Comtrend 5845N 2T2R Wireless-N Broadband Router User Manual User Guide W316
Comtrend Corporation 2T2R Wireless-N Broadband Router User Guide W316
Comtrend >
Users Manual


Contents
CHAPTER 1 PRODUCT INTRODUCTION ......................1
1.1 Package Contents ..................................1
1.2 LED Indicators and Port Description..........1
CHAPTER 2 PRODUCT INSTALLATION........................4
CHAPTER 3 HOW TO CONFIGURE TO ACCESS THE
INTERNET ............................................................................. 6
3.1 How to Set the Network Configurations.....6
3.2 Log in to the Router ............................. 11
3.3 Fast Internet Access............................. 11
3.4 Fast Encryption.................................... 11
CHAPTER 4 ADVANCED SETTINGS.............................. 13
4.1 System Status..................................... 13
4.2 WAN Settings...................................... 14
4.3 LAN Settings ....................................... 16
4.4 DNS Settings....................................... 16
4.5 WAN Medium Type ............................... 17
4.6 Bandwidth Control ............................... 18
4.7 Traffic Statistics................................... 19
CHAPTER 5 WLAN SETTINGS ....................................... 20
5.1 Wireless Basic Settings......................... 20
5.2 Wireless Security Settings..................... 21
5.2.1 WPS Settings.................................... 22
5.2.2 WPA- PSK ........................................ 22
5.2.3 WPA2- PSK....................................... 23
5.3 Wireless Access Control ........................ 23
5.4 Connection Status................................ 23

CHAPTER 6 DHCP SERVER............................................. 24
6.1 DHCP Server....................................... 24
6.2 DHCP Client List................................... 24
CHAPTER 7 VIRTUAL SERVER...................................... 25
7.1 Port Range Forwarding.......................... 25
7.2 DMZ Settings ...................................... 27
7.3 UPNP Settings ..................................... 27
CHAPTER 8 SECURITY SETTINGS ...............................29
8.1 Client Filter Settings............................. 29
8.2 MAC Address Filter............................... 30
8.3 URL Filter Settings ............................... 30
8.4 Remote Web Management..................... 31
CHAPTER 9 ROUTING SETTINGS.................................32
9.1 Routing Table ...................................... 32
9.2 Static Routing...................................... 32
CHAPTER 10 SYSTEM TOOLS........................................ 33
10.1 TIME SETTINGS ..................................... 33
10.2 DDNS............................................... 33
10.3 Backup/Restore ................................. 34
10.4 Restore to Factory Default ................... 35
10.5 Upgrade............................................ 35
10.6 Reboot the Router.............................. 36
10.7 Password Change............................... 36
10.8 Syslog.............................................. 36
10.9 Log out............................................. 36
APPENDIX 1 GLOSSARY..................................................37
APPENDIX 2 PRODUCT FEATURES.............................. 38
APPENDIX 3 FAQ ............................................................... 39

