Advance Multimedia Internet Technology ISL500001 IIoT 4G User Manual UM IDG500 IOG500
Advance Multimedia Internet Technology Inc. IIoT 4G UM IDG500 IOG500
Contents
- 1. Users Manual-1.pdf
- 2. Users Manual-2.pdf
Users Manual-2.pdf
M2MCellularGateway
100
Chapter3ObjectDefinition
3.1Scheduling
Schedulingprovidesabilityofadding/deletingtimeschedulerules,whichcanbeappliedtootherfunctionality.
3.1.1SchedulingConfiguration
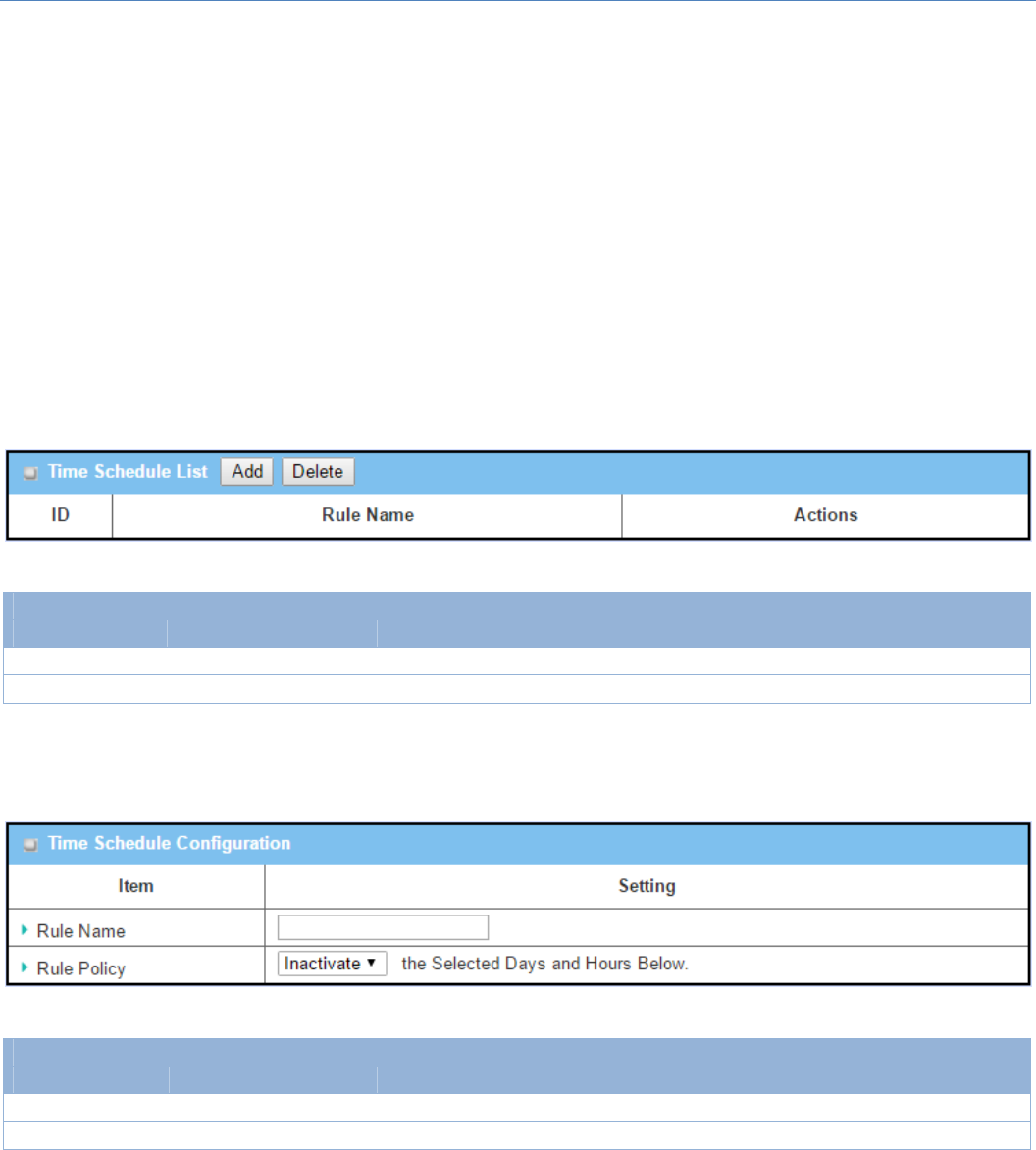
GotoObjectDefinition>Scheduling>Configurationtab.
Buttondescription
Item Valuesetting Description
Add N/A ClicktheAddbuttontoconfiguretimeschedulerule
Delete N/A ClicktheDeletebuttontodeleteselectedrule(s)
WhenAddbuttonisapplied,TimeScheduleConfigurationandTimePeriodDefinitionscreenswillappear.
TimeScheduleConfiguration
Item ValueSetting Description
RuleName String:anytext Setrulename
RulePolicy DefaultInactivate Inactivate/activatethefunctionbeenappliedtointhetimeperiodbelow
M2MCellularGateway
101
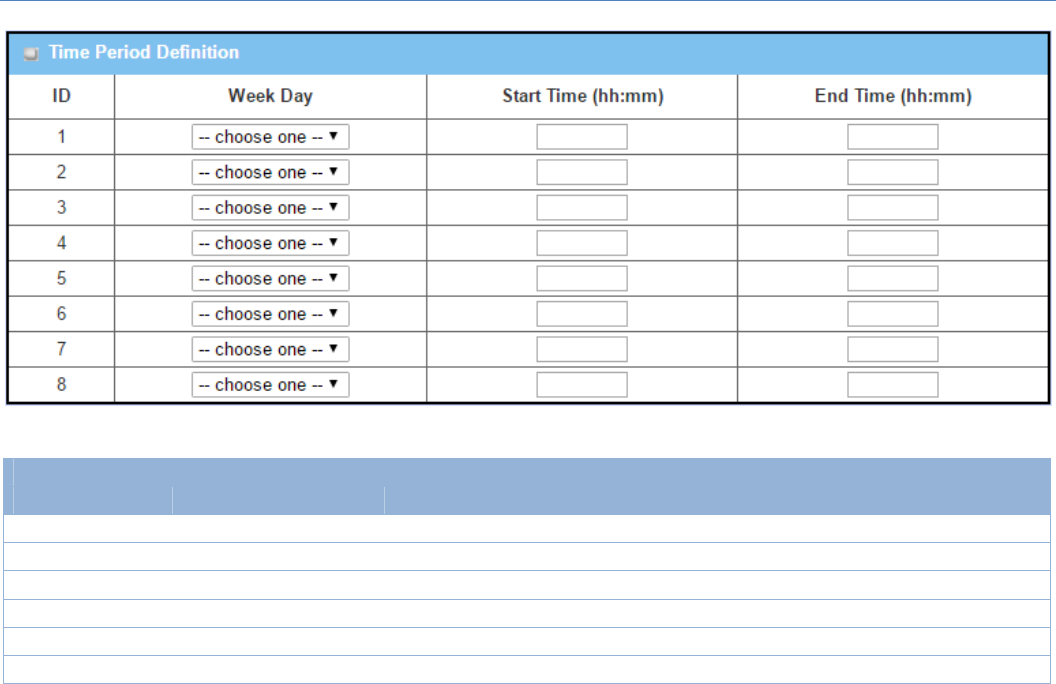
TimePeriodDefinition
Item ValueSetting Description
WeekDay Selectfrommenu Selecteverydayoroneofweekday
StartTime Timeformat(hh:mm) Starttimeinselectedweekday
EndTime Timeformat(hh:mm) Endtimeinselectedweekday
Save N/A Click Save to save the settings
Undo N/A Click Undo to cancel the settings
Refresh N/A Click the Refresh button to refresh the time schedule list.

M2MCellularGateway
102
3.2User(notsupported)
Not supported feature for the purchased product, leave it as blank.

M2MCellularGateway
103
3.3Grouping(notsupported)
Not supported feature for the purchased product, leave it as blank.
M2MCellularGateway
104
3.4ExternalServer
GotoObjectDefinition>ExternalServer>ExternalServertab.
TheExternalServersettingallowsusertoaddexternalserver.
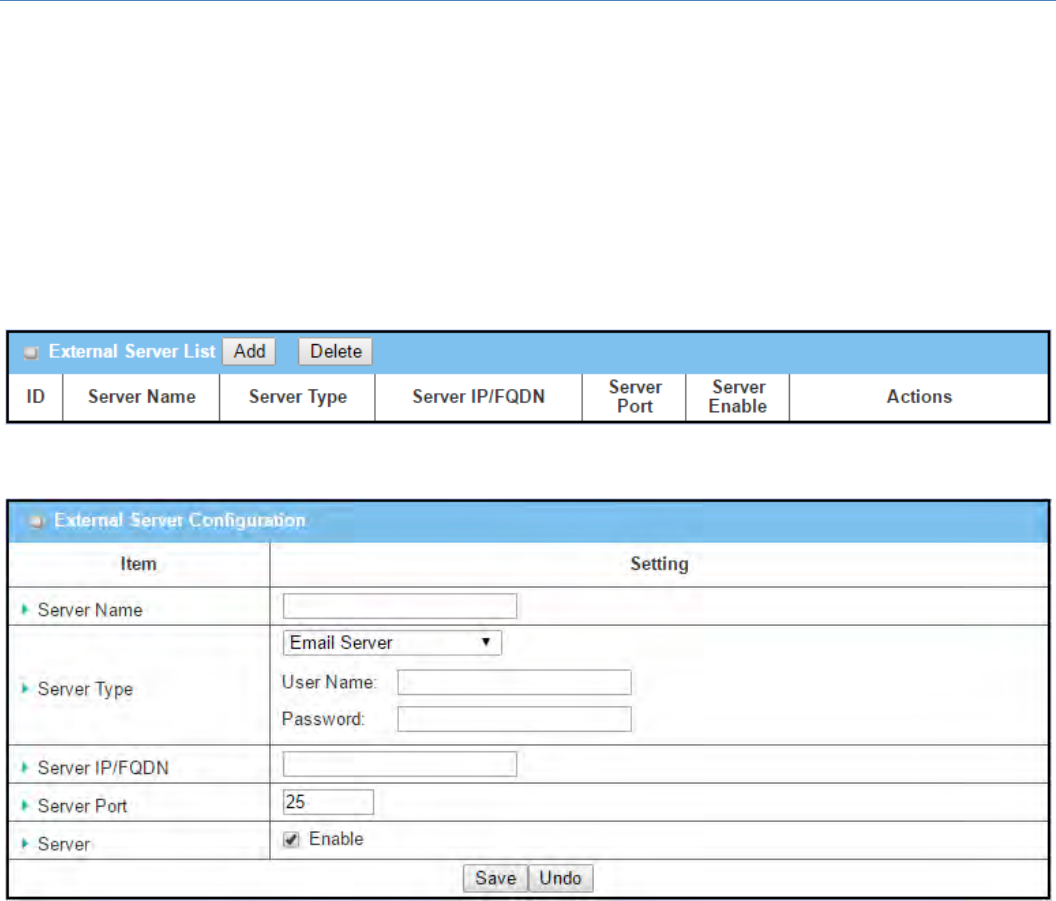
CreateExternalServer
WhenAddbuttonisapplied,ExternalServerConfigurationscreenwillappear.

M2MCellularGateway
105
ExternalServerConfiguration
Item Valuesetting Description
SeverName
1.Stringformatcanbe
anytext
2.AMustfilledsetting
Enteraservername.Enteranamethatiseasyforyoutounderstand.
ServerType AMustfilledsetting
SpecifytheServerTypeoftheexternalserver,andentertherequiredsettings
fortheaccessingtheserver.
EmailServer(AMustfilledsetting):
WhenEmailServerisselected,UserName,andPasswordarealsorequired.
UserName(Stringformat:anytext)
Password(Stringformat:anytext)
RADIUSServer(AMustfilledsetting):
WhenRADIUSServerisselected,thefollowingsettingsarealsorequired.
Primary:
SharedKey(Stringformat:anytext)
AuthenticationProtocol(BydefaultCHAPisselected)
SessionTimeout(Bydefault1)
Thevaluesmustbebetween1and60.
IdleTimeout:(Bydefault1)
Thevaluesmustbebetween1and15.
Secondary:
SharedKey(Stringformat:anytext)
AuthenticationProtocol(BydefaultCHAPisselected)
SessionTimeout(Bydefault1)
Thevaluesmustbebetween1and60.
IdleTimeout:(Bydefault1)
Thevaluesmustbebetween1and15.
FTP(SFTP)Server(AMustfilledsetting):
WhenFTP(SFTP)Serverisselected,thefollowingsettingsarealsorequired.
UserName(Stringformat:anytext)
Password(Stringformat:anytext)
Protocol(SelectFTPorSFTP)
Encryprion(SelectPlain,ExplicitFTPSorImplicitFTPS)
Transfermode(SelectPassiveorActive)
ServerIP/FQDN AMustfilledsetting SpecifytheIPaddressorFQDNusedfortheexternalserver.
ServerPort AMustfilledsetting
SpecifythePortusedfortheexternalserver.Ifyouselectedacertainserver
type,thedefaultserverportnumberwillbeset.
ForEmailServer25willbesetbydefault;
ForSyslogServer,port514willbesetbydefault;
ForRADIUSServer,port1812willbesetbydefault;
ForFTP(SFTP)Server,port21willbesetbydefault;
ValueRange:1~65535.
AccountPort 1.AMustfilledsetting
2.1813issetbydefault
SpecifytheaccountingportusedifyouselectedexternalRADIUSserver.
ValueRange:1~65535.

M2MCellularGateway
106
Server Theboxischeckedby
default ClickEnabletoactivatethisExternalServer.
Save N/A ClickSavetosavethesettings
Undo N/A ClickUndotocancelthesettings
Refresh N/A ClicktheRefreshbuttontorefreshtheexternalserverlist.

M2MCellularGateway
107
3.5 Certificate
In cryptography, a public key certificate (also known as a digital certificate or identity certificate) is an
electronicdocumentusedtoproveownershipofapublickey.Thecertificateincludesinformationaboutthe
key, information about its owner's identity, and the digital signature of an entity that has verified the
certificate'scontentsaregenuine.Ifthesignatureisvalid,andthepersonexaminingthecertificatetruststhe
signer,thentheyknowtheycanusethatkeytocommunicatewithitsowner9.
Inatypicalpublic‐keyinfrastructure(PKI)scheme,thesignerisacertificateauthority(CA),usuallyacompany
suchasVeriSignwhichchargescustomerstoissuecertificatesforthem.Inaweboftrustscheme,thesigneris
eitherthekey'sowner(aself‐signedcertificate)orotherusers("endorsements")whomthepersonexamining
thecertificatemightknowandtrust.ThedevicealsoplaysasaCArole.
CertificatesareanimportantcomponentofTransportLayerSecurity(TLS,sometimescalledbyitsoldername
SSL),wheretheypreventanattackerfromimpersonatingasecurewebsiteorotherserver.Theyarealsoused
inotherimportantapplications,suchasemailencryptionandcode signing. Here, it can be used in IPSec
tunnelingforuserauthentication.
3.5.1Configuration(notsupported)
Not supported feature for the purchased product, leave it as blank.
9 http://en.wikipedia.org/wiki/Public_key_certificate.
M2MCellularGateway
108
3.5.2MyCertificate
MyCertificateincludesaLocalCertificateList.LocalCertificateListshowsallgeneratedcertificatesbytheroot
CAforthegateway.AnditalsostoresthegeneratedCertificateSigningRequests(CSR)whichwillbesignedby
otherexternalCAs.Thesignedcertificatescanbeimportedasthelocalonesofthegateway.
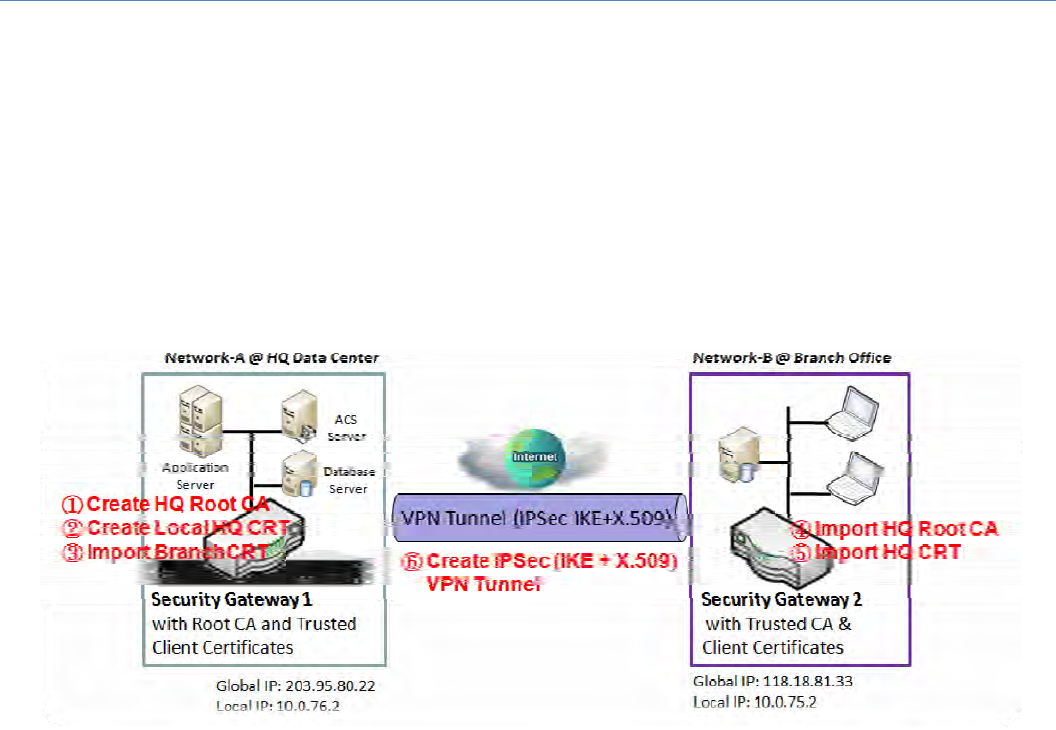
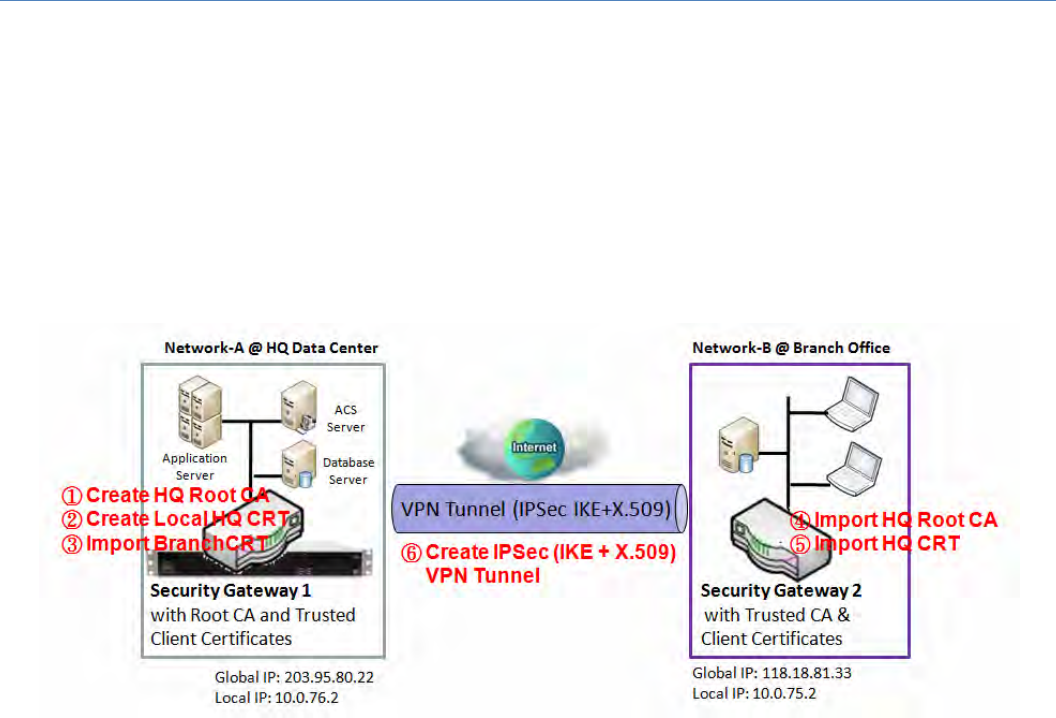
Self‐signedCertificateUsageScenario
ScenarioApplicationTiming
WhentheenterprisegatewayownstherootCAandVPNtunnelingfunction,itcangenerateitsown
localcertificatesbybeingsignedbyitselforimportanylocal certificates that are signed by other
externalCAs.AlsoimportthetrustedcertificatesforotherCAsandClients.Inaddition,sinceithasthe
rootCA,italsocansignCertificateSigningRequests(CSR)toformcorrespondingcertificatesforothers.
Thesecertificatescanbeusedfortworemotepeerstomakesuretheiridentityduringestablishinga
VPNtunnel.
ScenarioDescription
Gateway 1 generates the root CA and a local certificate (HQCRT) signed by itself. Import a trusted
certificate(BranchCRT)–aBranchCSRcertificateofGateway2signedbyrootCAofGateway1.
Gateway2createsaCSR(BranchCSR)tolettherootCAoftheGateway1signittobetheBranchCRT
certificate.ImportthecertificateintotheGateway2asalocalcertificate.Inaddition,alsoimportthe
certificatesoftherootCAoftheGateway1intotheGateway2asthetrustedones.(Pleasealsorefer
tofollowingtwosub‐sections)
Establish an IPSec VPN tunnel with IKE and X.509 protocols by starting from either peer, so that all

M2MCellularGateway
109
clienthostsinthesebothsubnetscancommunicatewitheachother.
ParameterSetupExample
ForNetwork‐AatHQ
Followingtableslisttheparameterconfigurationasanexampleforthe"MyCertificate"functionused
in the user authentication of IPSec VPN tunnel establishing, asshowninabovediagram.The
configuration example must be combined with the ones in followingtwosectionstocompletethe
wholeuserscenario.
Usedefaultvalueforthoseparametersthatarenotmentionedinthetables.
ConfigurationPath [MyCertificate]‐[RootCACertificateConfiguration]
Name HQRootCA
Key KeyType:RSAKeyLength:1024‐bits
SubjectName Country(C):T
W
State(ST):Taiwan Location(L):Tainan
Organization(O):AMITHQOrganizationUnit(OU):HQRD
CommonName(CN):HQRootCAE‐mail:hqrootca@amit.com.tw
ConfigurationPath [MyCertificate]‐[LocalCertificateConfiguration]
Name HQCRTSel
f
‐signed: ■
Key KeyType:RSAKeyLength:1024‐bits
SubjectName Country(C):T
W
State(ST):Taiwan Location(L):Tainan
Organization(O):AMITHQOrganizationUnit(OU):HQRD
CommonName(CN):HQCRTE‐mail:hqcrt@amit.com.tw
ConfigurationPath [IPSec]‐[Configuration]
IPSec ■Enable
ConfigurationPath [IPSec]‐[TunnelConfiguration]
Tunnel ■Enable
TunnelName s2s‐101
Interface WAN1
TunnelScenario
S
itetoSite
OperationMode
A
lwayson
ConfigurationPath [IPSec]‐[Local&RemoteConfiguration]
LocalSubnet 10.0.76.
0
LocalNetmask 255.255.255.
0
FullTunnel Disable
RemoteSubnet 10.0.75.
0
RemoteNetmask 255.255.255.
0
RemoteGateway 118.18.81.33
M2MCellularGateway
110
ConfigurationPath [IPSec]‐[Authentication]
KeyManagement IKE+X.509LocalCertificate:HQCRTRemoteCertificate:BranchCRT
LocalID UserNameNetwor
k
‐
A
RemoteID UserNameNetwor
k
‐B
ConfigurationPath [IPSec]‐[IKEPhase]
NegotiationMode MainMode
X‐Auth None
ForNetwork‐BatBranchOffice
Followingtableslisttheparameterconfigurationasanexampleforthe"MyCertificate"functionused
in the user authentication of IPSec VPN tunnel establishing, asshowninabovediagram.The
configuration example must be combined with the ones in followingtwosectionstocompletethe
wholeuserscenario.
Usedefaultvalueforthoseparametersthatarenotmentionedinthetables.
ConfigurationPath [MyCertificate]‐[LocalCertificateConfiguration]
Name BranchCRTSelf‐signed: □
Key KeyType:RSAKeyLength:1024‐bits
SubjectName Country(C):T
W
State(ST):Taiwan Location(L):Tainan
Organization(O):AMITBranchOrganizationUnit(OU):BranchRD
CommonName(CN):BranchCRTE‐mail:branchcrt@amit.com.tw
ConfigurationPath [IPSec]‐[Configuration]
IPSec ■Enable
ConfigurationPath [IPSec]‐[TunnelConfiguration]
Tunnel ■Enable
TunnelName s2s‐102
Interface WAN1
TunnelScenario
S
itetoSite
OperationMode
A
lwayson
ConfigurationPath [IPSec]‐[Local&RemoteConfiguration]
LocalSubnet 10.0.75.
0
LocalNetmask 255.255.255.
0
FullTunnel Disable
RemoteSubnet 10.0.76.
0

M2MCellularGateway
111
RemoteNetmask 255.255.255.
0
RemoteGateway 203.95.80.22
ConfigurationPath [IPSec]‐[Authentication]
KeyManagement IKE+X.509LocalCertificate:BranchCRTRemoteCertificate:HQCRT
LocalID UserNameNetwor
k
‐B
RemoteID UserNameNetwor
k
‐
A
ConfigurationPath [IPSec]‐[IKEPhase]
NegotiationMode MainMode
X‐Auth None
ScenarioOperationProcedure
Inabovediagram,"Gateway1"isthegatewayofNetwork‐Ainheadquarters and the subnet of its
Intranetis10.0.76.0/24.IthastheIPaddressof10.0.76.2forLANinterfaceand203.95.80.22forWAN‐
1interface."Gateway2"isthegatewayofNetwork‐BinbranchofficeandthesubnetofitsIntranetis
10.0.75.0/24.IthastheIPaddressof10.0.75.2forLANinterfaceand118.18.81.33forWAN‐1interface.
TheybothserveastheNATsecuritygateways.
Gateway 1 generates the root CA and a local certificate (HQCRT) that is signed by itself. Import the
certificates of the root CA and HQCRT into the "Trusted CA Certificate List" and "Trusted Client
CertificateList"ofGateway2.
Gateway 2 generates a Certificate Signing Request (BranchCSR) foritsowncertificate(BranchCRT)
(Pleasegenerateonenotself‐signedcertificateintheGateway2,andclickonthe"View"buttonfor
thatCSR.Justdownloadsit).TaketheCSRtobesignedbytherootCAofGateway1andobtainthe
BranchCRTcertificate(youneedrenameit).Importthecertificateintothe"TrustedClientCertificate
List"oftheGateway1andthe"LocalCertificateList"ofGateway2.
Gateway2canestablishanIPSecVPNtunnelwith"SitetoSite"scenarioandIKEandX.509protocolsto
Gateway1.
Finally,theclienthostsintwosubnetsof10.0.75.0/24and10.0.76.0/24cancommunicatewitheach
other.
M2MCellularGateway
112
MyCertificateSetting
GotoObjectDefinition>Certificate>MyCertificatetab.
The My Certificate setting allows user to create local certificates. In "My Certificate" page, there are two
configurationwindowsforthe"MyCertificate"function.The"LocalCertificateList"windowshowsthestored
certificatesorCSRsforrepresentingthegateway.The"LocalCertificateConfiguration"windowcanletyoufill
requiredinformationnecessaryforcorrespondingcertificatetobegeneratedbyitself,orcorrespondingCSR
tobesignedbyotherCAs.
CreateLocalCertificate
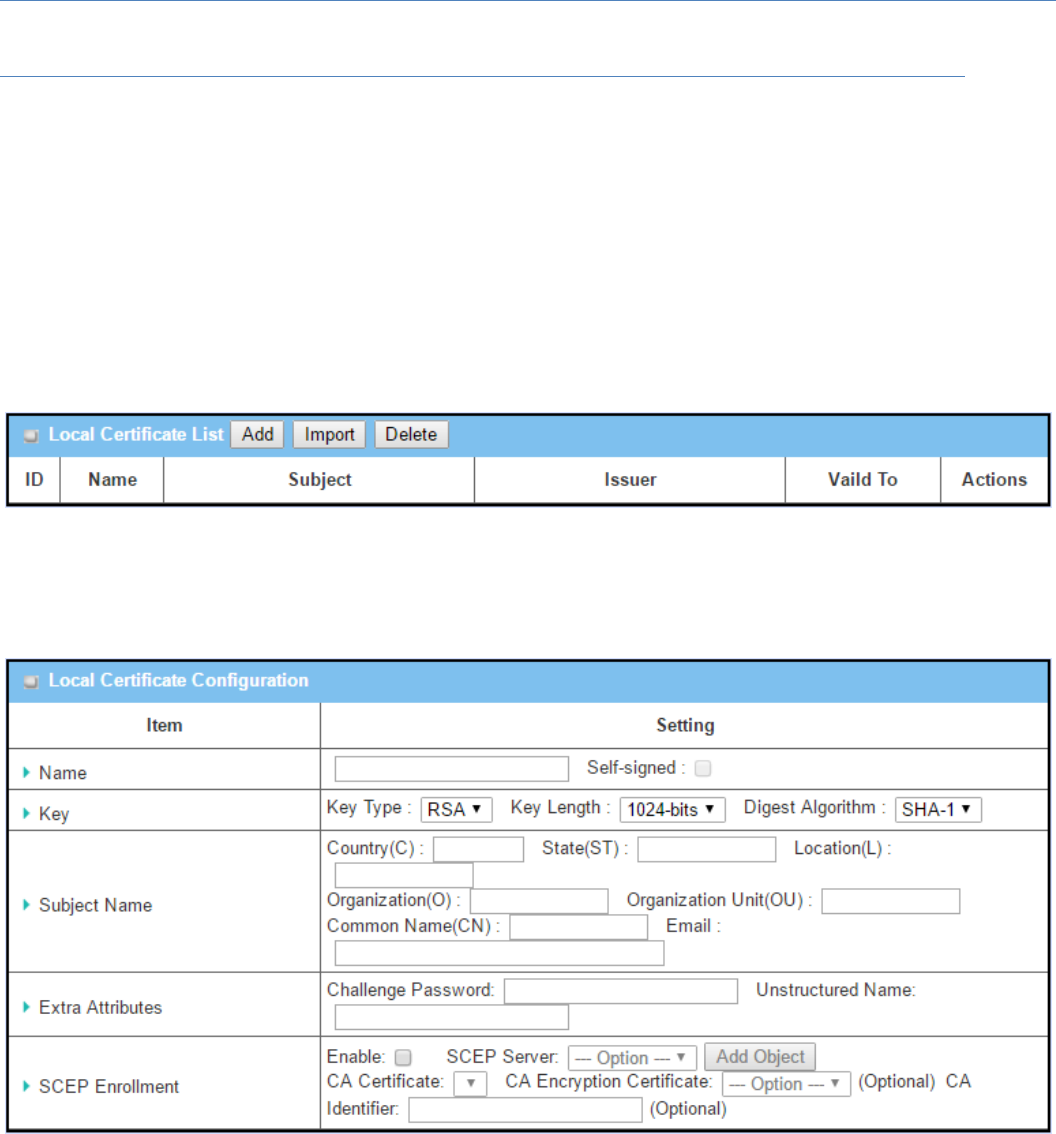
WhenAddbuttonisapplied,LocalCertificateConfigurationscreenwillappear.The required information to be
filled for the certificate or CSR includes the name, key and subject name. It is a certificate if the "Self-signed"
box is checked; otherwise, it is a CSR.

M2MCellularGateway
113
LocalCertificateConfiguration
Item Valuesetting Description
Name 1.Stringformatcanbeany
text
2.AMustfilledsetting
Enteracertificatename.Itwillbeacertificatefilename
IfSelf‐signedischecked,itwillbesignedbyrootCA.IfSelf‐signedisnot
checked,itwillgenerateacertificatesigningrequest(CSR).
Key AMustfilledsetting Thisfieldistospecifythekeyattributesofcertificate.
KeyTypetosetpublic‐keycryptosystems.Currently,onlyRSAissupported.
KeyLengthtosetthelengthinbitsofthekeyusedinacryptographicalgorithm.
Itcanbe512/768/1024/1536/2048.
DigestAlgorithmtosetidentifierinthesignaturealgorithmidentifierof
certificates.ItcanbeMD5/SHA‐1.
SubjectName AMustfilledsetting Thisfieldistospecify theinformationofcertificate.
Country(C)isthetwo‐letterISOcodeforthecountrywhereyourorganizationis
located.
State(ST)isthestatewhereyourorganizationislocated.
Location(L)isthelocationwhereyourorganizationislocated.
Organization(O)isthenameofyourorganization.
OrganizationUnit(OU)isthenameofyourorganizationunit.
CommonName(CN)isthenameofyourorganization.
Emailistheemailofyourorganization.Ithastobeemailaddresssettingonly.
ExtraAttributes AMustfilledsetting Thisfieldistospecify theextrainformationforgeneratingacertificate.
Challenge Password for the password you can use to request certificate
revocationinthefuture.
UnstructuredNameforadditionalinformation.
SCEPEnrollment AMustfilledsetting Thisfieldistospecify theinformationofSCEP.
Ifuserwantstogenerateacertificatesigningrequest(CSR)andthensignedby
SCEPserveronline,usercanchecktheEnablebox.
SelectaSCEPServertoidentifytheSCEPserverforuse.Theserverdetailed
informationcouldbespecifiedinExternalServers.RefertoObjectDefinition>
ExternalServer>ExternalServer.YoumayclickAddObjectbuttonto
generate.
SelectaCACertificatetoidentifywhichcertificatecouldbeacceptedbySCEP
serverforauthentication.ItcouldbegeneratedinTrustedCertificates.
SelectanoptionalCAEncryptionCertificate,ifitisrequired,toidentifywhich
certificatecouldbeacceptedbySCEPserverforencryptiondatainformation.It
couldbegeneratedinTrustedCertificates.
FillinoptionalCAIdentifiertoidentifywhichCAcouldbeusedforsigning
certificates.
Save N/A ClicktheSavebuttontosavetheconfiguration.
Back N/A WhentheBackbuttonisclicked,thescreenwillreturntopreviouspage.
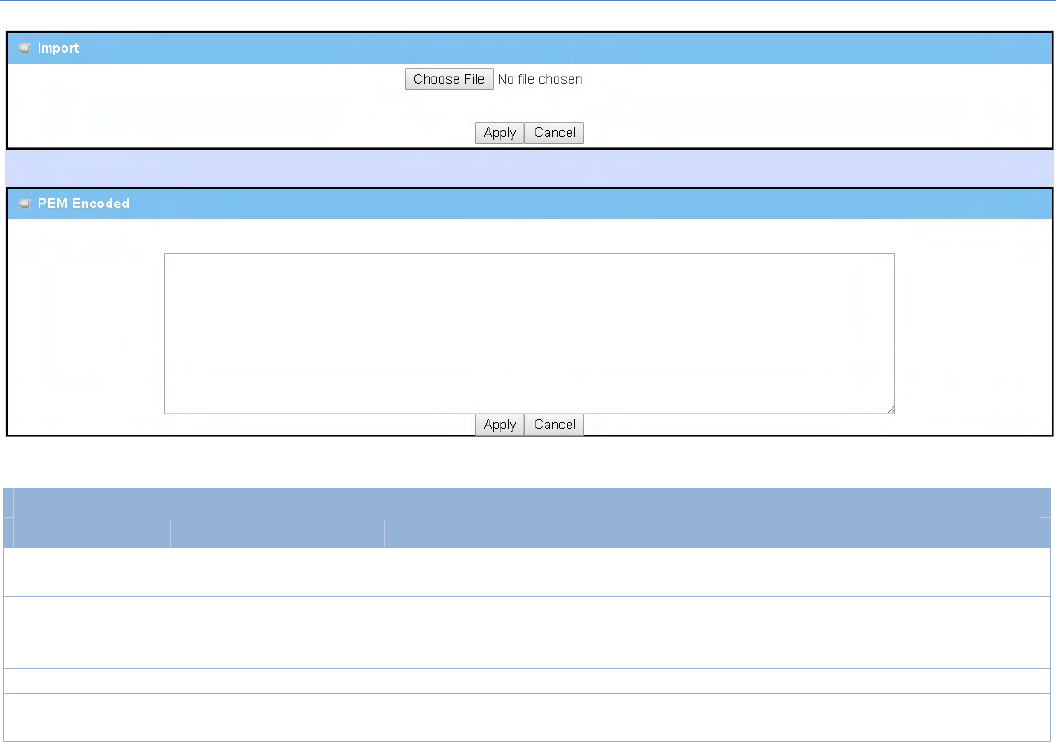
When Import button is applied, an Import screen will appear. You can import a certificate from an existed
certificatefile,ordirectlypasteaPEMencodedstringasthecertificate.
M2MCellularGateway
114
Import
Item Valuesetting Description
Import AMustfilledsetting Selectacertificatefilefromuser’scomputer,andclicktheApplybuttonto
importthespecifiedcertificatefiletothegateway.
PEMEncoded 1.Stringformatcanbeany
text
2.AMustfilledsetting
Thisisanalternativeapproachtoimportacertificate.
Youcandirectlyfillin(CopyandPaste)thePEMencodedcertificatestring,and
clicktheApplybuttontoimportthespecifiedcertificatetothegateway.
Apply N/A ClicktheApplybuttontoimportthecertificate.
Cancel N/A ClicktheCancelbuttontodiscardtheimportoperationandthescreenwill
returntotheMyCertificatespage.
M2MCellularGateway
115
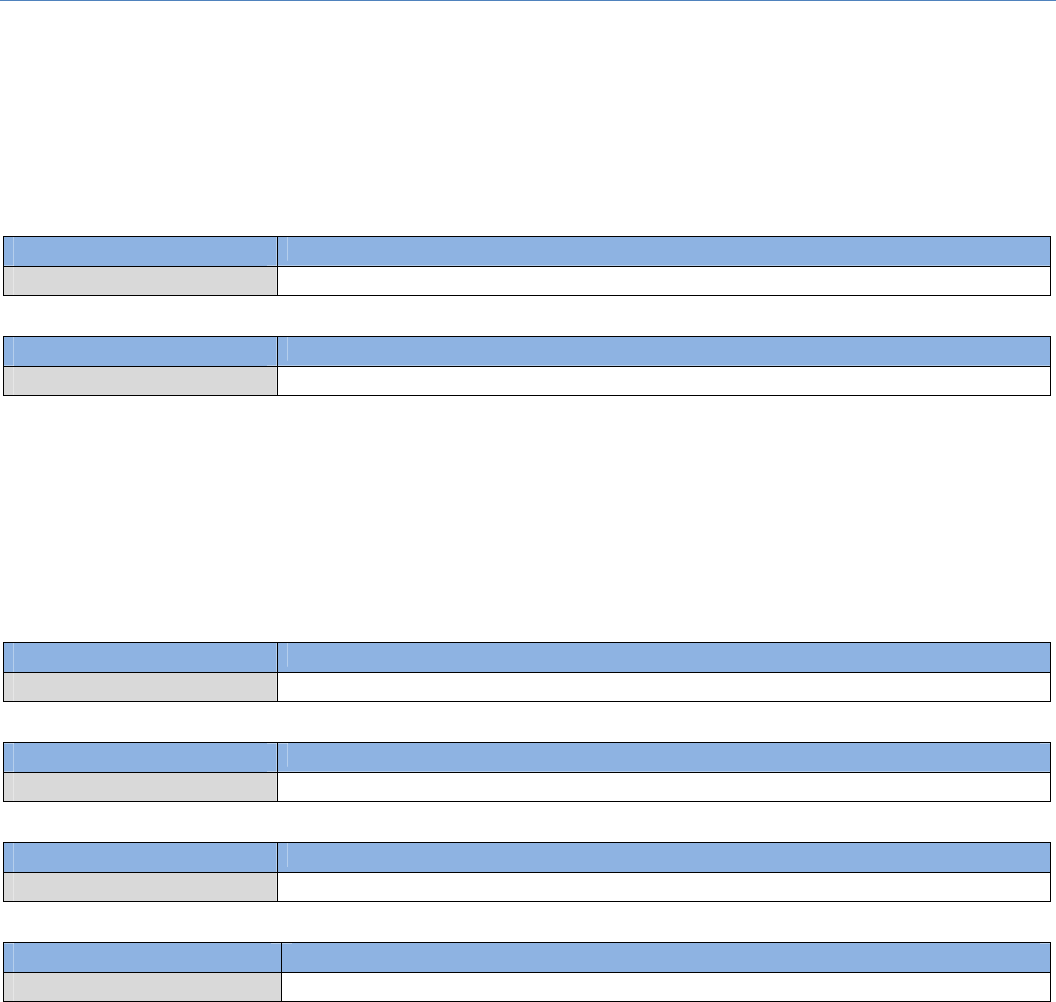
3.5.3TrustedCertificate
TrustedCertificateincludesTrustedCACertificateList,TrustedClientCertificateList,andTrustedClientKey
List. The Trusted CA Certificate List places the certificates of external trusted CAs. The Trusted Client
CertificateListplacestheothers'certificateswhatyoutrust.AndtheTrustedClientKeyListplacestheothers’
keyswhatyoutrusted.
Self‐signedCertificateUsageScenario
ScenarioApplicationTiming(sameastheonedescribedin"MyCertificate"section)
WhentheenterprisegatewayownstherootCAandVPNtunnelingfunction,itcangenerateitsown
localcertificatesbybeingsignedbyitself.AlsoimportsthetrustedcertificatesforotherCAsandClients.
Thesecertificatescanbeusedfortworemotepeerstomakesuretheiridentityduringestablishinga
VPNtunnel.
ScenarioDescription(sameastheonedescribedin"MyCertificate"section)
Gateway 1 generates the root CA and a local certificate (HQCRT) signed by itself. Import a trusted
certificate(BranchCRT)–aBranchCSRcertificateofGateway2signedbyrootCAofGateway1.
Gateway2createsaCSR(BranchCSR)tolettherootCAoftheGateway1signittobetheBranchCRT
certificate.ImportthecertificateintotheGateway2asalocalcertificate.Inaddition,alsoimportsthe
certificatesoftherootCAofGateway1intotheGateway2asthetrustedones.(Pleasealsoreferto
"MyCertificate"and"IssueCertificate"sections).
Establish an IPSec VPN tunnel with IKE and X.509 protocols by starting from either peer, so that all
clienthostsinthesebothsubnetscancommunicatewitheachother.
ParameterSetupExample(sameastheonedescribedin"MyCertificate"section)
M2MCellularGateway
116
ForNetwork‐AatHQ
Followingtableslisttheparameterconfigurationasanexampleforthe"TrustedCertificate"function
used in the user authentication of IPSec VPN tunnel establishing, as shown in above diagram. The
configuration example must be combined with the ones in "My Certificate" and "Issue Certificate"
sectionstocompletethesetupforthewholeuserscenario.
ConfigurationPath [TrustedCertificate]‐[TrustedClientCertificateList]
CommandButton Impor
t
ConfigurationPath [TrustedCertificate]‐[TrustedClientCertificateImportfromaFile]
File BranchCRT.cr
t
ForNetwork‐BatBranchOffice
Followingtableslisttheparameterconfigurationasanexampleforthe"TrustedCertificate"function
used in the user authentication of IPSec VPN tunnel establishing, as shown in above diagram. The
configuration example must be combined with the ones in "My Certificate" and "Issued Certificate"
sectionstocompletethesetupforthewholeuserscenario.
ConfigurationPath [TrustedCertificate]‐[TrustedCACertificateList]
CommandButton Impor
t
ConfigurationPath [TrustedCertificate]‐[TrustedCACertificateImportfromaFile]
File HQRootCA.cr
t
ConfigurationPath [TrustedCertificate]‐[TrustedClientCertificateList]
CommandButton Impor
t
ConfigurationPath [TrustedCertificate]‐[TrustedClientCertificateImportfromaFile]
File HQCRT.cr
t
ScenarioOperationProcedure(sameastheonedescribedin"MyCertificate"section)
Inabovediagram,the"Gateway1"isthegatewayofNetwork‐Ainheadquartersandthesubnetofits
Intranetis10.0.76.0/24.IthastheIPaddressof10.0.76.2forLANinterfaceand203.95.80.22forWAN‐
1interface.The"Gateway2"isthegatewayofNetwork‐Binbranch office and the subnet of its
Intranetis10.0.75.0/24.IthastheIPaddressof10.0.75.2forLANinterfaceand118.18.81.33forWAN‐
1interface.TheybothserveastheNATsecuritygateways.
InGateway2importthecertificatesoftherootCAandHQCRTthat were generated and signed by
Gateway1intothe"TrustedCACertificateList"and"TrustedClientCertificateList"ofGateway2.

M2MCellularGateway
117
Importthe obtainedBranchCRTcertificate(thederived BranchCSRcertificateafterGateway1’s root
CAsignature)intothe"TrustedClientCertificateList"oftheGateway1andthe"LocalCertificateList"
oftheGateway2.Formoredetails,refertotheNetwork‐Boperation procedure in "My Certificate"
sectionofthismanual.
Gateway2canestablishanIPSecVPNtunnelwith"SitetoSite"scenarioandIKEandX.509protocolsto
Gateway1.
Finally,theclienthostsintwosubnetsof10.0.75.0/24and10.0.76.0/24cancommunicatewitheach
other.
M2MCellularGateway
118
TrustedCertificateSetting
GotoObjectDefinition>Certificate>TrustedCertificatetab.
TheTrustedCertificatesettingallowsusertoimporttrustedcertificatesandkeys.
ImportTrustedCACertificate
When Import button is applied, a Trusted CA importscreenwillappear.YoucanimportaTrustedCA
certificatefromanexistedcertificatefile,ordirectlypasteaPEMencodedstringasthecertificate.
TrustedCACertificateList
Item Valuesetting Description
Importfroma
File
AMustfilledsetting SelectaCAcertificatefilefromuser’scomputer,andclicktheApply buttonto
importthespecifiedCAcertificatefiletothegateway.
Importfroma
PEM
1.Stringformatcanbeany
text
2.AMustfilledsetting
ThisisanalternativeapproachtoimportaCAcertificate.
Youcandirectlyfillin(CopyandPaste)thePEMencodedCAcertificatestring,
andclicktheApplybuttontoimportthespecifiedCAcertificatetothegateway.
Apply N/A ClicktheApplybuttontoimportthecertificate.
Cancel N/A ClicktheCancelbuttontodiscardtheimportoperationandthescreenwill
returntotheTrustedCertificatespage.
InsteadofimportingaTrustedCAcertificatewithmentionedapproaches,youcanalsogettheCAcertificate
fromtheSECPserver.
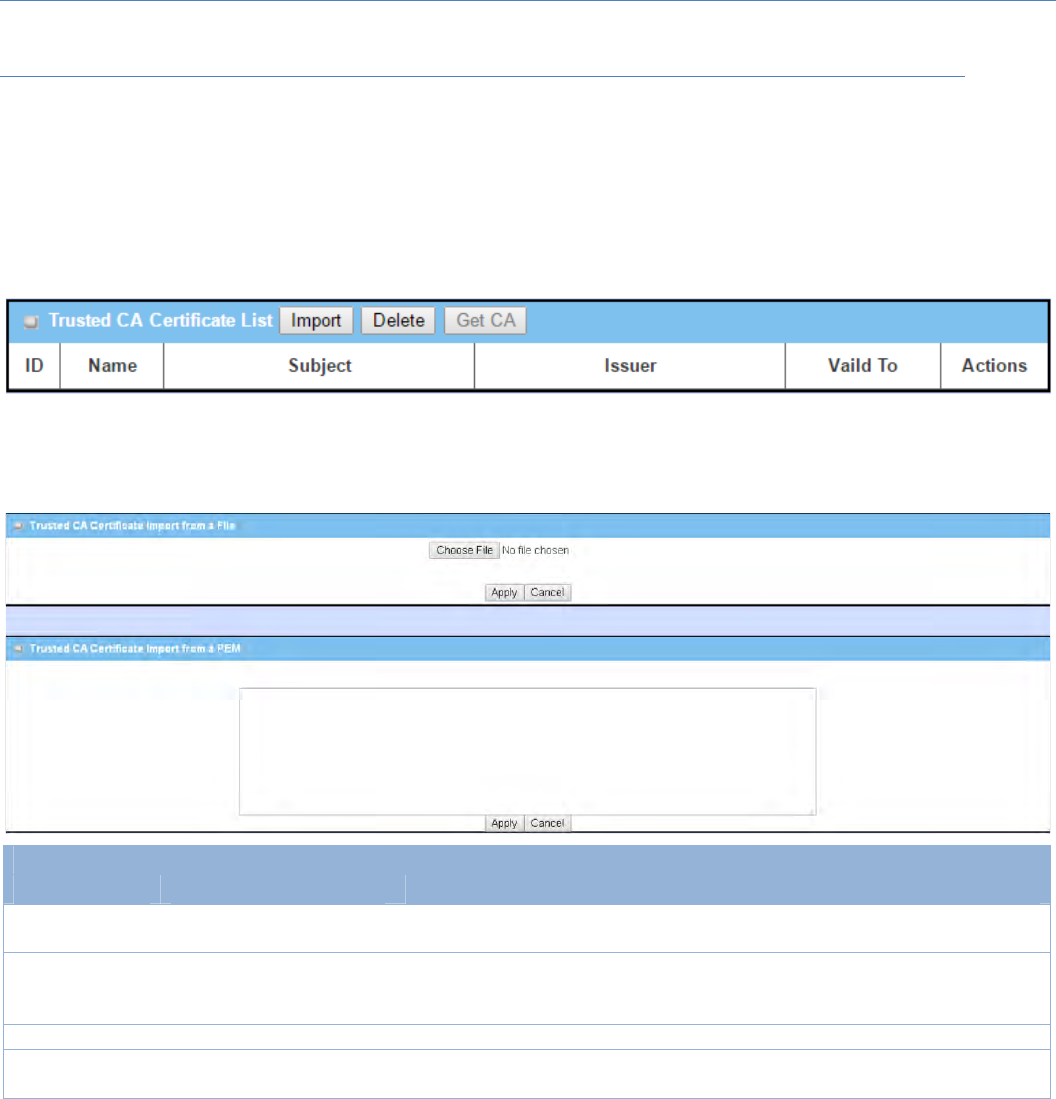
IfSCEPisenabled(RefertoObjectDefinition>Certificate>Configuration),youcanclickGetCAbutton,aGet
CAConfigurationscreenwillappear.
M2MCellularGateway
119
GetCAConfiguration
Item Valuesetting Description
SCEPServer AMustfilledsetting SelectaSCEPServer toidentifytheSCEPserverforuse.Theserverdetailed
informationcouldbespecifiedinExternalServers.RefertoObjectDefinition>
ExternalServer>ExternalServer.YoumayclickAddObjectbuttonto
generate.
CAIdentifier 1.Stringformatcanbeany
text
FillinoptionalCAIdentifier toidentifywhichCAcouldbeusedforsigning
certificates.
Save N/A ClickSave tosavethesettings.
Close N/A ClicktheClosebuttontoreturntotheTrustedCertificatespage.
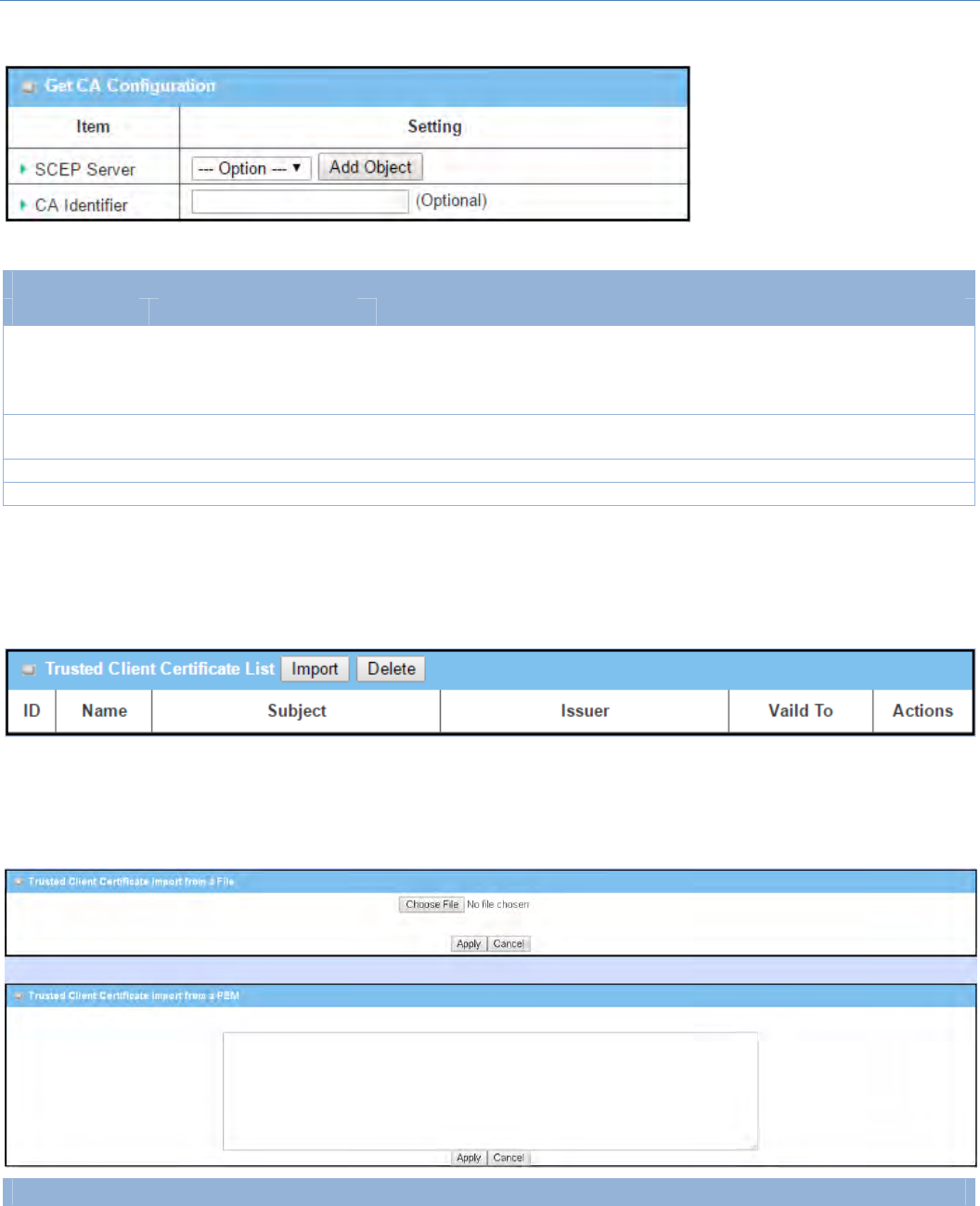
ImportTrustedClientCertificate
When Import button is applied, a Trusted Client Certificate Import screen will appear. You can import a
Trusted Client Certificate from an existed certificate file, or directly paste a PEM encoded string as the
certificate.
TrustedClientCertificateList
M2MCellularGateway
120
Item Valuesetting Description
Importfroma
File
AMustfilledsetting Selectacertificatefilefromuser’scomputer,andclicktheApplybuttontoimportthe
specifiedcertificatefiletothegateway.
Importfroma
PEM
1.Stringformatcanbeany
text
2.AMustfilledsetting
Thisisanalternativeapproachtoimportacertificate.
Youcandirectlyfillin(CopyandPaste)thePEMencodedcertificatestring,andclickthe
Applybuttontoimportthespecifiedcertificatetothegateway.
Apply N/A ClicktheApplybuttontoimportcertificate.
Cancel N/A ClicktheCancelbuttontodiscardtheimportoperationandthescreenwillreturntothe
TrustedCertificatespage.
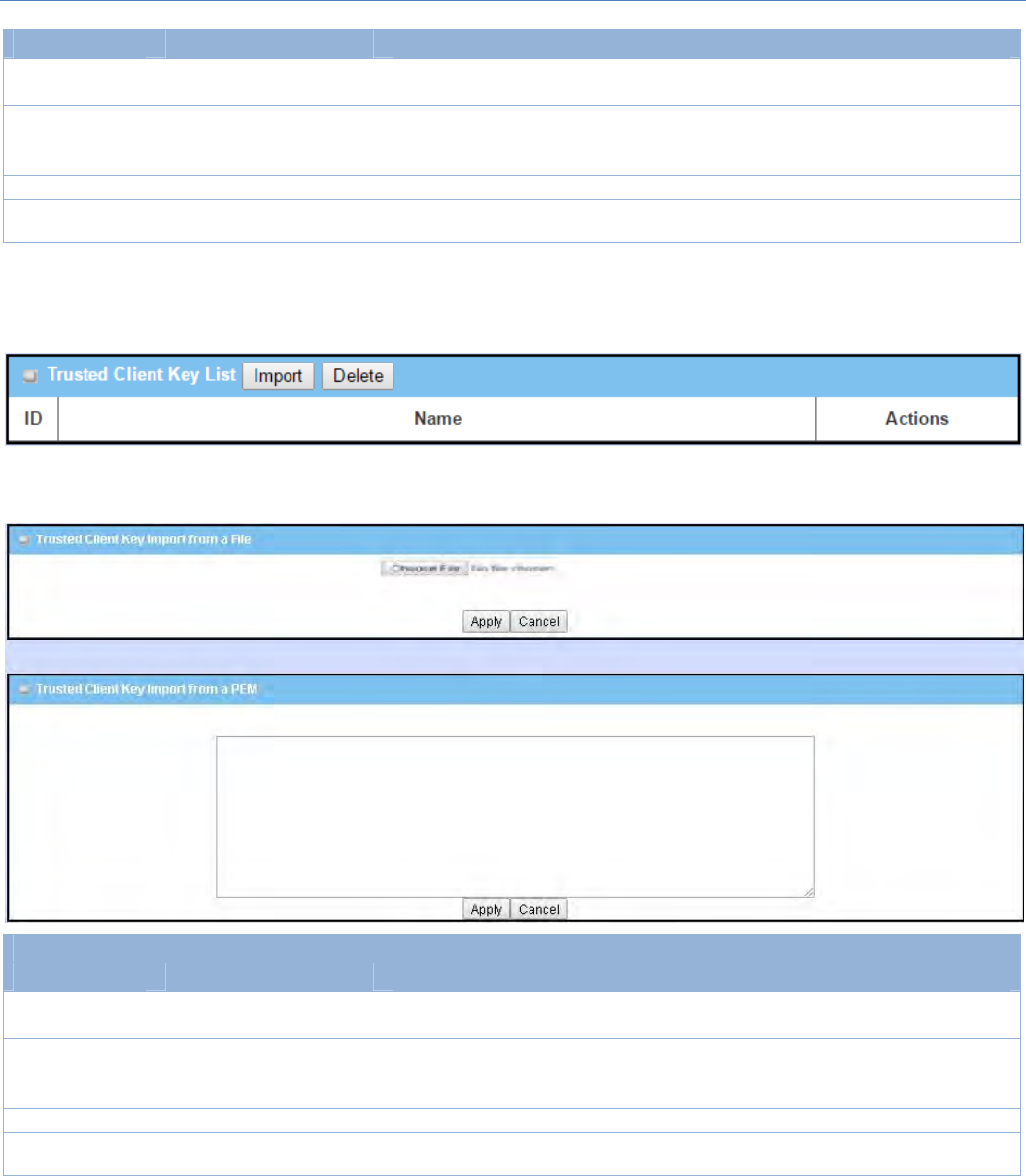
ImportTrustedClientKey
When Import button is applied, a Trusted Client Key Import screen will appear. You can import a Trusted
ClientKeyfromanexistedfile,ordirectlypasteaPEMencodedstringasthekey.
TrustedClientKeyList
Item Valuesetting Description
Importfroma
File
AMustfilledsetting Selectacertificatekeyfilefromuser’scomputer,andclicktheApplybuttontoimport
thespecifiedkeyfiletothegateway.
Importfroma
PEM
1.Stringformatcanbeany
text
2.AMustfilledsetting
Thisisanalternativeapproachtoimportacertificatekey.
Youcandirectlyfillin(CopyandPaste)thePEMencodedcertificatekeystring,andclick
theApplybuttontoimportthespecifiedcertificatekeytothegateway.
Apply N/A ClicktheApplybuttontoimportthecertificatekey.
Cancel N/A ClicktheCancelbuttontodiscardtheimportoperationandthescreenwillreturntothe
TrustedCertificatespage.

