Datalogic S r l JX2W JOYA X2 Basic Mobile Computer User Manual I
Datalogic ADC S.r.l. JOYA X2 Basic Mobile Computer I
Contents
- 1. user manual I
- 2. user manual II
- 3. user manual III
- 4. User Manual
user manual I

Datalogic JOYA
TM
X2 R2U
”Ready to Use”
User Guide

Datalogic ADC, S.r.l.
Via S. Vitalino, 13
40012 Lippo di Calderara di Reno
Bologna - Italy
Telephone: (+39) 051-3147011
Fax: (+39) 051-3147205
©2014 Datalogic ADC, S.r.l.
An Unpublished Work - All rights reserved. No part of the contents of this
documentation or the procedures described therein may be reproduced or
transmitted in any form or by any means without prior written permission of
Datalogic ADC, S.r.l. or its subsidiaries or affiliates ("Datalogic" or “Datalogic ADC”).
Owners of Datalogic products are hereby granted a non-exclusive, revocable
license to reproduce and transmit this documentation for the purchaser's own
internal business purposes. Purchaser shall not remove or alter any proprietary
notices, including copyright notices, contained in this documentation and shall
ensure that all notices appear on any reproductions of the documentation. Should
future revisions of this manual be published, you can acquire printed versions by
contacting your Datalogic representative. Electronic versions may either be
downloadable from the Datalogic website (www.datalogic.com) or provided on
appropriate media. If you visit our website and would like to make comments or
suggestions about this or other Datalogic publications, please let us know via the
"Contact Datalogic" page.
Disclaimer
Datalogic has taken reasonable measures to provide information in this manual that
is complete and accurate, however, Datalogic reserves the right to change any
specification at any time without prior notice. Datalogic and the Datalogic logo are
registered trademarks of Datalogic S.p.A. in many countries, including the U.S.A.
and the E.U.
Joya is a trademark of Datalogic ADC S.r.l. and the Joya logo is a registered
trademark of Datalogic ADC S.r.l. in the U.S.A. and the E.U.
All other brand and product names may be trademarks of their respective owners.
Patents
See www.patents.datalogic.com for patent list.
This product is covered by one or more of the following patents:
Design patents: AU323628, EP000891544, USD613289, ZL200830146270.9
Utility patents: EP0789315B1, EP1128315B1, EP1396811B1, EP1413971B1,
US5992740, US6808114, US6997385, US7387246, US7620475


ii
Datalogic ADC S.r.l.
Via S. Vitalino 13
40012 - Lippo di Calderara di Reno
Bologna - Italy
Datalogic JOYA™ X2 R2U - User's Manual
Ed.: REG REV3
ALL RIGHTS RESERVED
The Datalogic name and logo are registered trademarks of Datalogic S.p.A. in many
countries.
The JOYA name and logo are a trademarks of Datalogic ADC S.r.l.
All other brand and product names mentioned herein are for identification purposes only and
may be trademarks or registered trademarks of their respective owners.
Datalogic reserves the right to make modifications and improvements without prior
notification.
Datalogic shall not be liable for technical or editorial errors or omissions contained herein,
nor for incidental or consequential damages resulting from the use of this material.
© 2008 Datalogic ADC S.r.l. • All rights reserved. • Protected to the fullest extent under U.S.
and international laws. • Copying, or altering of this document is prohibited without express
written consent from Datalogic ADC S.r.l.

iii
CONTENTS
1
INTRODUCTION ............................................................................. 17
1.1
Datalogic JOYA™ X2 Description ................................................... 17
1.2
Model Description ........................................................................... 17
1.3
Package Contents ........................................................................... 19
1.4
Accessories .................................................................................... 19
2
CONNECTIONS .............................................................................. 20
2.1
USB Connection.............................................................................. 20
2.2
WLAN Connection .......................................................................... 22
2.3
WPAN Connections ........................................................................ 23
3
USE AND FUNCTIONING............................................................... 24
3.1
Startup ............................................................................................ 24
3.2
Avalanche Enabler .......................................................................... 27
3.3
Wavelink Avalanche System ........................................................... 28
3.4
Avalanche Management console .................................................... 29
3.4.1
Network profile ................................................................................ 29
3.4.2
ScanToConfig Profile ...................................................................... 31
3.4.3
Software profile ............................................................................... 34
3.4.4
DLdcu package ............................................................................... 36
3.5
Avalanche package builder ............................................................. 40
3.5.1
Wavelink software package ............................................................. 40
3.6
Datalogic configuration utility ........................................................... 41
3.6.1
Create JOYA™ X2 configuration profile .......................................... 42
3.7
Using the Stylus (available only on JOYA™ X2 Plus) ...................... 43
3.8
Data Capture ................................................................................... 43
3.8.1
Imager Data Capture ....................................................................... 44
3.9
Description of the Keys ................................................................... 47
3.9.1
Resetting the JOYA™ X2 ................................................................ 48
3.10
Status Indicators ............................................................................. 50
3.10.1
Taskbar ........................................................................................... 50
3.11
Data Capture Configuration ............................................................. 51
3.11.1
Configure ........................................................................................ 51
3.12
Control Panel .................................................................................. 60
3.12.1
Registry ........................................................................................... 60
3.12.2
Using Summit Radio Card Utility ..................................................... 61
3.12.3
Summit Radio Card : Starting client ................................................ 61
3.12.4
Summit Radio Card : Main screen ................................................... 62
3.12.5
Summit Radio Card : Profile screen ................................................ 63
3.12.6
Summit Radio Card : Status screen ................................................ 63
3.12.7
Summit Radio Card : Diagnostic screen .......................................... 65
3.12.8
Summit Radio Card : Global Settings screen .................................. 66
3.13
Stylus Calibration ............................................................................ 67
3.14
Windows Connections ..................................................................... 68
3.14.1
Microsoft® ActiveSync® .................................................................. 68
3.14.2
Microsoft® Windows Mobile Device Center® .................................. 68
3.14.3
ActiveSync® Remote ...................................................................... 68
3.14.4
Bluetooth® Manager Device Setup ................................................. 69
3.14.5
FTP Server Setup ........................................................................... 72

iv
3.15
Backup Directory File Management................................................. 73
3.16
Firmware Update ............................................................................. 75
3.16.1
Retrieving a Firmware Image Update .............................................. 75
3.16.2
Firmware Update Procedure ........................................................... 76
3.17
DAatalogic Configuration Utility ....................................................... 77
3.18
Datalogic Desktop Utility ................................................................. 77
4
MAINTENANCE .............................................................................. 78
4.1
Charging the Battery Pack .............................................................. 78
4.2
Replacing the Battery Pack ............................................................. 79
4.3
Cleaning the Mobile Computer ........................................................ 83
5
JOYA CRADLE DISPENSER ......................................................... 84
5.1
Introduction ..................................................................................... 84
5.2
Accessories .................................................................................... 84
5.3
Installation requirements ................................................................. 85
5.3.1
Base Unit Construction Details ........................................................ 86
5.3.2
JOYA Cradle Dispenser Supports ................................................... 87
5.3.3
Internal Cabinet Space and Openings ............................................. 88
5.3.4
Anchoring and Maintenance Issues................................................. 88
5.3.5
Power Supply Positioning and Cooling ............................................ 88
5.3.6
AC Power Cabling ........................................................................... 89
5.3.7
Wiring ............................................................................................. 90
5.3.8
Cable to Power Supply Connection ................................................. 92
5.3.9
Affixing Cables to Cabinet ............................................................... 92
5.3.10
Safety Precautions .......................................................................... 92
5.3.11
Connection to AC Line Voltage ....................................................... 94
5.4
JOYA™ X2 cradle dispenser firmware ............................................ 95
5.4.1
JOYA Cradle Tool installation ......................................................... 95
5.4.2
Starting program ............................................................................. 95
5.4.3
Reading firmware version ................................................................ 96
5.4.4
Firmware update procedure ............................................................ 97
5.5
JOYA™X2/JOYA cradle dispenser connection ............................. 100
5.6
Configuration ................................................................................. 100
5.7
Use and functioning ...................................................................... 100
6
TECHNICAL FEATURES .............................................................. 102
6.1
JOYA
TM
X2 technical datasheet .................................................... 102
7
TEST CODES ............................................................................... 103
8
GLOSSARY .................................................................................. 106