APPENDIX 4 CLEAR WIRELESS CONFIGURATION. 41
APPENDIX 5 REGULATORY INFORMATION .............43

1
Chapter 1 Product Introduction
Thank you for purchasing the ER-5840n/ER-5845n Wireless N Broadband Router!
This easy-to-use router provides simple configuration interface which enables you to
configure it with ease. It is based on the latest IEEE802.11n standard, and is backward
compatible with devices of IEEE802.11b/g standards.
The ER-5840n/ER-5845n wireless router,including router, wireless AP, four-port switch and
firewall in one,provides powerful online monitor function and supports URL filter and MAC
filter. With WDS function, it can repeat and amplify wireless signals so as to enlarge
network coverage area. It truly supports UPnP and WMM to make your audio and video
smoother. With QoS function, it can efficiently distribute the downloading rate for the clients.
With super compatibility, the router can break the access limits in some areas so that
multiple computers can share the Internet access. Additionally, it supports WISP function to
access to the ISP’s wireless hotspots (this function applies only to some of the products).
1.1 Package Contents
Please verify the following items after you open the package:
¾ One Wireless N Broadband Router
¾ One Quick Installation Guide
¾ One Power Adapter
¾ One Software CD
If any of the listed items are missing or damaged, please contact the ER-5840n/ER-5845n
reseller for immediate replacement.
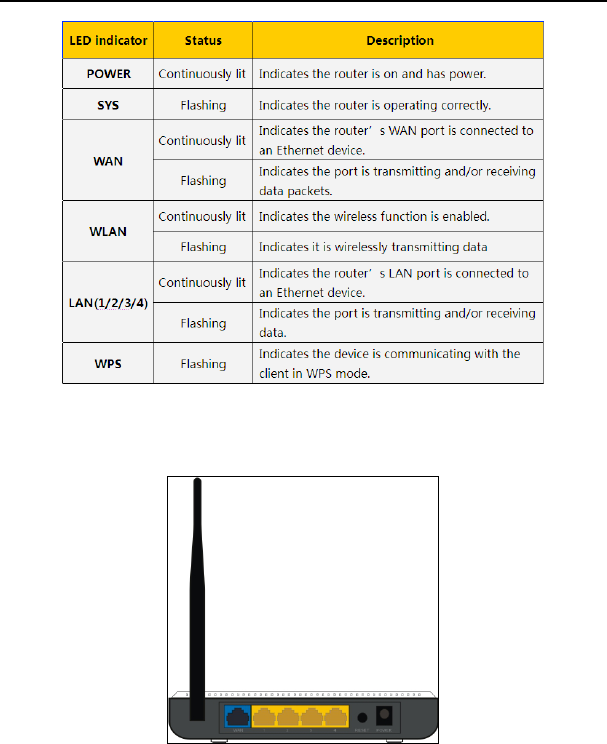
1.2 LED Indicators and Port Description
Panel and LED indicators show:
LED indicator description on the front panel
2
Back panel port show (take ER-5840N/ER-5845N as an example)
3
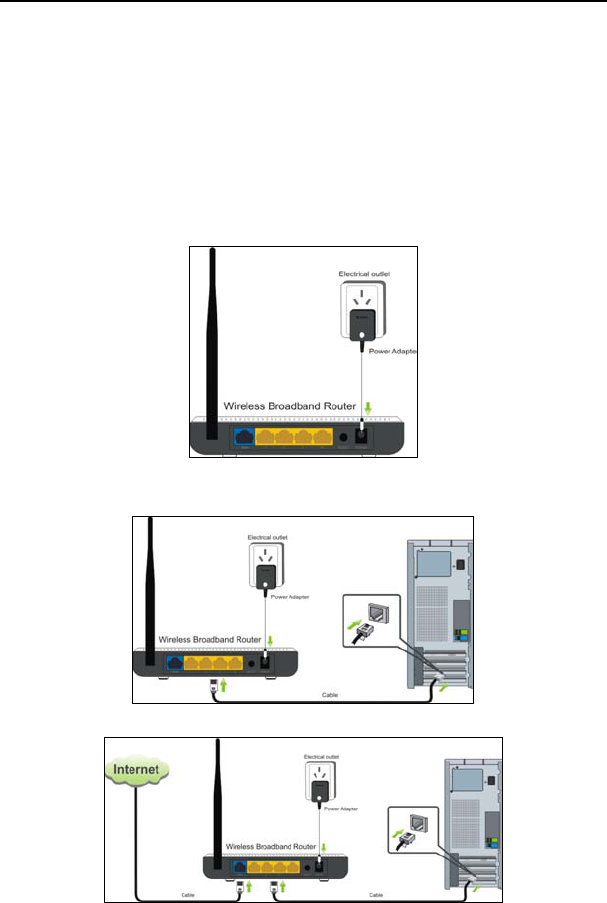
Back panel port description
4
Chapter 2 Product Installation
In this user guide, we take ER-5840N/ER-5845N as an example to explain the installation
steps. The installation steps of other products are similar to this one.
1. Please use only the included power adapter to power your router. (NOTE: Use of an
unmatched power adapter could cause damage to this product).
2. Please connect the router’s LAN port to your computer with an Ethernet cable as shown
below.
3. Please connect your broadband line provided by your ISP to the router’s WAN port.
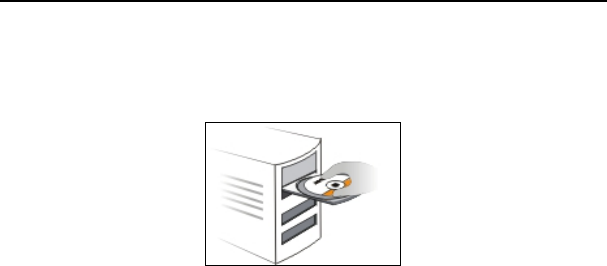
5
4. Insert the included software CD into the CD drive of your computer. After the software
automatically initiates, double click the “Setup” icon and follow the instructions to complete
the installation. You can also enter the router’s Web-based Utility to complete the
configuration.
6
Chapter 3 How to configure to access the Internet
3.1 How to Set the Network Configurations
Network Configurations under windows XP
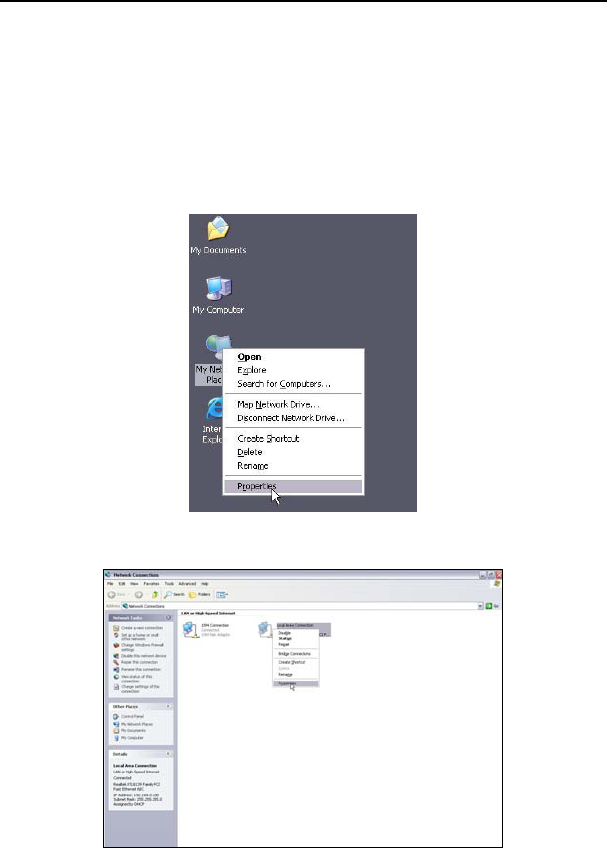
1. Right click “My Network Places” on your computer desktop and select “Properties”.
2. Right click “Local Area Connection” and select “Properties”.
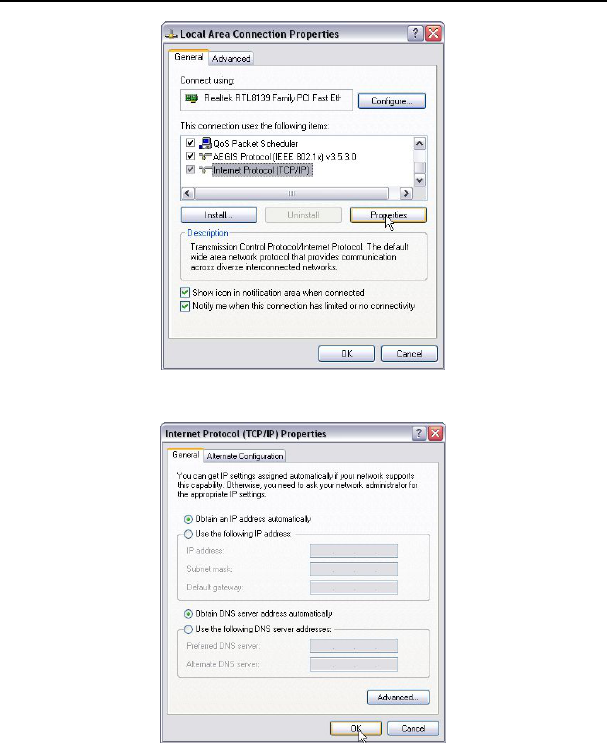
3. Select “Internet Protocol (TCP/IP)” and click “Properties”.
7
4. Select “Obtain an IP address automatically” and “Obtain DNS server address
automatically”. Click “OK” to save the configurations.
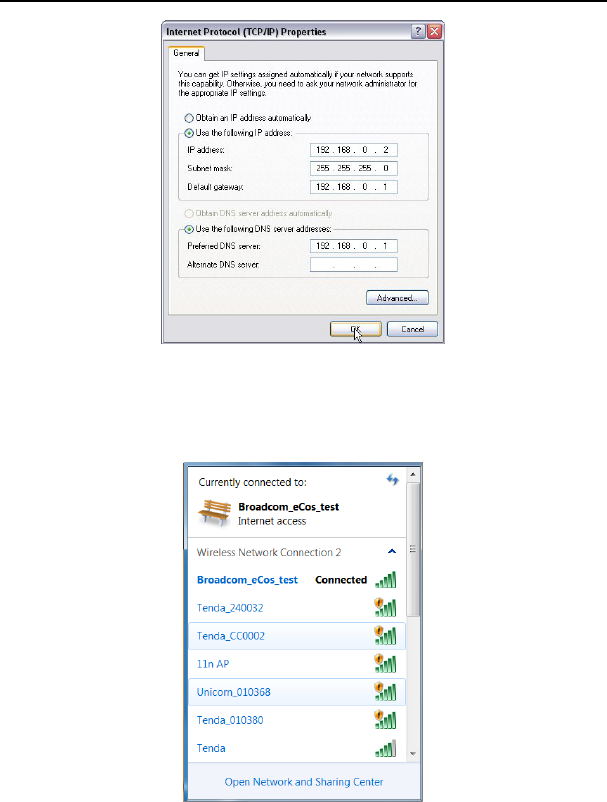
Or select “Use the following IP address” and enter the IP address, Subnet mask, Default
gateway as follows:
¾ IP Address: 192.168.0.XXX: (XXX is a number from 2~254)
¾ Subnet Mask: 255.255.255.0
¾ Gateway: 192.168.0.1
¾ DNS server: You should input the DNS server address provided by your ISP.
Otherwise, you can enter 192.168.0.1. Click “OK” to save the configurations.
8
Network Configurations under windows 7
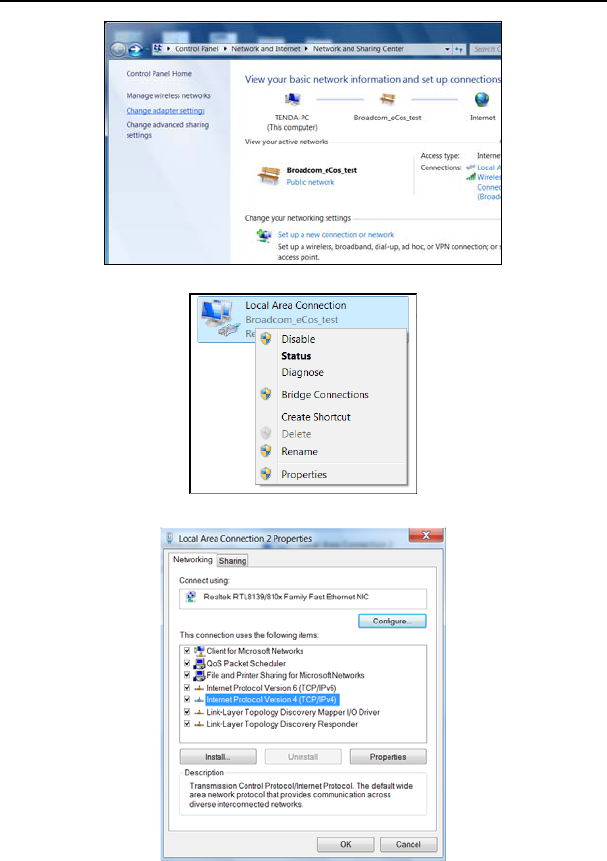
1. Click the network icon on the lower right corner of your computer desktop, and then
click” Open Network and Sharing Center”.
2. Click “Change adapter settings” on the left side of the window.
9
3. Right click “Local Area Connection” and select “Properties”.
4. Double click” Internet Protocol Version 4(TCP/IPv4)".
5. Select “Obtain an IP address automatically” and “Obtain DNS server address
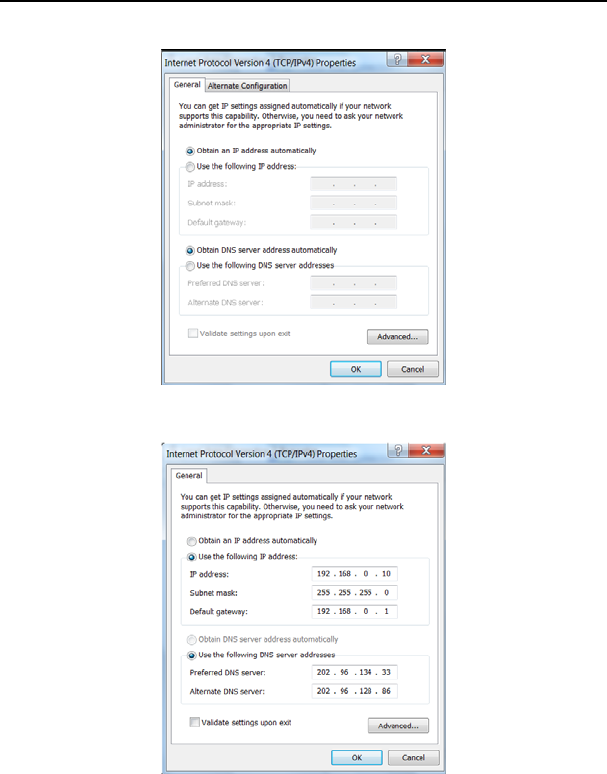
10
automatically”. Click “OK” to save the configurations.
Or select “Use the following IP address” and enter the IP address, Subnet mask, Default
gateway as follows:
¾ IP Address: 192.168.0.XXX: (XXX is a number from 2~254)
¾ Subnet Mask: 255.255.255.0
¾ Gateway: 192.168.0.1
¾ DNS server: You should input the DNS server address provided by your ISP.
Otherwise, you can enter 192.168.0.1. Click “OK” to save the configurations.
11
3.2 Log in to the Router
1. To access the Router’s Web-based Utility, launch a web browser such as Internet
Explorer or Firefox and enter http://192.168.0.1. Press “Enter”.
2. The system will automatically choose the corresponding web language in accordance
with the Browser’s language. For example, if your Browser’s language is French, the
router’s web language will display as French.
3. If your Browser language is English or beyond the 9 languages (Arabic, French, German,
Italian, Polish, Portuguese, Russian, Spanish, Turkish), the router’s web language will be
English.
3.3 Fast Internet Access
Two kinds of fast access methods are provided on the router’s web-based utility: ADSL
dial-up and DHCP.
If you select ADSL dial-up, you only need to enter the access account and access
password as well as the wireless password, and then click “Ok” to complete the settings.
If you select DHCP, you only need to enter the wireless password and click “Ok” to
complete the settings.
The default access method is ADSL dial-up and the access account and access password
are the same as the ADSL dial-up account and password, which you can inquire your
broadband ISP. For other access methods, please refer to WAN settings in chapter 4.The
wireless password can only consist of 8 characters, the default is 12345678 and you can
modify it when necessary.
3.4 Fast Encryption

