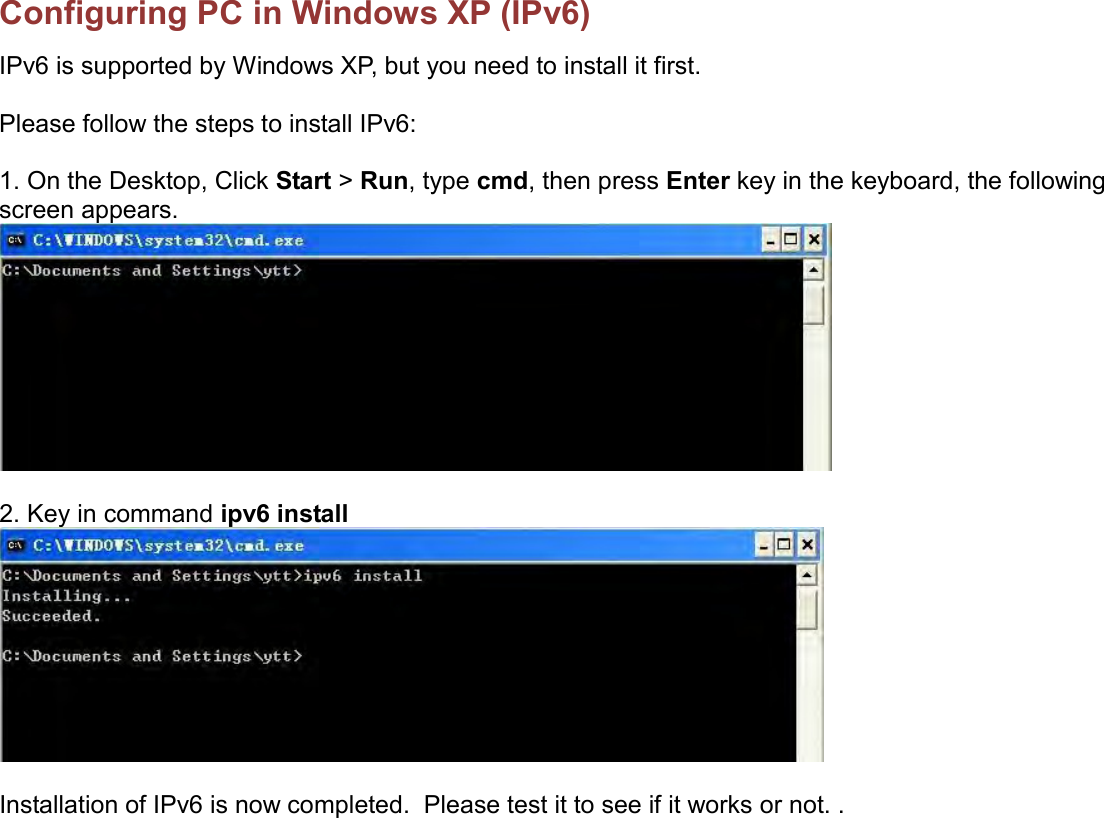
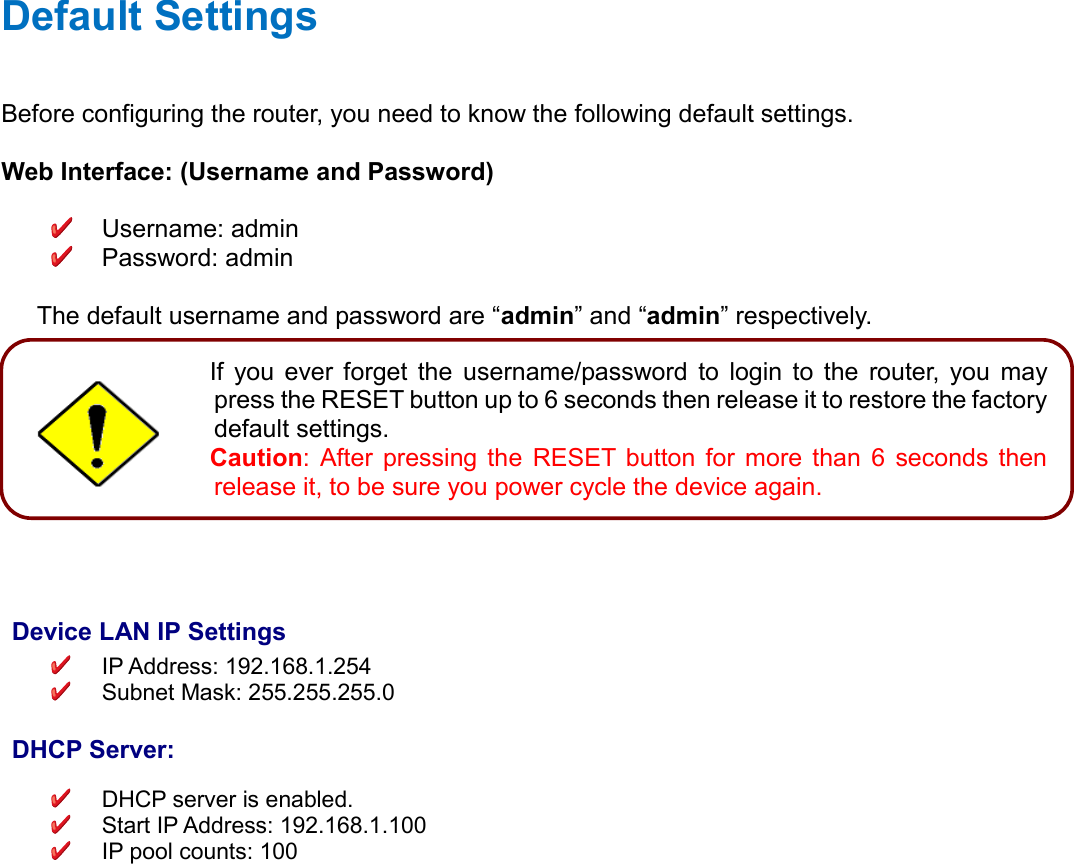
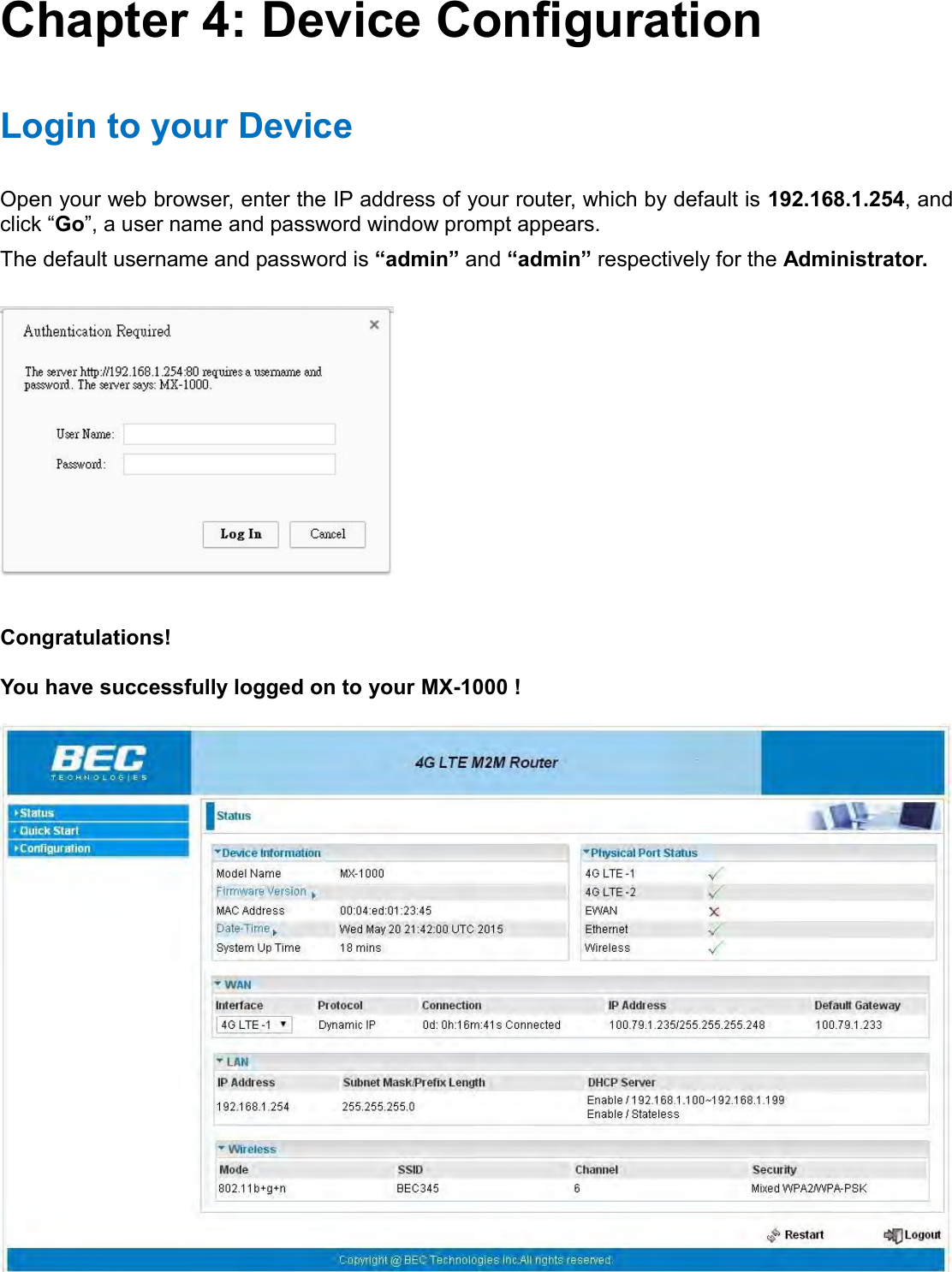
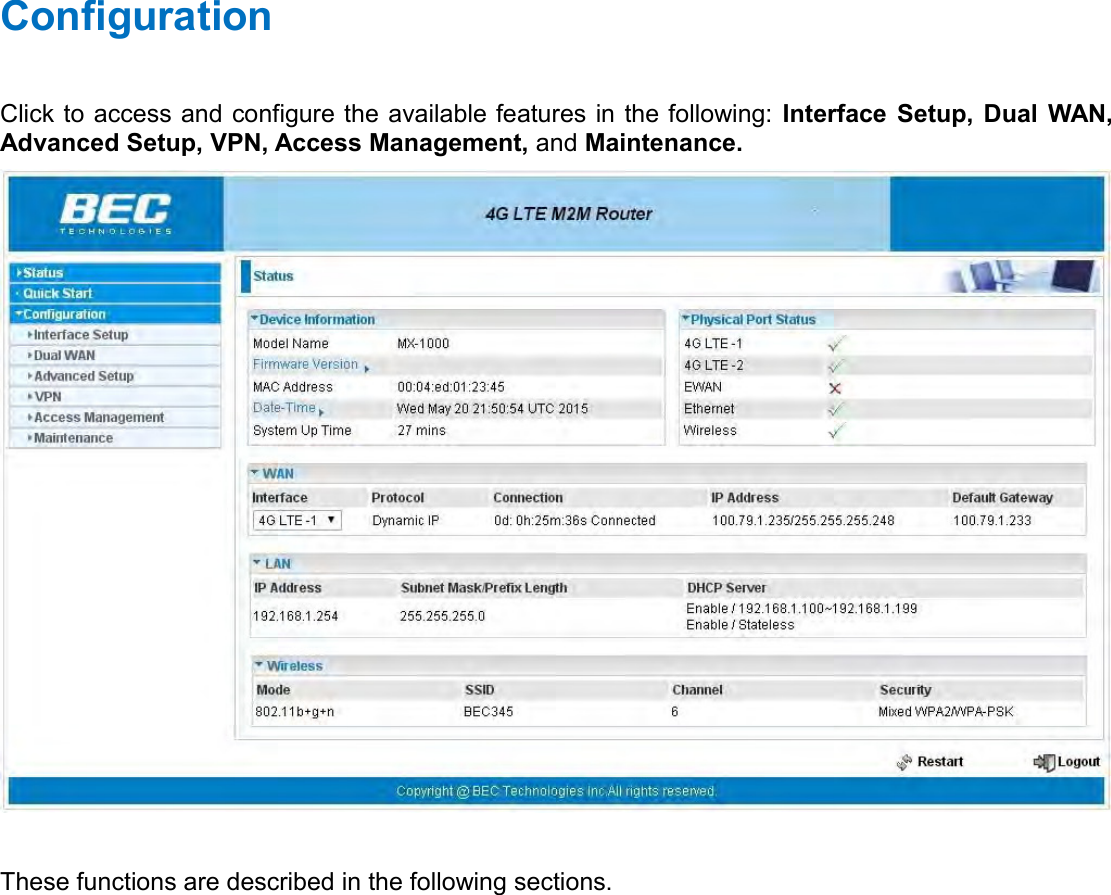