v
DATALOGIC END USER LICENSE AGREEMENT
BY DOWNLOADING OR INSTALLING THE SOFTWARE, OR BY USING DATALOGIC
EQUIPMENT THAT INCLUDES THIS SOFTWARE, YOU ARE CONSENTING TO BE
BOUND BY THIS AGREEMENT. IF YOU DO NOT AGREE TO ALL OF THE TERMS OF
THIS AGREEMENT, THEN DO NOT DOWNLOAD, INSTALL, USE THE SOFTWARE NOR
DATALOGIC EQUIPMENT.
The following terms and conditions govern your use of the Software except to the extent that a particular
program (a) is the subject of a separate written agreement with Datalogic or (b) includes a separate “click-
on” license agreement as part of the installation and/or download process. Should a conflict arise
between the provisions of the foregoing documents, the order of precedence shall be (1) the written
agreement, (2) the click-on agreement, and (3) this agreement (“Agreement”).
1. License. Subject to the terms and conditions of and except as otherwise provided in this Agreement,
Datalogic ADC S.r.l. (“Datalogic”) and its suppliers grant to Customer (“Customer”) a nonexclusive and
nontransferable license to use the specific program modules, feature set(s) or feature(s) in object code
form only as well as associated media, printed materials and “online” or electronic documentation (the
“Software”) for which Customer has paid, if required, the license fees. The Software is licensed not sold.
The license shall be subject to each of the following limitations:
• Unless otherwise expressly provided in the documentation, Customer shall use the Software solely
as embedded in, for execution on, or (where the applicable documentation permits installation on
non-Datalogic equipment) for communication with Datalogic equipment owned or leased by
Customer;
• Customer’s use of the Software shall be limited to use on a single hardware chassis, on a single
central processing unit, as applicable, or use on such greater number of chassis or central
processing units as Customer may have paid Datalogic the required license fee; and
• Customer’s use of the Software shall also be limited, as applicable and set forth in Customer’s
purchase order or in Datalogic’s product catalog, user documentation, or web site, to a maximum
number of (a) seats (i.e. users with access to the installed Software), (b) concurrent users,
sessions, ports, and/or issued and outstanding IP addresses, and/or (c) central processing unit
cycles or instructions per second. Customer’s use of the Software shall also be limited by any other
restrictions set forth in Customer’s purchase order or in Datalogic’s product catalog, user
documentation or web site for the Software.
2. General Limitations. Except as otherwise expressly provided under this Agreement, Customer shall
have no right, and Customer specifically agrees not to (i) transfer, assign or sublicense its license rights
to any other person, or use the Software on unauthorized or secondhand Datalogic equipment, and any
such attempted transfer, assignment or sublicense shall be void; (ii) correct errors to or otherwise modify
or adapt the Software or create derivative works based upon the Software, or to permit third parties to do
the same; or (iii) decompile, decrypt, reverse engineer, disassemble or otherwise reduce the Software to
human-readable form to gain access to trade secrets or confidential information in the Software. To the
extent required by law, at Customer's request, Datalogic shall provide Customer with the interface
information needed to achieve interoperability between the Software and another independently created
program, upon payment of Datalogic's applicable fee. Customer shall observe strict obligations of
confidentiality with respect to such information.
3. Upgrades and Additional Copies. For purposes of this Agreement, “Software” shall include (and the
terms and conditions of this Agreement shall apply to) any upgrades, updates, bug fixes or modified
versions (collectively, “Upgrades”) or backup copies of the Software licensed or provided to Customer by
Datalogic or an authorized distributor for which Customer has paid the applicable license fees.
Notwithstanding any other provision of this Agreement: (1) customer has no license or right to use any
such additional copies or upgrades unless customer, at the time of acquiring such copy or upgrade,
already holds a valid license to the original Software and has paid the applicable fee for the upgrade, if
required; (2) use of upgrades is limited to Datalogic equipment for which customer is the original end
user, purchaser or lessee or who otherwise holds a valid license to use the Software which is being
upgraded; and (3) use of additional copies is limited to backup purposes only.
4. Proprietary Notices. Customer agrees to maintain and reproduce all copyright and other proprietary
notices on all copies, in any form, of the Software in the same form and manner that such copyright and
other proprietary notices are included on the Software. Except as expressly authorized in this Agreement,
Customer shall not make any copies or duplicates or any Software without the prior written permission of
Datalogic. Customer may make such backup copies of the Software as may be necessary for Customer’s

vi
lawful use, provided Customer affixes to such copies all copyright, confidentiality, and proprietary notices
that appear on the original.
5. Protection of Information. Customer agrees that aspects of the Software and associated
documentation, including the specific design and structure of individual programs, constitute trade secrets
and/or copyrighted material of Datalogic. Customer shall not disclose, provide, or otherwise make
available such trade secrets or copyrighted material in any form to any third party without the prior written
consent of Datalogic. Customer shall implement reasonable security measures to protect such trade
secrets and copyrighted material. Software and documentation shall remain solely property of Datalogic.
6. Limited Warranty. If Customer obtained the Software directly from Datalogic, then Datalogic warrants that
during the Warranty Period (as defined below): (i) the media on which the Software is furnished will be free of
defects in materials and workmanship under normal use; and (ii) the Software will substantially conform to its
published specifications. The “Warranty Period” means a period beginning on the date of Customer’s receipt of
the Software and ending on the later of (a) ninety (90) days from the date of initial shipment of the Software by
Datalogic, or (b) the end of the minimum period required by the law of the applicable jurisdiction. The limited
warranties extend only to Customer as the original licensee. Customer's sole and exclusive remedy and the
entire liability of Datalogic and its suppliers under these limited warranties will be, at Datalogic’s sole option,
repair or replacement of the Software if reported (or, upon request, returned) to Datalogic. Except as expressly
granted in this Agreement, the Software is provided AS IS and with all faults. Datalogic does not warrant that
the Software is error free or that Customer will be able to operate the Software without problems or
interruptions. In addition, due to the continual development of new techniques for intruding upon and attacking
networks, Datalogic does not warrant that the Software or any equipment, system or network on which the
Software is used will be free of vulnerability to intrusion or attack. This warranty does not apply if the Software
(a) is licensed for beta, evaluation, testing or demonstration purposes for which Datalogic does not receive a
license fee, (b) has been altered, except by Datalogic, (c) has not been installed, operated, repaired, or
maintained in accordance with instructions supplied by Datalogic, (d) has been subjected to abnormal physical
or electrical stress, misuse, negligence, or accident, or (e) is used in ultra hazardous activities. If Customer
obtained the Software from a Datalogic reseller, the terms of any warranty shall be as provided by such
distributor, and Datalogic provides Customer no warranty with respect to such Software. The Software may
contain support for programs written in Java. Java technology is not fault tolerant and is not designed,
manufactured, or intended for use or resale as online control equipment in hazardous environments requiring
fail-safe performance, such as in the operation of nuclear facilities, aircraft navigation or communication
systems, air traffic control, direct life support machines, or weapons systems, in which the failure of Java
technology could lead directly to death, personal injury, or severe physical or environmental damage. Microsoft
Inc. has contractually obligated Datalogic to make this disclaimer.
7. Disclaimer of Warranties. Except as specified in this warranty, all expressed or implied conditions,
representations, and warranties including, without limitation, any implied warranty or condition of
merchantability, fitness for a particular purpose, non-infringement, satisfactory quality or arising from a course
of dealing, usage, or trade practice, are hereby excluded to the extent allowed by applicable law. To the extent
that an implied warranty cannot be excluded, such warranty is limited in duration to the warranty period.
8. Disclaimer of Liabilities. In no event will Datalogic or its suppliers be liable for any lost revenue, profit,
or data, or for special, indirect, consequential, incidental, or punitive damages however caused and
arising out of the use of or inability to use the Software even if Datalogic has been advised of the
possibility of such damages. In no event shall Datalogic or its suppliers' liability to customer, whether in
contract, tort (including negligence), or otherwise, exceed the price paid by customer. The foregoing
limitations shall apply even if the above-stated warranty fails of its essential purpose.
9. Term and Termination. This Agreement is effective until terminated. Customer may terminate this
Agreement at any time by destroying all copies of Software including any documentation. Customer’s
license rights under this Agreement will terminate immediately without notice from Datalogic if Customer
fails to comply with any provision of this Agreement. Upon termination, Customer must destroy all copies
of Software in its possession or control.
10. Customer Records. Customer grants to Datalogic and its independent accountants the right to
examine Customer’s books, records and accounts during Customer’s normal business hours to verify
compliance with this Agreement. In the event such audit discloses non-compliance with this Agreement,
Customer shall promptly pay to Datalogic the appropriate license fees.
11. General Provisions. This Agreement shall be governed by and construed in accordance with the
laws of Italy. All disputes arising out of or in connection with this Agreement will be subject to the
exclusive jurisdiction of the competent Court of the place where Datalogic has its registered office. If any
portion hereof is found to be void or unenforceable, the remaining provisions of this Agreement shall
remain in full force and effect. Except as expressly provided herein, this Agreement constitutes the entire
agreement between the parties with respect to the license of the Software and supercedes any conflicting
or additional terms contained in the purchase order.

INTRODUCTION
1
1
REFERENCES
CONVENTIONS
This manual uses the following conventions:
"JOYA ™ X2" refers to all possible JOYA ™ X2 hardware configurations,
unless otherwise specified.
“User” refers to anyone using a Datalogic JOYA™ X2 mobile computer.
“Mobile computer” and "Datalogic JOYA™" refer to Datalogic JOYA™ X2.
“You” refers to the System Administrator or Technical Support person using this
manual to install, configure, operate, maintain or troubleshoot a Datalogic
JOYA™ X2.
“Cradle” refers to Datalogic JOYA™ X2 Cradle Dispenser.
REFERENCE DOCUMENTATION
For further information regarding Datalogic JOYA™ X2 refer to the SDK Help
on-Line.

DATALOGIC JOYA™ X2
2
1
SAFETY REGULATIONS
Read this manual carefully before performing any type of
connection to the Datalogic JOYA™ X2 mobile computer.
The user is responsible for any damages caused by incorrect
use of the equipment or by inobservance of the indication
supplied in this manual.
NOTE
GENERAL SAFETY RULES
− Use only the components supplied by the manufacturer for the specific
Datalogic JOYA™ X2 being used.
− Do not attempt to disassemble the Datalogic JOYA™ X2 mobile
computer, as it does not contain parts that can be repaired by the user.
Any tampering will invalidate the warranty.
− When replacing the battery pack or at the end of the operative life of the
Datalogic JOYA™ X2 mobile computer, disposal must be performed in
compliance with the laws in force.
− Before using the device and the battery pack, see par. 0 and read every
warnings about the device and the battery pack.
− Do not submerge the Datalogic JOYA™ X2 in liquid products.
− The Datalogic JOYA™ X2 is designed and labelled to be compliant with
laws, rules and regulations in force in the countries where it is sold.
− For further information, refer to this manual and to the Datalogic ADC web
site: http://www.adc.datalogic.com.
BLUETOOTH® APPROVAL
For Bluetooth ® approval visit:
https://www.bluetooth.org/tpg/QLI_viewQDL.cfm?qid=23316

INTRODUCTION
3
1
FCC COMPLIACE – JOYA X2
FCC Regulations:
• This device complies with part 15 of the FCC Rules. Operation
is subject to the following two conditions: (1) This device
may not cause harmful interference, and (2) this device
must accept any interference received, including interference
that may cause undesired operation.
• This device has been tested and found to comply with the
limits for a Class B digital device, pursuant to Part 15 of
the FCC Rules. These limits are designed to provide
reasonable protection against harmful interference in a
residential installation. This equipment generates, uses and
can radiated radio frequency energy and, if not installed and
used in accordance with the instructions, may cause harmful
interference to radio communications. However, there is no
guarantee that interference will not occur in a
particular installation If this equipment does cause harmful
interference to radio or television reception, which can be
determined by turning the equipment off and on, the user
is encouraged to try to correct the interference by one or
more of the following measures:
- Reorient or relocate the receiving antenna.
- Increase the separation between the equipment and receiver.
- Connect the equipment into an outlet on a circuit different
from that to which
the receiver is connected.
- Consult the dealer or an experienced radio/TV technician for
help.
Change or Modifications that are not expressly approved by the
manufacturer could void the user's authority to operate the
equipment
The FCC/IC ID is located behind the battery. The product is sold
without the battery installed.

