D Link DIR855A1 Xtreme N DUO Media Router User Manual Manual Part 2
D Link Corporation Xtreme N DUO Media Router Manual Part 2
D Link >
Contents
- 1. Manual Part 1
- 2. Manual Part 2
- 3. Manual Part 3
Manual Part 2
39D-Link DIR-855 User Manual
Section 3 - Configuration
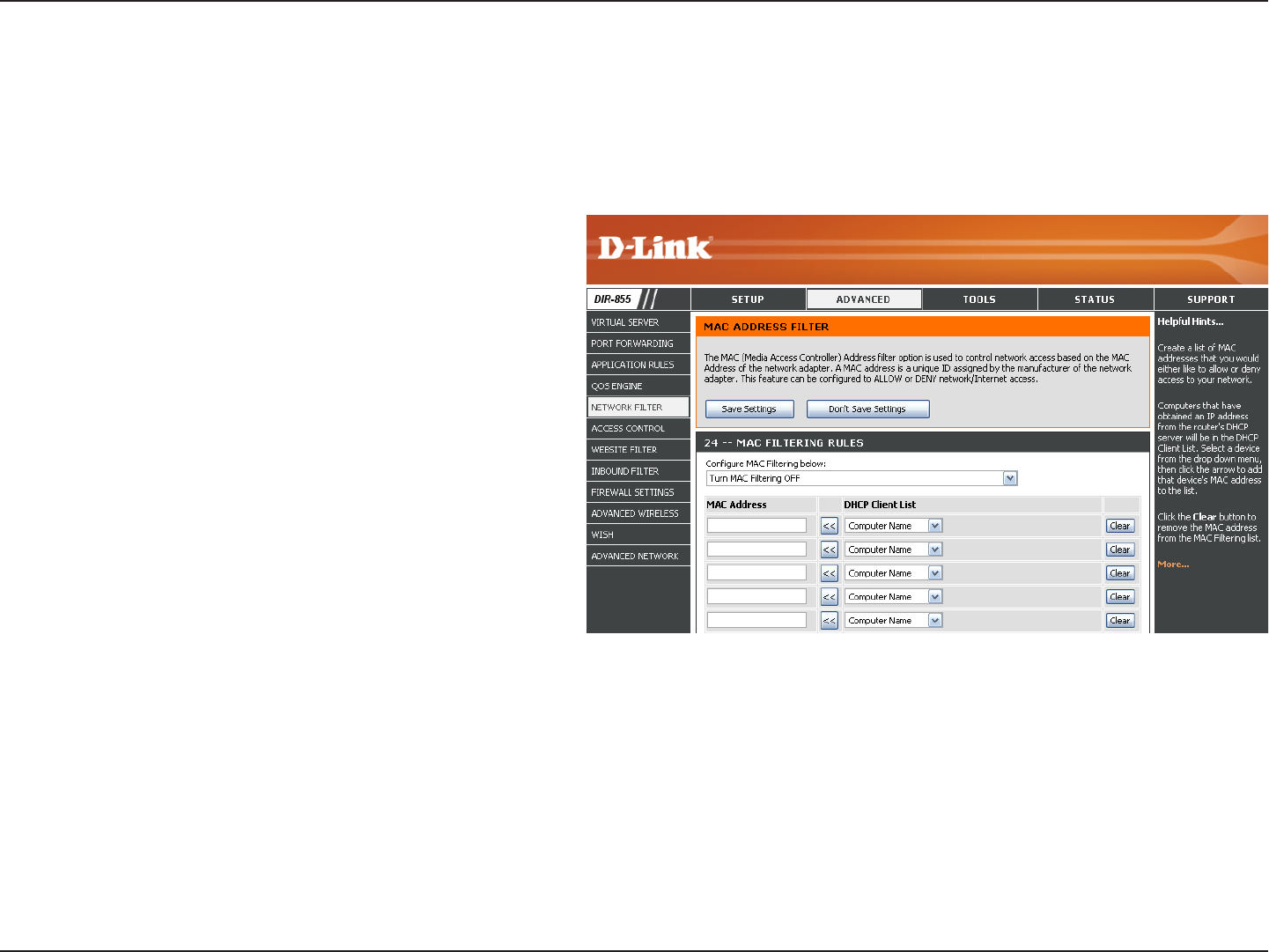
Network Filters
Select Turn MAC Filtering Off, Allow MAC
addresses listed below, or Deny MAC
addresses listed below from the drop-down
menu.
Enter the MAC address you would like to
filter.
To find the MAC address on a computer,
please refer to the Networking Basics section
in this manual.
Select a DHCP client from the drop-down menu
and click << to copy that MAC Address.
Click to remove the MAC address.
Configure MAC
Filtering:
MAC Address:
DHCP Client:
Clear:
Use MAC (Media Access Control) Filters to allow or deny LAN (Local Area Network) computers by their MAC addresses
from accessing the Network. You can either manually add a MAC address or select the MAC address from the list of
clients that are currently connected to the Broadband Router.
40D-Link DIR-855 User Manual
Section 3 - Configuration
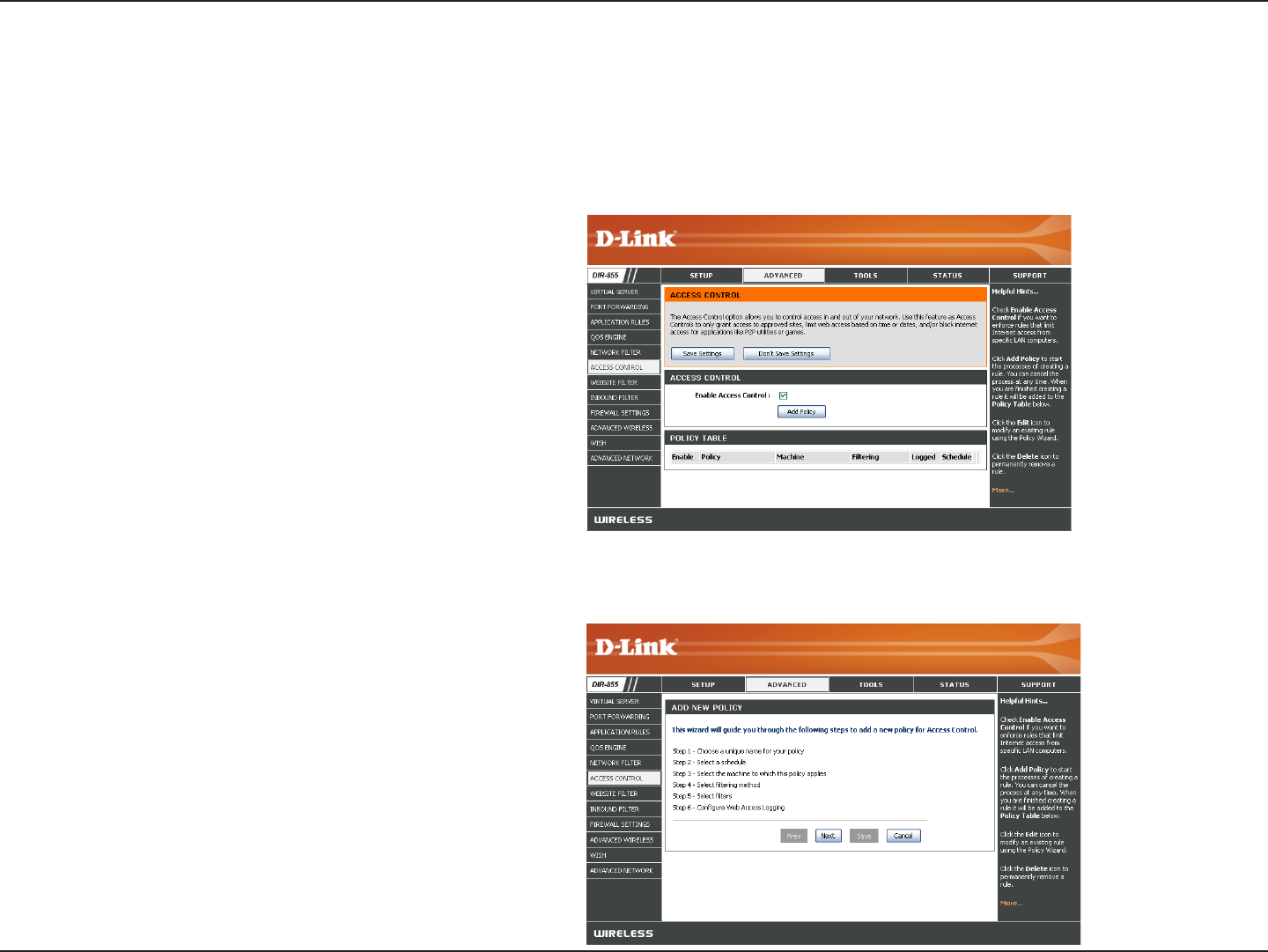
Access Control
Click the Add Policy button to start the Access
Control Wizard.
Add Policy:
The Access Control section allows you to control access in and out of your network. Use this feature as Parental Controls
to only grant access to approved sites, limit web access based on time or dates, and/or block access from applications
like P2P utilities or games.
Click Next to continue with the wizard.
Access Control Wizard
41D-Link DIR-855 User Manual
Section 3 - Configuration
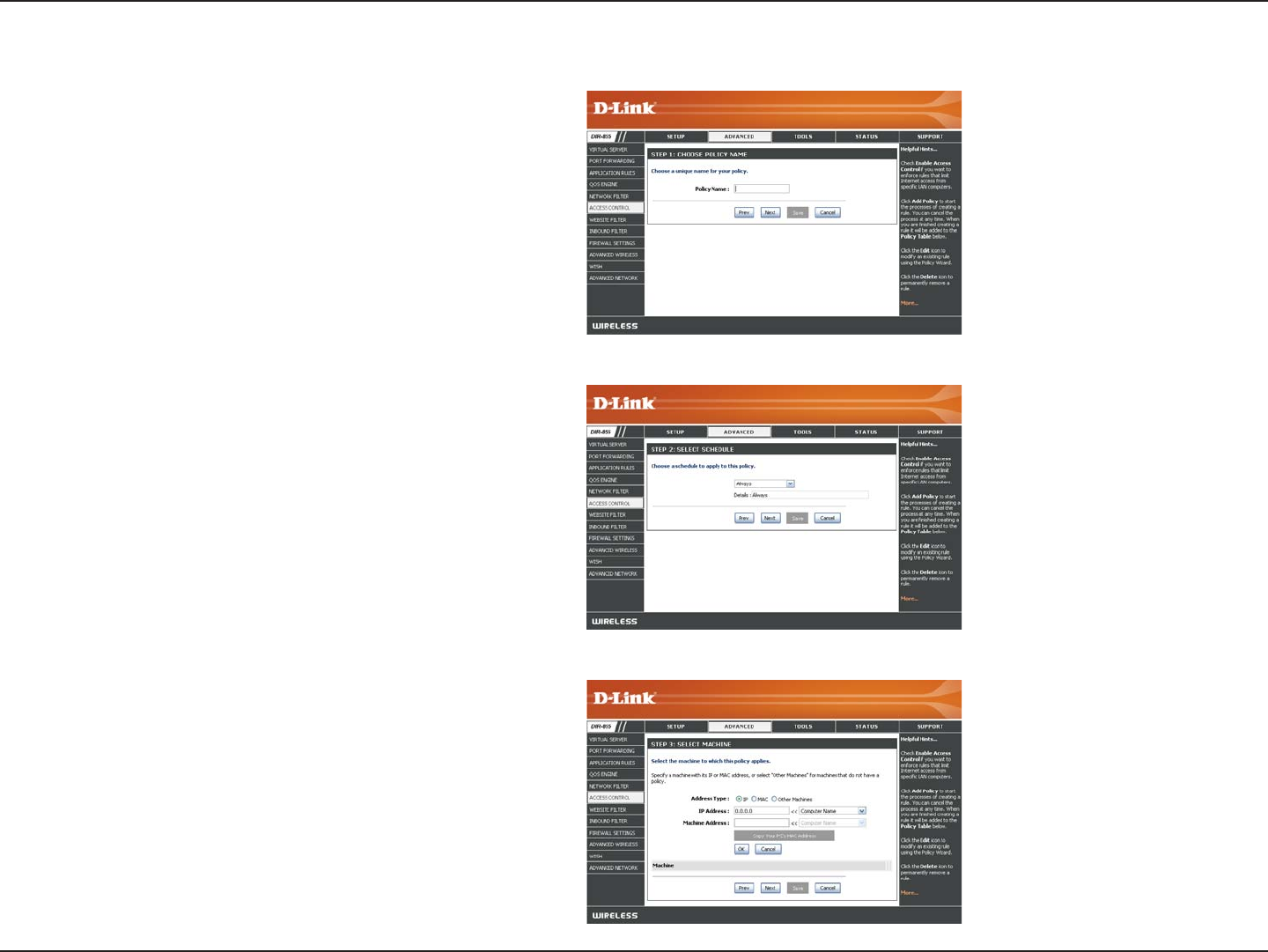
Enter a name for the policy and then click Next to continue.
Access Control Wizard (continued)
Select a schedule (I.E. Always) from the drop-down menu
and then click Next to continue.
Enter the following information and then click Next to
continue.
• Address Type - Select IP address, MAC address, or
Other Machines.
• IP Address - Enter the IP address of the computer
you want to apply the rule to.
42D-Link DIR-855 User Manual
Section 3 - Configuration
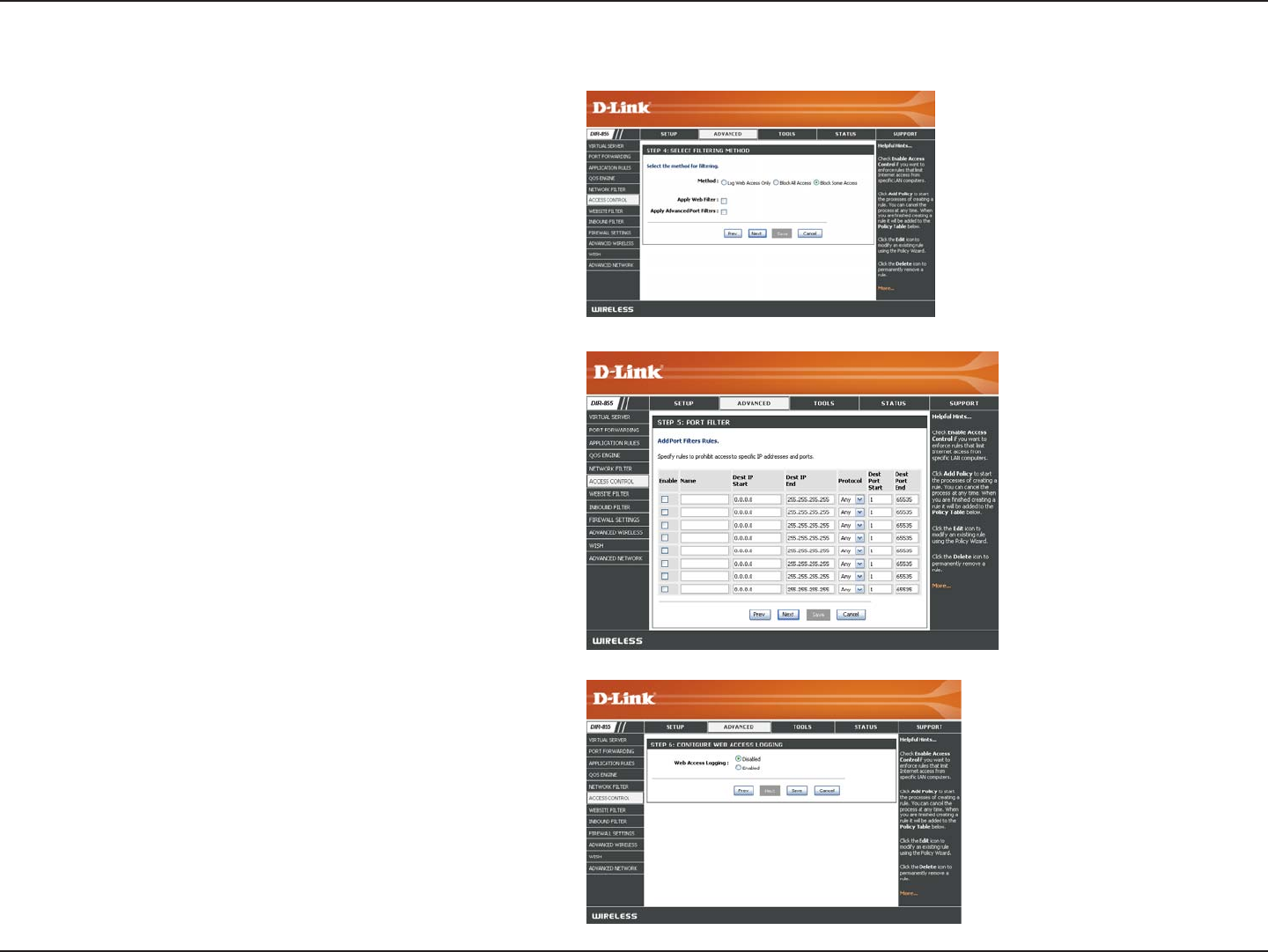
Select the filtering method and then click Next to continue.
Access Control Wizard (continued)
Enter the rule:
Enable - Check to enable the rule.
Name - Enter a name for your rule.
Dest IP Start - Enter the starting IP address.
Dest IP End - Enter the ending IP address.
Protocol - Select the protocol.
Dest Port Start - Enter the starting port number.
Dest Port End - Enter the ending port number.
To enable web logging, click Enable.
Click Save to save the access control rule.
43D-Link DIR-855 User Manual
Section 3 - Configuration
Add Website
Filtering Rule:
Website URL/
Domain:
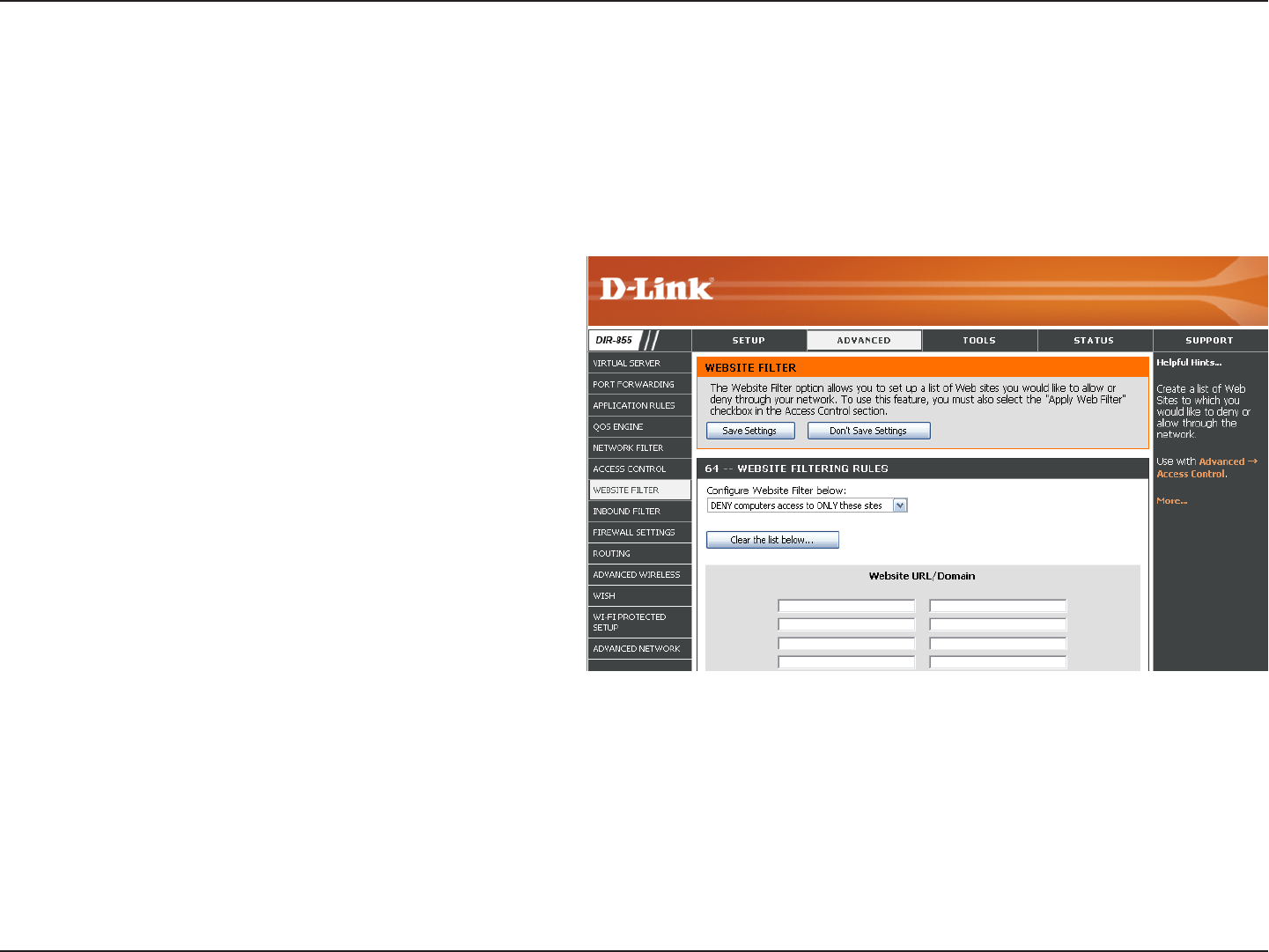
Website Filters
Select Allow or Deny.