M2MCellularGateway
121
Chapter4FieldCommunication(notsupported)
Not supported feature for the purchased product, leave it as blank.
M2MCellularGateway
122
Chapter5Security
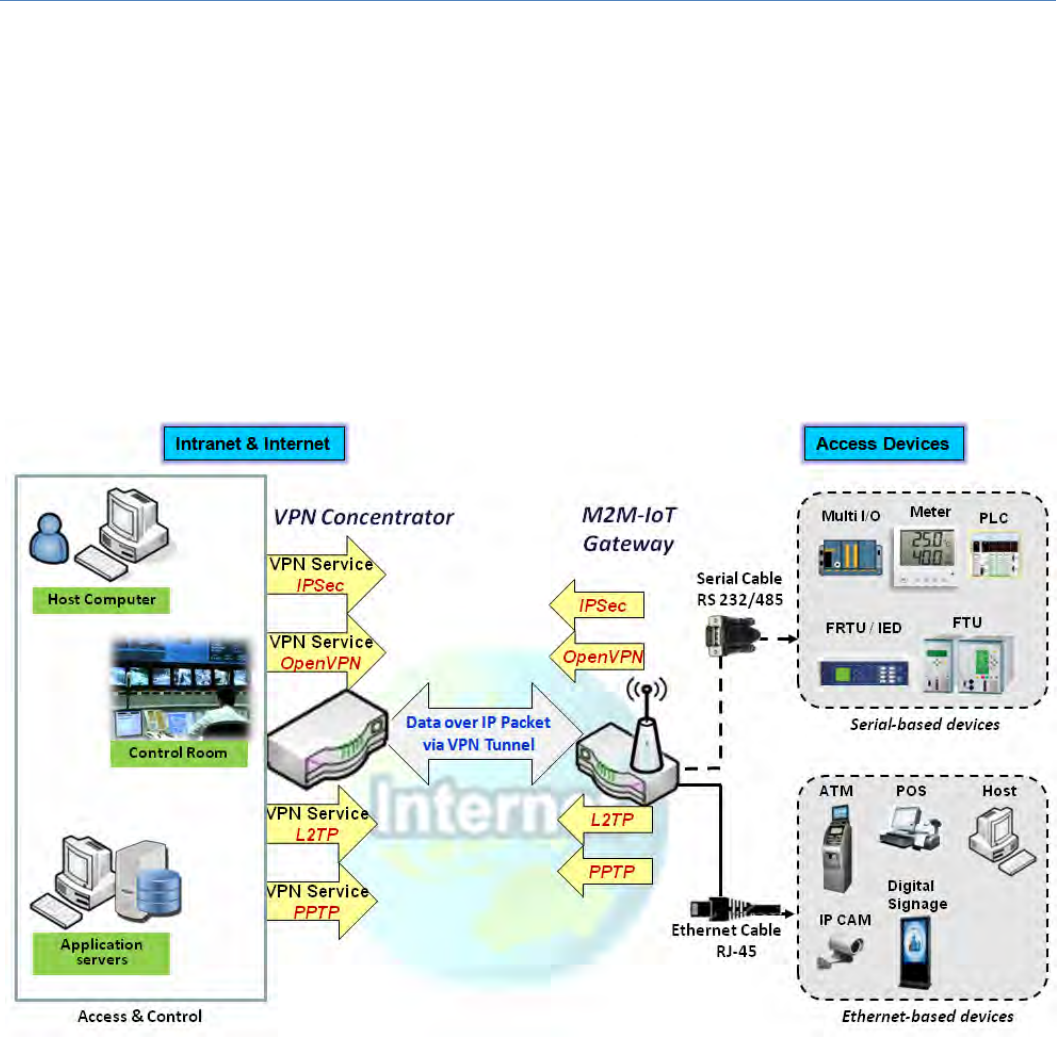
5.1 VPN
Avirtualprivatenetwork(VPN)extendsaprivatenetworkacross a public network, such as the Internet. It
enablesacomputertosendandreceivedataacrosssharedorpublicnetworksasifitweredirectlyconnected
totheprivatenetwork,whilebenefittingfromthefunctionality, security and management policies of the
privatenetwork.Thisisdonebyestablishingavirtualpoint‐to‐pointconnectionthroughtheuseofdedicated
connections, encryption, or a combination of the two. The tunnel technology supports data confidentiality,
data origin authentication and data integrity of network information by utilizing encapsulation protocols,
encryptionalgorithms,andhashingalgorithms.
The product series supports different tunneling technologies to establish secure tunnels between multiple
sitesfordatatransferring,suchasIPSec,OpenVPN,L2TP(overIPSec),PPTPandGRE.Besides,someadvanced
functions, like Full Tunnel, Tunnel Failover, Tunnel Load Balance, NetBIOS over IPSec, NAT Traversal and
DynamicVPN,arealsosupported.
M2MCellularGateway
123
5.1.1IPSec
InternetProtocolSecurity(IPSec)isaprotocolsuiteforsecuring Internet Protocol (IP) communications by
authenticating and encrypting each IP packet of a communication session. IPSec includes protocols for
establishingmutualauthenticationbetweenagentsatthebeginning of the session and negotiation of
cryptographickeystobeusedduringthesession.
AnIPSecVPNtunnelisestablishedbetweenIPSecclientandserver.Sometimes,wecalltheIPSecVPNclientas
theinitiatorandtheIPSecVPNserverastheresponder.Thisgatewaycanbeconfiguredasdifferentrolesand
establishnumberoftunnelswithvariousremotedevices.BeforegoingtosetuptheVPNconnections,youmay
needtodecidethescenariotypeforthetunneling.
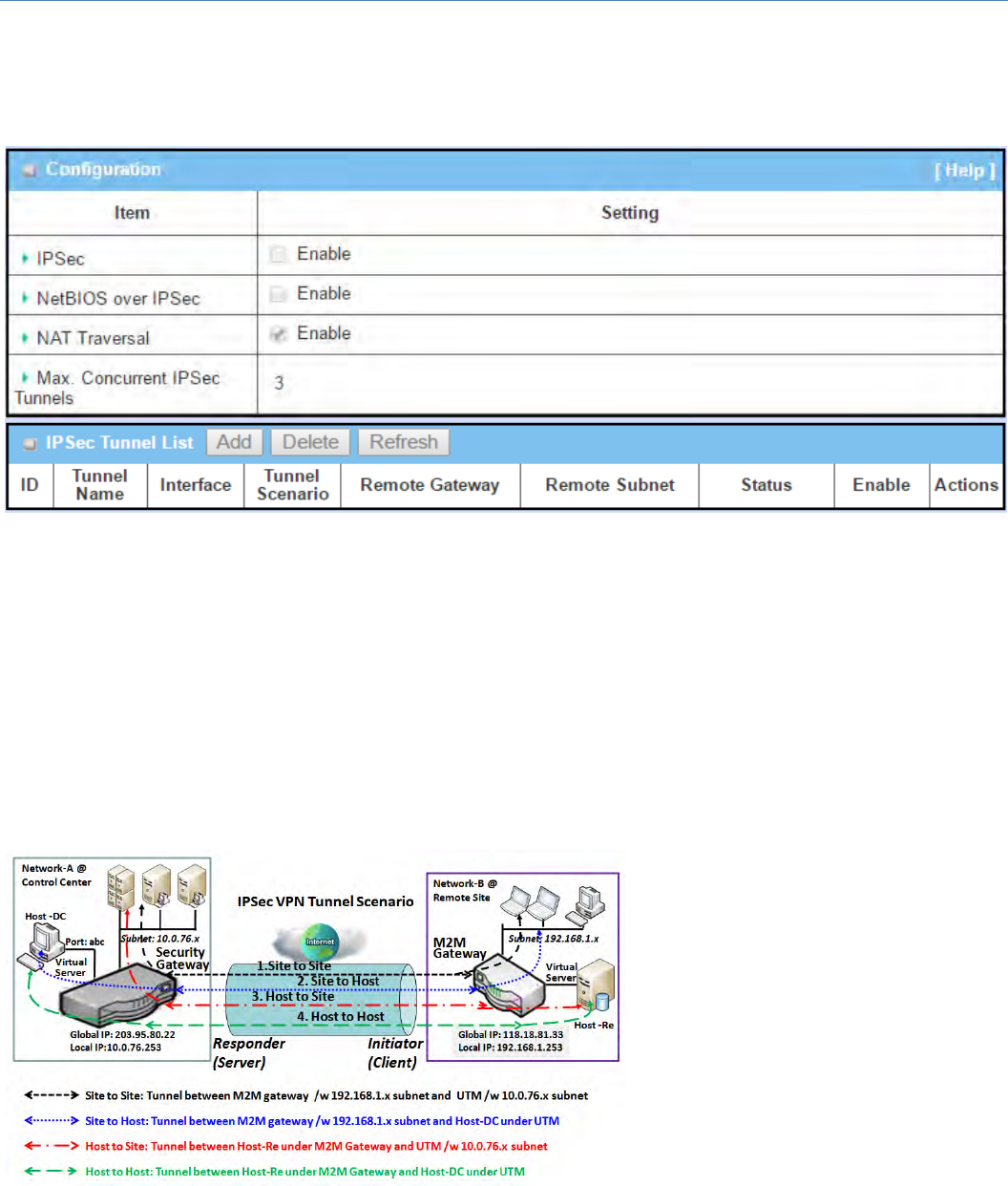
IPSecTunnelScenarios
TobuildIPSectunnel,youneedtofillin
remotegatewayglobalIP,andoptional
subnet if the hosts behind IPSec peer
canaccesstoremotesiteorhosts.
Under such configuration, there are
fourscenarios:
SitetoSite:Youneedtosetupremote
gateway IP and subnet of both
gateways. After the IPSec tunnel
established, hosts behind both
gatewayscancommunicationeach
otherthroughthetunnel.
SitetoHost:SitetoHostissuitablefortunnelingbetweenclientsinasubnetandanapplicationserver(host).
M2MCellularGateway
124
As in the diagram, the clients behind the M2M gateway can access to the host "Host‐DC" located in the
controlcenterthroughSitetoHostVPNtunnel.
Host to Site: On the contrast, for a single host (or mobile user to) to access the resources located in an
intranet,theHosttoSitescenariocanbeapplied.
HosttoHost:HosttoHostisaspecialconfigurationforbuildingaVPNtunnelbetweentwosinglehosts.
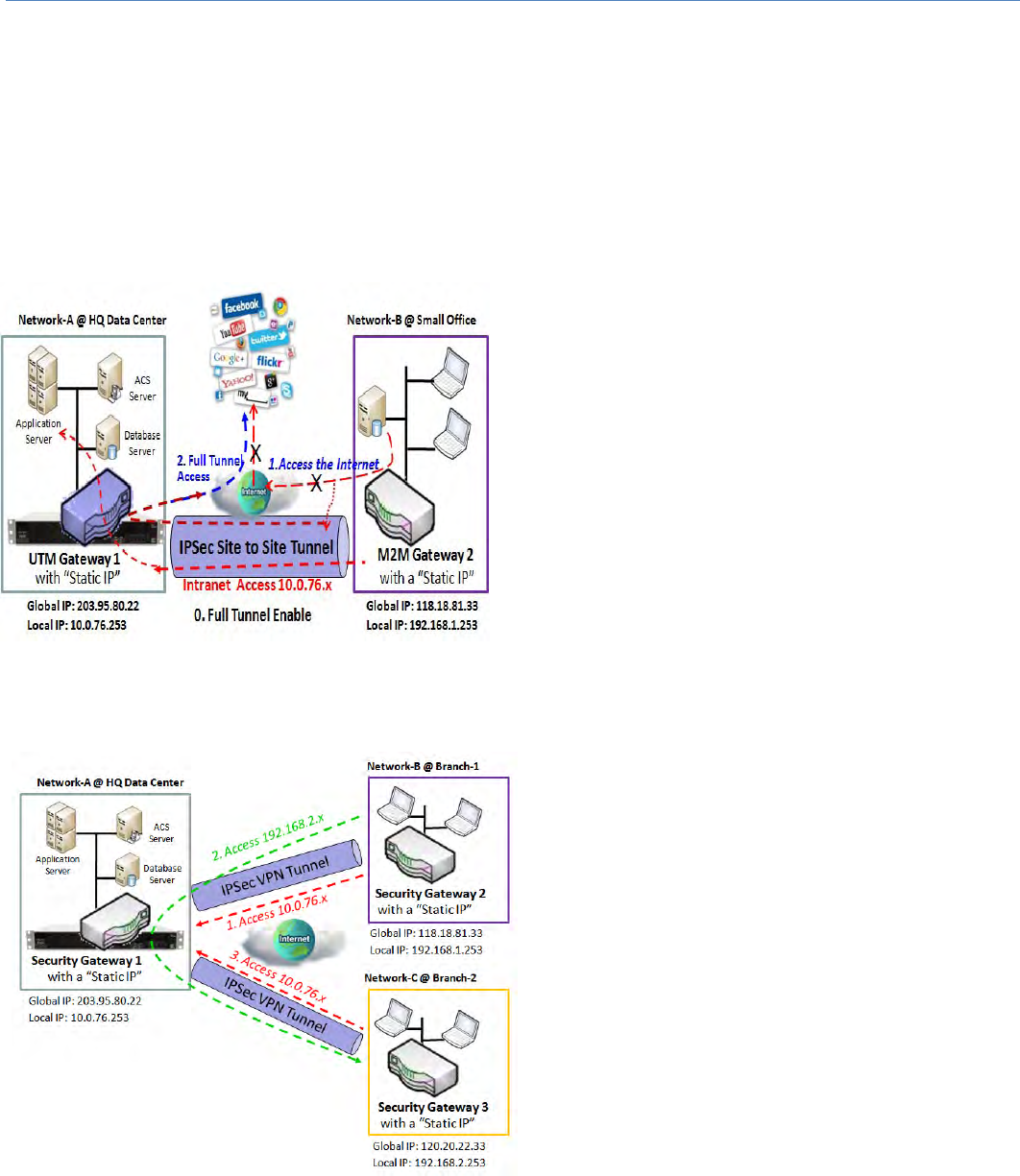
SitetoSitewith"FullTunnel"enabled
In"SitetoSite"scenario,clienthostsinremotesitecan
access the enterprise resources in the Intranet of HQ
gateway via an established IPSec tunnel, as described
above. However, Internet access originates from
remotesitestillgothroughitsregularWANconnection.
Ifyouwantallpacketsfromremotesitetoberouted
via this IPSec tunnel, including HQ server access and
Internet access, you can just enable the “Full Tunnel"
setting.Asaresult,everytimeuserssurfswebor
searchingdataonInternet,checkingpersonalemails,or
HQserveraccess,alltrafficswillgothroughthesecure
IPSec tunnel and route by the Security Gateway in
controlcenter.
SitetoSitewith"HubandSpoke"mechanism
Fora controlcenter tomanage thesecure Intranet
among all its remote sites, there is a simple
configuration,called HubandSpoke,forthewhole
VPNnetwork.AHubandSpokeVPNNetworkisset
up in organizations with centralized control center
over all its remote sites, like shops or offices. The
controlcenteracts as theHubroleand theremote
shopsorOfficesactasSpokes.AllVPNtunnelsfrom
remotesitesterminateatthisHub,whichactsasa
concentrator. Site‐to‐site connections between
spokes do not exist. Traffic originating from one
spokeanddestinedforanotherspokehastogovia
the Hub. Under such configuration, you don’t need
tomaintainVPNtunnelsbetweeneachtworemote
clients.
M2MCellularGateway
125
IPSecSetting
GotoSecurity>VPN>IPSectab.
TheIPSecSettingallowsusertocreateandconfigureIPSectunnels.
EnableIPSec
ConfigurationWindow
Item Valuesetting Description
IPsec Uncheckedbydefault ClicktheEnableboxtoenableIPSecfunction.
NetBIOSoverIPSec Uncheckedbydefault ClicktheEnableboxtoenableNetBIOSoverIPSecfunction.
NATTraversal Checkedbydefault ClicktheEnableboxtoenableNATTraversalfunction.
Max.Concurrent
IPSecTunnels
DependsonProduct
specification.
ThespecifiedvaluewilllimitthemaximumnumberofsimultaneousIPSec
tunnelconnection.Thedefaultvaluecanbedifferentforthepurchasedmodel.
Save N/A ClickSavetosavethesettings
Undo N/A ClickUndotocancelthesettings
Create/EditIPSectunnel
EnsurethattheIPSecenableboxischeckedtoenablebeforefurtherconfiguringtheIPSectunnelsettings.
WhenAdd/Editbuttonisapplied,aseriesofconfigurationscreenswillappear.TheyareTunnelConfiguration,
Local & Remote Configuration, Authentication, IKE Phase, IKE Proposal Definition, IPSec Phase, and IPSec
ProposalDefinition.YouhavetoconfigurethetunneldetailsforbothlocalandremoteVPNdevices.
M2MCellularGateway
126
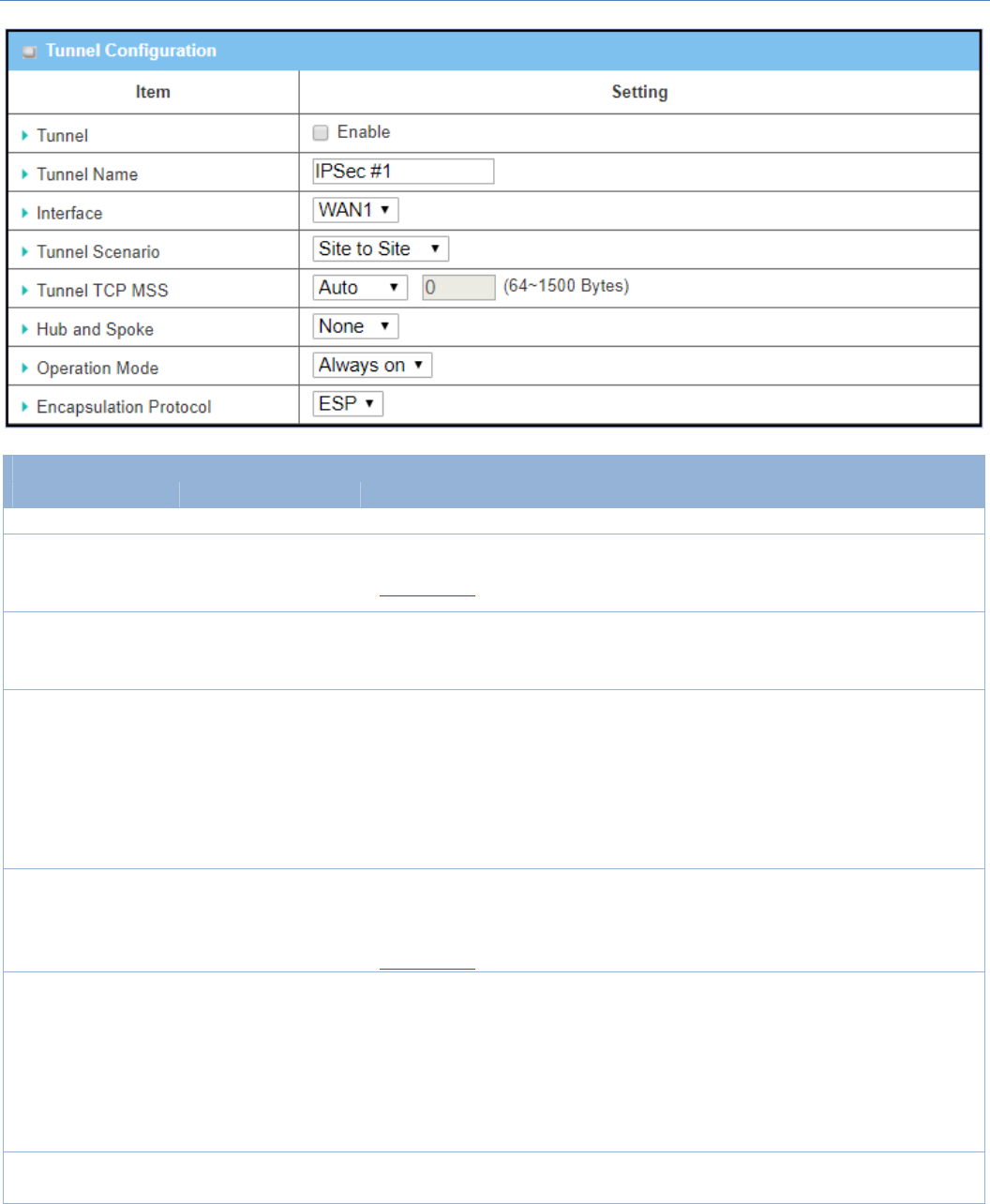
TunnelConfigurationWindow
Item Valuesetting Description
Tunnel Uncheckedbydefault ChecktheEnableboxtoactivatetheIPSectunnel
TunnelName
1.AMustfillsetting
2.Stringformatcanbe
anytext
Enteratunnelname.Enteranamethatiseasyforyoutoidentify.
ValueRange:1~19characters.
Interface
1.AMustfillsetting
2.WAN1isselected
bydefault
SelecttheinterfaceonwhichIPSectunnelistobeestablished.Itcanbethe
availableWANandLANinterfaces.
TunnelScenario
1.AMustfillsetting
2.Sitetositeis
selectedbydefault
SelectanIPSectunnelingscenariofromthedropdownboxforyourapplication.
SelectSite‐to‐Site,Site‐to‐Host,Host‐to‐Site,orHost‐to‐Host.IfLANinterface
isselected,onlyHost‐to‐Hostscenarioisavailable.
WithSite‐to‐SiteorSite‐to‐HostorHost‐to‐Site,IPSecoperatesintunnelmode.
Thedifferenceamongthemisthenumberofsubnets.WithHost‐to‐Host,IPSec
operatesintransportmode.
TunelTCPMSS
1.Anoptionalsetting
2.Autoissetby
default
SelectfromthedropdownboxtodefinethesizeofTunelTCPMSS.
SelectAuto,andalldeviceswilladjustthisparameterautomatically.
SelectManual,andspecifyanexpectedvauleforTunelTCPMSS.
ValueRange:64~1500bytes.
HubandSpoke
1.Anoptionalsetting
2.Noneissetby
default
SelectfromthedropdownboxtosetupyourgatewayforHub‐and‐SpokeIPSec
VPNDeployments.
SelectNoneifyourdeploymentswillnotsupportHuborSpokeencryption.
SelectHubforaHubroleintheIPSecdesign.
SelectSpokeforaSpokeroleintheIPSecdesign.
Note:HubandSpokeareavailableonlyforSite‐to‐SiteVPNtunnelingspecified
inTunnelScenario.ItisnotavailableforDynamicVPNtunnelingapplication.
OperationMode 1.AMustfillsetting
2.Alwayonisselected
DefineoperationmodefortheIPSecTunnel.ItcanbeAlwaysOn,orFailover.
Ifthistunnelissetasafailovertunnel,youneedtofurtherselectaprimary
M2MCellularGateway
127
bydefault tunnelfromwhichtofailoverto.
Note:FailovermodeisnotavailableforthegatewaywithsingleWAN.
Encapsulation
Protocol
1.AMustfillsetting
2.ESPisselectedby
default
SelecttheEncapsulationProtocolfromthedropdownboxforthisIPSectunnel.
AvailableencapsulationsareESPandAH.
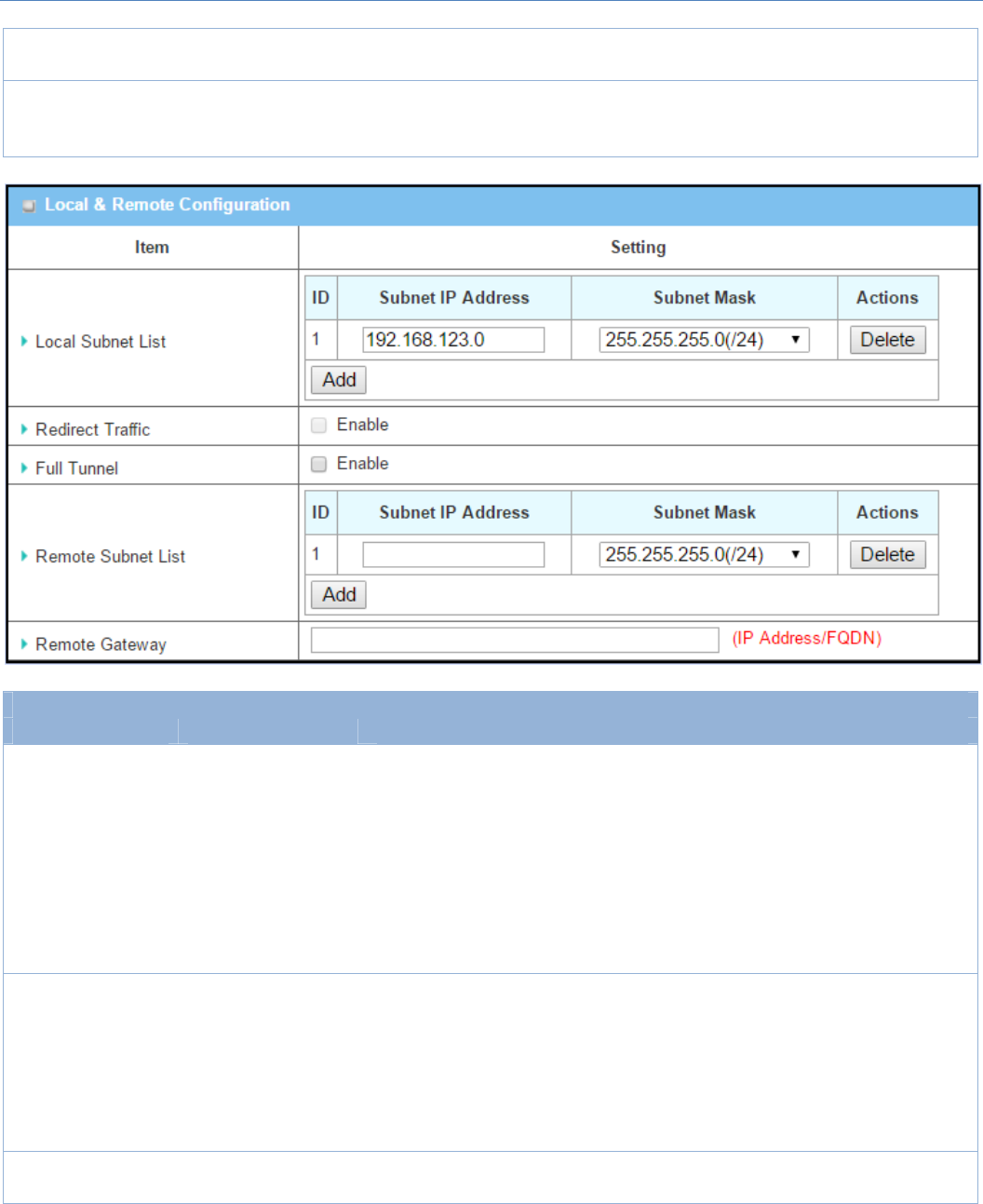
Local&RemoteConfigurationWindow
Item Valuesetting Description
LocalSubnetList AMustfillsetting
SpecifytheLocalSubnetIPaddressandSubnetMask.
ClicktheAddorDeletebuttontoaddordeleteaLocalSubnet.
Note_1:WhenDynamicVPNoptioninTunnelScenarioisselected,therewillbe
onlyonesubnetavailable.
Note_2:WhenHost‐to‐SiteorHost‐to‐HostoptioninTunnelScenariois
selected,LocalSubnetwillnotbeavailable.
Note_3:WhenHubandSpokeoptioninHubandSpokeisselected,therewillbe
onlyonesubnetavailable.
RedirectTraffic Uncheckedbydefault
ClickEnableboxtoactivatetheRedirectTrafficfunction.
Note:RedirectTrafficisavailableonlyforHost‐to‐SitespecifiedinTunnel
Scenario.Bydefault,itisdisabled,soitcanpreventtheun‐expectedand
dangerousaccesstothepeersubnet.Ifyouenablesuchfunction,allthe
networkdevicesbehindtheVPNhost(actually,itisanNATgateway)canaccess
tothepeersubnetwiththehostIP.
FullTunnel Uncheckedbydefault ClickEnableboxtoenableFullTunnel.
Note:FulltunnelisavailableonlyforSite‐to‐SitespecifiedinTunnelScenario.
M2MCellularGateway
128
RemoteSubnetList AMustfillsetting SpecifytheRemoteSubnetIPaddressandSubnetMask.
ClicktheAddorDeletebuttontoaddordeleteRemoteSubnetsetting.
RemoteGateway
1.AMustfillsetting.
2.Formatcanbea
ipv4addressorFQDN
SpecifytheRemoteGateway.
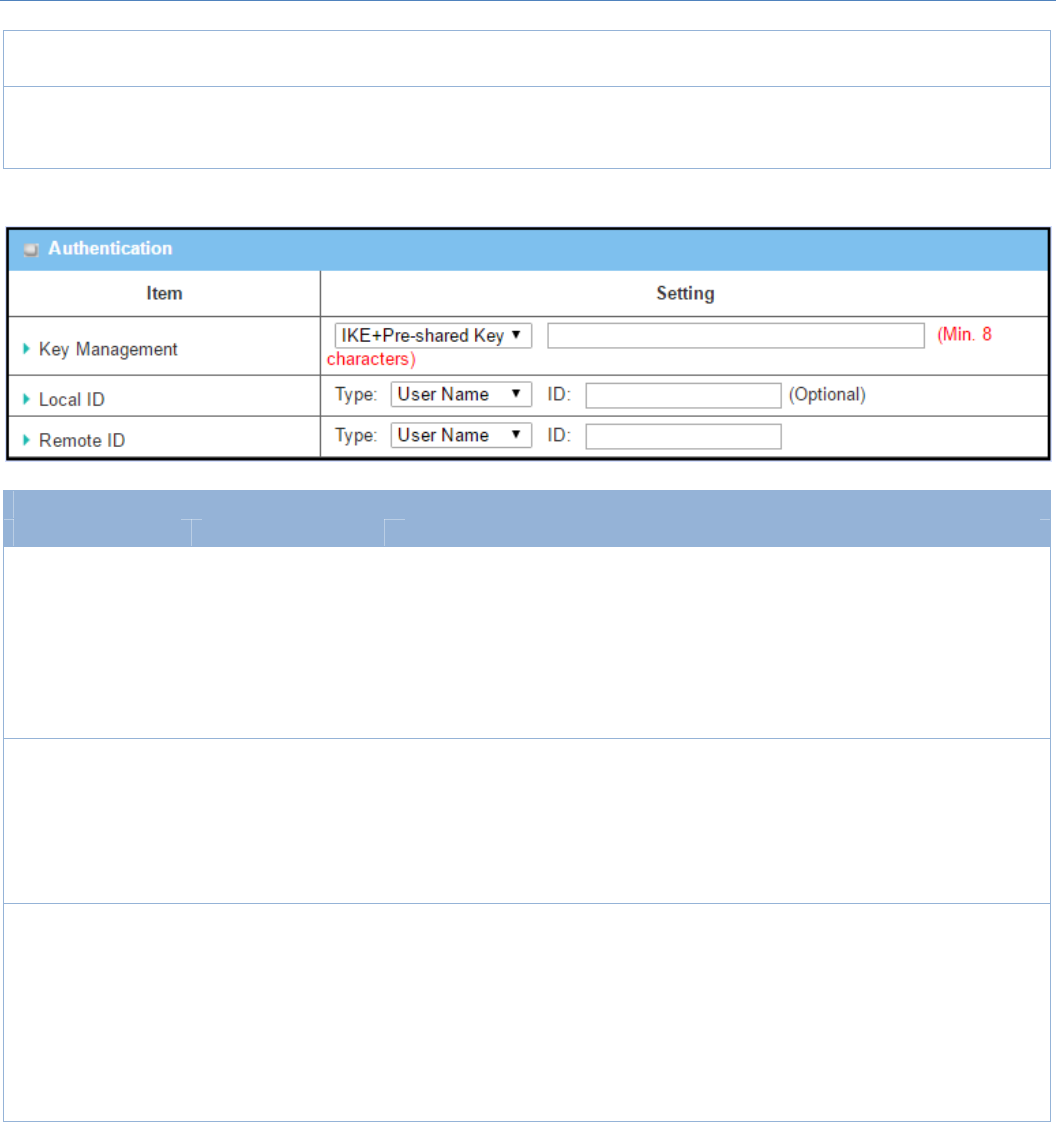
AuthenticationConfigurationWindow
Item Valuesetting Description
KeyManagement
1.AMustfillsetting
2.Pre‐sharedKey8to
32characters.
SelectKeyManagementfromthedropdownboxforthisIPSectunnel.
IKE+Pre‐sharedKey: userneedstosetakey(8~32characters).
IKE+X.509:userneedsCertificatetoauthenticate.IKE+X.509willbeavailable
onlywhenCertificatehasbeenconfiguredproperly.RefertoCertificatesection
ofthismanualandalsoObjectDefinition>Certificateinweb‐basedutility.
Manually:userneedstoenterkeyIDtoauthenticate.Manualkeyconfiguration
willbeexplainedinthefollowingManualKeyManagementsection.
LocalID Anoptionalsetting
SpecifytheLocalIDforthisIPSectunneltoauthenticate.
SelectUserNameforLocalIDandentertheusername.Theusernamemay
includebutcan’tbeallnumbers.
SelectFQDNforLocalIDandentertheFQDN.
SelectUser@FQDNforLocalIDandentertheUser@FQDN.
SelectKeyIDforLocalIDandentertheKeyID(Englishalphabetornumber).
RemoteID Anoptionalsetting
SpecifytheRemoteIDforthisIPSectunneltoauthenticate.
SelectUserNameforRemoteIDandentertheusername.Theusernamemay
includebutcan’tbeallnumbers.
SelectFQDNforLocalIDandentertheFQDN.
SelectUser@FQDNforRemoteIDandentertheUser@FQDN.
SelectKeyIDforRemoteIDandentertheKeyID(Englishalphabetornumber).
Note:RemoteIDwillbenotavailablewhenDynamicVPNoptioninTunnel
Scenarioisselected.
M2MCellularGateway
129
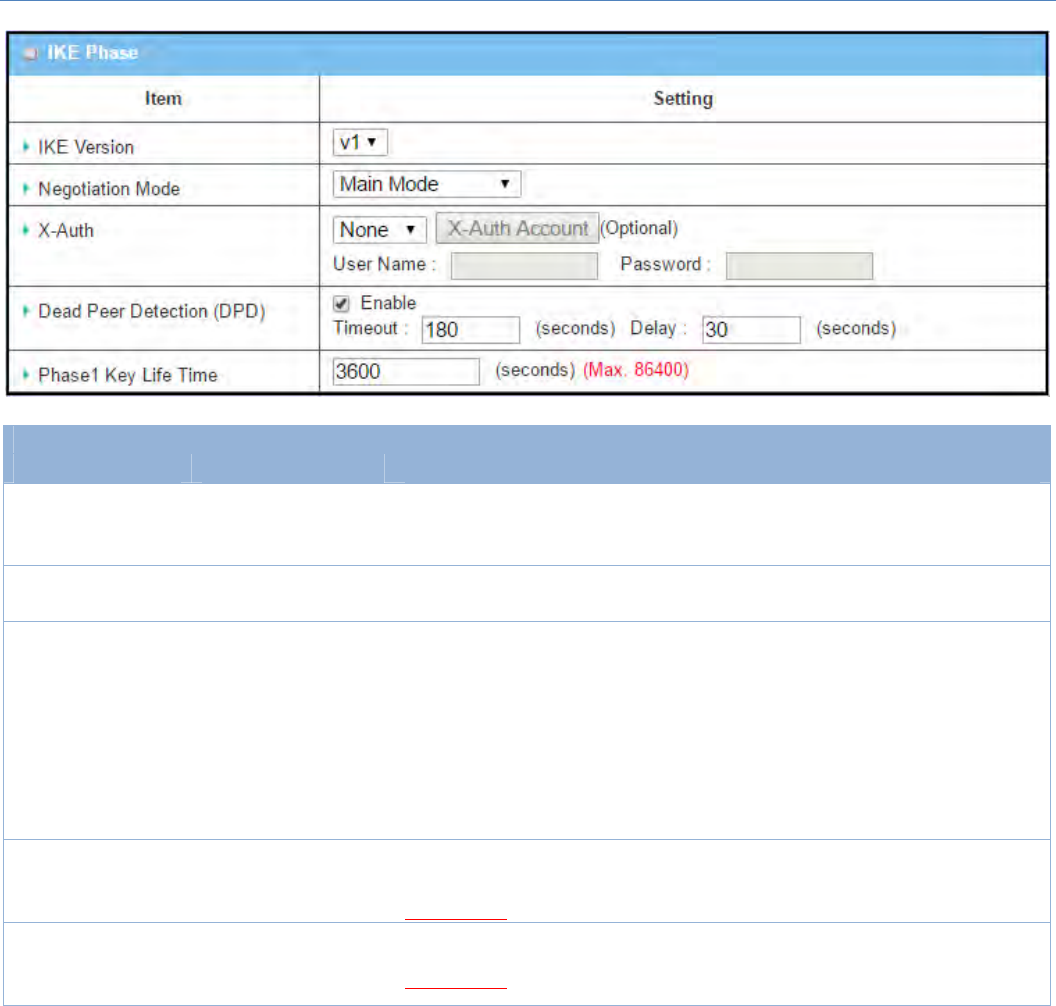
IKEPhaseWindow
Item Valuesetting Description
IKEVersion
1.Amustfillsetting
2.v1isselectedby
default
SpecifytheIKEversionforthisIPSectunnel.Selectv1orv2
Note:IKEversionswillnotbeavailablewhenDynamicVPNoptioninTunnel
Scenarioisselected,orAHoptioninEncapsulationProtocolisselected.
NegotiationMode MainModeissetby
defaultdefault
SpecifytheNegotiationModeforthisIPSectunnel.SelectMainModeor
AggressiveMode.
X‐Auth Noneisselectedby
default
SpecifytheX‐AuthroleforthisIPSectunnel.SelectServer,Client,orNone.
SelectedNonenoX‐Authauthenticationisrequired.
SelectedServerthisgatewaywillbeanX‐Authserver.ClickontheX‐Auth
AccountbuttontocreateremoteX‐Authclientaccount.
SelectedClientthisgatewaywillbeanX‐Authclient.EnterUsernameand
PasswordtobeauthenticatedbytheX‐Authservergateway.
Note:X‐AuthClientwillnotbeavailableforDynamicVPNoptionselectedin
TunnelScenario.
DeadPeerDetection
(DPD)
1.Checkedbydefault
2.DefaultTimeout
180sandDelay30s
ClickEnableboxtoenableDPDfunction.SpecifytheTimeoutandDelaytimein
seconds.
ValueRange:0~999secondsforTimeoutandDelay.
Phase1KeyLife
Time
1.AMustfillsetting
2.Default3600s
3.Max.86400s
SpecifythePhase1KeyLifeTime.
ValueRange:30~86400.
M2MCellularGateway
130
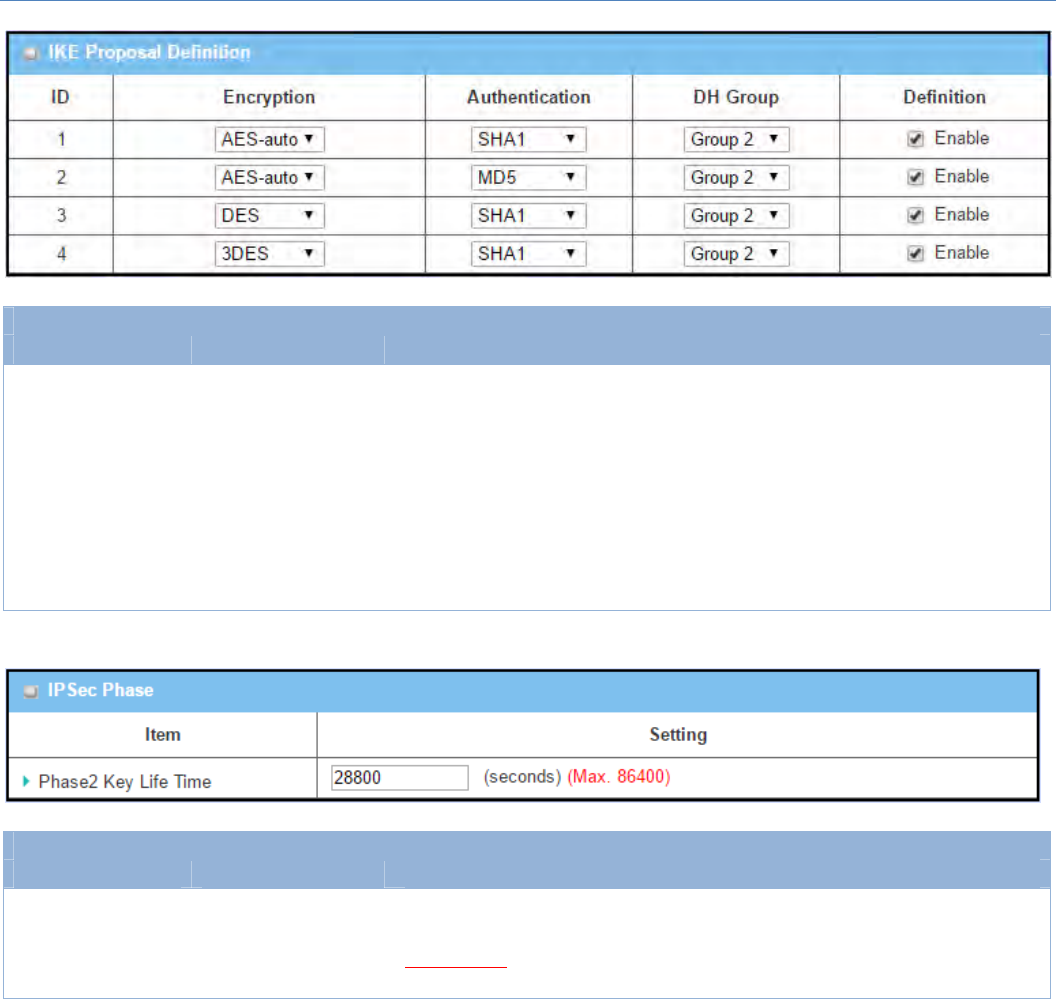
IKEProposalDefinitionWindow
Item Valuesetting Description
IKEProposal
Definition AMustfillsetting
SpecifythePhase1Encryptionmethod.ItcanbeDES/3DES/AES‐auto/AES‐
128/AES‐192/AES‐256.
SpecifytheAuthenticationmethod.ItcanbeNone/MD5/SHA1/SHA2‐256.
SpecifytheDHGroup.ItcanbeNone/Group1/Group2/Group5/Group14/
Group15/Group16/Group17/Group18.
CheckEnableboxtoenablethissetting
IPSecPhaseWindow
Item Valuesetting Description
Phase2KeyLifeTime
1.AMustfillsetting
2.28800sissetby
default
3.Max.86400s
SpecifythePhase2KeyLifeTimeinsecond.
ValueRange:30~86400.
M2MCellularGateway
131
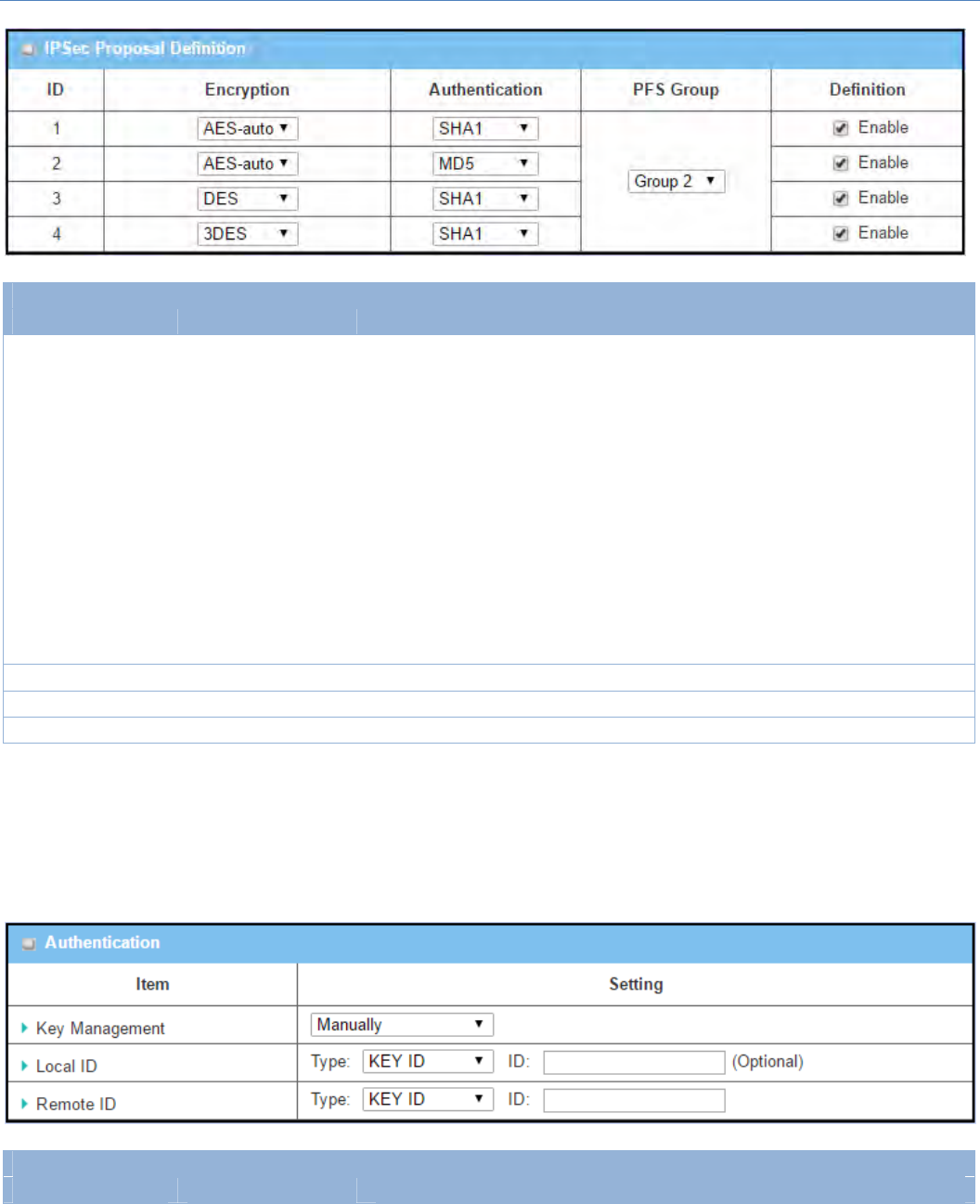
IPSecProposalDefinitionWindow
Item Valuesetting Description
IPSecProposal
Definition AMustfillsetting
SpecifytheEncryptionmethod.ItcanbeNone/DES/3DES/AES‐auto/AES‐
128/AES‐192/AES‐256.
Note:NoneisavailableonlywhenEncapsulationProtocolissetasAH;itisnot
availableforESPEncapsulation.
SpecifytheAuthenticationmethod.ItcanbeNone/MD5/SHA1/SHA2‐256.
Note:NoneandSHA2‐256areavailableonlywhenEncapsulationProtocolisset
asESP;theyarenotavailableforAHEncapsulation.
SpecifythePFSGroup.ItcanbeNone/Group1/Group2/Group5/Group14/
Group15/Group16/Group17/Group18.
ClickEnabletoenablethissetting
Save N/A ClickSavetosavethesettings
Undo N/A ClickUndotocancelthesettings
Back N/A ClickBacktoreturntothepreviouspage.
ManualKeyManagement
When the Manually option is selected for Key Management as described in Authentication Configuration
Window, a series of configuration windows for Manual IPSec Tunnel configuration will appear. The
configurationwindowsaretheLocal&RemoteConfiguration,theAuthentication,andtheManualProposal.
AuthenticationWindow
Item Valuesetting Description
M2MCellularGateway
132
KeyManagement AMustfillsetting SelectKeyManagementfromthedropdownboxforthisIPSectunnel.
InthissectionManuallyistheoptionselected.
LocalID Anoptionalsetting SpecifytheLocalIDforthisIPSectunneltoauthenticate.
SelecttheKeyIDforLocalIDandentertheKeyID(Englishalphabetornumber).
RemoteID Anoptionalsetting SpecifytheRemoteIDforthisIPSectunneltoauthenticate.
SelectKeyIDforRemoteIDandentertheKeyID(Englishalphabetornumber).
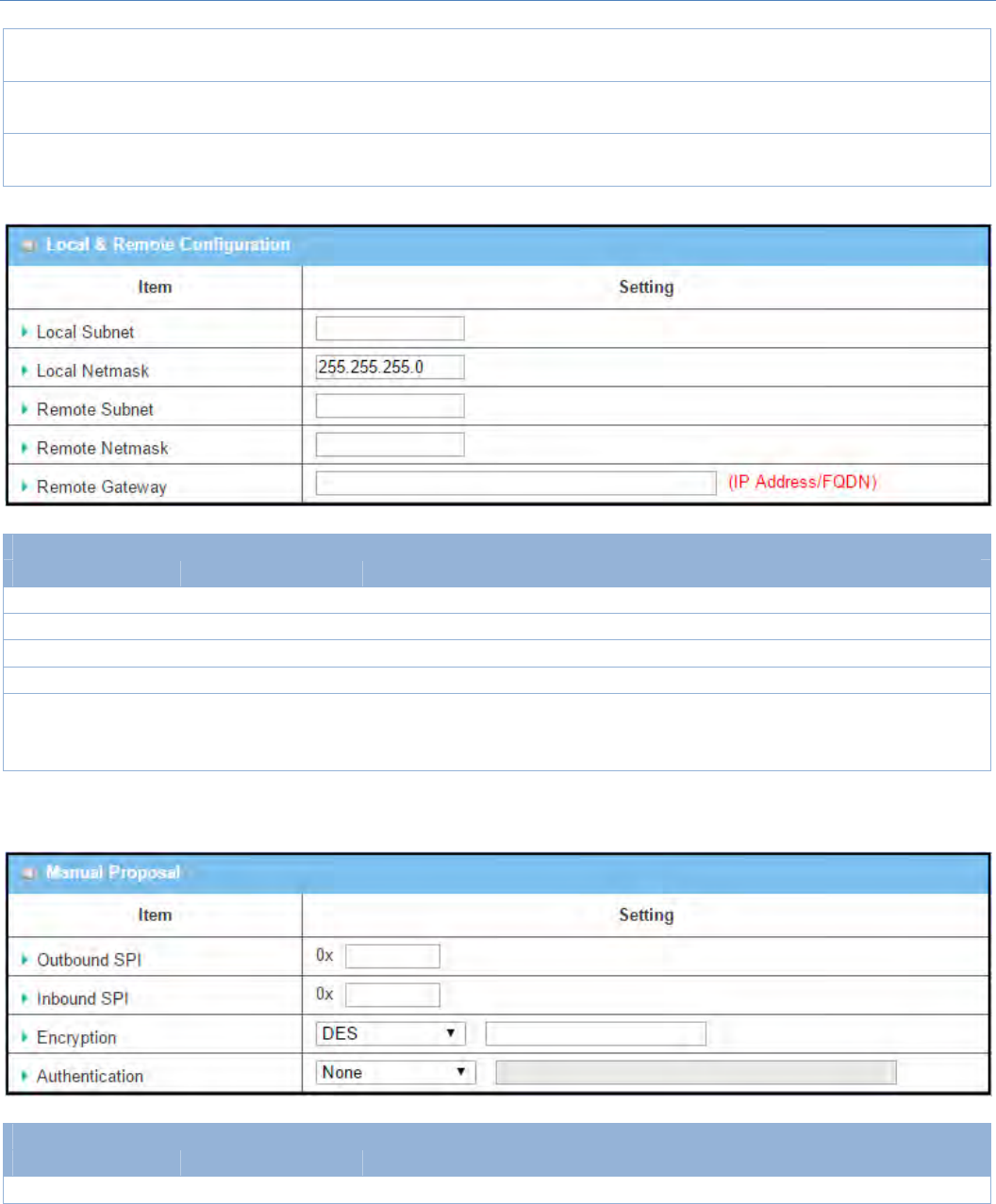
Local&RemoteConfigurationWindow
Item Valuesetting Description
LocalSubnet AMustfillsetting SpecifytheLocalSubnetIPaddressandSubnetMask.
LocalNetmask AMustfillsetting SpecifytheLocalSubnetMask.
RemoteSubnet AMustfillsetting SpecifytheRemoteSubnetIPaddress
RemoteNetmask AMustfillsetting SpecifytheRemoteSubnetMask.
RemoteGateway
1.AMustfillsetting
2.AnIPv4addressor
FQDNformat
SpecifytheRemoteGateway.TheRemoteGateway
Under the Manually Key Management authentication configuration, only one subnet is supported for both
LocalandRemoteIPSecpeer.
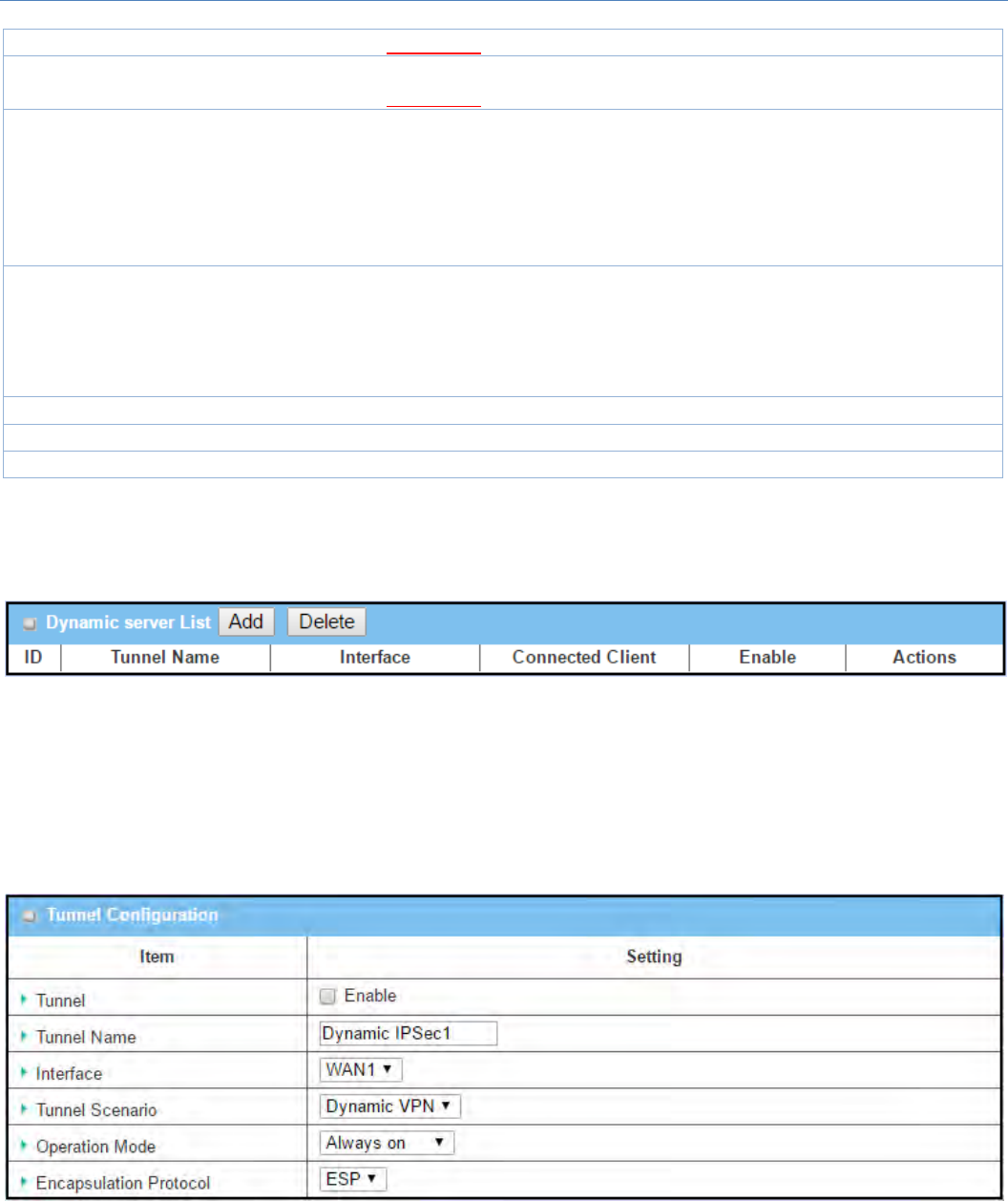
ManualProposalWindow
Item Valuesetting Description
OutboundSPI Hexadecimalformat SpecifytheOutboundSPIforthisIPSectunnel.
M2MCellularGateway
133
ValueRange:0~FFFF.
InboundSPI Hexadecimalformat SpecifytheInboundSPIforthisIPSectunnel.
ValueRange:0~FFFF.
Encryption 1.AMustfillsetting
2.Hexadecimalformat
SpecifytheEncryptionMethodandEncryptionkey.
AvailableencryptionmethodsareDES/3DES/AES‐128/AES‐192/AES‐256.
ThekeylengthforDESis16,3DESis48,AES‐128is32,AES‐192is48,andAES‐
256is64.
Note:WhenAHoptioninEncapsulationisselected,encryptionwillnotbe
available.
Authentication 1.AMustfillsetting
2.Hexadecimalformat
SpecifytheAuthenticationMethodandAuthenticationkey.
AvailableencryptionsareNone/MD5/SHA1/SHA2‐256.
ThekeylengthforMD5is32,SHA1is40,andSHA2‐256is64.
Note:WhenAHoptioninEncapsulationProtocolisselected,Noneoptionin
Authenticationwillnotbeavailable.
Save N/A ClickSavetosavethesettings
Undo N/A ClickUndotocancelthesettings
Back N/A ClickBacktoreturntothepreviouspage.
Create/EditDynamicVPNServerList
SimilartocreateanIPSecVPNTunnelforsite/hosttosite/hostscenario,whenEditbuttonisappliedaseries
of configuration screen will appear. They are Tunnel Configuration,Local&RemoteConfiguration,
Authentication, IKE Phase, IKE Proposal Definition, IPSec Phase, and IPSec Proposal Definition. You have to
configurethetunneldetailsforthegatewayasaDynamicVPNserver.
Note:Forthepurchasedgateway,youcanconfigureoneDynamicVPNserverforeachWANinterface.
M2MCellularGateway
134
TunnelConfigurationWindow
Item Valuesetting Description
Tunnel Uncheckedbydefault ChecktheEnableboxtoactivatetheDynamicIPSecVPNtunnel.
TunnelName
1.AMustfillsetting
2.Stringformatcanbe
anytext
Enteratunnelname.Enteranamethatiseasyforyoutoidentify.
ValueRange:1~19characters.
Interface
1.AMustfillsetting
2.WAN1isselected
bydefault
SelectWANinterfaceonwhichIPSectunnelistobeestablished.
TunnelScenario
1.AMustfillsetting
2.DynamicVPNis
selectedbydefault
TheIPSectunnelingscenarioisfixedtoDynamicVPN.
OperationMode
1.AMustfillsetting
2.Alwayonisselected
bydefault
TheavailableoperationmodeisAlwaysOn.Failoveroptionisnotavailablefor
theDynamicIPSecscenario.
Encapsulation
Protocol
1.AMustfillsetting
2.ESPisselectedby
default
SelecttheEncapsulationProtocolfromthedropdownboxforthisIPSectunnel.
AvailableencapsulationsareESPandAH.
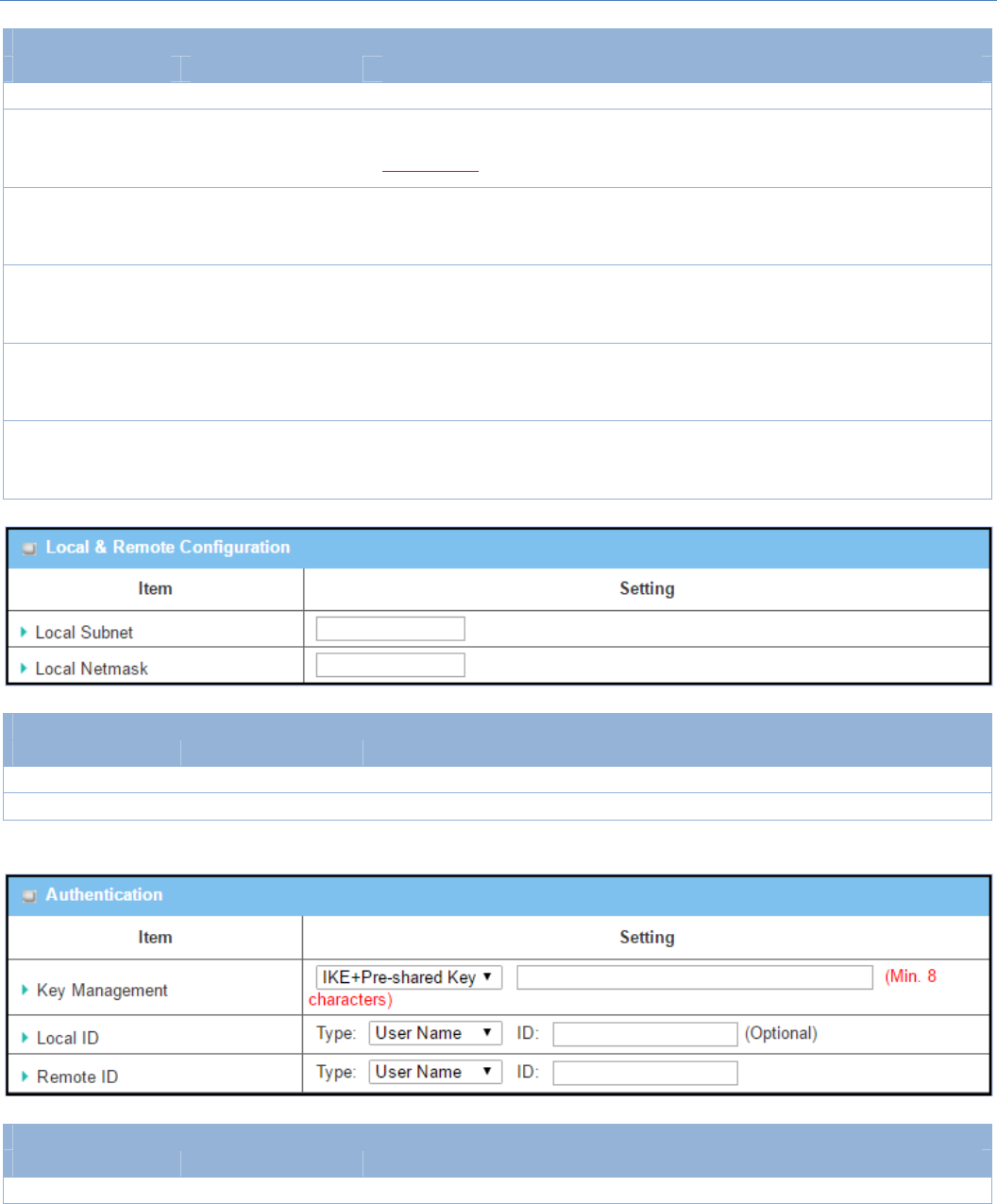
Local&RemoteConfigurationWindow
Item Valuesetting Description
LocalSubnet AMustfillsetting SpecifytheLocalSubnetIPaddress.
LocalNetmask AMustfillsetting SpecifytheLocalSubnetMask.
AuthenticationConfigurationWindow
Item Valuesetting Description
KeyManagement 1.AMustfillsetting SelectKeyManagementfromthedropdownboxforthisIPSectunnel.
M2MCellularGateway
135
2.Pre‐sharedKey8to
32characters.
IKE+Pre‐sharedKey: userneedstosetakey(8~32characters).
LocalID Anoptionalsetting
SpecifytheLocalIDforthisIPSectunneltoauthenticate.
SelectUserNameforLocalIDandentertheusername.Theusernamemay
includebutcan’tbeallnumbers.
SelectFQDNforLocalIDandentertheFQDN.
SelectUser@FQDNforLocalIDandentertheUser@FQDN.
SelectKeyIDforLocalIDandentertheKeyID(Englishalphabetornumber).
RemoteID Anoptionalsetting
SpecifytheRemoteIDforthisIPSectunneltoauthenticate.
SelectUserNameforRemoteIDandentertheusername.Theusernamemay
includebutcan’tbeallnumbers.
SelectFQDNforLocalIDandentertheFQDN.
SelectUser@FQDNforRemoteIDandentertheUser@FQDN.
SelectKeyIDforRemoteIDandentertheKeyID(Englishalphabetornumber).
Note:RemoteIDwillbenotavailablewhenDynamicVPNoptioninTunnel
Scenarioisselected.
FortherestIKEPhase,IKEProposalDefinition,IPSecPhase,andIPSecProposalDefinitionsettings,theyarethe
sameasthatofcreatinganIPSecTunneldescribedinprevioussection.Pleaserefertotherelateddescription.
M2MCellularGateway
136
5.1.2OpenVPN
OpenVPN is an application that implements virtual private network (VPN) techniques for creating secure
point‐to‐pointor site‐to‐siteconnectionsin routedor bridgedconfigurationsand remote access facilities.It
uses a custom security protocol that utilizes SSL/TLS for key exchange.Itiscapableoftraversingnetwork
addresstranslators(NATs)andfirewalls.
OpenVPN allows peers to authenticate each other using a Static Key (pre‐shared key) or certificates. When
used in a multi‐client‐server configuration,itallowstheserver to release an authentication certificate for
every client,using signatureand certificate authority.It uses the OpenSSL encryption library extensively, as
wellastheSSLv3/TLSv1protocol,andcontainsmanysecurityandcontrolfeatures.
OpenVPN Tunneling is a Client and Server based tunneling technology. The OpenVPN Server must have a
StaticIPoraFQDN,andmaintainaClientlist.TheOpenVPNClientmaybeamobileuserormobilesitewith
public IP or private IP, and requesting the OpenVPN tunnel connection. The product can only behave as a
OpenVPNClientroleforanOpenVPNtunnelconnection.
TherearetwoOpenVPNconnectionscenarios.TheyaretheTAPandTUNscenarios.Theproductcancreate
either alayer‐3based IP tunnel (TUN), or a layer‐2based Ethernet TAP that can carry any type of Ethernet
traffic.InadditiontoconfiguringthedeviceasaServerorClient,youhavetospecifywhichtypeofOpenVPN
connectionscenarioistobeadopted.
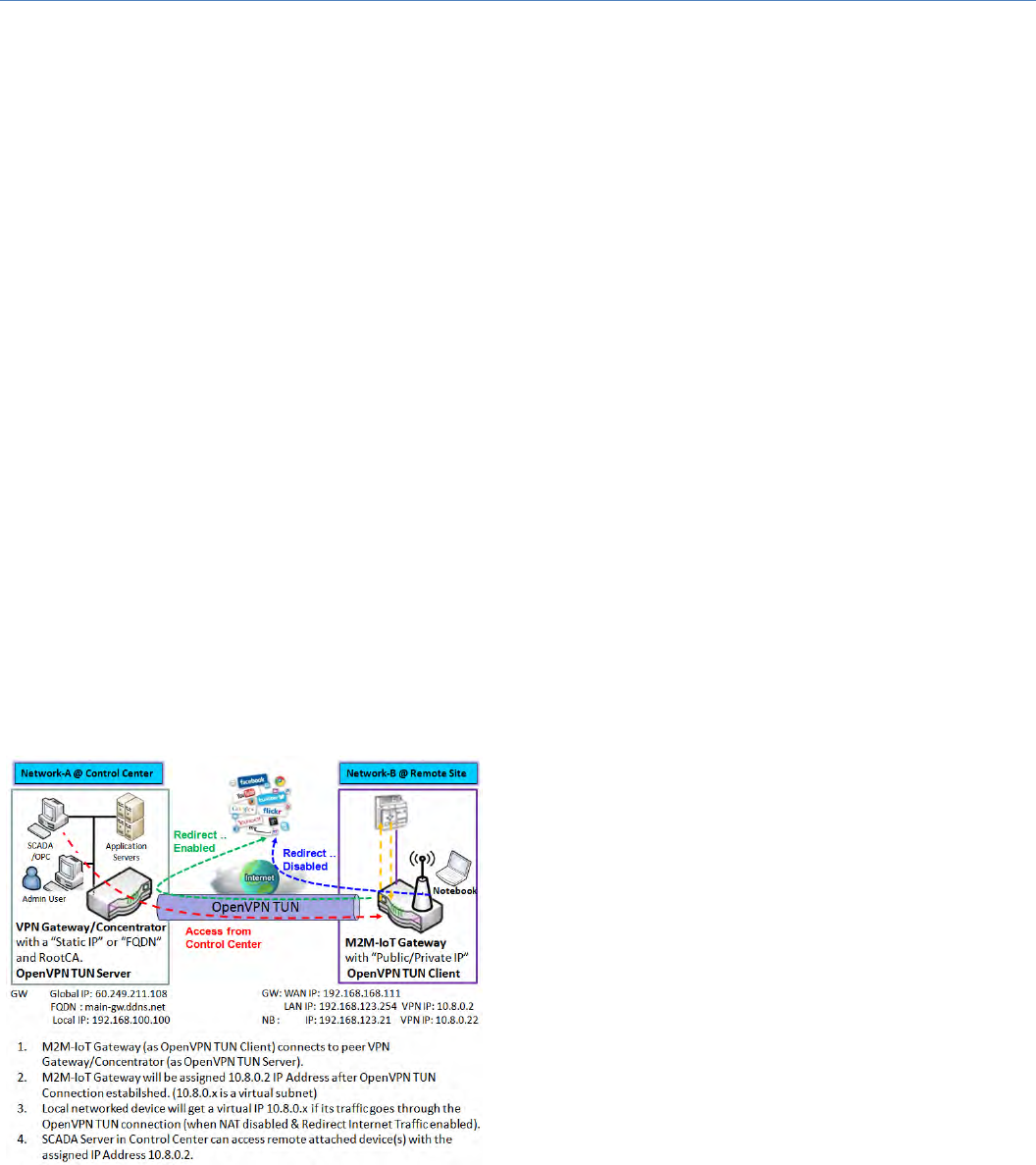
OpenVPNTUNScenario
Theterm"TUN"modeisreferredtoroutingmodeand
operateswithlayer3packets.Inroutingmode,theVPN
client is given an IP address on a different subnet than
the local LAN under the OpenVPN server. This virtual
subnet is created for connecting to any remote VPN
computers. In routing mode, the OpenVPN server
creates a "TUN" interface with its own IP address pool
which is different to the local LAN. Remote hosts that
dial‐in will get an IP address inside the virtual network
andwillhaveaccessonlytotheserverwhereOpenVPN
resides.
IfyouwanttoofferremoteaccesstoaVPNserverfrom
client(s),andinhibittheaccesstoremoteLANresources
under VPN server, OpenVPN TUN mode is the simplest
solution.
Asshowninthediagram,theM2M‐IoTGatewayisconfiguredasanOpenVPNTUNClient,andconnectstoan
OpenVPN UN Server. Once the OpenVPN TUN connection is established, the connected TUN client will be
M2MCellularGateway
137
assignedavirtualIP(10.8.0.2)whichisbelongtoavirtualsubnetthatisdifferenttothelocalsubnetinControl
Center. With such connection, the local networked devices will get a virtual IP 10.8.0.x if its traffic goes
throughtheOpenVPNTUNconnectionwhenRedirectInternetTrafficsettingsisenabled;Besides,theSCADA
ServerinControlCentercanaccessremoteattachedserialdevice(s)withthevirtualIPaddress(10.8.0.2).
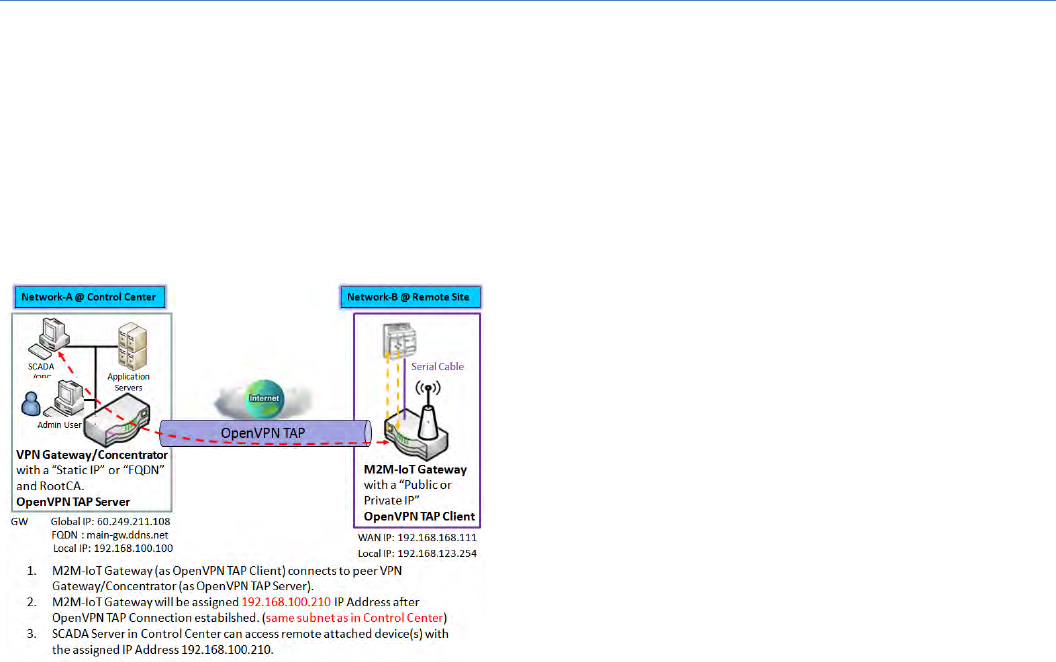
OpenVPNTAPScenario
Theterm"TAP"isreferredtobridgemodeandoperates
with layer 2 packets. In bridge mode, the VPN client is
given an IP address on the same subnet as the LAN
resided under the OpenVPN server. Under such
configuration, the OpenVPN client can directly access to
theresourcesinLAN.Ifyouwanttoofferremoteaccess
totheentireremoteLANforVPNclient(s),youhaveto
setupOpenVPNin“TAP”bridgemode.
As shown in the diagram, the M2M‐IoT Gateway is
configuredasanOpenVPNTAPClient,andconnectstoan
OpenVPNTAPServer.OncetheOpenVPNTAPconnection
isestablished,theconnectedTAPclientwillbeassigneda
virtualIP(192.168.100.210)whichisthe samesubnetas
thatoflocalsubnetinControlCenter.Withsuchconnection,theSCADAServerinControlCentercanaccess
remoteattachedserialdevice(s)withthevirtualIPaddress(192.168.100.210).
M2MCellularGateway
138
OpenVPNSetting
GotoSecurity>VPN>OpenVPNtab.
TheOpenVPNsettingallowsusertocreateandconfigureOpenVPNtunnels.
EnableOpenVPN
Configuration
Item Valuesetting Description
OpenVPN Theboxisuncheckedby
default
ChecktheEnable boxtoactivatetheOpenVPNfunction.
Client Clientisselectedby
default.
Only Clientis available,youcanspecifytheclientsettingsinanotherclient
configurationwindow.
M2MCellularGateway
139
AsanOpenVPNClient
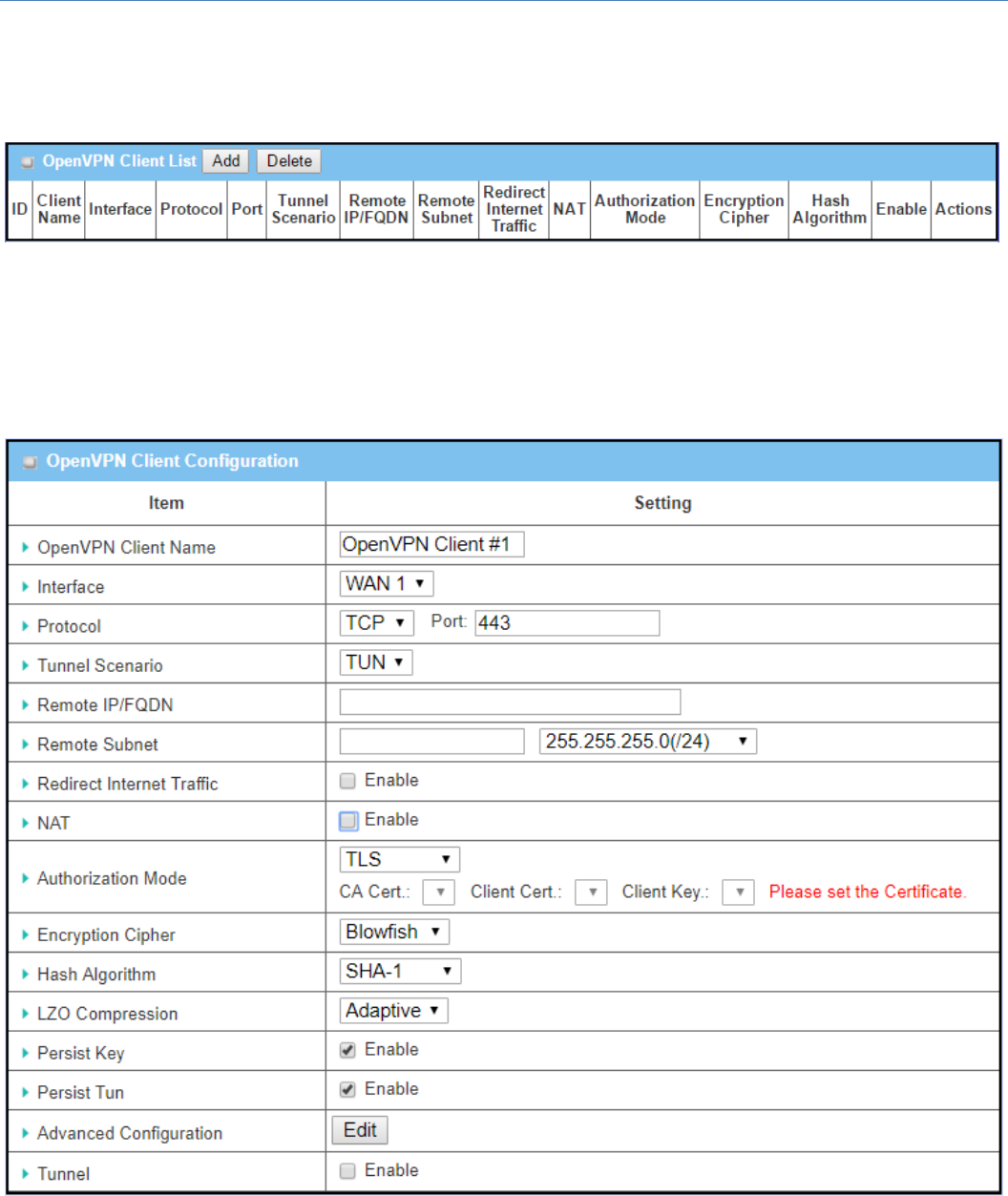
IfClientisselected,anOpenVPNClientListscreenwillappear.
WhenAddbuttonisapplied,OpenVPNClientConfigurationscreenwillappear.OpenVPNClientConfiguration
windowletyouspecifytherequiredparametersforanOpenVPNVPNclient,suchas"OpenVPNClientName",
"Interface", "Protocol", "Tunnel Scenario", "Remote IP/FQDN", "Remote Subnet", "Authorization Mode",
"EncryptionCipher","HashAlgorithm"andtunnelactivation.

