ARGtek Communication ARG-U27G 802.11b/g USB dongle User Manual
ARGtek Communication Inc. 802.11b/g USB dongle
User Manual
Before
you
proceed
with
the
installation,
please
notice
the
following
descriptions.
Note
1:
The
following
installation
was
operated
under
Windows
XP.
(Procedures
are
similar
to
Windows
98SE/Me/2000.)
Note
2:
If
you
have
installed
the
WLAN
USB
driver
&
utility
already,
please
uninstall
the
old
version
first.
Note
3:
Do
not
insert
the
wireless
LAN
adapter
into
your
computer
until
the
procedure
of
“
Install
the
Driver
&
Utility
"
has
been
performed.
1
.
I
n
s
t
a
ll
a
t
i
o
n
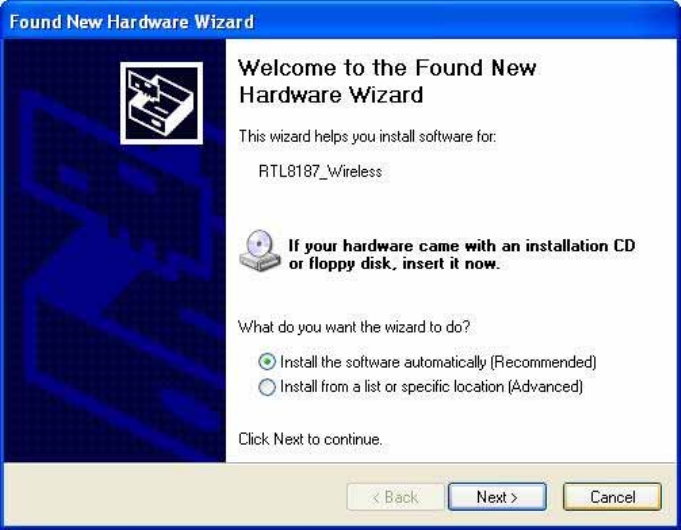
1.
If
you
insert
the
Wireless
LAN
USB
Adaptor
into
your
computer
USB
port
after
``installing
the
software
program
from
the
CD,
then
the
following
window
pops
up.
2.
Click
Cancel
.
3.
Choose
a
set
up
language.
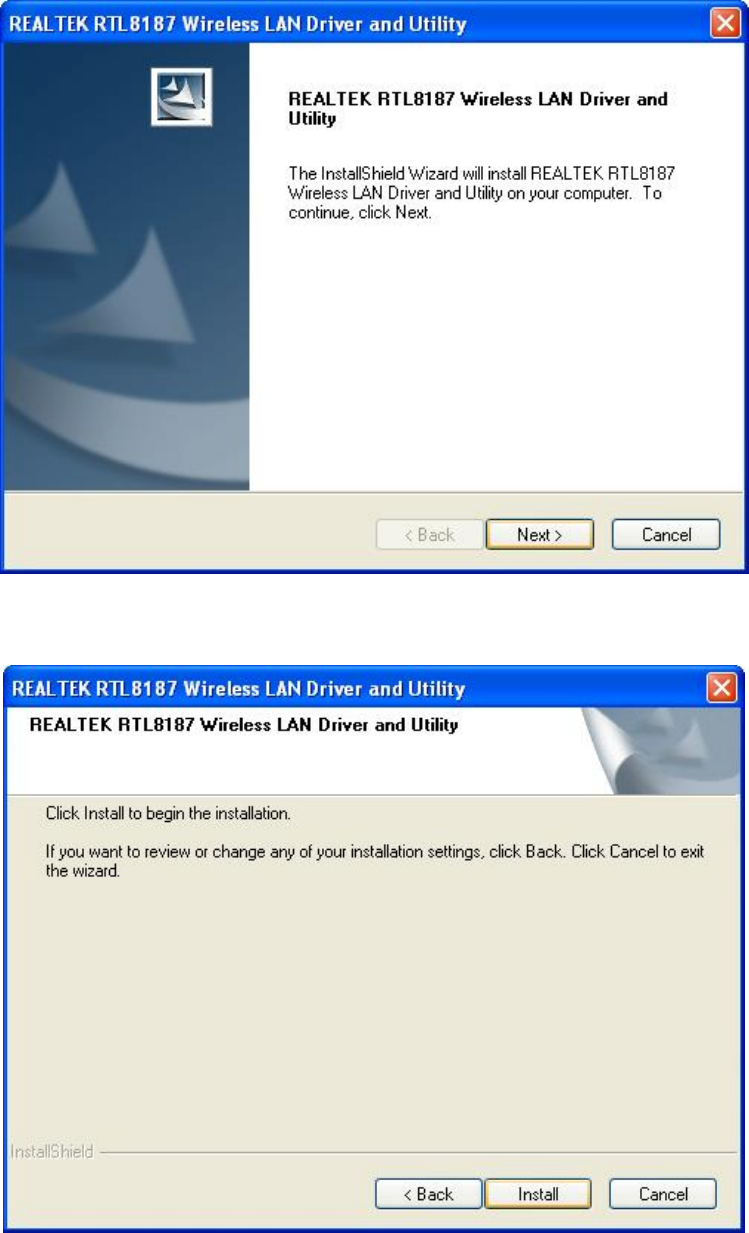
4.
Click
Next
to
process
the
installation.
.
5.
Click
Install
to
WLAN
USB
adaptor
installation.
6.
On
Windows
Logo
Software
Installation
screen,
click
Continue
Anyway
to
continue.
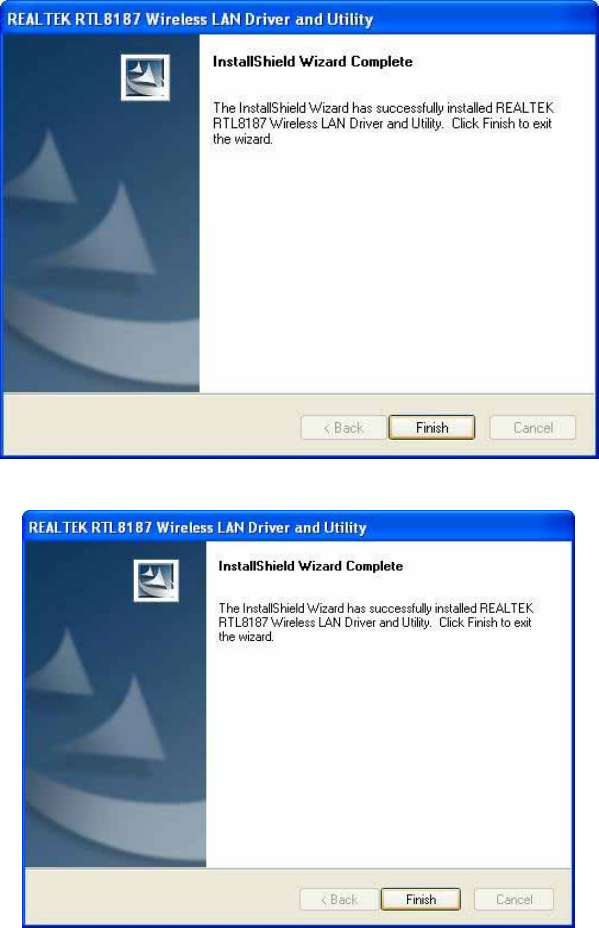
7.
Click
Finish
to
complete
the
installation.
8.
After
setup,
restart
your
computer
2
.
U
n
i
n
s
t
a
ll
a
t
i
o
n
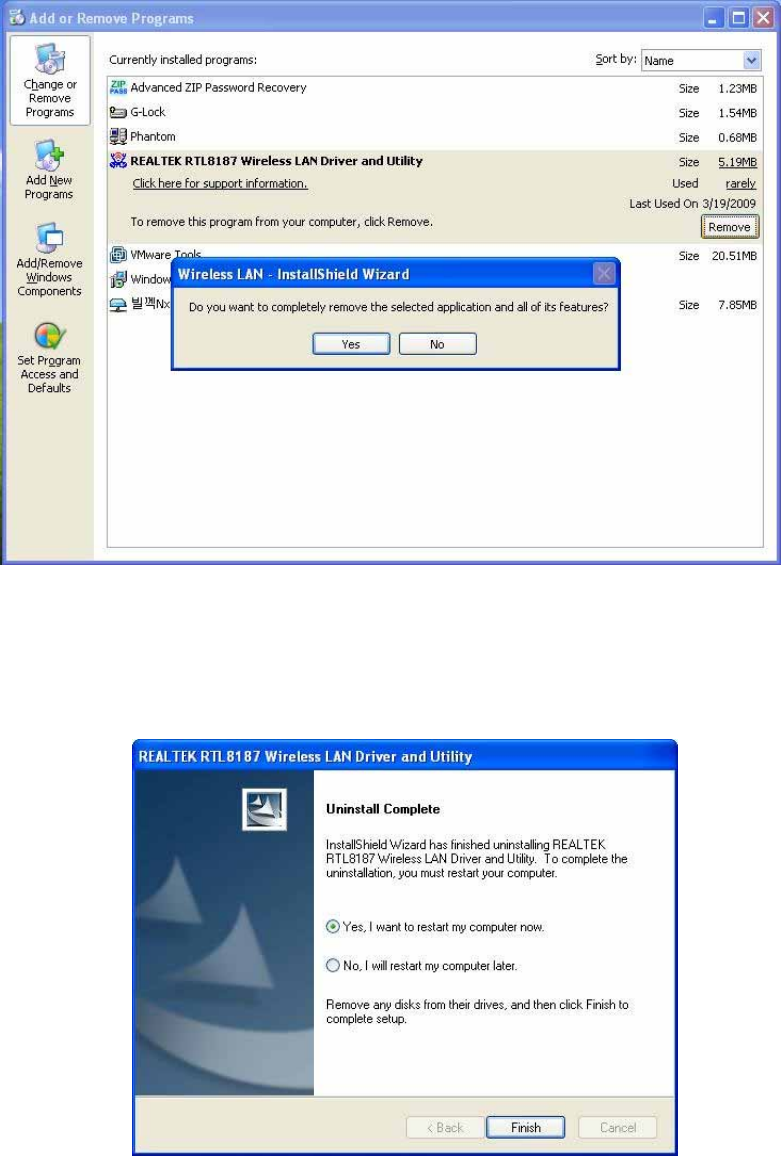
A.