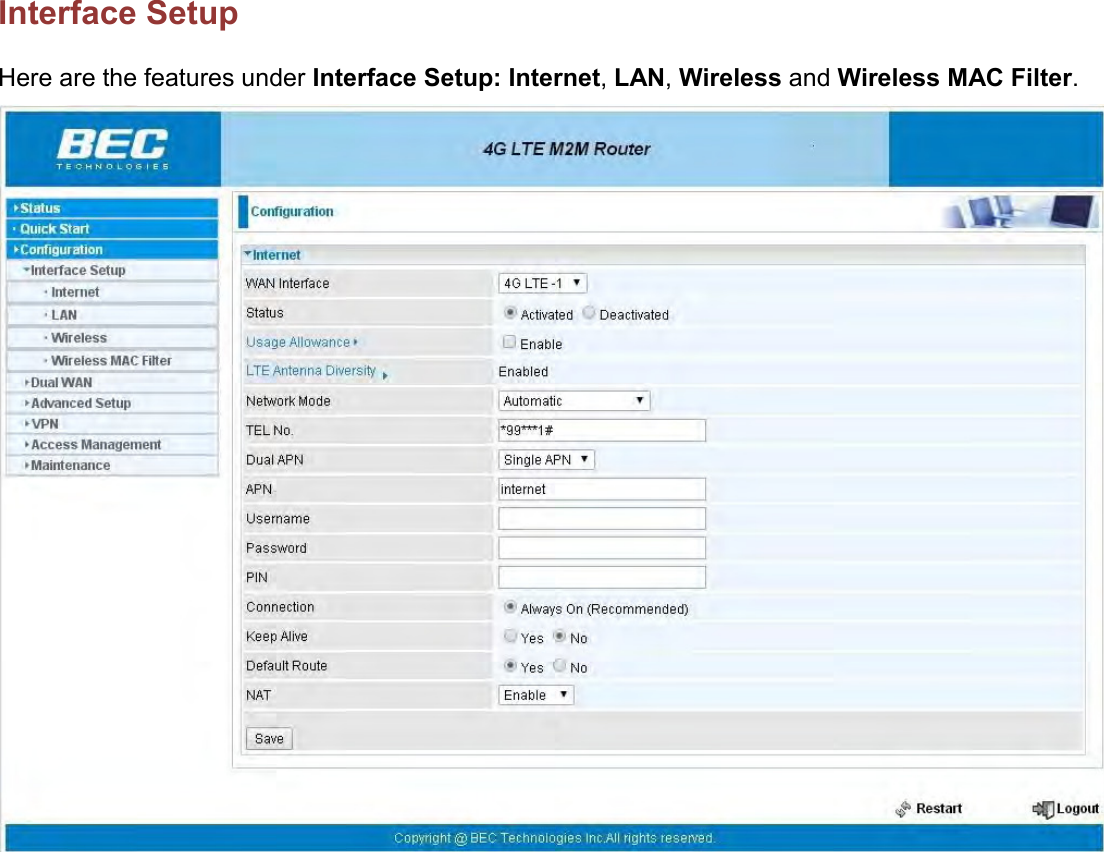
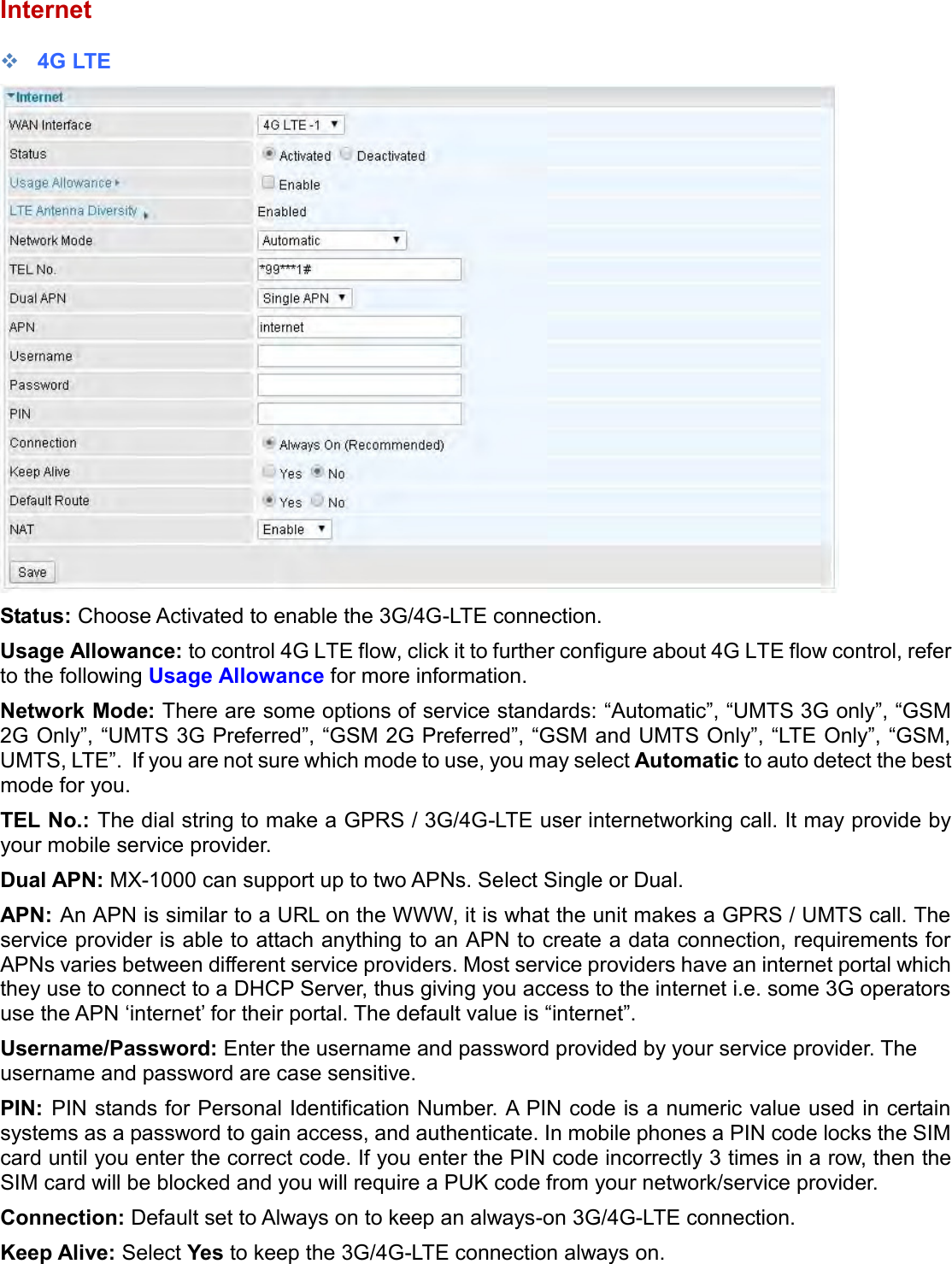
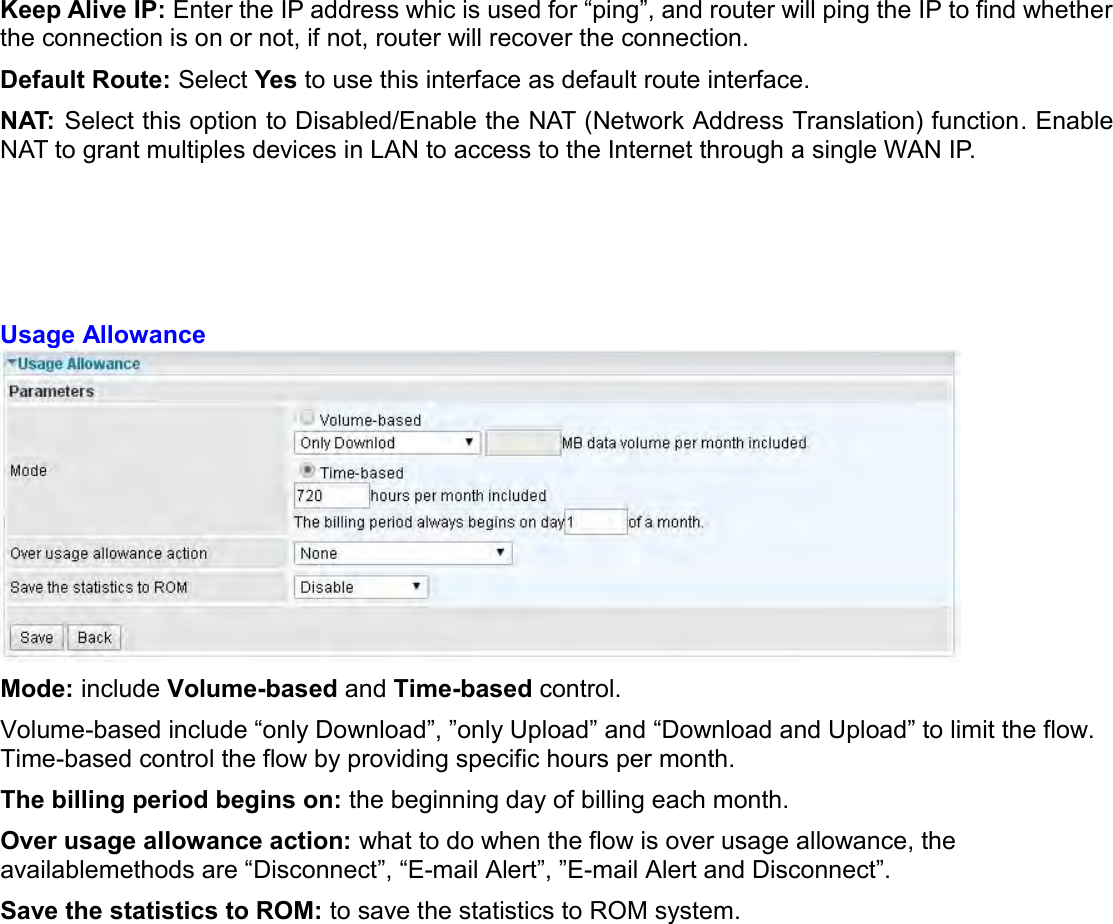
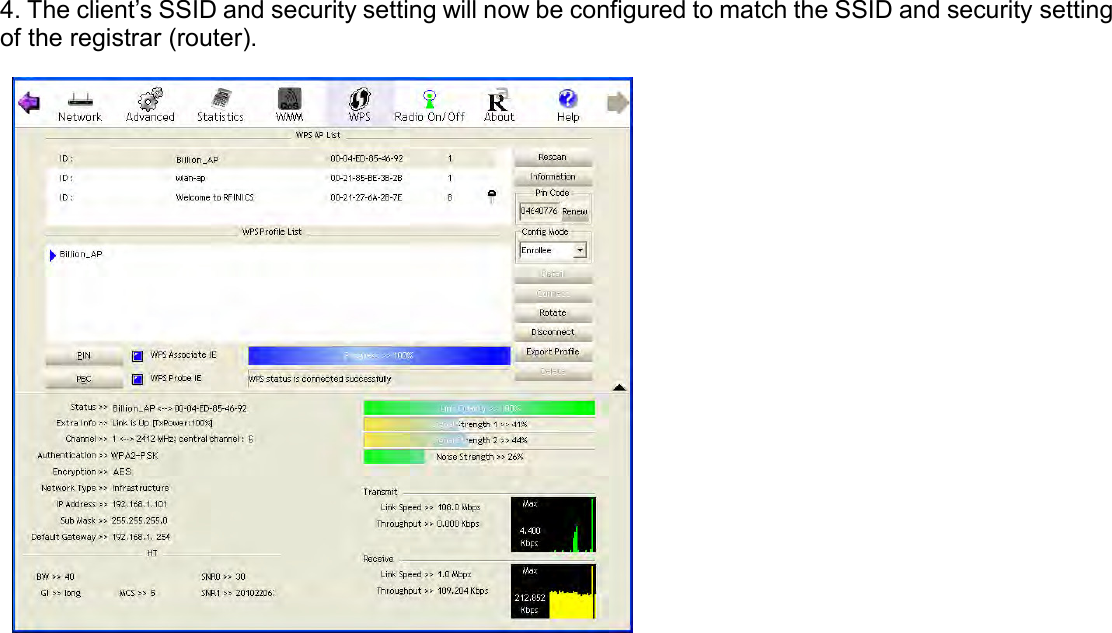
