Bosch Access PE 3.0 Offline Locking System En Us APE Operation Manual 16461045003
User Manual: Bosch en-us Access Professional Edition 3.0
Open the PDF directly: View PDF ![]() .
.
Page Count: 96
- Title Page
- Table of Contents
- System Overview
- General
- Offline Locking System
- Back Page

Access PE 3.0 - Offline Lock-
ing System
en Installation Manual

Table of contents
1System Overview 5
1.1 Restrictions and options 6
1.2 Installation on one computer 8
1.3 Installation on multiple computers 9
1.4 System Prerequisites 10
2General 12
2.1 Introduction 12
2.2 User Login 15
2.3 Menu and Tool bar 18
2.4 General system settings 22
2.5 Layout of the main dialog 27
2.6 Menu and tool bar 28
2.7 Layout of the main dialog 32
2.8 Menu and Tool bars 33
2.9 Enrollment Configuration 35
2.9.1 Enrollment via AMC connected readers 37
3Offline Locking System 42
3.1 Explanation of terms 43
3.2 Special features of the locking system 43
3.3 Locking system components 44
3.4 System Overview 46
3.4.1 Description of system components 47
3.4.2 System limits 51
3.5 Access PE - Configurator 52
3.5.1 Adding hardware components 52
3.5.2 Configuring the write-capable reader 53
3.5.3 Switching the reader protocol 55
3.6 Configurator - Offline Locking System 56
3.6.1 Offline locking system: System 57
3.6.2 Offline locking system: Entrances 60
3.6.3 Offline locking system: Time models 62
3.6.4 Offline locking system: Authorization groups 65
3.6.5 Offline locking system: Write transport cards 67
Access PE 3.0 - Offline
Locking System Table of Contents | en 3
Bosch Access Systems GmbH 2014-02 | 3.0 | IHB

3.6.6 Updating the date and time 70
3.6.7 Booking cards 71
3.7 Managing Personnel Data 72
3.7.1 Description of dialogs 72
3.7.2 Adding personnel data 76
3.7.3 Changing data 79
3.8 Description of Procedures 79
3.8.1 Access 80
3.8.2 Write process 81
3.9 Application Examples 82
3.10 LED display signals 87
4en | Table of Contents Access PE 3.0 - Offline
Locking System
2014-02 | 3.0 | IHB Bosch Access Systems GmbH

System Overview
Access Professional Edition System (hereunder referred to as
Access PE) consists of four modules
– LAC Service: a process which is in constant communication
with the LACs (Local Access Controllers – hereafter
referred to as Controllers). AMCs (Access Modular
Controllers) are used as Controllers.
– Configurator
– Personnel Management
– Logviewer
These four can be divided into server and client modules.
The LAC service needs to remain in constant contact with the
controllers because firstly it constantly receives messages from
them regarding movements, presence and absence of
cardholders, secondly because it transmits data modifications,
e.g. assignment of new cards, to the controllers, but mainly
because it carries out meta-level checks (access sequence
checks, anti-passback checks, random screening).
The Configurator should also run on the server; however it can
be installed on client workstations and operated from there.
The modules Personnel Management and Logviewer belong to
the Client component and can be run on the Server in addition,
or on a different PC with a network connection to the server.
The following Controllers can be used.
– AMC2 4W (with four Wiegand reader interfaces) - can be
extended with an AMC2 4W-EXT
– AMC2 4R4 (with four RS485 reader interfaces)
1
Access PE 3.0 - Offline
Locking System System Overview | en 5
Bosch Access Systems GmbH 2014-02 | 3.0 | IHB

Restrictions and options
You can use Access PE for systems that do not exceed the
following thresholds for connectable components and
manageable data volume.
– Max. 10,000 cards
– Up to three cards per person
– PIN length: 4 to 8 characters (configurable)
– PIN types:
– Verification PIN
– Identification PIN
– Arming PIN
– Door PIN
– Access variants:
– Only with card
– Only with PIN
– PIN or card
– Max. 255 time models
– Max. 255 access authorizations
– Max. 255 area-time authorizations
– Max. 255 authorization groups
– Max. 16 workstations
– Max. 128 readers
– Max. one I/O extension board (AMC2 8I-8O-EXT, AMC2
16I-16O-EXT or AMC2 16I-EXT) per Controller
– The following restrictions apply to each controller type:
1.1
6en | System Overview Access PE 3.0 - Offline
Locking System
2014-02 | 3.0 | IHB Bosch Access Systems GmbH

Controller AMC2 4W AMC2 4W
with AMC2
4W-EXT
AMC2 4R4
Readers/entrances
Max. readers per
AMC
4 8 8
Max. readers per
interface/bus
1 1 8
Table 1.1: System limits — readers and entrances
Video system — restrictions and options
– Max. 128 cameras
– Up to 5 cameras per entrance
– 1 identification camera
– 2 back surveillance cameras
– 2 front surveillance cameras
– You can configure one of these cameras as an alarm
and log book camera.
Offline Locking System (OLS) — restrictions and options
– Max. 1024 doors
– The number of entrances and authorization groups in the
authorizations depends on the dataset length that can be
written to the cards.
– Max. 15 time models
– Up to 4 periods per time model
– Max. 10 special days/holidays (from the online system)
Access PE 3.0 - Offline
Locking System System Overview | en 7
Bosch Access Systems GmbH 2014-02 | 3.0 | IHB
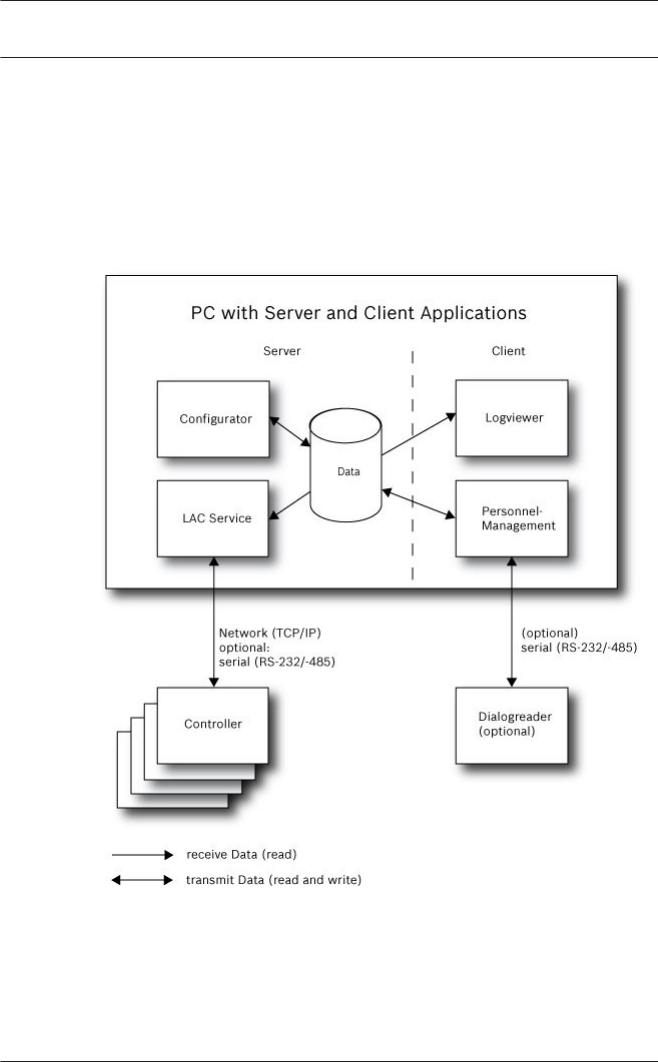
Installation on one computer
The following figure shows a complete Access PE system
installed on a single computer. Controllers can be connected via
a serial interface. If a dialog reader is used then this is also
connected via a serial interface.
Figure 1.1: System Overview – Single Computer Configuration
1.2
8en | System Overview Access PE 3.0 - Offline
Locking System
2014-02 | 3.0 | IHB Bosch Access Systems GmbH

Installation on multiple computers
The following figure shows an Access PE system distributed
across 2 computers. This is particularly beneficial in cases
where the Server to which the Controllers are connected is in a
locked computer room, but the personnel data is maintained,
for example, by the personnel department elsewhere.
The Access PE Client can be installed on up to 16 computers,
which access common data on the Server via the network.
Client workstations can be configured to use two monitors.
Window positions maintained by the operating system, ensure a
familiar operators’ environment across login sessions.
1.3
Access PE 3.0 - Offline
Locking System System Overview | en 9
Bosch Access Systems GmbH 2014-02 | 3.0 | IHB
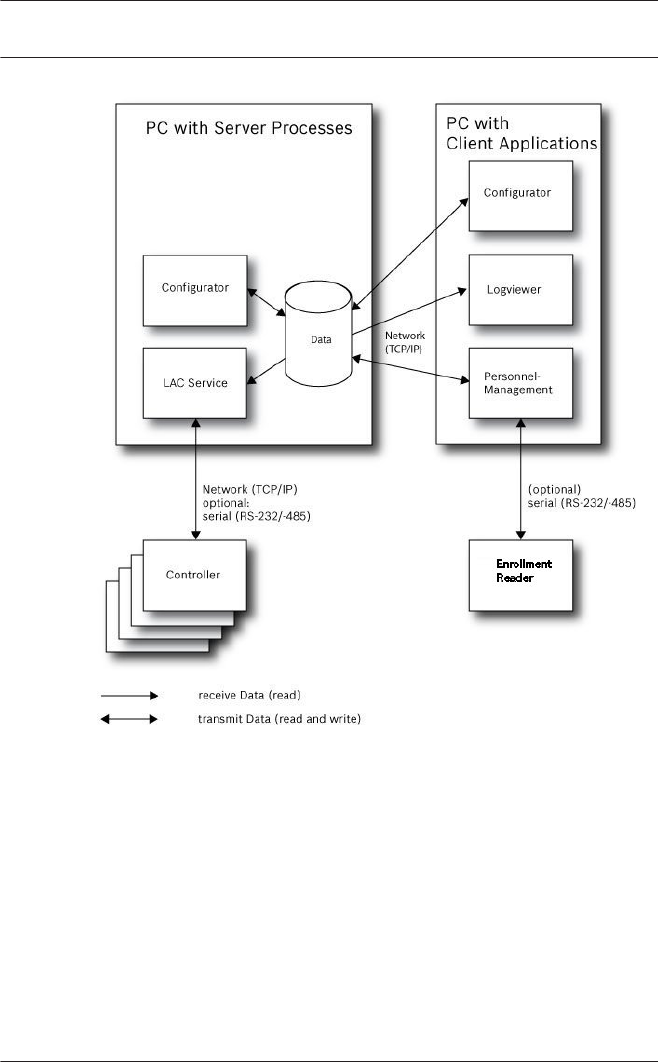
Figure 1.2: System overview – Distributed System
System Prerequisites
The installation of Access PE requires:
Operating Systems (one of):
– Windows XP SP2 Professional
– Windows XP SP3 Professional
– Windows 2008 Server
– Windows 7
Other software:
1.4
10 en | System Overview Access PE 3.0 - Offline
Locking System
2014-02 | 3.0 | IHB Bosch Access Systems GmbH

– To run the AmcIpConfig application supplied (and the
Bosch Video SDK), you need the .NET Framework 4.0
platform.
– To create and display lists and reports, you must install
Crystal Reports applications.
Separate setups are available on the installation CD.
Hardware Requirements
Both Server an Client require a Standard Windows PC with:
– 4 GHz CPU
– 4 GB RAM at least
– 20 GB free disk space (Server)
– 1 GB free disk space (Client)
– 100 Mbit Ethernet Network Card (PCI)
– Graphical adapter with 1024x768 resolution and 32k colors
– Resolution support:
– 1024 by 768
– 1280 by 1024
– 2048 by 768
– 2560 by 1024
– CD/DVD-ROM Drive
– I/O Expansion Option
– USB Keyboard and Mouse
Notice!
Microsoft Windows XP Professional is required for any video
integration.
Please consult the documentation of the chosen devices and
ensure that you can use an operating system supported by both
software and devices.
Access PE 3.0 - Offline
Locking System System Overview | en 11
Bosch Access Systems GmbH 2014-02 | 3.0 | IHB

General
Introduction
Access PE is an Access Control System which has been
designed to offer the highest standards of security and flexibility
to small and medium sized installations.
Access PE owes its stability and upgradeability to a 3-tier
design: The top tier is the administration level with its
controlling services. All administrative tasks are carried out
here, e.g. the registration of new cards and the assignment of
access rights.
The second tier is formed by the Local Access Controllers
(LACs) which govern each group of doors or entrances. Even
when the system is offline a LAC is able independently to make
access control decisions. LACs are responsible for controlling
the entrances, governing door opening times or requesting PIN-
codes at critical access points.
The third tier consists of card readers which, like the
Controllers, are identical across all BOSCH access controls.
They provide not only a consistently high degree of security, but
also a simple upgrade and expansion path for the system,
protecting previous investments.
Access PE multi-user version allows multiple workstations to
control the system. Customizable user rights levels regulate
access and guarantee security. In this way it is possible, for
example, to maintain card data from one workstation whilst
using another to verify whether an employee is present in the
building.
Access PE offers exceptionally flexible configuration of access
rights, time models and entrance parameters. The following list
gives an overview of the most important features:
Quick & Easy card Assignment
2
2.1
12 en | General Access PE 3.0 - Offline
Locking System
2014-02 | 3.0 | IHB Bosch Access Systems GmbH

Cards (up to three) can be assigned to persons either manually
or using a dialog reader connected to a PC via a serial
connection. Only one card can be active per person at any one
time. When upgrading cards the old card is automatically
overwritten and becomes invalid, thus preventing old cards from
gaining access even if those responsible forgot or were unable
to cancel them.
Access Rights (including Group Privileges)
Each person can inherit group privileges as well as having
individual rights assigned to him. Privileges can be restricted by
area and time to an accuracy of one minute. Group privileges
can be used to grant and limit access rights for any or all
cardholders simultaneously. Group privileges can be made
dependent on time models which restrict their access to certain
times of day.
Access tracking
By defining Areas it is possible to track and enforce a correct
sequence of accesses. Even without monitoring, this
configuration makes it possible to display a cardholder's
location.
Anti-Passback
When a card has been read it can be blocked for a defined
period from entering at the same access point. Hence it is
possible to prevent "passback", where a user hands his card
back across a barrier to provide access for an unauthorized
person.
Automatic Cancelation of cards upon Expiration
Visitors and temporary staff frequently require access for a
limited period only.
cards can be registered for a specific time period, so that they
automatically lose their validity when that period expires.
Time Models and Day Models
Access PE 3.0 - Offline
Locking System General | en 13
Bosch Access Systems GmbH 2014-02 | 3.0 | IHB

A cardholder can be assigned to specific time models which
regulate the hours in which that person has access. Time
models can be defined flexibly using day models which
determine how specific weekdays, weekends, holidays and
special days deviate from normal working days.
Identification via PIN-Code
Instead of a card a person can use a special PIN-Code to enter.
Verification via PIN-Code
Particularly sensitive areas can be programmed to require
additional PIN-Codes. This protection can in turn be made
dependent on time models, so that, for instance, a PIN-Code is
only required for access during holiday times or outside of
defined working hours.
Flexible Door Management
Flexible parameterization of individual door models allows an
optimum balance between security and comfort. The "shunt" or
alarm suppression period can be individually specified to
regulate for how long a door may remain open. In cooperation
with an alarm system the access point can then optionally be
locked.
Periodic Door Release
In order to facilitate access, door alarms can be shunted to
release doors for specific periods. Door release periods can be
defined manually or automatically via a time model.
Time and Attendance
Access points can be parameterized to record ingress and
egress for time & attendance purposes.
Card Design
The graphical add-in module Card Personalization (CP) is fully
integrated into the Access Control system to allow the operator
to create cards without switching applications.
Assignment of Photos
If the add-in module Card Personalization (CP) is not activated
photographic identification can nevertheless be imported and
associated with cardholders.
14 en | General Access PE 3.0 - Offline
Locking System
2014-02 | 3.0 | IHB Bosch Access Systems GmbH