M2MCellularGateway
140
OpenVPNClientConfiguration
Item Valuesetting Description
OpenVPNClient
Name
AMustfilledsetting TheOpenVPNClientName willbeusedtoidentifytheclientinthetunnellist.
ValueRange:1~32characters.
Interface 1.AMustfilledsetting
2.BydefaultWAN‐1is
selected.
DefinethephysicalinterfacetobeusedforthisOpenVPNClienttunnel.
Protocol 1.AMustfilledsetting
2.BydefaultTCPis
selected.
DefinetheProtocol fortheOpenVPNClient.
SelectTCP
‐>TheOpenVPNwilluseTCPprotocol,andPortwillbesetas443automatically.
SelectUDP
‐>TheOpenVPNwilluseUDPprotocol,andPortwillbesetas1194
automatically.
Port 1.AMustfilledsetting
2.Bydefault443is
set.
SpecifythePort fortheOpenVPNClienttouse.
Value Range: 1 ~ 65535.
TunnelScenario 1.AMustfilledsetting
2.BydefaultTUNis
selected.
Specify the type o
f
Tunnel Scenario for the OpenVPN Client to use. It can be
TUNforTUNtunnelscenario,orTAPforTAPtunnelscenario.
RemoteIP/FQDN AMustfilledsetting SpecifytheRemoteIP/FQDN ofthepeerOpenVPNServerforthisOpenVPN
Clienttunnel.
FillintheIPaddressorFQDN.
RemoteSubnet 1.AnOptionalsetting.
2.Theboxis
uncheckedbydefault.
ChecktheEnable boxtoactivateremotesubnetfunction,andspecify Remote
SubnetofthepeerOpenVPNServerforthisOpenVPNClienttunnel.
Fillintheremotesubnetaddressandremotesubnetmask.
RedirectInternet
Traffic
1.AnOptionalsetting.
2.Theboxis
uncheckedbydefault.
ChecktheEnable boxtoactivatetheRedirectInternetTrafficfunction.
NAT 1.AnOptionalsetting.
2.Theboxis
uncheckedbydefault.
ChecktheEnable boxtoactivatetheNAT function.
AuthorizationMode 1.AMustfilledsetting
2.BydefaultTLSis
selected.
Specify theauthorizationmode fortheOpenVPNServer.
TLS
‐>The OpenVPN will use TLS authorization mode, and the following items CA
Cert.,ClientCert.andClientKeywillbedisplayed.
CA Cert. could be selected in Trusted CA Certificate List. Refer to Object
Definition>Certificate>TrustedCertificate.
ClientCert.couldbeselectedinLocalCertificateList.RefertoObjectDefinition
>Certificate>MyCertificate.
ClientKeycouldbeselectedinTrustedClientkeyList.RefertoObjectDefinition
>Certificate>TrustedCertificate.
StaticKey
‐>TheOpenVPNwillusestatickeyauthorizationmode,andthefollowingitems
LocalEndpointIPAddress,RemoteEndpointIPAddressandStaticKeywillbe
displayed.
LocalEndpointIP
Address
AMustfilledsetting Specifythe virtual LocalEndpointIPAddress ofthisOpenVPNgateway.
ValueRange:TheIPformatis10.8.0.x,therangeofxis1~254.
Note:LocalEndpointIPAddresswillbeavailableonlywhenStaticKeyischosen
inAuthorizationMode.

M2MCellularGateway
141
RemoteEndpointIP
Address
AMustfilledsetting Specifythevirtual Remote EndpointIPAddressofthepeerOpenVPNgateway.
ValueRange:TheIPformatis10.8.0.x,therangeofxis1~254.
Note: Remote Endpoint IP Address will be available only when StaticKeyis
choseninAuthorizationMode.
StaticKe
y
AMustfilledsetting SpecifytheStaticKey.
Note:StaticKeywillbeavailableonlywhenStaticKeyischoseninAuthorization
Mode.
EncryptionCipher BydefaultBlowfishis
selected.
SpecifytheEncryptionCipher.
ItcanbeBlowfish/AES‐256/AES‐192/AES‐128/None.
HashAlgorithm BydefaultSHA‐1is
selected.
SpecifytheHashAlgorithm.
ItcanbeSHA‐1/MD5/MD4/SHA2‐256/SHA2‐512/None/Disable.
LZOCompression BydefaultAdaptiveis
selected.
SpecifytheLZOCompressionscheme.
ItcanbeAdaptive/YES/NO/Default.
PersisKey 1.AnOptionalsetting.
2.Theboxischecked
bydefault.
ChecktheEnable boxtoactivatethePersisKeyfunction.
PersisTun 1.AnOptionalsetting.
2.Theboxischecked
bydefault.
ChecktheEnable boxtoactivatethePersisTunfunction.
Advanced
Configuration
N/A Click the Edit button to specify the Advanced Configuration setting for the
OpenVPNserver.
Ifthebuttonisclicked,AdvancedConfigurationwillbedisplayedbelow.
Tunnel Theboxisunchecked
bydefault
Checkthe Enable boxtoactivate thisOpenVPNtunnel.
Save N/A Click Savetosavethesettings.
Undo N/A Click Undo tocancelthechanges.
Back N/A ClickBack toreturntolastpage.
M2MCellularGateway
142
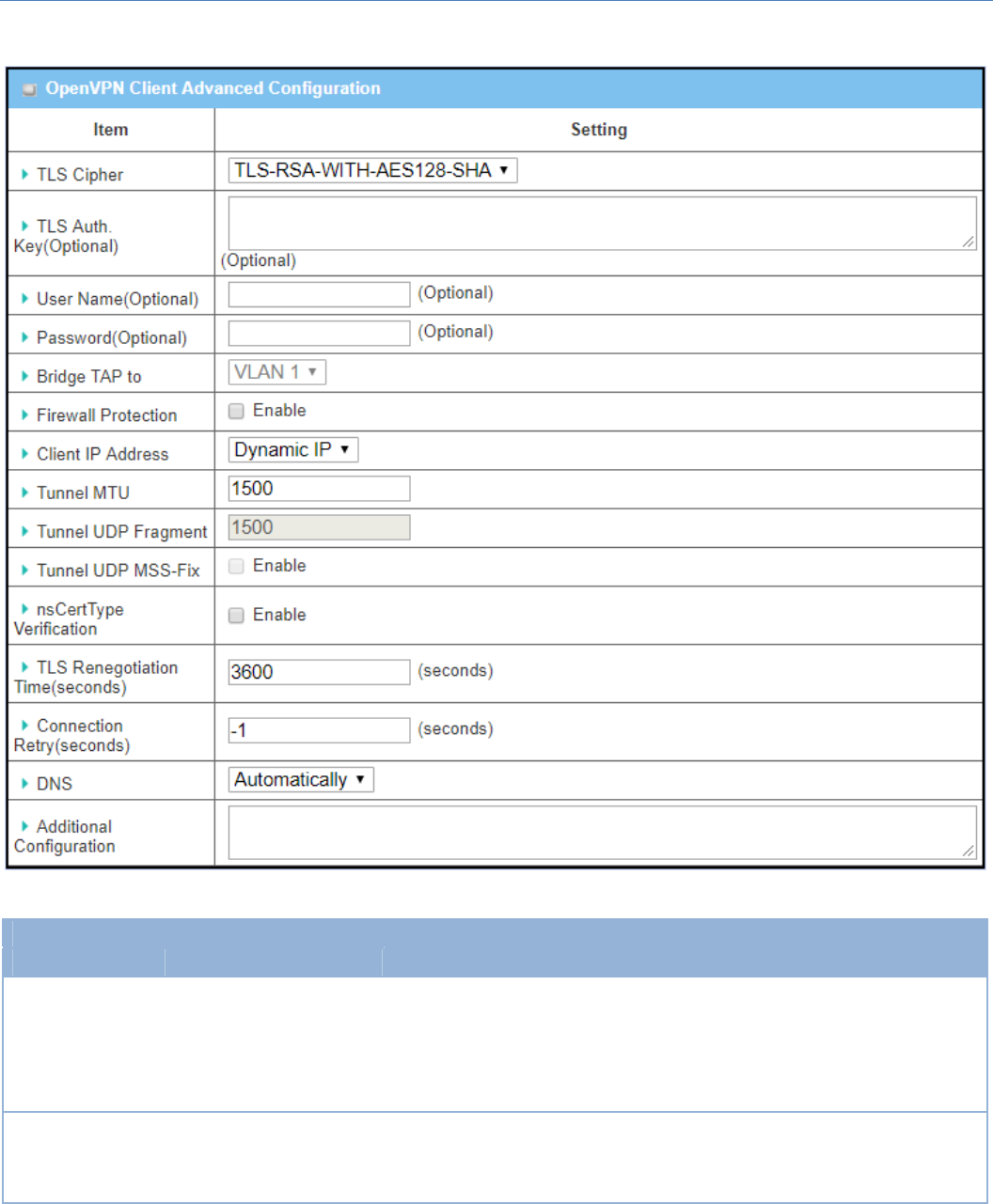
WhenAdvancedConfigurationisselected,anOpenVPNClientAdvancedConfigurationscreenwillappear.
OpenVPNAdvancedClientConfiguration
Item Valuesetting Description
TLSCipher 1.AMustfilledsetting.
2.TLS‐RSA‐WITH‐
AES128‐SHAisselected
bydefault
SpecifytheTLS Cipher from thedropdownlist.
ItcanbeNone/TLS‐RSA‐WITH‐RC4‐MD5/TLS‐RSA‐WITH‐AES128‐SHA/TLS‐
RSA‐WITH‐AES256‐SHA / TLS‐DHE‐DSS‐AES128‐SHA / TLS‐DHE‐DSS‐AES256‐
SHA.
Note: TLS Cipher will be available only when TLS is chosen in Authorization
Mode.
TLSAuth.Key 1.AnOptionalsetting.
2.Stringformat:anytext
SpecifytheTLSAuth.Key forconnectingtoanOpenVPNserver,iftheserver
requiredit.
Note:TLSAuth.KeywillbeavailableonlywhenTLSischoseninAuthorization
Mode.

M2MCellularGateway
143
UserName AnOptionalsetting. Enter the User account for connecting to an OpenVPN server, if the server
requiredit.
Note:UserNamewillbeavailableonlywhenTLSischoseninAuthorization
Mode.
Password AnOptionalsetting. Enter the Password forconnectingtoanOpenVPNserver,iftheserver
requiredit.
Note:UserNamewillbeavailableonlywhenTLSischoseninAuthorization
Mode.
BridgeTAPto BydefaultVLAN1is
selected
Specifythe settingof“BridgeTAPto” tobridgetheTAPinterfacetoacertain
localnetworkinterfaceorVLAN.
Note: Bridge TAP to will be available only when TAP is chosen in Tunnel
ScenarioandNATisunchecked.
FirewallProtection Theboxisuncheckedby
default.
Checktheboxtoactivatethe FirewallProtectionfunction.
Note:FirewallProtectionwillbeavailableonlywhenNATisenabled.
ClientIPAddress BydefaultDynamicIPis
selected
Specifythe virtualIPAddress fortheOpenVPNClient.
ItcanbeDynamicIP/StaticIP.
TunnelMTU 1.AMustfilledsetting
2.Thevalueis1500by
default
SpecifythevalueofTunnelMTU.
ValueRange:0~1500.
TunnelUDP
Fragment
Thevalueis1500by
default
SpecifythevalueofTunnelUDPFragment.
ValueRange:0~1500.
Note: Tunnel UDP Fragment will be available only when UDP is chosen in
Protocol.
TunnelUDPMSS‐
Fix
Theboxisuncheckedby
default.
ChecktheEnable boxto activate theTunnelUDPMSS‐Fixfunction.
Note: Tunnel UDP MSS‐Fix will be available only when UDP is chosen in
Protocol.
nsCerType
Verification
Theboxisuncheckedby
default.
ChecktheEnable boxtoactivatethensCerTypeVerificationfunction.
Note: nsCerType Verification will be available only when TLS is chosen in
AuthorizationMode.
TLSRenegotiation
Time(seconds)
Thevalueis3600by
default
SpecifythetimeintervalofTLSRenegotiationTime.
ValueRange:‐1~86400.
Connection
Retry(seconds)
Thevalueis‐1bydefault SpecifythetimeintervalofConnectionRetry.
Thedefault‐1meansthatitisnoneedtoexecuteconnectionretry.
ValueRange:‐1~86400,and‐1meansnoretryisrequired.
DNS BydefaultAutomatically
isselected
Specifythe settingo
f
DNS.
ItcanbeAutomatically/Manually.
Additional
Configuration
AnOptionalsetting. Enteroptionalconfigurationstringhere.Upto256charactersisallowable.
ValueRange:0~256characters.
Save N/A Click Savetosavethesettings.
Undo N/A Click Undo tocancelthechanges.
Back N/A ClickBack toreturntolastpage.
M2MCellularGateway
144
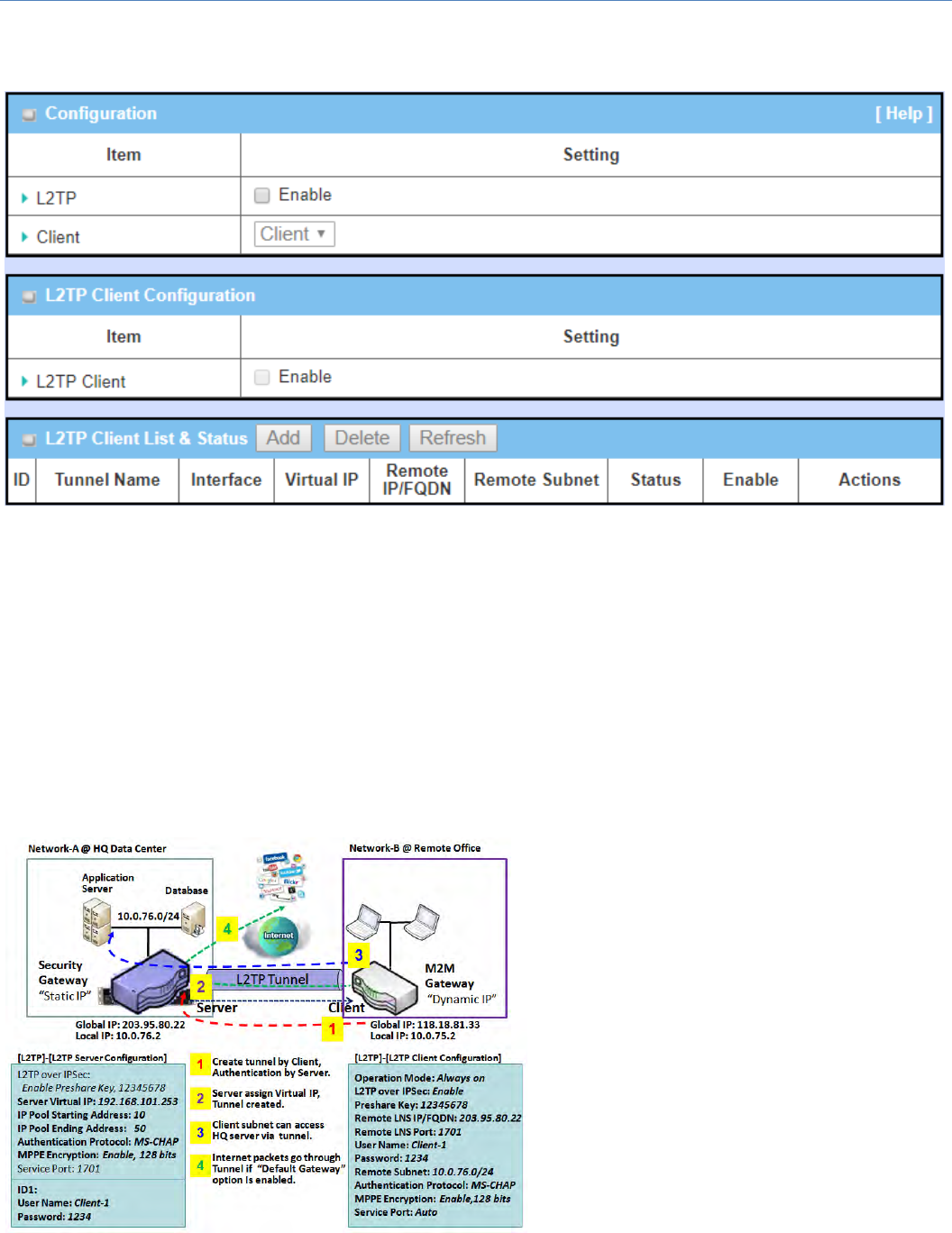
5.1.3L2TP
Layer2TunnelingProtocol(L2TP)isatunnelingprotocolusedtosupportvirtualprivatenetworks(VPNs)oras
partofthedeliveryofservicesbyISPs.Itdoesnotprovideanyencryptionorconfidentialitybyitself.Rather,it
relies on an encryption protocol that it passes within the tunnel to provide privacy. This Gateway can only
behaveasaL2TPclientforaL2TPVPNtunel.
L2TPClient:ItcanbemobileusersorgatewaysinremoteofficeswithdynamicIP.Tosetuptunnel,itshould
get“username”,“password”andserver’sglobalIP.Inaddition,itisrequiredtoidentifytheoperationmode
for each tunnel as main connection, failover for another tunnel, or load balance tunnel to increase overall
bandwidth.Itneedstodecide“DefaultGateway”or“RemoteSubnet”forpacketflow.Moreover,youcanalso
define what kind of traffics will pass through the L2TP tunnel in the “Default Gateway / Remote Subnet”
parameter.
Besides, for the L2TP client peer, a Remote
Subnetitemisrequired.ItisfortheIntranetof
L2TP server peer. So, at L2TP client peer, the
packets whose destination is in the dedicated
subnetwillbetransferredviatheL2TPtunnel.
Others will be transferred based on current
routing policy of the gateway at L2TP client
peer. But, if you entered 0.0.0.0/0 in the
Remote Subnet field, it will be treated as a
"DefaultGateway"settingfortheL2TPclient
peer, all packets, including the Internet
accessingofL2TPclientpeer,willgothrough
the established L2TP tunnel. That means the
M2MCellularGateway
145
remoteL2TPserverpeercontrolstheflowofanypacketsfromtheL2TPclientpeer.Certainly,thosepackets
comethroughtheL2TPtunnel.
L2TPSetting
GotoSecurity>VPN>L2TPtab.
TheL2TPsettingallowsusertocreateandconfigureL2TPtunnels.
EnableL2TP
EnableL2TPWindow
Item Valuesetting Description
L2TP Uncheckedbydefault ClicktheEnableboxtoactivateL2TPfunction.
Client AMustfilledsetting SpecifytheroleofL2TP.OnlyClientroleisavailableforthisgateway.Beloware
theconfigurationwindowsforL2TPClient.
Save N/A ClickSavebuttontosavethesettings
AsaL2TPClient
L2TPClientConfiguration
ItemSetting Valuesetting Description
L2TPClient Theboxisunchecked
bydefault ChecktheEnableboxtoenableL2TPclientroleofthegateway.
Save N/A ClickSavebuttontosavethesettings.
Undo N/A ClickUndobuttontocancelthesettings.

M2MCellularGateway
146
M2MCellularGateway
147
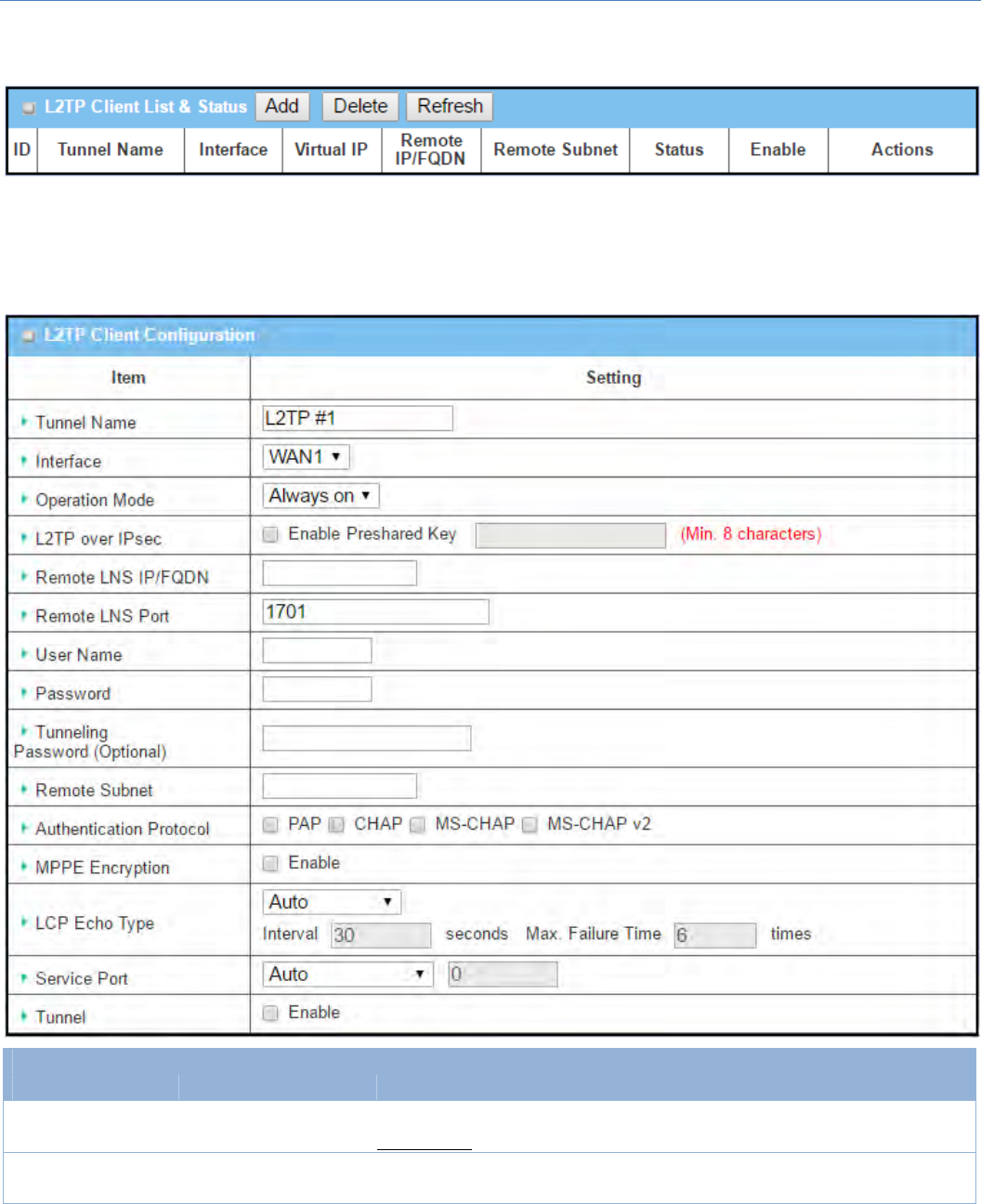
Create/EditL2TPClient
When Add/Editbuttonisapplied,aseriesofconfigurationscreenwillappear.Youcanaddupto8L2TP
Clients.
L2TPClientConfiguration
ItemSetting Valuesetting Description
TunnelName AMustfilledsetting Enteratunnelname.Enteranamethatiseasyforyoutoidentify.
ValueRange:1~32characters.
Interface AMustfilledsetting DefinetheselectedinterfacetobetheusedforthisL2TPtunnel
(WAN‐1isavailableonlywhenWAN‐1interfaceisenabled)

M2MCellularGateway
148
ThesameappliestootherWANinterfaces(e.g.WAN‐2).
OperationMode
1.AMustfilledsetting
2.Alwasyonis
selectedbydefault
DefineoperationmodefortheL2TPTunnel.ItcanbeAlwaysOn,orFailover.
Ifthistunnelissetasafailovertunnel,youneedtofurtherselectaprimary
tunnelfromwhichtofailoverto.
Note:FailovermodeisnotavailableforthegatewaywithsingleWAN.
L2TPoverIPSec Theboxisunchecked
bydefault
ChecktheEnableboxtoactivateL2TPoverIPSec,andfurtherspecifyaPre‐
sharedKey(8~32characters).
RemoteLNS
IP/FQDN AMustfilledsetting EnterthepublicIPaddressortheFQDNoftheL2TPserver.
RemoteLNSPort
1.AMustfilledsetting
2.1701issetby
default
EntertheRemoteLNSPortforthisL2TPtunnel.
ValueRange:1~65535.
UserName AMustfilledsetting
EntertheUserNameforthisL2TPtunneltobeauthenticatedwhenconnectto
L2TPserver.
ValueRange:1~32characters.
Password AMustfilledsetting EnterthePasswordforthisL2TPtunneltobeauthenticatedwhenconnectto
L2TPserver.
Tunneling
Password(Optional)
Theboxisunchecked
bydefault EntertheTunnelingPasswordforthisL2TPtunneltoauthenticate.
RemoteSubnet AMustfilledsetting
SpecifytheremotesubnetforthisL2TPtunneltoreachL2TPserver.
TheRemoteSubnetformatmustbeIPaddress/netmask(e.g.10.0.0.2/24).
ItisfortheIntranetofL2TPVPNserver.So,atL2TPclientpeer,thepackets
whosedestinationisinthededicatedsubnetwillbetransferredviatheL2TP
VPNtunnel.Otherswillbetransferredbasedoncurrentroutingpolicyofthe
securitygatewayatL2TPclientpeer.
Ifyouentered0.0.0.0/0intheRemoteSubnetfield,itwillbetreatedasa
defaultgatewaysettingfortheL2TPclientpeer,allpackets,includingthe
InternetaccessingofL2TPClientpeer,willgothroughtheestablishedL2TPVPN
tunnel.ThatmeanstheremoteL2TPVPNservercontrolstheflowofany
packetsfromtheL2TPclientpeer.Certainly,thosepacketscomethroughthe
L2TPVPNtunnel.
Authentication
Protocol
1.AMustfilledsetting
2.Uncheckedby
default
SpecifyoneoremultipleAuthenticationProtocolforthisL2TPtunnel.
AvailableauthenticationmethodsarePAP/CHAP/MS‐CHAP/MS‐CHAPv2.
MPPEEncryption
1.Uncheckedby
default
2.anoptionalsetting
SpecifywhetherL2TPserversupportsMPPEProtocol.ClicktheEnableboxto
enableMPPE.
Note:whenMPPEEncryptionisenabled,theAuthenticationProtocolPAP/
CHAPoptionswillnotbeavailable.
LCPEchoType
1.Autoissetby
default
SpecifytheLCPEchoTypeforthisL2TPtunnel.ItcanbeAuto,User‐defined,or
Disable.
Auto:thesystemsetstheIntervalandMax.FailureTime.
User‐defined:entertheIntervalandMax.FailureTime.Thedefaultvaluefor
Intervalis30seconds,andMaximumFailureTimesis6Times.
Disable:disabletheLCPEcho.
ValueRange:1~99999forIntervalTime,1~999forFailureTime.
ServicePort AMustfilledsetting SpecifytheServicePortforthisL2TPtunneltouse.ItcanbeAuto,(1701)for

M2MCellularGateway
149
Cisco),orUser‐defined.
Auto:Thesystemdeterminestheserviceport.
1701(forCisco):Thesystemuseport1701forconnectingwithCISCOL2TP
Server.
User‐defined:Entertheserviceport.Thedefaultvalueis0.
ValueRange:0~65535.
Tunnel Uncheckedbydefault ChecktheEnableboxtoenablethisL2TPtunnel.
Save N/A ClickSavebuttontosavethesettings.
Undo N/A ClickUndobuttontocancelthesettings.
M2MCellularGateway
150
5.1.4PPTP
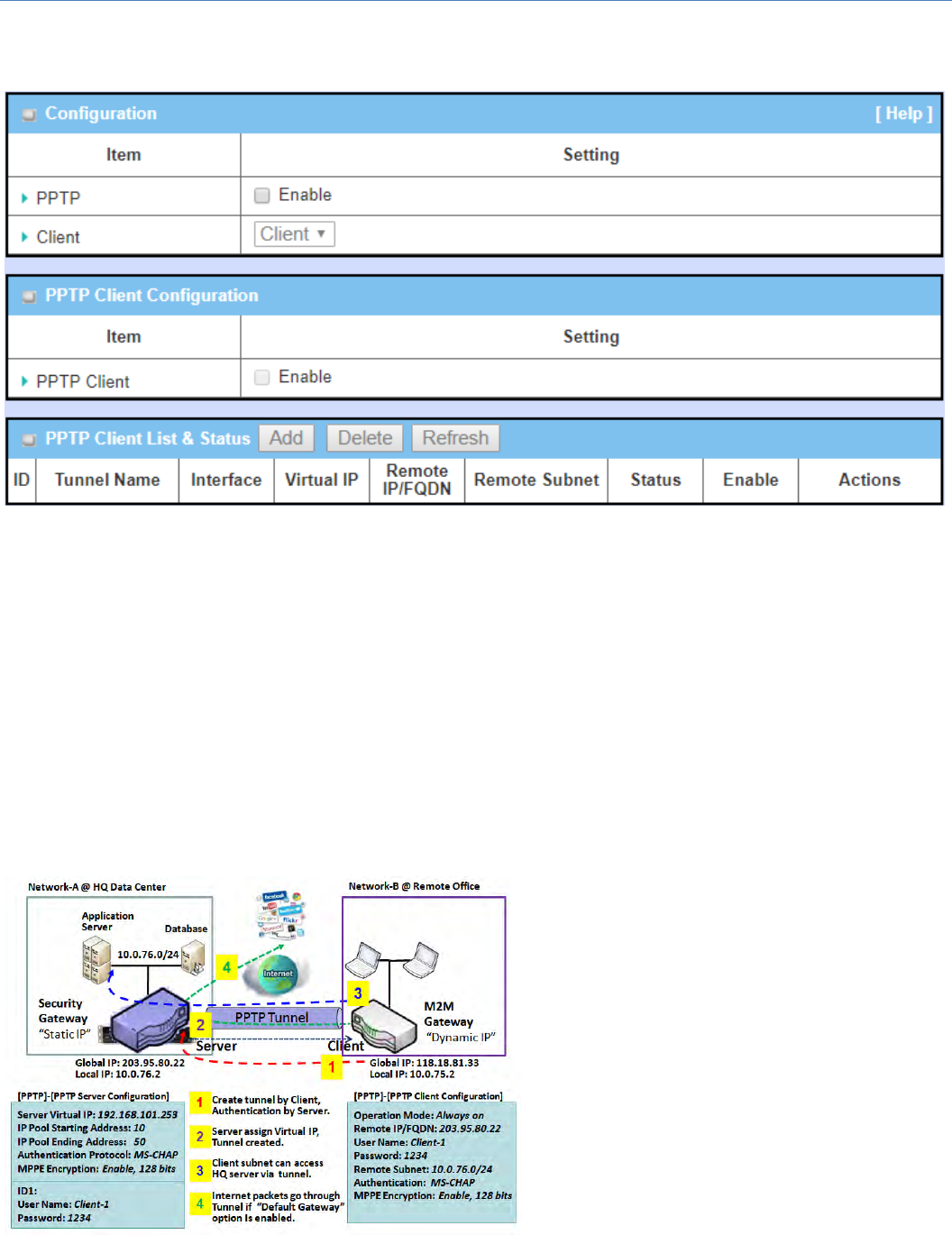
Point‐to‐PointTunnelingProtocol(PPTP)isamethodforimplementingvirtualprivatenetworks.PPTPusesa
controlchanneloverTCPandaGREtunneloperatingtoencapsulatePPPpackets.Itisaclient‐serverbased
technology.TherearevariouslevelsofauthenticationandencryptionforPPTPtunneling,usuallynativelyas
standardfeaturesoftheWindowsPPTPstack.Thesecuritygatewaycanonlyplay"PPTPClient"roleforaPPTP
VPNtunnel.PPTPtunnelprocessisnearlythesameasL2TP.
PPTPClient:ItcanbemobileusersorgatewaysinremoteofficeswithdynamicIP.Tosetuptunnel,itshould
get“username”,“password”andserver’sglobalIP.Inaddition,itisrequiredtoidentifytheoperationmode
for each tunnel as main connection, failover for another tunnel, or load balance tunnel to increase overall
bandwidth.Itneedstodecide“DefaultGateway”or“RemoteSubnet”forpacketflow.Moreover,youcanalso
define what kind of traffics will pass through the PPTP tunnel in the “Default Gateway / Remote Subnet”
parameter.
Besides,forthePPTPclientpeer,aRemote
Subnetitemisrequired.ItisfortheIntranetof
PPTP server peer. So, at PPTP client peer, the
packets whose destination is in the dedicated
subnetwillbetransferred via thePPTPtunnel.
Others will be transferred based on current
routing policy of the gateway at PPTP client
peer. But, if you entered 0.0.0.0/0 in the
Remote Subnet field, it will be treated as a
"DefaultGateway"settingforthePPTPclient
peer, all packets, including the Internet
M2MCellularGateway
151
accessingofPPTPclientpeer,willgothroughtheestablishedPPTPtunnel.ThatmeanstheremotePPTPserver
peercontrolstheflowofanypacketsfromthePPTPclientpeer.Certainly,thosepacketscomethroughthe
PPTPtunnel.
PPTPSetting
GotoSecurity>VPN>PPTPtab.
ThePPTPsettingallowsusertocreateandconfigurePPTPtunnels.
EnablePPTP
EnablePPTPWindow
Item Valuesetting Description
PPTP Uncheckedbydefault ClicktheEnableboxtoactivatePPTPfunction.
Client AMustfillsetting SpecifytheroleofPPTP.OnlyClientroleisavailableforthisgateway.Beloware
theconfigurationwindowsforPPTPClient.
Save N/A ClickSavebuttontosavethesettings.
AsaPPTPClient
PPTPClientConfiguration
Item Valuesetting Description
PPTPClient Uncheckedbydefault ChecktheEnableboxtoenablePPTPclientroleofthegateway.
Save N/A ClickSavebuttontosavethesettings.
Undo N/A ClickUndobuttontocancelthesettings.
M2MCellularGateway
152
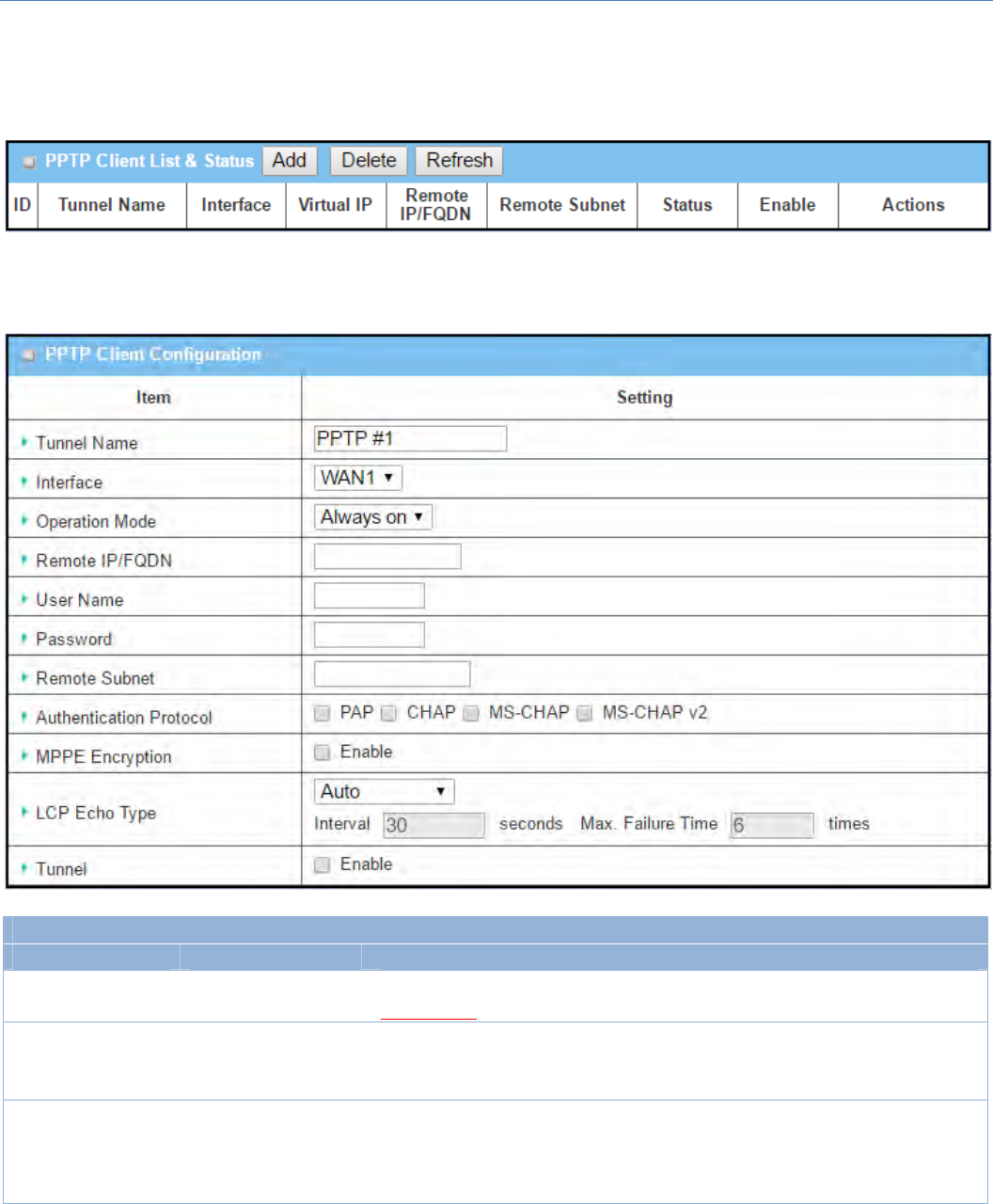
Create/EditPPTPClient
WhenAdd/Editbuttonisapplied,aseriesPPTPClientConfigurationwillappear.
PPTPClientConfigurationWindow
Item Valuesetting Description
TunnelName AMustfillsetting Enteratunnelname.Enteranamethatiseasyforyoutoidentify.
ValueRange:1~32characters.
Interface
1.AMustfillsetting
2.WAN1isselectedby
default
DefinetheselectedinterfacetobetheusedforthisPPTPtunnel
(WAN‐1isavailableonlywhenWAN‐1interfaceisenabled)
ThesameappliestootherWANinterfaces(e.g.WAN‐2).
OperationMode
1.AMustfillsetting
2.Alwasyonis
selectedbydefault
DefineoperationmodeforthePPTPTunnel.ItcanbeAlwaysOn,orFailover.
Ifthistunnelissetasafailovertunnel,youneedtofurtherselectaprimary
tunnelfromwhichtofailoverto.
Note:FailovermodeisnotavailableforthegatewaywithsingleWAN.

