Dell Networking N2000 Series Cli Reference Guide
2015-01-05
: Dell Dell-Dell-Networking-N2000-Series-Cli-Reference-Guide-136320 dell-dell-networking-n2000-series-cli-reference-guide-136320 dell pdf
Open the PDF directly: View PDF ![]() .
.
Page Count: 1823 [warning: Documents this large are best viewed by clicking the View PDF Link!]
- Command Groups
- Introduction
- Command Groups
- Mode Types
- Layer 2 Commands
- AAA
- Administrative Profiles
- ACL
- Address Table
- Auto-VoIP
- CDP Interoperability
- DHCP L2 Relay
- DHCP Management Interface
- DHCP Snooping
- Dynamic ARP Inspection
- E-mail Alerting
- Ethernet Configuration
- Ethernet CFM
- Green Ethernet
- GVRP
- IGMP Snooping
- IGMP Snooping Querier
- IP Addressing
- IPv6 ACL
- IPv6 MLD Snooping
- IPv6 MLD Snooping Querier
- IP Source Guard
- iSCSI Optimization
- Link Dependency
- LLDP
- MLAG
- Multicast VLAN Registration
- Port Channel
- Port Monitor
- QoS
- Radius
- Spanning Tree
- TACACS+
- VLAN
- Voice VLAN
- 802.1x
- Layer 3 Commands
- Utility Commands
- Auto-Install
- Captive Portal
- CLI Macro
- Clock
- Command Line Configuration Scripting
- Denial of Service
- Line
- Management ACL
- Password Management
- PHY Diagnostics
- Power Over Ethernet (PoE)
- RMON
- SDM Templates
- Serviceability Tracing
- sFlow
- SNMP
- SSH
- Syslog
- System Management
- Telnet Server
- Terminal Length
- Time Ranges
- USB Flash Drive
- User Interface
- Web Server
- Using the CLI
- Layer 2 Switching Commands
- AAA Commands
- TACACS+ Accounting
- Commands in this Chapter
- aaa authentication dot1x default
- aaa authentication enable
- aaa authentication login
- aaa authorization
- aaa authorization network default radius
- aaa ias-user username
- aaa new-model
- clear (IAS)
- authorization
- enable authentication
- enable password
- ip http authentication
- ip https authentication
- login authentication
- password (aaa IAS User Configuration)
- password (Line Configuration)
- password (User EXEC)
- show aaa ias-users
- show aaa statistics
- show authentication methods
- show authorization methods
- show users accounts
- show users login-history
- username
- username unlock
- Administrative Profiles Commands
- ACL Commands
- ACL Logging
- Commands in this Chapter
- ip access-list
- deny | permit (IP ACL)
- deny | permit (Mac-Access-List-Configuration)
- ip access-group
- mac access-group
- mac access-list extended
- mac access-list extended rename
- service-acl input
- show service-acl interface
- show access-lists interface
- show ip access-lists
- show mac access-lists
- Address Table Commands
- Commands in this Chapter
- clear mac address-table
- mac address-table aging-time
- mac address-table multicast forbidden address
- mac address-table static vlan
- port security
- port security max
- show mac address-table multicast
- show mac address-table
- show mac address-table address
- show mac address-table count
- show mac address-table dynamic
- show mac address-table interface
- show mac address-table static
- show mac address-table vlan
- show ports security
- show ports security addresses
- Auto-VoIP Commands
- CDP Interoperability Commands
- DHCP Layer 2 Relay Commands
- Commands in this Chapter
- dhcp l2relay (Global Configuration)
- dhcp l2relay (Interface Configuration)
- dhcp l2relay circuit-id
- dhcp l2relay remote-id
- dhcp l2relay trust
- dhcp l2relay vlan
- show dhcp l2relay all
- show dhcp l2relay interface
- show dhcp l2relay stats interface
- show dhcp l2relay subscription interface
- show dhcp l2relay agent-option vlan
- show dhcp l2relay vlan
- show dhcp l2relay circuit-id vlan
- show dhcp l2relay remote-id vlan
- clear dhcp l2relay statistics interface
- DHCP Management Interface Commands
- DHCP Snooping Commands
- Commands in this Chapter
- clear ip dhcp snooping binding
- clear ip dhcp snooping statistics
- ip dhcp snooping
- ip dhcp snooping binding
- ip dhcp snooping database
- ip dhcp snooping database write-delay
- ip dhcp snooping limit
- ip dhcp snooping log-invalid
- ip dhcp snooping trust
- ip dhcp snooping verify mac-address
- show ip dhcp snooping
- show ip dhcp snooping binding
- show ip dhcp snooping database
- show ip dhcp snooping interfaces
- show ip dhcp snooping statistics
- Dynamic ARP Inspection Commands
- E-mail Alerting Commands
- Commands in this Chapter
- logging email
- logging email urgent
- logging traps
- logging email message-type to-addr
- logging email from-addr
- logging email message-type subject
- logging email logtime
- logging email test message-type
- show logging email statistics
- clear logging email statistics
- security
- mail-server ip-address | hostname
- port (Mail Server Configuration Mode)
- username (Mail Server Configuration Mode)
- password (Mail Server Configuration Mode)
- show mail-server
- Ethernet Configuration Commands
- Commands in this Chapter
- clear counters
- description
- duplex
- flowcontrol receive
- interface
- interface range
- monitor capture (Global Configuration)
- monitor capture (Privileged Exec)
- rate-limit cpu
- show interfaces advertise
- show interfaces configuration
- show interfaces counters
- show interfaces description
- show interfaces detail
- show interfaces status
- show interfaces transceiver
- show monitor capture
- show statistics
- show statistics switchport
- show storm-control
- shutdown
- speed
- storm-control broadcast
- storm-control multicast
- storm-control unicast
- switchport protected
- switchport protected name
- show switchport protected
- show system internal pktmgr
- show system mtu
- system jumbo mtu
- Ethernet CFM Commands
- Commands in this Chapter
- ethernet cfm domain
- service
- ethernet cfm cc level
- ethernet cfm mep level
- ethernet cfm mep enable
- ethernet cfm mep active
- ethernet cfm mep archive-hold-time
- ethernet cfm mip level
- ping ethernet cfm
- traceroute ethernet cfm
- show ethernet cfm errors
- show ethernet cfm domain
- show ethernet cfm maintenance-points local
- show ethernet cfm maintenance-points remote
- show ethernet cfm statistics
- debug cfm
- Green Ethernet Commands
- GVRP Commands
- IGMP Snooping Commands
- Commands in this Chapter
- ip igmp snooping
- show ip igmp snooping
- show ip igmp snooping groups
- show ip igmp snooping mrouter
- ip igmp snooping vlan immediate-leave
- ip igmp snooping vlan groupmembership-interval
- ip igmp snooping vlan last-member-query- interval
- ip igmp snooping vlan mcrtrexpiretime
- ip igmp snooping report-suppression
- ip igmp snooping unregistered floodall
- ip igmp snooping vlan mrouter
- IGMP Snooping Querier Commands
- IP Addressing Commands
- Commands in this Chapter
- clear host
- clear ip address-conflict-detect
- interface out-of-band
- ip address (Out-of-Band)
- ip address-conflict-detect run
- ip address dhcp (Interface Configuration)
- ip default-gateway
- ip domain-lookup
- ip domain-name
- ip host
- ip name-server
- ipv6 address (Interface Configuration)
- ipv6 address (OOB Port)
- ipv6 address dhcp
- ipv6 enable (Interface Configuration)
- ipv6 enable (OOB Configuration)
- ipv6 gateway (OOB Configuration)
- show hosts
- show ip address-conflict
- show ip helper-address
- show ipv6 dhcp interface out-of-band statistics
- show ipv6 interface out-of-band
- IPv6 Access List Commands
- IPv6 MLD Snooping Commands
- Commands in this Chapter
- ipv6 mld snooping vlan groupmembership- interval
- ipv6 mld snooping vlan immediate-leave
- ipv6 mld snooping listener-message-suppression
- ipv6 mld snooping vlan last-listener-query- interval
- ipv6 mld snooping vlan mcrtexpiretime
- ipv6 mld snooping vlan mrouter
- ipv6 mld snooping (Global)
- show ipv6 mld snooping
- show ipv6 mld snooping groups
- show ipv6 mld snooping mrouter
- IPv6 MLD Snooping Querier Commands
- IP Source Guard Commands
- iSCSI Optimization Commands
- Link Dependency Commands
- LLDP Commands
- Commands in this Chapter
- clear lldp remote-data
- clear lldp statistics
- dcb enable
- lldp med
- lldp med confignotification
- lldp med faststartrepeatcount
- lldp med transmit-tlv
- lldp notification
- lldp notification-interval
- lldp receive
- lldp timers
- lldp transmit
- lldp transmit-mgmt
- lldp transmit-tlv
- show lldp
- show lldp interface
- show lldp local-device
- show lldp med
- show lldp med interface
- show lldp med local-device detail
- show lldp med remote-device
- show lldp remote-device
- show lldp statistics
- Multicast VLAN Registration Commands
- Port Channel Commands
- Static LAGS
- VLANs and LAGs
- LAG Thresholds
- LAG Hashing
- Enhanced LAG Hashing
- Manual Aggregation of LAGs
- Flexible Assignment of Ports to LAGs
- Commands in this Chapter
- channel-group
- interface port-channel
- interface range port-channel
- hashing-mode
- lacp port-priority
- lacp system-priority
- lacp timeout
- port-channel local-preference
- port-channel min-links
- show interfaces port-channel
- show lacp
- show statistics port-channel
- MLAG
- Commands in this Chapter
- clear vpc statistics
- debug vpc
- feature vpc
- peer-detection enable
- peer-keepalive destination
- peer-keepalive enable
- role priority
- show vpc
- show vpc brief
- show vpc consistency-parameters
- show vpc consistency-features
- show vpc peer-keepalive
- show vpc role
- show vpc statistics
- vpc
- vpc domain
- vpc peer-link
- Port Monitor Commands
- QoS Commands
- Access Control Lists
- Layer 2 ACLs
- Layer 3/4 IPv4 ACLs
- Class of Service (CoS)
- Queue Mapping
- Commands in this Chapter
- assign-queue
- class
- class-map
- class-map rename
- classofservice dot1p-mapping
- classofservice ip-dscp-mapping
- classofservice trust
- conform-color
- cos-queue min-bandwidth
- cos-queue random-detect
- cos-queue strict
- diffserv
- drop
- mark cos
- mark ip-dscp
- mark ip-precedence
- match class-map
- match cos
- match destination-address mac
- match dstip
- match dstip6
- match dstl4port
- match ethertype
- match ip6flowlbl
- match ip dscp
- match ip precedence
- match ip tos
- match protocol
- match source-address mac
- match srcip
- match srcip6
- match srcl4port
- match vlan
- mirror
- police-simple
- police-single-rate
- police-two-rate
- policy-map
- random-detect queue-parms
- random-detect exponential-weighting-constant
- redirect
- service-policy
- show class-map
- show classofservice dot1p-mapping
- show classofservice ip-dscp-mapping
- show classofservice trust
- show diffserv
- show diffserv service interface
- show diffserv service interface port-channel
- show diffserv service brief
- show interfaces cos-queue
- show interfaces random-detect
- show policy-map
- show policy-map interface
- show service-policy
- traffic-shape
- vlan priority
- RADIUS Commands
- Commands in this Chapter
- aaa accounting dot1x default start-stop
- accounting
- acct-port
- auth-port
- deadtime
- debug aaa accounting
- key
- key encrypted
- msgauth
- name (RADIUS server)
- primary
- priority
- radius-server attribute 4
- radius-server deadtime
- radius-server host
- radius-server key
- radius-server key encrypted
- radius-server retransmit
- radius-server source-ip
- radius-server timeout
- retransmit
- show aaa servers
- show accounting methods
- show radius statistics
- source-ip
- timeout
- usage
- Spanning Tree Commands
- Commands in this Chapter
- clear spanning-tree detected-protocols
- exit (mst)
- instance (mst)
- name (mst)
- revision (mst)
- show spanning-tree
- show spanning-tree summary
- show spanning-tree vlan
- spanning-tree
- spanning-tree auto-portfast
- spanning-tree backbonefast
- spanning-tree bpdu flooding
- spanning-tree bpdu-protection
- spanning-tree cost
- spanning-tree disable
- spanning-tree forward-time
- spanning-tree guard
- spanning-tree loopguard
- spanning-tree max-age
- spanning-tree max-hops
- spanning-tree mode
- spanning-tree mst configuration
- spanning-tree mst cost
- spanning-tree mst port-priority
- spanning-tree mst priority
- spanning-tree portfast
- spanning-tree portfast bpdufilter default
- spanning-tree portfast default
- spanning-tree port-priority (Interface Configuration)
- spanning-tree priority
- spanning-tree tcnguard
- spanning-tree transmit hold-count
- spanning-tree uplinkfast
- spanning-tree vlan
- spanning-tree vlan forward-time
- spanning-tree vlan hello-time
- spanning-tree vlan max-age
- spanning-tree vlan root
- spanning-tree vlan priority
- TACACS+ Commands
- UDLD Commands
- VLAN Commands
- Double VLAN Mode
- Independent VLAN Learning
- Protocol Based VLANs
- IP Subnet Based VLANs
- MAC-Based VLANs
- Private VLAN Commands
- Commands in this Chapter
- dvlan-tunnel ethertype
- interface vlan
- interface range vlan
- mode dvlan-tunnel
- name (VLAN Configuration)
- protocol group
- protocol vlan group
- protocol vlan group all
- show dvlan-tunnel
- show dvlan-tunnel interface
- show interfaces switchport
- show port protocol
- show vlan
- show vlan association mac
- show vlan association subnet
- switchport access vlan
- switchport general forbidden vlan
- switchport general acceptable-frame-type tagged-only
- switchport general allowed vlan
- switchport general ingress-filtering disable
- switchport general pvid
- switchport mode
- switchport trunk
- vlan
- vlan association mac
- vlan association subnet
- vlan makestatic
- vlan protocol group
- vlan protocol group add protocol
- vlan protocol group name
- vlan protocol group remove
- switchport private-vlan
- switchport mode private-vlan
- private-vlan
- show vlan private-vlan
- Voice VLAN Commands
- 802.1x Commands
- Local 802.1X Authentication Server
- MAC Authentication Bypass
- Guest VLAN
- 802.1x Monitor Mode
- RADIUS-based Dynamic VLAN Assignment
- Commands in this Chapter
- dot1x dynamic-vlan enable
- dot1x initialize
- dot1x eapolflood
- dot1x mac-auth-bypass
- dot1x max-req
- dot1x max-users
- dot1x port-control
- dot1x re-authenticate
- dot1x reauthentication
- dot1x system-auth-control
- dot1x system-auth-control monitor
- dot1x timeout guest-vlan-period
- dot1x timeout quiet-period
- dot1x timeout re-authperiod
- dot1x timeout server-timeout
- dot1x timeout tx-period
- authentication enable
- authentication order
- authentication priority
- authentication restart
- clear authentication statistics
- clear authentication authentication-history
- show authentication
- show authenticaton authentication-history
- show authentication statistics
- show dot1x
- show dot1x authentication-history
- show dot1x clients
- show dot1x interface
- show dot1x interface statistics
- show dot1x users
- clear dot1x authentication–history
- dot1x guest-vlan
- dot1x unauth-vlan
- show dot1x advanced
- Data Center Technology Commands
- Data Center Bridging Commands
- Data Center Bridging Exchange Protocol
- Interoperability with IEEE DCBX
- Port Roles
- Commands in this Chapter
- Data Center Bridging Capability Exchange Commands
- datacenter-bridging
- lldp dcbx version
- lldp tlv-select dcbxp (dcb enable)
- lldp dcbx port-role
- show lldp tlv-select
- show lldp dcbx
- Enhanced Transmission Selection (ETS) Commands
- classofservice traffic-class-group
- traffic-class-group max-bandwidth
- traffic-class-group min-bandwidth
- traffic-class-group strict
- traffic-class-group weight
- show classofservice traffic-class-group
- show interfaces traffic-class-group
- Priority Flow Control Commands
- Layer 3 Commands
- ARP Commands
- DHCP Server and Relay Agent Commands
- Commands in this Chapter
- ip dhcp pool
- bootfile
- clear ip dhcp binding
- clear ip dhcp conflict
- client-identifier
- client-name
- default-router
- dns-server (IP DHCP Pool Config)
- domain-name (IP DHCP Pool Config)
- hardware-address
- host
- ip dhcp bootp automatic
- ip dhcp conflict logging
- ip dhcp excluded-address
- ip dhcp ping packets
- lease
- netbios-name-server
- netbios-node-type
- network
- next-server
- option
- service dhcp
- sntp
- show ip dhcp binding
- show ip dhcp conflict
- show ip dhcp global configuration
- show ip dhcp pool
- show ip dhcp server statistics
- DHCPv6 Commands
- clear ipv6 dhcp
- dns-server (IPv6 DHCP Pool Config)
- domain-name (IPv6 DHCP Pool Config)
- ipv6 dhcp pool
- ipv6 dhcp relay
- ipv6 dhcp server
- prefix-delegation
- service dhcpv6
- show ipv6 dhcp
- show ipv6 dhcp binding
- show ipv6 dhcp interface (User EXEC)
- show ipv6 dhcp interface (Privileged EXEC)
- show ipv6 dhcp pool
- show ipv6 dhcp statistics
- DHCPv6 Snooping Commands
- clear ipv6 dhcp snooping binding
- clear ipv6 dhcp snooping statistics
- ipv6 dhcp snooping
- ipv6 dhcp snooping vlan
- ipv6 dhcp snooping binding
- ipv6 dhcp snooping database
- ipv6 dhcp snooping database write-delay
- ipv6 dhcp snooping limit
- ipv6 dhcp snooping log-invalid
- ipv6 dhcp snooping trust
- ipv6 dhcp snooping verify mac-address
- ipv6 verify binding
- ipv6 verify source
- show ipv6 dhcp snooping
- show ipv6 dhcp snooping binding
- show ipv6 dhcp snooping database
- show ipv6 dhcp snooping interfaces
- show ipv6 dhcp snooping statistics
- show ipv6 source binding
- show ipv6 verify
- show ipv6 verify source
- DVMRP Commands
- GMRP Commands
- IGMP Commands
- Commands in this Chapter
- ip igmp last-member-query-count
- ip igmp last-member-query-interval
- ip igmp mroute-proxy
- ip igmp query-interval
- ip igmp query-max-response-time
- ip igmp robustness
- ip igmp startup-query-count
- ip igmp startup-query-interval
- ip igmp version
- show ip igmp
- show ip igmp groups
- show ip igmp interface
- show ip igmp membership
- show ip igmp interface stats
- IGMP Proxy Commands
- IP Helper/DHCP Relay Commands
- Commands in this Chapter
- bootpdhcprelay maxhopcount
- bootpdhcprelay minwaittime
- clear ip helper statistics
- ip dhcp relay information check
- ip dhcp relay information check-reply
- ip dhcp relay information option
- ip dhcp relay information option-insert
- ip helper-address (global configuration)
- ip helper-address (interface configuration)
- ip helper enable
- show ip helper-address
- show ip dhcp relay
- show ip helper statistics
- IP Routing Commands
- Static Routes/ECMP Static Routes
- Static Reject Routes
- Default Routes
- Commands in this Chapter
- encapsulation
- ip address
- ip netdirbcast
- ip policy route-map
- ip route
- ip route default
- ip route distance
- ip routing
- match ip address
- match length
- match mac-list
- route-map
- set interface null0
- set ip default next-hop
- set ip next-hop
- set ip precedence
- show ip brief
- show ip interface
- show ip policy
- show ip protocols
- show ip route
- show ip route preferences
- show ip route summary
- show ip traffic
- show ip vlan
- show route-map
- show routing heap summary
- IPv6 Routing Commands
- IPv6 Limitations & Restrictions
- Commands in this Chapter
- clear ipv6 neighbors
- clear ipv6 statistics
- ipv6 address
- ipv6 enable
- ipv6 hop-limit
- ipv6 host
- ipv6 mld last-member-query-count
- ipv6 mld last-member-query-interval
- ipv6 mld host-proxy
- ipv6 mld host-proxy reset-status
- ipv6 mld host-proxy unsolicit-rprt-interval
- ipv6 mld query-interval
- ipv6 mld query-max-response-time
- ipv6 nd dad attempts
- ipv6 nd managed-config-flag
- ipv6 nd ns-interval
- ipv6 nd other-config-flag
- ipv6 nd prefix
- ipv6 nd ra-interval
- ipv6 nd ra-lifetime
- ipv6 nd reachable-time
- ipv6 nd suppress-ra
- ipv6 route
- ipv6 route distance
- ipv6 unicast-routing
- ping ipv6
- ping ipv6 interface
- rate-limit cpu
- show ipv6 brief
- show ipv6 interface
- show ipv6 interface management statistics
- show ipv6 mld groups
- show ipv6 mld host-proxy
- show ipv6 mld interface
- show ipv6 mld host-proxy
- show ipv6 mld host-proxy groups
- show ipv6 mld host-proxy groups detail
- show ipv6 mld host-proxy interface
- show ipv6 mld traffic
- show ipv6 neighbors
- show ipv6 route
- show ipv6 route preferences
- show ipv6 route summary
- show ipv6 traffic
- show ipv6 vlan
- traceroute ipv6
- Loopback Interface Commands
- Multicast Commands
- Commands in this Chapter
- clear ip mroute
- ip mcast boundary
- ip mroute
- ip multicast-routing
- ip multicast ttl-threshold
- ip pim
- ip pim bsr-border
- ip pim bsr-candidate
- ip pim dense-mode
- ip pim dr-priority
- ip pim hello-interval
- ip pim join-prune-interval
- ip pim rp-address
- ip pim rp-candidate
- ip pim sparse-mode
- ip pim ssm
- show ip multicast
- show ip pim boundary
- show ip multicast interface
- show ip mroute
- show ip mroute group
- show ip mroute source
- show ip mroute static
- show ip pim
- show ip pim bsr-router
- show ip pim interface
- show ip pim neighbor
- show ip pim rp hash
- show ip pim rp mapping
- IPv6 Multicast Commands
- clear ipv6 mroute
- ipv6 pim (VLAN Interface config)
- ipv6 pim bsr-border
- ipv6 pim bsr-candidate
- ipv6 pim dense-mode
- ipv6 pim dr-priority
- ipv6 pim hello-interval
- ipv6 pim join-prune-interval
- ipv6 pim register-threshold
- ipv6 pim rp-address
- ipv6 pim rp-candidate
- ipv6 pim sparse-mode
- ipv6 pim ssm
- show ipv6 pim
- show ipv6 pim bsr-router
- show ipv6 mroute group
- show ipv6 mroute source
- show ipv6 pim interface
- show ipv6 pim neighbor
- show ipv6 pim rp-hash
- show ipv6 pim rp mapping
- OSPF Commands
- Route Preferences
- OSPF Equal Cost Multipath (ECMP)
- Forwarding of OSPF Opaque LSAs Enabled by Default
- Passive Interfaces
- Graceful Restart
- Commands in this Chapter
- area default-cost (Router OSPF)
- area nssa (Router OSPF)
- area nssa default-info-originate (Router OSPF Config)
- area nssa no-redistribute
- area nssa no-summary
- area nssa translator-role
- area nssa translator-stab-intv
- area range (Router OSPF)
- area stub
- area stub no-summary
- area virtual-link
- area virtual-link authentication
- area virtual-link dead-interval
- area virtual-link hello-interval
- area virtual-link retransmit-interval
- area virtual-link transmit-delay
- auto-cost
- bandwidth
- capability opaque
- clear ip ospf
- clear ip ospf stub-router
- compatible rfc1583
- default-information originate (Router OSPF Configuration)
- default-metric
- distance ospf
- distribute-list out
- enable
- exit-overflow-interval
- external-lsdb-limit
- ip ospf area
- ip ospf authentication
- ip ospf cost
- ip ospf database-filter all out
- ip ospf dead-interval
- ip ospf hello-interval
- ip ospf mtu-ignore
- ip ospf network
- ip ospf priority
- ip ospf retransmit-interval
- ip ospf transmit-delay
- log adjacency-changes
- max-metric router-lsa
- maximum-paths
- network area
- nsf
- nsf helper
- nsf helper strict-lsa-checking
- nsf restart-interval
- passive-interface default
- passive-interface
- redistribute
- router-id
- router ospf
- show ip ospf
- show ip ospf abr
- show ip ospf area
- show ip ospf asbr
- show ip ospf database
- show ip ospf database database-summary
- show ip ospf interface
- show ip ospf interface brief
- show ip ospf interface stats
- show ip ospf neighbor
- show ip ospf range
- show ip ospf statistics
- show ip ospf stub table
- show ip ospf traffic
- show ip ospf virtual-link
- show ip ospf virtual-links brief
- timers pacing flood
- timers pacing lsa-group
- timers spf
- OSPFv3 Commands
- area default-cost (Router OSPFv3)
- area nssa (Router OSPFv3)
- area nssa default-info-originate (Router OSPFv3 Config)
- area nssa no-redistribute
- area nssa no-summary
- area nssa translator-role
- area nssa translator-stab-intv
- area range (Router OSPFv3)
- area stub
- area stub no-summary
- area virtual-link
- area virtual-link dead-interval
- area virtual-link hello-interval
- area virtual-link retransmit-interval
- area virtual-link transmit-delay
- default-information originate (Router OSPFv3 Configuration)
- default-metric
- distance ospf
- enable
- exit-overflow-interval
- external-lsdb-limit
- ipv6 ospf
- ipv6 ospf area
- ipv6 ospf cost
- ipv6 ospf dead-interval
- ipv6 ospf hello-interval
- ipv6 ospf mtu-ignore
- ipv6 ospf network
- ipv6 ospf priority
- ipv6 ospf retransmit-interval
- ipv6 ospf transmit-delay
- ipv6 router ospf
- maximum-paths
- nsf
- nsf helper
- nsf helper strict-lsa-checking
- nsf restart-interval
- passive-interface
- passive-interface default
- redistribute
- router-id
- show ipv6 ospf
- show ipv6 ospf abr
- show ipv6 ospf area
- show ipv6 ospf asbr
- show ipv6 ospf border-routers
- show ipv6 ospf database
- show ipv6 ospf database database-summary
- show ipv6 ospf interface
- show ipv6 ospf interface brief
- show ipv6 ospf interface stats
- show ipv6 ospf interface vlan
- show ipv6 ospf neighbor
- show ipv6 ospf range
- show ipv6 ospf stub table
- show ipv6 ospf virtual-links
- show ipv6 ospf virtual-link brief
- Router Discovery Protocol Commands
- Routing Information Protocol Commands
- Commands in this Chapter
- auto-summary
- default-information originate (Router RIP Configuration)
- default-metric
- distance rip
- distribute-list out
- enable
- hostroutesaccept
- ip rip
- ip rip authentication
- ip rip receive version
- ip rip send version
- redistribute
- router rip
- show ip rip
- show ip rip interface
- show ip rip interface brief
- split-horizon
- Tunnel Interface Commands
- Virtual Router Redundancy Protocol Commands
- Pingable VRRP Interface
- VRRP Route/Interface Tracking
- Interface Tracking
- Route Tracking
- Commands in this Chapter
- ip vrrp
- vrrp accept-mode
- vrrp authentication
- vrrp description
- vrrp ip
- vrrp mode
- vrrp preempt
- vrrp priority
- vrrp timers advertise
- vrrp timers learn
- vrrp track interface
- vrrp track ip route
- show vrrp
- show vrrp interface
- show vrrp interface brief
- show vrrp interface stats
- ip vrrp accept-mode
- show ip vrrp interface
- Utility Commands
- Auto-Install Commands
- Captive Portal Commands
- Commands in this Chapter
- authentication timeout
- captive-portal
- enable
- http port
- https port
- show captive-portal
- show captive-portal status
- block
- configuration
- enable
- group
- interface
- locale
- name (Captive Portal)
- protocol
- redirect
- redirect-url
- session-timeout
- verification
- captive-portal client deauthenticate
- show captive-portal client status
- show captive-portal configuration client status
- show captive-portal interface client status
- show captive-portal interface configuration status
- clear captive-portal users
- no user
- show captive-portal user
- user group
- user-logout
- user name
- user password
- user session-timeout
- show captive-portal configuration
- show captive-portal configuration interface
- show captive-portal configuration locales
- show captive-portal configuration status
- user group
- user group moveusers
- user group name
- CLI Macro Commands
- Clock Commands
- Real-time Clock
- Simple Network Time Protocol
- Commands in this Chapter
- show sntp configuration
- show sntp server
- show sntp status
- sntp authenticate
- sntp authentication-key
- sntp broadcast client enable
- sntp client poll timer
- sntp server
- sntp trusted-key
- sntp unicast client enable
- clock timezone hours-offset
- no clock timezone
- clock summer-time recurring
- clock summer-time date
- no clock summer-time
- show clock
- Command Line Configuration Scripting Commands
- Configuration and Image File Commands
- Denial of Service Commands
- Line Commands
- Management ACL Commands
- Password Management Commands
- Configurable Minimum Password Length
- Password History
- Password Aging
- User Lockout
- Password Strength
- Commands in this Chapter
- passwords aging
- passwords history
- passwords lock-out
- passwords min-length
- passwords strength-check
- passwords strength minimum uppercase-letters
- passwords strength minimum lowercase-letters
- passwords strength minimum numeric- characters
- passwords strength minimum special-characters
- passwords strength max-limit consecutive- characters
- passwords strength max-limit repeated- characters
- passwords strength minimum character-classes
- passwords strength exclude-keyword
- enable password encrypted
- show passwords configuration
- show passwords result
- PHY Diagnostics Commands
- Power Over Ethernet Commands
- Flexible Power Management
- Commands in this Chapter
- power inline
- power inline detection
- power inline high-power
- power inline limit
- power inline management
- power inline powered-device
- power inline priority
- power inline reset
- power inline usage-threshold
- clear power inline statistics
- show power inline
- show power inline firmware-version
- RMON Commands
- SDM Templates Commands
- Serviceability Tracing Packet Commands
- Commands in this Chapter
- debug arp
- debug authentication interface
- debug auto-voip
- debug clear
- debug console
- debug dot1ag
- debug dot1x
- debug igmpsnooping
- debug ip acl
- debug ip dvmrp
- debug ip igmp
- debug ip mcache
- debug ip pimdm packet
- debug ip pimsm packet
- debug ip vrrp
- debug ipv6 dhcp
- debug ipv6 mcache
- debug ipv6 mld
- debug ipv6 pimdm
- debug ipv6 pimsm
- debug isdp
- debug lacp
- debug mldsnooping
- debug ospf
- debug ospfv3
- debug ping
- debug rip
- debug sflow
- debug spanning-tree
- debug vrrp
- exception core-file
- exception dump
- exception protocol
- exception switch-chip-register
- show debugging
- show exception
- write core
- Sflow Commands
- SNMP Commands
- Commands in this Chapter
- show snmp
- show snmp engineID
- show snmp filters
- show snmp group
- show snmp user
- show snmp views
- show trapflags
- snmp-server community
- snmp-server community-group
- snmp-server contact
- snmp-server enable traps
- snmp-server engineID local
- snmp-server filter
- snmp-server group
- snmp-server host
- snmp-server location
- snmp-server user
- snmp-server view
- snmp-server v3-host
- SSH Commands
- Syslog Commands
- CLI Logged to Local File and Syslog Server
- Commands in this Chapter
- clear logging
- clear logging file
- description (Logging)
- level
- logging cli-command
- logging
- logging audit
- logging buffered
- logging console
- logging facility
- logging file
- logging monitor
- logging on
- logging protocol
- logging snmp
- logging web-session
- port
- show logging
- show logging file
- show syslog-servers
- terminal monitor
- System Management Commands
- asset-tag
- banner exec
- banner login
- banner motd
- banner motd acknowledge
- clear checkpoint statistics
- clear counters stack-ports
- connect
- cut-through mode
- exec-banner
- exit
- hardware profile portmode
- hostname
- initiate failover
- load-interval
- locate
- login-banner
- logout
- member
- motd-banner
- nsf
- ping
- quit
- reload
- service unsupported-transceiver
- set description
- slot
- show banner
- show checkpoint statistics
- show cut-through mode
- show hardware profile
- show idprom interface interface-id
- show interfaces advanced firmware
- show interfaces interface-id
- show interfaces utilization
- show memory cpu
- show nsf
- show power-usage-history
- show process cpu
- show sessions
- show slot
- show supported cardtype
- show supported switchtype
- show switch
- show system
- show system fan
- show system id
- show system power
- show system temperature
- show tech-support
- show users
- show version
- stack
- stack-port
- stack-port interface shutdown
- standby
- switch renumber
- telnet
- traceroute
- traceroute ipv6
- update bootcode
- Telnet Server Commands
- Terminal Length Commands
- Time Ranges Commands
- USB Flash Drive Commands
- User Interface Commands
- Web Server Commands
- Web Sessions
- Commands in this Chapter
- common-name
- country
- crypto certificate generate
- crypto certificate import
- crypto certificate request
- duration
- ip http port
- ip http server
- ip http secure-certificate
- ip http secure-port
- ip http secure-server
- key-generate
- location
- organization-unit
- show crypto certificate mycertificate
- show ip http server status
- show ip http server secure status
- state
- Appendix A: List of Commands

Dell Networking
2024/2048/3024/3048/4032/4064
CLI Reference Guide
Regulatory Model: N2024/N2024P/N2048/
N2048P/N3024/N3024F/N3024P/N3048/
N3048P/N4032/N4032F/N4064/N4064F
2CSNXXX_SWUM200.book Page 1 Tuesday, December 10, 2013 1:22 PM
Notes
NOTE: A NOTE indicates important information that helps you make better use of
your computer.
CAUTION: A CAUTION indicates potential damage to hardware or loss of data if
instructions are not followed.
____________________
Information in this publication is subject to change without notice.
© 2013 Dell Inc. All rights reserved.
Reproduction of these materials in any manner whatsoever without the written permission of Dell Inc.
is strictly forbidden.
Trademarks used in this text: Dell™, the DELL logo, and PowerConnect™ are trademarks of Dell
Inc. StrataXGS® is a registered trademark of Broadcom Corp. sFlow® is a registered trademark of
InMon Corporation. Cisco® is a registered trademark of Cisco Systems, Inc. and/or its affiliates in the
United States and certain other countries. Microsoft® and Windows®are registered trademarks of
Microsoft Corporation in the United States and/or other countries.
Other trademarks and trade names may be used in this publication to refer to either the entities claiming
the marks and names or their products. Dell Inc. disclaims any proprietary interest in trademarks and
trade names other than its own.
Regulatory Model N2024/N2024P/N2048/N2048P/N3024/N3024F/N3024P/N3048/N3048P/N4032/N4032F/N4064/N4064F
2013 - December Rev. A02
2CSNXXX_SWUM200.book Page 2 Tuesday, December 10, 2013 1:22 PM

Contents 3
Contents
1 Command Groups . . . . . . . . . . . . . . . . . . 83
Introduction . . . . . . . . . . . . . . . . . . . . . . . 83
Command Groups . . . . . . . . . . . . . . . . . . . . 83
Mode Types . . . . . . . . . . . . . . . . . . . . . . . 87
Layer 2 Commands . . . . . . . . . . . . . . . . . . . . 89
Layer 3 Commands . . . . . . . . . . . . . . . . . . . . 127
Utility Commands . . . . . . . . . . . . . . . . . . . . 156
2 Using the CLI . . . . . . . . . . . . . . . . . . . . . 179
Introduction . . . . . . . . . . . . . . . . . . . . . . . 179
Entering and Editing CLI Commands. . . . . . . . . . . 179
CLI Command Modes . . . . . . . . . . . . . . . . . . 190
Starting the CLI. . . . . . . . . . . . . . . . . . . . . . 203
Using CLI Functions and Tools. . . . . . . . . . . . . . 203
2CSNXXX_SWUM200.book Page 3 Tuesday, December 10, 2013 1:22 PM

Contents 4
3 Layer 2 Switching Commands . . . . . . . . 215
4 AAA Commands . . . . . . . . . . . . . . . . . . . 217
TACACS+ Accounting . . . . . . . . . . . . . . . . . . 218
Commands in this Chapter. . . . . . . . . . . . . . . . 219
aaa authentication dot1x default . . . . . . . . . . . . 220
aaa authentication enable. . . . . . . . . . . . . . . . 221
aaa authentication login. . . . . . . . . . . . . . . . . 223
aaa authorization . . . . . . . . . . . . . . . . . . . . 224
aaa authorization network default radius. . . . . . . . 227
aaa ias-user username . . . . . . . . . . . . . . . . . 227
aaa new-model . . . . . . . . . . . . . . . . . . . . . 228
clear (IAS) . . . . . . . . . . . . . . . . . . . . . . . . 229
authorization . . . . . . . . . . . . . . . . . . . . . . . 229
enable authentication . . . . . . . . . . . . . . . . . . 230
enable password . . . . . . . . . . . . . . . . . . . . 231
ip http authentication . . . . . . . . . . . . . . . . . . 232
ip https authentication. . . . . . . . . . . . . . . . . . 233
login authentication . . . . . . . . . . . . . . . . . . . 235
password (aaa IAS User Configuration). . . . . . . . . 236
password (Line Configuration) . . . . . . . . . . . . . 237
2CSNXXX_SWUM200.book Page 4 Tuesday, December 10, 2013 1:22 PM

Contents 5
password (User EXEC) . . . . . . . . . . . . . . . . . . 238
show aaa ias-users . . . . . . . . . . . . . . . . . . . 238
show aaa statistics . . . . . . . . . . . . . . . . . . . 239
show authentication methods. . . . . . . . . . . . . . 240
show authorization methods . . . . . . . . . . . . . . 241
show users accounts . . . . . . . . . . . . . . . . . . 242
show users login-history . . . . . . . . . . . . . . . . 243
username. . . . . . . . . . . . . . . . . . . . . . . . . 244
username unlock . . . . . . . . . . . . . . . . . . . . 246
5 Administrative Profiles Commands . . . . 249
Overview . . . . . . . . . . . . . . . . . . . . . . . . . 249
Commands in this Chapter. . . . . . . . . . . . . . . . 250
admin-profile. . . . . . . . . . . . . . . . . . . . . . . 251
description (Administrative Profile Configuration) . . . 251
rule . . . . . . . . . . . . . . . . . . . . . . . . . . . . 252
show admin-profiles. . . . . . . . . . . . . . . . . . . 253
show admin-profiles brief . . . . . . . . . . . . . . . . 254
show cli modes . . . . . . . . . . . . . . . . . . . . . 255
6 ACL Commands . . . . . . . . . . . . . . . . . . . 257
ACL Logging . . . . . . . . . . . . . . . . . . . . . . . 257
2CSNXXX_SWUM200.book Page 5 Tuesday, December 10, 2013 1:22 PM

Contents 6
Commands in this Chapter. . . . . . . . . . . . . . . . 260
ip access-list. . . . . . . . . . . . . . . . . . . . . . . 260
deny | permit (IP ACL) . . . . . . . . . . . . . . . . . . 261
deny | permit (Mac-Access-List-Configuration) . . . . 266
ip access-group . . . . . . . . . . . . . . . . . . . . . 268
mac access-group . . . . . . . . . . . . . . . . . . . . 270
mac access-list extended . . . . . . . . . . . . . . . . 271
mac access-list extended rename . . . . . . . . . . . 272
service-acl input. . . . . . . . . . . . . . . . . . . . . 273
show service-acl interface . . . . . . . . . . . . . . . 274
show access-lists interface . . . . . . . . . . . . . . . 274
show ip access-lists. . . . . . . . . . . . . . . . . . . 275
show mac access-lists . . . . . . . . . . . . . . . . . 276
7 Address Table Commands . . . . . . . . . . . 279
Commands in this Chapter. . . . . . . . . . . . . . . . 280
clear mac address-table. . . . . . . . . . . . . . . . . 280
mac address-table aging-time . . . . . . . . . . . . . 281
mac address-table multicast forbidden address . . . . 282
mac address-table static vlan . . . . . . . . . . . . . . 283
port security . . . . . . . . . . . . . . . . . . . . . . . 284
port security max . . . . . . . . . . . . . . . . . . . . 285
2CSNXXX_SWUM200.book Page 6 Tuesday, December 10, 2013 1:22 PM

Contents 7
show mac address-table multicast . . . . . . . . . . . 285
show mac address-table . . . . . . . . . . . . . . . . 287
show mac address-table address . . . . . . . . . . . . 287
show mac address-table count . . . . . . . . . . . . . 288
show mac address-table dynamic . . . . . . . . . . . 289
show mac address-table interface . . . . . . . . . . . 290
show mac address-table static . . . . . . . . . . . . . 291
show mac address-table vlan . . . . . . . . . . . . . . 292
show ports security . . . . . . . . . . . . . . . . . . . 293
show ports security addresses . . . . . . . . . . . . . 294
8 Auto-VoIP Commands . . . . . . . . . . . . . . 297
Commands in this Chapter. . . . . . . . . . . . . . . . 297
show switchport voice . . . . . . . . . . . . . . . . . 298
switchport voice detect auto . . . . . . . . . . . . . . 300
9 CDP Interoperability Commands . . . . . . 301
Commands in this Chapter. . . . . . . . . . . . . . . . 301
clear isdp counters . . . . . . . . . . . . . . . . . . . 301
clear isdp table . . . . . . . . . . . . . . . . . . . . . 302
isdp advertise-v2. . . . . . . . . . . . . . . . . . . . . 302
isdp enable. . . . . . . . . . . . . . . . . . . . . . . . 303
2CSNXXX_SWUM200.book Page 7 Tuesday, December 10, 2013 1:22 PM

Contents 8
isdp holdtime. . . . . . . . . . . . . . . . . . . . . . . 304
isdp timer . . . . . . . . . . . . . . . . . . . . . . . . 304
show isdp . . . . . . . . . . . . . . . . . . . . . . . . 305
show isdp entry . . . . . . . . . . . . . . . . . . . . . 306
show isdp interface . . . . . . . . . . . . . . . . . . . 307
show isdp neighbors. . . . . . . . . . . . . . . . . . . 308
show isdp traffic . . . . . . . . . . . . . . . . . . . . . 309
10 DHCP Layer 2 Relay Commands . . . . . . 311
Commands in this Chapter. . . . . . . . . . . . . . . . 311
dhcp l2relay (Global Configuration) . . . . . . . . . . . 312
dhcp l2relay (Interface Configuration) . . . . . . . . . 312
dhcp l2relay circuit-id . . . . . . . . . . . . . . . . . . 313
dhcp l2relay remote-id. . . . . . . . . . . . . . . . . . 314
dhcp l2relay trust . . . . . . . . . . . . . . . . . . . . 314
dhcp l2relay vlan. . . . . . . . . . . . . . . . . . . . . 315
show dhcp l2relay all . . . . . . . . . . . . . . . . . . 316
show dhcp l2relay interface. . . . . . . . . . . . . . . 316
show dhcp l2relay stats interface. . . . . . . . . . . . 317
show dhcp l2relay subscription interface . . . . . . . 318
show dhcp l2relay agent-option vlan . . . . . . . . . . 319
show dhcp l2relay vlan . . . . . . . . . . . . . . . . . 319
2CSNXXX_SWUM200.book Page 8 Tuesday, December 10, 2013 1:22 PM

Contents 9
show dhcp l2relay circuit-id vlan . . . . . . . . . . . . 320
show dhcp l2relay remote-id vlan. . . . . . . . . . . . 321
clear dhcp l2relay statistics interface . . . . . . . . . 322
11 DHCP Management Interface Commands 323
Commands in this Chapter. . . . . . . . . . . . . . . . 323
release dhcp . . . . . . . . . . . . . . . . . . . . . . . 324
renew dhcp . . . . . . . . . . . . . . . . . . . . . . . 325
debug dhcp packet . . . . . . . . . . . . . . . . . . . 326
show dhcp lease. . . . . . . . . . . . . . . . . . . . . 326
12 DHCP Snooping Commands . . . . . . . . . . 329
Commands in this Chapter. . . . . . . . . . . . . . . . 330
clear ip dhcp snooping binding . . . . . . . . . . . . . 330
clear ip dhcp snooping statistics . . . . . . . . . . . . 331
ip dhcp snooping. . . . . . . . . . . . . . . . . . . . . 331
ip dhcp snooping binding . . . . . . . . . . . . . . . . 332
ip dhcp snooping database . . . . . . . . . . . . . . . 333
ip dhcp snooping database write-delay . . . . . . . . 334
ip dhcp snooping limit . . . . . . . . . . . . . . . . . . 335
ip dhcp snooping log-invalid . . . . . . . . . . . . . . 336
ip dhcp snooping trust . . . . . . . . . . . . . . . . . . 337
2CSNXXX_SWUM200.book Page 9 Tuesday, December 10, 2013 1:22 PM

Contents 10
ip dhcp snooping verify mac-address . . . . . . . . . . 338
show ip dhcp snooping . . . . . . . . . . . . . . . . . 338
show ip dhcp snooping binding . . . . . . . . . . . . . 339
show ip dhcp snooping database . . . . . . . . . . . . 340
show ip dhcp snooping interfaces . . . . . . . . . . . 341
show ip dhcp snooping statistics . . . . . . . . . . . . 342
13 Dynamic ARP Inspection Commands . . 345
Commands in this Chapter. . . . . . . . . . . . . . . . 345
arp access-list . . . . . . . . . . . . . . . . . . . . . . 345
clear ip arp inspection statistics . . . . . . . . . . . . 346
ip arp inspection filter . . . . . . . . . . . . . . . . . . 347
ip arp inspection limit . . . . . . . . . . . . . . . . . . 347
ip arp inspection trust . . . . . . . . . . . . . . . . . . 348
ip arp inspection validate . . . . . . . . . . . . . . . . 349
ip arp inspection vlan . . . . . . . . . . . . . . . . . . 350
permit ip host mac host . . . . . . . . . . . . . . . . . 351
show arp access-list . . . . . . . . . . . . . . . . . . 351
show ip arp inspection . . . . . . . . . . . . . . . . . 352
show ip arp inspection vlan . . . . . . . . . . . . . . . 354
2CSNXXX_SWUM200.book Page 10 Tuesday, December 10, 2013 1:22 PM

Contents 11
14 E-mail Alerting Commands . . . . . . . . . . 357
Commands in this Chapter. . . . . . . . . . . . . . . . 358
logging email . . . . . . . . . . . . . . . . . . . . . . 358
logging email urgent. . . . . . . . . . . . . . . . . . . 359
logging traps . . . . . . . . . . . . . . . . . . . . . . . 360
logging email message-type to-addr . . . . . . . . . . 361
logging email from-addr . . . . . . . . . . . . . . . . . 362
logging email message-type subject . . . . . . . . . . 363
logging email logtime . . . . . . . . . . . . . . . . . . 363
logging email test message-type . . . . . . . . . . . . 364
show logging email statistics . . . . . . . . . . . . . . 364
clear logging email statistics . . . . . . . . . . . . . . 365
security. . . . . . . . . . . . . . . . . . . . . . . . . . 366
mail-server ip-address | hostname . . . . . . . . . . . 366
port (Mail Server Configuration Mode) . . . . . . . . . 367
username (Mail Server Configuration Mode) . . . . . . 368
password (Mail Server Configuration Mode) . . . . . . 368
show mail-server . . . . . . . . . . . . . . . . . . . . 369
15 Ethernet Configuration Commands . . . . 371
Commands in this Chapter. . . . . . . . . . . . . . . . 372
2CSNXXX_SWUM200.book Page 11 Tuesday, December 10, 2013 1:22 PM

Contents 12
clear counters . . . . . . . . . . . . . . . . . . . . . . 372
description . . . . . . . . . . . . . . . . . . . . . . . . 373
duplex . . . . . . . . . . . . . . . . . . . . . . . . . . 374
flowcontrol receive . . . . . . . . . . . . . . . . . . . 374
interface . . . . . . . . . . . . . . . . . . . . . . . . . 375
interface range. . . . . . . . . . . . . . . . . . . . . . 376
monitor capture (Global Configuration) . . . . . . . . . 377
monitor capture (Privileged Exec) . . . . . . . . . . . 382
rate-limit cpu. . . . . . . . . . . . . . . . . . . . . . . 383
show interfaces advertise. . . . . . . . . . . . . . . . 385
show interfaces configuration . . . . . . . . . . . . . 387
show interfaces counters . . . . . . . . . . . . . . . . 388
show interfaces description. . . . . . . . . . . . . . . 391
show interfaces detail. . . . . . . . . . . . . . . . . . 392
show interfaces status . . . . . . . . . . . . . . . . . 393
show interfaces transceiver. . . . . . . . . . . . . . . 396
show monitor capture . . . . . . . . . . . . . . . . . . 397
show statistics. . . . . . . . . . . . . . . . . . . . . . 398
show statistics switchport . . . . . . . . . . . . . . . 401
show storm-control . . . . . . . . . . . . . . . . . . . 403
shutdown. . . . . . . . . . . . . . . . . . . . . . . . . 403
2CSNXXX_SWUM200.book Page 12 Tuesday, December 10, 2013 1:22 PM

Contents 13
speed . . . . . . . . . . . . . . . . . . . . . . . . . . . 404
storm-control broadcast . . . . . . . . . . . . . . . . . 406
storm-control multicast . . . . . . . . . . . . . . . . . 406
storm-control unicast . . . . . . . . . . . . . . . . . . 407
switchport protected . . . . . . . . . . . . . . . . . . 408
switchport protected name . . . . . . . . . . . . . . . 409
show switchport protected . . . . . . . . . . . . . . . 410
show system internal pktmgr . . . . . . . . . . . . . . 410
show system mtu . . . . . . . . . . . . . . . . . . . . 411
system jumbo mtu . . . . . . . . . . . . . . . . . . . . 412
16 Ethernet CFM Commands . . . . . . . . . . . 415
Commands in this Chapter. . . . . . . . . . . . . . . . 415
ethernet cfm domain . . . . . . . . . . . . . . . . . . . 416
service . . . . . . . . . . . . . . . . . . . . . . . . . . 417
ethernet cfm cc level . . . . . . . . . . . . . . . . . . 417
ethernet cfm mep level . . . . . . . . . . . . . . . . . 418
ethernet cfm mep enable . . . . . . . . . . . . . . . . 419
ethernet cfm mep active . . . . . . . . . . . . . . . . . 420
ethernet cfm mep archive-hold-time . . . . . . . . . . 420
ethernet cfm mip level . . . . . . . . . . . . . . . . . . 421
ping ethernet cfm . . . . . . . . . . . . . . . . . . . . 422
2CSNXXX_SWUM200.book Page 13 Tuesday, December 10, 2013 1:22 PM

Contents 14
traceroute ethernet cfm . . . . . . . . . . . . . . . . . 423
show ethernet cfm errors . . . . . . . . . . . . . . . . 424
show ethernet cfm domain . . . . . . . . . . . . . . . 424
show ethernet cfm maintenance-points local . . . . . 425
show ethernet cfm maintenance-points remote . . . . 426
show ethernet cfm statistics . . . . . . . . . . . . . . 427
debug cfm . . . . . . . . . . . . . . . . . . . . . . . . 428
17 Green Ethernet Commands . . . . . . . . . . 431
Energy-Detect Mode. . . . . . . . . . . . . . . . . . . 431
Energy Efficient Ethernet . . . . . . . . . . . . . . . . 431
Commands in this Chapter. . . . . . . . . . . . . . . . 431
green-mode energy-detect . . . . . . . . . . . . . . . 432
green-mode eee . . . . . . . . . . . . . . . . . . . . . 433
clear green-mode statistics . . . . . . . . . . . . . . . 434
green-mode eee-lpi-history . . . . . . . . . . . . . . . 434
show green-mode interface-id . . . . . . . . . . . . . 435
show green-mode . . . . . . . . . . . . . . . . . . . . 439
show green-mode eee-lpi-history interface . . . . . . 440
18 GVRP Commands . . . . . . . . . . . . . . . . . . 443
Commands in this Chapter. . . . . . . . . . . . . . . . 443
2CSNXXX_SWUM200.book Page 14 Tuesday, December 10, 2013 1:22 PM

Contents 15
clear gvrp statistics . . . . . . . . . . . . . . . . . . . 443
garp timer . . . . . . . . . . . . . . . . . . . . . . . . 444
gvrp enable (global) . . . . . . . . . . . . . . . . . . . 445
gvrp enable (interface) . . . . . . . . . . . . . . . . . 446
gvrp registration-forbid . . . . . . . . . . . . . . . . . 447
gvrp vlan-creation-forbid . . . . . . . . . . . . . . . . 448
show gvrp configuration. . . . . . . . . . . . . . . . . 448
show gvrp error-statistics . . . . . . . . . . . . . . . . 450
show gvrp statistics . . . . . . . . . . . . . . . . . . . 451
19 IGMP Snooping Commands . . . . . . . . . . 453
Commands in this Chapter. . . . . . . . . . . . . . . . 454
ip igmp snooping. . . . . . . . . . . . . . . . . . . . . 454
show ip igmp snooping . . . . . . . . . . . . . . . . . 456
show ip igmp snooping groups . . . . . . . . . . . . . 457
show ip igmp snooping mrouter. . . . . . . . . . . . . 458
ip igmp snooping vlan immediate-leave . . . . . . . . 459
ip igmp snooping vlan groupmembership-interval . . . 460
ip igmp snooping vlan last-member-query-interval . . 461
ip igmp snooping vlan mcrtrexpiretime . . . . . . . . . 462
ip igmp snooping report-suppression . . . . . . . . . . 462
ip igmp snooping unregistered floodall. . . . . . . . . 463
2CSNXXX_SWUM200.book Page 15 Tuesday, December 10, 2013 1:22 PM

Contents 16
ip igmp snooping vlan mrouter . . . . . . . . . . . . . 464
20 IGMP Snooping Querier Commands . . . 467
Commands in this Chapter. . . . . . . . . . . . . . . . 467
ip igmp snooping querier . . . . . . . . . . . . . . . . 468
ip igmp snooping querier election participate . . . . . 469
ip igmp snooping querier query-interval . . . . . . . . 470
ip igmp snooping querier timer expiry . . . . . . . . . 471
ip igmp snooping querier version . . . . . . . . . . . . 472
show ip igmp snooping querier . . . . . . . . . . . . . 473
21 IP Addressing Commands . . . . . . . . . . . 477
Commands in this Chapter. . . . . . . . . . . . . . . . 477
clear host . . . . . . . . . . . . . . . . . . . . . . . . 478
clear ip address-conflict-detect . . . . . . . . . . . . 478
interface out-of-band . . . . . . . . . . . . . . . . . . 479
ip address (Out-of-Band) . . . . . . . . . . . . . . . . 479
ip address-conflict-detect run. . . . . . . . . . . . . . 481
ip address dhcp (Interface Configuration) . . . . . . . 481
ip default-gateway. . . . . . . . . . . . . . . . . . . . 483
ip domain-lookup . . . . . . . . . . . . . . . . . . . . 484
ip domain-name . . . . . . . . . . . . . . . . . . . . . 484
2CSNXXX_SWUM200.book Page 16 Tuesday, December 10, 2013 1:22 PM

Contents 17
ip host . . . . . . . . . . . . . . . . . . . . . . . . . . 485
ip name-server . . . . . . . . . . . . . . . . . . . . . . 486
ipv6 address (Interface Configuration) . . . . . . . . . 487
ipv6 address (OOB Port) . . . . . . . . . . . . . . . . . 488
ipv6 address dhcp . . . . . . . . . . . . . . . . . . . . 489
ipv6 enable (Interface Configuration) . . . . . . . . . . 490
ipv6 enable (OOB Configuration) . . . . . . . . . . . . 491
ipv6 gateway (OOB Configuration) . . . . . . . . . . . 491
show hosts . . . . . . . . . . . . . . . . . . . . . . . . 492
show ip address-conflict . . . . . . . . . . . . . . . . 493
show ip helper-address . . . . . . . . . . . . . . . . . 494
show ipv6 dhcp interface out-of-band statistics . . . . 495
show ipv6 interface out-of-band . . . . . . . . . . . . 496
22 IPv6 Access List Commands . . . . . . . . . 497
Commands in this Chapter. . . . . . . . . . . . . . . . 497
deny | permit (IPv6 ACL) . . . . . . . . . . . . . . . . . 498
ipv6 access-list . . . . . . . . . . . . . . . . . . . . . 504
ipv6 access-list rename . . . . . . . . . . . . . . . . . 504
ipv6 traffic-filter . . . . . . . . . . . . . . . . . . . . . 505
show ipv6 access-lists . . . . . . . . . . . . . . . . . 507
2CSNXXX_SWUM200.book Page 17 Tuesday, December 10, 2013 1:22 PM

Contents 18
23 IPv6 MLD Snooping Commands. . . . . . . 509
Commands in this Chapter. . . . . . . . . . . . . . . . 509
ipv6 mld snooping vlan groupmembership-interval . . 510
ipv6 mld snooping vlan immediate-leave . . . . . . . . 510
ipv6 mld snooping listener-message-suppression . . . 511
ipv6 mld snooping vlan last-listener-query-interval . . 512
ipv6 mld snooping vlan mcrtexpiretime. . . . . . . . . 513
ipv6 mld snooping vlan mrouter . . . . . . . . . . . . . 514
ipv6 mld snooping (Global) . . . . . . . . . . . . . . . 514
show ipv6 mld snooping . . . . . . . . . . . . . . . . . 515
show ipv6 mld snooping groups. . . . . . . . . . . . . 517
show ipv6 mld snooping mrouter . . . . . . . . . . . . 519
24 IPv6 MLD Snooping Querier Commands 521
Commands in this Chapter. . . . . . . . . . . . . . . . 521
ipv6 mld snooping querier . . . . . . . . . . . . . . . . 521
ipv6 mld snooping querier (VLAN mode) . . . . . . . . 522
ipv6 mld snooping querier address . . . . . . . . . . . 523
ipv6 mld snooping querier election participate. . . . . 523
ipv6 mld snooping querier query-interval. . . . . . . . 524
ipv6 mld snooping querier timer expiry . . . . . . . . . 525
2CSNXXX_SWUM200.book Page 18 Tuesday, December 10, 2013 1:22 PM

Contents 19
show ipv6 mld snooping querier . . . . . . . . . . . . 526
25 IP Source Guard Commands . . . . . . . . . 529
Commands in this Chapter. . . . . . . . . . . . . . . . 529
ip verify source . . . . . . . . . . . . . . . . . . . . . 529
ip verify source port-security . . . . . . . . . . . . . . 531
ip verify binding . . . . . . . . . . . . . . . . . . . . . 531
show ip verify . . . . . . . . . . . . . . . . . . . . . . 532
show ip verify source . . . . . . . . . . . . . . . . . . 533
show ip source binding . . . . . . . . . . . . . . . . . 534
26 iSCSI Optimization Commands . . . . . . . 535
Commands in this Chapter. . . . . . . . . . . . . . . . 536
iscsi aging time . . . . . . . . . . . . . . . . . . . . . 536
iscsi cos . . . . . . . . . . . . . . . . . . . . . . . . . 537
iscsi enable . . . . . . . . . . . . . . . . . . . . . . . 539
iscsi target port . . . . . . . . . . . . . . . . . . . . . 540
show iscsi . . . . . . . . . . . . . . . . . . . . . . . . 542
show iscsi sessions . . . . . . . . . . . . . . . . . . . 543
27 Link Dependency Commands . . . . . . . . 545
Commands in this Chapter. . . . . . . . . . . . . . . . 545
2CSNXXX_SWUM200.book Page 19 Tuesday, December 10, 2013 1:22 PM

Contents 20
action. . . . . . . . . . . . . . . . . . . . . . . . . . . 545
link-dependency group . . . . . . . . . . . . . . . . . 546
add . . . . . . . . . . . . . . . . . . . . . . . . . . . . 547
depends-on. . . . . . . . . . . . . . . . . . . . . . . . 547
show link-dependency . . . . . . . . . . . . . . . . . 548
28 LLDP Commands . . . . . . . . . . . . . . . . . . 551
Commands in this Chapter. . . . . . . . . . . . . . . . 552
clear lldp remote-data . . . . . . . . . . . . . . . . . . 552
clear lldp statistics . . . . . . . . . . . . . . . . . . . 553
dcb enable . . . . . . . . . . . . . . . . . . . . . . . . 554
lldp med . . . . . . . . . . . . . . . . . . . . . . . . . 554
lldp med confignotification . . . . . . . . . . . . . . . 555
lldp med faststartrepeatcount . . . . . . . . . . . . . . 555
lldp med transmit-tlv. . . . . . . . . . . . . . . . . . . 556
lldp notification . . . . . . . . . . . . . . . . . . . . . 557
lldp notification-interval. . . . . . . . . . . . . . . . . 557
lldp receive . . . . . . . . . . . . . . . . . . . . . . . 558
lldp timers . . . . . . . . . . . . . . . . . . . . . . . . 559
lldp transmit . . . . . . . . . . . . . . . . . . . . . . . 560
lldp transmit-mgmt. . . . . . . . . . . . . . . . . . . . 561
lldp transmit-tlv . . . . . . . . . . . . . . . . . . . . . 561
2CSNXXX_SWUM200.book Page 20 Tuesday, December 10, 2013 1:22 PM

Contents 21
show lldp. . . . . . . . . . . . . . . . . . . . . . . . . 562
show lldp interface . . . . . . . . . . . . . . . . . . . 563
show lldp local-device . . . . . . . . . . . . . . . . . 564
show lldp med . . . . . . . . . . . . . . . . . . . . . . 565
show lldp med interface. . . . . . . . . . . . . . . . . 566
show lldp med local-device detail . . . . . . . . . . . 567
show lldp med remote-device. . . . . . . . . . . . . . 568
show lldp remote-device . . . . . . . . . . . . . . . . 570
show lldp statistics . . . . . . . . . . . . . . . . . . . 571
29 Multicast VLAN Registration Commands 575
Commands in this Chapter. . . . . . . . . . . . . . . . 576
mvr . . . . . . . . . . . . . . . . . . . . . . . . . . . . 576
mvr group . . . . . . . . . . . . . . . . . . . . . . . . 576
mvr mode . . . . . . . . . . . . . . . . . . . . . . . . . 577
mvr querytime . . . . . . . . . . . . . . . . . . . . . . 578
mvr vlan . . . . . . . . . . . . . . . . . . . . . . . . . 579
mvr immediate . . . . . . . . . . . . . . . . . . . . . . 580
mvr type . . . . . . . . . . . . . . . . . . . . . . . . . 581
mvr vlan group . . . . . . . . . . . . . . . . . . . . . . 582
show mvr. . . . . . . . . . . . . . . . . . . . . . . . . 583
show mvr members . . . . . . . . . . . . . . . . . . . 584
2CSNXXX_SWUM200.book Page 21 Tuesday, December 10, 2013 1:22 PM

Contents 22
show mvr interface . . . . . . . . . . . . . . . . . . . 585
show mvr traffic . . . . . . . . . . . . . . . . . . . . . 587
30 Port Channel Commands . . . . . . . . . . . . 589
Static LAGS . . . . . . . . . . . . . . . . . . . . . . . 590
VLANs and LAGs . . . . . . . . . . . . . . . . . . . . . 590
LAG Thresholds . . . . . . . . . . . . . . . . . . . . . 590
LAG Hashing . . . . . . . . . . . . . . . . . . . . . . . 591
Enhanced LAG Hashing . . . . . . . . . . . . . . . . . 591
Manual Aggregation of LAGs . . . . . . . . . . . . . . 592
Flexible Assignment of Ports to LAGs. . . . . . . . . . 592
Commands in this Chapter. . . . . . . . . . . . . . . . 592
channel-group . . . . . . . . . . . . . . . . . . . . . . 593
interface port-channel. . . . . . . . . . . . . . . . . . 594
interface range port-channel . . . . . . . . . . . . . . 594
hashing-mode . . . . . . . . . . . . . . . . . . . . . . 595
lacp port-priority . . . . . . . . . . . . . . . . . . . . . 596
lacp system-priority . . . . . . . . . . . . . . . . . . . 597
lacp timeout . . . . . . . . . . . . . . . . . . . . . . . 598
port-channel local-preference . . . . . . . . . . . . . 599
port-channel min-links . . . . . . . . . . . . . . . . . 600
show interfaces port-channel . . . . . . . . . . . . . . 601
2CSNXXX_SWUM200.book Page 22 Tuesday, December 10, 2013 1:22 PM

Contents 23
show lacp . . . . . . . . . . . . . . . . . . . . . . . . 602
show statistics port-channel . . . . . . . . . . . . . . 604
31 MLAG . . . . . . . . . . . . . . . . . . . . . . . . . . . 607
Commands in this Chapter. . . . . . . . . . . . . . . . 607
clear vpc statistics . . . . . . . . . . . . . . . . . . . 607
debug vpc . . . . . . . . . . . . . . . . . . . . . . . . 608
feature vpc . . . . . . . . . . . . . . . . . . . . . . . . 609
peer-detection enable . . . . . . . . . . . . . . . . . . 610
peer-keepalive destination . . . . . . . . . . . . . . . 611
peer-keepalive enable. . . . . . . . . . . . . . . . . . 612
role priority. . . . . . . . . . . . . . . . . . . . . . . . 614
show vpc . . . . . . . . . . . . . . . . . . . . . . . . . 615
show vpc brief . . . . . . . . . . . . . . . . . . . . . . 616
show vpc consistency-parameters . . . . . . . . . . . 618
show vpc consistency-features . . . . . . . . . . . . . 619
show vpc peer-keepalive . . . . . . . . . . . . . . . . 619
show vpc role . . . . . . . . . . . . . . . . . . . . . . 620
show vpc statistics . . . . . . . . . . . . . . . . . . . 621
vpc . . . . . . . . . . . . . . . . . . . . . . . . . . . . 622
vpc domain . . . . . . . . . . . . . . . . . . . . . . . . 623
vpc peer-link . . . . . . . . . . . . . . . . . . . . . . . 624
2CSNXXX_SWUM200.book Page 23 Tuesday, December 10, 2013 1:22 PM

Contents 24
32 Port Monitor Commands . . . . . . . . . . . . 627
Commands in this Chapter. . . . . . . . . . . . . . . . 628
monitor session . . . . . . . . . . . . . . . . . . . . . 628
remote-span . . . . . . . . . . . . . . . . . . . . . . . 630
show monitor session . . . . . . . . . . . . . . . . . . 631
show vlan remote-span . . . . . . . . . . . . . . . . . 633
33 QoS Commands . . . . . . . . . . . . . . . . . . . 635
Access Control Lists . . . . . . . . . . . . . . . . . . . 635
Layer 2 ACLs . . . . . . . . . . . . . . . . . . . . . . . 636
Layer 3/4 IPv4 ACLs . . . . . . . . . . . . . . . . . . . 636
Class of Service (CoS) . . . . . . . . . . . . . . . . . . 636
Queue Mapping . . . . . . . . . . . . . . . . . . . . . 637
Commands in this Chapter. . . . . . . . . . . . . . . . 638
assign-queue. . . . . . . . . . . . . . . . . . . . . . . 639
class . . . . . . . . . . . . . . . . . . . . . . . . . . . 639
class-map . . . . . . . . . . . . . . . . . . . . . . . . 640
class-map rename . . . . . . . . . . . . . . . . . . . . 641
classofservice dot1p-mapping . . . . . . . . . . . . . 642
classofservice ip-dscp-mapping . . . . . . . . . . . . 643
classofservice trust . . . . . . . . . . . . . . . . . . . 646
2CSNXXX_SWUM200.book Page 24 Tuesday, December 10, 2013 1:22 PM

Contents 25
conform-color . . . . . . . . . . . . . . . . . . . . . . 647
cos-queue min-bandwidth . . . . . . . . . . . . . . . 649
cos-queue random-detect . . . . . . . . . . . . . . . . 650
cos-queue strict . . . . . . . . . . . . . . . . . . . . . 652
diffserv . . . . . . . . . . . . . . . . . . . . . . . . . . 653
drop. . . . . . . . . . . . . . . . . . . . . . . . . . . . 653
mark cos . . . . . . . . . . . . . . . . . . . . . . . . . 654
mark ip-dscp . . . . . . . . . . . . . . . . . . . . . . . 655
mark ip-precedence . . . . . . . . . . . . . . . . . . . 655
match class-map. . . . . . . . . . . . . . . . . . . . . 656
match cos . . . . . . . . . . . . . . . . . . . . . . . . 657
match destination-address mac. . . . . . . . . . . . . 658
match dstip. . . . . . . . . . . . . . . . . . . . . . . . 659
match dstip6 . . . . . . . . . . . . . . . . . . . . . . . 659
match dstl4port . . . . . . . . . . . . . . . . . . . . . 660
match ethertype . . . . . . . . . . . . . . . . . . . . . 661
match ip6flowlbl . . . . . . . . . . . . . . . . . . . . . 662
match ip dscp . . . . . . . . . . . . . . . . . . . . . . 662
match ip precedence . . . . . . . . . . . . . . . . . . 663
match ip tos . . . . . . . . . . . . . . . . . . . . . . . 664
match protocol . . . . . . . . . . . . . . . . . . . . . . 665
2CSNXXX_SWUM200.book Page 25 Tuesday, December 10, 2013 1:22 PM

Contents 26
match source-address mac . . . . . . . . . . . . . . . 666
match srcip. . . . . . . . . . . . . . . . . . . . . . . . 667
match srcip6 . . . . . . . . . . . . . . . . . . . . . . . 667
match srcl4port . . . . . . . . . . . . . . . . . . . . . 668
match vlan . . . . . . . . . . . . . . . . . . . . . . . . 669
mirror. . . . . . . . . . . . . . . . . . . . . . . . . . . 670
police-simple . . . . . . . . . . . . . . . . . . . . . . 670
police-single-rate . . . . . . . . . . . . . . . . . . . . 672
police-two-rate . . . . . . . . . . . . . . . . . . . . . 673
policy-map . . . . . . . . . . . . . . . . . . . . . . . . 674
random-detect queue-parms . . . . . . . . . . . . . . 675
random-detect exponential-weighting-constant . . . . 678
redirect. . . . . . . . . . . . . . . . . . . . . . . . . . 678
service-policy . . . . . . . . . . . . . . . . . . . . . . 679
show class-map . . . . . . . . . . . . . . . . . . . . . 680
show classofservice dot1p-mapping . . . . . . . . . . 682
show classofservice ip-dscp-mapping . . . . . . . . . 683
show classofservice trust . . . . . . . . . . . . . . . . 685
show diffserv. . . . . . . . . . . . . . . . . . . . . . . 686
show diffserv service interface . . . . . . . . . . . . . 686
show diffserv service interface port-channel . . . . . 687
2CSNXXX_SWUM200.book Page 26 Tuesday, December 10, 2013 1:22 PM

Contents 27
show diffserv service brief . . . . . . . . . . . . . . . 688
show interfaces cos-queue . . . . . . . . . . . . . . . 689
show interfaces random-detect . . . . . . . . . . . . . 691
show policy-map . . . . . . . . . . . . . . . . . . . . 691
show policy-map interface . . . . . . . . . . . . . . . 692
show service-policy . . . . . . . . . . . . . . . . . . . 693
traffic-shape . . . . . . . . . . . . . . . . . . . . . . . 694
vlan priority . . . . . . . . . . . . . . . . . . . . . . . 695
34 RADIUS Commands . . . . . . . . . . . . . . . . 697
Commands in this Chapter. . . . . . . . . . . . . . . . 700
aaa accounting dot1x default start-stop . . . . . . . . 701
accounting . . . . . . . . . . . . . . . . . . . . . . . . 702
acct-port . . . . . . . . . . . . . . . . . . . . . . . . . 703
auth-port . . . . . . . . . . . . . . . . . . . . . . . . . 704
deadtime . . . . . . . . . . . . . . . . . . . . . . . . . 705
debug aaa accounting . . . . . . . . . . . . . . . . . . 705
key . . . . . . . . . . . . . . . . . . . . . . . . . . . . 706
key encrypted . . . . . . . . . . . . . . . . . . . . . . 707
msgauth . . . . . . . . . . . . . . . . . . . . . . . . . 708
name (RADIUS server) . . . . . . . . . . . . . . . . . . 708
primary . . . . . . . . . . . . . . . . . . . . . . . . . . 709
2CSNXXX_SWUM200.book Page 27 Tuesday, December 10, 2013 1:22 PM

Contents 28
priority . . . . . . . . . . . . . . . . . . . . . . . . . . 710
radius-server attribute 4 . . . . . . . . . . . . . . . . . 711
radius-server deadtime . . . . . . . . . . . . . . . . . 712
radius-server host . . . . . . . . . . . . . . . . . . . . 713
radius-server key . . . . . . . . . . . . . . . . . . . . 714
radius-server key encrypted. . . . . . . . . . . . . . . 715
radius-server retransmit. . . . . . . . . . . . . . . . . 715
radius-server source-ip . . . . . . . . . . . . . . . . . 716
radius-server timeout . . . . . . . . . . . . . . . . . . 717
retransmit . . . . . . . . . . . . . . . . . . . . . . . . 718
show aaa servers . . . . . . . . . . . . . . . . . . . . 718
show accounting methods . . . . . . . . . . . . . . . 721
show radius statistics . . . . . . . . . . . . . . . . . . 721
source-ip . . . . . . . . . . . . . . . . . . . . . . . . . 725
timeout . . . . . . . . . . . . . . . . . . . . . . . . . . 726
usage . . . . . . . . . . . . . . . . . . . . . . . . . . . 726
35 Spanning Tree Commands . . . . . . . . . . . 729
Commands in this Chapter. . . . . . . . . . . . . . . . 730
clear spanning-tree detected-protocols . . . . . . . . 731
exit (mst) . . . . . . . . . . . . . . . . . . . . . . . . . 732
instance (mst) . . . . . . . . . . . . . . . . . . . . . . 732
2CSNXXX_SWUM200.book Page 28 Tuesday, December 10, 2013 1:22 PM

Contents 29
name (mst) . . . . . . . . . . . . . . . . . . . . . . . . 734
revision (mst). . . . . . . . . . . . . . . . . . . . . . . 735
show spanning-tree . . . . . . . . . . . . . . . . . . . 735
show spanning-tree summary . . . . . . . . . . . . . . 740
show spanning-tree vlan . . . . . . . . . . . . . . . . 741
spanning-tree . . . . . . . . . . . . . . . . . . . . . . 743
spanning-tree auto-portfast . . . . . . . . . . . . . . . 743
spanning-tree backbonefast. . . . . . . . . . . . . . . 744
spanning-tree bpdu flooding . . . . . . . . . . . . . . 745
spanning-tree bpdu-protection . . . . . . . . . . . . . 746
spanning-tree cost. . . . . . . . . . . . . . . . . . . . 747
spanning-tree disable . . . . . . . . . . . . . . . . . . 748
spanning-tree forward-time . . . . . . . . . . . . . . . 749
spanning-tree guard . . . . . . . . . . . . . . . . . . . 750
spanning-tree loopguard . . . . . . . . . . . . . . . . 750
spanning-tree max-age . . . . . . . . . . . . . . . . . 751
spanning-tree max-hops. . . . . . . . . . . . . . . . . 752
spanning-tree mode . . . . . . . . . . . . . . . . . . . 753
spanning-tree mst configuration . . . . . . . . . . . . 754
spanning-tree mst cost . . . . . . . . . . . . . . . . . 755
spanning-tree mst port-priority . . . . . . . . . . . . . 756
2CSNXXX_SWUM200.book Page 29 Tuesday, December 10, 2013 1:22 PM

Contents 30
spanning-tree mst priority . . . . . . . . . . . . . . . . 757
spanning-tree portfast . . . . . . . . . . . . . . . . . . 758
spanning-tree portfast bpdufilter default . . . . . . . . 759
spanning-tree portfast default. . . . . . . . . . . . . . 759
spanning-tree port-priority (Interface Configuration). . 760
spanning-tree priority . . . . . . . . . . . . . . . . . . 762
spanning-tree tcnguard . . . . . . . . . . . . . . . . . 763
spanning-tree transmit hold-count . . . . . . . . . . . 763
spanning-tree uplinkfast . . . . . . . . . . . . . . . . 764
spanning-tree vlan . . . . . . . . . . . . . . . . . . . 765
spanning-tree vlan forward-time . . . . . . . . . . . . 766
spanning-tree vlan hello-time . . . . . . . . . . . . . . 767
spanning-tree vlan max-age. . . . . . . . . . . . . . . 768
spanning-tree vlan root . . . . . . . . . . . . . . . . . 769
spanning-tree vlan priority . . . . . . . . . . . . . . . 769
36 TACACS+ Commands . . . . . . . . . . . . . . . 771
Commands in this Chapter. . . . . . . . . . . . . . . . 771
key . . . . . . . . . . . . . . . . . . . . . . . . . . . . 772
key encrypted . . . . . . . . . . . . . . . . . . . . . . 772
port . . . . . . . . . . . . . . . . . . . . . . . . . . . . 773
priority . . . . . . . . . . . . . . . . . . . . . . . . . . 774
2CSNXXX_SWUM200.book Page 30 Tuesday, December 10, 2013 1:22 PM

Contents 31
show tacacs . . . . . . . . . . . . . . . . . . . . . . . 774
tacacs-server host . . . . . . . . . . . . . . . . . . . . 775
tacacs-server key . . . . . . . . . . . . . . . . . . . . 776
tacacs-server key encrypted . . . . . . . . . . . . . . 777
tacacs-server timeout . . . . . . . . . . . . . . . . . . 778
timeout . . . . . . . . . . . . . . . . . . . . . . . . . . 778
37 UDLD Commands . . . . . . . . . . . . . . . . . . 781
Detecting Unidirectional Links on a Device Port . . . . 781
Processing UDLD Traffic from Neighbors . . . . . . . . 782
UDLD in Normal-mode. . . . . . . . . . . . . . . . . . 782
UDLD in Aggressive-mode. . . . . . . . . . . . . . . . 782
Commands in this Chapter. . . . . . . . . . . . . . . . 783
udld enable (Global Configuration) . . . . . . . . . . . 783
udld reset . . . . . . . . . . . . . . . . . . . . . . . . 784
udld message time. . . . . . . . . . . . . . . . . . . . 785
udld timeout interval. . . . . . . . . . . . . . . . . . . 785
udld enable (Interface Configuration). . . . . . . . . . 786
udld port . . . . . . . . . . . . . . . . . . . . . . . . . 787
show udld . . . . . . . . . . . . . . . . . . . . . . . . 787
debug udld . . . . . . . . . . . . . . . . . . . . . . . . 789
2CSNXXX_SWUM200.book Page 31 Tuesday, December 10, 2013 1:22 PM

Contents 32
38 VLAN Commands . . . . . . . . . . . . . . . . . . 791
Double VLAN Mode . . . . . . . . . . . . . . . . . . . 791
Independent VLAN Learning. . . . . . . . . . . . . . . 792
Protocol Based VLANs. . . . . . . . . . . . . . . . . . 792
IP Subnet Based VLANs . . . . . . . . . . . . . . . . . 793
MAC-Based VLANs . . . . . . . . . . . . . . . . . . . 793
Private VLAN Commands . . . . . . . . . . . . . . . . 793
Commands in this Chapter. . . . . . . . . . . . . . . . 796
dvlan-tunnel ethertype. . . . . . . . . . . . . . . . . . 797
interface vlan . . . . . . . . . . . . . . . . . . . . . . 799
interface range vlan . . . . . . . . . . . . . . . . . . . 800
mode dvlan-tunnel . . . . . . . . . . . . . . . . . . . . 801
name (VLAN Configuration) . . . . . . . . . . . . . . . 802
protocol group . . . . . . . . . . . . . . . . . . . . . . 803
protocol vlan group . . . . . . . . . . . . . . . . . . . 804
protocol vlan group all. . . . . . . . . . . . . . . . . . 805
show dvlan-tunnel . . . . . . . . . . . . . . . . . . . . 806
show dvlan-tunnel interface . . . . . . . . . . . . . . 807
show interfaces switchport . . . . . . . . . . . . . . . 808
show port protocol. . . . . . . . . . . . . . . . . . . . 811
show vlan . . . . . . . . . . . . . . . . . . . . . . . . 812
2CSNXXX_SWUM200.book Page 32 Tuesday, December 10, 2013 1:22 PM

Contents 33
show vlan association mac . . . . . . . . . . . . . . . 813
show vlan association subnet. . . . . . . . . . . . . . 814
switchport access vlan . . . . . . . . . . . . . . . . . 815
switchport general forbidden vlan . . . . . . . . . . . 816
switchport general acceptable-frame-type tagged-only 817
switchport general allowed vlan . . . . . . . . . . . . 817
switchport general ingress-filtering disable . . . . . . 818
switchport general pvid . . . . . . . . . . . . . . . . . 819
switchport mode . . . . . . . . . . . . . . . . . . . . . 820
switchport trunk . . . . . . . . . . . . . . . . . . . . . 821
vlan . . . . . . . . . . . . . . . . . . . . . . . . . . . . 823
vlan association mac . . . . . . . . . . . . . . . . . . 824
vlan association subnet . . . . . . . . . . . . . . . . . 825
vlan makestatic . . . . . . . . . . . . . . . . . . . . . 825
vlan protocol group . . . . . . . . . . . . . . . . . . . 826
vlan protocol group add protocol . . . . . . . . . . . . 827
vlan protocol group name . . . . . . . . . . . . . . . . 828
vlan protocol group remove . . . . . . . . . . . . . . . 829
switchport private-vlan . . . . . . . . . . . . . . . . . 830
switchport mode private-vlan . . . . . . . . . . . . . . 831
private-vlan . . . . . . . . . . . . . . . . . . . . . . . 832
2CSNXXX_SWUM200.book Page 33 Tuesday, December 10, 2013 1:22 PM

Contents 34
show vlan private-vlan . . . . . . . . . . . . . . . . . 833
39 Voice VLAN Commands . . . . . . . . . . . . . 835
Commands in this Chapter. . . . . . . . . . . . . . . . 836
voice vlan . . . . . . . . . . . . . . . . . . . . . . . . 836
voice vlan (Interface) . . . . . . . . . . . . . . . . . . 836
voice vlan data priority . . . . . . . . . . . . . . . . . 837
show voice vlan . . . . . . . . . . . . . . . . . . . . . 838
40 802.1x Commands . . . . . . . . . . . . . . . . . 841
Local 802.1X Authentication Server . . . . . . . . . . . 841
MAC Authentication Bypass. . . . . . . . . . . . . . . 842
Guest VLAN . . . . . . . . . . . . . . . . . . . . . . . 843
802.1x Monitor Mode . . . . . . . . . . . . . . . . . . 843
RADIUS-based Dynamic VLAN Assignment . . . . . . 844
Commands in this Chapter. . . . . . . . . . . . . . . . 844
dot1x dynamic-vlan enable . . . . . . . . . . . . . . . 845
dot1x initialize . . . . . . . . . . . . . . . . . . . . . . 846
dot1x eapolflood . . . . . . . . . . . . . . . . . . . . . 846
dot1x mac-auth-bypass . . . . . . . . . . . . . . . . . 847
dot1x max-req . . . . . . . . . . . . . . . . . . . . . . 848
dot1x max-users . . . . . . . . . . . . . . . . . . . . . 849
2CSNXXX_SWUM200.book Page 34 Tuesday, December 10, 2013 1:22 PM

Contents 35
dot1x port-control . . . . . . . . . . . . . . . . . . . . 849
dot1x re-authenticate . . . . . . . . . . . . . . . . . . 851
dot1x reauthentication. . . . . . . . . . . . . . . . . . 851
dot1x system-auth-control. . . . . . . . . . . . . . . . 852
dot1x system-auth-control monitor . . . . . . . . . . . 853
dot1x timeout guest-vlan-period . . . . . . . . . . . . 853
dot1x timeout quiet-period . . . . . . . . . . . . . . . 854
dot1x timeout re-authperiod . . . . . . . . . . . . . . . 855
dot1x timeout server-timeout . . . . . . . . . . . . . . 856
dot1x timeout tx-period . . . . . . . . . . . . . . . . . 857
authentication enable . . . . . . . . . . . . . . . . . . 858
authentication order . . . . . . . . . . . . . . . . . . . 859
authentication priority. . . . . . . . . . . . . . . . . . 859
authentication restart . . . . . . . . . . . . . . . . . . 860
clear authentication statistics . . . . . . . . . . . . . 861
clear authentication authentication-history . . . . . . 862
show authentication . . . . . . . . . . . . . . . . . . 862
show authenticaton authentication-history . . . . . . 863
show authentication statistics . . . . . . . . . . . . . 864
show dot1x . . . . . . . . . . . . . . . . . . . . . . . . 865
show dot1x authentication-history . . . . . . . . . . . 866
2CSNXXX_SWUM200.book Page 35 Tuesday, December 10, 2013 1:22 PM

Contents 36
show dot1x clients. . . . . . . . . . . . . . . . . . . . 868
show dot1x interface . . . . . . . . . . . . . . . . . . 870
show dot1x interface statistics . . . . . . . . . . . . . 871
show dot1x users . . . . . . . . . . . . . . . . . . . . 873
clear dot1x authentication–history . . . . . . . . . . . 874
dot1x guest-vlan . . . . . . . . . . . . . . . . . . . . . 875
dot1x unauth-vlan . . . . . . . . . . . . . . . . . . . . 875
show dot1x advanced . . . . . . . . . . . . . . . . . . 876
41 Data Center Technology Commands . . . 879
42 Data Center Bridging Commands . . . . . 881
Data Center Bridging Exchange Protocol . . . . . . . . 881
Interoperability with IEEE DCBX . . . . . . . . . . . . 885
Port Roles . . . . . . . . . . . . . . . . . . . . . . . . 885
Commands in this Chapter. . . . . . . . . . . . . . . . 889
Data Center Bridging Capability Exchange Commands 889
datacenter-bridging . . . . . . . . . . . . . . . . . . . 889
lldp dcbx version . . . . . . . . . . . . . . . . . . . . 890
lldp tlv-select dcbxp (dcb enable) . . . . . . . . . . . 891
lldp dcbx port-role . . . . . . . . . . . . . . . . . . . . 893
show lldp tlv-select . . . . . . . . . . . . . . . . . . . 894
2CSNXXX_SWUM200.book Page 36 Tuesday, December 10, 2013 1:22 PM

Contents 37
show lldp dcbx. . . . . . . . . . . . . . . . . . . . . . 895
Enhanced Transmission Selection (ETS) Commands . . 899
classofservice traffic-class-group . . . . . . . . . . . 899
traffic-class-group max-bandwidth. . . . . . . . . . . 901
traffic-class-group min-bandwidth . . . . . . . . . . . 902
traffic-class-group strict . . . . . . . . . . . . . . . . 903
traffic-class-group weight . . . . . . . . . . . . . . . 905
show classofservice traffic-class-group . . . . . . . . 906
show interfaces traffic-class-group . . . . . . . . . . 907
43 Priority Flow Control Commands . . . . . . 909
Commands in this Chapter. . . . . . . . . . . . . . . . 910
priority-flow-control mode . . . . . . . . . . . . . . . 910
priority-flow-control priority . . . . . . . . . . . . . . 911
clear priority-flow-control statistics . . . . . . . . . . 912
show interfaces priority-flow-control . . . . . . . . . 913
44 Layer 3 Commands . . . . . . . . . . . . . . . . 917
45 ARP Commands . . . . . . . . . . . . . . . . . . . 919
ARP Aging . . . . . . . . . . . . . . . . . . . . . . . . 920
Commands in this Chapter. . . . . . . . . . . . . . . . 920
2CSNXXX_SWUM200.book Page 37 Tuesday, December 10, 2013 1:22 PM

Contents 38
arp . . . . . . . . . . . . . . . . . . . . . . . . . . . . 920
arp cachesize . . . . . . . . . . . . . . . . . . . . . . 921
arp dynamicrenew. . . . . . . . . . . . . . . . . . . . 922
arp purge . . . . . . . . . . . . . . . . . . . . . . . . . 923
arp resptime . . . . . . . . . . . . . . . . . . . . . . . 924
arp retries . . . . . . . . . . . . . . . . . . . . . . . . 925
arp timeout . . . . . . . . . . . . . . . . . . . . . . . . 925
clear arp-cache . . . . . . . . . . . . . . . . . . . . . 926
clear arp-cache management . . . . . . . . . . . . . . 927
ip local-proxy-arp . . . . . . . . . . . . . . . . . . . . 928
ip proxy-arp . . . . . . . . . . . . . . . . . . . . . . . 928
show arp . . . . . . . . . . . . . . . . . . . . . . . . . 929
46 DHCP Server and Relay Agent Commands 931
Commands in this Chapter. . . . . . . . . . . . . . . . 932
ip dhcp pool . . . . . . . . . . . . . . . . . . . . . . . 932
bootfile . . . . . . . . . . . . . . . . . . . . . . . . . . 935
clear ip dhcp binding . . . . . . . . . . . . . . . . . . 935
clear ip dhcp conflict . . . . . . . . . . . . . . . . . . 936
client-identifier . . . . . . . . . . . . . . . . . . . . . 937
client-name . . . . . . . . . . . . . . . . . . . . . . . 937
default-router . . . . . . . . . . . . . . . . . . . . . . 938
2CSNXXX_SWUM200.book Page 38 Tuesday, December 10, 2013 1:22 PM

Contents 39
dns-server (IP DHCP Pool Config) . . . . . . . . . . . . 939
domain-name (IP DHCP Pool Config) . . . . . . . . . . 940
hardware-address . . . . . . . . . . . . . . . . . . . . 940
host. . . . . . . . . . . . . . . . . . . . . . . . . . . . 941
ip dhcp bootp automatic . . . . . . . . . . . . . . . . . 942
ip dhcp conflict logging . . . . . . . . . . . . . . . . . 943
ip dhcp excluded-address. . . . . . . . . . . . . . . . 943
ip dhcp ping packets. . . . . . . . . . . . . . . . . . . 944
lease . . . . . . . . . . . . . . . . . . . . . . . . . . . 945
netbios-name-server. . . . . . . . . . . . . . . . . . . 946
netbios-node-type . . . . . . . . . . . . . . . . . . . . 947
network . . . . . . . . . . . . . . . . . . . . . . . . . 947
next-server. . . . . . . . . . . . . . . . . . . . . . . . 948
option. . . . . . . . . . . . . . . . . . . . . . . . . . . 949
service dhcp . . . . . . . . . . . . . . . . . . . . . . . 953
sntp . . . . . . . . . . . . . . . . . . . . . . . . . . . . 953
show ip dhcp binding . . . . . . . . . . . . . . . . . . 954
show ip dhcp conflict . . . . . . . . . . . . . . . . . . 955
show ip dhcp global configuration . . . . . . . . . . . 955
show ip dhcp pool . . . . . . . . . . . . . . . . . . . . 956
show ip dhcp server statistics . . . . . . . . . . . . . 956
2CSNXXX_SWUM200.book Page 39 Tuesday, December 10, 2013 1:22 PM

Contents 40
47 DHCPv6 Commands . . . . . . . . . . . . . . . . 959
clear ipv6 dhcp. . . . . . . . . . . . . . . . . . . . . . 959
dns-server (IPv6 DHCP Pool Config). . . . . . . . . . . 960
domain-name (IPv6 DHCP Pool Config) . . . . . . . . . 960
ipv6 dhcp pool . . . . . . . . . . . . . . . . . . . . . . 961
ipv6 dhcp relay. . . . . . . . . . . . . . . . . . . . . . 962
ipv6 dhcp server . . . . . . . . . . . . . . . . . . . . . 963
prefix-delegation . . . . . . . . . . . . . . . . . . . . 965
service dhcpv6. . . . . . . . . . . . . . . . . . . . . . 966
show ipv6 dhcp . . . . . . . . . . . . . . . . . . . . . 967
show ipv6 dhcp binding . . . . . . . . . . . . . . . . . 967
show ipv6 dhcp interface (User EXEC) . . . . . . . . . 968
show ipv6 dhcp interface (Privileged EXEC) . . . . . . 970
show ipv6 dhcp pool . . . . . . . . . . . . . . . . . . . 973
show ipv6 dhcp statistics . . . . . . . . . . . . . . . . 973
48 DHCPv6 Snooping Commands . . . . . . . . 975
clear ipv6 dhcp snooping binding . . . . . . . . . . . . 975
clear ipv6 dhcp snooping statistics . . . . . . . . . . . 976
ipv6 dhcp snooping . . . . . . . . . . . . . . . . . . . 976
ipv6 dhcp snooping vlan . . . . . . . . . . . . . . . . . 977
2CSNXXX_SWUM200.book Page 40 Tuesday, December 10, 2013 1:22 PM

Contents 41
ipv6 dhcp snooping binding . . . . . . . . . . . . . . . 978
ipv6 dhcp snooping database . . . . . . . . . . . . . . 979
ipv6 dhcp snooping database write-delay . . . . . . . 980
ipv6 dhcp snooping limit. . . . . . . . . . . . . . . . . 981
ipv6 dhcp snooping log-invalid . . . . . . . . . . . . . 982
ipv6 dhcp snooping trust. . . . . . . . . . . . . . . . . 983
ipv6 dhcp snooping verify mac-address . . . . . . . . 983
ipv6 verify binding . . . . . . . . . . . . . . . . . . . . 984
ipv6 verify source . . . . . . . . . . . . . . . . . . . . 985
show ipv6 dhcp snooping . . . . . . . . . . . . . . . . 986
show ipv6 dhcp snooping binding. . . . . . . . . . . . 987
show ipv6 dhcp snooping database . . . . . . . . . . . 988
show ipv6 dhcp snooping interfaces . . . . . . . . . . 989
show ipv6 dhcp snooping statistics . . . . . . . . . . . 989
show ipv6 source binding . . . . . . . . . . . . . . . . 990
show ipv6 verify . . . . . . . . . . . . . . . . . . . . . 991
show ipv6 verify source . . . . . . . . . . . . . . . . . 992
49 DVMRP Commands . . . . . . . . . . . . . . . . 995
Commands in this Chapter. . . . . . . . . . . . . . . . 995
ip dvmrp . . . . . . . . . . . . . . . . . . . . . . . . . 995
ip dvmrp metric . . . . . . . . . . . . . . . . . . . . . 996
2CSNXXX_SWUM200.book Page 41 Tuesday, December 10, 2013 1:22 PM

Contents 42
show ip dvmrp . . . . . . . . . . . . . . . . . . . . . . 997
show ip dvmrp interface. . . . . . . . . . . . . . . . . 998
show ip dvmrp neighbor . . . . . . . . . . . . . . . . . 998
show ip dvmrp nexthop . . . . . . . . . . . . . . . . . 999
show ip dvmrp prune . . . . . . . . . . . . . . . . . 1000
show ip dvmrp route . . . . . . . . . . . . . . . . . . 1000
50 GMRP Commands . . . . . . . . . . . . . . . . 1003
Commands in this Chapter. . . . . . . . . . . . . . . 1004
gmrp enable . . . . . . . . . . . . . . . . . . . . . . 1004
show gmrp configuration . . . . . . . . . . . . . . . 1005
51 IGMP Commands . . . . . . . . . . . . . . . . . 1007
Commands in this Chapter. . . . . . . . . . . . . . . 1008
ip igmp last-member-query-count. . . . . . . . . . . 1009
ip igmp last-member-query-interval . . . . . . . . . 1009
ip igmp mroute-proxy . . . . . . . . . . . . . . . . . 1010
ip igmp query-interval . . . . . . . . . . . . . . . . . 1011
ip igmp query-max-response-time . . . . . . . . . . 1012
ip igmp robustness. . . . . . . . . . . . . . . . . . . 1013
ip igmp startup-query-count. . . . . . . . . . . . . . 1014
ip igmp startup-query-interval. . . . . . . . . . . . . 1014
2CSNXXX_SWUM200.book Page 42 Tuesday, December 10, 2013 1:22 PM

Contents 43
ip igmp version. . . . . . . . . . . . . . . . . . . . . 1015
show ip igmp. . . . . . . . . . . . . . . . . . . . . . 1016
show ip igmp groups. . . . . . . . . . . . . . . . . . 1017
show ip igmp interface . . . . . . . . . . . . . . . . 1017
show ip igmp membership . . . . . . . . . . . . . . 1018
show ip igmp interface stats . . . . . . . . . . . . . 1019
52 IGMP Proxy Commands . . . . . . . . . . . . 1021
Commands in this Chapter. . . . . . . . . . . . . . . 1021
ip igmp proxy-service . . . . . . . . . . . . . . . . . 1021
ip igmp proxy-service reset-status . . . . . . . . . . 1022
ip igmp proxy-service unsolicit-rprt-interval . . . . . 1023
show ip igmp proxy-service . . . . . . . . . . . . . . 1024
show ip igmp proxy-service interface . . . . . . . . 1025
show ip igmp-proxy groups . . . . . . . . . . . . . . 1025
show ip igmp proxy-service groups detail . . . . . . 1026
53 IP Helper/DHCP Relay Commands. . . . 1029
Commands in this Chapter. . . . . . . . . . . . . . . 1031
bootpdhcprelay maxhopcount. . . . . . . . . . . . . 1031
bootpdhcprelay minwaittime . . . . . . . . . . . . . 1032
clear ip helper statistics. . . . . . . . . . . . . . . . 1033
2CSNXXX_SWUM200.book Page 43 Tuesday, December 10, 2013 1:22 PM

Contents 44
ip dhcp relay information check . . . . . . . . . . . 1033
ip dhcp relay information check-reply . . . . . . . . 1034
ip dhcp relay information option . . . . . . . . . . . 1035
ip dhcp relay information option-insert . . . . . . . . 1036
ip helper-address (global configuration) . . . . . . . 1037
ip helper-address (interface configuration). . . . . . 1038
ip helper enable . . . . . . . . . . . . . . . . . . . . 1040
show ip helper-address . . . . . . . . . . . . . . . . 1041
show ip dhcp relay. . . . . . . . . . . . . . . . . . . 1042
show ip helper statistics . . . . . . . . . . . . . . . 1043
54 IP Routing Commands . . . . . . . . . . . . . 1045
Static Routes/ECMP Static Routes . . . . . . . . . . 1045
Static Reject Routes . . . . . . . . . . . . . . . . . . 1046
Default Routes . . . . . . . . . . . . . . . . . . . . . 1046
Commands in this Chapter. . . . . . . . . . . . . . . 1046
encapsulation . . . . . . . . . . . . . . . . . . . . . 1047
ip address . . . . . . . . . . . . . . . . . . . . . . . 1047
ip netdirbcast . . . . . . . . . . . . . . . . . . . . . 1049
ip policy route-map . . . . . . . . . . . . . . . . . . 1049
ip route . . . . . . . . . . . . . . . . . . . . . . . . . 1050
ip route default . . . . . . . . . . . . . . . . . . . . . 1051
2CSNXXX_SWUM200.book Page 44 Tuesday, December 10, 2013 1:22 PM

Contents 45
ip route distance . . . . . . . . . . . . . . . . . . . . 1053
ip routing . . . . . . . . . . . . . . . . . . . . . . . . 1053
match ip address. . . . . . . . . . . . . . . . . . . . 1054
match length . . . . . . . . . . . . . . . . . . . . . . 1056
match mac-list . . . . . . . . . . . . . . . . . . . . . 1057
route-map . . . . . . . . . . . . . . . . . . . . . . . 1058
set interface null0 . . . . . . . . . . . . . . . . . . . 1059
set ip default next-hop. . . . . . . . . . . . . . . . . 1060
set ip next-hop . . . . . . . . . . . . . . . . . . . . . 1061
set ip precedence . . . . . . . . . . . . . . . . . . . 1062
show ip brief . . . . . . . . . . . . . . . . . . . . . . 1063
show ip interface . . . . . . . . . . . . . . . . . . . 1064
show ip policy . . . . . . . . . . . . . . . . . . . . . 1065
show ip protocols . . . . . . . . . . . . . . . . . . . 1066
show ip route . . . . . . . . . . . . . . . . . . . . . 1070
show ip route preferences . . . . . . . . . . . . . . 1072
show ip route summary . . . . . . . . . . . . . . . . 1073
show ip traffic . . . . . . . . . . . . . . . . . . . . . 1074
show ip vlan . . . . . . . . . . . . . . . . . . . . . . 1075
show route-map . . . . . . . . . . . . . . . . . . . . 1076
show routing heap summary . . . . . . . . . . . . . 1078
2CSNXXX_SWUM200.book Page 45 Tuesday, December 10, 2013 1:22 PM

Contents 46
55 IPv6 Routing Commands . . . . . . . . . . . 1081
IPv6 Limitations & Restrictions . . . . . . . . . . . . 1081
Commands in this Chapter. . . . . . . . . . . . . . . 1081
clear ipv6 neighbors . . . . . . . . . . . . . . . . . . 1082
clear ipv6 statistics . . . . . . . . . . . . . . . . . . 1083
ipv6 address . . . . . . . . . . . . . . . . . . . . . . 1083
ipv6 enable . . . . . . . . . . . . . . . . . . . . . . . 1085
ipv6 hop-limit . . . . . . . . . . . . . . . . . . . . . 1086
ipv6 host . . . . . . . . . . . . . . . . . . . . . . . . 1086
ipv6 mld last-member-query-count . . . . . . . . . . 1087
ipv6 mld last-member-query-interval . . . . . . . . . 1088
ipv6 mld host-proxy . . . . . . . . . . . . . . . . . . 1088
ipv6 mld host-proxy reset-status . . . . . . . . . . . 1089
ipv6 mld host-proxy unsolicit-rprt-interval . . . . . . 1090
ipv6 mld query-interval . . . . . . . . . . . . . . . . 1090
ipv6 mld query-max-response-time . . . . . . . . . . 1091
ipv6 nd dad attempts . . . . . . . . . . . . . . . . . . 1092
ipv6 nd managed-config-flag . . . . . . . . . . . . . 1093
ipv6 nd ns-interval . . . . . . . . . . . . . . . . . . . 1093
ipv6 nd other-config-flag . . . . . . . . . . . . . . . 1094
ipv6 nd prefix. . . . . . . . . . . . . . . . . . . . . . 1095
2CSNXXX_SWUM200.book Page 46 Tuesday, December 10, 2013 1:22 PM

Contents 47
ipv6 nd ra-interval . . . . . . . . . . . . . . . . . . . 1096
ipv6 nd ra-lifetime . . . . . . . . . . . . . . . . . . . 1097
ipv6 nd reachable-time . . . . . . . . . . . . . . . . 1098
ipv6 nd suppress-ra . . . . . . . . . . . . . . . . . . 1099
ipv6 route. . . . . . . . . . . . . . . . . . . . . . . . 1099
ipv6 route distance. . . . . . . . . . . . . . . . . . . 1101
ipv6 unicast-routing . . . . . . . . . . . . . . . . . . 1101
ping ipv6 . . . . . . . . . . . . . . . . . . . . . . . . 1102
ping ipv6 interface . . . . . . . . . . . . . . . . . . . 1103
rate-limit cpu. . . . . . . . . . . . . . . . . . . . . . 1105
show ipv6 brief. . . . . . . . . . . . . . . . . . . . . 1107
show ipv6 interface . . . . . . . . . . . . . . . . . . 1107
show ipv6 interface management statistics . . . . . 1110
show ipv6 mld groups . . . . . . . . . . . . . . . . . 1111
show ipv6 mld host-proxy . . . . . . . . . . . . . . . 1113
show ipv6 mld interface . . . . . . . . . . . . . . . . 1114
show ipv6 mld host-proxy . . . . . . . . . . . . . . . 1116
show ipv6 mld host-proxy groups . . . . . . . . . . . 1118
show ipv6 mld host-proxy groups detail . . . . . . . 1119
show ipv6 mld host-proxy interface. . . . . . . . . . 1121
show ipv6 mld traffic . . . . . . . . . . . . . . . . . 1122
2CSNXXX_SWUM200.book Page 47 Tuesday, December 10, 2013 1:22 PM

Contents 48
show ipv6 neighbors. . . . . . . . . . . . . . . . . . 1123
show ipv6 route . . . . . . . . . . . . . . . . . . . . 1124
show ipv6 route preferences . . . . . . . . . . . . . 1125
show ipv6 route summary . . . . . . . . . . . . . . . 1126
show ipv6 traffic . . . . . . . . . . . . . . . . . . . . 1127
show ipv6 vlan . . . . . . . . . . . . . . . . . . . . . 1129
traceroute ipv6 . . . . . . . . . . . . . . . . . . . . . 1129
56 Loopback Interface Commands. . . . . . 1133
Commands in this Chapter. . . . . . . . . . . . . . . 1133
interface loopback. . . . . . . . . . . . . . . . . . . 1133
show interfaces loopback. . . . . . . . . . . . . . . 1134
57 Multicast Commands . . . . . . . . . . . . . . 1137
Commands in this Chapter. . . . . . . . . . . . . . . 1138
clear ip mroute. . . . . . . . . . . . . . . . . . . . . 1138
ip mcast boundary . . . . . . . . . . . . . . . . . . . 1140
ip mroute . . . . . . . . . . . . . . . . . . . . . . . . 1140
ip multicast-routing . . . . . . . . . . . . . . . . . . 1141
ip multicast ttl-threshold . . . . . . . . . . . . . . . 1142
ip pim. . . . . . . . . . . . . . . . . . . . . . . . . . 1143
ip pim bsr-border. . . . . . . . . . . . . . . . . . . . 1144
2CSNXXX_SWUM200.book Page 48 Tuesday, December 10, 2013 1:22 PM

Contents 49
ip pim bsr-candidate. . . . . . . . . . . . . . . . . . 1145
ip pim dense-mode. . . . . . . . . . . . . . . . . . . 1146
ip pim dr-priority . . . . . . . . . . . . . . . . . . . . 1146
ip pim hello-interval . . . . . . . . . . . . . . . . . . 1147
ip pim join-prune-interval . . . . . . . . . . . . . . . 1148
ip pim rp-address . . . . . . . . . . . . . . . . . . . 1149
ip pim rp-candidate . . . . . . . . . . . . . . . . . . 1150
ip pim sparse-mode . . . . . . . . . . . . . . . . . . 1150
ip pim ssm . . . . . . . . . . . . . . . . . . . . . . . 1151
show ip multicast . . . . . . . . . . . . . . . . . . . 1152
show ip pim boundary . . . . . . . . . . . . . . . . . 1153
show ip multicast interface . . . . . . . . . . . . . . 1154
show ip mroute . . . . . . . . . . . . . . . . . . . . 1154
show ip mroute group . . . . . . . . . . . . . . . . . 1155
show ip mroute source . . . . . . . . . . . . . . . . 1156
show ip mroute static . . . . . . . . . . . . . . . . . 1157
show ip pim . . . . . . . . . . . . . . . . . . . . . . 1157
show ip pim bsr-router. . . . . . . . . . . . . . . . . 1158
show ip pim interface . . . . . . . . . . . . . . . . . 1159
show ip pim neighbor . . . . . . . . . . . . . . . . . 1161
show ip pim rp hash . . . . . . . . . . . . . . . . . . 1162
2CSNXXX_SWUM200.book Page 49 Tuesday, December 10, 2013 1:22 PM

Contents 50
show ip pim rp mapping . . . . . . . . . . . . . . . . 1163
58 IPv6 Multicast Commands . . . . . . . . . . 1167
clear ipv6 mroute . . . . . . . . . . . . . . . . . . . 1167
ipv6 pim (VLAN Interface config) . . . . . . . . . . . 1168
ipv6 pim bsr-border . . . . . . . . . . . . . . . . . . 1169
ipv6 pim bsr-candidate . . . . . . . . . . . . . . . . 1170
ipv6 pim dense-mode . . . . . . . . . . . . . . . . . 1171
ipv6 pim dr-priority. . . . . . . . . . . . . . . . . . . 1171
ipv6 pim hello-interval. . . . . . . . . . . . . . . . . 1172
ipv6 pim join-prune-interval . . . . . . . . . . . . . . 1173
ipv6 pim register-threshold . . . . . . . . . . . . . . 1173
ipv6 pim rp-address . . . . . . . . . . . . . . . . . . 1174
ipv6 pim rp-candidate . . . . . . . . . . . . . . . . . 1175
ipv6 pim sparse-mode . . . . . . . . . . . . . . . . . 1176
ipv6 pim ssm . . . . . . . . . . . . . . . . . . . . . . 1176
show ipv6 pim . . . . . . . . . . . . . . . . . . . . . 1177
show ipv6 pim bsr-router . . . . . . . . . . . . . . . 1178
show ipv6 mroute group . . . . . . . . . . . . . . . . 1182
show ipv6 mroute source . . . . . . . . . . . . . . . 1183
show ipv6 pim interface . . . . . . . . . . . . . . . . 1184
show ipv6 pim neighbor . . . . . . . . . . . . . . . . 1185
2CSNXXX_SWUM200.book Page 50 Tuesday, December 10, 2013 1:22 PM

Contents 51
show ipv6 pim rp-hash. . . . . . . . . . . . . . . . . 1186
show ipv6 pim rp mapping. . . . . . . . . . . . . . . 1186
59 OSPF Commands . . . . . . . . . . . . . . . . . 1191
Route Preferences . . . . . . . . . . . . . . . . . . . 1192
OSPF Equal Cost Multipath (ECMP) . . . . . . . . . . 1192
Forwarding of OSPF Opaque LSAs Enabled by Default 1193
Passive Interfaces . . . . . . . . . . . . . . . . . . . 1194
Graceful Restart . . . . . . . . . . . . . . . . . . . . 1194
Commands in this Chapter. . . . . . . . . . . . . . . 1194
area default-cost (Router OSPF). . . . . . . . . . . . 1196
area nssa (Router OSPF) . . . . . . . . . . . . . . . . 1196
area nssa default-info-originate (Router OSPF Config) 1198
area nssa no-redistribute . . . . . . . . . . . . . . . 1199
area nssa no-summary. . . . . . . . . . . . . . . . . 1200
area nssa translator-role . . . . . . . . . . . . . . . 1200
area nssa translator-stab-intv . . . . . . . . . . . . . 1201
area range (Router OSPF) . . . . . . . . . . . . . . . 1202
area stub . . . . . . . . . . . . . . . . . . . . . . . . 1205
area stub no-summary . . . . . . . . . . . . . . . . . 1206
area virtual-link . . . . . . . . . . . . . . . . . . . . 1206
area virtual-link authentication . . . . . . . . . . . . 1209
2CSNXXX_SWUM200.book Page 51 Tuesday, December 10, 2013 1:22 PM

Contents 52
area virtual-link dead-interval . . . . . . . . . . . . 1210
area virtual-link hello-interval . . . . . . . . . . . . 1211
area virtual-link retransmit-interval . . . . . . . . . 1212
area virtual-link transmit-delay . . . . . . . . . . . . 1213
auto-cost . . . . . . . . . . . . . . . . . . . . . . . . 1213
bandwidth . . . . . . . . . . . . . . . . . . . . . . . 1214
capability opaque . . . . . . . . . . . . . . . . . . . 1215
clear ip ospf . . . . . . . . . . . . . . . . . . . . . . 1216
clear ip ospf stub-router . . . . . . . . . . . . . . . . 1217
compatible rfc1583. . . . . . . . . . . . . . . . . . . 1217
default-information originate (Router OSPF Configuration) 1218
default-metric . . . . . . . . . . . . . . . . . . . . . 1219
distance ospf. . . . . . . . . . . . . . . . . . . . . . 1220
distribute-list out . . . . . . . . . . . . . . . . . . . 1221
enable . . . . . . . . . . . . . . . . . . . . . . . . . 1222
exit-overflow-interval . . . . . . . . . . . . . . . . . 1223
external-lsdb-limit. . . . . . . . . . . . . . . . . . . 1224
ip ospf area. . . . . . . . . . . . . . . . . . . . . . . 1225
ip ospf authentication . . . . . . . . . . . . . . . . . 1225
ip ospf cost . . . . . . . . . . . . . . . . . . . . . . . 1226
ip ospf database-filter all out . . . . . . . . . . . . . 1227
2CSNXXX_SWUM200.book Page 52 Tuesday, December 10, 2013 1:22 PM

Contents 53
ip ospf dead-interval. . . . . . . . . . . . . . . . . . 1228
ip ospf hello-interval. . . . . . . . . . . . . . . . . . 1228
ip ospf mtu-ignore . . . . . . . . . . . . . . . . . . . 1229
ip ospf network . . . . . . . . . . . . . . . . . . . . 1230
ip ospf priority . . . . . . . . . . . . . . . . . . . . . 1231
ip ospf retransmit-interval. . . . . . . . . . . . . . . 1232
ip ospf transmit-delay . . . . . . . . . . . . . . . . . 1233
log adjacency-changes . . . . . . . . . . . . . . . . 1233
max-metric router-lsa . . . . . . . . . . . . . . . . . 1234
maximum-paths . . . . . . . . . . . . . . . . . . . . 1236
network area. . . . . . . . . . . . . . . . . . . . . . 1237
nsf . . . . . . . . . . . . . . . . . . . . . . . . . . . 1238
nsf helper . . . . . . . . . . . . . . . . . . . . . . . 1239
nsf helper strict-lsa-checking. . . . . . . . . . . . . 1239
nsf restart-interval . . . . . . . . . . . . . . . . . . . 1240
passive-interface default . . . . . . . . . . . . . . . 1241
passive-interface . . . . . . . . . . . . . . . . . . . 1242
redistribute. . . . . . . . . . . . . . . . . . . . . . . 1242
router-id . . . . . . . . . . . . . . . . . . . . . . . . 1244
router ospf . . . . . . . . . . . . . . . . . . . . . . . 1244
show ip ospf . . . . . . . . . . . . . . . . . . . . . . 1245
2CSNXXX_SWUM200.book Page 53 Tuesday, December 10, 2013 1:22 PM

Contents 54
show ip ospf abr . . . . . . . . . . . . . . . . . . . . 1251
show ip ospf area . . . . . . . . . . . . . . . . . . . 1252
show ip ospf asbr . . . . . . . . . . . . . . . . . . . 1254
show ip ospf database. . . . . . . . . . . . . . . . . 1254
show ip ospf database database-summary . . . . . . 1257
show ip ospf interface. . . . . . . . . . . . . . . . . 1259
show ip ospf interface brief . . . . . . . . . . . . . . 1261
show ip ospf interface stats . . . . . . . . . . . . . . 1262
show ip ospf neighbor . . . . . . . . . . . . . . . . . 1262
show ip ospf range. . . . . . . . . . . . . . . . . . . 1266
show ip ospf statistics. . . . . . . . . . . . . . . . . 1267
show ip ospf stub table . . . . . . . . . . . . . . . . 1269
show ip ospf traffic . . . . . . . . . . . . . . . . . . 1270
show ip ospf virtual-link. . . . . . . . . . . . . . . . 1272
show ip ospf virtual-links brief . . . . . . . . . . . . 1273
timers pacing flood . . . . . . . . . . . . . . . . . . 1273
timers pacing lsa-group . . . . . . . . . . . . . . . . 1274
timers spf. . . . . . . . . . . . . . . . . . . . . . . . 1275
60 OSPFv3 Commands . . . . . . . . . . . . . . . 1277
area default-cost (Router OSPFv3) . . . . . . . . . . 1278
area nssa (Router OSPFv3) . . . . . . . . . . . . . . 1279
2CSNXXX_SWUM200.book Page 54 Tuesday, December 10, 2013 1:22 PM

Contents 55
area nssa default-info-originate (Router OSPFv3 Config) 1280
area nssa no-redistribute . . . . . . . . . . . . . . . 1281
area nssa no-summary. . . . . . . . . . . . . . . . . 1282
area nssa translator-role . . . . . . . . . . . . . . . 1283
area nssa translator-stab-intv . . . . . . . . . . . . . 1284
area range (Router OSPFv3) . . . . . . . . . . . . . . 1285
area stub . . . . . . . . . . . . . . . . . . . . . . . . 1286
area stub no-summary . . . . . . . . . . . . . . . . . 1287
area virtual-link . . . . . . . . . . . . . . . . . . . . 1287
area virtual-link dead-interval . . . . . . . . . . . . 1289
area virtual-link hello-interval . . . . . . . . . . . . 1290
area virtual-link retransmit-interval . . . . . . . . . 1291
area virtual-link transmit-delay . . . . . . . . . . . . 1292
default-information originate (Router OSPFv3 Configuration) 1292
default-metric . . . . . . . . . . . . . . . . . . . . . 1293
distance ospf. . . . . . . . . . . . . . . . . . . . . . 1294
enable . . . . . . . . . . . . . . . . . . . . . . . . . 1295
exit-overflow-interval . . . . . . . . . . . . . . . . . 1296
external-lsdb-limit. . . . . . . . . . . . . . . . . . . 1297
ipv6 ospf . . . . . . . . . . . . . . . . . . . . . . . . 1297
ipv6 ospf area . . . . . . . . . . . . . . . . . . . . . 1298
2CSNXXX_SWUM200.book Page 55 Tuesday, December 10, 2013 1:22 PM

Contents 56
ipv6 ospf cost . . . . . . . . . . . . . . . . . . . . . 1299
ipv6 ospf dead-interval . . . . . . . . . . . . . . . . 1300
ipv6 ospf hello-interval . . . . . . . . . . . . . . . . 1300
ipv6 ospf mtu-ignore . . . . . . . . . . . . . . . . . . 1301
ipv6 ospf network . . . . . . . . . . . . . . . . . . . 1302
ipv6 ospf priority . . . . . . . . . . . . . . . . . . . . 1303
ipv6 ospf retransmit-interval . . . . . . . . . . . . . 1304
ipv6 ospf transmit-delay . . . . . . . . . . . . . . . . 1305
ipv6 router ospf . . . . . . . . . . . . . . . . . . . . 1305
maximum-paths . . . . . . . . . . . . . . . . . . . . 1306
nsf . . . . . . . . . . . . . . . . . . . . . . . . . . . 1307
nsf helper . . . . . . . . . . . . . . . . . . . . . . . 1308
nsf helper strict-lsa-checking. . . . . . . . . . . . . 1309
nsf restart-interval . . . . . . . . . . . . . . . . . . . 1309
passive-interface . . . . . . . . . . . . . . . . . . . 1310
passive-interface default . . . . . . . . . . . . . . . 1311
redistribute. . . . . . . . . . . . . . . . . . . . . . . 1312
router-id . . . . . . . . . . . . . . . . . . . . . . . . 1312
show ipv6 ospf . . . . . . . . . . . . . . . . . . . . . 1313
show ipv6 ospf abr . . . . . . . . . . . . . . . . . . . 1317
show ipv6 ospf area . . . . . . . . . . . . . . . . . . 1318
2CSNXXX_SWUM200.book Page 56 Tuesday, December 10, 2013 1:22 PM

Contents 57
show ipv6 ospf asbr . . . . . . . . . . . . . . . . . . 1319
show ipv6 ospf border-routers. . . . . . . . . . . . . 1319
show ipv6 ospf database . . . . . . . . . . . . . . . 1320
show ipv6 ospf database database-summary. . . . . 1322
show ipv6 ospf interface . . . . . . . . . . . . . . . 1323
show ipv6 ospf interface brief. . . . . . . . . . . . . 1324
show ipv6 ospf interface stats. . . . . . . . . . . . . 1325
show ipv6 ospf interface vlan . . . . . . . . . . . . . 1326
show ipv6 ospf neighbor. . . . . . . . . . . . . . . . 1327
show ipv6 ospf range . . . . . . . . . . . . . . . . . 1329
show ipv6 ospf stub table . . . . . . . . . . . . . . . 1329
show ipv6 ospf virtual-links . . . . . . . . . . . . . . 1330
show ipv6 ospf virtual-link brief . . . . . . . . . . . 1331
61 Router Discovery Protocol Commands 1333
Commands in this Chapter. . . . . . . . . . . . . . . 1333
ip irdp . . . . . . . . . . . . . . . . . . . . . . . . . 1333
ip irdp holdtime . . . . . . . . . . . . . . . . . . . . 1335
ip irdp maxadvertinterval . . . . . . . . . . . . . . . 1336
ip irdp minadvertinterval . . . . . . . . . . . . . . . 1337
ip irdp multicast . . . . . . . . . . . . . . . . . . . . 1338
ip irdp preference . . . . . . . . . . . . . . . . . . . 1338
2CSNXXX_SWUM200.book Page 57 Tuesday, December 10, 2013 1:22 PM

Contents 58
show ip irdp . . . . . . . . . . . . . . . . . . . . . . 1339
62 Routing Information Protocol Commands 1341
Commands in this Chapter. . . . . . . . . . . . . . . 1341
auto-summary . . . . . . . . . . . . . . . . . . . . . 1341
default-information originate (Router RIP Configuration) 1342
default-metric . . . . . . . . . . . . . . . . . . . . . 1343
distance rip . . . . . . . . . . . . . . . . . . . . . . 1344
distribute-list out . . . . . . . . . . . . . . . . . . . 1344
enable . . . . . . . . . . . . . . . . . . . . . . . . . 1345
hostroutesaccept . . . . . . . . . . . . . . . . . . . 1346
ip rip . . . . . . . . . . . . . . . . . . . . . . . . . . 1347
ip rip authentication . . . . . . . . . . . . . . . . . . 1347
ip rip receive version . . . . . . . . . . . . . . . . . 1348
ip rip send version . . . . . . . . . . . . . . . . . . . 1349
redistribute. . . . . . . . . . . . . . . . . . . . . . . 1350
router rip . . . . . . . . . . . . . . . . . . . . . . . . 1351
show ip rip . . . . . . . . . . . . . . . . . . . . . . . 1352
show ip rip interface. . . . . . . . . . . . . . . . . . 1353
show ip rip interface brief. . . . . . . . . . . . . . . 1354
split-horizon . . . . . . . . . . . . . . . . . . . . . . 1354
2CSNXXX_SWUM200.book Page 58 Tuesday, December 10, 2013 1:22 PM

Contents 59
63 Tunnel Interface Commands . . . . . . . . 1357
Commands in this Chapter. . . . . . . . . . . . . . . 1357
interface tunnel . . . . . . . . . . . . . . . . . . . . 1358
show interfaces tunnel . . . . . . . . . . . . . . . . 1358
tunnel destination . . . . . . . . . . . . . . . . . . . 1359
tunnel mode ipv6ip. . . . . . . . . . . . . . . . . . . 1360
tunnel source . . . . . . . . . . . . . . . . . . . . . 1361
64 Virtual Router Redundancy Protocol Commands
1363
Pingable VRRP Interface . . . . . . . . . . . . . . . 1363
VRRP Route/Interface Tracking . . . . . . . . . . . . 1364
Interface Tracking . . . . . . . . . . . . . . . . . . . 1365
Route Tracking . . . . . . . . . . . . . . . . . . . . . 1365
Commands in this Chapter. . . . . . . . . . . . . . . 1365
ip vrrp . . . . . . . . . . . . . . . . . . . . . . . . . 1366
vrrp accept-mode . . . . . . . . . . . . . . . . . . . 1366
vrrp authentication . . . . . . . . . . . . . . . . . . 1367
vrrp description . . . . . . . . . . . . . . . . . . . . 1368
vrrp ip . . . . . . . . . . . . . . . . . . . . . . . . . 1369
vrrp mode . . . . . . . . . . . . . . . . . . . . . . . 1370
vrrp preempt . . . . . . . . . . . . . . . . . . . . . . 1371
2CSNXXX_SWUM200.book Page 59 Tuesday, December 10, 2013 1:22 PM

Contents 60
vrrp priority. . . . . . . . . . . . . . . . . . . . . . . 1372
vrrp timers advertise. . . . . . . . . . . . . . . . . . 1372
vrrp timers learn . . . . . . . . . . . . . . . . . . . . 1373
vrrp track interface . . . . . . . . . . . . . . . . . . 1374
vrrp track ip route . . . . . . . . . . . . . . . . . . . 1375
show vrrp . . . . . . . . . . . . . . . . . . . . . . . 1376
show vrrp interface . . . . . . . . . . . . . . . . . . 1378
show vrrp interface brief . . . . . . . . . . . . . . . 1380
show vrrp interface stats . . . . . . . . . . . . . . . 1381
ip vrrp accept-mode . . . . . . . . . . . . . . . . . . 1382
show ip vrrp interface . . . . . . . . . . . . . . . . . 1382
65 Utility Commands. . . . . . . . . . . . . . . . . 1385
66 Auto-Install Commands . . . . . . . . . . . . 1387
Commands in this Chapter. . . . . . . . . . . . . . . 1388
boot auto-copy-sw . . . . . . . . . . . . . . . . . . . 1388
boot auto-copy-sw allow-downgrade . . . . . . . . 1389
boot host autoreboot . . . . . . . . . . . . . . . . . . 1390
boot host autosave . . . . . . . . . . . . . . . . . . . 1390
boot host dhcp . . . . . . . . . . . . . . . . . . . . . 1391
boot host retrycount . . . . . . . . . . . . . . . . . . 1392
2CSNXXX_SWUM200.book Page 60 Tuesday, December 10, 2013 1:22 PM

Contents 61
show auto-copy-sw . . . . . . . . . . . . . . . . . . 1393
show boot . . . . . . . . . . . . . . . . . . . . . . . 1393
67 Captive Portal Commands . . . . . . . . . . 1395
Commands in this Chapter. . . . . . . . . . . . . . . 1395
authentication timeout. . . . . . . . . . . . . . . . . 1397
captive-portal . . . . . . . . . . . . . . . . . . . . . 1397
enable . . . . . . . . . . . . . . . . . . . . . . . . . 1398
http port . . . . . . . . . . . . . . . . . . . . . . . . 1399
https port . . . . . . . . . . . . . . . . . . . . . . . . 1399
show captive-portal . . . . . . . . . . . . . . . . . . 1400
show captive-portal status . . . . . . . . . . . . . . 1401
block . . . . . . . . . . . . . . . . . . . . . . . . . . 1402
configuration. . . . . . . . . . . . . . . . . . . . . . 1402
enable . . . . . . . . . . . . . . . . . . . . . . . . . 1403
group . . . . . . . . . . . . . . . . . . . . . . . . . . 1404
interface . . . . . . . . . . . . . . . . . . . . . . . . 1404
locale. . . . . . . . . . . . . . . . . . . . . . . . . . 1405
name (Captive Portal) . . . . . . . . . . . . . . . . . 1406
protocol . . . . . . . . . . . . . . . . . . . . . . . . 1406
redirect. . . . . . . . . . . . . . . . . . . . . . . . . 1407
redirect-url. . . . . . . . . . . . . . . . . . . . . . . 1407
2CSNXXX_SWUM200.book Page 61 Tuesday, December 10, 2013 1:22 PM

Contents 62
session-timeout . . . . . . . . . . . . . . . . . . . . 1408
verification. . . . . . . . . . . . . . . . . . . . . . . 1409
captive-portal client deauthenticate . . . . . . . . . 1410
show captive-portal client status . . . . . . . . . . . 1410
show captive-portal configuration client status . . . 1411
show captive-portal interface client status . . . . . 1412
show captive-portal interface configuration status . 1413
clear captive-portal users . . . . . . . . . . . . . . . 1414
no user . . . . . . . . . . . . . . . . . . . . . . . . . 1415
show captive-portal user . . . . . . . . . . . . . . . 1415
user group . . . . . . . . . . . . . . . . . . . . . . . 1416
user-logout . . . . . . . . . . . . . . . . . . . . . . . 1417
user name . . . . . . . . . . . . . . . . . . . . . . . 1418
user password . . . . . . . . . . . . . . . . . . . . . 1419
user session-timeout . . . . . . . . . . . . . . . . . 1419
show captive-portal configuration . . . . . . . . . . 1420
show captive-portal configuration interface . . . . . 1421
show captive-portal configuration locales . . . . . . 1422
show captive-portal configuration status. . . . . . . 1423
user group . . . . . . . . . . . . . . . . . . . . . . . 1424
user group moveusers . . . . . . . . . . . . . . . . . 1424
2CSNXXX_SWUM200.book Page 62 Tuesday, December 10, 2013 1:22 PM

Contents 63
user group name . . . . . . . . . . . . . . . . . . . . 1425
68 CLI Macro Commands . . . . . . . . . . . . . 1427
Commands in this Chapter. . . . . . . . . . . . . . . 1428
macro name . . . . . . . . . . . . . . . . . . . . . . 1428
macro global apply . . . . . . . . . . . . . . . . . . 1429
macro global trace. . . . . . . . . . . . . . . . . . . 1430
macro global description . . . . . . . . . . . . . . . 1431
macro apply . . . . . . . . . . . . . . . . . . . . . . 1431
macro trace . . . . . . . . . . . . . . . . . . . . . . 1432
macro description . . . . . . . . . . . . . . . . . . . 1433
show parser macro . . . . . . . . . . . . . . . . . . 1433
69 Clock Commands . . . . . . . . . . . . . . . . . 1435
Real-time Clock . . . . . . . . . . . . . . . . . . . . 1435
Simple Network Time Protocol . . . . . . . . . . . . 1435
Commands in this Chapter. . . . . . . . . . . . . . . 1436
show sntp configuration. . . . . . . . . . . . . . . . 1436
show sntp server. . . . . . . . . . . . . . . . . . . . 1437
show sntp status . . . . . . . . . . . . . . . . . . . . 1438
sntp authenticate . . . . . . . . . . . . . . . . . . . 1439
sntp authentication-key . . . . . . . . . . . . . . . . 1440
2CSNXXX_SWUM200.book Page 63 Tuesday, December 10, 2013 1:22 PM

Contents 64
sntp broadcast client enable . . . . . . . . . . . . . 1441
sntp client poll timer. . . . . . . . . . . . . . . . . . 1441
sntp server . . . . . . . . . . . . . . . . . . . . . . . 1442
sntp trusted-key . . . . . . . . . . . . . . . . . . . . 1443
sntp unicast client enable . . . . . . . . . . . . . . . 1444
clock timezone hours-offset . . . . . . . . . . . . . . 1444
no clock timezone . . . . . . . . . . . . . . . . . . . 1445
clock summer-time recurring . . . . . . . . . . . . . 1446
clock summer-time date . . . . . . . . . . . . . . . . 1447
no clock summer-time . . . . . . . . . . . . . . . . . 1448
show clock. . . . . . . . . . . . . . . . . . . . . . . 1448
70 Command Line Configuration Scripting Commands
1451
Commands in this Chapter. . . . . . . . . . . . . . . 1451
script apply. . . . . . . . . . . . . . . . . . . . . . . 1451
script delete . . . . . . . . . . . . . . . . . . . . . . 1452
script list . . . . . . . . . . . . . . . . . . . . . . . . 1453
script show. . . . . . . . . . . . . . . . . . . . . . . 1453
script validate . . . . . . . . . . . . . . . . . . . . . 1454
2CSNXXX_SWUM200.book Page 64 Tuesday, December 10, 2013 1:22 PM

Contents 65
71 Configuration and Image File Commands 1457
File System Commands . . . . . . . . . . . . . . . . 1457
Command Line Interface Scripting . . . . . . . . . . 1457
Commands in this Chapter. . . . . . . . . . . . . . . 1457
boot system . . . . . . . . . . . . . . . . . . . . . . 1458
clear config . . . . . . . . . . . . . . . . . . . . . . 1459
copy . . . . . . . . . . . . . . . . . . . . . . . . . . 1460
delete. . . . . . . . . . . . . . . . . . . . . . . . . . 1465
delete backup-config . . . . . . . . . . . . . . . . . 1466
delete backup-image . . . . . . . . . . . . . . . . . 1466
delete startup-config . . . . . . . . . . . . . . . . . 1467
dir . . . . . . . . . . . . . . . . . . . . . . . . . . . 1467
erase . . . . . . . . . . . . . . . . . . . . . . . . . . 1468
filedescr . . . . . . . . . . . . . . . . . . . . . . . . 1469
rename . . . . . . . . . . . . . . . . . . . . . . . . . 1470
show backup-config. . . . . . . . . . . . . . . . . . 1470
show bootvar. . . . . . . . . . . . . . . . . . . . . . 1471
show running-config. . . . . . . . . . . . . . . . . . 1472
show startup-config . . . . . . . . . . . . . . . . . . 1473
write . . . . . . . . . . . . . . . . . . . . . . . . . . 1474
2CSNXXX_SWUM200.book Page 65 Tuesday, December 10, 2013 1:22 PM

Contents 66
72 Denial of Service Commands . . . . . . . 1477
Commands in this Chapter. . . . . . . . . . . . . . . 1478
dos-control firstfrag . . . . . . . . . . . . . . . . . . 1479
dos-control icmp. . . . . . . . . . . . . . . . . . . . 1479
dos-control l4port . . . . . . . . . . . . . . . . . . . 1480
dos-control sipdip . . . . . . . . . . . . . . . . . . . 1481
dos-control tcpflag . . . . . . . . . . . . . . . . . . 1482
dos-control tcpfrag . . . . . . . . . . . . . . . . . . 1482
ip icmp echo-reply . . . . . . . . . . . . . . . . . . . 1483
ip icmp error-interval . . . . . . . . . . . . . . . . . 1484
ip unreachables . . . . . . . . . . . . . . . . . . . . 1485
ip redirects. . . . . . . . . . . . . . . . . . . . . . . 1485
ipv6 icmp error-interval . . . . . . . . . . . . . . . . 1486
ipv6 unreachables . . . . . . . . . . . . . . . . . . . 1487
show dos-control . . . . . . . . . . . . . . . . . . . 1487
73 Line Commands . . . . . . . . . . . . . . . . . . 1489
exec-timeout . . . . . . . . . . . . . . . . . . . . . . 1489
history . . . . . . . . . . . . . . . . . . . . . . . . . 1490
history size . . . . . . . . . . . . . . . . . . . . . . . 1491
line . . . . . . . . . . . . . . . . . . . . . . . . . . . 1491
2CSNXXX_SWUM200.book Page 66 Tuesday, December 10, 2013 1:22 PM

Contents 67
show line. . . . . . . . . . . . . . . . . . . . . . . . 1492
speed . . . . . . . . . . . . . . . . . . . . . . . . . . 1493
74 Management ACL Commands . . . . . . . 1495
Commands in this Chapter. . . . . . . . . . . . . . . 1495
deny (management) . . . . . . . . . . . . . . . . . . 1496
management access-class . . . . . . . . . . . . . . 1497
management access-list . . . . . . . . . . . . . . . 1498
permit (management) . . . . . . . . . . . . . . . . . 1499
show management access-class . . . . . . . . . . . 1501
show management access-list . . . . . . . . . . . . 1502
75 Password Management Commands . . 1503
Configurable Minimum Password Length. . . . . . . 1503
Password History . . . . . . . . . . . . . . . . . . . 1503
Password Aging . . . . . . . . . . . . . . . . . . . . 1503
User Lockout . . . . . . . . . . . . . . . . . . . . . . 1503
Password Strength . . . . . . . . . . . . . . . . . . 1504
Commands in this Chapter. . . . . . . . . . . . . . . 1505
passwords aging. . . . . . . . . . . . . . . . . . . . 1506
passwords history . . . . . . . . . . . . . . . . . . . 1506
passwords lock-out . . . . . . . . . . . . . . . . . . 1507
2CSNXXX_SWUM200.book Page 67 Tuesday, December 10, 2013 1:22 PM

Contents 68
passwords min-length . . . . . . . . . . . . . . . . . 1508
passwords strength-check . . . . . . . . . . . . . . 1509
passwords strength minimum uppercase-letters. . . 1510
passwords strength minimum lowercase-letters. . . 1510
passwords strength minimum numeric-characters . 1511
passwords strength minimum special-characters . . 1512
passwords strength max-limit consecutive-characters 1513
passwords strength max-limit repeated-characters . 1513
passwords strength minimum character-classes . . 1514
passwords strength exclude-keyword . . . . . . . . 1515
enable password encrypted . . . . . . . . . . . . . . 1516
show passwords configuration . . . . . . . . . . . . 1516
show passwords result . . . . . . . . . . . . . . . . 1518
76 PHY Diagnostics Commands . . . . . . . . 1521
show copper-ports tdr . . . . . . . . . . . . . . . . . 1521
show fiber-ports optical-transceiver . . . . . . . . . 1522
test copper-port tdr . . . . . . . . . . . . . . . . . . 1523
77 Power Over Ethernet Commands . . . . 1525
Flexible Power Management . . . . . . . . . . . . . 1525
Commands in this Chapter. . . . . . . . . . . . . . . 1526
2CSNXXX_SWUM200.book Page 68 Tuesday, December 10, 2013 1:22 PM

Contents 69
power inline . . . . . . . . . . . . . . . . . . . . . . 1526
power inline detection . . . . . . . . . . . . . . . . 1527
power inline high-power . . . . . . . . . . . . . . . 1527
power inline limit . . . . . . . . . . . . . . . . . . . 1528
power inline management. . . . . . . . . . . . . . . 1529
power inline powered-device. . . . . . . . . . . . . 1533
power inline priority. . . . . . . . . . . . . . . . . . 1533
power inline reset . . . . . . . . . . . . . . . . . . . 1534
power inline usage-threshold . . . . . . . . . . . . . 1535
clear power inline statistics . . . . . . . . . . . . . 1535
show power inline. . . . . . . . . . . . . . . . . . . 1536
show power inline firmware-version . . . . . . . . . 1537
78 RMON Commands . . . . . . . . . . . . . . . . 1539
Commands in this Chapter. . . . . . . . . . . . . . . 1539
rmon alarm . . . . . . . . . . . . . . . . . . . . . . . 1539
rmon collection history . . . . . . . . . . . . . . . . 1541
rmon event . . . . . . . . . . . . . . . . . . . . . . . 1542
rmon hcalarm . . . . . . . . . . . . . . . . . . . . . 1543
show rmon alarm . . . . . . . . . . . . . . . . . . . 1545
show rmon alarms . . . . . . . . . . . . . . . . . . . 1547
show rmon collection history . . . . . . . . . . . . . 1548
2CSNXXX_SWUM200.book Page 69 Tuesday, December 10, 2013 1:22 PM

Contents 70
show rmon events . . . . . . . . . . . . . . . . . . . 1549
show rmon hcalarm . . . . . . . . . . . . . . . . . . 1550
show rmon history . . . . . . . . . . . . . . . . . . . 1551
show rmon log . . . . . . . . . . . . . . . . . . . . . 1554
show rmon statistics. . . . . . . . . . . . . . . . . . 1555
79 SDM Templates Commands . . . . . . . . . 1559
Commands in this Chapter. . . . . . . . . . . . . . . 1559
sdm prefer . . . . . . . . . . . . . . . . . . . . . . . 1559
show sdm prefer . . . . . . . . . . . . . . . . . . . . 1560
80 Serviceability Tracing Packet Commands 1565
Commands in this Chapter. . . . . . . . . . . . . . . 1565
debug arp . . . . . . . . . . . . . . . . . . . . . . . 1566
debug authentication interface . . . . . . . . . . . . 1567
debug auto-voip . . . . . . . . . . . . . . . . . . . . 1568
debug clear . . . . . . . . . . . . . . . . . . . . . . 1568
debug console . . . . . . . . . . . . . . . . . . . . . 1569
debug dot1ag. . . . . . . . . . . . . . . . . . . . . . 1569
debug dot1x . . . . . . . . . . . . . . . . . . . . . . 1571
debug igmpsnooping. . . . . . . . . . . . . . . . . . 1571
debug ip acl . . . . . . . . . . . . . . . . . . . . . . 1572
2CSNXXX_SWUM200.book Page 70 Tuesday, December 10, 2013 1:22 PM

Contents 71
debug ip dvmrp. . . . . . . . . . . . . . . . . . . . . 1573
debug ip igmp . . . . . . . . . . . . . . . . . . . . . 1573
debug ip mcache. . . . . . . . . . . . . . . . . . . . 1574
debug ip pimdm packet . . . . . . . . . . . . . . . . 1575
debug ip pimsm packet . . . . . . . . . . . . . . . . 1576
debug ip vrrp . . . . . . . . . . . . . . . . . . . . . . 1576
debug ipv6 dhcp . . . . . . . . . . . . . . . . . . . . 1577
debug ipv6 mcache . . . . . . . . . . . . . . . . . . 1578
debug ipv6 mld . . . . . . . . . . . . . . . . . . . . . 1578
debug ipv6 pimdm . . . . . . . . . . . . . . . . . . . 1579
debug ipv6 pimsm . . . . . . . . . . . . . . . . . . . 1580
debug isdp . . . . . . . . . . . . . . . . . . . . . . . 1581
debug lacp . . . . . . . . . . . . . . . . . . . . . . . 1581
debug mldsnooping . . . . . . . . . . . . . . . . . . 1582
debug ospf . . . . . . . . . . . . . . . . . . . . . . . 1583
debug ospfv3 . . . . . . . . . . . . . . . . . . . . . . 1583
debug ping . . . . . . . . . . . . . . . . . . . . . . . 1584
debug rip . . . . . . . . . . . . . . . . . . . . . . . . 1585
debug sflow . . . . . . . . . . . . . . . . . . . . . . 1585
debug spanning-tree. . . . . . . . . . . . . . . . . . 1586
debug vrrp . . . . . . . . . . . . . . . . . . . . . . . 1587
2CSNXXX_SWUM200.book Page 71 Tuesday, December 10, 2013 1:22 PM

Contents 72
exception core-file . . . . . . . . . . . . . . . . . . 1587
exception dump . . . . . . . . . . . . . . . . . . . . 1588
exception protocol. . . . . . . . . . . . . . . . . . . 1589
exception switch-chip-register . . . . . . . . . . . 1591
show debugging . . . . . . . . . . . . . . . . . . . . 1591
show exception . . . . . . . . . . . . . . . . . . . . 1592
write core . . . . . . . . . . . . . . . . . . . . . . . 1593
81 Sflow Commands . . . . . . . . . . . . . . . . . 1597
Commands in this Chapter. . . . . . . . . . . . . . . 1597
sflow destination . . . . . . . . . . . . . . . . . . . 1597
sflow polling . . . . . . . . . . . . . . . . . . . . . . 1599
sflow polling (Interface Mode) . . . . . . . . . . . . 1600
sflow sampling. . . . . . . . . . . . . . . . . . . . . 1601
sflow sampling (Interface Mode) . . . . . . . . . . . 1602
show sflow agent . . . . . . . . . . . . . . . . . . . 1603
show sflow destination . . . . . . . . . . . . . . . . 1604
show sflow polling . . . . . . . . . . . . . . . . . . 1605
show sflow sampling . . . . . . . . . . . . . . . . . 1606
82 SNMP Commands . . . . . . . . . . . . . . . . 1609
Commands in this Chapter. . . . . . . . . . . . . . . 1609
2CSNXXX_SWUM200.book Page 72 Tuesday, December 10, 2013 1:22 PM

Contents 73
show snmp . . . . . . . . . . . . . . . . . . . . . . . 1610
show snmp engineID . . . . . . . . . . . . . . . . . 1611
show snmp filters . . . . . . . . . . . . . . . . . . . 1611
show snmp group . . . . . . . . . . . . . . . . . . . 1612
show snmp user . . . . . . . . . . . . . . . . . . . . 1614
show snmp views . . . . . . . . . . . . . . . . . . . 1615
show trapflags . . . . . . . . . . . . . . . . . . . . . 1616
snmp-server community . . . . . . . . . . . . . . . . 1617
snmp-server community-group . . . . . . . . . . . . 1619
snmp-server contact. . . . . . . . . . . . . . . . . . 1620
snmp-server enable traps . . . . . . . . . . . . . . . 1621
snmp-server engineID local . . . . . . . . . . . . . . 1623
snmp-server filter . . . . . . . . . . . . . . . . . . . 1624
snmp-server group . . . . . . . . . . . . . . . . . . . 1625
snmp-server host . . . . . . . . . . . . . . . . . . . 1627
snmp-server location . . . . . . . . . . . . . . . . . 1628
snmp-server user . . . . . . . . . . . . . . . . . . . 1629
snmp-server view . . . . . . . . . . . . . . . . . . . 1631
snmp-server v3-host . . . . . . . . . . . . . . . . . . 1632
83 SSH Commands . . . . . . . . . . . . . . . . . . 1635
Commands in this Chapter. . . . . . . . . . . . . . . 1635
2CSNXXX_SWUM200.book Page 73 Tuesday, December 10, 2013 1:22 PM

Contents 74
cryptho key generate dsa . . . . . . . . . . . . . . . 1635
crypto key generate rsa . . . . . . . . . . . . . . . . 1636
crypto key pubkey-chain ssh . . . . . . . . . . . . . 1637
crypto key zeroize pubkey-chain . . . . . . . . . . . 1638
crypto key zeroize {rsa|dsa} . . . . . . . . . . . . . . 1638
ip ssh port . . . . . . . . . . . . . . . . . . . . . . . 1639
ip ssh pubkey-auth. . . . . . . . . . . . . . . . . . . 1640
ip ssh server . . . . . . . . . . . . . . . . . . . . . . 1640
key-string . . . . . . . . . . . . . . . . . . . . . . . 1641
no crypto certificate . . . . . . . . . . . . . . . . . . 1642
show crypto key mypubkey . . . . . . . . . . . . . . 1643
show crypto key pubkey-chain ssh . . . . . . . . . . 1644
show ip ssh . . . . . . . . . . . . . . . . . . . . . . 1645
84 Syslog Commands . . . . . . . . . . . . . . . . 1647
CLI Logged to Local File and Syslog Server. . . . . . 1647
Commands in this Chapter. . . . . . . . . . . . . . . 1648
clear logging. . . . . . . . . . . . . . . . . . . . . . 1648
clear logging file. . . . . . . . . . . . . . . . . . . . 1649
description (Logging) . . . . . . . . . . . . . . . . . 1650
level . . . . . . . . . . . . . . . . . . . . . . . . . . 1650
logging cli-command . . . . . . . . . . . . . . . . . 1651
2CSNXXX_SWUM200.book Page 74 Tuesday, December 10, 2013 1:22 PM

Contents 75
logging . . . . . . . . . . . . . . . . . . . . . . . . . 1652
logging audit . . . . . . . . . . . . . . . . . . . . . . 1654
logging buffered . . . . . . . . . . . . . . . . . . . . 1655
logging console . . . . . . . . . . . . . . . . . . . . 1656
logging facility. . . . . . . . . . . . . . . . . . . . . 1657
logging file . . . . . . . . . . . . . . . . . . . . . . . 1658
logging monitor . . . . . . . . . . . . . . . . . . . . 1659
logging on . . . . . . . . . . . . . . . . . . . . . . . 1660
logging protocol . . . . . . . . . . . . . . . . . . . . 1661
logging snmp. . . . . . . . . . . . . . . . . . . . . . 1662
logging web-session . . . . . . . . . . . . . . . . . 1663
port . . . . . . . . . . . . . . . . . . . . . . . . . . . 1664
show logging. . . . . . . . . . . . . . . . . . . . . . 1664
show logging file . . . . . . . . . . . . . . . . . . . 1665
show syslog-servers. . . . . . . . . . . . . . . . . . 1666
terminal monitor . . . . . . . . . . . . . . . . . . . . 1667
85 System Management Commands . . . . 1669
asset-tag . . . . . . . . . . . . . . . . . . . . . . . . 1670
banner exec . . . . . . . . . . . . . . . . . . . . . . 1670
banner login . . . . . . . . . . . . . . . . . . . . . . 1671
banner motd . . . . . . . . . . . . . . . . . . . . . . 1672
2CSNXXX_SWUM200.book Page 75 Tuesday, December 10, 2013 1:22 PM

Contents 76
banner motd acknowledge . . . . . . . . . . . . . . 1673
clear checkpoint statistics . . . . . . . . . . . . . . 1675
clear counters stack-ports. . . . . . . . . . . . . . . 1676
connect . . . . . . . . . . . . . . . . . . . . . . . . . 1676
cut-through mode . . . . . . . . . . . . . . . . . . . 1678
exec-banner . . . . . . . . . . . . . . . . . . . . . . 1678
exit . . . . . . . . . . . . . . . . . . . . . . . . . . . 1679
hardware profile portmode . . . . . . . . . . . . . . 1680
hostname . . . . . . . . . . . . . . . . . . . . . . . . 1681
initiate failover . . . . . . . . . . . . . . . . . . . . . 1682
load-interval . . . . . . . . . . . . . . . . . . . . . . 1683
locate. . . . . . . . . . . . . . . . . . . . . . . . . . 1684
login-banner . . . . . . . . . . . . . . . . . . . . . . 1685
logout. . . . . . . . . . . . . . . . . . . . . . . . . . 1685
member . . . . . . . . . . . . . . . . . . . . . . . . . 1687
motd-banner . . . . . . . . . . . . . . . . . . . . . . 1688
nsf . . . . . . . . . . . . . . . . . . . . . . . . . . . 1688
ping . . . . . . . . . . . . . . . . . . . . . . . . . . . 1689
quit . . . . . . . . . . . . . . . . . . . . . . . . . . . 1690
reload. . . . . . . . . . . . . . . . . . . . . . . . . . 1691
service unsupported-transceiver . . . . . . . . . . . 1693
2CSNXXX_SWUM200.book Page 76 Tuesday, December 10, 2013 1:22 PM

Contents 77
set description . . . . . . . . . . . . . . . . . . . . . 1693
slot . . . . . . . . . . . . . . . . . . . . . . . . . . . 1694
show banner . . . . . . . . . . . . . . . . . . . . . . 1696
show checkpoint statistics . . . . . . . . . . . . . . 1697
show cut-through mode . . . . . . . . . . . . . . . . 1698
show hardware profile . . . . . . . . . . . . . . . . 1698
show idprom interface interface-id . . . . . . . . . . 1699
show interfaces advanced firmware . . . . . . . . . 1701
show interfaces interface-id . . . . . . . . . . . . . 1701
show interfaces utilization . . . . . . . . . . . . . . 1703
show memory cpu . . . . . . . . . . . . . . . . . . . 1703
show nsf . . . . . . . . . . . . . . . . . . . . . . . . 1704
show power-usage-history . . . . . . . . . . . . . . 1705
show process cpu . . . . . . . . . . . . . . . . . . . 1706
show sessions . . . . . . . . . . . . . . . . . . . . . 1708
show slot . . . . . . . . . . . . . . . . . . . . . . . . 1709
show supported cardtype . . . . . . . . . . . . . . . 1710
show supported switchtype . . . . . . . . . . . . . . 1712
show switch . . . . . . . . . . . . . . . . . . . . . . 1714
show system . . . . . . . . . . . . . . . . . . . . . . 1722
show system fan . . . . . . . . . . . . . . . . . . . . 1723
2CSNXXX_SWUM200.book Page 77 Tuesday, December 10, 2013 1:22 PM

Contents 78
show system id . . . . . . . . . . . . . . . . . . . . 1724
show system power . . . . . . . . . . . . . . . . . . 1725
show system temperature . . . . . . . . . . . . . . . 1726
show tech-support . . . . . . . . . . . . . . . . . . . 1727
show users . . . . . . . . . . . . . . . . . . . . . . . 1729
show version. . . . . . . . . . . . . . . . . . . . . . 1730
stack . . . . . . . . . . . . . . . . . . . . . . . . . . 1731
stack-port . . . . . . . . . . . . . . . . . . . . . . . 1732
stack-port interface shutdown . . . . . . . . . . . . 1733
standby . . . . . . . . . . . . . . . . . . . . . . . . . 1734
switch renumber. . . . . . . . . . . . . . . . . . . . 1735
telnet . . . . . . . . . . . . . . . . . . . . . . . . . . 1736
traceroute . . . . . . . . . . . . . . . . . . . . . . . 1738
traceroute ipv6 . . . . . . . . . . . . . . . . . . . . . 1740
update bootcode . . . . . . . . . . . . . . . . . . . . 1742
86 Telnet Server Commands. . . . . . . . . . . 1745
Telnet Client Behaviors . . . . . . . . . . . . . . . . 1745
Commands in this Chapter. . . . . . . . . . . . . . . 1747
ip telnet server disable . . . . . . . . . . . . . . . . 1747
ip telnet port . . . . . . . . . . . . . . . . . . . . . . 1747
show ip telnet . . . . . . . . . . . . . . . . . . . . . 1748
2CSNXXX_SWUM200.book Page 78 Tuesday, December 10, 2013 1:22 PM

Contents 79
87 Terminal Length Commands . . . . . . . . 1749
terminal length. . . . . . . . . . . . . . . . . . . . . 1749
88 Time Ranges Commands . . . . . . . . . . . 1751
time-range . . . . . . . . . . . . . . . . . . . . . . . 1751
absolute . . . . . . . . . . . . . . . . . . . . . . . . 1752
periodic . . . . . . . . . . . . . . . . . . . . . . . . 1753
show time-range. . . . . . . . . . . . . . . . . . . . 1755
89 USB Flash Drive Commands . . . . . . . . 1757
Validation of Files Downloaded/Uploaded from USB Device 1757
Validation for Files Uploaded from Switch to USB Flash Drive 1758
Downloading and Uploading of Files . . . . . . . . . 1758
Commands in this Chapter. . . . . . . . . . . . . . . 1758
unmount usb . . . . . . . . . . . . . . . . . . . . . . 1758
show usb . . . . . . . . . . . . . . . . . . . . . . . . 1759
dir usb . . . . . . . . . . . . . . . . . . . . . . . . . 1760
90 User Interface Commands. . . . . . . . . . 1763
configure terminal . . . . . . . . . . . . . . . . . . . 1763
do. . . . . . . . . . . . . . . . . . . . . . . . . . . . 1764
enable . . . . . . . . . . . . . . . . . . . . . . . . . 1766
2CSNXXX_SWUM200.book Page 79 Tuesday, December 10, 2013 1:22 PM

Contents 80
end . . . . . . . . . . . . . . . . . . . . . . . . . . . 1766
exit . . . . . . . . . . . . . . . . . . . . . . . . . . . 1767
quit . . . . . . . . . . . . . . . . . . . . . . . . . . . 1768
91 Web Server Commands . . . . . . . . . . . . 1769
Web Sessions . . . . . . . . . . . . . . . . . . . . . 1769
Commands in this Chapter. . . . . . . . . . . . . . . 1770
common-name . . . . . . . . . . . . . . . . . . . . . 1770
country . . . . . . . . . . . . . . . . . . . . . . . . . 1771
crypto certificate generate . . . . . . . . . . . . . . 1772
crypto certificate import. . . . . . . . . . . . . . . . 1773
crypto certificate request . . . . . . . . . . . . . . . 1774
duration . . . . . . . . . . . . . . . . . . . . . . . . 1775
ip http port . . . . . . . . . . . . . . . . . . . . . . . 1775
ip http server . . . . . . . . . . . . . . . . . . . . . . 1776
ip http secure-certificate . . . . . . . . . . . . . . . 1777
ip http secure-port . . . . . . . . . . . . . . . . . . . 1778
ip http secure-server. . . . . . . . . . . . . . . . . . 1779
key-generate . . . . . . . . . . . . . . . . . . . . . . 1779
location . . . . . . . . . . . . . . . . . . . . . . . . 1780
organization-unit. . . . . . . . . . . . . . . . . . . . 1781
show crypto certificate mycertificate. . . . . . . . . 1781
2CSNXXX_SWUM200.book Page 80 Tuesday, December 10, 2013 1:22 PM

Contents 81
show ip http server status . . . . . . . . . . . . . . . 1782
show ip http server secure status . . . . . . . . . . . 1783
state . . . . . . . . . . . . . . . . . . . . . . . . . . 1784
A Appendix A: List of Commands . . . . . . 1787
2CSNXXX_SWUM200.book Page 81 Tuesday, December 10, 2013 1:22 PM

Contents 82
2CSNXXX_SWUM200.book Page 82 Tuesday, December 10, 2013 1:22 PM

Command Groups 83
1
Command Groups
Dell Networking N2000/N3000/N4000 Series Switches
Introduction
The Command Line Interface (CLI) is a network management application
operated through an ASCII terminal without the use of a Graphic User
Interface (GUI) driven software application. By directly entering commands,
the user has greater configuration flexibility. The CLI is a basic command-line
interpreter similar to the UNIX C shell.
A switch can be configured and maintained by entering commands from the
CLI, which is based solely on textual input and output with commands being
entered by a terminal keyboard and the output displayed as text via a terminal
monitor. The CLI can be accessed from a console terminal connected to an
EIA/TIA-232 port or through a Telnet/SSH session.
This guide describes how the CLI is structured, describes the command
syntax, and describes the command functionality.
This guide also provides information for configuring the Dell Networking
switch, details the procedures, and provides configuration examples. Basic
installation configuration is described in the
User’s Guide
and must be
completed before using this document.
Command Groups
The system commands can be broken down into three sets of functional
groups: Layer 2, Layer 3, and Utility.
Table 1-1. System Command Groups
Command Group Description
Layer 2 Commands
AAA
Configures connection security including authorization
and passwords.
2CSNXXX_SWUM200.book Page 83 Tuesday, December 10, 2013 1:22 PM
Command Groups 84
Administrative Profiles
Commands
Group commands into a profile and assign a profile to a
user upon authentication.
Administrative Profiles
Configures and displays ACL information.
Address Table
Configures bridging address tables.
Auto-VoIP
Configures Auto VoIP for IP phones on a switch.
CDP Interoperability
Configures Cisco® Discovery Protocol (CDP).
DHCP L2 Relay
Enables the Layer 2 DHCP Relay agent for an interface.
DHCP Management
Interface
Configures an interface to obtain an IP address via DHCP.
Dynamic ARP Inspection
Configures for rejection of invalid and malicious ARP
packets.
Ethernet Configuration
Configures all port configuration options for example
ports, storm control, port speed and auto-negotiation.
Ethernet CFM
Configures and displays GVRP configuration and
information.
IGMP Snooping
Configures IGMP snooping and displays IGMP
configuration and IGMP information.
IGMP Snooping Querier
Configures IGMP Snooping Querier and displays IGMP
Snooping Querier information.
IP Addressing
Configures and manages IP addresses on the switch.
IPv6 ACL
Configures and displays ACL information for IPv6.
IPv6 MLD Snooping
Configures IPv6 MLD Snooping.
IPv6 MLD Snooping
Querier
Configures IPv6 Snooping Querier and displays IPv6
Snooping Querier information.
iSCSI Optimization
Configures special QoS treatment for traffic between
iSCSI initiators and target systems.
Link Dependency
Configures and displays link dependency information.
LLDP
Configures and displays LLDP information.
Port Channel
Configures and displays Port channel information.
Port Monitor
Monitors activity on specific target ports.
Table 1-1. System Command Groups
(continued)
Command Group Description
2CSNXXX_SWUM200.book Page 84 Tuesday, December 10, 2013 1:22 PM
Command Groups 85
QoS
Configures and displays QoS information.
Radius
Configures and displays RADIUS information.
Spanning Tree
Configures and reports on Spanning Tree protocol.
TACACS+
Configures and displays TACACS+ information.
VLAN
Configures VLANs and displays VLAN information.
Voice VLAN
Configures voice VLANs and displays voice VLAN
information.
802.1x
Configures and displays commands related to 802.1x
security protocol.
Layer 3 Commands
ARP (IPv4)
Manages Address Resolution Protocol functions.
DHCP Server and Relay
Agent (IPv4)
Manages DHCP/BOOTP operations on the system.
DHCPv6
Configures IPv6 DHCP functions.
DHCPv6 Snooping
Configures DHCP v6 snooping and whether an interface
is trusted or untrusted.
DVMRP
(Mcast) Configures DVMRP operations.
IGMP
(Mcast) Configures IGMP operations.
IGMP Proxy
(Mcast) Manages IGMP Proxy on the system.
IP Helper/DHCP Relay
Configures relay of UDP packets.
IP Routing
(IPv4) Configures IP routing and addressing.
IPv6 Multicast
Manages IPv6 Multicasting on the system.
IPv6 Routing
Configures IPv6 routing and addressing.
Loopback Interface
(IPv6)
Manages Loopback configurations.
Multicast
(Mcast) Manages Multicasting on the system.
OSPF
(IPv4) Manages shortest path operations.
OSPFv3
(IPv6) Manages IPv6 shortest path operations.
Table 1-1. System Command Groups
(continued)
Command Group Description
2CSNXXX_SWUM200.book Page 85 Tuesday, December 10, 2013 1:22 PM
Command Groups 86
Router Discovery Protocol
(IPv4)
Manages router discovery operations.
Routing Information
Protocol
(IPv4)
Configures RIP activities.
Tu n ne l I n t er fa ce
(IPv6) Managing tunneling operations.
Virtual Router
Redundancy
(IPv4)
Controls virtual LAN routing.
Virtual Router
Redundancy
(IPv4)
Manages router redundancy on the system.
Utility Commands
Auto-Install
Automatically configures switch when a configuration file
is not found.
Captive Portal
Blocks clients from accessing network until user
verification is established.
Clock
Configures the system clock.
Command Line
Configuration Scripting
Manages the switch configuration files.
Denial of Service
Provides several Denial of Service options.
Line
Configures the console, SSH, and remote Telnet
connection.
Management ACL
Configures and displays management access-list
information.
Password Management
Provides password management.
PHY Diagnostics
Diagnoses and displays the interface status.
Power Over Ethernet
(PoE)
Configures PoE and displays PoE information.
RMON
Can be configured through the CLI and displays RMON
information.
Serviceability Tracing
Controls display of debug output to serial port or telnet
console.
sFlow
Configures sFlow monitoring.
Table 1-1. System Command Groups
(continued)
Command Group Description
2CSNXXX_SWUM200.book Page 86 Tuesday, December 10, 2013 1:22 PM
Command Groups 87
Mode Types
The tables on the following pages use these abbreviations for Command
Mode names.
• AAA — IAS User Configuration
• APC — Administrative Profile Configuration
• ARPA — ARP ACL Configuration
• CC — Crypto Configuration
• CP — Captive Portal Configuration
•CPI — Captive Portal Instance
• CMC — Class-Map Configuration
• DP — IP DHCP Pool Configuration
• GC — Global Configuration
• IC — Interface Configuration (reached via
interface vlan
xxx
command)
• IP — IP Access List Configuration
• IR — Interface Range
•KC — Key Chain
•KE — Key
SNMP
Configures SNMP communities, traps and displays SNMP
information.
SSH
Configures SSH authentication.
Syslog
Manages and displays syslog messages.
System Management
Configures the switch clock, name and authorized users.
Telnet Ser ve r
Configures Telnet service on the switch and displays
Telnet information.
User Interface
Describes user commands used for entering CLI
commands.
Web Ser ver
Configures web-based access to the switch.
Table 1-1. System Command Groups
(continued)
Command Group Description
2CSNXXX_SWUM200.book Page 87 Tuesday, December 10, 2013 1:22 PM

Command Groups 88
• L — Logging
• LC — Line Configuration
• LD — Link Dependency
• MA — Management Access-level
• MC — MST Configuration
• MD —MLAG Domain Configuration
• MDC — Maintenance Domain Configuration
• ML — MAC-List Configuration
• MSC — Mail Server Configuration
•MT — MAC-acl
• OG — OSPFv2 Global Configuration
• PE — Privileged EXEC
• PM — Policy Map Configuration
• PCGC — Policy Map Global Configuration
• PCMC — Policy Class Map Configuration
•R — Radius
• RIP — Router RIP Configuration
• RC — Router Configuration
• ROSPF — Router Open Shortest Path First
• ROSV3 — Router Open Shortest Path First Version 3
• SG — Stack Global Configuration
•SP — SSH Public Key
•SK — SSH Public Key-chain
• TC — TACACS Configuration
• TRC — Time Range Configuration
• UE — User EXEC
• VC — VLAN Configuration (reached via
vlan
command)
• v6ACL — IPv6 Access List Configuration
• v6CMC — IPv6 Class-Map Configuration
2CSNXXX_SWUM200.book Page 88 Tuesday, December 10, 2013 1:22 PM
Command Groups 89
• v6DP — IPv6 DHCP Pool Configuration
Layer 2 Commands
AAA
Command Description Modea
aaa authentication dot1x
default
Specifies an authentication method for 802.1x
clients.
GC
aaa authentication enable
Defines authentication method lists for
accessing higher privilege levels.
GC
aaa authentication login
Defines login authentication. GC
aaa authorization network
default radius
Enables the switch to accept VLAN assignment
by the RADIUS server.
GC
aaa ias-user username
Configures IAS users and their attributes. Also
changes the mode to aa user Configuration
mode.
GC
clear (IAS)
aaa ias-users Deletes all IAS users. PE
enable authentication
Specifies the authentication method list when
accessing a higher privilege level from a remote
telnet or console.
LC
enable password
Sets a local password to control access to the
normal level.
GC
ip http authentication
Specifies authentication methods for http. GC
ip https authentication
Specifies authentication methods for https. GC
login authentication
Specifies the login authentication method list
for a remote telnet or console.
LC
password (aaa IAS User
Configuration)
Configures a password for a user. AAA
password (Line
Configuration)
Specifies a password on a line. LC
password (User EXEC)
Specifies a user password UE
show aaa ias-users
Displays configured IAS users and their
attributes.
PE
2CSNXXX_SWUM200.book Page 89 Tuesday, December 10, 2013 1:22 PM
Command Groups 90
Administrative Profiles
show authentication
methods
Shows information about authentication
methods.
PE
show users accounts
Displays information about the local user
database.
PE
show users login-history
Displays information about login histories of
users.
PE
username
Establishes a username-based authentication
system. Optionally allows the specification of an
Administrative Profile for a local user.
GC
username unlock
Transfers local user passwords between devices
without having to know the passwords.
GC
a. For the meaning of each Mode abbreviation, see
Mode Types
on page 87
Command Description Modea
a. For the meaning of each Mode abbreviation, see
Mode Types
on page 87.
admin-profile
Creates an administrative profile. GC
description (Administrative
Profile Configuration)
Adds a description to an administrative profile. APC
rule
Adds a rule to an administrative profile. APC
show admin-profiles
Displays the administrative profiles. PE
show admin-profiles brief
Lists the names of the administrative
profiles defined on the switch.
PE
show cli modes
Lists the names of all the CLI modes. PE
show users
Shows which administrative profiles have been
assigned to local user accounts and to show
which profiles are active for logged-in users.
PE
username
Optionally allows the specification of an
Administrative Profile for a local user.
GC
Command Description Modea
2CSNXXX_SWUM200.book Page 90 Tuesday, December 10, 2013 1:22 PM
Command Groups 91
ACL
Command Description Modea
a. For the meaning of each Mode abbreviation, see
Mode Types
on page 87.
ip access-list
Creates an Access Control List (ACL) that is
identified by the parameter
accesslistnumber.
GC
deny | permit (IP ACL)
The deny command denies traffic if the
conditions defined in the deny statement are
matched. The permit command allows traffic if
the conditions defined in the permit statement
are matched.
ML
ip access-group
Attaches a specified access-control list to an
interface.
GC or
IC
mac access-group
Attaches a specific MAC Access Control List
(ACL) to an interface in the in-bound
direction.
GC or
IC
mac access-list extended
Creates the MAC Access Control List (ACL)
identified by the
name
parameter.
GC
mac access-list extended
rename
Renames the existing MAC Access Control List
(ACL) name.
GC
service-acl input
Blocks Link Local Protocol Filtering (LLPF)
protocol(s) on a given port.
IC
show service-acl interface
Displays the status of LLPF rules configured on
a particular port or on all the ports.
PE
show ip access-lists
Displays an Access Control List (ACL) and all
of the rules that are defined for the ACL.
PE
show mac access-lists
Displays a MAC access list and all of the rules
that are defined for the ACL.
PE
2CSNXXX_SWUM200.book Page 91 Tuesday, December 10, 2013 1:22 PM
Command Groups 92
Address Table
Command Description Modea
clear mac address-table
Removes any learned entries from the
forwarding database.
PE
mac address-table aging-
time
Sets the address table aging time. GC
mac address-table multicast
forbidden address
Forbids adding a specific multicast address to
specific ports.
IC
mac address-table static vlan
Registers MAC-layer multicast addresses to the
bridge forwarding table, and adds static ports to
the group.
IC
mac address-table static vlan
Adds a static MAC-layer station source address
to the bridge table.
IC
port security
Disables new address learning on an interface. IC
port security max
Configures the maximum addresses that can be
learned on the port while the port is in port
security mode.
IC
show mac address-table
Displays dynamically created entries in the
bridge-forwarding database.
PE
show mac address-table
address
Displays all entries in the bridge-forwarding
database for the specified MAC address.
UE or
PE
show mac address-table
count
Displays the number of addresses present in the
Forwarding Database.
PE
show mac address-table
dynamic
Displays all entries in the bridge-forwarding
database.
UE or
PE
show mac address-table
interface
Displays the mac forwarding table entries for a
specific interface.
UE or
PE
show mac address-table
multicast
Displays Multicast MAC address table
information.
PE
show mac address-table
static
Displays statically created entries in the bridge-
forwarding database.
PE
show mac address-table vlan
Displays all entries in the bridge-forwarding
database for the specified VLAN.
UE or
PE
2CSNXXX_SWUM200.book Page 92 Tuesday, December 10, 2013 1:22 PM
Command Groups 93
Auto-VoIP
CDP Interoperability
show ports security
Displays the port-lock status. PE
show ports security
addresses
Displays current dynamic addresses in locked
ports.
PE
a. For the meaning of each Mode abbreviation, see
Mode Types
on page 87.
Command Description Modea
a. For the meaning of each Mode abbreviation, see
Mode Types
on page 87.
switchport voice detect auto
Enables the VoIP Profile on all the interfaces of
the switch.
GC or
IC
show switchport voice
Displays the status of auto-voip on an interface
or all interfaces.
PE
Command Description Modea
clear isdp counters
Clears the ISDP counters. PE
clear isdp table
Clears entries in the ISDP table. PE
isdp advertise-v2
Enables the sending of ISDP version 2 packets
from the device.
GC
isdp enable
Enables ISDP on the switch. GC or
IC
isdp holdtime
Configures the hold time for ISDP packets that
the switch transmits.
GC
isdp timer
Sets period of time between sending new ISDP
packets.
GC
show isdp
Displays global ISDP settings. PE
show isdp interface
Displays ISDP settings for the specified
interface.
PE
show isdp entry
Displays ISDP entries. PE
show isdp neighbors
Displays the list of neighboring devices. PE
Command Description Modea
2CSNXXX_SWUM200.book Page 93 Tuesday, December 10, 2013 1:22 PM
Command Groups 94
DHCP L2 Relay
DHCP Management Interface
show isdp traffic
Displays ISDP statistics. PE
a. For the meaning of each Mode abbreviation, see
Mode Types
on page 87.
Command Description Modea
a. For the meaning of each Mode abbreviation, see
Mode Types
on page 87.
dhcp l2relay (Global
Configuration)
Enables the Layer 2 DHCP Relay agent for an
interface or globally.
GC or
IC
dhcp l2relay circuit-id
Enables user to set the DHCP Option 82
Circuit ID for a VLAN.
GC
dhcp l2relay remote-id
Enables user to set the DHCP Option 82
Remote ID for a VLAN.
GC
dhcp l2relay vlan
Enables the L2 DHCP Relay agent for a set of
VLANs.
GC
dhcp l2relay trust
Configures an interface to trust a received
DHCP Option 82.
IC
Command Description Modea
a. For the meaning of each Mode abbreviation, see
Mode Types
on page 87.
release dhcp
Forces the DHCPv4 client to release a leased
address.
PE
renew dhcp
Forces the DHCP client to immediately renew
an IPv4 address lane.
PE
debug dhcp packet
Displays debug information about DHCPv4
client activities and traces DHCP v4 packets to
and from the local DHCPv4 client.
PE
show dhcp lease
Displays IPv4 addresses leased from a DHCP
server.
PE
Command Description Modea
2CSNXXX_SWUM200.book Page 94 Tuesday, December 10, 2013 1:22 PM
Command Groups 95
DHCP Snooping
Command Description Modea
a. For the meaning of each Mode abbreviation, see
Mode Types
on page 87.
clear ip dhcp snooping
binding
Clears all DHCP Snooping entries. PE
clear ip dhcp snooping
statistics
Clears all DHCP Snooping statistics. PE
ip dhcp snooping
Enables DHCP snooping globally or on a
specific VLAN.
GC or
IC
ip dhcp snooping binding
Configures a static DHCP Snooping binding. GC
ip dhcp snooping database
Configures the persistent location of the DHCP
snooping database.
GC
ip dhcp snooping database
write-delay
Configures the interval in seconds at which the
DHCP Snooping database will be stored in
persistent storage.
GC
ip dhcp snooping limit
Controls the maximum rate of DHCP
messages.
IC
ip dhcp snooping log-invalid
Enables logging of DHCP messages filtered by
the DHCP Snooping application.
IC
ip dhcp snooping trust
Configure a port as trusted for DHCP snooping. IC
ip dhcp snooping verify mac-
address
Enables the verification of the source MAC
address with the client MAC address in the
received DHCP message.
GC
show ip dhcp snooping
Displays the DHCP snooping global and per
port configuration.
PE
show ip dhcp snooping
binding
Displays the DHCP snooping binding entries. PE
show ip dhcp snooping
database
Displays the DHCP snooping configuration
related to the database persistence.
PE
show ip dhcp snooping
interfaces
Displays the DHCP Snooping status of the
interfaces.
PE
show ip dhcp snooping
statistics
Displays the DHCP snooping filtration
statistics.
PE
2CSNXXX_SWUM200.book Page 95 Tuesday, December 10, 2013 1:22 PM
Command Groups 96
Dynamic ARP Inspection
Command Description Modea
a. For the meaning of each Mode abbreviation, see
Mode Types
on page 87.
arp access-list
Creates an ARP ACL. GC
clear ip arp inspection
statistics
Resets the statistics for Dynamic ARP
Inspection on all VLANs.
PE
ip arp inspection filter
Configures the ARP ACL to be used for a single
VLAN or a range of VLANs to filter invalid ARP
packets.
GC
ip arp inspection limit
Configures the rate limit and burst interval
values for an interface.
IC
ip arp inspection trust
Configures an interface as trusted for Dynamic
ARP Inspection.
IC
ip arp inspection validate
Enables additional validation checks like source
MAC address validation, destination MAC
address validation or IP address validation on
the received ARP packets.
GC
ip arp inspection vlan
Enables Dynamic ARP Inspection on a single
VLAN or a range of VLANs.
GC
permit ip host mac host
Configures a rule for a valid IP address and
MAC address combination used in ARP packet
validation.
ARPA
show arp access-list
Displays the configured ARP ACLs with the
rules.
PE
show ip arp inspection
Displays the Dynamic ARP Inspection
configuration.
PE
show ip arp inspection
interfaces
Displays the Dynamic ARP Inspection
configuration on all the DAI enabled interfaces.
PE
show ip arp inspection vlan
Displays the Dynamic ARP Inspection
configuration on all the VLANs in the given
VLAN range.
PE
2CSNXXX_SWUM200.book Page 96 Tuesday, December 10, 2013 1:22 PM
Command Groups 97
E-mail Alerting
Command Description Modea
logging email
Enables e-mail alerting and sets the lowest
severity level for which log messages are e-
mailed.
GC
logging email urgent
Sets the lowest severity level at which log
messages are e-mailed in an urgent manner.
GC
logging traps
Sets the lowest severity level at which SNMP
traps are logged.
GC
logging email message-type
to-addr
Configures the To address field of the e-mail. GC
logging email from-addr
Configures the From address of the e-mail. GC
logging email message-type
subject
Configures the subject. GC
logging email logtime
Configures the value of how frequently the
queued messages are sent.
GC
logging email test message-
type
Tests whether or not an e-mail is being sent to
an SMTP server.
GC
show logging email statistics
Displays information on how many e-mails are
sent, how many e-mails failed, when the last e-
mail was sent, how long it has been since the
last e-mail was sent, how long it has been since
the e-mail changed to disabled mode.
PE
clear logging email statistics
Clears the e-mail alerting statistics. GC
security
Sets the e-mail alerting security protocol. MSC
mail-server ip-address |
hostname
Configures the SMTP server IP address and
changes the mode to Mail Server Configuration
Mode.
GC
port (Mail Server
Configuration Mode)
Configures the TCP port to use for
communication with the SMTP servers.
MSC
username (Mail Server
Configuration Mode)
Configures the username required by the
authentication.
MSC
password (Mail Server
Configuration Mode)
Configures the password required to
authenticate to the e-mail server.
MSC
2CSNXXX_SWUM200.book Page 97 Tuesday, December 10, 2013 1:22 PM
Command Groups 98
Ethernet Configuration
show mail-server
Displays the configuration of all the mail servers
or a particular mail server.
PE
a. For the meaning of each Mode abbreviation, see
Mode Types
on page 87.
Command Description Modea
clear counters
Clears statistics on an interface. PE
description
Adds a description to an interface. IC
flowcontrol receive
Configures the flow control on a given interface. GC,
IC
interface
Enters the interface configuration mode to
configure parameters for an interface.
GC or
IC
interface range
Enters the interface configuration mode to
execute a command on multiple ports at the
same time.
GC,
IC, IR
monitor capture (Global
Configuration)
Captures packets transmitted or received from
the CPU.
GC
monitor capture (Privileged
Exec)
Capture packets transmitted or received from
the CPU
PE
rate-limit cpu
Sets the maximum transmission unit on an
interface by adjusting the maximum size of
received Ethernet frames.
IC
rate-limit cpu
Reduces the amount of unknown
unicast/multicast packets forwarded to the
CPU.
GC
show interfaces advertise
Displays information about auto negotiation
advertisement.
PE
show interfaces
configuration
Displays the configuration for all configured
interfaces.
UE
show interfaces counters
Displays traffic seen by the physical interface. UE
show interfaces description
Displays the description for all configured
interfaces.
UE
Command Description Modea
2CSNXXX_SWUM200.book Page 98 Tuesday, December 10, 2013 1:22 PM
Command Groups 99
show interfaces detail
Displays the detail for all configured interfaces. UE
show interfaces status
Displays the status for all configured interfaces. UE
show interfaces transceiver
Display the optic static parameters as well
as the Dell qualification.
PE
show monitor capture
Displays captured packets transmitted or
received from the CPU.
PE
show statistics
Displays statistics for one port or for the entire
switch.
PE
show statistics switchport
Displays detailed statistics for a specific port or
for the entire switch.
PE
show storm-control
Displays the storm control configuration. PE
shutdown
Disables interfaces. IC
speed
Configures the speed of a given Ethernet
interface when not using auto-negotiation.
IC
storm-control broadcast
Enables Broadcast storm control. IC
storm-control multicast
Enables the switch to count Multicast packets
together with Broadcast packets.
IC
storm-control unicast
Enables Unicast storm control. IC
switchport protected
Sets the port to Protected mode. IC
switchport protected name
Configures a name for a protected group. GC
show switchport protected
Displays protected group/port information. PE
show system internal pktmgr
Displays the configured CPU rate limit for
unknown packets in packets per second.
PE
show system mtu
Displays the configured MTU. PE
system jumbo mtu
Globally configures the Maximum
Transmission Unit (MTU) on all interfaces
for forwarded and system-generated
frames.
GC
a. For the meaning of each Mode abbreviation, see
Mode Types
on page 87.
Command Description Modea
2CSNXXX_SWUM200.book Page 99 Tuesday, December 10, 2013 1:22 PM
Command Groups 100
Ethernet CFM
Command Description Modea
a. For the meaning of each Mode abbreviation, see
Mode Types
on page 87.
ethernet cfm domain
Enters into maintenance domain Configuration
mode for an existing domain. Use the optional
level parameter to create a domain and enter
into maintenance domain Configuration mode.
GC
service
Associates a VLAN with a maintenance domain. MDC
ethernet cfm cc level
Initiates sending continuity checks (CCMs) at
the specified interval and level on a VLAN
monitored by an existing domain.
GC
ethernet cfm mep level
Creates a Maintenance End Point (MEP) on an
interface at the specified level and direction.
IC
ethernet cfm mep enable
Enables a MEP at the specified level and
direction.
IC
ethernet cfm mep active
Activates a MEP at the specified level and
direction.
IC
ethernet cfm mep archive-
hold-time
Maintains internal information on a missing
MEP.
IC
ethernet cfm mip level
Creates a Maintenance Intermediate Point
(MIP) at the specified level.
IC
ping ethernet cfm
Generates a loopback message (LBM) from
the configured MEP.
PE
traceroute ethernet cfm
Generates a link trace message (LTM) from the
configured MEP.
PE
show ethernet cfm errors
Displays the cfm errors. PE
show ethernet cfm domain
Displays the configured parameters in a
maintenance domain.
PE
show ethernet cfm
maintenance-points local
Displays the configured local maintenance
points.
PE
show ethernet cfm
maintenance-points remote
Displays the configured remote maintenance
points.
PE
show ethernet cfm statistics
Displays the CFM statistics. PE
debug cfm
Enables CFM debugging. PE
2CSNXXX_SWUM200.book Page 100 Tuesday, December 10, 2013 1:22 PM
Command Groups 101
Green Ethernet
GVRP
Command Description Modea
a. For the meaning of each Mode abbreviation, see
Mode Types
on page 87.
green-mode energy-detect
Enables a Dell proprietary mode of power
reduction on ports that are not connected to
another interface.
IC
green-mode eee
Enables EEE low power idle mode on an
interface or all the interfaces.
IC
clear green-mode statistics
Clears:
• The EEE LPI event count, and LPI duration
• The EEE LPI history table entries
• The Cumulative Power savings estimates
for a specified interface or for all the interfaces
based upon the argument.
PE
green-mode eee-lpi-history
Configures the Global EEE LPI history
collection interval and buffer size. This value is
applied globally on all interfaces on the stack.
GC
show green-mode interface-
id
Displays the green-mode configuration and
operational status of the port. This command is
also used to display the per port configuration
and operational status of the green-mode. The
status is shown only for the modes supported on
the corresponding hardware platform whether
enabled or disabled.
PE
show green-mode
Displays the green-mode configuration for the
whole system. The status is shown only for the
modes supported on the corresponding
hardware platform whether enabled or disabled.
PE
show green-mode eee-lpi-
history interface
Displays the interface green-mode EEE LPI
history.
PE
Command Description Modea
clear gvrp statistics
Clears all the GVRP statistics information. PE
2CSNXXX_SWUM200.book Page 101 Tuesday, December 10, 2013 1:22 PM
Command Groups 102
IGMP Snooping
garp timer
Adjusts the GARP application join, leave, and
leaveall GARP timer values.
IC
gvrp enable (global)
Enables GVRP globally. GC
gvrp enable (interface)
Enables GVRP on an interface. IC
gvrp registration-forbid
Deregisters all VLANs, and prevents dynamic
VLAN registration on the port.
IC
gvrp vlan-creation-forbid
Enables or disables dynamic VLAN creation. IC
show gvrp configuration
Displays GVRP configuration information,
including timer values, whether GVRP and
dynamic VLAN creation is enabled, and
which ports are running GVRP.
PE
show gvrp error-statistics
Displays GVRP error statistics. UE
show gvrp statistics
Displays GVRP statistics. UE
a. For the meaning of each Mode abbreviation, see
Mode Types
on page 87.
Command Description Modea
ip igmp snooping
In Global Configuration mode, Enables
Internet Group Management Protocol (IGMP)
snooping.
GC
show ip igmp snooping
groups
Displays Multicast groups learned by IGMP
snooping.
UE
show ip igmp snooping
mrouter
Displays information on dynamically learned
Multicast router interfaces.
PE
show ip igmp snooping
In VLAN Configuration mode, enables IGMP
snooping on a particular VLAN or on all
interfaces participating in a VLAN.
VC
ip igmp snooping vlan
immediate-leave
Enables or disables IGMP Snooping fast-leave
mode on a selected VLAN.
VC
ip igmp snooping vlan
groupmembership-interval
Sets the IGMP Group Membership Interval
time on a VLAN.
VC
Command Description Modea
2CSNXXX_SWUM200.book Page 102 Tuesday, December 10, 2013 1:22 PM
Command Groups 103
IGMP Snooping Querier
ip igmp snooping vlan last-
member-query-interval
Sets the IGMP Maximum Response time on a
particular VLAN.
VC
ip igmp snooping vlan
mcrtrexpiretime
Sets the Multicast Router Present Expiration
time.
VC
ip igmp snooping report-
suppression
Enables IGMP report suppression on a
specific VLAN.
GC
ip igmp snooping
unregistered floodall
Enables flooding of unregistered multicast
traffic to all ports in the VLAN.
GC
ip igmp snooping vlan
mrouter
Statically configures a port as connected to a
multicast router for a specified VLAN.
GC
a. For the meaning of each Mode abbreviation, see
Mode Types
on page 87.
Command Description Modea
a. For the meaning of each Mode abbreviation, see
Mode Types
on page 87.
ip igmp snooping querier
Enables/disables IGMP Snooping Querier on
the system (Global Configuration mode) or on
a VLAN.
GC,
VC
ip igmp snooping querier
election participate
Enables the Snooping Querier to participate in
the Querier Election process when it discovers
the presence of another Querier in the VLAN.
VC
ip igmp snooping querier
query-interval
Sets the IGMP Querier Query Interval time. GC
ip igmp snooping querier
timer expiry
Sets the IGMP Querier timer expiration period. GC
ip igmp snooping querier
version
Sets the IGMP version of the query that the
snooping switch is going to send periodically.
GC
show ip igmp snooping
querier
Displays IGMP Snooping Querier information. PE
Command Description Modea
2CSNXXX_SWUM200.book Page 103 Tuesday, December 10, 2013 1:22 PM
Command Groups 104
IP Addressing
Command Description Modea
clear host
Deletes entries from the host name-to-address
cache.
PE
clear ip address-conflict-
detect
Clears the address conflict detection status in
the switch.
PE
ip address (Out-of-Band)
Sets an IP address for the out-of-band interface. IC
ip address-conflict-detect
run
Triggers the switch to run active address conflict
detection by sending gratuitous ARP packets for
IPv4 addresses on the switch.
GC
ip address dhcp (Interface
Configuration)
Acquires an IP address on an interface from the
DHCP server.
IC
ip default-gateway
Defines a default gateway (router). GC
ip domain-lookup
Enables IP DNS-based host name-to-address
translation.
GC
ip domain-name
Defines a default domain name to complete
unqualified host names.
GC
ip host
Configures static host name-to-address
mapping in the host cache.
GC
ip name-server
Configures available name servers. GC
ipv6 address (Interface
Configuration)
Sets the IPv6 address of the management
interface.
IC
ipv6 address (OOB Port)
Sets the IPv6 prefix on the out-of-band port. IC
ipv6 address dhcp
Enables the DHCPv6 client on an IPv6
interface.
IC
ipv6 enable (Interface
Configuration)
Enables IPv6 on the management interface. GC
ipv6 enable (OOB
Configuration)
Enables IPv6 operation on the out-of-band
interface.
IC
ipv6 gateway (OOB
Configuration)
Configures the address of the IPv6 gateway. IC
2CSNXXX_SWUM200.book Page 104 Tuesday, December 10, 2013 1:22 PM
Command Groups 105
IPv6 ACL
IPv6 MLD Snooping
show hosts
Displays the default domain name, a list of
name server hosts, static and cached list of host
names and addresses.
UE
show ip address-conflict
Displays the status information corresponding
to the last detected address conflict.
UE or
PE
show ip helper-address
Displays the ip helper addresses configuration. PE
show ipv6 dhcp interface
out-of-band statistics
Displays IPv6 DHCP statistics for the out-of-
band interface.
PE
show ipv6 interface out-of-
band
Displays the IPv6 out-of-band port
configuration.
PE
a. For the meaning of each Mode abbreviation, see
Mode Types
on page 87.
Command Description Modea
a. For the meaning of each Mode abbreviation, see
Mode Types
on page 87.
deny | permit (IPv6
ACL)
Creates a new rule for the current IPv6 access
list.
v6ACL
ipv6 access-list
Creates an IPv6 Access Control List (ACL)
consisting of classification fields defined for the
IP header of an IPv6 frame.
GC
ipv6 access-list rename
Changes the name of an IPv6 ACL. GC
ipv6 traffic-filter
Attaches a specific IPv6 ACL to an interface or
associates it with a VLAN ID in a given
direction.
GC
IC
show ipv6 access-lists
Displays an IPv6 access list (and the rules
defined for it).
PE
Command Description Modea
ipv6 mld snooping vlan
immediate-leave
Enables or disables MLD Snooping immediate-
leave admin mode on a selected interface or
VLAN.
VC
Command Description Modea
2CSNXXX_SWUM200.book Page 105 Tuesday, December 10, 2013 1:22 PM
Command Groups 106
IPv6 MLD Snooping Querier
ipv6 mld snooping vlan
groupmembership-interval
Sets the MLD Group Membership Interval
time on a VLAN or interface.
VC
ipv6 mld snooping vlan last-
listener-query-interval
Sets the MLD Maximum Response time for an
interface or VLAN.
IC or
VC
ipv6 mld snooping listener-
message-suppression
Enables MLD listener message suppression on a
specific VLAN.
GC
ipv6 mld snooping vlan
mrouter
Statically configures a port as connected to
a multicast router for a specified VLAN.
GC
ipv6 mld snooping (Global)
Enables MLD Snooping on the system (Global
Configuration mode).
GC
show ipv6 mld snooping
Displays MLD Snooping information. PE
show ipv6 mld snooping
groups
Displays the MLD Snooping entries in the
MFDB table.
PE
a. For the meaning of each Mode abbreviation, see
Mode Types
on page 87.
Command Description Modea
a. For the meaning of each Mode abbreviation, see
Mode Types
on page 87.
ipv6 mld snooping querier
Enables MLD Snooping Querier on the system
or on a VLAN.
GC or
VC
ipv6 mld snooping querier
address
Sets the global MLD Snooping Querier address
on the system or on a VLAN.
GC or
VC
ipv6 mld snooping querier
election participate
Enables the Snooping Querier to participate in
the Querier Election process when it discovers
the presence of another Querier in the VLAN.
VC
ipv6 mld snooping querier
query-interval
Sets the MLD Querier Query Interval time. GC
ipv6 mld snooping querier
timer expiry
Sets the MLD Querier timer expiration period. GC
show ipv6 mld snooping
querier
Displays MLD Snooping Querier information. PE
Command Description Modea
2CSNXXX_SWUM200.book Page 106 Tuesday, December 10, 2013 1:22 PM
Command Groups 107
IP Source Guard
iSCSI Optimization
Link Dependency
Command Description Modea
a. For the meaning of each Mode abbreviation, see
Mode Types
on page 87.
ip verify source
Enables IP Source Guard on an interface. IC
ip verify source port-security
Enables IP Source Guard using both the IP
address and MAC address as filtering criteria.
IC
ip verify binding
Configures IPSG static bindings. GC
show ip verify
Displays IPSG interface configuration. PE
show ip verify source
Displays the bindings configured on a particular
interface.
PE
show ip source binding
Displays all bindings (static and dynamic). PE
Command Description Modea
a. For the meaning of each Mode abbreviation, see
Mode Types
on page 87.
iscsi aging time
Sets aging time for iSCSI sessions. GC
iscsi cos
Sets the quality of service profile that will be
applied to iSCSI flows.
GC
iscsi enable
Enables Global Configuration mode command
globally enables iSCSI awareness.
GC
iscsi target port
Configures an iSCSI target port (optionally
configures target port address and name).
GC
show iscsi
Displays the iSCSI settings. PE
show iscsi sessions
Displays the iSCSI sessions. PE
Command Description Modea
action
Indicates if the link-dependency group should
mirror or invert the status of the depended on
interfaces.
LD
2CSNXXX_SWUM200.book Page 107 Tuesday, December 10, 2013 1:22 PM
Command Groups 108
LLDP
link-dependency group
Enters the link-dependency mode to configure
a link-dependency group.
GC
add
Adds member gigabit Ethernet port(s) to the
dependency list.
LD
depends-on
Adds the dependent Ethernet ports or port
channels list.
LD
show link-dependency
Shows the link dependencies configured on a
particular group.
PE
a. For the meaning of each Mode abbreviation, see
Mode Types
on page 87.
Command Description Modea
clear lldp remote-data
Deletes all data from the remote data table. PE
clear lldp statistics
Resets all LLDP statistics. PE
lldp med
Enables/disables LLDP-MED on an interface. IC
lldp med confignotification
Enables sending the topology change
notification.
IC
lldp med
faststartrepeatcount
Sets the value of the fast start repeat count. GC
lldp med transmit-tlv
Specifies which optional TLVs in the LLDP
MED set are transmitted in the LLDPDUs.
IC
lldp notification
Enables remote data change notifications. IC
lldp notification-interval
Limits how frequently remote data change
notifications are sent.
GC
lldp receive
Enables the LLDP receive capability. IC
lldp timers
Sets the timing parameters for local data
transmission on ports enabled for LLDP.
GC
lldp transmit
Enables the LLDP advertise capability. IC
lldp transmit-mgmt
Specifies that transmission of the local system
management address information in the
LLDPDUs is included.
IC
Command Description Modea
2CSNXXX_SWUM200.book Page 108 Tuesday, December 10, 2013 1:22 PM
Command Groups 109
MLAG
lldp transmit-tlv
Specifies which optional TLVs in the 802.1AB
basic management set will be transmitted in the
LLDPDUs.
IC
show lldp
Displays the current LLDP configuration
summary.
PE
show lldp interface
Displays the current LLDP interface state. PE
show lldp local-device
Displays the LLDP local data. PE
show lldp med
Displays a summary of the current LLDP MED
configuration.
PE
show lldp med interface
Displays a summary of the current LLDP MED
configuration for a specific interface.
PE
show lldp med local-device
detail
Displays the advertised LLDP local data in
detail.
PE
show lldp med remote-
device
Displays the current LLDP MED remote data. PE
show lldp remote-device
Displays the current LLDP remote data. PE
show lldp statistics
Displays the current LLDP traffic statistics. PE
a. For the meaning of each Mode abbreviation, see
Mode Types
on page 87.
Command Description Modea
clear vpc statistics
Clears the counters for the keepalive
messages transmitted and received by the
MLAG switch.
PE
debug vpc
Enables debug traces for the specified
protocols.
GC
feature vpc
Globally enables MLAG. GC
peer-detection enable
Enables the Dual Control Plane
Detection Protocol.
MD
Command Description Modea
2CSNXXX_SWUM200.book Page 109 Tuesday, December 10, 2013 1:22 PM
Command Groups 110
peer-keepalive destination
Enables the Dual Control Plane Detection
Protocol with the configured IP address of
the peer MLAG, the local source address and
the peer timeout value.
MD
peer-keepalive enable
Enables the peer keep-alive protocol. MD
role priority
Configures the priority value used on a
switch for primary/secondary role selection.
MD
show vpc
Displays information about an MLAG. PE
show vpc brief
Displays the MLAG global status. PE
show vpc consistency-
parameters
Displays MLAG-related configuration
information in a format suitable for
comparison with the other MLAG peer.
PE
show vpc consistency-
features
Displays MLAG-related configuration
information in a format suitable for
comparison with the other MLAG peer.
PE
show vpc peer-keepalive
Displays the peer MLAG switch’s IP address
used by the dual control plane detection
protocol.
PE
show vpc role
Displays information about the keepalive
status, keepalive parameters, role of the
MLAG switch, and the system MAC and
priority.
PE
show vpc statistics
Displays counters for the keepalive messages
transmitted and received by the MLAG
switch
PE
vpc
Configures a port-channel (LAG) as part of
the MLAG domain.
IC
vpc domain
Enters into MLAG Configuration mode. GC
vpc peer-link
Configures a port channel as the MLAG peer
link for a domain and enables the peer link
protocol.
IC
a. For the meaning of each Mode abbreviation, see
Mode Types
on page 87.
Command Description Modea
2CSNXXX_SWUM200.book Page 110 Tuesday, December 10, 2013 1:22 PM
Command Groups 111
Multicast VLAN Registration
Port Channel
Command Description Modea
a. For the meaning of each Mode abbreviation, see
Mode Types
on page 87.
mvr
Enables MVR. GC or
IC
mvr group
Adds an MVR membership group. GC
mvr mode
Changes the MVR mode type. GC
mvr querytime
Sets the MVR query response time. GC
mvr vlan
Sets the MVR multicast VLAN. GC
mvr immediate
Enables MVR Immediate Leave mode. IC
mvr type
Sets the MVR port type. IC
mvr vlan group
Use to participate in the specific MVR group. IC
show mvr
Displays global MVR settings. PE
show mvr members
Displays the MVR membership groups
allocated.
PE
show mvr interface
Displays the MVR enabled interface
configuration.
PE
show mvr traffic
Displays global MVR statistics. PE
Command Description Modea
channel-group
Associates a port with a port-channel. IC
interface port-channel
Enables debug traces for the specified
protocols.
GC
interface port-channel
Enters the interface configuration mode of a
specific port-channel.
GC
interface range port-channel
Enters the interface configuration mode to
configure multiple port-channels.
GC
hashing-mode
Sets the hashing algorithm on trunk ports. IC (port-
channel)
2CSNXXX_SWUM200.book Page 111 Tuesday, December 10, 2013 1:22 PM
Command Groups 112
Port Monitor
QoS
lacp port-priority
Configures the priority value for physical
ports.
IC
lacp system-priority
Configures the system LACP priority. GC
lacp timeout
Assigns an administrative LACP timeout. IC
port-channel min-links
Sets the minimum number of links that must
be up in order for the port channel interface
to be declared up.
IC
show interfaces port-
channel
Displays port-channel information. PE
show lacp
Displays LACP information for ports. PE
show statistics port-channel
Displays port-channel statistics. PE
a. For the meaning of each Mode abbreviation, see
Mode Types
on page 87.
Command Description Modea
a. For the meaning of each Mode abbreviation, see
Mode Types
on page 87.
monitor session
Configures a port monitoring session. GC
remote-span
Configures a VLAN as an RSPAN VLAN. VC
show monitor session
Displays the port monitoring status. PE
show vlan remote-span
Displays the RSPAN VLAN IDs. UE or
PE
Command Description Modea
assign-queue
Modifies the queue ID to which the associated
traffic stream is assigned.
PCMC
class
Creates an instance of a class definition within
the specified policy for the purpose of defining
treatment of the traffic class through
subsequent policy attribute statements.
PMC
Command Description Modea
2CSNXXX_SWUM200.book Page 112 Tuesday, December 10, 2013 1:22 PM

Command Groups 113
class-map
Defines a new DiffServ class of type
match-all
,
match-any,
or
match-access-group
. For now,
only
match-all
is available in the CLI.
GC
class-map rename
Changes the name of a DiffServ class. GC
classofservice dot1p-
mapping
Maps an 802.1p priority to an internal traffic
class for a switch.
GC or
IC
classofservice ip-dscp-
mapping
Maps an IP DSCP value to an internal traffic
class.
GC
classofservice trust
Sets the class of service trust mode of an
interface.
GC or
IC
conform-color
Specifies the precoloring of packets conforming
to or exceeding the specified rate(s). The
possible actions are drop, setdscp-transmit, set-
prec-transmit, or transmit.
PCMC
cos-queue min-bandwidth
Specifies the minimum transmission
bandwidth for each interface queue.
GC or
IC
cos-queue random-detect
Configures WRED packet drop policy on an
interface CoS queue.
GC or
IC
cos-queue strict
Activates the strict priority scheduler mode for
each specified queue.
GC or
IC
diffserv
Sets the DiffServ operational mode to active. GC
drop
Use the drop policy-class-map configuration
command to specify that all packets for the
associated traffic stream are to be dropped at
ingress.
PCMC
mark cos
Marks all packets for the associated traffic
stream with the specified class of service value
in the priority field of the 802.1p header.
PCMC
mark ip-dscp
Marks all packets for the associated traffic
stream with the specified IP DSCP value.
PCMC
mark ip-precedence
Marks all packets for the associated traffic
stream with the specified IP precedence value.
PCMC
Command Description Modea
2CSNXXX_SWUM200.book Page 113 Tuesday, December 10, 2013 1:22 PM

Command Groups 114
match class-map
Adds add to the specified class definition the
set of match conditions defined for another
class.
CMC
match cos
Adds to the specified class definition a match
condition for the Class of Service value.
CMC
match destination-address
mac
Adds to the specified class definition a match
condition based on the destination MAC
address of a packet.
CMC
match dstip
Adds to the specified class definition a match
condition based on the destination IP address
of a packet.
CMC
match dstip6
Adds to the specified class definition a match
condition based on the destination IPv6
address of a packet.
v6CMC
match dstl4port
Adds to the specified class definition a match
condition based on the destination layer 4 port
of a packet using a single keyword, or a numeric
notation.
CMC
match ethertype
Adds to the specified class definition a match
condition based on the value of the ethertype.
CMC
match ip6flowlbl
Adds to the specified class definition a match
condition based on the IPv6 flow label of a
packet.
v6CMC
match ip dscp
Adds to the specified class definition a match
condition based on the value of the IP DiffServ
Code Point (DSCP) field in a packet.
CMC
match ip precedence
Adds to the specified class definition a match
condition based on the value of the IP.
CMC
match ip tos
Adds to the specified class definition a match
condition based on the value of the IP TOS
field in a packet.
CMC
match protocol
Adds to the specified class definition a match
condition based on the value of the IP Protocol
field in a packet using a single keyword
notation or a numeric value notation.
CMC
Command Description Modea
2CSNXXX_SWUM200.book Page 114 Tuesday, December 10, 2013 1:22 PM

Command Groups 115
match source-address mac
Adds to the specified class definition a match
condition based on the source MAC address of
the packet.
CMC
match srcip
Adds to the specified class definition a match
condition based on the source IP address of a
packet.
CMC
match srcip6
Adds to the specified class definition a match
condition based on the source IPv6 address of a
packet.
v6CMC
match srcl4port
Adds to the specified class definition a match
condition based on the source layer 4 port of a
packet using a single keyword, a numeric
notation, or a numeric range notation.
CMC
match vlan
Adds to the specified class definition a match
condition based on the value of the layer 2
VLAN Identifier field.
CMC
mirror
Mirrors all the data that matches the class
defined to the destination port specified.
PCMC
police-simple
Implements simple color aware marking for the
specified class.
PCMC
police-single-rate
Implements a single-rate Three Color
Marker (trTCM) per RFC 2698
PCMC
police-two-rate
Implements a two-rate Three Color
Marker (trTCM) per RFC 2698.
PCMC
policy-map
Establishes a new DiffServ policy or enters
policy map configuration mode.
GC
random-detect queue-
parms
Configures the green, yellow and red TCP and
non-TCP packet minimum and maximum
thresholds and corresponding drop
probabilities on an interface or all interfaces.
GC, IC,
or IR
random-detect exponential-
weighting-constant
Configures the decay in the calculation of the
average queue size user for WRED on an
interface or all interfaces.
GC, IC,
or IR
Command Description Modea
2CSNXXX_SWUM200.book Page 115 Tuesday, December 10, 2013 1:22 PM

Command Groups 116
redirect
Specifies that all incoming packets for the
associated traffic stream are redirected to a
specific egress interface (physical port or port-
channel).
PCMC
service-policy
Attaches a policy to an interface in a particular
direction.
GC or
IC
show class-map
Displays all configuration information for the
specified class.
PE
show classofservice dot1p-
mapping
Displays the current Dot1p (802.1p) priority
mapping to internal traffic classes for a specific
interface.
PE
show classofservice ip-dscp-
mapping
Displays the current IP DSCP mapping to
internal traffic classes for a specific interface.
PE
show classofservice trust
Displays the current trust mode setting for a
specific interface.
PE
show diffserv
Displays the DiffServ General Status
information.
PE
show diffserv service
interface
Displays policy service information for the
specified interface and direction.
PE
show diffserv service
interface port-channel
Displays policy service information for the
specified interface and direction.
PE
show diffserv service brief
Displays all interfaces in the system to which a
DiffServ policy has been attached.
PE
show interfaces cos-queue
Displays the class-of-service queue
configuration for the specified interface.
PE
show interfaces random-
detect
Displays the WRED policy on an interface. PE
show policy-map
Displays all configuration information for the
specified policy.
PE
show policy-map interface
Displays policy-oriented statistics information
for the specified interface and direction.
PE
show service-policy
Displays a summary of policy-oriented
statistics information for all interfaces.
PE
Command Description Modea
2CSNXXX_SWUM200.book Page 116 Tuesday, December 10, 2013 1:22 PM
Command Groups 117
Radius
traffic-shape
Specifies the maximum transmission
bandwidth limit for the interface as a whole.
GC or
IC
vlan priority
Assigns a default VLAN priority tag for
untagged frames ingressing an interface.
IC
a. For the meaning of each Mode abbreviation, see
Mode Types
on page 87.
Command Description Modea
aaa accounting dot1x
default start-stop
Creates an accounting method list GC
accounting
Applies an accounting method to a line
config.
LC
acct-port
Sets the port that connects to the RADIUS
accounting server.
R
auth-port Sets the port number for authentication requests
of the designated radius server
.
R
deadtime
Improves Radius response times when a server is
unavailable by causing the unavailable server to
be skipped.
R
debug aaa accounting
Enables debugging for accounting. PE
key Sets the authentication and encryption key for all
RADIUS communications between the switch
and the RADIUS daemon
.
R
key
Configures an encrypted key that is shared with
the RADIUS server.
R
msgauth
Enables the message authenticator attribute to
be used for the RADIUS Authenticating server
being configured.
R
name (RADIUS server)
Assigns a name to a RADIUS server. R
primary
Specifies that a configured server should be the
primary server in the group of authentication
servers which have the same server name.
R
Command Description Modea
2CSNXXX_SWUM200.book Page 117 Tuesday, December 10, 2013 1:22 PM
Command Groups 118
priority
Specifies the order in which the servers are to be
used, with 0 being the highest priority.
R
radius-server attribute 4
Sets the network access server (NAS) IP address
for the RADIUS server.
GC
radius-server deadtime
Improves RADIUS response times when servers
are unavailable. Causes the unavailable servers
to be skipped.
GC
radius-server host
Specifies a RADIUS server host. GC
radius-server key
Sets the authentication and encryption key for
all RADIUS communications between the
switch and the RADIUS daemon.
GC
radius-server key encrypted
Sets the authentication and encryption key for
communication between the switch and
RADIUS server.
GC
radius-server retransmit
Specifies the number of times the software
searches the list of RADIUS server hosts.
GC
radius-server source-ip
Specifies the source IP address used for
communication with RADIUS servers.
GC
radius-server timeout
Sets the interval for which a switch waits for a
server host to reply.
GC
retransmit
Specifies the number of times the software
searches the list of RADIUS server hosts before
stopping the search.
R
show aaa servers
Displays the list of configured RADIUS servers
and the values configured for the global
parameters of the RADIUS client.
UE or
PE
show accounting methods
Displays the configured accounting method
lists.
PE
show radius statistics
Shows the statistics for an authentication or
accounting server.
UE or
PE
source-ip
Specifies the source IP address to be used for
communication with RADIUS servers.
R
timeout
Sets the timeout value in seconds for the
designated radius server.
R
Command Description Modea
2CSNXXX_SWUM200.book Page 118 Tuesday, December 10, 2013 1:22 PM
Command Groups 119
Spanning Tree
usage
Specifies the usage type of the server. R
a. For the meaning of each Mode abbreviation, see
Mode Types
on page 87.
Command Description Modea
clear spanning-tree
detected-protocols
Restarts the protocol migration process on all
interfaces or on the specified interface.
PE
exit (mst)
Exits the MST configuration mode and applies
configuration changes.
MC
instance (mst)
Maps VLANs to an MST instance. MC
name (mst)
Defines the MST configuration name. MC
revision (mst)
Defines the configuration revision number. MC
show spanning-tree
Displays spanning tree configuration. PE
show spanning-tree
summary
Displays spanning tree settings and parameters
for the switch.
PE
show spanning-tree vlan
Displays spanning tree information per VLAN
and also lists the port roles and states as well as
the port cost.
PE
spanning-tree
Enables spanning-tree functionality. GC
spanning-tree auto-portfast
Sets the port to auto portfast mode. IC
spanning-tree backbonefast
Enables the detection of indirect link
failures and accelerate spanning tree
convergence on STP-PV/RSTP-PV
configured switches using Indirect Rapid
Convergence (IRC).
GC
spanning-tree bpdu flooding
Allows flooding of BPDUs received on
nonspanning-tree ports to all other non-
spanning-tree ports.
GC
spanning-tree bpdu-
protection
Enables BPDU protection on a switch. GC
Command Description Modea
2CSNXXX_SWUM200.book Page 119 Tuesday, December 10, 2013 1:22 PM
Command Groups 120
spanning-tree cost
Configures the spanning tree path cost for a
port.
IC
spanning-tree disable
Disables spanning tree on a specific port. IC
spanning-tree forward-time
Configures the spanning tree bridge forward
time.
GC
spanning-tree guard
Selects whether loop guard or root guard is
enabled on an interface.
IC
spanning-tree loopguard
Enables loop guard on all ports. GC
spanning-tree max-age
Configures the spanning tree bridge maximum
age.
GC
spanning-tree max-hops
Sets the MSTP Max Hops parameter to a new
value for the common and internal spanning
tree.
GC
spanning-tree mode
Configures the spanning tree protocol. GC
spanning-tree mst
configuration
Enables configuring an MST region by entering
the multiple spanning-tree (MST) mode.
GC
spanning-tree mst cost
Configures the path cost for multiple spanning
tree (MST) calculations.
IC
spanning-tree mst port-
priority
Configures port priority. IC
spanning-tree mst priority
Configures the switch priority for the specified
spanning tree instance.
GC
spanning-tree portfast
Enables PortFast mode. IC
spanning-tree portfast
bpdufilter default
Discards BPDUs received on spanningtree ports
in portfast mode.
GC
spanning-tree portfast
default
Enables Portfast mode on all ports. GC
spanning-tree port-priority
(Interface Configuration)
Configures port priority. IC
spanning-tree priority
Configures the spanning tree priority. GC
spanning-tree tcnguard
Prevents a port from propagating topology
change notifications.
IC
Command Description Modea
2CSNXXX_SWUM200.book Page 120 Tuesday, December 10, 2013 1:22 PM
Command Groups 121
TACACS+
spanning-tree transmit hold-
count
Set the maximum number of BPDUs that a
bridge is allowed to send within a hello time
window (2 seconds).
GC
spanning-tree uplinkfast
Configures the rate at which gratuitous
frames are sent after a switchover to an
alternate port and enables Direct Rapid
Convergence.
GC
spanning-tree vlan
Enables per VLAN spanning tree on a
VLAN.
GC
spanning-tree vlan forward-
time
Configures the spanning tree forward delay
time for a specified VLAN or a range of
VLANs.
GC
spanning-tree vlan hello-
time
Configures the spanning tree hello time for
a specified VLAN or a range of VLANs.
GC
spanning-tree vlan max-age
Configures the spanning tree maximum
age time for a set of VLANs.
GC
spanning-tree vlan root
Configures the switch to become the root
bridge or standby root bridge.
GC
spanning-tree vlan priority
Configures the bridge priority of a VLAN. GC
a. For the meaning of each Mode abbreviation, see
Mode Types
on page 87.
Command Description Modea
key
Specifies the authentication and encryption key
for all TACACS communications between the
device and the TACACS server.
TC
key encrypted
Configures an encrypted key that is shared with
the TACACS server.
TC
port
Specifies a server port number. TC
priority
Specifies the order in which servers are used. TC
Command Description Modea
2CSNXXX_SWUM200.book Page 121 Tuesday, December 10, 2013 1:22 PM
Command Groups 122
VLAN
show tacacs
Displays TACACS+ server settings and
statistics.
PE
tacacs-server host
Specifies a TACACS+ server host. GC
tacacs-server key
Sets the authentication and encryption key for
all TACACS+ communications between the
switch and the TACACS+ daemon.
GC
tacacs-server key
Sets the authentication and encryption key for
all communication between the switch and the
TACACS serve.
GC
tacacs-server timeout
Sets the interval for which the switch waits for a
server host to reply.
GC
timeout
Specifies the timeout value in seconds. TC
a. For the meaning of each Mode abbreviation, see
Mode Types
on page 87.
Command Description Modea
dvlan-tunnel ethertype
Configures the EtherType for the interface. GC
interface vlan
Enters the VLAN interface configuration mode. GC
interface range vlan
Enters the interface configuration mode to
configure multiple VLANs.
GC
mode dvlan-tunnel
Enables Double VLAN tunneling on the
specified interface.
IC
name (VLAN
Configuration)
Configures a name to a VLAN. IC
private-vlan
Defines a private VLAN association between
the primary and secondary VLANs.
VC
protocol group
Attaches a
vlanid
to the protocol-based VLAN
identified by
groupid
.
VC
protocol vlan group
Adds the physical unit/slot/port interface to the
protocol-based VLAN identified by
groupid
.
IC
protocol vlan group all
Adds all physical unit/slot/port interfaces to the
protocol-based VLAN identified by
groupid
.
GC
Command Description Modea
2CSNXXX_SWUM200.book Page 122 Tuesday, December 10, 2013 1:22 PM
Command Groups 123
show dvlan-tunnel
Displays all interfaces enabled for Double
VLAN Tunneling.
PE
show dvlan-tunnel interface
Displays detailed information about Double
VLAN Tunneling for the specified interface.
PE
show interfaces switchport
Displays switchport configuration. PE,
IC
show port protocol
Displays the Protocol-Based VLAN information
for either the entire system or for the indicated
group.
PE
show vlan
Displays detailed information, including
interface information and dynamic vlan type,
for a specific VLAN.
PE
show vlan association mac
Displays the VLAN associated with a specific
configured MAC address.
PE
show vlan association subnet
Displays the VLAN associated with a specific
configured IP subnet.
PE
show vlan private-vlan
switchport access vlan
Configures the VLAN ID when the interface is
in access mode.
IC
switchport general forbidden
vlan
Forbids adding specific VLANs to a port. IC
switchport general
acceptable-frame-type
tagged-only
Discards untagged frames at ingress. IC
switchport general allowed
vlan
Adds or removes VLANs from a port in General
mode.
IC
switchport general ingress-
filtering disable
Disables port ingress filtering. IC
switchport general pvid
Configures the PVID when the interface is in
general mode.
IC
switchport mode
Configures the VLAN membership mode of a
port.
IC
Command Description Modea
2CSNXXX_SWUM200.book Page 123 Tuesday, December 10, 2013 1:22 PM
Command Groups 124
Voice VLAN
switchport mode private-
vlan
Defines a private VLAN association for an
isolated or community port or a mapping for a
promiscuous port.
IC
switchport private-vlan
Defines a private-VLAN association for an
isolated or community port or a mapping for a
promiscuous port.
IC
switchport trunk
Adds or removes VLANs from a trunk port. IC
vlan
Configures a VLAN. GC
vlan association mac
Associates a MAC address to a VLAN. VC
vlan association subnet
Associates an IP subnet to a VLAN. VC
vlan makestatic
Changes a GVRP dynamically created VLAN to
a static VLAN.
GC
vlan protocol group
Adds protocol-based VLAN groups to the
system.
GC
vlan protocol group add
protocol
Adds a protocol to the protocol-based VLAN
identified by
groupid
.
GC
vlan protocol group name
Adds a group name to the protocol-based VLAN
identified by
groupid
.
GC
vlan protocol group remove
Removes the protocol-base VLAN group
identified by
groupid
.
GC
a. For the meaning of each Mode abbreviation, see
Mode Types
on page 87.
Command Description Modea
voice vlan
Enables the voice VLAN capability on the
switch.
GG
voice vlan (Interface)
Enables the voice VLAN capability on the
interface.
IC
voice vlan data priority
Trusts or not trusts the data traffic arriving on
the voice VLAN port.
IC
show voice vlan
Displays various properties of the voice VLAN. PE
Command Description Modea
2CSNXXX_SWUM200.book Page 124 Tuesday, December 10, 2013 1:22 PM
Command Groups 125
802.1x
a. For the meaning of each Mode abbreviation, see
Mode Types
on page 87.
Command Description Modea
dot1x dynamic-vlan enable
Enables the capability of creating VLANs
dynamically when a RADIUS-assigned VLAN
does not exist in the switch.
GC
dot1x initialize
Begins the initialization sequence on the
specified port.
PE
dot1x mac-auth-bypass
Enables MAB on an interface. IC
dot1x max-req
Sets the maximum number of times the switch
sends an EAP-request frame to the client before
restarting the authentication process.
IC
dot1x max-users
Sets the maximum number of clients supported
on the port when MAC-based 802.1X
authentication is enabled on the port.
IC
dot1x port-control
Enables manual control of the authorization
state of the port.
IC
dot1x re-authenticate
Manually initiates a reauthentication of all
802.1x-enabled ports or a specified 802.1X
enabled port.
PE
dot1x reauthentication
Enables periodic reauthentication of the client. IC
dot1x system-auth-control
monitor
Enables 802.1X globally. GC
dot1x timeout guest-vlan-
period
Sets the number of seconds that the switch
waits before authorizing the client if the client
is a dot1x unaware client.
IC
dot1x timeout quiet-period
Sets the number of seconds the switch remains
in the quiet state following a failed
authentication attempt.
IC
dot1x timeout re-authperiod
Sets the number of seconds between
reauthentication attempts.
IC
2CSNXXX_SWUM200.book Page 125 Tuesday, December 10, 2013 1:22 PM
Command Groups 126
dot1x timeout server-
timeout
Sets the number of seconds the switch waits for
a response from the authentication server
before resending the request.
IC
dot1x timeout tx-period
Sets the number of seconds the switch waits for
a response to an EAP-request/identify frame
from the client before resending the request.
IC
authentication enable
Enables the Authentication Manager. GC
authentication order
Sets the order of authentication methods used
on a port
IC
authentication priority
Sets the priority for the authentication methods
used on a port
IC
authentication restart
Sets the interval after which reauthentication
starts.
IC
clear authentication
statistics
Clears the authentication statistics. PE
clear authentication
authentication-history
Clears the authentication history logs. PE
show authentication
Displays the configured authentication
methods configured and if Tiered
Authentication is enabled.
PE
show authenticaton
authentication-history
Displays the authentication history on one or
more interfaces.
PE
show authentication
statistics
Displays the Authentication Manager statistics. PE
show dot1x
Displays 802.1X status for the switch or the
specified interface.
PE
show dot1x authentication-
history
Displays the dot1x authentication events and
information during successful and unsuccessful
dot1x authentication processes.
PE
show dot1x clients
Displays detailed information about the users
who have successfully authenticated on the
system or on a specified port.
PE
show dot1x interface
Shows the status of MAC Authentication
Bypass.
PE
Command Description Modea
2CSNXXX_SWUM200.book Page 126 Tuesday, December 10, 2013 1:22 PM
Command Groups 127
Layer 3 Commands
ARP (IPv4)
show dot1x interface
statistics
Displays 802.1X statistics for the specified
interface.
PE
show dot1x users
Displays active 802.1X authenticated users for
the switch.
PE
clear dot1x
authentication–history
Clears the authentication history table captured
during successful and unsuccessful
authentication.
PE
dot1x guest-vlan
Sets the guest VLAN on a port. IC
dot1x unauth-vlan
Specifies the unauthenticated VLAN on a port. IC
show dot1x advanced
Displays 802.1X advanced features for the
switch or specified interface.
PE
a. For the meaning of each Mode abbreviation, see
Mode Types
on page 87.
Command Description Modea
arp
Creates an Address Resolution Protocol (ARP)
entry.
GC
arp cachesize
Configures the maximum number of entries in
the ARP cache.
GC
arp dynamicrenew
Enables the ARP component to automatically
renew dynamic ARP entries when they age out.
GC
arp purge
Causes the specified IP address to be removed
from the ARP cache.
PE
arp resptime Configures the ARP request response timeout.
GC
arp retries
Configures the ARP count of maximum request
for retries.
GC
arp timeout
Configures the ARP entry age-out time. GC
clear arp-cache
Removes all ARP entries of type dynamic from
the ARP cache.
PE
Command Description Modea
2CSNXXX_SWUM200.book Page 127 Tuesday, December 10, 2013 1:22 PM
Command Groups 128
DHCP Server and Relay Agent (IPv4)
clear arp-cache management
Removes all entries from the ARP cache learned
from the management port.
PE
ip local-proxy-arp
Enables proxying of ARP requests. IC
ip proxy-arp
Enables proxy ARP on a router interface. IC
show arp
Displays the Address Resolution Protocol (ARP)
cache.
PE
show arp brief Displays the brief Address Resolution Protocol
(ARP) table information.
PE
a. For the meaning of each Mode abbreviation, see
Mode Types
on page 87.
Command Description Modea
ip dhcp pool
Defines a DHCP address pool that can be used
to supply addressing information to DHCP
client. This command puts the user into DHCP
Pool Configuration mode.
GC
bootfile
Sets the name of the image for the DHCP
client to load.
DP
clear ip dhcp binding
Removes automatic DHCP server bindings. PE
clear ip dhcp conflict
Removes DHCP server address conflicts. PE
client-identifier
Identifies a a Microsoft® DHCP client to be
manually assigned an address.
DP
client-name
Specifies the host name of a DHCP client. DP
default-router
Sets the IPv4 address of one or more routers for
the DHCP client to use.
DP
dns-server (IP DHCP Pool
Config)
Sets the IPv4 DNS server address which is
provided to a DHCP client by the DHCP server.
DP
domain-name (IP DHCP
Pool Config)
Sets the DNS domain name which is provided
to a DHCP client by the DHCP server.
DP
hardware-address
Specifies the MAC address of a client to be
manually assigned an address.
DP
Command Description Modea
2CSNXXX_SWUM200.book Page 128 Tuesday, December 10, 2013 1:22 PM
Command Groups 129
host
Specifies a manual binding for a DHCP client
host.
DP
ip dhcp bootp automatic
Enables automatic BOOTP address
assignments.
GC
ip dhcp conflict logging
Enables DHCP address conflict detection. GC
ip dhcp excluded-address
Excludes one or more DHCP addresses from
automatic assignment.
GC
ip dhcp ping packets
Configures the number of pings sent to detect if
an address is in use prior to assigning an address
from the DHCP pool.
GC
lease
Sets the period for which a dynamically
assigned DHCP address is valid.
DP
netbios-name-server
Configures the IPv4 address of the Windows®
Internet Naming Service (WINS) for a
Microsoft DHCP client.
DP
netbios-node-type
Sets the NetBIOS node type for a Microsoft
DHCP client.
DP
network
Defines a pool of IPv4 addresses for distributing
to clients.
DP
next-server
Sets the IPv4 address of the TFTP server to be
used during auto-install.
DP
option
Supplies arbitrary configuration information to
a DHCP client.
DP
service dhcp
Enables local IPv4 DHCP server on the switch. GC
sntp
Sets the IPv4 address of the NTP server to be
used for time synchronization of the client.
DP
show ip dhcp binding
Displays the configured DHCP bindings. PE
show ip dhcp conflict
Displays DHCP address conflicts for all relevant
interfaces or a specified interface.
PE
show ip dhcp global
configuration
Displays the DHCP global configuration. PE
show ip dhcp pool
Displays the configured DHCP pool or pools. UE or
PE
Command Description Modea
2CSNXXX_SWUM200.book Page 129 Tuesday, December 10, 2013 1:22 PM
Command Groups 130
DHCPv6
show ip dhcp server statistics
Displays the DHCP server binding and message
counters.
PE
a. For the meaning of each Mode abbreviation, see
Mode Types
on page 87.
Command Description Modea
a. For the meaning of each Mode abbreviation, see
Mode Types
on page 87.
clear ipv6 dhcp
Clears DHCPv6 statistics for all interfaces or for
a specific interface.
PE
dns-server (IPv6 DHCP Pool
Config)
Sets the IPv6 DNS server address which is
provided to a DHCPv6 client by the DHCPv6
server.
v6DP
domain-name (IPv6 DHCP
Pool Config)
Sets the DNS domain name which is provided
to a DHCPv6 client by the DHCPv6 server.
v6DP
ipv6 dhcp pool
Enters IPv6 DHCP Pool Configuration mode. GC
ipv6 dhcp relay
Configures an interface for DHCPv6 Relay
functionality.
IC
ipv6 dhcp server
Configures DHCPv6 server functionality on an
interface.
IC
prefix-delegation
Defines Multiple IPv6 prefixes within a pool for
distributing to specific DHCPv6 Prefix
delegation clients.
v6DP
service dhcpv6
Enables DHCPv6 configuration on the router. GC
show ipv6 dhcp
Displays the DHCPv6 server name and status. PE
show ipv6 dhcp binding
Displays the configured DHCP pool. PE
show ipv6 dhcp interface
(User EXEC)
Displays DHCPv6 information for all relevant
interfaces or a specified interface.
UE
PE
show ipv6 dhcp pool
Displays the configured DHCP pool. PE
show ipv6 dhcp statistics
Displays the DHCPv6 server name and status. UE
Command Description Modea
2CSNXXX_SWUM200.book Page 130 Tuesday, December 10, 2013 1:22 PM
Command Groups 131
DHCPv6 Snooping
Command Description Modea
clear ipv6 dhcp snooping
binding
Clears all IPv6 DHCP snooping entries. UE or
PE
clear ipv6 dhcp snooping
statistics
Clears all IPv6 DHCP snooping statistics. UE or
PE
ipv6 dhcp snooping
Globally enables IPv6 DHCP snooping. GC
ipv6 dhcp snooping vlan
Enables IPv6 DHCP snooping on a set of
VLANs.
GC
ipv6 dhcp snooping binding
Configures a static IPv6 DHCP snooping
binding.
GC
ipv6 dhcp snooping database
Configures the persistent location of the DHCP
snooping database.
GC
ipv6 dhcp snooping database
write-delay
Configures the time period between successive
writes of the binding database.
GC
ipv6 dhcp snooping limit
Configures an interface to disable itself if the
rate of received DHCP messages exceeds the
configured limit.
IC
ipv6 dhcp snooping log-
invalid
Configures the port to log invalid received
DHCP messages.
IC
ipv6 dhcp snooping trust
Configures the port as trusted. IC
ipv6 dhcp snooping verify
mac-address
Enables the additional verification of the source
MAC address with the client hardware address
in the received DHCP message.
GC
ipv6 verify binding
Configures a static IP source guard binding. GC
ipv6 verify source
Configures an interface to filter incoming
traffic from sources that are not present in the
DHCP binding database.
IC
show ipv6 dhcp snooping
Displays the IPv6 DHCP snooping
configuration.
UE or
PE
show ipv6 dhcp snooping
binding
Displays the IPv6 DHCP snooping
configuration.
UE or
PE
2CSNXXX_SWUM200.book Page 131 Tuesday, December 10, 2013 1:22 PM
Command Groups 132
DVMRP
show ipv6 dhcp snooping
database
Displays IPv6 DHCP snooping configurations
related to database persistency.
UE or
PE
show ipv6 dhcp snooping
statistics
Displays IPv6 DHCP snooping filtration
statistics.
UE or
PE
show ipv6 source binding
Displays the IPv6 source guard configurations
on all ports, an individual port, or on a VLAN.
UE or
PE
show ipv6 verify source
Displays the Ipv6 source guard configurations
on all ports.
UE or
PE
a. For the meaning of each Mode abbreviation, see
Mode Types
on page 87.
Command Description Modea
a. For the meaning of each Mode abbreviation, see
Mode Types
on page 87.
ip dvmrp
S
ets the administrative mode of DVMRP in the
router to active.
GC
IC
ip dvmrp metric
Configures the metric for an interface. IC
show ip dvmrp
Displays the system-wide information for
DVMRP.
PE
show ip dvmrp interface
Displays the interface information for DVMRP
on the specified interface.
PE
show ip dvmrp neighbor
Displays the neighbor information for DVMRP. PE
show ip dvmrp nexthop
D
isplays the next hop information on
outgoing interfaces for routing multicast
datagrams.
PE
show ip dvmrp prune
Displays the table that lists the router’s
upstream prune information.
PE
show ip dvmrp route
Displays the multicast routing information for
DVMRP.
PE
Command Description Modea
2CSNXXX_SWUM200.book Page 132 Tuesday, December 10, 2013 1:22 PM
Command Groups 133
GMRP
IGMP
Command Description Modea
a. For the meaning of each Mode abbreviation, see
Mode Types
on page 87.
gmrp enable
Enables GMRP globally or on a port. GC or
IC
show gmrp configuration
Displays GMRP configuration. GC or
IC
Command Description Modea
ip igmp last-member-query-
count
Sets the number of Group-Specific Queries
sent before the router assumes that there are
no local members on the interface.
IC
ip igmp last-member-query-
interval
Configures the Maximum Response Time
inserted in Group-Specific Queries which are
sent in response to Leave Group messages.
IC
ip igmp query-interval
Configures the query interval for the specified
interface. The query interval determines how
fast IGMP Host-Query packets are transmitted
on this interface.
IC
ip igmp query-max-response-
time
Configures the maximum response time
interval for the specified interface.
IC
ip igmp robustness
Configures the robustness that allows tuning
of the interface.
IC
ip igmp startup-query-count
Sets the number of queries sent out on
startup—at intervals equal to the startup
query interval for the interface.
IC
ip igmp startup-query-
interval
Sets the interval between general queries sent
at startup on the interface.
IC
ip igmp version
Configures the version of IGMP for an
interface.
IC
show ip igmp
Displays system-wide IGMP information. PE
2CSNXXX_SWUM200.book Page 133 Tuesday, December 10, 2013 1:22 PM
Command Groups 134
IGMP Proxy
IP Helper/DHCP Relay
show ip igmp groups
Displays the registered multicast groups on the
interface.
PE
show ip igmp interface
Displays the IGMP information for the
specified interface.
PE
show ip igmp membership
Displays the list of interfaces that have
registered in the multicast group.
PE
show ip igmp interface stats
Displays the IGMP statistical information for
the interface.
PE
a. For the meaning of each Mode abbreviation, see
Mode Types
on page 87.
Command Description Modea
a. For the meaning of each Mode abbreviation, see
Mode Types
on page 87.
ip igmp proxy-service
Enables the IGMP Proxy on the router. IC
ip igmp proxy-service reset-
status
Resets the host interface status parameters of
the IGMP Proxy router.
IC
ip igmp proxy-service
unsolicit-rprt-interval
Sets the unsolicited report interval for the
IGMP Proxy router.
IC
show ip igmp proxy-service
Displays a summary of the host interface status
parameters.
PE
show ip igmp proxy-service
interface
Displays a detailed list of the host interface
status parameters.
PE
show ip igmp-proxy groups
Displays a table of information about multicast
groups that IGMP Proxy reported.
PE
show ip igmp proxy-service
groups detail
Displays complete information about multicast
groups that IGMP Proxy has reported.
PE
Command Description Modea
bootpdhcprelay
maxhopcount
Configures the maximum allowable relay agent
hops for BootP/DHCP Relay on the system.
GC
Command Description Modea
2CSNXXX_SWUM200.book Page 134 Tuesday, December 10, 2013 1:22 PM
Command Groups 135
bootpdhcprelay
minwaittime
Configures the minimum wait time in seconds
for BootP/DHCP Relay on the system.
GC
clear ip helper statistics
Resets (to 0) the statistics displayed in show ip
helper statistics.
PE
ip dhcp relay information
check
Enables DHCP Relay to check that the relay
agent information option in forwarded
BOOTREPLY messages is valid.
GC
ip dhcp relay information
check-reply
Enables DHCP Relay to check that the relay
agent information option in forwarded
BOOTREPLY messages is valid.
IC
ip dhcp relay information
option
Enables the circuit ID option and remote agent
ID mode for BootP/DHCP Relay on the system
(also called option 82).
GC
ip dhcp relay information
option-insert
Enables the circuit ID option and remote agent
ID mode for BootP/DHCP Relay on the circuit
ID option and remote agent ID mode for
BootP/DHCP Relay on the interface (also called
option 82).
GC
ip helper-address (global
configuration)
Configures the relay of certain UDP broadcast
packets received on any interface.
GC
ip helper-address (interface
configuration)
Configures the relay of certain UDP broadcast
packets received on a specific interface.
IC
ip helper enable
Enables relay of UDP packets. GC
show ip helper-address
Displays the IP helper address configuration. PE
show ip dhcp relay
Displays the BootP/DHCP Relay information. UE or
PE
show ip helper statistics
Displays the number of DHCP and other UDP
packets processed and relayed by the UDP relay
agent.
PE
a. For the meaning of each Mode abbreviation, see
Mode Types
on page 87.
Command Description Modea
2CSNXXX_SWUM200.book Page 135 Tuesday, December 10, 2013 1:22 PM
Command Groups 136
IP Routing
Command Description Modea
encapsulation
Configures the link layer encapsulation type for
the packet.
IC
ip address
Configures an IP address on an interface. IC
ip netdirbcast
E
nables the forwarding of network-directed
broadcasts.
IC
ip policy route-map
Applies a route map on an interface. IC
ip route
Configures a static route. Use the no form of
the command to delete the static route.
GC
ip route default
Configures the default route. Use the no form
of the command to delete the default route.
GC
ip route distance
Sets the default distance (preference) for static
routes.
GC
ip routing
Globally enables IPv4 routing on the router. GC
match length
Configures packet length matching criteria for a
route map.
RM
match mac-list
Configures MAC ACL match criteria for a route
map.
RM
route-map
Creates a policy based route map. GC
match ip address
Specify IP address match criteria for a route
map.
RM
set interface null0
Routes packets to interface null 0. RM
set ip default next-hop
Sets a list of default next-hop IP addresses
to be used if no explicit route for the packet’s
destination address appears in the routing table.
RM
set ip next-hop
Specifies the adjacent next-hop router in the
path toward the destination to which the
packets should be forwarded.
RM
set ip precedence
Sets the IP precedence bits in the IP packet
header.
RM
show ip brief
Displays all the summary information of the IP. PE
2CSNXXX_SWUM200.book Page 136 Tuesday, December 10, 2013 1:22 PM
Command Groups 137
IPv6 Routing
show ip interface
Displays all pertinent information about the IP
interface.
PE
show ip policy
Displays the route maps used for policy based
routing on the router interfaces.
PE
show ip protocols
Displays the parameters and current state of the
active routing protocols.
PE
show ip route
Displays the routing table. PE
show ip route preferences
Displays detailed information about the route
preferences.
PE
show ip route summary
Shows the number of all routes, including best
and non-best routes.
PE
show ip traffic
Displays IP statistical information. UE or
PE
show ip vlan
Displays the VLAN routing information for all
VLANs with routing enabled.
PE
show route-map
Displays the route maps. PE
show routing heap summary
Displays a summary of the memory
allocation from the routing heap.
PE
a. For the meaning of each Mode abbreviation, see
Mode Types
on page 87.
Command Description Modea
clear ipv6 neighbors
Clears all entries in the IPv6 neighbor table
or an entry on a specific interface.
PE
clear ipv6 statistics
Clears IPv6 statistics for all interfaces or for a
specific interface, including loopback and
tunnel interfaces.
PE
ipv6 address
Configures an IPv6 address on an interface
(including tunnel and loopback interfaces).
IC
Command Description Modea
2CSNXXX_SWUM200.book Page 137 Tuesday, December 10, 2013 1:22 PM

