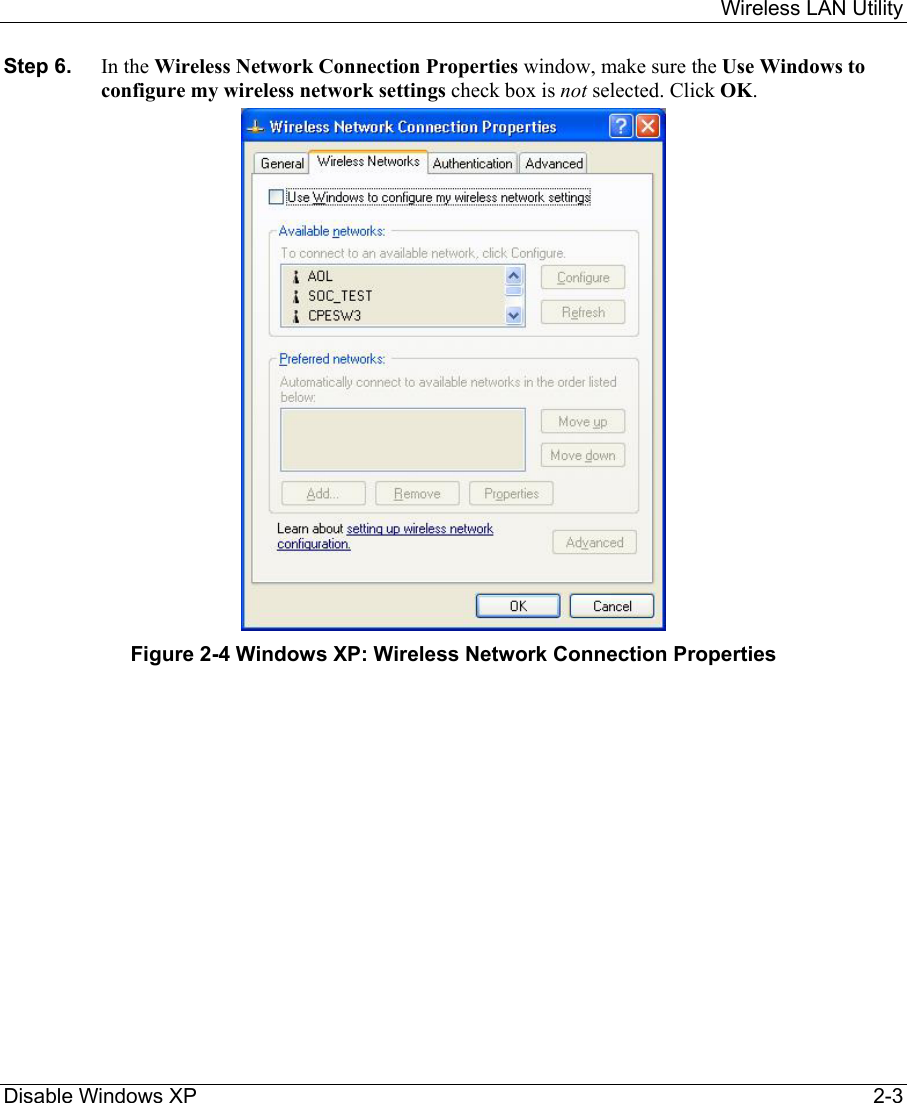
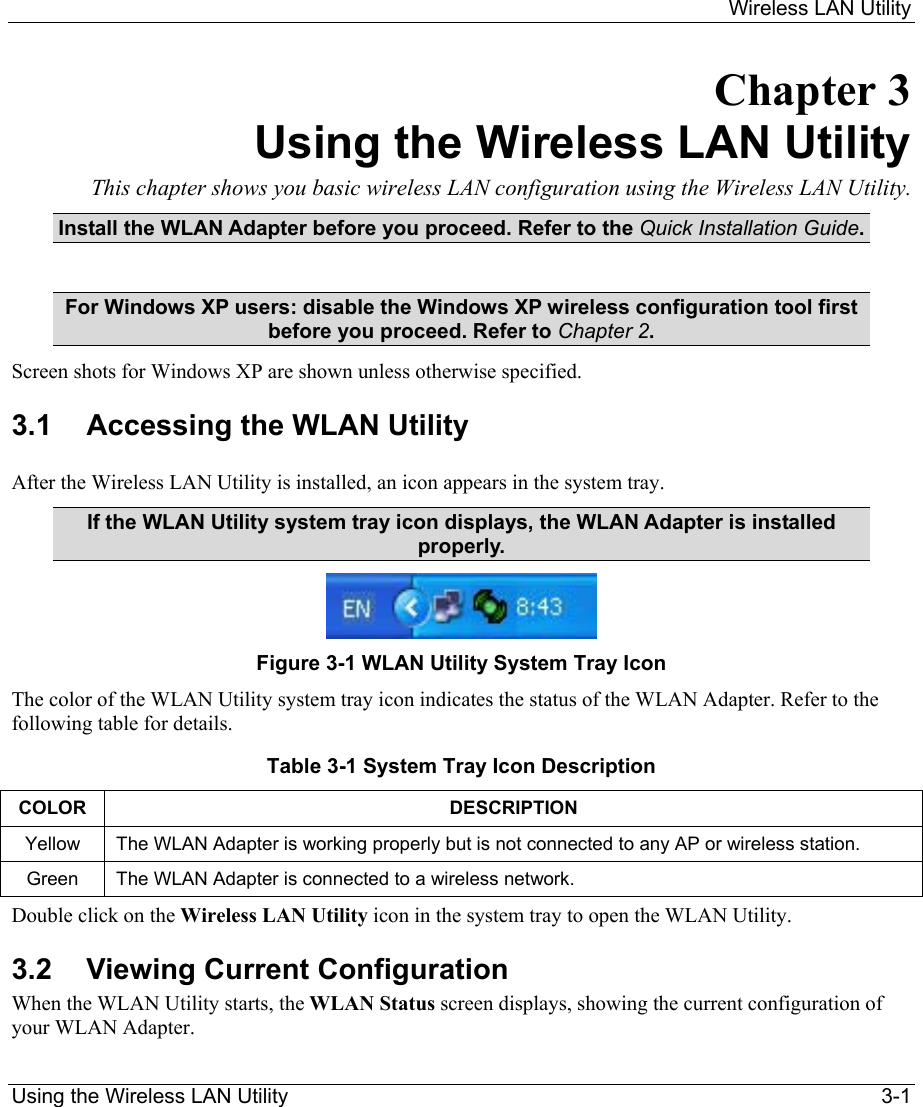
