Cogent Systems MOBILEIDENTII Cogent Multifunction Fingerprint Scanner User Manual Mobile Ident II MI2
Cogent Systems Inc Cogent Multifunction Fingerprint Scanner Mobile Ident II MI2
Users Manual

MobileIdentTMII 2008
Cogent Systems
Instruction of Mobile IdentTM II
1

MobileIdentTMII 2008
Table of Content
1. Power On………………………………………………………………...…………………..3
2. Login the Mobile Ident II (MI2)………………………………………………...………….3
3. Home Page………………………………………………………………...………………..4
4. Settings………………………………………………………………………………………..4
4.1. Volume…………………………………….…………………………………………….5
4.2. Date………………………………...…………………………………………………….5
4.3. Users………………………………………………………………………………………6
5. Wireless……………………………………...………………………………………………..6
6. Identify…………………………………….………………………………………………….7
6.1. Search………………………...………………………………………………………….7
6.2. Enroll………………………………………………………………………………………8
6.2.1. Demographics……..……………………………………………………………8
6.2.2. Fingerprints………………………………………………………………………..8
6.2.3. Photo………………………………………...…………………………………….9
6.2.4. Database………………………………...……………………………………….9
2

MobileIdentTMII 2008
1. Power On
To turn on and shut down the device, press power button for 2-3 seconds
(Figure 1).
Power
button
Figure 1
2. Login the Mobile IdentTM II
In order to access the systems, you have to get a valid user name and
password. Enter your user name and password and then tap ‘Login’, as Figure
2 shown below. Administrators create user accounts using ‘Users’. For details,
please refer to 4 ‘Users’.
Figure 2
Caps
Lock
3
MobileIdentTMII 2008
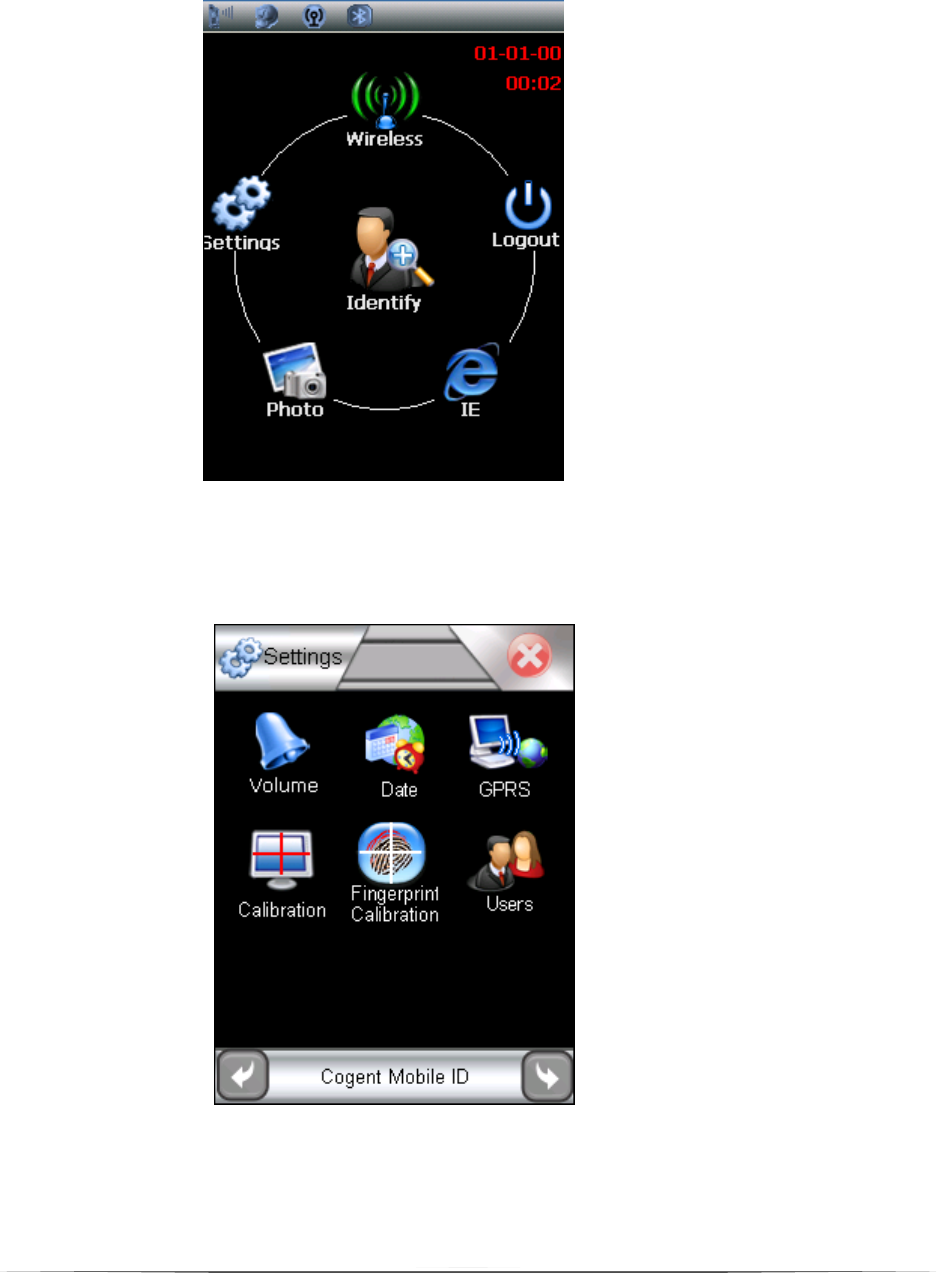
3. Home Page
After login, you will get into the main page of MI2 as Figure 3 shown below. All