M2MCellularGateway
153
RemoteIP/FQDN
1.AMustfillsetting.
2.Formatcanbea
ipv4addressorFQDN
EnterthepublicIPaddressortheFQDNofthePPTPserver.
UserName
AMustfillsetting EntertheUserNameforthisPPTPtunneltobeauthenticatedwhenconnectto
PPTPserver.
ValueRange:1~32characters.
Password AMustfillsetting EnterthePasswordforthisPPTPtunneltobeauthenticatedwhenconnectto
PPTPserver.
RemoteSubnet
AMustfillsetting SpecifytheremotesubnetforthisPPTPtunneltoreachPPTPserver.
TheRemoteSubnetformatmustbeIPaddress/netmask(e.g.10.0.0.2/24).
ItisfortheIntranetofPPTPVPNserver.So,atPPTPclientpeer,thepackets
whosedestinationisinthededicatedsubnetwillbetransferredviathePPTP
VPNtunnel.Otherswillbetransferredbasedoncurrentroutingpolicyofthe
securitygatewayatPPTPclientpeer.
Ifyouentered0.0.0.0/0intheRemoteSubnetfield,itwillbetreatedasa
defaultgatewaysettingforthePPTPclientpeer,allpackets,includingthe
InternetaccessingofPPTPClientpeer,willgothroughtheestablishedPPTPVPN
tunnel.ThatmeanstheremotePPTPVPNservercontrolstheflowofany
packetsfromthePPTPclientpeer.Certainly,thosepacketscomethroughthe
PPTPVPNtunnel.
Authentication
Protocol
1.AMustfillsetting
2.Uncheckedby
default
SpecifyoneoremultipleAuthenticationProtocolforthisPPTPtunnel.
AvailableauthenticationmethodsarePAP/CHAP/MS‐CHAP/MS‐CHAPv2.
MPPEEncryption
1.Uncheckedby
default
2.anoptionalsetting
SpecifywhetherPPTPserversupportsMPPEProtocol.ClicktheEnableboxto
enableMPPE.
Note:whenMPPEEncryptionisenabled,theAuthenticationProtocolPAP/
CHAPoptionswillnotbeavailable.
LCPEchoType
Autoissetbydefault
SpecifytheLCPEchoTypeforthisPPTPtunnel.ItcanbeAuto,User‐defined,or
Disable.
Auto:thesystemsetstheIntervalandMax.FailureTime.
User‐defined:entertheIntervalandMax.FailureTime.Thedefaultvaluefor
Intervalis30seconds,andMaximumFailureTimesis6Times.
Disable:disabletheLCPEcho.
ValueRange:1~99999forIntervalTime,1~999forFailureTime.
Tunnel Uncheckedbydefault ChecktheEnableboxtoenablethisPPTPtunnel.
Save N/A ClickSavebuttontosavethesettings.
Undo N/A ClickUndobuttontocancelthesettings.
Back N/A ClickBackbuttontoreturntothepreviouspage.
M2MCellularGateway
154
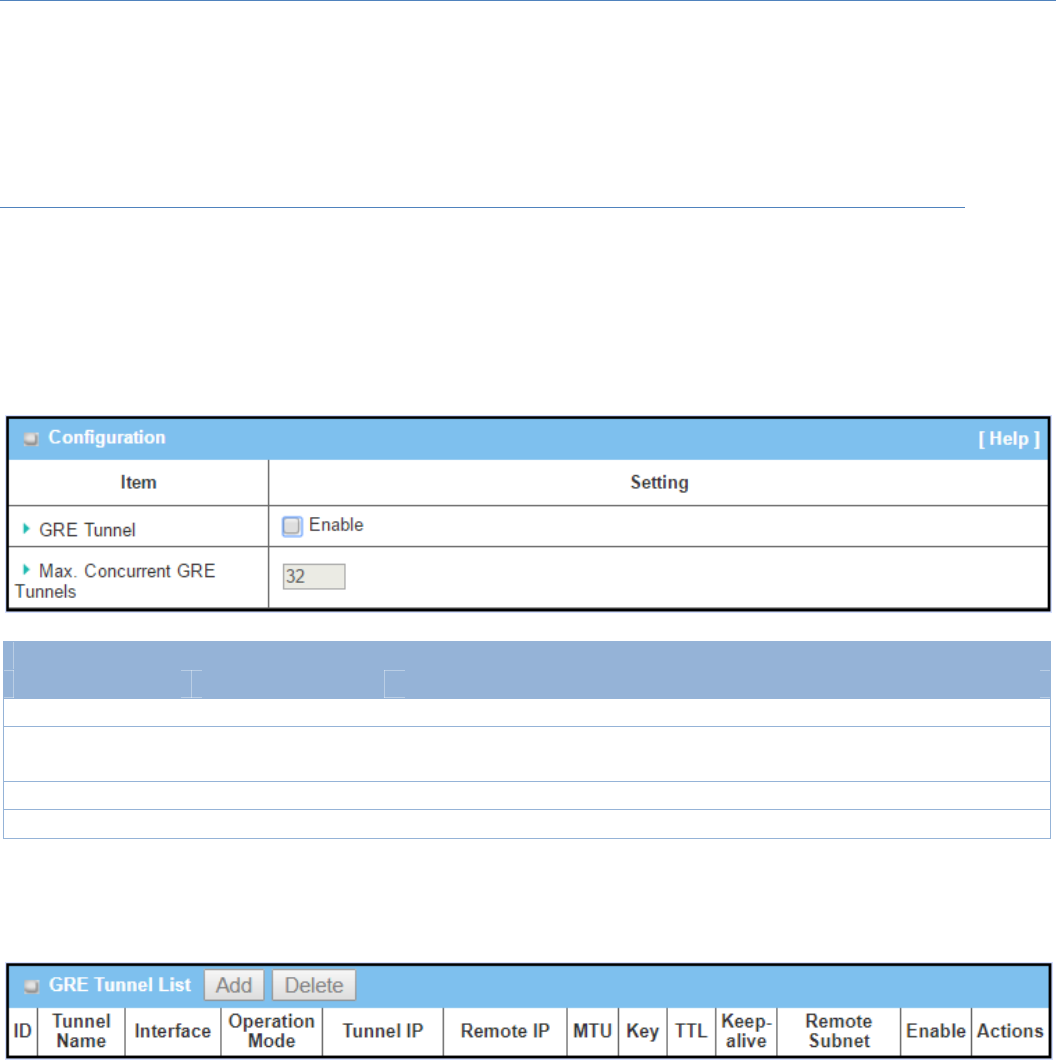
5.1.5GRE
GenericRoutingEncapsulation(GRE)isatunnelingprotocoldevelopedbyCiscoSystemsthatencapsulatesa
wide variety of network layer protocols inside virtual point‐to‐point links over an Internet Protocol
internetwork.
DeployaM2Mgatewayforremotesiteandestablishavirtualprivatenetworkwithcontrolcenterbyusing
GRE tunneling. So, all client hosts behind M2M gateway can make data communication with server hosts
behindcontrolcentergateway.
GRETunnelingissimilartoIPSecTunneling,clientrequestingthetunnelestablishmentwiththeserver.Both
theclientandtheservermusthaveaStaticIPoraFQDN.Anypeergatewaycanbeworkedaseitheraclient
oraserver,evenusingthesamesetofconfigurationrule.
GRETunnelScenario
To setup a GRE tunnel, each peer needs to
setup its global IP as tunnel IP and fill in the
other'sglobalIPasremoteIP.
Besides, each peer must further specify the
Remote Subnet item. It is for the Intranet of
GREserverpeer.So,atGREclientpeer,the
packets whose destination is in the dedicated
subnet will be transferred via the GRE tunnel.
Others will be transferred based on current
routingpolicyofthegatewayatGREclientpeer.
But, if you entered 0.0.0.0/0 in the Remote
Subnet field, it will be treated as a "Default
Gateway"settingfortheGREclientpeer,all
packets,includingtheInternetaccessingofGRE
clientpeer,willgothroughtheestablishedGRE
tunnel.Thatmeansthe remoteGREserverpeercontrolsthe flowofanypacketsfromtheGREclientpeer.
Certainly,thosepacketscomethroughtheGREtunnel.
M2MCellularGateway
155
IftheGREserversupportsDMVPNHubfunction,likeCiscorouterastheVPNconcentrator,theGREclientcan
activetheDMVPNspokefunctionheresinceitisimplementedbyGREoverIPSectunneling.
GRESetting
GotoSecurity>VPN>GREtab.
TheGREsettingallowsusertocreateandconfigureGREtunnels.
EnableGRE
EnableGREWindow
Item Valuesetting Description
GRETunnel Uncheckedbydefault ClicktheEnableboxtoenableGREfunction.
Max.Concurrent
GRETunnels
DependsonProduct
specification.
ThespecifiedvaluewilllimitthemaximumnumberofsimultaneousGREtunnel
connection.Thedefaultvaluecanbedifferentforthepurchasedmodel.
Save N/A ClickSavebuttontosavethesettings
Undo N/A ClickUndobuttontocancelthesettings
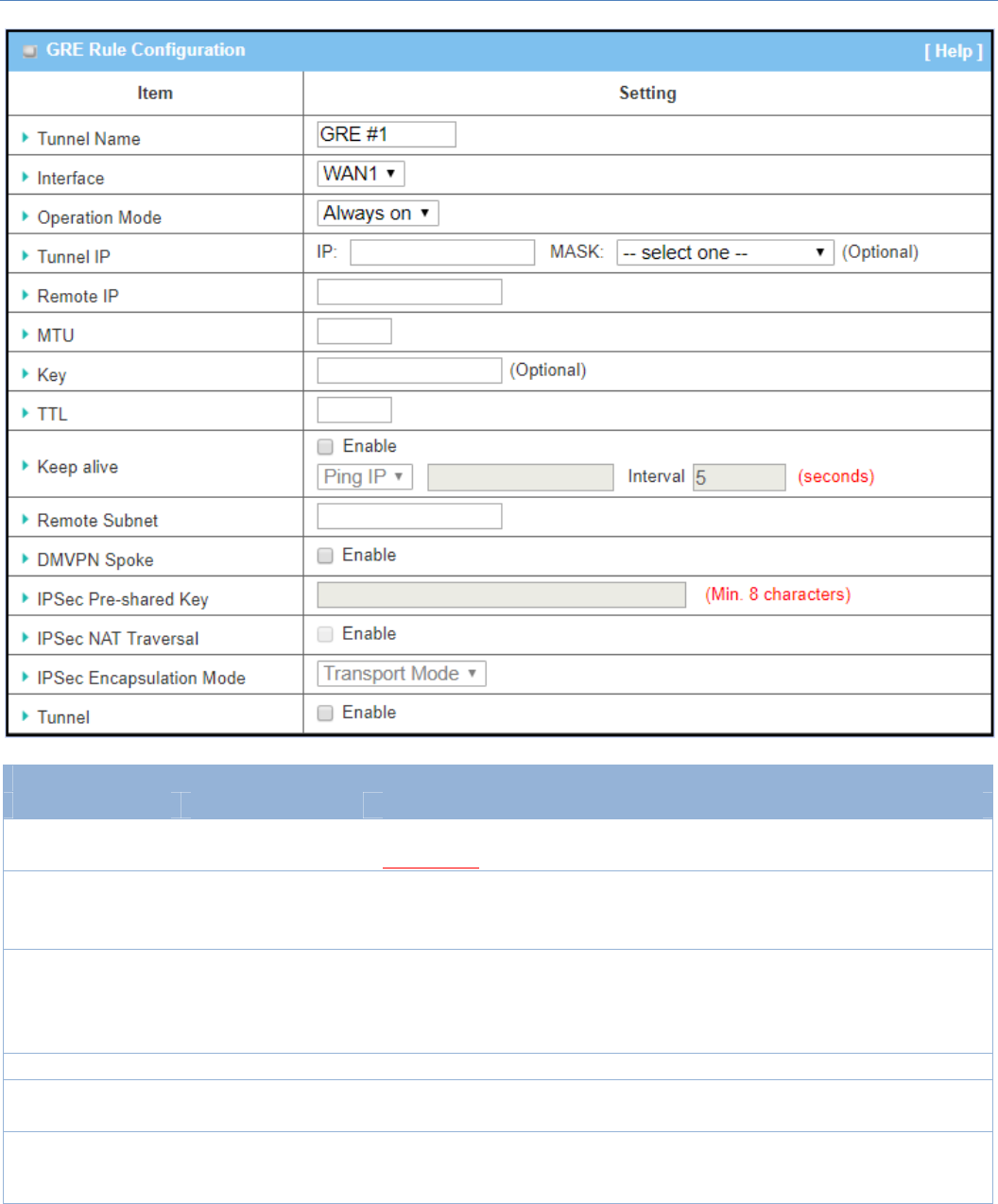
Create/EditGREtunnel
WhenAdd/Editbuttonisapplied,aGRERuleConfigurationscreenwillappear.
M2MCellularGateway
156
GRERuleConfigurationWindow
Item Valuesetting Description
TunnelName AMustfillsetting Enteratunnelname.Enteranamethatiseasyforyoutoidentify.
ValueRange:1~9characters.
Interface
1.AMustfillsetting
2.WAN1isselected
bydefault
SelecttheinterfaceonwhichGREtunnelistobeestablished.Itcanbethe
availableWANandLANinterfaces.
OperationMode
1.AMustfillsetting
2.Alwayonisselected
bydefault
DefineoperationmodefortheGRETunnel.ItcanbeAlwaysOn,orFailover.
Ifthistunnelissetasafailovertunnel,youneedtofurtherselectaprimary
tunnelfromwhichtofailoverto.
Note:FailovermodeisnotavailableforthegatewaywithsingleWAN.
TunnelIP AnOptionalsetting EntertheTunnelIPaddressandcorrespondingsubnetmask.
RemoteIP AMustfillsetting EntertheRemoteIPaddressofremoteGREtunnelgateway.Normallythisisthe
publicIPaddressoftheremoteGREgateway.
MTU
1.AMustfilledsetting
2.Auto(valuezero)is
setbydefault
MTUreferstoMaximumTransmissionUnit.Itspecifiesthelargestpacketsize
permittedforInternettransmission.
WhensettoAuto(value‘0’),therouterselectsthebestMTUforbestInternet
M2MCellularGateway
157
connectionperformance.
ValueRange:0~1500.
Key AnOptionalsetting EntertheKeyfortheGREconnection.
ValueRange:0~9999999999.
TTL 1.AMustfillsetting
2.1to255range
SpecifyTTLhop‐countvalueforthisGREtunnel.
ValueRange:1~255.
Keepalive
1.Uncheckedby
default
2.5sissetbydefault
ChecktheEnableboxtoenableKeepalivefunction.
SelectPingIPtokeepliveandentertheIPaddresstoping.
Enterthepingtimeintervalinseconds.
ValueRange:5~999seconds.
RemoteSubnet AMustfillsetting
SpecifytheremotesubnetforthisGREtunnel.
TheRemoteSubnetformatmustbeIPaddress/netmask(e.g.10.0.0.2/24).
ItisfortheIntranetofGREserverpeer.So,atGREclientpeer,thepackets
whosedestinationisinthededicatedsubnetwillbetransferredviatheGRE
tunnel.Otherswillbetransferredbasedoncurrentroutingpolicyofthesecurity
gatewayatGREclientpeer.
Ifyouentered0.0.0.0/0intheRemoteSubnetfield,itwillbetreatedasa
defaultgatewaysettingfortheGREclientpeer,allpackets,includingthe
InternetaccessingofGREclientpeer,willgothroughtheestablishedGRE
tunnel.ThatmeanstheremoteGREserverpeercontrolstheflowofanypackets
fromtheGREclientpeer.Certainly,thosepacketscomethroughtheGRE
tunnel.
DMVPNSpoke Uncheckedbydefault SpecifywhetherthegatewaywillsupportDMVPNSpokeforthisGREtunnel.
CheckEnableboxtoenableDMVPNSpoke.
IPSecPre‐shared
Key AMustfillsetting EnteraDMVPNspokeauthenticationPre‐sharedKey(8~32characters).
Note:Pre‐sharedKeyisavailableonlywhenDMVPNSpokeisenabled.
IPSecNATTraversal Uncheckedbydefault CheckEnableboxtoenableNAT‐Traversal.
Note:IPSecNATTraversalwillnotbeavailablewhenDMVPNisnotenabled.
IPSecEncapsulation
Mode Uncheckedbydefault
SpecifyIPSecEncapsulationModefromthedropdownbox.ThereareTransport
modeandTunnelmodesupported.
Note:IPSecEncapsulationModewillnotbeavailablewhenDMVPNisnot
enabled.
Tunnel Uncheckedbydefault CheckEnableboxtoenablethisGREtunnel.
Save N/A ClickSavebuttontosavethesettings.
Undo N/A ClickUndobuttontocancelthesettings.
Back N/A ClickBackbuttontoreturntothepreviouspage.
M2MCellularGateway
158
5.2Firewall
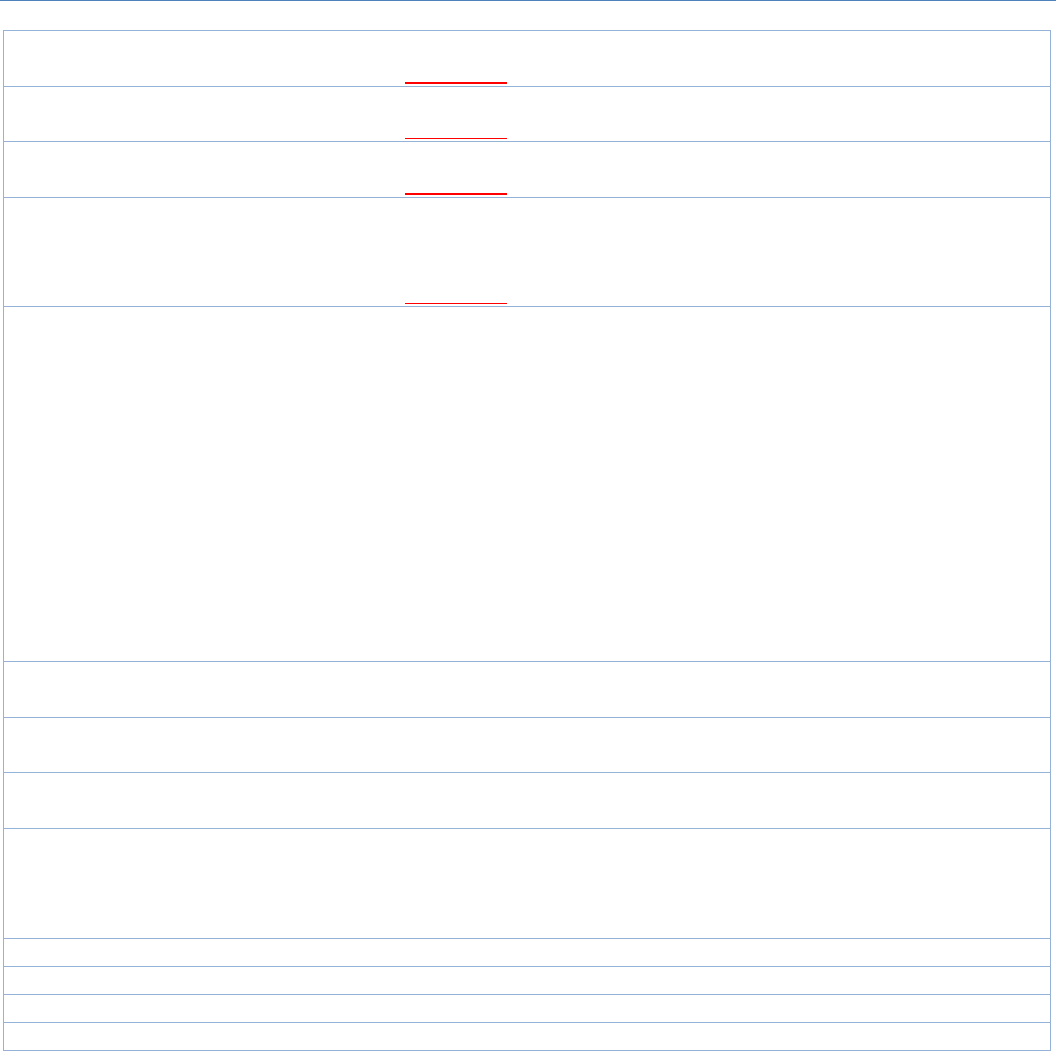
The firewall functions include Packet Filter, URL Blocking, Content Filter, MAC Control, Application Filter, IPS
andsomefirewalloptions.Thesupportedfunctioncanbedifferentforthepurchasedgateway.
5.2.1PacketFilter
M2MCellularGateway
159
"PacketFilter"functioncanletyoudefinesomefilteringrules for incoming and outgoing packets. So the
gatewaycancontrolwhatpacketsareallowedorblockedtopassthroughit.Apacketfilterruleshould
indicatefromandtowhichinterfacethepacketentersandleavesthegateway,thesourceanddestinationIP
addresses,anddestinationserviceporttypeandportnumber.Inaddition,thetimescheduletowhichtherule
willbeactive.
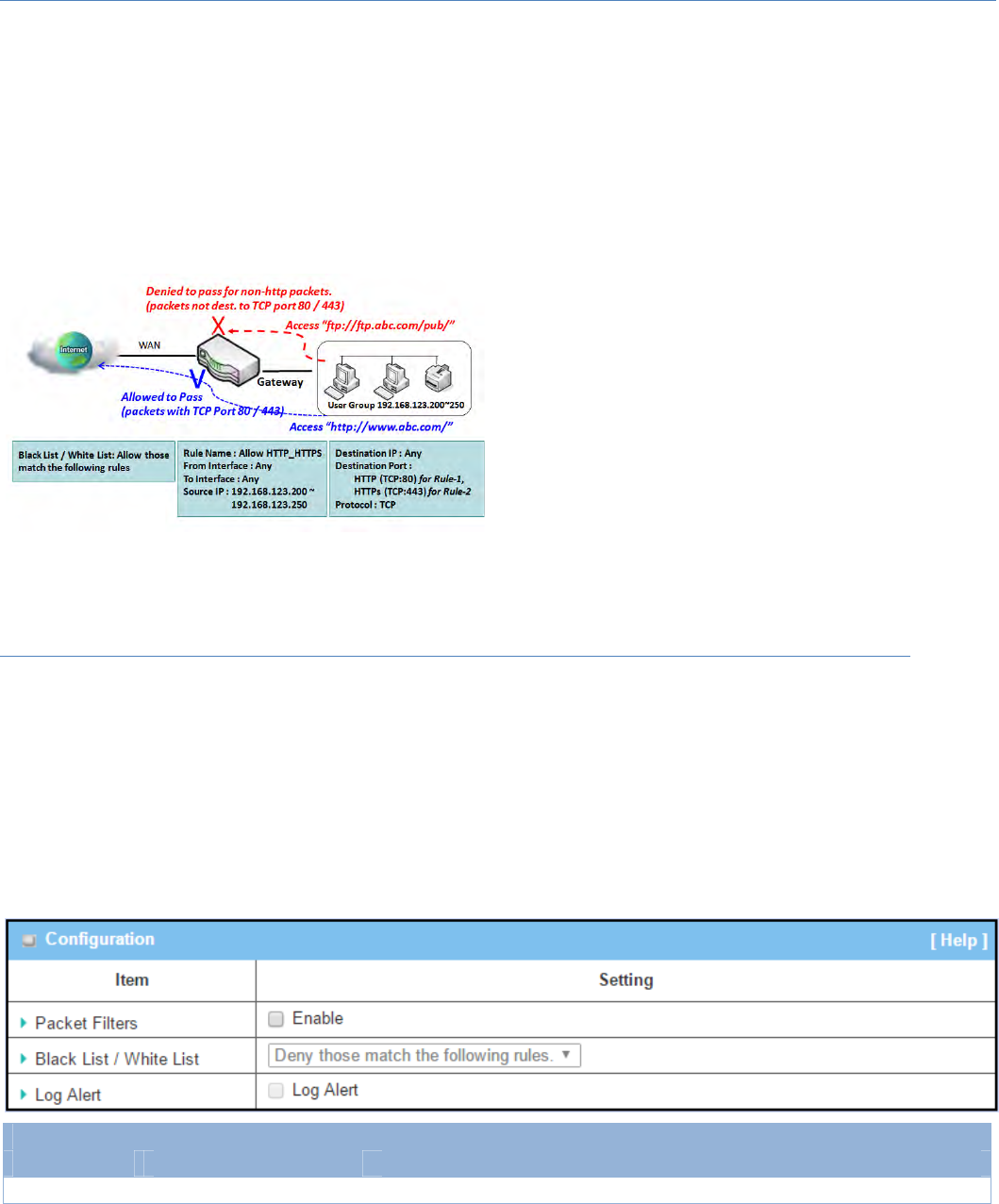
PacketFilterwithWhiteListScenario
Asshowninthediagram,specify"PacketFilterRule
List"aswhitelist(Allow those match the following
rules) and define the rules. Rule‐1 is to allow HTTP
packetstopass,andRule‐2istoallowHTTPSpackets
topass.
Undersuchconfiguration,thegatewaywillallowonly
HTTPandHTTPSpackets,issuedfromtheIPrange
192.168.123.200 to 250, which are targeted to TCP
port80or443topasstheWANinterface.
PacketFilterSetting
GotoSecurity>Firewall>PacketFilterTab.
Thepacketfiltersettingallowsusertocreateandcustomizepacketfilterpoliciestoallowor rejectspecific
inbound/outboundpacketsthroughtherouterbasedontheirofficesetting.
EnablePacketFilter
ConfigurationWindow
ItemName Valuesetting Description
PacketFilter Theboxisuncheckedby ChecktheEnableboxtoactivatePacketFilterfunction
M2MCellularGateway
160
default
BlackList/
WhiteList
Denythosematchthe
followingrulesissetby
default
WhenDenythosematchthefollowingrulesisselected,asthenamesuggest,
packetsspecifiedintheruleswillbeblocked–blacklisted.Incontrast,with
Allowthosematchthefollowingrules,youcanspecificallywhitelistthe
packetstopassandtherestwillbeblocked.
LogAlert Theboxisuncheckedby
default ChecktheEnableboxtoactivateEventLog.
Save N/A ClickSavetosavethesettings
Undo N/A ClickUndotocancelthesettings
Create/EditPacketFilterRules
Thegatewayallowsyoutocustomizeyourpacketfilteringrules.Itsupportsuptoamaximumof20filterrule
sets.
WhenAddbuttonisapplied,PacketFilterRuleConfigurationscreenwillappear.
PacketFilterRuleConfiguration
ItemName Valuesetting Description
RuleName 1.Stringformatcanbe Enterapacketfilterrulename.Enteranamethatiseasyforyoutoremember.

M2MCellularGateway
161
anytext
2.AMustfilledsetting
ValueRange:1~30characters.
FromInterface
1.AMustfilledsetting
2.BydefaultAnyis
selected
Definetheselectedinterfacetobethepacket‐enteringinterfaceoftherouter.
IfthepacketstobefilteredarecomingfromLANtoWANthenselectLANfor
thisfield.OrVLAN‐1toWANthenselectVLAN‐1forthisfield.Otherexamples
areVLAN‐1toVLAN‐2.VLAN‐1toWAN.
SelectAnytofilterpacketscomingintotherouterfromanyinterfaces.
Pleasenotethattwoidenticalinterfacesarenotacceptedbytherouter.e.g.,
VLAN‐1toVLAN‐1.
ToInterface
1.AMustfilledsetting
2.BydefaultAnyis
selected
Definetheselectedinterfacetobethepacket‐leavinginterfaceoftherouter.If
thepacketstobefilteredareenteringfromLANtoWANthenselectWANfor
thisfield.OrVLAN‐1toWANthenselectWANforthisfield.Otherexamplesare
VLAN‐1toVLAN‐2.VLAN‐1toWAN.
SelectAnytofilterpacketsleavingtherouterfromanyinterfaces.
Pleasenotethattwoidenticalinterfacesarenotacceptedbytherouter.e.g.,
VLAN‐1toVLAN‐1.
SourceIP
1.AMustfilledsetting
2.BydefaultAnyis
selected
ThisfieldistospecifytheSourceIPaddress.
SelectAnytofilterpacketscomingfromanyIPaddresses.
SelectSpecificIPAddresstofilterpacketscomingfromanIPaddress.
SelectIPRangetofilterpacketscomingfromaspecifiedrangeofIPaddress.
DestinationIP
1.AMustfilledsetting
2.BydefaultAnyis
selected
ThisfieldistospecifytheDestinationIPaddress.
SelectAnytofilterpacketsthatareenteringtoanyIPaddresses.
SelectSpecificIPAddresstofilterpacketsenteringtoanIPaddressenteredin
thisfield.
SelectIPRangetofilterpacketsenteringtoaspecifiedrangeofIPaddress
enteredinthisfield.
SourceMAC
1.AMustfilledsetting
2.BydefaultAnyis
selected
ThisfieldistospecifytheSourceMACaddress.
SelectAnytofilterpacketscomingfromanyMACaddresses.
SelectSpecificMACAddresstofilterpacketscomingfromaMACaddress.
Protocol
1.AMustfilledsetting
2.BydefaultAny(0)is
selected
ForProtocol,selectAnytofilteranyprotocolpackets
ThenforSourcePort,selectapredefinedportdropdownboxwhenWell‐known
Serviceisselected,otherwiseselectUser‐definedServiceandspecifyaport
range.
ThenforDestinationPort,selectapredefinedportdropdownboxwhenWell‐
knownServiceisselected,otherwiseselectUser‐definedServiceandspecifya
portrange.
ValueRange:1~65535forSourcePort,DestinationPort.
ForProtocol,selectICMPv4tofilterICMPv4packets
ForProtocol,selectTCPtofilterTCPpackets
ThenforSourcePort,selectapredefinedportdropdownboxwhenWell‐known
Serviceisselected,otherwiseselectUser‐definedServiceandspecifyaport
range.
ThenforDestinationPort,selectapredefinedportdropdownboxwhenWell‐
knownServiceisselected,otherwiseselectUser‐definedServiceandspecifya
portrange.
ValueRange:1~65535forSourcePort,DestinationPort.

M2MCellularGateway
162
ForProtocol,selectUDPtofilterUDPpackets
ThenforSourcePort,selectapredefinedportdropdownboxwhenWell‐known
Serviceisselected,otherwiseselectUser‐definedServiceandspecifyaport
range.
ThenforDestinationPort,selectapredefinedportdropdownboxwhenWell‐
knownServiceisselected,otherwiseselectUser‐definedServiceandspecifya
portrange.
ValueRange:1~65535forSourcePort,DestinationPort.
ForProtocol,selectGREtofilterGREpackets
ForProtocol,selectESPtofilterESPpackets
ForProtocol,selectSCTPtofilterSCTPpackets
ForProtocol,selectUser‐definedtofilterpacketswithspecifiedportnumber.
ThenenterapotnumberinProtocolNumberbox.
TimeSchedule AMustfilledsetting
ApplyTimeScheduletothisrule,otherwiseleaveitasAlways.
IfthedropdownlistisemptyensureTimeScheduleispre‐configured.Referto
ObjectDefinition>Scheduling>Configurationtab.
Rule Theboxisuncheckedby
default. ClickEnableboxtoactivatethisrulethensavethesettings.
Save N/A ClickSavetosavethesettings
Undo N/A ClickUndotocancelthesettings
Back N/A WhentheBackbuttonisclickedthescreenwillreturntothePacketFilter
Configurationpage.
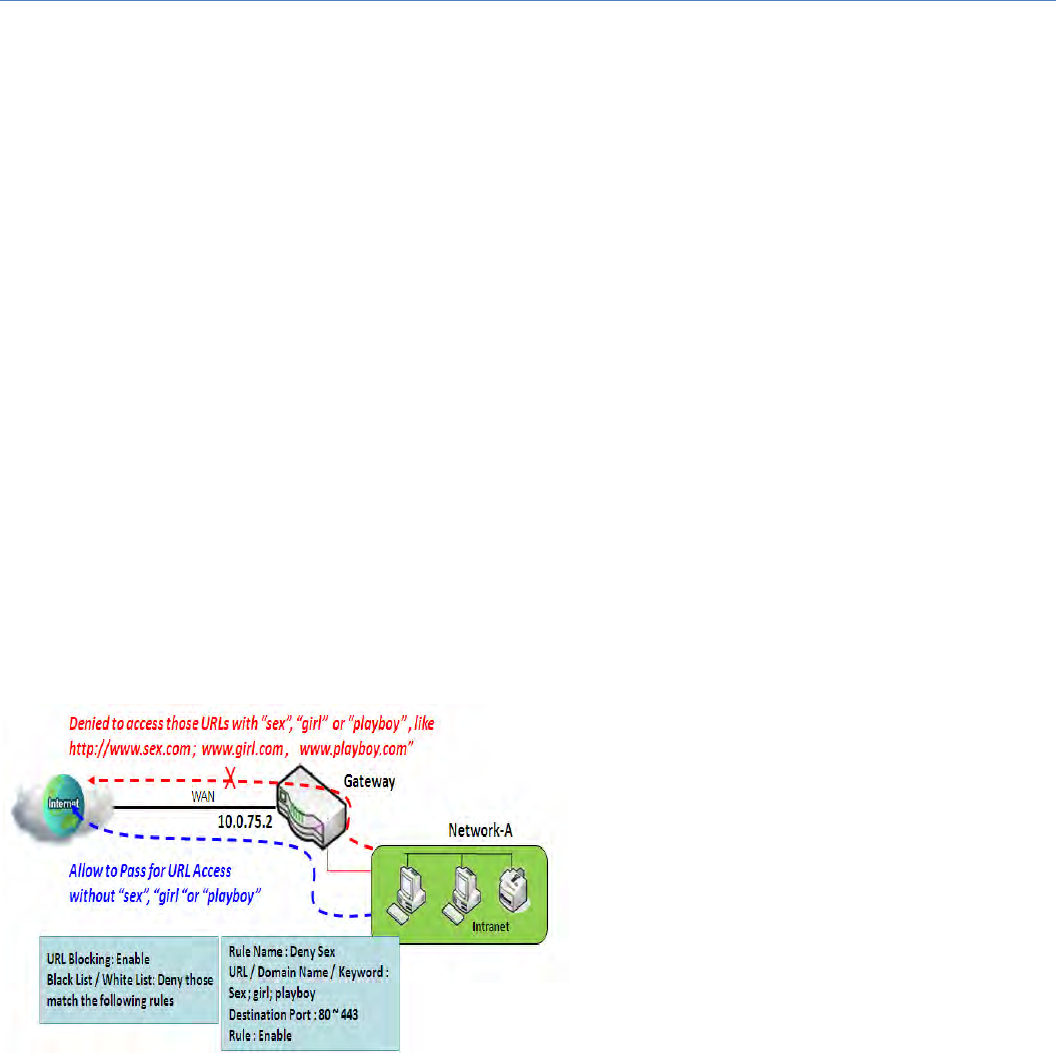
M2MCellularGateway
163
5.2.2URLBlocking
"URLBlocking"functioncanletyoudefineblockingorallowingrulesforincomingandoutgoingWebrequest
packets. With defined rules, gateway can control the Web requests containing the complete URL, partial
domainname,orpre‐definedkeywords.Forexample,onecanfilteroutorallowonlytheWebrequestsbased
ondomaininputsuffixeslike.comor.orgorkeywordslike“bct”or“mpe”.
AnURLblockingruleshouldspecifytheURL,partialdomainname,orincludedkeywordsintheWebrequests
fromandtothegatewayandalsothedestinationserviceport.Besides,acertaintimeschedulecanbeapplied
toactivatetheURLBlockingrulesduringpre‐definedtimeinterval(s).
The gateway will logs and displays the disallowed web accessing requests that matched the defined URL
blockingruleintheblack‐listorintheexclusionofthewhite‐list.
Whenyouchoose"Allowalltopassexceptthosematchthefollowingrules"forthe"URLBlockingRuleList",
youaresettingthedefinedURLblockingrulestobelongtotheblacklist.Thepackets,listedintherulelist,will
be blocked if one pattern in the requests matches to one rule. Other Web requests can pass through the
gateway.Incontrast,whenyouchoose"Denyalltopassexceptthosematchthefollowingrules"forthe"URL
BlockingRuleList",youaresettingthedefinedpacketfiltering rules to belong to the white list. The Web
requests, listed in the rule, will be allowed if one pattern in the requests matches to one rule. Other Web
requestswillbeblocked.
URLBlockingRulewithBlackList
Whentheadministratorofthegatewaywantsto
block the Web requests with some dedicated
patterns,hecanusethe"URLBlocking"function
to block specific Web requests by defining the
black listas shownin abovediagram.Certainly,
whentheadministratorwantstoallowonlythe
Web requests with some dedicated patterns to
go through the gateway, he can also use the
"URL Blocking" function by defining the white
listtomeettherequirement.
As shown in the diagram, enable the URL
blocking function and create the first rule to
denytheWebrequestswith"sex"or"sexygirl"patternsandthe other to deny the Web requests with
"playboy"patterntogothroughthegateway.Systemwillblockthe Web requests with "sex", "sexygirl" or
"playboy"patternstopassthroughthegateway.
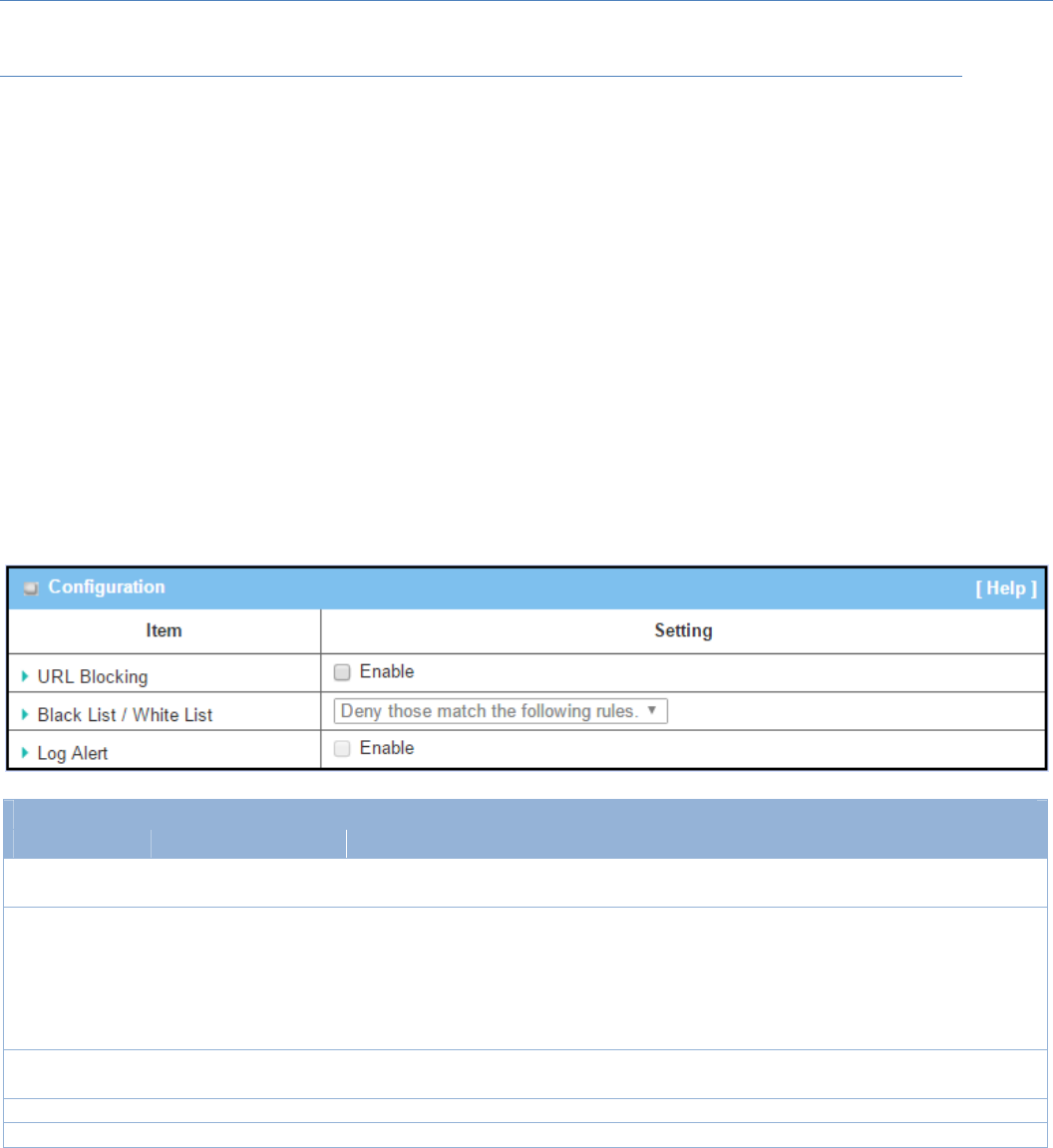
M2MCellularGateway
164
URLBlockingSetting
GotoSecurity>Firewall>URLBlockingTab.
In"URL Blocking"page,therearethree configurationwindows.Theyare the"Configuration"window,"URL
BlockingRuleList"window,and"URLBlockingRuleConfiguration"window.
The"Configuration"windowcanletyouactivatetheURLblockingfunctionandspecifytoblacklistingorto
whitelistingthepacketsdefinedinthe"URLBlockingRuleList"entry.Inaddition,logalertingcanbeenabled
torecordon‐goingeventsforanydisallowedWebrequestpackets.Referto"SystemStatus"in"6.1.1System
Related"sectioninthisusermanualforhowtoviewrecordedlog.
The"URLBlockingRuleList"windowlistsallyourdefinedURLblocking rule entry. And finally, the "URL
BlockingRuleConfiguration"windowcanletyoudefineURLblockingrules.Theparametersinaruleinclude
therulename,theSourceIPorMAC,theURL/DomainName/Keyword,thedestinationserviceports,the
integratedtimescheduleruleandtheruleactivation.
EnableURLBlocking
Configuration
Item Valuesetting Description
URLBlocking Theboxisunchecked
bydefault
ChecktheEnable boxtoactivateURLBlockingfunction.
BlackList/
WhiteList
Denythosematchthe
followingrulesisset
bydefault
SpecifytheURLBlockingPolicy,eitherBlackListorWhiteList.
BlackList:WhenDenythosematchthefollowingrulesisselected,asthename
suggest,thematchedWebrequestpacketswillbeblocked.
WhiteList:WhenAllowthosematchthefollowingrulesisselected,thematched
WebrequestpacketscanpassthroughtheGateway,andtheothersthatdon’tmatch
theruleswillbeblocked.
LogAlert Theboxisunchecked
bydefault
ChecktheEnable boxtoactivateEventLog.
Save NA ClickSave buttontosavethesettings
Undo NA ClickUndo buttontocancelthesettings
Create/EditURLBlockingRules
TheGatewaysupportsuptoamaximumof20URLblockingrulesets.EnsurethattheURLBlockingisenabledbeforewe
cancreateblockingrules.
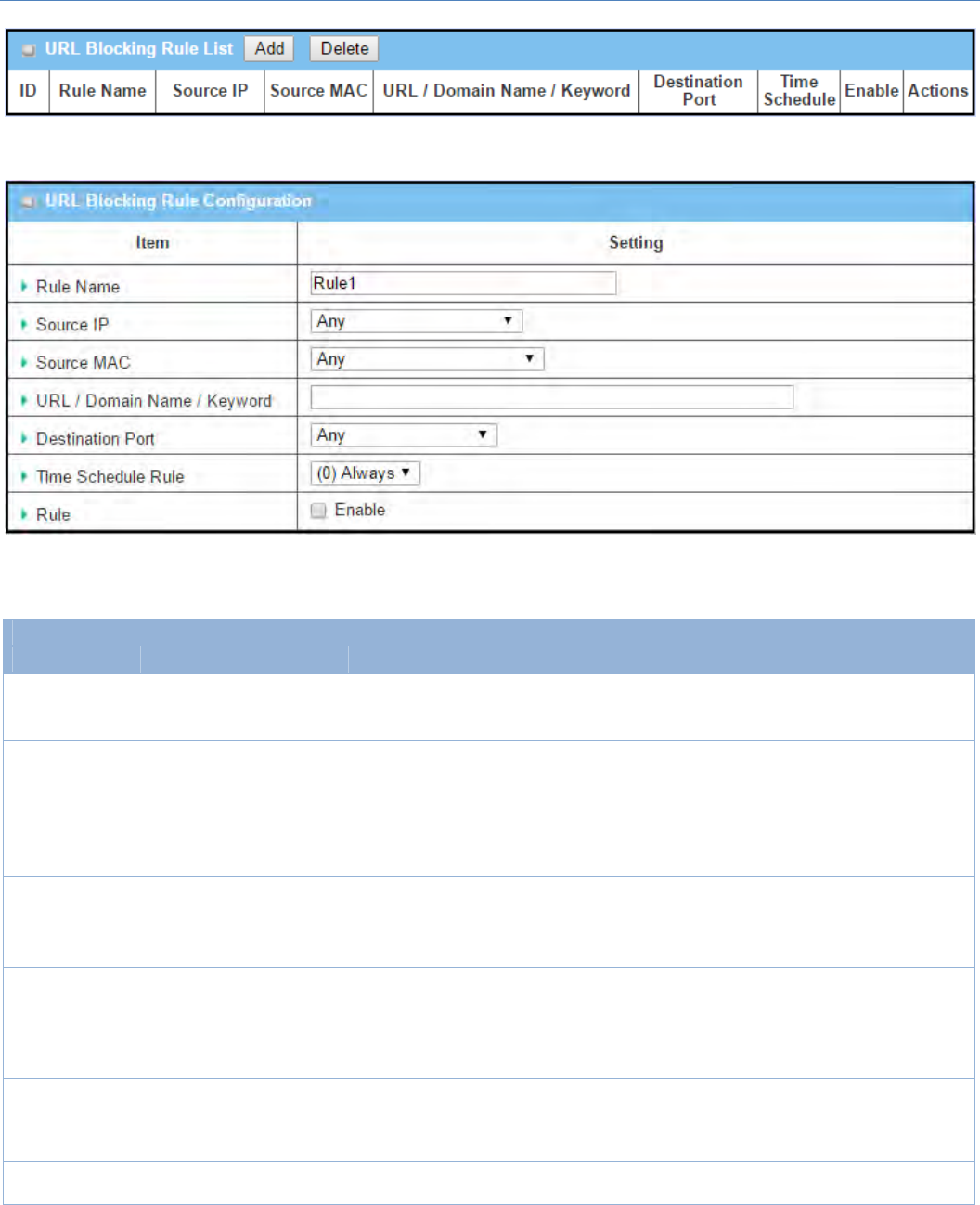
M2MCellularGateway
165
WhenAddbuttonisapplied,theURLBlockingRuleConfigurationscreenwillappear.
URLBlockingRulesConfiguration
Item Valuesetting Description
RuleName
1.Stringformatcanbeany
text
2.AMustfilledsetting
SpecifyanURLBlocking rulename.Enteranamethatiseasyforyouto
understand.
SourceIP
1. AMustfilledsetting
2. Anyissetbydefault
ThisfieldistospecifytheSourceIPaddress.
SelectAnytofilterpacketscomingfromanyIPaddresses.
SelectSpecificIPAddresstofilterpacketscomingfromanIPaddressenteredin
thisfield.
SelectIPRangetofilterpacketscomingfromaspecifiedrangeofIPaddress
enteredinthisfield.
SourceMAC
1. AMustfilledsetting
2. Anyissetbydefault
ThisfieldistospecifytheSourceMAC address.
SelectAnytofilterpacketscomingfromanyMACaddresses.
SelectSpecificMACAddresstofilterpacketscomingfromaMACaddress
enteredinthisfield.
URL/Domain
Name/
Keyword
1.AMustfilledsetting
2.Supportsuptoa
maximumof10Keywords
inarulebyusingthe
delimiter“;”.
SpecifyURL,DomainName,orKeywordlistforURLchecking.
IntheBlackListmode,ifamatchedruleisfound,thepacketswillbedropped.
IntheWhiteListmode,ifamatchedruleisfound,thepacketswillbeaccepted
andtheotherswhichdon’tmatchanyrulewillbedropped.
Destination
Port
1. AMustfilledsetting
2. Anyissetbydefault
ThisfieldistospecifytheDestinationPortnumber.
SelectAnytofilterpacketsgoingtoanyPort.
SelectSpecificServicePorttofilterpacketsgoingtoaspecificPortenteredinthisfield.
SelectPortRangetofilterpacketsgoingtoaspecificrangeofPortsenteredinthisfield.
Time AMustfilledsetting ApplyaspecificTimeScheduletothisrule;otherwiseleaveitas(0)Always.
IfthedropdownlistisemptyensureTimeScheduleispre‐configured.RefertoObject

M2MCellularGateway
166
ScheduleRule Definition>Scheduling>Configuration tab.
Rule Theboxisuncheckedby
default.
ClicktheEnableboxtoactivatethisrule.
Save NA ClicktheSave buttontosavethesettings.
Undo NA ClicktheUndo buttontocancelthechanges.
Back NAClicktheBackbuttontoreturntotheURLBlockingConfigurationpage.
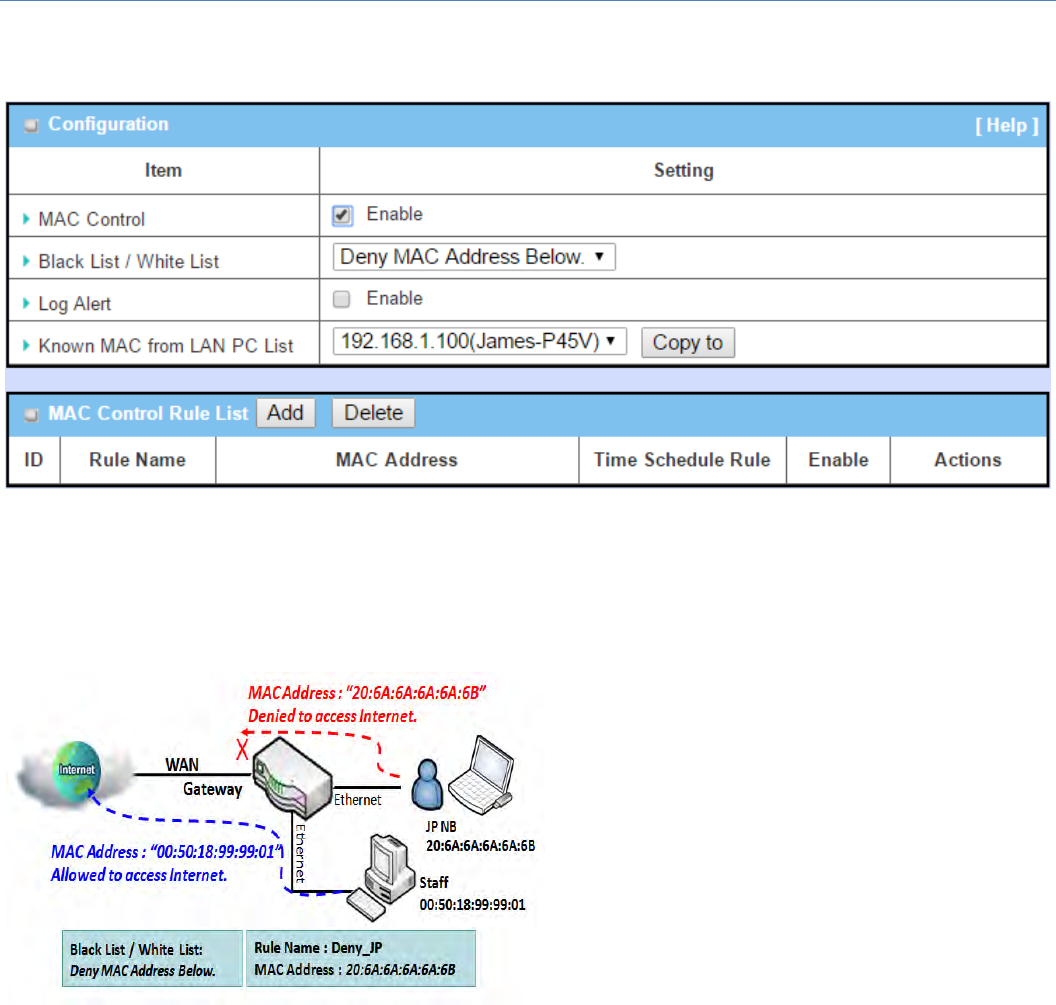
M2MCellularGateway
167
5.2.3MACControl
"MAC Control" function allows you to assign the accessibility to the gateway for different users based on
device’s MAC address. When the administrator wants to reject the traffics from some client hosts with specific
MAC addresses, he can use the "MAC Control" function to reject with the black list configuration.
MACControlwithBlackListScenario
Asshown inthe diagram,enabletheMACcontrol
functionandspecifythe"MACControlRuleList"is
ablacklist,andconfigureoneMACcontrolrulefor
thegatewayto denythe connectionrequestfrom
the "JP NB" with its own MAC address
20:6A:6A:6A:6A:6B.
Systemwillblocktheconnectingfromthe"JPNB"
tothegatewaybutallowothers.
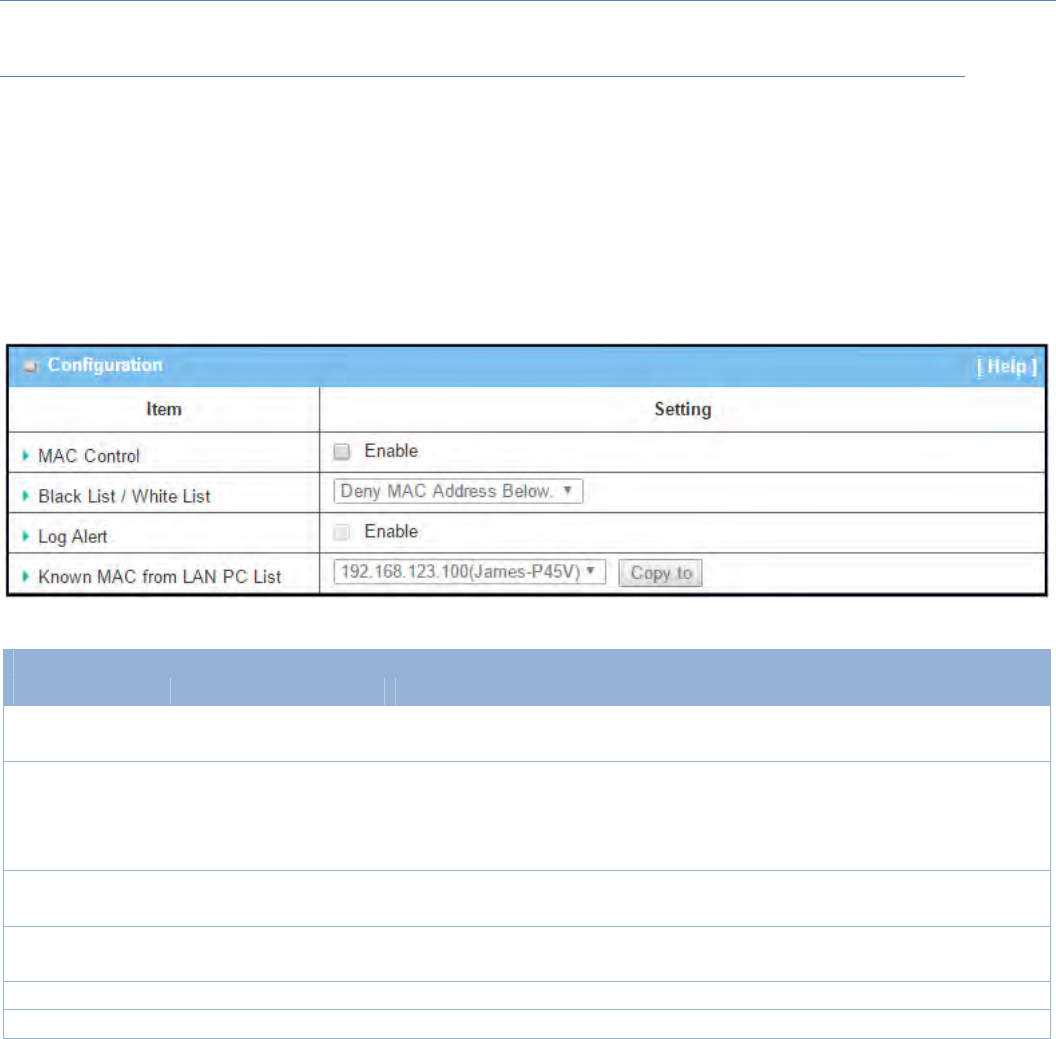
M2MCellularGateway
168
MACControlSetting
GotoSecurity>Firewall>MACControlTab.
TheMACcontrolsettingallowsusertocreateandcustomizeMACaddresspoliciestoalloworrejectpackets
withspecificsourceMACaddress.
EnableMACControl
ConfigurationWindow
Item Valuesetting Description
MACControl Theboxisuncheckedby
default ChecktheEnableboxtoactivatetheMACfilterfunction
BlackList/
WhiteList
DenyMACAddressBelow
issetbydefault
WhenDenyMACAddressBelowisselected,asthenamesuggest,packets
specifiedintheruleswillbeblocked–blacklisted.Incontrast,withAllowMAC
AddressBelow,youcanspecificallywhitelistthepacketstopassandtherest
willbeblocked.
LogAlert Theboxisuncheckedby
default ChecktheEnableboxtoactivatetoactivateEventLog.
KnownMAC
fromLANPCList N/A SelectaMACAddressfromLANClientList.ClicktheCopytotocopythe
selectedMACAddresstothefilterrule.
Save N/A ClickSavetosavethesettings
Undo N/A ClickUndotocancelthesettings
M2MCellularGateway
169
Create/EditMACControlRules
Thegatewaysupportsuptoamaximumof20filterrulesets.EnsurethattheMACControlisenabledbefore
wecancreatecontrolrules.
WhenAddbuttonisapplied,FilterRuleConfigurationscreenwillappear.
MACControlRuleConfiguration
Item Valuesetting Description
RuleName
1.Stringformatcanbeany
text
2.AMustfillsetting
EnteraMACControlrulename.Enteranamethatiseasyforyoutoremember.
MACAddress
(Use:to
Compose)
1.MACAddressstring
Format
2.AMustfillsetting
SpecifytheSourceMACAddresstofilterrule.
TimeSchedule AMustfillsetting
ApplyTimeScheduletothisrule;otherwiseleaveitas(0)Always.
Ifthedropdownlistisempty,ensureTimeScheduleispre‐configured.Referto
ObjectDefinition>Scheduling>Configurationtab
Enable Theboxisuncheckedby
default. ClickEnableboxtoactivatethisrule,andthensavethesettings.
Save N/A ClickSavetosavethesettings
Undo N/A ClickUndotocancelthesettings
Back N/A ClickBacktoreturntotheMACControlConfigurationpage.

M2MCellularGateway
170
5.2.4ContentFilter(notsupported)
Not supported feature for the purchased product, leave it as blank.