Enter the keywords or URLs that you want to
allow or block. Click Save Settings.
Website Filters are used to allow you to set up a list of allowed Web sites that can be used by multiple users through
the network. To use this feature select to Allow or Deny, enter the domain or website and click Save Settings. You
must also select Apply Web Filter under the Access Control section (page 40).
44D-Link DIR-855 User Manual
Section 3 - Configuration
Enter a name for the inbound filter rule.
Select Allow or Deny.
Check to enable rule.
Enter the starting IP address. Enter 0.0.0.0
if you do not want to specify an IP range.
Enter the ending IP address. Enter
255.255.255.255 if you do not want to
specify and IP range.
Click the Add button to apply your settings.
You must click Save Settings at the top to
save the settings.
This section will list any rules that are created.
You may click the Edit icon to change the
settings or enable/disable the rule, or click
the Delete icon to remove the rule.
Name:
Action:
Enable:
Remote IP Start:
Remote IP End:
Add:
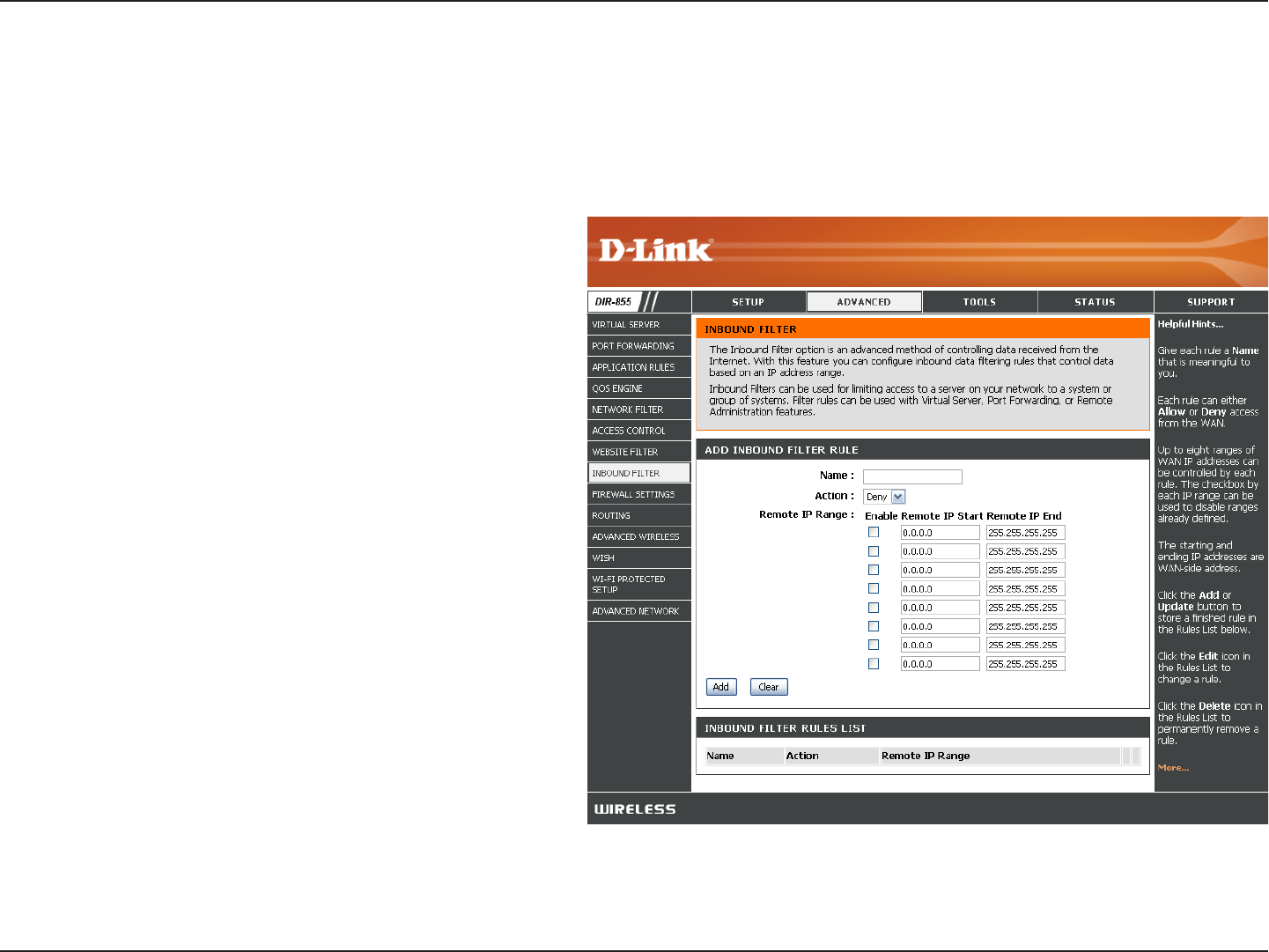
Inbound Filter
Rules List:
The Inbound Filter option is an advanced method of controlling data received from the Internet. With this feature you
can configure inbound data filtering rules that control data based on an IP address range. Inbound Filters can be used
with Virtual Server, Port Forwarding, or Remote Administration features.
Inbound Filters
45D-Link DIR-855 User Manual
Section 3 - Configuration
SPI (Stateful Packet Inspection, also known as dynamic packet
filtering) helps to prevent cyber attacks by tracking more state per
session. It validates that the traffic passing through the session
conforms to the protocol.
Select one of the following for TCP and UDP ports:
Endpoint Independent - Any incoming traffic sent to an open port
will be forwarded to the application that opened the port. The port
will close if idle for 5 minutes.
Address Restricted - Incoming traffic must match the IP address
of the outgoing connection.
Address + Port Restriction - Incoming traffic must match the IP
address and port of the outgoing connection.
Enable this feature to protect your network from certain kinds of
“spoofing” attacks.
If an application has trouble working from behind the router, you
can expose one computer to the Internet and run the application
on that computer.
Note: Placing a computer in the DMZ may expose that computer to
a variety of security risks. Use of this option is only recommended
as a last resort.
Specify the IP address of the computer on the LAN that you want to have unrestricted Internet communication. If this computer
obtains it’s IP address automatically using DHCP, be sure to make a static reservation on the Basic > DHCP page so that
the IP address of the DMZ machine does not change.
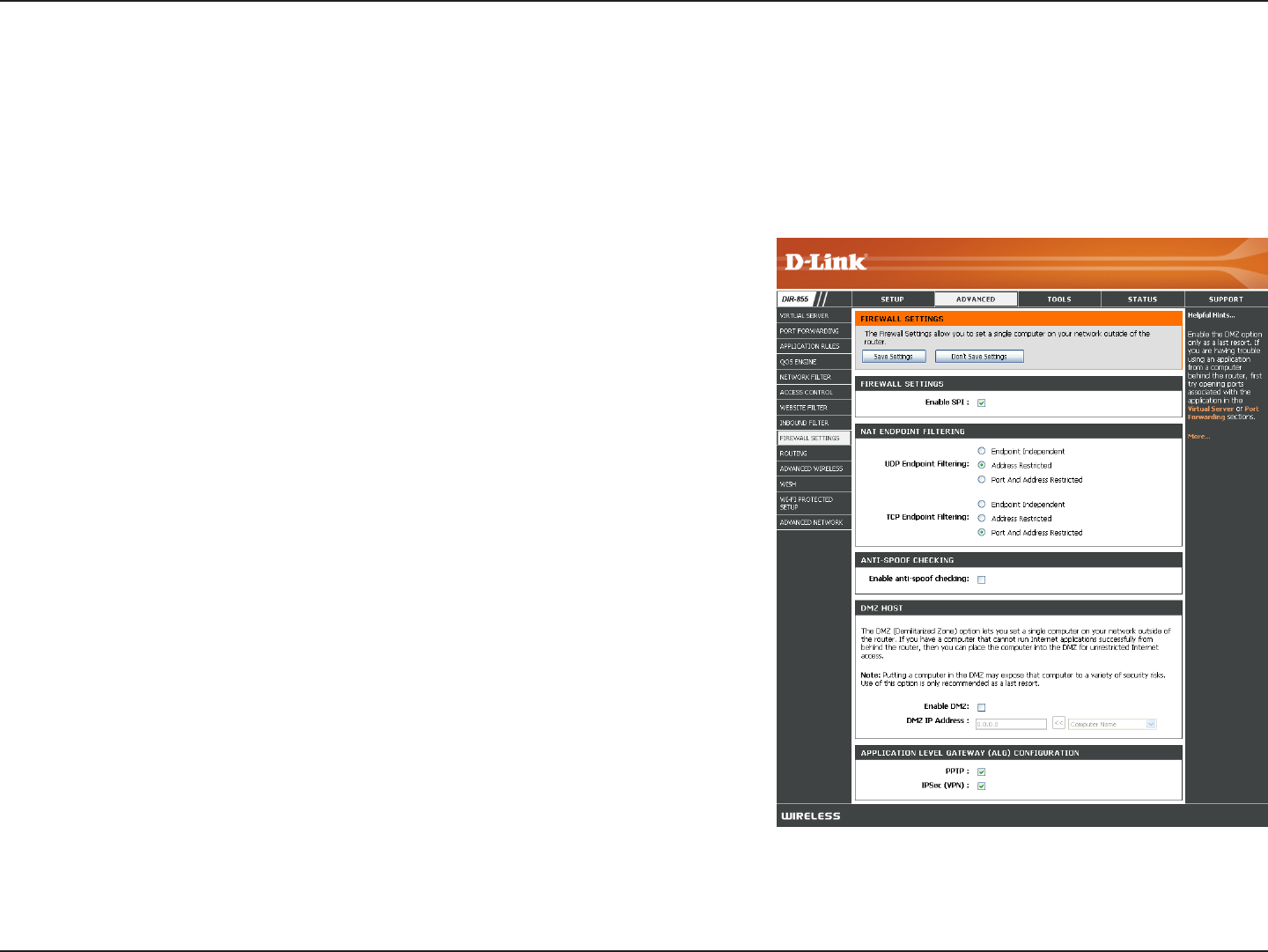
Enable SPI:
NAT Endpoint
Filtering:
Anti-Spoof Check:
Enable DMZ:
DMZ IP Address:
Firewall Settings
A firewall protects your network from the outside world. The DIR-855 offers a firewall type functionality. The SPI feature
helps prevent cyber attacks. Sometimes you may want a computer exposed to the outside world for certain types of
applications. If you choose to expose a computer, you can enable DMZ. DMZ is short for Demilitarized Zone. This option
will expose the chosen computer completely to the outside world.
46D-Link DIR-855 User Manual
Section 3 - Configuration
Application Level Gateway (ALG) Configuration
Here you can enable or disable ALG’s. Some protocols and applications require special handling of the IP payload to
make them work with network address translation (NAT). Each ALG provides special handling for a specific protocol
or application. A number of ALGs for common applications are enabled by default.
Allows multiple machines on the LAN to connect to their corporate network using PPTP protocol.
Allows multiple VPN clients to connect to their corporate network using IPSec. Some VPN clients support traversal of IPSec
through NAT. This ALG may interfere with the operation of such VPN clients. If you are having trouble connecting with your
corporate network, try turning this ALG off. Please check with the system adminstrator of your corporate network whether
your VPN client supports NAT traversal.
PPTP:
IPSEC (VPN):
47D-Link DIR-855 User Manual
Section 3 - Configuration
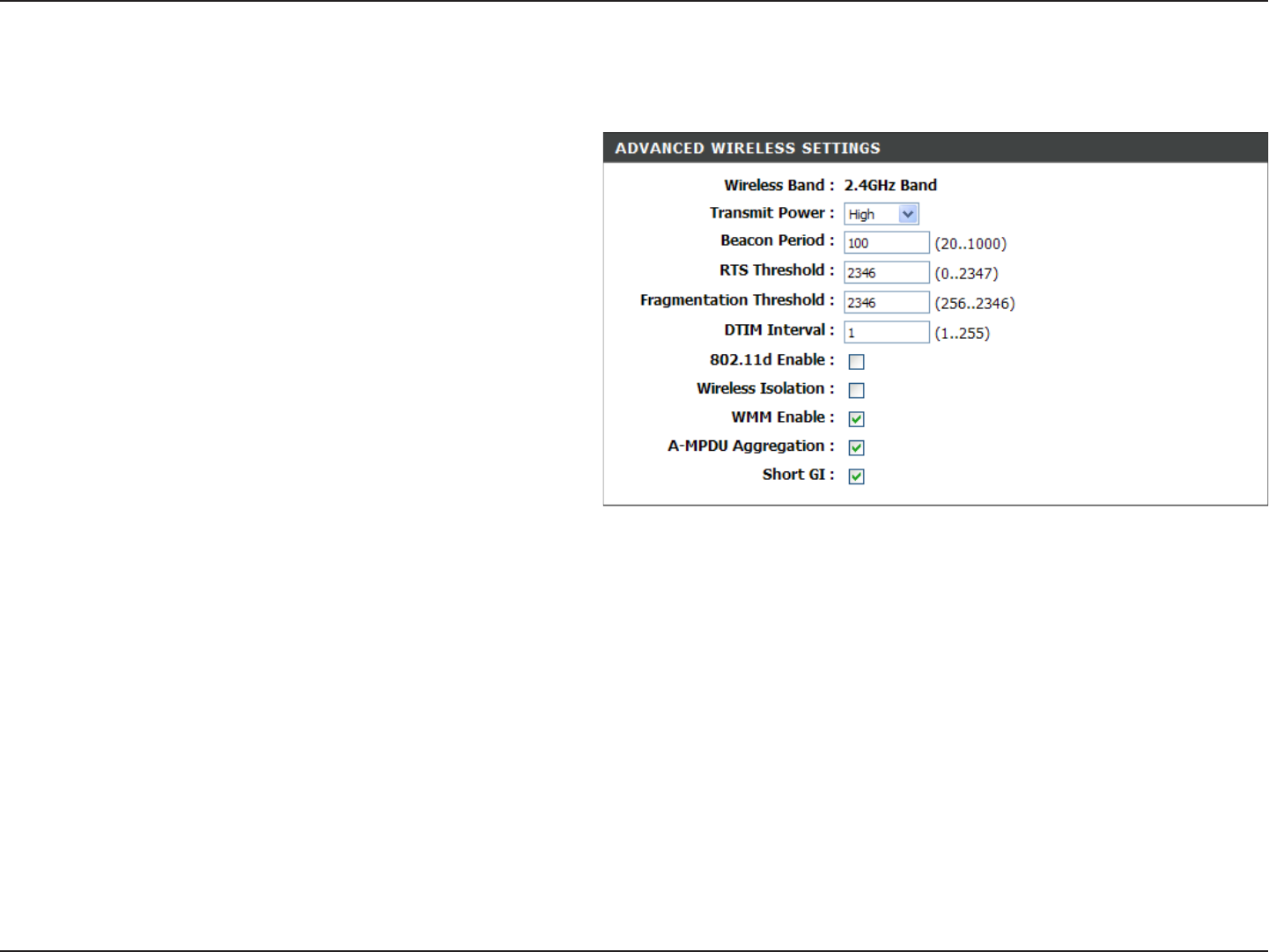
Set the transmit power of the antennas.
Beacons are packets sent by an Access Point to
synchronize a wireless network. Specify a value.
100 is the default setting and is recommended.
This value should remain at its default setting of
2432. If inconsistent data flow is a problem, only
a minor modification should be made.
The fragmentation threshold, which is specified
in bytes, determines whether packets will be
fragmented. Packets exceeding the 2346 byte
setting will be fragmented before transmission.
2346 is the default setting.
(Delivery Traffic Indication Message) 3 is the default setting. A DTIM is a countdown informing clients of the next window
for listening to broadcast and multicast messages.
This enables 802.11d operation. 802.11d is a wireless specification developed to allow implementation of wireless networks in
countries that cannot use the 802.11 standard. This feature should only be enabled if you are in a country that requires it.
When checked, it will disable the ability for computers on the wireless network from seeing each other, but will allow you to
see computers on the wired network.
WMM is QoS for your wireless network. This will improve the quality of video and voice applications for your wireless
clients.
Aggregated-MAC Packet Data Unit, is a group of MPDUs which built an PSDU (Physical Service Data Unit). It has lower
overhead and provides robust recovery in case of loss.
Check this box to reduce the guard interval time therefore increasing the data capacity. However, it’s less reliable and may
create higher data loss.
Transmit Power:
Beacon Period:
RTS Threshold:
Fragmentation
Threshold:
DTIM Interval:
802.11d:
Wireless Isolation:
WMM Function:
A-MPDU
Aggregation:
Short GI:
Advanced Wireless Settings
802.11n/g (2.4GHz)
48D-Link DIR-855 User Manual
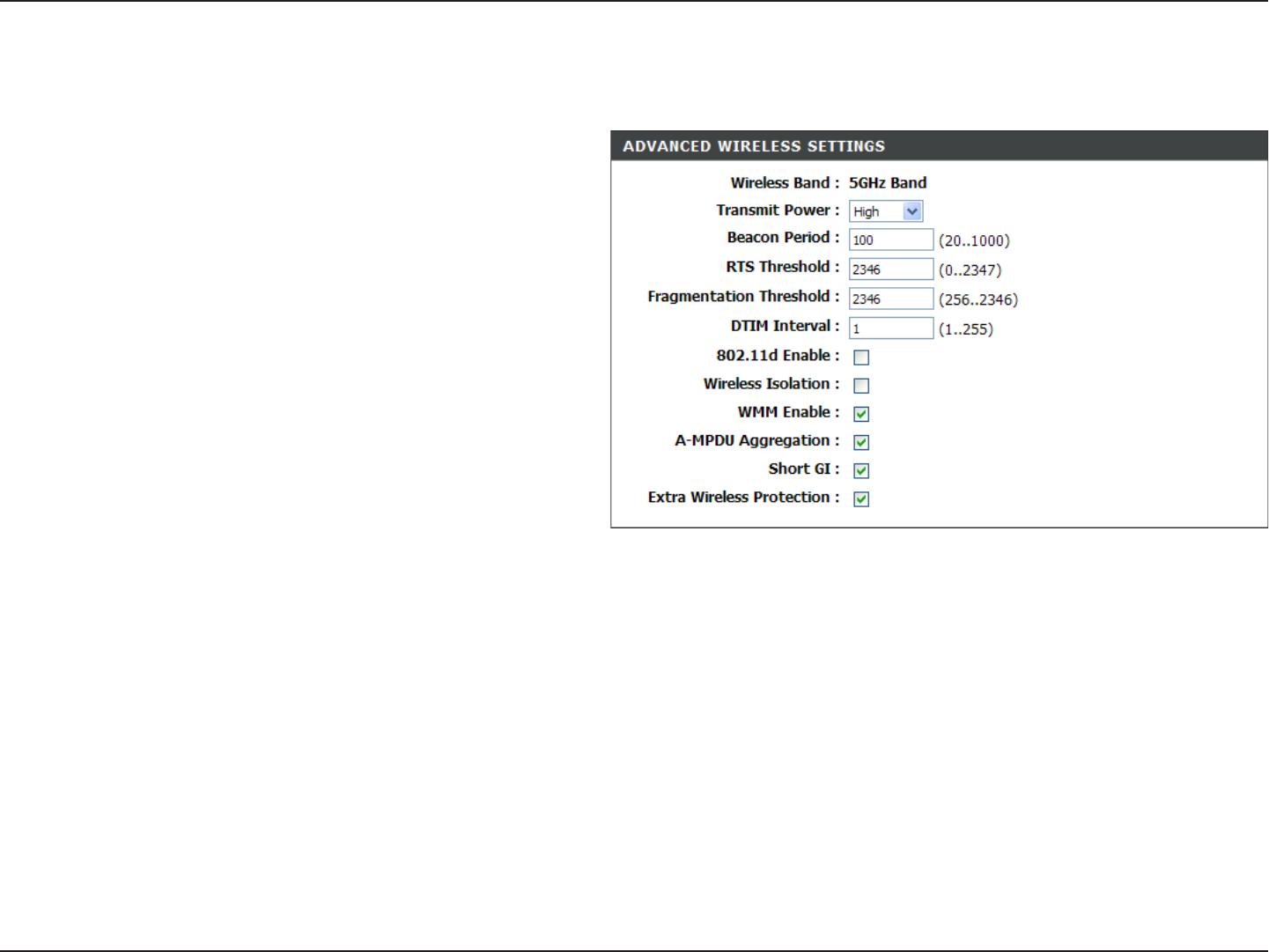
Section 3 - Configuration
Advanced Wireless Settings
802.11n/a (5GHz)
Set the transmit power of the antennas.
Beacons are packets sent by an Access Point to
synchronize a wireless network. Specify a value.
100 is the default setting and is recommended.
This value should remain at its default setting of
2432. If inconsistent data flow is a problem, only
a minor modification should be made.