12
The router provides two encryption setting screens, one is simple and easy, the other is
advanced (For advanced setting, please refer to chapter 5.2).
Simple and easy screen:
Log on to the router’s web-based utility and you may set encryption for the router. The
default adopts WPA-PSK mode and AES Algorithm. The default password is 12345678, as
shown below.
NOTE: The wireless password can only be 8 characters in length and the default
is 12345678, you can modify it when necessary.
13
Chapter 4 Advanced Settings
4.1 System Status
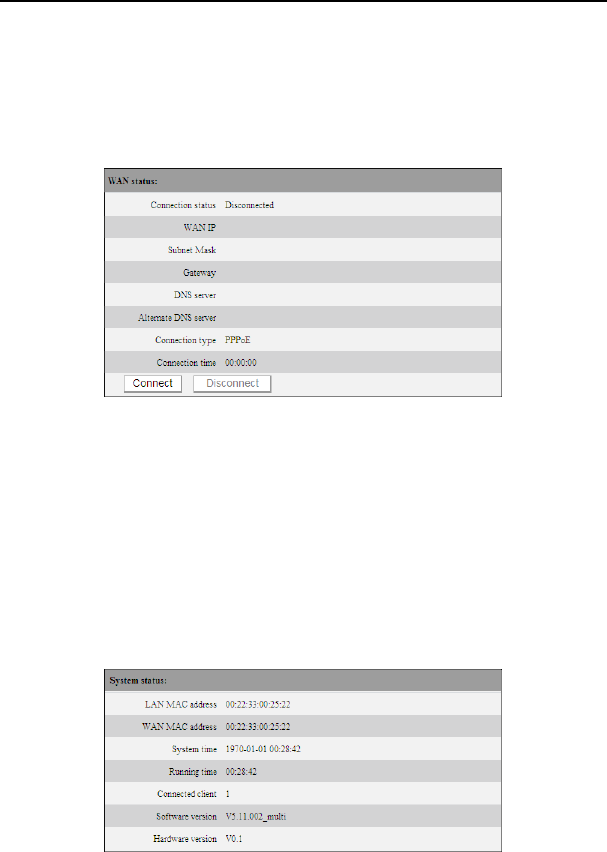
System status screen allows you to view the router’s WAN port status and system status.
¾ Connection status: It displays the router’s WAN connection status.
Disconnected: It indicates the router’s WAN port hasn’t been connected with the
network cable.
Connecting: It indicates the router’s WAN port is obtaining IP address.
Connected: It indicates the Router is well connected with the ISP.
¾ WAN IP:IP address obtained from ISP.
¾ Subnet mask: Obtained from ISP.
¾ Gateway: Obtained from ISP.
¾ DNS server: Obtained from ISP.
¾ Alternate DNS server: Obtained from ISP.
¾ Connection type: It displays your current access method.
¾ LAN MAC address:It displays the Router’s LAN MAC address.
¾ WAN MAC address:It displays the Router’s WAN MAC Address.

14
¾ System time:It displays the system’s updated time
¾ Connected client :It displays the number of the connected computers(normally it
displays the number of clients whose IP addresses obtained via DHCP server)
¾ Software version:It displays the Router’s software version;
¾ Hardware version:It displays the Router’s hardware version.
4.2 WAN Settings
Virtual Dial-up (PPPoE)
¾ Mode: Show your current connection mode.
¾ Access Account: Enter the account provided by your ISP.
¾ Access Password: Enter the password provided by your ISP.
¾ MTU: Maximum Transmission Unit. It is the size of the largest data packet that can
be sent over the network. The default value is 1492. Do NOT modify it unless
necessary, but if a specific website or web application software cannot open or be
enabled, you can try to change the MTU value to 1450, 1400, etc.
¾ Service Name: The connection name for current PPPOE, enter it if necessary,
otherwise, leave it blank.
¾ AC Name: The service name, enter it if necessary,otherwise, leave it blank.
¾ Connect Automatically: Connect automatically to the Internet after rebooting the
system or connection failure.
¾ Connect on Demand: Re-establish your connection to the Internet after the specific
time (Max Idle Time). Zero means you are connected to the Internet all times.
Otherwise, enter the minutes to be elapsed before you are disconnected from the
Internet.
¾ Connect Manually: Connect to the Internet by users manually.
¾ Connect on Fixed Time: Connect to the Internet during the time you fix
automatically.
NOTE:
The “Connect on Fixed Time” goes into effect only when you have set the current
time in “Time settings” from “System tools”.
Static IP
If your ISP provides you the static IP, please choose static IP, and you need to enter the IP
address, subnet mask, gateway, DNS server and alternate DNS server provided by your

15
ISP or network administrator。
¾ Mode: Show your current connection mode.
¾ IP address: Enter the WAN IP address provided by your ISP. If you are not clear,
please inquire your local ISP.
¾ Subnet mask: Enter the WAN Subnet Mask provided by your ISP. Generally it is
255.255.255.0。
¾ Gateway: Enter the Gateway provided by your ISP. If you are not clear, please
inquire your local ISP.
¾ DNS server: Enter the necessary DNS server provided by your ISP.
¾ Alternate DNS server: Enter the second DNS address if your ISP provides, which is
optional.
Dynamic IP (Via DHCP)
If your connection mode is Dynamic IP, it means every time you access the Internet, you
will get a different IP. You don’t need to enter any parameters in this mode, just Click “Ok” to
finish the settings.
PPTP
¾ Mode: Show your current connection mode.
¾ PPTP server address: The IP address or domain name of the destination server
and it is used to specify the destination address which needs for PPTP connection.
¾ Username/Password: Used to validate identity when connecting to the PPTP
server.
¾ Address mode: Set the router’s IP address mode, you can select either “Dynamic”
or “Static”. If your ISP doesn’t provide the IP address, please select “Dynamic”.
¾ IP address: Please enter the IP address provided by your ISP, inquire your local ISP
if you are not clear.
¾ Subnet mask: Please enter the subnet mask provided by your ISP ,generally its
255.255.255.0
¾ Gateway: Please enter the gateway provided by your ISP, inquire your local ISP if
you are not clear.
All the above parameters are provided by ISP.