Uninstall
the
WLAN
USB
Adaptor
Driver
from
“
Wireless
Network
Driver
and
Utility
"
or
“
Control
Panel
"
.
Click
“
Uninstall
"
(or
“
Change/Remove
"
)
to remove
Wireless
LAN
USB
Adaptor
driver.
B.
Click
“
OK
"
if
you
want
to
remove
Wireless
LAN
USB
Adaptor
Driver.
C.
Click
“
Finish
"
to
complete
the
uninstallation.
Making
a
Basic
Network
Connection
I
n
t
h
e
f
o
ll
o
w
i
n
g
i
n
s
t
r
u
c
t
i
o
n
f
o
r
m
a
ki
n
g
a
n
e
t
w
o
r
k
c
o
nn
ec
t
i
o
n
,
w
e
u
se
t
h
e
u
t
ili
t
y
w
e
p
r
o
vi
d
e
d
t
o
c
o
n
f
i
g
u
r
e
y
o
u
r
w
i
r
e
l
ess
n
e
t
w
o
r
k
se
tt
i
n
g
s
.
N
o
t
e
:
F
o
r
W
i
n
do
w
s X
P
u
se
r
s
t
h
a
t
w
a
n
t
t
o
c
o
n
f
i
g
u
r
e
y
o
u
r
w
i
r
e
l
ess
n
e
t
w
o
r
k
u
s
i
n
g
t
h
i
s
U
t
ili
t
y
,
p
l
ease
p
e
rf
o
r
m
t
h
e
f
o
ll
o
w
i
n
g
p
r
o
ce
d
u
r
es
t
o
d
i
sa
b
l
e
y
o
u
r
n
a
t
iv
e W
i
n
do
w
s X
P
w
i
r
e
l
ess s
u
ppo
r
t
(
W
i
r
e
l
ess
Z
e
r
o
C
o
n
f
i
g
u
r
a
t
i
o
n
Se
r
vi
ce
)
1
.
D
o
u
b
l
e c
li
c
k
t
h
e
i
c
o
n
o
n
y
o
u
r
d
es
k
t
op
t
o
s
t
a
r
t
t
h
e
u
t
ili
t
y
o
r
i
n
t
h
e
t
as
k
b
a
r
.
Ad-Hoc
Mode
A
n
A
d
-
H
o
c
m
od
e
w
i
r
e
l
ess
n
e
t
w
o
r
k
c
o
nn
ec
t
s
t
w
o
c
o
m
p
u
t
e
r
s
d
i
r
ec
t
ly
w
i
t
h
o
u
t
t
h
e
u
se
o
f
a
r
o
u
t
e
r
o
r
A
P
.
I
t
i
s a
l
s
o
known
as a
p
ee
r
-
t
o
-
p
ee
r
n
e
t
w
o
r
k
.
F
o
r
e
x
a
m
p
l
e
,
w
e ca
n
i
n
s
t
a
ll
t
h
i
s
w
i
r
e
l
ess a
d
a
p
t
e
r
t
o
t
w
o
c
o
m
p
u
t
e
r
s
r
es
p
ec
t
iv
e
ly
.
T
h
e
c
o
mmun
i
ca
t
i
o
n
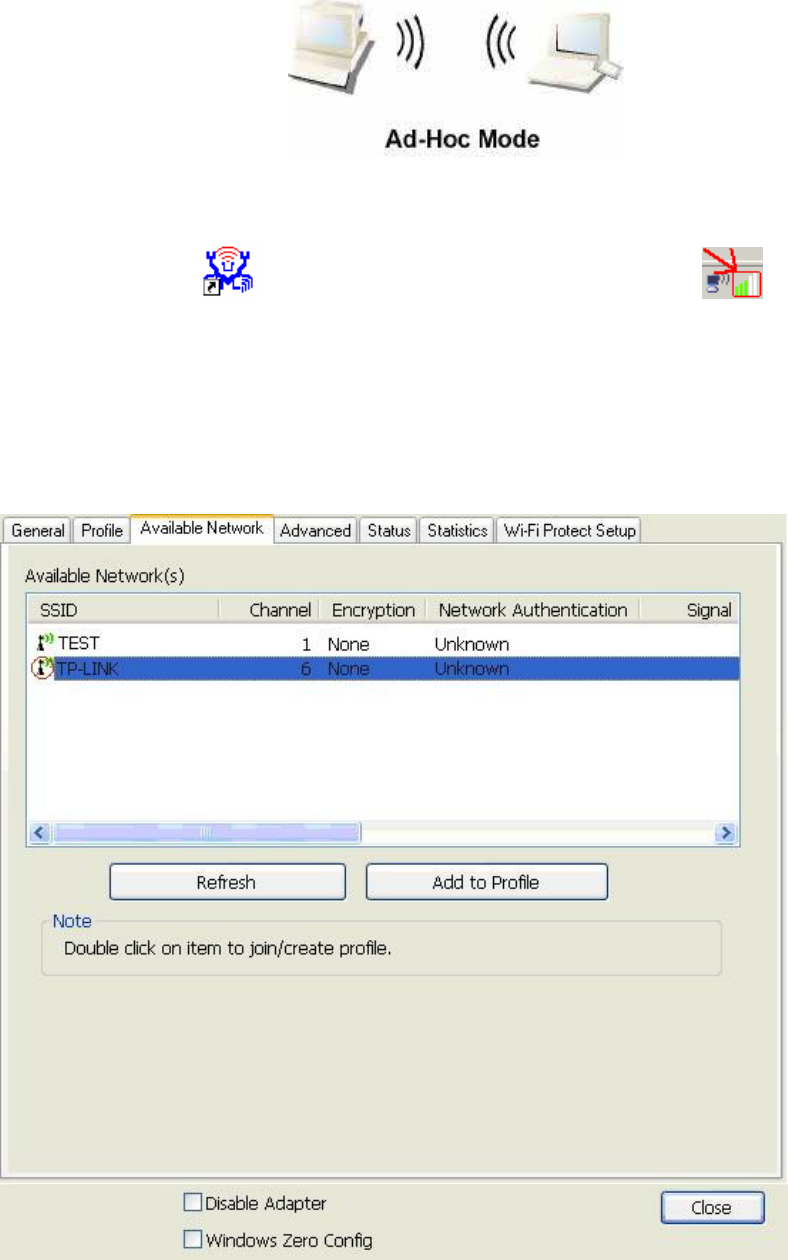
b
e
t
w
ee
n
t
h
e
t
w
o
c
o
m
p
u
t
e
r
s
i
s a
n
A
d
-
H
o
c
m
od
e
n
e
t
w
o
r
k
.
T
o
u
s
e
t
h
i
s
a
d
a
p
t
e
r
i
n
A
d
-
H
o
c
M
o
d
e
1
.
D
o
u
b
l
e c
li
c
k
t
h
e
i
c
o
n
o
n
y
o
u
r
d
es
k
t
op
t
o
s
t
a
r
t
t
h
e
u
t
ili
t
y
o
r
i
n
t
h
e
t
as
k
b
a
r
.
2
.
C
li
c
k
t
h
e
“
A
v
a
il
a
bl
e
N
e
t
w
o
r
k
"
b
u
tt
o
n
t
o
sca
n
a
v
a
il
a
b
l
e
w
i
r
e
l
ess
n
e
t
w
o
r
k
a
d
a
p
t
e
r
s
.
D
o
u
b
l
e c
li
c
k
o
n
t
h
e
n
e
t
w
o
r
k
a
d
a
p
t
e
r
t
h
a
t
y
o
u
a
r
e
go
i
n
g
t
o
c
o
nn
ec
t
t
o
.
3
.
C
li
c
k
t
h
e
O
K
b
u
tt
o
n
t
o
c
o
n
f
i
r
m
t
h
a
t
y
o
u
a
r
e c
o
nn
ec
t
i
n
g
t
o
a
n
op
e
n
w
i
r
e
l
ess
n
e
t
w
o
r
k
.
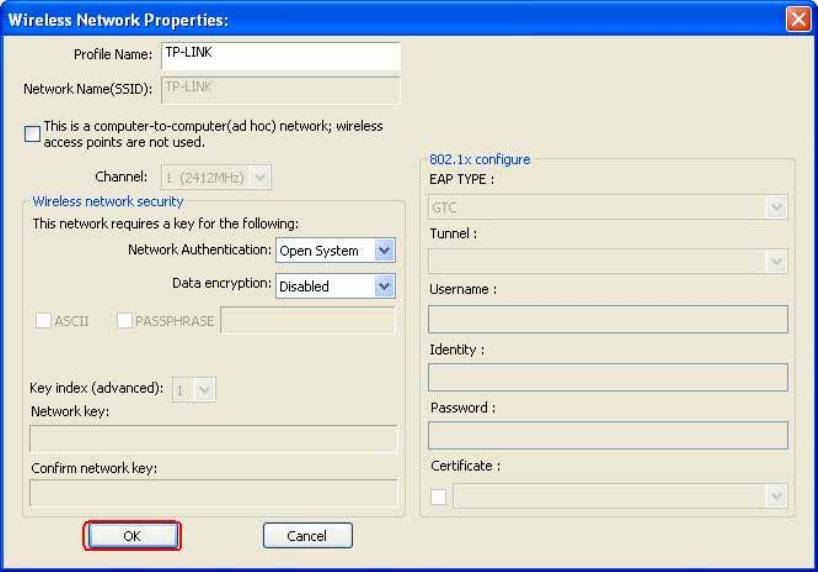
4
.