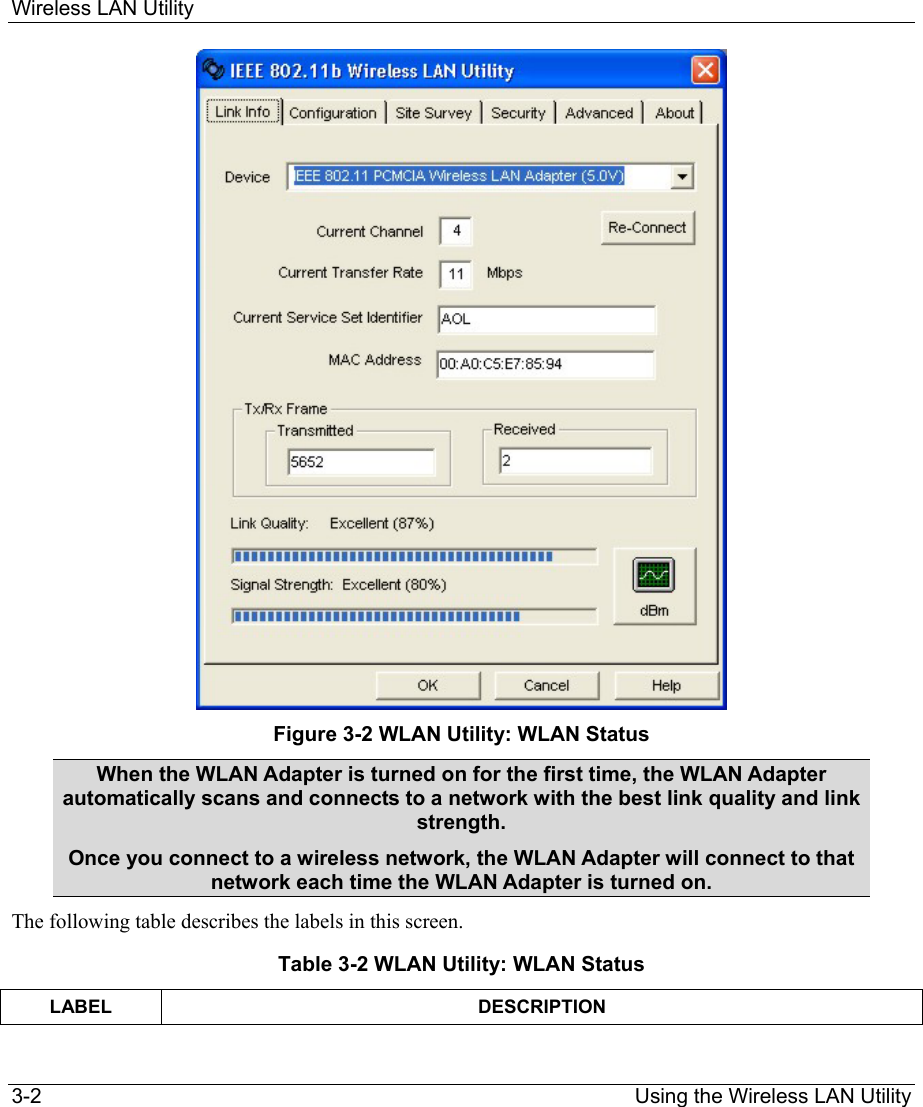
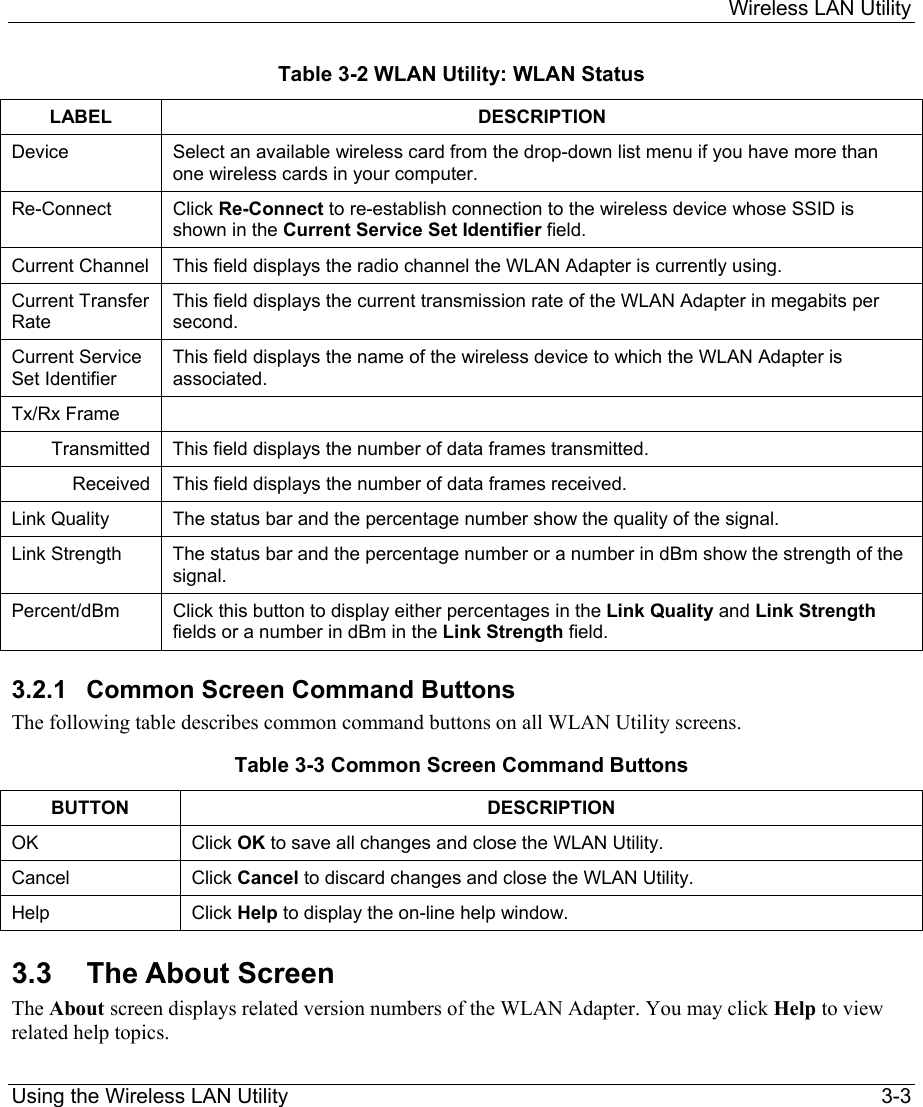
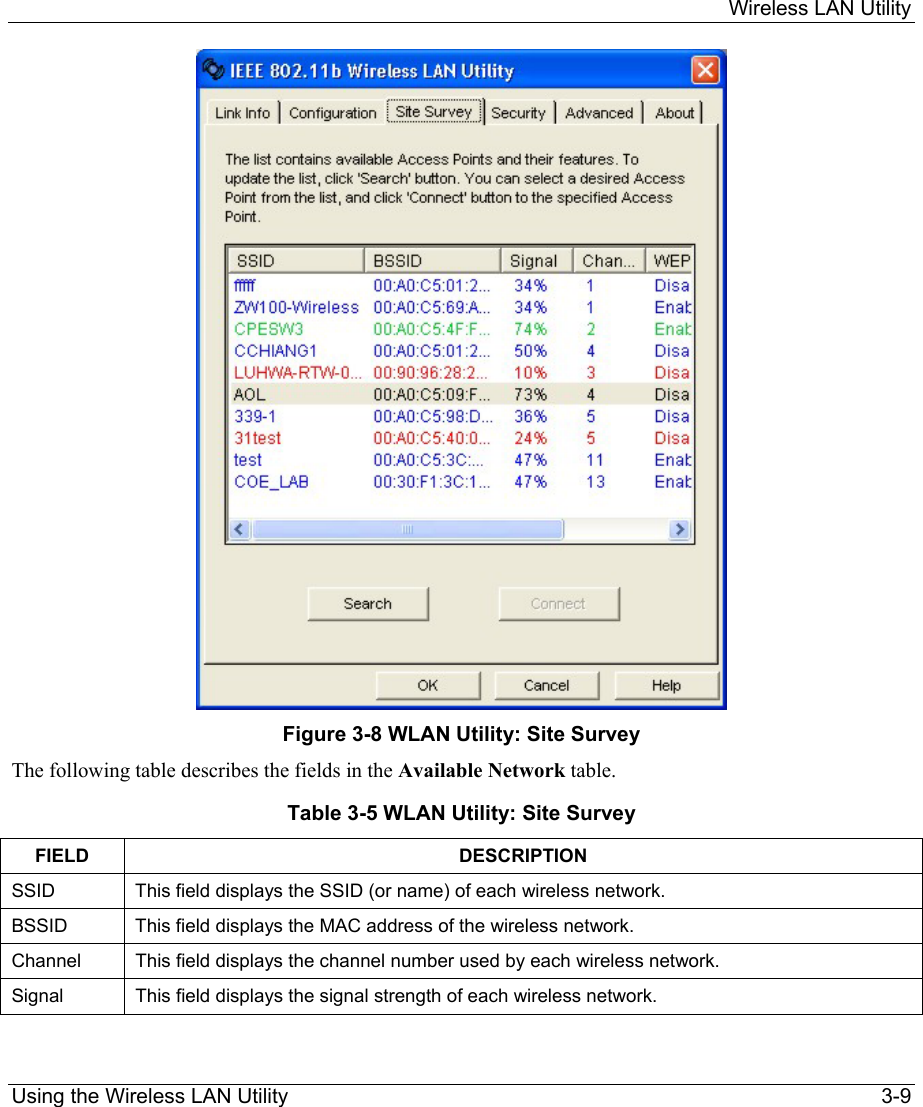