16
L2TP
¾ Mode: Show your current connection mode.
¾ L2TP server address: The IP address or domain name of the destination server and
it is used to specify the destination address which needs for L2TP connection.
¾ Username/Password: Used to validate identity when connecting to the L2TP
server.
¾ Address mode: Set the router’s IP address mode, you can select either “Dynamic”
or “Static”. If your ISP doesn’t provide the IP address, please select “Dynamic”.
¾ IP address: Please enter the IP address provided by your ISP, inquire your local ISP
if you are not clear.
¾ Subnet mask: Please enter the subnet mask provided by your ISP ,generally its
255.255.255.0
¾ Gateway: Please enter the gateway provided by your ISP, inquire your local ISP if
you are not clear.
All the above parameters are provided by ISP.
4.3 LAN Settings
Click “Advanced settings” –LAN settings to enter the following screen.
¾ LAN MAC address: The Router’s LAN MAC address, which is unchangeable.
¾ IP address: The Router’s LAN IP address (not your PC’s IP address).The default
value is 192.168.0.1; you can change it when necessary.
¾ Subnet mask: The Router’s LAN subnet mask. The default value is 255.255.255.0
NOTE:
Once you modify the IP address, you need to remember it for next time you log in to
the web-based utility.
4.4 DNS Settings
DNS stands for Domain Name System (or Service).
¾ DNS setting: Select to enable the DNS server.
¾ Primary DNS address: Enter the necessary address provided by your ISP.

17
¾ Alternate DNS address: Enter the second DNS address if your ISP provides, which
is optional.
NOTE:
After the settings are completed, reboot the device to activate the modified settings.
4.5 WAN Medium Type
Wired WAN and wireless WAN
NOTE: This function applies only to some of the products.
Wired WAN: In this mode, the cable is directly connected to the WAN port. Wired WAN is
the default mode.
Wireless WAN: Enable this mode if your ISP provides you wireless connection service or
you want to use it to amplify wireless signals.
SSID: SSID (Service Set Identifier) is the identity of the wireless device. You can only
access to the ISP’ network by entering the correct SSID, namely the SSID of the ISP’s
wireless device. You can click the “Open scan” button to let the router automatically search
the ISP’s available SSID. The SSID can also be the SSID of the superior wireless device
when using wireless bridge.
MAC: To connect to the ISP’s wireless device, you need to know the device’s MAC address.
You can click the “Open scan” button to let the router automatically search the wireless
device’s MAC or superior wireless device’s MAC.
Channel: The wireless device’s communication channel. You must select the same
channel as the ISP’s wireless device to enable their communications. It can also be
scanned by clicking the “Open scan” button.
Security mode: When the ISP wireless device is secured, the access device should set the
same security mode, encryption mode and key as the ISP’ wireless device.
For example
If your ISP wireless device’s SSID is “wireless”, then just enter the ISP’s SSID, wireless
MAC address, and channel respectively into the corresponding fields of the above picture.
If the ISP device is secured, please set your router’s encryption type the same as the ISP
device’s .Or you can click the “Open scan” button to let the router automatically fill in the
SSID, Channel and wireless MAC. After saving, come back to the WAN Setting screen to
select the corresponding WAN connection type to complete the settings (For example, if

18
your ISP wireless device’s connection type is dynamic IP, just select DHCP).
4.6 Bandwidth Control
Bandwidth control is used to limit the communication traffic of LAN computers when
accessing the Internet. It can simultaneously control maximum of 254 PCs' traffic. In
addition, IP address range configuration is supported.
¾ Enable Bandwidth Control: To enable or disable the internal IP bandwidth control.
The default is disabled.
¾ IP Address: The IP address range of the hosts whose traffic has been controlled. It
can be a single IP address or IP address range.
¾ Upload/Download: To specify the traffic heading way for the selected IP addresses:
upload or download.
¾ Bandwidth Range: The maximum and minimum upload/download data traffic of the
hosts in specified IP range. The unit is KByte/s. The uplink of upload and download
can not exceed the WAN port bandwidth limitation range.
¾ Enable: To enable the current edited rule. Otherwise, the rule will not go into effect.
¾ Add to list: After you edit the rule, click the “add to list” button to add the current
rule to the rule list.
Here we take 2Mbps bandwidth as an example. Theoretically, the biggest downloading rate
for 2Mbps bandwidth is 2Mbps=256KByte/s, and the biggest uploading rate is
512kbps=64KByte/s
Example 1
If you want to set the download rate of the computer at the IP address of 192.168.0.100 as
80-90KByte/s, upload rate as 10-15KByte/s, first add one upload rule as shown in the
picture below:
1. Enter 192.168.0.100 in the IP address field
2. Select upload in the Upload/Download field.
3. Enter 10-15 in the bandwidth range field
4. Select “Enable”
5. Click “Add to list”
6. Click “Ok” to finish the upload rule settings.
And then add a download rule as shown in the picture below.

19
The setting method is the same as the above.
Example 2 Set the download rate of all computers within the range of
192.168.0.2--192.168.0.254 as 100-120KByte/s, and the upload rate as 20-30KByte/s, as
shown in the picture below.
The setting method is the same as Example 1.
4.7 Traffic Statistics
Traffic statistics is used to display the bandwidth that LAN PC used.
Enable Traffic statistics: It is used to calculate the traffic used by the LAN computers. You
can enable it to calculate the traffic for you. Usually, disable it to improve the router’s data
packet processing ability, and the default is disabled. When this function is enabled, the
webpage will refresh automatically every five minutes, meanwhile, each computer’s traffic
value will refresh automatically.
¾ IP address: the IP address of the computer whose traffic is being calculated.
¾ Uplink rate: the data sending speed per second, the unit is KByte/s.
¾ Downlink rate: the data receiving speed per second, the unit is KByte/s.
¾ Sent message: the number of the calculated computer’s data packets that are sent
out through the router.
¾ Sent Bytes: the volume of the calculated computer’s statistics that is sent out
through the router
¾ Received message: the number of the calculated computer’s the data packets that
are received through the router.
¾ Received Bytes: the volume of the calculated computer’s statistics that is received
through the router.