The fragmentation threshold, which is specified
in bytes, determines whether packets will be
fragmented. Packets exceeding the 2346 byte
setting will be fragmented before transmission.
2346 is the default setting.
(Delivery Traffic Indication Message) 3 is the
default setting. A DTIM is a countdown informing clients of the next window for listening to broadcast and multicast
messages.
This enables 802.11d opration. 802.11d is a wireless specification developed to allow implementation of wireless networks in
countries that cannot use the 802.11 standard. This feature should only be enabled if you are in a country that requires it.
When checked, it will disable the ability for computers on the wireless network from seeing each other, but will allow you to
see computers on the wired network.
WMM is QoS for your wireless network. This will improve the quality of video and voice applications for your wireless
clients.
Aggregated-MAC Packet Data Unit, is a group of MPDUs which built an PSDU (Physical Service Data Unit). It will lower
overhead and provides robust recovery in case of loss.
Check this box to reduce the guard interval time therefore increasing the data capacity. However, it’s less reliable and may
create higher data loss.
Transmit Power:
Beacon Period:
RTS Threshold:
Fragmentation
Threshold:
DTIM Interval:
802.11d:
Wireless Isolation:
WMM Function:
A-MPDU
Aggregation:
Short GI:
49D-Link DIR-855 User Manual
Section 3 - Configuration
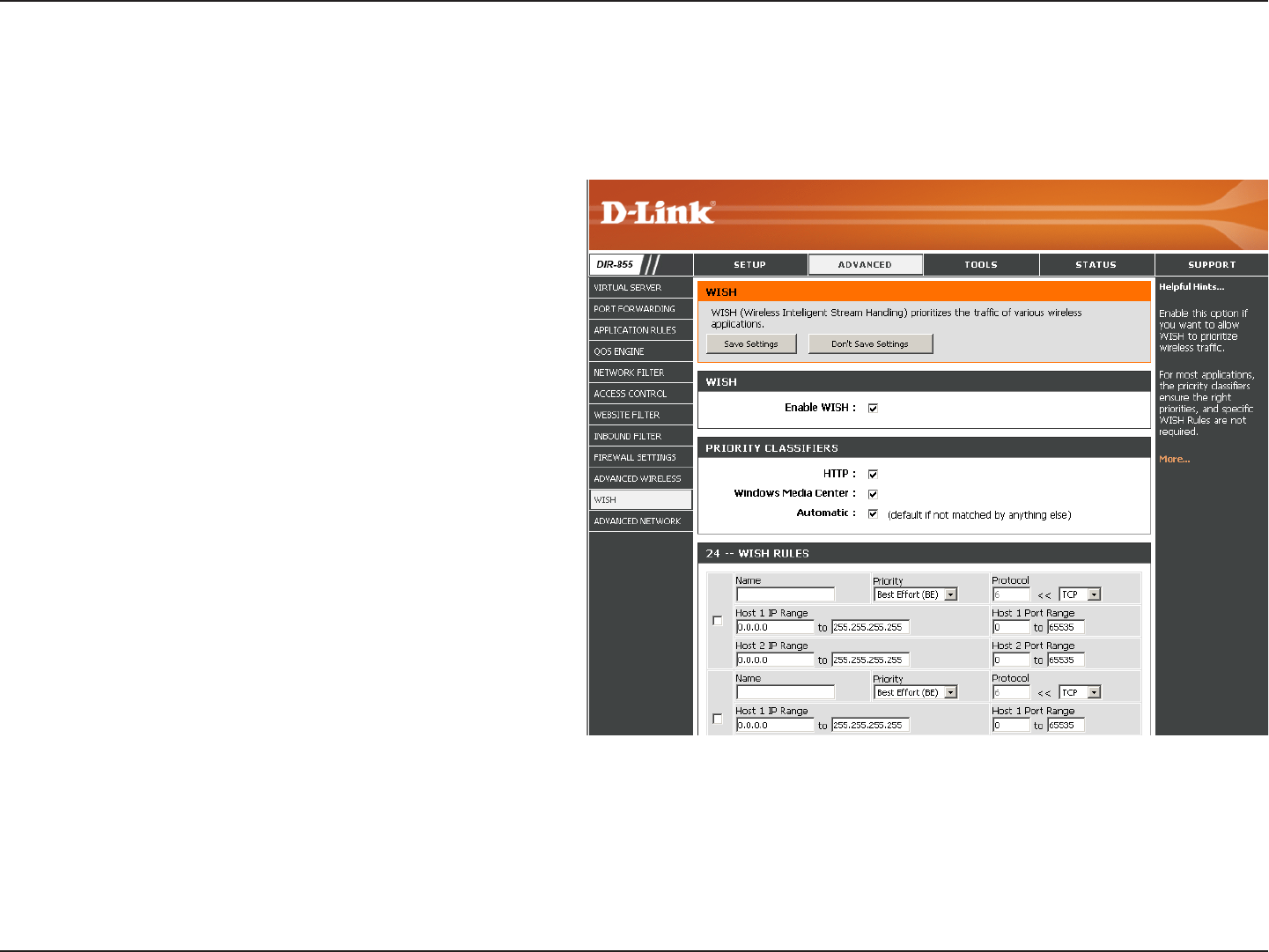
WISH Settings
WISH is short for Wireless Intelligent Stream Handling, a technology developed to enhance your experience of using
a wireless network by prioritizing the traffic of different applications.
Enable this option if you want to allow WISH
to prioritize your traffic.
Enable WISH:
Allows the router to recognize HTTP transfers
for many common audio and video streams
and prioritize them above other traffic. Such
streams are frequently used by digital media
players.
HTTP:
Enables the router to recognize certain audio
and video streams generated by a Windows
Media Center PC and to prioritize these above
other traffic. Such streams are used by systems
known as Windows Media Extenders, such as
the Xbox 360.
Windows Media
Center:
When enabled, this option causes the router
to automatically attempt to prioritize traffic
streams that it doesn’t otherwise recognize,
based on the behaviour that the streams
exhibit. This acts to deprioritize streams that
exhibit bulk transfer characteristics, such as
file transfers, while leaving interactive traffic,
such as gaming or VoIP, running at a normal
priority.
Automatic:
WISH Rules: A WISH Rule identifies a specific message flow and assigns a priority to that flow. For most applications, the priority classifiers
ensure the right priorities and specific WISH Rules are not required.
WISH supports overlaps between rules. If more than one rule matches for a specific message flow, the rule with the highest
priority will be used.

50D-Link DIR-855 User Manual
Section 3 - Configuration
Create a name for the rule that is meaningful
to you.
Name:
The priority of the message flow is entered
here. The four priorities are defined as:
BK: Background (least urgent)
BE: Best Effort.
VI: Video
VO: Voice (most urgent)
Priority:
The protocol used by the messages.
Protocol:
The rule applies to a flow of messages for which one computer’s IP address falls within the range set here.
Host IP Range:
The rule applies to a flow of messages for which host’s port number is within the range set here.
Host Port Range:
51D-Link DIR-855 User Manual
Section 3 - Configuration
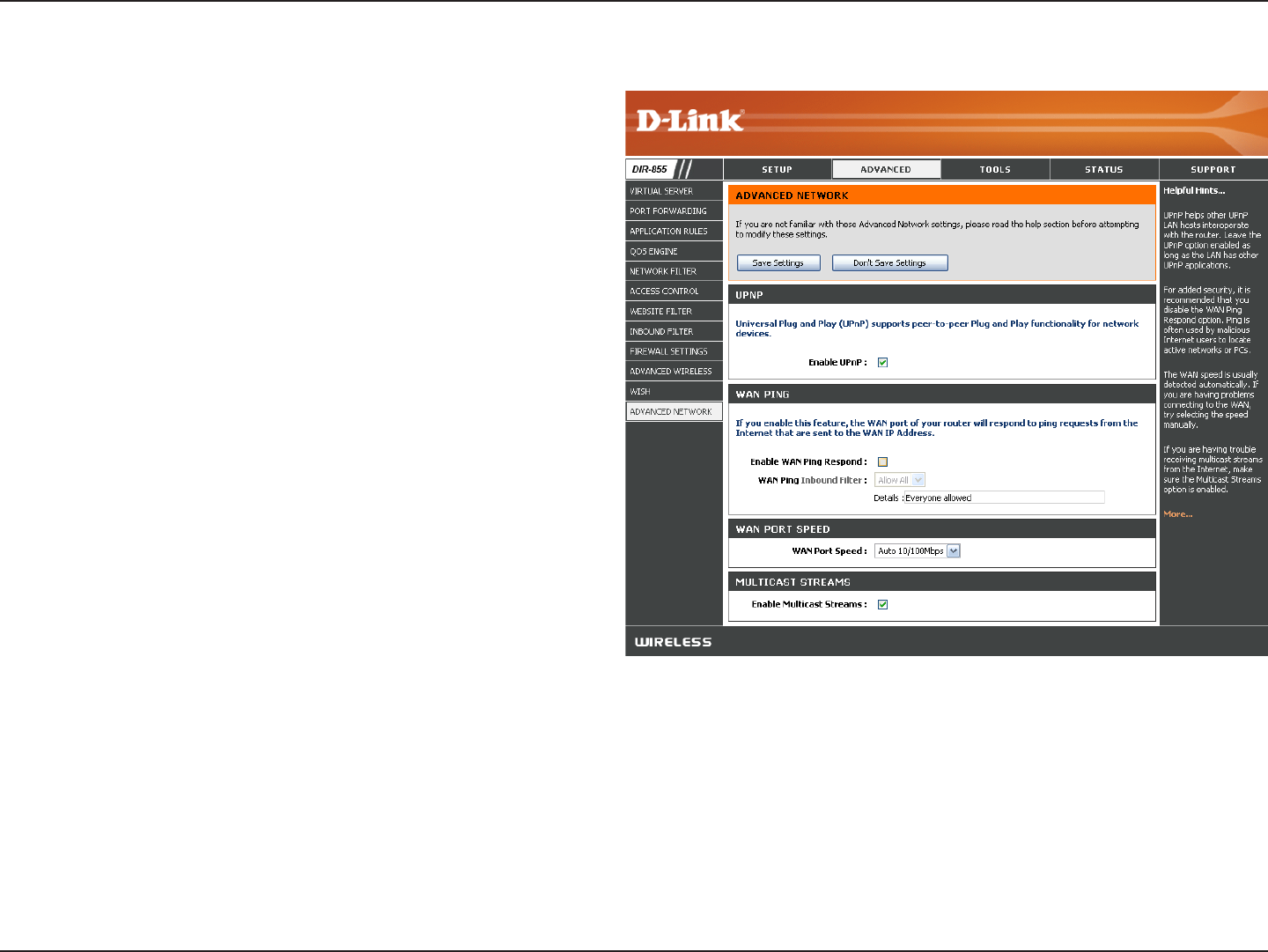
UPnP
Internet Ping Block
Internet Port Speed
Multicast Streams
To use the Universal Plug and Play (UPnP™) feature
click on Enabled. UPNP provides compatibility with
networking equipment, software and peripherals.
Unchecking the box will not allow the DIR-855 to
respond to pings. Blocking the Ping may provide
some extra security from hackers. Check the box
to allow the Internet port to be “pinged”.
Select from the drop-down menu if you would
like to apply the Inbound Filter to the WAN ping.
Refer to page 44 for more information regarding
Inbound Filter.
You may set the port speed of the Internet port
to 10Mbps, 100Mbps, or auto. Some older cable
or DSL modems may require you to set the port
speed to 10Mbps.
Check the box to allow multicast traffic to pass
through the router from the Internet.
Enable UPnP:
WAN Ping:
WAN Ping Inbound
Filter:
WAN Port Speed:
Multicast streams:
Advanced Network Settings
52D-Link DIR-855 User Manual
Section 3 - Configuration
Change Password
Remote Management
Enter a new password for the Administrator Login Name.
The administrator can make changes to the settings.
Enter the new password for the User login. If you login as
the User, you can only see the settings, but cannot change
them.
Enter a name for the DIR-855 router.
Remote management allows the DIR-855 to be configured
from the Internet by a web browser. A username and
password is still required to access the Web-Management
interface. In general, only a member of your network can
browse the built-in web pages to perform Administrator
tasks. This feature enables you to perform Administrator
tasks from the remote (Internet) host.
The port number used to access the DIR-855.
Example: http://x.x.x.x:8080 whereas x.x.x.x is the Internet
IP address of the DIR-855 and 8080 is the port used for
the Web Management interface.
This section will list any rules that are created. You may
click the Edit icon to change the settings or enable/disable
the rule, or click the Delete icon to remove the rule.
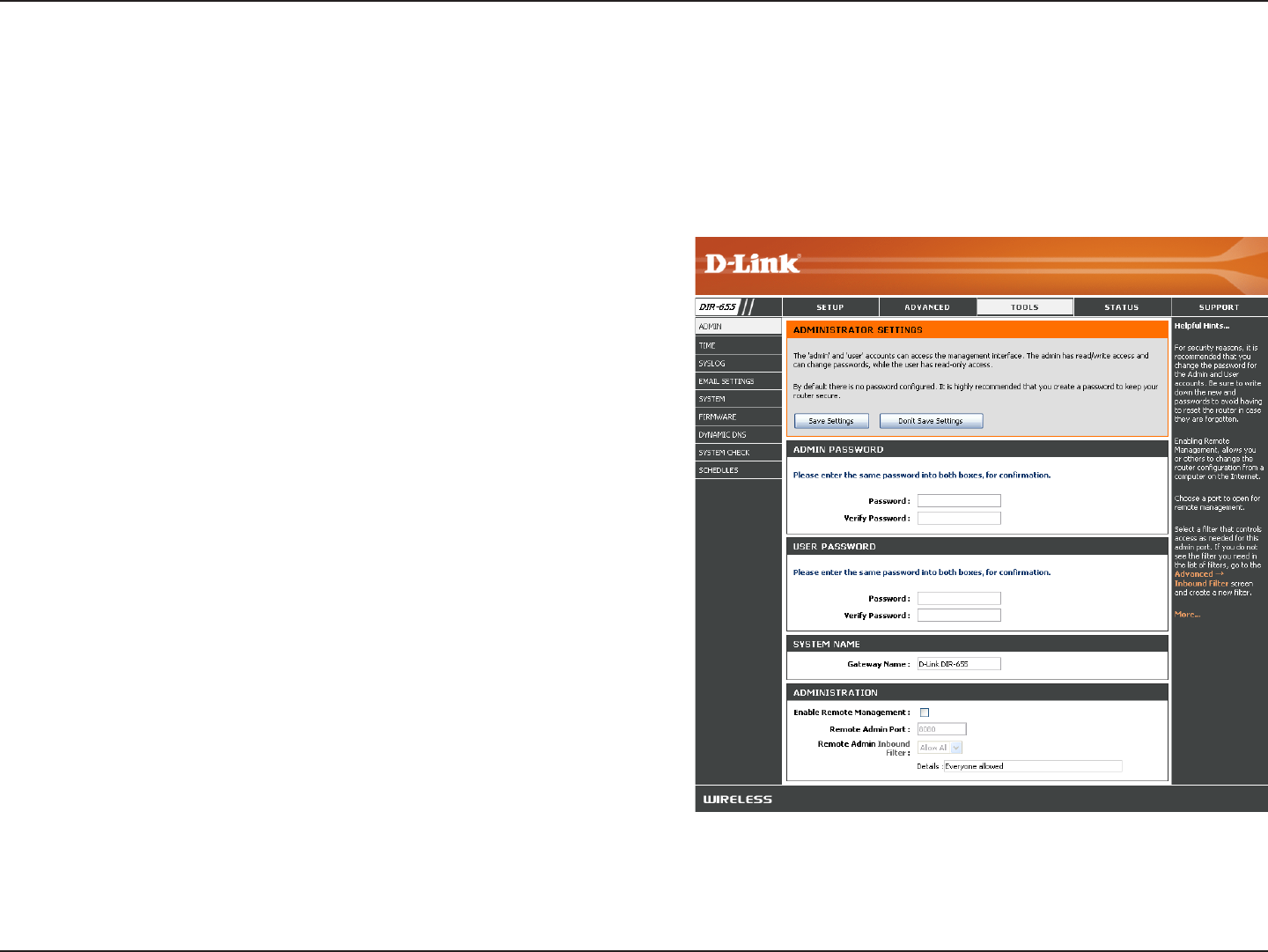
Admin Password:
User Password:
System Name:
Remote
Management:
Remote Admin Port:
Inbound Filter:
Administrator Settings
This page will allow you to change the Administrator and User passwords. You can also enable Remote Management.
There are two accounts that can access the management interface through the web browser. The accounts are admin
and user. Admin has read/write access while user has read-only access. User can only view the settings but cannot
make any changes. Only the admin account has the ability to change both admin and user account passwords.
53D-Link DIR-855 User Manual
Section 3 - Configuration
Time Settings
Select the Time Zone from the drop-down
menu.
To select Daylight Saving time manually, select
enabled or disabled, and enter a start date and
an end date for daylight saving time.
NTP is short for Network Time Protocol.
NTP synchronizes computer clock times in a
network of computers. Check this box to use a
NTP server. This will only connect to a server
on the Internet, not a local server.
Enter the NTP server or select one from the
drop-down menu.
To manually input the time, enter the values
in these fields for the Year, Month, Day, Hour,
Minute, and Second and then click Set Time.
You can also click Copy Your Computer’s
Time Settings.
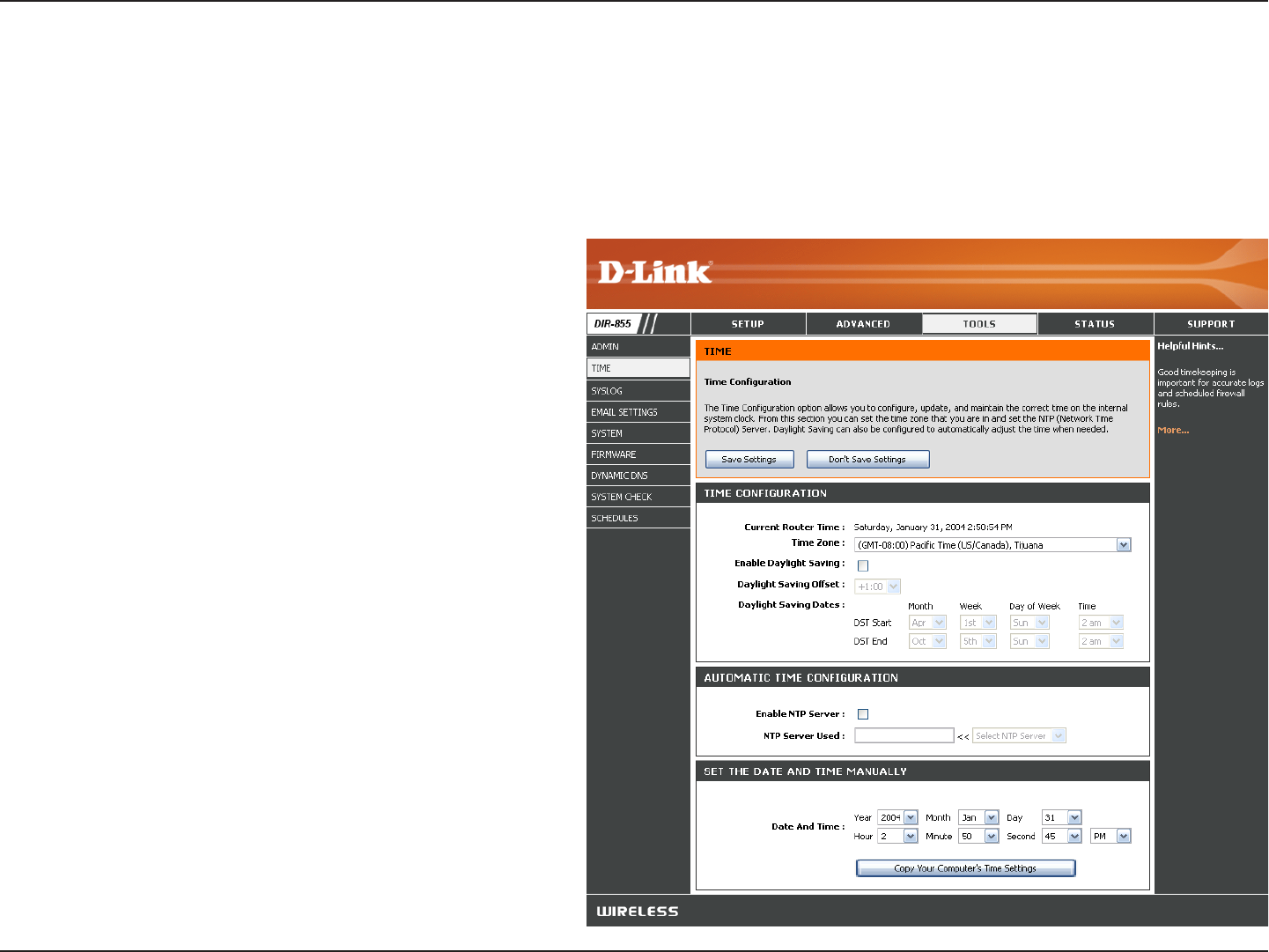
Time Zone:
Daylight Saving:
Enable NTP Server:
NTP Server Used:
Manual:
The Time Configuration option allows you to configure, update, and maintain the correct time on the internal system
clock. From this section you can set the time zone that you are in and set the Time Server. Daylight Saving can also
be configured to automatically adjust the time when needed.