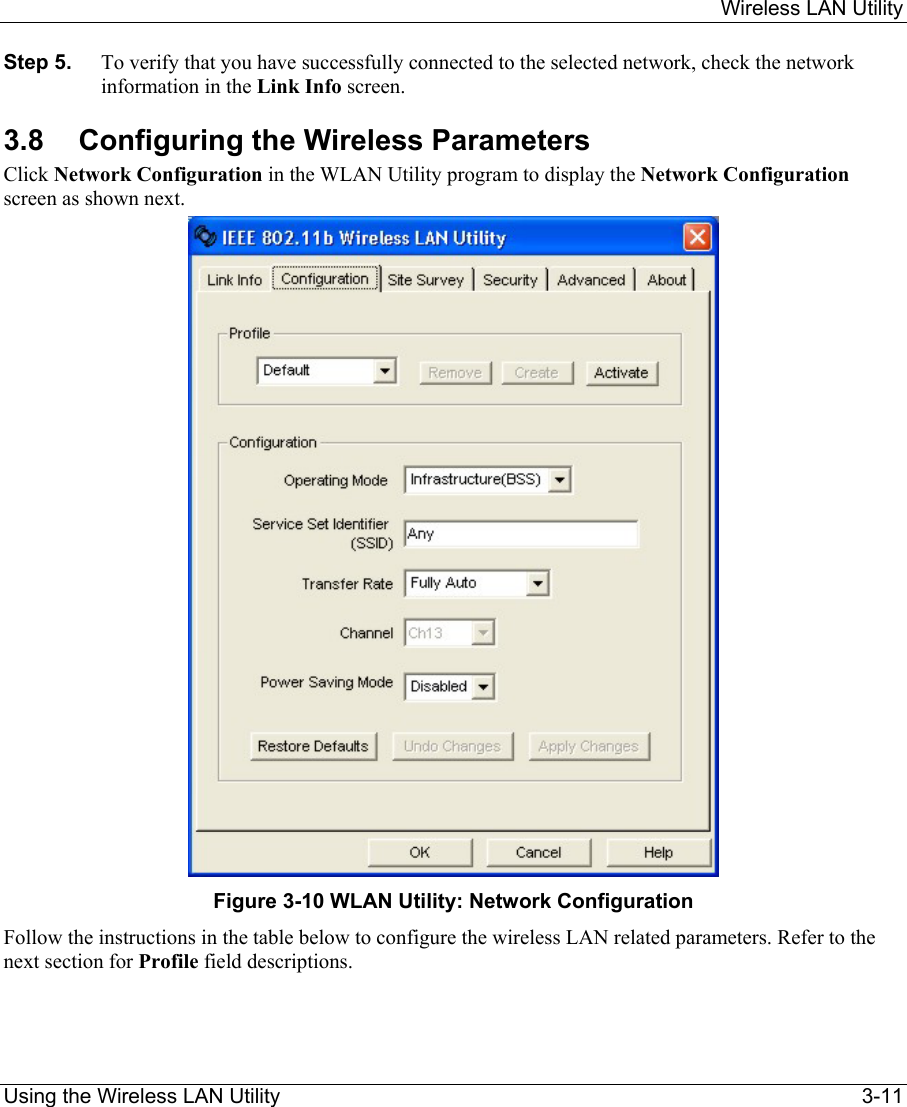
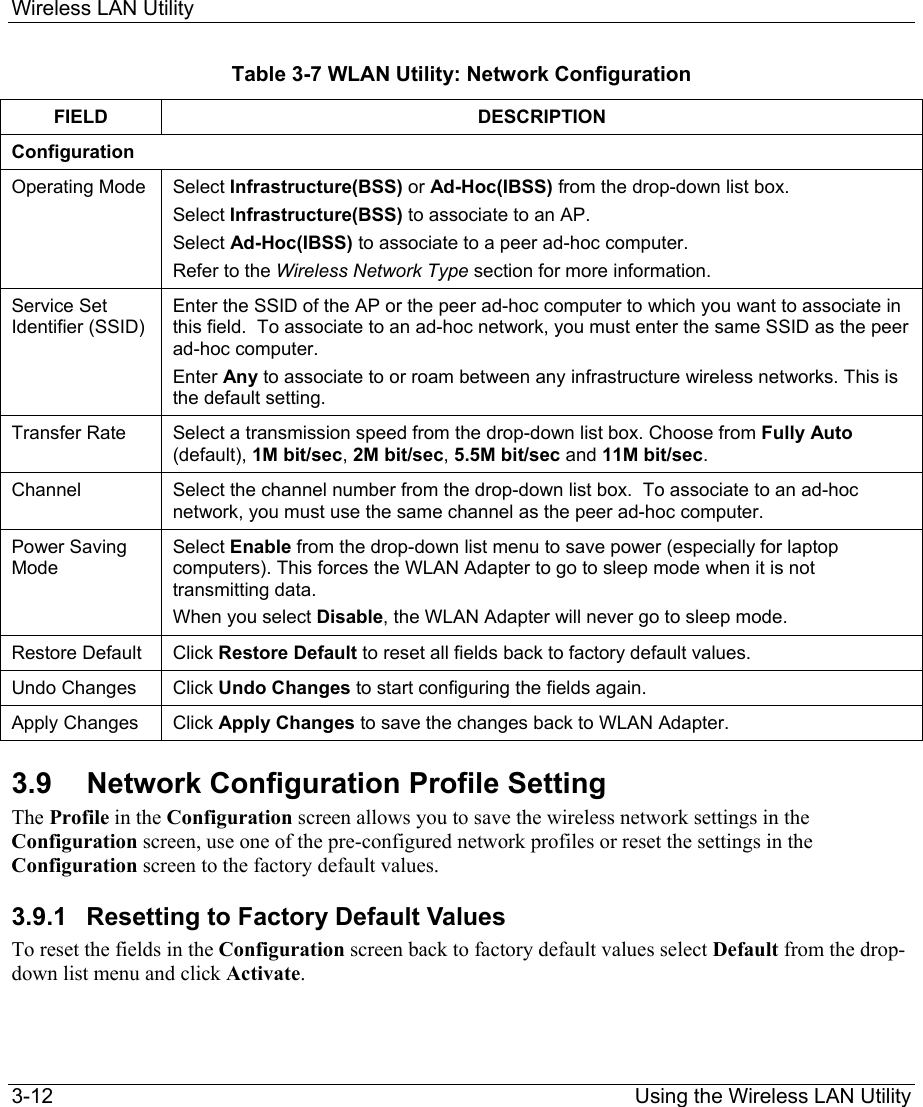