20
Chapter 5 WLAN Settings
5.1 Wireless Basic Settings
¾ Enable wireless function: Select to enable the Router’s wireless features; deselect
to disable it and all functions related with wireless are disabled.
¾ Wireless working mode: This router provides two kinds of working modes: Wireless
Access Point(AP) and Network Bridge (WDS)
Wireless Access Point (AP)
¾ Network Mode: Select one mode from the drop-down list.
11b mode:Select it if you have only Wireless-B clients in your network.
11g mode:Select it if you have only Wireless-G clients in your network.
11b/g mixed mode: Select it if you have only Wireless-B and Wireless-G clients
in your network.
11b/g/n mixed mode: Select it if you have Wireless-B, Wireless-G and
Wireless-N clients in your network.
¾ SSID: It is the unique name of the wireless network and can be modified. The SSID
must be entered.
¾ Broadcast (SSID): Select “Enable” to enable the router’ SSID to be scannable by
wireless devices. The default is enabled. If you disable it, the wireless devices must
know the SSID for communication.
¾ Channel: The currently used channel by the router. Select an effective channel (from
1 to 13\Auto) of the wireless network.
¾ WMM Capable: Enable it to enhance the transfer performance of the wirelessly
transferred multimedia data (such as video or online playing).We recommend
enabling this option if you are not familiar with WMM.
¾ APSD Capable: It is used for auto power-saved service. The default is disabled.
¾ Channel bandwidth: Select an appropriate channel bandwidth to enhance the
wireless performance. Select 20/40M when the network has 11b/g and 11n wireless
clients. Select 20M when the network has only non-11n wireless clients. Select
20/40M to promote its throughput when the wireless network is in 11n mode.
¾ Extension Channel: To confirm the network’s frequency range in 11n mode.
NOTE: Some products may have primary SSID and secondary SSID options, as

21
shown below. Primary SSID is necessary, secondary SSID is optional.
Network Bridge (WDS) Settings
WDS (Wireless Distribution System) is used to expand wireless coverage area.
¾ AP MAC address: Input the MAC address of another (opposing) wireless router you
want to connect.
Example: This example is to bridge two ER-5840N/ER-5845N routers.
1. If you know the connecting router’s MAC address, please enter it into the AP MAC
address field and click “Ok”.
2. You can also search for the wireless router’s signal by scanning.
a) Click “Open scan” and click the scanned signal and click the ”Ok” button on the dialog
box and the corresponding wireless MAC address will be added to the AP MAC address
field automatically.
b) Click “Ok” after the MAC address is added.
After finishing the above steps, you need to set the other ER-5840N/ER-5845N router in
the same way.
NOTE:
WDS feature requires both routers support this function and the SSID, channel,
encryption method and password are the same as those of the connecting router.
5.2 Wireless Security Settings
With the wireless security function, you can prevent others from connecting to your wireless
network and using the network resources without your consent. Meanwhile, you can also
block illegal users from intercepting or intruding your wireless network.

22
5.2.1 WPS Settings
WPS (Wi-Fi Protected Setting) makes it quick and easy to establish a secure connection
between the wireless clients and the router. The users only need to enter a PIN code or
press WPS button on the back panel to configure it without manually selecting an
encryption method or set a key.
¾ WPS settings: To enable or disable WPS function. The default is “Enable”.
¾ WPS mode: Provide two ways: PBC (Push-Button Configuration) and PIN code.
¾ PBC: Select the PBC and click Ok, or press and hold the WPS button on the back
panel of the device for about one second. The WPS LED indicator will be flashing for
2 minutes, which means the WPS is enabled. During this time (flashing WPS LED),
you can enable the wireless client to implement the WPS/PBC negotiation between
them. When the WPS connection is completed, the LED indicator will be
continuously lit. To add more clients, repeat the above steps.)
¾ PIN: If this option is enabled, you need to enter a wireless client’s PIN code in the
field and keep the same code in the WPS client.
¾ Reset OOB: Press this button, the WPS client will be in an idle state, and the WPS
indicator will turn off. AP will not respond to the WPS client’s connection request and
will set the security mode as Open-None (Disable) mode.
NOTE:
The use of WPS function requires the wireless adapter to support this function.
5.2.2 WPA- PSK
WPA guarantees to protect WLAN users’ data and only the authorized network users can
have access to WLAN.
¾ WPA Algorithms: Provides TKIP [Temporal Key Integrity Protocol] or AES
[Advanced Encryption Standard].
¾ Key: Enter the pass phrase that consists of 8-63 ASCII characters.
¾ Key Renewal Interval: Set the key’s renewal period, which tells the device how
often it should change the dynamic keys.

23
5.2.3 WPA2- PSK
WPA2 (Wi-Fi Protected Access version 2) provides higher security than and WPA (Wi-Fi
Protected Access).
¾ WPA Algorithms: Provides TKIP [Temporal Key Integrity Protocol] or AES
[Advanced Encryption Standard].
¾ Key: Enter the pass phrase that consists of 8-63 ASCII characters.
¾ Key Renewal Interval: Set the key’s renewal period, which tells the device how
often it should change the dynamic keys.
5.3 Wireless Access Control
Wireless access control is actually based on the MAC address to permit or forbid specific
clients to access the wireless network.
¾ MAC address filter: “Permit” indicates to allow the clients in the list to access the
wireless network, “Forbid” indicates to prevent the clients in the list from accessing
the wireless network.
¾ Configure MAC address: Input the MAC addresses of the wireless clients to
implement the filter policy. Click “Add” to finish the MAC add operation.
¾ MAC Address list: Show the added MAC addresses. You can add or delete them.
5.4 Connection Status
This screen shows wireless client’s connection status, including MAC address, Channel
bandwidth.
¾ MAC address: Shows the MAC addresses of the hosts connected to the Router.
¾ Bandwidth: Shows the channel bandwidth of the current connected hosts (wireless
clients).

24
Chapter 6 DHCP Server
6.1 DHCP Server
DHCP (Dynamic Host Control Protocol) is used to assign an IP address to the computers
on the LAN/private network. When you enable the DHCP Server, the DHCP Server will
allocate automatically an unused IP address from the IP address pool to the requesting
computer in premise of activating “Obtain an IP Address Automatically”. So specifying the
start and end address of the IP Address pool is needed.
¾ DHCP server: Check the Enable box to enable DHCP server.
¾ IP pool start/end address: Enter the range of IP addresses for DHCP server
distribution.
¾ Lease time: It indicates the valid time of the dynamic IP address which is distributed
to the DHCP client’s host computer by DHCP server. During this time, the server will
not distribute the IP address to any other host computer.
6.2 DHCP Client List
DHCP client list displays user computer’ IP address, MAC address, host name and other
information which are assigned by the DHCP server. You can manually enter the IP and
MAC address and convert them to static assignment.
¾ Host name: It displays the name of the computer whose IP is allocated by the DHCP
server.
¾ IP address: Enter the IP address which needs static binding.
¾ MAC address: Enter the MAC address of the computer you want to bind. Click
“Add” to add the entry in the list.
¾ Lease time: The remaining time length of the corresponding IP address lease.

25
Chapter 7 Virtual Server
7.1 Port Range Forwarding
¾ Start/End port: Enter the start/end port number which ranges the External ports
used to set the server or Internet applications.
¾ LAN IP: Enter the IP address of the PC which you want to set as the server.
¾ Protocol: Select the protocol (TCP/UDP/Both) for the application. If you are not
clear about the protocol you are using, you can select “Both”.
¾ Enable: Click the Enable checkbox to bring the set rule into effect.
¾ Delete: Clear all settings of this item.
¾ Well-known service port: The well-known protocol ports are listed in the drop-down
list. Select one and select a sequence number in the ID drop-down list and then click
“Add”, this port will be added automatically to the ID list. For other well known service
ports that are not listed, you can manually add them to the list.
¾ Add to: Add the selected well-known port to the policy ID.
For Example: You want to share some large files with your friends outside of your local
area network, however, they are too big, and it’s not convenient to transfer them. Then, you
can build a FTP server on your computer and set the router’s port range forwarding to
enable your friends to access to these files on your computer. Suppose that your FTP
server or your computer’s static IP address is 192.168.0.10, and you wish your friends can
access the server through the default port 21 and adopts TCP protocol.
Please follow the steps below to configure.
1.Enter 21 in both start port and end port fields, or you can also select FTP from the
well-known service port and its port 21 will be added to the corresponding field
automatically.
2. Enter 192.168.0.10 in the LAN IP column, and then select “Both” as the protocol and
select “Enable”.
3. As the picture shown below.
4. Click the “Ok” button to save the settings.
And now, when your friends want to visit the FTP server, they only need to enter
ftp://xxx.xxx.xxx.xxx:21 in the address field. Here, xxx.xxx.xxx.xxx means the router’s WAN
IP address. For example, when your router’s WAN IP address is 172.16.102.89; your
friends need to enter ftp://172.16.102.89:21 in the address field.

