D Link IR840LA1 Wireless N600 Cloud VPN Router , Wireless N600 VPN Router User Manual
D Link Corporation Wireless N600 Cloud VPN Router , Wireless N600 VPN Router
D Link >
user manual

User Manual
Wireless N600 VPN Router
DIR840
Version 1.0 | 07/02/2012
iD-Link DIR-840 User Manual
D-Link reserves the right to revise this publication and to make changes in the content hereof without obligation to notify any
person or organization of such revisions or changes.
Manual Revisions
Trademarks
D-Link and the D-Link logo are trademarks or registered trademarks of D-Link Corporation or its subsidiaries in the United
States or other countries. All other company or product names mentioned herein are trademarks or registered trademarks of
their respective companies.
Copyright © 2012 by D-Link Systems, Inc.
All rights reserved. This publication may not be reproduced, in whole or in part, without prior expressed written permission
from D-Link Systems, Inc.
Revision Date Description
1.0 July 02, 2012 • Initial release
Preface

iiD-Link DIR-840 User Manual
Table of Contents
Preface ................................................................................. i
Manual Revisions ........................................................................... i
Trademarks ...................................................................................... i
Product Overview .............................................................. 1
Package Contents ......................................................................... 1
System Requirements ................................................................. 2
Introduction ................................................................................... 3
Features ............................................................................................ 4
Hardware Overview ..................................................................... 5
Connections ...........................................................................5
LEDs ...........................................................................................6
Installation ......................................................................... 7
Before you Begin ........................................................................... 7
Wireless Installation Considerations ...................................... 8
Manual Setup .................................................................................9
Connect to an Existing Router ...............................................11
Conguration ...................................................................13
Web-based Conguration Utility ..........................................13
Internet Connection Setup .....................................................14
Static (assigned by ISP) .....................................................15
Dynamic (Cable) ..................................................................16
PPPoE (DSL) ...........................................................................17
PPTP .........................................................................................18
L2TP .........................................................................................20
Multi-SSID ......................................................................................22
Network Settings ........................................................................24
Router Settings ....................................................................24
DHCP Server Settings ........................................................25
VPN Settings .................................................................................26
IPSec Settings .......................................................................27
L2TP Settings ........................................................................29
Advanced Network Settings ...................................................30
Tools ..................................................................................31
Admin .............................................................................................31
Time .................................................................................................32
SysLog .............................................................................................33
System ............................................................................................34
Firmware ........................................................................................35
Dynamic DNS ...............................................................................36
System Check ...............................................................................37
Status ................................................................................38
Device Info ....................................................................................38
Log ...................................................................................................39
Statistics .........................................................................................40
Wireless ..........................................................................................41
VPN ..................................................................................................42
Troubleshooting ..............................................................43
Wireless Basics .................................................................47
What is Wireless? .........................................................................48
Table of Contents

iiiD-Link DIR-840 User Manual
Table of Contents
Tips ...................................................................................................50
Wireless Modes ............................................................................51
Networking Basics ...........................................................52
Check your IP address ...............................................................52
Statically Assign an IP address ...............................................53
Technical Specications ..................................................54
GPL Code Statement........................................................55
Safety Statements ...........................................................68

1D-Link DIR-840 User Manual
Section 1 - Product Overview
Product Overview
Package Contents
Note: Using a power supply with a dierent voltage rating than the one included with the DIR-840 will cause damage and void the warranty
for this product.
If any of the above items are missing, please contact your reseller.
DIR-840 Wireless N600 VPN Router
Ethernet Cable
Two Detachable Antennas
Power Adapter
2D-Link DIR-840 User Manual
Section 1 - Product Overview
Network Requirements
• An Ethernet-based Cable or DSL modem
• IEEE 802.11n or 802.11g wireless clients
• IEEE 802.11a wireless clients
• 10/100/1000 Ethernet
Web-based Conguration
Utility Requirements
Computer with the following:
• Windows®, Macintosh, or Linux-based operating system
• An installed Ethernet adapter
Browser Requirements:
• Internet Explorer 6 or higher
• Firefox 3.0 or higher
• Safari 3.0 or higher
• Chrome 2.0 or higher
Windows® Users: Make sure you have the latest version of Java
installed. Visit www.java.com to download the latest version.
System Requirements

3D-Link DIR-840 User Manual
Section 1 - Product Overview
Introduction
TOTAL PERFORMANCE
Combines award winning router features and IEEE 802.11a/g/n wireless technology to provide the best wireless performance.
TOTAL SECURITY
The most complete set of security features including Active Firewall and WPA/WPA2 to protect your network against outside intruders.
TOTAL COVERAGE
Provides greater wireless signal rates even at farther distances for best-in-class Whole Home Coverage.
ULTIMATE PERFORMANCE
The D-Link Wireless N600 VPN Router (DIR-840) is a 802.11n/802.11a compliant device that delivers real world performance of up to 14x
faster than an 802.11g wireless connection (also faster than a 100Mbps wired Ethernet connection). Create a secure wireless network
to share photos, les, music, video, printers, and network storage throughout your home. Connect the DIR-840 router to a cable or DSL
modem and share your high-speed Internet access with everyone on the network. In addition, this Router includes a Quality of Service
(QoS) engine that keeps digital phone calls (VoIP) and online gaming smooth and responsive, providing a better Internet experience.
EXTENDED WHOLE HOME COVERAGE
Powered by Wireless N technology, this high performance router provides superior Whole Home Coverage while reducing dead spots.
The router is designed for use in bigger homes and for users who demand higher performance networking. Add a Wireless N notebook
or desktop adapter and stay connected to your network from virtually anywhere in your home.
TOTAL NETWORK SECURITY
The Wireless N router supports all of the latest wireless security features to prevent unauthorized access, be it from over the wireless
network or from the Internet. Support for WPA/WPA2 standards ensure that you’ll be able to use the best possible encryption method,
regardless of your client devices. In addition, this router utilizes dual active rewalls (SPI and NAT) to prevent potential attacks from
across the Internet.
* Maximum wireless signal rate derived from IEEE Standard 802.11a, 802.11g and 802.11n specications. Actual data throughput will vary. Network conditions and environmental
factors, including volume of network trac, building materials and construction, and network overhead, lower actual data throughput rate. Environmental conditions will
adversely aect wireless signal range.

4D-Link DIR-840 User Manual
Section 1 - Product Overview
• Faster Wireless Networking - The DIR-840 provides up to 300Mbps* wireless connection with other 802.11n
wireless clients. This capability allows users to participate in real-time activities online, such as video streaming,
online gaming, and real-time audio. The performance of this 802.11n wireless router gives you the freedom of
wireless networking at speeds 14x faster than 802.11g.
• Compatible with 802.11a/g Devices - The DIR-840 is still fully compatible with the IEEE 802.11g and 802.11a
standards, so it can connect with existing 802.11g and 802.11a PCI, USB, and Cardbus adapters.
• Advanced Firewall Features - The Web-based user interface displays a number of advanced network
management features including:
• Secure Multiple/Concurrent Sessions - The DIR-840 can pass through VPN sessions. It supports
multiple and concurrent IPSec and PPTP sessions, so users behind the DIR-840 can securely access
corporate networks.
• User-friendly Setup Wizard - Through its easy-to-use Web-based user interface, the DIR-840 lets you control what
information is accessible to those on the wireless network, whether from the Internet or from your company’s
server. Congure your router to your specic settings within minutes.
* Maximum wireless signal rate derived from IEEE Standard 802.11g, 802.11a, and 802.11n specications. Actual data throughput will vary. Network conditions and environmental
factors, including volume of network trac, building materials and construction, and network overhead, lower actual data throughput rate. Environmental conditions will
adversely aect wireless signal range.
Features
5D-Link DIR-840 User Manual
Section 1 - Product Overview
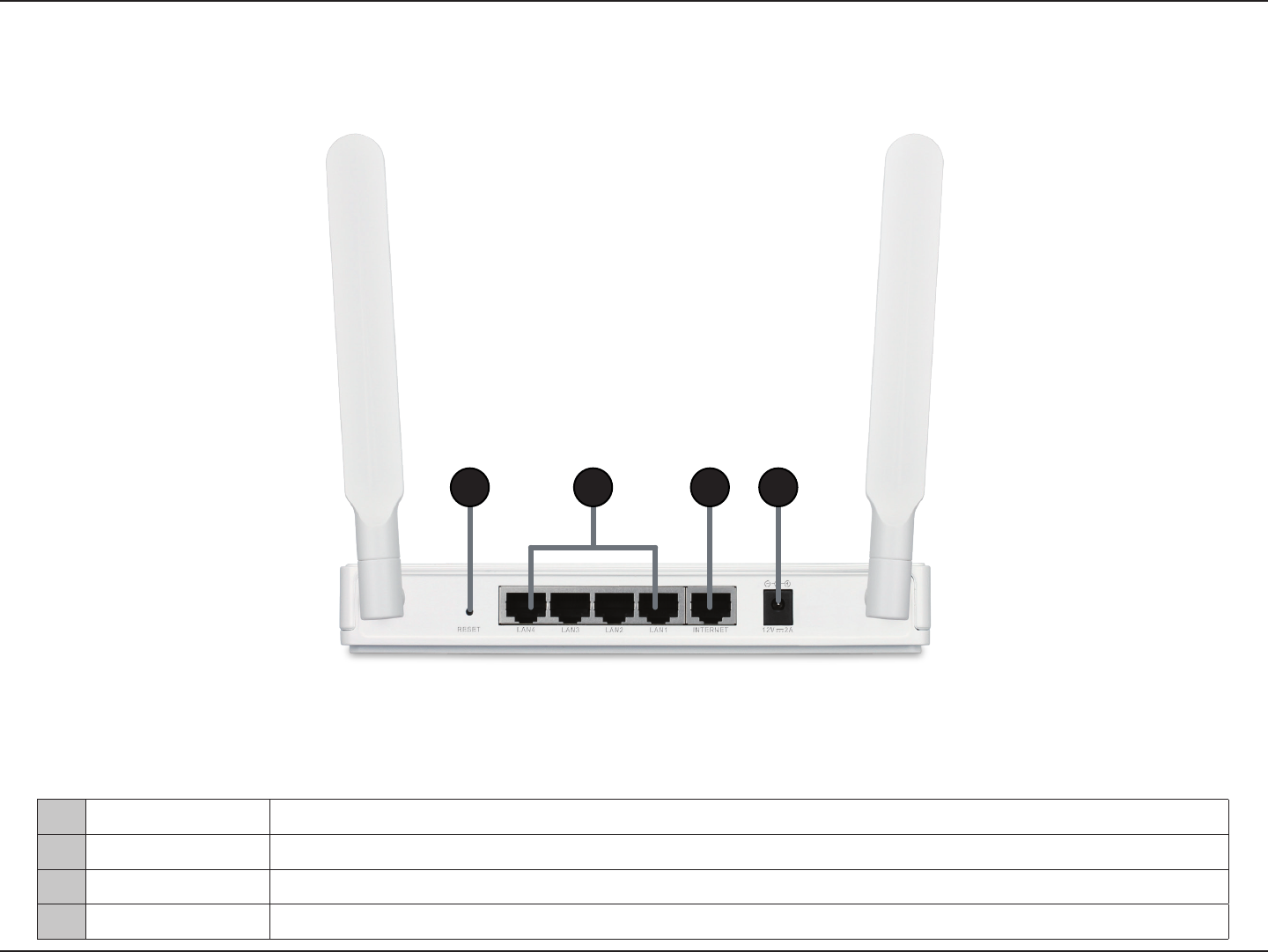
Hardware Overview
Connections
1Reset Button Pressing the Reset button restores the router to its original factory default settings.
2LAN Ports (1-4) Connect 10/100/1000 Ethernet devices such as computers, switches, and NAS.
3Internet Port The auto MDI/MDIX Internet port is the connection for the Ethernet cable to the cable or DSL modem.
4Power Receptor Receptor for the supplied power adapter.
1 2 43
6D-Link DIR-840 User Manual
Section 1 - Product Overview
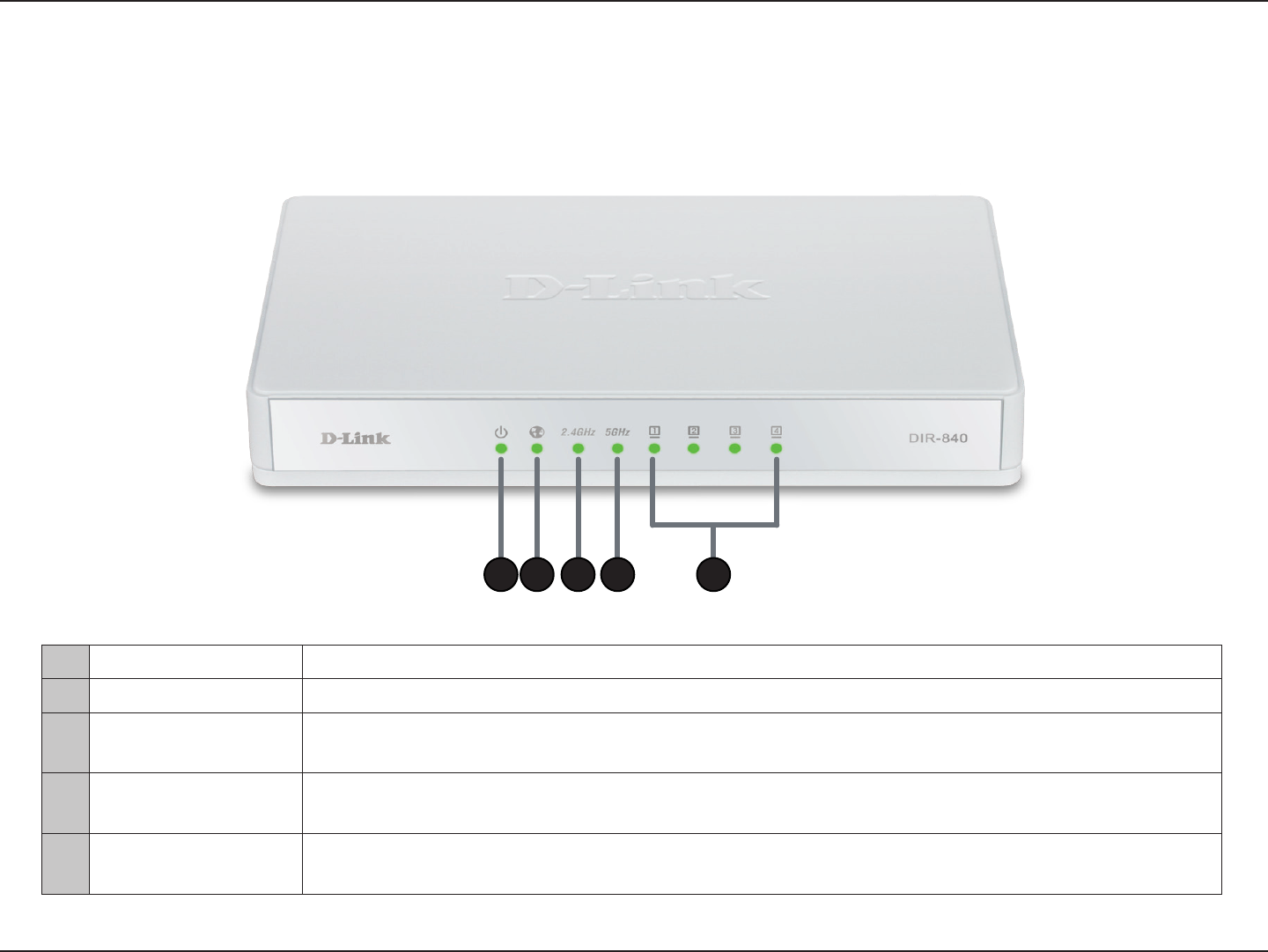
Hardware Overview
LEDs
1Power LED A solid light indicates a proper connection to the power supply.
2Internet LED A solid light indicates connection on the Internet port. This LED blinks during data transmission.
3WLAN LED (2.4GHz) A solid light indicates that the 2.4GHz wireless segment is ready. This LED blinks during wireless data
transmission.
4WLAN LED (5GHz) A solid light indicates that the 5GHz wireless segment is ready. This LED blinks during wireless data
transmission.
5LAN LEDs (1-4) A solid light indicates a connection to an Ethernet-enabled computer on ports 1-4. This LED blinks during
data transmission.
1 2 3 4 5

7D-Link DIR-840 User Manual
Section 2 - Installation
Before you Begin
Installation
This section will walk you through the installation process. Placement of the router is very important. Do not place the router
in an enclosed area such as a closet, cabinet, or in the attic or garage.
• Please congure the router with the computer that was last connected directly to your modem.
• You can only use the Ethernet port on your modem. If you were using the USB connection before using the router,
then you must turn o your modem, disconnect the USB cable and connect an Ethernet cable to the Internet port
on the router, and then turn the modem back on. In some cases, you may need to call your ISP to change connection
types (USB to Ethernet).
• If you have DSL and are connecting via PPPoE, make sure you disable or uninstall any PPPoE software such as WinPoet,
Broadjump, or Enternet 300 from your computer or you will not be able to connect to the Internet.

8D-Link DIR-840 User Manual
Section 2 - Installation
Wireless Installation Considerations
The D-Link wireless router lets you access your network using a wireless connection from virtually anywhere within the
operating range of your wireless network. Keep in mind, however, that the number, thickness and location of walls, ceilings,
or other objects that the wireless signals must pass through, may limit the range. Typical ranges vary depending on the types
of materials and background RF (radio frequency) noise in your home or business. The key to maximizing wireless range is to
follow these basic guidelines:
1. Keep the number of walls and ceilings between the D-Link router and other network devices to a minimum -
each wall or ceiling can reduce your adapter’s range from 3-90 feet (1-30 meters.) Position your devices so that
the number of walls or ceilings is minimized.
2. Be aware of the direct line between network devices. A wall that is 1.5 feet thick (.5 meters), at a 45-degree angle
appears to be almost 3 feet (1 meter) thick. At a 2-degree angle it looks over 42 feet (14 meters) thick! Position
devices so that the signal will travel straight through a wall or ceiling (instead of at an angle) for better reception.
3. Building Materials make a dierence. A solid metal door or aluminum studs may have a negative eect on range.
Try to position access points, wireless routers, and computers so that the signal passes through drywall or open
doorways. Materials and objects such as glass, steel, metal, walls with insulation, water (sh tanks), mirrors, le
cabinets, brick, and concrete will degrade your wireless signal.
4. Keep your product away (at least 3-6 feet or 1-2 meters) from electrical devices or appliances that generate RF
noise.
5. If you are using 2.4GHz cordless phones or X-10 (wireless products such as ceiling fans, lights, and home security
systems), your wireless connection may degrade dramatically or drop completely. Make sure your 2.4GHz phone
base is as far away from your wireless devices as possible. The base transmits a signal even if the phone in not
in use.
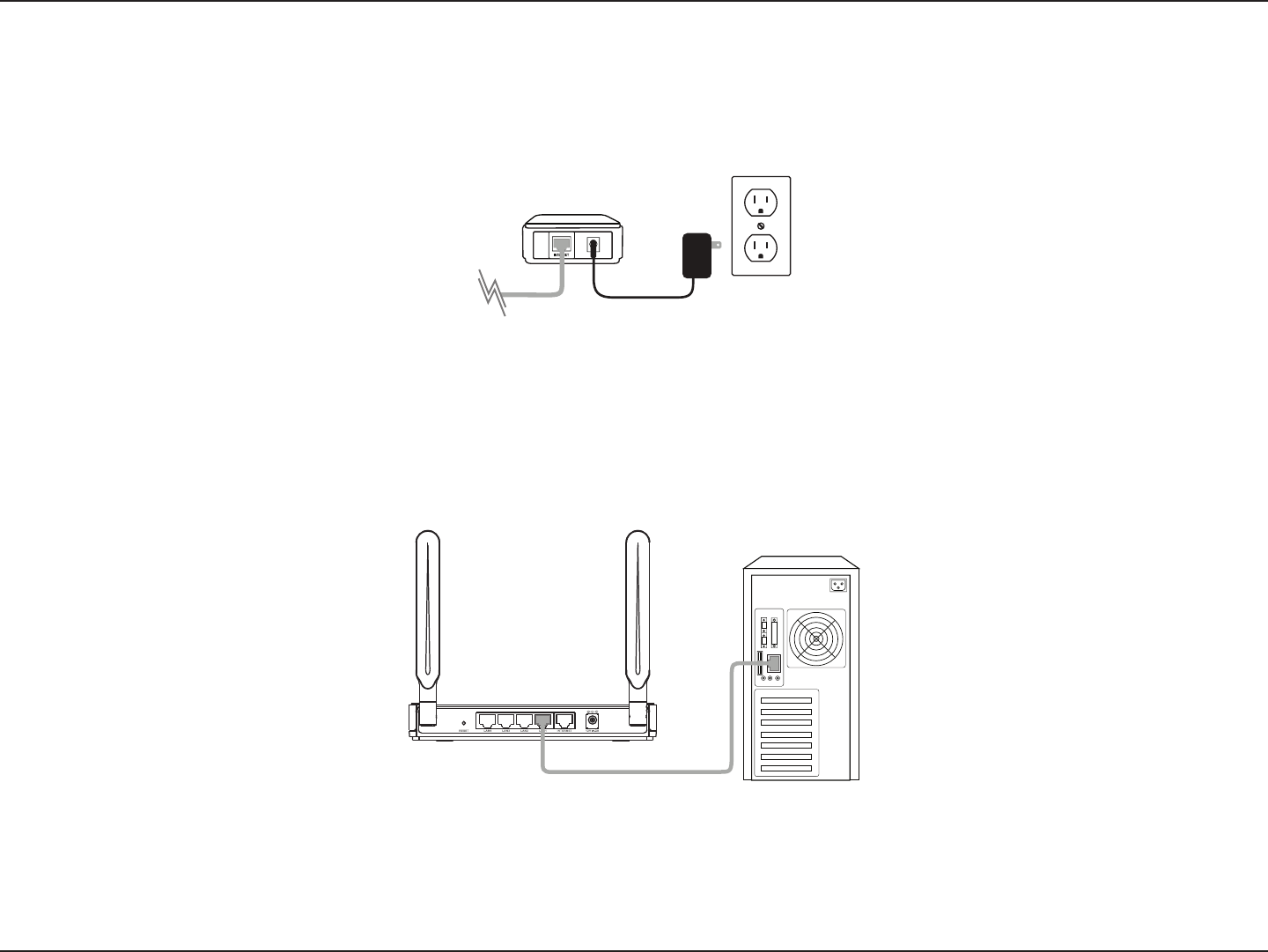
9D-Link DIR-840 User Manual
Section 2 - Installation
1. Turn o and unplug your cable or DSL broadband modem. This is required.
Manual Setup
2. Position your router close to your modem and a computer. Place the router in an open area of your intended
work area for better wireless coverage.
3. Unplug the Ethernet cable from your modem (or existing router if upgrading) that is connected to your computer.
Plug it into the blue port labeled 1 on the back of your router. The router is now connected to your computer.
Modem
DIR-840
Computer
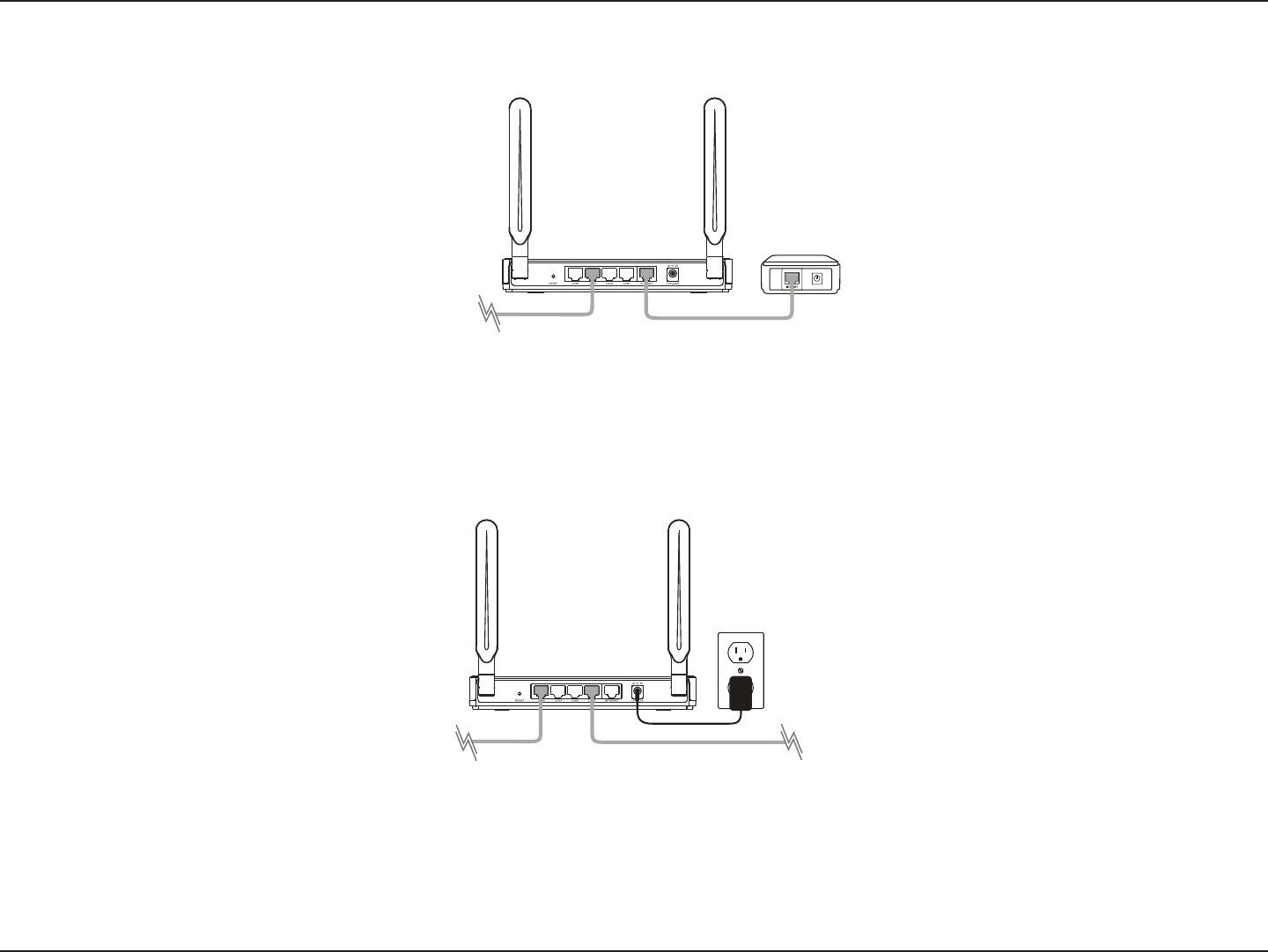
10D-Link DIR-840 User Manual
Section 2 - Installation
4. Plug one end of the included blue Ethernet cable that came with your router into the yellow port labeled
INTERNET on the back of the router. Plug the other end of this cable into the Ethernet port on your modem.
5. Reconnect the power adapter to your cable or DSL broadband modem and wait for two minutes.
6. Connect the supplied power adapter into the power port on the back of the router and then plug it into a power
outlet or surge protector. Press the power button and verify that the power LED is lit. Allow 1 minute for the
router to boot up.
7. If you are connecting to a Broadband service that uses a dynamic connection (not PPPoE), you may be online
already. Try opening a web browser and enter a web site. If you connect, you are nished with your Internet setup.
Please skip to page 13 to congure your router and use the manual setup procedure to congure your network
and wireless settings. If you did not connect to the Internet, use the D-Link Setup Wizard (refer to page 15).
DIR-840
DIR-840
Modem