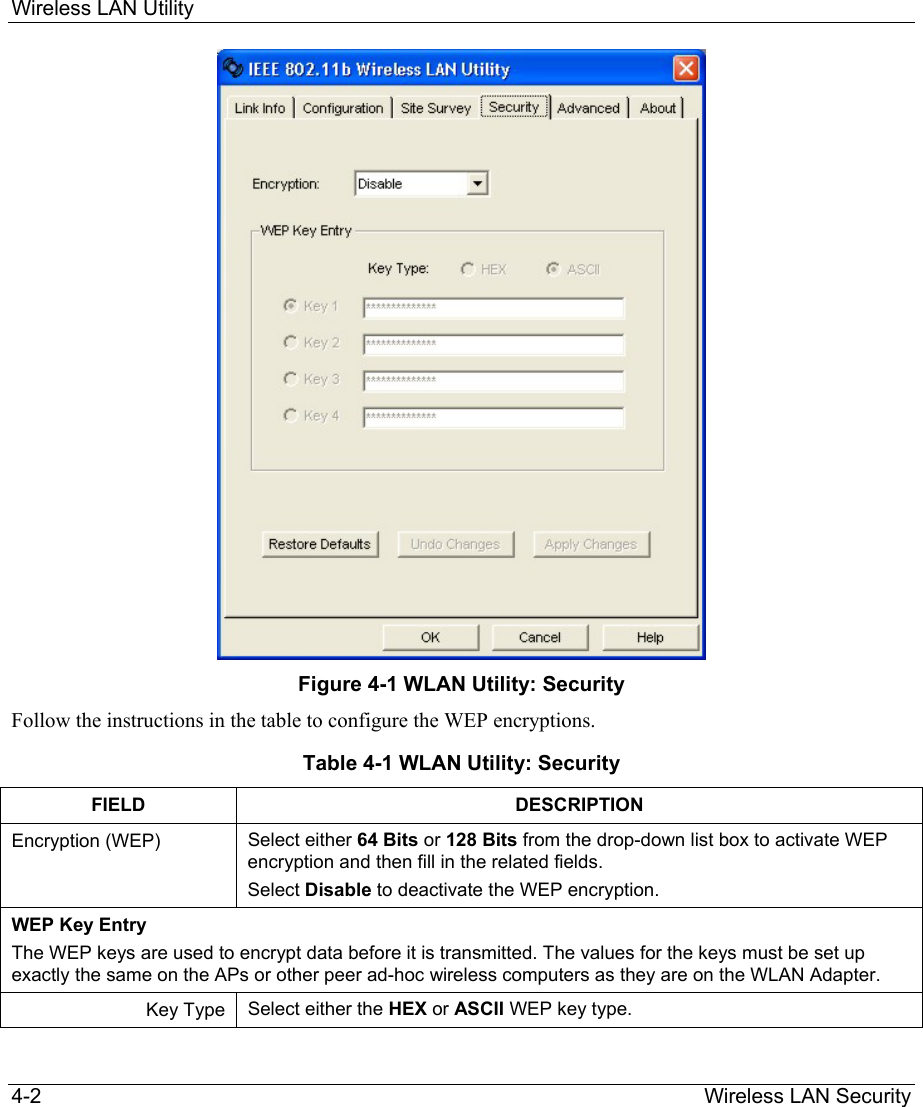
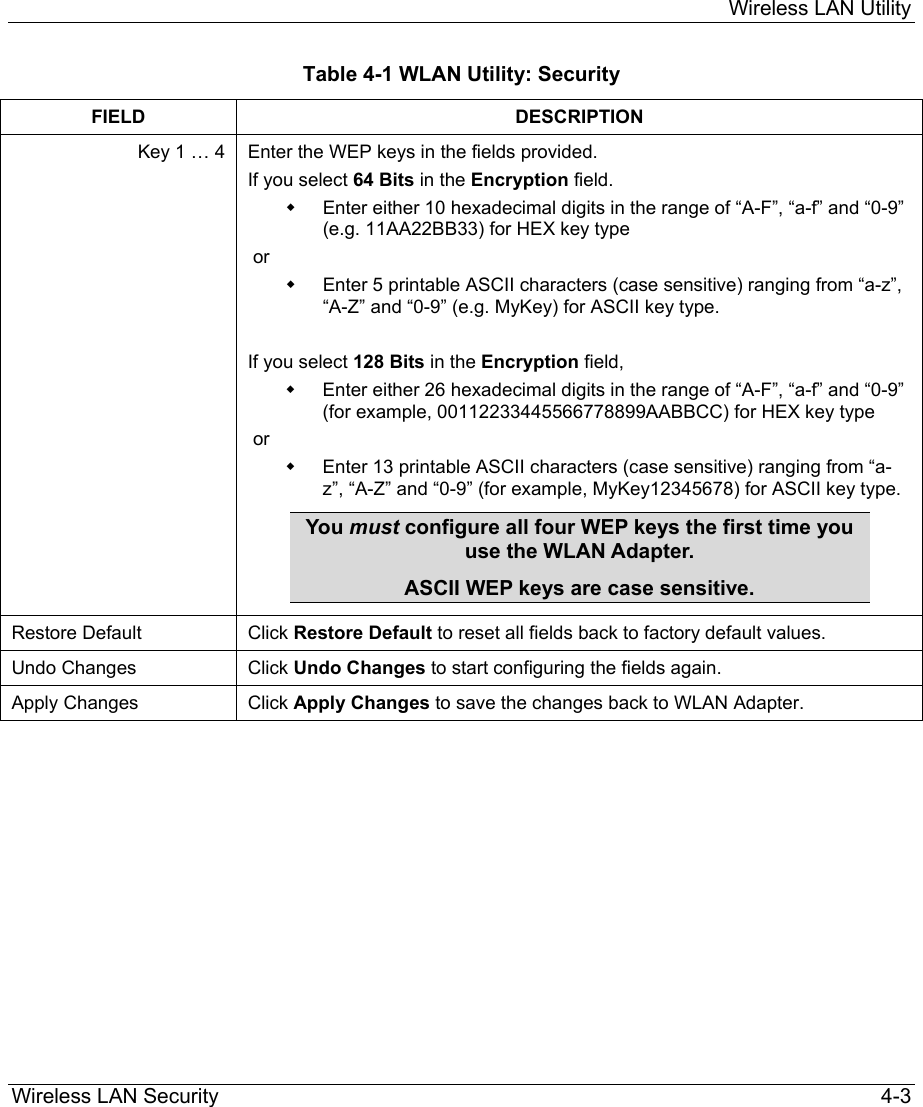