Offline locking system
Areas which are not covered, for whatever reason, by the high-
availability online access control system can nevertheless be
locked offline.
Administration of video devices
Entrances can be equipped additionally with cameras to identify
and track the movements of persons using them.
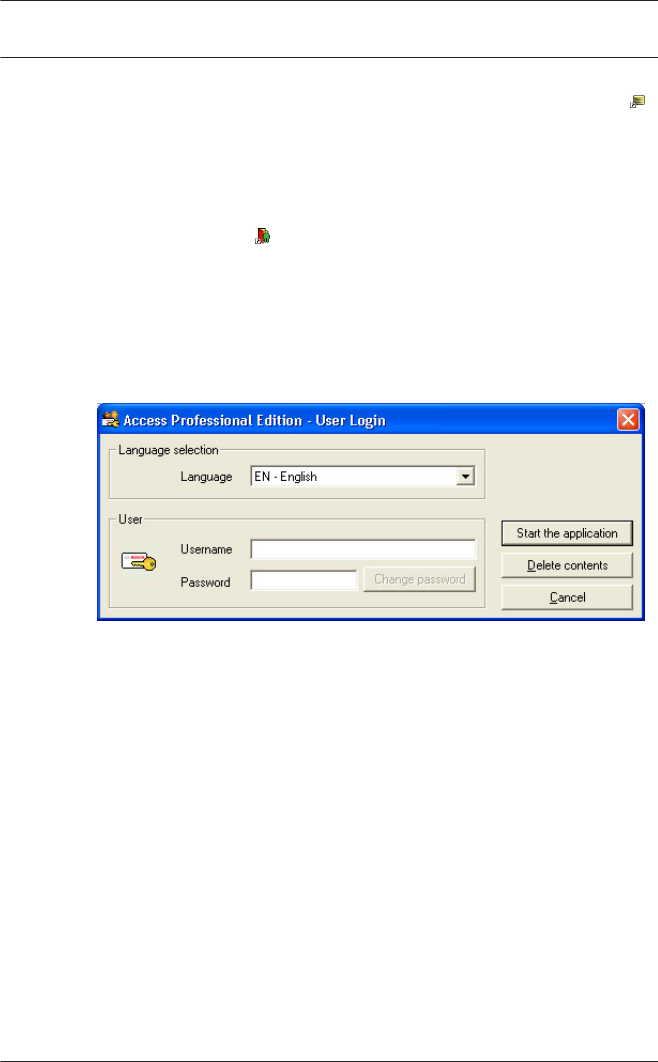
User Login
– Start the user applications using the desctop icons:
Personnel Management
Configurator
Logviewer
Map and Alarm Management
Video Verification
or choose the tools via : Start > Programs > Access
Professional Edition
– Start the : Map & Alarm Management application using the
desctop icon or via : Start > Programs > Access
Professional Edition > Map & Alarm Management.
– Start the : Video Verification application using the desctop
icon or via : Start > Programs > Access Professional
Edition > Video Verification.
– Start the : Configurator application using the desctop icon
or via : Start > Programs > Access Professional Edition >
Configurator.
2.2
Access PE 3.0 - Offline
Locking System General | en 15
Bosch Access Systems GmbH 2014-02 | 3.0 | IHB
– Start the : Logviewer application using the desctop icon
or via : Start > Programs > Access Professional Edition >
Logviewer.
– Start the : Personnel Management application using the
desctop icon or via : Start > Programs > Access
Professional Edition > Personnel Management.
The system's applications are protected from unauthorized use.
A login with a valid username and password is required in order
to invoke the dialog-based subsystems.
The upper drop-down list can be used to select the desired
interaction language. The default is that language which was
used to install the application. If there is a change of user
without restarting the application then the previous language is
retained. For this reason it is possible for a dialog box to appear
in an undesired language. In order to avoid this, please log in to
Access PE again.
Access PE applications can be run in the following languages:
– English
– German
– Russian
– Polish
– Chinese (PRC)
– Dutch
– Spanish
16 en | General Access PE 3.0 - Offline
Locking System
2014-02 | 3.0 | IHB Bosch Access Systems GmbH
– Portuguese (Brazil)
Notice!
All facilities such as device names, labels, models and user-
rights schemes are displayed in the language in which they
were entered.Similarly buttons and labels controlled by the
operating system may appear in the language of the operating
system.
If a valid username/password pair are entered then the button :
Change Password appears. This can be used to start a new
dialog to change the password.
The button Start the application checks the user's privileges
and, based on these, starts the application. If the system is
unable to authenticate the login then the following error
message appears: : Wrong username or password!
Login via Personnel Management
If the user is already logged into the Access PE Personnel
Management application, and if the user's rights include the
other tools, he can start the : LogViewer, : Configurator, : Alarm
Management and : Video Verification using the toolbar buttons.
If the user is already logged into the Access PE Personnel
Management application, and if the user's rights include :
LogViewer, then : LogViewer may be invoked directly using the
button in the tools list, without requiring a separate login to
the LogViewer application.
Access PE 3.0 - Offline
Locking System General | en 17
Bosch Access Systems GmbH 2014-02 | 3.0 | IHB

If the user is already logged into the Access PE Personnel
Management application, and if the user's rights include :
Configurator, then : Configurator may be invoked directly using
the button in the tools list, without requiring a separate
login to the Configurator application.
If the user is already logged into the Access PE Personnel
Management application, and if the user's rights include : Video
Verification, then : Video Verification may be invoked directly
using the button in the tools list, without requiring a separate
login to the Configurator application.
If the user is already logged into the Access PE Personnel
Management application, and if the user's rights include : Alarm
Management, then : Alarm Management may be invoked
directly using the button in the tools list, without requiring a
separate login to the Configurator application.
Menu and Tool bar
The following functions can be invoked via the menus, the icons
in the toolbar or specific keyed shortcuts.
Function Icon/
Shortcut
Description
Menu File
New
Crtl + N
Clears all configuration dialog
boxes (except for default
settings) in order to define a
new configuration.
2.3
18 en | General Access PE 3.0 - Offline
Locking System
2014-02 | 3.0 | IHB Bosch Access Systems GmbH
Function Icon/
Shortcut
Description
Open...
Crtl + O
Opens a dialog box to select a
different configuration for
loading.
Save
Crtl + S
Saves changes into the current
configuration file.
Save as... Saves the current configuration
into a new file.
Activate
Configuration
Activates a loaded configuration
and saves the hitherto active
configuration.
Send
Configuration to
LAC
Propagates saved configuration
changes to the LAC-Service.
List recently
active
configurations
Opens configurations directly,
circumventing the Open
function's selection dialog.
Exit Shuts down Access PE
Configurator.
Function Icon/
Shortcut
Description
Menu View
Tool bar Toggles display of the tool bar
(default = on).
Status bar Toggles display of the status bar
at the bottom edge of the
window (default = on).
Access PE 3.0 - Offline
Locking System General | en 19
Bosch Access Systems GmbH 2014-02 | 3.0 | IHB
Function Icon/
Shortcut
Description
Menu Configuration
General Opens the General Settings
dialog for setting up Controllers
and general system parameters.
Input signals Opens the dialog box for
parametrizing input signals.
Output signals Opens the dialog box for
parametrizing output signals.
Entrances Opens the Entrances dialog for
parametrizing doors and card
readers.
Areas Opens the Area Configuration
dialog for dividing the protected
installation into virtual areas.
Holidays Opens the Holidays dialog box
for defining holidays and special
days.
Day Models Opens the Day Models dialog
box for defining time periods
within a day for the activation of
access functions.
Time Models Opens the dialog Time Models
for defining timezones
dependent on days of the week
or calendar.
20 en | General Access PE 3.0 - Offline
Locking System
2014-02 | 3.0 | IHB Bosch Access Systems GmbH
Function Icon/
Shortcut
Description
Personnel
Groups
Opens the dialog box Personnel
Groups for dividing personnel
into logical groups.
Access
Authorization
Groups
Opens the dialog box Access
Authorization Groups for
defining groupings of
authorizations to entrances.
Offline locking
system
Opens the Offline locking
system dialog for configuring
special elements of the
installation (Entrances, Time
models, Authorization groups).
Display Texts Opens the dialog box Display
texts for editing the texts to be
displayed at the card readers.
Log Messages Opens the dialog box Log
Messages for editing and
categorizing log messages.
Additional
personnel fields
Opens the dialog box
Additional personnel fields for
defining data fields for
personnel.
Wiegand - cards Opens the dialog box Wiegand-
cards for defining the structures
of card data.
Administering
video devices
Opens the Video devices dialog
for configuring cameras to be
used in video verification.
Access PE 3.0 - Offline
Locking System General | en 21
Bosch Access Systems GmbH 2014-02 | 3.0 | IHB
Function Icon/
Shortcut
Description
Map Viewer and
Alarm
management
Opens the Map Viewer for an
areal view of maps and control
devices and the alarm list for
alarm handling.
Menu ? (Help)
Help topics Opens this help text.
About Access
Professional
Edition -
Configurator
Displays general information
about Access Professional
Edition - Configurator
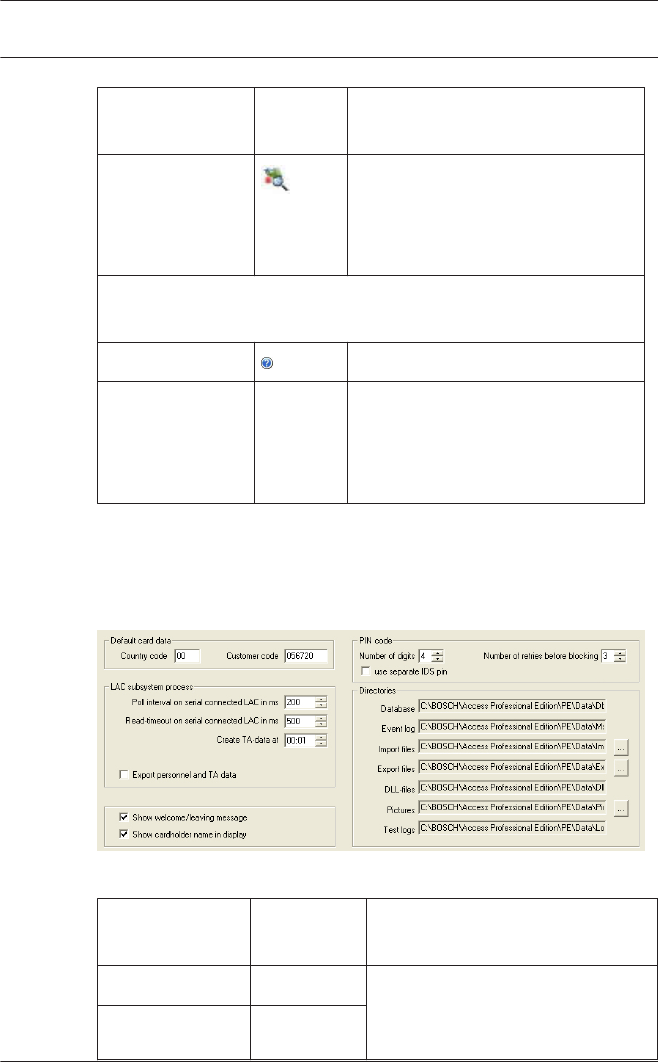
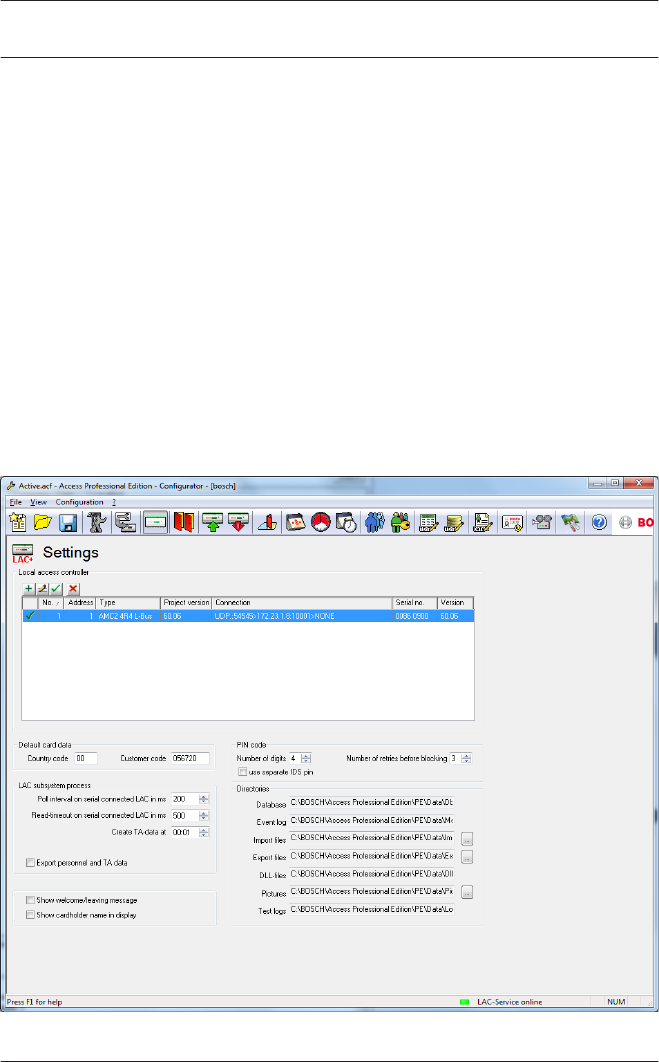
General system settings
General system settings are displayed below the list of
controller settings. These are valid for all installations.
Parameter Default
value
Description
Country Code 00 Some card data are appended
to the manually entered card
number.
Customer Code 056720
2.4
22 en | General Access PE 3.0 - Offline
Locking System
2014-02 | 3.0 | IHB Bosch Access Systems GmbH
Parameter Default
value
Description
Poll interval on
serial
connected LAC
in ms
200 The time interval in milliseconds
between pollings by the LAC-
Service to verify intact
connections to a controller.
Range of values for poll interval:
1 to 500
Possible values for read-
timeout: 1 to 3000
Read-Timeout
on serial
connected LAC
in ms
500
Create TA data
at
00:01 Specification of the time at
which the Time & Attendance
data file should be created.
Export
personnel and
TA data
deactivated When activated this option
causes time & attendance data
to written continuously to the
export file.
When not activated the data file
is created at the time specified
by the parameter Create TA
data at.
The file containing attendance time-stamps is created in the
following directory:
C:\Program Files\Bosch\Access Professional Edition\PE\Data
\Export
Under the name TA_<Current date YYYYMMDD>.dat
Access PE 3.0 - Offline
Locking System General | en 23
Bosch Access Systems GmbH 2014-02 | 3.0 | IHB

Parameter Default
value
Description
Show welcome/
leaving
message
activated Given appropriate reader type
and settings (Arriving, Leaving
or Check ok in the Entrances
dialog) the reader will display
those welcome and leaving
texts which are stored for the
cardholder in the Personnel
Data dialog of the Personnel
Management application.
Does not apply to Wiegand
readers.
Show
cardholder
name in display
aktiviert Readers with display will show
the Display Name as stored in
the cardholder's Personnel
Data.
Does not apply to Wiegand
readers.
Number of
digits
4 Determines the number of
digits a verification or arming
PIN requires.
This setting applies also to the
door PIN which can be set
during the configuration of
entrances.
Possible values: 4 to 8
24 en | General Access PE 3.0 - Offline
Locking System
2014-02 | 3.0 | IHB Bosch Access Systems GmbH
Parameter Default
value
Description
use separate
IDS PIN
If no separate IDS PIN is set,
then a verification PIN can be
used to arm the IDS.
Only if the check box is
selected do the input fields for
the arming-PIN become active
in the Personnel dialog screen.
In this case the verification PIN
can no longer be used to arm
the IDS.
Access PE 3.0 - Offline
Locking System General | en 25
Bosch Access Systems GmbH 2014-02 | 3.0 | IHB