DATALOGIC JOYA™ X2
4
1
RF EXPOSURE INFORMATION (SAR)
This device meets the government’s requirements for exposure
to radio waves. This device is designed and manufactured not
to exceed the emission limits for exposure to radio frequency
(RF) energy set by the Federal Communications Commission
of the U.S. Government.
The exposure standard for wireless devices employs a unit
of measurement known as the Specific Absorption Rate, or
SAR. The SAR limit set by the FCC is 1.6W/kg. Tests for SAR
are conducted using standard operating positions accepted
by the FCC with the device transmitting at its highest certified
power level in all tested frequency bands. Although the
SAR is determined at the highest certified power level, the
actual SAR level of the device while operating can be well below
the maximum value. This is because the device is designed
to operate at multiple power levels so as to use only the poser
required to reach the network. In general, the closer you are to a
wireless base station antenna, the lower the power output.
While there may be differences between the SAR levels of
various devices and at various positions, they all meet the
government requirement.
For body worn operation, this device has been tested and
meets FCC RF exposure guidelines when used with an
accessory that contains no metal and that positions the handset
a minimum distance of 0 cm from the body.
The maximum SAR value is 0,748 W/kg for Body
Use of other accessories may not ensure compliance with
FCC RF exposure guidelines.
The FCC has granted an Equipment Authorization for this model
device with all reported SAR levels evaluated as in compliance
with the FCC RF exposure guidelines. SAR information on this

INTRODUCTION
5
1
model device is on file with the FCC and can be found under
the Display Grant section of http://www.fcc.gov/oet/fccid
after searching on the below FCC IDs:
FCC ID: U4GJX2WB (for models with WLAN and BT)
FCC ID: U4GJX2W (for model with WLAN only)
This device is compliant with SAR for general population
/uncontrolled exposure limits in ANSI/IEEE C95.1-1999 and
had been tested in accordance with the measurement methods
and procedures specified in OET Bulletin 65 Supplement C.
INDUSTRY CANADA COMPLIANCE – JOYA X2
This device complies with Industry Canada licence-exempt
RSS standard(s).
Operation is subject to the following two conditions: (1)
this device may not cause interference, and (2) this device
must accept any interference, including interference that may
cause undesired operation of the device.
This Class B digital apparatus complies with Canadian ICES-
003.
This device and its antenna(s) must not be co-located or
operating in conjunction with any other antenna or transmitter.
The County Code Selection feature is disabled for products
marketed in the US/Canada.
Le présent appareil est conforme aux CNR d'Industrie Canada
applicables aux appareils radio exempts de licence.
L'exploitation est autorisée aux deux conditions suivantes :
(1) l'appareil ne doit pas produire de brouillage, et (2)
l'appareil doit accepter tout brouillage radioélectrique subi,
même si le brouillage est susceptible d'en compromettre le
fonctionnement. Cet appareil numérique de la classe B est
conforme à la norme NMB-003 du Canada.
This Class B digital apparatus complies with Canadian ICES-
003. Cet appareil numérique de la classe B est conforme à la
norme NMB-003 du Canada.

DATALOGIC JOYA™ X2
6
1
Ce dispositif et ses antennes ne doivent pas être co-implantés
ou utilisés avec une autre antenne ou an autre émetteur
La fonction de sélection de code de pays est désactivée
pour les produits commercialisés en Etats-Unis / Canada
IC RADIATION EXPOSURE STATEMENT
This EUT is compliant with SAR for general
population/uncontrolled exposure limits in IC RSS-102 and had
been tested in accordance with the measurement
methods and procedures specified in IEEE 1528. This
equipment can be installed and operated with minimum distance
of 0 cm between the radiator &
your body.
SAR COMPLIANCE
This product has been tested and found to comply with the
following standards:
• The portable device JOYA X2 from Datalogic is in compliance
with the IC RSS 102 Issue 4 [RSS 102] and Federal
Communications Commission (FCC) Guidelines [OET 65] for
uncontrolled exposure. SAR assessment in body worn was
conducted with the back of the device in direct contact
against the flat phantom.
• The portable device Joya ™ X2 from Datalogic is in
compliance European Standard EN 50566: Product standard to
demonstrate compliance of radio frequency fields from
handheld and body-mounted wireless communication
devices used by the general public (30 MHz - 6 GHz)

INTRODUCTION
7
1
WEEE COMPLIANCE
Informazione degli utenti ai sensi della Direttiva Europea
2012/19/EC
L’apparecchiatura che riporta il simbolo del bidone barrato
deve essere
smaltita, alla fine della sua vita utile, separatamente dai rifiuti
urbani.
Smaltire l’apparecchiatura in conformità alla presente Direttiva
consente di:
Evitare possibili conseguenze negative per l’ambiente e per la
salute
umana che potrebbero invece essere causati dall’errato
smaltimento
dello stesso;
Recuperare materiali di cui è composto al fine di
ottenere un
importante risparmio di energia e di risorse.
Per maggiori dettagli sulle modalità di smaltimento, contattare
il Fornitore dal
quale è stata acquistata l’apparecchiatura o consultare la
sezione dedicata sul
sito www.datalogic.com.
Information for the user in accordance with the European
Commission
Directive 2012/19/EC

DATALOGIC JOYA™ X2
8
1
At the end of its useful life, the product marked with the crossed
out wheeled
wastebin must be disposed of separately from urban waste.
Disposing of the product according to this Directive:
avoids potentially negative consequences to the
environment and
human health which otherwise could be caused by incorrect
disposal
enables the recovery of materials to obtain a significant
savings of
energy and resources.
For more detailed information about disposal, contact the
supplier that provided
you with the product in question or consult the dedicated section
at the website
www.datalogic.com.
Information aux utilisateurs concernant la Directive
Européenne
2012/19/EC
Au terme de sa vie utile, le produit qui porte le symbole d'un
caisson à ordures
barré ne doit pas être éliminé avec les déchets urbains.
Éliminer ce produit selon cette Directive permet de:
éviter les retombées négatives pour l'environnement et la
santé
dérivant d'une élimination incorrecte
récupérer les matériaux dans le but d'une économie
importante en
termes d'énergie et de ressources
Pour obtenir des informations complémentaires concernant
l'élimination,
veuillez contacter le fournisseur auprès duquel vous avez
acheté le produit ou
consulter la section consacrée au site Web www.datalogic.com.

INTRODUCTION
9
1
Información para el usuario de accuerdo con la Directiva
Europea
2012/19/CE
Al final de su vida útil, el producto marcado con un simbolo de
contenedor de
bassura móvil tachado no debe eliminarse junto a los desechos
urbanos.
Eliminar este producto de accuerdo con la Directiva permite de:
evitar posibles consecuencias negativas para el medio
ambiente y la
salud derivadas de una eliminación inadecuada
recuperar los materiales obteniendo así un ahorro
importante de
energía y recursos
Para obtener una información más detallada sobre la
eliminación, por favor,
póngase en contacto con el proveedor donde lo compró o
consultar la sección
dedicada en el Web site www.datalogic.com.
Benutzerinformation bezüglich Richtlinie 2012/19/EC der
europäischen
Kommission
Am Ende des Gerätelebenszyklus darf das Produkt nicht über
den städtischen
Hausmüll entsorgt werden. Eine entsprechende Mülltrennung ist
erforderlich.
Beseitigung des Produkts entsprechend der Richtlinie:
verhindert negative Auswirkungen für die Umwelt und die
Gesundheit
der Menschen
ermöglicht die Wiederverwendung der Materialien und
spart somit
Energie und Resourcen.

DATALOGIC JOYA™ X2
10
1
Weitere Informationen zu dieser Richtlinie erhalten sie von
ihrem Lieferanten
über den sie das Produkt erworben haben, oder besuchen sie
unsere Hompage
unter www.datalogic.com.

INTRODUCTION
11
1
WIRELESS AND RADIO FREQUENCIES WARNINGS
Most modern electronic equipment is shielded from RF signals.
However, certain electronic equipment may not be shielded
against the RF signals generated by Datalogic Joya™.
WARNING
Datalogic recommends persons with pacemakers or other
medical devices to follow the same recommendations provided
by Health Industry Manufacturers Associations for mobile
phones.
Persons with pacemakers:
• Should ALWAYS keep this device more than twenty five
(25) cm from their pacemaker and/or any other medical
device;
• Should not carry this device in a breast pocket;
• Should keep the device at the opposite side of the
pacemaker and/or any other medical device;
• Should turn this d
evice OFF or move it immediately AWAY
if there is any reason to suspect that interference is taking
place.
• Should ALWAYS read pacemaker or any other medical
device guides or should consult the manufacturer of the
medical device to determine if it is adequately shielded
from external RF energy.
In case of doubt concerning the use of wireless devices with an
implanted medical device, contact your doctor.
WARNING
Turn this device OFF in health care facilities when any
regulations posted in these areas instruct you to do so.
Hospitals or health care facilities may use equipment that could
be sensitive to external RF energy.
WARNING
Turn off the device when in any area with a potentially
explosive atmosphere. Observe restrictions and follow closely
any laws, regulations, warnings and best practices on the use
of radio equipment near fuel storage areas or distribution fuel
DATALOGIC JOYA™ X2
12
1
WARNING areas, chemical plants or where some operation involves use of
explosive materials.
Do not store or carry flammable liquids, explosive gases or
materials with the device or its parts or accessories.
Areas with a potentially explosive atmosphere are often, but not
always, clearly marked or showed.
Sparks in such areas could cause an explosion or fire, resulting
in injury or even death.
PATENTS
This product is covered by one or more of the following patents.
Design Pat.: EP 891,544; AU 323,628; US D 613,289 S; ZL 200830146270.9.
U.S. Pat. Nos: 5,992,740; 6,808,114 B1; 6,997,385 B2; 7,387,246 B2;
7,620,475 B2.
European Pat. Nos: 789,315 B1; 1,128,315 B1; 1,396,811 B1; 1,413,971 B1.
Additional patents pending.
WEEE COMPLIANCE
Informazione degli utenti ai sensi della Direttiva Europea 2012/19/EC
L’apparecchiatura che riporta il simbolo del bidone barrato deve essere
smaltita, alla fine della sua vita utile, separatamente dai rifiuti urbani.
Smaltire l’apparecchiatura in conformità alla presente Direttiva consente di:
Evitare possibili conseguenze negative per l’ambiente e per la salute
umana che potrebbero invece essere causati dall’errato smaltimento
dello stesso;
Recuperare materiali di cui è composto al fine di ottenere un
importante risparmio di energia e di risorse.
Per maggiori dettagli sulle modalità di smaltimento, contattare il Fornitore dal
quale è stata acquistata l’apparecchiatura o consultare la sezione dedicata sul
sito www.ADC.datalogic.com.
Information for the user in accordance with the European Commission
Directive 2012/19/EC

INTRODUCTION
13
1
At the end of its useful life, the product marked with the crossed out wheeled
wastebin must be disposed of separately from urban waste.
Disposing of the product according to this Directive:
avoids potentially negative consequences to the environment and
human health which otherwise could be caused by incorrect disposal
enables the recovery of materials to obtain a significant savings of
energy and resources.
For more detailed information about disposal, contact the supplier that provided
you with the product in question or consult the dedicated section at the website
www.ADC.datalogic.com.