Command Groups 138
ipv6 enable
Enables IPv6 routing on an interface
(including tunnel and loopback interfaces)
that has not been configured with an explicit
IPv6 address.
IC
ipv6 hop-limit
Configures the hop limit used in IPv6 PDUs
originated by the router.
GC
ipv6 host
Defines static host name-to- ipv6 address
mapping in the host cache.
GC
ipv6 mld last-member-
query-count
Sets the number of listener-specific queries
sent before the router assumes that there are
no local members on the interface.
IC (VC)
ipv6 mld last-member-
query-interval
Sets the last member query interval for the
MLD interface, which is the value of the
maximum response time parameter in the
group specific queries sent out of this
interface.
IC (VC)
ipv6 mld host-proxy
Enables MLD Proxy on the router. IC
ipv6 mld host-proxy reset-
status
Resets the host interface status parameters of
the MLD Proxy router.
IC
ipv6 mld host-proxy
unsolicit-rprt-interval
Sets the unsolicited report interval for the
MLD Proxy router.
IC
ipv6 mld query-interval
Sets the MLD router's query interval for the
interface.
IC
ipv6 mld query-max-
response-time
Sets MLD querier's maximum response time
for the interface.
IC
ipv6 nd dad attempts
Sets the number of duplicate address
detection probes transmitted while doing
neighbor discovery.
IC
ipv6 nd managed-config-
flag
Sets the managed address configuration flag
in router advertisements.
IC
ipv6 nd ns-interval
Sets the interval between router
advertisements for advertised neighbor
solicitations.
IC
Command Description Modea
2CSNXXX_SWUM200.book Page 138 Tuesday, December 10, 2013 1:22 PM

Command Groups 139
ipv6 nd other-config-flag
Sets the other stateful configuration flag in
router advertisements sent from the
interface.
IC
ipv6 nd prefix
Sets the IPv6 prefixes to include in the router
advertisement.
IC
ipv6 nd ra-interval
Sets the transmission interval between router
advertisements.
IC
ipv6 nd ra-lifetime
Sets the value that is placed in the Router
Lifetime field of the router advertisements
sent from the interface.
IC
ipv6 nd reachable-time
Sets the router advertisement time to
consider a neighbor reachable after neighbor
discovery confirmation.
IC
ipv6 nd suppress-ra
Suppresses router advertisement
transmission on an interface.
IC
ipv6 route
Configures an IPv6 static route GC
ipv6 route distance
Sets the default distance (preference) for
static routes.
GC
ipv6 unicast-routing
Enables forwarding of IPv6 unicast
datagrams.
GC
ping ipv6
Determines whether another computer is on
the network.
PE
ping ipv6 interface
Determines whether another computer is on
the network using Interface keyword.
PE
rate-limit cpu
Configures the rate in packets-per-
second for the number of IPv6 data
packets trapped to CPU when the packet
fails to be forwarded in the hardware due
to unresolved hardware address of the
destined IPv6 node.
GC
show ipv6 brief
Displays the IPv6 status of forwarding mode
and IPv6 unicast routing mode.
PE
show ipv6 interface
Shows the usability status of IPv6 interfaces. PE
Command Description Modea
2CSNXXX_SWUM200.book Page 139 Tuesday, December 10, 2013 1:22 PM

Command Groups 140
Loopback Interface
show ipv6 mld groups
Displays information about multicast groups
that MLD reported.
PE
show ipv6 mld interface
Displays MLD related information for an
interface.
PE
show ipv6 mld host-proxy
Displays a summary of the host interface
status parameters.
PE
show ipv6 mld host-proxy
groups
Displays information about multicast groups
that the MLD Proxy reported.
PE
show ipv6 mld host-proxy
groups detail
Displays information about multicast groups
that MLD Proxy reported.
PE
show ipv6 mld host-proxy
interface
Displays a detailed list of the host interface
status parameters.
PE
show ipv6 mld traffic
Displays MLD statistical information for the
router.
PE
show ipv6 neighbors
Displays information about IPv6 neighbors. PE
show ipv6 route
Displays the IPv6 routing table. PE
show ipv6 route
preferences
Shows the preference value associated with
the type of route.
PE
show ipv6 route summary
Displays a summary of the routing table. PE
show ipv6 traffic
Shows traffic and statistics for IPv6 and
ICMPv6.
UE
show ipv6 vlan
Displays IPv6 VLAN routing interface
addresses.
PE
traceroute ipv6
Discovers the routes that packets actually
take when traveling to their destination
through the network on a hop-by-hop basis.
PE
a. For the meaning of each Mode abbreviation, see
Mode Types
on page 87.
Command Description Modea
interface loopback
Enters the Interface Loopback configuration
mode.
GC
Command Description Modea
2CSNXXX_SWUM200.book Page 140 Tuesday, December 10, 2013 1:22 PM
Command Groups 141
Multicast
show interfaces loopback
Displays information about configured
loopback interfaces.
PE
a. For the meaning of each Mode abbreviation, see
Mode Types
on page 87.
Command Description Modea
ip mcast boundary
Adds an administrative scope multicast
boundary.
IC
ip mroute
Creates a static multicast route for a source
range.
GC
ip multicast-routing
Sets the administrative mode of the IP
multicast forwarder in the router to active.
GC
ip multicast ttl-threshold
Applies a
ttlvalue
to a routing interface. IC
ip pim
Administratively configures PIM mode for IP
multicast routing on a VLAN interface.
IC
ip pim bsr-border
Administratively disables bootstrap router
(BSR) messages from being sent or received
through an interface.
IC
ip pim bsr-candidate
Configures the router to advertise itself as a
bootstrap router (BSR).
GC
ip pim dense-mode
Administratively configures PIM dense mode
for IP multicast routing.
GC
ip pim dr-priority
Administratively configures the advertised
designated router (DR) priority value.
IC
ip pim hello-interval
Administratively configures the PIM Hello
messages on the specified interface.
IC
ip pim join-prune-interval
Administratively configures the frequency of
join/prune messages on the specified interface.
IC
ip pim rp-address
Defines the address of a PIM RP for a specific
multicast group range.
GC
Command Description Modea
2CSNXXX_SWUM200.book Page 141 Tuesday, December 10, 2013 1:22 PM
Command Groups 142
ip pim rp-candidate
Configures the router to advertise itself to the
bootstrap router (BSR) as a PIM candidate
rendezvous point (RP) for a specific multicast
group range.
IC
ip pim sparse-mode
Administratively configures PIM sparse mode
for IP multicast routing.
GC
ip pim ssm
Administratively configures PIM Source
Specific Multicast (SSM) range of addresses for
IP multicast routing.
GC
show ip multicast
Displays the system-wide multicast
information.
PE
show ip pim boundary
Displays the system-wide multicast
information.
PE
show ip multicast interface
Displays the multicast information for the
specified interface.
PE
show ip mroute
Displays a summary or all the details of the
multicast table.
PE
show ip mroute group
Displays the multicast configuration settings of
entries in the multicast mroute table.
PE
show ip mroute source
Displays the multicast configuration settings of
entries in the multicast mroute table.
PE
show ip mroute static
Displays all the static routes configured in the
static mcast table.
PE
show ip pim bsr-router
Displays the bootstrap router (BSR)
information.
PE
show ip pim interface
Displays PIM interface status parameters. If no
interface is specified, the command displays the
status parameters of all PIM-enabled interfaces.
UE or
PE
show ip pim neighbor
Displays PIM neighbors discovered by PIMv2
Hello messages. If no interface is specified, the
command displays the neighbors discovered on
all PIM-enabled interfaces.
UE or
PE
show ip pim rp hash
Displays the rendezvous point (RP) selected for
the specified group address.
UE or
PE
Command Description Modea
2CSNXXX_SWUM200.book Page 142 Tuesday, December 10, 2013 1:22 PM
Command Groups 143
IPv6 Multicast
show ip pim rp mapping
Displays the mappings for the PIM group to the
active rendezvous points (RPs).
UE or
PE
a. For the meaning of each Mode abbreviation, see
Mode Types
on page 87.
Command Description Modea
ipv6 pim (VLAN Interface
config)
Administratively enables PIM-SM multicast
routing mode on a particular IPv6 router
interface.
IC
ipv6 pim bsr-border
Prevents bootstrap router (BSR) messages from
being sent or received through an interface.
IC
ipv6 pim bsr-candidate
Configures the router to announce its
candidacy as a bootstrap router (BSR).
GC
ipv6 pim dense-mode
Administratively configures PIM dense mode
for IPv6 multicast routing.
GC
ipv6 pim dr-priority
Sets the priority value for which a router is
elected as the designated router (DR).
IC
ipv6 pim hello-interval
Administratively configures the PIM-SM Hello
Interval for the specified interface.
IC
ipv6 pim join-prune-interval
Administratively configures the interface
join/prune interval for the PIM-SM router.
IC
ipv6 pim register-threshold
Configures the Register Threshold rate for the
RP router to switch to the shortest path.
GC
ipv6 pim rp-address
Statically configures the Rendezvous Point (RP)
address for one or more multicast groups.
GC
ipv6 pim rp-candidate
Configures the router to advertise itself as a
PIM candidate rendezvous point (RP) to the
bootstrap router (BSR).
GC
ipv6 pim sparse-mode
Administratively configures PIM sparse mode
for multicast routing.
GC
ipv6 pim ssm
Defines the Source Specific Multicast (SSM)
range of multicast addresses.
GC
Command Description Modea
2CSNXXX_SWUM200.book Page 143 Tuesday, December 10, 2013 1:22 PM
Command Groups 144
OSPF
show ipv6 pim
Displays global status of IPv6 PIMSM and its
IPv6 routing interfaces.
PE or
GC
show ipv6 pim bsr-router
Display the bootstrap router (BSR)
information.
UE,
PE, or
GC
show ipv6 pim interface
Displays interface config parameters. PE or
GC
show ipv6 pim neighbor
Displays IPv6 PIMSM neighbors learned on the
routing interfaces.
PE or
GC
show ipv6 pim rp-hash
Displays which rendezvous point (RP) is being
selected for a specified group.
PE or
GC
show ipv6 pim rp mapping
Displays all group-to-RP mappings of which the
router is aware (either configured or learned
from the bootstrap router (BSR).
PE or
GC
a. For the meaning of each Mode abbreviation, see
Mode Types
on page 87.
Command Description Modea
area default-cost (Router
OSPF)
Configures the advertised default cost for the
stub area.
ROSPF
area nssa (Router OSPF)
Configures the specified area ID to function as an
NSSA.
ROSPF
area nssa default-info-
originate (Router OSPF
Config)
Configures the metric value and type for the
default route advertised into the NSSA.
ROSPF
area nssa no-redistribute
Configures the NSSA Area Border router (ABR)
so that learned external routes are not
redistributed to the NSSA.
ROSPF
area nssa no-summary
Configures the NSSA so that summary LSAs are
not advertised into the NSSA.
ROSPF
area nssa translator-role
Configures the translator role of the NSSA. ROSPF
area nssa translator-stab-
intv
Configures the translator stability interval of the
NSSA.
ROSPF
Command Description Modea
2CSNXXX_SWUM200.book Page 144 Tuesday, December 10, 2013 1:22 PM
Command Groups 145
area range (Router OSPF)
Creates a specified area range for a specified
NSSA.
ROSPF
area stub
Creates a stub area for the specified area ID. ROSPF
area stub no-summary
Prevents Summary LSAs from being advertised
into the NSSA.
ROSPF
area virtual-link
Creates the OSPF virtual interface for the
specified area-id and neighbor router.
ROSPF
area virtual-link
authentication
Configures the authentication type and key for
the OSPF virtual interface identified by the area
ID and neighbor ID.
ROSPF
area virtual-link dead-
interval
Configures the dead interval for the OSPF virtual
interface on the virtual interface identified by
area-id and neighbor router.
ROSPF
area virtual-link hello-
interval
Configures the hello interval for the OSPF virtual
interface on the virtual interface identified by the
area ID and neighbor ID.
ROSPF
area virtual-link
retransmit-interval
Configures the retransmit interval for the OSPF
virtual interface on the virtual interface identified
by the area ID and neighbor ID.
ROSPF
area virtual-link transmit-
delay
Configures the transmit delay for the OSPF
virtual interface on the virtual interface identified
by the area ID and neighbor ID.
ROSPF
auto-cost
Allows user to change the reference bandwidth
used in computing link cost.
ROSPF
bandwidth
Allows user to change the bandwidth used in
computing link cost.
IC
capability opaque
Enables Opaque Capability on the router. RC
clear ip ospf
Resets specific OSPF states. PE
compatible rfc1583
Enables OSPF 1583 compatibility. ROSPF
default-information
originate (Router OSPF
Configuration)
Controls the advertisement of default routes. ROSPF
default-metric
Sets a default for the metric of distributed routes. ROSPF
Command Description Modea
2CSNXXX_SWUM200.book Page 145 Tuesday, December 10, 2013 1:22 PM
Command Groups 146
distance ospf
Sets the route preference value of OSPF in the
router.
ROSPF
distribute-list out
Specifies the access list to filter routes received
from the source protocol.
ROSPF
enable
Resets the default administrative mode of OSPF
in the router (active).
ROSPF
exit-overflow-interval
Configures the exit overflow interval for OSPF. ROSPF
external-lsdb-limit
Configures the external LSDB limit for OSPF. ROSPF
ip ospf area
Enables OSPFv2 and sets the area ID of an
interface.
IC
ip ospf authentication
Sets the OSPF Authentication Type and Key for
the specified interface.
IC
ip ospf cost
Configures the cost on an OSPF interface. IC
ip ospf dead-interval
l Sets the OSPF dead interval for the specified
interface.
IC
ip ospf hello-interval
Sets the OSPF hello interval for the specified
interface.
IC
ip ospf mtu-ignore
Disables OSPF maximum transmission unit
(MTU) mismatch detection.
IC
ip ospf network
Configure OSPF to treat an interface as a point-
to-point, rather than broadcast interface.
IC
ip ospf priority
Sets the OSPF priority for the specified router
interface.
IC
ip ospf retransmit-interval
Sets the OSPF retransmit Interval for the
specified interface.
IC
ip ospf transmit-delay
Sets the OSPF Transit Delay for the specified
interface.
IC
maximum-paths
Sets the number of paths that OSPF can report
for a given destination.
ROSPF
nsf
Enables OSPF graceful restart. ROSPF
nsf helper
Allow OSPF to act as a helpful neighbor for a
restarting router.
ROSPF
Command Description Modea
2CSNXXX_SWUM200.book Page 146 Tuesday, December 10, 2013 1:22 PM
Command Groups 147
nsf helper strict-lsa-
checking
Set an OSPF helpful neighbor exit helper mode
whenever a topology change occurs.
ROSPF
nsf restart-interval
Configures the length of the grace period on the
restarting router.
ROSPF
network area
Enables OSPFv2 on an interface and sets its area
ID if the IP address of an interface is covered by
this network command.
ROSPF
passive-interface
Sets the interface or tunnel as passive. IC
passive-interface default
Enables the global passive mode by default for all
interfaces.
ROSPF
passive-interface
Sets the interface or tunnel as passive. ROSPF
redistribute
Configures OSPF protocol to allow redistribution
of routes from the specified source
protocol/routers.
ROSPF
router-id
Sets a 4-digit dotted-decimal number uniquely
identifying the router OSPF ID.
ROSPF
router ospf
Enters Router OSPF mode. GC
show ip ospf
Displays information relevant to the OSPF
router.
PE
show ip ospf abr
Displays the internal OSPF routing table entries
to Area Border Routers (ABR).
PE
show ip ospf area
Displays information about the identified OSPF
area.
PE
show ip ospf asbr
Displays the internal OSPF routing table entries
to Autonomous System Boundary Routes
(ASBR).
PE
show ip ospf database
Displays information about the link state
database when OSPF is enabled.
PE
show ip ospf database
database-summary
Displays the number of each type of LSA in the
database for each area and for the router.
PE
show ip ospf interface
Displays the information for the IFO object or
virtual interface tables.
PE
Command Description Modea
2CSNXXX_SWUM200.book Page 147 Tuesday, December 10, 2013 1:22 PM
Command Groups 148
OSPFv3
show ip ospf interface
brief
Displays brief information for the IFO object or
virtual interface tables.
PE
show ip ospf interface
stats
Displays the statistics for a specific interface. PE
show ip ospf neighbor
Displays information about OSPF neighbors. PE
show ip ospf range
Displays information about the area ranges for
the specified area-id.
PE
show ip ospf statistics
Displays information about recent Shortest Path
First (SPF) calculations.
PE
show ip ospf stub table
Displays the OSPF stub table. PE
show ip ospf virtual-link
Displays the OSPF Virtual Interface information
for a specific area and neighbor.
PE
show ip ospf virtual-links
brief
Displays the OSPF Virtual Interface information
for all areas in the system.
PE
timers pacing flood
Adjusts the rate at which OSPFv2 sends LS
Update packets
OG
timers pacing lsa-group
Tunes how OSPF groups LSAs for periodic
refresh.
OG
timers spf
Configures the SPF delay and hold time. ROSPF
a. For the meaning of each Mode abbreviation, see
Mode Types
on page 87.
Command Description Modea
area default-cost (Router
OSPFv3)
Configures the monetary default cost for the stub
area.
ROSV3
area nssa (Router
OSPFv3)
Configures the specified areaid to function as an
NSSA.
ROSV3
area nssa default-info-
originate (Router
OSPFv3 Config)
Configures the metric value and type for the
default route advertised into the NSSA.
ROSV3
Command Description Modea
2CSNXXX_SWUM200.book Page 148 Tuesday, December 10, 2013 1:22 PM
Command Groups 149
area nssa no-redistribute
Configures the NSSA ABR so that learned
external routes will not be redistributed to the
NSSA.
ROSV3
area nssa no-summary
Configures the NSSA so that summary LSAs are
not advertised into the NSSA.
ROSV3
area nssa translator-role
Configures the translator role of the NSSA. ROSV3
area nssa translator-stab-
intv
Configures the translator stability interval of the
NSSA.
ROSV3
area range (Router
OSPFv3)
Creates an area range for a specified NSSA. ROSV3
area stub
Creates a stub area for the specified area ID. ROSV3
area stub no-summary
Disables the import of Summary LSAs for the
stub area identified by
areaid.
ROSV3
area virtual-link
Creates the OSPF virtual interface for the
specified
areaid
and
neighbor
.
ROSV3
area virtual-link dead-
interval
Configures the dead interval for the OSPF virtual
interface on the virtual interface identified by
areaid
and
neighbor
.
ROSV3
area virtual-link hello-
interval
Configures the hello interval for the OSPF virtual
interface on the virtual interface identified by
areaid
and
neighbor
.
ROSV3
area virtual-link
retransmit-interval
Configures the retransmit interval for the OSPF
virtual interface on the virtual interface identified
by
areaid
and
neighbor
.
ROSV3
area virtual-link transmit-
delay
Configures the transmit delay for the OSPF
virtual interface on the virtual interface identified
by
areaid
and
neighbor
.
ROSV3
default-information
originate (Router
OSPFv3 Configuration)
Controls the advertisement of default routes. ROSV3
default-metric
Sets a default for the metric of distributed routes. ROSV3
distance ospf
Sets the route preference value of OSPF in the
router.
ROSV3
Command Description Modea
2CSNXXX_SWUM200.book Page 149 Tuesday, December 10, 2013 1:22 PM
Command Groups 150
enable
Resets the default administrative mode of OSPF
in the router (active).
ROSV3
exit-overflow-interval
Configures the exit overflow interval for OSPF. ROSV3
external-lsdb-limit
Configures the external LSDB limit for OSPF. ROSV3
ipv6 ospf
Enables OSPF on a router interface or loopback
interface.
IC
ipv6 ospf area
Sets the OSPF area to which the specified router
interface belongs.
IC
ipv6 ospf cost
Configures the cost on an OSPF interface. IC
ipv6 ospf dead-interval
Sets the OSPF dead interval for the specified
interface.
IC
ipv6 ospf hello-interval
Sets the OSPF hello interval for the specified
interface.
IC
ipv6 ospf mtu-ignore
Disables OSPF maximum transmission unit
(MTU) mismatch detection.
IC
ipv6 ospf network
Changes the default OSPF network type for the
interface.
IC
ipv6 ospf priority
Sets the OSPF priority for the specified router
interface.
IC
ipv6 ospf retransmit-
interval
Sets the OSPF retransmit interval for the
specified interface.
IC
ipv6 ospf transmit-delay
Sets the OSPF Transmit Delay for the specified
interface.
IC
ipv6 router ospf
Enters Router OSPFv3 Configuration mode. GC
maximum-paths
Sets the number of paths that OSPF can report
for a given destination.
ROSV3
nsf
Enables OSPF graceful restart. ROSV3
nsf helper
Allows OSPF to act as a helpful neighbor for a
restarting router.
ROSV3
nsf helper strict-lsa-
checking
Requires that an OSPF helpful neighbor exit
helper mode whenever a topology change occurs.
ROSV3
Command Description Modea
2CSNXXX_SWUM200.book Page 150 Tuesday, December 10, 2013 1:22 PM
Command Groups 151
nsf restart-interval
Configures the length of the grace period on the
restarting router.
ROSV3
passive-interface
Sets the interface or tunnel as passive. IC
passive-interface default
Enables the global passive mode by default for all
interfaces.
ROSV3
redistribute
Configures the OSPFv3 protocol to allow
redistribution of routes from the specified source
protocol/routers.
ROSV3
router-id
Sets a 4-digit dotted-decimal number uniquely
identifying the Router OSPF ID.
ROSV3
show ipv6 ospf
Displays information relevant to the OSPF
router.
PE
show ipv6 ospf abr
Displays the internal OSPFv3 routes to reach
Area Border Routers (ABR).
PE
show ipv6 ospf area
Displays information about the area. PE
show ipv6 ospf asbr
Displays the internal OSPFv3 routes to reach
Autonomous System Boundary Routes (ASBR).
PE
show ipv6 ospf border-
routers
Displays internal OSPFv3 routers to reach Area
Border Routers (ABR) and Autonomous System
Boundary Routers (ASBR).
UE or
PE
show ipv6 ospf database
Displays information about the link state
database when OSPFv3 is enabled.
PE
show ipv6 ospf database
database-summary
Displays the number of each type of LSA in the
database and the total number of LSAs in the
database.
PE
show ipv6 ospf interface
Displays the information for the IFO object or
virtual interface tables.
PE
show ipv6 ospf interface
brief
Displays brief information for the IFO object or
virtual interface tables.
PE
show ipv6 ospf interface
stats
Displays the statistics for a specific interface. UE
show ipv6 ospf interface
vlan
Displays OSPFv3 configuration and status
information for a specific VLAN.
PE
Command Description Modea
2CSNXXX_SWUM200.book Page 151 Tuesday, December 10, 2013 1:22 PM
Command Groups 152
Router Discovery Protocol
show ipv6 ospf neighbor
Displays information about OSPF neighbors. PE
show ipv6 ospf range
Displays information about the area ranges for
the specified area identifier.
PE
show ipv6 ospf stub table
Displays the OSPF stub table. PE
show ipv6 ospf virtual-
links
Displays the OSPF Virtual Interface information
for a specific area and neighbor.
PE
show ipv6 ospf virtual-
link brief
Displays the OSPFV3 Virtual Interface
information for all areas in the system.
PE
a. For the meaning of each Mode abbreviation, see
Mode Types
on page 87.
Command Description Modea
a. For the meaning of each Mode abbreviation, see
Mode Types
on page 87.
ip irdp
Enables Router Discovery on an interface. IC
ip irdp holdtime
Configures the value, in seconds, of the
holdtime field of the router advertisement sent
from this interface.
IC
ip irdp maxadvertinterval
Configures the maximum time, in seconds,
allowed between sending router advertisements
from the interface.
IC
ip irdp minadvertinterval
Configures the minimum time, in seconds,
allowed between sending router advertisements
from the interface.
IC
ip irdp multicast
Sends router advertisements as IP multicast
packets.
IC
ip irdp preference
Configures the preference of the address as a
default router address relative to other router
addresses on the same subnet.
IC
show ip irdp
Displays the router discovery information for all
interfaces, or for a specified interface.
PE
Command Description Modea
2CSNXXX_SWUM200.book Page 152 Tuesday, December 10, 2013 1:22 PM
Command Groups 153
Routing Information Protocol
Command Description Modea
auto-summary
Enables the RIP auto-summarization mode. RIP
default-information
originate (Router RIP
Configuration)
Controls the advertisement of default routes. RIP
default-metric
Sets a default for the metric of distributed
routes.
RIP
distance rip
Sets the route preference value of RIP in the
router.
RIP
distribute-list out
Specifies the access list to filter routes received
from the source protocol.
RIP
enable
Resets the default administrative mode of RIP
in the router (active).
RIP
hostroutesaccept
Enables the RIP hostroutesaccept mode. RIP
ip rip
Enables RIP on a router interface. IC
ip rip authentication
Sets the RIP Version 2 Authentication Type and
Key for the specified interface.
IC
ip rip receive version
Configures the interface to allow RIP control
packets of the specified version(s) to be
received.
IC
ip rip send version
Configures the interface to allow RIP control
packets of the specified version to be sent.
IC
redistribute
Configures OSPF protocol to allow
redistribution of routes from the specified
source protocol/routers.
PIP
router rip
Enters Router RIP mode. GC
show ip rip
Displays information relevant to the RIP router. PE
show ip rip interface
Displays information related to a particular RIP
interface.
PE
show ip rip interface brief
Displays general information for each RIP
interface.
PE
split-horizon
Sets the RIP split horizon mode. RIP
2CSNXXX_SWUM200.book Page 153 Tuesday, December 10, 2013 1:22 PM
Command Groups 154
Tunnel Interface
Virtual Router Redundancy
a. For the meaning of each Mode abbreviation, see
Mode Types
on page 87.
Command Description Modea
a. For the meaning of each Mode abbreviation, see
Mode Types
on page 87.
interface tunnel
Enables the interface configuration mode for a
tunnel.
GC
show interfaces tunnel
Displays the parameters related to tunnel such
as tunnel mode, tunnel source address and
tunnel destination address.
PE
tunnel destination
Specifies the destination transport address of
the tunnel.
IC
tunnel mode ipv6ip
Specifies the mode of the tunnel. IC
tunnel source
Specifies the source transport address of the
tunnel, either explicitly or by reference to an
interface.
IC
Command Description Modea
ip vrrp
Enables the administrative mode of Virtual
Router Redundancy Protocol (VRRP) for the
router.
GC
vrrp accept-mode
Enables the VRRP Master to accept ping
packets sent to one of the virtual router’s IP
addresses.
IC
vrrp authentication
Sets the authentication details value for the
virtual router configured on a specified
interface.
IC
vrrp description
Assigns a description to the VRRP group. IC
vrrp ip
Sets the virtual router IP address value for an
interface.
IC
2CSNXXX_SWUM200.book Page 154 Tuesday, December 10, 2013 1:22 PM
Command Groups 155
vrrp mode
Enables the virtual router configured on an
interface. Enabling the status field starts a
virtual router.
IC
vrrp preempt
Sets the preemption mode value for the virtual
router configured on a specified interface.
IC
vrrp priority
Sets the priority value for the virtual router
configured on a specified interface.
IC
vrrp timers advertise
Sets the frequency, in seconds, that an interface
on the specified virtual router sends a virtual
router advertisement.
IC
vrrp timers learn
Configures the router, when it is acting as
backup virtual router for a VRRR group, to learn
the advertisement interval used by the master
virtual router.
IC
vrrp track interface
Alters the priority of the VRRP router based on
the availability of its interfaces.
IC
vrrp track ip route
Tracks route reachability. IC
show vrrp
Displays the global VRRP configuration and
status as well as the brief or detailed status of
one or all VRRP groups.
UE or
PE
show vrrp interface
Displays all configuration information and
VRRP router statistics of a virtual router
configured on a specific interface.
UE or
PE
show vrrp interface brief
Displays information about each virtual router
configured on the switch.
PE
show vrrp interface stats
Displays the statistical information about each
virtual router configured on the switch.
PE
Pingable VRRP Commands
ip vrrp accept-mode
Enables the VRRP Master to accept ping
packets sent to one of the virtual router’s IP
addresses.
IC
show ip vrrp interface
Displays the configured value for Accept Mode. UE or
PE
a. For the meaning of each Mode abbreviation, see
Mode Types
on page 87.
Command Description Modea
2CSNXXX_SWUM200.book Page 155 Tuesday, December 10, 2013 1:22 PM
Command Groups 156
Utility Commands
Auto-Install
Captive Portal
Command Description Modea
a. For the meaning of each Mode abbreviation, see
Mode Types
on page 87.
boot auto-copy-sw
Enables or disables Stack Firmware
Synchronization.
GC
boot auto-copy-sw allow-
downgrade
Enables downgrading the firmware version on
the stack member if the firmware version on the
manager is older than the firmware version on
the member.
GC
boot host autoreboot
Enables rebooting the device (no administrative
intervention) when the auto-image is
successfully downloaded.
GC
boot host autosave
Enables/disables automatically saving the
downloaded configuration on the switch.
GC
boot host dhcp
Enables/disables Auto Config on the switch. GC
boot host retrycount
Set the number of attempts to download a
configuration.
GC
show auto-copy-sw
Displays Stack Firmware Synchronization
configuration status.
PE
show boot
Displays the current status of the Auto Config
process.
PE
Command Description Modea
authentication timeout
Configures the authentication timeout. CP
captive-portal
Enables the captive portal configuration mode. GC
enable
Globally enables captive portal. CPI
http port
Configures an additional HTTP port for captive
portal to monitor.
CP
2CSNXXX_SWUM200.book Page 156 Tuesday, December 10, 2013 1:22 PM
Command Groups 157
https port
Configures an additional HTTPS port for
captive portal to monitor.
CP
show captive-portal
Displays the status of captive portal. PE
show captive-portal status
Reports the status of all captive portal instances
in the system.
PE
block
Blocks all traffic for a captive portal
configuration.
CPI
configuration
Enables the captive portal instance mode. CP
enable
Enables a captive portal configuration. CPI
group
Configures the group number for a captive
portal configuration.
CPI
interface
Associates an interface with a captive portal
configuration.
CPI
locale
Associates an interface with a captive portal
configuration.
CPI
name (Captive Portal)
Configures the name for a captive portal
configuration.
CPI
protocol
Configures the protocol mode for a captive
portal configuration.
CPI
redirect
Enables the redirect mode for a captive portal
configuration.
CPI
redirect-url
Configures the redirect URL for a captive portal
configuration.
CPI
session-timeout
Configures the session timeout for a captive
portal configuration.
CPI
verification
Configures the verification mode for a captive
portal configuration.
CPI
captive-portal client
deauthenticate
Deauthenticates a specific captive portal client. PE
show captive-portal client
status
Displays client connection details or a
connection summary for connected captive
portal users.
PE
Command Description Modea
2CSNXXX_SWUM200.book Page 157 Tuesday, December 10, 2013 1:22 PM
Command Groups 158
show captive-portal
configuration client status
Displays the clients authenticated to all captive
portal configurations or a to specific
configuration.
PE
show captive-portal
interface client status
Displays information about clients
authenticated on all interfaces or a specific
interface.
PE
show captive-portal
interface configuration
status
Displays the clients authenticated to all captive
portal configurations or a to specific
configuration.
PE
clear captive-portal users
Deletes all captive portal user entries. PE
no user
Deletes a user from the local user database. CP
show captive-portal user
Displays all configured users or a specific user in
the captive portal local user database.
PE
user group
Associates a group with a captive portal user.
user-logout
Enables captive portal users to log out of the
portal.
CPI
user name
Modifies the user name for a local captive portal
user.
CP
user password
Creates a local user or changes the password for
an existing user.
CP
user session-timeout
Sets the session timeout value for a captive
portal user.
CP
show captive-portal
configuration
Displays the operational status of each captive
portal configuration.
PE
show captive-portal
configuration interface
Displays information about all interfaces
assigned to a captive portal configuration or
about a specific interface assigned to a captive
portal configuration.
PE
show captive-portal
configuration locales
Displays locales associated with a specific
captive portal configuration.
PE
show captive-portal
configuration status
Displays information about all configured
captive portal configurations or a specific
captive portal configuration.
PE
Command Description Modea
2CSNXXX_SWUM200.book Page 158 Tuesday, December 10, 2013 1:22 PM
Command Groups 159
CLI Macro
Clock
user group
Creates a user group. CP
user group moveusers
Moves a group's users to a different group. CP
user group name
Configures a group name. CP
a. For the meaning of each Mode abbreviation, see
Mode Types
on page 87.
Command Description Modea
a. For the meaning of each Mode abbreviation, see
Mode Types
on page 87.
macro name
Creates a user-defined macro. GC
macro global apply
Use to apply a macro. GC
macro global trace
Applies and traces a macro. GC
macro global description
Appends a line to the global macro description. GC
macro apply
Use to apply a macro. IC
macro trace
Applies and traces a macro. IC
macro description
Appends a line to the macro description. IC
show parser macro
Displays information about defined macros. PE
Command Description Modea
show sntp configuration
Displays the SNTP configuration. PE
show sntp server
Displays the preconfigured SNTP servers. PE
show sntp status
Displays the SNTP status. PE
sntp authenticate
Set to require authentication for received NTP
traffic from servers.
GC
sntp authentication-key
Defines an authentication key for SNTP. GC
sntp broadcast client enable
Enables SNTP Broadcast clients. GC
sntp client poll timer
Defines polling time for the SNTP client. GC
Command Description Modea
2CSNXXX_SWUM200.book Page 159 Tuesday, December 10, 2013 1:22 PM

Command Groups 160
Command Line Configuration Scripting
sntp server
Configures the SNTP server to use SNTP to
request and accept NTP traffic from it.
GC
sntp trusted-key
Authenticates the identity of a system to which
Simple Network Time Protocol (SNTP) will
synchronize.
GC
sntp unicast client enable
Enables clients to use Simple Network Time
Protocol (SNTP) predefined Unicast clients.
GC
clock timezone hours-offset
Sets the offset to Coordinated Universal Time. GC
clock summer-time
recurring
Sets the summertime offset to UTC recursively
every year.
GC
clock summer-time date
Sets the summertime offset to UTC. GC
show clock
Displays the time and date from the system
clock.
PE
a. For the meaning of each Mode abbreviation, see
Mode Types
on page 87.
Command Description Modea
a. For the meaning of each Mode abbreviation, see
Mode Types
on page 87.
Configuration and Image Files
script apply
Applies commands in the script to the switch. PE
script delete
Deletes a specific script. PE
script list
Lists all scripts present in the switch. PE
script show
Displays the contents of a script file. PE
script validate
Validates a script file. PE
Command Description Modea
boot system
Specifies the system image that the switch loads
at startup.
PE
clear config
Restores switch to default configuration. PE
copy
Copies files from a source to a destination. PE
Command Description Modea
2CSNXXX_SWUM200.book Page 160 Tuesday, December 10, 2013 1:22 PM
Command Groups 161
Denial of Service
delete
Deletes a file from a flash memory. PE
delete backup-image
Deletes a file from a flash memory device. PE
delete backup-config
Deletes the backup configuration file. PE
delete startup-config
Deletes the startup configuration file. PE
dir
Prints the contents of the flash file system. PE
erase
Erases the startup configuration, the backup
configuration, or the backup image.
PE
filedescr
Adds a description to a file. PE
rename
Renames the file present in flash. PE
show backup-config
Displays contents of a backup configuration
file.
PE
show bootvar
Displays the active system image file that the
switch loads at startup.
UE
show running-config
Displays the contents of the currently running
configuration file.
PE
show startup-config
Displays the startup configuration file contents. PE
write
Copies the running configuration image to the
startup configuration.
PE
a. For the meaning of each Mode abbreviation, see
Mode Types
on page 87.
Command Description Modea
dos-control firstfrag
Enables Minimum TCP Header Size Denial of
Service protection.
GC
dos-control icmp
Enables Maximum ICMP Packet Size Denial of
Service protections.
GC
dos-control l4port
Enables L4 Port Denial of Service protection. GC
dos-control sipdip
Enables Source IP Address = Destination IP
Address (SIP=DIP) Denial of Service protection.
GC
dos-control tcpflag
Enables TCP Flag Denial of Service protections. GC
Command Description Modea
2CSNXXX_SWUM200.book Page 161 Tuesday, December 10, 2013 1:22 PM
Command Groups 162
Line
dos-control tcpfrag
Enables TCP Fragment Denial of Service
protection.
GC
ip icmp echo-reply
Enables or disables the generation of ICMP Echo
Reply messages.
GC
ip icmp error-interval
Limits the rate at which IPv4 ICMP error
messages are sent.
GC
ip unreachables
Enables the generation of ICMP Destination
Unreachable messages.
IC
ip redirects
Enables the generation of ICMP Redirect
messages.
IC
ipv6 icmp error-interval
Limits the rate at which ICMPv6 error messages
are sent.
GC
ipv6 unreachables
Enables the generation of ICMPv6 Destination
Unreachable messages.
IC
show dos-control
Displays Denial of Service configuration
information.
PE
a. For the meaning of each Mode abbreviation, see
Mode Types
on page 87.
Command Description Modea
a. For the meaning of each Mode abbreviation, see
Mode Types
on page 87.
exec-timeout
Configures the interval that the system waits for
user input.
LC
history
Enables the command history function. LC
history size
Changes the command history buffer size for a
particular line.
LC
line
Identifies a specific line for configuration and
enters the line configuration command mode.
GC
show line
Displays line parameters. UE
speed
Sets the line baud rate. LC
Command Description Modea
2CSNXXX_SWUM200.book Page 162 Tuesday, December 10, 2013 1:22 PM
Command Groups 163
Management ACL
Password Management
Command Description Modea
a. For the meaning of each Mode abbreviation, see
Mode Types
on page 87.
deny (management)
Defines a deny rule. MA
management access-class
Defines which management access-list is used. GC
management access-list
Defines a management access-list, and enters
the access-list for configuration.
GC
permit (management)
Defines a permit rule. MA
show management access-
class
Displays the active management access-list. PE
show management access-
list
Displays management access-lists. PE
Command Description Modea
passwords aging
Implements aging on the passwords such that
users are required to change passwords when
they expire.
GC
passwords history
Enables the administrator to set the number of
previous passwords that are stored to ensure
that users do not reuse their passwords too
frequently.
GC
passwords lock-out
Enables the administrator to strengthen the
security of the switch by enabling the user
lockout feature. When a lockout count is
configured, a user who is logging in must enter
the correct password within that count.
GC
passwords min-length
Enables the administrator to enforce a
minimum length required for a password.
GC
passwords strength-check
Enables the Password Strength feature. GC
passwords strength
minimum uppercase-letters
Enforces a minimum number of uppercase
letters that a password should contain.
GC
2CSNXXX_SWUM200.book Page 163 Tuesday, December 10, 2013 1:22 PM
Command Groups 164
PHY Diagnostics
passwords strength
minimum lowercase-letters
Enforces a minimum number of lowercase
letters that a password must contain.
GC
passwords strength
minimum numeric-
characters
Enforces a minimum number of numeric
numbers that a password should contain.
GC
passwords strength
minimum special-characters
Enforces a minimum number of special
characters that a password may contain.
GC
passwords strength max-
limit consecutive-characters
Enforces a maximum number of consecutive
characters that a password can contain.
GC
passwords strength max-
limit repeated-characters
Enforces a maximum repeated characters that a
password should contain.
GC
passwords strength
minimum character-classes
Enforces the minimum number of character
classes (uppercase letters, lowercase letters,
numeric characters and special characters) that
a password must contain.
GC
passwords strength exclude-
keyword
Enforces a maximum number of consecutive
characters that a password can contain.
GC
enable password encrypted
Used by an Administrator to transfer the enable
password between devices without having to
know the password.
PE
show passwords
configuration
Displays the configuration parameters for
password configuration.
PE
show passwords result
Displays the last password set result
information.
PE
a. For the meaning of each Mode abbreviation, see
Mode Types
on page 87.
Command Description Modea
show copper-ports tdr
Displays the last TDR (Time Domain
Reflectometry) tests on specified ports.
PE
show fiber-ports optical-
transceiver
Displays the optical transceiver diagnostics. PE
Command Description Modea
2CSNXXX_SWUM200.book Page 164 Tuesday, December 10, 2013 1:22 PM
Command Groups 165
Power Over Ethernet (PoE)
test copper-port tdr
Diagnoses with TDR (Time Domain
Reflectometry) technology the quality and
characteristics of a copper cable attached to a
port.
PE
a. For the meaning of each Mode abbreviation, see
Mode Types
on page 87.
Command Description Modea
a. For the meaning of each Mode abbreviation, see
Mode Types
on page 87.
power inline
Enables/disables the ability of the port to
deliver power.
IC
(Ethernet)
power inline detection
Configures the detection type that tells
which types of PD’s will be detected and
powered by the switch.
IC
power inline high-power
Configures the port high power mode. IC
power inline limit
Configures the type of power limit. IC
power inline management
Sets the power management type. GC
power inline powered-
device
Adds a comment or description of the
powered device type.
IC
(Ethernet)
power inline priority
Configures the port priority level for the
delivery of power to an attached device.
IC
(Ethernet)
power inline reset
Use to reset the port. IC
power inline usage-
threshold
Configures the system power usage
threshold level at which lower priority
ports are disconnected.
GC
clear power inline statistics
Clears the PoE statistics. PE
show power inline
Reports current PoE configuration and
status.
PE
show power inline
firmware-version
Displays the version of the PoE controller
firmware present on the switch file system.
PE
Command Description Modea
2CSNXXX_SWUM200.book Page 165 Tuesday, December 10, 2013 1:22 PM
Command Groups 166
RMON
SDM Templates
Command Description Modea
a. For the meaning of each Mode abbreviation, see
Mode Types
on page 87.
rmon alarm
Configures alarm conditions. GC
rmon collection history
Enables a Remote Monitoring (RMON) MIB
history statistics group on an interface.
IC
rmon event
Configures an RMON event. GC
rmon hcalarm
Configures high capacity alarms. GC
show rmon alarm
Displays alarm configurations. UE
show rmon alarms
Displays the alarms summary table. UE
and
PE
show rmon collection history
Displays
the requested group of statistics.
UE
show rmon events
Displays the RMON event table. UE
show rmon hcalarm
Displays the high capacity alarms. PE
show rmon history
Displays RMON Ethernet Statistics history. UE
show rmon log
Displays the RMON logging table. UE
show rmon statistics
Displays RMON Ethernet Statistics. UE
Command Description Modea
a. For the meaning of each Mode abbreviation, see
Mode Types
on page 87.
sdm prefer
Changes the template that will be active after
the next reboot.
GC
show sdm prefer
Views the currently active SDM template and
its scaling parameters, or views the scaling
parameters for an inactive template.
PE
2CSNXXX_SWUM200.book Page 166 Tuesday, December 10, 2013 1:22 PM
Command Groups 167
Serviceability Tracing
Command Description Modea
debug arp
Enables tracing of ARP packets. PE
debug auto-voip
Enables Auto VOIP debug messages. PE
debug clear
Disables all debug traces. PE
debug console
Enables the display of debug trace output on
the login session in which it is executed.
PE
debug dot1ag
Enable the tracing of CFM components
for events and CFM PDUs based on the
type of packet for reception and
transmission.
PE
debug dot1x
Enables dot1x packet tracing. PE
debug igmpsnooping
Enables tracing of IGMP Snooping packets
transmitted and/or received by the switch.
PE
debug ip acl
Enables debug of IP Protocol packets matching
the ACL criteria.
PE
debug ip dvmrp
Traces DVMRP packet reception and
transmission.
PE
debug ip igmp
Traces IGMP packet reception and
transmission.
PE
debug ip mcache
Traces MDATA packet reception and
transmission.
PE
debug ip pimdm packet
Traces PIMDM packet reception and
transmission.
PE
debug ip pimsm packet
Traces PIMSM packet reception and
transmission.
PE
debug ip vrrp
Enables VRRP debug protocol messages. PE
debug ipv6 dhcp
Displays debug information about DHCPv6
client activities and to trace DHCPv6 packets to
and from the local DHCPv6 client.
PE
debug ipv6 mcache
Traces MDATAv6 packet reception and
transmission.
PE
debug ipv6 mld
Traces MLD packet reception and transmission. PE
2CSNXXX_SWUM200.book Page 167 Tuesday, December 10, 2013 1:22 PM
Command Groups 168
debug ipv6 pimdm
Traces PIMDMv6 packet reception and
transmission.
PE
debug ipv6 pimsm
Traces PIMSMv6 packet reception and
transmission.
PE
debug isdp
Traces ISDP packet reception and transmission. PE
debug lacp
Traces of LACP packets received and
transmitted by the switch.
PE
debug mldsnooping
Traces MLD snooping packet reception and
transmission.
PE
debug ospf
Enables tracing of OSPF packets received and
transmitted by the switch.
PE
debug ospfv3
Enables tracing of OSPFv3 packets received and
transmitted by the switch.
PE
debug ping
Enables tracing of ICMP echo requests and
responses.
PE
debug rip
Enables tracing of RIP requests and responses. PE
debug sflow
Enables sFlow debug packet trace. PE
debug spanning-tree
Traces spanning tree BPDU packet reception
and transmission.
PE
debug vrrp
Enables VRRP debug protocol messages. PE
exception core-file
Configures the core dump file name. GC
exception dump
Configures the core dump location. GC
exception protocol
Enables full core dumps. GC
exception switch-chip-
register
Enables the dumping of the switch chip
registers in case of an exception.
GC
show debugging
Displays packet tracing configurations. PE
show exception
Displays the core dump configuration
parameters.
PE
write core
Generates a core file on demand and either,
reboots the switch or tests the core file
configuration.
PE
a. For the meaning of each Mode abbreviation, see
Mode Types
on page 87.
Command Description Modea
2CSNXXX_SWUM200.book Page 168 Tuesday, December 10, 2013 1:22 PM
Command Groups 169
sFlow
SNMP
Command Description Modea
a. For the meaning of each Mode abbreviation, see
Mode Types
on page 87.
sflow destination
Configures sFlow collector parameters (owner
string, receiver timeout, ip address, and port).
GC
sflow polling
Enables a new sflow poller instance for the data
source if rcvr_idx is valid.
GC
sflow polling (Interface
Mode)
Enable a new sflow poller instance for this data
source if rcvr_idx is valid.
IC
sflow sampling
Enables a new sflow sampler instance for this
data source if rcvr_idx is valid.
GC
sflow sampling (Interface
Mode)
Enables a new sflow sampler instance for this
data source if rcvr_idx is valid.
IC
show sflow agent
Displays the sflow agent information. PE
show sflow destination
Displays all the configuration information
related to the sFlow receivers.
PE
show sflow polling
Displays the sFlow polling instances created on
the switch.
PE
show sflow sampling
Displays the sFlow sampling instances created
on the switch.
PE
Command Description Modea
show snmp
Displays the SNMP status. PE
show snmp engineID
Displays the SNMP engine ID. PE
show snmp filters
Displays the configuration of filters. PE
show snmp group
Displays the configuration of groups. PE
show snmp user
Displays the configuration of users. PE
show snmp views
Displays the configuration of views. PE
show trapflags
Displays SNMP traps globally or displays
specific SNMP traps.
PE
2CSNXXX_SWUM200.book Page 169 Tuesday, December 10, 2013 1:22 PM
Command Groups 170
SSH
snmp-server community
Sets up the community access string to permit
access to SNMP protocol.
GC
snmp-server community-
group
Maps SNMP v1 and v2 security models to the
group name.
GC
snmp-server contact
Set
s up a system contact (sysContact) string.
GC
snmp-server enable traps
Enables SNMP traps globally or enables specific
SNMP traps.
GC
snmp-server engineID local
Specifies the Simple Network Management
Protocol (SNMP) engine ID on the local switch.
GC
snmp-server filter
Creates or updates an SNMP server filter entry. GC
snmp-server group
Configures a new SNMP group or a table that
maps SNMP users to SNMP views.
GC
snmp-server host
Specifies the recipient of SNMP notifications. GC
snmp-server location
Sets
the system location string.
GC
snmp-server user
C
onfigures a new SNMP Version 3 user.
GC
snmp-server view
Creates or updates a Simple Network
Management Protocol (SNMP) server view
entry.
GC
snmp-server v3-host
Specifies the recipient of Simple Network
Management Protocol Version 3 (SNMPv3)
notifications.
GC
a. For the meaning of each Mode abbreviation, see
Mode Types
on page 87.
Command Description Modea
cryptho key generate dsa
Generates DSA key pairs for the switch. GC
crypto key generate rsa
Generates RSA key pairs for the switch. GC
crypto key pubkey-chain ssh
Enters SSH Public Key-chain configuration
mode.
GC
crypto key zeroize pubkey-
chain
Erases all public key chains or the public
key chain for a user.
GC
Command Description Modea
2CSNXXX_SWUM200.book Page 170 Tuesday, December 10, 2013 1:22 PM
Command Groups 171
Syslog
crypto key zeroize {rsa|dsa}
Deletes the RSA or DSA keys from the
switch.
GC
ip ssh port
Specifies the port to be used by the SSH server. GC
ip ssh pubkey-auth
Enables public key authentication for incoming
SSH sessions.
GC
ip ssh server
Enables the switch to be configured from a SSH
server connection.
GC
key-string
Manually specifies a SSH public key. SK
no crypto certificate
Removes the SSH public keys from the
switch.
GC
show crypto key mypubkey
Displays its own SSH public keys stored on the
switch.
PE
show crypto key pubkey-
chain ssh
Displays SSH public keys stored on the switch. PE
show ip ssh
Displays the SSH server configuration. PE
a. For the meaning of each Mode abbreviation, see
Mode Types
on page 87.
Command Description Modea
clear logging
Clears messages from the internal logging
buffer.
PE
clear logging file
Clears messages from the logging file. PE
description (Logging)
Describes the syslog server. L
level
Specifies the importance level of syslog
messages.
L
logging cli-command
Enable CLI command logging. GC
logging
Logs messages to a syslog server. GC
logging audit
Enables switch auditing. GC
logging buffered
Limits syslog messages displayed from an
internal buffer based on severity.
GC
Command Description Modea
2CSNXXX_SWUM200.book Page 171 Tuesday, December 10, 2013 1:22 PM
Command Groups 172
System Management
logging console
Limits messages logged to the console based on
severity.
GC
logging facility
Configures the facility to be used in log
messages.
GC
logging file
Limits syslog messages sent to the logging file
based on severity.
GC
logging on
Controls error messages logging. GC
logging protocol
Logs messages in RFC5424 format. GC
logging snmp
Enables SNMP Set command logging. GC
logging web-session
Enables web session logging. GC
port
Specifies the port number of syslog messages. L
show logging
Displays the state of logging and the syslog
messages stored in the internal buffer.
PE
show logging file
Displays the state of logging and the syslog
messages stored in the logging file.
PE
show syslog-servers
Displays the syslog servers settings. PE
terminal monitor
Enables the display of logging messages on the
terminal.
PE
a. For the meaning of each Mode abbreviation, see
Mode Types
on page 87.
Command Description Modea
asset-tag
Specifies the switch asset-tag. GC
banner exec
Sets the message that is displayed after a
successful login.
GC
banner login
Sets the message that is displayed just before
the login prompt.
GC
banner motd
Specifies message-of-the-day banner. GC
banner motd
acknowledge
Acknowledges message-of-the-day banner. GC
Command Description Modea
2CSNXXX_SWUM200.book Page 172 Tuesday, December 10, 2013 1:22 PM
Command Groups 173
clear checkpoint
statistics
Clears the statistics for the checkpointing
process.
GC
clear counters stack-
ports
Clears the statistics for all stack-ports. PE
connect
Connects to the serial console of a different
stack member.
PE
cut-through mode
Enables the cut-through mode on the switch. GC
exec-banner
Enables exec banner on the console, telnet or
SSH connection.
LC
exit
Disconnects the serial connection to the remote
unit.
UE
hostname
Specifies or modifies the switch host name. GC
initiate failover
Forces failover of management unit. GC
load-interval
Loads the interface utilization measurement
interval.
IC
locate
Locates a switch by LED blinking. PE
login-banner
Enables login banner on the console, telnet, or
SSH connection.
LC
logout
Disconnects the serial connection to a remote
unit on a stack member.
UE
member
Configures the switch. SG
motd-banner
Enables motd on the console, telnet, or SSH
connection.
LC
nsf
Specifies non-stop forwarding. GC
ping
Sends ICMP echo request packets to another
node on the network.
UE
quit
Disconnects the serial connection to the remote
unit on a stack member.
UE
reload
Reloads the operating system. PE
set description
Associates a text description with a switch in
the stack.
SG
Command Description Modea
2CSNXXX_SWUM200.book Page 173 Tuesday, December 10, 2013 1:22 PM
Command Groups 174
slot
Configures a slot in the system. GC
show banner
Displays banner information. PE
show checkpoint
statistics
Displays the statistics for the checkpointing
process.
PE
show cut-through mode
Show the cut-through mode on the switch. PE
show idprom interface
interface-id
Displays the optics EEPRM contents in a user-
readable format.
UE or PE
show interfaces
advanced firmware
Displays the firmware revision of the PHY for a
port.
PE
show interfaces
interface-id
Displays the static and dynamic parameters for
the optics.
UE or PE
show interfaces
utilization
Displays the interface utilization. PE
show memory cpu
Checks the total and available RAM space on
the switch.
PE
show nsf
Shows non-stop forwarding status. PE
show power-usage-
history
Shows the history of unit power consumption
for the unit specified in the command and total
stack power consumption.
PE
show process cpu
Checks the CPU utilization for each process
currently running on the switch.
PE
show sessions
Displays a list of the open telnet sessions to
remote hosts.
PE
show slot
Displays information about all the slots in the
system or for a specific slot.
UE
show supported cardtype
Displays information about all card types
supported in the system.
UE
show supported
switchtype
Displays information about all supported switch
types.
UE
show switch
Displays information about the switch status. UE
show system
Displays system information. UE
show system fan
Explicitly displays the fan status. UE or PE
Command Description Modea
2CSNXXX_SWUM200.book Page 174 Tuesday, December 10, 2013 1:22 PM
Command Groups 175
Telnet Server
show system id
Displays the service ID information. UE
show system power
Displays information about the system level
power consumption.
UE or PE
show system
temperature
Displays information about the system
temperature and fan status.
UE or PE
show tech-support
Displays system and configuration information
(for debugging/calls to technical support).
PE
show users
Displays information about the active users,
including which profiles have been assigned to
local user accounts and which profiles are active
for logged-in users.
PE
show version
Displays the system version information. UE
stack
Sets the mode to Stack Global Configuration
mode.
GC
stack-port
Sets the mode to Stack Global Configuration
mode to configure Stack ports as either
Stacking ports or as Ethernet ports.
GC
stack-port interface
shutdown
Enables or disable the stack port
administratively.
SC
standby
Configures the standby in the stack. SG
switch renumber
Changes the identifier for a switch in the stack. GC
telnet
Logs into a host that supports Telnet. PE
traceroute
Discovers the IP routes that packets actually
take when travelling to their destinations.
PE
a. For the meaning of each Mode abbreviation, see
Mode Types
on page 87.
Command Description Modea
ip telnet server disable
Enables/disables the Telnet service on the
switch.
GC
ip telnet port
Configures the Telnet TCP port number on the
switch.
GC
Command Description Modea
2CSNXXX_SWUM200.book Page 175 Tuesday, December 10, 2013 1:22 PM
Command Groups 176
Terminal Length
Time Ranges
USB Flash Drive
show ip telnet
Displays the status of the Telnet server and the
Telnet TCP port number.
PE
a. For the meaning of each Mode abbreviation, see
Mode Types
on page 87.
Command Description Modea
a. For the meaning of each Mode abbreviation, see
Mode Types
on page 87.
terminal length
Sets the terminal length. PE
Command Description Modea
a. For the meaning of each Mode abbreviation, see
Mode Types
on page 87.
time-range
Creates a time range identified by name,
consisting of one absolute time entry and/or one
or more periodic time entries.
GC
absolute
Adds an absolute time entry to a time range. TRC
periodic
Adds a periodic time entry to a time range. TRC
show time-range
Displays a time range and all the
absolute/periodic time entries that are defined
for the time range.
PE
Command Description Modea
a. For the meaning of each Mode abbreviation, see
Mode Types
.
unmount usb
Makes the USB flash device inactive. PE
show usb
Displays the USB flash device details. PE
dir usb
Displays the USB device contents and memory
statistics.
PE
Command Description Modea
2CSNXXX_SWUM200.book Page 176 Tuesday, December 10, 2013 1:22 PM
Command Groups 177
User Interface
Web Server
Command Description Modea
a. For the meaning of each Mode abbreviation, see
Mode Types
on page 87.
enable
Enters the privileged EXEC mode. UE
end
Gets the CLI user control back to the privileged
execution mode or user execution mode.
Any
exit
Exits any configuration mode to the previously
highest mode in the CLI mode hierarchy.
(All)
exit (EXEC) Closes an active terminal session by logging off
the switch.
UE
quit
Closes an active terminal session by logging off
the switch.
UE
Command Description Modea
common-name
Specifies the common-name for the device. CC
country
Specifies the country. CC
crypto certificate generate
Generates a HTTPS certificate. GC
crypto certificate import
Imports a certificate signed by the Certification
Authority for HTTPS.
GC
crypto certificate request
Generates and displays a certificate request for
HTTPS.
PE
duration
Specifies the duration in days. CC
ip http port
Specifies the TCP port for use by a web browser
to configure the switch.
GC
ip http server
Enables the switch to be configured from a
browser.
GC
ip http secure-certificate
Configures the active certificate for HTTPS. GC
ip http secure-port
Configures a TCP port for use by a secure web
browser to configure the switch.
GC
ip http secure-server
Enables the switch to be configured, monitored,
or modified securely from a browser.
GC
2CSNXXX_SWUM200.book Page 177 Tuesday, December 10, 2013 1:22 PM

Command Groups 178
key-generate
Specifies the key-generate. CC
location
Specifies the location or city name. CC
organization-unit
Specifies the organization-unit or department
name.
CC
show crypto certificate
mycertificate
Displays the SSL certificates of your switch. PE
show ip http server status
Displays the HTTP server status information. PE
show ip http server secure
status
Displays the HTTP secure server status
information.
UE or
PE
state
Specifies the state or province name. CC
a. For the meaning of each Mode abbreviation, see
Mode Types
on page 87.
Command Description Modea
2CSNXXX_SWUM200.book Page 178 Tuesday, December 10, 2013 1:22 PM

Using the CLI 179
2
Using the CLI
Dell Networking N2000/N3000/N4000 Series Switches
Introduction
This chapter describes the basics of entering and editing the Dell Networking
N2000/N3000/N4000 Series Command Line Interface (CLI) commands and
defines the command hierarchy. It also explains how to activate the CLI and
implement its major functions.
This chapter covers the following topics:
•Entering and Editing CLI Commands
•CLI Command Modes
•Starting the CLI
•Using CLI Functions and Tools
Entering and Editing CLI Commands
A CLI command is a series of keywords and arguments. The total number of
characters that may be entered in a single command is limited to 1536
characters. Keywords identify a command and arguments specify
configuration parameters. For example, in the command show interfaces
status gigabitethernet
1/0/5,
show, interfaces and status are keywords;
gigabitethernet is an argument that specifies the interface type, and
1/0/5
specifies the unit/slot/port.
When working with the CLI, the command options are not displayed. The
command is not selected by a menu but is entered manually. To see what
commands are available in each mode or within an Interface Configuration,
the CLI provides a method of displaying the available commands, the
command syntax requirements and in some instances parameters required to
complete the command. The standard command to request context-sensitive
help is the <?> key.
2CSNXXX_SWUM200.book Page 179 Tuesday, December 10, 2013 1:22 PM

Using the CLI 180
Two instances where the help information can be displayed are:
•
Keyword lookup
— The <?> key is entered in place of a command. A list
of all valid commands and corresponding help messages is displayed.
•
Partial keyword lookup
— A command is incomplete and the <?> key is
entered in place of a parameter. The matched parameters for this
command are displayed.
The following features and conventions are applicable to CLI command entry
and editing:
•History Buffer
•Negating Commands
•Show Command
•Command Completion
•Short Form Commands
•Keyboard Shortcuts
•Operating on Multiple Objects (Range)
•Command Scripting
•CLI Command Notation Conventions
•Interface Naming Conventions
History Buffer
Every time a command is entered in the CLI, it is recorded in an internally
managed Command History buffer. Commands are stored in the buffer,
which operates on a
First In First Out (FIFO)
basis. These commands can be
recalled, reviewed, modified, and reissued. This buffer is not preserved after
switch resets.
2CSNXXX_SWUM200.book Page 180 Tuesday, December 10, 2013 1:22 PM

Using the CLI 181
Table 2-1. History Buffer
By default, the history buffer system is enabled, but it can be disabled at any
time. The standard number of 10 stored commands can be increased to 216.
By configuring 0, the effect is the same as disabling the history buffer system.
For information about the command syntax for configuring the command
history buffer, see the
history size
command on page 1491 in the Line
command mode chapter of this guide.
Negating Commands
For many commands, the prefix keyword no is entered to cancel the effect of
a command or reset the configuration to the default value. Nearly all
configuration commands have this capability. This guide describes the
negation effect for all commands to which it applies.
Show Command
The show command executes in the User Executive (EXEC), Privileged
Executive (EXEC), Configuration mode, interface Configuration mode and
all configuration submodes such as interface Configuration mode with
command completion. Output from show commands is paginated. Use the
terminal length command to set the number of lines displayed in a page.
When the paging prompt appears, press the space bar to display the next page
of output or the enter key to display the next line of output.
Example:
console>en
console#configure
console(config)#interface gi1/0/1
Keyword Source or Destination
Up-arrow key
<Ctrl>+<P>
Recalls commands in the history buffer, beginning with the
most recent command. Repeats the key sequence to recall
successively older commands.
Down-arrow key
<Ctrl>+<N>
Returns to more recent commands in the history buffer after
recalling commands with the up-arrow key. Repeating the key
sequence recalls more recent commands in succession.
2CSNXXX_SWUM200.book Page 181 Tuesday, December 10, 2013 1:22 PM

Using the CLI 182
console(config-if-Gi1/0/1)#show interface status
Port Name Duplex Speed Neg Link Flow Control
State Status
--------- ------------------------- ------ ------- ---- ------ ------------
Gi1/0/1 N/A Unknown Auto Down Inactive
Gi1/0/2 N/A Unknown Auto Down Inactive
Gi1/0/3 N/A Unknown Auto Down Inactive
Gi1/0/4 N/A Unknown Auto Down Inactive
Gi1/0/5 N/A Unknown Auto Down Inactive
Gi1/0/6 N/A Unknown Auto Down Inactive
Command Completion
CLI can complete partially entered commands when the user presses the
<tab> or <space> key. If a command entered is not complete, is not valid,
or if some parameters of the command are not valid or missing, an error
message is displayed to assist in entering the correct command. By pressing
the <tab> key, an incomplete command is changed into a complete
command. If the characters already entered are not enough for the system to
identify a single matching command, the <?>key displays the available
commands matching the characters already entered.
Short Form Commands
The CLI supports the short forms of all commands. As long as it is possible to
recognize the entered command unambiguously, the CLI accepts the short
form of the command as if the user typed the full command.
Keyboard Shortcuts
The CLI has a range of keyboard shortcuts to assist in editing the CLI
commands. The help command, when used in the User EXEC and Privileged
EXEC modes, displays the keyboard short cuts.
Table 2-2 contains the CLI shortcuts displayed by the help command.
2CSNXXX_SWUM200.book Page 182 Tuesday, December 10, 2013 1:22 PM
Using the CLI 183
Table 2-2. CLI Shortcuts
Parameters
Command line parameters are entered by the user to choose an individual
value or range of values for the specific command. Command line parameters
are not syntax or range checked until the carriage return is entered.
Keyboard Key Description
<Delete, Backspace> Delete previous character
<Ctrl>+<A> Go to beginning of line
<Ctrl>+<E> Go to end of line
<Ctrl>+<F> Go forward one character
<Ctrl>+<B> Go backward one character
<Ctrl>+<D> Delete current character
<Ctrl>+<U,X> Delete to beginning of line
<Ctrl>+<K> Delete to the end of the line.
<Ctrl>+<W> Delete previous word
<Ctrl>+<T> Transpose previous character
<Ctrl>+<P> Go to previous line history buffer
<Ctrl>+<R> Rewrites or pastes the line
<Ctrl>+<N> Go to next line in history buffer
<Ctrl>+<Y> Print last deleted character
<Ctrl>+<Q> Pauses screen output.
<Ctrl>+<S> Resumes screen output.
<Ctrl>+<Z> Return to root command prompt
<Tab, SPACE> Command-line completion
end Return to the root command prompt
exit Go to next lower command prompt
<?> List choices
2CSNXXX_SWUM200.book Page 183 Tuesday, December 10, 2013 1:22 PM

Using the CLI 184
Operating on Multiple Objects (Range)
The CLI allows the user to operate on the set of objects at the same time.
The guidelines are as follows for range operation:
• Operations on objects with four or more instances support the range
operation, unless noted otherwise in the specific command
documentation.
•The
range
key word is used to identify the range of objects on which to
operate.
• The range may be specified in the following manner:
(#-#) — a range from a particular instance to another instance
(inclusive). For example, 1/0/1-10 indicates that the operation applies to
the gigabit Ethernet ports 1 to 10 on unit 1.
(#, #, #) — a list of non-consecutive instances. For example, (1/0/1,
1/0/1,1/0/3, 1/0/5) indicates that the operation applies to the gigabit
Ethernet ports 1, 3, and 5 on unit 1.
(#, #-#, #) — ranges and non-consecutive instances listed together. For
example, (1/0/1, 1/0/3-5, 1/0/7) indicates that the operation applies to the
gigabit Ethernet ports 1, 3, 4, 5, and 7 on unit 1.
NOTE: Each port must be a fully qualified port identifier in the format
unit
/
slot
/
port
. See Interface Naming Conventions on page 186.
• To specify a range of LAGs, use the following command:
interface range port-channel
1-48
• No spaces are allowed anywhere in a range parameter, e.g. gi1/0/1 -2 is not
accepted, nor is gi1/0/2, gi1/0/4. Use gi1/0/1-2 and gi/1/0/2,gi1/0/4
respectively.
• When operating on a range of objects, the CLI implementation hides the
parameters that may not be configured in a range (for example, parameters
that must be uniquely configured for each instance).
• The CLI uses best effort when operating on a list of objects. If the user
requests an operation on a list of objects, the CLI attempts to execute the
operation on as many objects in the list as possible even if failure occurs for
some of the items in the list. The CLI provides the user with a detailed list
of all failures, listing the objects and the reasons for the failures.
2CSNXXX_SWUM200.book Page 184 Tuesday, December 10, 2013 1:22 PM

Using the CLI 185
• Some parameters must be configured individually for each port or
interface.
Command Scripting
The CLI can be used as a programmable management interface. To facilitate
this function, any characters entered after the <!> character are treated as a
comment and ignored by the CLI. Also, the CLI allows the user to disable
session timeouts.
CLI Command Notation Conventions
When entering commands there are certain command-entry notations which
apply to all commands. Table 2-3 describes these conventions as they are used
in syntax definitions.
2CSNXXX_SWUM200.book Page 185 Tuesday, December 10, 2013 1:22 PM

Using the CLI 186
Table 2-3. CLI Command Notation Conventions
Interface Naming Conventions
The conventions for naming interfaces in CLI commands are as follows:
Ethernet Interfaces
The gigabit Ethernet and ten-gigabit Ethernet ports are identified in the CLI
by the variable
unit/slot/port
, where:
•
<Interface Type> Unit#/Slot#/Port# — Identifies a specific interface by
the interface type tag followed by the Unit# followed by a / symbol, then
the Slot# followed by a / symbol, and then the Port#.
For example,
gi
2/0/10
identifies the gigabit port 10 in slot 0 within the second unit on
a non-blade switch. Table 2-4 below lists the supported interface type
tags.
•
Unit
# — The unit number is greater than 1 only in a stacking solution
where a number of switches are stacked to form a virtual switch. In this
case, the Unit# indicates the logical position of the switch in a stack. The
range is 1–12. The unit value is 1 for standalone switches.
•
Slot
# — The slot number is an integer number assigned to a particular
slot. Front panel ports have a slot number of 0. Rear panel ports are
numbered from 1 and can be identified by the lexan on the rear panel. Use
the
show slot
command to retrieve information for a particular slot.
Convention Description
[ ]In a command line, square brackets indicate an optional entry.
{ }In a command line inclusive brackets indicate a selection of
compulsory parameters separated by the | character. One option
must be selected. For example: flowcontrol {auto | on | off}
means that for the flowcontrol command either auto, on or off
must be selected.
Italic
Indicates a variable.
<Enter> Any individual key on the keyboard.
<Ctrl>+<F4> Any combination of keys pressed simultaneously on the keyboard.
Screen Display Indicates system messages and prompts appearing on the
console.
all Indicates a literal parameter, entered into the command as it is.
2CSNXXX_SWUM200.book Page 186 Tuesday, December 10, 2013 1:22 PM
Using the CLI 187
•
Port
# — The port number is an integer number assigned to the physical
port on the switch and corresponds to the lexan printed next to the port on
the front or back panel. Ports are numbered from 1 to the maximum
number of ports available on the switch, typically 24 or 48.
Within this document, the tag interface–id refers to an interface identifier
that follows the naming convention above.
Table 2-4. Interface Identifiers
When listed in command line output, gigabit Ethernet interfaces are
preceded by the characters
Gi
, ten-gigabit Ethernet interfaces are preceded by
Te
, and forty-gigabit Ethernet interfaces are preceded by
Fo,
as shown in the
examples below.
Stacking Interfaces
Stacking interfaces are represented in the CLI with the same unit/slot/port
form as Ethernet interfaces. The fixed stacking interfaces on the
N2000/N3000 switches always use the TwentyGigabitStacking or Tw notation
and on the N4000 switches, are referred to using Ethernet notation.
Loopback Interfaces
Loopback interfaces are represented in the CLI by the variable
loopback-id
,
which can assume values from 0–7.
Interface Type Long Form Short Form Identifier
10-Gigabit
Ethernet
Tengigabitethernet Te unit/slot/port
21-Gigabit
Stacking
Twentygigabitstacking Tw unit/slot/port
40-Gigabit
Ethernet
Fortygigabitethernet Fo unit/slot/port
Gigabit Ethernet Gigabitethernet Gi unit/slot/port
Loopback Loopback Lo loopback-id (0-7)
Port Channel Port-channel Po port-channel-number
Tunnel Tunnel Tu tunnel-id (0-7)
Vlan VLAN Vl vlan-id (1-4093)
2CSNXXX_SWUM200.book Page 187 Tuesday, December 10, 2013 1:22 PM

Using the CLI 188
Port Channel Interfaces
Port-channel (or LAG) interfaces are represented in the CLI by the variable
port-channel-number
., which can assume values from 1-128 on most Dell
Networking switches.
When listed in command line output, port channel interfaces are preceded by
the characters
Po
.
Tunnel Interfaces
Tunnel interfaces are represented in the CLI by the variable
tunnel-id
, which
can assume values from 0–7.
VLAN Interfaces
VLAN interfaces are represented in the CLI by the variable
vlan-id
, which can
can assume values from 1-4093.
Examples
Example 1 shows the various forms of interface notation that can be entered
in the CLI. Examples 2 and 3 show various forms of CLI output using
shorthand interface notation.
Example #1
gigabitethernet 1/0/1
gigabitethernet1/0/1 (there is no space)
gi 1/0/1
gi1/0/1 (there is no space)
port-channel 1
vl 5
Example #2
console(config-if-Gi1/0/23)#show vlan
VLAN Name Ports Type
----- --------------- ------------- --------------
1 default Po1-128, Default
Gi1/0/1-24,
Te1/0/1-2
RSPAN Vlan
---------------------------------------------------------------------
None
2CSNXXX_SWUM200.book Page 188 Tuesday, December 10, 2013 1:22 PM

Using the CLI 189
console(config-if-Gi1/0/23)#show slot 2/0
Slot.............................. 2/0
Slot Status....................... Empty
Admin State....................... Enable
Power State....................... Enable
Configured Card:
Model Identifier............... Dell Networking N3024F
Card Description............... Dell 24 Port 10G Fiber
Pluggable......................... No
Example #3
console(config-if-Gi1/0/23)#show slot
Admin Power Configured Card
Slot Status State State Model ID Pluggable
----- ------ ------- ------- -------------------------------- ---------
1/0 Full Enable Enable Dell Networking N3024F No
1/1 Empty Disable Disable Yes
2/0 Empty Enable Enable Dell Networking N3024F No
2/1 Empty Enable Enable Yes
3/0 Empty Enable Enable Dell Networking N3048 No
3/1 Empty Enable Enable Yes
console(config-if-Gi1/0/23)#show slot 1/0
Slot.............................. 1/0
Slot Status....................... Full
Admin State....................... Enable
Power State....................... Enable
Inserted Card:
Model Identifier............... Dell Networking N3024F
Card Description............... Dell 24 Port 10G Fiber
Configured Card:
Model Identifier............... Dell Networking N3024F
Card Description............... Dell 24 Port 10G Fiber
Pluggable......................... No
2CSNXXX_SWUM200.book Page 189 Tuesday, December 10, 2013 1:22 PM

Using the CLI 190
CLI Command Modes
Since the set of CLI commands is very large, the CLI is structured as a
command-tree hierarchy, where related command sets are assigned to
command modes for easier access. At each level, only the commands related
to that level are available to the user and only those commands are shown in
the context sensitive help for that level.
In this guide, commands are organized into three categories:
• Layer 2 (IEEE 802.1 Bridging and Management) commands
• Layer 3 (Routing) commands
• Utility Commands
Layer 2 (IEEE 802.1 Bridging and Management) describes the commands
used for filtering and forwarding of packets within a VLAN based upon
learned MAC addresses.
Layer 3 (Routing) describes the commands used to forward packets within
and across VLANs based upon the IP addresses as well as management of the
routing protocols necessary to enable the distribution of routes.
Utility describes commands used to manage the switch.
Commands that cause specific actions to be taken immediately by the system
and do not directly affect the system configurations are defined at the top of
the command tree. For example, commands for rebooting the system or for
downloading or backing up the system configuration files are placed at the
top of the hierarchy tree.
Commands that result in configuration changes to the switch are grouped in
a Configuration sub tree.
There are levels beneath the Configuration mode for further grouping of
commands. The system prompt reflects these sub-Configuration modes.
All the parameters are provided with reasonable defaults where possible.
When starting a session, the initial mode is the User EXEC mode. Only a
limited subset of commands is available in this mode. This level is reserved
for tasks that do not change the configuration. To enter the next level, the
Privileged EXEC mode, a password is required.
2CSNXXX_SWUM200.book Page 190 Tuesday, December 10, 2013 1:22 PM

Using the CLI 191
The Privileged EXEC mode provides access to commands that can not be
executed in the User EXEC mode and permits access to the switch
Configuration mode.
The Global Configuration mode manages switch configuration on a global
level. For specific interface configurations, command modes exist at a
sublevel.
Entering a <?> at the system prompt displays a list of commands available
for that particular command mode. A specific command is used to navigate
from one command mode to another. The standard order to access the modes
is as follows: User EXEC mode, Privileged EXEC mode, Global
Configuration mode, and Interface Configuration and other specific
configuration modes.
User EXEC Mode
After logging into the switch, the user is automatically in the User EXEC
command mode unless the user is defined as a privileged user. In general, the
User EXEC commands allow the user to perform basic tests, and list system
information.
The user-level prompt consists of the switch host name followed by the angle
bracket (>).
console>
The default host name is Console unless it has been changed using the
hostname command in the Global Configuration mode.
Privileged EXEC Mode
Because many of the privileged commands set operating parameters,
privileged access is password-protected to prevent unauthorized use. The
password is not displayed on the screen and is case sensitive.
Privileged users enter into the Privileged EXEC mode from User EXEC
mode, where the following prompt is displayed.
console#
Global Configuration Mode
Global Configuration commands apply to features that affect the system as a
whole, rather than just a specific interface. The Privileged EXEC mode
command configure is used to enter the Global Configuration mode.
2CSNXXX_SWUM200.book Page 191 Tuesday, December 10, 2013 1:22 PM

Using the CLI 192
console(config)#
The following are the Global Configuration modes:
•
SNMP v3 Host Configuration
— Configures the parameters for the
SNMP v3 server host.
•
SNMP Community Configuration
— Configures the parameters for the
SNMP server community.
Preconfiguration
Nearly all switch features support a preconfiguration capability, even when
the feature is not enabled or the required hardware is not present.
Preconfigured capabilities become active only when enabled (typically via an
admin mode control) or when the required hardware is present (or both). For
example, a port can be preconfigured with both trunk and access mode
information. The trunk mode information is applied only when the port is
placed into trunk mode and the access mode information is only applied
when the port is placed into access mode. Likewise, OSPF routing can be
configured in the switch without being enabled on any port.
Interface and Other Specific Configuration Modes
Interface configuration modes are used to modify specific interface
operations. The following are the Interface Configuration and other specific
configuration modes:
•
MST
— The Global Configuration mode command spanning-tree mst
configuration is used to enter into the Multiple Spanning Tree
configuration mode.
•
Line Interface
— Contains commands to configure the management
connections. These include commands such as line speed and time-out
settings. The Global Configuration mode command
line
is used to enter
the Line Interface mode.
•
Router OSPF Configuration
— Global configuration mode command
router ospf
is used to enter into the Router OSPF Configuration mode.
•
Router RIP Configuration
— Global configuration mode command
router rip
is used to enter into the Router RIP Configuration mode.
2CSNXXX_SWUM200.book Page 192 Tuesday, December 10, 2013 1:22 PM

Using the CLI 193
•
Router OSPFv3 Configuration
— Global configuration mode command
ipv6 router ospf
is used to enter into the Router OSPFv3 Configuration
mode.
•
IPv6 DHCP Pool Mode
— Global configuration mode command
ipv6
dhcp pool
is used to enter into the IPv6 DHCP Pool mode.
•
Management Access List
— Contains commands to define management
access administration lists. The Global Configuration mode command
management access-list
is used to enter the Management Access List
configuration mode.
•
Policy-map
— Use the
policy-map
command to access the QoS policy
map configuration mode to configure the QoS policy map.
•
Policy Class
— Use the
class
command to access the QoS Policy-class
mode to attach or remove a diffserv class from a policy and to configure
the QoS policy class.
•
Class-Map —
This mode consists of class creation/deletion and matching
commands. The class matching commands specify layer 2, layer 3 and
general match criteria. Use the
class-map class-map-name
commands to
access the QoS Class Map Configuration mode to configure QoS class
maps.
•
Stack
— Use the stack command to access the Stack Configuration Mode.
•
Ethernet
— Contains commands to manage Ethernet port configuration.
The Global Configuration mode command
interface
enters the Interface
Configuration mode to configure an Ethernet interface.
•
Port Channel
— Contains commands to configure port-channels, i.e.,
assigning ports to a port-channel. Most of these commands are the same as
the commands in the Ethernet interface mode and are used to manage the
member ports as a single entity. The Global Configuration mode
command
interface port-channel
port-channel-number
is used to enter
the Port Channel mode.
•
Tunnel
— Contains commands to manage tunnel interfaces. The Global
Configuration mode command
interface tunnel
enters the Tunnel
Configuration mode to configure an tunnel type interface.
•
Loopback
— Contains commands to manage loopback interfaces. The
Global Configuration mode command
interface loopback
enters the
Loopback Configuration mode to configure an loopback type interface.
2CSNXXX_SWUM200.book Page 193 Tuesday, December 10, 2013 1:22 PM

Using the CLI 194
•
SSH Public Key-chain
— Contains commands to manually specify other
switch SSH public keys. The Global Configuration mode command
crypto
key pub-key chain ssh
is used to enter the SSH Public Key-chain
configuration mode.
•
SSH Public Key-string
— Contains commands to manually specify the
SSH Public-key of a remote SSH Client. The SSH Public-Key Chain
Configuration mode command
user-key
command is used to enter the
SSH Public-Key Configuration mode
.
•
MAC Access-List
— Configures conditions required to allow traffic based
on MAC addresses. The Global Configuration mode command
mac-
access-list
is used to enter the MAC Access-List configuration mode.
•
TACACS
— Configures the parameters for the TACACS server.
•
Radius
— Configures the parameters for the RADIUS server.
•
SNMP Host Configuration
— Configures the parameters for the SNMP
server host.
•
Crypto Certificate Request
— Configures the parameters for crypto
certificate request.
•
Crypto Certificate Generation
— Configures the parameters for crypto
certificate generate.
•
Logging
— Configures the parameters for syslog log server.
Identifying the Switch and Command Mode from the System Prompt
The system prompt provides the user with the name of the switch
(hostname) and identifies the command mode. The following is a formal
description of the system command prompt:
[
device name
][([
command mode-
[
object
]])][# | >]
[
device name
] — is the name of the managed switch, which is typically the
user-configured hostname established by the hostname command.
[
command mode
] — is the current configuration mode and is omitted for the
top configuration levels.
[
object
] — indicates specific object or range of objects within the
configuration mode.
2CSNXXX_SWUM200.book Page 194 Tuesday, December 10, 2013 1:22 PM
Using the CLI 195
For example, if the current configuration mode is config-if and the object
being operated on is gigabit ethernet 1 on unit 1, the prompt displays the
object type and unit (for example, 1/0/1).
[# | >] — The # sign is used to indicate that the system is in the Privileged
EXEC mode. The > symbol indicates that the system is in the User EXEC
mode, which is a read-only mode in which the system does not allow
configuration.
Navigating CLI Command Modes
Table 2-5 describes how to navigate through the CLI Command Mode
hierarchy.
Table 2-5. Navigating CLI Command Modes
Command Mode Access Method Command Prompt Exit or Access
Previous Mode
User EXEC The user is
automatically in
User EXEC mode
unless the user is
defined as a
privileged user.
console> logout
Privileged EXEC Use the enable
command to enter
into this mode. This
mode is password
protected.
console# Use the exit
command, or
press
<Ctrl>+<Z>
to return to the
User EXEC
mode.
Global
Configuration
From Privileged
EXEC mode, use
the configure
command.
console(config)# Use the exit
command, or
press
<Ctrl>+<Z>
to return to the
Privileged EXEC
mode.
2CSNXXX_SWUM200.book Page 195 Tuesday, December 10, 2013 1:22 PM
Using the CLI 196
Line Interface From Global
Configuration
mode, use the line
command.
console(config-line)# To exit to Global
Configuration
mode, use the
exit command,
or press
<Ctrl>+<Z>
to Privileged
EXEC mode.
Management
Access-List
From Global
Configuration
mode, use the
management
access-list
command.
console(config-macal)# To exit to Global
Configuration
mode, use the
exit command,
or press
<Ctrl>+<Z>
to Privileged
EXEC mode.
Policy-Class-Map From Global
Configuration
mode, use the
policy-map class
command.
console(config-policy-map)# To exit to Global
Configuration
mode, use the
exit command,
or press
<Ctrl>+<Z>
to Privileged
EXEC mode.
Class-Map From Global
Configuration
mode, use the class-
map command.
console(config-classmap)# To exit to Global
Configuration
mode, use the
exit command,
or press
<Ctrl>+<Z>
to Privileged
EXEC mode.
Table 2-5. Navigating CLI Command Modes
(continued)
Command Mode Access Method Command Prompt Exit or Access
Previous Mode
2CSNXXX_SWUM200.book Page 196 Tuesday, December 10, 2013 1:22 PM
Using the CLI 197
MAC Access List From Global
Configuration
mode, use the mac
access-list
command.
console(config-mac-access-
list)#
To exit to Global
Configuration
mode, use the
exit command,
or press
<Ctrl>+<Z>
to Privileged
EXEC mode.
SSH Public Key-
Chain
From Global
Configuration
mode, use the
crypto key pubkey-
chain ssh
command.
console(config-pubkey-
chain)#
To exit to Global
Configuration
mode, use the
exit command,
or press
<Ctrl>+<Z>
to Privileged
EXEC mode.
SSH Public Key
String
From the SSH
Public Key- Chain
mode, use the user-
key <
user name
>
{rsa | dsa}
command.
console(config-pubkey-key)# To return to the
SSH Public key-
chain mode, use
the exit
command, or
press
<Ctrl>+<Z>
to Privileged
EXEC mode.
TACACS From Global
Configuration
mode, use the
tacacs-server host
command.
console(tacacs)# To exit to Global
Configuration
mode, use the
exit command,
or press
<Ctrl>+<Z>
to Privileged
EXEC mode.
Table 2-5. Navigating CLI Command Modes
(continued)
Command Mode Access Method Command Prompt Exit or Access
Previous Mode
2CSNXXX_SWUM200.book Page 197 Tuesday, December 10, 2013 1:22 PM
Using the CLI 198
Radius From Global
Configuration
mode, use the
radius-server host
command.
console(Config-auth-
radius)#
To exit to Global
Configuration
mode, use the
exit command,
or press
<Ctrl>+<Z>
to Privileged
EXEC mode.
SNMP Host
Configuration
From Global
Configuration
mode, use the
snmp-server
command.
console(config-snmp)# To exit to Global
Configuration
mode, use the
exit command,
or press
<Ctrl>+<Z>
to Privileged
EXEC mode.
SNMP v3 Host
Configuration
From Global
Configuration
mode, use the
snmp-server v3-host
command.
console(config-snmp)# To exit to Global
Configuration
mode, use the
exit command,
or press
<Ctrl>+<Z>
to Privileged
EXEC mode.
SNMP
Community
Configuration
From Global
Configuration
mode, use the
snmp-server
community
command.
console(config-snmp)# To exit to Global
Configuration
mode, use the
exit command,
or press
<Ctrl>+<Z>
to Privileged
EXEC mode
Table 2-5. Navigating CLI Command Modes
(continued)
Command Mode Access Method Command Prompt Exit or Access
Previous Mode
2CSNXXX_SWUM200.book Page 198 Tuesday, December 10, 2013 1:22 PM
Using the CLI 199
Crypto
Certificate
Generation
From Global
Configuration
mode, use the
crypto certificate
number
generate
command.
console(config-crypto-cert)# To exit to Global
Configuration
mode, use the
exit command,
or press
<Ctrl>+<Z>
to Privileged
EXEC mode.
Crypto
Certificate
Request
From Privileged
EXEC mode, use
the crypto
certificate
number
request command.
console(config-crypto-cert)# To exit to
Privileged EXEC
mode, use the
exit command,
or press
<Ctrl>+<Z>.
Stack From Global
Configuration
mode, use the stack
command.
console(config-stack)# To exit to Global
Configuration
mode, use the
exit command,
or press
<Ctrl>+<Z>
to Privileged
EXEC mode.
Logging From Global
Configuration
mode, use the
logging command.
console(config-logging)# To exit to Global
Configuration
mode, use the
exit command,
or press
<Ctrl>+<Z>
to Privileged
EXEC mode.
Table 2-5. Navigating CLI Command Modes
(continued)
Command Mode Access Method Command Prompt Exit or Access
Previous Mode
2CSNXXX_SWUM200.book Page 199 Tuesday, December 10, 2013 1:22 PM
Using the CLI 200
MST From Global
Configuration
mode, use the
spanning-tree mst
configuration
command.
console(config-mst)# To exit to Global
Configuration
mode, use the
exit command,
or press
<Ctrl>+<Z>
to Privileged
EXEC mode.
VLAN Config From Global
Configuration
mode, use the vlan
command.
console(config-vlan)# To exit to Global
Configuration
mode, use the
exit command,
or press
<Ctrl>+<Z>
to Privileged
EXEC mode.
Router OSPF
Conf
From Global
Configuration
mode, use the
router ospf
command.
console(config-router)# To exit to Global
Configuration
mode, use the
exit command,
or press
<Ctrl>+<Z>
to Privileged
EXEC mode
Router RIP
Config
From Global
Configuration
mode, use the
router rip
command.
console(config-router)# To exit to Global
Configuration
mode, use the
exit command,
or press
<Ctrl>+<Z>
to Privileged
EXEC mode
Table 2-5. Navigating CLI Command Modes
(continued)
Command Mode Access Method Command Prompt Exit or Access
Previous Mode
2CSNXXX_SWUM200.book Page 200 Tuesday, December 10, 2013 1:22 PM
Using the CLI 201
Router OSPFv3
Config
From Global
Configuration
mode, use the ipv6
router ospf
command.
console(config-rtr)# To exit to Global
Configuration
mode, use the
exit command,
or press
<Ctrl>+<Z>
to Privileged
EXEC mode
IPv6 DHCP Pool
Mode
From Global
Configuration
mode, use the ipv6
dhcp pool
command.
console(config-dhcp6s-
pool)#
To exit to Global
Configuration
mode, use the
exit command,
or press
<Ctrl>+<Z>
to Privileged
EXEC mode
Interface Configuration Modes
Gigabit Ethernet From Global
Configuration
mode, use the
interface
gigabitethernet
command. Or, use
the abbreviation
interface gi.
console (config-if-
Gi
unit/slot/port
#
To exit to Global
Configuration
mode, use the
exit command,
or press
<Ctrl>+<Z>
to Privileged
EXEC mode.
10 Gigabit
Ethernet
From Global
Configuration
mode, use the
interface
tengigabitethernet
command. Or, use
the abbreviation
interface te.
console (config-if-
Te
unit/slot/port
#
To exit to Global
Configuration
mode, use the
exit command,
or press
<Ctrl>+<Z>
to Privileged
EXEC mode.
Table 2-5. Navigating CLI Command Modes
(continued)
Command Mode Access Method Command Prompt Exit or Access
Previous Mode
2CSNXXX_SWUM200.book Page 201 Tuesday, December 10, 2013 1:22 PM
Using the CLI 202
40 Gigabit
Ethernet
From Global
Configuration
mode, use the
interface
fortygigabitetherne
t command. Or, use
the abbreviation
interface fo.
console (config-if-
Fo
unit/slot/port
#
To exit to Global
Configuration
mode, use the
exit command,
or press
<Ctrl>+<Z>
to Privileged
EXEC mode.
Port Channel From Global
Configuration
mode, use the
interface port-
channel command.
Or, use the
abbreviation
interface po.
console (config-if-po
port-
channel-number
)#
To exit to Global
Configuration
mode, use the
exit command,
or
<Ctrl>+<Z>
to Privileged
EXEC mode.
VLAN From Global
Configuration
mode, use the
interface vlan
command.
console(config-if-vlan
vlan-
id
)#
To exit to Global
Configuration
mode, use the
exit command,
or press
<Ctrl>+<Z>
to Privileged
EXEC mode.
Tunnel From Global
Configuration
mode, use the
interface tunnel
command. Or, use
the abbreviation
interface tu.
console(config-tunnel
tunnel-
id
)#
To exit to Global
Configuration
mode, use the
exit command,
or press
<Ctrl>+<Z>
to Privileged
EXEC mode.
Table 2-5. Navigating CLI Command Modes
(continued)
Command Mode Access Method Command Prompt Exit or Access
Previous Mode
2CSNXXX_SWUM200.book Page 202 Tuesday, December 10, 2013 1:22 PM
Using the CLI 203
Starting the CLI
To begin running the CLI, perform the following steps:
NOTE: This procedure is for use on the console line only.
NOTE: The Easy Setup Wizard may appear if the system has no user configuration
saved. Follow the procedure in the Getting Started Guide to configure the switch
using the Easy Setup Wizard.
1
Start the switch and wait until the startup procedure is complete and the
User EXEC mode is entered. The prompt
console>
is displayed.
2
Configure the switch and complete any required tasks.
3
When finished, exit the session with the
quit
or
exit
command.
The switch can be managed over a direct connection to the switch console
port or through a Telnet connection. If access is through a Telnet connection,
the switch must have a defined IP address, corresponding management access
granted, and a connection to the network.
Using CLI Functions and Tools
The CLI has been designed to manage the switch’s configuration file system
and to manage switch security. A number of resident tools exist to support
these and other functions.
Loopback From Global
configuration mode,
use the interface
loopback
command. Or, use
the abbreviation
interface lo.
console(config-
loopback
loopback-id
)#
To exit to Global
Configuration
mode, use the
exit command,
or press
<Ctrl>+<Z>
to Privileged
EXEC mode.
Table 2-5. Navigating CLI Command Modes
(continued)
Command Mode Access Method Command Prompt Exit or Access
Previous Mode
2CSNXXX_SWUM200.book Page 203 Tuesday, December 10, 2013 1:22 PM

Using the CLI 204
Configuration Management
All managed systems have software images and databases that must be
configured, backed up and restored. Two software images may be stored on
the system, but only one of them is active. The other one is a backup image.
The same is true for configuration files, which store the configuration
parameters for the switch. The system has three configuration files. One file is
a memory-only file and is the current configuration file for the switch. The
second file is the one that is loaded by the system when it reboots. There is
one backup configuration file. The system also provides methods to back up
these files to a remote system.
File System Commands
All files are stored in a flat file system. The commands shown in Table 2-6 are
used to perform operations on these files.
Copying Files
The copy command not only provides a method for copying files within the
file system, but also to and from remote servers. With the copy command and
URLs to identify files, the user can back up images to local or remote systems
or restore images from local or remote systems.
To use the copy command, the user specifies the source file and the
destination file. For example, copy
tftp://remotehost/pub/backupfile backup-
config
copies a file from the remote TFTP server to a local backup
configuration file. In this case, if the local configuration file does not exist,
then it is created by the command. If it does exist, it is overwritten. If there is
not enough space on the local file system to accommodate the file, an error is
flagged.
Table 2-6. File System Commands
Command Description
delete
file
Deletes file.
filedescr
file description
Adds a description to a file (up to 20
characters can be used).
copy
source destination
Copies a file from source file to destination
file.
2CSNXXX_SWUM200.book Page 204 Tuesday, December 10, 2013 1:22 PM

Using the CLI 205
Refer to the
copy
command description on page 1460 in the Layer 2
commands section of the guide for command details.
Referencing External/Internal File systems
Configuration or software images are copied to or retrieved from remote file
systems using the TFTP protocol.
• tftp://server-name/path/filename — identifies a file on a remote file system
accessible through the server-name. Trivial file transfer protocol is a
simplified FTP and uses a UDP port instead of TCP and does not have
password protection.
Special System Files
The following special filenames are used to refer to special virtual system files,
which are under control of the system and may not be removed or added.
These file names are reserved and may not be used as user-defined files.
When the user copies a local source file into one of these special files and the
source file has an attached file description, it also is copied as the file
description for the special file.
•
backup-config
— This file refers to the backup configuration file.
•
running-config
— This file refers to the configuration file currently active
in the system. It is possible to copy the running-config image to a backup-
config file or to the startup-config file.
•
startup-config
— This file refers to the special configuration image stored
in flash memory which is loaded when the system next reboots. The user
may copy a particular configuration file (remote or local) to this special file
name and reboot the system to force it to use a particular configuration.
•
image1 & image2
— These files refer to software images. One of these will
be loaded when the system next reboots. Either image1 or image2 can be
chosen for the next reboot using the command
boot system.
The CLI prevents the user from accidentally copying a configuration image
onto a software image and vice versa.
2CSNXXX_SWUM200.book Page 205 Tuesday, December 10, 2013 1:22 PM

Using the CLI 206
Management Interface Security
This section describes the minimum set of management interface security
measures implemented by the CLI. Management interface security consists
of user account management, user access control and remote network/host
access controls.
CLI through Telnet, SSH, Serial Interfaces
The CLI is accessible through a local serial interface/console port, the out-of-
band interface, or in-band interfaces. Since the console port requires a
physical connection for access, it is used if all else fails. The console port
interface is the only interface from which the user may access the Easy Setup
Wizard. It is the only interface that the user can access if the remote
authentication servers are down and the user has not configured the system to
revert to local managed accounts.
The following rules and specifications apply to these interfaces:
• The CLI is accessible from remote telnet through the IP address for the
switch. IP addresses are assigned separately for the out-of-band interface
and the in-band ports.
• The CLI is accessible from a secure shell interface.
• The CLI generates keys for SSH locally.
• The serial session defaults to 9600 baud rate, eight data bits, non-parity
and one stop bit.
User Accounts Management
The CLI provides authentication for users either through remote
authentication servers supporting TACACS+ or Radius or through a set of
locally managed user accounts. The setup wizard asks the user to create the
initial administrator account and password at the time the system is booted.
The following rules and specifications apply:
• The user may create five local user accounts.
• User accounts have an access level, a user name, and a user password.
• The user is able to delete the user accounts but the user will not be able to
delete the last level 15 account.
2CSNXXX_SWUM200.book Page 206 Tuesday, December 10, 2013 1:22 PM

Using the CLI 207
• The user password is saved internally in encrypted format and never
appears in clear text anywhere on the CLI.
• The CLI supports TACACS+ and Radius authentication servers.
• The CLI allows the user to configure primary and secondary
authentication servers. If the primary authentication server fails to respond
within a configurable period, the CLI automatically tries the secondary
authentication server.
• The user can specify whether the CLI should revert to using local user
accounts when the remote authentication servers do not respond or if the
CLI simply fails the login attempt because the authentication servers are
down. This requirement applies only when the user is logged in through a
telnet or an SSH session.
• The CLI always allows the user to log in to a local serial port even if the
remote authentication server(s) are down. In this case, CLI reverts to using
the locally configured accounts to allow the user to log in.
User Access Control
In addition to authenticating a user, the CLI also assigns the user access to
one of two security levels. Level 1 has read-only access. This level allow the
user to read information but not configure the switch. The access to this level
cannot be modified. Level 15 is the special access level assigned to the
superuser of the switch. This level has full access to all functions within the
switch and can not be modified.
If the user account is created and maintained locally, each user is given an
access level at the time of account creation. If the user is authenticated
through remote authentication servers, the authentication server is
configured to pass the user access level to the CLI when the user is
authenticated. When Radius is used, the
Vendor-Specific Option
field
returns the access level for the user. Two vendor specific options are
supported. These are CISCO-AV-Pairs(Shell:priv-lvl=x) and Dell Radius VSA
(user-group=x). TACACS+ provides the appropriate level of access.
The following rules and specifications apply:
• The user determines whether remote authentication servers or locally
defined user authentication accounts are used.
2CSNXXX_SWUM200.book Page 207 Tuesday, December 10, 2013 1:22 PM

Using the CLI 208
• If authentication servers are used, the user can identify at least two remote
servers (the user may choose to configure only one server) and what
protocol to use with the server, TACACS+ or Radius. One of the servers is
primary and the other is the secondary server (the user is not required to
specify a secondary server). If the primary server fails to respond in a
configurable time period, the CLI automatically attempts to authenticate
the user with the secondary server.
• The user is able to specify what happens when both primary and secondary
servers fail to respond. In this case, the user is able to indicate that the CLI
should either use the local user accounts or reject all requests.
• Even if the user configures the CLI to fail login when the remote
authentication servers are down, the CLI allows the user to log in to the
serial interface authenticated by locally managed account data.
Syslogs
The CLI supports sending logging messages to a remote syslog server. The
user configures the switch to generate logging messages to a remote log server.
If no remote log server exists, then the CLI maintains a rolling log of at most
the last 1000 system events.
The following rules and specifications apply:
• The CLI permits the user to configure a remote syslog server to which
system logging messages are sent.
• Log messages are implementation-dependent but may contain debug
messages, security or fault events.
• If a log server is not specified by the user, the CLI maintains at most the
last 1000 system events.
Security Logs
The system log records security events including the following:
•User login.
•User logout.
•Denied login attempts.
• User attempt to exceed security access level.
• Denied attempts by external management system to access the system.
2CSNXXX_SWUM200.book Page 208 Tuesday, December 10, 2013 1:22 PM

Using the CLI 209
The security log record contains the following information:
• The user name, if available, or the protocol being accessed if the event is
related to a remote management system.
• The IP address from which the user is connecting or the IP address of the
remote management system.
• A description of the security event.
• A timestamp of the event
If syslog is available, the CLI sends security records to the syslog server.
Management ACL
In addition to user access control, the system also supports filtering of
management protocols packets addressed to the switch.. The system allows
individual hosts or subnets to access the switch using specific management
protocols.
The user defines a management profile, which identifies management
protocols such as the following:
•Telnet.
• SSH and the keying information to use for SSH.
• HTTP.
• HTTPS and the security certificate to be used.
• SNMPv1/v2c and the read and read/write community strings to be used.
• SNMPv3 and the security information for used this protocol.
For each of these management profiles, the user defines the list of hosts or
subnets from which the management profiles may be used.
Other CLI Tools and Capabilities
The CLI has several other capabilities associated with its primary functions.
Terminal Paging
The terminal width and length for CLI displays is 79 characters and 25 lines,
respectively. The length setting is used to control the number of lines the CLI
will display before it pauses. For example, the CLI pauses at 24 lines and
prompts the user with the
-more-
prompt on the 25th line. The CLI waits for
2CSNXXX_SWUM200.book Page 209 Tuesday, December 10, 2013 1:22 PM

Using the CLI 210
the user to press either <q> or any other key. If the user presses any key
except <q>, the CLI shows the next page. A <q> key stops the display and
returns to the CLI prompt.
Boot Message
The boot message is a system message that is not user-configurable and is
displayed when the system is booting.
To start the normal booting process, select item 1 in the Boot Menu. The
following is a sample log for booting information.
Select startup option within 5 seconds, else Operational Code will start
automatically...
Operational Code Startup -- Main Menu
1 - Start Operational Code
2 - Display Boot Menu
Select (1, 2)#
active = /dev/mtd7
Extracting Operational Code from .stk file...done.
Loading Operational Code...done.
Decompressing Operational Code...done.
Scanning devshell symbols file...
47544 symbols, loading...
Done.
PCI unit 0: Dev 0xb842, Rev 0x02, Chip BCM56842_A0, Driver BCM56840_B0
SOC unit 0 attached to PCI device BCM56842_A0
Adding BCM transport pointers
Configuring CPUTRANS TX
Configuring CPUTRANS RX
<186> Aug 26 08:18:23 0.0.0.0-1 General[72162340]: bootos.c(166) 4 %%
Event(0xaaaaaaaa) started!
(Unit 1 - Waiting to select management unit)>
Applying Global configuration, please wait ...
Applying Interface configuration, please wait ...
2CSNXXX_SWUM200.book Page 210 Tuesday, December 10, 2013 1:22 PM

Using the CLI 211
Boot Utility Menu
If a user is connected through the serial interface during the boot sequence,
the operator is presented with the option to enter the Boot Utility Menu
during the boot sequence. Selecting item 2 displays the menu and may be
typed only during the initial boot up sequence.
Select startup option within 5 seconds, else Operational Code will start
automatically...
Operational Code Startup -- Main Menu
1 - Start Operational Code
2 - Display Boot Menu
Select (1, 2)# 2
Boot Menu Rev: 6.0
Operational Code -- Boot Main Menu
1 - Start Operational Code
2 - Select Baud Rate
3 - Retrieve Logs
4 - Load New Operational Code
5 - Display Operational Code Details
9 - Reboot
10 - Restore Configuration to Factory Defaults
11 - Activate Backup Image
12 - Start Password Recovery
Enter Choice# 4
Creating tmpfs filesystem on /mnt/download for download...done.
Current Active Image# /dev/mtd7
Which Image to Update Active (/dev/mtd7) OR Back-Up (/dev/mtd6)? Select
(A/B): B
You selected to update Back-Up Image /dev/mtd6...
Select Mode of Transfer (Press T/X/Y/Z for TFTP/XMODEM/YMODEM/ZMODEM) []:T
Please ensure TFTP server is running to begin Transfer...
Enter Server IP []:10.27.9.99
Enter Host IP []:10.27.22.99
Enter Host Subnet Mask [255.255.255.0]:255.255.252.0
Enter Gateway IP []:10.27.20.1
Enter Filename []:jmclendo/N4000v8.21.17.20.stk
Do you want to continue? Press(Y/N): y
2CSNXXX_SWUM200.book Page 211 Tuesday, December 10, 2013 1:22 PM

Using the CLI 212
Bringing up eth0 interface...done.
Adding default gateway 10.27.20.1 to the Routing Table...done.
Bringing down eth0 interface...done.
Erasing /dev/mtd6!!!
Erasing 128 Kibyte @ 17e0000 -- 99 % complete.
Updating code file...
Code Update Instructions Found!
Critical components modified on Back-Up Partition -- Please activate Back-Up
Image to load the same on Reboot
Do you wish to activate Back-Up Image? (Y/N):
Cleaning tmpfs filesystem on /mnt/download...done.
Enter Choice# 5
active = /dev/mtd7
Extracting Operational Code from .stk file...done.
Loading Operational Code...done.
Decompressing Operational Code...done.
Product Details:-
Operational Code Image File Name - N4000v8.22.13.9
Rel 8, Ver 22, Maint Lev 13, Bld No 9
Timestamp - Thu Aug 22 13:09:33 EDT 2013
Number of components - 1
Device 776
ImageFlags 1
L7_MODULE_LIST=linux-kernel-bde.ko linux-user-bde.ko
Enter Choice# 10
Are sure you want to Erase Current Configuration? (Y/N): y
Erasing Current Configuration...done.
Boot Menu Rev: 6.0
Operational Code -- Boot Main Menu
1 - Start Operational Code
2 - Select Baud Rate
3 - Retrieve Logs
4 - Load New Operational Code
5 - Display Operational Code Details
9 - Reboot
10 - Restore Configuration to Factory Defaults
11 - Activate Backup Image
12 - Start Password Recovery
2CSNXXX_SWUM200.book Page 212 Tuesday, December 10, 2013 1:22 PM

Using the CLI 213
Enter Choice# 11
Current Active Image# /dev/mtd7
Checking for valid back-up image at /dev/mtd6...done.
Activating Back-Up Image /dev/mtd6...done.
Code Update Instructions Found!
Back-Up Image on /dev/mtd6 Activated -- System Reboot Recommended!
Reboot? (Y/N):
Enter Choice# 12
Starting Operational Code for Password Recovery...
active = /dev/mtd6
Extracting Operational Code from .stk file...done.
Loading Operational Code...done.
Decompressing Operational Code...done.
4 START_OPR_CODE_PASSWD_RECOVERY MODE
Uncompressing apps.lzma
SyncDB Running...
usbMount took 0 milliseconds
DMA pool size: 16777216
PCI unit 0: Dev 0xb842, Rev 0x02, Chip BCM56842_A1, Driver BCM56840_B0
SOC unit 0 attached to PCI device BCM56842_A1
hpc - No stack ports. Starting in stand-alone mode.
<186> Jul 12 02:40:46 0.0.0.0-1 General[63446620]: bootos.c(179) 11 %%
Event(0xaaaaaaaa) started!
(Unit 1 - Waiting to select management unit)>usbMount took 1 milliseconds
Applying Global configuration, please wait ...
usbMount took 0 milliseconds
Welcome to Dell Easy Setup Wizard
The setup wizard guides you through the initial switch configuration, and
gets you up and running as quickly as possible. You can skip the setup
wizard, and enter CLI mode to manually configure the switch. You must
respond to the next question to run the setup wizard within 60 seconds,
otherwise the system will continue with normal operation using the default
system configuration. Note: You can exit the setup wizard at any point
by entering [ctrl+z].
Would you like to run the setup wizard (you must answer this question within
60 seconds)? [Y/N] n
2CSNXXX_SWUM200.book Page 213 Tuesday, December 10, 2013 1:22 PM

Using the CLI 214
Thank you for using the Dell Easy Setup Wizard. You will now enter CLI mode.
usbMount took 1 milliseconds
Applying Interface configuration, please wait ...
Monitoring Traps from CLI
It is possible to connect to the CLI session and monitor the events or faults
that are being sent as traps from the system. This feature is equivalent to the
alarm-monitoring window in a typical network management system. The user
enables events or monitor traps from the CLI by entering the command
logging console. Traps generated by the system are dumped to all CLI
sessions that have requested monitoring mode to be enabled. The no logging
console command disables trap monitoring for the session. By default,
console logging is enabled.
Viewing System Messages
System messages autonomously display information regarding occurrences
that may affect switch operations. By default, system messages are not
displayed on CLI sessions connected via telnet or SSH. Use the terminal
monitor command to enable the autonomous display of system messages
when connecting to the switch via telnet or SSH. System messages are always
displayed on the serial console.
2CSNXXX_SWUM200.book Page 214 Tuesday, December 10, 2013 1:22 PM

Layer 2 Switching Commands 215
3
Layer 2 Switching Commands
The chapters that follow describe commands that conform to the OSI model
data link layer (Layer 2). Layer 2 commands provide a logical organization for
transmitting data bits on a particular medium. This layer defines the framing,
addressing, and checksum functions for Ethernet packets.
This section of the document contains the following Layer 2 topics:
AAA Commands E-mail Alerting
Commands
IPv6 MLD
Snooping
Commands
Port Monitor
Commands
ACL Commands Ethernet
Configuration
Commands
IPv6 MLD
Snooping Querier
Commands
QoS Commands
Address Table
Commands
Ethernet CFM
Commands
IP Source Guard
Commands
RADIUS Commands
Auto-VoIP
Commands
Green Ethernet
Commands
iSCSI
Optimization
Commands
Spanning Tree
Commands
CDP
Interoperability
Commands
GVRP Commands Link Dependency
Commands
TACACS+ Commands
DHCP Layer 2
Relay Commands
IGMP Snooping
Commands
LLDP Commands VLAN Commands
DHCP
Management
Interface
Commands
IGMP Snooping
Querier Commands
Multicast VLAN
Registration
Commands
Voice VLAN
Commands
DHCP Snooping
Commands
IP Addressing
Commands
–
802.1x Commands
Dynamic ARP
Inspection
Commands
IPv6 Access List
Commands
Port Channel
Commands
–
2CSNXXX_SWUM200.book Page 215 Tuesday, December 10, 2013 1:22 PM

216 Layer 2 Switching Commands
2CSNXXX_SWUM200.book Page 216 Tuesday, December 10, 2013 1:22 PM

AAA Commands 217
4
AAA Commands
Dell Networking N2000/N3000/N4000 Series Switches
Management access to the switch is via telnet, HTTP, SSH, or the serial
console (SNMP access is discussed in
SNMP Commands
). To ensure that only
authorized users can access and change the configuration of the switch, users
must be authenticated.
Users can be authenticated based on:
•Login mode
• Switch access method
• Access to Privileged EXEC mode
• Two levels of access:
–1 = Read-only
– 15 = Read-Write
The supported authentication methods for management access are:
• Local: The user's locally stored ID and password are used for
authentication.
• RADIUS: The user's ID and password are authenticated using the
RADIUS server.
• TACACS+: The user's ID and password are authenticated using the
TACACS+ server.
• None: No authentication is used.
• Enable: Uses the enable password for authentication.
• Line: Uses the line password for authentication.
• Authentication Preference Lists (APLs): An Authentication Preference List
is an ordered list of authentication methods.
To authenticate a user, the authentication methods in the APL for the access
line are attempted in order until an authentication attempt returns a success
or failure return code. If a method times out, the next method in the list is
attempted. The component requesting authentication is unaware of the
ultimate authentication source. If a method in the preference list does not
2CSNXXX_SWUM200.book Page 217 Tuesday, December 10, 2013 1:22 PM

218 AAA Commands
support the concept of time-out, subsequent entries in the list are never
attempted. For example, the local authentication method implementation
does not supply a time-out value. If a list contains the local method, followed
by the RADIUS authentication method, the RADIUS method is not
attempted.
Once an APL is created, a reference to that APL can be stored in the access
line configuration to determine how specific components should
authenticate users. The APL and associated component ID are stored
together. A single APL can be referenced by multiple users and components.
The administrator can enable/disable/reorder authentication methods on a
per method basis (see above).
TACACS+ Accounting
The administrator may choose to account user activity on the switch. The
following accounting types are supported:
• User exec sessions: User login and logout times are noted and conveyed to
an external AAA server.
• User executed commands: Commands executed by the user and the time
of execution are accounted and conveyed to an external AAA server.
User activity can be accounted for at the end and/or at the beginning of the
activity. For this purpose, the following record-types are defined:
• Start-stop
Accounting notifications are sent when the user logs into the switch and
when the user logs out of the exec mode. Accounting notifications are also
sent at the beginning and at the end of the user executed command.
Command execution does not wait for the accounting notification to be
recorded at the AAA server.
•Stop-only
Accounting notification is sent when user logs out of the exec mode. The
duration of the exec session is mentioned in the accounting notice.
Accounting notifications are sent at the end of each user executed
command. In the case of commands like
reload
, and
clear config
, an
exception is made and the stop accounting notice is sent at the beginning
of the command.
2CSNXXX_SWUM200.book Page 218 Tuesday, December 10, 2013 1:22 PM
AAA Commands 219
Accounting Method Lists
An Accounting Method List (AML) is an ordered list of accounting methods
that can be applied to the accounting types (exec or commands). Accounting
Method Lists are identified by the default keyword or by a user-defined name.
TACACS+ and RADIUS are supported as accounting methods.
TACACS+ accounts all accounting types. RADIUS only accounts exec
sessions.
Access Line Modes
AMLs can be applied to the following access line modes for accounting
purposes:
• Console: This mode is used when user logs in to the switch using serial
console.
• Telnet: This mode is used when user logs in through Telnet.
• SSH: This mode is used when user logs in through SSH.
By default, no accounting is enabled for any line Configuration modes.
The following default Accounting Methods List are available.
The default lists are not applied to any line-configuration modes by default.
Commands in this Chapter
This chapter explains the following commands:
Default List Name Accounting Type Record Type Accounting Method
Default Exec List exec Start-stop TACACS+
Default Command List commands Stop-only TACACS+
aaa authentication dot1x
default
clear (IAS) password (Line
Configuration)
aaa authentication enable enable authentication password (User EXEC)
aaa authentication login enable password show aaa ias-users
2CSNXXX_SWUM200.book Page 219 Tuesday, December 10, 2013 1:22 PM

220 AAA Commands
aaa authentication dot1x default
Use the aaa authentication dot1x default command in Global Configuration
mode to specify an authentication method for 802.1x clients. Use the no form
of the command to return the authentication method to its default settings.
Syntax
aaa authentication dot1x default {radius| ias|none}
no aaa authentication dot1x default
•radius—
Uses the list of all authentication servers for authentication.
•ias—
Uses the internal authentication server. Only EAP-MD5 authentication is
supported for the internal authentication server.
•none—
Uses no authentication.
Default Configuration
No default authentication method is defined.
Command Mode
Global Configuration mode
User Guidelines
Only one authentication method may be specified in the command. For the
RADIUS authentication method, if the RADIUS server cannot be contacted,
the supplicant fails authentication. The none method always allows access.
the ias method utilizes the internal authentication server. The internal
authentication server only supports the EAP-MD5 method.
aaa authorization ip http authentication show authentication
methods
aaa authorization network
default radius
ip https authentication show users accounts
aaa ias-user username login authentication show users login-history
aaa new-model password (aaa IAS User
Configuration)
username
2CSNXXX_SWUM200.book Page 220 Tuesday, December 10, 2013 1:22 PM

AAA Commands 221
Example
The following example configures 802.1x authentication to use no
authentication. Absent any other configuration, this command allows all
802.1x users to pass traffic through the switch.
console(config)# aaa authentication dot1x default none
The following example configures 802.1x authentication to use a RADIUS
server. A RADIUS server must be configured using the radius-server host auth
command for the radius method to succeed.
console(config)#aaa authentication dot1x default radius
aaa authentication enable
Use the aaa authentication enable command in Global Configuration mode
to set authentication for accessing higher privilege levels. To return to the
default configuration, use the no form of this command.
Syntax
aaa authentication enable {default |
list-name
}
method1
[
method2
...]
no aaa authentication enable {default |
list-name
}
•
default
— Uses the listed authentication methods that follow this
argument as the default list of methods, when using higher privilege levels.
•
list-name
— Character string used to name the list of authentication
methods activated, when using access higher privilege levels. (Range: 1-15
characters)
•
method1
[
method2
...
]
— Specify at least one from the following table:
Keyword Source or destination
enable Uses the enable password for authentication.
line Uses the line password for authentication.
none Uses no authentication.
radius Uses the list of all RADIUS servers for authentication.
tacacs Uses the list of all TACACS+ servers for authentication.
2CSNXXX_SWUM200.book Page 221 Tuesday, December 10, 2013 1:22 PM

222 AAA Commands
Default Configuration
The default enable list is enableList. It is used by console, telnet, and SSH
and only contains the method
none
.
Command Mode
Global Configuration mode
User Guidelines
The default and optional list names created with the aaa authentication
enable command are used with the enable authentication command.
Create a list by entering the aaa authentication enable
list-name method
command where
list-name
is any character string used to name this list. The
method
argument identifies the list of methods that the authentication
algorithm tries in the given sequence.
The additional methods of authentication are used only if the previous
method returns an error, not if it fails to authenticate the user. Only the
RADIUS or TACACS methods can return an error. To ensure that the
authentication succeeds even if all methods return an error, specify none as
the final method in the command line. Note that enable will not succeed for
a level one user if no authentication method is defined. A level one user must
authenticate to get to privileged EXEC mode. For example, if none is
specified as an authentication method after radius, no authentication is used
if the RADIUS server is down.
NOTE: Requests sent by the switch to a RADIUS server include the username
"$enabx$", where x is the requested privilege level. For enable to be authenticated
on Radius servers, add "$enabx$" users to them. The login user ID is also sent to
TACACS+ servers for enable authentication.
Example
The following example sets authentication when accessing higher privilege
levels.
console(config)# aaa authentication enable default enable
2CSNXXX_SWUM200.book Page 222 Tuesday, December 10, 2013 1:22 PM

AAA Commands 223
aaa authentication login
Use the aaa authentication login command in Global Configuration mode to
set the authentication method required for user at login. To return to the
default configuration, use the no form of this command.
Syntax
aaa authentication login {default |
list-name
}
method1
[
method2...
]
no aaa authentication login {default |
list-name
}
•
default
— Uses the listed authentication methods that follow this
argument as the default list of methods when a user logs in.
•
list-name
— Character string used to name the list of authentication
methods activated when a user logs in. (Range: 1-15 characters)
•
method1
[
method2
...
]
— Specify at least one from the following table:
Default Configuration
The default login lists are defaultList and networkList. defaultList is used by
the console and only contains the method
none
. networkList is used by telnet
and SSH and only contains the method
local
.
Command Mode
Global Configuration mode
Keyword Source or destination
enable Uses the enable password for authentication.
line Uses the line password for authentication.
local Uses the local username database for authentication.
none Uses no authentication.
radius Uses the list of all RADIUS servers for authentication.
tacacs Uses the list of all TACACS+ servers for authentication.
2CSNXXX_SWUM200.book Page 223 Tuesday, December 10, 2013 1:22 PM

224 AAA Commands
User Guidelines
The default and optional list names created with the aaa authentication
login command are used with the login authentication command. Create a
list by entering the aaa authentication login
list-name method
command for
a particular protocol, where
list-name
is any character string used to name
this list. The
method
argument identifies the list of methods that the
authentication algorithm tries, in the given sequence.
The additional methods of authentication are attempted only if the previous
method returns an error, not if there is an authentication failure. Only the
RADIUS, TACACS+, local and enable methods can return an error. To
ensure that authentication succeeds even if all methods return an error,
specify none as the final method in the command line. For example, if none is
specified as an authentication method after radius, no authentication is used
if the RADIUS server is down. If specified, none must be the last method in
the list.
NOTE: Auth-Type:=Local doesn’t work for recent versions of FreeRadius.
FreeRadius ignores the configuration if Local is used. Administrators should remove
Auth-Type=Local and use the PAP or CHAP modules instead.
Example
The following example configures the default authentication login to attempt
RADIUS authentication, then local authentication, then enable
authentication, and then, if all the previous methods returned an error, allow
the user access (none method).
console(config)# aaa authentication login default radius local enable none
aaa authorization
Use the aaa authorization command to create an authorization method list.
A list may be identified by a user-specified list-name or the keyword default.
Use the no form of the command to delete an authorization list.
Syntax
aaa authorization {commands|exec}{
default
|
list-name
} method1
[method2]
no aaa authorization {commands|exec} {
default
|
list-name
}
2CSNXXX_SWUM200.book Page 224 Tuesday, December 10, 2013 1:22 PM

AAA Commands 225
•
exec
—
Provides EXEC authorization. All methods are supported.
•
commands
—
Performs authorization of user commands. Only none and
TACACs methods are supported.
•
network
—
Performs RADIUS authorization. Only the default list is supported.
•
default
—
The default list of methods for authorization services
. The list
dfltCmdAuthList is the default list for command authorization and the
list dfltExecAuthList is the default list for EXEC authorization.
•
list-name
—
Character string used to name the list of authorization methods.
The list name can consist of any alphanumeric character up to 15 characters in
length. Use quotes around the list name if embedded blanks are contained in the
list name.
•
method
—The following authorization methods are supported:
– local—Perform local authorization (do not perform authorization—all
commands are authorized).
– none—Do not perform authorization. All commands are authorized.
– radius—Request authorization from the configured RADIUS servers.
– tacacs—Request authorization from the configured TACACS+
servers.
Default Configuration
Authorization is not enabled by default. Authorization supports EXEC
authorization and command authorization. Only TACACS is supported for
command authorization. Setting a none method for authorization authorizes
EXEC access or all commands.
The following default Authorization Methods List is present by default:
Command Mode
Global Configuration mode
Default List Name Description Authorization Method
dfltCmdAuthList Default Command List None
dfltExecAuthList Default EXEC list None
2CSNXXX_SWUM200.book Page 225 Tuesday, December 10, 2013 1:22 PM

226 AAA Commands
User Guidelines
A maximum of five authorization method lists may be created for command
types.
Command authorization attempts authorization for all EXEC mode
commands associated with a privilege level, including global configuration
commands. EXEC authorization attempts authorization when a user
attempts to enter Privileged EXEC mode.
If multiple authorization methods are listed, the switch will attempt
communication with each method in order, until successful communication
is established or all methods in the list have been tried. If authorization fails,
then the command is denied and no further attempts at authorization are
made for the user request.
The various utility commands like tftp,
ping
, outbound
telnet
also must pass
command authorization. Applying a script is treated as a single command
apply script which also must pass authorization. Startup-config commands
applied on device boot-up are not subject to the authorization process.
Example
Perform TACACS authorization on user commands. A TACACS server must
be configured.
console(config)#aaa authorization commands default tacacs
Perform exec authorization via RADIUS. A RADIUS server must be configured.
Method Notes
Local The local method is not supported for command authorization.
This method is equivalent to selecting the none method when
used for EXEC authorization.
TACACS Selects TACACS for command or exec authorization.
None Selecting the none method authorizes all commands. This
option is valid for both command and EXEC authorization.
Radius The radius method is only valid for EXEC authorization.
Command authorization with RADIUS will work only if the
applied authentication method is radius.
2CSNXXX_SWUM200.book Page 226 Tuesday, December 10, 2013 1:22 PM

AAA Commands 227
console(config)#aaa authorization exec "qwerty" radius
aaa authorization network default radius
Use the aaa authorization network default radius command in Global
Configuration mode to enable the switch to accept VLAN assignment by the
RADIUS server.
Syntax
aaa authorization network default radius
no aaa authorization network default radius
Default Configuration
By default, the switch does not accept VLAN assignments by the RADIUS
server.
Command Mode
Global Configuration mode
User Guidelines
The RADIUS server can place a port in a particular VLAN based on the result
of the authentication. VLAN assignment must be configured on the external
RADIUS server.
Example
The following example enables RADIUS-assigned VLANs.
console(config)#aaa authorization network default radius
aaa ias-user username
Use the aaa ias-user username command in Global Configuration mode to
configure IAS users and their attributes. Username and password attributes
are supported. The ias-user name is composed of up to 64 alphanumeric
characters. This command also changes the mode to a user Configuration
mode. Use the no form of this command to remove the user from the internal
user database.
2CSNXXX_SWUM200.book Page 227 Tuesday, December 10, 2013 1:22 PM

228 AAA Commands
Syntax
aaa ias-user username
user
no aaa ias-user username
user
Default Configuration
This command has no default configuration.
Command Mode
Global Configuration
User Guidelines
This command has no user guidelines.
Examples
console#configure
console(config)#aaa ias-user username client-1
console(Config-IAS-User)#exit
console(config)#no aaa ias-user username client-1
aaa new-model
The aaa new-model command in Global Configuration mode is a no-op
command. It is present only for compatibility purposes. Dell Networking
switches only support the new model command set.
Syntax
aaa new-model
Default Configuration
This command has no default configuration.
Command Mode
Global Configuration mode
User Guidelines
There are no user guidelines for this command.
2CSNXXX_SWUM200.book Page 228 Tuesday, December 10, 2013 1:22 PM

AAA Commands 229
Example
The following example configures the switch to use the new model command
set.
(config)# aaa new-model
clear (IAS)
Use the clear aaa ias-users command in Privileged EXEC mode to delete all
IAS users.
Syntax
clear aaa ias-users
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC mode
User Guidelines
There are no user guidelines for this command.
Example
console#clear aaa ias-users
authorization
Use the authorization command to apply a command authorization method
to a line config.
Use the no form of the command to return the authorization for the line
mode to the default.
Syntax
authorization {commands|exec} [default|
list_name
]
no authorization {commands|exec}
2CSNXXX_SWUM200.book Page 229 Tuesday, December 10, 2013 1:22 PM

230 AAA Commands
•
commands
—
Perform authorization for each command entered by the user.
•
exec
—
Perform EXEC authorization for the user (authorization required to
enter privileged EXEC mode).
•default
—
The default list of methods for command authorization
(cmdAuthList).
•list_name
—
Character string used to name the list of authorization methods.
The list name can consist of any printable character. Use quotes around the list
name if embedded blanks are contained in the list name.
Default Configuration
Authorization is not enabled on any line method by default.
Command Mode
Line console, line telnet, line SSH
User Guidelines
When command authorization is configured for a line-mode, the switch
sends information about the entered command to the method specified in
the command list. The authorization method validates the received
command and responds with either a PASS or FAIL response. If approved, the
command is executed. Otherwise, the command is denied and an error
message is shown to the user. If contact with the authorization method fails,
then the next method in the list is attempted.
Examples
Use the following command to enable TACACS command authorization for
telnet.
console(config)#line telnet
console(config-telnet)# authorization commands mycmdAuthList
enable authentication
Use the enable authentication command in Line Configuration mode to
specify the authentication method list when accessing a higher privilege level
from a remote telnet or console. To return to the default specified by the
enable authentication command, use the no form of this command.
2CSNXXX_SWUM200.book Page 230 Tuesday, December 10, 2013 1:22 PM

AAA Commands 231
Syntax
enable authentication {default |
list-name
}
no enable authentication
•
default
— Uses the default list created with the
aaa authentication enable
command.
•
list-name
— Uses the indicated list created with the
aaa authentication
enable
command. (Range: 1-12 characters)
Default Configuration
Uses the default set with the command aaa authentication enable.
Command Mode
Line Configuration mode
User Guidelines
Use of the no form of the command does not disable authentication. Instead,
it sets the authentication list to the default list (same as enable
authentication default).
Example
The following example specifies the default authentication method when
accessing a higher privilege level console.
console(config)# line console
console(config-line)# enable authentication default
enable password
Use the enable password command in Global Configuration mode to set a
local password to control access to the privileged EXEC mode. To remove the
password requirement, use the no form of this command.
Syntax
enable password
password
[encrypted]
no enable password
2CSNXXX_SWUM200.book Page 231 Tuesday, December 10, 2013 1:22 PM

232 AAA Commands
•
password
— Password for this level (Range: 8- 64 characters). The special
characters allowed in the password include ! # $ % & ‘ ( ) * + , - . /
: ; < = > @ [ \ ] ^ _ ` { | } ~. User names can contain blanks if
the name is surrounded by double quotes.
•
encrypted
— Encrypted password entered, copied from another switch
configuration.
Default Configuration
This command has no default configuration.
Command Mode
Global Configuration mode
User Guidelines
The DNOS firmware emulates industry standard behavior for enable mode
authentication over SSH and telnet. The default enable authentication
method for telnet and SSH uses the enableNetList method, which requires an
enable password. If users are unable to enter privileged mode when accessing
the switch via telnet or SSH, the administrator will need to either change the
enable authentication method, e.g. to enableList, or set an enable password.
If the encrypted parameter is specified, the password parameter is stored as
entered in the running-config. No attempt is made to decode the encrypted
password.
Example
The following example defines password "xxxyyyzzz" to control access to user
and privilege levels.
console(config)# enable password xxxyyyzzz
ip http authentication
Use the ip http authentication command in Global Configuration mode to
specify authentication methods for http server users. To return to the default,
use the no form of this command.
2CSNXXX_SWUM200.book Page 232 Tuesday, December 10, 2013 1:22 PM

AAA Commands 233
Syntax
ip http authentication
method1
[
method2
...]
no ip http authentication
•
method1
[
method2
...
]
— Specify at least one from the following table:
Default Configuration
The local user database is checked. This action has the same effect as the
command ip http authentication local.
Command Mode
Global Configuration mode
User Guidelines
The additional methods of authentication are used only if the previous
method returns an error, not if it fails. To ensure that the authentication
succeeds even if all methods return an error, specify none as the final method
in the command line. For example, if none is specified as an authentication
method after radius, no authentication is used if the RADIUS server is down.
Example
The following example configures the http authentication.
console(config)# ip http authentication radius local
ip https authentication
Use the ip https authentication command in Global Configuration mode to
specify authentication methods for https server users. To return to the default
configuration, use the no form of this command.
Keyword Source or destination
local Uses the local username database for authentication.
none Uses no authentication.
radius Uses the list of all RADIUS servers for authentication.
tacacs Uses the list of all TACACS+ servers for authentication.
2CSNXXX_SWUM200.book Page 233 Tuesday, December 10, 2013 1:22 PM

234 AAA Commands
Syntax
ip https authentication
method1
[
method2
...]
no ip https authentication
•
method1
[
method2
...] — Specify at least one from the following table:
Default Configuration
The local user database is checked. This action has the same effect as the
command ip https authentication local.
Command Mode
Global Configuration mode
User Guidelines
The additional methods of authentication are used only if the previous
method returns an error, not if it fails. To ensure that the authentication
succeeds even if all methods return an error, specify none as the final method
in the command line. If none is specified as an authentication method after
radius, no authentication is used if the RADIUS server is down.
When TACACS+ is used as the authentication method for HTTP/HTTPS,
the Cisco ACS must be configured to allow the shell service. In addition, for
admin privileges, the privilege level attribute must be set to 15.
Example
The following example configures https authentication.
console(config)# ip https authentication radius local
Keyword Source or destination
local Uses the local username database for authentication.
none Uses no authentication.
radius Uses the list of all RADIUS servers for authentication.
tacacs Uses the list of all TACACS+ servers for authentication.
2CSNXXX_SWUM200.book Page 234 Tuesday, December 10, 2013 1:22 PM

AAA Commands 235
login authentication
Use the login authentication command in Line Configuration mode to
specify the login authentication method list for a line (console, telnet, or
SSH). To return to the default specified by the authentication login
command, use the no form of this command.
Syntax
login authentication {default |
list-name
}
no login authentication
•
default
— Uses the default list created with the
aaa authentication login
command.
•
list-name
— Uses the indicated list created with the
aaa authentication
login
command.
Default Configuration
Uses the default set with the command aaa authentication login.
Command Mode
Line Configuration mode
User Guidelines
This command has no user guidelines.
Example
The following example specifies the default authentication method for a
console.
console(config)# line console
console(config-line)# login authentication default
2CSNXXX_SWUM200.book Page 235 Tuesday, December 10, 2013 1:22 PM

236 AAA Commands
password (aaa IAS User Configuration)
Use the password command in aaa IAS User Configuration mode to configure
a password for a user. The password is composed of up to 64 alphanumeric
characters. An optional parameter [encrypted] is provided to indicate that the
password given to the command is already pre-encrypted. To clear the user’s
password, use the no form of this command.
Syntax
password
password
[encrypted]
no password
•
password
— Password for this level. (Range: 8- 64 characters)
•
encrypted
— Encrypted password to be entered, copied from another
switch configuration.
Default Configuration
This command has no default configuration.
Command Mode
aaa IAS User Configuration
User Guidelines
This command has no user guidelines.
Example
console#configure
console(config)#aaa ias-user username client-1
console(Config-IAS-User)#password client123
console(Config-IAS-User)#no password
Example of adding a MAB Client to the Internal user database:
console#configure
console(config)#aaa ias-user username 1f3ccb1157
console(Config-IAS-User)#password 1f3ccb1157
console(Config-IAS-User)#exit
console(config)#
2CSNXXX_SWUM200.book Page 236 Tuesday, December 10, 2013 1:22 PM

AAA Commands 237
password (Line Configuration)
Use the password command in Line Configuration mode to specify a
password on a line. To remove the password, use the no form of this
command.
NOTE: For commands that configure password properties, see Password
Management Commands on page 1503.
Syntax
password
password
[encrypted]
no password
•
password
— Password for this level. (Range: 8- 64 characters) The special
characters allowed in the password include ! # $ % & ‘ ( ) * + , - . /
: ; < = > @ [ \ ] ^ _ ` { | } ~. User names can contain blanks if
the name is surrounded by double quotes.
•
encrypted
— Encrypted password to be entered, copied from another
switch configuration.
Default Configuration
No password is specified.
Command Mode
Line Configuration mode
User Guidelines
This command has no user guidelines.
Example
The following example specifies a password "mcmxxyyy" on a line.
console(config-line)# password mcmxxyyy
2CSNXXX_SWUM200.book Page 237 Tuesday, December 10, 2013 1:22 PM

238 AAA Commands
password (User EXEC)
Use the password command in User EXEC mode to allow a currently logged
in user to change the password for only that user without having read/write
privileges. This command should be used after the password has aged. The
user is prompted to enter the old password and the new password.
The special
characters allowed in the password include ! # $ % & ‘ ( ) * + , - . / : ; <
= > @ [ \ ] ^ _ ` { | } ~. User names can contain blanks if the name is
surrounded by double quotes.
NOTE: For commands that configure password properties, see Password
Management Commands.
Syntax
password
Default Configuration
There is no default configuration for this command.
Command Mode
User EXEC mode
User Guidelines
This command has no user guidelines.
Example
The following example shows the prompt sequence for executing the
password command.
console>password
Enter old password:********
Enter new password:********
Confirm new password:********
show aaa ias-users
Use the show aaa ias-users command in Privileged EXEC mode to display
configured IAS users and their attributes. Passwords configured are not shown
in the show command output.
2CSNXXX_SWUM200.book Page 238 Tuesday, December 10, 2013 1:22 PM

AAA Commands 239
Syntax
show aaa ias-users
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC, Configuration mode and all Configuration submodes
User Guidelines
This command has no user guidelines.
Example
console#show aaa ias-users
UserName
-------------------
Client-1
Client-2
show aaa statistics
Use the show aaa statistics command in Privileged EXEC mode to display
accounting statistics.
Syntax
show aaa statistics
Default Configuration
This command has no default setting.
Command Mode
Privileged EXEC mode, Configuration mode and all Configuration submodes
User Guidelines
This command has no user guidelines.
2CSNXXX_SWUM200.book Page 239 Tuesday, December 10, 2013 1:22 PM

240 AAA Commands
Examples
console#show aaa statistics
Number of Accounting Notifications sent at beginning of an EXEC session: 0
Errors when sending Accounting Notifications beginning of an EXEC session: 0
Number of Accounting Notifications sent at end of an EXEC session: 0
Errors when sending Accounting Notifications at end of an EXEC session: 0
Number of Accounting Notifications sent at beginning of a command execution:
0
Errors when sending Accounting Notifications at beginning of a command
execution: 0
Number of Accounting Notifications sent at end of a command execution: 0
Errors when sending Accounting Notifications at end of a command execution: 0
show authentication methods
Use the show authentication methods command in Privileged EXEC mode
to display information about the authentication methods.
Syntax
show authentication methods
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC mode, Configuration mode and all Configuration submodes
User Guidelines
This command has no user guidelines.
Example
The following example displays the authentication configuration.
console#show authentication methods
Login Authentication Method Lists
---------------------------------
defaultList : none
networkList : local
2CSNXXX_SWUM200.book Page 240 Tuesday, December 10, 2013 1:22 PM

AAA Commands 241
Enable Authentication Method Lists
----------------------------------
enableList : enable none
enableNetList : enable
Line Login Method List Enable Method List
------- ----------------- ------------------
Console defaultList enableList
Telnet networkList enableNetList
SSH networkList enableNetList
HTTPS :local
HTTP :local
DOT1X :
show authorization methods
Use the show authorization methods command in Privileged EXEC mode to
display the configured authorization method lists.
Syntax
show authorization methods
Default Configuration
This command has no default setting.
Command Mode
Privileged EXEC mode, Configuration mode and all Configuration submodes
User Guidelines
Command authorization is supported only for the line, telnet, and SSH
access methods.
Example
console#show authorization methods
Exec Authorization List Methods
---------------------------- ------------------------------
dfltExecAuthList none
Command Authorization List Methods
2CSNXXX_SWUM200.book Page 241 Tuesday, December 10, 2013 1:22 PM

242 AAA Commands
---------------------------- ------------------------------
dfltCmdAuthList none
Line Exec Method Lists Command Method Lists
--------- --------------------- ---------------------
Console dfltExecAuthList dfltCmdAuthList
Telnet dfltExecAuthList dfltCmdAuthList
SSH dfltExecAuthList dfltCmdAuthList
Network Authorization Methods
---------------------- -------
Dot1x radius
show users accounts
Use the show users accounts command in Privileged EXEC mode to display
the local user status with respect to user account lockout and password aging.
Syntax
show users accounts
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC mode, Configuration mode and all Configuration submodes
User Guidelines
The following fields are displayed by this command.
Parameter Description
User Name Local user account’s user name.
Privilege User’s access level (read only or
read/write).
Lockout Status Indicates whether the user account is
locked out or not.
Password Expiration Date Current password expiration date in date
format.
2CSNXXX_SWUM200.book Page 242 Tuesday, December 10, 2013 1:22 PM

AAA Commands 243
Example
The following example displays information about the local user database.
console#show users accounts
UserName Privilege Password Password Lockout
Aging Expiry date
----------- --------- --------- ----------- -------
admin 15 --- --- False
guest 15 --- --- False
brcm1 1 --- --- False
console#show users accounts long
User Name
------------
asd
thisisaverylongusernameitisquitelong
show users login-history
Use the show users login-history command in Global Configuration mode to
display information about the login history of users.
Syntax
show users login-history [long]
•
name
— name of user. (Range: 1-20 characters)
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC mode, Configuration mode and all Configuration submodes
User Guidelines
This command has no user guidelines.
Lockout Displays the user’s lockout status (True or
False).
Parameter Description
2CSNXXX_SWUM200.book Page 243 Tuesday, December 10, 2013 1:22 PM

244 AAA Commands
Example
The following example show user login history outputs.
console#show users login-history
Login Time Username Protocol Location
-------------------- --------- --------- -----------
Jan 19 2005 08:23:48 Bob Serial
Jan 19 2005 08:29:29 Robert HTTP 172.16.0.8
Jan 19 2005 08:42:31 John SSH 172.16.0.1
Jan 19 2005 08:49:52 Betty Telnet 172.16.1.7
username
Use the username command in Global Configuration mode to add a new user
to the local user database. The default privilege level is 1. The command
optionally allows the specification of an Administrative Profile for a local user.
Use the no form of this command to remove the username from the local user
database.
Syntax
username name {nopassword|password
password
} [privilege
level
|admin-
profile
profile
] [encrypted]
no username
name
•
name—
The name of the user. Range: 1-32 printable characters. The
special characters allowed in the password include ! # $ % & ‘ ( ) * +
, - . / : ; < = > @ [ \ ] ^ _ ` { | } ~. User names can contain
blanks if the name is surrounded by double quotes.
•
password
—The authentication password for the user. Range: 8-64
characters. This value can be 0 [zero] if the
no passwords min-length
command has been executed. The special characters allowed in the
password include ! # $ % & ‘ ( ) * + , - . / : ; < = > @ [ \ ] ^
_ ` { | } ~.
•
level
—The user’s privilege level. Level 0 can be assigned by a level 15 user
to another user to suspend that user’s access. Range: 0-15. Enter access
level 1 for Read Access or 15 for Read/Write Access.
•
profile
—
The name of the administrative profile(s) to apply to this user. An
administrative profile is mutually exclusive with a privilege level.
2CSNXXX_SWUM200.book Page 244 Tuesday, December 10, 2013 1:22 PM

AAA Commands 245
•encrypted—
Encrypted password entered, copied from another switch
configuration. Password strength checking is not applied to the encrypted
string.
Default Configuration
The default privilege level is 1.
Command Mode
Global Configuration mode
User Guidelines
To use the ! character as part of the username or password string, it should be
enclosed within quotation marks. For example, username “test!xyz” password
“test!xyz” includes an exclamation point in both the username and password.
Up to 8 users may be created. If the password strength feature is enabled, it
checks for password strength and returns an appropriate error if it fails to
meet the password strength criteria. If the encrypted keyword is entered, no
password strength checking is performed as the password is encrypted and the
system does not have the capability of decrypting the password.
The following table lists the completion messages.
Message Type Message Description
Successful Completion Message No message is displayed.
Error Completion Message Could not set user password!
2CSNXXX_SWUM200.book Page 245 Tuesday, December 10, 2013 1:22 PM

246 AAA Commands
Example
The following example configures user bob with password xxxyymmmm and
user level 15.
console(config)# username bob password ?
<password> Enter the password. The special characters allowed in the
password include ~ ` ! @ # $ % ^ & * ( ) _ - + = [ ] { } \ | : ; ' < > . , /.
console(config)# username bob password xxxyyymmm privilege 15
username unlock
Use the username unlock command in Global Configuration mode to unlock
a locked user account. Only a user with read/write access can reactivate a
locked user account.
Syntax
username
username
unlock
Reason behind the failure 1
Exceeds Minimum Length of a Password.
Password should be in the range of 8-64
characters in length. Set minimum password
length to 0 by using the passwords min-length
0 command.
2
Password should contain Minimum
< nu m be r > u p pe r c a s e - l e t te r s ,
<number> lowercase-letters, <number>
numeric numbers,
<n u m b e r > s p e c i a l c h a r a c t e r s a n d
< n u m b e r > c h a r a c t e r c l a s s e s a n d
Maximum limit of <number> consecutive
alphabetic and numeric
characters.
Ma x i m u m r e p et i t io n o f < n u m b e r >
alphabetic and number characters.
3
Pa s s w o rd s ho u l d no t c o nt a i n t h e
k e y w o r d s < k e y w o r d 1 > , < k e y w o r d 2 >
a n d < k e y w o r d 3 > i n a n y f o r m ( r e v e r s e d ,
substring or case-insensitive).
Message Type Message Description
2CSNXXX_SWUM200.book Page 246 Tuesday, December 10, 2013 1:22 PM

AAA Commands 247
Default Configuration
This command has no default configuration.
Command Mode
Global Configuration mode
User Guidelines
This command has no user guidelines.
2CSNXXX_SWUM200.book Page 247 Tuesday, December 10, 2013 1:22 PM

248 AAA Commands
2CSNXXX_SWUM200.book Page 248 Tuesday, December 10, 2013 1:22 PM

Administrative Profiles Commands 249
5
Administrative Profiles Commands
Dell Networking N2000/N3000/N4000 Series Switches
Overview
The administrative profiles capability provides the network administrator
control over which commands a user is allowed to execute. The administrator
is able to group commands into a “profile” and assign a profile to a user upon
authentication. This provides more granularity than simply allowing read-
only and read-write users. It may be, for example, that a particular user is only
allowed to manage the Captive Portal feature but not allowed to manage any
other of the switch features.
This capability is similar to the industry standard “User Roles” feature. The
main difference is that the Administrative Profile is obtained via
authentication rather than via authorization. This was necessary because Dell
Networking does not support AAA authorization of users.
Functionally, the Administrative Profiles feature allows the network
administrator to define a list of rules which control the commands which may
be executed by a user. These rules are collected in a “profile.” A rule defines a
set of commands to which a user is permitted or denied access. Alternatively,
a rule may define a CLI command mode to which the user is permitted or
denied access. The rule numbers determine the order in which the rules are
applied: Rules are applied in descending numerical order until there is a
match. Rules may use regular expressions for command matching. All profiles
have an implicit “deny all” rule such that any command which does not
match any rules in the profile is considered to have been denied by that
profile.
It is possible to assign a user more than one profile. If there are conflicting
rules in profiles, the “permit” rule always takes precedence over the “deny”
rule, i.e., if any profile assigned to a user permits a command, then the user is
permitted access to that command. A user may be assigned up to 16 profiles.
A number of profiles are provided by default. These profiles may not be
altered by the switch administrator.
2CSNXXX_SWUM200.book Page 249 Tuesday, December 10, 2013 1:22 PM

250 Administrative Profiles Commands
If the successful authentication method does not provide an Administrative
Profile for a user, then the user is permitted access based upon the user’s
privilege level (as in previous releases). This means that if a user successfully
passes enable authentication, the user is permitted access to all commands.
This is also true if none of the Administrative Profiles provided are configured
on the switch.
RADIUS and TACACS+
The network administrator may configure a custom attribute to be provided
by the server during authentication. The RADIUS and TACACS+
applications process this custom attribute and provide this data to the User
Manager for configuring the user profile.
The custom attribute is defined as:
cisco-av-pair=shell:roles=”roleA roleB …”
NOTE: If an “*” is used instead of an “=”, the attribute is considered optional and
devices which do not support this attribute will ignore it.
Commands in this Chapter
This chapter explains the following commands:
admin-profile show admin-profiles
description (Administrative Profile
Configuration)
show admin-profiles brief
rule show cli modes
2CSNXXX_SWUM200.book Page 250 Tuesday, December 10, 2013 1:22 PM

Administrative Profiles Commands 251
admin-profile
Use the admin-profile command in Global Configuration mode to create an
administrative profile. The system-defined administrative profiles cannot be
deleted. When creating a profile, the user is placed into Administrative
Profile Configuration mode.
Use the no form of the command to delete an administrative profile and all
its rules.
Syntax
admin-profile
profile-name
no admin-profile
profile-name
•
profile-name
—The name of the profile to create or delete. Range: 1 to 16
alphanumeric characters – may also include a hyphen.
Default Configuration
The administrative profiles are defined by default.
Command Mode
Global Configuration mode
User Guidelines
This command has no user guidelines.
Example
console(config)#admin-profile qos
console(admin-profile)#
description (Administrative Profile Configuration)
Use the description command in Administrative Profile Configuration mode
to add a description to an administrative profile.
Use the no form of this command to delete the description.
Syntax
description
text
2CSNXXX_SWUM200.book Page 251 Tuesday, December 10, 2013 1:22 PM

252 Administrative Profiles Commands
no description
•
text
—A description of, or comment about, the administrative profile. To
include white space, enclose the description in quotes. Range: 1 to 128
printable characters.
Default Configuration
This command has no default configuration.
Command Mode
Administrative Profile Configuration mode
User Guidelines
The description string is required to be enclosed in quotes if it contains
embedded white space.
Example
console(admin-profile)#description “This profile allows access to QoS
commands.”
rule
Use the rule command to add a rule to an administrative profile.
Use the no form of this command to delete a rule.
Syntax
rule
number
{deny|permit} {command
command-string
|mode
mode-
name
}
no rule
number
•
number
—The sequence number of the rule. Rules are applied from the highest
sequence number to the lowest. Range: 1 to 256.
•
command-string
—
Specifies which commands to permit or deny. The
command-string may contain spaces and regular expressions. Range: 1 to
128 characters). Regular expressions should conform to Henry Spencer’s
implementation of the POSIX 1003.2 specification.
Note: In this usage, the beginning and end of line meta-characters have no
meaning.
2CSNXXX_SWUM200.book Page 252 Tuesday, December 10, 2013 1:22 PM

Administrative Profiles Commands 253
•mode-name—
The name of the CLI mode to which the profile will permit
or deny access.
Default Configuration
This command has no default configuration.
Command Mode
Administrative Profile Configuration mode
User Guidelines
This command has no user guidelines.
Example
console(admin-profile)#rule 1 permit command “access-list *”
console(admin-profile)#
show admin-profiles
Use the show admin-profiles command in Privileged EXEC mode to show
the administrative profiles. If the optional profile name parameter is used,
only that profile will be shown.
Syntax
show admin-profiles [name
profile-name
]
•
profile-name
—The name of the administrative profile to display.
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC mode
User Guidelines
The following admin profiles are predefined and may not be deleted or
changed by the administrator:
• Profile: network-admin
2CSNXXX_SWUM200.book Page 253 Tuesday, December 10, 2013 1:22 PM

254 Administrative Profiles Commands
• Profile: network-security
• Profile: router-admin
• Profile: multicast-admin
• Profile: dhcp-admin
• Profile: CP-admin
• Profile: network-operator.
Example
console#show admin-profiles name qos
Profile: qos
Description: This profile allows access to QoS commands.
-----------------------------------------------------------
Rule Perm Type Entity
-----------------------------------------------------------
1 permit command access-list *
2 permit command access-group *
3 permit mode class-map
show admin-profiles brief
Use the show admin-profiles brief command in Privileged EXEC mode to list
the names of the administrative profiles defined on the switch.
Syntax
show admin-profiles brief
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC mode
User Guidelines
This command has no user guidelines.
2CSNXXX_SWUM200.book Page 254 Tuesday, December 10, 2013 1:22 PM

Administrative Profiles Commands 255
Example
console#show admin-profiles brief
Profile: network-admin
Profile: network-security
Profile: router-admin
Profile: multicast-admin
Profile: dhcp-admin
Profile: CP-admin
Profile: network-operator
show cli modes
Use the show cli modes command in Privileged EXEC mode to list the names
of all the CLI modes.
Syntax
show cli modes
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC mode
User Guidelines
These are the generic mode names to be used in the
rule
command above.
These are not the same as the prompt which is displayed in a particular mode.
Example
console#show cli modes
user-exec
privileged-exec
global-config
ethernet-config
port-channel-config
2CSNXXX_SWUM200.book Page 255 Tuesday, December 10, 2013 1:22 PM

256 Administrative Profiles Commands
2CSNXXX_SWUM200.book Page 256 Tuesday, December 10, 2013 1:22 PM

ACL Commands 257
6
ACL Commands
Dell Networking N2000/N3000/N4000 Series Switches
Access to a switch or router can be made more secure through the use of
Access Control Lists (ACLs) to control the type of traffic allowed into or out
of specific ports. An ACL consists of a series of rules, each of which describes
the type of traffic to be processed and the actions to take for packets that
meet the classification criteria. Rules within an ACL are evaluated
sequentially until a match is found, if any. An implicit deny-all rule is added
after the end of the last configured access group. ACLs can help ensure that
only authorized users have access to specific resources while blocking out any
unwarranted attempts to reach network resources.
ACLs may be used to restrict contents of routing updates, decide which types
of traffic are forwarded or blocked and, above all, provide security for the
network. ACLs are normally used in firewall routers that are positioned
between the internal network and an external network, such as the Internet.
They can also be used on a router positioned between two parts of the
network to control the traffic entering or exiting a specific part of the internal
network.
The Dell Networking ACL feature allows classification of packets based upon
Layer 2 through Layer 4 header information. An Ethernet IPv6 packet is
distinguished from an IPv4 packet by its unique Ethertype value; thus, all
IPv4 and IPv6 classifiers include the Ethertype field.
Multiple ACLs per interface are supported. The ACLs can be a combination
of Layer 2 and/or Layer 3/4 ACLs. ACL assignment is appropriate for both
physical ports and LAGs. ACLs can also be time based. The maximum
number of ACLs and rules supported depends on the resources consumed by
other processes and configured features running on the switch.
ACL Logging
Access list rules are monitored in hardware to either permit or deny traffic
matching a particular classification pattern, but the network administrator
currently has no insight as to which rules are being
hit
. Some hardware
platforms have the ability to count the number of hits for a particular
2CSNXXX_SWUM200.book Page 257 Tuesday, December 10, 2013 1:22 PM

258 ACL Commands
classifier rule. The ACL logging feature allows these hardware hit counts to be
collected on a per-rule basis and reported periodically to the network
administrator using the system logging facility and an SNMP trap.
The Dell Networking ACL permit/deny rule specification supports a log
parameter that enables hardware hit count collection and reporting.
Depending on platform capabilities, logging can be specified for deny rules,
permit rules, or both. A five minute logging interval is used, at which time
trap log entries are written for each ACL logging rule that accumulated a
nonzero hit count during that interval. The logging interval is not user
configurable.
How to Build ACLs
This section describes how to build ACLs that are less likely to exhibit false
matches.
Administrators are cautioned to specify ACL access-list, permit and deny rule
criteria as fully as is possible in order to avoid false matches. This is especially
true in networks with protocols such as FCoE that have newly introduced
Ether type values. As an example, rules that specify a TCP or UDP port value
should also specify the TCP or UDP protocol and the IPv4 or IPv6 Ether type.
Rules that specify an IP protocol should also specify the Ether type value for
the frame. In general, any rule that specifies matching on an upper layer
protocol field should also include matching constraints for each of the lower
layer protocols. For example, a rule to match packets directed to the well-
known UDP port number 22 (SSH) should also include matching constraints
on the IP protocol field (protocol = 0x11 or UDP) and the Ether type field
(Ether type = 0x0800 or IPv4). In Table 6-1 is a list of commonly used Ether
types and, in Table 6-2 commonly used IP protocol numbers.
2CSNXXX_SWUM200.book Page 258 Tuesday, December 10, 2013 1:22 PM
ACL Commands 259
Table 6-1. Common Ethertypes
EtherType Protocol
0x0800 Internet Protocol version 4 (IPv4)
0x0806 Address Resolution Protocol (ARP)
0x0842 Wake-on LAN Packet
0x8035 Reverse Address Resolution Protocol (RARP)
0x8100 VLAN tagged frame (IEEE 802.1Q)
0x86DD Internet Protocol version 6 (IPv6)
0x8808 MAC Control
0x8809 Slow Protocols (IEEE 802.3)
0x8870 Jumbo frames
0x888E EAP over LAN (EAPOL – 802.1x)
0x88CC Link Layer Discovery Protocol
0x8906 Fibre Channel over Ethernet
0x8914 FCoE Initialization Protocol
0x9100 Q in Q
Table 6-2. Common IP Protocol Numbers
IP Protocol Numbers Protocol
0x00 IPv6 Hop-by-hop option
0x01 ICMP
0x02 IGMP
0x06 TCP
0x08 EGP
0x09 IGP
0x11 UDP
2CSNXXX_SWUM200.book Page 259 Tuesday, December 10, 2013 1:22 PM

260 ACL Commands
Commands in this Chapter
This chapter explains the following commands:
ip access-list
Use the ip access-list command in Global Configuration mode to create an
Access Control List (ACL) that is identified by the parameter
list-name
and
to enter IPv4-Access-List configuration mode. If parameterized with the
name of an existing access list, additional match clauses are added to the end
of the access list..
ip access-list
list-name
[extended]
no ip access-list
list-name
•
list-name
—Access-list name up to 31 characters in length.
Default Configuration
This command has no default configuration.
Command Mode
Global Configuration mode
User Guidelines
Access lists now use the extended access list format. Multiple permit and
deny clauses and actions may be specified without requiring the access list
name to be entered each time. Permit and deny clauses are entered in order
from the first match clause when in Access List Configuration mode.
ip access-list mac access-list extended
deny | permit (IP ACL) mac access-list extended rename
deny | permit (Mac-Access-List-
Configuration)
service-acl input
ip access-group show service-acl interface
mac access-group show ip access-lists
–
show mac access-lists
2CSNXXX_SWUM200.book Page 260 Tuesday, December 10, 2013 1:22 PM

ACL Commands 261
ACL names are global. An IPv6 access list cannot have the same name as an
IPv4 access list. Access list names can consist of any printable character.
Names can be up to 31 characters in length.
deny | permit (IP ACL)
Use this command in Ipv4-Access-List Configuration mode to create a new
rule for the current IP access list. Each rule is appended to the list of
configured rules for the list.
Syntax
{deny | permit} {every | {{
ipv4-protocol
|
0-255
|
every
} {
srcip srcmask
|
any | host
srcip
} [{range {
portkey
|
startport
} {
portkey
|
endport
} | {eq |
neq | lt | gt} {
portkey
|
0-65535
} ] {
dstip dstmask
| any | host
dstip
}
[{range {
portkey
|
startport
} {
portkey
|
endport
} | {eq | neq | lt | gt}
{
portkey
|
0-65535
}] [flag [+fin | -fin] [+syn | -syn] [+rst | -rst] [+psh | -
psh] [+ack | -ack] [+urg | -urg] [established]] [icmp-type
icmp-type
[icmp-
code
icmp-code
] | icmp-message
icmp-message
] [igmp-type
igmp-type
]
[fragments] [precedence
precedence
| tos
tos
[
tosmask
] | dscp
dscp
]}}
[time-range
time-range-name
] [log] [assign-queue
queue-id
] [{mirror |
redirect}
unit/slot/port
] [rate-limit
rate burst-size
]
•{
deny | permit
}–Specifies whether the IP ACL rule permits or denies the
matching traffic.
•
{
ipv4-protocol
|
number
|
every
}—
Specifies the protocol to match for the IP
ACL rule.
– IPv4 protocols:
eigrp, gre, icmp, igmp, ip, ipinip, ospf, tcp, udp, pim
–
Every
: Match any protocol (don’t care)
•
srcip
srcmask
| any | host
srcip
—Specifies a source IP address and netmask
to match for the IP ACL rule.
– Specifying “any” implies specifying
srcip
as “0.0.0.0” and
srcmask
as
“255.255.255.255” for IPv4.
– Specifying “host A.B.C.D” implies
srcip
as “A.B.C.D” and
srcmask
as
“0.0.0.0”.
•
[{{eq | neq | lt | gt} {
portkey
|
number
} | range
startport endport
}]
—
Specifies the layer 4 destination port match condition for the IP ACL rule.
A destination port number, which ranges from 0-65535, can be entered, or
2CSNXXX_SWUM200.book Page 261 Tuesday, December 10, 2013 1:22 PM

262 ACL Commands
a
portkey
, which can be one of the following keywords: domain, echo, ftp,
ftp-data, http, smtp, snmp, telnet, tftp, and www. Each of these keywords
translates into its equivalent destination port number.
– When “range” is specified, IP ACL rule matches only if the layer 4
port number falls within the specified portrange. The
startport
and
endport
parameters identify the first and last ports that are part of the
port range. They have values from 0 to 65535. The ending port must
have a value equal or greater than the starting port. The starting port,
ending port, and all ports in between will be part of the layer 4 port
range.
– When “eq” is specified, IP ACL rule matches only if the layer 4 port
number is equal to the specified port number or portkey.
– When “lt” is specified, IP ACL rule matches if the layer 4 destination
port number is less than the specified port number or portkey. It is
equivalent to specifying the range as 0 to <specified port number –
1>.
– When “gt” is specified, IP ACL rule matches if the layer 4 destination
port number is greater than the specified port number or portkey. It is
equivalent to specifying the range as <specified port number + 1> to
65535.
– When “neq” is specified, IP ACL rule matches only if the layer 4
destination port number is not equal to the specified port number or
portkey.
– IPv4 TCP port names
: bgp, domain, echo, ftp, ftp-data, http, smtp,
telnet, www, pop2, pop3
– IPv4 UDP port names:
domain, echo, ntp, rip, snmp, tftp, time, who
•
dstip
dstmask
|
any | host
dstip
—Specifies a destination IP address and
netmask for match condition of the IP ACL rule.
– Specifying “any” implies specifying
dstip
as “0.0.0.0” and
dstmask
as
“255.255.255.255”.
– Specifying “host A.B.C.D” implies
dstip
as “A.B.C.D” and
dstmask
as
“0.0.0.0”.
•
[precedence
precedence
| tos
tos
[
tosmask
] | dscp
dscp
]—
Specifies the TOS
for an IP/TCP/UDP ACL rule depending on a match of precedence or
DSCP values using the parameters dscp, precedence, or tos tosmask.
2CSNXXX_SWUM200.book Page 262 Tuesday, December 10, 2013 1:22 PM

ACL Commands 263
•
flag [+fin | -fin] [+syn | -syn] [+rst | -rst] [+psh | -psh] [+ack | -ack] [+urg
| -urg] [established]—
Specifies that the IP/TCP/UDP ACL rule matches on
the TCP flags.
–
Ack
– Acknowledgement bit
–
Fin
– Finished bit
–
Psh
– push bit
–
Rst
– reset bit
–
Syn
– Synchronize bit
–
Urg
– Urgent bit
– When “+<tcpflagname>
”
is specified, a match occurs if specified
<tcpflagname> flag is set in the TCP header.
– When “-<tcpflagname>
”
is
specified, a match occurs if specified
<tcpflagname> flag is *NOT* set in the TCP header.
– When “established
” is
specified, a match occurs if either the RST or
ACK bits are set in the TCP header.
– This option is visible only if protocol is “tcp”.
•
[icmp-type
icmp-type
[icmp-code
icmp-code
] |
icmp-message
icmp-message
]
—
Specifies a match condition for ICMP packets.
– When icmp-type is specified, IP ACL rule matches on the specified
ICMP message type, a number from 0 to 255.
– When icmp-code is specified, IP ACL rule matches on the specified
ICMP message code, a number from 0 to 255.
– Specifying icmp-message implies both icmp-type and icmp-code are
specified.
– ICMP message is decoded into corresponding ICMP type and ICMP
code within that ICMP type. This option is visible only if the protocol
is “icmp”.
– IPv4 ICMP message types: echo echo-reply host-redirect mobile-
redirect net-redirect net-unreachable redirect packet-too-big port-
unreachable source-quench router-solicitation router-advertisement
time-exceeded ttl-exceeded unreachable
•igmp-type
igmp-type
—When igmp-type is specified, IP ACL rule matches
on the specified IGMP message type (i.e., a number from 0 to 255).
2CSNXXX_SWUM200.book Page 263 Tuesday, December 10, 2013 1:22 PM

264 ACL Commands
•
fragments—
Specifies the rule matches packets that are non-initial
fragments (fragment bit asserted). Not valid for rules that match L4
information such as TCP port number since that information is carried in
the initial packet.
This keyword is visible only if the protocol is IP, TCP, or UDP.
•
log—
Specifies that this rule is to be logged.
• time-range
time-range-name
—Allows imposing time limitation on the
ACL rule as defined by the parameter time-range-name. If a time range
with the specified name does not exist and the ACL containing this ACL
rule is applied to an interface or bound to a VLAN, then the ACL rule is
applied immediately. If a time range with specified name exists and the
ACL containing this ACL rule is applied to an interface or bound to a
VLAN, then the ACL rule is applied when the time-range with specified
name becomes active. The ACL rule is removed when the time-range with
specified name becomes inactive.
• assign-queue
queue-id
—Specifies the assign-queue, which is the queue
identifier to which packets matching this rule are assigned.
•
{mirror | redirect}
unit/slot/ port
—Specifies the mirror or redirect interface
which is the unit/slot/port to which packets matching this rule are copied
or forwarded, respectively.
•
rate-limit
rate burst-size
—Specifies the allowed rate of traffic as per the
configured rate in kbps, and burst-size in kbytes.
– Rate – the committed rate in kilobits per second
– Burst-size – the committed burst size in Kilobytes.
Default Configuration
No ACLs are configured by default.
Command Mode
Ipv4-Access-List Configuration mode
User Guidelines
Administrators are cautioned to specify permit and deny rule matches as fully
as is possible in order to avoid false matches. Rules that specify an IP port
value should also specify the protocol and and relevant IP addresses or
2CSNXXX_SWUM200.book Page 264 Tuesday, December 10, 2013 1:22 PM

ACL Commands 265
subnets. In general, any rule that specifies matching on an upper layer
protocol field should also include matching constraints for lower layer
protocol fields. For example, a rule to match packets directed to the well-
known UDP port number 22 (SSH) should also include constraints on the IP
protocol field (UDP). Below is a list of commonly used ethertypes:
In order to provide the greatest amount of flexibility in configuring ACLs, the
permit/deny syntax allows combinations of matching criteria that may not
make sense when applied in practice.
Port ranges are not supported for ACLs configured in egress (out) access-
groups. This means that only the eq operator is supported in an egress (out)
ACL.
The protocol type must be tcp or udp to specify a port range.
The fragment keyword is not supported for ACLs configured in egress (out)
IPv4 access-groups.
Ethertype Protocol
0x0800 Internet Protocol version 4 (IPv4)
0x0806 Address Resolution Protocol (ARP)
0x0842 Wake-on LAN Packet
0x8035 Reverse Address Resolution Protocol (RARP)
0x8100 VLAN tagged frame (IEEE 802.1Q)
0x86DD Internet Protocol version 6 (IPv6)
0x8808 MAC Control
0x8809 Slow Protocols (IEEE 802.3)
0x8870 Jumbo frames
0x888E EAP over LAN (EAPOL – 802.1x)
0x88CC Link Layer Discovery Protocol
0x8906 Fibre Channel over Ethernet
0x8914 FCoE Initialization Protocol
0x9100 Q in Q
2CSNXXX_SWUM200.book Page 265 Tuesday, December 10, 2013 1:22 PM

266 ACL Commands
The rate-limit command is not supported for ACLs configured in egress (out)
IPv4 access-groups.
Any – is equivalent to 0.0.0.0 255.255.255.255 for IPv4 access lists
Host – indicates specified address with mask equal to 255.255.255.255 and
address 0.0.0.0 for IPv4.
The command accepts the optional time-range parameter. The time-range
parameter allows imposing a time limitation on the IP ACL rule as defined by
the parameter
time-range-name
. If a time range with the specified name does
not exist, and the IP ACL containing this ACL rule is applied to an interface
or bound to a VLAN, then the ACL rule is applied immediately. If a time
range with the specified name exists, and the IP ACL containing this ACL
rule is applied to an interface or bound to a VLAN, then the ACL rule is
applied when the time-range with a specified name becomes active. The ACL
rule is removed when the time-range with a specified name becomes inactive.
The no form of this command is not supported, as the rules within an ACL
cannot be deleted individually. Rather the entire ACL must be deleted and
respecified.
Example
console(config-ip-acl)#deny ip any any precedence 3
deny | permit (Mac-Access-List-Configuration)
Use the deny command in Mac-Access-List Configuration mode to deny
traffic if the conditions defined in the deny statement are matched. Use the
permit command in Mac-Access-List Configuration mode to allow traffic if
the conditions defined in the permit statement are matched.
Use this command in Mac-Access-List Configuration mode to create a new
rule for the current MAC access list. Each rule is appended to the list of
configured rules for the list.
The command is enhanced to accept the optional time-range parameter. The
time-range parameter allows imposing a time limitation on the MAC ACL
rule as defined by the parameter
time-range-name
. If a time range with the
specified name does not exist, and the MAC ACL containing this ACL rule is
applied to an interface or bound to a VLAN, then the ACL rule is applied
immediately. If a time range with the specified name exists, and the MAC
ACL containing this ACL rule is applied to an interface or bound to a VLAN,
2CSNXXX_SWUM200.book Page 266 Tuesday, December 10, 2013 1:22 PM

ACL Commands 267
then the ACL rule is applied when the time-range with a specified name
becomes active. The ACL rule is removed when the time-range with a
specified name becomes inactive.
Syntax
{deny | permit} {{any |
srcmac srcmacmask
} {any | bpdu |
dstmac
dstmacmask}} [
ethertypekey
|
0x0600-0xFFFF
] vlan {eq
0-4095
}] [cos
0-7
]
[[log] [time-range
time-range-name
] [assign-queue
queue-id
] [{mirror |
redirect}
interface-id
]
•
srcmac
—Valid source MAC address in format xxxx.xxxx.xxxx.
•
srcmacmask
—Valid MAC address bitmask for the source MAC address in
format xxxx.xxxx.xxxx.
•
any
—Packets sent to or received from any MAC address.
•
dstmac
—Valid destination MAC address in format xxxx.xxxx.xxxx.
•
destmacmask
—Valid MAC address bitmask for the destination MAC
address in format xxxx.xxxx.xxxx.
•
bpdu
—Bridge protocol data unit
•
ethertypekey
—Either a keyword or valid four-digit hexadecimal number.
(Range: Supported values are appletalk, arp, ibmsna, ipv4, ipv6, ipx,
mplsmcast, mplsucast, Netbios, novell, pppoe, rarp.)
•
0x0600-0xFFFF
—Specify custom ethertype value (hexadecimal range
0x0600-0xFFFF).
•
vlan eq
—VLAN number. (Range 0-4095)
•
cos
—
Class of service. (Range 0-7)
•
log
—
Specifies that this rule is to be logged.
•
time-range-name
—Use the
time-range
parameter to impose a time
limitation on the MAC ACL rule as defined by the parameter.
•
assign-queue
—
Specifies particular hardware queue for handling traffic that
matches the rule.
•
queue-id
—
0-6, where n is number of user configurable queues available for that
hardware platform.
•
mirror
—
Copies the traffic matching this rule to the specified interface.
•
redirect
—
Forwards traffic matching this rule to the specified physical interface.
2CSNXXX_SWUM200.book Page 267 Tuesday, December 10, 2013 1:22 PM

268 ACL Commands
•
interface
—
Valid physical interface in
unit/slot/port
format, for example 1/0/12.
Default Configuration
This command has no default configuration.
Command Mode
Mac-Access-List Configuration mode
User Guidelines
The no form of this command is not supported, as the rules within an ACL
cannot be deleted individually. Rather the entire ACL must be deleted and
respecified.
The assign-queue and redirect parameters are only valid for permit
commands.
Example
The following example configures a MAC ACL to deny traffic from MAC
address 0806.c200.0000.
console(config)#mac access-list extended DELL123
console(config-mac-access-list)#deny 0806.c200.0000 ffff.ffff.ffff any
ip access-group
Use the ip access-group command in Global and Interface Configuration
modes to apply an IP-based ACL on an Ethernet interface or a group of
interfaces. An IP based ACL should have been created by the access-list
name
… command with the same name specified in this command.
Use the no ip access-group command to disable an IP-based ACL on an
Ethernet interface or a group of interfaces.
Syntax
ip access-group
name
[in | out | control-plane]
[seqnum]
no ip access-group
name
direction seqnum
•
name
— Access list name. (Range: Valid IP access-list name up to 31
characters in length)
2CSNXXX_SWUM200.book Page 268 Tuesday, December 10, 2013 1:22 PM

ACL Commands 269
•
in
— The access list is applied to ingress packets.
•
out
—The access list is applied to egress packets.
•
control-plane
—The access list is applied to egress control plane packets
only. This is only available in Global Configuration mode.
•
seqnum
— Precedence for this interface and direction. A lower sequence
number has higher precedence. Range: 1 – 4294967295. Default is
1
.
Default Configuration
This command has no default configuration.
Command Mode
Global Configuration and Interface Configuration (Ethernet, VLAN, or Port
Channel) modes
User Guidelines
Global mode command configures the ACL on all the interfaces, whereas the
interface mode command does so for the interface.
The optional control-plane keyword allows application of an ACL on the CPU
port. Control-plane matches actions occur in the egress direction. System
level rules are applied on ingress, after application of any user defined ingress
rules, therefore, it is not possible to rate limit packets matching the system
defined rules with an ACL having a control-plane target. Use the rate-limit
cpu command to reduce the effects of low priority traffic on the switch CPU.
An implicit deny-all rule is added after the end of the last access group in each
direction (in or out).
Examples
console(config)#ip access-group aclname in
console(config)#no ip access-group aclname in
console(config)#ip access-group aclname1 out
console(config)#interface te1/0/1
console(config-if-Te1/0/1)#ip access-group aclname out 2
console(config-if-Te1/0/1)#no ip access-group aclname out
2CSNXXX_SWUM200.book Page 269 Tuesday, December 10, 2013 1:22 PM

270 ACL Commands
mac access-group
Use the mac access-group command in Global Configuration or Interface
Configuration mode to attach a specific MAC Access Control List (ACL) to
an interface.
Syntax
mac access-group
name
[in | out | control-plane]
[
sequence
]
no mac access-group
name
• name — Name of the existing MAC access list. (Range: 1-31 characters)
• [in | out | control-plane]— The packet direction.
in
applies the access-list
to ingress packets.
out
applies the access-list to egress packets. control-
plane applies the access-list to ingress control plane packets. control-plane
is only valid in Global Configuration mode.
•
sequence
— Order of access list relative to other access lists already
assigned to this interface and direction. (Range: 1-4294967295)
Default Configuration
No ACLs are configured by default.
Command Mode
Global Configuration mode or Interface Configuration (Ethernet, VLAN or
Port Channel) mode
User Guidelines
An optional sequence number may be specified to indicate the order of this
access-list relative to the other access-lists already assigned to this interface
and direction. A lower number indicates higher precedence order. If a
sequence number already is in use for this interface and direction, the
specified access-list replaces the currently attached access list using that
sequence number. If the sequence number is not specified for this command,
a sequence number is selected that is one greater than the highest sequence
number currently in use for this interface and direction.
The optional control-plane keyword allows the application of a MAC ACL on
the CPU port.
2CSNXXX_SWUM200.book Page 270 Tuesday, December 10, 2013 1:22 PM

ACL Commands 271
This command specified in Interface Configuration mode only affects a
single interface.
Example
This example rate limits multicast traffic ingressing the internal CPU port to
8 kbps and a maximum burst of 4 kilobytes. This affects both unknown
multicast data plane traffic as well as control plane traffic. While this ACL
may be useful in mitigating the effect of unknown multicast traffic on the
switch CPU, use of this rule in the ingress or egress direction is highly likely to
disrupt normal multicast traffic.
11-11(config)# mac access-list extended unkn-multicast
11-11(config-mac-access-list)#permit 01:00:5e:00:00:00 ff:ff:ff:00:00:00 any
rate-limit 8 4
11-11(config-mac-access-list)#permit any any
11-11(config-mac-access-list)#exit
11-11(config)#mac access-group unkn-multicast control-plane
mac access-list extended
Use the mac access-list extended command in Global Configuration mode to
create the MAC Access Control List (ACL) identified by the
name
parameter
and enter MAC Access-list Configuration mode.
Syntax
mac access-list extended
name
no mac access-list extended
name
•
name
— Name of the access list. (Range: 1-31 characters)
Default Configuration
This command has no default configuration.
Command Mode
Global Configuration mode
2CSNXXX_SWUM200.book Page 271 Tuesday, December 10, 2013 1:22 PM

272 ACL Commands
User Guidelines
Use this command to create a mac access control list. The CLI mode is
changed to Mac-Access-List Configuration when this command is
successfully executed.
Example
The following example creates MAC ACL and enters MAC-Access-List-
Configuration mode.
console(config)#mac access-list extended LVL7DELL
console(config-mac-access-list)#
mac access-list extended rename
Use the mac access-list extended rename command in Global Configuration
mode to rename the existing MAC Access Control List (ACL).
Syntax
mac access-list extended rename
name newname
•
name
— Existing name of the access list. (Range: 1-31 characters)
•
newname
— New name of the access list. (Range: 1-31 characters)
Default Configuration
This command has no default configuration.
Command Mode
Global Configuration mode
User Guidelines
Command fails if the new name is the same as the old one.
Example
The following example shows the mac access-list extended rename
command.
console(config)#mac access-list extended rename DELL1 DELL2
2CSNXXX_SWUM200.book Page 272 Tuesday, December 10, 2013 1:22 PM

ACL Commands 273
service-acl input
Use the service-acl input command in Interface Configuration mode to block
Link Local Protocol Filtering (LLPF) protocol(s) on a given port. Use the no
form of this command to unblock link-local protocol(s) on a given port.
Syntax
service-acl input {blockcdp | blockvtp | blockdtp | blockudld | blockpagp |
blocksstp | blockall}
no service-acl input
•
blockcdp
—
To block CDP PDU’s from being forwarded.
•
blockvtp
—
To block VTP PDU’s from being forwarded.
•
blockdtp
—
To block DTP PDU’s from being forwarded.
•
blockudld
—
To block UDLD PDU’s from being forwarded.
•
blockpagp
—
To block PAgP PDU’s from being forwarded.
•
blocksstp
—
To block SSTP PDU’s from being forwarded.
•
blockall
—
To block all the PDU’s with MAC of 01:00:00:0c:cc:cx (x-don’t care)
from being forwarded.
Default Configuration
This command has no default configuration.
Command Mode
Interface Configuration (Ethernet, Port-channel)
User Guidelines
To specify multiple protocols, enter the protocol parameters together on the
command line, separated by spaces. This command can only be entered once
per interface if no intervening no service-acl input command has been
entered.
Example
console(config-if-Te1/0/1)#service-acl input blockall
2CSNXXX_SWUM200.book Page 273 Tuesday, December 10, 2013 1:22 PM

274 ACL Commands
show service-acl interface
This command displays the status of LLPF rules configured on a particular
port or on all the ports.
Syntax
show service-acl interface {
interface-id
| all}
•
interface-id—Any physical or logical interface. See
Interface Naming
Conventions
for interface representation.
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC mode, Configuration mode and all Configuration submodes
User Guidelines
This command has no user guidelines.
Example
console#show service-acl interface gi1/0/1
Block CDP................................ Enable
Block VTP.................................Enable
Block DTP..................................Enable
Block UDLD................................ Enable
Block PAGP.................................Enable
Block SSTP................................ Enable
Block All................................. Enable
show access-lists interface
Use the show access-lists interface command in Privileged EXEC mode to
display interface ACLs.
Syntax
show access-lists interface
interface-id
{in | out} | control-plane
•
interface-id
—
The interface identifier (physical, port-channel, or VLAN).
2CSNXXX_SWUM200.book Page 274 Tuesday, December 10, 2013 1:22 PM

ACL Commands 275
•
in
—
Show the ingress ACLs.
•
out
—
Show the egress ACLs.
•
control-plane
—
Show the control plane ACLs.
Default Configuration
No ACLs are configured by default.
Command Mode
Privileged EXEC mode, Configuration mode and all Configuration submodes
User Guidelines
There are no user guidelines for this command.
Examples
console#show access-lists interface control-plane
ACL Type ACL ID Sequence Number
-------- ------------------------------- ---------------
IPv6 ip61 1
show ip access-lists
Use the show ip access-lists command in Privileged EXEC mode to display an
IP ACL and time-range parameters.
Syntax
show ip access-lists [
accesslistnumber
]
•
accesslistnumber
—
The number used to identify the IP ACL.
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC mode, Configuration mode and all Configuration submodes
2CSNXXX_SWUM200.book Page 275 Tuesday, December 10, 2013 1:22 PM

276 ACL Commands
User Guidelines
There are no user guidelines for this command.
Examples
The following example displays IP ACLs configured on a device.
console#show ip access-lists
ACL Name: ip1
Inbound Interface(s): gi1/0/30
Rule Number: 1
Action......................................... permit
Match All...................................... FALSE
Protocol....................................... 1(icmp)
Committed Rate................................. 32
Committed Burst Size........................... 16
show mac access-lists
Use the show mac access-lists command in Privileged EXEC mode to display
a MAC access list and all the rules that are defined for the MAC ACL. Use
the [name] parameter to identify a specific MAC ACL to display.
Syntax
show mac access-lists
name
• name—Use this parameter to identify the specific MAC ACL to display.
Default Configuration
This command has no default configuration
Command Mode
Privileged EXEC mode, Configuration mode and all Configuration submodes
User Guidelines
This command has no user guidelines.
Example
11-11#show mac access-lists unkn-multicast
2CSNXXX_SWUM200.book Page 276 Tuesday, December 10, 2013 1:22 PM

ACL Commands 277
MAC ACL Name: unkn-multicast
Inbound Interface(s): control-plane
Rule Number: 1
Action......................................... permit
Source MAC Address............................. 0100.5E00.0000
Source MAC Mask................................ FFFF.FF00.0000
Committed Rate................................. 8
Committed Burst Size........................... 4
Rule Number: 2
Action......................................... permit
Match All...................................... TRUE
2CSNXXX_SWUM200.book Page 277 Tuesday, December 10, 2013 1:22 PM

278 ACL Commands
2CSNXXX_SWUM200.book Page 278 Tuesday, December 10, 2013 1:22 PM

Address Table Commands 279
7
Address Table Commands
Dell Networking N2000/N3000/N4000 Series Switches
Static MAC Filtering allows the administrator to add a number of unicast or
multicast MAC addresses directly to the forwarding database. This is typically
a small number relative to the total size of the database. Associated with each
static MAC address is a set of source ports, a set of destination ports and
VLAN information.
Any packet with a particular static MAC address in a particular VLAN is
admitted only if the ingress port is in the set of source ports; otherwise, the
packet is dropped. On the egress side, the packet, if admitted, is sent out of all
the ports that are in the set of destination ports.
Upon ingress, each packet's destination MAC address is compared against the
forwarding database. If the address is not in the table, the packet is flooded to
all other ports in the VLAN. If the address is in the table, then it is checked to
see if it has been defined as a filter. If the MAC address is not defined as a
filter, then the packet is forwarded.
If the specific destination MAC address is defined as a filter, then the ingress
port number is compared to the set of source ports listed for the address. If
the port of ingress is not in the set of source ports, then the packet is
immediately discarded. If the ingress port is a member of the set of source
ports, then the packet is admitted.
For packets admitted because of a MAC filter match only, the following
additional steps are performed. Note that all other egress processing remains
unchanged. At the egress port, if the destination port number is in the set of
destination ports, the packet is forwarded. If the destination port is not in the
set of destination ports, then the packet is discarded.
Static entries are never aged and can only be removed by user command.
2CSNXXX_SWUM200.book Page 279 Tuesday, December 10, 2013 1:22 PM

280 Address Table Commands
Commands in this Chapter
This chapter explains the following commands:
clear mac address-table
Use the clear mac address-table command in Privileged EXEC mode to
remove learned entries from the forwarding database.
Syntax
clear mac address-table dynamic [address
mac-addr
| interface
interface-id
|
vlan
vlan-id
]
•
mac-addr
—
Delete the specified MAC address.
•
interface-id
—
Delete all dynamic MAC addresses on the specified physical port
or port channel.
•
vlan-id
—
Delete all dynamic MAC addresses for the specified VLAN. The range
is 1 to 4093.
Default Configuration
This command has no default configuration.
clear mac address-table show mac address-table
multicast
show mac address-table
interface
mac address-table aging-
time
show mac address-table show mac address-table
static
mac address-table multicast
forbidden address
show mac address-table
address
show mac address-table vlan
mac address-table static
vlan
show mac address-table
count
show ports security
port security show mac address-table
count
show ports security
addresses
port security max show mac address-table
dynamic
–
2CSNXXX_SWUM200.book Page 280 Tuesday, December 10, 2013 1:22 PM

Address Table Commands 281
Command Mode
Privileged EXEC mode
User Guidelines
This command has no user guidelines.
Example
In this example, the mac address-table tables are cleared.
console#clear mac address-table dynamic
mac address-table aging-time
Use the mac address-table aging-time command in Global Configuration
mode to set the aging time of the address. To restore the default, use the no
form of the mac address table aging-time command.
Syntax
mac address-table aging-time
{0 |
10-1000000
}
no mac address-table aging-time
•
0
—
Disable aging time for the MAC Address Table.
•
10-1000000
—
Set the
number of seconds
aging time for the MAC Address
Tab le .
Default Configuration
300 seconds
Command Mode
Global Configuration mode
User Guidelines
This command has no user guidelines.
Example
In this example the MAC Address Table aging time is set to 400.
2CSNXXX_SWUM200.book Page 281 Tuesday, December 10, 2013 1:22 PM

282 Address Table Commands
console(config)#mac address-table aging-time 400
mac address-table multicast forbidden address
Use the mac address-table multicast forbidden address command in Global
Configuration mode to forbid adding a specific Multicast address to specific
ports. To return to the system default, use the no form of this command. If
routers exist on the VLAN, do not change the unregistered multicast
addresses state to
drop
on the routers ports.
Syntax
mac address-table multicast forbidden address vlan
vlan-id
{
mac-multicast-
address
|
ip-multicast-address
} {add | remove} interface {gigabitethernet |
port-channel | tengigabitethernet | fortygigabitethernet}
interface-list
no mac address-table multicast forbidden address vlan
vlan-id
{
mac-
multicast-address
|
ip-multicast-address
}
•
add
—
Adds ports to the group. If no option is specified, this is the default
option.
•
remove
—
Removes ports from the group.
•
vlan
vlan-id
—
A valid vlan-id. (Range 1-4093)
•
mac-multicast-address
—MAC Multicast address
in the format
xxxx.xxxx.xxxx.
•
ip-multicast-address
—
IP Multicast address.
•
interface-list
—
Specify a comma separated list of interfaces, a range of
interfaces, or a combination of both. Interfaces can be port-channel numbers or
physical ports in unit/slot/port format.
Default Configuration
No forbidden addresses are defined.
Command Mode
Global Configuration mode
User Guidelines
Before defining forbidden ports, ensure that the Multicast group is registered.
2CSNXXX_SWUM200.book Page 282 Tuesday, December 10, 2013 1:22 PM

Address Table Commands 283
Examples
In this example the MAC address 0100.5e02.0203 is forbidden on port 2/0/9
within VLAN 8.
console(config)#mac address-table multicast forbidden address vlan 8
0100.5e02.0203 add gigabitethernet 2/0/9
mac address-table static vlan
Use the mac address table static vlan command in Global Configuration
mode to add a static MAC-layer station source address to the bridge table. To
delete the MAC address, use the no form of the mac address table static
command.
Syntax
mac address-table static
mac-addr
vlan
vlan-id
interface
{gigabitethernet|port-channel|tengigabitethernet}
interface-id
no mac address table static
mac-addr
vlan
vlan-id
{gigabitethernet|port-
channel|tengigabitethernet}
interface-id]
•
mac-address
—
A valid MAC address in the format xxxx.xxxx.xxxx or
xx:xx:xx:xx:xx:xx
•
vlan-id
—
Valid VLAN ID (1-4093)
•
interface-id
—
The interface to which the received packet is forwarded.
Default Configuration
No static addresses are defined. The default mode for an added address is
permanent.
Command Mode
Global Configuration mode
User Guidelines
The MAC address may be a unicast or multicast MAC address. Static MAC
addresses are never overridden by dynamically learned addresses. This has
implications for protocols like IGMP snooping, where statically configuring
the MAC address of a multicast router keeps IGMP snooping from
dynamically adding the multicast router to a different port.
2CSNXXX_SWUM200.book Page 283 Tuesday, December 10, 2013 1:22 PM

284 Address Table Commands
Example
The following example adds a permanent static MAC-layer station source
address c2f3.220a.12f4 to the MAC address table.
console(config)# mac address-table static c2f3.220a.12f4 vlan 4 interface
gigabitethernet6/0/1
port security
Use the port security command in Interface Configuration mode to disable
the learning of new addresses on an interface. To enable new address learning,
use the no form of the port security command.
Syntax
port security [discard]
no port security
•
discard
— Discards frames with unlearned source addresses. This is the
default if no option is indicated.
Default Configuration
Disabled—No port security
Command Mode
Interface Configuration (gigabitethernet, port-channel, tengigabitethernet,
fortygigabitethernet) mode, Interface Range mode, Port-Channel Range
mode
User Guidelines
When port security is enabled on an interface, all dynamic entries learned up
to that point are flushed, and new entries can be learned only to the limit set
by the port security max command. The default limit is 100 dynamic MAC
addresses.
Example
In this example, frame forwarding is enabled without learning, and with traps
sent every 100 seconds on port gi1/0/1.
2CSNXXX_SWUM200.book Page 284 Tuesday, December 10, 2013 1:22 PM

Address Table Commands 285
console(config)#interface gigabitethernet te1/0/1
console(config-if-Te1/0/1)#port security trap 100
port security max
Use the port security max command in Interface Configuration mode to
configure the maximum addresses that can be learned on the port while the
port is in port security mode. To return to the system default, use the no form
of this command.
Syntax
port security max
max-addr
no port security max
•
max-addr
— The maximum number of addresses that can be learning on
the port. (Range: 0-600)
Default Configuration
The default value for this command is 100.
Command Mode
Interface Configuration (gigabitethernet, port-channel, tengigabitethernet,
fortygigabitethernet) mode, Configuration mode and all Configuration
submodes
User Guidelines
This command has no user guidelines.
Example
The following example shows using this command in Ethernet Interface
Configuration mode.
console(config-if-Te1/0/3)# port security max 80
show mac address-table multicast
Use the show mac address-table multicast command in Privileged EXEC
mode to display Multicast MAC address table information.
2CSNXXX_SWUM200.book Page 285 Tuesday, December 10, 2013 1:22 PM

286 Address Table Commands
Syntax
show mac address-table multicast [vlan
vlan-id
]
[address {
mac-multicast-
address
|
ip-multicast-address
}] [format {ip | mac}]
•
vlan_id
— A valid VLAN ID value.
•
mac-multicast-address
— A valid MAC Multicast address.
•
ip- multicast-address —
A valid IP Multicast address.
•
format
—
Multicast address format. Can be
ip
or
mac
.
Default Configuration
If format is unspecified, the default is mac.
Command Mode
Privileged EXEC mode, Configuration mode and all Configuration submodes
User Guidelines
A MAC address can be displayed in IP format only if it is in the range
01:00:5e:00:00:00 through 01:00:5e:7f:ff:ff.
Example
In this example, Multicast MAC address table information is displayed.
console#show mac address-table multicast
Vlan MAC Address Type Ports
----- ------------------- ------- ------------------
1 0100.5E05.0505 Static
Forbidden ports for multicast addresses:
Vlan MAC Address Ports
---- ----------------------- ---------------------------
1 0100.5E05.0505
NOTE: A multicast MAC address maps to multiple IP addresses, as shown above.
2CSNXXX_SWUM200.book Page 286 Tuesday, December 10, 2013 1:22 PM

Address Table Commands 287
show mac address-table
Use the show mac address-table command in User EXEC or Privileged EXEC
mode to display all entries in the bridge-forwarding database.
Syntax
show mac address-table
Default Configuration
This command has no default configuration.
Command Mode
User EXEC, Privileged EXEC mode, Configuration mode and all
Configuration submodes
User Guidelines
This command has no user guidelines.
Example
In this example, all classes of entries in the mac address-table are displayed.
console#show mac address-table
Aging time is 300 Sec
Vlan Mac Address Type Port
---- ---------------- ---------- -----------
0 001E.C9AA.AE19 Management CPU Interface: 0/5/
1 001E.C9AA.AC19 Dynamic Gi1/0/21
1 001E.C9AA.AE1B Management Vl1
10 001E.C9AA.AE1B Management Vl10
90 001E.C9AA.AE1B Management Vl90
Total MAC Addresses in use: 5
show mac address-table address
Use the show mac address-table address command in User EXEC or
Privileged EXEC mode to display all entries in the bridge-forwarding database
for the specified MAC address.
2CSNXXX_SWUM200.book Page 287 Tuesday, December 10, 2013 1:22 PM

288 Address Table Commands
Syntax
show mac address-table address
mac-address
[interface
interface-id
] [vlan
vlan-id
]
•
mac-address
—
A MAC address with the format xxxx.xxxx.xxxx.
•
interface-id
—
Display information for a specific interface. Valid interfaces
include physical ports and port channels.
•
vlan-id
—
Display entries for the specific VLAN only. The range is 1 to 4093.
Default Configuration
This command has no default configuration.
Command Mode
User EXEC, Privileged EXEC mode, Configuration mode and all
Configuration submodes
User Guidelines
This command has no user guidelines.
Example
In this example, the mac address table entry for 0000.E26D.2C2A is
displayed.
console#show mac address-table address 0000.E26D.2C2A
Vlan Mac Address Type Port
---- -------------- -------- -------------
1 0000.E26D.2C2A Dynamic 1/0/1
show mac address-table count
Use the show mac address-table count command in User EXEC or Privileged
EXEC mode to display the number of addresses present in the Forwarding
Database.
Syntax
show mac address-table count [vlan
vlan-id
| interface
interface-id
]
2CSNXXX_SWUM200.book Page 288 Tuesday, December 10, 2013 1:22 PM

Address Table Commands 289
•
interface-id
—
Specify an interface type; valid interfaces include physical ports
and port channels.
•
vlan-id
—
Specify a valid VLAN, the range is 1 to 4093.
Default Configuration
This command has no default configuration.
Command Mode
User EXEC, Privileged EXEC mode, Configuration mode and all
Configuration submodes
User Guidelines
This command has no user guidelines.
Example
The following example displays the addresses in the Forwarding Database:
console#show mac address-table count
Capacity: 8192
Used: 109
Static addresses: 2
Secure addresses: 1
Dynamic addresses: 97
Internal addresses: 9
show mac address-table dynamic
Use the show mac address-table command in User EXEC or Privileged EXEC
mode to display all dynamic entries in the bridge-forwarding database.
Syntax
show mac address-table dynamic [address
mac-address
] [interface
interface-
id
] [vlan
vlan-id
]
•
mac-address
—
A MAC address with the format xxxx.xxxx.xxxx.
•
interface-id
—
Display information for a specific interface. Valid interfaces
include physical ports and port channels.
•
vlan-id
—
Display entries for the specific VLAN only. The range is 1 to 4093.
2CSNXXX_SWUM200.book Page 289 Tuesday, December 10, 2013 1:22 PM

290 Address Table Commands
Default Configuration
This command has no default configuration.
Command Mode
User EXEC, Privileged EXEC mode, Configuration mode and all
Configuration submodes
User Guidelines
This command has no user guidelines.
Example
In this example, all dynamic entries in the mac address-table are displayed.
console#show mac address-table dynamic
Aging time is 300 Sec
Vlan Mac Address Type Port
---- -------------- ------- -------------
1 0000.0001.0000 Dynamic gi1/0/1
1 0000.8420.5010 Dynamic gi1/0/1
1 0000.E26D.2C2A Dynamic gi1/0/1
1 0000.E89A.596E Dynamic gi1/0/1
1 0001.02F1.0B33 Dynamic gi1/0/1
show mac address-table interface
Use the show mac address-table command in User EXEC or Privileged EXEC
mode to display all entries in the mac address-table.
Syntax
show mac address-table interface
interface-id
[vlan
vlan-id
]
•
interface-id
—
Specify an interface type.Valid interfaces include physical ports
and port channels.
•
vlan-id
—
Specify a valid VLAN. The range is 1 to 4093.
Default Configuration
This command has no default configuration.
2CSNXXX_SWUM200.book Page 290 Tuesday, December 10, 2013 1:22 PM

Address Table Commands 291
Command Mode
User EXEC, Privileged EXEC mode, Configuration mode and all
Configuration submodes
User Guidelines
This command has no user guidelines.
Example
In this example, all classes of entries in the bridge-forwarding database for
gigabit Ethernet interface 1/0/1 are displayed.
console#show mac address-table interface gigabitethernet 1/0/1
Aging time is 300 Sec
Vlan Mac Address Type Port
---- -------------- ---- -------------
1 0000.0001.0000 Dynamic gi1/0/1
1 0000.8420.5010 Dynamic gi1/0/1
1 0000.E26D.2C2A Dynamic gi1/0/1
1 0000.E89A.596E Dynamic gi1/0/1
1 0001.02F1.0B33 Dynamic gi1/0/1
show mac address-table static
Use the show mac address-table static command in User EXEC or Privileged
EXEC mode to display static entries in the bridge-forwarding database.
Syntax
show mac address-table static [address
mac-address
] [interface
interface-id
]
[vlan
vlan-id
]
•
mac-address
—
A MAC address with the format xxxx.xxxx.xxxx.
•
interface-id
—
Specify an interface type; valid interfaces include physical ports
and port channels.
•
vlan-id
—
Specify a valid VLAN; the range is 1 to 4093.
Default Configuration
This command has no default configuration.
2CSNXXX_SWUM200.book Page 291 Tuesday, December 10, 2013 1:22 PM

292 Address Table Commands
Command Mode
User EXEC, Privileged EXEC mode, Configuration mode and all
Configuration submodes
User Guidelines
This command has no user guidelines.
Example
In this example, all static entries in the bridge-forwarding database are
displayed.
console#show mac address-table static
Vlan Mac Address Type Port
---- -------------- ----- -----
1 0001.0001.0001 Static gi1/0/1
show mac address-table vlan
Use the show mac address-table vlan command in User EXEC or Privileged
EXEC mode to display all entries in the bridge-forwarding database for the
specified VLAN.
Syntax
show mac address-table [vlan
vlan-id
]
•
vlan-id
—
Specify a valid VLAN; the range is 1 to 4093.
Default Configuration
This command has no default configuration.
Command Mode
User EXEC, Privileged EXEC mode, Configuration mode and all
Configuration submodes
User Guidelines
This command has no user guidelines.
2CSNXXX_SWUM200.book Page 292 Tuesday, December 10, 2013 1:22 PM

Address Table Commands 293
Example
In this example, all classes of entries in the bridge-forwarding database are
displayed.
console#show mac address-table vlan 1
Mac Address Table
-------------------------------------
Vlan Mac Address Type Ports
---- --------------- ------- -------
1 0000.0001.0000 Dynamic gi1/0/1
1 0000.8420.5010 Dynamic gi1/0/1
1 0000.E26D.2C2A Dynamic gi1/0/1
1 0000.E89A.596E Dynamic gi1/0/1
1 0001.02F1.0B33 Dynamic gi1/0/1
Total Mac Addresses for this criterion: 5
show ports security
Use the show ports security command in Privileged EXEC mode to display
the port-lock status.
Syntax
show ports security [{gigabitethernet unit/slot/port|
port-channel
port-
channel-number
| tengigabitethernet unit/slot/port | fortygigabitethernet
unit/slot/port}]
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC mode, Configuration mode and all Configuration submodes
User Guidelines
This command has no user guidelines.
Example
In this example, all classes of entries in the port-lock status are displayed.
console#show ports security
2CSNXXX_SWUM200.book Page 293 Tuesday, December 10, 2013 1:22 PM

294 Address Table Commands
Port Status Action Maximum Trap Frequency
---- ------ ---------- -------- ------- -------
1/0/1 Locked Discard 3 Enable 100
1/0/2 Unlocked - 28 - -
1/0/3 Locked Discard 8 Disable -
The following table describes the fields in this example.
show ports security addresses
Use the show ports security addresses command in Privileged EXEC mode to
display current dynamic addresses in locked ports.
Syntax
show ports security addresses {gigabitethernet
unit/slot/port
|
port-channel
port-channel-number
| tengigabitethernet
unit/slot/port
|
fortygigabitethernet
unit/slot/port
}
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC mode, Configuration mode and all Configuration submodes
Field Description
Port The port number.
Status The status can be one of the following: Locked
or Unlocked.
Actions Action on violations.
Maximum The maximum addresses that can be associated
on this port in Static Learning mode or in
Dynamic Learning mode.
Trap Indicates if traps would be sent in case of
violation.
Frequency The minimum time between consecutive traps.
2CSNXXX_SWUM200.book Page 294 Tuesday, December 10, 2013 1:22 PM

Address Table Commands 295
User Guidelines
This command has no user guidelines.
Examples
The following example displays dynamic addresses for port channel number
1/0/1.
console#show ports security addresses Te1/0/1
Dynamic addresses: 83
Maximum addresses: 100
Learned addresses
------- ---------
2CSNXXX_SWUM200.book Page 295 Tuesday, December 10, 2013 1:22 PM

296 Address Table Commands
2CSNXXX_SWUM200.book Page 296 Tuesday, December 10, 2013 1:22 PM

Auto-VoIP Commands 297
8
Auto-VoIP Commands
Dell Networking N2000/N3000/N4000 Series Switches
Voice over Internet Protocol (VoIP) allows network users to make telephone
calls using a computer network over a data network like the Internet. With
the increased prominence of delay-sensitive applications (voice, video, and
other multimedia applications) deployed in networks today, proper QoS
configuration ensures high-quality application performance. The Auto-VoIP
feature is intended to provide an easy classification mechanism for voice
packets so that they can be prioritized above data packets in order to provide
better QoS.
The Auto-VoIP feature explicitly matches VoIP streams in Ethernet switches
and provides them with a better class of service than ordinary traffic. The
Auto VoIP module provides the capability to assign the highest priority for
the following VoIP packets:
• Session Initiation Protocol (SIP)
•H.323
• Skinny Client Control Protocol (SCCP)
Auto-VoIP borrows ACL lists from the global system pool. ACL lists allocated
by Auto-VoIP reduce the total number of ACLs available for use by the
network operator. Enabling Auto-VoIP uses one ACL list to monitor for VoIP
sessions. Each monitored VoIP session utilizes two rules from an additional
ACL list. This means that the maximum number of ACL lists allocated by
Auto-VoIP is two. The Auto-VoIP feature limits the maximum number of
simultaneous users to 16. Administrators should utilize the Voice VLAN
feature for deployment of IP voice service in an enterprise network because
Voice VLAN scales to significantly higher numbers of users.
Commands in this Chapter
This chapter explains the following commands:
show switchport voice switchport voice detect auto
2CSNXXX_SWUM200.book Page 297 Tuesday, December 10, 2013 1:22 PM

298 Auto-VoIP Commands
show switchport voice
Use the show switchport voice command to show the status of Auto-VoIP on
an interface or all interfaces.
Syntax
show switchport voice [gigabitethernet unit/slot/port|
port-channel
port-
channel-number
| tengigabitethernet unit/slot/port
|
fortygigabitethernet
unit/slot/port]
Default Configuration
There is no default configuration for this command.
Command Mode
Privileged EXEC mode, Configuration mode and all Configuration submodes
User Guidelines
There are no user guidelines for this command.
Examples
The following example shows command output when a port is not specified:
console#show switchport voice
Interface Auto VoIP Mode Traffic Class
--------- -------------- -------------
Gi1/0/1 Disabled 6
Gi1/0/2 Disabled 6
Gi1/0/3 Disabled 6
Gi1/0/4 Disabled 6
Gi1/0/5 Disabled 6
Gi1/0/6 Disabled 6
Gi1/0/7 Disabled 6
Gi1/0/8 Disabled 6
Gi1/0/9 Disabled 6
Gi1/0/10 Disabled 6
Gi1/0/11 Disabled 6
Gi1/0/12 Disabled 6
Gi1/0/13 Disabled 6
Gi1/0/14 Disabled 6
Gi1/0/15 Disabled 6
2CSNXXX_SWUM200.book Page 298 Tuesday, December 10, 2013 1:22 PM

Auto-VoIP Commands 299
Gi1/0/16 Disabled 6
Gi1/0/17 Disabled 6
Gi1/0/18 Disabled 6
Gi1/0/19 Disabled 6
Gi1/0/20 Disabled 6
Gi1/0/21 Disabled 6
Gi1/0/22 Disabled 6
Gi1/0/23 Disabled 6
Gi1/0/24 Disabled 6
Po1 Disabled 6
Po2 Disabled 6
Po3 Disabled 6
Po4 Disabled 6
Po5 Disabled 6
Po6 Disabled 6
Po7 Disabled 6
Po8 Disabled 6
Po9 Disabled 6
Po10 Disabled 6
Po11 Disabled 6
Po12 Disabled 6
Po13 Disabled 6
Po14 Disabled 6
Po15 Disabled 6
--More-- or (q)uit
The following example shows command output when a port is specified:
console#show switchport voice gigabitethernet 1/0/1
Interface Auto VoIP Mode Traffic Class
--------- -------------- -------------
Gi1/0/1 Disabled 6
The command output provides the following information:
•
AutoVoIP Mode
—The Auto VoIP mode on the interface.
•
Traffic Class
—The Cos Queue or Traffic Class to which all VoIP traffic is
mapped. This is not configurable and defaults to the highest COS queue
available in the system for data traffic.
2CSNXXX_SWUM200.book Page 299 Tuesday, December 10, 2013 1:22 PM

300 Auto-VoIP Commands
switchport voice detect auto
The switchport voice detect auto command is used to enable the VoIP Profile
on all the interfaces of the switch (global configuration mode) or for a specific
interface (interface configuration mode).Use the no form of the command to
disable the VoIP Profile.
Syntax
switchport voice detect auto
no switchport voice detect auto
Default Configuration
This feature is disabled by default.
Command Mode
Global Configuration mode, Configuration mode and all Configuration
submodes, Interface (gigabitethernet, port-channel, tengigabitethernet,
fortygigabitethernet) Configuration mode
User Guidelines
This command has no user guidelines
Example
console(config)#interface tengigabitethernet 1/0/1
console(config-if-Te1/0/1)#switchport voice detect auto
2CSNXXX_SWUM200.book Page 300 Tuesday, December 10, 2013 1:22 PM

CDP Interoperability Commands 301
9
CDP Interoperability Commands
Dell Networking N2000/N3000/N4000 Series Switches
Industry Standard Discovery Protocol (ISDP) is a proprietary Layer 2 network
protocol which inter-operates with Cisco network equipment and is used to
share information between neighboring devices. Dell Networking switches
participate in the ISDP protocol and are able to both discover and be
discovered by devices that support the Cisco Discovery Protocol (CDP).
ISDP is based on CDP, which is a precursor to LLDP.
Commands in this Chapter
This chapter explains the following commands:
clear isdp counters
The clear isdp counters command clears the ISDP counters.
Syntax
clear isdp counters
Default Configuration
There is no default configuration for this command.
Command Mode
Privileged EXEC mode
clear isdp counters show isdp
clear isdp table show isdp entry
isdp advertise-v2 show isdp interface
isdp enable show isdp neighbors
isdp holdtime show isdp traffic
isdp timer
–
2CSNXXX_SWUM200.book Page 301 Tuesday, December 10, 2013 1:22 PM

302 CDP Interoperability Commands
User Guidelines
There are no user guidelines for this command.
Example
console#clear isdp counters
clear isdp table
The clear isdp table command clears entries in the ISDP table.
Syntax
clear isdp table
Default Configuration
There is no default configuration for this command.
Command Mode
Privileged EXEC mode
User Guidelines
There are no user guidelines for this command.
Example
console#clear isdp table
isdp advertise-v2
The isdp advertise-v2 command enables the sending of ISDP version 2
packets from the device. Use the no form of this command to send version 1
packets.
Syntax
isdp advertise-v2
no isdp advertise-v2
2CSNXXX_SWUM200.book Page 302 Tuesday, December 10, 2013 1:22 PM

CDP Interoperability Commands 303
Default Configuration
ISDP sends version 2 packets by default.
Command Mode
Global Configuration mode
User Guidelines
There are no user guidelines for this command.
Example
console(config)#isdp advertise-v2
isdp enable
The isdp enable command enables ISDP on the switch. User the “no” form
of this command to disable ISDP. Use this command in global configuration
mode to enable the ISDP function on the switch. Use this command in
interface mode to enable sending ISDP packets on a specific interface.
Syntax
isdp enable
no isdp enable
Default Configuration
ISDP is enabled.
Command Mode
Global Configuration mode.
Interface (Ethernet) configuration mode.
User Guidelines
There are no user guidelines for this command.
Example
The following example enables isdp on interface 1/0/1.
2CSNXXX_SWUM200.book Page 303 Tuesday, December 10, 2013 1:22 PM

304 CDP Interoperability Commands
console(config)#interface gigabitethernet 1/0/1
console(config-if-Gi1/0/1)#isdp enable
isdp holdtime
The isdp holdtime command configures the hold time for ISDP packets that
the switch transmits. The hold time specifies how long a receiving device
should store information sent in the ISDP packet before discarding it. The
range is given in seconds. Use the no form of this command to reset the
holdtime to the default.
Syntax
isdp holdtime
time
no isdp holdtime
•
time
—The time in seconds (range 10–255 seconds).
Default Configuration
The default holdtime is 180 seconds.
Command Mode
Global Configuration mode
User Guidelines
There are no user guidelines for this command.
Example
The following example sets isdp holdtime to 40 seconds.
console(config)#isdp holdtime 40
isdp timer
The isdp timer command sets period of time between sending new ISDP
packets. The range is given in seconds. Use the “no” form of this command to
reset the timer to the default.
2CSNXXX_SWUM200.book Page 304 Tuesday, December 10, 2013 1:22 PM

CDP Interoperability Commands 305
Syntax
isdp timer
time
no isdp timer
•
time
—The time in seconds (range: 5–254 seconds).
Default Configuration
The default timer is 30 seconds.
Command Mode
Global Configuration mode
User Guidelines
There are no user guidelines for this command.
Example
The following example sets the isdp timer value to 40 seconds.
console(config)#isdp timer 40
show isdp
The show isdp command displays global ISDP settings.
Syntax
show isdp
Default Configuration
There is no default configuration for this command.
Command Mode
Privileged EXEC mode, Configuration mode and all Configuration submodes
User Guidelines
There are no user guidelines for this command.
2CSNXXX_SWUM200.book Page 305 Tuesday, December 10, 2013 1:22 PM

306 CDP Interoperability Commands
Example
console#show isdp
Timer................................ 30
Hold Time............................ 180
Version 2 Advertisements............. Enabled
Neighbors table last time changed.... 0 days 00:06:01
Device ID............................ QTFMPW82400020
Device ID format capability.......... Serial Number
Device ID format..................... Serial Number
show isdp entry
The show isdp entry command displays ISDP entries. If a device id specified,
then only the entry about that device is displayed.
Syntax
show isdp entry {all |
deviceid
}
•
all
—
Show ISDP settings for all devices.
•
deviceid
—
The device ID associated with a neighbor.
Default Configuration
There is no default configuration for this command.
Command Mode
Privileged EXEC mode, Configuration mode and all Configuration submodes
User Guidelines
There are no user guidelines for this command.
Example
console#show isdp entry Switch
Device ID N2000/N3000 SeriesSwitch
Address(es):
IP Address: 172.20.1.18
IP Address: 172.20.1.18
Capability Router IGMP
Platform cisco WS-C4948
Interface 1/0/1
2CSNXXX_SWUM200.book Page 306 Tuesday, December 10, 2013 1:22 PM

CDP Interoperability Commands 307
Port ID GigabitEthernet1/1
Holdtime 64
Advertisement Version 2
Entry last changed time 0 days 00:13:50
Version :
Cisco IOS Software, Catalyst 4000 L3 Switch Software (cat4000 I9K91S-M),
Version 12.2(25)EWA9, RELEASE SOFTWARE (fc3)
Technical Support: http://www.cisco.com/techsupport
Copyright (c) 1986-2007 by Cisco Systems, Inc.
Compiled Wed 21-Mar-07 12:20 by tinhuang
show isdp interface
The show isdp interface command displays ISDP settings for the specified
interface.
Syntax
show isdp interface {all | gigabitethernet unit/slot/port | tengigabitethernet
unit/slot/port | fortygigabitethernet unit/slot/port}
Default Configuration
There is no default configuration for this command.
Command Mode
Privileged EXEC mode, Configuration mode and all Configuration submodes
User Guidelines
There are no user guidelines for this command.
Example
console#show isdp interface all
Interface Mode
--------------- ----------
1/0/1 Enabled
1/0/2 Enabled
1/0/3 Enabled
1/0/4 Enabled
1/0/5 Enabled
1/0/6 Enabled
1/0/7 Enabled
2CSNXXX_SWUM200.book Page 307 Tuesday, December 10, 2013 1:22 PM

308 CDP Interoperability Commands
1/0/8 Enabled
1/0/9 Enabled
1/0/10 Enabled
1/0/11 Enabled
1/0/12 Enabled
1/0/13 Enabled
1/0/14 Enabled
1/0/15 Enabled
1/0/16 Enabled
1/0/17 Enabled
1/0/18 Enabled
1/0/19 Enabled
1/0/20 Enabled
1/0/21 Enabled
1/0/22 Enabled
1/0/23 Enabled
1/0/24 Enabled
console#show isdp interface gigabitethernet 1/0/1
Interface Mode
--------------- ----------
1/0/1 Enabled
show isdp neighbors
The show isdp neighbors command displays the list of neighboring devices.
Syntax
show isdp neighbors {[gigabitethernet
unit/slot/port
| tengigabitethernet
unit/slot/port
| fortygigabitethernet
unit/slot/port
| detail]}
Default Configuration
There is no default configuration for this command.
Command Mode
Privileged EXEC mode, Configuration mode and all Configuration submodes
User Guidelines
The information displayed varies based upon the information received from
the ISDP neighbor.
2CSNXXX_SWUM200.book Page 308 Tuesday, December 10, 2013 1:22 PM

CDP Interoperability Commands 309
Example
console#show isdp neighbors
Capability Codes: R - Router, T - Trans Bridge, B - Source Route, S - Switch,
H - Host, I - IGMP, r - Repeater
Device ID Intf Hold Cap. Platform Port ID
------------- ----- ---- ---------------
Switch1/0/1 165 RI cisco WS-C4948 GigabitEthernet1/1
console#show isdp neighbors detail
Device ID Switch
Address(es):
IP Address: 172.20.1.18
IP Address: 172.20.1.18
Capability Router IGMP
Platform cisco WS-C4948
Interface 1/0/1
Port ID GigabitEthernet1/1
Holdtime 162
Advertisement Version 2
Entry last changed time 0 days 00:55:20
Version :
Cisco IOS Software, Catalyst 4000 L3 Switch Software (cat4000-I9K91S-M),
Version 12.2(25)EWA9, RELEASE SOFTWARE (fc3)
Technical Support: http://www.cisco.com/techsupport
Copyright (c) 1986-2007 by Cisco Systems, Inc.
Compiled Wed 21-Mar-07 12:20 by tinhuang
show isdp traffic
The show isdp traffic command displays ISDP statistics.
Syntax
show isdp traffic
Default Configuration
There is no default configuration for this command.
Command Mode
Privileged EXEC mode, Configuration mode and all Configuration submodes
2CSNXXX_SWUM200.book Page 309 Tuesday, December 10, 2013 1:22 PM

310 CDP Interoperability Commands
User Guidelines
There are no user guidelines for this command.
Example
console#show isdp traffic
ISDP Packets Received.......................... 4253
ISDP Packets Transmitted....................... 127
ISDPv1 Packets Received........................ 0
ISDPv1 Packets Transmitted..................... 0
ISDPv2 Packets Received........................ 4253
ISDPv2 Packets Transmitted..................... 4351
ISDP Bad Header................................ 0
ISDP Checksum Error............................ 0
ISDP Transmission Failure...................... 0
ISDP Invalid Format............................ 0
ISDP Table Full................................ 392
ISDP Ip Address Table Full..................... 737
2CSNXXX_SWUM200.book Page 310 Tuesday, December 10, 2013 1:22 PM

DHCP Layer 2 Relay Commands 311
10
DHCP Layer 2 Relay Commands
Dell Networking N2000/N3000/N4000 Series Switches
In the majority of network configurations, DHCP clients and their associated
servers do not reside on the same IP network or subnet. Therefore, some kind
of third-party agent is required to transfer DHCP messages between clients
and servers. Such an agent is known as a DHCP Relay agent.
The DHCP Relay agent accepts DHCP requests from any routed interface,
including VLANs. The agent relays requests from a subnet without a DHCP
server to a server or next-hop agent on another subnet. Unlike a router which
switches IP packets transparently, a DHCP Relay agent processes DHCP
messages and generates new DHCP messages as a result.
The Dell Networking DHCP Relay supports DHCP Relay Option 82 circuit-
id and remote-id for a VLAN.
Commands in this Chapter
This chapter explains the following commands:
dhcp l2relay (Global Configuration) show dhcp l2relay stats interface
dhcp l2relay (Interface Configuration) show dhcp l2relay subscription interface
dhcp l2relay circuit-id show dhcp l2relay agent-option vlan
dhcp l2relay remote-id show dhcp l2relay vlan
dhcp l2relay trust show dhcp l2relay circuit-id vlan
dhcp l2relay vlan show dhcp l2relay remote-id vlan
show dhcp l2relay all clear dhcp l2relay statistics interface
show dhcp l2relay interface
–
2CSNXXX_SWUM200.book Page 311 Tuesday, December 10, 2013 1:22 PM

312 DHCP Layer 2 Relay Commands
dhcp l2relay (Global Configuration)
Use the dhcp l2relay command to enable Layer 2 DHCP Relay functionality.
The subsequent commands mentioned in this section can only be used when
the L2-DHCP Relay is enabled. Use the no form of this command to disable
L2-DHCP Relay.
Syntax
dhcp l2relay
no dhcp l2relay
Default Configuration
DHCP L2 Relay is disabled by default.
Command Mode
Global Configuration.
User Guidelines
There are no user guidelines for this command.
Example
console(config)#dhcp l2relay
dhcp l2relay (Interface Configuration)
Use the dhcp l2relay command to enable DHCP L2 Relay for an interface.
Use the no form of this command to disable DHCP L2 Relay for an interface.
Syntax
dhcp l2relay
no dhcp l2relay
Default Configuration
DHCP L2Relay is disabled on all interfaces by default.
2CSNXXX_SWUM200.book Page 312 Tuesday, December 10, 2013 1:22 PM

DHCP Layer 2 Relay Commands 313
Command Mode
Interface Configuration (Ethernet, Port-channel).
User Guidelines
There are no user guidelines for this command.
Example
console(config-if-Gi1/0/1)#dhcp l2relay
dhcp l2relay circuit-id
Use the dhcp l2relay circuit-id command to enable setting the DHCP
Option 82 Circuit ID for a VLAN. When enabled, the interface number is
added as the Circuit ID in DHCP option 82. Use the no form of this
command to disable setting the DHCP Option 82 Circuit ID.
Syntax
dhcp l2relay circuit-id vlan
vlan-range
no dhcp l2relay circuit-id vlan
vlan-range
•
vlan-range
—
The list of VLAN IDs.
Default Configuration
Setting the DHCP Option 82 Circuit ID is disabled by default.
Command Mode
Global Configuration
User Guidelines
There are no user guidelines for this command.
Example
console(config)#dhcp l2relay circuit-id vlan 340-350
2CSNXXX_SWUM200.book Page 313 Tuesday, December 10, 2013 1:22 PM

314 DHCP Layer 2 Relay Commands
dhcp l2relay remote-id
Use the dhcp l2relay remote-id command to enable setting the DHCP
Option 82 Remote ID for a VLAN. When enabled, the supplied string is used
for the Remote ID in DHCP Option 82. Use the no form of this command to
disable setting the DHCP Option 82 Remote ID.
Syntax
dhcp l2relay remote-id
remoteId
vlan
vlan-range
no dhcp l2relay remote-id
remoteId
vlan
vlan-range
•
remoteId
—
The string to be used as the remote ID in the Option 82 (Range: 1 -
128 characters).
•
vlan-range
—
The list of VLAN IDs.
Default Configuration
Setting the DHCP Option 82 Remote ID is disabled by default.
Command Mode
Global Configuration.
User Guidelines
There are no user guidelines for this command.
Example
console(config)#dhcp l2relay remote-id dslforum vlan 10,20-30
dhcp l2relay trust
Use the dhcp l2relay trust command to configure an interface to mandate
Option-82 on receiving DHCP packets.
Syntax
dhcp l2relay trust
no dhcp l2relay trust
2CSNXXX_SWUM200.book Page 314 Tuesday, December 10, 2013 1:22 PM

DHCP Layer 2 Relay Commands 315
Default Configuration
DHCP Option 82 is discarded by default.
Configuration Mode
Interface Configuration (Ethernet, Port-channel).
User Guidelines
There are no user guidelines for this command.
Example
console(config-if-Gi1/0/1)#dhcp l2relay trust
dhcp l2relay vlan
Use the dhcp l2relay vlan command to enable the L2 DHCP Relay agent for
a set of VLANs. All DHCP packets which arrive on interfaces in the
configured VLAN are subject to L2 Relay processing. Use the no form of this
command to disable L2 DHCP Relay for a set of VLANs.
Syntax
dhcp l2relay vlan
vlan-range
no dhcp l2relay vlan
vlan-range
•
vlan-range
—
The list of VLAN IDs.
Default Configuration
DHCP L2 Relay is disabled on all VLANs by default.
Command Mode
Global Configuration mode
User Guidelines
There are no user guidelines for this command.
Example
console(config)#dhcp l2relay vlan 10,340-345
2CSNXXX_SWUM200.book Page 315 Tuesday, December 10, 2013 1:22 PM

316 DHCP Layer 2 Relay Commands
show dhcp l2relay all
Use the show dhcp l2relay all command in Privileged EXEC mode to display
the summary of DHCP L2 Relay configuration.
Syntax
show dhcp l2relay all
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC mode, Configuration mode and all Configuration submodes
User Guidelines
There are no user guidelines for this command.
Example
console #show dhcp l2relay all
DHCP L2 Relay is Enabled.
Interface L2RelayMode TrustMode
---------- ----------- --------------
Gi1/0/2 Enabled untrusted
Gi1/0/4 Disabled trusted
VLAN Id L2 Relay CircuitId RemoteId
--------- ---------- ----------- ------------
3 Disabled Enabled --NULL--
5 Enabled Enabled --NULL--
6 Enabled Enabled broadcom
7 Enabled Disabled --NULL--
8 Enabled Disabled --NULL--
9 Enabled Disabled --NULL--
10 Enabled Disabled --NULL--
show dhcp l2relay interface
Use the show dhcp l2relay interface command in Privileged EXEC mode to
display DHCP L2 Relay configuration specific to interfaces.
2CSNXXX_SWUM200.book Page 316 Tuesday, December 10, 2013 1:22 PM

DHCP Layer 2 Relay Commands 317
Syntax
show dhcp l2relay interface {all |
interface-id
}
•
all
—
Show all interfaces.
•
interface-id
—
A physical interface.
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC mode, Configuration mode and all Configuration submodes
User Guidelines
There are no user guidelines for this command.
Example
console#show dhcp l2relay interface all
DHCP L2 Relay is Enabled.
Interface L2RelayMode TrustMode
---------- ----------- --------------
0/2 Enabled untrusted
0/4 Disabled trusted
show dhcp l2relay stats interface
Use the show dhcp l2relay stats interface command in Privileged EXEC
mode to display DHCP L2 Relay statistics specific to interfaces.
Syntax
show dhcp l2relay stats interface {all |
interface-id
}
•
all
—
Show all interfaces.
•
interface-id
—
A physical interface.
Default Configuration
This command has no default configuration.
2CSNXXX_SWUM200.book Page 317 Tuesday, December 10, 2013 1:22 PM

318 DHCP Layer 2 Relay Commands
Command Mode
Privileged EXEC mode, Configuration mode and all Configuration submodes
User Guidelines
There are no user guidelines for this command.
Example
console#show dhcp l2relay stats interface all
DHCP L2 Relay is Enabled.
Interface UntrustedServer UntrustedClient TrustedServer TrustedClient
MsgsWithOpt82 MsgsWithOpt82 MsgsWithoutOpt82 MsgsWithoutOpt82
--------- --------------- ----------------- ----------------- ----------
Gi1/0/1 0 0 0 0
Gi1/0/2 0 0 3 7
Gi1/0/3 0 0 0 0
show dhcp l2relay subscription interface
Use the show dhcp l2relay subscription interface command in Privileged
EXEC mode to display DHCP L2 Relay Option-82 configuration specific to
interfaces.
Syntax
show dhcp l2relay subscription interface {all |
interface-id
}
•
all
—
Show all interfaces.
•
interface-id
—
A physical interface.
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC mode, Configuration mode and all Configuration submodes
User Guidelines
There are no user guidelines for this command.
2CSNXXX_SWUM200.book Page 318 Tuesday, December 10, 2013 1:22 PM

DHCP Layer 2 Relay Commands 319
show dhcp l2relay agent-option vlan
Use the show dhcp l2relay agent-option vlan command in Privileged EXEC
mode to display DHCP L2 Relay Option-82 configuration specific to VLANs.
Syntax
show dhcp l2relay agent-option vlan
vlan-range
•
vlan-range
—
Show information for the specified VLAN range. A range may be a
single VLAN ID or two VLAN IDs separated by a single dash with no embedded
spaces.
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC mode, Configuration mode and all Configuration submodes
User Guidelines
There are no user guidelines for this command.
Example
console# show dhcp l2relay agent-option vlan 5-10
DHCP L2 Relay is Enabled.
VLAN Id L2 Relay CircuitId RemoteId
--------- ---------- ----------- ------------
5 Enabled Enabled --NULL--
6 Enabled Enabled broadcom
7 Enabled Disabled --NULL--
8 Enabled Disabled --NULL--
9 Enabled Disabled --NULL--
10 Enabled Disabled --NULL—
show dhcp l2relay vlan
Use the show dhcp l2relay vlan command in Privileged EXEC mode to
display whether DHCP L2 Relay is globally enabled on the specified VLAN or
VLAN range.
2CSNXXX_SWUM200.book Page 319 Tuesday, December 10, 2013 1:22 PM

320 DHCP Layer 2 Relay Commands
Syntax
show dhcp l2relay vlan
vlan-range
•
vlan-range
—
Show information for the specified VLAN range. A range may be a
single VLAN ID or two VLAN IDs separated by a single dash with no embedded
spaces.
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC mode, Configuration mode and all Configuration submodes
User Guidelines
There are no user guidelines for this command.
Example
console#show dhcp l2relay vlan 100
DHCP L2 Relay is Enabled.
DHCP L2 Relay is enabled on the following VLANs:
100
show dhcp l2relay circuit-id vlan
Use the show dhcp l2relay circuit-id vlan command in Privileged EXEC
mode to display whether DHCP L2 Relay is globally enabled and whether the
DHCP Circuit-ID option is enabled on the specified VLAN or VLAN range.
Syntax
show dhcp l2relay circuit-id vlan
vlan-range
•
vlan-range
—
Show information for the specified VLAN range. A range may be a
single VLAN ID or two VLAN IDs separated by a single dash with no embedded
spaces.
Default Configuration
This command has no default configuration.
2CSNXXX_SWUM200.book Page 320 Tuesday, December 10, 2013 1:22 PM