M2MCellularGateway
171
5.2.5ApplicationFilter(notsupported)
Not supported feature for the purchased product, leave it as blank.
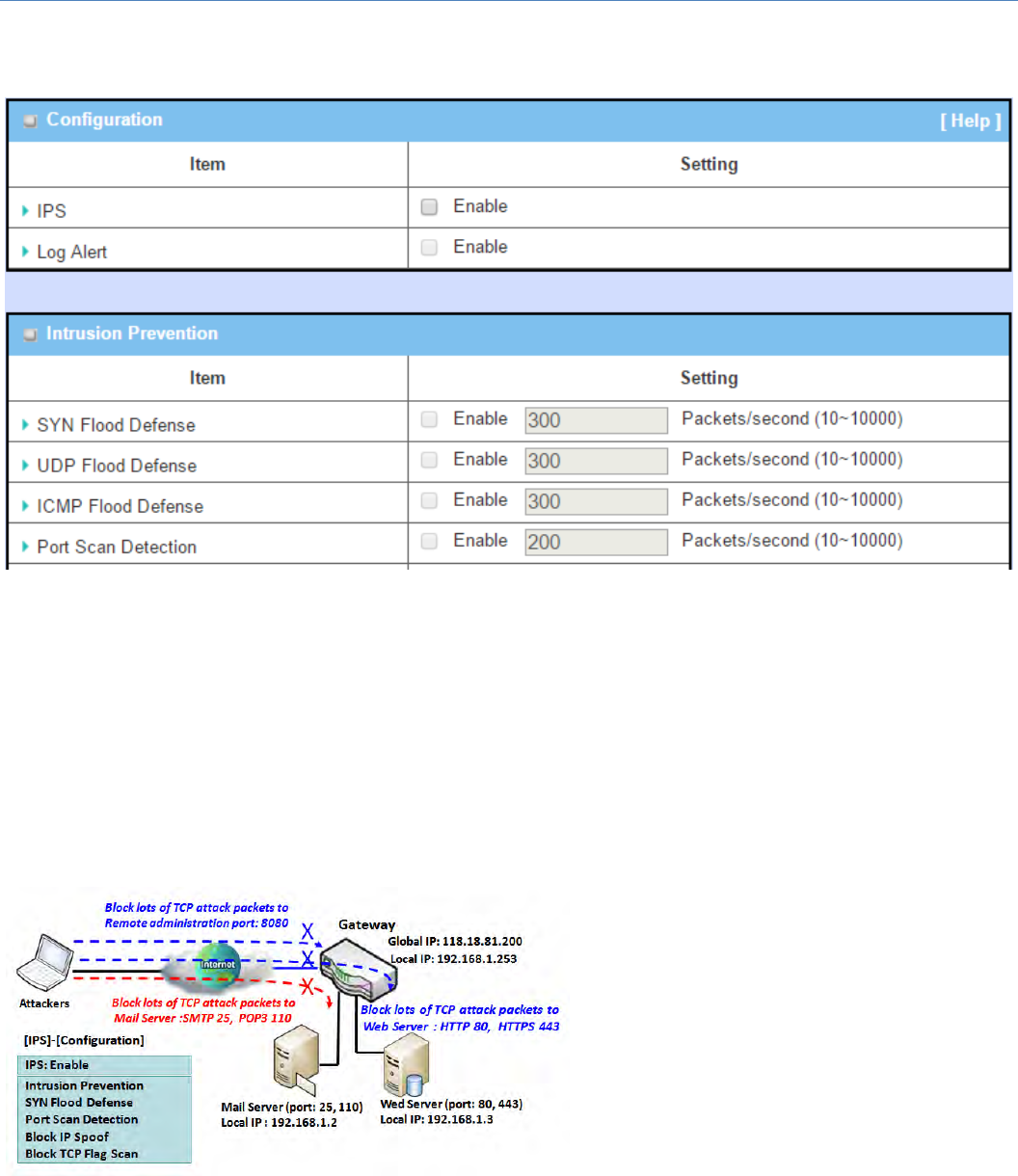
M2MCellularGateway
172
5.2.6IPS
ToprovideapplicationserversintheInternet,administratormayneedtoopenspecificportsfortheservices.
However,therearesomeriskstoalwaysopenserviceportsintheInternet.Inordertoavoidsuchattackrisks,
itisimportanttoenableIPSfunctions.
Intrusion Prevention System (IPS) is network security appliancesthatmonitornetworkand/orsystem
activitiesformaliciousactivity.ThemainfunctionsofIPSaretoidentifymaliciousactivity,loginformation
aboutthisactivity,attempttoblock/stopitandreportit.YoucanenabletheIPSfunctionandcheckthelisted
intrusion activities when needed. You can also enable the log alerting so that system will record Intrusion
eventswhencorrespondingintrusionsaredetected.
IPSScenario
Asshowninthediagram,thegatewayserves
asanE‐mailserver,WebServerandalso
provides TCP port 8080 for remote
administration. So, remote users or unknown
userscanrequestthoseservicesfromInternet.
With IPS enabled, the gateway can detect
incoming attack packets, including the TCP
ports(25,80,110,443and8080)withservices.
It will block the attack packets and let the
normalaccesstopassthroughthegateway
M2MCellularGateway
173
IPSSetting
GotoSecurity>Firewall>IPSTab.
TheIntrusionPreventionSystem(IPS)settingallowsusertocustomizeintrusionpreventionrulestoprevent
maliciouspackets.
EnableIPSFirewall
ConfigurationWindow
Item Valuesetting Description
IPS Theboxisuncheckedby
default ChecktheEnableboxtoactivateIPSfunction
LogAlert Theboxisuncheckedby
default ChecktheEnableboxtoactivatetoactivateEventLog.
Save N/A ClickSavetosavethesettings
Undo N/A ClickUndotocancelthesettings
SetupIntrusionPreventionRules
Therouterallowsyoutoselectintrusionpreventionrulesyoumaywanttoenable.EnsurethattheIPSis
enabledbeforewecanenablethedefensefunction.
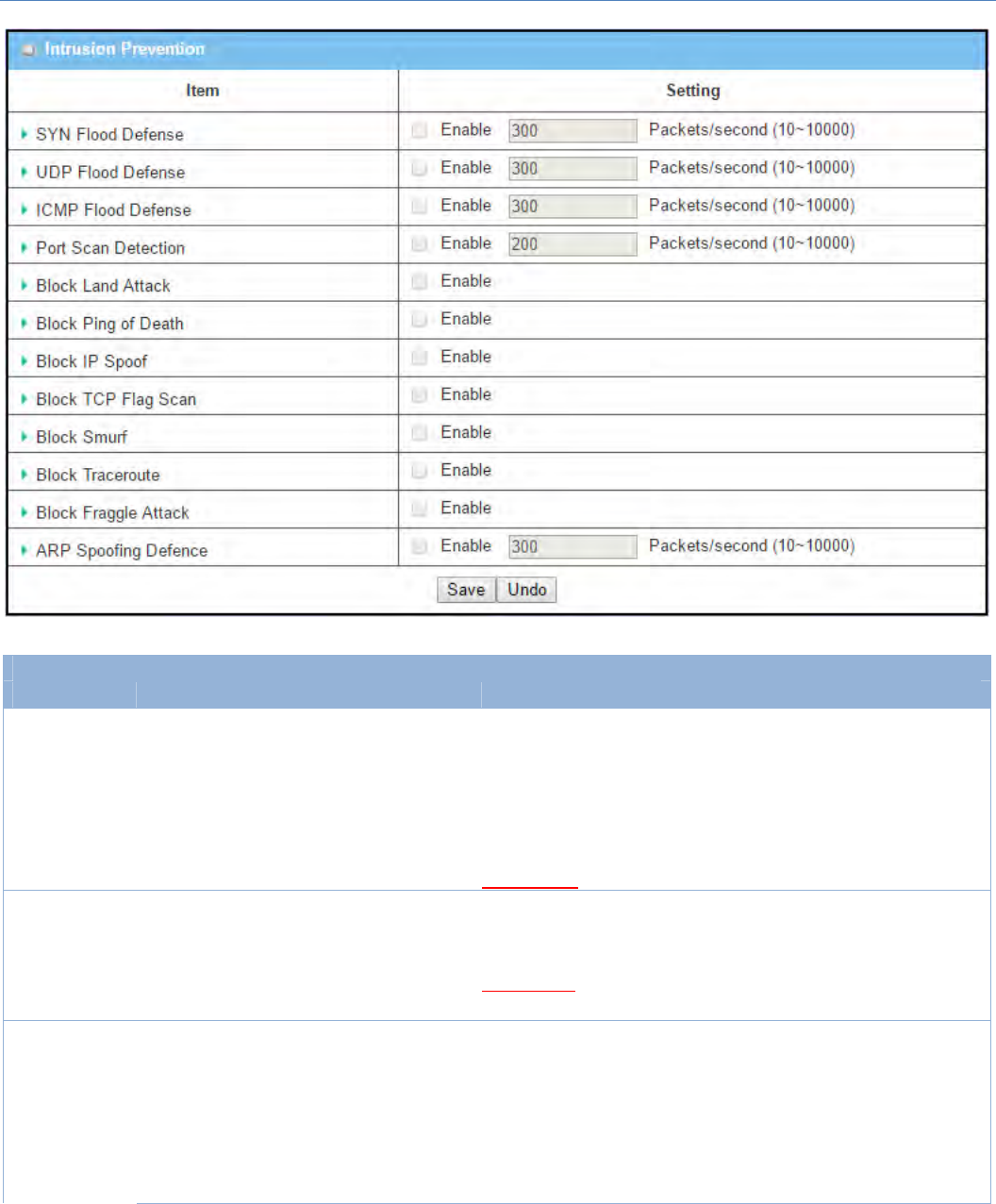
M2MCellularGateway
174
SetupIntrusionPreventionRules
ItemName Valuesetting Description
SYNFlood
Defense 1.AMustfilledsetting
2.Theboxisuncheckedbydefault.
3.Trafficthresholdissetto300bydefault
4.Thevaluerangecanbefrom10to
10000.
ClickEnableboxtoactivatethisintrusionpreventionruleand
enterthetrafficthresholdinthisfield.
UDPFlood
Defense
ClickEnableboxtoactivatethisintrusionpreventionruleand
enterthetrafficthresholdinthisfield.
ICMPFlood
Defense
ClickEnableboxtoactivatethisintrusionpreventionruleand
enterthetrafficthresholdinthisfield.
ValueRange:10~10000.
PortScan
Defection
1.AMustfilledsetting
2.Theboxisuncheckedbydefault.
3.Trafficthresholdissetto200bydefault
4.Thevaluerangecanbefrom10to
10000.
ClickEnableboxtoactivatethisintrusionpreventionruleand
enterthetrafficthresholdinthisfield.
ValueRange:10~10000.
BlockLand
Attack
Theboxisuncheckedbydefault. ClickEnableboxtoactivatethisintrusionpreventionrule.
BlockPingof
Death
BlockIPSpoof
BlockTCPFlag
Scan
BlockSmurf
M2MCellularGateway
175
Block
Traceroute
BlockFraggle
Attack
ARPSpoofing
Defence
1.AMustfilledsetting
2.Theboxisuncheckedbydefault.
3.Trafficthresholdissetto300bydefault
4.Thevaluerangecanbefrom10to
10000.
ClickEnableboxtoactivatethisintrusionpreventionruleand
enterthetrafficthresholdinthisfield.
ValueRange:10~10000.
Save NA ClickSavetosavethesettings
Undo NA ClickUndotocancelthesettings
M2MCellularGateway
176
5.2.7Options
Therearesomeadditionalusefulfirewalloptionsinthispage.
“StealthMode”letsgatewaynottorespondtoportscansfromtheWANsothatmakesitlesssusceptibleto
discoveryandattacksontheInternet.”SPI”enablesgatewaytorecordthepacketinformationlikeIPaddress,
portaddress,ACK,SEQnumberandsoonwhiletheypassthroughthegateway,andthegatewaychecksevery
incomingpackettodetectifthispacketisvalid.
“DiscardPingfromWAN”makesanyhostontheWANsidecan`tping this gateway. And finally, “Remote
AdministratorHosts”enablesyoutoperformadministrationtaskfromaremotehost.Ifthisfeatureisenabled,
onlyspecifiedIPaddress(es)canperformremoteadministration.
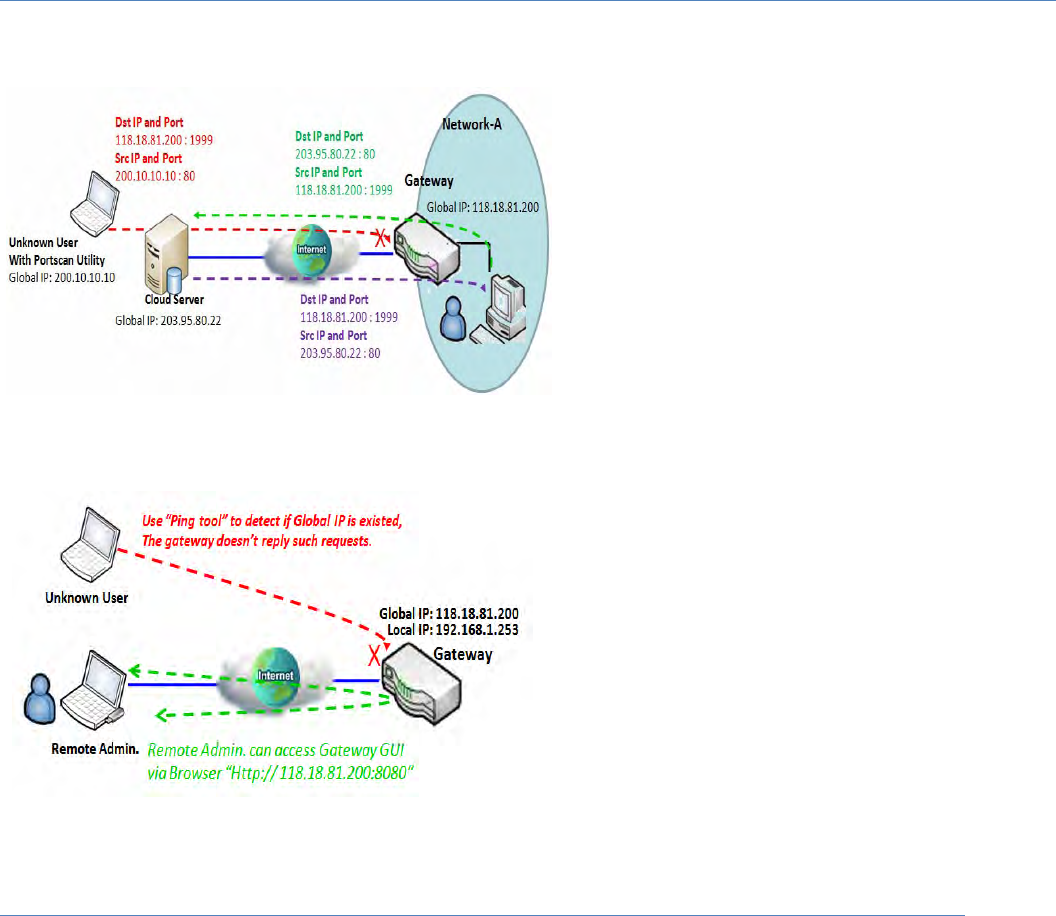
M2MCellularGateway
177
EnableSPIScenario
Asshowninthediagram,GatewayhastheIP
address of 118.18.81.200 for WAN interface and
192.168.1.253forLANinterface.ItservesasaNAT
gateway.UsersinNetwork‐Ainitiatetoaccess
cloud server through the gateway. Sometimes,
unknown users will simulate the packets but use
different source IP to masquerade. With the SPI
featurebeenenabledatthegateway,itwillblock
suchpacketsfromunknownusers.
DiscardPingfromWAN&RemoteAdministratorHostsScenario
“Discard Ping from WAN” makes any host on the
WANsidecan`tpingthisgatewayreplyanyICMP
packets.EnabletheDiscardPingfromWANfunction
to prevent security leak when local users surf the
internet.
Remoteadministratorknowsthegateway’sglobalIP,
and he can access the Gateway GUI via TCP port
8080.
FirewallOptionsSetting
GotoSecurity>Firewall>OptionsTab.
Thefirewalloptionssettingallowsnetworkadministratortomodifythebehaviorofthefirewallandtoenable
RemoteRouterAccessControl.
EnableFirewallOptions
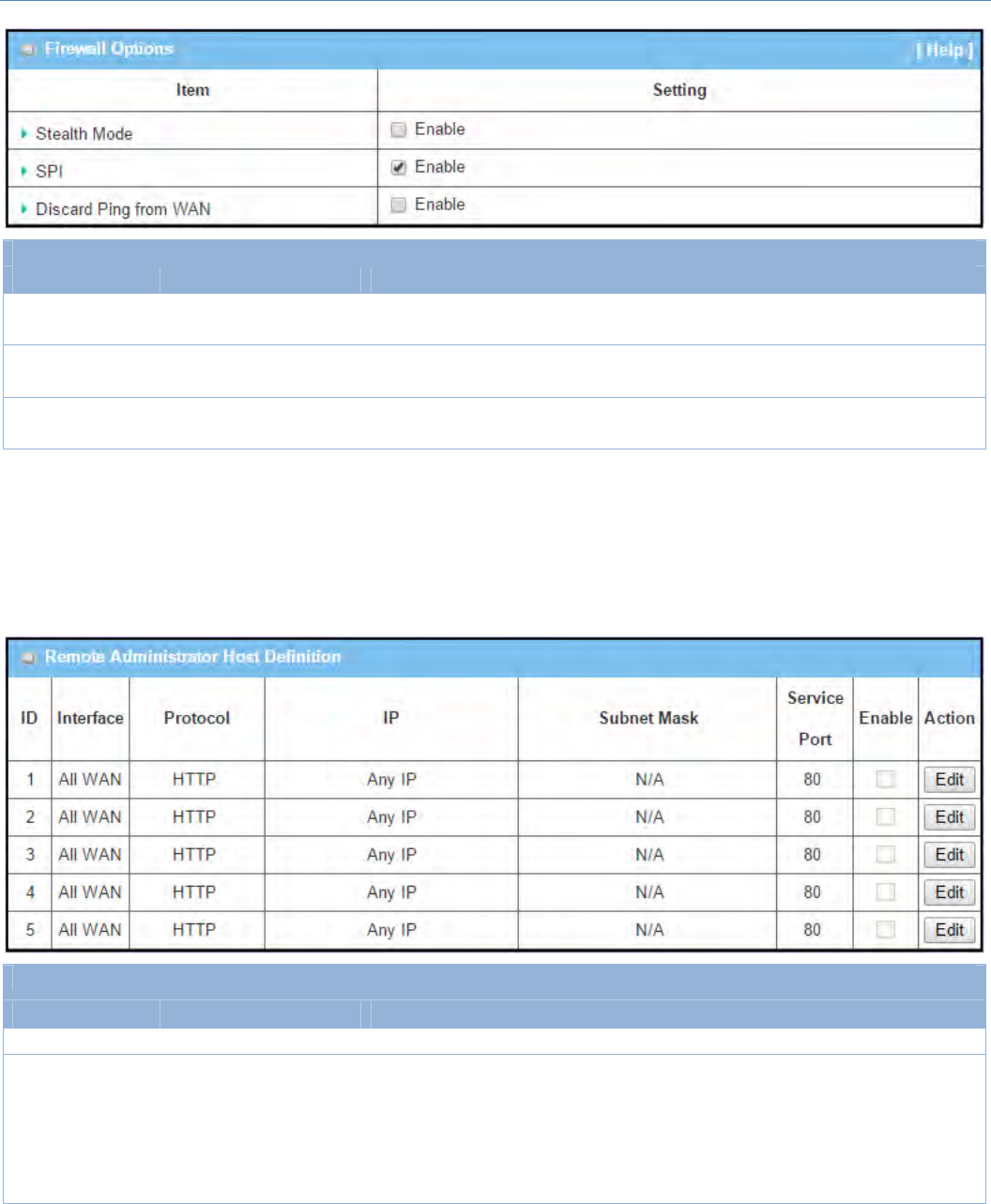
M2MCellularGateway
178
FirewallOptions
Item Valuesetting Description
StealthMode Theboxisuncheckedby
default ChecktheEnableboxtoactivatetheStealthModefunction
SPI Theboxischeckedby
default ChecktheEnableboxtoactivatetheSPIfunction
DiscardPing
fromWAN
Theboxisuncheckedby
default ChecktheEnableboxtoactivatetheDiscardPingfromWANfunction
DefineRemoteAdministratorHost
Therouter allowsnetwork administrator tomanagerouterremotely.Thenetworkadministrator canassign
specificIPaddressandserviceporttoallowaccessingtherouter.
RemoteAdministratorHostDefinition
Item Valuesetting Description
Protocol HTTPissetbydefault SelectHTTPorHTTPSmethodforrouteraccess.
IP AMustfilledsetting
Thisfieldistospecifytheremotehosttoassignaccessrightforremoteaccess.
SelectAnyIPtoallowanyremotehosts
SelectSpecificIPtoallowtheremotehostcomingfromaspecificsubnet.AnIP
addressenteredinthisfieldandaselectedSubnetMasktocomposethe
subnet.
M2MCellularGateway
179
ServicePort
1.80forHTTPbydefault
2.443forHTTPSby
default
ThisfieldistospecifyaServicePorttoHTTPorHTTPSconnection.
ValueRange:1~65535.
Enablingthe
rule
Theboxisuncheckedby
default. ClickEnableboxtoactivatethisrule.
Save N/A ClickEnableboxtoactivatethisrulethensavethesettings.
Undo N/A ClickUndotocancelthesettings
M2MCellularGateway
180
Chapter6Administration
6.1Configure&Manage
Configure&Managereferstoenterprise‐wideadministrationofdistributedsystemsincluding(andcommonly
inpractice)computersystems.Centralizedmanagementhasatimeandefforttrade‐offthatisrelatedtothe
sizeofthecompany,theexpertiseoftheITstaff,andtheamount of technology being used. This device
supportsmanysystemmanagementprotocols,suchasCommandScript,TR‐069,SNMP,andTelnetwithCLI.
Youcansetupthoseconfigurationsinthe"Configure&Manage"section.
M2MCellularGateway
181
6.1.1CommandScript
Command script configuration is the application that allows administrator to setup the pre‐defined
configurationinplaintextstyleandapplyconfigurationonstartup.
GotoAdministration>CommandScript>ConfigurationTab.
EnableCommandScriptConfiguration
Configuration
Item Valuesetting Description
Configuration Theboxisuncheckedby
default ChecktheEnableboxtoactivatetheCommandScriptfunction.
BackupScript N/A ClicktheViaWebUIorViaStoragebuttontobackuptheexistedcommand
scriptina.txtfile.YoucanspecifythescriptfilenameinScriptNamebelow.
UploadScript N/A ClicktheViaWebUIorViaStoragebuttontoUploadtheexistedcommand
scriptfromaspecified.txtfile.
ScriptName 1.AnOptionalsetting
2.Anyvalidfilename
Specifyascriptfilenameforscriptbackup,ordisplaytheselecteduploadscript
filename.
ValueRange:0~32characters.
Version 1.AnOptionalsetting
2.Anystring
SpecifytheversionnumberfortheappliedCommandscript.
ValueRange:0~32characters.
Description 1.AnOptionalsetting
2.Anystring EnterashortdescriptionfortheappliedCommandscript.
Updatetime N/A Itrecordstheuploadtimeforlastcommadscriptupload.
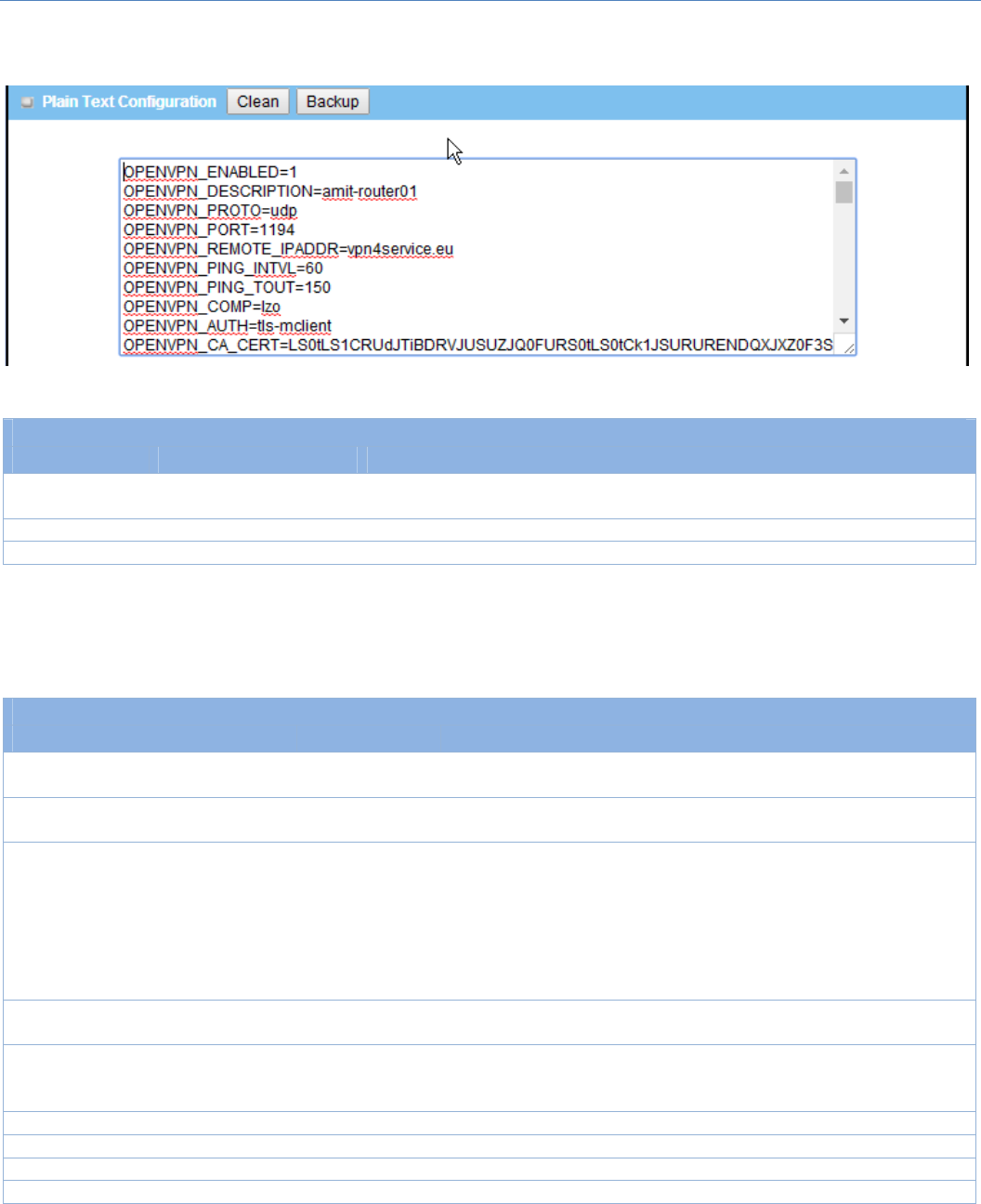
M2MCellularGateway
182
Edit/BackupPlainTextCommandScript
Youcanedittheplaintextconfigurationsettingsintheconfigurationscreenasabove.
PlainTextConfiguration
Item Valuesetting Description
Clean NA Cleantextarea.(YoushouldclickSave buttontofurthercleantheconfiguration
alreadysavedinthesystem.)
Backup NA Backupanddownloadconfiguration.
Save NA Saveconfiguration
The supported plain text configuration items are shown in the followinglist.Forthesettingsthatcanbe
executedwithstandardLinuxcommands,youcanputtheminascriptfile,andapplytothesystemconfigure
with STARTUP command. For those configurations without corresponding Linux command set to configure,
youcanconfigurethemwithproprietarycommandset.
ConfigurationContent
Key Valuesetting Description
OPENVPN_ENABLED 1:enable
0:disable
EnableordisableOpenVPNClientfunction.
OPENVPN_DESCRIPTION AMustfilled
Setting
SpecifythetunnelnamefortheOpenVPNClientconnection.
OPENVPN_PROTO udp
tcp
DefinetheProtocol fortheOpenVPNClient.
SelectTCPorTCP/UDP
‐>TheOpenVPNwilluseTCPprotocol,andPortwillbesetas443
automatically.
SelectUDP
‐>TheOpenVPNwilluseUDPprotocol,andPortwillbesetas1194
automatically.
OPENVPN_PORT AMustfilled
Setting
SpecifythePort fortheOpenVPNClienttouse.
OPENVPN_REMOTE_IPADDR IPorFQDN SpecifytheRemoteIP/FQDN ofthepeerOpenVPNServerforthis
OpenVPNClienttunnel.
FillintheIPaddressorFQDN.
OPENVPN_PING_INTVL seconds SpecifythetimeintervalforOpenVPNkeep‐alivechecking.
OPENVPN_PING_TOUT seconds SpecifythetimeoutvalueforOpenVPNClientkeep‐alivechecking.
OPENVPN_COMP Adaptive SpecifytheLZOCompression algorithmforOpenVPNclient.
OPENVPN_AUTH StaticKey/TLS Specifytheauthorizationmode fortheOpenVPNtunnel.

M2MCellularGateway
183
TLS
‐>TheOpenVPNwilluseTLSauthorizationmode,andthefollowing
itemsCACert.,ClientCert.andClientKeyneedtospecifyaswell.
OPENVPN_CA_CERT AMustfilled
Setting
SpecifytheTrustedCAcertificatefortheOpenVPNclient.Itwillgo
throughBase64Conversion.
OPENVPN_LOCAL_CERT AMustfilled
Setting
SpecifythelocalcertificateforOpenVPNclient.Itwillgothrough
Base64Conversion.
OPENVPN_LOCAL_KEY AMustfilled
Setting
SpecifythelocalkeyfortheOpenVPNclient.ItwillgothroughBase64
Conversion.
OPENVPN_EXTRA_OPTS Options SpecifytheextraoptionssettingfortheOpenVPNclient.
IP_ADDR1 Ip EthernetLANIP
IP_NETM1 Netmask EthernetLANMASK
PPP_MONITORING 1:enable
0:disable
WhentheNetworkMonitoringfeatureisenabled,therouterwilluse
DNSQueryorICMPtoperiodicallycheckInternetconnection–
connectedordisconnected.
PPP_PING 0:DNSQuery
1:ICMPQuery
With DNSQuery,thesystemcheckstheconnectionbysendingDNS
QuerypacketstothedestinationspecifiedinPPP_PING_IPADDR.
WithICMPQuery,thesystemwillcheckconnectionbysendingICMP
requestpacketstothedestinationspecifiedinPPP_PING_IPADDR.
PPP_PING_IPADDR IP SpecifyanIPaddressasthetargetforsendingDNSquery/ICMP
request.
PPP_PING_INTVL seconds Specifythetimeintervalfor betweentwoDNSQueryorICMP
checkingpackets.
STARTUP Scriptfile FortheconfigurationsthatcanbeconfiguredwithstandardLinux
commands,youcanputtheminascriptfile,andapplythescriptfile
withSTARTUPcommand.
Forexample,
STARTUP=#!/bin/sh
STARTUP=echo“startupdone”>/tmp/demo
PlainTextSystemConfigurationwithTelnet
Inadditiontotheweb‐styleplaintextconfigurationasmentionedabove,thegatewaysystemalsoallowthe
configurationviaTelnet CLI.Administratorcanusetheproprietarytelnetcommand“txtConfig” andrelated
actionitemstoperformtheplainsystemconfiguration.
Thecommandformatis:txtConfig(action)[option]
Action Option Description
clone Outputfile Duplicatetheconfigurationcontentfromdatabaseandstoredasa
configurationfile.
(ex:txtConfigclone/tmp/config)
Thecontentsintheconfigurationfilearethesameastheplaintextcommands
mentionedabove.Thisactionisexactlythesameasperformingthe“Backup”
plaintextconfiguration.
commit aexistingfile Committheconfigurationcontenttodatabase.
(ex:txtConfigcommit/tmp/config)
enable NA Enableplaintextsystemconfig.
M2MCellularGateway
184
(ex:txtConfigenable)
disable NA Disableplaintextsystemconfig.
(ex:txtConfigdisable)
run_immediately NA Applytheconfigurationcontentthathasbeencommittedindatabase.
(ex:txtConfigrun_immediately)
run_immediately aexistingfile Assignaconfigurationfiletoapply.
(ex:txtConfigrun_immediately/tmp/config)
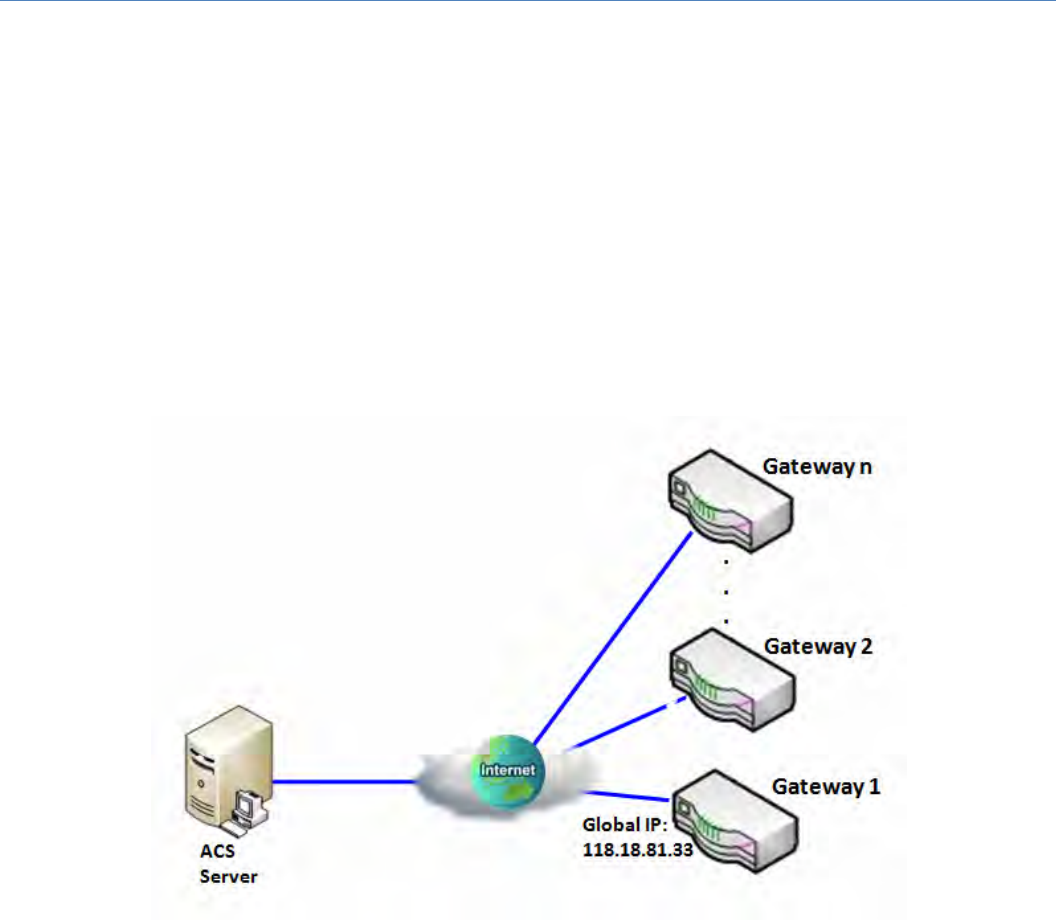
M2MCellularGateway
185
6.1.2TR‐069
TR‐069 (Technical Report 069)is a Broadband Forum technical specification entitledCPE WAN Management
Protocol(CWMP).Itdefinesanapplicationlayerprotocolforremotemanagementofend‐userdevices,likethis
gatewaydevice.AsabidirectionalSOAP/HTTP‐basedprotocol,it provides the communication between
customer‐premisesequipment(CPE)andAutoConfigurationServers(ACS).TheSecurityGatewayissuchCPE.
TR‐069isacustomizedfeatureforISP.Itisnotrecommendthatyouchangetheconfigurationforthis.Ifyou
haveanyprobleminusingthisfeaturefordevicemanagement,please contact with your ISP or the ACS
providerforhelp.AttherightuppercornerofTR‐069Settingscreen,one“[Help]”commandletyouseethe
samemessageaboutthat.
Scenario‐ManagingdeployedgatewaysthroughanACSServer
ScenarioApplicationTiming
When the enterprise data center wants to use an ACS server to manage remote gateways
geographically distributed elsewhere in the world, the gatewaysinallbranchofficesmusthavean
embeddedTR‐069agenttocommunicate withtheACSserver.SothattheACSservercanconfigure,
FWupgradeandmonitorthesegatewaysandtheircorrespondingIntranets.
ScenarioDescription
TheACSservercanconfigure,upgradewithlatestFWandmonitorthesegateways.
RemotegatewaysinquiretheACSserverforjobstodoineachtimeperiod.
TheACSservercanaskthegatewaystoexecutesomeurgentjobs.
ParameterSetupExample
M2MCellularGateway
186
Followingtableslisttheparameterconfigurationasanexample fortheGateway 1inabovediagram
with"TR‐069"enabling.
Usedefaultvalueforthoseparametersthatarenotmentionedinthetables.
ConfigurationPath [TR‐069]‐[Configuration]
TR‐069 ■Enable
ACSURL http://qa.acslite.com/cpe.php
ACSUserName
A
CSUserName
ACSPassword
A
CSPassword
ConnectionRequestPort 8099
ConnectionRequestUserName ConnReqUserName
ConnectionRequestPassword ConnReqPassword
Inform ■EnableInterval90
0
ScenarioOperationProcedure
Inabovediagram,theACSservercanmanagemultiple gatewaysintheInternet.The"Gateway 1"is
oneofthemandhas118.18.81.33IPaddressforitsWAN‐1interface.
Whenallremotegatewayshavebootedup,theywilltrytoconnecttotheACSserver.
Oncetheconnectionsareestablishedsuccessfully,theACSservercanconfigure,upgradewithlatest
FWandmonitorthesegateways.
RemotegatewaysinquiretheACSserverforjobstodoineachtimeperiod.
IftheACSserverneedssomeurgentjobstobedonebythegateways,itwillissuethe"Connection
Request"commandtothosegateways.Andthosegatewaysmakeimmediateconnectionsinresponse
totheACSserver’simmediateconnectionrequestforexecutingtheurgentjobs.
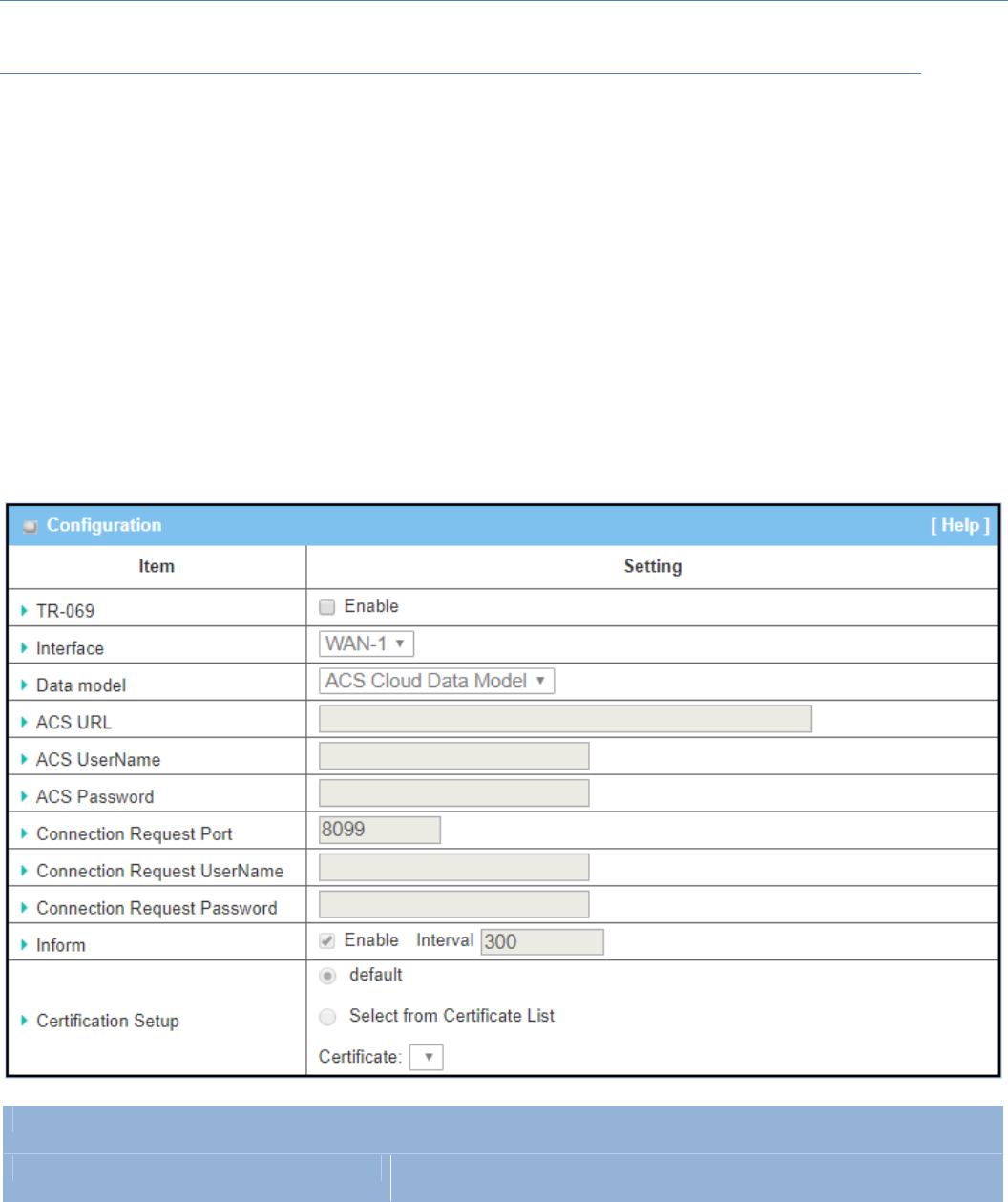
M2MCellularGateway
187
TR‐069Setting
GotoAdministration>Configure&Manage>TR‐069tab.
In "TR‐069" page, there is only one configuration window for TR‐069 function. In the window, you must
specifytherelatedinformationforyoursecuritygatewaytoconnecttotheACS.Drivethefunctiontoworkby
specifyingtheURLoftheACSserver,theaccountinformationtologintheACSserver,theserviceportandthe
account information for connection requesting from the ACS server, and the time interval for job inquiry.
Excepttheinquirytime,therearenoactivitiesbetweentheACSserverandthegatewaysuntilthenextinquiry
cycle.ButiftheACSserverhasnewjobsthatareexpectedtodobythegatewaysurgently,itwillaskthese
gatewaysbyusingconnectionrequestrelatedinformationforimmediate connection for inquiring jobs and
executing.
EnableTR‐069
TR‐069
Item Valuesetting Description

M2MCellularGateway
188
TR‐069 Theboxisuncheckedby
default ChecktheEnableboxtoactivateTR‐069function.
Interface WAN‐1isselectedby
default.
WhenyoufinishsetbasicnetworkWAN‐1~WAN‐n,youcanchooseWAN‐1~
WAN‐n
WhenyoufinishsetSecurity>VPN>IPSec/OpenVPN/PPTP/L2TP/GRE,you
canchooseIPSec/OpenVPN/PPTP/L2TP/GREtunnel,theinterfacejustlike
“IPSec#1”
DataModel ACSCloudDataModel
isselectedbydefault.
SelecttheTR‐069datmodelfortheremotemanagement.
Standard:theACSServerisastandardone,whichisfullycomplywithTR‐
069.
ACSCloudDataModel:SelectthisdatamodelifyouintendtouseCloudACS
Servertomanagingthedeployedgateways.
ACSURL AMustfilledsetting YoucanaskACSmanagerprovideACSURLandmanuallyset
ACSUsername AMustfilledsetting YoucanaskACSmanagerprovideACSusernameandmanuallyset
ACSPassword AMustfilledsetting YoucanaskACSmanagerprovideACSpasswordandmanuallyset
ConnectionRequest
Port
1.AMustfilledsetting.
2.Bydefault8099isset.
YoucanaskACSmanagerprovideACSConnectionRequestPortandmanually
set
ValueRange:0~65535.
ConnectionRequest
UserName AMustfilledsetting YoucanaskACSmanagerprovideACSConnectionRequestUsernameand
manuallyset
ConnectionRequest
Password AMustfilledsetting YoucanaskACSmanagerprovideACSConnectionRequestPasswordand
manuallyset
Inform
1.Theboxischeckedby
default.
2.TheIntervalvalueis
300bydefault.
WhentheEnableboxischecked,thegateway(CPE)willperiodiclysend
informmessagetoACSServeraccordingtotheIntervalsetting.
ValueRange:0~86400forInformInterval.
CertificationSetup Thedefaultboxis
selectedbydefault
Youcanleaveitasdefaultorselectanexpectedcertificateandkeyfromthe
dropdownlist.
RefertoObjectDefinition>CertificateSectionfortheCertificate
configuration.
Save N/A ClickSavetosavethesettings.
Undo N/A ClickUndotocancelthemodifications.
WhenyoufinishsetACSURLACSUsernameACSPassword,yourgateway(CPE,ClientPremiumEquipment)
cansendinformtoACSServer.
WhenyoufinishsetConnectionRequestPortConnectionRequest Username ConnectionRequest Password,
ACSServercanaskthegateway(CPE)tosendinformtoACSServer.
EnableSTUNServer
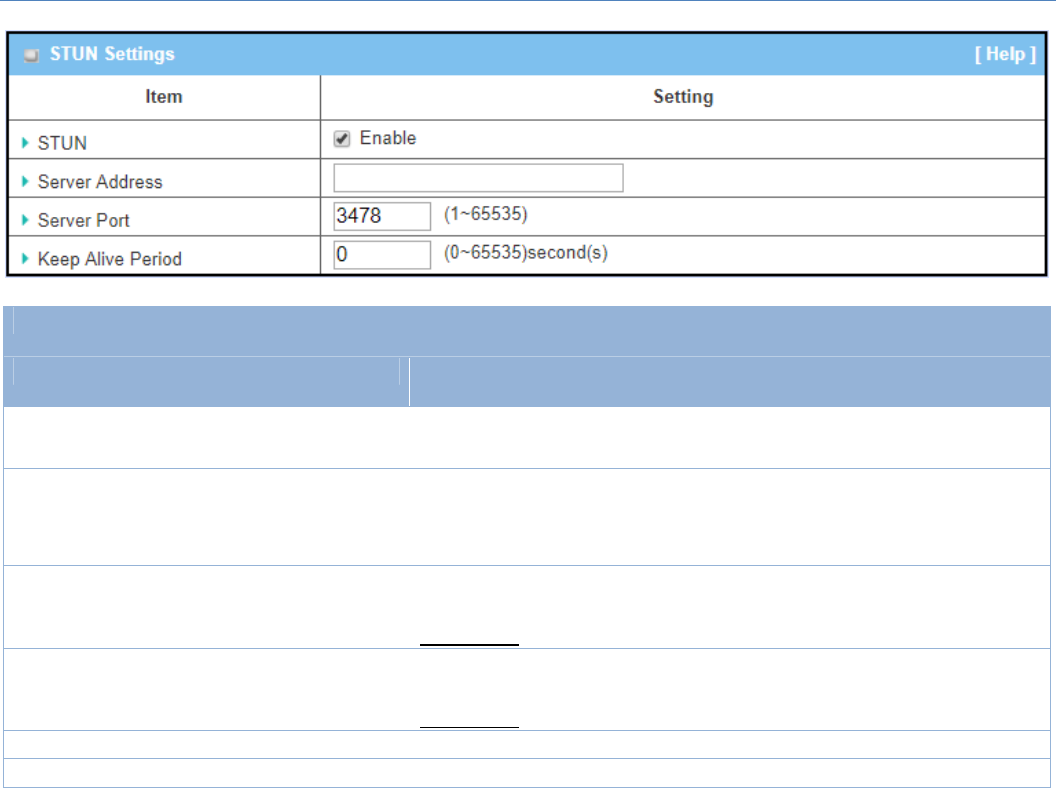
M2MCellularGateway
189
STUNSettingsConfiguration
Item Valuesetting Description
STUN Theboxischeckedby
default ChecktheEnableboxtoactivateSTUNfunction.
ServerAddress
1.Stringformat:any
IPv4address
2.Itisanoptionalitem.
SpecifytheIPaddressfortheexpectedSTUNServer.
ServerPort 1.Anoptionalsetting
2.3478issetbydefault
SpecifytheportnumberfortheexpectedSTUNServer.
ValueRange:1~65535.
KeepAlivePeriod 1.Anoptionalsetting
2.0issetbydefault
SpecifythekeepalivetimeperiodfortheconnectionwithSTUNServer.
ValueRange:0~65535.
Save N/A ClickSavetosavethesettings.
Undo N/A ClickUndotocancelthemodifications.
M2MCellularGateway
190
6.1.3SNMP
Inbrief,SNMP,theSimpleNetworkManagementProtocol,isaprotocoldesignedtogiveauserthecapability
toremotelymanageacomputernetworkbypollingandsettingterminal values and monitoring network
events.
IntypicalSNMPuses,oneormoreadministrativecomputers,calledmanagers,havethetaskofmonitoringor
managingagroupofhostsordevicesonacomputernetwork.Eachmanagedsystemexecutes,atalltimes,a
softwarecomponentcalledanagentwhichreportsinformationviaSNMPtothemanager.
SNMPagentsexposemanagementdataonthemanagedsystemsasvariables.Theprotocolalsopermitsactive
managementtasks,suchasmodifyingandapplyinganewconfigurationthroughremotemodificationofthese
variables.ThevariablesaccessibleviaSNMPareorganizedinhierarchies. These hierarchies, and other
metadata(suchastypeanddescriptionofthevariable),aredescribed by Management Information Bases
(MIBs).
ThedevicesupportsseveralpublicMIBsandoneprivateMIBfortheSNMPagent.ThesupportedMIBsareas
follow: MIB-II (RFC 1213, Include IPv6), IF-MIB, IP-MIB, TCP-MIB, UDP-MIB, SMIv1 and SMIv2,
SNMPv2-TM and SNMPv2-MIB, and AMIB (a Proprietary MIB)
SNMPManagementScenario
ScenarioApplicationTiming
TherearetwoapplicationscenariosofSNMPNetworkManagementSystems (NMS).LocalNMSisin
M2MCellularGateway
191
theIntranet andmanageall devices thatsupportSNMP protocolinthe Intranet.Anotheroneis the
Remote NMS to manage some devices whose WAN interfaces are connected together by using a
switch or a router with UDP forwarding. If you want to manage some devices and they all have
supportedSNMPprotocol,useeitheroneapplicationscenario,especiallythemanagementofdevices
intheIntranet.InmanagingdevicesintheInternet,theTR‐069isthebettersolution.Pleasereferto
lastsub‐section.
ScenarioDescription
TheNMSservercanmonitorandconfigurethemanageddevicesbyusingSNMPprotocol,andthose
devicesarelocatedatwhereUDPpacketscanreachfromNMS.
ThemanageddevicesreporturgenttrapeventstotheNMSservers.
UseSNMPv3versionofprotocolcanprotectedthetransmittingofSNMPcommandsandresponses.
TheremoteNMSwithprivilegeIPaddresscanmanagethedevices,butotherremoteNMScan't.
ParameterSetupExample
FollowingtableslisttheparameterconfigurationasanexamplefortheGateway1inabovediagram
with"SNMP"enablingatLANandWANinterfaces.
Usedefaultvalueforthoseparametersthatarenotmentionedinthetables.
ConfigurationPath [SNMP]‐[Configuration]
SNMPEnable ■LAN■WA
N
SupportedVersions ■v1■v2c■v3
Get/SetCommunity ReadCommunity/WriteCommunit
y
TrapEventReceiver1 118.18.81.11
WANAccessIPAddress 118.18.81.11
ConfigurationPath [SNMP]‐[UserPrivacyDefinition]
ID 12 3
UserName UserName1UserName2 UserName3
Password Password1 Password2 Disable
Authentication MD5
S
HA‐1 Disable
Encryption DE
S
Disable Disable
PrivacyMode authPri
v
authNoPriv noAuthNoPri
v
PrivacyKey 1234567
8
Disable Disable
Authority Read/Write Read Read
Enable ■Enable ■Enable ■Enable
ScenarioOperationProcedure
Inabovediagram,theNMSservercanmanagemultipledevicesin the Intranet or a UDP‐reachable
network.The"Gateway1"isoneofthemanageddevices,andithas theIPaddressof 10.0.75.2for
LANinterfaceand118.18.81.33forWAN‐1interface.ItservesasaNATrouter.

