Belkin F5D7632-4V5 ADSL2+ Modem with Wireless G Router User Manual P74725uk A F5D7632uk4 man indd
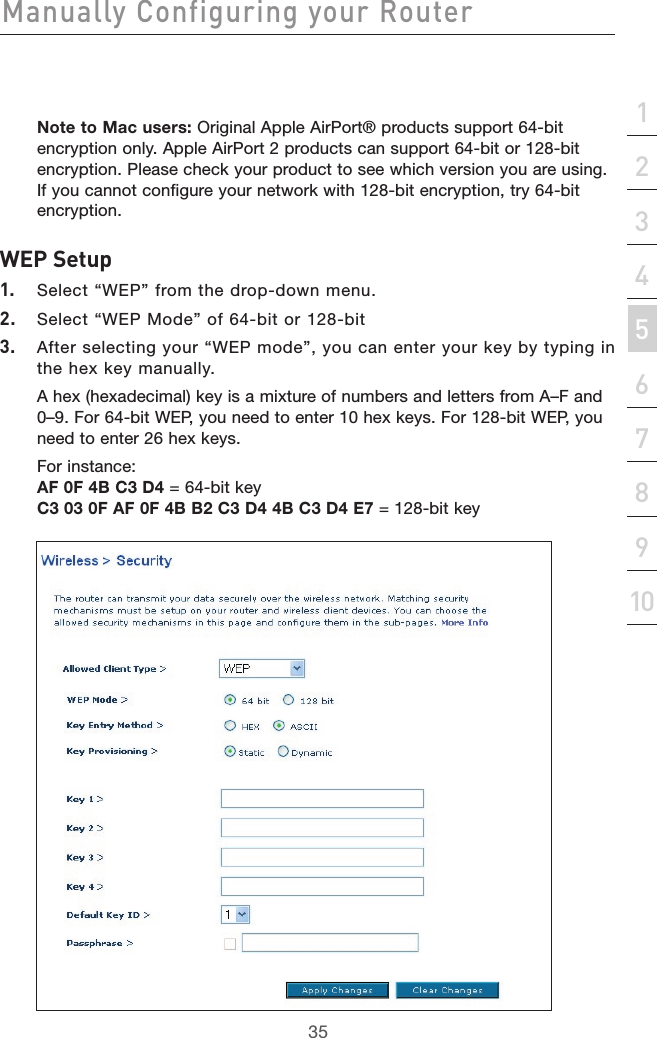
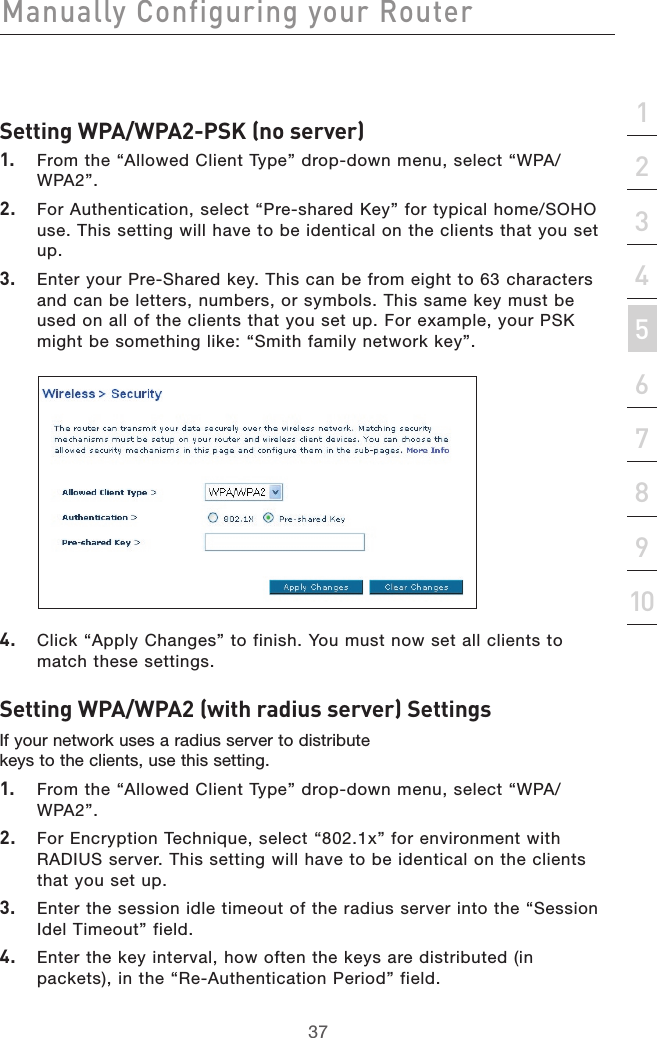
Belkin International, Inc. ADSL2+ Modem with Wireless G Router P74725uk A F5D7632uk4 man indd
Belkin >
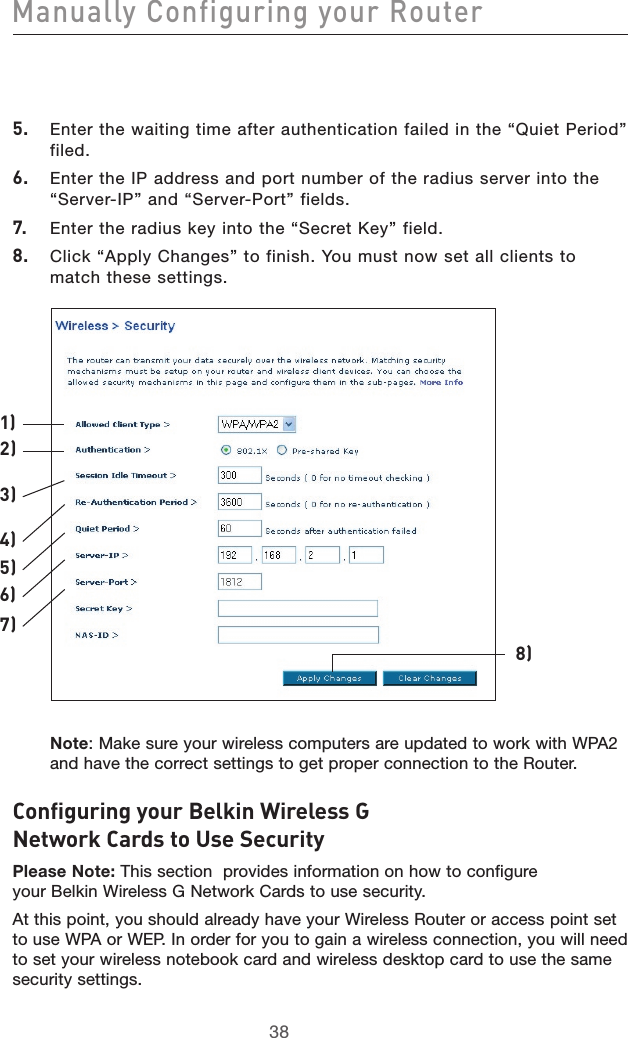
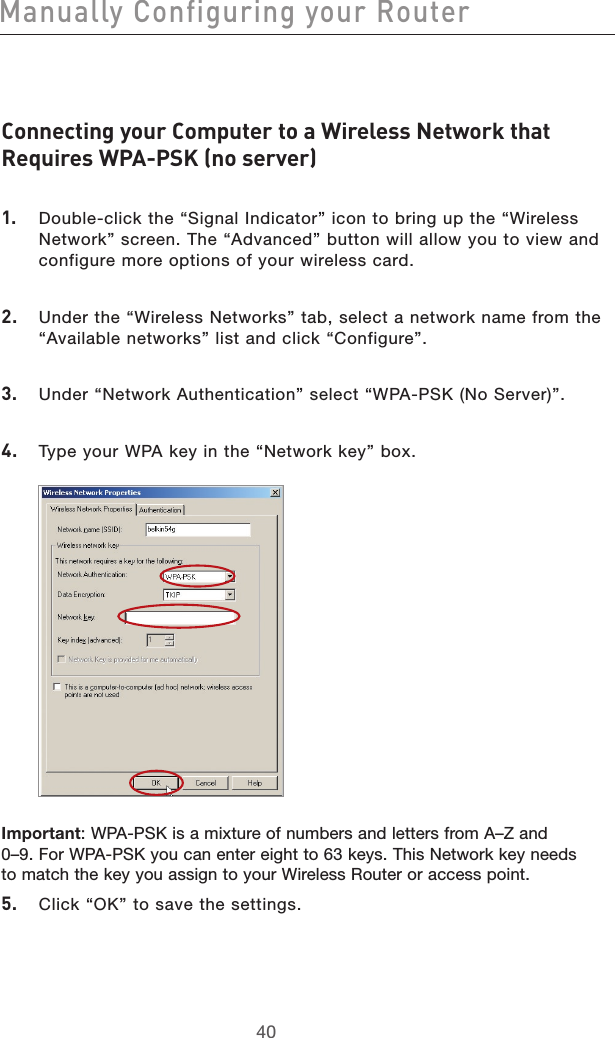
Contents