54D-Link DIR-855 User Manual
Section 3 - Configuration
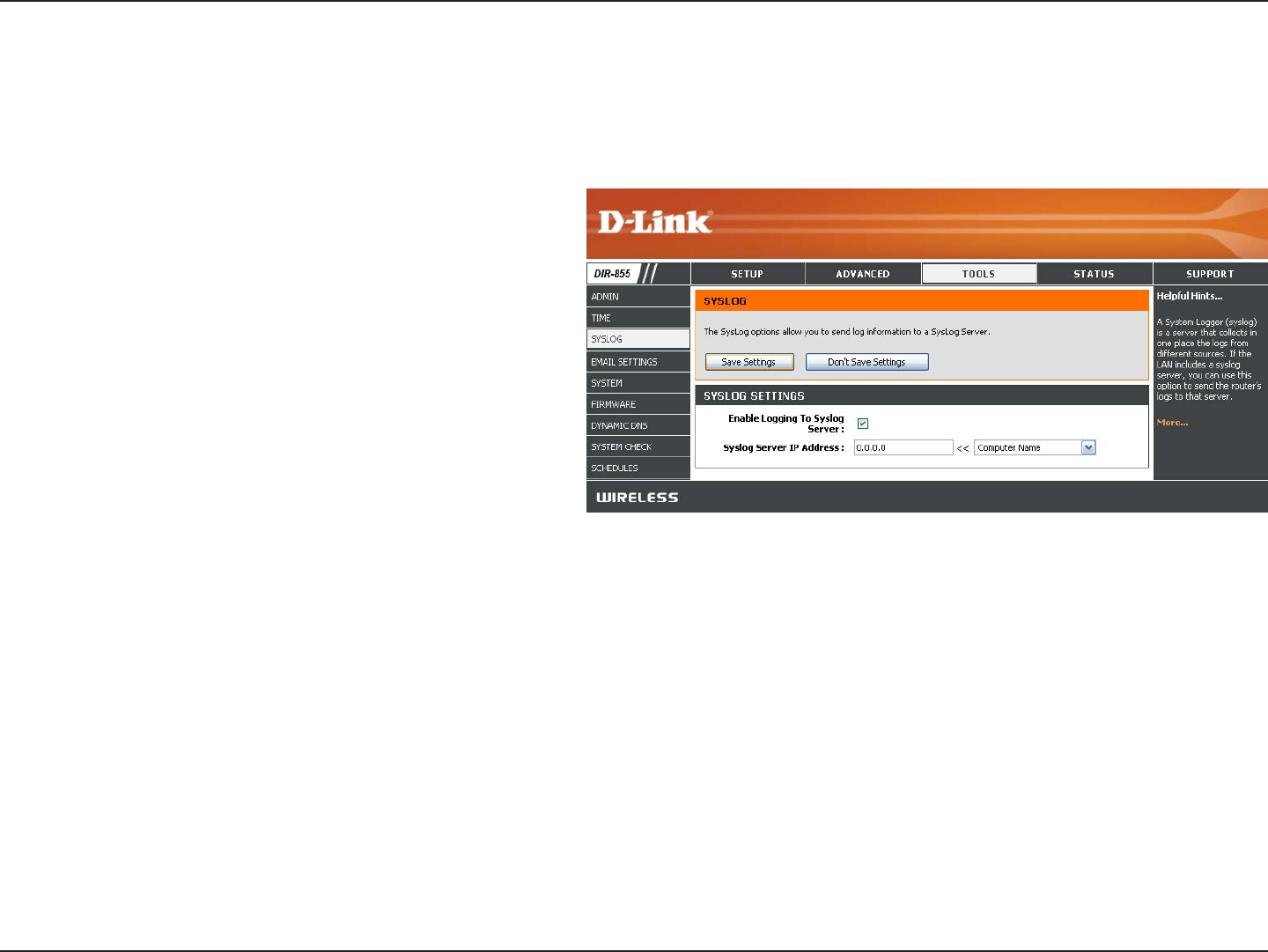
SysLog
The Broadband Router keeps a running log of events and activities occurring on the Router. You may send these logs
to a SysLog server on your network.
Enable Logging to
SysLog Server:
SysLog Server IP
Address:
Check this box to send the router logs to a
SysLog Server.
The address of the SysLog server that will be
used to send the logs. You may also select
your computer from the drop-down menu (only
if receiving an IP address from the router via
DHCP).
55D-Link DIR-855 User Manual
Section 3 - Configuration
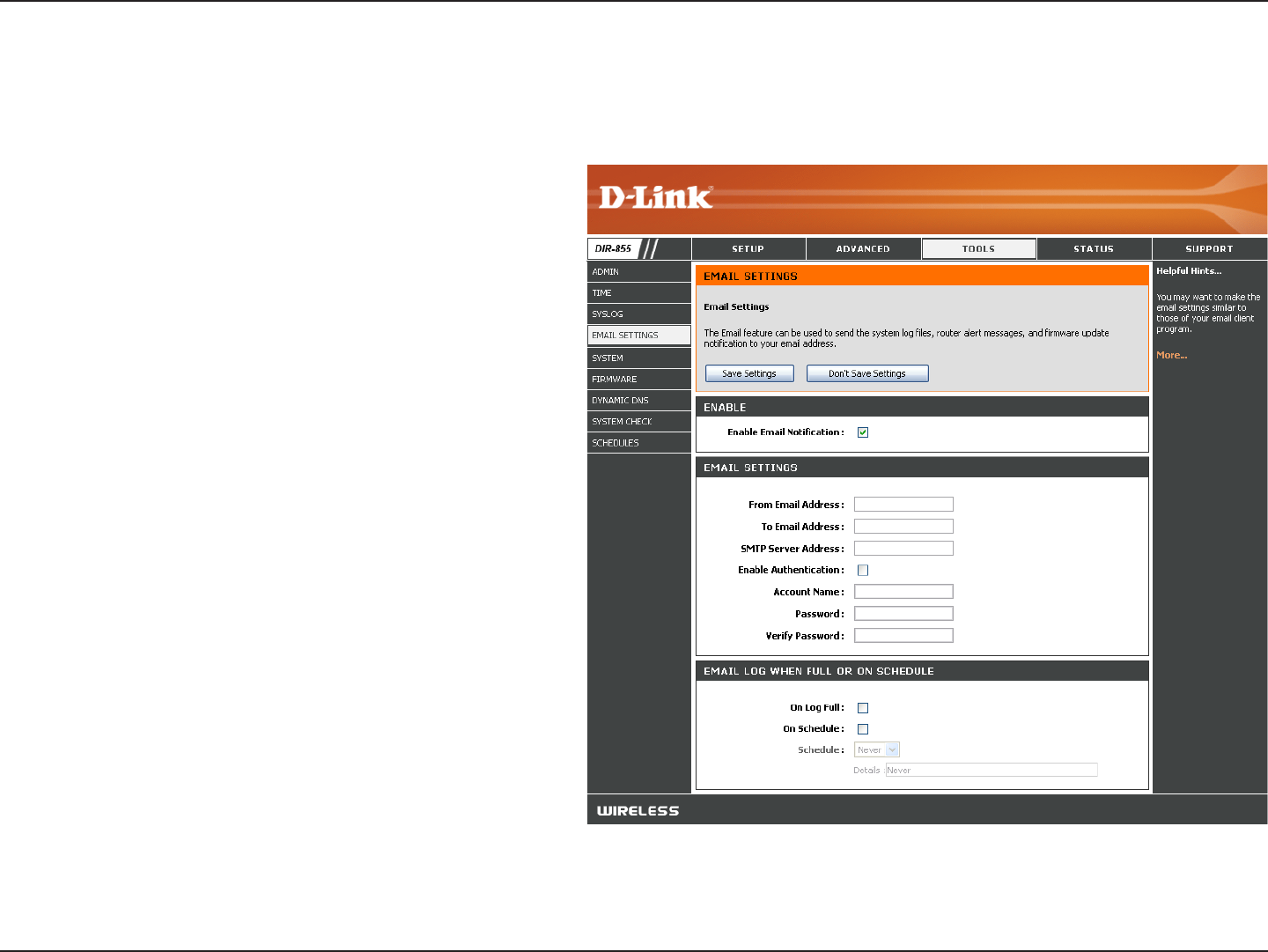
Email Settings
The Email feature can be used to send the system log files, router alert messages, and firmware update notification
to your email address.
Enable Email
Notification:
From Email
Address:
To Email Address:
SMTP Server
Address:
Enable
Authentication:
Account Name:
Password:
On Log Full:
On Schedule:
Schedule:
When this option is enabled, router activity logs
are e-mailed to a designated email address.
This email address will appear as the sender
when you receive a log file or firmware upgrade
notification via email.
Enter the email address where you want the
email sent.
Enter the SMTP server address for sending email.
If your SMTP server requires authentication,
select this option.
Check this box if your SMTP server requires
authentication.
Enter your account for sending email.
Enter the password associated with the
account. Re-type the password associated with
the account.
When this option is selected, logs will be sent
via email when the log is full.
Selecting this option will send the logs via email
according to schedule.
This option is enabled when On Schedule is selected. You can select a schedule from the list of defined schedules. To create
a schedule, go to Tools > Schedules.
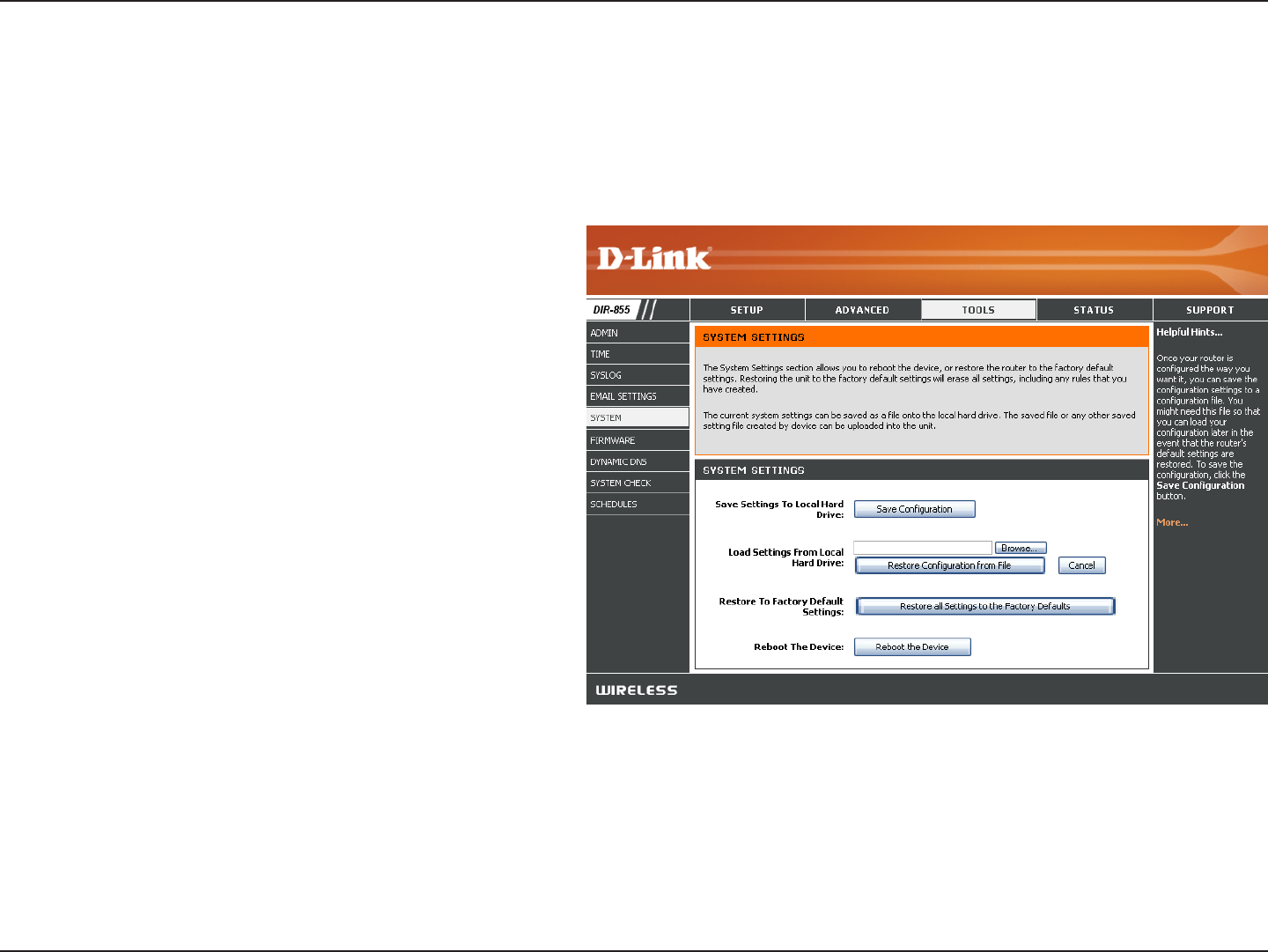
56D-Link DIR-855 User Manual
Section 3 - Configuration
Use this option to save the current router
configuration settings to a file on the hard disk
of the computer you are using. First, click the
Save button. You will then see a file dialog,
where you can select a location and file name
for the settings.
Use this option to load previously saved
router configuration settings. First, use the
Browse control to find a previously save
file of configuration settings. Then, click the
Load button to transfer those settings to the
router.
This option will restore all configuration
settings back to the settings that were in effect
at the time the router was shipped from the
factory. Any settings that have not been saved
will be lost, including any rules that you have
created. If you want to save the current router
configuration settings, use the Save button
above.
Click to reboot the router.
Save Settings to
Local Hard Drive:
Load Settings from
Local Hard Drive:
Restore to Factory
Default Settings:
Reboot Device:
System Settings
This section allows you to manage the router’s configuration settings, reboot the router, and restore the router to the
factory default settings. Restoring the unit to the factory default settings will erase all settings, including any rules that
you’ve created.
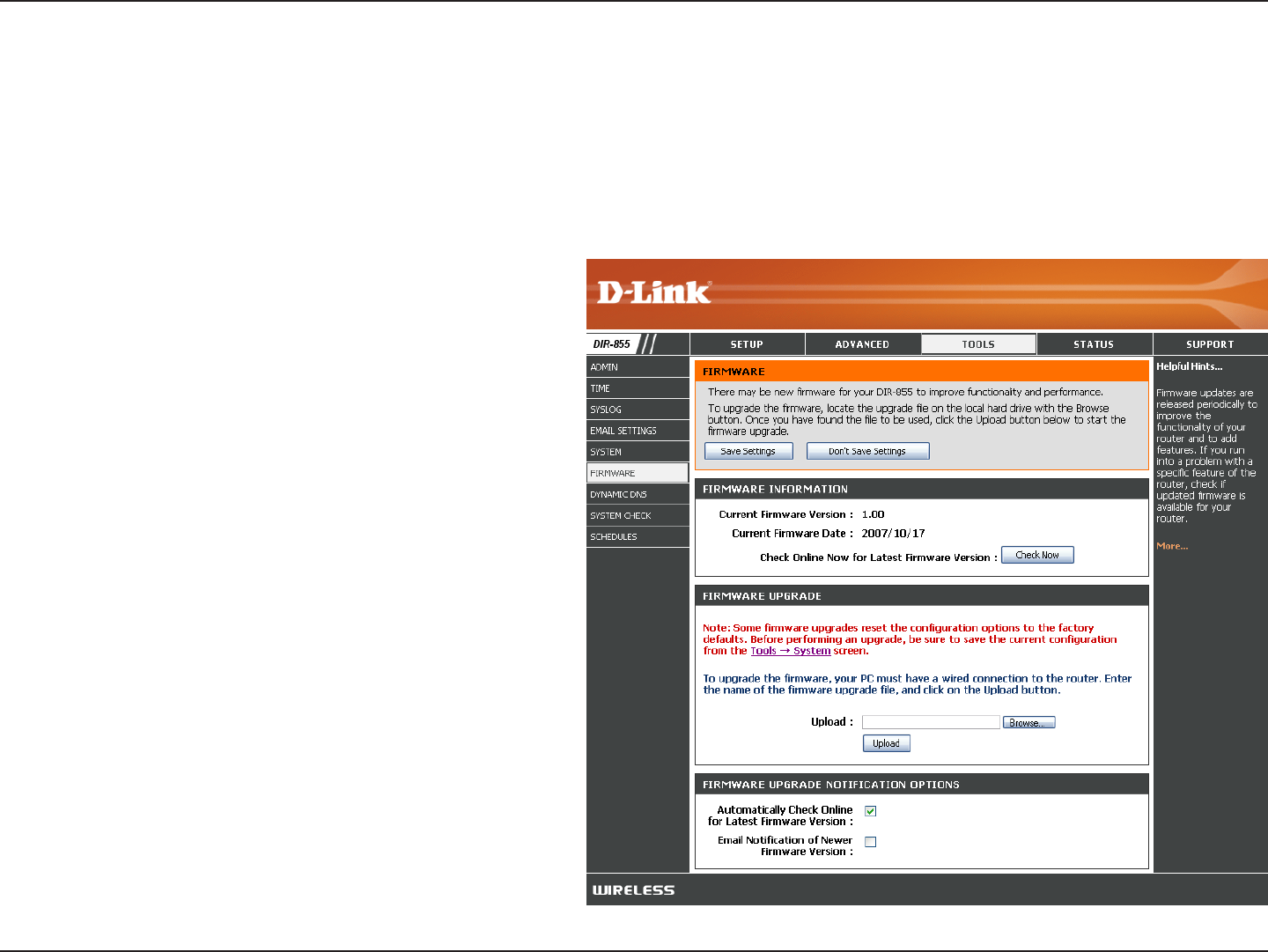
57D-Link DIR-855 User Manual
Section 3 - Configuration
Click on Check Now to find out if there is an
updated firmware; if so, download the new
firmware to your hard drive.
After you have downloaded the new firmware,
click Browse to locate the firmware update on
your hard drive. Click Upload to complete the
firmware upgrade.
Check Automatically Check Online for
Latest Firmware Version to have the router
check automatically to see if there is a new
firmware upgrade.
Check Email Notification of Newer Firmware
Version to have the router send an email when
there is a new firmware available.
Firmware Upgrade:
Browse:
Notifications
Options:
Update Firmware
You can upgrade the firmware of the Router here. Make sure the firmware you want to use is on the local hard drive of
the computer. Click on Browse to locate the firmware file to be used for the update. Please check the D-Link support
site for firmware updates at http://support.dlink.com. You can download firmware upgrades to your hard drive from the
D-Link support site.
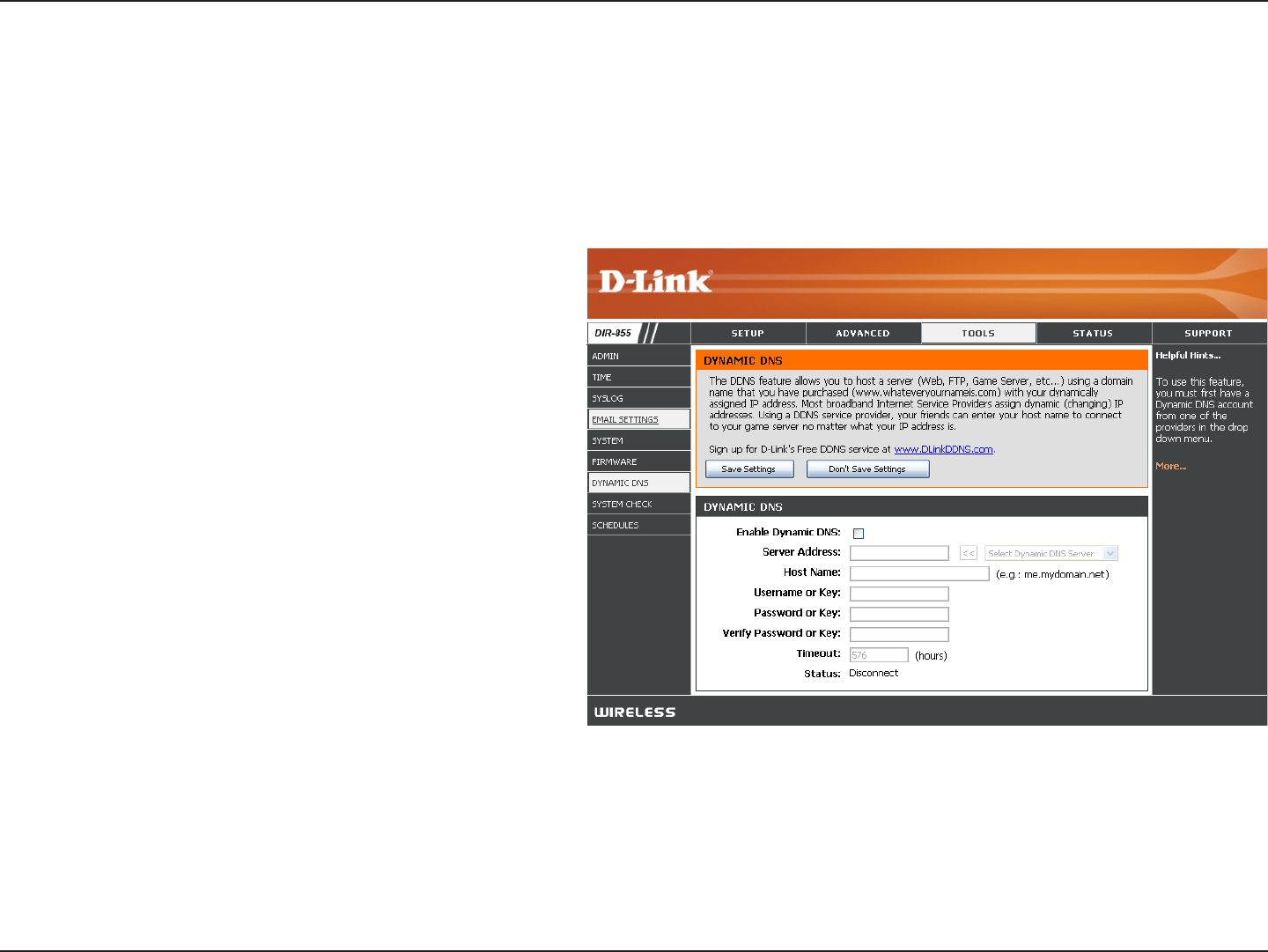
58D-Link DIR-855 User Manual
Section 3 - Configuration
Dynamic Domain Name System is a method of
keeping a domain name linked to a changing
IP Address. Check the box to enable DDNS.