C
li
c
k
O
K
t
o
a
dd
t
h
i
s
n
e
t
w
o
r
k
i
n
t
o
t
h
e
p
r
o
f
il
e
li
s
t
.
N
o
t
e
:
T
h
i
s e
x
a
m
p
l
e
i
s a
n
op
e
n
w
i
r
e
l
ess
n
e
t
w
o
r
k
.
I
f
y
o
u
a
r
e
go
i
n
g
t
o
c
o
nn
ec
t
t
o
a
W
i
r
e
l
ess a
d
a
p
t
e
r
w
i
t
h
sec
u
r
i
t
y
p
r
o
t
ec
t
i
o
n
,
y
o
u
w
ill
h
a
v
e
t
o
c
o
n
f
i
g
u
r
e
t
h
e e
n
c
r
y
p
t
i
o
n
se
tt
i
n
g
s
i
n
t
h
i
s
p
r
o
f
il
e
t
o
b
e c
o
rr
es
po
n
d
i
n
g
t
o
t
h
e
o
t
h
e
r
w
i
r
e
l
ess a
d
a
p
t
e
r
.
P
l
ease c
li
c
k
o
t
h
e
“
N
e
t
w
o
r
k
A
u
t
h
e
n
t
i
c
a
t
i
o
n
"
d
r
op
li
s
t
t
o
se
l
ec
t
a
n
a
u
t
h
e
n
t
i
ca
t
i
o
n
m
e
t
h
od
,
a
n
d
t
h
e
n
se
l
ec
t
a
“
D
a
t
a
e
n
c
r
y
pt
i
o
n
"
t
y
p
e
.
F
ill
i
n
eac
h
r
e
q
u
i
r
e
d
b
l
a
n
k
s a
n
d
c
li
c
k
“
O
K
"
.
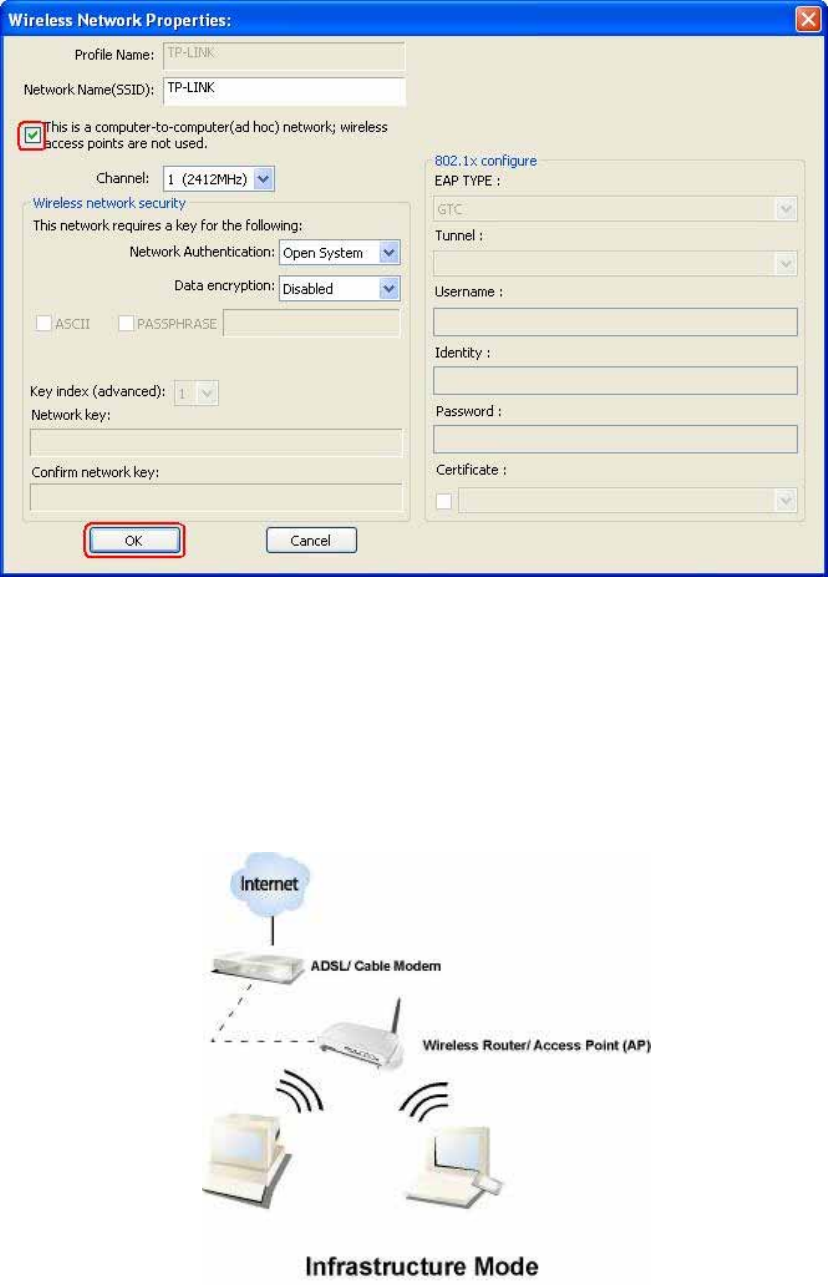
Infrastructure
mode
A
n
I
n
fr
as
t
r
u
c
t
u
r
e
M
od
e
n
e
t
w
o
r
k
c
o
n
t
a
i
n
s a
t
l
eas
t
o
n
e
w
i
r
e
l
ess c
li
e
n
t
a
n
d
o
n
e
w
i
r
e
l
ess A
P
o
r
r
o
u
t
e
r
.
T
h
i
s c
li
e
n
t
c
o
nn
ec
t
s
t
o
I
n
t
e
r
n
e
t
o
r
i
n
t
r
a
n
e
t
b
y
c
o
mmun
i
ca
t
i
n
g
w
i
t
h
t
h
i
s
w
i
r
e
l
ess A
P
.
T
o
u
s
e
t
h
i
s
a
d
a
p
t
e
r
i
n
I
n
f
r
a
s
t
r
u
c
t
u
r
e
M
o
d
e
:
1
.
D
o
u
b
l
e c
li
c
k
t
h
e
i
c
o
n
o
n
y
o
u
r
d
es
k
t
op
t
o
s
t
a
r
t
t
h
e
u
t
ili
t
y
o
r
i
n
t
h
e
t
as
k
b
a
r
.
2
.
C
li
c
k
t
h
e
“
A
v
a
il
a
b
l
e
N
e
t
w
o
r
k
"
b
u
tt
o
n
t
o
sca
n
a
v
a
il
a
b
l
e access
po
i
n
t
s
.
D
o
u
b
l
e c
li
c
k
o
n
t
h
e A
P
t
h
a
t
y
o
u
a
r
e
go
i
n
g
t
o
c
o
nn
ec
t
t
o
.
3
.
D
o
u
b
l
e c
li
c
k
t
o
c
r
ea
t
e
p
r
o
f
il
e
t
h
a
t
y
o
u
a
r
e c
o
nn
ec
t
i
n
g
t
o
a
n
op
e
n
w
i
r
e
l
ess
n
e
t
w
o
r
k
.
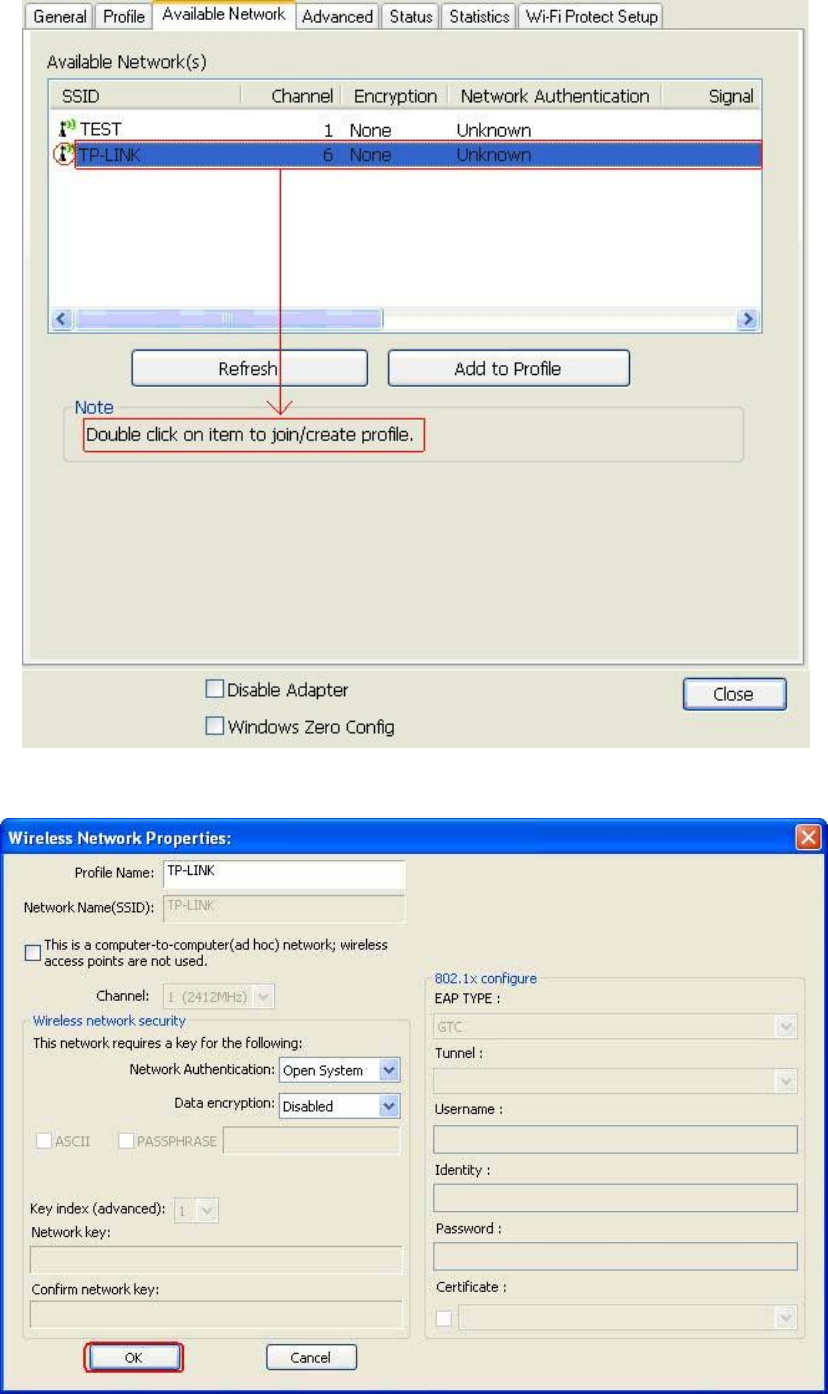
4
.