DATALOGIC JOYA™ X2
14
1
Information aux utilisateurs concernant la Directive Européenne
2012/19/EC
Au terme de sa vie utile, le produit qui porte le symbole d'un caisson à ordures
barré ne doit pas être éliminé avec les déchets urbains.
Éliminer ce produit selon cette Directive permet de:
éviter les retombées négatives pour l'environnement et la santé
dérivant d'une élimination incorrecte
récupérer les matériaux dans le but d'une économie importante en
termes d'énergie et de ressources
Pour obtenir des informations complémentaires concernant l'élimination,
veuillez contacter le fournisseur auprès duquel vous avez acheté le produit ou
consulter la section consacrée au site Web www.ADC.datalogic.com.
Información para el usuario de accuerdo con la Directiva Europea
2012/19/CE
Al final de su vida útil, el producto marcado con un simbolo de contenedor de
bassura móvil tachado no debe eliminarse junto a los desechos urbanos.
Eliminar este producto de accuerdo con la Directiva permite de:
evitar posibles consecuencias negativas para el medio ambiente y la
salud derivadas de una eliminación inadecuada
recuperar los materiales obteniendo así un ahorro importante de
energía y recursos
Para obtener una información más detallada sobre la eliminación, por favor,
póngase en contacto con el proveedor donde lo compró o consultar la sección
dedicada en el Web site www.ADC.datalogic.com.
Benutzerinformation bezüglich Richtlinie 2012/19/EC der europäischen
Kommission
Am Ende des Gerätelebenszyklus darf das Produkt nicht über den städtischen
Hausmüll entsorgt werden. Eine entsprechende Mülltrennung ist erforderlich.
Beseitigung des Produkts entsprechend der Richtlinie:
verhindert negative Auswirkungen für die Umwelt und die Gesundheit
der Menschen
ermöglicht die Wiederverwendung der Materialien und spart somit
Energie und Resourcen.
Weitere Informationen zu dieser Richtlinie erhalten sie von ihrem Lieferanten
über den sie das Produkt erworben haben, oder besuchen sie unsere Hompage
unter www.ADC.datalogic.com.

INTRODUCTION
15
1
GENERAL VIEW
A) Display * D) Bumper G) Loudspeaker
B) 6 keys keyboard E) Cold reset Hole H) Micro USB
C) TTL Serial connector F) Neck Strip Anchor I) Reader window
*Remove protective film cover before use

DATALOGIC JOYA™ X2
16
1

INTRODUCTION
17
1
1 INTRODUCTION
1.1 DATALOGIC JOYA™ X2 DESCRIPTION
The Datalogic JOYA™ X2 is a pocket-sized Windows powered mobile
computer.
This extremely compact, lightweight, and versatile device, combines fully
integrated automatic data capture (2D bar code) and wireless communication
capabilities, supporting nearly any application.
The Datalogic JOYA™ X2 system architecture is based on the blend of Intel
X-Scale series processors coupled with the Windows CE operating system and
it was developed to meet the most demanding customer needs.
A huge quantity of on-board memory is available. It enables the user to adapt
the terminal for any specific need.
Thanks to its great ergonomics and the state of the art architecture, the
Datalogic JOYA™ X2 is the right answer to enhance your business
opportunities.
1.2 MODEL DESCRIPTION
The brand new Datalogic JOYA™ X2 is available in several different models
depending on the options it is equipped with. All options are listed below:
xxxxxxxxx JOYA™ X2, 802.11 b/g/n CCX V4, 256 MB RAM/512 MB Flash,
2D SE4500 Imager with Green Spot, Windows CE Core 6.0 + Avalanche.
xxxxxxxxx JOYA™ X2, 802.11 b/g/n CCX V4, 256 MB RAM/512 MB Flash,
2D SE4500 Imager with Green Spot, Windows CE Professional 6.0 +
Avalanche.
xxxxxxxxx JOYA™ X2, 802.11 b/g/n CCX V4, 256 MB RAM/512 MB Flash,
2D SE4500 Imager with Green Spot, Windows CE Core 6.0 + Avalanche,
Bluetooth®.
xxxxxxxxx JOYA™ X2, 802.11 b/g/n CCX V4, 256 MB RAM/512 MB Flash,
2D SE4500 Imager with Green Spot, Windows CE Professional 6.0 +
Avalanche, Bluetooth®.
xxxxxxxxx JOYA™ X2, 802.11 b/g/n CCX V4, 256 MB RAM/512 MB Flash,
2D Halogen Imager with Green Spot, Windows CE Core 6.0 + Avalanche.
xxxxxxxxx JOYA™ X2, 802.11 b/g/n CCX V4, 256 MB RAM/512 MB Flash,
2D Halogen Imager with Green Spot, Windows CE Professional 6.0 +
Avalanche.

DATALOGIC JOYA™ X2
18
1
xxxxxxxxx JOYA™ X2, 802.11 b/g/n CCX V4, 256 MB RAM/512 MB Flash,
2D Halogen Imager with Green Spot, Windows CE Core 6.0 + Avalanche,
Bluetooth®.
xxxxxxxxx JOYA™ X2, 802.11 b/g/n CCX V4, 256 MB RAM/512 MB Flash,
2D Halogen Imager with Green Spot, Windows CE Professional 6.0 +
Avalanche, Bluetooth®.
xxxxxxxxx JOYA™ X2, 802.11 b/g/n CCX V4, 256 MB RAM/1 GB Flash, uSD
(4GB), touchscreen, 2D SE4500 Imager with Green Spot, Windows CE Core
6.0 + Avalanche.
xxxxxxxxx JOYA™ X2, 802.11 b/g/n CCX V4, 256 MB RAM/1 GB Flash, uSD
(4GB), touchscreen,2D SE4500 Imager with Green Spot, Windows CE
Professional 6.0 + Avalanche.
xxxxxxxxx JOYA™ X2, 802.11 b/g/n CCX V4, 256 MB RAM/1 GB Flash, uSD
(4GB), touchscreen,2D SE4500 Imager with Green Spot, Windows CE Core
6.0 + Avalanche, Bluetooth®.
xxxxxxxxx JOYA™ X2, 802.11 b/g/n CCX V4, 256 MB RAM/1 GB Flash, uSD
(4GB), touchscreen,2D SE4500 Imager with Green Spot, Windows CE
Professional 6.0 + Avalanche, Bluetooth®.
xxxxxxxxx JOYA™ X2, 802.11 b/g/n CCX V4, 256 MB RAM/1 GB Flash, uSD
(4GB), touchscreen,2D Halogen Imager with Green Spot, Windows CE Core
6.0 + Avalanche.
xxxxxxxxx JOYA™ X2, 802.11 b/g/n CCX V4, 256 MB RAM/1 GB Flash, uSD
(4GB), touchscreen,2D Halogen Imager with Green Spot, Windows CE
Professional 6.0 + Avalanche.
xxxxxxxxx JOYA™ X2, 802.11 b/g/n CCX V4, 256 MB RAM/1 GB Flash, uSD
(4GB), touchscreen,2D Halogen Imager with Green Spot, Windows CE Core
6.0 + Avalanche, Bluetooth®.
xxxxxxxxx JOYA™ X2, 802.11 b/g/n CCX V4, 256 MB RAM/1 GB Flash, uSD
(4GB), touchscreen,2D Halogen Imager with Green Spot, Windows CE
Professional 6.0 + Avalanche, Bluetooth®.
For further details about the Datalogic JOYA™ X2 models refer to the web site:
http://www.JOYA.datalogic.com.
19
1.3 PACKAGE CONTENTS
The Datalogic JOYA™ X2 package contains:
− 1 Datalogic JOYA™ X2 mobile computer
Remove all the components from their packaging; check their integrity and
congruity with the packing documents.
Keep the original packaging for use when sending products
to the technical assistance center. Damage caused by
improper packaging is not covered under the warranty.
CAUTION
Rechargeable battery packs are not initially charged.
Therefore the initial operation to perform is to charge them.
NOTE
1.4 ACCESSORIES
Cradle
912201000 Datalogic JOYA™ X2 Cradle Dispenser
Batteries
890002010 Datalogic JOYA™ X2 Battery Pack (10 pcs.)
Cradle Accessories
91ACC1000 Power Supply 12V 300W
91ACC0730 Power Junction Cable I90x/3 Cradle (8 pcs.)
91ACC0650 Term. Unlock Magnets (5 pcs.)
Various
94ACC1328 Datalogic JOYA™ X2 Stylus Pens (10 pcs)
91ACC1056 Datalogic JOYA™ X2 trolley holder (60 pcs.)
91ACC1057 Datalogic JOYA™ X2 checkout holder
Use only a Datalogic ADC-approved power supply and cables.
Use of an alternative power supply will invalidate any approval
given to this device and may be dangerous.
NOTE
DATALOGIC JOYA™ X2
20
2
2 CONNECTIONS
2.1 USB CONNECTION
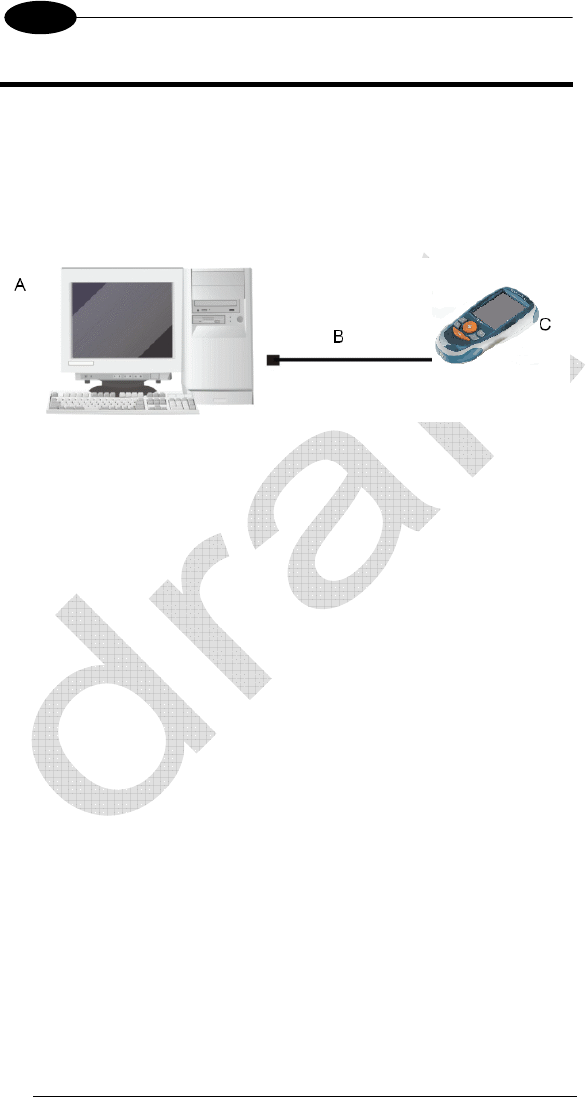
You can use any standard micro USB cable to directly connect the Datalogic
JOYA™ X2 to a host computer to transfer data through the USB interface.
Key:
A) Host Computer C) Datalogic JOYA™ X2
B) Standard Micro USB cable type USB A – micro USB B