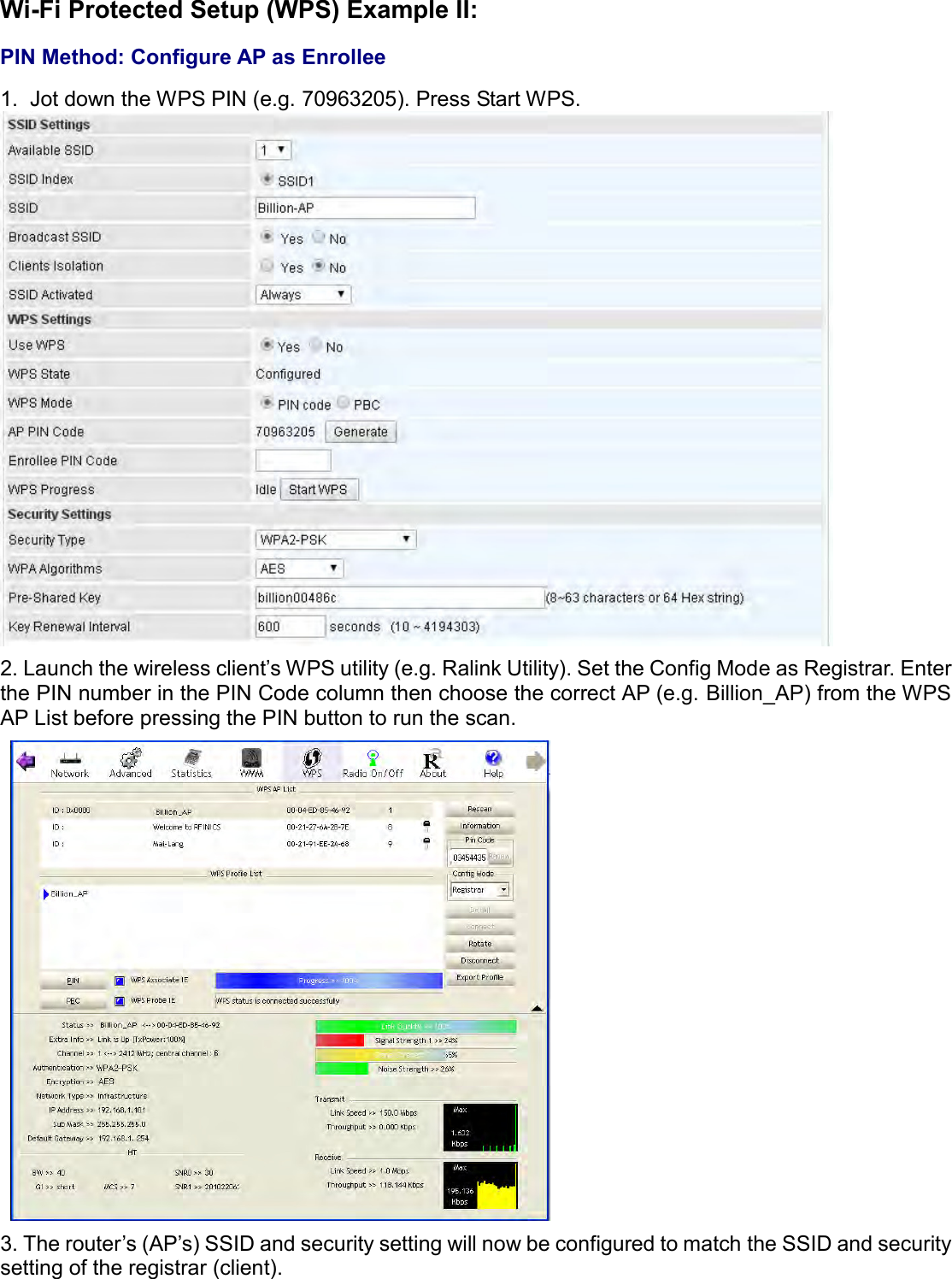
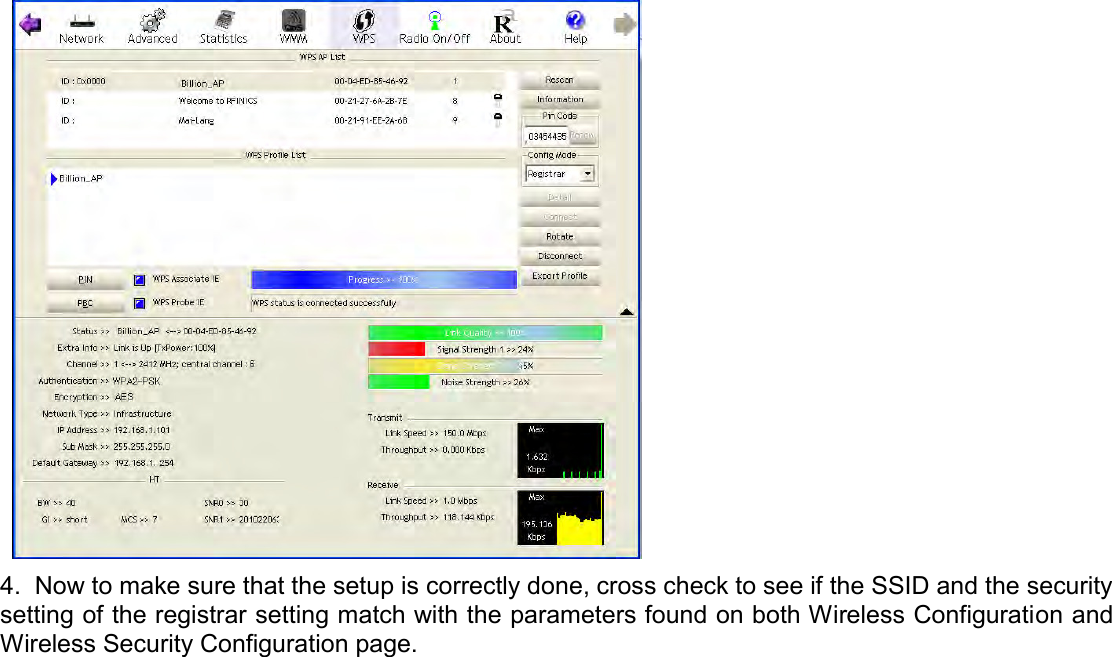
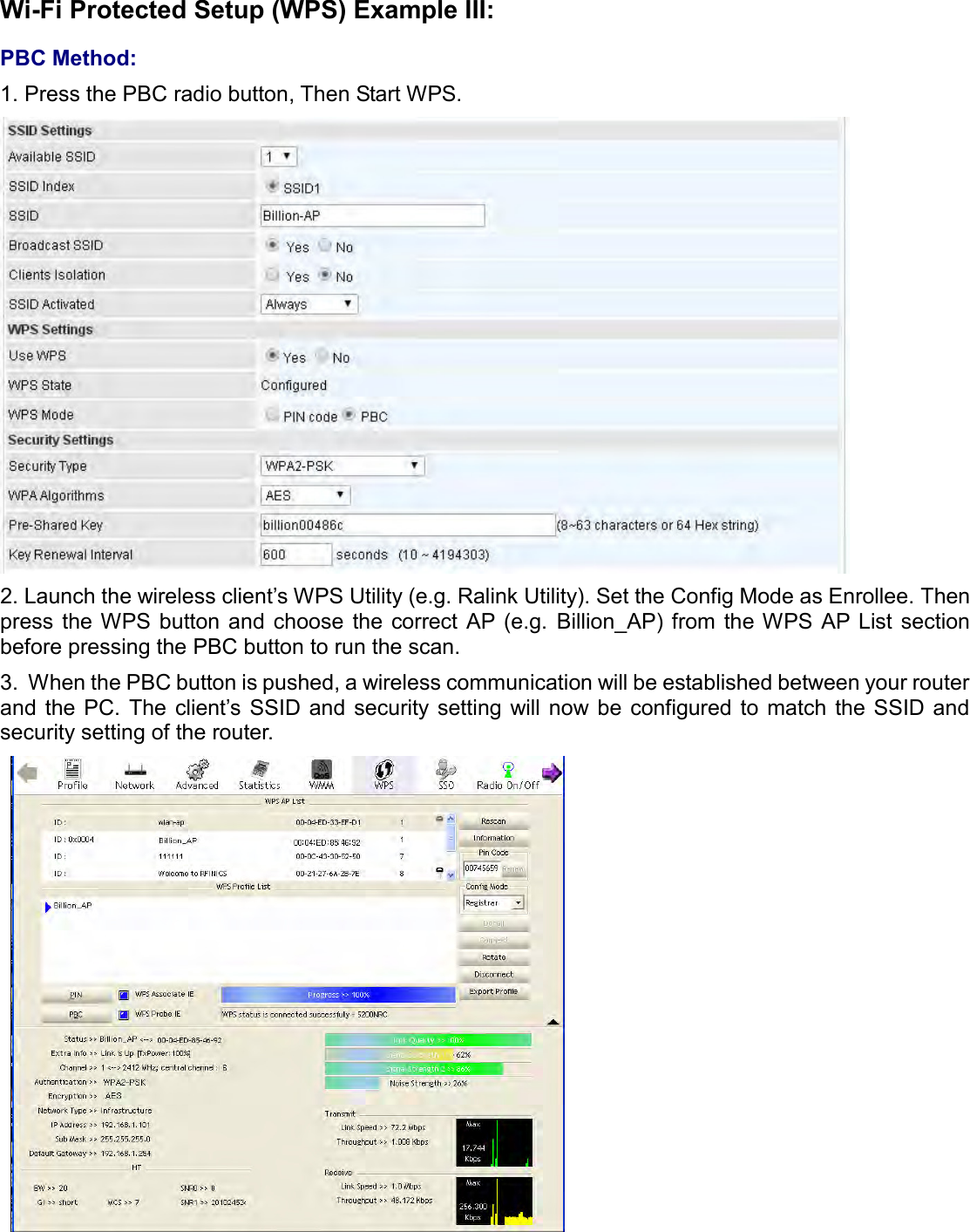
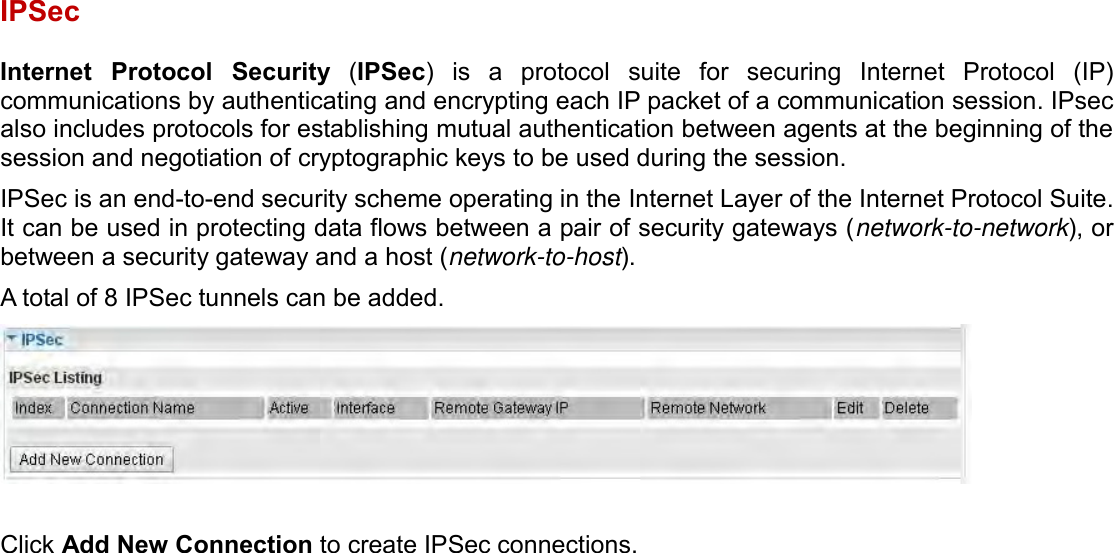