11D-Link DIR-840 User Manual
Section 2 - Installation
Note: It is strongly recommended to replace your existing router with the DIR-840 instead of using both. If your modem is a combo
router, you may want to contact your ISP or manufacturer’s user guide to put the router into Bridge mode, which will ‘turn o’ the
router (NAT) functions.
If you are connecting the DIR-840 router to an existing router to use as a wireless access point and/or switch, you will have to
do the following to the DIR-840 before connecting it to your network:
• Disable UPnP™
• Disable DHCP
• Change the LAN IP address to an available address on your network. The LAN ports on the router cannot accept
a DHCP address from your other router.
To connect to another router, please follow the steps below:
1. Plug the power into the router. Connect one of your computers to the router (LAN port) using an Ethernet cable. Make sure
your IP address on the computer is 192.168.0.xxx (where xxx is between 2 and 254). Please see the Networking Basics
section for more information. If you need to change the settings, write down your existing settings before making any
changes. In most cases, your computer should be set to receive an IP address automatically in which case you will not have
to do anything to your computer.
2. Open a web browser, enter http://192.168.89.1 and press Enter. When the login window appears, set the user name to
Admin and the password to nwtitfbipne. Click Log In to continue.
3. Click on Advanced and then click Advanced Network. Uncheck the Enable UPnP checkbox. Click Save Settings to continue.
4. Click Setup and then click Network Settings. Uncheck the Enable DHCP Server checkbox. Click Save Settings to continue.
Connect to an Existing Router
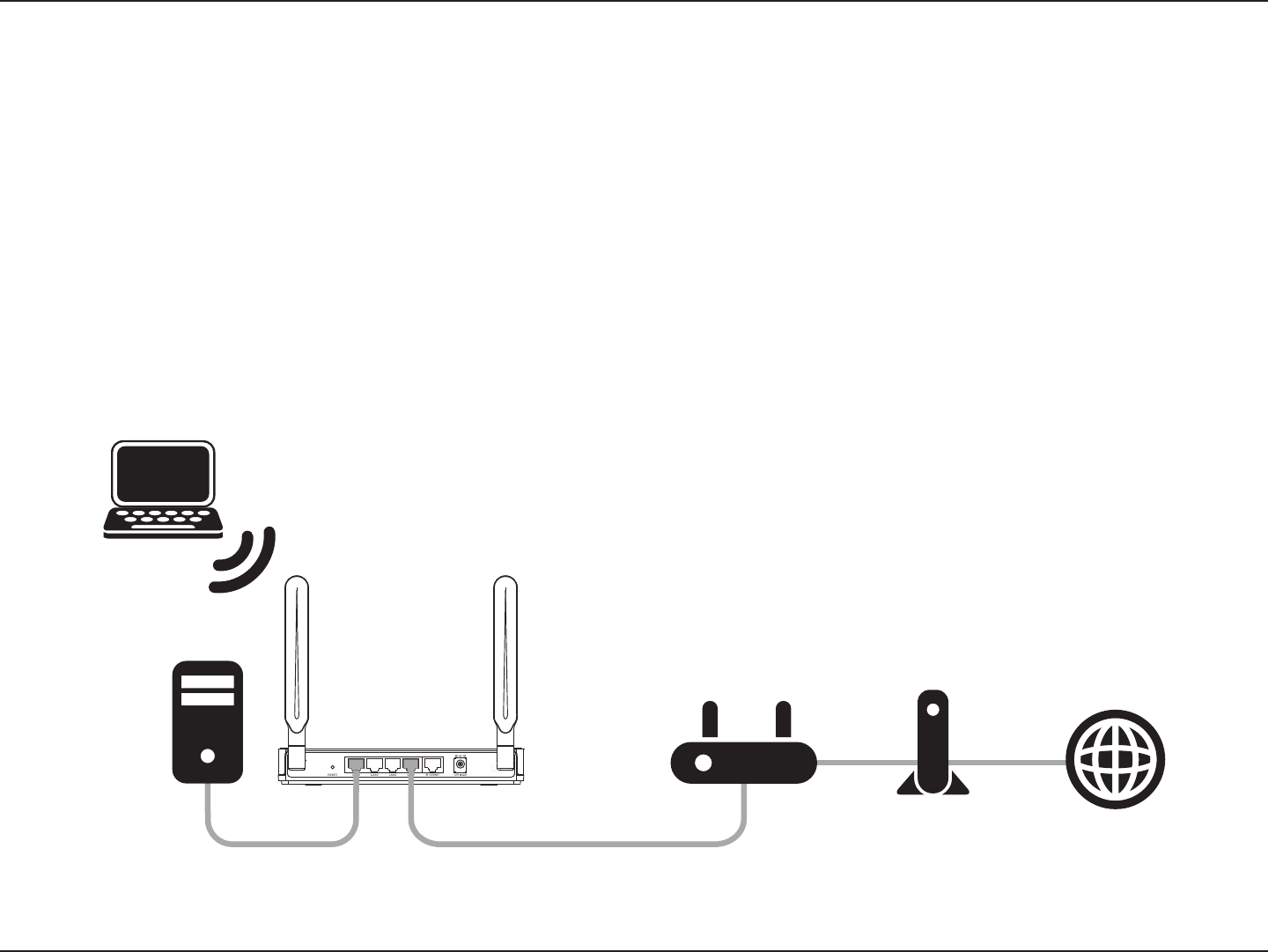
12D-Link DIR-840 User Manual
Section 2 - Installation
5. Under Router Settings, enter an available IP address and the subnet mask of your network. Click Save Settings to save your
settings. Use this new IP address to access the conguration utility of the router in the future. Close the browser and change
your computer’s IP settings back to the original values as in Step 1.
6. Disconnect the Ethernet cable from the router and reconnect your computer to your network.
7. Connect an Ethernet cable in one of the LAN ports of the router and connect it to your other router. Do not plug anything
into the Internet (WAN) port of the D-Link router.
8. You may now use the other 3 LAN ports to connect other Ethernet devices and computers. To congure your wireless network,
open a web browser and enter the IP address you assigned to the router. Refer to the Conguration and Wireless Security
sections for more information on setting up your wireless network.
Laptop
Computer
DIR-840
Existing Router Modem
Internet
13D-Link DIR-840 User Manual
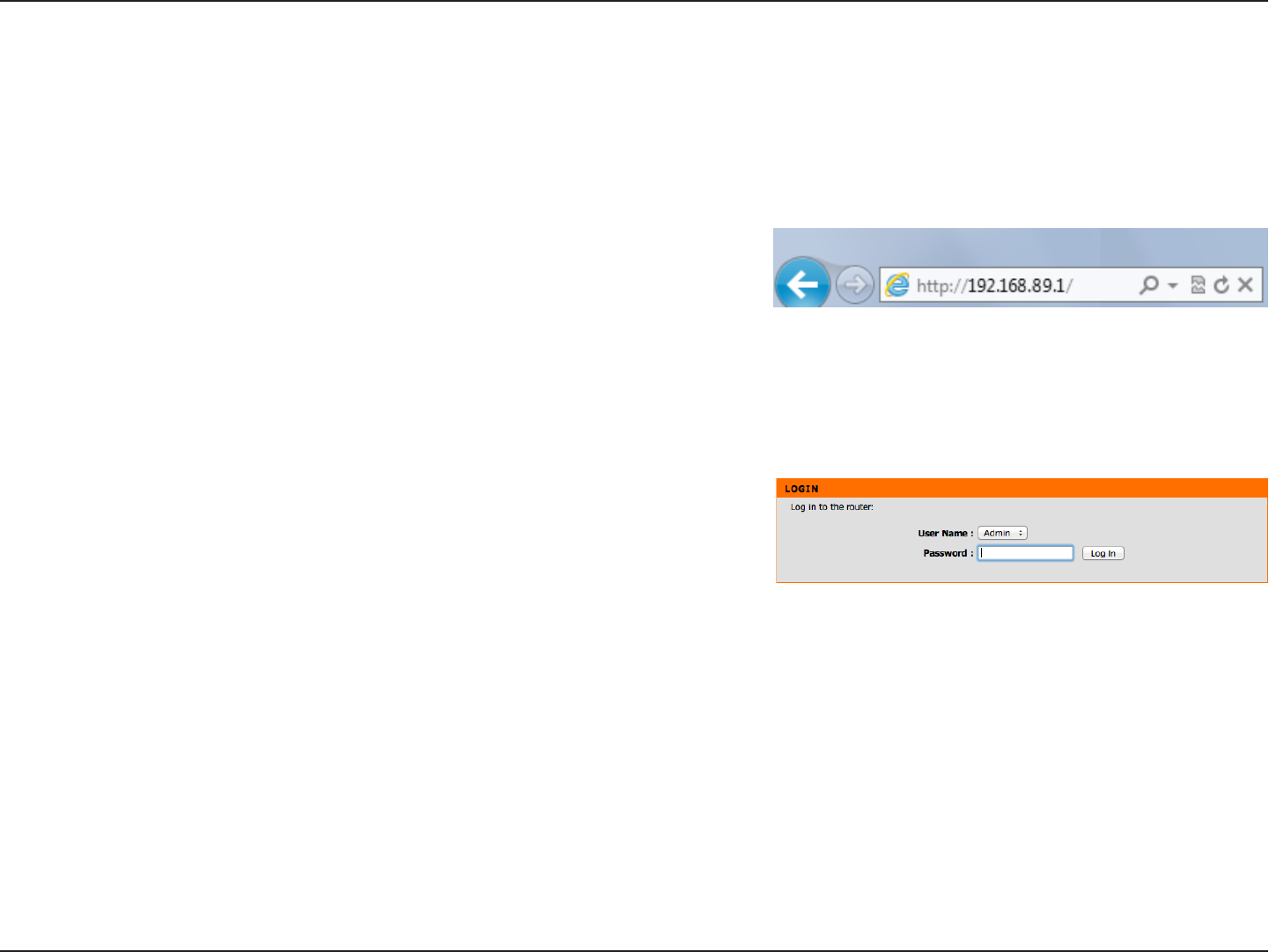
Section 3 - Conguration
Web-based Conguration Utility
Select Admin from the drop-down menu and then enter the password
nwtitfbipne.
To access the conguration utility, open a web-browser such as Internet
Explorer and enter the IP address of the router (http://192.168.89.1).
Conguration
14D-Link DIR-840 User Manual
Section 3 - Conguration
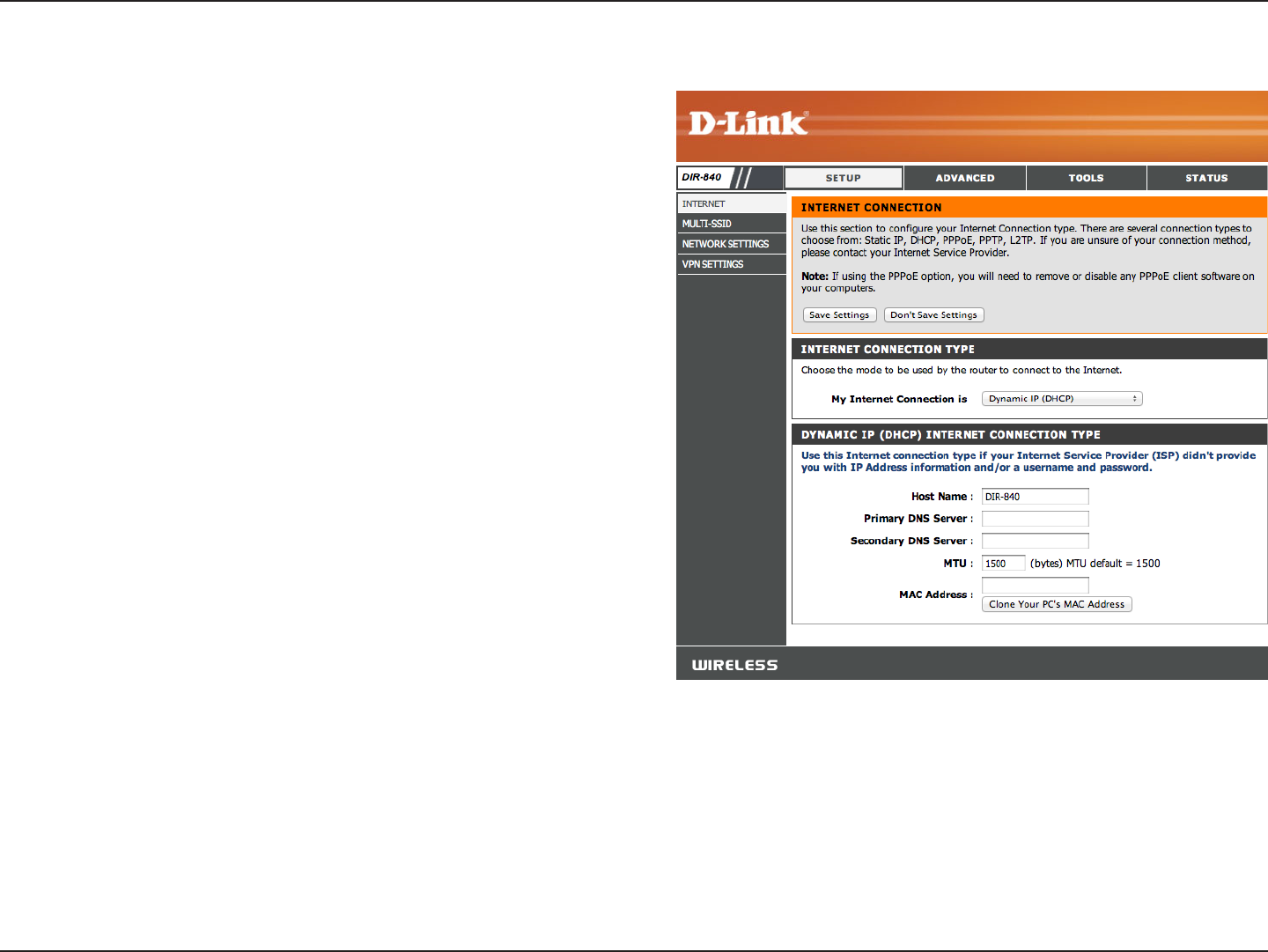
Internet Connection Setup
Use this tab to choose either Static IP, DHCP, PPPoE, PPTP, or
L2TP to congure your Internet connection. You may need to
get this information from your ISP (Internet Service Provider).
15D-Link DIR-840 User Manual
Section 3 - Conguration
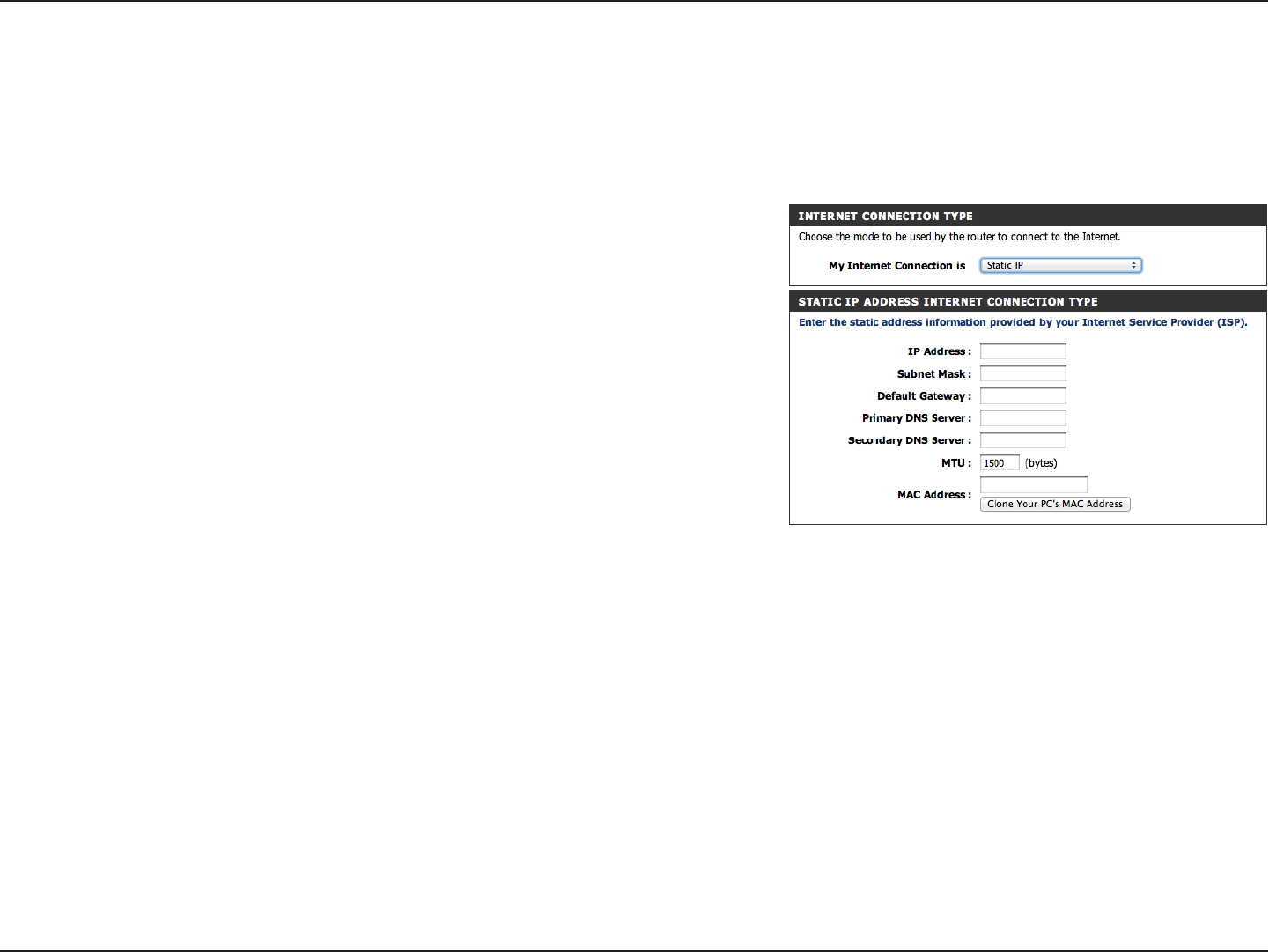
Select Static IP to manually enter the IP settings supplied by
your ISP.
Enter the IP address assigned by your ISP.
Enter the Subnet Mask assigned by your ISP.
Enter the Gateway assigned by your ISP.
The DNS server information will be supplied by your ISP (Internet
Service Provider.)
Maximum Transmission Unit - you may need to change the MTU
for optimal performance with your specic ISP. 1500 is the default
MTU.
The default MAC Address is set to the Internet port’s physical
interface MAC address on the Broadband Router. It is not
recommended that you change the default MAC address unless
required by your ISP. You can use the Copy Your PC’s MAC Address
button to replace the Internet port’s MAC address with the MAC
address of your Ethernet card.
My Internet Connection:
IP Address:
Subnet Mask:
Default Gateway:
DNS Servers:
MTU:
MAC Address:
Static (assigned by ISP)
Select Static IP Address if all the Internet port’s IP information is provided to you by your ISP. You will need to enter in the IP address, subnet mask,
gateway address, and DNS address(es) provided to you by your ISP. Each IP address entered in the elds must be in the appropriate IP form, which
are four octets separated by a dot (x.x.x.x). The Router will not accept the IP address if it is not in this format.
16D-Link DIR-840 User Manual
Section 3 - Conguration
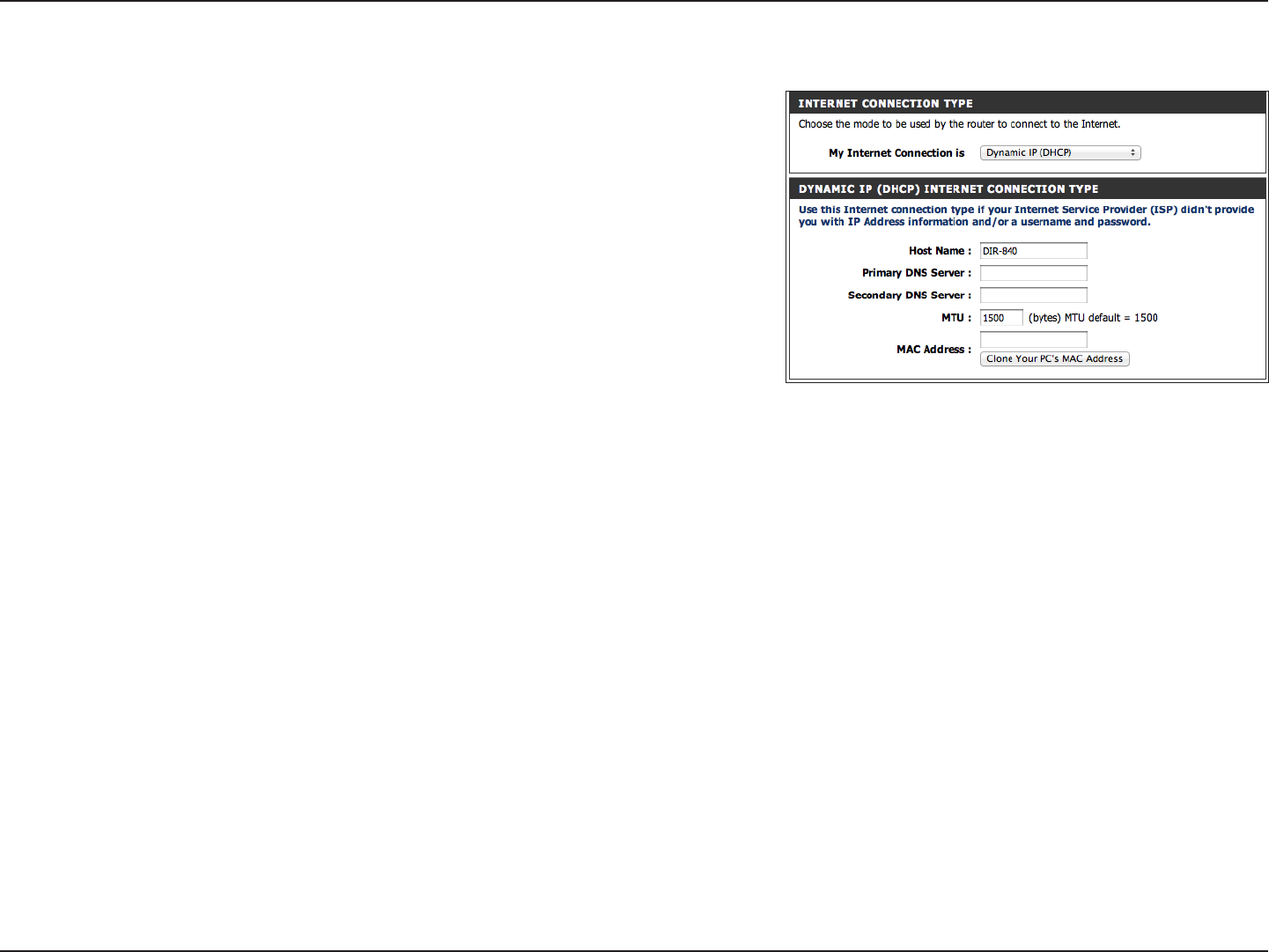
Select Dynamic IP (DHCP) to obtain IP Address information
automatically from your ISP. Select this option if your ISP does not give
you any IP numbers to use. This option is commonly used for cable
modem services.
The Host Name is optional but may be required by some ISPs. Leave
blank if you are not sure.
Enter the Primary and secondary DNS server IP addresses assigned by
your ISP. These addresses are usually obtained automatically from your
ISP. Leave at 0.0.0.0 if you did not specically receive these from your ISP.
Maximum Transmission Unit - you may need to change the MTU for
optimal performance with your specic ISP. 1500 is the default MTU.
The default MAC Address is set to the Internet port’s physical interface MAC address on the Broadband Router. It is not recommended
that you change the default MAC address unless required by your ISP. You can use the Copy Your PC’s MAC Address button to
replace the Internet port’s MAC address with the MAC address of your Ethernet card.
My Internet
Connection:
Host Name:
Primary/Secondary
DNS Server:
MTU:
MAC Address:
Dynamic (Cable)
17D-Link DIR-840 User Manual
Section 3 - Conguration
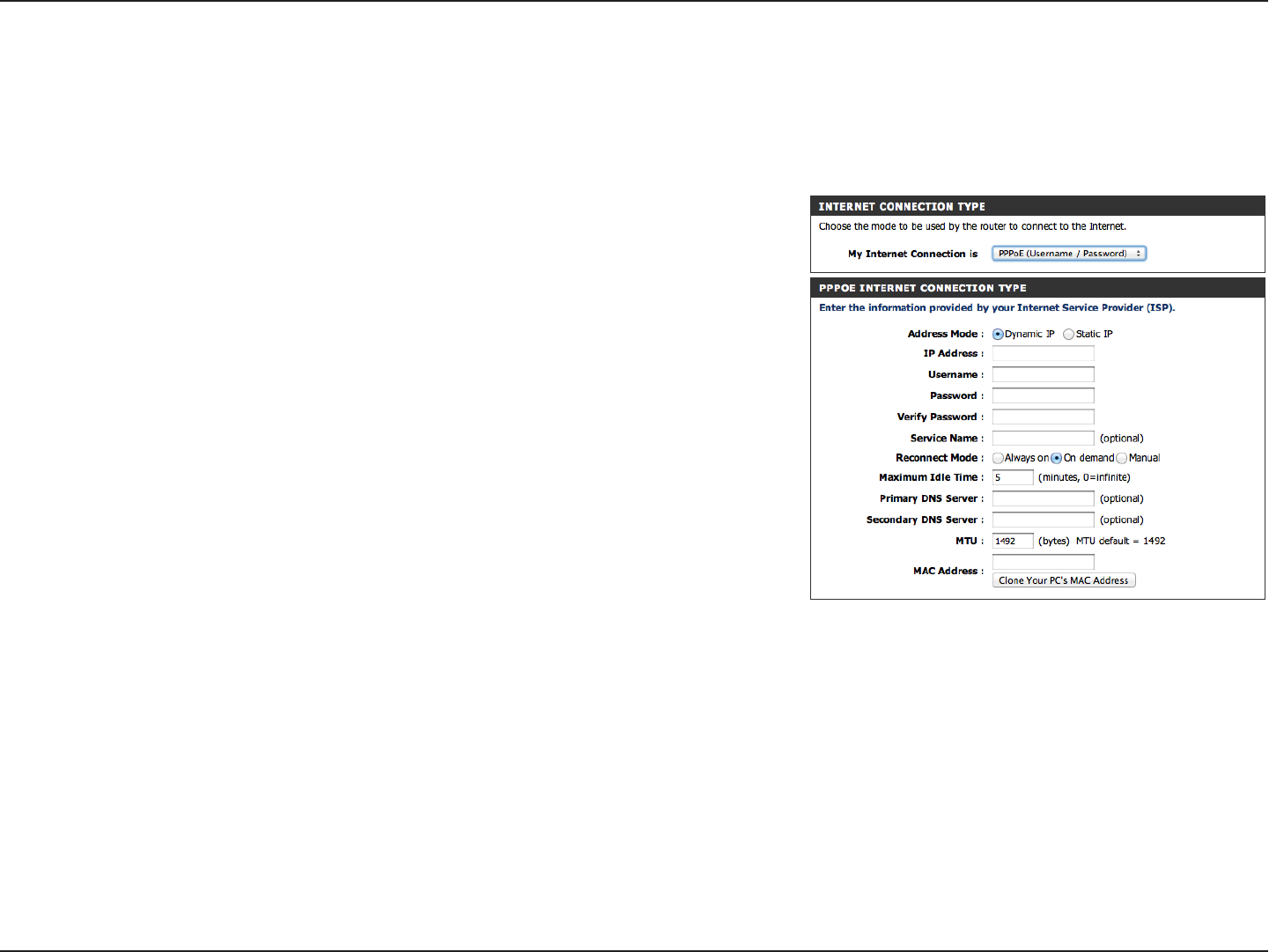
Select PPPoE (Username/Password) from the drop-down menu.
Select Static IP if your ISP assigned you the IP address, subnet mask, gateway,
and DNS server addresses. In most cases, select Dynamic.
Enter the IP address (Static PPPoE only).
Enter your PPPoE user name.
Enter your PPPoE password and then retype the password in the next box.
Enter the ISP Service Name (optional).
Select either Always-on, On-Demand, or Manual.
Enter a maximum idle time during which the Internet connection is maintained during inactivity. To disable this feature, enable
Auto-reconnect.
Enter the Primary and Secondary DNS Server Addresses (Static PPPoE only).
Maximum Transmission Unit - you may need to change the MTU for optimal performance with your specic ISP. 1492 is the default
MTU.
The default MAC Address is set to the Internet port’s physical interface MAC address on the Broadband Router. It is not recommended
that you change the default MAC address unless required by your ISP. You can use the Copy Your PC’s MAC Address button to
replace the Internet port’s MAC address with the MAC address of your Ethernet card.
My Internet
Connection:
Address Mode:
IP Address:
User Name:
Password:
Service Name:
Reconnect
Mode:
Maximum Idle
Time:
DNS Addresses:
MTU:
MAC Address:
PPPoE (DSL)
Choose PPPoE (Point to Point Protocol over Ethernet) if your ISP uses a PPPoE connection. Your ISP will provide you with a
username and password. This option is typically used for DSL services. Make sure to remove your PPPoE software from your
computer. The software is no longer needed and will not work through a router.
18D-Link DIR-840 User Manual
Section 3 - Conguration
Select PPTP (Username/Password) from the drop-down menu.
Select Static if your ISP assigned you the IP address, subnet mask,
gateway, and DNS server addresses. In most cases, select Dynamic.
Enter the IP address (Static PPTP only).
Enter the Primary and Secondary DNS Server Addresses (Static PPTP
only).
Enter the Gateway IP Address provided by your ISP.
Enter the Server IP provided by your ISP (optional).
Enter your PPTP username.
Enter your PPTP password and then retype the password.
Select either Always-on, On-Demand, or Manual.
Enter a maximum idle time to maintain the Internet connection
during inactivity. To disable this feature, enable Auto-reconnect.
The DNS server information will be supplied by your ISP (Internet
Service Provider.)
Maximum Transmission Unit - you may need to change the MTU for
optimal performance with your specic ISP. 1400 is the default MTU.
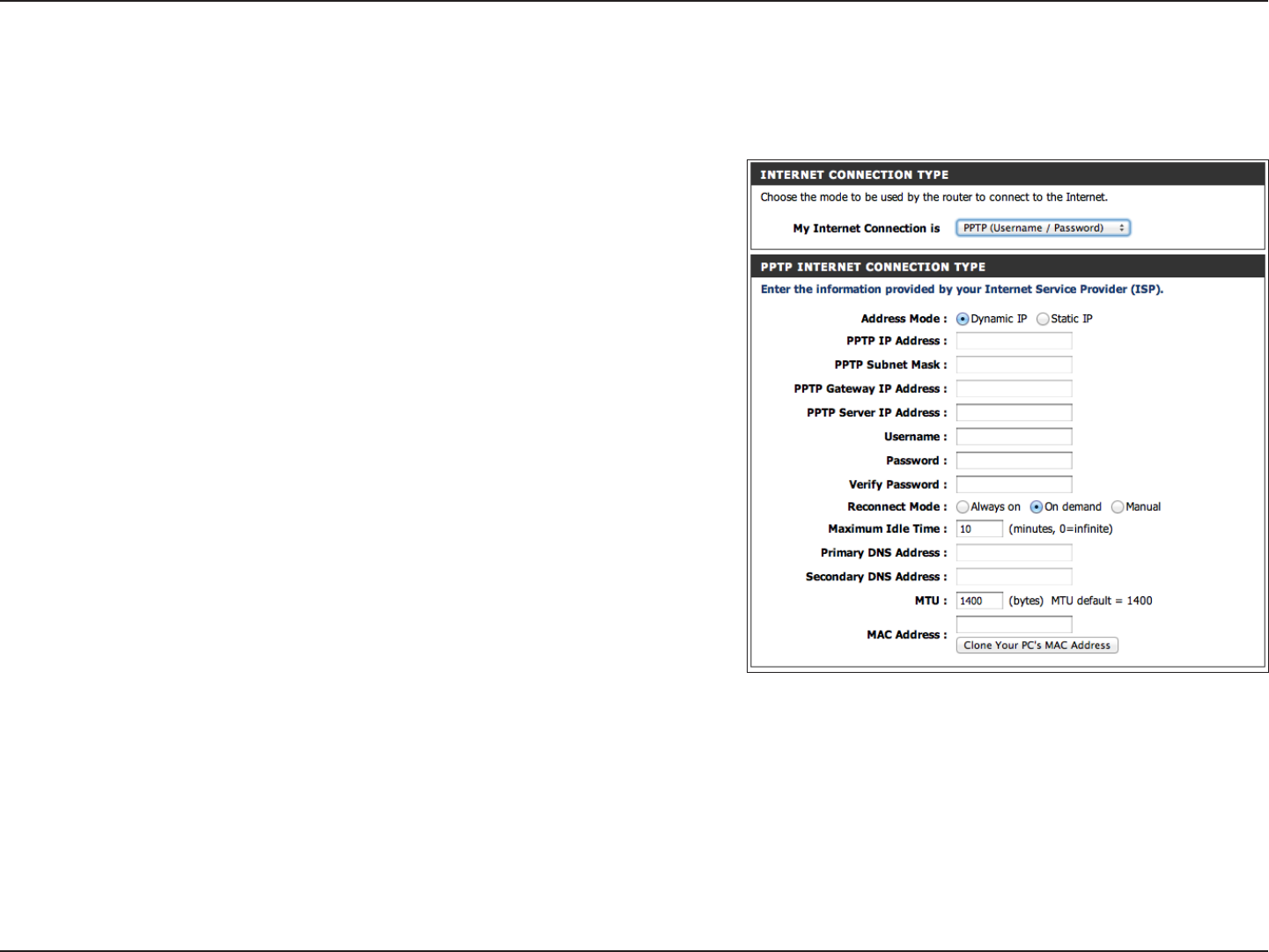
PPTP
Choose PPTP (Point-to-Point-Tunneling Protocol ) if your ISP uses a PPTP connection. Your ISP will provide you with a username
and password. This option is typically used for DSL services.
My Internet
Connection:
Address Mode:
PPTP IP Address:
PPTP Subnet
Mask:
PPTP Gateway:
PPTP Server IP:
Username:
Password:
Reconnect Mode:
Maximum Idle
Time:
DNS Servers:
MTU:

19D-Link DIR-840 User Manual
Section 3 - Conguration
The default MAC Address is set to the Internet port’s physical interface MAC address on the Broadband Router. It is not recommended
that you change the default MAC address unless required by your ISP. You can use the Clone Your PC’s MAC Address button to
replace the Internet port’s MAC address with the MAC address of your Ethernet card.
MAC Address:
20D-Link DIR-840 User Manual
Section 3 - Conguration
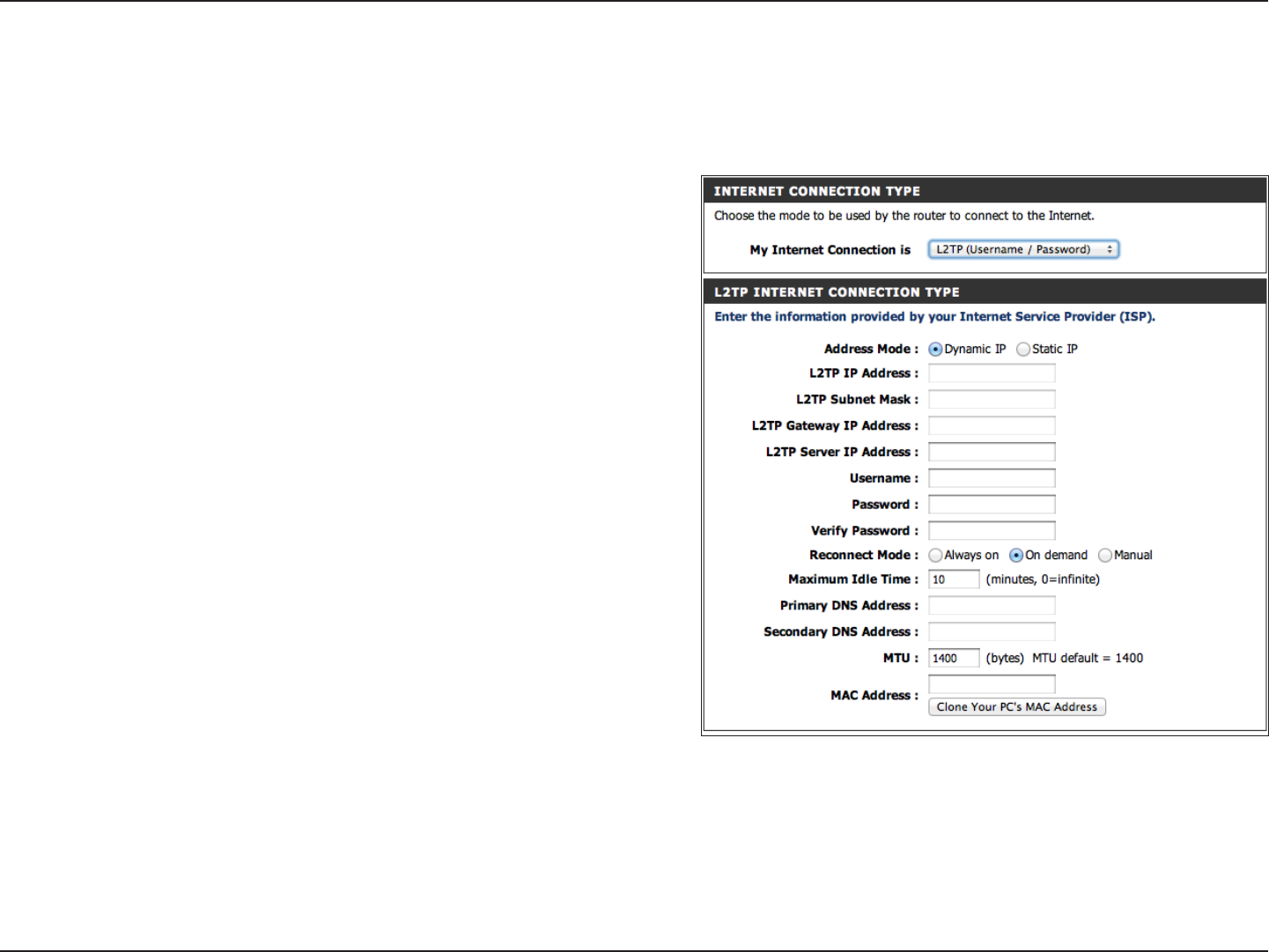
Select L2TP (Username/Password) from the drop-down menu.
Select Static if your ISP assigned you the IP address, subnet
mask, gateway, and DNS server addresses. In most cases, select
Dynamic.
Enter the L2TP IP address supplied by your ISP (Static only).
Enter the Subnet Mask supplied by your ISP (Static only).
Enter the Gateway IP Address provided by your ISP.
Enter the Server IP provided by your ISP (optional).
Enter your L2TP username.
Enter your L2TP password and then retype the password.
Select either Always-on, On-Demand, or Manual.
Enter a maximum idle time to maintain the Internet connection
during inactivity. To disable this feature, enable Auto-reconnect.
Enter the Primary and Secondary DNS Server Addresses (Static
L2TP only).
My Internet
Connection:
Address Mode:
L2TP IP Address:
L2TP Subnet
Mask:
L2TP Gateway IP:
L2TP Server IP:
Username:
Password:
Reconnect
Mode:
Maximum Idle
Time:
DNS Servers:
L2TP
Choose L2TP (Layer 2 Tunneling Protocol) if your ISP uses a L2TP connection. Your ISP will provide you with a username and
password. This option is typically used for DSL services.

21D-Link DIR-840 User Manual
Section 3 - Conguration
MTU:
MAC Address:
Maximum Transmission Unit - you may need to change the MTU for optimal performance with your specic ISP. 1400 is the default
MTU.
The default MAC Address is set to the Internet port’s physical interface MAC address on the Broadband Router. It is not recommended
that you change the default MAC address unless required by your ISP. You can use the Clone Your PC’s MAC Address button to
replace the Internet port’s MAC address with the MAC address of your Ethernet card.
22D-Link DIR-840 User Manual
Section 3 - Conguration
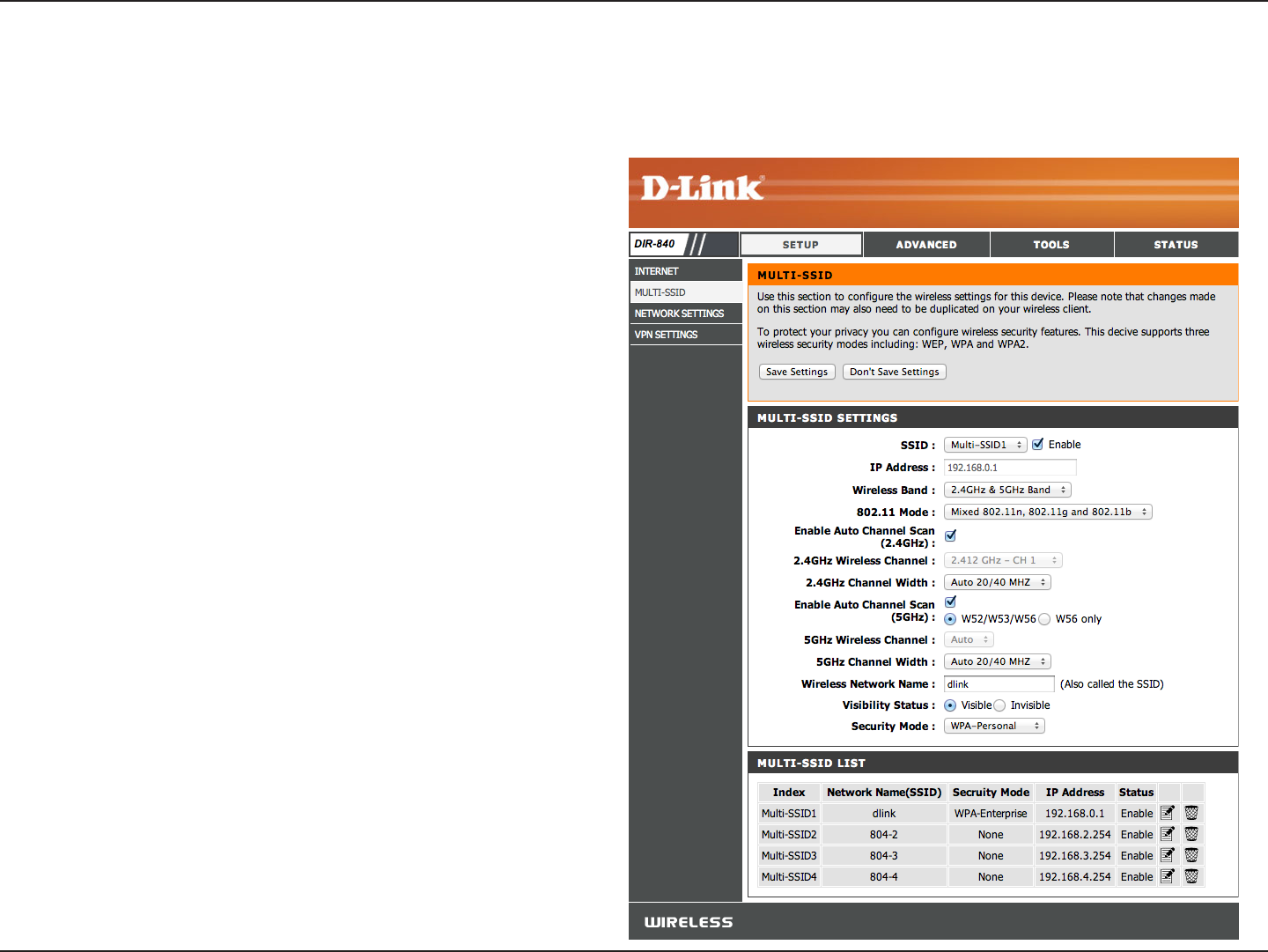
Enable SSID:
IP Address:
802.11 Mode:
Enable Auto
Channel Scan
(2.4GHz):
2.4GHz Wireless
Channel:
2.4GHz Wireless
Channel Width:
Check to enable the Multi-SSID wireless function. If you
do not want to use SSID wireless, uncheck the box to
disable all the wireless functions.
Input the IP Address of the router. (The default is
192.169.0.1)
Select one of the following:
802.11g Only - Select if all of your wireless clients are
802.11g.
802.11n Only - Select only if all of your wireless clients
are 802.11n.
Mixed 802.11n and 802.11g - Select if you are using a
mix of 802.11n and 11g wireless clients.
This setting can be selected to allow the DIR-840
to choose the channel with the least amount of
interference for the 2.4GHz band.
Indicates the channel setting for the DIR-840 on the
2.4GHz band. If you enable Auto Channel Scan, this
option will be greyed out.
Select the Channel Width for the 2.4GHz band:
Auto 20/40 - This is the default setting. Select if you are
using both 802.11n and non-802.11n wireless devices.
20MHz - Select if you are not using any 802.11n wireless
clients.
40MHz - Select if using only 802.11n wireless clients.
Multi-SSID
The Multi-SSID feature will allow you to create temporary zones that can be used by guests to access the Internet.
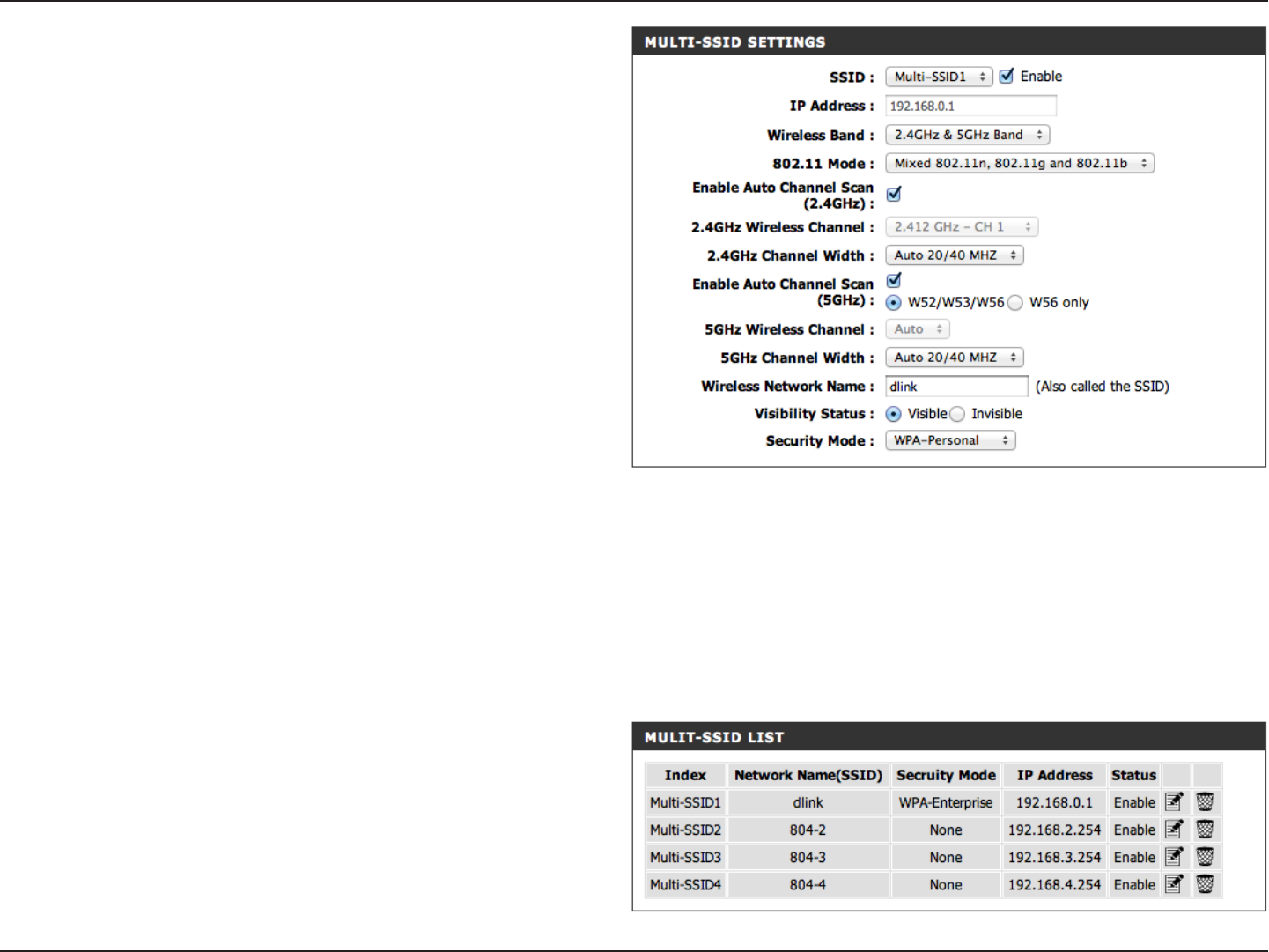
23D-Link DIR-840 User Manual
Section 3 - Conguration
This setting can be selected to allow the DIR-840
to choose the channel with the least amount of
interference for the 5GHz band.
Indicates the channel setting for the DIR-840 on the
5GHz band. If you enable Auto Channel Scan, this
option will be greyed out.
Select the Channel Width for the 5GHz band:
Auto 20/40 - This is the default setting. Select if you are
using both 802.11n and non-802.11n wireless devices.
20MHz - Select if you are not using any 802.11n wireless
clients.
40MHz - Select if using only 802.11n wireless clients.
Enter a wireless network name (SSID) that is dierent
from your main wireless network.
Select Invisible if you do not want the SSID of your
wireless network to be broadcasted by the DIR-840. If
Invisible is selected, the SSID will not be seen by Site
Survey utilities so your wireless clients will have to know
the SSID of the DIR-840.
Select the type of security or encryption you would like
to enable for the guest zone.
Enable Auto
Channel Scan
(5GHz):
5GHz Wireless
Channel:
5GHz Wireless
Channel Width:
Wireless
Network Name:
Visibility Status:
Security Mode:
MULTI-SSID List This displays a list of the wireless networks establish
by the DIR-840.
24D-Link DIR-840 User Manual
Section 3 - Conguration
This section will allow you to change the local network settings of the router and to congure the DHCP settings.
Network Settings
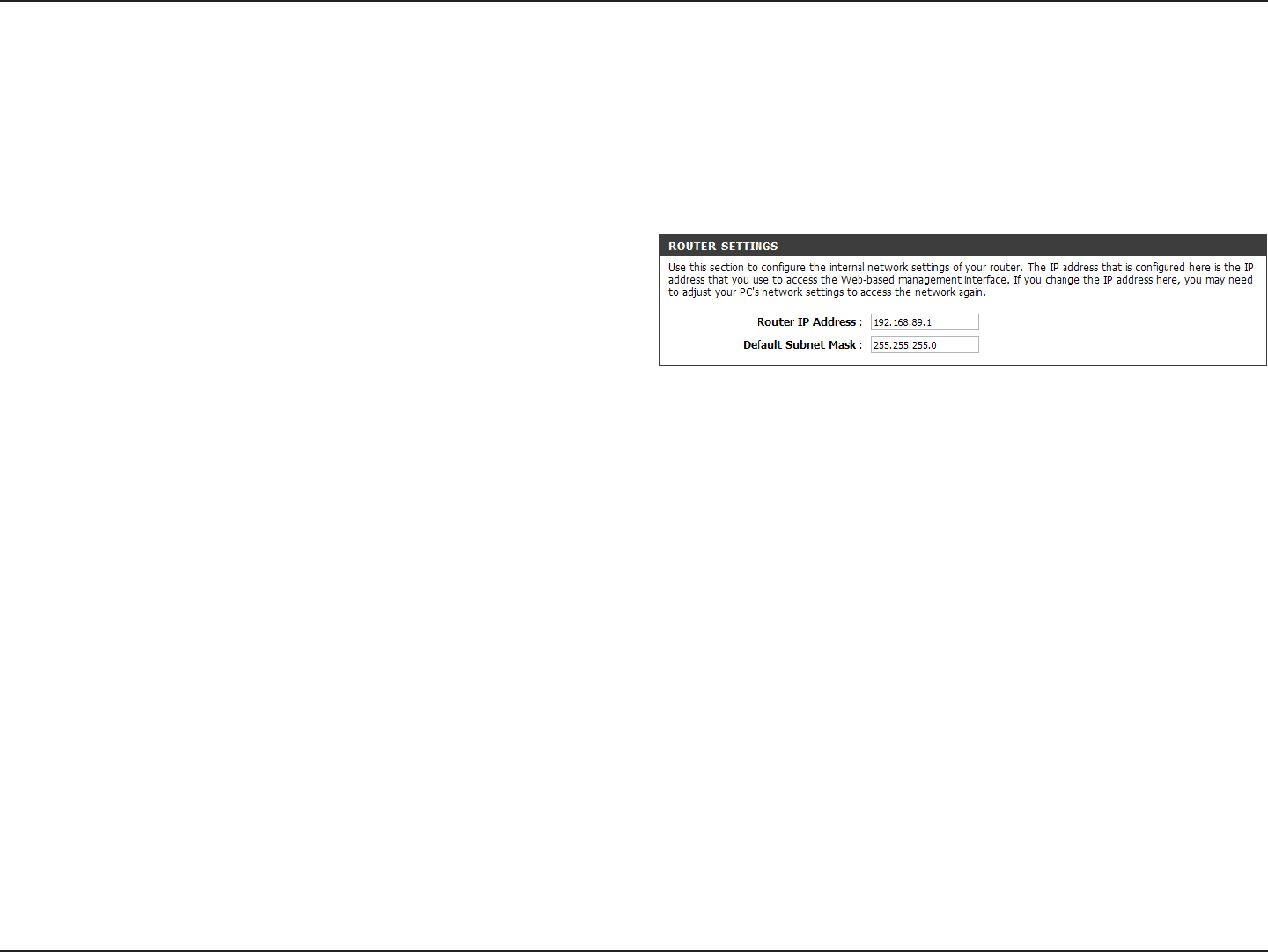
Enter the IP address of the router. The default IP address
is 192.168.89.1.
If you change the IP address, once you click Save Settings,
you will need to enter the new IP address in your browser
to get back into the conguration utility.
Enter the Subnet Mask. The default subnet mask is
255.255.255.0.
Router IP Address:
Subnet Mask:
Router Settings