26
NOTE:
If you set the service port of the virtual server as 80, you must set the Web
management port on Remote Web Management screen to be any value except 80
such as 8080. Otherwise, there will be a conflict to disable the virtual server.
27
7.2 DMZ Settings
The DMZ Settings screen allows one local computer to be exposed to the Internet for use
of a special-purpose service such as Internet gaming or videoconferencing. DMZ hosting
forwards all the ports at the same time to one PC.
¾ DMZ Host IP Address: The IP address of the LAN computer you want to set as
DMZ host.
¾ Enable: Check to enable the DMZ host.
For example:
Set the computer at the IP address of 192.168.0.10 as DMZ host to connect another host
on the Internet for intercommunication.
NOTE:
When the DMZ host is enabled, the firewall settings of the DMZ host will not function.
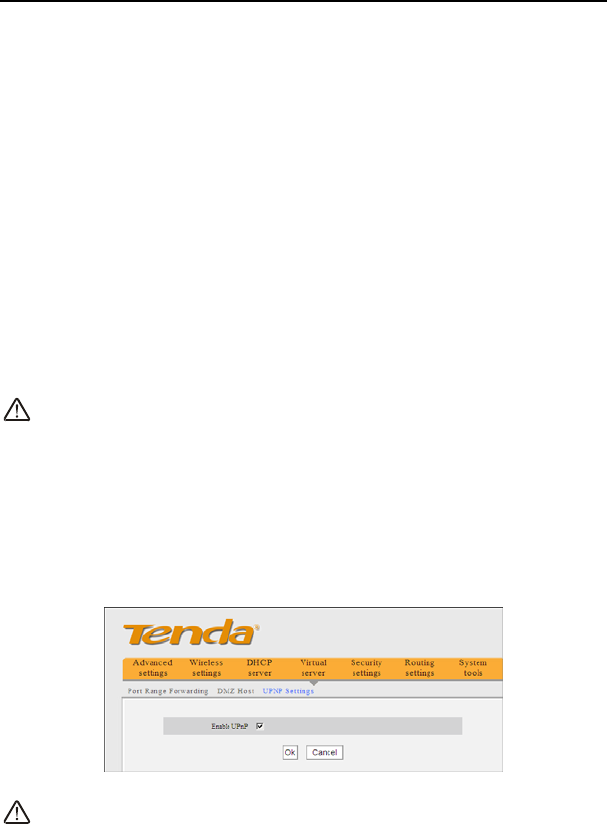
7.3 UPNP Settings
UPnP (Universal Plug and Play).With the UPnP function, the internal host can request the
router to process some special port switching so as to enable the external host to visit the
resources of the internal host.
¾ Enable UPnP: Click the checkbox to enable the UPnP.
NOTE:
This function goes into effect under Windows XP or Windows ME (NOTE: the system
should integrate or have installed the Directx 9.0) or this function would go into
effect if you have installed software that supports UPnP.

28
29
Chapter 8 Security Settings
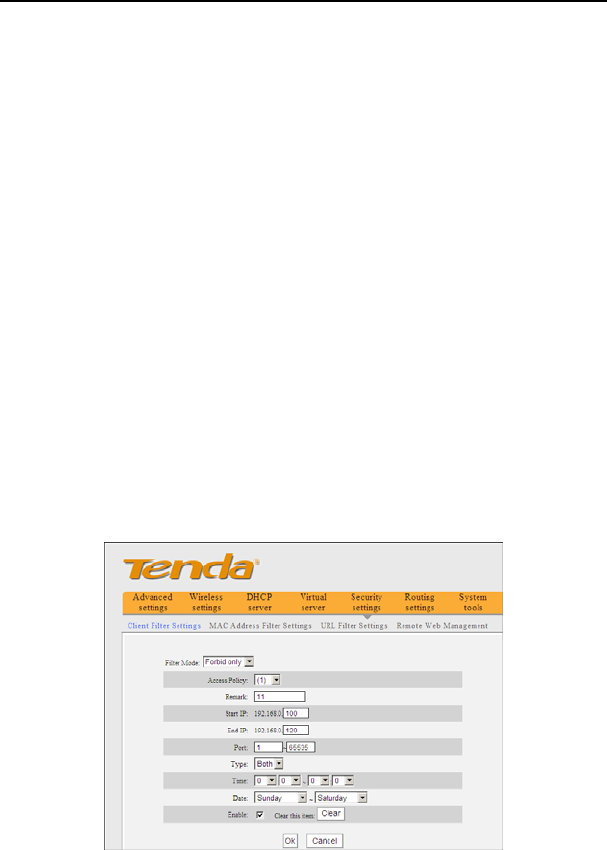
8.1 Client Filter Settings
You can enable client filter to control LAN computers’ access to some ports of the Internet。
¾ Filter Mode: You can select either “Permit only” or “Forbid only”.
¾ Access Policy: Select one number from the drop-down list.
¾ Remark: A simple description of the configured file. You can also leave it blank.
¾ Start/End IP: Enter the start/end IP address.
¾ Port: Enter the controlled TCP/UDP protocol port. You can specify a port or port
range.
¾ Type: Select one protocol (TCP/UDP/Both) from the drop-down list.
¾ Time: Select the time range of client filter.
¾ Date: Select the day(s) to run the access policy.
¾ Enable: To enable/disable the access policy (forbid/permit the packets matched with
the access policy to pass through the router.
Example1 Forbid LAN computers at the IP addresses of 192.168.0.100--192.168.0.120 to
access the Internet.
Example 2 Permit LAN computer with the IP address of 192.168.0.145 to access
websites during 8:00 to 18:00 from Sunday to Saturday.

30
8.2 MAC Address Filter
You can limit the computer’s access to Internet by MAC Address Filter.
¾ Filter mode: You can select either “Permit only” or “Forbid only”.
¾ Access Policy: Select one number from the drop-down list.
¾ Remark: A simple description of the configured file. You can also leave it blank.
¾ MAC Address: Enter the MAC address you want to run the access policy.
¾ Time: Select the time range of MAC address filter.
¾ Date: Select the day(s) to run the access policy.
¾ Enable: To enable/disable the access policy (forbid/permit the packets matched with
the access policy to pass through the router).
Example 1 Forbid the computer with the MAC address of 00:E0:4C:69:A3:23 to access
Internet during 8:00 to 18:00 from Monday to Friday.
Example 2 Permit the computer with the MAC address of 00:E4:A5:44:35:69 to access
Internet from Monday to Friday.
8.3 URL Filter Settings
You can use URL filtering to forbid their access to certain websites at a specified time.
¾ Filter Mode: You can select either “Permit only” or “Forbid only”.
¾ Access Policy: Select one number from the drop-down list.
¾ Remark: A simple description of the configured file. You can also leave it blank.
¾ Start/End IP: Enter the start/end IP address.
¾ URL character string: Specify the text strings or keywords needed to be filtered.
¾ Time: Select the time range of URL filter.
¾ Date: Select the day(s) to run the access policy.
¾ Enable: To enable/disable the access policy (forbid /permit the packets matched with
the access policy to pass through the router).

31
Example1 Forbid all computers on LAN to access baidu.com during 8:00 to 18:00 from
Monday to Friday.
Example2 Permit LAN computers with the IP addresses of 192.168.0.100- 192.168.0.115
to access yahoo.com.
NOTE:
Enter only one domain name for each access policy for one access policy can only
filter one domain name. So, if you want to filter multiple domain names, you need to
set multiple access policies
8.4 Remote Web Management
This section instructs how to allow the network administrator to manage the Router
remotely. If you want to access the Router from outside of the local network, please click
the checkbox after “Enable”.
¾ Enable: Check to enable remote web management.
¾ Port: The management port open to outside access. The default value is 80.
¾ IP Address: Specify the range of the IP addresses of the computers on the Internet
for remote management.
NOTE:
1. If you want to log in the device’s Web-based Utility via port 8080, you need to use
the format of WAN IP address: port (for example http://220.135.211.56:8080) to
implement remote login.
2. If your WAN IP address starts and ends with 0.0.0.0, it means all hosts on the
Internet can implement remote Web management. If you change the Internet IP
address as 218.88.93.33-218.88.93.35, then only the computers at the IP addresses of
218.88.93.33, 218.88.93.34 and 218.88.93.35 can access the Router to implement
remote web management.
For example:
If you want to configure the computer at the IP address of 218.88.93.33 to access the
router’s web-based utility via port 8080, please set the parameters as above.