C
li
c
k
O
K
t
o
a
dd
t
h
i
s
n
e
t
w
o
r
k
i
n
t
o
t
h
e
p
r
o
f
il
e
li
s
t
.
N
o
t
e
:
T
h
i
s e
x
a
m
p
l
e
i
s a
n
op
e
n
w
i
r
e
l
ess
n
e
t
w
o
r
k
.
I
f
y
o
u
a
r
e
go
i
n
g
t
o
c
o
nn
ec
t
t
o
a
n
A
P
w
i
t
h
sec
u
r
i
t
y
p
r
o
t
ec
t
i
o
n
,
y
o
u
w
ill
h
a
v
e
t
o
c
o
n
f
i
g
u
r
e
t
h
e e
n
c
r
y
p
t
i
o
n
se
tt
i
n
g
s
i
n
t
h
i
s
p
r
o
f
il
e
t
o
b
e c
o
rr
es
po
n
d
i
n
g
t
o
y
o
u
r
A
P
.
P
l
ease c
li
c
k
o
n
t
h
e
“
N
e
t
w
o
r
k
A
u
t
h
e
n
t
i
c
a
t
i
o
n
"
d
r
op
li
s
t
t
o
se
l
ec
t
a
n
a
u
t
h
e
n
t
i
ca
t
i
o
n
m
e
t
h
od
,
a
n
d
t
h
e
n
se
l
ec
t
a
“
D
a
t
a
e
n
c
r
y
pt
i
o
n
"
t
y
p
e
.
F
ill
i
n
eac
h
r
e
q
u
i
r
e
d
b
l
a
n
k
s a
n
d
c
li
c
k
“
O
K
"
.
T
i
p:
W
i
n
do
w
s X
P
a
n
d
W
i
n
do
w
s
2000
u
se
r
s
i
s a
l
s
o
a
ll
o
w
e
d
t
o
c
o
nn
ec
t
t
o
y
o
u
r
w
i
r
e
l
ess
n
e
t
w
o
r
k
w
i
t
h
t
h
e
“
R
T
-
Se
t
"
se
t
u
p
w
i
za
r
d
.
P
l
ease
r
e
f
e
r
t
o
“
A
pp
e
n
dix
"
f
o
r
m
o
r
e
i
n
f
o
r
m
a
t
i
o
n
.
Introduction
to
the
Wireless
LAN
Utility
N
o
t
e
:
T
h
i
s
m
a
n
a
g
e
m
e
n
t
i
n
s
t
r
u
c
t
i
o
n
u
ses W
i
n
do
w
s X
P
as
t
h
e
p
r
es
um
e
d op
e
r
a
t
i
o
n
s
y
s
t
e
m
.
S
o
m
e
f
un
c
t
i
o
n
s a
r
e
n
o
t
s
u
ppo
r
t
e
d
i
n
W
i
n
do
w
s
98
se
o
r
W
i
n
do
w
s
M
E
.
Starting
the
Wireless
LAN
Utility
Y
o
u
m
a
y
c
li
c
k
o
n
t
h
e
t
a
b
s a
bo
v
e
t
o
c
o
n
f
i
g
u
r
e
t
h
i
s a
d
a
p
t
e
r
.
T
h
e c
h
ec
k
bo
x
e
b
e
l
o
w
p
r
o
vi
d
e
t
h
e
f
o
ll
o
w
i
n
g
f
un
c
t
i
o
n
s
:
S
h
o
w
T
r
a
y
I
c
o
n
R
a
d
i
o
O
ff
D
i
sa
b
l
e
A
d
a
pt
e
r
C
h
ec
k
t
h
i
s c
h
ec
k
bo
x
t
o
s
h
o
w
t
h
e
u
t
ili
t
y
i
c
o
n
o
n
y
o
u
r
s
y
s
t
e
m
t
r
a
y
,
wh
i
c
h
i
s
i
n
t
h
e
n
o
t
i
f
i
ca
t
i
o
n
a
r
ea
a
t
t
h
e
l
o
w
e
r
-
r
i
g
h
t
c
o
r
n
e
r
o
f
t
h
e
w
i
n
do
w
s
d
es
k
t
op
.
Y
o
u
m
a
y
a
l
s
o
un
c
h
ec
k
i
t
t
o
r
e
m
o
v
e
t
h
e
u
t
ili
t
y
i
c
o
n
fr
o
m
s
y
s
t
e
m
t
r
a
y
.
C
h
ec
k
t
h
i
s c
h
ec
k
bo
x
t
o
p
r
e
v
e
n
t
t
h
i
s
a
d
a
p
t
e
r
f
o
r
m
t
r
a
n
s
m
i
tt
i
n
g
o
r
r
ece
ivi
n
g
s
i
g
n
a
l
s
.
U
n
c
h
ec
k
i
t
t
o
c
o
mmun
i
ca
t
e
.
C
h
ec
k
t
h
i
s c
h
ec
k
bo
x
t
o
d
i
sa
b
l
e
t
h
i
s
w
i
r
e
l
ess a
d
a
p
t
e
r
.
U
n
c
h
ec
k
i
t
t
o
e
n
a
b
l
e
t
h
i
s a
d
a
p
t
e
r
a
g
a
i
n
.
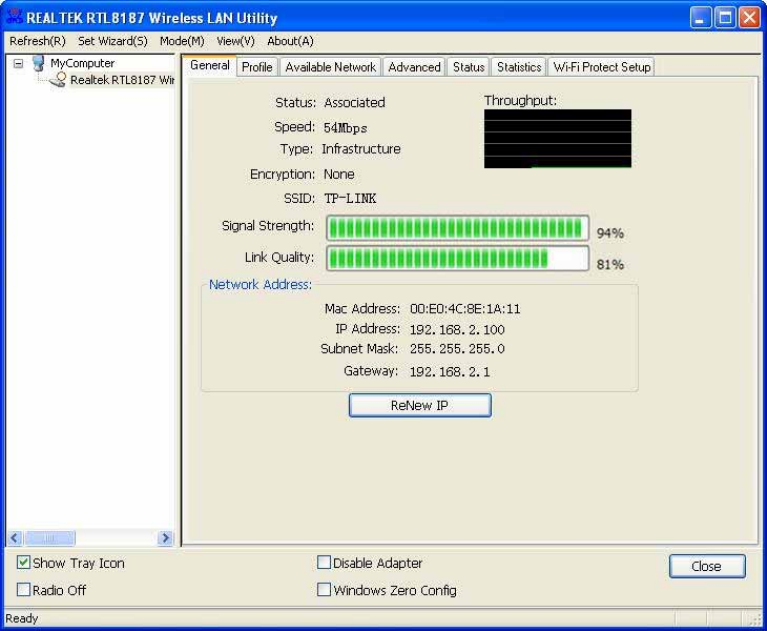
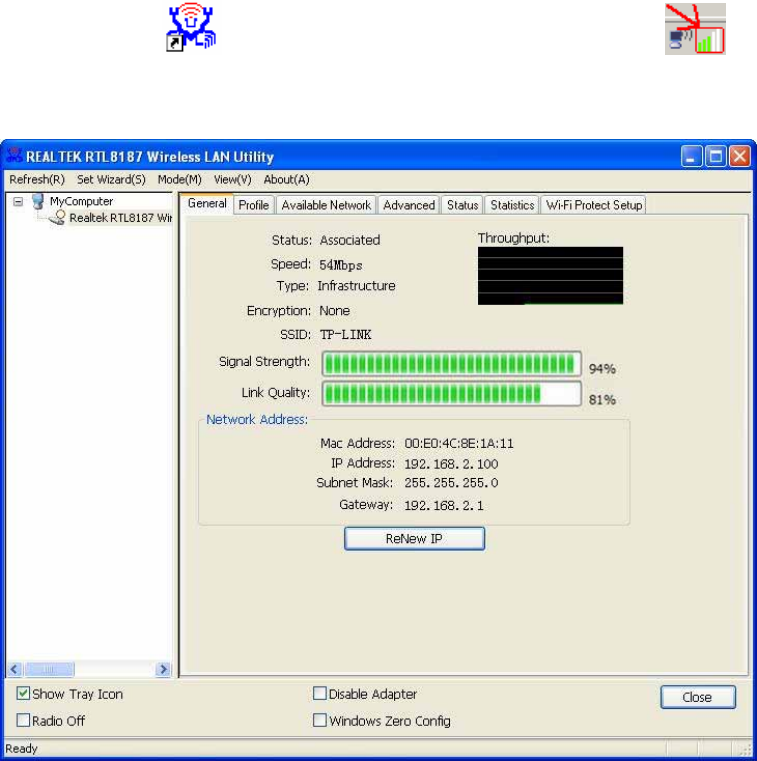
General
A
f
t
e
r
s
t
a
r
t
i
n
g
t
h
e
u
t
ili
t
y
,
t
h
e
g
e
n
e
r
a
l
p
a
g
e
pop
s
u
p
T
h
i
s
G
e
n
e
r
a
l
t
a
b p
r
o
vi
d
es
t
h
e
i
n
f
o
r
m
a
t
i
o
n
o
f
y
o
u
r
c
u
rr
e
n
t
w
i
r
e
l
ess
n
e
t
w
o
r
k
c
o
nn
ec
t
i
o
n
.