DHCP Layer 2 Relay Commands 321
Command Mode
Privileged EXEC mode, Configuration mode and all Configuration submodes
User Guidelines
There are no user guidelines for this command.
Example
console#show dhcp l2relay circuit-id vlan 300
DHCP L2 Relay is Enabled.
DHCP Circuit-Id option is enabled on the following VLANs:
300
show dhcp l2relay remote-id vlan
Use the show dhcp l2relay remote-id vlan command in Privileged EXEC
mode to display whether DHCP L2 Relay is globally enabled and shows the
remote ID configured on the specified VLAN or VLAN range.
Syntax
show dhcp l2relay remote-id vlan
vlan-range
•
vlan-range
—
Show information for the specified VLAN range. A range may be a
single VLAN ID or two VLAN IDs separated by a single dash with no embedded
spaces.
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC mode, Configuration mode and all Configuration submodes
User Guidelines
There are no user guidelines for this command.
Example
console#show dhcp l2relay remote-id vlan 200
DHCP L2 Relay is Enabled.
VLAN ID Remote Id
2CSNXXX_SWUM200.book Page 321 Tuesday, December 10, 2013 1:22 PM

322 DHCP Layer 2 Relay Commands
---------------------
200remote_22
clear dhcp l2relay statistics interface
Use the show dhcp l2relay statistics interface command in Privileged EXEC
mode to reset the DHCP L2 Relay counters to zero. Specify the port with the
counters to clear, or use the all keyword to clear the counters on all ports.
Syntax
clear dhcp l2relay statistics interface {all |
interface-id
}
•
all
—
Show all interfaces.
•
interface-id
—
A physical interface.
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC mode
User Guidelines
There are no user guidelines for this command.
Example
console#clear dhcp l2relay statistics interface gi1/0/1
2CSNXXX_SWUM200.book Page 322 Tuesday, December 10, 2013 1:22 PM

DHCP Management Interface Commands 323
11
DHCP Management Interface
Commands
Dell Networking N2000/N3000/N4000 Series Switches
Dell Networking switches support an embedded DHCP client. Any IP
interface can use DHCP to obtain an IP address. The DHCP client can run
on multiple interfaces simultaneously.
For IPv4, an IP interface can either use manually configured addresses or be
enabled for DHCP. The options are mutually exclusive. When the operator
enables DHCPv4 on an IP interface, all manually configured IP addresses on
that interface are removed from the running configuration. When the
operator configures an IP address, the system automatically releases any IPv4
address assigned by a DHCP server and disables DHCPv4 on the interface.
For IPv6, DHCP can coexist with configured addresses. The operator may
enable DHCPv6 and configure IPv6 addresses on the same interface. Only a
single in-band interface can be configured as a DHCPv6 client.
DHCP is disabled by default on all in-band interfaces.
The DHCP client retains an IP address even if the IP interface goes down.
The client does not attempt to renew its IP address until the lease expires,
regardless of changes in link state.
The operator may renew or release an IP address at any time using the new
release dhcp
and
renew dhcp
CLI commands (or web or SNMP equivalents).
When an IPv6 address is leased from a DHCP server, the address has a mask
length of 128. A local route for the network is only installed if the router
receives and accepts IPv6 router advertisements on the interface. Because
router advertisements are not accepted on a routing interface, a leased IPv6
address on a routing interface is not necessarily useful.
Commands in this Chapter
This chapter explains the following commands:
2CSNXXX_SWUM200.book Page 323 Tuesday, December 10, 2013 1:22 PM

324 DHCP Management Interface Commands
release dhcp
Use the release dhcp command in Privileged EXEC mode to force the
DHCPv4 client to release a leased address.
Syntax
release dhcp
interface-id
•
interface-id
—
Any valid VLAN interface. See
Interface Naming Conventions
for
interface representation.
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC
User Guidelines
The DHCP client sends a DHCP RELEASE message telling the DHCP
server that it no longer needs the IP address, and that the IP address can be
reassigned to another client. The interface method does not change and will
still be DHCP even after issuing this command. To lease an IP address again,
issue either the renew dhcp
interface-id
command below or
ip address dhcp
(Interface Configuration)
command on page 481 in interface mode. If the
IPv4 address on the interface was not assigned by DHCP, then the command
fails and displays the following error message:
The release dhcp option is applicable only for routing interfaces and not for
Out-of-Band port. Use the
ip address (Out-of-Band)
none
command on the
Out-of-Band interface to clear a DHCP-acquired address.
Example
console#release dhcp vlan2
release dhcp debug dhcp packet
renew dhcp show dhcp lease
2CSNXXX_SWUM200.book Page 324 Tuesday, December 10, 2013 1:22 PM

DHCP Management Interface Commands 325
renew dhcp
Use the renew dhcp command in Privileged EXEC mode to force the DHCP
client to immediately renew an IPv4 address lease.
Syntax
renew dhcp {
interface-id
| out-of-band}
•
interface-id
—Any valid routing interface. See Interface Naming
Conventions for interface representation.
•
out-of-band
—Keyword to identify the out-of-band interface. The DHCP
client renews the leased address on this interface.
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC
User Guidelines
If the interface has a leased IPv4 address when this command is issued, the
DHCP client sends a DHCP REQUEST message telling the DHCP server
that it wants to continue using the IP address. If DHCP is enabled on the
interface, but the interface does not currently have an IPv4 address (for
example, if the address was previously released), then the DHCP client sends
a DISCOVER to acquire a new address. If DHCP is not enabled on the
interface, then the command fails and displays the following error message:
DHCP is not enabled on this interface
Examples
The first example is for routing interfaces.
console#renew dhcp vlan 2
The second example is for an out-of-band port.
console#renew dhcp out-of-band
2CSNXXX_SWUM200.book Page 325 Tuesday, December 10, 2013 1:22 PM

326 DHCP Management Interface Commands
debug dhcp packet
Use the debug dhcp packet command in Privileged EXEC mode to display
debug information about DHCPv4 client activities and to trace DHCPv4
packets to and from the local DHCPv4 client. To disable debugging, use the
no form of this command.
Syntax
debug dhcp packet [transmit | receive]
no debug dhcp packet [transmit | receive]
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC
User Guidelines
DHCP client already has packet tracing. This command turns the packet
tracing on.
Example
The first example is for transmit and receive flows.
console#debug dhcp packet
The second example is for transmit flow.
console#debug dhcp packet transmit
The third example is for receive flow.
console#debug dhcp packet receive
show dhcp lease
Use the show dhcp lease command in Privileged EXEC mode to display IPv4
addresses leased from a DHCP server.
2CSNXXX_SWUM200.book Page 326 Tuesday, December 10, 2013 1:22 PM

DHCP Management Interface Commands 327
Syntax
show dhcp lease [interface { out-of-band | vlan
vlan-id
} ]
•
out-of-band
—The out-of-band interface.
•
vlan
—The VLAN and VLAN ID.
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC, Configuration mode and all Configuration submodes
User Guidelines
This command lists all IPv4 addresses currently leased from a DHCP server
on a routing interface. This command only applies to routing interfaces. To
see the IPv4 address leased on the out-of-band interface, use the command
show ip interface
out-of-band.
This command output provides the following information.
Term Description
IP address, Subnet
mask
The IP address and network mask leased from the DHCP server.
DHCP Lease server The IPv4 address of the DHCP server that leased the address.
State State of the DHCPv4 Client on this interface.
DHCP transaction
id
The transaction ID of the DHCPv4 Client.
Lease The time (in seconds) that the IP address was leased by the
server.
Renewal The time (in seconds) when the next DHCP renew Request is
sent by DHCPv4 Client to renew the leased IP address.
Rebind The time (in seconds) when the DHCP Rebind process starts.
Retry count Number of times the DHCPv4 client sends a DHCP
REQUEST message before the server responds.
2CSNXXX_SWUM200.book Page 327 Tuesday, December 10, 2013 1:22 PM

328 DHCP Management Interface Commands
Examples
The following example shows the output from this command when the
device has leased two IPv4 addresses from the DHCP server.
console#show dhcp lease
IP address: 10.1.20.1 on interface VLAN10
Subnet mask: 255.255.255.0
DHCP Lease server: 10.1.20.3, state: 5 Bound
DHCP transaction id: 0x7AD
Lease: 86400 secs, Renewal: 43200 secs, Rebind: 75600 secs
Retry count: 0
IP address: 10.1.1.2 on interface VLAN20
Subnet mask: 255.255.255.0
DHCP Lease server: 10.1.1.1, state: 5 Bound
DHCP transaction id: 0x11EB
Lease: 86400 secs, Renewal: 43200 secs, Rebind: 75600 secs
Retry count: 0
console#show dhcp lease interface vlan 10
IP address: 10.1.20.1 on interface VLAN10
Subnet mask: 255.255.255.0
DHCP Lease server: 10.1.20.3, state: 5 Bound
DHCP transaction id: 0x7AD
Lease: 86400 secs, Renewal: 43200 secs, Rebind: 75600 secs
Retry count: 0
2CSNXXX_SWUM200.book Page 328 Tuesday, December 10, 2013 1:22 PM

DHCP Snooping Commands 329
12
DHCP Snooping Commands
Dell Networking N2000/N3000/N4000 Series Switches
DHCP Snooping is a security feature that monitors DHCP messages between
DHCP clients and DHCP server to filter harmful DHCP messages and build
a bindings database of {MAC address, IP address, VLAN ID, interface} tuples
that are considered authorized.
The DHCP snooping application processes incoming DHCP messages. For
DHCPRELEASE and DHCPDECLINE messages, the application compares
the receive interface and VLAN with the client's interface and VLAN in the
bindings database. If the interfaces do not match, the application logs the
event and drops the message. For valid client messages, DHCP snooping
compares the source MAC address to the DHCP client hardware address.
When there is a mismatch, DHCP snooping logs and drops the packet.
DHCP Snooping forwards valid client messages on trusted members within
the VLAN. If DHCP Relay and/or DHCP Server coexist with DHCP
Snooping, the DHCP client message is sent to the DHCP Relay or/and
DHCP Server for further processing.
The DHCP Snooping application uses DHCP messages to build and
maintain the binding's database. The binding's database only includes data
for clients on untrusted ports. DHCP Snooping creates a tentative binding
from DHCP DISCOVER and REQUEST messages. Tentative bindings tie a
client to a port (the port where the DHCP client message was received).
Tentative bindings are completed when DHCP Snooping learns the client's IP
address from a DHCP ACK message on a trusted port. DHCP Snooping
removes bindings in response to DECLINE, RELEASE, and NACK messages.
The DHCP Snooping application ignores the ACK messages as a reply to the
DHCP Inform messages received on trusted ports. The network administrator
can enter static bindings into the binding database.
IP Source Guard and Dynamic ARP Inspection use the DHCP Snooping
bindings database for the validation of IP and ARP packets.
2CSNXXX_SWUM200.book Page 329 Tuesday, December 10, 2013 1:22 PM

330 DHCP Snooping Commands
Commands in this Chapter
This chapter explains the following commands:
clear ip dhcp snooping binding
Use the clear ip dhcp snooping binding command to clear all DHCP
Snooping bindings on a specific interface or on all interfaces.
Syntax
clear ip dhcp snooping binding {* | interface
interface-id
}
•*—
Clear all DHCP Snooping entries.
•
interface-id
—
Clear all DHCP Snooping entries on the specified interface.
Default Configuration
There is no default configuration for this command.
Command Mode
Privileged EXEC
User Guidelines
There are no user guidelines for this command.
clear ip dhcp snooping binding ip dhcp snooping trust
clear ip dhcp snooping statistics ip dhcp snooping verify mac-address
ip dhcp snooping show ip dhcp snooping
ip dhcp snooping binding show ip dhcp snooping binding
ip dhcp snooping database show ip dhcp snooping database
ip dhcp snooping database write-delay show ip dhcp snooping interfaces
ip dhcp snooping limit show ip dhcp snooping statistics
ip dhcp snooping log-invalid
2CSNXXX_SWUM200.book Page 330 Tuesday, December 10, 2013 1:22 PM

DHCP Snooping Commands 331
clear ip dhcp snooping statistics
Use the clear ip dhcp snooping statistics command to clear all DHCP
Snooping statistics.
Syntax
clear ip dhcp snooping statistics
Default Configuration
There is no default configuration for this command.
Command Mode
Privileged EXEC
User Guidelines
There are no user guidelines for this command.
Example
console#clear ip dhcp snooping statistics
ip dhcp snooping
Use the ip dhcp snooping command to enable DHCP snooping globally. Use
the “no” form of this command to disable DHCP snooping.
Syntax
ip dhcp snooping
no ip dhcp snooping
Default Configuration
DHCP Snooping is disabled by default.
Command Mode
Global Configuration mode
2CSNXXX_SWUM200.book Page 331 Tuesday, December 10, 2013 1:22 PM

332 DHCP Snooping Commands
User Guidelines
To enable DHCP snooping, do the following:
1
Enable DHCP Snooping globally.
2
Enable DHCP Snooping per VLAN.
3
Set DHCP Snooping trusted port on the port in the DHCP server
direction.
The bindings database populated by DHCP snooping is used by several other
services, including IP source guard and dynamic ARP inspection. DHCP
snooping must be enabled for these services to operate.
Example
The following configuration enables DHCP snooping on VLAN 1 for a switch
connected to a DHCP server over interface gi1/0/4:
console(config)#ip dhcp snooping
console(config-if-vlan1)#ip dhcp snooping
console(config-if-vlan1)#exit
console(config)#interface gi1/0/4
console(config-if-Gi1/0/4)#ip dhcp snooping trust
ip dhcp snooping binding
Use the ip dhcp snooping binding command to configure a static DHCP
Snooping binding. Use the “no” form of this command to remove a static
binding.
Syntax
ip dhcp snooping binding
mac-address
vlan
vlan-id ip-address
interface
{gigabitethernet unit/slot/port | tengigabitethernet unit/slot/port
|
fortygigabitethernet
unit/slot/port | port-channel
port-channel-id
}
no ip dhcp snooping binding
mac-address
•
mac-address
—
The client's MAC address.
•
vlan-id
—
The number of the VLAN the client is authorized to use.
•
ip-address
—
The IP address of the client.
•
interface
—
The interface on which the client is authorized. The interface may
be a physical interface or a port channel.
2CSNXXX_SWUM200.book Page 332 Tuesday, December 10, 2013 1:22 PM

DHCP Snooping Commands 333
Default Configuration
There are no static or dynamic DHCP snooping bindings by default.
Command Mode
Global Configuration mode
User Guidelines
There are no user guidelines for this command.
Example
console(config)#ip dhcp snooping binding 00:00:00:00:00:01 vlan 10
10.131.12.134 interface 1/0/1
ip dhcp snooping database
Use the ip dhcp snooping database command to configure the persistent
storage location of the DHCP snooping database. This can be local to the
switch or on a remote machine.
Syntax
ip dhcp snooping database {local | tftp://
hostIP
/
filename
}
•
hostIP
—
The IP address of the remote host.
•
filename
—
The name of the file for the database on the remote host. The
filename may contain any printable character and is checked only when
attempting to open the file. The file must reside in the working directory of the
TFTP server. Specification of a sub-directory in the file name parameter is not
supported.
Default Configuration
The database is stored locally by default.
Configuration Mode
Global Configuration mode.
User Guidelines
There are no user guidelines for this command.
2CSNXXX_SWUM200.book Page 333 Tuesday, December 10, 2013 1:22 PM

334 DHCP Snooping Commands
Example
The following example configures the storage location of the snooping
database as local.
console(config)#ip dhcp snooping database local
The following example configures the storage location of the snooping
database as remote.
console(config)#ip dhcp snooping database tftp://10.131.11.1/db.txt
ip dhcp snooping database write-delay
Use the ip dhcp snooping database write-delay command to configure the
interval in seconds at which the DHCP Snooping database will be stored in
persistent storage. Use the “no” form of this command to reset the write delay
to the default.
Syntax
ip dhcp snooping database write-delay
seconds
no ip dhcp snooping database write-delay
•
seconds
—
The write delay (Range: 15–86400 seconds).
Default Configuration
The write delay is 300 seconds by default.
Command Mode
Global Configuration mode
User Guidelines
There are no user guidelines for this command.
Example
console(config)#ip dhcp snooping database write-delay 500
2CSNXXX_SWUM200.book Page 334 Tuesday, December 10, 2013 1:22 PM

DHCP Snooping Commands 335
ip dhcp snooping limit
Use the ip dhcp snooping limit command to diagnostically disable itself if
the rate of received DHCP messages exceeds the configured limit. Use the no
shutdown command to re-enable the interface. Use the no form of this
command to disable automatic shutdown of the interface.
Syntax
ip dhcp snooping limit {rate
rate
[burst interval
seconds
]}
no ip dhcp snooping limit
•
rate
—The maximum number of packets per second allowed (Range:
0–300 pps).
•
seconds
—Interval over which to measure a burst of packets. (Range: 1–15
seconds).
Default Configuration
By default, DCHP messages do not cause an interface to be disabled.
Command Mode
Interface Configuration (gigabitethernet, port-channel, tengigabitethernet,
fortygigabitethernet) mode
User Guidelines
The switch hardware rate limits DHCP packets sent to the CPU from
snooping enabled interfaces to 512 Kbps.
To prevent DHCP packets from being used in a DoS attack when DHCP
snooping is enabled; the snooping application allows configuration of rate
limiting for received DHCP packets. DHCP snooping monitors the receive
rate on each interface separately. If the receive rate exceeds the configured
limit within the configured interval, DHCP snooping shuts down the
interface. The administrator must perform the “no shutdown” command on
the affected interface to re-enable the interface.
The administrator can configure the rate and burst interval. Rate limiting is
configured independently on each physical interface and may be enabled on
both trusted and untrusted interfaces. The rate limit is configurable in the
2CSNXXX_SWUM200.book Page 335 Tuesday, December 10, 2013 1:22 PM

336 DHCP Snooping Commands
range of 0-300 packets per second and the burst interval in the range of 1-15
seconds. In general, a rate limit of under 100 pps is valid for untrusted
interfaces.
Examples
console(config-if-Gi1/0/1)#ip dhcp snooping limit none
console(config-if-Gi1/0/1)#ip dhcp snooping limit rate 100 burst interval 1
ip dhcp snooping log-invalid
Use the ip dhcp snooping log-invalid command to enable logging of DHCP
messages filtered by the DHCP Snooping application. Use the no form of this
command to disable logging.
Syntax
ip dhcp snooping log-invalid
no ip dhcp snooping log-invalid
Default Configuration
Logging of filtered messages is disabled by default.
Invalid DHCP messages are not logged by default.
Command Mode
Interface Configuration (gigabitethernet, port-channel, tengigabitethernet,
fortygigabitethernet) mode
User Guidelines
There are no user guidelines for this command.
Example
console(config-if-Gi1/0/1)#ip dhcp snooping log-invalid
console(config-if-Gi1/0/1)#no ip dhcp snooping log-invalid
2CSNXXX_SWUM200.book Page 336 Tuesday, December 10, 2013 1:22 PM

DHCP Snooping Commands 337
ip dhcp snooping trust
Use the ip dhcp snooping trust command to configure a port as trusted. Use
the no form of this command to configure a port as untrusted.
Syntax
ip dhcp snooping trust
no ip dhcp snooping trust
Default Configuration
Ports are untrusted by default.
Command Mode
Interface Configuration (gigabitethernet, port-channel, tengigabitethernet,
fortygigabitethernet) mode
User Guidelines
Configuring an interface as trusted disables DHCP snooping validation of
DHCP packets and exposes the port to IPv4 DHCP DoS attacks. Configuring
an interface as untrusted indicates that the switch should firewall DHCP
messages and act as if the port is connected to a device outside the DMZ.
DHCP snooping must be enabled globally and on the VLAN for which the
port is a member for this command to have an effect.
Interfaces connected to the DHCP server must be configured as trusted in
order for DHCP snooping to operate.
Use the ip verify source command to disallow traffic from untrusted sources
on an interface.
Example
console(config-if-Gi1/0/1)#ip dhcp snooping trust
console(config-if-Gi1/0/1)#no ip dhcp snooping trust
2CSNXXX_SWUM200.book Page 337 Tuesday, December 10, 2013 1:22 PM

338 DHCP Snooping Commands
ip dhcp snooping verify mac-address
Use the ip dhcp snooping verify mac-address command to enable the
verification of the source MAC address with the client MAC address in the
received DHCP message. Use the “no” form of this command to disable
verification of the source MAC address.
Syntax
ip dhcp snooping verify mac-address
no ip dhcp snooping verify mac-address
Default Configuration
Source MAC address verification is enabled by default.
Command Mode
Global Configuration mode
User Guidelines
There are no user guidelines for this command.
Example
console(config)#ip dhcp snooping verify mac-address
show ip dhcp snooping
Use the show ip dhcp snooping command to display the DHCP snooping
global configuration.
Syntax
show ip dhcp snooping
Default Configuration
There is no default configuration for this command.
2CSNXXX_SWUM200.book Page 338 Tuesday, December 10, 2013 1:22 PM

DHCP Snooping Commands 339
Command Mode
User EXEC, Privileged EXEC mode, Configuration mode and all
Configuration submodes
User Guidelines
There are no user guidelines for this command.
Example
console#show ip dhcp snooping
DHCP snooping is Disabled
DHCP snooping source MAC verification is enabled
DHCP snooping is enabled on the following VLANs:
11 - 30, 40
Interface Trusted Log Invalid Pkts
--------- -------- ----------------
1/0/1 Yes No
1/0/2 No Yes
1/0/3 No Yes
1/0/4 No No
1/0/6 No No
show ip dhcp snooping binding
Use the show ip dhcp snooping binding command to display the DHCP
snooping binding entries.
Syntax
show ip dhcp snooping binding [{static | dynamic}] [interface
interface-id
|
port-channel
port-channel-id
] [vlan
vlan-id
]
•
static
|
dynamic
—Use these keywords to filter by static or dynamic
bindings.
•
interface-id
—The interface for which to show bindings.
•
vlan-id
—The number of the VLAN for which to show bindings.
Default Configuration
There is no default configuration for this command.
2CSNXXX_SWUM200.book Page 339 Tuesday, December 10, 2013 1:22 PM

340 DHCP Snooping Commands
Command Mode
User EXEC, Privileged EXEC mode, Configuration mode and all
Configuration submodes
User Guidelines
There are no user guidelines for this command.
Example
console#show ip dhcp snooping binding
Total number of bindings: 2
MAC Address IP Address VLAN Interface Type Lease (Secs)
----------------- --------------- ---- ----------- ------- ------------
00:02:B3:06:60:80 210.1.1.3 10 Gi1/0/1 Dyn 86400
00:02:FE:06:13:04 210.1.1.4 10 Gi1/0/1 Dyn 86400
show ip dhcp snooping database
Use the show ip dhcp snooping database command to display the DHCP
snooping configuration related to the database persistence.
Syntax
show ip dhcp snooping database
Default Configuration
There is no default configuration for this command.
Command Mode
User EXEC, Privileged EXEC, Configuration mode and all Configuration
submodes
User Guidelines
There are no user guidelines for this command.
Example
console#show ip dhcp snooping database
2CSNXXX_SWUM200.book Page 340 Tuesday, December 10, 2013 1:22 PM

DHCP Snooping Commands 341
agent url: /10.131.13.79:/sai1.txt
write-delay: 5000
show ip dhcp snooping interfaces
Use the show ip dhcp snooping interfaces command to show the DHCP
Snooping status of the interfaces.
Syntax
show ip dhcp snooping interfaces [
interface
]
• interface—A valid physical interface.
Default Configuration
There is no default configuration for this command.
Command Mode
Privileged EXEC, Configuration mode and all Configuration submodes
User Guidelines
There are no user guidelines for this command.
Example
console#show ip dhcp snooping interfaces
Interface Trust State Rate Limit Burst Interval
(pps) (seconds)
---------- ------------- ------------- ---------------
1/0/1 No 15 1
1/0/2 No 15 1
1/0/3 No 15 1
console#show ip dhcp snooping interfaces gigabitethernet 1/0/15
Interface Trust State Rate Limit Burst Interval
(pps) (seconds)
---------- ------------- ------------- ---------------
1/0/15 Yes 15 1
2CSNXXX_SWUM200.book Page 341 Tuesday, December 10, 2013 1:22 PM
342 DHCP Snooping Commands
show ip dhcp snooping statistics
Use the show ip dhcp snooping statistics command to display the DHCP
snooping filtration statistics.
Syntax
show ip dhcp snooping statistics
Default Configuration
There is no default configuration for this command.
Command Mode
User EXEC, Privileged EXEC, Configuration mode and all Configuration
submodes
User Guidelines
The following fields are displayed by this command:
Example
console#show ip dhcp snooping statistics
Interface MAC Verify Client Ifc DHCP Server
Failures Mismatch Msgs Rec'd
----------- ---------- ---------- -----------
1/0/2 0 0 0
1/0/3 0 0 0
1/0/4 0 0 0
1/0/5 0 0 0
1/0/6 0 0 0
Fields Description
MAC Verify
Failures
The number of DHCP messages that were filtered on an
untrusted interface because of source MAC address and client
MAC address mismatch.
Client Ifc
Mismatch
The number of DHCP release and Deny messages received on
the different ports than previously learned.
DHCP Server Msgs The number of DHCP server messages received on untrusted
ports.
2CSNXXX_SWUM200.book Page 342 Tuesday, December 10, 2013 1:22 PM

DHCP Snooping Commands 343
1/0/7 0 0 0
1/0/8 0 0 0
1/0/9 0 0 0
1/0/10 0 0 0
1/0/11 0 0 0
1/0/12 0 0 0
1/0/13 0 0 0
1/0/14 0 0 0
1/0/15 0 0 0
1/0/16 0 0 0
1/0/17 0 0 0
1/0/18 0 0 0
1/0/19 0 0 0
1/0/20 0 0 0
2CSNXXX_SWUM200.book Page 343 Tuesday, December 10, 2013 1:22 PM

344 DHCP Snooping Commands
2CSNXXX_SWUM200.book Page 344 Tuesday, December 10, 2013 1:22 PM

Dynamic ARP Inspection Commands 345
13
Dynamic ARP Inspection
Commands
Dell Networking N2000/N3000/N4000 Series Switches
Dynamic ARP Inspection (DAI) is a security feature that rejects invalid and
malicious ARP packets. The feature prevents a class of man-in-the-middle
attacks, where an unfriendly station intercepts traffic for other stations by
poisoning the ARP caches of its neighbors. The miscreant sends ARP requests
or responses mapping another station IP address to its own MAC address.
DAI drops ARP packets whose sender MAC address and sender IP address do
not match an entry in the DHCP Snooping bindings database.
Commands in this Chapter
This chapter explains the following commands:
arp access-list
Use the arp access-list command to create an ARP ACL. It will place the user
in ARP ACL Configuration mode. Use the “no” form of this command to
delete an ARP ACL.
Syntax
arp access-list
acl-name
no arp access-list
acl-name
arp access-list ip arp inspection vlan
clear ip arp inspection statistics permit ip host mac host
ip arp inspection filter show arp access-list
ip arp inspection limit show ip arp inspection
ip arp inspection trust show ip arp inspection vlan
ip arp inspection validate
–
2CSNXXX_SWUM200.book Page 345 Tuesday, December 10, 2013 1:22 PM

346 Dynamic ARP Inspection Commands
•
acl-name
— A valid ARP ACL name (Range: 1–31 characters).
Default Configuration
There are no ARP ACLs created by default.
Command Mode
Global Configuration mode
User Guidelines
There are no user guidelines for this command.
Example
console(config)#arp access-list tier1
clear ip arp inspection statistics
Use the clear ip arp inspection statistics command in Privileged EXEC mode
to reset the statistics for Dynamic Address Resolution Protocol (ARP)
inspection on all VLANs.
Syntax
clear ip arp inspection statistics
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC mode
User Guidelines
There are no user guidelines for this command.
Example
console#clear ip arp inspection statistics
2CSNXXX_SWUM200.book Page 346 Tuesday, December 10, 2013 1:22 PM

Dynamic ARP Inspection Commands 347
ip arp inspection filter
Use the ip arp inspection filter command to configure the ARP ACL to be
used for a single VLAN or a range of VLANs to filter invalid ARP packets. If
the static keyword is given, packets that do not match a permit statement are
dropped without consulting the DHCP snooping bindings. Use the “no” form
of this command to unconfigure the ARP ACL.
Syntax
ip arp inspection filter
acl-name
vlan
vlan-range
[static]
no ip arp inspection filter
acl-name
vlan
vlan-range
[static]
•
acl-name
—The name of a valid ARP ACL. (Range: 1–31 characters)
•
vlan-range
—A valid VLAN range.
Default Configuration
No ARP ACL is configured.
Command Mode
Global Configuration mode
User Guidelines
There are no user guidelines for this command.
Example
console(config)#ip arp inspection filter tier1 vlan 2-10 static
console(config)#ip arp inspection filter tier1 vlan 20-30
ip arp inspection limit
Use the ip arp inspection limit command to configure the rate limit and
burst interval values for an interface.
Configuring none for the limit means the interface is not rate limited for
Dynamic ARP Inspection.
Syntax
ip arp inspection limit {none | rate
pps
[burst interval
seconds
]}
2CSNXXX_SWUM200.book Page 347 Tuesday, December 10, 2013 1:22 PM

348 Dynamic ARP Inspection Commands
no ip arp inspection limit
•
none
— To set no rate limit.
•
pps
— The number of packets per second (Range: 0–300).
•
seconds
— The number of seconds (Range: 1–15).
Default Configuration
The default rate limit is 15 packets per second.
The default burst interval is 1 second.
Command Mode
Interface Configuration (gigabitethernet, port-channel, tengigabitethernet,
fortygigabitethernet) mode
User Guidelines
If Dynamic ARP Inspection packets are received on a port at a rate that
exceeds the threshold for a specified time, that port will be diagnostically
disabled. The threshold is configurable up to 300 pps, and the burst is
configurable up to 15s long. The default is 15 pps and 1s burst.
Use the no shut command to bring the port back in to service.
Example
console(config-if-Gi1/0/1)#ip arp inspection limit none
console(config-if-Gi1/0/1)#ip arp inspection limit rate 100 burst interval 2
ip arp inspection trust
The ip arp inspection trust command configures an interface as trusted for
Dynamic ARP Inspection. Use the no form of this command to configure an
interface as untrusted.
Syntax
ip arp inspection trust
no ip arp inspection trust
2CSNXXX_SWUM200.book Page 348 Tuesday, December 10, 2013 1:22 PM

Dynamic ARP Inspection Commands 349
Default Configuration
Interfaces are configured as untrusted by default.
Command Mode
Interface Configuration (gigabitethernet, port-channel, tengigabitethernet,
fortygigabitethernet) mode
User Guidelines
There are no user guidelines for this command.
Example
console(config-if-Gi1/0/3)#ip arp inspection trust
ip arp inspection validate
Use the ip arp inspection validate command to enable additional validation
checks like source MAC address validation, destination MAC address
validation or IP address validation on the received ARP packets. Each
command overrides the configuration of the previous command. For
example, if a command enables source MAC address and destination MAC
address validations and a second command enables IP address validation only,
the source MAC address and destination MAC address validations are
disabled as a result of the second command. Use the “no” form of this
command to disable additional validation checks.
Syntax
ip arp inspection validate {[src-mac] [dst-mac] [ip]}
no ip arp inspection validate {[src-mac] [dst-mac] [ip]}
•
src-mac
—
For validating the source MAC address of an ARP packet.
•
dst-mac
—
For validating the destination MAC address of an ARP packet.
•
ip
—
For validating the IP address of an ARP packet.
Default Configuration
There is no additional validation enabled by default.
2CSNXXX_SWUM200.book Page 349 Tuesday, December 10, 2013 1:22 PM

350 Dynamic ARP Inspection Commands
Command Mode
Global Configuration mode
User Guidelines
There are no user guidelines for this command
Example
console(config)#ip arp inspection validate src-mac dst-mac ip
console(config)#ip arp inspection validate src-mac ip
console(config)#ip arp inspection validate dst-mac ip
console(config)#ip arp inspection validate ip
ip arp inspection vlan
Use the ip arp inspection vlan command to enable Dynamic ARP Inspection
on a single VLAN or a range of VLANs. Use the no form of this command to
disable Dynamic ARP Inspection on a single VLAN or a range of VLANs.
Syntax
ip arp inspection vlan
vlan-range
[logging]
no ip arp inspection vlan
vlan-range
[logging]
•
vlan-range
— A valid range of VLAN IDs.
•
logging
— Use this parameter to enable logging of invalid packets.
Default Configuration
Dynamic ARP Inspection is disabled by default.
Command Mode
Global Configuration mode
User Guidelines
There are no user guidelines for this command.
Example
console(config)#ip arp inspection vlan 200-300
console(config)#ip arp inspection vlan 200-300 logging
2CSNXXX_SWUM200.book Page 350 Tuesday, December 10, 2013 1:22 PM

Dynamic ARP Inspection Commands 351
permit ip host mac host
Use the permit ip host mac host command to configure a rule for a valid IP
address and MAC address combination used in ARP packet validation. Use
the “no” form of this command to delete an ARP ACL rule.
Syntax
permit ip host
sender-ip
mac host
sender-mac
no permit ip host
sender-ip
mac host
sender-mac
•
sender-ip
— Valid IP address used by a host.
•
sender-mac
—Valid MAC address in combination with the above sender-ip
used by a host.
Default Configuration
There are no ARP ACL rules created by default.
Command Mode
ARP Access-list Configuration mode
User Guidelines
There are no user guidelines for this command.
Example
console(Config-arp-access-list)#permit ip host 1.1.1.1 mac host
00:01:02:03:04:05
show arp access-list
Use the show arp access-list command to display the configured ARP ACLs
with the rules. Giving an ARP ACL name as the argument would display only
the rules in that ARP ACL.
Syntax
show arp access-list [
acl-name
]
•
acl-name
— A valid ARP ACL name (Range: 1–31 characters).
2CSNXXX_SWUM200.book Page 351 Tuesday, December 10, 2013 1:22 PM

352 Dynamic ARP Inspection Commands
Default Configuration
There is no default configuration for this command.
Command Mode
Privileged EXEC, Configuration mode and all Configuration submodes
User Guidelines
There are no user guidelines for this command.
Example
console#show arp access-list
ARP access list H2
permit ip host 1.1.1.1 mac host 00:01:02:03:04:05
permit ip host 1.1.1.2 mac host 00:03:04:05:06:07
ARP access list H3
ARP access list H4
permit ip host 2.1.1.2 mac host 00:03:04:05:06:08
show ip arp inspection
Use the show ip arp inspection command in Privileged EXEC mode to
display the Dynamic ARP Inspection and status.
Syntax
show ip arp inspection [interfaces [
interface-id
] | statistics [vlan
vlan-range
]
| vlan
vlan-range
]
•
interfaces [
interface-id
]
—
Display the Dynamic ARP Inspection configuration
on all the DAI enabled interfaces. Giving an interface argument, it displays the
values for that interface.
•
statistics [vlan
vlan-range
]
—
Display the statistics of the ARP packets processed
by Dynamic ARP Inspection. Given vlan-range argument, it displays the
statistics on all DAI-enabled VLANs in that range. In the case of no argument, it
lists the summary of the forwarded and dropped ARP packets.
•
vlan
vlan-range
—
Display the Dynamic ARP Inspection configuration on all the
VLANs in the given VLAN range. It also displays the global configuration values
for source MAC validation, destination MAC validation and invalid IP
validation.
2CSNXXX_SWUM200.book Page 352 Tuesday, December 10, 2013 1:22 PM
Dynamic ARP Inspection Commands 353
Default Configuration
There is no default configuration for this command.
Command Mode
Privileged EXEC mode, Configuration mode and all Configuration submodes
User Guidelines
The following information is displayed for each VLAN when a VLAN range is
supplied:
Example
Following is an example of the show ip arp inspection command.
console#show ip arp inspection
Source MAC Validation................. Disabled
Destination MAC Validation............ Disabled
IP Address Validation................. Disabled
VLANConfigurationLog InvalidACL NameStatic flag
Field Description
VLAN The VLAN-ID for each displayed row.
Forwarded The total number of valid ARP packets forwarded in this VLAN.
Dropped The total number of invalid ARP packets dropped in this VLAN.
DHCP Drops The number of packets dropped due to DHCP Snooping binding
database match failure.
ACL Drops The number of packets dropped due to ARP ACL rule match failure.
DHCP Permits The number of packets permitted due to DHCP snooping binding
database match.
ACL Permits The number of packets permitted due to ARP ACL rule match.
Bad Src MAC The number of packets dropped due to Source MAC validation
failure.
Bad Dest
MAC
The number of packets dropped due to Destination MAC validation
failure.
Invalid IP The number of packets dropped due to invalid IP checks.
2CSNXXX_SWUM200.book Page 353 Tuesday, December 10, 2013 1:22 PM

354 Dynamic ARP Inspection Commands
-----------------------------------------------
1 Disabled Enabled
console#
Following is an example of the show ip arp inspection interfaces command.
console#show ip arp inspection interfaces
Interface Trust State Rate Limit Burst Interval
(pps) (seconds)
--------------- ----------- ---------- ---------------
1/0/1 Untrusted 15 1
1/0/2 Untrusted 10 10
Following is an example of the show ip arp inspection statistics command.
console#show ip arp inspection statistics
VLAN Forwarded Dropped
---- --------- -------
10 90 14
20 10 3
console#show ip arp inspection statistics vlan 10,20
VLAN DHCP ACL DHCP ACL Bad Src Bad Dest Invalid
Drops Drops Permits Permits MAC MAC IP
---- ---------- ---------- ---------- ---------- ---------- ---------- ------
10 11 1 65 25 1 1 0
20 1 0 8 2 0 1 1
show ip arp inspection vlan
Use the show ip arp inspection vlan command to display the Dynamic ARP
Inspection configuration on all the VLANs in the given VLAN range. It also
displays the global configuration values for source MAC validation,
destination MAC validation and invalid IP validation.
Syntax
show ip arp inspection vlan [
vlan-range
]
•
vlan-range
—
A valid VLAN range.
2CSNXXX_SWUM200.book Page 354 Tuesday, December 10, 2013 1:22 PM

Dynamic ARP Inspection Commands 355
Default Configuration
There is no default configuration for this command.
Command Mode
Privileged EXEC mode, Configuration mode and all Configuration submodes
User Guidelines
The following global parameters are displayed:
The following fields are displayed for each VLAN:
Example
console#show ip arp inspection vlan 10-12
Source Mac Validation : Disabled
Destination Mac Validation : Disabled
IP Address Validation : Disabled
Vlan Configuration Log Invalid ACL Name Static flag
---- ------------- ----------- --------- ----------
10 Enabled Enabled H2 Enabled
11 Disabled Enabled
Parameter Description
Source Mac Validation If Source Mac validation of ARP frame is enabled.
Destination Mac
Validation
If Destination Mac validation of ARP Response frame is
enabled.
IP Address Validation If IP address validation of ARP frame is enabled.
Field Description
VLAN The VLAN-ID for each displayed row.
Configuration Whether DAI is enabled on the VLAN.
Log Invalid Whether logging of invalid ARP packets is enabled on the
VLAN.
ACL Name ARP ACL Name if configured on the VLAN.
Static flag If the ARP ACL is configured static on the VLAN.
2CSNXXX_SWUM200.book Page 355 Tuesday, December 10, 2013 1:22 PM

356 Dynamic ARP Inspection Commands
12 Enabled Disabled
2CSNXXX_SWUM200.book Page 356 Tuesday, December 10, 2013 1:22 PM
E-mail Alerting Commands 357
14
E-mail Alerting Commands
Dell Networking N2000/N3000/N4000 Series Switches
E-mail Alerting is an extension of the logging system. The Dell Networking
logging system allows the user to configure a variety of destinations for log
messages. This feature adds e-mail configuration capabilities, by which the
log messages are sent to a configured SMTP server such that an operator may
receive the log in an e-mail account of their choice.
Figure 1: Log Messages Severity Level
The network operator can adjust the urgent and non-urgent severity levels.
These levels are global and apply to all destination e-mail addresses. Log
messages in the urgent group are sent immediately to SMTP server with each
log message in a separate mail. Log messages in the non-urgent group are
batched into a single e-mail message and after a configurable delay.
Only the minimum part (MUA functionality of RFC 4409) required by the
switch or router to send the messages to the SMTP server is supported. Some
SMTP servers insist on authentication before the messages may be received
by them. The minimum part (MUA functionality of RFC 4954) required by
the switch or router to become authenticated by the SMTP server is
supported. Only plain text authentication is supported.
emergency (0)
alert (1)
critical (2)
error (3)
warning (4)
notice (5)
info (6)
debug (7)
Urgent severity level
Non-urgent severity level
email immediately
email in batch
never email
2CSNXXX_SWUM200.book Page 357 Tuesday, December 10, 2013 1:22 PM

358 E-mail Alerting Commands
Commands in this Chapter
This chapter explains the following commands:
logging email
Use the logging email command in Global Configuration mode to enable e-
mail alerting and set the lowest severity level for which log messages are e-
mailed. Use the no form of the command to disable e-mail alerting.
Syntax
logging email [
severity
]
no logging email
•
severity
—If you specify a severity level, log messages at or above the
severity level are e-mailed. The severity level may either be specified by
keyword or as an integer from 0 to 7. The accepted keywords, and the
numeric severity level each represents, are as follows.
–emergency (0)
–alert (1)
–critical (2)
– error (3)
– warning (4)
logging email show logging email statistics
logging email urgent clear logging email statistics
logging traps security
logging email message-type to-addr mail-server ip-address | hostname
logging email from-addr port (Mail Server Configuration Mode)
logging email message-type subject username (Mail Server Configuration
Mode)
logging email logtime password (Mail Server Configuration
Mode)
logging email test message-type show mail-server
2CSNXXX_SWUM200.book Page 358 Tuesday, December 10, 2013 1:22 PM

E-mail Alerting Commands 359
–notice (5)
–info (6)
–debug (7)
Default Configuration
E-mail alerting is disabled by default. When e-mail alerting is enabled, log
messages at or above severity Warning are e-mailed.
Command Mode
Global Configuration mode
User Guidelines
The logging email command with no arguments enables e-mail alerting.
Specify a severity to set the severity level of log messages that are e-mailed in
a non-urgent manner. Log messages at or above this severity level, but below
the urgent severity level, are collected together until the log time expires (the
time specified in the
logging email logtime
command) and then e-mailed in a
single e-mail message. If you set the non-urgent severity level to the same
value as the urgent severity level, then no log messages are e-mailed non-
urgently. See the
logging email urgent
command to specify the urgent severity
level. The command no logging email disables all e-mail alerting.
logging email urgent
Use the logging email urgent command in Global Configuration mode to set
the lowest severity level at which log messages are e-mailed in an urgent
manner. To revert the urgent severity level to its default value, use the no
form of this command.
Syntax
logging email urgent {
severity
| none}
no logging email urgent
•
severity
—If you specify a severity level, log messages at or above the
severity level are e-mailed. The severity level may either be specified by
keyword or as an integer from 0 to 7. The accepted keywords, and the
numeric severity level each represents, are as follows.
2CSNXXX_SWUM200.book Page 359 Tuesday, December 10, 2013 1:22 PM

360 E-mail Alerting Commands
–emergency (0)
–alert (1)
–critical (2)
– error (3)
– warning (4)
–notice (5)
–info (6)
–debug (7)
•
none
—
If you specify this keyword, no log messages are e-mailed urgently. All log
messages at or above the non-urgent level (configured with the logging email
command) are e-mailed in batch.
Default Configuration
The default severity level is alert.
Command Mode
Global Configuration mode
User Guidelines
Log messages at or above this severity level are considered urgent. By default,
Emergency and Alert log messages are considered urgent. Urgent log
messages are e-mailed immediately, one log message per e-mail message, and
do not wait for the log time to expire. Urgent log messages are not e-mailed
unless you enable e-mail alerting with the logging email command.
logging traps
Use the logging traps command in Global Configuration mode to set the
lowest severity level at which SNMP traps are logged. To revert the urgent
severity level to its default value, use the no form of this command.
Syntax
logging traps
severity
no logging traps
2CSNXXX_SWUM200.book Page 360 Tuesday, December 10, 2013 1:22 PM

E-mail Alerting Commands 361
•
severity
—If you specify a severity level, log messages at or above the
severity level are e-mailed. The severity level may either be specified by
keyword or as an integer from 0 to 7. The accepted keywords, and the
numeric severity level each represents, are as follows.
–emergency (0)
–alert (1)
–critical (2)
– error (3)
–warning (4)
–notice (5)
–info (6)
–debug (7)
Default Configuration
The default severity level is info(6).
Command Mode
Global Configuration mode
User Guidelines
You can filter log messages that appear in the buffered log by severity level.
You can specify the severity level of log messages that are e-mailed. You can
use this command to specify the severity level at which SNMP traps are
logged, and thus control whether traps appear in the buffered log or are e-
mailed and, if they are e-mailed, whether traps are considered urgent or non-
urgent.
logging email message-type to-addr
Use the logging email message-type to-addr command in Global
Configuration mode to configure the To address field of the e-mail. The
message types supported now are urgent, non-urgent, and both. For each
supported severity level, multiple e-mail addresses can be configured. For
example, for urgent type of messages, there could be multiple addresses
configured.
2CSNXXX_SWUM200.book Page 361 Tuesday, December 10, 2013 1:22 PM

362 E-mail Alerting Commands
Syntax
logging email message-type {urgent | non-urgent | both} to-addr
to-email-
addr
no logging email to-addr
to-addr
message-type
no logging email message-type {urgent | non-urgent | both} to-addr
to-
email-addr
Default Configuration
This command has no default configuration.
Command Mode
Global Configuration
User Guidelines
This command removes the configured to-addr field of e-mail.
logging email from-addr
Use the logging email from-addr command in Global Configuration mode to
configure the From address of the e-mail. Use the no form of this command
to remove the e-mail source address.
Syntax
logging email from-addr
from-email-addr
no logging email from-addr
Default Configuration
This command has no default configuration.
Command Mode
Global Configuration
User Guidelines
There are no user guidelines for this command.
2CSNXXX_SWUM200.book Page 362 Tuesday, December 10, 2013 1:22 PM

E-mail Alerting Commands 363
logging email message-type subject
Use the logging email message-type subject command in Global
Configuration mode to configures subject of the e-mail. Use the no form of
this command to remove the existing subject and return to the default
subject.
Syntax
logging email message-type
message-type
subject
subject
no logging email message-type
message-type
subject
Default Configuration
This command has no default configuration.
Command Mode
Global Configuration
User Guidelines
The user must enter the message-type parameter manually as tab and space
bar completion do not work for this parameter.
logging email logtime
Use the logging email logtime command in Global Configuration mode to
configure the value of how frequently the queued messages are sent.
Syntax
logging email logtime
time duration
no logging email logtime
•
time duration
—
Time in minutes. Range: 30 – 1440.
Default Configuration
The default value is 30 minutes.
2CSNXXX_SWUM200.book Page 363 Tuesday, December 10, 2013 1:22 PM

364 E-mail Alerting Commands
Command Mode
Global Configuration
User Guidelines
This command has no user guidelines.
logging email test message-type
Use the logging email test message-type command in Global Configuration
mode to test whether or not an e-mail is being sent to an SMTP server.
Syntax
logging email test message-type
message-type
message-body
message-body
• message-type—
Urgent, non-urgent, or both
•
message-body
—
The message to log. Enclose the message in double quotes if it
contains any spaces.
Default Configuration
This command has no default configuration.
Command Mode
Global Configuration
User Guidelines
This command has no user guidelines.
show logging email statistics
Use the show logging email statistics command in Privileged EXEC mode to
show the statistics about the e-mails. The command displays information on
how many e-mails are sent, how many e-mails failed, when the last e-mail was
sent, how long it has been since the last e-mail was sent, how long it has been
since the e-mail changed to disabled mode.
2CSNXXX_SWUM200.book Page 364 Tuesday, December 10, 2013 1:22 PM

E-mail Alerting Commands 365
Syntax
show logging email statistics
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC
User Guidelines
This command has no user guidelines.
clear logging email statistics
Use the clear logging email statistics command in Privileged EXEC mode to
clear the e-mail alerting statistics.
Syntax
clear logging email statistics
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC
User Guidelines
This command has no user guidelines.
2CSNXXX_SWUM200.book Page 365 Tuesday, December 10, 2013 1:22 PM

366 E-mail Alerting Commands
security
Use the security command in Mail Server Configuration mode to set the e-
mail alerting security protocol. This enables and disables the switch to use
TLS authentication with the SMTP Server. If the administrator sets the TLS
mode and, if the SMTP sever does not support TLS mode, then no e-mail
goes to the SMTP server.
Syntax
security {tls | none}
Default Configuration
The default value is disabled.
Command Mode
Mail Server Configuration
User Guidelines
This command has no user guidelines.
mail-server ip-address | hostname
Use the mail-server ip-address | hostname command in Global
Configuration mode to configure the SMTP server IP address and change the
mode to Mail Server Configuration mode. The server address can be in the
IPv4, IPv6, or DNS name format. Use the no form of this command to
remove the configured SMTP server address.
Syntax
mail-server {ip-address
ip-address
| hostname
hostname
}
no mail-server {
ip-address
|
hostname
}
•
ip-address
—An IPv4 or IPv6 address.
•
hostname
—
The DNS name of an SMTP server.
2CSNXXX_SWUM200.book Page 366 Tuesday, December 10, 2013 1:22 PM

E-mail Alerting Commands 367
Default Configuration
The default configuration for a mail server is shown in the table below.
Command Mode
Global Configuration
User Guidelines
This command has no user guidelines.
port (Mail Server Configuration Mode)
Use the port command in Mail Server Configuration mode to configure the
TCP port to use for communication with the SMTP server. Port can be set to
465 or 25. Use the no form of the command to revert the SMTP port to the
default port.
Syntax
port
port
no port
Default Configuration
The default value is 25.
Command Mode
Mail Server Configuration
Field Default
Email Alert Mail Server Port 25
Email Alert Security Protocol none
Email Alert Username admin
Email Alert Password admin
2CSNXXX_SWUM200.book Page 367 Tuesday, December 10, 2013 1:22 PM

368 E-mail Alerting Commands
User Guidelines
Port 25 is the standard SMTP port for cleartext messages. Port 465 is the
standard port for messages sent using TLSv1. Messages are always sent in
plain text mode.
username (Mail Server Configuration Mode)
Use the username command in Mail Server Configuration mode to configure
the username required by the authentication. Use the no form of the
command to revert the username to the default value.
Syntax
username
username
no username
Default Configuration
The default value for username is admin.
Command Mode
Mail Server Configuration
User Guidelines
This command has no user guidelines.
password (Mail Server Configuration Mode)
Use the password command in Mail Server Configuration mode to configure
the password required to authenticate to the e-mail server. Use the no form of
the command to revert the password to the default value.
Syntax
password
password
no password
2CSNXXX_SWUM200.book Page 368 Tuesday, December 10, 2013 1:22 PM

E-mail Alerting Commands 369
Default Configuration
The default value for password is admin.
Command Mode
Mail Server Configuration
User Guidelines
This command has no user guidelines.
show mail-server
Use the show mail-server command in Privileged EXEC mode to display the
configuration of all the mail servers or a particular mail server.
Syntax
show mail-server {
ip-address
|
hostname
| all}
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC, Configuration mode and all Configuration submodes
User Guidelines
This command has no user guidelines.
Example
console#show mail-server all
Mail Servers configuration:
No of mail servers configured:2
Mail Serqy ver1 configuration:
SMTP server IP Address: 10.131.1.11
SMTP server Port: 465
SMTP server security protocol: tls
2CSNXXX_SWUM200.book Page 369 Tuesday, December 10, 2013 1:22 PM

370 E-mail Alerting Commands
SMTP server authentication details:
Username: admin
Mail server2 configuration:
SMTP server IP Address: 10.131.1.31
SMTP server Port: 465
SMTP server security protocol: tls
SMTP server authentication details:
Username: admin
console#show mail-server ip-address 10.131.1.11
SMTP server IP Address: 10.131.1.11
SMTP server Port: 465
SMTP server security protocol: tls
SMTP server authentication details:
Username: admin
2CSNXXX_SWUM200.book Page 370 Tuesday, December 10, 2013 1:22 PM

Ethernet Configuration Commands 371
15
Ethernet Configuration Commands
Dell Networking N2000/N3000/N4000 Series Switches
Dell Networking switches support a variety of configuration options to
optimize network operations. Features such as flow-control and jumbo frames
are supported along with a variety of commands to display traffic statistics as
well as limit the effects of network loops or other network issues.
Jumbo frame technology is employed in certain situations to reduce the task
load on a server CPU and to transmit large amounts of data efficiently. Jumbo
frames technology predominantly appears where certain applications would
benefit from using a larger frame size, e.g. Network File System (NFS). The
larger frame size eliminates some of the need for fragmentation, leading to
greater throughput. The increase in throughput is particularly valuable on
data center servers where the larger frame size increases efficiency of the
system and allows processing of more requests. The Dell Networking jumbo
frames feature extends the standard ethernet MTU (Max Frame Size) from
1518 (1522 with VLAN header) bytes to 9216 bytes. However, any device
connecting to the same broadcast domain should support the same or larger
MTU.
Flow control is a mechanism or protocol used to temporarily suspend
transmission of data to a device to avoid overloading the device receive path.
Dell Networking switching implements the flow control mechanism defined
in IEEE 802.3 Annexes 31A and 31B (formerly IEEE 802.3x). Dell
Networking switching is able to transmit a MAC Control frame containing
the PAUSE opcode to halt transmission by the device receiving the PAUSE
frame whenever internal congestion is detected by the switching fabric. Flow
control is enabled by default for all ports.
Storm control allows for rate limiting of specific types of packets through the
forwarding plane. The administrator can configure the absolute rate in
packets-per-second for the Storm control threshold. Each classified packet
type (broadcast, multicast, or unicast) can be enabled/disabled per port, and
the threshold level at which Storm-Control is active is also configurable per-
port and per-type (as a percentage of interface speed).
2CSNXXX_SWUM200.book Page 371 Tuesday, December 10, 2013 1:22 PM

372 Ethernet Configuration Commands
On a storm control enabled interface, if the ingress rate of that type of packet
(L2 broadcast, multicast, or unicast) is greater than the configured threshold
level (as a percentage of port speed or as an absolute packets-per-second rate),
the switch forwarding-plane discards the excess traffic.
The
speed
command controls interface link speeds and auto-negotiation. If
speed is set to something other than auto, auto-negotiation is disabled on the
interface. Auto-negotiation will link at the highest possible speed supported
on the interface at full duplex.
Commands in this Chapter
This chapter explains the following commands:
clear counters
Use the clear counters command in Privileged EXEC mode to clear statistics
on an interface.
clear counters show interfaces counters speed
description show interfaces description storm-control broadcast
flowcontrol receive show interfaces detail storm-control multicast
interface show interfaces status storm-control unicast
interface range show interfaces transceiver switchport protected
monitor capture (Global
Configuration)
show monitor capture switchport protected name
monitor capture (Privileged
Exec)
show statistics show switchport protected
rate-limit cpu show statistics switchport show system internal
pktmgr
show interfaces advertise show storm-control show system mtu
show interfaces
configuration
shutdown system jumbo mtu
2CSNXXX_SWUM200.book Page 372 Tuesday, December 10, 2013 1:22 PM

Ethernet Configuration Commands 373
Syntax
clear counters [{gigabitethernet unit/slot/port |
port-channel
port-channel-
number
| switchport | tengigabitethernet unit/slot/port |
fortygigabitethernet unit/slot/port}]
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC mode
User Guidelines
Use of the clear counters command with no parameters indicates that both
switch and all interface statistics are to be cleared. This command clears the
individual component counters. If port-channel is specified, the command
clears the port channel counters, including the flap counters.
Example
In the following example, the counters for port 1/0/1 are cleared.
console#clear counters gigabitethernet 1/0/1
description
Use the description command in Interface Configuration mode to add a
description to an interface. To remove the description use the no form of this
command.
Syntax
description
string
no description
•
string
— Comment or a description of the port attached to this interface.
(Range: 1 to 64 characters)
Default Configuration
By default, the interface does not have a description.
2CSNXXX_SWUM200.book Page 373 Tuesday, December 10, 2013 1:22 PM

374 Ethernet Configuration Commands
Command Mode
Interface Configuration (gigabitethernet, port-channel, tengigabitethernet,
fortygigabitethernet) mode
User Guidelines
This command has no user guidelines.
Example
The following example adds a description to the Ethernet port 5.
console(config)#interface gigabitethernet 1/0/5
console(config-if-Gi1/0/5)# description RD_SW#3
duplex
The duplex command is deprecated.
flowcontrol receive
Use the flowcontrol command in Global Configuration mode to configure
the flow control. To disable flow control, use the no form of this command.
Syntax
flowcontrol receive {on | off}
no flowcontrol receive
Default Configuration
Flow Control is enabled by default.
Command Mode
Global Configuration and Interface Configuration modes
User Guidelines
Dell Networking switches implement receive flow control only. They never
issue a flow control PAUSE frame when congested, but do respect received
flow control PAUSE frames received from other switches. Disabling flow
control causes the switch to ignore received PAUSE frames.
2CSNXXX_SWUM200.book Page 374 Tuesday, December 10, 2013 1:22 PM

Ethernet Configuration Commands 375
Interface specific configuration overrides any global configuration.
Changing the flow control setting on a copper port restarts auto-negotiation
and causes a brief link-flap while auto-negotiation occurs. Changing the flow
control setting on a fiber port may cause a brief link flap as the PHY is reset.
Enabling flow control on some ports and not others can lead to excessive
packet loss in situations where some ports on the switch have been paused
and the internal packet buffers are consumed. This situation may cause traffic
loss on other ports that are not congested or flow controlled.
Example
console(config)#flowcontrol receive off
console(config)#flowcontrol receive on
interface
Use this command to configure parameters for the gigabit Ethernet and ten-
gigabit Ethernet ports, and for port-channels. While in Global Configuration
mode, enter the interface command (with a specific interface). To exit to
Global Configuration mode, enter exit. To return to Privileged EXEC mode,
press Ctrl-Z or enter end.
Additional forms of the interface command enable configuring VLANs, tunnels, the
loopback interface, the out-of-band interface, and ranges of interfaces. See
interface vlan, interface tunnel, interface loopback, and interface range.
Syntax
interface {gigabitethernet unit/slot/port |
port-channel
port-channel-number
| tengigabitethernet unit/slot/port
|
fortygigabitethernet
unit/slot/port}
Default Configuration
This command has no default configuration.
Command Mode
Global Configuration, Interface Configuration
2CSNXXX_SWUM200.book Page 375 Tuesday, December 10, 2013 1:22 PM
376 Ethernet Configuration Commands
User Guidelines
Dell Networking switches implement receive flow control only. They never
issue a flow control PAUSE frame when congested, but will respect received
flow control PAUSE frames received from other switches. Disabling flow
control causes the switch to ignore received PAUSE frames.
Interface specific configuration overrides any global configuration.
Changing the flow control setting on a copper port will restart auto-
negotiation and cause a brief link-flap while auto-negotiation occurs.
Changing the flow control setting on a fiber port may cause a brief link flap as
the PHY is reset.
Enabling flow control on some ports and not others can lead to excessive
packet loss in situations where some ports on the switch have been paused
and the internal packet buffers are consumed. This situation may cause traffic
loss on other ports that are not congested or flow controlled. See
http://www.ieee802.org/3/cm_study/public/september04/thaler_3_0904.pdf
for more information.
Example
The following example enables gigabit port 2 on stack member 1 for
configuration.
console(config)# interface gigabitethernet 1/0/2
interface range
Use the interface range command in Global Configuration mode to execute a
command on multiple ports at the same time.
NOTE: An additional form of this command enables configuring a range of VLANs.
See interface range vlan.
Syntax
interface range {
port-rang
e |
port-type
all}
•
port-range
—A list of valid ports to configure. Separate non-consecutive
ports with a comma and no spaces; use a hyphen to designate a range of
ports. For more detailed information, see Operating on Multiple Objects
(Range). The command line buffer parses up to the maximum number of
command line characters possible in the port-range parameter.
2CSNXXX_SWUM200.book Page 376 Tuesday, December 10, 2013 1:22 PM

Ethernet Configuration Commands 377
•
port-type
—Shows all interfaces of the specified type.
Default Configuration
This command has no default configuration.
Command Mode
Global Configuration, Interface Range and Interface modes
User Guidelines
Commands under the interface range context are executed independently on
each active interface in the range. If the command returns an error on one of
the active interfaces, it does not stop executing commands on other active
interfaces.
Example
The following example shows how gigabitethernet ports 5/0/18 to 5/0/20 and
3/0/1 to 3/0/24 are ranged to receive the same command.
console(config)# interface range gigabitethernet 5/0/18-20,3/0/1-24
console(config-if-range)#
The following example shows how all gigabitethernet ports can be configured
at once.
console(config)# interface range gigabitethernet all
console(config-if-range)#
The following examples demonstrate various valid interface ranges:
console(config)#interface range gigabitEthernet 1/0/1-20
console(config)#interface range gi1/0/20-48
console(config)#interface range gi1/0/1,gi1/0/48
console(config)#interface range gi2/0/1-10,gi1/0/30
console(config)#interface range gi1/0/1-10,gi1/0/30-48
console(config)#interface range gi1/0/1,te1/1/1
console(config)#interface range gigabitEthernet 1/0/10,tengigabitEthernet
1/1/2
monitor capture (Global Configuration)
Use the monitor capture command to capture packets transmitted or
received from the CPU. This facility captures switch control plane traffic and
is useful in monitoring network control traffic and analyzing network security.
2CSNXXX_SWUM200.book Page 377 Tuesday, December 10, 2013 1:22 PM

378 Ethernet Configuration Commands
No monitor capture stops the capture and returns the configuration to the
defaults.
No monitor capture file size returns the capture file size to the defaults.
No monitor capture remote port returns the TCP port to the default.
Syntax
monitor capture [file [size
max-size
] | remote [port
id
] | line [wrap]]
no monitor capture [file size] [remote port] [line wrap]
•
max-size
—
The size of the capture file in bytes.
•
id
—
The local (switch) TCP port for use with Wireshark.
Default Configuration
Capture is not enabled by default.
The in memory buffer is 128 packets.
The file system buffer is 524288 bytes and is named cpuPktCapture.pcap.
Command Modes
Global Configuration mode
User Guidelines
Only one of file, remote, or line may be specified. Setting the file, remote, or
line stops the capture.
No monitor capture stops the capture and returns the configuration to the
defaults.
No monitor capture file size returns the capture file size to the defaults
No monitor capture remote port returns the TCP port to the default
The administrator can capture packets into one of the following locations:
memory, switch NVRAM, or directly to a Wireshark analyzer.
Memory Capture:
Captured packets can be displayed on the console using the show monitor
capture packets command. Captured packets can be displayed when actively
capturing or when stopped. When a capture session is active, it is possible to
2CSNXXX_SWUM200.book Page 378 Tuesday, December 10, 2013 1:22 PM

Ethernet Configuration Commands 379
display only the captured packets that were not previously displayed as the
show command empties the capture buffer. When a capture session is
stopped, it is possible to display all saved packets as often as is desired. The
command show monitor capture packets always displays the captured packets
in chronological order.
The memory buffer only stores the first 128 bytes of each packet captured.
The switch displays the following information from the captured packet when
it is displayed on CLI:
• Packet is transmitted or received.
• ID of the interface through which the packet was passed.
• The time when packet passed through CPU.
• The first 128 bytes of packet.
• The length of full packet (if greater than 128 bytes).
The in memory capture buffer can be configured to stop when full. This
mode is configured with the command no monitor capture line wrap.
Capturing packets is started by the command monitor capture start
command. Capturing packets is stopped automatically when 128 packets are
captured and saved into the RAM. Capturing packets can be stopped
manually before 128 packets have been captured. The command monitor
capture stop halts packet capture.
If capturing is in progress, the show monitor capture packets command
displays only captured packets which have not yet been displayed during
capturing session. If capturing is stopped, the first (after stopping) show
monitor capture packets command displays packets that have not yet been
displayed during capturing session. Next the show monitor capture packets
command displays all saved packets.
If the capturing session is stopped automatically during the period packet
display is in progress, the packet display continues until all saved packets are
shown and then the buffer is cleared. The next invocation of the show
capture packets command does not display any packets. Note that this
behavior is observed only if the capturing session is stopped automatically
when the packet displaying is in progress.
The in memory capture can also be configured to wrap. This makes it possible
to display more than 128 packets per capture session if command ‘show
capture packets' is periodically executed while capture is in progress. Saved
2CSNXXX_SWUM200.book Page 379 Tuesday, December 10, 2013 1:22 PM

380 Ethernet Configuration Commands
packets that have been already displayed during capturing session are
overwritten in RAM by new captured packets if capturing is still in progress.
In this manner, the limit of displaying 128 packets per session can be
overcome (but only in monitor capture line wrap mode). Packets that have
not been displayed are not overwritten.
Capturing packets is stopped automatically when 128 packets are captured
and have not yet been displayed during capturing session. It is guaranteed
that no packets will be lost (not be displayed or not be saved) when capturing
is in progress. In this case, the last 128 packets are saved into the RAM and
can be displayed many number of times by executing the show monitor
capture packets command.
If capturing is in progress and more than 128 packets are captured and user
configures no monitor capture line wrap mode - capturing is stopped
automatically. It is guaranteed that no packets will be lost when capturing is
in progress.
All captured packets can be displayed. No captured and not yet displayed
packet can be lost. Captured packets can be displayed when capturing is in
progress or after the moment when capturing is stopped. Only packets saved
in RAM (up to 128) can be displayed when capturing is stopped.
If capturing is in progress, the show monitor capture packets command
displays only captured packets which have not yet been displayed during
capturing session. If capturing is stopped: the first (after stopping) show
monitor capture packets command displays packets which have not yet been
displayed during capturing session; Next the show monitor capture packets
command displays up to 128 captured packets.
If the capturing session is stopped automatically when the packets displaying
is in progress, then packets displaying continues up to the moment when the
rest saved packets are shown. In this case, there are no packets that have not
been displayed during the capturing session. The next call of the 'show
capture packets' command displays nothing. Note that such behavior is
observed only if the capturing session is stopped automatically when the
packet displaying is in progress.
2CSNXXX_SWUM200.book Page 380 Tuesday, December 10, 2013 1:22 PM

Ethernet Configuration Commands 381
NVRAM Capture:
After packet capture is activated, packets are stored in NVRAM until the
capture file reaches its maximum size, or until the capture is stopped
manually. When the capture is started, the capture file from the previous
capture is deleted.
The captured file can be uploaded via TFTP, SFTP, SCP via CLI and SNMP
using the copy command. The name of the capture file is
cpuPktCapture.pcap.
Remote Capture:
Remote Packet Capture works in conjunction with the Wireshark® network
analyzer tool. A packet capture server runs on the Switch and sends the
captured packets via a TCP connection to the Wireshark tool. Once a
connection is established, packet capture is started and stopped via Wireshark
commands.
Remote capture can be enabled or disabled using the CLI. The network
operator should obtain a computer with the Wireshark tool to display the
captured traffic. When using remote capture mode, the switch doesn’t store
any captured data locally.
The local TCP port number can be configured for connecting Wireshark to
the switch. The default port number is 2002. If a firewall is installed between
the Wireshark PC and the switch, then these ports must be allowed to pass
through the firewall. The Firewall must be configured to allow the Wireshark
PC to initiate a TCP connection to the switch.
The remote capture application listens on the configured TCP port for a
connection request. Wireshark must send a request to that port to establish a
connection. Once the socket connection to Wireshark has been established,
captured CPU packets are written to the data socket. Wireshark receives the
packets and processes them locally. This continues till the session is
terminated by either end.
The following Wireshark request packets are supported:
• Request to list all the remote interfaces
• Request to open a remote device
• Request to start a capture on a remote device
• Request to close the connection with the remote peer
2CSNXXX_SWUM200.book Page 381 Tuesday, December 10, 2013 1:22 PM

382 Ethernet Configuration Commands
• Message that keeps the authentication parameters
• Request to get network statistics
• Request to stop the current capture, keeping the device open
Wireshark replies supported are:
• Reply which sends the list of all the remote interfaces
• Reply that remote device has been opened correctly
• Reply that capturing has started correctly
• Reply that says 'ok, authorization successful'
• Reply that keeps the network statistics
• Reply that confirms capturing stopped successfully
Remote packet capture is not supported for packets received via out-of-band
port.
Example
Configure capture for Wireshark remote access on port 2020:
console(config)#monitor capture remote port 2020
Copy the local capture file to a TFTP server
console#copy flash://cpuPktCapture.pcap tftp://10.267.9.99/mypkts.pcap
monitor capture (Privileged Exec)
Use the monitor capture command to capture packets transmitted or
received from the CPU. This facility captures switch control plane traffic and
is useful in monitoring network control traffic and analyzing network security.
Remote packet capture is not supported when the packets are received via
Service Port.
Syntax
monitor capture {start [transmit | receive | all] | stop}
•Transmit—Capture packets transmitted by the switch CPU.
• Receive—Capture packets forwarded to the switch CPU.
•All—Capture both transmitted and received packets.
2CSNXXX_SWUM200.book Page 382 Tuesday, December 10, 2013 1:22 PM

Ethernet Configuration Commands 383
Default Configuration
Capture is not enabled by default.
By default, both transmitted and received packets are captured.
Command Modes
Privileged EXEC mode
User Guidelines
In general, starting packet capture erases the previous capture buffer
contents.
Example
console# monitor capture start all
rate-limit cpu
Use the rate-limit cpu command to reduce the amount of unknown
unicast/multicast packets forwarded to the CPU. Use the no form of the
command to set the rate limit to the default value.
Syntax
rate-limit cpu direction input pps
pps_value
no rate-limit cpu direction input pps
•
pps_value
—The packets per second. The range is 100-1024 packets per
second (100-3000 packets per second for N4000 series switches).
Default Configuration
The default ingress rate limit is 1024 packets per second (3000 for
N4000
series switches
).
Command Modes
Global Configuration mode
2CSNXXX_SWUM200.book Page 383 Tuesday, December 10, 2013 1:22 PM

384 Ethernet Configuration Commands
User Guidelines
Unknown unicast and multicast packets are copied to the CPU on the lowest
priority QoS queue. Unknown packets are those that do not have hardware
forwarding entries. Known unicast/multicast packets are hardware forwarded
and are not queued to the CPU. Control plane packets (e.g. spanning tree
BPDUs) are copied or forwarded to the CPU on higher priority queues. The
rate limiting for unknown packets occurs on the internal CPU port and does
not affect hardware based traffic routing/forwarding in any way. Typically, the
switch examines the received packets in software to check if there is a
forwarding entry, create a forwarding entry (e.g., add a L2 MAC address or
ARP response), and then either discard the packet or software forward the
packet (only occurs during the brief transitional period when the system is
actively adding a hardware forwarding entry but the hardware is not yet
updated). Processing delays for higher priority packets may occur when the
internal CPU queue is continually kept busy handling low priority packets.
This command does not affect the rate limits for control plane packets. It is
almost never necessary to use this command to change from the default
value. The use of this command should be restricted to situations in which
moderate to high rates of unknown unicast/multicast are continually sent to
the switch CPU as evidenced by the show proc cpu command and where the
ipMapForwardingTask is showing high CPU usage. This occurs most
frequently in networks where a high number of ARPs are continually received
on untrusted ports, high numbers of L2 stations are timing out and
reappearing or multicast flooding is occurring in the network. If problems
with L2, L3 or multicast learning occur after changing this value, set the rate
limit back to the default value and take other steps to correct or mitigate the
underlying network issue directly.
Use the show system internal pktmgr command to show the configured
value.
Example
The following example shows output with higher than normal CPU usage due
to packets copied to the software forwarding task.
console#show process cpu
Memory Utilization Report
status bytes
2CSNXXX_SWUM200.book Page 384 Tuesday, December 10, 2013 1:22 PM

Ethernet Configuration Commands 385
------ ----------
free 1053933568
alloc 673873920
CPU Utilization:
PID Name 5 Secs 60 Secs 300 Secs
---------- ------------------- -------- -------- --------
1129 osapiTimer 0.00% 0.00% 0.01%
1133 _interrupt_thread 0.09% 0.01% 0.00%
1137 bcmCNTR.0 0.24% 0.31% 0.31%
1142 bcmRX 23.00% 27.01% 18.01%
1147 ipMapForwardingTas 32.97% 37.11% 29.92%
1155 bcmLINK.0 0.34% 0.36% 0.36%
1156 cpuUtilMonitorTask 0.09% 0.05% 0.04%
1170 nim_t 0.09% 0.08% 0.07%
1208 dot1s_timer_task 0.00% 0.00% 0.01%
1222 snoopTask 0.00% 0.00% 0.01%
1291 RMONTask 0.00% 0.02% 0.03%
1293 boxs Req 0.00% 0.01% 0.01%
------------------------------ -------- -------- --------
Total CPU Utilization 27.31% 28.97% 31.01%
show interfaces advertise
Use the show interfaces advertise command in Privileged EXEC mode to
display information about auto-negotiation advertisement. The display
includes the local configuration and link partner advertisement, in addition
to the local advertisement.
Syntax
show interfaces advertise [{gigabitethernet unit/slot/port
|
tengigabitethernet unit/slot/port
| fortygigabitethernet unit/slot/port}]
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC mode, Configuration mode and all Configuration submodes
2CSNXXX_SWUM200.book Page 385 Tuesday, December 10, 2013 1:22 PM

386 Ethernet Configuration Commands
User Guidelines
The priority resolution field indicates the auto-negotiated link speed and
duplex. The clock field indicates whether the local interface has auto-
negotiated to clock master or clock slave. When the link is down, the field will
show No link.
When the link is down, the Oper Peer Advertisement and Priority
Resolution fields will show dashes.
Examples
The following examples display information about auto negotiation
advertisement.
Example #1
console#show interfaces advertise
Port Type Neg Operational Link Advertisement
--------- ------------------------------ -------- --------------------------
----
Gi1/0/1 Gigabit - Level Enabled 1000f, 100f, 10f
Gi1/0/2 Gigabit - Level Enabled 1000f, 100f, 10f
Gi1/0/3 Gigabit - Level Enabled 1000f, 100f, 10f
Gi1/0/4 Gigabit - Level Enabled 1000f, 100f, 10f
Gi1/0/5 Gigabit - Level Enabled 1000f, 100f, 10f
Gi1/0/6 Gigabit - Level Enabled 1000f, 100f, 10f
Example #2
console#show interfaces advertise gi1/0/1
Port: Gi1/0/1
Type: Gigabit - Level
Link State: Down
Auto Negotiation: Enabled
802.3az EEE: Disabled
Clock: Master
10000f 1000f 1000h 100f 100h 10f 10h
------ ----- ----- ----- ----- ----- ----
Admin Local link Advertisement no yes no yes no yes no
Oper Local link Advertisement no yes no yes no yes no
Oper Peer Advertisement no yes no yes no yes no
Priority Resolution - - - yes - - -
2CSNXXX_SWUM200.book Page 386 Tuesday, December 10, 2013 1:22 PM
Ethernet Configuration Commands 387
show interfaces configuration
Use the show interfaces configuration command in User EXEC mode to
display the configuration for all configured interfaces.
Syntax
show interfaces configuration [{gigabitethernet unit/slot/port|
port-channel
port-channel-number
| tengigabitethernet unit/slot/port
|
fortygigabitethernet
unit/slot/port}]
Default Configuration
This command has no default configuration.
Command Mode
User EXEC mode, Configuration mode and all Configuration submodes
User Guidelines
The displayed port configuration information includes the following:
Example
The following example displays the configuration for all configured
interfaces:
console#show interfaces configuration gigabitethernet 1/0/1
Field Description
Port The port number.
Description The port designated IEEE shorthand identifier. For example
1000Base-T refers to 1000 Mbps baseband signaling including both
Tx and Rx transmissions.
Duplex Displays the port Duplex status.
Speed Refers to the port speed.
Neg Describes the Auto-negotiation status.
MTU The Maximum Transmission Unit.
Admin State Displays whether the port is enabled or disabled.
2CSNXXX_SWUM200.book Page 387 Tuesday, December 10, 2013 1:22 PM

388 Ethernet Configuration Commands
Port Description Duplex Speed Neg MTU Admin
State
--------- ------------------------------ ------ ------- ---- ----- -----
Gi1/0/1 Full 1000 Auto 1518 Up
show interfaces counters
Use the show interfaces counters command in User EXEC mode to display
traffic seen by the interface.
Syntax
show interfaces counters [errors] [gigabitethernet unit/slot/port |
port-
channel
port-channel-number
| tengigabitethernet unit/slot/port
|
fortygigabitethernet unit/slot/port]
•
errors
—Show the error counts (frame discards and reasons) in the in and
out direction.
•
gigabitethernet
—Shows the traffic for the specified Gigabit Ethernet port.
•
port-channel
—Shows the traffic for the specified port channel port.
•
tengigabitethernet
—Shows the traffic for the specified 10-Gigabit
Ethernet port.
•
fortygigabitethernet
—Shows the traffic for the specified 40-Gigabit
Ethernet port.
Default Configuration
This command has no default configuration.
Command Mode
User EXEC mode, Configuration mode and all Configuration submodes
User Guidelines
The following table describes the fields shown in the display:
Field Description
InOctets Counted received octets.
2CSNXXX_SWUM200.book Page 388 Tuesday, December 10, 2013 1:22 PM

Ethernet Configuration Commands 389
InUcastPkts Counted received Unicast packets.
InMcastPkts Counted received Multicast packets.
InBcastPkts Counted received Broadcast packets.
OutOctets Counted transmitted octets.
OutUcastPkts Counted transmitted Unicast packets.
OutMcastPkts Counted transmitted Multicast packets.
OutBcastPkts Counted transmitted Broadcast packets.
Alignment Errors A count of frames received that are not an integral number
of octets in length and do not pass the FCS check.
FCS Errors Counted frames received that are an integral number of
octets in length but do not pass the FCS check.
Single Collision Frames Counted frames that are involved in a single collision, and
are subsequently transmitted successfully.
Multiple Collision
Frames
A count of frames that are involved in a multiple collision,
and are subsequently transmitted successfully
Late Collisions Counted times that a collision is detected later than one
slot time into the transmission of a packet.
Excessive Collisions Counted frames for which transmission fails due to
excessive collisions.
Received packets
dropped > MTU
Count of received frames dropped due to frame length
greater than MTU
Transmitted packets
dropped> MTU
Count of frames queued for transmission dropped due to
frame length greater than MTU
Internal MAC Rx Errors A count of frames for which reception fails due to an
internal MAC sublayer receive error.
Received Pause Frames A count of MAC Control frames received with an opcode
indicating the PAUSE operation.
Tra ns mit ted Pa use
Frames
Counted MAC Control frames transmitted on this
interface with an opcode indicating the PAUSE operation.
Received PFC Frames A count of the received Priority Flow Control (PFC)
frames.
Field Description
2CSNXXX_SWUM200.book Page 389 Tuesday, December 10, 2013 1:22 PM
390 Ethernet Configuration Commands
Example
The following example displays traffic seen by the physical interface:
console>show interfaces counters
Port InOctets InUcastPkts
---- ---------- ---------
1/0/1 183892 1289
3/0/1 123899 1788
Port OutOctets OutUcastPkts
---- ---------- ---------
1/0/1 9188 9
2/0/1 0 0
3/0/1 8789 27
Ch InOctets InUcastPkts
---- ---------- ---------
1 27889 928
Ch OutOctets OutUcastPkts
---- ---------- ---------
1 23739 882
The following example displays counters for Ethernet port 1/0/1.
console(config-if-Te1/0/1)#show interfaces counters te1/0/1
Port InOctets InUcastPkts InMcastPkts InBcastPkts
--------- ---------------- ---------------- ---------------- ---------------
Te1/0/1 0 0 0 0
Port OutOctets OutUcastPkts OutMcastPkts OutBcastPkts
--------- ---------------- ---------------- ---------------- ---------------
Te1/0/1 0 0 0 0
Tra ns mit ted PFC
Frames
A count of the transmitted PFC frames.
Receive Packets
Discards
Count of frames discarded due to any reason
Transmit Packets
Discarded
Count of packet queued for transmission and discards for
any reason
Field Description
2CSNXXX_SWUM200.book Page 390 Tuesday, December 10, 2013 1:22 PM

Ethernet Configuration Commands 391
FCS Errors: ................................... 0
Single Collision Frames: ...................... 0
Late Collisions: .............................. 0
Excessive Collisions: ......................... 0
Multiple Collisions: .......................... 0
Received packets dropped > MTU: ............... 0
Transmitted packets dropped > MTU: ............ 0
Internal MAC Rx Errors: ....................... 0
Received Pause Frames: ........................ 0
Transmitted Pause Frames: ..................... 0
Received PFC Frames: .......................... 0
Transmitted PFC Frames: ....................... 0
show interfaces description
Use the show interfaces description command in User EXEC mode to
display the description for all configured interfaces.
Syntax
show interfaces description [gigabitethernet unit/slot/port |
port-channel
port-channel-number
| tengigabitethernet unit/slot/port |
fortygigabitethernet
unit/slot/port]
Default Configuration
This command has no default configuration.
Command Mode
User EXEC mode, Configuration mode and all Configuration submodes
User Guidelines
This command has no user guidelines.
Example
The following example displays the description for all interfaces.
console>show interfaces description
Port Description
---- ------------------------------------------------
1/0/1 Port that should be used for management only
2CSNXXX_SWUM200.book Page 391 Tuesday, December 10, 2013 1:22 PM

392 Ethernet Configuration Commands
2/0/1
2/0/2
Ch Description
---- -----------
1 Output
show interfaces detail
Use the show interfaces detail command in Privileged EXEC mode to display
detailed status and configuration of the specified interface.
Syntax
show interfaces detail <interface-id>
•
interface-id
—
A physical interface or port channel identifier.
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC mode, Configuration mode and all Configuration submodes
User Guidelines
This command has no user guidelines.
Example
The following example displays detailed status and configuration of the
specified interface.
console(config)#show interfaces detail gi1/0/1
Port Description Duplex Speed Neg MTU Admin Link
State State
--------- --------------------------- ------ ------- ---- ----- ----- -----
Gi1/0/1 N/A Unknown Auto 1518 Up Down
Port Description
--------- ------------------------------------------------------------------
Gi1/0/1
2CSNXXX_SWUM200.book Page 392 Tuesday, December 10, 2013 1:22 PM

Ethernet Configuration Commands 393
Flow Control: Enabled
Port: Gi1/0/1
VLAN Membership mode: Access Mode
Operating parameters:
PVID: 1
Ingress Filtering: Enabled
Acceptable Frame Type: Untagged
Default Priority: 0
GVRP status: Disabled
Protected: Disabled
Port Gi1/0/1 is member in:
VLAN Name Egress rule Type
---- --------------------------------- ----------- --------
1 default Untagged Default
Static configuration:
PVID: 1
Ingress Filtering: Enabled
Acceptable Frame Type: Untagged
Port Gi1/0/1 is statically configured to:
VLAN Name Egress rule
---- --------------------------------- -----------
Forbidden VLANS:
VLAN Name
---- ---------------------------------
Port Gi1/0/1 Enabled
State: Disabled Role: Disabled
Port id: 128.1 Port Cost: 0
Port Fast: No (Configured: no ) Root Protection: No
Designated bridge Priority: 32768 Address: 001E.C9DE.C52B
Designated port id: 0.0 Designated path cost: 0
CST Regional Root: 80:00:00:1E:C9:DE:C5:2B CST Port Cost: 0
BPDU: sent 0, received
show interfaces status
Use the show interfaces status command in Privileged EXEC mode to display
the status for all configured interfaces.
2CSNXXX_SWUM200.book Page 393 Tuesday, December 10, 2013 1:22 PM

394 Ethernet Configuration Commands
Syntax
show interfaces status
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC mode, Configuration mode and all Configuration submodes
User Guidelines
Port channels are only displayed if configured. Use the
show interfaces port-
channel
command to display configured and unconfigured port channels.
Interfaces configured as stacking ports will show as detached in the output of
the
show interfaces status
command.
The link state indicates the physical connectivity state of the link. It is
possible that the link is connected physically yet frames are not able to pass
over the link. Possible causes of this condition are speed or duplex mismatch.
The displayed port status information includes the following:
Example
The following example displays the status for all configured interfaces.
Field Description
Port The port or port channel number. Oob means Out-of-Band
Management Interface.
Description Description of the port.
Duplex Displays the port Duplex status.
VLAN The native VLAN for the port.
Speed Refers to the port speed.
Neg Describes the Auto-negotiation status.
Link State Displays the Link status, either Up or Down.
Flow Ctrl
Status
Displays the Flow Control status, either Active or Inactive.
2CSNXXX_SWUM200.book Page 394 Tuesday, December 10, 2013 1:22 PM

Ethernet Configuration Commands 395
Port Description Vlan Duplex Speed Neg Link Flow Ctrl
State Status
--------- ------------------------- ----- ------ ------- ---- ----- ---------
Te1/0/1 prom N/A Unknown Auto Down Inactive
Te1/0/2 2 N/A Unknown Auto Down Inactive
Te1/0/3 host N/A Unknown Auto Down Inactive
Te1/0/4 1 N/A Unknown Auto Down Inactive
Te1/0/5 trnk N/A Unknown Auto Down Inactive
Te1/0/6 1 N/A Unknown Auto Down Inactive
Te1/0/7 1 N/A Unknown Auto Down Inactive
Te1/0/8 1 N/A Unknown Auto Down Inactive
Te1/0/9 1 N/A Unknown Auto Down Inactive
console#show interfaces status gigabitethernet 1/0/1
Port Description VLAN Duplex Speed Neg Link Flow Ctrl
State Status
--------- ------------------------- ---- ------ ------- ---- ------ ---------
Gi1/0/1 1 Full 1000 Auto Up Disabled
console#show interfaces status po1
Port Description
Channel
------- ------------------------------
Po1
Operational State.............................. Down
Admin Mode..................................... Enabled
Port Channel Flap Count........................ 0
Member Device/ Port Port Flap
Ports Timeout Speed Active Count
-------- ------------- --------- ------- -----
Gi1/0/1 actor/long Auto True 0
partner/long
Gi1/0/2 actor/long Auto True 0
partner/long
Gi1/0/3 actor/long Auto False 36
partner/long
Gi1/0/4 actor/long Auto False 27
partner/long
2CSNXXX_SWUM200.book Page 395 Tuesday, December 10, 2013 1:22 PM

396 Ethernet Configuration Commands
show interfaces transceiver
Use the show interfaces transceiver command to display the optic static
parameters as well as the Dell qualification.
Syntax
show interfaces transceiver [properties]
• properties—Displays the static parameters for the optics.
Default Configuration
This command has no default configuration.
Command Modes
User EXEC, Privileged EXEC modes.
User Guidelines
This command only supports the display of 10G and 40G transceivers.
Example
The following example shows the qualifications status of the optics on the
switch.
console#show interfaces transceiver
Port Dell Qualified
------------- ----------------
Te1/0/9 Yes
Te1/0/11 Yes
Te1/0/13 N/A
Te1/0/15 No
Te1/0/17 No
The following example shows static parameters of the optics along with the
qualifications status.
console#show interfaces transceiver properties
Yes: Dell Qualified No: Not Qualified
N/A : Not Applicable
Port Type Media Serial Number Dell Qualified
------------ ------- --------------- -------------------- --------------
2CSNXXX_SWUM200.book Page 396 Tuesday, December 10, 2013 1:22 PM

Ethernet Configuration Commands 397
Te1/0/9 SFP+ 10GBASE-LRM ANF0L5J Yes
Te1/0/11 SFP+ 10GBASE-LRM ANF0L5R Yes
Te1/0/13 SFP 1GBASE-SX PCC1PT5 N/A
Te1/0/15 SFP+ 10GBASE-SR AD1125A002R No
Te1/0/17 SFP+ 10GBASE-SR AD0815E00PC No
show monitor capture
Use this command to display captured packets transmitted or received from
the CPU.
Syntax
show monitor capture [packets]
Default Configuration
This command has no default configuration.
Command Modes
Privileged EXEC mode (all SHOW modes)
User Guidelines
This command has no user guidelines.
Example
console#show monitor capture
Operational Status............................. Enabled
Current Capturing Type......................... Line
Capturing Traffic Mode......................... Tx/Rx
Line Wrap Mode................................. Disabled
RPCAP Listening Port........................... 2002
RPCAP dump file size (KB)...................... 45
console#show monitor capture packets
1/0/1 Length = 94 [RECEIVE]
===================
02:29:23.0000
0000 33 33 00 00 00 01 00 11 88 2f 8e 82 81 00 00 01
0010 86 dd 60 00 00 00 00 24 00 01 fe 80 00 00 00 00
0020 00 00 00 00 88 ff fe 2f 8e 82 ff 02 00 00 00 00
2CSNXXX_SWUM200.book Page 397 Tuesday, December 10, 2013 1:22 PM

398 Ethernet Configuration Commands
0030 00 00 00 00 00 00 00 00 00 01 3a 00 05 02 00 00
0040 01 00 82 00 43 62 27 10 00 00 00 00 00 00 00 00
0050 00 00 00 00 00 00 00 00 00 00 ff ff 00 00
===================
1/0/1 Length = 94 [RECEIVE]
===================
02:29:24.0000
0000 33 33 00 00 00 01 00 11 88 2f 8e 82 81 00 00 01
0010 86 dd 60 00 00 00 00 24 00 01 fe 80 00 00 00 00
0020 00 00 00 00 88 ff fe 2f 8e 82 ff 02 00 00 00 00
0030 00 00 00 00 00 00 00 00 00 01 3a 00 05 02 00 00
0040 01 00 82 00 43 62 27 10 00 00 00 00 00 00 00 00
0050 00 00 00 00 00 00 00 00 00 00 ff ff 00 00
===================
1/0/1 Length = 94 [RECEIVE]
===================
02:29:25.0000
0000 33 33 00 00 00 01 00 11 88 2f 8e 82 81 00 00 01
0010 86 dd 60 00 00 00 00 24 00 01 fe 80 00 00 00 00
0020 00 00 00 00 88 ff fe 2f 8e 82 ff 02 00 00 00 00
0030 00 00 00 00 00 00 00 00 00 01 3a 00 05 02 00 00
0040 01 00 82 00 43 62 27 10 00 00 00 00 00 00 00 00
0050 00 00 00 00 00 00 00 00 00 00 ff ff 00 00
===================
1/0/1 Length = 94 [RECEIVE]
===================
02:29:26.0000
0000 33 33 00 00 00 01 00 11 88 2f 8e 82 81 00 00 01
0010 86 dd 60 00 00 00 00 24 00 01 fe 80 00 00 00 00
0020 00 00 00 00 88 ff fe 2f 8e 82 ff 02 00 00 00 00
0030 00 00 00 00 00 00 00 00 00 01 3a 00 05 02 00 00
0040 01 00 82 00 43 62 27 10 00 00 00 00 00 00 00 00
0050 00 00 00 00 00 00 00 00 00 00 ff ff 00 00
show statistics
Use the show statistics command in Privileged EXEC mode to display
detailed statistics for a specific port or for the entire switch.
2CSNXXX_SWUM200.book Page 398 Tuesday, December 10, 2013 1:22 PM

Ethernet Configuration Commands 399
Syntax
show statistics {gigabitethernet unit/slot/port |switchport |
port-channel
port-channel-number
| tengigabitethernet unit/slot/port |
fortygigabitethernet unit/slot/port}
•
unit/slot/port
—
A valid interface. See
Interface Naming Conventions
for
interface representation.
•
switchport
—Displays statistics for the entire switch.
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC mode, Configuration mode and all Configuration submodes
User Guidelines
This command has no user guidelines.
Examples
The following example shows statistics for port 1/0/1.
console(config-if-Te1/0/1)#show statistics te1/0/1
Total Packets Received (Octets)................ 0
Packets Received 64 Octets..................... 0
Packets Received 65-127 Octets................. 0
Packets Received 128-255 Octets................ 0
Packets Received 256-511 Octets................ 0
Packets Received 512-1023 Octets............... 0
Packets Received 1024-1518 Octets.............. 0
Packets Received > 1518 Octets................. 0
Packets RX and TX 64 Octets.................... 0
Packets RX and TX 65-127 Octets................ 0
Packets RX and TX 128-255 Octets............... 0
Packets RX and TX 256-511 Octets............... 0
Packets RX and TX 512-1023 Octets.............. 0
Packets RX and TX 1024-1518 Octets............. 0
Packets RX and TX 1519-2047 Octets............. 0
Packets RX and TX 2048-4095 Octets............. 0
Packets RX and TX 4096-9216 Octets............. 0
2CSNXXX_SWUM200.book Page 399 Tuesday, December 10, 2013 1:22 PM

400 Ethernet Configuration Commands
Total Packets Received Without Errors.......... 0
Unicast Packets Received....................... 0
Multicast Packets Received..................... 0
Broadcast Packets Received..................... 0
Total Packets Received with MAC Errors......... 0
Jabbers Received............................... 0
Fragments/Undersize Received................... 0
Alignment Errors............................... 0
FCS Errors..................................... 0
Overruns....................................... 0
Total Received Packets Not Forwarded........... 0
802.3x Pause Frames Received................... 0
Unacceptable Frame Type........................ 0
Total Packets Transmitted (Octets)............. 0
Packets Transmitted 64 Octets.................. 0
Packets Transmitted 65-127 Octets.............. 0
Packets Transmitted 128-255 Octets............. 0
Packets Transmitted 256-511 Octets............. 0
Packets Transmitted 512-1023 Octets............ 0
Packets Transmitted 1024-1518 Octets........... 0
Packets Transmitted > 1518 Octets.............. 0
Max Frame Size................................. 1518
Total Packets Transmitted Successfully......... 0
Unicast Packets Transmitted.................... 0
Multicast Packets Transmitted.................. 0
Broadcast Packets Transmitted.................. 0
Total Transmit Errors.......................... 0
Total Transmit Packets Discarded............... 0
Single Collision Frames........................ 0
Multiple Collision Frames...................... 0
Excessive Collision Frames..................... 0
802.3x Pause Frames Transmitted................ 0
GVRP PDUs received............................. 0
GVRP PDUs Transmitted.......................... 0
GVRP Failed Registrations...................... 0
BPDU: sent 0, received 0
EAPOL Frames Transmitted....................... 0
EAPOL Start Frames Received.................... 0
2CSNXXX_SWUM200.book Page 400 Tuesday, December 10, 2013 1:22 PM

Ethernet Configuration Commands 401
Time Since Counters Last Cleared............... 0 day 13 hr 20 min 24 sec
show statistics switchport
Use the show statistics command in Privileged EXEC mode to display
detailed statistics for a specific port or for the entire switch.
Syntax
show statistics {
interface-id
|switchport}
•
interface-id
—The
interface ID. See
Interface Naming Conventions
for interface
representation.
•
switchport
—Displays statistics for the entire switch.
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC mode, Configuration mode and all Configuration submodes
User Guidelines
It is possible to enter interface configuration mode from global configuration
mode or from interface configuration mode.
RFC Cross Reference
Textual Explanation RFC 2863 MIB Identifier
Total Packets Received (Octets) ifHCInOctets
Unicast Packets Received ifHCInUcastPkts
Multicast Packets Received ifHCInMulticastPkts
Broadcast Packets Received ifHCInBroadcastPkts
Receive Packets Discarded ifInDiscards
Octets Transmitted ifHCOutOctets
2CSNXXX_SWUM200.book Page 401 Tuesday, December 10, 2013 1:22 PM

402 Ethernet Configuration Commands
Unicast Packets Transmitted ifHCOutUcastPkts
Multicast Packets Transmitted ifHCOutMulticastPkts
Broadcast Packets Transmitted ifHCOutBroadcastPkts
Transmit Packets Discarded ifOutDiscards
Example
The following example shows statistics for the entire switch.
console#show statistics switchport
Total Packets Received (Octets)................ 0
Packets Received Without Error................. 0
Unicast Packets Received....................... 0
Multicast Packets Received..................... 0
Broadcast Packets Received..................... 0
Receive Packets Discarded...................... 0
Octets Transmitted............................. 0
Packets Transmitted Without Errors............. 0
Unicast Packets Transmitted.................... 0
Multicast Packets Transmitted.................. 0
Broadcast Packets Transmitted.................. 0
Transmit Packets Discarded..................... 0
Most Address Entries Ever Used................. 3
Address Entries Currently in Use............... 3
Maximum VLAN Entries........................... 1024
Most VLAN Entries Ever Used.................... 2
Static VLAN Entries............................ 2
Dynamic VLAN Entries........................... 0
VLAN Deletes................................... 0
Time Since Counters Last Cleared............... 0 day 18 hr 1 min 59 sec
2CSNXXX_SWUM200.book Page 402 Tuesday, December 10, 2013 1:22 PM

Ethernet Configuration Commands 403
show storm-control
Use the show storm-control command in Privileged EXEC mode to display
the configuration of storm control.
Syntax
show storm-control [all | {gigabitethernet unit/slot/port |
tengigabitethernet unit/slot/port | fortygigabitethernet unit/slot/port}]
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC mode, Configuration mode and all Configuration submodes
User Guidelines
This command has no user guidelines.
Examples
The following example shows storm control configurations for a gigabit
Ethernet port. The second example shows flow control mode status.
console#show storm-control
802.3x Flow Control Mode....................... Disable
console#show storm-control gigabitethernet 1/0/1
Bcast Bcast Mcast Mcast Ucast Ucast Flow
Intf Mode Level Mode Level Mode Level Ctrl
---------- -------- --------- -------- --------- -------- --------- --------
Gi1/0/1 Disable 5 Disable 5 Disable 5 Disabled
shutdown
Use the shutdown command in Interface Configuration mode to disable an
interface. To restart a disabled interface, use the no form of this command.
2CSNXXX_SWUM200.book Page 403 Tuesday, December 10, 2013 1:22 PM

404 Ethernet Configuration Commands
Syntax
shutdown
no shutdown
Default Configuration
The interface is enabled.
Command Mode
Interface Configuration (Ethernet, Port-Channel, Tunnel, Loopback) mode
User Guidelines
This command has no user guidelines.
Examples
The following example disables gigabit Ethernet port 1/0/5.
console(config)#interface gigabitethernet 1/0/5
console(config-if-Gi1/0/5)# shutdown
The following example reenables gigabit ethernet port 1/0/5.
console(config)#interface gigabitethernet 1/0/5
console(config-if-Gi1/0/5)# no shutdown
speed
Use the speed command in Interface Configuration mode to configure the
speed of a given Ethernet interface. To restore the default, use the no form of
this command.
Syntax
speed {10 | 100 | 1000 | 10000 | auto [10 | 100 | 1000 | 10000]}
no speed
•
10
—Configures the port to 10 Mbps operation.
•
100
—Configures the port to 100 Mbps operation.
•
1000
—Configures the port to 1000 Mbps operation.
•
10000
—Configures the port to 10 Gbps operation.
2CSNXXX_SWUM200.book Page 404 Tuesday, December 10, 2013 1:22 PM

Ethernet Configuration Commands 405
•
40000
—Configures the port to 40 Gbps operation.
•
auto
—The port automatically detects the speed it should run based on the
port at the other end of the link. If you use the 10, 100, or 1000 keywords
with the auto keyword, the port only negotiates at the specified speeds.
Default Configuration
Auto-negotiation is enabled by default on copper ports.
Command Mode
Interface Configuration (Ethernet) mode
User Guidelines
To disable auto-negotiation on a port, it is necessary to enter the speed
command without using the auto parameter. Fiber ports do not support
auto-negotiation and therefore require the operator to enter the speed
command with the desired operating bandwidth. Disabling auto-negotiation
on 1G copper ports may lead to random frame loss as the clock master has not
been arbitrated by the auto-negotiation process. Auto-negotiation is required
on 10G/40G copper ports, and is always recommended for copper ports.
When the auto parameter is used with a set of speeds, only those speeds are
advertised during auto-negotiation. Alternatively, if no speed arguments are
configured, then all the speeds which the port is capable of supporting are
advertised. Not all ports support all speeds, even if they are available in the
command. Entering an unsupported speed will produce the following error
message An invalid interface has been used for this
function. Fiber ports do not support auto-negotiation. Both ends of fiber
connections must be set to the same speed.
Example
The following example configures the speed operation of Ethernet port 1/0/5
to advertise 100-Mbps operation only.
console(config)#interface gigabitethernet 1/0/5
console(config-if)#speed 100
2CSNXXX_SWUM200.book Page 405 Tuesday, December 10, 2013 1:22 PM

406 Ethernet Configuration Commands
storm-control broadcast
Use the storm-control broadcast command in Interface Configuration mode
to enable broadcast storm recovery mode for a specific interface. If the mode
is enabled, broadcast storm recovery is active, and if the rate of L2 broadcast
traffic ingressing on an interface increases beyond the configured threshold,
the traffic will be dropped. Therefore, the rate of broadcast traffic will be
limited to the configured threshold.
Syntax
storm-control broadcast [level |
rate
]
no storm-control broadcast
• level— The configured rate as a percentage of link-speed.
•
rate
— The configured rate in kilobits per second (Kbps). (Range: 0-100)
Default Configuration
The default value is 5.
Command Mode
Interface Configuration (Ethernet) mode
User Guidelines
This command has no user guidelines.
Example
console(config-if-Gi1/0/1)#storm-control broadcast level 5
storm-control multicast
Use the storm-control multicast command in Interface Configuration mode
to enable multicast storm recovery mode for an interface. If the mode is
enabled, multicast storm recovery is active, and if the rate of L2 multicast
traffic ingressing on an interface increases beyond the configured threshold,
the traffic will be dropped. Therefore, the rate of multicast traffic will be
limited to the configured threshold.
2CSNXXX_SWUM200.book Page 406 Tuesday, December 10, 2013 1:22 PM

Ethernet Configuration Commands 407
When you use the no storm-control multicast command to "disable" storm-
control after having set the level or rate to a non-default value, that value is
still set but is not active until you reenable storm-control.
Syntax
storm-control multicast [level |
rate
]
no storm-control multicast
• level— The configured rate as a percentage of link-speed.
•
rate
— The configured rate in kilobits per second (Kbps). (Range: 0-100)
Default Configuration
The default value is 5.
Command Mode
Interface Configuration (Ethernet) mode
User Guidelines
This command has no user guidelines.
Example
console(config-if-Gi1/0/1)#storm-control multicast level 5
storm-control unicast
Use the storm-control unicast command in Interface Configuration mode to
enable unknown unicast storm control for an interface. If the mode is
enabled, unicast storm recovery is active, and if the rate of unknown L2
unicast (destination lookup failure) traffic ingressing on an interface increases
beyond the configured threshold, the traffic will be dropped. Therefore, the
rate of unknown unicast traffic will be limited to the configured threshold.
When you use the no storm-control multicast command to "disable" storm-
control after having set the level or rate to a non-default value, that value is
still set but is not active until you reenable storm-control.
2CSNXXX_SWUM200.book Page 407 Tuesday, December 10, 2013 1:22 PM

408 Ethernet Configuration Commands
Syntax
storm-control unicast [level |
rate
]
no storm-control unicast
• level— The configured rate as a percentage of link-speed.
•
rate
— The configured rate in kilobits per second (Kbps). (Range: 0-100)
Default Configuration
The default value is 5.
Command Mode
Interface Configuration (Ethernet) mode
User Guidelines
This command has no user guidelines.
Example
console(config-if-Gi1/0/1)#storm-control unicast level 5
switchport protected
Use the switchport protected command in Interface Configuration mode to
configure a protected port. The
groupid
parameter identifies the set of
protected ports to which this interface is assigned. You can only configure an
interface as protected in one group. You are required to remove an interface
from one group before adding it to another group.
Port protection occurs within a single switch. Protected port configuration
does not affect traffic between ports on two different switches. No traffic
forwarding is possible between two protected ports. Ports in a protected group
will not forward traffic to other ports in the group.
Syntax
switchport protected
groupid
no switchport protected
•
groupid-
-Identifies which group this port will be protected in. (Range: 0-2)
2CSNXXX_SWUM200.book Page 408 Tuesday, December 10, 2013 1:22 PM

Ethernet Configuration Commands 409
Default Configuration
No protected switchports are defined.
Command Mode
Interface Configuration (Ethernet) mode
User Guidelines
This command has no user guidelines.
Example
The following example configures Ethernet port 1/0/1 as a member of
protected group 1.
console(config)#interface gigabitethernet 1/0/1
console(config-if-Gi1/0/1)#switchport protected 1
switchport protected name
Use the switchport protected name command in Global Configuration mode
to adds the port to the protected group 1 and also sets the group name to
"protected".
Syntax
switchport protected
groupid
name
name
no switchport protected
groupid
name
•
groupid
— Identifies which group the port is to be protected in.
(Range: 0–2)
•
name
— Name of the group. (Range: 0-32 characters)
Default Configuration
This command has no default configuration.
Command Mode
Global Configuration mode
2CSNXXX_SWUM200.book Page 409 Tuesday, December 10, 2013 1:22 PM

410 Ethernet Configuration Commands
User Guidelines
This command has no user guidelines.
Example
The following example assigns the name "protected" to group 1.
console(config-if-Gi1/0/1)#switchport protected 1 name protected
show switchport protected
Use the show switchport protected command in Privileged EXEC mode to
display the status of all the interfaces, including protected and unprotected
interfaces.
Syntax
show switchport protected
groupid
•
groupid
— Identifies which group the port is to be protected in.
(Range: 0–2)
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC mode, Configuration mode and all Configuration submodes
User Guidelines
This command has no user guidelines.
Example
The following example identifies test as the protected group.
console#show switchport protected 0
Name......................................... test
show system internal pktmgr
Use the show system internal pktmgr command to display the configured
CPU rate limit for unknown packets in packets per second.
2CSNXXX_SWUM200.book Page 410 Tuesday, December 10, 2013 1:22 PM

Ethernet Configuration Commands 411
Syntax
show system internal pktmgr internal control sw-rate-limit
Default Configuration
This command has no default configuration.
Command Modes
Privileged EXEC mode
User Guidelines
See the
rate-limit cpu
command for further information on the output of this
command.
Example
console# show system internal pktmgr internal control sw-rate-limit
Inband pps global threshold 1024
show system mtu
Use the show system mtu command to display the configured MTU. The
MTU is set using the global system jumbo mtu command. This command
deprecates the show interfaces mtu command.
Syntax
show system mtu
Default Configuration
The default mtu size is 1518 bytes (1522 bytes for VLAN tagged frames).
Command Modes
Privileged EXEC
User Guidelines
This command has no usage guidelines.
2CSNXXX_SWUM200.book Page 411 Tuesday, December 10, 2013 1:22 PM

412 Ethernet Configuration Commands
Example
a11-39#show system mtu
System Jumbo MTU size is 9216 bytes
system jumbo mtu
Use the system jumbo mtu command to globally configure the Maximum
Transmission Unit (MTU) on all interfaces, IP/IPv6 interfaces, VLAN
interfaces, and port channel interfaces for forwarded and system-generated
frames. The MTU is the size of the largest Ethernet frame that can be
transmitted on an interface without fragmentation. Frames received on an
interface are dropped if they exceed the MTU. Frames larger than this size
generated by the system are fragmented.
This command deprecates the mtu, ip mtu, and ipv6 mtu commands.
Use the no form of the command to reset the MTU to the default.
Syntax
system jumbo mtu
frame size
no system jumbo mtu
•
frame size
—The maximum frame size, in bytes, received by the system
which is not forwarded.
Default Configuration
The default MTU size is 1518 bytes (1522 bytes for VLAN tagged frames).
Command Modes
Global Configuration mode
User Guidelines
The IP and IPv6 MTU are set to the MTU minus 18 bytes. IP packets
forwarded in software are dropped if they exceed the IP MTU. Packets
originated on the router, such as OSPF packets, may be fragmented by the IP
stack. OSPF advertises the IP MTU in the Database Description packets it
sends to its neighbors during database exchange. If two OSPF neighbors
2CSNXXX_SWUM200.book Page 412 Tuesday, December 10, 2013 1:22 PM

Ethernet Configuration Commands 413
advertise different IP MTUs, they will not form an adjacency (unless OSPF
has been instructed to ignore differences in IP MTU with the ip ospf
mtuignore command).
2CSNXXX_SWUM200.book Page 413 Tuesday, December 10, 2013 1:22 PM

414 Ethernet Configuration Commands
2CSNXXX_SWUM200.book Page 414 Tuesday, December 10, 2013 1:22 PM

Ethernet CFM Commands 415
16
Ethernet CFM Commands
Dell Networking N4000 Series Switches
Connectivity Fault Management (CFM) is the OAM Protocol provision for
end-to-end service layer OAM in carrier Ethernet networks. CFM provides
mechanisms to support the operator in performing connectivity checks, fault
detection, fault verification and isolation, and fault notification per service in
the network domain of interest. Unlike Ethernet OAM defined in IEEE
802.3ah, where the faults are detected and notified on a single point-to-point
IEEE Std. 802.3 LAN, this specification deals with the fault diagnosis at
service layer across networks comprising multiple LANs, including LANs
other than 802.3 media.
Dell Networking CFM is only available on the N4000 series switches. CFM is
not compatible with iSCSI optimization. Disable iSCSI optimization before
enabling CFM.
Dell Networking CFM supports the following functionality:
• Path discovery (linktrace message)
• Fault detection (continuity check message)
• Fault verification and isolation (loopback and linktrace messages)
• Fault notification (alarm indication signal or SNMP trap)
Commands in this Chapter
This chapter explains the following commands:
ethernet cfm domain ping ethernet cfm
service traceroute ethernet cfm
ethernet cfm cc level show ethernet cfm errors
ethernet cfm mep level show ethernet cfm domain
2CSNXXX_SWUM200.book Page 415 Tuesday, December 10, 2013 1:22 PM

416 Ethernet CFM Commands
ethernet cfm domain
Use the ethernet cfm domain command in Global Configuration mode to
enter into maintenance domain Configuration mode for an existing domain.
Use the optional level parameter to create a domain and enter into
maintenance domain Configuration mode. In maintenance domain
Configuration mode, maintenance associations are created and per-
maintenance domain services can be configured. Use the no form of the
command to delete a maintenance domain.
Syntax
ethernet cfm domain
domain-name
[level
0-7
]
•
domain-name
—Name of the maintenance domain. Alphanumeric string
of up to 43 characters.
Default Configuration
No CFM domains are preconfigured.
Command Mode
Global Configuration mode
User Guidelines
Each domain must have a unique name and level, for example, one cannot
create a domain qwerty at level 2 if domain qwerty already exists at level 1.
Likewise, one cannot create a domain dvorak at level 2 if a domain of any
name exists at level 2.
ethernet cfm mep enable show ethernet cfm maintenance-points
local
ethernet cfm mep active show ethernet cfm maintenance-points
remote
ethernet cfm mep archive-hold-time show ethernet cfm statistics
ethernet cfm mip level debug cfm
2CSNXXX_SWUM200.book Page 416 Tuesday, December 10, 2013 1:22 PM

Ethernet CFM Commands 417
Example
In this example, a domain vin is created at level 1.
console(config)#ethernet cfm domain vin level 1
console(config-cfm-mdomain)#
service
Use the service command in maintenance domain Configuration mode to
associate a VLAN with a maintenance domain. Use the no form of the
command to remove the association.
Syntax
service
service-name
vlan
vlanid
•
service-name
—Unique service identifier.
•
vlanid
—VLAN ID representing a service instance that is monitored by this
maintenance association. The range is 1-4093.
Default Configuration
No VLANs are associated with a maintenance domain by default.
Command Mode
Maintenance domain Configuration mode
User Guidelines
This command has no user guidelines.
Example
console(config-cfm-mdomain)#service serv1 vlan 10
ethernet cfm cc level
Use the ethernet cfm cc level command in Global Configuration mode to
initiate sending continuity checks (CCMs) at the specified interval and level
on a VLAN monitored by an existing domain. Use the no form of the
command to cease send CCMs.
2CSNXXX_SWUM200.book Page 417 Tuesday, December 10, 2013 1:22 PM

418 Ethernet CFM Commands
Syntax
ethernet cfm cc level
0-7
vlan
vlan-list
interval
secs
•
vlanid
—VLAN ID representing a service instance that is monitored by this
maintenance association. The range is 1-4093.
• secs—Time interval between successive transmissions. The range is 1, 10,
60, and 600 seconds. The default is 1 second.
Default Configuration
CCMs are not sent by default.
Command Mode
Global Configuration mode
User Guidelines
This command has no user guidelines.
Example
console(config)#ethernet cfm cc level 1 vlan 15 interval 10
ethernet cfm mep level
Use the ethernet cfm mep level command in Interface Configuration mode
to create a Maintenance End Point (MEP) on an interface at the specified
level and direction. MEPs are configured per Maintenance Association per
Maintenance Domain. Use the no form of the command to delete a MEP.
Syntax
ethernet cfm mep level
0-7
direction
up|down
mpid
1-8191
vlan
1-4093
•
level
—Maintenance association level
•
direction
—
Up indicates the MEP is facing towards Bridge Relay Entity. Down
indicates the MEP is facing towards the LAN.
•
mpid
—
Maintenance entity identifier
•
vlan
—
VLAN on which the MEP operates.
2CSNXXX_SWUM200.book Page 418 Tuesday, December 10, 2013 1:22 PM

Ethernet CFM Commands 419
Default Configuration
No MEPs are preconfigured.
Command Mode
Interface Configuration
User Guidelines
This command has no user guidelines.
Example
The following example creates a maintenance endpoint at level 1 with mpid
1010 on vlan 10.
console(config-if-Gi1/0/3)#ethernet cfm mep level 1 direction up mpid 1010
vlan 10
ethernet cfm mep enable
Use the ethernet cfm mep enable command in Interface Configuration mode
to enable a MEP at the specified level and direction. Use the no form of the
command to disable the MEP.
Syntax
ethernet cfm mep enable level
0-7
vlan
1-4093
mpid
1-8191
•
level
—Maintenance association level
•
mpid
—
Maintenance entity identifier
•
vlan
—
VLAN on which the MEP operates.
Default Configuration
No MEPs are preconfigured.
Command Mode
Interface Configuration
User Guidelines
The maintenance domain must exist for it to be enabled.
2CSNXXX_SWUM200.book Page 419 Tuesday, December 10, 2013 1:22 PM

420 Ethernet CFM Commands
Example
The following example enables a maintenance endpoint at level 1 with mpid
1010 on vlan 10.
console(config-if-Gi1/0/3)#ethernet cfm mep enable level 1 vlan 10 mpid 1010
ethernet cfm mep active
Use the ethernet cfm mep active command in Interface Configuration mode
to activate a MEP at the specified level and direction. Use the no form of the
command to deactivate the MEP.
Syntax
ethernet cfm mep active level
0-7
vlan
1-4093
mpid
1-8191
•
level
—Maintenance association level
•
mpid
—
Maintenance entity identifier
•
vlan
—
VLAN on which the MEP operates.
Default Configuration
No MEPs are preconfigured.
Command Mode
Interface Configuration
User Guidelines
This command has no user guidelines.
ethernet cfm mep archive-hold-time
Use the ethernet cfm mep archive-hold-time command in Interface
Configuration mode to maintain internal information on a missing MEP. Use
the no form of the command to return the interval to the default value.
Syntax
ethernet cfm mep archive-hold-time
hold-time
2CSNXXX_SWUM200.book Page 420 Tuesday, December 10, 2013 1:22 PM

Ethernet CFM Commands 421
•
hold-time
—The time in seconds to maintain the data for a missing MEP
before removing the data. The default value is 600 seconds.
Default Configuration
No MEPs are preconfigured.
Command Mode
Interface Configuration
User Guidelines
The hold time should generally be less than the CCM message interval.
Example
The following example sets the hold time for maintaining internal
information regarding a missing MEP.
console(config)#ethernet cfm mep archive-hold-time 1200
ethernet cfm mip level
Use the ethernet cfm mip level command in Interface Configuration mode
to create a Maintenance Intermediate Point (MIP) at the specified level. The
MEPs are configured per Maintenance Domain per interface. Use the no
form of the command to delete a MIP.
Syntax
ethernet cfm mip level
0-7
•
level
—Maintenance association level
Default Configuration
No MIPs are preconfigured.
Command Mode
Interface Configuration
2CSNXXX_SWUM200.book Page 421 Tuesday, December 10, 2013 1:22 PM

422 Ethernet CFM Commands
User Guidelines
This command has no user guidelines.
Example
console(config-if-gi1/0/1)# ethernet cfm mip level <7>
ping ethernet cfm
Use the ping ethernet cfm command in Privileged EXEC mode to generate a
loopback message (LBM) from the configured MEP.
Syntax
ping ethernet cfm {mac
mac-addr
| remote-mpid
1-8191
} {domain
domain
name
| level
0-7
} vlan
vlan-id
mpid
1-8191
[count
1-255
]
•
level
—Maintenance association level
•
mac-addr
—
The destination MAC address for which the connectivity needs to
be verified. Either MEP ID or the MAC address option can be used.
•
remote-mpid
—
The MEP ID for which connectivity is to be verified; i.e. the
destination MEP ID.
•
domain
—
Name of the maintenance domain (an alphanumeric string of up to
43 characters in length).
•
vlan-id
—
A VLAN associated with the maintenance domain. Range: 1-4094.
•
mpid
—
The MEP ID from which the loopback message needs to be
transmitted.
•
count
—
The number of LBMs to be transmitted. The default number is 1.
Default Configuration
By default, this command will transmit one loopback message with a time-out
of five seconds.
Command Mode
Privileged EXEC
2CSNXXX_SWUM200.book Page 422 Tuesday, December 10, 2013 1:22 PM

Ethernet CFM Commands 423
User Guidelines
This command has no user guidelines.
Example
console #ping ethernet cfm mac 00:11:22:33:44:55 level 1 vlan 10 mpid 1 count
10
traceroute ethernet cfm
Use the traceroute ethernet command in Privileged EXEC mode to generate
a link trace message (LTM) from the configured MEP.
Syntax
traceroute ethernet cfm {mac
mac-addr
| remote-mpid
1-8191
} {domain
domain name
| level
0-7
} vlan
vlan-id
mpid
1-8191
[ttl
1-255
]
•
level
—Maintenance association level
•
mac-addr
—
The destination MAC address for which the connectivity needs to
be verified. Either MEP ID or the MAC address option can be used.
•
remote-mpid
—
The MEP ID for which connectivity is to be verified; i.e. the
destination MEP ID.
•
domain
—
Name of the maintenance domain (an alphanumeric string of up to
43 characters in length).
•
vlan-id
—
A VLAN associated with the maintenance domain. Range: 1-4094.
•
mpid
—
The MEP ID from which the loopback message needs to be
transmitted.
•
ttl
—
The number of hops over which the LTM is expected to be transmitted.
The default number is 64.
Default Configuration
By default, the traceroute command will send loopback trace messages with a
TTL of 64.
Command Mode
Privileged EXEC
2CSNXXX_SWUM200.book Page 423 Tuesday, December 10, 2013 1:22 PM

424 Ethernet CFM Commands
User Guidelines
This command has no user guidelines.
Example
console # linktrace src-mep 200 target-mep 400 ttl 64
show ethernet cfm errors
Use the show ethernet cfm errors command in Privileged EXEC mode to
display the cfm errors.
Syntax
show ethernet cfm errors {domain
domain-id
| level
0-7
}
•
level
—Maintenance association level
•
domain
—Name of the maintenance domain (an alphanumeric string of
up to 43 characters in length).
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC, Configuration mode and all Configuration submodes
User Guidelines
This command has no user guidelines.
Example
console#show ethernet cfm errors
----- ---- ---- --------- ------------ ------------ ----------- ----------
Level SVID MPID DefRDICcm DefMACStatus DefRemoteCCM DefErrorCCM DefXconCCM
----- ---- ---- --------- ------------ ------------ ----------- ----------
show ethernet cfm domain
Use the show ethernet cfm domain command in Privileged EXEC mode to
display the configured parameters in a maintenance domain.
2CSNXXX_SWUM200.book Page 424 Tuesday, December 10, 2013 1:22 PM

Ethernet CFM Commands 425
Syntax
show ethernet cfm domain {brief |
domain-id
}
•
domain
—Name of the maintenance domain (an alphanumeric string of
up to 43 characters in length).
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC, Configuration mode and all Configuration submodes
User Guidelines
This command has no user guidelines.
Example
console # show Ethernet cfm domain domain1
Domain Name : domain1
Level : 1
Total Services : 1
---- ----------------------------------- ------------------
VLAN ServiceName CC-Interval (secs)
---- ----------------------------------- ------------------
10 serv1 1
show ethernet cfm maintenance-points local
Use the show ethernet cfm maintenance-points local command in Privileged
EXEC mode to display the configured local maintenance points.
Syntax
show ethernet cfm maintenance-points local {level
0-7
| interface
interface-
id
| domain
domain-name
}
•
level
—Maintenance association level
•
domain
—Name of the maintenance domain (an alphanumeric string of
up to 43 characters in length).
•
interface-id
—
Show all MPs associated with the interface.
2CSNXXX_SWUM200.book Page 425 Tuesday, December 10, 2013 1:22 PM

426 Ethernet CFM Commands
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC, Configuration mode and all Configuration submodes
User Guidelines
This command has no user guidelines.
Example
show ethernet cfm maintenance-points local level 1
---- ----- ---- ---- ------ ----- -------- ------ ----------- -----
MPID Level Type VLAN Port Dire- CC MEP- Operational MAC
ction Transmit Active Status
---- ----- ---- ---- ------ ----- -------- ------ ----------- -----
1 1 MEP 10 1/0/1 UP Enabled True 00:02:bc:02:02:02
----- ---- ------ -----------------
Level Type Port MAC
----- ---- ------ -----------------
show ethernet cfm maintenance-points remote
Use the show ethernet cfm maintenance-points remote command in
Privileged EXEC mode to display the configured remote maintenance points.
Syntax
show ethernet cfm maintenance-points remote {level
0-7
| domain
domain-
name
| detail [mac
mac-address
| mep
MEPId
] [domain
domain-name
|
level
0-7
] [vlan
vlan-id
]}
•
domain
—Name of the maintenance domain (an alphanumeric string of
up to 43 characters in length).
•
level
—Maintenance association level
•
mac-addr
—
The destination MAC address for which the connectivity needs to
be verified. Either MEP ID or the MAC address option can be used.
•
vlan-id
—
A VLAN associated with the maintenance domain. Range: 1-4094.
•
mpid
—
The MEP ID from which the loopback message needs to be
transmitted.
2CSNXXX_SWUM200.book Page 426 Tuesday, December 10, 2013 1:22 PM

Ethernet CFM Commands 427
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC, Configuration mode and all Configuration submodes
User Guidelines
This command has no user guidelines.
Example
console# show ethernet cfm maintenance-points remove level 1
------ ------- ----- ----------------- ---- ----------------- -----------
MEP Id RMEP Id Level MAC VLAN Expiry Timer(sec) Service Id
------ ------- ----- ----------------- ---- ----------------- -----------
1 2 1 00:11:22:33:44:55 10 25 serv1
show ethernet cfm statistics
Use the show ethernet cfm maintenance-points remote command in
Privileged EXEC mode to display the CFM statistics.
Syntax
show ethernet cfm statistics [domain
domain-name
| level
0-7
]
•
domain
—Name of the maintenance domain (an alphanumeric string of
up to 43 characters in length).
•
level
—Maintenance association level
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC, Configuration mode and all Configuration submodes
User Guidelines
This command has no user guidelines.
2CSNXXX_SWUM200.book Page 427 Tuesday, December 10, 2013 1:22 PM

428 Ethernet CFM Commands
Example
show Ethernet cfm statistics [domain <domain-name> | level <0-7>]
Console# show ethernet cfm statistics
------------------------------------------------------------------
Statistics for 'Domain: domain1, Level: 1, Vlan: 11, MEP Id: 1'
------------------------------------------------------------------
Out-of-sequence CCM's received : 0
CCM's transmitted : 259
In-order Loopback Replies received : 5
Out-of-order Loopback Replies received: 0
Bad MSDU Loopback Replies received : 0
Loopback Replies transmitted : 5
Unexpected LTR's received : 0
------------------------------------------------------------------
Statistics for 'Domain: domain1, Level: 1, Vlan: 11, MEP Id: 2'
------------------------------------------------------------------
Out-of-sequence CCM's received : 0
CCM's transmitted : 1
In-order Loopback Replies received : 5
Out-of-order Loopback Replies received: 5
Bad MSDU Loopback Replies received : 0
Loopback Replies transmitted : 0
Unexpected LTR's received : 0
------------------------------------------------------------------
Statistics for 'Domain: domain1, Level: 1, Vlan: 11, MEP Id: 3'
------------------------------------------------------------------
Out-of-sequence CCM's received : 0
CCM's transmitted : 1
In-order Loopback Replies received : 0
Out-of-order Loopback Replies received: 0
Bad MSDU Loopback Replies received : 0
Loopback Replies transmitted : 5
Unexpected LTR's received : 0
debug cfm
Use the debug cfm command in Privileged EXEC mode to enable CFM
debugging. Use the no form of the command to disable debugging.
Syntax
debug cfm {event | {pdu {all | ccm | ltm | lbm |} {tx | rx}}}
2CSNXXX_SWUM200.book Page 428 Tuesday, December 10, 2013 1:22 PM

Ethernet CFM Commands 429
•
event
—CFM events
•
pdu
—CFM PDUs
•
ccm
—Continuity check messages
•
ltm
—Link trace messages
•
lbm
—Loopback messages
•
tx
—Transmit only
•
rx
—Receive only
•
all
—Everything
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC
User Guidelines
This command has no user guidelines.
Example
Console# show ethernet cfm statistics
------------------------------------------------------------------
Statistics for 'Domain: domain1, Level: 1, Vlan: 11, MEP Id: 1'
------------------------------------------------------------------
Out-of-sequence CCM's received : 0
CCM's transmitted : 259
In-order Loopback Replies received : 5
Out-of-order Loopback Replies received: 0
Bad MSDU Loopback Replies received : 0
Loopback Replies transmitted : 5
Unexpected LTR's received : 0
------------------------------------------------------------------
Statistics for 'Domain: domain1, Level: 1, Vlan: 11, MEP Id: 2'
------------------------------------------------------------------
Out-of-sequence CCM's received : 0
CCM's transmitted : 1
In-order Loopback Replies received : 5
Out-of-order Loopback Replies received: 5
2CSNXXX_SWUM200.book Page 429 Tuesday, December 10, 2013 1:22 PM

430 Ethernet CFM Commands
Bad MSDU Loopback Replies received : 0
Loopback Replies transmitted : 0
Unexpected LTR's received : 0
------------------------------------------------------------------
Statistics for 'Domain: domain1, Level: 1, Vlan: 11, MEP Id: 3'
------------------------------------------------------------------
Out-of-sequence CCM's received : 0
CCM's transmitted : 1
In-order Loopback Replies received : 0
Out-of-order Loopback Replies received: 0
Bad MSDU Loopback Replies received : 0
Loopback Replies transmitted : 5
Unexpected LTR's received : 0
2CSNXXX_SWUM200.book Page 430 Tuesday, December 10, 2013 1:22 PM

Green Ethernet Commands 431
17
Green Ethernet Commands
Dell Networking switches support various Green Ethernet modes, i.e., power
saving modes, namely:
•Energy-Detect Mode
•Energy Efficient Ethernet
These modes can enable significant operational cost reductions through
direct power savings and reducing cooling costs.
Energy-Detect Mode
With this mode enabled, when the port link is down the PHY automatically
goes down for short periods of time and then wakes up periodically to check
for link pulses. This reduces power consumption when no link partner is
present. This feature is currently available only on GE copper ports.
Energy Efficient Ethernet
Energy Efficient Ethernet (EEE) combines the MAC with a family of PHYs
that support operation in a Low Power Mode as defined by the IEEE 802.3az
Energy Efficient Ethernet Task Force. Lower Power Mode enables both the
send and receive sides of the link to disable some functionality for power
savings when lightly loaded. Transition to Low Power Mode does not change
the link status. Frames in transit are not dropped or corrupted in transition to
and from Low Power Mode. Transition time is transparent to upper layer
protocols and applications. LLDP must be enabled in order to EEE to operate
on a link.
Commands in this Chapter
This chapter explains the following commands:
green-mode energy-detect show green-mode interface-id
–
green-mode eee show green-mode
–
2CSNXXX_SWUM200.book Page 431 Tuesday, December 10, 2013 1:22 PM

432 Green Ethernet Commands
green-mode energy-detect
This command enables a Dell proprietary mode of power reduction on ports
that are not connected to another interface. Use the green-mode energy-
detect command in Interface Configuration mode to enable energy-detect
mode on an interface or all the interfaces. Energy-detect mode is disabled by
default on 1G copper interfaces and enabled by default on 10G copper
interfaces.
On combo ports, it is possible to configure energy-detect mode even if the
fiber port is enabled. If enabled, energy-detect mode will become active when
the copper port is used.
Use the no form of the command to disable energy-detect mode on the
interface(s).
Syntax
green-mode energy-detect
no green-mode energy-detect
Default Configuration
On N2000 and N3000 switches, energy-detect is disabled by default. Energy
detect mode is enabled by default and cannot be disabled on N4000 10G
copper interfaces.
Command Mode
Interface Configuration mode
User Guidelines
Cable diagnostics (show copper-ports commands) may give misleading
results if green mode is enabled on the port. Disable green mode prior to
running any cable diagnostics. EEE and energy-detect modes are only
supported on N4000 series 10G ports and on N2000/N3000 1G copper ports.
Energy-detect mode is always enabled on N4000 series 10G ports and cannot
clear green-mode statistics show green-mode eee-lpi-history interface
green-mode eee-lpi-history
–
2CSNXXX_SWUM200.book Page 432 Tuesday, December 10, 2013 1:22 PM

Green Ethernet Commands 433
be disabled. An error message (Unable to set energy-detect
mode) will be displayed if the user attempts to configure energy-detect on a
10G port on a N2000/N3000 series switch.
green-mode eee
Use the green-mode eee command in Interface Configuration mode to
enable EEE low power idle mode on an interface. The command enables both
send and receive sides of a link to disable some functionality for power savings
when lightly loaded. Transition to Low Power Mode does not change the link
status. Frames in transit are not dropped or corrupted in transition to and
from Low Power Mode.
On combo ports, eee mode can be enabled even if the port is using the fiber
interface. If enabled, eee mode is only active when the copper interface is
active.
Use the no form of the command to disable the feature.
Syntax
green-mode eee
no green-mode eee
Default Configuration
The default value is Disabled.
Command Mode
Interface Configuration
User Guidelines
Cable diagnostics (show copper-ports commands) may give misleading
results if green mode is enabled on the port. Disable green mode prior to
running any cable diagnostics. EEE mode is supported on N4000 series 10G
copper ports and on N2000/N3000 1G and 10G copper interfaces.
2CSNXXX_SWUM200.book Page 433 Tuesday, December 10, 2013 1:22 PM

434 Green Ethernet Commands
clear green-mode statistics
Use the clear green-mode statistics command in Privileged EXEC mode to
clear:
• The EEE LPI event count, and LPI duration
• The EEE LPI history table entries
• The Cumulative Power savings estimates
for a specified interface or for all the interfaces based upon the argument.
Syntax
clear green-mode statistics {
interface-id
| all}
•
interface-id
—
Any valid interface. See
Interface Naming Conventions
for
interface representation.
•
all
—All interfaces.
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC
User Guidelines
This command has no user guidelines.
green-mode eee-lpi-history
Use the green-mode eee-lpi-history command in Global Configuration mode
to configure the Global EEE LPI history collection interval and buffer size.
This value is applied globally on all interfaces on the stack. LPI history is only
collected on combo ports when the copper port is enabled. Use the no form of
the command to set the sampling interval or max-samples values to the
default.
2CSNXXX_SWUM200.book Page 434 Tuesday, December 10, 2013 1:22 PM

Green Ethernet Commands 435
Syntax
green-mode eee-lpi-history {sampling-interval
30 sec
–
36000 sec
| max-
samples
1
-
168
}
•
sampling-interval
—The interval in seconds at which power consumption
data needs to be collected.
•
max-samples
—Maximum number of samples to keep.
Default Configuration
The sampling-interval default value is 3600 seconds and the max-samples
default value is 168.
Command Mode
Global Configuration
User Guidelines
EEE and energy-detect modes are only supported on N4000 series 10G
copper ports and on N2000/N3000 1G and 10G copper ports.
Examples
Use the command below to set the EEE LPI History sampling interval to the
default.
console(config)# no green-mode eee-lpi-history sampling-interval
Use the command below to set the EEE LPI History max-samples to the
default.
console(config)#no green-mode eee-lpi-history max-samples
show green-mode
interface-id
Use the show green-mode
interface-id
command in Privileged EXEC mode
to display the green-mode configuration and operational status of the port.
This command is also used to display the per port configuration and
operational status of the green-mode. The status is shown only for the modes
supported on the corresponding hardware platform whether enabled or
disabled.
2CSNXXX_SWUM200.book Page 435 Tuesday, December 10, 2013 1:22 PM
436 Green Ethernet Commands
Syntax
show green-mode
interface-id
•
interface-id
—Any valid interface. See Interface Naming Conventions for
interface representation.
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC
User Guidelines
This command output provides the following information.
Term Description
Energy Detect
Energy-detect
admin mode
Energy-detect mode is enabled or disabled.
Energy-detect
operational status
Energy detect mode is currently active or inactive. The energy
detect mode may be administratively enabled, but the
operational status may be inactive. The reasons for the
operational status are described below.
Reason for Energy-
detect current
operational status
The energy detect mode may be administratively enabled, but
the operational status may be inactive. The possible reasons are:
1
Port is currently operating in the fiber mode
2
Link is up.
If the energy-detect operational status is active, then the reason
field shows up as:
1
No energy Detected
EEE
EEE Admin Mode EEE Admin Mode is enabled or disabled.
Rx Low Power Idle
Event Count
This field is incremented each time MAC RX enters LP IDLE
state. Shows the total number of Rx LPI Events since EEE
counters are last cleared.
2CSNXXX_SWUM200.book Page 436 Tuesday, December 10, 2013 1:22 PM

Green Ethernet Commands 437
Rx Low Power Idle
Duration (μSec)
This field indicates duration of Rx LPI state in 10us
increments. Shows the total duration of Rx LPI since the EEE
counters are last cleared.
Tx Low Power Idle
Event Count
This field is incremented each time MAC TX enters LP IDLE
state. Shows the total number of Tx LPI Events since EEE
counters are last cleared.
Rx Low Power Idle
Duration (μSec)
This field indicates duration of Tx LPI state in 10us
increments. Shows the total duration of Tx LPI since the EEE
counters are last cleared.
Tw_sys_tx (μSec) Integer that indicates the value of Tw_sys that the local system
can support. This value is updated by the EEE DLL
Transmitter state diagram. This variable maps into the
aLldpXdot3LocTxTwSys attribute.
Tw_ sy s E c ho ( μSec) Integer that indicates the remote system’s Transmit Tw_sys that
was used by the local system to compute the Tw_sys that it
wants to request from the remote system. This value maps into
the aLldpXdot3LocTxTwSysEcho attribute.
Tw_sys_rx (μSec) Integer that indicates the value of Tw_sys that the local system
requests from the remote system. This value is updated by the
EEE Receiver L2 state diagram. This variable maps into the
aLldpXdot3LocRxTwSys attribute.
Tw_sys_rx Echo
(μSec)
Integer that indicates the remote systems Receive Tw_sys that
was used by the local system to compute the Tw_sys that it can
support. This value maps into the
aLldpXdot3LocRxTwSysEcho attribute.
Fallback Tw_sys
(μSec)
Integer that indicates the value of fallback Tw_sys that the local
system requests from the remote system. This value is updated
by the local system software.
Remote Tw_sys_tx
(μSec)
Integer that indicates the value of Tw_sys that the remote
system can support. This value maps from the
aLldpXdot3RemTxTwSys attribute.
Remote Tw_sys
Echo (μSec)
Integer that indicates the value Transmit Tw_sys echoed back
by the remote system. This value maps from the
aLldpXdot3RemTxTwSysEcho attribute.
Term Description
2CSNXXX_SWUM200.book Page 437 Tuesday, December 10, 2013 1:22 PM
438 Green Ethernet Commands
Example
console#show green-mode gi1/0/1
Energy Detect Admin Mode........... Enabled
Operational Status............. Active
Reason......................... No Energy Detected
Short Reach Feature................. Not Available
EEE Admin Mode........................... Enabled
Rx Low Power Idle Event Count........ 0
Rx Low Power Idle Duration (uSec).... 0
Remote Tw_sys_rx
(μSec)
Integer that indicates the value of Tw_sys that the remote
system requests from the local system. This value maps from
the aLldpXdot3RemRxTwSys attribute.
Remote Tw_sys_rx
Echo (μSec)
Integer that indicates the value of Receive Tw_sys echoed back
by the remote system. This value maps from the
aLldpXdot3RemRxTwSysEcho attribute.
Remote Fallback
Tw _ sy s (μSec)
Integer that indicates the value of fallback Tw_sys that the
remote system is advertising.This attribute maps to the variable
RemFbSystemValue as defined in 78.4.2.3.
Tx_dll_enabled Initialization status of the EEE transmit Data Link Layer
management function on the local system.
Tx_dll_ready Data Link Layer ready: This variable indicates that the tx
system initialization is complete and is ready to update/receive
LLDPDU containing EEE TLV. This variable is updated by the
local system software.
Rx_dll_enabled Status of the EEE capability negotiation on the local system.
Rx_dll_ready Data Link Layer ready: This variable indicates that the rx
system initialization is complete and is ready to update/receive
LLDPDU containing EEE TLV. This variable is updated by the
local system software.
Power Saving (%) Percentage of Power saved by enabling EEE on the interface
since EEE counters are last cleared.
Time Since
Counters Last
Cleared
Time Since Counters Last Cleared (since the time of power up,
or after clear eee counters is executed)
Term Description
2CSNXXX_SWUM200.book Page 438 Tuesday, December 10, 2013 1:22 PM

Green Ethernet Commands 439
Tx Low Power Idle Event Count......... 0
Tx Low Power Idle Duration (uSec)......0
Tw_sys_tx (usec)..................... 17
Tw_sys_tx Echo(usec)................. 17
Tw_sys_rx (usec)..................... 17
Tw_sys_tx Echo(usec)................. 17
Fallback Tw_sys (usec)............... 17
Remote Tw_sys_tx (usec).............. 21
Remote Tw_sys_tx Echo(usec).......... 21
Remote Tw_sys_rx (usec)............... 21
Remote Tw_sys_tx Echo(usec).......... 21
Remote fallback Tw_sys (usec)........ 21
Tx DLL enabled........................ Yes
Tx DLL ready.......................... Yes
Rx DLL enabled........................ Yes
Rx DLL ready.......................... Yes
Cumulative Energy Saving (W * H)............... 2.37
Time Since Counters Last Cleared......... 1 day 20 hr 47 min 34 sec
show green-mode
Use the show green-mode command in Privileged EXEC mode to display the
green-mode configuration for the whole system. The status is shown only for
the modes supported on the corresponding hardware platform whether
enabled or disabled.
Syntax
show green-mode
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC
User Guidelines
This command output provides the following information.
2CSNXXX_SWUM200.book Page 439 Tuesday, December 10, 2013 1:22 PM

440 Green Ethernet Commands
Example
console#show green-mode
Current Power Consumption (mW)................. 11545
Power Saving /Stack (%)........................ 3
Cumulative Energy Saving /Stack (W * H)........ 17
Unit Green Ethernet Features Supported
---- -----------------------------------------------------------------------
1 Energy-Detect EEE LPI-History LLDP-Cap-Exchg Pwr-Usg-Est
Interface Energy-Detect Short-Reach-Config Short-Reach EEE
Config Opr Auto Forced Opr Config
--------- --------- --------- --------- --------- ----------- --------
gi1/0/1 Enabled Active Enabled Disabled In-Active Enabled
gi1/0/2 Enabled Active Enabled Disabled In-Active Enabled
gi1/0/3 Enabled Active Enabled Disabled In-Active Enabled
gi1/0/4 Enabled Active Enabled Disabled In-Active Enabled
gi1/0/5 Enabled Active Enabled Disabled In-Active Enabled
gi1/0/6 Enabled Active Enabled Disabled In-Active Enabled
gi1/0/7 Enabled Active Enabled Disabled In-Active Enabled
gi1/0/8 Enabled Active Enabled Disabled In-Active Enabled
show green-mode eee-lpi-history interface
Use the show green-mode eee-lpi-history interface command in Privileged
EXEC mode to display the interface green-mode EEE LPI history.
Term Description
Energy Detect
Energy-detect
Config
Energy-detect Admin mode is enabled or disabled.
Energy-detect Opr Energy detect mode is currently active or inactive. The energy
detect mode may be administratively enabled, but the
operational status may be inactive.
EEE
EEE Config EEE Admin Mode is enabled or disabled.
2CSNXXX_SWUM200.book Page 440 Tuesday, December 10, 2013 1:22 PM

Green Ethernet Commands 441
Syntax
show green-mode eee-lpi-history interface
interface-id
•
interface-id
—Any valid interface. See Interface Naming Conventions for
interface representation.
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC
User Guidelines
On combo ports, samples are only collected on the copper ports when
enabled.
The following fields are displayed by this command.
Example
This example is on a platform capable of providing power consumption
details.
Term Description
Sampling Interval Interval at which EEE LPI statistics is collected.
Total No. of
Samples to Keep
Maximum number of samples to keep.
Percentage LPI
Time per Stack
Percentage of total time spent in LPI mode by all ports in the
stack when compared to total time since reset.
Sample No. Sample index.
Sample Time Time since last reset.
%Time Spent in LPI
Mode Since Last
Sample
Percentage of time spent in LPI mode on this port when
compared to sampling interval.
%Time Spent in LPI
Mode Since Last
Reset
Percentage of total time spent in LPI mode on this port when
compared to time since reset.
2CSNXXX_SWUM200.book Page 441 Tuesday, December 10, 2013 1:22 PM

442 Green Ethernet Commands
Percentage of Percentage of
SampleTime Since Time Spent in Time Spent in
No. the SampleLPI Mode SinceLPI Mode Since
Was Recorded Last SampleLast Reset
------ -------------- -------------- --------------
10 0d:00:00:13 3 2
9 0d:00:00:44 3 2
8 0d:00:01:15 3 2
7 0d:00:01:46 3 2
6 0d:00:02:18 3 2
5 0d:00:02:49 3 2
4 0d:00:03:20 3 2
3 0d:00:03:51 3 1
2 0d:00:04:22 3 1
1 0d:00:04:53 3 1
2CSNXXX_SWUM200.book Page 442 Tuesday, December 10, 2013 1:22 PM

GVRP Commands 443
18
GVRP Commands
Dell Networking N2000/N3000/N4000 Series Switches
GARP VLAN Registration Protocol (GVRP) is used to propagate VLAN
membership information throughout the network. GVRP is based on the
Generic Attribute Registration Protocol (GARP), which defines a method of
propagating a defined attribute (that is, VLAN membership) throughout the
network. GVRP allows both end stations and the networking device to issue
and revoke declarations relating to membership in VLANs. End stations that
participate in GVRP register VLAN membership using GARP Protocol Data
Unit (GPDU) messages. Networking devices that implement the GVRP
protocol and enable GVRP then process the GPDUs. The VLAN registration
is made in the context of the port that receives the GPDU. The networking
device propagates this VLAN membership on all of its other ports in the
active topology. Thus, the end station VLAN ID is propagated throughout the
network. GVRP is an application defined in the IEEE 802.1p standard that
allows for the control of 802.1Q VLANs.
Commands in this Chapter
This chapter explains the following commands:
clear gvrp statistics
Use the clear gvrp statistics command in Privileged EXEC mode to clear all
the GVRP statistics information.
clear gvrp statistics gvrp vlan-creation-forbid
garp timer show gvrp configuration
gvrp enable (global) show gvrp error-statistics
gvrp enable (interface) show gvrp statistics
gvrp registration-forbid
–
2CSNXXX_SWUM200.book Page 443 Tuesday, December 10, 2013 1:22 PM

444 GVRP Commands
Syntax
clear gvrp statistics [{gigabitethernet unit/slot/port |
port-channel
port-
channel-number
| tengigabitethernet unit/slot/port | fortygigabitethernet
unit/slot/port}]
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC mode
User Guidelines
This command has no user guidelines.
Example
The following example clears all the GVRP statistics information on port
1/0/8.
console# clear gvrp statistics gigabitethernet 1/0/8
garp timer
Use the garp timer command in Interface Configuration mode to adjust the
GARP application join, leave, and leaveall GARP timer values. To reset the
timer to default values, use the no form of this command.
Syntax
garp timer {join | leave | leaveall}
timer_value
no garp timer
•
join
— Indicates the time in centiseconds that PDUs are transmitted.
•
leave
— Indicates the time in centiseconds that the device waits before
leaving its GARP state.
•
leaveall
— Used to confirm the port within the VLAN. The time is the
interval between messages sent, measured in centiseconds.
2CSNXXX_SWUM200.book Page 444 Tuesday, December 10, 2013 1:22 PM

GVRP Commands 445
•
timer_value —
Timer values in centiseconds. The range is 10-100 for
join
,
20-600 for
leave
, and 200-6000 for
leaveall
.
Default Configuration
The default timer values are as follows:
• Join timer — 20 centiseconds
• Leave timer — 60 centiseconds
• Leaveall timer — 1000 centiseconds
Command Mode
Interface Configuration (gigabitethernet, port-channel, tengigabitethernet,
fortygigabitethernet) mode
User Guidelines
The following
relationships
for the various timer values must be maintained:
• Leave time must be greater than or equal to three times the join time.
• Leaveall time must be greater than the leave time.
Set the same GARP timer values on all Layer 2-connected devices. If the
GARP timers are set differently on Layer 2-connected devices, the GARP
application will not operate successfully.
The
timer_value
setting must be a multiple of 10.
Example
The following example sets the leave timer for port 1/0/8 to 90 centiseconds.
console (config)# interface gigabitethernet 1/0/8
console (config-if-Gi1/0/8)# garp timer leave 90
gvrp enable (global)
Use the gvrp enable (global) command in Global Configuration mode to
enable GVRP globally on the switch. To disable GVRP globally on the switch,
use the no form of this command.
2CSNXXX_SWUM200.book Page 445 Tuesday, December 10, 2013 1:22 PM

446 GVRP Commands
Syntax
gvrp enable
no gvrp enable
Default Configuration
GVRP is globally disabled.
Command Mode
Global Configuration mode
User Guidelines
This command has no user guidelines.
Example
The following example globally enables GVRP on the device.
console(config)#gvrp enable
gvrp enable (interface)
Use the gvrp enable command in Interface Configuration mode to enable
GVRP on an interface. To disable GVRP on an interface, use the no form of
this command.
Syntax
gvrp enable
no gvrp enable
Default Configuration
GVRP is disabled on all interfaces by default.
Command Mode
Interface Configuration (gigabitethernet, port-channel, tengigabitethernet,
fortygigabitethernet) mode
2CSNXXX_SWUM200.book Page 446 Tuesday, December 10, 2013 1:22 PM

GVRP Commands 447
User Guidelines
An Access port cannot join dynamically to a VLAN because it is always a
member of only one VLAN.
Membership in untagged VLAN would be propagated in a same way as a
tagged VLAN. In such cases it is the administrator’s responsibility to set the
PVID to be the untagged VLAN VID.
Example
The following example enables GVRP on gigabit ethernet 1/0/8.
console(config)#interface gigabitethernet 1/0/8
console(config-if-Gi1/0/8)#gvrp enable
gvrp registration-forbid
Use the gvrp registration-forbid command in Interface Configuration mode
to deregister all VLANs on a port and prevent any dynamic registration on the
port. To allow dynamic registering for VLANs on a port, use the no form of
this command.
Syntax
gvrp registration-forbid
no gvrp registration-forbid
Default Configuration
Dynamic registering and deregistering for each VLAN on the port is not
forbidden.
Command Mode
Interface Configuration (gigabitethernet, port-channel, tengigabitethernet,
fortygigabitethernet) mode
User Guidelines
This command has no user guidelines.
2CSNXXX_SWUM200.book Page 447 Tuesday, December 10, 2013 1:22 PM

448 GVRP Commands
Example
The following example shows how default dynamic registering and
deregistering is forbidden for each VLAN on port 1/0/8.
console(config)#interface gigabitethernet 1/0/8
console(config-if-Gi1/0/8)#gvrp registration-forbid
gvrp vlan-creation-forbid
Use the gvrp vlan-creation-forbid command in Interface Configuration mode
to disable dynamic VLAN creation. To enable dynamic VLAN creation, use
the no form of this command.
Syntax
gvrp vlan-creation-forbid
no gvrp vlan-creation-forbid
Default Configuration
By default, dynamic VLAN creation is enabled.
Command Mode
Interface Configuration (gigabitethernet, port-channel, tengigabitethernet,
fortygigabitethernet) mode
User Guidelines
This command has no user guidelines.
Example
The following example disables dynamic VLAN creation on port 1/0/8.
console(config)#interface gigabitethernet 1/0/8
console(config-if-Gi1/0/8)#gvrp vlan-creation-forbid
show gvrp configuration
Use the show gvrp configuration command in Privileged EXEC mode to
display GVRP configuration information. Timer values are displayed. Other
data shows whether GVRP is enabled and which ports are running GVRP.
2CSNXXX_SWUM200.book Page 448 Tuesday, December 10, 2013 1:22 PM

GVRP Commands 449
Syntax
show gvrp configuration [{gigabitethernet unit/slot/port |
port-channel
port-
channel-number
| tengigabitethernet unit/slot/port
| fortygigabitethernet
unit/slot/port}]
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC mode, Configuration mode and all Configuration submodes
User Guidelines
This command has no user guidelines.
Example
The following example shows how to display GVRP configuration
information:
console# show gvrp configuration
Global GVRP Mode: Disabled
Join Leave LeaveAll Port VLAN
Interface Timer Timer Timer GVRP Mode Create Register
(centisecs) (centisecs) (centisecs) Forbid Forbid
----------- ----------- ----------- ----------- ----------- ------ ------
1/0/1 20 60 1000 Disabled
1/0/2 20 60 1000 Disabled
1/0/3 20 60 1000 Disabled
1/0/4 20 60 1000 Disabled
1/0/5 20 60 1000 Disabled
1/0/6 20 60 1000 Disabled
1/0/7 20 60 1000 Disabled
1/0/8 20 60 1000 Disabled
1/0/9 20 60 1000 Disabled
1/0/10 20 60 1000 Disabled
1/0/11 20 60 1000 Disabled
1/0/12 20 60 1000 Disabled
1/0/13 20 60 1000 Disabled
1/0/14 20 60 1000 Disabled
2CSNXXX_SWUM200.book Page 449 Tuesday, December 10, 2013 1:22 PM

450 GVRP Commands
show gvrp error-statistics
Use the show gvrp error-statistics command in User EXEC mode to display
GVRP error statistics.
Syntax
show gvrp error-statistics [{gigabitethernet unit/slot/port|
port-channel
port-
channel-number
| tengigabitethernet unit/slot/port | fortygigabitethernet
unit/slot/port}]
Default Configuration
This command has no default configuration.
Command Mode
User EXEC mode, Configuration mode and all Configuration submodes
User Guidelines
This command has no user guidelines.
Example
The following example displays GVRP error statistics information.
console>show gvrp error-statistics
GVRP error statistics:
----------------
Legend:
INVPROT: Invalid Protocol Id INVATYP: Invalid Attribute Type
INVALEN: Invalid Attribute Length INVAVAL: Invalid Attribute Value
INVEVENT: Invalid Event
Port INVPROT INVATYP INVAVAL INVALEN INVEVENT
---- ------- ------- ------- ------- --------
1/0/1 0 0 0 0 0
1/0/2 0 0 0 0 0
1/0/3 0 0 0 0 0
1/0/4 0 0 0 0 0
2CSNXXX_SWUM200.book Page 450 Tuesday, December 10, 2013 1:22 PM

GVRP Commands 451
show gvrp statistics
Use the show gvrp statistics command in User EXEC mode to display GVRP
statistics.
Syntax
show gvrp statistics [{gigabitethernet unit/slot/port|
port-channel
port-
channel-number
| tengigabitethernet unit/slot/port
| fortygigabitethernet
unit/slot/port}]
Default Configuration
This command has no default configuration.
Command Mode
User EXEC mode, Configuration mode and all Configuration submodes
User Guidelines
This command has no user guidelines.
Example
This example shows output of the show gvrp statistics command.
console>show gvrp statistics
GVRP statistics:
------------------------------
Legend:
rJE : Join Empty Received rJIn : Join In Received
rEmp : Empty Received rLIn : Leave In Received
rLE : Leave Empty Received rLA : Leave All Received
sJE : Join Empty Sent JIn : Join In Sent
sEmp : Empty Sent sLIn : Leave In Sent
sLE : Leave Empty Sent sLA : Leave All Sent
Port rJE rJIn rEmp rLIn rLE rLA sJE sJIn sEmp sLIn sLE sLA
---- --- ---- ---- ---- --- --- --- --- --- ---- ---- ---
1/0/1000 0 0000 0 0 00
1/0/2000 0 0000 0 0 00
1/0/3000 0 0000 0 0 00
1/0/4000 0 0000 0 0 00
2CSNXXX_SWUM200.book Page 451 Tuesday, December 10, 2013 1:22 PM

452 GVRP Commands
1/0/5 0 0 0 0 0 0 0 0 0 0 0 0
1/0/6 0 0 0 0 0 0 0 0 0 0 0 0
1/0/7 0 0 0 0 0 0 0 0 0 0 0 0
1/0/8 0 0 0 0 0 0 0 0 0 0 0 0
2CSNXXX_SWUM200.book Page 452 Tuesday, December 10, 2013 1:22 PM

IGMP Snooping Commands 453
19
IGMP Snooping Commands
Dell Networking N2000/N3000/N4000 Series Switches
Snooping of Internet Group Management Protocol (IGMP) messages is a
feature that allows Dell Networking switches to forward multicast traffic
intelligently on the switch. Multicast traffic is traffic that is destined to a host
group. Host groups are identified by the destination MAC address, i.e. the
range 01:00:5e:00:00:00-01:00:5e:7f:ff:ff:ff for IPv4 multicast traffic or
33:33:xx:xx:xx:xx for IPv6 multicast traffic. Based on the IGMP query and
report messages, the switch forwards traffic only to the ports that request the
multicast traffic. This prevents the switch from broadcasting the traffic to all
ports and possibly affecting network performance.
IGMP snooping switches build forwarding lists by monitoring for, and in
some cases intercepting, IGMP messages. Although the software processing
the IGMP messages could maintain state information based on the full IP
group addresses, the forwarding tables in Dell Networking are mapped to link
layer addresses.
The Multicast Forwarding Database (MFDB) manages the forwarding
address table for Layer 2 multicast protocols, such as IGMP Snooping.
The IGMP Snooping code in the CPU ages out IGMP entries in the MFDB.
If a report for a particular group on a particular interface is not received
within a certain time interval (query interval), the IGMP Snooping code
deletes that interface from the group. The value for query interval time is
configurable using management.
If an IGMP Leave Group message is received on an interface, the IGMP
Snooping code sends a query on that interface and waits a specified length of
time (maximum response time). If no response is received within that time,
that interface is removed from the group. The value for maximum response
time is configurable using management.
In addition to building and maintaining lists of multicast group
memberships, the snooping switch also maintains a list of multicast routers.
When forwarding multicast packets, they should be forwarded on ports that
have joined using IGMP and also on ports on which multicast routers are
attached. The reason for this is that in IGMP there is only one active query
2CSNXXX_SWUM200.book Page 453 Tuesday, December 10, 2013 1:22 PM

454 IGMP Snooping Commands
mechanism. This means that all other routers on the network are suppressed
and thus not detectable by the switch. If a query is not received on an
interface within a specified length of time (multicast router present
expiration time), that interface is removed from the list of interfaces with
multicast routers attached. The multicast router present expiration time is
configurable using management. The default value for the multicast router
expiration time is zero, which indicates an infinite time-out (that is, no
expiration).
Commands in this Chapter
This chapter explains the following commands:
ip igmp snooping
Use the ip igmp snooping command in Global Configuration mode without
parameters to globally enable Internet Group Management Protocol (IGMP)
snooping. Use the vlan form of the command to enable IGMP snooping on a
specific VLAN. Use the no form of this command to disable IGMP snooping
globally.
Syntax
ip igmp snooping [vlan
vlan-id
]
no ip igmp snooping [vlan
vlan-id
]
•
vlan-id
—Specifies a VLAN ID value.
ip igmp snooping ip igmp snooping vlan groupmembership-
interval
show ip igmp snooping ip igmp snooping vlan last-member-query-
interval
show ip igmp snooping groups ip igmp snooping vlan mcrtrexpiretime
show ip igmp snooping mrouter ip igmp snooping report-suppression
ip igmp snooping vlan immediate-leave ip igmp snooping unregistered floodall
–
ip igmp snooping vlan mrouter
2CSNXXX_SWUM200.book Page 454 Tuesday, December 10, 2013 1:22 PM

IGMP Snooping Commands 455
Default Configuration
IGMP snooping is enabled globally and on all VLANs by default.
Command Mode
Global Configuration mode
User Guidelines
Use this command without parameters to globally enable IGMP snooping.
Use the no form of the command to disable IGMP snooping. Use the vlan
parameter to enable IGMP snooping on a specific VLAN. GMRP is
incompatible with IGMP snooping and should be disabled on any VLANs on
which IGMP snooping is enabled. It is recommended that MLD snooping
should be enabled whenever IGMP snooping is enabled to ensure that
unwanted pruning of multicast protocol packets used by other protocols does
not occur.
Enabling IGMP snooping on a VLAN in which L3 multicast is enabled is not
recommended. If a multicast source is connected to a VLAN on which both
L3 multicast and IGMP/MLD snooping are enabled, the multicast source is
forwarded to the mrouter ports that have been discovered when the multicast
source is first seen. If a new mrouter is later discovered on a different port, the
multicast source data is not forwarded to the new port. Likewise, if an existing
mrouter times out or stops querying, the multicast source data continues to
be forwarded to that port. If a host in the VLAN subsequently joins or leaves
the group, the list of mrouter ports is not updated for the multicast source
and the forwarding of the multicast source is not adjusted. The workaround
to this limitation is to avoid the use of multi-access VLANs in L3 multicast
routed topologies.
IGMP snooping (and IGMP querier) validates IGMP packets. As part of the
validation, IGMP checks for the router alert option. If other devices in the
network do not send IGMP packets with the router alert option, IGMP
snooping (and snoooping querier) will discard the packet. Use the no ip igmp
snooping router-alert-check command to disable checking for the router alert
option.
Example
console(config)#ip igmp snooping
console(config)#no ip igmp snooping vlan 1
2CSNXXX_SWUM200.book Page 455 Tuesday, December 10, 2013 1:22 PM

456 IGMP Snooping Commands
show ip igmp snooping
Use the show ip igmp snooping command in Privileged EXEC mode to
display the IGMP snooping configuration and SSM statistics.
Syntax
show ip igmp snooping [vlan
vlan-id
]
•
vlan-id
—Specifies a VLAN ID value.
Default Configuration
This command has no default configuration.
Command Mode
User EXEC, Privileged EXEC, Configuration mode and all Configuration
submodes
User Guidelines
This command has no user guidelines.
Example
console(config)#show ip igmp snooping
Admin Mode..................................... Enable
IGMP Router-Alert check........................ Enabled
Multicast Control Frame Count.................. 0
SSM FDB Capacity............................... 0
SSM FDB Current Entries........................ 0
SSM FDB High Water Mark. ...................... 0
Flooding Unregistered to All Ports............. Disabled
Vlan 1:
--------
IGMP Snooping Admin Mode....................... Enabled
Immediate Leave Mode........................... Disabled
Group Membership Interval...................... 260
Last Member Query Interval..................... 10
Multicast Router Expiry Time................... 300
Report Suppression Mode........................ Enabled
2CSNXXX_SWUM200.book Page 456 Tuesday, December 10, 2013 1:22 PM

IGMP Snooping Commands 457
show ip igmp snooping groups
Use the show ip igmp snooping groups command in User EXEC mode to
display the Multicast groups learned by IGMP snooping and IGMP SSM
entries.
Syntax
show ip igmp snooping groups [vlan
vlan-id
]
[address
ip-multicast-address
]
•
vlan_id — Specifies a
VLAN ID value.
•
ip-multicast-address — Specifies an
IP Multicast address.
Default Configuration
This command has no default configuration.
Command Mode
User EXEC mode, Configuration mode and all Configuration submodes
User Guidelines
To see the full Multicast address table (including static addresses) use the
show mac address-table
command.
Example
This example shows IGMPv2 snooping entries
console(config)#show ip igmp snooping groups
Vlan Group Type OIFs
---- ----------------------- ------- ------------------------------------
1 224-239.129|1.2.3 Dynamic Te1/0/1,Te1/0/17
IGMP SSM Entries:
-------------------
VLAN Group Reporter Filter IIF Source Address
---- ------------------ ----------------- ------- ---------- ---------------
1 224.2.2.2 192.168.10.2 include Te1/0/1 1.1.1.2
2.2.2.2
1 224.3.3.3 192.168.10.2 include Te1/0/1 4.4.4.4
2CSNXXX_SWUM200.book Page 457 Tuesday, December 10, 2013 1:22 PM

458 IGMP Snooping Commands
VLAN Group Reporter Filter IIF Source Address
---- --------------------- ----------------- ------- ---------- -----------
1 224.2.2.2 192.168.10.2 include Te1/0/1 1.1.1.2
console(config)#show ip igmp snooping
Admin Mode..................................... Enable
IGMP Router-Alert check........................ Disabled
Multicast Control Frame Count.................. 6847
SSM FDB Capacity............................... 128
SSM FDB High Water Mark........................ 1
SSM FDB Current Entries........................ 1
Flooding Unregistered to All Ports............. Disabled
Vlan 1:
--------
IGMP Snooping Admin Mode....................... Enabled
Immediate Leave Mode........................... Disabled
Group Membership Interval...................... 260
Last Member Query Interval..................... 10
Multicast Router Expiry Time................... 300
Report Suppression Mode........................ Enabled
show ip igmp snooping mrouter
Use the show ip igmp snooping mrouter command in Privileged EXEC mode
to display information on dynamically learned Multicast router interfaces.
Syntax
show ip igmp snooping mrouter
Default Configuration
This command has no default configuration.
Command Mode
User EXEC, Privileged EXEC modes, Configuration mode and all
Configuration submodes
2CSNXXX_SWUM200.book Page 458 Tuesday, December 10, 2013 1:22 PM

IGMP Snooping Commands 459
User Guidelines
This command has no user guidelines.
Example
The following example shows IGMP snooping mrouter information.
console#show ip igmp snooping mrouter
VLAN ID Port
------- -----------
10 Gi2/0/1
ip igmp snooping vlan immediate-leave
This command enables or disables IGMP Snooping immediate-leave mode
on a selected VLAN. Enabling immediate-leave allows the switch to
immediately remove the layer 2 LAN interface from its forwarding table entry
upon receiving an IGMP leave message for that multicast group without first
sending out MAC-based general queries to the interface. The no form of this
command disables IGMP Snooping immediate-leave mode on a VLAN.
You should enable immediate-leave admin mode only on VLANs where only
one host is connected to each layer 2 LAN port. This setting prevents the
inadvertent dropping of the other hosts that were connected to the same layer
2 LAN port but were still interested in receiving multicast traffic directed to
that group. Also, immediate-leave processing is supported only with IGMP
version 2 hosts.
Syntax
ip igmp snooping vlan
vlan-id
immediate-leave
no ip igmp snooping vlan
vlan-id
immediate-leave
•
vlan id
— Number assigned to the VLAN.
Default Configuration
IGMP snooping immediate-leave mode is disabled on VLANs by default.
Command Mode
Global Configuration mode
2CSNXXX_SWUM200.book Page 459 Tuesday, December 10, 2013 1:22 PM

460 IGMP Snooping Commands
User Guidelines
This command has no user guidelines.
Example
The following example enables IGMP snooping immediate-leave mode on
VLAN 2.
console(config)#ip igmp snooping vlan 2 immediate-leave
ip igmp snooping vlan groupmembership-interval
This command sets the IGMP Group Membership Interval time on a VLAN.
The Group Membership Interval time is the amount of time in seconds that a
switch waits for a report from a particular group on a particular interface
before deleting the interface from the entry. This value must be greater than
the IGMPv3 Maximum Response time value. The range is 2 to 3600 seconds.
The no form of this command sets the IGMPv3 Group Membership Interval
time to the default value.
Syntax
ip igmp snooping vlan
vlan-id
groupmembership-interval
time
no ip igmp snooping groupmembership-interval
•
vlan-id
— Number assigned to the VLAN
• time — IGMP group membership interval time in seconds. (Range:
2–3600)
Default Configuration
The default group membership interval time is 260 seconds.
Command Mode
Global Configuration mode
User Guidelines
This command has no user guidelines.
2CSNXXX_SWUM200.book Page 460 Tuesday, December 10, 2013 1:22 PM

IGMP Snooping Commands 461
Example
The following example configures an IGMP snooping group membership
interval of 1500 seconds on VLAN 2.
console(config)#ip igmp snooping vlan 2 groupmembership-interval 1500
ip igmp snooping vlan last-member-query-
interval
This command sets the last-member-query interval on a particular VLAN.
The last-member-query-interval is the amount of time in seconds after which
a host is considered to have left the group. This value must be less than the
IGMP Query Interval time value. The range is 1 to 25 seconds. The no form
of this command sets the last-member-query-interval on the VLAN to the
default value.
Syntax
ip igmp snooping vlan
vlan-id
last-member-query-interval
time
no ip igmp snooping vlan
vlan-id
last-member-query-interval
time
•
vlan-id
— Number assigned to the VLAN.
•
time
— Number of seconds after which a host is considered to have left
the group. (Range: 1-25)
Default Configuration
The default maximum response time is 10 seconds.
Command Mode
Global Configuration mode
User Guidelines
When using IGMP Snooping Querier, this parameter should be less than the
value for the IGMP Snooping Querier query interval.
Example
The following example sets the maximum response time to 7 seconds on
VLAN 2.
2CSNXXX_SWUM200.book Page 461 Tuesday, December 10, 2013 1:22 PM

462 IGMP Snooping Commands
console(config)#ip igmp snooping vlan 2 last-member-query-interval 7
ip igmp snooping vlan mcrtrexpiretime
This command sets the Multicast Router Present Expiration time. The time
is set on a particular VLAN. This is the amount of time in seconds that a
switch waits for a query to be received on an interface before the interface is
removed from the list of interfaces with multicast routers attached. The range
is 1–2147483647 seconds. A value of 0 indicates an infinite time-out (no
expiration). The no form of this command sets the Multicast Router Present
Expiration time to 0. The time is set for a particular VLAN.
Syntax
ip igmp snooping vlan
vlan-id
mcrtexpiretime
time
no igmp snooping vlan
vlan-id
mcrtexpiretime
time
•
vlan id
— Number assigned to the VLAN
•
time
— Multicast router present expiration time. (Range: 1–3600)
Default Configuration
The default multicast router present expiration time is 300 seconds.
Command Mode
Global Configuration mode
User Guidelines
The mcrexpiretime should be less than the group membership interval.
Example
The following example sets the multicast router present expiration time on
VLAN 2 to 60 seconds.
console(config)#ip igmp snooping vlan 2 mcrtexpiretime 1500
ip igmp snooping report-suppression
This command enables IBMP report suppression on a specific VLAN. The no
form of this command disables report suppression.
2CSNXXX_SWUM200.book Page 462 Tuesday, December 10, 2013 1:22 PM

IGMP Snooping Commands 463
Syntax
ip igmp snooping vlan
vlan-id
report-suppression
no ip igmp report-suppression
•
vlan id
— Number assigned to the VLAN
Default Configuration
Report suppression is enabled by default.
Command Mode
Global Configuration mode
User Guidelines
When IGMP report suppression is enabled, the switch only sends the first
report received for a group in response to a query. Report suppression is only
applicable to IGMPv1 and IGMPv2.
Example
The following example sets the multicast router present expiration time on
VLAN 2 to 60 seconds.
console(config)#ip igmp snooping report suppression vlan 10
ip igmp snooping unregistered floodall
This command enables flooding of unregistered multicast traffic to all ports
in the VLAN. Use the no form of this command to only flood unregistered
multicast traffic to router ports.
Syntax
ip igmp snooping unregistered floodall
no ip igmp snooping unregistered floodall
Default Configuration
Unregistered multicast traffic is only flooded to router ports by default.
2CSNXXX_SWUM200.book Page 463 Tuesday, December 10, 2013 1:22 PM

464 IGMP Snooping Commands
Command Mode
Global Configuration mode.
User Guidelines
There is no equivalent MLD command since this setting applies to both
protocols.
Example
console(config)#ip igmp snooping unregistered floodall
ip igmp snooping vlan mrouter
This command statically configures a port as connected to a multicast router
for a specified VLAN. Use the no form of this command to remove the static
binding.
Syntax
ip igmp snooping vlan
vlan-id
mrouter interface
interface-id
no ip igmp snooping vlan mrouter
•
vlan id
— The number assigned to the VLAN.
• interface-id—The next-hop interface to the multicast router.
Default Configuration
There are no multicast router ports configured by default.
Command Mode
Global Configuration mode.
User Guidelines
It is preferable to configure mrouter ports for IGMP snooping as opposed to
configuring a static MAC address entry for the router. A static MAC address
entry is tied to a specific port whereas an mrouter configuration will
dynamically learn the MAC address of the router. Multiple mrouter ports may
be configured for a VLAN.
2CSNXXX_SWUM200.book Page 464 Tuesday, December 10, 2013 1:22 PM

IGMP Snooping Commands 465
Example
console(config)#ip igmp snooping vlan 10 mrouter interface Gi1/0/2
2CSNXXX_SWUM200.book Page 465 Tuesday, December 10, 2013 1:22 PM

466 IGMP Snooping Commands
2CSNXXX_SWUM200.book Page 466 Tuesday, December 10, 2013 1:22 PM

IGMP Snooping Querier Commands 467
20
IGMP Snooping Querier Commands
Dell Networking N2000/N3000/N4000 Series Switches
The IGMP Snooping Querier is an extension to the IGMP Snooping feature.
IGMP Snooping Querier allows the switch to simulate an IGMP router in a
Layer 2-only network, thus removing the need to have an IGMP Router to
collect and refresh the multicast group membership information. The querier
function simulates a small subset of the IGMP router functionality. IGMP
Snooping Querier is not recommended for networks in which a multicast
router is reachable.
In a network with IP multicast routing, an IP multicast router acts as the
IGMP querier. However, if it is required that the IP-multicast traffic in a
VLAN be switched and no multicast router is present in the network, the Dell
Networking switch can be configured as an IGMP querier. When IGMP
Snooping Querier is enabled, the Querier sends out periodic IGMP General
Queries that trigger the multicast listeners/members to send their joins to the
querier so as to receive the multicast data traffic. IGMP snooping listens to
these reports to establish the appropriate L2 forwarding table entries.
The Dell Networking supports version IGMP V1 and 2 for snooping IGMP
queries.
Commands in this Chapter
This chapter explains the following commands:
ip igmp snooping querier ip igmp snooping querier timer expiry
ip igmp snooping querier election
participate
ip igmp snooping querier version
ip igmp snooping querier query-interval show ip igmp snooping querier
2CSNXXX_SWUM200.book Page 467 Tuesday, December 10, 2013 1:22 PM

468 IGMP Snooping Querier Commands
ip igmp snooping querier
This command enables IGMP Snooping Querier on the system (Global
Configuration mode) or on a VLAN. Using this command, you can specify
the IP address that the snooping querier switch should use as the source
address when generating periodic queries. The no form of this command
disables IGMP Snooping Querier on the system. Use the optional address
parameter to set or reset the querier address.
If a VLAN has IGMP Snooping Querier enabled, and IGMP Snooping is
operationally disabled on the VLAN, IGMP Snooping Querier functionality is
disabled on that VLAN. IGMP Snooping Querier functionality is reenabled if
IGMP Snooping becomes operational on the VLAN.
The IGMP Snooping Querier application sends periodic general queries on
the VLAN to solicit membership reports.
Syntax
ip igmp snooping querier [vlan
vlan-id
]
[address
ip-address
]
no ip igmp snooping querier [vlan
vlan-id
][address]
•
vlan-id
— A valid VLAN number.
•
ip-address
— An IPv4 address used for the source address.
Default Configuration
The IGMP Snooping Querier feature is globally disabled on the switch.
When enabled, the IGMP Snooping Querier stops sending queries if it
detects IGMP queries from a multicast-enabled router. The Snooping
Querier periodically (querier timer expiry) wakes up and listens for IGMP
queries, and if found, goes back to sleep. If no IGMP queries are heard, then
the Snooping Querier will resume querying.
Command Mode
Global Configuration mode
2CSNXXX_SWUM200.book Page 468 Tuesday, December 10, 2013 1:22 PM

IGMP Snooping Querier Commands 469
User Guidelines
When using the command in Global Configuration mode to configure a
snooping querier source address, the IPv4 address is the global querier
address. When using the command in VLAN Configuration mode to
configure a snooping querier source address, the IPv4 address is the querier
address for the VLAN. If there are no global or VLAN querier addresses
configured, then the management IP address is used as the IGMP snooping
querier source address. Using all zeros for the querier IP address disables it.
The VLAN IP address takes precedence over the global IP address when both
are configured. IGMP Querier does not detect when the local switch is
configured as a multicast router. It is not recommended to configure both L3
multicast routing and IGMP Querier on the same switch.
IGMP snooping (and IGMP querier) validates IGMP packets. As part of the
validation, IGMP checks for the router alert option. If other devices in the
network do not send IGMP packets with the router alert option, IGMP
snooping (and snoooping querier) will discard the packet. Use the no ip igmp
snooping router-alert-check command to disable checking for the router alert
option.
Example
The following example enables IGMP snooping querier in Global
Configuration mode.
console(config)#ip igmp snooping querier vlan 1 address 10.19.67.1
ip igmp snooping querier election participate
This command enables the Snooping Querier to participate in the Querier
Election process when it discovers the presence of another Snooping Querier
in the VLAN. When election mode is enabled, if the Snooping Querier finds
that the other Querier source address is numerically higher than the
Snooping Querier address, it stops sending periodic queries. The Snooping
Querier with the numerically lower IP address wins the election, and
continues sending periodic queries. The no form of this command sets the
snooping querier not to participate in the querier election but to stop sending
queries as soon as it discovers the presence of another querier in the VLAN.
2CSNXXX_SWUM200.book Page 469 Tuesday, December 10, 2013 1:22 PM

470 IGMP Snooping Querier Commands
Syntax
ip igmp snooping querier election participate
vlan-id
no ip igmp snooping querier election participate
vlan-id
Default Configuration
The snooping querier is configured to not participate in the querier election
by default. If the switch detects another querier in the VLAN, it will cease
sending queries for the querier timeout period.
Command Mode
Global Configuration mode
User Guidelines
This command has no user guidelines.
Example
The following example configures the snooping querier to participate in the
querier election.
console(config)#ip igmp snooping querier election participate
ip igmp snooping querier query-interval
This command sets the IGMP Querier Query Interval time, which is the
amount of time in seconds that the switch waits before sending another
periodic query. The no form of this command sets the IGMP Querier Query
Interval time to its default value.
Syntax
ip igmp snooping querier query-interval
interval-count
no ip igmp snooping querier query-interval
•
interval–count
— Amount of time in seconds that the switch waits before
sending another general query. (Range: 1-1800)
Default Configuration
The query interval default is 60 seconds.
2CSNXXX_SWUM200.book Page 470 Tuesday, December 10, 2013 1:22 PM

IGMP Snooping Querier Commands 471
Command Mode
Global Configuration mode
User Guidelines
The value of this parameter should be larger than the IGMP Max Response
Time value inserted into general query messages by the querier. The default
IGMP Max Response Time is defined in RFC 3376 as 10 seconds. DNOS
queriers use this value when sending general query messages.
Use the show ip igmp snooping querier vlan command to display the
operational max response time value.
Example
The following example sets the query interval to 1800:
console(config)#ip igmp snooping querier query_interval 1800
ip igmp snooping querier timer expiry
This command sets the IGMP Querier timer expiration period which is the
time period that the switch remains in Non-Querier mode after it has
discovered that there is a Multicast Querier in the network. The no form of
this command sets the IGMP Querier timer expiration period to its default
value.
Syntax
ip igmp snooping querier timer expiry
seconds
no ip igmp snooping querier timer expiry
•
seconds
— The time in seconds that the switch remains in Non-Querier
mode after it has discovered that there is a multicast querier in the
network. The range is 60–300 seconds.
Default Configuration
The query interval default is 60 seconds.
Command Mode
Global Configuration mode
2CSNXXX_SWUM200.book Page 471 Tuesday, December 10, 2013 1:22 PM

472 IGMP Snooping Querier Commands
User Guidelines
This command has no user guidelines.
Example
The following example sets the querier timer expiry time to 100 seconds.
console(config)#ip igmp snooping querier timer expiry 100
ip igmp snooping querier version
This command sets the IGMP version of the query that the snooping switch
is going to send periodically. The no form of this command sets the IGMP
Querier Version to its default value.
Syntax
ip igmp snooping querier version
version
no ip igmp snooping querier version
•
version
— IGMP version. (Range: 1–2)
Default Configuration
The querier version default is 2.
Command Mode
Global Configuration mode
User Guidelines
This command has no user guidelines.
Example
The following example sets the IGMP version of the querier to 1.
console(config)#ip igmp snooping querier version 1
2CSNXXX_SWUM200.book Page 472 Tuesday, December 10, 2013 1:22 PM

IGMP Snooping Querier Commands 473
show ip igmp snooping querier
This command displays IGMP Snooping Querier information. Configured
information is displayed whether or not IGMP Snooping Querier is enabled.
If a querier is active in the network and IGMP snooping querier is enabled,
the querier’s IP address is shown in the Last Querier Address field.
Syntax
show ip igmp snooping querier [detail | vlan
vlan_id
]
•
vlan_id
—Specifies a VLAN ID value.
Default Configuration
This command has no default configuration.
Command Mode
User EXEC, Privileged Exec modes
User Guidelines
When the optional argument
vlan_id
is not used, the command shows the
following information.
When you specify a value for
vlan_id
, the following information appears.
Parameter Description
Admin Mode Indicates whether or not IGMP Snooping Querier is active on
the switch.
Admin Version Indicates the version of IGMP that will be used while sending
out the queries.
Source IP Address Shows the IP address that is used in the IPv4 header when
sending out IGMP queries. It can be configured using the
appropriate command.
Query Interval Shows the amount of time in seconds that a Snooping Querier
waits before sending out the periodic general query.
Querier Timeout Displays the amount of time to wait in the Non-Querier
operational state before moving to a Querier state.
2CSNXXX_SWUM200.book Page 473 Tuesday, December 10, 2013 1:22 PM
474 IGMP Snooping Querier Commands
When the optional argument detail is used, the command shows the global
information and the information for all Querier enabled VLANs.
Example
The following example shows querier information for VLAN 2.
console#show ip igmp snooping querier vlan 2
Vlan 2 : IGMP Snooping querier status
----------------------------------------------
IGMP Snooping Querier Vlan Mode.......... Enable
Querier Election Participate Mode........ Enable
Querier Vlan Address..................... 1.1.1.1
Parameter Description
VLAN Admin Mode Indicates whether IGMP Snooping Querier is active on the
VLAN.
VLAN Operational
State
Indicates whether IGMP Snooping Querier is in the Querier or
Non-Querier state. When the switch is in Querier state it sends
out periodic general queries. When in Non-Querier state it
waits for moving to Querier state and does not send out any
queries.
VLAN Operational
Max Response Time
Indicates the time to wait before removing a Leave from a host
upon receiving a Leave request. This value is calculated
dynamically from the Queries received from the network. If the
Snooping Switch is in Querier state, then it is equal to the
configured value.
Querier Election
Participate
Indicates whether the IGMP Snooping Querier participates in
querier election if it discovers the presence of a querier in the
VLAN.
Last Querier
Address
Indicates the IP address of the most recent Querier from which
a Query was received.
Last Querier Version Indicates the IGMP version of the most recent Querier from
which a Query was received on this VLAN.
Elected Querier Indicates the IP address of the Querier that has been
designated as the Querier based on its source IP address. This
field will be 0.0.0.0 when Querier Election Participate mode is
disabled.
2CSNXXX_SWUM200.book Page 474 Tuesday, December 10, 2013 1:22 PM

IGMP Snooping Querier Commands 475
Operational State........................ Querier
Last Querier Address..................... 2.2.2.2
Operational version.................... 2
Operational Max Resp Time.............. 10
2CSNXXX_SWUM200.book Page 475 Tuesday, December 10, 2013 1:22 PM

476 IGMP Snooping Querier Commands
2CSNXXX_SWUM200.book Page 476 Tuesday, December 10, 2013 1:22 PM

IP Addressing Commands 477
21
IP Addressing Commands
Dell Networking N2000/N3000/N4000 Series Switches
Interfaces on the Dell Networking switches support a variety of capabilities to
support management of the switch. In addition to performing switching and
routing of network traffic, Dell Networking switches act as a host for
management of the switch. Commands in this category allow the network
operator to configure the local host address, utilize the embedded DHCP
client to obtain an address, resolve names to addresses using DNS servers, and
detect address conflicts on the local subnet.
There are two management interface types on Dell Networking switches. In-
band interfaces allow management of the switch through the network
switching/routing interfaces. Out-of-band management is always through the
dedicated out-of-band interface. The serial port on the stack master provides
a direct console interface supporting a CLI. In-band management interfaces
can employ a variety of protection mechanisms including VLAN assignment
and Management ACLs. The out-of-band port does not support such
protection mechanisms and, therefore, it is recommended that the out-of-
band interface only be connected to a physically segregated management
network.
Commands in this Chapter
This chapter explains the following commands:
clear host ip host
clear ip address-conflict-detect ip name-server
ip address (Out-of-Band) ipv6 address (Interface Configuration)
ip address-conflict-detect run ipv6 address dhcp
ip address dhcp (Interface Configuration) ipv6 enable (Interface Configuration)
ip default-gateway show hosts
ip domain-lookup show ip address-conflict
ip domain-name show ip helper-address
2CSNXXX_SWUM200.book Page 477 Tuesday, December 10, 2013 1:22 PM

478 IP Addressing Commands
clear host
Use the clear host command in Privileged EXEC mode to delete entries from
the host name-to-address cache.
Syntax
clear host {
name
| *}
•
name
— Host name to be deleted from the host name-to-address cache.
(Range: 1-255 characters)
•
*
— Deletes all entries in the host name-to-address cache.
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC mode
User Guidelines
This command has no user guidelines.
Example
The following example deletes all entries from the host name-to-address
cache.
console#clear host *
clear ip address-conflict-detect
Use the clear ip address-conflict-detect command in Privileged EXEC mode
to clear the address conflict detection status in the switch.
Syntax
clear ip address-conflict-detect
Default Configuration
This command has no default configuration.
2CSNXXX_SWUM200.book Page 478 Tuesday, December 10, 2013 1:22 PM

IP Addressing Commands 479
Command Mode
Privileged EXEC mode
User Guidelines
This command has no user guidelines.
Example
console#
console#configure
console(config)#clear ip address-conflict-detect
interface out-of-band
Use the interface out-of-band command to enter into OOB interface
configuration mode.
Syntax
interface out-of-band
Default Configuration
This command has no default configuration.
Command Mode
Global Configuration
User Guidelines
No specific guidelines.
Example
console(config)#interface out-of-band
console(config-if)#
ip address (Out-of-Band)
Use the ip address command in Interface Configuration mode to set an IP
address for the out-of-band interface. Use the no form of this command to
return the ip address configuration to its default value.
2CSNXXX_SWUM200.book Page 479 Tuesday, December 10, 2013 1:22 PM

480 IP Addressing Commands
Syntax
ip address {
ip-address
{
mask
|
prefix-length
} | dhcp}
no ip address
•
ip-address
—Specifies a valid IP address.
•
mask
—Specifies a valid subnet (network) mask IP address.
•
prefix-length
—The number of bits that comprise the IP address prefix.
The prefix length must be preceded by a forward slash (/). (Range: 1-30
bits)
•
dhcp
—Obtain the out-of-band interface address via DHCPv4.
Default Configuration
The out-of-band interface (service port) obtains an IP address via DHCP by
default.
Command Mode
Interface (Out-of-Band) Configuration mode
User Guidelines
When setting the netmask/prefix length on an IPv4 address, a space is
required between the address and the mask or prefix length. Setting an IP
address on the out-of-band port enables switch management over the service
port.
In order to ensure the security of the switches from intruders, it is strongly
recommended that the out-of-band interface be isolated on a physically
separate network from the in-band ports.
Example
The following examples configure the out-of-band interface with an IP
address 131.108.1.27 and subnet mask 255.255.255.0 and the same IP address
with prefix length of 24 bits.
console(config)#interface out-of-band
console(config-if)#ip address 131.108.1.27 255.255.255.0
console(config-if)#ip address 131.108.1.27 /24
2CSNXXX_SWUM200.book Page 480 Tuesday, December 10, 2013 1:22 PM

IP Addressing Commands 481
ip address-conflict-detect run
Use the ip address-conflict-detect run command in Global Configuration
mode to trigger the switch to run active address conflict detection by sending
gratuitous ARP packets for IPv4 addresses on the switch.
Syntax
ip address–conflict–detect run
Default Configuration
This command has no default configuration.
Command Mode
Global Configuration
User Guidelines
This command has no user guidelines.
Example
console#
console#configure
console(config)#ip address-conflict-detect run
ip address dhcp (Interface Configuration)
Use the ip address dhcp command in Interface (VLAN) Configuration mode
to enable the DHCPv4 client on an interface.
Syntax
ip address dhcp
no ip address dhcp
Default Configuration
DHCPv4 is disabled by default on routing interfaces.
2CSNXXX_SWUM200.book Page 481 Tuesday, December 10, 2013 1:22 PM

482 IP Addressing Commands
Command Mode
Interface (VLAN) Configuration mode
User Guidelines
This command only applies to routing interfaces. When DHCP is enabled on
a routing interface, the system automatically deletes all manually configured
IPv4 addresses on the interface.
• The command
no ip address
removes the interface’s primary address
(Manual/DHCP) including the secondary addresses, if configured, and sets
the Interface method to
None
.
• The command
no ip address dhcp
removes the interface’s primary address
only if configured through DHCP and sets the interface method to
None
.
It does not remove a manually configured address.
In addition to leasing an IP address and subnet mask, the DHCP client may
learn the following parameters from a DHCP server:
• The IPv4 address of a default gateway. If the device learns different default
gateways on different interfaces, the system uses the first default gateway
learned. The system installs a default route in the routing table, with the
default gateway’s address as the next hop address. This default route has a
preference of 254.
• The IPv4 address of a DNS server. The DNS client stores each DNS server
address in its server list.
• A domain name. The DNS client stores each domain name in its domain
name list.
Examples
To enable DHCPv4 on vlan 2:
console#config
console(config)#interface vlan 2
console(config-if-vlan2)#ip address dhcp
2CSNXXX_SWUM200.book Page 482 Tuesday, December 10, 2013 1:22 PM

IP Addressing Commands 483
ip default-gateway
Use the ip default-gateway command in Global Configuration mode to
configure a default gateway (router).
Syntax
ip default-gateway
ip-address
no ip default-gateway
ip-address
•
ip-address
—Valid IPv4 address of an attached router.
Default Configuration
No default gateway is defined.
Command Mode
Global Configuration mode
User Guidelines
When the system does not have a more specific route to a packet’s
destination, it sends the packet to the default gateway. The system installs a
default IPv4 route with the gateway address as the next hop address. The
route preference is 253. A default gateway configured with this command is
more preferred than a default gateway learned from a DHCP server, which has
a route preference of 254. It is less preferred than a static route configured via
the
ip route
command, which has a route preference of 1. Use the
show ip
route
command to display the active default gateway.
Only one default gateway can be configured. If you invoke this command
multiple times, each command replaces the previous value.
Example
The following example sets the default-gateway to 10.1.1.1.
console(config)#ip default-gateway 10.1.1.1.
2CSNXXX_SWUM200.book Page 483 Tuesday, December 10, 2013 1:22 PM

484 IP Addressing Commands
ip domain-lookup
Use the ip domain-lookup command in Global Configuration mode to
enable IP Domain Naming System (DNS)-based host name-to-address
translation. To disable the DNS, use the no form of this command.
Syntax
ip domain-lookup
no ip domain-lookup
Default Configuration
DNS name resolution is enabled by default.
Command Mode
Global Configuration mode
User Guidelines
This command has no user guidelines.
Example
The following example enables the IP Domain Naming System (DNS)-based
host name-to-address translation.
console(config)#ip domain-lookup
ip domain-name
Use the ip domain-name command in Global Configuration mode to define
a default domain name used to complete unqualified host names. To delete
the default domain name, use the no form of this command.
Syntax
ip domain-name
name
no ip domain-name
2CSNXXX_SWUM200.book Page 484 Tuesday, December 10, 2013 1:22 PM

IP Addressing Commands 485
•
name
— Default domain name used to complete an unqualified host
name. Do not include the initial period that separates the unqualified host
name from the domain name (Range: 1-255 characters).
Default Configuration
This command has no default configuration.
Command Mode
Global Configuration mode
User Guidelines
This command has no user guidelines.
Example
The following example defines a default domain name of dell.com.
console(config)#ip domain-name dell.com
ip host
Use the ip host command in Global Configuration mode to define static host
name-to-address mapping in the host cache. To delete the name-to-address
mapping, use the no form of this command.
Syntax
ip host
name address
no ip host
name
•
name
— Host name.
•
address
— IP address of the host.
Default Configuration
No host is defined.
Command Mode
Global Configuration mode
2CSNXXX_SWUM200.book Page 485 Tuesday, December 10, 2013 1:22 PM

486 IP Addressing Commands
User Guidelines
This command has no user guidelines.
Example
The following example defines a static host name-to-address mapping in the
host cache.
console(config)#ip host accounting.dell.com 176.10.23.1
ip name-server
Use the ip name-server command in Global Configuration mode to define
available IPv4 or IPv6 name servers. To delete a name server, use the no form
of this command.
Syntax
ip name-server
server-address1
[
server-address2 … server-address8
]
no ip name-server [
server-address1 … server-address8
]
•
server-address
—Valid IPv4 or IPv6 addresses of the name server. (Range:
1–255 characters)
Default Configuration
No name server IP addresses are specified.
Command Mode
Global Configuration mode
User Guidelines
Server preference is determined by entry order.
Up to eight servers can be defined in one command or by using multiple
commands. Use the
show hosts
command on page 492 to display the
configured name servers.
Example
The following example sets the available name server.
console(config)#ip name-server 176.16.1.18
2CSNXXX_SWUM200.book Page 486 Tuesday, December 10, 2013 1:22 PM

IP Addressing Commands 487
ipv6 address (Interface Configuration)
Use the ipv6 address command to set the IPv6 address of the management
interface. Use the no form of this command to reset the IPv6 address to the
default.
Syntax
ipv6 address {
prefix/prefix-length
[eui64] | autoconfig | dhcp}
no ipv6 address
•
prefix
—Consists of the bits of the address to be configured.
•
prefix-length
—Designates how many of the high-order contiguous bits of
the address make up the prefix.
•
eui64
—The optional eui-64 field designates that IPv6 processing on the
interfaces is enabled using an EUI-64 interface ID in the low order 64 bits
of the address. If this option is used, the value of prefix_length must be 64
bits.
•
autoconfig
—Use this keyword to set the IPv6 address auto configuration
mode.
•
dhcp
—Use this keyword to obtain an IPv6 address via DHCP.
Default Configuration
There is no IPv6 address configured by default.
Command Mode
Interface Configuration mode (VLAN, loopback, port-channel)
User Guidelines
When setting the prefix length on an IPv6 address, no space can be present
between the address and the mask.
Example
Configure ipv6 routing on vlan 10 and obtain an address via DHCP. Assumes
vlan 10 already exists.
console(config)#ip routing
console(config)#interface vlan 10
2CSNXXX_SWUM200.book Page 487 Tuesday, December 10, 2013 1:22 PM

488 IP Addressing Commands
console(config-if-vlan10)#ipv6 enable
console(config-if-vlan10)#ipv6 address dhcp
Configure a default gateway on vlan 10
console(config)#no ipv6 address autoconfig
console(config)#no ipv6 address 2003::6/64
console(config)#no ipv6 address 2001::/64 eui64
console(config)#no ipv6 address
ipv6 address (OOB Port)
Use the ipv6 address command in Interface (out-of-band) Configuration
mode to set the IPv6 prefix on the out-of-band port. If a prefix is specified,
the address will be configured using the prefix and length A link local address
in EUI-64 format may also be assigned.
The autoconfig parameter specifies that a link local address in the EUI-64
format is assigned to the interface.
The DHCP parameter indicates that the port should obtain its address va
DHCP.
Use the no form of the command to remove a specific address or to return the
address assignment to its default value. Using the no form of the command
with no parameters removes all IPv6 prefixes from the interface.
Syntax
ipv6 address {
prefix/prefix-length
[eui64] | autoconfig | dhcp}
no ipv6 address {
prefix/prefix-length
[eui64] | autoconfig | dhcp}
•
prefix/prefix-length
—An IPv6 prefix in global format address format.
•
eui64
—Formulate the prefix in EUI-64 format.
•
autoconfig
—Perform IPv6 auto-configuration.
•
dhcp
—Obtain the prefix via DHCP.
Default Configuration
No address is assigned to the out-of-band interface by default.
2CSNXXX_SWUM200.book Page 488 Tuesday, December 10, 2013 1:22 PM

IP Addressing Commands 489
Command Mode
Interface (out-of-band) Configuration mode
User Guidelines
When DHCPv6 is enabled on the Out-of-Band interface, the system
automatically deletes all manually configured IPv6 addresses on the interface.
DHCPv6 can be enabled on the Out-of-Band interface only when IPv6 auto
configuration or DHCPv6 is not enabled on any of the in-band management
interfaces.
IPv6 auto configuration mode can be enabled in the Out-of-Band interface
only when IPv6 auto configuration or DHCPv6 is not enabled on any of the
in-band management interfaces.
ipv6 address dhcp
Use the ipv6 address dhcp command in Interface (VLAN) Configuration
mode to enable the DHCPv6 client on an IPv6 interface.
Syntax
ipv6 address dhcp
no ipv6 address dhcp
Default Configuration
DHCPv6 is disabled by default on routing interfaces.
Command Mode
Interface (VLAN) Configuration mode
User Guidelines
This command only applies to VLAN routing interfaces. When DHCPv6 is
enabled on a VLAN routing interface, the system automatically deletes all
manually configured IPv6 addresses on the interface.
Use the no ipv6 address dhcp command to release a leased address and to
disable DHCPv6 on an interface. The command no ipv6 address does not
disable the DHCPv6 client on the interface.
2CSNXXX_SWUM200.book Page 489 Tuesday, December 10, 2013 1:22 PM

490 IP Addressing Commands
This command will fail if DHCPv6 server has been configured on the
interface.
Examples
In the following example, DHCPv6 is enabled on interface vlan2.
console#config
console(config)#interface vlan2
console(config-if-vlan2)#ipv6 address dhcp
ipv6 enable (Interface Configuration)
Use the ipv6 enable command in Interface Configuration mode to enable
IPv6 on a routing interface. Use the no form of this command to reset the
IPv6 configuration to the defaults.
Syntax
ipv6 enable
no ipv6 enable
Default Configuration
IPv6 is not enabled by default.
Command Mode
Interface Configuration mode (VLAN, loopback)
User Guidelines
There are no user guidelines for this command.
Example
console(config)#no ipv6 enable
2CSNXXX_SWUM200.book Page 490 Tuesday, December 10, 2013 1:22 PM

IP Addressing Commands 491
ipv6 enable (OOB Configuration)
Use the ipv6 enable command in Interface (out-of-band) Configuration
mode to enable IPv6 operation on the out-of-band interface. Prefixes
configured by the ipv6 address command are not configured until the
interface is enabled.
Syntax
ipv6 enable
no ipv6 enable
Default Configuration
By default, IPv6 is not enabled on the out-of-band port.
Command Mode
Interface (out-of-band) Configuration mode
User Guidelines
There are no user guidelines for this command.
ipv6 gateway (OOB Configuration)
Use the ipv6 gateway command in Interface (out-of-band) Configuration
mode to configure the address of the IPv6 gateway. The gateway is used as a
default route for packets addressed to network devices not present on the
local subnet. Use the no form of the command to remove the gateway
configuration.
Syntax
ipv6 gateway
ipv6-address
no ipv6 gateway
•
ipv6-address
—An IPv6 address (not a prefix).
Default Configuration
By default, no IPv6 gateway is configured.
2CSNXXX_SWUM200.book Page 491 Tuesday, December 10, 2013 1:22 PM

492 IP Addressing Commands
Command Mode
Interface (out-of-band) Configuration mode
User Guidelines
There are no user guidelines for this command.
show hosts
Use the show hosts command in User EXEC mode to display the default
domain name, a list of name server hosts, and the static and cached list of
host names and addresses.
Syntax
shows hosts [
hostname
].
•
hostname
—(Range: 1–255 characters). The command allows spaces in the
host name when specified in double quotes. For example,
console(config)#snmp-server host "host name"
Default Configuration
This command has no default configuration.
Command Mode
User EXEC mode, Configuration mode and all Configuration submodes
User Guidelines
This command has no user guidelines.
Example
The following example displays information about IP hosts.
console>show hosts
Host name:
Default domain: gm.com, sales.gm.com, usa.sales.gm.com
Name/address lookup is enabled
Name servers (Preference order): 176.16.1.18 176.16.1.19
Configured host name-to-address mapping:
Host Addresses
2CSNXXX_SWUM200.book Page 492 Tuesday, December 10, 2013 1:22 PM

IP Addressing Commands 493
-------------------------- ----------------------------
accounting.gm.com 176.16.8.8
Cache: TTL (Hours)
Host Total Elapsed Type Addresses
---------------- ----- ------- ------- -------------
www.stanford.edu 72 3 IP 171.64.14.203
show ip address-conflict
Use the show ip address-conflict command in User EXEC or Privileged
EXEC mode to display the status information corresponding to the last
detected address conflict.
Syntax
show ip address-conflict
Default Configuration
This command has no default configuration.
Command Mode
User EXEC, Privileged EXEC mode, Configuration mode and all
Configuration submodes
User Guidelines
The command provides the following information.
Term Description
Address Conflict
Detection Status
Whether the switch has detected an address conflict on any IP
address. Set to Conflict Detected if detected, No Conflict
Detected otherwise.
Last Conflicting IP
Address
The IP address that was last detected as conflicting on any
interface.
Last Conflicting
MAC Address
The MAC Address of the conflicting host that was last detected
on any interface.
Time Since Conflict
Detected
The time in days, hours, minutes, and seconds since the last
address conflict was detected.
2CSNXXX_SWUM200.book Page 493 Tuesday, December 10, 2013 1:22 PM

494 IP Addressing Commands
Example
console#show ip address-conflict
Address Conflict Detection Status...Conflict Detected
Last Conflicting IP Address.........10.131.12.56
Last Conflicting MAC Address........00:01:02:04:5A:BC
Time Since Conflict Detected........5 days 2 hrs 6 mins 46 secs
console#show ip address-conflict
Address Conflict Detection Status..No Conflict Detected
show ip helper-address
Use the show ip helper-address command in Privileged EXEC mode to
display IP helper addresses configuration.
Syntax
show ip helper-address [
intf-address
]
•
intf-address
— IP address of a routing interface. (Range: Any valid IP
address)
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC mode, Configuration mode and all Configuration submodes
User Guidelines
This command has no user guidelines.
Example
console#show ip helper-address
IP helper is enabled
Interface UDP Port Discard Hit Count Server Address
-------------------- ----------- ---------- ---------- ----------------
vlan 25 domain No 0 192.168.40.2
vlan 25 dhcp No 0 192.168.40.2
2CSNXXX_SWUM200.book Page 494 Tuesday, December 10, 2013 1:22 PM

IP Addressing Commands 495
vlan 30 dhcp Yes 0
vlan 30 162 No 0 192.168.23.1
Any dhcp No 0 192.168.40.1
show ipv6 dhcp interface out-of-band statistics
Use the show ipv6 dhcp interface out-of-band statistics command in
Privileged EXEC mode to display IPv6 DHCP statistics for the out-of-band
interface.
Syntax
show ipv6 dhcp interface out-of-band statistics
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC, Configuration mode and all Configuration submodes
User Guidelines
This command has no user guidelines.
Example
console#show ipv6 dhcp interface out-of-band statistics
DHCPv6 Client Statistics
-------------------------
DHCPv6 Advertisement Packets Received.......... 0
DHCPv6 Reply Packets Received.................. 0
Received DHCPv6 Advertisement Packets Discard.. 0
Received DHCPv6 Reply Packets Discarded........ 0
DHCPv6 Malformed Packets Received.............. 0
Total DHCPv6 Packets Received.................. 0
DHCPv6 Solicit Packets Transmitted............. 8
DHCPv6 Request Packets Transmitted............. 0
DHCPv6 Renew Packets Transmitted............... 0
DHCPv6 Rebind Packets Transmitted.............. 0
DHCPv6 Release Packets Transmitted............. 0
Total DHCPv6 Packets Transmitted............... 8
2CSNXXX_SWUM200.book Page 495 Tuesday, December 10, 2013 1:22 PM

496 IP Addressing Commands
show ipv6 interface out-of-band
Use the show ipv6 interface out-of-band command in Privileged EXEC mode
to show the IPv6 out-of-band port configuration.
Syntax
show ipv6 interface out-of-band
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC, Configuration mode and all Configuration submodes
User Guidelines
This command has no user guidelines.
Example
console(config-if)#do show ipv6 interface out-of-band
IPv6 Administrative Mode........Enabled
IPv6 Prefix is..................FE80::21E:C9FF:FEAA:AD79/64
::/128
IPv6 Default Router.............FE80::A912:FEC2:A145:FEAD
Configured IPv6 Protocol........None
IPv6 AutoConfiguration mode............Enabled
Burned In MAC Address...........001E.C9AA.AD79
2CSNXXX_SWUM200.book Page 496 Tuesday, December 10, 2013 1:22 PM

IPv6 Access List Commands 497
22
IPv6 Access List Commands
Dell Networking N2000/N3000/N4000 Series Switches
Access to a switch or router can be made more secure through the use of
Access Control Lists (ACLs) to control the type of traffic allowed into or out
of specific ports. An ACL consists of a series of rules, each of which describes
the type of traffic to be processed and the actions to take for packets that
meet the classification criteria. Rules within an ACL are evaluated
sequentially until a match is found, if any. Every ACL is terminated by an
implicit deny all rule, which covers any packet not matching a preceding
explicit rule. ACLs can help to ensure that only authorized users have access
to specific resources while blocking out any unwarranted attempts to reach
network resources.
ACLs may be used to restrict contents of routing updates, decide which types
of traffic are forwarded or blocked and, above all, provide security for the
network. ACLs are normally used in firewall routers that are positioned
between the internal network and an external network, such as the Internet.
They can also be used on a router positioned between two parts of the
network to control the traffic entering or exiting a specific part of the internal
network.
The Dell Networking ACL feature allows classification of packets based upon
Layer 2 through Layer 4 header information. An Ethernet IPv6 packet is
distinguished from an IPv4 packet by its unique Ethertype value; thus all IPv6
classifiers include the Ethertype field.
Multiple ACLs per interface are supported. The ACLs can be combination of
Layer 2 and/or Layer 3/4 ACLs. ACL assignment is appropriate for both
physical ports and LAGs. ACLs can also be time based.
Commands in this Chapter
This chapter explains the following commands:
deny | permit (IPv6 ACL) ipv6 traffic-filter
ipv6 access-list show ipv6 access-lists
2CSNXXX_SWUM200.book Page 497 Tuesday, December 10, 2013 1:22 PM

498 IPv6 Access List Commands
deny | permit (IPv6 ACL)
This command creates a new rule for the current IPv6 access list. Each rule is
appended to the list of configured rules for the list.
A rule may either deny or permit traffic according to the specified
classification fields. At a minimum, either the every keyword or the protocol,
source address, and destination address values must be specified. The source
and destination IPv6 address fields may be specified using the keyword any to
indicate a match on any value in that field. The remaining command
parameters are all optional, but the most frequently used parameters appear
in the same relative order as shown in the command format.
The assign-queue parameter allows specification of a particular hardware
queue for handling traffic that matches this rule. The assign-queue parameter
is valid only for a permit rule.
The command is enhanced to accept the optional time-range parameter. The
time-range parameter allows imposing a time limitation on the IPv6 ACL rule
as defined by the parameter
time-range-name
. If a time range with the
specified name does not exist, and the IPv6 ACL containing this ACL rule is
applied to an interface or bound to a VLAN, then the ACL rule is applied
immediately. If a time range with the specified name exists, and the IPv6
ACL containing this ACL rule is applied to an interface or bound to a VLAN,
then the ACL rule is applied when the time-range with a specified name
becomes active. The ACL rule is removed when the time-range with a
specified name becomes inactive.
Syntax
{deny | permit} {ipv6-protocol | number | every} {
source-ipv6-
prefix/prefix-length
| any |
host source-ipv6-address
} [{range {
portkey
|
startport
} {
portkey
|
endport
} | {eq | neq | lt | gt} {
portkey
|
0-65535
}]
{
destination-ipv6-prefix/prefix-length
| any |
host destination-ipv6-address
}
[{range {
portkey
|
startport
} {
portkey
|
endport
} | {eq | neq | lt | gt}
{
portkey
|
0-65535
}] [flag [+fin | -fin] [+syn | -syn] [+rst | -rst] [+psh | -
psh] [+ack | -ack] [+urg | -urg] [established]] [flow-label
value
] [icmp-
ipv6 access-list rename
–
2CSNXXX_SWUM200.book Page 498 Tuesday, December 10, 2013 1:22 PM

IPv6 Access List Commands 499
type
icmp-type
[icmp-code
icmp-code
] | icmp-message
icmp-message
]
[routing] [fragments] [dscp
dscp
]}} [log] [assign-queue
queue-id
] [{mirror
| redirect}
unit/slot/port
] [rate-limit
rate burst-size
]
•{
deny | permit
}–Specifies whether the IP ACL rule permits or denies the
matching traffic.
•{
ipv6-protocol
|
number
|
every
}—Specifies the protocol to match for the IP
ACL rule.
– IPv4 protocols:
icmpv6, ipv6, tcp and udp
–
Every
: Match any protocol (don’t care)
•
source-ipv6-prefix
/prefixlength |
any | host
src-ipv6-address
—Specifies a
source IP address and netmask to match for the IP ACL rule.
– For IPv6 ACLs, “any” implies a 0::/128 prefix and a mask of all ones.
– Specifying “host X::X” implies a prefix length as “/128” and a mask of
0::/128.
•[{range {
portkey
|
startport
} {
portkey
|
endport
} | {eq | neq | lt | gt}
{
portkey
|
0-65535
}]—Specifies the layer 4 destination port match
condition for the IP/TCp/UDP ACL rule. A destination port number,
which ranges from 0-65535, can be entered, or a
portkey
, which can be one
of the following keywords: bgp, domain, echo, ftp, ftp-data, http, ntp,
pop2, pop3, rip, smtp, snmp, telnet, tftp, telnet, time, who and www. Each
of these keywords translates into its equivalent destination port number.
– When “range” is specified, IPv6 ACL rule matches only if the layer 4
port number falls within the specified portrange. The
startport
and
endport
parameters identify the first and last ports that are part of the
port range. They have values from 0 to 65535. The ending port must
have a value equal or greater than the starting port. The starting port,
ending port, and all ports in between will be part of the layer 4 port
range.
– When “eq” is specified, IPv6 ACL rule matches only if the layer 4 port
number is equal to the specified port number or portkey.
– When “lt” is specified, IPv6 ACL rule matches if the layer 4
destination port number is less than the specified port number or
portkey. It is equivalent to specifying the range as 0 to <specified port
number – 1>.
2CSNXXX_SWUM200.book Page 499 Tuesday, December 10, 2013 1:22 PM

500 IPv6 Access List Commands
– When “gt” is specified, IPv6 ACL rule matches if the layer 4
destination port number is greater than the specified port number or
portkey. It is equivalent to specifying the range as <specified port
number + 1> to 65535.
– When “neq” is specified, IPv6 ACL rule matches only if the layer 4
destination port number is not equal to the specified port number or
portkey.
– IPv6 TCP port names:
bgp, domain, echo, ftp, ftp-data, http, smtp,
telnet, www, pop2, pop3
– IPv6 UDP port names:
domain, echo, ntp, rip, snmp, time, who
•
destination-ipv6-prefix
/
prefix-length
|
any
|
host
destination-ipv6-
address
—Specifies a destination IP address and netmask for match
condition of the IP ACL rule.
– For IPv6 ACLs, “any” implies 0::/128 prefix and a mask of all ones.
– Specifying host implies prefix length as “/128” and a mask of 0::/128.
• [precedence
precedence
| tos
tos
[
tosmask
] | dscp
dscp
]—Specifies the
TOS for an IP/TCP/UDP ACL rule depending on a match of precedence
or DSCP values using the parameters dscp, precedence, or tos tosmask.
• flag [+fin | -fin] [+syn | -syn] [+rst | -rst] [+psh | -psh] [+ack | -ack]
[+urg | -urg] [established]—Specifies that the IP/TCP/UDP ACL rule
matches on the TCP flags.
– When “+<tcpflagname>
” is
specified, a match occurs if specified
<tcpflagname> flag is set in the TCP header.
– When “-<tcpflagname>
” is
specified, a match occurs if specified
<tcpflagname> flag is *NOT* set in the TCP header.
– When “established
” is
specified, a match occurs if specified either
RST or ACK bits are set in the TCP header.
– This option is visible only if the protocol is tcp.
–
Ack
– Acknowledgement bit
–
Fin
– Finished bit
–
Psh
– push bit
–
Rst
– reset bit
–
Syn
– Synchronize bit
2CSNXXX_SWUM200.book Page 500 Tuesday, December 10, 2013 1:22 PM

IPv6 Access List Commands 501
–
Urg
– Urgent bit
•[icmp-type
icmp-type
[icmp-code
icmp-code
] | icmp-message
icmp-
message
]—Specifies a match condition for ICMP packets.
– When icmp-type is specified, IP ACL rule matches on the specified
ICMP message type, a number from 0 to 255.
– When icmp-code is specified, IP ACL rule matches on the specified
ICMP message code, a number from 0 to 255.
– Specifying icmp-message implies both icmp-type and icmp-code are
specified.
– ICMP message is decoded into corresponding ICMP type and ICMP
code within that ICMP type. This option is visible only if the protocol
is “icmpv6”.
– ICMPv6 message types: destination-unreachable echo-reply echo-
request header hop-limit mld-query mld-reduction mld-report nd-na
nd-ns next-header no-admin no-route packet-too-big port-
unreachable router-solicitation router-advertisement router-
renumbering time-exceeded unreachable
– The icmpv6 message types are available only if the protocol is icmpv6.
• fragments—Specifies the rule matches packets that are non-initial
fragments (fragment bit asserted). Not valid for rules that match L4
information such as TCP port number since that information is carried in
the initial packet. IPv6 fragments contain an IPv6 Fragment extension
header.
• routing—Specifies that IP ACL rule matches on routed packets. Routed
packets contain an IPv6 “routing” extension header.
• log—Specifies that this rule is to be logged.
• time-range
time-range-name
—Allows imposing time limitation on the
ACL rule as defined by the parameter time-range-name. If a time range
with the specified name does not exist and the ACL containing this ACL
rule is applied to an interface or bound to a VLAN, then the ACL rule is
applied immediately. If a time range with specified name exists and the
ACL containing this ACL rule is applied to an interface or bound to a
VLAN, then the ACL rule is applied when the time-range with specified
name becomes active. The ACL rule is removed when the time-range with
specified name becomes inactive.
2CSNXXX_SWUM200.book Page 501 Tuesday, December 10, 2013 1:22 PM

502 IPv6 Access List Commands
• assign-queue
queue-id
—Specifies the assign-queue, which is the queue
identifier to which packets matching this rule are assigned.
• {mirror | redirect}
unit/slot/ port
—Specifies the mirror or redirect
interface which is the unit/slot/port to which packets matching this rule
are copied or forwarded, respectively.
•rate-limit
rate burst-size
—Specifies the allowed rate of traffic as per the
configured rate in kbps, and burst-size in kbytes.
– Rate – the committed rate in kilobits per second
– Burst-size – the committed burst size in Kilobytes.
Default Configuration
This command has no default configuration.
Command Mode
IPv6-Access-List Configuration mode
User Guidelines
Users are permitted to add rules, but if a packet does not match any user-
specified rules, the packet is dropped by the implicit “deny all” rule.
In order to provide the greatest amount of flexibility in configuring ACLs, the
permit/deny syntax allows combinations of matching criteria that may not
make sense when applied in practice.
The rate-limit command is not supported in egress (out) access groups.
Any – is equivalent to ::/0 for IPv6 access lists.
Host - indicates /128 prefix length for IPv6.
Port ranges are not supported for egress (out) IPv6 traffic-filters. This means
that only the eq operator is supported for egress (out) ACLs.
The protocol type must be TCP or UDP to specify a port range.
The IPv6 “fragment” and “routing” keywords are not supported on egress
(out) access groups.
2CSNXXX_SWUM200.book Page 502 Tuesday, December 10, 2013 1:22 PM

IPv6 Access List Commands 503
Since ACLs have an implicit deny all at the end of the last access-group, IPv6
ACLs need an explicit permit icmp any any nd-na and permit icmp any any
nd-ns statements as match conditions. These additional conditions allow for
ICMPv6 neighbor discovery to occur.
The 'no' form of this command is not supported, since the rules within an
IPv6 ACL cannot be deleted individually. Rather, the entire IPv6 ACL must
be deleted and reentered.
For the N4000 series:
• The IPv6 ACL “routing” keyword is not supported when an IPv6 address is
specified.
• For ingress (in) ACLs, the IPv6 ACL “fragment” keyword matches only on
the first two IPv6 extension headers for the fragment header (next header
code 44). If the fragment header appears in the third or subsequent header,
it is not matched.
For the N2000/N3000 Series series, for ingress (in) ACLs:
• The IPv6 ACL “fragment” keyword matches only on the first IPv6
extension header for the fragment header (next header code 44). If the
fragment header appears in the second or a subsequent header, it is not
matched.
• The IPv6 ACL “routing” keyword matches only on the first IPv6 extension
header for the routing header (next header code 43). If the fragment
header appears in the second or a subsequent header, it is not matched.
• For all series switches, port ranges are not supported on egress (out) ACLs.
Only the eq operator is supported in an egress ACL.
Example
The following example creates rules in an IPv6 ACL named "STOP_HTTP"
to discard any HTTP traffic from the 2001:DB8::/32 network, but allow all
other traffic from that network:
console(config)#ipv6 access-list STOP_HTTP
console(Config-ipv6-acl)#deny ipv6 2001:DB8::/32 any eq http
console(Config-ipv6-acl)#permit ipv6 2001:DB8::/32 any
console(Config-ipv6-acl)#
2CSNXXX_SWUM200.book Page 503 Tuesday, December 10, 2013 1:22 PM

504 IPv6 Access List Commands
ipv6 access-list
The ipv6 access-list command creates an IPv6 Access Control List (ACL)
consisting of classification fields defined for the IP header of an IPv6 frame.
The
name
parameter is a case-sensitive alphanumeric string from 1 to 31
characters uniquely identifying the IPv6 access list.
If an IPv6 ACL with this name already exists, this command enters Ipv6-
Access-List Configuration mode to update the existing IPv6 ACL.
Use the no form of the command to delete an IPv6 ACL from the system.
Syntax
ipv6 access-list
name
no ipv6 access-list
name
•
name
— Alphanumeric string of 1 to 31 characters uniquely identifying
the IPv6 access list.
Default Configuration
There is no default configuration for this command.
Command Mode
Global Configuration mode
User Guidelines
There are no user guidelines for this command
Example
The following example creates an IPv6 ACL named "DELL_IP6" and enters
the IPv6-Access-List Configuration mode:
console(config)#ipv6 access-list DELL_IP6
console(Config-ipv6-acl)#
ipv6 access-list rename
The ipv6 access-list rename command changes the name of an IPv6 Access
Control List (ACL). This command fails if an IPv6 ACL with the new name
already exists.
2CSNXXX_SWUM200.book Page 504 Tuesday, December 10, 2013 1:22 PM

IPv6 Access List Commands 505
Syntax
ipv6 access-list rename
name newname
•
name
— the name of an existing IPv6 ACL.
•
newname
— alphanumeric string from 1 to 31 characters uniquely
identifying the IPv6 access list.
Default Configuration
There is no default configuration for this command.
Command Mode
Global Configuration mode
User Guidelines
There are no user guidelines for this command.
Example
console(Config)#ipv6 access-list rename DELL_IP6 DELL_IP6_NEW_NAME
ipv6 traffic-filter
The ipv6 traffic-filter command either attaches a specific IPv6 Access
Control List (ACL) to an interface or associates it with a VLAN ID in a given
direction.
An optional sequence number may be specified to indicate the order of this
access list relative to other IPv6 access lists already assigned to this interface
and direction. A lower number indicates higher precedence order. If a
sequence number is already in use for this interface and direction, the
specified IPv6 access list replaces the currently attached IPv6 access list using
that sequence number. If the sequence number is not specified for this
command, a sequence number that is one greater than the highest sequence
number currently in use for this interface and direction is used.
Use the “no” form of the command to remove an IPv6 ACL from the
interface(s) in a given direction.
2CSNXXX_SWUM200.book Page 505 Tuesday, December 10, 2013 1:22 PM

506 IPv6 Access List Commands
Syntax
ipv6 traffic-filter
name
[in | out | control-plane][
seq-num
]
no ipv6 traffic-filter
name
•
name
— Alphanumeric string of 1 to 31 characters uniquely identifying
the IPv6 access list.
• in — The access list is applied to ingress packets.
• out—The access list is applied to egress packets.
• control-plane—The access list is applied to ingress control plane pakcets.
This is only available in Global Configuration mode
•
seq-num
— Order of access list relative to other access lists already
assigned to this interface and direction. (Range: 1–4294967295)
Default Configuration
No IPv6 traffic filters are configured by default.
Command Modes
Global Configuration mode, Interface Configuration (Ethernet, Port-
channel, VLAN) mode
User Guidelines
This command specified in Interface Configuration mode only affects a
single interface, whereas the Global Configuration mode setting is applied to
all interfaces. The optional control-plane keyword allows application of an
ACL on the CPU port ingress queue. Control plane packets (e.g., BPDUs) are
dropped because of the implicit deny all rule added at the end of every access
control list. To mitigate this behavior, permit rules must be added by the
operator to allow the appropriate control plane packets to ingress the CPU
(i.e., ARP, DHCP, LACP, STP BPDU, etc.). The control-plane keyword does
not filter traffic received over the out-of-band port.
Example
The following example attaches an IPv6 access control list to an interface.
console(config-if-Gi1/0/1)#ipv6 traffic-filter DELL_IP6 in
2CSNXXX_SWUM200.book Page 506 Tuesday, December 10, 2013 1:22 PM

IPv6 Access List Commands 507
show ipv6 access-lists
Use the show ipv6 access-lists command in User EXEC and Privileged EXEC
mode to display an IPv6 access list and all of the rules that are defined for the
IPv6 ACL. Use the [
name
] parameter to identify a specific IPv6 ACL to
display.
Syntax
show ipv6 access-lists [
name
]
•
name
—
The name used to identify the IPv6 ACL.
Default Configuration
There is no default configuration for this command.
Command Mode
User EXEC, Privileged EXEC mode, Configuration mode and all
Configuration submodes
User Guidelines
There are no user guidelines for this command.
Example
ACL Name: ip1
Outbound Interface(s): control-plane
Rule Number: 1
Action......................................... permit
Match All...................................... FALSE
Protocol....................................... 1(icmp)
Committed Rate................................. 32
Committed Burst Size........................... 16
Rule Number: 2
Action......................................... permit
Match All...................................... TRUE
2CSNXXX_SWUM200.book Page 507 Tuesday, December 10, 2013 1:22 PM

508 IPv6 Access List Commands
2CSNXXX_SWUM200.book Page 508 Tuesday, December 10, 2013 1:22 PM

IPv6 MLD Snooping Commands 509
23
IPv6 MLD Snooping Commands
Dell Networking N2000/N3000/N4000 Series Switches
In IPv6, Multicast Listener Discover (MLD) snooping performs functions
similar to IGMP snooping in IPv4. With MLD snooping, IPv6 multicast data
is selectively forwarded to a list of ports that want to receive the data, instead
of being flooded to all ports in a VLAN. This list is constructed by snooping
IPv6 multicast control packets.
MLD is a protocol used by IPv6 multicast routers to discover the presence of
multicast listeners (nodes wishing to receive IPv6 multicast packets) on its
directly-attached links and to discover which multicast packets are of interest
to neighboring nodes. MLD is derived from IGMP. MLD version 1 (MLDv1)
is equivalent to IGMPv2. MLD version 2 (MLDv2) is equivalent to IGMPv3.
MLD is a subprotocol of Internet Control Message Protocol version 6
(ICMPv6), and MLD messages are a subset of ICMPv6 messages, identified
in IPv6 packets by a preceding Next Header value of 58.
Dell Networking switches can snoop on both MLDv1 and MLDv2 protocol
packets and bridge IPv6 multicast data based on destination IPv6 Multicast
MAC Addresses. The switch can be configured to perform MLD Snooping
and IGMP Snooping simultaneously. The Dell Networking implementation is
compliant to RFC 4541.
Commands in this Chapter
This chapter explains the following commands:
ipv6 mld snooping vlan groupmembership-
interval
ipv6 mld snooping vlan mrouter
ipv6 mld snooping vlan immediate-leave ipv6 mld snooping (Global)
ipv6 mld snooping listener-message-
suppression
show ipv6 mld snooping
ipv6 mld snooping vlan last-listener-query-
interval
show ipv6 mld snooping groups
ipv6 mld snooping vlan mcrtexpiretime show ipv6 mld snooping mrouter
2CSNXXX_SWUM200.book Page 509 Tuesday, December 10, 2013 1:22 PM

510 IPv6 MLD Snooping Commands
ipv6 mld snooping vlan groupmembership-
interval
The ipv6 mld snooping vlan groupmembership-interval command sets the
MLD Group Membership Interval time on a VLAN or interface. The Group
Membership Interval time is the amount of time in seconds that a switch
waits for a report from a particular group on a particular interface before
deleting the interface from the entry. This value must be greater than the
MLDv2 Maximum Response time value. The range is 2 to 3600 seconds.
Syntax
ipv6 mld snooping vlan
vlan-id
groupmembership-interval
time
no ipv6 mld snooping
vlan-id
groupmembership-interval
time
•
vlan-id
— Specifies a VLAN ID value.
•
time
— MLD group membership interval time in seconds. (Range: 2-
3600)
Default Configuration
The default group membership interval time is 260 seconds.
Command Mode
Global Configuration mode
User Guidelines
This command has no user guidelines.
Example
console(config)#ipv6 mld snooping vlan 2 groupmembership-interval 1500
ipv6 mld snooping vlan immediate-leave
This command enables or disables MLD Snooping immediate-leave mode on
a selected VLAN. Enabling immediate-leave allows the switch to immediately
remove the layer 2 LAN interface from its forwarding table entry upon
receiving an MLD done message for that multicast group without first
sending out MAC-based general queries to the interface.
2CSNXXX_SWUM200.book Page 510 Tuesday, December 10, 2013 1:22 PM

IPv6 MLD Snooping Commands 511
You should enable immediate-leave admin mode only on VLANs where only
one host is connected to each layer 2 LAN port. This prevents the inadvertent
dropping of the other hosts that were connected to the same layer 2 LAN
port, but were still interested in receiving multicast traffic directed to that
group. Also, immediate-leave processing is supported only with MLD version
1 hosts.
Syntax
ipv6 mld snooping vlan
vlan-id
immediate-leave
•
vlan-id
— Specifies the VLAN.
Default Configuration
Immediate leave is disabled on all VLANs by default.
Command Mode
Global Configuration mode.
User Guidelines
There are no user guidelines for this command.
Example
This example enables mld snooping immediate-leave for VLAN 2.
console(config)#ipv6 mld snooping vlan 2 immediate-leave
ipv6 mld snooping listener-message-suppression
This command enables MLD listener message suppression on a specific
VLAN. Use the no form of this command to disable listener message
suppression.
Syntax
ipv6 mld snooping vlan
vlan-id
listener-message-suppression
no ipv6 mld snooping vlan
vlan-id
listener-message-suppression
•
vlan_id
— Specifies a VLAN ID value.
2CSNXXX_SWUM200.book Page 511 Tuesday, December 10, 2013 1:22 PM

512 IPv6 MLD Snooping Commands
Default Configuration
Listener message suppression is enabled by default.
Command Mode
Global Configuration mode.
User Guidelines
MLD listener message suppression is equivalent to IGMP report suppression.
When MLD listener message suppression is enabled, the switch only sends
the first report received for a group in response to a query. Listener message
suppression is only applicable to MLDv1.
Example
console(config)#ipv6 mld snooping vlan 10 listener-message-suppression
ipv6 mld snooping vlan last-listener-query-
interval
The ipv6 mld snooping vlan last-listener-query-interval command sets the
number of seconds after which a host is considered to have left the group.
This value must be less than the MLD Query Interval time value. The range
is 1 to 25 seconds.
Syntax
ipv6 mld snooping vlan
vlan-id
last-listener-query-interval
time
no ipv6 mld snooping vlan
vlan-id
last-listener-query-interval
•
vlan-id
— Specifies a VLAN ID value.
•
time
— The number of seconds after which a host is considered to have
left the group. (Range: 1–25 seconds)
Default Configuration
The default maximum response time is 1000 ms.
Command Mode
Global Configuration mode
2CSNXXX_SWUM200.book Page 512 Tuesday, December 10, 2013 1:22 PM

IPv6 MLD Snooping Commands 513
User Guidelines
This command has no user guidelines.
Example
console(config)#ipv6 mld snooping vlan 2 last-listener-query-interval 7
ipv6 mld snooping vlan mcrtexpiretime
The ipv6 mld snooping mcrtexpiretime command sets the Multicast Router
Present Expiration time. The time is set for a particular interface or VLAN.
This is the amount of time in seconds that a switch waits for a query to be
received on an interface before the interface is removed from the list of
interfaces with multicast routers attached. The range is 1 to 3600 seconds.
Syntax
ipv6 mld snooping vlan
vlan-id
mcrtexpiretime
time
no ipv6 mld snooping vlan
vlan-id
mcrtexpiretime
•
vlan-id
— Specifies a valid VLAN ID.
•
time
— Multicast router present expiration time in seconds. (Range:
1–3600)
Default Configuration
The default multicast router present expiration time is 300 seconds.
Command Mode
Global Configuration mode.
User Guidelines
This command has no user guidelines
Example
console(config)#ipv6 mld snooping vlan 2 mcrtrexpiretime 1500
2CSNXXX_SWUM200.book Page 513 Tuesday, December 10, 2013 1:22 PM

514 IPv6 MLD Snooping Commands
ipv6 mld snooping vlan mrouter
This command statically configures a port as connected to a multicast router
for a specified VLAN. The no form of this command removes the static
binding.
Syntax
ipv6 mld snooping vlan
vlan-id
mrouter interface
interface
no ipv6 mld snooping vlan
vlan-id
mrouter interface
interface
•
vlan-id
— Specifies a valid VLAN ID.
•
interface-id
— The next-hop interface to the Multicast router.
Default Configuration
There are no multicast router ports configured by default.
Command Mode
Global Configuration mode.
User Guidelines
This command has no user guidelines
Example
console(config)#ipv6 mld snooping vlan 10 mrouter interface Gi1/0/2
ipv6 mld snooping (Global)
Use the ipv6 mld snooping (Global) command to globally enable MLD
Snooping on the system (Global Configuration Mode). Use the no form of
the command to disable MLD snooping. Use the vlan parameter to enable
MLD Snooping on a specific VLAN.
Syntax
ipv6 mld snooping [vlan
vlan-id
]
no ipv6 mld snooping [vlan
vlan-id
]
•
vlan-id
— Specifies a VLAN ID value.
2CSNXXX_SWUM200.book Page 514 Tuesday, December 10, 2013 1:22 PM

IPv6 MLD Snooping Commands 515
Default Configuration
MLD Snooping is enabled globally and on all VLANs by default.
Command Mode
Global Configuration mode.
User Guidelines
Use this command without parameters to globally enable MLD Snooping.
Use the no form of the command to disable MLD Snooping. Use the vlan
parameter to enable MLD Snooping on a specific VLAN.
It is recommended that IGMP snooping should be enabled whenever MLD
snooping is enabled to ensure that unwanted pruning of multicast protocol
packets used by other protocols does not occur.
Enabling MLD snooping on an IPv6 L3 multicast router is not recommended.
If a multicast source is connected to a VLAN on which both L3 multicast and
IGMP/MLD snooping are enabled, the multicast source is forwarded to the
mrouter ports that have been discovered when the multicast source is first
seen. If a new mrouter is later discovered on a different port, the multicast
source data is not forwarded to the new port. Likewise, if an existing mrouter
times out or stops querying, the multicast source data continues to be
forwarded to that port. If a host in the VLAN subsequently joins or leaves the
group, the list of mrouter ports is updated for the multicast source and the
forwarding of the multicast source is adjusted. The workaround to this
limitation is to statically configure mrouter ports when enabling MLD
snooping in L3 multicast enabled VLANs.
Example
console(config)#ipv6 mld snooping
console(config)#no ipv6 mld snooping vlan 1
show ipv6 mld snooping
The show ipv6 mld snooping command displays MLD Snooping information
and SSM statistics. Configured information is displayed whether or not MLD
Snooping is enabled.
2CSNXXX_SWUM200.book Page 515 Tuesday, December 10, 2013 1:22 PM