25D-Link DIR-840 User Manual
Section 3 - Conguration
DHCP Server Settings
DHCP stands for Dynamic Host Control Protocol. The DIR-840 has a built-in DHCP server. The DHCP Server will automatically
assign an IP address to the computers on the LAN/private network. Be sure to set your computers to be DHCP clients by setting
their TCP/IP settings to “Obtain an IP Address Automatically.” When you turn your computers on, they will automatically load
the proper TCP/IP settings provided by the DIR-840. The DHCP Server will automatically allocate an unused IP address from
the IP address pool to the requesting computer. You must specify the starting and ending address of the IP address pool.
Check this box to enable the DHCP server on your router.
Uncheck to disable this function.
Enter the starting and ending IP addresses for the DHCP server’s
IP assignment.
Note: If you statically (manually) assign IP addresses to your
computers or devices, make sure the IP addresses are outside
of this range or you may have an IP conict.
The length of time for the IP address lease. Enter the Lease time in minutes.
Enter your primary WINS Server IP address.
Enter your secondary WINS Server IP address.
Enable DHCP
Server:
DHCP IP Address
Range:
DHCP Lease Time:
Primary WINS IP
Address:
Secondary WINS
IP Address:
26D-Link DIR-840 User Manual
Section 3 - Conguration
Choose either IPSec or L2TPv3/L2TPv3 over IPSec
from the drop-down menu and click Add to begin
conguring a VPN prole.
This list allows you to Enable established VPN proles
as well as Edit and Delete them.
Check this box to enable NAT Traversal options.
Check this box to automatically keep IPSec connections
alive.
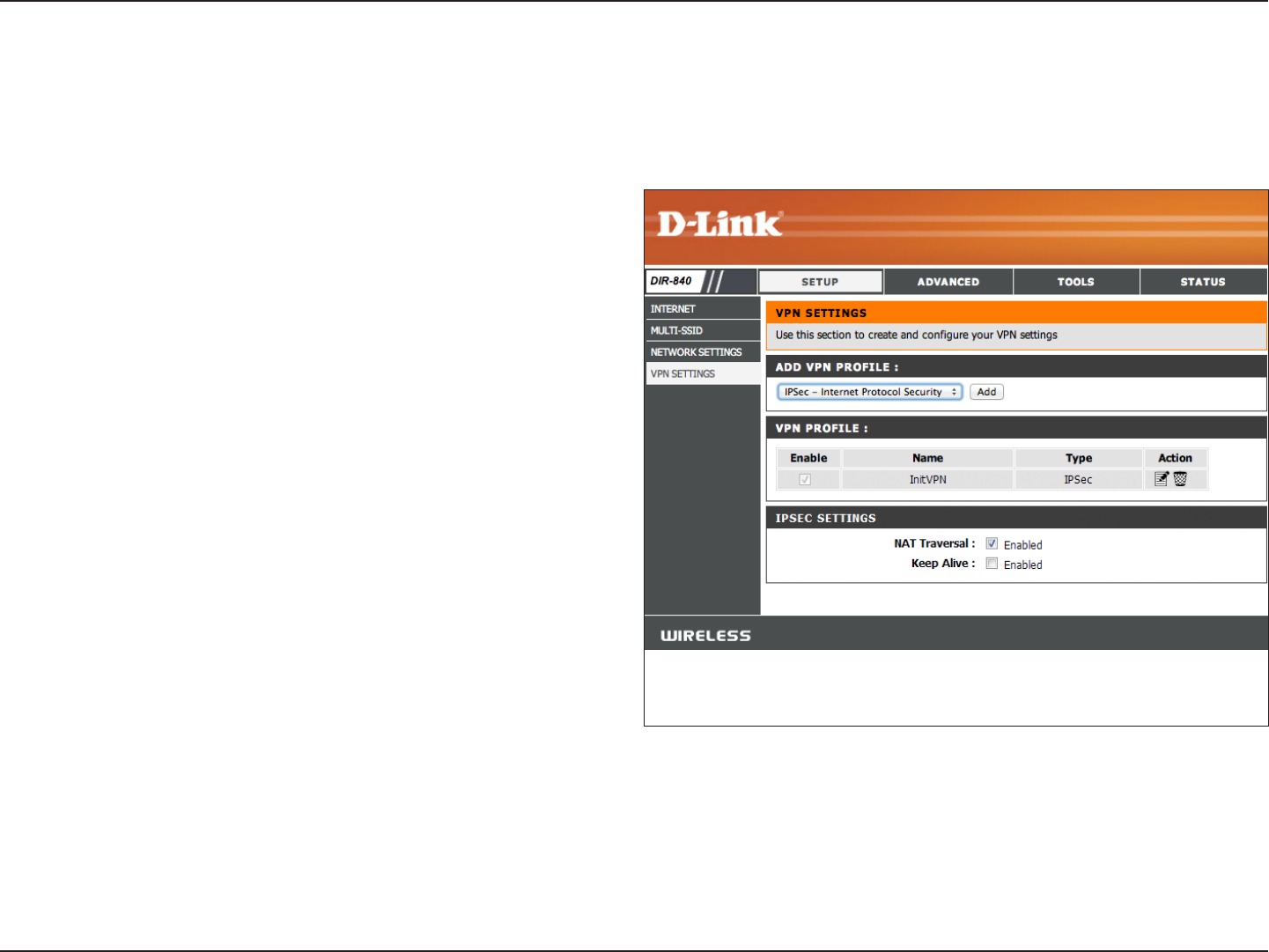
Add VPN Prole:
VPN Prole:
NAT Traversal:
Keep Alive:
On this page you can set up advanced options for a Virtual Private Network (VPN). The DIR-840 supports both IPSec and L2TP
as the Server Endpoint. IPSec (Internet Protocol Security) is a set of protocols that can provide IP security at the network layer.
VPN Settings
27D-Link DIR-840 User Manual
Section 3 - Conguration
Check this box to enable IPSec.
Enter a name for your VPN.
Choose either IKE or Manual from the drop-down menu.
Choose either Tunnel Mode or Transport Mode from the
drop-down menu.
Enter the local (LAN) subnet and mask.
(ex. 192.168.0.0/24)
Enter the remote subnet and mask.
Enter the amount of time in seconds that the Phase 1 and
Phase 2 keys should last.
Choose either ESP, AH or ESP + AH from the drop-down menu.
Enable or Disable the PFS Group option using the drop-down
menu. PFS is an additional security protocol.
Select this option to congure IKE Phase 1 of the VPN Tunnel
to carry out negotiation in a shorter amount of time. (This
option is not recommended as it is less secure)
Manually enter an ASCII passphrase in box.
Choose Always on or Manual from the drop-down menu.
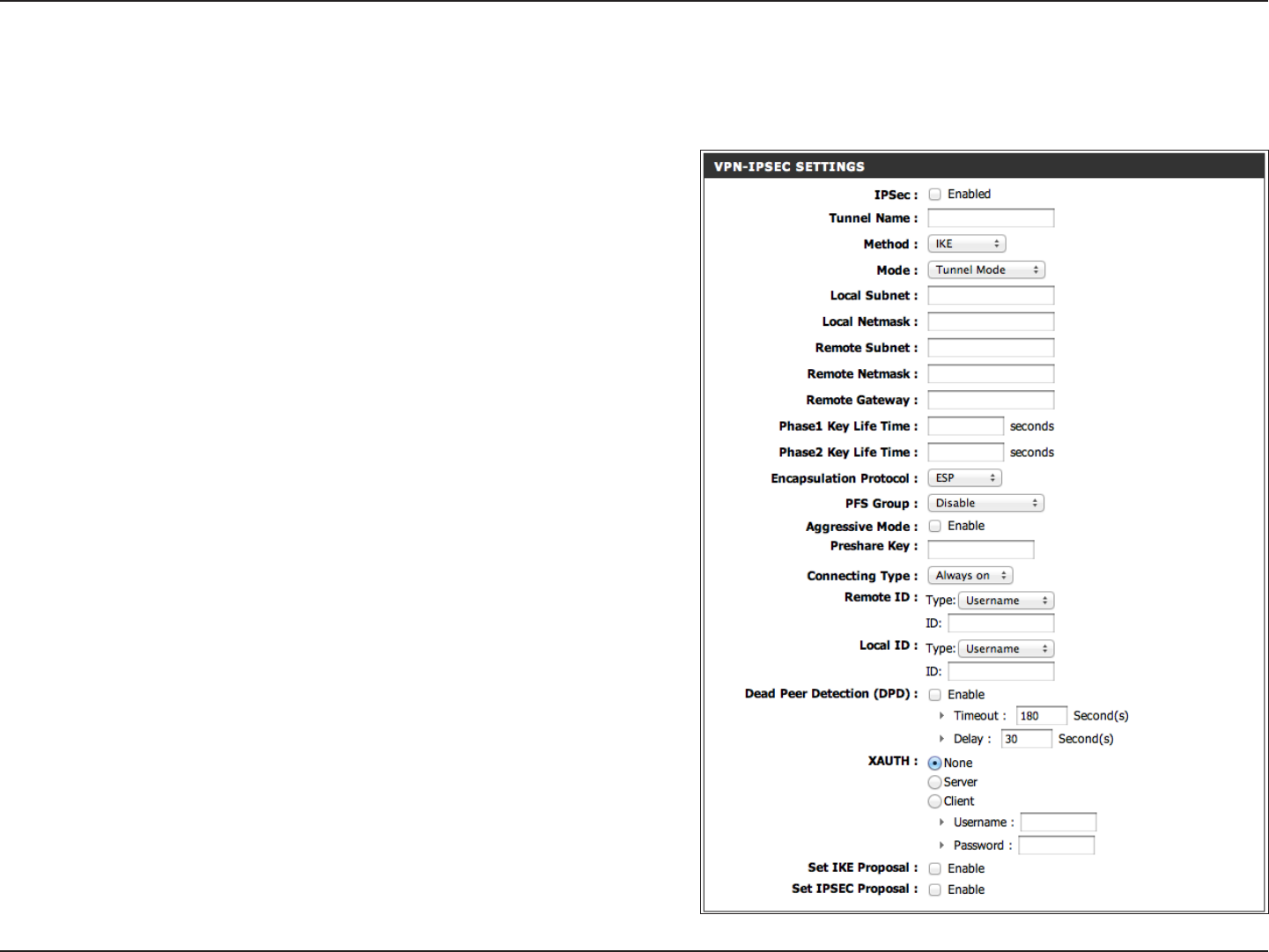
IPSec:
Tunnel Name:
Method:
Mode:
Local Subnet/
Netmask:
Remote Subnet/
Netmask:
Phase1/2 Key
Life Time:
Encapsulation
Protocol:
PFS Group:
Aggressive
Mode:
Preshare Key:
Connecting Type:
IPSec Settings
The DIR-840 supports IPSec as the Server Endpoint. IPSec (Internet Protocol Security) is a set of protocols that can provide IP
security at the network layer.
28D-Link DIR-840 User Manual
Section 3 - Conguration
Choose from Username, FQDN, User@FQDN, or Key ID using the drop-down menu and then the ID in the box.
Choose from Username, FQDN, User@FQDN, or Key ID using the drop-down menu and then the ID in the box.
Check this box to enable Dead Peer Detection, then enter the time in seconds in which a peer is determined to be no longer active.
You may also enter a delay period in seconds.
Check this box to include additional username and password authentication requirements for the VPN. Select Server Mode, Client
Mode, or None. Then enter the user name and password if required by the remote VPN server endpoint congured in xAuth Server
Mode.
Check this box to enable IKE Proposal.
Check this box to enable IPSec Proposal.
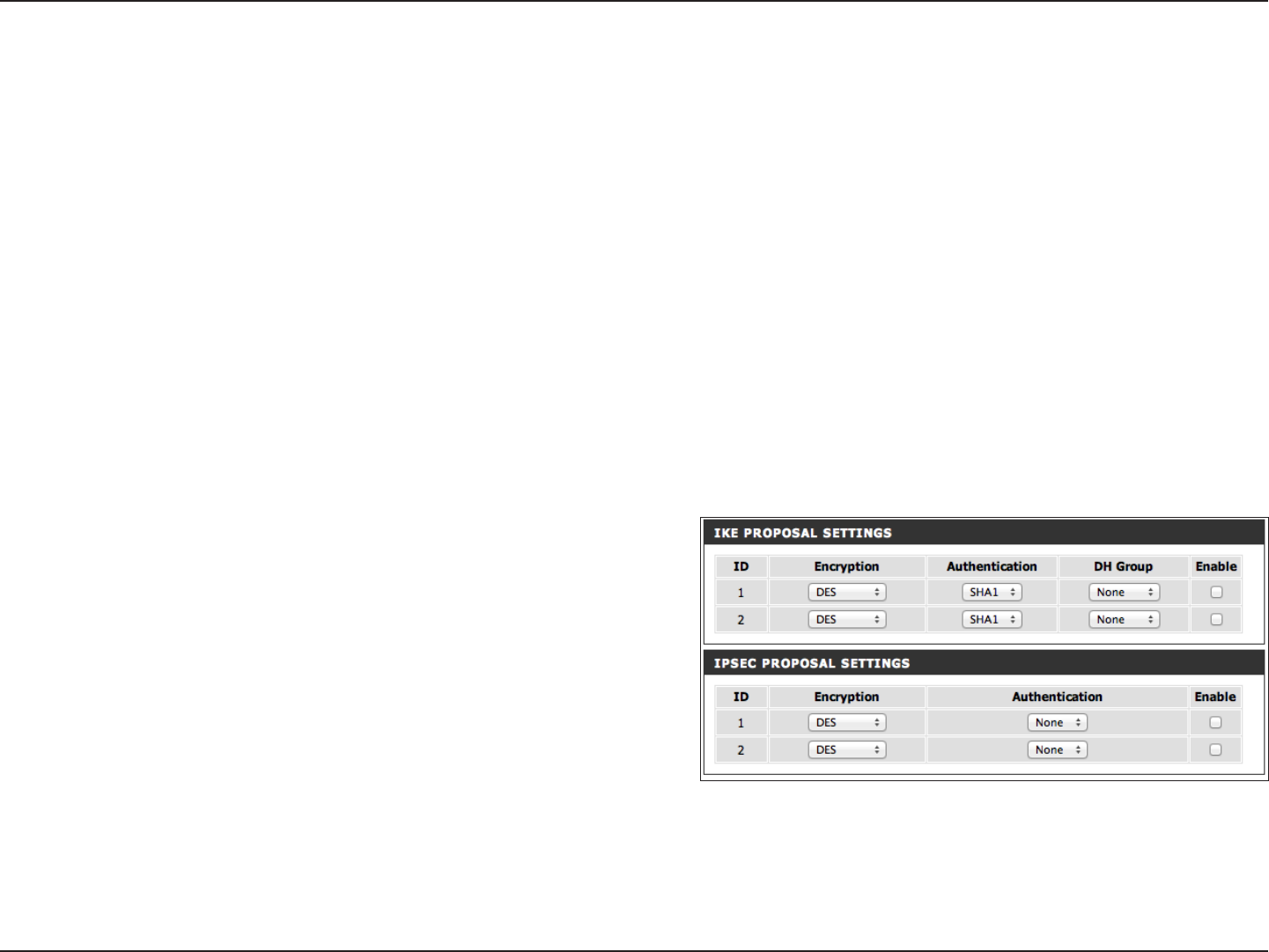
Remote ID:
Local ID:
Dead Peer
Detection (DPD):
XAUTH:
Set IKE Proposal:
Set IPSEC
Proposal:
Use this area to Enable IKE Proposals. Then determine the
Encryption and Authentication types, as well as the DH
Group from the drop-down menus.
Use this area to Enable IPSec Proposals. Then determine the
Encryption and Authentication types from the drop-down
menus.
IKE Proposal
Settings:
IPSEC Proposal
Settings:

29D-Link DIR-840 User Manual
Section 3 - Conguration
L2TP Settings
L2TPv3 uses UDP protocol to transport the PPP data. This is often encapsulated in IPsec encryption instead of MPPE.
Check this box to enable L2TP VPN settings.
You can establish VPN settings on multiple SSIDs by enabling
each of them here.
Enter a name for your VPN.
Select L2TPv3 or L2TPv3 over IPsec.
Enter the IP address of the remote LCCE.
Enter the name of the remote LCCE.
Enter the router ID of the remote LCCE.
Enter the router ID of the local LCCE.
L2TP:
Multi-SSID 1-4:
Host Name:
Connection Type:
Remote Address:
Remote Host
Name:
Remote Router
ID:
Local Router ID:
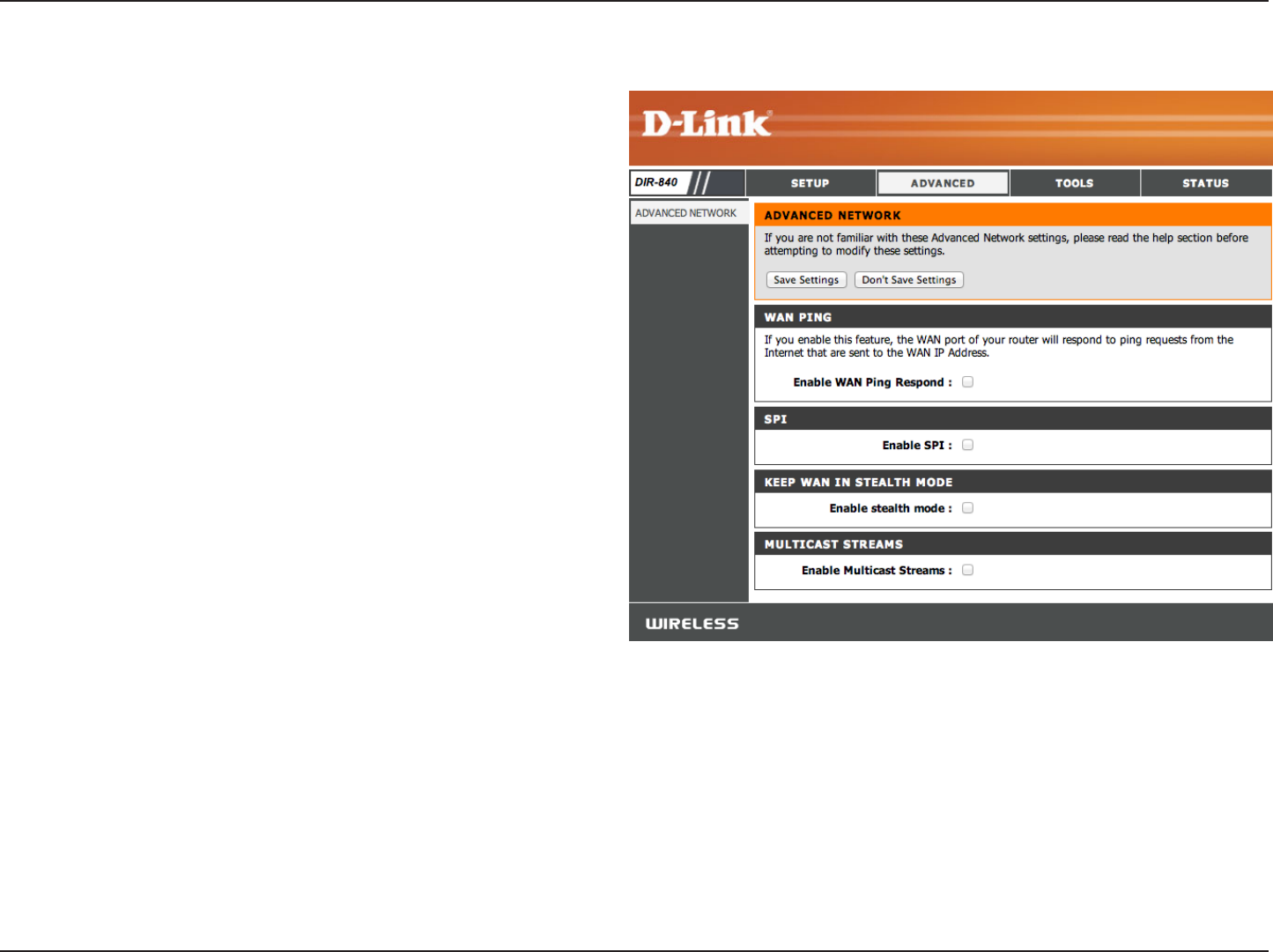
30D-Link DIR-840 User Manual
Section 4 - Advanced
Checking the box will allow the DIR-840 to respond to
pings. Unchecking the box may provide some extra
security from hackers.
Check this box to enable Stateful Packet Inspection
which will only allow packets from known active
connections and reject all others.
Check this box to prevent the DIR-840 from responding
to port scans from the WAN making it less susceptible
to discovery.
Check the box to allow multicast trac to pass through
the router from the Internet.
Enable WAN Ping
Respond:
Enable SPI:
Enable Stealth
Mode:
Enable IPV6
Multicast Streams:
Advanced Network Settings
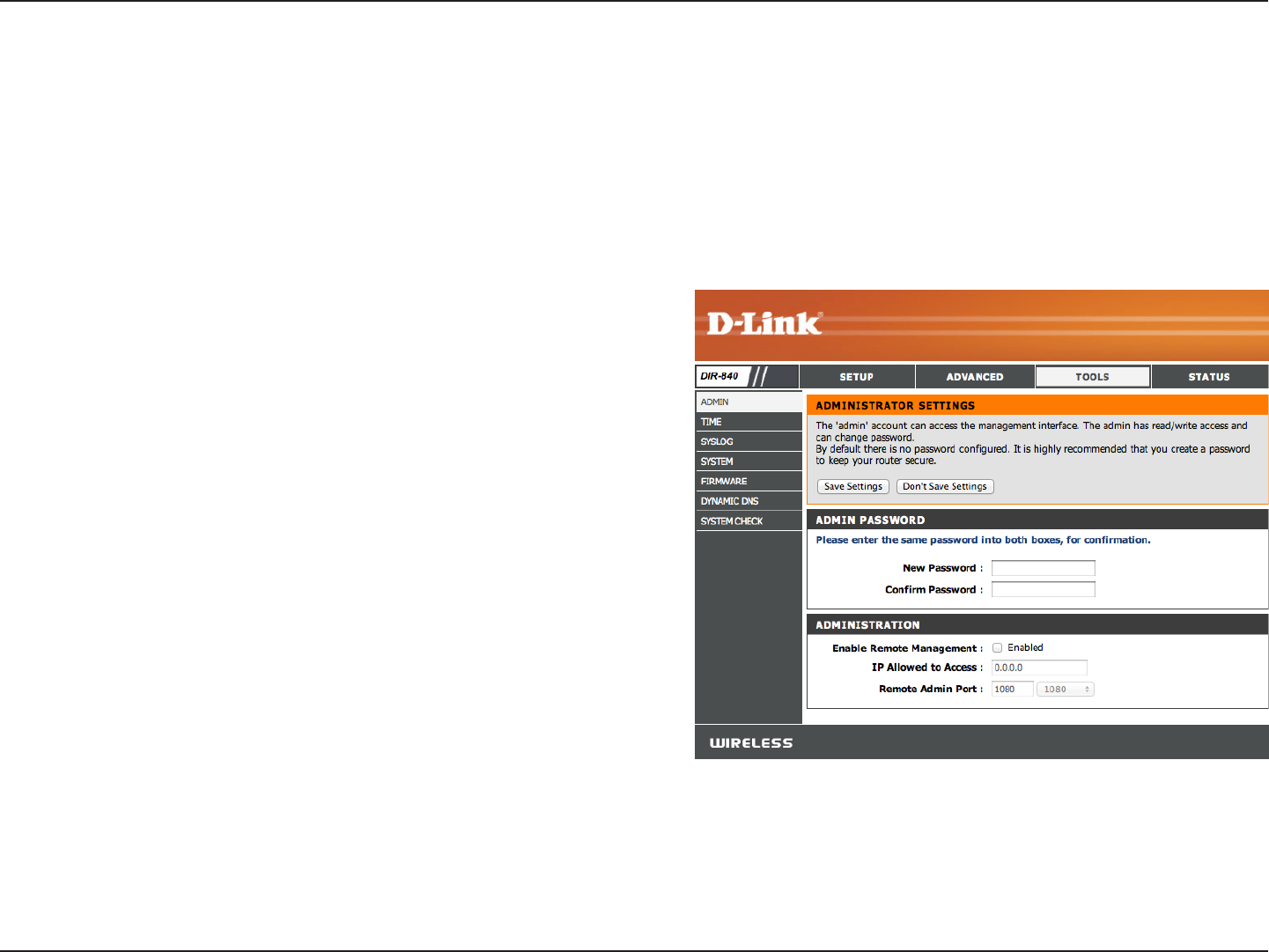
31D-Link DIR-840 User Manual
Section 5 - Tools
Admin
This page will allow you to change the Administrator and User passwords. You can also enable Remote Management. There are
two accounts that can access the management interface through the web browser. The accounts are admin and user. Admin
has read/write access while user has read-only access. User can only view the settings but cannot make any changes. Only the
admin account has the ability to change both admin and user account passwords.
Tools
Enter a new password for the Administrator Login Name. And
type it again in the next box.
Remote management allows the DIR-840 to be congured
from the Internet by a web browser. A username/password is
still required to access the Web Management interface.
Enter the IP address used to access the DIR-840.
Enter the port number used to access the DIR-840 is used in
the URL. Example: http://x.x.x.x:8080 whereas x.x.x.x is the
Internet IP address of the DIR-840 and 8080 is the port used
for the Web Management interface.
Admin
Password:
Enable Remote
Management:
IP Allowed to
Access:
Remote Admin
Port:
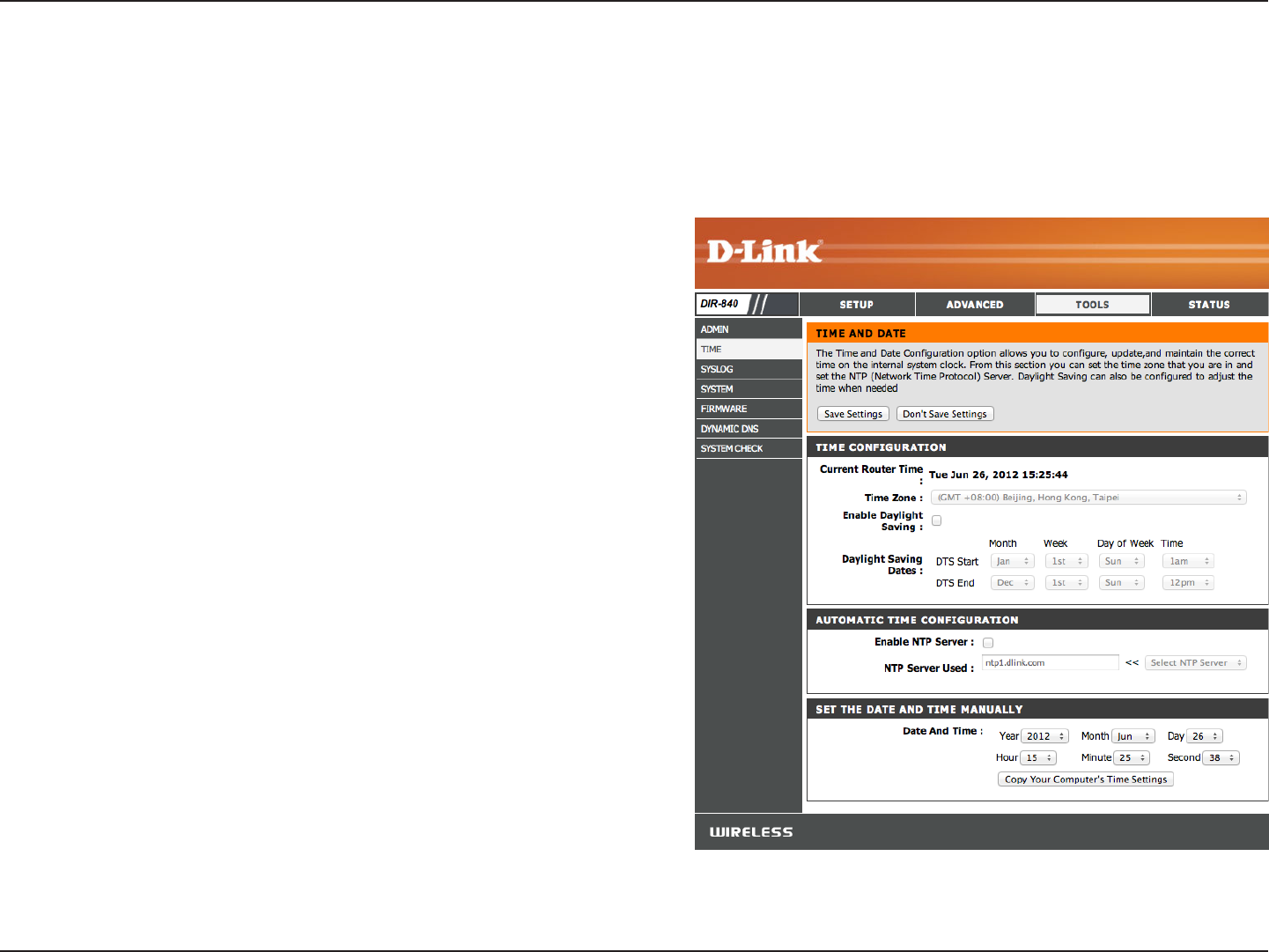
32D-Link DIR-840 User Manual
Section 5 - Tools
Time
Displays the current date and time of the router.
Select your Time Zone from the drop-down menu.
To select Daylight Saving time manually, select enabled or
disabled, and enter a start date and an end date for daylight
saving time.
If Daylight Saving is enabled, you may specify the date it
begins and ends.
NTP is short for Network Time Protocol. A NTP server will
synch the time and date with your router. This will only
connect to a server on the Internet, not a local server. Check
the box to enable this feature.
Enter the IP address of a NTP server or select one from the
drop-down menu.
To manually input the time, enter the values in these elds
for the Year, Month, Day, Hour, Minute, and Second and then
click Set Time.
You can also click Copy Your Computer’s Time Settings to
synch the date and time with the computer you are currently
on.
Current Router
Time:
Time Zone:
Enable Daylight
Saving:
Daylight Saving
Dates:
Enable NTP Server:
NTP Server Used:
Date And Time:
The Time Conguration option allows you to congure, update, and maintain the correct time on the internal system clock.
From this section you can set the time zone that you are in and set the Time Server. Daylight Saving can also be congured to
automatically adjust the time when needed.
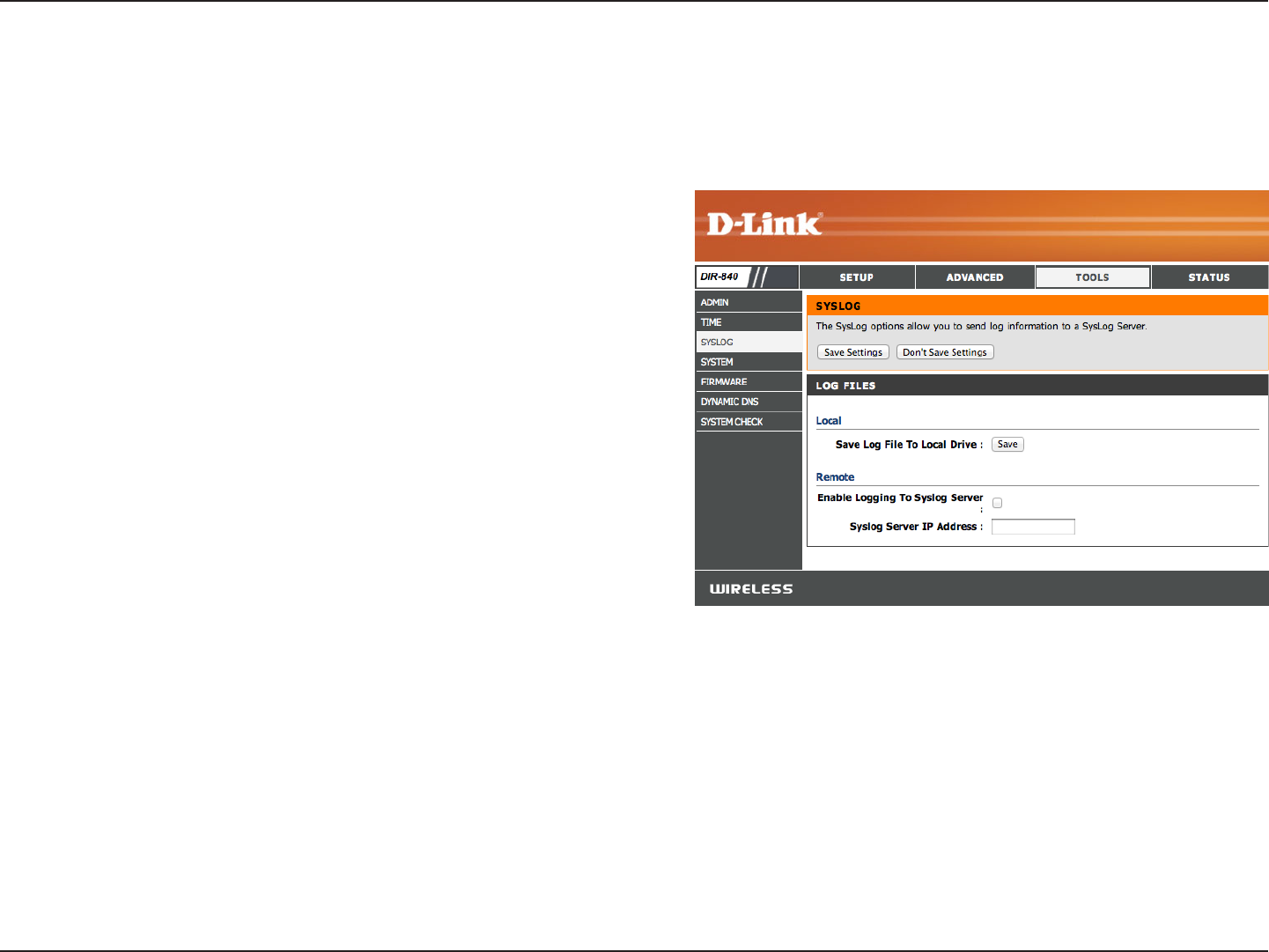
33D-Link DIR-840 User Manual
Section 5 - Tools
SysLog
The Broadband Router keeps a running log of events and activities occurring on the Router. You may send these logs to a
SysLog server on your network.
Save Log File To
Local Drive:
Enable Logging to
SysLog Server:
SysLog Server IP
Address:
Click the Save button to save a local copy of the Log le on
your PC.
Check this box to send the router logs to a SysLog Server.
The address of the SysLog server that will be used to send the
logs. You may also select your computer from the drop-down
menu (only if receiving an IP address from the router via DHCP).
34D-Link DIR-840 User Manual
Section 5 - Tools
Use this option to save the current router conguration settings
to a le on the hard disk of the computer you are using. First, click
the Save button. A le dialog will appear, allowing you to select
a location and le name for the settings.
Use this option to load previously saved router conguration
settings. First, use the Browse option to nd a previously saved le
of conguration settings. Then, click the Load button to transfer
those settings to the router.
This option will restore all conguration settings back to the
settings that were in eect at the time the router was shipped
from the factory. Any settings that have not been saved will be
lost, including any rules that you have created. If you want to save
the current router conguration settings, use the Save button
above.
Click to reboot the router.
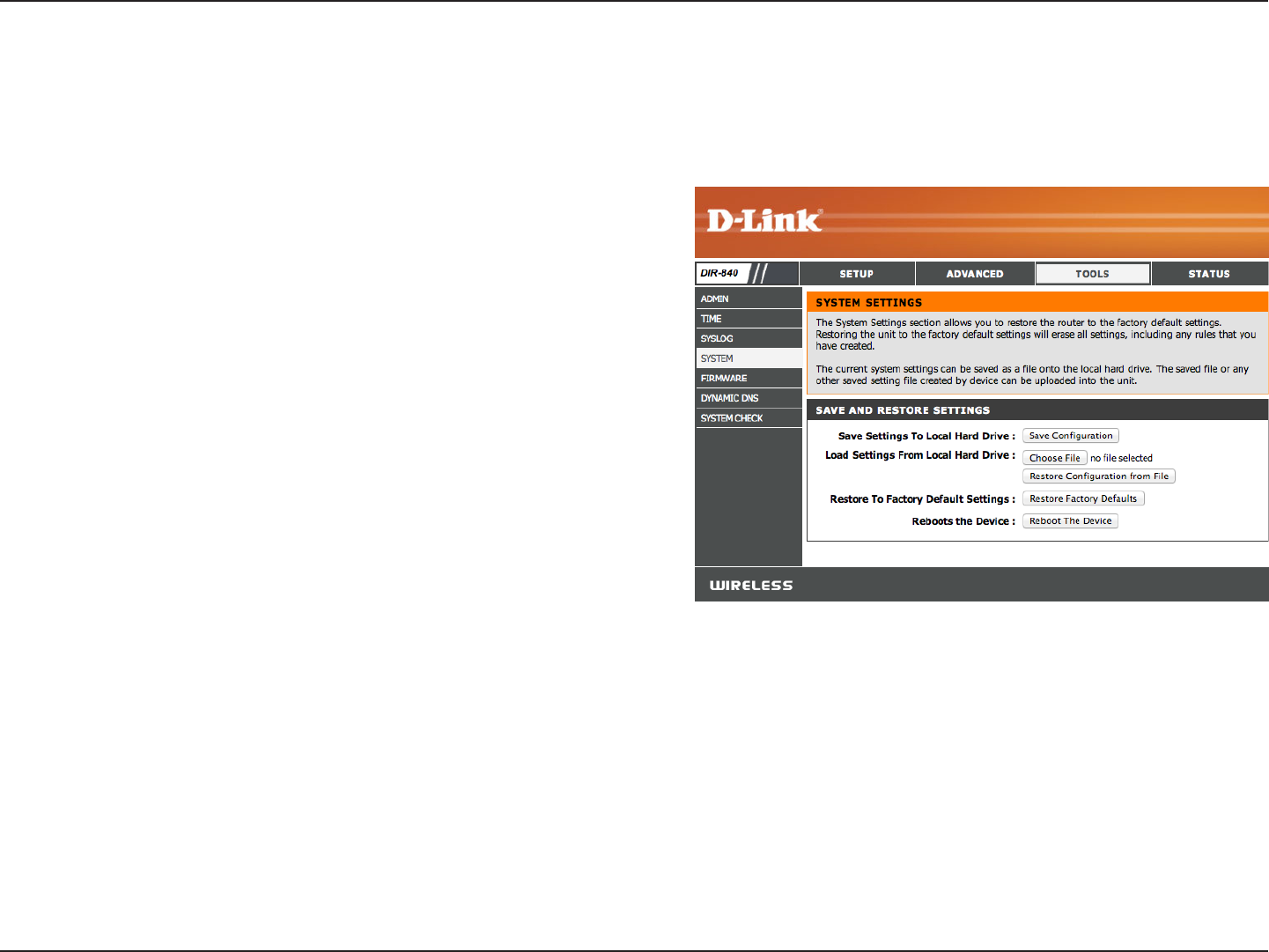
Save Settings to
Local Hard Drive:
Load Settings
from Local Hard
Drive:
Restore to
Factory Default
Settings:
Reboot Device:
System
This section allows you to manage the router’s conguration settings, reboot the router, and restore the router to the factory
default settings. Restoring the unit to the factory default settings will erase all settings, including any rules that you’ve created.
35D-Link DIR-840 User Manual
Section 5 - Tools
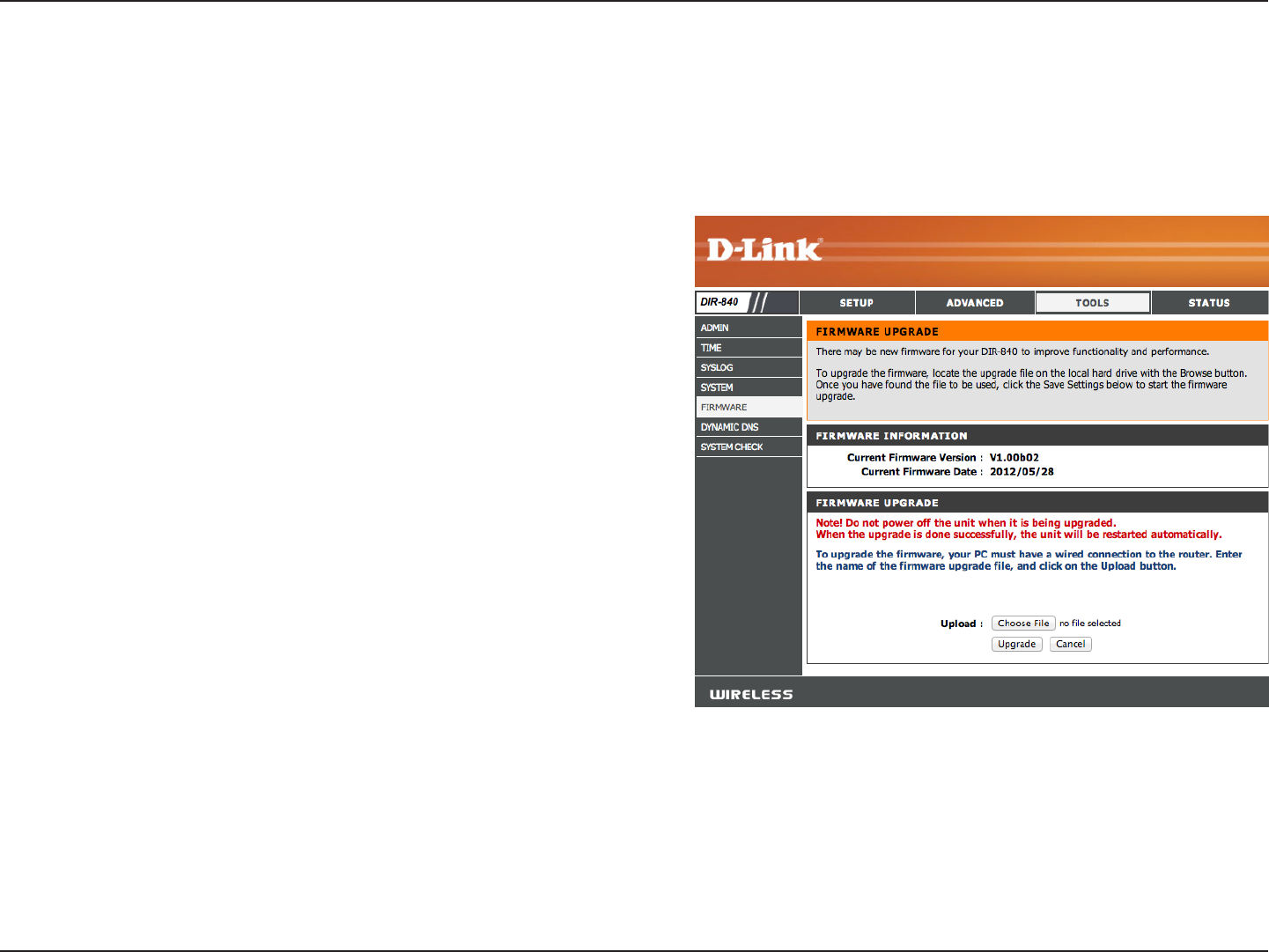
Firmware
Upload: After you have downloaded the new rmware, click Choose
File to locate the rmware update on your hard drive. Click
Upgrade to complete the rmware upgrade.
Once you have a rmware update on your computer, use this
option to browse for the le and then upload the information
into the access point.
You can upgrade the rmware of the access point here. Make sure the rmware you want to use is on the local hard drive of
the computer. Click on Browse to locate the rmware le to be used for the update. Please check the D-Link support website
for rmware updates at http://support.dlink.com. You can download rmware upgrades to your hard drive from this site.
36D-Link DIR-840 User Manual
Section 5 - Tools
Dynamic Domain Name System is a method of keeping a
domain name linked to a changing IP Address. Check the
box to enable DDNS.
Select your DDNS provider from the drop-down menu or
enter the DDNS server address.
Enter the Host Name that you registered with your DDNS
service provider.
Enter the Username or key for your DDNS account.
Enter the Password or key for your DDNS account.
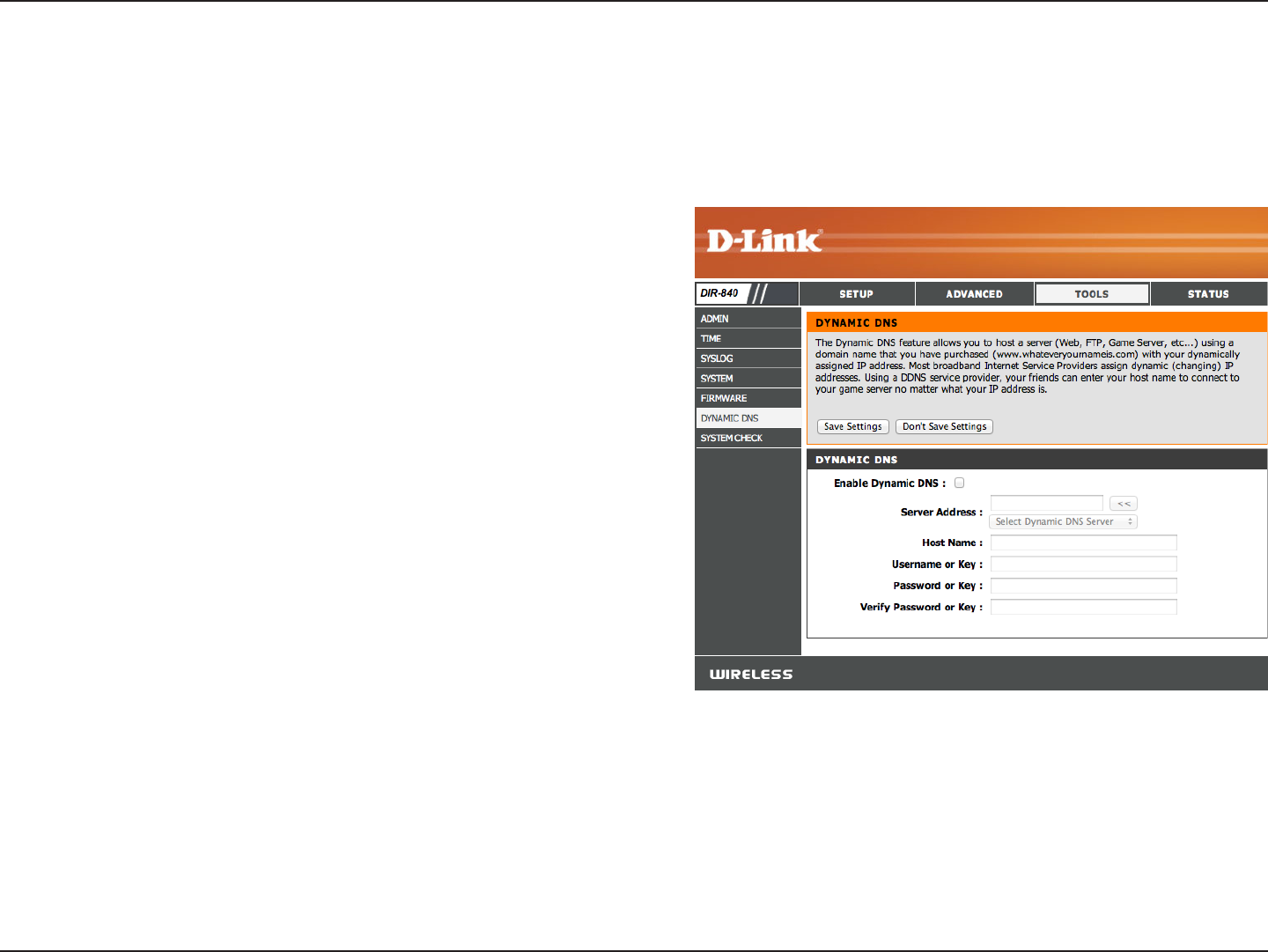
Enable
Dynamic DNS:
Server
Address:
Host Name:
Username or
Key:
Password or
Key:
Dynamic DNS
The DDNS feature allows you to host a server (Web, FTP, Game Server, etc…) using a domain name that you have purchased
(www.whateveryournameis.com) with your dynamically assigned IP address. Most broadband Internet Service Providers assign
dynamic (changing) IP addresses. Using a DDNS service provider, your friends can enter in your domain name to connect to
your server no matter what your IP address is.
37D-Link DIR-840 User Manual
Section 5 - Tools
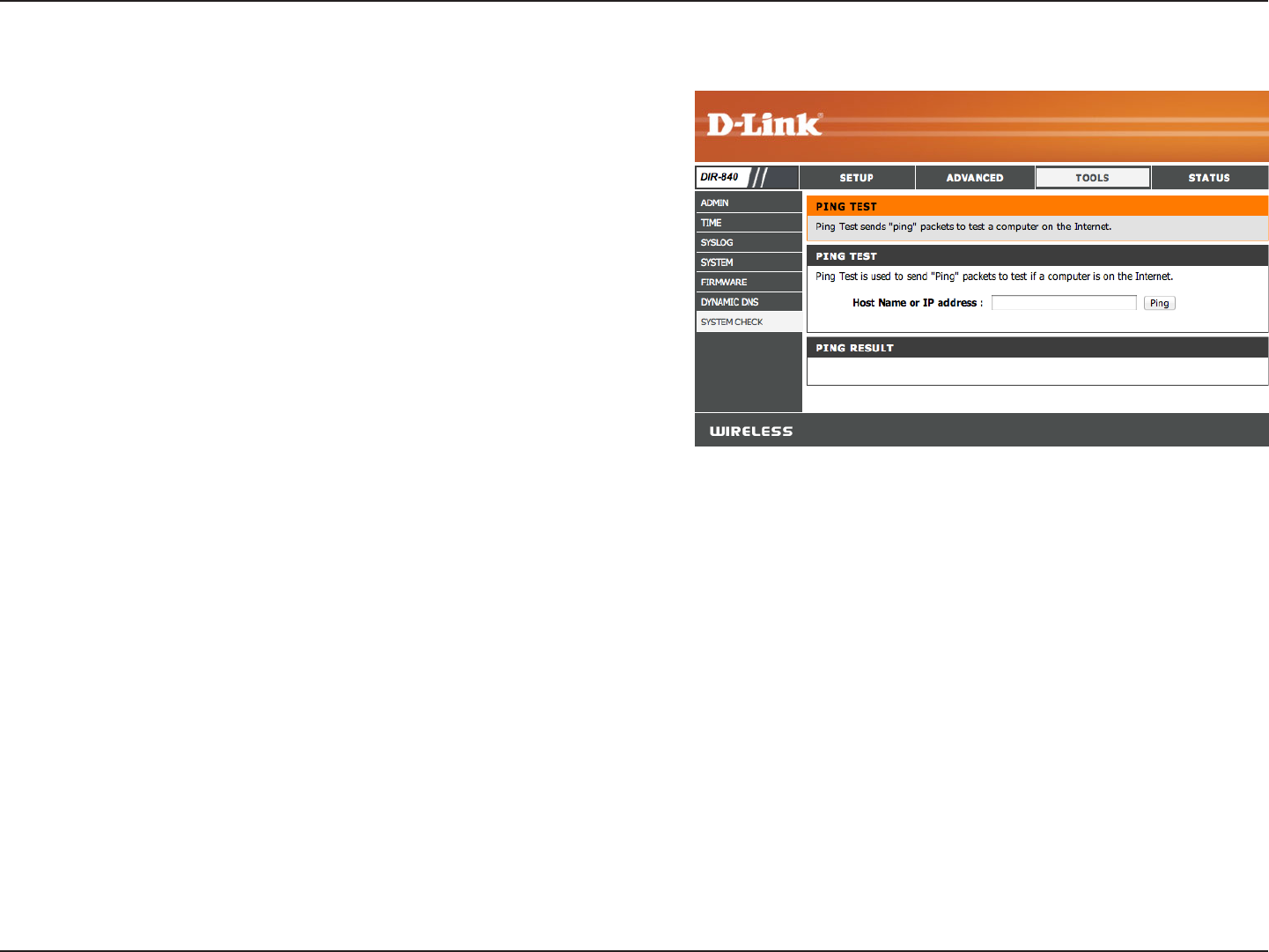
The Ping Test is used to send Ping packets to test if a
computer is on the Internet. Enter the IP address that you
wish to Ping and click Ping.
The results of your ping attempts will be displayed here.
System Check
Host Name or IP
Address:
Ping Result:
38D-Link DIR-840 User Manual
Section 6 - Status
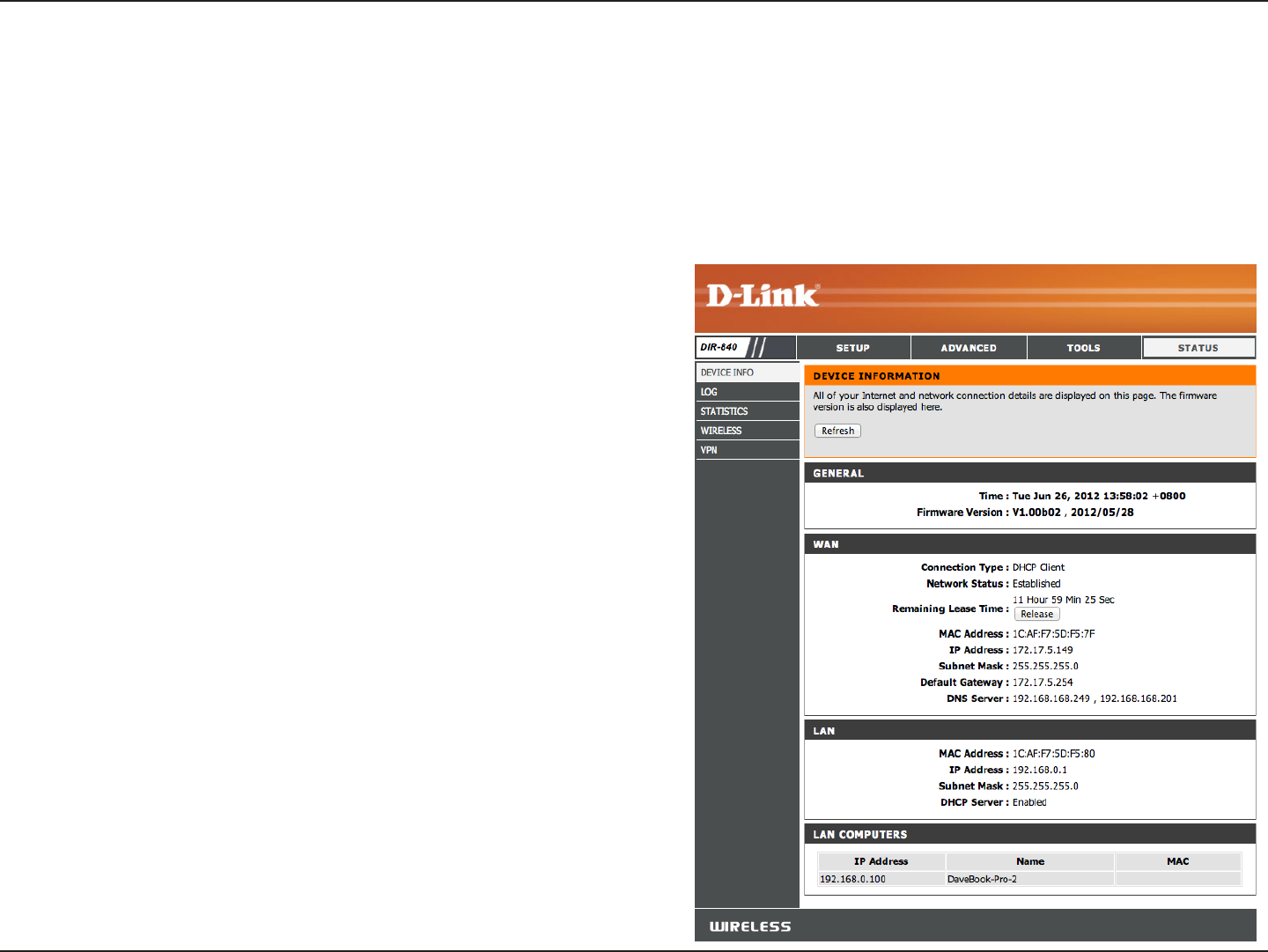
This page displays the current information for the DIR-840. It will display the LAN, WAN (Internet), and Wireless information. If
your Internet connection is set up for a Dynamic IP address then a Release button and a Renew button will be displayed. Use
Release to disconnect from your ISP and use Renew to connect to your ISP.
If your Internet connection is set up for PPPoE, a Connect button
and a Disconnect button will be displayed. Use Disconnect to
drop the PPPoE connection and use Connect to establish the
PPPoE connection.
Displays the router’s time and rmware version.
Displays the MAC address and the public IP settings.
Displays the MAC address and the private (local) IP settings
for the router.
Displays computers and devices that are connected to the
router via Ethernet and that are receiving an IP address
assigned by the router (DHCP).
General:
WAN:
LAN:
LAN Computers:
Device Info
Status
39D-Link DIR-840 User Manual
Section 6 - Status
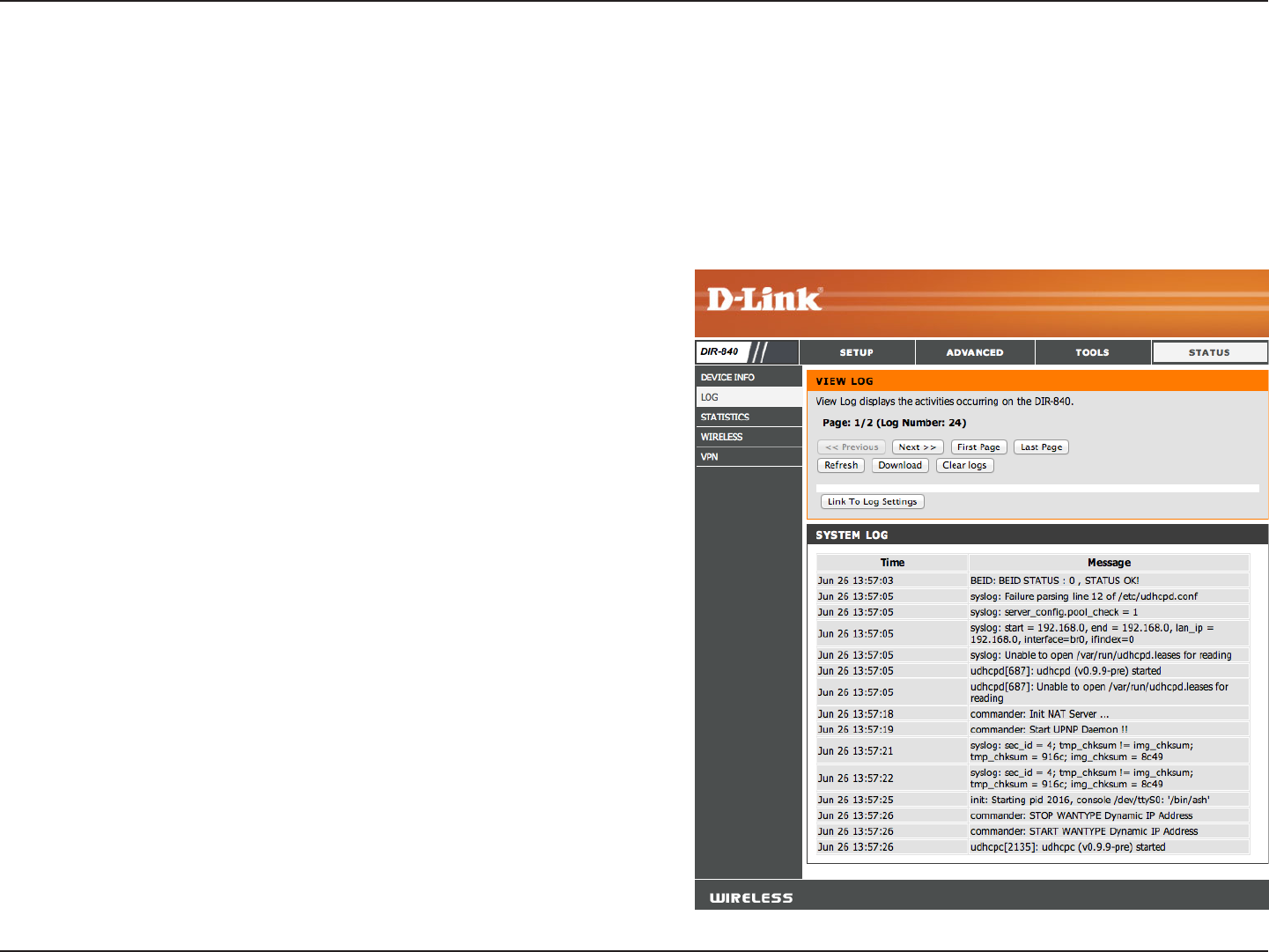
Log
Refresh:
Download:
Clear Logs:
Link To Log
Settings:
Updates the log details on the screen so it displays any recent
activity.
This option will save the router log to a le on your computer.
Clears all of the log contents.
This option will jump to Tools > Syslog settings.
The router automatically logs (records) events of possible interest in its internal memory. If there isn’t enough internal memory
for all events, logs of older events are deleted but logs of the latest events are retained. The Logs option allows you to view
the router logs. You can dene what types of events you want to view and the level of the events to view. This router also has
external Syslog Server support so you can send the log les to a computer on your network that is running a Syslog utility.
40D-Link DIR-840 User Manual
Section 6 - Status
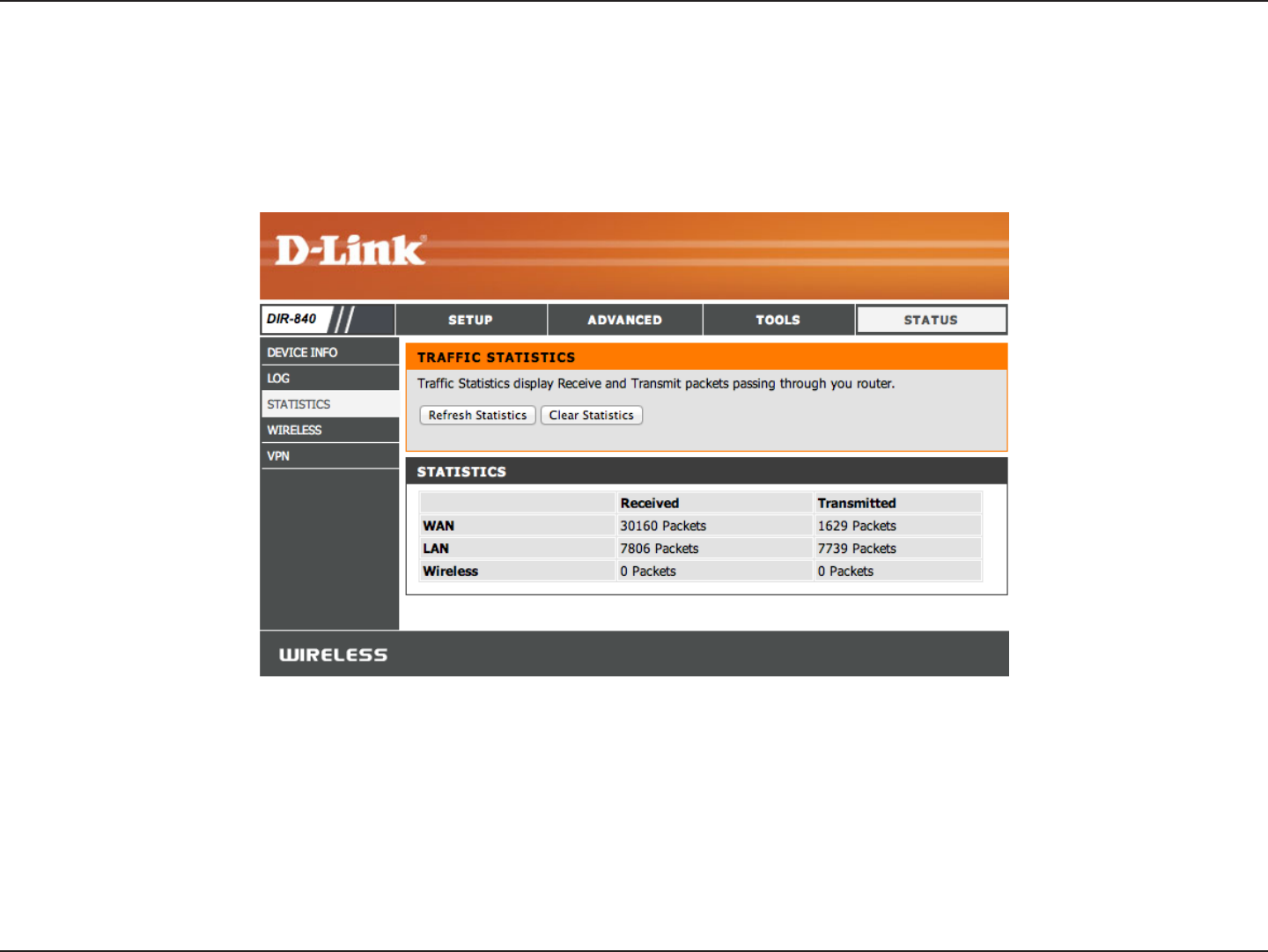
Statistics
The screen below displays the Trac Statistics. Here you can view the amount of packets that pass through the DIR-840 on both
the WAN, LAN ports and both the 802.11n/g (2.4GHz) and 802.11n/a (5GHz) wireless bands. The trac counter will reset if the
device is rebooted.
41D-Link DIR-840 User Manual
Section 6 - Status
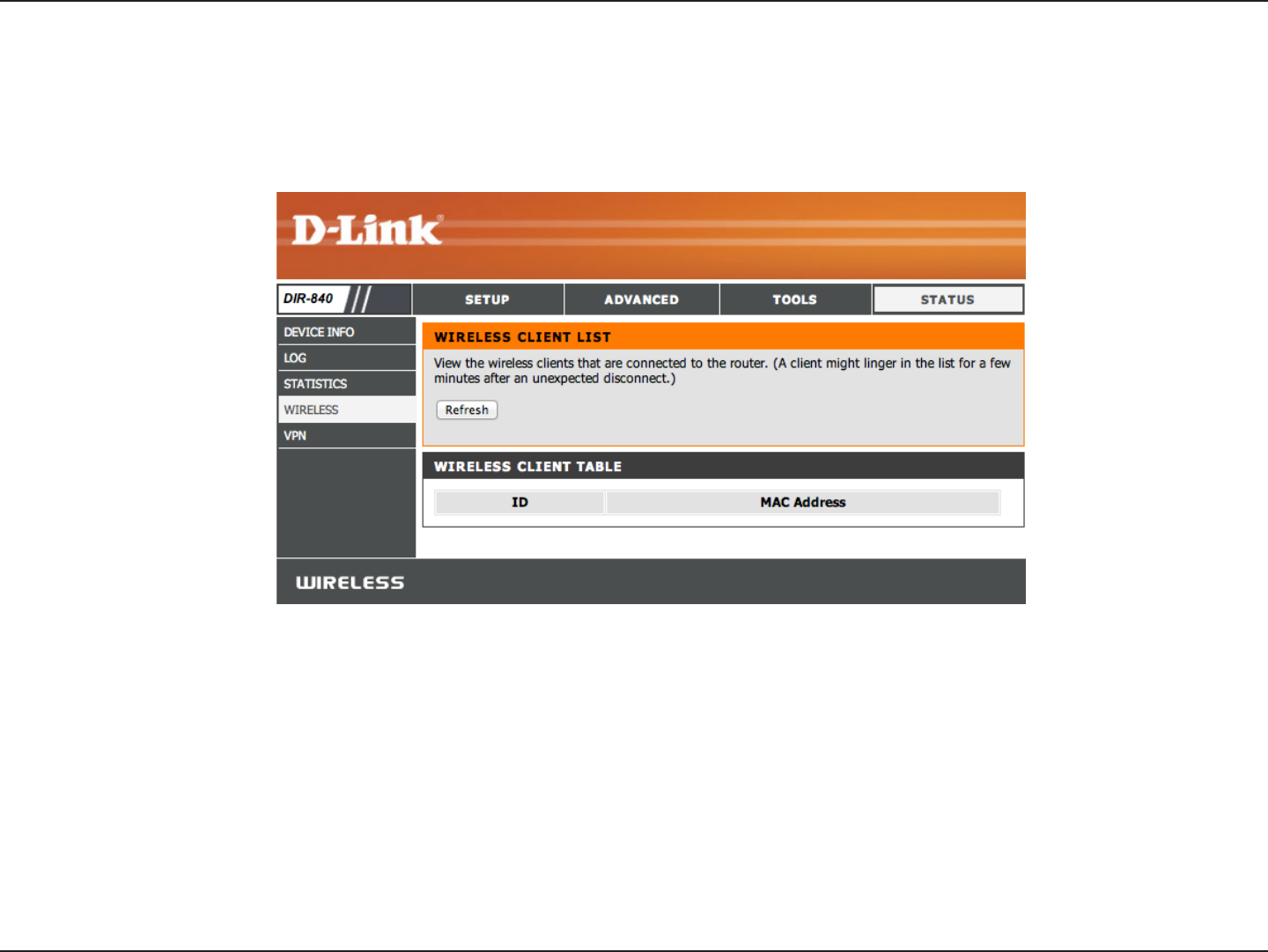
The wireless client table displays a list of current connected wireless clients. This table also displays the connection time and
MAC address of the connected wireless clients.
Wireless
42D-Link DIR-840 User Manual
Section 6 - Status
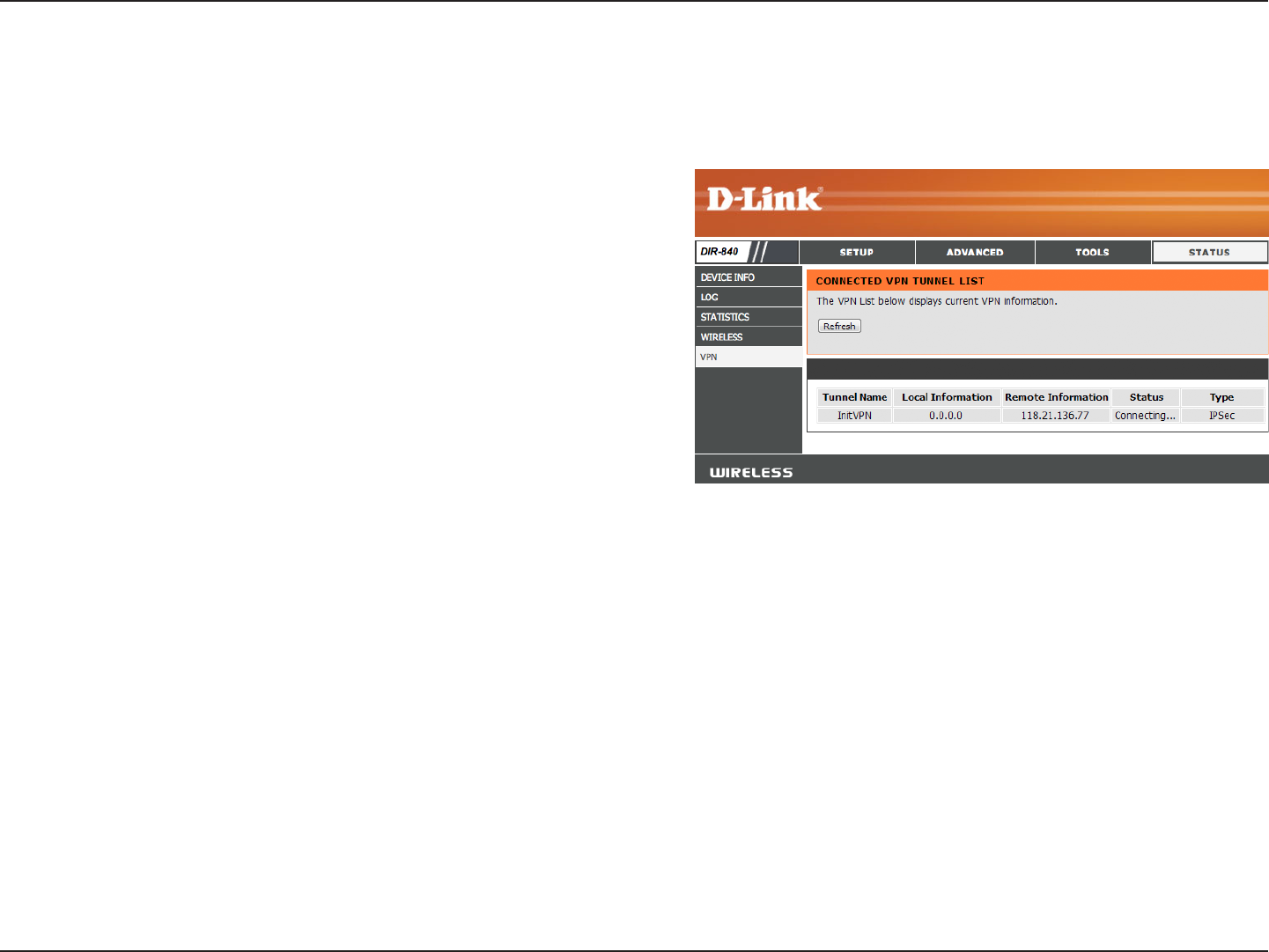
VPN
Refresh: Updates the VPN details on the screen so it displays any
recent activity.
This page is where the router displays information on the the current VPN tunnels.