CONNECTIONS
21
2
To comply with the FCC rules the EMI ferrite filter (Fair-Rite™
p.n. 0444164951) must be used and installed round the cable
(see pictures below)
WARNING
DATALOGIC JOYA™ X2
22
2
2.2 WLAN CONNECTION
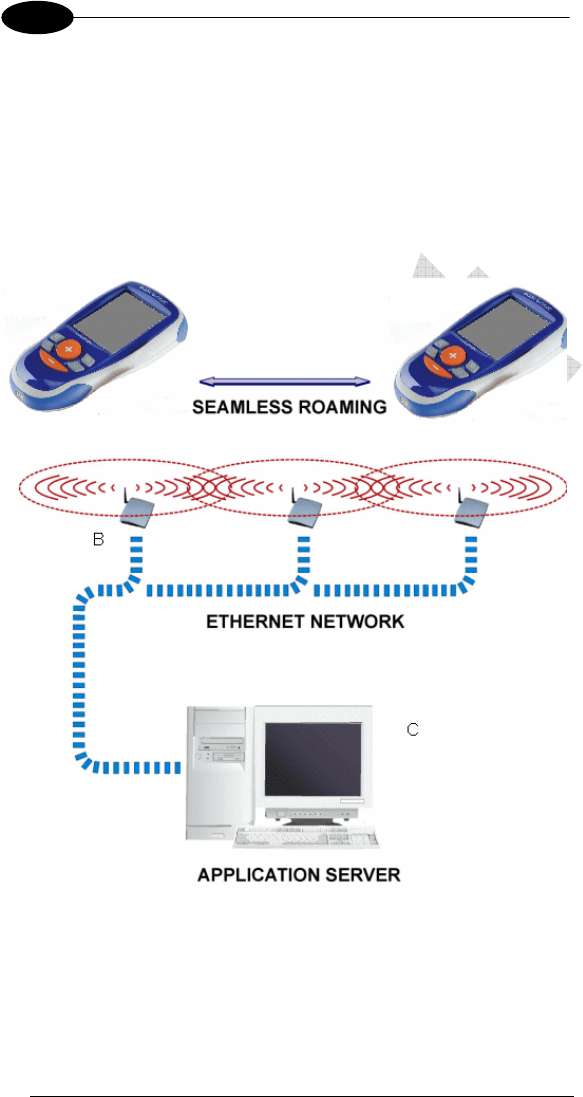
Datalogic JOYA™ X2 Wi-Fi 802.11 b/g/n radio models can communicate with
the host using the on-board radio frequency component and an Access Point
connected to the host computer.
To launch this utility you can tap the specific icon if it's visible on the taskbar or
you can open Connections folder or Control Panel from desktop and select the
'Summit Client Utility' icon.
A
Key:
Datalogic JOYA™ X2
Access Point
Host – Application Server
CONNECTIONS
23
2
Wi-Fi module is on by default, in order to avoid wasting
energy, you can switch it off using the Wireless
Communications applet.
NOTE
Suspending the terminal powers off the 802.11b/g/n radio and
drops the radio connection. When the terminal resumes,
depending on the radio power mode and security protocol
selected, it may take up to 30 seconds for the 802.11b/g/n
radio driver to re-associate the radio to the network.
NOTE
Area coverage and radio performance may vary, due to
environmental conditions, access points types or interference
caused by other devices (microwave ovens, radio
transmitters, etc.)
NOTE
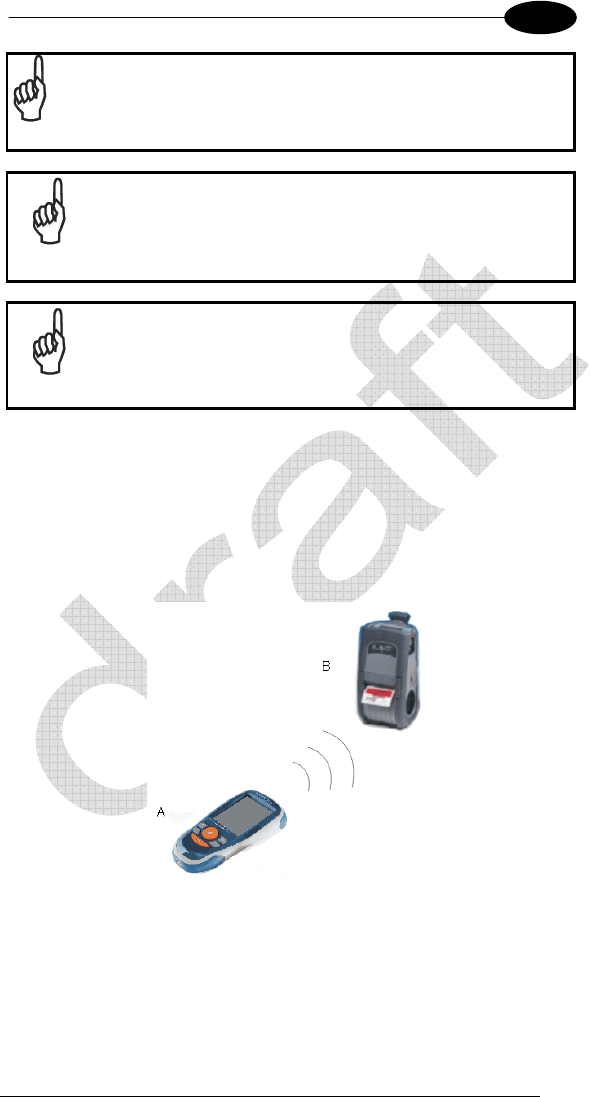
2.3 WPAN CONNECTIONS
Datalogic JOYA™ X2 mobile computer models can communicate with a
Bluetooth device, such as a printer, within a range of 10 m, using the on-
board Bluetooth module.
Key:
A) Datalogic JOYA™ X2
B) Bluetooth printer
DATALOGIC JOYA™ X2
24
2
In order to avoid wasting energy, the Bluetooth® module is
off by default. If you need to have Bluetooth® working, the
module must be powered on using the Wireless
Communications applet and perform the Discovery
procedure.
NOTE
Suspending the terminal powers off the Bluetooth
radio and
drops the piconet (Bluetooth
connection). When the
terminal resumes, it takes approximately 10 seconds for the
Bluetooth
radio driver to re-initialize the radio.
NOTE
Area coverage and Bluetooth
radio performance may vary,
due to environmental conditions or interference caused by
other devices (microwave ovens, radio transmitters, etc.), etc.
NOTE
3 USE AND FUNCTIONING
The use of the Datalogic JOYA™ X2 depends on the application software
loaded. However there are several parameters that can be set and utilities that