516 IPv6 MLD Snooping Commands
Syntax
show ipv6 mld snooping [interface {{gigabitethernet unit/slot/port|
port-
channel
port-channel-number
| tengigabitethernet unit/slot/port |
fortygigabitethernet unit/slot/port}} | vlan
vlan-id
}]
Default Configuration
This command has no default configuration
Command Mode
Privileged EXEC mode, Configuration mode and all Configuration submodes
User Guidelines
With no optional arguments, the command displays the following
information:
• Admin Mode — Indicates whether or not MLD Snooping is active on the
switch.
• Multicast Control Frame Count— Displays the total number of IGMP or
PIM packets which have been received (same as IPv4).
• Flooding Unregistered to All Ports—Indicates if Flooding Unregistered to
All Ports is enabled. If enabled, multicast data traffic for which no listeners
have registered is flooded to all ports in a VLAN instead of only flooded to
multicast router ports.
• SSM FDB Capacity—The capacity of the SSM FDB.
• SSM FDB Current Entries—The current count of SSM FDB entries.
• SSM FDB High Water Mark—The highest count of FDB entries since the
last clear counters all.
When you specify an interface or VLAN, the following information displays:
• MLD Snooping Admin Mode — Indicates whether MLD Snooping is
active on the interface or VLAN.
• Fast Leave Mode — Indicates whether MLD Snooping Fast-leave is active
on the VLAN.
2CSNXXX_SWUM200.book Page 516 Tuesday, December 10, 2013 1:22 PM

IPv6 MLD Snooping Commands 517
• Group Membership Interval — Shows the amount of time in seconds that
a switch will wait for a report from a particular group on a particular
interface, which is participating in the VLAN, before deleting the interface
from the entry. This value may be configured.
• Last Listener Query Interval—Displays the amount of time the switch
waits after it sends a query on an interface, participating in the VLAN,
because it did not receive a report for a particular group on that interface.
This value may be configured.
• Multicast Router Present Expiration Time — Displays the amount of time
to wait before removing an interface that is participating in the VLAN
from the list of interfaces with multicast routers attached. The interface is
removed if a query is not received. This value may be configured.
• Listener Message Suppression Mode—Sends only
the first report received
in response to a query to the router.
Example
console(config)#show ipv6 mld snooping
Admin Mode..................................... Enable
Multicast Control Frame Count.................. 6255
SSM FDB Capacity............................... 64
SSM FDB High Water Mark........................ 1
SSM FDB Current Entries........................ 1
Flooding Unregistered to All Ports............. Disabled
Vlan 1:
--------
MLD Snooping Admin Mode........................ Enabled
Immediate Leave Mode........................... Disabled
Group Membership Interval...................... 260
Last Listener Query Interval................... 10
Multicast Router Expiry Time................... 300
Listener Message Suppression Mode.............. Enabled
show ipv6 mld snooping groups
The show ipv6 mld snooping groups command displays the MLD Snooping
and SSM entries in the MFDB table.
2CSNXXX_SWUM200.book Page 517 Tuesday, December 10, 2013 1:22 PM

518 IPv6 MLD Snooping Commands
Syntax
show ipv6 mld snooping groups [{vlan
vlan-id
| address
ipv6-multicast-
address
}]
•
vlan_id
— Specifies a VLAN ID value.
•
ipv6-multicast-address
— Specifies an IPv6 Multicast address.
Default configuration
This command has no default configuration.
Command Mode
Privileged EXEC mode, Configuration mode and all Configuration submodes
User Guidelines
This user guideline applies to all switch models.To see the full Multicast
address table (including static addresses) use the
show mac address-table
command.
Example
This example shows MLDv2 snooping entries
console#show ipv6 mld snooping groups
Vlan Group Type OIFs
---- ----------------------- ------- ------------------------------------
1 3333.0000.0003 Dynamic Te1/0/1,Te1/0/17
MLD SSM Entries :
-----------------
VLAN Group Reporter Filter IIF Source Address
---- ---------------- ---------------- --------- ---------- ----------------
1 ff1e:2222:2222: fe80::200:3ff:f include Te1/0/1 2001::2
2222:2222:2222: e00:b00
2222:2222
2CSNXXX_SWUM200.book Page 518 Tuesday, December 10, 2013 1:22 PM

IPv6 MLD Snooping Commands 519
show ipv6 mld snooping mrouter
Use the show ipv6 mld snooping mrouter command in Privileged EXEC
mode to display information on dynamically learned Multicast router
interfaces.
Syntax
show ipv6 mld snooping mrouter
Default configuration
This command has no default configuration.
Command Mode
Privileged EXEC mode, Configuration mode and all Configuration submodes
User Guidelines
This command has no user guidelines.
Example
console# show ipv6 mld snooping mrouter
VLAN ID Port
------- -----------
10 Gi2/0/1
2CSNXXX_SWUM200.book Page 519 Tuesday, December 10, 2013 1:22 PM

520 IPv6 MLD Snooping Commands
2CSNXXX_SWUM200.book Page 520 Tuesday, December 10, 2013 1:22 PM

IPv6 MLD Snooping Querier Commands 521
24
IPv6 MLD Snooping Querier
Commands
Dell Networking N2000/N3000/N4000 Series Switches
The MLD Snooping Querier is an extension of the MLD Snooping feature.
MLD Snooping Querier allows the switch to simulate an MLD router in a
Layer 2-only network, thus removing the need to have an MLD Router to
collect the multicast group membership information. The querier function
simulates a small subset of the MLD router functionality.
In a network with IP multicast routing, the IP multicast router acts as the
MLD querier. However, if it is required that the IP-multicast traffic in a
VLAN be switched, the switch can be configured as an MLD querier. When
MLD Snooping Querier is enabled, the Querier sends out periodic MLD
General Queries that trigger the Multicast listeners/member to send their
joins so as to receive the Multicast data traffic. MLD Snooping listens to
these reports to establish the appropriate forwarding table entries.
Commands in this Chapter
This chapter explains the following commands:
ipv6 mld snooping querier
Use the ipv6 mld snooping querier command to enable MLD Snooping
Querier on the system. Use the no form of this command to disable MLD
Snooping Querier.
ipv6 mld snooping querier ipv6 mld snooping querier query-interval
ipv6 mld snooping querier (VLAN mode) ipv6 mld snooping querier timer expiry
ipv6 mld snooping querier address show ipv6 mld snooping querier
ipv6 mld snooping querier election
participate
–
2CSNXXX_SWUM200.book Page 521 Tuesday, December 10, 2013 1:22 PM

522 IPv6 MLD Snooping Querier Commands
Syntax
ipv6 mld snooping querier
no ipv6 mld snooping querier
Default Configuration
MLD Snooping Querier is disabled by default.
Command Mode
Global Configuration mode
User Guidelines
It is not recommended the MLD Snooping Querier be enabled on a switch
enabled for IPv6 multicast routing.
Example
console(config)#ipv6 mld snooping querier
ipv6 mld snooping querier (VLAN mode)
Use the ipv6 mld snooping querier command in VLAN mode to enable MLD
Snooping Querier on a VLAN. Use the no form of this command to disable
MLD Snooping Querier on a VLAN.
Syntax
ipv6 mld snooping querier vlan
vlan-id
no ipv6 mld snooping querier vlan
vlan-id
•
vlan-id
— A valid VLAN ID. (Range: 1–4093)
Default Configuration
MLD Snooping Querier is disabled by default on all VLANs.
Command Mode
Global Configuration mode
2CSNXXX_SWUM200.book Page 522 Tuesday, December 10, 2013 1:22 PM

IPv6 MLD Snooping Querier Commands 523
User Guidelines
There are no user guidelines for this command.
Example
console(config)#ipv6 mld snooping querier vlan 10
ipv6 mld snooping querier address
Use the ipv6 mld snooping querier address command to set the global MLD
Snooping Querier address. Use the no form of this command to reset the
global MLD Snooping Querier address to the default.
Syntax
ipv6 mld snooping querier address
prefix
[
/prefix-length
]
no ipv6 mld snooping querier address
•
prefix
— The bits of the address to be configured.
•
prefix-length
— Designates how many of the high-order contiguous bits of
the address make up the prefix.
Default Configuration
There is no global MLD Snooping Querier address configured by default.
Command Mode
Global Configuration mode
User Guidelines
There are no user guidelines for this command.
Example
console(config)#ipv6 mld snooping querier address Fe80::5
ipv6 mld snooping querier election participate
Use the ipv6 mld snooping querier election participate command to enable
the Snooping Querier to participate in the Querier Election process when it
discovers the presence of another Querier in the VLAN. When this mode is
2CSNXXX_SWUM200.book Page 523 Tuesday, December 10, 2013 1:22 PM

524 IPv6 MLD Snooping Querier Commands
enabled, if the Snooping Querier finds that the other Querier's source address
is numerically lower than the Snooping Querier's address, it stops sending
periodic queries. If the Snooping Querier wins the election then it will
continue sending periodic queries. Use the no form of this command to
disable election participation on a VLAN.
Syntax
ipv6 mld snooping querier election participate
vlan-id
no ipv6 mld snooping querier election participate
vlan-id
•
vlan-id
— A valid VLAN ID. (Range: 1 - 4093)
Default Configuration
Election participation is disabled by default.
Command Mode
Global Configuration mode
User Guidelines
If there is another querier in the network and the local querier is in election
mode, then the querier with the lower IP address is elected and the other
querier stops querying. If the local querier is not in election mode and
another querier is detected, the local querier stops querying.
Example
console(config-vlan)#ipv6 mld snooping querier election participate 10
ipv6 mld snooping querier query-interval
Use the ipv6 mld snooping querier query-interval command to set the MLD
Querier Query Interval time. It is the amount of time in seconds that the
switch waits before sending another general query. Use the no form of this
command to reset the Query Interval to the default.
Syntax
ipv6 mld snooping querier query-interval
interval
ipv6 mld snooping querier query-interval
2CSNXXX_SWUM200.book Page 524 Tuesday, December 10, 2013 1:22 PM

IPv6 MLD Snooping Querier Commands 525
•
interval
— Amount of time that the switch waits before sending another
general query. (Range: 1–1800 seconds)
Default Configuration
The default query interval is 60 seconds.
Command Mode
Global Configuration mode
User Guidelines
There are no user guidelines for this command
Example
console(config)#ipv6 mld snooping querier 120
ipv6 mld snooping querier timer expiry
Use the ipv6 mld snooping querier timer expiry command to set the MLD
Querier timer expiration period. It is the time period that the switch remains
in Non-Querier mode once it has discovered that there is another Multicast
Querier in the network. Use the no form of this command to reset the timer
expiration period to the default.
Syntax
ipv6 mld snooping querier timer expiry
timer
ipv6 mld snooping querier timer expiry
•
timer
— The time that the switch remains in Non-Querier mode after it
has discovered that there is a multicast querier in the network. (Range:
60–300 seconds)
Default Configuration
The default timer expiration period is 60 seconds.
Command Mode
Global Configuration mode
2CSNXXX_SWUM200.book Page 525 Tuesday, December 10, 2013 1:22 PM
526 IPv6 MLD Snooping Querier Commands
User Guidelines
There are no user guidelines for this command.
Example
console(config)#ipv6 mld snooping querier timer expiry 222
show ipv6 mld snooping querier
Use the show ipv6 mld snooping querier command to display MLD
Snooping Querier information. Configured information is displayed whether
or not MLD Snooping Querier is enabled.
Syntax
show ipv6 mld snooping querier [detail | vlan
vlan-id
]
•
vlan-id
— A valid VLAN ID. (Range: 1 - 4093)
Default Configuration
There is no default configuration for this command.
Command Mode
Privileged EXEC mode, Configuration mode and all Configuration submodes
User Guidelines
When the optional argument vlan vlan-id is not used, the command shows
the following information:
Parameter Description
MLD Snooping Querier
Mode
Indicates whether or not MLD Snooping Querier is
active on the switch.
Querier Address Shows the IP Address which will be used in the IPv6
header while sending out MLD queries.
MLD Version Indicates the version of MLD that will be used while
sending out the queries. This is defaulted to MLD v1
and it can not be changed.
2CSNXXX_SWUM200.book Page 526 Tuesday, December 10, 2013 1:22 PM
IPv6 MLD Snooping Querier Commands 527
When the optional argument vlan vlan-id is used, the following additional
information appears:
When the optional argument detail is used, the command shows the global
information and the information for all Querier enabled VLANs as well as the
following information:
Querier Query Interval Shows the amount of time that a Snooping Querier
waits before sending out a periodic general query.
Querier Expiry Interval Displays the amount of time to wait in the Non-Querier
operational state before moving to a Querier state.
Parameter Description
MLD Snooping Querier
VLAN Mode
Indicates whether MLD Snooping Querier is active on
the VLAN.
Querier Election
Participate Mode
Indicates whether the MLD Snooping Querier
participates in querier election if it discovers the
presence of a querier in the VLAN.
Querier VLAN Address Shows the IP Address which will be used in the IPv6
header while sending out MLD queries.
Operational State Indicates whether MLD Snooping Querier is in
"Querier" or "Non-Querier" state. When the switch is in
Querier state it will send out periodic general queries.
When in Non-Querier state it will wait for moving to
Querier state and does not send out any queries.
Operational Version Indicates the version of MLD that will be used while
sending out the queries. This is defaulted to MLD v1
and it can not be changed.
Last Querier Address Indicates the IP address of the most recent Querier from
which a Query was received.
MLD Version Indicates the version of MLD.
2CSNXXX_SWUM200.book Page 527 Tuesday, December 10, 2013 1:22 PM

528 IPv6 MLD Snooping Querier Commands
2CSNXXX_SWUM200.book Page 528 Tuesday, December 10, 2013 1:22 PM

IP Source Guard Commands 529
25
IP Source Guard Commands
Dell Networking N2000/N3000/N4000 Series Switches
IP Source Guard (IPSG) is a security feature that filters IP packets based on
source ID. The source ID may either be source IP address or a {source IP
address, source MAC address} pair. The network administrator configures
whether enforcement includes the source MAC address. The network
administrator can configure static authorized source IDs. The DHCP
Snooping binding database and static IPSG entries identify authorized source
IDs. IPSG may be enabled on physical and LAG ports. IPSG is disabled by
default.
If the network administrator enables IPSG on a port where DHCP snooping is
disabled or where DHCP snooping is enabled but the port is trusted, all IP
traffic received on that port is dropped depending upon the admin-
configured IPSG entries. IPSG cannot be enabled on a port-based routing
interface.
IPSG uses two enforcement mechanisms: the L2FDB to enforce the source
MAC address and ingress VLAN and an ingress classifier to enforce the source
IP address or {source IP, source MAC} pair.
Commands in this Chapter
This chapter explains the following commands:
ip verify source
Use the ip verify source command in Interface Configuration mode to enable
filtering of IP packets from hosts which have not been assigned an IP address
via DHCP on the specified interface.
ip verify source show ip verify
ip verify source port-security show ip verify source
ip verify binding show ip source binding
2CSNXXX_SWUM200.book Page 529 Tuesday, December 10, 2013 1:22 PM

530 IP Source Guard Commands
Use the no form of the command to enable unverified traffic to flow over the
interfaces.
Syntax
ip verify source {port-security}
no ip verify source
•
port-security
—Enables filtering based on IP address, VLAN, and MAC
address.
Default Configuration
By default, no sources are blocked.
Command Mode
Interface Configuration mode
User Guidelines
DHCP snooping should be enabled on any ports for which ip verify source is
configured. If ip verify source is configured on an interface for which DHCP
snooping is disabled, or for which DHCP snooping is enabled and the port is
trusted, incoming traffic on the interface is dropped.
Incoming traffic is filtered based on the source IP address and VLAN. When
the port-security keyword is configured, filtering occurs based upon source IP
address, VLAN and source MAC address.
IP source guard also interacts with the port security component. Use the port
security command in interface mode to optionally add checking of learned
MAC addresses. When port security is enabled, MAC learning coordinates
with the IP Source Guard to verify that the MAC address is in the DHCP
binding database. If it is not, port security is notified that the frame is in
violation of the security policy.
Example
console(config-if-Gi1/0/1)#ip verify source
2CSNXXX_SWUM200.book Page 530 Tuesday, December 10, 2013 1:22 PM

IP Source Guard Commands 531
ip verify source port-security
Use the ip verify source port-security command in Interface Configuration
mode to enable filtering of IP packets that do not match the source IP address
and the source MAC address bindings in the DHCP snooping database..
Syntax
ip verify source port-security
Default Configuration
By default, IPSG is disabled on all interfaces.
Command Mode
Interface Configuration mode
User Guidelines
Use the no ip verify source command to disable IPSG on an interface.
Example
console(config-if-Gi1/0/1)#ip verify source port-security
ip verify binding
Use the ip verify binding command in Global Configuration mode to
configure static bindings. Use the no form of the command to remove the
IPSG entry.
Syntax
ip verify binding
macaddr
vlan
ipaddr
interface
Default Configuration
By default, there are no static bindings configured.
Command Mode
Global Configuration mode
2CSNXXX_SWUM200.book Page 531 Tuesday, December 10, 2013 1:22 PM

532 IP Source Guard Commands
User Guidelines
The configured IP address and MAC address are used to match the source IP
address and source MAC address for packets received on the interface. Hosts
sending packets using the configured source IP address and source MAC
address are trusted on the interface.
Example
console(config)#ip verify binding 00:11:22:33:44:55 vlan 1 1.2.3.4 interface
gigabitethernet 1/0/2
show ip verify
Use the show ip verify command to display the IP Source Guard
configuration on all interfaces or the specified interface.
Syntax
show ip verify [interface
if-id
]
•
if-id
—A valid interface ID (physical)
Default Configuration
There is no default configuration for this command.
Command Modes
User EXEC, Privileged EXEC (all show modes)
User Guidelines
The filter type is one of the following values:
• ipv4-mac: User has configure MAC address filtering on this interface
• ip: IPv4 address filtering is configured on this interface
• N/A: No filtering is configured on the interface
Example
console(config-if-Gi1/0/5)#show ip verify
Interface Filter Type
2CSNXXX_SWUM200.book Page 532 Tuesday, December 10, 2013 1:22 PM

IP Source Guard Commands 533
----------- -----------
Gi1/0/1 ipv4
Gi1/0/2 ipv4-mac
Gi1/0/3 N/A
Gi1/0/4 N/A
Gi1/0/5 ipv4-mac
Gi1/0/6 N/A
Gi1/0/7 N/A
Gi1/0/8 N/A
Gi1/0/9 N/A
console(config-if-Gi1/0/5)#show ip verify interface gi1/0/5
Interface Filter Type
----------- -----------
Gi1/0/5 ipv6-mac
show ip verify source
Use the show ip verify source command in Privileged EXEC mode to display
the bindings configured on a particular interface or all interfaces.
Syntax
show ip verify source [interface
interface-id
]
•
interface-id
: A valid physical interface or port-channel identifier
Default Configuration
There is no default configuration for this command.
Command Mode
User EXEC, Privileged EXEC mode, Configuration mode and all
Configuration submodes
User Guidelines
This command has no user guidelines.
Example
console#show ip verify source interface gigabitethernet 1/0/1
2CSNXXX_SWUM200.book Page 533 Tuesday, December 10, 2013 1:22 PM

534 IP Source Guard Commands
show ip source binding
Use the show ip source binding command in Privileged EXEC mode to
display all bindings (static and dynamic).
Syntax
show ip source binding
Default Configuration
There is no default configuration for this command.
Command Mode
User EXEC, Privileged EXEC mode, Configuration mode and all
Configuration submodes
User Guidelines
This command has no user guidelines.
Example
console#show ip source binding
2CSNXXX_SWUM200.book Page 534 Tuesday, December 10, 2013 1:22 PM

iSCSI Optimization Commands 535
26
iSCSI Optimization Commands
Dell Networking N2000/N3000/N4000 Series Switches
iSCSI Optimization provides a means of performing configuration specific to
storage traffic and optionally giving traffic between iSCSI initiator and target
systems special Quality of Service (QoS) treatment.
iSCSI Optimization is best applied to mixed-traffic networks where iSCSI
packets constitutes a portion of overall traffic. In these cases, the assignment
of iSCSI packets to non-default CoS queues can provide flows with lower
latency and avoid queue resource contention.
If iSCSI frames comprise most of the traffic passing through the switch, the
system provides optimal throughput when all traffic is assigned to the default
queue. An example of this situation is a Storage Area Network (SAN) where
the switch is dedicated to interconnecting iSCSI Targets with Initiators.
Using the default queue for this homogenous traffic provides the best
performance in traffic burst handling and the most accurate 802.3x Flow
Control Pause Frame generation. In these cases, the application of QoS
treatment other than the default policy may result in less overall throughput
or more packet loss.
By default, iSCSI optimization is enabled and iSCSI QoS treatment is
disabled.
LLDP is used to detect the presence of EqualLogic storage arrays. When
iSCSI optimization is enabled, and LLDP detects an EQL array on a port,
that port configuration is changed to enable portfast and disable unicast
storm control. Configuration changes appear in the running config and are
not removed by disabling the feature or disconnecting the EQl array.
QoS treatment is accomplished by monitoring traffic to detect packets used
by iSCSI stations to establish iSCSI sessions and connections. Data from
these exchanges is used to create classification rules that assign the traffic
between the stations to a configured traffic class. Packets in the flow are
queued and scheduled for egress on the destination port based on these rules.
2CSNXXX_SWUM200.book Page 535 Tuesday, December 10, 2013 1:22 PM

536 iSCSI Optimization Commands
In addition, if configured, the packets can be updated with IEEE 802.1p or
IP-DSCP values. This is done by enabling remark. Remarking packets with
priority data provides special QoS treatment as the packets continue through
the network.
iSCSI Optimization borrows ACL lists from the global system pool. ACL lists
allocated by iSCSI Optimization reduce the total number of ACLs available
for use by the network operator. Enabling iSCSI Optimization uses one ACL
list to monitor for iSCSI sessions. Each monitored iSCSI session utilizes two
rules from additional ACL lists up to a maximum of two ACL lists. This
means that the maximum number of ACL lists allocated by iSCSI is three.
Commands in this Chapter
This chapter explains the following commands:
iscsi aging time
The iscsi aging time command sets the time out value for iSCSI sessions. To
reset the aging time to the default value, use the no form of this command.
Syntax
iscsi aging time
time
no iscsi aging time
•
time
— The number of minutes a session must not be active prior to it's
removal. (Range: 1 43,200)
Default Configuration
The default aging time is 10 minutes.
Command Mode
Global Configuration mode.
iscsi aging time iscsi target port
iscsi cos show iscsi
iscsi enable show iscsi sessions
2CSNXXX_SWUM200.book Page 536 Tuesday, December 10, 2013 1:22 PM

iSCSI Optimization Commands 537
User Guidelines
Changing the aging time has the following behavior:
• When aging time is increased, current sessions will be timed out according
to the new value.
• When aging time is decreased, any sessions that have been dormant for a
time exceeding the new setting will be immediately deleted from the table.
All other sessions will continue to be monitored against the new time out
value.
Example
The following example sets the aging time for iSCSI sessions to 100 minutes.
console(config)#iscsi aging time 100
iscsi cos
Use the iscsi cos command in Global Configuration mode to set the quality
of service profile that will be applied to iSCSI flows. To return the VPT/DSCP
setting to the default value, use the no form of this command. VPT/DSCP
values can be configured independently from the application of QoS
treatment.
Syntax
iscsi cos {enable | disable | vpt
vpt
| dscp
dscp
} [remark]
no iscsi cos
•
enable
—Enables application of preferential QoS treatment to iSCSI
frames.
•
disable
—Disables application of preferential QoS treatment to iSCSI
frames.
•
vpt/dscp
—The VLAN Priority Tag or DSCP value to assign received iSCSI
session packets.
•
remark
—Mark the iSCSI frames with the configured DSCP when
egressing the switch.
2CSNXXX_SWUM200.book Page 537 Tuesday, December 10, 2013 1:22 PM

538 iSCSI Optimization Commands
Default Configuration
By default, frames are not remarked. The default vpt setting for iSCSI is 4,
which the default class of service dot1p mapping assigns to queue 2.
Command Mode
Global Configuration mode.
User Guidelines
The remark option only applies to DSCP values. Remarking is not available
for vpt values.
In general, the use of iSCSI CoS is not required. By default, iSCSI flows are
assigned to the highest VPT/DSCP value that is mapped to the highest queue
not used for stack management or the voice VLAN. Make sure you configure
the relevant Class of Service parameters for the queue in order to complete
the setting.
Configuring the VPT/DSCP value sets the QoS profile which selects the
egress queue to which the frame is mapped. The default setting for egress
queues scheduling is Weighted Round Robin (WRR).
You may alter the QoS setting by configuring the relevant ports to work in
other scheduling and queue management modes via the Class of Service
settings. These choices may include strict priority for the queue used for
iSCSI traffic. The downside of strict priority is that, in certain circumstances
(under heavy high priority traffic), other lower priority traffic may get starved.
In WRR, the queue to which the flow is assigned to can be set to get the
required percentage using the min-bandwidth settings.
If an EqualLogic array is detected when QoS is enabled, two additional TCP
ports receive preferential QoS treatment (TCP ports 25555 and 9876). This
QoS policy is applied globally. The iscsi cos enable command enables
the generation of the iSCSI Application Priority TLV over DCBX using the
value set by the iscsi cos vpt command on switches that support
DCBX.
Example
The following example configures iSCSI packets to receive CoS treatment
using DiffServ Code Point AF 41 and configures remarking of transmitted
iSCSI packets.
2CSNXXX_SWUM200.book Page 538 Tuesday, December 10, 2013 1:22 PM

iSCSI Optimization Commands 539
console(config)#iscsi cos dscp 10 remark
iscsi enable
The iscsi enable command globally enables iSCSI optimization. To disable
iSCSI optimization, use the no form of this command.
Syntax
iscsi enable
no iscsi enable
Default Configuration
iSCSI is enabled by default.
Command Mode
Global Configuration mode
User Guidelines
This command modifies the running config to enable flow control on all
interfaces.
Connectivity fault management is not compatible with iSCSI monitoring.
Disable CFM before enabling iSCSI monitoring.
Monitoring for EqualLogic Storage arrays via LLDP is also enabled by this
command. Upon detection of an EQL array, the specific interface involved
will have spanning-tree portfast enabled and unicast storm control disabled.
These changes appear in the running config. Disabling iSCSI Optimization
does not disable flow control, portfast or storm control configuration applied
as a result of enabling iSCSI Optimization.
On the N4000 switches, enabling iSCSI will locally generate a DCBX
Application Priority TLV with the following parameters when the following
conditions are met:
•DCBX is enabled
• CoS Queuing is enabled on the port using VPT (
iscsi cos enable
)
The Application Priority TLV sent will contain the following information in
addition to any other information contained in the TLV:
2CSNXXX_SWUM200.book Page 539 Tuesday, December 10, 2013 1:22 PM

540 iSCSI Optimization Commands
AE Selector = 1
AE Protocol = 3260
AE Priority = priority configured for iSCSI PFC (the VPT value above). This
TLV is sent in addition to any Application Priority TLV information received
from the configuration source. If the configuration source is sending iSCSI or
FCoE application priority information, it is not necessary to enable iscsi cos
to send the iSCSI Application Priority TLV.
Example
In the following example, iSCSI is globally enabled.
console(config)#iscsi enable
iscsi target port
Use the iscsi target port command in Global Configuration mode to
configure iSCSI port(s), target addresses and names. To delete iSCSI port(s)
or target ports, use the no form of this command.
Syntax
iscsi target port
tcp-port-1
[
tcp-port-2.… tcp-port-16
[address
ip-address
]
[name
targetname
]
no iscsi target port
tcp-port-1
[
tcp-port-2.… tcp-port-16
[address
ip-address
]
•
tcp-port
—TCP port number or list of TCP port numbers on which iSCSI
target(s) listen to requests. Up to 16 TCP ports can be defined in the
system in one command or by using multiple commands.
•
ip-address
—IP address of the iSCSI target. When the
no
form is used, and
the tcp port to be deleted is one bound to a specific IP address, the address
field must be present.
•
targetname
—iSCSI name of the iSCSI target. The name can be statically
configured; however, it can be obtained from iSNS or from sendTargets
response. The initiator MUST present both its iSCSI Initiator Name and
the iSCSI Target Name to which it wishes to connect in the first login
request of a new session or connection. The target name can consist of any
printable character except for an exclamation point or a double quote as
2CSNXXX_SWUM200.book Page 540 Tuesday, December 10, 2013 1:22 PM

iSCSI Optimization Commands 541
the first character. A question mark may not appear anywhere in the target
name. The name can contain embedded blanks if enclosed in double
quotes.
Default Configuration
iSCSI well-known ports 3260 and 860 are configured by default but can be
removed as any other configured target.
Command Mode
Global Configuration mode.
User Guidelines
• When working with private iSCSI ports (not IANA assigned iSCSI ports
3260/860), it is recommended to specify the target IP address as well, so
the switch will only snoop frames with which the TCP destination port is
one of the configured TCP ports, AND their destination IP is the target's
IP address. This way the CPU is not be falsely loaded by non-iSCSI flows
(if by chance other applications also choose to use these {non-standard}
ports).
• When a port is already defined and not bound to an IP address, and you
want to bind the port to an IP address, first remove the port by using the
no
form of the command and then add it again, this time together with
the relevant IP address.
• Target names are only for display when using the show iscsi command.
These names are not used to match (or for doing any sanity check) with
the iSCSI session information acquired by snooping.
• A maximum of 16 TCP ports can be configured either bound to IP or not.
Example
The following example configures TCP Port 49154 to target IP address
172.16.1.20.
console(config)#iscsi target port 49154 address 172.16.1.20
2CSNXXX_SWUM200.book Page 541 Tuesday, December 10, 2013 1:22 PM

542 iSCSI Optimization Commands
show iscsi
Use the show iscsi command in Privileged EXEC mode to display the iSCSI
configuration.
Syntax
show iscsi
Default Configuration
There is no default configuration for this command.
Command Mode
Privileged EXEC mode, Configuration mode and all Configuration submodes
User Guidelines
There are no user guidelines for this command.
Example
The following example displays the iSCSI configuration.
console#show iscsi
iSCSI enabled
iSCSI CoS enabled
iSCSI vpt is 5
Session aging time: 10 min
Maximum number of sessions is 192
------------------------------------------------
iSCSI Targets and TCP Ports:
------------------------------------------------
TCP Port Target IP Address Name
860 --
3260 --
30001 172.16.1.1iqn.1993-11.com.disk
vendor:diskarrays.sn.45678.tape:sys1.xyz
30033172.16.1.10
------------------------------------------------
iSCSI Static Rule Table
------------------------------------------------
Index TCP Port IP Address IP Address Mask
TCP Port Target IP AddressName
2CSNXXX_SWUM200.book Page 542 Tuesday, December 10, 2013 1:22 PM

iSCSI Optimization Commands 543
show iscsi sessions
Use the show iscsi sessions command in Privileged EXEC mode to display the
iSCSI status.
Syntax
show iscsi sessions [detailed]
•
detailed
— Displayed list has additional data when this option is used.
Default Configuration
If not specified, sessions are displayed in short mode (not detailed).
Command Mode
Privileged EXEC mode, Configuration mode and all Configuration submodes
User Guidelines
The N2000/N3000 Series switches support monitoring for up to 1024
sessions. The N4000 switches support monitoring for up to 512 sessions.
Example
The following examples show summary and detailed information about the
iSCSI sessions.
console#show iscsi sessions
Target: iqn.1993-11.com.disk-vendor:diskarrays.sn.45678
-----------------------------------------------------
Initiator: iqn.1992-04.com.os-vendor.plan9:cdrom.12
ISID: 11
Initiator: iqn.1995-05.com.os-vendor.plan9:cdrom.10
ISID: 222
-----------------------------------------------------
Target: iqn.103-1.com.storage-vendor:sn.43338.
storage.tape:sys1.xyz
Session 3:
Initiator: iqn.1992-04.com.os-vendor.plan9:cdrom.12
Session 4:
Initiator: iqn.1995-05.com.os-vendor.plan9:cdrom.10
Console# show iscsi sessions detailed
Target: iqn.1993-11.com.disk-vendor:diskarrays.sn.45678
2CSNXXX_SWUM200.book Page 543 Tuesday, December 10, 2013 1:22 PM

544 iSCSI Optimization Commands
-----------------------------------------------------
Session 1:
Initiator: iqn.1992-04.com.os
vendor.plan9:cdrom.12.storage:sys1.xyz
-----------------------------------------------------
Time started: 17-Jul-2008 10:04:50
Time for aging out: 10 min
ISID: 11
Initiator Initiator Target Target
IP address TCP port IP address IP port
172.16.1.3 49154 172.16.1.20 30001
172.16.1.4 49155 172.16.1.21 30001
172.16.1.5 49156 172.16.1.22 30001
Session 2:
-----------------------------------------------------
Initiator: iqn.1995-05.com.os-vendor.plan9:cdrom.10
Time started: 17-Aug-2008 21:04:50
Time for aging out: 2 min
ISID: 22
Initiator Initiator Target Target
IP address TCP port IP address IP port
172.16.1.30 49200 172.16.1.20 30001
172.16.1.30 49201 172.16.1.21 30001
2CSNXXX_SWUM200.book Page 544 Tuesday, December 10, 2013 1:22 PM

Link Dependency Commands 545
27
Link Dependency Commands
Dell Networking N2000/N3000/N4000 Series Switches
Link dependency allows the link status of a group of interfaces to be made
dependent on the link status of other interfaces. The effect is that the link
status of a group that depends on another interface either mirrors or inverts
the link status of the depended-on interface.
Commands in this Chapter
This chapter explains the following commands:
action
Use the action command in Link Dependency mode to indicate if the link-
dependency group should mirror or invert the status of the depended-on
interfaces.
Syntax
action {down|up}
•
down
—Mirror the depended on interface(s) status.
•
up
—Invert the depended on interface(s) status.
Default Configuration
The default configuration for a group is down, i.e. the group members will
mirror the depended-on link status by going down when all depended-on
interfaces are down.
action
–
link-dependency group depends-on
add show link-dependency
2CSNXXX_SWUM200.book Page 545 Tuesday, December 10, 2013 1:22 PM

546 Link Dependency Commands
Command Mode
Link Dependency mode
User Guidelines
The action up command will cause the group members to be up when no
depended-on interfaces are up.
Example
console(config-depend-1)#action up
link-dependency group
Use the link-dependency group command to enter the link-dependency
mode to configure a link-dependency group.
Syntax
link-dependency group
GroupId
no link-dependency group
GroupId
•
GroupId
— Link dependency group identifier. (Range: 1–72)
Default Configuration
This command has no default configuration.
Command Mode
Global Configuration mode
User Guidelines
The preference of a group is to remain in the up state. A group will be in the
up state if any depends-on interface is up and will be in the down state only if
all depends-on interfaces are down.
Example
console(config)#link-dependency group 1
console(config-linkDep-group-1)#
2CSNXXX_SWUM200.book Page 546 Tuesday, December 10, 2013 1:22 PM

Link Dependency Commands 547
add
Use this command to add member ten gigabit or gigabit Ethernet port(s) or
port channels to the dependency list.
Syntax
add {gigabitethernet | tengigabitethernet | port-channel}
intf-list
•
intf-list
— List of Ethernet interfaces in unit/slot/port format. Separate
nonconsecutive ports with a comma and no spaces. Use a hyphen to
designate the range of ports. (Range: Valid Ethernet interface list or range)
Default Configuration
This command has no default configuration.
Command Mode
Link Dependency mode
User Guidelines
Adding an interface to a dependency list brings the interface down until the
depends-on command is entered. The link status will then follow the
interface specified in the depends-on command.
To avoid bringing down interfaces, enter the depends-on command prior to
entering the add command.
Example
console(config-depend-1)#add gigabitethernet 1/0/1
console(config-depend-1)#add tengigabitethernet 1/0/1
console(config-depend-1)#add port-channel 10-12
depends-on
Use this command to add the dependent Ethernet ports or port channels list.
Use the no depends-on command to remove the dependent Ethernet ports or
port-channels list.
2CSNXXX_SWUM200.book Page 547 Tuesday, December 10, 2013 1:22 PM

548 Link Dependency Commands
Syntax
depends-on {gigabitethernet | port-channel | tengigabitethernet |
fortygigabitethernet}
intf-list
no depends-on {gigabitethernet | port-channel | tengigabitethernet |
fortygigabitethernet}
intf-list
•
intf-list
— List of ports in unit/slot/port format or port-channel numbers.
Separate nonconsecutive items with a comma and no spaces. Use a hyphen
to designate the range of ports or port-channel numbers. (Range: Valid
Ethernet interface or port-channel list or range)
Default Configuration
This command has no default configuration.
Command Mode
Link Dependency mode
User Guidelines
Circular dependencies are not allowed, i.e. interfaces added to the group may
not also appear in the depends-on list.
Examples
console(config-linkDep-group-1)#depends-on gigabitethernet 1/0/10
console(config-linkDep-group-1)#depends-on port-channel 6
show link-dependency
Use the show link-dependency command to show the link dependencies
configured for a particular group. If no group is specified, then all the
configured link-dependency groups are displayed.
Syntax
show link-dependency [
group GroupId
] [detail]
•
GroupID
—Link dependency group identifier. (Range: Valid Group Id,
1–16)
•
detail
—Show detailed information about the state of members and the
dependent ports.
2CSNXXX_SWUM200.book Page 548 Tuesday, December 10, 2013 1:22 PM

Link Dependency Commands 549
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC, Configuration mode and all Configuration submodes
User Guidelines
No specific guidelines.
Example
The following command shows link dependencies for all groups.
console#show link-dependency
GroupId Member Ports Ports Depended On Link Action Group State
------- -----------------------------------------------------
1 Gi4/0/2-3,Gi4/0/5 Gi4/0/10-12 Link Up Up/Down
The following command shows link dependencies for group 1 only.
console#show link-dependency group 1
GroupId Member Ports Ports Depended On Link Action Group State
------- -----------------------------------------------------
1 Gi4/0/2-3,Gi4/0/5 Gi4/0/10-12 Link Up Up/Down
The following command shows detailed information for group 1.
console#show link-dependency group 1 detail
GroupId: 1
Link Action: Link UpGroup
State: Up
Ports Depended On State:
Link Up: Gi4/0/10
Link Down: Gi4/0/11-12
Member Ports State:
Link Up: Gi4/0/2-3
Link Down: Gi4/0/5
2CSNXXX_SWUM200.book Page 549 Tuesday, December 10, 2013 1:22 PM

550 Link Dependency Commands
2CSNXXX_SWUM200.book Page 550 Tuesday, December 10, 2013 1:22 PM

LLDP Commands 551
28
LLDP Commands
Dell Networking N2000/N3000/N4000 Series Switches
The IEEE 802.1AB standard defines the Link Layer Discovery Protocol
(LLDP). This protocol allows stations residing on an 802 LAN to advertise
major capabilities, physical descriptions, and management information to
physically adjacent devices, allowing a network management system (NMS)
to access and display this information.
The standard is designed to be extensible, providing for the optional
exchange of organizational specific information and data related to other
IEEE standards. The base implementation supports only the required basic
management set of type length values (TLVs).
LLDP is a one-way protocol; there are no request/response sequences.
Information is advertised by stations implementing the transmit function.
The information is received and processed by stations implementing the
receive function. Devices are not required to implement both transmit and
receive functions and each function can be enabled or disabled separately by
the network manager. Dell Networking supports both the transmit and
receive functions in order to support device discovery.
The LLDP component transmit and receive functions can be
enabled/disabled separately per physical port. By default, both transmit and
receive functions are enabled on all ports. The application starts each
transmit and receive state machine appropriately based on the configured
status and operational state of the port.
The transmit function is configurable with respect to packet construction and
timing parameters. The required Chassis ID, Port ID, and Time to Live
(TTL) TLVs are always included in the Link Layer Discovery Protocol Data
Unit (LLDPDU). However, inclusion of the optional TLVs in the
management set is configurable by the administrator. By default, they are not
included. The transmit function extracts the local system information and
builds the LLDPDU based on the specified configuration for the port. In
addition, the administrator has control over timing parameters affecting the
TTL of LLDPDUs and the interval in which they are transmitted.
2CSNXXX_SWUM200.book Page 551 Tuesday, December 10, 2013 1:22 PM

552 LLDP Commands
The receive function accepts incoming LLDPDU frames and stores
information about the remote stations. Both local and remote data may be
displayed by the user interface and retrieved using SNMP as defined in the
LLDP MIB definitions. The component maintains one remote entry per
physical network connection.
The LLDP component manages a number of statistical parameters
representing the operation of each transmit and receive function on a per-port
basis. These statistics may be displayed by the user interface and retrieved
using SNMP as defined in the MIB definitions.
Commands in this Chapter
This chapter explains the following commands:
clear lldp remote-data
Use the clear lldp remote-data command in Privileged EXEC mode to delete
all LLDP information from the remote data table.
Syntax
clear lldp remote-data
clear lldp remote-data lldp receive show lldp med
clear lldp statistics lldp timers show lldp med interface
lldp med lldp transmit show lldp med local-device
detail
lldp med confignotification lldp transmit-mgmt show lldp med remote-
device
lldp med
faststartrepeatcount
lldp transmit-tlv show lldp remote-device
lldp med transmit-tlv show lldp show lldp statistics
lldp notification show lldp interface
–
lldp notification-interval show lldp local-device
–
2CSNXXX_SWUM200.book Page 552 Tuesday, December 10, 2013 1:22 PM

LLDP Commands 553
Default Configuration
By default, data is removed only on system reset.
Command Mode
Privileged EXEC mode
User Guidelines
This command has no user guidelines.
Example
The following example displays how to clear the LLDP remote data.
console#clear lldp remote-data
clear lldp statistics
Use the clear lldp statistics command in Privileged EXEC mode to reset all
LLDP statistics.
Syntax
clear lldp statistics
Default Configuration
By default, the statistics are only cleared on a system reset.
Command Mode
Privileged EXEC mode
User Guidelines
This command has no user guidelines.
Example
The following example displays how to reset all LLDP statistics.
console#clear lldp statistics
2CSNXXX_SWUM200.book Page 553 Tuesday, December 10, 2013 1:22 PM

554 LLDP Commands
dcb enable
This command enables the sending of DCBX information in LLDP frames.
Syntax
dcb enable
no dcb enable
Command Mode
Global Configuration mode
Default Value
The sending of DCBX information in enabled by default.
User Guidelines
Use this command to disable the sending of DCBX information when it is
desirable to utilize legacy QoS and disable the automatic configuration of
CNAs based on transmitted DCBX information.
Example
console(config)#no dcb enable
lldp med
This command is used to enable/disable LLDP-MED on an interface. By
enabling MED, the transmit and receive functions of LLDP are effectively
enabled.
Syntax
lldp med
no lldp med
Command Mode
Interface (Ethernet) Configuration
2CSNXXX_SWUM200.book Page 554 Tuesday, December 10, 2013 1:22 PM

LLDP Commands 555
Default Value
LLDP-MED is disabled on all supported interfaces.
User Guidelines
No specific guidelines.
Example
console(config)#interface gigabitethernet 1/0/1
console(config-if-Gi1/0/1)#lldp med
lldp med confignotification
This command is used to enable sending the topology change notification.
Syntax
lldp med confignotification
no lldp med confignotification
Command Mode
Interface (Ethernet) Configuration
Default Value
By default, notifications are disabled on all supported interfaces.
User Guidelines
No specific guidelines.
Example
console(config)#lldp med confignotification
lldp med faststartrepeatcount
This command is used to set the value of the fast start repeat count.
Syntax
lldp med faststartrepeatcount
count
2CSNXXX_SWUM200.book Page 555 Tuesday, December 10, 2013 1:22 PM

556 LLDP Commands
no lldp med faststartrepeatcount
•
count
— Number of LLDPPDUs that are transmitted when the protocol is
enabled. (Range 1–10)
Command Mode
Global Configuration
Default Value
3
User Guidelines
No specific guidelines.
Example
console(config)# lldp med faststartrepeatcount 2
lldp med transmit-tlv
This command is used to specify which optional TLVs in the LLDP MED set
are transmitted in the LLDPDUs. There are certain conditions that have to
be met for this port to be MED compliant. These conditions are explained in
the normative section of the specification. For example, the MED TLV
'capabilities' is mandatory. By disabling this bit, MED is effectively disable on
this interface.
Syntax
lldp med transmit-tlv [capabilities] [network-policy] [ex-pse] [ex-pd]
[location] [inventory]
no med lldp transmit-tlv [capabilities] [network-policy] [ex-pse] [ex-pd]
[location] [inventory]
Command Mode
Interface (Ethernet) Configuration
Default Value
By default, the capabilities and network policy TLVs are included.
2CSNXXX_SWUM200.book Page 556 Tuesday, December 10, 2013 1:22 PM

LLDP Commands 557
Example
console(config)#interface gigabitethernet 1/0/1
console(config-if-Gi1/0/1)#lldp med transmit-tlv capabilities
console(config-if-Gi1/0/1)#lldp med transmit-tlv network-policies
lldp notification
Use the lldp notification command in Interface Configuration mode to
enable remote data change notifications. To disable notifications, use the no
form of this command.
Syntax
lldp notification
no lldp notification
Default Configuration
By default, notifications are disabled on all supported interfaces.
Command Mode
Interface Configuration (Ethernet) mode
User Guidelines
This command has no user guidelines.
Example
The following example displays how to enable remote data change
notifications.
console(config-if-Gi1/0/3)#lldp notification
lldp notification-interval
Use the lldp notification-interval command in Global Configuration mode
to limit how frequently remote data change notifications are sent. To return
the notification interval to the factory default, use the no form of this
command.
2CSNXXX_SWUM200.book Page 557 Tuesday, December 10, 2013 1:22 PM

558 LLDP Commands
Syntax
lldp notification-interval
interval
no lldp notification-interval
• interval — The smallest interval in seconds at which to send remote data
change notifications. (Range: 5–3600 seconds)
Default Configuration
The default value is 5 seconds.
Command Mode
Global Configuration mode
User Guidelines
This command has no user guidelines.
Example
The following example displays how to set the interval value to 10 seconds.
console(config)#lldp notification-interval 10
lldp receive
Use the lldp receive command in Interface Configuration mode to enable the
LLDP receive capability. To disable reception of LLDPDUs, use the no form
of this command.
Syntax
lldp receive
no lldp receive
Default Configuration
The default lldp receive mode is enabled.
Command Mode
Interface Configuration (Ethernet) mode
2CSNXXX_SWUM200.book Page 558 Tuesday, December 10, 2013 1:22 PM

LLDP Commands 559
User Guidelines
This command has no user guidelines.
Example
The following example displays how to enable the LLDP receive capability.
console(config-if-Gi1/0/3)#lldp receive
lldp timers
Use the lldp timers command in Global Configuration mode to set the
timing parameters for local data transmission on ports enabled for LLDP. To
return any or all parameters to factory default, use the no form of this
command.
Syntax
lldp timers [interval transmit-interval] [hold hold-multiplier] [reinit reinit-
delay]
no lldp timers [interval] [hold] [reinit]
•
transmit-interval —
The interval in seconds at which to transmit local data
LLDPDUs. (Range: 5–32768 seconds)
•
hold-multiplier —
Multiplier on the transmit interval used to set the TTL
in local data LLDPDUs. (Range: 2–10)
•
reinit-delay —
The delay in seconds before reinitialization. (Range: 1–10
seconds)
Default Configuration
The default transmit interval is 30 seconds.
The default hold-multiplier is 4.
The default delay before reinitialization is 2 seconds.
Command Mode
Global Configuration mode
2CSNXXX_SWUM200.book Page 559 Tuesday, December 10, 2013 1:22 PM

560 LLDP Commands
User Guidelines
This command has no user guidelines.
Examples
The following example displays how to configure LLDP to transmit local
information every 1000 seconds.
console(config)#lldp timers interval 1000
The following example displays how to set the timing parameter at 1000
seconds with a hold multiplier of 8 and a 5 second delay before
reinitialization.
console(config)#lldp timers interval 1000 hold 8 reinit 5
lldp transmit
Use the lldp transmit command in Interface Configuration mode to enable
the LLDP advertise (transmit) capability. To disable local data transmission,
use the no form of this command.
Syntax
lldp transmit
no lldp transmit
Default Configuration
LLDP is enabled on all supported interfaces.
Command Mode
Interface Configuration (Ethernet) mode
User Guidelines
This command has no user guidelines.
Example
The following example displays how enable the transmission of local data.
console(config-if-Gi1/0/3)#lldp transmit
2CSNXXX_SWUM200.book Page 560 Tuesday, December 10, 2013 1:22 PM

LLDP Commands 561
lldp transmit-mgmt
Use the lldp transmit-mgmt command in Interface Configuration mode to
include transmission of the local system management address information in
the LLDPDUs. To cancel inclusion of the management information, use the
no form of this command.
Syntax
lldp transmit-mgmt
no lldp transmit-mgmt
Default Configuration
By default, management address information is not included.
Command Mode
Interface Configuration (Ethernet) mode
User Guidelines
This command has no user guidelines.
Example
The following example displays how to include management information in
the LLDPDU.
console(config-if-Gi1/0/3)#lldp transmit-mgmt
lldp transmit-tlv
Use the lldp transmit-tlv command in Interface Configuration mode to
specify which optional type-length-value settings (TLVs) in the 802.1AB basic
management set will be transmitted in the LLDPDUs. To remove an optional
TLV, use the no form of this command.
Syntax
lldp transmit-tlv [sys-desc][sys-name][sys-cap][port-desc]
no lldp transmit-tlv [sys-desc][sys-name][sys-cap][port-desc]
2CSNXXX_SWUM200.book Page 561 Tuesday, December 10, 2013 1:22 PM

562 LLDP Commands
•
sys-name
— Transmits the system name TLV
•
sys-desc
— Transmits the system description TLV
•
sys-cap
— Transmits the system capabilities TLV
•
port desc
— Transmits the port description TLV
Default Configuration
By default, no optional TLVs are included.
Command Mode
Interface Configuration (Ethernet) mode
User Guidelines
This command has no user guidelines.
Example
The following example shows how to include the system description TLV in
local data transmit.
console(config-if-1/0/3)#lldp transmit-tlv sys-desc
show lldp
Use the show lldp command in Privileged EXEC mode to display the current
LLDP configuration summary.
Syntax
show lldp
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC mode, Configuration mode and all Configuration submodes
2CSNXXX_SWUM200.book Page 562 Tuesday, December 10, 2013 1:22 PM

LLDP Commands 563
User Guidelines
This command has no user guidelines.
Example
The following example displays the current LLDP configuration summary.
console# show lldp
Global Configurations:
Transmit Interval: 30 seconds
Transmit TTL Value: 120 seconds
Reinit Delay: 2 seconds
Notification Interval: limited to every 5 seconds
console#show lldp
LLDP transmit and receive disabled on all interfaces
show lldp interface
Use the show lldp interface command in Privileged EXEC mode to display
the current LLDP interface state.
Syntax
show lldp interface {gigabitethernet unit/slot/port
| tengigabitethernet
unit/slot/port | fortygigabitethernet unit/slot/port| all}
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC mode, Configuration mode and all Configuration submodes
User Guidelines
This command has no user guidelines.
Examples
This example show how the information is displayed when you use the
command with the all parameter.
console#show lldp interface all
Interface Link Transmit Receive Notify TLVs Mgmt
2CSNXXX_SWUM200.book Page 563 Tuesday, December 10, 2013 1:22 PM

564 LLDP Commands
--------- ---- -------- -------- -------- ------- ----
1/0/1 Up Enabled Enabled Enabled 0,1,2,3 Y
1/0/2 Down Enabled Enabled Disabled Y
1/0/3 Down Disabled Disabled Disabled 1,2 N
TLV Codes: 0 – Port Description, 1 – System Name, 2 – System Description, 3 –
System Capability
console# show lldp interface 1/0/1
Interface Link Transmit Receive Notify TLVs Mgmt
--------- ---- -------- -------- -------- ------- ----
1/0/1 Up Enabled Enabled Enabled 0,1,2,3 Y
TLV Codes: 0 – Port Description, 1 – System Name, 2 – System Description, 3 –
System Capability
show lldp local-device
Use the show lldp local-device command in Privileged EXEC mode to display
the advertised LLDP local data. This command can display summary
information or detail for each interface.
Syntax
show lldp local-device {detail
interface
|
interface
| all}
•
detail
— includes a detailed version of remote data.
•
interface
— Specifies a valid physical interface on the device. Specify
either
gigabitethernet
unit/slot/port
or tengigabitethernet
unit/slot/port
or
fortygigabitethernet
unit/slot/port.
•
all
— Shows lldp local device information on all interfaces.
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC mode, Configuration mode and all Configuration submodes
User Guidelines
This command has no user guidelines.
Examples
These examples show advertised LLDP local data in two levels of detail.
2CSNXXX_SWUM200.book Page 564 Tuesday, December 10, 2013 1:22 PM

LLDP Commands 565
console#show lldp local-device all
LLDP Local Device Summary
Interface Port ID Port Description
--------- -------------------- --------------------
1/0/1 00:62:48:00:00:02
console# show lldp local-device detail 1/0/1
LLDP Local Device Detail
Interface: 1/0/1
Chassis ID Subtype: MAC Address
Chassis ID: 00:62:48:00:00:00
Port ID Subtype: MAC Address
Port ID: 00:62:48:00:00:02
System Name:
System Description: Routing
Port Description:
System Capabilities Supported: bridge, router
System Capabilities Enabled: bridge
Management Address:
Type: IPv4
Address: 192.168.17.25
show lldp med
This command displays a summary of the current LLDP MED configuration.
Syntax
show lldp med
Command Mode
Privileged EXEC, Configuration mode and all Configuration submodes
Default Value
Not applicable
User Guidelines
No specific guidelines.
Example
console(config)#show lldp med
LLDP MED Global Configuration
2CSNXXX_SWUM200.book Page 565 Tuesday, December 10, 2013 1:22 PM

566 LLDP Commands
Fast Start Repeat Count: 3
Device Class: Network Connectivity
show lldp med interface
This command displays a summary of the current LLDP MED configuration
for a specific interface.
Syntax
show lldp med interface {gigabitethernet unit/slot/port | tengigabitethernet
unit/slot/port| all}
•
all
— Shows information for all valid LLDP interfaces.
Command Mode
Privileged EXEC, Configuration mode and all Configuration submodes
Default Value
Not applicable
Example
console#show lldp med interface all
LLDP MED Interface Configuration
Interface Link configMED operMED ConfigNotify TLVsTx
--------- ------ --------- -------- ------------ -----------
Gi1/0/1 Detach Enabled EnabledEnabled0,1
Gi1/0/2 Detach Disabled Disabled Disabled 0,1
Gi1/0/3 Detach Disabled Disabled Disabled 0,1
Gi1/0/4 Detach Disabled Disabled Disabled 0,1
Gi1/0/5 Detach Disabled Disabled Disabled 0,1
console #show lldp med interface 1/0/1
LLDP MED Interface Configuration
Interface Link configMED operMED ConfigNotify TLVsTx
--------- ------ -------- -------- -------- -------
1/0/1 Up Enabled Enabled Disabled 0,1
TLV Codes: 0- Capabilities, 1- Network Policy
2-Location, 3- Extended PSE, 4- Extended PD, 5-Inventory
2CSNXXX_SWUM200.book Page 566 Tuesday, December 10, 2013 1:22 PM

LLDP Commands 567
show lldp med local-device detail
This command displays the advertised LLDP local data in detail.
Syntax
show lldp med local-device detail {gigabitethernet unit/slot/port |
tengigabitethernet unit/slot/port}
Command Mode
Privileged EXEC, Configuration mode and all Configuration submodes
Default Value
Not applicable
Example
Console#show lldp med local-device detail 1/0/1
LLDP MED Local Device Detail
Interface: 1/0/8
Network Policies
Media Policy Application Type : voice
Vlan ID: 10
Priority: 5
DSCP: 1
Unknown: False
Tagged: True
Media Policy Application Type : streamingvideo
Vlan ID: 20
Priority: 1
DSCP: 2
Unknown: False
Tagged: True
Inventory
Hardware Rev: xxx xxx xxx
Firmware Rev: xxx xxx xxx
Software Rev: xxx xxx xxx
Serial Num: xxx xxx xxx
Mfg Name: xxx xxx xxx
Model Name: xxx xxx xxx
2CSNXXX_SWUM200.book Page 567 Tuesday, December 10, 2013 1:22 PM

568 LLDP Commands
Asset ID: xxx xxx xxx
Location
Subtype: elin
Info: xxx xxx xxx
Extended POE
Device Type: pseDevice
Extended POE PSE
Available: 0.3 watts
Source: primary
Priority: critical
Extended POE PD
Required: 0.2 watts
Source: local
Priority: low
show lldp med remote-device
This command displays the current LLDP MED remote data. This command
can display summary information or detail for each interface.
Syntax
show lldp med remote-device {gigabitethernet unit/slot/port |
tengigabitethernet unit/slot/port | all}
show lldp med remote-device detail {gigabitethernet unit/slot/port |
tengigabitethernet unit/slot/port}
•
all
— Indicates all valid LLDP interfaces.
•
detail
— Includes a detailed version of remote data for the indicated
interface.
Command Mode
Privileged EXEC, Configuration mode and all Configuration submodes
Default Value
Not applicable
2CSNXXX_SWUM200.book Page 568 Tuesday, December 10, 2013 1:22 PM

LLDP Commands 569
Example
Console#show lldp med remote-device all
LLDP MED Remote Device Summary
Local
InterfaceDevice Class
---------------------
1/0/1Class I
1/0/2 Not Defined
1/0/3Class II
1/0/4Class III
1/0/5Network Con
Console#show lldp med remote-device detail 1/0/1
LLDP MED Remote Device Detail
Local Interface: 1/0/1
Capabilities
MED Capabilities Supported: capabilities, networkpolicy, location,
extendedpse
MED Capabilities Enabled: capabilities, networkpolicy
Device Class: Endpoint Class I
Network Policies
Media Policy Application Type : voice
Vlan ID: 10
Priority: 5
DSCP: 1
Unknown: False
Tagged: True
Media Policy Application Type : streamingvideo
Vlan ID: 20
Priority: 1
DSCP: 2
Unknown: False
Tagged: True
Inventory
Hardware Rev: xxx xxx xxx
Firmware Rev: xxx xxx xxx
Software Rev: xxx xxx xxx
Serial Num: xxx xxx xxx
Mfg Name: xxx xxx xxx
2CSNXXX_SWUM200.book Page 569 Tuesday, December 10, 2013 1:22 PM

570 LLDP Commands
Model Name: xxx xxx xxx
Asset ID: xxx xxx xxx
Location
Subtype: elin
Info: xxx xxx xxx
Extended POE
Device Type: pseDevice
Extended POE PSE
Available: 0.3 Watts
Source: primary
Priority: critical
Extended POE PD
Required: 0.2 Watts
Source: local
Priority: low
show lldp remote-device
Use the lldp remote-device command in Privileged EXEC mode to display
the current LLDP remote data. This command can display summary
information or detail for each interface.
Syntax
show lldp remote-device {detail
interface
|
interface
| all}
• detail — Includes detailed version of remote data.
•
interface
— Specifies a valid physical interface on the device. Substitute
gigabitethernet
unit/slot/port
or tengigabitethernet
unit/slot/port
or
fortygigabitethernet
unit/slot/port
}
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC mode, Configuration mode and all Configuration submodes
2CSNXXX_SWUM200.book Page 570 Tuesday, December 10, 2013 1:22 PM

LLDP Commands 571
User Guidelines
This command has no user guidelines.
Examples
These examples show current LLDP remote data, including a detailed
version.
console#show lldp remote-device
Local Remote
Interface Device ID Port ID TTL
--------- ----------------- ----------------- ----------
1/0/1 01:23:45:67:89:AB 01:23:45:67:89:AC 60 seconds
1/0/2 01:23:45:67:89:CD 01:23:45:67:89:CE 120 seconds
1/0/3 01:23:45:67:89:EF 01:23:45:67:89:FG 80 seconds
console# show lldp remote-device detail 1/0/1
Ethernet1/0/1,
Remote ID: 01:23:45:67:89:AB
System Name: system-1
System Description:
System Capabilities: Bridge
Port ID: 01:23:45:67:89:AC
Port Description: 1/0/4
Management Address: 192.168.112.1
TTL: 60 seconds
show lldp statistics
Use the show lldp statistics command in Privileged EXEC mode to display
the current LLDP traffic statistics.
Syntax
show lldp statistics {
unit/slot/port
| all}
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC mode, Configuration mode and all Configuration submodes
2CSNXXX_SWUM200.book Page 571 Tuesday, December 10, 2013 1:22 PM

572 LLDP Commands
User Guidelines
This command has no user guidelines.
Examples
The following examples shows an example of the display of current LLDP
traffic statistics.
console#show lldp statistics all
LLDP Device Statistics
Last Update.................................. 0 days 22:58:29
Total Inserts................................ 1
Total Deletes................................ 0
Total Drops.................................. 0
Total Ageouts................................ 1
Tx Rx TLV TLV TLV TLV TLV
Interface Total Total Discards Errors Ageout Discards Unknowns MED 802.1
802.3
--------- ----- ----- -------- ------ ------ -------- -------- ---- ----- --
---
1/0/11 29395 82562 0 0 1 0 0 0 1 4
The following table explains the fields in this example.
Fields Description
Last Update The value of system of time the last time a remote data entry
was created, modified, or deleted.
Total Inserts The number of times a complete set of information advertised
by a remote device has been inserted into the table.
Total Deletes The number of times a complete set of information advertised
by a remote device has been deleted from the table.
Total Drops Number of times a complete set of information advertised by a
remote device could not be inserted due to insufficient
resources.
2CSNXXX_SWUM200.book Page 572 Tuesday, December 10, 2013 1:22 PM

LLDP Commands 573
Total Ageouts Number of times any remote data entry has been deleted due to
time-to-live (TTL) expiration.
Transmit Total Total number of LLDP frames transmitted on the indicated
port.
Receive Total Total number of valid LLDP frames received on the indicated
port.
Discards Number of LLDP frames received on the indicated port and
discarded for any reason.
Errors Number of non-valid LLDP frames received on the indicated
port.
Ageouts Number of times a remote data entry on the indicated port has
been deleted due to TTL expiration.
TLV Discards Number LLDP TLVs (Type, Length, Value sets) received on the
indicated port and discarded for any reason by the LLDP agent.
TLV Unknowns Number of LLDP TLVs received on the indicated port for a type
not recognized by the LLDP agent.
TLV MED Number of OUI specific MED (Media Endpoint Device) TLVs
received.
TLV 802.1 Number of OUI specific 802.1 specific TLVs received.
TLV 802.3 Number of OUI specific 802.3 specific TLVs received.
Fields Description
2CSNXXX_SWUM200.book Page 573 Tuesday, December 10, 2013 1:22 PM

574 LLDP Commands
2CSNXXX_SWUM200.book Page 574 Tuesday, December 10, 2013 1:22 PM

Multicast VLAN Registration Commands 575
29
Multicast VLAN Registration
Commands
Dell Networking N2000/N3000/N4000 Series Switches
Multicast VLAN registration (MVR) is a method for consolidating multicast
traffic from multiple VLANs onto a single VLAN. A typical usage scenario
would be the distribution of a multicast group to a switch using a single
VLAN where the switch has users in different VLANs subscribing to the
multicast group. MVR enables the distribution of the multicast group from
the single consolidated VLAN onto the multiple user VLANs.
MVR, like the IGMP Snooping protocol, allows a Layer 2 switch to snoop on
the IGMP control protocol. Both protocols operate independently from each
other. Both protocols may be enabled on the switch interfaces at the same
time. In such a case, MVR is listening to the join and report messages only for
groups configured statically. All other groups are managed by IGMP snooping.
There are two types of MVR ports: source and receiver.
• Source port is the port to which the multicast traffic is flowing using the
multicast VLAN.
• Receiver port is the port where a listening host is connected to the switch.
It can utilize any (or no) VLAN, except the multicast VLAN. This implies
that the MVR switch will perform VLAN tag substitution from the
multicast VLAN Source port to the VLAN tag used by the receiver port.
The Multicast VLAN is the VLAN that is configured in the specific network
for MVR purposes. It must be manually specified by the operator for all
multicast source ports in the network. It is this VLAN that is used to transfer
multicast traffic over the network to avoid duplication of multicast streams
for clients in different VLANs.
NOTE: MVR can only be enabled on physical interfaces, not on LAGs or VLANs.
2CSNXXX_SWUM200.book Page 575 Tuesday, December 10, 2013 1:22 PM

576 Multicast VLAN Registration Commands
Commands in this Chapter
This chapter explains the following commands:
mvr
Use the mvr command in Global Configuration and Interface Configuration
modes to enable MVR. Use the no form of this command to disable MVR.
Syntax
mvr
no mvr
Default Configuration
The default value is Disabled.
Command Mode
Global Configuration, Interface Configuration
User Guidelines
MVR can only be configured on physical interfaces.
mvr group
Use the mvr group command in Global Configuration mode to add an MVR
membership group. Use the no form of the command to remove an MVR
membership group.
mvr mvr type
mvr group mvr vlan group
mvr mode show mvr
mvr querytime show mvr members
mvr vlan show mvr interface
mvr immediate show mvr traffic
2CSNXXX_SWUM200.book Page 576 Tuesday, December 10, 2013 1:22 PM
Multicast VLAN Registration Commands 577
Syntax
mvr group
A.B.C.D
[
count
]
no mvr group
A.B.C.D
[
count
]
•
A.B.C.D
—Specify a multicast group.
•
count
—Specifies the number of multicast groups to configure. Groups are
configured contiguously by incrementing the first group specified.
Default Configuration
This command has no default configuration.
Command Mode
Global Configuration
User Guidelines
The following table lists the completion messages.
Example
console(config)#mvr
console(config)#mvr group 239.0.1.0 100
console(config)#mvr vlan 10
mvr mode
Use the mvr mode command in Global Configuration mode to change the
MVR mode type. Use the no form of the command to set the mode type to
the default value.
Syntax
mvr mode {compatible | dynamic}
Message Type Message Description
Successful Completion Message None
Error Completion Message
• Not an IP multicast group address
• Illegal IP multicast group address
2CSNXXX_SWUM200.book Page 577 Tuesday, December 10, 2013 1:22 PM

578 Multicast VLAN Registration Commands
no mvr mode
•
compatible
—Do not allow membership joins on source ports.
•
dynamic
—Send IGMP joins to the multicast source when IGMP joins are
received on receiver ports.
Default Configuration
The default mode is compatible.
Command Mode
Global Configuration
User Guidelines
This command has no user guidelines.
mvr querytime
Use the mvr querytime command in Global Configuration mode to set the
MVR query response time. The query time is the maximum time to wait for
an IGMP membership report on a receiver port before removing the port from
the multicast group. The query time only applies to receiver ports and is
specified in tenths of a second.
Use the no form of the command to set the MVR query response time to the
default value.
Syntax
mvr querytime
1–100
no mvr querytime
Default Configuration
The default value is 5 tenths of a second.
Command Mode
Global Configuration
2CSNXXX_SWUM200.book Page 578 Tuesday, December 10, 2013 1:22 PM

Multicast VLAN Registration Commands 579
User Guidelines
The following table lists the completion messages.
Example
console(config)#interface Gi1/0/1
console(config-if-Gi1/0/1)#switchport access vlan 10
console(config-if-Gi1/0/1)#mvr
console(config-if-Gi1/0/1)#mvr type receiver
console(config-if-Gi1/0/1)#exit
console(config)#mvr mode dynamic
console(config)#mvr querytime 10
mvr vlan
Use the mvr vlan command in Global Configuration mode to set the MVR
multicast VLAN. Use the no form of the command to set the MVR multicast
VLAN to the default value.
Syntax
mvr vlan
1–4094
no mvr vlan
•
1–4094
—
Specifies the port on which multicast data is expected to be received.
Source ports should belong to this VLAN.
Default Configuration
The default value is 1.
Command Mode
Global Configuration
User Guidelines
The following table lists the completion messages.
Message Type Message Description
Successful Completion Message Defaulting MVR query response time.
Error Completion Message None
2CSNXXX_SWUM200.book Page 579 Tuesday, December 10, 2013 1:22 PM

580 Multicast VLAN Registration Commands
mvr immediate
Use the mvr immediate command in Interface Configuration mode to enable
MVR Immediate Leave mode. Use the no form of this command to set the
MVR multicast VLAN to the default value.
Syntax
mvr immediate
no mvr immediate
Default Configuration
The default value is Disabled.
Command Mode
Interface Configuration
User Guidelines
Immediate leave should only be configured on ports with a single receiver.
When immediate leave is enabled, a receiver port will leave a group on receipt
of a leave message. Without immediate leave, upon receipt of a leave
message, the port sends an IGMP query and waits for an IGMP membership
report.
Example
console(config)#interface Gi1/0/1
console(config-if-Gi1/0/1)#switchport access vlan 10
console(config-if-Gi1/0/1)#mvr
console(config-if-Gi1/0/1)#mvr type receiver
console(config-if-Gi1/0/1)#mvr mode dynamic
console(config-if-Gi1/0/1)#mvr immediate
Message Type Message Description
Successful Completion Message MVR multicast VLAN ID is set to the
default value which is equal to 1.
Error Completion Message Receiver port in mVLAN, operation failed.
2CSNXXX_SWUM200.book Page 580 Tuesday, December 10, 2013 1:22 PM
Multicast VLAN Registration Commands 581
mvr type
Use the mvr type command in Interface Configuration mode to set the MVR
port type. Use the no form of this command to set the MVR port type to
None.
Syntax
mvr type {receiver | source}
no mvr type
•
receiver
—Configure the port as a receiver port. Receiver ports are ports
over which multicast data will be sent but not received.
•
source
—Configure the port as a source port. Source ports are ports over
which multicast data is received or sent.
Default Configuration
The default value is None.
Command Mode
Interface Configuration
User Guidelines
The following table lists the completion messages.
Example
console(config)#mvr
console(config)#mvr group 239.1.1.1
console(config)#exit
console(config)#interface Gi1/0/1
console(config-if-Gi1/0/1)#switchport access vlan 10
console(config-if-Gi1/0/1)#mvr
console(config-if-Gi1/0/1)#mvr type receiver
Message Type Message Description
Successful Completion Message None
Error Completion Message
• Port is a Trunk port, operation failed.
• Receiver port in mVLAN, operation failed.
2CSNXXX_SWUM200.book Page 581 Tuesday, December 10, 2013 1:22 PM

582 Multicast VLAN Registration Commands
console(config-if-Gi1/0/1)#interface Gi1/0/24
console(config-if-Gi1/0/24)#switchport mode trunk
console(config-if-Gi1/0/24)#switchport trunk native vlan 99
console(config-if-Gi1/0/24)#switchport trunk allowed vlan add 99
console(config-if-Gi1/0/24)#mvr
console(config-if-Gi1/0/24)#mvr type source
console(config-if-Gi1/0/24)#exit
mvr vlan group
Use the mvr vlan group command in Interface Configuration mode to
participate in the specific MVR group. Use the no form of this command to
remove the port participation from the specific MVR group.
Syntax
mvr vlan
mVLAN
group
A.B.C.D
no mvr vlan
mVLAN
group
A.B.C.D
•
VLAN
—The VLAN over which multicast data from the specified group is
to be received.
•
A.B.C.D.
—The multicast group for which multicast data is to be received
over the specified VLAN.
Default Configuration
This command has no default configuration.
Command Mode
Interface Configuration
User Guidelines
This command statically configures a port to receive the specified multicast
group on the specified VLAN. This command only applies to receiver ports in
compatible mode. It also applies to source ports in dynamic mode. In
dynamic mode, receiver ports can also join multicast groups using IGMP
messages.
Example
console(config-if-Gi1/0/1)#interface Te1/1/1
console(config-if-Gi1/0/24)#switchport mode trunk
2CSNXXX_SWUM200.book Page 582 Tuesday, December 10, 2013 1:22 PM
Multicast VLAN Registration Commands 583
console(config-if-Gi1/0/24)#switchport trunk native vlan 2000
console(config-if-Gi1/0/24)#switchport trunk allowed vlan add 2000
console(config-if-Gi1/0/24)#mvr
console(config-if-Gi1/0/24)#mvr type source
console(config-if-Gi1/0/24)#mvr vlan 2000 group 239.1.1.1
show mvr
Use the show mvr command in Privileged EXEC mode to display global MVR
settings.
Syntax
show mvr
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC, Configuration mode and all Configuration submodes
User Guidelines
The following table lists the completion messages.
The following table explains the output parameters.
Message Type Message Description
Successful Completion Message None
Error Completion Message MVR disabled
Parameter Description
MVR Running MVR running state. It can be enabled or
disabled.
MVR Multicast VLAN Current MVR multicast VLAN. It can be in
the range from 1 to 4094.
MVR Max Multicast Groups The maximum number of multicast groups
that is supported by MVR.
2CSNXXX_SWUM200.book Page 583 Tuesday, December 10, 2013 1:22 PM

584 Multicast VLAN Registration Commands
Example
console #show mvr
MVR Running.............................. TRUE
MVR multicast VLAN....................... 1200
MVR Max Multicast Groups................. 256
MVR Current multicast groups............. 1
MVR Global query response time........... 10 (tenths of sec)
MVR Mode................................. compatible
show mvr members
Use the show mvr members command in Privileged EXEC mode to display
the MVR membership groups allocated.
Syntax
show mvr members [
A.B.C.D
]
•
A.B.C.D
—A valid multicast address in IPv4 dotted notation.
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC, Configuration mode and all Configuration submodes
User Guidelines
The following table lists the completion messages.
MVR Current Multicast groups The current number of MVR groups
allocated.
MVR Query Response Time The current MVR query response time.
MVR Mode The current MVR mode. It can be
compatible or dynamic.
Message Type Message Description
Successful Completion Message None
Parameter Description
2CSNXXX_SWUM200.book Page 584 Tuesday, December 10, 2013 1:22 PM
Multicast VLAN Registration Commands 585
The following table explains the output parameters.
Examples
console#show mvr members
MVR Group IP Status Members
------------------ --------------- ---------------------
224.1.1.1 INACTIVE 1/0/1, 1/0/2, 1/0/3
console#show mvr members 224.1.1.1
MVR Group IP Status Members
------------------ --------------- ---------------------
224.1.1.1 INACTIVE 1/0/1, 1/0/2, 1/0/3
show mvr interface
Use the show mvr interface command in Privileged EXEC mode to display
the MVR enabled interfaces configuration.
Syntax
show mvr interface [
interface-id
[members [vlan
vid
]]]
•
interface-id
—Identifies a specific interface.
•
vid
—VLAN identifier.
Default Configuration
This command has no default configuration.
Error Completion Message MVR disabled
Parameter Description
MVR Group IP MVR group multicast IP address.
Status The status of the specific MVR group. It can
be active or inactive.
Members The list of ports which participates in the
specific MVR group.
Message Type Message Description
2CSNXXX_SWUM200.book Page 585 Tuesday, December 10, 2013 1:22 PM
586 Multicast VLAN Registration Commands
Command Mode
Privileged EXEC, Configuration mode and all Configuration submodes
User Guidelines
The following table lists the completion messages.
The following table explains the output parameters.
Examples
console#show mvr interface
Port Type Status Immediate Leave
--------- --------------- --------------------- --------------------
1/0/9 RECEIVER ACTIVE/inVLAN DISABLED
console#show mvr interface 1/0/9
Type: RECEIVER Status: ACTIVE Immediate Leave: DISABLED
console#show mvr interface Fa1/0/23 members
235.0.0.1 STATIC ACTIVE
Message Type Message Description
Successful Completion Message None
Error Completion Message MVR disabled
Parameter Description
Port Interface number
Type The MVR port type. It can be None,
Receiver, or Source type.
Status The interface status. It consists of two
characteristics:
1
active
or
inactive
indicating if port is
forwarding.
2
inVLAN
or
notInVLAN
indicating if the
port is part of any VLAN
Immediate Leave The state of immediate mode. It can be
enabled or disabled.
2CSNXXX_SWUM200.book Page 586 Tuesday, December 10, 2013 1:22 PM
Multicast VLAN Registration Commands 587
console#show mvr interface Fa1/0/23 members vlan 12
235.0.0.1 STATIC ACTIVE
235.1.1.1 STATIC ACTIVE
show mvr traffic
Use the show mvr traffic command in Privileged EXEC mode to display
global MVR statistics.
Syntax
show mvr traffic
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC, Configuration mode and all Configuration submodes
User Guidelines
The following table lists the completion messages.
Examples
The following table explains the output parameters.
Message Type Message Description
Successful Completion Message None
Error Completion Message MVR disabled
Parameter Description
IGMP Query Received Number of received IGMP Queries.
IGMP Report V1 Received Number of received IGMP Reports V1.
IGMP Report V2 Received Number of received IGMP Reports V2.
IGMP Leave Received Number of received IGMP Leaves.
IGMP Query Transmitted Number of transmitted IGMP Queries.
2CSNXXX_SWUM200.book Page 587 Tuesday, December 10, 2013 1:22 PM

588 Multicast VLAN Registration Commands
console#show mvr traffic
IGMP Query Received............................ 2
IGMP Report V1 Received........................ 0
IGMP Report V2 Received........................ 3
IGMP Leave Received............................ 0
IGMP Query Transmitted......................... 2
IGMP Report V1 Transmitted..................... 0
IGMP Report V2 Transmitted..................... 3
IGMP Leave Transmitted......................... 1
IGMP Packet Receive Failures................... 0
IGMP Packet Transmit Failures.................. 0
IGMP Report V1 Transmitted Number of transmitted IGMP Reports V1.
IGMP Report V2 Transmitted Number of transmitted IGMP Reports V2.
IGMP Leave Transmitted Number of transmitted IGMP Leaves.
IGMP Packet Receive Failures Number of failures on receiving the IGMP
packets.
IGMP Packet Transmit Failures Number of failures on transmitting the
IGMP packets.
Parameter Description
2CSNXXX_SWUM200.book Page 588 Tuesday, December 10, 2013 1:22 PM

Port Channel Commands 589
30
Port Channel Commands
Dell Networking N2000/N3000/N4000 Series Switches
A port channel is a set of one or more links that can be aggregated together to
form a bonded channel (Link Aggregation Group or LAG or port channel).
Individual conversations in a particular direction always travel over a single
link in the port channel, however, in aggregate, the bandwidth usage of all of
the links is fairly evenly distributed. Port channels have the advantage of
allowing incremental bandwidth to be added as needed (by adding additional
links) and supporting a form of fault tolerance (traffic on failed links is
redistributed among other links in the LAG). LAGs are formed from similarly
configured physical links, i.e. the speed, duplex, auto-negotiation, PFC
configuration, DCBX configuration, etc. must be identical on all member
links.
Care must be taken while enabling this type of configuration. If the Partner
System is not 802.3AD compliant or the Link Aggregation Control protocol is
not enabled, there may be network instability. Network instability occurs
when one side assumes that the members in an aggregation are one single
link, while the other side is oblivious to this aggregation and continues to
treat the 'members' as individual links.
In the Dell Networking system, the Actor System waits for 3 seconds before
aggregating manually. The 3 second wait time is specified by the protocol
standard.
If a manual LAG member sees an LACPDU that contains information
different from the currently configured default partner values, that particular
member drops out of the LAG. This configured member does not aggregate
with the LAG until all the other active members see the new information.
When each of the other active members sees the new information, they
continue to drop out of the LAG. When all the members have dropped out of
the LAG, they form an aggregate with the new information.
2CSNXXX_SWUM200.book Page 589 Tuesday, December 10, 2013 1:22 PM

590 Port Channel Commands
Static LAGS
A static LAG is fundamentally no different from a dynamically configured
LAG. All the requirements for the member ports hold true (member ports
must be physical, same speed, and so on). The only difference is this LAG has
an additional parameter static which makes this LAG not require a partner
system running Link Aggregation Control Protocol (LACP) to be able to
aggregate it's member ports.
A static LAG does not transmit or process received LACPDUs, that is, the
member ports do not transmit LACPDUs and all the LACPDUs it may
receive are dropped. A dropped counter is maintained to count the number of
such PDUs.
Configured members are added to the LAG (active participation)
immediately if the LAG is configured to be static. There is no wait time
before we add the port to the LAG.
A LAG can be either static or dynamic, but not both. It cannot have some
member ports participate in the protocol while other member ports do not
participate. Additionally, it is not possible to change a LAG from static to
dynamic via the CLI. You must remove the member ports from the static
LAG and then add them to the dynamic LAG.
VLANs and LAGs
When physical interfaces are added to a LAG, they are removed from all
existing physical link VLAN membership and take on the VLAN membership
of the LAG. When members are removed from a LAG, the members regain
the physical interface VLAN membership as per the configuration file.
LAG Thresholds
In many implementations, a LAG is declared as up if any one of its member
ports is active. This enhancement provides configurability for the minimum
number of member links to be active to declare a LAG up. Network
administrators can also utilize this feature to automatically declare a LAG
down when only some of the links have failed.
2CSNXXX_SWUM200.book Page 590 Tuesday, December 10, 2013 1:22 PM

Port Channel Commands 591
LAG Hashing
The purpose of link aggregation is to increase bandwidth between two
switches. It is achieved by aggregating multiple ports in one logical group. A
common problem of port channels is the possibility of changing packets order
in a particular TCP session. The resolution of this problem is correct selection
of a physical port within the port channel for transmitting the packet to keep
original packets order.
The hashing algorithm is configurable for each LAG. Typically, an
administrator is able to choose from hash algorithms utilizing the following
attributes of a packet to determine the outgoing port:
• Source MAC, VLAN, EtherType, and incoming port associated with the
packet.
• Source IP and Source TCP/UDP fields of the packet.
• Destination MAC, VLAN, EtherType, and incoming port associated with
the packet.
• Source MAC, Destination MAC, VLAN, EtherType, and incoming port
associated with the packet.
• Destination IP and Destination TCP/UDP Port fields of the packet.
• Source/Destination MAC, VLAN, EtherType, and incoming port
associated with the packet.
• Source/Destination IP and source/destination TCP/UDP Port fields of the
packet.
Enhanced LAG Hashing
Dell Networking devices based on Broadcom XGS-IV silicon support
configuration of hashing algorithms for each LAG interface. The hashing
algorithm is used to distribute traffic load among the physical ports of the
LAG while preserving the per-flow packet order.
One limitation with earlier LAG hashing techniques is that the packet
attributes were fixed for all type of packets. Also, there was no MODULO-N
operation involved, which can result in poor load balancing performance.
The LAG hashing support supports an enhanced hashing mode, which has
the following advantages:
2CSNXXX_SWUM200.book Page 591 Tuesday, December 10, 2013 1:22 PM

592 Port Channel Commands
• MODULO-N operation based on the number of ports in the LAG.
• Packet attributes selection based on the packet type. For L2 packets,
Source and Destination MAC address are used for hash computation. For
IP packets, Source IP, Destination IP address, TCP/UDP ports are used.
• Non-Unicast traffic and Unicast traffic is hashed using a common hash
algorithm.
• Excellent load balancing performance.
• Enhanced LAG hashing is the default hashing mode for LAGs.
Manual Aggregation of LAGs
Dell Networking switching supports the manual addition and deletion of links
to aggregates.
In the manual configuration of aggregates, the ports send their Actor
Information (LACPDUs) to the partner system in order to find a suitable
Partner to form an aggregation. When the Partner System neglects to respond
using LACPDUs, the Dell Networking switching aggregates manually. The
Dell Networking switching uses the currently configured default Partner
Values for Partner Information.
Flexible Assignment of Ports to LAGs
Assignment of interfaces to dynamic LAGs is based upon a maximum of 144
interfaces assigned to dynamic LAGs, a maximum of 128 dynamic LAGs and
a maximum of 8 interfaces per dynamic LAG. For example, 128 LAGs may be
assigned 2 interfaces each or 18 LAGs may be assigned 8 interfaces each.
Commands in this Chapter
This chapter explains the following commands:
channel-group lacp timeout
interface port-channel port-channel local-preference
interface port-channel port-channel min-links
interface range port-channel show interfaces port-channel
2CSNXXX_SWUM200.book Page 592 Tuesday, December 10, 2013 1:22 PM

Port Channel Commands 593
channel-group
Use the channel-group command in Interface Configuration mode to
associate a port with a port channel. To remove the channel-group
configuration from the interface, use the no form of this command.
Syntax
channel-group
port-channel-number
mode {on | active}
no channel-group
•
port-channel-number
— Number of a valid port-channel with which to
associate the current interface.
•
on
— Forces the port to join a channel without LACP (static LAG).
•
active
— Forces the port to join a channel with LACP (dynamic LAG).
Default Configuration
This command has no default configuration.
Command Mode
Interface Configuration (Ethernet) mode
User Guidelines
This command has no user guidelines.
Example
The following example shows how port 1/0/5 is configured to port-channel 1
without LACP
(static LAG)
.
console(config)# interface gigabitethernet 1/0/5
console(config-if-Gi1/0/5)# channel-group 1 mode on
The following example shows how port 1/0/6 is configured to port-channel 1
with LACP
(dynamic LAG)
.
console(config)# interface gigabitethernet 1/0/6
hashing-mode show lacp
lacp port-priority show statistics port-channel
lacp system-priority
–
2CSNXXX_SWUM200.book Page 593 Tuesday, December 10, 2013 1:22 PM

594 Port Channel Commands
console(config-if-Gi1/0/6)# channel-group 1 mode active
interface port-channel
Use the interface port-channel command in Global Configuration mode to
enter port-channel configuration mode.
Syntax
interface
port-channel
port-channel-number
Default Configuration
This command has no default configuration.
Command Mode
Global Configuration mode
User Guidelines
Port channel numbers range from 1 to 128.
Example
The following example enters the context of port-channel 1.
console(config)# interface port-channel 1
console(config-if-po1)#
interface range port-channel
Use the interface range port-channel command in Global Configuration
mode to execute a command on multiple port channels at the same time.
Syntax
interface range port-channel {
port-channel-range
| all}
•
port-channel-range
— List of port-channels to configure. Separate non-
consecutive port-channels with a comma and no spaces. A hyphen
designates a range of port-channels. (Range: valid port-channel)
•
all
— All the channel-ports.
2CSNXXX_SWUM200.book Page 594 Tuesday, December 10, 2013 1:22 PM

Port Channel Commands 595
Default Configuration
This command has no default configuration.
Command Mode
Global Configuration mode
User Guidelines
Commands in the interface range context are executed independently on
each interface in the range. If the command returns an error on one of the
interfaces, it stops the execution of the command on subsequent interfaces.
Example
The following example shows how port-channels 1, 2 and 8 are grouped to
receive the same command.
console(config)# interface range port-channel 1-2,8
console(config-if)#
hashing-mode
Use the hashing-mode command to set the hashing algorithm on trunk ports.
Use the no hashing-mode command to set the hashing algorithm on trunk
ports to the default (7).
Syntax
hashing-mode
mode
•
mode
— Mode value in the range of 1 to 7.
Range: 1–7:
• 1 — Source MAC, VLAN, EtherType, source module, and port ID
• 2 — Destination MAC, VLAN, EtherType, source module, and port ID
• 3 — Source IP and source TCP/UDP port
• 4 — Destination IP and destination TCP/UDP port
• 5 — Source/destination MAC, VLAN, EtherType, and source
MODID/port
• 6 — Source/destination IP and source/destination TCP/UDP port
2CSNXXX_SWUM200.book Page 595 Tuesday, December 10, 2013 1:22 PM

596 Port Channel Commands
• 7 — Enhanced hashing mode
Default Configuration
The default hashing mode is 7—Enhanced hashing mode.
Command Mode
Interface Configuration (port-channel)
User Guidelines
No specific guidelines.
Example
console(config)#interface port-channel l
console(config-if-po1)#hashing-mode 4
console(config-if-po1)#no hashing mode
lacp port-priority
Use the lacp port-priority command to configure the priority value for
physical ports. To reset to default priority value, use the no form of this
command.
Syntax
lacp port-priority
value
no lacp port-priority
•
value
— Port priority value. (Range: 1–65535)
Default Configuration
The default port priority value is 1.
Command Mode
Interface Configuration (Ethernet) mode
Interface Range mode
2CSNXXX_SWUM200.book Page 596 Tuesday, December 10, 2013 1:22 PM

Port Channel Commands 597
User Guidelines
Per IEEE 802.1AX-2008 Section 5.6, ports are selected for aggregation by each
switch based upon the port priority assigned by the switch with the higher
system priority, starting with the highest priority port of the switch with the
higher switch priority, and working downward through the ordered list of port
priority values for the ports.
The port priority of each port is a four octet binary number, formed by using
the configured port priority as the two most significant octets and the port
number as the two least significant octets. For any given set of ports, the port
with the numerically lower value of port priority has the higher priority.
The selection algorithm is reapplied upon changes in the membership of the
port channel (for example, if a link fails, or if a new link joins the group) and
any subsequent changes to the set of active links are made according to the
above algorithm.
Example
The following example configures the priority value for port 1/0/8 to 247.
console(config)#interface gigabitethernet 1/0/8
console(config-if-Gi1/0/8)#lacp port-priority 247
lacp system-priority
Use the lacp system-priority command in Global Configuration mode to
configure the Link Aggregation system priority. To reset to default, use the no
form of this command.
Syntax
lacp system-priority
value
no lacp system-priority
•
value
— Port priority value. (Range: 1–65535)
Default Configuration
The default system priority value is 1.
2CSNXXX_SWUM200.book Page 597 Tuesday, December 10, 2013 1:22 PM

598 Port Channel Commands
Command Mode
Global Configuration mode
User Guidelines
Per IEEE 802.1AX-2008 Section 5.6, ports are selected for aggregation by each
switch based upon the port priority assigned by the switch with the higher
system priority, starting with the highest priority port of the switch with the
higher switch priority, and working downward through the ordered list of port
priority values for the ports.
The system priority of each switch is an eight octet binary number, formed by
using the configured system priority as the two most significant octets and
the switch id (MAC address) as the least significant six octets. For a given
switch and link aggregation partner, the switch with the numerically lower
value of system priority has the higher priority.
The selection algorithm is reapplied upon changes in the membership of the
port channel (for example, if a link fails, or if a new link joins the group) and
any subsequent changes to the set of active links are made according to the
above algorithm.
Example
The following example configures the system priority to 120.
console(config)#lacp system-priority 120
lacp timeout
Use the lacp timeout command to assign an administrative LACP timeout.
To reset the default administrative LACP timeout, use the no form of this
command.
Syntax
lacp timeout {long | short}
no lacp timeout
•
long
— Specifies a long timeout value.
•
short
— Specifies a short timeout value.
2CSNXXX_SWUM200.book Page 598 Tuesday, December 10, 2013 1:22 PM

Port Channel Commands 599
Default Configuration
The default port timeout value is long.
Command Mode
Interface Configuration (Ethernet) mode
Interface Range mode
User Guidelines
The LACP time-out setting indicates a local preference for the rate of
LACPDU transmission and the period of time before invalidating received
LACPDU information. This setting is negotiated with the link partner. Long
time-outs are 90 seconds with a transmission rate of once every 30 seconds.
Short time-outs are 3 seconds with a transmission rate of once every second.
For further information, refer to the LACP_Timeout setting in IEEE Std.
802.1AX-2008.
Example
The following example assigns an administrative LACP timeout for port
Gi1/0/8 to a long timeout value.
console(config)#interface gigabitethernet 1/0/8
console(config-if-Gi1/0/8)#lacp timeout long
port-channel local-preference
Use the port-channel local-preference command in Interface Configuration
mode to enable the local-preference mode on a port-channel (LAG) interface
or range of port-channel interfaces.
Use the no form of the command to remove the local preference.
Syntax
port-channel local-preference
no port-channel local-preference
Default Configuration
By default, port channels are not configured with local preference.
2CSNXXX_SWUM200.book Page 599 Tuesday, December 10, 2013 1:22 PM

600 Port Channel Commands
Command Mode
Interface Configuration (port-channel) mode
User Guidelines
For a LAG that contains links distributed across stacking units, the default
behavior is to distribute locally received ingress traffic across all LAG links in
the stack per the selected hashing algorithm. When enabled, this command
disables forwarding of ingress unicast traffic across stacking links for a LAG
that is comprised of links on multiple stack units. It does this by restricting
LAG hashing to only select egress links on the stack unit where the traffic
ingresses.
CAUTION: If the capacity of the local egress LAG links is exceeded, traffic will
be discarded. Therefore, use of this option should be carefully considered, and the
operator must ensure that sufficient egress bandwidth is available in the LAG links
on every stack member to avoid excessive discards.
By default, the local-preference mode for a port-channel is disabled. This
command can be used only on port-channel interfaces.
port-channel min-links
Use the port-channel min-links command in Interface Configuration (port-
channel) mode to set the minimum number of links that must be up in order
for the port channel interface to be declared up. Use the no form of the
command to return the configuration to the default value (1).
Syntax
port-channel min-links
1-8
no port-channel min-links
•
min-links
—The minimum number of links that must be active before the
link is declared up. Range 1-8. The default is 1.
Default Configuration
This command has no default configuration.
2CSNXXX_SWUM200.book Page 600 Tuesday, December 10, 2013 1:22 PM

Port Channel Commands 601
Command Mode
Interface Configuration (port-channel) mode
User Guidelines
This command has no user guidelines.
show interfaces port-channel
Use the show interfaces port-channel command to show port-channel
information.
Syntax
show interfaces port-channel [
port-channel-number
]
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC, Configuration mode and all Configuration submodes
User Guidelines
The command displays the following information.
Example #1
console#show interfaces port-channel
ChannelPorts ChTypeHash Algorithm Typemin-Links
------------------------- -----------------------------------
Po1Inactive: Gi1/0/3Dynamic31
Parameter Description
[
index
]
Number of the port channel to show. This parameter is
optional. If the port channel number is not given, all the
channel groups are displayed. (Range: Valid port-channel
number, 1 to 48).
Local Prf An additional field added to support the display of the local
preference.
2CSNXXX_SWUM200.book Page 601 Tuesday, December 10, 2013 1:22 PM

602 Port Channel Commands
Po2No Configured PortsStatic31
Hash Algorithm Type
1 - Source MAC, VLAN, Ethertype, source module and port ID
2 - Destination MAC, VLAN, Ethertype, source module and port ID
3 - Source IP and source TCP/UDP port
4 - Destination IP and destination TCP/UDP port
5 - Source/Destination MAC, VLAN, Ethertype, source MODID/port
6 - Source/Destination IP and source/destination TCP/UDP port
7 - Enhanced hashing mode
Example #2
console#show interfaces port-channel 1
Channel Ports Ch-Type Hash Type Min-links Local Prf
------- ----------------------------- -------- ---------- --------- --------
-
Po1 Inactive: Gi1/0/1, Gi1/0/2, Dynamic 3 1 Enabled
Gi1/0/3, Gi1/0/4
show lacp
Use this command in Privileged EXEC mode to display LACP information
for Ethernet ports.
Syntax
show lacp {gigabitethernet unit/slot/port| tengigabitethernet unit/slot/port
|
fortygigabitethernet unit/slot/port [{parameters | statistics}]
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC mode, Configuration mode and all Configuration submodes
User Guidelines
This command has no user guidelines.
2CSNXXX_SWUM200.book Page 602 Tuesday, December 10, 2013 1:22 PM

Port Channel Commands 603
Example
The following example shows how to display LACP Ethernet interface
information.
console#show lacp gigabitethernet 1/0/1
Port 1/0/1 LACP parameters:
Actor
system priority: 1
system mac addr: 00:00:12:34:56:78
port Admin key: 30
port Oper key: 30
port Oper priority: 1
port Admin timeout: LONG
port Oper timeout: LONG
LACP Activity: ACTIVE
Aggregation: AGGREGATABLE
synchronization: FALSE
collecting: FALSE
distributing: FALSE
expired: FALSE
Partner
system priority: 0
system mac addr: 00:00:00:00:00:00
port Admin key: 0
port Oper key: 0
port Admin priority: 0
port Oper priority: 0
port Oper timeout: LONG
LACP Activity: ASSIVE
Aggregation: AGGREGATABLE
synchronization: FALSE
collecting: FALSE
distributing: FALSE
expired: FALSE
Port 1/0/1 LACP Statistics:
LACP PDUs sent: 2
LACP PDUs received: 2
2CSNXXX_SWUM200.book Page 603 Tuesday, December 10, 2013 1:22 PM

604 Port Channel Commands
show statistics port-channel
Use the show statistics port-channel command in Privileged EXEC mode to
display statistics about a specific port-channel.
Syntax
show statistics
port-channel
port-channel-number
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC mode, Configuration mode and all Configuration submodes
User Guidelines
This command has no user guidelines.
Example
The following example shows statistics about port-channel 1.
console#show statistics port-channel 1
Total Packets Received (Octets)................ 0
Packets Received > 1522 Octets................. 0
Packets RX and TX 64 Octets.................... 1064
Packets RX and TX 65-127 Octets................ 140
Packets RX and TX 128-255 Octets............... 201
Packets RX and TX 256-511 Octets............... 418
Packets RX and TX 512-1023 Octets.............. 1
Packets RX and TX 1024-1518 Octets............. 0
Packets RX and TX 1519-1522 Octets............. 0
Packets RX and TX 1523-2047 Octets............. 0
Packets RX and TX 2048-4095 Octets............. 0
Packets RX and TX 4096-9216 Octets............. 0
Total Packets Received Without Errors.......... 0
Unicast Packets Received....................... 0
Multicast Packets Received..................... 0
Broadcast Packets Received..................... 0
Total Packets Received with MAC Errors......... 0
Jabbers Received............................... 0
Fragments/Undersize Received................... 0
Alignment Errors............................... 0
2CSNXXX_SWUM200.book Page 604 Tuesday, December 10, 2013 1:22 PM

Port Channel Commands 605
--More-- or (q)uit
FCS Errors..................................... 0
Overruns....................................... 0
Total Received Packets Not Forwarded........... 0
Local Traffic Frames........................... 0
802.3x Pause Frames Received................... 0
Unacceptable Frame Type........................ 0
Multicast Tree Viable Discards................. 0
Reserved Address Discards...................... 0
Broadcast Storm Recovery....................... 0
CFI Discards................................... 0
Upstream Threshold............................. 0
Total Packets Transmitted (Octets)............. 263567
Max Frame Size................................. 1518
Total Packets Transmitted Successfully......... 1824
Unicast Packets Transmitted.................... 330
Multicast Packets Transmitted.................. 737
Broadcast Packets Transmitted.................. 757
Total Transmit Errors.......................... 0
FCS Errors..................................... 0
--More-- or (q)uit
Tx Oversized................................... 0
Underrun Errors................................ 0
Total Transmit Packets Discarded............... 0
Single Collision Frames........................ 0
Multiple Collision Frames...................... 0
Excessive Collision Frames..................... 0
Port Membership Discards....................... 0
802.3x Pause Frames Transmitted................ 0
GVRP PDUs received............................. 0
GVRP PDUs Transmitted.......................... 0
GVRP Failed Registrations...................... 0
Time Since Counters Last Cleared............... 0 day 0 hr 17 min 52 sec
console#
2CSNXXX_SWUM200.book Page 605 Tuesday, December 10, 2013 1:22 PM

606 Port Channel Commands
2CSNXXX_SWUM200.book Page 606 Tuesday, December 10, 2013 1:22 PM

MLAG 607
31
MLAG
Dell Networking N2000/N3000/N4000 Series Switches
MLAG enables a LAG to be created across two independent switches, so that
some member ports of a MLAG can reside on one switch and the other
members of a MLAG can reside on another switch. The partner switch on the
remote side can be a MLAG-unaware unit. To the MLAG unaware switch, the
MLAG appears to be a single LAG connected to a single switch.
Commands in this Chapter
This chapter explains the following commands:
clear vpc statistics
Use the clear vpc statistics command to clear the counters for the keepalive
messages trasmitted and received by the MLAG switch.
Syntax
clear vpc statistics {peer-keepalive | peer-link}
clear vpc statistics show vpc consistency-parameters
debug vpc show vpc consistency-features
feature vpc show vpc peer-keepalive
peer-detection enable show vpc role
peer-keepalive destination show vpc statistics
peer-keepalive enable vpc
role priority vpc domain
show vpc vpc peer-link
show vpc brief
–
2CSNXXX_SWUM200.book Page 607 Tuesday, December 10, 2013 1:22 PM

608 MLAG
Default Configuration
There is no default configuration for this command.
Command Modes
Privileged EXEC mode
User Guidelines
There are no user guidelines for this command.
Example
console#clear vpc statistics
debug vpc
Use the debug vpc command to enable debug traces for the specified
protocols. Use the no form of the command to disable all or some of the
debug trace display.
Syntax
debug vpc {peer-keepalive [packet]| peer-link {control-message | data-
message} | peer detection | core}
no debug vpc [{peer-keepalive [packet]| peer-link {control-message | data-
message} | peer detection | core]
•
peer-keepalive
—Displays the debug traces for the keepalive state machine
transitions. The packet option enables debug traces for the keep-alive
packets exchanged between the MLAG peer devices on the peer link.
•
peer-link
—In error cases, enables the debug traces for the control
messages or data messages exchanged between the MLAG devices on the
peer link.
•
peer detection
—Enables the debug traces dual control plane detection
protocol. Traces are seen when DCPDP state changes occur
(enable/disable, peer detected, ...).
•
core
—Displays the MLAG core messages.
2CSNXXX_SWUM200.book Page 608 Tuesday, December 10, 2013 1:22 PM

MLAG 609
Default Configuration
This command has no default configuration.
Command Modes
Global Configuration mode
User Guidelines
This command has no user guidelines.
Example
console#debug vpc peer-link data-message
VPC peer link data message tracing enabled.
feature vpc
The feature vpc command globally enables MLAG. Use the no form of the
command to globally disable MLAG.
Syntax
feature vpc
no feature vpc
Default Configuration
By default, the MLAG feature is not globally enabled.
Command Modes
Global Configuration mode
User Guidelines
The MLAG configuration is retained even when the feature is disabled. The
peer link will not be enabled if the VPC feature is not enabled.
MLAG role election occurs if the MLAG feature is enabled and the keepalive
state machine is enabled.
2CSNXXX_SWUM200.book Page 609 Tuesday, December 10, 2013 1:22 PM

610 MLAG
Example
console#configure terminal
console(config)#feature vpc
peer-detection enable
Use the peer-detection enable command to enable the Dual Control Plane
Detection Protocol. This enables the detection of peer MLAG switches and
suppresses state transitions out of the secondary state in the presence of peer
link failures.
Use the no form of the command to disable the dual control plane detection
protocol.
Syntax
peer-detection enable
no peer-detection enable
Default Configuration
Dual Control Plane Detection Protocol is disabled by default.
Command Modes
MLAG Domain Configuration mode
Usage Guidelines
Use of the Dual Control Plane Detection Protocol is optional. It provides a
second layer of redundancy beyond that provided by the peer link protocol.
System that operate without the DCPDP protocol enabled (and use static
LAGs) run the risk of a split brain scenario in the case of peer link failure.
Example
console(config)#vpc domain 1
console(config-vpc 1)#peer-keepalive enable
console(config-vpc 1)#peer-keepalive destination 192.168.0.2 source
192.168.0.1
console(config-vpc 1)#peer detection enable
console(config-vpc 1)#exit
2CSNXXX_SWUM200.book Page 610 Tuesday, December 10, 2013 1:22 PM

MLAG 611
peer-keepalive destination
Use the peer-keepalive destination command to enable the Dual Control
Plane Detection Protocol with the configured IP address of the peer MLAG,
the local source address and the peer timeout value. The UDP port on which
the MLAG switch listens to the Dual Control Plane Detection Protocol
messages is also configurable with this command.
Use the no form of the command to return the configuration to the default.
Syntax
peer-keepalive destination
ipaddress
source
srcaddr
[udp-port
port
] [timeout
seconds
]
no peer-keepalive destination
•
ipaddress
—The ip address of the MLAG peer.
•
port
—The UDP port number to use to listen for peer Dual Control Plane
Detection Protocol packets.
•
srcaddr
—The local source address to use.
•
seconds
—The timeout value used to expire the Dual Control Plane
Detection Protocol peer. The range is 2-15 seconds; the default is 5.
Default Configuration
There are no Dual Control Plane Detection Protocol peers configured by
default.
Command Modes
MLAG Domain Configuration mode
User Guidelines
Changes to the DCPDP configuration do not take effect until the protocol is
disabled and then re-enabled. Both the local switch and the MLAG peer
switch must be configured identically. The recommended procedure to
update these parameters is to disable the DCPDP protocol on both switches,
configure the new parameters on both switches, and then re-enable the
DCPDP protocol on both switches.
2CSNXXX_SWUM200.book Page 611 Tuesday, December 10, 2013 1:22 PM

612 MLAG
The Dual Control Plane Detection Protocol is a UDP-based protocol. The
administrator must configure this protocol on an IP interface with a VLAN
that is not shared with any of the MLAG interfaces. This can include the out-
of-band port. When enabled, the dual-control plane detection protocol sends
a control plane detection message to the peer once every second. The
message is unidirectional and contains the sender’s MAC address. When a
switch receives a control plane detection message it sets the ‘peer is UP’
variable to TRUE to indicate that a peer is detected.
Example
console(config)#vpc domain 1
console(config-vpc 1)#peer-keepalive enable
console(config-vpc 1)#peer-keepalive destination 192.168.0.2 source
192.168.0.1
console(config-vpc 1)#peer detection enable
console(config-vpc 1)#exit
peer-keepalive enable
Use the peer-keepalive enable command to enable the peer keep-alive
protocol on the peer link. When enabled, if an MLAG switch does not receive
keepalive messages from the peer within the timeout value and DCPDP is
disabled, the switch begins the process of transitioning to the primary role (if
standby).
Use the no form of the command to disable the peer keep-alive protocol.
Syntax
peer-keepalive enable
no peer-keepalive enable
Default Configuration
The peer keep-alive protocol is disabled by default.
Command Modes
MLAG Domain Configuration mode
2CSNXXX_SWUM200.book Page 612 Tuesday, December 10, 2013 1:22 PM

MLAG 613
User Guidelines
MLAG will not become operational until the peer keepalive protocol detects
a peer and syncs the peer information. Peer keepalive timeout state
transitions are suppressed if the Dual Control Plan Detection (DCPDP) is
enabled and detects that the peer is still alive.
Two failure situations cause state transitions:
• The peer device fails: A peer does not receive any more advertisements and
the timeout timer expires.
• Secondary device fails: All MLAG members’ port information
regarding the secondary device that the primary switch maintains are
removed from the primary switch. Forwarding and control processing
continues on the local MLAG ports on the primary switch. Once the
secondary comes back up again, it starts the keepalive protocol and, if
successful in contacting the primary device, moves to the secondary
state. It then initiates an FDB sync and becomes operational again.
• Primary device fails: The secondary device transitions to primary state
and continues forwarding traffic on its local MLAG ports. It also starts
processing control messages. The MLAG connected devices see a
change in the source MAC address. Once the peer device comes up
again, it starts the keepalive protocol and transitions to the secondary
state.
• The peer-link fails: This occurs when either switch cannot contact the peer
through the peer keepalive protocol and the DCPDP protocol. The
secondary switch transitions to a primary role which results in two primary
switches. Both primaries continue forwarding traffic. Each primary also
processes control traffic and sends LACP and BPDU packets with a unique
source MAC address (the system MAC of the local switch). The MLAG
connected devices become aware that they are connected to two devices
and, if LACP is enabled, block the links to one of the peers as a new actor
id is received. STP re-convergence may also occur in this scenario.
Example
console(config)#vpc domain 1
console(config-vpc 1)#peer-keepalive enable
console(config-vpc 1)#peer-keepalive destination 192.168.0.2 source
192.168.0.1
console(config-vpc 1)#peer detection enable
console(config-vpc 1)#exit
2CSNXXX_SWUM200.book Page 613 Tuesday, December 10, 2013 1:22 PM

614 MLAG
role priority
Use the role priority command to configure the priority value used on a
switch for primary/secondary role selection. The primary switch is responsible
for maintaining and propagating spanning-tree and link-aggregation to the
secondary switch.
Use the no form of the command to return the switch priority to the default
value.
Syntax
role priority
value
no role priority
• Value—The local switch priority value. (The range is 1-255.)
Default Configuration
The default priority value is 100.
Command Modes
MLAG Domain Configuration mode
User Guidelines
This value is used for the MLAG role election and is sent to the MLAG peer
in the MLAG keepalive messages. The MLAG switch with the numerically
lower priority value becomes the Primary and the switch with higher priority
becomes the Secondary. If both the MLAG peer switches have the same role
priority, the device with lower system MAC address becomes the Primary
switch.
Changes to the priority value are not preemptive. The keepalive role selection
state machine is not restarted even if the keepalive priority is modified post
election. This means that priority value changes in a running MLAG domain
do not affect the selection of the primary and secondary switches. In order for
changes to take effect, disable the VPC with the no feature vpc command
and re-enable it.
Example
console(config-vpc 1)#role priority 30
2CSNXXX_SWUM200.book Page 614 Tuesday, December 10, 2013 1:22 PM

MLAG 615
show vpc
Use the show vpc command to display MLAG information. The
configuration and operational modes of the MLAG are displayed. The MLAG
is operationally enabled if all preconditions are met. The port channel
configured as an MLAG interface is also displayed along with the member
ports on the current switch and peer switch (plus their link status).
Syntax
show vpc
id
•
id
—A valid MLAG identifier.
Default Configuration
There is no default configuration for this command.
Command Modes
Privileged EXEC mode and above
User Guidelines
There are no user guidelines for this command.
Example
(console)# show vpc 10
VPC Id 10
-----------------
Configuration mode......................Enabled
Operational mode........................Enabled
Port channel................................Po1
Self member ports Status
------------------------ ---------
Gi1/0/2 Up
Gi1/0/6 Down
2CSNXXX_SWUM200.book Page 615 Tuesday, December 10, 2013 1:22 PM

616 MLAG
show vpc brief
Use the show vpc brief command to display the MLAG global status. The
command displays the current MLAG operational mode as well as the
peerlink and keepalive status is also displayed. The number of configured and
operational MLAGs along with the system MAC and role are also displayed.
Syntax
show vpc brief
Default Configuration
There is no default configuration for this command.
Command Modes
Privileged EXEC mode and above
User Guidelines
Only the Primary switch maintains the member status of the Secondary
switch. The Secondary switch does not maintain or show the status of the
Primary switch peer members.
A VPC instance may show as enabled even if all of the port-channels that are
members of the VPC are disabled or all of the links in the port channels are
disabled. A VPC will show as disabled if peer-link (or DCPDP) connectivity is
lost.
The Keep-alive admin status field shows the status of the peer-link protocol.
The VPC operational status shows the overall MLAG status.
The Peer detection admin status field shows the status of the DCPDP
protocol.
Example
MLAG-Peer-A#show vpc brief
VPC config Mode................................ Enabled
Keepalive config mode.......................... Enabled
VPC operational Mode........................... Enabled
Self Role...................................... Primary
Peer Role...................................... Secondary
2CSNXXX_SWUM200.book Page 616 Tuesday, December 10, 2013 1:22 PM

MLAG 617
Peer detection................................. Peer detected, VPC
Operational
Peer-Link details
-----------------
Interface...................................... Po1
Peer link status............................... UP
Peer-link STP Mode............................. Disabled
Configured Vlans............................... 1,10,11,12,13,14,15,16,17
Egress tagging................................. 10,11,12,13,14,15,16,17
VPC Details
-----------
Number of VPCs configured...................... 2
Number of VPCs operational..................... 2
VPC id# 1
-----------
Interface...................................... Po2
Configured Vlans............................... 1,10,11,12,13,14,15,16,17
VPC Interface State............................ Active
Local MemberPorts Status
----------------- ------
Gi1/0/23 UP
Gi1/0/24 UP
Peer MemberPorts Status
---------------- ------
Gi1/0/23 UP
Gi1/0/24 UP
VPC id# 2
-----------
Interface...................................... Po3
Configured Vlans............................... 1,10,11,12,13,14,15,16,17
VPC Interface State............................ Active
show vpc example
MLAG-Peer-A#show vpc 1
2CSNXXX_SWUM200.book Page 617 Tuesday, December 10, 2013 1:22 PM

618 MLAG
VPC id# 1
-----------------
Config mode.................................... Enabled
Operational mode............................... Enabled
Port channel................................... Po2
Local MemberPorts Status
----------------- ------
Gi1/0/23 UP
Gi1/0/24 UP
Peer MemberPorts Status
---------------- ------
Gi1/0/23 UP
Gi1/0/24 UP
show vpc consistency-parameters
Use the show vpc consistency parameters on both MLAG peers to display
MLAG related configuration information in a format suitable for comparison
with the other MLAG peer.
Syntax
show vpc consistency-parameters { global | interface
port-channel-number
}
•
port-channel-number
—A valid port-channel identifier (range 1-128).
Default Configuration
There is no default configuration for this command.
Command Modes
Privileged EXEC mode and above
User Guidelines
There are no user guidelines for this command.
2CSNXXX_SWUM200.book Page 618 Tuesday, December 10, 2013 1:22 PM

MLAG 619
show vpc consistency-features
Use the show vpc consistency parameters on both MLAG peers to display
MLAG related configuration information in a format suitable for comparison
with the other MLAG peer.
Syntax
show vpc consistency-features { global | interface
port-channel-number
}
•
port-channel-number
—A valid port-channel identifier (range 1-128).
Default Configuration
There is no default configuration for this command.
Command Modes
Privileged EXEC mode and above
User Guidelines
There are no user guidelines for this command.
show vpc peer-keepalive
Use the show vpc peer-keepalive command to display the peer MLAG
switch’s IP address used by the Dual Control Plane Detection Protocol. The
port used for the Dual Control Plane Detection Protocol is shown, as well as if
peer detection is enabled or not. If enabled, the detection status is displayed.
Syntax
show vpc peer-keepalive
Default Configuration
There is no default configuration for this command.
Command Modes
Privileged EXEC mode and above
2CSNXXX_SWUM200.book Page 619 Tuesday, December 10, 2013 1:22 PM

620 MLAG
User Guidelines
There are no user guidelines for this command.
Example
(console) # show vpc peer-keepalive
Peer IP address …………………………………10.130.14.55
UDP port ……………………………………………………50000
Peer detection ……………………………………Enabled
Peer is detected ………………………………True
show vpc role
Use the show vpc role command to display information about the keepalive
status and parameters. The role of the MLAG switch and the system MAC
and priority are displayed.
Syntax
show vpc role
Default Configuration
There is no default configuration for this command.
Command Modes
Privileged EXEC mode and above
User Guidelines
There are no user guidelines for this command.
Example
(console) # show vpc role
Keepalive admin mode…………… Enabled
Priority……………………………… 100
VPC Role……………………………… Primary
System MAC…………………………… 0001.0002.0003
2CSNXXX_SWUM200.book Page 620 Tuesday, December 10, 2013 1:22 PM

MLAG 621
show vpc statistics
Use the show vpc statistics command to display the counters for the keepalive
messages trasmitted and received by the MLAG switch.
Syntax
show vpc statistics {peer-keepalive | peer-link}
Default Configuration
There is no default configuration for this command.
Command Modes
Privileged EXEC mode and above
User Guidelines
There are no user guidelines for this command.
Example
(console) # show vpc statistics peer-keepalive
Total trasmitted .......................................123
Tx successful...........................................118
Tx errors...............................................5
Total received..........................................115
Rx successful...........................................108
Rx Errors...............................................7
Timeout counter.........................................6
(console) # show vpc statistics peer-link
Peer link control messages transmitted..................123
Peer link control messages Tx errors................... 5
Peer link control messages Tx timeout.................. 4
Peer link control messages ACK transmitted............. 34
Peer link control messages ACK Tx erorrs............... 5
Peer link control messages received.................... 115
Peer link data messages trasmitted..................... 123
Peer link data messages Tx errors...................... 5
Peer link data messages Tx imeout...................... 4
Peer link data messages ACK transmitted................ 34
Peer link data messages ACK Tx erorrs.................. 5
Peer link data messages received....................... 115
Peer link BPDU’s tranmsitted to peer................... 123
2CSNXXX_SWUM200.book Page 621 Tuesday, December 10, 2013 1:22 PM

622 MLAG
Peer link BPDU’s Tx error.............................. 9
Peer link BPDU’s received from peer.................... 143
Peer link BPDU’s Rx error.............................. 1
Peer link LACPDU’s tranmsitted to peer................. 123
Peer link LACPDU’s Tx error............................ 9
Peer link LACPDU’s received from peer.................. 143
Peer link LACPDU’s Rx error............................ 1
(console) #show vpc statistics peer-link
Peer link control messages transmitted......... 24
Peer link control messages Tx errors........... 0
Peer link control messages Tx timeout.......... 0
Peer link control messages ACK transmitted..... 23
Peer link control messages ACK Tx errors....... 0
Peer link control messages received............ 23
Peer link data messages transmitted............ 73
Peer link data messages Tx errors.............. 0
Peer link data messages Tx timeout............. 0
Peer link data messages received............... 73
Peer link BPDU's transmitted to peer........... 0
Peer link BPDU's Tx errors..................... 0
Peer link BPDU's received from peer............ 0
Peer link BPDU's Rx errors..................... 0
Peer link LACPDU's tranmsitted to peer......... 73
Peer link LACPDU's Tx errors................... 0
Peer link LACPDU's received from peer.......... 73
Peer link LACPDU's Rx errors................... 0
vpc
Use the vpc command to configure a port-channel (LAG) as part of an
MLAG instance. Upon issuing this command, the port-channel is down until
the port-channel member information is exchanged and agreed between the
MLAG peer switches.
Use the no form of the command to remove the LAG from the MLAG
domain.
Syntax
vpc
vpc-id
no vpc
vpc-id
• vpd-id—The MLAG identifier.
2CSNXXX_SWUM200.book Page 622 Tuesday, December 10, 2013 1:22 PM

MLAG 623
Default Configuration
LAGs are not members of an MLAG domain by default. It is expected that all
links belonging to an MLAG instance are connected to switch (or switches)
which consider the links to be members of a single LAG.
This configuration must be present on both the primary and secondary
switches.
The port channel number and VPC number can be different from each other
but the mapping must be the same on the primary and secondary MLAG
peers (i.e., the port channel number must map to the same VPC number on
both MLAG peers).
Command Modes
Port-channel mode
User Guidelines
The peer keep-alive protocol is required for MLAG operation. Configure a
LAG between the two MLAG peers as an MLAG peer link before executing
this command.
Example
console(config)#interface po3
console(config-if-Po3)#switchport mode trunk
console(config-if-Po3)#switchport trunk allowed vlan 1-99,101-4093
console(config-if-Po3)#vpc 2
console(config-if-Po3)#exitconsole(config)#interface po3
console(config-if-Po3)#switchport mode trunk
console(config-if-Po3)#switchport trunk allowed vlan 1-99,101-4093
console(config-if-Po3)#vpc 2
console(config-if-Po3)#exit
vpc domain
Use the vpc domain command to enter into MLAG configuration mode.
Syntax
vpc domain
domain-id
• domain-id—The MLAG domain instance. The range is 1.
2CSNXXX_SWUM200.book Page 623 Tuesday, December 10, 2013 1:22 PM

624 MLAG
Default Configuration
By default, no MLAG domains are configured.
Command Modes
Global Configuration mode
User Guidelines
Only one MLAG domain (domain 1) is supported.
Example
console(config)#vpc domain 1
console(config-vpc 1)#peer-keepalive enable
console(config-vpc 1)#peer-keepalive destination 192.168.0.2 source
192.168.0.1
console(config-vpc 1)#peer detection enable
console(config-vpc 1)#exit
vpc peer-link
Use the vpc peer-link command to configure a port channel as the MLAG
peer link for a domain and enables the peer link protocol.
Use the no form of the command to remove the peer link configuration from
an MLAG domain and disable the peer link protocol.
Syntax
vpc peer-link
no vpc peer-link
Default Configuration
There are no peer links configured by default.
Command Modes
Port-channel configuration mode
2CSNXXX_SWUM200.book Page 624 Tuesday, December 10, 2013 1:22 PM

MLAG 625
User Guidelines
This configuration must the present on both the primary and secondary
switches. The peer keep-alive protocol is required for MLAG operation.
Configure and enable a LAG between the two MLAG peers as an MLAG peer
link before executing this command.
Example
console(config)#interface port-channel 1
console(config-if-Po1)#description "MLAG-Peer-Link"
console(config-if-Po1)#spanning-tree disable
console(config-if-Po1)#switchport mode trunk
console(config-if-Po1)#switchport trunk allowed vlan 1-99,101-4093
console(config-if-Po1)#vpc peer-link
console(config-if-Po1)#exit
2CSNXXX_SWUM200.book Page 625 Tuesday, December 10, 2013 1:22 PM

626 MLAG
2CSNXXX_SWUM200.book Page 626 Tuesday, December 10, 2013 1:22 PM

Port Monitor Commands 627
32
Port Monitor Commands
Dell Networking N2000/N3000/N4000 Series Switches
Dell Networking switches allow the user to monitor traffic with an external
network analyzer. The external network analyzer can use any of the Ethernet
ports as a probe port. The probe port transmits a mirror copy of the traffic
being probed. Network traffic transmission is always disrupted whenever a
configuration change is made for port monitoring. Therefore, whenever port
monitoring is enabled, the probe port does not always forward traffic as a
normal port. When diagnosing problems, an operator should always check the
status of port monitoring.
The port monitoring feature allows the user to configure a single probe
session. A session consists of one destination or probe port and one or
multiple source ports. When a session is enabled, any traffic entering or
leaving the source ports of that session is copied (mirrored) onto the
corresponding destination port. A network traffic analyzer can be attached to
destination ports to analyze the traffic patterns of source ports.
A session is operationally active only if both a destination port and at least
one source port are configured. If neither is true, the session is inactive. A port
configured as a destination port acts as a mirroring port when the session is
operationally active. If it is not, the port acts as a normal port and participates
in all normal operation with respect to transmitting traffic.
Any Ethernet port may be configured as a source port.
Caveats:
• Platforms may behave unpredictably if an attempt is made to mirror a port
of greater speed than the probe port.
• Once configured, there is no network connectivity on the probe
(destination) port. The probe port does not forward any traffic and does
not receive any traffic. The probe tool attached to the probe port is unable
to ping the networking device or ping through the networking device, and
no device is able to ping the probe tool.
• ACL attributes redirect, mirror, log, rate-limit, assign-queue, time-range,
IGMP type, ICMP type, ICMP code, routing, fragments, and TCP
established are not supported when applied to a mirroring session.
2CSNXXX_SWUM200.book Page 627 Tuesday, December 10, 2013 1:22 PM

628 Port Monitor Commands
Commands in this Chapter
This chapter explains the following commands:
monitor session
Use the monitor session command in Global Configuration mode to
configure a probe port and a monitored port for monitor session (port
monitoring). Use the src-interface parameter to specify the interface to
monitor. Use rx to monitor only ingress packets, or use tx to monitor only
egress packets. If you do not specify an {rx | tx} option, the destination port
monitors both ingress and egress packets. Use the destination interface to
specify the interface to receive the monitored traffic. Use the mode parameter
to enabled the administrative mode of the session. If enabled, the probe port
monitors all the traffic received and transmitted on the physical monitored
port.
Use the no form of the command to remove the monitoring session.
Syntax
monitor session
session_number
{source {interface
interface–id
|vlan
vlan-
id
| remote vlan
rspan-vlan-id
}[rx | tx] | destination {interface
interface–id
| remote vlan
rspan-vlan-id
reflector-port
interface-id
} | filter {ip access-
group [
acl-name
|
acl-number
] | mac access-group
acl-name
no monitor session
[no] monitor session
session_number
destination {interface
interface–id
|
remote vlan
rspan-vlan-id
reflector-port
interface-id
}
[no] monitor session
session_number
filter {ip access-group [
acl-name
|
acl-
number
] | mac access-group
acl-name
}
•
session _number
— Session identification number.
•
interface interface–id
— Ethernet interface (Range: Any valid Ethernet
Port), CPU interface. CPU interface is not supported as a destination
interface or a source interface for RSPAN..
monitor session show monitor session
remote-span show vlan remote-span
2CSNXXX_SWUM200.book Page 628 Tuesday, December 10, 2013 1:22 PM

Port Monitor Commands 629
•
vlan
vlan-id
— The source VLAN identifier. All the ports in this VLAN are
mirrored. The source VLAN must not be the RSPAN VLAN.
•
acl-name
— An IP or MAC ACL name.
•
remote vlan
rspan-vlan-id
— An RSPAN VLAN.
•
reflector-port
interface-id
— Any physical interface on the destination
switch. It is required that the reflector port be configured as a trunk port or
otherwise have VLAN tagging enabled. The relector port cannot be a port
channel.
•
rx
— Monitors received packets only. If no option specified, monitors both
rx and tx.
•
tx
— Monitors transmitted packets only. If no option is specified, monitors
both rx and tx.
•
both
—Monitors both ingress and egress. This is the default.
Default Configuration
The default is to monitor both transmit and receive directions. If neither tx or
rx is configured, both directions are monitored.
Command Mode
Global Configuration mode
User Guidelines
The source of a monitoring session must be configured before the destination
can be configured. Only one session with a single destination is supported,
however, that session supports multiple sources. The internal CPU port
cannot be configured as an RSPAN source.
Reserve a few VLANs across the network for the exclusive use of RSPAN. Do
not assign access ports to these VLANs. The source VLAN (if configured),
cannot be the same as the RSPAN VLAN. The destination interface must be
configured as a member of the RSPAN VLAN on the source switch. The
source interface must be configured as a member of the RSPAN VLAN on the
destination switch.If an ACL name is specified, the ACL must be created
prior to its use in an RSPAN configuration.
RSPAN VLANs must be configured with the remote-span command.
2CSNXXX_SWUM200.book Page 629 Tuesday, December 10, 2013 1:22 PM

630 Port Monitor Commands
Example
This example shows how to configure a source switch using VLAN 723 as the
destination RSPAN VLAN and Gi1/0/3 as the source interface. Gi1/0/10 is
configured as the reflector port. It is recommended that interface gi1/0/10 be
configured as a trunk port. Interface gi1/0/10 must be configured as a member
of VLAN 723.
console(config)# monitor session 1 source interface gi1/0/3 both
console(config)# monitor session 1 destination remote vlan 723 reflector-port
gi1/0/10
console(config)# monitor session 1 mode
This example shows how to configure a destination switch using VLAN 723 as
the source RSPAN VLAN and Gi1/0/10 as the destination interface.
console(config)# monitor session 1 source remote vlan 723
console(config)# monitor session 1 destination interface gi1/0/10
console(config)# monitor session 1 mode
remote-span
Use this command to configure a VLAN as an RSPAN VLAN. Use the no
form of the command to remove the remote SPAN characteristics from a
VLAN and revert it to a VLAN.
Syntax
remote-span
no remote-span
Default Configuration
There is no default configuration for this command.
Command Modes
VLAN Configuration mode.
2CSNXXX_SWUM200.book Page 630 Tuesday, December 10, 2013 1:22 PM

Port Monitor Commands 631
User Guidelines
Traffic in a RSPAN VLAN is always flooded as MAC address learning is
disabled on RSPAN VLANs. VLANs on transit switches should be configured
as remote-span VLANs in order to ensure delivery of all mirrored packets.
Example
console(config-vlan10)#remote-span
console(config)#
show monitor session
Use the show monitor session command in Privileged EXEC mode to display
status of port monitoring, VLAN-based mirroring, Flow-based mirroring, and
mirroring across RSPAN.
Syntax
show monitor session
session_number
[detail]
•
session
_number
— Session identification number.
• detail—Displays additional information.
Default Configuration
This command has no default configuration.
Command Mode
User EXEC, Privileged EXEC modes, Configuration mode and all
Configuration submodes
User Guidelines
This command has no user guidelines.
Examples
The following example shows port monitor status.
console(config)#show monitor session 1
Session : 1
Admin mode : Disabled
2CSNXXX_SWUM200.book Page 631 Tuesday, December 10, 2013 1:22 PM

632 Port Monitor Commands
Type : Local session
Source ports :
Both : Te1/0/10
Destination ports : Te2/0/20
IP access-group : a1
The following example shows the detailed status of the port based mirroring
session that is constrained to a local switch.
console(config)#show monitor session 1 detail
Session : 1
Admin mode : Disabled
Type : Local session
Source ports :
Rx only : None
Tx only : None
Both : Te1/0/10
Source VLANs :
Rx only : None
Source RSPAN VLAN : None
Destination ports : Te2/0/20
Destination RSPAN VLAN : None
IP access-group : a1
MAC access-group : None
The following example shows the detailed status of a VLAN session on source
switch, where session is span across multiple switches.
console# show monitor session 1 detail
Session : 1
Type : Remote Destination Session
Source Ports :
RX Only : None
TX Only : None
Both : None
Source VLANs :
RX Only : 100
Source RSPAN VLAN : None
Destination Ports : None
Dest RSPAN VLAN : 999
The following example shows the detailed status of a VLAN session on
destination switch, where session is span across multiple switches.
2CSNXXX_SWUM200.book Page 632 Tuesday, December 10, 2013 1:22 PM

Port Monitor Commands 633
console# show monitor session 1 detail
Session : 1
Type : Remote Destination Session
Source Ports :
RX Only : None
TX Only : None
Both : None
Source VLANs :
RX Only : None
Source RSPAN VLAN : 999
Destination Ports : Gi1/0/15
Dest RSPAN VLAN : None
show vlan remote-span
Use this command to display the RSPAN VLAN IDs.
Syntax
show vlan remote-span
Default Configuration
This command has no default configuration.
Command Modes
User EXEC, Privileged EXEC modes.
User Guidelines
This command has no user guidelines.
Example
The following example shows the RSPAN VLANs configured on the switch.
console# show vlan remote-span
RSPAN Vlan
-----------------------------------------------------
10
2CSNXXX_SWUM200.book Page 633 Tuesday, December 10, 2013 1:22 PM

634 Port Monitor Commands
2CSNXXX_SWUM200.book Page 634 Tuesday, December 10, 2013 1:22 PM

QoS Commands 635
33
QoS Commands
Dell Networking N2000/N3000/N4000 Series Switches
Quality of Service (QoS) technologies are intended to provide guaranteed
timely delivery of specific application data to a particular destination. In
contrast, standard IP-based networks are designed to provide best effort data
delivery service. Best effort service implies that the network delivers the data
in a timely fashion, although there is no guarantee. During times of
congestion, packets may be delayed, sent sporadically, or dropped. For typical
Internet applications, such as electronic mail and file transfer, a slight
degradation in service is acceptable and, in many cases, unnoticeable.
Conversely, any degradation of service has undesirable effects on applications
with strict timing requirements, such as voice or multimedia.
QoS is a means of providing consistent, predictable data delivery by
distinguishing between packets that have strict timing requirements from
those that are more tolerant of delay. Packets with strict timing requirements
are given special treatment in a QoS-capable network. To accomplish this, all
elements of the network must be QoS-capable. If one node is unable to meet
the necessary timing requirements, this creates a deficiency in the network
path and the performance of the entire packet flow is compromised.
Access Control Lists
The Dell Networking ACL feature allows classification of packets based upon
Layer 2 through Layer 4 header information. An Ethernet IPv6 packet is
distinguished from an IPv4 packet by its unique Ether-type value; thus, all
IPv4 and IPv6 classifiers include the Ether-type field.
Multiple ACLs per interface are supported. The ACLs can be combination of
Layer 2 and/or Layer 3/4 ACLs.
ACL assignment is appropriate for both physical ports and LAGs.
2CSNXXX_SWUM200.book Page 635 Tuesday, December 10, 2013 1:22 PM

636 QoS Commands
A user configures an ACL permit rule to force its matching traffic stream to a
specific egress interface, bypassing any forwarding decision normally
performed by the device. The interface can be a physical port or a LAG. The
redirect interface rule action is independent of, but compatible with, the
assign queue rule action.
ACLs can be configured to apply to a VLAN instead of an interface. Traffic
tagged with a VLAN ID (either receive-tagged or tagged by ingress process
such as PVID) is evaluated for a match regardless of the interface on which it
is received.
Layer 2 ACLs
The Layer 2 ACL feature provides access list capability by allowing
classification on the Layer 2 header of an Ethernet frame, including the
802.1Q VLAN tag(s). In addition, the rule action set is enhanced to designate
which (egress) CoS queue should handle the traffic, and whether the traffic
flow is to be redirected to a specific outgoing interface.
MAC access lists are identified by a user-specified name instead of a number.
Layer 3/4 IPv4 ACLs
The Layer 3/4 ACL feature supports IP access lists, both standard and
extended. These lists check the Layer 3 portion of a packet, looking
specifically at information contained in the IP header and, in certain cases,
the TCP or UDP header. An Ethertype of 0x0800 is assumed in the case of IP
access lists. Permit and deny actions are supported for each ACL rule.
Standard layer 3/4 ACLs can be classified based on the source IP address and
netmask or other extended classification criteria.
Class of Service (CoS)
The Dell Networking CoS Queueing feature allows the user to directly
configure device queueing and, therefore, provide the desired QoS behavior
without the complexities of DiffServ. The CoS feature allows the user to
determine the following queue behavior:
•Queue Mapping
– Trusted Port Queue Mapping
2CSNXXX_SWUM200.book Page 636 Tuesday, December 10, 2013 1:22 PM

QoS Commands 637
– Untrusted Port Default Priority
• Queue Configuration
This enables Dell Networking switches to support a wide variety of delay
sensitive video and audio multicast applications.
CoS mapping tables, port default priority, and hardware queue parameters
may be configured on LAG interfaces as well as physical port interfaces.
Queue Mapping
The priority of a packet arriving at an interface is used to steer the packet to
the appropriate outbound CoS queue through a mapping table. Network
packets arriving at an ingress port are directed to one of n queues in an egress
port(s) based on the translation of packet priority to CoS queue. The CoS
mapping tables define the queue used to handle each enumerated type of
user priority designated in either the 802.1p, IP precedence, or IP DSCP
contents of a packet. If none of these fields are trusted to contain a
meaningful COS queue designation, the ingress port can be configured to use
its default priority to specify the CoS queue.
CoS queue mappings use the concept of trusted and untrusted ports.
A trusted port is one that takes at face value a certain priority designation
within arriving packets. Specifically, a port may be configured to trust one of
the following packet fields:
• 802.1p User Priority
• IP Precedence
•IP DSCP
Packets arriving at the port ingress are inspected and their trusted field value
is used to designate the COS queue that the packet is placed when forwarded
to the appropriate egress port. A mapping table associates the trusted field
value with the desired COS queue.
Alternatively, a port may be configured as untrusted, whereby it does not trust
any incoming packet priority designation and uses the port default priority
value instead. All packets arriving at the ingress of an untrusted port are
directed to a specific COS queue on the appropriate egress port(s) in
accordance with the configured default priority of the ingress port. This
2CSNXXX_SWUM200.book Page 637 Tuesday, December 10, 2013 1:22 PM

638 QoS Commands
process is also used for cases where a trusted port mapping is unable to be
honored, such as when a nonIP packet arrives at a port configured to trust the
IP precedence or IP DSCP value.
Commands in this Chapter
This chapter explains the following commands:
assign-queue mark ip-dscp match source-
address mac
show classofservice
dot1p-mapping
class mark ip-precedence match srcip show classofservice ip-
dscp-mapping
class-map match class-map match srcip6 show classofservice
trust
class-map rename match cos match srcl4port show diffserv
classofservice
dot1p-mapping
match destination-
address mac
match vlan show diffserv service
interface
classofservice ip-
dscp-mapping
match dstip mirror show diffserv service
interface port-channel
classofservice trust match dstip6 police-simple show diffserv service
brief
conform-color match dstl4port police-single-rate show interfaces cos-
queue
cos-queue min-
bandwidth
match ethertype police-two-rate show interfaces
random-detect
cos-queue random-
detect
match ip6flowlbl policy-map show policy-map
cos-queue strict match ip dscp random-detect
queue-parms
show policy-map
interface
diffserv match ip
precedence
random-detect
exponential-
weighting-constant
show service-policy
drop match ip tos redirect traffic-shape
mark cos match protocol service-policy vlan priority
2CSNXXX_SWUM200.book Page 638 Tuesday, December 10, 2013 1:22 PM

QoS Commands 639
assign-queue
Use the assign-queue command in Policy-Class-Map Configuration mode to
modify the queue ID to which the associated traffic stream is assigned.
Syntax
assign-queue
queueid
•
queueid
— Specifies a valid queue ID. (Range: integer from 0–6.)
Default Configuration
This command has no default configuration.
Command Mode
Policy-Class-Map Configuration mode
User Guidelines
This command has no user guidelines.
Example
The following example displays how to change the queue ID to 4 for the
associated traffic stream.
console(config-policy-classmap)#assign-queue 4
class
Use the class command in Policy-Map Class Configuration mode to create an
instance of a class definition within the specified policy for the purpose of
defining treatment of the traffic class through subsequent policy attribute
statements.
Syntax
class
classname
no class
––
show class-map
–
2CSNXXX_SWUM200.book Page 639 Tuesday, December 10, 2013 1:22 PM

640 QoS Commands
•
classname
— Specifies the name of an existing DiffServ class. (Range:
1–31 characters)
Default Configuration
This command has no default configuration.
Command Mode
Policy Map Configuration mode
User Guidelines
This command causes the specified policy to create a reference to the class
definition. The command mode is changed to Policy-Class-Map
Configuration when this command is executed successfully.
Example
The following example shows how to specify the DiffServ class name of
"DELL."
console(config)#policy-map DELL1
console(config-classmap)#class DELL
class-map
Use the class-map command in Global Configuration mode to define a new
DiffServ class of type
match-all
. To delete the existing class, use the no form
of this command.
Syntax
class-map match-all
class-map-name
[{ipv4 | ipv6}]
no class-map match-all
class-map-name
•
class-map-name
— a case-sensitive alphanumeric string from 1 to 31
characters uniquely identifying an existing DiffServ class.
Default Configuration
The class-map defaults to ipv4.
2CSNXXX_SWUM200.book Page 640 Tuesday, December 10, 2013 1:22 PM

QoS Commands 641
Command Mode
Global Configuration mode
User Guidelines
There are no user guidelines for this command.
Example
The following example creates a class-map named "DELL" which requires all
ACE’s to be matched.
console(config)#class-map DELL
console(config-cmap)#
class-map rename
Use the class-map rename command in Global Configuration mode to
change the name of a DiffServ class.
Syntax
class-map rename
classname
newclassname
•
classname
— The name of an existing DiffServ class. (Range: 1–31
characters)
•
newclassname
— A case-sensitive alphanumeric string. (Range: 1–31
characters)
Default Configuration
This command has no default configuration.
Command Mode
Global Configuration mode
User Guidelines
This command has no user guidelines.
2CSNXXX_SWUM200.book Page 641 Tuesday, December 10, 2013 1:22 PM
642 QoS Commands
Example
The following example displays how to change the name of a DiffServ class
from "DELL" to "DELL1."
console(config)#class-map rename DELL DELL1
console(config)#
classofservice dot1p-mapping
Use the classofservice dot1p-mapping command in Global Configuration
mode to map an 802.1p priority to an internal traffic class. In Interface
Configuration mode, the mapping is applied only to packets received on that
interface. Use the no form of the command to remove mapping between an
802.1p priority and an internal traffic class.
Syntax
classofservice dot1p-mapping
802.1ppriority
trafficclass
no classofservice dot1p-mapping
•
802.1ppriority
— Specifies the user priority mapped to the specified traffic
class for this switch. (Range: 0–7)
•
trafficclass
— Specifies the traffic class for this switch. (Range: 0–6)
Default Configuration
The default dot1p mapping is as follows:
User Priority Traffic Class
01
10
20
31
42
52
63
73
2CSNXXX_SWUM200.book Page 642 Tuesday, December 10, 2013 1:22 PM
QoS Commands 643
Command Mode
Global Configuration or Interface Configuration (Ethernet, Port-channel)
mode
User Guidelines
None
Example
The following example configures mapping for user priority 1 and traffic class
2.
console(config)#classofservice dot1p-mapping 1 2
classofservice ip-dscp-mapping
Use the classofservice ip-dscp-mapping command in Global Configuration
mode to map an IP DSCP value to an internal traffic class. Use the no form of
the command to return the classofservice mapping to the default, and remove
a traffic class mapping for an IP DSCP value.
Syntax
classofservice ip-dscp-mapping
ipdscp
trafficclass
no classofservice ip-dscp-mapping ipdscp
•
ipdscp
—Specifies the IP DSCP value to which you map the specified
traffic class. (Range: 0–63 or an IP DSCP keyword – af11, af12, af13, af21,
af22, af23, af31, af32, af33, af41, af42, af43, be, cs0, cs1, cs2, cs3, cs4, cs5,
cs6, cs7, ef).
•
trafficclass
—Specifies the traffic class for this value mapping. (Range:
0–6).
Default Configuration
The default DSCP mapping is as follows:
IP DSCP Traffic Class
0(be/cs0) 1
2CSNXXX_SWUM200.book Page 643 Tuesday, December 10, 2013 1:22 PM
644 QoS Commands
11
21
31
41
51
61
71
8(cs1) 0
90
10(af11) 0
11 0
12(af12) 0
13 0
14(af13) 0
15 0
16(cs2) 0
17 0
18(af21) 0
19 0
20(af22) 0
21 0
22(af23) 0
23 0
24(cs3) 1
25 1
26(af31) 1
27 1
28(af32) 1
IP DSCP Traffic Class
2CSNXXX_SWUM200.book Page 644 Tuesday, December 10, 2013 1:22 PM

QoS Commands 645
29 1
30(af33) 1
31 1
32(cs4) 2
33 2
34(af41) 2
35 2
36(af42) 2
37 2
38(af43) 2
39 2
40(cs5) 2
41 2
42 2
43 2
44 2
45 2
46(ef) 2
47 2
48(cs6) 3
49 3
50 3
51 3
52 3
53 3
54 3
55 3
56(cs7) 3
IP DSCP Traffic Class
2CSNXXX_SWUM200.book Page 645 Tuesday, December 10, 2013 1:22 PM

646 QoS Commands
Command Mode
Global Configuration mode
User Guidelines
This command has no user guidelines.
Example
The following example displays mapping for IP DSCP 1 and traffic class 2.
console(config)#classofservice ip-dscp-mapping 1 2
classofservice trust
Use the classofservice trust command in either Global Configuration mode
or Interface Configuration mode to set the class of service trust mode of an
interface. To set the interface mode to untrusted, use the no form of this
command.
Syntax
classofservice trust {dot1p | untrusted | ip-dscp}
no classofservice trust
•
dot1p
— Specifies that the mode be set to trust dot1p (802.1p) packet
markings.
•
untrusted
— Sets the Class of Service Trust Mode for all interfaces to
Untrusted.
57 3
58 3
59 3
60 3
61 3
62 3
63 3
IP DSCP Traffic Class
2CSNXXX_SWUM200.book Page 646 Tuesday, December 10, 2013 1:22 PM

QoS Commands 647
•
ip-dscp
— Specifies that the mode be set to trust IP DSCP packet
markings.
Default Configuration
This command has no default configuration.
Command Mode
Global Configuration mode or Interface Configuration (gigabitethernet,
port-channel, tengigabitethernet
,
fortygigabitethernet) mode
User Guidelines
This command has no user guidelines.
Examples
The following example displays how you set the class of service trust mode of
an interface to trust dot1p (802.1p) packet markings when in Global
Configuration mode.
console(config)#classofservice trust dot1p
The following example displays how you set the class of service trust mode of
an interface to trust IP Precedence packet mark
console(config)#classofservice trust ip-precedence
conform-color
Use the conform-color command in Policy-Class-Map Configuration mode
to enable color-aware marking for a policy. This command must be preceded
by a police command. If the conform-color command is not entered, the
police algorithm uses the color-blind version, meaning in the incoming color
is ignored. The conform-color command can be used with both the simple
police algorithm and the two-rate police algorithm. In the simple algorithm,
only the conform color class can be configured which precolors packets as
green. Non-conforming packets are precolored red. With the two-rate police
algorithm, the conform color class precolors packets as green and the exceed
color class precolors packets as yellow. Non-conforming packets are precolored
red.
2CSNXXX_SWUM200.book Page 647 Tuesday, December 10, 2013 1:22 PM

648 QoS Commands
Syntax
conform-color {class-map-name} [exceed-color { class-map-name } ]
Default Configuration
This command has no default configuration.
Command Mode
Policy-Class-Map Configuration mode
User Guidelines
Color conforming classes must be one of the following types:
• Primary COS
•Secondary COS
•DSCP
• IP Precedence
This includes both the input and color aware classes. The conform color class
may not be the same as the input class, nor may the match criteria be of the
same type. The input class map may have a match type of "any."
The exceed color class may only be specified for the two-rate police
algorithm.
Example
The following example uses a simple policer to color TCP packets that exceed
an average rate of 1000 Kbps or a burst size of 16 Kbytes as red. Conforming
packets are colored green. The example configuration below also shows the
configuration of WRED drop thresholds and probabilities for colored traffic.
console(config)#class-map match-all class-ipv4 ipv4
console(config-classmap)#match any
console(config-classmap)#exit
console(config)#class-map match-all class-cos1 ipv4
console(config-classmap)#match cos 1
console(config-classmap)#exit
console(config)#policy-map color in
console(config-policy-map)#class class-ipv4
console(config-policy-classmap)#police-simple 1000 16 conform-action
transmit violate-action transmit
2CSNXXX_SWUM200.book Page 648 Tuesday, December 10, 2013 1:22 PM

QoS Commands 649
console(config-policy-classmap)#conform-color class-cos1
console(config-policy-classmap)#exit
console(config-policy-map)#exit
console(config)#
cos-queue min-bandwidth
Use the cos-queue min-bandwidth command in either Global Configuration
mode or Interface Configuration mode to specify the minimum transmission
bandwidth for each interface queue. To restore the default for each queue’s
minimum bandwidth value, use the no form of this command.
Syntax
cos-queue min-bandwidth
bw-0
bw-1
…
bw-n
no cos-queue min-bandwidth
•
bw-0
— Specifies the minimum transmission bandwidth guarantee for an
interface. You must specify as many bandwidth parameters as there are
COS queues (bw-0 through bw-n). (Range: 0–100 in increments of 5)
Default Configuration
By default, all CoS queues are configured with a 0% minimum bandwidth
guarantee.
Command Mode
Global Configuration mode or Interface Configuration (gigabitethernet,
port-channel, tengigabitethernet
,
fortygigabitethernet) mode
User Guidelines
The maximum number of queues supported per interface is seven. It is
recommended that the operator avoid the use of queue 5-7 in order to avoid
conflicts with inter- and intra-network control traffic.
In order to better accommodate bursty traffic, it is recommended that the
sum of the configured min-bandwidths be much less than 100%. Configuring
the minimum bandwidths such that they sum to 100% effectively locks the
scheduler such that bandwidth sharing by lower priority queues cannot be
accommodated under congestion conditions.
2CSNXXX_SWUM200.book Page 649 Tuesday, December 10, 2013 1:22 PM

650 QoS Commands
When ETS is operational on a switch, this command overrides the ETS
assignments and assigns minimum bandwidth constraints across traffic class
groups. This allows the administrator to ensure that the frame scheduler does
not completely starve lower priority groups when strict priority is enabled on a
high numbered TCG. Specifically, assigning a minimum bandwidth to a
lower numbered TCG, even when strict priority is enabled on a higher
numbered TCG, will alter the normal scheduler behavior and cause the
scheduler to process frames from the lower numbered TCG to conform to the
min-bandwidth constraint.
Example
The following example displays how to specify the minimum transmission
bandwidth guarantee for cos-queues 0 through 6.
console(config)#cos-queue min-bandwidth 5 5 10 10 0 0 0
cos-queue random-detect
Use the cos-queue random-detect command in Global Configuration or
Interface Configuration mode to enable WRED queue management policy
on an interface CoS queue. Use the no form of the command to disable
WRED policy for a CoS queue on an interface.
Syntax
cos-queue {random-detect
queue-id1
[
queue-id2
..
queue-idn
]}
no cos-queue {random-detect
queue-id1
[
queue-id2
..
queue-idn
]}
•
queue-id
—An integer indicating the queue-id which is to be enabled for
WRED. Range 0-6. Up to 7 queues may be simultaneously specified.
Default Configuration
WRED queue management policy is disabled by default. Tail-drop queue
management policy is enabled by default. The threshold for invoking tail-
drop behavior when WRED is disabled is approximately 1/2 of the remaining
free packet buffer in the switch.
2CSNXXX_SWUM200.book Page 650 Tuesday, December 10, 2013 1:22 PM

QoS Commands 651
Command Mode
Interface Configuration (physical or port-channel) mode or Global
Configuration mode
User Guidelines
When used on a port-channel, this command will override the settings on the
individual interfaces that are part of the port channel. Removing an interface
from the port channel restores the individual interface settings.
This command can be used in Interface Range mode.
Use the
cos-queue min-bandwidth
command to configure the minimum
bandwidth percentage guarantee for the CoS queues.
Use the
show interfaces random-detect
command to display the WRED
configuration.
Use the
policy-map
and
conform-color
commands to mark traffic with a color
other than default green color.
The drop probability scale supports values in the range 0-10% and the discrete
values 25%, 50%, 75%, and 100%. Other values are truncated to the next lower
value by the hardware.
Example
Enable WRED on the default CoS 0 queue for unmarked packets and set the
green, yellow, and red colored traffic to utilize WRED starting at 3% of port
congestion with a drop probability of 1%, 2% and 3%, respectively. In this
configuration, non-TCP traffic uses tail-drop queue discipline with a drop
threshold at 100% of the statically calculated port queue length vs. the
dynamically calculated value used by the normal tail-drop mechanism
(approx. 1/2 remaining free memory).
console(config)# cos-queue random-detect 0
console(config)# random-detect queue-parms 0 min-thresh 3 3 3 100 max-thresh
10 10 10 100 drop-prob-scale 1 2 3 0
2CSNXXX_SWUM200.book Page 651 Tuesday, December 10, 2013 1:22 PM

652 QoS Commands
cos-queue strict
Use the cos-queue strict command in either Global Configuration mode or
Interface Configuration mode to activate the strict priority scheduler mode
for each specified queue. To restore the default weighted scheduler mode for
each specified queue, use the no form of this command.
Syntax
cos-queue strict {
queue-id-1
} [{
queue-id-2
} … {
queue-id-n
}]
no cos-queue strict {
queue-id-1
} [{
queue-id-2
} … {
queue-id-n
}]
•
queue-id-1
— Specifies the queue ID for which you are activating the
strict priority scheduler. You can specify a queue ID for as many queues as
you have (queue-id 1 through queue-id-n). (Range: 0–6)
Default Configuration
This command has no default configuration.
Command Mode
Global Configuration mode or Interface Configuration (gigabitethernet,
port-channel, tengigabitethernet
,
fortygigabitethernet) mode
User Guidelines
Strict priority (SP) queues are scheduled in priority order ahead of WRR
queues. Strict priority queues are allocated unlimited bandwidth. Use the
cos-queue min-bandwidth command on lower priority SP and WRR queues
to ensure fairness to lower priority queues.
Example
The following example displays how to activate the strict priority scheduler
mode for two queues.
console(config)#cos-queue strict 1 2
The following example displays how to activate the strict priority scheduler
mode for three queues.
console(config)#cos-queue strict 1 2 4
2CSNXXX_SWUM200.book Page 652 Tuesday, December 10, 2013 1:22 PM

QoS Commands 653
diffserv
Use the diffserv command in Global Configuration mode to set the DiffServ
operational mode to active. While disabled, the DiffServ configuration is
retained and can be changed, but it is not activated. When enabled, DiffServ
services are activated. To set the DiffServ operational mode to inactive, use
the no form of this command.
Syntax
diffserv
no diffserv
Default Configuration
This command default is enabled.
Command Mode
Global Configuration mode
User Guidelines
This command has no user guidelines.
Example
The following example displays how to set the DiffServ operational mode to
active.
console(Config)#diffserv
drop
Use the drop command in Policy-Class-Map Configuration mode to specify
that all packets for the associated traffic stream are to be dropped at ingress.
Syntax
drop
Default Configuration
This command has no default configuration.
2CSNXXX_SWUM200.book Page 653 Tuesday, December 10, 2013 1:22 PM

654 QoS Commands
Command Mode
Policy-Class-Map Configuration mode
User Guidelines
This command has no user guidelines.
Example
The following example displays how to specify that matching packets are to
be dropped at ingress.
console(config-policy-classmap)#drop
mark cos
Use the mark cos command in Policy-Class-Map Configuration mode to
mark all packets for the associated traffic stream with the specified class of
service value in the priority field of the 802.1p header. If the packet does not
already contain this header, one is inserted.
Syntax
mark cos
cos-value
•
cos-value
— Specifies the CoS value as an integer. (Range: 0–7)
Default Configuration
There is no default cos-value for this command. Packets are not remarked by
default.
Command Mode
Policy-Class-Map Configuration mode
User Guidelines
This command has no user guidelines.
Example
The following example displays how to mark all packets with a CoS value.
console(config-policy-classmap)#mark cos 7
2CSNXXX_SWUM200.book Page 654 Tuesday, December 10, 2013 1:22 PM

QoS Commands 655
mark ip-dscp
Use the mark ip-dscp command in Policy-Class-Map Configuration mode to
mark all packets for the associated traffic stream with the specified IP DSCP
value.
Syntax
mark ip-dscp
dscpval
•
dscpval
— Specifies a DSCP value (10, 12, 14, 18, 20, 22, 26, 28, 30, 34, 36,
38, 0, 8, 16, 24, 32, 40, 48, 56, 46) or a DSCP keyword (af11, af12, af13,
af21, af22, af23, af31, af32, af33, af41, af42, af43, be, cs0, cs1, cs2, cs3, cs4,
cs5, cs6, cs7, ef).
Default Configuration
This command has no default configuration.
Command Mode
Policy-Class-Map Configuration mode
User Guidelines
This command has no user guidelines.
Example
The following example displays how to mark all packets with an IP DSCP
value of "cs4."
console(config-policy-classmap)#mark ip-dscp cs4
mark ip-precedence
Use the mark ip-precedence command in Policy-Class-Map Configuration
mode to mark all packets for the associated traffic stream with the specified
IP precedence value.
Syntax
mark ip-precedence
prec-value
•
prec-value
— Specifies the IP precedence value as an integer. (Range: 0–7)
2CSNXXX_SWUM200.book Page 655 Tuesday, December 10, 2013 1:22 PM

656 QoS Commands
Default Configuration
This command has no default configuration.
Command Mode
Policy-Class-Map Configuration mode
User Guidelines.
This command has no user guidelines.
Example
The following example displays
console(config)#policy-map p1 in
console(config-policy-map)#class c1
console(config-policy-classmap)#mark ip-precedence 2
console(config-policy-classmap)#
match class-map
Use the match class-map command to add to the specified class definition
the set of match conditions defined for another class. Use the no form of this
command to remove from the specified class definition the set of match
conditions defined for another class.
Syntax
match class-map
refclassname
no match class-map
refclassname
•
refclassname
— The name of an existing DiffServ class whose match
conditions are being referenced by the specified class definition.
Default Configuration
This command has no default configuration.
Command Mode
Class-Map Configuration mode
2CSNXXX_SWUM200.book Page 656 Tuesday, December 10, 2013 1:22 PM

QoS Commands 657
User Guidelines
• The parameters
refclassname
and
class-map-name
can not be the same.
• Only one other class may be referenced by a class.
• Any attempts to delete the
refclassname
class while the class is still
referenced by any
class-map-name
fails.
• The combined match criteria of
class-map-name
and
refclassname
must
be an allowed combination based on the class type.
• Any subsequent changes to the
refclassname
class match criteria must
maintain this validity, or the change attempt fails.
• The total number of class rules formed by the complete reference class
chain (including both predecessor and successor classes) must not exceed
a platform-specific maximum. In some cases, each removal of a refclass
rule reduces the maximum number of available rules in the class definition
by one.
Example
The following example adds match conditions defined for the Dell class to
the class currently being configured.
console(config-classmap)#match class-map Dell
The following example deletes the match conditions defined for the Dell
class from the class currently being configured.
console(config-classmap)#no match class-map Dell
match cos
Use the match cos command in Class-Map Configuration mode to add a
match condition for the class of service value (the only tag in a single-tagged
packet or the first or outer 802.1Q tag of a double-VLAN tagged packet).
Syntax
match cos
• cos-value — Specifies the CoS value as an integer (Range: 0–7)
Default Configuration
This command has no default configuration.
2CSNXXX_SWUM200.book Page 657 Tuesday, December 10, 2013 1:22 PM

658 QoS Commands
Command Mode
Class-Map Configuration mode
User Guidelines
This command has no user guidelines.
Example
The following example displays adding a match condition to the specified
class.
console(config-classmap)#match cos 1
match destination-address mac
Use the match destination-address mac command in Class-Map
Configuration mode to add a match condition based on the destination MAC
address of a packet.
Syntax
match destination-address mac
macaddr
macmask
•
macaddr
— Specifies any valid layer 2 MAC address formatted as six two-
digit hexadecimal numbers separated by colons.
•
macmask
— Specifies a valid layer 2 MAC address bit mask formatted as
six two-digit hexadecimal numbers separated by colons. This address bit
mask does not need to be contiguous.
Default Configuration
This command has no default configuration.
Command Mode
Class-Map Configuration mode
User Guidelines
This command has no user guidelines.
2CSNXXX_SWUM200.book Page 658 Tuesday, December 10, 2013 1:22 PM

QoS Commands 659
Example
The following example displays adding a match condition for the specified
MAC address and bit mask.
console(config-classmap)#match destination-address mac AA:ED:DB:21:11:06
FF:FF:FF:EF:EE:EE
match dstip
Use the match dstip command in Class-Map Configuration mode to add a
match condition based on the destination IP address of a packet.
Syntax
match dstip
ipaddr
ipmask
•
ipaddr
— Specifies a valid IP address.
•
ipmask
— Specifies a valid IP address bit mask. Note that even though this
parameter is similar to a standard subnet mask, it does not need to be
contiguous.
Default Configuration
This command has no default configuration.
Command Mode
Class-Map Configuration mode
User Guidelines
This command has no user guidelines.
Example
The following example displays adding a match condition using the specified
IP address and bit mask.
console(config-classmap)#match dstip 10.240.1.1 10.240.0.0
match dstip6
The match dstip6 command adds a match condition based on the
destination IPv6 address of a packet.
2CSNXXX_SWUM200.book Page 659 Tuesday, December 10, 2013 1:22 PM

660 QoS Commands
Syntax
match dstip6
destination-ipv6-prefix/prefix-length
•
destination-ipv6-prefix
—IPv6 prefix in IPv6 global address format.
•
prefix-length
—IPv6 prefix length value.
Default Configuration
There is no default configuration for this command.
Command Mode
Ipv6-Class-Map Configuration mode.
User Guidelines
There are no user guidelines for this command.
Example
console(config-classmap)#match dstip6 2001:DB8::/32
match dstl4port
Use the match dstl4port command in Class-Map Configuration mode to add
a match condition based on the destination layer 4 port of a packet using a
single keyword or a numeric notation.
Syntax
match dstl4port {
portkey
|
port-number
}
•
portkey
— Specifies one of the supported port name keywords. A match
condition is specified by one layer 4 port number. The currently supported
values are: domain, echo, ftp, ftpdata, http, smtp, snmp, telnet, tftp, and
www.
•
port-number
— Specifies a layer 4 port number (Range: 0–65535).
Default Configuration
This command has no default configuration.
2CSNXXX_SWUM200.book Page 660 Tuesday, December 10, 2013 1:22 PM

QoS Commands 661
Command Mode
Class-Map Configuration mode
User Guidelines
This command has no user guidelines.
Example
The following example displays adding a match condition based on the
destination layer 4 port of a packet using the "echo" port name keyword.
console(config-classmap)#match dstl4port echo
match ethertype
Use the match ethertype command in Class-Map Configuration mode to add
a match condition based on the value of the ethertype.
Syntax
match ethertype {keyword |
0x0600-0xffff
}
•
keyword
— Specifies either a valid keyword or a valid hexadecimal number.
The supported keywords are
appletalk
,
arp, ibmsna
,
ipv4, ipv6
,
ipx
,
mplsmcast
,
mplsucast
,
netbios
,
novell
,
pppoe
,
rarp
. (Range:
0x0600–0xFFFF)
Default Configuration
This command has no default configuration.
Command Mode
Class-Map Configuration mode
User Guidelines
This command has no user guidelines.
Example
The following example displays how to add a match condition based on
ethertype.
2CSNXXX_SWUM200.book Page 661 Tuesday, December 10, 2013 1:22 PM

662 QoS Commands
console(config-classmap)#match ethertype arp
match ip6flowlbl
The match ip6flowlbl command adds to the specified class definition a
match condition based on the IPv6 flow label of a packet.
Syntax
match ip6flowlbl
label
•
label
- The value to match in the Flow Label field of the IPv6 header
(Range 0-1048575).
Default Configuration
There is no default configuration for this command.
Command Mode
Ipv6-Class-Map Configuration mode.
User Guidelines
There are no user guidelines for this command.
Example
The following example adds a rule to match packets whose IPv6 Flow Label
equals 32312.
console(config-classmap)#match ip6flowlbl 32312
match ip dscp
Use the match ip dscp command in Class-Map Configuration mode to add to
the specified class definition a match condition based on the value of the IP
DiffServ Code Point (DSCP) field in a packet. This field is defined as the
high-order six bits of the Service Type octet in the IP header. The low-order
two bits are not checked.
Syntax
match ip dscp
dscpval
2CSNXXX_SWUM200.book Page 662 Tuesday, December 10, 2013 1:22 PM

QoS Commands 663
•
dscpval
— Specifies an integer value or a keyword value for the DSCP
field. (Integer Range: 0–63) (Keyword Values:
af11
,
af12
,
af13
,
af21
,
af22
,
af23
,
af31
,
af32
,
af33
,
af41
,
af42
,
af43
,
be
,
cs0
,
cs1
,
cs2
,
cs3
,
cs4
,
cs5
,
cs6
,
cs7
,
ef
)
Default Configuration
This command has no default configuration.
Command Mode
Class-Map Configuration mode
User Guidelines
The ip dscp, ip precedence, and ip tos match conditions are alternative ways
to specify a match criterion for the same Service Type field in the IP header
but with a slightly different user notation.
To specify a match on all DSCP values, use the match ip tos
tosbits tosmask
command with tosbits set to "0" (zero) and tosmask set to hex "03."
Example
The following example displays how to add a match condition based on the
DSCP field.
console(config-classmap)# match ip dscp 3
match ip precedence
Use the match ip precedence command in Class-Map Configuration mode to
add to the specified class definition a match condition based on the value of
the IP precedence field.
Syntax
match ip precedence
precedence
•
precedence
— Specifies the precedence field in a packet. This field is the
high-order three bits of the Service Type octet in the IP header. (Integer
Range: 0–7)
2CSNXXX_SWUM200.book Page 663 Tuesday, December 10, 2013 1:22 PM

664 QoS Commands
Default Configuration
This command has no default configuration.
Command Mode
Class-Map Configuration mode
User Guidelines
The ip dscp, ip precedence, and ip tos match conditions are alternative ways
to specify a match criterion for the same Service Type field in the IP header
but with a slightly different user notation.
To specify a match on all precedence values, use the match ip tos
tosbits
tosmask
command with tosbits set to "0" (zero) and tosmask set to hex "1F."
Example
The following example displays adding a match condition based on the value
of the IP precedence field.
console(config-classmap)#match ip precedence 1
match ip tos
Use the match ip tos command in Class-Map Configuration mode to add to
the specified class definition a match condition based on the value of the IP
TOS field in a packet. This field is defined as all eight bits of the Service Type
octet in the IP header.
Syntax
match ip tos
tosbits
tosmask
•
tosbits
— Specifies a two-digit hexadecimal number. (Range: 00–ff)
•
tosmask
— Specifies the bit positions in the tosbits parameter that are
used for comparison against the IP TOS field in a packet. This value of this
parameter is expressed as a two-digit hexadecimal number. (Range: 00–ff)
Default Configuration
This command has no default configuration.
2CSNXXX_SWUM200.book Page 664 Tuesday, December 10, 2013 1:22 PM

QoS Commands 665
Command Mode
Class-Map Configuration mode
User Guidelines
The ip dscp, ip precedence, and ip tos match conditions are alternative ways
to specify a match criterion for the same Service Type field in the IP header
but with a slightly different user notation.
This specification is the
free form
version of the IP DSCP/Precedence/TOS
match specification in that you have complete control of specifying which
bits of the IP Service Type field are checked.
Example
The following example displays adding a match condition based on the value
of the IP TOS field in a packet.
console(config-classmap)#match ip tos AA EF
match protocol
Use the match protocol command in Class-Map Configuration mode to add
to the specified class definition a match condition based on the value of the
IP Protocol field in a packet using a single keyword notation or a numeric
value notation.
Syntax
match protocol {
protocol-name
|
protocol-number
}
•
protocol-name
— Specifies one of the supported protocol name keywords.
The supported values are
icmp
,
igmp
,
ip
,
tcp
, and
udp
.
•
protocol-number
— Specifies the standard value assigned by IANA.
(Range 0–255)
Default Configuration
This command has no default configuration.
Command Mode
Class-Map Configuration mode
2CSNXXX_SWUM200.book Page 665 Tuesday, December 10, 2013 1:22 PM

666 QoS Commands
User Guidelines
This command has no user guidelines.
Example
The following example displays adding a match condition based on the "ip"
protocol name keyword.
console(config-classmap)#match protocol ip
match source-address mac
Use the match source-address mac command in Class-Map Configuration
mode to add to the specified class definition a match condition based on the
source MAC address of the packet.
Syntax
match source-address mac
address
macmask
•
macaddr
— Specifies any valid layer 2 MAC address formatted as six two-
digit hexadecimal numbers separated by colons.
•
macmask
— Specifies a layer 2 MAC address bit mask formatted as six
two-digit hexadecimal numbers separated by colons. This bit mask does
not need to be contiguous.
Default Configuration
This command has no default configuration.
Command Mode
Class-Map Configuration mode
User Guidelines
This command has no user guidelines.
Example
The following example adds to the specified class definition a match
condition based on the source MAC address of the packet.
2CSNXXX_SWUM200.book Page 666 Tuesday, December 10, 2013 1:22 PM

QoS Commands 667
console(config-classmap)# match source-address mac 10:10:10:10:10:10
11:11:11:11:11:11
match srcip
Use the match srcip command in Class-Map Configuration mode to add to
the specified class definition a match condition based on the source IP
address of a packet.
Syntax
match srcip
ipaddr
ipmask
•
ipaddr
— Specifies a valid IP address.
•
ipmask
— Specifies a valid IP address bit mask. Note that although this IP
address bit mask is similar to a subnet mask, it does not need to be
contiguous.
Default Configuration
This command has no default configuration.
Command Mode
Class-Map Configuration mode
User Guidelines
Only one srcip matching criteria can be specified. To remove the matching
criteria, delete the class map.
Example
The following example displays adding a match condition for the specified IP
address and address bit mask.
console(config-classmap)#match srcip 10.240.1.1 10.240.0.0
match srcip6
The match srcip6 command adds to the specified class definition a match
condition based on the source IPv6 address of a packet.
2CSNXXX_SWUM200.book Page 667 Tuesday, December 10, 2013 1:22 PM

668 QoS Commands
Syntax
match srcip6
source-ipv6-prefix/prefix-length
•
source-ipv6-prefix
—IPv6 prefix in IPv6 global address format.
•
prefix-length
—IPv6 prefix length value.
Default Configuration
There is no default configuration for this command.
Command Mode
Ipv6-Class-Map Configuration mode.
User Guidelines
There are no user guidelines for this command.
Example
console(config-classmap)#match srcip6 2001:DB8::/32
match srcl4port
Use the match srcl4port command in Class-Map Configuration mode to add
to the specified class definition a match condition based on the source layer 4
port of a packet using a single keyword or a numeric notation.
Syntax
match srcl4port {
portkey
|
port-number
}
•
portkey
— Specifies one of the supported port name keywords. A match
condition is specified by one layer 4 port number. The currently supported
values are: domain, echo, ftp, ftpdata, http, smtp, snmp, telnet, tftp, and
www.
•
port-number
— Specifies a layer 4 port number (Range: 0–65535).
Default Configuration
This command has no default configuration.
2CSNXXX_SWUM200.book Page 668 Tuesday, December 10, 2013 1:22 PM

QoS Commands 669
Command Mode
Class-Map Configuration mode
User Guidelines
Only one srcl4port matching criteria can be specified. To remove the
matching criteria, delete the class map.
Example
The following example displays how to add a match condition using the
"snmp" port name keyword.
console(config-classmap)#match srcl4port snmp
match vlan
Use the match vlan command in Class-Map Configuration mode to add to
the specified class definition a match condition based on the value of the
layer 2 VLAN Identifier field. This field is the only tag in a single tagged
packet or the first or outer tag of a double VLAN packet.
Syntax
match vlan
vlan-id
•
vlan-id
— Specifies a VLAN ID as an integer. (Range: 0–4095)
Default Configuration
This command has no default configuration.
Command Mode
Class-Map Configuration mode
User Guidelines
Only a single VLAN can be specified for each class map. To remove the
matching criteria, delete the class map.
2CSNXXX_SWUM200.book Page 669 Tuesday, December 10, 2013 1:22 PM

670 QoS Commands
Example
The following example displays adding a match condition for the VLAN ID
"2."
console(config-classmap)#match vlan 2
mirror
Use the mirror command in Policy-Class-Map Configuration mode to mirror
all the data that matches the class defined to the destination port specified.
Syntax
mirror
interface
•
interface
— Specifies the Ethernet port to which data needs to be copied.
Default Configuration
This command has no default configuration.
Command Mode
Policy-Class-Map Configuration mode
User Guidelines
The port identified in this command is identical to the destination port of the
monitor command.
Example
The following example displays how to copy all the data to port 1/0/5.
console(config-policy-classmap)#mirror 1/0/5
police-simple
Use the police-simple command in Policy-Class-Map Configuration mode to
applying a policing meter for the specified class. The simple form of the
police command uses a single data rate and burst size, resulting in two
outcomes: conform and violate. Conforming packets are colored green and
non-conforming packets are colored red for use by the WRED mechanism.
2CSNXXX_SWUM200.book Page 670 Tuesday, December 10, 2013 1:22 PM

QoS Commands 671
Syntax
police-simple {
datarate
burstsize
conform-action {drop | set-prectransmit
cos
| set-dscp-transmit
dscpval
| transmit} [violate-action {drop | set-cos-
transmit
cos
| set-prec-transmit
cos
| set-dscp-transmit
dscpval
|
transmit}]}
•
datarate
— Data rate in kilobits per second (kbps). (Range:
1–4294967295)
•
burstsize
— Burst size in Kbytes (Range: 1–128)
•
conform action
— Indicates what happens when the packet is conforming
to the policing rule: it could be dropped, it could have its COS modified, it
could have its IP precedence modified, or it could have its DSCP
modified. The same actions are available for packets that violate the
policing rule.
•
cos
— Class of Service value. (Range: 0–7)
• dscpval — DSCP value. (Range: 0–63 or a keyword from this list:
af11
,
af12
,
af13
,
af21
,
af22
,
af23
,
af31
,
af32
,
af33
,
af41
,
af42
,
af43
,
be
,
cs0
,
cs1
,
cs2
,
cs3
,
cs4
,
cs5
,
cs6
,
cs7
,
ef
)
Default Configuration
This command has no default configuration.
Command Mode
Policy-Class-Map Configuration mode
User Guidelines
Only one style of police command (simple or two-rate) is allowed for a given
class instance in a particular policy. The
conform-color
command can be used
to precolor packets prior to policing. Packets precolored red are not recolored
by the policer.
Example
The following example configures a single rate ingress meter with packets
received at a rate below 1000 Kbps and 4096 byte burst size are transmitted
and packets above that rate are dropped. The transmitted packets are colored
green should the operator desire to configure a WRED drop policy.
2CSNXXX_SWUM200.book Page 671 Tuesday, December 10, 2013 1:22 PM

672 QoS Commands
console(config-policy-classmap)#police-simple 1000 64 conform-action
transmit violate-action drop
police-single-rate
Use the police-single-rate command to implement a single-rate Three Color
Market (srTCM) per RFC 2697. An srTCM meters a traffic stream and colors
packets according to three parameters: Committed Information Rate (CIR),
Committed Burst Size (CBS), and Peak Burst Size (PBS). A packet is colored
red if it exceeds the CBS and the PBS, yellow if it exceeds the CBS, and green
if it exceeds neither. An srTCM is useful in situations where only the length of
the burst, but not the peak rate, determines the service assignment.
Syntax
police-single-rate
datarate burstsize excess-burstsize
conform-action
action
exceed-action
action
violate-action
action
•
datarate
—Data rate in kilobits per second (Kbps). (Range 1-4294967295)
•
burstsize
—Burst size in kilobits per seconds (Kbps). (Range 1-128)
•
excess-burstsize
—Excess burst size in kilobits per seconds (Kbps). (Range
1-128)
•
action
—The action to take according to the color. Select one:
–
drop
: Drop the packet.
–
set-prec-transmit
ip-prec
: Remark the IP precedence in the packet to
ip-prec
and transmit. (Range 0-7)
–
set-dscp-transmit
dscp-val
: Remark the DSCP in the packet to
dscp-
val
and transmit. (Range 0-63)
–
set-cos-transmit
802.1p-priority
: Remark the 802.1p priority in the
packet to
802.1p-priority
and transmit. (Range 0-7)
–
transmit
: Transmit the packet unmodified.
Default Configuration
There no default configuration for this command.
Command Modes
Policy-Class-Map Configuration mode
2CSNXXX_SWUM200.book Page 672 Tuesday, December 10, 2013 1:22 PM

QoS Commands 673
User Guidelines
The CIR is measured in Kbps, the CBS in Kbytes, and the PBS in Kbytes. It is
recommended that the CBS and PBS be configured to be larger than the
largest expected IP packet. A class command in policy-map mode must be
issued for an existing class-map before entering this command.
Example
console#police-single-rate 100000000 32 64 conform-action set-cos-transmit 7
exceed-action set-prec-transmit 7 violate-action drop
police-two-rate
Use the police-two-rate command to implement a two-rate Three Color
Market (trTCM) per RFC 2698. A trTCM meters a traffic stream and colors
packets according to four parameters:
Committed Information Rate (CIR)
Committed Burst Size (CBS)
Peak Information Rate (PIR)
Peak Burst Size (PBS)
A packet is colored red if it exceeds the PIR, yellow if it exceeds the CIR, and
green if it does not exceed either. A trTCM is useful when a peak rate needs to
be enforced separately from a committed rate.
Syntax
police-two-rate
datarate burstsize peak-data-rate excess-burstsize
conform-
action
action
exceed-action
action
violate-action
action
•
datarate
— Data rate in kilobits per second (kbps). (Range:
1–4294967295)
•
burstsize
— Burst size in Kbytes (Range: 1–128)
•
peak-data-rate
— Peak data rate in kilobits per second (kbps). (Range 1-
4294967295)
•
excess-burstsize
— Excess burst size in kilobits per seconds (kbps). (Range
1-128)
•
action
— The action to take according to the color. Select one of:
– drop— Drop the packet.
2CSNXXX_SWUM200.book Page 673 Tuesday, December 10, 2013 1:22 PM

674 QoS Commands
–
set-prec-transmit
ip-prec
— Remark the IP precedence in the packet to
ip-prec
and transmit. (Range 0-7)
–
set-dscp-transmit
dscp-val
— Remark the DSCP in the packet to
dscp-
val
and transmit. (Range 0-63)
–
set-cos-transmit
802.1p-priority
— Remark the 802.1p priority in the
packet to
802.1p-priority
and transmit. (Range 0-7)
– transmit— Transmit the packet unmodified.
Default Configuration
This command has no default configuration.
Command Mode
Policy-Class-Map Configuration mode
User Guidelines
The CIR and PIR are measured in Kbps (not pps as indicated in the RFC),
the CBS in Kbytes, and the PBS in Kbytes. It is recommended that the CBS
and PBS be configured to be larger than the largest expected IP packet. A
class command in policy-map mode must be issued for an existing class-map
before entering this command.
Example
console#police-two-rate 100000000 64 1000000000 32 conform-action set-cos-
transmit 7 exceed-action set-prec-transmit 7 violate-action drop
policy-map
Use the policy-map command in Global Configuration mode to establish a
new DiffServ policy or to enter policy map configuration mode. To remove
the policy, use the no form of this command.
Syntax
policy-map
policyname
[in|out]
no policy-map
policyname
2CSNXXX_SWUM200.book Page 674 Tuesday, December 10, 2013 1:22 PM

QoS Commands 675
•
policyname
— Specifies the DiffServ policy name as a unique case-
sensitive alphanumeric string of characters. (Range: 1–31 alphanumeric
characters.)
•
in
—The policy is applied on ingress. Must be specified to create new
DiffServ policies. An existing policy can be selected without specifying "in"
or "out".
•
out
—The policy is applied on egress. Either "in" or "out" must be specified
to create a new DiffServ policy. An existing policy may be selected without
the "in" or "out" parameter.
Default Configuration
This command has no default configuration.
Command Mode
Global Configuration mode
User Guidelines
The CLI mode is changed to Policy-Class-Map Configuration when this
command is successfully executed.
The policy type dictates which of the individual policy attribute commands
are valid within the policy definition.
Example
The following example shows how to establish a new ingress DiffServ policy
named "DELL."
console(config)#policy-map DELL in
console(config-policy-classmap)#
random-detect queue-parms
Use the random-detect queue-parms command to configure the WRED
green, yellow and red TCP and non-TCP packet minimum and maximum
thresholds and corresponding drop probabilities on an interface or all
interfaces.
2CSNXXX_SWUM200.book Page 675 Tuesday, December 10, 2013 1:22 PM
676 QoS Commands
Syntax
random-detect queue-parms
queue-id
[queue-id] ... min-thresh
minthresh-
green minthresh-yellow minthresh-red minthresh-nontcp
max-thresh
max-
thresh-green max-thresh-yellow max-thresh-red maxthresh-nontcp
no random-detect queue-parms
queue-id
[queue-id] ...
•
queue-id
—The class of service queue. Range 0 to 6.
•
min-thresh
—The minimum threshold at which to begin dropping, based
on the configured maximum drop probability for each color and for non-
TCP packets. Range 0 to 100.
•
max-thresh
—The maximum threshold to ene dropping at the configured
maximum drop probability for each color and for non-TCP packets. Range
0 to 100.
•
drop-prob-scale
—The maximum drop probability. Range 0-100.
Default Configuration
The table below shows the default green, yellow, and red TCP and non-TCP
minimum/maximum drop thresholds and the green, yellow and red TCP and
non-TCP drop probabilities.
Command Mode
Global Configuration mode, Interface Configuration mode (physical and
port-channel), Interface Range mode
Queue ID WRED Minimum
Threshold
WRED Maximum
Threshold
WRED Drop Probability
Scale
0 40/30/20/100 100/ 90/ 80/100 10/ 10/ 10/ 10
1 40/30/20/100 100/ 90/ 80/100 10/ 10/ 10/ 10
2 40/30/20/100 100/ 90/ 80/100 10/ 10/ 10/ 10
3 40/30/20/100 100/ 90/ 80/100 10/ 10/ 10/ 10
4 40/30/20/100 100/ 90/ 80/100 10/ 10/ 10/ 10
5 40/30/20/100 100/ 90/ 80/100 10/ 10/ 10/ 10
6 40/30/20/100 100/ 90/ 80/100 10/ 10/ 10/ 10
2CSNXXX_SWUM200.book Page 676 Tuesday, December 10, 2013 1:22 PM

QoS Commands 677
User Guidelines
The Green/Yellow/Red Ranges may overlap and are applied to each color
independently. Within a color, the range from minimum to maximum is
divided into eight (0...7) fixed probabilities at which packets are dropped
based on the instantaneous egress queue size:
0 - 6.25% of maximum drop probability
1 - 18.75% of maximum drop probability
2 - 30.25% of maximum drop probability
3 - 43.75% of maximum drop probability
4 - 56.25% of maximum drop probability
5 - 68.75% of maximum drop probability
6 - 81.25% of maximum drop probability
7 - 92.75% of maximum drop probability
Packets are dropped at 100% when the queue size exceeds the maximum
value and at 0% when the queue size is below the minimum value.
Configuring a queue with a drop probability of 0% effectively applies tail-drop
behavior when the queue length exceeds the maximum threshold.
If the max thresh parameter is less than the corresponding min-thresh
parameter, it is adjusted to be the min-thresh plus one.
Example
This example configures interface te2/0/1 to drop packets queued for egress
on the all interfaces (global config) or a single interface (interface config)
with a piecewise linear approximation of the configured probability when the
average queue size is within the given range:
• TCP Green Range: 5 to 15% - 1% maximum drop probability
• TCP Yellow Range: 10% to 25% - 2% maximum drop probability
• TCP Red Range: 15% to 50% - 3% maximum drop probability
• Non-TCP traffic: 50 to 98% - 25% maximum drop probability
console(config-if-Te2/0/1)#random-detect queue-parms 0 min-thresh 5 10 15 50
max-thresh 15 25 50 98 drop-prob-scale 1 2 3 25
2CSNXXX_SWUM200.book Page 677 Tuesday, December 10, 2013 1:22 PM

678 QoS Commands
random-detect exponential-weighting-constant
Use the random-detect exponential-weighting-constant command to
configure the decay in the calculation of the average queue size user for
WRED on an interface or all interfaces.
Syntax
random-detect exponential-weighting-constant
0-15
no random-detect exponential-weighting-constant
•
0–15
— The weighting constant is used to smooth the calculation of the
queue size using the following formula where the 0-15 value is N.
Default Configuration
The default value is 15.
Command Mode
Global Configuration mode, Interface Configuration mode (physical and
port-channel), Interface Range mode
User Guidelines
To use the instantaneous queue size in the calculation of WRED drops, set
the weighting constant to 0. Larger values of N reduce the effect of
instantaneous changes. To update the current queue size to ½ the difference
between the previous size and the current instantaneous queue size, set the
weighting constant to 1. To update the current queue size to 1/4 the
difference between the previous size and the current instantaneous queue
size, set the weighting constant to 2, ....
redirect
Use the redirect command in Policy-Class-Map Configuration mode to
specify that all incoming packets for the associated traffic stream are
redirected to a specific egress interface (physical port or port-channel).
Syntax
redirect
interface
2CSNXXX_SWUM200.book Page 678 Tuesday, December 10, 2013 1:22 PM

QoS Commands 679
•
interface
— Specifies any valid interface. Interface is Ethernet port or
port-channel (Range: po1-po32 or gi1/0/1-gi1/0/24)
Default Configuration
This command has no default configuration.
Command Mode
Policy-Class-Map Configuration mode
User Guidelines
This command has no user guidelines.
Example
The following example shows how to redirect incoming packets to port 1/0/1.
console(config-policy-classmap)#redirect 1/0/1
service-policy
Use the service-policy command in either Global Configuration mode (for all
system interfaces) or Interface Configuration mode (for a specific interface)
to attach a policy to an interface. To return to the system default, use the no
form of this command.
Syntax
service-policy {in|out}
policymapname
no service-policy {in|out}
policymapname
•
policymapname
—Specifies the DiffServ policy name as a unique case-
sensitive alphanumeric string. (Range: 1–31 alphanumeric characters.)
•
in
—Apply the policy on ingress.
•
out
—Apply the policy on egress.
Default Configuration
This command has no default configuration.
2CSNXXX_SWUM200.book Page 679 Tuesday, December 10, 2013 1:22 PM

680 QoS Commands
Command Mode
Global Configuration mode (for all system interfaces)
Interface Configuration (Ethernet, Port-channel) mode (for a specific
interface)
User Guidelines
This command enables DiffServ on an interface. No separate interface
administrative mode command for DiffServ is available. Use the policy-map
command to configure the DiffServ policy. The service-policy direction must
catch the direction given for the policy map.
Ensure that no attributes within the policy definition exceed the capabilities
of the interface. When a policy is attached to an interface successfully, any
attempt to change the policy definition, such that it would result in a
violation of the interface capabilities, causes the policy change attempt to
fail. ACLs and DiffServ policies may not both exist on the same interface in
the same direction.
Example
The following example shows how to attach a service policy named "DELL" to
all interfaces.
console(config)#service-policy DELL
show class-map
Use the show class-map command in Privileged EXEC mode to display all
configuration information for the specified class.
Syntax
show class-map [
classname
]
•
classname
— Specifies the valid name of an existing DiffServ class.
(Range: 1–31 characters)
Default Configuration
This command has no default configuration.
2CSNXXX_SWUM200.book Page 680 Tuesday, December 10, 2013 1:22 PM

QoS Commands 681
Command Mode
Privileged EXEC mode, Configuration mode and all Configuration submodes
User Guidelines
This command has no user guidelines.
Example
The following example displays all the configuration information for the class
named "Dell".
console#show class-map
Class L3
Class Name Type Proto Reference Class Name
------------------------------- ----- ----- -----------------------------
ipv4 All ipv4
ipv6 All ipv6
stop_http_class All ipv6
match_icmp6 All ipv6
console#show class-map ipv4
Class Name..................................... ipv4
Class Type..................................... All
Class Layer3 Protocol.......................... ipv4
Match Criteria Values
---------------------------- -------------------------------------
Source IP Address 2.2.2.2 (255.255.255.0)
console#show class-map stop_http_class
Class Name..................................... stop_http_class
Class Type..................................... All
Class Layer3 Protocol.......................... ipv6
Match Criteria Values
---------------------------- -------------------------------------
Source IP Address 2001:DB8::/32
Source Layer 4 Port 80(http/www)
2CSNXXX_SWUM200.book Page 681 Tuesday, December 10, 2013 1:22 PM

682 QoS Commands
show classofservice dot1p-mapping
Use the show classofservice dot1p-mapping command in Privileged EXEC
mode to display the current Dot1p (802.1p) priority mapping to internal
traffic classes for a specific interface.
Syntax
show classofservice dot1p-mapping [{gigabitethernet unit/slot/port |
port-
channel
port-channel-number
| tengigabitethernet unit/slot/port
|
fortygigabitethernet unit/slot/port}]
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC mode, Configuration mode and all Configuration submodes
User Guidelines
If the interface is specified, the 802.1p mapping table of the interface is
displayed. If omitted, the most recent global configuration settings are
displayed.
The following table lists the parameters in the example and gives a
description of each.
Example
The following example displays the dot1p traffic class mapping and user
priorities.
console#show classofservice dot1p-mapping
User Priority Traffic Class
------------- ---------------
01
Parameter Description
User Priority The 802.1p user priority value.
Traffic Class The traffic class internal queue identifier to which
the user priority value is mapped.
2CSNXXX_SWUM200.book Page 682 Tuesday, December 10, 2013 1:22 PM

QoS Commands 683
11
26
34
43
54
65
76
show classofservice ip-dscp-mapping
Use the show classofservice ip-dscp-mapping command in Privileged EXEC
mode to display the current IP DSCP mapping to internal traffic classes for a
specific interface.
Syntax
show classofservice ip-dscp-mapping
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC mode, Configuration mode and all Configuration submodes
User Guidelines
Command is supported only globally.
Example
console#show classofservice ip-dscp-mapping
IP DSCP Traffic Class
------------- -------------
0(be/cs0 1
11
21
31
41
51
61
71
8(cs1) 0
90
2CSNXXX_SWUM200.book Page 683 Tuesday, December 10, 2013 1:22 PM

684 QoS Commands
10(af11) 0
11 0
12(af12) 0
13 0
14(af13) 0
15 0
16(cs2) 0
17 0
18(af21) 0
19 0
--More-- or (q)uit
20(af22) 0
21 0
22(af23) 0
23 0
24(cs3) 1
25 1
26(af31) 1
27 1
28(af32) 1
29 1
30(af33) 1
31 1
32(cs4) 2
33 2
34(af41) 2
35 2
36(af42) 2
37 2
38(af43) 2
39 2
40(cs5) 2
41 2
42 2
--More-- or (q)uit
43 2
44 2
45 2
46(ef) 2
47 2
48(cs6) 3
49 3
50 3
51 3
52 3
53 3
54 3
2CSNXXX_SWUM200.book Page 684 Tuesday, December 10, 2013 1:22 PM

QoS Commands 685
55 3
56(cs7) 3
57 3
58 3
59 3
60 3
61 3
62 3
63 3
console#
show classofservice trust
Use the show classofservice trust command in Privileged EXEC mode to
display the current trust mode setting for a specific interface.
Syntax
show classofservice trust [{gigabitethernet unit/slot/port|
port-channel
port-
channel-number
| tengigabitethernet unit/slot/port
|
fortygigabitethernet
unit/slot/port}]
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC mode, Configuration mode and all Configuration submodes
User Guidelines
If the interface is specified, the port trust mode of the interface is displayed.
If omitted, the port trust mode for global configuration is shown.
Example
The following example displays the current trust mode settings for the
specified port.
console#show classofservice trust 1/0/2
Class of Service Trust Mode: Dot1P
2CSNXXX_SWUM200.book Page 685 Tuesday, December 10, 2013 1:22 PM

686 QoS Commands
show diffserv
Use the show diffserv command in Privileged EXEC mode to display the
DiffServ general information, which includes the current administrative
mode setting as well as the current and maximum number of DiffServ
components.
Syntax
show diffserv
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC mode, Configuration mode and all Configuration submodes
User Guidelines
This command has no user guidelines.
Example
The following example displays the DiffServ information.
console#show diffserv
DiffServ Admin mode.......................... Enable
Class Table Size Current/Max................. 5 / 25
Class Rule Table Size Current/Max............ 6 / 150
Policy Table Size Current/Max................ 2 / 64
Policy Instance Table Size Current/Max....... 2 / 640
Policy Attribute Table Size Current/Max...... 2 / 1920
Service Table Size Current/Max............... 26 / 214
show diffserv service interface
Use this command in Privileged EXEC mode to display policy service
information for the specified interface.
2CSNXXX_SWUM200.book Page 686 Tuesday, December 10, 2013 1:22 PM

QoS Commands 687
Syntax
show diffserv service interface {gigabitethernet unit/slot/port|
tengigabitethernet unit/slot/port
|
fortygigabitethernet unit/slot/port}
{in|out}
•
in
—Show ingress policies.
•
out
—Show egress policies.
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC, Configuration mode and all Configuration submodes
User Guidelines
This command has no user guidelines.
Example
console#show diffserv service interface gigabitethernet 1/0/1 in
DiffServ Admin Mode........................... Enable
Interface..................................... 1/0/1
Direction..................................... In
No policy is attached to this interface in this direction.
show diffserv service interface port-channel
Syntax
show diffserv service interface port-channel
channel-group
{in|out}
•
channel-group
— A valid port-channel in the system. (Range: 1–18)
•
in
—Show ingress policies.
•
out
—Show egress policies.
Default Configuration
This command has no default configuration.
2CSNXXX_SWUM200.book Page 687 Tuesday, December 10, 2013 1:22 PM

688 QoS Commands
Command Mode
Privileged EXEC, Configuration mode and all Configuration submodes
User Guidelines
Not applicable
Example
console#show diffserv service interface port-channel 1 in
DiffServ Admin Mode........................... Enable
Interface..................................... po1
Direction..................................... In
No policy is attached to this interface in this direction
show diffserv service brief
Use the show diffserv service brief command in Privileged EXEC mode to
display all interfaces in the system to which a DiffServ policy has been
attached.
Syntax
show diffserv service brief
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC mode, Configuration mode and all Configuration submodes
User Guidelines
This command has no user guidelines.
Example
The following example shows how to display all interfaces in the system to
which a DiffServ policy has been attached.
console# show diffserv service brief
Interface Direction OperStatus Policy Name
2CSNXXX_SWUM200.book Page 688 Tuesday, December 10, 2013 1:22 PM

QoS Commands 689
----------- ----------- ------------ -------------------
1/0/1 in Down DELL
show interfaces cos-queue
Use the show interfaces cos-queue command in Privileged EXEC mode to
display the class-of-service queue configuration for the specified interface.
Syntax
show interfaces cos-queue [{gigabitethernet unit/slot/port |
port-channel
port-channel-number
| tengigabitethernet unit/slot/port |
fortygigabitethernet unit/slot/port}]
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC mode, Configuration mode and all Configuration submodes
User Guidelines
If the interface is specified, the class-of-service queue configuration of the
interface is displayed. If omitted, the most recent global configuration
settings are displayed.
Examples
The following example displays the COS configuration with no unit/slot/port
or port-channel parameter.
console#show interfaces cos-queue
Global Configuration
Interface Shaping Rate......................... 0
Queue Id Min. Bandwidth Scheduler Type Queue Management Type
-------- -------------- -------------- --------------
0 0 Weighted Tail Drop
1 0 Weighted Tail Drop
2 0 Weighted Tail Drop
3 0 Weighted Tail Drop
4 0 Weighted Tail Drop
2CSNXXX_SWUM200.book Page 689 Tuesday, December 10, 2013 1:22 PM
690 QoS Commands
5 0 Weighted Tail Drop
6 0 Weighted Tail Drop
This example displays the COS configuration for the specified interface 1/0/1.
console#show interfaces cos-queue gigabitethernet 1/0/1
Interface...................................... 1/0/1
Interface Shaping Rate......................... 0
Queue Id Min. Bandwidth Scheduler Type Queue Management Type
-------- -------------- -------------- --------------
0 0 Weighted Tail Drop
1 0 Weighted Tail Drop
2 0 Weighted Tail Drop
3 0 Weighted Tail Drop
4 0 Weighted Tail Drop
5 0 Weighted Tail Drop
6 0 Weighted Tail Drop
The following table lists the parameters in the examples and gives a
description of each.
Parameter Description
Interface The port of the interface. If displaying the global
configuration, this output line is replaced with a
global configuration indication.
Intf Shaping Rate The maximum transmission bandwidth limit for
the interface as a whole. It is independent of any
per-queue maximum bandwidth values in effect
for the interface. This value is a configured value.
Queue Mgmt Type The queue depth management technique used for
all queues on this interface.
Queue An interface supports
n
queues numbered 0 to
(
n
-1).The specific
n
value is platform-dependent.
Internal egress queue of the interface; queues 0–6
are available.
Minimum Bandwidth The minimum transmission bandwidth guarantee
for the queue, expressed as a percentage. A value of
0 means bandwidth is not guaranteed and the
queue operates using best-effort scheduling. This
value is a configured value.
2CSNXXX_SWUM200.book Page 690 Tuesday, December 10, 2013 1:22 PM

QoS Commands 691
show interfaces random-detect
Use the show interfaces random-detect command in Privileged EXEC mode
to display WRED policy on an interface.
Syntax
show interfaces random-detect
interface-id
•
interface-id
—Specify an interface type. Valid interfaces include physical
ports and port channels.
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC mode, Configuration mode and all Configuration submodes
User Guidelines
Use the
show interfaces cos-queue
command to show the global or per
interface scheduler type and queue management types.
show policy-map
Use the show policy-map command in Privileged EXEC mode to display all
configuration information for the specified policy.
Syntax
show policy-map [
policyname
]
•
policyname
— Specifies the name of a valid existing DiffServ policy.
(Range: 1-31)
Scheduler Type Indicates whether this queue is scheduled for
transmission using a strict priority or a weighted
scheme. This value is a configured value.
Parameter Description
2CSNXXX_SWUM200.book Page 691 Tuesday, December 10, 2013 1:22 PM

692 QoS Commands
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC mode, Configuration mode and all Configuration submodes
User Guidelines
This command has no user guidelines.
Example
The following example displays the DiffServ information.
console#show policy-map
Policy Name Policy Type Class Members
----------- ----------- -------------
POLY1 xxx DellClass
DELL xxx DellClass
show policy-map interface
Use the show policy-map interface command in Privileged EXEC mode to
display policy-oriented statistics information for the specified interface.
Syntax
show policy-map interface {gigabithethernet unit/slot/port|
tengigabitethernet unit/slot/port
|
fortygigabitethernet unit/slot/port port-
channel
port-channel number
} {in|out}
•
port-channel number
—A valid port-channel identifier.
•
in
—Show inbound service policies. The offered value indicates the
number of packets received by the classifier.
•
out
—Show outbound service policies. The discarded value indicates the
number of packets discarded by the policy.
Default Configuration
This command has no default configuration.
2CSNXXX_SWUM200.book Page 692 Tuesday, December 10, 2013 1:22 PM

QoS Commands 693
Command Mode
Privileged EXEC mode, Configuration mode and all Configuration submodes
User Guidelines
This command has no user guidelines.
Example
The following example displays the statistics information for port te1/0/1.
console#show policy-map interface te1/0/1 in
Interface..................................... te1/0/1
Operational Status............................ Down
Policy Name................................... DELL
Interface Summary:
Class Name.................................... Dell Networking
In Offered Packets............................ 1003
In Discarded Packets.......................... 11
show service-policy
Use the show service-policy command in Privileged EXEC mode to display a
summary of policy-oriented statistics information for all interfaces.
Syntax
show service-policy
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC mode, Configuration mode and all Configuration submodes
User Guidelines
This command has no user guidelines.
2CSNXXX_SWUM200.book Page 693 Tuesday, December 10, 2013 1:22 PM

694 QoS Commands
Example
The following example displays a summary of policy-oriented statistics
information.
console#show service-policy
Oper Policy
Intf Stat Name
------ ----- -------------------------------
1/0/1 Down DELL
1/0/2 Down DELL
1/0/3 Down DELL
1/0/4 Down DELL
1/0/5 Down DELL
1/0/6 Down DELL
1/0/7 Down DELL
1/0/8 Down DELL
1/0/9 Down DELL
1/0/10 Down DELL
traffic-shape
Use the traffic-shape command in Global Configuration mode and Interface
Configuration mode to specify the maximum transmission bandwidth limit
for the interface as a whole. This process, also known as
rate shaping
, has the
effect of smoothing temporary traffic bursts over time so that the transmitted
traffic rate is bounded. To restore the default interface shaping rate value, use
the no form of this command.
Syntax
traffic-shape
bw
kbps
no traffic-shape
•
bw
— Maximum transmission bandwidth value expressed in Kbps.
(Range: 64 - 4294967295)
Default Configuration
This command has no default configuration.
2CSNXXX_SWUM200.book Page 694 Tuesday, December 10, 2013 1:22 PM

QoS Commands 695
Command Mode
Global Configuration mode, Interface Configuration (gigabitethernet, port-
channel, tengigabitethernet
,
fortygigabitethernet) mode
User Guidelines
This command implements a true shaper where bursts of traffic are buffered
and smoothed. Shaping occurs if the average rate exceeds the configured
limit or a burst exceeds 2% of the configured limit. Effectively, all CoS queues
are configured with the configured rate limit in the scheduler.
Example
The following example rate limits interface gi1/0/1 to a maximum bandwidth
of 1024 Kbps.
console(config-if-gi1/0/1)#traffic-shape 1024 kbps
vlan priority
Use the vlan priority command to assign a default VLAN priority tag for
untagged frames ingressing an interface.
Syntax
vlan priority
cos value
•
cos-value
– A value ranging from 0-7.
Default Configuration
By default, untagged frames are processed with VLAN priority 0. The VLAN
priority is mapped to a class of service value which determines the handling of
the frame. Use the show interfaces detail command to display the configured
priority. Use the show classofservice dot1p-mapping command to display the
mapping of VLAN priorities to COS values.
Command Modes
Interface (physical) Configuration mode
2CSNXXX_SWUM200.book Page 695 Tuesday, December 10, 2013 1:22 PM

696 QoS Commands
User Guidelines
This command has no user guidelines.
Example
The following example configures the default VLAN priority to 1 for
untagged frames ingressing interface Te1/0/1.
console(config-if-Te1/0/1)#vlan priority 1
2CSNXXX_SWUM200.book Page 696 Tuesday, December 10, 2013 1:22 PM

RADIUS Commands 697
34
RADIUS Commands
Dell Networking N2000/N3000/N4000 Series Switches
Managing and determining the validity of users in a large network can be
significantly simplified by making use of a single database of accessible
information supplied by an Authentication Server. These servers commonly
use the Remote Authentication Dial In User Service (RADIUS) protocol as
defined by RFC 2865.
RADIUS permits access to a user’s authentication and configuration
information contained on the server only when requests are received from a
client that shares an encrypted secret with the server. This secret is never
transmitted over the network in an attempt to maintain a secure
environment. Any requests from clients that are not appropriately configured
with the secret or access from unauthorized devices are silently discarded by
the server.
RADIUS conforms to a client/server model with secure communications
using UDP as a transport protocol. It is extremely flexible, supporting a
variety of methods to authenticate and statistically track users. It is very
extensible allowing for new methods of authentication to be added without
disrupting existing network functionality.
Dell Networking supports a RADIUS client in conformance with RFC 2865
and accounting functions in conformance with RFC2866. The RADIUS
client will apply user policies under control of the RADIUS server, e.g.
password lockout or login time of day restrictions. The RADIUS client
supports up to 32 named authentication and accounting servers.
Tab le 34 -1
below indicates the RADIUS attributes supported by various Dell
Networking switch service. Administrators may configure these attributes on
the RADIUS server(s) when utilizing the switch RADIUS service.
Table 34-1. RADIUS Attributes Supported by Dell Networking Switch Service
Type RADIUS Attribute Name 802.1X User Manager Captive Portal
1USER-NAME Yes No No
2 USER-PASSWORD Yes No No
2CSNXXX_SWUM200.book Page 697 Tuesday, December 10, 2013 1:22 PM

698 RADIUS Commands
4 NAS-IP-ADDRESS Yes No No
5NAS-PORT Yes No No
6SERVICE-TYPE No Yes No
11 FILTER-ID Yes No No
12 FRAMED-MTU Yes No No
18 REPLY-MESSAGE Yes Yes No
24 STATE Yes Yes No
25 CLASS Yes No No
26 VENDOR-SPECIFIC No No Yes
27 SESSION-TIMEOUT Yes No Yes
28 IDLE-TIMEOUT No No Yes
29 TERMINATION-ACTION Yes No No
30 CALLED-STATION-ID Yes No No
31 CALLING-STATION-ID Yes No No
32 NAS-IDENTIFIER Yes No No
40 ACCT-STATUS-TYPE Set by
RADIUS
client for
Accounting
No No
42 ACCT-INPUT-OCTETS Yes No No
43 ACCT-OUTPUT-OCTETS Yes No No
44 ACCT-SESSION-ID Set by
RADIUS
client for
Accounting
No No
46 ACCT-SESSION-TIME Yes No No
49 ACCT-TERMINATE-CAUSE Yes No No
52 ACCT-INPUT-GIGAWORDS Yes No No
53 ACCT-OUTPUT-GIGAWORDS Yes No No
Table 34-1. RADIUS Attributes Supported by Dell Networking Switch Service
Type RADIUS Attribute Name 802.1X User Manager Captive Portal
2CSNXXX_SWUM200.book Page 698 Tuesday, December 10, 2013 1:22 PM

RADIUS Commands 699
The following attributes are processed in the RADIUS Access-Accept
message received from a RADIUS server:
•NAS-PORT
– ifIndex of the port to be authenticated
• REPLY-MESSAGE
– Trigger to respond to the Access-Accept message with an EAP
notification
•STATE
– RADIUS server state. Transmitted in Access-Request and Accounting-
Request messages.
• SESSION-TIMEOUT
– Session time-out value for the session (in seconds). Used by both
802.1x and Captive Portal.
• TERMINATION-ACTION
– Indication as to the action taken when the service is completed.
• EAP-MESSAGE
– Contains an EAP message to be sent to the user. This is typically used
for MAB clients.
• VENDOR-SPECIFIC
– No actions configured at this time.
61 NAS-PORT-TYPE Yes No No
64 TUNNEL-TYPE Yes No No
65 TUNNEL-MEDIUM-TYPE Yes No No
79 EAP-MESSAGE Yes No No
80 MESSAGE-AUTHENTICATOR Set by
RADIUS
client for
Accounting
No No
81 TUNNEL-PRIVATE-GROUP-ID Yes No No
Table 34-1. RADIUS Attributes Supported by Dell Networking Switch Service
Type RADIUS Attribute Name 802.1X User Manager Captive Portal
2CSNXXX_SWUM200.book Page 699 Tuesday, December 10, 2013 1:22 PM

700 RADIUS Commands
• FILTER-ID
– Name of the filter list for this user.
• TUNNEL-TYPE
– Used to indicate that a VLAN is to be assigned to the user when set to
tunnel type VLAN (13).
• TUNNEL-MEDIUM-TYPE
– Used to indicate the tunnel medium type. Must be set to medium
type 802 (6) to enable VLAN assignment.
• TUNNEL-PRIVATE-GROUP-ID
– Used to indicate the VLAN to be assigned to the user. May be a string
which matches a preconfigured VLAN name or a VLAN id. If a VLAN
id is given, the string must only contain decimal digits.
Commands in this Chapter
This chapter explains the following commands:
aaa accounting dot1x
default start-stop
name (RADIUS server) radius-server source-ip
accounting primary radius-server timeout
acct-port priority retransmit
auth-port radius-server attribute 4 show aaa servers
deadtime radius-server deadtime show accounting methods
debug aaa accounting radius-server host show accounting methods
debug aaa accounting radius-server key source-ip
key radius-server key encrypted timeout
key encrypted radius-server retransmit usage
msgauth
––
2CSNXXX_SWUM200.book Page 700 Tuesday, December 10, 2013 1:22 PM

RADIUS Commands 701
aaa accounting dot1x default start-stop
The aaa accounting network default start-stop group radius command has
been migrated to the aaa accounting dot1x default start-stop {radius|none}
command. Use the aaa accounting dot1x default start-stop command in
Global Configuration mode to create an accounting method list.
Use the no form of the command to delete a list. A list may be identified by
the default keyword or a user-specified listname.
Use either the aaa accounting dot1x default none or no aaa accounting
dot1x default command to disable dot1x accounting.
Syntax
aaa accounting dot1x default start-stop {radius|none }
no aaa accounting dot1x default
aaa accounting dot1x default none
aaa accounting {exec|commands} {
listname
|default} {none|start-
stop|stop-only} {radius|tacacs|radius tacacs|tacacs radius}
no aaa accounting {exec|commands} {default|list}
•
commands
—Perform accounting on all user executed commands
(TACACS only).
•
exec
—Perform accounting on EXEC terminal sessions.
•
listname
—The name of an Accounting Method List. The list name can
consist of any printable character. Use quotes around the list name if
embedded blanks are contained in the list name.
•
none
—Disable issuing accounting notices for the specified list.
Default Configuration
IEEE 802.1x accounting is not enabled by default.
Command Mode
Global Configuration mode
2CSNXXX_SWUM200.book Page 701 Tuesday, December 10, 2013 1:22 PM

702 RADIUS Commands
User Guidelines
Accounting records, when enabled for a line mode, are sent at both the
beginning and at the end (start-stop) of command execution or only at the
end (stop-only) of command execution. If none is specified, then accounting
is disabled for RADIUS. If radius is the specified accounting method,
accounting records are forwarded to the list of RADIUS servers.
For the same set of accounting type and list name, the administrator can
change the record type, or the methods list, without having to first delete the
previous configuration.
A maximum of five accounting method lists can be created for each exec and
commands accounting type.
The same list-name can be used for both exec and commands accounting
types.
AAA accounting for commands with RADIUS as the accounting method is
not supported. TACACS+ supports both exec and commands accounting
types.
There is exactly one accounting method list for dot1x: default.
accounting
Use the accounting command in Line Configuration mode to apply an
accounting method to a line config.
Use the no form of the command to return the accounting for the line mode
to the default.
Syntax
accounting {exec|commands} [default|list_name]
no accounting
•
exec
—Provides accounting for a user EXEC terminal session.
•
commands
—Provides accounting for all user-executed commands.
•
default
—The default list of methods for accounting services.
2CSNXXX_SWUM200.book Page 702 Tuesday, December 10, 2013 1:22 PM

RADIUS Commands 703
•
list_name
—Character string of not more than 15 characters used to name
the list of accounting methods. The list name can consist of any printable
character. Use quotes around the list name if embedded blanks are
contained in the list name.
Default Configuration
Accounting is not enabled by default.
Command Mode
Line Configuration
User Guidelines
When enabling accounting for exec mode for the current line-configuration
type, users logged in with that mode will be logged out.
Examples
Use the following command to enable exec type accounting for telnet.
console(config)#line telnet
console(config-telnet)# accounting exec default
acct-port
Use the acct-port command to set the port on which RADIUS accounting
server listens for connections. Use the no form of this command to reset the
port to the default.
Syntax
acct-port
port
no acct-port
•
port
— The layer 4 port number of the accounting server (Range: 1 -
65535).
Default Configuration
The default value of the port number is 1813.
2CSNXXX_SWUM200.book Page 703 Tuesday, December 10, 2013 1:22 PM

704 RADIUS Commands
Command Mode
Radius (accounting) mode
User Guidelines
There are no user guidelines for this command.
Example
The following example sets port number 56 for accounting requests.
console(config)#radius-server host acct 3.2.3.2
console(Config-acct-radius)#acct-port 56
auth-port
Use the auth-port command in Radius mode to set the port number on which
the RADIUS server listens for authentication requests.
Syntax
auth-port
auth-port-number
•
auth-port-number
— Port number for authentication requests. (Range: 1 -
65535)
Default Configuration
The default value of the port number is 1812.
Command Mode
Radius mode
User Guidelines
User must enter the mode corresponding to a specific Radius server before
executing this command.
Example
The following example sets the port number 2412 for authentication
requests.
console(config)#radius-server host 192.143.120.123
2CSNXXX_SWUM200.book Page 704 Tuesday, December 10, 2013 1:22 PM

RADIUS Commands 705
console(config-radius)#auth-port 2412
deadtime
Use the deadtime command in Radius mode to configure the minimum
amount of time to wait before attempting to recontact an unresponsive
RADIUS server. If a RADIUS server is currently active and responsive, that
server will be used until it no longer responds. RADIUS servers whose
deadtime interval has not expired are skipped when searching for a new
RADIUS server to contact.
Syntax
deadtime
deadtime
•
deadtime —
The amount of time that the unavailable server is skipped
over. (Range: 0-2000 minutes)
Default Configuration
The default deadtime interval is 0 minutes.
Command Mode
Radius mode
User Guidelines
If only one RADIUS server is configured, it is recommended to use a
deadtime interval of 0.
Example
The following example specifies a deadtime interval of 60 minutes.
console(config)#radius-server host 192.143.120.123
console(config-radius)#deadtime 60
debug aaa accounting
Use the debug aaa accounting command in Privileged EXEC mode to enable
debugging for accounting.
Use the no form of the command to disable accounting debugging.
2CSNXXX_SWUM200.book Page 705 Tuesday, December 10, 2013 1:22 PM

706 RADIUS Commands
Syntax
debug aaa accounting
no debug aaa accounting
Default Configuration
Debugging is disabled by default.
Command Mode
Privileged EXEC mode
User Guidelines
This command has no user guidelines.
key
Use the key command to specify the encryption key which is shared with the
RADIUS server. Use the no form of this command to remove the key.
Syntax
key
key-string
•
key-string
— A string specifying the encryption key (Range: 0 - 128
characters).
Default Configuration
There is no key configured by default.
Command Mode
Radius mode
User Guidelines
There are no user guidelines for this command.
2CSNXXX_SWUM200.book Page 706 Tuesday, December 10, 2013 1:22 PM

RADIUS Commands 707
Example
The following example specifies an authentication and encryption key of
“
lion-king
”.
console(config)#radius-server host acct 3.2.3.2
console(Config-acct-radius)#key keyacct
key encrypted
Use the key encrypted command to configure an encrypted key that is shared
with the RADIUS server. Use the no form of the command to remove the key.
Syntax
key encrypted
key-string
•
key-string
— The key string in encrypted form. It should be 256 characters
in length.
Default Configuration
There is no default configuration for this command.
Command Modes
Radius mode
User Guidelines
This command has no user guidelines.
Example
console(Config-auth-radius)# key encrypted
f6fdffe48c908deb0f4c3bd36c032e72f6fdffe48c908deb0f4c3bd36c032e72f6fdffe48c90
8deb0f4c3bd36c032e72f6fdffe48c908deb0f4c3bd36c032e72f6fdffe48c908deb0f4c3bd3
6c032e72f6fdffe48c908deb0f4c3bd36c032e72f6fdffe48c908deb0f4c3bd36c032e72f6fd
ffe48c908deb0f4c3bd36c032e72
console(config)#
2CSNXXX_SWUM200.book Page 707 Tuesday, December 10, 2013 1:22 PM

708 RADIUS Commands
msgauth
Use the msgauth command to enable the message authenticator attribute to
be used for the RADIUS Authenticating server being configured. Use the
“no” form of this command to disable the message authenticator attribute.
Syntax
msgauth
no msgauth
Default Configuration
The message authenticator attribute is enabled by default.
Command Mode
Radius mode
User Guidelines
There are no user guidelines for this command.
Example
console(Config-auth-radius)#msgauth
name (RADIUS server)
Use the name command to assign a name to a RADIUS server. Use the no
form of the command to return the name to the default (unspecified). The
no form of the command does not require the user to enter the configured
name.
Syntax
name servername
no name
•
servername
—The name for the RADIUS server (Range: 1 - 32 characters).
2CSNXXX_SWUM200.book Page 708 Tuesday, December 10, 2013 1:22 PM

RADIUS Commands 709
Default Configuration
The default RADIUS server name is Default-RADIUS-Server.
Command Mode
Radius Configuration mode
User Guidelines
Names may only be set for authentication servers, not for accounting servers.
Names may consist of alphanumeric characters and the underscore, dash and
blanks.Embed the name in double quotes to use a name with blanks.
NOTE: When multiple RADIUS servers are configured with different names, e.g.
ServerName is name1 and address is 1.1.1.1
ServerName is name2 and address is 1.1.1.2
The RADIUS request is always sent to the first ordered name server list, i.e. name1 server
list would be tried before moving on to name2. Even if the priority value of servers in
name2 is lower (lower value indicates high priority) the request would be sent to the
name1 servers. If for name1 list, the configured servers fail to respond, the request
is sent to the second configured name list.
Within the same server list, the first primary server would be tried. You can have multiple
secondary servers in the same name list. From the multiple secondary servers, the
one with the lowest priority value would be tried. For a different named server list,
the server name would be based on lexicographic order. For e.g. if name9, name1,
name6 are configured in this order, name1, then name6, then name9 would be tried.
Example
console(config)#radius-server host 44.44.44.44
console(Configuration-auth-radius)#name NAME
console(Config-auth-radius)#no name
primary
Use the primary command to specify that a configured server should be the
primary server in the group of authentication servers which have the same
server name. Multiple primary servers can be configured for each group of
servers which have the same name. When the RADIUS client has to perform
transactions with an authenticating RADIUS server of the specified name, it
uses the primary server that has the specified server name by default. If it fails
2CSNXXX_SWUM200.book Page 709 Tuesday, December 10, 2013 1:22 PM

710 RADIUS Commands
to communicate with the primary server for any reason, it uses the backup
servers configured with the same server name. These backup servers are
identified as the “Secondary” type.
Syntax
primary
Default Configuration
There is no primary authentication server by default.
Command Mode
Radius mode
User Guidelines
There are no user guidelines for this command.
Example
console(Config-auth-radius)#primary
priority
Use the priority command in Radius mode to specify the order in which the
servers are to be used, with 0 being the highest priority.
Syntax
priority
priority
•
priority —
Sets server priority level. (Range 0-65535)
Default Configuration
The default priority is 0.
Command Mode
Radius mode
2CSNXXX_SWUM200.book Page 710 Tuesday, December 10, 2013 1:22 PM

RADIUS Commands 711
User Guidelines
User must enter the mode corresponding to a specific Radius server before
executing this command.
Example
The following example specifies a priority of 10 for the designated server.
console(config)#radius-server host 192.143.120.123
console(config-radius)#priority 10
radius-server attribute 4
Use the radius-server attribute 4 command in Global Configuration mode to
set the network access server (NAS) IP address for the RADIUS server. The
NAS IP address is RADIUS attribute number 4. Use the no version of the
command to set the value to the default.
Syntax
radius-server attribute 4
ip-address
no radius-server attribute 4
•
ip-address
— Specifies the IP address to be used as the RADIUS attribute
4, the NAS IP address.
Default Configuration
If a RADIUS server has been configured on the switch, the default attribute 4
value is the RADIUS server IP address.
Command Mode
Global Configuration mode
User Guidelines
This command does not change the address in the IP header for the request
sent to the RADIUS server. It only changes the address sent to the RADIUS
server inside the RADIUS packet.
2CSNXXX_SWUM200.book Page 711 Tuesday, December 10, 2013 1:22 PM

712 RADIUS Commands
Example
The following example sets the NAS IP address in RADIUS attribute 4 to
192.168.10.22.
console(config)#radius-server attribute 4 192.168.10.22
radius-server deadtime
Use the radius-server deadtime command in Global Configuration mode to
configure the minimum amount of time to wait before attempting to
recontact an unresponsive RADIUS server. If a RADIUS server is currently
active and responsive, that server will be used until it no longer responds.
RADIUS servers whose deadtime interval has not expired are skipped when
searching for a new RADIUS server to contact. To set the deadtime to 0, use
the no form of this command.
Syntax
radius-server deadtime
deadtime
no radius-server deadtime
•
deadtime
— Length of time in minutes, for which a Radius server is
skipped over by transaction requests. (Range: 0–2000 minutes).
Deadtime
is used to mark an unavailable Radius server as dead until this user-
configured time expires.
Deadtime
is configurable on a Radius server basis.
Default Configuration
The default dead time is 0 minutes.
Command Mode
Global Configuration mode
User Guidelines
If only one RADIUS server is configured, it is recommended that the
deadtime interval be left at 0.
2CSNXXX_SWUM200.book Page 712 Tuesday, December 10, 2013 1:22 PM

RADIUS Commands 713
Example
The following example sets the minimum interval for a RADIUS server will
not be contacted after becoming unresponsive.
console(config)#radius-server deadtime 10
radius-server host
Use the radius-server host command in Global Configuration mode to specify
a RADIUS server host and enter RADIUS Configuration mode. To delete the
specified Radius host, use the no form of this command.
Syntax
radius-server host [acct | auth] {
ip–address
|
hostname
}
no radius-server host [acct | auth] {
ip–address
|
hostname
}
•
acct
|
auth
—The type of server (accounting or authentication).
•
ip–address
—The RADIUS server host IP address.
•
hostname
—Host name of the Radius server host. (Range: 1–255
characters).
Default Configuration
The default server type is authentication. The default server name is Default
RADIUS Server. The default port number is 1812 for an authentication
server and 1813 for an accounting server.
Command Mode
Global Configuration mode
User Guidelines
Radius servers are keyed by the host name, therefore it is advisable to use
unique server host names.
Example
The following example specifies a Radius server host with the following
characteristics:
2CSNXXX_SWUM200.book Page 713 Tuesday, December 10, 2013 1:22 PM

714 RADIUS Commands
Server host IP address — 192.168.10.1
console(config)#radius-server host 192.168.10.1
radius-server key
Use the radius-server key command in Global Configuration mode to set the
authentication and encryption key for all Radius communications between
the switch and the Radius server. To reset to the default, use the no form of
this command.
Syntax
radius-server key [
key-string
]
no radius-server key
•
key-string
— Specifies the authentication and encryption key for all Radius
communications between the switch and the Radius server. This key must
match the encryption used on the Radius server. (Range: 1-128 characters)
Default Configuration
The default is an empty string.
Command Mode
Global Configuration mode
User Guidelines
This command has no user guidelines.
Example
The following example sets the authentication and encryption key for all
Radius communications between the device and the Radius server to “dell-
server
.”
console(config)#radius-server key dell-server
2CSNXXX_SWUM200.book Page 714 Tuesday, December 10, 2013 1:22 PM

RADIUS Commands 715
radius-server key encrypted
Use the radius-server key encrypted command to set the authentication and
encryption key for the communication between the switch and radius server.
Use the no form of the command to disable the key.
Syntax
radius-server key encrypted
key-string
•
key-string
— The key string in encrypted form. It should be 256 characters
in length.
Default Configuration
There is no default configuration for this command.
Command Modes
Global Configuration mode
User Guidelines
This command has no user guidelines.
Example
console(config)# radius-server key encrypted
f6fdffe48c908deb0f4c3bd36c032e72f6fdffe48c908deb0f4c3bd36c032e72f6fdffe48c90
8deb0f4c3bd36c032e72f6fdffe48c908deb0f4c3bd36c032e72f6fdffe48c908deb0f4c3bd3
6c032e72f6fdffe48c908deb0f4c3bd36c032e72f6fdffe48c908deb0f4c3bd36c032e72f6fd
ffe48c908deb0f4c3bd36c032e72
console(config)#
radius-server retransmit
Use the radius-server retransmit command in Global Configuration mode to
specify the number of times the Radius client will retransmit requests to the
Radius server. To reset the default configuration, use the no form of this
command.
Syntax
radius-server retransmit
retries
2CSNXXX_SWUM200.book Page 715 Tuesday, December 10, 2013 1:22 PM

716 RADIUS Commands
no radius-server retransmit
•
retries
— Specifies the retransmit value. (Range: 1–10)
Default Configuration
The default is 3 attempts.
Command Mode
Global Configuration mode
User Guidelines
This command has no user guidelines.
Example
The following example configures the number of times the Radius client
attempts to retransmit requests to the Radius server to 5 attempts.
console(config)#radius-server retransmit 5
radius-server source-ip
Use the radius-server source-ip command in Global Configuration mode to
specify the source IP address used for communication with Radius servers. To
return to the default, use the no form of this command. 0.0.0.0 is interpreted
as a request to use the IP address of the outgoing IP interface.
Syntax
radius-server source-ip
source
no radius-server source-ip
•
source
— Specifies the source IP address.
Default Configuration
The default IP address is the outgoing IP interface.
Command Mode
Global Configuration mode
2CSNXXX_SWUM200.book Page 716 Tuesday, December 10, 2013 1:22 PM

RADIUS Commands 717
User Guidelines
This command has no user guidelines.
Example
The following example configures the source IP address used for
communication with Radius servers to 10.1.1.1.
console(config)#radius-server source-ip 10.1.1.1
radius-server timeout
Use the radius-server timeout command in Global Configuration mode to set
the interval for which a switch waits for a server host to reply. To restore the
default, use the no form of this command.
Syntax
radius-server timeout
timeout
no radius-server timeout
•
timeout
— Specifies the timeout value in seconds. (Range: 1–30)
Default Configuration
The default value is 3 seconds.
Command Mode
Global Configuration mode
User Guidelines
This command has no user guidelines.
Example
The following example sets the interval for which a switch waits for a server
host to reply to 5 seconds.
console(config)#radius-server timeout 5
2CSNXXX_SWUM200.book Page 717 Tuesday, December 10, 2013 1:22 PM

718 RADIUS Commands
retransmit
Use the retransmit command in Radius mode to specify the number of times
the Radius client retransmits requests to the Radius server.
Syntax
retransmit
retries
•
retries —
Specifies the retransmit value. (Range: 1-10 attempts)
Default Configuration
The default number for attempts is 3.
Command Mode
Radius mode
User Guidelines
User must enter the mode corresponding to a specific Radius server before
executing this command.
Example
The following example of the retransmit command specifies five retries.
console(config)#radius-server host 192.143.120.123
console(config-radius)#retransmit 5
show aaa servers
Use the show aaa servers command to display the list of configured RADIUS
servers and the values configured for the global parameters of the RADIUS
client.
Syntax
show aaa servers [accounting | authentication] [name [
servername
]]
•
accounting
—This optional parameter will cause accounting servers to be
displayed.
2CSNXXX_SWUM200.book Page 718 Tuesday, December 10, 2013 1:22 PM

RADIUS Commands 719
•
authentication
—This optional parameter will cause authentication servers
to be displayed.
•
name
—This optional parameter will cause the server names to be
displayed instead of the server configuration parameters.
•
servername
—Will cause only the server(s) with
server-name
name to be
displayed. There are no global parameters displayed when this parameter is
specified.
Default Configuration
Authentication servers are displayed by default.
Command Mode
User EXEC, Privileged EXEC, Configuration mode and all Configuration
submodes
User Guidelines
The following fields are displayed:
Field Description
Configured
Authentication Servers
The number of RADIUS Authentication servers that have
been configured.
Configured Accounting
Servers
The number of RADIUS Accounting servers that have
been configured.
Named Authentication
Server Groups
The number of configured named RADIUS server groups.
Named Accounting
Server Groups
The number of configured named RADIUS server groups.
Timeout The configured timeout value, in seconds, for request
retransmissions.
Retransmit The configured value of the maximum number of times a
request packet is retransmitted.
Deadtime The length of time an unavailable RADIUS server is
skipped.
2CSNXXX_SWUM200.book Page 719 Tuesday, December 10, 2013 1:22 PM

720 RADIUS Commands
Example
console#show aaa servers
IP address Type Port TimeOut Retran. DeadTime Source IP Prio.Usage
---------------- ----- ----- ------- ------- -------- ---------- ----- ------
6.6.6.6 Auth 1812 Global Global Global Global 0 all
5.5.5.5 Auth 1812 Global Global Global Global 0 all
4.4.4.4 Auth 1812 Global Global Global Global 0 all
3.3.3.3 Auth 1812 Global Global Global Global 0 all
2.2.2.2 Auth 1812 Global Global Global Global 0 all
1.1.1.1 Acct 1813 N/A N/A N/A N/A N/A N/A
Global values
--------------------------------------------
Number of Configured Authentication Servers.... 5
Number of Configured Accounting Servers........ 1
Number of Named Authentication Server Groups... 2
Number of Named Accounting Server Groups....... 1
Number of Retransmits.......................... 3
Timeout Duration............................... 15
Deadtime....................................... 0
Source IP...................................... 0.0.0.0
RADIUS Accounting Mode......................... Disable
RADIUS Attribute 4 Mode........................ Disable
--More-- or (q)uit
RADIUS Attribute 4 Value....................... 0.0.0.0
console#show aaa servers name
Server Name Host Address Port Secret
Configured
-------------------------------- ------------------------ ------ ----------
RADIUS Accounting
Mode
A Global parameter to indicate whether the accounting
mode for all the servers is enabled or not.
RADIUS Attribute 4
Mode
A Global parameter to indicate whether the NAS-IP-
Address attribute has been enabled to use in RADIUS
requests.
RADIUS Attribute 4
Value
A Global parameter that specifies the IP address to be
used in NAS-IP-Address attribute to be used in RADIUS
requests.
Field Description
2CSNXXX_SWUM200.book Page 720 Tuesday, December 10, 2013 1:22 PM

RADIUS Commands 721
Default-RADIUS-Server 4.4.4.4 1812 No
test 6.6.6.6 1812 No
show accounting methods
Use the show accounting methods command in Privileged EXEC mode to
display the configured accounting method lists.
Syntax
show accounting methods
Default Configuration
This command has no default setting.
Command Mode
Privileged EXEC mode, Configuration mode and all Configuration submodes
User Guidelines
This command has no user guidelines.
Examples
console#show accounting methods
Acct Type Method Name Record Type Method Type
---------- ------------ ------------ ------------
Exec dfltExecList start-stop TACACS
Commands dfltCmdsList stop-only TACACS
Commands UserCmdAudit start-stop TACACS
Line EXEC Method List Command Method List
------- ---------------------------------------
Console dfltExecList dfltCmdsList
Telnet dfltExecList dfltCmdsList
SSH dfltExecList UserCmdAudit
show radius statistics
Use the show radius statistics command to show the statistics for an
authentication or accounting server.
2CSNXXX_SWUM200.book Page 721 Tuesday, December 10, 2013 1:22 PM

722 RADIUS Commands
Syntax
show radius statistics [accounting | authentication] [{
ipaddress
|
hostname
| name
servername
}]
•
accounting | authentication
—The type of server (accounting or
authentication).
•
ipaddress
—The RADIUS server host IP address.
•
hostname
—Host name of the Radius server host. (Range: 1–158
characters). The command allows spaces in the host name when specified
in double quotes. For example, console(config)#snmp-server host "host
name"
•
servername
—The alias used to identify the server.
Default Configuration
There is no default configuration for this command.
Command Mode
User EXEC, Privileged EXEC modes, Configuration mode and all
Configuration submodes
User Guidelines
The following fields are displayed for accounting servers:
Field Description
RADIUS
Accounting Server
Name
Name of the accounting server.
Server Host
Address
IP address of the host.
Round Trip Time The time interval, in hundredths of a second, between the most
recent Accounting Response and the Accounting Request that
matched it from this RADIUS accounting server.
Requests The number of RADIUS Accounting Request packets sent to this
server not including the retransmissions.
2CSNXXX_SWUM200.book Page 722 Tuesday, December 10, 2013 1:22 PM

RADIUS Commands 723
The following fields are displayed for authentication servers:
Retransmissions The number of RADIUS Accounting Request packets
retransmitted to this RADIUS accounting server.
Responses The number of RADIUS packets received on the accounting port
from this server.
Malformed
Responses
The number of malformed RADIUS Accounting Response
packets received from this server. Malformed packets include
packets with an invalid length. Bad authenticators or signature
attributes or unknown types are not included as malformed
accounting responses.
Bad
Authenticators
The number of RADIUS Accounting Response packets
containing invalid authenticators received from this accounting
server.
Pending Requests The number of RADIUS Accounting Request packets destined
for this server that have not yet timed out or received a response.
Timeouts The number of accounting timeouts on this server.
Unknown Types The number of packets unknown type which were received from
this server on accounting port.
Packets Dropped The number of RADIUS packets received from this server on
accounting port and dropped for some other reason.
Field Description
RADIUS Server
Name
Name of the authenticating server.
Server Host
Address
IP address of the host.
Access Requests The number of RADIUS Access Request packets sent to this
server. This number does not include retransmissions.
Access
Retransmissions
The number of RADIUS Access Request packets retransmitted
to this RADIUS authentication server.
Access Accepts The number of RADIUS Access Accept packets, including both
valid and invalid packets, that were received from this server.
Field Description
2CSNXXX_SWUM200.book Page 723 Tuesday, December 10, 2013 1:22 PM