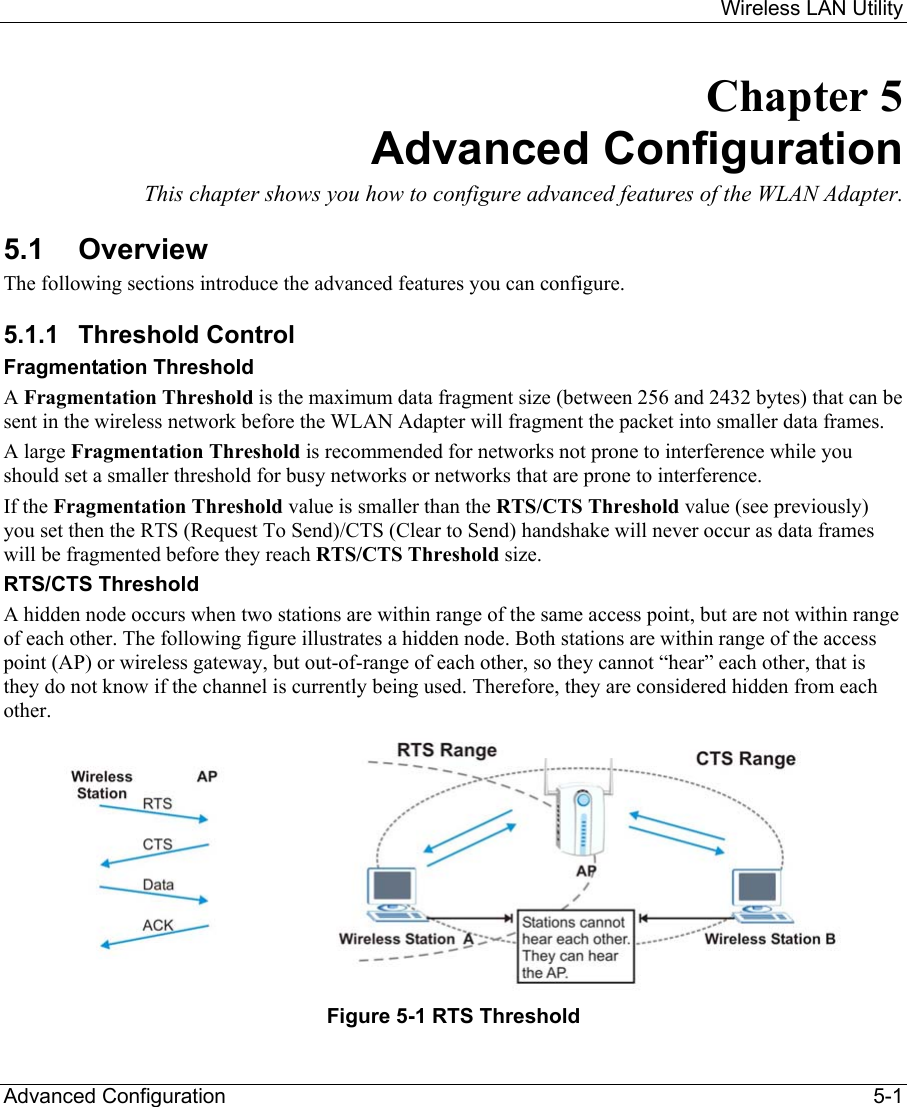
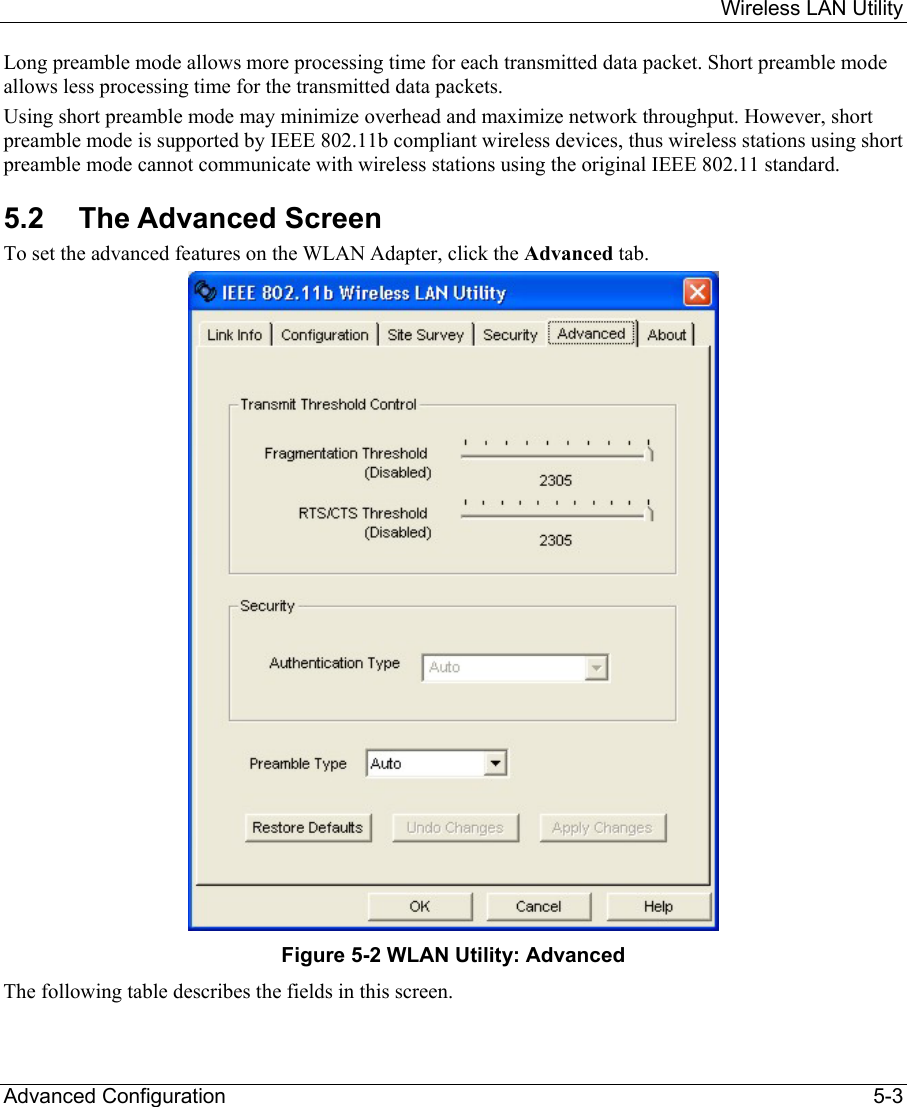
ZyXEL Communications B-120 802.11b Mobile Module User Manual ZyAIR Wireless Utility OEM
ZyXEL Communications Corporation 802.11b Mobile Module ZyAIR Wireless Utility OEM
Contents
- 1. DoC Statement
- 2. Users Manual Revised 052203
- 3. Quick Install Guide
- 4. Revised Installation Guide
Revised Installation Guide