43D-Link DIR-840 User Manual
Section 9 - Troubleshooting
Troubleshooting
This chapter provides solutions to problems that can occur during the installation and operation of the DIR-840. Read the
following descriptions if you are having problems. The examples below are illustrated in Windows® XP. If you have a dierent
operating system, the screenshots on your computer will look similar to the following examples.
1. Why can’t I access the web-based conguration utility?
When entering the IP address of the D-Link router (192.168.89.1 for example), you are not connecting to a website nor do you
have to be connected to the Internet. The device has the utility built-in to a ROM chip in the device itself. Your computer must
be on the same IP subnet to connect to the web-based utility.
• Make sure you have an updated Java-enabled web browser. We recommend the following:
- Microsoft Internet Explorer® 6.0 and higher
- Mozilla Firefox 3.0 and higher
- Google™ Chrome 2.0 and higher
- Apple Safari 3.0 and higher
• Verify physical connectivity by checking for solid link lights on the device. If you do not get a solid link light, try using a
dierent cable or connect to a dierent port on the device if possible. If the computer is turned o, the link light may not be
on.
• Disable any Internet security software running on the computer. Software rewalls such as Zone Alarm, Black Ice, Sygate,
Norton Personal Firewall, and Windows® XP rewall may block access to the conguration pages. Check the help les included
with your rewall software for more information on disabling or conguring it.