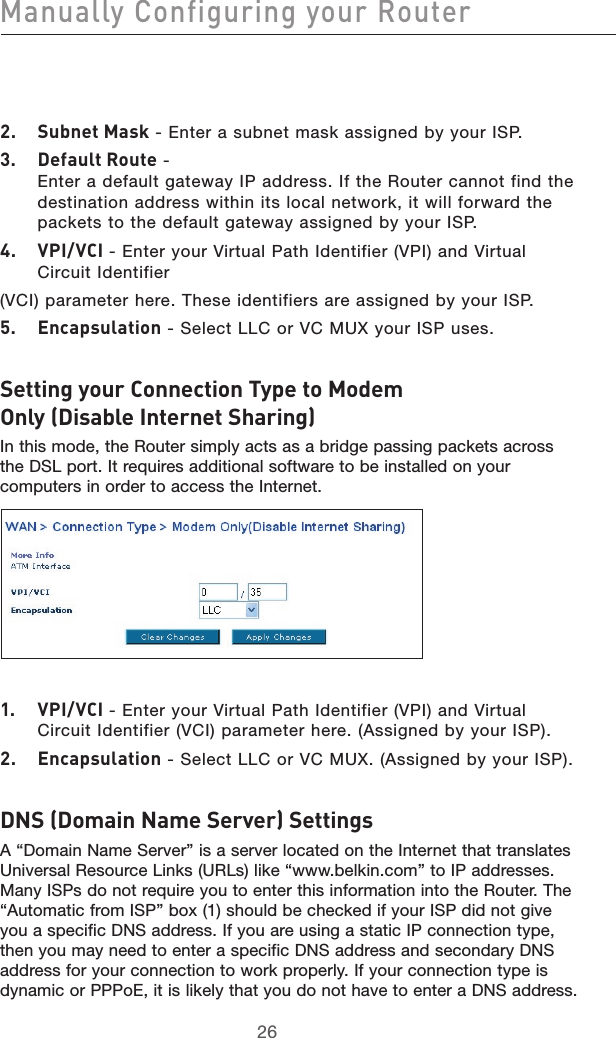
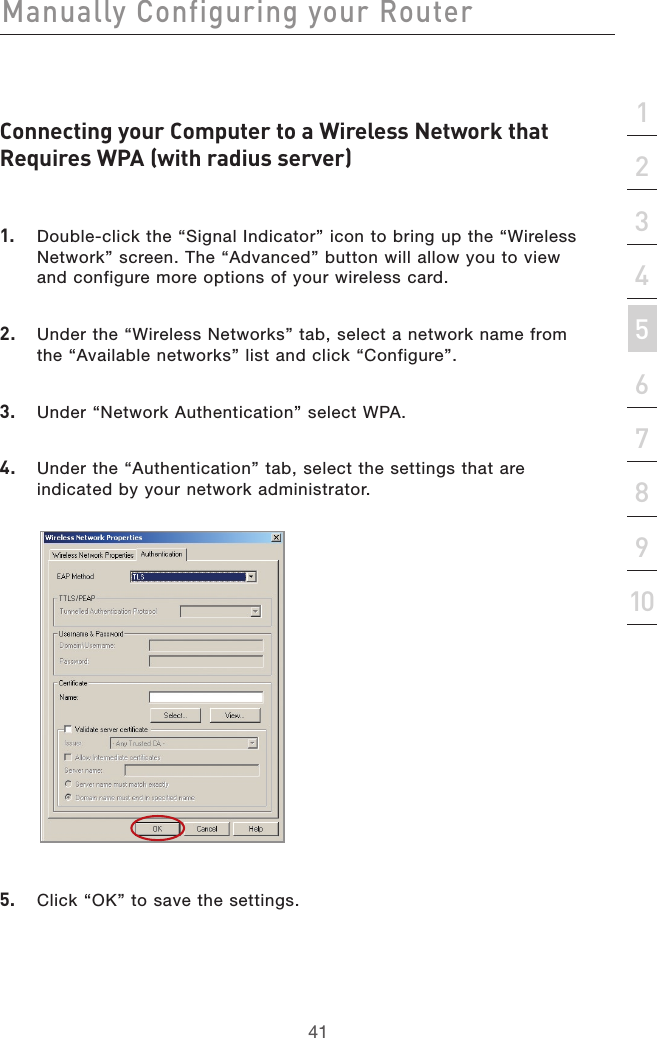
- 1. user manual part 1
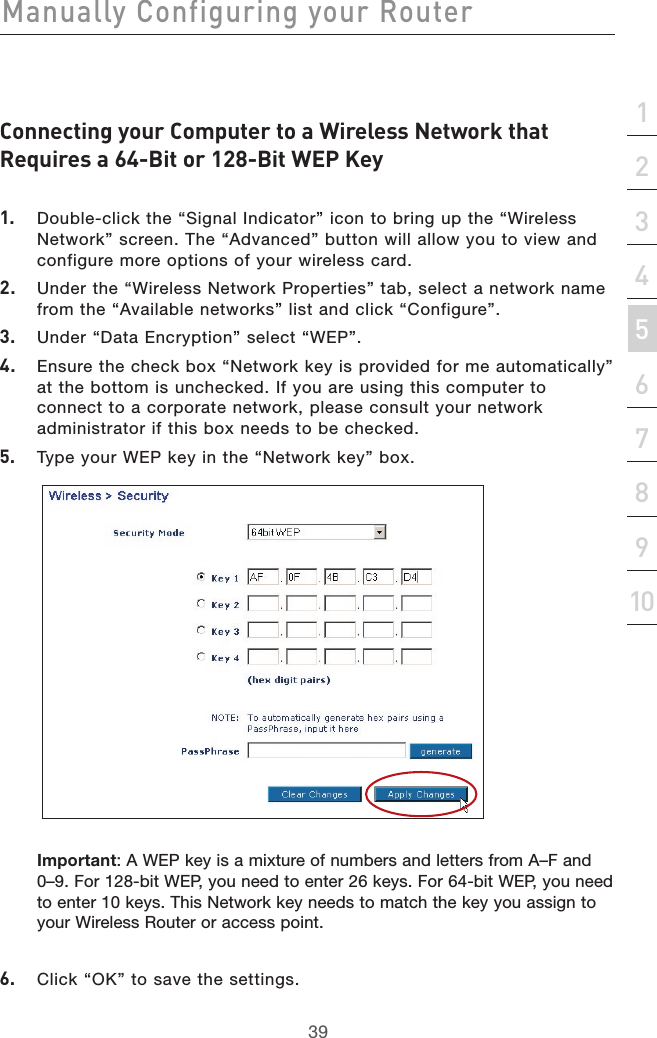
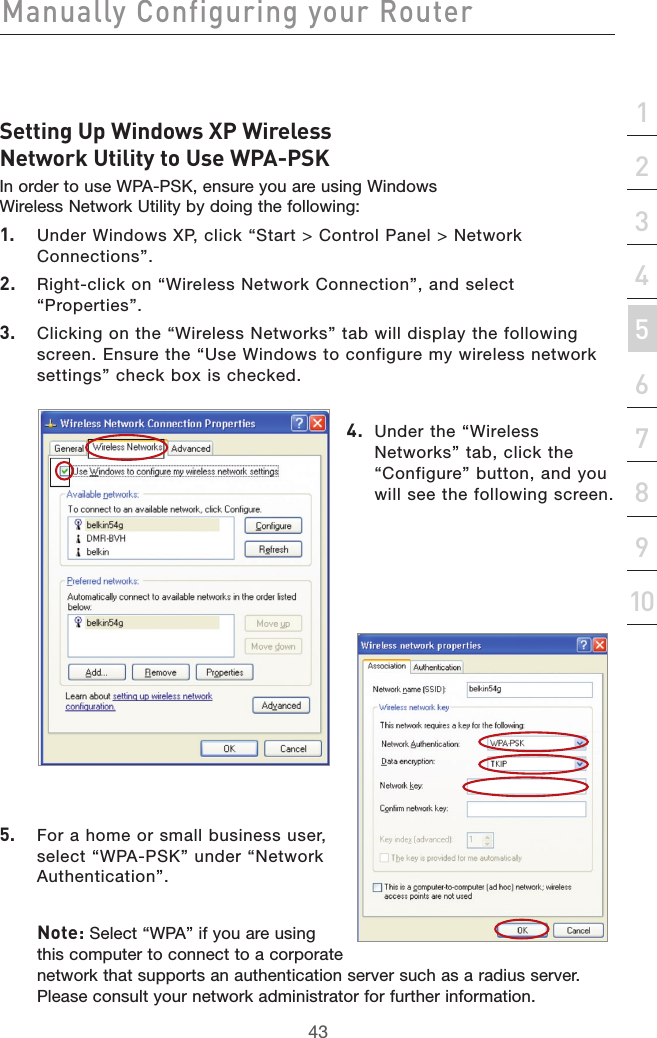
- 2. user manual part 2
- 3. user manual part 3
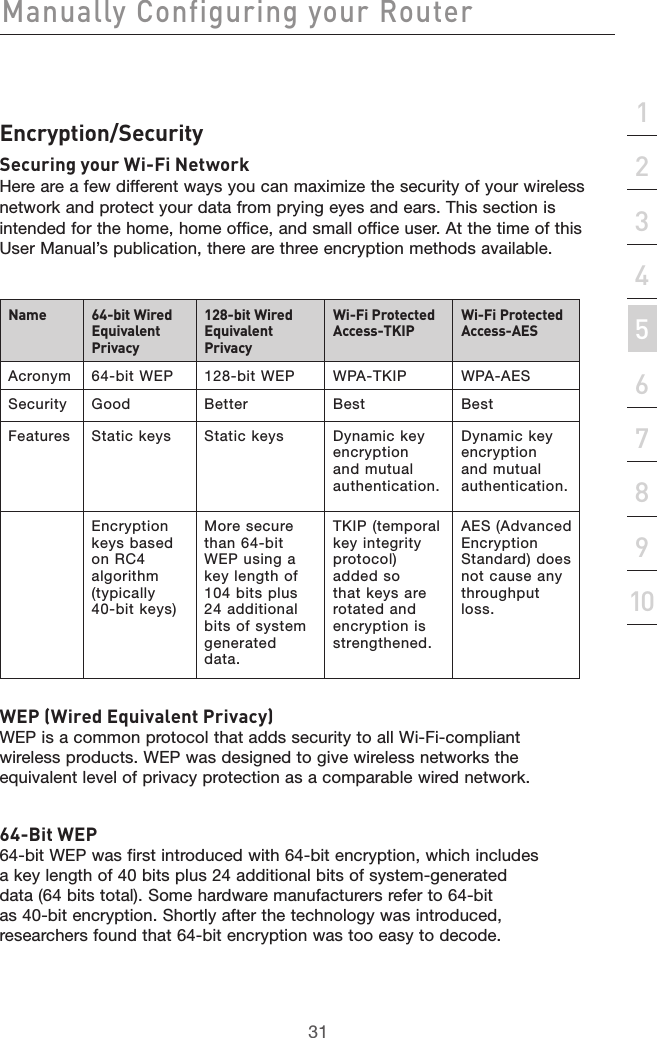
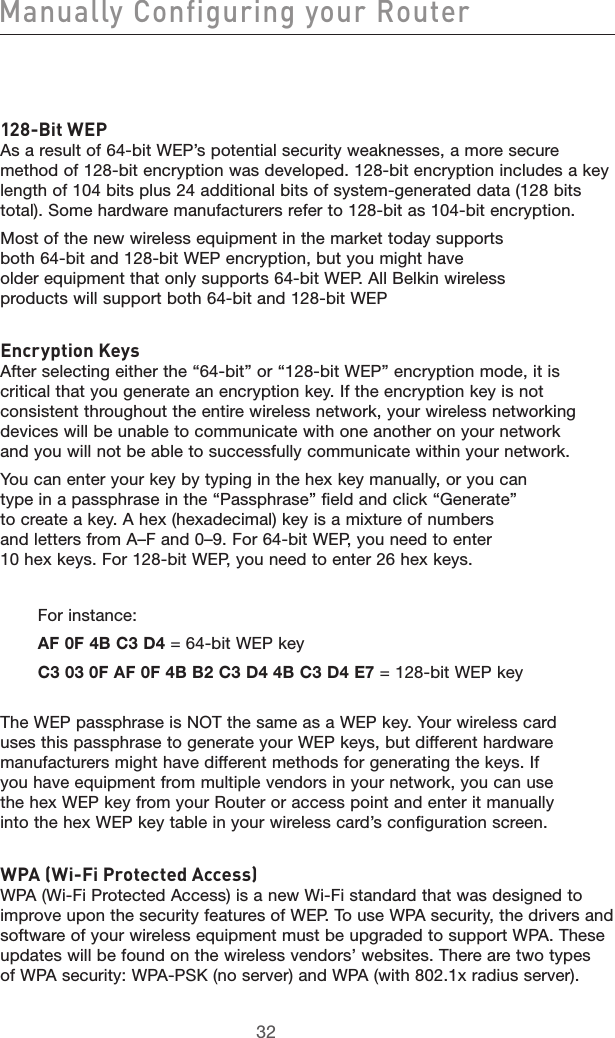
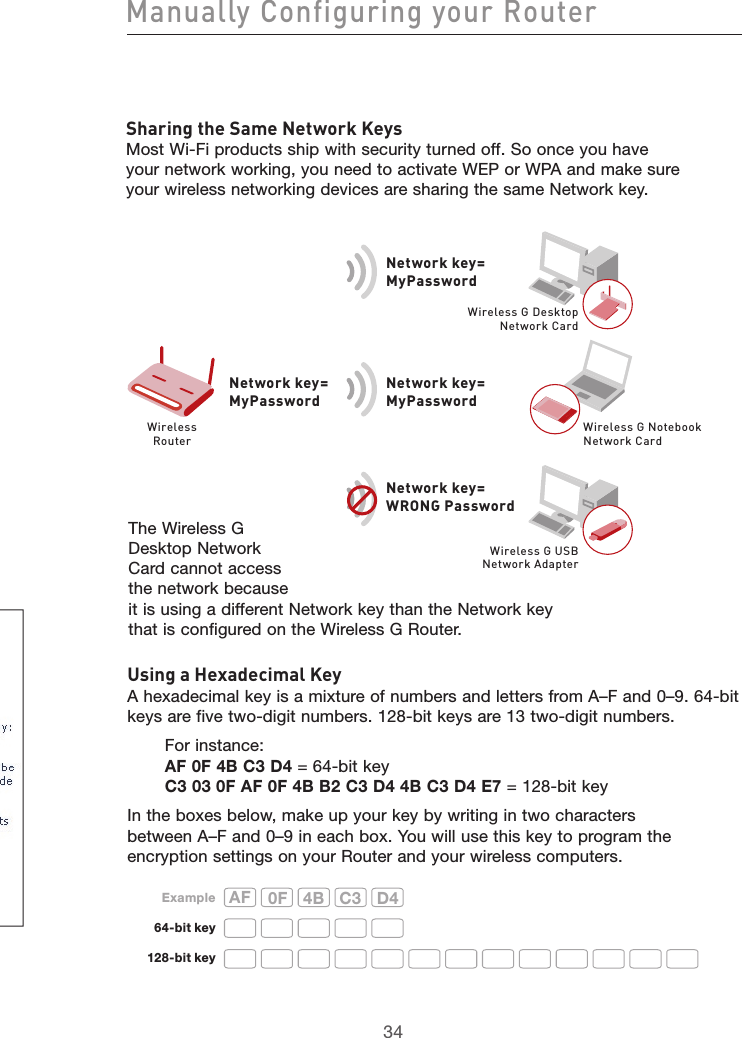
user manual part 2