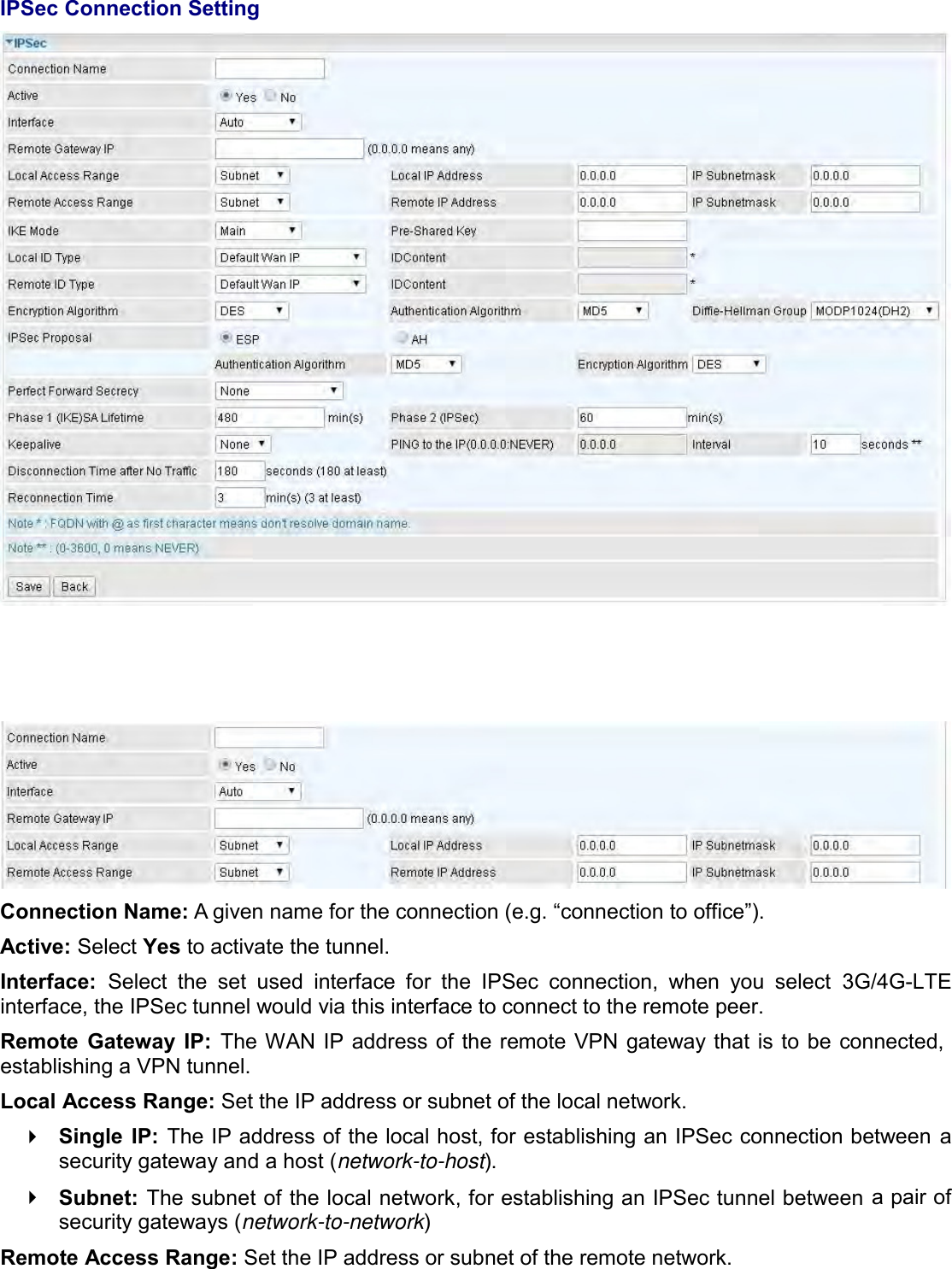
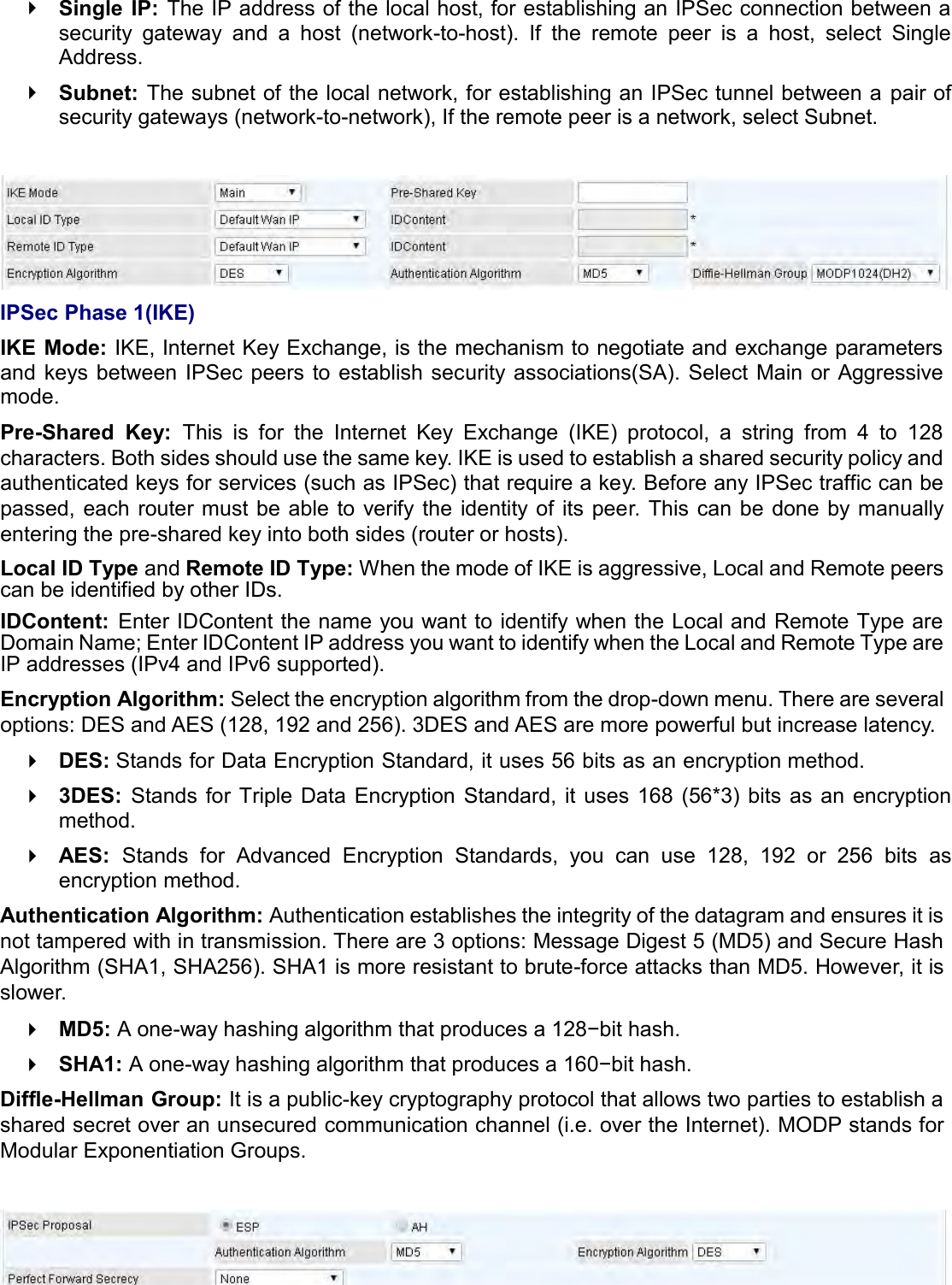
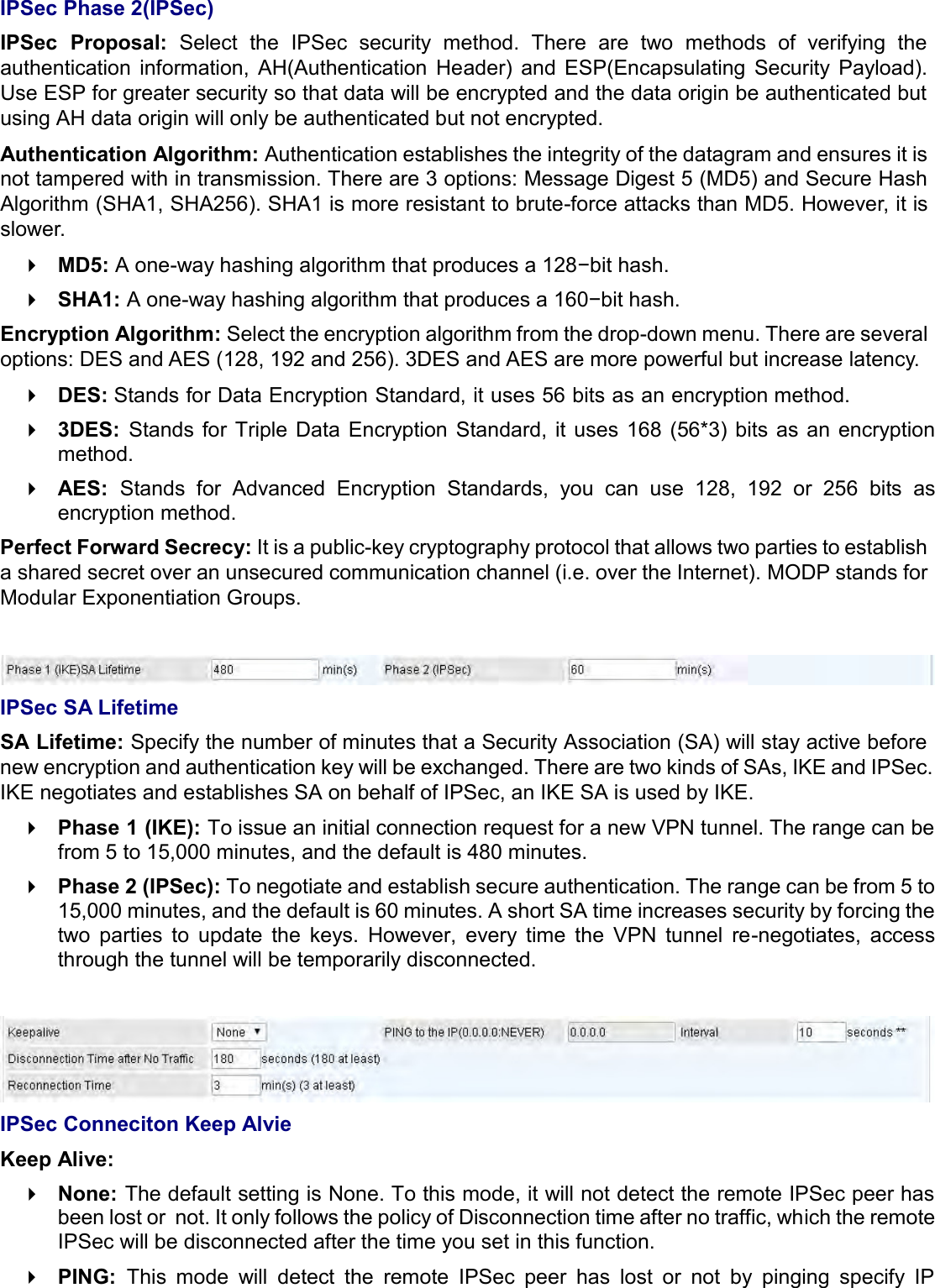
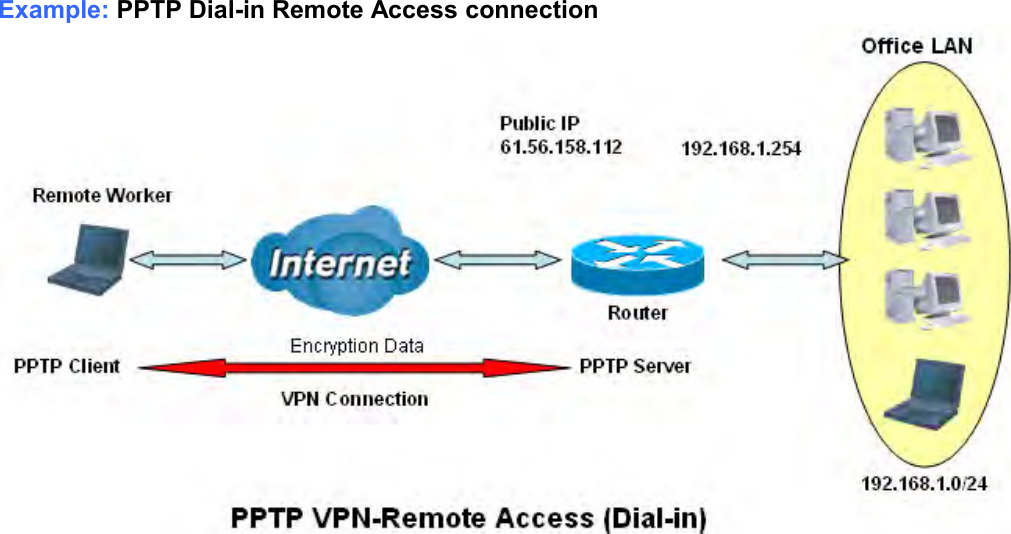