can be used to perform some basic functions such as data capture,
communications, file management, etc.
Furthermore there are two major utilities embedded in the software provided
from factory:
• ScanToConfig
• Avalanche Enabler
3.1 STARTUP
The Datalogic JOYA™ X2 turns on when a charged battery pack is inserted.
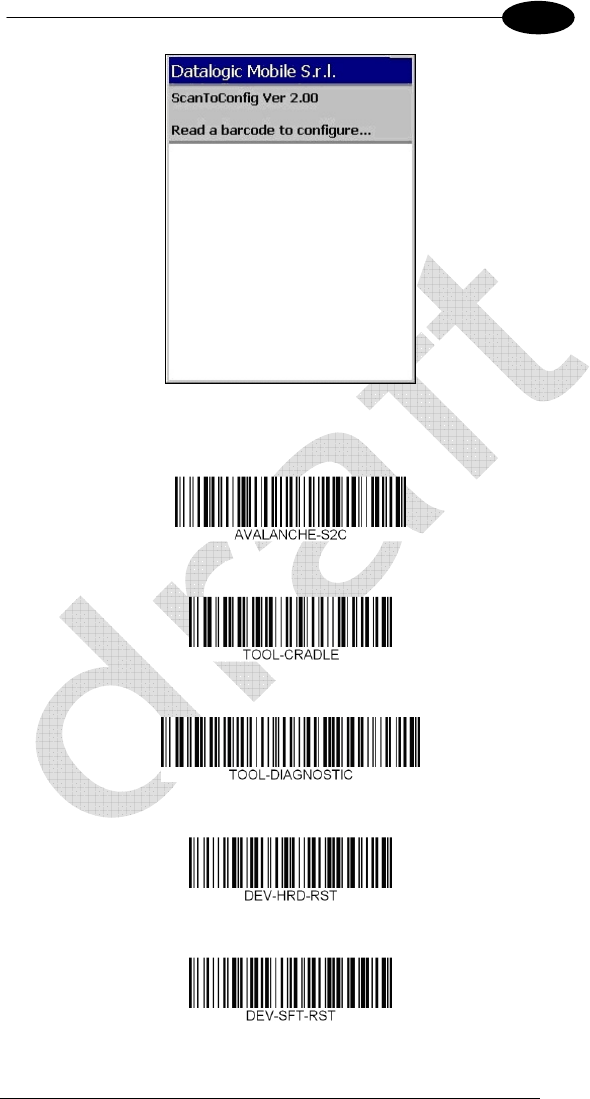
As soon as the mobile computer is on, the “ScanToConfig” request screen
appears and stays on for five seconds:
USE AND FUNCTIONING
25
3
By pressing the “+” key, the reader beam is lit. By reading different predefined
barcodes, different actions are performed. In particular it is possible to:
Start the Wavelink Avalanche Enabler-application interface (embedded);
Start the "JOYA Cradle Tool" application if present in \BACKUP\CTOOLS;
Start “JOYA Diagnostic Tool" application if present in \BACKUP\CTOOLS;
Perform a hardware reset;
DATALOGIC JOYA™ X2
26
1 3
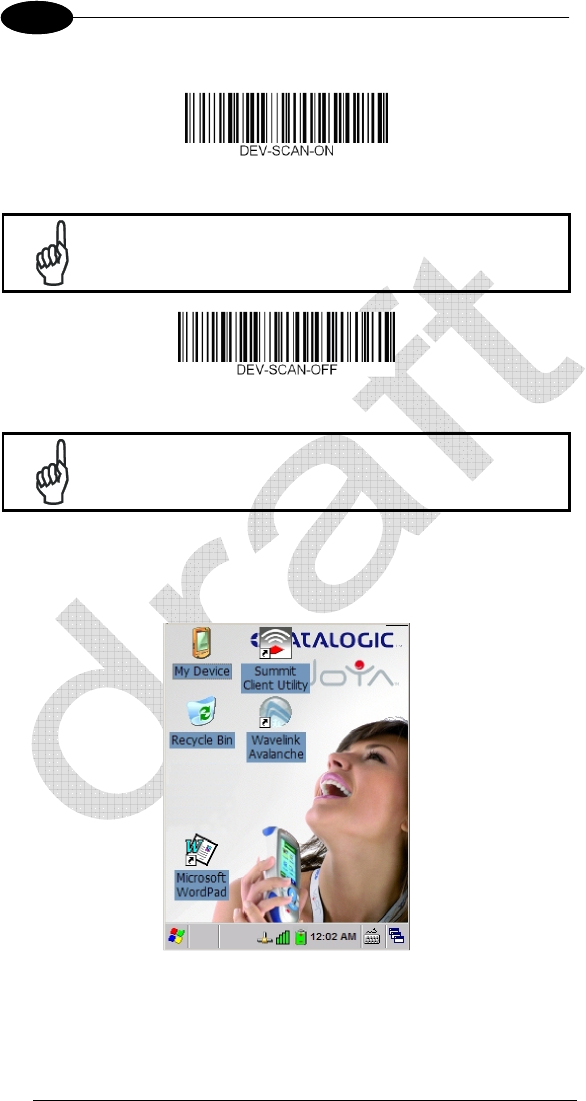
Perform a software reset;
Enable the reader trigger when the "+" key is pressed. Default is “enabled”;
A reset (either HW or SW) is required to confirm the choice.
Disable the reader trigger when the "+" key is pressed.
A reset (either HW or SW) is required to confirm the choice.
When the ScanToConfig timeout expires, Windows CE desktop will appear on
the screen. Wait a few seconds before starting any activity so that the mobile
computer completes its startup procedure.
The mobile computer goes into power-off (low power with display and keyboard
backlight off), when it is no longer used for more than a programmable timeout,
USE AND FUNCTIONING
27
3
which is defined in the POWER applet of the Control Panel. In this mode it can
be awakened (resuming operation) pressing the “Up” Key.
The mobile computer can also be awakened or turned off
by the application program.
NOTE
3.2 AVALANCHE ENABLER
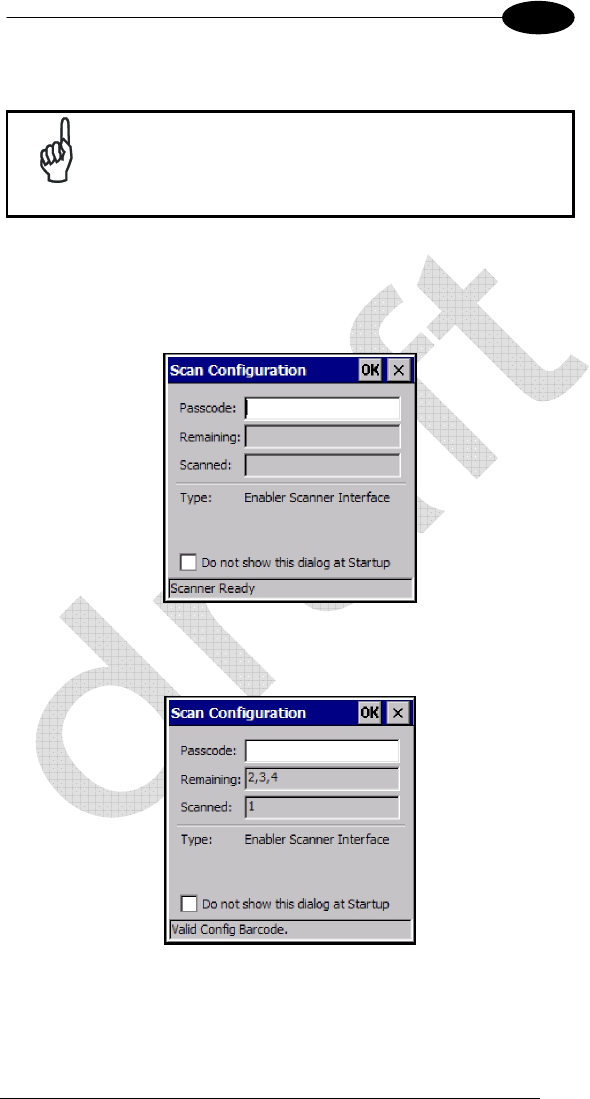
By scanning the AVALANCHE-S2C barcode, user can start the avalanche
enabler interface. First screen ask for the barcode setup sequence
At this point, user must scan the previously generated barcodes to properly
configure the radio interface. Barcodes can be scanned in any order, Scan
Configuration screen will report about scanned and remaining barcodes.
Then Avalanche Enabler connects the server and downloads suitable
information in term of “packages”. These packages are previously created by
using the Avalanche Package Builder.