Choose your DDNS provider from the drop
down menu.
Enter the Host Name that you registered with
your DDNS service provider.
Enter the Username for your DDNS account.
Enter the Password for your DDNS account.
Enter a time (in hours).
Enable Dynamic
DNS:
Server Address:
Host Name:
Username or Key:
Password or Key:
Timeout:
DDNS
The DDNS feature allows you to host a server (Web, FTP, Game Server, etc…) using a domain name that you have
purchased (www.whateveryournameis.com) with your dynamically assigned IP address. Most broadband Internet
Service Providers assign dynamic (changing) IP addresses. Using a DDNS service provider, your friends can enter in
your domain name to connect to your server no matter what your IP address is.
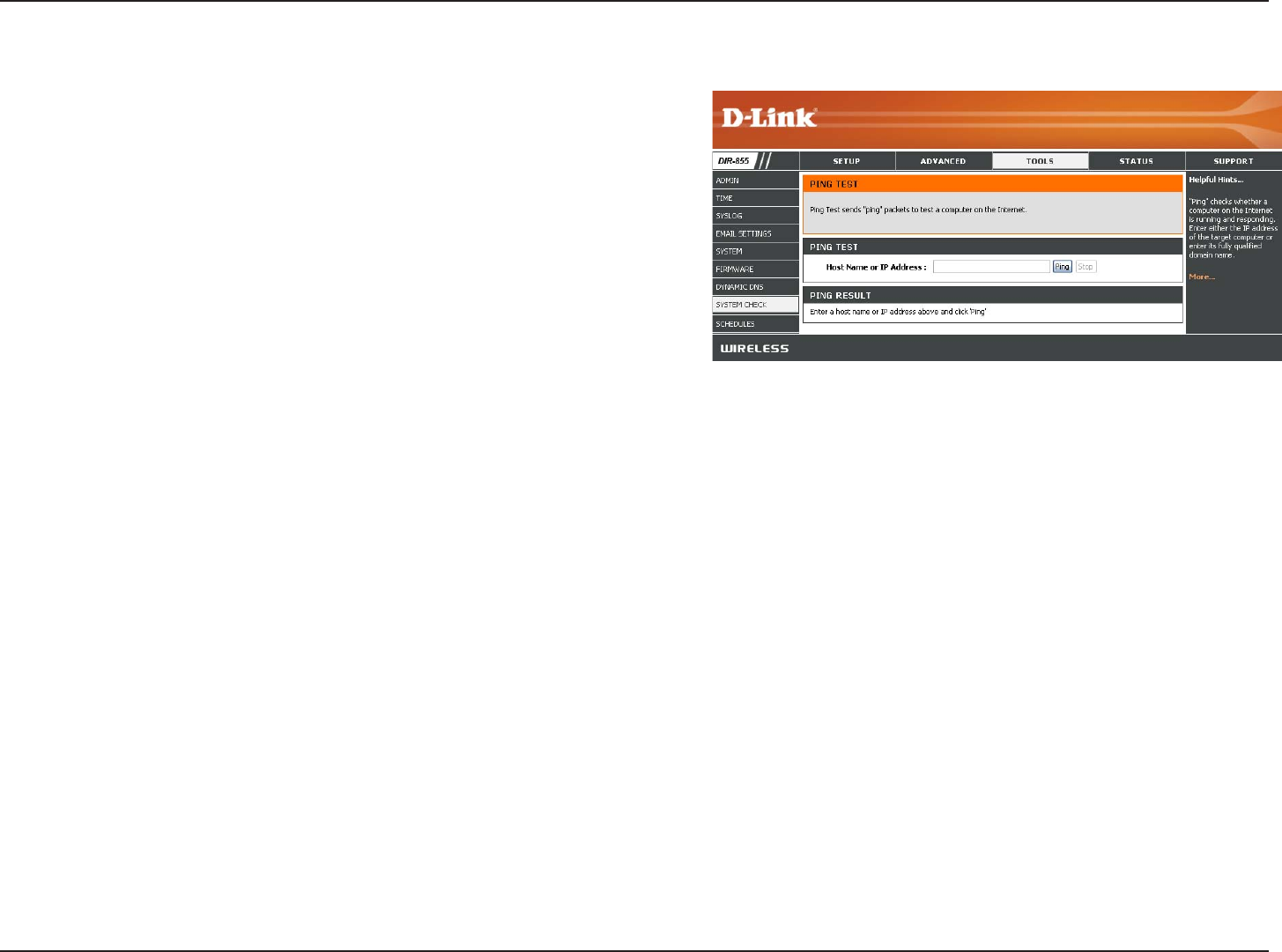
59D-Link DIR-855 User Manual
Section 3 - Configuration
The Ping Test is used to send Ping packets to test if a
computer is on the Internet. Enter the IP Address that you
wish to Ping, and click Ping.
The results of your ping attempts will be displayed here.
System Check
Ping Test:
Ping Results:
60D-Link DIR-855 User Manual
Section 3 - Configuration
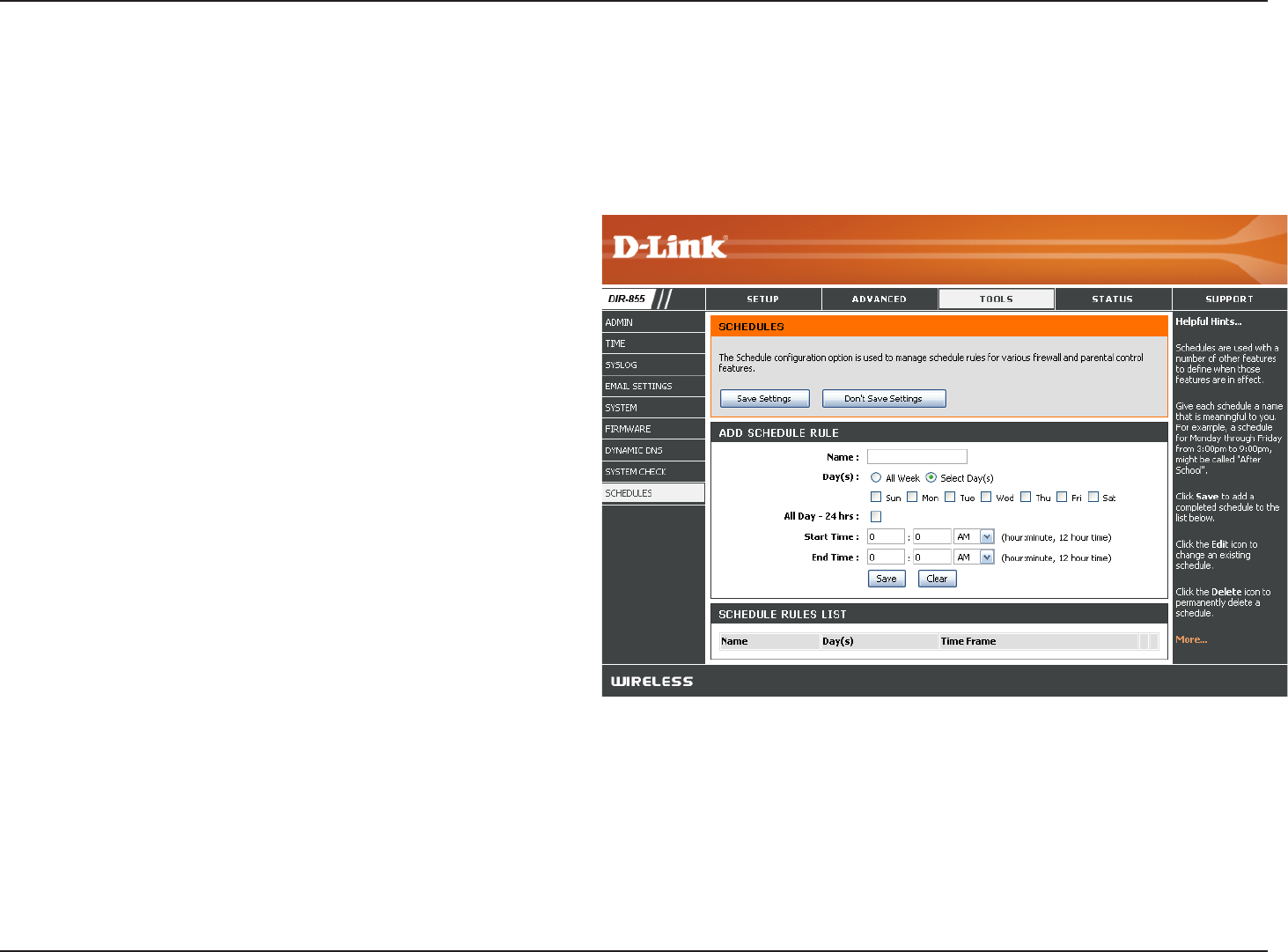
Enter a name for your new schedule.
Select a day, a range of days, or All Week to
include every day.
Check All Day - 24hrs or enter a start and end
time for your schedule.
Click Save to save your schedule. You must click
Save Settings at the top for your schedules to
go into effect.
The list of schedules will be listed here. Click the
Edit icon to make changes or click the Delete
icon to remove the schedule.
Name:
Days:
Time:
Save:
Schedule Rules
List:
Schedules
Schedules can be created for use with enforcing rules. For example, if you want to restrict web access to Mon-Fri from
3pm to 8pm, you could create a schedule selecting Mon, Tue, Wed, Thu, and Fri and enter a Start Time of 3pm and
End Time of 8pm.
61D-Link DIR-855 User Manual
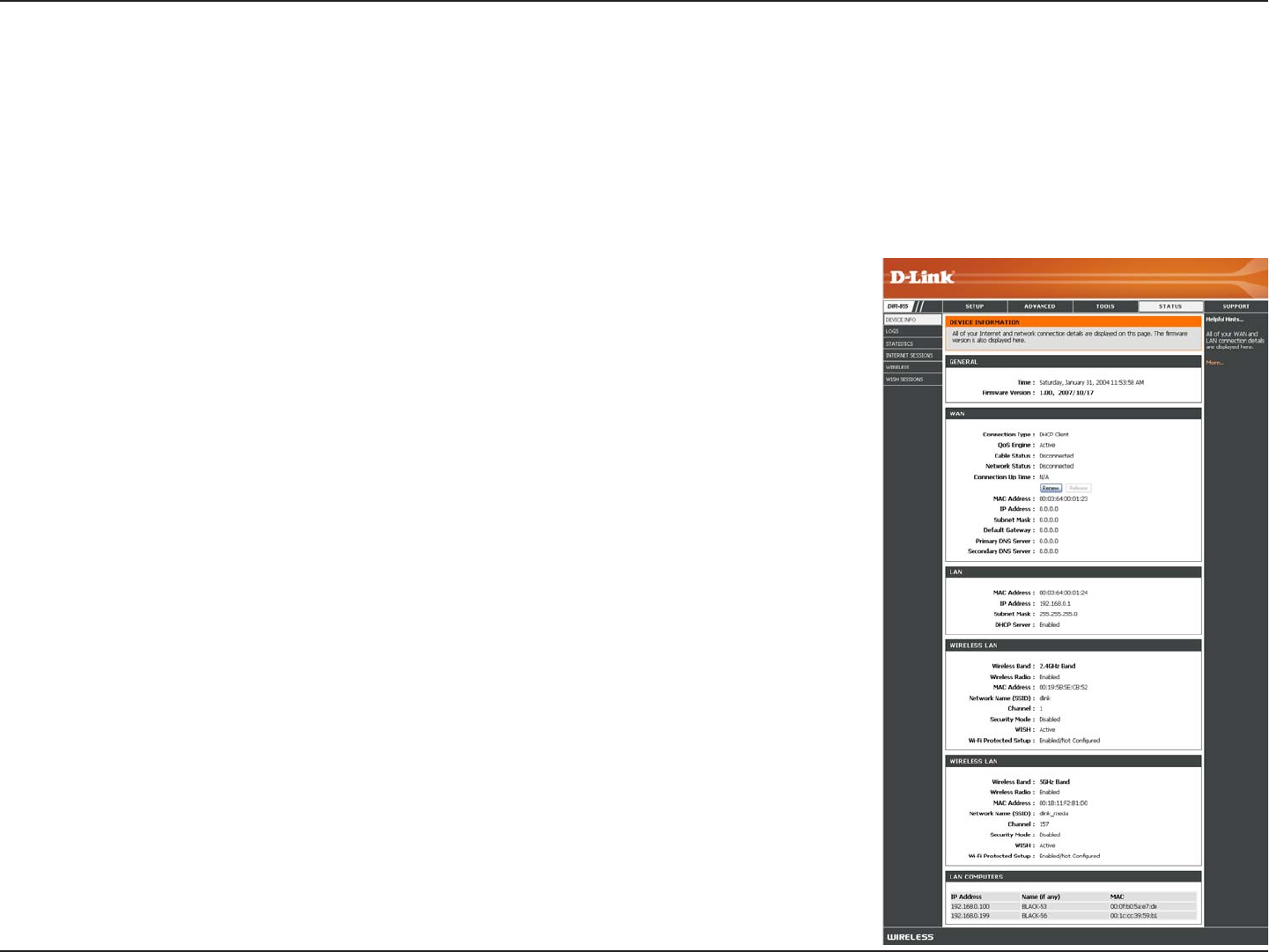
Section 3 - Configuration
This page displays the current information for the DIR-855. It will display the LAN, WAN (Internet), and Wireless
information. If your Internet connection is set up for a Dynamic IP address then a Release button and a Renew button
will be displayed. Use Release to disconnect from your ISP and use Renew to connect to your ISP.
If your Internet connection is set up for PPPoE, a Connect button and a Disconnect button will be displayed. Use
Disconnect to drop the PPPoE connection and use Connect to establish the PPPoE connection.
Displays the router’s time and firmware version.
Displays the MAC address and the public IP settings for the router.
Displays the MAC address and the private (local) IP settings for the
router.
Displays the wireless MAC address and your wireless settings such as
SSID and Channel.
Displays computers and devices that are connected to the router via Ethernet
and that are receiving an IP address assigned by the router (DHCP).
Displays the Multicast Group IP Address.
General:
WAN:
LAN:
Wireless LAN:
LAN Computers:
IGMP Multicast
Memberships:
Device Information
62D-Link DIR-855 User Manual
Section 3 - Configuration
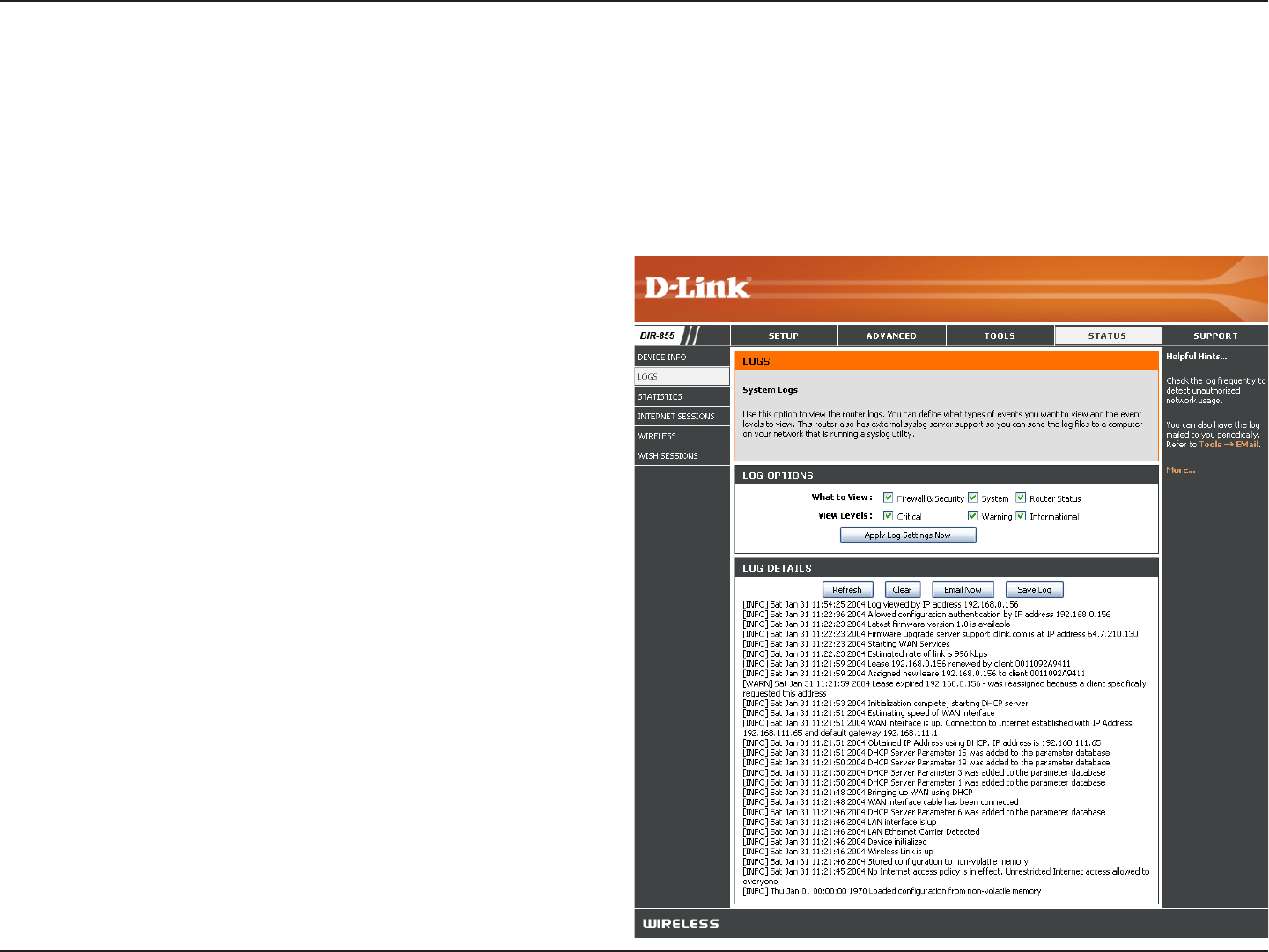
Log
What to View:
View Levels:
Apply Log Settings:
Refresh:
Clear:
Email Now:
Save Log:
You can select the types of messages that you want
to display from the log. Firewall & Security, System,
and Router Status messages can be selected.
There are three levels of message importance:
Informational, Warning, and Critical. Select the
levels that you want displayed in the log.
Will filter the log results so that only the selected
options appear.
Updates the log details on the screen so it displays
any recent activity.
Clears all of the log contents.
This option will send a copy of the router log to
the email address configured in the Tools > Email
screen.
This option will save the router to a log file on your
computer.
The router automatically logs (records) events of possible interest in it’s internal memory. If there isn’t enough internal
memory for all events, logs of older events are deleted but logs of the latest events are retained. The Logs option allows
you to view the router logs. You can define what types of events you want to view and the level of the events to view.
This router also has external Syslog Server support so you can send the log files to a computer on your network that
is running a Syslog utility.