44D-Link DIR-840 User Manual
Section 9 - Troubleshooting
• Congure your Internet settings:
• Go to Start > Settings > Control Panel. Double-click the Internet Options Icon. From the Security tab, click
the button to restore the settings to their defaults.
• Click the Connection tab and set the dial-up option to Never Dial a Connection. Click the LAN Settings button.
Make sure nothing is checked. Click OK.
• Go to the Advanced tab and click the button to restore these settings to their defaults. Click OK three times.
• Close your web browser (if open) and open it.
• Access the web management. Open your web browser and enter the IP address of your D-Link router in the address bar. This
should open the login page for your web management.
• If you still cannot access the conguration, unplug the power to the router for 10 seconds and plug back in. Wait about 30
seconds and try accessing the conguration. If you have multiple computers, try connecting using a dierent computer.
2. What can I do if I forgot my password?
If you forgot your password, you must reset your router. Unfortunately this process will change all your settings back to the
factory defaults.
To reset the router, locate the reset button (hole) on the rear panel of the unit. With the router powered on, use a paperclip
to hold the button down for 10 seconds. Release the button and the router will go through its reboot process. Wait about 30
seconds to access the router. The default IP address is 192.168.89.1. When logging in, the username is admin and the password
is nwtitfbipne.
45D-Link DIR-840 User Manual
Section 9 - Troubleshooting
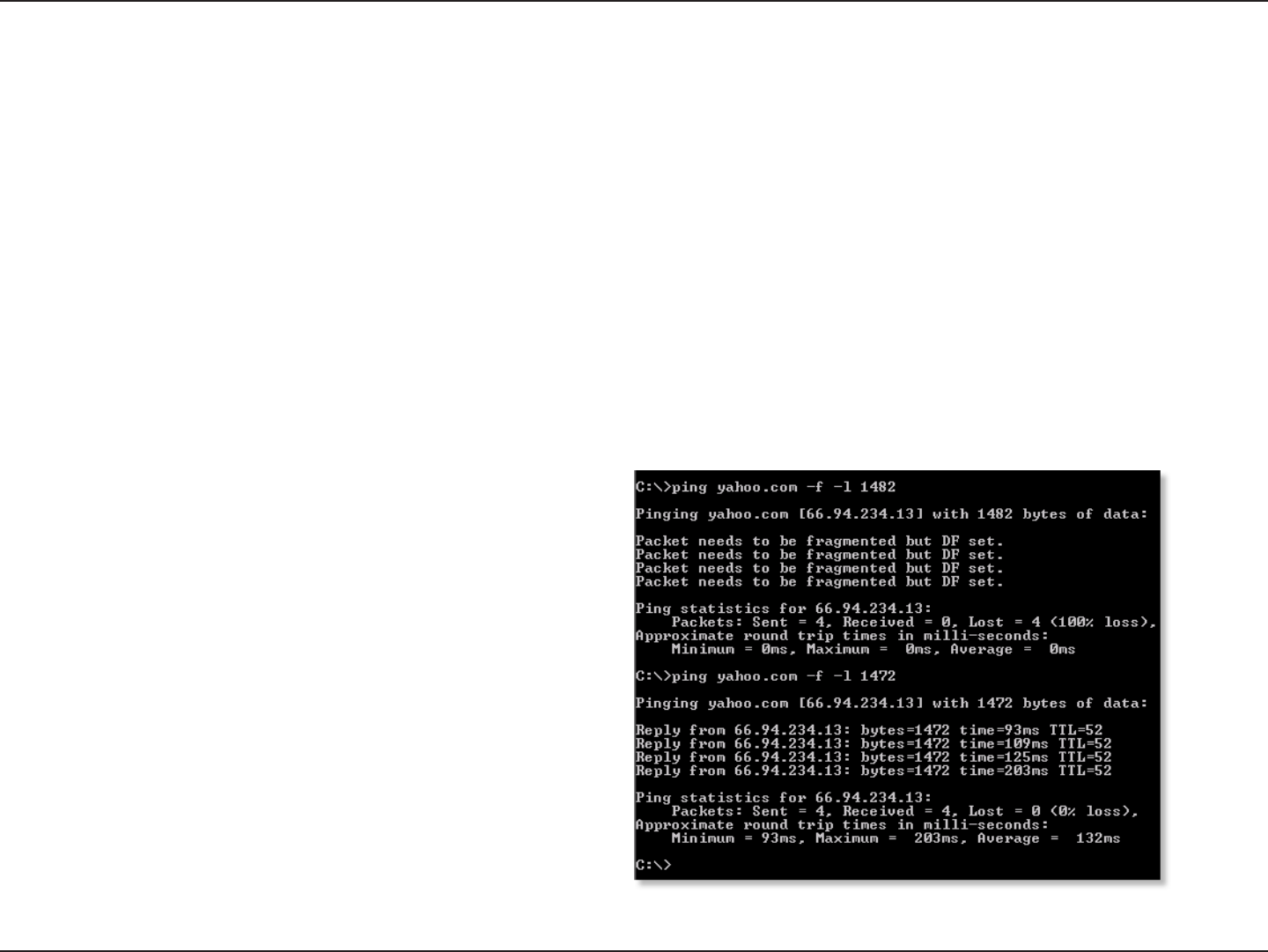
3. Why can’t I connect to certain sites or send and receive emails when connecting through my router?
If you are having a problem sending or receiving email, or connecting to secure sites such as eBay, banking sites, and Hotmail,
we suggest lowering the MTU in increments of ten (Ex. 1492, 1482, 1472, etc).
To nd the proper MTU Size, you’ll have to do a special ping of the destination you’re trying to go to. A destination could be
another computer, or a URL.
• Click on Start and then click Run.
• Windows® 95, 98, and Me users type in command (Windows® NT, 2000, XP, Vista®, and 7 users type in cmd) and
press Enter (or click OK).
• Once the window opens, you’ll need to do a special ping. Use the following syntax:
ping [url] [-f] [-l] [MTU value]
Example: ping yahoo.com -f -l 1472

46D-Link DIR-840 User Manual
Section 9 - Troubleshooting
You should start at 1472 and work your way down by 10 each time. Once you get a reply, go up by 2 until you get a fragmented
packet. Take that value and add 28 to the value to account for the various TCP/IP headers. For example, lets say that 1452 was the
proper value, the actual MTU size would be 1480, which is the optimum for the network we’re working with (1452+28=1480).
Once you nd your MTU, you can now congure your router with the proper MTU size.
To change the MTU rate on your router follow the steps below:
• Open your browser, enter the IP address of your router (http://192.168.89.1) and click OK.
• Enter your username (admin) and password (nwtitfbipne). Click OK to enter the web conguration page for
the device.
• Click on Setup and then click Manual Congure.

47D-Link DIR-840 User Manual
Appendix A - Wireless Basics
D-Link wireless products are based on industry standards to provide easy-to-use and compatible high-speed wireless
connectivity within your home, business or public access wireless networks. Strictly adhering to the IEEE standard, the D-Link
wireless family of products will allow you to securely access the data you want, when and where you want it. You will be able
to enjoy the freedom that wireless networking delivers.
A wireless local area network (WLAN) is a cellular computer network that transmits and receives data with radio signals instead of
wires. Wireless LANs are used increasingly in both home and oce environments, and public areas such as airports, coee shops
and universities. Innovative ways to utilize WLAN technology are helping people to work and communicate more eciently.
Increased mobility and the absence of cabling and other xed infrastructure have proven to be benecial for many users.
Wireless users can use the same applications they use on a wired network. Wireless adapter cards used on laptop and desktop
systems support the same protocols as Ethernet adapter cards.
Under many circumstances, it may be desirable for mobile network devices to link to a conventional Ethernet LAN in order to
use servers, printers or an Internet connection supplied through the wired LAN. A Wireless Router is a device used to provide
this link.
Wireless Basics

48D-Link DIR-840 User Manual
Appendix A - Wireless Basics
What is Wireless?
Wireless or Wi-Fi technology is another way of connecting your computer to the network without using wires. Wi-Fi uses radio
frequency to connect wirelessly, so you have the freedom to connect computers anywhere in your home or oce network.
Why D-Link Wireless?
D-Link is the worldwide leader and award winning designer, developer, and manufacturer of networking products. D-Link
delivers the performance you need at a price you can aord. D-Link has all the products you need to build your network.
How does wireless work?
Wireless works similar to how cordless phone work, through radio signals to transmit data from one point A to point B. But
wireless technology has restrictions as to how you can access the network. You must be within the wireless network range area
to be able to connect your computer. There are two dierent types of wireless networks Wireless Local Area Network (WLAN),
and Wireless Personal Area Network (WPAN).
Wireless Local Area Network (WLAN)
In a wireless local area network, a device called an Access Point (AP) connects computers to the network. The access point has
a small antenna attached to it, which allows it to transmit data back and forth over radio signals. With an indoor access point
as seen in the picture, the signal can travel up to 300 feet. With an outdoor access point the signal can reach out up to 30 miles
to serve places like manufacturing plants, industrial locations, college and high school campuses, airports, golf courses, and
many other outdoor venues.
Wireless Personal Area Network (WPAN)
Bluetooth is the industry standard wireless technology used for WPAN. Bluetooth devices in WPAN operate in a range up to
30 feet away.

49D-Link DIR-840 User Manual
Appendix A - Wireless Basics
Compared to WLAN the speed and wireless operation range are both less than WLAN, but in return it doesn’t use nearly as
much power which makes it ideal for personal devices, such as mobile phones, PDAs, headphones, laptops, speakers, and other
devices that operate on batteries.
Who uses wireless?
Wireless technology as become so popular in recent years that almost everyone is using it, whether it’s for home, oce, business,
D-Link has a wireless solution for it.
Home
• Gives everyone at home broadband access
• Surf the web, check email, instant message, etc.
• Gets rid of the cables around the house
• Simple and easy to use
Small Oce and Home Oce
• Stay on top of everything at home as you would at oce
• Remotely access your oce network from home
• Share Internet connection and printer with multiple computers
• No need to dedicate oce space

50D-Link DIR-840 User Manual
Appendix A - Wireless Basics
Where is wireless used?
Wireless technology is expanding everywhere not just at home or oce. People like the freedom of mobility and it’s becoming
so popular that more and more public facilities now provide wireless access to attract people. The wireless connection in public
places is usually called “hotspots”.
Using a D-Link Cardbus Adapter with your laptop, you can access the hotspot to connect to Internet from remote locations
like: Airports, Hotels, Coee Shops, Libraries, Restaurants, and Convention Centers.
Wireless network is easy to setup, but if you’re installing it for the rst time it could be quite a task not knowing where to start.
That’s why we’ve put together a few setup steps and tips to help you through the process of setting up a wireless network.
Tips
Here are a few things to keep in mind, when you install a wireless network.
Centralize your router or Access Point
Make sure you place the router/access point in a centralized location within your network for the best performance. Try to
place the router/access point as high as possible in the room, so the signal gets dispersed throughout your home. If you have
a two-story home, you may need a repeater to boost the signal to extend the range.
Eliminate Interference
Place home appliances such as cordless telephones, microwaves, and televisions as far away as possible from the router/access
point. This would signicantly reduce any interference that the appliances might cause since they operate on same frequency.
Security
Don’t let you next-door neighbors or intruders connect to your wireless network. Secure your wireless network by turning on
the WPA or WEP security feature on the router. Refer to product manual for detail information on how to set it up.

51D-Link DIR-840 User Manual
Appendix A - Wireless Basics
There are basically two modes of networking:
• Infrastructure – All wireless clients will connect to an access point or wireless router.
• Ad-Hoc – Directly connecting to another computer, for peer-to-peer communication, using wireless network
adapters on each computer, such as two or more DIR-840 wireless network Cardbus adapters.
An Infrastructure network contains an Access Point or wireless router. All the wireless devices, or clients, will connect to the
wireless router or access point.
An Ad-Hoc network contains only clients, such as laptops with wireless cardbus adapters. All the adapters must be in Ad-Hoc
mode to communicate.
Wireless Modes
52D-Link DIR-840 User Manual
Appendix B - Networking Basics
Networking Basics
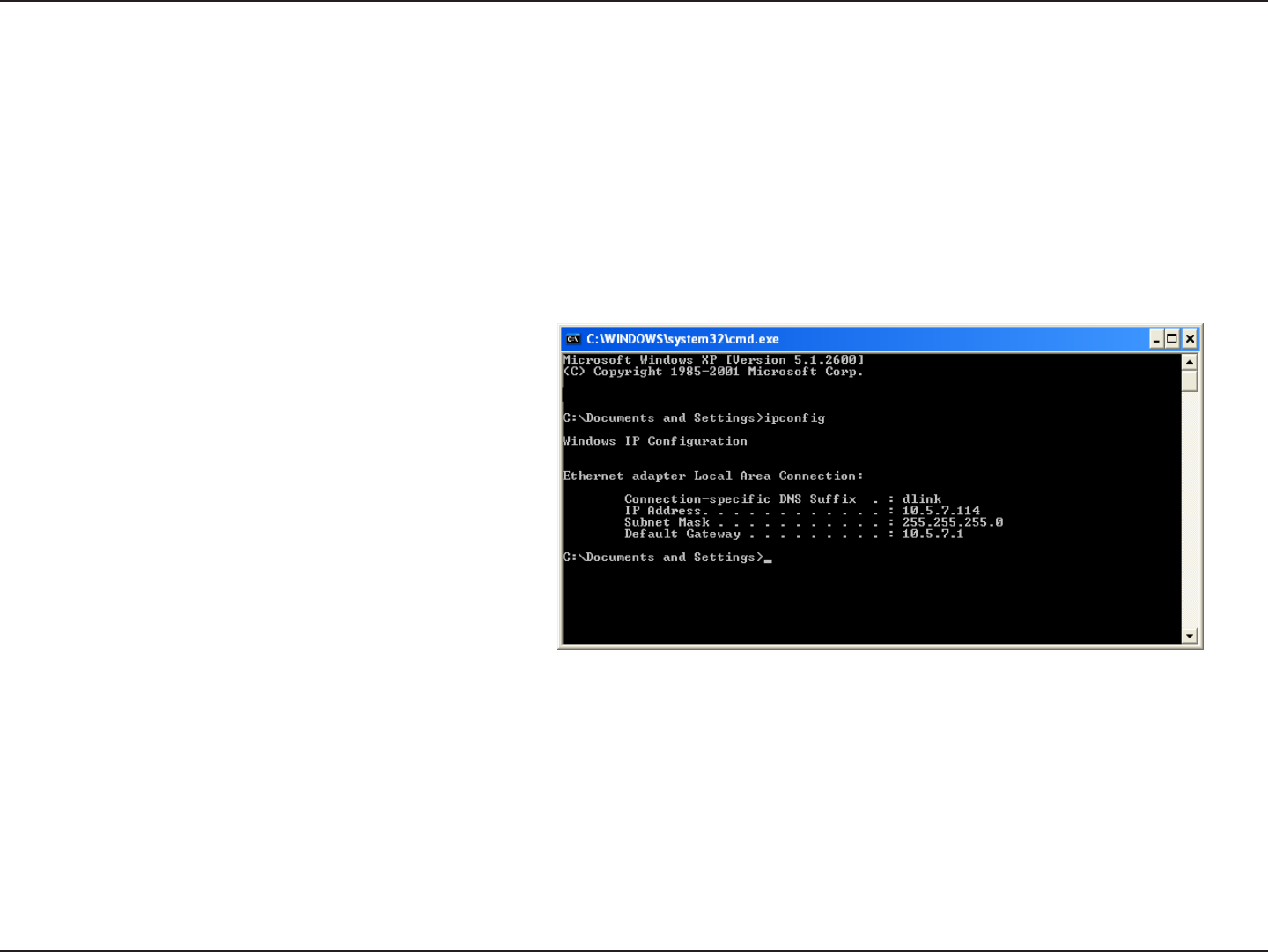
Check your IP address
After you install your new D-Link adapter, by default, the TCP/IP settings should be set to obtain an IP address from a DHCP
server (i.e. wireless router) automatically. To verify your IP address, please follow the steps below.
Click on Start > Run. In the run box type cmd and click OK. (Windows® 7/Vista® users type cmd in the Start Search box.)
At the prompt, type ipcong and press Enter.
This will display the IP address, subnet mask, and the
default gateway of your adapter.
If the address is 0.0.0.0, check your adapter installation,
security settings, and the settings on your router.
Some rewall software programs may block a DHCP
request on newly installed adapters.
53D-Link DIR-840 User Manual
Appendix B - Networking Basics
Statically Assign an IP address
If you are not using a DHCP capable gateway/router, or you need to assign a static IP address, please follow the steps below:
Step 1
Windows® 7 - Click on Start > Control Panel > Network and Internet > Network and Sharing Center.
Windows Vista® - Click on Start > Control Panel > Network and Internet > Network and Sharing Center > Manage Network
Connections.
Windows® XP - Click on Start > Control Panel > Network Connections.
Windows® 2000 - From the desktop, right-click My Network Places > Properties.
Step 2
Right-click on the Local Area Connection which represents your network adapter and select Properties.
Step 3
Highlight Internet Protocol (TCP/IP) and click Properties.
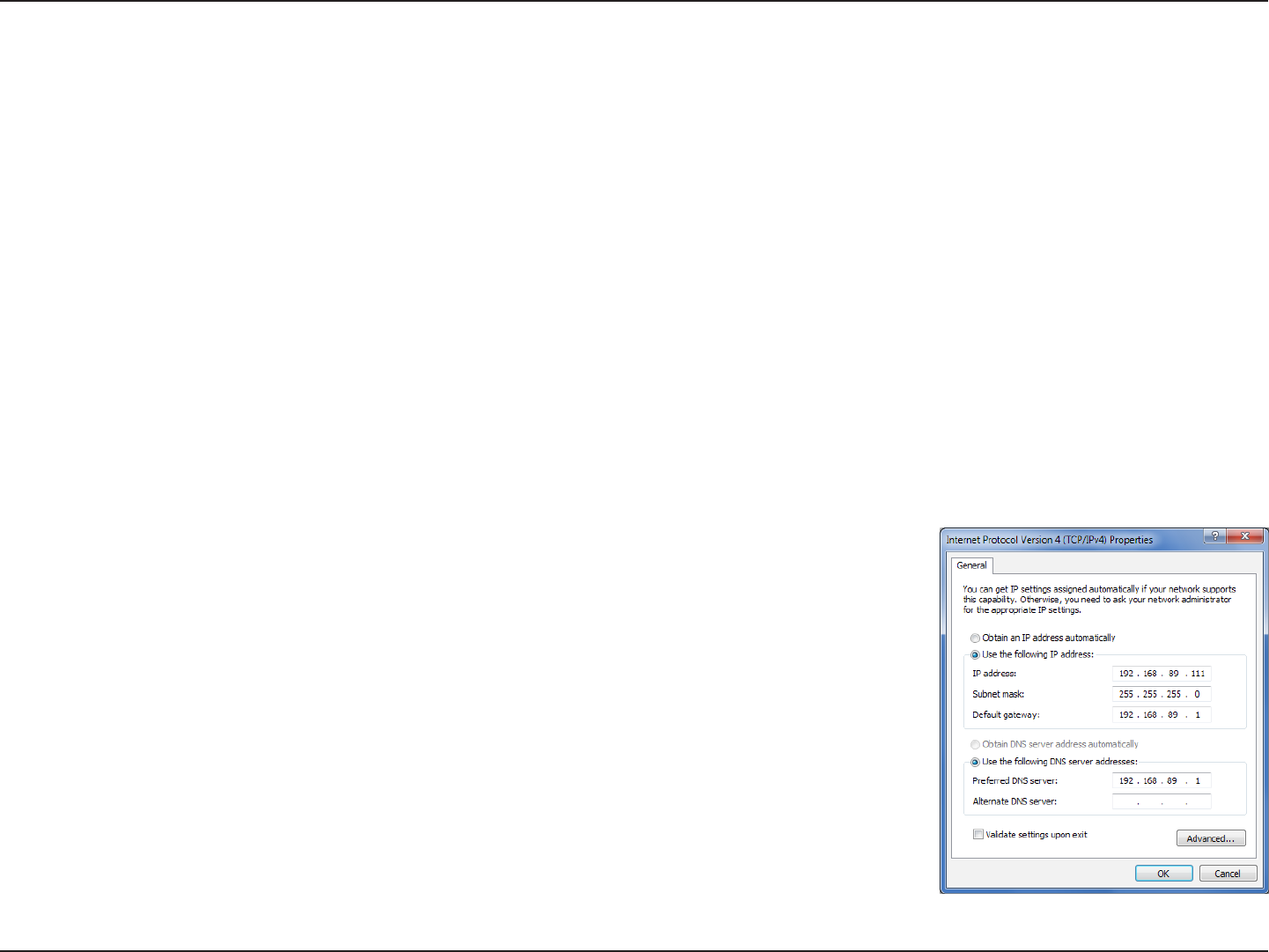
Step 4
Click Use the following IP address and enter an IP address that is on the same subnet as your network or the LAN IP address
on your router.
Example: The router’s LAN IP address is 192.168.89.1, make your IP address 192.168.0.X
where X is a number between 2 and 99. Make sure that the number you choose is not in
use on the network. Set the Default Gateway the same as the LAN IP address of your router
(I.E. 192.168.89.1).
Set Primary DNS the same as the LAN IP address of your router (192.168.89.1). The Secondary
DNS is not needed or you may enter a DNS server from your ISP.
Step 5
Click OK twice to save your settings.

54D-Link DIR-840 User Manual
Appendix C - Technical Specications
Technical Specications
Standards
• IEEE 802.11n
• IEEE 802.11g
• IEEE 802.11a
• IEEE 802.3
• IEEE 802.3u
• IEEE 802.3ab
Security
• WPA™ - Personal/Enterprise
• WPA2™ - Personal/Enterprise
Wireless Signal Rates1
IEEE 802.11n 2.4GHz(HT20/40):
• 144.4 Mbps (300) · 130 Mbps (270)
• 115.6 Mbps (240) · 86.7 Mbps (180)
• 72.2 Mbps (150) · 65 Mbps (135)
• 57.8 Mbps (120) · 43.3 Mbps (90)
• 28.9 Mbps (60) · 21.7 Mbps (45)
•14.4 Mbps (30) · 7.2 Mbps (15)
IEEE 802.11n 5GHz(HT20/40):
• 144.4 Mbps (300) · 130 Mbps (270)
• 115.6 Mbps (240) · 86.7 Mbps (180)
• 72.2 Mbps (150) · 65 Mbps (135)
• 57.8 Mbps (120) · 43.3 Mbps (90)
• 28.9 Mbps (60) · 21.7 Mbps (45)
•14.4 Mbps (30) · 7.2 Mbps (15)
IEEE 802.11g:
• 54 Mbps • 48 Mbps • 36 Mbps
• 24 Mbps • 18 Mbps • 12 Mbps
• 11 Mbps • 9 Mbps • 6 Mbps
• 5.5 Mbps • 2 Mbps • 1 Mbps
Frequency Range2 (North America)
• 2.412 GHz to 2.462 GHz (802.11g/n)
• 5.15 GHz to 5.825 GHz (802.11a/n)3
External Antenna Type
• Two (2) detachable Antennas
Operating Temperature
• 32°F to 104°F ( 0°C to 40°C)
Humidity
• 95% maximum (non-condensing)
Safety & Emissions
• FCC
• IC
Dimensions
• L = 7.4 inches
• W = 4.4 inches
• H = 1.1 inches
Warranty
• 1 Year
1 Maximum wireless signal rate derived from IEEE Standard 802.11a, 802.11g, and 802.11n specications. Actual data throughput will vary. Network conditions and environmental factors, including
volume of network trac, building materials and construction, and network overhead, lower actual data throughput rate. Environmental factors will adversely aect wireless signal range.
2 Frequency Range varies depending on country’s regulation
3 The DIR-840 does not include 5.25-5.35 GHz & 5.47-5.725 GHz in some regions.

55D-Link DIR-840 User Manual
Appendix D - GPL Code Statement
GPL Code Statement
This D-Link product includes software code developed by third parties, including software code subject to the GNU General Public License (“GPL”)
or GNU Lesser General Public License (“LGPL”). As applicable, the terms of the GPL and LGPL, and information on obtaining access to the GPL
code and LGPL code used in this product, are available to you at:
http://tsd.dlink.com.tw/GPL.asp
The GPL code and LGPL code used in this product is distributed WITHOUT ANY WARRANTY and is subject to the copyrights of one or more
authors. For details, see the GPL code and the LGPL code for this product and the terms of the GPL and LGPL.
WRITTEN OFFER FOR GPL AND LGPL SOURCE CODE
Where such specic license terms entitle you to the source code of such software, D-Link will provide upon written request via email and/or
traditional paper mail the applicable GPL and LGPLsource code files via CD-ROM for a nominal cost to cover shipping and media charges as
allowed under the GPL and LGPL.
Please direct all inquiries to:
Email: GPLCODE@DLink.com
Snail Mail:
Attn: GPLSOURCE REQUEST
D-Link Systems, Inc.
17595 Mt. Herrmann Street
Fountain Valley, CA 92708
GNU GENERAL PUBLIC LICENSE
Version 3, 29 June 2007
Copyright (C) 2007 Free Software Foundation, Inc. <http://fsf.org/> Everyone is permitted to copy and distribute verbatim copies of this license
document, but changing it is not allowed.