Y
o
u
m
a
y
c
li
c
k
t
h
e
R
e
n
e
w
I
P
b
u
tt
o
n
t
o
r
e
fr
es
h
t
h
o
se
li
s
t
e
d
i
n
f
o
r
m
a
t
i
o
n
.
S
t
a
t
u
s
:
C
h
ec
k
i
f
t
h
e
d
e
vi
ce ass
o
c
i
a
t
e
d
t
o
t
a
r
g
e
t
n
e
t
w
o
r
k
.
S
p
ee
d
:
T
h
e c
u
rr
e
n
t
c
o
nn
ec
t
i
o
n
s
p
ee
d
T
yp
e
:
I
n
fr
as
t
r
u
c
t
u
r
e
m
od
e
o
r
A
d
-
H
o
c
m
od
e
.
E
n
c
r
yp
t
i
o
n
:
T
h
e
p
e
rf
o
r
m
i
n
g
e
n
c
r
y
p
t
i
o
n
m
od
e
f
o
r
c
o
nn
ec
t
i
n
g
t
o
c
u
rr
e
n
t
n
e
t
w
o
r
k
p
r
o
f
il
e
.
SS
I
D
:
T
h
e SS
I
D
(
n
e
t
w
o
r
k
n
a
m
e
)
o
f
t
h
e c
o
nn
ec
t
e
d
w
i
r
e
l
ess
n
e
t
w
o
r
k
.
S
i
gn
a
l
S
t
r
e
ng
t
h
:
I
n
d
i
ca
t
es
t
h
e s
i
g
n
a
l
s
t
r
e
n
g
t
h
d
e
t
ec
t
e
d
b
y
t
h
i
s a
d
a
p
t
e
r
.
L
i
n
k
Q
u
a
li
t
y
I
n
d
i
ca
t
es
t
h
e
li
n
k
q
u
a
li
t
y
o
f
t
h
i
s
w
i
r
e
l
ess c
o
nn
ec
t
i
o
n
.
N
e
t
w
o
r
k
A
dd
r
e
ss
:
S
h
o
w
s
t
h
e c
u
rr
e
n
t
I
P
a
dd
r
esses se
tt
i
n
g
s
f
o
r
t
h
i
s a
d
a
p
t
e
r
.
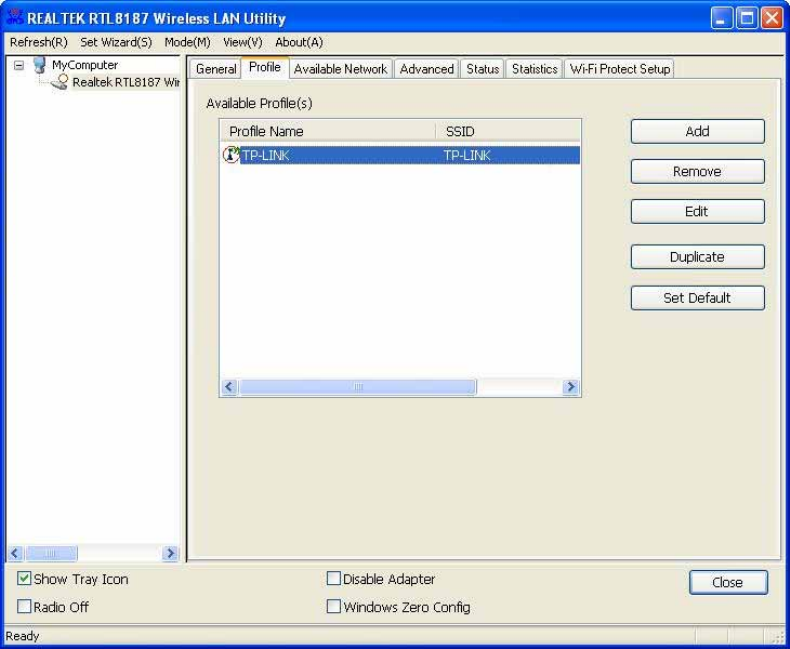
Profile
T
h
e
P
r
o
fil
e
t
a
b
li
s
t
s
t
h
e
p
r
e
f
e
rr
e
d
c
o
nn
ec
t
i
o
n
s
.
Y
o
u
ca
n
c
li
c
k
t
h
e
b
u
tt
o
n
s
b
es
i
d
e
t
o
do
c
o
n
f
i
g
u
r
e eac
h
c
o
nn
ec
t
i
o
n
.
A
dd
C
li
c
k
t
h
i
s
b
u
tt
o
n
t
o
a
dd
a c
o
nn
ec
t
i
o
n
p
r
o
f
il
e
f
o
r
t
h
i
s a
d
a
p
t
e
r
.
R
e
m
o
v
e
T
o
r
e
m
o
v
e a c
o
nn
ec
t
i
o
n
p
r
o
f
il
e
,
c
li
c
k
t
h
i
s
p
r
o
f
il
e
o
n
t
h
e
p
r
o
f
il
e
li
s
t
a
n
d
c
li
c
k
t
h
i
s
b
u
tt
o
n
t
o
d
e
l
e
t
e
i
t
.
E
di
t
T
o
m
od
i
f
y
t
h
e c
o
n
f
i
g
u
r
a
t
i
o
n
s
f
o
r
a
p
r
o
f
il
e
,
c
li
c
k
t
h
i
s
p
r
o
f
il
e
o
n
t
h
e
p
r
o
f
il
e
li
s
t
a
n
d
c
li
c
k
t
h
i
s
b
u
tt
o
n
t
o
e
d
i
t
.
D
u
pl
i
c
a
t
e
T
o
m
a
k
e a c
op
y
o
f
a
p
r
o
f
il
e
,
c
li
c
k
t
h
e
p
r
o
f
il
e
t
h
a
t
go
i
n
g
t
o
b
e
c
op
i
e
d
,
a
n
d
c
li
c
k
t
h
i
s
b
u
tt
o
n
t
o
c
op
y
i
t
.
S
e
t
D
e
f
a
u
l
t
T
o
se
l
ec
t
a
p
r
o
f
il
e as
y
o
u
r
d
e
f
a
u
l
t
w
i
r
e
l
ess c
o
nn
ec
t
i
o
n
,
c
li
c
k
t
h
i
s
p
r
o
f
il
e
o
n
t
h
e
li
s
t
a
n
d
c
li
c
k
t
h
i
s
b
u
tt
o
n
.
Y
o
u
m
a
y
a
l
s
o
do
u
b
l
e c
li
c
k
o
eac
h
p
r
o
f
il
e
t
o
se
l
ec
t
i
t
as
y
o
u
r
d
e
f
a
u
l
t
w
i
r
e
l
ess c
o
nn
ec
t
i
o
n
.
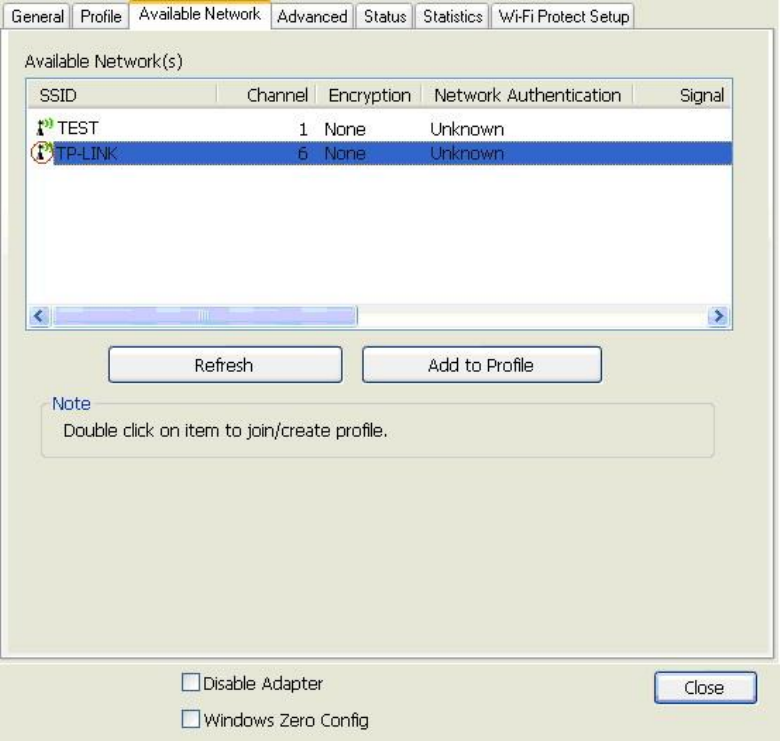
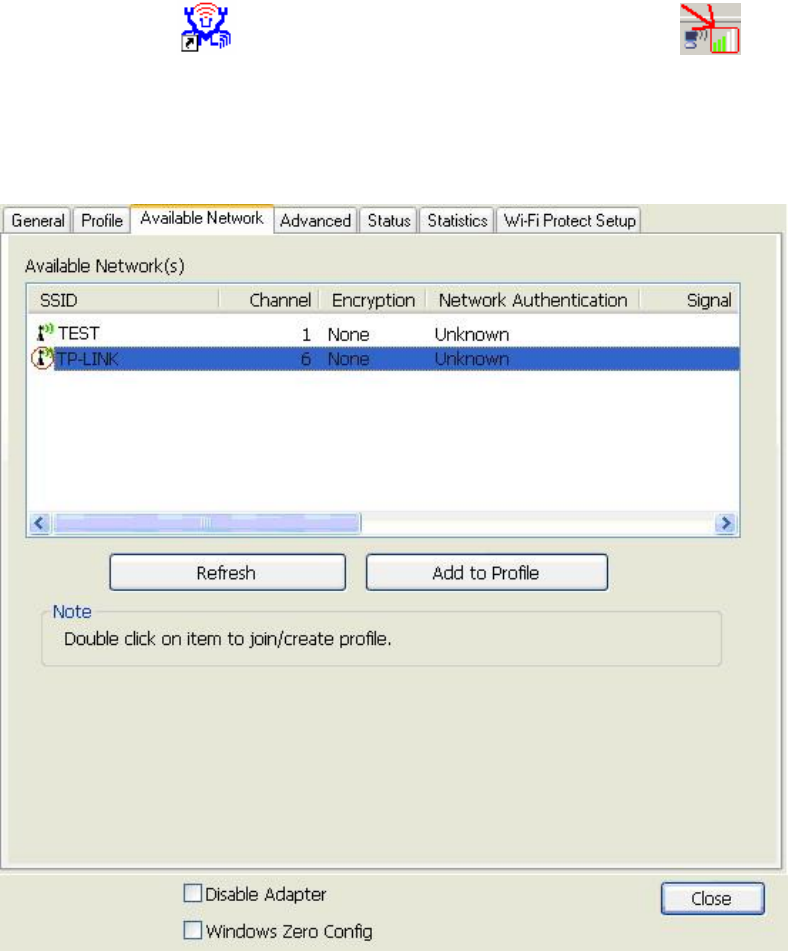
Available
Network
T
h
i
s a
v
a
il
a
b
l
e
t
a
b
li
s
t
s
t
h
e
r
eac
h
a
b
l
e
w
i
r
e
l
ess
n
e
t
w
o
r
k
o
f
t
h
i
s a
d
a
p
t
e
r
.