function of Mobile IdentTM II will display in this page. Tap the icon (function) you
wish to operate.
Figure 3
4. Settings
Select and enter ‘Settings’, you can set the data be yourself (Figure 4).
Figure 4
4
MobileIdentTMII 2008
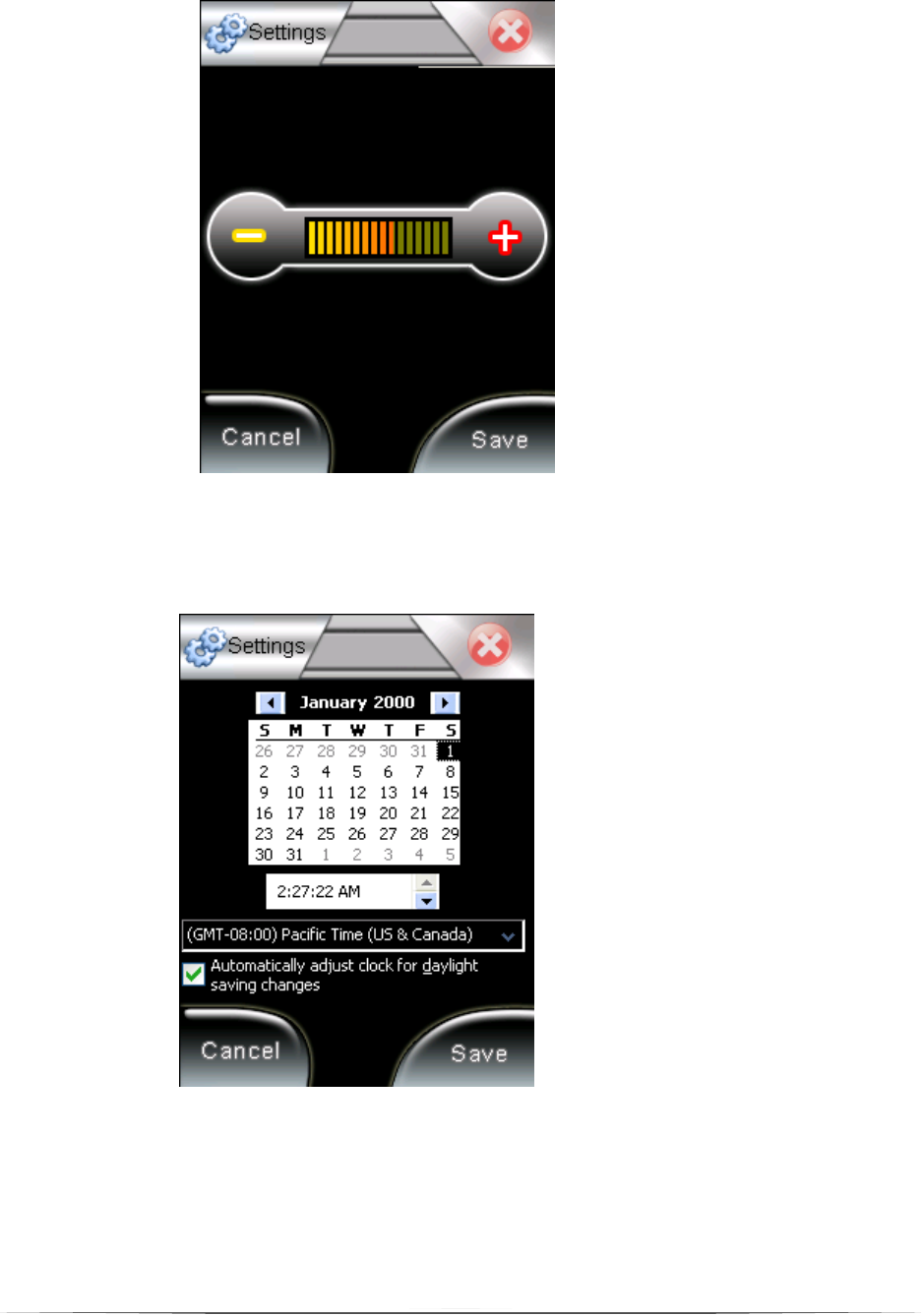
4.1. Volume
Tap ‘Save’ to save your setting (Figure 5).
Figure 5
4.2. Date
Set the time, date and time zone, then tap save (Figure 6).
Figure 6
5
MobileIdentTMII 2008
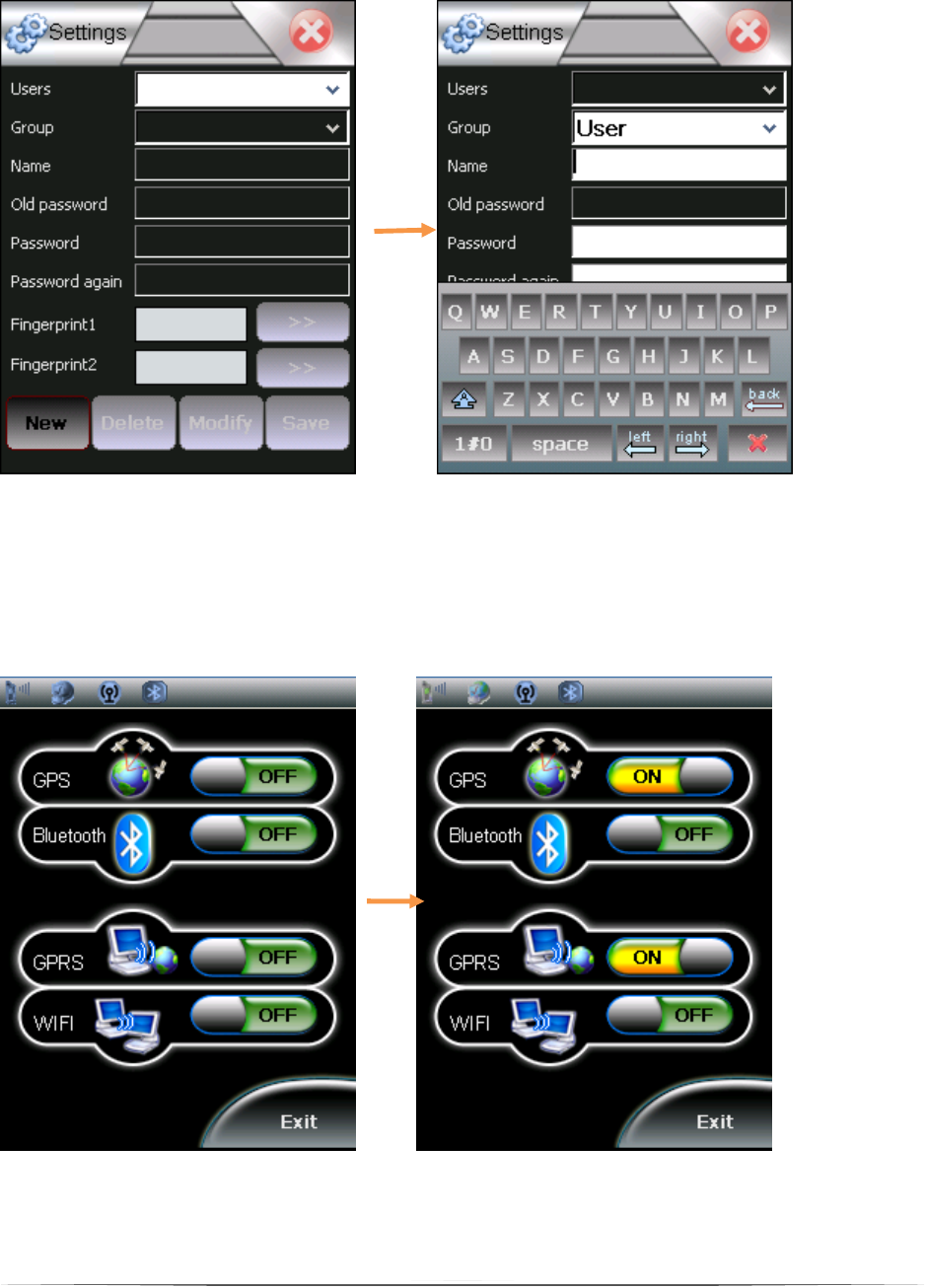
4.3. Users
Tap ‘New’ to add user. Enter the information in the page, then tap save to
save your setting (Figure 7).
Figure7
5. Wireless
Select ‘Wireless’ and get into the power control. Tap the On-Off button to
control the wireless function (Figure 8). Please note that GPRS, WIFI and
BLUETHOOTH cannot work together. It is impossible to send data with all
systems at the same time and it cannot send data during the scan process.