56D-Link DIR-840 User Manual
Appendix D - GPL Code Statement
Preamble
The GNU General Public License is a free, copyleft license for software and other kinds of works.
The licenses for most software and other practical works are designed to take away your freedom to share and change the works. By contrast, the
GNU General Public License is intended to guarantee your freedom to share and change all versions of a program--to make sure it remains free
software for all its users. We, the Free Software Foundation, use the GNU General Public License for most of our software; it applies also to any other
work released this way by its authors. You can apply it to your programs, too.
When we speak of free software, we are referring to freedom, not price. Our General Public Licenses are designed to make sure that you have the
freedom to distribute copies of free software (and charge for them if you wish), that you receive source code or can get it if you want it, that you
can change the software or use pieces of it in new free programs, and that you know you can do these things.
To protect your rights, we need to prevent others from denying you these rights or asking you to surrender the rights. Therefore, you have certain
responsibilities if you distribute copies of the software, or if you modify it: responsibilities to respect the freedom of others.
For example, if you distribute copies of such a program, whether gratis or for a fee, you must pass on to the recipients the same freedoms that you
received. You must make sure that they, too, receive or can get the source code. And you must show them these terms so they know their rights.
Developers that use the GNU GPL protect your rights with two steps:
(1) assert copyright on the software, and (2) oer you this License giving you legal permission to copy, distribute and/or modify it.
For the developers’ and authors’ protection, the GPL clearly explains that there is no warranty for this free software. For both users’ and authors’
sake, the GPL requires that modied versions be marked as changed, so that their problems will not be attributed erroneously to authors of
previous versions.
Some devices are designed to deny users access to install or run modied versions of the software inside them, although the manufacturer can
do so. This is fundamentally incompatible with the aim of protecting users’ freedom to change the software. The systematic pattern of such abuse
occurs in the area of products for individuals to use, which is precisely where it is most unacceptable. Therefore, we have designed this version of
the GPL to prohibit the practice for those products. If such problems arise substantially in other domains, we stand ready to extend this provision
to those domains in future versions of the GPL, as needed to protect the freedom of users.
Finally, every program is threatened constantly by software patents. States should not allow patents to restrict development and use of software
on general-purpose computers, but in those that do, we wish to avoid the special danger that patents applied to a free program could make it
eectively proprietary. To prevent this, the GPL assures that patents cannot be used to render the program non-free.
The precise terms and conditions for copying, distribution and modication follow.

57D-Link DIR-840 User Manual
Appendix D - GPL Code Statement
TERMS AND CONDITIONS
0. Denitions.
“This License” refers to version 3 of the GNU General Public License.
“Copyright” also means copyright-like laws that apply to other kinds of works, such as semiconductor masks.
“The Program” refers to any copyrightable work licensed under this License. Each licensee is addressed as “you”. “Licensees” and “recipients” may
be individuals or organizations.
To “modify” a work means to copy from or adapt all or part of the work in a fashion requiring copyright permission, other than the making of an
exact copy. The resulting work is called a “modied version” of the earlier work or a work “based on” the earlier work.
A “covered work” means either the unmodied Program or a work based on the Program.
To “propagate” a work means to do anything with it that, without permission, would make you directly or secondarily liable for infringement under
applicable copyright law, except executing it on a computer or modifying a private copy. Propagation includes copying, distribution (with or
without modication), making available to the public, and in some countries other activities as well.
To “convey” a work means any kind of propagation that enables other parties to make or receive copies. Mere interaction with a user through a
computer network, with no transfer of a copy, is not conveying.
An interactive user interface displays “Appropriate Legal Notices” to the extent that it includes a convenient and prominently visible feature that
(1) displays an appropriate copyright notice, and (2) tells the user that there is no warranty for the work (except to the extent that warranties are
provided), that licensees may convey the work under this License, and how to view a copy of this License. If the interface presents a list of user
commands or options, such as a menu, a prominent item in the list meets this criterion.
1. Source Code.
The “source code” for a work means the preferred form of the work for making modications to it. “Object code” means any non-source form of a
work.
A “Standard Interface” means an interface that either is an ocial standard dened by a recognized standards body, or, in the case of interfaces
specied for a particular programming language, one that is widely used among developers working in that language.

58D-Link DIR-840 User Manual
Appendix D - GPL Code Statement
The “System Libraries” of an executable work include anything, other than the work as a whole, that (a) is included in the normal form of packaging
a Major Component, but which is not part of that Major Component, and (b) serves only to enable use of the work with that Major Component,
or to implement a Standard Interface for which an implementation is available to the public in source code form. A “Major Component”, in this
context, means a major essential component (kernel, window system, and so on) of the specic operating system (if any) on which the executable
work runs, or a compiler used to produce the work, or an object code interpreter used to run it.
The “Corresponding Source” for a work in object code form means all the source code needed to generate, install, and (for an executable work)
run the object code and to modify the work, including scripts to control those activities. However, it does not include the work’s System Libraries,
or general-purpose tools or generally available free programs which are used unmodied in performing those activities but which are not part of
the work. For example, Corresponding Source includes interface denition les associated with source les for the work, and the source code for
shared libraries and dynamically linked subprograms that the work is specically designed to require, such as by intimate data communication or
control ow between those subprograms and other parts of the work.
The Corresponding Source need not include anything that users can regenerate automatically from other parts of the Corresponding Source.
The Corresponding Source for a work in source code form is that same work.
2. Basic Permissions.
All rights granted under this License are granted for the term of copyright on the Program, and are irrevocable provided the stated conditions
are met. This License explicitly arms your unlimited permission to run the unmodied Program. The output from running a covered work is
covered by this License only if the output, given its content, constitutes a covered work. This License acknowledges your rights of fair use or other
equivalent, as provided by copyright law.
You may make, run and propagate covered works that you do not convey, without conditions so long as your license otherwise remains in force.
You may convey covered works to others for the sole purpose of having them make modications exclusively for you, or provide you with facilities
for running those works, provided that you comply with the terms of this License in conveying all material for which you do not control copyright.
Those thus making or running the covered works for you must do so exclusively on your behalf, under your direction and control, on terms that
prohibit them from making any copies of your copyrighted material outside their relationship with you.
Conveying under any other circumstances is permitted solely under the conditions stated below. Sublicensing is not allowed; section 10 makes it
unnecessary.

59D-Link DIR-840 User Manual
Appendix D - GPL Code Statement
3. Protecting Users’ Legal Rights From Anti-Circumvention Law.
No covered work shall be deemed part of an eective technological measure under any applicable law fullling obligations under article 11 of the
WIPO copyright treaty adopted on 20 December 1996, or similar laws prohibiting or restricting circumvention of such measures.
When you convey a covered work, you waive any legal power to forbid circumvention of technological measures to the extent such circumvention
is eected by exercising rights under this License with respect to the covered work, and you disclaim any intention to limit operation or modication
of the work as a means of enforcing, against the work’s users, your or third parties’ legal rights to forbid circumvention of technological measures.
4. Conveying Verbatim Copies.
You may convey verbatim copies of the Program’s source code as you receive it, in any medium, provided that you conspicuously and appropriately
publish on each copy an appropriate copyright notice; keep intact all notices stating that this License and any non-permissive terms added in
accord with section 7 apply to the code; keep intact all notices of the absence of any warranty; and give all recipients a copy of this License along
with the Program.
You may charge any price or no price for each copy that you convey, and you may oer support or warranty protection for a fee.
5. Conveying Modied Source Versions.
You may convey a work based on the Program, or the modications to produce it from the Program, in the form of source code under the terms of
section 4, provided that you also meet all of these conditions:
a) The work must carry prominent notices stating that you modied it, and giving a relevant date.
b) The work must carry prominent notices stating that it is released under this License and any conditions added under section 7.
This requirement modies the requirement in section 4 to “keep intact all notices”.
c) You must license the entire work, as a whole, under this License to anyone who comes into possession of a copy. This License
will therefore apply, along with any applicable section 7 additional terms, to the whole of the work, and all its parts, regardless
of how they are packaged. This License gives no permission to license the work in any other way, but it does not invalidate such
permission if you have separately received it.
d) If the work has interactive user interfaces, each must display Appropriate Legal Notices; however, if the Program has interactive
interfaces that do not display Appropriate Legal Notices, your work need not make them do so.

60D-Link DIR-840 User Manual
Appendix D - GPL Code Statement
A compilation of a covered work with other separate and independent works, which are not by their nature extensions of the covered work, and
which are not combined with it such as to form a larger program, in or on a volume of a storage or distribution medium, is called an “aggregate”
if the compilation and its resulting copyright are not used to limit the access or legal rights of the compilation’s users beyond what the individual
works permit. Inclusion of a covered work in an aggregate does not cause this License to apply to the other parts of the aggregate.
6. Conveying Non-Source Forms.
You may convey a covered work in object code form under the terms of sections 4 and 5, provided that you also convey the machine-readable
Corresponding Source under the terms of this License, in one of these ways:
a) Convey the object code in, or embodied in, a physical product (including a physical distribution medium), accompanied by the
Corresponding Source xed on a durable physical medium customarily used for software interchange.
b) Convey the object code in, or embodied in, a physical product (including a physical distribution medium), accompanied by a
written oer, valid for at least three years and valid for as long as you oer spare parts or customer support for that product
model, to give anyone who possesses the object code either (1) a copy of the Corresponding Source for all the software in the
product that is covered by this License, on a durable physical medium customarily used for software interchange, for a price no
more than your reasonable cost of physically performing this conveying of source, or (2) access to copy the Corresponding Source
from a network server at no charge.
c) Convey individual copies of the object code with a copy of the written oer to provide the Corresponding Source. This alternative
is allowed only occasionally and noncommercially, and only if you received the object code with such an oer, in accord with
subsection 6b.
d) Convey the object code by oering access from a designated place (gratis or for a charge), and oer equivalent access to the
Corresponding Source in the same way through the same place at no further charge. You need not require recipients to copy the
Corresponding Source along with the object code. If the place to copy the object code is a network server, the Corresponding
Source may be on a dierent server (operated by you or a third party) that supports equivalent copying facilities, provided you
maintain clear directions next to the object code saying where to nd the Corresponding Source. Regardless of what server hosts
the Corresponding Source, you remain obligated to ensure that it is available for as long as needed to satisfy these requirements.
e) Convey the object code using peer-to-peer transmission, provided you inform other peers where the object code and
Corresponding Source of the work are being oered to the general public at no charge under subsection 6d.
A separable portion of the object code, whose source code is excluded from the Corresponding Source as a System Library, need not be
included in conveying the object code work.

61D-Link DIR-840 User Manual
Appendix D - GPL Code Statement
A “User Product” is either (1) a “consumer product”, which means any tangible personal property which is normally used for personal, family, or
household purposes, or (2) anything designed or sold for incorporation into a dwelling. In determining whether a product is a consumer product,
doubtful cases shall be resolved in favor of coverage. For a particular product received by a particular user, “normally used” refers to a typical
or common use of that class of product, regardless of the status of the particular user or of the way in which the particular user actually uses,
or expects or is expected to use, the product. A product is a consumer product regardless of whether the product has substantial commercial,
industrial or non-consumer uses, unless such uses represent the only signicant mode of use of the product.
“Installation Information” for a User Product means any methods, procedures, authorization keys, or other information required to install and
execute modied versions of a covered work in that User Product from a modied version of its Corresponding Source. The information must
suce to ensure that the continued functioning of the modied object code is in no case prevented or interfered with solely because modication
has been made.
If you convey an object code work under this section in, or with, or specically for use in, a User Product, and the conveying occurs as part of a
transaction in which the right of possession and use of the User Product is transferred to the recipient in perpetuity or for a xed term (regardless of
how the transaction is characterized), the Corresponding Source conveyed under this section must be accompanied by the Installation Information.
But this requirement does not apply if neither you nor any third party retains the ability to install modied object code on the User Product (for
example, the work has been installed in ROM).
The requirement to provide Installation Information does not include a requirement to continue to provide support service, warranty, or updates
for a work that has been modied or installed by the recipient, or for the User Product in which it has been modied or installed. Access to a
network may be denied when the modication itself materially and adversely aects the operation of the network or violates the rules and
protocols for communication across the network.
Corresponding Source conveyed, and Installation Information provided, in accord with this section must be in a format that is publicly documented
(and with an implementation available to the public in source code form), and must require no special password or key for unpacking, reading or
copying.
7. Additional Terms.
“Additional permissions” are terms that supplement the terms of this License by making exceptions from one or more of its conditions. Additional
permissions that are applicable to the entire Program shall be treated as though they were included in this License, to the extent that they are valid
under applicable law. If additional permissions apply only to part of the Program, that part may be used separately under those permissions, but
the entire Program remains governed by this License without regard to the additional permissions.

62D-Link DIR-840 User Manual
Appendix D - GPL Code Statement
When you convey a copy of a covered work, you may at your option remove any additional permissions from that copy, or from any part of it.
(Additional permissions may be written to require their own removal in certain cases when you modify the work). You may place additional
permissions on material, added by you to a covered work, for which you have or can give appropriate copyright permission.
Notwithstanding any other provision of this License, for material you add to a covered work, you may (if authorized by the copyright holders of
that material) supplement the terms of this License with terms:
a) Disclaiming warranty or limiting liability dierently from the terms of sections 15 and 16 of this License; or
b) Requiring preservation of specied reasonable legal notices or author attributions in that material or in the Appropriate Legal
Notices displayed by works containing it; or
c) Prohibiting misrepresentation of the origin of that material, or requiring that modied versions of such material be marked in
reasonable ways as dierent from the original version; or
d) Limiting the use for publicity purposes of names of licensors or authors of the material; or
e) Declining to grant rights under trademark law for use of some trade names, trademarks, or service marks; or
f) Requiring indemnication of licensors and authors of that material by anyone who conveys the material (or modied versions of
it) with contractual assumptions of liability to the recipient, for any liability that these contractual assumptions directly impose
on those licensors and authors.
All other non-permissive additional terms are considered “further restrictions” within the meaning of section 10. If the Program as you received
it, or any part of it, contains a notice stating that it is governed by this License along with a term that is a further restriction, you may remove that
term. If a license document contains a further restriction but permits relicensing or conveying under this License, you may add to a covered work
material governed by the terms of that license document, provided that the further restriction does not survive such relicensing or conveying.
If you add terms to a covered work in accord with this section, you must place, in the relevant source les, a statement of the additional terms that
apply to those les, or a notice indicating where to nd the applicable terms.
Additional terms, permissive or non-permissive, may be stated in the form of a separately written license, or stated as exceptions; the above
requirements apply either way.

63D-Link DIR-840 User Manual
Appendix D - GPL Code Statement
8. Termination.
You may not propagate or modify a covered work except as expressly provided under this License. Any attempt otherwise to propagate or modify
it is void, and will automatically terminate your rights under this License (including any patent licenses granted under the third paragraph of
section 11).
However, if you cease all violation of this License, then your license from a particular copyright holder is reinstated (a) provisionally, unless and until
the copyright holder explicitly and nally terminates your license, and (b) permanently, if the copyright holder fails to notify you of the violation
by some reasonable means prior to 60 days after the cessation.
Moreover, your license from a particular copyright holder is reinstated permanently if the copyright holder noties you of the violation by some
reasonable means, this is the rst time you have received notice of violation of this License (for any work) from that copyright holder, and you cure
the violation prior to 30 days after your receipt of the notice.
Termination of your rights under this section does not terminate the licenses of parties who have received copies or rights from you under this
License. If your rights have been terminated and not permanently reinstated, you do not qualify to receive new licenses for the same material
under section 10.
9. Acceptance Not Required for Having Copies.
You are not required to accept this License in order to receive or run a copy of the Program. Ancillary propagation of a covered work occurring
solely as a consequence of using peer-to-peer transmission to receive a copy likewise does not require acceptance. However, nothing other than
this License grants you permission to propagate or modify any covered work. These actions infringe copyright if you do not accept this License.
Therefore, by modifying or propagating a covered work, you indicate your acceptance of this License to do so.
10. Automatic Licensing of Downstream Recipients.
Each time you convey a covered work, the recipient automatically receives a license from the original licensors, to run, modify and propagate that
work, subject to this License. You are not responsible for enforcing compliance by third parties with this License.
An “entity transaction” is a transaction transferring control of an organization, or substantially all assets of one, or subdividing an organization, or
merging organizations. If propagation of a covered work results from an entity transaction, each party to that transaction who receives a copy of
the work also receives whatever licenses to the work the party’s predecessor in interest had or could give under the previous paragraph, plus a
right to possession of the Corresponding Source of the work from the predecessor in interest, if the predecessor has it or can get it with reasonable
eorts.

64D-Link DIR-840 User Manual
Appendix D - GPL Code Statement
You may not impose any further restrictions on the exercise of the rights granted or armed under this License. For example, you may not impose
a license fee, royalty, or other charge for exercise of rights granted under this License, and you may not initiate litigation (including a cross-claim
or counterclaim in a lawsuit) alleging that any patent claim is infringed by making, using, selling, oering for sale, or importing the Program or any
portion of it.

65D-Link DIR-840 User Manual
Appendix D - GPL Code Statement
11. Patents.
A “contributor” is a copyright holder who authorizes use under this License of the Program or a work on which the Program is based. The work thus
licensed is called the contributor’s “contributor version”.
A contributor’s “essential patent claims” are all patent claims owned or controlled by the contributor, whether already acquired or hereafter acquired,
that would be infringed by some manner, permitted by this License, of making, using, or selling its contributor version, but do not include claims
that would be infringed only as a consequence of further modication of the contributor version. For purposes of this denition, “control” includes
the right to grant patent sublicenses in a manner consistent with the requirements of this License.
Each contributor grants you a non-exclusive, worldwide, royalty-free patent license under the contributor’s essential patent claims, to make, use,
sell, oer for sale, import and otherwise run, modify and propagate the contents of its contributor version.
In the following three paragraphs, a “patent license” is any express agreement or commitment, however denominated, not to enforce a patent
(such as an express permission to practice a patent or covenant not to sue for patent infringement). To “grant” such a patent license to a party
means to make such an agreement or commitment not to enforce a patent against the party.
If you convey a covered work, knowingly relying on a patent license, and the Corresponding Source of the work is not available for anyone to
copy, free of charge and under the terms of this License, through a publicly available network server or other readily accessible means, then you
must either (1) cause the Corresponding Source to be so available, or (2) arrange to deprive yourself of the benet of the patent license for this
particular work, or (3) arrange, in a manner consistent with the requirements of this License, to extend the patent license to downstream recipients.
“Knowingly relying” means you have actual knowledge that, but for the patent license, your conveying the covered work in a country, or your
recipient’s use of the covered work in a country, would infringe one or more identiable patents in that country that you have reason to believe
are valid.
If, pursuant to or in connection with a single transaction or arrangement, you convey, or propagate by procuring conveyance of, a covered work,
and grant a patent license to some of the parties receiving the covered work authorizing them to use, propagate, modify or convey a specic copy
of the covered work, then the patent license you grant is automatically extended to all recipients of the covered work and works based on it.

66D-Link DIR-840 User Manual
Appendix D - GPL Code Statement
A patent license is “discriminatory” if it does not include within the scope of its coverage, prohibits the exercise of, or is conditioned on the non-
exercise of one or more of the rights that are specically granted under this License. You may not convey a covered work if you are a party to an
arrangement with a third party that is in the business of distributing software, under which you make payment to the third party based on the
extent of your activity of conveying the work, and under which the third party grants, to any of the parties who would receive the covered work
from you, a discriminatory patent license (a) in connection with copies of the covered work conveyed by you (or copies made from those copies), or
(b) primarily for and in connection with specic products or compilations that contain the covered work, unless you entered into that arrangement,
or that patent license was granted, prior to 28 March 2007.
Nothing in this License shall be construed as excluding or limiting any implied license or other defenses to infringement that may otherwise be
available to you under applicable patent law.
12. No Surrender of Others’ Freedom.
If conditions are imposed on you (whether by court order, agreement or otherwise) that contradict the conditions of this License, they do not
excuse you from the conditions of this License. If you cannot convey a covered work so as to satisfy simultaneously your obligations under this
License and any other pertinent obligations, then as a consequence you may not convey it at all. For example, if you agree to terms that obligate
you to collect a royalty for further conveying from those to whom you convey the Program, the only way you could satisfy both those terms and
this License would be to refrain entirely from conveying the Program.
13. Use with the GNU Aero General Public License.
Notwithstanding any other provision of this License, you have permission to link or combine any covered work with a work licensed under version
3 of the GNU Aero General Public License into a single combined work, and to convey the resulting work. The terms of this License will continue
to apply to the part which is the covered work, but the special requirements of the GNU Aero General Public License, section 13, concerning
interaction through a network will apply to the combination as such.

67D-Link DIR-840 User Manual
Appendix D - GPL Code Statement
14. Revised Versions of this License.
The Free Software Foundation may publish revised and/or new versions of the GNU General Public License from time to time. Such new versions
will be similar in spirit to the present version, but may dier in detail to address new problems or concerns.
Each version is given a distinguishing version number. If the Program species that a certain numbered version of the GNU General Public License
“or any later version” applies to it, you have the option of following the terms and conditions either of that numbered version or of any later version
published by the Free Software Foundation. If the Program does not specify a version number of the GNU General Public License, you may choose
any version ever published by the Free Software Foundation. If the Program species that a proxy can decide which future versions of the GNU
General Public License can be used, that proxy’s public statement of acceptance of a version permanently authorizes you to choose that version
for the Program.
Later license versions may give you additional or dierent permissions. However, no additional obligations are imposed on any author or copyright
holder as a result of your choosing to follow a later version.
15. Disclaimer of Warranty.
THERE IS NO WARRANTY FOR THE PROGRAM, TO THE EXTENT PERMITTED BY APPLICABLE LAW. EXCEPT WHEN OTHERWISE STATED IN WRITING
THE COPYRIGHT HOLDERS AND/OR OTHER PARTIES PROVIDE THE PROGRAM “AS IS” WITHOUT WARRANTY OF ANY KIND, EITHER EXPRESSED OR
IMPLIED, INCLUDING, BUT NOT LIMITED TO, THE IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR PURPOSE. THE
ENTIRE RISK AS TO THE QUALITY AND PERFORMANCE OF THE PROGRAM IS WITH YOU. SHOULD THE PROGRAM PROVE DEFECTIVE, YOU ASSUME
THE COST OF ALL NECESSARY SERVICING, REPAIR OR CORRECTION.
16. Limitation of Liability.
IN NO EVENT UNLESS REQUIRED BY APPLICABLE LAW OR AGREED TO IN WRITING WILL ANY COPYRIGHT HOLDER, OR ANY OTHER PARTY WHO
MODIFIES AND/OR CONVEYS THE PROGRAM AS PERMITTED ABOVE, BE LIABLE TO YOU FOR DAMAGES, INCLUDING ANY GENERAL, SPECIAL,
INCIDENTAL OR CONSEQUENTIAL DAMAGES ARISING OUT OF THE USE OR INABILITY TO USE THE PROGRAM (INCLUDING BUT NOT LIMITED TO
LOSS OF DATA OR DATA BEING RENDERED INACCURATE OR LOSSES SUSTAINED BY YOU OR THIRD PARTIES OR A FAILURE OF THE PROGRAM TO
OPERATE WITH ANY OTHER PROGRAMS), EVEN IF SUCH HOLDER OR OTHER PARTY HAS BEEN ADVISED OF THE POSSIBILITY OF SUCH DAMAGES.
17. Interpretation of Sections 15 and 16.
If the disclaimer of warranty and limitation of liability provided above cannot be given local legal eect according to their terms, reviewing courts
shall apply local law that most closely approximates an absolute waiver of all civil liability in connection with the Program, unless a warranty or
assumption of liability accompanies a copy of the Program in return for a fee.

68D-Link DIR-840 User Manual
Appendix E - Safety Statements
Safety Statements
CE Mark Warning:
This is a Class B product. In a domestic environment, this product may cause radio interference, in which case the user may be required to take
adequate measures.
FCC Statement:
This equipment has been tested and found to comply with the limits for a Class B digital device, pursuant to Part 15 of the FCC Rules. These limits are
designed to provide reasonable protection against harmful interference in a residential installation. This equipment generates, uses and can radiate
radio frequency energy and, if not installed and used in accordance with the instructions, may cause harmful interference to radio communications.
However, there is no guarantee that interference will not occur in a particular installation. If this equipment does cause harmful interference to radio
or television reception, which can be determined by turning the equipment o and on, the user is encouraged to try to correct the interference by
one of the following measures:
• Reorient or relocate the receiving antenna.
• Increase the separation between the equipment and receiver.
• Connect the equipment into an outlet on a circuit dierent from that to which the receiver is connected.
• Consult the dealer or an experienced radio/TV technician for help.
This device complies with Part 15 of the FCC Rules. Operation is subject to the following two conditions: (1) This device may not cause harmful
interference, and (2) this device must accept any interference received, including interference that may cause undesired operation.
FCC Caution:
Any changes or modications not expressly approved by the party responsible for compliance could void the user’s authority to operate this
equipment.
IMPORTANT NOTICE:
FCC Radiation Exposure Statement:
This equipment complies with FCC radiation exposure limits set forth for an uncontrolled environment. This equipment should be installed and
operated with minimum distance 20cm between the radiator & your body. To maintain compliance with FCC RF exposure compliance requirements,
please avoid direct contact to the transmitting antenna during transmitting.
If this device is going to be operated in 5.15 ~ 5.25GHz frequency range, then it is restricted in indoor environment only. This transmitter must not

69D-Link DIR-840 User Manual
Appendix E - Safety Statements
be co-located or operating in conjunction with any other antenna or transmitter.
The availability of some specic channels and/or operational frequency bands are country dependent and are rmware programmed at the factory
to match the intended destination. The rmware setting is not accessible by the end user.
ICC Notice:
Operation is subject to the following two conditions:
1) This device may not cause interference and
2) This device must accept any interference, including interference that may cause undesired operation of the device.
IMPORTANT NOTE:
IC Radiation Exposure Statement:
This equipment complies with IC radiation exposure limits set forth for an uncontrolled environment. End users must follow the specic operating
instructions for satisfying RF exposure compliance. This equipment should be installed and operated with minimum distance 20cm between the
radiator & your body.
This transmitter must not be co-located or operating in conjunction with any other antenna or transmitter.
(i) The device for the band 5150-5250 MHz is only for indoor usage to reduce potential for harmful interference to
co-channel mobile satellite systems;
(ii) The maximum antenna gain (2dBi) permitted (for devices in the band 5725-5825 MHz) to comply with the e.i.r.p. limits specied
for point-to-point and non point-to-point operation as appropriate, as stated in section A9.2(3).
Règlement d’Industry Canada
Les conditions de fonctionnement sont sujettes à deux conditions:
(1) Ce périphérique ne doit pas causer d’interférence et.
(2) Ce périphérique doit accepter toute interférence, y compris les interférences pouvant perturber le bon fonctionnement de
ce périphérique.