63D-Link DIR-855 User Manual
Section 3 - Configuration
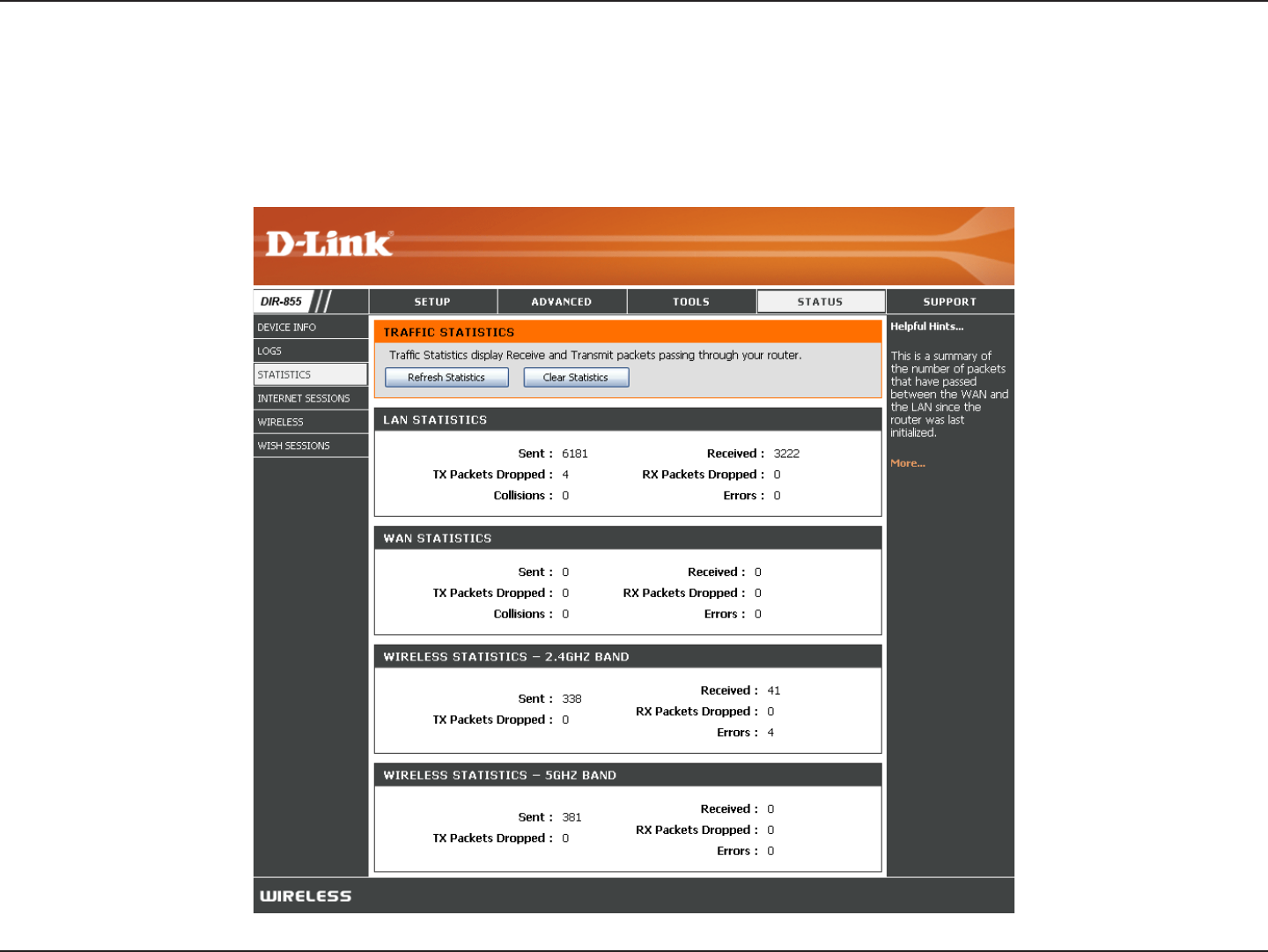
Stats
The screen below displays the Traffic Statistics. Here you can view the amount of packets that pass through the DIR-855 on
both the Internet, LAN ports and both the 802.11n/g and 802.11a wireless bands. The traffic counter will reset if the
device is rebooted.
64D-Link DIR-855 User Manual
Section 3 - Configuration
Internet Sessions
The Internet Sessions page displays full details of active Internet sessions through your router. An Internet session is a
conversation between a program or application on a LAN-side computer and a program or application on a WAN-side
computer.
65D-Link DIR-855 User Manual
Section 3 - Configuration
The wireless client table displays a list of current connected wireless clients. This table also displays the connection
time and MAC address of the connected wireless clients.
Wireless
The WISH details page displays full details of wireless clients that are connected when WISH is enabled.
WISH
66D-Link DIR-855 User Manual
Section 3 - Configuration
Support
67D-Link DIR-855 User Manual
Section 4 - Security
Wireless Security
This section will show you the different levels of security you can use to protect your data from intruders. The
DIR-855 offers the following types of security:
• WPA2 (Wi-Fi Protected Access 2) • WPA2-PSK (Pre-Shared Key)
• WPA (Wi-Fi Protected Access) • WPA-PSK (Pre-Shared Key)
What is WPA?
WPA, or Wi-Fi Protected Access, is a Wi-Fi standard that was designed to improve the security features of WEP (Wired
Equivalent Privacy).
The 2 major improvements over WEP:
• Improved data encryption through the Temporal Key Integrity Protocol (TKIP). TKIP scrambles the keys
using a hashing algorithm and, by adding an integrity-checking feature, ensures that the keys haven’t
been tampered with. WPA2 is based on 802.11i and uses Advanced Encryption Standard (AES) instead
of TKIP.
• User authentication, which is generally missing in WEP, through the extensible authentication protocol
(EAP). WEP regulates access to a wireless network based on a computer’s hardware-specific MAC
address, which is relatively simple to be sniffed out and stolen. EAP is built on a more secure public-key
encryption system to ensure that only authorized network users can access the network.
WPA-PSK/WPA2-PSK uses a passphrase or key to authenticate your wireless connection. The key is an alpha-numeric
password between 8 and 63 characters long. The password can include symbols (!?*&_) and spaces. This key must
be the exact same key entered on your wireless router or access point.
WPA/WPA2 incorporates user authentication through the Extensible Authentication Protocol (EAP). EAP is built on a
more secure public key encryption system to ensure that only authorized network users can access the network.
68D-Link DIR-855 User Manual
Section 4 - Security
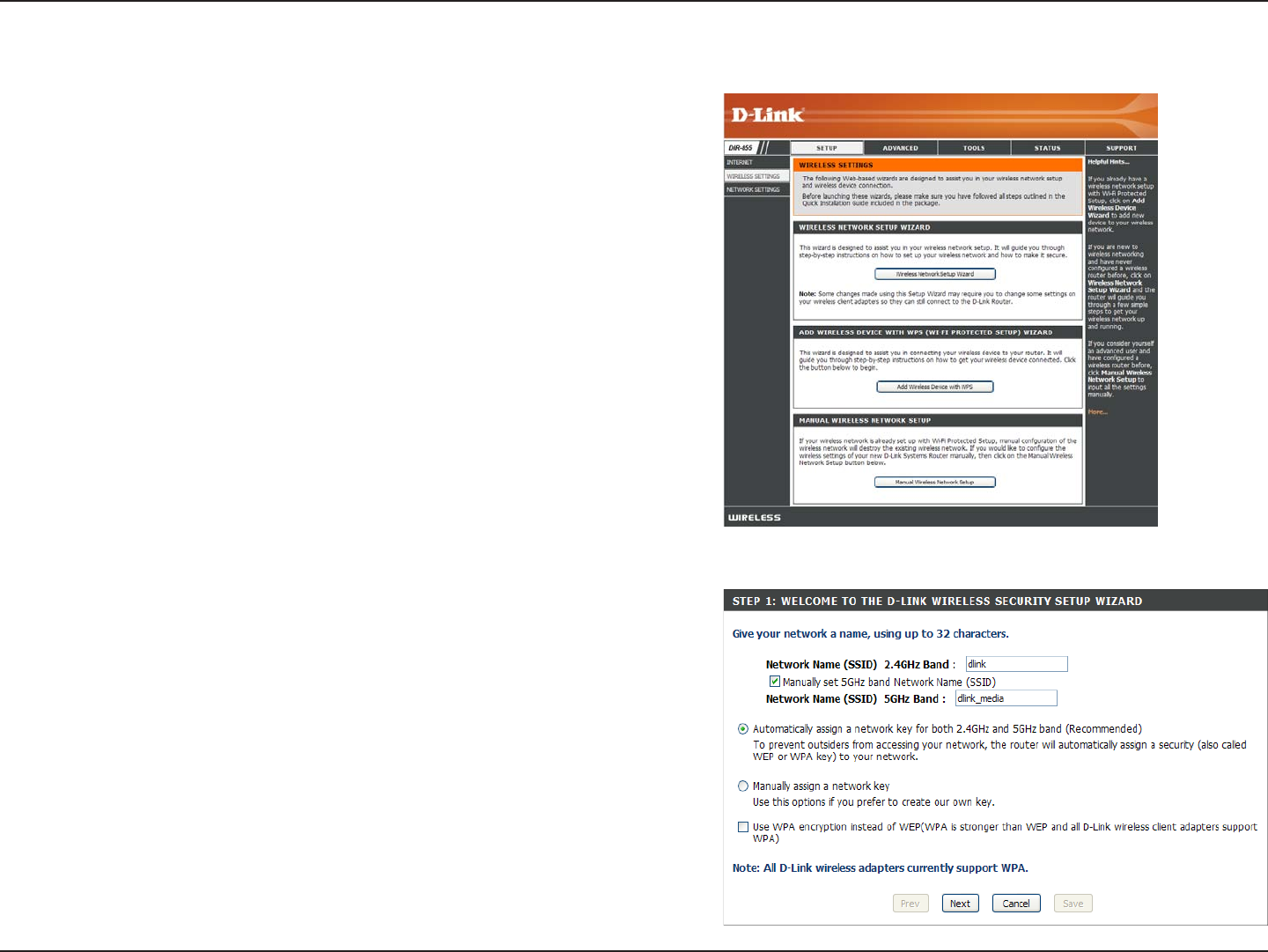
Wireless Security Setup Wizard
To run the security wizard, click on Setup at the top and then
click Launch Wireless Security Setup Wizard.
Check the Manually set 5GHz band Network Name... box to
manually set your desired wireless network name for the 5GHz
band.
Type your desired wireless network name (SSID).
Automatically: Select this option to automatically generate
the router’s network key and click Next.
Manually: Select this option to manually enter your network
key and click Next.
Check the “Use WPA encryption...” box to use WPA.
69D-Link DIR-855 User Manual
Section 4 - Security
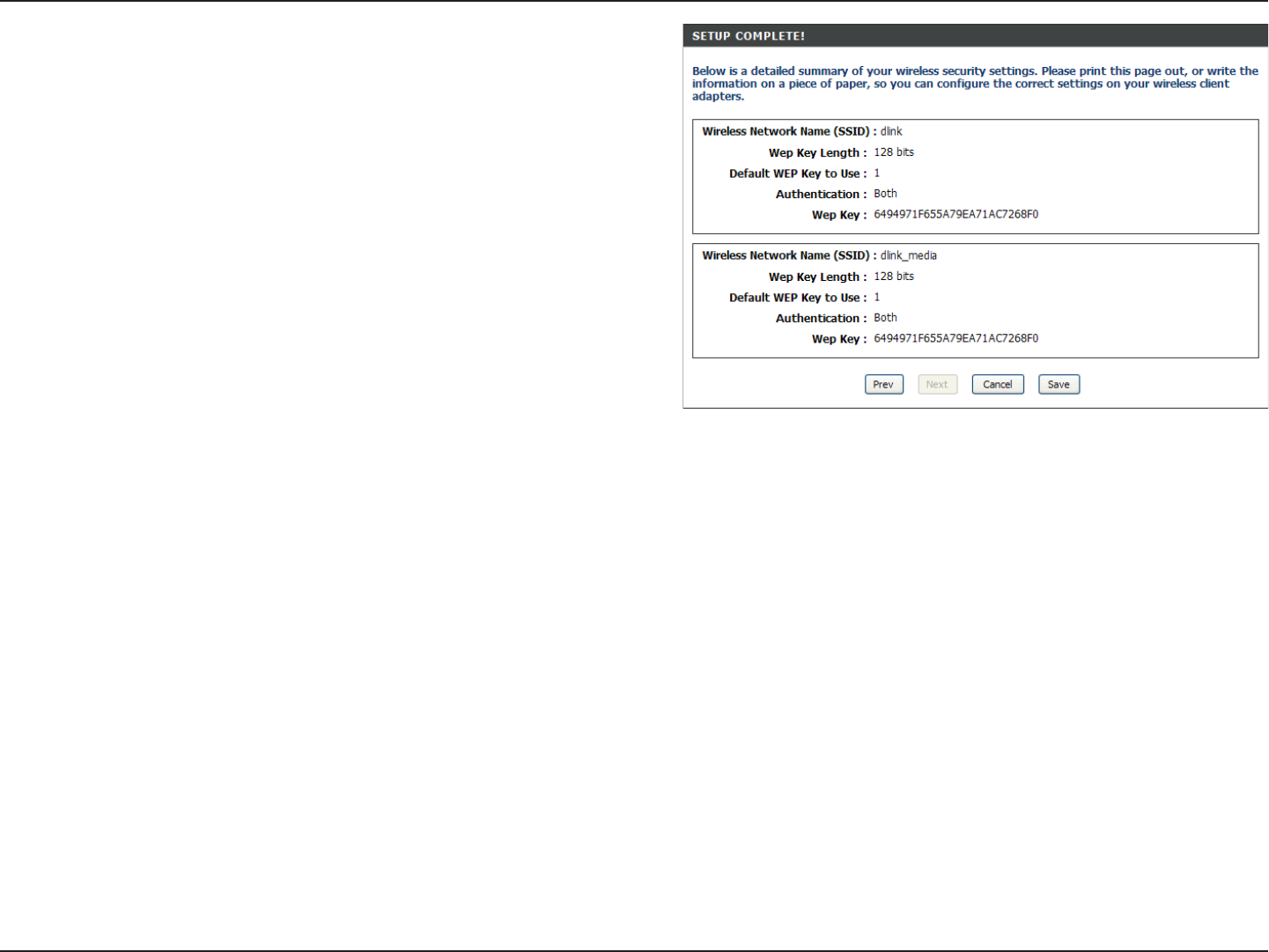
If you selected Automatically, the summary window will
display your settings. Write down the security key and
enter this on your wireless clients. Click Save to save your
settings.
70D-Link DIR-855 User Manual
Section 4 - Security
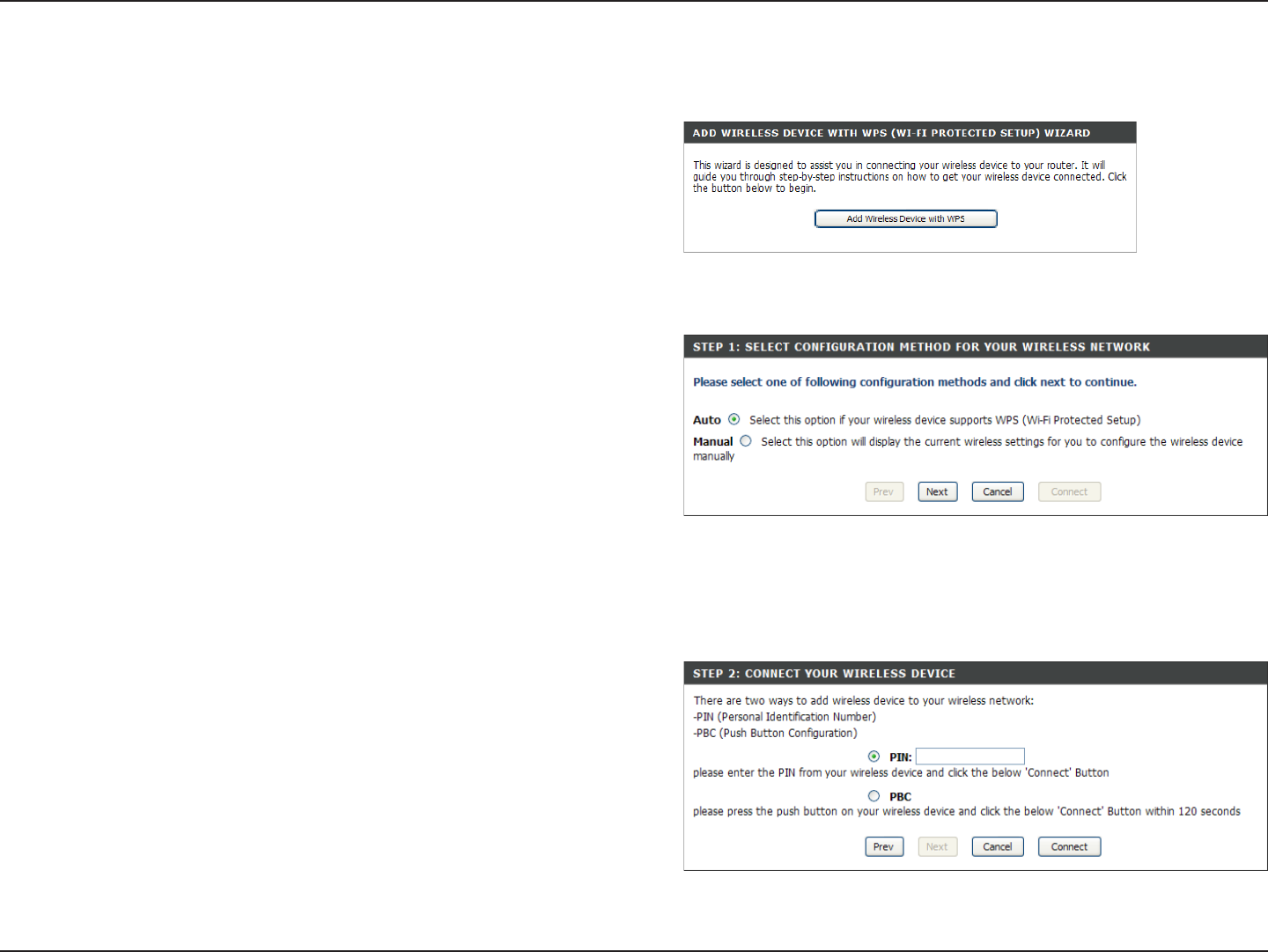
From the Basic > Wizard screen, click Add Wireless Device
with WPS.
Add Wireless Device with WPS Wizard
PIN: Select this option to use PIN method. In order to use this
method you must know the wireless client’s 8 digit PIN and
click Connect.
PBC: Select this option to use PBC (Push Button) method to
add a wireless client. Click Connect.
Select Auto to add a wireless client using WPS (Wi-Fi Protected
Setup). Once you select Auto and click Connect, you will have
a 120 second time limit to apply the settings to your wireless
client(s) and successfully establish a connection.
If you select Manual, a settings summary screen will appear.
Write down the security key and enter this on your wireless
clients.
71D-Link DIR-855 User Manual
Section 4 - Security
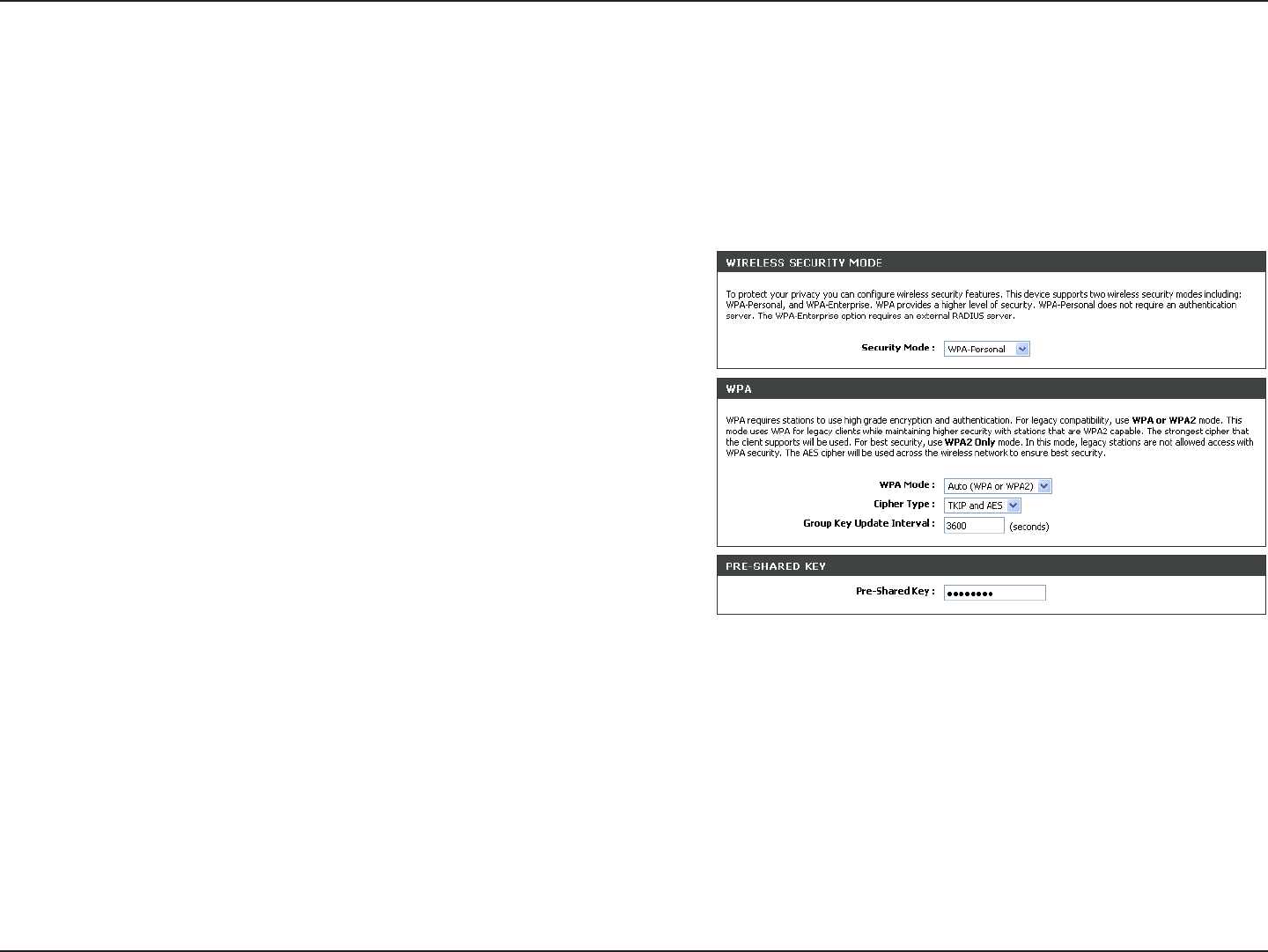
Configure WPA-Personal (PSK)
It is recommended to enable encryption on your wireless router before your wireless network adapters. Please establish
wireless connectivity before enabling encryption. Your wireless signal may degrade when enabling encryption due to
the added overhead.