R
e
f
r
es
h
C
li
c
k
t
h
i
s
b
u
tt
o
n
t
o
r
esca
n
a
v
a
il
a
b
l
e
n
e
t
w
o
r
k
s a
r
o
un
d
t
h
e a
d
a
p
t
e
r
.
A
dd
t
o
P
r
o
fil
e
T
o
a
dd
a
n
a
v
a
il
a
b
l
e Ne
t
w
o
r
k
t
o
y
o
u
r
p
r
o
f
il
e
li
s
t
,
se
l
ec
t
the
“
A
v
a
il
a
b
l
e
N
e
t
w
o
r
k
"
a
n
d
c
li
c
k
t
h
i
s
b
u
tt
o
n
t
o
a
dd
.
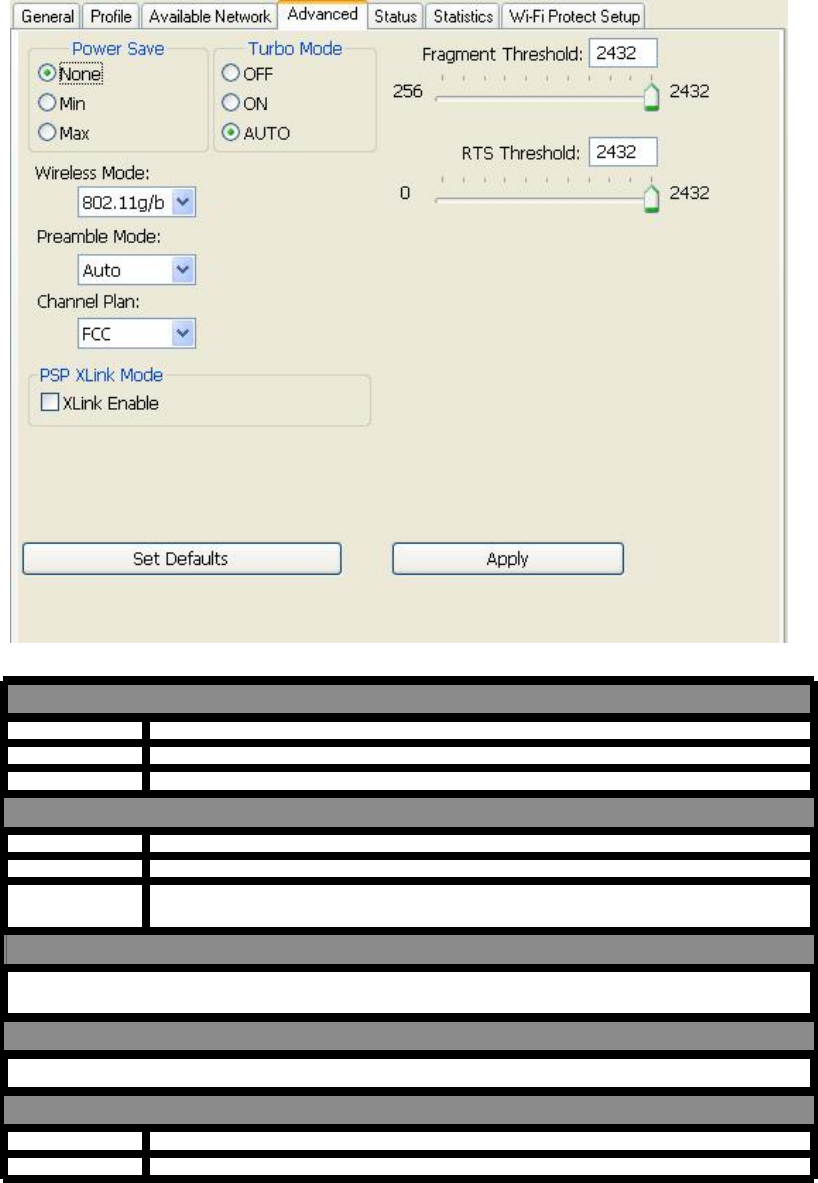
Advanced
T
h
i
s A
d
v
a
n
ce
d
t
a
b
p
r
o
vi
d
es a
d
v
a
n
ce
d
c
o
n
f
i
g
u
r
a
t
i
o
n
s
t
o
t
h
i
s a
d
a
p
t
e
r
.
E
v
e
r
y
m
od
i
f
i
ca
t
i
o
n
i
n
t
h
i
s
t
a
b
w
ill
b
e
p
e
rf
o
r
m
e
d
a
f
t
e
r
c
li
c
ki
n
g
t
h
e
A
p
ply
b
u
tt
o
n
.
T
o
r
es
t
o
r
e
t
h
e
d
e
f
a
u
l
t
se
tt
i
n
g
s
o
f
t
h
e a
d
v
a
n
ce
d
t
a
b
,
c
li
c
k
t
h
e S
e
t
d
e
f
a
u
l
t
s
b
u
tt
o
n
t
o
p
e
rf
o
r
m
r
es
t
o
r
i
n
g
.
P
o
w
e
r
S
a
v
e
N
o
n
e
D
i
sa
b
l
e
P
o
w
e
r
sa
vi
n
g
f
un
c
t
i
o
n
.
M
i
n
M
i
n
i
mum
po
w
e
r
c
o
n
s
um
p
t
i
o
n
M
a
x
M
a
xi
mum
po
w
e
r
c
o
n
s
um
p
t
i
o
n
T
u
r
bo
M
ode
O
FF D
i
sa
b
l
e
t
u
r
bo
m
od
e
O
N
E
n
a
b
l
e
t
u
r
bo
m
od
e
A
UTO
E
n
a
b
l
e
o
r
d
i
sa
b
l
e
t
u
r
bo
mode a
u
t
o
m
a
t
i
ca
lly
acc
o
r
d
i
n
g
t
o
t
h
e
d
e
t
ec
t
e
d
e
n
vi
r
o
nm
e
n
t
F
r
a
gm
e
n
t
T
h
r
es
h
o
l
d
T
h
e
m
a
xi
mum
s
i
ze
o
f
a
p
ac
k
e
t
t
h
a
t
i
s
go
i
n
g
t
o
b
e
se
g
m
e
n
t
e
d
a
n
d
t
r
a
n
s
m
i
tt
e
d
.
Se
l
ec
t
t
h
e s
i
ze
fr
o
m
256
t
o
2432
(
d
e
f
a
u
l
t
)
b
y
t
es
.
RT
S
T
h
r
es
h
o
l
d
Se
l
ec
t
t
h
e
R
T
S
T
h
r
es
h
o
l
d
f
o
r
m
0
t
o
2432
(
d
e
f
a
u
l
t
)
W
i
r
e
l
ess
M
ode
802
.
11
g/
b
C
o
nn
ec
t
t
o
a
802
.
11
b
/
g
n
e
t
w
o
r
k
(
2
.
4
G
Hz
/
54
M
bp
s
)
802
.
11b
C
o
nn
ec
t
t
o
a
802
.
11
b
n
e
t
w
o
r
k
(
2
.
4
G
Hz
/
11
M
bp
s
)
802
.
11b
P
r
ea
mb
l
e
M
ode
Se
l
ec
t
t
h
e
p
r
ea
m
b
l
e
m
od
e
t
o
b
e
l
o
n
g
,
s
h
o
r
t
o
r
a
u
t
o
d
e
t
ec
t
i
o
n
m
od
e
.
C
h
a
nn
e
l
P
l
a
n
Se
l
ec
t
y
o
u
r
r
e
g
i
o
n
fr
o
m
t
h
e
d
r
op
li
s
t
.
P
l
ease
n
o
t
e
t
h
a
t
i
t
i
s
n
ecessa
r
y
f
o
r
y
o
u
t
o
se
l
ec
t
a c
o
rr
ec
t
r
e
g
i
o
n
.
Se
l
ec
t
i
n
g
a
n
i
n
c
o
rr
ec
t
r
e
g
i
o
n
m
a
y
a
g
a
i
n
t
h
e a
pp
li
ca
b
l
e
l
a
w
.