M2MCellularGateway
192
Atfirststage,theNMSmanagerpreparesrelatedinformationfor all managed devices and records
themintheNMSsystem.ThenNMSsystemgetsthestatusofallmanageddevicesbyusingSNMPget
commands.
Whenthemanagerwantstoconfigurethemanageddevices,theNMSsystemallowshimtodothatby
usingSNMPsetcommands.The"UserName1"accountisusedifthemanagerusesSNMPv3protocol
forconfiguringthe"Gateway 1".Onlythe"UserName1"accountcanletthe"Gateway1"acceptthe
configurationfromtheNMSsincetheauthorityoftheaccountis"Read/Write".
Once a managed device has an urgent event to send, the device will issue a trap to the Trap Event
Receivers.TheNMSitselfcouldbeoneamongthem.
If you want to secure the transmitted SNMP commands and responsesbetweentheNMSandthe
manageddevices,useSNMPv3versionofprotocol.
TheremoteNMSwithoutprivilegeIPaddresscan'tmanagethe"Gateway1",since"Gateway1"allows
onlytheNMSwithprivilegeIPaddresscanmanageitviaitsWANinterface.
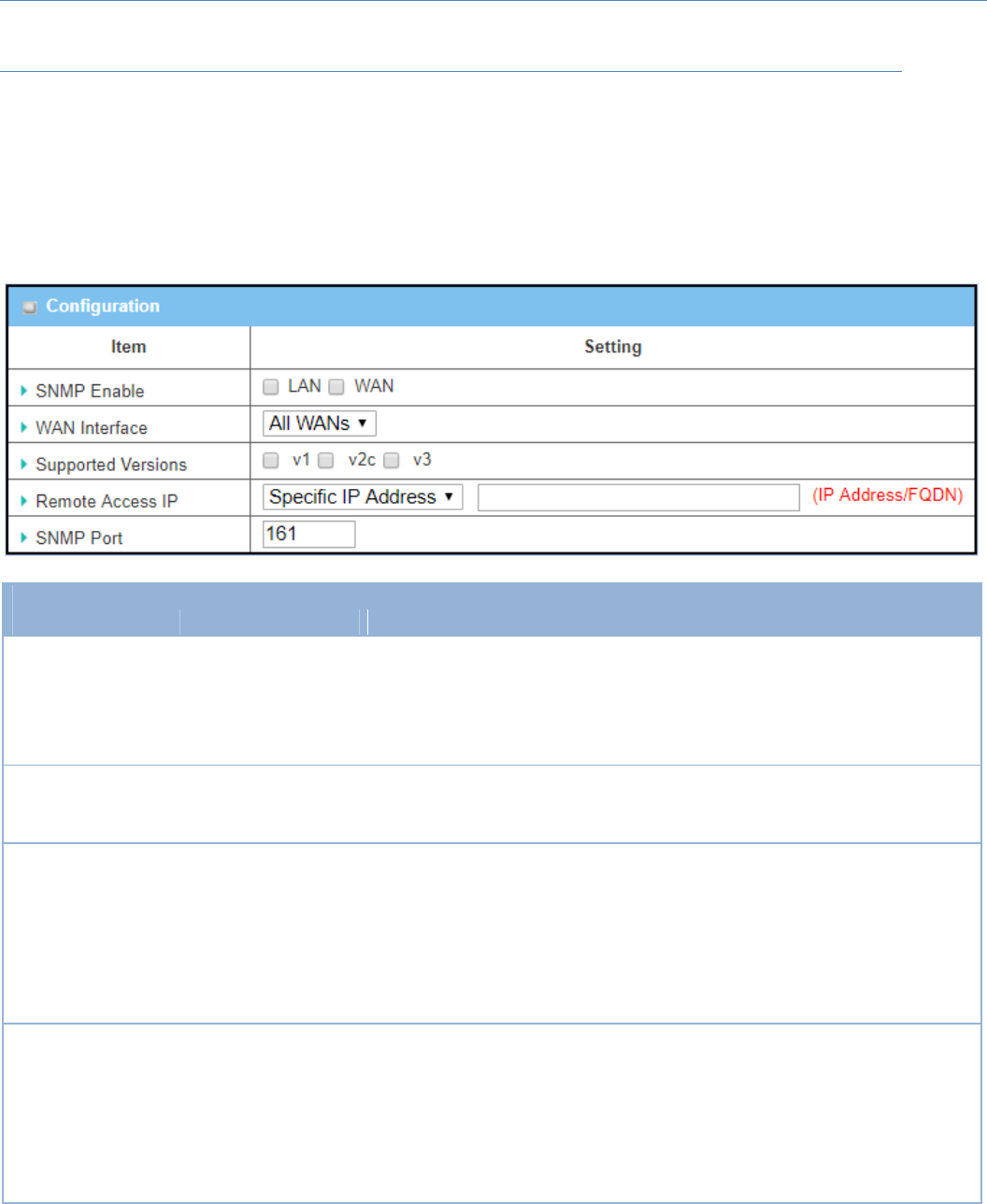
M2MCellularGateway
193
SNMPSetting
GotoAdministration>Configure&Manage>SNMPtab.
TheSNMPallowsusertoconfigureSNMPrelevantsettingwhichincludes interface, version, access control
andtrapreceiver.
EnableSNMP
SNMP
Item Valuesetting Description
SNMPEnable 1.Theboxesare
uncheckedbydefault
SelecttheinterfacefortheSNMPandenableSNMPfunctions.
WhenChecktheLANbox,itwillactivateSNMPfunctionsandyoucanaccess
SNMPfromLANside;
WhenChecktheWANbox,itwillactivateSNMPfunctionsandyoucanaccess
SNMPfromWANside.
WANInterface
1.AMustfilledsetting
2.ALLWANsis
selectedbydefault
SpecifytheWANinterfacethataremoteSNMPhostcanaccesstothedevice.
Bydefault,AllWANsisselected,andthereisnolimitationfortheWAN
inferface.
SupportedVersions
1.AMustfilledsetting
2.Theboxesare
uncheckedbydefault
SelecttheversionfortheSNMP
WhenCheckthev1box.
ItmeansyoucanaccessSNMPbyversion1.
WhenCheckthev2cbox.
ItmeansyoucanaccessSNMPbyversion2c.
WhenCheckthev3box.
ItmeansyoucanaccessSNMPbyversion3.
RemoteAceessIP
1.Stringformat:any
IPv4address
2.Itisanoptional
item.
SpecifytheRemoteAccessIPforWAN.
SelectSpecificIPAddress,andfillinacertainIPaddress.ItmeansonlythisIP
addresscanaccessSNMPfromLAN/WANside.
SelectIPRange,andfillinarangeofIPaddresses.ItmeanstheIPaddress
withinspecifiedrangecanaccessSNMPfromLAN/WANside.
Ifyouleftitasblank,itmeansanyIPaddresscanaccessSNMPfromWANside.
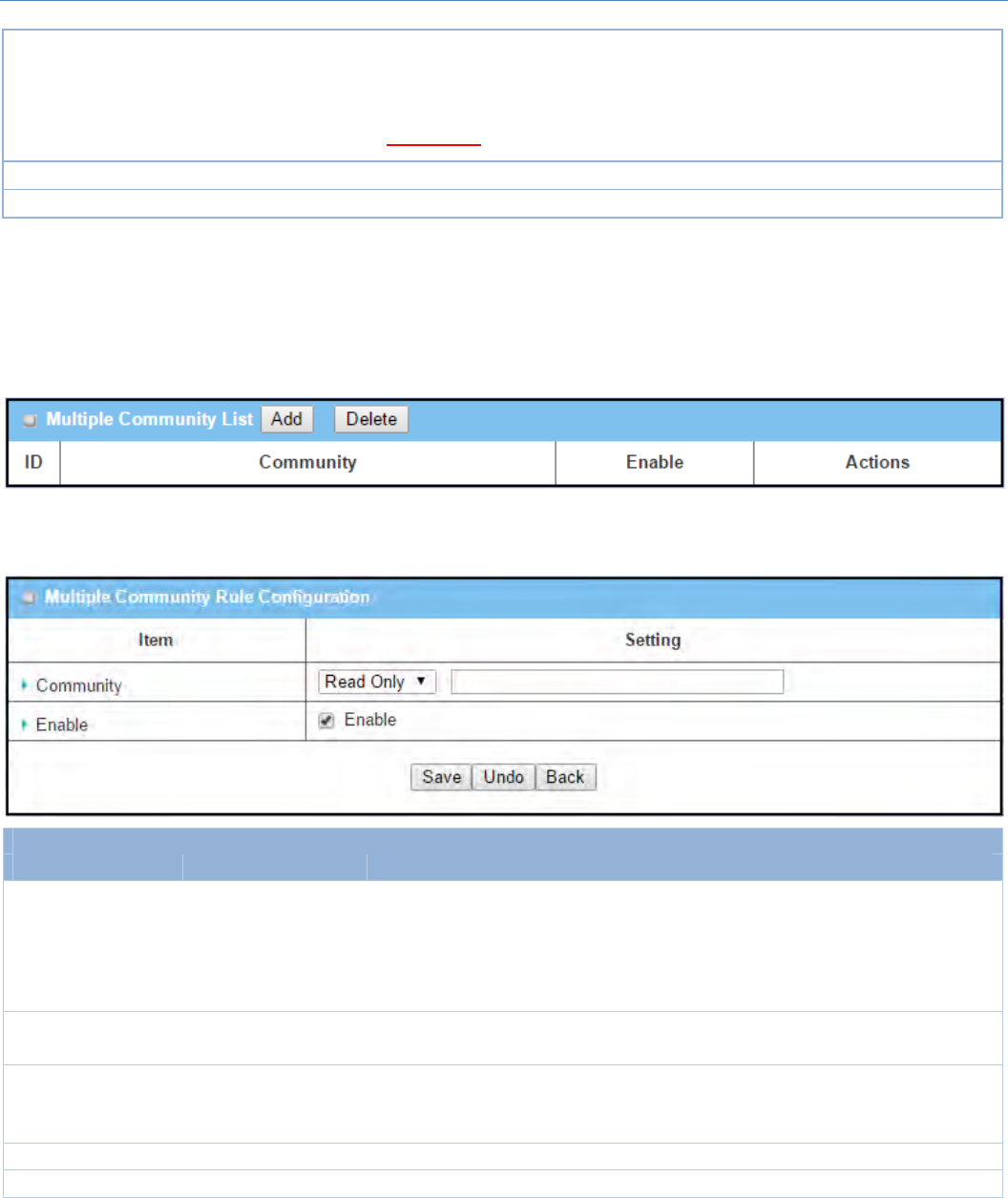
M2MCellularGateway
194
SNMPPort
1.Stringformat:any
portnumber
2.ThedefaultSNMP
portis161.
3.AMustfilledsetting
SpecifytheSNMPPort.
Youcanfillinanyportnumber.Butyoumustensuretheportnumberisnotto
beused.
ValueRange:1~65535.
Save N/A ClickSavetosavethesettings
Undo N/A ClickUndotocancelthesettings
Create/EditMultipleCommunity
TheSNMPallowsyoutocustomyouraccesscontrolforversion1andversion2user.Theroutersupportsupto
amaximumof10communitysets.
WhenAddbuttonisapplied,MultipleCommunityRuleConfigurationscreenwillappear.
MultipleCommunityRuleConfiguration
Item Valuesetting Description
Community
1.ReadOnlyis
selectedbydefault
2.AMustfilledsetting
3.Stringformat:any
text
Specifythisversion1orversionv2cuser’scommunitythatwillbeallowedRead
Only(GETandGETNEXT)orRead‐Write(GET,GETNEXTandSET)access
respectively.
Themaximumlengthofthecommunityis32.
Enable 1.Theboxischecked
bydefault ClickEnabletoenablethisversion1orversionv2cuser.
Save N/A
ClicktheSavebuttontosavetheconfiguration.ButitdoesnotapplytoSNMP
functions.WhenyoureturntotheSNMPmainpage.Itwillshow“Clickonsave
buttontoapplyyourchanges”remindusertoclickmainpageSavebutton.
Undo N/A ClicktheUndobuttontocancelthesettings.
Back N/A ClicktheBackbuttontoreturntolastpage.
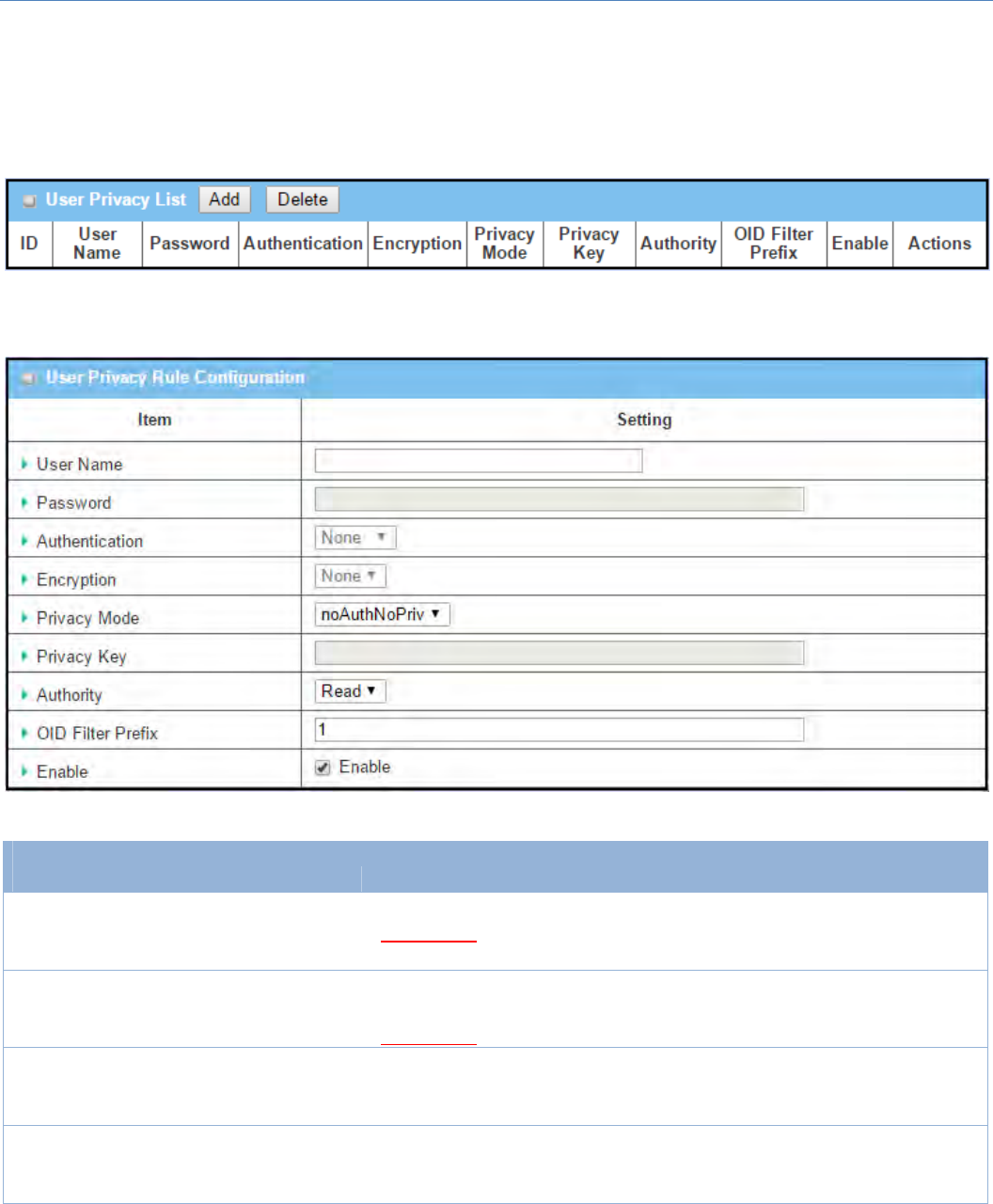
M2MCellularGateway
195
Create/EditUserPrivacy
TheSNMPallowsyoutocustomyouraccesscontrolforversion3user.Theroutersupportsuptoamaximum
of128UserPrivacysets.
WhenAddbuttonisapplied,UserPrivacyRuleConfigurationscreenwillappear.
UserPrivacyRuleConfiguration
Item Valuesetting Description
UserName 1.AMustfilledsetting
2.Stringformat:any
text
SpecifytheUserNameforthisversion3user.
ValueRange:1~32characters.
Password 1.Stringformat:any
text
WhenyourPrivacyModeisauthNoPrivorauthPriv,youmustspecifythe
Passwordforthisversion3user.
ValueRange:8~64characters.
Authentication 1.Noneisselectedby
default
WhenyourPrivacyModeisauthNoPrivorauthPriv,youmustspecifythe
Authenticationtypesforthisversion3user.
SelectedtheauthenticationtypesMD5/SHA‐1touse.
Encryption 1.Noneisselectedby
default
WhenyourPrivacyModeisauthPriv,youmustspecifytheEncryption
protocolsforthisversion3user.
SelectedtheencryptionprotocolsDES/AEStouse.
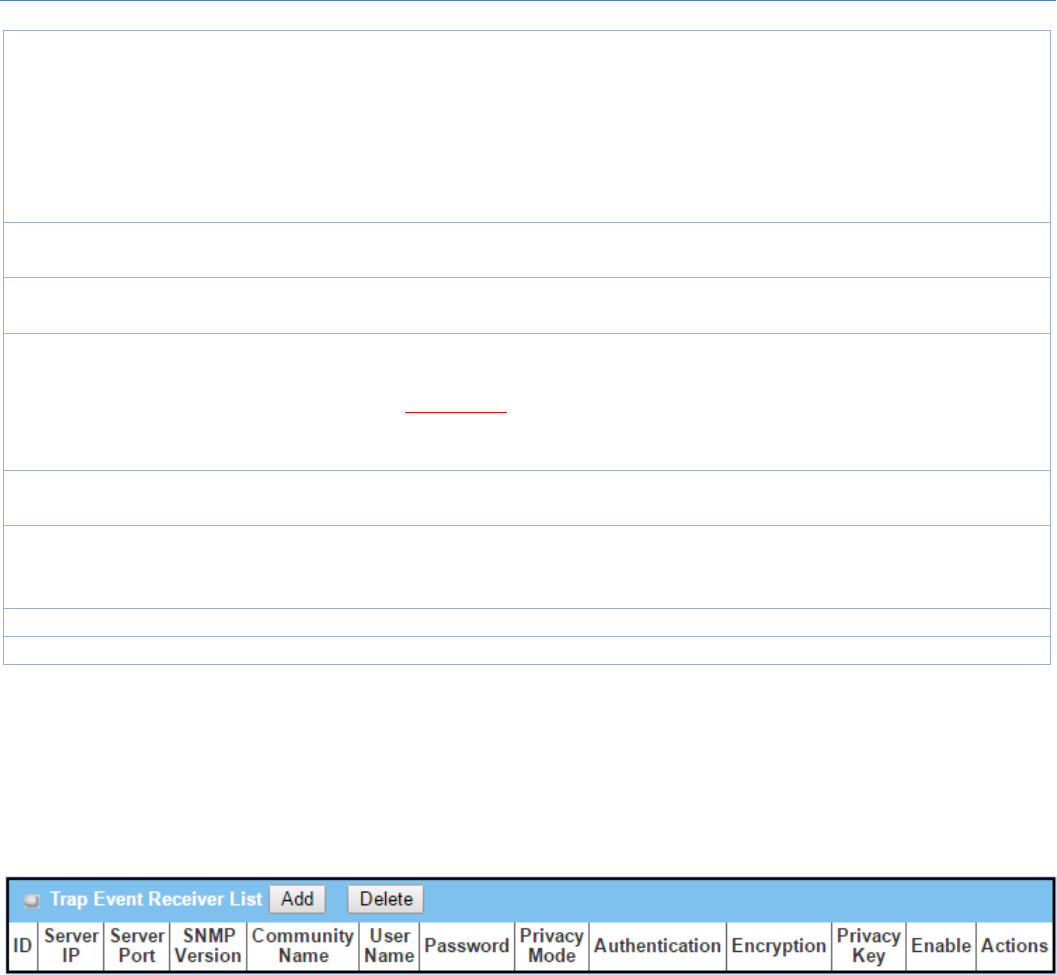
M2MCellularGateway
196
PrivacyMode 1.noAuthNoPrivis
selectedbydefault
SpecifythePrivacyModeforthisversion3user.
SelectedthenoAuthNoPriv.
Youdonotuseanyauthenticationtypesandencryptionprotocols.
SelectedtheauthNoPriv.
YoumustspecifytheAuthenticationandPassword.
SelectedtheauthPriv.
YoumustspecifytheAuthentication,Password,EncryptionandPrivacyKey.
PrivacyKey 1.Stringformat:any
text
WhenyourPrivacyModeisauthPriv,youmustspecifythePrivacyKey(8~64
characters)forthisversion3user.
Authority 1.Readisselectedby
default
Specifythisversion3user’sAuthoritythatwillbeallowedReadOnly(GETand
GETNEXT)orRead‐Write(GET,GETNEXTandSET)accessrespectively.
OIDFilterPrefix 1.Thedefaultvalueis
1
2.AMustfilledsetting
3.Stringformat:any
legalOID
TheOIDFilterPrefixrestrictsaccessforthisversion3usertothesub‐tree
rootedatthegivenOID.
ValueRange:1~2080768.
Enable 1.Theboxischecked
bydefault
ClickEnabletoenablethisversion3user.
Save N/A ClicktheSavebuttontosavetheconfiguration.ButitdoesnotapplytoSNMP
functions.WhenyoureturntotheSNMPmainpage.Itwillshow“Clickonsave
buttontoapplyyourchanges”remindusertoclickmainpageSavebutton.
Undo N/A ClicktheUndobuttontocancelthesettings
Back N/A ClicktheBackbuttontoreturnthelastpage.
Create/EditTrapEventReceiver
The SNMP allows you to custom your trap event receiver. The router supports up to a maximum of4 Trap
EventReceiversets.
WhenAddbuttonisapplied,TrapEventReceiverRuleConfigurationscreenwillappear.ThedefaultSNMP
Versionisv1.Theconfigurationscreenwillprovidetheversion1mustfilleditems.
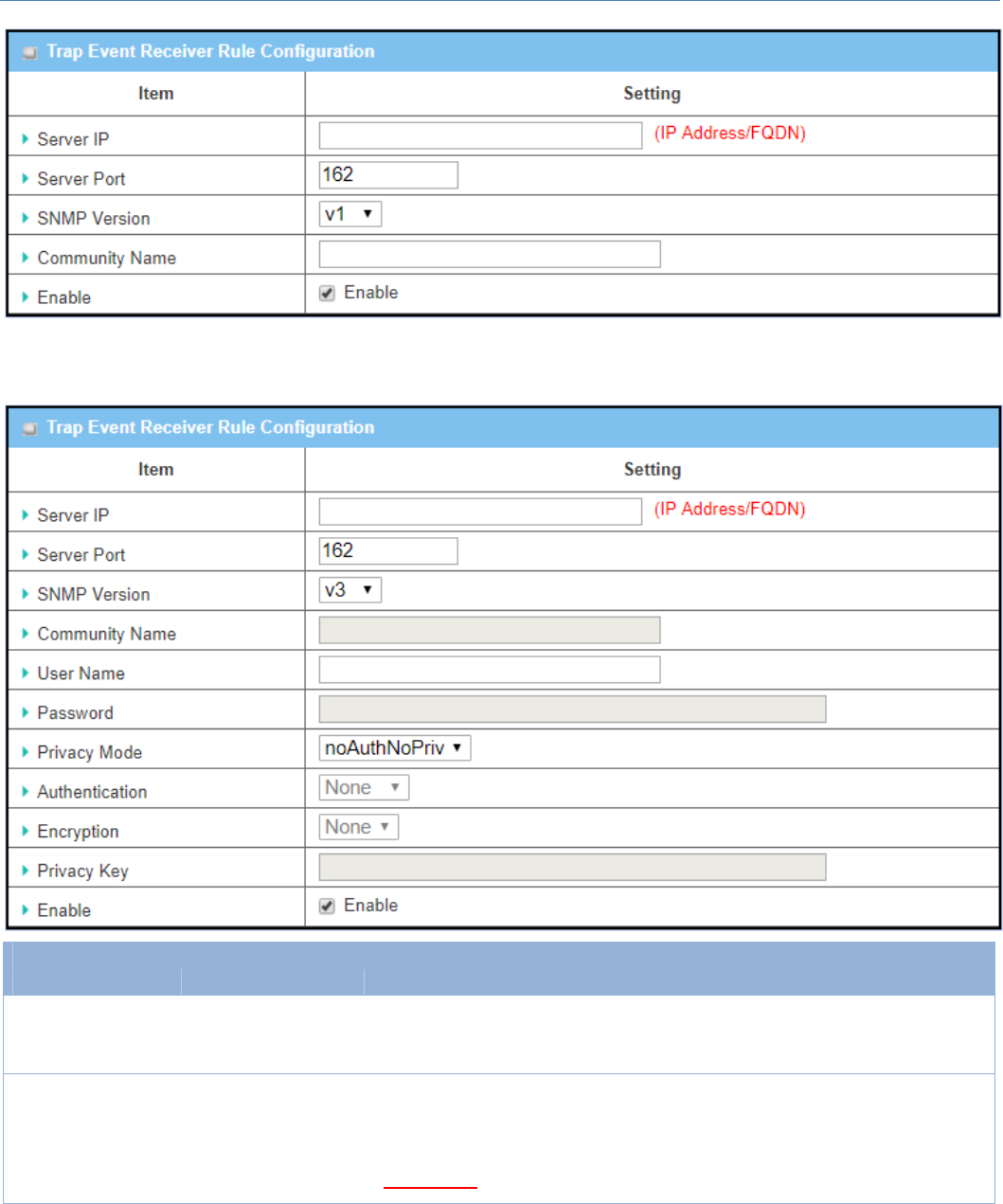
M2MCellularGateway
197
Whenyouselectedv2c,theconfigurationscreenisexactlythesameasthatofv1,excepttheversion.
Whenyouselectedv3,theconfigurationscreenwillprovidemoresettingitemsfortheversion3Trap.
TrapEventReceiverRuleConfiguration
Item Valuesetting Description
ServerIP
1.AMustfilledsetting
2.Stringformat:any
IPv4addressorFQDN
SpecifythetrapServerIPorFQDN.
TheDUTwillsendtraptotheserverIP/FQDN.
ServerPort
1.Stringformat:any
portnumber
2.ThedefaultSNMP
trapportis162
3.AMustfilledsetting
SpecifythetrapServerPort.
Youcanfillinanyportnumber.Butyoumustensuretheportnumberisnotto
beused.
ValueRange:1~65535.

M2MCellularGateway
198
SNMPVersion 1.v1isselectedby
default
Selecttheversionforthetrap
Selectedthev1.
Theconfigurationscreenwillprovidetheversion1mustfilleditems.
Selectedthev2c.
Theconfigurationscreenwillprovidetheversion2cmustfilleditems.
Selectedthev3.
Theconfigurationscreenwillprovidetheversion3mustfilleditems.
CommunityName
1.Av1andv2cMust
filledsetting
2.Stringformat:any
text
SpecifytheCommunityNameforthisversion1orversionv2ctrap.
ValueRange:1~32characters.
UserName
1.Av3Mustfilled
setting
2.Stringformat:any
text
SpecifytheUserNameforthisversion3trap.
ValueRange:1~32characters.
Password
1.Av3Mustfilled
setting
2.Stringformat:any
text
WhenyourPrivacyModeisauthNoPrivorauthPriv,youmustspecifythe
Passwordforthisversion3trap.
ValueRange:8~64characters.
PrivacyMode
1.Av3Mustfilled
setting
2.noAuthNoPrivis
selectedbydefault
SpecifythePrivacyModeforthisversion3trap.
SelectedthenoAuthNoPriv.
Youdonotuseanyauthenticationtypesandencryptionprotocols.
SelectedtheauthNoPriv.
YoumustspecifytheAuthenticationandPassword.
SelectedtheauthPriv.
YoumustspecifytheAuthentication,Password,EncryptionandPrivacyKey.
Authentication
1.Av3Mustfilled
setting
2.Noneisselectedby
default
WhenyourPrivacyModeisauthNoPrivorauthPriv,youmustspecifythe
Authenticationtypesforthisversion3trap.
SelectedtheauthenticationtypesMD5/SHA‐1touse.
Encryption
1.Av3Mustfilled
setting
2.Noneisselectedby
default
WhenyourPrivacyModeisauthPriv,youmustspecifytheEncryption
protocolsforthisversion3trap.
SelectedtheencryptionprotocolsDES/AEStouse.
PrivacyKey
1.Av3Mustfilled
setting
2.Stringformat:any
text
WhenyourPrivacyModeisauthPriv,youmustspecifythePrivacyKey(8~64
characters)forthisversion3trap.
Enable 1.Theboxischecked
bydefault ClickEnabletoenablethistrapreceiver.
Save N/A
ClicktheSavebuttontosavetheconfiguration.ButitdoesnotapplytoSNMP
functions.WhenyoureturntotheSNMPmainpage.Itwillshow“Clickonsave
buttontoapplyyourchanges”remindusertoclickmainpageSavebutton.
Undo N/A ClicktheUndobuttontocancelthesettings.
Back N/A ClicktheBackbuttontoreturnthelastpage.
M2MCellularGateway
199
SpecifySNMPMIB‐2System
Ifrequired,youcanalsospecifytherequiredonformationthetheMIB‐2System.
SNMPMIB‐2SystemConfiguration
Item Valuesetting Description
sysContact 1.AnOptionalfilled
setting
2.Stringformat:any
text
SpecifythecontactinformationforMIB‐2system.
ValueRange:0~64characters.
sysLocation 1.AnOptionalfilled
setting
2.Stringformat:any
text
SpecifythelocationinformationforMIB‐2system.
ValueRange:0~64characters.
EditSNMPOptions
IfyouusesomeparticularprivateMIB,youmustfilltheenterprisename,numberandOID.
Options
M2MCellularGateway
200
Item Valuesetting Description
EnterpriseName
1.Thedefaultvalueis
Default
2.AMustfilledsetting
3.Stringformat:any
text
SpecifytheEnterpriseNamefortheparticularprivateMIB.
ValueRange:1~10characters,andonlystringwithA~Z,a~z,0~9,’–‘,‘_’.
EnterpriseNumber
Thedefaultvalueis
12823
(DefaultEnterprise
Number)
2.AMustfilledsetting
3.Stringformat:any
number
SpecifytheEnterpriseNumberfortheparticularprivateMIB.
ValueRange:1~2080768.
EnterpriseOID
1.Thedefaultvalueis
1.3.6.1.4.1.12823.4.4.9
(DefaultEnterpriseOID)
2.AMustfilledsetting
3.Stringformat:any
legalOID
SpecifytheEnterpriseOIDfortheparticularprivateMIB.
TherangeoftheeachOIDnumberis1‐2080768.
ThemaximumlengthoftheenterpriseOIDis31.
Theseventhnumbermustbeidenticalwiththeenterprisenumber.
Save N/A ClicktheSavebuttontosavetheconfigurationandapplyyourchangesto
SNMPfunctions.
Undo N/A ClicktheUndobuttontocancelthesettings.
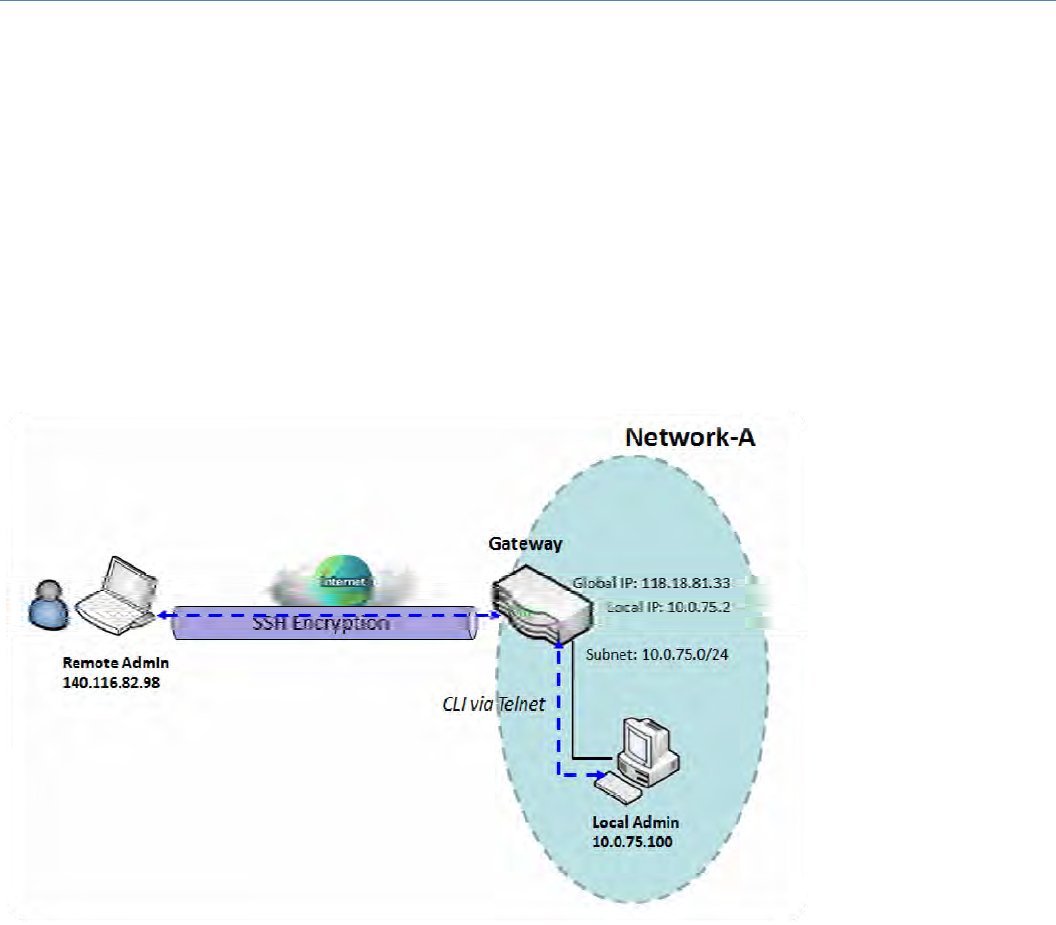
M2MCellularGateway
201
6.1.4Telnet&SSH
Acommand‐lineinterface(CLI),also knownascommand‐line userinterface,and consoleuserinterfaceare
meansofinteractingwithacomputerprogramwheretheuser(orclient)issuescommandstotheprogramin
theformofsuccessivelinesoftext(commandlines).Theinterfaceisusuallyimplementedwithacommand
lineshell,which isaprogram thatacceptscommands as textinputandconverts commandstoappropriate
operating system functions. Programs with command‐line interfacesaregenerallyeasiertoautomatevia
scripting. The device supports both Telnet and SSH (Secure Shell) CLI with default service port 23 and 22,
respectively.
Telnet&SSHScenario
ScenarioApplicationTiming
WhentheadministratorofthegatewaywantstomanageitfromremotesiteintheIntranetorInternet,
hemayuse"TelnetwithCLI"functiontodothatbyusing"Telnet"or"SSH"utility.
ScenarioDescription
TheLocalAdminortheRemoteAdmincanmanagetheGatewaybyusing"Telnet"or"SSH"utilitywith
privilegedusernameandpassword.
ThedatapacketsbetweentheLocalAdminandtheGatewayorbetweentheRemoteAdminandthe
Gateway can be plain texts or encrypted texts. Suggest they are plain texts in the Intranet for Local
Admintouse"Telnet"utility,andencryptedtextsintheInternetforRemoteAdmintouse"SSH"utility.
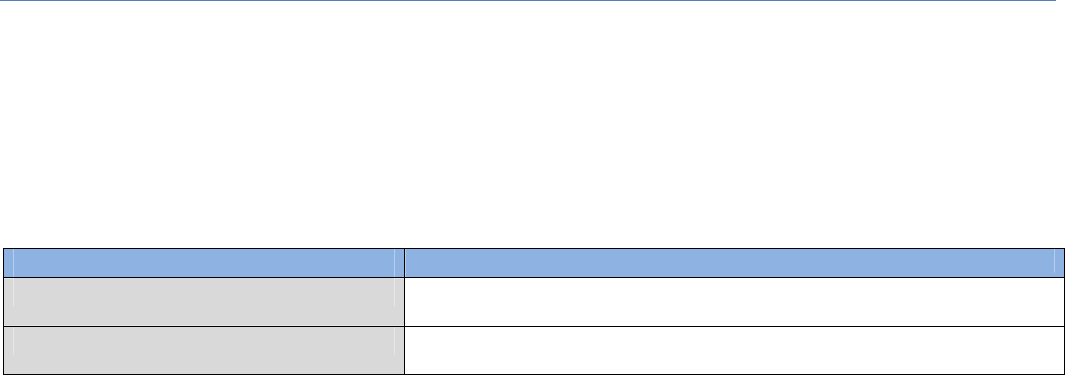
M2MCellularGateway
202
ParameterSetupExample
FollowingtableliststheparameterconfigurationasanexamplefortheGatewayinabovediagramwith
"TelnetwithCLI"enablingatLANandWANinterfaces.
Usedefaultvalueforthoseparametersthatarenotmentionedinthetable.
ConfigurationPath [Telnet
&
SSH]‐[Configuration]
Telnet LAN: ■EnableWAN: Enable
ServicePort:23
SSH LAN: ■EnableWAN: ■Enable
ServicePort:22
ScenarioOperationProcedure
Inabovediagram,"LocalAdmin"or"RemoteAdmin"canmanagethe "Gateway" in the Intranet or
Internet.The"Gateway"isthegatewayofNetwork‐A,andthesubnetofitsIntranetis10.0.75.0/24.It
hastheIPaddressof10.0.75.2forLANinterfaceand118.18.81.33forWAN‐1interface.Itservesasa
NATgateway.
The"LocalAdmin"intheIntranetuses"Telnet"utilitywithprivilegedaccounttologintheGateway.
Orthe"RemoteAdmin"intheInternetuses"SSH"utilitywithprivilegedaccounttologintheGateway.
Theadministratorofthegatewaycancontrolthedeviceaslikeheisinfrontofthegateway.
M2MCellularGateway
203
Telnet&SSHSetting
GotoAdministration>Configure&Manage>Telnet&SSHtab.
TheTelnet&SSHsettingallowsadministratortoaccessthisdevicethroughthetraditionalTelnetorSSH
Telnetprogram.Beforeyoucantelnet(login)tothedevice,please configure the related settings and
passwordwithcare.Thepasswordmanagementpartallowsyoutosetrootpasswordforloggingtelnetand
SSH.
Configuration
Item Valuesetting Description
Telnet 1. TheLANEnableboxis
checkedbydefault.
2. BydefaultService
Portis23.
ChecktheEnableboxtoactivatetheTelnetfunctionforconnectingfromLANorWAN
interfaces.
You can set which number of Service Portyouwanttoprovideforthecorresponding
service.
ValueRange:1~65535.
SSH 3. TheLANEnableboxis
checkedbydefault.
4. BydefaultService
Portis22.
ChecktheEnableboxtoactivatetheSSHTelnetfunctionforconnectingfromLANor
WANinterfaces.
You can set which number of Service Portyouwanttoprovideforthecorresponding
service.
ValueRange:1~65535.
Save N/A ClickSavetosavethesettings
Undo N/A ClickUndotocancelthesettings

M2MCellularGateway
204
Configuration
Item Valuesetting Description
root 1.String:anytextbutno
blankcharacter
2.Thedefaultpassword
fortelnetis
‘wirelessm2m’.
Typeoldpasswordandspecifynewpasswordtochangerootpassword.
Note_1:Youarehighlyrecommendedtochangethedefaulttelnetpasswordwith
yoursbeforethedeviceisdeployed.
Note_2:IfyouhavetroubleforthedefaultpasswordforpreviousFWversion,please
checkthecorrespondingUserManualtogetthecorrectone.
Save N/A ClickSavetosavethesettings
Undo N/A ClickUndotocancelthesettings
M2MCellularGateway
205
6.2SystemOperation
System Operation allows the network administrator to manage system, settings such as web‐based utility
access password change, system information, system time, system log, firmware/configuration backup &
restore,andreset&reboot.
6.2.1Password&MMI
GotoAdministration>SystemOperation>Password&MMItab.
ChangeUserName
ChangeUsernamescreenallowsnetworkadministratortochangetheweb‐basedMMIloginaccounttoaccess
gateway.ClicktheModifybuttonandprovidethenewusernamesetting.
UsernameConfiguration
Item Valuesetting Description
Username
1.ThedefaultUsername
forweb‐basedMMIis
‘admin’.
DisplaythecurrentMMIloginaccount(Username).
NewUsername String:anytext EnternewUsernametoreplacethecurrentsetting.
Password String:anytext Entercurrentpasswordtoverifyifyouhavethepermissiontochangethe
usernamesetting.
Save N/A ClickSavebuttontosavethesettings
Undo N/A ClickUndobuttontocancelthesettings
ChangePassword
Changepasswordscreenallowsnetworkadministratortochangetheweb‐basedMMIloginpasswordto
accessgateway.
M2MCellularGateway
206
PasswordConfiguration
Item Valuesetting Description
OldPassword
1.String:anytext
2.Thedefaultpassword
forweb‐basedMMIis
‘admin’.
Enterthecurrentpasswordtoenableyouunlocktochangepassword.
NewPassword String:anytext Enternewpassword
NewPassword
Confirmation String:anytext Enternewpasswordagaintoconfirm
Save N/A ClickSavebuttontosavethesettings
Undo N/A ClickUndobuttontocancelthesettings
ChangeMMISettingforAccessing
This is the gateway’s web‐based MMI access which allows administrator to access the gateway for
management.Thegateway’sweb‐basedMMIwillautomaticallylogoutwhentheidletime haselapsed.The
settingallowsadministratortoenableautomaticlogoutandsetthelogoutidletime.Whenthelogintimeout
isdisabled,thesystemwon’tlogouttheadministratorautomatically.
M2MCellularGateway
207
MMIConfiguration
Item Valuesetting Description
Login 3timesissetbydefault
Enterthelogintrialcountingvalue.
ValueRange:3~10.
IfsomeonetriedtologinthewebGUIwithincorrectpasswordformore
thanthecountingvalue,anwarningmessage“Alreadyreachingmaximum
Password‐Guessingtimes,pleasewaitafewseconds!”willbedisplayed
andignorethefollowinglogintrials.
LoginTimeout
TheEnableboxis
checked,and300isset
bydefault.
ChecktheEnableboxtoactivatetheautologoutfunction,andspecifythe
maximumidletimeaswell.
ValueRange:30~65535.
GUIAccessProtocol http/httpsis
selectedbydefault.
SelecttheprotocolthatwillbeusedforGUIaccess.Itcanbehttp/https,
httponly,orhttpsonly.
HTTPsCertificate
Setup
Thedefaultboxis
selectedbydefault
IfthehttpsAccessProtocolisselected,theHTTPsCertificateSetupoption
willbeavailableforfurtherconfiguration.
Youcanleaveitasdefaultorselectaexpectedcertificateandkeyfromthe
dropdownlist.
RefertoObjectDefinition>CertificateSectionfortheCertificate
configuration.
httpCompression Theboxisuncheckedby
default.
Checkthebox(gzip,ordeflate)ifanycomprerssionmethodispreferred.
SystemBootMode NormalModeisselected
bydefault.
Selectthesystembootmodethatwillbeadoptedtobootupthedevice.
NormalMode:Ittakeslongerbootuptime,about200seconds,with
completefirmwareimagecheckduringthedevicebooting.
FastMode:Ittakesshorterbootuptime,about120seconds,without
checkingthefirmwareimageduringthedevicebooting.
QuickMode:Ittakesshorterbootuptime,about90seconds,without
checkingthefirmwareimageandcreatetheinternaldatabasefor
User/Group/CaptivePortalfunctions.
Note:UseQuickModewithcare,onceselected,theUser/Group/Captive
Portalfunctionwillbecomenon‐functional.
Save N/A ClickSavebuttontosavethesettings
Undo N/A ClickUndobuttontocancelthesettings
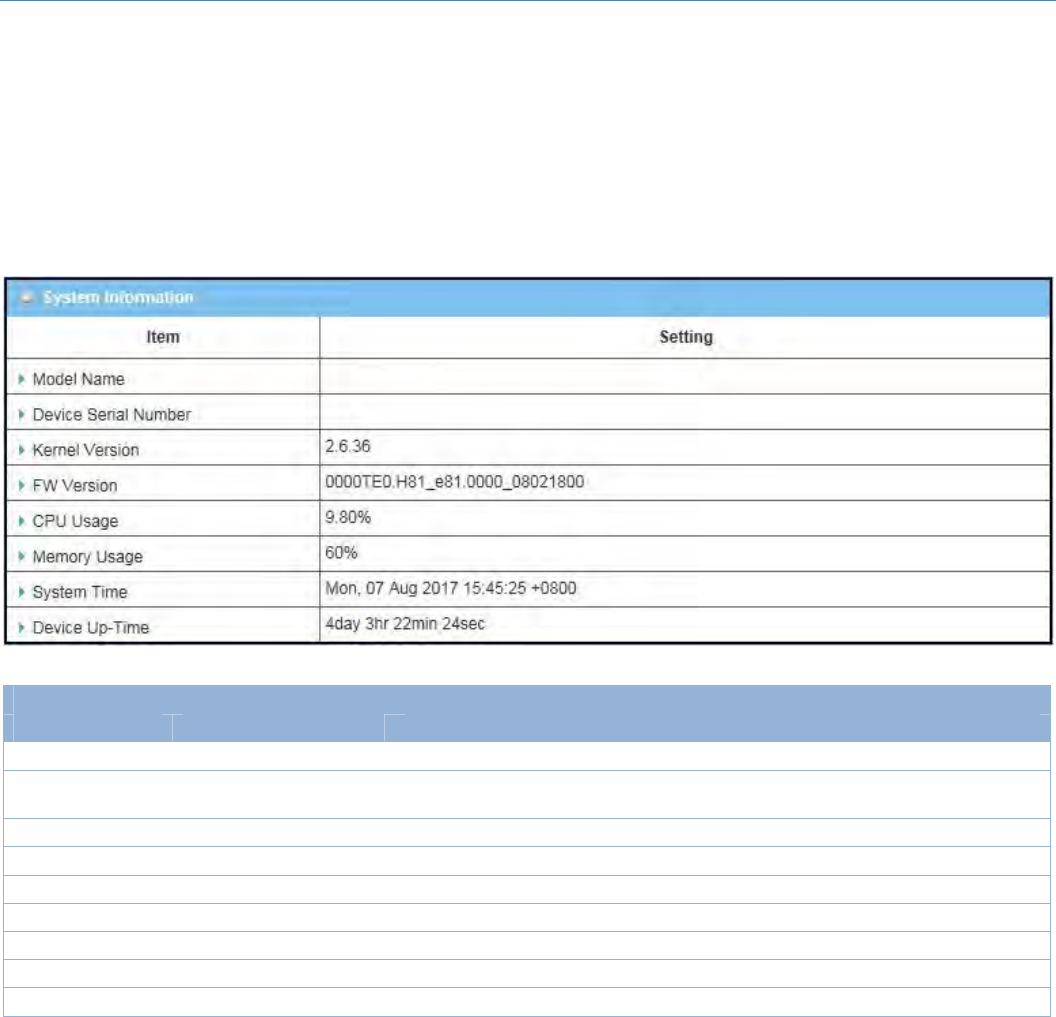
M2MCellularGateway
208
6.2.2SystemInformation
SystemInformationscreengivesnetwork administrator a quick look up on the device information for the
purchadesgateway.
GotoAdministration>SystemOperation>SystemInformationtab.
SystemInformation
Item ValueSetting Description
ModelName N/A Itdisplaysthemodelnameofthisproduct.
DeviceSerial
Number N/A Itdisplaystheserialnumberofthisproduct.
KernelVersion N/A ItdisplaystheLinuxkernelversionoftheproduct
FWVersion N/A Itdisplaysthefirmwareversionoftheproduct
CPUUsage N/A ItdisplaysthepercentageofCPUutilization.
MemoryUsage N/A Itdisplaysthepercentageofdevicememoryutilization.
SystemTime N/A Itdisplaysthecurrentsystemtimethatyoubrowsedthiswebpage.
DeviceUp‐Time N/A Itdisplaysthestatisticsforthedeviceup‐timesincelastbootup.
Refresh N/A ClicktheRefreshbuttontoupdatethesystemInformationimmediately.
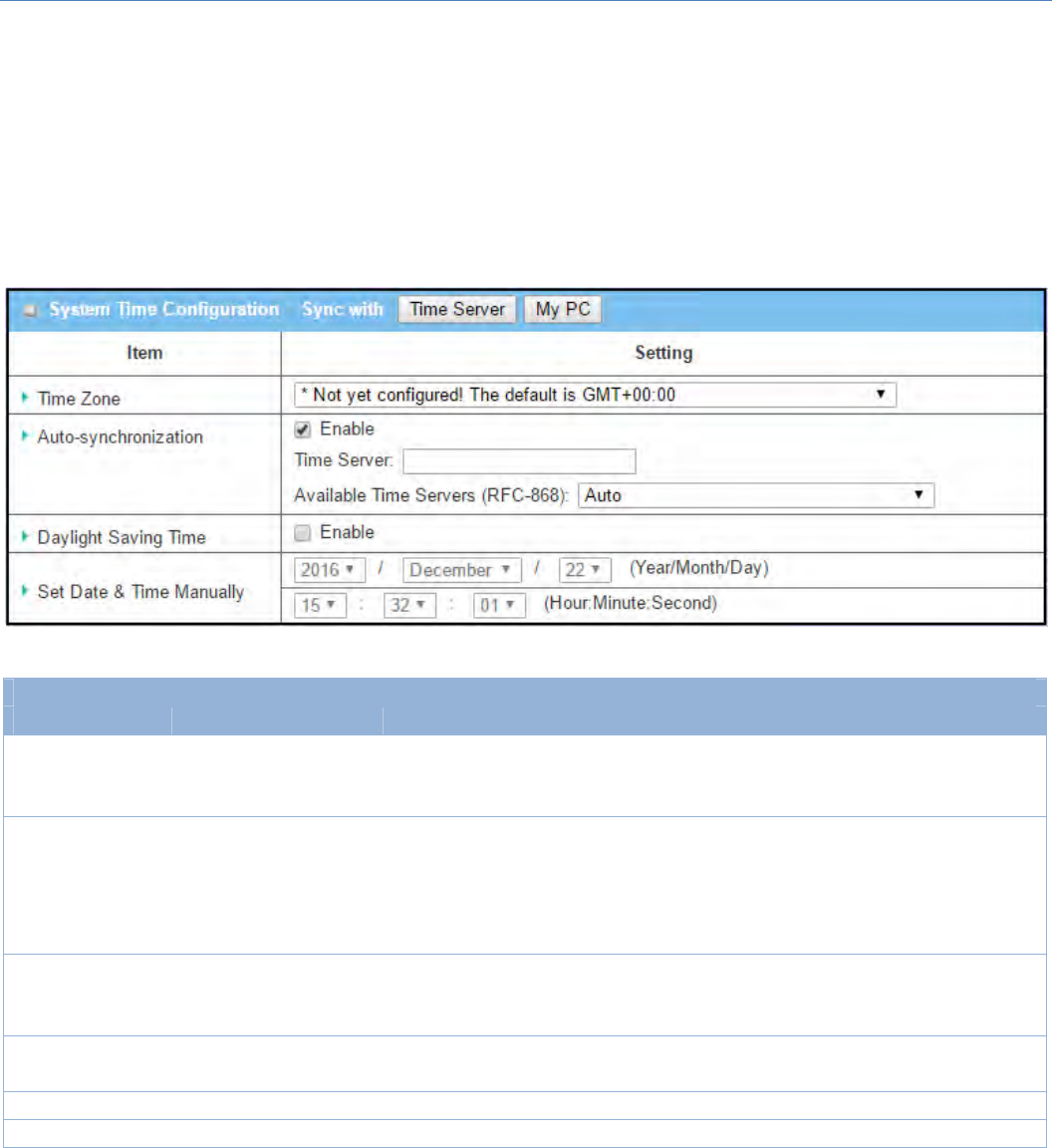
M2MCellularGateway
209
6.2.3SystemTime
Thegatewayprovidesmanuallysetupandauto‐synchronizedapproachesfortheadministratortosetupthe
systemtimeforthegateway.
GotoAdministration>SystemOperation>SystemTimetab.
SystemTimeInformation
Item ValueSetting Description
TimeZone
1.Itisanoptionalitem.
2.GMT+00:00is
selectedbydefault.
Select a time zone where this device locates.
Auto‐
synchronization
1.Checkedbydefault.
2.Autoisselectedby
default.
ChecktheEnablebuttontoactivatethetimeauto‐synchronizationfunctionwith
acertainNTPserver.
YoucanentertheIPorFQDNfortheNTPserveryouexpected,orleaveitas
automodesothattheavailableserverwillbeusedfortimesynchronizationone
byone.
DaylightSaving
Time
1.Itisanoptionalitem.
2.Un‐checkedbydefault
ChecktheEnablebuttontoactivatethedaylightsavingfunction.
When you enabled this function, you have to specify the start date and end date
for the daylight saving time duration.
SetDate&Time 1.Itisanoptionalitem. If you do not enable the time auto-synchronization function, you can also
manually set the date (Year/Month/Day) and time (Hour:Minute:Second).
Save N/A ClicktheSavebuttontosavethesettings.
Refresh N/A ClicktheRefreshbuttontoupdatethesystemtimeimmediately.
Insteadofmanuallyconfiguringthesystemtimeforthegateway,therearetwosimpleandquicksolutionsfor
youtosetthecorrecttimeinformationandsetitasthesystemtimeforthegateway.

M2MCellularGateway
210
Thefirstoneis“SyncwithTimerServer”.Basedonyourselectionoftimezoneandtimeserverinabovetime
informationconfigurationwindow,systemwillcommunicatewithtimeserverbyNTPProtocoltogetsystem
dateandtimeafteryouclickontheSyncwithTimerServerbutton.
Note:Remembertoselectacorrecttimezoneforthedevice,otherwise,youwilljustgettheUTC
(CoordinatedUniversalTime)time,notthelocaltimeforthedevice.
Thesecondoneis“SyncwithmyPC”.ClickontheSyncwithmyPCbuttontoletsystemsynchronizeitsdate
andtimetothetimeoftheadministrationPC.
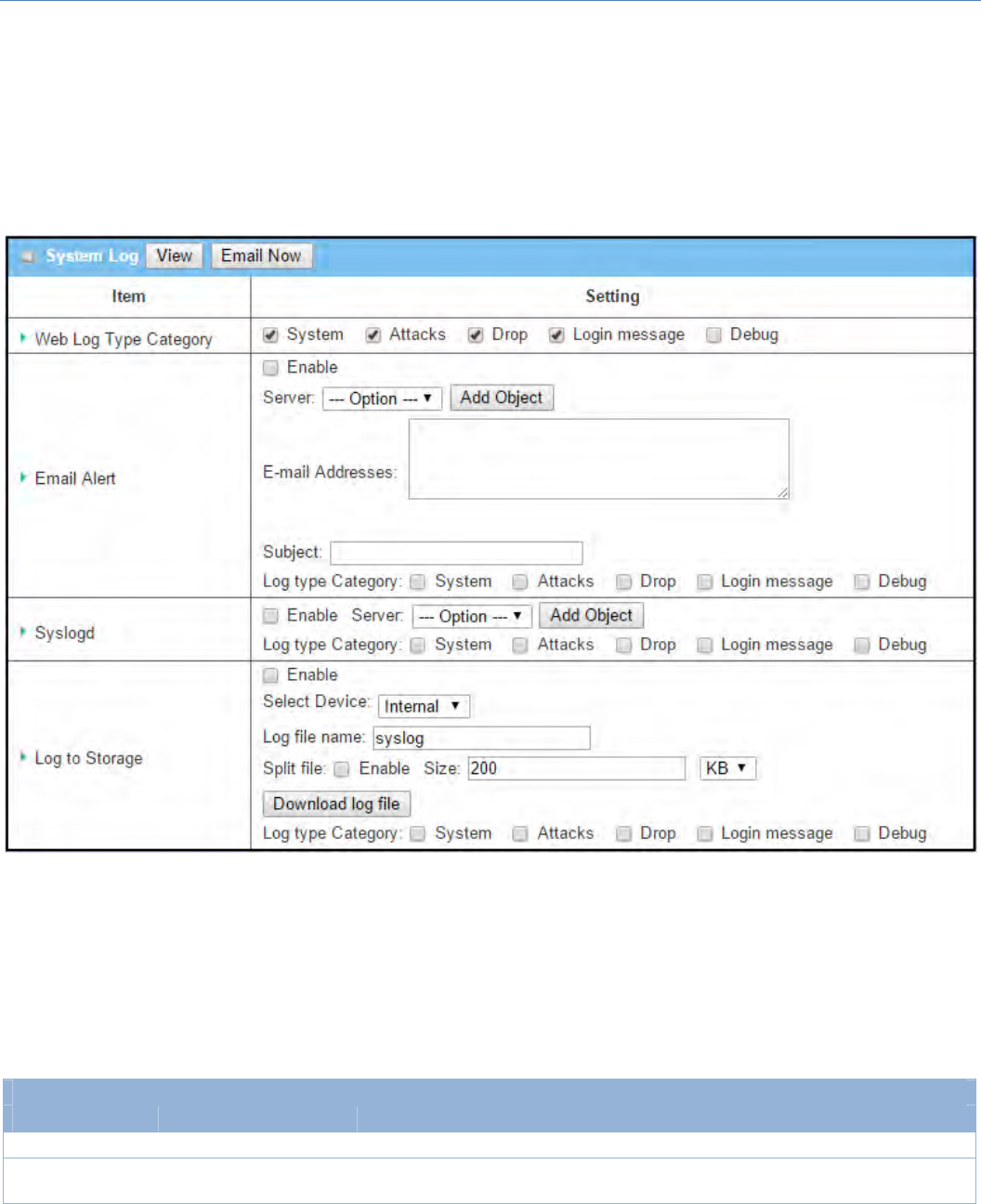
M2MCellularGateway
211
6.2.4SystemLog
SystemLogscreencontainsvariouseventlogtoolsfacilitatingnetworkadministratortoperformlocalevent
loggingandremotereporting.
GotoAdministration>SystemOperation>SystemLogtab.
View&EmailLogHistory
View button is provided for network administrator to view log history on the gateway. Email Now button
enablesadministratortosendinstantEmailforanalysis.
View&EmailLogHistory
Item Valuesetting Description
Viewbutton N/A ClicktheViewbuttontoviewLogHistoryinWebLogListWindow.
EmailNow
button N/A ClicktheEmailNowbuttontosendLogHistoryviaEmailinstantly.
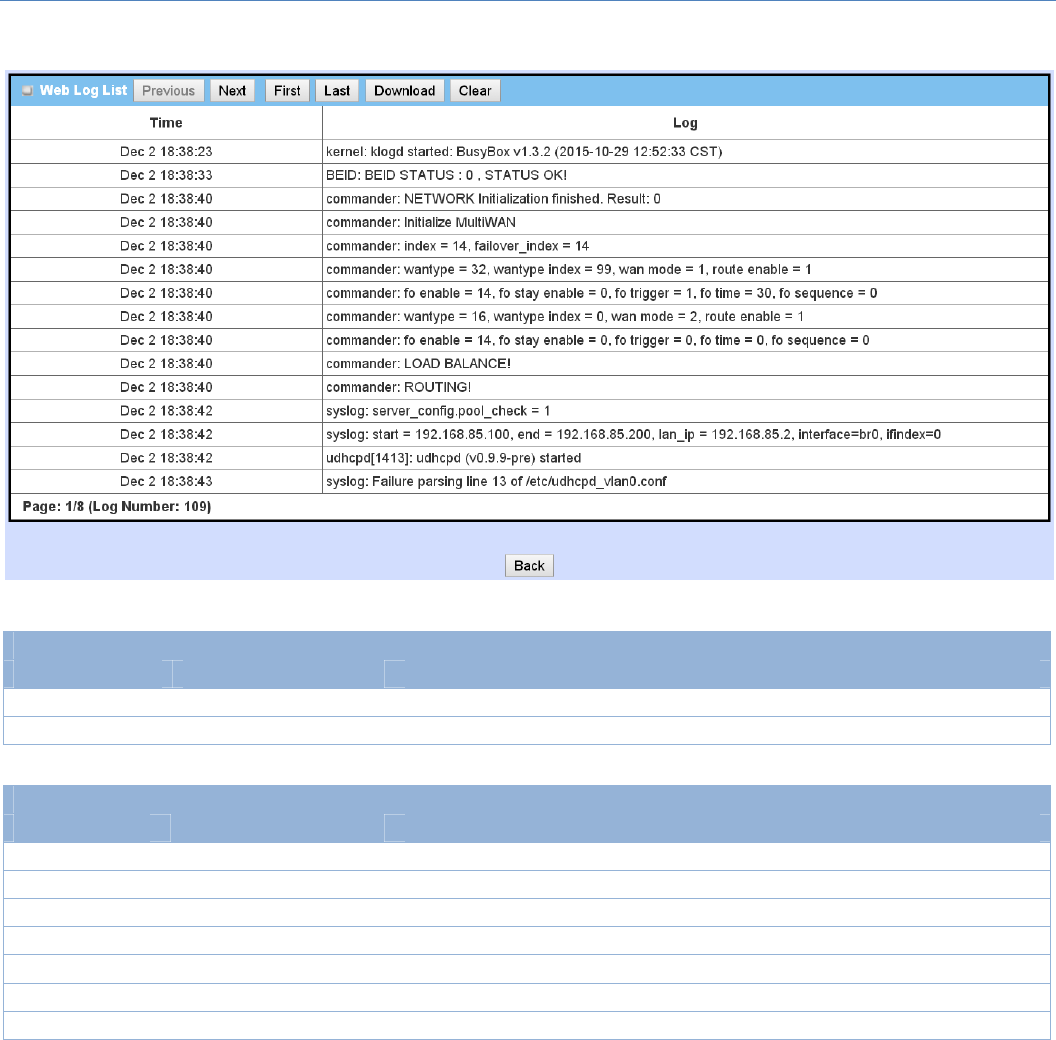
M2MCellularGateway
212
WebLogListWindow
Item ValueSetting Description
Timecolumn N/A Itdisplayseventtimestamps
Logcolumn N/A ItdisplaysLogmessages
WebLogListButtonDescription
Item Valuesetting Description
Previous N/A ClickthePreviousbuttontomovetothepreviouspage.
Next N/A ClicktheNextbuttontomovetothenextpage.
First N/A ClicktheFirstbuttontojumptothefirstpage.
Last N/A ClicktheLastbuttontojumptothelastpage.
Download N/A ClicktheDownloadbuttontodownloadlogtoyourPCintarfileformat.
Clear N/A ClicktheClearbuttontoclearalllog.
Back N/A ClicktheBackbuttontoreturntothepreviouspage.
WebLogTypeCategory
WebLogTypeCategoryscreenallowsnetworkadministratortoselect the type of events to log and be
displayedintheWebLogListWindowasdescribedintheprevioussection.ClickontheViewbuttontoview
LogHistoryintheWebLogListwindow.
M2MCellularGateway
213
WebLogTypeCategorySettingWindow
Item ValueSetting Description
System Checkedbydefault ChecktologsystemeventsandtodisplayintheWebLogListwindow.
Attacks Checkedbydefault ChecktologattackeventsandtodisplayintheWebLogListwindow.
Drop Checkedbydefault ChecktologpacketdropeventsandtodisplayintheWebLogListwindow.
Loginmessage Checkedbydefault ChecktologsystemlogineventsandtodisplayintheWebLogListwindow.
Debug Un‐checkedbydefault ChecktologdebugeventsandtodisplayintheWebLogListwindow.
EmailAlert
EmailAlertscreenallowsnetworkadministratortoselectthetypeofeventtologandbesenttothedestined
Emailaccount.
EmailAlertSettingWindow
Item ValueSetting Description
Enable Un‐checkedbydefault CheckEnableboxtoenablesendingeventlogmessagestodestinedEmail
accountdefinedintheE‐mailAddressesblankspace.
Server N/A
SelectoneemailserverfromtheServerdropdownboxtosendEmail.Ifnone
hasbeenavailable,clicktheAddObjectbuttontocreateanoutgoingEmail
server.
You may also add an outgoing Email server from Object Definition > External
Server > External Server tab.
E‐mailaddress String:emailformat
Entertherecipient’sEmailaddress.SeparateEmailaddresseswithcomma‘,’or
semicolon‘;’
EntertheEmailaddressintheformatof‘myemail@domain.com’
Subject String:anytext EnteranEmailsubjectthatiseasyforyoutoidentifyontheEmailclient.
Logtypecategory Defaultunchecked Select the type of events to log and be sent to the designated Email account.
AvailableeventsareSystem,Attacks,Drop,Loginmessage,andDebug.
M2MCellularGateway
214
Syslogd
Syslogdscreenallowsnetworkadministratortoselectthetypeofeventtologandbesenttothedesignated
Syslogserver.
SyslogdSettingWindow
Item ValueSetting Description
Enable Un‐checkedbydefault CheckEnableboxtoactivatetheSyslogdfunction,andsendeventlogstoasyslogserver
Server N/A
SelectonesyslogserverfromtheServerdropdownboxtosenteventlogto.
Ifnonehasbeenavailable,clicktheAddObjectbuttontocreateasystemlogserver.
You may also add an system log server from the Object Definition > External Server >
External Server tab.
Logtype
category Un‐checkedbydefault Selectthetypeofeventtologandbesenttothedestinedsyslogserver.Available
eventsareSystem,Attacks,Drop,Loginmessage,andDebug.
LogtoStorage
Log to Storagescreen allowsnetworkadministratorto select the type of events tolog and be stored at an
internaloranexternalstorage.
LogtoStorageSettingWindow
Item ValueSetting Description
Enable Un‐checkedbydefault Checktoenablesendinglogtostorage.
SelectDevice Internalisselectedby
default Selectinternalorexternalstorage.
Logfilename Un‐checkedbydefault Enterlogfilenametosavelogsindesignatedstorage.
SplitfileEnable Un‐checkedbydefault Checkenableboxtosplitfilewheneverlogfilereachingthespecifiedlimit.
SplitfileSize 200KBissetbydefault Enterthefilesizelimitforeachsplitlogfile.
ValueRange:10~1000.
Logtypecategory Un‐checkedbydefault Checkwhichtypeoflogstosend:System,Attacks,Drop,Loginmessage,Debug
LogtoStorageButtonDescription
Item Valuesetting Description
Downloadlog
file
N/A ClicktheDownloadlogfilebuttontodownloadlogfilestoalog.tarfile.
M2MCellularGateway
215
6.2.5Backup&Restore
IntheBackup&Restorewindow,youcanupgradethedevicefirmwarewhennewfirmwareisavailableand
alsobackup/restorethedeviceconfiguration.
In addition to the factory defaultsettings,youcanalsocustomizeaspecialconfigurationsettingasa
customizeddefaultvalue.Withthiscustomizeddefaultvalue,youcanresetthedevicetotheexpecteddefault
settingifneeded.
GotoAdministration>SystemOperation>Backup&Restoretab.
FWBackup&Restore
Item ValueSetting Description
FWUpgrade ViaWebUIisselectedby
default
Ifnewfirmwareisavailable,clicktheFWUpgradebuttontoupgradethedevice
firmwareviaWebUI,orViaStorage.
Afterclickingonthe“FWUpgrade”commandbutton,youneedtospecifythe
filenameofnewfirmwarebyusing“Browse”button,andthenclick“Upgrade”
buttontostarttheFWupgradingprocessonthisdevice.Ifyouwanttoupgrade
afirmwarewhichisfromGPLpolicy,pleasecheck“Acceptunofficialfirmware”
Backup
Configuration
Settings
Downloadisselectedby
default
YoucanbackuporrestorethedeviceconfigurationsettingsbyclickingtheVia
WebUIbutton.
Download:forbackupthedeviceconfigurationtoaconfig.binfile.
Upload:forrestoreadesignatedconfigurationfiletothedevice.
ViaWebUI:toretrievetheconfigurationfileviaWebGUI.
AutoRestore
Configuration
TheEnableboxis
uncheckedbydefault
ChicktheEnablebuttontoactivatethecustomizeddefaultsettingfunction.
Oncethefunctionisactivated,youcansavetheexpectedsettingasa
customizeddefaultsettingbyclickingtheSaveConf.button,orclickingthe
CleanConf.buttontoerasethestoredcustomizedconfiguration.
M2MCellularGateway
216
6.2.6Reboot&Reset
Forsomespecialreasonorsituation,youmayneedtorebootthegatewayorresetthedeviceconfigurationto
itsdefault value.Inadditionto performtheseoperationsthroughthePowerON/OFF,orpressingthereset
buttononthedevicepanel,youcandoitthroughthewebGUItoo.
GotoAdministration>SystemOperation>Reboot&Resettab.
In the Reboot & Reset window, you can reboot this device by clicking the “Reboot” button, and reset this
devicetodefaultsettingsbyclickingthe“Reset”button.
SystemOperationWindow
Item ValueSetting Description
Reboot Nowisselectedby
default
ChicktheRebootbuttontorebootthegatewayimmediatelyoronapre‐defined
timeschedule.
Now:Rebootimmediately
TimeSchedule:Selectapre‐definedauto‐reboottimescheduleruletoreboot
theautodeviceonadesignatedtim.Todefineatimeschedulerule,goto
ObjectDefinition>Scheduling>Configurationtab.
ResettoDefault N/A ClicktheResetbuttontoresetthedeviceconfigurationtoitsdefaultvalue.