1. Log into the web-based configuration by opening a web browser
and entering the IP address of the router (192.168.0.1). Click
on Setup and then click Wireless Settings on the left side.
2. Next to Security Mode, select WPA-Personal.
3. Next to WPA Mode, select Auto, WPA2 Only, or WPA Only. Use
Auto if you have wireless clients using both WPA and WPA2.
4. Next to Cypher Type, select TKIP and AES, TKIP, or AES.
5. Next to Group Key Update Interval, enter the amount of time
before the group key used for broadcast and multicast data is
changed (3600 is default).
6. Next to Pre-Shared Key, enter a key (passphrase). The key is entered as a pass-phrase in ASCII format at both ends
of the wireless connection. The pass-phrase must be between 8-63 characters.
7. Click Save Settings to save your settings. If you are configuring the router with a wireless adapter, you will lose
connectivity until you enable WPA-PSK on your adapter and enter the same passphrase as you did on the router.
72D-Link DIR-855 User Manual
Section 4 - Security
It is recommended to enable encryption on your wireless router before your wireless network adapters. Please establish
wireless connectivity before enabling encryption. Your wireless signal may degrade when enabling encryption due to
the added overhead.
1. Log into the web-based configuration by opening a web browser
and entering the IP address of the router (192.168.0.1). Click
on Setup and then click Wireless Settings on the left side.
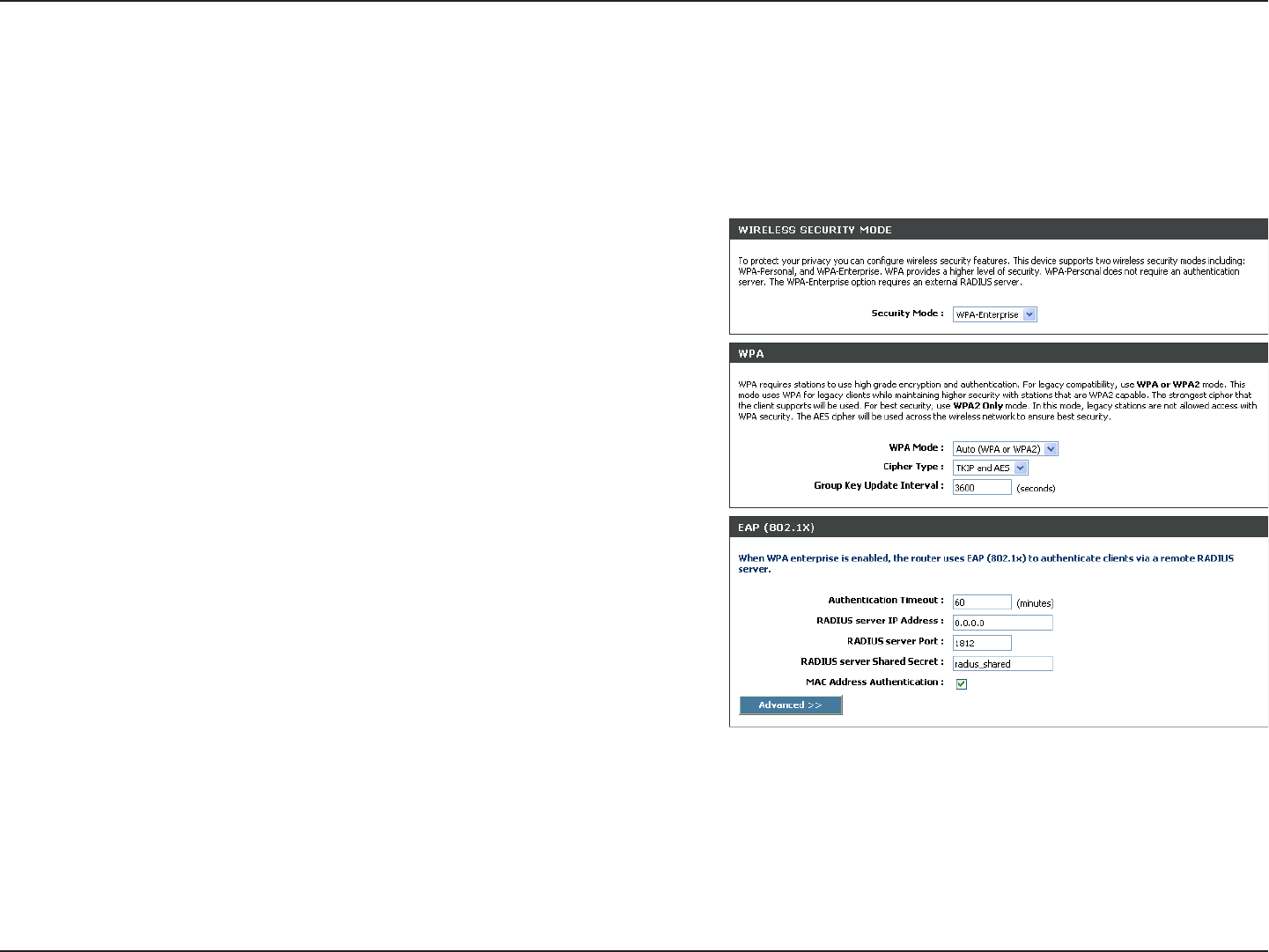
2. Next to Security Mode, select WPA-Enterprise.
3. Next to WPA Mode, select Auto, WPA2 Only, or WPA Only. Use
Auto if you have wireless clients using both WPA and WPA2.
4. Next to Cypher Type, select TKIP and AES, TKIP, or AES.
5. Next to Group Key Update Interval, enter the amount of time
before the group key used for broadcast and multicast data is
changed (3600 is default).
6. Next to Authentication Timeout, enter the amount of time before
a client is required to re-authenticate (60 minutes is default).
7. Next to RADIUS Server IP Address enter the IP Address of your RADIUS server.
Configure WPA-Enterprise (RADIUS)
73D-Link DIR-855 User Manual
Section 4 - Security
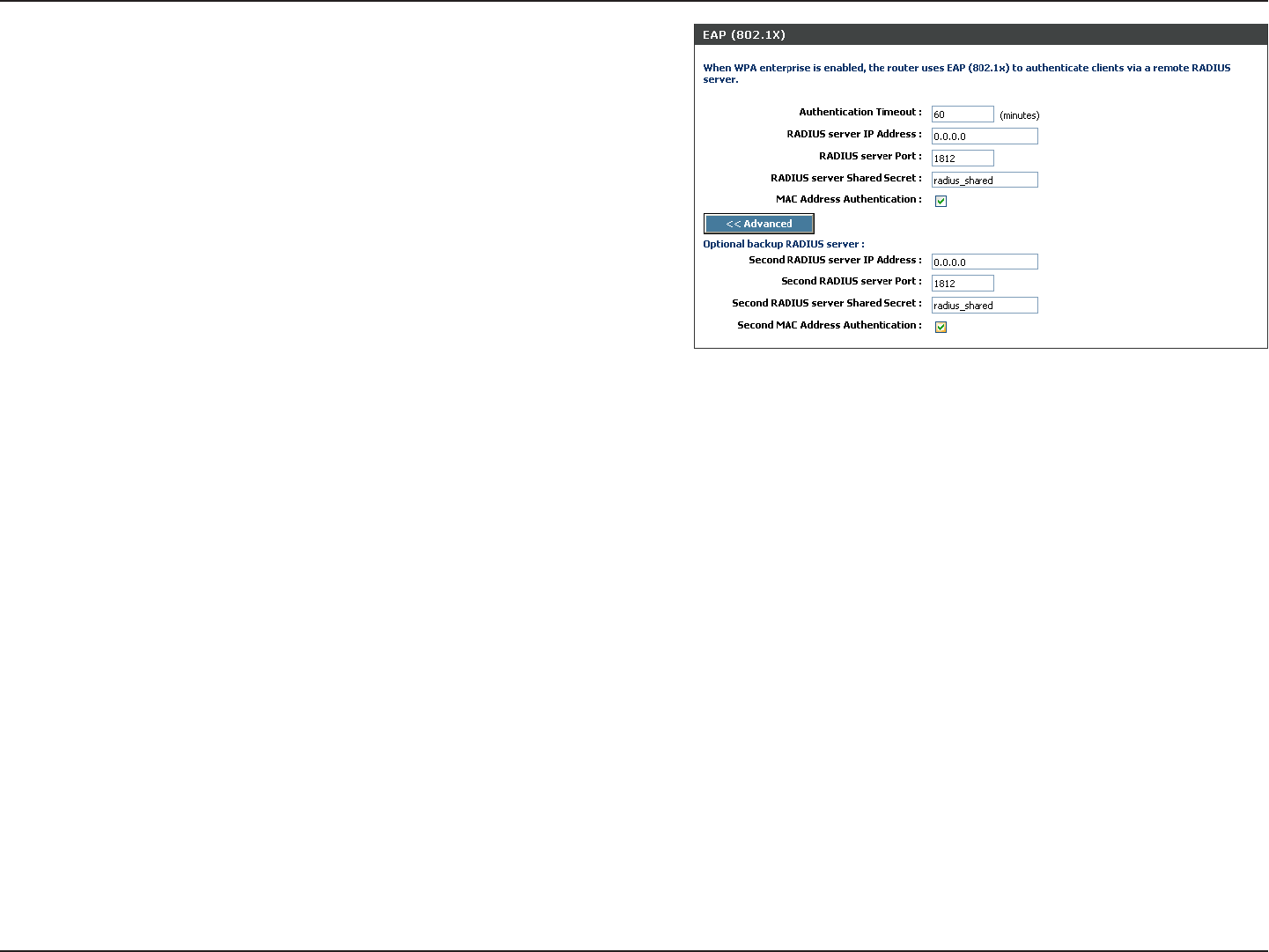
8. Next to RADIUS Server Port, enter the port you are using with
your RADIUS server. 1812 is the default port.
9. Next to RADIUS Server Shared Secret, enter the security
key.
10. If the MAC Address Authentication box is selected then the
user will need to connect from the same computer whenever
logging into the wireless network.
11. Click Advanced to enter settings for a secondary RADIUS
Server.
12. Click Apply Settings to save your settings.
74D-Link DIR-855 User Manual
Section 4 - Security
Connect to a Wireless Network
Using Windows® Vista™
Windows® Vista™ users may use the built-in wireless utility. If you are using another company’s utility or Windows® 2000,
please refer to the user manual of your wireless adapter for help with connecting to a wireless network. Most utilities
will have a “site survey” option similar to the Windows® Vista™ utility as seen below.
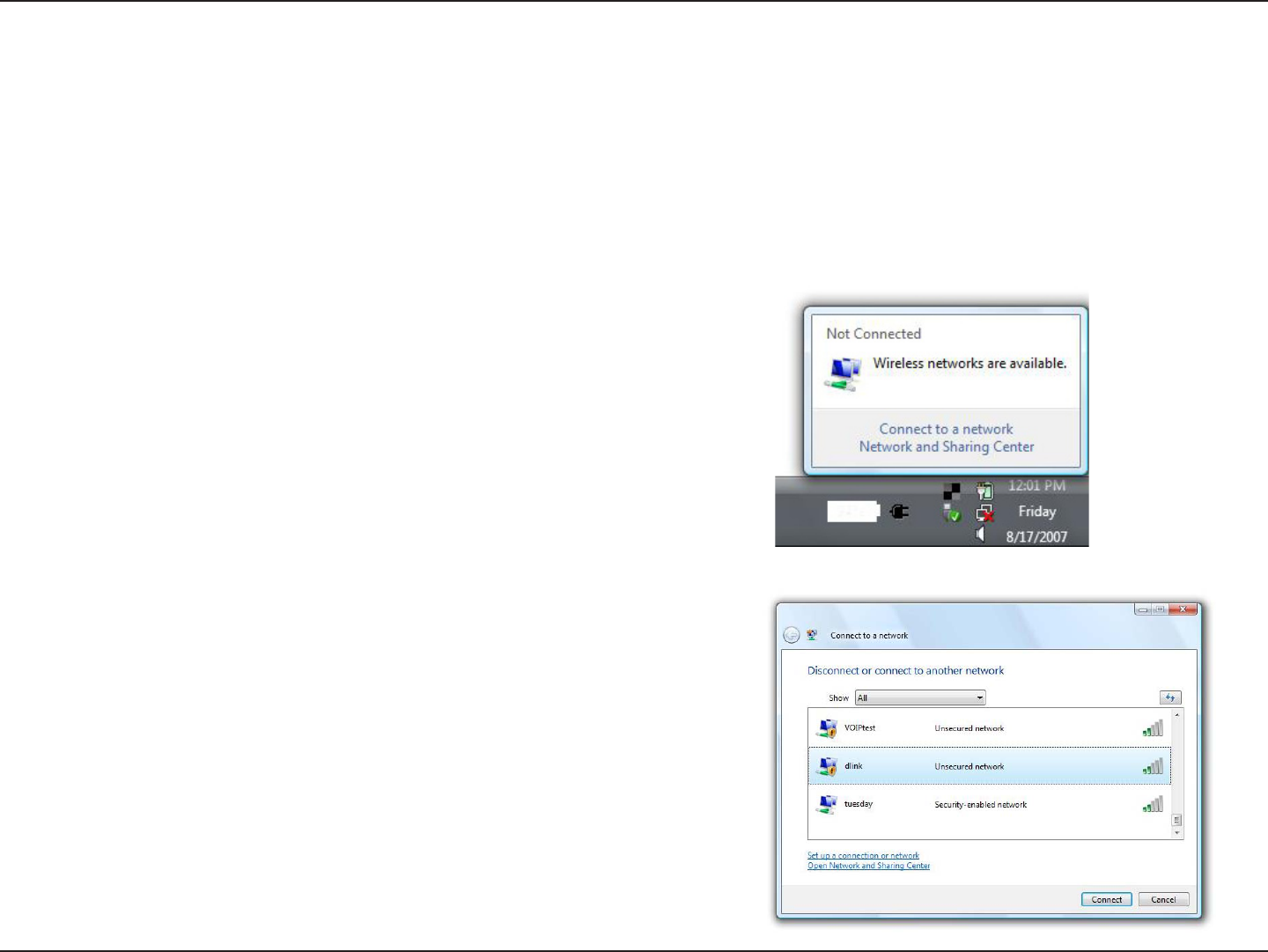
Right-click on the wireless computer icon in your system tray
(lower-right corner next to the time). Select Connect to a
network.
If you receive the Wireless Networks Detected bubble, click on
the center of the bubble to access the utility.
or
The utility will display any available wireless networks in your
area. Click on a network (displayed using the SSID) and click
the Connect button.
If you get a good signal but cannot access the Internet, check you
TCP/IP settings for your wireless adapter. Refer to the Networking
Basics section in this manual for more information.
75D-Link DIR-855 User Manual
Section 5 - Connecting to a Wireless Network
Configure Wireless Security
It is recommended to enable wireless security (WPA/WPA2) on your wireless router or access point before configuring
your wireless adapter. If you are joining an existing network, you will need to know the security key or passphrase
being used.
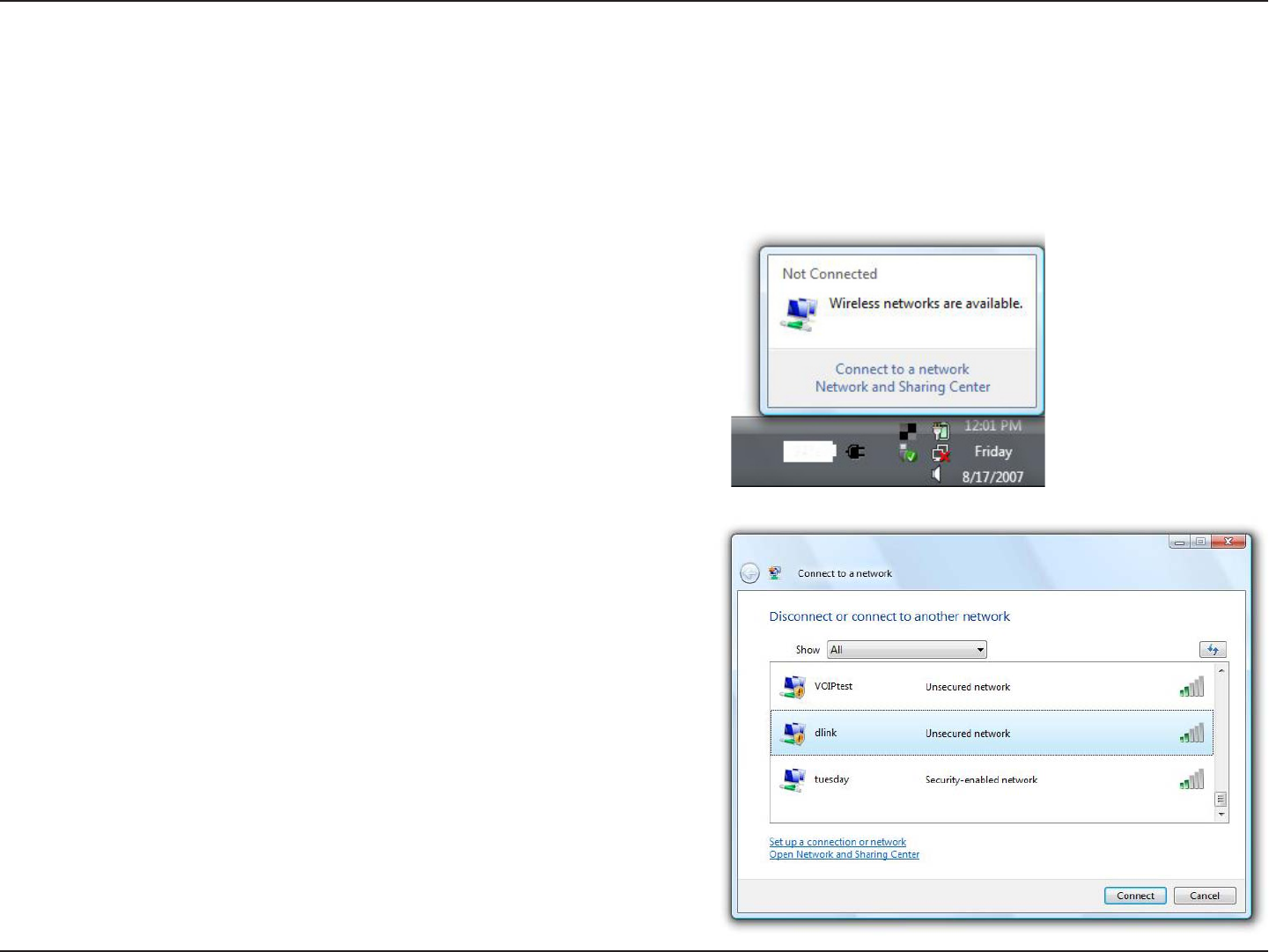
2. Highlight the wireless network (SSID) you would like to
connect to and click Connect.
1. Open the Windows® Vista™ Wireless Utility by right-clicking
on the wireless computer icon in your system tray (lower right
corner of screen). Select Connect to a network.