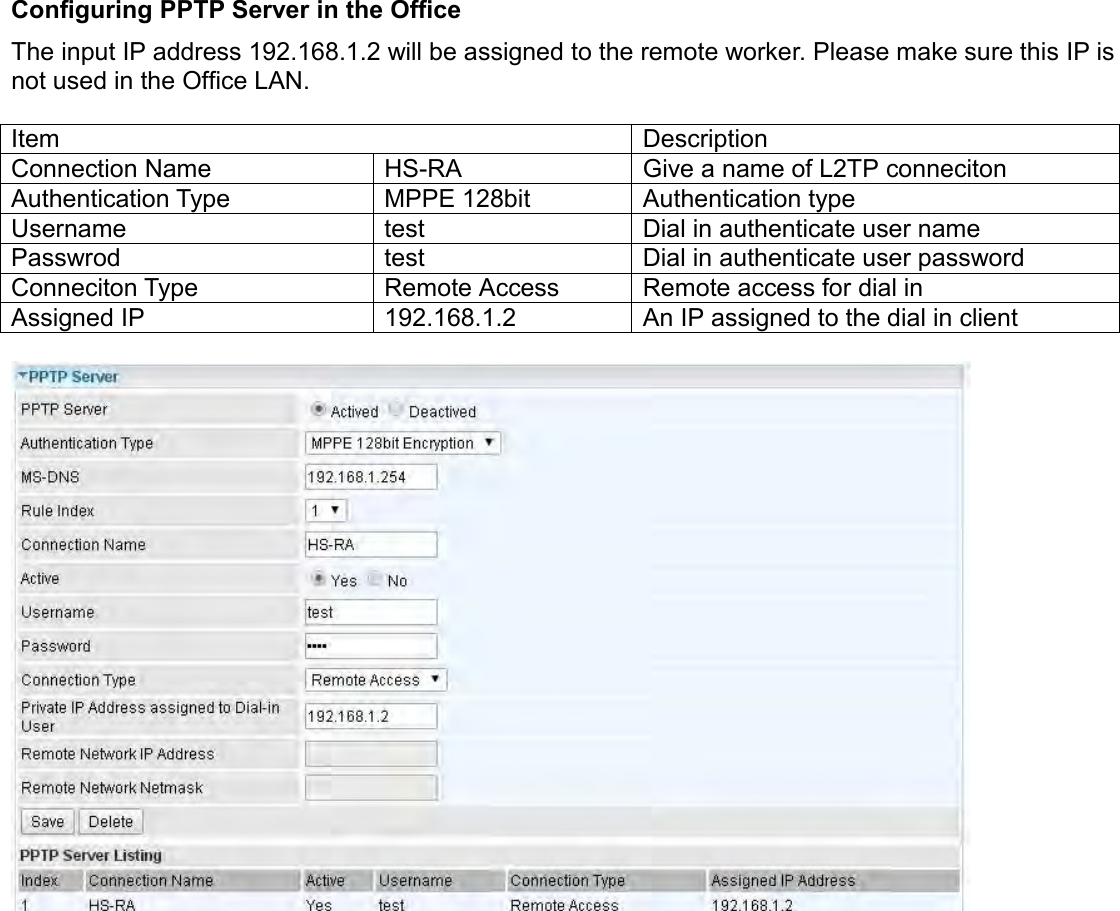
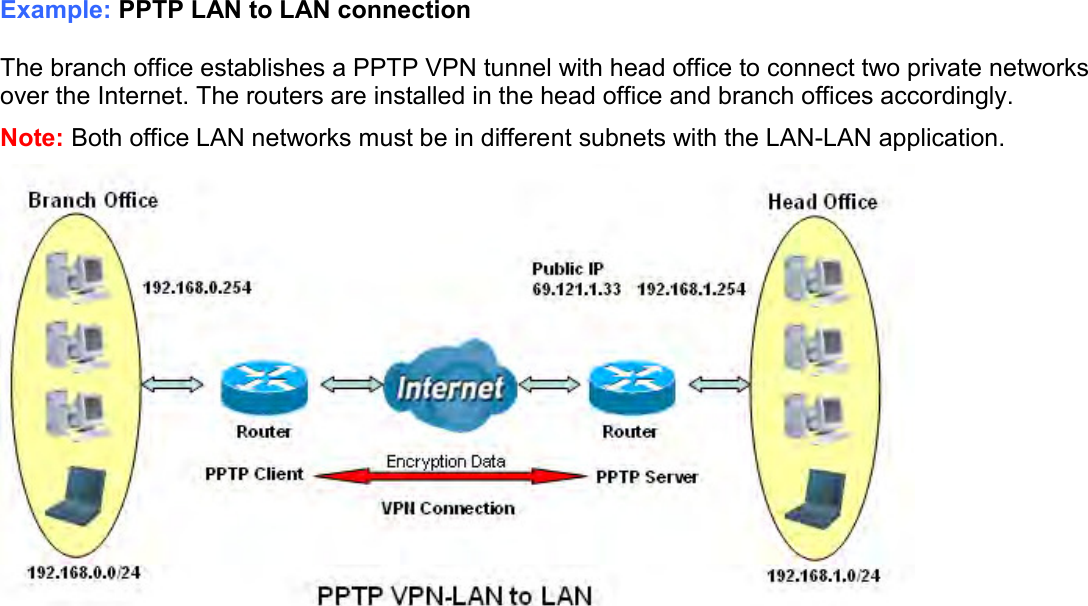
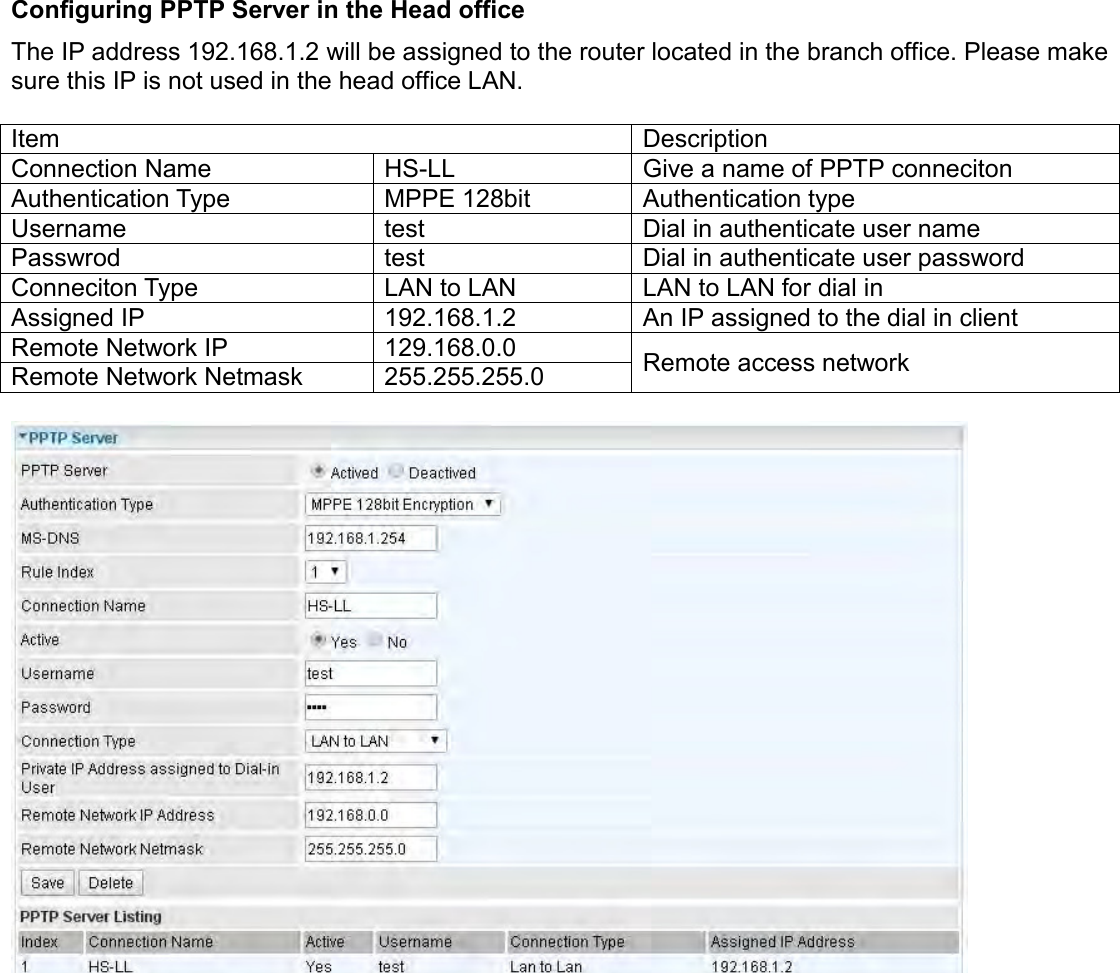