DATALOGIC JOYA™ X2
28
1 3
3.3 WAVELINK AVALANCHE SYSTEM
Is a client management system that automatically deploys software and
configuration updates to JOYA™ X2. Avalanche uses "push/pull" technology to
install, update, and manage the software and configurations of JOYA™ X2 and
other mobile devices. For detailed information please refer directly to the
Wavelink website: http://www.wavelink.com/
The Wavelink Avalanche system includes three primary components:
Avalanche Manager: This tool provides centralized client management within
a network. The Avalanche Manager consists of two applications: Avalanche
Manager Agent and the Avalanche Management Console. The Agent performs
the management functions on the LAN or WAN, while the Management
Console provides an administrative interface to one or more Manager Agents
Avalanche Enabler: This tool is an agent that runs on each JOYA™ X2 to
allow device management via Avalanche Manager.
Avalanche-enabled software packages: These software packages are
intended to run on the JOYA™ X2 and include settings and applications. The
Avalanche Enabler is embedded in the JOYA™ X2 allowing communicating
directly with the Avalanche Manager over a wireless connection. The Enabler
and the Avalanche Manager work together to synchronize software on the
JOYA™ X2 to an associated profile on the Management Console. The profile
can include one or more distinct software packages, as well as RF and TCP/IP
configurations, and can apply to multiple devices.
USE AND FUNCTIONING
29
3
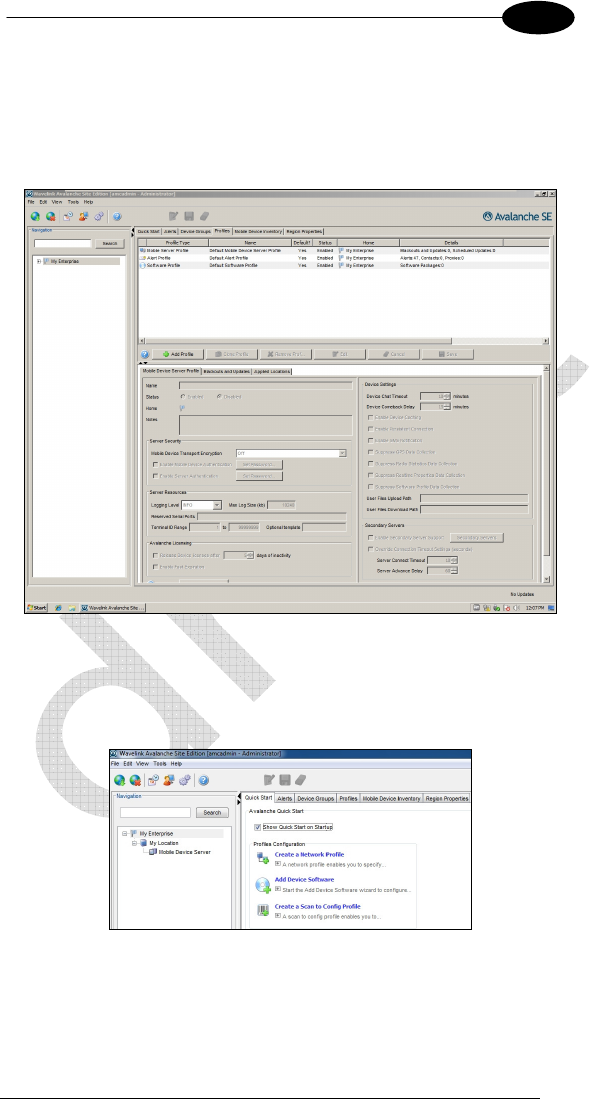
3.4 AVALANCHE MANAGEMENT CONSOLE
The Avalanche Management Console provides an administrative interface to
one or more Manager Agents. After installing, click on the Avalanche shortcut
on desktop or select Avalanche SE Console from All Programs -> Wavelink
Avalanche SE menu.
3.4.1 Network profile
Define the way each JOYA™ X2 terminal will connect the network.
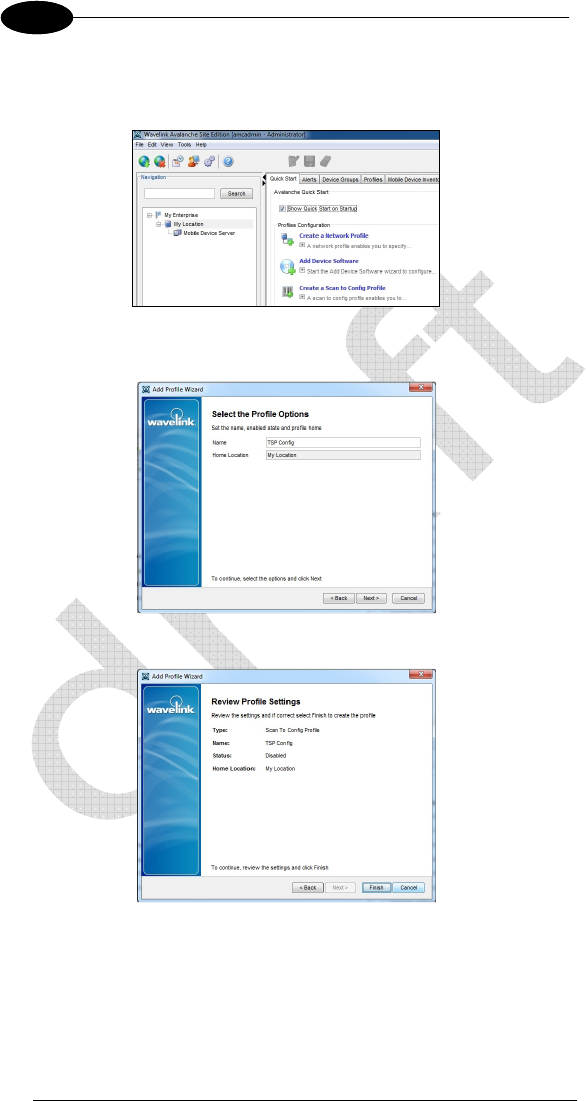
To create a Network Profile select the tab Quick Star, click on Create a
Network Profile.
DATALOGIC JOYA™ X2
30
1 3
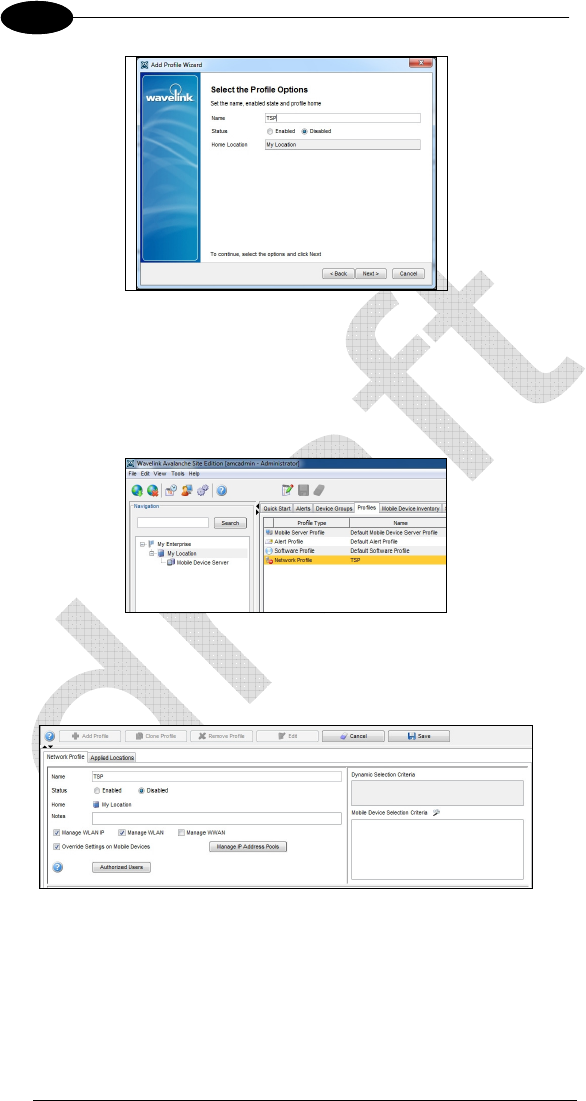
Insert a suitable profile name, leave status disabled then click Next.
Skip the Profile Selection Criteria screen then select Finish in the Review
Profile Settings screen. A new line named Network Profile will appear on the
right part of the main screen
Keep the Network profile line previously created highlighted. Click on the Edit
button on the top lower part of the main screen. Check the Manage WLAN IP,
the Manage WLAN and the Override Settings on Mobile Devices boxes.
On the lower part of the main screen select the WLAN IP Settings tab.
Check the box Manage IP Assignment and select DHCP Server on the side
drop-down menu.
Check the box Server Address and enter the DHCP server IP address in
decimal dotted notation.
USE AND FUNCTIONING
31
3
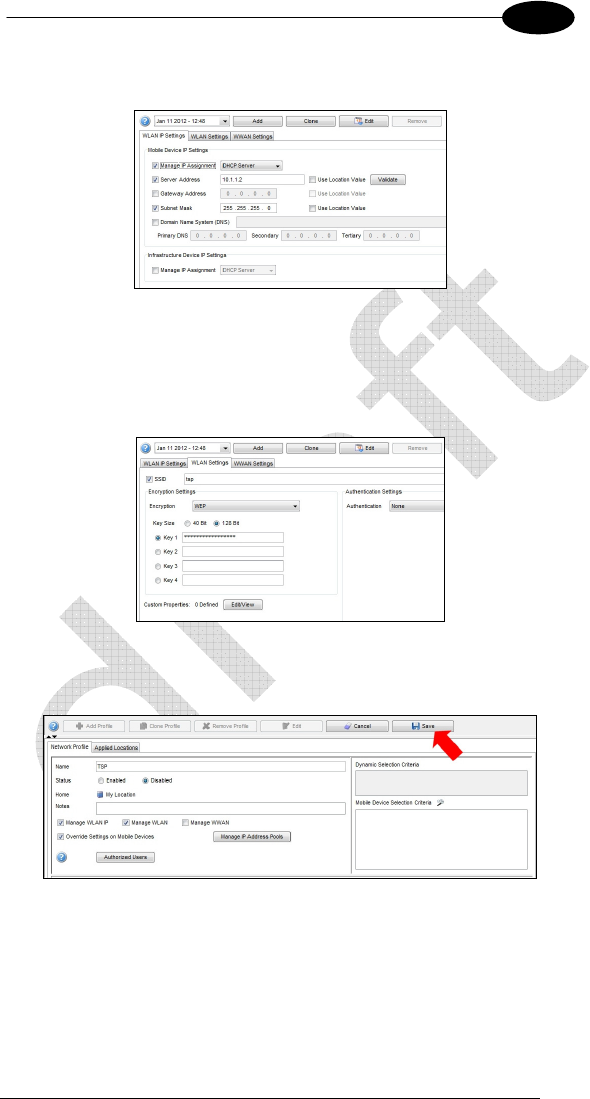
Check the box Subnet Mask and enter the subnet mask in decimal dotted
notation.
On the lower part of the main screen select the WLAN Settings tab.
Check the box SSID and enter the wifi SSID key.
In the Encryption Settings area enter the suitable values for the wifi
communication (encryption type and key value).
Click on the Save button to confirm modifications.
3.4.2 ScanToConfig Profile
Avalanche allows creating ScanToConfig profiles (setup by scanning barcodes)
that are configured with network settings. User can then print the profiles as
barcodes and a JOYA™ X2 can scan these barcodes. The information from the
scanned barcodes is used to configure the network settings on the JOYA™ X2
DATALOGIC JOYA™ X2
32
1 3