Parameter Default
value
Description
Count of retries
before blocking
3 Number of failed attempts to
enter the PIN. If the cardholder
mistypes the PIN this many
times then s/he will incur a
system-wide block which can
only be removed by an
authorized system user
(Personnel Management).
Possible values: 1 to 9
Directory paths
to:
Database
Log file
Import files
Export files
DLL files
Image data
Test-Logging
C:\Program
Files
\BOSCH
\Access
Professiona
l Edition\PE
\Data...
\Db
\MsgLog
\Import
\Export
\Dll
\Pictures
\Log
These are the default paths. The
directories for import, export
and image files can be changed.
Notice!
When using Wiegand controllers and readers, in order to use
Identification-, arming- or door-PINs the Wiegand card definition
PIN or Card (Nr. 6) needs to be activated.
26 en | General Access PE 3.0 - Offline
Locking System
2014-02 | 3.0 | IHB Bosch Access Systems GmbH
Layout of the main dialog
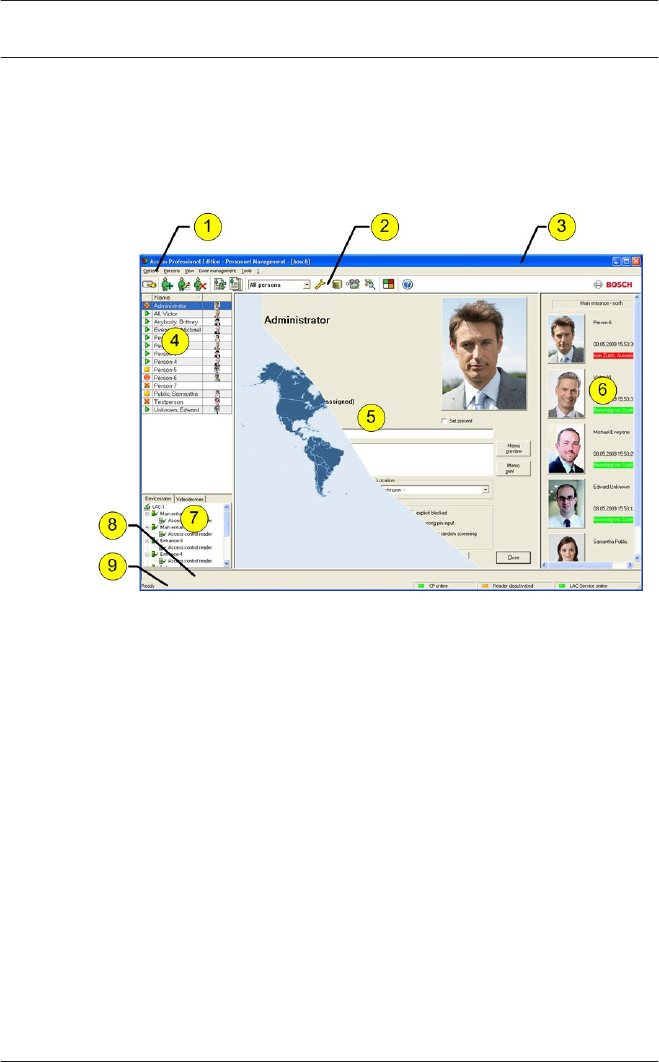
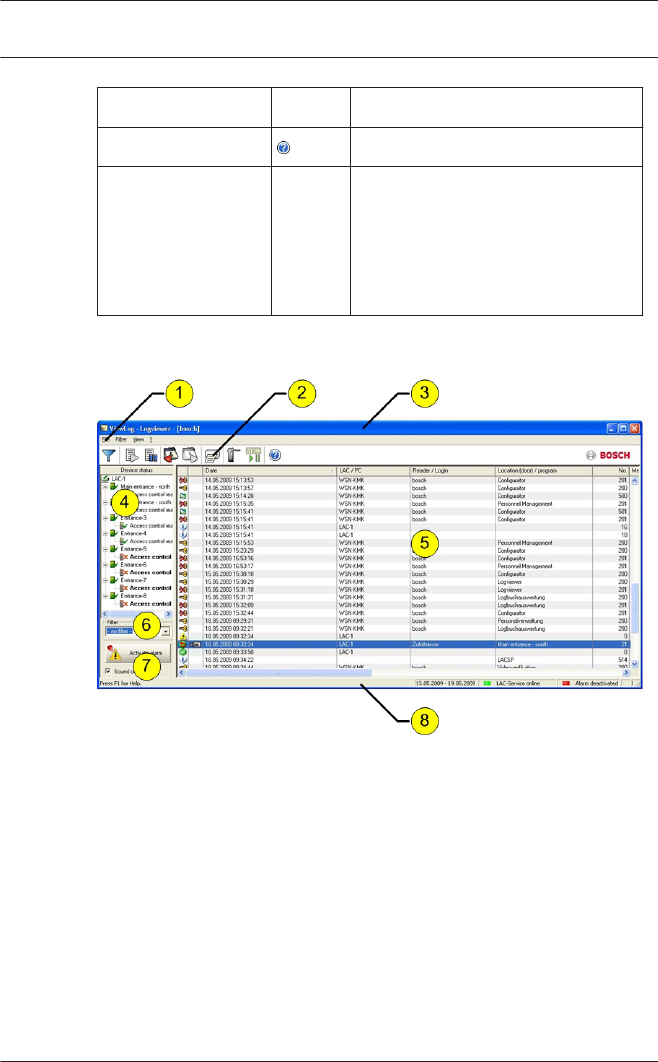
The dialog consists of the following parts:
1 = Menu bar — contains dialog functions displayed
according to the menu order.
2 = Toolbar — contains shortcut keys for the most
important dialog functions.
3 = Title bar — conforms to Windows standard and
contains buttons for minimizing or closing the dialog
window. The name of the registered user appears in
square brackets.
4 = Personnel table — lists all people known in the system
along with their attendance status (authorization and
location).
2.5
Access PE 3.0 - Offline
Locking System General | en 27
Bosch Access Systems GmbH 2014-02 | 3.0 | IHB

5 = Dialog field — the first time this field is opened or
when no user is logged in, it shows a neutral image
(map of the world). When an entry is selected from the
Personnel list, this person's data is displayed.
6 = Online swipe — lists the last five people (with
database image) that have swiped their cards at the
entrance selected.
7 = Device status — lists the configured devices and
entrances along with their connection status. Enables
door control functions.
8 = Event display — faults are indicated by a flashing red
bar (flashes three times) with details on the cause.
9 = Status bar — displays information on buttons and
menu entries that are controlled with the cursor.
Status display on card personalization program (CP),
dialog readers and LAC service.
When you enable the Video Verification component, additional
facilities will be added to this dialog; see Personnel
Management.
When you enable the Video Verification component, additional
facilities will be added to this dialog.
Menu and tool bar
The following functions are available via the menus or the icon
buttons.
Function Icon Description
Menu Options
Refresh Refreshes the Personnel list
2.6
28 en | General Access PE 3.0 - Offline
Locking System
2014-02 | 3.0 | IHB Bosch Access Systems GmbH
Function Icon Description
Exit Exits the Access PE Personnel
Management application
Menu Persons
New person Opens a blank personnel and
card data dialog
Modify person Opens the personnel and card
data dialog with the data of the
selected person.
Delete person Deletes the selected person
(after confirming a safety check
dialog).
Transmit selected
person to the LAC
service
Transmits the selected person's
data to the LAC service and
reports success.
Transmit all
persons to the
LAC service
Transmits all persons' data to
the LAC service and reports
success.
Set all persons
absent
Sets all persons absent (after
confirming a safety check
dialog).
Set location of all
persons present
to unknown
Sets the location of all persons
to unknown and deactivates
access tracing for the next
booking of each person.
View/print reports Calls the dialog for creating
report lists.
Access PE 3.0 - Offline
Locking System General | en 29
Bosch Access Systems GmbH 2014-02 | 3.0 | IHB
Function Icon Description
List
control
Restricts the persons shown to
those of the selected group.
Menu View
Symbol bar Toggles display of the tool bar.
Default = on.
Status bar Toggles display of the status
bar. Default = on.
Personnel data:
State
Card No.
Personnel-No.
Company
Personnel Group
Phone
Location
Choice of columns displayed in
the personnel overview in
addition to symbol and name
columns.
Default = State - Company -
Location
Menu Door management
open door These
functio
ns are
also
availabl
e via
The entrance selected in the
device list is displayed and can
be opened (one-off).
30 en | General Access PE 3.0 - Offline
Locking System
2014-02 | 3.0 | IHB Bosch Access Systems GmbH
Function Icon Description
Long-term open the
context
menu
(right
click on
the
desired
door/
entranc
e)
The entrance selected in the
device list is displayed and can
be opened (long-term).
lock door The entrance selected in the
device list is displayed and can
be locked.
Menu Tools
User logon Log in/off Personnel
management.
Execute the
Configurator
Executes Configurator and
transfers data from personnel
management.
Execute log
viewer
Executes Log viewer and
transfers data from personnel
management.
Execute Video
verification
Starts the application for
executing video verification.
Execute Alarm and
Map management
Starts the Map viewer and
Alarm management processing
application.
Video panel Shows four displays in the
dialog field for individual video
camera feeds.
Properties Opens a dialog box for general
system settings.
Menu ? (Help)
Access PE 3.0 - Offline
Locking System General | en 31
Bosch Access Systems GmbH 2014-02 | 3.0 | IHB
Function Icon Description
Help topics Opens this help file.
About Access
Professional
Edition -
Personnel
Management
Displays information about
Personnel Management.
Layout of the main dialog
1 = Menu bar - Contains all dialog functions arranged in
menus.
2 = Tool bar - Contains the most important dialog
functions as icon buttons
3 = Title bar - Conforms to Windows standard and
contains buttons to minimize and close the main
dialog window. The name of the current user is
displayed in square brackets.
2.7
32 en | General Access PE 3.0 - Offline
Locking System
2014-02 | 3.0 | IHB Bosch Access Systems GmbH
4 = Device status - List of the configured devices and
entrances along with their connection status.
5 = Message list - List of messages arrived hitherto. The
display can be modified by specific filter settings.
6 = Filter selection - Predefined and customized filters
can be selected from the combo-box.
7 = Alarm activation - Triggers the activation/
deactivation of alarms for messages. An incoming
message can be accompanied by an acoustic signal.
8 = Status bar - Dates of the log files opened. Status of
the LAC Service. Alarm settings.
Menu and Tool bars
The following functions are available for log evaluation via
menus and icon buttons.
Menu Function Icon
button
Description
File Print... Print the log messages
displayed
Exit Closes the LogViewer
application.
Filter Filter
definition
Opens the message
filtering dialog.
2.8
Access PE 3.0 - Offline
Locking System General | en 33
Bosch Access Systems GmbH 2014-02 | 3.0 | IHB
Menu Function Icon
button
Description
Continuous
mode on
Starts continuous
message display. This
icon is only active
when the function is
not already running
and the message filter
is set to the current
day.
Continuous message
display is the default
setting.
Continuous
mode off
Pauses the continuous
message display. This
icon is only active
when continuous
message display is
running.
Events
previous
day
Switch to previous
day's messages.
Events next
day
Switch to next day's
messages.
View Symbol bar Hides/Displays the
tool bar.
Default = on.
Status bar Hides/Displays the
status bar.
Default = on.
without a menuitem
34 en | General Access PE 3.0 - Offline
Locking System
2014-02 | 3.0 | IHB Bosch Access Systems GmbH
Menu Function Icon
button
Description
? (Help) Help topics Opens this help file.
About
LogViewer
Opens Help About
Access PE LogViewer.
Enrollment Configuration
Enrollment Readers (RS 232) > Tools > Settings calls a dialog
in which it is possible to perform basic configuration tasks
(activate, modify) from any workstation.
– Administrative workplaces, where persons are assigned
cards, can be fitted with an enrollment reader. This must be
parameterized and configured according to the
manufacturer's specifications, or those delivered with the
device. If an enrollment reader is set up then manual card
checking is deactivated.
The required settings for supported readers are:
Reader name BAUD D P S
DELTA 1200 Prox RS232 9600 8 N 1
DELTA 1200 iClass RS232 57600 8 E 1
DELTA 1200 USB Hitag, Legic, Mifare 9600 8 N 1
DELTA 1200 RS232 Hitag, Legic, Mifare 19200 8 N 1
Rosslare ARD-1200EM USB 9600 8 N 1
LECTUS secure 5000 MD 9600 8 N 1
2.9
Access PE 3.0 - Offline
Locking System General | en 35
Bosch Access Systems GmbH 2014-02 | 3.0 | IHB
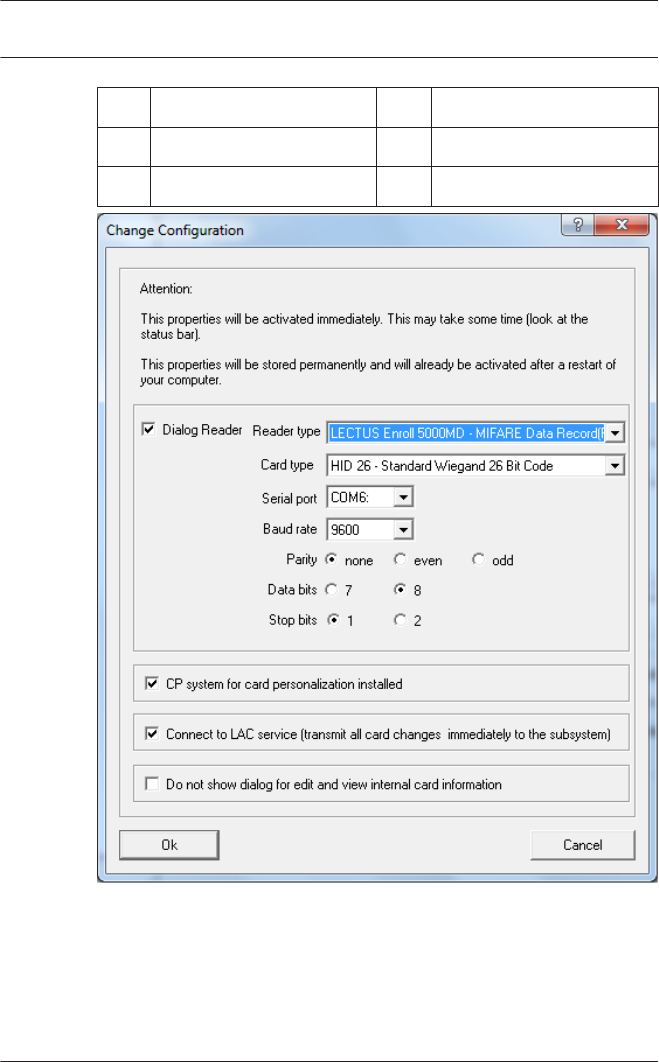
D = Data bits N = none
P = Parity E = even
S = Stop bits O = odd
– If the system has been installed with the optional Card
Personalization (CP) module then the corresponding check
box is selected in settings. Unchecking this box blocks all
functions for card design/creation.
36 en | General Access PE 3.0 - Offline
Locking System
2014-02 | 3.0 | IHB Bosch Access Systems GmbH
– In addition the automatic transfer of personnel data via
Connection to the LAC Server is also checked. This box
should always remain checked.
– The display of card information during card assignment can
be disabled here. This display is only necessary when,
contrary to default settings (see General Settings in Access
PE Configurator) card data are required which do not
conform to the company standard settings.
Enrollment via AMC connected readers
Make sure that at least one reader is configured with a Door
Model 06c, which is the door model for enrollment.
Start the Configuration Browser and select a Local Access
Controller (LAC) (e.g. AMC2…)
2.9.1
Access PE 3.0 - Offline
Locking System General | en 37
Bosch Access Systems GmbH 2014-02 | 3.0 | IHB
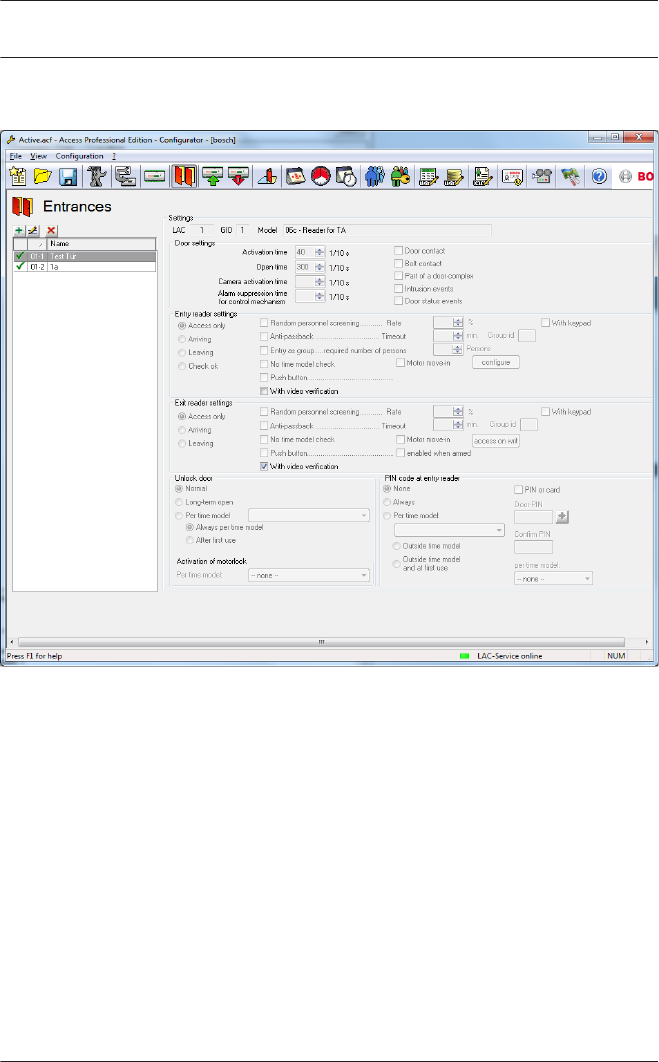
Click the Entrances symbol an add a new Entrance reader:
The dialog window Define Entrance opens:
38 en | General Access PE 3.0 - Offline
Locking System
2014-02 | 3.0 | IHB Bosch Access Systems GmbH
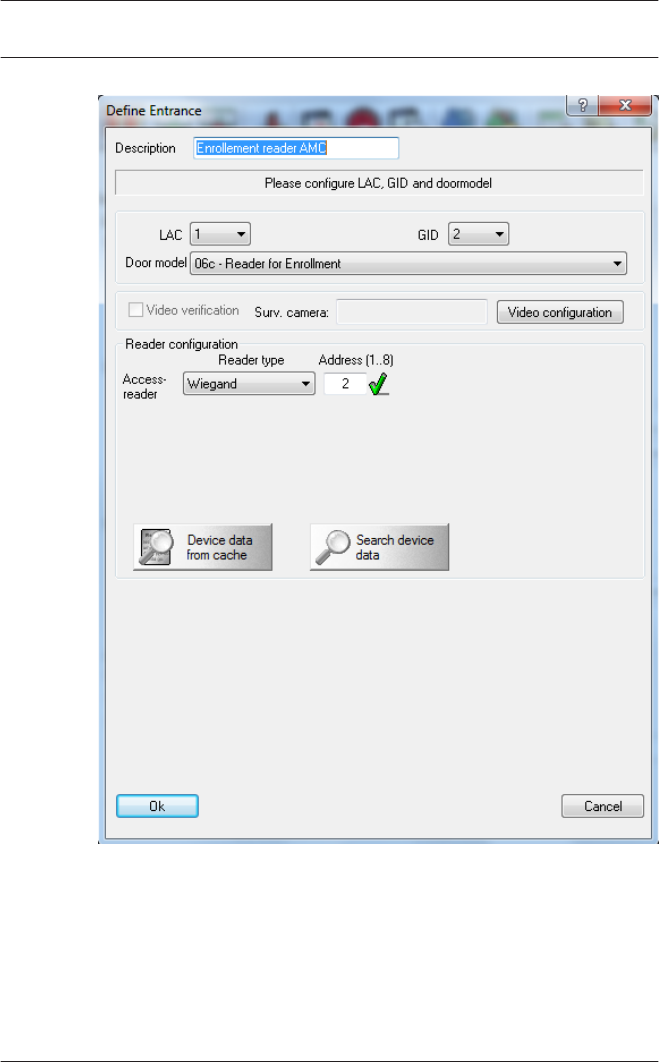
In this dialog:
– Enter a Description (e.g. Enrollment Reader AMC)
– Select a LAC and a group ID (GID)
– Select a reader type (e.g. Wiegand)
– Select a number between 1 and 8 as Access Reader
Address
Click OK to conform the enrollment configuration.
Access PE 3.0 - Offline
Locking System General | en 39
Bosch Access Systems GmbH 2014-02 | 3.0 | IHB
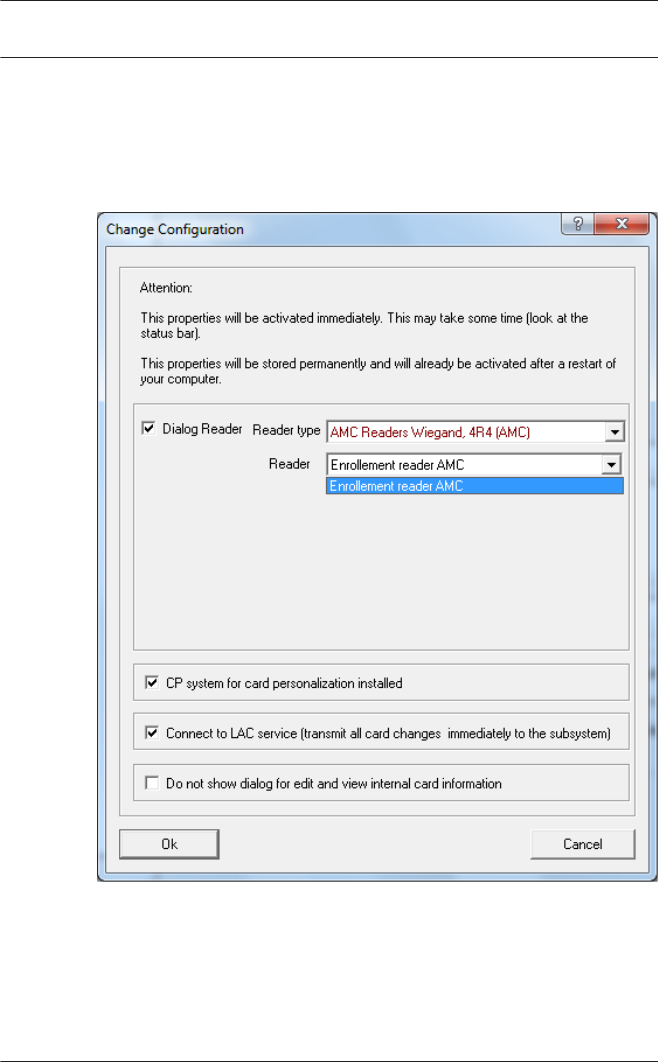
To assign the configured enrollment reader to a specific
workstation, you have to change tot he APE client.
– Select Tool > Properties.
Select an available enrollment reader to activate the enrollment
process.
Confirm that your enrollment reader is online.
If you don’t get an immediate response, restart the Personnel
Management dialog.
40 en | General Access PE 3.0 - Offline
Locking System
2014-02 | 3.0 | IHB Bosch Access Systems GmbH
Access PE 3.0 - Offline
Locking System General | en 41
Bosch Access Systems GmbH 2014-02 | 3.0 | IHB