Figure 8
6
MobileIdentTMII 2008
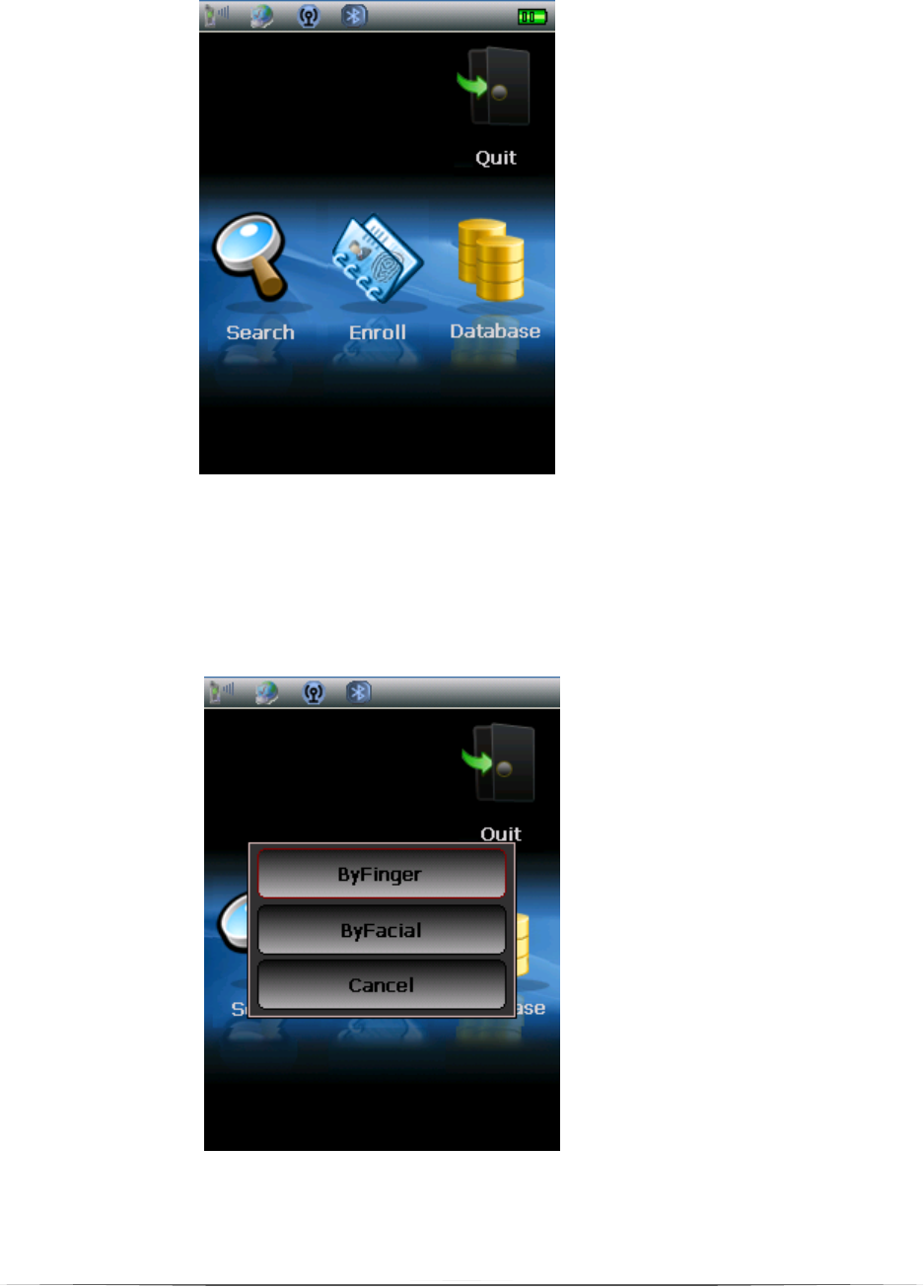
6. Identify
‘Identify’ is the main function of MI2. It is use to enroll fingerprint, edit and
search the demographics (Figure 9).
Figure 9
6.1. Search
‘Search’ is for searching the data in the database. You can search by
finger and facial (Figure 10). If it finds a match in the database, the
information will be displayed.
Figure 10
7
MobileIdentTMII 2008
6.2. Enroll
6.2.1. Demographics
Tap ‘Enroll’ and get into the demographics. Tap the information you
wish to enter and edit it. After editing demographics, tap ‘OK’ go to
the nest step (Figure 11).
Figure 11
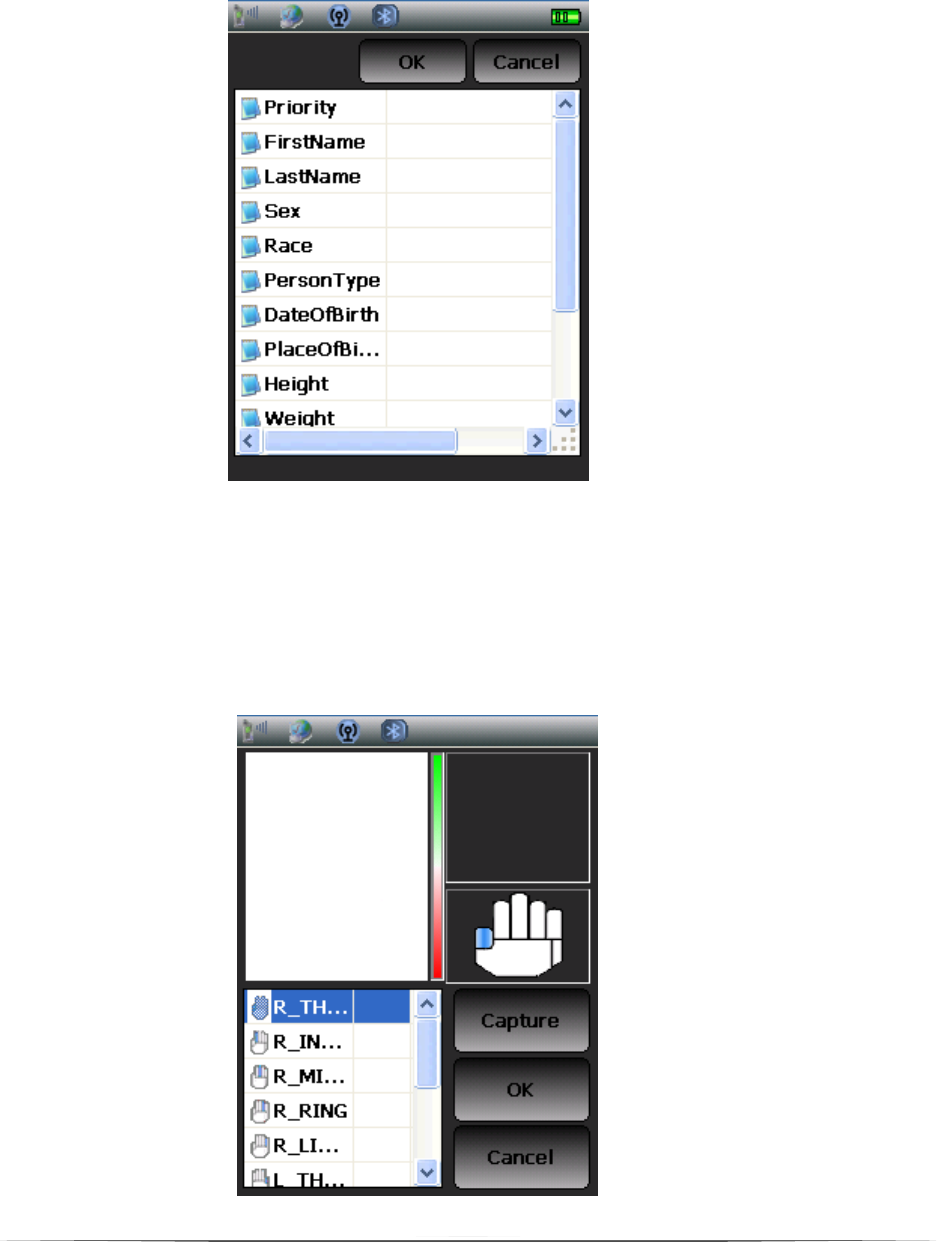
6.2.2. Fingerprints
Tenprints is required. Follow the instruction to enroll tenprints (from R
Thumb to L Little) (Figure 12). Select the finger you wish to enroll. If