M2MCellularGateway
217
6.3FTP(notsupported)
Not supported feature for the purchased product, leave it as blank.
M2MCellularGateway
218
6.4Diagnostic
Thisgatewaysupportssimplenetworkdiagnosistoolsfortheadministratortotroubleshootandfindtheroot
causeoftheabnormalbehaviorortrafficspassingthroughthe gateway.TherecanbeaPacketAnalyzerto
helprecordthepacketsforadesignatedinterfaceorspecificsource/destinationhost,andanotherPingand
Tracerttoolsfortestingthenetworkconnectivityissues.
6.4.1DiagnosticTools
TheDiagnosticToolsprovidesomefrequentlyusednetworkconnectivitydiagnostictools(approaches)forthe
networkadministratortocheckthedeviceconnectivity.
GotoAdministration>Diagnostic>DiagnosticToolstab.
DiagnosticTools
Item Valuesetting Description
PingTest OptionalSetting
ThisallowsyoutospecifyanIP/FQDNandthetestinterface(LAN,WAN,or
Auto),sosystemwilltrytopingthespecifieddevicetotestwhetheritisalive
afterclickingonthePingbutton.Atestresultwindowwillappearbeneathit.
TracertTest Optionalsetting
Traceroute(tracert)commandisanetworkdiagnostictoolfordisplayingthe
route(path)andmeasuringtransitdelaysofpacketsacrossanIPnetwork.
Tracerouteproceedsuntilall(three)sentpacketsarelostformorethan
twice,thentheconnectionislostandtheroutecannotbeevaluated.
First,youneedtospecifyanIP/FQDN,thetestinterface(LAN,WAN,or
Auto)andtheprotocol(UDPorICMP),andbydefault,itisUDP.
Then,systemwilltrytotracethespecifiedhosttotestwhetheritisalive
afterclickingonTracertbutton.Atestresultwindowwillappearbeneathit.
WakeonLAN Optionalsetting
WakeonLAN(WOL)isanEthernetnetworkingstandardthatallowsa
computertobeturnedonorawakenedbyanetworkmessage.Youcan
specifytheMACaddressofthecomputer,inyourLANnetwork,tobe
remotelyturnedonbyclickingontheWakeupcommandbutton.
Save N/A ClicktheSavebuttontosavetheconfiguration.
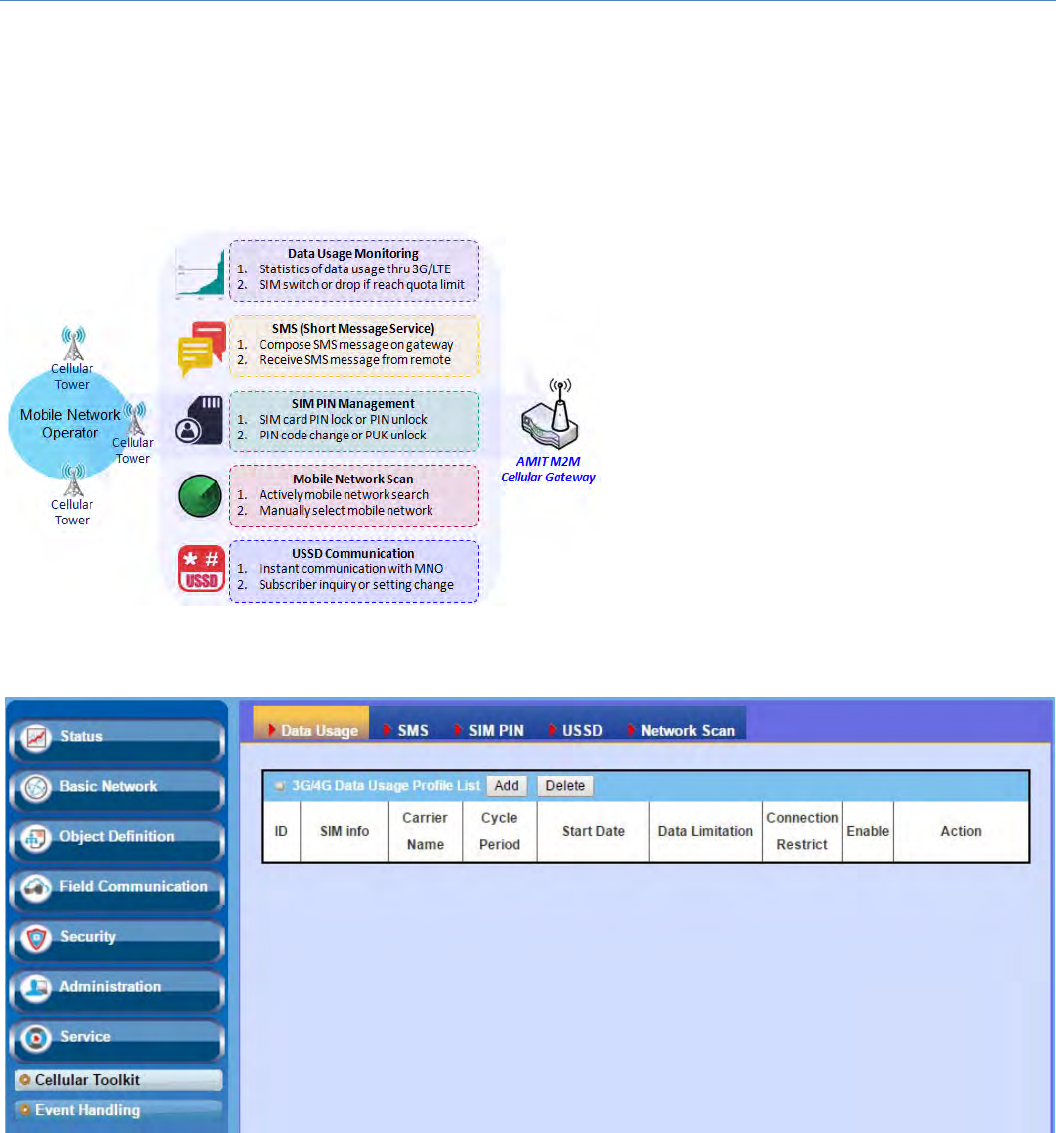
M2MCellularGateway
219
Chapter7Service
7.1 CellularToolkit
Besides cellular data connection, you may
alsoliketomonitordatausageofcellular
WAN,sendingtextmessagethroughSMS,
changing PIN code of SIM card,
communicating with carrier/ISP by USSD
command, or doing a cellular network scan
fordiagnosticpurpose.
In Cellular Toolkit section, it includes several
useful features that are related to cellular
configuration or application. You can
configure settings of Data Usage, SMS, SIM
PIN, USSD, and Network Scan here. Please
noteatleastavalidSIMcardisrequiredtobe
insertedtodevicebeforeyoucontinuesettingsinthissection.
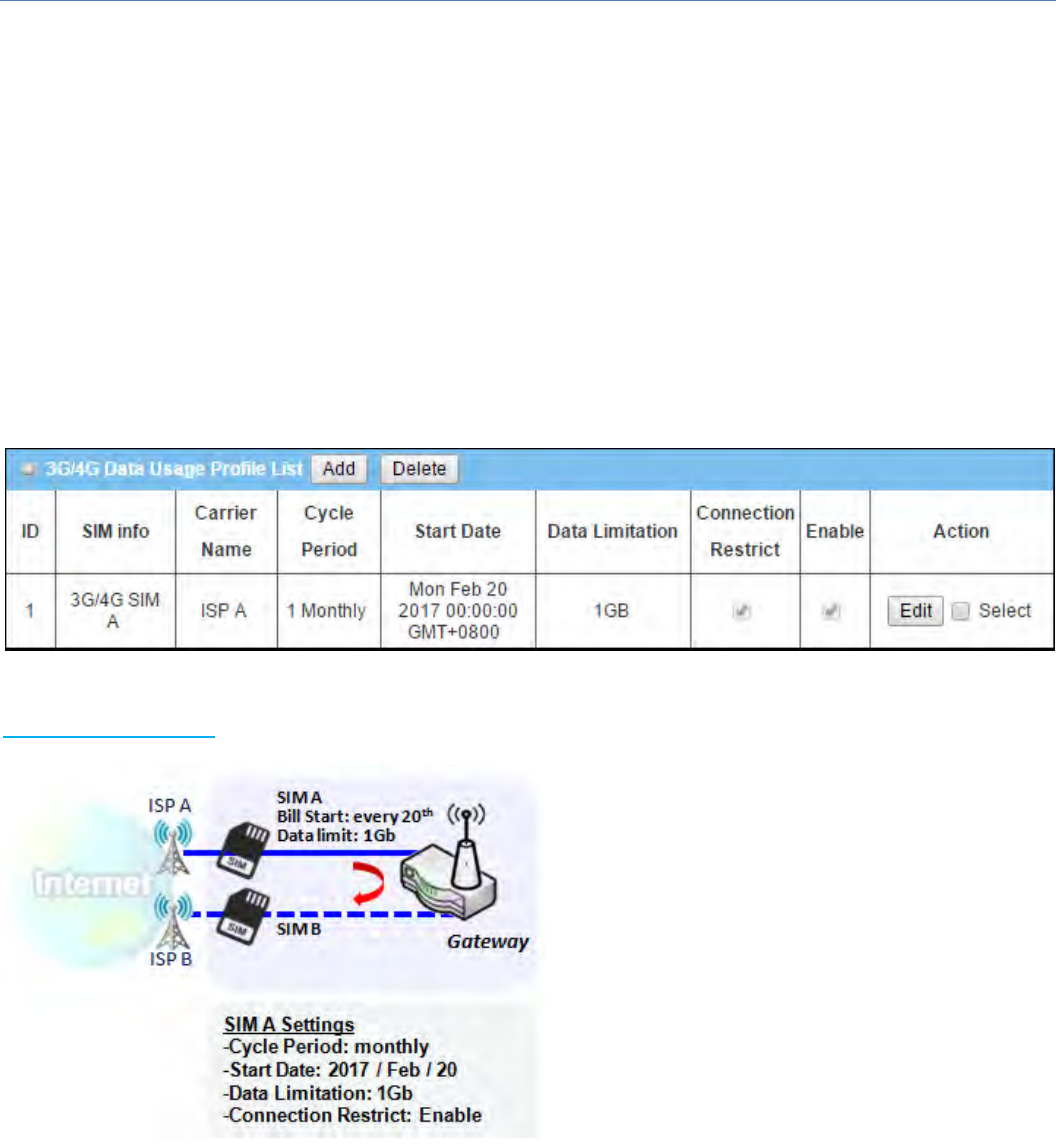
M2MCellularGateway
220
7.1.1DataUsage
Mostofdataplanforcellularconnectioniswithalimitedamountofdatausage.Ifdatausagehasbeenover
limitedquota,eitheryouwillgetmuchlowerdatathroughputthatmayaffectyourdailyoperation,oryouwill
geta‘billshock’inthenextmonthbecausecarrier/ISPchargesalotfortheover‐quotadatausage.
WithhelpfromDataUsagefeature,devicewillmonitorcellulardatausagecontinuouslyandtakeactions.If
datausagereacheslimitedquota,devicecanbesettodropthecellulardataconnectionrightaway.Otherwise,
if secondary SIM card is inserted, device will switch to secondary SIM and establish another cellular data
connectionwithsecondarySIMautomatically.
IfDataUsagefeatureisenabled,allhistoryofcellulardatausage can be viewed at Status>Statistics &
Reports>CellularUsagetab.
3G/4GDataUsage
DataUsagefeatureenablinggatewaydeviceto
continuously monitor cellular data usage and take
actions.Inthediagram,quotalimitofSIMAis1Gb
permonthandbillstartdateis20thofeverymonth.
Thedeviceissmarttostartanewcalculationof
data usage on every 20th of month. Enable
Connection Restrict will force gateway device to
dropcellularconnectionofSIMAwhendatausage
reaches quota limit (1Gb in this case). If SIM
failover feature is configured in Internet Setup,
then gateway will switch to SIM B and establish a
newcellulardataconnectionautomatically.
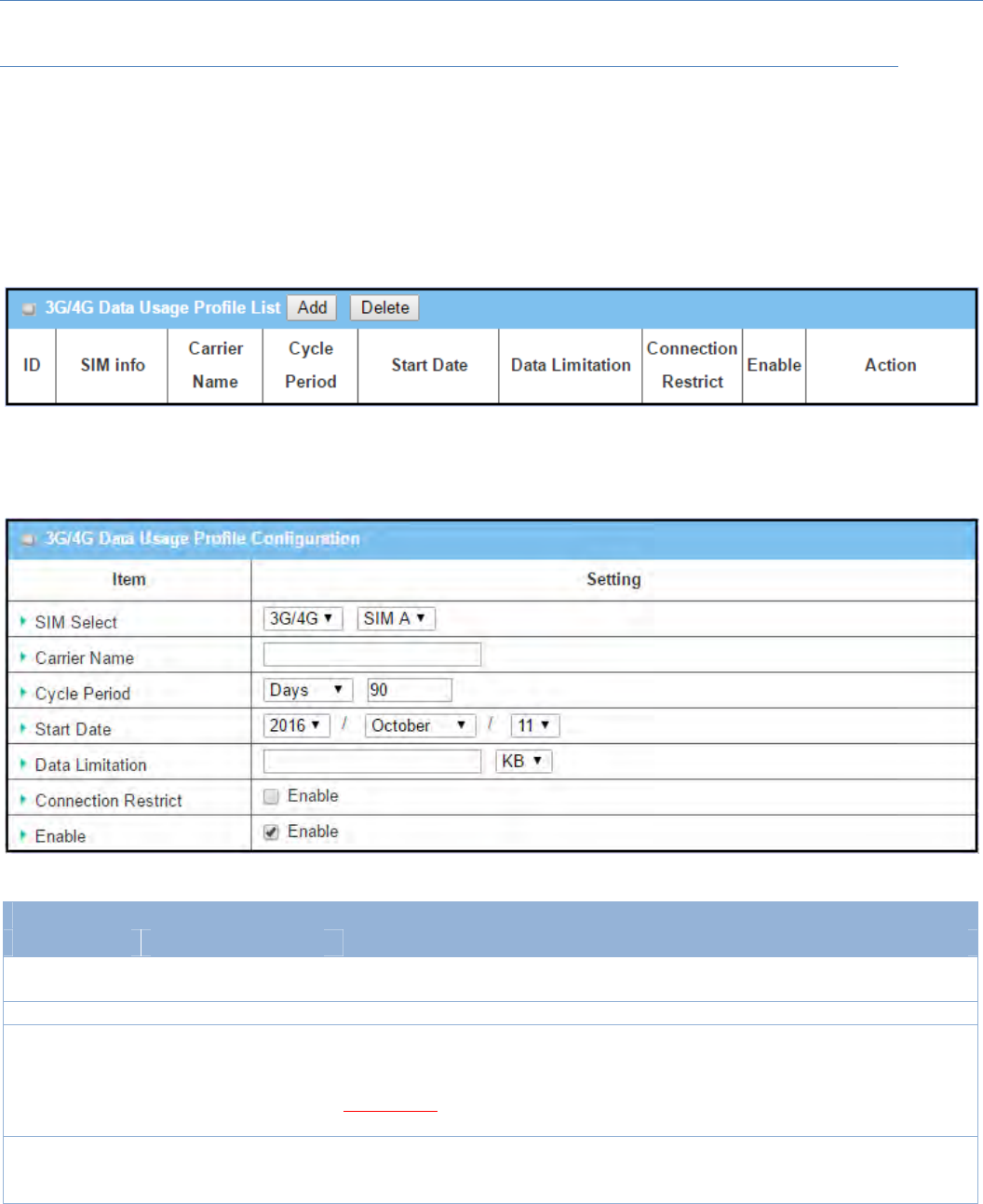
M2MCellularGateway
221
DataUsageSetting
GotoService>CellularToolkit>DataUsagetab.
BeforefinishedsettingsforDataUsage,youneedtoknowbillstartdate,billperiod,andquotalimitofdata
usageaccordingtoyourdataplan.YoucanaskthisinformationfromyourcarrierorISP.
Create/Edit3G/4GDataUsageProfile
WhenAddbuttonisapplied,3G/4GDataUsageProfileConfigurationscreenwillappear.Youcancreateupto
fourdatausageprofiles,oneprofileforeachSIMcardusedintheGateway.
3G/4GDataUsageProfileConfiguration
ItemSetting Valuesetting Description
SIMSelect 3G/4G‐1andSIMAby
default.
Chooseacellularinterface (3G/4G‐1or3G/4G‐2),andaSIMcardboundtothe
selectedcellularinterfacetoconfigureitsdatausageprofile.
CarrierName Itisanoptionalitem. FillintheCarrierNamefortheselectedSIMcardforidentification.
CyclePeriod Daysbydefault Thefirstboxhas threetypes forcycleperiod.TheyareDays,WeeklyandMonthly.
Days:ForperDayscycleperiods,youhavetofurtherspecifythenumberofdaysin
thesecondbox.
ValueRange:1~90days.
Weekly,Monthly:Thecycleperiodisoneweekoronemonth.
StartDate N/A Specifythedateto startmeasurenetworktraffic.
Pleasedon’tselectthedaybeforenow,otherwise,thetrafficstatisticswillbe
incorrect.

M2MCellularGateway
222
DataLimitation N/A Specifytheallowabledatalimitationforthedefinedcycleperiod.
Connection
Restrict
Un‐Checkedbydefault. ChecktheEnable boxtoactivate theconnectionrestrictionfunction.
Duringthespecifiedcycleperiod,iftheactualdatausageexceedstheallowabledata
limitation,thecellularconnectionwillbeforcedtodisconnect.
Enable Un‐Checkedbydefault. ChecktheEnable boxtoactivate thedatausageprofile.
M2MCellularGateway
223
7.1.2SMS
ShortMessageService(SMS)isatextmessagingservice,whichisusedtobewidely‐usedonmobilephones.It
usesstandardizedcommunicationsprotocolstoallowmobilephonesorcellulardevicestoexchangeshorttext
messagesinaninstantandconvenientway.
SMSSetting
GotoService>CellularToolkit>SMStab
Withthisgatewaydevice,youcansendSMStextmessagesorbrowsereceivedSMSmessagesasyouusually
doonacellularphone.
SetupSMSConfiguration
Configuration
Item Valuesetting Description
Physical
Interface
Theboxis3G/4G‐1by
default
Chooseacellularinterface(3G/4G‐1or3G/4G‐2)forthefollowingSMSfunction
configuration.
SMS Theboxischeckedby
default
ThisistheSMSswitch.IftheboxcheckedthattheSMSfunctionenable,ifthe
boxuncheckedthattheSMSfunctiondisable.
SIMStatus N/A DependoncurrentlySIMstatus.ThepossiblevaluewillbeSIM_AorSIM_B.
SMSStorage TheboxisSIMCardOnly
bydefaultThisistheSMSstoragelocation.CurrentlytheoptiononlySIMCardOnly.
Save N/A ClicktheSavebuttontosavethesettings
M2MCellularGateway
224
SMSSummary
ShowUnreadSMS,ReceivedSMS,RemainingSMS,andeditSMScontexttosend,readSMSfromSIMcard.
SMSSummary
Item Valuesetting Description
UnreadSMS N/A IfSIMcardinserttorouterfirsttime,unreadSMSvalueiszero.Whenreceivedthe
newSMSbutdidn’tread,thisvalueplusone.
ReceivedSMS N/A ThisvaluerecordtheexistingSMSnumbersfromSIMcard,Whenreceivedthenew
SMS,thisvalueplusone.
RemainingSMS N/A ThisvalueisSMScapacityminusreceivedSMS,WhenreceivedthenewSMS,this
valueminusone.
NewSMS N/AClickNewSMSbutton,aNewSMSscreenappears.UsercansettheSMSsetting
fromthisscreen.RefertoNewSMSinthenextpage.
SMSInbox N/A
ClickSMSInboxbutton,aSMSInboxListscreenappears.Usercanreadordelete
SMS,replySMSorforwardSMSfromthisscreen.RefertoSMSInboxListinthe
nextpage.
Refresh N/A ClicktheRefreshbuttontoupdatetheSMSsummaryimmediately.
NewSMS
YoucansettheSMSsettingfromthisscreen.
M2MCellularGateway
225
NewSMS
Item Valuesetting Description
Receivers N/A WritethereceiverstosendSMS.Userneedtoaddthesemicolonandcompose
multiplereceiversthatcangroupsendSMS.
TextMessage N/A WritetheSMScontexttosendSMS.Theroutersupportsuptoamaximumof
1023characterforSMScontextlength.
Send N/A ClicktheSendbutton,abovetextmessagewillbesentasaSMS.
Result N/AIfSMShasbeensentsuccessfully,itwillshowSendOK,otherwiseSendFailed
willbedisplayed.
SMSInboxList
YoucanreadordeleteSMS,replySMSorforwardSMSfromthisscreen.
SMSInboxList
Item Valuesetting Description
ID N/A ThenumberorSMS.
FromPhone
Number N/A WhatthephonenumberfromSMS
Timestamp N/AWhattimereceiveSMS
SMSText
Preview N/A PreviewtheSMStext.ClicktheDetailbuttontoreadacertainmessage.
Action Theboxisuncheckedby
default
ClicktheDetailbuttontoreadtheSMSdetail;ClicktheReply/Forwardbutton
toreply/forwardSMS.
Besides,youcancheckthebox(es),andthenclicktheDeletebuttontodelete
thecheckedSMS(s).
Refresh N/A RefreshtheSMSInboxList.
Delete N/A DeletetheSMSforallcheckedboxfromAction.
Close N/A ClosetheDetailSMSMessagescreen.

M2MCellularGateway
226
7.1.3SIMPIN
Withmostcasesintheworld,usersneedtoinsertaSIMcard(a.k.a.UICC)intoenddevicestogetoncellular
networkforvoiceserviceordatasurfing.TheSIMcardisusually released by mobile operators or service
providers. Each SIMcard hasa unique number(so‐called ICCID) fornetworkowners orserviceproviders to
identifyeachsubscriber.AsSIMcardplaysanimportantrolebetweenserviceprovidersandsubscribers,some
securitymechanismsarerequiredonSIMcardtopreventanyunauthorizedaccess.
EnablingaPINcodeinSIMcardisaneasyandeffectivewayofprotectingcellulardevicesfromunauthorized
access.ThisgatewaydeviceallowsyoutoactivateandmanagePINcodeonaSIMcardthroughitswebGUI.
ActivatePINcodeonSIMCard
ThisgatewaydeviceallowsyoutoactivatePINcodeonSIMcard.This
exampleshowshow toactivatePINcodeon SIM‐Afor3G/4G‐1with
defaultPINcode“0000”.
ChangePINcodeonSIMCard
ThisgatewaydeviceallowsyoutochangePINcodeonSIMcard.
Followingtheexampleabove,youneed to type original PIN code
“0000”,andthentypenewPINcodewith‘1234’ifyouliketosetnew
PINcodeas‘1234’.ToconfirmthenewPINcodeyoutypeiswhatyou
want,youneedtotypenewPINcode‘1234’inVerifiedNewPINCode
again.
UnlockSIMcardbyPUKCode
IfyouenteredincorrectPINcodeatconfigurationpagefor3G/4G‐1
WANoverthreetimes,andthenitwillcauseSIMcardtobelockedby
PUKcode.ThenyouhavetocallservicenumbertogetaPUKcodeto
unlockSIMcard.Inthediagram,thePUKcodeis“12345678”andnew
PINcodeis“5678”.
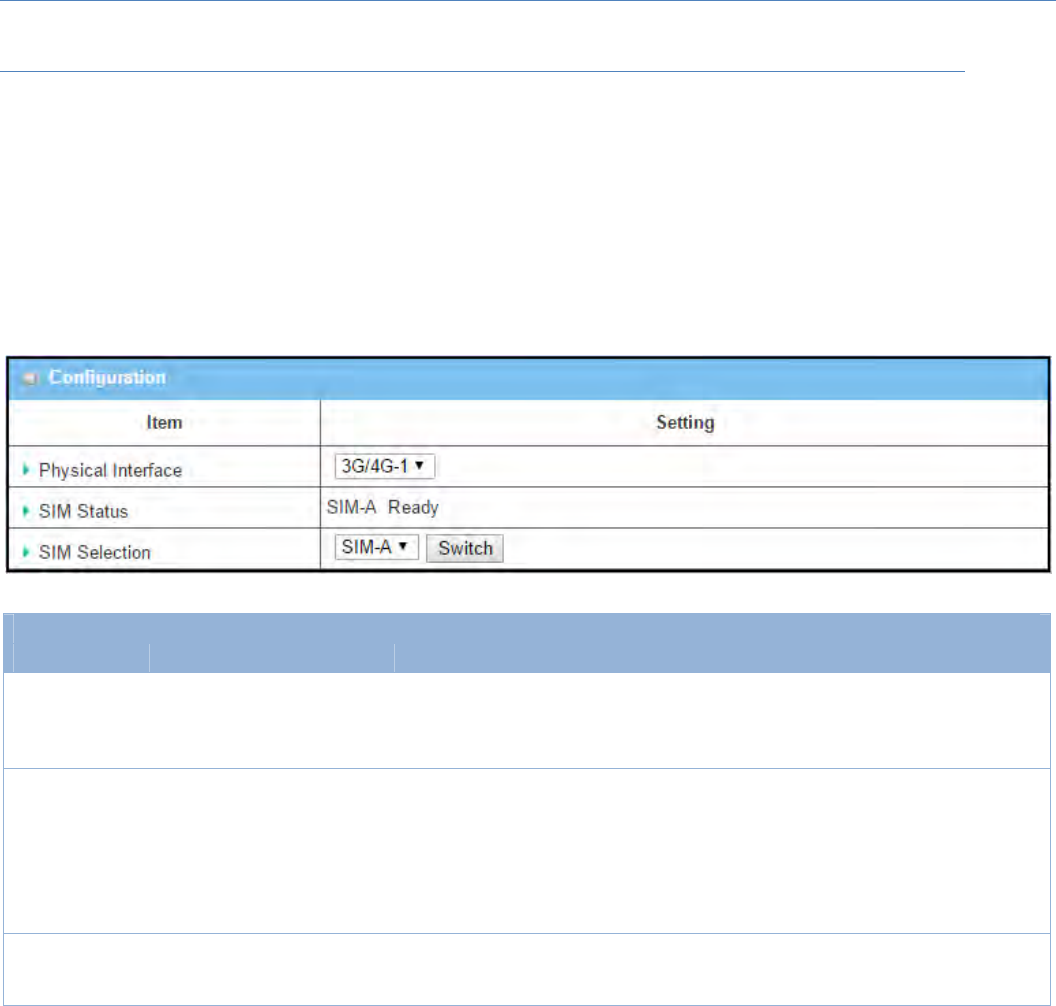
M2MCellularGateway
227
SIMPINSetting
GotoService>CellularToolkit>SIMPINTab
WiththeSIMPINFunctionwindow,itallowsyoutoenableordisableSIMlock(whichmeansprotectedbyPIN
code),orchangePINcode.Youcanalsoseetheinformationofremaining times of failure trials as we
mentionedearlier.Ifyourunoutofthesefailuretrials,youneedtogetaPUKcodetounlockSIMcard.
SelectaSIMCard
ConfigurationWindow
Item Valuesetting Description
Physical
Interface
Theboxis3G/4G‐1by
default
Chooseacellularinterface(3G/4G‐1or3G/4G‐2)tochangetheSIMPINsetting
fortheselectedSIMCard.
Thenumberofphysicalmodemsdependsonthegatewaymodelyou
purchased.
SIMStatus N/A IndicationfortheselectedSIMcardandtheSIMcardstatus.
The status could be Ready, Not Insert, or SIM PIN.
Ready -- SIM card is inserted and ready to use. It can be a SIM card without PIN
protection or that SIM card is already unlocked by correct PIN code.
Not Insert -- No SIM card is inserted in that SIM slot.
SIM PIN -- SIM card is protected by PIN code, and it’s not unlocked by a
correct PIN code yet. That SIM card is still at locked status.
SIMSelection N/A SelecttheSIMcardforfurtherSIMPINconfiguration.
PresstheSwitchbutton,thentheGatewaywillswitchSIMcardtoanotherone.
Afterthat,youcanconfiguretheSIMcard.
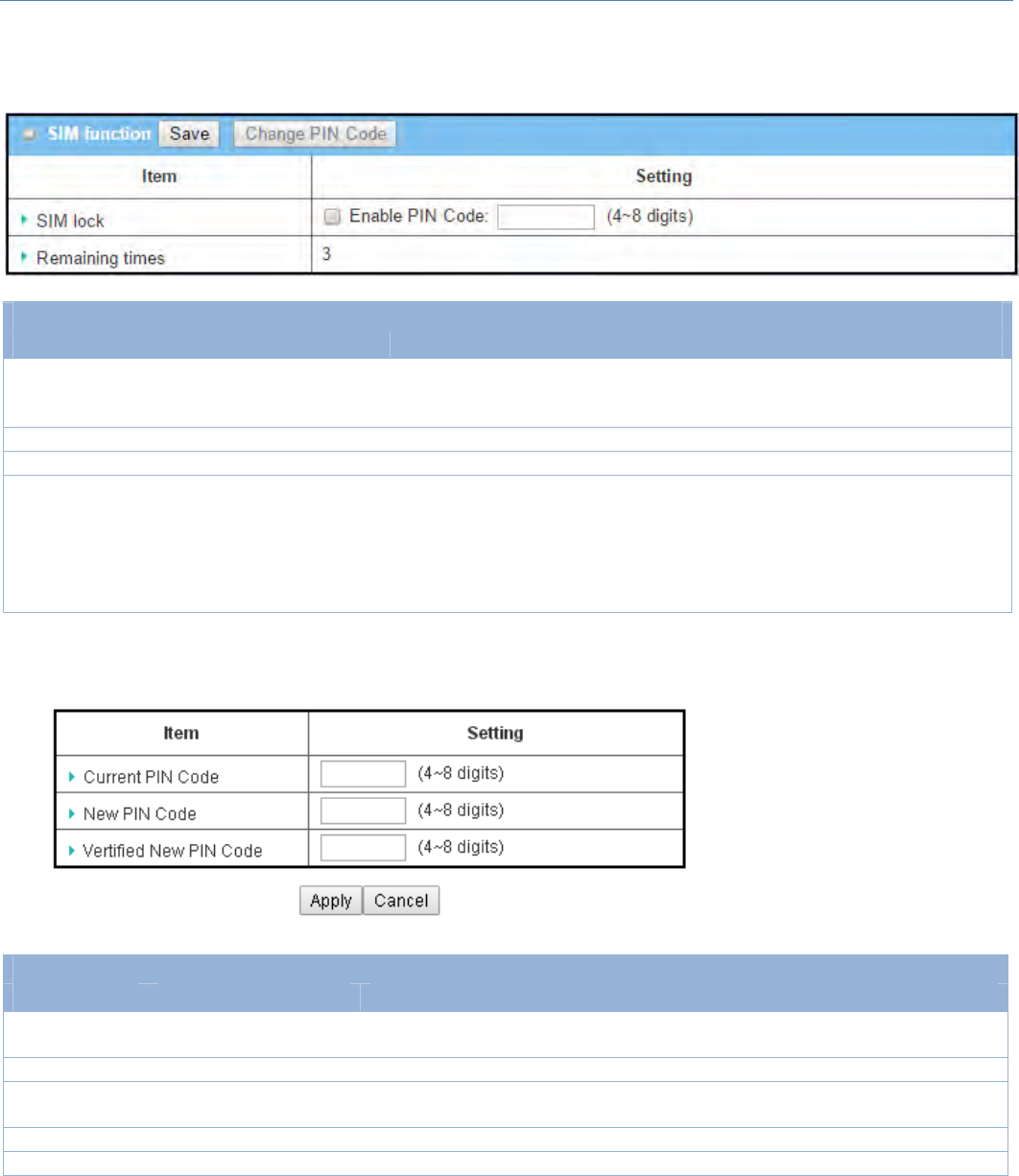
M2MCellularGateway
228
Enable/ChangePINCode
Enable or Disable PIN code (password) function, and even change PIN code function.
SIMfunctionWindow
ItemSetting Valuesetting Description
SIMlock DependonSIMcard ClicktheEnable buttontoactivatetheSIMlockfunction.
ForthefirsttimeyouwanttoenabletheSIMlockfunction,youhaveto
fillinthePINcodeaswell,andthenclickSavebuttontoapplythesetting.
Remainingtimes DependonSIMcard RepresenttheremainingtrialtimesfortheSIMPINunlocking.
Save N/A ClicktheSavebuttontoapplythesetting.
ChangePINCode N/A ClicktheChangePINcodebuttontochangethePINcode(password).
IftheSIMLockfunctionisnotenabled,theChangePINcodebuttonis
disabled.Inthecase,ifyoustillwanttochangethePINcode,youhaveto
enabletheSIMLockfunctionfirst,fillinthePINcode,andthenclicktheSave
buttontoenable.Afterthat,YoucanclicktheChangePINcodebuttonto
changethePINcode.
WhenChangePINCodebuttonisclicked,thefollowingscreenwillappear.
Item ValueSetting Description
CurrentPIN
Code
AMustfilledsetting Fillinthecurrent (old)PINcodeoftheSIMcard.
NewPINCode AMustfilledsetting FillinthenewPINCodeyouwanttochange.
VerifiedNew
PINCode
AMustfilledsettingConfirmthenewPINCodeagain.
Apply N/A ClicktheApplybuttontochangethePINcodewithspecifiednewPINcode.
Cancel N/A ClicktheCancel buttontocancelthechangesandkeepcurrentPINcode.
Note:IfyouchangedthePINcodeforacertainSIMcard,youmustalsochangethecorrespondingPINcode
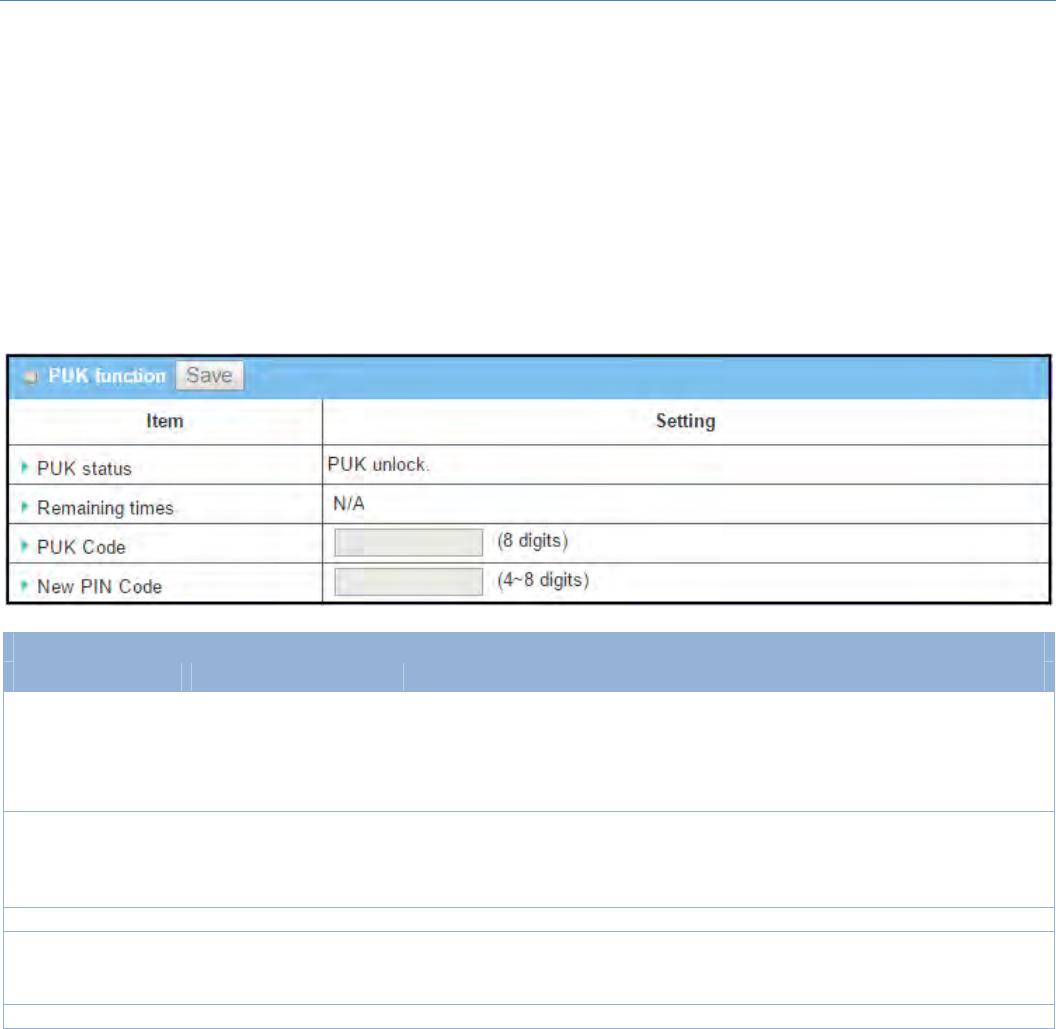
M2MCellularGateway
229
specified in the Basic Network>WAN & Uplink>Internet Setup>Connection with SIM Cardpage.
Otherwise,itmayresultinwrongSIMPINtrialswithinvalid(old)PINcode.
UnlockwithaPUKCode
ThePUKFunctionwindowisonlyavailableforconfigurationifthatSIMcardislockedbyPUKcode.Itmeans
thatSIMcardislockedandneedsadditionalPUKcodetounlock.Usuallyithappensaftertoomanytrialsof
incorrectPINcode,andtheremainingtimesinSIMFunctiontable turnsto0. Inthissituation, youneed to
contactyourserviceproviderandrequestaPUKcodeforyourSIMcard,andtrytounlockthelockedSIMcard
withtheprovidedPUKcode.AfterunlockingaSIMcardbyPUKcodesuccessfully,theSIMlockfunctionwillbe
activatedautomatically.
PUKFunctionWindow
Item Valuesetting Description
PUKstatus PUKUnlock
/PUKLock
IndicationforthePUKstatus.
ThestatuscouldbePUKLockorPUKUnlock.Asmentionedearlier,theSIMcard
willbelockedbyPUKcodeaftertoomanytrialsoffailurePINcode.Inthiscase,
thePUKStatuswillturnstoPUKLock.Inanormalsituation,itwilldisplayPUK
Unlock.
Remainingtimes DependonSIMcard Represent theremainingtrialtimesforthePUKunlocking.
Note:DONOTmaketheremainingtimesdowntozero,itwilldamagetheSIM
cardFOREVER!CallforyourISP’shelptogetacorrectPUKandunlocktheSIMif
youdon’thavethePUKcode.
PUKCode AMustfilledsetting FillinthePUKcode(8digits)thatcanunlocktheSIMcardinPUKunlockstatus.
NewPINCode AMustfilledsetting FillintheNewPINCode(4~8digits)fortheSIMcard.
YouhavetodetermineyournewPINcodetoreplacetheold,forgottenone.
KeepthePINcode(password)inmindwithcare.
Save N/A ClicktheSavebuttontoapplythesetting.
Note:IfyouchangedthePUKcodeandPINcodeforacertainSIMcard, you must also change the
correspondingPINcodespecifiedintheBasicNetwork>WAN&Uplink>InternetSetup>Connectionwith
SIMCardpage.Otherwise,itmayresultinwrongSIMPINtrialswithinvalid(old)PINcode.
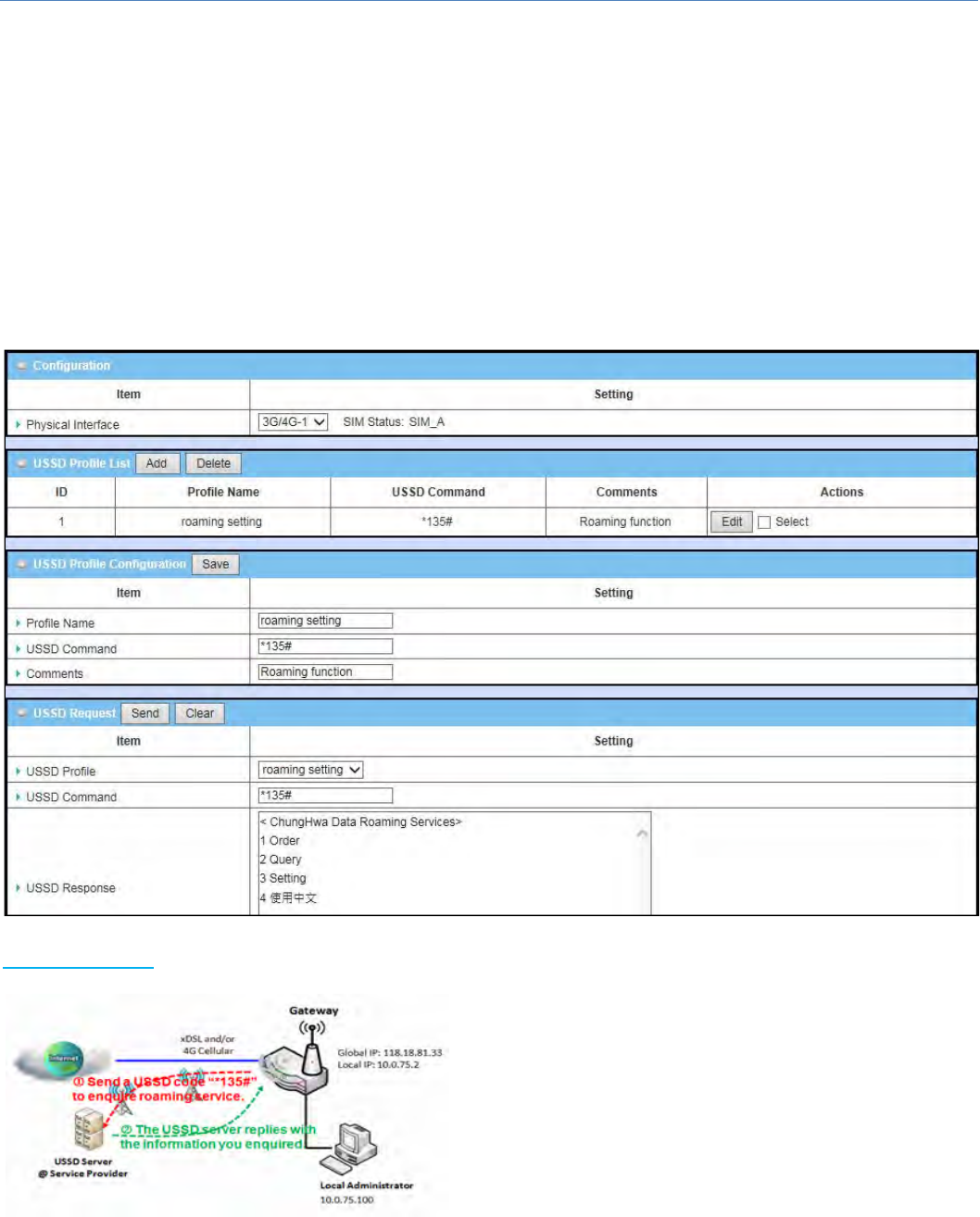
M2MCellularGateway
230
7.1.4USSD
Unstructured Supplementary Service Data (USSD) is a protocol used by GSM cellular telephones to
communicate with theservice provider's computers. USSD can be usedforWAPbrowsing,prepaidcallback
service, mobile‐money services, location‐based content services, menu‐based information services, and as
partofconfiguringthephoneonthenetwork.
An USSD message is up to 182 alphanumeric characters in length. Unlike Short Message Service (SMS)
messages, USSD messages create a real‐time connection during an USSD session. The connection remains
open,allowingatwo‐wayexchangeofasequenceofdata.ThismakesUSSDmoreresponsivethanservices
thatuseSMS.
USSDScenario
USSDallowsyoutohaveaninstantbi‐directional
communicationwithcarrier/ISP.Inthediagram,theUSSD
command ‘*135#’isreferredtodataroamingservices.
AftersendingthatUSSDcommandtocarrier,youcanget
a response at window USSD Response. Please note the
USSDcommandvariesfordifferentcarriers/ISP.
M2MCellularGateway
231
USSDSetting
GotoService>CellularToolkit>USSDtab.
In"USSD"page,therearefourwindowsfortheUSSDfunction.The"Configuration"windowcanletyouspecify
which3G/4Gmodule(physicalinterface)isusedfortheUSSDfunction,andsystemwillshowwhichSIMcardin
themoduleisthecurrentusedone.Thesecondwindowisthe"USSDProfileList"anditshowsallyourdefined
USSDprofilesthatstorepre‐commandsforactivatinganUSSDsession.An"Add"buttoninthewindowcanlet
youaddonenewUSSDprofileanddefinethecommandfortheprofileinthethirdwindow,the"USSDProfile
Configuration".WhenyouwanttostarttheactivationofanUSSD connection session to the USSD server,
selecttheUSSDprofileortypeinthecorrectpre‐command,andthenclickonthe"Send"buttonforthe
session. The responses from the USSD server will be displayed beneath the "USSD Command" line. When
commandstypedinthe"USSDCommand"fieldaresent,receivedresponses will be displayed in the "USSD
Response"blankspace.UsercancommunicatewiththeUSSDserverbysendingUSSDcommandsandgetting
USSDresponsesviathegateway.
USSDConfiguration
Configuration
Item Valuesetting Description
PhysicalInterface Theboxis3G/4G‐1by
default.
Chooseacellularinterface(3G/4G‐1or3G/4G‐2)toconfiguretheUSSDsetting
fortheconnectedcellularservice(identifiedwithSIM_AorSIM_B).
SIMStatus N/A Showtheconnectedcellularservice(identifiedwithSIM_AorSIM_B).
Create/EditUSSDProfile
ThecellulargatewayallowsyoutocustomyourUSSDprofile.Itsupportsuptoamaximumof35USSDprofiles.
WhenAddbuttonisapplied,USSDProfileConfigurationscreenwillappear.
M2MCellularGateway
232
USSDProfileConfiguration
Item Valuesetting Description
ProfileName N/A EnteranamefortheUSSDprofile.
USSDCommand N/A
EntertheUSSDcommanddefinedfortheprofile.
Normally,itisacommandstringcomposedwithnumerickeypad“0~9”,“*”,
and“#”.TheUSSDcommandsarehighlyrelatedtothecellularservice,please
checkwithyourserviceproviderforthedetails.
Comments N/A Enterabriefcommentfortheprofile.
SendUSSDRequest
WhensendtheUSSDcommand,theUSSDResponsescreenwillappear.
WhenclicktheClearbutton,theUSSDResponsewilldisappear.
USSDRequest
Item Valuesetting Description
USSDProfile N/A SelectaUSSDprofilenamefromthedropdownlist.
USSDCommand N/A TheUSSDCommandstringoftheselectedprofilewillbeshownhere.
USSDResponse N/A
ClicktheSendbuttontosendtheUSSDcommand,andtheUSSDResponse
screenwillappear.Youwillseetheresponsemessageofthecorresponding
service,receivetheserviceSMS.
M2MCellularGateway
233
7.1.5NetworkScan
"Network Scan" function can let administrator specify the device how to connect to the mobile system for
data communication in each 3G/4G interface. For example, administrator can specify which generation of
mobilesystemisusedforconnection,2G,3GorLTE.Moreover,hecandefinetheirconnectionsequencefor
the gateway device to connect to the mobile system automatically.Administratoralsocanscanthemobile
systemsintheairmanually,selectthetargetoperatorsystemandapplyit.Themanualscanningapproachis
usedforproblemdiagnosis.
NetworkScanSetting
GotoService>CellularToolkit>NetworkScantab.
In"NetworkScan"page,therearetwowindowsfortheNetworkScanfunction.The"Configuration"window
canletyouselectwhich3G/4Gmodule(physicalinterface)isusedtoperformNetworkScan,andsystemwill
showthecurrentusedSIMcardinthemodule.Youcanconfigureeach3G/4GWANinterfacebyexecutingthe
networkscanningoneafteranother.Youcanalsospecifytheconnectionsequenceofthetargetedgeneration
ofmobilesystem,2G/3G/LTE.
NetworkScanConfiguration
Configuration
Item Valuesetting Description
Physical
Interface
Theboxis3G/4G‐1by
default
Chooseacellularinterface(3G/4G‐1or3G/4G‐2)forthenetworkscanfunction.
Note:3G/4G‐2isonlyavailableforfortheproductwithdualcellularmodule.
SIMStatus N/A Showtheconnectedcellularservice(identifiedwithSIM_AorSIM_B).
NetworkType Autoisselectedby
default.
Specifythenetworktypeforthenetworkscanfunction.
ItcanbeAuto,2GOnly,2Gprefer,3GOnly,3Gprefer,orLTEOnly.
WhenAutoisselected,thenetworkwillberegisterautomatically;
Ifthepreferoptionisselected,networkwillberegisterforyouroptionfirst;
Iftheonlyoptionisselected,networkwillberegisterforyouroptiononly.
ScanApproach Autoisselectedby
default.
WhenAutoselected,cellularmoduleregisterautomatically.
IftheManuallyoptionisselected,aNetworkProviderListscreenappears.
PressScanbuttontoscanforthenearestbasestations.Select(checkthebox)
thepreferredbasestationsthenclickApplybuttontoapplysettings.
M2MCellularGateway
234
Save N/A ClickSavetosavethesettings
Thesecondwindowisthe"NetworkProviderList"windowanditappearswhentheManuallyScanApproach
isselectedintheConfigurationwindow.Byclickingonthe"Scan"buttonandwaitfor1to3minutes,thefound
mobileoperatorsystemwillbedisplayedforyoutochoose.Clickagainonthe"Apply"buttontodrivesystem
toconnecttothatmobileoperatorsystemforthededicated3G/4Ginterface.