724 RADIUS Commands
Example
console#show radius statistics accounting 192.168.37.200
RADIUS Accounting Server Name................. Default_RADIUS_Server
Host Address.................................. 192.168.37.200
Round Trip Time............................... 0.00
Requests...................................... 0
Retransmissions............................... 0
Responses..................................... 0
Malformed Responses........................... 0
Bad Authenticators............................ 0
Pending Requests.............................. 0
Timeouts...................................... 0
Unknown Types................................. 0
Packets Dropped............................... 0
console#show radius statistics name Default_RADIUS_Server
Access Rejects The number of RADIUS Access Reject packets, including both
valid and invalid packets, that were received from this server.
Access Challenges The number of RADIUS Access Challenge packets, including
both valid and invalid packets, that were received from this
server.
Malformed Access
Responses
The number of malformed RADIUS Access Response packets
received from this server. Malformed packets include packets
with an invalid length. Bad authenticators or signature attributes
or unknown types are not included as malformed access
responses.
Bad
Authenticators
The number of RADIUS Access Response packets containing
invalid authenticators or signature attributes received from this
server.
Pending Requests The number of RADIUS Access Request packets destined for
this server that have not yet timed out or received a response.
Timeouts The number of authentication timeouts to this server.
Unknown Types The number of packets unknown type which were received from
this server on the authentication port.
Packets Dropped The number of RADIUS packets received from this server on
authentication port and dropped for some other reason.
Field Description
2CSNXXX_SWUM200.book Page 724 Tuesday, December 10, 2013 1:22 PM

RADIUS Commands 725
RADIUS Server Name............................ Default_RADIUS_Server
Server Host Address........................... 192.168.37.200
Access Requests............................... 0.00
Access Retransmissions........................ 0
Access Accepts................................ 0
Access Rejects................................ 0
Access Challenges............................. 0
Malformed Access Responses.................... 0
Bad Authenticators............................ 0
Pending Requests.............................. 0
Timeouts...................................... 0
Unknown Types................................. 0
Packets Dropped............................... 0
source-ip
Use the source-ip command in Radius mode to specify the source IP address
to be used for communication with Radius servers. 0.0.0.0 is interpreted as a
request to use the IP address of the outgoing IP interface.
Syntax
source-ip
source
•
source —
A valid source IP address.
Default Configuration
The IP address is of the outgoing IP interface.
Command Mode
Radius mode
User Guidelines
User must enter the mode corresponding to a specific Radius server before
executing this command.
Example
The following example specifies 10.240.1.23 as the source IP address.
console(config)#radius-server host 192.143.120.123
console(config-radius)#source-ip 10.240.1.23
2CSNXXX_SWUM200.book Page 725 Tuesday, December 10, 2013 1:22 PM

726 RADIUS Commands
timeout
Use the timeout command in Radius mode to set the timeout value in
seconds for the designated Radius server.
Syntax
timeout
timeout
•
timeout —
Timeout value in seconds for the specified server. (Range: 1-30
seconds.)
Default Configuration
The default value is 3 seconds.
Command Mode
Radius mode
User Guidelines
User must enter the mode corresponding to a specific Radius server before
executing this command.
Example
The following example specifies the timeout setting for the designated
Radius Server.
console(config)#radius-server host 192.143.120.123
console(config-radius)#timeout 20
usage
Use the usage command in Radius mode to specify the usage type of the
server.
Syntax
usage
type
•
type —
Variable can be one of the following values:
login
,
802.1x
or
all
.
2CSNXXX_SWUM200.book Page 726 Tuesday, December 10, 2013 1:22 PM

RADIUS Commands 727
Default Configuration
The default variable setting is
all.
Command Mode
Radius mode
User Guidelines
User must enter the mode corresponding to a specific Radius server before
executing this command.
Example
The following example specifies usage type
login
.
console(config)#radius-server host 192.143.120.123
console(config-radius)#usage login
2CSNXXX_SWUM200.book Page 727 Tuesday, December 10, 2013 1:22 PM

728 RADIUS Commands
2CSNXXX_SWUM200.book Page 728 Tuesday, December 10, 2013 1:22 PM

Spanning Tree Commands 729
35
Spanning Tree Commands
Dell Networking N2000/N3000/N4000 Series Switches
The Multiple Spanning Tree Protocol (MSTP) component complies with
IEEE 802.1s by efficiently navigating VLAN traffic over separate interfaces
for multiple instances of Spanning Tree. IEEE 802.1D, Spanning Tree and
IEEE 802.1w, Rapid Spanning Tree are supported through the IEEE 802.1s
implementation. The difference between the RSTP and STP (IEEE 802.1D)
is the ability to configure and recognize full-duplex connectivity and ports
that are connected to end stations. The difference enables RSTP to rapidly
transition to the Forwarding state and to suppress the Topology Change
Notification PDUs, where possible.
A VLAN ID does not have to be preconfigured before mapping it to an MST
instance.
Management of MSTP is compliant with the requirements of RFC5060.
The following features are supported by Dell Networking MSTP:
STP Loop Guard - The Loop Guard feature is an enhancement of the
Multiple Spanning Tree Protocol. Loop guard protects a network from
forwarding loops induced by BPDU packet loss. It can be configured to
prevent a blocked port from transitioning to the forwarding state when the
port stops receiving BPDUs for some reason (such as a uni-directional link
failure).
STP BPDU Guard - The STP BPDU guard allows the network administrator
to enforce the STP domain borders and keep the active topology consistent
and predictable. The switches behind the edge ports that have STP BPDU
guard enabled are not able to influence the overall STP topology. At the
reception of BPDUs, the BPDU guard operation diagnostically disables a port
that is configured with this option.
STP Root Guard - The root guard ensures that the port on which root guard
is enabled is the designated port. In a root bridge ports are all designated
ports, unless two or more ports of the root bridge are connected together. If
the bridge receives superior STP BPDUs on a root guard enabled port, root
guard moves this port to a root inconsistent STP state. This root inconsistent
state is effectively equal to a listening state. No traffic is forwarded across this
2CSNXXX_SWUM200.book Page 729 Tuesday, December 10, 2013 1:22 PM

730 Spanning Tree Commands
port. In this way, the root guard enforces the position of the root bridge. In
MSTP scenario the port may be designated in one of the instances while
being alternate in the CIST, and so on. Root guard is a per port (not a per port
per instance command) configuration so all the MSTP instances this port
participates in should not be in root role.
STP BPDU Filtering - STP BPDU filtering applies to all operational edge
ports. Edge Port in an operational state is supposed to be connected to hosts
that typically drop BPDUs. If an operational edge port receives a BPDU, it
immediately loses its operational status. In that case, if BPDU filtering is
enabled on this port then it drops the BPDUs received on this port.
STP BPDU Flooding - STP BPDU flooding feature applies to the STP
disabled switch. To enable BPDU flooding on a port, STP should be disabled
on the switch administratively. When this feature is enabled on the switch, it
floods all the ports which have the BPDU flood feature enabled.
BPDU Storm Protection - If STP BPDUs are received at a rate of 15 pps or
greater for 3 consecutive seconds on a port, the port will be diagnostically
disabled. A message of the following form is logged:
<188> MAY 04 09:45:23 10.10.10.10-1 DOT1S[276072720]: dot1s_ih.c(1587)
15855515 %% Diagnostically disabling interface 2/0/41
Use the no shut command to return the port to service.
Commands in this Chapter
This chapter explains the following commands:
clear spanning-tree
detected-protocols
spanning-tree
backbonefast
spanning-tree mode spanning-tree priority
exit (mst) spanning-tree bpdu
flooding
spanning-tree mst
configuration
spanning-tree tcnguard
instance (mst) spanning-tree
bpdu-protection
spanning-tree mst
cost
spanning-tree transmit
hold-count
name (mst) spanning-tree cost spanning-tree mst
port-priority
spanning-tree
uplinkfast
revision (mst) spanning-tree
disable
spanning-tree mst
priority
spanning-tree vlan
2CSNXXX_SWUM200.book Page 730 Tuesday, December 10, 2013 1:22 PM

Spanning Tree Commands 731
clear spanning-tree detected-protocols
Use the clear spanning-tree detected-protocols command in Privileged
EXEC mode to restart the protocol migration process (force the renegotiation
with neighboring switches) on all interfaces or on the specified interface.
Syntax
clear spanning-tree detected-protocols [{gigabitethernet unit/slot/port |
port-channel
port-channel-number
| tengigabitethernet unit/slot/port
|
fortygigabitethernet unit/slot/port}]
Default Configuration
This command has no default setting.
Command Mode
Privileged EXEC mode
User Guidelines
This feature is used only when working in RSTP or MSTP mode.
show spanning-tree spanning-tree
forward-time
spanning-tree
portfast
spanning-tree vlan
forward-time
show spanning-tree
summary
spanning-tree guard spanning-tree
portfast bpdufilter
default
spanning-tree vlan
hello-time
show spanning-tree
vlan
spanning-tree
loopguard
spanning-tree
portfast default
spanning-tree vlan
max-age
spanning-tree spanning-tree max-
age
spanning-tree port-
priority (Interface
Configuration)
spanning-tree vlan root
spanning-tree auto-
portfast
spanning-tree max-
hops
–
spanning-tree vlan
priority
2CSNXXX_SWUM200.book Page 731 Tuesday, December 10, 2013 1:22 PM

732 Spanning Tree Commands
Example
The following example restarts the protocol migration process (forces the
renegotiation with neighboring switches) on 1/0/1.
console#clear spanning-tree detected-protocols gigabitethernet 1/0/1
exit (mst)
Use the exit command in MST mode to exit the MST configuration mode
and apply all configuration changes.
Syntax
exit
Default Configuration
MST configuration.
Command Mode
MST mode
User Guidelines
This command has no user guidelines.
Example
The following example shows how to exit the MST configuration mode and
save changes.
console(config)#spanning-tree mst configuration
console(config-mst)#exit
instance (mst)
Use the instance command in MST mode to map VLANS to an MST
instance.
Syntax
instance
instance-id
{add | remove} vlan
vlan-range
•
instance-ID —
ID of the MST instance. (Range: 1-4094)
2CSNXXX_SWUM200.book Page 732 Tuesday, December 10, 2013 1:22 PM

Spanning Tree Commands 733
•
vlan-range —
VLANs to be added to the existing MST instance. To specify
a range of VLANs, use a hyphen. To specify a series of VLANs, use a
comma. (Range: 1-4093)
Default Configuration
VLANs are mapped to the common and internal spanning tree (CIST)
instance (instance 0).
Command Mode
MST mode
User Guidelines
Before mapping VLANs to an instance use the spanning-tree mst enable
command to enable the instance.
All VLANs that are not explicitly mapped to an MST instance are mapped to
the common and internal spanning tree (CIST) instance (instance 0) and
cannot be unmapped from the CIST.
For two or more switches to be in the same MST region, they must have the
same VLAN mapping, the same configuration revision number, and the same
name.
Dell Networking MSTP supports mapping of VLANs to MST instances, even
though the underlying VLAN may not be defined on the switch. Traffic
received on VLANs not defined on the port received is dropped.
Example
The following example maps the entire range of VLANs to MST instances
(MST instance 0 is mapped to VLAN 1 by default). Additionally, two 10G
ports have some, but not all, of the VLANs mapped to MST instances.
console(config)#spanning-tree mode mst
console(config)#spanning-tree mst 1 priority 8192
console(config)#spanning-tree mst 2 priority 28672
console(config)#spanning-tree mst configuration
console(config-mst)#instance 1 add vlan 2-199
console(config-mst)#instance 1 add vlan 350
console(config-mst)#instance 1 add vlan 400-449
console(config-mst)#instance 1 add vlan 500-1999
console(config-mst)#instance 1 add vlan 2200-2499
2CSNXXX_SWUM200.book Page 733 Tuesday, December 10, 2013 1:22 PM

734 Spanning Tree Commands
console(config-mst)#instance 1 add vlan 2600-2799
console(config-mst)#instance 1 add vlan 3000-4093
console(config-mst)#instance 2 add vlan 200-349
console(config-mst)#instance 2 add vlan 351-399
console(config-mst)#instance 2 add vlan 450-499
console(config-mst)#instance 2 add vlan 2000-2199
console(config-mst)#instance 2 add vlan 2500-2599
console(config-mst)#instance 2 add vlan 2800-2999
console(config-mst)#exit
console(config)#interface te1/1/1
console(config-if-Te1/1/1)#switchport mode trunk
console(config-if-Te1/1/1)#switchport trunk allowed vlan add 2-150
console(config-if-Te1/1/1)#spanning-tree mst 1 port-priority 16
console(config-if-Te1/1/1)#interface te1/1/2
console(config-if-Te1/1/2)#switchport mode trunk
console(config-if-Te1/1/2)#switchport trunk allowed vlan add 200-349
console(config-if-Te1/1/2)#spanning-tree mst 2 port-priority 16
console(config-if-Te1/1/2)#exit
name (mst)
Use the name command in MST mode to define the configuration name. To
return to the default setting, use the no form of this command.
Syntax
name
string
•
string — Case sensitive
MST configuration name. (Range: 1-32
characters)
Default Configuration
Bridge address.
Command Mode
MST mode
User Guidelines
This command has no user guidelines.
2CSNXXX_SWUM200.book Page 734 Tuesday, December 10, 2013 1:22 PM

Spanning Tree Commands 735
Example
The following example sets the configuration name to “region1”.
console(config)#spanning-tree mst configuration
console(config-mst)#name region1
revision (mst)
Use the revision command in MST mode to identify the configuration
revision number. To return to the default setting, use the no form of this
command.
Syntax
revision
version
no revision
•
version —
Configuration revision number. (Range: 0-65535)
Default Configuration
Revision number is 0.
Command Mode
MST mode
User Guidelines
This command has no user guidelines.
Example
The following example sets the configuration revision to 1.
console(config)#spanning-tree mst configuration
console(config-mst)#revision 1
show spanning-tree
Use the show spanning-tree command in Privileged EXEC mode to display
the spanning-tree configuration.
2CSNXXX_SWUM200.book Page 735 Tuesday, December 10, 2013 1:22 PM

736 Spanning Tree Commands
Syntax
show spanning-tree [{gigabitethernet unit/slot/port |
port-channel
port-
channel-number
| tengigabitethernet unit/slot/port | fortygigabitethernet
unit/slot/port}]
[instance
instance-id
]
show spanning-tree [detail] [active | blockedports] | [instance
instance-id
]
show spanning-tree mst-configuration
show spanning-tree {uplinkfast | backbonefast}
•
detail
—Displays detailed information.
•
active
—Displays active ports only.
•
blockedports
—Displays blocked ports only.
•
mst-configuration
—Displays the MST configuration identifier.
•
instance -id
—ID of the spanning tree instance.
•
uplinkfast
—Displays Direct Rapid Convergence information.
•
backbonefast
—Displays Indirect Rapid Convergence information.
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC mode, Configuration mode and all Configuration submodes
User Guidelines
This command has no user guidelines.
Examples
The following examples display spanning-tree information.
console#show spanning-tree
Spanning tree :Enabled - BPDU Flooding :Disabled - Portfast BPDU filtering
:Disabled - mode :rstp
CST Regional Root: 80:00:00:1E:C9:AA:AD:1B
Regional Root Path Cost: 0
ROOT ID
Priority 32768
Address 0010.1882.1C53
Path Cost 20000
2CSNXXX_SWUM200.book Page 736 Tuesday, December 10, 2013 1:22 PM

Spanning Tree Commands 737
Root Port Gi1/0/1
Hello Time 2 Sec Max Age 20 sec Forward Delay 15 sec TxHoldCount
6 sec
Bridge ID
Priority 32768
Address 001E.C9AA.AD1B
Hello Time 2 Sec Max Age 20 sec Forward Delay 15 sec
Interfaces
Name State Prio.Nbr Cost Sts Role Restricted
------ -------- --------- --------- ---- ----- ----------
Gi1/0/1 Enabled 128.1 20000 FWD Root No
Gi1/0/2 Enabled 128.2 0 DIS Disb No
Gi1/0/3 Enabled 128.3 0 DIS Disb No
Gi1/0/4 Enabled 128.4 0 DIS Disb No
console#show spanning-tree gigabitethernet 1/0/1
Port Gi1/0/1 Enabled
State: Forwarding Role: Root
Port id: 128.1 Port Cost: 20000
Port Fast: No Root Protection: No
Designated bridge Priority: 32768 Address: 0010.1882.1C53
Designated port id: 128.48 Designated path cost: 0
CST Regional Root: 80:00:00:10:18:82:1C:53 CST Port Cost: 0
Root Guard..................................... FALSE
Loop Guard..................................... FALSE
TCN Guard...................................... FALSE
Auto Portfast.................................. TRUE
Port Up Time Since Counters Last Cleared....... 0 day 0 hr 17 min 1 sec
BPDU: sent 24, received 496
console#show spanning-tree detail
Spanning tree Enabled (BPDU flooding : Disabled) Portfast BPDU filtering
Disabled mode rstp
CST Regional Root: 80:00:00:1E:C9:AA:AD:1B
Regional Root Path Cost: 0
ROOT ID
Priority 32768
Address 0010.1882.1C53
Path Cost 20000
Root Port Gi1/0/1
Hello Time 2 Sec Max Age 20 sec Forward Delay 15 sec
Bridge ID
2CSNXXX_SWUM200.book Page 737 Tuesday, December 10, 2013 1:22 PM

738 Spanning Tree Commands
Priority 32768
Address 001E.C9AA.AD1B
Hello Time 2 Sec Max Age 20 sec Forward Delay 15 sec
Number of topology changes 1 last change occurred 0d0h17m7s ago
Times: hold 6, hello 2, max age 20, forward delay 15
Port Gi1/0/1 Enabled
State: Forwarding Role: Root
Port id: 128.1 Port Cost: 20000
Root Protection: No
Designated bridge Priority: 32768 Address: 0010.1882.1C53
Designated port id: 128.48 Designated path cost: 0
CST Regional Root: 80:00:00:10:18:82:1C:53 CST Port Cost: 0
BPDU: sent 24, received 500
console#show spanning-tree detail active
Spanning tree Enabled (BPDU flooding : Disabled) Portfast BPDU filtering
Disabled mode rstp
CST Regional Root: 80:00:00:1E:C9:AA:AD:1B
Regional Root Path Cost: 0
ROOT ID
Priority 32768
Address 0010.1882.1C53
Path Cost 20000
Root Port Gi1/0/1
Hello Time 2 Sec Max Age 20 sec Forward Delay 15 sec
Bridge ID
Priority 32768
Address 001E.C9AA.AD1B
Hello Time 2 Sec Max Age 20 sec Forward Delay 15 sec
Number of topology changes 1 last change occurred 0d0h17m15s ago
Times: hold 6, hello 2, max age 20, forward delay 15
Port Gi1/0/1 Enabled
State: Forwarding Role: Root
Port id: 128.1 Port Cost: 20000
Root Protection: No
Designated bridge Priority: 32768 Address: 0010.1882.1C53
Designated port id: 128.48 Designated path cost: 0
CST Regional Root: 80:00:00:10:18:82:1C:53 CST Port Cost: 0
BPDU: sent 24, received 504
Port Gi1/0/5 Enabled
State: Forwarding Role: Designated
Port id: 128.5 Port Cost: 20000
2CSNXXX_SWUM200.book Page 738 Tuesday, December 10, 2013 1:22 PM

Spanning Tree Commands 739
Root Protection: No
Designated bridge Priority: 32768 Address: 001E.C9AA.AD1B
Designated port id: 128.5 Designated path cost: 20000
CST Regional Root: 80:00:00:1E:C9:AA:AD:1B CST Port Cost: 0
BPDU: sent 524, received 0
console#show spanning-tree detail blockedports
Spanning tree Enabled (BPDU flooding : Disabled) Portfast BPDU filtering
Disabled mode rstp
CST Regional Root: 80:00:00:1E:C9:AA:AD:1B
Regional Root Path Cost: 0
ROOT ID
Priority 32768
Address 0010.1882.1C53
Path Cost 20000
Root Port Gi1/0/1
Hello Time 2 Sec Max Age 20 sec Forward Delay 15 sec
Bridge ID
Priority 32768
Address 001E.C9AA.AD1B
Hello Time 2 Sec Max Age 20
console#show spanning-tree backbonefast
Backbonefast Statistics
-----------------------
Transitions via Backbonefast (all VLANs) : 0
Inferior BPDUs received (all VLANs) : 0
RLQ request PDUs received (all VLANs) : 0
RLQ response PDUs received (all VLANs) : 0
RLQ request PDUs sent (all VLANs) : 0
RLQ response PDUs sent (all VLANs) : 0
console#show spanning-tree uplinkfast
Uplinkfast is enabled
BPDU update rate: 150 packets/sec
Uplinkfast statistics
-----------------------
Uplinkfast transitions (all VLANs) : 0
Proxy multicast addresses transmitted (all VLANs) : 0
Name Interface List
-------------------- ------------------------------------
Vl1 gi1/0/1,gi1/0/2
2CSNXXX_SWUM200.book Page 739 Tuesday, December 10, 2013 1:22 PM

740 Spanning Tree Commands
show spanning-tree summary
Use the show spanning-tree summary command to display spanning tree
settings and parameters for the switch.
Syntax
show spanning-tree summary
Default Configuration
There is no default configuration for this command.
Command Mode
Privileged EXEC mode, Configuration mode and all Configuration submodes
User Guidelines
The following fields are displayed:
Field Description
Spanning Tree Admin
Mode
Enabled or disabled
Spanning Tree Version Version of 802.1 currently supported (IEEE 802.1s,
IEEE 802.1w, or IEEE 802.1d) based upon the mode
parameter.
BPDU Protection Mode Enabled or disabled.
BPDU Filter Mode Enabled or disabled.
BPDU Flooding Mode Enabled or disabled.
Configuration Name Identifier used to identify the configuration currently
being used.
Configuration Revision
Level
Identifier used to identify the configuration currently
being used.
Configuration Digest Key A generated Key used in the exchange of the BPDUs.
Configuration Format
Selector
Specifies the version of the configuration format being
used in the exchange of BPDUs. The default value is
zero.
2CSNXXX_SWUM200.book Page 740 Tuesday, December 10, 2013 1:22 PM

Spanning Tree Commands 741
Example
console#show spanning-tree summary
Spanning Tree Adminmode........... Enabled
Spanning Tree Version............. IEEE 802.1w
BPDU Guard Mode................... Disabled
BPDU Flood Mode................... Disabled
BPDU Filter Mode.................. Disabled
Configuration Name................ 00-1E-C9-AA-AC-84
Configuration Revision Level...... 0
Configuration Digest Key.......... 0xac36177f50283cd4b83821d8ab26de62
Configuration Format Selector..... 0
show spanning-tree vlan
Use the show spanning-tree vlan command to display spanning tree
information per VLAN and also list out the port roles and states as well as
port cost.
Syntax
show spanning-tree vlan
vlan-list
• vlan-list — A list of VLANs or VLAN ranges separated by commas and
with no embedded blank spaces. VLAN ranges are of the form X-Y where X
and Y are valid VLAN identifiers and X < Y.
Default Configuration
There is no default configuration for this command.
Command Modes
Privileged EXEC and above
User Guidelines
There are no user guidelines for this command.
Example
console(config-vlan)#show spanning-tree vlan 1-3
MST Instances List of all multiple spanning tree instances configured
on the switch.
2CSNXXX_SWUM200.book Page 741 Tuesday, December 10, 2013 1:22 PM

742 Spanning Tree Commands
VLAN0001
Spanning tree enabled protocol rstp
Root ID Priority 32768
Address 0000.0000.0001
Cost 4
Port 1 (1/0/1)
Hello Time 2 sec Max Age 20 sec Forward Delay 15 sec
Bridge ID Priority 32769 (priority 32768 sys-id-ext 1)
Address 0000.0000.0003
Hello Time 2 sec Max Age 20 sec Forward Delay 15 sec
Aging Time 300 sec
Interface Role Sts Cost Prio.Nbr
------------------- ---- --- --------- -------- ----------------------------
Gi1/0/1 Desg FWD 4 128.19
Gi1/0/2 Desg FWD 4 128.21
VLAN0002
Spanning tree enabled protocol rstp
Root ID Priority 32768
Address 0000.0000.0001
Cost 4
Port 1 (1/0/1)
Hello Time 2 sec Max Age 20 sec Forward Delay 15 sec
Bridge ID Priority 32770 (priority 32768 sys-id-ext 2)
Address 0000.0000.0003
Hello Time 2 sec Max Age 20 sec Forward Delay 15 sec
Aging Time 300 sec
Interface Role Sts Cost Prio.Nbr
------------------- ---- --- --------- -------- ----------------------------
Gi1/0/3 Desg FWD 4 128.19
Gi1/0/4 Desg FWD 4 128.21
VLAN0003
Spanning tree enabled protocol rstp
Root ID Priority 32768
Address 0000.0000.0001
Cost 4
Port 1 (GigabitEthernet1/0/1)
Hello Time 2 sec Max Age 20 sec Forward Delay 15 sec
Bridge ID Priority 32771 (priority 32768 sys-id-ext 3)
Address 0000.0000.0003
2CSNXXX_SWUM200.book Page 742 Tuesday, December 10, 2013 1:22 PM

Spanning Tree Commands 743
Hello Time 2 sec Max Age 20 sec Forward Delay 15 sec
Aging Time 300 sec
Interface Role Sts Cost Prio.Nbr
------------------- ---- --- --------- -------- ----------------------------
Gi1/0/5 Desg FWD 4 128.19
Gi1/0/6 Desg FWD 4 128.21
spanning-tree
Use the spanning-tree command in Global Configuration mode to enable
spanning-tree functionality. To disable spanning-tree functionality, use the no
form of this command.
Syntax
spanning-tree
no spanning-tree
Default Configuration
Spanning-tree is enabled.
Command Mode
Global Configuration mode
User Guidelines
This command has no user guidelines.
Example
The following example enables spanning-tree functionality.
console(config)#spanning-tree
spanning-tree auto-portfast
Use the spanning-tree auto-portfast command to set the port to auto portfast
mode. This enables the port to become a portfast port if it does not see any
BPDUs for 3 seconds. Use the no form of this command to disable auto
portfast mode.
2CSNXXX_SWUM200.book Page 743 Tuesday, December 10, 2013 1:22 PM

744 Spanning Tree Commands
Syntax
spanning-tree auto-portfast
no spanning-tree auto-portfast
Default Configuration
Auto portfast mode is enabled by default.
Command Mode
Interface Configuration (Ethernet, Port Channel) mode
User Guidelines
There are no user guidelines for this command.
Example
The following example enables spanning-tree functionality on gigabit
ethernet interface 4/0/1.
console#config
console(config)#interface gigabitethernet 4/0/1
console(config-if-4/0/1)#spanning-tree auto-portfast
spanning-tree backbonefast
Use the spanning-tree backbonefast command to enable the detection of
indirect link failures and accelerate spanning tree convergence on
STP-PV/RSTP-PV configured switches using Indirect Rapid Convergence
(IRC). IRC accelerates finding an alternate path when an indirect link to the
root port goes down. Use the no form of the command to disable the IRC
feature.
Syntax
spanning-tree backbonefast
no spanning-tree backbonefast
Default Configuration
This command has no default configuration.
2CSNXXX_SWUM200.book Page 744 Tuesday, December 10, 2013 1:22 PM

Spanning Tree Commands 745
Command Modes
Global Configuration Mode
User Guidelines
IRC can be configured even if the switch is configured for MST(RSTP) or
RSTP-PV mode. It only has an effect when the switch is configured for
STP-PV mode.
If an IRC-enabed switch receives an inferior BPDU from its designated switch
on a root or blocked port, it sets the maximum aging time on the interfaces
on which it received the inferior BPDU if there are alternate paths to the
designated switch. This allows a blocked port to immediately move to the
listening state where the port can be transitioned to the forwarding state in
the normal manner.
Example
console(config)#spanning-tree backbonefast
spanning-tree bpdu flooding
The spanning-tree bpdu flooding command allows flooding of BPDUs
received on non-spanning-tree ports to all other non-spanning-tree ports. Use
the “no” form of the command to disable flooding.
Syntax
spanning-tree bpdu flooding
no spanning-tree bpdu flooding
Default Configuration
This feature is disabled by default.
Command Mode
Global Configuration mode
User Guidelines
There are no user guidelines for this command.
2CSNXXX_SWUM200.book Page 745 Tuesday, December 10, 2013 1:22 PM

746 Spanning Tree Commands
Example
console#spanning-tree bpdu flooding
spanning-tree bpdu-protection
Use the spanning-tree bpdu-protection command in Global Configuration
mode to enable BPDU protection on a switch. Use the no form of this
command to resume the default status of BPDU protection function.
For an access layer device, the access port is generally connected to the user
terminal (such as a desktop computer) or file server directly and configured as
an edge port to implement the fast transition. When the port receives a
BPDU packet, the system sets it to non-edge port and recalculates the
spanning tree, which causes network topology flapping. In normal cases, these
ports do not receive any BPDU packets. However, someone may forge BPDU
to maliciously attack the switch and cause network flapping.
RSTP provides BPDU protection function against such attack. After BPDU
protection function is enabled on a switch, the system disables an edge port
that has received BPDU and notifies the network manager about it. The
disabled port can only be enabled by the no version of the command.
Syntax
spanning-tree bpdu-protection
no spanning-tree bpdu-protection
Default Configuration
BPDU protection is not enabled.
Command Mode
Global Configuration mode
User Guidelines
This command has no user guidelines.
Example
The following example enables BPDU protection.
console(config)#spanning-tree bpdu-protection
2CSNXXX_SWUM200.book Page 746 Tuesday, December 10, 2013 1:22 PM

Spanning Tree Commands 747
spanning-tree cost
Use the spanning-tree cost command in Interface Configuration mode to
configure the externally advertised spanning-tree path cost for a port. To
return to the default port path cost, use the no form of this command.
The path cost is used in the selection of an interface for the forwarding or
blocking states. Use the no form of the command to automatically select the
path cost based upon the speed of the interface.
Syntax
spanning-tree [vlan
vlan-list
] cost
cost
no spanning-tree cost
•
cost
— The port path cost. (Range: 1–200,000,000)
Default Configuration
The default value is to select the path cost based on the link speed.
• 40G Port path cost
— 1400
•
10G Port path cost
— 2000
•
1000 mbps (giga)
— 20,000
•
100 mbps
— 200,000
•
10 mbps
— 2,000,000
• Port Channel—200,000,000 divided by the sum of the unidirectional link
speed (in Mbps) of each active member multiplied by 10 per section 13.6.1
of IEEE 802.1s.
Command Mode
Interface Configuration (gigabitethernet, port-channel, tengigabitethernet,
fortygigabitethernet) mode
User Guidelines
If the VLAN parameter is given, the path cost is configured only for the
selected VLANs (applies only when pvst or rapid-pvst mode is selected).
Configuration without the VLAN parameter configures the interface path
cost for RSTP, RSTP-PV, and STP-PV.
2CSNXXX_SWUM200.book Page 747 Tuesday, December 10, 2013 1:22 PM

748 Spanning Tree Commands
If an interface is configured with both the spanning-tree vlan
vlan-id
cost
cost
command and the spanning-tree cost
cost
command, the spanning-tree vlan
vlan-id
cost
cost
value is used in the spanning tree calculation.
Example
The following example configures the external path cost to be 8192 for
VLANs 12, 13, 24, 25, and 26.
console(config-if-Gi1/0/1)#spanning-tree vlan 12,13,24-26 cost 8192
spanning-tree disable
Use the spanning-tree disable command in Interface Configuration mode to
disable spanning-tree on a specific port. To enable spanning-tree on a port,
use the no form of this command.
Syntax
spanning-tree disable
no spanning-tree disable
Default Configuration
By default, all ports are enabled for spanning-tree.
Command Mode
Interface Configuration (gigabitethernet, port-channel, tengigabitethernet,
fortygigabitethernet) mode
User Guidelines
This command has no user guidelines.
Example
The following example disables spanning-tree on 1/0/5.
console(config)#interface gigabitethernet 1/0/5
console(config-if-Gi1/0/5)#spanning-tree disable
2CSNXXX_SWUM200.book Page 748 Tuesday, December 10, 2013 1:22 PM

Spanning Tree Commands 749
spanning-tree forward-time
Use the spanning-tree forward-time command in Global Configuration
mode to configure the spanning-tree bridge forward time, which is the
amount of time a port remains in the listening and learning states before
entering the forwarding state.
To reset the default forward time, use the no form of this command.
Syntax
spanning-tree forward-time
seconds
no spanning-tree forward-time
•
seconds
— Time in seconds. (Range: 4–30)
Default Configuration
The default forwarding-time for IEEE Spanning-tree Protocol (STP) is 15
seconds.
Command Mode
Global Configuration mode.
User Guidelines
When configuring the Forward-Time the following relationship should be
satisfied:
2*(Forward-Time - 1) >= Max-Age.
Example
The following example configures spanning-tree bridge forward time to 25
seconds.
console(config)#spanning-tree forward-time 25
2CSNXXX_SWUM200.book Page 749 Tuesday, December 10, 2013 1:22 PM

750 Spanning Tree Commands
spanning-tree guard
The spanning-tree guard command selects whether loop guard or root guard
is enabled on an interface. If neither is enabled, the port operates in
accordance with the multiple spanning tree protocol. Use the “no” form of
this command to disable loop guard or root guard on the interface.
Syntax
spanning-tree guard {root | loop | none}
•
root
— Enables root guard.
•
loop
— Enables loop guard
•
none
— Disables root and loop guard.
Default Configuration
Neither root nor loop guard is enabled.
Command Mode
Interface Configuration (Ethernet, Port Channel) mode.
User Guidelines
There are no user guidelines for this command.
Example
The following example disables spanning-tree guard functionality on gigabit
ethernet interface 4/0/1.
console#config
console(config)#interface gigabitethernet 4/0/1
console(config-if-4/0/1)#spanning-tree guard none
spanning-tree loopguard
Use the spanning-tree loopguard command to enable loop guard on all ports.
Use the “no” form of this command to disable loop guard on all ports.
Syntax
spanning-tree loopguard default
2CSNXXX_SWUM200.book Page 750 Tuesday, December 10, 2013 1:22 PM

Spanning Tree Commands 751
no spanning-tree loopguard default
Default Configuration
Loop guard is disabled by default.
Command Mode
Global Configuration mode
User Guidelines
There are no user guidelines for this command.
Example
The following example enables spanning-tree loopguard functionality on all
ports.
console(config)#spanning-tree loopguard default
spanning-tree max-age
Use the spanning-tree max-age command in Global Configuration mode to
configure the spanning-tree bridge maximum age. To reset the default
maximum age, use the no form of this command.
Syntax
spanning-tree max-age
seconds
no spanning-tree max-age
•
seconds
-Time in seconds. (Range: 6–40)
Default Configuration
The default max-age for IEEE STP is 20 seconds.
Command Mode
Global Configuration mode
2CSNXXX_SWUM200.book Page 751 Tuesday, December 10, 2013 1:22 PM

752 Spanning Tree Commands
User Guidelines
When configuring the Max-Age the following relationships should be
satisfied:
2*(Forward-Time - 1) >= Max-Age
Max-Age >= 2*(Hello-Time + 1)
Example
The following example configures the spanning-tree bridge maximum-age to
10 seconds.
console(config)#spanning-tree max-age 10
spanning-tree max-hops
Use the spanning-tree max-hops command to set the MSTP Max Hops
parameter to a new value for the common and internal spanning tree. Use the
“no” form of this command to reset the Max Hops to the default.
Syntax
spanning-tree max-hops
hops
no spanning-tree max-hops
•
hops
— The maximum number of hops to use (Range: 6 to 40).
Default Configuration
The maximum number of hops is 20 by default.
Command Mode
Global Configuration mode
User Guidelines
There are no user guidelines for this command.
Example
console(config)#spanning-tree max-hops 32
2CSNXXX_SWUM200.book Page 752 Tuesday, December 10, 2013 1:22 PM

Spanning Tree Commands 753
spanning-tree mode
Use the spanning-tree mode command in Global Configuration mode to
configure the spanning-tree protocol. To return to the default configuration,
use the no form of this command.
Syntax
spanning-tree mode {stp | rstp | mst | pvst | rapid-pvst}
no spanning-tree mode
•
stp
— Spanning Tree Protocol (STP) is enabled.
•
rstp
— Rapid Spanning Tree Protocol (RSTP) is enabled.
•
mst
— Multiple Spanning Tree Protocol (MSTP) is enabled.
•
pvst
—
Spanning-tree operates in Per-VLAN mode.
•
rapid-pvst
—
Spanning-tree operates in Rapid Per-VLAN mode.
Default Configuration
Rapid Spanning Tree Protocol (RSTP) is supported.
Command Mode
Global Configuration mode
User Guidelines
In RSTP mode, the switch uses STP when the neighbor switch is using STP.
In MSTP mode, the switch uses RSTP when the neighbor switch is using
RSTP and uses STP when the neighbor switch is using STP.
Only one of STP, RSTP, MSTP (RSTP), STP-PV or RSTP-PV can be enabled
on a switch. This command stops all spanning-tree instances in the current
mode and enables spanning-tree per VLAN in the new mode. By default,
RSTP is enabled.
In the STP-PV or RSTP-PV modes, BPDUs contain per-VLAN information
instead of the common spanning-tree information (MST/RSTP).
2CSNXXX_SWUM200.book Page 753 Tuesday, December 10, 2013 1:22 PM

754 Spanning Tree Commands
RSTP-PV maintains independent spanning tree information about each
configured VLAN. RSTP-PV uses IEEE 802.1Q trunking and allows a trunked
VLAN to maintain blocked or forwarding state per port on a per VLAN basis.
This allows a trunk port to be forwarding for some VLANs and blocked on
other VLANs.
RSTP-PV extends the IEEE 802.1w standard. It supports faster convergence
than IEEE 802.1D. RSTP-PV is compatible with IEEE 802.1D spanning tree.
RSTP-PV sends BPDUs on all ports instead of only the root bridge sending
BPDUs and supports the discarding, learning, and forwarding states.
When the mode is changed to rapid-pvst, version 0 STP BPDUs are no longer
transmitted and version 2 RSTP-PV BPDUs that carry per-VLAN information
are transmitted on the VLANs enabled for spanning-tree. If a version 0 BPDU
is seen, RSTP-PV reverts to sending version 0 BPDUs.
RSTP-PV embeds support for STP-PV Indirect Rapid Convergence and
Direct Rapid Convergence. There is no provision to enable or disable these
features in RSTP-PV.
Example
The following example configures the spanning-tree protocol to MSTP.
console(config)#spanning-tree mode mst
spanning-tree mst configuration
Use the spanning-tree mst configuration command in Global Configuration
mode to enable configuring an MST region by entering the multiple
spanning-tree (MST) mode.
Syntax
spanning-tree mst configuration
Default Configuration
This command has no default configuration.
Command Mode
Global Configuration mode
2CSNXXX_SWUM200.book Page 754 Tuesday, December 10, 2013 1:22 PM

Spanning Tree Commands 755
User Guidelines
For two or more switches to be in the same MST region, they must have the
same VLAN mapping, the same configuration revision number and the same
name.
Example
The following example configures an MST region.
console (config)#spanning-tree mst configuration
console (config-mst)#instance 1 add vlan 10-20
console (config-mst)#name region1
console (config-mst)#revision 1
spanning-tree mst cost
Use the spanning-tree mst cost command in Interface Configuration mode
to configure the internal path cost for multiple spanning tree (MST)
calculations. If a loop occurs, the spanning tree considers path cost when
selecting an interface to put in the forwarding state. To return to the default
port path cost, use the no form of this command.
Syntax
spanning-tree mst
instance-id
cost
cost
no spanning-tree mst
instance-id
cost
•
instance-ID —
ID of the spanning -tree instance. (Range: 1-4094)
•
cost —
The port path cost. (Range: 0–200,000,000)
Default Configuration
The default value is 0, which signifies that the cost will be automatically
calculated based on port speed.
The default configuration is:
• Ethernet (10 Mbps)
—
2,000,000
•Fast Ethernet (100 Mbps)
—
200,000
• Gigabit Ethernet (1000 Mbps)
—
20,000
•Port-Channel
—
20,000
2CSNXXX_SWUM200.book Page 755 Tuesday, December 10, 2013 1:22 PM

756 Spanning Tree Commands
Command Mode
Interface Configuration (gigabitethernet, port-channel, tengigabitethernet,
fortygigabitethernet) mode
User Guidelines
MST instance id 0 is the common internal spanning tree instance (CIST).
Example
The following example configures the MSTP instance 1 path cost for
interface 1/0/9 to 4.
console(config)#interface gigabitethernet 1/0/9
console(config-if-Gi1/0/9)#spanning-tree mst 1 cost 4
spanning-tree mst port-priority
Use the spanning-tree mst port-priority command in Interface Configuration
mode to configure port priority. To return to the default port priority, use the
no form of this command.
Syntax
spanning-tree mst
instance-id
port-priority
priority
no spanning-tree mst
instance-id
port-priority
•
instance-id
—ID of the spanning-tree instance. (Range: 1-4094)
•
priority
—The port priority. (Range: 0-240 in multiples of 16.)
Default Configuration
The default port-priority for IEEE STP is 128. The default priority for a port-
channel is 96.
Command Mode
Interface Configuration (gigabitethernet, port-channel, tengigabitethernet,
fortygigabitethernet) mode
2CSNXXX_SWUM200.book Page 756 Tuesday, December 10, 2013 1:22 PM

Spanning Tree Commands 757
User Guidelines
The priority will be set to the nearest multiple of 4096 if not an exact multiple
of 4096.
Example
The following example configures the port priority of gigabit Ethernet
interface 1/0/5 to 144.
console(config)#interface gigabitethernet 1/0/5
console(config-if)#spanning-tree mst 1 port-priority 144
spanning-tree mst priority
Use the spanning-tree mst priority command in Global Configuration mode
to set the switch priority for the specified spanning-tree instance. To return to
the default setting, use the no form of this command.
Syntax
spanning-tree mst
instance-id
priority
priority
no spanning-tree mst
instance-id
priority
•
instance-id
—ID of the spanning-tree instance. (Range: 1-4094)
•
priority
—Sets the switch priority for the specified spanning-tree instance.
This setting affects the likelihood that the switch is selected as the root
switch. A lower value increases the probability that the switch is selected as
the root switch. (Range: 0-61440)
Default Configuration
The default bridge priority for IEEE STP is 32768.
Command Mode
Global Configuration mode
User Guidelines
The priority value must be a multiple of 4096. The priority will be set to the
nearest multiple of 4096 if not an exact multiple of 4096.
The switch with the lowest priority is selected as the root of the spanning tree.
2CSNXXX_SWUM200.book Page 757 Tuesday, December 10, 2013 1:22 PM

758 Spanning Tree Commands
Example
The following example configures the spanning tree priority of instance 1 to
4096.
console(config)#spanning-tree mst 1 priority 4096
spanning-tree portfast
Use the spanning-tree portfast command in Interface Configuration mode to
enable PortFast mode. In PortFast mode, the interface is immediately put
into the forwarding state upon linkup, without waiting for the timer to expire.
To disable PortFast mode, use the no form of this command.
Syntax
spanning-tree portfast
no spanning-tree portfast
Default Configuration
PortFast mode is disabled.
Command Mode
Interface Configuration (gigabitethernet, port-channel, tengigabitethernet,
fortygigabitethernet) mode
User Guidelines
This command only applies to access ports. The command is to be used only
with interfaces connected to end stations. Otherwise, an accidental topology
loop could cause a data packet loop and disrupt switch and network
operations.
An interface with PortFast mode enabled is moved directly to the spanning
tree forwarding state when linkup occurs without waiting the standard
forward-time delay.
Example
The following example enables PortFast on 1/0/5.
console(config)#interface gigabitethernet 1/0/5
console(config-if-Gi1/0/5)#spanning-tree portfast
2CSNXXX_SWUM200.book Page 758 Tuesday, December 10, 2013 1:22 PM

Spanning Tree Commands 759
spanning-tree portfast bpdufilter default
The spanning-tree portfast bpdufilter default command discards BPDUs
received on spanning-tree ports in portfast mode. Use the “no” form of the
command to disable discarding.
Syntax
spanning-tree portfast bpdufilter default
no spanning-tree portfast bpdufilter default
Default Configuration
This feature is disabled by default.
Command Mode
Global Configuration mode
User Guidelines
There are no user guidelines for this command.
Example
The following example discards BPDUs received on spanning-tree ports in
portfast mode.
console#spanning-tree portfast bpdufilter default
spanning-tree portfast default
Use the spanning-tree portfast default command to enable Portfast mode
only on access ports. Use the no form of this command to disable Portfast
mode on all ports.
Syntax
spanning-tree portfast default
no spanning-tree portfast default
2CSNXXX_SWUM200.book Page 759 Tuesday, December 10, 2013 1:22 PM

760 Spanning Tree Commands
Default Configuration
Portfast mode is disabled by default.
Command Mode
Global Configuration mode
User Guidelines
This command only applies to access ports.
NOTE: This command should be used with care. An interface with
PortFast mode enabled is moved directly to the spanning tree forwarding
state when linkup occurs without waiting for the standard forward-time delay.
Setting a port connected to another switch into PortFast mode may cause an
accidental topology loop and disrupt switch and network operations.
Example
The following example enables Portfast mode on all access ports.
console(config)#spanning-tree portfast default
spanning-tree port-priority (Interface
Configuration)
Use the spanning-tree port-priority command in Interface Configuration
mode to configure the priority value of an edge-port or point-to-point
interface to allow the operator to select the relative importance of the
interface in the selection process for forwarding. Set this value to a lower
number to prefer an operationally enabled interface for forwarding of frames.
Use the no form of the command to return the priority to the default value.
Syntax
spanning-tree [vlan
vlan-id
] port-priority
priority
no spanning-tree [vlan
vlan-id
] port-priority
•
vlan-id
— An optional parameter specifying the VLAN to which the
priority applies when the port is configured as an edge-port. Range 1-4094.
•
priority
— The priority of the edge-port or point-to-point link in the
forwarding port selection process. Range is 0 to 240 in increments of 16.
2CSNXXX_SWUM200.book Page 760 Tuesday, December 10, 2013 1:22 PM

Spanning Tree Commands 761
Default Configuration
The default port-priority for IEEE STP is 128.
Command Mode
Interface Configuration mode
User Guidelines
If the VLAN parameter is given, the priority is configured only for the
selected VLANs (applies only when pvst or rapid-pvst mode is selected).
Configuration without the VLAN parameter configures the port priority for
RSTP, STP-PV, and RSTP-PV.
If an interface is configured with both the spanning-tree vlan
vlan-id
port-
priority
priority
command and the spanning-tree port-priority
priority
command, the spanning-tree vlan
vlan-id
port-priority
priority
value is used
as the port priority.
If a VLAN parameter is provided, the VLAN must have been previously
configured or an error is thrown.
An edge port is a port with spanning-tree port-fast enabled. A point-to-point
link is a link configured as full-duplex. Edge-ports and point-to-point links
can directly transition to the forwarding state and do not delay for the
listening and learning stages of spanning-tree. An edge port that receives a
BPDU is no longer considered an edge-port and will utilize the configured
port priority value.
All interfaces and VLANs have 128 as priority value by default. By default,
spanning-tree puts the lowest numbered operationally enabled interface in
the forwarding state and blocks other interfaces. The priority value is used to
override this default behavior. Interfaces with lower port priorities are
preferred for forwarding over interfaces with numerically higher priority
values. STP-PV/RSTP-PV uses the port priority value when the LAN port is
configured as an edge port and uses the VLAN priority value when the
interface is configured as a point-to-point link. MSTP uses the port priority
regardless of whether the port is an edge port or not.
2CSNXXX_SWUM200.book Page 761 Tuesday, December 10, 2013 1:22 PM

762 Spanning Tree Commands
Example
The following example configures a port connected to a host to be least likely
to be selected for forwarding to the root bridge, even if the host begins to
send BPDUs.
console(config-if-Gi1/0/1)#spanning-tree port-priority 240
console(config-if-Gi1/0/1)#spanning-tree vlan 10 port-priority 240
spanning-tree priority
Use the spanning-tree priority command in Global Configuration mode to
configure the spanning-tree priority. The priority value is used to determine
which bridge is elected as the root bridge. To reset the default spanning-tree
priority use the no form of this command.
Syntax
spanning-tree priority
priority
no spanning-tree priority
•
priority
— Priority of the bridge. (Range: 0–61440)
Default Configuration
The default bridge priority for IEEE STP is 32768.
Command Mode
Global Configuration mode
User Guidelines
The priority value must be a multiple of 4096.
The switch with the lowest priority is the root of the spanning tree.
Example
The following example configures spanning-tree priority to 12288.
console(config)#spanning-tree priority 12288
2CSNXXX_SWUM200.book Page 762 Tuesday, December 10, 2013 1:22 PM

Spanning Tree Commands 763
spanning-tree tcnguard
Use the spanning-tree tcnguard command to prevent a port from propagating
topology change notifications. Use the “no” form of the command to enable
TCN propagation.
Syntax
spanning-tree tcnguard
no spanning-tree tcnguard
Default Configuration
TCN propagation is disabled by default.
Command Mode
Interface Configuration (Ethernet, Port Channel) mode
User Guidelines
There are no user guidelines for this command.
Example
The following example configures spanning-tree tcnguard on 4/0/1.
console(config-if-4/0/1)#spanning-tree tcnguard
spanning-tree transmit hold-count
Use the spanning-tree transmit hold-count command to set the maximum
number of BPDUs that a bridge is allowed to send within a hello time window
(2 seconds). Use the no form of this command to reset the hold count to the
default value.
Syntax
spanning-tree transmit [hold-count] [
value
]
no spanning-tree transmit
•
value
— The maximum number of BPDUs to send (Range: 1–10).
2CSNXXX_SWUM200.book Page 763 Tuesday, December 10, 2013 1:22 PM

764 Spanning Tree Commands
Default Configuration
The default hold count is 6 BPDUs.
Command Mode
Global Configuration mode
User Guidelines
There are no user guidelines for this command.
Example
The following example sets the maximum number of BPDUs sent to 6.
console(config)#spanning-tree transmit hold-count 6
spanning-tree uplinkfast
Use the spanning-tree uplinkfast command to configure the rate at which
gratuitous frames are sent (in packets per second) after a switchover to an
alternate port on STP-PV and RSTP-PV configured switches and enable
Direct Rapid Convergence on STP-PV switches. This command assists in
accelerating spanning-tree convergence after switchover to an alternate port.
Use the no form of the command to return the configured rate to the default
value (or disable uplinkfast on STP-PV configured switches).
Syntax
spanning-tree uplinkfast [max-update-rate
packets/s
]
no spanning-tree uplinkfast [max-update-rate]
•
max-update-rate
—The rate at which update packets are sent. (Range: 0-
3200
Default Configuration
The default rate is 150.
Command Modes
Global Configuration Mode
2CSNXXX_SWUM200.book Page 764 Tuesday, December 10, 2013 1:22 PM

Spanning Tree Commands 765
User Guidelines
DirectLink Rapid Convergence (DRC) can be configured even if the switch is
configured for MST(RSTP) mode. It only has an effect when the switch is
configured for STP-PV or RSTP-PV modes. Enabling DRC sets the switch
priority to 49152. Path costs less than 3000 have an additional 3000 added
when DRC is enabled. This reduces the probability that the switch will
become the root switch.
DRC immediately changes to an alternate root port on detecting a root port
failure and change the new root port directly to the fowarding state. A TCN is
sent for this event.
After a switchover to an alternate port (new root port), DRC multicasts a
gratuitous frame on the new root port on behalf of each attached machine so
that the rest of the network knows to use the secondary link to reach that
machine.
RSTP-PV embeds support for IRC and DRC. There is no provision to enable
or disable these features in RSTP-PV configured switches.
Example
console(config)#spanning-tree uplinkfast
spanning-tree vlan
Use the spanning-tree vlan command to enable per VLAN spanning tree on a
VLAN. Use the no form of the command to remove the VLAN as a separate
spanning tree instance.
Syntax
spanning-tree vlan {
vlan-list
}
no spanning-tree vlan {
vlan-list
}
•
vlan-list
–A single VLAN ID or a list of VLAN IDs in comma delineated or
range format with no embedded blanks. Range 1-4094.
Default Configuration
By default, each configured VLAN is automatically associated with a per
VLAN spanning tree instance. If more than eight VLANs are configured, the
excess VLANs do not participate in per VLAN spanning tree.
2CSNXXX_SWUM200.book Page 765 Tuesday, December 10, 2013 1:22 PM

766 Spanning Tree Commands
To change the allocation of spanning-tree instances to VLANs, use the no
spanning-tree vlan command to disassociate a VLAN from a per VLAN
spanning-tree instance and use the spanning-tree vlan command to associate
the spanning-tree instance with the desired VLAN.
Command Modes
Global Configuration mode
User Guidelines
This command can be configured even if the switch is configured for
MST(RSTP) mode. It is only used when the switch is configured for PVST or
RPVST modes.
Example
This example configures a switch to use per VLAN spanning tree for VLANS
12, 13 and 24-26
console(config)#spanning-tree vlan 12,13,24-26
spanning-tree vlan forward-time
Use the spanning-tree vlan forward-time command to configure the
spanning tree forward delay time for a specified VLAN or a range of VLANs.
Use the no form of the command to return the forward time to its default
value.
Syntax
spanning-tree vlan
vlan-list
forward-time
4-30
no spanning-tree vlan
vlan-list
forward-time
• forward-time — The interval (time spent in listening and learning states)
before transitioning a port to the forwarding state. (Range: 4-30 seconds)
Default Configuration
The default forward delay time is 15.
2CSNXXX_SWUM200.book Page 766 Tuesday, December 10, 2013 1:22 PM

Spanning Tree Commands 767
Command Modes
Global Configuration Mode
User Guidelines
Set this value to a lower number to accelerate the transition to forwarding.
The network operator should take into account the end to end BPDU
propagation delay, the maximum frame lifetime, the maximum transmission
halt delay and the message age overestimate values specific to their network
when configuring this parameter.
Example
console(config)#spanning-tree vlan 3 forward-time 12
spanning-tree vlan hello-time
Use the spanning-tree vlan hello-time command to configure the spanning
tree hello time for a specified VLAN or a range of VLANs.
Syntax
spanning-tree vlan
vlan-list
hello-time
1-10
no spanning-tree vlan
vlan-list
hello-time
• Hello-time–The interval between sending successive BDPUs. Default: 2
seconds.
Default Configuration
The default hello time is 2 seconds.
Command Modes
Global Configuration Mode
User Guidelines
This command can be configured even if the switch is configured for
MST(RSTP) mode. It is only used when the switch is configured for PVST or
RPVST modes.
Set this value to a lower number to accelerate discovery of topology changes.
2CSNXXX_SWUM200.book Page 767 Tuesday, December 10, 2013 1:22 PM

768 Spanning Tree Commands
Use the
no
form of the command to return the hello time to its default value.
Example
console(config)#spanning-tree vlan 3 hello-time 1
spanning-tree vlan max-age
Use the spanning-tree vlan max-age command to configure the spanning tree
maximum age time for a set of VLANs. Use the no form of the command to
return the maximum age timer to the default value.
Syntax
spanning-tree vlan
vlan-list
max-age
6-40
no spanning-tree vlan
vlan-list
> max-age
• max-age — The maximum age time before a bridge port saves its
configuration information.
Default Configuration
The default maximum aging time is 20 seconds.
Command Modes
Global Configuration Mode
User Guidelines
Set this value to a lower number to accelerate discovery of topology changes.
The network operator must take into account the end to end BPDU
propagation delay and message age overestimate for their specific topology
when configuring this value.
The default setting of 20 seconds is suitable for a network of diameter 7, lost
message value of 3, transit delay of 1, hello interval of 2 seconds, overestimate
per bridge of 1 second, and a BPDU delay of 1 second. For a network of
diameter 4, a setting of 16 seconds is appropriate if all other timers remain at
their default values.
Example
console(config)#spanning-tree vlan 3 max-age 18
2CSNXXX_SWUM200.book Page 768 Tuesday, December 10, 2013 1:22 PM

Spanning Tree Commands 769
spanning-tree vlan root
Use the spanning-tree vlan root primary command to configure the switch to
become the root bridge or standby root bridge by modifying the bridge
priority from the default value to a lower value calculated to ensure the bridge
is the root (or standby) bridge. Use the no form of the command to let the
network elect the root bridge.
Syntax
spanning-tree vlan
vlan-list
root {primary | secondary}
no spanning tree vlan
vlan-list
root
Default Configuration
The default bridge priority value is 32768.
Command Modes
Global Configuration mode
User Guidelines
This command can be configured even if the switch is configured for MST
(RSTP) mode. It is only used when the switch is configured for PVST or
RPVST modes.
The logic sets the bridge priority to a value lower (primary) or next lower
(secondary) than the lowest bridge priority for the specified VLAN or a range
of VLANs. This command only applies when STP-PV or RSTP-PV is enabled.
Example
console(config)#spanning-tree vlan 3 root primary
spanning-tree vlan priority
Use the spanning-tree vlan priority command to configure the bridge priority
of a VLAN. The bridge priority is combined with the MAC address of the
switch and is used to select the root bridge for the VLAN. Use the no form of
the command to return the priority to the default value.
2CSNXXX_SWUM200.book Page 769 Tuesday, December 10, 2013 1:22 PM

770 Spanning Tree Commands
Syntax
spanning-tree vlan {
vlan-list
} priority
priority
no spanning-tree vlan {
vlan-list
} priority
•
vlan-list
–A single VLAN ID or a list of VLAN IDs in comma delineated or
range format with no embedded blanks. Range 1-4094.
•
priority
–The bridge priority advertised when combined with the switch
MAC address. Range 0-61440.
Default Configuration
The default bridge priority is 32768.
Valid values are 0, 4096, 8192, 12288, 16384, 20480, 24576, 28672, 32768,
36864, 40960, 45056, 49152, 53248, 57344, and 61440. The default value is
32768.
If the value configured is not among the specifed values, it will be rounded off
to the nearest valid value.
Command Modes
Global Configuration mode
User Guidelines
This command can be configured even if the switch is configured for
MST(RSTP) mode. It is only used when the switch is configured for PVST or
RPVST modes.
The root bridge for a VLAN should be carefully selected to provide optimal
paths for traffic through the network. Generally, this means selecting a switch
that is well-connected with other switches in the network.
Example
This example configures a switch to be the spanning tree root bridge for
VLANs 12, 13, 24, 25, and 26. This presumes other switches in the network
utilize the default bridge priority configuration.
console(config)#spanning-tree vlan 12,13,24-26 priority 8192
2CSNXXX_SWUM200.book Page 770 Tuesday, December 10, 2013 1:22 PM

TACACS+ Commands 771
36
TACACS+ Commands
Dell Networking N2000/N3000/N4000 Series Switches
TACACS+ provides access control for networked devices via one or more
centralized servers, similar to RADIUS this protocol simplifies authentication
by making use of a single database that can be shared by many clients on a
large network. TACACS+ is based on the TACACS protocol (described in
RFC1492) but additionally provides for separate authentication,
authorization and accounting services. The original protocol was UDP based
with messages passed in clear text over the network; TACACS+ uses TCP to
ensure reliable delivery and a shared key configured on the client and daemon
server to encrypt all messages.
Dell Networking supports authentication of a user using a TACACS+ server.
When TACACS+ is configured as the authentication method for a user login
type (CLI/HTTP/HTTPS), the NAS will prompt for the user login credentials
and request services from the TACACS+ client; the client will then use the
configured list of servers for authentication and provide results back to the
NAS. The TACACS+ server list is configured with one or more hosts defined
via their network IP address; each can be assigned a priority to determine the
order in which the TACACS+ client will contact them, a server is contacted
when a connection attempt fails or times out for a higher priority server. Each
server host can be separately configured with a specific connection type, port,
time-out, and shared key, or the global configuration may be used for the key
and time-out. Like RADIUS, the TACACS+ server may do the
authentication itself, or redirect the request to another back-end device, all
sensitive information is encrypted and the shared secret is never passed over
the network.
Commands in this Chapter
This chapter explains the following commands:
key tacacs-server host
key encrypted tacacs-server key
2CSNXXX_SWUM200.book Page 771 Tuesday, December 10, 2013 1:22 PM

772 TACACS+ Commands
key
Use the key command in TACACS Configuration mode to specify the
authentication and encryption key for all TACACS communications between
the device and the TACACS server. This key must match the key used on the
TACACS daemon.
Syntax
key [
key-string
]
•key-string
— To specify the key name. (Range: 1
–
128 characters)
Default Configuration
If left unspecified, the key-string parameter defaults to the global value.
Command Mode
TACACS Configuration mode
User Guidelines
This command has no user guidelines.
Example
The following example specifies an encryption and authentication key of 12.
console(tacacs)#key 12
key encrypted
Use the key encrypted command to configure an encrypted key that is shared
with the TACACS server. Use the no form of the command to remove the key.
Syntax
key encrypted
key-string
port tacacs-server key encrypted
priority tacacs-server timeout
show tacacs timeout
2CSNXXX_SWUM200.book Page 772 Tuesday, December 10, 2013 1:22 PM

TACACS+ Commands 773
•
key-string —
The key string in encrypted form. It should be 256 characters
in length
.
Default Configuration
There is no default configuration for this command.
Command Modes
TACACS Configuration mode.
Usage Guidelines
This command has no user guidelines.
Example
console(tacacs)# key encrypted
f6fdffe48c908deb0f4c3bd36c032e72f6fdffe48c908deb0f4c3bd36c032e72f6fdffe48c90
8deb0f4c3bd36c032e72f6fdffe48c908deb0f4c3bd36c032e72f6fdffe48c908deb0f4c3bd3
6c032e72f6fdffe48c908deb0f4c3bd36c032e72f6fdffe48c908deb0f4c3bd36c032e72f6fd
ffe48c908deb0f4c3bd36c032e72
console(config)#
port
Use the port command in TACACS Configuration mode to specify a port
number on which a TACACS server listens for connections.
Syntax
port [port-number]
•
port-number
— The server port number. If left unspecified, the default
port number is 49. (Range: 0–65535)
Default Configuration
The default port number is 49.
Command Mode
TACACS Configuration mode
2CSNXXX_SWUM200.book Page 773 Tuesday, December 10, 2013 1:22 PM

774 TACACS+ Commands
User Guidelines
This command has no user guidelines.
Example
The following example displays how to specify TACACS server port number
1200.
console(tacacs)#port 1200
priority
Use the priority command in TACACS Configuration mode to specify the
order in which servers are used, where 0 (zero) is the highest priority.
Syntax
priority [
priority
]
•
priority
— Specifies the priority for servers. 0 (zero) is the highest priority.
(Range: 0–65535).
Default Configuration
If left unspecified, this parameter defaults to 0 (zero).
Command Mode
TACACS Configuration mode
User Guidelines
This command has no user guidelines.
Example
The following example shows how to specify a server priority of 10000.
console(tacacs)#priority 10000
show tacacs
Use the show tacacs command in Privileged EXEC mode to display the
configuration and statistics of a TACACS+ server.
2CSNXXX_SWUM200.book Page 774 Tuesday, December 10, 2013 1:22 PM

TACACS+ Commands 775
Syntax
show tacacs [
ip-address
]
•
ip-address
—
The name or IP address of the host.
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC mode, Configuration mode and all Configuration submodes
User Guidelines
This command has no user guidelines.
Examples
The following example displays TACACS+ server settings.
console#show tacacs
Global Timeout: 5
IP address Port Timeout Priority
--------------- ----- ------- --------
10.254.24.162 49 Global 0
tacacs-server host
Use the tacacs-server host command in Global Configuration mode to
configure a TACACS+ server. This command enters into the TACACS+
configuration mode. To delete the specified hostname or IP address, use the
no form of this command.
Syntax
tacacs-server host {
ip-address
|
hostname
}
no tacacs-server host {
ip-address
|
hostname
}
•
ip-address
—
The IP address of the TACACS+ server.
2CSNXXX_SWUM200.book Page 775 Tuesday, December 10, 2013 1:22 PM

776 TACACS+ Commands
•
hostname —
The hostname of the TACACS+ server. (Range: 1-255
characters).
Default Configuration
No TACACS+ host is specified.
Command Mode
Global Configuration mode
User Guidelines
To specify multiple hosts, multiple tacacs-server host commands can be used.
TACACS servers are keyed by the host name, therefore it is advisable to use
unique host names.
Example
The following example specifies a TACACS+ host.
console(config)#tacacs-server host 172.16.1.1
console(tacacs)#
tacacs-server key
Use the tacacs-server key command in Global Configuration mode to set the
authentication and encryption key for all TACACS+ communications
between the switch and the TACACS+ daemon. To disable the key, use the
no form of this command.
Syntax
tacacs-server key [
key-string
]
no tacacs-server key
•
key-string — Specifies
the authentication and encryption key for all
TACACS communications between the switch and the TACACS+ server.
This key must match the key used on the TACACS+ daemon. (Range:
0–128 printable characters except for question marks and double quotes.)
Default Configuration
The default is an empty string.
2CSNXXX_SWUM200.book Page 776 Tuesday, December 10, 2013 1:22 PM

TACACS+ Commands 777
Command Mode
Global Configuration mode
User Guidelines
The tacacs-server key command accepts any printable characters for the key
except a double quote or question mark. Enclose the string in double quotes
to include spaces within the key. The surrounding quotes are not used as part
of the name. The CLI does not filter illegal characters and may accept entries
up to the first illegal character or reject the entry entirely.
Example
The following example sets the authentication encryption key.
console(config)#tacacs-server key "I've got a secret"
console(config)#tacacs-server key @#$%^&*()_+=-{}][<>.,/';:|
tacacs-server key encrypted
Use this command to set the authentication and encryption key for the
communication between the switch and TACACS server. Use the no form of
the command to disable the key.
Syntax
tacacs-server key encrypted
key-string
•
key-string
—The key string in encrypted form. It should be 256 characters
in length.
Default Configuration
There is no default configuration for this command.
Command Modes
Global Configuration mode.
User Guidelines
This command has no user guidelines.
2CSNXXX_SWUM200.book Page 777 Tuesday, December 10, 2013 1:22 PM

778 TACACS+ Commands
Example
console(config)# tacacs-server key encrypted
f6fdffe48c908deb0f4c3bd36c032e72f6fdffe48c908deb0f4c3bd36c032e72f6fdffe48c90
8deb0f4c3bd36c032e72f6fdffe48c908deb0f4c3bd36c032e72f6fdffe48c908deb0f4c3bd3
6c032e72f6fdffe48c908deb0f4c3bd36c032e72f6fdffe48c908deb0f4c3bd36c032e72f6fd
ffe48c908deb0f4c3bd36c032e72
console(config)#
tacacs-server timeout
Use the tacacs-server timeout command in Global Configuration mode to set
the interval during which a switch waits for a server host to reply. To restore
the default, use the no form of this command.
Syntax
tacacs-server timeout [
timeout
]
no tacacs-server timeout
•
timeout —
The timeout value in seconds. (Range: 1–30)
Default Configuration
The default value is 5 seconds.
Command Mode
Global Configuration mode
User Guidelines
This command has no user guidelines.
Example
The following example sets the timeout value as 30.
console(config)#tacacs-server timeout 30
timeout
Use the timeout command in TACACS Configuration mode to specify the
timeout value in seconds. If no timeout value is specified, the global value is
used.
2CSNXXX_SWUM200.book Page 778 Tuesday, December 10, 2013 1:22 PM

TACACS+ Commands 779
Syntax
timeout [
timeout
]
•
timeout —
The timeout value in seconds. (Range: 1–30)
Default Configuration
If left unspecified, the timeout defaults to the global value.
Command Mode
TACACS Configuration mode
User Guidelines
This command has no user guidelines.
Example
This example shows how to specify the timeout value.
console(tacacs)#timeout 23
2CSNXXX_SWUM200.book Page 779 Tuesday, December 10, 2013 1:22 PM

780 TACACS+ Commands
2CSNXXX_SWUM200.book Page 780 Tuesday, December 10, 2013 1:22 PM

UDLD Commands 781
37
UDLD Commands
The UDLD feature detects unidirectional links on physical ports. A
unidirectional link is a forwarding anomaly in a Layer 2 communication
channel in which a bi-directional link stops passing traffic in one direction.
UDLD must be enabled on the both sides of the link in order to detect a
unidirectional link. The UDLD protocol operates by exchanging packets
containing information about neighboring devices.
UDLD enabled devices send announcements to the multicast destination
address 01-00-0c-cc-cc-cc. UDLD packets are transmitted using SNAP
encapsulation, with OUI value 0x00000c (Cisco) and protocol ID 0x0111.
UDLD is supported on individual physical ports that are members of port
channel interface. If any of the aggregated links becomes unidirectional,
UDLD detects it and disables the individual link, but not the entire port
channel. This improves fault tolerance of port-channel.
UDLD PDUs act as network control packets. They are unaffected by
Spanning Tree state. Thus, they are transmitted and received regardless of
Spanning Tree state.
For the successful operation of UDLD, it is required that its neighbors are
UDLD-capable and UDLD is enabled on the corresponding ports. All ports
should also be configured to use the same mode of UDLD, either normal or
aggressive mode.
Detecting Unidirectional Links on a Device Port
A device detects unidirectional links on its port via UDLD. Every UDLD-
capable device distributes service information over the network via a layer 2
broadcast frame. This service frame contains information about sender
(source device) and all discovered neighbors. Every sender expects to receive
an UDLD echo frame. If an echo frame is received, but does not contain
information about the sender itself, it implies that the sender's frames have
not reached the neighbors. This can happen when the link is able to receive
traffic but cannot send traffic. In other words, a UDLD-capable device can
2CSNXXX_SWUM200.book Page 781 Tuesday, December 10, 2013 1:22 PM

782 UDLD Commands
recognize only the sending failures on unidirectional links. If all devices in the
network support UDLD, this functionality is enough to detect all
unidirectional links.
Processing UDLD Traffic from Neighbors
Every UDLD-capable device collects information about all other UDLD-
capable devices. Each device populates UDLD echo packets with collected
neighbor information to help neighbors identify unidirectional links. Every
frame basically contains the device ID of the sender and the collection of
device IDs of its discovered neighbors.
UDLD in Normal-mode
In normal mode, a port’s state is classified as undetermined if an anomaly
exists. These include the absence of its own information in received UDLD
messages or the failure to receive UDLD messages. The state of
undetermined has no effect on the operation of the port. The port is not
disabled and continues operating as it previously did. When in normal mode,
a port is disagnostically disabled for the following cases:
a
UDLD PDU is received from partner that does not have the port’s
own details (echo).
b
When there is a loopback. Information sent out on a port is received
back as it is.
UDLD in Aggressive-mode
Aggressive mode differs from normal UDLD mode – it can diagnostically
disable a port if the port does not receive any UDLD echo packets after a
bidirectional connection was established. It expands the cases when port can
be disabled. There can be several causes for a port not to receive UDLD
echoes. These include:
• A link is up on one side and down on the other. This can occur on fiber
ports if the transmit port is unplugged on one side.
• Loss of connectivity, i.e. the port is neither transmitting nor receiving, but
the port also reports it is up.
2CSNXXX_SWUM200.book Page 782 Tuesday, December 10, 2013 1:22 PM

UDLD Commands 783
UDLD will put the port into the diagnostically disabled state in the following
cases:
a
When there is a loopback. The device ID and port ID sent out on a
port is received back.
b
UDLD PDU is received from a partner does not have its own details
(echo).
c
Bidirectional connection is established and no UDLD packets are
received from the partner device within three times the message
interval.
d
In aggressive mode, when the partner does not respond to an ECHO
within 7 seconds.
Commands in this Chapter
This chapter explains the following commands:
udld enable (Global Configuration)
Use the udld enable command in Global Configuration mode to enable
UDLD on all physical interfaces on a switch.
Use the no form of the command to disable UDLD on all interfaces.
Syntax
udld enable
no udld enable
Default Configuration
UDLD is disabled by default.
udld enable (Global Configuration) udld enable (Interface Configuration)
udld reset udld port
udld message time show udld
udld timeout interval debug udld
2CSNXXX_SWUM200.book Page 783 Tuesday, December 10, 2013 1:22 PM

784 UDLD Commands
Command Mode
Global Configuration mode
User Guidelines
This command globally enables UDLD. Interfaces which are not connected
or enabled at the Ethernet layer at the time the command is issued will be
enabled for UDLD when connected or enabled.
udld reset
Use the udld reset command in Privileged EXEC mode to reset (enable) all
interfaces disabled by UDLD.
Syntax
udld reset
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC mode
User Guidelines
The following commands will reset an interface disabled by UDLD:
• Use udld reset in Privileged EXEC mode to reset all interfaces disabled by
UDLD.
• The shutdown command followed by no shutdown interface configuration
command.
• The no udld enable global configuration command followed by the udld
enable command.
• The no udld port interface configuration command followed by the udld
port or udld port aggressive interface configuration command.
2CSNXXX_SWUM200.book Page 784 Tuesday, December 10, 2013 1:22 PM

UDLD Commands 785
udld message time
Use the udld message time command in Global Configuration mode to
configure the interval between the transmission of UDLD probe messages on
ports that are in the advertisement phase.
Use the no form of the command to return the message transmission interval
to the default value.
Syntax
udld message time
message-interval
no udld message time
•
message-interval
—
UDLD message transmit interval in seconds. Range
is 7 to 90 seconds.
Default Configuration
The default message transmit interval is 15 seconds.
Command Mode
Global Configuration mode
User Guidelines
Lower message time values will detect the unidirectional links more quickly
at the cost of higher CPU utilization.
The message interval is also used to age out UDLD entries from the internal
database. UDLD entries are removed after three times the message interval
and the discovery process starts again.
udld timeout interval
Use the udld timeout interval command in Global Configuration mode to
configure the interval for the receipt of ECHO replies.
Use the no form of the command to return the value to the default setting.
Syntax
udld timeout interval
timeout-interval
2CSNXXX_SWUM200.book Page 785 Tuesday, December 10, 2013 1:22 PM

786 UDLD Commands
no udld timeout interval
•
timeout-interval
—UDLD timeout interval. Range is 5 to 60 seconds.
Default Configuration
The default timeout interval is 5 seconds.
Command Mode
Global Configuration mode
User Guidelines
This command sets the time interval used to determine if the link has
bidirectional or unidirectional connectivity. If no ECHO replies are received
within three times the message interval, then the link is considered to have
unidirectional connectivity.
udld enable (Interface Configuration)
Use the udld enable command in Interface (physical) Configuration mode to
enable UDLD on a specific interface.
Use the no form of the command to disable UDLD on an interface.
Syntax
udld enable
no udld enable
Default Configuration
UDLD is disabled by default on an interface.
Command Mode
Interface (physical) Configuration mode
User Guidelines
UDLD cannot be enabled on a port channel. Instead, enable UDLD on the
physical interfaces of a port channel.
2CSNXXX_SWUM200.book Page 786 Tuesday, December 10, 2013 1:22 PM

UDLD Commands 787
udld port
Use the udld port command in Interface (physical) Configuration mode to
select the UDLD operating mode on a specific interface.
Use the no form of the command to reset the operating mode to the default
(normal).
Syntax
udld port aggressive
no udld port
• aggressive—Sets the port to discover peers in aggressive mode.
Default Configuration
Normal mode is configured by default when UDLD is enabled on an
interface.
Command Mode
Interface (physical) Configuration mode
User Guidelines
In aggressive mode, UDLD will attempt to detect a peer by sending an
ECHO packet every seven seconds until a peer is detected.
show udld
Use the show udld command in User EXEC or Privileged EXEC mode to
display the global settings for UDLD.
Syntax
show udld [
interface-id
|all]
Default Configuration
This command has no default setting.
2CSNXXX_SWUM200.book Page 787 Tuesday, December 10, 2013 1:22 PM
788 UDLD Commands
Command Mode
Privileged EXEC or User EXEC mode, Configuration mode and all
Configuration submodes
User Guidelines
When no interface is specified, the following fields are shown:
When an interface ID is specified, the following fields are shown:
Field Description
Admin Mode The global administrative mode of UDLD.
Message Interval The time period (in seconds) between the transmission of
UDLD probe packets.
Timeout Interval The time period (in seconds) before making decision that link
is unidirectional.
Field Description
Interface Id The interface identifier in short form, e.g. te1/0/1.
Admin Mode The administrative mode of UDLD configured on this
interface. This is either Enabled or Disabled.
UDLD Mode The UDLD mode configured on this interface. This is either
Normal or Aggressive.
2CSNXXX_SWUM200.book Page 788 Tuesday, December 10, 2013 1:22 PM

UDLD Commands 789
debug udld
Use the debug udld command in Privileged EXEC mode to enable the
display of UDLD packets or event processing.
Use the no form of the command to disable debugging.
Syntax
debug udld {packet [receive|transmit]|events}
no debug udld {packet [receive|transmit]|events}
•
Packet
—Display transmitted and received UDLD packets.
•
Receive
—Debug packets received by the switch.
•
Transmit
—Debug packets transmitted by the switch.
•
Events
—Display UDLD events.
Default Configuration
By default, debugging is disabled.
Command Mode
Privileged EXEC mode
UDLD Status The status of the link as determined by UDLD. The options
are:
•
Undetermined
– UDLD has not collected enough information
to determine the state of the port.
•
Not applicable
– UDLD is disabled, either globally or on the
port.
•
Shutdown
– UDLD has detected a unidirectional link and
shutdown the port. That is, the port is in an errDisabled state.
•
Bidirectional
- UDLD has detected a bidirectional link.
•
Undetermined (Link Down)
– The port would transition into
this state when the port link physically goes down due to any
reasons other than the port being put into D-Disable mode by
the UDLD protocol on the switch.
Field Description
2CSNXXX_SWUM200.book Page 789 Tuesday, December 10, 2013 1:22 PM

790 UDLD Commands
User Guidelines
This command has no user guidelines.
2CSNXXX_SWUM200.book Page 790 Tuesday, December 10, 2013 1:22 PM

VLAN Commands 791
38
VLAN Commands
Dell Networking N2000/N3000/N4000 Series Switches
Dell Networking 802.1Q VLANs are an implementation of the Virtual Local
Area Network, specification 802.1Q. Operating at Layer 2 of the OSI model,
the VLAN is a means of parsing a single network into logical user groups or
organizations as if they physically resided on a dedicated LAN segment of
their own. In reality, this virtually defined community may have individual
members scattered across a large, extended LAN. The VLAN identifier is part
of the 802.1Q tag, which is added to an Ethernet frame by an 802.1Q-
compliant switch or router. Devices recognizing 802.1Q-tagged frames
maintain appropriate tables to track VLANs. The first 3 bits of the 802.1Q tag
are used by 802.1p to establish priority for the packet.
Dell Networking switches supports 802.1Q VLANs. As such, ports may
simultaneously belong to multiple VLANs. VLANs allow a network to be
logically segmented without regard to the physical locations of devices in the
network.
Dell Networking switches supports up to 4093 VLANs for forwarding.
Interfaces can be configured in trunk mode (multiple VLAN support) or
access mode (single VLAN support).
VLANs can be allocated by subnet and netmask pairs, thus allowing
overlapping subnets. For example, subnet 10.10.128.0 with Mask
255.255.128.0 and subnet 10.10.0.0 with Mask 255.255.0.0 can have different
VLAN associations.
Double VLAN Mode
An incoming frame is identified as tagged or untagged based on Tag Protocol
Identifier (TPID) value it contains. The 802.1Q standard specifies a TPID
value (0x8100) to recognize an incoming frame as tagged or untagged. Any
valid Ethernet frame with a value 0x8100 in the 12th and 13th bytes is
recognized as tagged frame. 802.1Q switches check the 12th and 13th bytes to
decide the tag status of incoming frame.
2CSNXXX_SWUM200.book Page 791 Tuesday, December 10, 2013 1:22 PM

792 VLAN Commands
The Dell Networking switching component can be configured to enable the
port in double-VLAN (DVLAN) mode. In this mode switch looks for 12th,
13th, 16th, and 17th bytes for the tag status in the incoming frame. The outer
tag (S-TAG) TPID is identified with the 12th and 13th bytes values. The
inner tag (C-TAG) TPID is identified with 16th and 17th bytes values. These
two TPID values can be different or the same. VLAN normalization, source
MAC learning, and forwarding are based on the S-TAG value in a received
frame.
Dell Networking supports configuring one outer VLAN TPID value per
switch. The global default TPID is 0x88A8, which indicates a Virtual
Metropolitan Area Network (VMAN).
Independent VLAN Learning
Independent VLAN Learning (IVL) allows unicast address-to-port mappings
to be created based on a MAC Address in conjunction with a VLAN ID.
This arrangement associates the MAC Address only with the VLAN on which
the frame was received. Therefore, frames are forwarded based on their
unicast destination address as well as their VLAN membership. This
configuration affords multiple occurrences of an address in the forwarding
database. Each address associates with a unique VLAN. Care must be taken
in the administration of networks, as multiple instances of a MAC address,
each on a different VLAN, can quickly eat up address entries.
Each VLAN is associated with its own forwarding database. Hence the
number of forwarding databases equals the number of VLANs supported.
The MAC address stored is supplemented by a 2-byte VLAN ID. The first 2
bytes of a forwarding database entry contain the VLAN ID associated, and the
next 6 bytes contain the MAC address. There is a one-to-one relationship
between VLAN ID and FID (forwarding database ID).
Protocol Based VLANs
The main purpose of Protocol-based VLANs (PBVLANs) is to selectively
process packets based on their upper-layer protocol by setting up protocol-
based filters. Packets are bridged through user-specified ports based on their
protocol.
2CSNXXX_SWUM200.book Page 792 Tuesday, December 10, 2013 1:22 PM

VLAN Commands 793
In PBVLANs, the VLAN classification of a packet is based on its protocol (IP,
IPX, NetBIOS, and so on). PBVLANs help optimize network traffic because
protocol-specific broadcast messages are sent only to end stations using that
protocol. End stations do not receive unnecessary traffic, and bandwidth is
used more efficiently. It is a flexible method that provides a logical grouping
of users. An IP subnet or an IPX network, for example, can each be assigned
its own VLAN. Additionally, protocol-based classification allows an
administrator to assign nonrouting protocols, such as NetBIOS or DECnet, to
larger VLANs than routing protocols like IPX or IP. This maximizes the
efficiency gains that are possible with VLANs.
In port-based VLAN classification, the Port VLAN Identifier (PVID) is
associated with the physical ports. The VLAN ID (VID) for an untagged
packet is equal to the PVID of the port. In port-and protocol-based VLAN
classifications, multiple VIDs are associated with each of the physical ports.
Each VID is also associated with a protocol. The ingress rules used to classify
incoming packets include the use of the packet's protocol, in addition to the
PVID, to determine the VLAN to which the packet belongs. This approach
requires one VID on each port for each protocol for which the filter is desired.
IP Subnet Based VLANs
This feature allows an untagged packet to be placed in a configured VLAN
based upon its IP address.
MAC-Based VLANs
This feature allows an untagged packet to be placed in a configured VLAN
based upon its MAC address.
Private VLAN Commands
The Dell Networking Private VLAN feature separates a regular VLAN domain
into two or more subdomains. Each subdomain is defined (represented) by a
primary VLAN and a secondary VLAN. The primary VLAN ID is the same for
all subdomains that belong to a private VLAN. The secondary VLAN ID
differentiates subdomains from each another and provides Layer 2 isolation
between ports of the same private VLAN. There are the following types of
VLANs within a private VLAN:
2CSNXXX_SWUM200.book Page 793 Tuesday, December 10, 2013 1:22 PM

794 VLAN Commands
• Primary VLAN
Forwards the traffic from the promiscuous ports to isolated ports,
community ports and other promiscuous ports in the same private VLAN.
Only one primary VLAN can be configured per private VLAN. All ports
within a private VLAN share the same primary VLAN.
•Isolated VLAN
Is a secondary VLAN. It carries traffic from isolated ports to promiscuous
ports. Only one isolated VLAN can be configured per private VLAN.
• Community VLAN
Is a secondary VLAN. It forwards traffic between ports which belong to the
same community and to the promiscuous ports. There can be multiple
community VLANs per private VLAN.
Three types of port designations exist within a private VLAN:
• Promiscuous port
Belongs to a primary VLAN and can communicate with all interfaces in
the private VLAN, including other promiscuous ports, community ports
and isolated ports. An endpoint connected to a promiscuous port is
allowed to communicate with any endpoint within the private VLAN.
Multiple promiscuous ports can be defined for a single private VLAN
domain.
•Host port
Belongs to a secondary VLAN and depending upon the type of secondary
VLAN can either communicate with other ports in the same community
(if the secondary VLAN is the community VLAN) and with the
promiscuous ports or can communicate only with the promiscuous ports
(if the secondary VLAN is an isolated VLAN).
The Private VLANs can be extended across multiple switches through inter-
switch/stack links that transport primary, community and isolated VLANs
between devices, as shown in
Figure 38-1
.
2CSNXXX_SWUM200.book Page 794 Tuesday, December 10, 2013 1:22 PM
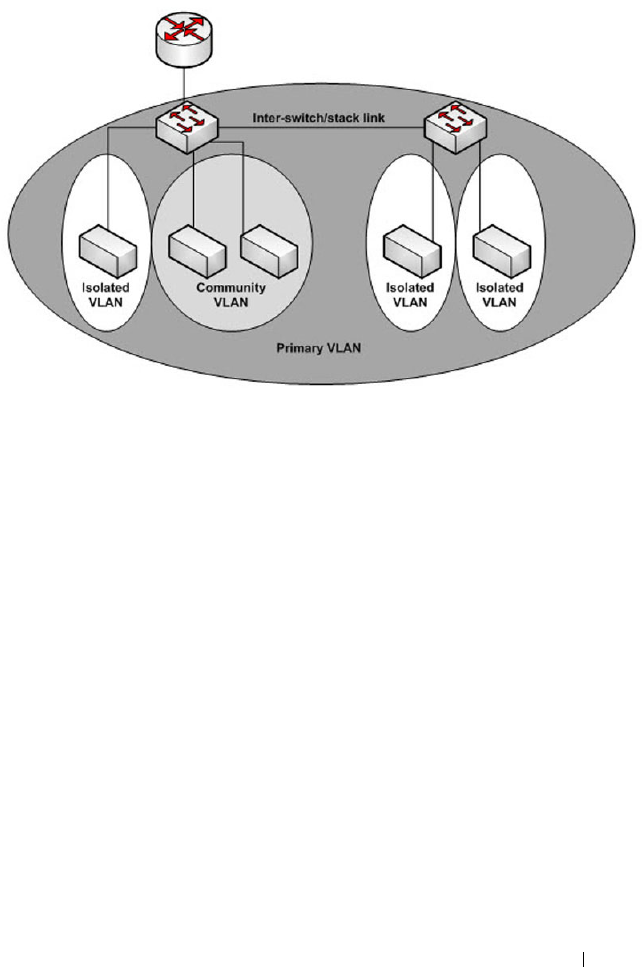
VLAN Commands 795
Figure 38-1. Private VLANs
Isolated VLAN
An endpoint connected over an isolated VLAN is allowed to communicate
with endpoints connected to promiscuous ports only. Endpoints connected to
adjacent endpoints over an isolated VLAN cannot communicate with each
other.
Community VLAN
An endpoint connected over a community VLAN is allowed to communicate
with the endpoints within the community and can also communicate with
any configured promiscuous port. The endpoints which belong to one
community cannot communicate with endpoints which belong to a different
community or with endpoints connected over isolated VLANs.
Private VLAN Operation in the Switch Environment
The Private VLAN feature operates in a stacked or single switch environment.
The stack links are transparent to the configured VLAN, thus there is no need
for special private VLAN configuration. Any private VLAN port can reside on
any stack member.
2CSNXXX_SWUM200.book Page 795 Tuesday, December 10, 2013 1:22 PM

796 VLAN Commands
In order to enable Private VLAN operation across multiple switches which are
not stacked, the inter-switch links should carry VLANs which belong to a
private VLAN. The trunk ports which connect neighbor switches have to be
assigned to the primary, isolated, and community VLANs of a private VLAN.
In regular VLANs, ports in the same VLAN switch traffic at L2. However for
private VLAN, the promiscuous port is in the primary VLAN whereas the
isolated or community ports are in the secondary VLAN. Similarly, for
broadcasts, in regular VLANs, ports in the same VLAN receive broadcast
traffic. However, for private VLANs, the ports to which the broadcast traffic is
forwarded depend on the type of port on which the traffic was received. If the
received port is a host port; the traffic is forwarded to all promiscuous and
trunk ports. If the received port is community port the broadcast traffic is
forwarded to promiscuous, trunk and community ports in the same VLAN. A
promiscuous port sends traffic to other promiscuous ports, isolated and
community ports.
Commands in this Chapter
This chapter explains the following commands:
dvlan-tunnel
ethertype
show dvlan-tunnel switchport general
acceptable-frame-
type tagged-only
vlan association subnet
interface vlan show dvlan-tunnel
interface
switchport general
allowed vlan
vlan makestatic
interface range vlan show interfaces
switchport
switchport general
ingress-filtering
disable
vlan makestatic
mode dvlan-tunnel show port protocol switchport general
pvid
vlan protocol group
name (VLAN
Configuration)
show vlan switchport mode vlan protocol group add
protocol
protocol group show vlan
association mac
switchport trunk vlan protocol group
name
protocol vlan group show vlan
association subnet
vlan vlan protocol group
remove
2CSNXXX_SWUM200.book Page 796 Tuesday, December 10, 2013 1:22 PM

VLAN Commands 797
dvlan-tunnel ethertype
Use the dvlan-tunnel ethertype command in Global Configuration mode to
enable the configuration of the inner and outer VLAN tag ethertype.
To configure the EtherType to its default value, use the no form of this
command.
Syntax
dvlan-tunnel ethertype {802.1Q | vman | custom
1-65535
[
primary-tpid
]}
no dvlan-tunnel ethertype
•
802.1Q
—Configures the EtherType as 0x8100 (default).
•
vman
—Configures the EtherType as 0x88A8
•
custom
—Configures a custom EtherType for the DVLAN tunnel. The
value must be in the range 1-65535.
•
primary-tpid
—Globally configures the tag protocol identifier on the outer
VLAN tag on all interfaces. If this parameter is not given, the inner vlan is
configured.
Default Configuration
The default outer tag type (secondary TPID) is 802.1Q. The default inner tag
type (primary TPID) is 802.1Q.
protocol vlan group
all
switchport access
vlan
vlan association
mac
show vlan private-vlan
–
–
switchport general
forbidden vlan
––
Private VLAN Commands
switchport private-
vlan
private-vlan show interfaces
switchport
show vlan private-vlan
switchport mode
private-vlan
–––
2CSNXXX_SWUM200.book Page 797 Tuesday, December 10, 2013 1:22 PM

798 VLAN Commands
Command Mode
Global Configuration, Interface Configuration, Interface Range, and Port-
Channel Range modes
User Guidelines
This command configures the outer VLAN tag type (primary TPID) for
double VLAN tagging when used in global CONFIG mode with the primary-
tpid parameter. Only one outer tag type can be configured for the switch. The
outer tag is added on egress and removed on ingress on uplink (service
provider) ports. Frames normally transmitted untagged (access ports) will
have a single (outer) tag added prior to transmission out of the SP port.
Frames normally transmitted tagged will have an inner tag (the original tag)
and an outer tag (the dvlan tag) added prior to transmission on the SP port.
When used without the primary-tpid parameter, this command configures
the inner VLAN tag type (secondary TPID) for all switch interfaces when
used in global CONFIG mode.
When used in interface mode, this command configures the inner VLAN tag
type (secondary TPID) for an individual switch interface or port channel.
DVLAN capable service provider interfaces must be configured for egress
tagging in order for double tags to be observed on frames egressing the
interface. MAC address learning on DVLAN enabled uplink ports occurs on
the DVLAN port's native VLAN. All participating ports must have the service
provider port PVID configured.
Example
The following example configures two customer ports (Gi1/0/2 and Gi1/0/3
on isolated VLANs 200 and 300) and a single service provider port (Gi1/0/1).
console(config)#vlan 100,200,300
console(config-vlan100,200,300)#exit
!!Configure 0x88A8 as primary TPID.
console(config)#dvlan-tunnel ethertype vman primary-tpid
SP port config
console(config)#interface Gi1/0/1
console(config-if-Gi1/0/1)#exit
console(config-if-Gi1/0/1)#switchport mode general
console(config-if-Gi1/0/1)#switchport general pvid 100
2CSNXXX_SWUM200.book Page 798 Tuesday, December 10, 2013 1:22 PM

VLAN Commands 799
Service provider port is participating in service provider VLAN 100 and egress
tagging is enabled
console(config-if-Gi1/0/1)#switchport general allowed vlan add 100 tagged
console(config-if-Gi1/0/1)#mode dvlan-tunnel
console(config-if-Gi1/0/1)#vlan-tunnel ethertype vman
console(config-if-Gi1/0/1)#exit
Customer port config
console(config)#interface Gi1/0/2
console(config-if-Gi1/0/2)#switchport mode general
Service provider VLAN 100 configured as the PVID on the customer port
console(config-if-Gi1/0/2)#switchport general pvid 100
Customer port is participating in service provider VLAN 100 and egress
tagging is disabled
console(config-if-Gi1/0/2)#switchport general allowed vlan add 100
!! Customer port can use vlan 200 for local traffic. Forwarding is based on
VLAN 100 learning
console(config-if-Gi1/0/2)#switchport general allowed vlan add 200
console(config-if-Gi1/0/2)#dvlan-tunnel ethertype vman
console(config-if-Gi1/0/2)#exit
Customer port configuration
console(config)#interface gi1/0/3
Customer port is participating in service provider VLAN 100 and egress
tagging is disabled
console(config-if-Gi1/0/3)#switchport general allowed vlan add 100
console(config-if-Gi1/0/3)#switchport general allowed vlan add 300
console(config-if-Gi1/0/3)#switchport mode general
Service provider VLAN 100 configured as the PVID on the customer port
console(config-if-Gi1/0/3)#switchport general pvid 100
console(config-if-Gi1/0/3)#dvlan-tunnel ethertype vman
console(config-if-Gi1/0/3)#exit
interface vlan
Use the interface vlan command in Global Configuration mode to enter
VLAN Interface Configuration mode.
Syntax
interface vlan {
vlan-id
} [nsf-index]
2CSNXXX_SWUM200.book Page 799 Tuesday, December 10, 2013 1:22 PM

800 VLAN Commands
•
vlan-id
—The ID of a valid VLAN (Range 1–4093).
Default Configuration
By default, routing is enabled on VLAN 1. However, VLAN 1 does not route
packets until an IP address is assigned to the VLAN. DHCP is not enabled on
VLAN 1 by default.
Command Mode
VLAN Configuration or Global Configuration modes
User Guidelines
Assigning an IP address to a VLAN interface enables routing on the VLAN
interface.
Examples
console(config-vlan10)# interface vlan 10
console(config-if-vlan10)#
interface range vlan
Use the interface range vlan command in Global Configuration mode to
execute a command on multiple VLANs at the same time.
Syntax
interface range vlan {
vlan-range
|
all
}
•
vlan-range
— A list of valid VLAN IDs to add. Separate nonconsecutive
VLAN IDs with a comma and no spaces; use a hyphen to designate a range
of IDs. (Range: 2–4093)
•
all
— All existing static VLANs.
Default Configuration
This command has no default configuration.
Command Mode
Global Configuration mode
2CSNXXX_SWUM200.book Page 800 Tuesday, December 10, 2013 1:22 PM

VLAN Commands 801
User Guidelines
Commands used in the interface range context are executed independently
on each interface in the range. If the command returns an error on one of the
interfaces, an error message is displayed and execution continues on other
interfaces.
Example
The following example groups VLAN 221 through 228 and VLAN 889 to
execute the commands entered in interface range mode.
console(config)#interface range vlan 221-228,889
console(config-if)#
mode dvlan-tunnel
Use the mode dvlan-tunnel command in Interface Configuration mode to
enable Double VLAN Tunneling on the specified interface. To disable Double
VLAN Tunneling on the specified interface, use the no form of this
command.
Syntax
mode dvlan-tunnel
no mode dvlan-tunnel
Default Configuration
By default, Double VLAN Tunneling is
disabled
.
Command Mode
Interface Configuration (gigabitethernet, port-channel, tengigabitethernet,
fortygigabitethernet) mode
User Guidelines
Use the global configuration command
dvlan-tunnel ethertype
to configure
the inner and outer TPIDs.When dvlan-tunnel is enabled on an interface, the
interface is configured as an uplink or service provider (SP) port. All other
interfaces on the switch behave like access (customer) ports.
2CSNXXX_SWUM200.book Page 801 Tuesday, December 10, 2013 1:22 PM

802 VLAN Commands
Uplink Port Behavior
If a single-tagged (SP tagged) or double-tagged (SP tag as outer tag) packet
ingresses an uplink port, the switch strips the outer tag prior to forwarding it
to the respective access ports.
If an untagged or single tagged (802.1Q tagged) packet egresses an uplink
port, the switch tags it with the configured ethertype and service provider
VLAN ID taken from the service port PVID.
Access Port Behavior
Ingress packets on an access port are always tagged by the switch. Packets are
tagged on ingress with the configured ethertype and the service provider ID
taken from the PVID of the service provider port. On egress, the access port
strips the outer tag belonging to service provider VLANS.
Example
The following example displays how to enable Double VLAN Tunneling on
gigabit ethernet port 1/0/1.
console(config-if-Gi1/0/1)#mode dvlan-tunnel
name (VLAN Configuration)
Use the name command in VLAN Configuration mode to configure the
VLAN name. To return to the default configuration, use the no form of this
command.
NOTE: This command cannot be configured for a range of interfaces (range
context).
Syntax
name
vlan–name
no name
•
vlan–name
—The name of the VLAN. Must be 1–32 characters in length.
Default Configuration
The default VLAN name is default.
2CSNXXX_SWUM200.book Page 802 Tuesday, December 10, 2013 1:22 PM

VLAN Commands 803
Command Mode
VLAN Configuration mode
User Guidelines
The VLAN name may include any alphanumeric characters including a space,
underscore, or dash. Enclose the string in double quotes to include spaces
within the name. The surrounding quotes are not used as part of the name.
The CLI does not filter illegal characters and may truncate entries at the first
illegal character or reject the entry entirely. The name of VLAN 1 cannot be
changed.
Example
The following example configures a VLAN name of office2 for VLAN 2.
console(config)#vlan 2
console(config-vlan2)#name "RDU-NOC Management VLAN"
protocol group
Use the protocol group command in VLAN Configuration mode to attach a
VLAN ID to the protocol-based group identified by
groupid
. A group may
only be associated with one VLAN at a time. However, the VLAN association
can be changed. The referenced VLAN should be created prior to the creation
of the protocol-based group except when GVRP is expected to create the
VLAN.
To detach the VLAN from this protocol-based group identified by this
groupid
, use the no form of this command.
Syntax
protocol group
groupid vlanid
no protocol group
groupid
vlanid
•
groupid
— The protocol-based VLAN group ID, which is automatically
generated when you create a protocol-based VLAN group with the
vlan
protocol group
command. To see the group ID associated with the name
of a protocol group, use the
show port protocol all
command.
•
vlanid
— A valid VLAN ID.
2CSNXXX_SWUM200.book Page 803 Tuesday, December 10, 2013 1:22 PM

804 VLAN Commands
Default Configuration
This command has no default configuration.
Command Mode
VLAN Configuration mode
User Guidelines
This command has no user guidelines.
Example
The following example displays how to attach the VLAN ID "100" to the
protocol-based VLAN group "3."
console(config-vlan)#protocol group 3 100
protocol vlan group
Use the protocol vlan group command in Interface Configuration mode to
add the physical unit/slot/port interface to the protocol-based group
identified by
groupid
. A group may have more than one interface associated
with it. Each interface and protocol combination can be associated with one
group only. If adding an interface to a group causes any conflicts with
protocols currently associated with the group, this command fails and the
interface(s) are not added to the group. Ensure that the referenced VLAN is
created prior to the creation of the protocol-based group except when GVRP
is expected to create the VLAN.
To remove the interface from this protocol-based VLAN group that is
identified by this
groupid
, use the no form of this command.
If you select all, all ports are removed from this protocol group.
Syntax
protocol vlan group
groupid
no protocol vlan group
groupid
2CSNXXX_SWUM200.book Page 804 Tuesday, December 10, 2013 1:22 PM

VLAN Commands 805
•
groupid
— The protocol-based VLAN group ID, which is automatically
generated when you create a protocol-based VLAN group with the
vlan
protocol group
command. To see the group ID associated with the name
of a protocol group, use the
show port protocol all
command.
Default Configuration
This command has no default configuration.
Command Mode
Interface Configuration (Ethernet) mode
User Guidelines
This command has no user guidelines.
Example
The following example displays how to add a physical port interface to the
group ID of "2."
console(config-if-Gi1/0/1)#protocol vlan group 2
protocol vlan group all
Use the protocol vlan group all command in Global Configuration mode to
add all physical interfaces to the protocol-based group identified by
groupid
.
A group may have more than one interface associated with it. Each interface
and protocol combination can be associated with one group only. If adding an
interface to a group causes any conflicts with protocols currently associated
with the group, this command fails and the interface(s) are not added to the
group. Ensure that the referenced VLAN is created prior to the creation of the
protocol-based group except when GVRP is expected to create the VLAN.
To remove all interfaces from this protocol-based group that is identified by
this
groupid
, use
the no form of the command
Syntax
protocol vlan group all
groupid
no protocol vlan group all
groupid
2CSNXXX_SWUM200.book Page 805 Tuesday, December 10, 2013 1:22 PM

806 VLAN Commands
•
groupid
— The protocol-based VLAN group ID, which is automatically
generated when you create a protocol-based VLAN group with the
vlan
protocol group
command. To see the group ID associated with the name
of a protocol group, use the
show port protocol all
command.
Default Configuration
This command has no default configuration.
Command Mode
Global Configuration mode
User Guidelines
This command has no user guidelines.
Example
The following example displays how to add all physical interfaces to the
protocol-based group identified by group ID "2."
console(config)#protocol vlan group all 2
show dvlan-tunnel
Use the show dvlan-tunnel command in Privileged EXEC mode to display all
interfaces enabled for Double VLAN Tunneling.
Syntax
show dvlan-tunnel
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC mode, Configuration mode and all Configuration submodes
User Guidelines
This command has no user guidelines.
2CSNXXX_SWUM200.book Page 806 Tuesday, December 10, 2013 1:22 PM

VLAN Commands 807
Example
The following example shows how to display all interfaces for Double VLAN
Tu n n e l i n g .
console#show dvlan-tunnel
Interfaces Enabled for DVLAN Tunneling......... 1/0/1
show dvlan-tunnel interface
Use the show dvlan-tunnel interface command in Privileged EXEC mode to
display detailed information about Double VLAN Tunneling for the specified
interface or all interfaces.
Syntax
show dvlan-tunnel interface {gigabithethernet unit/slot/port |
tengigabitethernet unit/slot/port | fortygigabitethernet unit/slot/port| all}
•
all
— Displays information for all interfaces.
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC mode, Configuration mode and all Configuration submodes
User Guidelines
The following table describes the significant fields shown in the example.
Field Description
Mode This field specifies the administrative mode through which
Double VLAN Tunneling can be enabled or disabled. The default
value for this field is
disabled
.
Interface Interface Number.
2CSNXXX_SWUM200.book Page 807 Tuesday, December 10, 2013 1:22 PM

808 VLAN Commands
Example
The following example displays detailed information for port 1/0/1.
console#show dvlan-tunnel interface 1/0/1
Interface Mode EtherType
--------- ------- --------------
1/0/1 Enable vMAN
show interfaces switchport
Use the show interfaces switchport command in Privileged EXEC mode to
display switchport configuration, including the private VLAN mappings.
Syntax
show interfaces switchport {{gigabitethernet unit/slot/port |
port-channel
port-channel-number
| tengigabitethernet unit/slot/port|
fortygigabitethernet unit/slot/port}}
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC mode, Interface Configuration mode and all Configuration
submodes
User Guidelines
Do not configure private VLANs on ports configured with any of these
features:
• Link Aggregation Control Protocol (LACP)
• Multicast VLAN Registration (MVR)
EtherType This field represents a 2-byte hex EtherType to be used as the first
16 bits of the DVLAN tunnel. The three different EtherType tags
are: (1) 802.1Q, which represents the commonly used value of
0x8100. (2) vMAN, which represents the commonly used value of
0x88A8. (3) If EtherType is not one of these two values, it is a
custom tunnel value, representing any value in the range of 0 to
65535.
2CSNXXX_SWUM200.book Page 808 Tuesday, December 10, 2013 1:22 PM

VLAN Commands 809
• Voice VLAN
It is recommended that the private VLAN host ports be configured as
spanning-tree portfast.
The command displays the following information.
Examples
The following example displays switchport configuration individually for
gi1/0/1.
console#show interface switchport gigabitethernet 1/0/1
Port 1/0/1:
VLAN Membership mode: General
Operating parameters:
PVID: 1 (default)
Ingress Filtering: Enabled
Acceptable Frame Type: All
GVRP status: Enabled
Protected: Enabled
Port 1/0/1 is member in:
VLAN Name Egress rule Type
---- --------- ----------- -----
1 default untagged Default
8 VLAN008 tagged Dynamic
11 VLAN0011 tagged Static
19 IPv6 VLAN untagged Static
72 VLAN0072 untagged Static
Static configuration:
PVID: 1 (default)
Ingress Filtering: Enabled
Acceptable Frame Type: All
Port 1/0/1 is statically configured to:
VLAN Name Egress rule
---- --------- -----------
11 VLAN0011 tagged
19 IPv6 VLAN untagged
72 VLAN0072 untagged
Parameter Description
private-vlan host-
association
Displays VLAN association for the private-VLAN host ports.
private-vlan
mapping
Displays VLAN mapping for the private-VLAN promiscuous
ports.
2CSNXXX_SWUM200.book Page 809 Tuesday, December 10, 2013 1:22 PM

810 VLAN Commands
Forbidden VLANS:
VLAN Name
---- ---------
73 Out
The following example displays switchport configuration individually for
1/0/2.
console#show interface switchport gigabitethernet 1/0/2
Port 1/0/2:
VLAN Membership mode: General
Operating parameters:
PVID: 4095 (discard vlan)
Ingress Filtering: Enabled
Acceptable Frame Type: All
Port 1/0/1 is member in:
VLAN Name Egress rule Type
---- --------- ----------- -----
91 IP Telephony tagged Static
Static configuration:
PVID: 8
Ingress Filtering: Disabled
Acceptable Frame Type: All
Port 1/0/2 is statically configured to:
VLAN Name Egress rule
---- --------- -----------
8 VLAN0072 untagged
91 IP Telephony tagged
Forbidden VLANS:
VLAN Name
---- ---------
73 Out
The following example displays switchport configuration individually for
2/0/19.
console#show interfaces switchport gigabitethernet 2/0/19
Port 2/0/19:
Operating parameters:
PVID: 2922
Ingress Filtering: Enabled
Acceptable Frame Type: Untagged
GVRP status: Disabled
Port 2/0/19 is member in:
VLAN Name Egress rule Type
---- --------- ----------- -----
2921 Primary A untagged Static
2CSNXXX_SWUM200.book Page 810 Tuesday, December 10, 2013 1:22 PM

VLAN Commands 811
2922 Community A1 untagged Static
Static configuration:
PVID: 2922
Ingress Filtering: Enabled
Acceptable Frame Type: Untagged
GVRP status: Disabled
Port 2/0/19 is member in:
VLAN Name Egress rule Type
---- --------- ----------- -----
2921 Primary A untagged Static
2922 Community A1 untagged Static
show port protocol
Use the show port protocol command in Privileged EXEC mode to display
the Protocol-Based VLAN information for either the entire system or for the
indicated group.
Syntax
show port protocol {
groupid
| all}
•
groupid
— The protocol-based VLAN group ID, which is automatically
generated when you create a protocol-based VLAN group with the
vlan
protocol group
command.
•
all
— Enter
all
to show all interfaces.
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC mode, Configuration mode and all Configuration submodes
User Guidelines
This command has no user guidelines.
Example
The following example displays the Protocol-Based VLAN information for
either the entire system.
console#show port protocol all
2CSNXXX_SWUM200.book Page 811 Tuesday, December 10, 2013 1:22 PM

812 VLAN Commands
Group
Group Name ID Protocol(s VLAN Interface(s)
--------------- ----- ---------- ---- ------------
test 1 IP 1 1/0/1
show vlan
Use the show vlan command in Privileged EXEC mode to display detailed
information, including interface information and dynamic VLAN type, for a
specific VLAN or RSPAN VLAN. The ID is a valid VLAN identification
number.
Syntax
show vlan [id
vlanid
|
name vlan-name
]
•
vlanid
—VLAN identifier
•
vlan-name
—A valid VLAN name (Range 1-32 characters)
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC mode, Configuration mode and all Configuration submodes
User Guidelines
This command has no user guidelines.
Example
This shows all VLANs and RSPAN VLANs.
console#show vlan
VLAN Name Ports Type
----- --------------- ------------- --------------
1 default Po1-128, Default
Gi1/0/1-48
10 Static
RSPAN Vlan
------------------------------------------------------------------
2CSNXXX_SWUM200.book Page 812 Tuesday, December 10, 2013 1:22 PM

VLAN Commands 813
10
This example shows information for a specific VLAN ID.
console#show vlan id 10
VLAN Name Ports Type
----- --------------- ------------- --------------
10 Te1/0/1 Static
RSPAN Vlan
------------------------------------------------------------------
Enabled
This example shows information for a specific VLAN name.
console#show vlan name myspan
VLAN Name Ports Type
----- --------------- ------------- --------------
10 myspan Te1/0/1 Static
RSPAN Vlan
------------------------------------------------------------------
Enabled
show vlan association mac
Use the show vlan association mac command in Privileged EXEC mode to
display the VLAN associated with a specific configured MAC address. If no
MAC address is specified, the VLAN associations of all the configured MAC
addresses are displayed.
Syntax
show vlan association mac [
mac-address
]
•
mac-address
— Specifies the MAC address to be entered in the list.
(Range: Any valid MAC address)
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC mode, Configuration mode and all Configuration submodes
2CSNXXX_SWUM200.book Page 813 Tuesday, December 10, 2013 1:22 PM

814 VLAN Commands
User Guidelines
This command has no user guidelines.
Example
The following example shows no entry in MAC address to VLAN cross-
reference.
console#show vlan association mac
MAC Address VLAN ID
----------------------- -------
0001.0001.0001.0001 1
console#
show vlan association subnet
Use the show vlan association subnet command in Privileged EXEC mode to
display the VLAN associated with a specific configured IP-Address and
netmask. If no IP Address and net mask are specified, the VLAN associations
of all the configured IP-subnets are displayed.
Syntax
show vlan association subnet [
ip-address ip-mask
]
•
ip-address
— Specifies IP address to be shown
•
ip-mask
— Specifies IP mask to be shown
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC mode, Configuration mode and all Configuration submodes
User Guidelines
The command has no user guidelines.
2CSNXXX_SWUM200.book Page 814 Tuesday, December 10, 2013 1:22 PM

VLAN Commands 815
Example
The following example shows the case if no IP Subnet to VLAN association
exists.
console#show vlan association subnet
IP Address IP Mask VLAN ID
---------------- ---------------- -------
The IP Subnet to VLAN association does not exist.
switchport access vlan
Use the switchport access vlan command in Interface Configuration mode to
configure the VLAN ID when the interface is in access mode. To reconfigure
the default, use the no form of this command.
Syntax
switchport access vlan
vlan-id
no switchport access vlan
•
vlan-id
— A valid VLAN ID of the VLAN to which the port is configured.
Default Configuration
The default value for the
vlan-id
parameter is 1.
Command Mode
Interface Configuration (gigabitethernet, port-channel, tengigabitethernet,
fortygigabitethernet) mode
User Guidelines
This command removes the port from the previous VLAN membership and
adds it to the specified VLAN. The no form of the command sets the port
VLAN membership to VLAN 1.
Example
The following example configures interface gi1/0/8 to operate in access mode
with a VLAN membership of 23. Received untagged packets are processed on
VLAN 23. Received packets tagged with VLAN 23 are also accepted. Other
received tagged packets are discarded.
2CSNXXX_SWUM200.book Page 815 Tuesday, December 10, 2013 1:22 PM

816 VLAN Commands
console(config)#interface gigabitethernet 1/0/8
console(config-if-Gi1/0/8)#switchport access vlan 23
switchport general forbidden vlan
Use the switchport general forbidden vlan command in Interface
Configuration mode to forbid adding specific VLANs to a general mode port.
To revert to allowing the addition of specific VLANs to the port, use the
remove parameter of this command.
Syntax
switchport general forbidden vlan {add
vlan-list
| remove
vlan-list
}
•
add
vlan-list
— List of valid VLAN IDs to add to the forbidden list.
Separate nonconsecutive VLAN IDs with a comma and no spaces. Use a
hyphen to designate a range of IDs.
•
remove
vlan-list
— List of valid VLAN IDs to remove from the forbidden
list. Separate nonconsecutive VLAN IDs with a comma and no spaces. Use
a hyphen to designate a range of IDs.
Default Configuration
All VLANs allowed.
Command Mode
Interface Configuration (gigabitethernet, port-channel, tengigabitethernet,
fortygigabitethernet) mode
User Guidelines
This configuration only applies to ports configured in general mode.
Example
The following example forbids adding VLAN numbers 234 through 256 to
port 1/0/8.
console(config)#interface gigabitethernet 1/0/8
console(config-if-Gi1/0/8)#switchport general forbidden vlan add 234-256
2CSNXXX_SWUM200.book Page 816 Tuesday, December 10, 2013 1:22 PM

VLAN Commands 817
switchport general acceptable-frame-type
tagged-only
Use the switchport general acceptable-frame-type tagged-only command in
Interface Configuration mode to discard untagged frames at ingress. To
enable untagged frames at ingress, use the no form of this command.
Syntax
switchport general acceptable-frame-type tagged-only
no switchport general acceptable-frame-type tagged-only
Default Configuration
All frame types are accepted at ingress.
Command Mode
Interface Configuration (gigabitethernet, port-channel, tengigabitethernet,
fortygigabitethernet) mode
User Guidelines
This command has no user guidelines.
Example
The following example configures 1/0/8 to discard untagged frames at ingress.
console(config)#interface gigabitethernet 1/0/8
console(config-if-Gi1/0/8)#switchport general acceptable-frame-type tagged-
only
switchport general allowed vlan
Use the switchport general allowed vlan command in Interface
Configuration mode to add VLANs to or remove VLANs from a general port.
Syntax
switchport general allowed vlan add
vlan-list
[tagged | untagged]
switchport general allowed vlan remove
vlan-list
2CSNXXX_SWUM200.book Page 817 Tuesday, December 10, 2013 1:22 PM

818 VLAN Commands
•
add
vlan-list
— List of VLAN IDs to add. Separate nonconsecutive VLAN
IDs with a comma and no spaces. Use a hyphen to designate a range of
IDs.
•
remove
vlan-list
— List of VLAN IDs to remove. Separate nonconsecutive
VLAN IDs with a comma and no spaces. Use a hyphen to designate a range
of IDs.
•
tagged
— Sets the port to transmit tagged packets for the VLANs. If the
port is added to a VLAN without specifying tagged or untagged, the
default is untagged.
•
untagged
— Sets the port to transmit untagged packets for the VLANs.
Default Configuration
Untagged.
Command Mode
Interface Configuration (gigabitethernet, port-channel, tengigabitethernet,
fortygigabitethernet) mode
User Guidelines
You can use this command to change the egress rule (for example, from
tagged to untagged) without first removing the VLAN from the list.
Example
The following example shows how to add VLANs 1, 2, 5, and 8 to the allowed
list.
console(config-if-Gi1/0/8)#switchport general allowed vlan add 1,2,5,8
tagged
switchport general ingress-filtering disable
Use the switchport general ingress-filtering disable command in Interface
Configuration mode to disable port ingress filtering. To enable ingress
filtering on a port, use the no form of this command.
Syntax
switchport general ingress-filtering disable
2CSNXXX_SWUM200.book Page 818 Tuesday, December 10, 2013 1:22 PM

VLAN Commands 819
no switchport general ingress-filtering
disable
Default Configuration
Ingress filtering is enabled.
Command Mode
Interface Configuration (gigabitethernet, port-channel, tengigabitethernet,
fortygigabitethernet) mode
User Guidelines
Ingress filtering, when enabled, discards received frames that are not tagged
with a VLAN for which the port is a member. If ingress filtering is disabled,
tagged frames from all VLANs are processed by the switch.
Example
The following example shows how to enables port ingress filtering on 1/0/8.
console(config)#interface gigabitethernet 1/0/8
console(config-if-1/0/8)#switchport general ingress-filtering disable
switchport general pvid
Use the switchport general pvid command in Interface Configuration mode
to configure the Port VLAN ID (PVID) when the interface is in general mode.
Use the switchport mode general command to set the VLAN membership
mode of a port to "general." To configure the default value, use the no form of
this command.
Syntax
switchport general pvid
vlan-id
no switchport general pvid
•
vlan-id
— PVID. The VLAN ID may belong to a non-existent VLAN.
Default Configuration
The default value for the
vlan-id
parameter is 1 when the VLAN is enabled.
Otherwise, the value is 4093.
2CSNXXX_SWUM200.book Page 819 Tuesday, December 10, 2013 1:22 PM

820 VLAN Commands
Command Mode
Interface Configuration (gigabitethernet, port-channel, tengigabitethernet,
fortygigabitethernet) mode
User Guidelines
Setting a new PVID does NOT remove the previously configured PVID VLAN
from the port membership.
Example
The following example shows how to configure the PVID for 1/0/8, when the
interface is in general mode.
console(config)#interface gigabitethernet 1/0/8
console(config-if-Gi1/0/8)#switchport general pvid 234
switchport mode
Use the switchport mode command in Interface Configuration mode to
configure the VLAN membership mode of a port. To reset the mode to the
appropriate default for the switch, use the no form of this command.
Syntax
switchport mode {access | trunk | general}
no switchport mode
•
access
—An access port connects to a single end station belonging to a
single VLAN. An access port is configured with ingress filtering enabled
and will accept either an untagged frame or a packet tagged with the access
port VLAN. Tagged packets received with a VLAN other than the access
port VLAN are discarded. An access port transmits only untagged packets.
•
trunk
—A trunk port connects two switches. A trunk port may belong to
multiple VLANs. A trunk port accepts only packets tagged with the VLAN
IDs of the VLANs to which the trunk is a member or untagged packets if
configured with a native VLAN. A trunk port only transmits tagged packets
for member VLANs other than the native VLAN and untagged packets for
the native VLAN.
2CSNXXX_SWUM200.book Page 820 Tuesday, December 10, 2013 1:22 PM

VLAN Commands 821
•
general
—Full 802.1q support VLAN interface. A general mode port is a
combination of both trunk and access ports capabilities. It is possible to
fully configure all VLAN features on a general mode port. Both tagged and
untagged packets may be accepted and transmitted.
Default Configuration
The default switchport mode is access.
Command Mode
Interface Configuration (gigabitethernet, port-channel, tengigabitethernet,
fortygigabitethernet) mode
User Guidelines
This command has no user guidelines.
Example
The following example configures 1/0/5 to access mode.
console(config)#interface gigabitethernet 1/0/5
console(config-if-1/0/5)#switchport mode access
switchport trunk
Use the switchport trunk command in Interface Configuration mode to add
VLANs to or remove VLANs from a trunk port, or to set the native VLAN for
an interface in Trunk Mode.
Syntax
switchport trunk {allowed vlan
vlan–list
| native vlan
vlan–id
}
no switchport trunk allowed vlan
•
vlan–list
—Set the list of allowed VLANs that can receive and send traffic
on this interface in tagged format when in trunking mode. The default is
all
. The vlan–list format is as follows:
The vlan-list format is all | [add | remove | except] vlan–atom
[, vlan–atom...] where:
2CSNXXX_SWUM200.book Page 821 Tuesday, December 10, 2013 1:22 PM

822 VLAN Commands
–
all
specifies all VLANs from 1 to 4093. This keyword is not allowed on
commands that do not permit all VLANs in the list to be set at the
same time.
–
add
adds the defined list of VLANs to those currently set instead of
replacing the list.
–
remove
removes the defined list of VLANs from those currently set
instead of replacing the list. Valid IDs are from 1 to 4093; extended-
range VLAN IDs of the form X-Y or X,Y,Z are valid in this command.
–
except
lists the VLANs that should be calculated by inverting the
defined list of VLANs. (VLANs are added except the ones specified.)
–
vlan-atom
is either a single VLAN number from 1 to 4093 or a
continuous range of VLANs described by two VLAN numbers, the
lesser one first, separated by a hyphen.
•
valid–id
—A valid VLAN id from 1–4093.
Default Configuration
All VLANs are members of a trunk port.
VLAN 1 is the native VLAN on a trunk port. VLAN 1 is the default VLAN for
access mode ports.
Command Mode
Interface Configuration (gigabitethernet, port-channel, tengigabitethernet,
fortygigabitethernet) mode
Interface Range mode
Port-Channel Range mode
User Guidelines
Untagged traffic received on a trunk port is forwarded on the native VLAN, if
configured.
To drop untagged traffic on a trunk port, remove the native VLAN from the
trunk port. (Ex. switchport trunk allowed vlan remove 1.) Management
traffic is still allowed on the trunk port in this configuration.
The no form of the command sets the trunk port back to the defaults.
2CSNXXX_SWUM200.book Page 822 Tuesday, December 10, 2013 1:22 PM

VLAN Commands 823
It is possible to exclude VLANs that have not yet been created from trunk
port membership.
Example
console(config-if-Gi1/0/1)#switchport trunk allowed vlan 1-1024
console(config-if-Gi1/0/1)#switchport trunk allowed vlan except
1,2,3,5,7,11,13
vlan
Use the vlan command in Global Configuration mode to configure a VLAN.
To delete a VLAN, use the no form of this command.
Syntax
vlan {
vlan–id
|
vlan–range
}
no vlan {
vlan–id
|
vlan–range
}
•
vlan–id
—A valid VLAN ID. (Range: 1–4093)
•
vlan–range
—A list of valid VLAN IDs. List separate, non-consecutive
VLAN IDs separated by commas (without spaces). Use a hyphen to
designate a range of IDs. (Range: 1–4093)
Default Configuration
This command has no default configuration.
Command Mode
Global Configuration (Config)
User Guidelines
Deleting the VLAN assigned as the PVID on an access port will cause VLAN 1
to be assigned as the PVID for the access port. Deleting the VLAN assigned as
the native VLAN for a trunk port will cause the trunk port to discard
untagged frames received on the port.. Creating a VLAN adds it to the
allowed list for all trunk ports except those where it is specifically excluded.
Ports and port channels can be configured with VLANs that do not exist.
They will not forward traffic on nonexisting VLANs.
2CSNXXX_SWUM200.book Page 823 Tuesday, December 10, 2013 1:22 PM

824 VLAN Commands
Example
The following example shows how to create (add) VLAN IDs 22, 23, and 56.
console(config)#vlan 22,23,56
console(config-vlan)#
vlan association mac
Use the vlan association mac command in VLAN Configuration mode to
associate a MAC address to a VLAN. The maximum number of MAC-based
VLANs is 256. Only packets with a matching source IP address are placed in
the VLAN.
Syntax
vlan association mac
mac-address
no vlan association mac
mac-address
•
mac-address
— MAC address to associate to the VLAN. (Range: Any MAC
address in the format xxxx.xxxx.xxxx or xx:xx:xx:xx:xx:xx)
Default Configuration
No assigned MAC address.
Command Mode
VLAN Configuration mode
User Guidelines
This command has no user guidelines.
Example
The following example associates MAC address with VLAN ID 1.
console(config)# vlan 1
console(config-vlan-1)#vlan association mac 0001.0001.0001
2CSNXXX_SWUM200.book Page 824 Tuesday, December 10, 2013 1:22 PM

VLAN Commands 825
vlan association subnet
Use the vlan association subnet command in VLAN Configuration mode to
associate a VLAN to a specific IP-subnet. Only packets with a matching
source IP address are placed into the VLAN.
Syntax
vlan association subnet
ip-address subnet-mask
no vlan association subnet
ip-address subnet-mask
•
ip-address
— Source IP address. (Range: Any valid IP address)
•
subnet-mask
— Subnet mask. (Range: Any valid subnet mask)
Default Configuration
No assigned ip-subnet.
Command Mode
VLAN Configuration mode
User Guidelines
This command has no user guidelines.
Example
The following example associates the 192.168.0.xxx IP address with VLAN ID
1.
console(config)# vlan 1
console(config-vlan-1)#vlan association subnet 192.168.0.0 255.255.255.0
vlan makestatic
This command changes a dynamically created VLAN (one that is created by
GVRP registration) to a static VLAN (one that is permanently configured and
defined). The ID is a valid VLAN identification number. VLAN range is 2-
4093.
2CSNXXX_SWUM200.book Page 825 Tuesday, December 10, 2013 1:22 PM

826 VLAN Commands
Syntax
vlan makestatic
vlan-id
•
vlan-id
— Valid vlan ID. Range is 2–4093.
Default Configuration
This command has no default configuration.
Command Mode
Global Configuration Mode
User Guidelines
The dynamic VLAN (created via GRVP) should exist prior to executing this
command. See the Type column in output from the
show vlan
command to
determine that the VLAN is dynamic.
Example
The following changes vlan 3 to a static VLAN.
console(config-vlan)#vlan makestatic 3
vlan protocol group
Use the vlan protocol group command in Global Configuration mode to add
protocol-based groups to the system. When a protocol group is created, it is
assigned a unique group ID number. The group ID is used to identify the
group in subsequent commands. Use the no form of the command to remove
the specified VLAN protocol group name from the system.
Syntax
vlan protocol group
groupid
no vlan protocol group
groupid
•
groupid
— The protocol-based VLAN group ID, to create a protocol-based
VLAN group. To see the created protocol groups, use the
show port
protocol al
l command.
2CSNXXX_SWUM200.book Page 826 Tuesday, December 10, 2013 1:22 PM

VLAN Commands 827
Default Configuration
This command has no default configuration.
Command Mode
Global Configuration mode
User Guidelines
This command has no user guidelines.
Example
console(config)# vlan protocol group 1
vlan protocol group add protocol
Use the vlan protocol group add protocol command in Global Configuration
mode to add a protocol to the protocol-based VLAN groups identified by
groupid
. A group may have more than one protocol associated with it. Each
interface and protocol combination can be associated with one group only. If
adding a protocol to a group causes any conflicts with interfaces currently
associated with the group, this command fails and the protocol is not added
to the group.
To remove the protocol from the protocol-based VLAN group identified by
groupid
, use the no form of this command.
Syntax
vlan protocol group add protocol
groupid
ethertype
value
no vlan protocol group add protocol
groupid
ethertype
value
•
groupid
— The protocol-based VLAN group ID, which is automatically
generated when you create a protocol-based VLAN group with the
vlan
protocol group
command. To see the group ID associated with the name
of a protocol group, use the
show port protocol all
command.
•
ethertype
value
— The protocol you want to add. The ethertype value can
be any valid hexadecimal number in the range 0x0600 to 0xffff.
2CSNXXX_SWUM200.book Page 827 Tuesday, December 10, 2013 1:22 PM

828 VLAN Commands
Default Configuration
This command has no default configuration.
Command Mode
Global Configuration mode
User Guidelines
This command has no user guidelines.
Example
The following example displays how to add the "ip" protocol to the protocol
based VLAN group identified as "2."
console(config)#vlan protocol group add protocol 2 ethertype 0xXXXX
vlan protocol group name
This is a new command for assigning a group name to
vlan protocol group id
.
Syntax
vlan protocol group name
groupid
groupName
no vlan protocol group name
groupid
•
groupid
—The protocol-based VLAN group ID, which is automatically
generated when you create a protocol-based VLAN group with the
vlan
protocol group
command. To see the group ID associated with the name
of a protocol group, use the
show port protocol all
command
•
groupName
—The group name you want to add. The group name can be
up to 16 characters length. It can be any valid alpha numeric characters.
Default Configuration
This command has no default configuration.
Command Mode
Global Configuration mode
2CSNXXX_SWUM200.book Page 828 Tuesday, December 10, 2013 1:22 PM

VLAN Commands 829
User Guidelines
This command has no user guidelines.
Example
console(config)# vlan protocol group name 1 usergroup
vlan protocol group remove
Use the vlan protocol group remove command in Global Configuration
mode to remove the protocol-based VLAN group identified by
groupid
.
Syntax
vlan protocol group remove
groupid
•
groupid
— The protocol-based VLAN group ID, which is automatically
generated when you create a protocol-based VLAN group with the
vlan
protocol group
command. To see the group ID associated with the name
of a protocol group, use the
show port protocol all
command.
Default Configuration
This command has no default configuration.
Command Mode
Global Configuration mode
User Guidelines
This command has no user guidelines.
Example
The following example displays the removal of the protocol-based VLAN
group identified as "2."
console(config)#vlan protocol group remove 2
2CSNXXX_SWUM200.book Page 829 Tuesday, December 10, 2013 1:22 PM

830 VLAN Commands
switchport private-vlan
Use the switchport private-vlan command in Interface Configuration mode
to define a private VLAN association for an isolated or community port or a
mapping for a promiscuous port.
Use the no form of the command to remove the private VLAN association or
mapping from the interface.
Syntax
switchport private-vlan {host-association primary-vlan-id secondary-vlan-id
| mapping primary-vlan-id [add|remove] secondary-vlan-list}
no switchport private-vlan {host-association|mapping}
•
host-association
—Defines VLAN associations for community or host
ports.
•
mapping
—Defines the private VLAN mapping for promiscuous ports.
•
primary-vlan-id
—Primary VLAN ID of a private VLAN.
•
secondary-vlan-id
—Secondary (isolated or community) VLAN ID of a
private VLAN.
•
add
—Associates the secondary VLAN with the primary one.
•
remove
—Deletes the secondary VLANs from the primary VLAN
association.
•
secondary-vlan-list
—A list of secondary VLANs to be mapped to a primary
VLAN.
Default Configuration
This command has no default association or mapping configuration.
Command Mode
Interface Configuration (physical or port-channel)
User Guidelines
This command has no user guidelines.
2CSNXXX_SWUM200.book Page 830 Tuesday, December 10, 2013 1:22 PM

VLAN Commands 831
switchport mode private-vlan
Use the switchport mode private-vlan command in Interface Configuration
mode to define a private VLAN association for an isolated or community
interface or a mapping for a promiscuous interface.
Use the no form of the command to remove the private VLAN association or
mapping from the interface.
Syntax
switchport mode private-vlan {host|promiscuous}
no switchport mode
•
host-association
—Configure the interface as a private VLAN host port.
Host ports are community or isolated ports, depending on the VLAN to
which they belong.
•
promiscuous
—Configure the interface as a private VLAN promiscuous
port. Promiscuous ports are members of the primary VLAN.
Default Configuration
This command has no default configuration. By default, a port is neither
configured as promiscuous or host.
Command Mode
Interface Configuration (physical or port-channel)
User Guidelines
Do not configure private VLANs on ports configured with any of these
features:
• Link Aggregation Control Protocol (LACP)
• Multicast VLAN Registration (MVR)
• Voice VLAN
It is recommended that the private VLAN host ports be configured as
spanning-tree portfast.
2CSNXXX_SWUM200.book Page 831 Tuesday, December 10, 2013 1:22 PM

832 VLAN Commands
private-vlan
Use the private-vlan command in VLAN Configuration mode to define a
private VLAN association between the primary and secondary VLANs.
Use the no form of the command to remove the private VLAN association.
Syntax
private-vlan {primary|isolated|community|association [add|remove]
vlan-
list
}
no private-vlan [association]
•
association
—Defines an association between the primary VLAN and
secondary VLANs.
•
primary
—Specify that the selected VLAN is the primary VLAN.
•
community
—Specify that the selected VLAN is the community VLAN.
•
isolated
—Specify that the selected VLAN is the isolated VLAN.
•
add
—Associates a secondary VLAN with the primary VLAN.
•
remove
—Deletes the secondary VLAN association with the primary
VLAN.
•
vlan-list
—A list of secondary VLAN ids to be mapped to a primary VLAN.
The VLAN list can contain multiple entries separated by commas and
containing no spaces. Each entry can be a single VLAN id or a hyphenated
range of VLANs.
Default Configuration
This command has no default setting.
Command Mode
VLAN Configuration mode
User Guidelines
A community VLAN carries traffic among community ports and from
community ports to the promiscuous ports on the corresponding primary
VLAN.
2CSNXXX_SWUM200.book Page 832 Tuesday, December 10, 2013 1:22 PM

VLAN Commands 833
An isolated VLAN is used by isolated ports to communicate with
promiscuous ports. It does not carry traffic to other community ports or other
isolated ports with the same primary VLAN.
The primary VLAN is the VLAN that carries traffic from a promiscuous port
to the private ports.
VLAN 1 cannot be configured in a private VLAN configuration.
Examples
console# configure terminal
console(config)# vlan 10
console(config-vlan)# private-vlan primary
console(config-vlan)# exit
console(config)# vlan 1001
console(config-vlan)# private-vlan isolated
console(config-vlan)# exit
console(config)# vlan 1002
console(config-vlan)# private-vlan community
console(config-vlan)# exit
console(config)# vlan 1003
console(config-vlan)# private-vlan community
console(config-vlan)# exit
console(config)# vlan 20
console(config-vlan)# private-vlan association 1001-1003
console(config-vlan)# end
show vlan private-vlan
Use the show vlan private-vlan command in Privileged EXEC mode to
display information about the configured private VLANs including primary
and secondary VLAN IDs, type (community, isolated, or primary), and the
ports which belong to a private VLAN.
Syntax
show vlan private-vlan [type]
Default Configuration
This command has no default setting.
2CSNXXX_SWUM200.book Page 833 Tuesday, December 10, 2013 1:22 PM

834 VLAN Commands
Command Mode
Privileged EXEC mode, Configuration mode and all Configuration submodes
User Guidelines
Do not configure private VLANs on ports configured with any of these
features:
• Link Aggregation Control Protocol (LACP)
• Multicast VLAN Registration (MVR)
• Voice VLAN
It is recommended that the private VLAN host ports be configured as
spanning-tree portfast.
The command displays the following information.
Parameter Description
Primary Primary VLAN ID.
Secondary Secondary VLAN ID.
Type Secondary VLAN type. Use the type parameter to display only
private VLAN ID and its type.
Ports Ports that are associated with a private VLAN.
2CSNXXX_SWUM200.book Page 834 Tuesday, December 10, 2013 1:22 PM

Voice VLAN Commands 835
39
Voice VLAN Commands
Dell Networking N2000/N3000/N4000 Series Switches
The Voice VLAN feature enables switch ports to carry voice traffic with an
administrator-defined priority so as to enable prioritization of voice traffic
over data traffic. Using Voice VLAN helps to ensure that the sound quality of
an IP phone is protected from deterioration when the data traffic utilization
on the port is high.
Voice VLAN is the preferred solution for applying QoS to voice traffic in an
enterprise environment. Voice VLAN scales with the number of ports and
does not make significant demands on the switch CPU for classification of
voice traffic. However, Voice VLAN does require the administrator to perform
the additional configuration step of defining the QoS policy to be applied to
voice traffic.
The switch can be configured to support voice VLAN on a port connecting to
the VoIP phone. When a VLAN is associated with the voice VLAN port, then
the VLAN ID information is passed onto the VoIP phone using the LLDP-
MED mechanism. The voice data coming from the VoIP phone is tagged with
the exchanged VLAN ID; thus, regular data arriving on the switch is given the
default PVID of the port, and the voice traffic is received on a predefined
VLAN. The two types of traffic are therefore segregated so that better service
can be provided to the voice traffic.
When a dot1p priority is associated with the voice VLAN port instead of
VLAN ID, then the priority information is passed onto the VoIP phone using
the LLDP-MED mechanism. Thus, the voice data coming from the VoIP
phone is tagged with VLAN 0 and with the exchanged priority. Regular data
arriving on the switch is given the default priority of the port (default 0), and
the voice traffic is received with higher priority, thus segregating both the
traffic to provide better service to the voice traffic.
The switch can be configured to override the data traffic CoS. This feature
enables overriding the 802.1P priority of the data traffic packets arriving at
the port enabled for voice VLAN. Thus, a rogue client that is also connected
to the voice VLAN port does not deteriorate the voice traffic. Voice VLAN is
recommended for enterprise-wide deployment of voice services on the IP
network.
2CSNXXX_SWUM200.book Page 835 Tuesday, December 10, 2013 1:22 PM

836 Voice VLAN Commands
Commands in this Chapter
This chapter explains the following commands:
voice vlan
This command is used to enable the voice VLAN capability on the switch.
Syntax
voice vlan
no voice vlan
Command Mode
Global Configuration
User Guidelines
Not applicable
Default Value
This feature is disabled by default.
Example
console(config)#voice vlan
console(config)#no voice vlan
voice vlan (Interface)
This command is used to enable the voice vlan capability on the interface.
Syntax
voice vlan {
vlanid
| dot1p
priority
| none | untagged | data priority {trust |
untrust} | auth { enable | disable} | dscp
dscp
}
no voice vlan
voice vlan voice vlan data priority
voice vlan (Interface) show voice vlan
2CSNXXX_SWUM200.book Page 836 Tuesday, December 10, 2013 1:22 PM

Voice VLAN Commands 837
•
auth
—Enables/disables authentication on the voice vlan port.
•
data
—Observe the priority on received voice vlan traffic (trusted mode).
•
dot1p
—Configure Voice VLAN 802.1p priority tagging for voice traffic.
•
dscp
—Configure DSCP value for voice traffic on the voice vlan port.
(Range: 0–64).
•
none
—Allow the IP phone to use its own configuration to send untagged
voice traffic
•
priority
—The Dot1p priority for the voice VLAN on the port.
•trust—
Trust the dot1p priority or DSCP values contained in packets
arriving on the voice vlan port.
•
untagged
—Configure the phone to send untagged voice traffic.
•
untrust
—Do not trust the dot1p priority or DSCP values contained in
packets arriving on the voice vlan port.
•
vlanid
—The voice VLAN ID.
Default Configuration
The default DSCP value is 46.
Command Mode
Interface Configuration (Ethernet) mode.
User Guidelines
There are no user guidelines for this command.
Example
console(config-if-Gi1/0/1)#voice vlan 1
console(config-if-Gi1/0/1)#voice vlan dot1p 1
console(config-if-Gi1/0/1)#voice vlan none
console(config-if-Gi1/0/1)#voice vlan untagged
voice vlan data priority
This command is to either trust or not trust (untrust) the data traffic arriving
on the voice VLAN port.
2CSNXXX_SWUM200.book Page 837 Tuesday, December 10, 2013 1:22 PM

838 Voice VLAN Commands
Syntax
voice vlan data priority {trust | untrust}
•
trust—
Trust the dot1p priority or DSCP values contained in packets
arriving on the voice vlan port.
•
untrust—
Do not trust the dot1p priority or DSCP values contained in
packets arriving on the voice vlan port.
Command Mode
Interface Configuration
Default Value
trust
Example
console(config-if-1/0/1)#voice vlan data priority untrust
console(config-if-1/0/1)#voice vlan data priority trust
show voice vlan
This command displays information about the voice VLAN.
Syntax
show voice vlan [interface {gigabitethernet unit/slot/port |
tengigabitethernet unit/slot/port | fortygigabitethernet unit/slot/port| all}]
Command Mode
Privileged EXEC, Configuration mode and all Configuration submodes
User Guidelines
• When the
interface
parameter is not specified, only the global mode of the
voice VLAN is displayed.
• When the
interface
parameter is specified, the following is displayed:
2CSNXXX_SWUM200.book Page 838 Tuesday, December 10, 2013 1:22 PM

Voice VLAN Commands 839
Example
(console) #show voice vlan interface 1/0/1
Interface....................................1/0/1
Voice VLAN Interface Mode....................Enabled
Voice VLAN ID................................1
Voice VLAN COS Override......................False
Voice VLAN Port Status.......................Disabled
When the interface parameter is specified:
Voice VLAN Mode The admin mode of the voice VLAN on the interface.
Voice VLAN ID The voice VLAN ID.
Voice VLAN Priority The Dot1p priority for the voice VLAN on the port.
Voice VLAN
Untagged
The tagging option for the voice VLAN traffic.
Voice VLAN COS
Override
The Override option for the voice traffic arriving on the port.
Voice VLAN Status The operational status of voice VLAN on the port.
2CSNXXX_SWUM200.book Page 839 Tuesday, December 10, 2013 1:22 PM

840 Voice VLAN Commands
2CSNXXX_SWUM200.book Page 840 Tuesday, December 10, 2013 1:22 PM

802.1x Commands 841
40
802.1x Commands
Dell Networking N2000/N3000/N4000 Series Switches
Local Area Networks (LANs) are often deployed in environments that permit
the attachment of unauthorized devices. The networks also permit
unauthorized users to attempt to access the LAN through existing
equipment. In such environments, the administrator may desire to restrict
access to the services offered by the LAN.
Port-based network access control makes use of the physical characteristics of
LAN infrastructures to provide a means of authenticating and authorizing
devices attached to a LAN port. Port-based network access control prevents
access to the port in cases in which the authentication and authorization
process fails. A port is defined as a single point of attachment to the LAN.
The Dell Networking supports an 802.1x Authenticator service with a local
authentication server or authentication using remote RADIUS or TACACS
servers.
Supported security methods for communication with remote servers include
MD5, PEAP, EAP-TTL, EAP-TTLS, and EAP-TLS.
Local 802.1X Authentication Server
The Dell Networking switch supports a dedicated database for local
authentication of users for network access through the Dot1x feature. This
functionality is distinct from management access for the switch. This feature
supports creating users for Dot1x (port) access only.
The Internal Authentication Server feature provides support for the creation
of users for Dot1x access only, i.e. without management access. This feature
maintains a separate database (known as the Dot1x user database) of users
allowed for Dot1x access.
A new authentication method internal is added to the list of methods
supported by authentication list creation in order to support the IDAS user
database lookup. The internal method cannot be added in the same
authentication list that has other methods like local, radius and reject.
2CSNXXX_SWUM200.book Page 841 Tuesday, December 10, 2013 1:22 PM

842 802.1x Commands
Whenever an operator configures a port in Dot1x authentication mode and
selects the authentication method as internal, then the user credentials
received from the Dot1x supplicant is validated against the IDAS by Dot1x
component. The Dot1x application accesses the Dot1x user database to
check whether the user credentials present in the authentication message
corresponds to a valid user or not. If so then an event is generated which
triggers the Dot1x state machine to send a challenge to the supplicant.
Otherwise a failure is returned to the Dot1x state machine and the user is not
granted access to the port.
If user(s) credentials are changed, the existing user connection(s) are not
disturbed and the changed user(s) credentials are only used when a new EAP
request arises.
A CLI configuration mode is added in order to configure dot1x users and
their attributes. The Dot1x maintained user database can be exported
(uploaded) or imported (downloaded) to/from a central location using a
TFTP server.
MAC Authentication Bypass
Today, 802.1x has become the recommended port-based authentication
method at the access layer in enterprise networks. However, there may be
802.1x unaware devices such as printers, fax-machines etc that would require
access to the network without 802.1x authentication. MAC Authentication
Bypass (MAB) is a supplemental authentication mechanism to allow 802.1x
unaware clients to authenticate to the network. It uses the 802,1x
infrastructure and MAB cannot be supported independent of the Dot1x
component.
MAC Authentication Bypass (MAB) provides 802.1x unaware clients
controlled access to the network using the devices’ MAC address as an
identifier. This requires that the known and allowable MAC address and
corresponding access rights be prepopulated in the authentication server.
MAB only works when the port control mode of the port is MAC-based.
Port access by MAB clients is allowed if the Dot1x user database has
corresponding entries added for the MAB clients with user name and
password attributes set to the MAC address of MAB clients.
2CSNXXX_SWUM200.book Page 842 Tuesday, December 10, 2013 1:22 PM

802.1x Commands 843
Guest VLAN
The Guest VLAN feature allows a Dell Networking switch to provide a
distinguished service to unauthenticated users (not rogue users who fail
authentication). This feature provides a mechanism to allow visitors and
contractors to have network access to reach external network with no ability
to surf internal LAN.
When a client that does not support 802.1X is connected to an unauthorized
port that is 802.1X-enabled, the client does not respond to the 802.1X
requests from the switch. Therefore, the port remains in the unauthorized
state, and the client is not granted access to the network. If a guest VLAN is
configured for that port, then the port is placed in the configured guest
VLAN, and the port is moved to the authorized state, allowing access to the
client.
802.1x Monitor Mode
Monitor mode is a special mode that can be enabled in conjunction with
Dot1x authentication. It allows network access even in case where there is a
failure to authenticate but logs the results of the authentication process for
diagnostic purposes. The exact details are described in the below sections.
The main aim of the monitor mode is to provide a mechanism to the operator
to be able to identify the short-comings in the configuration of a Dot1x
authentication on the switch without affecting the network access to the
users of the switch.
There are three important aspects to this feature after activation:
1
To allow successful authentications using the returned information from
authentication server.
2
To provide a mechanism to report unsuccessful authentications without
negative repercussions to the user due to operator errors or failure cases
from the Authentication server or supplicants.
3
To accurately report the data received from the successful and
unsuccessful operations so that the operator can make the appropriate
changes or learn where the problem areas are.
The monitor mode can be configured globally on a switch. If the switch fails
to authenticate the user for any reason (say RADIUS access reject from
RADIUS server, RADIUS time-out, or the client itself is Dot1x unaware), the
2CSNXXX_SWUM200.book Page 843 Tuesday, December 10, 2013 1:22 PM

844 802.1x Commands
client is authenticated and is undisturbed by the failure condition(s). The
reasons for failure are logged and buffered into the local logging database such
that the operator can track the failure conditions. Clients authenticated when
monitor mode is enabled are always assigned to the default VLAN, regardless
of the RADIUS assignment.
RADIUS-based Dynamic VLAN Assignment
If VLAN assignment is enabled in the RADIUS server then as part of the
response message, the RADIUS server sends the VLAN ID which the client is
requested to use in the 802.1x tunnel attributes. If dynamic VLAN creation is
enabled on the switch and the RADIUS assigned VLAN does not exist, then
the assigned VLAN is dynamically created. This implies that the client can
connect from any port and be assigned to the appropriate VLAN. This gives
flexibility for clients to move around the network with out requiring the
operator to perform additional provisioning for each network interface.
Commands in this Chapter
This chapter explains the following commands:
dot1x dynamic-vlan enable dot1x timeout re-
authperiod
show authentication
statistics
dot1x initialize dot1x timeout server-
timeout
show dot1x
dot1x mac-auth-bypass dot1x timeout tx-period show dot1x authentication-
history
dot1x max-req authentication enable show dot1x clients
dot1x max-users authentication order show dot1x interface
dot1x port-control authentication priority show dot1x interface
statistics
dot1x re-authenticate authentication restart show dot1x users
dot1x reauthentication clear authentication
statistics
clear dot1x
authentication–history
dot1x system-auth-control dot1x guest-vlan
2CSNXXX_SWUM200.book Page 844 Tuesday, December 10, 2013 1:22 PM

802.1x Commands 845
802.1x Advanced Features
dot1x dynamic-vlan enable
Use the dot1x dynamic-vlan enable command in Global Configuration mode
to enable the capability of creating VLANs dynamically when a
RADIUS–assigned VLAN does not exist in the switch. Use the no form of the
command to disable this capability.
Syntax
dot1x dynamic-vlan enable
no dot1x dynamic-vlan enable
Default Configuration
The default value is Disabled.
Command Mode
Global Configuration
User Guidelines
This command has no user guidelines.
dot1x system-auth-control
monitor
clear authentication
authentication-history
dot1x unauth-vlan
dot1x timeout guest-vlan-
period
show authentication show dot1x advanced
dot1x timeout quiet-period show authenticaton
authentication-history
–
dot1x guest-vlan dot1x unauth-vlan show dot1x advanced
2CSNXXX_SWUM200.book Page 845 Tuesday, December 10, 2013 1:22 PM

846 802.1x Commands
dot1x initialize
This command begins the initialization sequence on the specified port. This
command is only valid if the control mode for the specified port is auto or
mac-based. If the control mode is not auto or mac-based, an error will be
returned.
Syntax
dot1x initialize [interface interface-id]
•
interface-id
—The port to be initialized.
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC mode
User Guidelines
There are no user guidelines for this command.
dot1x eapolflood
This command enables the flooding of received IEEE 802.1x frames in the
VLAN.
Syntax
dot1x eapolflood
Default Configuration
By default, the switch does not forward received IEEE 802.1x frames, even if
802.1x is not enabled on the switch. This is the default behavior required by
IEEE 802.1x-2010.
Command Mode
Global Configuration mode
2CSNXXX_SWUM200.book Page 846 Tuesday, December 10, 2013 1:22 PM

802.1x Commands 847
User Guidelines
Local processing of IEEE 802.1x frames must be disabled (no dot1x system-
auth-control) for this capability to be enabled. This capability is useful in
situations where the authenticator device is placed one or more hops away
from the authenticating host. The intervening switch will flood all received
IEEE 802.1x frames in the VLAN.
Flooding of IEEE 802.1x frames makes end stations vulnerable to a denial of
service attack should another end station record and play back certain flooded
EAPOL frames at a high rate.
dot1x mac-auth-bypass
Use the dot1x mac-auth-bypass command to enable MAB on an interface.
Use the no form of this command to disable MAB on an interface.
Syntax
dot1x mac-auth-bypass
no dot1x mac-auth-bypass
Default Configuration
MAC Authentication Bypass is disabled by default.
Command Mode
Interface Configuration (Ethernet) mode
User Guidelines
Authentication of a user via mac-auth-bypass will not occur until the "dot1x
time-out guest-vlan-period" timer expires.
Example
The following example sets MAC Authentication Bypass on interface
gigabitethernet 1/0/2:
console(config-if-Gi1/0/2)#dot1x mac-auth-bypass
2CSNXXX_SWUM200.book Page 847 Tuesday, December 10, 2013 1:22 PM

848 802.1x Commands
dot1x max-req
Use the dot1x max-req command in Interface Configuration mode to set the
maximum number of times that the switch sends an Extensible
Authentication Protocol (EAP)-request frame (assuming that no response is
received) to the client before restarting the authentication process. To return
to the default setting, use the no form of this command.
Syntax
dot1x max-req
count
no dot1x max-req
•
count
—
Number of times that the switch sends an EAP-request/identity
frame before restarting the authentication process. (Range: 1–10)
Default Configuration
The default value for the
count
parameter is 2.
Command Mode
Interface Configuration (Ethernet) mode
User Guidelines
Change the default value of this command only to adjust for unusual
circumstances, such as unreliable links or specific behavioral problems with
certain clients and authentication servers.
Example
The following example sets the number of times that the switch sends an
EAP-request/identity frame to 6.
console(config)# interface gigabitethernet 1/0/16
console(config-if-Gi1/0/16)# dot1x max-req 6
2CSNXXX_SWUM200.book Page 848 Tuesday, December 10, 2013 1:22 PM

802.1x Commands 849
dot1x max-users
Use the dot1x max-users command in Interface Configuration mode to set
the maximum number of clients supported on the port when MAC-based
802.1X authentication is enabled on the port. Use the no version of the
command to reset the maximum number of clients supported on the port
when MAC-based 802.1X authentication is enabled on the port.
Syntax
dot1x max-users
users
no dot1x max-users
•
users
—
The number of users the port supports for MAC-based 802.1X
authentication (Range: 1–64)
Default Configuration
The default number of clients supported on a port with MAC-based 802.1X
authentication is 64.
Command Mode
Interface Configuration (Ethernet) mode
User Guidelines
This command has no user guidelines.
Example
The following command limits the number of devices that can authenticate
on port gigabitethernet 1/0/2 to 3.
console(config-if-Gi1/0/2)#dot1x max-users 3
dot1x port-control
Use the dot1x port-control command in Interface Configuration mode to
enable the IEEE 802.1X operation on the port.
2CSNXXX_SWUM200.book Page 849 Tuesday, December 10, 2013 1:22 PM

850 802.1x Commands
Syntax
dot1x port-control {force-authorized | force-unauthorized | auto | mac-
based}
no dot1x port-control
•
auto
— Enables 802.1x authentication on the interface and causes the
port to transition to the authorized or unauthorized state based on the
802.1x authentication exchange between the switch and the client.
•
force-authorized
— Disables 802.1x authentication on the interface and
causes the port to transition to the authorized state without any
authentication exchange required. The port sends and receives normal
traffic without 802.1x-based authentication of the client.
•
force-unauthorized
—
Denies all access through this interface by forcing
the port to transition to the unauthorized state, ignoring all attempts by
the client to authenticate. The switch cannot provide authentication
services to the client through the interface.
•
mac-based
— Enables 802.1x authentication on the interface and allows
multiple hosts to authenticate on a single port. The hosts are distinguished
by their MAC addresses.
Default Configuration
The default configuration is auto.
Command Mode
Interface Configuration (Ethernet) mode
User Guidelines
It is recommended that you disable spanning tree or enable spanning-tree
PortFast mode on 802.1x edge ports (ports in auto state that are connected to
end stations), in order to go immediately to the forwarding state after
successful authentication.
When configuring a port to use MAC-based authentication, the port must be
in switchport general mode.
Example
The following command enables MAC-based authentication on port 1/0/2
2CSNXXX_SWUM200.book Page 850 Tuesday, December 10, 2013 1:22 PM

802.1x Commands 851
console(config)# interface gigabitethernet 1/0/2
console(config-if-Gi1/0/2)# dot1x port-control mac-based
dot1x re-authenticate
Use the dot1x re-authenticate command in Privileged EXEC mode to enable
manually initiating a re-authentication of all 802.1x-enabled ports or the
specified 802.1x-enabled port.
Syntax
dot1x re-authenticate [gigabitethernet unit/slot/port | tengigabitethernet
unit/slot/port | fortygigabitethernet unit/slot/port]
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC mode
User Guidelines
This command has no user guidelines.
Example
The following command manually initiates a reauthentication of the 802.1x-
enabled port.
console# dot1x re-authenticate gigabitethernet 1/0/16
dot1x reauthentication
Use the dot1x reauthentication command in Interface Configuration mode
to enable periodic re-authentication of the client. To return to the default
setting, use the no form of this command.
Syntax
dot1x reauthentication
no dot1x reauthentication
2CSNXXX_SWUM200.book Page 851 Tuesday, December 10, 2013 1:22 PM

852 802.1x Commands
Default Configuration
Periodic reauthentication is disabled.
Command Mode
Interface Configuration (Ethernet) mode
User Guidelines
This command has no user guidelines.
Example
The following example enables periodic reauthentication of the client.
console(config)# interface gigabitethernet 1/0/16
console(config-if-Gi1/0/16)# dot1x reauthentication
dot1x system-auth-control
Use the dot1x system-auth-control command in Global Configuration mode
to enable 802.1x globally. To disable 802.1x globally, use the no form of this
command.
Syntax
dot1x system-auth-control
no dot1x system-auth-control
Default Configuration
The default for this command is disabled.
Command Mode
Global Configuration mode
User Guidelines
This command enables local processing of IEEE 802.1x frames on the switch.
Dot1x eapolflood mode must be disabled for local processing to occur.
2CSNXXX_SWUM200.book Page 852 Tuesday, December 10, 2013 1:22 PM

802.1x Commands 853
Example
The following example enables 802.1x globally.
console(config)# dot1x system-auth-control
dot1x system-auth-control monitor
Use the dot1x system-auth-control monitor command in Global
Configuration mode to enable 802.1x monitor mode globally. To disable this
function, use the no form of this command.
Syntax
dot1x system-auth-control monitor
no dot1x system-auth-control monitor
Default Configuration
Dot1x monitor mode is disabled.
Command Mode
Global Configuration mode
User Guidelines
This command has no user guidelines.
Example
The following example enables 802.1x globally.
console(config)# dot1x system-auth-control monitor
dot1x timeout guest-vlan-period
Use the dot1x timeout guest-vlan-period command in Interface
Configuration mode to set the number of seconds that the switch waits
before authorizing the client if the client is a dot1x unaware client. Use the
no form of the command to return the timeout to the default value.
2CSNXXX_SWUM200.book Page 853 Tuesday, December 10, 2013 1:22 PM

854 802.1x Commands
Syntax
dot1x timeout guest-vlan-period
seconds
no dot1x timeout guest-vlan-period
•
seconds —
Time in seconds that the switch waits before authorizing the
client if the client is a dot1x unaware client. Range 1-300.
Default Configuration
The switch remains in the quiet state for 90 seconds.
Command Mode
Interface Configuration (Ethernet) mode
User Guidelines
It is recommended that the user set the dot1x timeout guest-vlan-period to at
least three times the while timer so that at least three EAP Requests are sent,
before assuming that the client is a dot1x unaware client.
Example
The following example sets the dot1x timeout guest vlan period to 100
seconds.
console(config)# dot1x timeout guest-vlan-period 100
dot1x timeout quiet-period
Use the dot1x timeout quiet-period command in Interface Configuration
mode to set the number of seconds that the switch remains in the quiet state
following a failed authentication exchange (for example, the client provided
an invalid password). To return to the default setting, use the no form of this
command.
Syntax
dot1x timeout quiet-period
seconds
no dot1x timeout quiet-period
2CSNXXX_SWUM200.book Page 854 Tuesday, December 10, 2013 1:22 PM

802.1x Commands 855
•
seconds —
Time in seconds that the switch remains in the quiet state
following a failed authentication exchange with the client. (Range:
0–65535 seconds)
Default Configuration
The switch remains in the quiet state for 60 seconds.
Command Mode
Interface Configuration (Ethernet) mode
User Guidelines
During the quiet period, the switch does not accept or initiate any
authentication requests.
Change the default value of this command only to adjust for unusual
circumstances, such as unreliable links or specific behavioral problems with
certain clients and authentication servers.
To provide a faster response time to the user, enter a smaller number than the
default.
Example
The following example sets the number of seconds that the switch remains in
the quiet state following a failed authentication exchange to 3600.
console(config)# interface gigabitethernet 1/0/16
console(config-if-Gi1/0/16)# dot1x timeout quiet-period 3600
dot1x timeout re-authperiod
Use the dot1x timeout re-authperiod command in Interface Configuration
mode to set the number of seconds between reauthentication attempts. To
return to the default setting, use the no form of this command.
Syntax
dot1x timeout re-authperiod
seconds
no dot1x timeout re-authperiod
2CSNXXX_SWUM200.book Page 855 Tuesday, December 10, 2013 1:22 PM

856 802.1x Commands
•
seconds —
Number of seconds between re-authentication attempts.
(Range: 300–4294967295)
Default Configuration
Re-authentication period is 3600 seconds.
Command Mode
Interface Configuration (Ethernet) mode
User Guidelines
This command has no user guidelines.
Example
The following example sets the number of seconds between re-authentication
attempts to 300.
console(config)# interface gigabitethernet 1/0/16
console(config-if-Gi1/0/16)# dot1x timeout re-authperiod 300
dot1x timeout server-timeout
Use the dot1x timeout server-timeout command in Interface Configuration
mode to set the time that the switch waits for a response from the
authentication server. To return to the default setting, use the no form of this
command.
Syntax
dot1x timeout server-timeout
seconds
no dot1x timeout server-timeout
•
seconds
—
Time in seconds that the switch waits for a response from the
authentication server. (Range: 1–65535)
Default Configuration
The period of time is set to 30 seconds.
2CSNXXX_SWUM200.book Page 856 Tuesday, December 10, 2013 1:22 PM

802.1x Commands 857
Command Mode
Interface Configuration (Ethernet) mode
User Guidelines
The actual timeout is this parameter or the product of the Radius
transmission times the Radius timeout, whichever is smaller.
Example
The following example sets the time for the retransmission to the
authentication server to 3600 seconds.
console(config-if-1/0/1)# dot1x timeout server-timeout 3600
dot1x timeout tx-period
Use the dot1x timeout tx-period command in Interface Configuration mode
to set the number of seconds that the switch waits for a response to an
Extensible Authentication Protocol (EAP)-request/identity frame from the
client before resending the request. To return to the default setting, use the
no form of this command.
Syntax
dot1x timeout tx-period
seconds
no dot1x timeout tx-period
•
seconds
—
Time in seconds that the switch should wait for a response to
an EAP-request/identity frame from the client before resending the
request. (Range: 1–65535)
Default Configuration
The period of time is set to 30 seconds.
Command Mode
Interface Configuration (Ethernet) mode
2CSNXXX_SWUM200.book Page 857 Tuesday, December 10, 2013 1:22 PM

858 802.1x Commands
User Guidelines
Change the default value of this command only to adjust for unusual
circumstances, such as unreliable links or specific behavioral problems with
certain clients and authentication servers.
Example
The following command sets the number of seconds that the switch waits for
a response to an EAP-request/identity frame to 3600 seconds.
console(config)# interface gigabitethernet 1/0/16
console(config-if-Gi1/0/16)# dot1x timeout tx-period 3600
authentication enable
Use this command to globally enable the Authentication Manager. Interface
configuration takes effect only if the Authentication Manager is enabled with
this command.
Use the no form of this command to set the feature to factory default value.
Syntax
authentication enable
no authentication enable
Default Configuration
The default value is Disabled.
Command Mode
Global Configuration mode
User Guidelines
There are no user guidelines for this command.
Example
console(config)# authentication enable
2CSNXXX_SWUM200.book Page 858 Tuesday, December 10, 2013 1:22 PM

802.1x Commands 859
authentication order
This command sets the order of authentication methods used on a port. The
available authentication methods are Dot1x, MAB, and captive portal.
Ordering sets the order of methods that the switch attempts when trying to
authenticate a new device connected to a port. If one method is unsuccessful
or timed out, the next method is attempted.
Use the no form of this command to return the port to the default
authentication order.
Syntax
authentication order [dot1x [mab] | mab [dot1x]] [captive portal]
no authentication order
Default Configuration
There is no default configuration for this command.
Command Modes
Interface VLAN Configuration mode
User Guidelines
Each method can only be entered once. Ordering is only possible between
802.1x and MAB. Captive portal can be configured either as a stand-alone
method or as the last method in the order.
Example
console(config-if-Gi1/0/1)# authentication order dot1x mab captive-portal
console(config-if-Gi1/0/1)# no authentication order
authentication priority
Use this command to set the priority for the authentication methods used on
a port. The available authentication methods are Dot1x, MAB, and captive
portal. The authentication priority decides if a previously authenticated client
is reauthenticated with a higher-priority method when the same is received.
Captive portal is always the last method in the list.
2CSNXXX_SWUM200.book Page 859 Tuesday, December 10, 2013 1:22 PM

860 802.1x Commands
Use the no form of this command to return the port to the default order of
priority for the authentication methods.
Syntax
authentication priority [mab | dot1x | captive-portal] [mab | dot1x |
captive-portal] [mab | dot1x | captive-portal]
no authentication priority
Default Configuration
There is no default configuration for this command.
Command Modes
Interface VLAN Configuration mode.
User Guidelines
Each method can only be entered once. There are no restrictions on the
priority ordering of methods.
Example
console(config-if-Gi1/0/1)# authentication priority mab dot1x captive-portal
console(config-if-Gi1/0/1)# no authentication priority
authentication restart
Use this command to set the interval after which reauthentication starts. This
timer starts only if all the authentication methods fail.
Use the no form of this command to set the authentication restart timer to
factory default value.
Syntax
authentication restart
time
no authentication restart
•
time
—The time, in seconds, after which reauthentication starts, if all the
authentication methods have failed. Range: 300-65535.
2CSNXXX_SWUM200.book Page 860 Tuesday, December 10, 2013 1:22 PM

802.1x Commands 861
Default Configuration
The default timer value is 300 seconds.
Command Modes
Interface VLAN Configuration mode
User Guidelines
None
Example
console(config-if-Gi1/0/1)# authentication timer restart 1800
console(config-if-Gi1/0/1)# no authentication timer restart
clear authentication statistics
Use this command to clear the authentication statistics.
Syntax
clear authentication statistics
{
interface-id
| all}
Default Configuration
There is no default configuration for this command.
Command Modes
Privileged EXEC mode
User Guidelines
There are no user guidelines for this command.
Example
console(config)# clear authentication statistics Gi1/0/1
Are you sure you want to clear authentication manager port stats? (y/n)
2CSNXXX_SWUM200.book Page 861 Tuesday, December 10, 2013 1:22 PM

862 802.1x Commands
clear authentication authentication-history
Use this command to clear the authentication history logs.
Syntax
clear authentication authentication-history {
interface-id
| all}
•
interface-id
—The interface.
•
all
—All interfaces.
Default Configuration
There is no default configuration for this command.
Command Modes
Privileged EXEC mode
User Guidelines
None
Example
console(config)# clear authentication authentication-history Gi1/0/1
show authentication
Use this command to list the authentication methods configured on the
interface and display if the Tiered Authentication feature is enabled.
Syntax
show authentication [interface {
interface-id
| all}]
•
interface-id
—The physical interface.
•
all
—All interfaces.
Default Configuration
There is no default configuration for this command.
2CSNXXX_SWUM200.book Page 862 Tuesday, December 10, 2013 1:22 PM

802.1x Commands 863
Command Modes
Privileged EXEC mode
User Guidelines
This command has no user guidelines.
Example
console# show authentication
Tiered Authentication.......................... Enabled
console# show authentication interface Gi1/0/1
Port........................................... Gi1/0/1
Authentication Restart timer................... 300
Configured method order........................ dot1x mab captive-portal
Enabled method order........................... dot1x mab undefined
Configured method priority..................... undefined undefined
undefined
Enabled method priority........................ undefined undefined
undefined
Number of authenticated clients................ 1
Logical Interface.............................. 0
client mac addr:............................... 00:00:00:00:00:01
Authenticated Method:.......................... dot1x
Auth State..................................... success
Auth Status.................................... Authenticated
show authenticaton authentication-history
Use this command to display the authentication history on one or more
interfaces.
Syntax
show authentication authentication-history {
interface-id
| all}
•
interface-id
—Any physical interface.
Default Configuration
There is no default configuration for this command.
2CSNXXX_SWUM200.book Page 863 Tuesday, December 10, 2013 1:22 PM

864 802.1x Commands
Command Modes
Privileged EXEC mode
User Guidelines
This command has no user guidelines.
Example
console#show authentication authentication-history Gi1/0/1
Time Stamp Interface MAC-Address Auth Status Method
--------------------- --------- ----------------- ------------ ------
Jul 21 1919 15:06:15 Gi1/0/1 00:00:00:00:00:01 Authorized 802.1X
show authentication statistics
Use this command to display the Authentication Manager statistics on one or
more interfaces.
Syntax
show authentication statistics
interface-id
•
interface-id
—The physical interface.
Default Configuration
There is no default configuration for this command.
Command Modes
Privileged EXEC mode
User Guidelines
This command has no user guidelines.
Example
config# show authentication statistics Gi1/0/1
Port........................................... Gi1/0/1
802.1X attempts................................ 1
802.1X failed attempts......................... 0
2CSNXXX_SWUM200.book Page 864 Tuesday, December 10, 2013 1:22 PM

802.1x Commands 865
Mab attempts................................... 0
Mab failed attempts............................ 0
Captive-portal attempts........................ 0
Captive-Portal failed attempts................. 0
show dot1x
Use the show dot1x command in Privileged EXEC mode to display:
•
A summary of
the global dot1x configuration.
• Summary information of the dot1x configuration for a specified port or all
ports.
• Detailed dot1x configuration for a specified port
• Dot1x statistics for a specified port, depending on the tokens used.
Syntax
show dot1x [interface
interface-id
[statistics]]
•
interface-id
—Any valid interface. See Interface Naming Conventions for
interface representation.
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC mode, Configuration mode and all Configuration submodes
User Guidelines
If you do not use the optional parameters, the command displays the global
dot1x mode and the VLAN Assignment mode.
Field Description
Administrative
Mode
Indicates whether authentication control on the switch is
enabled or disabled.
VLAN Assignment
Mode
Indicates whether assignment of an authorized port to a
RADIUS assigned VLAN is allowed (enabled) or not (disabled).
2CSNXXX_SWUM200.book Page 865 Tuesday, December 10, 2013 1:22 PM

866 802.1x Commands
Example
console(config-if-Gi1/0/1)#show dot1x
Administrative Mode............... Disabled
Dynamic VLAN Creation Mode........ Disabled
VLAN Assignment Mode.............. Disabled
Monitor Mode...................... Disabled
EAPOL Flood Mode.................. Disabled
Port Admin Mode Oper Mode Reauth Reauth
Control Period
--------- ------------------ ------------ -------- ----------
Gi1/0/1 auto N/A FALSE 3600
Gi1/0/2 auto N/A FALSE 3600
Gi1/0/3 auto N/A FALSE 3600
show dot1x authentication-history
Use the show dot1x authentication-history command in Privileged EXEC
mode to display the dot1x authentication events and information during
successful and unsuccessful dot1x authentication processes. The command is
available to display all events, or events per interface, or only failure
authentication events in summary or in detail.
Syntax
show dot1x authentication-history {
interface-id
| all} [failed-auth-only]
[detail]
• interface-id— Any valid interface. See Interface Naming Conventions for
interface representation.
• all—All interfaces.
Monitor Mode Indicates whether the Dot1x Monitor mode on the switch is
enabled or disabled.
Dynamic VLAN
Creation Mode
Indicates if VLANs assigned by the RADIUS server are
dynamically created by the dot1x client.
EAPOL flood mode Indicates whether EAPOL frames are flooded on the interface
or are processed locally by the switch.
Field Description
2CSNXXX_SWUM200.book Page 866 Tuesday, December 10, 2013 1:22 PM

802.1x Commands 867
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC mode, Configuration mode and all Configuration submodes
User Guidelines
The following table explains the output parameters.
Example
console#show dot1x authentication-history all detail
Time Stamp............................... Mar 22 2010 01:16:31
Interface................................ Gi1/0/2
MAC-Address.............................. 00:01:02:03:04:05
VLAN Assigned............................ 111
VLAN Assigned Reason..................... Guest VLAN
Auth Status.............................. Authorized
Reason...... ............................ Dot1x Authentication
due to Guest VLAN
Timer Expiry.
......
......
console#show dot1x authentication-history all
Time Stamp Interface MAC-Address VLANID Auth Status
Parameter Description
Time Stamp Exact time at which the event occurs.
Interface Physical Port on which the event occurs.
MAC-Address Supplicant/Client MAC Address
VLAN assigned VLAN assigned to the client/port on authentication.
VLAN assigned
Reason
Type of VLAN ID assigned i.e Guest VLAN, Unauth,
Default, Radius Assigned or Monitor Mode VLAN ID.
Auth Status Authentication Status
Reason Actual reason behind the successful or failure authentication.
2CSNXXX_SWUM200.book Page 867 Tuesday, December 10, 2013 1:22 PM

868 802.1x Commands
--------------------- --------- ----------------- ------ ----------
Mar 22 2010 01:16:31 gi1/0/2 00:01:02:03:04:05 111 Authorized
Mar 22 2010 01:20:33 gi1/0/7 00:00:0D:00:00:00 222 Authorized
console#show dot1x authentication-history gi1/0/1
Time Stamp Interface MAC-Address VLANID Auth Status
--------------------- --------- ----------------- ------ ----------
Mar 22 2010 01:16:31 gi1/0/1 00:01:02:03:04:05 111 Authorized
Mar 22 2010 01:18:22 gi1/0/1 00:00:00:03:04:05 0 Unauthorized
console#show dot1x authentication-history gi1/0/1 failed-auth-only
Time Stamp Interface MAC-Address VLANID Auth Status
--------------------- --------- ----------------- ------ ----------
Mar 22 2010 01:18:22 gi1/0/2 00:00:00:03:04:05 0 Unauthorized
show dot1x clients
Use the show dot1x clients command in Privileged EXEC mode to display
802.1x client information. The client information is displayed in summary or
in detail. The command also displays the statistics of the number of clients
that are authenticated using Monitor Mode and using 802.1x.
Syntax
show dot1x clients {
interface–id
| all}
•
interface–id
—Any valid interface. See Interface Naming Conventions for
interface representation.
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC mode, Configuration mode and all Configuration submodes
User Guidelines
The following fields are displayed by this command.
2CSNXXX_SWUM200.book Page 868 Tuesday, December 10, 2013 1:22 PM
802.1x Commands 869
The following table describes the significant fields shown in the display.
Example
The following example displays information about the 802.1x clients.
console#show dot1x clients all
Clients Authenticated using Monitor Mode....... 1
Clients Authenticated using Dot1x.............. 1
Logical Interface.............................. 16
Interface...................................... gi1/0/2
Field Description
Clients
Authenticated using
Monitor Mode
Indicates the number of Dot1x clients authenticated using
Monitor mode.
Clients
Authenticated using
Dot1x
Indicates the number of Dot1x clients authenticated using
802.1x authentication process.
Field Description
Interface The port number.
Username The username representing the identity of the Supplicant.
This field shows the username when the port control is
auto or mac-based. If the port is Authorized, it shows the
username of the current user. If the port is unauthorized it
shows the last user that was authenticated successfully.
Supp MAC Address The MAC-address of the supplicant
Session Time The amount of time, in seconds, since the client was
authenticated on the port.
Filter ID The Filter ID assigned to the client by the RADIUS server.
This field is not applicable when the Filter-ID feature is
disabled on the RADIUS server and client.
VLAN Assigned The VLAN assigned to the client by the radius server.
When VLAN assignments are disabled, RADIUS server
does not assign any VLAN to the port, and this field is set
to 0.
2CSNXXX_SWUM200.book Page 869 Tuesday, December 10, 2013 1:22 PM

870 802.1x Commands
User Name...................................... 000102030405
Supp MAC Address............................... 00:01:02:03:04:05
Session Time................................... 518
Filter Id......................................
VLAN Id........................................ 1
VLAN Assigned.................................. Default
Session Timeout................................ 0
Session Termination Action..................... Default
Logical Interface.............................. 96
Interface...................................... gi1/0/7
User Name...................................... brcm
Supp MAC Address............................... 00:08:A1:7E:45:1A
Session Time................................... 67
VLAN Id........................................ 1
VLAN Assigned.................................. Monitor Mode
Session Timeout................................ 0
Session Termination Action..................... Default
show dot1x interface
This command shows the status of MAC Authentication Bypass. This feature
is an extension of Dot1x Option 81 feature added in Dell Networking Release
2.1. to accept a VLAN name as an alternative to a number when RADIUS
indicates the Tunnel-Private-Group-ID for a supplicant.
Syntax
show dot1x interface {gigabitethernet unit/slot/port| tengigabitethernet
unit/slot/port | fortygigabitethernet unit/slot/port}
Default Configuration
There is no default configuration for this command.
Command Mode
Privileged EXEC mode, Configuration mode and all Configuration submodes
User Guidelines
There are no user guidelines for this command.
2CSNXXX_SWUM200.book Page 870 Tuesday, December 10, 2013 1:22 PM

802.1x Commands 871
Example
console#show dot1x interface gigabitethernet 1/0/10
Administrative Mode............... Disabled
Dynamic VLAN Creation Mode........ Disabled
Monitor Mode...................... Disabled
Port Admin Oper Reauth Reauth
Mode Mode Control Period
------- ------------------ ------------ -------- ----------
Gi1/0/10 auto N/A FALSE 3600
Quiet Period................................... 60
Transmit Period................................ 30
Maximum Requests............................... 2
Max Users...................................... 16
VLAN Assigned..................................
Supplicant Timeout............................. 30
Guest-vlan Timeout............................. 30
Server Timeout (secs).......................... 30
MAB mode (configured).......................... Disabled
MAB mode (operational)......................... Disabled
Authenticator PAE State........................ Initialize
Backend Authentication State................... Initialize
show dot1x interface statistics
Use the show dot1x interface statistics command in Privileged EXEC mode
to display 802.1x statistics for the specified interface.
Syntax
show dot1x interface {gigabitethernet unit/slot/port| tengigabitethernet
unit/slot/port | fortygigabitethernet unit/slot/port} statistics
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC mode, Configuration mode and all Configuration submodes
2CSNXXX_SWUM200.book Page 871 Tuesday, December 10, 2013 1:22 PM

872 802.1x Commands
User Guidelines
The following table describes the significant fields shown in the display.
Example
The following example displays 802.1x statistics for the specified interface.
Field Description
EAPOL Frames Received The number of valid EAPOL frames of any type that
have been received by this Authenticator.
EAPOL Frames
Tra ns mit ted
The number of EAPOL frames of any type that have
been transmitted by this Authenticator.
EAPOL Start Frames
Received
The number of EAPOL Start frames that have been
received by this Authenticator.
EAPOL Logoff Frames
Received
The number of EAPOL Logoff frames that have been
received by this Authenticator.
EAP Response/ID Frames
Received
The number of EAP Resp/Id frames that have been
received by this Authenticator.
EAP Response Frames
Received
The number of valid EAP Response frames (other than
Resp/Id frames) that have been received by this
Authenticator.
EAP Request/ID Frames
Tra ns mit ted
The number of EAP Req/Id frames that have been
transmitted by this Authenticator.
EAP Request Frames
Tra ns mit ted
The number of EAP Request frames (other than Rq/Id
frames) that have been transmitted by this
Authenticator.
Invalid EAPOL Frames
Received
The number of EAPOL frames that have been received
by this Authenticator in which the frame type is not
recognized.
EAPOL Length Error
Frames Received
The number of EAPOL frames that have been received
by this Authenticator in which the Packet Body Length
field is invalid.
Last EAPOL Frame
Version
The protocol version number carried in the most recently
received EAPOL frame.
Last EAPOL Frame
Source
The source MAC address carried in the most recently
received EAPOL frame.
2CSNXXX_SWUM200.book Page 872 Tuesday, December 10, 2013 1:22 PM

802.1x Commands 873
console#show dot1x interface gigabitethernet 1/0/2 statistics
Port......................................... gi1/0/2
EAPOL Frames Received.......................... 0
EAPOL Frames Transmitted....................... 0
EAPOL Start Frames Received.................... 0
EAPOL Logoff Frames Received................... 0
Last EAPOL Frame Version....................... 0
Last EAPOL Frame Source........................ 0000.0000.0000
EAP Response/Id Frames Received................ 0
EAP Response Frames Received................... 0
EAP Request/Id Frames Transmitted.............. 0
EAP Request Frames Transmitted................. 0
Invalid EAPOL Frames Received.................. 0
EAPOL Length Error Frames Received............. 0
show dot1x users
Use the show dot1x users command in Privileged EXEC mode to display
802.1x authenticated users for the switch.
Syntax
show dot1x users [username
username
]
•
username
— Supplicant
username (Range: 1–160 characters)
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC mode, Configuration mode and all Configuration submodes
User Guidelines
This command has no user guidelines.
Example
The following example displays 802.1x users.
console#show dot1x users
Port Username
--------- ---------
2CSNXXX_SWUM200.book Page 873 Tuesday, December 10, 2013 1:22 PM

874 802.1x Commands
1/0/1 Bob
1/0/2 John
Switch# show dot1x users username Bob
Port Username
--------- ---------
1/0/1 Bob
The following table describes the significant fields shown in the display:
clear dot1x authentication–history
Use the clear dot1x authentication–history command in Privileged EXEC
mode to clear the authentication history table captured during successful and
unsuccessful authentication.
Syntax
show dot1x authentication–history [
interface–id
]
•
interface–id
—Any valid interface. See Interface Naming Conventions for
interface representation.
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC mode
User Guidelines
This command has no user guidelines.
Example
console#clear dot1x authentication-history
Purge all entries from the log.
console#clear dot1x authentication-history gi1/0/1
Purge all entries for the specified interface from the log.
Field Description
Username The username representing the identity of the Supplicant.
Port The port that the user is using.
2CSNXXX_SWUM200.book Page 874 Tuesday, December 10, 2013 1:22 PM

802.1x Commands 875
802.1x Advanced Features
dot1x guest-vlan
Use the dot1x guest-vlan command in Interface Configuration mode to set
the guest VLAN on a port. The VLAN must already have been defined. The
no form of this command sets the guest VLAN id to zero, which disables the
guest VLAN on a port.
Syntax
dot1x guest-vlan
vlan-id
no dot1x guest-vlan
•
vlan-id
— The ID of a valid VLAN to use as the guest VLAN (Range: 0-
4093).
Default Configuration
The guest VLAN is disabled on the interface by default.
Command Mode
Interface Configuration (Ethernet) mode
User Guidelines
Configure the guest VLAN before using this command.
Example
The following example sets the guest VLAN on port 1/0/2 to VLAN 10.
console(config-if-Gi1/0/2)#dot1x guest-vlan 10
dot1x unauth-vlan
Use the dot1x unauth-vlan command in Interface Configuration mode to
specify the unauthenticated VLAN on a port. The unauthenticated VLAN is
the VLAN to which supplicants that fail 802.1X authentication are assigned.
2CSNXXX_SWUM200.book Page 875 Tuesday, December 10, 2013 1:22 PM

876 802.1x Commands
Syntax
dot1x unauth-vlan
vlan-id
no dot1x unauth-vlan
•
vlan-id
— The ID of a valid VLAN to use for unauthenticated clients
(Range: 0-4093).
Default Configuration
The unauthenticated VLAN is disabled on the interface by default.
Command Mode
Interface Configuration (Ethernet) mode
User Guidelines
Configure the unauthenticated VLAN before using this command.
Example
The following example set the unauthenticated VLAN on port 1/0/2 to VLAN
20.
console(config-if-Gi1/0/2)#dot1x unauth-vlan 20
show dot1x advanced
Use the show dot1x advanced command in Privileged EXEC mode to display
802.1x advanced features for the switch or for the specified interface. The
output of this command has been updated in release 2.1 to remove the
Multiple Hosts column and add an Unauthenticated VLAN column, which
indicates whether an unauthenticated VLAN is configured on a port. The
command has also been updated to show the Guest VLAN ID (instead of the
status) since it is now configurable per port.
Syntax
show dot1x advanced [{gigabitethernet unit/slot/port| tengigabitethernet
unit/slot/port | fortygigabitethernet unit/slot/port}]
2CSNXXX_SWUM200.book Page 876 Tuesday, December 10, 2013 1:22 PM

802.1x Commands 877
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC mode, Configuration mode and all Configuration submodes
User Guidelines
This command has no user guidelines.
Example
The following example displays 802.1x advanced features for the switch.
console#show dot1x advanced
Port Guest Unauthenticated
VLAN Vlan
--------- --------- ---------------
1/0/1 Disabled Disabled
1/0/2 10 20
1/0/3 Disabled Disabled
1/0/4 Disabled Disabled
1/0/5 Disabled Disabled
1/0/6 Disabled Disabled
console#show dot1x advanced gigabitethernet 1/0/2
Port Guest Unauthenticated
VLAN Vlan
--------- --------- ---------------
1/0/2 10 20
2CSNXXX_SWUM200.book Page 877 Tuesday, December 10, 2013 1:22 PM

878 802.1x Commands
2CSNXXX_SWUM200.book Page 878 Tuesday, December 10, 2013 1:22 PM

Data Center Technology Commands 879
41
Data Center Technology Commands
The data center commands allow network operators to deploy lossless
Ethernet capabilities in support of a converged network with Fibre Channel
and Ethernet data, as specified by the FC-BB-5 working group of ANSI T11.
This capability allows operators to deploy networks at a lower cost while still
maintaining the same SAN network management operations that exists
today.
NOTE: Data Center Technologies such as ETS, DCBX, and PFC are only available on
N4000 series switches.
This section of the document contains the following FCoE commands:
Data Center Bridging Commands
Priority Flow Control Commands
2CSNXXX_SWUM200.book Page 879 Tuesday, December 10, 2013 1:22 PM

880 Data Center Technology Commands
2CSNXXX_SWUM200.book Page 880 Tuesday, December 10, 2013 1:22 PM

Data Center Bridging Commands 881
42
Data Center Bridging Commands
Dell Networking N2000/N3000/N4000 Series Switches
NOTE: Enhanced Transmission Selection commands are only supported on N4000 series
switches. CLI commands and Dell OpenManage Switch Administrator pages are
not available for other switch models.
Data Center Bridging Exchange Protocol
The Data Center Bridging Exchange Protocol (DCBX) is used by DCB
devices to exchange configuration information with directly connected peers.
The protocol is also used to detect misconfiguration of the peer DCB devices
and, optionally, for configuration of peer DCB devices.
DCBX is expected to be deployed in support of lossless operation for FCoE or
iSCSI traffic. In these scenarios, all network elements are DCBX-enabled
(DCBX is enabled end-to-end).
The Dell Networking implementation of the DCBX protocol supports the
propagation of configuration information for the following features:
1
Enhanced Transmission Selection (ETS)
2
Priority-based Flow Control (PFC)
3
Application Priorities
The features listed above use DCBX to send and receive device configuration
and capability information and configuration details to peer DCBX devices.
The PFC and ETS information exchange is discussed in
Priority Flow Control
Commands
and
Enhanced Transmission Selection
. Application Priority
information is captured from the configuration source and propagated to
other auto-configuration peers by the DCBX component. When iSCSI is
enabled on an operationally active PFC port, the application priority
information is supplemented with the configured iSCSI priority.
Enhanced Transmission Selection
NOTE: Enhanced Transmission Selection commands are only supported on N4000 series
switches. CLI commands and Dell OpenManage Switch Administrator pages are
not available for other switch models.
2CSNXXX_SWUM200.book Page 881 Tuesday, December 10, 2013 1:22 PM

882 Data Center Bridging Commands
Overview
In a typical switch or router, each physical port supports one or more queues
for transmitting packets on the attached network. Multiple queues per port
are often provided to give preference to certain packets over others based on
user-defined criteria. When a packet is queued for transmission in a port, the
rate at which it is serviced depends on how the queue is configured and
possibly the amount of traffic present in the other queues of the port. If a
delay is necessary, packets get held in the queue until the scheduler
authorizes the queue for transmission. As queues become full, packets have
no place to be held for transmission and get dropped by the device.
The drop precedence of a packet is an indication of whether the packet is
more or less likely to be dropped during times of queue congestion. Often
referred to as packet coloring, a low drop precedence (green) allows the packet
to be transmitted under most circumstances, a higher drop precedence
(yellow) subjects the packet to dropping when bursts become excessive, while
the highest drop precedence (red) discards the packet whenever the queue is
congested. In some hardware implementations, the queue depth can be
managed using tail dropping or a weighted random early discard, or a
weighted random early discard (WRED), technique. These methods often
use customizable threshold parameters that are specified on a per-drop-
precedence basis.
The Dell Networking QoS implementation contains Differentiated Services
(DiffServ) support that allows traffic to be classified into streams and given
certain QOS treatment in accordance with defined per-hop behaviors.
However, the DiffServ feature does not offer direct configuration of the
hardware CoS queue resources.
The CoS Queuing feature offers a new capability for the user to directly
configure certain aspects of device queuing to provide the desired QOS
behavior for different types of network traffic when the complexities of
DiffServ are not required. The priority of a packet arriving at an interface can
be used to steer the packet to the appropriate outbound CoS queue through a
mapping table. CoS queue characteristics such as minimum guaranteed
bandwidth, transmission rate shaping, etc. are now user configurable at the
queue (or port) level.
The CoS queue feature provides a method to configure Traffic Class Groups
(TCGs) to extend the CoS queue management. Multiple CoS queues can be
mapped to a single TCG. Each TCG can have a configured minimum
2CSNXXX_SWUM200.book Page 882 Tuesday, December 10, 2013 1:22 PM

Data Center Bridging Commands 883
guaranteed bandwidth allocation and a scheduling algorithm similar to the
CoS queue configuration. The TCG scheduling and bandwidth enforcement
occurs after the CoS queue scheduling and bandwidth enforcement is
performed. Therefore all CoS queues mapped to the same TCG share the
scheduling and bandwidth properties of the TCG.
ETS Operations
ETS provides an operational model for priority processing and bandwidth
allocation for the switch in a Data Center Bridging environment. Using
priority-based processing and bandwidth allocations, different Traffic Class
Groups (TCGs) within different types of traffic such as LAN, SAN and
Management can be configured to provide bandwidth allocation or best effort
transmit characteristics.
For ETS to be operational, the following configuration steps need to be
performed:
1
Configure CoS queues to Traffic Class Group mapping for the egress
ports.
2
Configure weight percentage (bandwidth allocation) for each TCG.
3
Enable appropriate scheduling algorithm for each TCG
CoS information is exchanged with peer DCBX devices using ETS TLVs. As
part of the transmitted ETS TLVs, by default, DCBX advertises the following
parameters, and these parameters are populated in the switch hardware on a
per port basis.
1
Mapping between ingress ports 802.1p priority to Traffic Class Group
(TCG).
2
Bandwidth percentage (weight percentage) of each Traffic Class Group.
3
Scheduling algorithm for each Traffic Class Group.
For Dell Networking switches which do not support configuration of ETS
traffic classes in the hardware, the ETS information is propagated from the
configuration source to the other DCBX peers.
The mapping between the ingress port’s 802.1p priority and TCG is not
direct. The mapping depends upon:
• The CoS map defining the CoS queue that a packet is egress forwarded for
the ingress 802.1p priority.
2CSNXXX_SWUM200.book Page 883 Tuesday, December 10, 2013 1:22 PM

884 Data Center Bridging Commands
• Traffic Class Group map defining the CoS queue to TCG mapping.
The indirect mapping between the 802.1p priorities and the associated Traffic
Class Group mapping is advertised by DCBX as part of ETS TLVs. For this
indirect mapping to be valid, the following parameters need to be configured
in addition to the configuration of the TCGs.
1
Configure 8021.p priority to CoS mapping for the ingress ports.
2
Enable Trust mode on the ingress ports to trust the 802.1p priority present
in the frames.
ETS TLVs use DCBX Asymmetric attribute exchange mechanism to
exchange ETS information between the peers. In this exchange, each peer
device sends its ETS configuration via the “configuration” ETS TLV and
recommended ETS settings for the peer using the “recommend” ETS TLV.
Both the configuration and recommendation ETS TLVs are implemented for
Dell Networking switches in release 4.2.
The peer ETS TLVs are stored in the DCBX database and are accessible using
show commands.
The Application Priority TLV is accepted from auto-upstream devices and
propagated to auto-downstream devices. In addition, if iSCSI CoS is enabled,
an additional entry in the Application Priority TLV is added as discussed in
the iSCSI section.
Data Center Bridging Exchange Protocol Main Objective
The DCBX protocol implementation conforms to the IEEE 802.1Qaz
specification with some exceptions. To be interoperable with legacy industry
implementations of DCBX protocol, a hybrid model is used to support both
the IEEE version of DCBX and legacy DCBX versions. The hybrid version of
the DCBX conforms to all aspects of the legacy standards to the degree
necessary to support interoperability with a wide variety of FCoE capable
switches.
The main objective of DCBX is to perform the following operations:
• Discovery of DCB capability in a peer
DCBX is used to learn about the capabilities of the peer device. It is a
means to determine if the peer device supports a particular feature such as
PFC.
• DCB feature misconfiguration detection
2CSNXXX_SWUM200.book Page 884 Tuesday, December 10, 2013 1:22 PM

Data Center Bridging Commands 885
DCBX can be used to detect misconfiguration of a feature between the
peers on a link. Misconfiguration detection is feature-specific because
some features may allow asymmetric configuration.
• Peer configuration of DCB features
DCBX can be used by a device to perform configuration of DCB features
in its peer device if the peer device is willing to accept configuration.
Interoperability with IEEE DCBX
The Dell Networking switch automatically detects if a peer is operating with
either of the two CEE DCBX versions or the IEEE standard DCBX version.
This is the default mode. DCBX can also be configured to manually select
one of the legacy versions or IEEE standard mode. In auto-detect mode, the
switch starts operating in IEEE DCBX mode on a port and if it detects a
legacy DCBX device based on the OUI of the organization TLV, then the
switch changes its DCBX mode on that port to support the version detected.
There is no time out mechanism to move back to IEEE mode. Once the
DCBX peer times out, multiple peers are detected, the link is reset (link
down/up) or as commanded by the operator, DCBX resets its operational
mode to IEEE.
The interaction between DCBX component and other components remains
the same irrespective of the operational mode it is executing. For instance,
DCBX component interacts with PFC to get needed information to pack the
TLVs to be sent out on the interface. Based on the operational control mode
of the port, DCBX packs it in the proper frame format.
Port Roles
Each port’s behavior is dependent on the operational mode of that port and
of other ports in the stack. The port mode is a DCBX configuration item that
is passed to the DCBX clients to control the processing of their configuration
information. There are four port roles:
1
Manual
2
Auto-Upstream
3
Auto-Downstream
4
Configuration Source
2CSNXXX_SWUM200.book Page 885 Tuesday, December 10, 2013 1:22 PM

886 Data Center Bridging Commands
Manual
Ports operating in the Manual role do not have their configuration affected
by peer devices or by internal propagation of configuration. These ports have
their operational mode and TC and bandwidth information specified
explicitly by the operator. These ports will advertise their configuration to
their peer if DCBX is enabled on that port. Incompatible peer configurations
will be logged and counted with an error counter.
The default operating mode for each port is Manual for Dell Networking
releases; however, customer platforms may change the default mode for
selected ports to either Auto-Upstream or Auto-Downstream mode. An
example of this would be a blade switch that needed to support touchless
configuration and has certain ports that are upstream ports and other ports
that are downstream ports. A port that is set to manual mode sets the willing
bit for DCBX client TLVs to false. Manually configured ports never internally
propagate or accept internal or external configuration from other ports.
Manually configured ports may notify the operator of incompatible
configurations if client configuration exchange over DCBX is enabled.
Manually configured ports are always operationally enabled for DCBX clients,
regardless of whether DCBX is enabled.
Auto-Upstream
Advertises a configuration, but is also willing to accept a configuration from
the link-partner and propagate it internally to the auto-downstream ports as
well as receive configuration propagated internally by other auto-upstream
ports. The local configuration parameters for PFC and ETS, if any, are
overridden with the negotiated configuration. Specifically, the willing
parameter is enabled on the port and the recommendation TLV is sent to the
peer and processed if received locally. The first auto-upstream port to
successfully accept a compatible configuration becomes the configuration
source. The configuration source propagates its configuration to other auto-
upstream and auto-downstream ports. Only the configuration source may
propagate configuration to other ports internally. Auto-upstream ports that
receive internally propagated information ignore their local configuration and
utilize the internally propagated information.
Peer configurations received on auto-upstream ports other than the
configuration source result in one of two possibilities.
2CSNXXX_SWUM200.book Page 886 Tuesday, December 10, 2013 1:22 PM

Data Center Bridging Commands 887
1
If the configuration is compatible with the configuration source, then the
DCBX client becomes operationally active on the upstream port.
2
If the configuration is not compatible with the configuration source, then
a message is logged indicating an incompatible configuration, an error
counter is incremented, and the DCBX client is operationally disabled on
the port. The expectation is that the network administrator configures the
upstream devices appropriately so that all such devices advertise a
compatible configuration.
Auto-Downstream
Advertises a configuration but is not willing to accept one from the link
partner. However, the port will accept a configuration propagated internally
by the configuration source. The local configuration parameters for PFC and
ETS, if any, are overridden with the negotiated configuration.Specifically, the
willing parameter is disabled on auto-downstream ports. By default, auto-
downstream ports have the recommendation TLV parameter enabled. Auto-
downstream ports that receive internally propagated information ignore their
local configuration and utilize the internally propagated information.
Configuration Source
In this role, the port has been manually selected to be the configuration
source. Configuration received over this port is propagated to the other auto-
configuration ports, however, no automatic election of a new configuration
source port is allowed. Only one port can be configured as the configuration
source. The local configuration parameters for PFC and ETS, if any, are
overridden with the received configuration. Events that cause selection of a
new configuration source are ignored. The configuration received over the
configuration source port is maintained until cleared by the operator (set the
port to the manual role). FIP snooping must be enabled to set a port to
configuration source. For interfaces configured in a port-channel for which it
is desirable to receive configuration information, it is strongly recommended
that the auto-up setting be used on the physical interfaces in the port channel
in preference to the configuration source parameter.
2CSNXXX_SWUM200.book Page 887 Tuesday, December 10, 2013 1:22 PM

888 Data Center Bridging Commands
Configuration Source Port Selection Process
When an auto-upstream or auto-downstream port receives a configuration
from a peer, the DCBX client first checks if there is an active configuration
source. If there is a configuration source already selected, the received
configuration is checked against the local port operational values as received
from the configuration source, and if compatible, the client marks the port as
operationally enabled. If the configuration received from the peer is
determined to not be compatible, a message is logged, an error counter is
incremented and the DCBX clients become operationally disabled on the
port. The port continues to keep link up and exchanges DCBX packets. If a
compatible configuration is later received, the DCBX clients will become
operationally enabled.
If there is no configuration source, a port may elect itself as the configuration
source on a first-come, first-serve basis from the set of eligible ports. A port is
eligible to become the configuration source if:
• No other port is the configuration source.
• The port role is auto-upstream.
• The port is enabled with link up and DCBX enabled.
• The port has negotiated a DCBX relationship with the partner.
• The switch is capable of supporting the received configuration values,
either directly or by translating the values into an equivalent configuration
N.B. Whether or not the peer configuration is compatible with the
configured values is NOT considered.
The newly elected configuration source propagates DCBX client information
to the other ports and is internally marked as being the port over which
configuration has been received. Configuration changes received from the
peer over the configuration source port are propagated to the other auto-
configuration ports. Ports receiving auto-configuration information from the
configuration source ignore their current settings and utilize the
configuration source information.
When a configuration source is selected, local ETS and PFC configuration
for all auto-up, auto-down and config-source ports is overridden by the
configuration received from the configuration source.
2CSNXXX_SWUM200.book Page 888 Tuesday, December 10, 2013 1:22 PM

Data Center Bridging Commands 889
In order to reduce flapping of configuration information, if the configuration
source port is disabled, disconnected or loses LLDP connectivity, the system
clears the selection of configuration source port (if not manually selected)
and enables the willing bit on all auto-upstream ports. The configuration on
the auto-configuration ports is not cleared (configuration holdover). If the
user wishes to clear the configuration on the system in this scenario, the user
can put the configuration source port into manual mode.
When a new port is selected as configuration source, it is marked as the
configuration source, the DCBX configuration is refreshed on all auto-
configuration ports and each port may begin configuration negotiation with
their peer again (if any information has changed).
Commands in this Chapter
This chapter explains the following commands:
Data Center Bridging Capability Exchange
Commands
datacenter-bridging
Use the datacenter-bridging command for an ethernet interface in order to
enter the DataCenterBridging mode. Priority-Flow-Control is configurable
from within the DataCenterBridging mode.
Data Center Bridging Capability Exchange Commands
datacenter-bridging lldp dcbx port-role
lldp dcbx version show lldp tlv-select
lldp tlv-select dcbxp (dcb enable) show lldp dcbx
Enhanced Transmission Selection Commands
classofservice traffic-class-group traffic-class-group weight
traffic-class-group max-bandwidth show classofservice traffic-class-group
traffic-class-group min-bandwidth show interfaces traffic-class-group
traffic-class-group strict
–
2CSNXXX_SWUM200.book Page 889 Tuesday, December 10, 2013 1:22 PM

890 Data Center Bridging Commands
Syntax
datacenter-bridging
Default Configuration
This command has no default configuration.
Command Mode
Interface Configuration (Ethernet) mode
User Guidelines
NOTE: This command is only available on N40xx series switches.
Datacenter bridging mode is only available on physical interfaces, not on
port-channel interfaces. To ensure proper operation, users must configure all
physical interfaces in a port channel to have the same data-center bridging
configuration.
Example
console#config
console(config)#interface range ethernet all
console(config-if)#datacenter-bridging
console(config-if-dcb)#priority-flow-control mode on
console(config-if-dcb)#priority-flow-control priority 1 no-drop
lldp dcbx version
Use the lldp dcbx version command in Global Configuration mode to
configure the administrative version for the Data Center Bridging Capability
Exchange (DCBX) protocol. This command enables the switch to support a
specific version of the DCBX protocol or to detect the peer version and match
it. DCBX can be configured to operate in IEEE mode or CEE mode or CIN
mode. In auto mode, version detection is based on the peer device DCBX
version. The switch operates in either IEEE or one of the legacy modes on
each interface.
NOTE: CIN is Cisco Intel Nuova DCBX (version 1.0). CEE is converged enhanced
ethernet DCBX (version 1.06).
Use the no form of the command to reset the dcbx version to the default
value of auto.
2CSNXXX_SWUM200.book Page 890 Tuesday, December 10, 2013 1:22 PM

Data Center Bridging Commands 891
Syntax
lldp dcbx version {auto | cin | cee | ieee}
no lldp dcbx version
•
auto
—Automatically select the version based on the peer response.
•
CIN
—Force the mode to Cisco-Intel-Nuova. (DCBX 1.0)
•
CEE
—Force the mode to CEE (DCBX 1.06)
•
IEEE
—Force the mode to IEEE 802.1Qaz
Default Configuration
The default version is auto.
Command Mode
Global Config
User Guidelines
NOTE: This command is only available on N40xx series switches.
In auto mode, the switch will attempt to jump start the exchange by sending
an IEEE frame, followed by a CEE frame followed by a CIN frame. The
switch will parse the received response and immediately switch to the peer
version. Because LLDP is a link local protocol, it cannot be configured on a
port channel or VLAN interface. It is recommended that all ports configured
in a port channel utilize the same LLDP configuration.
Example
The following example configures the switch to use CEE DCBX.
s1(config)#lldp dcbx version cee
lldp tlv-select dcbxp (dcb enable)
Use the lldp tlv-select dcbxp command in Global Configuration or Interface
Configuration mode to enable the LLDP to send DCBX TLVs if LLDP is
enabled to transmit on the given interface. If no parameter is given, all DCBX
TLVs are enabled for transmission. The default is all DCBX TLVs are enabled
2CSNXXX_SWUM200.book Page 891 Tuesday, December 10, 2013 1:22 PM

892 Data Center Bridging Commands
for transmission. If executed in Interface mode, the interface configuration
overrides the global configuration for that interface. Entering the command
with no parameters enables transmission of all TLVs.
Use the no form of the command to return the configuration to the default
settings.
Syntax
lldp tlv-select dcbxp [ets-config|ets-recommend|pfc|application-
priority|congestion-notification] [dcb enable]
no lldp tlv-select dcbxp [ets-config|ets-recommend|pfc|application-
priority|congestion-notification] [dcb enable]
•
Ets-config
—Transmit the ETS configuration TLV.
•
Ets-recommend
—Transmit the ETS recommendation TLV.
•
Pfc
—Transmit the PFC configuration TLV.
•
Application-priority
—Transmit the application priority TLV.
•
Congestion-notification
—Transmit the congestion notification TLV.
Default Configuration
The default value is to transmit all DCBX TLVs as received from the auto-
configuration configuration source port. In manual mode, the default is to
transmit all DCBX TLVs per the switch (global or interface) configuration.
Command Mode
Global Config, Interface Config
User Guidelines
NOTE: This command is only available on N40xx series switches.
Global configuration and interface configuration are separate. Interface
configuration overrides the global configuration on a configured interface.
Example
The following example configures the port to not transmit any DCBX TLVs.
console(interface-config-te1/0/1)#no lldp tlv-select dcbxp
2CSNXXX_SWUM200.book Page 892 Tuesday, December 10, 2013 1:22 PM

Data Center Bridging Commands 893
The following example globally configures all ports to not transmit any DCBX
TLVs.
console(config)#no dcb enable
lldp dcbx port-role
Use the lldp dcbx port-role command in Interface Configuration mode to
configure the port role to manual, auto-upstream, auto-downstream and
configuration source. The default port role is manual.
Syntax
lldp dcbx port-role {auto-up |auto-down | manual | configuration-source}
•
Manual
—Ports operating in the ‘Manual’ role do not have their
configuration affected by peer devices or by internal propagation of
configuration. These ports will advertise their configuration to their peer if
DCBX is enabled on that port. The willing bit is set to disabled on manual
role ports.
•
Auto-up
—Advertises a configuration, but is also willing to accept a
configuration from the link-partner and propagate it internally to the auto-
downstream ports as well as receive configuration propagated internally by
other auto-upstream ports. These ports have the willing bit enabled. These
ports should be connected to FCFs.
•
Auto-down
—Advertises a configuration but is not willing to accept one
from the link partner. However, the port will accept a configuration
propagated internally by the configuration source. These ports have the
willing bit set to disabled. Selection of a port based upon compatibility of
the received configuration is suppressed. These ports should be connected
to a trusted FCF.
•
Configuration Source
—In this role, the port has been manually selected
to be the configuration source. Configuration received over this port is
used to configure the switch and is propagated to the other auto-
configuration ports. Selection of a port based upon compatibility of the
received configuration is suppressed. These ports should be connected to a
trusted FCF. These ports have the willing bit enabled.
2CSNXXX_SWUM200.book Page 893 Tuesday, December 10, 2013 1:22 PM

894 Data Center Bridging Commands
Default Configuration
The default port role is manual.
Command Mode
Interface Config
User Guidelines
NOTE: This command is only available on N40xx series switches.
In order to reduce configuration flapping, ports that obtain configuration
information from a configuration source port will maintain that configuration
for 2x the LLDP time out, even if the configuration source port becomes
operationally disabled.
Examples
This example configures an FCF facing port:
console(config-if-Te1/1/1)#lldp dcbx port-role auto-up
This example configures an FCoE host facing port:
console(config-if-Te1/1/1)#lldp dcbx port-role auto-down
show lldp tlv-select
Use the lldp tlv-select command in Privileged EXEC mode to display the
Traffic Class to Traffic Class Group mapping.
Syntax
show lldp tlv-select interface [all|
interface-id
]
•
interface-id
—A valid physical interface specifier
•
all
—All interfaces
Default Configuration
The default is to show the per interface TLV configuration.
Command Mode
Privileged EXEC
2CSNXXX_SWUM200.book Page 894 Tuesday, December 10, 2013 1:22 PM

Data Center Bridging Commands 895
User Guidelines
NOTE: This command is only available on N40xx series switches.
This command has no user guidelines.
Examples
console# show lldp tlv-select interface te1/0/1
Interface ETS Config ETS Recommend PFC App Priority QCN
------------ ---------- ------------- --- ------------ ---
te1/0/1Yes No Yes No Yes
console# show lldp tlv-select interface all
Interface ETS Config ETS Recommend PFC App Priority QCN
----------- ---------- ------------- --- ------------ ---
te1/0/1Yes No Yes No Yes
te1/0/2No No Yes No Yes
show lldp dcbx
Use the show lldp dcbx command in Privileged EXEC mode to display the
Traffic Class to Traffic Class Group mapping.
Syntax
show lldp dcbx [interface <all|interface-id <detail|status>>]
•
interface-id
—A valid physical interface specifier.
•
all
—All interfaces.
•
detail
—Display detailed DCBX information.
•
status
—Display a status summary.
Default Configuration
This command has no default setting.
Command Mode
Privileged EXEC
User Guidelines
NOTE: This command is only available on N40xx series switches.
2CSNXXX_SWUM200.book Page 895 Tuesday, December 10, 2013 1:22 PM

896 Data Center Bridging Commands
This command has no user guidelines.
Example #1
DCBX Status:
console# show lldp dcbx interface all status
Config DCBX DCBX Frame TLV
Interface Status Role Version Rx Tx Errors Dscrd Dscrd
---------- ------- -------- -------- ------ ------ ------ ------ -----
te1/0/1 Enabled Auto-up CEE 1.06 Yes 32 37 0 0
te1/0/2 Enabled Auto-up IEEE 32 37 0 0
te2/0/1 Enabled Auto-dn CIN 1.0 32 37 0 0
te2/0/2 Enabled Auto-dn IEEE 32 37 0 0
te3/0/1 Enabled Auto-dn CIN 1.0 32 37 0 0
te3/0/2 Disabled Manual IEEE 0 0 0 0
Example #2
DCBX not enabled:
console# show lldp dcbx interface te1/0/1
Interface te1/0/1
DCBX Admin Status: Disabled
Configured DCBX Version: Auto-detect
Peer DCBX Version:
Peer MAC:
Peer Description:
Auto-configuration Port Role: Manual
Peer Is Configuration Source: False
Error Counters:
ETS Incompatible Configuration: 0
PFC Incompatible Configuration: 0
Disappearing Neighbor: 0
Multiple Neighbors Detected: 0
Example #3
DCBX enabled – legacy device (CIN/CEE):
console# show lldp dcbx interface te1/0/1
Interface te1/0/1
DCBX Admin Status: Enabled
Configured Version: Auto-detect
Peer DCBX Version: CIN Version 1.0
Peer MAC: 00:23:24:A4:21:03
Peer Description: Cisco Nexus 5020 IOS Version 5.00
2CSNXXX_SWUM200.book Page 896 Tuesday, December 10, 2013 1:22 PM

Data Center Bridging Commands 897
Auto-configuration Port Role: Auto-downstream
Peer Is Configuration Source: False
Local Configuration:
Max/Oper
Type Subtype Version En/Will/Adv
PFC(3) 000 000 Y/Y/Y
PG(2) 000 000 Y/Y/Y
APP(4) 000 000 Y/Y/Y
Number of TCs Supported: 3
Priority Group Id: 0:00 1:01 2:02 3:03 4:04 5:05 6:06 7:07
PG Percentage (%): 0:12 1:10 2:12 3:00 4:00 5:66 6:00 7:00
Strict Priority: 0:0 1:2 2:0 3:0 4:0 5:0 6:0 7:0
PFC Enable Vector: 0:0 1:1 2:0 3:0 4:0 5:0 6:0 7:0
Peer Configuration:
Operation version: 00 Max version: 00 Seq no: 23 Ack no: 22
Max/Oper
Type Subtype Version En/Will/Err
PFC(3) 000 000/000 Y/N/N
PG(2) 000 000/000 Y/N/N
APP(4) 000 000/000 Y/N/N
Number of TCs Supported: 3
Priority Group Id: 0:00 1:01 2:02 3:03 4:04 5:05 6:06 7:07
PG Percentage (%): 0:0 1:10 2:12 3:00 4:00 5:78 6:00 7:00
PFC Enable Vector: 0:0 1:1 2:0 3:0 4:0 5:1 6:0 7:0
Application Priority (TX Enabled)
Type Application Priority Status
---------------------------------------------------
Ethernet FC0E 3 Enabled
TCP/SCTP 860 4 Disabled
TCP/SCTP 3260 4 Disabled
Error Counters:
ETS Incompatible Configuration: 0
PFC Incompatible Configuration: 0
Disappearing Neighbor: 0
Multiple Neighbors Detected: 0
2CSNXXX_SWUM200.book Page 897 Tuesday, December 10, 2013 1:22 PM

898 Data Center Bridging Commands
Example #4
DCBX enabled – IEEE device (DCBX Version Forced):
console# show lldp dcbx interface te1/0/1
Interface te1/0/1
DCBX Admin Status: Enabled
Configured DCBX Version: CIN 1.0
Peer DCBX Version: CEE 1.6
Peer MAC: 00:23:24:A4:21:03
Peer Description: Cisco Nexus 5020 IOS Version 5.00
Auto-configuration Port Role: Auto-upstream
Peer Is Configuration Source: True
Error Counters:
ETS Incompatible Configuration: 7
PFC Incompatible Configuration: 0
Disappearing Neighbor: 0
Multiple Neighbors Detected: 0
Example #5
DCBX enabled – detailed view:
console# show lldp dcbx interface te1/0/1 detail
Interface te1/0/1
DCBX Admin Status: Enabled
Configured Version: Auto-detect
Auto-configuration Port Role: Configuration Source
Peer Is Configuration Source: True
PFC Capability (TX Enabled)
Willing: True MBC: False Max PFC classes supported: 3
PFC Enable Vector: 0:0 1:1 2:0 3:0 4:0 5:1 6:0 7:0
ETS Configuration (TX Enabled)
Willing: True Credit Shaper: True Traffic Classes Supported: 8
Priority Assignment: 0:0 1:1 2:2 3:3 4:4 5:5 6:6 7:7
Traffic Class Bandwidth (%): 0:00 1:10 2:12 3:00 4:00 5:78 6:00 7:00
Traffic Selection Algorithm: 0:0 1:1 2:2 3:0 4:0 5:3 6:0 7:0
ETS Recommendation (TX Enabled)
Peer DCBX Version: CEE 1.6
Peer Description: Cisco Nexus 5020 IOS Version 5.00
Peer MAC: 00:23:24:A4:21:03
Peer PFC Capability:
Willing: False MBC: False Max PFC classes supported: 3
PFC Enable Vector 0:0 1:1 2:0 3:0 4:0 5:1 6:0 7:0
2CSNXXX_SWUM200.book Page 898 Tuesday, December 10, 2013 1:22 PM

Data Center Bridging Commands 899
Peer ETS Configuration:
Willing: False Peer ETS Detected: True Credit Shaper: True
Traffic Classes Supported: 8
Priority Assignment: 0:0 1:1 2:1 3:0 4:0 5:1 6:0 7:0
Traffic Class Bandwidth: 0:00 1:10 2:12 3:00 4:00 5:78 6:00 7:00
Traffic Selection Algorithm: 0:0 1:1 2:2 3:0 4:0 5:3 6:0 7:0
Peer ETS Recommendation:
Traffic Class Bandwidth: 0:0 1:1 2:2 3:0 4:0 5:3 6:0 7:0
Traffic Selection Algorithm: 0:0 1:1 2:2 3:0 4:0 5:3 6:0 7:0
Peer Application Priority
Type Application Priority
-------------------------------------
Ethernet FC0E 3
TCP/SCTP 3260 4
Enhanced Transmission Selection (ETS)
Commands
NOTE: Enhanced Transmission Selection commands are only supported on N4000 series
switches. CLI commands and Dell OpenManage Switch Administrator pages are
not available for other switch models.
classofservice traffic-class-group
This command maps the internal Traffic Class to an internal Traffic Class
Group (TCG). The Traffic Class can range from 0-6, although the actual
number of available traffic classes depends on the platform.
Use the no form of this command to return system (Global Configuration
mode) or interface (Interface Configuration mode) to the default mapping.
Syntax
classofservice traffic-class-group <trafficclass> <traffic class group>
no classofservice traffic-class-group
•
trafficclass
—
The selected traffic class. Range is 0-6.
•
trafficclassgroup
—
The selected group. Range 0-2.
2CSNXXX_SWUM200.book Page 899 Tuesday, December 10, 2013 1:22 PM

900 Data Center Bridging Commands
Default Configuration
By default, all the traffic classes are mapped to TCG 0. In the default
configuration, all the Traffic Classes are grouped as one Traffic Class Group
and TCG0 is configured as weighted round robin.
Command Mode
Global Config, Interface Configuration modes
User Guidelines
NOTE: This command is only available on N40xx series switches.
For a given Traffic Class, a value specified in Interface Configuration mode
only affects a single interface, whereas a change in Global Configuration
mode is applied to all interfaces. The Interface Configuration mode
command is only available on platforms that support independent per-port
class of service mappings. Ports that are configured to use the DCBX auto-
configuration roles (auto-up or auto-down) have their ETS settings
overridden. Only ports configured as DCBX manual role utilize the
configured ETS settings.
It is recommended that all strict priority traffic classes be mapped to a single
TCG.
Internally, frames are selected for transmission from the strict priority TCGs
first, then, once the constraints of the TCGs are satisfied, frames from the
WRR TCGs are selected for transmission. For example, grouping strict
priority assignments into TCG 1 and weighted assignments into TCG 0 will
result in all frames of the highest priority in TCG 1 being transmitted first,
then the next lower priority, et. seq. until no frames remain for transmission
in TCG 1. Then the scheduler will process frames from TCG 0, giving them
appropriate treatment based upon the weights, minimum bandwidth and
maximum bandwidth constraints.
Traffic class group 7 is reserved by the system for internal use.
Example
The following example demonstrates how to globally map priorities 1 and 2 to
TCG 1.
console(config)# classofservice traffic-class-group 1 1
console(config)# classofservice traffic-class-group 2 1
2CSNXXX_SWUM200.book Page 900 Tuesday, December 10, 2013 1:22 PM

Data Center Bridging Commands 901
traffic-class-group max-bandwidth
Use this command in Global Config or Interface Configuration mode to
specify the maximum transmission bandwidth limit for each TCG as a
percentage of the interface rate. Also known as rate shaping, this has the
effect of smoothing temporary traffic bursts over time so that the transmitted
traffic rate is bound.
Syntax
traffic-class-group max-bandwidth <bw-0> <bw-1> … <bw-n>
no traffic-class-group max-bandwidth
•
bw-0..7
—The maximum percentage bandwidth to be transmitted by the
TCG. Range 0 to 100.
Default Configuration
The default maximum bandwidth for all TCGs is 0% (unlimited).
Command Mode
Global Config, Interface Configuration modes
User Guidelines
NOTE: This command is only available on N40xx series switches.
This command specified in Interface Configuration mode only affects a
single interface; whereas, the Global Configuration mode setting is applied to
all interfaces. Interface configuration overrides the global configuration on
the designated interface. The Interface Configuration mode command is only
available on platforms that support independent per-port class of service
queue configuration.
Each bw-x value is a percentage that ranges from 0 to 100 in increments of 1.
All n bandwidth values must be specified with this command and each is
independent of the others. The number n is platform dependent and
corresponds to the number of supported traffic classes groups. The default
maximum bandwidth value for each TCG is 0, meaning no upper limit is
enforced, which allows the TCG queue to consume any available non-
guaranteed bandwidth of the interface.
2CSNXXX_SWUM200.book Page 901 Tuesday, December 10, 2013 1:22 PM

902 Data Center Bridging Commands
If a non-zero value is specified for any bw-x maximum bandwidth parameter,
it must not be less than the current minimum bandwidth value for the
corresponding queue. A bw-x maximum bandwidth parameter value of 0 may
be specified at any time without restriction.
The maximum bandwidth limits may be used with either a weighted or strict
priority scheduling scheme. Note that a value of 0 (the default) implies an
unrestricted upper transmission limit, which is similar to 100%, although
there may be subtle operational differences depending on how the device
handles a no limit case versus limit to 100%.
Example
The following example demonstrates how to limit the maximum bandwidth
percentage for TCG 1 and 2 to 25% each.
console(config)# traffic-class-group max-bandwidth 50 25 25
traffic-class-group min-bandwidth
Use this command in Global Config or Interface Configuration mode to
specify the minimum transmission bandwidth guaranteed for each TCG
before processing frames from other TCGs on an interface.
Use the no form of the command to return the bandwidth reservations to the
default values.
Syntax
traffic-class-group min-bandwidth <bw-0> <bw-1> … <bw-n>
no traffic-class-group min-bandwidth
•
bw-0..7
—The maximum percentage bandwidth to be transmitted by the
TCG. Range 0 to 100.
Default Configuration
The default minimum bandwidth for all TCGs is 0% (no minimum
guarantee).
Command Mode
Global Configuration mode, Interface Configuration mode
2CSNXXX_SWUM200.book Page 902 Tuesday, December 10, 2013 1:22 PM

Data Center Bridging Commands 903
User Guidelines
NOTE: This command is only available on N40xx series switches.
This command specified in Interface Configuration mode only affects a
single interface, whereas the Global Configuration mode setting is applied to
all interfaces. The Interface Configuration mode command is only available
on the N4000 series switches.
Each bw-x value is a percentage that ranges from 0 to 100 in increments of 1.
All n bandwidth values must be specified with this command, and their
combined sum must not exceed 100%. The default minimum bandwidth
value for each TCG is 0, meaning no bandwidth is guaranteed (best effort) In
order to better accommodate bursty traffic, it is recommended that the sum
of the minimum bandwidths configured be much less than 100%.
If the value of any bw-x minimum bandwidth parameter is specified as greater
than the current maximum bandwidth value for the corresponding TCG,
then its corresponding maximum bandwidth automatically increases the
maximum to the same value. Min-bandwidth may be configured manually by
the operator on manual and auto-configuration ports. If the port is an auto-
configuration port, the weights received via ETS TLVs are taken into account
by the scheduler along with the min-bandwidth parameters supplied by the
operator.
Refer to the
cos-queue min-bandwidth
command for information regarding
scheduling frame for transmission across TCGs.
Example
The following example demonstrates how to reserve the minimum bandwidth
percentage for TCG 1 and 2 to 25% each and reserve the remaining
bandwidth for TCG 0.
console(config)# traffic-class-group min-bandwidth 50 25 25
traffic-class-group strict
Use this command in Global Config or Interface Configuration mode to
activate the strict priority scheduler mode for each specified TCG.
Use the no form of the command to return the TCGs to the default weighted
scheduler mode.
2CSNXXX_SWUM200.book Page 903 Tuesday, December 10, 2013 1:22 PM

904 Data Center Bridging Commands
Syntax
traffic-class-group strict <tcg-id> [<tcg-id> … <tcg-id>]
no traffic-class-group strict
•
tcg-id
—The TCG identifier. Range is 0 to 2
Default Configuration
The default scheduling mode for all TCGs is weighted scheduling.
Command Mode
Global Configuration mode, Interface Configuration mode
User Guidelines
NOTE: This command is only available on N40xx series switches.
This command specified in Interface Configuration mode only affects a
single interface, whereas the Global Configuration mode setting is applied to
all interfaces. The Interface Configuration mode command is only available
on platforms that support independent per-port class of service queue
configuration.
At least one, but no more than n, tcg-id values are specified with this
command. Duplicate tcg-id values are ignored. Each tcg-id value ranges from
0 to (n-1), where n is the total number of TCG supported per interface. The
number n is platform dependent and corresponds to the number of supported
Traffic Class Groups.
When strict priority scheduling is used for a TCG, the minimum bandwidth
setting for the TCG is ignored and packets are scheduled for transmission as
soon as they arrive. A maximum bandwidth setting for the queue, if
configured, serves to limit the outbound transmission rate of a strict priority
TCG queue so that it does not consume the entire capacity of the interface.
If multiple TCGs on the same interface are configured for strict priority
mode, the method of handling their packet transmission, gives preference
among the strict priority TCGs to the one with the highest tcg-id. Strict
priority or weighted scheduling may be configured manually or via DCBX
using the ETS TLVs.
2CSNXXX_SWUM200.book Page 904 Tuesday, December 10, 2013 1:22 PM

Data Center Bridging Commands 905
Example
The following example demonstrates how to set TCGs 1 and 2 to strict
priority scheduling.
console(config)# traffic-class-group strict 1 2
traffic-class-group weight
Use the traffic-class-group weight command in Global Config or Interface
Configuration mode to specify the scheduling weight for each TCG. The
scheduler attempts to balance the traffic selected for transmission from the
TCGs such that, when the switch is congested, traffic is selected from the
round robin configured TCGs in proportion to their weights.
Use the no form of the command to return the TCGs to the default weighted
scheduler mode.
Syntax
traffic-class-group weight <wp-0> <wp-1> <wp-2>
no traffic-class-group strict
•
wp-n
—The weight percentage. Range 0 to 100.
Default Configuration
The default weight is in the ratio of 1:2:3 for
TCG0:TCG1:TCG2(100%:0%:0%).
Command Mode
Global Configuration mode, Interface Configuration mode
User Guidelines
NOTE: This command is only available on N40xx series switches.
This command specified in Interface Configuration mode only affects a
single interface, whereas the Global Configuration mode setting is applied to
all interfaces. The Interface Configuration mode command is only available
on platforms that support independent per-port class of service queue
configuration.
2CSNXXX_SWUM200.book Page 905 Tuesday, December 10, 2013 1:22 PM

906 Data Center Bridging Commands
The weight percentage is not considered for Traffic Class Groups that are
configured for strict priority scheduling. Auto-configuration ports utilize the
weights received from the auto-configuration source but do no alter the
manual settings. Manually configured ports enabled for DCBX transmit the
manually configured weights in the TC Bandwidth table in the ETS TLVs.
Each wp-x (weight percentage) value is a percentage that ranges from 0 to
100 in increments of 1. All n bandwidth values must be specified with this
command, and their combined sum must equal 100%. The weight percentage
may be configured manually or via the DCBX protocol using the ETS TLVs.
Example
The following example demonstrates how to set TCG 0 to 50% weight and
TCG 1 to 50%.
console(config)# traffic-class-group weight 50 5 0
show classofservice traffic-class-group
Use the show classofservice traffic-class-group command in Privileged EXEC
mode to display the Traffic Class to Traffic Class Group mapping.
Syntax
show classofservice traffic-class-group [<interface-id>]
•
wp-n
—The weight percentage. Range 0 to 100.
Default Configuration
The default is to show the global traffic class to group mapping.
Command Mode
Privileged EXEC mode
User Guidelines
NOTE: This command is only available on N40xx series switches.
The <interface-id> parameter is optional. If specified, the TCG mapping
table of the interface is displayed. If omitted, the global configuration settings
are displayed (these may have been subsequently overridden by per-port
configuration).
2CSNXXX_SWUM200.book Page 906 Tuesday, December 10, 2013 1:22 PM

Data Center Bridging Commands 907
Traffic class group 7 is reserved by the system and is not shown.
Auto-configuration ports utilize the traffic class group mappings received
from the auto-configuration source. Manually configured ports enabled for
DCBX transmit the traffic class groups in the ETS TLVs.
Example
The following example demonstrates how to display the global traffic class to
group mappings:
s1# show classofservice traffic-class-group
Traffic Class Traffic Class Group
------------- ---------------------
0 0
1 1
2 1
3 1
4 2
5 1
6 1
show interfaces traffic-class-group
Use the show interfaces traffic-class-group command in Privileged EXEC
mode to display the Traffic Class to Traffic Class Group mapping.
Syntax
show interfaces traffic-class-group [
interface-id
]
•
interface-id
—A valid physical interface specifier.
Default Configuration
The default is to show the global traffic class group configuration.
Command Mode
Privileged EXEC mode
User Guidelines
NOTE: This command is only available on N40xx series switches.
2CSNXXX_SWUM200.book Page 907 Tuesday, December 10, 2013 1:22 PM
908 Data Center Bridging Commands
The <interface-id> parameter is optional. If specified, the TCG mapping
table of the interface is displayed. If omitted, the global configuration settings
are displayed (these may have been subsequently overridden by per-port
configuration).
The following information is displayed:
Example
The following example demonstrates how to display the global traffic class
group configuration:
s1# show interfaces traffic-class-group
Global Configuration
TCG Id Min. Max Scheduler Weight
Bandwidth Bandwidth Type Percentage
------- ---------- --------- --------- ----------
0 0 0 Strict 0
1 0 0 WDRR 50
2 0 0 WDRR 50
Field Description
Interface Displays the slot/port of the interface. If displaying the global
configuration, this output line is replaced with a Global Config
indication.
Traffic Class Group The traffic class Group identifier.
Min-Bandwidth The minimum transmission bandwidth, expressed as a
percentage. A value of 0 means bandwidth is not guaranteed.
This is a configured value.
Max-Bandwidth The maximum transmission bandwidth g, expressed as a
percentage. A value of 0 means no upper limit is enforced, so
the queue may use any or all of the available bandwidth of the
interface. This is a configured value.
Scheduler Type Indicates whether this queue is scheduled for transmission
using a strict priority or a weighted scheme. Strict priority
scheduler is to provide lower latency to the higher CoS classes
of traffic. Weighted scheduling is a round robin mechanism
with weights associated to each CoS class of traffic. This is a
configured value.
Weight Percentage The weight of the TCG used during non-strict scheduling.
2CSNXXX_SWUM200.book Page 908 Tuesday, December 10, 2013 1:22 PM

Priority Flow Control Commands 909
43
Priority Flow Control Commands
Dell Networking N4000 Series Switches
Priority Flow Control (PFC) provides a means of pausing frames based on
individual priorities on a single physical link. By pausing the congested
priority or priorities independently, protocols that are highly loss sensitive can
share the same link with traffic that has different loss tolerances with less
congestion spreading than standard flow control. The priorities are
differentiated by the priority field of the 802.1Q VLAN header. PFC is
standardized by the IEEE 802.1Qbb specification.
PFC uses a new control packet defined in 802.1Qbb and therefore is not
compatible with standard flow control. An interface that is configured for
PFC will be automatically disabled for 802.3x flow control. When PFC is
disabled on an interface, the flow control configuration for the interface
becomes active. Any flow control frames received on a PFC configured
interface are ignored.
Each priority is configured as either drop or no-drop. If a priority that is
designated as no-drop is congested, the priority is paused. Drop priorities do
not participate in pause. By default there are no priority classifications
configured and PFC is not enabled.
While several no-drop priorities may be configured on a supporting system,
the actual number of lossless priorities supported on a given system is a
function of the switch chips packet buffer, the maximum supported MTU
size, pause delay, the media type and the total number of ports enabled for
lossless behavior. In order to guarantee lossless behavior, the switch chip must
send a pause message prior to exhausting its available packet buffer and have
sufficient buffer to absorb the delay. In order to accomplish this, it must
reserve enough memory (headroom) to handle the max delay in processing
the pause packet.
The maximum number of lossless priorities per interface is two. The
headroom is only used for guaranteeing lossless behavior. There must be
enough dynamic memory to handle the typical work load of the switch in
addition to the headroom. With two no-drop priorities per interface and
static allocations, there is only about 30 percent of the buffer space available
for normal forwarding behavior.
2CSNXXX_SWUM200.book Page 909 Tuesday, December 10, 2013 1:22 PM

910 Priority Flow Control Commands
The effective default behavior on an interface enabled for PFC without a no-
drop priority is that no flow control (legacy or PFC) is enabled. If the user
enables PFC but does not create any no-drop priorities, the interface will not
be lossless.
Changing the drop and no-drop capabilities on an interface, either in flow
control or priority flow control, may require that all ports briefly drop link.
The priority to flow control group cannot be changed while traffic is running.
When 802.3 link flow control is enabled, all priorities are mapped to a single
flow control group. When 802.1Qbb is enabled, the priorities are each
mapped into their own flow control group, where lossless groups have
additional buffer to handle the round trip delay for flow control. In order to
minimize the impact, the link will only be dropped when changing between
802.3 and 802.1Qbb.
Commands in this Chapter
This chapter explains the following commands:
priority-flow-control mode
Use the priority-flow-control mode on command in Datacenter-Bridging
Configuration mode to enable Priority-Flow-Control (PFC) on an interface.
To disable Priority-Flow-Control, use the no form of the command.
Syntax
priority-flow-control mode on
priority-flow-control mode off
no priority-flow-control mode
•
on
—Enable PFC on the interface.
•
off
—Disable PFC on the interface.
priority-flow-control mode
priority-flow-control priority
clear priority-flow-control statistics
show interfaces priority-flow-control
2CSNXXX_SWUM200.book Page 910 Tuesday, December 10, 2013 1:22 PM