the quality of fingerprint is poor, the system will ask for capture
again. If the quality of the image is good, then it will go to capture
the next finger.
Figure 12
8
MobileIdentTMII 2008
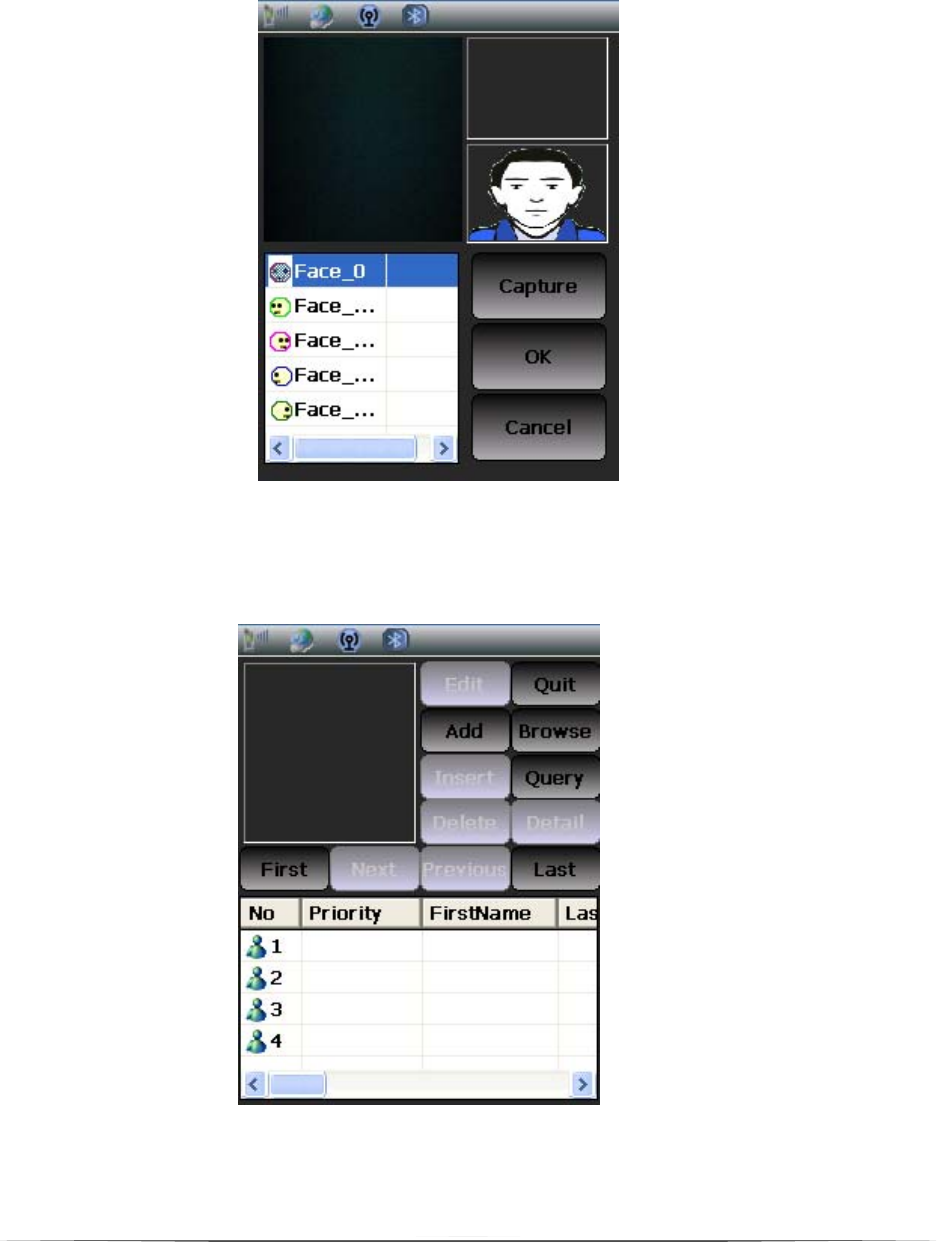
6.2.3. Photo
After capturing the fingerprint, it will go to the next step ‘Photo’
automatically. It will take 5 photos for 5 different face angles. One
photo captured at front, two captured at 90 degree (left and right),
two captured at 45 degree (left and right) (Figure 13).
Figure 13
6.3. Database
Check the data you entered (Figure 14). You can edit the information you
entered previously.
Figure 14
9

MobileIdentTMII 2008
FCC INFORMATION
This device complies with Part 15 of the FCC Rules. Operation is subject to the
following two conditions: (1) this device may not cause harmful interference, and
(2) this device must accept any interference received, including interference that
may cause undesired operation.
Changes or modifications not expressly approved by the party responsible for
compliance could void the user's authority to operate the equipment.
This equipment complies with FCC radiation exposure limits set forth for an
uncontrolled environment. End users must follow the specific operating instructions
for satisfying RF exposure compliance. This transmitter must not be co-located or
operating in conjunction with any other antenna or transmitter.
NOTE: This equipment has been tested and found to comply with the limits for a
Class B digital device, pursuant to Part 15 of the FCC Rules. These limits are
designed to provide reasonable protection against harmful interference in a
residential installation. This equipment generates, uses and can radiate radio
frequency energy and, if not installed and used in accordance with the
instructions, may cause harmful interference to radio communications.
However, there is no guarantee that interference will not occur in a particular
installation. If this equipment does cause harmful interference to radio or
television reception, which can be determined by turning the equipment off
and on, the user is encouraged to try to correct the interference by one or
more of the following measures:
-- Reorient or relocate the receiving antenna.
-- Increase the separation between the equipment and receiver.
-- Connect the equipment into an outlet on a circuit different from that to
which the receiver is connected.
-- Consult the dealer or an experienced radio/TV technician for help.
10