such as the IP address, subnet mask, and gateway as well as wireless
parameters such as SSID, encryption rules and keys etc... The length of the
barcode is configurable.
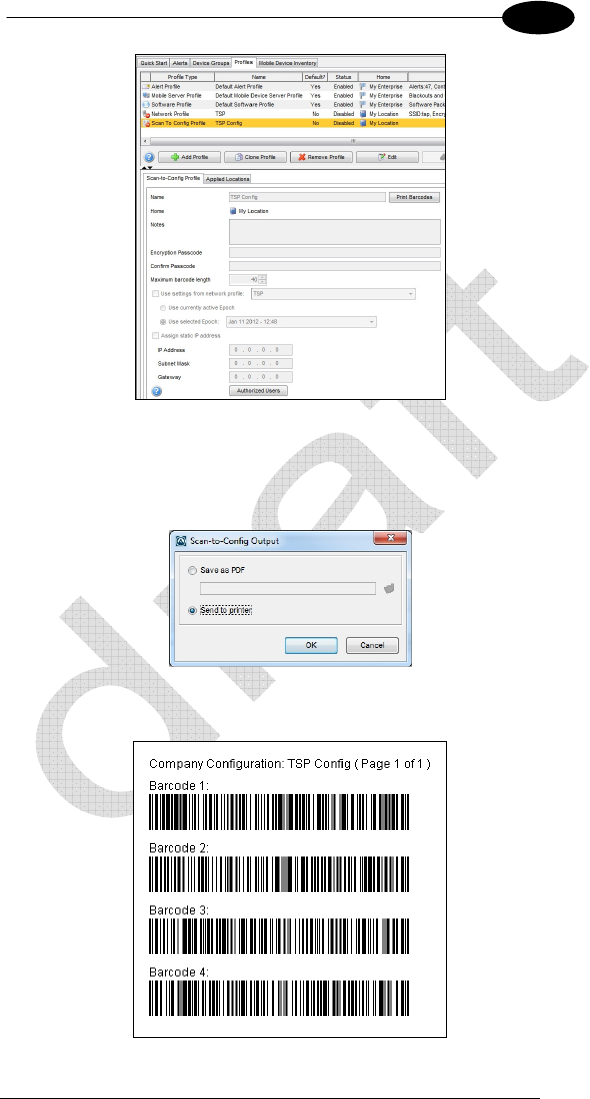
To create a Network Profile select the tab Quick Star, click on Create a Scan to
Config Profile.
Enter a suitable Network Profile name then click Next
Verify and confirm by clicking on Finish. A new line named Scan To Config
Profile will appear on the right part of the main screen
USE AND FUNCTIONING
33
3
Be sure that the Scan To Config Profile line is highlighted then press the Edit
key. Check the box Use settings from network profile and verify the network
profile name selected in the right windows. Confirm by clicking the Save key.
Select the Scan To Config Profile line then press the Print Barcodes key.
Select Save as PDF then click on the folder icon and enter a suitable name and
path for the output file. Then a PDF file will be created.
DATALOGIC JOYA™ X2
34
1 3
Make a paper copy and use it for JOYA™ X2 configuration.
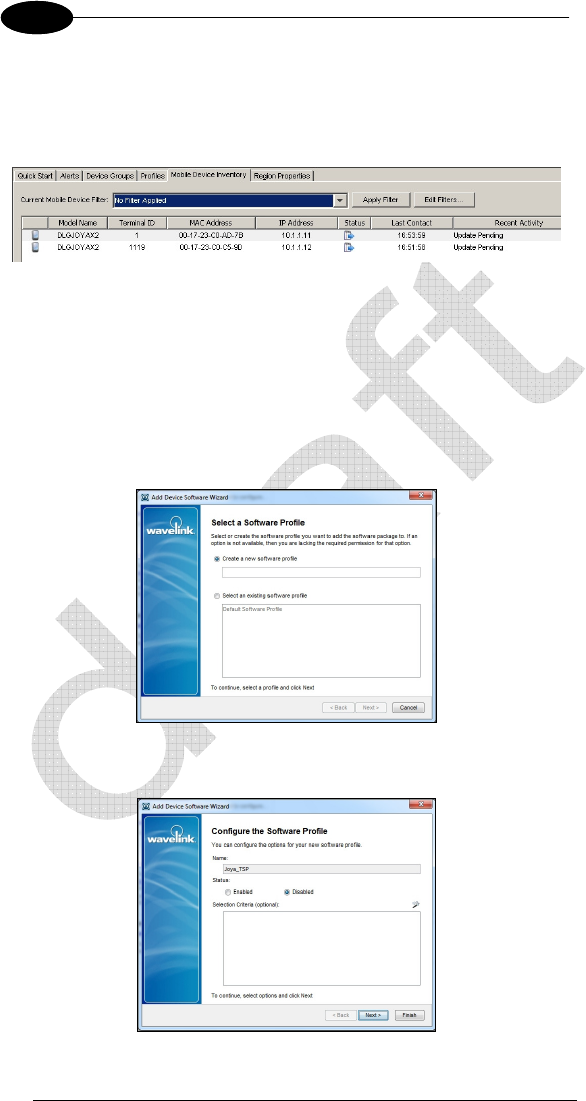
When the device is properly configured and connected to the Avalanche server
it will be reported in the Mobile Device Inventory tab.
3.4.3 Software profile
Software profiles allow user to organize and configure software for deployment
to JOYA™ X2 terminal, as well as change device parameters. Add software
packages to the profile, configure them, and schedule how and when they will
be installed. When the profile is enabled and applied to a location, the software
packages associated with the profile are installed on JOYA™ X2 terminals
meeting the selection criteria for the profile and packages.
To create new software profile, from the Quick Start tab select Add Device
Software.
USE AND FUNCTIONING
35
3
Insert a suitable software profile name, leave status disabled then click Next.
You can add packages, copy packages that have already been added to a
different profile, or create custom software packages from the Avalanche
Console. Before you create a custom package, ensure you know the location of
all the files you want to include and ensure that the files are valid.
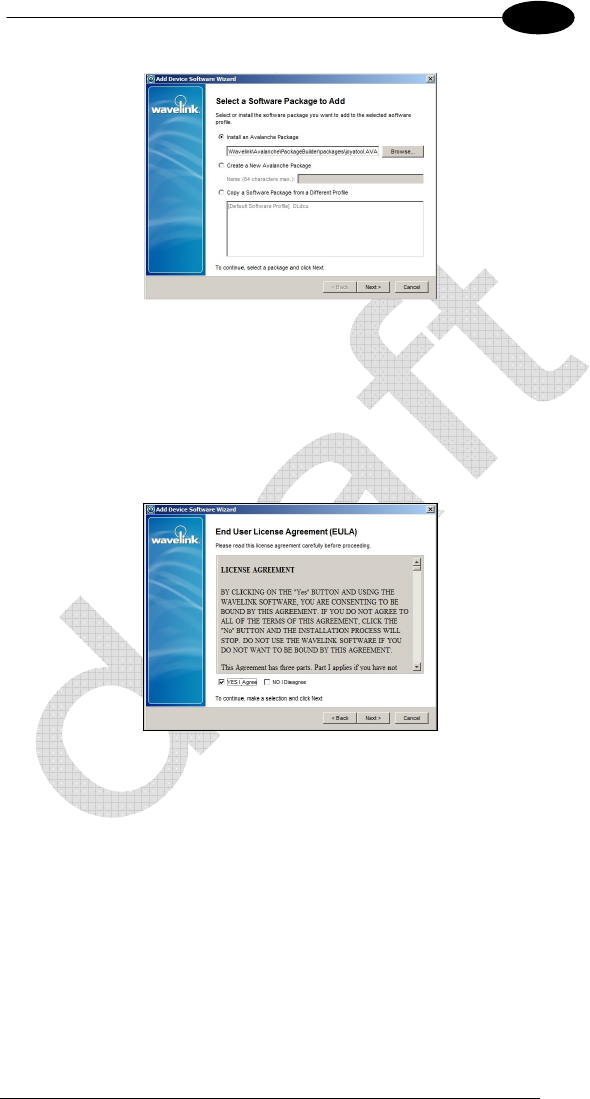
In the example select a previously created Software Package (AVA extension)
then Next.
Check the license agreement and confirm with Next.
DATALOGIC JOYA™ X2
36
1 3
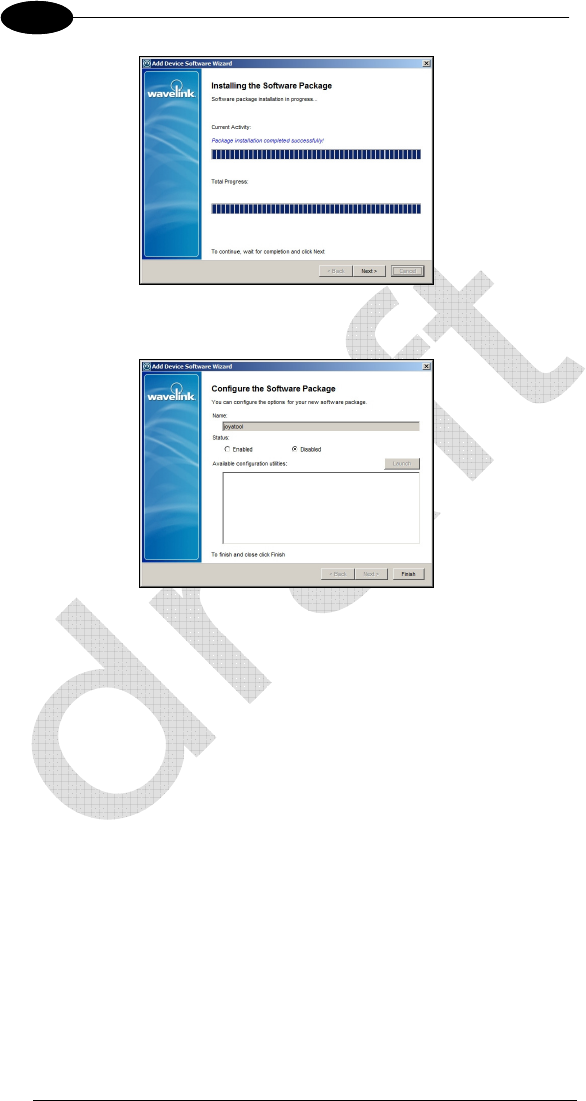
Wait for installation then click Next.
Close this wizard with Finish.
Once you create a software profile, you must enable/disable and add/remove
the software packages to that profile. Through the software profile you can
configure the software package settings and then deploy the packages to
specific mobile devices.
When working in software profiles, you do not need to be in Edit Mode to add or
configure software packages. Software package configuration changes are
saved to the actual package. However, you must enter Edit Mode to configure
any other software package options.
3.4.4 DLdcu package
The Datalogic Configuration Utility for Avalanche is a preassembled Avalanche
package (AVA extension) specifically created and freely distributed, aimed to
deploy configuration parameters on different mobile devices manufactured by
Datalogic through the Avalanche platform. Usually this package is assigned to
the default profile.
USE AND FUNCTIONING
37
3
In order to install the DLdcu Avalanche Package you first
must install the DCU program in the PC.
From the Profiles tab select Software profile/Default Software Profile.
On the lower part of the screen click on Install Package
Check Install an Avalanche package. Browse and select the DLdcuxx.AVA file