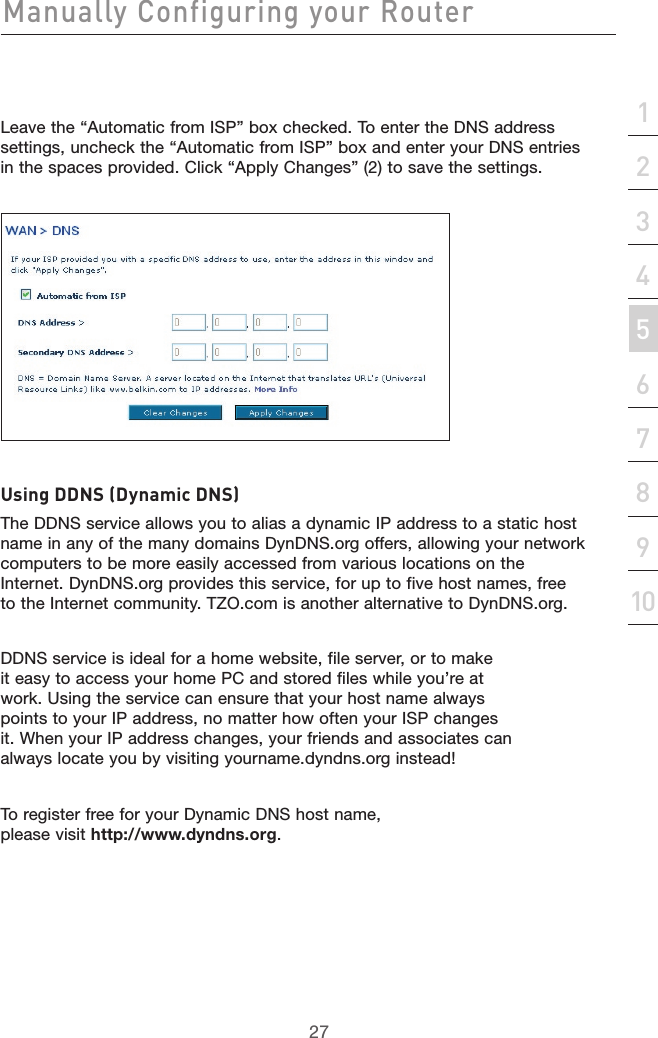


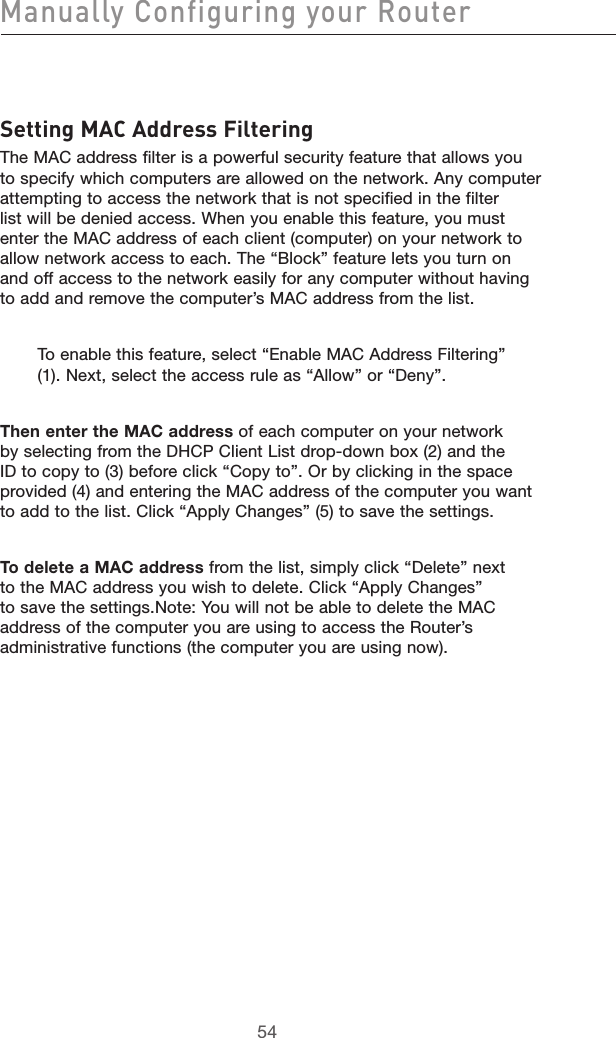
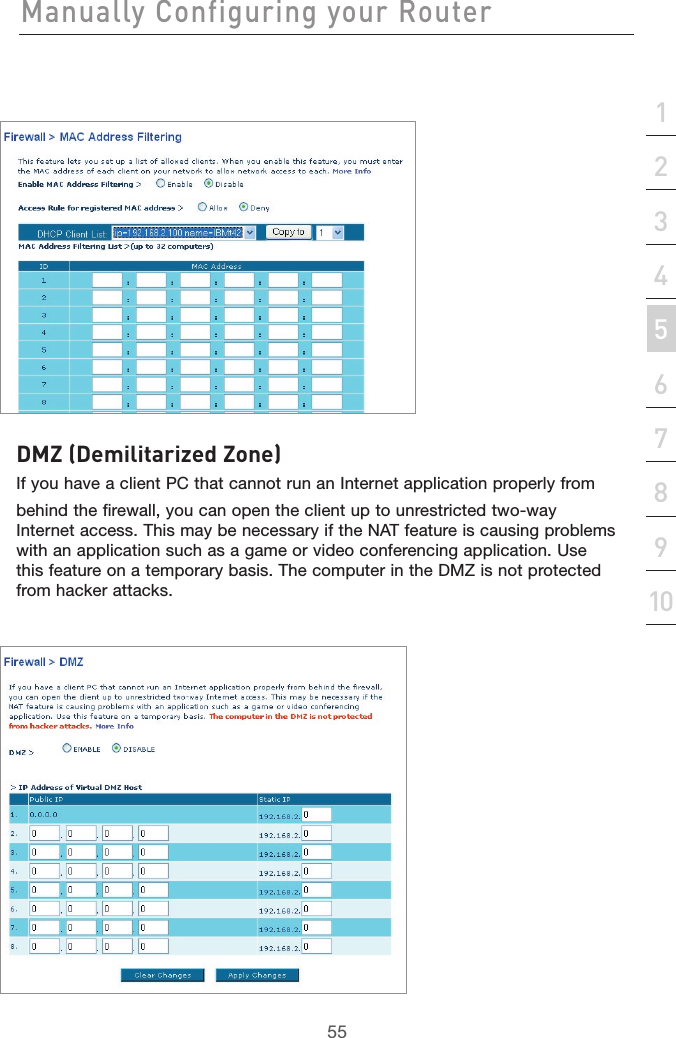
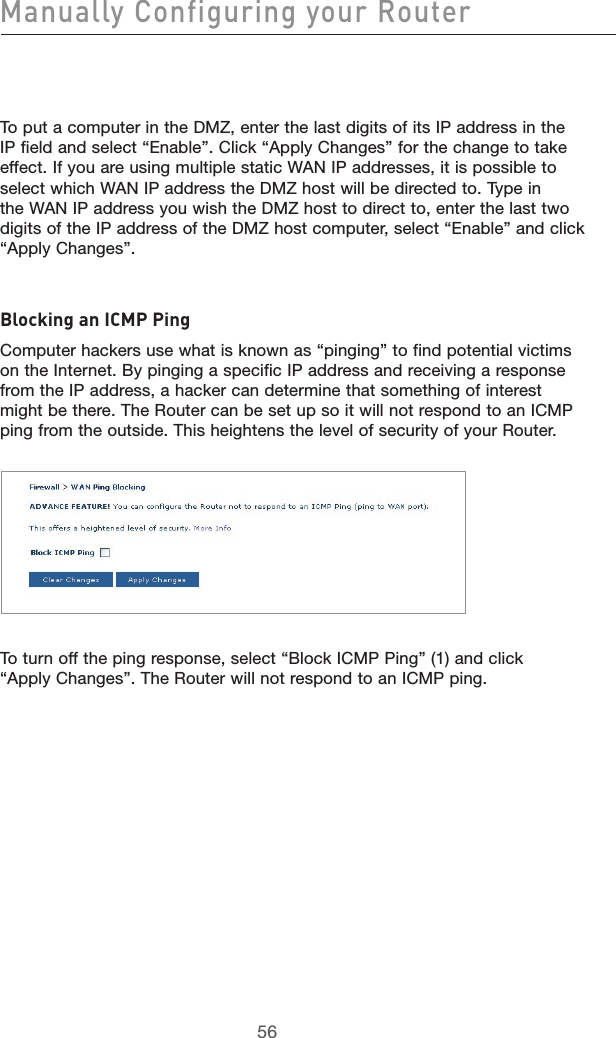
![49Manually Configuring your Router49section21345678910Virtual ServersVirtual servers allow you to route external (Internet) calls for services such as a web server (port 80), FTP server (Port 21), or