Billion Electric BIL-MX1000 MXConnect M2M Advanced In-Vehicle 4G/LTE Wireless Router, MXConnect M2M Wireless Router User Manual Basic Installation
Billion Electric Co., Ltd. MXConnect M2M Advanced In-Vehicle 4G/LTE Wireless Router, MXConnect M2M Wireless Router Basic Installation
Contents
- 1. User manual
- 2. Users Manual
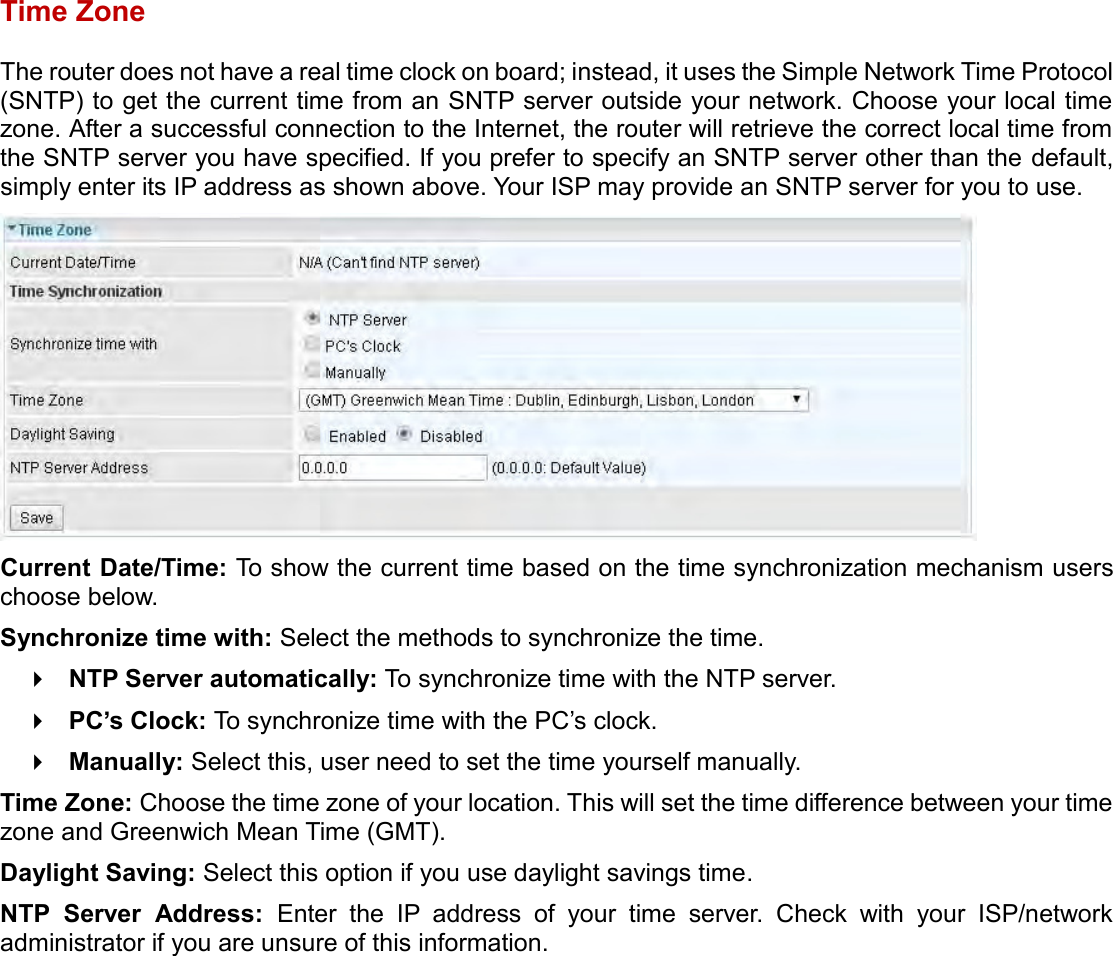
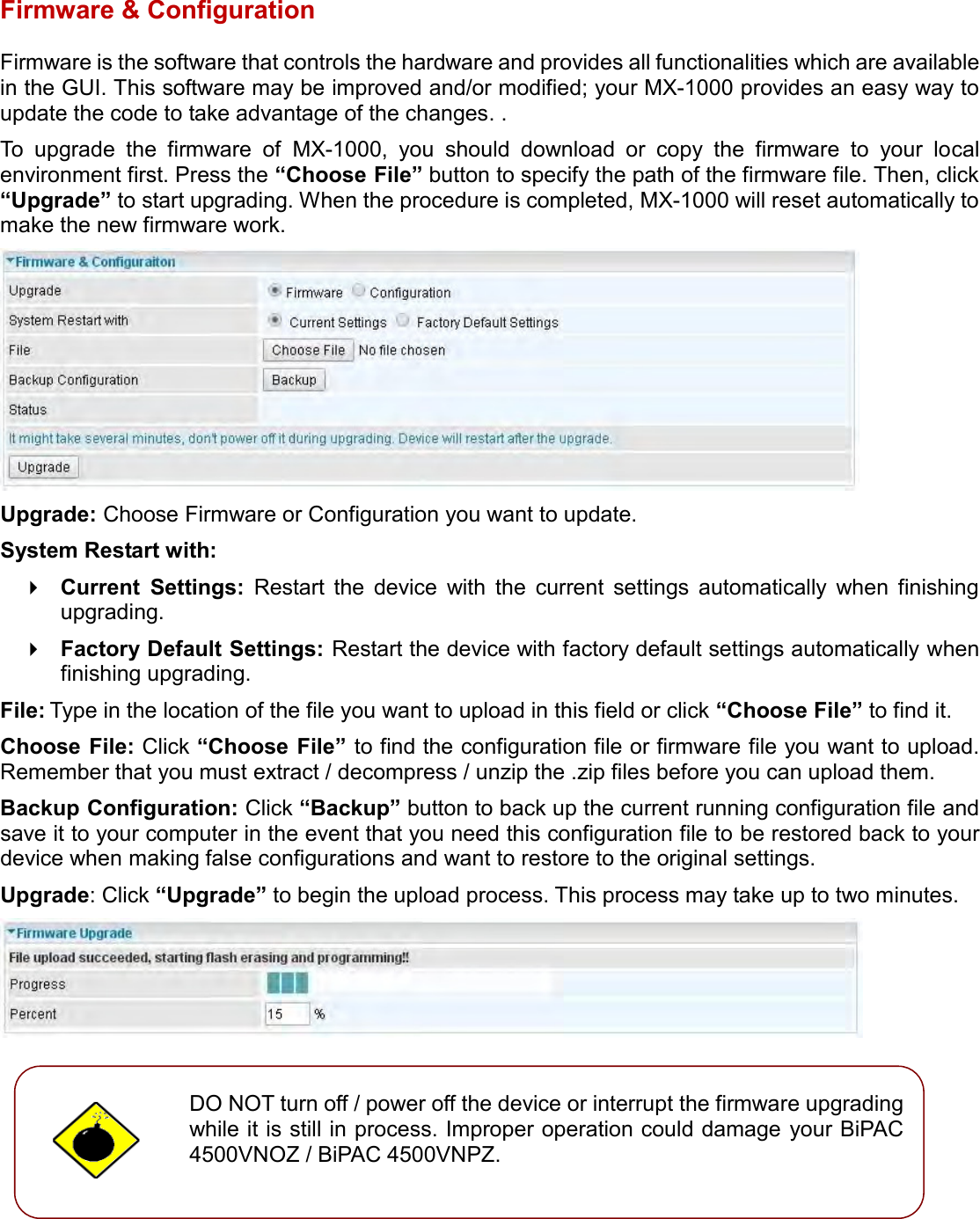
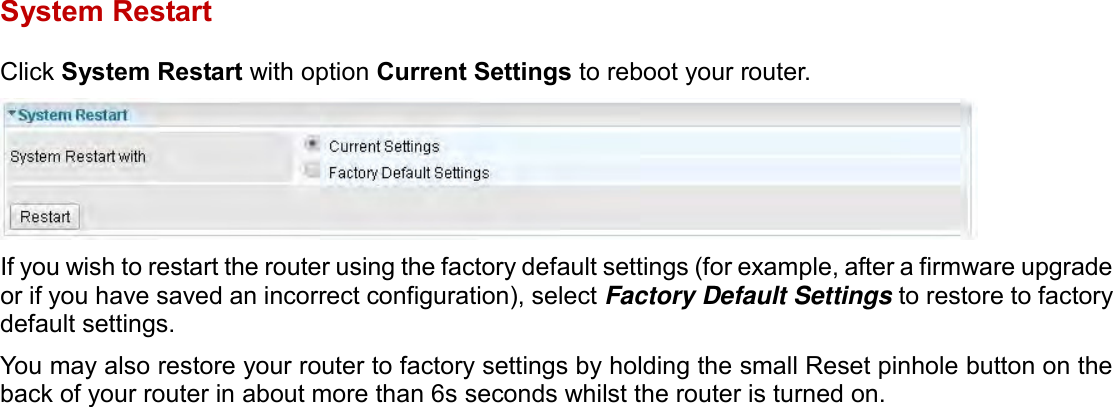
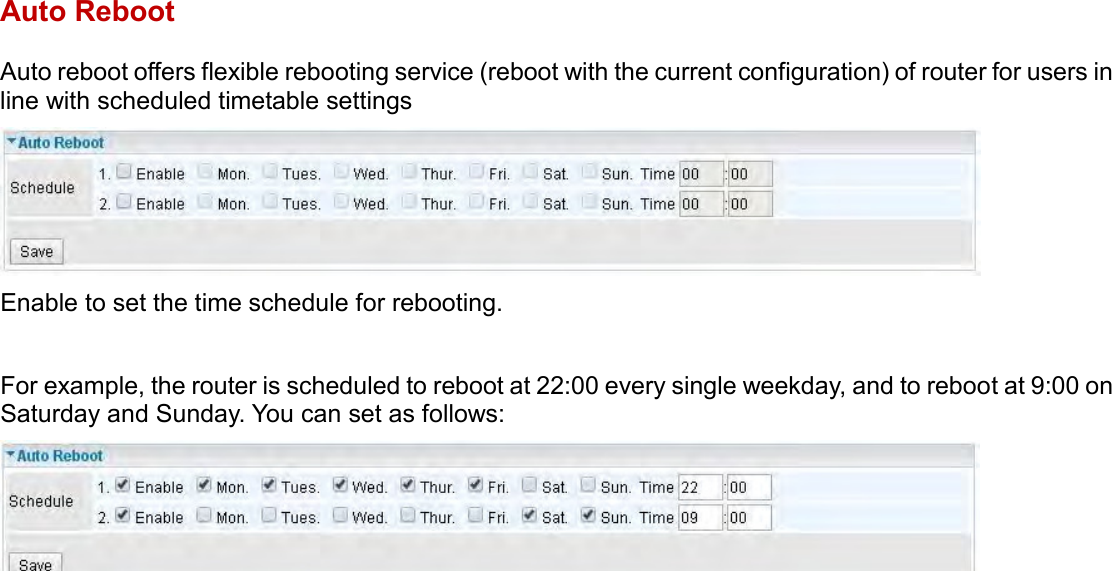
User manual