32
Chapter 9 Routing Settings
9.1 Routing Table
This page shows the router’s core routing table.
The main duty for a router is to look for a best path for every data packet, and transfer this
data packet to a destination station. In order to fulfill this function, many transferring paths,
i.e. routing table, are saved in the router, for choosing when needed.
9.2 Static Routing
This screen is used to set the router’s static routing.
A static route is a pre-determined pathway that network information must travel to reach a
specific host or network.
¾ Destination network IP address: The destination host or IP segment you visit.
¾ Subnet mask: Enter the subnet mask, generally it is 255.255.255.0
¾ Gateway: The entry IP address of the next router.
NOTE:
1. The gateway must be at the same net segment with the router’s LAN IP.
2. If the destination IP address is one host’ address, then the subnet mask must be
255.255.255.255.
3. If the destination IP address is an IP segment, then it must match with the subnet
mask. For example, if the destination IP is 10.0.0.0 then the subnet mask must be
255.0.0.0

33
Chapter 10 System Tools
10.1 Time Settings
This section is to configure the router’s system time. You can set it manually or obtain the
GMT time from the Internet.
¾ Time zone: Select the time zone where you are operating the Router from the
drop-down list.
¾ Customized time: Enter the time you wish to configure.
NOTE:
When the Router is powered off, the time settings will be lost. The router will obtain
the GMT time automatically when you next time access the Internet. Only when you
connect to the Internet and obtain the GMT time or set the time on this screen, can
the time settings in other functions (e.g. security settings) take effect.
10.2 DDNS
The DDNS (Dynamic Domain Name System) is supported in this Router. It is used to
assign a fixed host and domain name to a dynamic Internet IP address. Every time you
access the Internet, the dynamic domain name software installed on your host will tell the
ISP’S host server its dynamic IP address by sending messages. And the server software is
responsible for providing DNS service and implementing dynamic domain name resolution.
¾ Main features:
1. Mostly, your ISP provides a dynamic IP address and the DDNS is used to capture
the changeable IP address and match to the fixed domain. Then users can have
access to the Internet to communicate with others outside the network.
2. DDNS can help you to establish a virtual host in your home or company.
¾ DDNS: Click the radio button to enable or disable the DDNS service.
¾ Service provider: Select one from the drop-down list and click “Sign up” for
registration.
¾ Username: Enter the username that you use to register from the DDNS provider
¾ Password: Enter the password that you use to register from the DDNS provider
34
¾ Domain name: Enter the effective registered domain name
For example:
Establish a Web server in the local host 192.168.0.10 and register in 3322.org as follows:
Username ER-5840n/ER-5845n
Password 123456
Domain Name ER-5840n/ER-5845n.3322.org
After mapping the port in the virtual server, and setting account information in DDNS server,
you can then access the web page by entering http://ER-5840n/ER-5845n.3322.org in the
address field.
10.3 Backup/Restore
On this screen, you can back up the router’s current settings or restore previous settings.
¾ Backup Setting:
Click the Backup button to back up the Router’s settings and select a path to save
them.
Click the “Save” button to save the configuration files.
¾ Restore Setting:
Click the “Browse” button to select the backup files.
35
Click the “Restore” button to restore previous settings.
10.4 Restore to Factory Default
This screen allows you to restore all settings to the factory default values.
¾ Restore: Click this button to restore to default settings.
¾ Factory default settings:
Password: NULL(the default password displays as null)
IP address: 192.168.0.1
Subnet mask: 255.255.255.0
NOTE:
After restoring to default settings, please restart the router to make the default
settings effective.
10.5 Upgrade
By upgrading the router’s software, you’ll get better software version and appreciated
routing function. Before upgrading, download the Router’s software upgrade file from our
website, www.ER-5840n/ER-5845n.cn.

36
¾ Browse: Click this button to select the upgrade file.
¾ Upgrade: Click this button to start the upgrading process. After the upgrade is
completed, the router will reboot automatically.
10.6 Reboot the Router
Reboot the router to make the configuration effective. The router will cut its WAN
connection automatically after rebooting.
¾ Reboot the router: Click this button to reboot the router.
10.7 Password Change
This section is to set a new password to better secure your router and network.
¾ Old password: Enter the old password.
¾ New password: Enter a new password.
¾ Confirm new password: Re-enter to confirm the new password.
NOTE:
The default password displays as null, users can log on the web-based utility
without any authentication. To secure the router and your network, it is highly
recommended that you change the initial password.
10.8 Syslog
The section is to view the system log. You can view various conditions appearing after
system start, and also check whether there’s an attack on the network. The log can record
at most 150 entries.
¾ Refresh: Click this button to update the log.
¾ Clear: Click this button to clear the current shown log.
10.9 Log out

37
After all settings are finished, please click’” Log out” to exit securely and completely.
Appendix 1 Glossary
Channel:
An instance of medium use for the purpose of passing protocol data units (PDUs) that may
be used simultaneously, in the same volume of space, with other instances of medium
use(on other channels) by other instances of the same physical layer (PHY),with an
acceptably low frame error ratio(FER) due to mutual interference.
SSID:
SSID (Service Set Identifier) is the network name shared by all devices in a wireless
network. Your network’s SSID should be unique to your network and identical for all
devices within the network. It is case-sensitive and must not exceed 20 characters (use any
of the characters on the keyboard).Make sure this setting is the same for all devices in your
wireless network.
WPA/WPA2 Encryption:
A security protocol for wireless networks that builds on the basic foundations of WEP. It
secures wireless data transmission by using a key similar to WEP, but the added strength
of WPA is that the key changes dynamically. The changing key makes it much more difficult
for a hacker to learn the key and gain access to the network.WPA2 is the second
generation of WPA security and provides a stronger encryption mechanism through
Advanced Encryption Standard (AES), which is a requirement for some government users.
802,1x authentication
Static WEP key is difficult to manage for when you change the key, you will have to inform
all others, and if the key is disclosed in one of the places, the key can no longer provide
security. Besides, there’s severe security loophole about static WEP encryption. The WEP
key can be decrypted after one person receives a specific amount of data via wireless
intercepting. 802,1x is initially used for wired Ethernet authentication access to prevent
illegal users from accessing the network. Later, it is found that 802.1x can better solve the
wireless network security problem. EAP-TLS of the 802.1x successfully achieves the
two-way authentication between users and networks, i.e. can prevent illegal users from
accessing the network and can also prevent users from accessing the illegal AP. 802.1x
utilizes dynamic WEP encryption to protect the WEP key from being decrypted. To solve
the publishing problem for digital certification, people make some changes to TLS
authentication and TTLS and EAP come into exist, which enable you to access the network
by using the traditional way of authentication: username and password.

38
Appendix 2 Product Features
Supports IEEE 802.11n, IEEE 802.11g, IEEE 802.11b, IEEE 802.3 and IEEE 802.3u
standards.
High gain omni-directional antenna, with strong signals and long transmission
distance.
Wireless transmission rate up to 150Mbps or 300 Mbps
Provides one 10/100Mbps auto-negotiation Ethernet WAN port to connect to the
Wide Area Network
Provides four 10/100Mbps auto-negotiation Ethernet LAN ports to connect to the
Local Area Network
Supports Auto MDI/MDIX
Supports xDSL/Cable MODEM, static and dynamic IP in community broadband
networking
Includes router, wireless access point, four-port switch and firewall all in one
SupportsWPA-PSK,WPA2-PSK,andWPA-PSK&WPA2-PSK mixed security modes
Supports WPS button
Supports hidden SSID function and MAC address-based access control
Supports WMM to make your audio and video smoother
Supports SNTP
Supports UPnP and DDNS
Supports WDS to extend wireless network
Supports wireless WAN and allows access to ISP’s wireless hotspots to share
Internet access with multiple computers (this function applies only to some of the
products).
Supports virtual server, DMZ host
Provides syslog to record the running status of the router