M2MCellularGateway
235
Chapter8Status
8.1Dashboard(notsupported)
Not supported feature for the purchased product, leave it as blank.
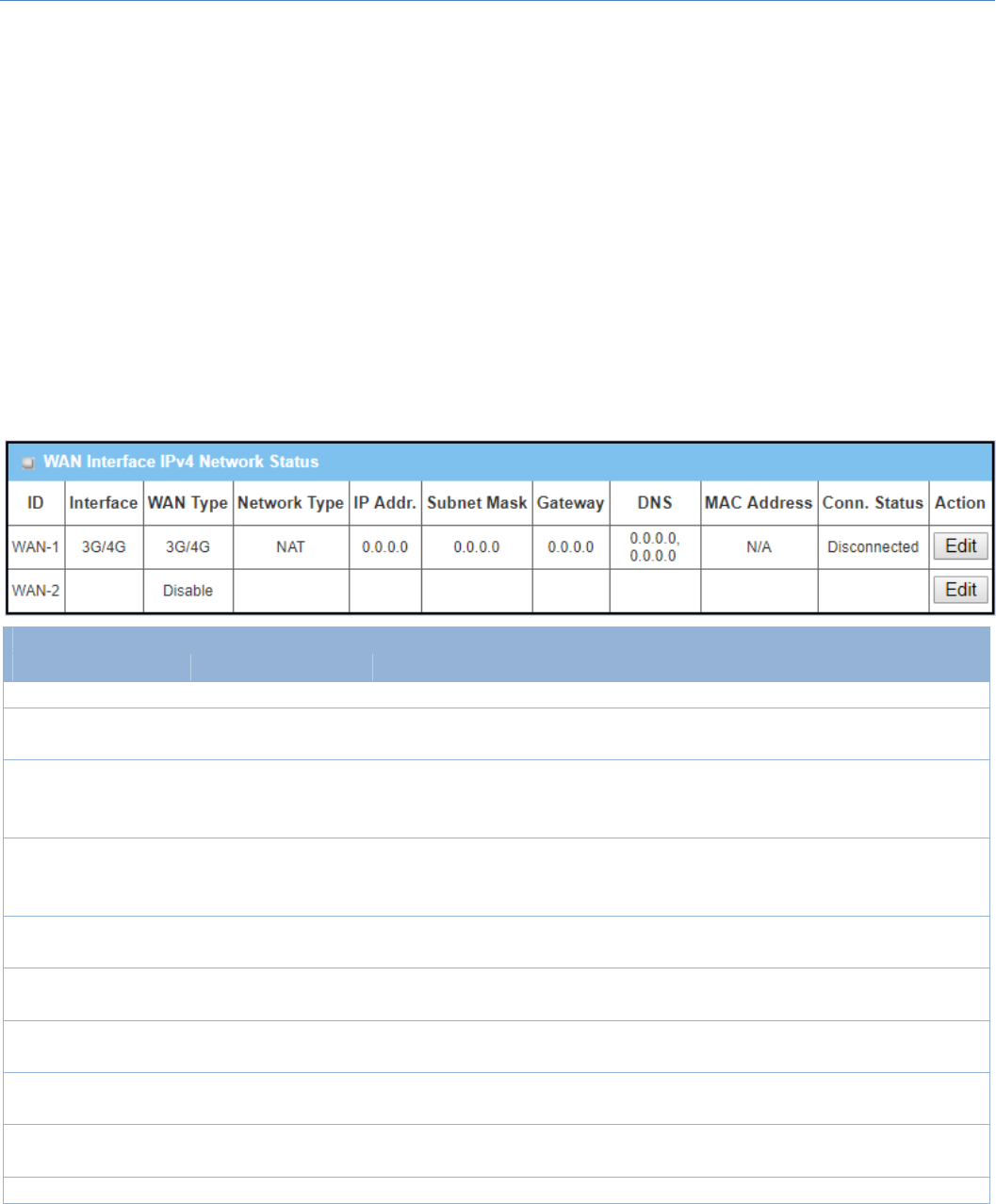
M2MCellularGateway
236
8.2BasicNetwork
8.2.1WAN&UplinkStatus
GotoStatus>BasicNetwork>WAN&Uplinktab.
The WAN & Uplink Status window shows the current status for different network type, including network
configuration, connecting information, modem status and trafficstatistics.Thedisplaywillberefreshedon
everyfiveseconds.
WANinterfaceIPv4NetworkStatus
WANinterfaceIPv4NetworkStatusscreenshowsstatusinformationforIPv4network.
WANinterfaceIPv4NetworkStatus
Item Valuesetting Description
ID N/A ItdisplayscorrespondingWANinterfaceWANIDs.
Interface N/A ItdisplaysthetypeofWANphysicalinterface.
Dependingonthemodelpurchased,itcanbeEthernet,3G/4G,etc...
WANType N/A
ItdisplaysthemethodwhichpublicIPaddressisobtainedfromyourISP.
Dependingonthemodelpurchased,itcanbeStaticIP,DynamicIP,PPPoE,
PPTP,L2TP,3G/4G.
NetworkType N/A
ItdisplaysthenetworktypefortheWANinterface(s).
Dependingonthemodelpurchased,itcanbeNAT,Routing,Bridge,orIPPass‐
through.
IPAddr. N/A ItdisplaysthepublicIPaddressobtainedfromyourISPforInternet
connection.Defaultvalueis0.0.0.0ifleftunconfigured.
SubnetMask N/A ItdisplaystheSubnetMaskforpublicIPaddressobtainedfromyourISPfor
Internetconnection.Defaultvalueis0.0.0.0ifleftunconfigured.
Gateway N/A ItdisplaystheGatewayIPaddressobtainedfromyourISPforInternet
connection.Defaultvalueis0.0.0.0ifleftunconfigured.
DNS N/A ItdisplaystheIPaddressofDNSserverobtainedfromyourISPforInternet
connection.Defaultvalueis0.0.0.0ifleftunconfigured.
MACAddress N/A ItdisplaystheMACAddressforyourISPtoallowyouforInternetaccess.Note:
NotallISPmayrequirethisfield.
Conn.Status N/A ItdisplaystheconnectionstatusofthedevicetoyourISP.
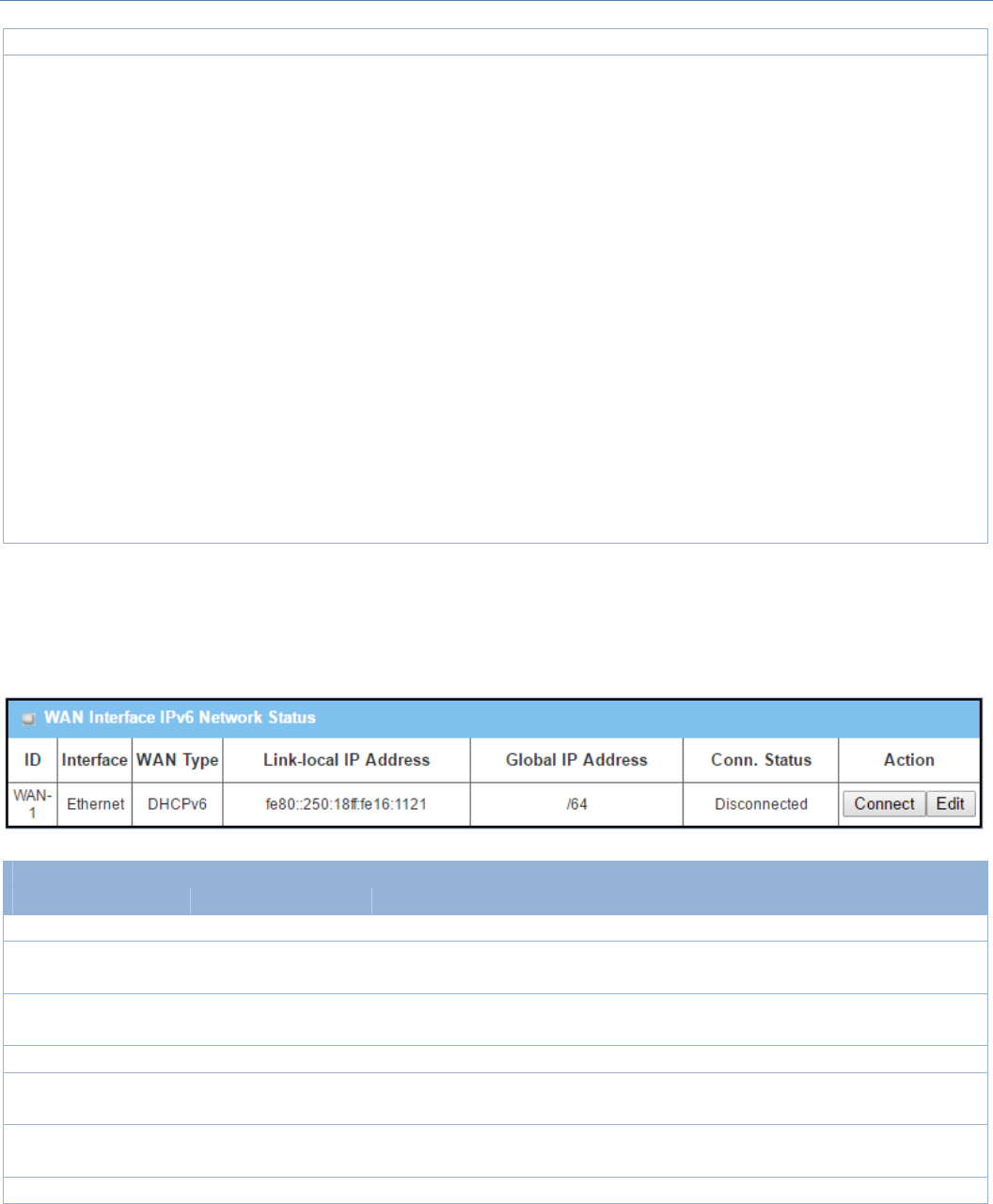
M2MCellularGateway
237
StatusareConnectedordisconnected.
Action N/A
Thisareaprovidesfunctionalbuttons.
RenewbuttonallowsusertoforcethedevicetorequestanIPaddressfrom
theDHCPserver.Note:RenewbuttonisavailablewhenDHCPWANTypeis
usedandWANconnectionisdisconnected.
ReleasebuttonallowsusertoforcethedevicetoclearitsIPaddresssettingto
disconnectfromDHCPserver.Note:ReleasebuttonisavailablewhenDHCP
WANTypeisusedandWANconnectionisconnected.
ConnectbuttonallowsusertomanuallyconnectthedevicetotheInternet.
Note:ConnectbuttonisavailablewhenConnectionControlinWANType
settingissettoConnectManually(RefertoEditbuttoninBasicNetwork>
WAN&Uplink>InternetSetup)andWANconnectionstatusisdisconnected.
Disconnectbuttonallowsusertomanuallydisconnectthedevicefromthe
Internet.Note:ConnectbuttonisavailablewhenConnectionControlinWAN
TypesettingissettoConnectManually(RefertoEditbuttoninBasicNetwork
>WAN&Uplink>InternetSetup)andWANconnectionstatusisconnected.
WANinterfaceIPv6NetworkStatus
WANinterfaceIPv6NetworkStatusscreenshowsstatusinformationforIPv6network.
WANinterfaceIPv6NetworkStatus
Item Valuesetting Description
ID N/A ItdisplayscorrespondingWANinterfaceWANIDs.
Interface N/A ItdisplaysthetypeofWANphysicalinterface.
Dependingonthemodelpurchased,itcanbeEthernet,3G/4G,etc...
WANType N/A ItdisplaysthemethodwhichpublicIPaddressisobtainedfromyourISP.WAN
typesettingcanbechangedfromBasicNetwork>IPv6>Configuration.
Link‐localIPAddress N/A ItdisplaystheLANIPv6Link‐Localaddress.
GlobalIPAddress N/A ItdisplaystheIPv6globalIPaddressassignedbyyourISPforyourInternet
connection.
Conn.Status N/A Itdisplaystheconnectionstatus.Thestatuscanbeconnected,disconnected
andconnecting.
Action N/A Thisareaprovidesfunctionalbuttons.
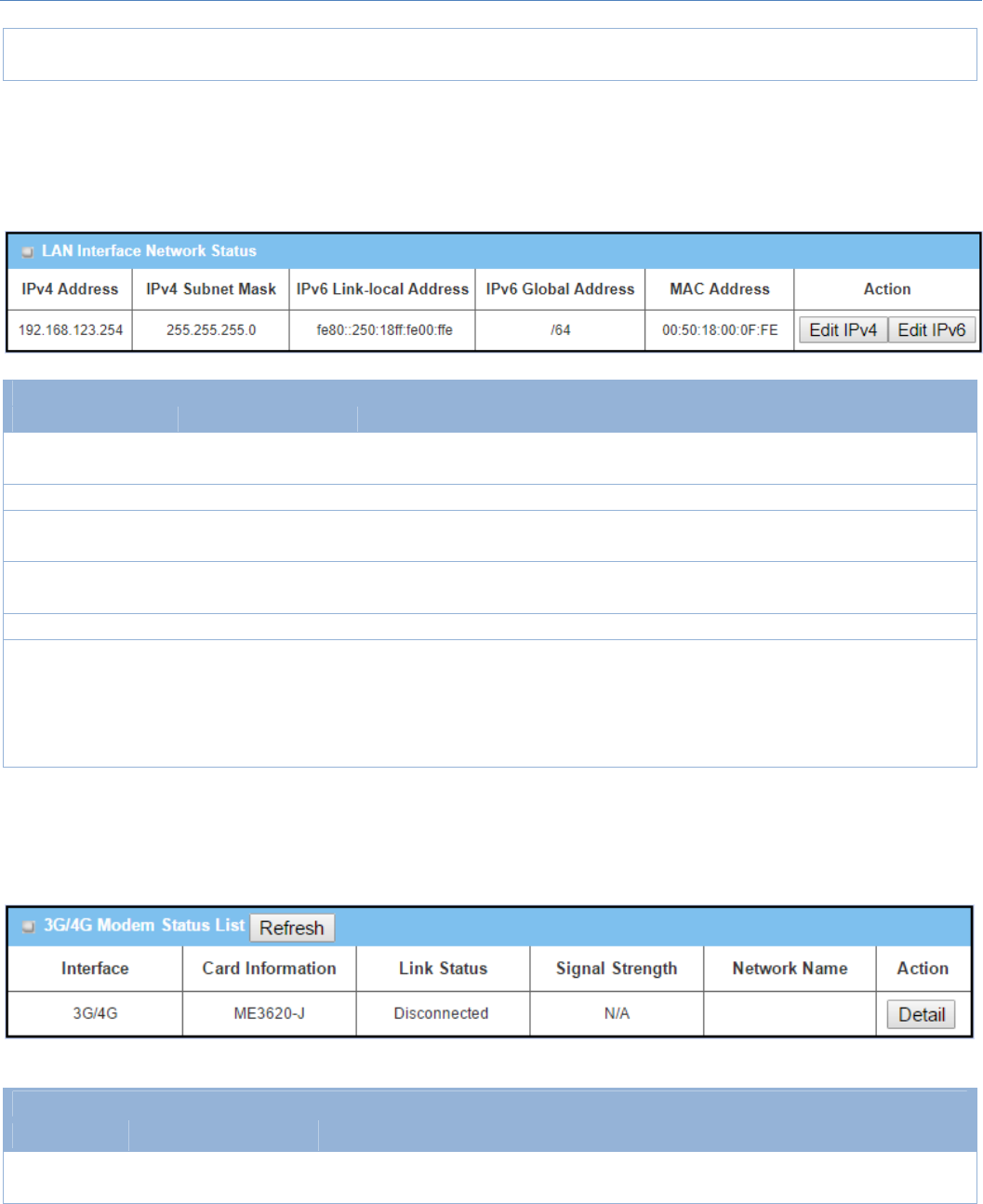
M2MCellularGateway
238
EditButtonwhenpressed,web‐basedutilitywilltakeyoutotheIPv6
configurationpage.(BasicNetwork>IPv6>Configuration.)
LANInterfaceNetworkStatus
LANInterfaceNetworkStatusscreenshowsIPv4andIPv6informationofLANnetwork.
LANInterfaceNetworkStatus
Item Valuesetting Description
IPv4Address N/A ItdisplaysthecurrentIPv4IPAddressofthegateway
ThisisalsotheIPAddressuserusetoaccessRouter’sWeb‐basedUtility.
IPv4SubnetMask N/A Itdisplaysthecurrentmaskofthesubnet.
IPv6Link‐local
Address N/A ItdisplaysthecurrentLANIPv6Link‐Localaddress.
ThisisalsotheIPv6IPAddressuserusetoaccessRouter’sWeb‐basedUtility.
IPv6GlobalAddress N/A ItdisplaysthecurrentIPv6globalIPaddressassignedbyyourISPforyour
Internetconnection.
MACAddress N/A ItdisplaystheLANMACAddressofthegateway
Action N/A
Thisareaprovidesfunctionalbuttons.
EditIPv4Buttonwhenpress,web‐basedutilitywilltakeyoutotheEthernet
LANconfigurationpage.(BasicNetwork>LAN&VLAN>EthernetLANtab).
EditIPv6Buttonwhenpress,web‐basedutilitywilltakeyoutotheIPv6
configurationpage.(BasicNetwork>IPv6>Configuration.)
3G/4GModemStatus
3G/4GModemStatusListscreenshowsstatusinformationfor3G/4GWANnetwork(s).
3G/4GModemStatusList
Item Valuesetting Description
Physical
Interface N/A ItdisplaysthetypeofWANphysicalinterface.
Note:Somedevicemodelmaysupporttwo3G/4Gmodules.Theirphysicalinterface
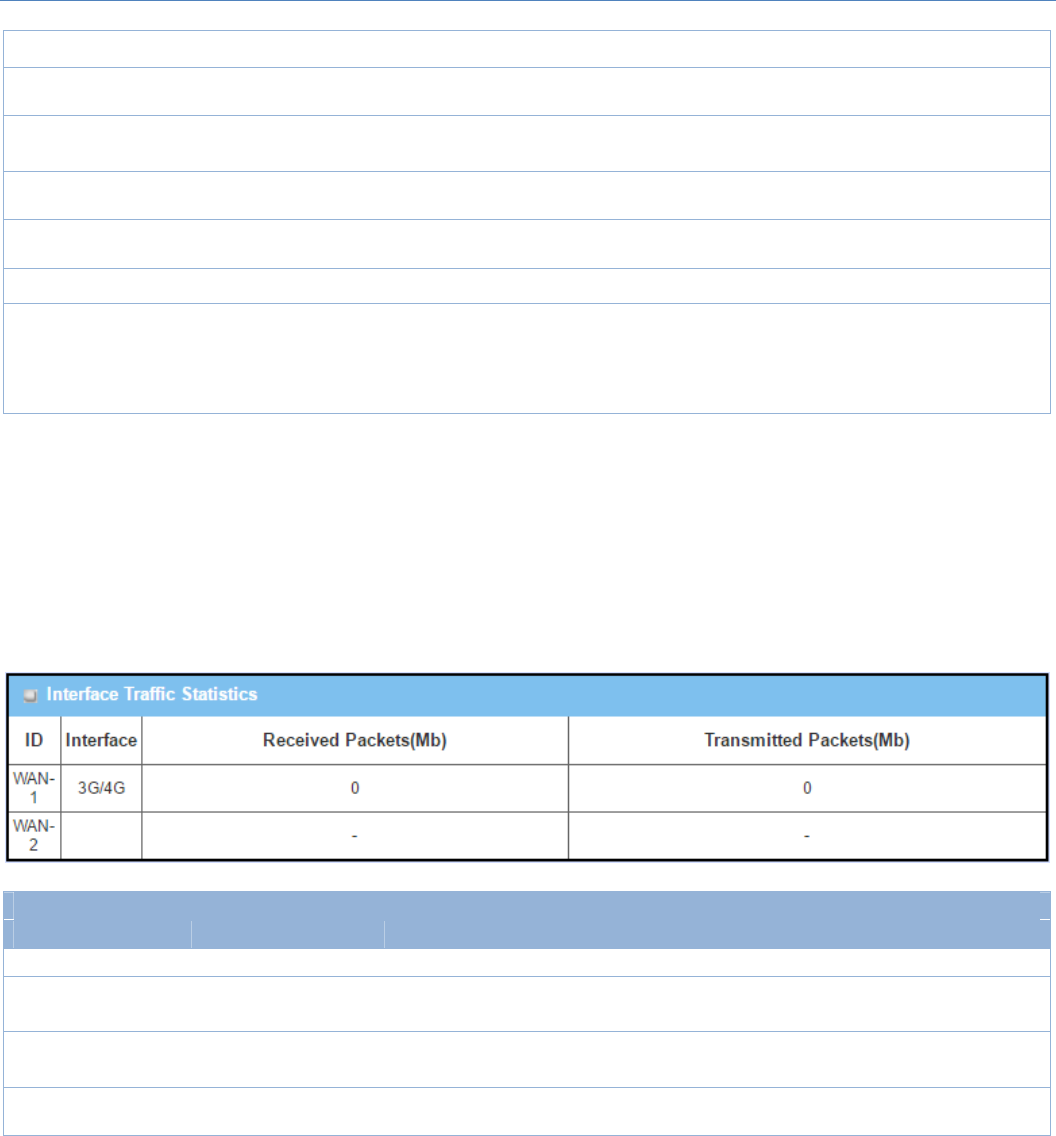
M2MCellularGateway
239
namewillbe3G/4G‐1and3G/4G‐2.
Card
Information N/A Itdisplaysthevendor’s3G/4Gmodemmodelname.
LinkStatus N/A Itdisplaysthe3G/4Gconnectionstatus.ThestatuscanbeConnecting,Connected,
Disconnecting,andDisconnected.
Signal
Strength N/A Itdisplaysthe3G/4Gwirelesssignallevel.
Network
Name N/A Itdisplaysthenameoftheservicenetworkcarrier.
Refresh N/A ClicktheRefreshbuttontorenewtheinformation.
Action N/A
Thisareaprovidesfunctionalbuttons.
DetailButtonwhenpress,windowsofdetailinformationwillappear.Theyarethe
ModemInformation,SIMStatus,andServiceInformation.Refertonextpagefor
more.
When the Detail button is pressed, 3G/4G modem information windows such as Modem Information, SIM
Status,ServiceInformation,SignalStrength/Quality,andErrorMessagewillappear.
InterfaceTrafficStatistics
InterfaceTrafficStatisticsscreendisplaystheInterface’stotaltransmittedpackets.
InterfaceTrafficStatistics
Item Valuesetting Description
ID N/A ItdisplayscorrespondingWANinterfaceWANIDs.
Interface N/A ItdisplaysthetypeofWANphysicalinterface.
Dependingonthemodelpurchased,itcanbeEthernet,3G/4G,etc…
ReceivedPackets
(Mb) N/A Itdisplaysthedownstreampackets(Mb).Itisresetwhenthedeviceis
rebooted.
TransmittedPackets
(Mb) N/A Itdisplaystheupstreampackets(Mb).Itisresetwhenthedeviceisrebooted.
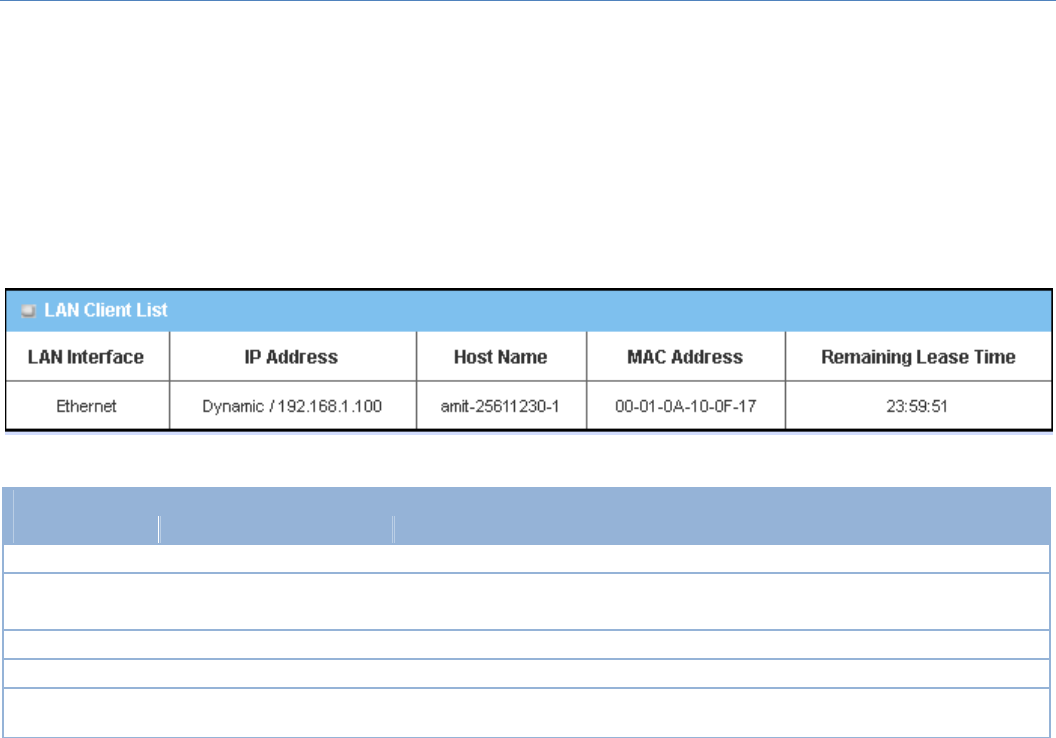
M2MCellularGateway
240
8.2.2LAN&VLANStatus
GotoStatus> BasicNetwork>LAN&VLANtab.
ClientList
TheClientListshowsyoutheLANInterface,IPaddress,HostName,MACAddress,andRemainingLeaseTime
ofeachdevicethatisconnectedtothisgateway.
LANClientList
Item Valuesetting Description
LANInterface N/A ClientrecordofLANInterface.StringFormat.
IPAddress N/A ClientrecordofIPAddressTypeandtheIPAddress.TypeisStringFormatand
theIPAddressisIPv4Format.
HostName N/A ClientrecordofHostName.StringFormat.
MACAddress N/A ClientrecordofMACAddress.MACAddressFormat.
RemainingLease
Time N/A ClientrecordofRemainingLeaseTime.TimeFormat.

M2MCellularGateway
241
8.2.3WiFiStatus(notsupported)
Not supported feature for the purchased product, leave it as blank.
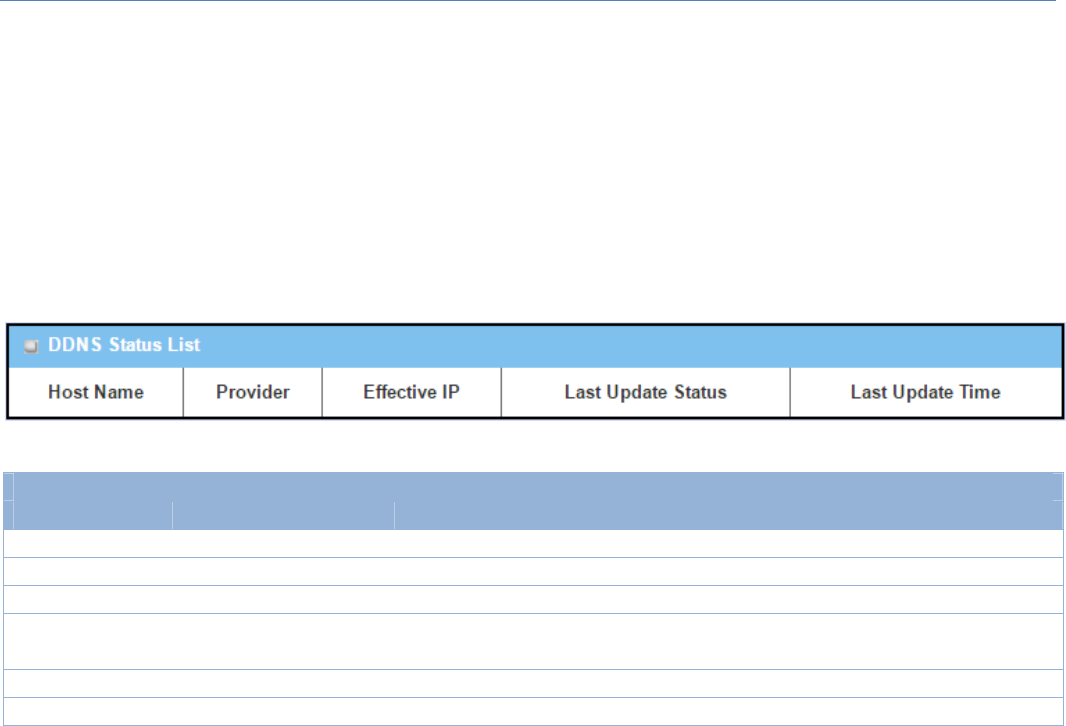
M2MCellularGateway
242
8.2.4DDNSStatus
GotoStatus> BasicNetwork>DDNStab.
TheDDNSStatuswindowshowsthecurrentDDNSserviceinuse,thelastupdatestatus,andthelastupdate
timetotheDDNSserviceserver.
DDNSStatus
DDNSStatus
Item ValueSetting Description
HostName N/A It displays the name you entered to identifyDDNSserviceprovider
Provider N/A It displays the DDNS server of DDNSserviceprovider
EffectiveIP N/A It displays the public IP address of the device updated to the DDNS server
LastUpdate
Status N/A It displays whether the last update of the device public IP address to the DDNS
server has been successful (Ok) or failed (Fail).
LastUpdateTime N/A It displays time stamp of the last update of public IP address to the DDNS server.
Refresh N/A Therefreshbuttonallowsusertoforcethedisplaytorefreshinformation.
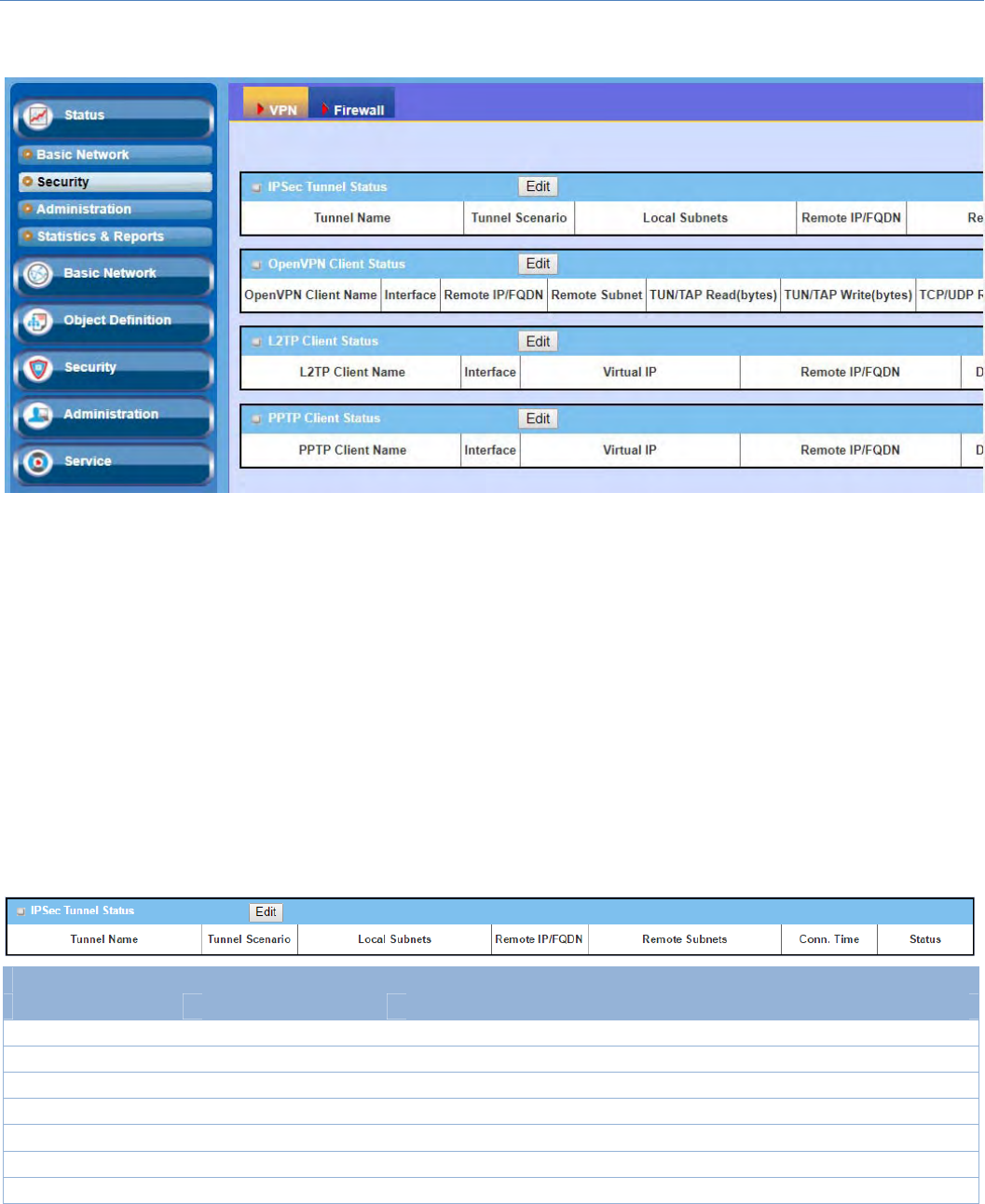
M2MCellularGateway
243
8.3Security
8.3.1VPNStatus
GotoStatus> Security>VPNtab.
TheVPNStatus widow shows the overall VPN tunnel status. The display will berefreshedoneveryfive
seconds.
IPSecTunnelStatus
IPSec Tunnel Status windows show the configuration for establishing IPSec VPN connection and current
connectionstatus.
IPSecTunnelStatus
Item Valuesetting Description
TunnelName N/A Itdisplaysthetunnelnameyouhaveenteredtoidentify.
TunnelScenario N/A ItdisplaystheTunnelScenariospecified.
LocalSubnets N/A ItdisplaystheLocalSubnetsspecified.
RemoteIP/FQDN N/A ItdisplaystheRemoteIP/FQDNspecified.
RemoteSubnets N/A ItdisplaystheRemoteSubnetsspecified.
Conn.Time N/A ItdisplaystheconnectiontimefortheIPSectunnel.
Status N/A ItdisplaystheStatusoftheVPNconnection.Thestatusdisplaysare
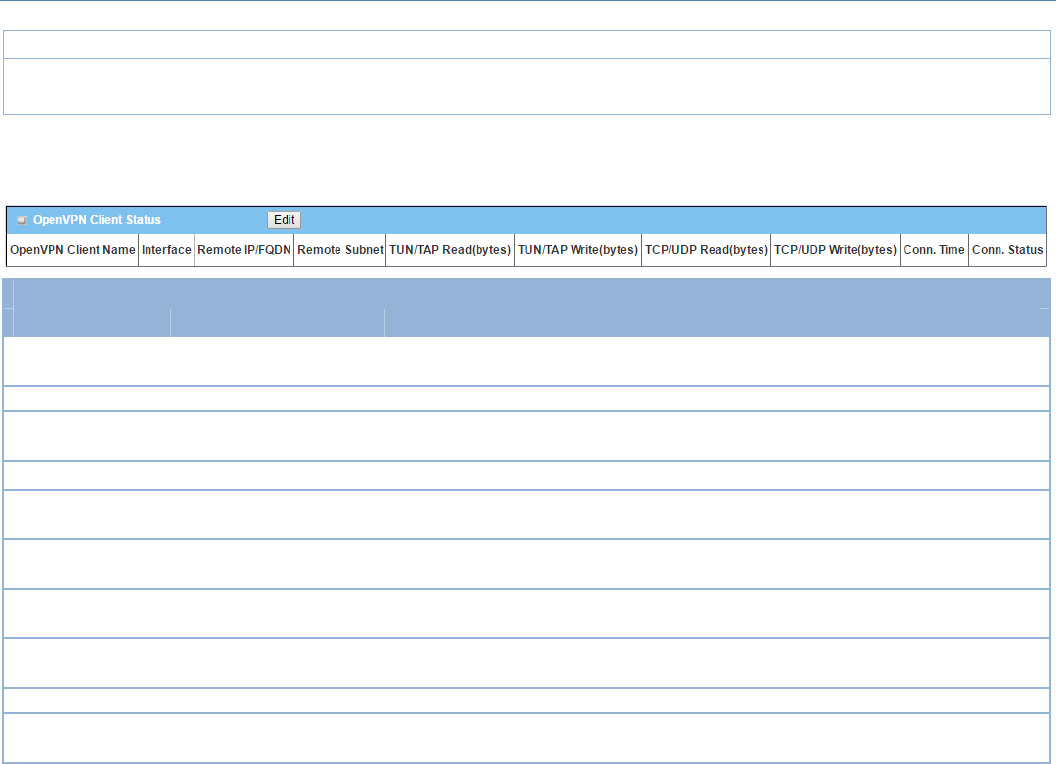
M2MCellularGateway
244
Connected,Disconnected,Waitfortraffic,andConnecting.
EditButton N/A ClickonEditButtontochangeIPSecsetting,web‐basedutilitywilltakeyou
totheIPSecconfigurationpage.(Security>VPN>IPSectab)
OpenVPNClientStatus
OpenVPNClientStatus
Item Valuesetting Description
OpenVPNClient
Name
N/A Itdisplaysthe Client nameyouhaveenteredforidentification.
Interface N/A ItdisplaystheWANinterfacespecifiedfortheOpenVPNclientconnection.
Remote
IP/FQDN
N/A Itdisplaysthe peer OpenVPN Server’sPublicIPaddress(theWANIPaddress)or
FQDN.
RemoteSubnet N/A ItdisplaystheRemoteSubnetspecified.
TUN/TAP
Read(bytes)
N/A ItdisplaystheTUN/TAPReadBytesofOpenVPNClient.
TUN/TAP
Write(bytes)
N/A Itdisplaysthe TUN/TAPWriteBytesofOpenVPNClient.
TCP/UDP
Read(bytes)
N/A ItdisplaystheTCP/UDPReadBytesofOpenVPNClient.
TCP/UDP
Write(bytes)
N/A ItdisplaystheTCP/UDPWriteBytesofOpenVPNClient.
Connection
Conn.Time N/A Itdisplays the connectiontimeforthecorrespondingOpenVPNtunnel.
Conn.Status N/A ItdisplaystheconnectionstatusofthecorrespondingOpenVPNtunnel.
ThestatuscanbeConnected,orDisconnected.
M2MCellularGateway
245
L2TPClientStatus
LT2TPClientStatusshowstheconfigurationforestablishingLT2TPtunnelandcurrentconnectionstatus.
L2TPClientStatus
Item Valuesetting Description
ClientName N/A ItdisplaysNamefortheL2TPClientspecified.
Interface N/A ItdisplaystheWANinterfacewithwhichthegatewaywillusetorequest
PPTPtunnelingconnectiontothePPTPserver.
VirtualIP N/A ItdisplaystheIPaddressassignedbyVirtualIPserverofL2TPserver.
RemoteIP/FQDN N/A ItdisplaystheL2TPServer’sPublicIPaddress(theWANIPaddress)or
FQDN.
Default
Gateway/Remote
Subnet
N/A
ItdisplaysthespecifiedIPaddressofthegatewaydeviceusedtoconnectto
theinternettoconnecttotheL2TPserver–thedefaultgateway.Orother
specifiedsubnetifthedefaultgatewayisnotusedtoconnecttotheL2TP
server–theremotesubnet.
Conn.Time N/A ItdisplaystheconnectiontimefortheL2TPtunnel.
Status N/A ItdisplaystheStatusoftheVPNconnection.ThestatusdisplaysConnected,
Disconnect,andConnecting.
Edit N/A ClickonEditButtontochangeL2TPclientsetting,web‐basedutilitywilltake
youtotheL2TPclientpage.(Security>VPN>L2TPtab)
M2MCellularGateway
246
PPTPClientStatus
PPTPClientStatusshowstheconfigurationforestablishingPPTPtunnelandcurrentconnectionstatus.
PPTPClientStatus
Item Valuesetting Description
ClientName N/A ItdisplaysNameforthePPTPClientspecified.
Interface N/A ItdisplaystheWANinterfacewithwhichthegatewaywillusetorequest
PPTPtunnelingconnectiontothePPTPserver.
VirtualIP N/A ItdisplaystheIPaddressassignedbyVirtualIPserverofPPTPserver.
RemoteIP/FQDN N/A ItdisplaysthePPTPServer’sPublicIPaddress(theWANIPaddress)or
FQDN.
DefaultGateway/
RemoteSubnet N/A
ItdisplaysthespecifiedIPaddressofthegatewaydeviceusedtoconnectto
theinternettoconnecttothePPTPserver–thedefaultgateway.Orother
specifiedsubnetifthedefaultgatewayisnotusedtoconnecttothePPTP
server–theremotesubnet.
Conn.Time N/A ItdisplaystheconnectiontimeforthePPTPtunnel.
Status N/A ItdisplaystheStatusoftheVPNconnection.ThestatusdisplaysConnected,
Disconnect,andConnecting.
EditButton N/A ClickonEditButtontochangePPTPclientsetting,web‐basedutilitywill
takeyoutothePPTPserverpage.(Security>VPN>PPTPtab)
M2MCellularGateway
247
8.3.2FirewallStatus
GotoStatus>Security>FirewallStatusTab.
TheFirewallStatusprovidesuseraquickviewofthefirewallstatusandcurrentfirewallsettings.Italsokeeps
the log history of the dropped packets by the firewall rule policies, and includes the administrator remote
loginsettingsspecifiedintheFirewallOptions.
Byclickingtheicon[+],thestatustablewillbeexpandedtodisplayloghistory.Clicking the Editbuttonthe
screenwillbeswitchedtotheconfigurationpage.
PacketFilterStatus
PacketFilterStatus
Item Valuesetting Description
ActivatedFilter
Rule N/A ThisisthePacketFilterRulename.
Detected
Contents N/A
Thisistheloggedpacketinformation,includingthesourceIP,destinationIP,
protocol,anddestinationport–theTCPorUDP.
Stringformat:
SourceIPtoDestinationIP:DestinationProtocol(TCPorUDP)
IP N/A TheSourceIP(IPv4)oftheloggedpacket.
Time N/A TheDateandTimestampoftheloggedpacket.Date&timeformat.("Month"
"Day""Hours":"Minutes":"Seconds")
Note:EnsurePacketFilterLogAlertisenabled.
RefertoSecurity>Firewall>PacketFiltertab.CheckLogAlertandsavethesetting.
URLBlockingStatus
URLBlockingStatus
Item Valuesetting Description
Activated
BlockingRule N/A ThisistheURLBlockingRulename.
BlockedURL N/A Thisistheloggedpacketinformation.
M2MCellularGateway
248
IP N/A TheSourceIP(IPv4)oftheloggedpacket.
Time N/A TheDateandTimestampoftheloggedpacket.Date&timeformat.("Month"
"Day""Hours":"Minutes":"Seconds")
Note:EnsureURLBlockingLogAlertisenabled.
RefertoSecurity>Firewall>URLBlockingtab.CheckLogAlertandsavethesetting.
WebContentFilterStatus
WebContentFilterStatus
Item Valuesetting Description
ActivatedFilter
Rule N/A Loggedpacketoftherulename.Stringformat.
Detected
Contents N/A Loggedpacketofthefilterrule.Stringformat.
IP N/A LoggedpacketoftheSourceIP.IPv4format.
Time N/A LoggedpacketoftheDateTime.Datetimeformat("Month""Day"
"Hours":"Minutes":"Seconds")
Note:EnsureWebContentFilterLogAlertisenabled.
RefertoSecurity>Firewall>WebContentFiltertab.CheckLogAlertandsavethesetting.
M2MCellularGateway
249
MACControlStatus
MACControlStatus
Item Valuesetting Description
Activated
ControlRule N/A ThisistheMACControlRulename.
BlockedMAC
Addresses N/A ThisistheMACaddressoftheloggedpacket.
IP N/A TheSourceIP(IPv4)oftheloggedpacket.
Time N/A TheDateandTimestampoftheloggedpacket.Date&timeformat.("Month"
"Day""Hours":"Minutes":"Seconds")
Note:EnsureMACControlLogAlertisenabled.
RefertoSecurity>Firewall>MACControltab.CheckLogAlertandsavethesetting.
ApplicationFiltersStatus
ApplicationFiltersStatus
Item Valuesetting Description
FilteredApplication
Category N/A ThenameoftheApplicationCategorybeingblocked.
FilteredApplication
Name N/A ThenameoftheApplicationbeingblocked.
IP N/A TheSourceIP(IPv4)oftheloggedpacket.
Time N/A TheDateandTimestampoftheloggedpacket.Date&timeformat.("Month"
"Day""Hours":"Minutes":"Seconds")
Note:EnsureApplicationFilterLogAlertisenabled.
RefertoSecurity>Firewall>ApplicationFiltertab.CheckLogAlertandsavethesetting.
M2MCellularGateway
250
IPSStatus
IPSFirewallStatus
Item Valuesetting Description
Detected
Intrusion N/A Thisistheintrusiontypeofthepacketsbeingblocked.
IP N/A TheSourceIP(IPv4)oftheloggedpacket.
Time N/A TheDateandTimestampoftheloggedpacket.Date&timeformat.("Month""Day"
"Hours":"Minutes":"Seconds")
Note:EnsureIPSLogAlertisenabled.
RefertoSecurity>Firewall>IPStab.CheckLogAlertandsavethesetting.
FirewallOptionsStatus
FirewallOptionsStatus
Item Valuesetting Description
StealthMode N/A EnableorDisablesettingstatusofStealthModeonFirewallOptions.
StringFormat:DisableorEnable
SPI N/A EnableorDisablesettingstatusofSPIonFirewallOptions.
StringFormat:DisableorEnable
Discard Ping from
WAN N/A
EnableorDisablesettingstatusofDiscardPingfromWANonFirewall
Options.
StringFormat:DisableorEnable
Remote
Administrator
Management
N/A
EnableorDisablesettingstatusofRemoteAdministrator.
IfRemoteAdministratorisenabled,itshowsthecurrentlyloggedin
administrator’ssourceIPaddressandloginusernameandthelogintime.
Format:
IP:"SourceIP",UserName:"LoginUserName",Time:"Datetime"
Example:
IP:192.168.127.39,UserName:admin,Time:Mar301:34:13
Note:EnsureFirewallOptionsLogAlertisenabled.
RefertoSecurity>Firewall>Optionstab.CheckLogAlertandsavethesetting.
M2MCellularGateway
251
8.4Administration
8.4.1Configure&ManageStatus
GotoStatus>Administration>Configure&Managetab.
TheConfigure&ManageStatuswindowshowsthestatusformanagingremotenetworkdevices.Thetypeof
managementavailableinyourdeviceisdependedonthedevicemodelpurchased.Thecommonlyusedones
aretheSNMP,TR‐069,andUPnP.
SNMPLinkingStatus
SNMPLinkStatusscreenshowsthestatusofcurrentactiveSNMPconnections.
SNMPLinkStatus
Item Valuesetting Description
UserName N/A Itdisplaystheusernameforauthentication.ThisisonlyavailableforSNMP
version3.
IPAddress N/A ItdisplaystheIPaddressofSNMPmanager.
Port N/A ItdisplaystheportnumberusedtomaintainconnectionwiththeSNMP
manager.
Community N/A ItdisplaysthecommunityforSNMPversion1orversion2conly.
Auth.Mode N/A ItdisplaystheauthenticationmethodforSNMPversion3only.
PrivacyMode N/A Itdisplaystheprivacymodeforversion3only.
SNMPVersion N/A ItdisplaystheSNMPVersionemployed.
SNMPTrapInformation
SNMPTrapInformationscreenshowsthestatusofcurrentreceivedSNMPtraps.
SNMPTrapInformation
Item Valuesetting Description
TrapLevel N/A Itdisplaysthetraplevel.
Time N/A Itdisplaysthetimestampoftrapevent.
TrapEvent N/A ItdisplaystheIPaddressofthetrapsenderandeventtype.
M2MCellularGateway
252
TR‐069Status
TR‐069StatusscreenshowsthecurrentconnectionstatuswiththeTR‐068server.
TR‐069Status
Item Valuesetting Description
LinkStatus N/A
ItdisplaysthecurrentconnectionstatuswiththeTR‐068server.Theconnection
statusiseitherOnwhenthedeviceisconnectedwiththeTR‐068serverorOff
whendisconnected.
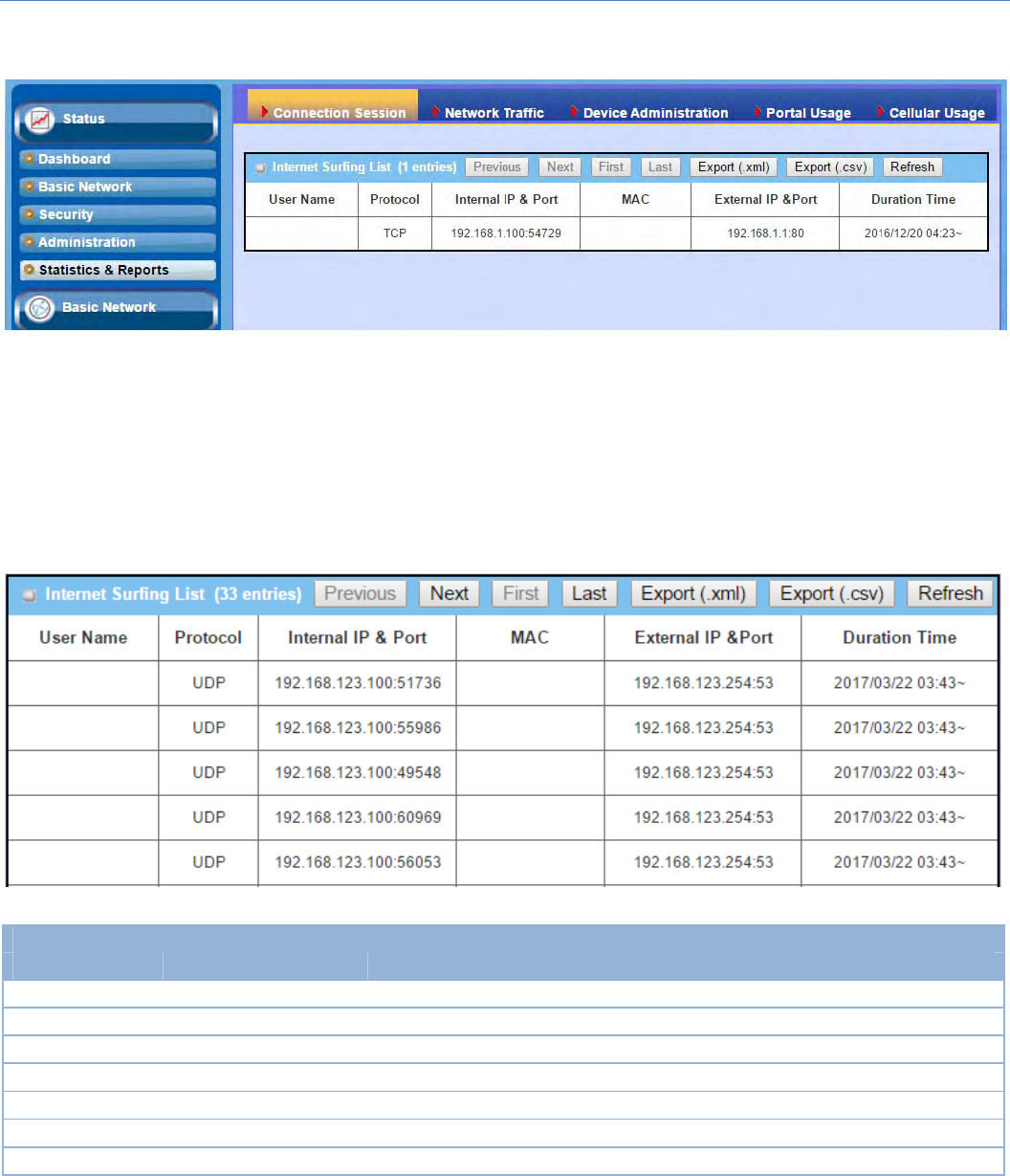
M2MCellularGateway
253
8.5Statistics&Report
8.5.1ConnectionSession
GotoStatus>Statistics&Reports>ConnectionSessiontab.
InternetSurfingStatisticshowstheconnectiontracksonthisrouter.
InternetSurfingStatistic
Item Valuesetting Description
Previous N/A ClickthePreviousbutton;youwillseethepreviouspageoftracklist.
Next N/A ClicktheNextbutton;youwillseethenextpageoftracklist.
First N/A ClicktheFirstbutton;youwillseethefirstpageoftracklist.
Last N/A ClicktheLastbutton;youwillseethelastpageoftracklist.
Export(.xml) N/A ClicktheExport(.xml)buttontoexportthelisttoxmlfile.
Export(.csv) N/A ClicktheExport(.csv)buttontoexportthelisttocsvfile.
Refresh N/A ClicktheRefreshbuttontorefreshthelist.

M2MCellularGateway
254
8.5.2NetworkTraffic(notsupported)
Not supported feature for the purchased product, leave it as blank.
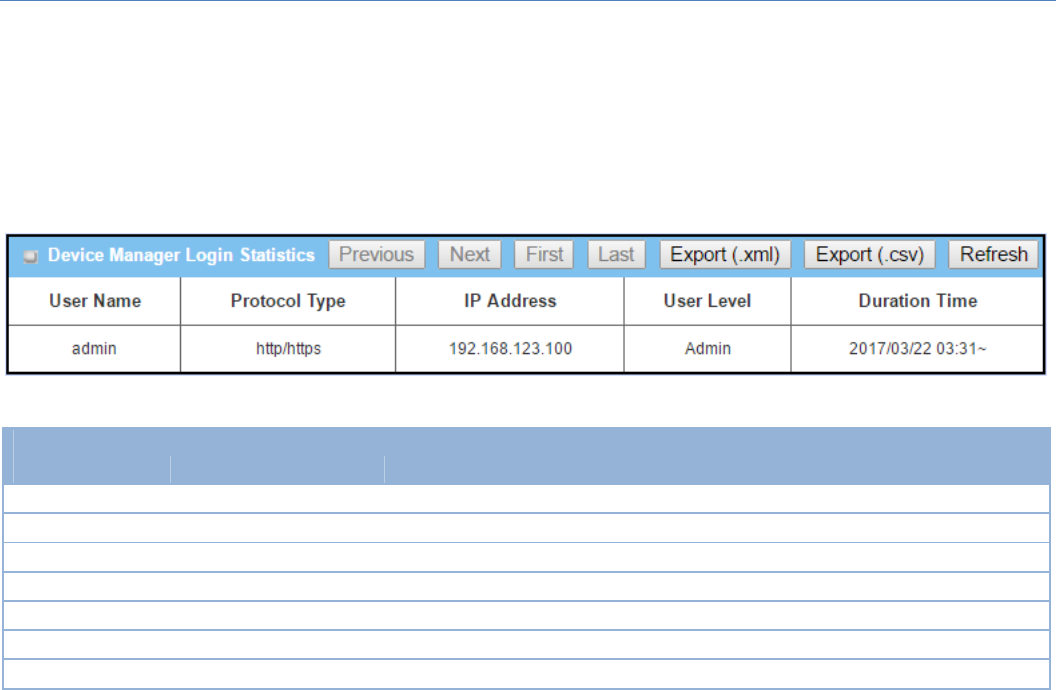
M2MCellularGateway
255
8.5.3DeviceAdministration
GotoStatus>Statistics&Reports>DeviceAdministrationtab.
DeviceAdministrationshowsthelogininformation.
DeviceManagerLoginStatistic
Item Valuesetting Description
Previous N/A ClickthePreviousbutton;youwillseethepreviouspageofloginstatistics.
Next N/A ClicktheNextbutton;youwillseethenextpageofloginstatistics.
First N/A ClicktheFirstbutton;youwillseethefirstpageofloginstatistics.
Last N/A ClicktheLastbutton;youwillseethelastpageofloginstatistics.
Export(.xml) N/A ClicktheExport(.xml)buttontoexporttheloginstatisticstoxmlfile.
Export(.csv) N/A ClicktheExport(.csv)buttontoexporttheloginstatisticstocsvfile.
Refresh N/A ClicktheRefreshbuttontorefreshtheloginstatistics.
M2MCellularGateway
256
8.5.4CellularUsage
GotoStatus>Statistics&Reports>CellularUsagetab.
Cellular Usage screenshowsdata usagestatisticsfortheselectedcellularinterface.Thecellulardatausage
canbeaccumulatedperhourorperday.

M2MCellularGateway
257
AppendixAGPLWRITTENOFFER
This product incorporates open source software components covered by the terms of third party copyright notices
and license agreements contained below.
GPSBabel
Version 1.4.4
Copyright (C) 2002-2005 Robert Lipe<robertlipe@usa.net>
GPL License: https://www.gpsbabel.org/
Curl
Version 7.19.6
Copyright (c) 1996-2009, Daniel Stenberg, <daniel@haxx.se>.
MIT/X derivate License: https://curl.haxx.se/
OpenSSL
Version 1.0.2c
Copyright (C) 1995-1998 Eric Young (eay@cryptsoft.com)
GPL License: https://www.openssl.org/
brctl - ethernet bridge administration
Stephen Hemminger <shemminger@osdl.org>
Lennert Buytenhek <buytenh@gnu.org>
version 1.1
GNU GENERAL PUBLIC LICENSE Version 2, June 1991
tc - show / manipulate traffic control settings
Stephen Hemminger<shemminger@osdl.org>
Alexey Kuznetsov<kuznet@ms2.inr.ac.ru>
version iproute2-ss050330
GNU GENERAL PUBLIC LICENSE Version 2, June 1991
dhcp-fwd — starts the DHCP forwarding agent
Enrico Scholz <enrico.scholz@informatik.tu-chemnitz.de>
version 0.7
GNU GENERAL PUBLIC LICENSE Version 2, June 1991
lftp - Sophisticated file transfer program
Alexander V. Lukyanov <lav@yars.free.net>
version:4.5.x
Copyright (c) 1996-2014 by Alexander V. Lukyanov (lav@yars.free.net)
dnsmasq - A lightweight DHCP and caching DNS server.
Simon Kelley <simon@thekelleys.org.uk>
version:2.72
dnsmasq is Copyright (c) 2000-2014 Simon Kelley

M2MCellularGateway
258
socat - Multipurpose relay
Version: 2.0.0-b8
GPLv2
http://www.dest-unreach.org/socat/
LibModbus
Version: 3.0.3
LGPL v2
http://libmodbus.org/news/
LibIEC60870
GPLv2
Copyright (C) 1989, 1991 Free Software Foundation, Inc. 59 Temple Place, Suite 330, Boston, MA 02111-
1307 USA
https://sourceforge.net/projects/mrts/
Openswan
Version: v2.6.38 GNU GENERAL PUBLIC LICENSE Version 2, June 1991
Copyright (C) 1989, 1991 Free Software Foundation, Inc. 59 Temple Place, Suite 330, Boston, MA 02111-
1307 USA
Everyone is permitted to copy and distribute verbatim copies
of this license document, but changing it is not allowed.
https://www.openswan.org/
Opennhrp
Version: v0.14.1
OpenNHRP is an NHRP implementation for Linux. It has most of the RFC2332
and Cisco IOS extensions.
Project homepage: http://sourceforge.net/projects/opennhrp
Git repository: git://opennhrp.git.sourceforge.net/gitroot/opennhrp
LICENSE
OpenNHRP is licensed under the MIT License. See MIT-LICENSE.txt for
additional details.
OpenNHRP embeds libev. libev is dual licensed with 2-clause BSD and
GPLv2+ licenses. See libev/LICENSE for additional details.
OpenNHRP links to c-ares. c-ares is licensed under the MIT License.
https://sourceforge.net/projects/opennhrp/
IPSec-tools
Ve r sio n: v0 .8
No GPL be written
http://ipsec-tools.sourceforge.net/
PPTP
Version: pptp-1.7.1
GNU GENERAL PUBLIC LICENSE Version 2, June 1991

M2MCellularGateway
259
Copyright (C) 1989, 1991 Free Software Foundation, Inc. 675 Mass Ave, Cambridge, MA 02139, USA
Everyone is permitted to copy and distribute verbatim copies
of this license document, but changing it is not allowed.
http://pptpclient.sourceforge.net/
PPTPServ
Version: 1.3.4
GNU GENERAL PUBLIC LICENSE Version 2, June 1991
Copyright (C) 1989, 1991 Free Software Foundation, Inc. 675 Mass Ave, Cambridge, MA 02139, USA
Everyone is permitted to copy and distribute verbatim copies
of this license document, but changing it is not allowed. http://poptop.sourceforge.net/
L2TP
Version: 0.4
Copying All software included in this package is Copyright 2002 Roaring
Penguin Software Inc. You may distribute it under the terms of the
GNU General Public License (the "GPL"), Version 2, or (at your option)
any later version.
http://www.roaringpenguin.com/
L2TPServ
Version: v 1.3.1 GNU GENERAL PUBLIC LICENSEVersion 2, June 1991
Copyright (C) 1989, 1991 Free Software Foundation, Inc.59 Temple Place, Suite 330, Boston, MA 02111-
1307 USA
Everyone is permitted to copy and distribute verbatim copies
of this license document, but changing it is not allowed.
http://www.xelerance.com/software/xl2tpd/
Mpstat: from sysstat, system performance tools for Linux
Version: 10.1.6
Copyright: (C) 1999-2013 by Sebastien Godard (sysstat <at> orange.fr)
SSHD: dropbear, a SSH2 server
Version: 0.53.1
Copyright: (c) 2002-2008 Matt Johnston
Libncurses: The ncurses (new curses) library is a free software emulation of curses in System V Release 4.0
(SVr4), and more.
Version: 5.9
Copyright: (c) 1998,2000,2004,2005,2006,2008,2011,2015 Free Software Foundation, Inc., 51 Franklin Street,
Boston, MA 02110-1301, USA
MiniUPnP: The miniUPnP daemon is an UPnP IGD (internet gateway device) which provide NAT traversal
services to any UPnP enabled client on the network.
Version: 1.7
Copyright: (c) 2006-2011, Thomas BERNARD

M2MCellularGateway
260
CoovaChilli is an open-source software access controller for captive portal (UAM) and 802.1X access
provisioning.
Version: 1.3.0
Copyright: (C) 2007-2012 David Bird (Coova Technologies) <support@coova.com>
Krb5: Kerberos is a network authentication protocol. It is designed to provide strong authentication for
client/server applications by using secret-key cryptography.
Version: 1.11.3
Copyright: (C) 1985-2013 by the Massachusetts Institute of Technology and its contributors
OpenLDAP: a suite of the Lightweight Directory Access Protocol (v3) servers, clients, utilities, and
development tools.
Version: 2.4
Copyright: 1998-2014 The OpenLDAP Foundation
Samba3311: the free SMB and CIFS client and server for UNIX and other operating systems
Version: 3.3.11
Copyright: (C) 2007 Free Software Foundation, Inc. <http://fsf.org/>
NTPClient: an NTP (RFC-1305, RFC-4330) client for unix-alike computers
Version: 2007_365
Copyright: 1997, 1999, 2000, 2003, 2006, 2007 Larry Doolittle
exFAT: FUSE-based exFAT implementation
Version: 0.9.8
Copyright: (C) 2010-2012 Andrew Nayenko
ONTFS_3G: The NTFS-3G driver is an open source, freely available read/write NTFS driver for Linux,
FreeBSD, Mac OS X, NetBSD, Solaris and Haiku.
Version: 2009.4.4
Copyright: (C) 1989, 1991 Free Software Foundation, Inc., 51 Franklin Street, Fifth Floor, Boston, MA 02110-
1301 USA
mysql-5_1_72: a release of MySQL, a dual-license SQL database server
Version: 5.1.72
Copyright: (c) 2000, 2013, Oracle and/or its affiliates
FreeRadius: a high performance and highly configurable RADIUS server
Version: 2.1.12
Copyright: (C) 1999-2011 The FreeRADIUS server project and contributors
Linux IPv6 Router Advertisement Daemon – radvd
Version: V 1.15
Copyright (c) 1996,1997 by Lars Fenneberg<lf@elemental.net>
BSD License: http://www.litech.org/radvd/
WIDE-DHCPv6
Dynamic Host Configuration Protocol for IPv6 (DHCPv6) clients, servers, and relay agents.

M2MCellularGateway
261
Version: 20080615
Copyright (C) 1998-2004 WIDE Project.
BSD License: https://sourceforge.net/projects/wide-dhcpv6/
Federal Communication Commission Interference Statement
This device complies with Part 15 of the FCC Rules. Operation is subject to
the following two conditions: (1) This device may not cause harmful
interference, and (2) this device must accept any interference received,
including interference that may cause undesired operation.
This equipment has been tested and found to comply with the limits for a
Class B digital device, pursuant to Part 15 of the FCC Rules. These limits
are designed to provide reasonable protection against harmful interference in a
residential installation. This equipment generates, uses and can radiate radio
frequency energy and, if not installed and used in accordance with the
instructions, may cause harmful interference to radio communications.
However, there is no guarantee that interference will not occur in a particular
installation. If this equipment does cause harmful interference to radio or
television reception, which can be determined by turning the equipment off
and on, the user is encouraged to try to correct the interference by one of the
following measures:
- Reorient or relocate the receiving antenna.
- Increase the separation between the equipment and receiver.
- Connect the equipment into an outlet on a circuit different from that
to which the receiver is connected.
- Consult the dealer or an experienced radio/TV technician for help.
FCC Caution: Any changes or modifications not expressly approved by the
party responsible for compliance could void the user's authority to operate this
equipment.
This transmitter must not be co-located or operating in conjunction with any
other antenna or transmitter.

FOR MOBILE DEVICE USAGE (>20cm/low power)
Radiation Exposure Statement:
This equipment complies with FCC radiation exposure limits set forth for an
uncontrolled environment. This equipment should be installed and operated
with minimum distance 20cm between the radiator & your body.
M2MCellularGateway
262