P
S
P
XL
i
n
k
M
o
d
e
I
f
y
o
u
a
r
e
u
s
i
n
g
t
h
e
P
S
2
o
r
X
-
bo
x
f
o
r
w
i
r
e
l
ess c
o
nn
ec
t
i
o
n
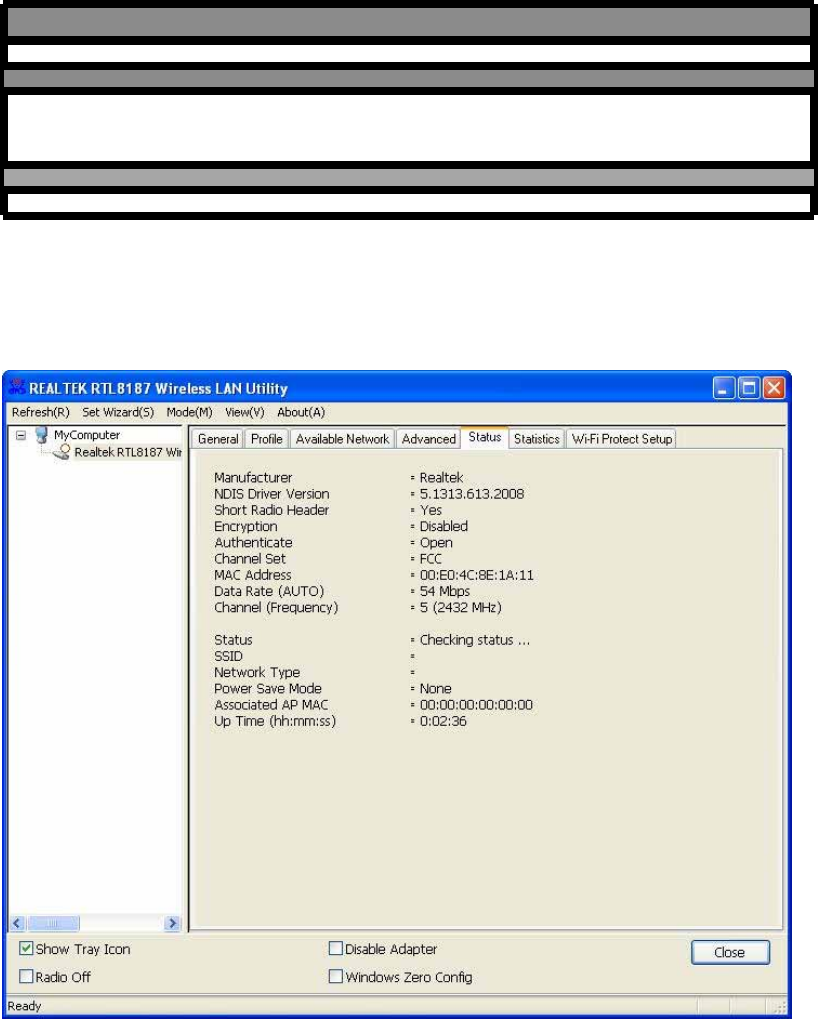
Status
T
h
i
s
t
a
b
s
h
o
w
s
t
h
e c
u
rr
e
n
t
c
o
nn
ec
t
i
o
n
s
t
a
t
u
s
o
f
t
h
i
s a
d
a
p
t
e
r
.
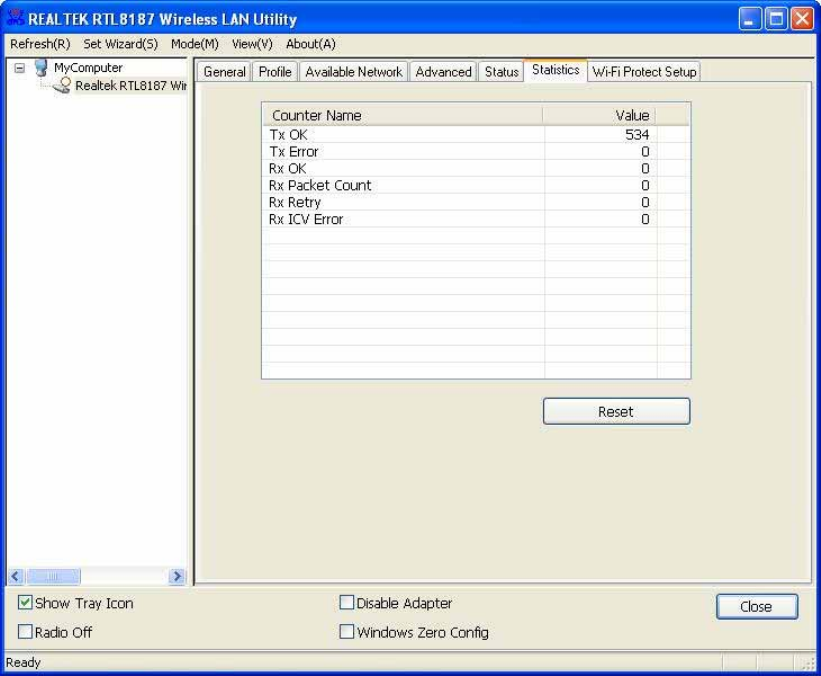
Statistics
See
t
h
i
s
t
a
b
t
o
s
h
o
w
t
h
e
t
r
a
n
s
m
i
ss
i
o
n
ac
t
ivi
t
y
r
ec
o
r
d
.
C
li
c
ki
n
g
t
h
e
“
R
ese
t
"
b
u
tt
o
n
r
ec
o
un
t
s
t
h
e
v
a
l
u
es
fr
o
m
ze
r
o
.
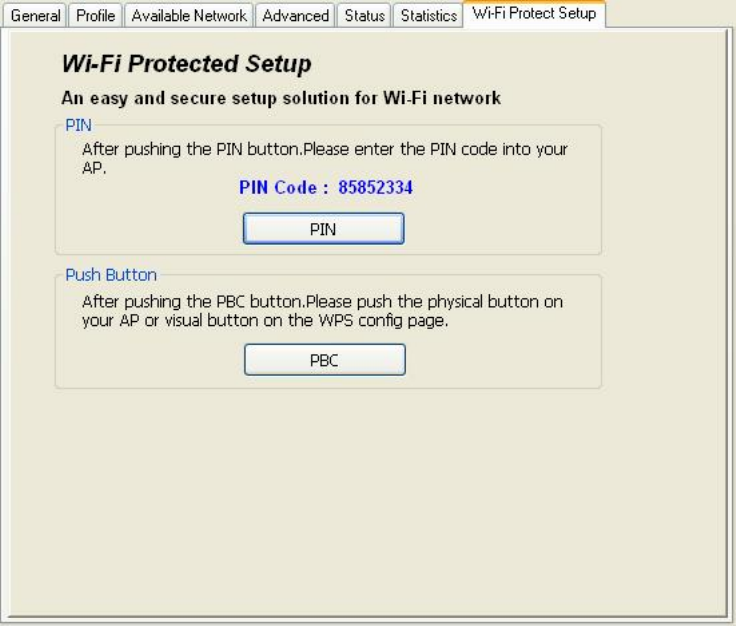
Wi-Fi Protected Setup
This device provides Wi-Fi Protected Setup, an easy and secure Wi-Fi network setup solution,
which contains two options of operation methods, each one will be functional.
PIN Method: After pushing the PIN button, please enter your PIN code into your AP.
PBC Method: After pushing the PBC button, please push the physical button on your AP or visual
button on the WPS configuration page.
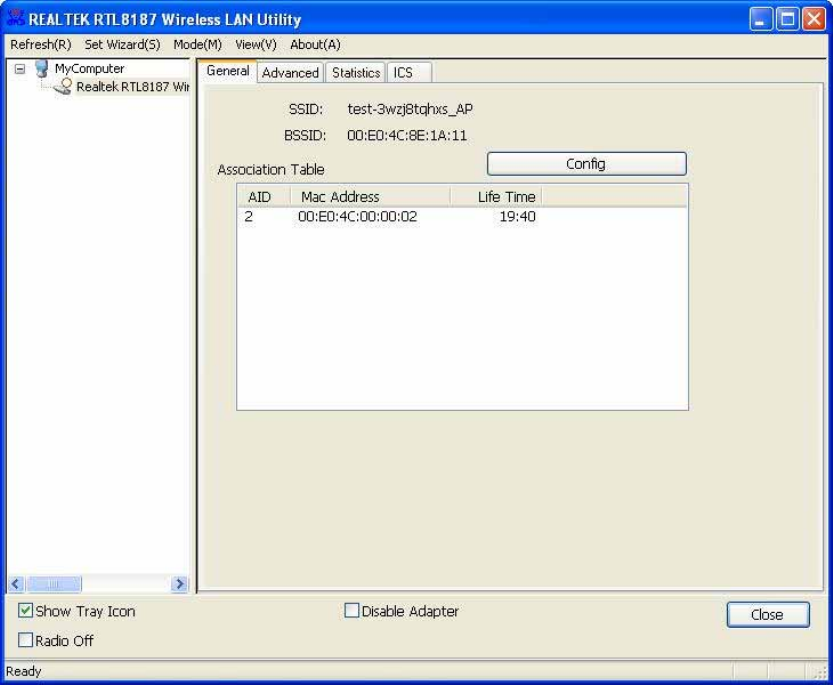
AP
mode
management
guide
General
A
f
t
e
r
c
o
n
fi
g
u
ri
n
g
t
h
e
adap
t
e
r
i
n
A
P
m
ode
,
t
h
i
s
“
G
e
n
e
r
a
l
"
page
s
h
o
w
s
u
p
,
wh
i
c
h
s
h
o
w
s
t
h
e
ge
n
e
r
a
l
i
n
f
o
r
m
a
t
i
o
n
o
f
t
h
i
s A
P
.
SS
I
D
:
T
h
e SS
I
D
(
n
e
t
w
o
r
k
n
a
m
e
)
o
f
t
h
e
w
i
r
e
l
ess
n
e
t
w
o
r
k
c
o
n
s
t
r
u
c
t
e
d
b
y
t
h
i
s A
P
.