Priority Flow Control Commands 911
Default Configuration
Priority-flow-control mode is off (disabled) by default.
Command Mode
Datacenter-Bridging Configuration mode
User Guidelines
NOTE: This command is only available on N40xx series switches.
PFC must be enabled before FIP snooping can operate over the interface. Use
the no form of the command to return the mode to the default (off). VLAN
tagging (trunk or general mode) must be enabled on the interface in order to
carry the dot1p value through the network. Additionally, the dot1mapping to
class-of-service must be set to one-to-one. Ports that are configured to use the
DCBX auto-configuration roles (auto-up or auto-down) have their PFC
settings overridden. Only ports configured as DCBX manual role utilize the
configured PFC settings.
When PFC is enabled on an interface, the normal PAUSE control mechanism
is operationally disabled. Because PFC is a link local protocol, it must be
configured on all the interfaces aggregated in a port channel. Only
configuring some of the ports in a port channel to use PFC will cause
unexpected results and is not supported.
Example
The following example enables PFC on an interface.
s1(config)#interface te1/0/1
s1(config-if-Te1/0/1)#datacenter-bridging
s1(config-if-dcb)#priority-flow-control mode on
priority-flow-control priority
Use the priority-flow-control priority command in Datacenter-Bridging
Configuration mode to enable the priority group for lossless (no-drop) or
lossy (drop) behavior on the selected interface. Up to two lossless priorities
can be enabled on an interface.
Use the no form of the command to return all priorities to their default lossy
behavior.
2CSNXXX_SWUM200.book Page 911 Tuesday, December 10, 2013 1:22 PM

912 Priority Flow Control Commands
Syntax
priority-flow-control priority
priority-list
{drop | no-drop}
no priority-flow-control priority
•
drop
—Disable lossless behavior on the selected priorities.
•
no-drop
—Enable lossless behavior on the selected priorities.
Default Configuration
The default behavior for all priorities is drop.
Command Mode
Datacenter-Bridging Configuration mode
User Guidelines
NOTE: This command is only available on N40xx series switches.
The administrator must configure the same no-drop priorities across the
network in order to ensure end-to-end lossless behavior. Ports that are
configured to use the DCBX auto-configuration roles (auto-up or auto-down)
have their PFC settings overridden. Only ports configured as DCBX manual
role utilize the configured PFC settings.
Example
The following example sets priority 3 to no drop behavior.
s1(config)#interface te1/0/1
s1(config-if-Te1/0/1)#datacenter-bridging
s1(config-if-dcb)#priority-flow-control mode on
s1(config-if-dcb)#priority-flow-control priority 1 no-drop
clear priority-flow-control statistics
Use the clear priority-flow-control statistics command to clear all or interface
Priority-Flow-Control statistics.
Syntax
clear priority-flow-control statistics [ethernet
interface
]
•
interface —
A valid Ethernet port.
2CSNXXX_SWUM200.book Page 912 Tuesday, December 10, 2013 1:22 PM

Priority Flow Control Commands 913
Command Mode
Privileged EXEC mode
User Guidelines
This command has no user guidelines.
Example #1
console#clear priority-flow-control statistics tengigabitethernet 1/0/1
Example #2
console#clear priority-flow-control statistics
show interfaces priority-flow-control
Use the show interfaces priority-flow-control command in Privileged EXEC
mode to display the global or interface priority flow control status and
statistics.
Syntax
show interfaces
interface-id
priority-flow-control
•
interface-id
—A valid Ethernet port identifier.
Command Mode
Privileged EXEC, Configuration mode and all Configuration submodes
User Guidelines
NOTE: This command is only available on N40xx series switches.
This command has no user guidelines.
Examples
The following examples show the priority flow control status and statistics.
s1#show interfaces tengigabitethernet 1/0/1 priority-flow-control
Interface Detail:te1/0/1
PFC Configured State: Disabled
PFC Operational State: Enabled
Configured Drop Priorities: 2-7
2CSNXXX_SWUM200.book Page 913 Tuesday, December 10, 2013 1:22 PM

914 Priority Flow Control Commands
Operational Drop Priorities: 2-7
Configured No-Drop Priorities: 0-1
Operational No-Drop Priorities:0-1
Delay Allowance: 32456 bit times
Peer Configuration Compatible: True
Compatible Configuration Count: 3
Incompatible Configuration Count: 1
Priority Received PFC Frames Transmitted PFC Frames
-------- ----------------- ----------------------
00 0
10 0
20 0
30 0
40 0
50 0
60 0
70 0
console#show interfaces priority-flow-control
Port Drop No-Drop Operational
Priorities Priorities Status
-------- --------------- --------------- ----------
Te1/0/1 0-2,4-7 3 Active
Te1/0/2 0-2,4-7 3 Active
Te1/0/3 0-7 Inactive
Te1/0/4 0-7 Inactive
Te1/0/5 0-7 Inactive
Te1/0/6 0-7 Inactive
Te1/0/7 0-7 Inactive
Te1/0/8 0-7 Inactive
Te1/0/9 0-7 Inactive
Te1/0/10 0-7 Inactive
Te1/0/11 0-7 Inactive
Te1/0/12 0-7 Inactive
Te1/0/13 0-7 Inactive
Te1/0/14 0-7 Inactive
Te1/0/15 0-7 Inactive
Te1/0/16 0-7 Inactive
Te1/0/17 0-7 Inactive
Te1/0/18 0-7 Inactive
Te1/0/19 0-7 Inactive
--More-- or (q)uit
Te1/0/20 0-7 Inactive
Te1/0/21 0-7 Inactive
Te1/0/22 0-7 Inactive
2CSNXXX_SWUM200.book Page 914 Tuesday, December 10, 2013 1:22 PM

Priority Flow Control Commands 915
Te1/0/23 0-2,4-7 3 Active
Te1/0/24 0-7 Inactive
2CSNXXX_SWUM200.book Page 915 Tuesday, December 10, 2013 1:22 PM

916 Priority Flow Control Commands
2CSNXXX_SWUM200.book Page 916 Tuesday, December 10, 2013 1:22 PM

Layer 3 Commands 917
44
Layer 3 Commands
The chapters that follow describe commands that conform to the OSI
model’s Network Layer (Layer 3). Layer 3 commands perform a series of
exchanges over various data links to deliver data between any two nodes in a
network. These commands define the addressing and routing structure of the
Internet.
This section of the document contains the following Layer 3 topics:
ARP Commands Loopback Interface Commands
DHCP Server and Relay Agent Commands Multicast Commands
DHCPv6 Commands IPv6 Multicast Commands
DVMRP Commands OSPF Commands
GMRP Commands OSPFv3 Commands
IGMP Commands Router Discovery Protocol Commands
IGMP Proxy Commands Routing Information Protocol Commands
IP Helper/DHCP Relay Commands Tunnel Interface Commands
IP Routing Commands Virtual Router Redundancy Protocol
Commands
IPv6 Routing Commands
–
2CSNXXX_SWUM200.book Page 917 Tuesday, December 10, 2013 1:22 PM

918 Layer 3 Commands
2CSNXXX_SWUM200.book Page 918 Tuesday, December 10, 2013 1:22 PM

ARP Commands 919
45
ARP Commands
Dell Networking N2000/N3000/N4000 Series Switches
When a host has an IP packet to send on an Ethernet network, it must
encapsulate the IP packet in an Ethernet frame. The Ethernet header requires
a destination MAC address. If the destination IP address is on the same
network as the sender, the sender uses the Address Resolution Protocol (ARP)
to determine the MAC address associated with destination IP address. The
network device broadcasts an ARP request, identifying the IP address for
which it wants a corresponding MAC address. The IP address is called the
target IP. If a device on the same physical network is configured with the
target IP, it sends an ARP response giving its MAC address. This MAC address
is called the target MAC.
If the destination IP address is not on the same network as the sender, the
sender generally forwards the packet to a default gateway. The default
gateway is a router that forwards the packet to its destination. The host may
be configured with a default gateway or may dynamically learn a default
gateway.
The router discovery protocol is one method that enables hosts to learn a
default gateway. If a host does not know a default gateway, it can learn the
first hop to the destination through proxy ARP. Proxy ARP (RFC 1027) is a
technique used to make a machine physically located on one network appear
to be logically part of a different physical network connected to the same
router (may also be a firewall). Typically Proxy ARP hides a machine with a
public IP address on a private network behind a router and still allows the
machine to appear to be on the public network. The router proxies ARP
requests and all network traffic to and from the hidden machine to make this
fiction possible.
Proxy ARP is implemented by making a small change to a router's processing
of ARP requests. Without proxy ARP, a router only responds to an ARP
request if the target IP address is an address configured on the interface where
the ARP request arrived. With proxy ARP, the router may also respond if it
has a route to the target IP address. The router only responds if all next hops
on its route to the destination are through interfaces other than the interface
where the ARP request was received.
2CSNXXX_SWUM200.book Page 919 Tuesday, December 10, 2013 1:22 PM

920 ARP Commands
ARP Aging
Dynamic entries in the ARP cache are aged. When an entry for a neighbor
router reaches its maximum age, the system sends an ARP request to the
neighbor router to renew the entry. Entries for neighbor routers should
remain in the ARP cache as long as the neighbor continues to respond to ARP
requests. ARP cache entries for neighbor hosts are renewed more selectively.
When an ARP cache entry for a neighbor host reaches its maximum age, the
system checks if the cache entry has been used recently to forward data
traffic. If so, the system sends an ARP request to the entry's target IP address.
If a response is received, the cache entry is retained and its age is reset to 0. By
enabling the dynamic renew option, the system administrator can configure
ARP to attempt to renew aged ARP entries regardless of their use for
forwarding.
If the system learns a new ARP entry but the hardware does not have space to
add the new ARP entry, the system attempts to remove entries that have not
been used for forwarding recently. This action may create space for new
entries in the hardware's ARP table.
Commands in this Chapter
This chapter explains the following commands:
arp
Use the arp command in Global Configuration mode to create an Address
Resolution Protocol (ARP) entry. Use the no form of the command to remove
the entry.
arp clear arp-cache
arp cachesize clear arp-cache management
arp purge ip local-proxy-arp
arp resptime ip proxy-arp
arp retries show arp
arp timeout
–
2CSNXXX_SWUM200.book Page 920 Tuesday, December 10, 2013 1:22 PM

ARP Commands 921
Syntax
arp
ip-address hardware-address
no arp
ip-address
•
ip-address
— IP address of a device on a subnet attached to an existing
routing interface.
•
hardware-address
— A unicast MAC address for that device.
Default Configuration
This command has no default configuration.
Command Mode
Global Configuration mode
User Guidelines
This command has no user guidelines.
Example
The following example creates an ARP entry consisting of an IP address and a
MAC address.
console(config)#arp 192.168.1.2 00A2.64B3.A245
arp cachesize
Use the arp cachesize command in Global Configuration mode to configure
the maximum number of entries in the ARP cache. To return the maximum
number ARP cache entries to the default value, use the no form of this
command.
Syntax
arp cachesize
integer
no arp cachesize
•
integer
— Maximum number of ARP entries in the cache. Use the
show
sdm prefer
command to display the supported ARP cache size.
2CSNXXX_SWUM200.book Page 921 Tuesday, December 10, 2013 1:22 PM

922 ARP Commands
Default Configuration
The switch defaults to using the maximum allowed cache size.
Command Mode
Global Configuration mode
User Guidelines
The ARP cache size is dependant on the switching hardware used. Values
different from the default given above may exist in a given switch model.
Example
The following example defines an arp cachesize of 500.
console(config)#arp cachesize 500
arp dynamicrenew
Use the arp dynamicrenew command in Global Configuration mode to
enable the ARP component to automatically renew dynamic ARP entries
when they age out. To disable the automatic renewal of dynamic ARP entries
when they age out, use the no form of the command.
Syntax
arp dynamicrenew
no arp dynamicrenew
Default Configuration
The default state is disabled.
Command Mode
Global Configuration mode
User Guidelines
When an ARP entry reaches its maximum age, the system must decide
whether to retain or delete the entry. If the entry has recently been used to
forward data packets, the system will renew the entry by sending an ARP
2CSNXXX_SWUM200.book Page 922 Tuesday, December 10, 2013 1:22 PM

ARP Commands 923
request to the neighbor. If the neighbor responds, the age of the ARP cache
entry is reset to 0 without removing the entry from the hardware. Traffic to
the host continues to be forwarded in hardware without interruption. If the
entry is not being used to forward data packets, then the entry is deleted from
the ARP cache, unless the dynamic renew option is enabled. If the dynamic
renew option is enabled, the system sends an ARP request to renew the entry.
When an entry is not renewed, it is removed from the hardware and
subsequent data packets to the host trigger an ARP request. Traffic to the
host is lost until the router receives an ARP reply from the host. Gateway
entries, entries for a neighbor router, are always renewed. The dynamic renew
option only applies to host entries.
The disadvantage of enabling dynamic renew is that once an ARP cache entry
is created, that cache entry continues to take space in the ARP cache as long
as the neighbor continues to respond to ARP requests, even if no traffic is
being forwarded to the neighbor. In a network where the number of potential
neighbors is greater than the ARP cache capacity, enabling dynamic renew
could prevent some neighbors from communicating because the ARP cache is
full.
Example
console#configure
console(config)#arp dynamicrenew
console(config)#no arp dynamicrenew
arp purge
Use the arp purge command in Privileged EXEC mode to cause the specified
IP address to be removed from the ARP cache. Only entries of type dynamic
or gateway are affected by this command.
Syntax
arp purge
ip-address
•
ip-address
— The IP address to be removed from ARP cache.
Default Configuration
This command has no default configuration.
2CSNXXX_SWUM200.book Page 923 Tuesday, December 10, 2013 1:22 PM

924 ARP Commands
Command Mode
Privileged EXEC mode
User Guidelines
This command has no user guidelines.
Example
The following example removes the specified IP address from arp cache.
console#arp purge 192.168.1.10
arp resptime
Use the arp resptime command in Global Configuration mode to configure
the ARP request response time-out. To return the response time-out to the
default value, use the no form of this command.
Syntax
arp resptime
integer
no arp resptime
•
integer
— IP ARP entry response time out. (Range: 1-10 seconds)
Default Configuration
The default value is 1 second.
Command Mode
Global Configuration mode
User Guidelines
This command has no user guidelines.
Example
The following example defines a response time-out of 5 seconds.
console(config)#arp resptime 5
2CSNXXX_SWUM200.book Page 924 Tuesday, December 10, 2013 1:22 PM

ARP Commands 925
arp retries
Use the arp retries command in Global Configuration mode to configure the
ARP count of maximum requests for retries. To return to the default value,
use the no form of this command.
Syntax
arp retries
integer
no arp retries
•
integer
— The maximum number of requests for retries. (Range: 0-10)
Default Configuration
The default value is 4 retries.
Command Mode
Global Configuration mode
User Guidelines
This command has no user guidelines.
Example
The following example defines 6 as the maximum number of retries.
console(config)#arp retries 6
arp timeout
Use the arp timeout command in Global Configuration mode to configure
the ARP entry ageout time. Use the no form of the command to set the
ageout time to the default.
Syntax
arp timeout
integer
no arp timeout
•
integer
— The IP ARP entry ageout time. (Range: 15-21600 seconds)
2CSNXXX_SWUM200.book Page 925 Tuesday, December 10, 2013 1:22 PM

926 ARP Commands
Default Configuration
The default value is 1200 seconds.
Command Mode
Global Configuration mode
User Guidelines
This command has no user guidelines.
Example
The following example defines 900 seconds as the timeout.
console(config)#arp timeout 900
clear arp-cache
Use the clear arp-cache command in Privileged EXEC mode to remove all
ARP entries of type dynamic from the ARP cache.
Syntax
clear arp-cache [gateway]
•
gateway
— Removes the dynamic entries of type
gateway
, as well.
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC mode
User Guidelines
This command has no user guidelines.
Example
The following example clears all entries ARP of type dynamic, including
gateway, from ARP cache.
2CSNXXX_SWUM200.book Page 926 Tuesday, December 10, 2013 1:22 PM

ARP Commands 927
console#clear arp-cache gateway
clear arp-cache management
Use the clear arp-cache management command to clear all entries that show
as management arp entries in the show arp command.
Syntax
clear arp-cache management
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC mode
User Guidelines
This command has no user guidelines.
Example
In the example below, out-of-band management entries are shown, for
example, those from the out-of-band interface.
console#show arp
Age Time (seconds)............................. 1200
Response Time (seconds).................... 1
Retries................................................... 4
Cache Size............................................ 6144
Dynamic Renew Mode....................... Disable
Total Entry Count Current / Peak...... 0 / 0
Static Entry Count Configured / Active / Max.. 0 / 0 / 128
IP Address MAC Address Interface Type Age
--------------- ----------------- -------------- -------- -----------
10.27.20.241 001A.A0FF.F662 Management Dynamic n/a
10.27.20.243 0019.B9D1.29A3 Management Dynamic n/a
console#clear arp-cache management
2CSNXXX_SWUM200.book Page 927 Tuesday, December 10, 2013 1:22 PM

928 ARP Commands
ip local-proxy-arp
Use the ip local proxy-arp command in Interface Configuration mode to
enable proxying of ARP requests. This allows the switch to respond to ARP
requests within a subnet where routing is not enabled.
Syntax
ip local-proxy-arp
no ip local-proxy-arp
Default Configuration
Proxy arp is disabled by default.
Command Mode
Interface (VLAN) Configuration
User Guidelines
This command has no user guidelines.
ip proxy-arp
Use the ip proxy-arp command in Interface Configuration mode to enable
proxy ARP on a router interface. Without proxy ARP, a device only responds
to an ARP request if the target IP address is an address configured on the
interface where the ARP request arrived. With proxy ARP, the device may also
respond if the target IP address is reachable. The device only responds if all
next hops in its route to the destination are through interfaces other than the
interface that received the ARP request. Use the no form of the command to
disable proxy ARP on a router interface.
Syntax
ip proxy-arp
no ip proxy-arp
Default Configuration
Enabled is the default configuration.
2CSNXXX_SWUM200.book Page 928 Tuesday, December 10, 2013 1:22 PM

ARP Commands 929
Command Mode
Interface Configuration (VLAN) mode
User Guidelines
The ip proxy-arp command is not available in interface range mode.
Example
The following example enables proxy arp for VLAN 15.
(config)#interface vlan 15
console(config-if-vlan15)#ip proxy-arp
show arp
Use the show arp command in Privileged EXEC mode to display all entries in
the Address Resolution Protocol (ARP) cache. The displayed results are not
the total ARP entries. To view the total ARP entries, the operator should view
the show ARP results.
Syntax
show arp [brief]
• brief — Display ARP parameters.
Default Configuration
This command has no default configuration.
Command Mode
User EXEC and Privileged EXEC modes, Configuration mode and all
Configuration submodes
User Guidelines
The show arp command will display static (user-configured) ARP entries
regardless of whether they are reachable over an interface or not.
Example
The following example shows show arp command output.
2CSNXXX_SWUM200.book Page 929 Tuesday, December 10, 2013 1:22 PM

930 ARP Commands
console#show arp
Static ARP entries are only active
when the IP address is reachable on a local subnet
Age Time (seconds)............................. 1200
Response Time (seconds)........................ 1
Retries........................................ 4
Cache Size..................................... 6144
Dynamic Renew Mode............................ Disable
Total Entry Count Current / Peak.............. 0 / 0
Static Entry Count Configured / Active / Max .. 1 / 0 / 128
IP Address MAC Address Interface Type Age
---------- -------------- --------- ------ -------
1.1.1.3 0000.0000.0022 n/a Static n/a
2CSNXXX_SWUM200.book Page 930 Tuesday, December 10, 2013 1:22 PM

DHCP Server and Relay Agent Commands 931
46
DHCP Server and Relay Agent
Commands
Dell Networking N2000/N3000/N4000 Series Switches
DHCP is based on the Bootstrap Protocol (BOOTP). It also captures the
behavior of BOOTP relay agents and DHCP participants can inter operate
with BOOTP participants.
The host RFC’s standardize the configuration parameters which can be
supplied by the DHCP server to the client. After obtaining parameters via
DHCP, a DHCP client should be able to exchange packets with any other host
in the Internet. DHCP is based on a client-server model.
DHCP consists of the following components:
• A protocol for delivering host-specific configuration parameters from a
DHCP server to a host.
• A mechanism for allocation of network addresses to hosts.
DHCP offers the following features and benefits:
• It supports the definition of "pools" of IP addresses that can be allocated to
clients by the server. Many implementations use the term
scope
instead of
pool
.
• Configuration settings like the subnet mask, default router, DNS server,
that are required to make TCP/ IP work correctly can be passed to the
client using DHCP.
• DHCP is supported by most TCP/ IP routers this allows it to allocate an IP
address according to the subnet the original request came from. This
means that a single DHCP server can be used in multiple subnets and that
there is no need to reconfigure a client that changed subnets.
• Addresses can be leased out for a specific duration after which they need to
be explicitly renewed. This allows DHCP to reclaim expired addresses and
put back in the unallocated pool.
2CSNXXX_SWUM200.book Page 931 Tuesday, December 10, 2013 1:22 PM

932 DHCP Server and Relay Agent Commands
• Internet access cost is greatly reduced by using automatic assignment as
Static IP addresses are considerably more expensive to purchase than are
automatically allocated IP addresses.
• Using DHCP a centralized management policy can be implemented as the
DHCP server keeps information about all the subnets. This allows a
system operator to update a single server when configuration changes take
place.
Commands in this Chapter
This chapter explains the following commands:
ip dhcp pool
Use the ip dhcp pool command in Global Configuration mode to define a
DHCP address pool that can be used to supply addressing information to
DHCP clients. Upon successful completion, this command puts the user into
DHCP Pool Configuration mode. Use the no form of the command to
remove an address pool definition.
ip dhcp pool dns-server (IP
DHCP Pool
Config)
ip dhcp ping
packets
service dhcp
bootfile domain-name (IP
DHCP Pool
Config)
lease sntp
clear ip dhcp
binding
hardware-address netbios-name-
server
show ip dhcp binding
clear ip dhcp
conflict
host netbios-node-type show ip dhcp conflict
client-identifier ip dhcp bootp
automatic
network show ip dhcp global
configuration
client-name ip dhcp conflict
logging
next-server show ip dhcp pool
default-router ip dhcp excluded-
address
option show ip dhcp server
statistics
2CSNXXX_SWUM200.book Page 932 Tuesday, December 10, 2013 1:22 PM

DHCP Server and Relay Agent Commands 933
Syntax
ip dhcp pool [
pool-name
]
no ip dhcp pool [
pool-name
]
•
pool-name
—The name of an existing or new DHCP address pool. The
pool name can be up to 31 characters in length and can contain the
following characters: a-z, A-Z, 0-9, ’-’, ’_’, ’ ’. Enclose the entire pool name
in quotes if an embedded blank is to appear in the pool name.
Default Configuration
The command has no default configuration.
Command Mode
Global Configuration mode
User Guidelines
This capability requires the DHCP service to be enabled. Enable the DHCP
service using the service dhcp command. Dell Networking supports dynamic,
automatic, and manual address assignment. Dynamic address assignment
leases an address to the client for a limited period of time. Automatic
assignment assigns a permanent address to a client. Manual (static)
assignment simply conveys an address assigned by the administrator to the
client.
In DHCP Pool Configuration mode, the administrator can configure the
address space and other parameters to be supplied to DHCP clients. By
default, the DHCP server assumes that all addresses specified are available for
assignment to clients. Use the
ip dhcp excluded-address
command in Global
Configuration mode to specify addresses that should never be assigned to
DHCP clients.
To configure a dynamic DHCP address pool, configure the following pool
properties using the listed DHCP pool commands:
• Address pool subnet and mask – network
• Client domain name – domain-name
• Client DNS server – dns-server
• NetBIOS WINS Server – netbios-name-server
2CSNXXX_SWUM200.book Page 933 Tuesday, December 10, 2013 1:22 PM

934 DHCP Server and Relay Agent Commands
• NetBIOS Node Type – netbios-node-type
• Client default router – default-router
• Client address lease time – lease
Administrators may also configure manual bindings for clients using the host
command in DHCP Pool Configuration mode. This is the most often used
for DHCP clients for which the administrator wishes to reserve an ip address,
for example a computer server or a printer. A DHCP pool can contain
automatic or dynamic address assignments or a single static address
assignment.
To configure a manual address binding, configure the pool properties using
the DHCP pool commands listed below. It is only necessary to configure a
DHCP client identifier or a BOOTP client MAC address for a manual
binding. To configure a manual binding, the client identifier or hardware
address must be specified before specifying the host address.
• DHCP client identifier – client-identifier
• BOOTP client MAC address – hardware-address
• Host address – host
• Client name (optional) – client-name
Examples
Example 1 – Manual Address Pool
console(config)#service dhcp
console (config)#ip dhcp pool “Printer LP32 R1-101”
console(config-dhcp-pool)#client-identifier 00:23:12:43:23:54
console(config-dhcp-pool)#host 10.1.1.1 255.255.255.255
console(config-dhcp-pool)#client-name PRT_PCL_LP32_R1-101
Example 2 – Dynamic Address Pool
console(config)#service dhcp
console(config)#ip dhcp pool "Windows PCs"
console(config-dhcp-pool)#network 192.168.21.0 /24
console(config-dhcp-pool)#domain-name power-connect.com
console(config-dhcp-pool)#dns-server 192.168.22.3 192.168.23.3
console(config-dhcp-pool)#netbios-name-server 192.168.22.2 192.168.23.2
console(config-dhcp-pool)#netbios-node-type h-node
console(config-dhcp-pool)#lease 2 12
console(config-dhcp-pool)#default-router 192.168.22.1 192.168.23.1
2CSNXXX_SWUM200.book Page 934 Tuesday, December 10, 2013 1:22 PM

DHCP Server and Relay Agent Commands 935
bootfile
Use the bootfile command in DHCP Pool Configuration mode to set the
name of the image for the DHCP client to load. Use the no form of the
command to remove the bootfile configuration. Use the
show ip dhcp pool
command to display pool configuration parameters.
Syntax
bootfile
filename
no bootfile
•
filename
—The name of the file for the DHCP client to load.
Default Configuration
There is no default bootfile filename.
Command Mode
DHCP Pool Configuration mode
User Guidelines
This command has no user guidelines.
Example
console(config-dhcp-pool)#bootfile ntldr
clear ip dhcp binding
Use the clear ip dhcp binding command in Privileged EXEC mode to remove
automatic DHCP server bindings.
Syntax
clear ip dhcp binding {ip-address | *}
•
*
—Clear all automatic dhcp bindings.
•
ip-address
—Clear a specific binding.
2CSNXXX_SWUM200.book Page 935 Tuesday, December 10, 2013 1:22 PM

936 DHCP Server and Relay Agent Commands
Default Configuration
The command has no default configuration.
Command Mode
Privileged EXEC mode
User Guidelines
This command has no user guidelines.
Example
console#clear ip dhcp binding 1.2.3.4
clear ip dhcp conflict
Use the clear ip dhcp conflict command in Privileged EXEC mode to remove
DHCP server address conflicts. Use the
show ip dhcp conflict
command to
display address conflicts detected by the DHCP server.
Syntax
clear ip dhcp conflict {ip-address | *}
•
*
—Clear all automatic dhcp bindings.
•
ip-address
—Clear a specific address conflict.
Default Configuration
The command has no default configuration.
Command Mode
Privileged EXEC mode
User Guidelines
This command has no user guidelines.
Example
console#clear ip dhcp conflict *
2CSNXXX_SWUM200.book Page 936 Tuesday, December 10, 2013 1:22 PM

DHCP Server and Relay Agent Commands 937
client-identifier
Use the client-identifier command in DHCP Pool Configuration mode to
identify a Microsoft DHCP client to be manually assigned an address. Use the
no form of the command to remove the client identifier configuration.
Syntax
client-identifier
unique-identifier
no client-identifier
•
unique-identifier
—The identifier of the Microsoft DHCP client. The
client identifier is specified as 7 bytes of the form
XX:XX:XX:XX:XX:XX:XX where X is a hexadecimal digit.
Default Configuration
This command has no default configuration.
Command Mode
DHCP Pool Configuration mode
User Guidelines
For Microsoft DHCP clients, the identifier consists of the media type
followed by the MAC address of the client. The media type 01 indicates
Ethernet media.
Use the
show ip dhcp pool
command to display pool configuration
parameters.
Example
console(config-dhcp-pool)#client-identifier 01:03:13:18:22:33:11
console(config-dhcp-pool)#host 192.168.21.34 32
client-name
Use the client-name command in DHCP Pool Configuration mode to specify
the host name of a DHCP client. Use the no form of the command to remove
the client name configuration.
2CSNXXX_SWUM200.book Page 937 Tuesday, December 10, 2013 1:22 PM

938 DHCP Server and Relay Agent Commands
Syntax
client-name
name
no client-name
•
name
—The name of the DHCP client. The client name is specified as up
to 31 printable characters.
Default Configuration
There is no default client name.
Command Mode
DHCP Pool Configuration mode
User Guidelines
Use the
show ip dhcp pool
command to display pool configuration
parameters. The client name should not include the domain name as it is
specified separately by the
domain-name (IP DHCP Pool Config)
command. It
is not recommended to use embedded blanks in client names.
Example
console(config-dhcp-pool)#client-identifier 01:03:13:18:22:33:11
console(config-dhcp-pool)#host 192.168.21.34 32
console(config-dhcp-pool)#client-name Line_Printer_Hallway
default-router
Use the default-router command in DHCP Pool Configuration mode to set
the IPv4 address of one or more routers for the DHCP client to use. Use the
no form of the command to remove the default router configuration. Use the
show ip dhcp pool
command to display pool configuration parameters.
Syntax
default-router {
ip-address1
}[
ip address2
]
no default-router
•
ip-address1
—The IPv4 address of the first default router for the DHCP
client.
2CSNXXX_SWUM200.book Page 938 Tuesday, December 10, 2013 1:22 PM

DHCP Server and Relay Agent Commands 939
•
ip-address2
—The IPv4 address of the second default router for the DHCP
client.
Default Configuration
No default router is configured.
Command Mode
DHCP Pool Configuration mode
User Guidelines
This command has no user guidelines.
Example
console(config-dhcp-pool)#default-router 192.168.22.1 192.168.23.1
dns-server (IP DHCP Pool Config)
Use the dns-server command in IP DHCP Pool Configuration mode to set
the IP DNS server address which is provided to a DHCP client by the DHCP
server. DNS server address is configured for stateless server support.
Syntax
dns-server
ip-address1
no dns-server
•
ip-address1
—A valid IPv4 address.
Default Configuration
This command has no default configuration.
Command Mode
IP DHCP Pool Configuration mode
User Guidelines
This command has no user guidelines.
2CSNXXX_SWUM200.book Page 939 Tuesday, December 10, 2013 1:22 PM

940 DHCP Server and Relay Agent Commands
domain-name (IP DHCP Pool Config)
Use the domain-name command in IP DHCP Pool Configuration mode to
set the DNS domain name which is provided to a DHCP client by the DHCP
server. The DNS name is an alphanumeric string up to 255 characters in
length. Use the no form of the command to remove the domain name.
Syntax
domain-name
domain
no domain-name
domain
•
domain
— DHCP domain name. (Range: 1–255 characters)
Default Configuration
This command has no default configuration.
Command Mode
IP DHCP Pool Configuration mode
hardware-address
Use the hardware-address command in DHCP Pool Configuration mode to
specify the MAC address of a client to be manually assigned an address. Use
the no form of the command to remove the MAC address assignment.
Syntax
hardware-address
hardware-address
no hardware-address
•
hardware-address
—MAC address of the client. Either the
XXXX.XXXX.XXXX or XX:XX:XX:XX:XX:XX form of MAC address may
be used where XX is a hexadecimal digit.
Default Configuration
There are no default MAC address manual bindings.
2CSNXXX_SWUM200.book Page 940 Tuesday, December 10, 2013 1:22 PM

DHCP Server and Relay Agent Commands 941
Command Mode
DHCP Pool Configuration mode
User Guidelines
Use the
show ip dhcp pool
command to display pool configuration
parameters. It may be necessary to use the no host command prior to
executing the no hardware-address command.
Example
console(config-dhcp-pool)#hardware-address 00:23:12:43:23:54
console(config-dhcp-pool)#host 192.168.21.131 32
host
Use the host command in DHCP Pool Configuration mode to specify a
manual binding for a DHCP client host. Use the no form of the command to
remove the manual binding.
Syntax
host ip-address [netmask|prefix-length]
no host
•
ip-address
—IPv4 address to be manually assigned to the host identified by
the client identifier.
•
netmask
—An IPv4 address indicating the applicable bits of the address,
typically 255.255.255.255.
•
prefix-length
—A decimal number ranging from 1-30.
Default Configuration
The default is a 1 day lease.
Command Mode
DHCP Pool Configuration mode
2CSNXXX_SWUM200.book Page 941 Tuesday, December 10, 2013 1:22 PM

942 DHCP Server and Relay Agent Commands
User Guidelines
Use the
client-identifier
or
hardware-address
command prior to using this
command for an address pool. Use the
show ip dhcp pool
command to display
pool configuration parameters.
Example
console(config-dhcp-pool)#client-identifier 00:23:12:43:23:54
console(config-dhcp-pool)#host 192.168.21.131 32
ip dhcp bootp automatic
Use the ip dhcp bootp automatic command in Global Configuration mode
to enable automatic BOOTP address assignment. By default, BOOTP clients
are not automatically assigned addresses, although they may be assigned a
static address. Use the no form of the command to disable automatic BOOTP
client address assignment. Use the
show ip dhcp global configuration
command to display the automatic address assignment configuration.
Syntax
ip dhcp bootp automatic
no ip dhcp bootp automatic
Default Configuration
Automatic BOOTP client address assignment is disabled by default.
Command Mode
Global Configuration mode
User Guidelines
This command has no user guidelines.
Example
console#ip dhcp bootp automatic
2CSNXXX_SWUM200.book Page 942 Tuesday, December 10, 2013 1:22 PM

DHCP Server and Relay Agent Commands 943
ip dhcp conflict logging
Use the ip dhcp conflict logging command in Global Configuration mode to
enable DHCP address conflict detection. Use the no form of the command to
disable DHCP conflict logging.
Syntax
ip dhcp conflict logging
no ip dhcp conflict logging
Default Configuration
Conflict logging is enabled by default.
Command Mode
Global Configuration mode
User Guidelines
This command has no user guidelines.
Example
console#ip dhcp conflict logging
ip dhcp excluded-address
Use the ip dhcp excluded-address command in Global Configuration mode
to exclude one or more DHCP addresses from automatic assignment. Use the
no form of the command to allow automatic address assignment for the
specified address or address range.
Syntax
ip dhcp excluded-address
low-address
{
high-address
}
no ip dhcp excluded-address
low-address
{
high-address
}
•
low-address
—An IPv4 address indicating the starting range for exclusion
from automatic DHCP address assignment.
2CSNXXX_SWUM200.book Page 943 Tuesday, December 10, 2013 1:22 PM

944 DHCP Server and Relay Agent Commands
•
high-address
—An IPv4 address indicating the ending range for exclusion
from automatic DHCP address assignment. The high-address must be
numerically greater than the low-address.
Default Configuration
By default, no IP addresses are excluded from the lists configured by the IP
DHCP pool configuration.
Command Mode
Global Configuration mode
User Guidelines
This command has no user guidelines.
Example
console#ip dhcp excluded-address 192.168.20.1 192.168.20.3
ip dhcp ping packets
Use the ip dhcp ping packets command in Global Configuration mode to
configure the number of pings sent to detect if an address is in use prior to
assigning an address from the DHCP pool. If neither ping is answered, the
DHCP server presumes the address is not in use and assigns the selected IP
address.
Syntax
ip dhcp ping packets {0,
2-10
}
no ip dhcp ping packets
•
count
—
The number of ping packets sent to detect an address in use. The
default is 2 packets. Range 0, 2-10. A value of 0 turns off address detection. Use
the no form of the command to return the setting to the default value.
Default Configuration
The command has no default configuration.
2CSNXXX_SWUM200.book Page 944 Tuesday, December 10, 2013 1:22 PM

DHCP Server and Relay Agent Commands 945
Command Mode
Global Configuration mode
User Guidelines
This command has no user guidelines.
Example
console#ip dhcp ping packets 5
lease
Use the lease command in DHCP Pool Configuration mode to set the period
for which a dynamically assigned DHCP address is valid. Use the infinite
parameter to indicate that addresses are to be automatically assigned. Use the
no form of the command to return the lease configuration to the default. Use
the
show ip dhcp pool
command to display pool configuration parameters.
Use the
show ip dhcp binding
command to display the expiration time of the
leased IP address.
Syntax
lease {
days
[
hours
][
minutes
]|infinite}
no lease
•
days
—The number of days for the lease duration. Range 0-59. Default is 1.
•
hours
—The number of hours for the lease duration. Range 0-23. There is
no default.
•
minutes
—The number of minutes for the lease duration. Range 0-59.
There is no default.
•
infinite
—The lease does not expire.
Default Configuration
The default is a 1 day lease.
Command Mode
DHCP Pool Configuration mode
2CSNXXX_SWUM200.book Page 945 Tuesday, December 10, 2013 1:22 PM

946 DHCP Server and Relay Agent Commands
User Guidelines
This command has no user guidelines.
Example
console(config-dhcp-pool)#lease 1 12 59
netbios-name-server
Use the netbios-name-server command in DHCP Pool Configuration mode
to configure the IPv4 address of the Windows Internet Naming Service
(WINS) for a Microsoft DHCP client. Use the no form of the command to
remove the NetBIOS name server configuration.
Syntax
netbios-name-server
ip-address
[
ip-address2...ip-address8
]
no netbios-name-server
•
ip-address
—IPv4 address
Default Configuration
There is no default name server configured.
Command Mode
DHCP Pool Configuration mode
User Guidelines
Use the
show ip dhcp pool
command to display pool configuration
parameters. Up to eight name server addresses may be specified. The
NetBIOS WINS information is conveyed in the Option 44 TLV of the DHCP
OFFER, DCHP ACK, DHCP INFORM ACK and DHCP BOOTREPLY
messages.
Example
console(config-dhcp-pool)#netbios-name-server 192.168.21.1 192.168.22.1
2CSNXXX_SWUM200.book Page 946 Tuesday, December 10, 2013 1:22 PM

DHCP Server and Relay Agent Commands 947
netbios-node-type
Use the netbios-node-type command in DHCP Pool Configuration mode to
set the NetBIOS node type for a Microsoft DHCP client. Use the no form of
the command to remove the netbios node configuration.
Syntax
netbios-node-type
type
no netbios-node-type
•
type
—The NetBIOS node type can be
b-node
,
h-node
,
m-node
or
p-node
.
Default Configuration
There is no default NetBIOS node type configured.
Command Mode
DHCP Pool Configuration mode
User Guidelines
Use the
show ip dhcp pool
command to display pool configuration
parameters. The NetBIOS node type information is conveyed in the Option
46 TLV of the DHCP OFFER, DHCP ACK, DHCP INFORM ACK and
DHCP BOOTREPLY messages. Supported NetBIOS node types are:
• broadcast (b-node)
• peer-to-peer (p-node)
• mixed (m-node)
•hybrid (h-node)
Example
console(config-dhcp-pool)#netbios-node-type h-node
network
Use the network command in IP DHCP Pool Configuration mode to define a
pool of IPv4 addresses for distributing to clients.
2CSNXXX_SWUM200.book Page 947 Tuesday, December 10, 2013 1:22 PM

948 DHCP Server and Relay Agent Commands
Syntax
network
network-number
[
mask
|
prefix-length
]
•
network-number
—A valid IPv4 address
•mask—
A valid IPv4 network mask with contiguous left-aligned bits.
•
prefix-length
—An integer indicating the number of leftmost bits in the
network-number to use as a prefix for allocating cells.
Default Configuration
This command has no default configuration.
Command Mode
IP DHCP Pool Configuration mode
next-server
Use the next-server command in DHCP Pool Configuration mode to set the
IPv4 address of the TFTP server to be used during auto-install. Use the no
form of the command to remove the next server configuration.
Syntax
next-server
ip-address
no next-server
•
ip-address
—The IPv4 address of the TFTP server to use during auto-
configuration.
Default Configuration
There is no default IPv4 next server configured.
Command Mode
DHCP Pool Configuration mode
2CSNXXX_SWUM200.book Page 948 Tuesday, December 10, 2013 1:22 PM

DHCP Server and Relay Agent Commands 949
User Guidelines
Use the
show ip dhcp pool
command to display pool configuration
parameters. The IPv4 address is conveyed in the SIADDR field of the DHCP
OFFER, DHCP ACK, DHCP INFORM ACK and DHCP BOOTREPLY
messages.
Example
console(config-dhcp-pool)#next-server 192.168.21.2
option
Use the option command in DHCP Pool Configuration mode to supply
arbitrary configuration information to a DHCP client. Use the no form of the
command to remove the option configuration. Use the
show ip dhcp pool
command to display pool configuration parameters.
Syntax
option code {ascii string1|hex[
string1...string8
]|ip[
ip-address1...ip-
address8]}
no option code
•
code
—The DHCP TLV option code.
•
ascii string1
—An ASCII character string. Strings with embedded blanks
must be wholly contained in quotes.
•
hex string1
—A hexadecimal string containing the characters [0-9A-F].
The string should not begin with 0x. A hex string consists of two characters
which are parsed to fill a single byte. Multiple values are separated by
blanks.
•
ip-address1
—An IPv4 address in dotted decimal notation.
Default Configuration
There is no default option configured.
Command Mode
DHCP Pool Configuration mode
2CSNXXX_SWUM200.book Page 949 Tuesday, December 10, 2013 1:22 PM

950 DHCP Server and Relay Agent Commands
User Guidelines
The option information must match the selected option type and length.
Options cannot be longer than 255 characters in length. The option
information is conveyed in the TLV specified by the code parameter in the
DHCP OFFER, DHCP ACK, DHCP INFORM ACK and DHCP
BOOTREPLY messages.
Figure 46-1 lists the options that can be configured and their fixed length,
minimum length, and length multiple requirements.
Figure 46-1. Option Codes and Lengths
Option Code Fixed Length Minimum Length Multiple Of
2 (Time Offset) 4 – –
4 (Time Server) – 4 4
7 (Log Server) – 4 4
8 (Cookie Server) – 4 4
9 (LPR Server)–44
10 (Impress Server) – 4 4
11 (Resource Location
Server)
–44
12 (Host Name) –1–
13 (Boot File Size) 2 – –
14 (Merit File Dump) – 1 –
16 (Swap Server) 4––
17 (Root Path) – 1 –
18 (Extensions Path) – 1 –
19 (IP Forwarding
Enable)
1––
20 (Non-local Source
Routing)
1––
21 (Policy Filter) –88
22 (Max Datagram
Reassembly)
2––
2CSNXXX_SWUM200.book Page 950 Tuesday, December 10, 2013 1:22 PM

DHCP Server and Relay Agent Commands 951
23 (IP TTL) 1––
24 (Path MTU Aging)4––
25 (Path MTU Plateau) – 2 2
26 (Interface MTU) 2––
27 (Subnets are local) 1––
28 (Broadcast Address)4––
29 (Perform Mask)1––
30 (Mask Supplier)1––
31 (Perform Router
Discovery)
1––
32 (Router Solicitation
Address)
4––
33 (Static Router Option) – 8 8
34 (Trailer
Encapsulation)
1––
35 (ARP Cache Timeout)4––
36 (Ethernet
Encapsulation)
1––
37 (TCP TTL) 1––
38 (TCP Keepalive
Interval)
4––
39 (TCP Keepalive
Garbage)
1––
40 (Network Information
Service)
–1–
41 (Network Information
Servers)
–44
42 (NTP Servers) –44
43 (Vendor Specific
Information)
1––
Figure 46-1. Option Codes and Lengths
(continued)
Option Code Fixed Length Minimum Length Multiple Of
2CSNXXX_SWUM200.book Page 951 Tuesday, December 10, 2013 1:22 PM

952 DHCP Server and Relay Agent Commands
Options 19, 20, 27, 29, 30, 31, 34, 36, and 39 only accept hex 00 or hex 01
values.
Example
console(config-dhcp-pool)#option 4 ascii "ntpservice.com "
console(config-dhcp-pool)#option 42 ip 192.168.21.1
45 (NetBIOS Datagram
Distribution)
–44
47 (Netbois Scope) – 1 –
48 (X-Windows Font
Server)
–44
49 (X-Windows Display
Manager)
–44
58 (Renewal Time T1) 4 – –
59 (Rebinding Time T2)4––
60 (Vendor Class)–1–
64 (NIS Domain) – 1 –
65 (NIS Servers) –44
66 (TFTP Server) –1–
68 (Mobile IP Home
Agent)
–04
69 (SMTP Server)–44
70 (POP3 Server)–44
71 (NNTP Server) – 4 4
72 (WWW Server) – 4 4
73 (Finger Server) – 4 4
74 (IRC Server) – 4 4
75 (Streettalk Server) – 4 4
76 (STDA Server) – 4 4
Figure 46-1. Option Codes and Lengths
(continued)
Option Code Fixed Length Minimum Length Multiple Of
2CSNXXX_SWUM200.book Page 952 Tuesday, December 10, 2013 1:22 PM

DHCP Server and Relay Agent Commands 953
console(config-dhcp-pool)#option 29 hex 01
console(config-dhcp-pool)#option 59 hex 00 00 10 01
console(config-dhcp-pool)#option 25 hex 01 ff
service dhcp
Use the service dhcp command in Global Configuration mode to enable local
IPv4 DHCP server on the switch. Use the no form of the command to disable
the DHCPv4 service.
Syntax
service dhcp
no service dhcp
Default Configuration
The service is disabled by default.
Command Mode
Global Configuration mode
User Guidelines
This command has no user guidelines.
sntp
Use the sntp command in DHCP Pool Configuration mode to set the IPv4
address of the NTP server to be used for time synchronization of the client.
Use the no form of the command to remove the NTP server configuration.
Syntax
sntp
ip-address
no sntp
•
ip-address
—The IPv4 address of the NTP server to use for time services.
Default Configuration
There is no default IPv4 NTP server configured.
2CSNXXX_SWUM200.book Page 953 Tuesday, December 10, 2013 1:22 PM

954 DHCP Server and Relay Agent Commands
Command Mode
DHCP Pool Configuration mode
User Guidelines
Use the
show ip dhcp pool
command to display pool configuration
parameters. The IPv4 address of the NTP server is conveyed in the Option 42
TLV of the DHCP OFFER, DHCP ACK, DHCP INFORM ACK and DHCP
BOOTREPLY messages.
Example
console(config-dhcp-pool)#sntp 192.168.21.2
show ip dhcp binding
Use the show ip dhcp binding command in Privileged EXEC mode to display
the configured DHCP bindings.
Syntax
show ip dhcp binding [address]
•
address
—A valid IPv4 address
Default Configuration
The command has no default configuration.
Command Mode
Privileged EXEC mode, Configuration mode and all Configuration submodes
User Guidelines
This command has no user guidelines.
Example
console(config)# show ip dhcp binding
IP address Hardware Address Expires Type client-DUID
----------- ----------------- --------- ----- --------------
10.10.10.3 00:0e:c6:88:0e:98 00:23:56 Auto
00:01:01:02:03:04:05:06:00:0e:c6:88:0e:98
2CSNXXX_SWUM200.book Page 954 Tuesday, December 10, 2013 1:22 PM

DHCP Server and Relay Agent Commands 955
show ip dhcp conflict
Use the show ip dhcp conflict command in User EXEC mode to display
DHCP address conflicts for all relevant interfaces or a specified interface. If
an interface is specified, the optional statistics parameter is available to view
statistics for the specified interface.
Syntax
show ip dhcp conflict [
address
]
•
address
—A valid IPv4 address for which the conflict information is
desired.
Default Configuration
The command has no default configuration.
Command Mode
Privileged EXEC mode, Configuration mode and all Configuration submodes
User Guidelines
This command has no user guidelines.
show ip dhcp global configuration
Use the show ip dhcp global configuration command in Privileged EXEC
mode to display the DHCP global configuration.
Syntax
show ip dhcp server statistics
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC mode, Configuration mode and all Configuration submodes
2CSNXXX_SWUM200.book Page 955 Tuesday, December 10, 2013 1:22 PM

956 DHCP Server and Relay Agent Commands
User Guidelines
This command has no user guidelines.
Example
console#show ip dhcp server statistics
show ip dhcp pool
Use the show ip dhcp pool command in User EXEC or Privileged EXEC
mode to display the configured DHCP pool or pools. If no pool name is
specified, information about all pools is displayed.
Syntax
show ip dhcp pool [all |
poolname
]
•
poolname
—Name of the pool. (Range: 1-32 characters)
Default Configuration
This command has no default configuration.
Command Mode
User EXEC, Privileged EXEC mode, Configuration mode and all
Configuration submodes
User Guidelines
This command has no user guidelines.
show ip dhcp server statistics
Use the show ip dhcp server statistics command in Privileged EXEC mode to
display the DHCP server binding and message counters.
Syntax
show ip dhcp server statistics
Default Configuration
This command has no default configuration.
2CSNXXX_SWUM200.book Page 956 Tuesday, December 10, 2013 1:22 PM

DHCP Server and Relay Agent Commands 957
Command Mode
Privileged EXEC mode, Configuration mode and all Configuration submodes
User Guidelines
This command has no user guidelines.
Example
console#show ip dhcp server statistics
Automatic Bindings............................. 100
Expired Bindings............................... 32
Malformed Bindings............................. 0
Messages Received
---------- ----------
DHCP DISCOVER.................................. 132
DHCP REQUEST................................... 132
DHCP DECLINE................................... 0
DHCP RELEASE................................... 32
DHCP INFORM.................................... 0
Messages Sent
---------- ------
DHCP OFFER..................................... 132
DHCP ACK....................................... 132
DHCP NACK...................................... 0
2CSNXXX_SWUM200.book Page 957 Tuesday, December 10, 2013 1:22 PM

958 DHCP Server and Relay Agent Commands
2CSNXXX_SWUM200.book Page 958 Tuesday, December 10, 2013 1:22 PM

DHCPv6 Commands 959
47
DHCPv6 Commands
Dell Networking N2000/N3000/N4000 Series Switches
This chapter explains the following commands:
clear ipv6 dhcp
Use the clear ipv6 dhcp command in Privileged EXEC mode to clear
DHCPv6 statistics for all interfaces or for a specific interface.
Syntax
clear ipv6 dhcp {statistics | interface vlan
vlan-id
statistics}
•
vlan-id
— Valid VLAN ID.
•
statistics
— Indicates statistics display if VLAN is specified.
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC mode
clear ipv6 dhcp service dhcpv6
dns-server (IPv6 DHCP Pool Config) show ipv6 dhcp
domain-name (IPv6 DHCP Pool Config) show ipv6 dhcp binding
ipv6 dhcp pool show ipv6 dhcp interface (User EXEC)
ipv6 dhcp relay show ipv6 dhcp interface (Privileged
EXEC)
ipv6 dhcp server show ipv6 dhcp pool
prefix-delegation show ipv6 dhcp statistics
2CSNXXX_SWUM200.book Page 959 Tuesday, December 10, 2013 1:22 PM

960 DHCPv6 Commands
User Guidelines
This command has no user guidelines.
Examples
The following examples clears DHCPv6 statistics for VLAN 11.
console#clear ipv6 dhcp interface vlan 11 statistics\
dns-server (IPv6 DHCP Pool Config)
Use the dns-server command in IPv6 DHCP Pool Configuration mode to set
the IPv6 DNS server address which is provided to a DHCPv6 client by the
DHCPv6 server. DNS server address is configured for stateless server support.
Syntax
dns-server
ipv6-address
no dns-server
ipv6-address
•
ipv6-address
—Valid IPv6 address.
Default Configuration
This command has no default configuration.
Command Mode
IPv6 DHCP Pool Configuration mode
User Guidelines
This command has no user guidelines.
domain-name (IPv6 DHCP Pool Config)
Use the domain-name command in IPv6 DHCP Pool Configuration mode to
set the DNS domain name which is provided to a DHCPv6 client by the
DHCPv6 server. DNS domain name is configured for stateless server support.
Syntax
domain-name
domain
2CSNXXX_SWUM200.book Page 960 Tuesday, December 10, 2013 1:22 PM

DHCPv6 Commands 961
no domain-name
domain
•
domain
— DHCPv6 domain name. (Range: 1–255 characters)
Default Configuration
This command has no default configuration.
Command Mode
IPv6 DHCP Pool Configuration mode
User Guidelines
DHCPv6 pool can have multiple number of domain names with maximum of
8.
Example
The following example sets the DNS domain name "test", which is provided
to a DHCPv6 client by the DHCPv6 server.
console(config)#ipv6 dhcp pool addrpool
console(config-dhcp6s-pool)#domain-name test
console(config-dhcp6s-pool)#no domain-name test
ipv6 dhcp pool
This capability requires the IPv6 DHCP service to be enabled. Use the service
dhcpv6 command to enable the DHCPv6 service. Use the ipv6 dhcp pool
command in Global Configuration mode to enter IPv6 DHCP Pool
Configuration mode. DHCPv6 pools are used to specify information for
DHCPv6 server to distribute to DHCPv6 clients. These pools are shared
between multiple interfaces over which DHCPv6 server capabilities are
configured.
Syntax
ipv6 dhcp pool
pool-name
no ipv6 dhcp pool
pool-name
•
pool-name
— DHCPv6 pool name. (Range: 1-31 characters)
2CSNXXX_SWUM200.book Page 961 Tuesday, December 10, 2013 1:22 PM

962 DHCPv6 Commands
Default Configuration
This command has no default configuration.
Command Mode
Global Configuration mode
User Guidelines
This command has no user guidelines.
Example
The following example enters IPv6 DHCP Pool Configuration mode.
console(config)#service dhcpv6
console(config)#ipv6 dhcp pool addrpool
console(config-dhcp6s-pool)#
ipv6 dhcp relay
Use the ipv6 dhcp relay command in Interface Configuration mode to
configure an interface for DHCPv6 relay functionality.
Syntax
ipv6 dhcp relay {destination
relay-address
[interface vlan
vlan-id
] | interface
vlan
vlan-id
}[remote-id {duid-ifid |
user-defined-string
}]
•
destination
— Keyword that sets the relay server IPv6 address.
•
relay-address
— An IPv6 address of a DHCPv6 relay server.
•
interface
— Sets the relay server interface.
•
vlan-id
— A valid VLAN ID.
•
[
remote-id
{
duid-ifid
|
user-defined-string
}]
— The Relay Agent
Information Option “remote ID” suboption to be added to relayed
messages. This can either be the special keyword duid-ifid, which causes
the “remote ID” to be derived from the DHCPv6 server DUID and the
relay interface number, or it can be specified as a user-defined string.
Default Configuration
This command has no default configuration.
2CSNXXX_SWUM200.book Page 962 Tuesday, December 10, 2013 1:22 PM

DHCPv6 Commands 963
Command Mode
Interface Configuration (VLAN, Tunnel) mode
User Guidelines
The IPv6 DHCP service must be enavbled to use this feature. Enable the
IPv6 DHCP service using the service dhcpv6 command. If
relay-address
is an
IPv6 global address, then
relay-interface
is not required. If
relay-address
is a
link-local or multicast address, then
relay-interface
is required. Finally, a value
for
relay-address
is not specified, then a value for
relay-interface
must be
specified and the DHCPV6-ALLAGENTS multicast address (i.e. FF02::1:2)
is used to relay DHCPv6 messages to the relay server. An IP interface (VLAN)
can be configured in DHCP relay mode or DHCP server mode. Configuring
an interface in DHCP relay mode overwrites the DHCP server mode and vice-
versa.
An IP interface configured in relay mode cannot be configured as a DHCP
client (ip address dhcp).
Example
The following example configures VLAN 15 for DHCPv6 relay functionality.
console(config)#service dhcpv6
console(config)#interface vlan 15
console(config-if-vlan15)#ipv6 dhcp relay destination 2020:1::1
ipv6 dhcp server
Use the ipv6 dhcp server command in Interface Configuration mode to
configure DHCPv6 server functionality on an interface. For a particular
interface DHCPv6 server and DHCPv6 relay functions are mutually exclusive.
Syntax
ipv6 dhcp server
pool-name
[rapid-commit] [preference
pref-value
]
•
pool-name
— The name of the DHCPv6 pool containing stateless and/or
prefix delegation parameters
•
rapid-commit
— An option that allows for an abbreviated exchange
between the client and server.
2CSNXXX_SWUM200.book Page 963 Tuesday, December 10, 2013 1:22 PM

964 DHCPv6 Commands
•
pref-value
— Preference value
—
used by clients to determine preference
between multiple DHCPv6 servers. (Range: 0-4294967295)
Default Configuration
The default preference value is 20. Rapid commit is not enabled by default.
Command Mode
Interface Configuration (VLAN, Tunnel) mode
User Guidelines
This feature requires the IPv6 DHCP service. Enable the IPv6 DHCP service
using the service dhcpv6 command. The ipv6 dhcp server command enables
DHCP for IPv6 service on a specified interface using the pool for prefix
delegation and other configuration through that interface.
The rapid-commit keyword enables the use of the two-message exchange for
prefix delegation and other configuration. If a client has included a rapid
commit option in the solicit message and the rapid-commit keyword is
enabled for the server, the server responds to the solicit message with a reply
message.
If the preference keyword is configured with a value other than 0, the server
adds a preference option to carry the preference value for the advertise
messages. This action affects the selection of a server by the client. Any
advertise message that does not include a preference option is considered to
have a preference value of 0. If the client receives an advertise message that
includes a preference option with a preference value of 255, the client
immediately sends a request message to the server from which the advertise
message was received.
The DHCP for IPv6 client, server, and relay functions are mutually exclusive
on an interface. When one of these functions is already enabled and a user
tries to configure a different function on the same interface, a message is
displayed.
Example
console#configure
console(config)#service dhcpv6
console(config)# ipv6 dhcp pool pool1
2CSNXXX_SWUM200.book Page 964 Tuesday, December 10, 2013 1:22 PM

DHCPv6 Commands 965
console(config-dhcp6s-pool)# address prefix-delegation 2001::/64
00:01:32:00:32:00
console(config-dhcp6s-pool)# exit
console(config)#interface vlan 10
console(config-if-vlan10)#ipv6 dhcp server pool1
console(config-if-vlan10)#
prefix-delegation
Use the prefix-delegation command in IPv6 DHCP Pool Configuration mode
to define multiple IPv6 prefixes within a pool for distributing to specific
DHCPv6 Prefix delegation clients.
Syntax
prefix-delegation
ipv6-prefix/prefix-length client-DUID
[name
hostname
]
[valid-lifetime {
valid-lifetime
| infinite}] [preferred-lifetime {
preferred-
lifetime
| infinite}]
no prefix-delegation ipv6-prefix/prefix-length
•
prefix/prefix-length
—Delegated IPv6 prefix.
•
client-DUID
—Client DUID (e.g. 00:01:00:09:f8:79:4e:00:04:76:73:43:76').
•
hostname
—Client hostname used for logging and tracing. (Range: 0-31
characters.) The command allows spaces in the host name when specified
in double quotes. For example,
console(config)#snmp-server
host "host name"
•
valid-lifetime
—Valid lifetime for delegated prefix. (Range: 0-4294967295
seconds) or use the keyword
infinite
. Using the value 0 for the valid-
lifetime sets the value to the default.
•
preferred-lifetime
—Preferred lifetime for delegated prefix. (Range: 0-
4294967295 seconds) or use the keyword
infinite
. Using the value 0 for the
preferred-lifetime sets the value to the default.
Default Configuration
604800 seconds (30 days) is the default value for
preferred-lifetime
. 2592000
seconds (7 days) is the default value for
valid-lifetime
.
Command Mode
IPv6 DHCP Pool Configuration mode
2CSNXXX_SWUM200.book Page 965 Tuesday, December 10, 2013 1:22 PM

966 DHCPv6 Commands
User Guidelines
This command has no user guidelines.
Example
The following example defines a Multiple IPv6 prefix and client DUID within
a pool for distributing to specific DHCPv6 Prefix delegation clients.
console(config)#ipv6 dhcp pool addrpool
console(config-dhcp6s-pool)#prefix-delegation 2020:1::1/64
00:01:00:09:f8:79:4e:00:04:76:73:43:76
The following example defines a unique local address prefix with the MAC
address 00:1D:BA:06:37:64 converted to EUI-64 format and a preferred
lifetime of 5 days.
console(config-dhcp6s-pool)#prefix-delegation fc00::/7
00:1D:BA:FF:FE:06:37:64 preferred-lifetime 43200
service dhcpv6
Use the service dhcpv6 command in Global Configuration mode to enable
local IPv6 DHCP server on the switch. Use the no form of the command to
disable the DHCPv6 service.
Syntax
service dhcpv6
no service dhcpv6
Default Configuration
The service dhcpv6 is disabled by default.
Command Mode
Global Configuration mode
User Guidelines
IPv6 DHCP relay and IPv6 DHCPv6 pool assignments require the DHCPv6
service to be enabled.
2CSNXXX_SWUM200.book Page 966 Tuesday, December 10, 2013 1:22 PM

DHCPv6 Commands 967
Example
The following example enables DHCPv6 globally.
console#configure
console(config)#service dhcpv6
console(config)#no service dhcpv6
show ipv6 dhcp
Use the show ipv6 dhcp command in Privileged EXEC mode to display the
DHCPv6 server name and status.
Syntax
show ipv6 dhcp
Default Configuration
This command has no default configuration.
Command Mode
User EXEC, Privileged EXEC modes, Configuration mode and all
Configuration submodes
User Guidelines
The DUID value of the server will only appear in the output when a DHCPv6
lease is active.
Example
The following example displays the DHCPv6 server name and status.
console#show ipv6 dhcp
DHCPv6 is disabled
Server DUID:
show ipv6 dhcp binding
Use the show ipv6 dhcp binding command in Privileged EXEC mode to
display the configured DHCP pool.
2CSNXXX_SWUM200.book Page 967 Tuesday, December 10, 2013 1:22 PM

968 DHCPv6 Commands
Syntax
show ipv6 dhcp binding [
ipv6-address
]
•
ipv6-address
— Valid IPv6 address.
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC and User EXEC modes, Configuration mode and all
Configuration submodes
User Guidelines
This command has no user guidelines.
Example
The following example displays the configured DHCP pool based on the
entered IPv6 address.
console#show ipv6 dhcp binding 2020:1::
show ipv6 dhcp interface (User EXEC)
Use the show ipv6 dhcp interface command in User EXEC mode to display
DHCPv6 information for all relevant interfaces or for the specified interface.
If an interface is specified, the optional statistics parameter is available to
view statistics for the specified interface.
Syntax
show ipv6 dhcp interface [type number] [statistics]
•
type number
—
Tunnel tunnel-id (Range: 0-7) or VLAN vlan-id (Valid VLAN id)
•
statistics
—
Enables statistics display if interface is specified.
Default Configuration
This command has no default configuration.
2CSNXXX_SWUM200.book Page 968 Tuesday, December 10, 2013 1:22 PM

DHCPv6 Commands 969
Command Mode
User EXEC, Privileged EXEC modes, Configuration mode and all
Configuration submodes
User Guidelines
Statistics are shown depending on the interface mode (relay, server, or client).
Examples
The following examples display DHCPv6 information for VLAN 11 when
configured in relay mode.
console> show ipv6 dhcp interface vlan 11
IPv6 Interface................................. vlan11
Mode........................................... Relay
Relay Address.................................. 2020:1::1
Relay Interface Number......................... Relay
Relay Remote ID................................
Option Flags...................................
console> show ipv6 dhcp interface vlan 11 statistics
DHCPv6 Interface vlan11 Statistics
------------------------------------
DHCPv6 Solicit Packets Received................ 0
DHCPv6 Request Packets Received................ 0
DHCPv6 Confirm Packets Received................ 0
DHCPv6 Renew Packets Received.................. 0
DHCPv6 Rebind Packets Received................. 0
DHCPv6 Release Packets Received................ 0
DHCPv6 Decline Packets Received................ 0
DHCPv6 Inform Packets Received................. 0
DHCPv6 Relay-forward Packets Received.......... 0
DHCPv6 Relay-reply Packets Received............ 0
DHCPv6 Malformed Packets Received.............. 0
Received DHCPv6 Packets Discarded.............. 0
Total DHCPv6 Packets Received.................. 0
DHCPv6 Advertisement Packets Transmitted....... 0
DHCPv6 Reply Packets Transmitted............... 0
DHCPv6 Reconfig Packets Transmitted............ 0
DHCPv6 Relay-reply Packets Transmitted......... 0
DHCPv6 Relay-forward Packets Transmitted....... 0
Total DHCPv6 Packets Transmitted............... 0
2CSNXXX_SWUM200.book Page 969 Tuesday, December 10, 2013 1:22 PM
970 DHCPv6 Commands
show ipv6 dhcp interface (Privileged EXEC)
Use the show ipv6 dhcp interface command in Privileged EXEC mode to
display configuration and status information about an IPv6 DHCP interface
or all interfaces.
Syntax
show ipv6 dhcp interface [
interface-id
]{statistics}
•
interface-id
—Any valid IP interface. See Interface Naming Conventions
for interface representation.
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC, Configuration mode and all Configuration submodes
User Guidelines
This command shows the DHCP status. Information displayed depends on
the mode.
The command output provides the following information for an interface
configured in client mode. Not all fields will be shown for an inactive client.
Term Description
Mode Displays whether the specified interface is in Client, Relay, or
Server mode.
State State of the DHCPv6 Client on this interface. The valid values
are:
INACTIVE, SOLICIT, REQUEST, ACTIVE, RENEW,
REBIND, RELEASE.
S er ve r D UI D D H C Pv 6 U ni q ue Id e nt if i er of t he D HC Pv 6 S er v er on th i s
interface.
T1 Time The T1 (in seconds) time as indicated by the DHCPv6 Server.
T1 value indicates the time interval after which the address is
requested for renewal.
2CSNXXX_SWUM200.book Page 970 Tuesday, December 10, 2013 1:22 PM
DHCPv6 Commands 971
Example
The following example shows the output from this command when the
device has leased an IPv6 address from the DHCPv6 server on interface 1/0/1.
NOTE: Note that the interface is in client mode.
console#show ipv6 dhcp interface vlan 2
IPv6 Interface................................. Vl2
Mode........................................... Client
State.......................................... ACTIVE
Server DUID....................................
00:03:00:01:00:13:c4:db:6c:00
T1 Time........................................ 0 days 12 hrs 0 mins 0 secs
T2 Time........................................ 0 days 19 hrs 12 mins 0 secs
Interface IAID................................. 20
Leased Address................................. 2017::309D:161:4EF1:DBB1/128
Preferred Lifetime............................. 1 days 0 hrs 0 mins 0 secs
Valid Lifetime................................. 2 days 0 hrs 0 mins 0 secs
Renew Time..................................... 0 days 11 hrs 55 mins 28 secs
Expiry Time.................................... 1 days 23 hrs 55 mins 28 secs
console#show ipv6 dhcp interface vlan 10
T2 Time The T2 (in seconds) time as indicated by the DHCPv6 Server.
T2 value indicates the time interval after which the Client
sends Rebind message to the Server in case there are no replies
to the Renew messages.
Interface IAID An identifier for an identity association chosen by this Client.
Leased Address The IPv6 address leased by the DHCPv6 Server for this
interface.
Preferred Lifetime The preferred life time (in seconds) of the IPv6 Address leased
by the DHCPv6 Server.
Valid Lifetime The valid life time (in seconds) of the IPv6 Address leased by
the DHCPv6 Server.
Renew Time The time remaining (in seconds) to send a DHCPv6 Renew
request to DHCPv6 Server for the leased address.
Expiry Time The time (in seconds) when the DHCPv6 leased address
expires.
Term Description
2CSNXXX_SWUM200.book Page 971 Tuesday, December 10, 2013 1:22 PM

972 DHCPv6 Commands
IPv6 Interface................................. Vl10
Mode........................................... Relay
Relay Address.................................. 3030::3
Relay Interface Number......................... Relay
Relay Remote ID................................
Option Flags...................................
console#show ipv6 dhcp interface vlan 10
IPv6 Interface................................. Vl10
Mode........................................... Server
Pool Name...................................... asd
Server Preference.............................. 20
Option Flags...................................
console#show ipv6 dhcp interface vlan 10 statistics
DHCPv6 Server Interface Vl10 Statistics
DHCPv6 Solicit Packets Received................ 0
DHCPv6 Request Packets Received................ 0
DHCPv6 Confirm Packets Received................ 0
DHCPv6 Renew Packets Received.................. 0
DHCPv6 Rebind Packets Received................. 0
DHCPv6 Release Packets Received................ 0
DHCPv6 Decline Packets Received................ 0
DHCPv6 Inform Packets Received................. 0
DHCPv6 Relay-forward Packets Received.......... 0
DHCPv6 Relay-reply Packets Received............ 0
DHCPv6 Malformed Packets Received.............. 0
Received DHCPv6 Packets Discarded.............. 0
Total DHCPv6 Packets Received.................. 0
DHCPv6 Advertisement Packets Transmitted....... 0
DHCPv6 Reply Packets Transmitted............... 0
DHCPv6 Reconfig Packets Transmitted............ 0
DHCPv6 Relay-reply Packets Transmitted......... 0
DHCPv6 Relay-forward Packets Transmitted....... 0
Total DHCPv6 Packets Transmitted............... 0
console#show ipv6 dhcp interface vlan 10 statistics
DHCPv6 Client Interface Vl10 Statistics
---------------------------------------------------------
DHCPv6 Advertisement Packets Received................. 0
DHCPv6 Reply Packets Received......................... 0
Received DHCPv6 Advertisement Packets Discarded....... 0
Received DHCPv6 Reply Packets Discarded............... 0
2CSNXXX_SWUM200.book Page 972 Tuesday, December 10, 2013 1:22 PM

DHCPv6 Commands 973
DHCPv6 Malformed Packets Received..................... 0
Total DHCPv6 Packets Received......................... 0
DHCPv6 Solicit Packets Transmitted.................... 0
DHCPv6 Request Packets Transmitted.................... 0
DHCPv6 Renew Packets Transmitted...................... 0
DHCPv6 Rebind Packets Transmitted..................... 0
DHCPv6 Release Packets Transmitted.................... 0
Total DHCPv6 Packets Transmitted...................... 0
show ipv6 dhcp pool
Use the show ipv6 dhcp pool command in Privileged EXEC mode to display
the configured DHCP pool.
Syntax
show ipv6 dhcp pool
poolname
•
poolname
— Name of the pool. (Range: 1-32 characters)
Default Configuration
This command has no default configuration.
Command Mode
User EXEC, Privileged EXEC modes, Configuration mode and all
Configuration submodes
User Guidelines
This command has no user guidelines.
Example
The following example displays the configured DHCP pool.
console#show ipv6 dhcp pool test
DHCPv6 Pool: test
show ipv6 dhcp statistics
Use the show ipv6 dhcp statistics command in User EXEC mode to display
the global DHCPv6 server and relay statistics.
2CSNXXX_SWUM200.book Page 973 Tuesday, December 10, 2013 1:22 PM

974 DHCPv6 Commands
Syntax
show ipv6 dhcp statistics
Default Configuration
This command has no default configuration.
Command Mode
User EXEC mode, Configuration mode and all Configuration submodes
User Guidelines
This command has no user guidelines.
Example
The following example displays the DHCPv6 server name and status.
console> show ipv6 dhcp statistics
DHCPv6 Interface Global Statistics
------------------------------------
DHCPv6 Solicit Packets Received................ 0
DHCPv6 Request Packets Received................ 0
DHCPv6 Confirm Packets Received................ 0
DHCPv6 Renew Packets Received.................. 0
DHCPv6 Rebind Packets Received................. 0
DHCPv6 Release Packets Received................ 0
DHCPv6 Decline Packets Received................ 0
DHCPv6 Inform Packets Received................. 0
DHCPv6 Relay-forward Packets Received.......... 0
DHCPv6 Relay-reply Packets Received............ 0
DHCPv6 Malformed Packets Received.............. 0
Received DHCPv6 Packets Discarded.............. 0
Total DHCPv6 Packets Received.................. 0
DHCPv6 Advertisement Packets Transmitted....... 0
DHCPv6 Reply Packets Transmitted............... 0
DHCPv6 Reconfig Packets Transmitted............ 0
DHCPv6 Relay-reply Packets Transmitted......... 0
DHCPv6 Relay-forward Packets Transmitted....... 0
Total DHCPv6 Packets Transmitted............... 0
2CSNXXX_SWUM200.book Page 974 Tuesday, December 10, 2013 1:22 PM

DHCPv6 Snooping Commands 975
48
DHCPv6 Snooping Commands
Dell Networking N2000/N3000/N4000 Series Switches
This chapter explains the following commands:
clear ipv6 dhcp snooping binding
Use the clear ipv6 dhcp snooping binding command to clear all IPv6 DHCP
Snooping entries.
Syntax
clear ipv6 dhcp snooping binding {* | interface
interface-id
}
• *—Clears all snooping bindings.
• interface-id—Clears all snooping bindings on a specified physical
interface.
Default Configuration
This command has no default configuration.
clear ipv6 dhcp snooping binding ipv6 dhcp snooping verify mac-address
clear ipv6 dhcp snooping statistics ipv6 verify binding
ipv6 dhcp snooping ipv6 verify source
ipv6 dhcp snooping vlan show ipv6 dhcp snooping
ipv6 dhcp snooping vlan show ipv6 dhcp snooping binding
ipv6 dhcp snooping binding show ipv6 dhcp snooping database
ipv6 dhcp snooping database show ipv6 dhcp snooping interfaces
ipv6 dhcp snooping database write-delay show ipv6 dhcp snooping statistics
ipv6 dhcp snooping limit show ipv6 source binding
ipv6 dhcp snooping log-invalid show ipv6 verify
ipv6 dhcp snooping trust show ipv6 verify source
2CSNXXX_SWUM200.book Page 975 Tuesday, December 10, 2013 1:22 PM

976 DHCPv6 Snooping Commands
Command Modes
User EXEC, Privileged EXEC
User Guidelines
This command has no user guidelines.
Example
(console) #clear ipv6 dhcp snooping binding
clear ipv6 dhcp snooping statistics
Use the clear ipv6 dhcp snooping statistics command to clear all IPv6 DHCP
Snooping statistics.
Syntax
clear ipv6 dhcp snooping statistics
Default Configuration
This command has no default configuration.
Command Modes
User EXEC, Privileged EXEC
User Guidelines
The IPv6 snooping statistics are also cleared by the clear counters all
command.
Example
(console) #clear ipv6 dhcp snooping statistics
ipv6 dhcp snooping
Use the ipv6 dhcp snooping command to globally enable IPv6 DHCP
snooping. Use the no form of the command to globally disable IPv6 DHCP
snooping.
2CSNXXX_SWUM200.book Page 976 Tuesday, December 10, 2013 1:22 PM

DHCPv6 Snooping Commands 977
Syntax
ipv6 dhcp snooping
no ipv6 dhcp snooping
Default Configuration
By default, DHCP snooping is not enabled.
Command Modes
Global Configuration mode
User Guidelines
The DHCP snooping application processes incoming DHCP messages. For
RELEASE and DECLINE messages from a DHCPv6 client and
RECONFIGURE messages from a DHCPv6 server received on an untrusted
interface, the application compares the receive interface and VLAN with the
client’s interface and VLAN in the bindings database. If the interfaces do not
match, the application logs the event and drops the packet. If configured, for
valid client messages, DHCP snooping additionally compares the source
MAC address to the DHCP client hardware address. If there is a mismatch,
DHCP snooping logs a message and drops the packet. The network
administrator can disable this option using the no ip dhcpv6 snooping verify
mac-address for DHCPv6. DHCP snooping always forwards client messages
on trusted interfaces within the VLAN. If DHCP relay or/and DHCP server
are enabled simultaneously with DHCP snooping, the DHCP client message
will be sent to the DHCP relay or/and DHCP server to process further.
Example
console(config)#ipv6 dhcp snooping
ipv6 dhcp snooping vlan
Use the ipv6 dhcp snooping vlan command to globally enable IPv6 DHCP on
a set of VLANs. Use the no form of the command to globally disable IPv6
DHCP snooping on a set of VLANs.
2CSNXXX_SWUM200.book Page 977 Tuesday, December 10, 2013 1:22 PM

978 DHCPv6 Snooping Commands
Syntax
ipv6 dhcp snooping vlan
vlan-range
no ipv6 dhcp snooping
vlan-range
•
vlan-range
—A single VLAN, one or more VLANs separated by commas, or
two VLANs separated by a single dash indicating all VLANs between the
first and second inclusive. Multiple VLAN identifiers can be entered
provided that no embedded spaces are contained within the
vlan-range
.
Default Configuration
By default, DHCP snooping is not enabled on any VLANs.
Command Modes
Global Configuration mode
User Guidelines
DHCP snooping must be enabled on at least one VLAN and globally enabled
to become operational.
Example
console(config)#ipv6 dhcp snooping
console(config)#ipv6 dhcp snooping vlan 5-10,15,30
console(config)#interface te1/0/1
console(config-if-te1/0/1)#switchport mode access
console(config-if-te1/0/1)#switchport access vlan 10
console(config-if-te1/0/1)#no ipv6 dhcp snooping trust
ipv6 dhcp snooping binding
Use the ipv6 dhcp snooping binding command to configure a static IPv6
DHCP snooping binding. Use the no form of the command to remove the
entry from the binding database.
Syntax
ipv6 dhcp snooping binding
mac-address
vlan
vlan-id ip-address
interface
{gigabitethernet
unit/slot/port
| tengigabitethernet
unit/slot/port
|
fortygigabitethernet
unit/slot/port
| port-channel
port-channel-id
}
no ipv6 dhcp snooping binding
mac-address
2CSNXXX_SWUM200.book Page 978 Tuesday, December 10, 2013 1:22 PM

DHCPv6 Snooping Commands 979
•
mac-address
—
A valid mac address in standard format.
•
vlan-id
—
A configured VLAN id. (Range 1-4093)
•
ip-address
—
A valid IPv6 address.
•
interface-id
—
A valid interface ID in short or long format. Physical interfaces
and port channels are supported.
Default Configuration
By default, no static DHCP bindings are configured.
Command Modes
Global Configuration mode
User Guidelines
Static bindings do not age out of the DHCP binding database.
ipv6 dhcp snooping database
Use the ipv6 dhcp snooping database command to configure the persistent
location of the DHCP snooping database. This can be a local or remote file
on a TFTP server.
Syntax
ipv6 dhcp snooping database {local | tftp://hostIP/filename}
no ipv6 dhcp snooping database
Default Configuration
By default, the local database is used.
Command Modes
Global Configuration mode
2CSNXXX_SWUM200.book Page 979 Tuesday, December 10, 2013 1:22 PM

980 DHCPv6 Snooping Commands
User Guidelines
The DHCP binding database is persistently stored on a configured external
server or locally in flash, depending on the user configuration. A row-wise
checksum is placed in the text file that is stored on the configured TFTP
server. On switch startup, the switch reads the text file and uses the contents
to build the DHCP snooping database. If the calculated checksum value
equals the stored checksum, the switch uses the entries from the binding file
and populates the binding database. Checksum failure or a connection
problem to the external configured server causes the switch to lose the
bindings and may cause connectivity loss for hosts if IPSG or DAI is enabled.
ipv6 dhcp snooping database write-delay
Use the ipv6 dhcp snooping database write-delay command to configure the
time period between successive writes of the binding database. The binding
database is used to persistently store the DHCP bindings. Use the no form of
the command to return the write delay to the default value.
Syntax
ipv6 dhcp snooping database write-delay
seconds
no ipv6 dhcp snooping write-delay
•
seconds
—The period of time between successive writes of the binding
database to persistent storage. (Range 15-86400 seconds.)
Default Configuration
By default, the write delay is 300 seconds.
Command Modes
Global Configuration mode
User Guidelines
The binding database is cached in memory and written to storage every
write-
delay
seconds.
2CSNXXX_SWUM200.book Page 980 Tuesday, December 10, 2013 1:22 PM

DHCPv6 Snooping Commands 981
ipv6 dhcp snooping limit
Use the ipv6 dhcp snooping limit command configures an interface to be
diagnostically disabled if the rate of received DHCP messages exceeds the
configured limit. Use the no shutdown command to reenable the interface.
Use the no form of the command to disable diagnostic disabling of the
interface.
Syntax
ipv6 dhcp snooping limit {rate
pps
[burst interval
seconds
]}
no ipv6 dhcp snooping limit
• pps—The rate in packets per interval. (Range 0-300.)
• seconds—The time interval over which to measure a burst of packets.
(Range 1-15, default 1 second.)
Default Configuration
By default, DHCP messages do not shut down the interface.
Command Modes
Interface Configuration mode
User Guidelines
The switch hardware rate limits DHCP packets sent to the CPU from
snooping enabled interfaces to 512 Kbps.
To prevent DHCP packets from being used in a DoS attack when DHCP
snooping is enabled, the snooping application allows configuration of rate
limiting for received DHCP packets. DHCP snooping monitors the receive
rate on each interface separately. If the receive rate exceeds the configured
limit within the configured interval, DHCP snooping diagnostically
disablesthe interface. The administrator must perform the no shutdown
command on the affected interface to reenable the interface.
2CSNXXX_SWUM200.book Page 981 Tuesday, December 10, 2013 1:22 PM

982 DHCPv6 Snooping Commands
The administrator can configure the rate and burst interval. Rate limiting is
configured independently on each physical interface and may be enabled on
both trusted and untrusted interfaces. The rate limit is configurable in the
range of 0-300 packets per second and the burst interval in the range of 1-15
seconds.
ipv6 dhcp snooping log-invalid
Use the ipv6 dhcp snooping log-invalid command to configure the port to
log invalid received DHCP messages.
Syntax
ipv6 dhcp snooping log-invalid
no ipv6 dhcp snooping log-invalid
Default Configuration
By default, invalid DHCP messages are not logged.
Command Modes
Interface Configuration mode
User Guidelines
An invalid DHCP message is one that is received on an untrusted interface
that is not a member of the VLAN over which the IP address (and optionally
the MAC address) has been learned. Receiving large number of invalid
messages may be an indication of an attack.
Logging invalid messages can use valuable CPU resources if the switch
receives such messages at a high rate. To avoid allowing the switch to be
vulnerable to a DoS attack, DHCP snooping only logs invalid messages if the
user has enabled logging. Logging is enabled on individual interfaces so that
only messages on interfaces of interest are logged. To further protect the
system, invalid message logging is rate limited to 1 per second.
2CSNXXX_SWUM200.book Page 982 Tuesday, December 10, 2013 1:22 PM

DHCPv6 Snooping Commands 983
ipv6 dhcp snooping trust
Use the ipv6 dhcp snooping trust command to configure an interface as
trusted. Use the no form of the command to return the interface to the
default configuration.
Syntax
ipv6 dhcp snooping trust
no ipv6 dhcp snooping trust
Default Configuration
By default, interfaces are untrusted.
Command Modes
Interface Configuration mode (physical and port-channel)
User Guidelines
Configuring an interface as trusted disables DHCP snooping address
validation checking and exposes the port to IPv6 DHCP DoS attacks.
DHCP snooping must be enabled globally and on the VLAN for which the
port is a member for this command to have an effect. Configuring a port as
trusted indicates that the port is connected to an IPv6 DHCP server or to a
trusted device. Configuring a port as untrusted indicates that the switch
should firewall IPv6 DHCP messages and act as if the port is connected to an
untrusted device.
Use the ipv6 verify source command to disable traffic from untrusted sources
on an interface.
ipv6 dhcp snooping verify mac-address
Use the ipv6 dhcp snooping verify mac-address command to enable the
additional verification of the source MAC address with the client hardware
address in the received DHCP message.
Syntax
ipv6 dhcp snooping verify mac-address
2CSNXXX_SWUM200.book Page 983 Tuesday, December 10, 2013 1:22 PM

984 DHCPv6 Snooping Commands
no ipv6 dhcp snooping verify mac-address
Default Configuration
By default, MAC address verification is not enabled.
Command Modes
Global Configuration mode
User Guidelines
DHCP MAC address verification operates on DHCP messages received over
untrusted interfaces. The source MAC address of DHCP packet is different
from the client hardware if:
• A DHCP discovery/request broadcast packet that was forwarded by the
relay agent.
• A DHCP unicast request packet was routed in renew process.
For DHCP servers and relay agents connected to untrusted interfaces, source
MAC verification should be disabled.
DHCP snooping must be enabled on at least one VLAN and globally enabled
to become operational.
Example
console(config)#ipv6 dhcp snooping
console(config)#ipv6 dhcp snooping vlan 5-10,15,30
console(config)#interface te1/0/1
console(config-if-te1/0/1)#switchport mode access
console(config-if-te1/0/1)#switchport access vlan 10
console(config-if-te1/0/1)#no ipv6 dhcp snooping trust
console(config-if-te1/0/1)#exit
console(config)#ipv6 dhcp snooping verify mac-address
ipv6 verify binding
Use the ipv6 verify binding command to configure a static IP
source guard binding.
2CSNXXX_SWUM200.book Page 984 Tuesday, December 10, 2013 1:22 PM

DHCPv6 Snooping Commands 985
Syntax
ipv6 verify binding
mac-address
vlan
vlan-id
ip-address
interface
interface id
no ipv6 verify binding
mac-address
vlan
vlan-id
ip-address
interface
interface
id
•
mac-address
—A valid mac address in standard format.
•
vlan-id
—A configured VLAN id. (Range 1-4093.
•
ip-address
—A valid IPv6 address.
•
interface-id
—A valid interface ID in short or long format.
Default Configuration
By default, no static IP Source Guard entries are configured.
Command Modes
Global Configuration mode
User Guidelines
Traffic is filtered based upon the source IPv6 address and VLAN. Use the port
security command in interface mode to optionally add MAC address filtering
in addition to source IPv6 address filtering. If port security is enabled, the
filtering is based upon IPv6 address, MAC address and VLAN.
ipv6 verify source
Use the ipv6 verify source command to configure an interface to filter (drop)
incoming traffic from sources that are not present in the DHCP binding
database. Use the no form of the command to enable unverified traffic to
flow over the interfaces.
Syntax
ipv6 verify source [port-security]
no ipv6 verify source
•
port-security
— Enables filtering based upon source IP address, VLAN and
MAC address.
2CSNXXX_SWUM200.book Page 985 Tuesday, December 10, 2013 1:22 PM

986 DHCPv6 Snooping Commands
Default Configuration
By default, no sources are blocked.
Command Modes
Interface Configuration mode (physical and port-channel)
User Guidelines
DHCP snooping should be enabled on any interfaces for which ipv6 verify
source is configured. If ipv6 verify source is configured on an interface for
which DHCP snooping is disabled, or for which DHCP snooping is enabled
and the interface is trusted, incoming traffic on the interface is dropped.
Traffic is filtered based on the source IP address and VLAN. When the port-
security keyword is configured, filtering occur based upon source IP address,
VLAN and source MAC address.
IP source guard also interacts with the port security component. Use the port
security command in interface mode to optionally add checking of learned
MAC addresses. When port security is enabled, MAC learning coordinates
with the IP Source Guard component to verify that the MAC address is in the
DHCP binding database. If it is not, port security is notified that the frame is
in violation of the security policy.
show ipv6 dhcp snooping
Use the show ipv6 dhcp snooping command to display the IPv6 DHCP
snooping configuration
Syntax
show ipv6 dhcp snooping
Default Configuration
This command has no default configuration.
Command Modes
User EXEC, Privileged EXEC (all show modes)
2CSNXXX_SWUM200.book Page 986 Tuesday, December 10, 2013 1:22 PM

DHCPv6 Snooping Commands 987
User Guidelines
This command has not user guidelines.
Example
(console)#show ipv6 dhcp snooping
DHCP snooping is Disabled
DHCP snooping source MAC verification is enabled
DHCP snooping is enabled on the following VLANs:
11 - 30, 40
Interface Trusted Log Invalid Pkts
--------- -------- ----------------
Gi1/0/1 Yes No
Gi1/0/2 No Yes
Gi1/0/3 No Yes
Gi1/0/4 No No
Gi1/0/6 No No
show ipv6 dhcp snooping binding
Use the show ipv6 dhcp snooping binding command to display the IPv6
DHCP snooping configuration
Syntax
show ipv6 dhcp snooping binding [{static|dynamic}] [interface
interface-id
| port-channel
port-channel-id
] [vlan
vlan-id
]
•
static
—Only show static entries.
•
dynamic
—Only show dynamic entries.
•
interface-id
—Limit the display to entries associated with
interface-id
.
•
vlan-id
—Limit the display to entries associated with VLAN
vlan-id
.
Default Configuration
This command has no default configuration.
Command Modes
User EXEC, Privileged EXEC (all show modes)
2CSNXXX_SWUM200.book Page 987 Tuesday, December 10, 2013 1:22 PM

988 DHCPv6 Snooping Commands
User Guidelines
There are no user guidelines for this command.
Example
(console)#show ipv6 dhcp snooping binding
Total number of bindings: 2
MAC Address IPv6 Address VLAN Interface Lease time(Secs)
------------------ ------------ ---- --------- -------------
00:02:B3:06:60:80 2000::1/64 10 0/1 86400
00:0F:FE:00:13:04 3000::1/64 10 0/1 86400
show ipv6 dhcp snooping database
Use the show ipv6 dhcp snooping database command to display IPv6 DHCP
snooping configuration related to database persistency.
Syntax
show ipv6 dhcp snooping database
Default Configuration
This command has no default configuration.
Command Modes
User EXEC, Privileged EXEC (all show modes)
User Guidelines
This command has no user guidelines.
Example
(console) #show ipv6 dhcp snooping database
agent url: /10.131.13.79:/sai1.txt
write-delay: 5000
2CSNXXX_SWUM200.book Page 988 Tuesday, December 10, 2013 1:22 PM

DHCPv6 Snooping Commands 989
show ipv6 dhcp snooping interfaces
Use the show ipv6 dhcp snooping interfaces command to show the DHCP
Snooping status of IPv6 interfaces.
Syntax
show ipv6 dhcp snooping interfaces [
interface id
]
•
interface id
—A valid physical interface.
Default Configuration
There is no default configuration for this command.
Command Modes
User EXEC, Privileged EXEC (all show modes)
User Guidelines
If no parameter is given, all interfaces are shown.
Example
(console) #show ipv6 dhcp interfaces
Interface Trust State Rate Limit Burst Interval
(pps) (seconds)
---------- ------------- ------------- ---------------
Gi1/0/1 No 15 1
Gi1/0/2 No 15 1
Gi1/0/3 No 15 1
show ipv6 dhcp snooping statistics
Use the show ipv6 dhcp snooping statistics command to display IPv6 dhcp
snooping filtration statistics.
Syntax
show ipv6 dhcp snooping statistics
2CSNXXX_SWUM200.book Page 989 Tuesday, December 10, 2013 1:22 PM

990 DHCPv6 Snooping Commands
Default Configuration
This command has no default configuration.
Command Modes
User EXEC, Privileged EXEC (all show modes)
User Guidelines
The following statistics are displayed.
Example
(console) #show ipv6 dhcp snooping statistics
Interface MAC Verify Client Ifc DHCP Server
Failures Mismatch Msgs Rec'd
----------- ---------- ---------- -----------
Gi1/0/2 0 0 0
Gi1/0/3 0 0 0
Gi1/0/4 0 0 0
Gi1/0/5 0 0 0
Gi1/0/6 0 0 0
show ipv6 source binding
Use the show ipv6 source binding command to display the IPv6 Source
Guard configurations on all ports, on an individual port, or on a VLAN.
Parameter Description
MAC Verify Failures The number of DHCP messages that got filtered
on an untrusted interface because of the source
MAC address and client hardware address
mismatch.
Client Ifc mismatch The number of DHCP release and reply messages
received on different ports than the ones they were
learned on previously.
DHCP Server Msgs It represents the number of DHCP server messages
received on Untrusted ports.
2CSNXXX_SWUM200.book Page 990 Tuesday, December 10, 2013 1:22 PM

DHCPv6 Snooping Commands 991
Syntax
show ipv6 source binding [{dhcp-snooping | static}] [interface
interface-id
]
[vlan vlan-id]
• dhcp-snooping — Displays the DHCP snooping bindings.
• static —Displays the statically configured bindings.
Default Configuration
This command has no default configuration.
Command Modes
User EXEC, Privileged EXEC (all show modes)
User Guidelines
This command has no user guidelines.
Example
(console) #show ipv6 source binding
MAC Address IP Address Type Vlan Interface
----------------- --------------- ------------- ----- ---------
00:00:00:00:00:08 2000::1 dhcpv6-snooping 2 Gi1/0/1
00:00:00:00:00:09 3000::1 dhcpv6-snooping 3 Gi1/0/1
00:00:00:00:00:0A 4000::1 dhcpv6-snooping 4 Gi1/0/1
show ipv6 verify
Use the show ipv6 verify command to display the IPv6 Source Guard
configuration on all interfaces or the specified interface.
Syntax
show ipv6 verify [interface
if-id
]
•
if-id
—A valid interface ID (physical)
Default Configuration
There is no default configuration for this command.
2CSNXXX_SWUM200.book Page 991 Tuesday, December 10, 2013 1:22 PM

992 DHCPv6 Snooping Commands
Command Modes
User EXEC, Privileged EXEC (all show modes)
User Guidelines
The filter type is one of the following values:
• ipv6-mac: User has configure MAC address filtering on this interface
• ipv6: IPv6 address filtering is configured on this interface
• N/A: No filtering is configured on the interface
Example
console(config-if-Gi1/0/5)#show ipv6 verify
Interface Filter Type
----------- -----------
Gi1/0/1 ipv6
Gi1/0/2 ipv6-mac
Gi1/0/3 N/A
Gi1/0/4 N/A
Gi1/0/5 ipv6-mac
Gi1/0/6 N/A
Gi1/0/7 N/A
Gi1/0/8 N/A
Gi1/0/9 N/A
console(config-if-Gi1/0/5)#show ipv6 verify interface gi1/0/5
Interface Filter Type
----------- -----------
Gi1/0/5 ipv6-mac
show ipv6 verify source
Use the show ipv6 verify source command to display the IPv6 Source Guard
configurations on all ports.
Syntax
show ipv6 verify source
2CSNXXX_SWUM200.book Page 992 Tuesday, December 10, 2013 1:22 PM

DHCPv6 Snooping Commands 993
Default Configuration
There is no default configuration for this command.
Command Modes
User EXEC, Privileged EXEC (all show modes)
User Guidelines
If MAC address filtering is not configured on the interface, the MAC Address
field is empty. If port security is disabled on the interface, the MAC Address
field displays permit-all.
The filter type is one of the following:
• ipv6-mac: User has configured MAC address filtering on this interface.
• ipv6: Only IPv6 address filtering is configured on this interface.
Example
show ipv6 verify source
Interface Filter Type IPv6 Address MAC Address Vlan
--------- ----------- --------------- ----------------- -----
Gi1/0/1 ipv6-mac 2000::1/64 00:02:B3:06:60:80 10
Gi1/0/1 ipv6-mac 3000::1/64 00:0F:FE:00:13:04 10
2CSNXXX_SWUM200.book Page 993 Tuesday, December 10, 2013 1:22 PM

994 DHCPv6 Snooping Commands
2CSNXXX_SWUM200.book Page 994 Tuesday, December 10, 2013 1:22 PM

DVMRP Commands 995
49
DVMRP Commands
Dell Networking N3000/N4000 Series Switches
Distance Vector Multicast Routing Protocol (DVMRP) is a dense mode
multicast protocol and is most appropriate for use in networks where
bandwidth is relatively plentiful and there is at least one multicast group
member in each subnet. DVMRP assumes that all hosts are part of a
multicast group until it is informed of multicast group changes. When the
dense-mode multicast router is informed of a group membership change, the
multicast delivery tree is pruned. DVMRP uses a distributed routing
algorithm to build per-source-group multicast trees. It is also called Broadcast
and Prune Multicasting protocol. It dynamically generates per-source-group
multicast trees using Reverse Path Multicasting. Trees are calculated and
updated dynamically to track membership of individual groups.
Commands in this Chapter
This chapter explains the following commands:
ip dvmrp
Use the ip dvmrp command to set the administrative mode of DVMRP in the
router to active. Enabling DVMRP concurrently enables IGMP/MLD. Using
the no form of the command sets the administrative mode to inactive and
disables IGMP/MLD. This command does not affect IP multicast routing.
Syntax
ip dvmrp
no ip dvmrp
ip dvmrp show ip dvmrp neighbor
ip dvmrp metric show ip dvmrp nexthop
show ip dvmrp show ip dvmrp prune
show ip dvmrp interface show ip dvmrp route
2CSNXXX_SWUM200.book Page 995 Tuesday, December 10, 2013 1:22 PM

996 DVMRP Commands
Default Configuration
Disabled is the default configuration.
Command Mode
Global Configuration
Interface Configuration (VLAN) mode
User Guidelines
PIM must be disabled before DVMRP can be enabled.
Example
The following example sets VLAN 15’s administrative mode of DVMRP to
active.
console(config)#interface vlan 15
console(config-if-vlan15)#ip dvmrp
ip dvmrp metric
Use the ip dvmrp metric command in Interface Configuration mode to
configure the metric for an interface. This value is used in the DVMRP
messages as the cost to reach this network.
Syntax
ip dvmrp metric
metric
no ip dvmrp metric
•
metric
— Cost to reach the network. (Range: 1-31)
Default Configuration
1 the default value.
Command Mode
Interface Configuration (VLAN) mode
2CSNXXX_SWUM200.book Page 996 Tuesday, December 10, 2013 1:22 PM

DVMRP Commands 997
User Guidelines
This command has no user guidelines.
Example
The following example configures a metric of 5 for VLAN 15.
console(config)#interface vlan 15
console(config-if-vlan15)#ip dvmrp metric 5
show ip dvmrp
Use the show ip dvmrp command in Privileged EXEC mode to display the
system-wide information for DVMRP.
Syntax
show ip dvmrp
Default Configuration
This command has no default condition.
Command Mode
Privileged EXEC mode, Configuration mode and all Configuration submodes
User Guidelines
This command has no user guidelines.
Example
The following example displays system-wide information for DVMRP.
console(config)#show ip dvmrp
Admin Mode................................. Enabled
Version.................................... 3
Total Number of Routes..................... 0
Reachable Routes........................... 0
DVMRP INTERFACE STATUS
Interface Interface Mode Operational-Status
--------- -------------- ------------------
2CSNXXX_SWUM200.book Page 997 Tuesday, December 10, 2013 1:22 PM

998 DVMRP Commands
show ip dvmrp interface
Use the show ip dvmrp interface command in Privileged EXEC mode to
display the interface information for DVMRP on the specified interface.
Syntax
show ip dvmrp interface vlan
vlan-id
•
vlan-id
— Valid VLAN ID.
Default Configuration
This command has no default condition.
Command Mode
Privileged EXEC mode, Configuration mode and all Configuration submodes
User Guidelines
This command has no user guidelines.
Example
The following example displays interface information for VLAN 11 DVMRP.
console(config)#show ip dvmrp interface vlan 11
Interface Mode................................. Enabled
Interface Metric .............................. 1
Local Address ................................. 10.1.0.2
show ip dvmrp neighbor
Use the show ip dvmrp neighbor command in Privileged EXEC mode to
display the neighbor information for DVMRP.
Syntax
show ip dvmrp neighbor
Default Configuration
This command has no default condition.
2CSNXXX_SWUM200.book Page 998 Tuesday, December 10, 2013 1:22 PM

DVMRP Commands 999
Command Mode
Privileged EXEC mode, Configuration mode and all Configuration submodes
User Guidelines
This command has no user guidelines.
Example
The following example displays the neighbor information for DVMRP.
console(config)#show ip dvmrp neighbor
No neighbors available.
show ip dvmrp nexthop
Use the show ip dvmrp nexthop command in Privileged EXEC mode to
display the next hop information on outgoing interfaces for routing multicast
datagrams.
Syntax
show ip dvmrp nexthop
Default Configuration
This command has no default condition.
Command Mode
Privileged EXEC mode, Configuration mode and all Configuration submodes
User Guidelines
This command has no user guidelines.
Example
The following example displays the next hop information on outgoing
interfaces for routing multicast datagrams.
console(config)#show ip dvmrp nexthop
Next Hop
Source IP Source Mask Interface Type
-------------- -------------- --------- ------
2CSNXXX_SWUM200.book Page 999 Tuesday, December 10, 2013 1:22 PM

1000 DVMRP Commands
show ip dvmrp prune
Use the show ip dvmrp prune command in Privileged EXEC mode to display
the table that lists the router’s upstream prune information.
Syntax
show ip dvmrp prune
Default Configuration
This command has no default condition.
Command Mode
Privileged EXEC mode, Configuration mode and all Configuration submodes
User Guidelines
This command has no user guidelines.
Example
The following example displays the table that lists the router’s upstream
prune information.
console(config)#show ip dvmrp prune
Group IP Source IP Source Mask Expiry Time(secs)
-------------- -------------- -------------- ----------------
239.0.1.43 10.1.0.3 255.255.0.0 237
show ip dvmrp route
Use the show ip dvmrp route command in Privileged EXEC mode to display
the multicast routing information for DVMRP.
Syntax
show ip dvmrp route
Default Configuration
This command has no default.
2CSNXXX_SWUM200.book Page 1000 Tuesday, December 10, 2013 1:22 PM

DVMRP Commands 1001
Command Mode
Privileged EXEC mode, Configuration mode and all Configuration submodes
User Guidelines
This command has no user guidelines.
Example
The following example displays the multicast routing information for
DVMRP.
console#show ip dvmrp route
console(config)#show ip dvmrp route
Upstream Expiry
Source Address Source Mask Neighbor Intf Metric Time
UpTime
2CSNXXX_SWUM200.book Page 1001 Tuesday, December 10, 2013 1:22 PM

1002 DVMRP Commands
2CSNXXX_SWUM200.book Page 1002 Tuesday, December 10, 2013 1:22 PM

GMRP Commands 1003
44
GMRP Commands
Dell Networking N2000/N3000/N4000 Series Switches
The GARP Multicast Registration Protocol provides a mechanism that allows
networking devices to dynamically register (and deregister) Group
membership information with the MAC networking devices attached to the
same segment, and for that information to be disseminated across all
networking devices in the bridged LAN that support Extended Filtering
Services. The operation of GMRP relies upon the services provided by the
Generic Attribute Registration Protocol (GARP). GMRP is supported as
described below.
The information registered, deregistered and disseminated via GMRP is in
the following forms:
1
Group Membership information: This indicates that there exists one or
more GMRP participants which are members of a particular Group, and
carry the group MAC addresses associated with the Group.
2
Group service requirements information: This indicates that one or more
GMRP participants require Forward all Groups or Forward Unregistered to
be the default filtering behavior.
NOTE: The Group Service capability is not supported.
Registration of group membership information allow networking devices to
be made aware that frames destined for that group MAC address concerned
should be forwarded in the direction of registered members of the group.
Forwarding of frames destined for that group MAC address occur on ports on
which such membership registration has been received.
Registration of group services requirement information allow networking
devices to be made aware that any of their ports that can forward frames in
the direction from which the group service requirement information has been
received should modify their default group behavior in accordance with the
group service requirement expressed.
2CSNXXX_SWUM200.book Page 1003 Tuesday, December 10, 2013 1:22 PM

1004 GMRP Commands
NOTE: The Group Service capability is not supported.
The registration and deregistration of membership results in the multicast
table being updated with a new entry or the existing entry modified.
This ensures that the networking device receives multicast frames from all
ports but forwards them through only those ports for which GMRP has
created Group registration entry (for that multicast address). Registration
entries created by GMRP ensures that frames are not transmitted on LAN
segments which neither have registered GMRP participants nor are in the
path through the active topology between the sources of the frames and the
registered group members.
Commands in this Chapter
This chapter explains the following commands:
gmrp enable
Use the gmrp enable command in Global Configuration mode to enable
GMRP globally or Interface Configuration mode to enable GMRP on a port.
Syntax
gmrp enable
no gmrp enable
Default Configuration
GMRP is disabled by default.
Command Mode
Global Configuration and Interface Configuration modes
User Guidelines
IGMP snooping is incompatible with GMRP and must be disabled on any
VLANs running GMRP.
gmrp enable show gmrp configuration
2CSNXXX_SWUM200.book Page 1004 Tuesday, December 10, 2013 1:22 PM

GMRP Commands 1005
Example
In this example, GMRP is globally enabled.
console(config)#gmrp enable
show gmrp configuration
Use the show gmrp configuration command in Global Configuration mode
and Interface Configuration mode to display GMRP configuration.
Syntax
show gmrp configuration
Default Configuration
GMRP is disabled by default.
Command Mode
Global Configuration and Interface Configuration modes
User Guidelines
This command has no user guidelines.
Example
console#show gmrp configuration
Global GMRP Mode: Disabled
Join Leave LeaveAll Port
Interface Timer Timer Timer GMRP Mode
(centisecs) (centisecs) (centisecs)
----------- ----------- ----------- ----------- -----------
Gi1/0/1 20 60 1000 Disabled
Gi1/0/2 20 60 1000 Disabled
Gi1/0/3 20 60 1000 Disabled
Gi1/0/4 20 60 1000 Disabled
Gi1/0/5 20 60 1000 Disabled
Gi1/0/6 20 60 1000 Disabled
2CSNXXX_SWUM200.book Page 1005 Tuesday, December 10, 2013 1:22 PM

1006 GMRP Commands
2CSNXXX_SWUM200.book Page 1006 Tuesday, December 10, 2013 1:22 PM

IGMP Commands 1007
45
IGMP Commands
Dell Networking N3000/N4000 Series Switches
The Dell Network N2000 series supports limited routing and multicast capabilities.
See the Users Configuration Guide section “Feature Limitations and Platform
Constants” for supported capabilities.
Internet Group Management Protocol (IGMP) is the multicast group
membership discovery protocol used for IPv4 multicast groups. Three
versions of IGMP exist. Versions one and two are widely deployed. Since
IGMP is used between end systems (often desktops) and the multicast router,
the version of IGMP required depends on the end-user operating system
being supported. Any implementation of IGMP must support all earlier
versions.
The following list describes the basic operation of IGMP, common to all
versions. A multicast router can act as both an IGMP host and an IGMP
router and as a result can respond to its own IGMP messages. The Dell
Networking implementation of IGMPv3 supports the multicast router
portion of the protocol (that is, not the host portion). It is backward
compatible with IGMPv1 and IGMPv2.
• One router periodically broadcasts IGMP Query messages onto the
network.
• Hosts respond to the Query messages by sending IGMP Report messages
indicating their group memberships.
• All routers receive the Report messages and note the memberships of hosts
on the network.
• If a router does not receive a Report message for a particular group for a
period of time, the router assumes there are no more members of the
group on the network.
All IGMP messages are raw IP data grams and are sent to multicast group
addresses, with a time to leave (TTL) of 1. Since raw IP does not provide
reliable transport, some messages are sent multiple times to aid reliability.
2CSNXXX_SWUM200.book Page 1007 Tuesday, December 10, 2013 1:22 PM

1008 IGMP Commands
IGMPv3 is a major revision of the protocol and provides improved group
membership latency. When a host joins a new multicast group on an
interface, it immediately sends an unsolicited IGMP Report message for that
group.
IGMPv2 introduced a Leave Group message, which is sent by a host when it
leaves a multicast group for which it was the last host to send an IGMP
Report message. Receipt of this message causes the Querier possibly to
reduce the remaining lifetime of its state for the group, and to send a group-
specific IGMP Query message to the multicast group.The Leave Group
message is not used with IGMPv3, since the source address filtering
mechanism provides the same functionality.
IGMPv3 also allows hosts to specify the list of hosts from which they want to
receive traffic. Traffic from other hosts is blocked inside the network. It also
allows hosts to block packets for all sources sending unwanted traffic.
IGMPv3 adds the capability for a multicast router to learn which sources are
of interest to neighboring systems for packets sent to any particular multicast
address. This information gathered by IGMP is provided to the multicast
routing protocol (that is, DVMRP, PIM-DM, and PIM-SM) that is currently
active on the router in order to ensure multicast packets are delivered to all
networks where there are interested receivers.
IGMP mode is automatically enabled when PIM, DVMRP, or IGMP Proxy is
enabled.
Commands in this Chapter
This chapter explains the following commands:
ip igmp last-member-query-count ip igmp startup-query-interval
ip igmp last-member-query-interval ip igmp version
ip igmp mroute-proxy show ip igmp
ip igmp query-interval show ip igmp groups
ip igmp query-max-response-time show ip igmp interface
ip igmp robustness show ip igmp membership
ip igmp startup-query-count show ip igmp interface stats
2CSNXXX_SWUM200.book Page 1008 Tuesday, December 10, 2013 1:22 PM

IGMP Commands 1009
ip igmp last-member-query-count
Use the ip igmp last-member-query-count command in Interface
Configuration mode to set the number of Group-Specific Queries sent before
the router assumes that there are no local members on the interface.
Syntax
ip igmp last-member-query-count
Imqc
no ip igmp last-member-query-count
•
Imqc
— Query count. (Range: 1-20)
Default Configuration
The default last member query count is 2.
Command Mode
Interface Configuration (VLAN) mode
User Guidelines
This command has no user guidelines.
Example
The following example sets 10 as the number of VLAN 2 Group-Specific
Queries.
console#configure
console(config)#interface vlan 2
console(config-if-vlan2)#ip igmp last-member-query-count 10
console(config-if-vlan2)#no ip igmp last-member-query-count
ip igmp last-member-query-interval
Use the ip igmp last-member-query-interval command in Interface
Configuration mode to configure the Maximum Response Time inserted in
Group-Specific Queries which are sent in response to Leave Group messages.
Syntax
ip igmp last-member-query-interval
tenthsofseconds
2CSNXXX_SWUM200.book Page 1009 Tuesday, December 10, 2013 1:22 PM

1010 IGMP Commands
no ip igmp last-member-query-interval
•
tenthsofseconds
— Maximum Response Time in tenths of a second
(Range: 0-255)
Default Configuration
The default Maximum Response Time value is ten (in tenths of a second).
Command Mode
Interface Configuration (VLAN) mode
User Guidelines
This command has no user guidelines.
Example
The following example configures 2 seconds as the Maximum Response Time
inserted in VLAN 15’s Group-Specific Queries.
console(config)#interface vlan 15
console(config-if-vlan15)#ip igmp last-member-query-interval 20
ip igmp mroute-proxy
This command configures downstream IGMP proxy on the selected VLAN
interface associated with multicast hosts. Use this command to enable the
proxying of IGMP messages received on the local interface to the multicast
router connected interface enabled with the ip igmp proxy-service command.
PIM and DVMRP are not compatible with IGMP proxy. Disable
PIM/DVMRP before enabling IGMP proxy.
Multicast routing must be enabled for the IGMP proxy service to become
operationally enabled.
IGMP is enabled when ip pim sparse-mode, ip pim dense-mode, ip dvmrp,
or ip igmp-proxy are enabled. IP multicast routing must be globally enabled
and an upstream interfaces must be configured using the the ip igmp proxy-
service command. If ip pim or ip dvmrp is enabled, this command is not
displayed in the running-config.
2CSNXXX_SWUM200.book Page 1010 Tuesday, December 10, 2013 1:22 PM

IGMP Commands 1011
Syntax
ip igmp mroute-proxy
no ip igmp mroute-proxy
Default Configuration
Disabled is the default state.
Command Mode
Interface VLAN Configuration mode
User Guidelines
IGMP is enabled when ip pim sparse-mode, ip pim dense-mode, ip dvmrp,
or ip igmp-proxy are enabled.
A multicast routing protocol (e.g. PIM) should be enabled whenever IGMP is
enabled.
L3 IP multicast must be enabled for IGMP to operate.
Example
The following example globally enables IGMP the IGMP proxy service on
VLAN 1.
console(config)#ip multicast-routing
console(config)#interface vlan 1
console(config-if-vlan1)#ip igmp mroute-proxy
ip igmp query-interval
Use the ip igmp query-interval command in Interface Configuration mode to
configure the query interval for the specified interface. The query interval
determines how fast IGMP Host-Query packets are transmitted on this
interface.
Syntax
ip igmp query-interval
seconds
no ip igmp query-interval
2CSNXXX_SWUM200.book Page 1011 Tuesday, December 10, 2013 1:22 PM

1012 IGMP Commands
•
seconds
— Query interval. (Range: 1-3600)
Default Configuration
The default query interval value is 125 seconds.
Command Mode
Interface Configuration (VLAN) mode
User Guidelines
This command has no user guidelines.
Example
The following example configures a 10-second query interval for VLAN 15.
console(config)#interface vlan 15
console(config-if-vlan15)#ip igmp query-interval 10
ip igmp query-max-response-time
Use the ip igmp query-max-response-time command in Internet
Configuration mode to configure the maximum response time interval for
the specified interface. It is the maximum query response time advertised in
IGMPv2 queries on this interface. The time interval is specified in seconds.
Syntax
ip igmp query-max-response-time
seconds
no ip igmp query-max-response-time
•
seconds
— Maximum response time. (Range: 0-25 seconds)
Default Configuration
The default maximum response time value is 10 seconds.
Command Mode
Interface Configuration (VLAN) mode
2CSNXXX_SWUM200.book Page 1012 Tuesday, December 10, 2013 1:22 PM

IGMP Commands 1013
User Guidelines
This command has no user guidelines.
Example
The following example configures a maximum response time interval of one
second for VLAN 15.
console(config)#interface vlan 15
console(config-if-vlan15)#ip igmp query-max-response-time 10
ip igmp robustness
Use the ip igmp robustness command in Interface VLAN Configuration
mode to configure the robustness that allows tuning of the interface, that is,
tuning for the expected packet loss on a subnet. If a subnet is expected to
have significant loss, the robustness variable may be increased for the
interface.
Syntax
ip igmp robustness
robustness
no ip igmp robustness
•
robustness
— Robustness variable. (Range: 1-255)
Default Configuration
The default robustness value is 2.
Command Mode
Interface Configuration (VLAN) mode
User Guidelines
This command has no user guidelines.
Example
The following example configures a robustness value of 10 for VLAN 15.
console(config)#interface vlan 15
console(config-if-vlan15)#ip igmp robustness 10
2CSNXXX_SWUM200.book Page 1013 Tuesday, December 10, 2013 1:22 PM

1014 IGMP Commands
ip igmp startup-query-count
Use the ip igmp startup-query-count command in Interface VLAN
Configuration mode to set the number of queries sent out on startup—at
intervals equal to the startup query interval for the interface.
Syntax
ip igmp startup-query-count
count
no ip igmp startup-query-count
•
count
— The number of startup queries. (Range: 1-20)
Default Configuration
The default count value is 2.
Command Mode
Interface Configuration (VLAN) mode
User Guidelines
This command has no user guidelines.
Example
The following example sets for VLAN 15 the number of queries sent out on
startup at 10.
console(config)#interface vlan 15
console(config-if-vlan15)#ip igmp startup-query-count 10
ip igmp startup-query-interval
Use the ip igmp startup-query-interval command in Interface Configuration
mode to set the interval between general queries sent at startup on the
interface.
Syntax
ip igmp startup-query-interval
seconds
no ip igmp startup-query-interval
2CSNXXX_SWUM200.book Page 1014 Tuesday, December 10, 2013 1:22 PM

IGMP Commands 1015
•
seconds
— Startup query interval. (Range: 1-300 seconds)
Default Configuration
The default interval value is 31 seconds.
Command Mode
Interface Configuration (VLAN) mode
User Guidelines
This command has no user guidelines.
Example
The following example sets at 10 seconds the interval between general queries
sent at startup for VLAN 15.
console(config)#interface vlan 15
console(config-if-vlan15)#ip igmp startup-query-interval 10
ip igmp version
Use the ip igmp version command in Interface Configuration mode to
configure the version of IGMP for an interface.
Syntax
ip igmp version
version
•
version
— IGMP version. (Range: 1-3)
Default Configuration
The default version is 3.
Command Mode
Interface Configuration (VLAN) mode
User Guidelines
This command has no user guidelines.
2CSNXXX_SWUM200.book Page 1015 Tuesday, December 10, 2013 1:22 PM

1016 IGMP Commands
Example
The following example configures version 2 of IGMP for VLAN 15.
console#interface vlan 15
console(config-if-vlan15)#ip igmp version 2
show ip igmp
Use the show ip igmp command in Privileged EXEC mode to display system-
wide IGMP information.
Syntax
show ip igmp
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC mode, Configuration mode and all Configuration submodes
User Guidelines
This command has no user guidelines.
Example
The following example displays system-wide IGMP information.
console#show ip igmp
IGMP Admin Mode............................. Enabled
IGMP Router-Alert check..................... Disabled
IGMP INTERFACE STATUS
Interface Interface-Mode Operational-Status
--------- -------------- ----------------
vlan 3 Enabled Non-Operational
2CSNXXX_SWUM200.book Page 1016 Tuesday, December 10, 2013 1:22 PM

IGMP Commands 1017
show ip igmp groups
Use the show ip igmp groups command in User EXEC or Privileged EXEC
modes to display the registered multicast groups on the interface. If detail is
specified, this command displays the registered multicast groups on the
interface in detail.
Syntax
show ip igmp groups [
interface-type interface-number
] [detail]
•
interface-type interface-number
—Interface type of VLAN and a valid VLAN
ID
Default Configuration
This command has no default configuration.
Command Mode
User EXEC, Privileged EXEC modes, Configuration mode and all
Configuration submodes
User Guidelines
This command has no user guidelines.
Example
The following example displays the registered multicast groups for VLAN 1.
console#show ip igmp groups interface vlan 3 detail
REGISTERED MULTICAST GROUP DETAILS
Version1 Version2 Group
Multicast Last Up Expiry Host Host Compat
IP Address Reporter Time Time Timer Timer Mode
--------------- ------------ ---------- --------- ------- -------- -----
225.0.0.5 1.1.1.5 00:00:05 00:04:15 ------ 00:04:15 v2
show ip igmp interface
Use the show ip igmp interface command in Privileged EXEC mode to
display the IGMP information for the specified interface.
2CSNXXX_SWUM200.book Page 1017 Tuesday, December 10, 2013 1:22 PM

1018 IGMP Commands
Syntax
show ip igmp interface [stats][
interface-type interface-number
]
•
interface-type interface-number
—Interface type of VLAN and a valid VLAN
ID
•
stats
—Displays IGMP statistics for the specified VLAN.
Default Configuration
This command has no default configuration.
Command Mode
User EXEC, Privileged EXEC modes, Configuration mode and all
Configuration submodes
User Guidelines
This command has no user guidelines.
Example
The following example displays IGMP information for VLAN 11.
console#show ip igmp vlan 11
Interface..................................... 11
IGMP Admin Mode............................... Enable
Interface Mode................................ Enable
IGMP Version.................................. 3
Query Interval (secs)......................... 125
Query Max Response Time (1/10 of a second).... 100
Robustness..................................... 2
Startup Query Interval (secs)................. 31
Startup Query Count............................ 2
Last Member Query Interval (1/10 of a second). 10
Last Member Query Count........................ 2
show ip igmp membership
Use the show ip igmp membership command in Privileged EXEC mode to
display the list of interfaces that have registered in the multicast group. If
detail is specified, this command displays detailed information about the
listed interfaces.
2CSNXXX_SWUM200.book Page 1018 Tuesday, December 10, 2013 1:22 PM

IGMP Commands 1019
Syntax
show ip igmp membership [
groupaddr
]
[detail]
•
groupaddr
— Group IP address
Default Configuration
This command has no default configuration.
Command Mode
User EXEC, Privileged EXEC modes, Configuration mode and all
Configuration submodes
User Guidelines
This command has no user guidelines.
Examples
The following examples display the list of interfaces that have registered in
the multicast group at IP address 224.5.5.5, the latter in detail mode.
console#show ip igmp interface membership 224.5.5.5
console(config)#show ip igmp interface membership 224.5.5.5 detail
show ip igmp interface stats
Use the show ip igmp interface stats command in User EXEC mode to
display the IGMP statistical information for the interface. The statistics are
only displayed when the interface is enabled for IGMP.
Syntax
show ip igmp interface stats vlan
vlan-id
•
vlan-id
— Valid VLAN ID
Default Configuration
This command has no default configuration.
2CSNXXX_SWUM200.book Page 1019 Tuesday, December 10, 2013 1:22 PM

1020 IGMP Commands
Command Mode
Privileged EXEC, Configuration mode and all Configuration submodes
User Guidelines
This command has no user guidelines.
Examples
The following example displays the IGMP statistical information for VLAN 7.
console#show ip igmp interface stats vlan 7
Querier Status............................... Querier
Querier IP Address........................... 7.7.7.7
Querier Up Time (secs)...................... 55372
Querier Expiry Time (secs).................. 0
Wrong Version Queries........................ 0
Number of Joins.............................. 7
Number of Groups............................. 1
2CSNXXX_SWUM200.book Page 1020 Tuesday, December 10, 2013 1:22 PM

IGMP Proxy Commands 1021
46
IGMP Proxy Commands
Dell Networking N3000/N4000 Series Switches
IGMP Proxy is used by the router on IPv4 systems to enable the system to
issue IGMP host messages on behalf of hosts that the system discovered
through standard IGMP router interfaces, thus acting as proxy to all its hosts
residing on its router interfaces.
Dell Networking supports IGMP Version 3, Version 2 and Version 1. Version 3
adds support for source filtering [SSM] is interoperable with Versions 1 and 2.
Version 2 enhances group membership terminations to be quickly reported to
overcome leave latency and is interoperable with IGMP Version 1.
Commands in this Chapter
This chapter explains the following commands:
ip igmp proxy-service
Use the ip igmp proxy-service command in Interface Configuration mode to
enable the IGMP Proxy on the VLAN interface. Use this command to enable
the sending of IGMP messages received on interfaces configured with the ip
igmp mroute-proxy command to an attached multicast router.
IGMP is enabled with IGMP proxy. Only one interface can be configured with
the IGMP proxy service. This interface forwards IGMP reports to a multicast
router on behalf of IGMP clients configured with the ip igmp mroute-proxy
command.
ip igmp proxy-service show ip igmp proxy-service interface
ip igmp proxy-service reset-status show ip igmp-proxy groups
ip igmp proxy-service unsolicit-rprt-
interval
show ip igmp proxy-service groups detail
show ip igmp proxy-service
–
2CSNXXX_SWUM200.book Page 1021 Tuesday, December 10, 2013 1:22 PM

1022 IGMP Proxy Commands
Syntax
ip igmp proxy-service
no ip igmp proxy-service
Default Configuration
Disabled is the default configuration.
Command Mode
Interface Configuration (VLAN) mode
User Guidelines
This command enables IGMP proxy on the VLAN interface. Use this
command to enable sending of IGMP messages received on interfaces
configured with the ip igmp mroute-proxy command to an attached
multicast router.
PIM and DVMRP are not compatible with IGMP proxy. Disable
PIM/DVMRP before enabling IGMP proxy.
Multicast routing must be enabled for the IGMP proxy service to become
operationally enabled.
Example
The following example enables the IGMP Proxy on the VLAN 15 router.
console(config)#interface vlan 15
console(config-if-vlan15)#ip igmp-proxy
ip igmp proxy-service reset-status
Use the ip igmp proxy-service reset-status command in Interface
Configuration mode to reset the host interface status parameters of the
IGMP Proxy router. This command is valid only when IGMP Proxy is enabled
on the interface.
Syntax
ip igmp proxy-service reset-status
2CSNXXX_SWUM200.book Page 1022 Tuesday, December 10, 2013 1:22 PM

IGMP Proxy Commands 1023
Default Configuration
This command has no default configuration.
Command Mode
Interface Configuration (VLAN) mode
User Guidelines
This command has no user guidelines.
Example
The following example resets the host interface status parameters of the
IGMP Proxy router.
console(config)#interface vlan 15
console(config-if-vlan15)#ip igmp proxy-service reset-status
ip igmp proxy-service unsolicit-rprt-interval
Use the ip igmp proxy-service unsolicit-rprt-interval command in Interface
Configuration mode to set the unsolicited report interval for the IGMP Proxy
router. This command is valid only if IGMP Proxy on the interface is enabled.
Syntax
ip igmp proxy-service unsolicit-rprt-interval
seconds
•
seconds
— Unsolicited report interval. (Range: 1-260 seconds)
Default Configuration
The default configuration is 1 second.
Command Mode
Interface Configuration (VLAN) mode
User Guidelines
This command has no user guidelines.
2CSNXXX_SWUM200.book Page 1023 Tuesday, December 10, 2013 1:22 PM

1024 IGMP Proxy Commands
Example
The following example sets 10 seconds as the unsolicited report interval for
the IGMP Proxy router.
console(config)#interface vlan 15
console(config-if-vlan15)#ip igmp proxy-service unsolicit-rpt-interval 10
show ip igmp proxy-service
Use the show ip igmp proxy-service command in Privileged EXEC mode to
display a summary of the host interface status parameters. It displays status
parameters only when IGMP Proxy is enabled.
Syntax
show ip igmp proxy-service
Default Configuration
This command has no default configuration.
Command Mode
User EXEC, Privileged EXEC mode, Configuration mode and all
Configuration submodes
User Guidelines
This command has no user guidelines.
Example
The following example displays a summary of the host interface status
parameters.
console#show ip igmp proxy-service
Interface Index............................... vlan13
Admin Mode.................................... Enable
Operational Mode.............................. Enable
Version....................................... 3
Number of Multicast Groups.................... 0
Unsolicited Report Interval................... 1
Querier IP Address on Proxy Interface......... 0.0.0.0
Older Version 1 Querier Timeout............... 0
Older Version 2 Querier Timeout............... 0
2CSNXXX_SWUM200.book Page 1024 Tuesday, December 10, 2013 1:22 PM

IGMP Proxy Commands 1025
Proxy Start Frequency........................ 1
show ip igmp proxy-service interface
Use the show ip igmp proxy-service interface command in Privileged EXEC
mode to display a detailed list of the host interface status parameters. It
displays status parameters only when IGMP Proxy is enabled.
Syntax
show ip igmp proxy-service interface
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC mode, Configuration mode and all Configuration submodes
User Guidelines
This command has no user guidelines.
Example
The following example fails to display status parameters because IGMP Proxy
is not enabled.
console#show ip igmp proxy-service interface
Interface Index................................ vlan13
Ver Query Rcvd Report Rcvd Report Sent Leave Rcvd Leave Sent
-----------------------------------------------------------------
1 0 0 0 ----- -----
200000
3 0 0 0 ----- -----
show ip igmp-proxy groups
Use the show ip igmp proxy-service groups command in Privileged EXEC
mode to display a table of information about multicast groups that IGMP
Proxy reported. It displays status parameters only when IGMP Proxy is
enabled.
2CSNXXX_SWUM200.book Page 1025 Tuesday, December 10, 2013 1:22 PM

1026 IGMP Proxy Commands
Syntax
show ip igmp proxy-service groups
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC mode, Configuration mode and all Configuration submodes
User Guidelines
This command has no user guidelines.
Example
The following example attempts to display a table of information about
multicast groups that IGMP Proxy reported.
console#show ip igmp proxy-service groups
Interface Index................................ vlan13
Group Address Last Reporter Up Time Member State Filter Mode Sources
------------- --------------- ------- ------------ ----------- ------
225.0.1.1 13.13.13.1 7 DELAY-MEMBER Exclude 0
225.0.1.2 13.13.13.1 48 DELAY-MEMBER Exclude 0
show ip igmp proxy-service groups detail
Use the show ip igmp proxy-service groups detail command in Privileged
EXEC mode to display complete information about multicast groups that
IGMP Proxy has reported.
Syntax
show ip igmp proxy-service groups detail
Default Configuration
This command has no default configuration.
2CSNXXX_SWUM200.book Page 1026 Tuesday, December 10, 2013 1:22 PM

IGMP Proxy Commands 1027
Command Mode
Privileged EXEC mode, Configuration mode and all Configuration submodes
User Guidelines
This command has no user guidelines.
Example
The following example displays complete information about multicast groups
that IGMP Proxy has reported.
console#show ip igmp proxy-service groups detail
Interface Index................................ vlan13
Group Address Last Reporter Up Time Member State Filter Mode Sources
------------- --------------- ------- ------------ ----------- -------
225.0.1.1 13.13.13.1 26 DELAY-MEMBER Exclude 0
225.0.1.2 13.13.13.1 67 DELAY-MEMBER Exclude 0
2CSNXXX_SWUM200.book Page 1027 Tuesday, December 10, 2013 1:22 PM

1028 IGMP Proxy Commands
2CSNXXX_SWUM200.book Page 1028 Tuesday, December 10, 2013 1:22 PM

IP Helper/DHCP Relay Commands 1029
47
IP Helper/DHCP Relay Commands
Dell Networking N2000/N3000/N4000 Series Switches
The IP Helper feature provides the ability for a router to forward configured
UDP broadcast packets to a particular IP address. This allows applications to
reach servers on non-local subnets. This is possible even when the application
is designed to assume a server is always on a local subnet or when the
application uses broadcast packets to reach the server (with the limited
broadcast address 255.255.255.255, or a network directed broadcast address).
Network administrators can configure relay entries globally and on routing
interfaces. Each relay entry maps an ingress interface and destination UDP
port number to a single IPv4 address (the helper address). Multiple relay
entries may be configured for the same interface and UDP port, in which case
the relay agent relays matching packets to each server address. Interface
configuration takes priority over global configuration. If the destination UDP
port for a packet matches any entry on the ingress interface, the packet is
handled according to the interface configuration. If the packet does not
match any entry on the ingress interface, the packet is handled according to
the global IP helper configuration.
Network administrators can configure discard relay entries. Discard entries are
used to discard packets received on a specific interface when those packets
would otherwise be relayed according to a global relay entry. Discard relay
entries may be configured on interfaces, but are not configured globally.
Additionally, administrators can configure which UDP ports are forwarded.
Certain UDP port numbers can be specified by name in the UI, but network
administrators can configure a relay entry with any UDP port number.
Administrators may configure relay entries that do not specify a destination
UDP port. The relay agent assumes that these entries match packets with the
UDP destination ports listed in
Tab le 47 -1
.
2CSNXXX_SWUM200.book Page 1029 Tuesday, December 10, 2013 1:22 PM

1030 IP Helper/DHCP Relay Commands
Table 47-1. UDP Destination Ports
Certain preexisting configurable DHCP relay options do not apply to relay of
other protocols. These options are unchanged. The user may optionally set a
DHCP maximum hop count or minimum wait time.
The relay agent relays DHCP packets in both directions. It relays broadcast
packets from the client to one or more DHCP servers, and relays packets to
the client that the DHCP server unicasts back to the relay agent. For other
protocols, the relay agent only relays broadcast packets from the client to the
server. Packets from the server back to the client are assumed to be unicast
directly to the client. Because there is no relay in the return direction for
protocols other than DHCP, the relay agent retains the source IP address from
the original client packet. The relay agent uses a local IP address as the source
IP address of relayed DHCP client packets.
When a switch receives a broadcast UDP packet on a routing interface, the
relay agent verifies that the interface is configured to relay to the destination
UDP port. If so, the relay agent unicasts the packet to the configured server IP
addresses. Otherwise, the relay agent verifies that there is a global
configuration for the destination UDP port. If so, the relay agent unicasts the
packet to the configured server IP addresses. Otherwise the packet is not
relayed.
The relay agent only relays packets that meet the following conditions:
• The destination MAC address must be the all-ones broadcast address
(FF:FF:FF:FF:FF:FF).
Protocol UDP Port Number
IEN-116 Name Service 42
DNS 53
NetBIOS Name Server 137
NetBIOS Datagram Server 138
TACACS Server 49
Time Service 37
DHCP 67
Trivial File Transfer Protocol 69
2CSNXXX_SWUM200.book Page 1030 Tuesday, December 10, 2013 1:22 PM

IP Helper/DHCP Relay Commands 1031
• The destination IP address must be the limited broadcast address
(255.255.255.255) or a directed broadcast address for the receive interface.
• The IP time-to-live (TTL) must be greater than 1.
• The protocol field in the IP header must be UDP (17).
• The destination UDP port must match a configured relay entry.
DHCP relay cannot be enabled and disabled globally. IP helper can be
enabled or disabled globally. Enabling IP helper enables DHCP relay.
Commands in this Chapter
This chapter explains the following commands:
bootpdhcprelay maxhopcount
Use the bootpdhcprelay maxhopcount command in Global Configuration
mode to configure the maximum allowable relay agent hops for BootP/DHCP
Relay on the system. Use the no form of the command to set the maximum
hop count to the default value.
Syntax
bootpdhcprelay maxhopcount
integer
no bootpdhcprelay maxhopcount
•
integer
— Maximum allowable relay agent hops for BootP/DHCP Relay on
the system. (Range: 1-16)
bootpdhcprelay maxhopcount ip helper-address (global configuration)
bootpdhcprelay minwaittime ip helper-address (interface configuration)
clear ip helper statistics ip helper enable
ip dhcp relay information check show ip helper-address
ip dhcp relay information check-reply show ip dhcp relay
ip dhcp relay information option show ip helper statistics
ip dhcp relay information option-insert
–
2CSNXXX_SWUM200.book Page 1031 Tuesday, December 10, 2013 1:22 PM

1032 IP Helper/DHCP Relay Commands
Default Configuration
The default
integer
configuration is 4.
Command Mode
Global Configuration mode
User Guidelines
Enable DHCP Relay using the
ip helper enable
command.
Example
The following example defines a maximum hopcount of 6.
console(config)#bootpdhcprelay maxhopcount 6
bootpdhcprelay minwaittime
Use the bootpdhcprelay minwaittime command in Global Configuration
mode to configure the minimum wait time in seconds for BootP/DHCP Relay
on the system. When the BOOTP relay agent receives a BOOTREQUEST
message, it might use the seconds-sinceclient- began-booting field of the
request as a factor in deciding whether to relay the request or not. Use the no
form of the command to set the minimum wait time to the default value.
Syntax
bootpdhcprelay minwaittime
integer
no bootpdhcprelay minwaittime
•
integer
— Minimum wait time for BootP/DHCP Relay on the system.
(Range: 0-100 seconds)
Default Configuration
0 is the default
integer
configuration.
Command Mode
Global Configuration mode
2CSNXXX_SWUM200.book Page 1032 Tuesday, December 10, 2013 1:22 PM

IP Helper/DHCP Relay Commands 1033
User Guidelines
Enable DHCP Relay using the ip helper enable command.
Example
The following example defines a minimum wait time of 10 seconds.
console(config)#bootpdhcprelay minwaittime 10
clear ip helper statistics
Use the clear ip helper statistics command to reset to 0 the statistics
displayed in show ip helper statistics.
Syntax
clear ip helper statistics
Default Configuration
There is no default configuration for this command.
Command Mode
Privileged EXEC mode
User Guidelines
There are no user guidelines for this command.
Example
console#clear ip helper statistics
ip dhcp relay information check
Use the ip dhcp relay information check command to enable DHCP Relay to
check that the relay agent information option in forwarded BOOTREPLY
messages is valid. If an invalid message is received, the relay agent drops it.
This information check will take effect, though enabled, only when the relay
agent interface is enabled to insert the suboptions.
2CSNXXX_SWUM200.book Page 1033 Tuesday, December 10, 2013 1:22 PM

1034 IP Helper/DHCP Relay Commands
Syntax
ip dhcp relay information check
no ip dhcp relay information check
Default Configuration
This is enabled by default for a DHCP relay agent.
Command Mode
Global Configuration mode
User Guidelines
Enable DHCP Relay using the ip helper enable command. Interface
configuration takes precedence over global configuration. However if there is
no interface configuration then global configuration is followed.
This check is enabled by default. The administrator has to ensure that the
relay should be configured such that only it should insert option-82 fields and
no other device near the client has the facility to insert options.
Example
The following example enables relay information check globally:
console(config)#ip dhcp relay information check
ip dhcp relay information check-reply
Use the ip dhcp relay information check-reply command to enable DHCP
Relay to check that the relay agent information option in forwarded
BOOTREPLY messages is valid. If an invalid message is received, the relay
agent drops it. This information check will take effect, though enabled, only
when the relay agent interface is enabled to insert the suboptions.
Syntax
ip dhcp relay information check-reply [none]
no ip dhcp relay information check-reply
•
none
—(Optional) Disables the command function.
2CSNXXX_SWUM200.book Page 1034 Tuesday, December 10, 2013 1:22 PM

IP Helper/DHCP Relay Commands 1035
Default Configuration
This check is enabled by default.
Command Mode
Interface Configuration (VLAN) mode
User Guidelines
Enable DHCP Relay using the ip helper enable command. Use the global
configuration command ip dhcp relay information option command to
enable processing of DHCP circuit ID and remote agent ID options. DHCP
replies are checked by default. The network administrator should ensure that
only one switch in the path between the DHCP client and server processes
DHCP information options.
Example
The following example enables relay information check on the interface:
console(config)#interface vlan 10
console(config-if-vlan10)#ip dhcp relay information check
ip dhcp relay information option
Use the ip dhcp relay information option command in Global Configuration
mode to enable the circuit ID option and remote agent ID mode for
BootP/DHCP Relay on the system (also called option 82). Use the no form of
the command to disable the circuit ID option and remote agent ID mode for
BootP/DHCP Relay.
Syntax
ip dhcp relay information option
no ip dhcp relay information option
Default Configuration
Disabled is the default configuration.
Command Mode
Global Configuration mode
2CSNXXX_SWUM200.book Page 1035 Tuesday, December 10, 2013 1:22 PM

1036 IP Helper/DHCP Relay Commands
User Guidelines
Enable DHCP Relay using the ip helper enable command.
Example
The following example enables the circuit ID and remote agent ID options.
console(config)#ip dhcp relay information option
ip dhcp relay information option-insert
Use the ip dhcp relay information option-insert command in Interface
Configuration mode to enable the circuit ID option and remote agent ID
mode for BootP/DHCP Relay on the interface (also called option 82). Use the
no form of the command to return the option insert configuration to the
default.
Syntax
ip dhcp relay information option-insert [none]
no ip dhcp relay information option-insert
•
none
—Use to disable insertion of circuit id and remote agent id options
into DHCP messages.
Default Configuration
Disabled is the default configuration.
Command Mode
Interface (VLAN) Configuration mode
User Guidelines
Enable DHCP Relay using the ip helper enable command. The interface
configuration always takes precedence over global configuration. However, if
there is no interface configuration, then global configuration is followed.
Example
The following example enables the circuit ID and remote agent ID options on
vlan 10.
2CSNXXX_SWUM200.book Page 1036 Tuesday, December 10, 2013 1:22 PM

IP Helper/DHCP Relay Commands 1037
console(config)#interface vlan 10
console(config-if-vlan10)#ip dhcp relay information option-insert
ip helper-address (global configuration)
Use the ip helper-address (global configuration) command to configure the
relay of certain UDP broadcast packets received on any interface. To delete an
IP helper entry, use the no form of this command.
Syntax
ip helper-address
server-address
[
dest-udp-port
| dhcp | domain | isakmp |
mobile-ip | nameserver | netbios-dgm | netbios-ns | ntp | pim-auto-rp | rip
| tacacs | tftp | time]
no ip helper-address [
server-address
] [
dest-udp-port
| dhcp | domain |
isakmp | mobile-ip | nameserver | netbios-dgm | netbios-ns | ntp | pim-
auto-rp | rip | tacacs | tftp | time]
•
server-address
— The IPv4 unicast or directed broadcast address to which
relayed UDP broadcast packets are sent. The server address cannot be an
IP address configured on any interface of the local router.
•
dest-udp-port
— A destination UDP port number from 0 to 65535.
•
port-name
— The destination UDP port may be optionally specified by its
name. Whether a port is specified by its number or its name has no effect
on behavior. The names recognized are as follows:
dhcp
(port 67),
domain
(port 53),
isakmp
(port 500),
mobile-ip
(port 434),
nameserver
(port 42),
netbios-dgm
(port 138),
netbios-ns
(port 137),
ntp
(port 123),
pim-auto-
rp
(port 496),
rip
(port 520),
tacacs
(port 49),
tftp
(port 69), and
time
(port 37). Other ports must be specified by number.
Default Configuration
No helper addresses are configured.
Command Mode
Global Configuration mode.
2CSNXXX_SWUM200.book Page 1037 Tuesday, December 10, 2013 1:22 PM

1038 IP Helper/DHCP Relay Commands
User Guidelines
This command can be invoked multiple times, either to specify multiple
server addresses for a given port number or to specify multiple port numbers
handled by a specific server.
The command no ip helper-address with no arguments clears all global IP
helper addresses.
Example
To relay DHCP packets received on any interface to two DHCP servers,
10.1.1.1 and 10.1.2.1, use the following commands:
console#config
console(config)#ip helper-address 10.1.1.1 dhcp
console(config)#ip helper-address 10.1.2.1 dhcp
To relay UDP packets received on any interface for all default ports (see
Tab le 47 -1
) to the server at 20.1.1.1, use the following commands:
console#config
console(config)#ip helper-address 20.1.1.1
ip helper-address (interface configuration)
Use the ip helper-address (interface configuration) command to configure
the relay of certain UDP broadcast packets received on a specific interface. To
delete a relay entry on an interface, use the no form of this command.
Syntax
ip helper-address {server-address | discard} [dest-udp-port | dhcp | domain
| isakmp | mobile ip | nameserver | netbios-dgm | netbios-ns | ntp | pim-
auto-rp | rip | tacacs | tftp | time]
no ip helper-address [
server-address
| discard] [
dest-udp-port
| dhcp |
domain | isakmp | mobile-ip | nameserver | netbios-dgm | netbios-ns | ntp
| pim-auto-rp | rip | tacacs | tftp | time]
•
server-address
— The IPv4 unicast or directed broadcast address to which
relayed UDP broadcast packets are sent. The server address cannot be an
IP address configured on any interface of the local router.
2CSNXXX_SWUM200.book Page 1038 Tuesday, December 10, 2013 1:22 PM

IP Helper/DHCP Relay Commands 1039
•
discard
— Matching packets should be discarded rather than relayed, even
if a global ip helper-address configuration matches the packet.
•
dest-udp-port
— A destination UDP port number from 0 to 65535.
•
port-name
— The destination UDP port may be optionally specified by its
name. Whether a port is specified by its number or its name has no effect
on behavior. The names recognized are as follows:
dhcp
(port 67),
domain
(port 53),
isakmp
(port 500),
mobile-ip
(port 434),
nameserver
(port 42),
netbios-dgm
(port 138),
netbios-ns
(port 137),
ntp
(port 123),
pim-auto-
rp
(port 496),
rip
(port 520),
tacacs
(port 49),
tftp
(port 69), and
time
(port 37). Other ports must be specified by number.
Default Configuration
No helper addresses are configured.
Command Mode
Interface Configuration (VLAN) mode.
User Guidelines
This command can be invoked multiple times on routing interface, either to
specify multiple server addresses for a given port number or to specify
multiple port numbers handled by a specific server.
The command no ip helper-address with no arguments clears all helper
addresses on the interface.
Example
To relay DHCP packets received on vlan 5 to two DHCP servers, 192.168.10.1
and 192.168.20.1, use the following commands:
console#config
console(config)#interface vlan 5
console(config-if-vlan5)#ip helper-address 192.168.10.1 dhcp
console(config-if-vlan5)#ip helper-address 192.168.20.1 dhcp
To relay both DHCP and DNS packets to 192.168.30.1, use the following
commands:
console#config
console(config)#interface vlan 5
console(config-if-vlan5)#ip helper-address 192.168.30.1 dhcp
console(config-if-vlan5)#ip helper-address 192.168.30.1 dns
2CSNXXX_SWUM200.book Page 1039 Tuesday, December 10, 2013 1:22 PM

1040 IP Helper/DHCP Relay Commands
This command takes precedence over an ip helper-address command given in
global configuration mode. With the following configuration, the relay agent
relays DHCP packets received on any interface other than vlan 5 and vlan 6 to
192.168.40.1, relays DHCP and DNS packets received on vlan 5 to
192.168.40.2, relays SNMP traps (port 162) received on interface vlan 6 to
192.168.23.1, and drops DHCP packets received on vlan 6:
console#config
console(config)#ip helper-address 192.168.40.1 dhcp
console(config)#interface vlan 5
console(config-if-vlan5)#ip helper-address 192.168.40.2 dhcp
console(config-if-vlan5)#ip helper-address 192.168.40.2 domain
console(config-if-vlan5)#exit
console(config)#interface 2/6
console(config-if-vlan6)#ip helper-address 192.168.23.1 162
console(config-if-vlan6)#ip helper-address discard dhcp
ip helper enable
Use the ip helper enable command to enable relay of UDP packets. To
disable relay of all UDP packets, use the “no” form of this command.
Syntax
ip helper enable
no ip helper enable
Default Configuration
IP helper is enabled by default.
Command Mode
Global Configuration mode.
User Guidelines
This command can be used to temporarily disable IP helper without deleting
all IP helper addresses.
This command replaces the bootpdhcprelay enable command, but affects not
only relay of DHCP packets, but also relay of any other protocols for which an
IP helper address has been configured.
2CSNXXX_SWUM200.book Page 1040 Tuesday, December 10, 2013 1:22 PM

IP Helper/DHCP Relay Commands 1041
Example
console(config)#ip helper enable
show ip helper-address
Use the show ip helper-address command to display the IP helper address
configuration.
Syntax
show ip helper-address [
interface
]
•
interface
— Optionally specify an interface to limit the output to the
configuration of a single interface. The interface is identified as vlan vlan-
id.
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC mode, Configuration mode and all Configuration submodes
User Guidelines
Field Description
Interface The relay configuration is applied to packets that arrive on this
interface. This field is set to “any” for global IP helper entries.
UDP Port The relay configuration is applied to packets whose destination
UDP port is this port. Entries whose UDP port is identified as
“any” are applied to packets with the destination UDP ports listed
in
Table 47-1
.
Discard If “Yes”, packets arriving on the given interface with the given
destination UDP port are discarded rather than relayed. Discard
entries are used to override global IP helper address entries which
otherwise might apply to a packet.
Hit Count The number of times the IP helper entry has been used to relay or
discard a packet.
Server Address The IPv4 address of the server to which packets are relayed.
2CSNXXX_SWUM200.book Page 1041 Tuesday, December 10, 2013 1:22 PM

1042 IP Helper/DHCP Relay Commands
Example
show ip helper-address
IP helper is enabled
Interface UDP Port Discard Hit Count Server Address
--------------- ----------- -------- ---------- ---------------
vlan 100 dhcp No 10 10.100.1.254
10.100.2.254
vlan 101 any Yes 2
any dhcp No 0 10.200.1.254
show ip dhcp relay
Use the show ip dhcp relay command in User EXEC mode to display the
BootP/DHCP Relay information.
Syntax
show ip dhcp relay
Default Configuration
The command has no default configuration.
Command Mode
User EXEC and Privileged EXEC modes, Configuration mode and all
Configuration submodes
User Guidelines
This command has no user guidelines.
Example
The following example defines the Boot/DHCP Relay information.
console#show ip dhcp relay
Maximum Hop Count.............................. 4
Minimum Wait Time(Seconds)..................... 0
Circuit Id Option Mode....................... Disable
Circuit Id Option Check Mode................. Enable
2CSNXXX_SWUM200.book Page 1042 Tuesday, December 10, 2013 1:22 PM
IP Helper/DHCP Relay Commands 1043
show ip helper statistics
Use the show ip helper statistics command to display the number of DHCP
and other UDP packets processed and relayed by the UDP relay agent.
Syntax
show ip helper statistics
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC mode, Configuration mode and all Configuration submodes
User Guidelines
Field Description
DHCP client
messages received
The number of valid messages received from a DHCP client.
The count is only incremented if IP helper is enabled globally,
the ingress routing interface is up, and the packet passes a
number of validity checks, such as having a TTL > 1 and having
valid source and destination IP addresses.
DHCP client
messages relayed
The number of DHCP client messages relayed to a server. If a
message is relayed to multiple servers, the count is incremented
once for each server.
DHCP server
messages received
The number of DHCP responses received from the DHCP
server. This count only includes messages that the DHCP server
unicasts to the relay agent for relay to the client.
DHCP server
messages relayed
The number of DHCP server messages relayed to a client.
UDP client
messages received
The number of valid UDP packets received. This count includes
DHCP messages and all other protocols relayed. Conditions are
similar to those for the first statistic in this table.
UDP client
messages relayed
The number of UDP packets relayed. This count includes
DHCP messages relayed as well as all other protocols. The count
is incremented for each server to which a packet is sent.
2CSNXXX_SWUM200.book Page 1043 Tuesday, December 10, 2013 1:22 PM

1044 IP Helper/DHCP Relay Commands
Example
console#show ip helper statistics
DHCP client messages received.................. 8
DHCP client messages relayed................... 2
DHCP server messages received.................. 2
DHCP server messages relayed................... 2
UDP client messages received................... 8
UDP client messages relayed.................... 2
DHCP message hop count exceeded max............ 0
DHCP message with secs field below min......... 0
DHCP message with giaddr set to local address.. 0
Packets with expired TTL....................... 0
Packets that matched a discard entry........... 0
DHCP message
hop count
exceeded max
The number of DHCP client messages received whose hop
count is larger than the maximum allowed. The maximum hop
count is a configurable value listed in
show ip dhcp relay
. A log
message is written for each such failure. The DHCP relay agent
does not relay these packets.
DHCP message
with secs field
below min
The number of DHCP client messages received with secs fields
that are less than the minimum value. The minimum secs value
is a configurable value and is displayed in
show ip dhcp relay
. A
log message is written for each such failure. The DHCP relay
agent does not relay these packets.
DHCP message
with giaddr set to
local address
The number of DHCP client messages received whose gateway
address, giaddr, is already set to an IP address configured on one
of the relay agent's own IP addresses. In this case, another device
is attempting to spoof the relay agent's address. The relay agent
does not relay such packets. A log message gives details for each
occurrence.
Packets with
expired TTL
The number of packets received with TTL of 0 or 1 that might
otherwise have been relayed.
Packets that
matched a discard
entry
The number of packets ignored by the relay agent because they
match a discard relay entry.
2CSNXXX_SWUM200.book Page 1044 Tuesday, December 10, 2013 1:22 PM

IP Routing Commands 1045
48
IP Routing Commands
Dell Networking N2000/N3000/N4000 Series Switches
The Dell Network N2000 series supports limited routing and multicast capabilities.
See the Users Configuration Guide section “Feature Limitations and Platform
Constants” for supported capabilities.
The Routing Module provides the base Layer 3 support for Local Area
Network (LAN) and Wide Area Network (WAN) environments. The Dell
Networking switches allows the network operator to build a complete Layer
3+ configuration with advanced functionality. As the Dell Networking
defaults to Layer 2 switching functionality, routing must be explicitly enabled
on the Dell Networking to perform Layer 3 forwarding. For Dell Networking
switches, routing is only supported on VLAN and Loopback interfaces for in-
band ports. It is not possible to route packets to or from the out-of-band
interface.
Static Routes/ECMP Static Routes
The operator is able to configure static and default routes with multiple next
hops to any given destination. Permitting the additional routes creates several
options for the Dell Networking network operator.
1
The operator configures multiple next hops to a given destination,
intending for the router to load share across the next hops.
2
The operator configures multiple next hops to a given destination,
intending for the router to use the primary next hops and only use the
other next hops if the primary next hops are unusable.
The operator distinguishes static routes by specifying a route preference
value. A static route with a lower preference value is a more preferred static
route. Next hops with the same preference are grouped into a single ECMP
route. A less preferred static route is used if the more preferred static route is
unusable. (The link is down or the next hop IP address cannot be resolved to a
MAC address.)
2CSNXXX_SWUM200.book Page 1045 Tuesday, December 10, 2013 1:22 PM

1046 IP Routing Commands
In Dell Networking, the operator deletes an individual next hop from a static
route or deletes an entire static route at once. The cost of a static route is
always 1 unless configured otherwise by the operator.
The addition of a preference option has a side benefit. The preference option
allows the operator to control the preference of individual static routes
relative to routes learned from other sources (such as OSPF). When routes
from different sources have the same preference, Dell Networking routing
prefers a static route over a dynamic route.
Static Reject Routes
To administratively control the traffic destined to a particular network so that
it is not forwarded through the router, Dell Networking enables configuring a
static reject route for that network on the router. Such traffic is discarded and
an ICMP destination unreachable message is sent back to the source. Static
reject routes are typically used to prevent routing loops.
Default Routes
Dell Networking routing provides a preference option for the configuration of
default routes. A configured default route is treated exactly like a static route.
Therefore, default routes and static routes have the same default preference
(1).
Commands in this Chapter
This chapter explains the following commands:
encapsulation match length show ip policy
ip address match mac-list show ip protocols
ip netdirbcast route-map show ip route
ip policy route-map set interface null0 show ip route preferences
ip route set ip default next-hop show ip route summary
ip route default set ip next-hop show ip traffic
ip route distance set ip precedence show ip vlan
2CSNXXX_SWUM200.book Page 1046 Tuesday, December 10, 2013 1:22 PM

IP Routing Commands 1047
encapsulation
Use the encapsulation command in Interface Configuration (VLAN) mode
to configure the Link Layer encapsulation type for the packet. Routed frames
are always Ethernet-encapsulated when a frame is routed to a VLAN.
Syntax
encapsulation {ethernet | snap}
•
ethernet —
Specifies Ethernet encapsulation.
•
snap —
Specifies SNAP encapsulation.
Default Configuration
Ethernet encapsulation is the default configuration.
Command Mode
Interface Configuration (VLAN) mode
User Guidelines
This command has no user guidelines.
Example
The following example applies SNAP encapsulation for VLAN 15.
console(config)#interface vlan 15
console(config-if-vlan15)#encapsulation snap
ip address
Use the ip address command in Interface Configuration mode to configure
an IP address on an in-band interface. Also use this command to configure
one or more secondary IP addresses on the interface. The ip address none
command clears the currently assigned IPv4 address and sets the IP address
configuration method to none. The no ip address command clears the
ip routing show ip brief show route-map
match ip address show ip interface show routing heap summary
2CSNXXX_SWUM200.book Page 1047 Tuesday, December 10, 2013 1:22 PM

1048 IP Routing Commands
currently assigned IPv4 address sets the IP address configuration method to
the default (whatever the default is). Use the show ip interface command to
display the configured IP addresses.
Syntax
ip address
ip-address
{
subnet-mask
|
prefix-length
} [secondary]
no ip address
ip-address
{
subnet-mask
|
prefix-length
} [secondary]
•
ip-address
— IP address of the interface.
•
subnet-mask
— Subnet mask of the interface
•
prefix-length
— Length of the prefix. Must be preceded by a forward slash
(/). (Range: 1-30 bits)
•
secondary
— Indicates the IP address is a secondary address.
Default Configuration
The N2000 default IPv4 address assignment method is DHCP on VLAN 1.
The N3000/N4000 default IPv4 address assignment method is none.
Command Mode
Interface Configuration (VLAN, Loopback) mode
User Guidelines
This command also implicitly enables the VLAN or loopback interface for
routing (i.e. as if the user had issued the ‘routing’ interface command). By
default, configuring an IP address on a VLAN enables in-band management
for interfaces configured with that VLAN. Setting up an IP address on VLAN
1 enables switch management on all in-band interfaces except for those where
VLAN 1 is specifically excluded.
Example
The following example defines the IP address and subnet mask for VLAN 15
and enables the VLAN for routing.
console(config)#interface vlan 15
console(config-if-vlan15)#ip address 192.168.10.10 255.255.255.0
2CSNXXX_SWUM200.book Page 1048 Tuesday, December 10, 2013 1:22 PM

IP Routing Commands 1049
ip netdirbcast
Use the ip netdirbcast command in Interface Configuration mode to enable
the forwarding of network-directed broadcasts. When enabled, network
directed broadcasts are forwarded. When disabled they are dropped. Use the
no form of the command to disable the broadcasts.
Syntax
ip netdirbcast
no ip netdirbcast
Default Configuration
Disabled is the default configuration.
Command Mode
Interface Configuration (VLAN) mode
User Guidelines
This command has no user guidelines.
Example
The following example defines the IP address and subnet mask for VLAN 15.
console(config)#interface vlan 15
console(config-if-vlan15)#ip netdirbcast
ip policy route-map
Use this command to apply a route map on an interface. Use the no form of
this command to delete a route map from the interface.
Syntax
ip policy route-map
map-tag
no ip policy route-map
map-tag
•
map-tag
—Name of the route map to use for policy based routing. It must
match a map tag specified by the route-map command.
2CSNXXX_SWUM200.book Page 1049 Tuesday, December 10, 2013 1:22 PM

1050 IP Routing Commands
Default Configuration
No route maps are configured by default.
Command Mode
Interface Configuration (VLAN) mode
User Guidelines
Policy-based routing must be configured on the VLAN interface that receives
the packets, not on the VLAN interface from which the packets are sent.
Packets matching a deny route map are routed using the routing table. Policy
maps with no set clause are ignored.
Example
Considering equal-access as a route-map configured earlier, the following
sequence is an example of how a route map is applied to a VLAN.
console(config)#interface vlan 10
console(config-if-vlan10)#ip policy route-map equal-access
ip route
Use the ip route command in Global Configuration mode to configure a
static route. Use the no form of the command to delete the static route. The
IP route command sets a value for the route preference. Among routes to the
same destination, the route with the lowest preference value is the route
entered into the forwarding database. Specifying the preference of a static
route controls whether a static route is more or less preferred than routes from
dynamic routing protocols. The preference also controls whether a static
route is more or less preferred than other static routes to the same
destination.
Syntax
ip route
networkaddr
{
subnetmask
|
prefix-length
}
nexthopip
[
preference
]
no ip route
networkaddr
{
subnetmask
|
prefix-length
}
nexthopip
[
preference
]
•
networkaddr
— IP address of destination interface.
•
subnetmask
— Subnet mask of destination interface.
2CSNXXX_SWUM200.book Page 1050 Tuesday, December 10, 2013 1:22 PM

IP Routing Commands 1051
•
prefix-length
— Length of prefix. Must be preceded with a forward slash
(/). (Range: 0-32 bits)
•
nexthopip
— IP address of the next hop router.
•
preference
— Specifies the preference value, a.k.a. administrative distance,
of an individual static route. (Range: 1-255)
Default Configuration
Default value of preference is 1. The router will prefer a route with a smaller
administrative distance that a route with a higher administrative distance.
Command Mode
Global Configuration mode
User Guidelines
For the static routes to be visible, you must:
• Enable ip routing globally.
• Enable ip routing for the interface.
• Confirm that the associated link is also up.
Example
The following example identifies the
ip-address subnet-mask, next-hop-ip
and a preference value of 200.
console(config)#ip route 192.168.10.10 255.255.255.0 192.168.20.1 200
ip route default
Use the ip route default command in Global Configuration mode to
configure the next hop address of the default route. Use the no form of the
command to delete the default route.
Syntax
ip route default
next-hop-ip
[
preference
]
no ip route default
next-hop-ip
[
preference
]
•
next-hop-ip
— IP address of the next hop router.
2CSNXXX_SWUM200.book Page 1051 Tuesday, December 10, 2013 1:22 PM

1052 IP Routing Commands
•
preference
— Specifies the preference value, a.k.a administrative distance,
of an individual static route. (Range: 1-255)
Default Configuration
Default value of preference is 1.
Command Mode
Global Configuration mode
User Guidelines
For routed management traffic:
1
Router entries are checked for applicable destinations.
2
The globally assigned default-gateway is consulted.
If DHCP is enabled on multiple in-band interfaces and the system learns a
different default gateway on each, the system retains the first default gateway
it learns and ignores any others. If the first default gateway is lost, the system
does not revert to an alternate default gateway until it renews its IP address.
Using this command, the administrator may manually configure a single,
global default gateway. The switch installs a default route for a configured
default gateway with a preference of 253, making it more preferred than the
default gateways learned via DHCP, but less preferred than a static default
route. The preference of these routes is not configurable.
The switch installs a default route for the default gateway whether or not
routing is globally enabled. When the user displays the routing table (e.g.
show ip route
), the display identifies the default gateway, if one is known.
Use the show ip route static all command to display the configured static
routes and preferences.
Example
The following example identifies the
next-hop-ip
and a preference value of
200.
console(config)#ip route default 192.168.10.1.200
2CSNXXX_SWUM200.book Page 1052 Tuesday, December 10, 2013 1:22 PM

IP Routing Commands 1053
ip route distance
Use the ip route distance command in Global Configuration mode to set the
default distance (preference) for static routes. Lower route preference values
are preferred when determining the best route. The ip route and ip route
default commands allow optional setting of the distance of an individual
static route. The default distance is used when no distance is specified in
these commands. Changing the default distance does not update the
distance of existing static routes, even if they were assigned the original
default distance. The new default distance are applied to static routes created
after invoking the ip route distance command.
Syntax
ip route distance
integer
no ip route distance
integer
•
integer
— Specifies the distance (preference) of an individual static route.
(Range 1-255)
Default Configuration
Default value of distance is 1.
Command Mode
Global Configuration mode
User Guidelines
Lower route distance values are preferred when determining the best route.
Example
The following example sets the default route metric to 80.
console(config)#ip route distance 80
ip routing
Use the ip routing command in Global Configuration mode to globally
enable IPv4 routing on the router. To disable IPv4 routing globally, use the no
form of the command.
2CSNXXX_SWUM200.book Page 1053 Tuesday, December 10, 2013 1:22 PM

1054 IP Routing Commands
Syntax
ip routing
no ip routing
Default Configuration
Disabled is the default configuration.
Command Mode
Global Configuration mode
User Guidelines
Use the
show ip brief
command to determine if routing is enabled or disabled.
Example
The following example enables IPv4 and IPv6 routing for VLAN 15
console(config)#ip routing
match ip address
Use this command to specify IP address match criteria for a route map. Use
the
no
form of this command to delete a match statement from a route map.
Syntax
match ip address
access-list-name
[
access-list-name
]
no match ip address [
access-list-name
]
•
access-list-name
—
The access-list name that identifies the named IP ACLs. The
name can be up to 31 characters in length.
Default Configuration
There is no default configuration for this command.
Command Mode
Route Map mode
2CSNXXX_SWUM200.book Page 1054 Tuesday, December 10, 2013 1:22 PM

IP Routing Commands 1055
User Guidelines
The IP ACL must be configured before it can be linked to a route-map.
Specifying an unconfigured IP ACL causes an error.
Actions in the IP ACL configuration are applied with other actions present in
the route-map. If an IP ACL referenced by a route-map is removed, the route-
map rule is also removed.
If a list of IP access lists is specified in this command and a packet matches at
least one of these access list match criteria, the corresponding set of actions in
the route map are applied to the packet. Duplicate IP access list names are
ignored.
It is strongly recommended that access lists used in a route map not be re-
used for normal access list processing. This is because:
• ACLs inherit the priority of the route map. This overrides the priority of
the including access group.
• Route maps do not have a implicit deny all at the end of the list. Instead,
non-matching packets for a permit route map use the routing table.
Example
The example below creates two access lists (R1 and R2) and two route-maps
with IP address match clauses and that associate the route-map to an
interface.
In the example, the ip policy route-map equal-access command is applied to
interface VLAN 11. All packets ingressing VLAN 11 are policy-routed.
Route map sequence 10 in route map
equal-access
is used to match all
packets sourced from any host in subnet 10.1.0.0. If there is a match, and if
the router has no explicit route for the packet’s destination, it is sent to next-
hop address 192.168.6.6.
Route map sequence 20 in route map
equal-access
is used to match all
packets sourced from any host in subnet 10.2.0.0. If there is a match, and if
the router has no explicit route for the packet’s destination, it is sent to next-
hop address 172.16.7.7.
All other packets are forwarded as per normal L3 destination-based routing.
console(config-if-vlan3)#ip policy route-map equal-access
console(config)#ip access-list R1
2CSNXXX_SWUM200.book Page 1055 Tuesday, December 10, 2013 1:22 PM

1056 IP Routing Commands
console(config-ip-acl)#permit ip 10.1.0.0 0.0.255.255 any
console(config-ip-acl)#exit
console(config)#ip access-list R2
console(config-ip-acl)#permit ip 10.2.0.0 0.0.255.255 any
console(config-ip-acl)#exit
console(config)#route-map equal-access permit 10
console(config-route-map)#match ip address R1
console(config-route-map)#set ip default next-hop 192.168.6.6
console(config-route-map)#exit
console(config)#route-map equal-access permit 20
console(config-route-map)#match ip address R2
console(config-route-map)#set ip default next-hop 172.16.7.7
console(config-route-map)#exit
console(config)#interface vlan 11
console(config-if-vlan11)#ip address 10.1.1.1 255.255.255.0
console(config-if-vlan11)#ip policy route-map equal-access
console(config)#interface vlan 12
console(config-if-vlan12)#ip address 10.1.1.1 255.255.255.0
console(config-if-vlan12)#ip policy route-map equal-access
console(config)#interface vlan 13
console(config-if-vlan13)#ip address 192.168.6.5 255.255.255.0
console(config)#interface vlan 16
console(config-if-vlan16)#ip address 172.16.7.6 255.255.255.0
match length
Use this command to configure packet length matching criteria for a route
map. Use the no form of this command to delete a match statement from a
route map.
Syntax
match length
min
max
no match length
•
min
—
Specifies the minimum Layer 3 length for the packet, inclusive, allowing
for a match.
•
max
—
Specifies the maximum Layer 3 length for the packet, inclusive, allowing
for a match.
2CSNXXX_SWUM200.book Page 1056 Tuesday, December 10, 2013 1:22 PM

IP Routing Commands 1057
Default Configuration
There is no default configuration for this command.
Command Mode
Route Map mode
User Guidelines
The match criteria specified by this command acts on the packet length as it
appears in the IP header and is not necessarily correlated with the frame
length as it appears on the wire.
Example
console(config-route-map)#match length 64 1500
match mac-list
Use this command to configure MAC ACL match criteria for a route map.
Use the no form of this command to delete the match statement from a route
map.
Syntax
match mac-list
mac-list-name
[
mac-list-name
]
no match mac-list [
mac-list-name
]
•
mac-list-name
—The MAC ACL name that identifies the MAC ACLs. The
name can be between 0 and 31 characters.
Default Configuration
There is no default configuration for this command.
Command Mode
Route Map mode
User Guidelines
The MAC ACL must be configured before it is linked to a route map. Trying
to link to an unconfigured MAC ACL causes an error.
2CSNXXX_SWUM200.book Page 1057 Tuesday, December 10, 2013 1:22 PM

1058 IP Routing Commands
Actions in the MAC ACL configuration are applied with other actions
configured in the route map. When a MAC ACL referenced by a route map is
removed, the route map rule is also removed.
Example
console(config-route-map)#match mac-list mac-test
route-map
Use this command to create a policy based route map. Use the no form of this
command to delete a route map or one of its statements.
Syntax
route-map
map-tag
[permit | deny] [
sequence-number
]
no route-map
map-tag
[permit | deny] [
sequence-number
]
•
map-tag
—
Text name of the route map. Route maps with the same name are
grouped together in order of their sequence numbers. A route map name may be
up to 32 characters long and comprised of any printable character. Enclose the
map-tag in quotes to embed blanks in the name.
•
permit
—
(Optional) Permit routes that match all of the match conditions in the
route map.
•
deny
—
(Optional) Deny routes that match all of the match conditions in the
route map. Packets matching deny routes use the routing table.
•
sequence-number
—
(Optional) An integer used to order the set of route maps.
Route maps are ordered from lowest to greatest sequence number, with lower
sequence numbers being considered first. If no sequence number is specified,
the system assigns a value ten greater than the last statement in the route map.
The range is 0 to 65,535.
Default Configuration
No route maps are configured by default. If no permit or deny tag is specified,
permit is the default.
Command Mode
Global Configuration mode
2CSNXXX_SWUM200.book Page 1058 Tuesday, December 10, 2013 1:22 PM

IP Routing Commands 1059
User Guidelines
Apply an ACL rule on the VLAN interface to perform policy based routing
based on the VLAN ID as a matching criteria for incoming packets. Packets
matching a deny rule or a deny route-map are routed using the routing table.
There is no implicit deny all at the end of a route map. Packets not matching
any clause are routed using the routing table.
Route maps with no set clause are ignored.
Example
The following example creates (or edits) the route map
equal-access
as the
first route map in the system for allowing matching packets into the system.
Route-map mode is also entered.
console(config)#route-map equal-access permit 0
set interface null0
Use this command to drop a packet instead of reverting to normal routing for
packets that do not match the route map criteria. This command should be
configured as the last entry in the route-map as no further set clauses will
operate on a dropped packet. Use the no form of this command to remove the
set clause from a route map.
Syntax
set interface
null0
no set interface
null0
•
null0
—
Specifies the null0 interface used to drop packets.
Default Configuration
There is no default configuration for this command.
Command Mode
Route Map mode
2CSNXXX_SWUM200.book Page 1059 Tuesday, December 10, 2013 1:22 PM

1060 IP Routing Commands
User Guidelines
A route-map statement used for policy based routing is configured as permit
or deny. If the statement is marked as deny, traditional destination-based
routing is performed on the packet meeting the match criteria. If the
statement is marked as permit and the packet meets all the match criteria,
the set clauses in the route-map statement are applied. If no match is found
in the route-map, the packet is forwarded using the routing decision resulting
from traditional destination-based routing. If the network administrator does
not want to revert to normal forwarding but instead want to drop packets that
do not match the specified criteria, a set clause routing the packets to
interface null0 may be configured as the last (highest numbered) route-map.
Example
console(config-route-map)#set interface null0
set ip default next-hop
Use this route map clause to override default entries in the routing table.
Packets that can routed by an active explicit route in the routing table are not
affected by this clause. Use this command to set a list of default next-hop IP
addresses to be used if no explicit route for the packet’s destination address
appears in the routing table. If more than one IP address is specified, the
reachable address in the list is used. Use the no form of this command to
remove a set command from a route map.
Syntax
set ip default next-hop ip-address [ip-address]
no set ip default next-hop ip-address [ip-address]
ip-address
—
The IP address of the next hop to which packets are routed. It must be
the address of an adjacent router.
•
ip-address
—A maximum of 16 next-hop IP addresses can be specified.
Default Configuration
There is no default configuration for this command.
2CSNXXX_SWUM200.book Page 1060 Tuesday, December 10, 2013 1:22 PM

IP Routing Commands 1061
Command Mode
Route Map mode
User Guidelines
A packet is routed to the next hop specified by this command only if there is
no active explicit route for the packet’s destination address in the routing
table. A default route in the routing table is not considered an explicit route
for an unknown destination address.
Only one of set ip next-hop, set ip default next-hop, or set interface null0
may be specified in a route map.
Example
console(config-route-map)#set ip default next-hop 192.0.2.2
set ip next-hop
Use this command to specify an adjacent next-hop router in the path toward
the destination to which the packets should be forwarded. If more than one
IP address is specified, the first IP address associated with a link up interface
is used to route the packets. Use the no form of this command to remove a set
command from a route map.
Syntax
set ip next-hop ip-address [ip-address]
no set ip next-hop ip-address [ip-address]
•
ip-address
—The IP address of the next hop to which packets are routed. It
must be the address of an adjacent router (i.e., the next hop must be in a
subnet configured on the local router). A maximum of 16 next-hop IP
addresses can be specified.
Default Configuration
There is no default configuration for this command.
Command Mode
Route Map mode
2CSNXXX_SWUM200.book Page 1061 Tuesday, December 10, 2013 1:22 PM

1062 IP Routing Commands
User Guidelines
Use this route map clause to override active routes in the routing table. This
command affects all matching packet types and is used if an active route for
the next hop exists in the routing table. The next hop IP address must be
associated with a directly connected subnet on the router. If no resolvable
active interface is present in the route table, the packet is routed using the
default routing table.
Only one of set ip next-hop, set ip default next-hop, or set interface null0
may be specified in a route map.
Example
console(config-route-map)#set ip next-hop 192.0.2.1
set ip precedence
Use this command to set the three IP precedence bits in the IP packet header
on ingress. Values 0 through 7 are supported. This precedence value may be
used by other QoS services in the switch such as weighted fair queuing
(WFQ) or weighted random early detection (WRED). Use the no form of
this command to remove a set clause from a route map.
Syntax
set ip precedence 0-7
no set ip precedence
•
0
—
Sets the routine precedence.
•
1
—
Sets the priority precedence.
•
2
—
Sets the immediate precedence.
•
3
—
Sets the Flash precedence.
•
4
—
Sets the Flash override precedence.
•
5
—
Sets the critical precedence.
•
6
—
Sets the internetwork control precedence.
•
7
—
Sets the network control precedence.
2CSNXXX_SWUM200.book Page 1062 Tuesday, December 10, 2013 1:22 PM

IP Routing Commands 1063
Default Configuration
There is no default configuration for this command.
Command Mode
Route Map mode
User Guidelines
The set ip precedence clause may be combined with set ip next-hop or set ip
default next-hop clause in a route map.
Example
console(config-route-map)#set ip precedence 5
show ip brief
Use the show ip brief command in Privileged EXEC mode to display all the
summary information of the IP.
Syntax
show ip brief
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC mode, Configuration mode and all Configuration submodes
User Guidelines
This command has no user guidelines.
Example
The following example displays IP summary information.
console#show ip brief
Default Time to Live....................... 30
Routing Mode............................... Disabled
IP Forwarding Mode......................... Enabled
2CSNXXX_SWUM200.book Page 1063 Tuesday, December 10, 2013 1:22 PM

1064 IP Routing Commands
Maximum Next Hops.......................... 2
show ip interface
Use the show ip interface command in Privileged EXEC mode to display
information about one or more IP interfaces. The output shows how each IP
address was assigned.
Syntax
show ip interface [
type number
]
•
type
—Interface type (loopback, out-of-band, or vlan)
•
number
—Interface number. Valid only for loopback and VLAN types.
Default Configuration
This command has no default configuration.
Command Mode
User EXEC, Privileged EXEC modes, Configuration mode and all
Configuration submodes
User Guidelines
The Method field contains one of the following values.
Example
console(config-if)#show ip interface
Default Gateway................................ 0.0.0.0
L3 MAC Address..........................
Routing Interfaces:
Interface State IP Address IP Mask Method
---------- ----- --------------- --------------- -------
Field Description
DHCP The address is leased from a DHCP server.
Manual The address is manually configured.
2CSNXXX_SWUM200.book Page 1064 Tuesday, December 10, 2013 1:22 PM

IP Routing Commands 1065
Vl1 Down 0.0.0.0 0.0.0.0 None
The following examples display all IP information and information specific to
VLAN 2.
console#show ip interface
Default Gateway....................... 0.0.0.0
L3 MAC Address................. 001E.C9AA.AC84
Routing Interfaces:
Interface State IP Address IP Mask Method
---------- ----- --------------- --------------- -------
Vl1 Down 0.0.0.0 0.0.0.0 None
console#show ip interface vlan2
Routing Interface Status......... Up
Primary IP Address.........192.168.75.1/255.255.255.0
Method........................... DHCP
Routing Mode..................... Enable
Administrative Mode.............. Enable
Forward Net Directed Broadcasts.... Disable
Proxy ARP.......................... Enable
Local Proxy ARP.................... Disable
Active State....................... Active
Link Speed Data Rate............... 100 Half
MAC address........................ 00:11:88:2A:3C:B3
Encapsulation Type................. Ethernet
IP MTU............................. 1500
Bandwidth.......................... 100000 kbps
Destination Unreachables........... Enabled
ICMP Redirects..................... Enabled
console#show ip interface out-of-band
IP Address............................. 10.131.11.66
Subnet Mask............................ 255.255.255.0
Default Gateway........................ 10.131.11.1
Configured IPv4 Protocol................. DHCP
Burned In MAC Address............... 001E.C9AA.AD1C
show ip policy
Use the show ip policy command in Privileged EXEC mode to display the
route maps used for policy based routing on the router interfaces.
2CSNXXX_SWUM200.book Page 1065 Tuesday, December 10, 2013 1:22 PM

1066 IP Routing Commands
Syntax
show ip policy
map-name
•
map-name
—The name of a specific route map.
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC mode
User Guidelines
This command has no user guidelines.
Example
console#show ip policy
Interface Route map
Gi1/0/24 pbr-rmap
show ip protocols
Use the show ip protocols command in Privileged EXEC mode to display a
summary of the configuration and status for each unicast routing protocol.
The command lists all supported routing protocols, regardless of whether they
are currently configured or enabled.
Syntax
show ip protocols
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC mode
2CSNXXX_SWUM200.book Page 1066 Tuesday, December 10, 2013 1:22 PM

IP Routing Commands 1067
User Guidelines
The command displays the following information.
Parameter Description
BGP Section:
Routing Protocol BGP.
Router ID The router ID configured for BGP.
Local AS Number The AS number that the local router is in.
BGP Admin Mode Whether BGP is globally enabled or disabled.
Maximum Paths The maximum number of next hops in an internal or external
BGP route.
Distance The default administrative distance (or route preference) for
external, internal, and locally-originated BGP routes. The table
that follows lists ranges of neighbor addresses that have been
configured to override the default distance with a neighbor-
specific distance. If a neighbor’s address falls within one of
these ranges, routes from that neighbor are assigned the
configured distance. If a prefix list is configured, then the
distance is only assigned to prefixes from the neighbor that are
permitted by the prefix list.
Prefix List In The global prefix list used to filter inbound routes from all
neighbors.
Prefix List Out The global prefix list used to filter outbound routes to all
neighbors.
Neighbors A list of configured neighbors and the inbound and outbound
policies configured for each.
OSPFv2 Section
Routing Protocol OSPFv2.
Router ID The router ID configured for OSPFv2.
OSPF Admin Mode Whether OSPF is enabled or disabled globally.
Maximum Paths The maximum number of next hops in an OSPF route.
Routing for
Networks
The address ranges configured with an OSPF network
command.
2CSNXXX_SWUM200.book Page 1067 Tuesday, December 10, 2013 1:22 PM

1068 IP Routing Commands
Distance The administrative distance (or “route preference”) for intra-
area, inter-area, and external routes.
Default Route
Advertise
Whether OSPF is configured to originate a default route.
Always Whether default advertisement depends on having a default
route in the common routing table.
Metric The metric configured to be advertised with the default route.
Metric Type The metric type to advertise for redistributed routes of this
type.
Redist Source The type of routes OSPF is redistributing.
Metric The metric to advertise for redistributed routes of this type.
Metric Type The metric type to advertise for redistributed routes of this
type.
Subnets Whether OSPF redistributes subnets of classful addresses, or
only classful prefixes.
Dist List A distribute list used to filter routes of this type. Only routes
that pass the distribute list are redistributed.
Number of Active
Areas
The number of OSPF areas with at least one interface running
on this router. Also broken down by area type.
ABR Status The number of OSPF areas with at least one interface running
on this router. Also broken down by area type.
ASBR Status Whether the router is an autonomous system boundary router.
The router is an ASBR if it is redistributing any routes or
originating a default route.
RIP Section
RIP Admin Mode Whether RIP is globally enabled.
Split Horizon Mode Whether RIP advertises routes on the interface where they were
received.
Default Metric The metric assigned to redistributed routes.
Default Route
Advertise
Whether this router is originating a default route.
Distance The administrative distance for RIP routes.
Parameter Description
2CSNXXX_SWUM200.book Page 1068 Tuesday, December 10, 2013 1:22 PM

IP Routing Commands 1069
Example
The following shows example CLI display output for the command.
console# show ip protocols
Routing Protocol.......................... BGP
Router ID................................. 6.6.6.6
Local AS Number........................... 65001
BGP Admin Mode............................ Enable
Maximum Paths............................. Internal 32, External 32
Distance.................................. Ext 20 Int 200 Local 200
Address Wildcard Distance Pfx List
------- -------- -------- --------
172.20.0.0 0.0.255.255 40 None
172.21.0.0 0.0.255.255 45 1
Prefix List In............................ PfxList1
Prefix List Out........................... None
Neighbors:
172.20.1.100
Filter List In........................ 1
Filter List Out....................... 2
Prefix List In........................ PfxList2
Prefix List Out....................... PfxList3
Route Map In.......................... rmapUp
Route Map Out......................... rmapDown
172.20.5.1
Prefix List Out....................... PfxList12
Routing Protocol.......................... OSPFv2
Router ID................................. 6.6.6.6
OSPF Admin Mode........................... Enable
Maximum Paths............................. 32
Routing for Networks...................... 172.24.0.0 0.0.255.255 area 0
10.0.0.0 0.255.255.255 area 1
192.168.75.0 0.0.0.255 area 2
Distance.................................. Intra 110 Inter 110 Ext 110
Interface The interfaces where RIP is enabled and the version sent and
accepted on each interface.
Parameter Description
2CSNXXX_SWUM200.book Page 1069 Tuesday, December 10, 2013 1:22 PM

1070 IP Routing Commands
Default Route Advertise................... Disabled
Always.................................... FALSE
Metric.................................... Not configured
Metric Type............................... External Type 2
Redist
Source Metric Metric Type Subnets Dist List
--------- ------- ----------- ------- ---------
static default 2 Yes None
connected 10 2 Yes 1
Number of Active Areas.................... 3 (3 normal, 0 stub, 0 nssa)
ABR Status................................ Yes
ASBR Status............................... Yes
Routing Protocol.......................... RIP
RIP Admin Mode............................ Enable
Split Horizon Mode........................ Simple
Default Metric............................ Not configured
Default Route Advertise................... Disable
Distance.................................. 120
Interface Send Recv
--------- ---- ----
0/25 RIPv2 RIPv2
show ip route
Use the show ip route command in Privileged EXEC mode to display the
current state of the routing table. The output of the command also displays
the IPv4 address of the default gateway and the default route associated with
the gateway.
This command deprecates the show ip route configured and show ip route
connected commands.
Syntax
show ip route [ip-address [mask |
prefix-length
] [longer-prefixes] ]
•
ip-address
—Specifies the network for which the route is to be displayed
and displays the best matching route for the address.
•
mask
—Subnet mask of the IP address.
2CSNXXX_SWUM200.book Page 1070 Tuesday, December 10, 2013 1:22 PM

IP Routing Commands 1071
•
prefix-length
—Length of prefix, in bits. Must be preceded with a forward
slash (/). (Range: 0-32 bits.)
•
longer-prefixes
—Indicates that the
ip-address
and
subnet-mask
pair
becomes the prefix, and the command displays the routes to the addresses
that match that prefix.
Default Configuration
This command has no default configuration.
Command Mode
User EXEC, Privileged EXEC modes, Configuration mode and all
Configuration submodes
User Guidelines
• If the subnet mask is specified, then only routes with an exact match are
displayed. For example:
show ip route 192.168.2.0 /24
• If only an IP address is specified, the best route for the IP address is
displayed. For example:
show ip route 192.168.2.0
•If the
longer-prefixes option is specified, then the subnets within an
aggregate are displayed. For example:
show ip route 192.168.2.0 /23 longer-prefixes
Example
The following example displays the IPv4 address of the default gateway and
the default route associated with the gateway.
console#show ip route
Route Codes: R - RIP Derived, O - OSPF Derived,
C - Connected, S - Static
B - BGP Derived, IA - OSPF Inter Area
E1 - OSPF External Type 1, E2 - OSPF External Type 2
N1 - OSPF NSSA External Type 1, N2 - OSPF NSSA External Type 2
*Indicates the best (lowest metric) route for the subnet
Default gateway 10.1.20.1 is configured
2CSNXXX_SWUM200.book Page 1071 Tuesday, December 10, 2013 1:22 PM

1072 IP Routing Commands
S 0.0.0.0/0 [254/0] via 10.1.20.1
C *10.1.20.0/24 [0/1] directly connected, Vl2
C *4.4.0.0/16 [0/1] directly connected, Lo1
C *20.1.20.0/24 [0/1] directly connected, Vl4
console# show ip route 10.2.0.0
Routing entry for 10.2.0.0 (mask 255.255.0.0)
Known via "ospf", distance 100, metric 0
Redistributing via rip
Last update from 10.2.35.13, 0:0:23 ago
Routing Descriptor Blocks:
* 10.2.35.13, from 10.2.35.13, 0:00:24 ago
Route metric is 0, traffic share count is 1
show ip route preferences
Use the show ip route preferences command in Privileged EXEC mode
displays detailed information about the route preferences. Route preferences
are used in determining the best route. Lower router preference values are
preferred over higher router preference values.
The user can configure a global default gateway using the ip default-gateway
command, creating a default route with a preference of 253. The show ip
route preferences command lists the new preference value. The show
command also displays the preference of default routes learned from a DHCP
server.
Syntax
show ip route preferences
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC mode, Configuration mode and all Configuration submodes
User Guidelines
This command has no user guidelines.
2CSNXXX_SWUM200.book Page 1072 Tuesday, December 10, 2013 1:22 PM

IP Routing Commands 1073
Example
The following example displays IP route preferences.
console#show ip route preferences
Local.......................................... 0
Static......................................... 1
OSPF Intra..................................... 110
OSPF Inter..................................... 110
OSPF External.................................. 110
RIP............................................ 120
Configured Default Gateway..................... 253
DHCP Default Gateway........................... 254
show ip route summary
Use the show ip route summary command in Privileged EXEC mode to
display the routing table summary, including best and non-best routes.
Syntax
show ip route summary [best]
•
best
—
Shows the number of best routes. To include the number of all routes, do
not use this optional parameter.
Default Configuration
This command has no default configuration.
Command Mode
User EXEC, Privileged EXEC modes, Configuration mode and all
Configuration submodes
User Guidelines
This command has no user guidelines.
Example
The following example displays the IP route summary.
console#show ip route summary
Connected Routes............................... 0
Static Routes.................................. 0
2CSNXXX_SWUM200.book Page 1073 Tuesday, December 10, 2013 1:22 PM

1074 IP Routing Commands
RIP Routes..................................... 0
OSPF Routes.................................... 0
Intra Area Routes.............................. 0
Inter Area Routes.............................. 0
External Type-1 Routes......................... 0
External Type-2 Routes......................... 0
Total routes................................... 0
show ip traffic
Use the show ip traffic command in User EXEC mode to display IP statistical
information of the software IP stack. Refer to RFC 1213 for more information
about the fields that are displayed.
Syntax
show ip traffic
Default Configuration
This command has no default configuration.
Command Mode
User EXEC, Privileged EXEC modes, Configuration mode and all
Configuration submodes
User Guidelines
This command displays statistics for the software IP stack, not the hardware
routing information.
Example
The following example displays IP route preferences.
console>show ip traffic
IpInReceives................................... 24002
IpInHdrErrors.................................. 1
IpInAddrErrors................................. 925
IpForwDatagrams................................ 0
IpInUnknownProtos.............................. 0
IpInDiscards................................... 0
IpInDelivers................................... 18467
IpOutRequests.................................. 295
2CSNXXX_SWUM200.book Page 1074 Tuesday, December 10, 2013 1:22 PM

IP Routing Commands 1075
IpOutDiscards.................................. 0
IpOutNoRoutes.................................. 0
IpReasmTimeout................................. 0
IpReasmReqds................................... 0
IpReasmOKs..................................... 0
IpReasmFails................................... 0
IpFragOKs...................................... 0
IpFragFails.................................... 0
IpFragCreates.................................. 0
IpRoutingDiscards.............................. 0
IcmpInMsgs..................................... 3
IcmpInErrors................................... 0
IcmpInDestUnreachs............................. 0
IcmpInTimeExcds................................ 0
IcmpInParmProbs................................ 0
IcmpInSrcQuenchs............................... 0
IcmpInRedirects................................ 0
IcmpInEchos.................................... 3
IcmpInEchoReps................................. 0
IcmpInTimestamps............................... 0
IcmpInTimestampReps............................ 0
IcmpInAddrMasks................................ 0
IcmpInAddrMaskReps............................. 0
IcmpOutMsgs.................................... 3
IcmpOutErrors.................................. 0
IcmpOutDestUnreachs............................ 0
IcmpOutTimeExcds............................... 0
IcmpOutParmProbs............................... 0
IcmpOutSrcQuenchs.............................. 0
IcmpOutRedirects............................... 0
IcmpOutEchos................................... 3
IcmpOutEchoReps................................ 3
IcmpOutTimestamps.............................. 0
IcmpOutTimestampReps........................... 0
IcmpOutAddrMasks............................... 0
show ip vlan
Use the show ip vlan command in Privileged EXEC mode to display the
VLAN routing information for all VLANs with routing enabled.
Syntax
show ip vlan
2CSNXXX_SWUM200.book Page 1075 Tuesday, December 10, 2013 1:22 PM

1076 IP Routing Commands
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC mode, Configuration mode and all Configuration submodes
User Guidelines
This command has no user guidelines.
Example
The following example displays VLAN routing information.
console#show ip vlan
MAC Address used by Routing VLANs: 00:00:00:01:00:02
VLAN ID IP Address Subnet Mask
------- --------------- ---------------
10 0.0.0.0 0.0.0.0
20 0.0.0.0 0.0.0.0
show route-map
Use this command to display the route maps.
Syntax
show route-map
map-name
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC mode
User Guidelines
This command has no user guidelines.
2CSNXXX_SWUM200.book Page 1076 Tuesday, December 10, 2013 1:22 PM

IP Routing Commands 1077
Example
For each sequence number, the match count is shown in terms of number of
packets and number of bytes. This counter displays the match count in
packets and bytes when a route map is applied. When a route map is
created/removed from interface, this count is shown as zero. The following is
an example of the behavior of counters as well as how they are displayed when
a route-map is applied and removed from interface:
console# show route-map test
route-map test, permit, sequence 10
Match clauses:
ip address prefix-lists: orange
Set clauses:
set metric 50
console #show ip policy
Interface Route-Map
------------ -----------------------------------------
console #show route-map simplest
route-map simplest permit 10
Match clauses:
ip address (access-lists) : 1
Set clauses:
ip next-hop 3.3.3.3
ip precedence 3
Policy routing matches: 0 packets, 0 bytes
route-map simplest permit 20
Match clauses:
ip address (access-lists) : 1
Set clauses:
ip default next-hop 4.4.4.4
ip precedence 4
Policy routing matches: 0 packets, 0 bytes
route-map simplest permit 30
Match clauses:
Set clauses:
interface null0
Policy routing matches: 0 packets, 0 bytes
console #configure
console (Config)#interface Te1/0/2
console (config-if-Te1/0/2)#ip policy simplest
console (config-if-Te1/0/2)#show route-map simplest
route-map simplest permit 10
Match clauses:
ip address (access-lists) : 1
Set clauses:
ip next-hop 3.3.3.3
ip precedence 3
2CSNXXX_SWUM200.book Page 1077 Tuesday, December 10, 2013 1:22 PM

1078 IP Routing Commands
Policy routing matches: 5387983 packets, 344831232 bytes
route-map simplest permit 20
Match clauses:
ip address (access-lists) : 1
Set clauses:
ip default next-hop 4.4.4.4
ip precedence 4
Policy routing matches: 0 packets, 0 bytes
route-map simplest permit 30
Match clauses:
Set clauses:
interface null0
Policy routing matches: 0 packets, 0 bytes
console (config-if-Te1/0/2)
console (config-if-Te1/0/2)# no ip policy simplest
console (config-if-Te1/0/2)# exit
console (config)# exit
console # show route-map simplest
route-map simplest permit 10
Match clauses:
ip address (access-lists) : 1
Set clauses:
ip next-hop 3.3.3.3
ip precedence 3
Policy routing matches: 0 packets, 0 bytes
route-map simplest permit 20
Match clauses:
ip address (access-lists) : 1
Set clauses:
ip default next-hop 4.4.4.4
ip precedence 4
Policy routing matches: 0 packets, 0 bytes
route-map simplest permit 30
Match clauses:
Set clauses:
interface null0
Policy routing matches: 0 packets, 0 bytes
console #show ip policy
Interface Route-Map
------------ -----------------------------------------
console #
show routing heap summary
Use the show routing heap summary command in Privileged EXEC mode to
display a summary of the memory allocation from the routing heap. The
routing heap is a section of memory set aside when the system boots for use
by the routing applications.
2CSNXXX_SWUM200.book Page 1078 Tuesday, December 10, 2013 1:22 PM

IP Routing Commands 1079
Syntax
show routing heap summary
Default Configuration
This command has no default setting.
Command Mode
Privileged EXEC mode
User Guidelines
The command displays the following information.
Examples
The following shows example CLI display output for the command.
console# show routing heap summary
Heap Size....................... 92594000 bytes
Memory In Use................... 149598 bytes (0%)
Memory on Free List............. 78721 bytes (0%)
Memory Available in Heap........ 92365249 bytes (99%)
In Use High Water Mark.......... 210788 bytes (0%)
Parameter Description
Heap Size The amount of memory, in bytes, allocated at startup for the
routing heap.
Memory In Use The number of bytes currently allocated.
Memory on Free
List
The number of bytes currently on the free list. When a chunk
of memory from the routing heap is freed, it is placed on a free
list for future reuse.
Memory Available in
Heap
The number of bytes in the original heap that have never been
allocated.
In Use High Water
Mark
The maximum memory in use since the system last rebooted.
2CSNXXX_SWUM200.book Page 1079 Tuesday, December 10, 2013 1:22 PM

1080 IP Routing Commands
2CSNXXX_SWUM200.book Page 1080 Tuesday, December 10, 2013 1:22 PM

IPv6 Routing Commands 1081
49
IPv6 Routing Commands
Dell Networking N2000/N3000/N4000 Series Switches
The Dell Network N2000 series supports limited routing and multicast capabilities.
See the Users Configuration Guide section “Feature Limitations and Platform
Constants” for supported capabilities.
The IPv6 version of the routing table manager provides a repository for IPv6
routes learned by dynamic routing protocols or static configuration. RTO6
manages dynamic and static IPv6 routes, redistributes routes to registered
protocols, supports ECMP routes, and supports multiple routes to the same
destination, sorted by preference. IPv6 routing only operates over VLAN
interfaces.
IPv6 Limitations & Restrictions
The following limitations apply:
• IPSec support is not available.
• The DHCPv6 server does not support stateful address configuration.
• Automated router renumbering is not supported.
Commands in this Chapter
This chapter explains the following commands:
clear ipv6 neighbors ipv6 mld query-
max-response-time
ipv6 route distance show ipv6 mld host-
proxy groups
clear ipv6 statistics ipv6 nd dad
attempts
ipv6 unicast-
routing
show ipv6 mld host-
proxy groups detail
ipv6 address ipv6 nd managed-
config-flag
ping ipv6 show ipv6 mld host-
proxy interface
ipv6 enable ipv6 nd ns-interval ping ipv6 interface show ipv6 mld traffic
ipv6 hop-limit ipv6 nd other-
config-flag
rate-limit cpu show ipv6 neighbors
2CSNXXX_SWUM200.book Page 1081 Tuesday, December 10, 2013 1:22 PM

1082 IPv6 Routing Commands
clear ipv6 neighbors
Use the clear ipv6 neighbors command in Privileged EXEC mode to clear all
entries in the IPv6 neighbor table or an entry on a specific interface.
Syntax
clear ipv6 neighbors [vlan
vlan-id
]
•
vlan-id
— Valid VLAN ID.
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC mode.
User Guidelines
This command has no user guidelines.
ipv6 host ipv6 nd prefix show ipv6 brief show ipv6 route
ipv6 mld last-
member-query-
count
ipv6 nd ra-interval show ipv6 interface show ipv6 route
preferences
ipv6 mld last-
member-query-
interval
ipv6 nd ra-lifetime show ipv6 interface
management
statistics
show ipv6 route
summary
ipv6 mld host-proxy ipv6 nd reachable-
time
show ipv6 mld
groups
show ipv6 traffic
ipv6 mld host-proxy
reset-status
ipv6 nd suppress-ra show ipv6 mld
interface
show ipv6 vlan
ipv6 mld host-proxy
unsolicit-rprt-
interval
ipv6 route show ipv6 mld host-
proxy
traceroute ipv6
ipv6 mld query-
interval
–––
2CSNXXX_SWUM200.book Page 1082 Tuesday, December 10, 2013 1:22 PM

IPv6 Routing Commands 1083
Example
The following example clears all entries in the IPv6 neighbor table.
console(config)#clear ipv6 neighbors
clear ipv6 statistics
Use the clear ipv6 statistics command in Privileged EXEC mode to clear IPv6
statistics for all interfaces or for a specific interface, including loopback and
tunnel interfaces. IPv6 statistics display in the output of the show ipv6 traffic
command.
Syntax
clear ipv6 statistics [vlan
vlan-id
| tunnel
tunnel-id
| loopback
loopback-id
]
•
vlan-id
— Valid VLAN ID.
•
tunnel-id
— Tunnel identifier. (Range: 0-7)
•
loopback-id
— Loopback identifier. (Range: 0-7)
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC mode.
User Guidelines
This command has no user guidelines.
Example
The following example clears IPv6 statistics for VLAN 11.
console(config)#clear ipv6 statistics vlan 11
ipv6 address
Use the ipv6 address command in Interface Configuration mode to configure
an IPv6 address on an interface (including tunnel and loopback interfaces)
and to enable IPv6 processing on this interface. Multiple globally reachable
2CSNXXX_SWUM200.book Page 1083 Tuesday, December 10, 2013 1:22 PM

1084 IPv6 Routing Commands
addresses can be assigned to an interface by using this command. There is no
need to assign a link-local address by using this command since one is
automatically created. IPv6 addresses can be expressed in eight blocks. Also
of note is that instead of a period, a colon separates each block. For
simplification, leading zeros of each 16-bit block can be omitted. One
sequence of 16-bit blocks containing only zeros can be replaced with a double
colon “::”, but not more than one at a time (otherwise it is no longer a unique
representation).
Dropping zeros: 3ffe:ffff:100:f101:0:0:0:1 becomes 3ffe:ffff:100:f101::1
Local host: 0000:0000:0000:0000:0000:0000:0000:0001 becomes ::1
Any host: 0000:0000:0000:0000:0000:0000:0000:0000 becomes ::
The hexadecimal letters in the IPv6 addresses are not case-sensitive. An
example of an IPv6 prefix and prefix length is 3ffe:1::1234/64.
Syntax
ipv6 address
prefix/prefix-length
[eui64]
no ipv6 address [
prefix/prefix-length
]
[eui64]
•
prefix
— Consists of the bits of the address to be configured.
•
prefix-length
— Designates how many of the high-order contiguous bits of
the address make up the prefix.
•
eui64
— The optional eui-64 field designates that IPv6 processing on the
interfaces is enabled using an EUI-64 interface ID in the low order 64 bits
of the address. If this option is used, the value of
prefix_length
must be 64
bits.
Default Configuration
This command has no default configuration.
Command Mode
Interface Configuration (VLAN, Tunnel, Loopback) mode.
User Guidelines
This command has no user guidelines.
2CSNXXX_SWUM200.book Page 1084 Tuesday, December 10, 2013 1:22 PM

IPv6 Routing Commands 1085
Example
The following example configures an IPv6 address and enables IPv6
processing.
console(config)#interface vlan 15
console(config-if-vlan15)#ipv6 address 2020:1::1/64
ipv6 enable
Use the ipv6 enable command in Interface Configuration mode to enable
IPv6 routing on an interface (including tunnel and loopback interfaces) that
has not been configured with an explicit IPv6 address. Command execution
automatically configures the interface with a link-local address. The
command is not required if an IPv6 global address is configured on the
interface.
Syntax
ipv6 enable
no ipv6 enable
Default Configuration
Disabled is the default configuration.
Command Mode
Interface Configuration (VLAN, Tunnel, Loopback) mode.
User Guidelines
This command has no user guidelines.
Example
The following example enables IPv6 routing, which has not been configured
with an explicit IPv6 address.
console(config)#interface vlan 15
console(config-if-vlan15)#ipv6 enable
2CSNXXX_SWUM200.book Page 1085 Tuesday, December 10, 2013 1:22 PM

1086 IPv6 Routing Commands
ipv6 hop-limit
Use the ipv6 hop-limit command to configure the hop limit used in IPv6
PDUs originated by the router. Use the no form of the command to return
the hop limit to the default setting.
Syntax
ipv6 hop-limit
count
no ipv6 hop-limit
•
count
—The number of hops before the PDU expires (Range 0-255).
Default Configuration
The default count is 64 hops.
Command Mode
Global Configuration
ipv6 host
The ipv6 host command is used to define static host name-to- ipv6 address
mapping in the host cache.
Syntax
ipv6 host
name
ipv6-address
no ipv6 host
name
•
name
— Host name.
•
ipv6-address
— IPv6 address of the host.
Default Configuration
No IPv6 hosts are defined.
Command Mode
Global Configuration mode.
2CSNXXX_SWUM200.book Page 1086 Tuesday, December 10, 2013 1:22 PM

IPv6 Routing Commands 1087
User Guidelines
This command has no user guidelines.
Example
console(config)#ipv6 host Dell 2001:DB8::/32
ipv6 mld last-member-query-count
The ipv6 mld last-member-query-count command sets the number of
listener-specific queries sent before the router assumes that there are no local
members on the interface. Use the “no” form of this command to set the last
member query count to the default.
Syntax
ipv6 mld last-member-query-count
last-member-query-count
no ipv6 mld last-member-query-count
•
last-member-query-count
— Query count (Range: 1–20).
Default Configuration
The default last member query count is 2.
Command Mode
Interface Configuration (VLAN) mode.
User Guidelines
There are no user guidelines for this command.
Example
console(config-if-vlan3)#ipv6 mld last-member-query-count 5
2CSNXXX_SWUM200.book Page 1087 Tuesday, December 10, 2013 1:22 PM

1088 IPv6 Routing Commands
ipv6 mld last-member-query-interval
The ipv6 mld last-member-query-interval command sets the last member
query interval for the MLD interface, which is the value of the maximum
response time parameter in the group-specific queries sent out of this
interface. Use the “no” form of this command to set the last member query
interval to the default.
Syntax
ipv6 mld last-member-query-interval
last-member-query-interval
no ipv6 mld last-member-query-interval
•
last-member-query-interval
— The last member query interval (Range:
0–65535 milliseconds).
Default Configuration
The default last member query interval is 1 second.
Command Mode
Interface Configuration (VLAN) mode.
User Guidelines
There are no user guidelines for this command.
Example
console(config-if-vlan3)#ipv6 mld last-member-query-interval 5000
ipv6 mld host-proxy
This command enables MLD and MLD Proxy on the specified interface.
PIM and DVMRP are not compatible with MLD proxy. Disable PIM/DVMRP
before enabling MLD proxy.
Multicast routing must be enabled for the MLD proxy service to become
operationally enabled
Also, ensure that there are no other multicast routing protocols enabled on
the router and that ip multicast routing is globally enabled. Use the “no”
form of this command to disable MLD Proxy globally.
2CSNXXX_SWUM200.book Page 1088 Tuesday, December 10, 2013 1:22 PM

IPv6 Routing Commands 1089
Syntax
ipv6 mld host-proxy [interface
vlan-id
]
no ipv6 mld host-proxy [interface
vlan-id
]
Default Configuration
MLD Proxy is disabled by default.
Command Mode
Interface Configuration (VLAN) mode.
User Guidelines
There are no user guidelines for this command.
Example
console(config-if-vlan3)#ipv6 mld host-proxy
ipv6 mld host-proxy reset-status
Use the ipv6 mld host-proxy reset-status command to reset the host interface
status parameters of the MLD Proxy router. This command is only valid when
MLD Proxy is enabled on the interface.
Syntax
ipv6 mld host-proxy reset-status
Command Mode
Interface Configuration (VLAN) mode.
Default Configuration
There is no default configuration for this command.
User Guidelines
There are no user guidelines for this command.
2CSNXXX_SWUM200.book Page 1089 Tuesday, December 10, 2013 1:22 PM

1090 IPv6 Routing Commands
Example
console(config-if-vlan3)#ipv6 mld host-proxy reset-status
ipv6 mld host-proxy unsolicit-rprt-interval
Use the ipv6 mld host-proxy unsolicit-rprt-interval command to set the
unsolicited report interval for the MLD Proxy router. This command is only
valid when MLD Proxy is enabled on the interface. Use the “no” form of this
command to reset the MLD Proxy router's unsolicited report interval to the
default value.
Syntax
ipv6 mld host-proxy unsolicited-report-interval
interval
no ipv6 mld host-proxy unsolicited-report-interval
•
interval
—The interval between unsolicited reports (Range: 1–260
seconds).
Default Configuration
The unsolicited report interval is 1 second by default.
Command Mode
Interface Configuration (VLAN) mode.
User Guidelines
This command has no user guidelines
Example
console(config-if-vlan3)#ipv6 mld host-proxy unsolicit-rprt-interval 10
ipv6 mld query-interval
The ipv6 mld query-interval command sets the MLD router's query interval
for the interface. The query-interval is the amount of time between the
general queries sent when the router is querying on that interface. Use the
“no” form of this command to set the query interval to the default.
2CSNXXX_SWUM200.book Page 1090 Tuesday, December 10, 2013 1:22 PM

IPv6 Routing Commands 1091
Syntax
ipv6 mld query-interval
query-interval
no ipv6 mld query-interval
•
query-interval
— Query interval (Range: 1–3600).
Default Configuration
The default query interval is 125 seconds.
Command Mode
Interface Configuration (VLAN) mode.
User Guidelines
There are no user guidelines for this command.
Example
console(config-if-vlan3)#ipv6 mld query-interval 130
ipv6 mld query-max-response-time
The ipv6 mld query-max-response-time command sets MLD query
maximum response time for the interface. This value is used in assigning the
maximum response time in the query messages that are sent on that
interface. Use the “no” form of this command to set the maximum query
response time to the default.
Syntax
ipv6 mld query-max-response-time
query-max-response-time
no ipv6 mld query-max-response-time
•
query-max-response-time
— Maximum query response time (Range:
1–65535 milliseconds).
Default Configuration
The default query maximum response time is 10 seconds.
2CSNXXX_SWUM200.book Page 1091 Tuesday, December 10, 2013 1:22 PM

1092 IPv6 Routing Commands
Command Mode
Interface Configuration (VLAN) mode
User Guidelines
There are no user guidelines for this command.
Example
console(config-if-vlan3)#ipv6 mld query-max-response-time 4500
ipv6 nd dad attempts
Use the ipv6 nd dad attempts command in Interface Configuration mode to
set the number of duplicate address detection probes transmitted while doing
neighbor discovery. Duplicate address detection verifies that an IPv6 address
on an interface is unique.
Syntax
ipv6 nd dad attempts
value
no ipv6 nd dad attempts
•
value
—Probes transmitted. (Range: 0-600)
Default Configuration
The default value for attempts is 1.
Command Mode
Interface Configuration (VLAN, Tunnel, Loopback) mode
User Guidelines
This command has no user guidelines.
Example
The following example sets at 10 the number of duplicate address detection
probes transmitted while doing neighbor discovery.
console(config)#interface vlan 15
console(config-if-vlan15)#ipv6 nd dad attempts 10
2CSNXXX_SWUM200.book Page 1092 Tuesday, December 10, 2013 1:22 PM

IPv6 Routing Commands 1093
ipv6 nd managed-config-flag
Use the ipv6 nd managed-config-flag command in Interface Configuration
mode to set the “managed address configuration” flag in router
advertisements. When the value is true,
end nodes use DHCPv6. When the value is false, end nodes automatically
configure addresses.
Syntax
ipv6 nd managed-config-flag
no ipv6 nd managed-config-flag
Default Configuration
False is the default configuration.
Command Mode
Interface Configuration (VLAN, Tunnel, Loopback) mode
User Guidelines
This command has no user guidelines.
Example
In the following example, the end node uses DHCPv6.
console(config)#interface vlan 15
console(config-if-vlan15)#ipv6 nd managed-config-flag
ipv6 nd ns-interval
Use the ipv6 nd ns-interval command in Interface Configuration mode to set
the interval between router advertisements for advertised neighbor
solicitations. An advertised value of 0 means the interval is unspecified.
Syntax
ipv6 nd ns-interval
milliseconds
no ipv6 nd ns-interval
2CSNXXX_SWUM200.book Page 1093 Tuesday, December 10, 2013 1:22 PM

1094 IPv6 Routing Commands
•
milliseconds
— Interval duration. (Range: 0, 1000–4294967295)
Default Configuration
0 is the default value for
milliseconds
.
Command Mode
Interface Configuration (VLAN, Tunnel, Loopback) mode
User Guidelines
This command has no user guidelines.
Example
The following example sets the interval between router advertisements for
advertised neighbor solicitations at 5000 ms.
console(config)#interface vlan 15
console(config-if-vlan15)#ipv6 nd ns-interval 5000
ipv6 nd other-config-flag
Use the ipv6 nd other-config-flag command in Interface Configuration mode
to set the “other stateful configuration” flag in router advertisements sent
from the interface.
Syntax
ipv6 nd other-config-flag
no ipv6 nd other-config-flag
Default Configuration
False is the default configuration.
Command Mode
Interface Configuration (VLAN, Tunnel, Loopback) mode
User Guidelines
This command has no user guidelines.
2CSNXXX_SWUM200.book Page 1094 Tuesday, December 10, 2013 1:22 PM

IPv6 Routing Commands 1095
Example
The following example sets to true the “other stateful configuration” flag in
router advertisements
console(config)#interface vlan 15
console(config-if-vlan15)#ipv6 nd other-config-flag
ipv6 nd prefix
Use the ipv6 nd prefix command to configure parameters associated with
prefixes that the router advertises in its router advertisements.
Syntax
ipv6 nd prefix
ipv6-prefix/prefix-length
[{valid-lifetime | infinite}
{preferred-lifetime | infinite}] [no-autoconfig] [off-link]
no ipv6 nd prefix
ipv6-prefix/prefix-length
•
ipv6-prefix
—IPv6 prefix.
•
prefix-length
—IPv6 prefix length.
•
valid-lifetime
—Valid lifetime of the router in seconds. (Range:
0–4294967295 seconds.)
•
infinite
—Indicates lifetime value is infinite.
•
preferred-lifetime
—Preferred-lifetime of the router in seconds. (Range:
0–4294967295 seconds.)
•
no-autoconfig
—Do not use Prefix for autoconfiguration.
•
off-link
—Do not use Prefix for onlink determination.
Default Configuration
604800 seconds is the default value for valid-lifetime, 2592000 seconds for
preferred lifetime.
Command Mode
Interface Configuration (VLAN, Tunnel, Loopback) mode
2CSNXXX_SWUM200.book Page 1095 Tuesday, December 10, 2013 1:22 PM

1096 IPv6 Routing Commands
User Guidelines
The router advertises its global IPv6 prefixes in its router advertisements
(RAs). An RA only includes the prefixes of the IPv6 addresses configured on
the interface where the RA is transmitted. Addresses are configured using the
ipv6 address interface configuration command. Each prefix advertisement
includes information about the prefix, such as its lifetime values and whether
hosts should use the prefix for on-link determination or address auto-
configuration. Use the ipv6 nd prefix command to configure these values.
The ipv6 nd prefix command will allow you to preconfigure RA prefix values
before you configure the associated interface address. In order for the prefix
to be included in RAs, you must configure an address that matches the prefix
using the ipv6 address command. Prefixes specified using ipv6 nd prefix
without an associated interface address will not be included in RAs and will
not be committed to the device configuration.
Example
The following example sets the IPv6 prefixes to include in the router
advertisement.
console(config)#interface vlan 11
console(config-if-vlan11)#ipv6 nd prefix 2020:1::1/64
ipv6 nd ra-interval
Use the ipv6 nd ra-interval command in Interface Configuration mode to set
the transmission interval between router advertisements.
Syntax
ipv6 nd ra-interval
maximum
minimum
no ipv6 nd ra-interval
•
maximum
— The maximum interval duration (Range: 4–1800 seconds).
•
minimum
— The minimum interval duration (Range: 3 – (0.75 *
maximum) seconds).
Default Configuration
600 is the default value for
seconds
.
2CSNXXX_SWUM200.book Page 1096 Tuesday, December 10, 2013 1:22 PM

IPv6 Routing Commands 1097
Command Mode
Interface Configuration (VLAN, Tunnel, Loopback) mode
User Guidelines
The minimum interval cannot be larger than 75% of the maximum interval.
Example
The following example sets the transmission interval between router
advertisements at 1000 seconds.
console(config)#interface vlan 15
console(config-if-vlan15)#ipv6 nd ra-interval 1000
ipv6 nd ra-lifetime
Use the ipv6 nd ra-lifetime command in Interface Configuration mode to set
the value that is placed in the Router Lifetime field of the router
advertisements sent from the interface.
Syntax
ipv6 nd ra-lifetime
seconds
no ipv6 nd ra-lifetime
•
seconds
— Lifetime duration. The value must be zero, or it must be an
integer between the value of the router advertisement transmission
interval and 9000 seconds. A value of zero means this router is not to be
used as the default router. (Range: 0-9000)
Default Configuration
1800 is the default value for
seconds
.
Command Mode
Interface Configuration (VLAN, Tunnel, Loopback) mode
User Guidelines
This command has no user guidelines.
2CSNXXX_SWUM200.book Page 1097 Tuesday, December 10, 2013 1:22 PM

1098 IPv6 Routing Commands
Example
The following example sets at 1000 seconds the value that is placed in the
Router Lifetime field of the router advertisements.
console(config)#interface vlan 15
console(config-if-vlan15)#ipv6 nd ra-lifetime 1000
ipv6 nd reachable-time
Use the ipv6 nd reachable-time command in Interface Configuration mode
to set the router advertisement time to consider a neighbor reachable after
neighbor discovery confirmation.
Syntax
ipv6 nd reachable-time
milliseconds
no ipv6 nd reachable-time
•
milliseconds
— Reachable-time duration. A value of zero means the time
is unspecified by the router. (Range: 0-3600000 milliseconds)
Default Configuration
The default value for neighbor discovery reachable times is 0 milliseconds.
Command Mode
Interface Configuration (VLAN, Tunnel, Loopback) mode
User Guidelines
This command has no user guidelines.
Example
The following example sets the router advertisement time at 5000
milliseconds to consider a neighbor reachable after neighbor discovery
confirmation.
console(config)#interface vlan 15
console(config-if-vlan15)#ipv6 nd reachable-time 5000
2CSNXXX_SWUM200.book Page 1098 Tuesday, December 10, 2013 1:22 PM

IPv6 Routing Commands 1099
ipv6 nd suppress-ra
Use the ipv6 nd suppress-ra command in Interface Configuration mode to
suppress router advertisement transmission on an interface.
Syntax
ipv6 nd suppress-ra
no ipv6 nd suppress-ra
Default Configuration
Disabled is the default configuration.
Command Mode
Interface Configuration (VLAN, Tunnel, Loopback) mode
User Guidelines
This command has no user guidelines.
Example
The following example suppresses router advertisement transmission.
console(config)#interface vlan 15
console(config-if-vlan15)#ipv6 nd suppress-ra
ipv6 route
Use the ipv6 route command in Global Configuration mode to configure an
IPv6 static route. Use the no form of the command to remove a preference,
an individual next hop, or all next hops for a route. Using the no ipv6 route
distance form causes the system to use the system default administrative
distance.
Syntax
ipv6 route
distance
ipv6 route
ipv6-prefix/prefix-length
{ipv6-address |
interface-type
ipv6-
address} [
preference
]
2CSNXXX_SWUM200.book Page 1099 Tuesday, December 10, 2013 1:22 PM

1100 IPv6 Routing Commands
no ipv6 route
ipv6-prefix/prefix-length
ipv6-address
preference
no ipv6 route
ipv6-prefix/prefix-length interface-type ipv6-address
no ipv6 route
ipv6-prefix/prefix-length interface
•
distance
—The default administrative distance for static routes. (Range 1-
255)
•
ipv6-prefix
—An IPv6 prefix representing the subnet that can be reached
via the next-hop neighbor.
•
prefix-length
—The length of the IPv6 prefix — a decimal value (usually 0-
64) that shows how many of the high-order contiguous bits of the address
comprise the prefix (the network portion of the address). A slash mark
must separate the prefix from the prefix-length with no spaces on either
side of the slash mark.
•
interface-type
—Distinguishes direct static routes from point-to-point and
broadcast interfaces, and must be specified when using a link-local address
as the next hop. Interface-type can be Null or vlan plus vlan-id or tunnel
plus tunnel-id.
•
ipv6-address
—The IPv6 address of the next hop neighbor.
•
preference
—The administrative distance the router uses to compare this
route with routes from other route sources that have the same destination.
(Range: 1-255)
Default Configuration
1 is the default value for
preference
.
Command Mode
Global Configuration mode
User Guidelines
This command has no user guidelines.
Example
The following example configure an IPv6 static route.
console(config)#ipv6 route 2020:1::1/64 2030:1::2
2CSNXXX_SWUM200.book Page 1100 Tuesday, December 10, 2013 1:22 PM

IPv6 Routing Commands 1101
ipv6 route distance
Use the ipv6 route distance command in Global Configuration mode to set
the default distance (preference) for static routes. Lower route preference
values are preferred when determining the best route. The ipv6 route and
ipv6 route default commands allow optional setting of the distance of an
individual static route. The default distance is used when no distance is
specified in these commands. Changing the default distance does not update
the distance of existing static routes, even if they were assigned the original
default distance. The new default distance is applied to static routes created
after invoking the ipv6 route distance command.
Syntax
ipv6 route distance
integer
no ipv6 route distance
integer
•
integer
— Specifies the distance (preference) of an individual static route.
(Range 1-255)
Default Configuration
Default value of
integer
is 1.
Command Mode
Global Configuration mode
User Guidelines
Lower route distance values are preferred when determining the best route.
Example
The following example sets the default distance to 80.
console(config)#ipv6 route distance 80
ipv6 unicast-routing
Use the ipv6 unicast-routing command in Global Configuration mode to
enable forwarding of IPv6 unicast datagrams.
2CSNXXX_SWUM200.book Page 1101 Tuesday, December 10, 2013 1:22 PM

1102 IPv6 Routing Commands
Syntax
ipv6 unicast-routing
no ipv6 unicast-routing
Default Configuration
Disabled is the default configuration.
Command Mode
Global Configuration mode
User Guidelines
This command has no user guidelines.
Example
The following example globally enables Ipv6 unicast datagram forwarding.
console(config)#ipv6 unicast-routing
console(config)#no ipv6 unicast-routing
ping ipv6
Use ping ipv6 command in Privileged EXEC mode to determine whether
another computer is reachable on the network. The target device must have
the ping responses enabled.
Syntax
ping ipv6 {
ipv6-address
|
hostname
} [repeat
1-15
] | [timeout
1-60
] | [size
0-
13000
] | [source {
ipv6-address
| | loopback
0-7
| vlan
0-4093
| tunnel
0-7
|
out-of-band}]
•
ipv6-address
|
hostname
—The target IP address or host to ping.
• repeat—The number of ping packets to send. Range 1-15.
• timeout—The period in seconds to wait for an ICMP echo reply.
• size—The packet size padding in bytes. Range 0-13000
2CSNXXX_SWUM200.book Page 1102 Tuesday, December 10, 2013 1:22 PM

IPv6 Routing Commands 1103
• source—Use the specified source IP address, loopback address, VLAN
address, tunnel, or out-of-band interface address in the transmitted
packets
• loopback—Use the source address from the loopback port index.
• VLAN—The source VLAN over which to send the echo request.
• out-of-band—Sends the ping over the out-of-band interface.
Default Configuration
It is not possible to ping from a specific interface when a VLAN is specified as
the source of the ping. The system selects the first available interface in the
VLAN from which to send the ping packets.
Command Mode
User EXEC and Privileged EXEC modes
User Guidelines
This command has no user guidelines.s
Example
The following example determines whether another computer is on the
network at the IPv6 address specified.
console#ping ipv6 2030:1::1/64
Send count=3, Receive count=0 from 2030:1::1/64
Average round trip time = 0.00 ms
ping ipv6 interface
Use ping ipv6 interface command in the Privileged EXEC mode to
determine whether another computer is on the network. To use the
command, configure the switch for network (in-band) connection. The
source and target devices must have the ping utility enabled and running on
top of TCP/IP. The switch can be pinged from any IP workstation with which
the switch is connected through the default VLAN (VLAN 1), as long as there
is a physical path between the switch and the workstation. The terminal
2CSNXXX_SWUM200.book Page 1103 Tuesday, December 10, 2013 1:22 PM

1104 IPv6 Routing Commands
interface sends three pings to the target station. Use the interface keyword to
ping an interface by using the link-local address or the global IPv6 address of
the interface. The source can be a loopback, tunnel, or logical interface.
Syntax
ping ipv6 interface {loopback
0-7
| out-of-band | vlan
0-4093
| tunnel
0-7
}
link-local-address
[repeat
1-15
] | [timeout
1-60
] | [size
0-13000
] | [source
{
ipv6-address
| loopback
0-7
| vlan
0-4093
| tunnel
0-7
| out-of-band}]
• loopback—Use the source address from the loopback port index.
• out-of-band—Sends the ping over the out-of-band interface.
• VLAN—The source VLAN over which to send the echo request.
•
link-local-address
—The target IP address or host to ping.
• repeat—The number of ping packets to send. Range 1-15.
• timeout—The period in seconds to wait for an ICMP echo reply.
• size—The packet size padding in bytes. Range 0-13000
• source—Use the specified source IP address, loopback address, VLAN
address, tunnel, or out-of-band interface address in the transmitted
packets
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC mode
User Guidelines
This command has no user guidelines.
Example
The following example determines whether another computer is on the
network at the IPv6 address specified.
console(config)#ping ipv6 interface loopback 1 FE80::202:BCFF:FE00:3068/128
Send count=3, Receive count=0 from FE80::202:BCFF:FE00:3068/128
Average round trip time = 0.00 ms
2CSNXXX_SWUM200.book Page 1104 Tuesday, December 10, 2013 1:22 PM

IPv6 Routing Commands 1105
rate-limit cpu
Use the rate-limit cpu command to reduce the amount of unknown
unicast/multicast packets forwarded to the CPU on CoS queues 0 and 1.
This command also configures the rate in packets-per-second for the number
of IPv4 and IPv6 data packets trapped to CPU when the packet fails to be
forwarded in the hardware due to unresolved MAC address of the destination
IPv6 node. Packets exceeeding the rate limit are silently discarded.
Use the no form of the command to return the rate limit to the default value.
Syntax
rate-limit cpu direction input pps
pps-value
no rate-limit cpu direction input pps
• pps-value—Range of 100-1024 packets per second (100-3000 for N4000
switches)
Default Configuration
The default is 1024 packets per second
(3000 for N4000 switches)
Command Modes
Global Configuration mode
User Guidelines
Unknown multicast and IPv4/IPv6 data packets destined to hosts in the
connected networks on the router for which the MAC address is not resolved
are trapped to CPU to trigger the ARP/neighbor discovery resolution of those
hosts.
When the ARP or neighbor table is filled, the switch cannot accommodate
new entries. In this case, there is no value in receiving the unresolved
IPv4/IPv6 packets. Likewise, in cases of a L2 network re-convergence, a large
number of neighbors may not be discovered but may be transmitting traffic.
In the case of multicast data, certain multicast topologies using multiaccess
VLANs may result in packets being forwarded to the CPU with no associated
PIM or MFDB state.
2CSNXXX_SWUM200.book Page 1105 Tuesday, December 10, 2013 1:22 PM

1106 IPv6 Routing Commands
Receiving large numbers unresolved packets spikes the CPU usage to high
levels at no benefit. For Ipv6, it also results in delayed processing of the NUD
packets (NS/NA) for the existing neighbor entries leading to NUD anomalies
and deletions of existing neighbor entries.
To avoid such an unnecessary CPU load leading to NUD anomalies when the
ARP or IPV6 neighbor table is close to full (crossing 95% of table size) or
other failures, the switch automatically reduces the rate limit to an empirical
value of 50 pps irrespective of the configured rate limit. When the table size
falls below 95% of the table size, it is restored to the configured rate limit
value.
Use this command to limit the CPU load in situations where large numbers of
unknown multicast or IPv4/IPv6 packets with an unknown multicast or
unicast IPv4/IPv6 destination are being handled in software. The symptom
can be diagnosed by high CPU usage of the ipMapForwardingTask.
Example
An example output is showing higher than normal CPU usage due to packets
copied to the software forwarding task below:
console#show process cpu
Memory Utilization Report
status bytes
------ ----------
free 1055653888
alloc 672153600
CPU Utilization:
PID Name 5 Secs 60 Secs 300 Secs
---------- ------------------- -------- -------- --------
1129 osapiTimer 0.09% 0.02% 0.01%
1137 bcmCNTR.0 0.19% 0.28% 0.30%
1142 bcmRX 18.00% 12.04% 11.10%
1155 bcmLINK.0 0.39% 0.37% 0.36%
1156 cpuUtilMonitorTask 0.09% 0.04% 0.04%
1170 nim_t 0.09% 0.07% 0.07%
1222 snoopTask 0.09% 0.02% 0.02%
1243 ipMapForwardingTask 27.30% 24.19% 29.06%
1257 tRtrDiscProcessingT 0.09% 0.01% 0.00%
1291 RMONTask 0.00% 0.02% 0.03%
2CSNXXX_SWUM200.book Page 1106 Tuesday, December 10, 2013 1:22 PM

IPv6 Routing Commands 1107
1293 boxs Req 0.00% 0.01% 0.01%
------------------------------ -------- -------- --------
Total CPU Utilization 55.91% 45.40% 48.02%
show ipv6 brief
Use the show ipv6 brief command in Privileged EXEC mode to display the
IPv6 status of forwarding mode and IPv6 unicast routing mode.
Syntax
show ipv6 brief
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC mode, Configuration mode and all Configuration submodes
User Guidelines
This command has no user guidelines.
Example
The following example displays the IPv6 status of forwarding mode and IPv6
unicast routing mode.
console#show ipv6 brief
IPv6 Unicast Routing Mode.................... Enable
IPv6 Hop Limit............................... Unconfigured
ICMPv6 Rate Limit Error Interval............. 1000 msec
ICMPv6 Rate Limit Burst Size................. 100 messages
show ipv6 interface
Use the show ipv6 interface command in Privileged EXEC mode to show the
usability status of IPv6 interfaces. The output of the command includes the
method of assignment for each IPv6 address that is either autoconfigured or
leased from a DHCP server. Global addresses with no annotation are assumed
to be manually configured.
2CSNXXX_SWUM200.book Page 1107 Tuesday, December 10, 2013 1:22 PM
1108 IPv6 Routing Commands
Syntax
show ipv6 interface [brief] [loopback
loopback-id
| tunnel
tunnel-id
| vlan
vlan-id
[prefix]]
•
loopback-id
—Valid loopback interface ID
•
tunnel-id
—Valid tunnel interface ID
•
vlan-id
—Valid VLAN ID
•
prefix
—Display IPv6 Interface Prefix Information.
Default Configuration
Displays all IPv6 interfaces.
Command Mode
User EXEC, Privileged EXEC modes, Configuration mode and all
Configuration submodes
User Guidelines
The Method field contains one of the following values.
The long form of the command includes the same annotations and shows
whether address autoconfiguration or DHCP client are enabled on the
interface. When the interface acts as a host interface, the output also shows
the default gateway on the interface, if one exists.
Examples
The following example shows the method of assignment for each IPv6 address
that is either autoconfigured or leased from a DHCP server.
console#show ipv6 interface
Field Description
Auto The IPv6 address is automatically generated using IPv6 auto
address configuration (RFC 2462).
Config The IPv6 address is manually configured.
DHCP The IPv6 address is leased from a DHCP server.
TENT Tentative address.
2CSNXXX_SWUM200.book Page 1108 Tuesday, December 10, 2013 1:22 PM

IPv6 Routing Commands 1109
Oper.
Interface Mode IPv6 Address/Length
---------- -------- ---------------------------------
Vl3 Enabled FE80::211:88FF:FE2A:3E3C/128
2033::211:88FF:FE2A:3E3C/64
Vl5 Enabled FE80::211:88FF:FE2A:3E3C/128
2017::A42A:26DB:1049:43DD/128 [DHCP]
Vl7 Enabled FE80::211:88FF:FE2A:3E3C/128
2001::211:88FF:FE2A:3E3C/64 [AUTO]
Vl9 Disabled FE80::211:88FF:FE2A:3E3C/128 [TENT]
The Method column shows one of the following values:
• Auto – The IPv6 address was automatically generated using IPv6 auto
address configuration (RFC 2462)
• Config – The IPv6 address was manually configured.
• DHCP – The IPv6 address was leased from a DHCP server.
• TENT – Tentative address.
The following example displays the long form of the command, and indicates
whether address autoconfiguration or DHCP client are enabled on the
interface. When the interface acts as a host interface, the output also shows
the default gateway on the interface, if one exists.
console#show ipv6 interface vlan2
IPv6 is enabled
IPv6 Prefix is ................................ FE80::211:88FF:FE2A:3E3C/128
2017::A42A:26DB:1049:43DD/128
[DHCP]
Routing Mode................................... Enabled
Administrative Mode............................ Enabled
IPv6 Routing Operational Mode.................. Enabled
Bandwidth...................................... 100000 kbps
Interface Maximum Transmit Unit................ 1500
Router Duplicate Address Detection Transmits... 1
Address Autoconfigure Mode..................... Disabled
Address DHCP Mode.............................. Enabled
Router Advertisement NS Interval............... 0
Router Advertisement Lifetime.................. 1800
Router Advertisement Reachable Time............ 0
Router Advertisement Interval.................. 600
Router Advertisement Managed Config Flag....... Disabled
Router Advertisement Other Config Flag......... Disabled
Router Advertisement Router Preference......... medium
Router Advertisement Suppress Flag............. Disabled
2CSNXXX_SWUM200.book Page 1109 Tuesday, December 10, 2013 1:22 PM