Offline Locking System
The offline locking system is a PegaSys system from Normbau
(hereafter referred to as the "locking system" or "offline
system"). This is used to secure objects that cannot, should not
or must not be monitored online.
Offline systems are normally used where non-real-time data
transfer means that high availability of individual components is
not necessary, where the infrastructure does not permit a direct
connection (e.g. cabling for installations set up at a
considerable distance) or where the installation of online
components is too expensive. In comparison with conventional
locking systems (security locks with specially manufactured
keys), the advantage of offline systems is that significant
investment costs are only incurred when installing or extending
the system. Locks and keys do not need to be updated or
replaced (e.g. in the event of loss or theft), as the software can
deactivate the units concerned (cards) and therefore render
them unusable.
Suitable objects for offline systems are generally installations
with a number of individual areas to secure, such as hotels,
student residences and hospitals.
PegaSys components are integrated into the Access PE access
control system and managed from there.
3
42 en | Offline Locking System Access PE 3.0 - Offline
Locking System
2014-02 | 3.0 | IHB Bosch Access Systems GmbH

Explanation of terms
In order to differentiate between the individual access control
components, the following terms are used for the various
components:
–Access control system
This refers to the online components
These include
–
– The data recording level (dialog system, database,
logbook etc.) i.e. top level
– Controllers, which take decisions regarding access on
the basis of data they receive from the top level.
– Readers, which read the code data from the cards and
forward it to the controllers.
–Locking system
This includes the offline system elements
–
– Cards, which contain the authorization data.
– Door terminals, which take decisions regarding access
on the basis of the authorization data that is read.
The locking system as an integrated unit also makes partial use
of the dialog system and the access control system's controllers
and readers.
Special features of the locking system
In access control systems (for example, the Access PE) code
data is read off the card and stored in the database in
combination with the personnel data and access authorizations.
When scanned at an access control reader, the code number is
read again and compared with the stored data. If this check is
positive, the person in question is granted access.
A connection to a data storage element of the system (= online
system) is therefore essential.
3.1
3.2
Access PE 3.0 - Offline
Locking System Offline Locking System | en 43
Bosch Access Systems GmbH 2014-02 | 3.0 | IHB

With offline systems, access authorizations for certain doors are
stored on the card. [The locking system variants for which
authorizations are stored in the door terminal (armature or
cylinder) are not described here.] When scanned, these
authorizations are read and a check is carried out to ascertain
whether or not the card contains the identification for the door
concerned and has up-to-date data.
The offline variant poses a basic security risk, as it is essentially
impossible to prevent misuse in the event of loss or theft. In
access control systems, cards of this kind can be blocked,
deleted or assigned a validity expiration date, whereas offline
systems offer no means of direct intervention. However, in order
to keep the risk of misuse as low as possible, the authorizations
are assigned an expiration date/time. If this deadline elapses,
the authorizations are no longer valid. In order to reactivate
them, the validity period must be extended. This is carried out
via a special reader with write capability (e.g. DELTA 7020). If
the authorizations have not been deleted or blocked in the
meantime, they are extended or renewed when the card is
scanned at this online reader.
Locking system components
When the offline system is installed, the following necessary
applications and extensions are set up:
–Software
–
– Configurator > Offline locking system
This application is used to set up the features and
make all the general settings, create time models, and
configure doors and door groups.
– Configurator > Entrances
3.3
44 en | Offline Locking System Access PE 3.0 - Offline
Locking System
2014-02 | 3.0 | IHB Bosch Access Systems GmbH

When setting up entrances, write capability can be
activated and configured for the readers.
– Personnel Management > Personnel data
This dialog contains (after initialization with a facility
card) another tab called Offline Access
Authorizations; this is where you can allocate
authorizations and record cards for the locking system.
–Hardware
–
–System cards
System cards are used to initialize the door terminal
and to update data (e.g. blacklists).
– A read-write device for user cards and system cards
must be connected to the workstation(s) at which
offline system data is processed.
– A mobile read-write device (timesetter) which
updates door and time model initialization cards,
which in turn are used to update/initialize the door
terminals (optional).
–Terminals to read the user and system cards at the
doors in the locking system.
– At least one write-capable reader for distributing and
extending access authorizations for the locking system.
Access PE 3.0 - Offline
Locking System Offline Locking System | en 45
Bosch Access Systems GmbH 2014-02 | 3.0 | IHB
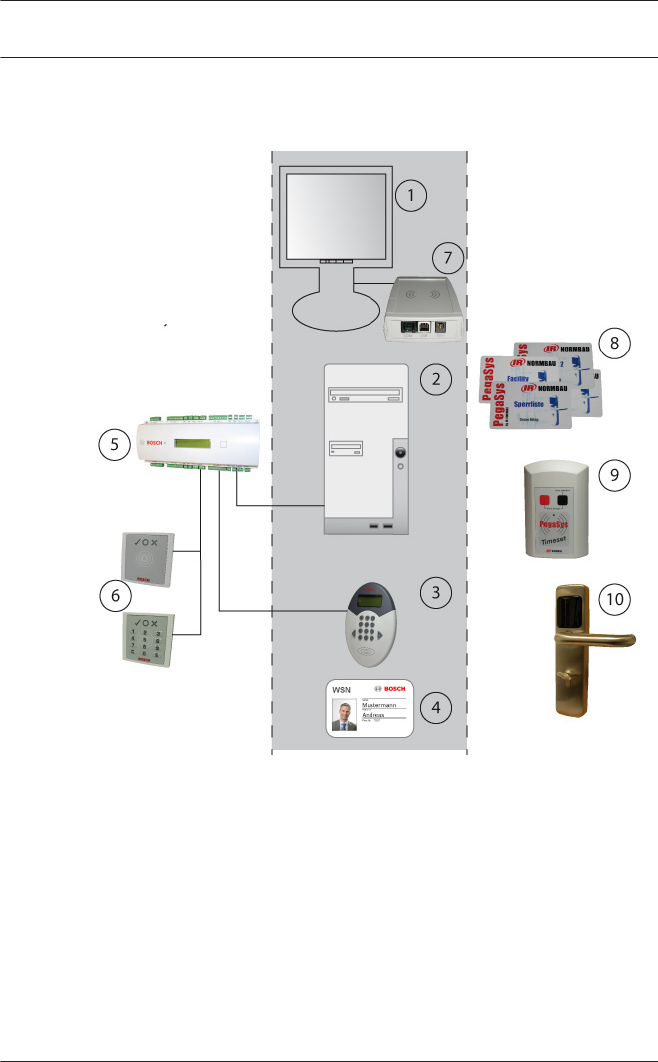
System Overview
When the locking system is integrated into the Access PE access
control system, certain components are used by both systems.
The gray area in the diagram above contains the system
components that are used by both the access control system
and the locking system. The items on the left are purely access
control installations and the items on the right belong only to
the locking system.
1. Workstation
2. Server with configuration application and database
3.4
46 en | Offline Locking System Access PE 3.0 - Offline
Locking System
2014-02 | 3.0 | IHB Bosch Access Systems GmbH

3. Access control reader with write unit ("write-capable
reader")
4. Card - for both systems
5. AMC2 4R4 Access Control Panel
6. Access control readers
7. Dialog read-write unit for online and offline system data
8. Various system cards for the locking system
9. Mobile read-write units for date/time stamping
10. Door terminal with read unit
Description of system components
The following sections describe the components listed above for
both systems, focusing mainly on the function of the common
elements.
Workstation
The same dialog interface [1] is used to create personnel data
for the access control system and for the locking system. Only a
single step is required to allocate both access authorizations for
the Access PE and access rights for the offline system.
Lists outlining the status of authorization allocations for the
locking system can be called up via the same menu items as
used for access control.
Server
The software for the access control system and the locking
system run on this computer [2]. The Access PE Configurator is
also used to configure the readers [3] for the locking system.
Data for the offline system is managed in special tables of the
Access PE database.
3.4.1
Access PE 3.0 - Offline
Locking System Offline Locking System | en 47
Bosch Access Systems GmbH 2014-02 | 3.0 | IHB
Write-capable readers
At least one reader of this type [3] must be available. Ideally,
these are placed at entrances used on a frequent basis (e.g. the
main entrance) so that authorization for the locking system is
extended at the same time as access is granted to the secured
facility.
However, it is also possible to install these readers at special
locations, independently of the access control system, so that
rights are not extended automatically but have to be specifically
obtained.
An RS485 reader is configured on an AMC2 4R4 with L-bus
protocol for setup.
Notice!
Don’t activate Videoverification to this reader.
This reader type cannot be used for arming/disarming (DM 10
and 14).
Card
No special cards [4] are required for the offline system. The
data required for the locking system is written to separate
sectors of the access control card.
Notice!
For the offline system, only a person's card 1 can be used.
AMC2 4R4 Controller
An AMC2 4R4 L bus [5] (= access control panel with RS485
reader interface) is required for the write-capable reader [3]
that is used as a read-write unit for the locking system.
48 en | Offline Locking System Access PE 3.0 - Offline
Locking System
2014-02 | 3.0 | IHB Bosch Access Systems GmbH