39
Appendix 3 FAQ
This section provides some solutions to the problems which may occur during the router’s
installation or usage. The instructions below may help you deal with the problems. If your
problem is not in the list, please log into our website www.ER-5840n/ER-5845n.cn or send
an E-mail to support@ER-5840n/ER-5845n.cn, and we will reply to you at the earliest time.
1. Can not log in to the Web-based Utility of the router after you enter the IP address in the
address field?
Step 1: Check if the router is working correctly, after the device is powered on for a few
seconds, the SYS indicator on the front panel should light up. If it is not, please contact us.
Step 2: Check the network cables are connected correctly and the corresponding LED
indicator lights up. Sometimes, the indicator lights up, but it does not mean it is functioning.
Step 3: Run “Ping” command and check if it can ping the Router’s LAN IP address
192.168.0.1 (open “Command Prompt” and type “Ping 192.168.0.1” and then enter). If it is
OK, please make sure your browser does not access the Internet by proxy server. If the
ping fails, you can press the “RESET” button for 7 seconds to restore to default settings.
And then repeat the ping operation. If it still does not work, please contact us.
2. Forgot the login password and cannot enter the Web-based Utility. What can I
do?
Press the “RESET” button for 7 seconds to restore the Router to default settings.
3. The computer connected with the Router shows IP address conflict. What can
do?
Check if there are other DHCP servers in the LAN and if there are then disable them. The
default IP address of the router is 192.168.0.1 please maker sure the address is not being
used by any other device. If there are two computers with the same IP address, please
change one of them.
4. I cannot use E-mail and access the Internet. What can I do?
Sometimes happens with ADSL connection and Dynamic IP users. You may need to modify
the default MTU value (1492). Please open the “WAN Setting” and modify the MTU value
with the recommended value as 1450 or 1400.
40
5.How to share my computer’s resource with other users in Internet?
If you want Internet users to access the internal server via the router such as: e-mail server,
Web, FTP. You can configure the “Virtual Server”.
Step 1: create your internal server, make sure the LAN users can access these servers
and know related service port. For example, Web server’s port is 80; FTP is 21; SMTP is 25
and POP3 is 110.
Step 2: In the router’s web click “Virtual Server” and select “Port Range Forwarding”.
Step 3: Input the service port provided by the router (i.e. the external port) for mapping the
internal and external network, for example, 80-80.
Step 4: input the internal Web service port, for example, 80-80.
Step 5: Input the internal server’s IP address. For example, if your Web server’s IP address
is 192.168.0.10, please input it.
Step 6: select the communication protocol used by your internal host: TCP, UDP, Both.
Step 7: click “Ok” to activate the settings.
The following table lists some well-known applications and their respective service ports:
Server Protocol Service Port
WEB Server TCP 80
FTP Server TCP 21
Telnet TCP 23
NetMeeting TCP 1503、1720
MSN
Messenger TCP/UDP
File Send:6891-6900(TCP)
Voice:1863、6901(TCP)
Voice:1863、5190(UDP)
PPTP VPN TCP 1723
Iphone5.0 TCP 22555
SMTP TCP 25
POP3 TCP 110
41
Appendix 4 Clear Wireless Configuration
Clear Wireless configuration file under windows XP
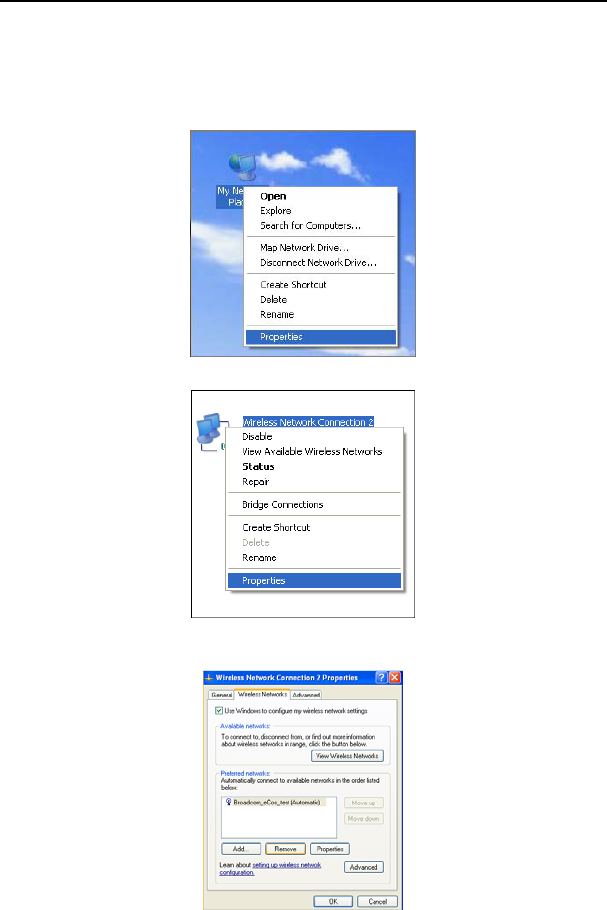
1. Right click “My Network Places” on your computer desktop and select “Properties”.
2. Right click “Wireless Network Connections” and select “Properties”.
3. Click “Wireless Network Configuration” and clear the corresponding wireless
configuration file as shown below.
42
Clear Wireless configuration file under windows 7
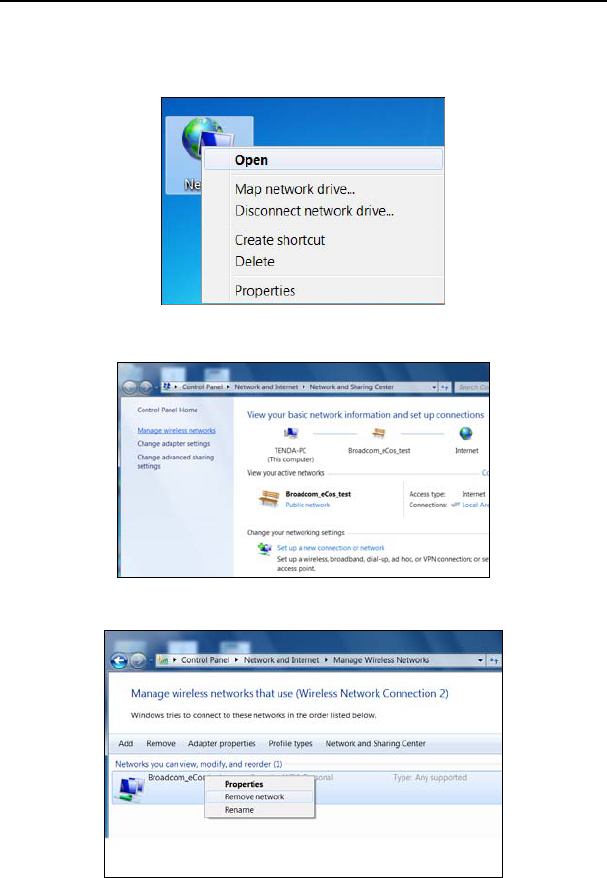
1. Right click “Network” and click “Properties”.
2. Click “Manage wireless networks” on the left side of the window.
3. Delete the corresponding configured file in the “Manage wireless networks”.

43
Appendix 5 Regulatory Information
EU Declaration or Declaration of Conformity
Hereby, SHENZHEN ER-5840N/ER-5845N TECHNOLOGY CO.,LTD, declares that this
Wireless Broadband Router is in compliance with the essential requirements and other
relevant provisions of Directive 1999/5/EC.
FCC Statement
This equipment has been tested and found to comply with the limits for a Class B digital
device, pursuant to part 15 of the FCC rules. These limits are designed to provide
reasonable protection against harmful interference in a residential installation. This
equipment generates uses and can radiate radio frequency energy and, if not installed and
used in accordance with the instructions, may cause harmful interference to radio
communications. However, there is no guarantee that interference will not occur in a
particular installation. If this equipment does cause harmful interference
to radio or television reception, which can be determined by turning the equipment off and
on, the user is encouraged to try to correct the interference by one or more of the following
measures:
-Reorient or relocate the receiving antenna.
-Increase the separation between the equipment and receiver.
-Connect the equipment into an outlet on a circuit different from that to which the receiver is
connected.
-Consult the dealer or an experienced radio/TV technician for help.
To assure continued compliance, any changes or modifications not expressly approved by
the party responsible for compliance could void the user’s authority to operate this
equipment. (Example- use only shielded interface cables when connecting to computer or
peripheral devices).
“The antenna(s) used for this transmitter must not be co-located or operating in conjunction
with any other antenna or transmitter.”
FCC Radiation Exposure Statement
This equipment complies with FCC radiation exposure limits set forth for an uncontrolled
environment. This equipment should be installed and operated with the minimum distance
of 20 cm. Operation is subject to the following two conditions:
1) This device may not cause interference, and
2) This device must accept any interference, including interference that may cause

44
undesired operation of the device.
Caution!
The manufacturer is not responsible for any radio or TV interference caused by
unauthorized modifications to this equipment. Such modifications could void the user
authority to operate the equipment.