1110 IPv6 Routing Commands
IPv6 Destination Unreachables.................. Enabled
IPv6 Default Router............................ fe80::213:c4ff:fedb:6c42
show ipv6 interface management statistics
Use the show ipv6 interface management statistics command in Privileged
EXEC mode to show the DCHPv6 client statistics.
Syntax
show ipv6 interface management statistics
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC mode, Configuration mode and all Configuration submodes
User Guidelines
This command has no user guidelines.
Example
console#show ipv6 interface management statistics
DHCPv6 Client Statistics
-------------------------
DHCPv6 Advertisement Packets Received.......... 0
DHCPv6 Reply Packets Received.................. 0
Received DHCPv6 Advertisement Packets Discard.. 0
Received DHCPv6 Reply Packets Discarded........ 0
DHCPv6 Malformed Packets Received.............. 0
Total DHCPv6 Packets Received.................. 0
DHCPv6 Solicit Packets Transmitted............. 0
DHCPv6 Request Packets Transmitted............. 0
DHCPv6 Renew Packets Transmitted............... 0
DHCPv6 Rebind Packets Transmitted.............. 0
DHCPv6 Release Packets Transmitted............. 0
Total DHCPv6 Packets Transmitted............... 0
2CSNXXX_SWUM200.book Page 1110 Tuesday, December 10, 2013 1:22 PM
IPv6 Routing Commands 1111
show ipv6 mld groups
The show ipv6 mld groups command is used to display information about
multicast groups that MLD reported. The information is displayed only when
MLD is enabled on at least one interface. If MLD was not enabled on any
interfaces, there is no group information to be displayed.
Syntax
show ipv6 mld groups {
group-address
| vlan
vlan-id
}
•
group-address
— The group address to display.
•
vlan-id
— A valid VLAN id.
Default Configuration
There is no default configuration for this command.
Command Mode
Privileged EXEC mode, Configuration mode and all Configuration submodes
User Guidelines
The following fields are displayed as a table when vlan
vlan-id
is specified:
Field Description
Number of (*, G)
entries
Displays the number of groups present in the MLD Table.
Number of (S, G)
entries
Displays the number of include and exclude mode sources
present in the MLD Table.
Group Address The address of the multicast group.
Interface Interface through which the multicast group is reachable.
Uptime Time elapsed in seconds since the multicast group has been
known.
Expiry Time Time left in seconds before the entry is removed from the
MLD membership table.
2CSNXXX_SWUM200.book Page 1111 Tuesday, December 10, 2013 1:22 PM

1112 IPv6 Routing Commands
If vlan
vlan-id
is not specified, the following fields are displayed for each
multicast group and each interface:
The following table is displayed to indicate all the sources associated with this
group:
Example
console#show ipv6 mld groups ff1e::5
Interface..................................... vlan 6
Group Address................................ FF1E::5
Last Reporter................... FE80::200:FF:FE00:22
Up Time (hh:mm:ss).......................... 00:03:43
Expiry Time (hh:mm:ss)......................... -----
Filter Mode..........................................Include
Field Description
Group Address The address of the multicast group.
Interface Interface through which the multicast group is reachable.
Uptime Time elapsed in seconds since the multicast group has been
known.
Expiry Time Time left in seconds before the entry is removed from the MLD
membership table of this interface.
Last Reporter The IP Address of the source of the last membership report
received for this multicast group address on that interface.
Filter Mode The filter mode of the multicast group on this interface. The
values it can take are INCLUDE and EXCLUDE.
Compatibility
Mode
The compatibility mode of the multicast group on this interface.
The values it can take are MLDv1 and MLDv2.
Version 1 Host
Timer
The time remaining until the router assumes there are no longer
any MLD version-1 Hosts on the specified interface.
Field Description
Source Address The IP address of the source.
Uptime Time elapsed in seconds since the source has been known.
Expiry Time Time left in seconds before the entry is removed.
2CSNXXX_SWUM200.book Page 1112 Tuesday, December 10, 2013 1:22 PM

IPv6 Routing Commands 1113
Version1 Host Timer............................ -----
Group compat mode.............................. v2
Source Address ExpiryTime
----------------- -----------
4001::6 00:03:15
4001::7 00:03:15
4001::8 00:03:15
console#show ipv6 mld groups vlan 6
Group Address................................ FF1E::1
Interface..................................... vlan 6
Up Time (hh:mm:ss).......................... 00:04:23
Expiry Time (hh:mm:ss)........................ ------
Group Address................................ FF1E::2
Interface..................................... vlan 6
Up Time (hh:mm:ss).......................... 00:04:23
Expiry Time (hh:mm:ss)........................ ------
Group Address................................ FF1E::3
Interface..................................... vlan 6
Up Time (hh:mm:ss).......................... 00:04:23
Expiry Time (hh:mm:ss)........................ ------
Group Address................................ FF1E::4
Interface..................................... vlan 6
Up Time (hh:mm:ss).......................... 00:04:23
Expiry Time (hh:mm:ss)........................ ------
show ipv6 mld host-proxy
Use the show ipv6 mld host-proxy command to display a summary of the host
interface status parameters.
This command deprecates the show ipv6 mld mroute-proxy command.
Syntax
show ipv6 mld host-proxy
Default Configuration
There is no default configuration for this command.
2CSNXXX_SWUM200.book Page 1113 Tuesday, December 10, 2013 1:22 PM

1114 IPv6 Routing Commands
Command Mode
Privileged EXEC mode, Configuration mode and all Configuration submodes
User Guidelines
There are no user guidelines for this command.
Example
console#show ipv6 mld host-proxy
Admin Mode..................................... Disabled
show ipv6 mld interface
The show ipv6 mld interface command is used to display MLD related
information for an interface.
Syntax
show ipv6 mld interface { vlan
vlan-id
| all}
•
vlan-id
— A valid VLAN id.
Default Configuration
There is no default configuration for this command.
Command Mode
Privileged EXEC mode, Configuration mode and all Configuration submodes
User Guidelines
The following information is displayed for the specified interface:
Field Description
Interface The interface number in unit/slot/port format.
MLD Global
Admin Mode
This field displays the configured global administrative status of
MLD.
MLD Interface
Admin Mode
This field displays the configured interface administrative status
of MLD.
2CSNXXX_SWUM200.book Page 1114 Tuesday, December 10, 2013 1:22 PM

IPv6 Routing Commands 1115
The following information is displayed if the operational mode of the MLD
interface is enabled:
MLD Operational
Mode
The operational status of MLD on the interface.
MLD Version This field indicates the version of MLD configured on the
interface.
Query Interval This field indicates the configured query interval for the
interface.
Query Max
Response Time
This field indicates the configured maximum query response
time (in seconds) advertised in MLD queries on this interface.
Robustness This field displays the configured value for the tuning for the
expected packet loss on a subnet attached to the interface.
Startup Query
Interval
This value indicates the configured interval between General
Queries sent by a Querier on startup.
Startup Query
Count
This value indicates the configured number of Queries sent out
on startup, separated by the Startup Query Interval.
Last Member
Query Interval
This value indicates the configured Maximum Response Time
inserted into Group-Specific Queries sent in response to Leave
Group messages.
Last Member
Query Count
This value indicates the configured number of Group-Specific
Queries sent before the router assumes that there are no local
members.
Field Description
Querier Status This value indicates whether the interface is a MLD querier or
non-querier on the subnet with which it is associated.
Querier Address The IP address of the MLD querier on the subnet the interface
with which it is associated.
Querier Up Time Time elapsed in seconds since the querier state has been
updated.
Querier Expiry
Time
Time left in seconds before the Querier losses its title as querier.
Wrong Version
Queries
Indicates the number of queries received whose MLD version
does not match the MLD version of the interface.
2CSNXXX_SWUM200.book Page 1115 Tuesday, December 10, 2013 1:22 PM

1116 IPv6 Routing Commands
Example
console#show ipv6 mld interface vlan 2
Interface................................... vlan 2
MLD Global Admin Mode....................... Enabled
MLD Interface Admin Mode.................... Disabled
MLD Operational Mode........................ Disabled
MLD Version................................. 2
Query Interval (secs)....................... 100
Query Max Response Time(milli-secs)........ 1111
Robustness.................................. 2
Startup Query Interval (secs).............. 31
Startup Query Count......................... 2
Last Member Query Interval (milli-secs)..... 1111
Last Member Query Count..................... 2
show ipv6 mld host-proxy
Use the show ipv6 mld host-proxy command to display a summary of the host
interface status parameters.
Syntax
show ipv6 mld host-proxy
Command Mode
Privileged EXEC mode, Configuration mode and all Configuration submodes
Default Configuration
There is no default configuration for this command.
Number of Joins The number of times a group membership has been added on
this interface.
Number of Leaves The number of times a group membership has been removed on
this interface.
Number of Groups The current number of membership entries for this interface.
2CSNXXX_SWUM200.book Page 1116 Tuesday, December 10, 2013 1:22 PM

IPv6 Routing Commands 1117
User Guidelines
The command displays the following parameters only when you enable MLD
Proxy:
Example
console#show ipv6 mld host-proxy
Interface Index.............................. vlan 10
Admin Mode................................... Enabled
Operational Mode............................. Enabled
Version............................................ 3
Num of Multicast Groups............................ 0
Unsolicited Report Interval........................ 1
Querier IP Address on Proxy Interface..... fe80::1:2:5
Older Version 1 Querier Timeout............. 00:00:00
Proxy Start Frequency...............................1
Field Description
Interface Index The interface number of the MLD Proxy interface.
Admin Mode Indicates whether MLD Proxy is enabled or disabled. This is a
configured value.
Operational Mode Indicates whether MLD Proxy is operationally enabled or
disabled. This is a status parameter.
Version The present MLD host version that is operational on the proxy
interface.
Number of
Multicast Groups
The number of multicast groups that are associated with the
MLD-Proxy interface.
Unsolicited Report
Interval
The time interval at which the MLD-Proxy interface sends
unsolicited group membership reports.
Querier IP Address
on Proxy Interface
The IP address of the Querier, if any, in the network attached to
the upstream interface (MLD-Proxy interface).
Older Version 1
Querier Timeout
The interval used to timeout the older version 1 queriers.
Proxy Start
Frequency
The number of times the MLD-Proxy has been stopped and
started.
2CSNXXX_SWUM200.book Page 1117 Tuesday, December 10, 2013 1:22 PM

1118 IPv6 Routing Commands
show ipv6 mld host-proxy groups
Use the show ipv6 mld host-proxy groups command to display information
about multicast groups that the MLD Proxy reported.
Syntax
show ipv6 mld host-proxy groups
Default Configuration
There is no default configuration for this command.
Command Mode
Privileged EXEC, Configuration mode and all Configuration submodes
User Guidelines
The following parameters are displayed by this command:
Field Description
Interface The MLD Proxy interface.
Group Address The IP address of the multicast group.
Last Reporter The IP address of the host that last sent a membership report for the
current group on the network attached to the MLD-Proxy interface
(upstream interface).
Up Time (in
secs)
The time elapsed in seconds since last created.
Member State Possible values are:
• Idle_Member—The interface has responded to the latest group
membership query for this group.
• Delay_Member—The interface is going to send a group
membership report to respond to a group membership query for
this group.
Filter Mode Possible values are Include or Exclude.
Sources The number of sources attached to the multicast group.
2CSNXXX_SWUM200.book Page 1118 Tuesday, December 10, 2013 1:22 PM

IPv6 Routing Commands 1119
Example
console#show ipv6 mld host-proxy groups
Interface................................ vlan 10
Group Address Last Reporter Up Time Member State Filter Mode Sources
------------- -------------- ---------- ----------------- ------------ -----
--
FF1E::1 FE80::100:2.3 00:01:40 DELAY_MEMBER Exclude 2
FF1E::2 FE80::100:2.3 00:02:40 DELAY_MEMBER Include 1
FF1E::3 FE80::100:2.3 00:01:40 DELAY_MEMBER Exclude 0
FF1E::4 FE80::100:2.3 00:02:44 DELAY_MEMBER Include 4
show ipv6 mld host-proxy groups detail
Use the show ipv6 mld host-proxy groups detail command to display
information about multicast groups that MLD Proxy reported.
Syntax
show ipv6 mld host-proxy groups detail
Default Configuration
There is no default configuration for this command.
Command Mode
Privileged EXEC, Configuration mode and all Configuration submodes
User Guidelines
The following parameters are displayed by this command:
Field Description
Interface The interface number of the MLD-Proxy.
Group Address The IP address of the multicast group.
Last Reporter The IP address of the host that last sent a membership report for
the current group on the network attached to the MLD Proxy
interface (upstream interface).
Up Time (in
secs)
The time elapsed in seconds since last created.
2CSNXXX_SWUM200.book Page 1119 Tuesday, December 10, 2013 1:22 PM

1120 IPv6 Routing Commands
Example
console#show ipv6 mld host-proxy groups
Interface................................ vlan 10
Group Address Last Reporter Up Time Member State Filter Mode
Sources
------------- ---------------- --------- ----------------- ------------- ---
FF1E::1 FE80::100:2.3 244 DELAY_MEMBER Exclude 2
Group Source List Expiry Time
------------------ ---------------
2001::1 00:02:40
2001::2 --------
FF1E::2 FE80::100:2.3 243 DELAY_MEMBER Include 1
Group Source List Expiry Time
------------------ ---------------
3001::1 00:03:32
3002::2 00:03:32
FF1E::3 FE80::100:2.3 328 DELAY_MEMBER Exclude 0
FF1E::4 FE80::100:2.3 255 DELAY_MEMBER Include 4
Group Source List Expiry Time
------------------ ---------------
4001::1 00:03:40
5002::2 00:03:40
4001::2 00:03:40
5002::2 00:03:40
Member State Possible values are:
• Idle_Member—The interface has responded to the latest group
membership query for this group.
• Delay_Member—The interface is going to send a group
membership report to respond to a group membership query for
this group.
Filter Mode Possible values are Include or Exclude.
Sources The number of sources attached to the multicast group.
Group Source
List
The list of IP addresses of the sources attached to the multicast
group.
Expiry Time The time left for a source to get deleted.
2CSNXXX_SWUM200.book Page 1120 Tuesday, December 10, 2013 1:22 PM

IPv6 Routing Commands 1121
show ipv6 mld host-proxy interface
Use the show ipv6 mld-proxy interface command to display a detailed list of
the host interface status parameters.
Syntax
show ipv6 mld host-proxy interface
Default Configuration
There is no default configuration for this command.
Command Mode
Privileged EXEC, Configuration mode and all Configuration submodes
User Guidelines
The following parameters are displayed only when MLD Proxy is enabled:
The column headings of the table associated with the interface are as follows:
Example
console#show ipv6 mld host-proxy interface
Interface................................ vlan 10
Parameter Description
Interface The MLD Proxy interface.
Parameter Description
Ver The MLD version.
Query Rcvd Number of MLD queries received.
Report Rcvd Number of MLD reports received.
Report Sent Number of MLD reports sent.
Leaves Rcvd Number of MLD leaves received. Valid for version 2 only.
Leaves Sent Number of MLD leaves sent on the Proxy interface. Valid for version 2
only.
2CSNXXX_SWUM200.book Page 1121 Tuesday, December 10, 2013 1:22 PM

1122 IPv6 Routing Commands
Ver Query Rcvd Report Rcvd Report Sent Leave Rcvd Leave Sent
-----------------------------------------------------------
1 2 0 0 0 2
2 3 0 4 ----- -----
show ipv6 mld traffic
The show ipv6 mld traffic command is used to display MLD statistical
information for the router.
Syntax
show ipv6 mld traffic
Default Configuration
There is no default configuration for this command.
Command Mode
Privileged EXEC mode, Configuration mode and all Configuration submodes
User Guidelines
The following fields are displayed:
Field Description
Valid MLD Packets
Received
The number of valid MLD packets received by the
router.
Valid MLD Packets Sent The number of valid MLD packets sent by the router.
Queries Received The number of valid MLD queries received by the
router.
Queries Sent The number of valid MLD queries sent by the router.
Reports Received The number of valid MLD reports received by the
router.
Reports Sent The number of valid MLD reports sent by the router.
Leaves Received The number of valid MLD leaves received by the router.
Leaves Sent The number of valid MLD leaves sent by the router.
2CSNXXX_SWUM200.book Page 1122 Tuesday, December 10, 2013 1:22 PM

IPv6 Routing Commands 1123
Example
console#show ipv6 mld traffic
Valid MLD Packets Received..................... 52
Valid MLD Packets Sent......................... 7
Queries Received............................... 0
Queries Sent................................... 7
Reports Received............................... 52
Reports Sent................................... 0
Leaves Received................................ 0
Leaves Sent.................................... 0
show ipv6 neighbors
Use the show ipv6 neighbors command in Privileged EXEC mode to display
information about the IPv6 neighbors.
Syntax
show ipv6 neighbors
Default Configuration
This command has no default configuration.
Command Mode
User EXEC, Privileged EXEC modes, Configuration mode and all
Configuration submodes
User Guidelines
This command has no user guidelines.
Example
The following example displays information about the IPv6 neighbors.
console(config)#show ipv6 neighbors
Bad Checksum MLD
Packets
The number of bad checksum MLD packets received by
the router.
Malformed MLD Packets The number of malformed MLD packets received by the
router.
2CSNXXX_SWUM200.book Page 1123 Tuesday, December 10, 2013 1:22 PM

1124 IPv6 Routing Commands
Neighbor Last
IPv6 Address MAC Address isRtr State Updated
Interface
-------------------- ----------------- ----- ------- ---------
show ipv6 route
Use the show ipv6 route command in User EXEC or Privileged EXEC mode
to display the IPv6 routing table. The output of the command also displays
the IPv6 address of the default gateway and the default route associated with
the gateway.
Syntax
show ipv6 route [ipv6-address |
ipv6-prefix
/
prefix-length
| protocol |
i
nterface-type interface-number
] [best]
•
ipv6-address
—Specifies an IPv6 address for which the best-matching
route would be displayed.
•
protocol
—Specifies the protocol that installed the routes. Is one of the
following keywords: connected, ospf, static.
•
ipv6-prefix/ prefix-length
—Specifies an IPv6 network for which the
matching route would be displayed.
•
interface-type interface-number
—Valid IPv6 interface. Specifies that the
routes with next-hops on the selected interface be displayed. Supported
interface types are VLAN, Tunnel, and Loopback.
•
best
—Specifies that only the best routes are displayed. If the connected
keyword is selected for protocol, the best option is not available because
there are no best or non-best connected routes.
Default Configuration
This command has no default configuration.
Command Mode
User EXEC, Privileged EXEC modes, Configuration mode and all
Configuration submodes
2CSNXXX_SWUM200.book Page 1124 Tuesday, December 10, 2013 1:22 PM

IPv6 Routing Commands 1125
User Guidelines
This command has no user guidelines.
Example
The following example displays the IPv6 address of the default gateway and
the default route associated with the gateway.
console(config)#show ipv6 route
IPv6 Routing Table - 0 entries
Route Codes: C - connected, S - static
O - OSPF Intra, OI - OSPF Inter, OE1 - OSPF Ext 1, OE2 - OSPF Ext 2
ON1 - OSPF NSSA Ext Type 1, ON2 - OSPF NSSA Ext Type 2
Default gateway is 10.1.20.1
S 0.0.0.0/0 [254/0] via 10.1.20.1
C 10.1.20.0/24 [0/1] directly connected, vlan2
C 20.1.20.0/24 [0/1] directly connected, vlan4
show ipv6 route preferences
Use the show ipv6 route preferences command in Privileged EXEC mode to
show the preference value associated with the type of route. Lower numbers
have a greater preference.
Syntax
show ipv6 route preferences
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC mode, Configuration mode and all Configuration submodes
User Guidelines
This command has no user guidelines.
2CSNXXX_SWUM200.book Page 1125 Tuesday, December 10, 2013 1:22 PM

1126 IPv6 Routing Commands
Example
The following example shows the preference value associated with the type of
route.
console#show ipv6 route preferences
Local.......................................... 0
Static......................................... 1
OSPF Intra-area routes......................... 110
OSPF Inter-area routes......................... 110
OSPF External routes........................... 110
show ipv6 route summary
Use the show ipv6 route summary command in Privileged EXEC mode to
display a summary of the routing table for all routes, including best and non-
best routes. Use best to display the count summary for only best routes.
Syntax
show ipv6 route summary [best]
•
best
— Displays the count summary for only best routes.
Default Configuration
This command has no default configuration.
Command Mode
User EXEC, Privileged EXEC modes, Configuration mode and all
Configuration submodes
User Guidelines
This command has no user guidelines.
Example
The following example displays a summary of the routing table.
console#show ipv6 route summary
IPv6 Routing Table Summary - 0 entries
Connected Routes............................. 0
Static Routes................................ 0
2CSNXXX_SWUM200.book Page 1126 Tuesday, December 10, 2013 1:22 PM

IPv6 Routing Commands 1127
OSPF Routes.................................. 0
Intra Area Routes............................ 0
Inter Area Routes............................ 0
External Type-1 Routes....................... 0
External Type-2 Routes....................... 0
Total routes................................. 0
Number of Prefixes:
show ipv6 traffic
Use the show ipv6 traffic command in User EXEC mode to show traffic and
statistics for IPv6 and ICMPv6.
Syntax
show ipv6 traffic [vlan
vlan-id
| tunnel
tunnel-id
| loopback
loopback-id
]
•
vlan-id
— Valid VLAN ID, shows information about traffic on a specific
interface or, without the optional parameter, shows information about
traffic on all interfaces.
• tunnel — Tunnel identifier. (Range: 0-7)
• loopback — Loopback identifier. (Range: 0-7)
Default Configuration
This command has no default configuration.
Command Mode
User EXEC mode, Configuration mode and all Configuration submodes
User Guidelines
This command has no user guidelines.
Examples
The following examples show traffic and statistics for IPv6 and ICMPv6, first
for all interfaces and an individual VLAN.
console> show ipv6 traffic
IPv6 STATISTICS
Total Datagrams Received........................................... 0
Received Datagrams Locally
Delivered.......................................... 0
2CSNXXX_SWUM200.book Page 1127 Tuesday, December 10, 2013 1:22 PM

1128 IPv6 Routing Commands
Received Datagrams Discarded Due To Header Errors.. 0
Received Datagrams Discarded Due To MTU............ 0
Received Datagrams Discarded Due To No Route....... 0
Received Datagrams With Unknown Protocol........... 0
Received Datagrams Discarded Due To Invalid Address.0
Received Datagrams Discarded Due To Truncated Data. 0
Received Datagrams Discarded Other................. 0
Received Datagrams Reassembly Required............. 0
Datagrams Successfully Reassembled................. 0
Datagrams Failed To Reassemble..................... 0
Datagrams Forwarded................................ 0
Datagrams Locally Transmitted...................... 0
Datagrams Transmit Failed.......................... 0
Datagrams Successfully Fragmented.................. 0
Datagrams Failed To Fragment....................... 0
Fragments Created.................................. 0
Multicast Datagrams Received....................... 0
Multicast Datagrams Transmitted.................... 0
console> show ipv6 traffic vlan 11
Interface ........................................ 11
IPv6 STATISTICS
Total Datagrams Received........................... 0
Received Datagrams Locally Delivered............... 0
Received Datagrams Discarded Due To Header Errors.. 0
Received Datagrams Discarded Due To MTU............ 0
Red Datagrams Discarded Due To No Route............ 0
Received Datagrams With Unknown Protocol........... 0
Received Datagrams Discarded Due To Invalid Address 0
Received Datagrams Discarded Due To Truncated Data. 0
Received Datagrams Discarded Other................. 0
Received Datagrams Reassembly Required............. 0
Datagrams Successfully Reassembled................. 0
Datagrams Failed To Reassemble..................... 0
Datagrams Forwarded................................ 0
Datagrams Locally Transmitted...................... 0
Datagrams Transmit Failed.......................... 0
Datagrams Successfully Fragmented.................. 0
Datagrams Failed To Fragment....................... 0
Fragments Created.................................. 0
Multicast Datagrams Received....................... 0
Multicast Datagrams Transmitted.................... 0
2CSNXXX_SWUM200.book Page 1128 Tuesday, December 10, 2013 1:22 PM

IPv6 Routing Commands 1129
show ipv6 vlan
Use the show ipv6 vlan command in Privileged EXEC mode to display IPv6
VLAN routing interface addresses.
Syntax
show ipv6 vlan
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC mode, Configuration mode and all Configuration submodes
User Guidelines
This command has no user guidelines.
Example
The following example displays IPv6 VLAN routing interface addresses.
console#show ipv6 vlan
MAC Address used by Routing VLANs: 00:02:BC:00:30:68
VLAN ID IPv6 Address/Prefix Length
------- ---------------------------------------
1
traceroute ipv6
Use the traceroute ipv6 command in Privileged EXEC mode to determine
the path and measure the transit delay to another device in the network. The
transit delays are measured for each hop in the network.
Syntax
traceroute ipv6 {ipv6-address|hostname} [count
1-10
] [init-ttl
1-255
]
[interval
1-60
] [max-fail
0-255
] [max-ttl
1-255
] [port
1-65535
] [size
0-
39936
] [source {
ipv6-address
| loopback
0-7
| vlan
1-4093
}]
• ipv6-address | hostname—The target IP address or host to ping.
2CSNXXX_SWUM200.book Page 1129 Tuesday, December 10, 2013 1:22 PM

1130 IPv6 Routing Commands
• out-of-band—Send the ping over the out-of-band interface.
• vlan—The source vlan over which to send the echo request.
• count—The number of echo request packets to send for each ttl value.
(Range 1-10. Default 3).
• interval—The time (in seconds) between successive echo requests.
Default 3.
• init-ttl—The initial TTL sent in the ICMP echo request packets (Range 1-
255. Default 1).
• max-ttl—The maximum ttl sent in the ICMP echo request packet (Range
1-255, default 30). Must be equal to or larger than init-ttl.
• port—The destination UDP port of the probe. (Range 1-65535).
• size—The packet size padding in bytes. (Range 0-39936, default 0).
• source—Use the specified source IP address, loopback address, VLAN
address, tunnel or out-of-band interface address in the transmitted
packets.
Default Configuration
There is no default configuration for this command.
Command Mode
Privileged EXEC and User EXEC modes
User Guidelines
Traceroute operates by sending a sequence of Internet Control Message
Protocol (ICMP) echo request packets. The time-to-live (TTL) value, is used
in determining the intermediate routers through which the packet flows
toward the destination address. Routers decrement a packet’s TTL value and
discard packets whose TTL equals 0. On discarding a packet, the router
returns an ICMP time exceeded message to the source.
Example
(console) # traceroute ipv6 2001::2 init-ttl 1 max-ttl 4 max-fail 0 interval
1 count 3 port 33434 size 43
Traceroute to 2001::2, 4 hops max, 43 byte packets:
1 2001::2 708 msec 41 msec 11 msec
2CSNXXX_SWUM200.book Page 1130 Tuesday, December 10, 2013 1:22 PM

IPv6 Routing Commands 1131
2 2001::2 12 msec 13 msec 12 msec
3 2001::2 14 msec 9 msec 11 msec
2CSNXXX_SWUM200.book Page 1131 Tuesday, December 10, 2013 1:22 PM

1132 IPv6 Routing Commands
2CSNXXX_SWUM200.book Page 1132 Tuesday, December 10, 2013 1:22 PM

Loopback Interface Commands 1133
50
Loopback Interface Commands
Dell Networking N2000/N3000/N4000 Series Switches
Dell Networking provides for the creation, deletion, and management of
loopback interfaces. They are dynamic interfaces that are created and deleted
by user configuration.
A loopback interface is always expected to be up. As such, it provides a means
to configure a stable IP address on the device which may be referred to by
other switches in the network. This interface never transmits data but may
receive data. It is typically expected to be used by routing protocols.
Support for the internal loopback address, if present, is limited to testing the
IP stack.
Commands in this Chapter
This chapter explains the following commands:
interface loopback
Use the interface loopback command in Global Configuration mode to enter
the Interface Loopback configuration mode.
Syntax
interface loopback
loopback-id
no interface loopback
loopback-id
• loopback-id — Loopback identifier. (Range: 0-7)
Default Configuration
This command has no default configuration.
interface loopback show interfaces loopback
2CSNXXX_SWUM200.book Page 1133 Tuesday, December 10, 2013 1:22 PM

1134 Loopback Interface Commands
Command Mode
Global Configuration mode.
User Guidelines
This command has no user guidelines.
Example
The following example enters the Interface Loopback 1 configuration mode.
console(config)#interface loopback 1
console(config-if-loopback0)#ip address 192.168.22.1 255.255.255.255
console(config-if-loopback0)#exit
console(config)#ex
console#ping 192.168.22.1
Pinging 192.168.22.1 with 0 bytes of data:
Reply From 192.168.22.1: icmp_seq = 0. time <10 msec.
Reply From 192.168.22.1: icmp_seq = 1. time <10 msec.
Reply From 192.168.22.1: icmp_seq = 2. time <10 msec.
Reply From 192.168.22.1: icmp_seq = 3. time <10 msec.
show interfaces loopback
Use the show interfaces loopback command in Privileged EXEC mode to
display information about one or all configured loopback interfaces.
Syntax
show interfaces loopback [
loopback-id
]
•
loopback-id
— Loopback identifier. (Range: 0-7)
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC mode, Configuration mode and all Configuration submodes
User Guidelines
This command has no user guidelines.
2CSNXXX_SWUM200.book Page 1134 Tuesday, December 10, 2013 1:22 PM

Loopback Interface Commands 1135
Examples
The following examples display information about configured loopback
interfaces.
console# show interfaces loopback
Loopback Id Interface IP Address Received Packets Sent Packets
----------- --------- ---------- ---------------- ------------
1 loopback 1 0.0.0.0 0 0
console# show interfaces loopback 1
Interface Link Status.......................... Up
IP Address..................................... 0.0.0.0 0.0.0.0
MTU size....................................... 1500 bytes
2CSNXXX_SWUM200.book Page 1135 Tuesday, December 10, 2013 1:22 PM

1136 Loopback Interface Commands
2CSNXXX_SWUM200.book Page 1136 Tuesday, December 10, 2013 1:22 PM

Multicast Commands 1137
51
Multicast Commands
Dell Networking N3000/N4000 Series Switches
The Dell Network N2000 series supports limited routing and multicast capabilities.
See the Users Configuration Guide section “Feature Limitations and Platform
Constants” for supported capabilities.
The Dell Networking Multicast component is best suited for video and audio
traffic requiring multicast packet control for optimal operation. The
Multicast component includes support for IGMPv2, IGMPv3, PIM-DM,
PIM-SM, and DVMRP. Communication from point to multipoint is called
Multicasting. The source host (point) transmits a message to a group of zero
or more hosts (multipoint) that are identified by a single IP destination
address. Although the task may be accomplished by sending unicast (point-
to-point) messages to each of the destination hosts, multicasting is the more
desirable method for this type of transmission. A multicast message is
delivered to all members of its destination host group with the same best-
efforts reliability as regular unicast IP messages. The message is not
guaranteed to arrive intact at all members of the destination group or in the
same order relative to other messages. The advantages of multicasting are
explained below:
• Network Load Decrease: A number of applications are required to transmit
packets to hundreds of stations. The packets transmitted to these stations
share a group of links on their paths to their destinations. Multicast
transmission can conserve much needed network bandwidth, since
multicasting transmission requires the transmission of only a single packet
by the source and replicates this packet only if it is necessary (at forks of
the multicast delivery tree).
• Discovery of resources: A number of applications require a host to find out
whether a certain type of service is available. Internet protocols such as
Bootstrap Protocol (BOOTP) and Open Shortest Path First (OSPF)
protocol are among these applications. Using multicast messages and
sending the query to those hosts which are potentially capable of providing
this service speeds the gathering of this information considerably.
Although a group of hosts residing on the same network are the intended
target for the majority of multicast packets, this limitation is not
2CSNXXX_SWUM200.book Page 1137 Tuesday, December 10, 2013 1:22 PM

1138 Multicast Commands
mandatory. Discovering the local domain-name server is the intended use
of multicast messages on remote networks when there is less than one
server per network.
• Applications used for datacasting: Since multimedia transmission has
become increasingly popular, multicast transmission use has increased.
Multicast transmission may be used to efficiently accommodate this type
of communication. For instance, the audio and video signals are captured,
compressed and transmitted to a group of receiving stations. Instead of
using a set of point-to-point connections between the participating nodes,
multicasting can be used for distribution of the multimedia data to the
receivers. The participating stations are free to join or leave an audio-cast
or a video-cast as needed. The variable membership maintenance is
managed efficiently through multicasting.
Commands in this Chapter
This chapter explains the following commands:
clear ip mroute
Use this command to selectively clear IPv4 multicast entries from the cache.
clear ip mroute ip pim dense-mode show ip multicast show ip mroute static
ip mcast boundary ip pim dr-priority show ip multicast show ip pim
ip mroute ip pim hello-
interval
show ip pim
boundary
show ip pim bsr-router
ip multicast-routing ip pim join-prune-
interval
show ip multicast
interface
show ip pim interface
ip multicast ttl-
threshold
ip pim rp-address show ip mroute show ip pim neighbor
ip pim ip pim rp-candidate show ip mroute
group
show ip pim rp hash
ip pim bsr-border ip pim sparse-mode show ip mroute
source
show ip pim rp
mapping
ip pim bsr-
candidate
ip pim ssm
––
2CSNXXX_SWUM200.book Page 1138 Tuesday, December 10, 2013 1:22 PM

Multicast Commands 1139
Syntax
clear ip mroute { * |
group-address
[
source-address
] }
•
*
—Deletes all IPv4 entries from the IP multicast routing table.
•
group-address
— IP address of the multicast group.
•
source-address
—IP address of a multicast srouce that is sending multicast
traffic to the group.
Default configuration
There is no default configuration for this command.
Command Mode
User EXEC, Privileged EXEC modes, Configuration mode and all
Configuration submodes
User Guidelines
When a * entry is deleted through this command, it cannot be formed again
until it is expired in IGMP and started again via the host. The default mcache
time-out is 210 seconds.
Example
The following example deletes all entries from the IP multicast routing table:
console# clear ip mroute *
The following example deletes from the IP multicast routing table all entries
that match the given multicast group address (224.1.2.1), irrespective of
which source is sending for this group:
console# clear ip mroute 224.1.2.1
The following example deletes from the IP multicast routing table all entries
that match the given multicast group address (224.1.2.1) and the multicast
source address (192.168.10.10):
console# clear ip mroute 224.1.2.1 192.168.10.10
2CSNXXX_SWUM200.book Page 1139 Tuesday, December 10, 2013 1:22 PM

1140 Multicast Commands
ip mcast boundary
Use the ip multicast boundary command in Interface Configuration mode to
add an administrative scope multicast boundary specified by
groupipaddr
and
mask
for which this multicast administrative boundary is applicable.
groupipaddr
is a group IP address and
mask
is a group IP mask.
Syntax
ip multicast boundary
groupipaddr mask
no ip multicast boundary
groupipaddr
•
groupipaddr
— IP address of multicast group. Valid range is 239.0.0.0 to
239.255.255.255.
•
mask
—The group address mask in dotted quad notation.
Default Configuration
This command has no default configuration.
Command Mode
Interface Configuration (VLAN) mode
User Guidelines
This command has no user guidelines.
Example
The following example adds an administrative scope multicast boundary.
console(config)#interface vlan 15
console(config-if-vlan15)#ip multicast boundary 239.5.5.5 255.255.255.255
ip mroute
Use the ip mroute command to create a static multicast route for a source
range. Use the no form of this command to delete a static multicast route.
Syntax
ip mroute
source-address mask rpf-address preference
2CSNXXX_SWUM200.book Page 1140 Tuesday, December 10, 2013 1:22 PM

Multicast Commands 1141
no ip mroute
source-address mask
•
source-address
— The IP address of the multicast data source.
•
mask
— The IP subnet mask of the multicast data source.
•
rpf-address
— The IP address of the next hop towards the source.
•
preference
— The cost of the route (Range: 1 - 255).
Default Configuration
There is no default configuration for this command.
Command Mode
Global Configuration mode
User Guidelines
There are no user guidelines for this command.
Example
console(config)#
console(config)#ip mroute 1.1.1.1 255.255.0.0 192.168.20.1 34
ip multicast-routing
Use the ip multicast-routing command in Global Configuration mode to set
the administrative mode of the IP multicast forwarder in the router to active.
It enables both IPv4 and IPv6 multicast routing. For multicast routing to
become operational, IGMP must be currently enabled. An error message is
displayed on the CLI if multicast routing is enabled while IGMP is disabled.
However, the IP multicast mode configuration is stored in the multicast
configuration file and is automatically enabled once IGMP is enabled. This
command is not affected by enabling/disabling PIM or DVMRP.
Syntax
ip multicast-routing
no ip multicast-routing
2CSNXXX_SWUM200.book Page 1141 Tuesday, December 10, 2013 1:22 PM

1142 Multicast Commands
Default Configuration
This command has no default configuration.
Command Mode
Global Configuration mode
User Guidelines
Use of a multicast routing protocol is recommended (e.g., PIM, when ip
multicast is enabled).
Unless required, IGMP/MLD snooping should be disabled when ip multicast
is enabled. If a multicast source is connected to a VLAN on which both L3
multicast and IGMP/MLD snooping are enabled, the multicast source is
forwarded to the mrouter ports that have been discovered when the multicast
source is first seen. If a new mrouter is later discovered on a different port, the
multicast source data is not forwarded to the new port. Likewise, if an existing
mrouter times out or stops querying, the multicast source data continues to
be forwarded to that port. If a host in the VLAN subsequently joins or leaves
the group, the list of mrouter ports is updated for the multicast source and
the forwarding of the multicast source is adjusted. The workaround to this
limitation is to statically configure mrouter ports when enabling IGMP/MLD
snooping in L3 multicast enabled VLANs.
This command is not affected by enabling/disabling PIM or DVMRP.
This command enables both ipv4 and ipv6 multicast routing.
Example
The following example enables IP multicast on the router.
console#configure
console(config)#ip multicast
ip multicast ttl-threshold
Use the ip multicast ttl-threshold command in Interface VLAN
Configuration mode to apply a
ttlvalue
to a routing interface.
ttlvalue
is the
TTL threshold which is applied to the multicast Data packets forwarded
through the interface.
2CSNXXX_SWUM200.book Page 1142 Tuesday, December 10, 2013 1:22 PM

Multicast Commands 1143
Syntax
ip multicast ttl-threshold
ttlvalue
no ip multicast ttl-threshold
•
ttlvalue
— Specifies TTL threshold. (Range: 0-255)
Default Configuration
This command has no default configuration.
Command Mode
Interface Configuration (VLAN) mode
User Guidelines
This command has no user guidelines.
Example
The following example applies a
ttlvalue
of 5
to the VLAN 15 routing
interface.
console(config)#interface vlan 15
console(config-if-vlan15)#ip multicast ttl-threshold 5
ip pim
Use the ip pim command in Interface (VLAN) Configuration mode to
administratively configure PIM mode for IP multicast routing on a VLAN
interface. Enabling or disabling PIM mode concurrently enables/disables
IGMP. Use the no form of the command to disable PIM on the interface.
Syntax
ip pim
no ip pim
Default Configuration
PIM is not enabled on interfaces by default.
2CSNXXX_SWUM200.book Page 1143 Tuesday, December 10, 2013 1:22 PM

1144 Multicast Commands
Command Mode
Interface (VLAN) Configuration mode
User Guidelines
PIM requires that routing, multicast, and IGMP be enabled.
Example
console(config)#ip routing
console(config)#ip multicast
console(config)#interface vlan 10
console(if-vlan-10)#ip pim
ip pim bsr-border
The ip pim bsr-border command is used in Interface (VLAN) Configuration
mode to administratively disable bootstrap router (BSR) messages on the
interface. Use the no form of this command to return the configuration to the
default.
Syntax
ip pim bsr-border
no ip pim bsr-border
Default Configuration
BSR messages are enabled on the interface by default.
Command Mode
Interface (VLAN) Configuration mode
User Guidelines
This command only has an effect if sparse mode is enabled. Lower values are
preferred.
Example
console(if-vlan-10)#ip pim bsr-border
2CSNXXX_SWUM200.book Page 1144 Tuesday, December 10, 2013 1:22 PM

Multicast Commands 1145
ip pim bsr-candidate
The ip pim bsr-candidate command is used to configure the router to
advertise itself as a bootstrap router (BSR). Use the no form of this command
to return to the default configuration. This command replaces the ip pimsm
bsr-candidate, ip pimsm cbsrhaskmasklength and ip pimsm cbsrpreference
commands.
Syntax
ip pim bsr-candidate vlan {
vlan-id hash-mask-length
bsr-priority
[interval
interval
]}
no ip pim bsr-candidate vlan {
vlan-id}
•
vlan-id
—A valid VLAN identifier with multicast routing enabled.
•
hash-mask-length
—Length of the BSR hash to be ANDed with the
multicast group address. (Range 0–32 bits). Default 0.
•
bsr-priority
—The advertised priority of the BSR candidate. Range 0-255.
Default 0.
•
interval
—(Optional) Indicates the RP candidate advertisement interval.
The range is from 1 to 16383 seconds. The default value is 60 seconds.
Default Configuration
None - the router does not advertise itself as a BSR candidate.
Command Mode
Global Configuration mode
User Guidelines
All multicast groups with the same hash value correspond to the same RP.
Lower priority values are preferred.
Example
console(config)#ip pim bsr-candidate vlan 10 16 0 interval 30
2CSNXXX_SWUM200.book Page 1145 Tuesday, December 10, 2013 1:22 PM

1146 Multicast Commands
ip pim dense-mode
Use the ip pim dense-mode command in Global Configuration mode to
administratively configure PIM dense mode for IP multicast routing. Use the
no form of this command to disable PIM.
Syntax
ip pim dense-mode
no ip pim
Default Configuration
PIM is not enabled by default.
Command Mode
Global Configuration mode
User Guidelines
Only one of sparse or dense mode can be configured on a router. IGMP is
automatically enabled if PIM is enabled and disabled when PIM is disabled.
ip multicast-routing is not enabled or disabled by this command.
PIM is not compatible with DVMRP. DVMRP must be disabled before
enabling PIM.
Example
console(config)#ip multicast-routing
console(config)#ip pim dense-mode
ip pim dr-priority
The ip pim dr-priority command in Interface (VLAN) Configuration mode
to administratively configure the advertised designated router (DR) priority
value. Use the no form of this command to return the configuration to the
default.
Syntax
ip pim dr-priority
priority
2CSNXXX_SWUM200.book Page 1146 Tuesday, December 10, 2013 1:22 PM

Multicast Commands 1147
no ip pim dr-priority
•
priority
— The administratively configured priority (Range:
0–2147483647).
Default Configuration
The default election priority is 1.
Command Mode
Interface (VLAN) Configuration mode
User Guidelines
This command only has an effect if sparse mode is enabled. Lower values are
preferred.
Example
console(if-vlan10)#ip pim dr-priority 32768
ip pim hello-interval
The ip pim hello-interval command in Interface (VLAN) Configuration
mode to administratively configure the frequency of PIM Hello messages on
the specified interface. Use the no form of this command to return the
configuration to the default.
Syntax
ip pim hello-interval
interval
no ip pim hello-interval
•
interval
— The number of seconds between successive hello transmissions.
Range: 0–18000 seconds. Default is 30.
Default Configuration
The default hello interval is 30 seconds.
Command Mode
Interface (VLAN) Configuration mode
2CSNXXX_SWUM200.book Page 1147 Tuesday, December 10, 2013 1:22 PM

1148 Multicast Commands
User Guidelines
There are no user guidelines for this command.
Example
console(config-if-vlan10)#ip pim hello-interval 20
ip pim join-prune-interval
The ip pim join-prune-interval command in Interface (VLAN)
Configuration mode to administratively configure the frequency of
join/prune messages on the specified interface. Use the no form of this
command to return the configuration to the default.
Syntax
ip pim join-prune-interval
interval
no ip pim join-prune-interval
•
interval
— The number of seconds between successive join-prune
transmissions. Range: 0–18000 seconds. Default is 60.
Default Configuration
The default join/prune interval is 60 seconds.
Command Mode
Interface (VLAN) Configuration mode
User Guidelines
This command only has an effect if sparse mode is enabled.
Example
console(if-vlan10)#ip pim join-prune-interval 30
2CSNXXX_SWUM200.book Page 1148 Tuesday, December 10, 2013 1:22 PM

Multicast Commands 1149
ip pim rp-address
Use the ip pim rp-address command in Global Configuration mode to define
the address of a PIM Rendezvous point (RP) for a specific multicast group
range. Use the no form of this command to remove a configured RP. This
command replaces the ip pimsm rp-address command.
Syntax
ip pim rp-address
{rp-address group-address group-mask
[override]}
no ip pim rp-address {
rp-address group-address group-mask}
•
rp-address
—
The valid IPv4 address for the rendezvous point.
•
group-address
—
A valid multicast group address to be sourced from the
rendezvous point.
•
group-mask
—
A mask indicating the range of multicast groups sourced from the
RP.
•
override
—
A flag indicating that the static entry should override dynamically
learned entries for the configured multicast group.
Default Configuration
None —no static multicast groups are configured for an RP.
Command Mode
Global Configuration mode
User Guidelines
There are no user guidelines for this command.
Example
console(config)#ip pim rp-address 192.168.21.1 239.1.0.0 255.255.0.0
override
2CSNXXX_SWUM200.book Page 1149 Tuesday, December 10, 2013 1:22 PM

1150 Multicast Commands
ip pim rp-candidate
Use the ip pim rp-candidate command in Global Configuration mode to
configure the router to advertise itself to the bootstrap router (BSR) router as
a PIM candidate rendezvous point (RP) for a specific multicast group range.
Use the no form of this command to return to the default configuration. This
command replaces the ip pimsm rp-candidate command.
Syntax
ip pim rp-candidate vlan {
vlanid group-address group-mask
[interval
interval
]}
no ip pim rp-candidate vlan
vlanid group-address group-mask}
•
vlan-id
—A valid VLAN identifier with multicast routing enabled.
•
group-address
—
A valid multicast group address.
•
group-mask
—A mask indicating the range of multicast groups for which
the router should advertise itself as an RP-candidate.
•
interval
—(Optional) Indicates the RP candidate advertisement interval.
The range is from 1 to 16383 seconds. The default value is 60 seconds.
Default Configuration
None - the router does not advertise itself as an RP candidate by default.
Command Mode
Global Configuration mode
User Guidelines
There are no user guidelines for this command.
Example
console(config)#ip pim rp-candidate vlan 10 239.1.0.0 255.255.0.0 interval 30
ip pim sparse-mode
Use the ip pim sparse-mode command in Global Configuration mode to
administratively configure PIM sparse mode for IP multicast routing. Use the
no form of this command to disable PIM.
2CSNXXX_SWUM200.book Page 1150 Tuesday, December 10, 2013 1:22 PM

Multicast Commands 1151
Syntax
ip pim sparse-mode
no ip pim
Default Configuration
PIM not enabled by default.
Command Mode
Global Configuration mode
User Guidelines
Only one of sparse or dense mode can be configured on a router.IGMP is
automatically enabled if PIM is enabled and disabled when PIM is disabled.
IP multicast must be enabled for PIM to operate. ip multicast-routing is not
disabled or enabled by this command.
It is recommended that IGMP snooping be disabled if IP multicast is enabled
unless specifically required.
PIM is not compatible with DVMRP. DVMRP must be disabled before
enabling PIM.
Example
console(config)#ip pim sparse-mode
ip pim ssm
Use the ip pim ssm command in Global Configuration mode to
administratively configure PIM source specific multicast range of addresses
for IP multicast routing. Use the no form of this command to remove
configured ranges of addresses from the router.
Syntax
ip pim ssm {default |
group-address group-mask
}
no ip pim ssm {default |
group-address group-mask
}
•
default
—Defines the SSM range access list to 232/8.
2CSNXXX_SWUM200.book Page 1151 Tuesday, December 10, 2013 1:22 PM

1152 Multicast Commands
•
group-address
—An IP multicast group address.
• group-mask—An IPv4 mask in a.b.c.d form where a, b, c and d range from
0-255.
Default Configuration
There are no group addresses configured by default.
Command Mode
Global Configuration mode
User Guidelines
There are no user guidelines for this command.
Example
console(config)#ip pim ssm 239.0.10.0 255.255.255.0
show ip multicast
Use the show ip multicast command in Privileged EXEC mode to display the
system-wide multicast information.
Syntax
show ip multicast
Default Configuration
This command has no default configuration.
Command Mode
User EXEC, Privileged EXEC modes, Configuration mode and all
Configuration submodes
User Guidelines
This command has no user guidelines.
2CSNXXX_SWUM200.book Page 1152 Tuesday, December 10, 2013 1:22 PM

Multicast Commands 1153
Example
The following example displays system-wide multicast information.
console#show ip multicast
Admin Mode........................... Enabled
Protocol State....................... Non-Operational
Table Max Size....................... 768
Protocol............................. PIMDM
Multicast forwarding cache entry count 0
show ip pim boundary
Use the show ip pim boundary command in Privileged EXEC mode to
display all the configured administrative scoped multicast boundaries.
Syntax
show ip pim boundary {vlan
vlan-id
| all}
•
vlan-id
— Valid VLAN ID.
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC mode, Configuration mode and all Configuration submodes
User Guidelines
This command has no user guidelines.
Example
The following example displays all the configured administrative scoped
multicast boundaries.
console#show ip pim boundary all
MULTICAST BOUNDARY
Interface Group IP Mask
-------- ------ ---------------
2CSNXXX_SWUM200.book Page 1153 Tuesday, December 10, 2013 1:22 PM

1154 Multicast Commands
show ip multicast interface
Use the show ip multicast interface command in Privileged EXEC mode to
display the multicast information for the specified interface.
Syntax
show ip multicast interface [
type number
]
•
type number
—Interface type and number for which to display IP
multicast information. VLAN Vlan-ID is the only supported type and
number.
Default Configuration
Show information for all multicast interfaces.
Command Mode
User EXEC, Privileged EXEC modes, Configuration mode and all
Configuration submodes
User Guidelines
This command has no user guidelines.
Example
The following example displays the multicast information for VLAN 15.
console#show ip mcast interface vlan 15
Interface TTL
--------- -----
Vl15 1
show ip mroute
Use the show ip mroute command in Privileged EXEC mode to display a
summary or details of the multicast table.
Syntax
show ip mroute
2CSNXXX_SWUM200.book Page 1154 Tuesday, December 10, 2013 1:22 PM

Multicast Commands 1155
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC mode, Configuration mode and all Configuration submodes
User Guidelines
This command has no user guidelines.
Example
console#show ip mroute
Multicast route table
Expiry Up Time
Source IP Group IP (mm:ss) (hh:mm:ss) RPF Neighbor Flags
--------------- --------------- -------- ----------- --------------- -----
192.168.0.11 239.0.5.7 3:03 15:54:12 192.168.0.10
show ip mroute group
Use the show ip mroute group command in Privileged EXEC mode to display
the multicast configuration settings such as flags, timer settings, incoming
and outgoing interfaces, RPF neighboring routers, and expiration times of all
the entries in the multicast mroute table containing the
groupipaddr
value.
Syntax
show ip mroute group
groupipaddr
[summary]
•
groupipaddr
— IP address of the multicast group.
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC mode, Configuration mode and all Configuration submodes
User Guidelines
This command has no user guidelines.
2CSNXXX_SWUM200.book Page 1155 Tuesday, December 10, 2013 1:22 PM

1156 Multicast Commands
Example
The following example displays the multicast configuration settings such as
flags, timer settings, incoming and outgoing interfaces.
console#show ip mroute group 224.5.5.5 summary
console#show ip mroute group 224.5.5.5
show ip mroute source
Use the show ip mroute source command in Privileged EXEC mode to
display the multicast configuration settings such as flags, timer settings,
incoming and outgoing interfaces, RPF neighboring routers, and expiration
times of all the entries in the multicast mroute table containing the
sourceipaddr
or
sourceipaddr
|
groupipaddr
pair value(s).
Syntax
show ip mroute source
sourceipaddr
{summary}
•
sourceipaddr
— IP address of source.
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC mode, Configuration mode and all Configuration submodes
User Guidelines
Use the summary option to summarize the information displayed.
Example
The following example displays multicast configuration settings.
console#show ip mroute source 10.1.1.1 summary
console#show ip mroute source 10.1.1.1 224.5.5.5
2CSNXXX_SWUM200.book Page 1156 Tuesday, December 10, 2013 1:22 PM

Multicast Commands 1157
show ip mroute static
Use the show ip mroute static command in Privileged EXEC mode to display
all the static routes configured in the static mcast table if it is specified or
display the static route associated with the particular
sourceipaddr
.
Syntax
show ip mroute static [
sourceipaddr
]
•
sourceipaddr
— IP address of source.
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC mode, Configuration mode and all Configuration submodes
User Guidelines
This command has no user guidelines.
Example
The following example displays the static routes configured in the static
mcast table.
console#show ip mroute static
MULTICAST STATIC ROUTES
Source IP Source Mask RPF Address Preference
--------------- --------------- --------------- ----------
1.1.1.1 255.255.255.0 2.2.2.2 23
show ip pim
The show ip pim command displays information about the interfaces
enabled for PIM.
Syntax
show ip pim
2CSNXXX_SWUM200.book Page 1157 Tuesday, December 10, 2013 1:22 PM

1158 Multicast Commands
Default Configuration
There is no default configuration for this command.
Command Mode
User EXEC, Privileged EXEC mode, Configuration mode and all
Configuration submodes
User Guidelines
The following information is displayed:
Example
console#show ip pim
PIM Mode............................. None
If no routers are enabled for PIM, the following message is displayed.
None of the routing interfaces are enabled for PIM.
show ip pim bsr-router
The show ip pim bsr-router command displays information about a bootstrap
router (BSR).
Syntax
show ip pim bsr-router {candidate|elected}
• candidate – Shows the candidate routers capable of acting as the bootstrap
router.
• elected – Shows the router elected as the PIM bootstrap router.
Default Configuration
There is no default configuration for this command.
Field Description
PIM Mode The routers that are enabled for PIM.
2CSNXXX_SWUM200.book Page 1158 Tuesday, December 10, 2013 1:22 PM

Multicast Commands 1159
Command Mode
User EXEC, Privileged EXEC mode, Configuration mode and all
Configuration submodes
User Guidelines
The following information is displayed:
Example
console#show ip pim bsr-router
BSR Address............................. 192.168.10.1
BSR Priority............................ 0
BSR Hash Mask Length.................... 30
C-BSR Advertisement Interval (secs)........60
Next Bootstrap message(hh:mm:ss).......... NA
If no configured/elected BSRs exist on the router, the following message is
displayed.
No BSR’s exist/learned on this router.
show ip pim interface
The show ip pim interface command displays the PIM interface status
parameters. If the interface number is not is specified, the command displays
the status parameters of all the PIM-enabled interfaces.
Syntax
show ip pim interface [vlan
vlan-id
]
Field Description
BSR address IP address of the BSR.
BSR Priority The configured BSR priority.
BSR Hash Mask Length The configured hash mask length (32 bits maximum).
Next Bootstrap Message
in
Time remaining (in hours, minutes, and seconds) until a
BSR message is sent.
Next Candidate RP
Advertisement
Time remaining (in hours, minutes, and seconds) until the
next RP advertisement is sent.
2CSNXXX_SWUM200.book Page 1159 Tuesday, December 10, 2013 1:22 PM
1160 Multicast Commands
•
vlan-id
— A valid VLAN ID for which multicast routing has been enabled.
Field Descriptions
Default Configuration
There is no default configuration for this command.
Command Mode
User EXEC and Privileged EXEC modes, Configuration mode and all
Configuration submodes
User Guidelines
There are no user guidelines for this command.
Example
(console) #show ip pim interface
InterfaceVLAN0010
ModeSparse
Hello Interval (secs)30
Join Prune Interval (secs)60
DR Priority1
BSR BorderDisabled
Neighbor Count1
Designated Router192.168.10.1
InterfaceVLAN0001
Field Description
Mode Active PIM Protocol
Interface Interface number
Hello Interval Hello interval value
Join-prune Interval Join-prune interval value
DR Priority DR Priority configured on this interface
BSR Border Whether or not this interface is configured as a BSR Border
Neighbor Count Number of PIM Neighbors learnt on this interface
Designated-Router IP address of the elected DR on the interface
2CSNXXX_SWUM200.book Page 1160 Tuesday, December 10, 2013 1:22 PM

Multicast Commands 1161
ModeSparse
Hello Interval (secs)30
Join Prune Interval (secs)60
DR Priority1
BSR BorderDisabled
Neighbor Count1
Designated Router192.168.10.1
If none of the interfaces are enabled for PIM, the following message is
displayed:
None of the routing interfaces are enabled for PIM
show ip pim neighbor
Use the show ip pim neighbor command in User EXEC or Privileged EXEC
modes to display PIM neighbors discovered by PIMv2 Hello messages. If the
interface number is not specified, this command displays the neighbors
discovered on all the PIM-enabled interfaces.
Syntax
show ip pim neighbor [vlan
vlan-id
]
•
vlan-id
— A valid VLAN ID for which multicast routing has been enabled.
Default Configuration
This command has no default configuration.
Command Mode
User EXEC, Privileged EXEC modes, Configuration mode and all
Configuration submodes
User Guidelines
The following information is displayed.
Field Description
Neighbor Addr IP address of the PIM neighbor
Interface Interface number
Uptime Time since the neighbor is learned
2CSNXXX_SWUM200.book Page 1161 Tuesday, December 10, 2013 1:22 PM

1162 Multicast Commands
Example
(console)#show ip pim neighbor vlan 10
Up Time Expiry Time
Neighbor Addr Interface hh:mm:ss hh:mm:ss
--------------- ---------- --------- -----------
192.168.10.2 VLAN0010 00:02:55 00:01:15
(console) #show ip pim neighbor
Neighbor Addr Interface Uptime Expiry Time
(HH:MM::SS) (HH:MM::SS)
--------------- --------- ----------- -----------
192.168.10.2 VLAN0001 00:02:55 00:01:15
192.168.20.2 VLAN0010 00:03:50 00:02:10
If no neighbors are learned on any of the interfaces, the following message is
displayed.
No neighbors are learned on any interface.
show ip pim rp hash
The show ip pim rp hash command displays the rendezvous point (RP)
selected for the specified group address.
Syntax
show ip pim rp hash
group-address
•
group-address
— A valid multicast address supported by RP.
Default Configuration
There is no default configuration for this command.
Command Mode
User EXEC, Privileged EXEC mode, Configuration mode and all
Configuration submodes
Expiry Time Time remaining for the neighbor to expire
Field Description
2CSNXXX_SWUM200.book Page 1162 Tuesday, December 10, 2013 1:22 PM

Multicast Commands 1163
User Guidelines
The following fields are displayed:
Example
console#show ip pim rp hash 224.1.2.0
RP Address192.168.10.1
TypeStatic
If no RP Group mapping exists on the router, the following message is
displayed:
No RP-Group mappings exist/learned on this router.ny interface.
show ip pim rp mapping
The show ip pim rp mapping command is used in User EXEC and Privileged
EXEC modes to display the mappings for the PIM group to the active
rendezvous points.
Syntax
show ip pim rp mapping [
rp-address
|candidate|static]
rp-address
— An RP address.
Default configuration
There is no default configuration for this command.
Command Mode
User EXEC, Privileged EXEC modes, Configuration mode and all
Configuration submodes
User Guidelines
The following fields are displayed.
Field Description
RP Address Address of the RP
Type Origin from where this group mapping was learned.
2CSNXXX_SWUM200.book Page 1163 Tuesday, December 10, 2013 1:22 PM

1164 Multicast Commands
Example
console#show ip pim rp mapping candidate
RP Address.................................... 192.168.10.1
Group Address.............................. 224.1.2.1
Group Mask................................. 255.255.0.0
Origin..................................... BSR
C-RP Advertisement Interval (secs)......... 60
Next Candidate RP Advertisement (hh:mm:ss). 00:00:15
If no RP Group mapping exists on the router, the following message is
displayed:
No RP-Group mappings exist on this router.
If no static RP Group mapping exists on the router, the following message is
displayed:
No Static RP-Group mappings exist on this router.
Field Description
RP Address Address of the RP
Group Address Address of the multicast group.
Group Mask Mask for the group address.
Origin Origin from where this group mapping is learned.
2CSNXXX_SWUM200.book Page 1164 Tuesday, December 10, 2013 1:22 PM

Multicast Commands 1165
2CSNXXX_SWUM200.book Page 1165 Tuesday, December 10, 2013 1:22 PM

1166 Multicast Commands
2CSNXXX_SWUM200.book Page 1166 Tuesday, December 10, 2013 1:22 PM

IPv6 Multicast Commands 1167
52
IPv6 Multicast Commands
Dell Networking N3000/N4000 Series Switches
The Dell Network N2000 series supports limited routing and multicast capabilities.
See the Users Configuration Guide section “Feature Limitations and Platform
Constants” for supported capabilities.
This chapter explains the following commands:
clear ipv6 mroute
This command is used to selectively clear dynamic IPv6 multicast entries
from the cache.
Syntax
clear ipv6 mroute { * |
group-address
[
source-address
] }
*
—Deletes all IPv6 entries from the IP multicast routing table.
group-address
— IPv6 address of the multicast group.
source-address
—IPv6 address of a multicast srouce that is sending multicast
traffic to the group.
clear ipv6 mroute ipv6 pim rp-address
ipv6 pim (VLAN Interface config) ipv6 pim rp-candidate
ipv6 pim bsr-border ipv6 pim sparse-mode
ipv6 pim bsr-candidate ipv6 pim ssm
ipv6 pim dense-mode show ipv6 pim
ipv6 pim dr-priority ipv6 pim dense-mode
ipv6 pim hello-interval show ipv6 pim interface
ipv6 pim join-prune-interval show ipv6 pim neighbor
ipv6 pim register-threshold show ipv6 pim rp-hash
–show ipv6 pim rp mapping
2CSNXXX_SWUM200.book Page 1167 Tuesday, December 10, 2013 1:22 PM

1168 IPv6 Multicast Commands
Default Configuration
There is no default configuration for this command.
Command Mode
Privileged EXEC mode, Configuration mode and all Configuration submodes
User Guidelines
This command does not clear static multicast route entries.
When a * entry is deleted through this command, it cannot be formed again
until it is expired in MLD and started again via the host. The default mcache
time-out is 210 seconds.
Example
The following example deletes all entries from the IPv6 multicast routing
table:
console# clear ipv6 mroute *
The following example deletes from the IPv6 multicast routing table all
entries that match the given multicast group address (FF4E::1), irrespective
of which source is sending for this group:
console# clear ipv6 mroute FF4E::1
The following example deletes from the IPv6 multicast routing table all
entries that match the given multicast group address (FF4E::1) and the
multicast source address (2001::2):
console# clear ipv6 mroute FF4E::1 2001::2
ipv6 pim (VLAN Interface config)
Use the ipv6 pim command in VLAN Interface configuration mode to
administratively enable PIM multicast routing mode on a particular IPv6
router interface. Use the no form of this command to disable PIM on an
interface.
Syntax
ipv6 pim
no ipv6 pim
2CSNXXX_SWUM200.book Page 1168 Tuesday, December 10, 2013 1:22 PM

IPv6 Multicast Commands 1169
Default Configuration
PIM is disabled by default.
Command Mode
Interface Configuration (VLAN) mode
User Guidelines
Either PIM-SM or PIM-DM are enabled by this command depending on the
globally configured mode. Refer to the ip pim sparse-mode and ip pim
dense-mode commands for further information.
Example
console(config-if-vlan3)#ipv6 pim
ipv6 pim bsr-border
Use the ipv6 pim bsr-border command to prevent bootstrap router (BSR)
messages from being sent or received through an interface. Use the no form
of this command to disable the interface from being the BSR border.
Syntax
ipv6 pim bsr-border
no ipv6 pim bsr-border
Default Configuration
BSR-border is disabled by default.
Command Mode
Interface Configuration (VLAN) mode
User Guidelines
There are no user guidelines for this command.
Example
console(config-if-vlan3)#ipv6 pim bsr-border
2CSNXXX_SWUM200.book Page 1169 Tuesday, December 10, 2013 1:22 PM

1170 IPv6 Multicast Commands
ipv6 pim bsr-candidate
Use the ipv6 pim bsr-candidate command to configure the router to
announce its candidacy as a bootstrap router (BSR). Use the no form of this
command to stop the router from announcing its candidacy as a bootstrap
router.
Syntax
ipv6 pim bsr-candidate vlan
vlan-id hash-mask-len
[
priority
][interval]
no ipv6 pim bsr-candidate vlan
vlan-id
•
vlan-id
—A valid VLAN ID value.
•
hash-mask-len
—The length of a mask that is to be ANDed with the group
address before the hash function is called. All groups with the same seed
hash correspond to the same RP. For example, if this value is 24, only the
first 24 bits of the group addresses matter. This allows you to get one RP
for multiple groups. (Range 0–128 bits).
•
priority
—The priority of the candidate BSR. The BSR with the higher
priority is preferred. If the priority values are the same, the router with the
higher IP address is the BSR. (Range: 0–255).
• interval—The interval at which candidate rendezvous point
advertisements are sent.
Default Configuration
The router will not announce its candidacy by default.
The default hash mask length is 126 bits.
The default priority is 0.
The default C-RP advertisement interval is 60 seconds.
Command Mode
Global Configuration mode
User Guidelines
There are no user guidelines for this command.
2CSNXXX_SWUM200.book Page 1170 Tuesday, December 10, 2013 1:22 PM

IPv6 Multicast Commands 1171
Example
console(config)#ipv6 pim bsr-candidate vlan 9 10 34
ipv6 pim dense-mode
Use the ipv6 pim dense-mode command in Global configuration mode to
administratively configure PIM dense mode for IPv6 multicast routing. This
command also enables MLD. Use the no form of this command to disable
PIM and MLD. This command does not affect ip multicast-routing.
Syntax
ipv6 pim dense-mode
no ipv6 pim
Default Configuration
PIM dense mode is disabled by default.
Command Mode
Global Configuration mode
User Guidelines
Only one of sparse or dense mode can be configured on a router. DVMRP
must be disabled before enabling PIM.
Example
console(config)#ipv6 pim dense
ipv6 pim dr-priority
Use the ipv6 pim dr-priority command to set the priority value for which a
router is elected as the designated router (DR). Use the no form of this
command to set the priority to the default.
Syntax
ipv6 pim dr-priority
priority
no ipv6 pim dr-priority
2CSNXXX_SWUM200.book Page 1171 Tuesday, December 10, 2013 1:22 PM

1172 IPv6 Multicast Commands
•
priority
—The election priority (Range: 0–2147483647).
Default Configuration
The default election priority is 1.
Command Mode
Interface Configuration (VLAN) mode
User Guidelines
There are no user guidelines for this command.
Example
console(config-if-vlan3)#ipv6 pim dr-priority 10
ipv6 pim hello-interval
Use the ipv6 pim hello-interval command to configure the PIM-SM Hello
Interval for the specified interface. Use the no form of this command to set
the hello interval to the default.
Syntax
ipv6 pim hello-interval
interval
no ipv6 pim hello-interval
• interval—The hello interval (Range: 0–18000 seconds).
Default Configuration
The default hello interval is 30 seconds.
Command Mode
Interface Configuration (VLAN) mode
User Guidelines
Setting the hello interval to 0 disables sending on PIM Hellos.
2CSNXXX_SWUM200.book Page 1172 Tuesday, December 10, 2013 1:22 PM

IPv6 Multicast Commands 1173
Example
console(config-if-vlan3)#ipv6 pim hello-interval 45
ipv6 pim join-prune-interval
Use the ipv6 pim join-prune-interval command to configure the interface
join/prune interval for the PIM-SM router. Use the no form of this command
to set the join/prune interval to the default.
Syntax
ipv6 pim join-prune-interval
interval
no ipv6 pim join-prune-interval
• interval—The join/prune interval (Range: 0–18000 seconds).
Default Configuration
The default join/prune interval is 60 seconds.
Command Mode
Interface Configuration (VLAN) mode
User Guidelines
There are no user guidelines for this command.
Example
console(config-if-vlan3)#ipv6 pim join-prune-interval 90
ipv6 pim register-threshold
Use the ipv6 pim register-threshold command to configure the Register
Threshold rate for the RP router to switch to the shortest path. Use the no
form of this command to set the register threshold rate to the default.
Syntax
ipv6 pim register-threshold
threshold
no ipv6 pim register-threshold
• threshold—The threshold rate (Range: 0–2000 Kbps).
2CSNXXX_SWUM200.book Page 1173 Tuesday, December 10, 2013 1:22 PM

1174 IPv6 Multicast Commands
Default Configuration
The default threshold rate is 0.
Command Mode
Global Configuration mode
User Guidelines
There are no user guidelines for this command.
Example
console(config)#ipv6 pim register-threshold 250
ipv6 pim rp-address
Use the ipv6 pim rp-address command to statically configure the RP address
for one or more multicast groups. The optional keyword override indicates
that if there is a conflict, the RP configured with this command prevails over
the RP learned by BSR. Use the no form of this command to remove the RP
address for one or more multicast groups.
Syntax
ipv6 pim rp-address
rp-address group-address/prefixlength
[ override ]
no ipv6 pim rp-address
•
rp-address
—An RP address.
•
group-address
—The group address to display.
•
prefixlength
—This parameter specifies the prefix length of the IP address
for the media gateway. (Range: 1–32)
Default Configuration
There are no static RP addresses configured by default.
Command Mode
Global Configuration mode
2CSNXXX_SWUM200.book Page 1174 Tuesday, December 10, 2013 1:22 PM

IPv6 Multicast Commands 1175
User Guidelines
There are no user guidelines for this command.
Example
console(config)#ipv6 pim rp-address 2001::1 ff1e::/64
ipv6 pim rp-candidate
Use the ipv6 pim rp-candidate command to configure the router to advertise
itself as a PIM candidate rendezvous point (RP) to the bootstrap router
(BSR). Use the no form of this command to disable the router from
advertising itself as a PIM candidate rendezvous point (RP) to the bootstrap
router (BSR).
Syntax
ipv6 pim rp-candidate vlan
vlan-id group-address/prefixlength
[interval
c_rp_interval
]
no ipv6 pim rp-candidate vlan
vlan-id
• vlan-id—A valid VLAN ID value.
• group-address—The group address to display.
• prefixlength—This parameter specifies the prefix length of the IP address
for the media gateway. (Range: 1–32)
• c_rp_interval—The Candiate RP advertisement interval (range 1-16383
seconds, default 60 seconds).
Default Configuration
The router does not advertise itself as a PIM candidate rendezvous point by
default.
Command Mode
Global Configuration mode
User Guidelines
The default interval for a Candidate Rendezvous Point (C-RP) to send C-RP
Advertisement messages to the Bootstrap Router (BSR) is 60 seconds.
2CSNXXX_SWUM200.book Page 1175 Tuesday, December 10, 2013 1:22 PM

1176 IPv6 Multicast Commands
Example
console(config)#ipv6 pim rp-candidate vlan 6 ff1e::/64
ipv6 pim sparse-mode
Use the ipv6 pim sparse-mode command to administratively configure PIM
sparse mode for multicast routing. This command also enables MLD. Use the
no form of this command to disable PIM and MLD.
Syntax
ipv6 pim sparse-mode
no ipv6 pim
Default Configuration
IPv6 PIM sparse mode is disabled by default.
Command Mode
Global Configuration mode
User Guidelines
Only one of sparse or dense mode can be configured on a router. DVMRP
must be disabled before enabling PIM.
Example
console(config)#ipv6 pim sparse-mode
ipv6 pim ssm
Use the ipv6 pim ssm command to define the Source Specific Multicast
(SSM) range of multicast addresses.
Syntax
ipv6 pim ssm {default |
group-address
/
prefixlength
}
•
default
—Defines the SSM range access list to FF3x::/32.
•
group-address
—Group IP address supported by RP.
2CSNXXX_SWUM200.book Page 1176 Tuesday, December 10, 2013 1:22 PM

IPv6 Multicast Commands 1177
•
prefixlength
—This parameter specifies the prefix length of the IP address
for the media gateway. (Range: 1–32)
Default Configuration
The default range is FF3x::/32.
Command Mode
Global Configuration mode
User Guidelines
There are no user guidelines for this command.
Example
console(config)#ipv6 pim ssm ff1e::/64
show ipv6 pim
Use the show ipv6 pim command to display global status of IPv6 PIMSM and
its IPv6 routing interfaces.
Syntax
show ipv6 pim
Default Configuration
There is no default configuration for this command.
Command Mode
Privileged EXEC mode, Configuration mode and all Configuration submodes
User Guidelines
There are no user guidelines for this command.
Example
console(config)#show ipv6 pim
PIM Mode....................................... Sparse
2CSNXXX_SWUM200.book Page 1177 Tuesday, December 10, 2013 1:22 PM

1178 IPv6 Multicast Commands
Interface Interface-Mode Operational-Status
--------- -------------- ------------------
Vl1 Enabled Operational
show ipv6 pim bsr-router
Use the show ipv6 pim bsr-router command to display the bootstrap router
(BSR) information.
Syntax
show ipv6 pim bsr-router { candidate | elected }
• candidate—Show the IPv6 PIM candidate bootstrap router information.
• elected—Show the IPv6 elected PIM bootstrap router information.
Default Configuration
There is no default configuration for this command.
Command Mode
User EXEC, Privileged EXEC modes, Configuration mode and all
Configuration submodes
User Guidelines
Field descriptions are shown in the following table.
Field Description
BSR Address Address of the BSR
BSR Priority Configured BSR priority
BSR Hash Mask
Length
Configured hash mask length
Next Bootstrap
Message
Remaining time until a BSR message is sent
Next Candidate RP
Advertisement
Time remaining until the next RP advertisement is sent.
2CSNXXX_SWUM200.book Page 1178 Tuesday, December 10, 2013 1:22 PM

IPv6 Multicast Commands 1179
Example
console(config)#show ipv6 pim bsr-router candidate
BSR Address.................................... 2001:0db8:0:badc::1
BSR Priority................................. 0
BSR Hash Mask Length......................... 64
C-BSR Advertisement Interval (secs).......... 60
Next Bootstrap message (hh:mm:ss)............ 00:00:32
If no configured/elected BSR’s exist on the router, the following message is
displayed:
No BSR’s exist/learned on this router.
2CSNXXX_SWUM200.book Page 1179 Tuesday, December 10, 2013 1:22 PM

1180 IPv6 Multicast Commands
show ipv6 mroute
Use the show ipv6 mroute command in Privileged EXEC mode to display a
summary or all the details of the multicast table.
Syntax
show ipv6 mroute [group
groupip
[summary] | source
sourceip
[summary] |
static summary]
• group—Show the multicast route information for the specified multicast
group.
• source—Show the multicast route information for the specified multicast
source.
• static—Show the multicast route information for the specified static
multicast group.
• summary—Summarize the information.
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC mode, Configuration mode and all Configuration submodes
User Guidelines
This command has no user guidelines.
Example
console#show ipv6 mroute summary
Multicast Route Table Summary
Source IP Group IP Protocol IIF OIF Expiry
--------------- --------------- -------- --------- --------- -------
* FF43::5 PIMSM Vl11
Vl13
2001::5 FF43::5 PIMSM Vl12 Vl11
Vl13
console#show ipv6 mroute summary
2CSNXXX_SWUM200.book Page 1180 Tuesday, December 10, 2013 1:22 PM

IPv6 Multicast Commands 1181
Multicast Route Table Summary
Source IP Group IP Protocol IIF OIF Expiry
--------------- --------------- -------- --------- --------- -------
* FF43::5 PIMSM Vl11
Vl13
2001::5 FF43::5 PIMSM Vl12 Vl11
Vl13
console#show ipv6 mroute source 2001::5 ?
<cr> Press enter to execute the command.
| Output filter options.
summary Display the IPV6 multicast routing table summary.
console#show ipv6 mroute source 2001::5
Multicast Route Table
Expiry Up Time
Source IP Group IP (mm:ss) (hh:mm:ss) RPF Neighbor Flags
--------------- --------------- -------- ----------- --------------- -----
2001::5 FF43::5 03:08 00:00:21 2001::5 SPT
console#show ipv6 mroute source 2001::5 summary
Multicast Route Table Summary
Source IP Group IP Protocol IIF OIF Expiry
--------------- --------------- -------- --------- --------- -------
2001::5 FF43::5 PIMSM Vl12 Vl11
Vl13
console#show ipv6 mroute group FF43::5 ?
<cr> Press enter to execute the command.
| Output filter options.
summary Display the IPV6 multicast routing table summary.
console#show ipv6 mroute group FF43::5
Multicast Route Table
Expiry Up Time
Source IP Group IP (mm:ss) (hh:mm:ss) RPF Neighbor Flags
--------------- --------------- -------- ----------- --------------- -----
* FF43::5 00:00 00:01:00 :: RPT
2001::5 FF43::5 02:54 00:00:35 2001::5 SPT
2CSNXXX_SWUM200.book Page 1181 Tuesday, December 10, 2013 1:22 PM

1182 IPv6 Multicast Commands
console#show ipv6 mroute group FF43::5 summary
Multicast Route Table Summary
Source IP Group IP Protocol IIF OIF Expiry
--------------- --------------- -------- --------- --------- -------
* FF43::5 PIMSM Vl11
Vl13
2001::5 FF43::5 PIMSM Vl12 Vl11
Vl13
show ipv6 mroute group
Use the show ipv6 mroute group command in Privileged EXEC mode to
display the multicast configuration settings such as flags, timer settings,
incoming and outgoing interfaces, RPF neighboring routers, and expiration
times of all the entries in the multicast mroute table containing the
groupipaddr
value.
Syntax
show ipv6 mroute group
groupipaddr
[summary]
•
groupipaddr
— IP address of the multicast group.
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC mode, Configuration mode and all Configuration submodes
User Guidelines
This command has no user guidelines.
Example
console#show ipv6 mroute group FF43::5 ?
<cr> Press enter to execute the command.
| Output filter options.
summary Display the IPV6 multicast routing table summary.
2CSNXXX_SWUM200.book Page 1182 Tuesday, December 10, 2013 1:22 PM

IPv6 Multicast Commands 1183
console#show ipv6 mroute group FF43::5
Multicast Route Table
Expiry Up Time
Source IP Group IP (mm:ss) (hh:mm:ss) RPF Neighbor Flags
--------------- --------------- -------- ----------- --------------- -----
* FF43::5 00:00 00:01:00 :: RPT
2001::5 FF43::5 02:54 00:00:35 2001::5 SPT
console#show ipv6 mroute group FF43::5 summary
Multicast Route Table Summary
Source IP Group IP Protocol IIF OIF Expiry
--------------- --------------- -------- --------- --------- ------
* FF43::5 PIMSM Vl11
Vl13
2001::5 FF43::5 PIMSM Vl12 Vl11
Vl13
show ipv6 mroute source
Use the show ipv6 mroute source command in Privileged EXEC mode to
display the multicast configuration settings such as flags, timer settings,
incoming and outgoing interfaces, RPF neighboring routers, and expiration
times of all the entries in the multicast mroute table containing the
sourceipaddr
or
sourceipaddr
|
groupipaddr
pair value(s).
Syntax
show ipv6 mroute source
sourceipaddr
{summary |
groupipaddr
}
•
sourceipaddr
— IP address of source.
•
groupipaddr
— IP address of multicast group.
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC mode, Configuration mode and all Configuration submodes
2CSNXXX_SWUM200.book Page 1183 Tuesday, December 10, 2013 1:22 PM

1184 IPv6 Multicast Commands
User Guidelines
This command has no user guidelines.
Example
console#show ipv6 mroute source 2001::5 ?
<cr> Press enter to execute the command.
| Output filter options.
summary Display the IPV6 multicast routing table summary.
console#show ipv6 mroute source 2001::5
Multicast Route Table
Expiry Up Time
Source IP Group IP (mm:ss) (hh:mm:ss) RPF Neighbor Flags
--------------- --------------- -------- ----------- --------------
2001::5 FF43::5 03:08 00:00:21 2001::5 SPT
console#show ipv6 mroute source 2001::5 summary
Multicast Route Table Summary
Source IP Group IP Protocol IIF OIF Expiry
--------------- --------------- -------- --------- --------- ------
2001::5 FF43::5 PIMSM Vl12 Vl11
Vl13
show ipv6 pim interface
Use the show ipv6 pim interface command to display interface config
parameters. If no interface is specified, all interfaces are displayed.
Syntax
show ipv6 pim interface [ vlan
vlan-id
]
• vlan-id—A valid VLAN ID value.
Default Configuration
There is no default configuration for this command.
2CSNXXX_SWUM200.book Page 1184 Tuesday, December 10, 2013 1:22 PM

IPv6 Multicast Commands 1185
Command Mode
Privileged EXEC mode, Configuration mode and all Configuration submodes
User Guidelines
There are no user guidelines for this command.
Example
console#show ipv6 pim interface vlan 6
Slot/Port...................................... vlan 6
IP Address..................................... FE80::2FF:EDFF:FED0:2/128
Hello Interval (secs).......................... 30
Join Prune Interval (secs)..................... 60
Neighbor Count ................................ 0
Designated Router.............................. FE80::2FF:EDFF:FED0:2
DR Priority.................................... 1
BSR Border..................................... Disabled
show ipv6 pim neighbor
Use the show ipv6 pim neighbor command to display IPv6 PIMSM neighbors
learned on the routing interfaces.
Syntax
show ipv6 pim neighbor [interface vlan
vlan-id
]
•
vlan-id
—A valid VLAN ID value.
Default Configuration
There is no default configuration for this command.
Command Mode
Privileged EXEC mode, Configuration mode and all Configuration submodes
User Guidelines
If a VLAN interface is not specified, all neighbors are shown.
Example
console#show ipv6 pim neighbor
2CSNXXX_SWUM200.book Page 1185 Tuesday, December 10, 2013 1:22 PM

1186 IPv6 Multicast Commands
Slot/Port...................................... vlan 6
Neighbor Address............................... FE80::200:FF:FE00:33
Up Time (hh:mm:ss)............................. 00:00:12
Expiry Time (hh:mm:ss)......................... 00:01:34
DR Priority.................................... 0
show ipv6 pim rp-hash
Use the show ipv6 pim rp-hash command to display which rendezvous point
(RP) is being selected for a specified group.
Syntax
show ipv6 pim rp-hash
group-address
group-address
—Group IP address supported by RP.
Default Configuration
There is no default configuration for this command.
Command Mode
Privileged EXEC mode, Configuration mode and all Configuration submodes
User Guidelines
There are no user guidelines for this command.
Example
console#show ipv6 pim rp-hash ff1e::/64
RP Type
Address
------------------------ -----
3001::1 BSR
show ipv6 pim rp mapping
Use the show ipv6 pim rp mapping command to display all group-to-RP
mappings of which the router is aware (either configured or learned from the
bootstrap router (BSR). If no RP is specified, all active RPs are displayed
2CSNXXX_SWUM200.book Page 1186 Tuesday, December 10, 2013 1:22 PM

IPv6 Multicast Commands 1187
Syntax
show ipv6 pim rp mapping [
rp-address
|
candidate
|
static
]
•
rp-address
—IP address of RP.
• candidate—Show candidate rendezvous point mappings.
• static—Show static rendezvous point mappings.
Default Configuration
There is no default configuration for this command.
Command Mode
Privileged EXEC mode, Configuration mode and all Configuration submodes
User Guidelines
There are no user guidelines for this command.
Example
console#show ipv6 pim rp mapping
Group Address.................................. FF1E::/64
RP Address..................................... 2001::1
origin......................................... Static
Group Address.................................. FF1E::/64
RP Address..................................... 3001::1
origin......................................... BSR
2CSNXXX_SWUM200.book Page 1187 Tuesday, December 10, 2013 1:22 PM

1188 IPv6 Multicast Commands
2CSNXXX_SWUM200.book Page 1188 Tuesday, December 10, 2013 1:22 PM

IPv6 Multicast Commands 1189
2CSNXXX_SWUM200.book Page 1189 Tuesday, December 10, 2013 1:22 PM

1190 IPv6 Multicast Commands
2CSNXXX_SWUM200.book Page 1190 Tuesday, December 10, 2013 1:22 PM

OSPF Commands 1191
53
OSPF Commands
Dell Networking N3000/N4000 Series Switches
The Dell Network N2000 series supports limited routing and multicast capabilities.
See the Users Configuration Guide section “Feature Limitations and Platform
Constants” for supported capabilities.
OSPF is a link-state protocol. Dell Networking OSPF supports variable-
length subnet masks. Dell Networking OSPF only operates over VLAN
interfaces.
OSPF operates within a hierarchy. The largest entity within the hierarchy is
the autonomous system (AS), a collection of networks under a common
administration sharing a common routing strategy. This is sometimes called a
routing domain. An AS can be divided into a number of areas or groups of
contiguous networks and attached hosts. Routers within the same area share
the same information, so they have identical topological databases.
Information is sent in the form of link-state advertisements (LSAs) to all
other routers within the same hierarchical area. An area's topology is not
visible to routers outside the area.
Two different types of OSPF routing occur as a result of area partitioning:
Intra-area and Inter-area. Intra-area routing occurs if a source and destination
are in the same area. Inter-area routing occurs when a source and destination
are in different areas. An OSPF backbone distributes information between
areas.
For IPv4 networks, Dell Networking routing supports OSPF version 2 in
accordance with RFC 2328. The Dell Networking routing also provides a
compatibility mode for the RFC 1583 OSPF specification, which allows
interoperability with OSPF version 2 routers using the older implementation.
The Dell Networking OSFPv2 implementation supports point-to-point
operation on Ethernet interfaces. The user can configure an OSPFv2
interface to run in broadcast or point-to-point mode. When there are only
two routers attached to the link, OSPFv2 point-to-point mode has the
advantage of not requiring designated router election or origination of a
network LSA for the LAN. This makes the protocol more efficient. Dell
Networking also supports OSPFv3 for use with IPv6 networks.
2CSNXXX_SWUM200.book Page 1191 Tuesday, December 10, 2013 1:22 PM

1192 OSPF Commands
The Dell Networking routing OSPF NSSA feature supports RFC 3101, The
OSPF Not-So-Stubby Area (NSSA) Option.
Route Preferences
Normally, OSPF select routes in the following order:
•Local
• Static
•Intra-area
•Inter-area
•External
•RIP
Dell Networking OSPF allows the administrator to change the preference for
selecting intra, inter, and external routes according to the following rules:
a
External route preferences apply to all ospf external routes like type1,
type2, nssa-type1, nssa-type2 equally.
b
Multiple route types may be configured with equal preference values.
c
Configuring a route preference of 255 makes the route ineligible to be
selected as the best route to its destination. That is, a route type with
a preference of 255 shall never be used for forwarding.
The RIP preference is not used in IPv6 routing.
OSPF Equal Cost Multipath (ECMP)
A device running the IP routing protocol OSPF maintains multiple equal-cost
routes to all destinations. The multiple routes are of the same type (intra-
area, inter-area, type 1 external or type 2 external), cost, and have the same
associated area. However, each route is defined by a separate advertising
router and next hop.
With ECMP, a device forwards traffic to a specified destination through
multiple paths thereby taking advantage of the bandwidth of both links.
ECMP routes are configured statically or learned dynamically as follows:
2CSNXXX_SWUM200.book Page 1192 Tuesday, December 10, 2013 1:22 PM

OSPF Commands 1193
• Configured Statically: If an operator configures multiple static routes to
the exact same destination but with different next hops, those routes are
treated as a single route with two next hops.
• Learned Dynamically: Routing protocols can learn ECMP routes. For
example, if OSPF is configured on both links connecting Router A to
Router B with interface addresses 10.1.1.2 and 10.1.2.2 respectively, and
Router B advertises its connection to 20.0.0.0/ 8, then Router A computes
an OSPF route to 20.0.0.0/8 with next hops of 10.1.1.2 and 10.1.2.2.
Dell Networking routing stores static and dynamic routes in a single
combined routing table. RTO accepts ECMP routes, but it is important to
understand that RTO does not combine routes from different sources to
create ECMP routes. Referring to the above configuration, assume OSPF is
only configured on the 10.1.1.2 Router B interface connecting Router A and
Router B. Then on Router A, OSPF reports to RTO a route to 20.0.0.0/8 with
a next hop of 10.1.1.2. If the user configures a static route to 20.0.0.0/8 with a
single next hop of 10.1.2.2, RTO does NOT combine the OSPF and static
route into a single route to 20.0.0.0/8 with two next hops. All next hops within
an ECMP route must be provided by the same source.
On Dell Networking N3000 and N4000 platforms, the ECMP hashing
support utilizes Enhanced hashing mode, which provides improved load-
balancing performance. ECMP hashing on these platforms has the following
features:
• MODULO-N operation based on the number N of next hops in the route.
• Packet attributes selection based on the packet type. For IP packets, the
following fields are used: Source IP address, Destination IP address,
TCP/UDP port, IPv4 Protocol, IPv6 next header.
Forwarding of OSPF Opaque LSAs Enabled by
Default
Dell Networking supports the flooding capability of opaque LSAs. Dell
Networking cannot originate or process opaque LSAs. In the past, the
capability to flood opaque LSAs was disabled by default.
2CSNXXX_SWUM200.book Page 1193 Tuesday, December 10, 2013 1:22 PM

1194 OSPF Commands
Passive Interfaces
The passive interface feature is used to disable sending OSPF routing updates
on an interface. An OSPF adjacency will not be formed on such an interface.
On a passive interface, subnet prefixes for IP addresses configured on the
interface will continue to be advertised as stub networks.
Graceful Restart
The Dell Networking implementation of OSPFv2 supports graceful restart as
specified in RFC 3623. Graceful restart works in concert with Dell
Networking nonstop forwarding to enable the hardware to continue
forwarding IPv4 packets using OSPFv2 routes while a backup unit takes over
management unit responsibility. When OSPF executes a graceful restart, it
informs its neighbors that the OSPF control plane is restarting, but that it
will be back shortly. Helpful neighbors continue to advertise to the rest of the
network that they have full adjacencies with the restarting router, avoiding
announcement of a topology change and everything that goes with that (i.e.,
flooding of LSAs, SPF runs). Helpful neighbors continue to forward packets
through the restarting router. The restarting router relearns the network
topology from its helpful neighbors.
Dell Networking implements both the restarting router and helpful neighbor
features described in RFC 3623.
Commands in this Chapter
This chapter explains the following commands:
area default-cost
(Router OSPF)
capability opaque ip ospf priority show ip ospf asbr
area nssa (Router
OSPF)
clear ip ospf ip ospf retransmit-
interval
show ip ospf database
area nssa default-
info-originate
(Router OSPF
Config)
clear ip ospf stub-
router
ip ospf transmit-
delay
show ip ospf database
database-summary
2CSNXXX_SWUM200.book Page 1194 Tuesday, December 10, 2013 1:22 PM

OSPF Commands 1195
area nssa no-
redistribute
compatible rfc1583 log adjacency-
changes
show ip ospf interface
area nssa no-
summary
default-information
originate (Router
OSPF
Configuration)
max-metric router-
lsa
show ip ospf interface
brief
area nssa translator-
role
default-metric maximum-paths show ip ospf interface
stats
area nssa translator-
stab-intv
distance ospf network area show ip ospf area
area range (Router
OSPF)
distribute-list out nsf show ip ospf neighbor
area stub enable nsf helper Example
area stub no-
summary
exit-overflow-
interval
nsf helper strict-lsa-
checking
show ip ospf statistics
area virtual-link external-lsdb-limit nsf restart-interval show ip ospf stub table
area virtual-link
authentication
ip ospf area passive-interface
default
show ip ospf traffic
area virtual-link
dead-interval
ip ospf
authentication
passive-interface show ip ospf virtual-link
area virtual-link
hello-interval
ip ospf cost redistribute show ip ospf virtual-
links brief
area virtual-link
retransmit-interval
ip ospf database-
filter all out
router-id timers pacing flood
area virtual-link
transmit-delay
ip ospf dead-
interval
router ospf timers pacing lsa-group
auto-cost ip ospf hello-
interval
show ip ospf timers spf
bandwidth ip ospf mtu-ignore show ip ospf abr
–
–
ip ospf network
––
2CSNXXX_SWUM200.book Page 1195 Tuesday, December 10, 2013 1:22 PM

1196 OSPF Commands
area default-cost (Router OSPF)
Use the area default-cost command in Router OSPF Configuration mode to
configure the advertised default cost for the stub area. Use the no form of the
command to return the cost to the default value.
Syntax
area
area-id
default-cost
integer
no area
area-id
default-cost
•
area-id
— Identifies the OSPF stub area to configure. (Range: IP address
or decimal from 0-4294967295)
•
integer
— The default cost for the stub area. (Range: 1–16777215)
Default Configuration
10 is the default configuration for
integer
.
Command Mode
Router OSPF Configuration mode.
User Guidelines
This command has no user guidelines.
Example
The following example identifies a stub area of 10 and default cost of 100.
console(config)#router ospf
console(config-router)#area 10 default-cost 100
area nssa (Router OSPF)
Use the area nssa command in Router OSPF Configuration mode to
configure the specified area ID to function as an NSSA. If the area has not
been previously created, this command creates the area and then applies the
NSSA distinction. If the area already exists, the NSSA distinction is added or
modified. Use the no form of the command to remove the NSSA distinction
from the specified area ID.
2CSNXXX_SWUM200.book Page 1196 Tuesday, December 10, 2013 1:22 PM

OSPF Commands 1197
Syntax
area
area-id
nssa [no-redistribution] [default-information-originate [metric
metric-value
] [metric-type
metric-type-value
]] [no-summary] [translator-
role role] [translator-stab-intv interval]
no area
area-id
nssa [no-redistribution] [default-information-originate] [no-
summary] [translator-role] [translator-stab-intv]
•
area-id
—Identifies the OSPF stub area to configure. (Range: IP address or
decimal from 0–4294967295)
•
metric-value
—Specifies the metric of the default route advertised to the
NSSA. (Range: 1–16777214)
•
metric-type-value
—The metric type can be one of the following :
– A metric type of nssa-external 1
– A metric type of nssa-external 2 (default)
•
role
—The translator role where role is one of the following :
– always - The router assumes the role of the translator when it becomes
a border router.
– candidate - The router to participate in the translator election process
when it attains border router status.
•
interval
—The period of time that an elected translator continues to
perform its duties after it determines that its translator status has been
deposed by another router. (Range: 0–3600)
Default Configuration
If no metric is defined, 10 is the default configuration.
The default role is candidate. The default metric is type 2.
Command Mode
Router OSPF Configuration mode.
User Guidelines
Specifying a metric with no metric type is equivalent to specifying a metric
with a metric type of 2.
2CSNXXX_SWUM200.book Page 1197 Tuesday, December 10, 2013 1:22 PM

1198 OSPF Commands
Example
The following example configures not-so-stubby-area 10 as an NSSA.
console(config)#router ospf
console(config-router)#area 10 nssa
The following example configures the metric value and type for the default
route advertised into the NSSA and configures the NSSA so that summary
LSAs are not advertised into the NSSA.
console(config-router)#area 20 nssa default-info-originate metric 250
metric-type 2 no-summary
area nssa default-info-originate (Router OSPF
Config)
Use the area nssa default-info-originate command in Router OSPF
Configuration mode to configure the metric value and type for the default
route advertised into the NSSA. The metric type can be comparable (nssa-
external 1) or noncomparable (nssa-external 2). Use the no form of the
command to return the metric value and type to the default value.
Syntax
area
area-id
nssa default-info-originate [
integer
] [comparable | non-
comparable]
no area
area-id
nssa default-info-originate
•
area-id
— Identifies the OSPF NSSA to configure. (Range: IP address or
decimal from 0–4294967295)
•
integer
— Specifies the metric of the default route advertised to the
NSSA. (Range: 1–16777214)
•
comparable
— A metric type of nssa-external 1
•
non-comparable
— A metric type of nssa-external 2
Default Configuration
If no metric is defined, 10 is the default configuration.
Command Mode
Router OSPF Configuration mode.
2CSNXXX_SWUM200.book Page 1198 Tuesday, December 10, 2013 1:22 PM

OSPF Commands 1199
User Guidelines
This command has no user guidelines.
Example
The following example configures the metric value and type for the default
route advertised into the NSSA.
console(config-router)#area 20 nssa default-info-originate 250 non-
comparable
area nssa no-redistribute
Use the area nssa no-redistribute command in Router OSPF Configuration
mode to configure the NSSA Area Border router (ABR) so that learned
external routes are not redistributed to the NSSA.
Syntax
area
area-id
nssa no-redistribute
no area
area-id
nssa no-redistribute
•
area-id
— Identifies the OSPF NSSA to configure. (Range: IP address or
decimal from 0–4294967295)
Default Configuration
This command has no default configuration.
Command Mode
Router OSPF Configuration mode.
User Guidelines
This command has no user guidelines.
Example
The following example configures the NSSA ABR.
console(config-router)#area 20 nssa no-redistribute
2CSNXXX_SWUM200.book Page 1199 Tuesday, December 10, 2013 1:22 PM

1200 OSPF Commands
area nssa no-summary
Use the area nssa no-summary command in Router OSPF Configuration
mode to configure the NSSA so that summary LSAs are not advertised into
the NSSA.
Syntax
area
area-id
nssa no-summary
no area
area-id
nssa no-summary
•
area-id
— Identifies the OSPF NSSA to configure. (Range: 0–4294967295)
Default Configuration
This command has no default configuration.
Command Mode
Router OSPF Configuration mode.
User Guidelines
This command has no user guidelines.
Example
The following example configures the NSSA so that summary LSAs are not
advertised into the NSSA.
console(config-router)#area 20 nssa no-summary
area nssa translator-role
Use the area nssa translator-role command in Router OSPF Configuration
mode to configure the translator role of the NSSA.
Syntax
area
area-id
nssa translator-role {always | candidate}
no area
area-id
nssa translator-role
•
area-id
— Identifies the OSPF NSSA to configure. (Range: IP address or
decimal from 0–4294967295)
2CSNXXX_SWUM200.book Page 1200 Tuesday, December 10, 2013 1:22 PM

OSPF Commands 1201
• always — The router assumes the role of the translator when it becomes a
border router.
• candidate — The router to participate in the translator election process
when it attains border router status.
Default Configuration
The default role is candidate.
Command Mode
Router OSPF Configuration mode.
User Guidelines
This command has no user guidelines.
Example
The following example configures the translator role of the NSSA.
console(config-router)#area 20 nssa translator-role always
area nssa translator-stab-intv
Use the area nssa translator-stab-intv command in Router OSPF
Configuration mode to configure the translator stability interval of the NSSA.
Syntax
area
area-id
nssa translator-stab-intv
integer
no area
area-id
nssa translator-stab-intv
•
area-id
— Identifies the OSPF NSSA to configure. (Range: IP address or
decimal from 0–4294967295)
•
integer
— The period of time that an elected translator continues to
perform its duties after it determines that its translator status has been
deposed by another router. (Range: 0–3600)
Default Configuration
This command has no default configuration.
2CSNXXX_SWUM200.book Page 1201 Tuesday, December 10, 2013 1:22 PM

1202 OSPF Commands
Command Mode
Router OSPF Configuration mode.
User Guidelines
This command has no user guidelines.
Example
The following example configures the translator stability interval of the area
20 NSSA.
console(config-router)#area 20 nssa translator-stab-intv 2000
area range (Router OSPF)
Use the area range command in Router OSPF Configuration mode to
configure a summary prefix that an area border router advertises for a specific
area. There are two types of area ranges. An area range can be configured to
summarize intra-area routes. An ABR advertises the range rather than the
specific intra-area route as a type 3 summary LSA. Also, an area range can be
configured at the edge of an NSSA to summarize external routes reachable
within the NSSA. The range is advertised as a type 5 external LSA.
Use the no form of the command to delete an area range or revert an option
to its default.
Syntax
area
area-id
range
prefix netmask
{summarylink | nssaexternallink}
[advertise | not-advertise][cost
cost
]
no area
area-id
range
prefix netmask
{summarylink | nssaexternallink}
•
area-id
—
Identifies the OSPF NSSA to configure. (Range: IP address or decimal
from 0–4294967295)
•
prefix netmask
—
The summary prefix to be advertised when the ABR computes
a route to one or more networks within this prefix in this area.
•
summarylink
—
When this keyword is given, the area range is used when
summarizing prefixes advertised in type 3 summary LSAs.
•
nssaexternallink
—
When this keyword is given, the area range is used when
translating type 7 LSAs to type 5 LSAs.
2CSNXXX_SWUM200.book Page 1202 Tuesday, December 10, 2013 1:22 PM

OSPF Commands 1203
•
advertise
—
[Optional] When this keyword is given, the summary prefix is
advertised when the area range is active. This is the default.
•
not-advertise
—
[Optional] When this keyword is given, neither the summary
prefix nor the contained prefixes are advertised when the area range is active.
Then the not-advertise option is given, any static cost previously configured is
removed from the system configuration.
•
cost
—
[Optional] If an optional cost is given, OSPF sets the metric field in the
summary LSA to the configured value, rather than setting the metric to the
largest cost among the networks covered by the area range. A static cost may only
be configured if the area range is configured to advertise the summary. The range
is 0 to 16,777,215. If the cost is set to 16,777,215 for type 3 summarization, a
type 3 summary LSA is not advertised, but contained networks are suppressed.
This behavior is equivalent to specifying the not-advertise option. If the range is
configured for type 7 to type 5 translation, a type 5 LSA is sent if the metric is set
to 16,777,215; however, other routers will not compute a route from a type 5
LSA with this metric.
Default Configuration
No area ranges are configured by default. No cost is configured by default.
Command Mode
OSPFv2 Router Configuration mode
User Guidelines
The no form of this command can be used to delete an area range. For
example:
!! Create area range
console (config-router)#area 1 range 10.0.0.0 255.0.0.0 summarylink
!! Delete area range
console (config-router)#no area 1 range 10.0.0.0 255.0.0.0 summarylink
The no form may be used to revert the [advertise | not-advertise] option to
its default without deleting the area range. Deleting and recreating the area
range would cause OSPF to termporarily advertise the prefixes contained
within the range. Note that using either the advertise or not-advertise
keyword reverts the configuration to the default. For example:
!! Create area range. Suppress summary.
2CSNXXX_SWUM200.book Page 1203 Tuesday, December 10, 2013 1:22 PM

1204 OSPF Commands
console (config-router)#area 1 range 10.0.0.0 255.0.0.0 summarylink not-
advertise
!! Advertise summary.
console (config-router)#no area 1 range 10.0.0.0 255.0.0.0 summarylink not-
advertise
The no form may be use to remove a static area range cost, so that OSPF sets
the cost to the largest cost among the contained routes. For example:
!! Create area range with static cost.
console (config-router)#area 1 range 10.0.0.0 255.0.0.0 summarylink cost 1000
!! Remove static cost.
console (config-router)#no area 1 range 10.0.0.0 255.0.0.0 summarylink cost
If the user tries to configure both types of ranges for the same prefix and area:
A T3 range with the same prefix is already configured on this area.
If the network mask is invalid:
console (config-router)#area 1 range 0.0.0.0 0.0.0.0 summarylink
An area range mask must have contiguous ones and be no longer than 31 bits.
If the prefix is not a valid area range prefix:
console (config-router)#area 1 range 0.0.0.0 255.0.0.0 summarylink
Cannot create this area range because it represents a default route.
console (config-router)#area 1 range 225.0.0.0 255.0.0.0 summarylink
225.0.0.0 255.0.0.0 is an invalid prefix for an area range.
If the maximum number of ranges is already configured:
console (config-router)#area 3 range 90.0.0.0 255.0.0.0 summarylink cost 50
The maximum number of area ranges (60) is alrady configured.
If the user tries to delete an area range that does not exist:
console (config-router)#no area 4 range 40.0.0.0 255.0.0.0 summarylink
Delete failed. No matching area range configured.
2CSNXXX_SWUM200.book Page 1204 Tuesday, December 10, 2013 1:22 PM

OSPF Commands 1205
Example
The following example defines an area range for the area 20.
console(config-router)#area 20 range 192.168.6.0 255.255.255.0 summarylink
advertise
area stub
Use the area stub command in Router OSPF Configuration mode to create a
stub area for the specified area ID. A stub area is characterized by the fact
that AS External LSAs are not propagated into the area. Removing AS
External LSAs and Summary LSAs can significantly reduce the link state
database of routers within the stub area. Use the no form of the command to
remove the stub area.
Syntax
area
area-id
stub
no area
area-id
stub
•
area-id
— Identifies the area identifier of the OSPF stub. (Range: IP
address or decimal from 0–4294967295)
Default Configuration
This command has no default configuration.
Command Mode
Router OSPF Configuration mode.
User Guidelines
This command has no user guidelines.
Examples
The following examples define area 3 for the stub and then removes the stub
area.
console(config-router)#area 3 stub
console(config-router)#no area 3 stub
2CSNXXX_SWUM200.book Page 1205 Tuesday, December 10, 2013 1:22 PM

1206 OSPF Commands
area stub no-summary
Use the area stub no-summary command in Router OSPF Configuration
mode to prevent Summary LSAs from being advertised into the NSSA. Use
the no form of the command to return the Summary LSA mode to the
default value.
Syntax
area
area-id
stub no-summary
no area
area-id
stub no-summary
•
area-id
— Identifies the OSPF area to configure. (Range: IP address or
decimal from 0–4294967295)
Default Configuration
Disabled is the default configuration.
Command Mode
Router OSPF Configuration mode.
User Guidelines
This command has no user guidelines.
Example
The following example prevents the Summary LSA from being advertised
into the area 3 NSSA.
console(config-router)#area 3 stub no-summary
area virtual-link
Use the area virtual-link command in Router OSPF Configuration mode to
create the OSPF virtual interface for the specified area-id and neighbor
router. To remove the link, use the no form of the command. Use the optional
parameters to configure authentication, dead-interval, hello-interval,
retransmit-interval and transmit-delay. If the area has not been previously
created, it is created by this command. If the area already exists, the virtual-
link information is added or modified.
2CSNXXX_SWUM200.book Page 1206 Tuesday, December 10, 2013 1:22 PM

OSPF Commands 1207
Syntax
area
area-id
virtual-link
router-id
[authentication [message-digest | null]]
[hello-interval
seconds
] [retransmit-interval
seconds
] [transmit-delay
seconds
] [dead-interval
seconds
] [[authentication-key
key
] | [message-
digest-key
key-id
md5
key
]]
no area
area-id
virtual-link
router-id
[authentication [message-digest | null]]
[hello-interval] [retransmit-interval] [transmit-delay] [dead-interval]
[[authentication-key] | [message-digest-key]]
•
area-id
—Identifies the OSPF stub area to configure. (Range: IP address or
decimal from 0-4294967295)
•
router-id
—Valid IP address.
•
authentication
—Specifies authentication type.
•
message-digest
—Specifies that message-digest authentication is used.
•
null
—No authentication is used. Overrides password or message-digest
authentication if configured for the area.
•
hello-interval
seconds
—Number of seconds to wait before sending hello
packets to the OSPF virtual interface. (Range: 1–65535)
•
dead-interval
seconds
—Number of seconds to wait before the OSPF
virtual interface on the virtual interface is assumed to be dead. (Range:
1–65535)
•
retransmit-interval
seconds
—The number of seconds to wait between
retransmitting LSAs if no acknowledgement is received. (Range: 0–3600)
•
transmit-delay
seconds
—Number of seconds to increment the age of the
LSA before sending, based on the estimated time it takes to transmit from
the interface. (Range: 0–3600)
•
md5
—Use MD5 Encryption for an OSPF Virtual Link.
•
key
—Authentication key for the specified interface. (Range: 8 bytes or less
if the authentication type is simple and 16 bytes or less if the type is
encrypt.)
•
key-id
—Authentication key identifier for the authentication type encrypt.
(Range: 0–255)
2CSNXXX_SWUM200.book Page 1207 Tuesday, December 10, 2013 1:22 PM
1208 OSPF Commands
Default Configuration
Command Mode
Router OSPF Configuration mode.
User Guidelines
Unauthenticated interfaces cannot be configured with an authentication key.
Use the
area virtual-link authentication
command on page 1209 to enable
configuration of an authentication key.
Example
The following example establishes a virtual link with a 40-second transmit-
delay interval and default values for all other optional parameters:
router ospf
network 10.50.50.0 0.0.0.255 area 10
area 10 virtual-link 192.168.2.2 transmit-delay 40
The following example establishes a virtual link with MD5 authentication:
router ospf
Parameter Default
area-id No area ID is predefined.
router-id No router ID is predefined.
hello-interval
seconds
10 seconds
retransmit-interval
seconds
5 seconds
transmit-delay
seconds
1 second
dead-interval
seconds
40 seconds
authentication-key
key
No key is predefined.
message-digest-key
key-id md5 key
No key is predefined.
2CSNXXX_SWUM200.book Page 1208 Tuesday, December 10, 2013 1:22 PM

OSPF Commands 1209
network 10.50.50.0 0.0.0.255 area 10
area 10.0.0.0 virtual-link 10.3.4.5 message-digest-key 100 md5 test123
area virtual-link authentication
Use the area virtual-link authentication command in Router OSPF
Configuration mode to configure the authentication type and key for the
OSPF virtual interface identified by the area ID and neighbor ID. Use the no
form of the command to return the authentication type to the default value.
Syntax
area
area-id
virtual-link
neighbor-id
authentication [none | simple
key
|
encrypt
key
key-id
]
no area
area-id
virtual-link
neighbor-id
authentication
•
area-id
— Identifies the OSPF area to configure. (Range: IP address or
decimal from 0–4294967295)
•
neighbor-id
— Identifies the Router identifier of the neighbor.
• encrypt — Use MD5 Encryption for an OSPF Virtual Link.
•
key
— Authentication key for the specified interface. (Range: 8 bytes or
less if the authentication type is simple and 16 bytes or less if the type is
encrypt.)
•
key-id
— Authentication key identifier for the authentication type
encrypt. (Range: 0–255)
Default Configuration
This command has no default configuration.
Command Mode
Router OSPF Configuration mode.
User Guidelines
Unauthenticated interfaces cannot be configured with an authentication key.
If no parameters are specified after the authentication keyword, then plain-
text password authentication is used.
2CSNXXX_SWUM200.book Page 1209 Tuesday, December 10, 2013 1:22 PM

1210 OSPF Commands
Example
The following example configures the authentication type and key for the
area 10 OSPF virtual interface and neighbor ID.
console(config-router)#area 10 virtual-link 192.168.2.7 authentication
console(config-router)#area 10 virtual-link 192.168.2.7 authentication
encrypt test123 1001010
area virtual-link dead-interval
Use the area virtual-link dead-interval command in Router OSPF
Configuration mode to configure the dead interval for the OSPF virtual
interface on the virtual interface identified by area-id and neighbor router.
Use the no form of the command to return the dead interval to the default
value.
Syntax
area
area-id
virtual-link
neighbor-id
dead-interval
seconds
no area
area-id
virtual-link
neighbor-id
dead-interval
•
area-id
— Identifies the OSPF area to configure. (Range: IP address or
decimal from 0–4294967295)
•
neighbor-id
— Identifies the Router ID of the neighbor.
•
seconds
— Number of seconds to wait before the OSPF virtual interface
on the virtual interface is assumed to be dead. (Range: 1–2147483647)
Default Configuration
40 seconds is the default configuration.
Command Mode
Router OSPF Configuration mode.
User Guidelines
This command has no user guidelines.
2CSNXXX_SWUM200.book Page 1210 Tuesday, December 10, 2013 1:22 PM

OSPF Commands 1211
Example
The following example configures the dead interval for the area 10 OSPF
virtual interface on the virtual interface and neighbor router.
console(config-router)#area 10 virtual-link 192.168.2.2 dead-interval 655555
area virtual-link hello-interval
Use the area virtual-link hello-interval command in Router OSPF
Configuration mode to configure the hello interval for the OSPF virtual
interface on the virtual interface identified by the area ID and neighbor ID.
Use the no form of the command to return the hello interval to the default
value.
Syntax
area
area-id
virtual-link
neighbor-id
hello-interval
seconds
no area
area-id
virtual-link
neighbor-id
hello-interval
•
area-id
— Identifies the OSPF area to configure. (Range: IP address or
decimal from 0–4294967295)
•
neighbor-id
— Identifies the Router ID of the neighbor.
•
seconds
— Number of seconds to wait before sending hello packets to the
OSPF virtual interface. (Range: 1–65535)
Default Configuration
10 seconds is the default configuration.
Command Mode
Router OSPF Configuration mode.
User Guidelines
This command has no user guidelines.
Example
The following example configures a 50-second wait interval.
console(config-router)#area 10 virtual-link 192.168.2.2 hello-interval 50
2CSNXXX_SWUM200.book Page 1211 Tuesday, December 10, 2013 1:22 PM

1212 OSPF Commands
area virtual-link retransmit-interval
Use the area virtual-link retransmit-interval command in Router OSPF
Configuration mode to configure the retransmit interval for the OSPF virtual
interface on the virtual interface identified by the area ID and neighbor ID.
Use the no form of the command to return the retransmit interval to the
default value.
Syntax
area
area-id
virtual-link
neighbor-id
retransmit-interval
seconds
no area
area-id
virtual-link
neighbor-id
retransmit-interval
•
area-id
— Identifies the OSPF area to configure. (Range: IP address or
decimal from 0–4294967295)
•
neighbor-id
— Identifies the Router ID of the neighbor.
•
seconds
— The number of seconds to wait between retransmitting LSAs if
no acknowledgement is received. (Range: 0–3600)
Default Configuration
The default configuration is 5 seconds.
Command Mode
Router OSPF Configuration mode.
User Guidelines
This command has no user guidelines.
Example
The following example configures a 500-second retransmit wait interval.
console(config-router)#area 10 virtual-link 192.168.2.2 retransmit-interval
500
2CSNXXX_SWUM200.book Page 1212 Tuesday, December 10, 2013 1:22 PM

OSPF Commands 1213
area virtual-link transmit-delay
Use the area virtual-link transmit-delay command in Router OSPF
Configuration mode to configure the transmit delay for the OSPF virtual
interface identified by the area ID and neighbor ID. Use the no form of the
command to return the transmit delay to the default value.
Syntax
area
area-id
virtual-link
neighbor-id
transmit-delay
seconds
no area
area-id
virtual-link
neighbor-id
transmit-delay
•
area-id
— Identifies the OSPF area to configure. (Range: IP address or
decimal from 0–4294967295)
•
neighbor-id
— Identifies the Router ID of the neighbor.
•
seconds
— Number of seconds to increment the age of the LSA before
sending, based on the estimated time it takes to transmit from the
interface. (Range: 0–3600)
Default Configuration
1 second is the default configuration.
Command Mode
Router OSPF Configuration mode.
User Guidelines
This command has no user guidelines.
Example
The following example configures a 40-second transmit-delay interval.
console(config-router)#area 10 virtual-link 192.168.2.2 transmit-delay 40
auto-cost
By default, OSPF computes the link cost of each interface from the interface
bandwidth. The link cost is computed as the ratio of a “reference bandwidth”
to the interface bandwidth (ref_bw / interface bandwidth), where interface
2CSNXXX_SWUM200.book Page 1213 Tuesday, December 10, 2013 1:22 PM

1214 OSPF Commands
bandwidth is defined by the “bandwidth” command. Because the default
reference bandwidth is 100 Mbps, OSPF uses the same default link cost for all
interfaces whose bandwidth is 100 Mbps or greater. To change the reference
bandwidth, use the auto-cost command, specifying the reference bandwidth
in megabits per second. The different reference bandwidth can be
independently configured for OSPFv2 and OSPFv3.
Syntax
auto-cost reference-bandwidth
ref_bw
•
ref_bw
— The reference bandwidth in Mbps (Range: 1–4294967).
Default Configuration
The default reference bandwidth is 100 Mbps.
Command Mode
OSPFv2 or OSPFv3 Router Configuration mode.
User Guidelines
There are no user guidelines for this command.
Example
The following example configures a reference bandwidth of 500 Mbps.
console(config-router)#auto-cost reference-bandwidth 500
bandwidth
By default, OSPF computes the link cost of an interface as the ratio of the
reference bandwidth to the interface bandwidth. Reference bandwidth is
specified with the auto-cost command. For the purpose of the OSPF link cost
calculation, the bandwidth command specifies the interface bandwidth. The
bandwidth is specified in kilobits per second. If no bandwidth is configured,
the bandwidth defaults to the actual interface bandwidth for port-based
routing interfaces and to 10 Mbps for VLAN routing interfaces. This
command does not affect the actual speed of an interface.
2CSNXXX_SWUM200.book Page 1214 Tuesday, December 10, 2013 1:22 PM

OSPF Commands 1215
Syntax
bandwidth
bw
•
bw
— Interface bandwidth in Kbps (Range: 1–10000000).
Default Configuration
The default reference bandwidth is 10 Mbps
Command Mode
Interface Configuration (VLAN) mode.
User Guidelines
There are no user guidelines for this command.
Example
The following example configures the interface bandwidth to 500000 Kbps.
console(config-if-vlan1)#bandwidth 500000
capability opaque
Use the capability opaque command to enable Opaque Capability on the
router. Use the “no” form of this command to disable Opaque Capability.
Syntax
capability opaque
no capability opaque
Default Configuration
Opaque Capability is enabled by default.
Command Mode
Router Configuration mode.
User Guidelines
There are no user guidelines for this command.
2CSNXXX_SWUM200.book Page 1215 Tuesday, December 10, 2013 1:22 PM

1216 OSPF Commands
Example
console(config-router)#capability opaque
clear ip ospf
Use the clear ip ospf command to reset specific OSPF states. If no
parameters are specified, OSPF is disabled and then reenabled.
Syntax
clear ip ospf [{configuration | redistribution | counters | neighbor
[interface vlan
vlan id
[
neighbor id
]]}]
•
configuration
— Reset the OSPF configuration to factory defaults.
•
redistribution
— Flush all self-originated external LSAs. Reapply the
redistribution configuration and re originate prefixes as necessary.
•
counters
— Reset global and interface statistics.
•
neighbor
— Drop the adjacency with all OSPF neighbors. On each
neighbor's interface, send a one-way hello. Adjacencies may then be
reestablished.
•
interface vlan
vlan-id
— Drop adjacency with all neighbors on a specific
interface.
•
neighbor-id
— Drop adjacency with a specific router ID on a specific
interface.
Default Configuration
There is no default configuration for this command.
Command Mode
Privileged EXEC mode.
User Guidelines
There are no user guidelines for this command.
Example
The following example shows the options for the clear ip ospf command.
console#clear ip ospf ?
2CSNXXX_SWUM200.book Page 1216 Tuesday, December 10, 2013 1:22 PM

OSPF Commands 1217
<cr> Press enter to execute the command.
configuration Restore OSPF configuration to defaults
counters Clear OSPF counters
neighbor Bounce all OSPF neighbors
redistribution Flush and reoriginate external LSAs
clear ip ospf stub-router
Use the clear ip ospf stub-router command in Privileged EXEC mode to force
OSPF to exit stub router mode when it has automatically entered stub router
mode because of a resource limitation.
Syntax
clear ip ospf stub-router
Default Configuration
There is no default configuration for this command.
Command Mode
Privileged EXEC mode
User Guidelines
OSPF only exits stub router mode if it entered stub router mode because of a
resource limitation or if it is in stub router mode at startup. This command
has not effect is OSPF is configured to be in stub router mode permanently.
compatible rfc1583
Use the compatible rfc1583 command in Router OSPF Configuration mode
to enable OSPF 1583 compatibility. Use the no form of the command to
disable it.
Syntax
compatible rfc1583
no compatible rfc1583
2CSNXXX_SWUM200.book Page 1217 Tuesday, December 10, 2013 1:22 PM

1218 OSPF Commands
Syntax Description
This command has no arguments or keywords.
Default Configuration
Compatible with RFC 1583.
Command Mode
Router OSPF Configuration mode.
User Guidelines
If all OSPF routers in the routing domain are capable of operating according
to RFC 2328, OSPF 1583 compatibility mode should be disabled.
Example
The following example enables 1583 compatibility.
console(config-router)#compatible rfc1583
default-information originate (Router OSPF
Configuration)
Use the default-information originate command in Router OSPF
Configuration mode to control the advertisement of default routes. Use the
no form of the command to return the default route advertisement settings
to the default value.
Syntax
default-information originate [always] [metric
metric-value
] [metric-type
type-value]
no default-information originate [metric] [metric-type]
•
always
—Always advertise default routes.
•
metric-value
—The metric (or preference) value of the default route.
(Range: 1–16777214)
•
type-value
—One of the following:
1
External type-1 route.
2CSNXXX_SWUM200.book Page 1218 Tuesday, December 10, 2013 1:22 PM

OSPF Commands 1219
2
External type-2 route.
Default Configuration
The default configuration is no default-information originate. The default
metric is none and the default type is 2.
Command Mode
Router OSPF Configuration mode.
User Guidelines
The only routers that actually have Internet connectivity should advertise a
default route. All other routers in the network should learn the default route
from the routers that have connections to the Internet. The edge router
should also have a static default route configured with an upstream ISP router
as the destination. The always keyword will cause the router to advertise a
default route to its neighbors, even if no valid default route is known.
Example
The following example always advertises default routes.
console(config-router)#default-information originate always metric 100
metric-type 1
default-metric
Use the default-metric command in Router OSPF Configuration mode to set
a default for the metric of distributed routes. Use the no form of the
command to remove the metric from the distributed routes. If the area has
not been previously created, it is created by this command. If the area already
exists, the default-metric information is added or modified.
Syntax
default-metric
metric-value
no default-metric
•
metric-value
— The metric (or preference) value of the default route.
(Range: 1–16777214)
2CSNXXX_SWUM200.book Page 1219 Tuesday, December 10, 2013 1:22 PM

1220 OSPF Commands
Default Configuration
This command has no default configuration.
Command Mode
Router OSPF Configuration mode.
User Guidelines
This command has no user guidelines.
Example
The following example sets a value of 50 for the default metric.
console(config-router)#default-metric 50
distance ospf
The distance ospf command sets the preference values of OSPF route types
in the router. Lower route preference values are preferred when determining
the best route. The type of OSPF route can be intra, inter, external. All the
external type routes are given the same preference value. Use the no form of
this command to reset the preference values to the default.
Syntax
distance ospf {[
intra-area dist1
]
[
inter-area dist2
]
[
external dist3
]}
no distance ospf
{
intra-area
|
inter-area
|
external
}
•
intra-area dist1
—Used to select the best path within an area when there
are two or more routes to the same destination from two different routing
protocols (Range: 1–255).
•
inter-area dist2
—Used to select the best path from one area to another
area when there are two or more routes to the same destination from two
different routing protocols (Range: 1–255).
•
external dist3
—Used to select the best path for routes from other routing
domains, learned by redistribution when there are two or more routes to
the same destination from two different routing protocols (Range: 1–255).
2CSNXXX_SWUM200.book Page 1220 Tuesday, December 10, 2013 1:22 PM

OSPF Commands 1221
Default Configuration
The default preference value is 110 for dist1, dist2 and dist3.
Command Mode
Router OSPF Configuration mode.
Router OSPFv3 Configuration mode.
User Guidelines
There are no user guidelines for this command.
Examples
The following examples set route preference values of OSPF in the router.
console(config-router)#distance ospf intra 4
console(config-router)#distance ospf type1 19
distribute-list out
Use the distribute-list out command in Router OSPF Configuration mode to
specify the access list to filter routes received from the source protocol. Use
the no form of the command to remove the specified source protocol from
the access list.
Syntax
distribute-list
name
out {rip | static
\
connected}
no distribute-list
name
out {rip | static
\
connected}
•
name
—The name used to identify an existing ACL. The range is 1–31
characters.
•
rip
—Apply the specified access list when RIP is the source protocol.
•
static
—Apply the specified access list when packets come through the
static route.
•
connected
—Apply the specified access list when packets come from a
directly connected route.
2CSNXXX_SWUM200.book Page 1221 Tuesday, December 10, 2013 1:22 PM

1222 OSPF Commands
Default Configuration
This command has no default configuration.
Command Mode
Router OSPF Configuration mode.
User Guidelines
This command has no user guidelines.
Example
The following example specifies the access list to filter routes received from
the RIP source protocol.
console(config-router)#distribute-list ACL40 out rip
enable
This command has been deprecated. Use the enable command in Router
OSPF Configuration mode to reset the default administrative mode of OSPF
in the router (active). OSPF is now globally enabled using the router ospf
command. Use the no form of the command to disable the administrative
mode for OSPF.
Syntax
enable
no enable
Default Configuration
Enabled is the default configuration.
Command Mode
Router OSPF Configuration mode.
User Guidelines
This command has no user guidelines.
2CSNXXX_SWUM200.book Page 1222 Tuesday, December 10, 2013 1:22 PM

OSPF Commands 1223
Example
The following example enables OSPF router mode.
console(config-router)#enable
exit-overflow-interval
Use the exit-overflow-interval command in Router OSPF Configuration
mode to configure the exit overflow interval for OSPF. When a router leaves
the overflow state it can originate non-default AS-external-LSAs. When set to
0, the router will not leave Overflow State until restarted. Use the no form of
the command to return the interval to the default value.
Syntax
exit-overflow-interval
seconds
no exit-overflow-interval
•
seconds
— Number of seconds after entering overflow state that a router
will wait before attempting to leave the overflow state. (Range:
0–2147483647)
Default Configuration
0 seconds is the default configuration.
Command Mode
Router OSPF Configuration mode.
User Guidelines
This command has no user guidelines.
Example
The following example sets the exit overflow interval for OSPF at 10 seconds.
console(config-router)#exit-overflow-interval 10
2CSNXXX_SWUM200.book Page 1223 Tuesday, December 10, 2013 1:22 PM

1224 OSPF Commands
external-lsdb-limit
Use the external-lsdb-limit command in Router OSPF Configuration mode
to configure the external LSDB limit for OSPF. If the value is -1, then there is
no limit. When the number of non-default AS-external-LSAs in a router's
link-state database reaches the external LSDB limit, the router enters
overflow state. The router never holds more than the external LSDB limit
non-default AS-external-LSAs in it database. Use the no form of the
command to return the limit to the default value.
Syntax
external-lsdb-limit
integer
no external-lsdb-limit
•
integer
— Maximum number of non-default AS-external-LSAs allowed in
the router's link-state database. (Range: –1 to 2147483647)
Default Configuration
-1 is the default configuration.
Command Mode
Router OSPF Configuration mode.
User Guidelines
The external LSDB limit MUST be set identically in all routers attached to
the OSPF backbone and/or any regular OSPF area.
Example
The following example configures the external LSDB limit for OSPF with the
number of non-default AS-external-LSAs set at 20.
console(config-router)#external-lsdb-limit 20
2CSNXXX_SWUM200.book Page 1224 Tuesday, December 10, 2013 1:22 PM

OSPF Commands 1225
ip ospf area
The ip ospf area command enables OSPFv2 and sets the area ID of an
interface. This command supersedes the effects of network area command. It
can also configure the advertisability of the secondary addresses on this
interface into OSPFv2 domain. Use the “no” form of this command to
disable OSPFv2 on an interface.
Syntax
ip ospf area
area-id
[secondaries none]
no ip ospf area [secondaries none]
•
area-id
— The ID of the area (Range: IP address or decimal from 0
–4294967295).
Default Configuration
OSPFv2 is disabled by default.
Command Mode
Interface Configuration (VLAN) mode.
User Guidelines
There are no user guidelines for this command.
Example
console(config-if-vlan1)#ip ospf area 192.168.1.10
console(config-if-vlan1)#ip ospf area 3232235786
ip ospf authentication
Use the ip ospf authentication command in the Interface Configuration
mode to set the OSPF Authentication Type and Key for the specified
interface. Use the no form of the command to return the authentication type
to the default value.
Syntax
ip ospf authentication {none | {simple
key
} | {encrypt
key key-id
}}
2CSNXXX_SWUM200.book Page 1225 Tuesday, December 10, 2013 1:22 PM

1226 OSPF Commands
no ip ospf authentication
• encrypt — MD5 encrypted authentication key.
•
key
— Authentication key for the specified interface. (Range: 8 bytes or
less if the authentication type is
simple
and 16 bytes or less if the type is
encrypt
.)
•
key-id
— Authentication key identifier for the authentication type
encrypt
. (Range: 0–25)
Default Configuration
This command has no default configuration.
Command Mode
Interface Configuration (VLAN) mode.
User Guidelines
Unauthenticated interfaces do not need an authentication key or
authentication key ID.
Example
The following example sets the OSPF Authentication Type and Key for VLAN
15.
console(config-if-vlan15)#ip ospf authentication encrypt test123 100
ip ospf cost
Use the ip ospf cost command in Interface Configuration mode to configure
the cost on an OSPF interface. Use the no form of the command to return
the cost to the default value.
Syntax
ip ospf cost
interface-cost
no ip ospf cost
•
inte
rface-cost
— Specifies the cost (link-state metric) of the OSPF
interface. (Range: 1–65535)
2CSNXXX_SWUM200.book Page 1226 Tuesday, December 10, 2013 1:22 PM

OSPF Commands 1227
Default Configuration
10 is the default link-state metric configuration.
Command Mode
Interface Configuration (VLAN) mode.
User Guidelines
This command has no user guidelines.
Example
The following example configures the cost on the OSPF interface at 5.
console(config-if-vlan1)#ip ospf cost 5
ip ospf database-filter all out
Use the ip ospf database-filter all out command in Interface Configuration
mode to prevent flooding of OSPF LSAs on an interface.
Use the no form of the command to enable flooding of LSAs on an interface.
Syntax
ip ospf database-filter all out
no ip ospf database-filter all out
Default Configuration
By default, LSAs are flooded on all interfaces in a routed VLAN.
Command Mode
Interface Configuration mode
User Guidelines
This command is only applicable to OSPFv2 routing configurations.
2CSNXXX_SWUM200.book Page 1227 Tuesday, December 10, 2013 1:22 PM

1228 OSPF Commands
ip ospf dead-interval
Use the ip ospf dead-interval command in Interface Configuration to set the
OSPF dead interval for the specified interface. Use the no form of the
command to return the interval to the default value.
Syntax
ip ospf dead-interval
seconds
no ip ospf dead-interval
•
seconds
— Number of seconds that a router's Hello packets have not been
seen before its neighbor routers declare that the router is down. (Range:
1–65535)
Default Configuration
40 is the default number of seconds.
Command Mode
Interface Configuration (VLAN) mode
User Guidelines
The value for the length of time must be the same for all routers attached to a
common network. This value should be some multiple of the Hello Interval
(i.e., 4).
Example
The following example sets the dead interval at 30 seconds.
console(config-if-vlan1)#ip ospf dead-interval 30
ip ospf hello-interval
Use the ip ospf hello-interval command in Interface Configuration mode to
set the OSPF hello interval for the specified interface. Use the no form of the
command to return the interval to the default value.
Syntax
ip ospf hello-interval
seconds
2CSNXXX_SWUM200.book Page 1228 Tuesday, December 10, 2013 1:22 PM

OSPF Commands 1229
no ip ospf hello-interval
•
seconds
— Number of seconds to wait before sending Hello packets from
the interface. (Range: 1–65535)
Default Configuration
10 is the default number of seconds.
Command Mode
Interface Configuration (VLAN) mode.
User Guidelines
The value for the length of time must be the same for all routers attached to a
network.
Example
The following example sets the OSPF hello interval at 30 seconds.
console(config-if-vlan1)#ip ospf hello-interval 30
ip ospf mtu-ignore
Use the ip ospf mtu-ignore command in Interface Configuration mode to
disable OSPF maximum transmission unit (MTU) mismatch detection.
OSPF Database Description packets specify the size of the largest IP packet
that can be sent without fragmentation on the interface. When a router
receives a Database Description packet, it examines the MTU advertised by
the neighbor. By default, if the MTU is larger than the router can accept, the
Database Description packet is rejected and the OSPF adjacency is not
established. Use the no form of the command to enable OSPF maximum
transmission unit (MTU) mismatch detection.
Syntax
ip ospf mtu-ignore
no ip ospf mtu-ignore
2CSNXXX_SWUM200.book Page 1229 Tuesday, December 10, 2013 1:22 PM

1230 OSPF Commands
Default Configuration
This command has no default configuration.
Command Mode
Interface Configuration (VLAN) mode.
User Guidelines
This command has no user guidelines.
Example
The following example disables OSPF MTU mismatch detection on VLAN
interface 15.
console(config-if-vlan1)#ip ospf mtu-ignore
ip ospf network
Use the ip ospf network command to configure OSPF to treat an interface as
a point-to-point rather than broadcast interface. To return to the default
value, use the no form of this command.
Syntax
ip ospf network {
broadcast
|
point-to-point
}
no ip ospf network
•
broadcast
— Set the network type to broadcast.
•
point-to-point
— Set the network type to point-to-point
Default Configuration
Interfaces operate in broadcast mode by default.
Command Mode
Interface Configuration (VLAN) mode.
2CSNXXX_SWUM200.book Page 1230 Tuesday, December 10, 2013 1:22 PM

OSPF Commands 1231
User Guidelines
OSPF treats interfaces as broadcast interfaces by default. Loopback interfaces
have a special loopback network type, which cannot be changed. When there
are only two routers on the network, OSPF can operate more efficiently by
treating the network as a point-to-point network. For point-to-point
networks, OSPF does not elect a designated router or generate a network link
state advertisement (LSA). Both endpoints of the link must be configured to
operate in point-to-point mode.
Example
The following example shows the options for the ip ospf network command.
console(config-if-vlan1)#ip ospf network ?
broadcast Set the OSPF network type to Broadcast
point-to-point Set the OSPF network type to Point-to-Point
ip ospf priority
Use the ip ospf priority command in Interface Configuration mode to set the
OSPF priority for the specified router interface. Use the no form of the
command to return the priority to the default value.
Syntax
ip ospf priority
number-value
no ip ospf priority
•
number-value
— Specifies the OSPF priority for the specified router
interface. (Range: 0–255)
Default Configuration
1 is the default integer value.
Command Mode
Interface Configuration (VLAN) mode.
2CSNXXX_SWUM200.book Page 1231 Tuesday, December 10, 2013 1:22 PM

1232 OSPF Commands
User Guidelines
A value of 1 is the highest router priority. A value of 0 indicates that the
interface is not eligible to become the designated router on this network.
Example
The following example sets the OSPF priority for the VLAN 15 router at 100.
console(config-if-vlan1)#ip ospf priority 100
ip ospf retransmit-interval
Use the ip ospf retransmit-interval command in Interface Configuration
mode to set the OSPF retransmit Interval for the specified interface. Use the
no form of the command to return the interval to the default value.
Syntax
ip ospf retransmit-interval
seconds
no ip ospf retransmit-interval
•
seconds
— Number of seconds between link-state advertisement
retransmissions for adjacencies belonging to this router interface. This
value is also used when retransmitting database description and link-state
request packets. (Range: 0–3600 seconds)
Default Configuration
5 is the default number of seconds.
Command Mode
Interface Configuration (VLAN) mode.
User Guidelines
A value of 1 is the highest router priority. A value of 0 indicates that the
interface is not eligible to become the designated router on this network.
Example
The following example sets the OSPF retransmit Interval for VLAN 15 at 50
seconds.
2CSNXXX_SWUM200.book Page 1232 Tuesday, December 10, 2013 1:22 PM

OSPF Commands 1233
console(config-if-vlan1)#ip ospf retransmit-interval 50
ip ospf transmit-delay
Use the ip ospf transmit-delay command in Interface Configuration mode to
set the OSPF Transit Delay for the specified interface. Use the no form of the
command to return the delay to the default value.
Syntax
ip ospf transmit-delay
seconds
no ip ospf transmit-delay
•
seconds
— Sets the estimated number of seconds it takes to transmit a link
state update packet over this interface. (Range: 1–3600 seconds)
Default Configuration
1 is the default number of seconds.
Command Mode
Interface Configuration (VLAN) mode.
User Guidelines
This command has no user guidelines.
Example
The following example sets the OSPF Transit Delay for VLAN 15 at 20
seconds.
console(config-if-vlan1)#ip ospf transmit-delay 20
log adjacency-changes
Use the log adjacency-changes command in OSPFv2 Router Configuration
mode to enable logging of OSPFv2 neighbor state changes.
Use the no form of the command to disable state change logging.
2CSNXXX_SWUM200.book Page 1233 Tuesday, December 10, 2013 1:22 PM

1234 OSPF Commands
Syntax
log-adjacency-changes [detail]
no log-adjacency-changes [detail]
•
detail
—(Optional) When this keyword is specified, all adjacency state
changes are logged. Otherwise, OSPF only logs transitions to FULL state
and when a backwards transition occurs.
Default Configuration
Adjacency changes are not logged by default.
Command Mode
OSPFv2 Router Configuration mode
User Guidelines
State changes are logged with INFORMATIONAL severity.
max-metric router-lsa
Use the max-metric router-lsa command in router OSPF Global
Configuration mode to configure OSPF to enable stub router mode.
To disable stub router mode, use the no max-metric router-lsa command in
OSPFv2 Global Router Configuration mode.
Syntax
max-metric router-lsa [on-startup
seconds
] [summary-lsa {
metric
}]
no max-metric router-lsa [on-startup] [summary-lsa]
•
on-startup
—(Optional) OSPF starts in stub router mode after a reboot.
•
seconds
—(Required if on-startup) The number of seconds that OSPF
remains in stub router mode after a reboot. The range is 5 to 86,400
seconds. There is no default value.
•
summary-lsa
—(Optional) Set the metric in type 3 and 4 summary LSAs to
LsInfinity (0xFFFFFF).
•
metric
—(Optional) Metric to send in summary LSAs when in stub router
mode. Range is 1 to 16,777,215. Default is 16,711,680 (0xFF0000).
2CSNXXX_SWUM200.book Page 1234 Tuesday, December 10, 2013 1:22 PM

OSPF Commands 1235
Default Configuration
By default, OSPF is not in stub router mode.
Command Mode
OSPFv2 Global Configuration mode
User Guidelines
When OSPF is in stub router mode, as defined by RFC 3137, OSPF sets the
metric in the non-stub links in its router LSA to LsInfinity. Other routers
therefore compute very long paths through the stub router, and prefer any
alternate path. Doing so eliminates all transit traffic through the stub router,
when alternate routes are available. Stub router mode is useful when adding
or removing a router from a network or to avoid transient routes when a
router reloads.
One can administratively force OSPF into stub router mode. OSPF remains
in stub router mode until OSPF is taken out of stub router mode.
Alternatively, one can configure OSPF to start in stub router mode for a
specific period of time after the router boots up.
If the summary LSA metric is set to 16,777,215, other routers will skip the
summary LSA when they compute routes.
If the router is configured to enter stub router mode on startup (max-metric
router-lsa on-startup), and one then enters max-metric router lsa, there is no
change. If OSPF is administratively in stub router mode (the max-metric
router-lsa command has been given), and one configures OSPF to enter stub
router mode on startup (max-metric router-lsa on-startup), OSPF exits stub
router mode (assuming the startup period has expired) and the configuration
is updated.
The command no max-metric router-lsa clears either type of stub router
mode (always or on-startup) and resets the summary-lsa option. If OSPF is
configured to enter global configuration mode on startup, and during normal
operation one wants to immediately place OSPF in stub router mode, one
may issue the command no max-metric router-lsa on-startup. The command
no max-metric router-lsa summary-lsa causes OSPF to send summary LSAs
with metrics computed using normal procedures defined in RFC 2328.
2CSNXXX_SWUM200.book Page 1235 Tuesday, December 10, 2013 1:22 PM

1236 OSPF Commands
maximum-paths
Use the maximum-paths command in Router OSPF Configuration mode to
set the number of paths that OSPF can report for a given destination. Use the
no form of the command to reset the number to the default value.
Syntax
maximum-paths
integer
no maximum-paths
•
integer
— Number of paths that OSPF can report for a given destination.
(Range: 1–4.)
Default Configuration
4 is the
integer
default value.
Command Mode
Router OSPF Configuration mode.
User Guidelines
OSPF is only enabled on an interface if the primary IPv4 address on the
interface matches a network area range. Any individual interface can only be
attached to a single area. If an interface address matches multiple network
area ranges, the interface is assigned to the area for the first matching range.
If the ip ospf area command is given for an interface, it overrides any
matching network area command.
OSPF only advertises IP subnets for secondary IP addresses if the secondary
address is within the range of a network area command for the same area as
the primary address on the same interface.
When a network area command is deleted, matching interfaces are
reevaluated against all remaining network area commands.
Example
The following example sets the number of paths at 2 that OSPF can report
for a given destination.
console(config-router)#maximum-paths 2
2CSNXXX_SWUM200.book Page 1236 Tuesday, December 10, 2013 1:22 PM

OSPF Commands 1237
network area
The network area command enables OSPFv2 on an interface and sets its area
ID if the ip-address of an interface is covered by this network command. Use
the “no” form of this command to disable OSPFv2 on an interface.
Syntax
network
ip-address wildcard-mask
area
area-id
no network
ip-address wildcard-mask
area
area-id
•
ip-address
— Base IPv4 address of the network area.
•
wildcard-mask
— The network mask indicating the subnet.
•
area-id
— The ID of the area (Range: IPv4 address or 32-bit decimal in the
range 0–4294967295).
Default Configuration
OSPFv2 is disabled
Command Mode
Router OSPF Configuration mode.
User Guidelines
OSPF is only enabled on an interface if the primary IPv4 address on the
interface matches a network area range. Any individual interface can only be
attached to a single area. If an interface address matches multiple network
area ranges, the interface is assigned to the area for the first matching range.
If the ip ospf area command is given for an interface, it overrides any
matching network area command.
OSPF only advertises IP subnets for secondary IP addresses if the secondary
address is within the range of a network area command for the same area as
the primary address on the same interface.
When a network area command is deleted, matching interfaces are
reevaluated against all remaining network area commands.
Example
console(config-router)#network 10.50.50.0 0.0.0.255 area 4
2CSNXXX_SWUM200.book Page 1237 Tuesday, December 10, 2013 1:22 PM

1238 OSPF Commands
nsf
Use this command to enable OSPF graceful restart. Use the no form of this
command to disable graceful restart.
Syntax
nsf [ietf] [planned-only]
no nsf [ietf]
•
ietf
— This keyword is used to distinguish the IETF standard
implementation of graceful restart from other implementations. Since the
IETF implementation is the only one supported, this keyword is optional.
•
planned-only
— This keyword indicates that OSPF should only perform a
graceful restart when the restart is planned (i.e., when the restart is a result
of the
initiate failover
command).
Default Configuration
Graceful restart is disabled by default
Command Mode
Router OSPF Configuration mode
User Guidelines
Graceful restart works in concert with nonstop forwarding to enable the
hardware to continue forwarding IPv4 packets using OSPFv2 routes while a
backup unit takes over management unit responsibility. When OSPF
executes a graceful restart, it informs its neighbors that the OSPF control
plane is restarting, but that it will be back shortly. Helpful neighbors continue
to advertise to the rest of the network that they have full adjacencies with the
restarting router, avoiding announcement of a topology change and
everything that goes with that (i.e., flooding of LSAs, SPF runs). Helpful
neighbors continue to forward packets through the restarting router. The
restarting router relearns the network topology from its helpful neighbors.
This implementation of graceful restart restarting router behavior is only
useful with a router stack. Graceful restart does not work on a standalone,
single-unit router.
2CSNXXX_SWUM200.book Page 1238 Tuesday, December 10, 2013 1:22 PM

OSPF Commands 1239
nsf helper
Use the nsf-helper to allow OSPF to act as a helpful neighbor for a restarting
router. Use the “no” form of this command to prevent OSPF from acting as a
helpful neighbor.
Syntax
nsf [ietf] helper[planned-only]
no nsf [ietf] helper
•
planned-only
— This keyword indicates that OSPF should only help a
restarting router performing a planned restart.
Default Configuration
OSPF may act as a helpful neighbor for both planned and unplanned restarts
Command Mode
Router OSPF Configuration mode
User Guidelines
The grace LSA announcing the graceful restart includes a restart reason.
Reasons 1 (software restart) and 2 (software reload/upgrade) are considered
planned restarts. Reasons 0 (unknown) and 3 (switch to redundant control
processor) are considered unplanned restarts.
nsf ietf helper disable is functionally equivalent to no nsf helper and is
supported solely for IS CLI compatibility.
nsf helper strict-lsa-checking
Use the nsf-helper strict-lsa-checking command to require that an OSPF
helpful neighbor exit helper mode whenever a topology change occurs. Use
the “no” form of this command to allow OSPF to continue as a helpful
neighbor in spite of topology changes.
Syntax
nsf [ietf] helper strict-lsa-checking
2CSNXXX_SWUM200.book Page 1239 Tuesday, December 10, 2013 1:22 PM

1240 OSPF Commands
no nsf [ietf] helper strict-lsa-checking
•
ietf
—This keyword is used to distinguish the IETF standard
implementation of graceful restart from other implementations. Since the
IETF implementation is the only one supported, this keyword is optional.
Default Configuration
A helpful neighbor exits helper mode when a topology change occurs.
Command Mode
Router OSPF Configuration mode
User Guidelines
The restarting router is unable to react to topology changes. In particular, the
restarting router will not immediately update its forwarding table; therefore, a
topology change may introduce forwarding loops or black holes that persist
until the graceful restart completes. By exiting the graceful restart on a
topology change, a router tries to eliminate the loops or black holes as quickly
as possible by routing around the restarting router.
A helpful neighbor considers a link down with the restarting router to be a
topology change, regardless of the strict LSA checking configuration.
nsf restart-interval
Use the nsf restart-interval command to configure the length of the grace
period on the restarting router. Use the “no” form of this command to revert
the grace period to its default.
Syntax
nsf [ietf] restart-interval
seconds
no nsf [ietf] restart-interval
•
ietf
— This keyword is used to distinguish the IETF standard
implementation of graceful restart from other implementations. Since the
IETF implementation is the only one supported, this keyword is optional.
2CSNXXX_SWUM200.book Page 1240 Tuesday, December 10, 2013 1:22 PM

OSPF Commands 1241
•
seconds
— The number of seconds that the restarting router asks its
neighbors to wait before exiting helper mode. The restarting router
includes the restart interval in its grace LSAs (range 1–1800 seconds).
Default Configuration
The default restart interval is 120 seconds.
Command Mode
Router OSPF
User Guidelines
The grace period must be set long enough to allow the restarting router to
reestablish all of its adjacencies and complete a full database exchange with
each of those neighbors.
Example
console(config-router)#nsf restart-interval 180
passive-interface default
The passive-interface default command enables the global passive mode by
default for all interfaces. It overrides any interface level passive mode. Use the
“no” form of this command to disable the global passive mode by default for
all interfaces. Any interface previously configured to be passive reverts to non-
passive mode.
Syntax
passive-interface default
no passive-interface default
Default Configuration
Global passive mode is disabled by default.
Command Mode
Router OSPF Configuration mode.
2CSNXXX_SWUM200.book Page 1241 Tuesday, December 10, 2013 1:22 PM

1242 OSPF Commands
User Guidelines
There are no user guidelines for this command.
Example
console(config-router)#passive-interface
passive-interface
Use the passive-interface command to set the interface as passive. It
overrides the global passive mode that is currently effective on the interface.
Use the “no” form of this command to set the interface as non-passive.
Syntax
passive-interface vlan
vlan-id
no passive-interface vlan
vlan-id
•
vlan-id
— The vlan number
Default Configuration
Passive interface mode is disabled by default.
Command Mode
Router OSPF Configuration mode.
User Guidelines
There are no user guidelines for this command.
Example
console(config-router)#passive-interface vlan 1
redistribute
Use the redistribute command in Router OSPF Configuration mode to
configure OSPF protocol to allow redistribution of routes from the specified
source protocol/routers. Use the no version of the command to disable
redistribution from the selected source or to reset options to their default
values.
2CSNXXX_SWUM200.book Page 1242 Tuesday, December 10, 2013 1:22 PM

OSPF Commands 1243
Syntax
redistribute protocol [metric metric-value] [metric-type type-value] [tag
tag-value] [subnets]
no redistribute protocol [metric] [metric-type] [tag] [subnets]
•
protocol
—One of the following:
– rip - Specifies RIP as the source protocol.
– static - Specifies that the source is a static route.
– connected - Specifies that the source is a directly connected route.
•
static
—Specifies that the source is a static route.
•
connected
—Specifies that the source is a directly connected route.
•
metric-value
—Specifies the metric to use when redistributing the route.
(Range: 0–16777214)
•
type-value
—One of the following:
– Type 1 external route.
– Type 2 external route.
•
tag-value
—Value attached to each external route, which might be used to
communicate information between ASBRs. (Range: 0–4294967295)
•
subnets
—Specifies whether to redistribute the routes to subnets.
Default Configuration
0 is the tag-value default configuration.
Command Mode
Router OSPF Configuration mode.
User Guidelines
This command has no user guidelines.
Example
The following example configures OSPF protocol to allow redistribution of
routes from the specified source protocol/routers.
2CSNXXX_SWUM200.book Page 1243 Tuesday, December 10, 2013 1:22 PM

1244 OSPF Commands
console(config-router)#redistribute rip metric 90 metric-type 1 tag 555
subnets
router-id
Use the router-id command in Router OSPF Configuration mode to set a 32-
bit integer in 4-digit dotted-decimal number uniquely identifying the router
ID.
Syntax
router-id
router-id
•
router-id
— A 32-bit interface (in IPv4 address format) that uniquely
identifies the router ID.
Default Configuration
There is no default router ID.
Command Mode
Router OSPF Configuration mode.
User Guidelines
The router-id must be set in order for OSPF to become operationally enabled.
It is recommended that the router ID be set to the IP address of a loopback
interface to ensure that the router remains up internally.
Example
The following example defines the router ID as 5.5.5.5.
console(config)#router ospf
console(config-router)#router-id 5.5.5.5
router ospf
Use the router ospf command in Global Configuration mode to enter Router
OSPF mode and globally enable OSPF. Using the no form of the command
disables OSPF and removes the OSPF interface and global configuration.
2CSNXXX_SWUM200.book Page 1244 Tuesday, December 10, 2013 1:22 PM

OSPF Commands 1245
Syntax
router ospf
no router ospf
Default Configuration
OSPF routing is not enabled by default
Command Mode
Global Configuration mode.
User Guidelines
The command prompt changes when the router ospf command executes.
Example
The following example enters into router OSPF mode.
console(config)#router ospf
console(config-router)#
show ip ospf
Use the show ip ospf command to display information relevant to the OSPF
router. This command has been modified to show additional fields.
Syntax
show ip ospf
Syntax Description
This command has no arguments or keywords.
Default Configuration
There is no default configuration for this command.
Command Mode
User EXEC, Privileged EXEC modes, Configuration mode and all
Configuration submodes
2CSNXXX_SWUM200.book Page 1245 Tuesday, December 10, 2013 1:22 PM
1246 OSPF Commands
User Guidelines
Some of the information below displays only if you enable OSPF and
configure certain features. The following fields may be displayed:
Field Description
Router ID A 32-bit integer in dotted decimal format identifying the router
about which information is displayed. This is a configured value.
OSPF Admin
Mode
Shows whether OSPF is administratively enabled or disabled.
RFC 1583
Compatibility
This configuration option controls the preference rules used
when choosing among multiple external LSAs advertising the
same destination. When enabled, the preference rules remain
those specified by RFC 1583. When disabled, the preference
rules are those stated in Section 16.4.1 of RFC 2328. These rules
prevent routing loops when external LSAs for the same
destination have been originated from different areas.
External LSDB
Limit
Shows the maximum number of non-default external LSAs
entries that can be stored in the link-state database.
Exit Overflow
Interval
Shows the number of seconds that, after entering
OverflowState, as defined by RFC 1765, a router will attempt to
leave OverflowState.
Spf Delay Time The number of seconds to wait before running a routing table
calculation after a topology change.
Spf Hold Time The minimum number of seconds between routing table
calculations.
Flood Pacing
Interval
The average time, in milliseconds, between LS Update packet
transmissions on an interface. This is the value configured with
the timers pacing flood command.
LSA Refresh
Group Pacing
Time
The size of the LSA refresh group window, in seconds. This is the
value configured with the timers pacing lsa-group command.
Opaque Capability Shows whether router is capable of sending Opaque LSAs.
AutoCost Ref BW The configured autocost reference bandwidth. This value is used
to determine the OSPF metric on its interfaces. The reference
bandwidth is divided by the interface speed to compute the
metric.
2CSNXXX_SWUM200.book Page 1246 Tuesday, December 10, 2013 1:22 PM
OSPF Commands 1247
Default Passive
Setting
When enabled, OSPF interfaces are passive by default.
Maximum Paths Shows the maximum number of paths that OSPF can report for
a given destination.
Default Metric Default metric for redistributed routes.
Stub Router
Configuration
One of Always, Startup, or None.
Stub Router
Startup Time
Configured value in seconds. This row is only listed if OSPF is
configured to be a stub router at startup.
Summary LSA
Metric Override
One of Enabled (
met
), Disabled, where
met
is the metric to be
sent in summary LSAs when in stub router mode.
Default Route
Advertise
When enabled, OSPF originates a type 5 LSA advertising a
default route.
Always When this option is configured, OSPF only originates a default
route when the router has learned a default route from another
source.
Metric Shows the metric for the advertised default routes. If the metric
is not configured, this field is not configured.
Metric Type Shows whether the metric for the default route is advertised as
External Type 1 or External Type 2.
Number of Active
Areas
The number of OSPF areas to which the router is attached on
interfaces that are up.
ABR Status Shows whether the router is an OSPF Area Border Router.
ASBR Status Indicates whether the router is an autonomous system border
router. Router automatically becomes an ASBR when it is
configured to redistribute routes learned from another protocol.
The possible values for the ASBR status is enabled (if the router
is configured to redistribute routes learned by other protocols) or
disabled (if the router is not configured for the same).
Stub Router Status One of Active or Active.
Stub Router
Reason
One of Configured, Startup, or Resource Limitation. This row
is only listed if stub router is active.
Stub Router Time
Remaining
The remaining time until OSPF exits stub router mode. This
row is only listed if OSPF is in startup stub router mode.
2CSNXXX_SWUM200.book Page 1247 Tuesday, December 10, 2013 1:22 PM
1248 OSPF Commands
External LSDB
Overflow
OSPF enters this state when the number of external LSAs
exceeds a configured limit, as described in RFC 1765.
External LSA
Count
Shows the number of external (LS type 5) link-state
advertisements in the link-state database.
External LSA
Checksum
Shows the sum of the LS checksums of external link-state
advertisements contained in the link-state database.
AS_OPAQUE LSA
Count
Shows the number of AS Opaque LSAs received.
AS_OPAQUE LSA
Checksum
Sum of the checksums of all AS Opaque LSAs in the link state
database.
New LSAs
Originated
Shows the number of link-state advertisements that have been
originated.
LSAs Received Shows the number of link-state advertisements received
determined to be new instantiations.
LSA Count The number of LSAs in the link state database.
Maximum Number
of LSAs
The limit on the number of LSAs that the router can store in its
link state database.
LSA High Water
Mark
The maximum number of LSAs that have been in the link state
database since OSPF began operation.
AS Scope LSA
Flood List Length
The number of LSAs currently in the global flood queue waiting
to be flooded through the OSPF domain. LSAs with AS flooding
scope, such as type 5 external LSAs and type 11 Opaque LSAs.
Retransmit List
Entries
The current number of entries on all neighbors’ retransmit lists.
Maximum Number
of Retransmit
Entries
The maximum number of entries that can be on neighbors’
retransmit lists at any given time. This is the sum for all
neighbors. When OSPF receives an LSA and cannot allocate a
new retransmit list entry, the router does not acknowledge the
LSA, expecting the sender to retransmit.
Retransmit Entries
High Water Mark
The maximum number of retransmit list entries that have been
on all neighbors’ retransmit lists at one time.
NSF Support Whether graceful restart is administratively enabled. Possible
values are Support Always, Disabled, or Planned.
NSF Restart
Interval
The number of seconds a helpful neighbor allows a restarting
router to complete its graceful restart.
2CSNXXX_SWUM200.book Page 1248 Tuesday, December 10, 2013 1:22 PM
OSPF Commands 1249
Example #1
The following example displays OSPF router information.
console#show ip ospf
Router ID................................ 1.1.1.1
OSPF Admin Mode.......................... Enable
RFC 1583 Compatibility................... Enable
External LSDB Limit...................... No Limit
Exit Overflow Interval................... 0
Spf Delay Time........................... 5
Spf Hold Time............................ 10
Opaque Capability........................ Disable
AutoCost Ref BW.......................... 100 Mbps
Default Passive Setting.................. Disabled
Maximum Paths........................ 4
Default Metric....................... Not configured
NSF Restart Status Whether the router is currently performing a graceful restart.
NSF Restart Age The number of seconds until a graceful restart expires. Only
non-zero when the router is in graceful restart.
NSF Restart Exit
Reason
The reason the previous graceful restart ended. Possible values
are Not attempted, In progress, Completed, Timed out,
Topology change, and Manual clear.
NSF Helper
Support
Whether this router is configured to act as a graceful restart
helpful neighbor. Possible values are: Helper Support Always,
Disabled, or Planned.
NSF Helper Strict
LSA Checking
As a graceful restart helpful neighbor, whether to terminate the
helper relationship if a topology change occurs during a
neighbor's graceful restart.
Redistributing This field is a heading and appears only if you configure the
system to take routes learned from a non-OSPF source and
advertise them to its peers.
Source Shows source protocol/routes that are being redistributed.
Possible values are static, connected, or RIP.
Tag Shows the decimal value attached to each external route.
Subnets When this option is not configured, OSPF will only redistribute
classful prefixes.
Distribute-List Shows the access list used to filter redistributed routes.
2CSNXXX_SWUM200.book Page 1249 Tuesday, December 10, 2013 1:22 PM

1250 OSPF Commands
Default Route Advertise.............. Disabled
Always............................... FALSE
Metric............................... Not configured
Metric Type.......................... External Type 2
Number of Active Areas... 1 (1 normal, 0 stub, 0 nssa)
ABR Status........................... Disable
ASBR Status.......................... Disable
Stub Router.......................... FALSE
External LSDB Overflow............... FALSE
External LSA Count................... 0
External LSA Checksum................ 0
AS_OPAQUE LSA Count.................. 0
AS_OPAQUE LSA Checksum............... 0
New LSAs Originated.................. 25
LSAs Received........................ 7
LSA Count............................ 4
Maximum Number of LSAs............... 18200
LSA High Water Mark.................. 4
Retransmit List Entries.............. 0
Maximum Number of Retransmit Entries..72800
Retransmit Entries High Water Mark... 2
NSF Support........................... Disabled
NSF Restart Interval.................. 120
NSF Restart Status.................... Not Restarting
NSF Restart Age....................... 0 seconds
NSF Restart Exit Reason............... Not Attempted
NSF Helper Support.................... Always
NSF Helper Strict LSA Checking........ Enabled
Example #2
The following example displays the length of the global flood queue for LSAs
with AS flooding scope and for stub router configuration. Also displayed are
the values of the LSA pacing configuration parameters.
console#show ip ospf
Router ID...................................... 1.1.1.1
OSPF Admin Mode................................ Enable
RFC 1583 Compatibility......................... Enable
External LSDB Limit............................ No Limit
Exit Overflow Interval......................... 0
Spf Delay Time................................. 5
Spf Hold Time.................................. 10
2CSNXXX_SWUM200.book Page 1250 Tuesday, December 10, 2013 1:22 PM

OSPF Commands 1251
Flood Pacing Interval.......................... 33 ms
LSA Refresh Group Pacing Time.................. 60 sec
Opaque Capability.............................. Enable
AutoCost Ref BW................................ 100 Mbps
Default Passive Setting........................ Disabled
Maximum Paths.................................. 4
Default Metric................................. Not configured
Stub Router Configuration...................... <val>
Stub Router Startup Time.................... <val> seconds
Summary LSA Metric Override................. Enabled (<met>)
Default Route Advertise........................ Disabled
Always......................................... FALSE
Metric......................................... Not configured
Metric Type.................................... External Type 2
Number of Active Areas......................... 2 (2 normal, 0 stub, 0 nssa)
ABR Status..................................... Enable
ASBR Status.................................... Disable
Stub Router Status............................. Inactive
Stub Router Reason............................. <reason>
Stub Router Time Remaining..................... <duration> seconds
External LSDB Overflow......................... FALSE
External LSA Count............................. 0
External LSA Checksum.......................... 0
AS_OPAQUE LSA Count............................ 0
AS_OPAQUE LSA Checksum......................... 0
New LSAs Originated............................ 300269
LSAs Received.................................. 300276
LSA Count...................................... 6020
Maximum Number of LSAs......................... 36968
LSA High Water Mark............................ 6020
AS Scope LSA Flood List Length................. 0
Retransmit List Entries........................ 0
Maximum Number of Retransmit Entries........... 147872
Retransmit Entries High Water Mark............. 32616
NSF Helper Support............................. Always
NSF Helper Strict LSA Checking................. Enabled
show ip ospf abr
The show ip ospf abr command displays the internal OSPF routing table
entries to Area Border Routers (ABR). This command takes no options.
2CSNXXX_SWUM200.book Page 1251 Tuesday, December 10, 2013 1:22 PM

1252 OSPF Commands
Syntax
show ip ospf abr
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC mode, Configuration mode and all Configuration submodes
User Guidelines
There are no user guidelines for this command.
Example
console#show ip ospf abr
Type Router Id Cost Area ID Next Hop Next Hop
Intf
----- --------- ----- --------------- --------- --------
INTRA 3.3.3.3 1 0.0.0.1 10.1.23.3 vlan11
INTRA 4.4.4.4 10 0.0.0.1 10.1.24.4 vlan12
show ip ospf area
Use the show ip ospf area command in Privileged EXEC mode to display
information about the identified OSPF area.
Syntax
show ip ospf area area-id
•
area-id
—Identifies the OSPF area whose ranges are being displayed.
(Range: 0–4294967295)
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC mode, Configuration mode and all Configuration submodes
2CSNXXX_SWUM200.book Page 1252 Tuesday, December 10, 2013 1:22 PM

OSPF Commands 1253
User Guidelines
This command has no user guidelines.
Example #1
The following example displays OSPF router information.
console#show ip ospf area 10
AreaID......................................... 0.0.0.10
External Routing............................... Import External LSAs
Spf Runs....................................... 0
Area Border Router Count....................... 0
Area LSA Count................................. 0
Area LSA Checksum.............................. 0
Import Summary LSAs............................ Enable
Example #2
console#show ip ospf area 20
AreaID......................................... 0.0.0.20
External Routing............................... Import NSSAs
Spf Runs....................................... 0
Area Border Router Count....................... 0
Area LSA Count................................. 0
Area LSA Checksum.............................. 0
OSPF NSSA Specific Information.
Import Summary LSAs............................ Enable
Redistribute into NSSA......................... Enable
Default Information Originate.................. TRUE
Default Metric................................. 250
Default Metric Type............................ Non-Comparable
Translator Role................................ Candidate
Translator Stability Interval.................. 2000
Translator State............................... Disabled
Example #3
The following example shows the length of the area’s flood queue for LSAs
waiting to be flooded within the area.
console #show ip ospf area 1
AreaID......................................... 0.0.0.1
External Routing............................... Import External LSAs
Spf Runs....................................... 10
Area Border Router Count....................... 0
Area LSA Count................................. 3004
2CSNXXX_SWUM200.book Page 1253 Tuesday, December 10, 2013 1:22 PM

1254 OSPF Commands
Area LSA Checksum.............................. 0x5e0abed
Flood List Length.............................. 0
Import Summary LSAs............................ Enable
show ip ospf asbr
The show ip ospf asbr command displays the internal OSPF routing table
entries to Autonomous System Boundary Routes (ASBR). This command
takes no options.
Syntax
show ip ospf asbr
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC mode, Configuration mode and all Configuration submodes
User Guidelines
This command has no user guidelines.
Example
console#show ip ospf asbr
Type Router Id Cost Area ID Next Hop Next Hop
Intf
----- ---------- ---- -------- ----------- -----------
INTRA 1.1.1.1 1 0.0.0.1 10.1.12.1 vlan10
INTRA 4.4.4.4 10 0.0.0.1 10.1.24.4 vlan12
show ip ospf database
Use the show ip ospf database command in Privileged EXEC mode to display
information about the link state database when OSPF is enabled. If
parameters are entered, the command displays the LSA headers. Use the
optional parameters to specify the type of link state advertisements to display.
2CSNXXX_SWUM200.book Page 1254 Tuesday, December 10, 2013 1:22 PM

OSPF Commands 1255
Syntax
show ip ospf [
area-id
] database [{asbr-summary | external | network | nssa-
external | router | summary}][
ls-id
] [adv-router [
ip-address
] | self-originate]
[opaque-area] [opaque-as] [opaque-link]
•
area-id
— Identifies a specific OSPF area
for which link state database
information will be displayed.
• asbr-summary — Display the autonomous system boundary router (ASBR)
summary LSAs.
• external — Display the external LSAs.
• network — Display the network LSAs.
• nssa-external — Display NSSA external LSAs.
• router — Display router LSAs.
• summary — Display the LSA database summary information.
• ls-id — Specifies the link state ID (LSID). (Range: IP address or an integer
in the range of 0–4294967295)
•
adv-router
— Display the LSAs that are restricted by the advertising
router. To specify a router, enter the IP address of the router.
• self-originate — Display the LSAs in that are self-originated.
• opaque-area— Display the area opaque LSAs.
• opaque-as— Display AS opaque LSAs.
• opaque-link— Display link opaque LSAs.
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC mode, Configuration mode and all Configuration submodes
User Guidelines
Information is only displayed if OSPF is enabled.
2CSNXXX_SWUM200.book Page 1255 Tuesday, December 10, 2013 1:22 PM

1256 OSPF Commands
Example
The following example displays information about the link state database
when OSPF is enabled.
console#show ip ospf database
Router Link States (Area 0.0.0.0)
Link Id Adv Router Age Sequence Chksm Options Rtr Opt
--------------- --------------- ----- -------- ------ ------- -----
5.2.0.0 0.0.0.0 1360 80000006 3a1f ------ -----
5.2.0.0 5.2.0.0 1360 80000009 a47e ------ ---E-
20.20.20.20 20.20.20.20 1165 8000000b 0f80 -E---- -----
Network Link States (Area 0.0.0.0)
Link Id Adv Router Age Sequence Chksm Options Rtr Opt
--------------- --------------- ----- -------- ------ ------- -----
2.2.2.2 20.20.20.20 1165 80000005 f86d -E--O-
Network Summary States (Area 0.0.0.0)
Link Id Adv Router Age Sequence Chksm Options Rtr Opt
--------------- --------------- ----- -------- ------ ------- -----
5.2.0.0 0.0.0.0 1360 80000007 242e ------
Summary ASBR States (Area 0.0.0.0)
Link Id Adv Router Age Sequence Chksm Options Rtr Opt
--------------- --------------- ----- -------- ------ ------- -----
5.2.0.0 0.0.0.0 1361 80000006 183a ------
Link Opaque States (Area 0.0.0.0)
Link Id Adv Router Age Sequence Chksm Options Rtr Opt
--------------- --------------- ----- -------- ------ ------- -----
5.2.0.0 0.0.0.0 1361 80000005 ef59 ------
Area Opaque States (Area 0.0.0.0)
2CSNXXX_SWUM200.book Page 1256 Tuesday, December 10, 2013 1:22 PM

OSPF Commands 1257
Link Id Adv Router Age Sequence Chksm Options Rtr Opt
--------------- --------------- ----- -------- ------ ------- -----
5.2.0.0 0.0.0.0 1362 80000005 e166 ------
AS External States
Link Id Adv Router Age Sequence Chksm Options Rtr Opt
--------------- --------------- ----- -------- ------ ------- -----
6.0.0.0 5.2.0.0 1364 80000008 e35d
AS Opaque States
Link Id Adv Router Age Sequence Chksm Options Rtr Opt
--------------- --------------- ----- -------- ------ ------- -----
5.2.0.0 0.0.0.0 1364 80000005 d373
show ip ospf database database-summary
Use the show ip ospf database database-summary command to display the
number of each type of LSA in the database for each area and for the router.
The command also displays the total number of LSAs in the database. This
command has been modified.
Syntax
show ip ospf database database-summary
Default Configuration
There is no default configuration for this command.
Command Mode
Privileged EXEC mode, Configuration mode and all Configuration submodes
User Guidelines
The following fields are displayed:
2CSNXXX_SWUM200.book Page 1257 Tuesday, December 10, 2013 1:22 PM

1258 OSPF Commands
Example
The following example displays the number of each type of LSA in the
database for each area and for the router.
console#show ip ospf database database-summary
OSPF Router with ID (5.5.5.5)
Area 0.0.0.0 database summary
Router......................................... 0
Network........................................ 0
Summary Net.................................... 0
Summary ASBR................................... 0
Type-7 Ext..................................... 0
Self Originated Type-7......................... 0
Opaque Link.................................... 0
Opaque Area.................................... 0
Subtotal....................................... 0
Area 0.0.0.10 database summary
Router......................................... 0
Network........................................ 0
Summary Net.................................... 0
Field Description
Router Shows Total number of router LSAs in the OSPF link state database.
Network Shows Total number of network LSAs in the OSPF link state
database.
Summary Net Shows Total number of summary network LSAs in the database.
Summary
ASBR
Shows Number of summary ASBR LSAs in the database.
Type-7 Ext Shows Total number of Type-7 external LSAs in the database.
Self-
Originated
Ty p e - 7
Shows Total number of self originated AS external LSAs in the
OSPFv3 link state database.
Opaque Link Shows Number of opaque link LSAs in the database.
Opaque Area Shows Number of opaque area LSAs in the database.
Subtotal Shows Number of entries for the identified area.
Opaque AS Shows Number of opaque AS LSAs in the database.
Total Shows Number of entries for all areas.
2CSNXXX_SWUM200.book Page 1258 Tuesday, December 10, 2013 1:22 PM

OSPF Commands 1259
Summary ASBR................................... 0
Type-7 Ext..................................... 0
Self Originated Type-7......................... 0
Opaque Link.................................... 0
Opaque Area.................................... 0
Subtotal....................................... 0
Router database summary
Router......................................... 0
Network........................................ 0
Summary Net.................................... 0
Summary ASBR................................... 0
Type-7 Ext..................................... 0
Opaque Link.................................... 0
Opaque Area.................................... 0
Type-5 Ext..................................... 0
Self-Originated Type-5 Ext..................... 0
Opaque AS...................................... 0
Total.......................................... 0
show ip ospf interface
Use the show ip ospf interface command in Privileged EXEC mode to display
the information for the VLAN or loopback interface. The long form of the
command displays the configuration of flood blocking.
Syntax
show ip ospf interface [
interface-type interface-number
]
•
interface-type
—Vlan or loopback
•
interface-number
—Valid VLAN ID or loopback interface number (Range:
0–7).
•
Flood Blocking
—Indicates if flood blocking is enabled or disabled.
Default Configuration
This command has no default configuration.
Command Mode
User EXEC, Privileged EXEC modes, Configuration mode and all
Configuration submodes
2CSNXXX_SWUM200.book Page 1259 Tuesday, December 10, 2013 1:22 PM

1260 OSPF Commands
User Guidelines
This command has no user guidelines.
Example #1
The following example displays the information for the IFO object or virtual
interface tables associated with VLAN 10.
console#show ip ospf interface vlan 10
IP Address..................................... 1.1.1.1
Subnet Mask.................................... 255.255.255.0
Secondary IP Address(es).......................
OSPF Admin Mode................................ Enable
OSPF Area ID................................... 0.0.0.0
OSPF Network Type.............................. Broadcast
Router Priority................................ 1
Retransmit Interval............................ 5
Hello Interval................................. 10
Dead Interval.................................. 40
LSA Ack Interval............................... 1
Iftransit Delay Interval....................... 1
Authentication Type............................ None
Metric Cost.................................... 10 (computed)
Passive Status................................. Non-passive interface
OSPF Mtu-ignore................................ Disable
State.......................................... designated-router
Designated Router.............................. 1.1.1.1
Backup Designated Router....................... 0.0.0.0
Number of Link Events.......................... 2
Example #2
The following example shows the configuration of flood blocking.
console#show ip ospf interface gi2/0/11
IP Address........................... 172.20.11.2
Subnet Mask.......................... 255.255.255.0
Secondary IP Address(es).............
OSPF Admin Mode...................... Enable
OSPF Area ID......................... 0.0.0.0
OSPF Network Type.................... Point-to-Point
Router Priority...................... 1
Retransmit Interval.................. 5
Hello Interval....................... 3
Dead Interval........................ 12
2CSNXXX_SWUM200.book Page 1260 Tuesday, December 10, 2013 1:22 PM

OSPF Commands 1261
LSA Ack Interval..................... 1
Transmit Delay....................... 1
Authentication Type.................. None
Metric Cost.......................... 100 (computed)
Passive Status....................... Non-passive interface
OSPF Mtu-ignore...................... Disable
Flood Blocking....................... Disable
State................................ point-to-point
Number of Link Events................ 1
Local Link LSAs...................... 0
Local Link LSA Checksum.............. 0
show ip ospf interface brief
Use the show ip ospf interface brief command in Privileged EXEC mode to
display brief information for the IFO object or virtual interface tables.
Syntax
show ip ospf interface brief
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC mode, Configuration mode and all Configuration submodes
User Guidelines
This command has no user guidelines.
Example
The following example displays brief information for the IFO object or virtual
interface tables.
console#show ip ospf interface brief
Hello Dead Retrax LSA
Admin Router Int. Int. Int. Tranx Ack
Interface Mode Area ID Prior. Cost Val. Val. Val. Delay Intval
------------ -------- ----------- ------ ----- ----- ----- ------ ------ ------
Vl10 Enable 0.0.0.10 1 10 10 40 5 1 1
Vl20 Enable 0.0.0.1 1 10 10 40 5 1 1
Vl100 Enable 0.0.0.111 1 10 10 40 5 1 1
loopback 1 Enable 0.0.0.0 1 1 10 40 5 1 1
2CSNXXX_SWUM200.book Page 1261 Tuesday, December 10, 2013 1:22 PM

1262 OSPF Commands
show ip ospf interface stats
Use the show ip ospf interface stats command in User EXEC mode to display
the statistics for a specific interface. The information is only displayed if
OSPF is enabled.
Syntax
show ip ospf interface stats vlan
vlan-id
•
vlan-id
— Valid VLAN ID.
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC mode, Configuration mode and all Configuration submodes
User Guidelines
This command has no user guidelines.
Example
The following example displays the ospf statistics for VLAN 15.
console>show ip ospf interface stats vlan 15
OSPF Area ID....................................... 0.0.0.0
Area Border Router Count................................. 0
AS Border Router Count................................... 0
Area LSA Count........................................... 1
IP Address......................................... 2.2.2.2
OSPF Interface Events.................................... 1
Virtual Events........................................... 0
Neighbor Events.......................................... 0
External LSA Count....................................... 0
show ip ospf neighbor
Use the show ip ospf neighbor command in Privileged EXEC mode to display
information about OSPF neighbors. The information below only displays if
OSPF is enabled and the interface has a neighbor.
2CSNXXX_SWUM200.book Page 1262 Tuesday, December 10, 2013 1:22 PM

OSPF Commands 1263
Syntax
show ip ospf neighbor [
interface-type interface-number
] [
neighbor-id
]
•
interface-type
—Interface type – only supported type is vlan.
•
interface-number
—A valid interface number.
•
neighbor-id
—Valid IP address of the neighbor.
Default Configuration
This command has no default configuration.
Command Mode
User EXEC, Privileged EXEC modes, Configuration mode and all
Configuration submodes
User Guidelines
The following information is output.
Field Description
Interface The name of the interface on which the adjacency is formed.
Neighbor IP Address
The IPv4 address on the neighbor's interface used to form the
adjacency.
Interface Index The SNMP interface index.
Area Id The OSPF area in which the adjacency is formed.
Options
The options advertised by the neighbor.
Router Priority The router priority advertised by the neighbor.
Dead timer The number of seconds until the dead timer expires.
Up Time How long this adjacency has been in FULL state.
State The current state of the adjacency.
Events Incremented for the following events:
• A DD is received from the neighbor with an MTU mismatch.
• The neighbor sent an ACK for an LSA not on the neighbor's
retransmit list.
• The state of the adjacency changed.
2CSNXXX_SWUM200.book Page 1263 Tuesday, December 10, 2013 1:22 PM
1264 OSPF Commands
Retransmitted LSAs The number of LSAs retransmitted to a given neighbor.
Retransmission
Queue Length
The number of LSAs on the neighbor's retransmit queue
waiting for the neighbor to acknowledge.
Restart Helper
Status
One of two values:
• Helping — This router is acting as a helpful neighbor to this
neighbor. A helpful neighbor does not report an adjacency
change during graceful restart, but continues to advertise the
restarting router as a FULL adjacency. A helpful neighbor
continues to forward data packets to the restarting router,
trusting that the restarting router's forwarding table is
maintained during the restart.
• Not Helping — This router is not a helpful neighbor at this
time.
Field Description
2CSNXXX_SWUM200.book Page 1264 Tuesday, December 10, 2013 1:22 PM

OSPF Commands 1265
Example
The following examples display information about OSPF neighbors on the
specified Ethernet and IP interfaces.
Restart Helper
Exit Reason
One of the following values:
• Restart Reason — When the router is in helpful neighbor
mode, the output includes the restart reason the restarting
router sent in its grace LSA. The Restart Reason is the value in
the Graceful Restart Reason TLV in the grace LSA sent by the
restarting router. Possible values for the Restart Reason are
defined in RFC 3623 as follows:
– Unknown (0)
– Software restart (1)
– Software reload/upgrade (2)
– Switch to redundant control processor (3)
– Unrecognized - a value not defined in RFC 3623
When the switch sends a grace LSA, it sets the Restart Reason
to
Software Restart
on a planned warm restart (when the
initiate failover command is invoked), and to
Unknown
on an
unplanned warm restart.
• Remaining Grace Time — The number of seconds remaining
in the current graceful restart interval. This row is only
included if the router is currently acting as a restart helper for
the neighbor.
• Restart Exit Reason — One of the following:
– None — graceful restart has not been attempted
– In Progress — restart is in progress
– Completed — the previous graceful restart completed
successfully
– Timed Out — the previous graceful restart timed out
– Topology Changed — The previous graceful restart
terminated prematurely because of a topology change. A
helpful neighbor declares a topology change when it
forwards a changed LSA to the restarting router. An LSA is
considered changed if its contents are changed, not if it is
simply a periodic refresh.
Field Description
2CSNXXX_SWUM200.book Page 1265 Tuesday, December 10, 2013 1:22 PM

1266 OSPF Commands
console#show ip ospf neighbor 3.3.3.3
Interface...................................... 0/25
Neighbor IP Address............................ 172.20.25.3
Interface Index................................ 25
Area Id........................................ 0.0.0.0
Options........................................ 0x2
Router Priority................................ 1
Dead timer due in (secs)....................... 10
Up Time........................................ 4 days 3 hrs 33 mins 36 secs
State.......................................... Full/PtP
Events......................................... 4
Retransmitted LSAs............................. 32
Retransmission Queue Length.................... 0
Restart Helper Status........................ Not helping
Restart Helper Exit Reason................... Not attempted
show ip ospf range
Use the show ip ospf range command in Privileged EXEC mode to display
information about the area ranges for the specified area-id.
Syntax
show ip ospf range
area-id
•
area-id
—Identifies the OSPF area whose ranges are being displayed.
(Range: IP address or decimal from 0–4294967295)
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC mode, Configuration mode and all Configuration submodes
User Guidelines
The following information is displayed.
Field Description
••
2CSNXXX_SWUM200.book Page 1266 Tuesday, December 10, 2013 1:22 PM

OSPF Commands 1267
Example
The following example displays information about the area ranges configured
for the specified area-id.
console#show ip ospf range 0
Prefix Subnet Mask Type Action Cost Active
10.1.0.0 255.255.0.0 S Advertise Auto N
172.20.0.0 255.255.0.0 S Advertise 500 Y
show ip ospf statistics
This command displays information about recent Shortest Path First (SPF)
calculations. The SPF is the OSPF routing table calculation. The output lists
the number of times the SPF has run for each OSPF area. A table follows this
information. For each of the 15 most recent SPF runs, the table lists how long
ago the SPF ran, how long the SPF took, and the reasons why the SPF was
scheduled.
Syntax
show ip ospf statistics
Default Configuration
This command has no default configuration.
Prefix The summary prefix.
Subnet Mask The subnetwork mask of the summary prefix.
Type S (Summary Link) or E (External Link)
Action Advertise or Suppress
Cost Metric to be advertised when the range is active. If a static cost
is not configured, the field displays Auto. If the action is
Suppress, the field displays N/A.
Active Whether the range is currently active (Y) or not (N).
Field Description
2CSNXXX_SWUM200.book Page 1267 Tuesday, December 10, 2013 1:22 PM

1268 OSPF Commands
Command Mode
User EXEC, Privileged EXEC modes, Configuration mode and all
Configuration submodes
User Guidelines
This command outputs the following.
Example
console# show ip ospf statistics
Area 0.0.0.0: SPF algorithm executed 15 times
Delta T Intra Summ Ext SPF Total RIB Update Reason
00:05:33 0 0 0 0 0 R
00:05:30 0 0 0 0 0 R
00:05:19 0 0 0 0 0 N, SN
Field Description
Delta T The time since the routing table was computed, in hours, minutes,
and seconds (hh:mm:ss).
Intra The time taken to compute intra-area routes, in milliseconds.
Summ The time taken to compute inter-area routes, in milliseconds.
Ext The time taken to compute external routes, in milliseconds.
SPF Total The total time to compute routes, in milliseconds. The total may
exceed the sum of the Intra, Summ, and Ext times.
RIB Update The time from the completion of the routing table calculation until
all changes have been made in the common routing table (the
Routing Information Base, or RIB), in milliseconds.
Reason The event or events that triggered the SPF. Reasons may include the
following:
•R – New router LSA
•N – New network LSA
• SN –New network summary LSA
• SA – New ASBR summary LSA
•X – New external LSA
2CSNXXX_SWUM200.book Page 1268 Tuesday, December 10, 2013 1:22 PM

OSPF Commands 1269
00:05:15 0 10 0 10 0 R, N, SN
00:05:11 0 0 0 0 0 R
00:04:50 0 60 0 60 460 R, N
00:04:46 0 90 0 100 60 R, N
00:03:42 0 70 10 90 160 R
00:03:39 0 70 40 120 240 X
00:03:36 0 60 60 130 160 X
00:01:28 0 60 50 130 240 X
00:01:25 0 30 50 110 310 SN
00:01:22 0 0 40 50 260 SN
00:01:19 0 0 20 20 190 X
00:01:16 0 0 0 0 110 R, X
show ip ospf stub table
Use the show ip ospf stub table command in Privileged EXEC mode to
display the OSPF stub table. The information below will only be displayed if
OSPF is initialized on the switch.
Syntax
show ip ospf stub table
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC mode, Configuration mode and all Configuration submodes
User Guidelines
This command has no user guidelines.
Example
The following example displays the OSPF stub table.
console(config)#show ip ospf stub table
AreaId TypeofService Metric Val Import SummaryLSA
------------- ------------- ---------- -----------------
0.0.0.1 Normal 1 Enable
2CSNXXX_SWUM200.book Page 1269 Tuesday, December 10, 2013 1:22 PM
1270 OSPF Commands
show ip ospf traffic
Use the show ip ospf traffic command in Privileged EXEC mode to display
OSPFv2 packet and LSA statistics and OSPFv2 message queue statistics.
Packet statistics count packets and LSAs since OSPFv2 counters were last
cleared (using the
clear ip ospf
counters command.)
NOTE: Note that the clear ip ospf counters command does not clear the message
queue high water marks.
Syntax
show ip ospf traffic
Default Configuration
This command has no default setting.
Command Mode
Privileged EXEC mode
User Guidelines
The clear ip ospf counters command does not clear the message queue high
water marks.
The following is output.
Parameter Description
OSPFv2 Packet
Statistics
The number of packets of each type sent and received since
OSPF counters were last cleared.
LSAs Retransmitted The number of LSAs retransmitted by this router since OSPF
counters were last cleared.
LS Update Max
Receive Rate
The maximum rate of LS Update packets received during any
5-second interval since OSPF counters were last cleared. The
rate is in packets per second.
LS Update Max
Send Rate
The maximum rate of LS Update packets transmitted during
any 5-second interval since OSPF counters were last cleared.
The rate is in packets per second.
2CSNXXX_SWUM200.book Page 1270 Tuesday, December 10, 2013 1:22 PM

OSPF Commands 1271
Example
console# show ip ospf traffic
Time Since Counters Cleared: 4000 seconds
OSPFv2 Packet Statistics
Hello Database Desc LS Request LS Update LS ACK Total
Recd: 500 10 20 50 20 600
Sent: 400 8 16 40 16 480
LSAs Retransmitted................0
LS Update Max Receive Rate........20 pps
LS Update Max Send Rate...........10 pps
Number of LSAs Received
T1 (Router).......................10
T2 (Network)......................0
T3 (Net Summary)..................300
T4 (ASBR Summary).................15
T5 (External).....................20
T7 (NSSA External)................0
T9 (Link Opaque)..................0
T10 (Area Opaque).................0
T11 (AS Opaque)...................0
Total.............................345
OSPFv2 Queue Statistics
Current Max Drops Limit
Hello 0 10 0 500
ACK 2 12 0 1680
Data 24 47 0 500
Event 1 8 0 1000
Number of LSAs
Received
The number of LSAs of each type received since OSPF
counters were last cleared.
OSPFv2 Queue
Statistics
For each OSPFv2 message queue, the current count, the high
water mark, the number of packets that failed to be enqueued,
and the queue limit. The high water marks are not cleared when
OSPF counters are cleared.
Parameter Description
2CSNXXX_SWUM200.book Page 1271 Tuesday, December 10, 2013 1:22 PM

1272 OSPF Commands
show ip ospf virtual-link
Use the show ip ospf virtual-link command in Privileged EXEC mode to
display the OSPF Virtual Interface information for a specific area and
neighbor or for all.
Syntax
show ip ospf virtual-link [
area-id neighbor-id
]
•
area-id
— Identifies the OSPF area whose ranges are being displayed.
(Range: IP address or decimal from 0–4294967295)
•
neighbor-id
— Identifies the neighbor’s router ID. (Range: Valid IP
address)
Default Configuration
Show information for all OSPF Virtual Interfaces.
Command Mode
User EXEC, Privileged EXEC modes, Configuration mode and all
Configuration submodes
User Guidelines
This command has no user guidelines.
Example
The following example displays the OSPF Virtual Interface information for
area 10 and its neighbor.
console#show ip ospf virtual-link 10 192.168.2.2
Area ID........................................ 10
Neighbor Router ID............................. 192.168.2.2
Hello Interval................................. 10
Dead Interval.................................. 655555
Iftransit Delay Interval....................... 1
Retransmit Interval............................ 5
State.......................................... down
Metric......................................... 0
Neighbor State................................. down
Authentication Type............................ MD5
Authentication Key............................. "test123"
2CSNXXX_SWUM200.book Page 1272 Tuesday, December 10, 2013 1:22 PM

OSPF Commands 1273
Authentication Key ID.......................... 100
show ip ospf virtual-links brief
Use the show ip ospf virtual-link brief command in Privileged EXEC mode
to display the OSPF Virtual Interface information for all areas in the system
in table format.
Syntax
show ip ospf virtual-link brief
Default Configuration
This command has no default configuration.
Command Mode
User EXEC, Privileged EXEC modes, Configuration mode and all
Configuration submodes
User Guidelines
This command has no user guidelines.
Example
The following example displays the OSPF Virtual Interface information in
the system.
console#show ipv6 ospf virtual-link brief
Hello Dead Retransmit Transit
Area ID Neighbor Interval Interval Interval Delay
------- -------- -------- -------- ---------- -------
0.0.0.2 5.5.5.5 10 40 5 1
timers pacing flood
Use the timers pacing flood command in router OSPF Global Configuration
mode to adjust the rate at which OSPFv2 sends LS Update packets.
Use the no form of the command to return the timer pacing to the default
value.
2CSNXXX_SWUM200.book Page 1273 Tuesday, December 10, 2013 1:22 PM

1274 OSPF Commands
Syntax
timers pacing flood
milliseconds
no timers pacing flood
•
milliseconds
—The average time between transmission of LS Update
packets. The range is from 5 ms to 100 ms. The default is 33 ms.
Default Configuration
The default pacing between LS Update packets is 33 ms.
Command Mode
OSPFv2 Global Configuration mode
User Guidelines
OSPF distributes routing information in Link State Advertisements (LSAs),
which are bundled into Link State Update (LS Update) packets. To reduce
the likelihood of sending a neighbor more packets than it can buffer, OSPF
rate limits the transmission of LS Update packets. By default, OSPF sends up
to 30 updates per second on each interface (1/the pacing interval). Use this
command to adjust the LS Update transmission rate.
timers pacing lsa-group
Use the timers pacing lsa-group command in router OSPF Global
Configuration mode to tune how OSPF groups LSAs for periodic refresh.
Syntax
timers pacing lsa-group
seconds
•
seconds
—Width of the window in which LSAs are refreshed. The range for
the pacing group window is from 10 to 1800 seconds.
Default Configuration
The default timer pacing is 60 seconds.
Command Mode
OSPFv2 Global Configuration mode
2CSNXXX_SWUM200.book Page 1274 Tuesday, December 10, 2013 1:22 PM

OSPF Commands 1275
User Guidelines
OSPF refreshes self-originated LSAs approximately once every 30 minutes.
When OSPF refreshes LSAs, it considers all self-originated LSAs whose age is
from 1800 to 1800 plus the pacing group size. Grouping LSAs for refresh
allows OSPF to combine refreshed LSAs into a minimal number of LS
Update packets. Minimizing the number of Update packets makes LSA
distribution more efficient.
When OSPF originates a new or changed LSA, it selects a random refresh
delay for the LSA. When the refresh delay expires, OSPF refreshes the LSA.
By selecting a random refresh delay, OSPF avoids refreshing a large number of
LSAs at one time, even if a large number of LSAs are originated at one time.
timers spf
Use the timers spf command in Router OSPF Configuration mode to
configure the SPF delay and hold time. Use the no form of the command to
reset the numbers to the default value.
Syntax
timers spf
delay-time hold-time
no timers spf
•
delay-time
— SPF delay time. (Range: 0–65535 seconds)
•
hold-time
— SPF hold time. (Range: 0–65535 seconds)
Default Configuration
The default value for
delay-time
is 5. The default value for
hold-time
is 10.
Command Mode
Router OSPF Configuration mode.
User Guidelines
This command has no user guidelines.
Example
The following example configures the SPF delay and hold time.
2CSNXXX_SWUM200.book Page 1275 Tuesday, December 10, 2013 1:22 PM

1276 OSPF Commands
console(config-router)#timers spf 20 30
2CSNXXX_SWUM200.book Page 1276 Tuesday, December 10, 2013 1:22 PM

OSPFv3 Commands 1277
54
OSPFv3 Commands
Dell Networking N3000/N4000 Series Switches
The Dell Network N2000 series supports limited routing and multicast capabilities.
See the Users Configuration Guide section “Feature Limitations and Platform
Constants” for supported capabilities.
This chapter explains the following commands:
area default-cost
(Router OSPFv3)
area virtual-link
transmit-delay
ipv6 ospf priority show ipv6 ospf abr
area nssa (Router
OSPFv3)
default-information
originate (Router
OSPFv3
Configuration)
ipv6 ospf
retransmit-interval
show ipv6 ospf area
area nssa default-
info-originate
(Router OSPFv3
Config)
default-metric ipv6 ospf transmit-
delay
show ipv6 ospf asbr
area nssa no-
redistribute
distance ospf ipv6 router ospf show ipv6 ospf database
area nssa no-
summary
enable maximum-paths show ipv6 ospf database
database-summary
area nssa translator-
role
exit-overflow-
interval
nsf show ipv6 ospf interface
area nssa translator-
stab-intv
external-lsdb-limit nsf helper show ipv6 ospf interface
brief
area range (Router
OSPFv3)
ipv6 ospf nsf helper strict-lsa-
checking
show ipv6 ospf interface
stats
area stub ipv6 ospf area nsf restart-interval show ipv6 ospf interface
vlan
area stub no-
summary
ipv6 ospf cost passive-interface show ipv6 ospf
neighbor
2CSNXXX_SWUM200.book Page 1277 Tuesday, December 10, 2013 1:22 PM

1278 OSPFv3 Commands
area default-cost (Router OSPFv3)
Use the area default-cost command in Router OSPFv3 Configuration mode
to configure the monetary default cost for the stub area. The operator must
specify the area id and an integer value between 1-16777215. Use the no form
of the command to return the cost to the default value. If the area has not
been previously created, this command creates the area and then applies the
default-cost.
Syntax
area
area-id
default-cost
cost
no area
area-id
default-cost
•
areaid
— Valid area identifier.
•
cost
— Default cost. (Range: 1-16777215)
Default Configuration
This command has no default configuration.
Command Mode
Router OSPFv3 Configuration mode
User Guidelines
This command has no user guidelines.
area virtual-link ipv6 ospf dead-
interval
passive-interface
default
show ipv6 ospf range
area virtual-link
dead-interval
ipv6 ospf hello-
interval
redistribute show ipv6 ospf stub
table
area virtual-link
hello-interval
ipv6 ospf mtu-
ignore
router-id show ipv6 ospf virtual-
links
area virtual-link
retransmit-interval
ipv6 ospf network show ipv6 ospf show ipv6 ospf virtual-
link brief
2CSNXXX_SWUM200.book Page 1278 Tuesday, December 10, 2013 1:22 PM

OSPFv3 Commands 1279
Example
The following example configures the monetary default cost at 100 for stub
area 1.
console(config)#ipv6 router ospf
console(config-rtr)#area 1 default-cost 100
area nssa (Router OSPFv3)
Use the area nssa command in Router OSPF Configuration mode to
configure the specified area ID to function as an NSSA. If the area has not
been previously created, this command creates the area and then applies the
NSSA distinction. If the area already exists, the NSSA distinction is added or
modified. Use the no form of the command to remove the NSSA distinction
from the area.
Syntax
area
area-id
nssa [no-redistribution] [default-information-originate [metric
metric-value
] [metric-type
metric-type-value
]] [no-summary] [translator-
role
role
] [translator-stab-intv
interval
]
no area
area-id
nssa [no-redistribution] [default-information-originate] [no-
summary] [translator-role] [translator-stab-intv]
•
area-id
—Identifies the OSPFv3 stub area to configure. (Range: IP address
or decimal from 0–4294967295)
•
metric-value
—Specifies the metric of the default route advertised to the
NSSA. (Range: 1–16777214)
•
metric-type-value
—The metric type can be one of the following :
– A metric type of nssa-external 1 (comparable)
– A metric type of nssa-external 2 (non-comparable)
•
role
—The translator role where role is one of the following :
– always - The router assumes the role of the translator when it becomes
a border router.
– candidate - The router to participate in the translator election process
when it attains border router status.
2CSNXXX_SWUM200.book Page 1279 Tuesday, December 10, 2013 1:22 PM

1280 OSPFv3 Commands
•
interval
—The period of time that an elected translator continues to
perform its duties after it determines that its translator status has been
deposed by another router. (Range: 0–3600)
Default Configuration
If no metric is defined, 10 is the default configuration.
The default role is candidate.
Command Mode
Router OSPFv3 Configuration mode.
User Guidelines
This command has no user guidelines.
Example
The following example configures not-so-stubby-area 10 as an NSSA.
console(config)#ipv6 router ospf
console(config-router)#area 10 nssa
The following example configures the metric value and type for the default
route advertised into the NSSA and configures the NSSA so that summary
LSAs are not advertised into the NSSA.
console(config-router)#area 20 nssa default-info-originate metric 250
metric-type 2 no-summary
area nssa default-info-originate (Router OSPFv3
Config)
Use the area nssa default-info-originate command in Router OSPFv3
Configuration mode to configure the metric value and type for the default
route advertised into the NSSA. The optional metric parameter specifies the
metric of the default route. The metric type can be comparable (nssa-external
1) or noncomparable (nssa-external 2). Use the no form of the command to
return the metric value and type to the default value
2CSNXXX_SWUM200.book Page 1280 Tuesday, December 10, 2013 1:22 PM

OSPFv3 Commands 1281
Syntax
area
areaid
nssa default-info-originate [
metric
[comparable | non-
comparable]]
no area
areaid
nssa default-info-originate
•
areaid
— Valid OSPFv3 area identifier.
•
metric
— Metric value for default route. (Range: 1-16777214)
•
comparable
— Metric Type (nssa-external 1).
•
non-comparable
— Metric Type (nssa-external 2).
Default Configuration
If no metric is defined, 10 is the default configuration.
Command Mode
Router OSPFv3 Configuration mode.
User Guidelines
This command has no user guidelines.
Example
The following example configures the default metric value for the default
route advertised into the NSSA.
console(config)#ipv6 router ospf
console(config-rtr)#area 1 nssa default-info-originate
area nssa no-redistribute
Use the area nssa no-redistribute command in Router OSPFv3 Configuration
mode to configure the NSSA ABR so that learned external routes will not be
redistributed to the NSSA. Use the no form of the command to remove the
configuration.
Syntax
area
areaid
nssa no-redistribute
no area
areaid
nssa no-redistribute
2CSNXXX_SWUM200.book Page 1281 Tuesday, December 10, 2013 1:22 PM

1282 OSPFv3 Commands
•
areaid
— Valid OSPF area identifier.
Default Configuration
This command has no default configuration.
Command Mode
Router OSPFv3 Configuration mode.
User Guidelines
This command has no user guidelines.
Example
The following example configures the area 1 NSSA ABR so that learned
external routes will not be redistributed to the NSSA.
console(config)#ipv6 router ospf
console(config-rtr)#area 1 nssa no-redistribute
area nssa no-summary
Use the area nssa no-summary command in Router OSPFv3 Configuration
mode to configure the NSSA so that summary LSAs are not advertised into
the NSSA. Use the no form of the command to remove the configuration.
Syntax
area
areaid
nssa no-summary
no area
area-id
nssa no-summary
•
areaid
— Valid OSPF area identifier.
Default Configuration
This command has no default configuration.
Command Mode
Router OSPFv3 Configuration mode.
2CSNXXX_SWUM200.book Page 1282 Tuesday, December 10, 2013 1:22 PM

OSPFv3 Commands 1283
User Guidelines
This command has no user guidelines.
Example
The following example configures the area 1 NSSA so that summary LSAs are
not advertised into the NSSA.
console(config)#ipv6 router ospf
console(config-rtr)#area 1 nssa no-summary
area nssa translator-role
Use the area nssa translator-role command in Router OSPFv3 Configuration
mode to configure the translator role of the NSSA. Use the no form of the
command to remove the configuration.
Syntax
area
areaid
nssa translator-role {always | candidate}
no area
areaid
nssa translator-role
•
areaid
— Valid OSPF area identifier.
•
always —
Causes the router to assume the role of the translator the instant
it becomes a border router.
•
candidate —
Causes the router to participate in the translator election
process when it attains border router status.
Default Configuration
This command has no default configuration.
Command Mode
Router OSPFv3 Configuration mode.
User Guidelines
This command has no user guidelines.
2CSNXXX_SWUM200.book Page 1283 Tuesday, December 10, 2013 1:22 PM

1284 OSPFv3 Commands
Example
The following example configures the always translator role of the area 1
NSSA.
console(config)#ipv6 router ospf
console(config-rtr)#area 1 nssa translator-role always
area nssa translator-stab-intv
Use the area nssa translator-stab-intv command in Router OSPFv3
Configuration mode to configure the translator stability interval of the NSSA.
The stability interval is the period of time that an elected translator continues
to perform its duties after it determines that its translator status has been
deposed by another router.
Syntax
area
areaid
nssa translator-stab-intv
seconds
no area
areaid
nssa translator-stab-intv
•
areaid
— Valid OSPF area identifier.
•
seconds
— Translator stability interval of the NSSA. (Range: 0-3600
seconds)
Default Configuration
This command has no default configuration.
Command Mode
Router OSPFv3 Configuration mode.
User Guidelines
This command has no user guidelines.
Example
The following example configures a translator stability interval of 100 seconds
for the area 1 NSSA.
console(config)#ipv6 router ospf
console(config-rtr)#area 1 nssa translator-stab-intv 100
2CSNXXX_SWUM200.book Page 1284 Tuesday, December 10, 2013 1:22 PM

OSPFv3 Commands 1285
area range (Router OSPFv3)
Use the area range command in Router OSPF Configuration mode to
configure a summary prefix for routes learned in a given area. If the area has
not been previously created, this command creates the area and then applies
the range parameters. There are two types of area ranges. An area range can be
configured to summarize intra-area routes. An ABR advertises the range
rather than the specific intra-area route as a type 3 summary LSA. Also, an
area range can be configured at the edge of an NSSA to summarize external
routes reachable within the NSSA. The range is advertised as a type 5 external
LSA. Use the no form of the command to remove the summary prefix
configuration for routes learned in the specified area.
Syntax
area
area-id
range
ipv6-prefix/prefix-length
{summarylink |
nssaexternallink} [advertise | not-advertise]
no area
area-id
range
ipv6-prefix/prefix-length
{summarylink |
nssaexternallink}
•
areaid
—Valid OSPFv3 area identifier.
•
ipv6-prefix/prefix-length
—Valid route prefix.
•
summarylink
—LSDB type
•
nssaexternallink
—LSDB type.
•
advertise
—Allows area range to be advertised.
•
not-advertise
—Suppresses area range from being advertised.
Default Configuration
This command has no default configuration.
Command Mode
Router OSPFv3 Configuration mode.
User Guidelines
The LSDB type must be specified by either summarylink or nssaexternallink,
and the advertising of the area range can be allowed or suppressed.
2CSNXXX_SWUM200.book Page 1285 Tuesday, December 10, 2013 1:22 PM

1286 OSPFv3 Commands
Example
The following example creates an area range for the area 1 NSSA.
console(config)#ipv6 router ospf
console(config-rtr)#area 1 range 2020:1::1/64 summarylink
area stub
Use the area stub command in Router OSPFv3 Configuration mode to create
a stub area for the specified area ID. If the area has not been previously
created, this command creates the area and then applies the stub distinction.
A stub area is characterized by the fact that AS External LSAs are not
propagated into the area. Removing AS External LSAs and Summary LSAs
can significantly reduce the size of the link state database of routers within
the stub area.
Syntax
area
area-id
stub [no summary]
no area
area-id
stub [no summary]
•
area-id
— Valid OSPFv3 area identifier.
•
no-summary
—Disable the import of Summary LSAs for the stub area
identified by area-id.
Default Configuration
This command has no default configuration.
Command Mode
Router OSPFv3 Configuration mode.
User Guidelines
This command has no user guidelines.
Example
The following example creates a stub area for area 1.
console(config)#ipv6 router ospf
console(config-rtr)#area 1 stub
2CSNXXX_SWUM200.book Page 1286 Tuesday, December 10, 2013 1:22 PM

OSPFv3 Commands 1287
area stub no-summary
Use the area stub no-summary command in Router OSPFv3 Configuration
mode disable the import of Summary LSAs for the stub area identified by
area-id.
Syntax
area
area-id
stub no-summary
no area
area-id
stub no-summary
•
area-id
— Valid OSPFv3 area identifier.
• so-summary
— Disable the import of Summary LSAs for the stub area
identified by area-id.
Default Configuration
This command has no default configuration.
Command Mode
Router OSPFv3 Configuration mode.
User Guidelines
This command has no user guidelines.
Example
The following example prevents Summary LSAs from being advertised into
the area 1 NSSA.
console(config)#ipv6 router ospf
console(config-rtr)#area 1 stub no-summary
area virtual-link
Use the area virtual-link command in Router OSPFv3 Configuration mode
to create the OSPF virtual interface for the specified
area-id
and
neighbor
router. If the area has not been previously created, this command creates the
area and then applies the virtual-link parameters. To remove the link, use the
no form of the command. Use the optional parameters to configure dead-
interval, hello-interval, retransmit-interval and transmit-delay.
2CSNXXX_SWUM200.book Page 1287 Tuesday, December 10, 2013 1:22 PM
1288 OSPFv3 Commands
Syntax
area
area-id
virtual-link
router-id
[hello-interval
seconds
] [retransmit-
interval
seconds
] [transmit-delay
seconds
] [dead-interval
seconds
]
no area
area-id
virtual-link
router-id id
[hello-interval] [retransmit-interval]
[transmit-delay] [dead-interval]
•
area-id
—Valid OSPFv3 area identifier (or decimal value in the range of 0-
4294967295).
•
router-id
—Identifies the Router ID or valid IP address of the neighbor.
•
hello-interval
seconds
—Number of seconds to wait before sending hello
packets to the OSPF virtual interface. (Range: 1–65535)
•
dead-interval
seconds
—Number of seconds to wait before the OSPF
virtual interface on the virtual interface is assumed to be dead. (Range:
1–65535)
•
retransmit-interval
seconds
—The number of seconds to wait between
retransmitting LSAs if no acknowledgement is received. (Range: 0–3600)
•
transmit-delay
seconds
—Number of seconds to increment the age of the
LSA before sending, based on the estimated time it takes to transmit from
the interface. (Range: 0–3600)
Default Configuration
Parameter Default
area-id No area ID is predefined.
router-id No router ID is predefined.
hello-interval
seconds
10 seconds
retransmit-interval
seconds
5 seconds
transmit-delay
seconds
1 second
dead-interval
seconds
40 seconds
2CSNXXX_SWUM200.book Page 1288 Tuesday, December 10, 2013 1:22 PM

OSPFv3 Commands 1289
Command Mode
Router OSPFv3 Configuration mode.
User Guidelines
This command has no user guidelines.
Example
The following example creates the OSPF virtual interface for area 1 and its
neighbor router.
console(config)#ipv6 router ospf
console(config-rtr)#area 1 virtual-link 2
The following example configures a 20-second dead interval, a hello interval
of 20 seconds, a retransmit interval of 20 seconds, and a 20-second transmit
delay for the OSPF virtual interface on the virtual interface identified by area
1 and its neighbor.
console(config)#ipv6 router ospf
console(config-rtr)#area 1 virtual-link 2 dead-interval 20 hello-interval 20
retransmit-interval 20 transmit-delay 20
area virtual-link dead-interval
Use the area virtual-link dead-interval command in Router OSPFv3
Configuration mode to configure the dead interval for the OSPF virtual
interface on the virtual interface identified by
areaid
and
neighbor
.
Syntax
area
areaid
virtual-link
neighbor
dead-interval
seconds
no area
areaid
virtual-link
neighbor
dead-interval
•
areaid
— Valid OSPFv3 area identifier.
•
neighbor
— Router ID of neighbor.
•
seconds
— Dead interval. (Range: 1-65535)
Default Configuration
40 is the default value for
seconds
.
2CSNXXX_SWUM200.book Page 1289 Tuesday, December 10, 2013 1:22 PM

1290 OSPFv3 Commands
Command Mode
Router OSPFv3 Configuration mode.
User Guidelines
This command has no user guidelines.
Example
The following example configures a 20-second dead interval for the OSPF
virtual interface on the virtual interface identified by area 1 and its neighbor.
console(config)#ipv6 router ospf
console(config-rtr)#area 1 virtual-link 2 dead-interval 20
area virtual-link hello-interval
Use the area virtual-link hello-interval command in Router OSPFv3
Configuration mode to configure the hello interval for the OSPF virtual
interface on the virtual interface identified by
areaid
and
neighbor
.
Syntax
area
areaid
virtual-link
neighbor
hello-interval
seconds
no area
areaid
virtual-link
neighbor
hello-interval
•
areaid
— Valid OSPFv3 area identifier.
•
neighbor
— Router ID of neighbor.
•
seconds
— Hello interval. (Range: 1-65535)
Default Configuration
10 is the default value for
seconds
.
Command Mode
Router OSPFv3 Configuration mode.
User Guidelines
This command has no user guidelines.
2CSNXXX_SWUM200.book Page 1290 Tuesday, December 10, 2013 1:22 PM

OSPFv3 Commands 1291
Example
The following example configures a hello interval of 20 seconds for the OSPF
virtual interface on the virtual interface identified by area 1
and its neighbor.
console(config)#ipv6 router ospf
console(config-rtr)#area 1 virtual-link 2 hello-interval 20
area virtual-link retransmit-interval
Use the area virtual-link retransmit-interval command in Router OSPFv3
Configuration mode to configure the retransmit interval for the OSPF virtual
interface on the virtual interface identified by
areaid
and
neighbor
.
Syntax
area
areaid
virtual-link
neighbor
retransmit-interval
seconds
no area
areaid
virtual-link
neighbor
retransmit-interval
•
areaid
— Valid OSPFv3 area identifier.
•
neighbor
— Router ID of neighbor.
•
seconds
— Retransmit interval. (Range: 0-3600)
Default Configuration
5 is the default value for
seconds
.
Command Mode
Router OSPFv3 Configuration mode.
User Guidelines
This command has no user guidelines.
Example
The following example configures the retransmit interval of 20 seconds for
the OSPF virtual interface on the virtual interface identified by area 1 and its
neighbor.
(config)#ipv6 router ospf
(config-rtr)#area 1 virtual-link 2 retransmit-interval 20
2CSNXXX_SWUM200.book Page 1291 Tuesday, December 10, 2013 1:22 PM

1292 OSPFv3 Commands
area virtual-link transmit-delay
Use the area virtual-link transmit-delay command in Router OSPFv3
Configuration mode to configure the transmit delay for the OSPF virtual
interface on the virtual interface identified by
areaid
and
neighbor
.
Syntax
area
areaid
virtual-link
neighbor
transmit-delay
seconds
no area
areaid
virtual-link
neighbor
transmit-delay
•
areaid
— Valid OSPFv3 area identifier.
•
neighbor
— Router ID of neighbor.
•
seconds
— Transmit delay interval. (Range: 0-3600)
Default Configuration
1 is the default value for
seconds
.
Command Mode
Router OSPFv3 Configuration mode.
User Guidelines
This command has no user guidelines.
Example
The following example configures a 20-second transmit delay for the OSPF
virtual interface on the virtual interface identified by area 1
and its neighbor.
console(config)#ipv6 router ospf
console(config-rtr)#area 1 virtual-link 2 transmit-delay 20
default-information originate (Router OSPFv3
Configuration)
Use the default-information originate command in Router OSPFv3
Configuration mode to control the advertisement of default routes. Use the
no form of the command to return the default route advertisement settings
to the default value.
2CSNXXX_SWUM200.book Page 1292 Tuesday, December 10, 2013 1:22 PM

OSPFv3 Commands 1293
Syntax
default-information originate [always] [metric
metric-value
] [metric-type
type-value]
no default-information originate [metric] [metric-type]
•
always
—Always advertise default routes.
•
metric-value
—
•
type-value
—The metric (or preference) value of the default route. (Range:
1–16777214)
• One of the following:
1
External type-1 route.
2
External type-2 route.
Default Configuration
The default metric is none and the default type is 2.
Command Mode
Router OSPFv3 Configuration mode.
User Guidelines
This command has no user guidelines.
Example
The following example controls the advertisement of default routes by
defining a metric value of 100 and metric type 2.
console(config)#ipv6 router ospf
console(config-rtr)#default-information originate metric 100 metric-type 2
default-metric
Use the default-metric command in Router OSPFv3 Configuration mode to
set a default for the metric of distributed routes. Use the no form of the
command to remove the metric from the distributed routes.
2CSNXXX_SWUM200.book Page 1293 Tuesday, December 10, 2013 1:22 PM

1294 OSPFv3 Commands
Syntax
default-metric
metric-value
no default-metric
•
metric-value
— The metric (or preference) value of the default route.
(Range: 1–16777214)
Default Configuration
This command has no default configuration.
Command Mode
Router OSPFv3 Configuration mode.
User Guidelines
This command has no user guidelines.
Example
The following example sets a default of 100 for the metric of distributed
routes.
console(config)#ipv6 router ospf
console(config-rtr)#default-metric 100
distance ospf
The distance ospf command sets the preference values of OSPF route types
in the router. Lower route preference values are preferred when determining
the best route. The type of OSPF route can be intra, inter, external. All the
external type routes are given the same preference value. Use the “no” form of
this command to reset the preference values to the default.
Syntax
distance ospf {external | inter-area | intra-area}
distance
no distance ospf {external | inter-area | intra-area}
distance
•
distance
— Used to select the best path when there are two or more routes
to the same destination from two different routing protocols (Range:
1–255).
2CSNXXX_SWUM200.book Page 1294 Tuesday, December 10, 2013 1:22 PM

OSPFv3 Commands 1295
Default Configuration
The default preference value is 110.
Command Mode
Router OSPF Configuration mode.
Router OSPFv3 Configuration mode.
User Guidelines
There are no user guidelines for this command.
Example
The following example sets a route preference value of 100 for intra OSPF in
the router.
console(config)#ipv6 router ospf
console(config-rtr)#distance ospf intra 100
enable
Use the enable command in Router OSPFv3 Configuration mode to enable
administrative mode of OSPF in the router (active).
Syntax
enable
no enable
Default Configuration
Enabled is the default state.
Command Mode
Router OSPFv3 Configuration mode.
User Guidelines
This command has no user guidelines.
2CSNXXX_SWUM200.book Page 1295 Tuesday, December 10, 2013 1:22 PM

1296 OSPFv3 Commands
Example
The following example enables administrative mode of OSPF in the router
(active).
console(config)#ipv6 router ospf
console(config-rtr)#enable
exit-overflow-interval
Use the exit-overflow-interval command in Router OSPFv3 Configuration
mode to configure the exit overflow interval for OSPF. It describes the
number of seconds after entering Overflow state that a router will wait before
attempting to leave the Overflow State. This allows the router to originate
non-default AS-external-LSAs again. When set to 0, the router will not leave
Overflow State until restarted.
Syntax
exit-overflow-interval
seconds
no exit-overflow-interval
•
seconds
— Exit overflow interval for OSPF (Range: 0-2147483647)
Default Configuration
0 is the default value for
seconds
.
Command Mode
Router OSPFv3 Configuration mode
User Guidelines
This command has no user guidelines.
Example
The following example configures the exit overflow interval for OSPF at 100
seconds.
console(config)#ipv6 router ospf
console(config-rtr)#exit-overflow-interval 100
2CSNXXX_SWUM200.book Page 1296 Tuesday, December 10, 2013 1:22 PM

OSPFv3 Commands 1297
external-lsdb-limit
Use the external-lsdb-limit command in Router OSPFv3 Configuration
mode to configure the external LSDB limit for OSPF. If the value is -1, then
there is no limit. When the number of non-default AS-external-LSAs in a
router's link-state database reaches the external LSDB limit, the router enters
overflow state. The router never holds more than the external LSDB limit
non-default AS-external- LSAs in it database. The external LSDB limit
MUST be set identically in all routers attached to the OSPF backbone and/or
any regular OSPF area.
Syntax
external-lsdb-limit
limit
no external-lsdb-limit
•
limit
— External LSDB limit for OSPF (Range: -1-2147483647)
Default Configuration
-1 is the default value for
limit
.
Command Mode
Router OSPFv3 Configuration mode.
User Guidelines
This command has no user guidelines.
Example
The following example sets the external LSDB limit at 100 for OSPF.
console(config)#ipv6 router ospf
console(config-rtr)#external-lsdb-limit 100
ipv6 ospf
Use the ipv6 ospf command in Interface Configuration mode to enable
OSPF on a router interface or loopback interface.
2CSNXXX_SWUM200.book Page 1297 Tuesday, December 10, 2013 1:22 PM

1298 OSPFv3 Commands
Syntax
ipv6 ospf
no ipv6 ospf
Default Configuration
Disabled is the default configuration.
Command Mode
Interface Configuration (VLAN, Tunnel, Loopback) mode
User Guidelines
This command has no user guidelines.
Example
The following example enables OSPF on VLAN 15.
console(config)#interface vlan 15
console(config-if-vlan15)#ipv6 ospf
ipv6 ospf area
Use the ipv6 ospf area
areaid
command in Interface Configuration mode to
set the OSPF area to which the specified router interface belongs.
Syntax
ipv6 ospf area
areaid
no ipv6 ospf area
areaid
•
areaid
— Is a 32-bit integer, formatted as a 4-digit dotted-decimal number
or a decimal value. It uniquely identifies the area to which the interface
connects. Assigning an area id which does not exist on an interface causes
the area to be created with default values. (Range: 0-4294967295).
Default Configuration
This command has no default configuration.
2CSNXXX_SWUM200.book Page 1298 Tuesday, December 10, 2013 1:22 PM

OSPFv3 Commands 1299
Command Mode
Interface Configuration (VLAN, Tunnel, Loopback) mode.
User Guidelines
This command has no user guidelines.
Example
The following example defines the OSPF area to which VLAN 15 belongs.
console(config)#interface vlan 15
console(config-if-vlan15)#ipv6 ospf area 100
ipv6 ospf cost
Use the ipv6 ospf cost command in Interface Configuration mode to
configure the cost on an OSPF interface. Use the no form of the command to
return the cost to the default value.
Syntax
ipv6 ospf cost
interface-cost
no ipv6 ospf cost
•
inte
rface-cost
— Specifies the cost (link-state metric) of the OSPF
interface. (Range: 1–65535)
Default Configuration
10 is the default link-state metric configuration.
Command Mode
Interface Configuration (VLAN) mode.
User Guidelines
This command has no user guidelines.
Example
The following example configures a cost of 100.
console(config)#interface vlan 15
2CSNXXX_SWUM200.book Page 1299 Tuesday, December 10, 2013 1:22 PM

1300 OSPFv3 Commands
console(config-if-vlan15)#ipv6 ospf cost 100
ipv6 ospf dead-interval
Use the ipv6 ospf dead-interval command in Interface Configuration mode
to set the OSPF dead interval for the specified interface.
Syntax
ipv6 ospf dead-interval
seconds
no ipv6 ospf dead-interval
•
seconds
— A valid positive integer, which represents the length of time in
seconds that a router's Hello packets have not been seen before its
neighbor routers declare that the router is down. The value for the length
of time must be the same for all routers attached to a common network.
This value should be some multiple of the Hello Interval (i.e. 4).
(Range: 1-65535)
Default Configuration
40 seconds is the default value of
seconds
.
Command Mode
Interface Configuration (VLAN, Tunnel, Loopback) mode.
User Guidelines
This command has no user guidelines.
Example
The following example sets the OSPF dead interval at 100 seconds.
console(config)#interface vlan 15
console(config-if-vlan15)#ipv6 ospf dead-interval 100
ipv6 ospf hello-interval
Use the ipv6 ospf hello-interval command in Interface Configuration mode
to set the OSPF hello interval for the specified interface.
2CSNXXX_SWUM200.book Page 1300 Tuesday, December 10, 2013 1:22 PM

OSPFv3 Commands 1301
Syntax
ipv6 ospf hello-interval
seconds
no ipv6 ospf hello-interval
•
seconds
— A valid positive integer which represents the length of time of
the OSPF hello interval. The value must be the same for all routers
attached to a network. (Range: 1-65535 seconds)
Default Configuration
10 seconds is the default value of
seconds
.
Command Mode
Interface Configuration (VLAN, Tunnel, Loopback) mode.
User Guidelines
This command has no user guidelines.
Example
The following example sets the OSPF hello interval at 15 seconds.
console(config)#interface vlan 15
console(config-if-vlan15)#ipv6 ospf hello-interval 15
ipv6 ospf mtu-ignore
Use the ipv6 ospf mtu-ignore command in Interface Configuration mode to
disable OSPF maximum transmission unit (MTU) mismatch detection. Use
the no form of the command to reset mismatch detection to the default
value.
Syntax
ipv6 ospf mtu-ignore
no ipv6 ospf mtu-ignore
Default Configuration
The default state is Disabled.
2CSNXXX_SWUM200.book Page 1301 Tuesday, December 10, 2013 1:22 PM

1302 OSPFv3 Commands
Command Mode
Interface Configuration (VLAN, Tunnel, Loopback) mode.
User Guidelines
OSPF Database Description packets specify the size of the largest IP packet
that can be sent without fragmentation on the interface. When a router
receives a Database Description packet, it examines the MTU advertised by
the neighbor. By default, if the MTU is larger than the router can accept, the
Database Description packet is rejected and the OSPF adjacency is not
established.
Example
The following example disables OSPF maximum transmission unit (MTU)
mismatch detection.
console(config)#interface vlan 15
console(config-if-vlan15)#ipv6 ospf mtu-ignore
ipv6 ospf network
Use the ipv6 ospf network command in Interface Configuration mode to
change the default OSPF network type for the interface. Use the no form of
the command to return the network setting to the default value.
Syntax
ipv6 ospf network {broadcast | point-to-point}
no ipv6 ospf network
•
broadcast
— The network type is broadcast.
•
point-to-point
— The network type is point-to-point.
Default Configuration
The default state is point-to-point.
Command Mode
Interface Configuration (VLAN, Tunnel, Loopback) mode
2CSNXXX_SWUM200.book Page 1302 Tuesday, December 10, 2013 1:22 PM

OSPFv3 Commands 1303
User Guidelines
Normally, the network type is determined from the physical IP network type.
By default all Ethernet networks are OSPF-type broadcast. Similarly, tunnel
interfaces default to point-to-point. When an Ethernet port is used as a single
large bandwidth IP network between two routers, the network type can be
point-to-point since there are only two routers. Using point-to-point as the
network type eliminates the overhead of the OSPF designated router
election. It is normally not useful to set a tunnel to OSPF network type
broadcast.
Example
The following example changes the default OSPF network type to point-to-
point.
console(config)#interface vlan 15
console(config-if-vlan15)#ipv6 ospf network point-to-point
ipv6 ospf priority
Use the ipv6 ospf priority command in Interface Configuration mode to set
the OSPF priority for the specified router interface. Use the no form of the
command to return the priority to the default value.
Syntax
ipv6 ospf priority
number-value
no ipv6 ospf priority
•
number-value
— Specifies the OSPF priority for the specified router
interface. (Range: 0–255) A value of 0 indicates that the router is not
eligible to become the designated router on this network.
Default Configuration
1, the highest router priority, is the default value.
Command Mode
Interface Configuration (VLAN, Tunnel, Loopback) mode.
2CSNXXX_SWUM200.book Page 1303 Tuesday, December 10, 2013 1:22 PM

1304 OSPFv3 Commands
User Guidelines
This command has no user guidelines.
Example
The following example sets the OSPF priority at 50 for VLAN 15.
console(config)#interface vlan 15
console(config-if-vlan15)#ipv6 ospf priority 50
ipv6 ospf retransmit-interval
Use the ipv6 ospf retransmit-interval command in Interface Configuration
mode to set the OSPF retransmit interval for the specified interface.
Syntax
ipv6 ospf retransmit-interval
seconds
no ipv6 ospf retransmit-interval
•
seconds
— The number of seconds between link-state advertisement
retransmissions for adjacencies belonging to this router interface. This
value is also used when retransmitting database description and link-state
request packets. (Range: 0 to 3600 seconds)
Default Configuration
5 seconds is the default value.
Command Mode
Interface Configuration (VLAN, Tunnel, Loopback) mode.
User Guidelines
This command has no user guidelines.
Example
The following example sets the OSPF retransmit interval at 100 seconds.
console(config)#interface vlan 15
console(config-if-vlan15)#ipv6 ospf retransmit-interval 100
2CSNXXX_SWUM200.book Page 1304 Tuesday, December 10, 2013 1:22 PM

OSPFv3 Commands 1305
ipv6 ospf transmit-delay
Use the ipv6 ospf transmit-delay command in Interface Configuration mode
to set the OSPF Transmit Delay for the specified interface.
Syntax
ipv6 ospf transmit-delay
seconds
no ipv6 ospf transmit-delay
•
seconds
— OSPF transmit delay for the specified interface. In addition, it
sets the estimated number of seconds it takes to transmit a link state
update packet over this interface. (Range: 1 to 3600 seconds)
Default Configuration
No default value.
Command Mode
Interface Configuration (VLAN, Tunnel, Loopback) mode.
User Guidelines
This command has no user guidelines.
Example
The following example sets the OSPF Transmit Delay at 100 seconds for
VLAN 15.
console(config)#interface vlan 15
console(config-if-vlan15)#ipv6 ospf transmit-delay 100
ipv6 router ospf
Use the ipv6 router ospf command in Global Configuration mode to enable
OSPFv3 and enter Router OSPFv3 Configuration mode. Use the no form of
the command to disable OSPFv3 and remove the OSPFv3 interface and
global configuration.
Syntax
ipv6 router ospf
2CSNXXX_SWUM200.book Page 1305 Tuesday, December 10, 2013 1:22 PM

1306 OSPFv3 Commands
no ipv6 router ospf
Default Configuration
This command has no default configuration.
Command Mode
Global Configuration mode.
User Guidelines
This command has no user guidelines.
Example
Use the following command to enable OSPFv3.
console(config)#ipv6 router ospf
maximum-paths
Use the maximum-paths command in Router OSPFv3 Configuration mode
to set the number of paths that OSPF can report for a given destination.
Syntax
maximum-paths
maxpaths
no maximum-paths
•
maxpaths
— Number of paths that can be reported. (Range: 1-2)
Default Configuration
2 is the default value for
maxpaths
.
Command Mode
Router OSPFv3 Configuration mode.
User Guidelines
This command has no user guidelines.
2CSNXXX_SWUM200.book Page 1306 Tuesday, December 10, 2013 1:22 PM

OSPFv3 Commands 1307
Example
The following example sets the number of paths that OSPF can report for a
destination to 1.
console(config)#ipv6 router ospf
console(config-rtr)#maximum-paths 1
nsf
Use this command to enable OSPF graceful restart. Use the no form of this
command to disable graceful restart.
Syntax
nsf [ietf] [planned-only]
no nsf [ietf]
•
ietf
— This keyword is used to distinguish the IETF standard
implementation of graceful restart from other implementations. Since the
IETF implementation is the only one supported, this keyword is optional.
•
planned-only
— This keyword indicates that OSPF should only perform a
graceful restart when the restart is planned (i.e., when the restart is a result
of the
initiate failover
command).
Default Configuration
Graceful restart is disabled by default
Command Mode
Router OSPFv3 Configuration mode
User Guidelines
Graceful restart works in concert with nonstop forwarding to enable the
hardware to continue forwarding IPv6 packets using OSPFv3 routes while a
backup unit takes over management unit responsibility. When OSPF
executes a graceful restart, it informs its neighbors that the OSPF control
plane is restarting, but that it will be back shortly. Helpful neighbors continue
to advertise to the rest of the network that they have full adjacencies with the
restarting router, avoiding announcement of a topology change and
2CSNXXX_SWUM200.book Page 1307 Tuesday, December 10, 2013 1:22 PM

1308 OSPFv3 Commands
everything that goes with that (i.e., flooding of LSAs, SPF runs). Helpful
neighbors continue to forward packets through the restarting router. The
restarting router relearns the network topology from its helpful neighbors.
This implementation of graceful restart restarting router behavior is only
useful with a router stack. Graceful restart does not work on a standalone,
single-unit router.
nsf helper
Use the nsf-helper to allow OSPF to act as a helpful neighbor for a restarting
router. Use the no form of this command to prevent OSPF from acting as a
helpful neighbor.
Syntax
nsf helper[planned-only]
no nsf helper
•
planned-only
— This keyword indicates that OSPF should only help a
restarting router performing a planned restart.
Default Configuration
OSPF may act as a helpful neighbor for both planned and unplanned restarts
Command Mode
Router OSPFv3 Configuration mode
User Guidelines
The grace LSA announcing the graceful restart includes a restart reason.
Reasons 1 (software restart) and 2 (software reload/upgrade) are considered
planned restarts. Reasons 0 (unknown) and 3 (switch to redundant control
processor) are considered unplanned restarts.
nsf ietf helper disable is functionally equivalent to no nsf helper and is
supported solely for IS CLI compatibility.
2CSNXXX_SWUM200.book Page 1308 Tuesday, December 10, 2013 1:22 PM

OSPFv3 Commands 1309
nsf helper strict-lsa-checking
Use the nsf-helper strict-lsa-checking command to require that an OSPF
helpful neighbor exit helper mode whenever a topology change occurs. Use
the “no” form of this command to allow OSPF to continue as a helpful
neighbor in spite of topology changes.
Syntax
nsf [ietf] helper strict-lsa-checking
no nsf [ietf] helper strict-lsa-checking
•
ietf
—This keyword is used to distinguish the IETF standard
implementation of graceful restart from other implementations. Since the
IETF implementation is the only one supported, this keyword is optional.
Default Configuration
A helpful neighbor exits helper mode when a topology change occurs.
Command Mode
Router OSPFv3 Configuration mode
User Guidelines
The restarting router is unable to react to topology changes. In particular, the
restarting router will not immediately update its forwarding table; therefore, a
topology change may introduce forwarding loops or black holes that persist
until the graceful restart completes. By exiting the graceful restart on a
topology change, a router tries to eliminate the loops or black holes as quickly
as possible by routing around the restarting router.
A helpful neighbor considers a link down with the restarting router to be a
topology change, regardless of the strict LSA checking configuration.
nsf restart-interval
Use the nsf restart-interval command to configure the length of the grace
period on the restarting router. Use the “no” form of this command to revert
the grace period to its default.
2CSNXXX_SWUM200.book Page 1309 Tuesday, December 10, 2013 1:22 PM

1310 OSPFv3 Commands
Syntax
nsf [ietf] restart-interval
seconds
no nsf [ietf] restart-interval
•
ietf
— This keyword is used to distinguish the IETF standard
implementation of graceful restart from other implementations. Since the
IETF implementation is the only one supported, this keyword is optional.
•
seconds
— The number of seconds that the restarting router asks its
neighbors to wait before exiting helper mode. The restarting router
includes the restart interval in its grace LSAs (range 1–1800 seconds).
Default Configuration
The default restart interval is 120 seconds.
Command Mode
Router OSPFv3 Configuration mode
User Guidelines
The grace period must be set long enough to allow the restarting router to
reestablish all of its adjacencies and complete a full database exchange with
each of those neighbors.
passive-interface
Use the passive-interface command to set the interface or tunnel as passive.
It overrides the global passive mode that is currently effective on the interface
or tunnel. Use the “no” form of this command to set the interface or tunnel
as non-passive.
Syntax
passive-interface {vlan
vlan-id
| tunnel
tunnel-id
}
no passive-interface {vlan
vlan-id
| tunnel
tunnel-id
}
•
vlan-id
— The vlan number
•
tunnel-id
— Tunnel identifier. (Range: 0–7)
2CSNXXX_SWUM200.book Page 1310 Tuesday, December 10, 2013 1:22 PM