The readers dedicated solely to access control [6] can use any
protocols and read procedures, and can be operated with any
AMC2 variant.
Access control readers
These readers [6] have nothing to do with the locking system;
they simply regulate access requests in the Access PE system.
Card holders who are able to use the doors in the locking
system [9] can also have authorizations for doors in the access
control system.
Dialog read-write unit
This device [7] is connected directly to the workstation
computer via a USB interface and is used to transfer
authorizations to user cards and system-related data (e.g. door
and time initialization data) to special system cards [8]. It is also
used to enroll online cards.
System cards
Different system cards [8] (time, door and facility cards) are
required for the locking system to transfer relevant data — e.g.
initialization data — to the door terminals [9].
Mobile read-write units (optional) - timesetter
In order for the terminals to be updated, current terminal
initialization data is written to door and time model initialization
cards via this unit.
PegaSys - door terminal
This read unit uses the individual door identification or its own
door group identification to check the access rights for the card
holder.
The access rights on the card must be continually updated via
special readers with write capability [3].
Access PE 3.0 - Offline
Locking System Offline Locking System | en 49
Bosch Access Systems GmbH 2014-02 | 3.0 | IHB

If an emergency opening is required, e.g. if the electronics fail,
the terminals have mechanical cylinder locks.
50 en | Offline Locking System Access PE 3.0 - Offline
Locking System
2014-02 | 3.0 | IHB Bosch Access Systems GmbH
System limits
The following values apply as the upper limits for individual
installations in the locking system.
Entrances (doors) There are no restrictions governing
the creation and configuration of
entrances.
The number that can be allocated as
individual door authorizations
depends on the length of the datasets
ordered; see , page 51.
Door groups The maximum number depends on
the length of datasets for the offline
data; see , page 51.
Time models 15
Periods/Time model 4
Holidays 10
Door groups
Individual doors
256 512 768 1024
248
(= default)
80 112 144
452 84 116 148
860 92 124 156
16 76 108 140 172
Table 3.1: The figures refer to the dataset length in bytes.
3.4.2
Access PE 3.0 - Offline
Locking System Offline Locking System | en 51
Bosch Access Systems GmbH 2014-02 | 3.0 | IHB

Notice!
When Hitag1 cards are used, only 2 individual doors can be
created; similarly, only 240 (instead of the specified 256) door
groups can be created — no other formats are possible here.
The dataset length should be selected in line with current
requirements. Do not order storage space in anticipation of
possible requirements. As data is written to all enabled sectors,
increasing the storage space can significantly lengthen the time
required for extending or renewing authorizations.
Access PE - Configurator
Special write-capable readers are required to extend and renew
access authorizations for the locking system.
These readers with write capability are created as access
control readers and are usually also assigned door control
functions. However, they can also be used purely as "rechargers"
for offline system authorizations.
Adding hardware components
In the Access PE access control system, no specific reader types
are selected when hardware components are added; the
appropriate protocol used by the AMCs is selected for each
reader.
To add and configure the locking system components, please
carry out the following steps:
– Start the Access PE Configurator.
– Switch to the Settings tab.
–
– Add an AMC2 4R4 L-Bus.
– Switch to the Entrances tab.
–
3.5
3.5.1
52 en | Offline Locking System Access PE 3.0 - Offline
Locking System
2014-02 | 3.0 | IHB Bosch Access Systems GmbH
– Add an entrance with any door model (except DM 10
and 14) and one or two RS485 readers. There must be
at least one write-capable reader at this entrance.
– For the write-capable reader, select read/write in the
Write access field.
– Confirm the new entry with OK to close the dialog.
– For the reader options, set the Grant access on write
error and Write without access rights parameters if
these apply to your system.
Configuring the write-capable reader
If this reader is also used as an access control reader and the
settings are different to the default settings, configure it
according to your requirements. For further information about
the parameters in question, please see the section on adding
entrances.
Notice!
Don’t activate Videoverification to this reader.
This reader type cannot be used for arming/disarming (DM 10
and 14).
The following parameters are of importance for the locking
system.
3.5.2
Access PE 3.0 - Offline
Locking System Offline Locking System | en 53
Bosch Access Systems GmbH 2014-02 | 3.0 | IHB

Write access read only
This reader is purely an access control
reader and is not part of the locking system.
read/write
This reader has access control functions and
is also activated for the locking system.
Grant access on
write error
Access checking and safeguarding (in the
online system) does not depend on the
success of the locking system write process.
The door is released following several
unsuccessful write attempts.
Deactivated (unchecked): If it is not
possible to write to the card, access is also
denied.
Activated (checked): The write process has
no impact on the access check.
Write without
access rights
Rights for the locking system will only be
written to the card if the card holder has
(online) access authorization for the
entrance.
Deactivated (unchecked): Data is only
written to the card if valid authorization is
present.
Activated (checked): Data is always written
to the card.
Notice!
If the parameter is deactivated, the write process will be
prohibited even if the authorizations are only temporarily invalid
(e.g. if time models are used).
54 en | Offline Locking System Access PE 3.0 - Offline
Locking System
2014-02 | 3.0 | IHB Bosch Access Systems GmbH

Switching the reader protocol
As a rule, readers with write capability are installed at central
entrances (e.g. as the entry reader at the main entrance), so
that when personnel enter the site in the morning, the access
rights for the locking system are automatically updated.
When subsequently setting up the offline system, at least one
reader in the facility must be replaced with a write-capable
reader. If this involves adding an entrance again, the existing
entrance would be deleted and would need to be added again
with the write-capable reader.
If the existing entrance was deleted, this entrance would also be
removed from all access authorizations. All authorizations would
therefore need to be added to the new entrance.
To avoid this laborious process, which could lead to errors, the
AMC in question can be reconfigured.
– Go to the Settings tab in Access PE Configurator.
– Select the relevant AMC from the list field.
– Click the button to open the Edit dialog.
–
– In the Device type field, select the AMC2 4R4 L-Bus
entry.
– Test the AMC so that the new software is downloaded
and confirm the changes with OK.
– Save the changes and send them to the LAC Service
process .
Notice!
Other readers on this AMC must also understand this protocol.
If necessary, these readers must also be replaced.
If you have changed the device type from AMC2 4W to AMC2
4R4 L-Bus, the AMC must also be replaced.
3.5.3
Access PE 3.0 - Offline
Locking System Offline Locking System | en 55
Bosch Access Systems GmbH 2014-02 | 3.0 | IHB