B
SS
I
D
:
T
h
e
MA
C
add
r
e
ss
o
f
t
h
i
s A
P
C
on
fi
g
:
C
li
c
k
t
h
i
s
b
u
tt
o
n
t
o
c
h
a
n
ge
c
o
n
fi
g
u
r
a
t
i
o
n
s
t
o
t
h
i
s A
P
A
ss
o
c
i
a
t
i
on
T
a
b
l
e
:
S
h
o
w
s
t
h
e
i
n
f
o
r
m
a
t
i
o
n
o
f
t
h
o
s
e
de
v
i
c
e
s
t
h
a
t
a
ss
o
c
i
a
t
ed
w
i
t
h
t
h
i
s A
P
i
n
c
l
u
d
i
n
g
t
h
e
ir
MA
C
add
r
e
ss
e
s
a
n
d
t
h
e
t
i
m
e
t
h
a
t
t
h
e
y
c
o
nn
e
c
t
ed
w
i
t
h
t
h
i
s
de
v
i
c
e
.
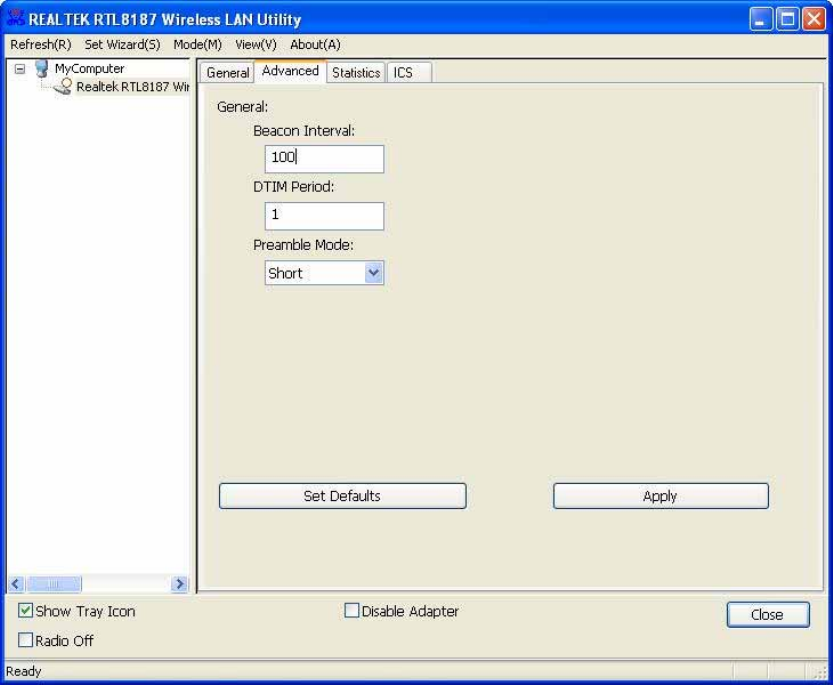
Advanced
B
eac
on
I
n
t
e
r
v
a
l
:
D
e
fi
n
e
t
h
e
i
n
t
e
r
v
a
l
be
t
w
ee
n
bea
c
o
n
s
fr
o
m
20
~
1000
D
T
I
M
P
e
r
i
od
:
S
e
t
t
h
e
D
T
I
M
pe
ri
od
be
t
w
ee
n
1
~
255
P
r
ea
mb
l
e
M
od
e
:
C
li
c
k
t
h
e
d
r
op
li
s
t
t
o
s
e
l
e
c
t
t
h
e
p
r
ea
m
b
l
e
t
o
be
l
o
n
g
,
s
h
o
r
t
o
r
a
u
t
o
S
e
t
D
e
f
a
u
l
t
s
:
C
li
c
k
t
h
i
s
b
u
tt
o
n
t
o
r
e
s
t
o
r
e
t
h
e
s
e
tt
i
n
g
s
abo
v
e
t
o
de
f
a
u
l
t
A
pp
l
y
:
C
li
c
k
t
h
i
s
b
u
tt
o
n
t
o
e
x
e
c
u
t
e
c
h
a
n
ge
s
.
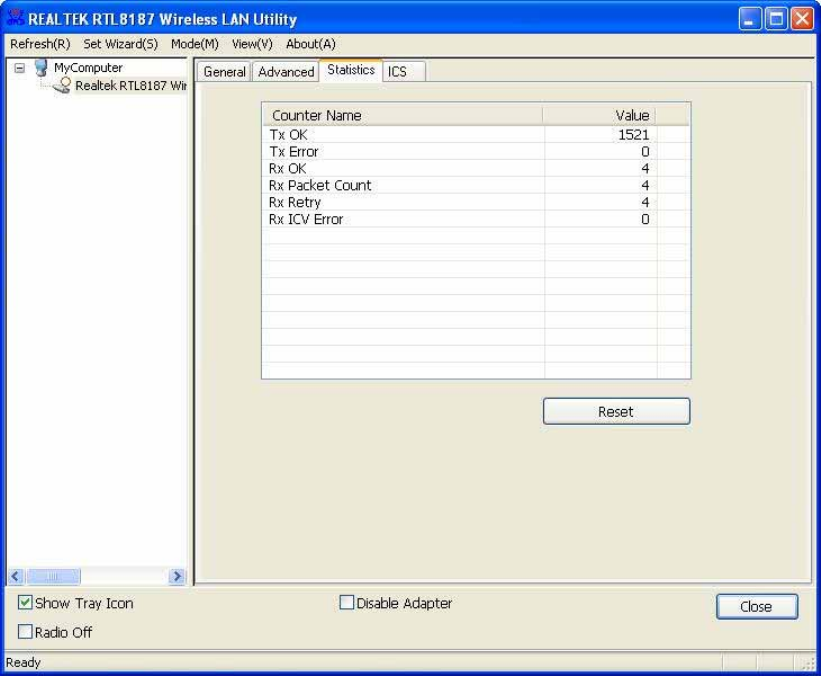
Statistics
See
t
h
i
s
t
a
b
t
o
s
h
o
w
t
h
e
t
r
a
n
s
m
i
ss
i
o
n
ac
t
ivi
t
y
r
ec
o
r
d
.
C
li
c
ki
n
g
t
h
e
“
R
ese
t
"
b
u
tt
o
n
r
ec
o
un
t
s
t
h
e
v
a
l
u
es
fr
o
m
ze
r
o
.
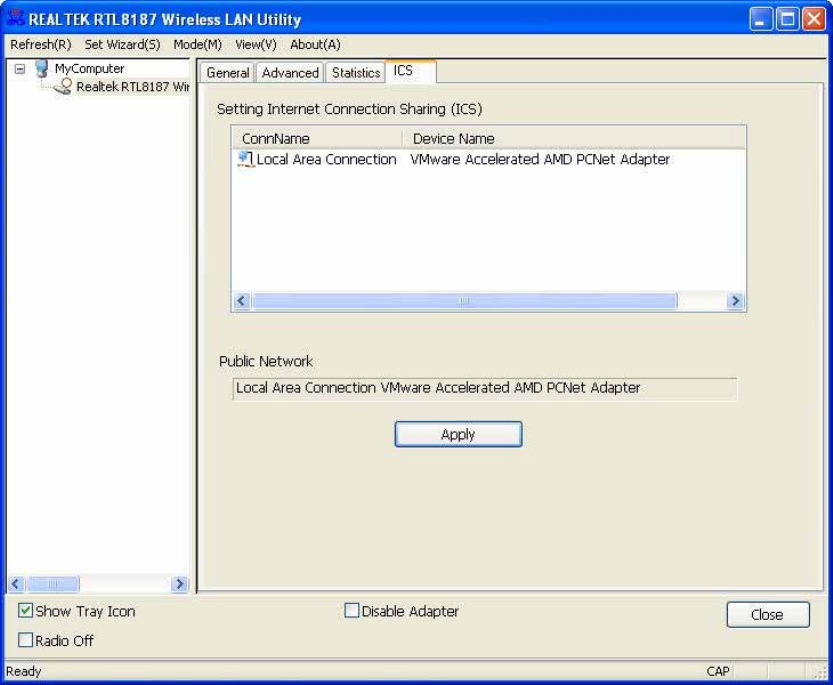
Internet
Connection
Sharing
(ICS)
T
h
i
s
p
a
g
e a
ll
o
w
s
u
se
r
s
t
o
se
l
ec
t
t
h
e a
d
a
p
t
e
r
f
o
r
c
o
nn
ec
t
t
o
p
u
b
li
c
n
e
t
w
o
r
k
.
P
l
ease c
li
c
k
o
n
t
h
e
d
e
vi
ce
t
h
a
t
a
r
e
u
se
d
f
o
r
c
o
nn
ec
t
i
n
g
t
o
p
u
b
li
c
n
e
t
w
o
r
k
a
n
d
c
li
c
k
t
h
e
“
Se
l
ec
t
"
b
u
tt
o
n
,
a
n
d
t
h
e
n
c
li
c
k
t
h
e
“
A
pp
ly
"
b
u
tt
o
n
t
o
e
x
ec
u
t
e
.
Federal Communication Commission Interference Statement
This equipment has been tested and found to comply with the limits for
a Class B digital device, pursuant to Part 15 of the FCC Rules. These
limits are designed to provide reasonable protection against harmful
interference in a residential installation. This equipment generates,
uses and can radiate radio frequency energy and, if not installed and
used in accordance with the instructions, may cause harmful
interference to radio communications. However, there is no guarantee
that interference will not occur in a particular installation. If this
equipment does cause harmful interference to radio or television
reception, which can be determined by turning the equipment off and
on, the user is encouraged to try to correct the interference by one of
the following measures:
- Reorient or relocate the receiving antenna.
- Increase the separation between the equipment and receiver.
- Connect the equipment into an outlet on a circuit different from that
to which the receiver is connected.
- Consult the dealer or an experienced radio/TV technician for help.
This device complies with Part 15 of the FCC Rules. Operation is
subject to the following two conditions: (1) This device may not cause
harmful interference, and (2) this device must accept any interference
received, including interference that may cause undesired operation.
FCC Caution: Any changes or modifications not expressly approved by
the party responsible for compliance could void the user's authority to
operate this equipment.
IMPORTANT NOTE:
FCC Radiation Exposure Statement:
This equipment complies with FCC radiation exposure limits set forth
for an uncontrolled environment.
This transmitter must not be co-located or operating in conjunction with
any other antenna or transmitter.