76D-Link DIR-855 User Manual
Section 5 - Connecting to a Wireless Network
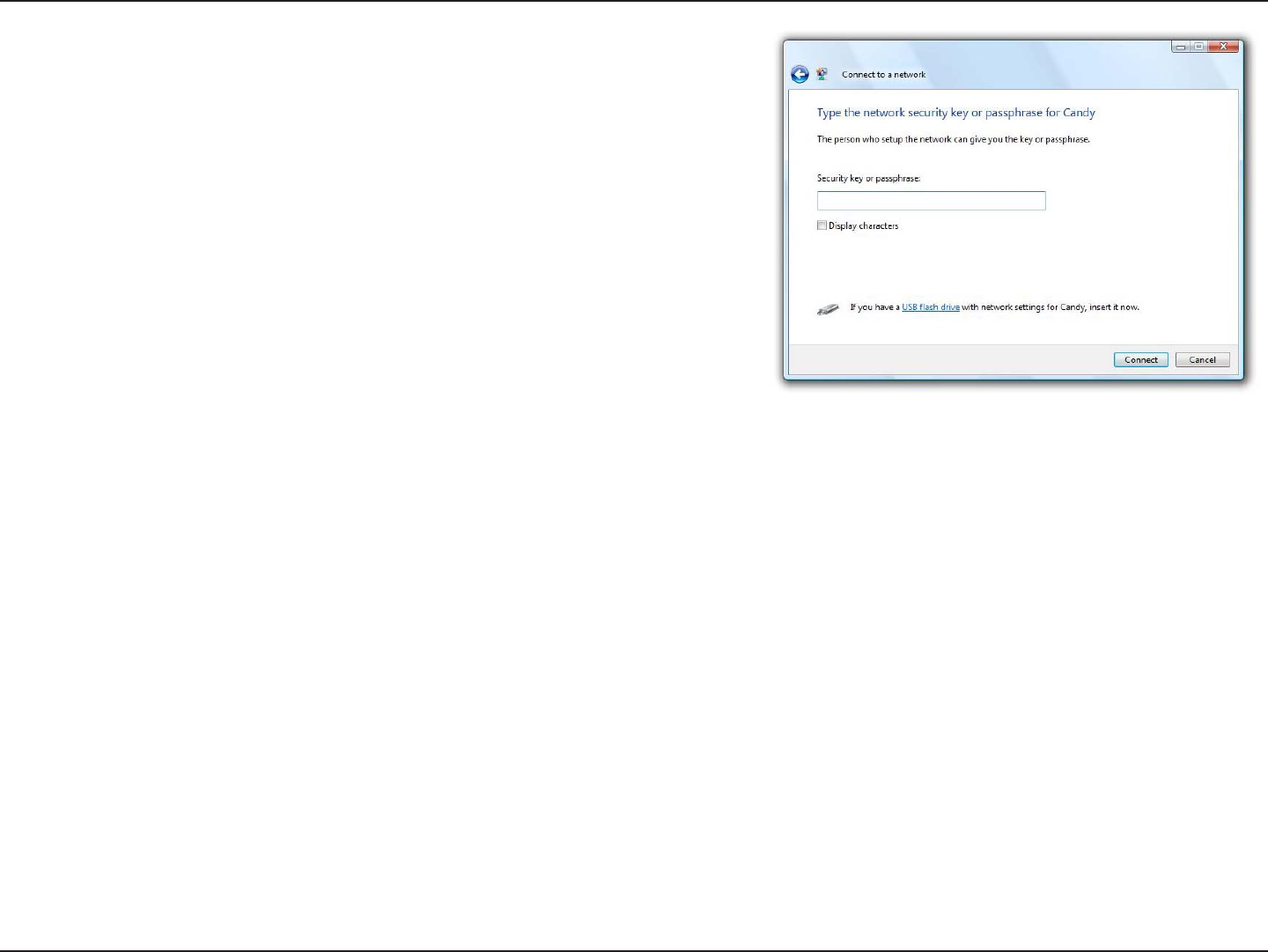
3. Enter the same security key or passphrase that is on your router
and click Connect.
It may take 20-30 seconds to connect to the wireless network. If the
connection fails, please verify that the security settings are correct.
The key or passphrase must be exactly the same as on the wireless
router.
77D-Link DIR-855 User Manual
Section 5 - Connecting to a Wireless Network
Connect Using WCN 2.0 in Windows Vista™
The router supports Wi-Fi protection, referred to as WCN 2.0 in Windows Vista™. The following instructions for setting
this up depends on whether you are using Windows Vista™ to configure the router or third party software.
When you first set up the router, Wi-Fi protection is disabled and unconfigured. To enjoy the benefits of Wi-Fi protection,
the router must be both enabled and configured. There are three basic methods to accomplish this: use Windows Vista’s
built-in support for WCN 2.0, use software provided by a third party, or manually configure.
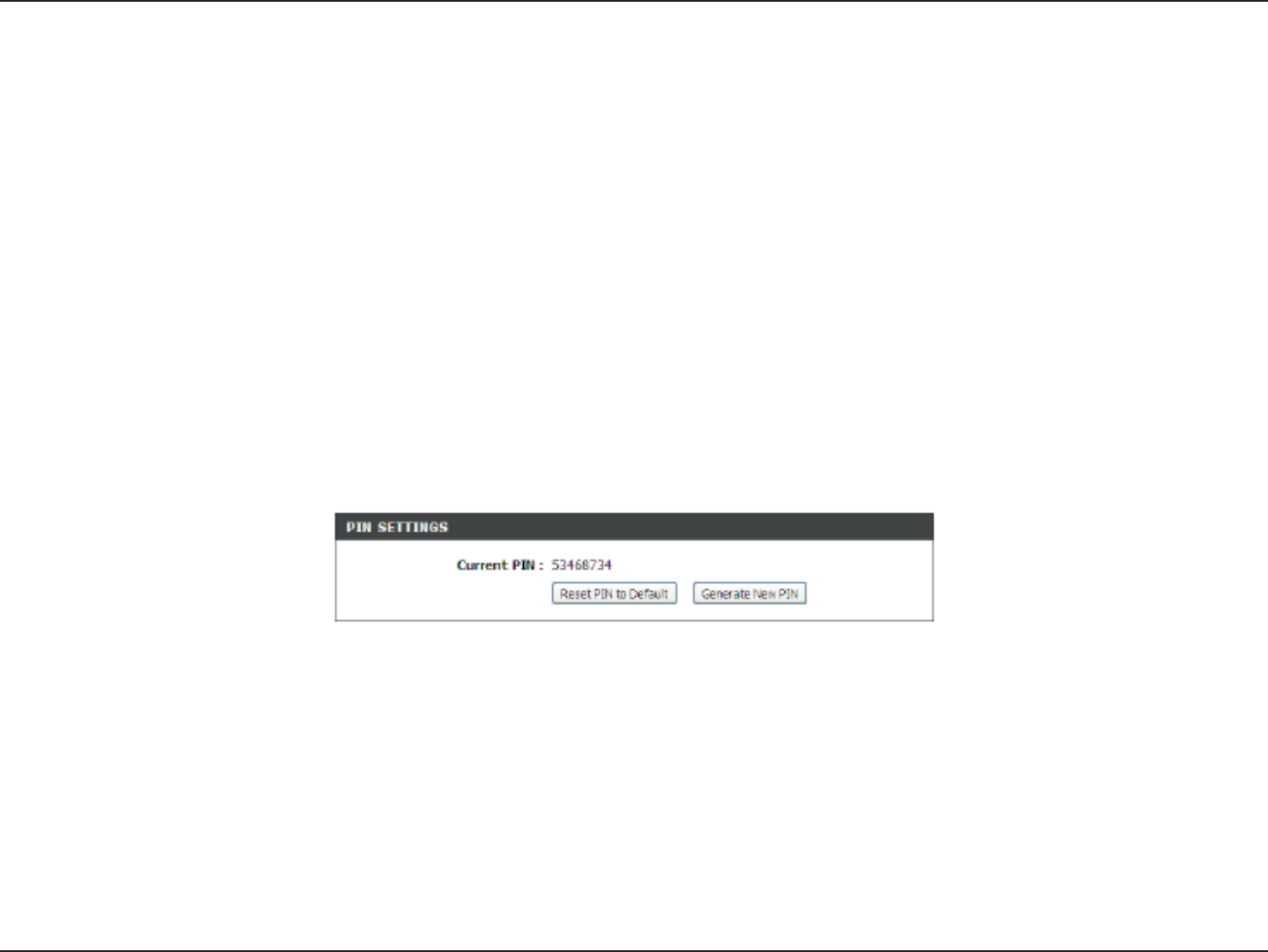
If you are running Windows Vista™, log into the router and click the Enable checkbox in the Basic > Wireless section.
Use the Current PIN that is displayed on the Advanced > Wi-Fi Protected Setup section or choose to click the Generate
New PIN button or Reset PIN to Default button.
For additional information, please refer to page 47.
If you are using third party software to set up Wi-Fi Protection, carefully follow the directions. When you are finished,
proceed to the next section to set up the newly-configured router.
78D-Link DIR-855 User Manual
Section 5 - Connecting to a Wireless Network
Connect to a Wireless Network
Using Windows® XP
Windows® XP users may use the built-in wireless utility (Zero Configuration Utility). The following instructions are for
Service Pack 2 users. If you are using another company’s utility or Windows® 2000, please refer to the user manual
of your wireless adapter for help with connecting to a wireless network. Most utilities will have a “site survey” option
similar to the Windows® XP utility as seen below.
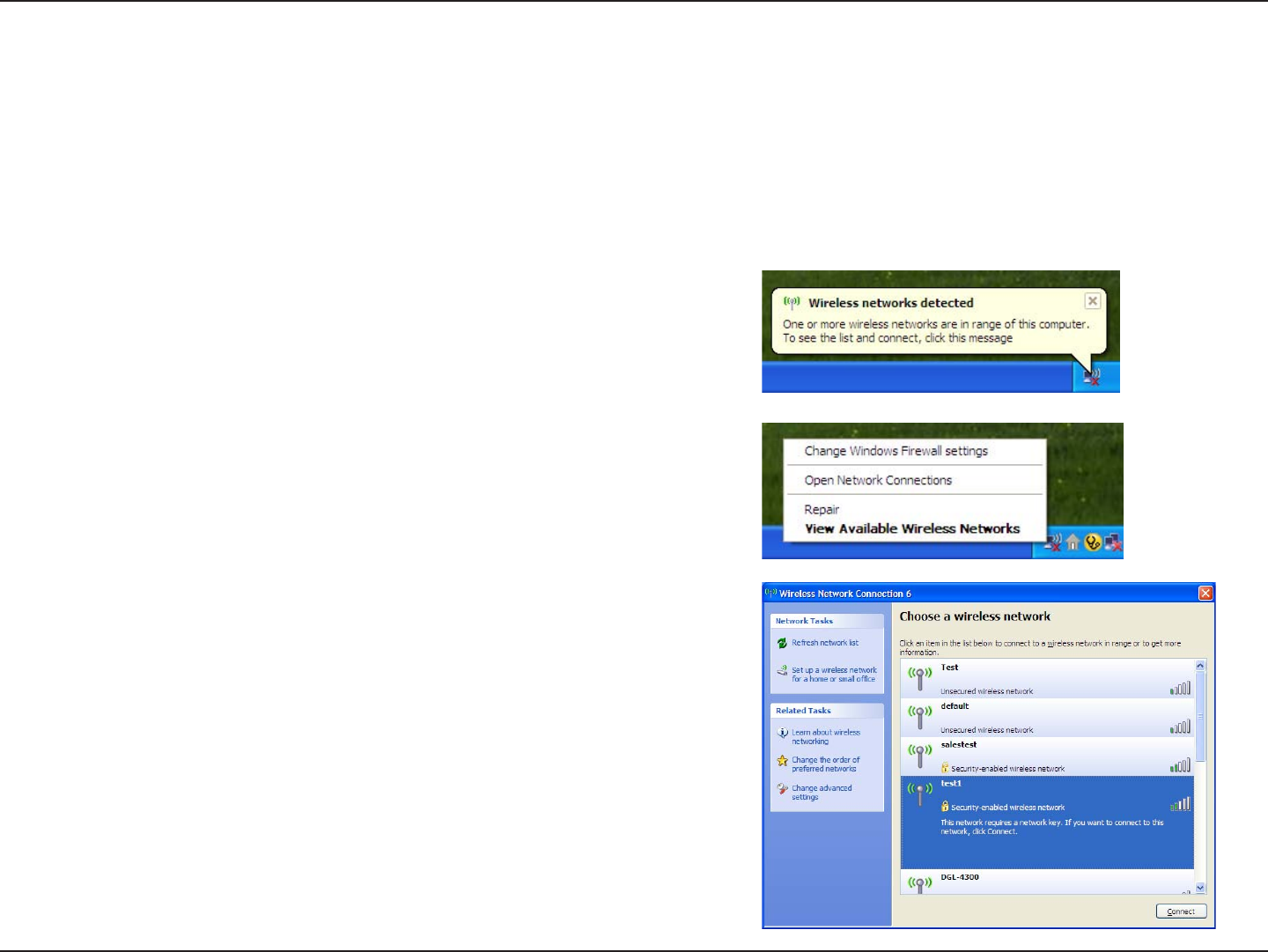
Right-click on the wireless computer icon in your system tray
(lower-right corner next to the time). Select View Available
Wireless Networks.
If you receive the Wireless Networks Detected bubble, click on
the center of the bubble to access the utility.
or
The utility will display any available wireless networks in your
area. Click on a network (displayed using the SSID) and click the
Connect button.
If you get a good signal but cannot access the Internet, check you
TCP/IP settings for your wireless adapter. Refer to the Networking
Basics section in this manual for more information.
79D-Link DIR-855 User Manual
Section 5 - Connecting to a Wireless Network
Configure WPA-PSK
It is recommended to enable WPA on your wireless router or access point before configuring your wireless adapter. If
you are joining an existing network, you will need to know the WPA key being used.
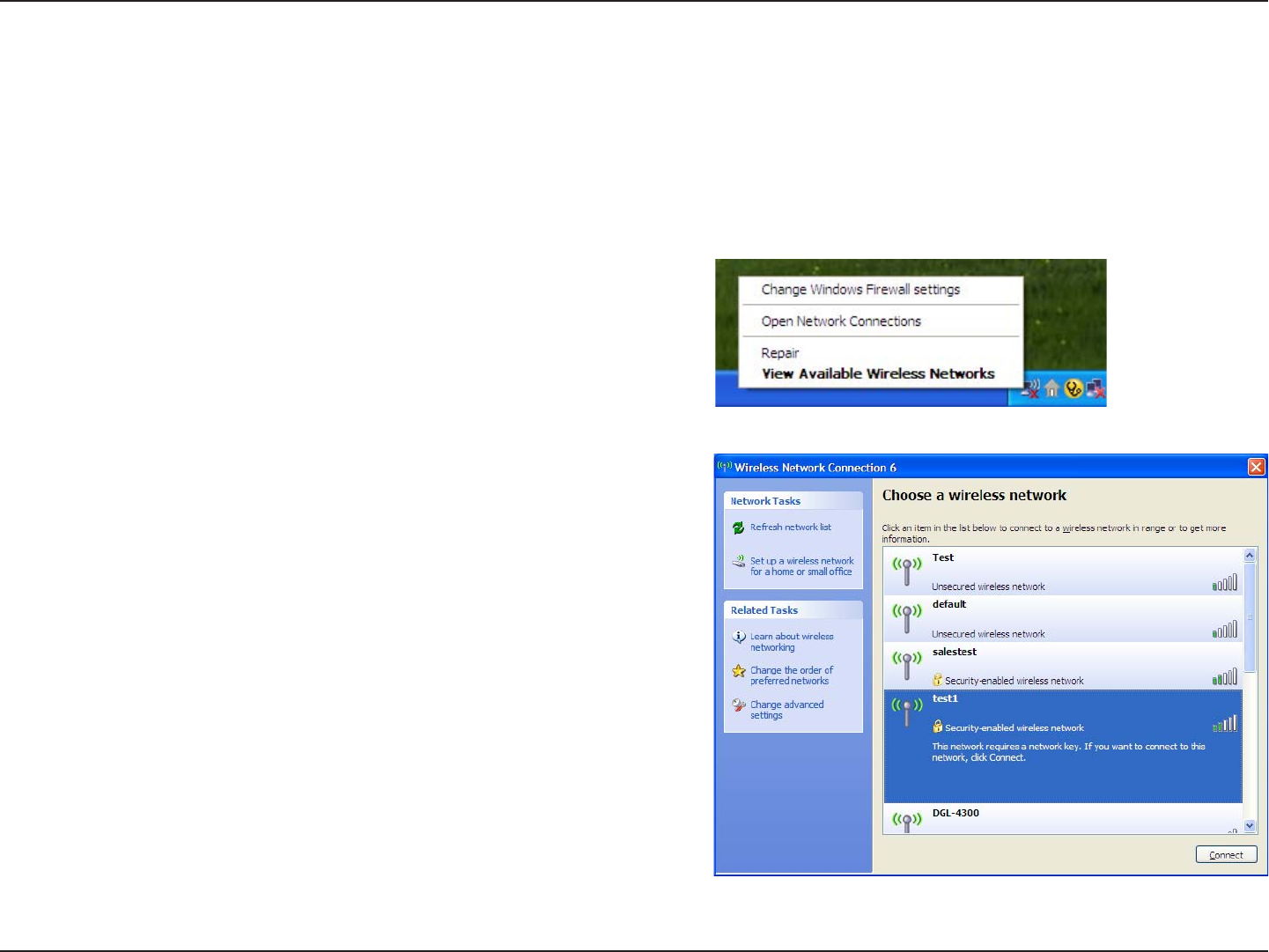
2. Highlight the wireless network (SSID) you would like to
connect to and click Connect.
1. Open the Windows® XP Wireless Utility by right-clicking
on the wireless computer icon in your system tray
(lower-right corner of screen). Select View Available
Wireless Networks.
80D-Link DIR-855 User Manual
Section 5 - Connecting to a Wireless Network
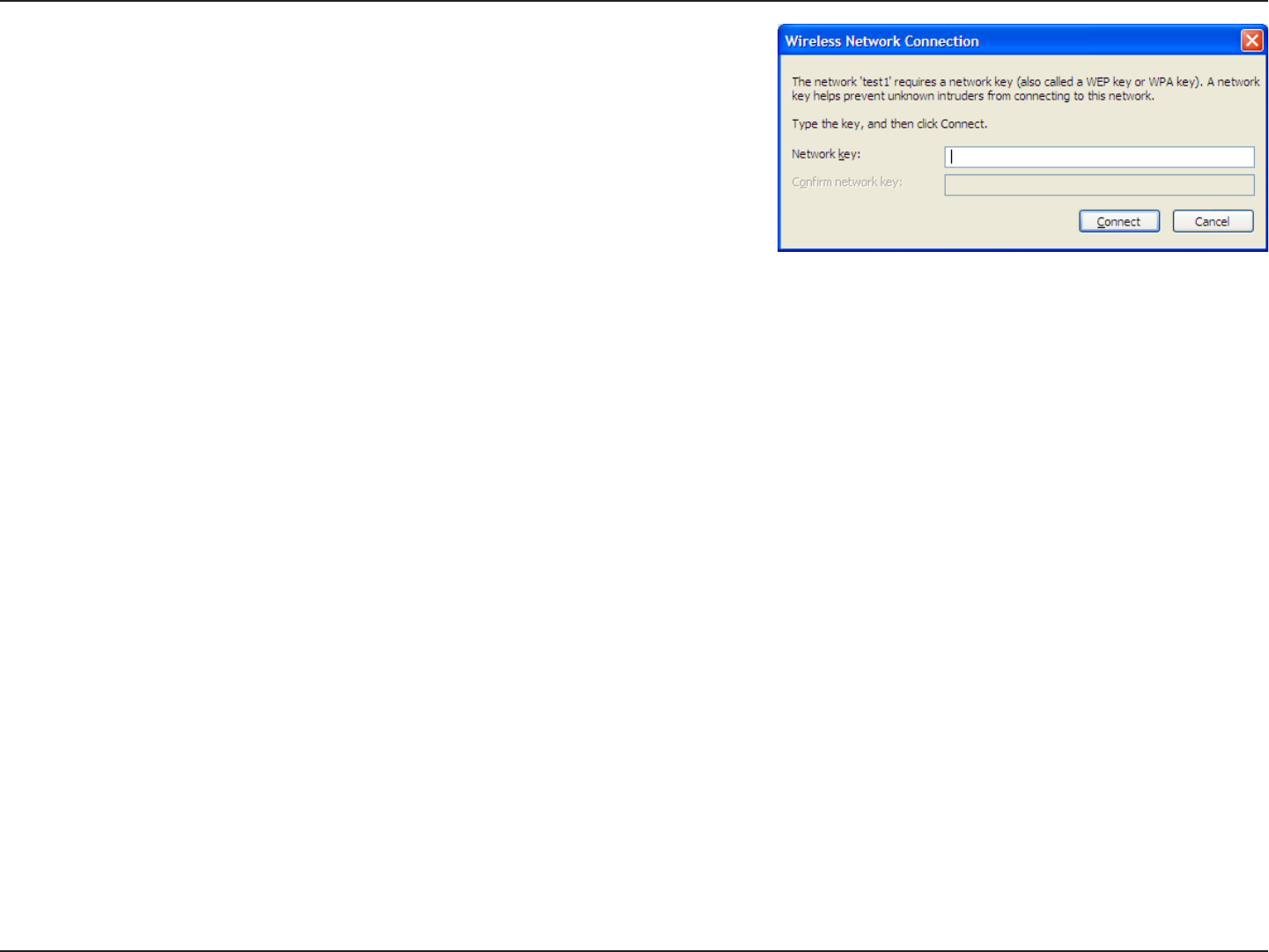
3. The Wireless Network Connection box will appear. Enter the
WPA-PSK passphrase and click Connect.
It may take 20-30 seconds to connect to the wireless network. If the
connection fails, please verify that the WPA-PSK settings are correct.
The WPA-PSK passphrase must be exactly the same as on the
wireless router.