Configurator - Offline Locking System
In this dialog, which is accessed by clicking the button in the
Configurator toolbar, the necessary locking system settings are
configured on five different tabs. In the interests of user-
friendliness, the tabs for configuring the locking system have the
same names and icons as the corresponding access control
dialogs. Insofar as this was possible given the specific data
structure of the offline system, the structure and data
processing characteristics of the online configuration process
were also used.
The individual tabs are used to manage the following data:
–System
Special offline system data, such as system limits, keys and
serial numbers.
–Entrances
As in the dialog of the same name in the access control
system, this is where the entrances are managed, but in
this case the locking system entrances.
–Time models
As the offline system cannot use the access control time
models, these must be set up separately for the locking
system, if required.
–Authorization groups
As with the dialog of the same name in the access control
system, this tab is also used for combining a number of
entrances in the locking system into authorization groups.
–Write transport cards
In order to receive updated data on the locking system
installations, individual entrances and time models can be
written to transport cards. These are read by the terminals.
3.6
56 en | Offline Locking System Access PE 3.0 - Offline
Locking System
2014-02 | 3.0 | IHB Bosch Access Systems GmbH
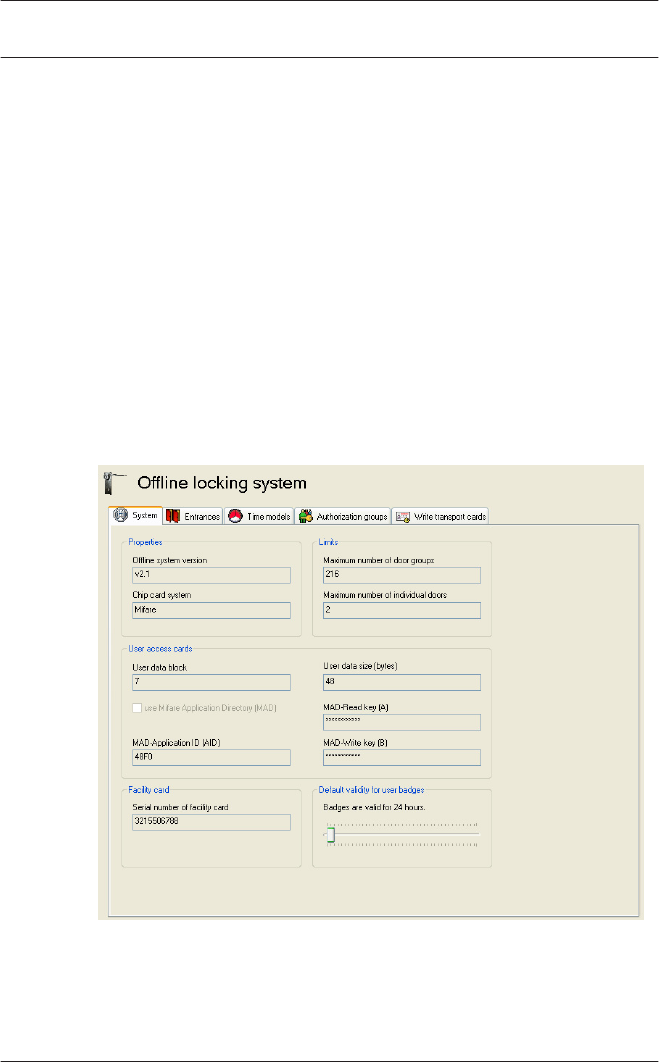
Offline locking system: System
When the locking system is purchased, one of the items the
customer receives is a "facility card". This contains details of the
system settings that the customer specified on the
manufacturer's order form.
All of the fields on this page are read-only fields and cannot be
overwritten. Their content is read from the facility card and
entered into the corresponding fields.
Before the locking system is set up, the Facility card dialog field
at the bottom of the page contains the Initialize system with
facility card button. The system data is transferred and set
when the facility card is placed on the dialog reader for the
offline system and the button is clicked.
Properties dialog field
–Offline system version
3.6.1
Access PE 3.0 - Offline
Locking System Offline Locking System | en 57
Bosch Access Systems GmbH 2014-02 | 3.0 | IHB
Locking system software version — only Version V2.0
functionalities are used in Access PE.
–Chip card system
Displays the card technology — Mifare and Hitag1 can be
used for Access PE.
Limits dialog field
–Maximum number of door groups
Maximum possible number of access authorization groups.
–Maximum number of singular door permissions
Maximum possible number of individual door
authorizations.
These entries correlate with one another and define the
available dataset lengths [= User data size (bytes)] on the cards
— see also , page 51.
User access cards dialog field
–User data block
Details on the card sector in which the offline data write
process begins.
–User data size (bytes)
Length of the datasets — this also determines the maximum
values for the authorizations.
Notice!
If using Hitag1, these values should be checked when a system
is set up for the first time, as these card types do not have a
function to prevent areas that are already in use from being
unintentionally overwritten.
Data is only written to the following four fields if the MAD has
been activated in the MIFARE card technology.
–use Mifare Application Directory (MAD)
If this check box is activated (checked), data for the other
MAD fields will also be displayed.
58 en | Offline Locking System Access PE 3.0 - Offline
Locking System
2014-02 | 3.0 | IHB Bosch Access Systems GmbH
When the MAD is activated, the user data block is simply
the default sector and is dynamically defined for each user
card if the specified block is occupied.
–MAD-Application ID (AID)
Identification number for the MAD of this system.
–MAD-Read key (A)
Read key for this system.
–MAD-Write key (B)
Write key for this system.
Facility card dialog field
–Serial number of facility card
Serial number of the facility card that has been read in — if
this serial number is saved, the facility card cannot be
overwritten.
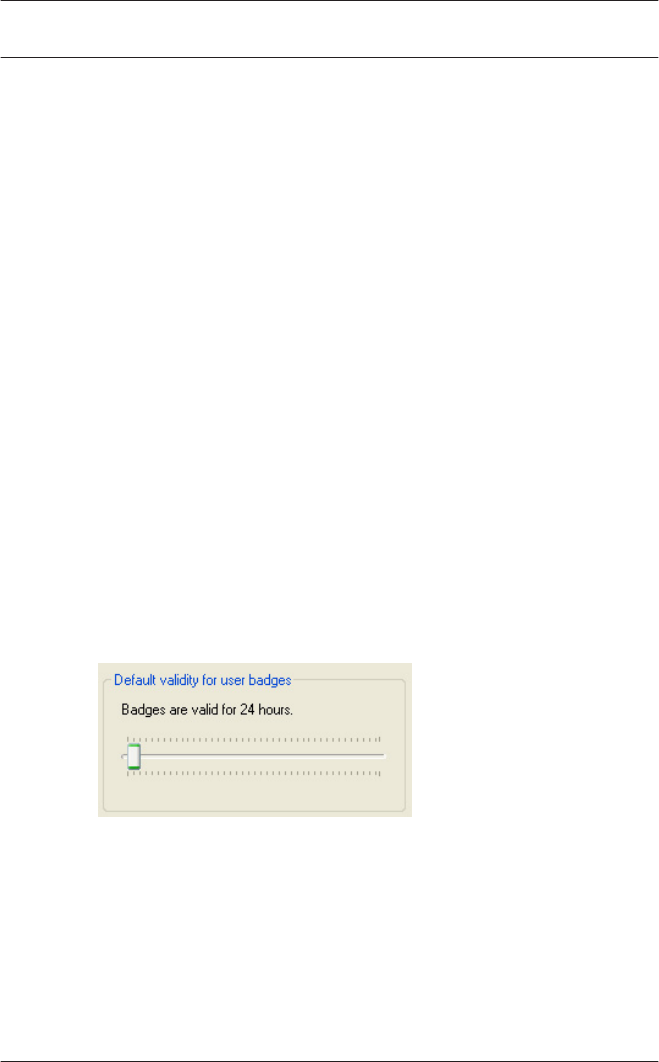
Dialog field Default validity for access cards
– Use the slider to set the default validity period in hours for
the offline system’s access cards. Values from 1 to 1000
can be used. First hold the left mouse button and slide to
set an approximate value, then use the arrow keys to set
values exact to the hour.
Immediately after initialization, the offline locking system is
activated within the displayed limits. The Offline Access
Authorizations tab is now displayed in Personnel Management.
Access PE 3.0 - Offline
Locking System Offline Locking System | en 59
Bosch Access Systems GmbH 2014-02 | 3.0 | IHB
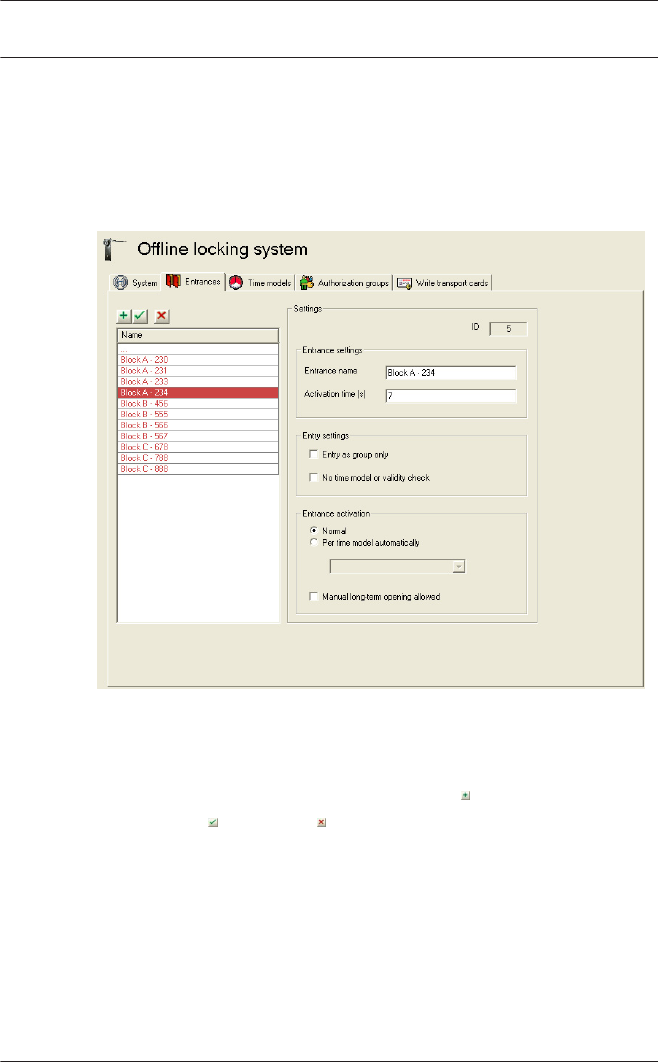
Offline locking system: Entrances
A list entry must be created and configured in this dialog for
each door terminal in the locking system. These can then be
assigned to certain door groups.
The list field contains all entrances that have been set up and
are fitted with locking system terminals. The button above the
list enables new list entries to be created , and existing entries
to be edited or deleted .
The parameters for the entrance selected in the list are
displayed in the fields to the right, where they can be entered
and edited.
3.6.2
60 en | Offline Locking System Access PE 3.0 - Offline
Locking System
2014-02 | 3.0 | IHB Bosch Access Systems GmbH
Parameter Description
ID Assigned by the system when the list
entry is created and cannot be edited.
Sequential number that uniquely
identifies the dataset.
Entrance settings
Entrance name The entrance can be specified more
precisely via the name.
Max. 29 characters
Activation time (s) Entry in seconds defining how long
the door remains unlocked after a
positive check.
Default = 7
Entry settings
Entry as group only A group is defined as two people. This
ensures the dual control principle is
used, as it is always necessary for two
authorized people to scan their cards
at these entrances for the door to be
opened.
Offers added security.
No time model or
validity check
When this option is activated, only the
general authorization for this entrance
is checked — any restrictions such as
time models or expiration dates are
ignored.
Offers reduced security.
Entrance activation
Access PE 3.0 - Offline
Locking System Offline Locking System | en 61
Bosch Access Systems GmbH 2014-02 | 3.0 | IHB
Parameter Description
Normal Each authorized person is permitted
to open the door for access purposes.
If the Manual long-term opening
allowed parameter is set and the card
holder has the relevant authorization,
long-term unlock is also possible.
Per time model
automatically
Outside the time model = normal
operation
Within = long-term unlock
For automatic locking, only the end
times of the periods are set.
Manual long-term
opening allowed
It is only possible to unlock the door
on a long-term basis if this parameter
is set and the card holder is
authorized for this feature.
A card with authorization must also be
held to the door terminal reader for 5
seconds.
Offline locking system: Time models
The list field contains all time models that have been set up. The
buttons above the list can be used to create further list entries
, edit existing entries or deleted them .
The parameters for the entrance selected in the list are
displayed in the fields to the right, where they can be entered
and edited.
3.6.3
62 en | Offline Locking System Access PE 3.0 - Offline
Locking System
2014-02 | 3.0 | IHB Bosch Access Systems GmbH
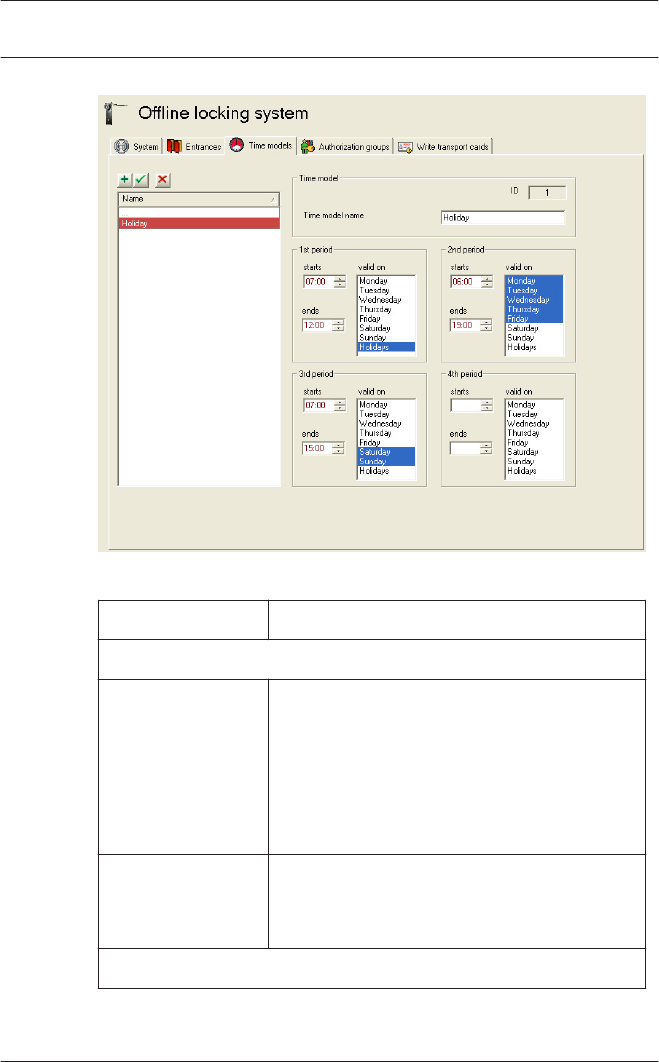
Parameter Description
Time model
ID Assigned by the system when the list
entry is created and cannot be edited.
Sequential number that uniquely
identifies the dataset.
A maximum of 15 time models can be
defined for the locking system.
Time model name The time model can be specified more
precisely via the name.
Max. 29 characters
1. 1st period to 4th period
Access PE 3.0 - Offline
Locking System Offline Locking System | en 63
Bosch Access Systems GmbH 2014-02 | 3.0 | IHB
Parameter Description
starts ... ends Start and end time of the period
concerned.
If only end times are specified, these time
models can be used for automatic door
locking.
valid on Days of the week on which the period is
valid are selected.
Entries are selected by clicking on them
with the mouse — selected days are
shown in blue. Clicking again removes the
selection.
Holidays
Holidays and special days are taken from the list in the online
system.
In the Special days dialog, up to ten holidays can be selected
for the offline system by activating the active for offline locking
system parameter. Irrespective of the category given to the
holiday for the online system or its activation status in that
system, it can be used as a holiday in the offline system.
An activation for the locking system is independent of the use of
the holiday in the access control system — this means that
holidays deactivated for the online system can nevertheless be
activated for the offline system.
Time model vs time period
A time model can contain up to four time periods in one 24 hour
day. Defining start and end times of a period means that a
different regulation applies in this period (e.g. long-term door
unlock) compared with the rest of the day. The periods can be
as long as necessary and can overlap. If only end times are
specified, this can be used for automatic door locking, but when
allocated to specific persons, they have no access at all.
64 en | Offline Locking System Access PE 3.0 - Offline
Locking System
2014-02 | 3.0 | IHB Bosch Access Systems GmbH
Each period can be allocated to any day of the week or holiday.
The user is thereby responsible for ensuring that the period
limits are set and allocated to the days in a logical and
consistent manner.
The entirety of all time periods and their allocations to days
makes up the time model, which can be used as an entity in the
system.
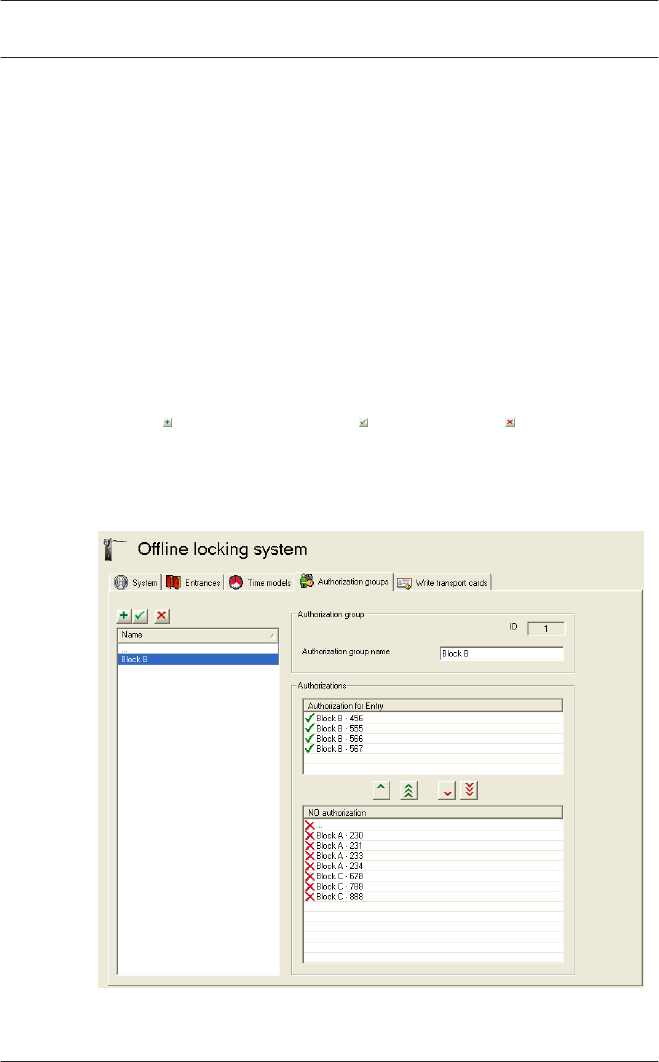
Offline locking system: Authorization groups
The list field contains all authorization groups that have been set
up. The buttons above the list can be used to create further list
entries , edit existing entries or delete them .
The parameters for the entrance selected in the list are
displayed in the fields to the right, where they can be entered
and edited.
3.6.4
Access PE 3.0 - Offline
Locking System Offline Locking System | en 65
Bosch Access Systems GmbH 2014-02 | 3.0 | IHB
Parameter Description
Authorization group
ID Assigned by the system when the list
entry is created and cannot be edited.
Sequential number that uniquely
identifies the dataset.
The number of door groups that can be
created is determined by the data size (,
page 51) and corresponds to the data for
Maximum number of door groups on the
System tab.
Authorization
group name
The authorization group can be specified
more precisely via the name.
Max. 29 characters
Authorizations
Authorization for
Entry
All entrances, allocated from the bottom
list, for which access authorization has
been granted.
NO authorization All doors in the offline system that have
been defined on the Entrances tab but
have not been transferred to the top list.
Individual selected entries can be added to or removed from
the top list using the arrow keys between the two list fields; it is
also possible to transfer all entries from one list to the other or
.
66 en | Offline Locking System Access PE 3.0 - Offline
Locking System
2014-02 | 3.0 | IHB Bosch Access Systems GmbH
Notice!
The segmentation of cards allows only a relatively low
allocation of individual doors in comparison with door groups.
However, given that individual door authorizations are only
used in special circumstances, that authorizations for certain
doors are usually allocated by combining a number of doors
together into a door group, and that it is also possible to form a
door group containing only one door, the number of permitted
individual door authorizations is sufficient.
Offline locking system: Write transport cards
In contrast to the online system, configuration data in the offline
systems cannot be distributed via system components and
transmitted to the relevant installations; instead, it must be
brought to the devices via another route. In System Overview,
page 46, various system cards have already been mentioned,
including door initialization and time model cards, to which
door parameter settings and time models are written and which
are scanned at the door terminals.
3.6.5
Access PE 3.0 - Offline
Locking System Offline Locking System | en 67
Bosch Access Systems GmbH 2014-02 | 3.0 | IHB
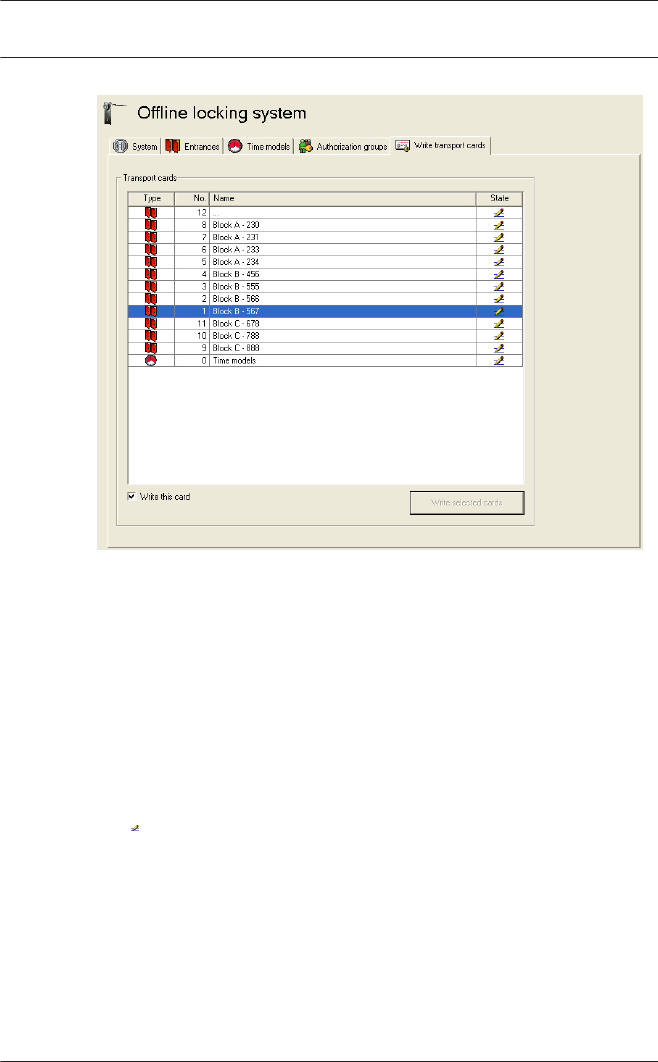
Transport cards for doors (door initialization cards)
The list field on the Write transport cards dialog page contains
one entry for each individual configured door. To facilitate
selection and for the purposes of carrying out the write process,
the doors for which transport cards need to be written are
highlighted in the list after configuration. If the appropriate list
entry is selected and the Write this card check box is activated
(or if the list entry is double-clicked), these entries are assigned
the icon in the State column and are therefore selected for the
next write process. In addition to this identification mark, doors
that have not been selected are shown grayed out.
The Write selected cards button is used to activate the dialog
reader; this writes a separate transport card for each door.
68 en | Offline Locking System Access PE 3.0 - Offline
Locking System
2014-02 | 3.0 | IHB Bosch Access Systems GmbH
Notice!
Please ensure that the necessary number of transport cards is
available for the selected number of doors.
A dialog box prompts you to place the card in position and then
shows the progress of the write process.
If door data has been written to the transport card that is
currently in position, the user will be prompted to place a new
card in position for the next dataset.
Notice!
Door data also contains information about the authorization
groups to which this door belongs.
If several door initialization cards are used these should be
clearly marked, so that data is assigned to the correct door. For
this reason, the data on the card is deleted once the door
initialization card has been scanned at the relevant terminal.
Transport cards for time models (time model cards)
There is also a list entry for the time model; this is always added
to the end of the list. In contrast to the doors, the time models
are combined together and all of them—up to 15—are written
with the current time to a single card.
Accordingly, all time models are also scanned at all door
terminals.
Checking the card type
Before the current card is written, the system checks whether it
is actually a door initialization card. If the card has already been
encoded in a different way (e.g. as a user or facility card), a
warning to this effect is displayed.
Access PE 3.0 - Offline
Locking System Offline Locking System | en 69
Bosch Access Systems GmbH 2014-02 | 3.0 | IHB