other applications, through your Router to your internal network. Since your internal computers are protected by a firewall, machines from the Internet cannot get to them because they cannot be “seen”. If you need to configure the virtual server function for a specific application, you will need to contact the application vendor to find out which port settings you need. You can manually input this port information into the Router.Choosing an ApplicationSelect your application from the drop-down list. Click “Add”. The settings will be transferred to the next available space in the screen. Click “Apply Changes” to save the setting for that application. To remove an application, select the number of the row that you want to remove then click “Clear”.Manually Entering Settings into the Virtual ServerTo manually enter settings, enter the IP address in the space provided for the internal (server) machine, the port(s) required to pass, select the port type (TCP or UDP), and click “Apply Changes”. Each inbound port entry has two fields with 5 characters maximum per field that allows a start and end port range, e.g. [xxxxx]-[xxxxx]. For each entry, you can enter a single port value by filling in the two fields with the same value (e.g. [7500]-[7500] or a wide range of ports (e.g. [7500]-[9000]). If you need multiple single port value or mixture of ranges and a single value, you must use multiple entries up to the maximum of 20 entries (e.g. 1. [7500]-[7500], 2. [8023]-[8023], 3. [9000]-[9000]). You can only pass one port per internal IP address. Opening ports in your firewall can pose a security risk. You can enable and disable settings very quickly. It is recommended that you disable the settings when you are not using a specific application.](https://usermanual.wiki/Belkin/F5D7632-4V5.user-manual-part-2/User-Guide-663729-Page-25.png)