Updating the date and time
In addition to the door and time model data, the current time
stamp (date/time) is also written to the transport cards.
Depending on the size of the facility being secured, there is a
certain time delay before the cards can be scanned at the doors.
The time delay will increase significantly with the number of
doors to configure, particularly in the case of time model cards.
In order to gain the most precise time data, above all for when
cards are scanned, a mobile read-write device (timesetter)
should be used. This unit allows the times to be updated on the
transport cards immediately before scanning at the terminal, to
ensure that the time delay remains within the tolerable limits.
Scanning the system card
1. The timesetter must first be initialized with the facility-
specific data. To achieve this, it must be "christened" with a
facility card once.
2. In addition to the door and time model data, the transport
cards described above (door initialization and time model
cards) also contain the current system time. These can be
used to provide the timesetter with the time data.
3.
– Place the system card (facility or transport card) on
the read head of the device (gray field).
– Press 1.
– Hold down 1 and press 2.
Writing to the transport cards
Immediately before the transport cards are scanned, their time
data should be updated — door and time model data remain
unaffected.
– Place the transport card (door initialization or time model
card) on the read head of the device (gray field).
– Press 2.
3.6.6
70 en | Offline Locking System Access PE 3.0 - Offline
Locking System
2014-02 | 3.0 | IHB Bosch Access Systems GmbH

Notice!
The write and read process is indicated by an LED display. For
details on what the color sequences mean, please see LED
display signals, page 87.
Booking cards
In addition to the transport cards for the doors and time
models, other special cards are also used for data transfer in the
offline system. These are called access or booking cards; these
are used to copy recordings of access attempts from the door
terminals and transfer them to the management system.
Successful and unsuccessful opening attempts are saved in the
door terminals. The last 800 bookings are saved in a ring buffer.
These can be retrieved with special booking cards and entered
in the database.
The different card types allow varying numbers of bookings to
be written to one card: Hitag1 holds 32, MIFARE holds 244,
Legic holds 294. You must therefore create sufficient booking
cards and set up appropriate retrieval deadlines.
Reading the bookings on the terminal
The system card is held to the read unit of the corresponding
terminal. While the LED shows orange, the terminal is writing
data to the booking card. When the LED flashes green three
times, the bookings have been successfully written to the card.
If the booking card is removed during the terminal is writing, the
data transfer will be interrupted.
Scanning booking cards
The cards with the transferred bookings are then scanned via
the dialog reader and displayed in the LogViewer dialog.
The messages are automatically transferred to the log file and
can be retrieved at any time in the same way as the online
messages.
3.6.7
Access PE 3.0 - Offline
Locking System Offline Locking System | en 71
Bosch Access Systems GmbH 2014-02 | 3.0 | IHB
As the offline messages are listed together with the online
messages in the standard view, a predefined filter in the toolbar
of the dialog can be used to restrict the view to just the offline
messages.
Notice!
The data is deleted from the transferring unit:
When the terminal is read, its memory is erased.
When the booking card is scanned at the workstation, the card
is erased.
Managing Personnel Data
The database of the Access PE access control system is used to
store personnel data for the offline system as well.
Accordingly this data is entered via the access control system
dialogs.
Notice!
Each card holder for the offline system requires a valid card for
the access control system (online system).
Description of dialogs
When the offline system is active (after the facility card has
been scanned), the dialog for entering personnel and card data
contains the additional page Offline Access Authorizations.
Here all personnel-related settings are configured for the locking
system.
3.7
3.7.1
72 en | Offline Locking System Access PE 3.0 - Offline
Locking System
2014-02 | 3.0 | IHB Bosch Access Systems GmbH
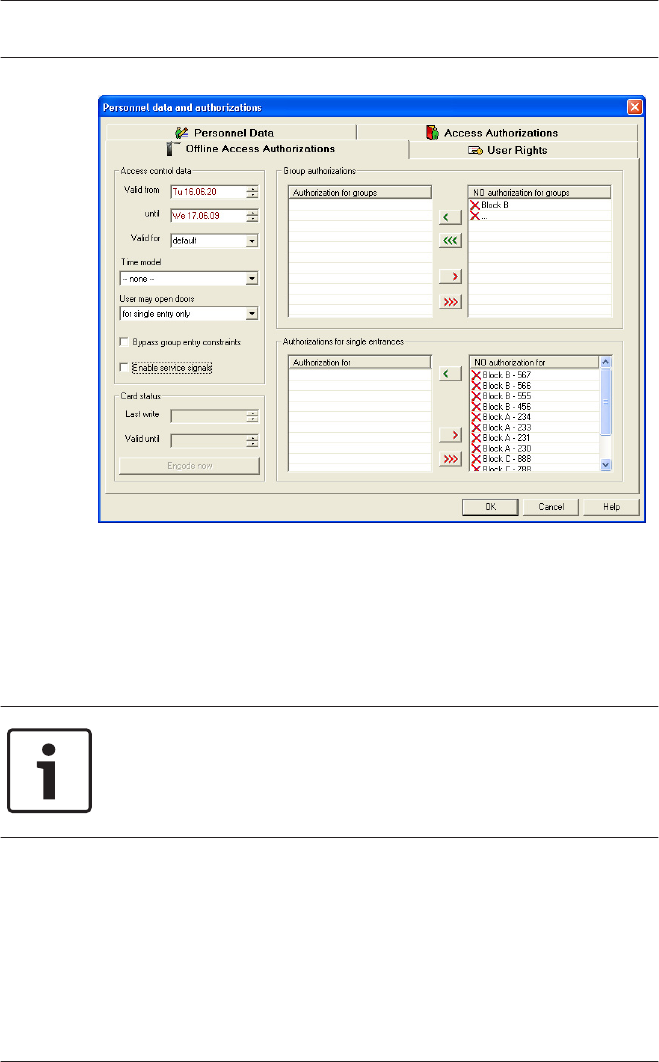
The four list fields on the right of the dialog are used to assign
Group authorizations (top list fields) and Authorizations for
single entrances (bottom list fields). The process of assigning
and withdrawing authorizations is the same as the process for
online access authorizations.
Notice!
Individual authorizations can only be assigned in line with the
data size. The maximum number for each locking system can be
found in the system data in Access PE Configurator.
Other settings for the offline cards are configured to the left of
the list fields for access authorizations.
Access control data dialog field
–Valid from ... until
Access PE 3.0 - Offline
Locking System Offline Locking System | en 73
Bosch Access Systems GmbH 2014-02 | 3.0 | IHB

The card's general duration of use can be defined here.
Extensions (Valid for) can be set up for no longer than the
specified "until" date. The start date (Valid from) can be set
as a date in the future, in which case the set extensions are
only written to the card on this date.
If no entries are made, the card is valid indefinitely from the
time of encoding.
The validity of assigned access authorizations, however, is
regulated by the settings in the Valid for field. Only when
the end of validity entry has been selected here is the
"until" date also applied to the access authorizations.
–Valid for
This field is used to define the extension periods for
authorizations. It contains a list of predefined periods for
quick selection, but other time data can also be entered.
[Depending on the time unit, time periods of up to four
years can be defined. If necessary, time data can be
expressed in larger units, e.g. 14 days as 2 weeks].
In addition to the time periods 1 hour, 1 day, 1 week, 1
month and 1 year, the list also contains the entries default
and end of validity.
–
– Default
This is a predefined entry and corresponds to an
extension period of two days.
– End of validity
This is used to extend the period to the general card
validity period ("until" date) during the encoding
process or the initial write process.
Note: If no end date is set for use of the card, the card
is extended indefinitely.
–Time model
Selecting a time model restricts the use of the card to the
defined time periods.
74 en | Offline Locking System Access PE 3.0 - Offline
Locking System
2014-02 | 3.0 | IHB Bosch Access Systems GmbH

The only time models that can be selected are those that
have been created in the dialog of the same name for the
offline locking system in Access PE Configurator. Time
models for access control (online system) cannot be used
here.
–User may open doors
–
–for single entry only
Corresponds to a normal access authorization —
depending on the authorization, the card holder may or
may not open the door.
–long-term only
The standard access authorization does not apply for
this card holder. He can only open correspondingly
configured doors (Manual long-term opening allowed
parameter) on a long-term basis by briefly presenting
his card to the door terminal reader.
–both
Depending on his authorizations the card holder is
able to unlock the door either long-term (by presenting
his card to the reader for 5 seconds, provided the door
in question has been configured appropriately) or for a
single entry (by presenting the card briefly i.e less than
5 seconds).
–Bypass group entry constraints
With this authorization selected, a card holder can access
doors configured with Entry as group only on his own, i.e.
override the group requirement.
–Enable service signals
When the battery status at the door terminal is low, optical
signals will only be displayed for users for whom this option
is activated. This also allows the signaling to be restricted
to people who are responsible for system repairs and
maintenance.
Access PE 3.0 - Offline
Locking System Offline Locking System | en 75
Bosch Access Systems GmbH 2014-02 | 3.0 | IHB

Card status dialog field
–Last write
The date and time of the last extension is displayed on the
encoding reader of the workstation or on the write-capable
reader.
–Valid until
Expiration date (date/time) for access authorizations based
on the last extension.
–Encode now
Data for the locking system can be written to the user card
via a connected encoding reader (Interflex - RWD).
If the card is not available when setting up or changing the
offline settings, the card will be rewritten the next time it is
scanned at a write-capable reader.
Adding personnel data
People to be granted access authorizations for the locking
system (offline system) must be added as records in the access
control system (online system).
As the same card is used for both systems and access
authorizations are extended for the offline system via (write-
capable) readers (e.g. DELTA 7020) in the online systems, card
holders must also have valid access authorizations for the
access control system, in line with the Write without access
rights parameter setting.
Prerequisites
In order to encode the cards at the workstation, you require an
appropriate dialog read-write unit. This is connected directly to
the workstation computer and set up via Access PE Personnel
Management.
1. Connect the reader to the workstation.
2. Open Access PE Personnel Management.
3. In the Tools menu, use the Properties function to openthe
Change configuration dialog.
3.7.2
76 en | Offline Locking System Access PE 3.0 - Offline
Locking System
2014-02 | 3.0 | IHB Bosch Access Systems GmbH

4. Activate the Dialog reader check box.
5. In the Reader field, select the Interflex USB Hitag, Mifare
(IFRW) entry.
6. Click OK to close the dialog.
You also require a write-capable reader (e.g. DELTA 7020) to
extend the offline authorizations. This reader can be installed as
an access control reader in the online system, e.g. at frequently
used entrances (main entrance), and can be configured at the
same time with write capabilities for the locking system; see
also Configuring the write-capable reader, page 53.
Online data
For people who have not yet been created in the system, a
record must first be added. To add personnel data and to assign
authorizations for the access control system, follow the steps
below:
1. Open Personnel Management.
2.
– To add a new dataset, click or open the Persons
> New person ... menu and then go to the Personnel
data and authorizations dialog.
– On the Personnel Data tab, complete at least the
mandatory fields with the data for the person in
question.
– Assign a card to the person.
3. Switch to the Access Authorizations tab.
4.
– Assign the person the necessary access authorizations
for the online system.
– If the Write without access rights (Configuring the
write-capable reader, page 53) parameter is not
activated for the write-capable reader, the access
authorization for this entrance must also be assigned.
Access PE 3.0 - Offline
Locking System Offline Locking System | en 77
Bosch Access Systems GmbH 2014-02 | 3.0 | IHB
You can distribute the offline access authorizations immediately,
without closing the dialog.
Offline data
If you wish to add to offline data for an existing dataset, or if
you have closed the creation dialog when setting up a new
dataset, you can open it either by double-clicking the relevant
entry in the list of available items or by selecting the entry and
clicking the button.
Notice!
Only people with a valid card for the access control system
(online system) can be assigned authorizations for the locking
system (offline system).
1. Switch to the Offline Access Authorizations tab.
2. Assign the person the necessary authorization groups and
individual authorizations.
3. Enter any use restrictions (validity dates, validity period,
time model etc.).
4. Place the card on the dialog reader.
5. Click the Encode now button to encode the card.
The Last write and Valid until fields are populated with the
relevant dates.
[If the physical card is not available, encoding is
automatically carried out the next time it is scanned at a
write-capable reader].
6. Once encoding has been successfully completed, click OK
to close the dialog.
Data check during write process
When the Encode now button is clicked, a dialog box appears
prompting you to place the card on the read-write unit.
78 en | Offline Locking System Access PE 3.0 - Offline
Locking System
2014-02 | 3.0 | IHB Bosch Access Systems GmbH
The following circumstances result in error messages and in the
termination of the write process.
– No card is place on the unit or the code data cannot be
read.
– The card is not a user card.
– The card does not belong to the selected person.
Display of the validity period indicates that the write process
has been successful.
Changing data
Any changes made to offline data (extensions or reductions of
access authorizations, new extension cycles etc.) are distributed
to the controllers, as with online data. The next time the card is
scanned at a write-capable reader, the changed data is
transferred to the card.
Notice!
Certain online data can also have an impact on offline
authorizations.
For people who are blocked in the online system, all offline
data will be deleted from the card during the next read/write
process.
Description of Procedures
The following procedural descriptions are intended to provide a
brief overview of the required steps and processes, with a view
to demonstrating and explaining the peculiarities of offline
systems — in particular in connection with access control
systems (online).
3.7.3
3.8
Access PE 3.0 - Offline
Locking System Offline Locking System | en 79
Bosch Access Systems GmbH 2014-02 | 3.0 | IHB
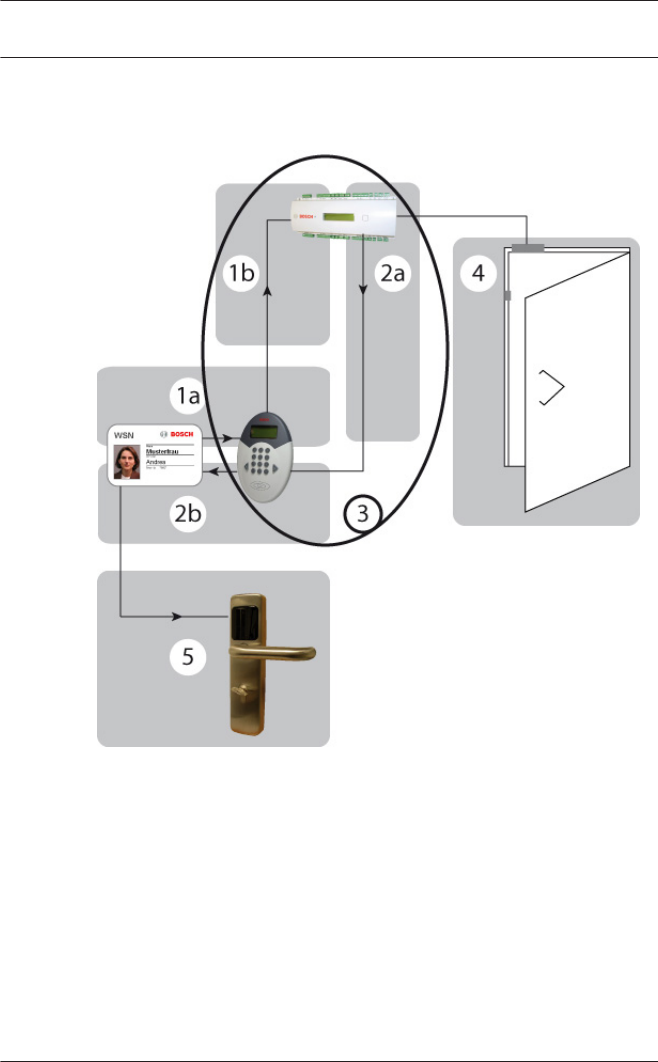
Access
1a Card read
1b Card number sent to the AMC
2a Current data shared with the reader
2b Current data written to the card
3For details on the checking and write process on the
AMC, please see the flow diagram in Write process,
page 81.
3.8.1
80 en | Offline Locking System Access PE 3.0 - Offline
Locking System
2014-02 | 3.0 | IHB Bosch Access Systems GmbH
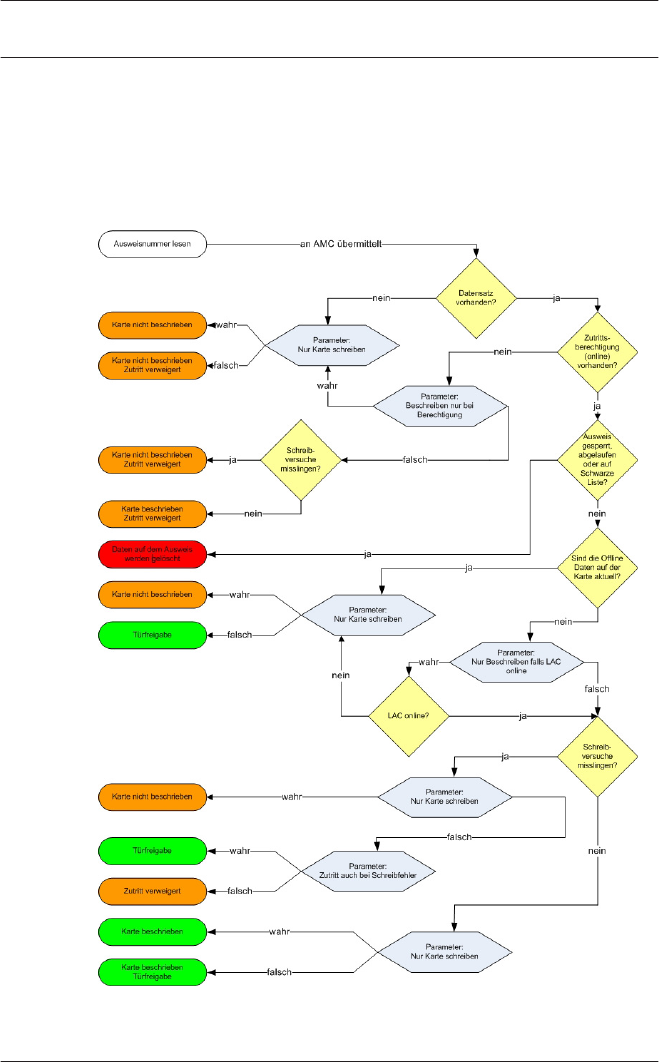
4Door release for the online system (if configured)
5Authorization check at door terminals
Write process
3.8.2
Access PE 3.0 - Offline
Locking System Offline Locking System | en 81
Bosch Access Systems GmbH 2014-02 | 3.0 | IHB

In the majority of cases write processes are used to extend
access authorizations by the amount of time specified.
For this reason, the last write date is also stored in the
database. The need for extension is determined by means of a
comparison with the current date or the current time. However,
as this would mean that expiration data would be updated every
time the card is scanned, a write process would also need to be
carried out each time. To avoid unnecessary waiting times and
delays at read-write units, a validity period is used to determine
a point in time until which the card data is considered valid.
Data is only updated when a third of the validity period has
expired.
Example
Validity period: 1 day = 24 hours
1/3 of the validity period: 8 hours
If a card holder scans the card when he starts work and his
expiration date is updated, he can pass the read-write unit
during the subsequent eight hours without a new write process
being triggered — the data is only updated at the end of the
eight hours.
Tip: If the validity period in the example above is doubled (= 48
hours), the updating period increases accordingly (= 16 hours).
This ensures that the validity period is only updated once a day.
Application Examples
The following examples demonstrate how the system can be set
up for special requirements or events via the relevant parameter
settings. The examples are restricted to one specific element.
Other variations can occur when a combination of parameter
settings is used. The examples can also be combined with each
other accordingly.
3.9
82 en | Offline Locking System Access PE 3.0 - Offline
Locking System
2014-02 | 3.0 | IHB Bosch Access Systems GmbH

Access control reader and/or write-capable reader?
The decision regarding the way in which the write-capable
reader is used depends on a number of different factors; it can
make sense not to integrate the reader into the access control
system (online).
– Is there an entrance (e.g. main entrance) that must be
passed by most of the card holders?
–
–Yes: A write-capable reader with simultaneous access
control function for the online system is
recommended.
–No (There are a number of possible entrances, for
example): The use of write-capable readers at each
entrance would not be recommended for cost reasons.
In this case, the reader (or possibly two readers)
should be installed in the most frequented area as a
simple recharging station.
– Should extensions of authorizations be possible at all
times?
–
–Yes: We recommend the use of a write-capable reader
(with or without access control function) in the most
frequented area.
–No (As a rule, fixed expiration dates are used): If the
read-write unit at the operator workstation is not
enough, any write-capable reader will suffice for these
special extensions.
Example 1: Read-write unit only
Ideally a hotel should be accessible to everyone, at least as far
as the reception desk. For this reason, access control readers
are predominantly installed at doors that require particular
security, in the event that the settings in the second example in
Single doors or door groups?, page 85 are not sufficient.
Access PE 3.0 - Offline
Locking System Offline Locking System | en 83
Bosch Access Systems GmbH 2014-02 | 3.0 | IHB

Accordingly, the write-capable reader is not linked with access
control functions; instead, it is configured purely as a read-write
unit for the offline system.
Requirements:
The Reader function reader parameter must be set to Write
locking system and the Only write card parameter is activated
(= checked).
The write-capable reader need only be installed in a central
location for hotel personnel, so that their rights can be updated
and extended. If possible, choose a position that all relevant
people pass on a regular basis, e.g. staff room.
For hotel guests, authorization for the hotel room door is
assigned in accordance with the room booking and written to
the card via a write-capable reader at reception. Authorizations
do not normally need to be changed, but this is carried out at
reception if required; the reader does not need to be installed in
a freely accessible area.
Example 2: Read-write unit with access control function
Student residences: Here, only residents must be allowed
access. One access control reader for the main entrance can
secure the building against unauthorized access. One write-
capable reader can update and extend rights for the locking
system for authorized people at the same time.
Requirements:
The Reader function reader parameter must be set to Write
locking system and the Only write card parameter is
deactivated (= unchecked).
If the Write without access rights parameter is not set
(checked), only people with access authorization (online) for
the main entrance will have their offline rights updated and
extended.
84 en | Offline Locking System Access PE 3.0 - Offline
Locking System
2014-02 | 3.0 | IHB Bosch Access Systems GmbH

Single doors or door groups?
Each door created in the system can be assigned as an
individual authorization and belong to any number of door
groups. The following examples are intended to demonstrate
how these two types of authorization should be handled.
Example 1: Hotel
At reception, the validity period for the room in question is
assigned as an individual authorization in accordance with the
booking. It is also possible, for example, to assign another door
group containing all general-use areas (restaurant, breakfast
room, sauna, sports facilities etc.), provided that these areas are
secured by terminals.
In contrast, hotel personnel are assigned a door group
containing all (or at least most) doors.
Requirements:
The Check door groups parameter must be selected.
Procedure:
The guest can open the door to his room, in line with the
assigned individual authorization, and can also open all doors in
the door group. Hotel personnel are able to open all doors in the
assigned door group, which also includes all doors to the guest
rooms.
Example 2: Areas within the offline system that are subject to
increased security requirements and may only be accessed by
certain people.
The authorized people are assigned these doors as individual
authorizations. It is irrelevant whether these doors belong to
door groups and it is also irrelevant to whom these door groups
have been assigned.
Requirements:
The Check door groups parameter must be cleared
(unchecked).
Procedure:
Access PE 3.0 - Offline
Locking System Offline Locking System | en 85
Bosch Access Systems GmbH 2014-02 | 3.0 | IHB

Only individual authorizations are accepted at the doors. People
who are only assigned door group authorizations for these doors
will not be granted access.
Normal or long-term unlock
If the card is valid, the LED on the terminal flashes green three
times. The door is unlocked for a set door opening time (the
default is 3 seconds). If the door is in Long-term unlock mode,
the LED again flashes green three times when a valid card is
presented.
A card with permission for single entry can only open the door
for single entry. A card with long-term unlock function
immediately activates long-term unlock (no five second
presentation necessary). Cards that are authorized for both can
be used for normal opening if the card is removed during the
three flashes. If, instead, the card continues to be presented to
the terminal's read unit (> five seconds), a continuous green
signal is displayed and the door remains unlocked until a card
with long-term unlock [both] authorization is presented to the
terminal (for at least five seconds). The door is then locked; i.e.
access is only possible with authorized cards.
Requirements:
The long-term unlock (Toggle) parameter must also be selected
(checked) for the terminal.
By time model:
The same function can be controlled via a time model. A time
model is selected for the Opening time model door parameter
and the door is unlocked ("from time") or locked ("until time")
on a long-term basis in line with the specified time periods.
Time models containing only "until times" can be used to lock
doors which have been unlocked long-term.
86 en | Offline Locking System Access PE 3.0 - Offline
Locking System
2014-02 | 3.0 | IHB Bosch Access Systems GmbH

Notice!
Unlocks governed by time models always contain the risk that
unsupervised areas could be made freely accessible.
Examples: Office buildings with public access
1. Manual long-term unlock/lock
The office is unlocked each morning using the long-term
unlocking function and made accessible to the public.
When the office closes, long-term locking is carried out,
meaning that only people with a valid card can access the
office during this time.
2. Long-term unlock/lock controlled via a time model
If the public visiting hours are not the same as the staff
hours, door opening and closing can also be controlled via
a time model.
Personnel hours: 8:00-12:00 and 13:00-17:00
Public visiting hours: 9:00-11:00 and 14:00-16:00
To correctly comply with the hours and avoid the need for
manual unlocking/locking, a time model can be used with
two periods that correspond to the public visiting hours.
3. Long-term locking controlled via time model
The office is unlocked manually each morning by the first
associate to arrive, using the long-term unlocking function.
A time model without start times is used to initiate long-
term locking at a certain point in time.
LED display signals
Signals for user cards
Door opened with single-unlock function
3.10
Access PE 3.0 - Offline
Locking System Offline Locking System | en 87
Bosch Access Systems GmbH 2014-02 | 3.0 | IHB
Meaning The door is unlocked with a single-unlock
card. This message also appears if the
door is already unlocked on a long-term
basis.
Booking entry access, single door permission
or
access, door group permission
Door opened with long-term unlock function
Meaning The door has been unlocked by long-term
unlock card, or by time model.
Booking entry Door unlocked
Door closed with long-term unlock function
Meaning The door has been locked by long-term
unlock card, or by time model.
Booking entry Door in normal mode
Battery change request
88 en | Offline Locking System Access PE 3.0 - Offline
Locking System
2014-02 | 3.0 | IHB Bosch Access Systems GmbH
Meaning Red LED signal of one to three seconds'
duration. As long as the battery is not
completely empty, a card-specific signal
will follow.
If the batteries are empty, no further
signal will be displayed and no bookings
will be possible.
The battery change request is only
displayed for user cards.
Booking entry The battery voltage too low entry is
shown after every 25 bookings.
Solution Replace batteries.
Special signals
Read-write confirmation for system cards
Meaning A system card was successfully read or
written.
Booking entry Initialization
No card in range
Meaning The electronics have been activated,
however no card was recognized in front
of the reader.
Booking entry <No entry made>
Solution Present the card to the reader again.
Read/write error
Access PE 3.0 - Offline
Locking System Offline Locking System | en 89
Bosch Access Systems GmbH 2014-02 | 3.0 | IHB
Meaning It was not possible to read or write to a
system card successfully.
Booking entry <No entry made>
Solution Present the system card to the reader
again.
Invalid authorization
Meaning The card has no valid authorization.
Booking entry Access denied, card status blocked,
Not authorized,
Access denied, card expired
or
Access denied, outside time model
Solution If necessary, change the authorization for
this card.
Time invalid
90 en | Offline Locking System Access PE 3.0 - Offline
Locking System
2014-02 | 3.0 | IHB Bosch Access Systems GmbH
Meaning The terminal does not know the current
time.
Booking entry <No entry made>
Solution A time initialization card must be created
and scanned at the terminal.
Door initialization missing
Meaning The terminal has not been initialized.
Booking entry <No entry made>
Solution A door initialization card must be created
and scanned at the terminal.
Facility data missing
Meaning The terminal has not been initialized for
this facility.
Booking entry <No entry made>
Solution The terminal must be initialized with a
facility card.
Data transmission
Access PE 3.0 - Offline
Locking System Offline Locking System | en 91
Bosch Access Systems GmbH 2014-02 | 3.0 | IHB
Meaning The LED lights up orange while data is
being exchanged between a system card
and a terminal.
The duration depends on the volume of
data to be transferred. The read/write
process is then signaled.
LED displays for mobile read-write device
Write-confirmation for time model cards
Meaning Data has been successfully written to
time model card.
Read-confirmation for the time model card
Meaning The time model card has been
successfully read.
Read-confirmation for facility card
Meaning The facility card has been successfully
read.
Read/write error
92 en | Offline Locking System Access PE 3.0 - Offline
Locking System
2014-02 | 3.0 | IHB Bosch Access Systems GmbH
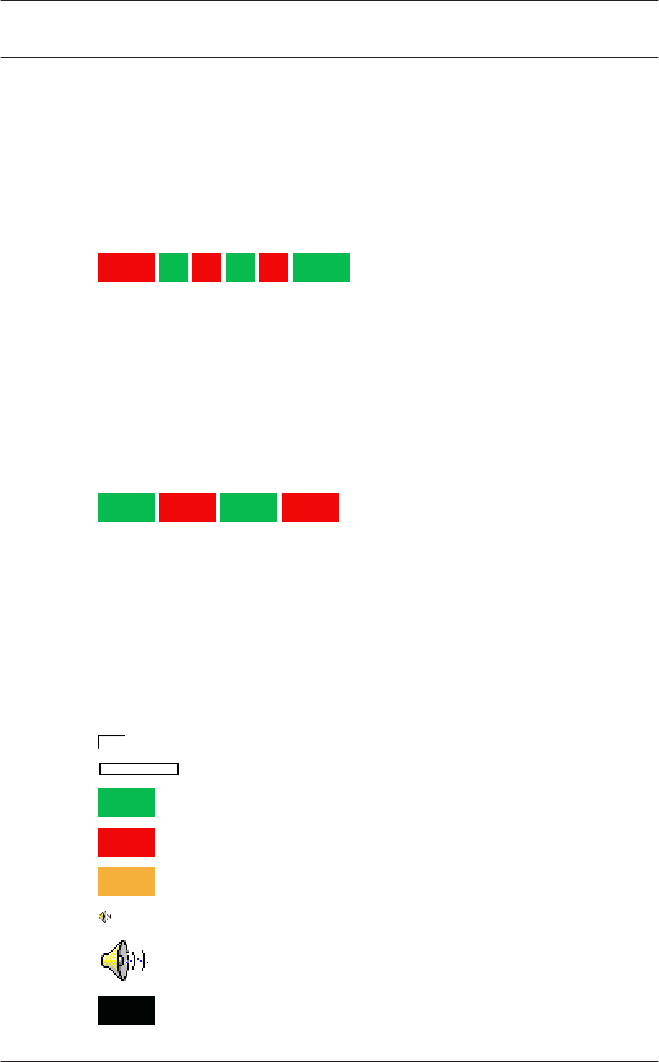
Meaning It was not possible to read or write to the
system card successfully.
Solution Hold the system card to the reader again.
Facility data missing
Meaning The timesetter has not been initialized for
this facility.
Solution The timesetter must be reinitialized with
the facility card.
Time invalid
Meaning The timesetter does not know the current
time.
Solution An appropriate time initialization card
must be created and the timesetter must
be synchronized.
Key:
- LED signal lasting one second.
- LED signal lasting up to three seconds.
- green LED
- red LED
- orange LED
- additional acoustic signal
- additional acoustic signal
- signal interrupted
Access PE 3.0 - Offline
Locking System Offline Locking System | en 93
Bosch Access Systems GmbH 2014-02 | 3.0 | IHB

94 en | Offline Locking System Access PE 3.0 - Offline
Locking System
2014-02 | 3.0 | IHB Bosch Access Systems GmbH

Bosch Access Systems GmbH
Charlottenburger Allee 50
52068 Aachen
Germany
www.boschsecurity.com
© Bosch Access Systems GmbH, 2014