OSPFv3 Commands 1311
Default Configuration
Passive interface mode is disabled by default.
Command Mode
Router OSPFv3 Configuration mode.
User Guidelines
There are no user guidelines for this command.
Example
console(config-router)#passive-interface vlan 1
passive-interface default
The passive-interface default command enables the global passive mode by
default for all interfaces. It overrides any interface level passive mode. Use the
“no” form of this command to disable the global passive mode by default for
all interfaces. Any interface previously configured to be passive reverts to non-
passive mode.
Syntax
passive-interface default
no passive-interface default
Default Configuration
Global passive mode is disabled by default.
Command Mode
Router OSPFv3 Configuration mode.
User Guidelines
There are no user guidelines for this command.
Example
console(config-rtr)#passive-interface default
2CSNXXX_SWUM200.book Page 1311 Tuesday, December 10, 2013 1:22 PM

1312 OSPFv3 Commands
redistribute
Use the redistribute command in Router OSPFv3 Configuration mode to
configure the OSPFv3 protocol to allow redistribution of routes from the
specified source protocol/routers.
Syntax
redistribute {static | connected} [metric
metric
] [metric-type {1 | 2}] [tag
tag
]
no redistribute {static | connected} [
metric
] [metric-type] [
tag
]
•
metric
— Metric value used for default routes. (Range: 0-16777214)
•
tag
— Tag. (Range: 0-4294967295)
Default Configuration
2 is the default value for metric-type, 0 for
tag
.
Command Mode
Router OSPFv3 Configuration mode
User Guidelines
This command has no user guidelines.
Example
The following example configures the OSPFv3 protocol to allow
redistribution of routes from the specified source protocol/routers.
console(config)#ipv6 router ospf
console(config-rtr)#redistribute connected
router-id
Use the router-id command in Router OSPFv3 Configuration mode to set a
4-digit dotted-decimal number uniquely identifying the Router OSPF ID.
Syntax
router-id
router-id
2CSNXXX_SWUM200.book Page 1312 Tuesday, December 10, 2013 1:22 PM

OSPFv3 Commands 1313
•
router-id
— Router OSPF identifier. (Range: 0-4294967295)
Default Configuration
This command has no default configuration.
Command Mode
Router OSPFv3 Configuration mode.
User Guidelines
This command has no user guidelines.
Example
The following example sets a 4-digit dotted-decimal number identifying the
Router OSPF ID as 2.3.4.5.
console(config)#ipv6 router ospf
console(config-rtr)#router-id 2.3.4.5
show ipv6 ospf
Use the show ipv6 ospf command in Privileged EXEC mode to display
information relevant to the OSPF router.
Syntax
show ipv6 ospf [
area-id
]
area-id
— Identifier for the OSPF area being displayed.
Default Configuration
This command has no default configuration.
Command Mode
User EXEC, Privileged EXEC mode, Configuration mode and all
Configuration submodes
2CSNXXX_SWUM200.book Page 1313 Tuesday, December 10, 2013 1:22 PM

1314 OSPFv3 Commands
User Guidelines
Some of the information below displays only if you enable OSPF and
configure certain features. The following fields may be displayed:
Field Description
Router ID A 32-bit integer in dotted decimal format identifying the router
about which information is displayed. This is a configured value.
OSPF Admin
Mode
Shows whether OSPF is administratively enabled or disabled.
External LSDB
Limit
Shows the maximum number of non-default external LSAs
entries that can be stored in the link-state database.
Exit Overflow
Interval
Shows the number of seconds that, after entering
OverflowState, as defined by RFC 1765, a router will attempt to
leave OverflowState.
AutoCost Ref BW The configured autocost reference bandwidth. This value is used
to determine the OSPF metric on its interfaces. The reference
bandwidth is divided by the interface speed to compute the
metric.
Default Passive
Setting
When enabled, OSPF interfaces are passive by default.
Maximum Paths Shows the maximum number of paths that OSPF can report for
a given destination.
Default Metric Default metric for redistributed routes.
Default Route
Advertise
When enabled, OSPF originates a type 5 LSA advertising a
default route.
Always When this option is configured, OSPF only originates a default
route when the router has learned a default route from another
source.
Metric Shows the metric for the advertised default routes. If the metric
is not configured, this field is not configured.
Metric Type Shows whether the metric for the default route is advertised as
External Type 1 or External Type 2.
Number of Active
Areas
The number of OSPF areas to which the router is attached on
interfaces that are up.
2CSNXXX_SWUM200.book Page 1314 Tuesday, December 10, 2013 1:22 PM
OSPFv3 Commands 1315
ABR Status Shows whether the router is an OSPF Area Border Router.
ASBR Status Indicates whether the router is an autonomous system border
router. Router automatically becomes an ASBR when it is
configured to redistribute routes learned from another protocol.
The possible values for the ASBR status is enabled (if the router
is configured to redistribute routes learned by other protocols) or
disabled (if the router is not configured for the same).
Stub Router OSPF enters stub router mode, as described in RFC 3137, when
it encounters a resource limitation that prevents it from
computing a complete routing table. In this state, OSPF sets the
link metrics of non-stub links in its own router LSAs to the
largest possible value, discouraging other routers from
computing paths through the stub router, but allowing other
routers to compute routes to destinations attached to the stub
router. To restore OSPF to normal operation, resolve the
condition that caused the resource overload, then disable and
reenable OSPF globally.
External LSDB
Overflow
OSPF enters this state when the number of external LSAs
exceeds a configured limit, as described in RFC 1765.
External LSA
Count
Shows the number of external (LS type 5) link-state
advertisements in the link-state database.
External LSA
Checksum
Shows the sum of the LS checksums of external link-state
advertisements contained in the link-state database.
New LSAs
Originated
Shows the number of link-state advertisements that have been
originated.
LSAs Received Shows the number of link-state advertisements received
determined to be new instantiations.
LSA Count The number of LSAs in the link state database.
Maximum Number
of LSAs
The limit on the number of LSAs that the router can store in its
link state database.
LSA High Water
Mark
The maximum number of LSAs that have been in the link state
database since OSPF began operation.
Retransmit List
Entries
The current number of entries on all neighbors’ retransmit lists.
2CSNXXX_SWUM200.book Page 1315 Tuesday, December 10, 2013 1:22 PM
1316 OSPFv3 Commands
Example
The following example enables OSPF traps.
Maximum Number
of Retransmit
Entries
The maximum number of entries that can be on neighbors’
retransmit lists at any given time. This is the sum for all
neighbors. When OSPF receives an LSA and cannot allocate a
new retransmit list entry, the router does not acknowledge the
LSA, expecting the sender to retransmit.
Retransmit Entries
High Water Mark
The maximum number of retransmit list entries that have been
on all neighbors’ retransmit lists at one time.
NSF Support Whether graceful restart is administratively enabled. Possible
values are Support Always, Disabled, or Planned.
NSF Restart
Interval
The number of seconds a helpful neighbor allows a restarting
router to complete its graceful restart.
NSF Restart Status Whether the router is currently performing a graceful restart.
NSF Restart Age The number of seconds until a graceful restart expires. Only
non-zero when the router is in graceful restart.
NSF Restart Exit
Reason
The reason the previous graceful restart ended. Possible values
are Not attempted, In progress, Completed, Timed out,
Topology change, and Manual clear.
NSF Helper
Support
Whether this router is configured to act as a graceful restart
helpful neighbor. Possible values are: Helper Support Always,
Disabled, or Planned.
NSF Helper Strict
LSA Checking
As a graceful restart helpful neighbor, whether to terminate the
helper relationship if a topology change occurs during a
neighbor's graceful restart.
Redistributing This field is a heading and appears only if you configure the
system to take routes learned from a non-OSPF source and
advertise them to its peers.
Source Shows source protocol/routes that are being redistributed.
Possible values are static, connected, or RIP.
Tag Shows the decimal value attached to each external route.
Subnets When this option is not configured, OSPF will only redistribute
classful prefixes.
Distribute-List Shows the access list used to filter redistributed routes.
2CSNXXX_SWUM200.book Page 1316 Tuesday, December 10, 2013 1:22 PM

OSPFv3 Commands 1317
console#show ipv6 ospf
Router ID...................................... 0.0.0.2
OSPF Admin Mode................................ Enable
ASBR Mode...................................... Disable
ABR Status..................................... Disable
Exit Overflow Interval......................... 0
External LSA Count............................. 0
External LSA Checksum.......................... 0
New LSAs Originated............................ 0
LSAs Received.................................. 0
External LSDB Limit............................ No Limit
Default Metric................................. Not Configured
Maximum Paths.................................. 2
Default Route Advertise........................ Disabled
Always......................................... FALSE
Metric.........................................
Metric Type.................................... External Type 2
NSF Support.................................... Disabled
NSF Restart Interval........................... 120 seconds
NSF Helper Support............................. Always
NSF Helper Strict LSA Checking................. Enabled
show ipv6 ospf abr
This command displays the internal OSPFv3 routes to reach Area Border
Routers (ABR). This command takes no options.
Syntax
show ipv6 ospf abr
Default Configuration
This command has no default configuration.
Command Mode
User EXEC mode, Configuration mode and all Configuration submodes
User Guidelines
This command has no user guidelines.
Example
console#show ipv6 ospf abr
2CSNXXX_SWUM200.book Page 1317 Tuesday, December 10, 2013 1:22 PM

1318 OSPFv3 Commands
Type Router Id Cost Area ID Next Hop Next Hop
Intf
---- -------- ---- -------- ----------------------- -----
INTRA 3.3.3.3 10 0.0.0.1 FE80::211:88FF:FE2A:3CB3 vlan11
INTRA 4.4.4.4 10 0.0.0.1 FE80::210:18FF:FE82:8E1 vlan12
show ipv6 ospf area
Use the show ipv6 ospf area command in Privileged EXEC mode to display
information about the area.
Syntax
show ipv6 ospf area
areaid
•
areaid
— Identifier for the OSPF area being displayed.
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC mode, Configuration mode and all Configuration submodes
User Guidelines
This command has no user guidelines.
Example
The following example displays information about area 1.
console#show ipv6 ospf area 1
AreaID........................................ 0.0.0.1
External Routing.............................. Import External LSAs
Spf Runs...................................... 0
Area Border Router Count...................... 0
Area LSA Count................................ 0
Area LSA Checksum............................. 0
Stub Mode..................................... Disable
Import Summary LSAs........................... Enable
2CSNXXX_SWUM200.book Page 1318 Tuesday, December 10, 2013 1:22 PM

OSPFv3 Commands 1319
show ipv6 ospf asbr
The show ipv6 ospf asbr command displays the internal OSPFv3 routes to
reach Autonomous System Boundary Routes (ASBR). This command takes
no options.
Syntax
show ipv6 ospf asbr
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC mode, Configuration mode and all Configuration submodes
User Guidelines
This command has no user guidelines.
Example
console#show ipv6 ospf asbr
Type Router Id Cost Area ID Next Hop Next Hop
Intf
---- --------- ---- -------- ----------------------- -------
INTRA 1.1.1.1 10 0.0.0.1 FE80::213:C4FF:FEDB:6C41 vlan10
INTRA 4.4.4.4 10 0.0.0.1 FE80::210:18FF:FE82:8E1 vlan12
show ipv6 ospf border-routers
Use the show ipv6 ospf command to display internal OSPFv3 routes to reach
Area Border Routers (ABR) and Autonomous System Boundary Routers
(ASBR). This command takes no options.
Syntax
show ipv6 ospf border-routers
Default Configuration
This command has no default configuration.
2CSNXXX_SWUM200.book Page 1319 Tuesday, December 10, 2013 1:22 PM

1320 OSPFv3 Commands
Command Mode
User EXEC, Privileged EXEC mode, Configuration mode and all
Configuration submodes
show ipv6 ospf database
Use the show ipv6 ospf database command in Privileged EXEC mode to
display information about the link state database when OSPFv3 is enabled. If
no parameters are entered, the command displays the LSA headers. Optional
parameters specify the type of link state advertisements to display.
The information below is only displayed if OSPF is enabled.
Syntax
show ipv6 ospf [
area-id
] database [{external | inter-area {prefix | router} |
link | network | nssaexternal | prefix | router | unknown [area | as | link]}]
[
link-state-id
] [adv-router [
router-id
] | self-originate]
•
area-id
— Identifies a specific OSPF area for which link state database
information will be displayed.
•
external —
Displays the external LSAs.
•
inter-area —
Displays the inter-area LSAs.
•
link —
Displays the link LSAs.
•
network —
Displays the network LSAs.
•
nssa-external —
Displays NSSA external LSAs.
•
prefix —
Displays intra-area Prefix LSA.
•
router —
Displays router LSAs.
•
unknown —
Displays unknown area, AS or link-scope LSAs.
•
l
ink-state-
id
—
Specifies a valid link state identifier (LSID).
•
adv-router —
Shows the LSAs that are restricted by the advertising router.
•
router-id
— Specifies a valid router identifier.
•
self-originate —
Displays the LSAs in that are self originated.
Default Configuration
This command has no default configuration.
2CSNXXX_SWUM200.book Page 1320 Tuesday, December 10, 2013 1:22 PM

OSPFv3 Commands 1321
Command Mode
User EXEC, Privileged EXEC mode, Configuration mode and all
Configuration submodes
User Guidelines
This command has no user guidelines.
Example
The following example displays information about the link state database
when OSPFv3 is enabled.
console#show ipv6 ospf database
Router Link States (Area 0.0.0.0)
Adv Router Link Id Age Sequence Csum Options Rtr Opt
-------------- --------------- ----- -------- ---- ------- -------
1.1.1.1 0 4 80000034 54BD V6E--R- ----B
2.2.2.2 0 2 80000044 95A5 V6E--R- ----B
Network Link States (Area 0.0.0.0)
Adv Router Link Id Age Sequence Csum Options Rtr Opt
-------------- --------------- ----- -------- ---- ------- -------
2.2.2.2 636 636 80000001 8B0D V6E--R-
Inter Network States (Area 0.0.0.0)
Adv Router Link Id Age Sequence Csum Options Rtr Opt
-------------- --------------- ----- -------- ---- ------- -------
1.1.1.1 1 323 80000001 3970
2.2.2.2 1 322 80000001 1B8A
1.1.1.1 2 293 80000001 3529
2.2.2.2 2 375 80000001 FC5E
Link States (Area 0.0.0.0)
Adv Router Link Id Age Sequence Csum Options Rtr Opt
-------------- --------------- ----- -------- ---- ------- -------
1.1.1.1 634 700 80000008 2D89 V6E--R-
2.2.2.2 634 689 8000000A 6F82 V6E--R-
2.2.2.2 635 590 80000001 7782 V6E--R-
Intra Prefix States (Area 0.0.0.0)
Adv Router Link Id Age Sequence Csum Options Rtr Opt
-------------- --------------- ----- -------- ---- ------- -------
1.1.1.1 0 1 8000003C 9F31
2.2.2.2 0 2 8000004D 9126
2CSNXXX_SWUM200.book Page 1321 Tuesday, December 10, 2013 1:22 PM

1322 OSPFv3 Commands
Router Link States (Area 0.0.0.1)
Adv Router Link Id Age Sequence Csum Options Rtr Opt
-------------- --------------- ----- -------- ---- ------- -------
1.1.1.1 0 1 8000002E 35AD V6E--R- --V-B
2.2.2.2 0 0 8000004A D2F3 V6E--R- ----B
Network Link States (Area 0.0.0.1)
Adv Router Link Id Age Sequence Csum Options Rtr Opt
-------------- --------------- ----- -------- ---- ------- -------
1.1.1.1 634 621 80000001 B9E2 V6E--R-
Inter Network States (Area 0.0.0.1)
Adv Router Link Id Age Sequence Csum Options Rtr Opt
-------------- --------------- ----- -------- ---- ------- -------
1.1.1.1 16 4 80000001 CA7C
2.2.2.2 18 3 80000001 B28D
Link States (Area 0.0.0.1)
Adv Router Link Id Age Sequence Csum Options Rtr Opt
-------------- --------------- ----- -------- ---- ------- -------
1.1.1.1 634 441 80000003 B877 V6E--R-
2.2.2.2 634 433 80000003 FE6E V6E--R-
Intra Prefix States (Area 0.0.0.1)
Adv Router Link Id Age Sequence Csum Options Rtr Opt
-------------- --------------- ----- -------- ---- ------- -------
1.1.1.1 0 6 8000003A 37C4
2.2.2.2 0 1 8000004F 439A
1.1.1.1 10634 434 80000002 440A
show ipv6 ospf database database-summary
Use the show ipv6 ospf database database-summary command in Privileged
EXEC mode to display the number of each type of LSA in the database and
the total number of LSAs in the database.
Syntax
show ipv6 ospf database database-summary
Default Configuration
This command has no default configuration.
2CSNXXX_SWUM200.book Page 1322 Tuesday, December 10, 2013 1:22 PM

OSPFv3 Commands 1323
Command Mode
User EXEC, Privileged EXEC mode, Configuration mode and all
Configuration submodes
User Guidelines
This command has no user guidelines.
Example
The following example displays the number of each type of LSA in the
database and the total number of LSAs in the database.
console#show ipv6 ospf database database-summary
OSPF Router with ID (0.0.0.2)
Router database summary
Router......................................... 0
Network........................................ 0
Inter-area Prefix.............................. 0
Inter-area Router.............................. 0
Type-7 Ext..................................... 0
Link........................................... 0
Intra-area Prefix.............................. 0
Link Unknown................................... 0
Area Unknown................................... 0
AS Unknown..................................... 0
Type-5 Ext..................................... 0
Self-Originated Type-5 Ext..................... 0
Total.......................................... 0
show ipv6 ospf interface
Use the show ipv6 ospf interface command in Privileged EXEC mode to
display the information for the IFO object or virtual interface tables.
Syntax
show ipv6 ospf interface [
interface-type interface-number
]
•
interface-type
—The interface type, VLAN, tunnel or loopback
•
interface-number
—The valid interface number, a valid VLAN ID, tunnel
identifier (Range: 0–7) or loopback identifier (Range: 0–7).
2CSNXXX_SWUM200.book Page 1323 Tuesday, December 10, 2013 1:22 PM

1324 OSPFv3 Commands
Default Configuration
This command has no default configuration.
Command Mode
User EXEC, Privileged EXEC mode, Configuration mode and all
Configuration submodes
User Guidelines
This command has no user guidelines.
Example
The following example displays the information in VLAN 11’s virtual
interface tables.
console#show ipv6 ospf interface vlan 11
IP Address..................................... 11.11.11.11
ifIndex........................................ 1
OSPF Admin Mode................................ Enable
OSPF Area ID................................... 0.0.0.0
Router Priority................................ 1
Retransmit Interval............................ 5
Hello Interval................................. 10
Dead Interval.................................. 40
LSA Ack Interval............................... 1
Iftransit Delay Interval....................... 1
Authentication Type............................ None
Metric Cost.................................... 10 (computed)
OSPF Mtu-ignore................................ Disable
OSPF cannot be initialized on this interface.
show ipv6 ospf interface brief
Use the show ipv6 ospf interface brief command in Privileged EXEC mode to
display brief information for the IFO object or virtual interface tables.
Syntax
show ipv6 ospf interface brief
2CSNXXX_SWUM200.book Page 1324 Tuesday, December 10, 2013 1:22 PM

OSPFv3 Commands 1325
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC mode, Configuration mode and all Configuration submodes
User Guidelines
This command has no user guidelines.
Example
The following example displays brief ospf interface information.
console#show ipv6 ospf interface brief
Hello Dead Retrax LSA
Admin Router Int. Int. Int. Retrax Ack
Interface Mode Area ID Prior. Cost Val. Val. Val. Delay Intval
--------- -------- -------- ------ ----- ----- ----- ------ ------ -----
show ipv6 ospf interface stats
Use the show ipv6 ospf interface stats command in User EXEC mode to
display the statistics for a specific interface. The command only displays
information if OSPF is enabled.
Syntax
show ipv6 ospf interface stats vlan
vlan-id
•
vlan-id
— Valid VLAN ID.
Default Configuration
This command has no default configuration.
Command Mode
User EXEC mode, Configuration mode and all Configuration submodes
User Guidelines
This command has no user guidelines.
2CSNXXX_SWUM200.book Page 1325 Tuesday, December 10, 2013 1:22 PM

1326 OSPFv3 Commands
Example
The following example displays the interface statistics for VLAN 5.
console>show ipv6 ospf interface stats vlan 5
OSPFv3 Area ID................................. 0.0.0.1
Spf Runs....................................... 265
Area Border Router Count....................... 1
AS Border Router Count......................... 0
Area LSA Count................................. 6
IPv6 Address...................................
FE80::202:BCFF:FE00:3146/1283FFE::2/64
OSPF Interface Events.......................... 53
Virtual Events................................. 13
Neighbor Events................................ 6
External LSA Count............................. 0
LSAs Received.................................. 660
Originate New LSAs............................. 853
Sent Packets................................... 1013
Received Packets............................... 893
Discards....................................... 48
Bad Version.................................... 0
Virtual Link Not Found......................... 9
Area Mismatch.................................. 39
Invalid Destination Address.................... 0
No Neighbor at Source Address.................. 0
Invalid OSPF Packet Type....................... 0
Packet Type Sent Received
-------------------- ---------- ----------
Hello 295 219
Database Description 10 14
LS Request 4 4
LS Update 521 398
LS Acknowledgement 209 282
show ipv6 ospf interface vlan
Use the show ipv6 ospf interface vlan command in Privileged EXEC mode to
display OSPFv3 configuration and status information for a specific vlan.
Syntax
show ipv6 ospf interface vlan {
vlan-id
| brief}
•
vlan-id
— Valid VLAN ID. Range is 1-4093.
•
brief —
Displays a snapshot of configured interfaces.
2CSNXXX_SWUM200.book Page 1326 Tuesday, December 10, 2013 1:22 PM

OSPFv3 Commands 1327
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC mode, Configuration mode and all Configuration submodes
User Guidelines
This command has no user guidelines.
Example
The following example displays ospf interface vlan information.
console#show ipv6 ospf interface vlan 10
IPv6 Address............................. FE80::2FC:E3FF:FE90:44
ifIndex.................................. 634
OSPF Admin Mode.......................... Enable
OSPF Area ID............................. 0.0.0.1
Router Priority.......................... 1
Retransmit Interval...................... 5
Hello Interval........................... 10
Dead Interval............................ 40
LSA Ack Interval......................... 1
Iftransit Delay Interval................. 1
Authentication Type...................... None
Metric Cost.............................. 10 (computed)
OSPF Mtu-ignore.......................... Disable
OSPF Interface Type...................... broadcast
State.................................... backup-designated-router
Designated Router........................ 1.1.1.1
Backup Designated Router................. 2.2.2.2
Number of Link Events.................... 46
show ipv6 ospf neighbor
Use the show ipv6 ospf neighbor command in Privileged EXEC mode to
display information about OSPF neighbors. If a neighbor IP address is not
specified, the output displays summary information in a table. If an interface
or tunnel is specified, only the information for that interface or tunnel
displays. The information below only displays if OSPF is enabled and the
interface has a neighbor.
2CSNXXX_SWUM200.book Page 1327 Tuesday, December 10, 2013 1:22 PM

1328 OSPFv3 Commands
Syntax
show ipv6 ospf neighbor [
interface-type interface-number
] [
neighbor-id
]
•
interface-type
—Interface type, vlan or tunnel.
•
interface-number
—A valid interface number, a valid VLAN ID or tunnel
identifier. (Range is 0-7).
•
neighbor-id
—Valid IP address of the neighbor about which information is
displayed.
Default Configuration
This command has no default configuration.
Command Mode
User EXEC, Privileged EXEC mode, Configuration mode and all
Configuration submodes
User Guidelines
This command has no user guidelines.
Examples
The following examples display information about OSPF neighbors, in the
first case in a summary table, and in the second in a table specific to tunnel 1.
console#show ipv6 ospf neighbor
Router ID Priority Intf Interface State Dead
ID Time
--------- -------- ---- ----------- ------------- ----
console#show ipv6 ospf neighbor interface tunnel 1
IP Address..................................... 2.4.6.8
ifIndex........................................ 619
OSPF Admin Mode................................ Enable
OSPF Area ID................................... 0.0.0.0
Router Priority................................ 1
Retransmit Interval............................ 5
Hello Interval................................. 10
Dead Interval.................................. 40
LSA Ack Interval............................... 1
Iftransit Delay Interval....................... 1
Authentication Type............................ None
2CSNXXX_SWUM200.book Page 1328 Tuesday, December 10, 2013 1:22 PM

OSPFv3 Commands 1329
Metric Cost.................................... 1 (computed)
OSPF Mtu-ignore................................ Disable
OSPF cannot be initialized on this interface.
show ipv6 ospf range
Use the show ipv6 ospf range command in Privileged EXEC mode to display
information about the area ranges for the specified area identifier.
Syntax
show ipv6 ospf range
areaid
•
areaid
— Identifies the OSPF area whose ranges are being displayed.
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC mode, Configuration mode and all Configuration submodes
User Guidelines
This command has no user guidelines.
Example
The following example displays information about the area ranges for area 1.
console#show ipv6 ospf range 1
Area ID IPv6 Prefix/Prefix Length Lsdb Type Advertisement
--------- ------------------------- --------------- -------------
show ipv6 ospf stub table
Use the show ipv6 ospf stub table command in Privileged EXEC mode to
display the OSPF stub table. The information below will only be displayed if
OSPF is initialized on the switch.
Syntax
show ipv6 ospf stub table
2CSNXXX_SWUM200.book Page 1329 Tuesday, December 10, 2013 1:22 PM

1330 OSPFv3 Commands
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC mode, Configuration mode and all Configuration submodes
User Guidelines
This command has no user guidelines.
Example
The following example displays the OSPF stub table.
console#show ipv6 ospf stub table
AreaId TypeofService Metric Val Import SummaryLSA
------------ ------------- ---------- -----------------
0.0.0.10 Normal 1 Enable
show ipv6 ospf virtual-links
Use the show ipv6 ospf virtual-links command in Privileged EXEC mode to
display the OSPF Virtual Interface information for a specific area and
neighbor or for all areas in the system.
Syntax
show ipv6 ospf virtual-link [
area-id
neighbor-id
| brief]
•
area-id
— Identifies the OSPF area whose virtual interface information is
being displayed.
•
neighbor-id
— Router ID of neighbor.
Default Configuration
This command has no default configuration.
Command Mode
User EXEC, Privileged EXEC mode, Configuration mode and all
Configuration submodes
2CSNXXX_SWUM200.book Page 1330 Tuesday, December 10, 2013 1:22 PM

OSPFv3 Commands 1331
User Guidelines
This command has no user guidelines.
Example
The following example displays the OSPF Virtual Interface information for
area 1 and its neighbor.
console#show ipv6 ospf virtual-link 1 1.1.1.1
Area ID........................................ 1
Neighbor Router ID............................. 1.1.1.1
Hello Interval................................. 10
Dead Interval.................................. 40
Iftransit Delay Interval....................... 1
Retransmit Interval............................ 5
State.......................................... point-to-point
Metric......................................... 10
Neighbor State................................. Full
show ipv6 ospf virtual-link brief
Use the show ipv6 ospf virtual-link brief command in Privileged EXEC mode
to display the OSPFV3 Virtual Interface information for all areas in the
system.
Syntax
show ipv6 ospf virtual-link brief
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC mode, Configuration mode and all Configuration submodes
User Guidelines
This command has no user guidelines.
Example
The following example displays the OSPF stub table.
2CSNXXX_SWUM200.book Page 1331 Tuesday, December 10, 2013 1:22 PM

1332 OSPFv3 Commands
console(config)#show ipv6 ospf virtual-link brief
Hello Dead Retransmit Transit
Area ID Neighbor Interval Interval Interval Delay
----------- ----------- ---------- ---------- ---------- --------
2CSNXXX_SWUM200.book Page 1332 Tuesday, December 10, 2013 1:22 PM

Router Discovery Protocol Commands 1333
55
Router Discovery Protocol
Commands
Dell Networking N3000/N4000 Series Switches
Routers can be configured to periodically send router discovery messages to
announce their presence to locally attached hosts. The router discovery
message advertises one or more IP addresses on the router that hosts can use
as their default gateway. Hosts can send a router solicitation message asking
any router that receives the message to immediately send a router
advertisement, so that the host does not have to wait for the next periodic
message.
Router discovery enables hosts to select from among multiple default
gateways and switch to a different default gateway if an initially designated
gateway goes down.
Commands in this Chapter
This chapter explains the following commands:
ip irdp
Use the ip irdp command in Interface Configuration mode to enable Router
Discovery on an interface. Use the no form of the command to disable Router
Discovery.
Syntax
ip irdp [multicast | holdtime
seconds
| maxadvertinterval
seconds
|
minadvertinterval
seconds
| preference
number
| address
address
]
ip irdp ip irdp multicast
ip irdp holdtime ip irdp preference
ip irdp maxadvertinterval show ip irdp
ip irdp minadvertinterval
–
2CSNXXX_SWUM200.book Page 1333 Tuesday, December 10, 2013 1:22 PM

1334 Router Discovery Protocol Commands
no ip irdp holdtime
•
multicast
—Configure the address that the interface uses to send the
router discovery advertisements to be 224.0.0.1, the all-hosts IP multicast
address. Use the
no
form of the command to use 255.255.255.255, the
limited broadcast address.
•
holdtime
seconds
—Integer value in seconds of the holdtime field of the
router advertisement sent from this interface. (Range: 4-9000 seconds)
•
maxadvertinterval
seconds
—Maximum time in seconds allowed between
sending router advertisements from the interface. (Range: 4 or the
minimum advertisement interval, whichever is greater, and 1800 seconds).
•
minadvertinterval
seconds
—Minimum time in seconds allowed between
sending router advertisements from the interface. (Range: 3 to value of
maximum advertisement interval in seconds)
•
preference
number
—Preference of the address as a default router address,
relative to other router addresses on the same subnet. (Range: -
2147483648 to 2147483647)
•
address
address
—IP address for router discovery advertisements. (Range:
224.0.0.1 [all-hosts IP multicast address] or 255.255.255.255 [limited
broadcast address])
Default Configuration
• Router discovery is disabled by default.
• 1800 seconds is the default value for holdtime.
• 600 seconds is the default value for maxadvertinterval.
• The minadvertinterval default value is 450.
• The preference default value is 0.
• IP address 224.0.0.1 is the default configuration for address.
Command Mode
Interface Configuration (VLAN) mode
User Guidelines
This command has no user guidelines.
2CSNXXX_SWUM200.book Page 1334 Tuesday, December 10, 2013 1:22 PM

Router Discovery Protocol Commands 1335
Example
The following example enables router discovery on the selected interface.
console(config)#interface vlan 15
console(config-if-vlan15)#ip irdp
ip irdp holdtime
Use the ip irdp holdtime command in Interface Configuration mode to
configure the value, in seconds, of the holdtime field of the router
advertisement sent from this interface. Use the no form of the command to
set the time to the default value.
Syntax
ip irdp holdtime
integer
no ip irdp holdtime
•
integer
— Integer value in seconds of the holdtime field of the router
advertisement sent from this interface. The holdtime must be no less than
the maximum advertisement interval and cannot be greater than 9000
seconds.
Default Configuration
The holdtime defaults to 3 times the maximum advertisement interval.
Command Mode
Interface Configuration (VLAN) mode.
User Guidelines
The holdtime is the length of time that a host considers the router
advertisement valid. After the holdtime expires, a host will no longer use the
router as its default gateway.
Example
The following example sets hold time at 2000 seconds for VLAN 15.
console(config)#interface vlan 15
console(config-if-vlan15)#ip irdp holdtime 2000
2CSNXXX_SWUM200.book Page 1335 Tuesday, December 10, 2013 1:22 PM

1336 Router Discovery Protocol Commands
ip irdp maxadvertinterval
Use the ip irdp maxadvertinterval command in Interface Configuration
mode to configure the maximum time, in seconds, allowed between sending
router advertisements from the interface. Use the no form of the command to
set the time to the default value.
Syntax
ip irdp maxadvertinterval
integer
no ip irdp maxadvertinterval
•
integer
— Maximum time in seconds allowed between sending router
advertisements from the interface. (Range: 4 or the minimum
advertisement interval, whichever is greater, and 1800 seconds)
Default Configuration
600 seconds is the default value.
Command Mode
Interface Configuration (VLAN) mode.
User Guidelines
The default values of the minimum advertisement interval and the holdtime
depend on the value of the maximum advertisement interval. Setting the
maximum advertisement interval changes the minimum advertisement
interval and holdtime if those values are at their defaults; so, the maximum
advertisement interval should always be set first. If the minimum
advertisement interval has been configured to a non-default value, the
maximum advertisement interval cannot be configured to a lower value than
the minimum advertisement interval. If the holdtime has been configured to
a non-default value, the maximum advertisement interval cannot be
configured to a value larger than the holdtime.
Example
The following example sets maximum advertisement interval at 600 seconds
for VLAN 15.
console(config)#interface vlan 15
2CSNXXX_SWUM200.book Page 1336 Tuesday, December 10, 2013 1:22 PM

Router Discovery Protocol Commands 1337
console(config-if-vlan15)#ip irdp maxadvertinterval 600
ip irdp minadvertinterval
Use the ip irdp minadvertinterval command in Interface Configuration
mode to configure the minimum time, in seconds, allowed between sending
router advertisements from the interface. Use the no form of the command to
set the time to the default value.
Syntax
ip irdp minadvertinterval
integer
no ip irdp minadvertinterval
•
integer
— Minimum time in seconds allowed between sending router
advertisements from the interface. (Range: 3 to value of maximum
advertisement interval in seconds)
Default Configuration
The default value is 0.75 times the maximum advertisement interval.
Command Mode
Interface Configuration (VLAN) mode.
User Guidelines
This command has no user guidelines.
Example
The following example sets minimum advertisement interval at 100 seconds
for VLAN 15.
console(config)#interface vlan 15
console(config-if-vlan15)#ip irdp minadvertinterval 100
2CSNXXX_SWUM200.book Page 1337 Tuesday, December 10, 2013 1:22 PM

1338 Router Discovery Protocol Commands
ip irdp multicast
To send router advertisements as IP multicast packets, use the ip irdp
multicast command in Interface Configuration mode. To send router
advertisements to the limited broadcast address (255.255.255.255), use the
no form of this command.
Syntax
ip irdp multicast
no ip irdp multicast
Default Configuration
Router discovery packets are sent to the all hosts IP multicast address
(224.0.0.1) by default.
Command Mode
Interface Configuration (VLAN) mode
User Guidelines
If a subnet includes any hosts that do not accept IP multicast packets, send
router advertisements to the limited broadcast address.
Example
The following example configures router discovery to send to the limited
broadcast address:
console(config)#interface vlan 15804 Router Discovery Protocol Commands www.
d e l l . c om | s u p p o r t . d e l l .com console(config-if-vlan15)#no ip
irdp multicast
ip irdp preference
Use the ip irdp preference command in Interface Configuration mode to
configure the preference of the address as a default router address relative to
other router addresses on the same subnet. Use the no form of the command
to set the preference to the default value.
2CSNXXX_SWUM200.book Page 1338 Tuesday, December 10, 2013 1:22 PM

Router Discovery Protocol Commands 1339
Syntax
ip irdp preference
integer
no ip irdp preference
•
integer
— Preference of the address as a default router address, relative to
other router addresses on the same subnet. (Range: -2147483648 to
2147483647
)
Default Configuration
0 is the default value.
Command Mode
Interface Configuration (VLAN) mode.
User Guidelines
This command has no user guidelines.
Example
The following example sets the ip irdp preference to 1000 for VLAN 15.
console(config)#interface vlan 15
console(config-if-vlan15)#ip irdp preference 1000
show ip irdp
Use the show ip irdp command in Privileged EXEC mode to display the
router discovery information for all interfaces, or for a specified interface.
Syntax
show ip irdp [vlan
vlan-id
]
•
vlan-id
— Valid VLAN ID
Default Configuration
This command has no default configuration.
2CSNXXX_SWUM200.book Page 1339 Tuesday, December 10, 2013 1:22 PM

1340 Router Discovery Protocol Commands
Command Mode
User EXEC, Privileged EXEC mode, Configuration mode and all
Configuration submodes
User Guidelines
This command has no user guidelines.
Example
The following example shows router discovery information for VLAN 15.
console#show ip irdp vlan 15
Interface Ad Mode Advertise Address Max Int Min Int Hold Time Preference
--------- ------- ----------------- ------- ------- -------- ----------
vlan15 Enable 224.0.0.1 600 450 1800 0
2CSNXXX_SWUM200.book Page 1340 Tuesday, December 10, 2013 1:22 PM
Routing Information Protocol Commands 1341
56
Routing Information Protocol
Commands
Dell Networking N2000/N3000/N4000 Series Switches
The Routing Information Protocol (RIP) has been a long-standing protocol
used by routers for exchanging route information. RIP is a distance vector
protocol whereby each route is characterized by the number of gateways, or
hops, a packet must traverse to reach its intended destination. Categorized as
an interior gateway protocol, RIP operates within the scope of an autonomous
system. RIP is a simple protocol. Its usefulness is limited to moderately sized
networks whose physical interconnections are of similar type and speed.
Dell Networking routing supports RIPv2 as specified in RFC 2453.
Commands in this Chapter
This chapter explains the following commands:
auto-summary
Use the auto-summary command in Router RIP Configuration mode to
enable the RIP auto-summarization mode. Use the no form of the command
to disable auto-summarization mode.
auto-summary hostroutesaccept router rip
default-information
originate (Router RIP
Configuration)
ip rip show ip rip
default-metric ip rip authentication show ip rip interface
distance rip ip rip receive version show ip rip interface brief
distribute-list out ip rip send version split-horizon
enable redistribute
–
2CSNXXX_SWUM200.book Page 1341 Tuesday, December 10, 2013 1:22 PM

1342 Routing Information Protocol Commands
Syntax
auto-summary
no auto-summary
Default Configuration
Disabled is the default configuration.
Command Mode
Router RIP Configuration mode.
User Guidelines
This command has no user guidelines.
Example
console(config-router)#auto-summary
default-information originate (Router RIP
Configuration)
Use the default-information originate command in Router RIP
Configuration mode to control the advertisement of default routes.
Syntax
default-information originate
no default-information originate
Default Configuration
The default configuration is no default-information originate.
Command Mode
Router RIP Configuration mode.
2CSNXXX_SWUM200.book Page 1342 Tuesday, December 10, 2013 1:22 PM

Routing Information Protocol Commands 1343
User Guidelines
Only routers that actually have Internet connectivity should advertise a
default route. All other routers in the network should learn the default route
from routers that have connections out to the Internet.
Example
console(config-router)#default-information originate
default-metric
Use the default-metric command in Router RIP Configuration mode to set a
default for the metric of distributed routes. Use the no form of the command
to return the metric to the default value.
Syntax
default-metric
number-value
no default-metric
•
number-value
— Metric for the distributed routes. (Range: 1-15)
Default Configuration
Default metric is not configured by default.
Command Mode
Router RIP Configuration mode.
User Guidelines
This command has no user guidelines.
Example
The following example sets a default of 12 for the metric of distributed
routes.
console(config-router)#default-metric 12
2CSNXXX_SWUM200.book Page 1343 Tuesday, December 10, 2013 1:22 PM

1344 Routing Information Protocol Commands
distance rip
Use the distance rip command in Router RIP Configuration mode to set the
route preference value of RIP in the router. Lower route preference values are
preferred when determining the best route. Use the no form of the command
to return the preference to the default value.
Syntax
distance rip
integer
no distance rip
•
integer
— RIP route preference. (Range: 1-255)
Default Configuration
15 is the default configuration.
Command Mode
Router RIP Configuration mode.
User Guidelines
This command has no user guidelines.
Example
The following example sets the route preference value of RIP in the router at
100.
console(config-router)#distance rip 100
distribute-list out
Use the distribute-list out command in Router RIP Configuration mode to
specify the access list to filter routes received from the source protocol. Use
the no form of the command to remove the access list from the specified
source protocol.
Syntax
distribute-list
accesslistname
out {ospf | static | connected}
2CSNXXX_SWUM200.book Page 1344 Tuesday, December 10, 2013 1:22 PM

Routing Information Protocol Commands 1345
no distribute-list
accesslistname
out {ospf | static | connected}
•
accesslistname
— The name used to identify the existing ACL. The range
is 1-31 characters.
•
ospf
— Apply the specific access list when OSPF is the source protocol.
•
static
— Apply the specified access list when packets come through a static
route.
•
connected
— Apply the specified access list when packets come from a
directly connected route.
Default Configuration
This command has no default configuration.
Command Mode
Router RIP Configuration mode.
User Guidelines
This command has no user guidelines.
Example
The following example elects access list ACL40 to filter routes received from
the source protocol.
console(config-router)#distribute-list ACL40 out static
enable
Use the enable command in Router RIP Configuration mode to reset the
default administrative mode of RIP in the router (active). Use the no form of
the command to disable the administrative mode for RIP.
Syntax
enable
no enable
2CSNXXX_SWUM200.book Page 1345 Tuesday, December 10, 2013 1:22 PM

1346 Routing Information Protocol Commands
Default Configuration
Enabled is the default configuration.
Command Mode
Router RIP Configuration mode.
User Guidelines
This command has no user guidelines.
Example
console(config-router)#enable
hostroutesaccept
Use the hostroutesaccept command in Router RIP Configuration mode to
enable the RIP hostroutesaccept mode. Use the no form of the command to
disable the RIP hostroutesaccept mode.
Syntax
hostroutesaccept
no hostroutesaccept
Default Configuration
Enabled is the default configuration.
Command Mode
Router RIP Configuration mode.
User Guidelines
This command has no user guidelines.
Example
console(config-router)#hostroutesaccept
2CSNXXX_SWUM200.book Page 1346 Tuesday, December 10, 2013 1:22 PM

Routing Information Protocol Commands 1347
ip rip
Use the ip rip command in Interface Configuration mode to enable RIP on a
router interface. Use the no form of the command to disable RIP on the
interface.
Syntax
ip rip
no ip rip
Default Configuration
Disabled is the default configuration.
Command Mode
Interface Configuration (VLAN) mode.
User Guidelines
This command has no user guidelines.
Example
console(config-if-vlan2)#ip rip
console(config-if-vlan2)#no ip rip
ip rip authentication
Use the ip rip authentication command in Interface Configuration Mode to
set the RIP Version 2 Authentication Type and Key for the specified VLAN.
Use the no form of the command to return the authentication to the default
value.
Syntax
ip rip authentication {none | {simple
key
} | {encrypt
key
key-id
}}
no ip rip authentication
• none—Do not use RIP authentication on the VLAN.
• simple—Use simple authentication on the VLAN.
2CSNXXX_SWUM200.book Page 1347 Tuesday, December 10, 2013 1:22 PM

1348 Routing Information Protocol Commands
•
key
— Authentication key for the VLAN. (Range: 16 bytes or less)
• encrypt — Use MD5 encryption for the RIP interface.
•
key-id
— Authentication key identifier for authentication type encrypt.
(Range: 0-255)
Default Configuration
This command has no default configuration.
Command Mode
Interface Configuration (VLAN) mode.
User Guidelines
This command has no user guidelines.
Example
The following example sets the RIP Version 2 Authentication Type and Key
for VLAN 11.
console(config-if-vlan11)#ip rip authentication encrypt pass123 35
ip rip receive version
Use the ip rip receive version command in Interface Configuration mode to
configure the interface to allow RIP control packets of the specified version(s)
to be received. Use the no form of the command to return the version to the
default value.
Syntax
ip rip receive version {rip1 | rip2 | both | none}
no ip rip receive version
•
rip1
— Receive only RIP version 1 formatted packets.
•
rip2
— Receive only RIP version 2 formatted packets.
•
both
— Receive packets from either format.
•
none
— Do not allow any RIP control packets to be received.
2CSNXXX_SWUM200.book Page 1348 Tuesday, December 10, 2013 1:22 PM

Routing Information Protocol Commands 1349
Default Configuration
Both is the default configuration.
Command Mode
Interface Configuration (VLAN) mode.
User Guidelines
This command has no user guidelines.
Example
The following example allows no RIP control packets to be received by VLAN
11.
console(config-if-vlan11)#ip rip receive version none
ip rip send version
Use the ip rip sent version command in Interface Configuration mode to
configure the interface to allow RIP control packets of the specified version to
be sent. Use the no form of the command to return the version to the default
value.
Syntax
ip rip send version {rip1 | rip1c | rip2 | none}
no ip rip send version
• rip1 — Send RIP version 1 formatted packets.
• rip1c — Send RIP version 1 compatibility mode, which sends RIP version
2 formatted packets via broadcast.
• rip2 — Send RIP version 2 using multicast.
• none — Do not allow any RIP control packets to be sent.
Default Configuration
RIP2 is the default configuration.
2CSNXXX_SWUM200.book Page 1349 Tuesday, December 10, 2013 1:22 PM

1350 Routing Information Protocol Commands
Command Mode
Interface Configuration (VLAN) mode.
User Guidelines
This command has no user guidelines.
Example
The following example allows no RIP control packets to be sent by VLAN 11.
console(config-if-vlan11)#ip rip send version none
redistribute
The redistribute command configures RIP protocol to redistribute routes
from the specified source protocol/routers. If the source protocol is OSPF,
there are five possible match options.
Syntax
redistribute ospf [metric
integer
] [match [internal] [external 1] [external 2]
[nssa-external 1] [nssa-external 2]]
no redistribute ospf
redistribute {static | connected} [metric
integer
]
•metric
integer
— Specifies the metric to use when redistributing the route.
Range: 0-15.
• match internal — Adds internal matches to any match types presently
being redistributed.
• match external 1 — Adds routes imported into OSPF as Type-1 external
routes into any match types presently being redistributed.
• match external 2 — Adds routes imported into OSPF as Type-2 external
routes into any match types presently being redistributed.
• match nssa-external 1 — Adds routes imported into OSPF as NSSA Type-
1 external routes into any match types presently being redistributed.
• match nssa-external 2 — Adds routes imported into OSPF as NSSA Type-
2 external routes into any match types presently being redistributed.
•
static
— Redistributes static routes.
2CSNXXX_SWUM200.book Page 1350 Tuesday, December 10, 2013 1:22 PM

Routing Information Protocol Commands 1351
• connected — Redistributes directly-connected routes.
Default Configuration
metric
integer
— not configured
match — internal
Command Mode
Router RIP Configuration mode.
User Guidelines
This command has no user guidelines.
Example
console(config-router)#redistribute ospf metric 10 match nssa-external 1
console(config-router)#redistribute connected metric 1
router rip
Use the router rip command in Global Configuration mode to enter Router
RIP mode.
Syntax
router rip
Default Configuration
This command has no default configuration.
Command Mode
Global Configuration mode.
User Guidelines
This command has no user guidelines.
Example
The following example enters Router RIP mode.
console(config)#router rip
2CSNXXX_SWUM200.book Page 1351 Tuesday, December 10, 2013 1:22 PM

1352 Routing Information Protocol Commands
console(config-router)#
show ip rip
Use the show ip rip command in Privileged EXEC mode to display
information relevant to the RIP router.
Syntax
show ip rip
Default Configuration
The command has no default configuration.
Command Mode
Privileged EXEC mode, Configuration mode and all Configuration submodes
User Guidelines
This command has no user guidelines.
Example
The following example displays information relevant to the RIP router.
console#show ip rip
RIP Admin Mode................................. Enable
Split Horizon Mode............................. Simple
Auto Summary Mode.............................. Enable
Host Routes Accept Mode........................ Enable
Global route changes........................... 0
Global queries................................. 0
Default Metric................................. 12
Default Route Advertise........................ 0
Redistributing.................................
Source......................................... Connected
Metric......................................... 2
Distribute List................................ Not configured
Redistributing.................................
Source......................................... ospf
Metric......................................... 10
Match Value.................................... 'nssa-external 1'
Distribute List................................ Not configured
2CSNXXX_SWUM200.book Page 1352 Tuesday, December 10, 2013 1:22 PM

Routing Information Protocol Commands 1353
show ip rip interface
Use the show ip rip interface command in Privileged EXEC mode to display
information related to a particular RIP interface.
Syntax
show ip rip interface vlan
vlan-id
•
vlan-id
— Valid VLAN ID.
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC mode, Configuration mode and all Configuration submodes
User Guidelines
This command has no user guidelines.
Example
The following example displays information related to the VLAN 15 RIP
interface.
console#show ip rip interface vlan 15
Interface...................................... 15
IP Address..................................... -----
Send version................................... RIP-2
Receive version................................ Both
RIP Admin Mode................................. Disable
Link State..................................... -----
Authentication Type............................ MD5
Authentication Key............................. "pass123"
Authentication Key ID.......................... 35
Bad Packets Received........................... -----
Bad Routes Received............................ -----
Updates Sent................................... -----
2CSNXXX_SWUM200.book Page 1353 Tuesday, December 10, 2013 1:22 PM

1354 Routing Information Protocol Commands
show ip rip interface brief
Use the show ip rip interface brief command in Privileged EXEC mode to
display general information for each RIP interface. For this command to
display successful results routing must be enabled per interface (i.e. ip rip).
Syntax
show ip rip interface brief
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC mode, Configuration mode and all Configuration submodes
User Guidelines
This command has no user guidelines.
Example
The following example displays general information for each RIP interface.
console#show ip rip interface brief
Send Receive RIP Link
Interface IP Address Version Version Mode State
---------- ---------- -------- ----------- --------- ----------
vlan1 0.0.0.0 RIP-2 Both Disable Down
vlan2 0.0.0.0 RIP-2 Both Disable Down
split-horizon
Use the split-horizon command in Router RIP Configuration mode to set the
RIP split horizon mode. Use the no form of the command to return the mode
to the default value.
Syntax
split-horizon {none | simple | poison}
no split-horizon
2CSNXXX_SWUM200.book Page 1354 Tuesday, December 10, 2013 1:22 PM

Routing Information Protocol Commands 1355
•
none
— RIP does not use split horizon to avoid routing loops.
•
simple
— RIP uses split horizon to avoid routing loops.
•
poison
— RIP uses split horizon with poison reverse (increases routing
packet update size).
Default Configuration
Simple is the default configuration.
Command Mode
Router RIP Configuration mode.
User Guidelines
This command has no user guidelines.
Example
The following example does not use split horizon.
console(config-router)#split-horizon none
2CSNXXX_SWUM200.book Page 1355 Tuesday, December 10, 2013 1:22 PM

1356 Routing Information Protocol Commands
2CSNXXX_SWUM200.book Page 1356 Tuesday, December 10, 2013 1:22 PM

Tunnel Interface Commands 1357
57
Tunnel Interface Commands
Dell Networking N3000/N4000 Series Switches
Dell Networking provides for the creation, deletion, and management of
tunnel interfaces. They are dynamic interfaces that are created and deleted by
user configuration.
Tunnel interfaces are used for the following purposes.
• IPv4 tunnels
• IPv6 tunnels
Each router interface (port or VLAN interface) may have associated tunnel
interfaces. Each interface can have multiple tunnel interfaces. There is no set
limit to the number of tunnel interfaces associated with a router interface.
There is a compile platform limitation to the number of tunnel interfaces
available to the entire system.
To support IPv4 to IPv6 transition, Dell Networking supports configured
tunnels (RFC 4213) and automatic 6to4 tunnels (RFC 3056). 6to4 tunnels
are automatically formed for IPv4 tunnels carrying IPv6 traffic. The
automatic tunnels IPv4 destination address is derived from the 6to4 IPv6
address of the tunnel’s next hop. Dell Networking can act as a 6to4 border
router that connects a 6to4 site to a 6to4 domain. The border router sends
and receives tunneled traffic from routers in the 6to4 domain that include
other 6to4 border routers and 6to4 relay routers.
Commands in this Chapter
This chapter explains the following commands:
interface tunnel tunnel mode ipv6ip
show interfaces tunnel tunnel source
tunnel destination
–
2CSNXXX_SWUM200.book Page 1357 Tuesday, December 10, 2013 1:22 PM

1358 Tunnel Interface Commands
interface tunnel
Use the interface tunnel command in Global Configuration mode to enter
the interface configuration mode for a tunnel.
Syntax
interface tunnel
tunnel-id
no interface tunnel
tunnel-id
•
tunnel-id
— Tunnel identifier. (Range: 0–7)
Default Configuration
This command has no default configuration.
Command Mode
Global Configuration mode.
User Guidelines
This command has no user guidelines.
Example
The following example enables the interface configuration mode for tunnel 1.
console(config)#interface tunnel 1
console(config-if-tunnel1)#
show interfaces tunnel
Use the show interfaces tunnel command in Privileged EXEC mode to
display the parameters related to tunnel such as tunnel mode, tunnel source
address and tunnel destination address.
Syntax
show interfaces tunnel [
tunnel-id
]
•
tunnel-id
— Tunnel identifier. (Range: 0–7)
2CSNXXX_SWUM200.book Page 1358 Tuesday, December 10, 2013 1:22 PM

Tunnel Interface Commands 1359
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC mode, Configuration mode and all Configuration submodes
User Guidelines
This command has no user guidelines.
Examples
The following examples show the parameters related to an individual tunnel
and to all tunnel interfaces.
console#show interfaces tunnel 1
Interface Link Status.......................... down
MTU size....................................... 1480 bytes
console#show interfaces tunnel
TunnelId Interface TunnelMode SourceAddress DestinationAddress
-------- --------- ---------- ------------- ----------------
1 tunnel 1 IPv6OVER4 10.254.25.14 10.254.25.10
2 tunnel 2 IPv6OVER4 10.254.20.10
tunnel destination
Use the tunnel destination command in Interface Configuration mode to
specify the destination transport address of the tunnel.
Syntax
tunnel destination
ip-address
no tunnel destination
•
ip-addr
ess — Valid IPv4 address.
Default Configuration
This command has no default configuration.
2CSNXXX_SWUM200.book Page 1359 Tuesday, December 10, 2013 1:22 PM

1360 Tunnel Interface Commands
Command Mode
Interface Configuration (Tunnel) mode.
User Guidelines
This command has no user guidelines.
Example
The following example specifies the destination transport address of tunnel 1.
console(config)#interface tunnel 1
console(config-if-tunnel1)#tunnel destination 10.1.1.1
tunnel mode ipv6ip
Use the tunnel mode ipv6ip command in Interface Configuration mode to
specify the mode of the tunnel.
Syntax
tunnel mode ipv6ip [6to4]
no tunnel mode
•
6to4
— Sets the tunnel mode to automatic.
Default Configuration
This command has no default configuration.
Command Mode
Interface Configuration (Tunnel) mode.
User Guidelines
This command has no user guidelines.
Example
The following example specifies ipv6ip mode for tunnel 1.
console(config)#interface tunnel 1
console(config-if-tunnel1)#tunnel mode ipv6ip
console(config-if-tunnel1)#tunnel mode ipv6ip 6to4
2CSNXXX_SWUM200.book Page 1360 Tuesday, December 10, 2013 1:22 PM

Tunnel Interface Commands 1361
tunnel source
Use the tunnel source command in Interface Configuration mode to specify
the source transport address of the tunnel, either explicitly or by reference to
an interface.
Syntax
tunnel source {
ip-address
|
interface-type interface-number
}
no tunnel source
•
ip-address
—Valid IPv4 address.
•
interface-type
—Valid interface type. VLAN is the only type supported.
•
interface-number
—Valid interface number.
Default Configuration
This command has no default configuration.
Command Mode
Interface Configuration (Tunnel) mode.
User Guidelines
This command has no user guidelines.
Example
The following example specifies VLAN 11 as the source transport address of
the tunnel.
console(config)#interface tunnel 1
console(config-if-tunnel1)#tunnel source vlan 11
2CSNXXX_SWUM200.book Page 1361 Tuesday, December 10, 2013 1:22 PM

1362 Tunnel Interface Commands
2CSNXXX_SWUM200.book Page 1362 Tuesday, December 10, 2013 1:22 PM

Virtual Router Redundancy Protocol Commands 1363
58
Virtual Router Redundancy Protocol
Commands
Dell Networking N3000/N4000 Series Switches
An end station running IP needs to know the address of its first hop router.
While some network administrators choose to install dynamic router
discovery protocols such as DHCP, others prefer to statically allocate router
addresses. If the router identified by such a statically allocated address goes
down, the end station loses connectivity. The Virtual Router Redundancy
Protocol (VRRP) is designed to provide backup for the failing router without
requiring any action on the part of the end station. It is based on the concept
of having more than one router recognize the same IP address. One of the
routers is elected the master router and handles all traffic sent to the specified
virtual router IP address. If the master router fails, one of the backup routers
is elected in its place and starts handling traffic sent to the address. This
change is transparent to end stations.
VRRP increases the availability of the default path without requiring
configuration of dynamic routing or router discovery protocols on every end
station.
Multiple virtual routers can be defined on a single router interface.
Pingable VRRP Interface
RFC 3768 specifies that a router may only accept IP packets sent to the
virtual router’s IP address if the router is the address owner. In practice, this
restriction makes it more difficult to troubleshoot network connectivity
problems. When a host cannot communicate, it is common to ping (send an
ICMP Echo Request) the host’s default gateway to determine whether the
problem is in the first hop of the path to the destination. When the default
gateway is a virtual router that does not respond to pings, the operator cannot
use this troubleshooting technique. Because of this, it has been common for
VRRP implementations to respond to pings, in spite of the prohibition in the
RFC. The IETF has recognized the issue, and a draft revision of the VRRP
2CSNXXX_SWUM200.book Page 1363 Tuesday, December 10, 2013 1:22 PM

1364 Virtual Router Redundancy Protocol Commands
RFC defines a new configuration option that allows the router to accept any
packet sent to a VRRP address, regardless of whether the VRRP Master is the
address owner.
The Pingable VRRP Interface feature, when enabled, allows the VRRP master
to respond to both fragmented and unfragmented ICMP echo requests
packets destined to a VRRP address (or addresses). A virtual router in backup
state discards these. For any packet destined to a VRRP address (or
addresses), the VRRP master responds with VRRP address as the source IPv4
address and VRMAC as the source MAC address. A configuration option
controls whether the router responds to Echo Requests sent to a VRRP IP
address.
Dell Networking 4.0 includes a separate configuration option that controls
whether the router responds to ICMP Echo Requests. When Echo Replies are
disabled using that option, the VRRP master does not respond to Echo
Requests, even if this new option is enabled.
VRRP Route/Interface Tracking
The VRRP Route/Interface Tracking feature extends the capability of the
Virtual Router Redundancy Protocol (VRRP) to allow tracking of specific
route/interface IP states, within the router, that can alter the priority level of a
virtual router for a VRRP group. Exception to this is, if that VRRP group is
the IP address owner, and, in that case, its priority is fixed at 255 and cannot
be reduced through the tracking process.
VRRP Route/Interface Tracking provides a way to ensure the best VRRP
router is master for the group by altering VRRP priorities to the status of
tracked objects, such as IP interface or IP route states. In the process of
altering the VRRP priorities the priority must not go below 1 or above the
configured priority.
NOTE: Note that the mastership only switches on a priority change if
preempt is enabled.
2CSNXXX_SWUM200.book Page 1364 Tuesday, December 10, 2013 1:22 PM
Virtual Router Redundancy Protocol Commands 1365
Interface Tracking
For interface tracking, VRRP is a routing event client. When a routing
interface goes up or down (or routing is disabled globally, implying all routing
interfaces are down), VRRP checks if the interface is tracked. If so, it adjusts
the priority. Interface tracking is useful for tracking interfaces that are not
configured for VRRP. Only IP interfaces are tracked.
Route Tracking
The network operator may perform this task to track the reachability of an IP
route. A tracked route is considered up when a routing table entry exists for
the route and the route is accessible. For route tracking, make VRRP a best
route client of RTO. When a tracked route is added or deleted, change the
priority. For simplicity, routes are not distinguished with the next hop
interface that has VRRP enabled. So VRRP Route Tracking can ignore route
modifications.
Commands in this Chapter
This chapter explains the following commands:
Virtual Router Redundancy Protocol Commands
Pingable VRRP Commands
ip vrrp vrrp timers advertise
vrrp accept-mode vrrp timers learn
vrrp authentication vrrp track interface
vrrp description vrrp track ip route
vrrp ip show vrrp
vrrp mode show vrrp interface
vrrp preempt show vrrp interface brief
vrrp priority show vrrp interface stats
ip vrrp accept-mode show ip vrrp interface
2CSNXXX_SWUM200.book Page 1365 Tuesday, December 10, 2013 1:22 PM

1366 Virtual Router Redundancy Protocol Commands
Virtual Router Redundancy Protocol Commands
ip vrrp
Use the ip vrrp command in Global Configuration mode to enable the
administrative mode of VRRP for the router. Use the no form of the
command to disable the administrative mode of VRRP for the router.
Syntax
ip vrrp
no ip vrrp
Default Configuration
VRRP is disabled by default.
Command Mode
Global Configuration mode.
User Guidelines
This command has no user guidelines.
Example
The following example enables VRRP protocol on the router.
console(config)#ip vrrp
vrrp accept-mode
Use the vrrp accept-mode command in Interface (VLAN) Configuration
mode to enable the VRRP Master to accept ping packets sent to one of the
virtual router’s IP addresses from an external device. Use the no form of the
command to disable responding to ping packets.
Syntax
vrrp
vrid
accept-mode
no vrrp
vrid
accept-mode
2CSNXXX_SWUM200.book Page 1366 Tuesday, December 10, 2013 1:22 PM

Virtual Router Redundancy Protocol Commands 1367
• vrid — Virtual router identification. (Range: 1-255)
Default Configuration
The default configuration is disabled.
Command Mode
Interface Configuration (VLAN) mode.
User Guidelines
The VRRP IP address is not pingable from within the switch.
vrrp authentication
Use the vrrp authentication command in Interface Configuration mode to
set the authentication details value for the virtual router configured on a
specified interface. Use the no form of the command to return the
authentication type to the default value.
Syntax
vrrp group authentication
{none | simple
key
}
no vrrp group authentication
•
group
—The virtual router identifier. (Range: 1-255)
•
none
—Indicates authentication type is none.
•
simple
—Authentication type is a simple text password.
•
key
—The key for simple authentication. (Range: String values)
Default Configuration
None is the default configuration.
Command Mode
Interface Configuration (VLAN) mode.
User Guidelines
This command has no user guidelines.
2CSNXXX_SWUM200.book Page 1367 Tuesday, December 10, 2013 1:22 PM

1368 Virtual Router Redundancy Protocol Commands
Example
The following example sets the authorization details value for VRRP router
group 5 on VLAN 15.
console(config)#interface vlan 15
console(config-if-vlan15)#vrrp 2 authentication simple test123
vrrp description
Use the vrrp description command in Interface Configuration mode to assign
a description to the Virtual Router Redundancy Protocol (VRRP) group. To
remove the description, use the no form of the command.
Syntax
vrrp group description
text
no vrrp group description
•
group
—The virtual router identifier. (Range: 1-255)
•
text
—Description for the virtual router group up to 80 characters.
Default Configuration
No description is present.
Command Mode
Interface Configuration (VLAN) mode.
User Guidelines
This command accepts any printable characters for the name. Descriptions
containing spaces must be wrapped with quotes.
Example
The following example creates virtual router group 5 on VLAN 15 and
configures its description.
console(config)#interface vlan 15
console(config-if-vlan15)#vrrp 5
console(config-if-vlan15)#vrrp 5 description “Sales and Marketing”
2CSNXXX_SWUM200.book Page 1368 Tuesday, December 10, 2013 1:22 PM

Virtual Router Redundancy Protocol Commands 1369
vrrp ip
Use the vrrp ip command in Interface Configuration mode to enable VRRP
and set the virtual router IP address value for an interface. Use the no form of
the command remove the secondary IP address. It is not possible to remove
the primary IP address once assigned. Remove the VRRP group instead.
Syntax
vrrp
group
ip
ip-address
[secondary]
no vrrp
group
ip
ip-address
vlan
secondary
•
group
—The virtual router identifier. (Range: 1-255)
•
ip-address
—The IP address of the virtual router.
•
secondary
—Designates the virtual router IP address as a secondary IP
address on an interface.
Default Configuration
VRRP is not configured on the interface.
Command Mode
Interface Configuration (VLAN) mode.
User Guidelines
The virtual router IP addresses must be a valid host address on the local
subnet based on the IP address and subnet mask configured on the VLAN
interface. The VRRP IP address cannot be either the broadcast address or a
network address. To configure vrrp, perform the following steps:
1
Enable ip routing in global configuration mode.
2
Enable ip vrrp globally.
3
Set an IP address on the desired interface where VRRP is to be configured.
4
Configure the VRRP group ID on the selected interface.
5
Set the virtual router ID and address on the selected interface.
6
Enable VRRP on the interface using the
vrrp mode
command.
2CSNXXX_SWUM200.book Page 1369 Tuesday, December 10, 2013 1:22 PM

1370 Virtual Router Redundancy Protocol Commands
Example
The following example configures VRRP on VLAN 15.
console#configure
console(config)#ip routing
console(config)#ip vrrp
console(config-vlan)#vlan 15
console(config-vlan)#vlan routing 15
console(config-vlan)#exit
console(config)#interface vlan 15
console(config-if-vlan15)#ip address 192.168.5.1 255.255.255.0
console(config-if-vlan15)#vrrp 20
console(config-if-vlan15)#vrrp 20 ip 192.168.5.20
console(config-if-vlan15)#vrrp 20 mode
vrrp mode
Use the vrrp mode command in Interface Configuration mode to enable the
virtual router configured on an interface. Enabling the status field starts a
virtual router. Use the no form of the command to disable the virtual router.
Syntax
vrrp
vr-id
mode
no vrrp
vr-id
mode
•
vr-id
— The virtual router identifier. (Range: 1-255)
Default Configuration
Disabled is the default configuration.
Command Mode
Interface Configuration (VLAN) mode.
User Guidelines
This command has no user guidelines.
Example
The following example enables the virtual router for VLAN 15.
console(config)#interface vlan 15
2CSNXXX_SWUM200.book Page 1370 Tuesday, December 10, 2013 1:22 PM

Virtual Router Redundancy Protocol Commands 1371
console(config-if-vlan15)#vrrp 5 mode
vrrp preempt
Use the vrrp preempt command in Interface Configuration mode to set the
preemption mode value for the virtual router configured on a specified
interface. Use the no form of the command to disable preemption mode.
Syntax
vrrp
group
preempt [delay
seconds
]
no vrrp
group
preempt
•
group
—The virtual router identifier. (Range: 1-255)
•
seconds
—The number of seconds the VRRP router will wait before issuing
an advertisement claiming master ownership.
Default Configuration
Enabled is the default configuration. Delay defaults to 0 seconds.
Command Mode
Interface Configuration (VLAN) mode.
User Guidelines
As per the VRRP RFC, when preemption is enabled, the backup router
discards the advertisements until the masterdowntimer starts. This feature
requires immediate sending of advertisements when the preemption case
occurs and the delay is 0. This is a violation according to the RFC 3768.
Delay, if configured, will cause the VRRP router to wait the specified number
of seconds before issuing an advertisement claiming master ownership.
Example
The following example sets the preemption mode value for the virtual router
for VLAN 15.
console(config)#interface vlan 15
console(config-if-vlan15)#vrrp 5 preempt
2CSNXXX_SWUM200.book Page 1371 Tuesday, December 10, 2013 1:22 PM

1372 Virtual Router Redundancy Protocol Commands
vrrp priority
Use the vrrp priority command in Interface Configuration mode to set the
priority value for the virtual router configured on a specified interface. Use
the no form of the command to return the priority to the default value.
Syntax
vrrp
group
priority
level
no vrrp
group
priority
level
•
group
— The virtual router identifier. (Range: 1-255)
•
level
— Priority value for the interface. (Range: 1-254)
Default Configuration
Priority
has a default value of 100.
Command Mode
Interface Configuration (VLAN) mode.
User Guidelines
The VRRP router with the highest numerical value for priority will become
the VR master. When the VRRP priorities are equal, the router with the
numerically highest IP address will win the election and become master. If the
VRRP router is the owner of the VR IP address, its priority will be 255, and
this value cannot be changed.
Example
The following example sets the priority value for the virtual router 5 on VLAN
15.
console(config-if-vlan15)#vrrp 5 priority 20
vrrp timers advertise
Use the vrrp timers advertise command in Interface Configuration mode to
set the frequency, in seconds, that an interface on the specified virtual router
sends a virtual router advertisement. Use the no form of the command to
return the advertisement frequency to the default value.
2CSNXXX_SWUM200.book Page 1372 Tuesday, December 10, 2013 1:22 PM

Virtual Router Redundancy Protocol Commands 1373
Syntax
vrrp
group
timers advertise
interval
no vrrp
group
timers advertise
interval
•
group
— The virtual router identifier. (Range: 1-255)
•
interval
— The frequency at which an interface on the specified virtual
router sends a virtual router advertisement. (Range: 1-255 seconds)
Default Configuration
Interval
has a default value of 1.
Command Mode
Interface Configuration (VLAN) mode.
User Guidelines
This command has no user guidelines.
Example
The following example sets the frequency at which the VLAN 15 virtual
router 5 sends a virtual router advertisement.
console(config-if-vlan15)#vrrp 5 timers advertise 10
vrrp timers learn
Use the vrrp timers learn command in Interface Configuration mode to
configure the router, when it is acting as backup virtual router for a Virtual
Router Redundancy Protocol (VRRP) group, to learn the advertisement
interval used by the master virtual router. Use the no form of the command to
prevent the router from learning the advertisement interval from the master
virtual router.
Syntax
vrrp
group
timers learn
no vrrp
group
timers learn
•
group
— The virtual router identifier. (Range: 1-255)
2CSNXXX_SWUM200.book Page 1373 Tuesday, December 10, 2013 1:22 PM

1374 Virtual Router Redundancy Protocol Commands
Default Configuration
Timer learning is disabled by default and the router uses the configured
advertisement.
Command Mode
Interface Configuration (VLAN) mode.
User Guidelines
This command has no user guidelines.
Example
The following configures VLAN 15 virtual router to learn the advertisement
interval used by the master virtual router.
console(config-if-vlan15)#vrrp 5 timers learn
vrrp track interface
Use the vrrp track interface command in Interface Configuration mode to
alter the priority of the VRRP router based on the availability of its interfaces.
It is useful for tracking interfaces that are not configured for VRRP. Only
routing interfaces may be tracked. A tracked interface is up if routing on that
interface is up. Otherwise, the tracked interface is down.
When the tracked interface is down, or the interface has been removed from
the router, the priority of the VRRP router will be decremented by the value
specified in the priority argument. When the interface is up for the IP
protocol, the priority will be incremented by the priority value.
A VRRP configured interface can track more than one interface. When a
tracked interface goes down, then the priority of the router will be decreased
by 10 (default priority decrement) for each downed interface. The default
priority decrement is changed using the priority argument. The default
priority of the virtual router is 100, and the default decrement priority is 10.
By default, no interfaces are tracked. If you specify, just the interface to be
tracked without giving the priority, which is optional, then the default priority
will be set.
2CSNXXX_SWUM200.book Page 1374 Tuesday, December 10, 2013 1:22 PM

Virtual Router Redundancy Protocol Commands 1375
Use the no form of this command to remove the interface from the tracked
list or to restore the priority decrement to its default. When removing an
interface from the tracked list, the priority is incremented by the decrement
value if that interface is down.
Syntax
vrrp
group
track interface vlan
vlan-id
[decrement
priority
]
no vrrp
group
track interface vlan
vlan-id
•
group
—The virtual router identifier. (Range: 1-255)
•
vlan
vlan-id
—Valid VLAN ID.
•
priority
—Priority decrement value for the tracked interface. (Range: 1-
254)
Default Configuration
No interfaces are tracked. The default decrement priority is 10.
Command Mode
Interface Configuration (VLAN) mode.
User Guidelines
This command has no user guidelines.
Example
The following example adds VLAN 2 to the virtual router tracked list (with a
priority decrement value of 20.)
(config-if-vlan10)#vrrp 1 track interface vlan 2 decrement 20
vrrp track ip route
Use the vrrp track ip route command to track the route reachability. When
the tracked route is deleted, the priority of the VRRP router is decremented
by the value specified in the priority argument. When the tracked route is
added, the priority is incremented by the same. A VRRP configured interface
can track more than one route. When a tracked route goes down, the priority
of the router is decreased by 10 (default priority decrement) for each downed
2CSNXXX_SWUM200.book Page 1375 Tuesday, December 10, 2013 1:22 PM

1376 Virtual Router Redundancy Protocol Commands
route. By default no routes are tracked. If we specify just the route to be
tracked without specifying the optional parameter, then the default priority
will be set.
Use the no form of this command to remove the route from the tracked list or
to restore the priority decrement to its default. When removing a tracked IP
route from the tracked list, priority should be incremented by the decrement
value if the route is not reachable.
Syntax
vrrp
group
track ip route
ip-address/prefix-length
[decrement
priority
]
no vrrp
group
track ip route
ip-address/prefix-length
•
group
—
The virtual router identifier. (Range: 1–255).
•
ip-address/prefix-length
—
Specifies the route to be tracked.
•
priority
—
Priority decrement value for the tracked route. (Range: 1–254).
Default Configuration
There are no routes tracked by default.
The default decrement priority is 10.
Command Mode
Interface Configuration (VLAN) mode.
User Guidelines
There are no user guidelines for this command.
Example
The following example adds the route 2.2.2.0/24 to the virtual router tracked
list (with a priority decrement value of 20).
console(config-if-vlan10)#vrrp 1 track ip route 2.2.2.0/24 decrement 20
show vrrp
Use the show vrrp command in User EXEC or Privileged EXEC mode to
display the global VRRP configuration and status as well as the brief or
detailed status of one or all VRRP groups.
2CSNXXX_SWUM200.book Page 1376 Tuesday, December 10, 2013 1:22 PM

Virtual Router Redundancy Protocol Commands 1377
Syntax
show vrrp [brief |
group
]
•
group
—The virtual router group identifier. Range 1-255.
•
brief
—Provide a summary view of the VRRP group information.
Default Configuration
Show information on all VRRP groups.
Command Mode
User EXEC, Privileged EXEC mode, Configuration mode and all
Configuration submodes
User Guidelines
This command has no user guidelines.
Example
The following example displays detailed VRRP status.
console# show vrrp
Admin Mode..................................... Enable
Router Checksum Errors......................... 0
Router Version Errors.......................... 0
Router VRID Errors............................. 0
Vlan 7 – Group 1
Primary IP Address............................. 192.168.5.55
VMAC Address................................... 0000.5E00.0101
Authentication Type............................ None
Priority....................................... 60
Configured Priority............................ 100
Advertisement Interval (secs).................. 10
Accept Mode.................................... Enable
Pre-empt Mode.................................. Enable
Pre-empt Delay.................................. Enable
Administrative Mode............................ Enable
State.......................................... Initialized
Timers Learn Mode................................ Enable
Description .....................................
Track Interface................................ vlan 3
2CSNXXX_SWUM200.book Page 1377 Tuesday, December 10, 2013 1:22 PM

1378 Virtual Router Redundancy Protocol Commands
Track Interface State ......................... Down
Track Interface DecrementPriority ............. 20
Track Route (pfx/len) ......................... 10.10.10.0/24
Track Route Reachable ......................... False
Track Route DecrementPriority ................. 20
Vlan 7 – Group 2
Primary IP Address............................. 192.168.5.65
VMAC Address................................... 0000.5E00.0202
Authentication Type............................ None
Priority....................................... 60
Configured Priority............................ 100
Advertisement Interval (secs).................. 10
Accept Mode ................................... Enable
Pre-empt Mode.................................. Enable
Pre-empt Delay................................. 0
Administrative Mode............................ Enable
State.......................................... Initialized
Timers Learn Mode............................ Disable
Description .....................................
Track Interface................................ vlan 3
Track Interface State ......................... Down
Track Interface DecrementPriority ............. 20
Track Route (pfx/len) ......................... 10.10.10.0/24
Track Route Reachable ......................... False
Track Route DecrementPriority ................. 20
console#show vrrp brief
Interface Grp Prio IP Address Mode State
--------- --- ---- -------------- ------ ------------
V1 1 2 60 0.0.0.0 Disable Initialize
V1 2 5 70 192.168.5.55 Enable Initialize
show vrrp interface
Use the show vrrp interface command in User EXEC or Privileged EXEC
mode to display all configuration information and VRRP router statistics of a
virtual router configured on a specific interface.
Syntax
show vrrp interface [brief | vlan
vlan-id
{stats}]
•
brief
—
Display summary information about each virtual router configured on
the switch.
2CSNXXX_SWUM200.book Page 1378 Tuesday, December 10, 2013 1:22 PM

Virtual Router Redundancy Protocol Commands 1379
•
stats
—
Display the statistical information about each virtual router configured
on the VLAN.
•
vlan-id
—
Display information about each virtual router configured on the
VLAN. Valid interface type (VLAN) and interface number (vlan-id).
Default Configuration
Show information for each group in the specified interface.
Command Mode
User EXEC, Privileged EXEC mode, Configuration mode and all
Configuration submodes
User Guidelines
This command has no user guidelines.
Example
The following example displays all configuration information about the
VLAN 15 virtual router.
console#show vrrp interface vlan 7
Vlan 7 – Group 1
Primary IP Address........................... 192.168.5.55
VMAC Address................................ 0000.5E00.0101
Authentication Type............................ None
Priority....................................... 100
Configured Priority............................ 100
Advertisement Interval (secs).................. 10
Accept Mode.................................... Disable
Pre-empt Mode.................................. Enable
Pre-empt Delay................................. 0
Administrative Mode............................ Enable
State.......................................... Initialized
Timers Learn Mode.............................. Disable
Description.................................... GoodStuff
The following example displays all configuration information about the
virtual router on the selected interface.
console#show vrrp interface brief
Interface VRID IP Address Mode State
--------- ---- -------------- ------ ------------
vlan1 2 0.0.0.0 Disable Initialize
2CSNXXX_SWUM200.book Page 1379 Tuesday, December 10, 2013 1:22 PM

1380 Virtual Router Redundancy Protocol Commands
vlan2 5 192.168.5.55 Enable Initialize
The following example displays all statistical information about the VLAN 15
virtual router.
console#show vrrp interface vlan 15 stats
Vlan 15 – Group 5
UpTime........................... 0 days 0 hrs 0 mins 0 secs
Protocol....................................... IP
State Transitioned to Master................... 0
Advertisement Received......................... 0
Advertisement Interval Errors.................. 0
Authentication Failure......................... 0
IP TTL Errors.................................. 0
Zero Priority Packets Received................. 0
Zero Priority Packets Sent..................... 0
Invalid Type Packets Received.................. 0
Address List Errors ........................... 0
Invalid Authentication Type.................... 0
Authentication Type Mismatch................... 0
Packet Length Errors........................... 0
show vrrp interface brief
Use the show vrrp interface brief command in Privileged EXEC mode to
display information about each virtual router configured on the switch. It
displays information about each virtual router.
Syntax
show vrrp interface brief
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC mode, Configuration mode and all Configuration submodes
User Guidelines
This command has no user guidelines.
2CSNXXX_SWUM200.book Page 1380 Tuesday, December 10, 2013 1:22 PM

Virtual Router Redundancy Protocol Commands 1381
Example
The following example displays all configuration information about the
virtual router on the selected interface.
console#show vrrp interface brief
Interface VRID IP Address Mode State
--------- ---- -------------- ------ ------------
vlan1 2 0.0.0.0 Disable Initialize
vlan2 5 192.168.5.55 Enable Initialize
show vrrp interface stats
Use the show vrrp interface stats command in User EXEC mode to display
the statistical information about each virtual router configured on the switch.
Syntax
show vrrp interface stats vlan
vlan-id vr-id
•
vlan-id
— Valid VLAN ID.
•
vr-id
— The virtual router identifier. (Range: 1-255)
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC mode, Configuration mode and all Configuration submodes
User Guidelines
This command has no user guidelines.
Example
The following example displays all statistical information about the VLAN 15
virtual router.
console#show vrrp interface stats vlan 15 5
UpTime..................... 0 days 0 hrs 0 mins 0 secs
Protocol....................................... IP
State Transitioned to Master................... 0
Advertisement Received......................... 0
Advertisement Interval Errors.................. 0
2CSNXXX_SWUM200.book Page 1381 Tuesday, December 10, 2013 1:22 PM

1382 Virtual Router Redundancy Protocol Commands
Authentication Failure......................... 0
IP TTL Errors.................................. 0
Zero Priority Packets Received................. 0
Zero Priority Packets Sent..................... 0
Invalid Type Packets Received.................. 0
Address List Errors ........................... 0
Invalid Authentication Type.................... 0
Authentication Type Mismatch................... 0
Packet Length Errors........................... 0
Pingable VRRP Commands
ip vrrp accept-mode
Use the ip vrrp accept-mode command in Interface (VLAN) Configuration
mode to enable the VRRP Master to accept ping packets sent to one of the
virtual router’s IP addresses. Use the no form of the command to disable
responding to ping packets.
Syntax
ip vrrp
vrid
accept-mode
no vrrp
vrid
accept-mode
• vrid — Virtual router identification. (Range: 1-255)
Default Configuration
The default configuration is disabled.
Command Mode
Interface Configuration (VLAN) mode.
User Guidelines
This command has no user guidelines.
show ip vrrp interface
Use the show ip vrrp interface command in User EXEC or Privileged EXEC
mode to display the configured value for Accept Mode.
2CSNXXX_SWUM200.book Page 1382 Tuesday, December 10, 2013 1:22 PM

Virtual Router Redundancy Protocol Commands 1383
Syntax
show ip vrrp interface
interface-id
vrid
•
interface-id
—
Any valid routing interface. See
Interface Naming Conventions
for
interface representation.
•
vrid
—The virtual router identifier. (Range: 1-255)
Default Configuration
The command has no default configuration.
Command Mode
User EXEC, Privileged EXEC mode, Configuration mode and all
Configuration submodes
User Guidelines
This command has no user guidelines.
Example
The following example displays all configuration information about the
VLAN 15 virtual router.
console#show ip vrrp interface vlan2 1
Primary IP Address........................... 10.10.10.1
VMAC Address............................. 00:00:5E:00:01:01
Authentication Type............................ None
Priority....................................... 100
Configured Priority............................ 100
Advertisement Interval (secs).................. 1
Pre-empt Mode.................................. Enable
Administrative Mode............................ Disable
Accept Mode.................................... Enable
State.......................................... Initialized
Track Interface State Decrement Priority
--------------- ------------- ------------
No interfaces are tracked for this vrid and interface combination.
Track Route(pfx/len) Reachable Decrement Priority
--------------- ------------- ------------
No routes are tracked for this vrid and interface combination.
2CSNXXX_SWUM200.book Page 1383 Tuesday, December 10, 2013 1:22 PM

1384 Virtual Router Redundancy Protocol Commands
2CSNXXX_SWUM200.book Page 1384 Tuesday, December 10, 2013 1:22 PM

Utility Commands 1385
59
Utility Commands
This section of the document contains the following Utility command topics:
Auto-Install
Commands
Line Commands SDM Templates
Commands
Telnet Server
Commands
Captive Portal
Commands
Management ACL
Commands
Serviceability
Traci ng Packet
Commands
Ter mi nal L ength
Commands
CLI Macro
Commands
Mode Commands Sflow Commands Time Ranges
Commands
Clock Commands Password
Management
Commands
SNMP Commands USB Flash Drive
Commands
Command Line
Configuration
Scripting
Commands
PHY Diagnostics
Commands
SSH Commands User Interface
Commands
Configuration and
Image File
Commands
Power Over
Ethernet
Commands
Syslog Commands Web Server Commands
Denial of Service
Commands
RMON Commands System
Management
Commands
–
2CSNXXX_SWUM200.book Page 1385 Tuesday, December 10, 2013 1:22 PM

1386 Utility Commands
2CSNXXX_SWUM200.book Page 1386 Tuesday, December 10, 2013 1:22 PM

Auto-Install Commands 1387
60
Auto-Install Commands
Dell Networking N2000/N3000/N4000 Series Switches
Auto-Install provides automatic update of the image and configuration of
Dell Networking devices on boot up from a TFTP server as controlled by
received DHCP options. It plays a critical role in the Dell Networking offering
of touchless or low-touch provisioning, in which configuration and imaging of
a device is greatly simplified. This is highly desirable as device can be setup
with minimum interaction from a skilled technician.
In Dell Networking devices, Auto-Install provides for network-based auto-
configuration and auto-imaging. Other aspects provide support for auto-
configuration and auto-imaging from attached devices.
Auto-Install is available on Dell Networking devices as per the specification
listed below.
Auto-Install features in this release include:
1
Support download of image from TFTP server using DHCP option 125.
The image update can result in a downgrade or upgrade of the firmware on
the switch or stack of switches.
2
Support for automatic download of a configuration file from a TFTP
server when the device is booted with no saved configuration file located in
designated storage. This release extends the designated storage to USB
flash drives. In previous releases, the only supported storage was the
device’s embedded flash or non-volatile memory.
3
Support for automatic download of an image from a TFTP server in the
following situations:
a
When the device is booted with no saved configuration found in the
designated storage areas.
b
When the device is booted with a saved configuration that has Auto-
Install enabled.
2CSNXXX_SWUM200.book Page 1387 Tuesday, December 10, 2013 1:22 PM

1388 Auto-Install Commands
4
Support for the Auto-Install process from a TFTP server operationally
enabling the DHCP client on designated management interfaces during
the Auto-Install process. The end user configuration remains unchanged.
Management interfaces include the out-of-band interface or routing
interfaces in a saved config.
Commands in this Chapter
This chapter explains the following commands:
boot auto-copy-sw
Use the boot auto-copy-sw command in Privileged EXEC mode to enable or
disable Stack Firmware Synchronization.
Use the no form of the command to disable Stack Firmware Synchronization.
Syntax
boot auto-copy-sw
no boot auto-copy-sw
Default Configuration
Stack firmware synchronization is enabled by default.
Command Mode
Global Config
boot auto-copy-sw boot auto-copy-sw allow-downgrade
boot host autoreboot boot host autoreboot
boot host autosave boot host autosave
boot host dhcp boot host dhcp
boot host retrycount boot host retrycount
boot auto-copy-sw show auto-copy-sw
–
show boot
2CSNXXX_SWUM200.book Page 1388 Tuesday, December 10, 2013 1:22 PM

Auto-Install Commands 1389
User Guidelines
The configuration on the master switch controls the stack as if it is a single
switch. No configuration steps need to be taken on the member switches to
synchronize the firmware.
boot auto-copy-sw allow-downgrade
Use the boot auto-copy-sw allow-downgrade command in Privileged EXEC
mode to enable downgrading the firmware version on the stack member if the
firmware version on the manager is older than the firmware version on the
member.
Use the no form of the command to disable downgrading the image.
Syntax
boot auto-copy-sw allow-downgrade
no boot auto-copy-sw allow-downgrade
Default Configuration
The default value is Enable.
Command Mode
Global Configuration
User Guidelines
The configuration on the stack master switch controls the stack as if it is a
single switch. No configuration steps need to be taken on the member
switches to downgrade the firmware. Configuration migration during a
downgrade is not assured. The operator should ensure that the configuration
can be downgraded before allowing the downgrade to occur or otherwise take
steps to reconfigure the switches.
During a downgrade, meta-data regarding the stack configuration is not
migrated. For example, Ethernet ports configured as stacking ports will revert
to the default Ethernet configuration during a downgrade. When this occurs,
the stack will almost certainly be split into individual switches, each of which
must have the relevant Ethernet ports individually configured a stacking
before the stack can be reconstituted.
2CSNXXX_SWUM200.book Page 1389 Tuesday, December 10, 2013 1:22 PM

1390 Auto-Install Commands
boot host autoreboot
Use the boot host autoreboot command in Global Configuration mode to
enable rebooting the device (no administrative intervention) when the auto-
image is successfully downloaded. Use the no form of this command to
disable rebooting the device (no administrative intervention) when the auto-
image is successfully downloaded.
Syntax
boot host autoreboot
no boot host autoreboot
Default Configuration
The default value is enabled.
Command Mode
Global Configuration mode
User Guidelines
The configuration on the master switch controls the stack as if it is a single
switch. No configuration steps need to be taken on the member switches to
enable rebooting the member switches after auto-image download.
Example
console#
console#configure
console(config)#boot host autoreboot
console(config)#no boot host autoreboot
boot host autosave
Use the boot host autosave command in Global Configuration mode to
enable automatically saving the downloaded configuration on the switch. Use
the no form of this command to disable automatically saving the downloaded
configuration on the switch.
2CSNXXX_SWUM200.book Page 1390 Tuesday, December 10, 2013 1:22 PM

Auto-Install Commands 1391
Syntax
boot host autosave
no boot host autosave
Default Configuration
The default value is disabled.
Command Mode
Global Configuration mode
User Guidelines
This command has no user guidelines
Example
console#
console#configure
console(config)#boot host auto-save
console(config)#no boot host auto-save
boot host dhcp
Use the boot host dhcp command in Global Configuration mode to enable
Auto-Install and Auto Configuration on the switch. When a switch boots
with a saved startup configuration that includes this command, the Auto-
Install process is triggered. Use the no form of this command to disable Auto-
Install on the next reboot if the reboot occurs with a saved startup
configuration. If you give this command while the Auto-Install process is
running, the Auto-Install process terminates. The Auto-Install process has an
internal timer that retries failed installations for ten minutes.
Syntax
boot host dhcp
no boot host dhcp
Default Configuration
The default value is Enabled.
2CSNXXX_SWUM200.book Page 1391 Tuesday, December 10, 2013 1:22 PM

1392 Auto-Install Commands
Command Mode
Global Configuration.
User Guidelines
This command has no user guidelines
Example
console#
console#configure
console(config)#boot host dhcp
console(config)#no boot host dhcp
boot host retrycount
The boot host retrycount command sets the number of attempts to
download a configuration. Use the no form of this command to reset the
number of attempts to download a configuration to the default.
Syntax
boot host retrycount
count
no boot host retrycount
•
count
—
The number of attempts to download a configuration (Range:
1–6).
Default Configuration
The default number of configuration download attempts is three.
Command Mode
Global Configuration mode
User Guidelines
This command has no user guidelines
Example
console#
console#configure
console(config)#boot host retrycount 5
2CSNXXX_SWUM200.book Page 1392 Tuesday, December 10, 2013 1:22 PM

Auto-Install Commands 1393
console(config)#no boot host retrycount
show auto-copy-sw
Use the show auto-copy-sw command in Privileged EXEC mode to display
Stack Firmware Synchronization configuration status.
Syntax
show auto-copy-sw
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC mode, Configuration mode and all Configuration submodes
User Guidelines
The show switch command also displays the switch firmware synchronization
status.
Example
console#show auto-copy-sw
Stack Firmware Synchronization
Synchronization: Enabled
SNMP Trap status: Enabled
Allow Downgrade: Enabled
show boot
Use the show boot command in Privileged EXEC mode to display the auto
install configuration and the status.
Syntax
show boot
2CSNXXX_SWUM200.book Page 1393 Tuesday, December 10, 2013 1:22 PM

1394 Auto-Install Commands
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC, Configuration mode and all Configuration submodes
User Guidelines
This command has no user guidelines.
Example
console#show boot
AutoInstall Mode………………………… Started
AutoSave Mode………………………………… Enabled
AutoReboot Mode…………………………… Enabled
AutoInstall Retry Count……… 3
AutoInstall State……………………… Waiting for boot options
2CSNXXX_SWUM200.book Page 1394 Tuesday, December 10, 2013 1:22 PM

Captive Portal Commands 1395
61
Captive Portal Commands
Dell Networking N2000/N3000/N4000 Series Switches
The Captive Portal feature is a software implementation that blocks both
wired and wireless clients from accessing the network until user verification
has been established. Verification can be configured to allow access for both
guest and authenticated users. Authenticated users must be validated against
a database of authorized Captive Portal users before access is granted.
The Authentication server supports both HTTP and HTTPS web
connections. In addition, Captive Portal can be configured to use an optional
HTTP port (in support of HTTP Proxy networks) or an optional HTTPS port.
If configured, this additional port or ports are then used exclusively by
Captive Portal.
NOTE: This optional HTTP port is in addition to the standard HTTP port 80 which is
currently being used for all other web traffic, and the optional HTTPS port is in
addition to the standard HTTPS port 443 used for secure web traffic.
Commands in this Chapter
This chapter explains the following commands:
Captive Portal Global Commands
Captive Portal Configuration Commands
authentication timeout https port
captive-portal show captive-portal
enable show captive-portal status
http port
–
block name (Captive Portal)
configuration protocol
enable redirect
2CSNXXX_SWUM200.book Page 1395 Tuesday, December 10, 2013 1:22 PM

1396 Captive Portal Commands
Captive Portal Client Connection Commands
Captive Portal Local User Commands
Captive Portal Status Commands
Captive Portal User Group Commands
group redirect-url
interface session-timeout
locale verification
captive-portal client deauthenticate show captive-portal interface client status
show captive-portal client status show captive-portal interface configuration
status
show captive-portal configuration client
status
–
clear captive-portal users user-logout
no user user name
show captive-portal user user password
user group user session-timeout
show captive-portal configuration show captive-portal configuration locales
show captive-portal configuration interface show captive-portal configuration status
user group user group name
user group moveusers
–
2CSNXXX_SWUM200.book Page 1396 Tuesday, December 10, 2013 1:22 PM

Captive Portal Commands 1397
Captive Portal Global Commands
authentication timeout
Use the authentication timeout command to configure the authentication
timeout. If the user does not enter valid credentials within this time limit, the
authentication page needs to be served again in order for the client to gain
access to the network. Use the “no” form of this command to reset the
authentication timeout to the default.
Syntax
authentication timeout
timeout
no authentication timeout
•
timeout
—The authentication timeout (Range: 60–600 seconds).
Default Configuration
The default authentication timeout is 300 seconds.
Command Mode
Captive Portal Configuration mode.
User Guidelines
There are no user guidelines for this command.
Example
console(config-CP)#authentication timeout 600
console(config-CP)#no authentication timeout
captive-portal
Use the captive-portal command to enter the captive portal configuration
mode.
Syntax
captive-portal
2CSNXXX_SWUM200.book Page 1397 Tuesday, December 10, 2013 1:22 PM

1398 Captive Portal Commands
Default Configuration
There is no default configuration for this command.
Command Mode
Global Configuration mode
User Guidelines
There are no user guidelines for this command.
Example
console(config)#captive-portal
console(config-CP)#
enable
Use the enable command to globally enable captive portal. Use the “no” form
of this command to globally disable captive portal.
Syntax
enable
no enable
Default Configuration
Captive Portal is disabled by default.
Command Mode
Captive Portal Configuration mode.
User Guidelines
There are no user guidelines for this command.
Example
console(config-CP)#enable
2CSNXXX_SWUM200.book Page 1398 Tuesday, December 10, 2013 1:22 PM

Captive Portal Commands 1399
http port
Use the http port command to configure an additional HTTP port for captive
portal to listen for connections. Use the “no” form of this command to
remove the additional HTTP port from monitoring.
Syntax
http port
port-num
no http port
•
port-num
—The port number on which the HTTP server listens for
connections
(
Range: 1025–65535).
Default Configuration
Captive portal only monitors port 80 by default.
Command Mode
Captive Portal Configuration mode
User Guidelines
The port number should not be set to a value that might conflict with other well-
known protocol port numbers used on this switch.
Example
console(config-CP)#http port 32768
console(config-CP)#no http port
https port
Use the https port command to configure an additional HTTPS port for
captive portal to monitor. Use the “no” form of this command to remove the
additional HTTPS port.
Syntax
https port
port-num
no https port
2CSNXXX_SWUM200.book Page 1399 Tuesday, December 10, 2013 1:22 PM

1400 Captive Portal Commands
•
port-num
—The port number on which the HTTPS server listens for
connections (Range: 1025–65535).
Default Configuration
Captive portal listens on port 443 by default.
Command Mode
Captive Portal Configuration mode.
User Guidelines
The port number should not be set to a value that might conflict with other well-
known protocol port numbers used on this switch.
Example
console(config-CP)#https port 1443
console(config-CP)#no https port
show captive-portal
Use the show captive-portal command to display the status of the captive
portal feature.
Syntax
show captive-portal
Default Configuration
There is no default configuration for this command
Command Mode
Privileged EXEC mode, Configuration mode and all Configuration submodes
User Guidelines
There are no user guidelines for this command.
Example
console#show captive-portal
2CSNXXX_SWUM200.book Page 1400 Tuesday, December 10, 2013 1:22 PM

Captive Portal Commands 1401
Administrative Mode....................... Disabled
Operational Status........................ Disabled
Disable Reason................ Administrator Disabled
Captive Portal IP Address................. 1.2.3.4
show captive-portal status
Use the show captive-portal status command to report the status of all
captive portal instances in the system.
Syntax
show captive-portal status
Default Configuration
There is no default configuration for this command.
Command Mode
Privileged EXEC mode, Configuration mode and all Configuration submodes
User Guidelines
There are no user guidelines for this command.
Example
console#show captive-portal status
Additional HTTP Port........................... 81
Additional HTTP Secure Port.................... 1443
Authentication Timeout......................... 300
Supported Captive Portals...................... 10
Configured Captive Portals..................... 1
Active Captive Portals......................... 0
Local Supported Users.......................... 128
Configured Local Users......................... 3
System Supported Users......................... 1024
Authenticated Users............................ 0
Captive Portal Configuration Commands
The commands in this section are related to captive portal configurations.
2CSNXXX_SWUM200.book Page 1401 Tuesday, December 10, 2013 1:22 PM

1402 Captive Portal Commands
block
Use the block command to block all traffic for a captive portal configuration.
Use the “no” form of this command to unblock traffic.
Syntax
block
no block
Default Configuration
Traffic is not blocked by default.
Command Mode
Captive Portal Instance mode.
User Guidelines
There are no user guidelines for this command.
Example
console(config-CP 2)#block
configuration
Use the configuration command to enter the captive portal instance mode.
The captive portal configuration identified by CP ID 1 is the default CP
configuration. The system supports a total of ten CP configurations. Use the
“no” form of this command to delete a configuration. The default
configuration (1) cannot be deleted.
Syntax
configuration
cp-id
no configuration
cp-id
•
cp-id
—Captive Portal ID (Range: 1–10).
2CSNXXX_SWUM200.book Page 1402 Tuesday, December 10, 2013 1:22 PM

Captive Portal Commands 1403
Default Configuration
Configuration 1 is enabled by default.
Command Mode
Captive Portal Configuration mode.
User Guidelines
There are no user guidelines for this command.
Example
console(config-CP)#configuration 2
console(config-CP 2)#
enable
Use the enable command to enable a captive portal configuration. Use the no
form of this command to disable a configuration.
Syntax
enable
no enable
Default Configuration
Configurations are enabled by default
Command Mode
Captive Portal Instance mode.
User Guidelines
There are no user guidelines for this command.
Example
console(config-CP 2)#no enable
2CSNXXX_SWUM200.book Page 1403 Tuesday, December 10, 2013 1:22 PM

1404 Captive Portal Commands
group
Use the group command to configure the group number for a captive portal
configuration. If a group number is configured, the user entry (Local or
RADIUS) must be configured with the same name and the group to
authenticate to this captive portal instance. Use the no form of this
command to reset the group number to the default.
Syntax
group
group-number
no group
•
group-number
—The number of the group to associate with this
configuration (Range: 1–10).
Default Configuration
The default group number is 1.
Command Mode
Captive Portal Instance mode.
User Guidelines
There are no user guidelines for this command.
Example
console(config-CP 2)#group 2
interface
Use the interface command to associate an interface with a captive portal
configuration. Use the no form of this command to remove an association.
Syntax
interface
interface
no interface
interface
•
interface
—An interface or range of interfaces.
2CSNXXX_SWUM200.book Page 1404 Tuesday, December 10, 2013 1:22 PM

Captive Portal Commands 1405
Default Configuration
No interfaces are associated with a configuration by default.
Command Mode
Captive Portal Instance Configuration mode.
User Guidelines
There are no user guidelines for this command.
Example
console(config-CP 2)#interface 1/0/2
locale
The locale command is not intended to be a user command. The
administrator must use the Web UI to create and customize captive portal
web content. This command is primarily used by the show running-config
command and process as it provides the ability to save and restore
configurations using a text based format.
Syntax
locale
web-id
•
web-id
—The locale number (Range: Only locale 1 is supported)
Default Configuration
Locale 1 is configured by default.
Command Mode
Captive Portal Instance mode.
User Guidelines
There are no user guidelines for this command.
2CSNXXX_SWUM200.book Page 1405 Tuesday, December 10, 2013 1:22 PM

1406 Captive Portal Commands
name (Captive Portal)
Use the name command to configure the name for a captive portal
configuration. Use the no form of this command to remove a configuration
name.
Syntax
name
cp-name
no name
•
cp-name
—CP configuration name (Range: 1–32 characters).
Default Configuration
Configuration 1 has the name “Default” by default. All other configurations
have no name by default.
Command Mode
Captive Portal Instance mode.
User Guidelines
There are no user guidelines for this command.
Example
console(config-CP 2)#name cp2
protocol
Use the protocol command to configure the protocol mode for a captive
portal configuration.
Syntax
protocol {http | https}
Default Configuration
The default protocols mode is https.
2CSNXXX_SWUM200.book Page 1406 Tuesday, December 10, 2013 1:22 PM

Captive Portal Commands 1407
Command Mode
Captive Portal Instance mode.
User Guidelines
There are no user guidelines for this command.
Example
console(config-CP 2)#protocol http
redirect
Use the redirect command to enable the redirect mode for a captive portal
configuration. Use the “no” form of this command to disable redirect mode.
Syntax
redirect
no redirect
Default Configuration
Redirect mode is disabled by default.
Command Mode
Captive Portal Instance mode.
User Guidelines
There are no user guidelines for this command.
Example
console(config-CP 2)#redirect
redirect-url
Use the redirect-url command to configure the redirect URL for a captive
portal configuration.
2CSNXXX_SWUM200.book Page 1407 Tuesday, December 10, 2013 1:22 PM

1408 Captive Portal Commands
Syntax
redirect-url
url
•
url
—The URL for redirection (Range: 1–512 characters).
Default Configuration
There is no redirect URL configured by default.
Command Mode
Captive Portal Instance mode.
User Guidelines
There are no user guidelines for this command.
Example
console(config-CP 2)#redirect-url www.dell.com
session-timeout
Use the session-timeout command to configure the session timeout for a
captive portal configuration. Use the no form of this command to reset the
session timeout to the default.
Syntax
session-timeout
timeout
no session-timeout
•
timeout
—Session timeout. 0 indicates timeout not enforced (Range:
0–86400 seconds).
Default Configuration
There is no session timeout by default.
Command Mode
Captive Portal Instance mode.
2CSNXXX_SWUM200.book Page 1408 Tuesday, December 10, 2013 1:22 PM

Captive Portal Commands 1409
User Guidelines
There are no user guidelines for this command.
Example
console(config-CP 2)#session-timeout 86400
console(config-CP 2)#no session-timeout
verification
Use the verification command to configure the verification mode for a
captive portal configuration.
Syntax
verification { guest | local | radius }
• guest—Allows access for unauthenticated users (users that do not have
assigned user names and passwords).
• local—Authenticates users against a local user database.
• radius—Authenticates users against a remote RADIUS database.
Default Configuration
The default verification mode is guest.
Command Mode
Captive Portal Instance mode.
User Guidelines
There are no user guidelines for this command.
Example
console(config-CP 2)#verification local
2CSNXXX_SWUM200.book Page 1409 Tuesday, December 10, 2013 1:22 PM

1410 Captive Portal Commands
Captive Portal Client Connection Commands
captive-portal client deauthenticate
Use the captive-portal client deauthenticate command to deauthenticate a
specific captive portal client.
Syntax
captive-portal client deauthenticate
macaddr
•
macaddr
—Client MAC address.
Default Configuration
There is no default configuration for this command.
Command Mode
Privileged EXEC mode.
User Guidelines
There are no user guidelines for this command.
Example
console#captive-portal client deauthenticate 0002.BC00.1290
show captive-portal client status
Use the show captive-portal client status command to display client
connection details or a connection summary for connected captive portal
users.
Syntax
show captive-portal client [
macaddr
] status
•
macaddr
—Client MAC address.
Default Configuration
There is no default configuration for this command.
2CSNXXX_SWUM200.book Page 1410 Tuesday, December 10, 2013 1:22 PM

Captive Portal Commands 1411
Command Mode
Privileged EXEC mode, Configuration mode and all Configuration submodes
User Guidelines
There are no user guidelines for this command.
Example
console#show captive-portal client status
Client MAC Address Client IP Address Protocol Verification Session Time
------------------ ----------------- -------- ------------ ------------
0002.BC00.1290 10.254.96.47 https Local 0d:00:01:20
0002.BC00.1291 10.254.96.48 https Local 0d:00:05:20
0002.BC00.1292 10.254.96.49 https Radius 0d:00:00:20
console#show captive-portal client 0002.BC00.1290 status
Client MAC Address........................ 0002.BC00.1290
Client IP Address......................... 10.254.96.47
Protocol Mode............................. https
Verification Mode......................... Local
CP ID..................................... 1
CP Name................................... cp1
Interface................................. 1/0/1
Interface Description..................... Unit: 1 Slot: 0 Port: 1 Gigabit -
Level
User Name................................. user123
Session Time.............................. 0d:00:00:13
show captive-portal configuration client status
Use the show captive-portal configuration client status command to display
the clients authenticated to all captive portal configurations or a to specific
configuration.
Syntax
show captive-portal configuration [
cp-id
] client status
•
cp-id
—Captive Portal ID.
Default Configuration
There is no default configuration for this command.
2CSNXXX_SWUM200.book Page 1411 Tuesday, December 10, 2013 1:22 PM

1412 Captive Portal Commands
Command Mode
Privileged EXEC mode, Configuration mode and all Configuration submodes
User Guidelines
There are no user guidelines for this command.
Example
console#show captive-portal configuration client status
CP ID CP Name Client MAC Address Client IP Address Interface
----- --------------- ------------------ ----------------- ---------
1 cp1 0002.BC00.1290 10.254.96.47 1/0/1
0002.BC00.1291 10.254.96.48 1/0/2
2 cp2 0002.BC00.1292 10.254.96.49 1/0/3
3 cp3 0002.BC00.1293 10.254.96.50 1/0/4
console#show captive-portal configuration 1 client status
CP ID..................................... 1
CP Name................................... cp1
Client Client
MAC Address IP Address Interface Interface Description
-------------- --------------- --------- --------------------------------
0002.BC00.1290 10.254.96.47 1/0/1 Unit: 1 Slot: 0 Port: 1 Gigabit
0002.BC00.1291 10.254.96.48 1/0/2 Unit: 1 Slot: 0 Port: 2 Gigabit
show captive-portal interface client status
Use the show captive-portal interface client status command to display
information about clients authenticated on all interfaces or a specific
interface.
Syntax
show captive-portal interface {gigabitethernet unit/slot/port|
tengigabitethernet unit/slot/port | fortygigabitethernet unit/slot/port} client
status
Default Configuration
There is no default configuration for this command.
2CSNXXX_SWUM200.book Page 1412 Tuesday, December 10, 2013 1:22 PM

Captive Portal Commands 1413
Command Mode
Privileged EXEC mode, Configuration mode and all Configuration submodes
User Guidelines
There are no user guidelines for this command.
Example
console#show captive-portal interface client status
Client Client
Intf Intf Description MAC Address IP Address
------ ----------------------------------- ----------------- ---------------
1/0/1 Unit: 1 Slot: 0 Port: 1 Gigabit 0002.BC00.1290 10.254.96.47
0002.BC00.1291 10.254.96.48
1/0/2 Unit: 1 Slot: 0 Port: 2 Gigabit 0002.BC00.1292 10.254.96.49
1/0/3 Unit: 1 Slot: 0 Port: 3 Gigabit 0002.BC00.1293 10.254.96.50
console#show captive-portal interface 1/0/1 client status
Interface................................. 1/0/1
Interface Description..................... Unit: 1 Slot: 0 Port: 1 Gigabit
Client Client
MAC Address IP Address CP ID CP Name Protocol Verification
----------------- --------------- ----- ----------------- -------- ---------
0002.BC00.1290 10.254.96.47 1 cp1 http local
0002.BC00.1291 10.254.96.48 2 cp2 http local
Captive Portal Interface Commands
show captive-portal interface configuration
status
Use the show captive-portal interface configuration status command to
display the interface to configuration assignments for all captive portal
configurations or for a specific configuration.
Syntax
show captive-portal interface configuration [
cp-id
] status
•
cp-id
—Captive Portal ID.
2CSNXXX_SWUM200.book Page 1413 Tuesday, December 10, 2013 1:22 PM

1414 Captive Portal Commands
Default Configuration
There is no default configuration for this command.
Command Mode
Privileged EXEC mode, Configuration mode and all Configuration submodes
User Guidelines
There are no user guidelines for this command.
Example
console#show captive-portal interface configuration status
CP ID CP Name Interface Interface Description Type
----- ------------------ --------- ----------------------------------- -----
1 Default 1/0/1 Unit: 1 Slot: 0 Port: 1 Gigabit .. Physical
console#show captive-portal interface configuration 1 status
CP ID..................................... 1
CP Name................................... cp1
Interface Interface Description Type
--------- ----------------------------------- --------
1/0/1 Unit: 1 Slot: 0 Port: 1 Gigabit ... Physical
Captive Portal Local User Commands
clear captive-portal users
Use the clear captive-portal users command to delete all captive portal user
entries.
Syntax
clear captive-portal users
Default Configuration
There is no default configuration for this command.
2CSNXXX_SWUM200.book Page 1414 Tuesday, December 10, 2013 1:22 PM

Captive Portal Commands 1415
Command Mode
Privileged EXEC mode.
User Guidelines
There are no user guidelines for this command.
Example
console#clear captive-portal users
no user
Use the no user command to delete a user from the local user database. If the
user has an existing session, it is disconnected.
Syntax
no user
user-id
•
user-id
—User ID (Range: 1–128).
Default Configuration
There is no default configuration for this command.
Command Mode
Captive Portal Configuration mode.
User Guidelines
There are no user guidelines for this command.
Example
console(config-CP)#no user 1
show captive-portal user
Use the show captive-portal user command to display all configured users or a
specific user in the captive portal local user database.
2CSNXXX_SWUM200.book Page 1415 Tuesday, December 10, 2013 1:22 PM

1416 Captive Portal Commands
Syntax
show captive-portal user [
user-id
]
•
user-id
—User ID (Range: 1–128).
Default Configuration
There is no default configuration for this command.
Command Mode
Privileged EXEC mode, Configuration mode and all Configuration submodes
User Guidelines
There are no user guidelines for this command.
Example
console#show captive-portal user
Session
User ID User Name Timeout Group ID Group Name
------- --------------------- ------- ------------ ------------
1 user123 14400 1 Default
2 user234 0 1 Default
2 group2
console#show captive-portal user 1
User ID........................................ 1
User Name...................................... user123
Password Configured............................ Yes
Session Timeout................................ 0
Group ID Group Name
-------- --------------------------------
1 Default
2 group2
user group
Use the user group command to associate a group with a captive portal user.
Use the “no” form of this command to disassociate a group and user. A user
must be associated with at least one group so the last group cannot be
disassociated.
2CSNXXX_SWUM200.book Page 1416 Tuesday, December 10, 2013 1:22 PM

Captive Portal Commands 1417
Syntax
user
user-id
group
group-id
•
user-id
—User ID (Range: 1–128).
•
group-id
—Group ID (Range: 1–10).
Default Configuration
A user is associated with group 1 by default.
Command Mode
Captive Portal Configuration mode.
User Guidelines
There are no user guidelines for this command.
Example
console(config-CP)#user 1 group 3
user-logout
Use the user-logout command in Captive Portal Instance mode to enable
captive portal users to log out of the portal (versus having the session time
out). Use the no form of the command to return the user logout
configuration to the default.
Syntax
user-logout
no user-logout
Default Configuration
User-logout is disabled by default.
Command Mode
Captive-portal Instance mode
2CSNXXX_SWUM200.book Page 1417 Tuesday, December 10, 2013 1:22 PM

1418 Captive Portal Commands
User Guidelines
There are no user guidelines for this command.
Example
In this example, all classes of entries in the mac address-table are displayed.
console(config)#captive-portal
console(config-CP)#user 1 name asd
console(config-CP)#configuration 1
console(config-CP 1)#user-logout
console(config-CP 1)#no user-logout
user name
Use the user name command to modify the user name for a local captive
portal user.
Syntax
user
user-id
name
name
•
user-id
—User ID (Range: 1–128).
•
name
—user name (Range: 1–32 characters).
Default Configuration
There is no name for a user by default.
Command Mode
Captive Portal Configuration mode.
User Guidelines
There are no user guidelines.
Example
console(config-CP)#user 1 name johnsmith
2CSNXXX_SWUM200.book Page 1418 Tuesday, December 10, 2013 1:22 PM

Captive Portal Commands 1419
user password
Use the user password command to create a local user or change the password
for an existing user.
Syntax
user
user-id
password {
password
| encrypted
enc-password
}
•
user-id
—User ID (Range: 1–128).
•
password
—User password (Range: 8–64 characters).
•
enc-password
—User password in encrypted form.
Default Configuration
There are no users configured by default.
Command Mode
Captive Portal Configuration mode.
User Guidelines
There are no user guidelines for this command.
Example
console(Config-CP)#user 1 password
Enter password (8 to 64 characters): ********
Re-enter password: ********
user session-timeout
Use the user session-timeout command to set the session timeout value for a
captive portal user. Use the no form of this command to reset the session
timeout to the default.
Syntax
user
user-id
session-timeout
timeout
no user
user-id
session-timeout
•
user-id
—User ID (Range: 1–128).
2CSNXXX_SWUM200.book Page 1419 Tuesday, December 10, 2013 1:22 PM

1420 Captive Portal Commands
•
timeout
—Session timeout. 0 indicates use global configuration (Range:
0–86400 seconds).
Default Configuration
The global session timeout is used by default.
Command Mode
Captive Portal Configuration mode.
User Guidelines
There are no user guidelines for this command.
Example
console(config-CP)#user 1 session-timeout 86400
console(config-CP)#no user 1 session-timeout
Captive Portal Status Commands
show captive-portal configuration
Use the show captive-portal configuration command to display the
operational status of each captive portal configuration.
Syntax
show captive-portal configuration
cp-id
•
cp-id
—Captive Portal ID.
Default Configuration
There is no default configuration for this command.
Command Mode
Privileged EXEC mode, Configuration mode and all Configuration submodes
User Guidelines
There are no user guidelines for this command.
2CSNXXX_SWUM200.book Page 1420 Tuesday, December 10, 2013 1:22 PM

Captive Portal Commands 1421
Example
console#show captive-portal configuration 1
CP ID..................................... 1
CP Name................................... cp1
Operational Status........................ Disabled
Disable Reason............................ Administrator Disabled
Blocked Status............................ Not Blocked
Configured Locales........................ 1
Authenticated Users....................... 0
show captive-portal configuration interface
Use the show captive-portal configuration interface command to display
information about all interfaces assigned to a captive portal configuration or
about a specific interface assigned to a captive portal configuration.
Syntax
show captive-portal configuration
cp-id
interface [{gigabitethernet
unit/slot/port| tengigabitethernet unit/slot/port | fortygigabitethernet
unit/slot/port}]
•
cp-id
—Captive Portal ID.
Default Configuration
There is no default configuration for this command.
Command Mode
Privileged EXEC mode, Configuration mode and all Configuration submodes
User Guidelines
There are no user guidelines for this command.
Example
console#show captive-portal configuration 1 interface
CP ID..................................... 1
CP Name................................... cp1
Operational Block
Interface Interface Description Status Status
--------- ---------------------------------------- ------------ ---------
2CSNXXX_SWUM200.book Page 1421 Tuesday, December 10, 2013 1:22 PM

1422 Captive Portal Commands
1/0/1 Unit: 1 Slot: 0 Port: 1 Gigabit - Level Disabled Blocked
console#show captive-portal configuration 1 interface 1/0/1
CP ID..................................... 1
CP Name................................... cp1
Interface................................. 1/0/1
Interface Description..................... Unit: 1 Slot: 0 Port: 1 Gigab...
Operational Status........................ Disabled
Disable Reason............................ Interface Not Attached
Block Status.............................. Not Blocked
Authenticated Users....................... 0
show captive-portal configuration locales
Use the show captive-portal configuration locales command to display
locales associated with a specific captive portal configuration.
Syntax
show captive-portal configuration
cp-id
locales
•
cp-id
—Captive Portal Configuration ID.
Default Configuration
There is no default configuration for this command.
Command Mode
Privileged EXEC mode, Configuration mode and all Configuration submodes
User Guidelines
There are no user guidelines for this command.
Example
console#show captive-portal configuration 1 locales
Locale Code
---------------
en
2CSNXXX_SWUM200.book Page 1422 Tuesday, December 10, 2013 1:22 PM

Captive Portal Commands 1423
show captive-portal configuration status
Use the show captive-portal configuration status command to display
information about all configured captive portal configurations or about a
specific captive portal configuration.
Syntax
show captive-portal configuration [
cp-id
] status
•
cp-id
—Captive Portal ID.
Default Configuration
There is no default configuration for this command.
Command Mode
Privileged EXEC mode, Configuration mode and all Configuration submodes
User Guidelines
There are no user guidelines for this command.
Example
console#show captive-portal configuration status
CP ID CP Name Mode Protocol Verification
----- --------------- -------- -------- ------------
1 cp1 Enable https Guest
2 cp2 Enable http Local
3 cp3 Disable https Guest
console#show captive-portal configuration 1 status
CP ID.......................................... 1
CP Name........................................ cp1
Mode........................................... Enabled
Protocol Mode.................................. https
Verification Mode.............................. Guest
Group Name..................................... group123
Redirect URL Mode.............................. Enabled
Redirect URL................................... www.cnn.com
Session Timeout (seconds)...................... 86400
2CSNXXX_SWUM200.book Page 1423 Tuesday, December 10, 2013 1:22 PM

1424 Captive Portal Commands
Captive Portal User Group Commands
user group
Use the user group command to create a user group. Use the no form of this
command to delete a user group. The default user group (1) cannot be
deleted.
Syntax
user group
group-id
no user group
group-id
group-id
—
Group ID (Range: 1–10).
Default Configuration
User group 1 is created by default and cannot be deleted.
Command Mode
Captive Portal Configuration mode.
User Guidelines
There are no user guidelines for this command.
Example
console(config-CP)#user group 2
console(config-CP)#no user group 2
user group moveusers
Use the user group moveusers command to move a group's users to a different
group.
Syntax
user group
group-id
moveusers
new-group-id
•
group-id
—Group ID (Range: 1–10).
•
new-group-id
—Group ID (Range: 1–10).
2CSNXXX_SWUM200.book Page 1424 Tuesday, December 10, 2013 1:22 PM

Captive Portal Commands 1425
Default Configuration
There is no default configuration for this command.
Command Mode
Captive Portal Configuration mode
User Guidelines
The new group-id must already exist.
Example
console(config-CP)#user group 2 moveusers 3
user group name
Use the user group name command to configure a group name.
Syntax
user group
group-id
name
name
•
group-id
—Group ID (Range: 1–10).
•
name
—Group name (Range: 1–32 characters).
Default Configuration
User groups have no names by default.
Command Mode
Captive Portal Configuration mode.
User Guidelines
There are no user guidelines for this command.
Example
console(config-CP)#user group 2 name group2
2CSNXXX_SWUM200.book Page 1425 Tuesday, December 10, 2013 1:22 PM

1426 Captive Portal Commands
2CSNXXX_SWUM200.book Page 1426 Tuesday, December 10, 2013 1:22 PM

CLI Macro Commands 1427
62
CLI Macro Commands
Dell Networking N2000/N3000/N4000 Series Switches
CLI Macros provides a convenient way to save and distribute common
configurations. A CLI macro is a set of the CLI commands having a unique
name. When a CLI macro is applied, the CLI commands contained within
the macro are executed and added to the Running Configuration File. When
the macro is applied to an interface, the existing configuration is not lost; the
new commands are added configuration.
A CLI Macro may have keywords (variables) which are replaced by values
provided when the macro is applied (up to 3 keywords per macro). Macros can
be applied to specific interfaces, a range of interfaces, or the global
configuration.
There are two types of Macros:
• Built-In Macros, or Default Macros – the predefined macros which cannot
be changed or deleted.
• User-Defined Macros, or Custom Macros – the macros which allow the
operator to bundle some prerequisites or global configurations as a macro
and then apply them to one or more interfaces at a time, which can then
be copied or used by other switches. Up to 50 user-defined macros are
supported.
The software includes 6 built-in macros:
• profile-global, the global configuration, used to enable RSTP and loop
guard.
• profile-desktop, the interface configuration, for increased network security
and reliability when connecting a desktop device, such as a PC, to a switch
port.
• profile-phone, the interface configuration, used when connecting a
desktop device such as a PC with an IP Phone to a switch port.
• profile-switch, the interface configuration, used when connecting an
access switch and a distribution switch or between access switches.
• profile-router, the interface configuration, used when connecting the
switch and a WAN router.
2CSNXXX_SWUM200.book Page 1427 Tuesday, December 10, 2013 1:22 PM
1428 CLI Macro Commands
• profile-wireless, the interface configuration, used when connecting the
switch and a wireless access point.
• profile-compellent-nas, the interface configuration, used when connecting
the switch to a Dell Compellent NAS.
Commands in this Chapter
This chapter explains the following commands:
macro name
Use the macro name command in Global Configuration mode to create a
user-defined macro. Use the no form of the command to delete a macro.
Syntax
macro name
name
no macro name
name
•
name
—The name of the macro. A macro name can consist of any
printable characters, including blanks. A macro name may be up to 31
characters in length. Embed the name in quotes if a blank is desired in the
name. Use the
no
form of the command to delete a macro.
Default Configuration
The following macros are defined by default and may not be deleted or
altered:
macro name macro apply
macro global apply macro trace
macro global trace macro description
macro global description show parser macro
Macro Default Definition
default global :profile-global
default interface :profile-desktop
2CSNXXX_SWUM200.book Page 1428 Tuesday, December 10, 2013 1:22 PM

CLI Macro Commands 1429
Command Mode
Global Configuration mode
User Guidelines
Macros consist of text commands with one command per line. Enter the
commands and terminate macro input mode by entering a single at sign (@)
on a line by itself.
A macro may utilize up to 3 parameters. Parameters are text strings that begin
with a dollar sign ($). Parameters are substituted by specifying the parameter
on the command line when the macro is applied.
Macros may be applied to a specific interface, a range of interfaces, or to the
global configuration. Up to 50 user-defined macros may be configured.
macro global apply
Use the macro global apply command in Global Configuration mode to
apply a macro.
Syntax
macro global apply
macro-name
[
parameter value
] [
parameter
value
][
parameter value
]
•
macro-name
—The name of the macro.
•
parameter
—
The name of the parameter recognized by the macro. The
parameter must begin with a dollar sign ($).
•
value
—
The string to be substituted within the macro for the specified
parameter name.
default interface :profile-phone
default interface :profile-switch
default interface :profile-router
default interface :profile-wireless
default global :profile-compellent-nas
Macro Default Definition
2CSNXXX_SWUM200.book Page 1429 Tuesday, December 10, 2013 1:22 PM

1430 CLI Macro Commands
Default Configuration
No parameters are substituted unless supplied on the command line.
Command Mode
Global Configuration mode
User Guidelines
Commands applied are additive in nature. That is, they do not remove
existing configuration information by default.
macro global trace
Use the macro global trace command in Global Configuration mode to apply
and trace a macro. The trace command will display each line of the macro as
it is executed and list any errors encountered.
Syntax
macro global trace
macro-name
[
parameter value
] [
parameter
value
][
parameter value
]
•
macro-name
—
The name of the macro.
•
parameter
—
The name of the parameter recognized by the macro. The
parameter must begin with a dollar sign ($).
•
value
—
The string to be substituted within the macro for the specified
parameter name.
Default Configuration
No parameters are substituted unless supplied on the command line.
Command Mode
Global Configuration mode
User Guidelines
The line number of the first error encountered is printed. The script is
aborted after the first error.
2CSNXXX_SWUM200.book Page 1430 Tuesday, December 10, 2013 1:22 PM

CLI Macro Commands 1431
Commands applied are additive in nature. That is, they do not remove
existing configuration information by default.
macro global description
Use the macro global description command in Global Configuration mode
to append a line to the global macro description. Use the no form of the
command to clear the description.
Syntax
macro global description
line
•
line
—The macro description. All text up to the new line is included in the
description.
Default Configuration
There is no description by default.
Command Mode
Global Configuration mode
User Guidelines
This command is intended to give the administrator an easy way to remember
which macros have been applied globally. All text up to the new line is
included in the description. The line is appended to the global description.
macro apply
Use the macro apply command in Interface Configuration mode to apply a
macro.
Syntax
macro apply
macro-name
[
parameter value
] [
parameter value
][
parameter
value
]
•
macro-name
—
The name of the macro.
•
parameter
—
The name of the parameter recognized by the macro. The
parameter must begin with a dollar sign ($).
2CSNXXX_SWUM200.book Page 1431 Tuesday, December 10, 2013 1:22 PM

1432 CLI Macro Commands
•
value
—
The string to be substituted within the macro for the specified
parameter name.
Default Configuration
No parameters are substituted unless supplied on the command line.
Command Mode
Interface Configuration mode
User Guidelines
Commands applied are additive in nature. That is, they do not remove
existing configuration information by default.
macro trace
Use the macro trace command in Interface Configuration mode to apply and
trace a macro. The command will display each line of the macro as it is
executed and list any errors encountered.
Syntax
macro trace
macro-name
[
parameter value
] [
parameter value
][
parameter
value
]
no macro name
name
•
macro-name
—The name of the macro.
•
parameter
—The name of the parameter recognized by the macro. The
parameter must begin with a dollar sign ($).
•
value
—The string to be substituted within the macro for the specified
parameter name.
Default Configuration
No parameters are substituted unless supplied on the command line.
Command Mode
Interface Configuration mode
2CSNXXX_SWUM200.book Page 1432 Tuesday, December 10, 2013 1:22 PM

CLI Macro Commands 1433
User Guidelines
The line number of the first error encountered is printed. The script is
aborted after the first error.
Commands applied are additive in nature. That is, they do not remove
existing configuration information by default.
macro description
Use the macro description command in Interface Configuration mode to
append a line to the macro description. Use the no form of the command to
clear the description.
Syntax
macro description
line
•
line
—The macro description. All text up to the new line is included in the
description.
Default Configuration
There is no description by default.
Command Mode
Interface Configuration mode
User Guidelines
This command is intended to give the administrator an easy way to remember
which macros have been applied to an interface. All text up to the new line is
included in the description. The line is appended to the interface description.
show parser macro
Use the show parser macro command in Privileged EXEC mode to display
information about defined macros.
Syntax
show parser macro [
brief
|
description
[
interface interface-id
] |
name macro
2CSNXXX_SWUM200.book Page 1433 Tuesday, December 10, 2013 1:22 PM

1434 CLI Macro Commands
•
brief
—Shows the list of defined macros and their type.
•
description
—Shows the macro descriptions.
•
name
—Shows an individual macro, including its contents.
•
macro
—The name of the macro to display.
•
interface-id
—The interface for which to show the macro description.
Default Configuration
No parameters are substituted unless supplied on the command line.
Command Mode
Privileged EXEC mode, Configuration mode and all Configuration submodes
User Guidelines
There are no user guidelines for this command.
2CSNXXX_SWUM200.book Page 1434 Tuesday, December 10, 2013 1:22 PM

Clock Commands 1435
63
Clock Commands
Dell Networking N2000/N3000/N4000 Series Switches
Real-time Clock
The Dell Networking supports a real-time clock that maintains the system
time across reboots. The system time is used to timestamp messages in the
logging subsystem as well as for the application of time based ACLs. The
administrator has the ability to configure and view the current time, time
zone, and summer time settings.
The earliest date that can be configured is Jan 1, 2010.
Simple Network Time Protocol
The Simple Network Time Protocol (SNTP) is widely used for synchronizing
network resources. SNTP Version 4 is described in RFC 2030. SNTP is an
adaptation of the Network Time Protocol (RFC 1305) useful for situations
where the full performance of NTP is not justified. SNTP can operate in
unicast mode (point-to-point) or broadcast mode (point-to-multipoint).
Various NTP implementations can operate as either a client or a server. To an
NTP or SNTP server, NTP and SNTP clients are indistinguishable. Likewise,
to an NTP or SNTP client, NTP and SNTP servers are indistinguishable.
Furthermore, any version of NTP is compatible with any other version of NTP.
Dell Networking SNTP implements the client side of SNTP.
Support for IPv6 address configuration is provided to the existing SNTP
client. The end user can configure either an IPv4 or IPv6 address or a host
name for an SNTP server among the list of servers. In unicast mode, one of
the servers from the list is selected as the active server to be used for polling
based on priority and configured order. The servers are treated alike
independent of IPv4 or IPv6 or hostname address formats. At any given point
of time, the client operates in unicast or broadcast mode. In broadcast mode,
SNTP client listens on the well known multicast group address 224.0.1.1
(reserved for NTP) for server packets from IPv4 networks on port number 123.
On IPv6 networks, the SNTP client listens to the link-local scoped IANA
2CSNXXX_SWUM200.book Page 1435 Tuesday, December 10, 2013 1:22 PM

1436 Clock Commands
multicast address ff02::101 (reserved for SNTP) for server packets on port
number 123. The client logic to handle packet contents doesn’t change with
support for IPv6 networks.
Commands in this Chapter
This chapter explains the following commands:
show sntp configuration
Use the show sntp configuration command in Privileged EXEC mode to
show the configuration of the Simple Network Time Protocol (SNTP).
Syntax
show sntp configuration
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC mode, Configuration mode and all Configuration submodes
User Guidelines
This command has no user guidelines.
show sntp configuration sntp trusted-key
show sntp server sntp unicast client enable
show sntp status clock timezone hours-offset
sntp authenticate no clock timezone
sntp authentication-key clock summer-time recurring
sntp broadcast client enable clock summer-time date
sntp client poll timer no clock summer-time
sntp server show clock
2CSNXXX_SWUM200.book Page 1436 Tuesday, December 10, 2013 1:22 PM

Clock Commands 1437
Example
The following example displays the current SNTP configuration of the
device.
console#show sntp configuration
Polling interval: 64 seconds
MD5 Authentication keys:
Authentication is not required for synchronization.
Trusted keys:
No trusted keys.
Unicast clients: Disable
Unicast servers:
Server Key Polling Priority
--------- ----------- ----------- ----------
10.27.128.21 Disabled Enabled 1
show sntp server
Use the show sntp server command in Privileged EXEC mode to display the
preconfigured SNTP servers. The configured servers can be either IPv4 or
IPv6 format.
Syntax
show sntp server
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC, Configuration mode and all Configuration submodes
User Guidelines
This command has no user guidelines.
Examples
console#show sntp server
Server Host Address: 2001::01
2CSNXXX_SWUM200.book Page 1437 Tuesday, December 10, 2013 1:22 PM

1438 Clock Commands
Server Type: IPv6
Server Stratum: 2
Server Reference Id: NTP Srv: 158.108.96.32
Server Mode: Server
Server Maximum Entries: 3
Server Current Entries: 2
SNTP Servers
------------
Host Address: 2001::01
Address Type: IPv6
Priority: 1
Version: 4
Port: 123
Last Update Time: Dec 22 11:10:00 2009
Last Attempt Time: Dec 22 11:10:00 2009
Last Update Status: Success
Total Unicast Requests: 955
Failed Unicast Requests: 1
--More-- or (q)uit
Host Address: 3.north-america.pool.ntp.org
Address Type: DNS
Priority: 1
Version: 4
Port: 123
Last Update Time: Dec 22 07:30:31 2009
Last Attempt Time: Dec 22 07:32:41 2009
Last Update Status: Server Unsynchronized
Total Unicast Requests: 157
Failed Unicast Requests: 2
show sntp status
Use the show sntp status command in Privileged EXEC mode to show the
status of the Simple Network Time Protocol (SNTP).
Syntax
show sntp status
2CSNXXX_SWUM200.book Page 1438 Tuesday, December 10, 2013 1:22 PM

Clock Commands 1439
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC mode, Configuration mode and all Configuration submodes
User Guidelines
This command has no user guidelines.
Examples
The following example shows the status of the SNTP.
console#show sntp status
Client Mode: Unicast
Last Update Time: MAR 30 21:21:20 2009
Unicast servers:
Server Status Last response
--------- ----------- --------------------------
192.168.0.1 Up 21:21:20 Mar 30 2009
sntp authenticate
Use the sntp authenticate command in Global Configuration mode to
require server authentication for received Network Time Protocol (NTP)
traffic. To disable the feature, use the no form of this command.
Syntax
sntp authenticate
no sntp authenticate
Default Configuration
No authentication.
Command Mode
Global Configuration mode
2CSNXXX_SWUM200.book Page 1439 Tuesday, December 10, 2013 1:22 PM

1440 Clock Commands
User Guidelines
The command is relevant for both Unicast and Broadcast.
Example
The following example, after defining the authentication key for SNTP, grants
authentication.
console(config)# sntp authentication-key 8 md5 ClkKey
console(config)# sntp trusted-key 8
console(config)# sntp authenticate
sntp authentication-key
Use the sntp authentication-key command in Global Configuration mode to
define an authentication key for Simple Network Time Protocol (SNTP). To
remove the authentication key for SNTP, use the no form of this command.
Syntax
sntp authentication-key
key-number
md5
value
no sntp authentication-key
number
•
key-number —
number (Range: 1–4294967295)
•
value —
value (Range: 1-8 characters)
Default value
No authentication is defined.
Command Mode
Global Configuration mode
User Guidelines
This command has no user guidelines.
Examples
The following examples define the authentication key for SNTP.
console(config)# sntp authentication-key 8 md5 ClkKey
console(config)# sntp trusted-key 8
2CSNXXX_SWUM200.book Page 1440 Tuesday, December 10, 2013 1:22 PM

Clock Commands 1441
console(config)# sntp authenticate
sntp broadcast client enable
Use the sntp broadcast client enable command in Global Configuration
mode to enable a Simple Network Time Protocol (SNTP) Broadcast client. To
disable an SNTP Broadcast client, use the no form of this command.
Syntax
sntp broadcast client enable
no sntp broadcast client enable
Default Configuration
The SNTP Broadcast client is disabled.
Command Mode
Global Configuration mode
User Guidelines
This command has no user guidelines.
Example
The following example enables a Simple Network Time Protocol (SNTP)
Broadcast client.
console(config)# sntp broadcast client enable
sntp client poll timer
Use the sntp client poll timer command in Global Configuration mode to set
the polling time for the Simple Network Time Protocol (SNTP) client. To
return to the default settings, use the no form of this command.
Syntax
sntp client poll timer
seconds
no sntp client poll timer
2CSNXXX_SWUM200.book Page 1441 Tuesday, December 10, 2013 1:22 PM

1442 Clock Commands
•
seconds —
Polling interval. (Range: 64-1024 seconds, in powers of 2)
Default Configuration
The polling interval is 64 seconds.
Command Mode
Global Configuration mode
User Guidelines
If a user enters a value which is not an exact power of two, the nearest power-
of-two value is applied.
Example
The following example sets the polling time for the Simple Network Time
Protocol (SNTP) client to 1024 seconds.
console(config)# sntp client poll timer 1024
sntp server
Use the sntp server command in Global Configuration mode to configure an
SNTP server address or a host name. The server address can be either an IPv4
address or an IPv6 address. Use the no form of this command to unconfigure
an SNTP server address or a host name.
Syntax
sntp server {
ip-address
|
ipv6-address
|
hostname
}
no sntp server {
ip-address
|
ipv6-address
|
hostname
}
•
ip-address
— IP address of the server.
•
hostname —
Hostname of the server. (Range: 1-158 characters)
Default Configuration
This command has no default configuration.
Command Mode
Global Configuration mode
2CSNXXX_SWUM200.book Page 1442 Tuesday, December 10, 2013 1:22 PM

Clock Commands 1443
User Guidelines
This command has no user guidelines.
Example
The following example configures the device to accept Simple Network Time
Protocol (SNTP) traffic from the server at IP address 192.1.1.1.
console(config)# sntp server 192.1.1.1
sntp trusted-key
Use the sntp trusted-key command in Global Configuration mode to
authenticate the identity of a system to which Simple Network Time Protocol
(SNTP) will synchronize. To disable authentication of the identity of the
system, use the no form of this command.
Syntax
sntp trusted-key
key-number
no sntp trusted-key
key-number
•
key-number —
Key number of authentication key to be trusted. (Range:
1–4294967295)
Default Configuration
No keys are trusted.
Command Mode
Global Configuration mode
User Guidelines
This command is relevant for both received Unicast and Broadcast.
Example
The following defines SNTP trusted-key.
console(config)# sntp authentication-key 8 md5 ClkKey
console(config)# sntp trusted-key 8
console(config)# sntp authenticate
2CSNXXX_SWUM200.book Page 1443 Tuesday, December 10, 2013 1:22 PM

1444 Clock Commands
sntp unicast client enable
Use the sntp unicast client enable command in Global Configuration mode
to enable a client to use Simple Network Time Protocol (SNTP) predefined
Unicast clients. To disable an SNTP Unicast client, use the no form of this
command.
Syntax
sntp unicast client enable
no sntp unicast client enable
Default Configuration
The SNTP Unicast client is disabled.
Command Mode
Global Configuration mode
User Guidelines
Use the sntp server command to define SNTP servers.
Examples
The following example enables the device to use Simple Network Time
Protocol (SNTP) to request and accept SNTP traffic from servers.
console(config)# sntp unicast client enable
clock timezone hours-offset
Use the clock timezone [ hours-offset ] [minutes
minutes-offset
] [zone
acronym
] command to set the offset to Coordinated Universal Time (UTC).
If the optional parameters are not specified, they will be read as either '0' or
'\0, as appropriate.
Syntax
clock timezone hours-offset [minutes
minutes-offset
] [zone
acronym
]
•
hours-offset —
Hours difference from UTC. (Range: –12 to +13)
2CSNXXX_SWUM200.book Page 1444 Tuesday, December 10, 2013 1:22 PM

Clock Commands 1445
•
minutes-offset —
Minutes difference from UTC. (Range: 0–59)
•
acronym —
The acronym for the time zone. (Range: Up to four
characters)
Command Mode
Global Configuration
Default Value
No default setting
User Guidelines
No specific guidelines
Example
console(config)#clock timezone -5 minutes 30 zone IST
no clock timezone
Use the no clock timezone command to reset the time zone settings.
Syntax
no clock timezone
Default Configuration
This command has no default configuration.
Command Mode
Global Configuration
User Guidelines
This command has no specific user guidelines.
Example
console(config)#no clock timezone
2CSNXXX_SWUM200.book Page 1445 Tuesday, December 10, 2013 1:22 PM

1446 Clock Commands
clock summer-time recurring
Use the clock summer-time recurring {usa | eu | {
week day month hh:mm
week day month hh:mm
}} [offset
offset
] [zone
acronym
] command to set
the summertime offset to UTC recursively every year. If the optional
parameters are not specified, they are read as either '0' or '\0', as appropriate.
Syntax
clock summer-time recurring {usa | eu | {
week day month hh:mm week day
month hh:mm
}} [offset
offset
] [zone
acronym
]
•
week
— Week of the month. (Range: 1–5, first, last)
•
day —
Day of the week. (Range: The first three letters by name; sun, for
example.)
•
month —
Month. (Range: The first three letters by name; jan, for
example.)
•
hh:mm
— Time in 24-hour format in hours and minutes. (Range: hh:
0–23, mm: 0–59)
•
offset
— Number of minutes to add during the summertime.
(Range:1–1440)
•
acronym
— The acronym for the time zone to be displayed when
summertime is in effect. (Range: Up to four characters)
Default Value
No default setting
Command Mode
Global Configuration
User Guidelines
No specific guidelines
Examples
console(config)# clock summer-time recurring 1 sun jan 00:10 2 mon mar 10:00
offset 1 zone ABC
2CSNXXX_SWUM200.book Page 1446 Tuesday, December 10, 2013 1:22 PM

Clock Commands 1447
clock summer-time date
Use the clock summer-time date {date | month} {month | date}
year
hh:mm
{date | month} {month | date}
year hh:mm
[offset
offset
] [zone
acronym
] command to set the summertime offset to UTC. If the optional
parameters are not specified, they are read as either '0' or '\0', as appropriate.
Syntax
clock summer-time date {date | month} {month | date}
year hh:mm
{date
| month} {month | date}
year hh:mm
[offset
offset
] [zone
acronym
]
•
date
— Day of the month. (Range: 1–31)
•
month
— Month. (Range: The first three letters by name; jan, for
example.)
•
year
— Year. (Range: 2000–2097)
•
hh:mm
— Time in 24-hour format in hours and minutes. (Range: hh:
0–23, mm: 0–59)
•
offset
— Number of minutes to add during the summertime. (Range:
1–1440)
•
acronym
— The acronym for the time zone to be displayed when
summertime is in effect. (Range: Up to four characters)
Default Configuration
This command has no default configuration.
Command Mode
Global Configuration
User Guidelines
No specific guidelines
Examples
console(config)# clock summer-time date 1 Apr 2007 02:00 28 Oct 2007 offset
90 zone EST
or
console(config)# clock summer-time date Apr 1 2007 02:00 Oct 28 2007 offset
90 zone EST
2CSNXXX_SWUM200.book Page 1447 Tuesday, December 10, 2013 1:22 PM

1448 Clock Commands
no clock summer-time
Use the no clock summer-time command to reset the summertime
configuration.
Syntax
no clock summer-time
Default Configuration
This command has no default configuration.
Command Mode
Global Configuration
User Guidelines
No specific guidelines
Example
console(config)#no clock summer-time
show clock
Use the show clock command in Privileged EXEC or User EXEC mode to
display the time and date from the system clock. Use the show clock detail
command to show the time zone and summertime configuration.
Syntax
show clock [detail]
Default Configuration
This command has no default configuration.
Command Mode
User EXEC, Privileged EXEC, Configuration mode and all Configuration
submodes
2CSNXXX_SWUM200.book Page 1448 Tuesday, December 10, 2013 1:22 PM

Clock Commands 1449
User Guidelines
This command has no user guidelines.
Example
The following example shows the time and date only.
console# show clock
15:29:03 PDT(UTC-7) Jun 17 2005
Time source is SNTP
The following example shows the time, date, timezone, and summertime
configuration.
console# show clock detail
15:29:03 PDT(UTC-7) Jun 17 2005
Time source is SNTP
Time zone:
Acronym is PST
Offset is UTC-7
Summertime:
Acronym is PDT
Recurring every year.
Begins at first Sunday of April at 2:00.
Ends at last Sunday of October at 2:00.
Offset is 60 minutes.
The following example displays the time and date from the system clock
console>show clock
15:29:03 Jun 17 2002
Time source is SNTP
2CSNXXX_SWUM200.book Page 1449 Tuesday, December 10, 2013 1:22 PM

1450 Clock Commands
2CSNXXX_SWUM200.book Page 1450 Tuesday, December 10, 2013 1:22 PM

Command Line Configuration Scripting Commands 1451
64
Command Line Configuration
Scripting Commands
Dell Networking N2000/N3000/N4000 Series Switches
The Configuration Scripting feature allows the user to generate text-
formatted files representing the current system configuration. These
configuration script files can be uploaded to a computer and edited, then
downloaded to the system and applied to the system. This feature allows the
flexibility of creating command configuration scripts that can be applied to
several switches with minor or no modifications.
Commands applied from a script are additive in nature. That is, they modify,
but do not automatically replace the current configuration. Any valid
command can be placed in a script, including show commands.
Scripts execute in Privileged EXEC mode. The script author must add a
command (configure) in order to enter Global Configuration mode.
Commands in this Chapter
This chapter explains the following commands:
script apply
Use the script apply command in Privileged EXEC mode to apply the
commands in the script to the switch.
Syntax
script apply
scriptname
•
scriptname
— Name of the script file to apply. (Range 1–31 characters)
script apply script show
script delete script validate
script list
–
2CSNXXX_SWUM200.book Page 1451 Tuesday, December 10, 2013 1:22 PM

1452 Command Line Configuration Scripting Commands
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC mode
User Guidelines
This command has no user guidelines.
Example
The following example applies the
config.scr
script to the switch.
console#script apply config.scr
script delete
Use the script delete command in Privileged EXEC mode to delete a
specified script.
Syntax
script delete {
scriptname
| all}
•
scriptname
— Script name of the file being deleted. (Range 1-31
characters)
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC mode
User Guidelines
This command has no user guidelines.
Example
The following example deletes all scripts from the switch.
2CSNXXX_SWUM200.book Page 1452 Tuesday, December 10, 2013 1:22 PM

Command Line Configuration Scripting Commands 1453
console#script delete all
script list
Use the script list command in Privileged EXEC mode to list all scripts
present on the switch as well as the remaining available space.
Syntax
script list
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC mode
User Guidelines
This command has no user guidelines.
Example
The following example displays all scripts present on the switch.
console#script list
Configuration Script Name Size(Bytes)
-------------------------------- -----------
0 configuration script(s) found.
2048 Kbytes free.
script show
Use the script show command in Privileged EXEC mode to display the
contents of a script file.
Syntax
script show
scriptname
•
scriptname
— Name of the script file to be displayed. (Range: 1-31
characters)
2CSNXXX_SWUM200.book Page 1453 Tuesday, December 10, 2013 1:22 PM

1454 Command Line Configuration Scripting Commands
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC mode
User Guidelines
This command has no user guidelines.
Example
The following example displays the contents of the script file
config.scr
.
console#script show config.scr
interface gigabitethernet 1/0/1
ip address 176.242.100.100 255.255.255.0
exit
script validate
Use the script validate command in Privileged EXEC mode to validate a
script file by parsing each line in the script file.The validate option is
intended for use as a tool in script development. Validation identifies
potential problems though it may not identify all problems with a given
script.
Syntax
script validate
scriptname
•
scriptname
— Name of the script file being validated. (Range: 1-31
characters)
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC mode
2CSNXXX_SWUM200.book Page 1454 Tuesday, December 10, 2013 1:22 PM

Command Line Configuration Scripting Commands 1455
User Guidelines
This command has no user guidelines.
Example
The following example validates the contents of the script file
config.scr
.
console#script validate config.scr
2CSNXXX_SWUM200.book Page 1455 Tuesday, December 10, 2013 1:22 PM

1456 Command Line Configuration Scripting Commands
2CSNXXX_SWUM200.book Page 1456 Tuesday, December 10, 2013 1:22 PM

Configuration and Image File Commands 1457
65
Configuration and Image File
Commands
Dell Networking N2000/N3000/N4000 Series Switches
File System Commands
CLI commands allow the user to show the contents of the current directory in
the flash file system (dir command). These files may also be deleted from the
flash using the delete command or renamed with the rename command.
Also, the syntax of the copy command has been changed slightly to add
additional flash targets and sources for the above commands.
Command Line Interface Scripting
The configuration scripting feature allows the user to save the current Dell
Networking configuration in text format. To modify the configuration script
file, follow these procedures:
1
Upload the file to a personal computer.
2
Edit the file.
3
Download the file to a Dell Networking switch.
4
Apply it to the Dell Networking system. With this feature in place, the
Dell Networking administrator has the flexibility of creating configuration
scripts and then applying the scripts to several devices.
Commands in this Chapter
This chapter explains the following commands:
boot system erase
clear config filedescr
copy rename
2CSNXXX_SWUM200.book Page 1457 Tuesday, December 10, 2013 1:22 PM

1458 Configuration and Image File Commands
boot system
Use the boot system command in Privileged EXEC mode to specify the
system image that the device loads at startup.
Syntax
boot system [unit-id][active|backup]
•
unit-id
—Unit to be used for this operation. If absent, command executes
on this node.
•
active
—Boot from the currently active image.
•
backup
—Boot from the backup image.
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC mode
User Guidelines
Use the show bootvar command to find out which image is the active image.
Example
console#boot system ?
<unit> Unit to be used for this operation. If absent,
command executes on this node.
active Marks the given image as active for subsequent
re-boots.
backup Marks the given image as active for subsequent
re-boots.
delete show backup-config
delete backup-config show bootvar
delete backup-image show running-config
delete startup-config show startup-config
dir write
2CSNXXX_SWUM200.book Page 1458 Tuesday, December 10, 2013 1:22 PM

Configuration and Image File Commands 1459
console#show version
Machine Description............... Dell Networking Switch
System Model ID................... N4032
Machine Type...................... Dell Networking N4032
Serial Number..................... X00-32C-10
Manufacturer...................... 0xbc00
Operating System.................. Linux 2.6.32.9
Burned In MAC Address............. 001E.C9F0.0039
System Object ID.................. 1.3.6.1.4.1.674.10895.3042
CPU Version....................... XLP308L
SOC Version....................... BCM56842_A1
HW Version........................ 1
CPLD Version...................... 17
unit active backup current-active next-active
---- ----------- ----------- -------------- --------------
1 6.0.0.1 6.0.0.0 6.0.0.1 6.0.0.1
clear config
Use the clear config command in Privileged EXEC mode to restore the
switch to the default configuration.
Syntax
clear config
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC mode
User Guidelines
This command has no user guidelines.
Example
The following example restores the switch to its default configuration.
console#clear config
2CSNXXX_SWUM200.book Page 1459 Tuesday, December 10, 2013 1:22 PM
1460 Configuration and Image File Commands
copy
Use the copy command in Privileged EXEC mode to copy files within the
switch and to upload and download files from and to the switch.
Syntax
copy
source
-url
destination-url
Parameter Description
source-url
The location URL or or reserved keyword of the source file being
copied. (Range: 1-160 characters.)
List of valid source parameters for uploading from the switch:
backup-config Uploads Backup Config file.
image Uploads code file via tftp.
operational-log Uploads Operational Log file.
running-config Copies system config file.
script Uploads Configuration Script file.
startup-config Uploads Startup Config file.
startup-log Uploads Startup Log file.
Valid source URLs for downloading to the switch:
tftp://{ipaddress | hostname}/filepath/filename
scp://{user@ipaddresss | hostname}/filepath/filename
sftp://{user@ipaddress | hostname}/filepath/filename
ftp://{user@ipaddress | hostname}/filepath/filename
flash://
filename
usb://
filepath
/
filename
2CSNXXX_SWUM200.book Page 1460 Tuesday, December 10, 2013 1:22 PM

Configuration and Image File Commands 1461
The following list describes syntax keywords.
•
source-url
— The location URL or reserved keyword of the source file
being copied. (Range: 1–160 characters.)
•
destination-url
— The URL or reserved keyword of the destination file.
(Range: 1–160 characters.)
•
ipaddr
— The IPv4 or IPv6 address of the server.
•
hostname
— Hostname of the server. (Range: 1–158 characters). The
command allows spaces in the host name when specified in double quotes.
•
filepath
— The path to the file on the server.
•
filename
— The name of the file on the server.
•
username
— The user name for logging into the remote server via SSH.
The following table lists and describes reserved keywords.
destination-url
The URL or reserved keyword of the destination file. (Range: 1-160
characters.
List of valid destination parameters for downloading to the switch:
backup-config Downloads config file using sftp or tftp.
image Downloads code file by ftp, sftp, or tftp.
script Downloads configuration script by sftp
or tftp.
startup-config Downloads config file using tftp.
ias-users Downloads the ias-users database file.
Valid destination URLs for uploading from the switch:
tftp://{ipaddress | hostname}/filepath/filename
scp://{user@ipaddresss | hostname}/filepath/filename
sftp://{user@ipaddress | hostname}/filepath/filename
flash://
filename
usb://
filename/filename
Parameter Description
2CSNXXX_SWUM200.book Page 1461 Tuesday, December 10, 2013 1:22 PM
1462 Configuration and Image File Commands
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC mode
Reserved
Keyword
Description
running-config Represents the current running configuration file.
startup-config Represents the startup configuration file.
startup-log Represents the startup syslog file. This can only be the source of a
copy operation.
operational-log Represents the operational syslog file. This can only be the source
of a copy operation.
script
scriptname
Represents a CLI script file.
image Represents the software image file. When "image" is the target of a
copy command, it refers to the backup image. When "image" is
the source of a copy command, it refers to the active image. If this
is destination, the file will be distributed to all units in the stack.
ftp: Source or destination URL for an FTP network server. The syntax
for this alias is ftp:
//ipaddr/filepath/filename image
.
tftp: Source or destination URL for a TFTP network server. The syntax
for this alias is tftp:[[
//location
]
/directory
]
/filename
. An out-of-
band IP address can be specified as described in the User
Guidelines.
usb: Source or destination URL for a file on a mounted USB file
system. Subdirectories are not supported on USB devices.
flash: Source or destination URL for the switch flash-based file system.
backup-config Represents the backup configuration file.
unit Indicates which unit in the stack is the target of the copy
command.
2CSNXXX_SWUM200.book Page 1462 Tuesday, December 10, 2013 1:22 PM

Configuration and Image File Commands 1463
User Guidelines
When copying files from the switch, match a source parameter with a
destination URL. When copying to the switch, match a source URL to a
destination parameter. FTP is only supported for image download to the
switch. URLs may not exceed 160 characters in length, including filename,
file path, hostname, ip address, user, and reserved keywords. Script download
performs syntax checking of downloaded scripts. If a syntax error is detected,
the user is prompted to save the file. If no error is detected, the file is saved in
the target file name.
When copying scripts to the switch, use the script <filename> target syntax.
Internally, all scripts, including the startup-config and backup-config, are
stored with a header. The header is added when the script is downloaded to
the switch and removed when the script is uploaded from the switch. Using
the flash://<filename> syntax as the target or source bypasses adding of the
script header, ensuring that when a script is applied on the switch which was
previously copied to the switch using the flash://<filename> syntax, a syntax
error will result.
Downloaded scripts are executed from privileged exec mode and should
contain a configure command as the first line of the script in order to enter
global configuration mode.
Examples
Example – Backing up the running-config
console#copy running-config backup-config
This operation may take a few minutes.
Management interfaces will not be available during this time.
Are you sure you want to save? (y/n) y
Configuration saved!
Example – Downloading new code to the switch
console#copy tftp://10.27.9.99/jmclendo/N4000v8.22.13.9.stk backup
Transfer Mode.................................. TFTP
Server IP Address.............................. 10.27.9.99
Source File Path............................... jmclendo/
Source Filename................................ N4000v8.22.13.9.stk
Data Type...................................... Code
Destination Filename........................... backup
2CSNXXX_SWUM200.book Page 1463 Tuesday, December 10, 2013 1:22 PM

1464 Configuration and Image File Commands
Management access will be blocked for the duration of the transfer
Are you sure you want to start? (y/n) y
File transfer in progress. Management access will be blocked for the duration
of the transfer. please wait...
TFTP Code transfer starting...
17128797 bytes transferred...
File contents are valid. Copying file to flash...
Attempting to send the STK file to other units in the stack...
File transfer operation completed successfully.
console#show bootvar
Image Descriptions
active :
backup :
Images currently available on Flash
unit active backup current-active next-active
----- ------------ ------------ ----------------- -----------------
1 6.0.0.1 6.0.0.0 6.0.0.1 6.0.0.1
After the file transfer completes, use the boot system command to select the
new image to run.
Example – Downloading and applying ias users file
console#copy tftp://10.131.17.104/aaa_users.txt ias-users
Transfer Mode.................................. TFTP
Server IP Address.............................. 10.131.17.104
File Path...................................... ./
File Name...................................... aaa_users.txt
Data Type...................................... IAS Users
Management access will be blocked for the duration of the transfer
Are you sure you want to start? (y/n) y
File transfer operation completed successfully.
2CSNXXX_SWUM200.book Page 1464 Tuesday, December 10, 2013 1:22 PM

Configuration and Image File Commands 1465
Validating and updating the users to the IAS users database.
Updated IAS users database successfully.
Example – Script Download
copy tftp://10.27.9.99/jmclendo/max-acl.scr script maxacl.scr
Example – USB copy operations
console#copy usb:/start-config startup-config
console#copy operational-log usb://olog.txt
console#copy usb://backup-config.txt backup-config
console#copy active usb://image1.stk
console#copy flash://crashdump.0 usb://crashdump.0
delete
Use the delete command to delete files from flash. Files cannot be deleted
from the USB device.
Syntax
delete
file
•
file
— Name of the file to be deleted.
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC mode
User Guidelines
This command has no user guidelines.
Example
console#delete file1.scr
Delete file1.scr (Y/N)?y
2CSNXXX_SWUM200.book Page 1465 Tuesday, December 10, 2013 1:22 PM

1466 Configuration and Image File Commands
delete backup-config
Use the delete backup-config command in Privileged EXEC mode to delete
the backup-config file.
Syntax
delete backup-config
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC mode
User Guidelines
This command has no user guidelines.
Example
The following example deletes the backup-config file.
console#delete backup-config
Delete backup-config (Y/N)?y
delete backup-image
Use the delete backup-image command in Privileged EXEC mode to delete a
file from a flash memory device.
Syntax
delete
backup-image
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC mode
2CSNXXX_SWUM200.book Page 1466 Tuesday, December 10, 2013 1:22 PM

Configuration and Image File Commands 1467
User Guidelines
NOTE: The active image cannote be deleted.
Example
The following example deletes test file in Flash memory.
console#delete backup-image
Delete: image2 (y/n)?
delete startup-config
Use the delete startup-config command in Privileged EXEC mode to delete
the startup-config file.
Syntax
delete startup-config
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC mode
User Guidelines
If the startup-config file is not present when system reboots, it reboots with
default settings.
Example
The following example deletes the startup-config file.
console# delete startup-config
Delete startup-config (y/n)?
dir
Use the dir command to print the contents of the flash file system.
2CSNXXX_SWUM200.book Page 1467 Tuesday, December 10, 2013 1:22 PM

1468 Configuration and Image File Commands
Syntax
dir
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC mode
User Guidelines
This command has no user guidelines.
Example
console#dir
0 drwx 2048 Jan 13 2031 17:19:54 .
0 drwx 2048 Jan 10 2031 15:58:10 ..
0 -rwx 256 Jan 22 2005 08:00:48 vpd.bin
0 -rwx 16380 Jan 10 2031 15:58:18 log2.bin
0 -rwx 72 Jan 10 2031 15:58:14 boot.dim
0 -rwx 0 Jan 10 2031 15:58:18 slog2.txt
0 -rwx 53205 Jan 22 2005 09:45:04 rc.soc
0 -rwx 148 Jan 10 2031 15:58:22 hpc_broad.cfg
0 -rwx 11224 Jan 22 2005 09:45:04 helixmem.soc
--More-- or (q)uit
console#
erase
Use the erase command to erase the startup configuration, the backup
configuration, or the backup image.
Syntax
erase {filename | startup-config | backup-image | backup-config}
•
filename
—
The name of a file on the flash drive.
•
startup-config
—
Erases the contents of the startup configuration file.
•
backup-image
—
Erase the backup image.
•
backup-config
—
Erases the backup configuration.
2CSNXXX_SWUM200.book Page 1468 Tuesday, December 10, 2013 1:22 PM

Configuration and Image File Commands 1469
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC mode
User Guidelines
This command is not supported on USB drives.
filedescr
Use the filedescr command in Privileged EXEC mode to add a description to
a file. Use the no version of this command to remove the description from the
filename.
Syntax
filedescr {image 1 | image2}
description
no filedescr {image 1 | image2}
•
image1
|
image2
— Image file.
•
description
— Block of descriptive text. (Range: 0-128 characters)
Default Configuration
No description is attached to the file.
Command Mode
Privileged EXEC mode
User Guidelines
The description accepts any printable characters except a double quote or
question mark. Enclose the string in double quotes to include spaces within
the description. The surrounding quotes are not used as part of the
description. The CLI does not filter illegal combinations of characters on
entry and may accept entries up to the first illegal character or reject the entry
entirely.
2CSNXXX_SWUM200.book Page 1469 Tuesday, December 10, 2013 1:22 PM

1470 Configuration and Image File Commands
Example
The following example attaches a file description to image2.
console#filedescr image2 "backedup on 03-22-05"
rename
Use the rename command in Privileged EXEC mode to rename a file present
in flash.
Syntax
rename
source
dest
•
source
— Source file name
•
dest
— Destination file name
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC mode
User Guidelines
This command has no user guidelines.
Example
console#rename file1.scr file2.scr
show backup-config
Use the show backup-config command in Privileged EXEC mode to display
the contents of the backup configuration file.
Syntax
show backup-config
2CSNXXX_SWUM200.book Page 1470 Tuesday, December 10, 2013 1:22 PM

Configuration and Image File Commands 1471
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC mode, Configuration mode and all Configuration submodes
User Guidelines
This command has no user guidelines.
Example
The following example shows backup-config data.
console#show backup-config
!Current Configuration:
!System Description "Dell Networking N4032, 6.0.0.0, Linux 2.6.32.9"
!System Software Version 6.0.0.0
!Cut-through mode is configured as disabled
!
configure
slot 1/0 1 ! Dell Networking N4032
stack
member 1 1 ! N4032
exit
interface vlan 1
exit
snmp-server engineid local 800002a203001122334455
exit
show bootvar
Use the show bootvar command in User EXEC mode to display the active
system image file that the device loads at startup.
Syntax
show bootvar [
unit
]
•
unit
—Unit number.
2CSNXXX_SWUM200.book Page 1471 Tuesday, December 10, 2013 1:22 PM

1472 Configuration and Image File Commands
Default Configuration
This command has no default configuration.
Command Mode
User EXEC mode, Configuration mode and all Configuration submodes
User Guidelines
This command has no user guidelines.
Example
The following example displays the active system image file that the device
loads at startup.
console(config)#show bootvar
Image Descriptions
active :
backup :
Images currently available on Flash
unit active backup current-active next-active
----- ------------ ------------ ----------------- -----------------
1 6.0.0.0 9.25.16.57 6.0.0.0 6.0.0.0
show running-config
Use the show running-config command in Privileged EXEC mode to display
the contents of the currently running configuration file, including banner
configuration. The command only displays the configurations that are non-
default.
NOTE: All non-default configurations for the Captve Portal branding images and
encoded Unicode are not displayed via the standard show running-config
command. If desired, you can view this data in the script files or by using the all
mode for the show running-config command. In addition, please note that this non-
readable data is contained and displayed at the end of the script files.
2CSNXXX_SWUM200.book Page 1472 Tuesday, December 10, 2013 1:22 PM

Configuration and Image File Commands 1473
Syntax
show running-config [
all
|
scriptname
]
•
all
—To display or capture the commands with settings and
configuration that are equal to the default value, include the
all
option.
•
scriptname
—If the optional
scriptname
is provided, the output is
redirected to a script file.
NOTE: If you issue the show running-config command from a serial connection,
access to the switch through remote connections (such as Telnet) is suspended
while the output is being generated and displayed.
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC mode
, Configuration mode and all Configuration
submodes
User Guidelines
This command has no user guidelines.
Example
console# show running-config
...
line ssh
no exec-banner
exit
line telnet
no login-banner
exit
banner exec "===exec====="
banner login "===login====="
banner motd "===motd====="
exit
show startup-config
Use the show startup-config command in Privileged EXEC mode to display
the startup configuration file contents.
2CSNXXX_SWUM200.book Page 1473 Tuesday, December 10, 2013 1:22 PM

1474 Configuration and Image File Commands
Syntax
show startup-config
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC mode, Configuration mode and all Configuration submodes
User Guidelines
This command has no user guidelines.
Example
The following example displays the contents of the startup-config file.
console#show startup-config
!Current Configuration:
!System Description "Dell Networking 7048R, 10.0.0.0, Linux 6.6"
!System Software Version 6.0.0.0
!
configure
vlan routing 1 1
exit
slot 1/0 7 ! Dell Networking N3048
slot 1/1 11 ! SFP+ Card
slot 1/2 9 ! CX4 Card
stack
member 1 7 ! N3048
exit
logging console informational
logging cli-command
logging file informational
interface vlan 1
exit
snmp-server community "public" su
exit
write
Use the write command to copy the running configuration image to the
startup configuration.
2CSNXXX_SWUM200.book Page 1474 Tuesday, December 10, 2013 1:22 PM

Configuration and Image File Commands 1475
Syntax
write
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC mode
User Guidelines
This command is equivalent to the copy running-config startup-config
command functionally.
Example
console#write
2CSNXXX_SWUM200.book Page 1475 Tuesday, December 10, 2013 1:22 PM

1476 Configuration and Image File Commands
2CSNXXX_SWUM200.book Page 1476 Tuesday, December 10, 2013 1:22 PM

Denial of Service Commands 1477
66
Denial of Service Commands
Dell Networking N2000/N3000/N4000 Series Switches
The following list shows the DoS attack detection Dell Networking supports.
•SIP=DIP:
– Source IP address = Destination IP address.
•First Fragment:
– TCP Header size smaller then configured value.
•TCP Fragment:
–IP Fragment Offset = 1.
• TCP Flag:
– TCP Flag SYN set and Source Port < 1024 or TCP Control Flags = 0
and
– TCP Sequence Number = 0 or TCP Flags FIN, URG, and PSH set
and
– TCP Sequence Number = 0 or TCP Flags SYN and FIN set.
•L4 Port:
– Source TCP/UDP Port = Destination TCP/UDP Port.
•ICMP:
– Limiting the size of ICMP Ping packets.
•SMAC=DMAC:
– Source MAC address = Destination MAC address.
•TCP Port:
– Source TCP Port = Destination TCP Port.
•UDP Port:
– Source UDP Port = Destination UDP Port.
• TCP Flag & Sequence:
– TCP Flag SYN set and Source Port < 1024 or TCP Control Flags = 0
and
2CSNXXX_SWUM200.book Page 1477 Tuesday, December 10, 2013 1:22 PM

1478 Denial of Service Commands
– TCP Sequence Number = 0 or TCP Flags FIN, URG, and PSH set
and
– TCP Sequence Number = 0 or TCP Flags SYN and FIN set.
• TCP Offset:
– Checks for TCP header offset =1.
•TCP SYN:
–TCP Flag SYN set.
• TCP SYN & FIN:
– TCP Flags SYN and FIN set.
• TCP FIN & URG & PSH:
– TCP Flags FIN and URG and PSH set and TCP Sequence Number =
0.
•ICMP V6:
– Limiting the size of ICMPv6 Ping packets.
•ICMP Fragment:
– Checks for fragmented ICMP packets.
Commands in this Chapter
This chapter explains the following commands:
dos-control firstfrag ip icmp error-interval
dos-control icmp ip unreachables
dos-control l4port ip redirects
dos-control sipdip ipv6 icmp error-interval
dos-control tcpflag ipv6 unreachables
dos-control tcpfrag show dos-control
ip icmp echo-reply
–
2CSNXXX_SWUM200.book Page 1478 Tuesday, December 10, 2013 1:22 PM

Denial of Service Commands 1479
dos-control firstfrag
Use the dos-control firstfrag command in Global Configuration mode to
enable Minimum TCP Header Size Denial of Service protection. If the mode
is enabled, Denial of Service prevention is active for this type of attack. If
packets ingress having a TCP Header Size smaller than the configured value,
the packets are dropped.
Syntax
dos-control firstfrag [
size
]
no dos-control firstfrag
•
size
—TCP header size. (Range: 0-255). The default TCP header size is 20.
ICMP packet size is 512.
Default Configuration
Denial of Service is disabled.
Command Mode
Global Configuration mode
User Guidelines
This command has no user guidelines.
Example
The following example defines a minimum TCP header size of 20. Packets
entering with a smaller header size are dropped.
console(config)#dos-control firstfrag 20
dos-control icmp
Use the dos-control icmp command in Global Configuration mode to enable
Maximum ICMP Packet Size Denial of Service protections. If the mode is
enabled, Denial of Service prevention is active for this type of attack. If ICMP
Echo Request (PING) packets ingress having a size greater than the
configured value, the packets are dropped.
2CSNXXX_SWUM200.book Page 1479 Tuesday, December 10, 2013 1:22 PM

1480 Denial of Service Commands
Syntax
dos-control icmp [
size
]
no dos-control icmp
•
size
— Maximum ICMP packet size. (Range: 0-16376). If size is
unspecified, the value is 512.
Default Configuration
Denial of Service is disabled.
Command Mode
Global Configuration mode
User Guidelines
This command has no user guidelines.
Example
The following example activates the Maximum ICMP Packet Denial of
Service protection with a maximum packet size of 1023.
console(config)#dos-control icmp 1023
dos-control l4port
Use the dos-control l4port command in Global Configuration mode to
enable L4 Port Denial of Service protection. If the mode is enabled, Denial of
Service prevention is active for this type of attack. If packets ingress having
Source TCP/UDP Port Number equal to Destination TCP/UDP Port
Number, the packets are dropped.
Syntax
dos-control l4port
no dos-control l4port
Default Configuration
Denial of Service is disabled.
2CSNXXX_SWUM200.book Page 1480 Tuesday, December 10, 2013 1:22 PM

Denial of Service Commands 1481
Command Mode
Global Configuration mode
User Guidelines
This command has no user guidelines.
Example
The following example activates L4 Port Denial of Service protection.
console(config)#dos-control l4port
dos-control sipdip
Use the dos-control sipdip command in Global Configuration mode to
enable Source IP Address = Destination IP Address (SIP=DIP) Denial of
Service protection. If the mode is enabled, Denial of Service prevention is
active for this type of attack. If packets ingress with SIP=DIP, the packets is
dropped if the mode is enabled.
Syntax
dos-control sipdip
no dos-control sipdip
Default Configuration
Denial of Service is disabled.
Command Mode
Global Configuration mode
User Guidelines
This command has no user guidelines.
Example
The following example activates SIP=DIP Denial of Service protection.
console(config)#dos-control sipdip
2CSNXXX_SWUM200.book Page 1481 Tuesday, December 10, 2013 1:22 PM

1482 Denial of Service Commands
dos-control tcpflag
Use the dos-control tcpflag command in Global Configuration mode to
enable TCP Flag Denial of Service protections. If the mode is enabled, Denial
of Service prevention is active for this type of attack. If packets ingress having
TCP Flag SYN set and a source port less than 1024, having TCP Control
Flags set to 0 and TCP Sequence Number set to 0, having TCP Flags FIN,
URG, and PSH set and TCP Sequence Number set to 0, or having TCP Flags
SYN and FIN both set, the packets are dropped.
Syntax
dos-control tcpflag
no dos-control tcpflag
Default Configuration
Denial of Service is disabled.
Command Mode
Global Configuration mode.
User Guidelines
This command has no user guidelines.
Example
The following example activates TCP Flag Denial of Service protections.
console(config)#dos-control tcpflag
dos-control tcpfrag
Use the dos-control tcpfrag command in Global Configuration mode to
enable TCP Fragment Denial of Service protection. If the mode is enabled,
Denial of Service prevention is active for this type of attack. If packets ingress
having IP Fragment Offset equal to one (1), the packets are dropped.
Syntax
dos-control tcpfrag
2CSNXXX_SWUM200.book Page 1482 Tuesday, December 10, 2013 1:22 PM

Denial of Service Commands 1483
no dos-control tcpfrag
Default Configuration
Denial of Service is disabled.
Command Mode
Global Configuration mode
User Guidelines
This command has no user guidelines.
Example
The following example activates TCP Fragment Denial of Service protection.
console(config)#dos-control tcpfrag
ip icmp echo-reply
Use the ip icmp echo-reply command to enable or disable the generation of
ICMP Echo Reply messages. Use the no form of this command to prevent the
generation of ICMP Echo Replies.
Syntax
ip icmp echo-reply
no ip icmp echo-reply
Default Configuration
ICMP Echo Reply messages are enabled by default.
Command Mode
Global Configuration mode
User Guidelines
There are no user guidelines for this command.
2CSNXXX_SWUM200.book Page 1483 Tuesday, December 10, 2013 1:22 PM

1484 Denial of Service Commands
Example
console(config)#ip icmp echo-reply
ip icmp error-interval
Use the ip icmp error-interval command to limit the rate at which IPv4
ICMP error messages are sent. The rate limit is configured as a token bucket
with two configurable parameters: Burst-size and burst-interval.
To disable ICMP rate limiting, set burst-interval to zero. Use the no form of
this command to return burst-interval and burst-size to their default values.
Syntax
ip icmp error-interval
burst-interval
[
burst-size
]
no ip icmp error-interval
•
burst-interval
— How often the token bucket is initialized (Range:
0–2147483647 milliseconds).
•
burst-size
— The maximum number of messages that can be sent during a
burst interval (Range: 1–200).
Default Configuration
Rate limiting is enabled by default.
The default burst-interval is 1000 milliseconds.
The default burst-size is 100 messages.
Command Mode
Global Configuration mode
User Guidelines
There are no user guidelines for this command
Example
console(config)#ip icmp error-interval 1000 20
2CSNXXX_SWUM200.book Page 1484 Tuesday, December 10, 2013 1:22 PM

Denial of Service Commands 1485
ip unreachables
Use the ip unreachables command to enable the generation of ICMP
Destination Unreachable messages. Use the no form of this command to
prevent the generation of ICMP Destination Unreachable messages.
Syntax
ip unreachables
no ip unreachables
Default Configuration
ICMP Destination Unreachable messages are enabled.
Command Mode
Interface Configuration (VLAN) mode
User Guidelines
There are no user guidelines for this command.
Example
console(config-if-vlan10)#ip unreachables
ip redirects
Use the ip redirects command to enable the generation of ICMP Redirect
messages. Use the no form of this command to prevent the sending of ICMP
Redirect Messages. In global configuration mode, this command affects all
interfaces. In interface configuration mode, it only affects that interface.
Syntax
ip redirects
no ip redirects
Default Configuration
ICMP Redirect messages are enabled by default.
2CSNXXX_SWUM200.book Page 1485 Tuesday, December 10, 2013 1:22 PM

1486 Denial of Service Commands
Command Mode
Interface Configuration (VLAN) mode
User Guidelines
There are no user guidelines for this command.
Example
console(config-if-vlan10)#ip redirects
ipv6 icmp error-interval
Use the icmp error-interval command to limit the rate at which ICMP error
messages are sent. The rate limit is configured as a token bucket with two
configurable parameters: Burst-size and burst interval. Use the no form of this
command to return burst-interval and burst-size to their default values. To
disable ICMP rate limiting, set burst-interval to zero.
Syntax
ipv6 icmp error-interval
burst-interval
[
burst-size
]
no ipv6 icmp error-interval
•
burst-interval
— How often the token bucket is initialized (Range:
0–2147483647 milliseconds).
•
burst-size
— The maximum number of messages that can be sent during a
burst interval (Range: 1–200).
Default Configuration
Rate limiting is enabled by default.
The default burst-interval is 1000 milliseconds.
The default burst-size is 100 messages.
Command Mode
Global Configuration mode
User Guidelines
There are no user guidelines for this command.
2CSNXXX_SWUM200.book Page 1486 Tuesday, December 10, 2013 1:22 PM

Denial of Service Commands 1487
Example
console(config)#ipv6 icmp error-interval 2000 20
ipv6 unreachables
Use the ipv6 unreachables command to enable the generation of ICMPv6
Destination Unreachable messages. Use the no form of this command to
prevent the generation of ICMPv6 Destination Unreachable messages.
Syntax
ipv6 unreachables
no ipv6 unreachables
Default Configuration
ICMPv6 Destination Unreachable messages are enabled by default.
Command Mode
Interface Configuration (VLAN) mode
User Guidelines
There are no user guidelines for this command.
Example
console(config-if-vlan10)#ipv6 unreachables
show dos-control
Use the show dos-control command in Privileged EXEC mode to display
Denial of Service configuration information.
Syntax
show dos-control
Default Configuration
This command has no default configuration.
2CSNXXX_SWUM200.book Page 1487 Tuesday, December 10, 2013 1:22 PM

1488 Denial of Service Commands
Command Mode
Privileged EXEC mode, Configuration mode and all Configuration submodes
User Guidelines
This command has no user guidelines.
Example
The following example displays Denial of Service configuration information.
console#show dos-control
SIPDIP Mode...............................Disable
First Fragment Mode.......................Disable
Min TCP Hdr Size..........................20
TCP Fragment Mode........................ Disable
TCP Flag Mode.............................Disable
L4 Port Mode..............................Disable
ICMP Mode.................................Disable
Max ICMP Pkt Size.........................512
2CSNXXX_SWUM200.book Page 1488 Tuesday, December 10, 2013 1:22 PM

Line Commands 1489
67
Line Commands
Dell Networking N2000/N3000/N4000 Series Switches
This chapter explains the following commands:
Authentication commands related to line configuration mode are in
AAA
Commands
.
exec-timeout
Use the exec-timeout command in Line Configuration mode to set the
interval that the system waits for user input before timeout. The exec-
timeout command is also used by the web for timing out web sessions. To
restore the default setting, use the no form of this command.
Syntax
exec-timeout
minutes
[
seconds
]
no exec-timeout
•
minutes
— Integer that specifies the number of minutes. (Range:
0–65535)
•
seconds
— Additional time intervals in seconds. (Range: 0–59)
Default Configuration
The default configuration is 10 minutes.
Command Mode
Line Configuration mode
exec-timeout line
history show line
history size speed
2CSNXXX_SWUM200.book Page 1489 Tuesday, December 10, 2013 1:22 PM

1490 Line Commands
User Guidelines
To specify no timeout, enter the exec-timeout 0 command.
Example
The following example configures the interval that the system waits until user
input is detected to 20 minutes.
console(config)#line console
console(config-line)#exec-timeout 20
history
Use the history command in Line Configuration mode to enable the
command history function. To disable the command history function, use the
no form of this command.
Syntax
history
no history
Default Configuration
The default value for this command is
enabled
.
Command Mode
Line Interface mode
User Guidelines
This command has no user guidelines.
Example
The following example disables the command history function for the current
terminal session.
console(config-line)# no history
2CSNXXX_SWUM200.book Page 1490 Tuesday, December 10, 2013 1:22 PM

Line Commands 1491
history size
Use the history size command in Line Configuration mode to change the
command history buffer size for a particular line. To reset the command
history buffer size to the default setting, use the no form of this command.
Syntax
history size
number-of-commands
no history size
•
number-of-commands
—Specifies the number of commands the system
may record in its command history buffer. (Range: 0-216)
Default Configuration
The default command history buffer size is 10.
Command Mode
Line Configuration mode
User Guidelines
This command has no user guidelines.
Example
The following example configures the command history buffer size to 20
commands for the current terminal session.
console(config-line)#history size 20
line
Use the line command in Global Configuration mode to identify a specific
line for configuration and enter the line configuration command mode.
Syntax
line {console | telnet | ssh}
•
console
— Console terminal line.
•
telnet
— Virtual terminal for remote console access (Telnet).
2CSNXXX_SWUM200.book Page 1491 Tuesday, December 10, 2013 1:22 PM

1492 Line Commands
•
ssh
— Virtual terminal for secured remote console access (SSH).
Default Configuration
This command has no default configuration.
Command Mode
Global Configuration mode
User Guidelines
The default authentication list for telnet and SSH is enableNetList. The
enableNetList uses a single method: enable. This implies that users accessing
the switch via telnet or SSH must have an enable password defined in order to
access privileged mode. Alternatively, the administrator can set the telnet and
ssh lists to enableList, which has the enable and none methods defined.
When using line ssh authentication with a RADIUS server as the primary
authentication method, be aware that the default 802.1x timeout is 45
seconds. This is the same timeout value as SSH. Thus a secondary
authentication method is unlikely to be invoked due to SSH timing out and
dropping the connection attempt.
Examples
The following example sets the telnet authentication list to enableList:
console(config)#line telnet
console(config-telnet)#enable authentication enableList
The following example enters Line Configuration mode to configure Telnet.
console(config)#line telnet
console(config-line)#
show line
Use the show line command in User EXEC or Privileged EXEC modes to
display line parameters.
Syntax
show line [console | telnet | ssh]
•
console
— Console terminal line.
2CSNXXX_SWUM200.book Page 1492 Tuesday, December 10, 2013 1:22 PM

Line Commands 1493
•
telnet
— Virtual terminal for remote console access (Telnet).
•
ssh
— Virtual terminal for secured remote console access (SSH).
Default Configuration
This command has no default configuration.
Command Mode
User EXEC and Privileged EXEC mode, Configuration mode and all
Configuration submodes
User Guidelines
This command has no user guidelines.
Example
The following example displays the line configuration.
console>show line
Console configuration:
Interactive timeout: Disabled
History: 10
Baudrate: 9600
Databits: 8
Parity: none
Stopbits: 1
Telnet configuration:
Interactive timeout: 10 minutes 10 seconds
History: 10
SSH configuration:
Interactive timeout: 10 minutes 10 seconds
History: 10
speed
Use the speed command in Line Configuration mode to set the line baud
rate. Use the no form of the command to restore the default settings.
Syntax
speed {
bps
}
no speed
2CSNXXX_SWUM200.book Page 1493 Tuesday, December 10, 2013 1:22 PM

1494 Line Commands
•
bps
— Baud rate in bits per second (bps). The options are 2400, 9600,
19200, 38400, 57600, and 115200.
Default Configuration
This default speed is 9600.
Command Mode
Line Interface (console) mode
User Guidelines
This configuration applies only to the current session.
Example
The following example configures the console baud rate to 9600.
console(config-line)#speed 9600
2CSNXXX_SWUM200.book Page 1494 Tuesday, December 10, 2013 1:22 PM

Management ACL Commands 1495
68
Management ACL Commands
Dell Networking N2000/N3000/N4000 Series Switches
In order to ensure the security of the switch management features, the
administrator may elect to configure a management access control list. The
Management Access Control and Administration List (ACAL) component is
used to ensure that only known and trusted devices are allowed to remotely
manage the switch via TCP/IP. Management ACLs are only configurable on
IP (in-band) interfaces, not on the out-of-band interface or the serial port.
Management ACLs are applied after all hardware based ACLs (ip access-list
and ipv6 access-list) have been applied. This allows the administrator to
configure hardware based filtering criteria for the in-band management and
then further refine that criteria with firmware based filtering supplied by the
management ACL capability.
When a Management ACAL is enabled, incoming TCP packets initiating a
connection (TCP SYN) and all UDP packets will be filtered based on their
source IP address and destination port. Additionally, other attributes such as
incoming port (or port-channel) and VLAN ID can be used to determine if
the traffic should be allowed to the management interface. When the
component is disabled, incoming TCP/UDP packets are not filtered and are
processed normally.
There is also an option to restrict all the above packets from the network
interface. This is done by specifying “console only” in the MACAL
component. If this is enabled, the systems management interface is only
accessible via the serial port. All TCP SYN packets and UDP packets are
dropped except UDP packets sent to the DHCP Server or DHCP Client
ports.
Commands in this Chapter
This chapter explains the following commands:
deny (management) permit (management)
management access-class show management access-class
2CSNXXX_SWUM200.book Page 1495 Tuesday, December 10, 2013 1:22 PM

1496 Management ACL Commands
deny (management)
Use the deny command in Management Access-List Configuration mode to
set conditions for the management access list.
Syntax
deny [gigabitethernet unit/slot/port | vlan
vlan-id
|
port-channel
port-
channel-number
| tengigabitethernet unit/slot/port | fortygigabitethernet
unit/slot/port] [service
service
] [priority
priority
]
deny ip-source
ip-address
[mask
mask
|
prefix-length
] [gigabitethernet
unit/slot/port | vlan
vlan-id
|
port-channel
port-channel-number
|
tengigabitethernet unit/slot/port | fortygigabitethernet unit/slot/port]
[service
service
] [priority
priority
]
•
gigabitethernet
unit/slot/port — A valid 1-gigabit Ethernet-routed port
number.
•
vlan
vlan-id
— A valid VLAN number.
•
port-channel
port-channel-number
— A valid routed port-channel
number.
•
tengigabitethernet
unit/slot/port — A valid 10-gigabit Ethernet-routed
port number.
•
fortygigabitethernet
unit/slot/port
–
A valid 40-gigabit Ethernet-routed
port number.
•
ip-address
— Source IP address.
•
mask
mask
— Specifies the network mask of the source IP address.
•
mask
prefix-length
— Specifies the number of bits that comprise the
source IP address prefix. The prefix length must be preceded by a forward
slash (/). (Range: 0–32)
•
service
service
— Indicates service type. Can be one of the following:
telnet
,
ssh
,
http
,
https
,
tftp
,
snmp
,
sntp
, or
any
. The
any
keyword indicates
that the service match for the ACL is effectively "don’t care".
•
priority
priority
— Priority for the rule. (Range: 1–64)
management access-list show management access-list
2CSNXXX_SWUM200.book Page 1496 Tuesday, December 10, 2013 1:22 PM

Management ACL Commands 1497
Default Configuration
This command has no default configuration.
Command Mode
Management Access-list Configuration mode
User Guidelines
Rules with gigabitethernet, tengigabitethernet, fortygigabitethernet, vlan,
and port-channel parameters are valid only if an IP address is defined on the
appropriate interface. Ensure that each rule has a unique priority.
Example
The following example shows how all ports are denied in the access-list called
mlist
.
console(config)# management access-list mlist
console(config-macal)# deny
management access-class
Use the management access-class command in Global Configuration mode
to restrict management connections. To disable restriction, use the no form
of this command.
Syntax
management access-class {console-only |
name
}
no management access-class
•
name
— A valid access-list name. (Range: 1–32 characters)
•
console-only
— The switch can be managed only from the console.
Default Configuration
This command has no default configuration.
Command Mode
Global Configuration mode
2CSNXXX_SWUM200.book Page 1497 Tuesday, December 10, 2013 1:22 PM

1498 Management ACL Commands
User Guidelines
This command has no user guidelines.
Example
The following example configures an access-list called
mlist
as the
management access-list.
console(config)# management access-class mlist
management access-list
Use the management access-list command in Global Configuration mode to
define an access list for management, and enter the access-list for
configuration. Once in the access-list configuration mode, the denied or
permitted access conditions are configured with the deny and permit
commands. To remove an access list, use the no form of this command.
Syntax
management access-list
name
no management access-list
name
•
name
— The access list name. (Range: 1–32 printable characters)
Default Configuration
This command has no default configuration.
Command Mode
Global Configuration mode
User Guidelines
This command enters the access-list configuration mode, where the denied or
permitted access conditions with the deny and permit commands must be
defined.
If no match criteria are defined the default is deny.
If reentering to an access-list context, the new rules are entered at the end of
the access-list.
2CSNXXX_SWUM200.book Page 1498 Tuesday, December 10, 2013 1:22 PM

Management ACL Commands 1499
Use the management access-class command to select the active access-list.
The active management list cannot be updated or removed.
Management access list names can consist of any printable character,
including blanks. Enclose the name in quotes to embed blanks in the name.
Examples
The following example shows how to configure two management interfaces,
gigabit Ethernet 1/0/1 and gigabit Ethernet 2/0/9.
console(config)#management access-list mlist
console(config-macal)# permit gigabitethernet 1/0/1 priority 1
console(config-macal)# permit gigabitethernet 2/0/9 priority 1
console(config-macal)# exit
console(config)#management access-class mlist
The following example shows how to configure all the interfaces to be
management interfaces except for two interfaces, gigabit Ethernet 1/0/1 and
gigabit Ethernet 2/0/9.
console(config)# management access-list mlist
console(config-macal)# deny gigabitethernet 1/0/1 priority 1
console(config-macal)# deny gigabitethernet 2/0/9 priority 2
console(config-macal)# permit priority 2
console(config-macal)# exit
console(config) # management access-class mlist
permit (management)
Use the permit command in Management Access-List configuration mode to
set conditions for the management access list.
Syntax
permit ip-source
ip-address
[mask
mask
|
prefix-length
] [gigabitethernet
unit/slot/port | vlan
vlan-id
|
port-channel
port-channel-number
|
tengigabitethernet unit/slot/port |fortygigabitethernet unit/slot/port][
service
service
] [ priority
priority-value
]
permit {gigabitethernet unit/slot/port | vlan
vlan-id
|
port-channel
port-
channel-number
| tengigabitethernet unit/slot/port |fortygigabitethernet
unit/slot/port} [service
service
] [priority
priority-value
]
permit service
service
[priority
priority-value
]
2CSNXXX_SWUM200.book Page 1499 Tuesday, December 10, 2013 1:22 PM

1500 Management ACL Commands
permit priority
priority-value
•
gigabitethernet
unit/slot/port — A valid 1-gigabit Ethernet-routed port
number.
•
vlan
vlan-id
— A valid VLAN number.
•
port-channel
port-channel-number
— A valid port channel number.
•
tengigabitethernet
unit/slot/port — A valid 10-gigabit Ethernet-routed
port number.
•
fortygigabitethernet
unit/slot/port
–
A valid 40-gigabit Ethernet-routed
port number.
•
ip-address
— Source IP address.
•
mask
mask
— Specifies the network mask of the source IP address.
•
mask
prefix-length
— Specifies the number of bits that comprise the
source IP address prefix. The prefix length must be preceded by a forward
slash (/). (Range: 0–32)
•
service
service
— Indicates service type. Can be one of the following:
telnet
,
ssh
,
http
,
https
,
tftp
,
snmp
,
sntp
, or
any
. The
any
keyword indicates
that the service match for the ACL is effectively "don’t care".
•
priority
priority-value
— Priority for the rule. (Range: 1 – 64)
Default Configuration
This command has no default configuration.
Command Mode
Management Access-list Configuration mode
User Guidelines
Rules with gigabitethernet, tengigabitethernet, fortygigabitethernet, vlan,
and port-channel parameters are valid only if an IP address is defined on the
appropriate interface. Ensure that each rule has a unique priority.
Examples
The following example shows how to configure two management interfaces,
gigabit Ethernet 1/0/1 and gigabit Ethernet 2/0/9.
console(config)#management access-list mlist
2CSNXXX_SWUM200.book Page 1500 Tuesday, December 10, 2013 1:22 PM

Management ACL Commands 1501
console(config-macal)# permit gigabitethernet 1/0/1 priority 1
console(config-macal)# permit gigabitethernet 2/0/9 priority 1
console(config-macal)# exit
console(config)# management access-class mlist
The following example shows how to configure all the interfaces to be
management interfaces except for two interfaces, gigabit Ethernet 1/0/1 and
2/0/9.
console(config)# management access-list mlist
console(config-macal)# deny gigabitethernet 1/0/1 priority 1
console(config-macal)# deny gigabitethernet 2/0/9 priority 2
console(config-macal)# permit priority 2
console(config-macal)# exit
console(config)# management access-class mlist
show management access-class
Use the show management access-class command in Privileged EXEC mode
to display information about the active management access list.
Syntax
show management access-class
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC mode, Configuration mode and all Configuration submodes
User Guidelines
This command has no user guidelines.
Example
The following example displays the management access-list information.
console# show management access-class
Management access-class is enabled, using access list mlist
2CSNXXX_SWUM200.book Page 1501 Tuesday, December 10, 2013 1:22 PM

1502 Management ACL Commands
show management access-list
Use the show management access-list command in Privileged EXEC mode to
display management access-lists.
Syntax
show management access-list [
name
]
•
name
— A valid access list name. (Range: 1–32 characters)
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC mode, Configuration mode and all Configuration submodes
User Guidelines
This command has no user guidelines.
Example
The following example displays the active management access-list.
console# show management access-list
mlist
-----
permit priority 1 gigabitethernet 1/0/1
permit priority 2 gigabitethernet 2/0/1
! (Note: all other access implicitly denied)
2CSNXXX_SWUM200.book Page 1502 Tuesday, December 10, 2013 1:22 PM

Password Management Commands 1503
69
Password Management Commands
Dell Networking N2000/N3000/N4000 Series Switches
The Password Management component supports the features below.
Passwords are masked when entered by the user and in the running config.
Configurable Minimum Password Length
The administrator has the option of requiring user passwords to be a
minimum length. The administrator can choose to have the switch enforce a
minimum length between 8 and 64 characters. The default minimum length
is 8 although there is no default password (zero length string).
Password History
Keeping a history of previous passwords ensures that users cannot reuse
passwords often. The administrator can configure the switch to store up to 10
of the last passwords for each user. The default operation is that no history is
stored.
Password Aging
The switch can implement an aging process on passwords and require users to
change them when they expire. The administrator can configure the switch to
force a password change between 1 and 365 days. By default, password aging
is disabled. When a password expires, the user must enter a new password
before continuing.
User Lockout
The administrator may choose to strengthen the security of the switch by
enabling the user lockout feature. A lockout count between 1 and 5 attempts
can be configured. When a lockout count is configured, then a user that is
logging in must enter the correct password within that count. Otherwise, that
user is locked out form further remote switch access. Only an administrator
with read/write access can reactivate that user. The user lockout feature is
2CSNXXX_SWUM200.book Page 1503 Tuesday, December 10, 2013 1:22 PM

1504 Password Management Commands
disabled by default. The user lockout feature applies to all users on all ports.
The administrator can access the serial port even if he/she is locked out and
reset the password or clear the config to regain control of the switch. This
ensures that if a hacker tries to log in as admin and causes the account to be
locked out, then the administrator with physical access to the switch can still
log in and reactivate the admin account.
Password Strength
Password Strength is a measure of the effectiveness of a password in resisting
guessing and brute-force attacks. The strength of a password is a function of
length, complexity and randomness. Using strong passwords lowers overall
risk of a security breach. The scope of this feature is to enforce a baseline
Password Strength for all locally administered users.
The feature doesn’t affect users with an existing password until their
password ages out. Password Strength is only enforced when a user is
configuring a new password or changing their existing password. The default
action is Disabled in FP and is independent of any platform. The network
operator has to take care that the Password Strength check is Disabled before
downloading scripts containing old users to avoid password configuration
failure for such users.
Password Strength Definition:
The feature ensures that any password configured on the switch for local
administration purpose is a Strong password and it must conform to each of
the following characteristics:
• Minimum number of uppercase letters.
• Minimum number of lowercase letters.
• Minimum number of numeric characters.
• Minimum number of special characters from the set (`! " ? $ ? % ^ & * ( )
_ - + = { [ } ] : ; @ ' ~ # | \ < , > . ? / ).
• Does not contain the associated login name.
• Maximum number of consecutive characters (such as abcd).
• Maximum number of consecutive numbers (such as 1234).
2CSNXXX_SWUM200.book Page 1504 Tuesday, December 10, 2013 1:22 PM

Password Management Commands 1505
• Maximum number of repetition of characters or numbers (such as 1111 or
aaaa).
Configuring minimum value of 0 for the above parameters means no
restriction on that set of characters and configuring maximum of 0 means
disabling the restriction (or no limit on the maximum number of course
limited by minimum password length).
The Password strength feature applies to all login passwords (user, line and
enable).
Commands in this Chapter
This chapter explains the following commands for viewing and configuring
properties of passwords:
NOTE: To change a password, use the passwords command, which is described in
AAA Commands.
passwords aging passwords strength minimum special-
characters
passwords history passwords strength max-limit consecutive-
characters
passwords lock-out passwords strength max-limit repeated-
characters
passwords min-length passwords strength minimum character-
classes
passwords strength-check passwords strength exclude-keyword
passwords strength minimum uppercase-
letters
enable password encrypted
passwords strength minimum lowercase-
letters
show passwords configuration
passwords strength minimum numeric-
characters
show passwords result
2CSNXXX_SWUM200.book Page 1505 Tuesday, December 10, 2013 1:22 PM

1506 Password Management Commands
passwords aging
Use the passwords aging command in Global Configuration mode to
implement aging on passwords for local users. When a user’s password
expires, the user is prompted to change it before logging in again. Use the no
form of this command to set the password aging to the default value.
Syntax
passwords aging
1-365
no passwords aging
Default Configuration
The default value is 0.
Command Mode
Global Configuration mode
User Guidelines
A value of 0 days disables password aging.
Example
The following example sets the password age limit to 100 days.
console(config)#passwords aging 100
passwords history
As administrator, use the passwords history command in Global
Configuration mode to set the number of previous passwords that are stored
for each user account. When a local user changes his or her password, the user
is not able to reuse any password stored in password history. This setting
ensures that users do not reuse their passwords often. The default is 0. Use
the no form of this command to set the password history to the default value
of 0.
Syntax
passwords history
0-10
2CSNXXX_SWUM200.book Page 1506 Tuesday, December 10, 2013 1:22 PM

Password Management Commands 1507
no passwords history
Default Configuration
The default value is 0.
Command Mode
Global Configuration mode
User Guidelines
This command has no user guidelines.
Example
The following example sets the number of previous passwords remembered by
the system at 10.
console(config)#passwords history 10
passwords lock-out
Use the passwords lock-out command in Global Configuration mode to
strengthen the security of the switch by locking user accounts that have failed
login due to wrong passwords. When a lockout count is configured, a user
who is logging in must enter the correct password within that count.
Otherwise that user is locked out from further switch access. Only a user with
read/write access can reactivate a locked user account. Password lockout does
not apply to logins from the serial console. Use the no form of this command
to set the password lockout count to the default value.
Syntax
passwords lock-out
1-5
no passwords lock-out
Default Configuration
The default value is 0 or no lockout count is enforced.
2CSNXXX_SWUM200.book Page 1507 Tuesday, December 10, 2013 1:22 PM

1508 Password Management Commands
Command Mode
Global Configuration mode.
User Guidelines
Password lockout only applies to users with authentication configured to
local. RADIUS or TACACS authenticated users will use policies configured
on the respective RADIUS/TACACS servers.
Example
The following example sets the number of user attempts before lockout at 2.
console(config)#passwords lock-out 2
passwords min-length
Use the passwords min-length command in Global Configuration mode to
enforce a minimum length password length for local users. The value also
applies to the enable password. The valid range is 8–64. The default is 8. Use
the no version of this command to set the minimum password length to 8.
Syntax
passwords min-length
length
no passwords min-length
•
length
— The minimum length of the password (Range: 8–64 characters)
Default Configuration
By default, the minimum password length is 8 characters.
Command Mode
Global Configuration mode
User Guidelines
This command has no user guidelines.
2CSNXXX_SWUM200.book Page 1508 Tuesday, December 10, 2013 1:22 PM

Password Management Commands 1509
Example
The following example configures user bob with password xxxyymmmm and
user level 15.
(config)# username bob password xxxyyymmm level 15
passwords strength-check
Use the passwords strength-check command in Global Configuration mode
to enable the Password Strength feature. The command is used to enable the
checking of password strength during user configuration. Use the no form of
the command to disable the Password Strength feature.
Syntax
passwords strength-check
no passwords strength-check
Default Configuration
The password strength feature is disabled by default.
Command Mode
Global Configuration
User Guidelines
This command enables/disables enforcement of password strength checking
policy as configured by the following commands:
passwords strength minimum uppercase-letters
passwords strength minimum lowercase-letters
passwords strength minimum special-characters
passwords strength minimum numeric-characters
passwords strength max-limit consecutive-characters
passwords strength max-limit repeated-characters
passwords strength minimum character-classes
2CSNXXX_SWUM200.book Page 1509 Tuesday, December 10, 2013 1:22 PM

1510 Password Management Commands
passwords strength minimum uppercase-letters
Use this command to enforce a minimum number of uppercase letters that a
password must contain. The valid range is 0–16. The default is 1. A minimum
of 0 means no restriction on that set of characters. Use the no form of the
command to reset the minimum uppercase letters to the default value.
Syntax
passwords strength minimum uppercase-letters
0–16
no passwords strength minimum uppercase-letters
Default Configuration
The default value is 1.
Command Mode
Global Configuration
User Guidelines
This limit is not enforced unless the passwords strength minimum character-
classes command is configured with a value greater than 0.
Example
console(config)#passwords strength minimum uppercase-letters 6
passwords strength minimum lowercase-letters
Use this command to enforce a minimum number of lowercase letters that a
password must contain. The valid range is 0–16. The default is 1. A setting of
0 means no restriction. Use the no form of this command to reset the
minimum lowercase letters to the default value.
Syntax
passwords strength minimum lowercase-letters
0–16
no passwords strength minimum lowercase-letters
2CSNXXX_SWUM200.book Page 1510 Tuesday, December 10, 2013 1:22 PM

Password Management Commands 1511
Default Configuration
The default value is 1.
Command Mode
Global Configuration
User Guidelines
This command has no effect unless enabled by the passwords strength
minimum character-classes command. This limit is not enforced unless the
passwords strength minimum character-classes command is configured with
a value greater than 0.
Example
console(config)#passwords strength minimum lowercase-letters 6
passwords strength minimum numeric-
characters
Use this command to enforce a minimum number of numeric numbers that a
password should contain. The valid range is 0–16. The default is 1. A
minimum of 0 means no restriction on that set of characters. Use the no form
of this command to reset the minimum numeric characters to the default
value.
Syntax
passwords strength minimum numeric–characters
0–16
no passwords strength minimum numeric–characters
Default Configuration
The default value is 1.
Command Mode
Global Configuration
2CSNXXX_SWUM200.book Page 1511 Tuesday, December 10, 2013 1:22 PM

1512 Password Management Commands
User Guidelines
This command has no effect unless the passwords strength minimum
character-classes command has been enabled.
Example
console(config)#passwords strength minimum numeric–characters 6
passwords strength minimum special-characters
Use this command to enforce a minimum number of special characters that a
password may contain. The valid range is 0–16. The default is 1. A setting of 0
means no restriction. Special characters are one of the following characters (`!
$ % ^ & * ( ) _ - + = { [ } ] : ; @ ' ~ # | \ < , > . / ) Use the no form of this
command to reset the minimum special characters to the default value.
Syntax
passwords strength minimum special–characters
0–16
no passwords strength minimum special–characters
Default Configuration
The default value is 1.
Command Mode
Global Configuration
User Guidelines
This limit is not enforced unless the passwords strength minimum character-
classes command is configured with a value greater than 0.
Example
console(config)#passwords strength minimum special–characters 6
2CSNXXX_SWUM200.book Page 1512 Tuesday, December 10, 2013 1:22 PM

Password Management Commands 1513
passwords strength max-limit consecutive-
characters
Use this command to enforce a maximum number of consecutive characters
that a password can contain. If a user enters a password that has more
consecutive characters than the configured limit, the system rejects the
password. The valid range of consecutive characters is 0–15. The default is 0.
A maximum of 0 means there is no restriction on consecutive characters.
Examples of consecutive characters are ABCDEF or 123456 or !”#$%&’().
Use the no form of this command to reset the maximum consecutive
characters accepted to the default value.
Syntax
passwords strength max-limit consecutive–characters
0–15
no passwords strength max-limit consecutive-characters
Default Configuration
The default value is 0.
Command Mode
Global Configuration
User Guidelines
This command has no user guidelines.
Example
console(config)#passwords strength max-limit consecutive-characters 3
passwords strength max-limit repeated-
characters
Use this command to enforce a maximum repeated characters that a
password should contain. If password has repetition of characters more than
the configured max-limit, it fails to configure. The valid range is 0-15. The
2CSNXXX_SWUM200.book Page 1513 Tuesday, December 10, 2013 1:22 PM

1514 Password Management Commands
default is 0. A maximum of 0 means again disabling the restriction. Use the
no form of this command to reset the maximum repeated characters to the
default value.
Syntax
passwords strength max-limit repeated-characters
0-15
no passwords strength max-limit repeated-characters
Default Configuration
The default value is 0.
Command Mode
Global Configuration
User Guidelines
This command has no user guidelines.
Example
console(config)# passwords strength max-limit repeated-characters 3
passwords strength minimum character-classes
Use this command to enforce a minimum number of character classes that a
password should contain. Character classes are uppercase letters, lowercase
letters, numeric characters and special characters. The valid range is 0-4. The
default is 0. If a value of 0 is configured then no character class checking is
performed, i.e. for special characters, uppercase characters, lower-case
characters, etc. Use the no form of this command to reset the minimum
character-classes to the default value.
Syntax
passwords strength minimum character-classes
0-4
no passwords strength minimum character–classes
2CSNXXX_SWUM200.book Page 1514 Tuesday, December 10, 2013 1:22 PM

Password Management Commands 1515
Default Configuration
The default value is 0. This limit is not enforced unless the passwords
strength minimum character-classes command is configured with a value
greater than 0.
Command Mode
Global Configuration
User Guidelines
This command is used to enable password character class checking using the
parameters set by the following commands:
• passwords strength minimum uppercase-letters
• passwords strength minimum lowercase-letters
• passwords strength minimum special-characters
• passwords strength minimum numeric-characters
A value greater than 0 specifies the minimum number of character class tests
a password must pass. A value of 0 disables the minimum strength checking
set by the above commands.
Example
console(config)#passwords strength minimum character-classes 4
passwords strength exclude-keyword
Use this command to exclude the keyword while configuring the password.
The password does not accept the keyword in any form (inbetween the string,
case insensitive and reverse) as a substring. You can configure up to a
maximum of three keywords. Use the no form of this command to reset the
restriction for a given string or all the strings configured.
Syntax
passwords strength exclude–keyword
string
no passwords strength exclude–keyword [
string
]
2CSNXXX_SWUM200.book Page 1515 Tuesday, December 10, 2013 1:22 PM

1516 Password Management Commands
Default Configuration
This command has no default configuration.
Command Mode
Global Configuration
User Guidelines
This command has no user guidelines.
Example
console(config)#passwords strength exclude-keyword brcm
enable password encrypted
This command is used by an Administrator to transfer the enable password
between devices without having to know the password. The
password
parameter must be exactly 128 hexadecimal characters.
Syntax
enable password encrypted
password
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC mode
User Guidelines
This command has no user guidelines.
show passwords configuration
Use the show passwords configuration command in Privileged EXEC mode
to display the configured password management settings.
2CSNXXX_SWUM200.book Page 1516 Tuesday, December 10, 2013 1:22 PM

Password Management Commands 1517
Syntax
show passwords configuration
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC mode, Configuration mode and all Configuration submodes
User Guidelines
The following fields are displayed by this command.
Parameter Description
Minimum Password Length Minimum number of characters required
when changing passwords.
Password History Number of passwords to store for reuse
prevention.
Password Aging Length in days that a password is valid.
Lockout Attempts Number of failed password login attempts
before lockout.
Minimum Password Uppercase Letters Minimum number of uppercase
characters required when configuring
passwords.
Minimum Password Lowercase Letters Minimum number of uppercase
characters required when configuring
passwords.
Minimum Password Numeric Characters Minimum number of numeric characters
required when configuring passwords.
Maximum Password Consecutive
Characters
Maximum number of consecutive
characters required that the password
should contain when configuring
passwords.
Maximum Password Repeated Characters Maximum number of repetition of
characters that the password should
contain when configuring passwords.
2CSNXXX_SWUM200.book Page 1517 Tuesday, December 10, 2013 1:22 PM

1518 Password Management Commands
Example
The following example displays the command output.
console#show passwords configuration
Passwords Configuration
-----------------------
Minimum Password Length........................ 8
Password History............................... 0
Password Aging (days).......................... 0
Lockout Attempts............................... 0
Password Strength Check........................ Enable
Minimum Password Uppercase Letters............. 4
Minimum Password Lowercase Letters............. 4
Minimum Password Numeric Characters............ 3
Minimum Password Special Characters............ 3
Maximum Password Consecutive Characters........ 3
Maximum Password Repeated Characters........... 3
Minimum Password Character Classes............. 4
Password Exclude Keywords...................... brcm, brcm1,brcm2
show passwords result
Use the show passwords result command in Privileged EXEC mode to display
the last password set result information.
Syntax
show passwords result
Default Configuration
This command has no default configuration.
Minimum Password Character Classes Minimum number of character classes
(uppercase, lowercase, numeric and
special) required when configuring
passwords.
Password Exclude-Keywords Minimum number of character classes
(uppercase, lowercase, numeric and
special) required when configuring
passwords.
Parameter Description
2CSNXXX_SWUM200.book Page 1518 Tuesday, December 10, 2013 1:22 PM

Password Management Commands 1519
Command Mode
Privileged EXEC mode, Configuration mode and all Configuration submodes
User Guidelines
This command has no user guidelines.
Example
The following example displays the command output.
console#show passwords result
Last User whose password is set ...................... brcm
Password strength check ........................... Enable
Last Password Set Result:
Reason for failure: Could not set user password! Password should contain at
least 4 uppercase letters.
2CSNXXX_SWUM200.book Page 1519 Tuesday, December 10, 2013 1:22 PM

1520 Password Management Commands
2CSNXXX_SWUM200.book Page 1520 Tuesday, December 10, 2013 1:22 PM

PHY Diagnostics Commands 1521
70
PHY Diagnostics Commands
Dell Networking N2000/N3000/N4000 Series Switches
This chapter explains the following commands:
show copper-ports tdr
Use the show copper-ports tdr command in Privileged EXEC mode to display
the stored information regarding cable lengths.
Syntax
show copper-ports tdr [
interface
]
•
interface
— A valid Ethernet port. The full syntax is
unit / port.
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC mode, Configuration mode and all Configuration submodes
User Guidelines
The copper-related commands do not apply to the stacking or 10GBaseT
ports associated with these plug-in modules.
The maximum length of the cable for the Time Domain Reflectometry
(TDR) test is 120 meters. Disable green-mode on the port in order to obtain
accurate results.
Example
The following example displays the last TDR tests on all ports.
show copper-ports tdr test copper-port tdr
show fiber-ports optical-transceiver
–
2CSNXXX_SWUM200.book Page 1521 Tuesday, December 10, 2013 1:22 PM

1522 PHY Diagnostics Commands
console#show copper-ports tdr
Port Result Length [meters]Date
---- -------- --------------- ---------------
1/0/1 OK
1/0/2 Short 50 13:32:00 23 July 2004
1/0/3 Test has not been performed
1/0/4 Open 128 13:32:08 23 July 2004
1/0/5 Fiber - -
show fiber-ports optical-transceiver
Use the show fiber-ports optical-transceiver command in Privileged EXEC
mode to display the optical transceiver diagnostics.
Syntax
show fiber-ports optical-transceiver [
interface
]
•
interface —
A valid fiber port.
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC mode, Configuration mode and all Configuration submodes
User Guidelines
The show fiber ports command is applicable to all fiber ports, including SFP,
SFP+, and XFP ports. It will display an error if executed against a copper port
or passive or active direct attach cables.
Examples
The following examples display the optical transceiver diagnostics.
console#show fiber-ports optical-transceiver
Port Temp Voltage Current Output Input TX LOS
Power Power Fault
----------- ------ ------- ------- ------ ----- ----- ---
1/0/3 w OK E OK OK OK OK
1/0/4 OK OK OK OK OK E OK
1/0/1 Copper
2CSNXXX_SWUM200.book Page 1522 Tuesday, December 10, 2013 1:22 PM

PHY Diagnostics Commands 1523
Temp - Internally measured transceiver temperature
Voltage - Internally measured supply voltage
Current - Measured TX bias current
Output Power - Measured TX output power in milliWatts
Input Power - Measured RX received power in milliWatts
TX Fault - Transmitter fault
LOS - Loss of signal
test copper-port tdr
Use the test copper-port tdr command in Privileged EXEC mode to diagnose
with Time Domain Reflectometry (TDR) technology the quality and
characteristics of a copper cable attached to a 1GBaseT or 10GBaseT port.
Syntax
test copper-port tdr
interface
•
interface
— A valid Ethernet port.
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC mode
User Guidelines.
This command prompts the user to shut down the port for the duration of
the test. Passive or active direct attach SFP/SFP+ cables are not based on
BaseT technology and do not support TDR testing.
The maximum distance the Virtual Cable Tester (VCT) can function is 120 meters.
Examples
The following example results in a report on the cable attached to port 1/0/3.
console#test copper-port tdr te1/0/1
This command takes the port offline to measure the cable length.
Use the show copper-port tdr command to view the results..
Do you wish to continue and take the port offline (Y/N)?y
2CSNXXX_SWUM200.book Page 1523 Tuesday, December 10, 2013 1:22 PM

1524 PHY Diagnostics Commands
The following example results in a failure to report on the cable attached to
port te2/0/3.
console#test copper-port tdr te2/0/3
Can’t perform the test on fiber ports
2CSNXXX_SWUM200.book Page 1524 Tuesday, December 10, 2013 1:22 PM

Power Over Ethernet Commands 1525
71
Power Over Ethernet Commands
Dell Networking N2000/N3000 Series Switches
The Dell Networking PoE solution implements the PoE+ specification
(IEEE 802.3at). IEEE 802.3at allows power to be supplied to Class 4 PD
devices that require power greater than 15.4 Watts and up to 34.2 Watts. This
allows the PoE+ enabled network switches and routers to be used for
deployment with devices that require more power than the 802.3AF
specification allows. PoE+ 802.3at is compatible with 802.1AF.
NOTE: This section applies to the N2024P/N2048P/N3024P/N3048P switches.
Flexible Power Management
The Dell Networking PoE solution provides power management which
supports power reservation, power prioritization and power limiting. The
operator can assign a priority to each PoE port. When the power budget of
the PoE switch has been exhausted, the higher priority ports are given
preference over the lower priority ports. Lower priority ports are forcibly
stopped to supply power in order to provide power to higher priority ports.
The static power management feature allows operators to reserve a
guaranteed amount of power for a PoE port. This is useful for powering up
devices which draw variable amounts of power and provide them an assured
power range within which to operate. Class based power management
allocates power at class limits as opposed to user defined limits.
In the Dynamic Power management feature, power is not reserved for a given
port at any point of time. The power available with the PoE switch is
calculated by subtracting the instantaneous power drawn by all the ports from
the maximum available power. Thus, more ports can be powered at the same
time. This feature is useful to efficiently power up more devices when the
available power with the PoE switch is limited.
The Dell Networking PoE solution also provides a global usage threshold
feature in order to limit the PoE switch from reaching an overload condition.
The operator can specify the limit as a percentage of the maximum power.
NOTE: PoE commands are only applicable to copper ports.
2CSNXXX_SWUM200.book Page 1525 Tuesday, December 10, 2013 1:22 PM

1526 Power Over Ethernet Commands
Commands in this Chapter
This chapter explains the following commands:
power inline
The power inline command enables/disables the ability of the port to deliver
power.
Syntax
power inline { auto | never }
no power inline
•
auto
— Enables device discovery and, if a device is found using the
method specified by the power inline detection setting,
supplies power to
the device.
•
never
— Disables the device discovery protocol and stops supplying power
to the device.
Command Mode
Interface Configuration (Ethernet).
User Guidelines
Auto enables the switch to negotiate with the powered device via LLDP to
learn the device's desired power draw. The power inline detection parameter
should be set to class.
power inline power inline priority
power inline detection power inline reset
power inline high-power power inline usage-threshold
power inline limit clear power inline statistics
power inline management show power inline
power inline powered-device show power inline firmware-version
2CSNXXX_SWUM200.book Page 1526 Tuesday, December 10, 2013 1:22 PM

Power Over Ethernet Commands 1527
Default Value
auto
Examples
console(config)#interface gigabitethernet 1/0/1
console(config-if-Gi1/0/1)# power inline auto
power inline detection
Use the power inline detection command in Interface Configuration mode
to configure the detection type that tells which types of PD’s will be detected
and powered by the switch. Use the no form of this command to set the
detection type to the default.
Syntax
power inline detection {dot3af+legacy | dot3af}
no power inline detection
•
dot3af+legacy
—IEEE 802.3af 4-point detection followed by legacy
capacitive detection.
•
dot3af
—IEEE 802.3af 4-point detection only. Legacy capacitive detection
is disabled.
Default Value
The default value is dot3af+legacy.
Command Mode
Global Configuration
User Guidelines
This command has no user guidelines.
power inline high-power
Use this command to enable high power mode. Use the no form of this
command to disable high power mode. In high power mode, the switch (PSE)
negotiates the power budget with the powered device (PD) via LLDP.
2CSNXXX_SWUM200.book Page 1527 Tuesday, December 10, 2013 1:22 PM

1528 Power Over Ethernet Commands
Syntax
power inline high-power
no power inline high-power
Default Configuration
The default value is disabled.
Command Mode
Interface Configuration.
User Guidelines
The system does not apply high power to the interface until an LLDP-MED
packet is received from the link partner requesting the application of high
power.
power inline limit
Use the power inline limit command to configure the type of power limit.
Use the no form of this command to set the power limit type to the default.
Syntax
power inline limit user-defined
limit
no power inline limit
•
user-defined
limit
—Allows the port to draw up to user-defined configured
value. The range of limit is 3000-32000 milliwatts.
Default Configuration
The default power limit is 32000 milliwatts.
Command Mode
Interface Configuration
2CSNXXX_SWUM200.book Page 1528 Tuesday, December 10, 2013 1:22 PM

Power Over Ethernet Commands 1529
User Guidelines
User defined limits are only operational if the power management mode is
configured as static. By default, the power management mode is dynamic. If
the operator attempts to set the limit to user defined and the power
management mode is not configured as static, a warning is issued and the
command has no effect.
power inline management
Use the power inline management command in Global Configuration mode
to set the power management type. This command is used along with the
power inline priority
command on page 1533. Use the no form of this
command to set the management mode to the default.
Syntax
power inline management {dynamic | static | class}
no power inline management
•
dynamic
—Dynamic power management
•
static
—Static power management
•
class
—Class-based power management
Default Configuration
Default management is dynamic.
Command Mode
Global Configuration
User Guidelines
Static and dynamic modes differ in how the available power is calculated:
Static Power Management
Available Power = Power limit of the Sources – Total Configured power
Where Total Configured Power is calculated as sum of the configured power
limit configured on the port.
2CSNXXX_SWUM200.book Page 1529 Tuesday, December 10, 2013 1:22 PM
1530 Power Over Ethernet Commands
Dynamic Power Management
Available Power = Power limit of the Sources – Total Allocated power
Where Total Allocated Power is calculated as the sum of the power consumed
by each port.
Class-Based Power Management
Available Power = Power limit of the Sources – Total Class Configured power
Where Total Class Configured Power is calculated as the sum of the class
based power allocation for each port.
Class-based power management allocates power based on the class selected
by the device using LLDP. Power is supplied to the device in class mode per
the following table:
There are three power banks on a switch: one for the fixed power supply, one
for the external power supply (EPS) and one for both. The power limits are
shown in the following table.
Class Usage Current (mA) Power (Watts)
0 Default 600 34.2
1 Optional 350 15.4
2 Optional 350 15.4
3Optional 350 15.4
4 Valid for 802.3at (Type 2) devices, not
supported for 802.3af devices
600 34.2
2CSNXXX_SWUM200.book Page 1530 Tuesday, December 10, 2013 1:22 PM

Power Over Ethernet Commands 1531
Model
Name
System
Power
Maximum
Dissipation
PoE Power Budget Limit
One PSU Two PSUs
Maximum
PSU
output
ability
POE+ power turn
on limitation
Maximum
PSUs
output
ability
POE+ power turn
on limitation
N3024P 110W 715W Power budget is
550W
The total POE
supplied power
cannot exceed
950W.
715W Power budget is
1100W
All PoE+/UPOE
ports can be
turned on.
N3048P 140W 1100W Power budget is
950W
The total POE
supplied power
cannot exceed
950W.
2200W Power budget is
1900W
All PoE+/UPOE
ports can be
turned on.
N2024P 90W 1000W Power budget is
850W
The total POE
supplied power
cannot exceed
850W.
2000W Power budget is
1700W
All PoE+/UPOE
ports can be
turned on.
N2048P 110W 1000W Power budget is
850W
The total POE
supplied power
cannot exceed
850W.
2000W Power budget is
1700W
All PoE+/UPOE
ports can be
turned on.
2CSNXXX_SWUM200.book Page 1531 Tuesday, December 10, 2013 1:22 PM

1532 Power Over Ethernet Commands
The default guard band is 90% of maximum power supplied to the system.
Assuming a maximum current draw of 31.2W per device and the default
settings for PoE, the N2024P can power 32 devices using a single power
supply and the N2048P can power 31 devices with a single power supply and
48 devices when using two power supplies. If a PD is detected that is
requesting class-based power allocation via LLDP and either static or
dynamic power allocation is configured, a log message is issued indicating
that a class based PD is requesting power. The device will not be powered
until class based power management is configured.
Example
In the following example, no port is specified so the command displays global
configuration and status of all the ports. Configure the global power
management scheme as dynamic with dot3af+legacy detection and enable
PoE capability on ports gi1/0/1-10.
console(config)#power inline management dynamic
console(config)#power inline detection dot3af+legacy
console(config)#interface range gi1/0/1-10
console(config-if)#power inline auto
console(config-if)#exit
console#show power inline
Unit Status
===========
Unit........................................... 1
Power.......................................... On
Total Power.................................... 765 Watts
Consumed Power................................. 0 Watts
Global Configuration
====================
Usage Threshold................................ 90%
Power Management Mode.......................... Dynamic
Power Detection Mode........................... dot3af
Power Priority Mode............................ Disabled
Port Configuration
==================
2CSNXXX_SWUM200.book Page 1532 Tuesday, December 10, 2013 1:22 PM

Power Over Ethernet Commands 1533
power inline powered-device
The power inline powered-device command adds a comment or description
of the powered device type to enable the user to remember what is attached
to the interface. To remove the description, use the no form of this command.
Syntax
power inline powered-device
pd-type
no power inline powered-device
•
pd-type
— Specifies the type of powered device attached to the interface.
(Range:
1–20 characters)
Command Mode
Interface Configuration (Ethernet).
User Guidelines
No specific guidelines.
Examples
console(config)#interface gigabitethernet 1/0/1
console(config-if-Gi1/0/1)# power inline powered-device IP-phone
power inline priority
The power inline priority command configures the port priority level, for the
delivery of power to an attached device. The switch may not be able to supply
power to all connected devices, so the port priority is used to determine which
ports will supply power if adequate power capacity is not available for all
enabled ports. For ports that have the same priority level, the lower-numbered
port has higher priority.
For a system delivering peak power to a certain number of devices, if a new
device is attached to a high-priority port, power to a low-priority port is shut
down and the new device is powered up.
Syntax
power inline priority {critical | high | low}
2CSNXXX_SWUM200.book Page 1533 Tuesday, December 10, 2013 1:22 PM

1534 Power Over Ethernet Commands
no power inline priority
Command Mode
Interface Configuration (Ethernet).
User Guidelines
Priority is always enabled for all ports. If all ports have equal priority in an
overload condition, the switch will shut down the lowest numbered ports
first.
Default Value
Low
Examples
console(config)#interface gigabitethernet 1/0/1
console(config-if-Gi1/0/1)# power inline priority high
power inline reset
Use the power inline reset command to reset the port.
Syntax
power inline reset
Default Configuration
This command has no default configuration.
Command Mode
Interface Configuration
User Guidelines
This command is useful if the port is stuck in an Error state. Power to the
powered devices may be interrupted.
2CSNXXX_SWUM200.book Page 1534 Tuesday, December 10, 2013 1:22 PM

Power Over Ethernet Commands 1535
power inline usage-threshold
The power inline usage-threshold command configures the system power
usage threshold level at which lower priority ports are disconnected. The
threshold is configured as a percentage of the total available power. Use the
no form of the command to set the threshold to the default value.
Syntax
power inline usage-threshold
threshold
no power inline usage-threshold
•
threshold
— Power threshold at which ports are disconnected. The range is
1-99%.
Default Configuration
The default threshold is 90%.
Command Mode
Global Configuration.
User Guidelines
The power limit beyond which ports are disconnected has a configurable
range as a percentage of total available power. The maximum power available
is given in the table shown in the power inline management command. When
ports are disconnected due to the threshold being exceeded, a trap is
generated.
Examples
console(config)# power inline usage-threshold 90
clear power inline statistics
Use this command to clear the PoE statistics.
Syntax
clear power inline statistics
interface identifier
•
interface identifier
—A physical interface capable of supplying PoE power.
2CSNXXX_SWUM200.book Page 1535 Tuesday, December 10, 2013 1:22 PM

1536 Power Over Ethernet Commands
Default Configuration
This command has no default configuration.
Command Modes
Privileged EXEC
User Guidelines
This command has no user guidelines.
show power inline
Use the show power inline command to report current PoE configuration and
status. If no port is specified, the command displays global configuration and
status of all the ports. If a port is specified, then the command displays the
details for the single port. Use the detailed parameter to show power limits,
detection type and high power mode for the interface.
Syntax
show power inline [
interface-id
] [detailed]
•
interface-id
—Any physical interface. See Interface Naming Conventions
for interface representation.
Command Mode
Privileged EXEC
User Guidelines
No specific guidelines.
Examples
In the next example, the port is specified and the command displays the
configuration and status for the specified port.
console#show power inline gigabitethernet 1/0/13
Port Powered Device State Priority Status Class[W]
Power[mW]
--------- ------------------------ ----- -------- --------- -------
Gi1/0/13 Auto Low On 3.84 - 6.49 5000
2CSNXXX_SWUM200.book Page 1536 Tuesday, December 10, 2013 1:22 PM

Power Over Ethernet Commands 1537
Overload Counter............................... 0
Short Counter ................................. 0
Denied Counter................................. 0
Absent Counter................................. 0
Invalid Signature Counter...................... 0
Output Volts................................... 0
Output Current................................. 0
Temperature.................................... 39
In the next example, the port is specified and the command displays the
details for the single port.
console#show power inline gigabitethernet 1/0/13
Port Powered Device State Priority Status Class[W] Power[mW]
----- ------------------------ ----- -------- --------- ------------- ------
1/0/13 auto Low On 3.84 - 6.49 5000
Overload Counter............................... 0
Short Counter ................................. 0
Denied Counter................................. 0
Absent Counter................................. 0
Invalid Signature Counter...................... 0
console#
show power inline firmware-version
Use the show power inline firmware-version command in Privileged EXEC
mode to display the version of the PoE controller firmware present on the
switch file system.
Syntax
show power inline firmware-version
Command Mode
Privileged EXEC
User Guidelines
This command has no user guidelines.
2CSNXXX_SWUM200.book Page 1537 Tuesday, December 10, 2013 1:22 PM

1538 Power Over Ethernet Commands
Example
console(config)#show power inline firmware-version
Unit Firmware Version
---- ----------------
1 248_48
2CSNXXX_SWUM200.book Page 1538 Tuesday, December 10, 2013 1:22 PM

RMON Commands 1539
72
RMON Commands
Dell Networking N2000/N3000/N4000 Series Switches
The Dell Networking SNMP component includes an RMON (remote
monitoring) agent. RMON is a base technology used by network
management applications to manage a network. Troubleshooting and
network planning can be accomplished through the network management
applications. The network monitor monitors traffic on a network and records
selected portions of the network traffic and statistics. The collected traffic
and statistics are retrieved using SNMP. The data collected is defined in the
RMON MIB, RFC 2819. A device that supports gathering and reporting the
RMON data is referred to as an RMON probe or RMON Agent. An RMON
probe provides RMON data to an RMON Manager for analysis and
presentation to the user. An RMON probe may be embedded in an existing
network device or stand-alone.
Commands in this Chapter
This chapter explains the following commands:
rmon alarm
Use the rmon alarm command in Global Configuration mode to configure
alarm conditions. To remove an alarm, use the no form of this command. See
also the related
show rmon alarm
command.
rmon alarm show rmon collection history
rmon collection history show rmon events
rmon event show rmon hcalarm
rmon hcalarm show rmon history
show rmon alarm show rmon log
show rmon alarms show rmon statistics
2CSNXXX_SWUM200.book Page 1539 Tuesday, December 10, 2013 1:22 PM

1540 RMON Commands
Syntax
rmon alarm
number
variable
interval
{delta | absolute}
rising-threshold
value
[event-number]
falling-threshold value
[event-number] [owner
string
]
[startup
direction
]
no rmon alarm
number
•
number
—The alarm index. (Range: 1–65535)
•
variable
—A fully qualified SNMP object identifier that resolves to a
particular instance of a MIB object.
•
interval
—The interval in seconds over which the data is sampled and
compared with the rising and falling thresholds. (Range: 1– 2147483647)
•
rising-threshold value
—Rising Threshold value. (Range: -2147483648 –
2147483647)
•
falling-threshold value
—Falling Threshold value. (Range: -2147483648 –
2147483647)
•
event-number
—The index of the Event that is used when a rising or
falling threshold is crossed. (Range: 1- 65535)
•
delta
—The sampling method for the selected variable and calculating the
value to be compared against the thresholds. If the method is delta, the
selected variable value at the last sample is subtracted from the current
value, and the difference compared with the thresholds.
•
absolute
—The sampling method for the selected variable and calculating
the value to be compared against the thresholds. If the method is absolute,
the value of the selected variable is compared directly with the thresholds
at the end of the sampling interval.
•
startup
direction
—The alarm that may be sent when this entry is first set
to valid. If the first sample (after this entry becomes valid) is greater than
or equal to the rising-threshold, and direction is equal to rising or rising-
falling, then a single rising alarm is generated. If the first sample (after this
entry becomes valid) is less than or equal to the falling-threshold, and
direction is equal to falling or rising-falling, then a single falling alarm is
generated.
•
owner
string
—Enter a name that specifies who configured this alarm. If
unspecified, the name is an empty string.
2CSNXXX_SWUM200.book Page 1540 Tuesday, December 10, 2013 1:22 PM

RMON Commands 1541
Default Configuration
No alarms are configured.
Command Mode
Global Configuration mode
User Guidelines
This command has no user guidelines.
Example
The following example configures the following alarm conditions:
•Alarm index —
1
•Variable
identifier —
1.3.6.1.2.1.2.2.1.10.5
• Sample interval —
10 seconds
• Rising threshold —
500000
• Falling threshold —
10
• Rising threshold event index —
1
• Falling threshold event index —
1
console(config)#rmon alarm 1 1.3.6.1.2.1.2.2.1.1.10.5 10 50000 10 1 1
rmon collection history
Use the rmon collection history command in Interface Configuration mode
to enable a Remote Monitoring (RMON) MIB history statistics group on an
interface. To remove a specified RMON history statistics group, use the no
form of this command. Also see the
show rmon collection history
command.
Syntax
rmon collection history
index
[owner
ownername
] [buckets
bucket-number
]
[interval
seconds
]
no rmon collection history
index
•
index
— The requested statistics index group. (Range: 1–65535)
2CSNXXX_SWUM200.book Page 1541 Tuesday, December 10, 2013 1:22 PM

1542 RMON Commands
•
owner
ownername
— Records the RMON statistics group owner name. If
unspecified, the name is an empty string.
•
buckets
bucket-number
— A value associated with the number of buckets
specified for the RMON collection history group of statistics. If
unspecified, defaults to 50. (Range: 1 - 65535)
•
interval
seconds
— The number of seconds in each polling cycle. If
unspecified, defaults to 1800. (Range: 1–3600)
Default Configuration
The buckets configuration is 50. The interval configuration is 1800 seconds.
Command Mode
Interface Configuration (gigabitethernet, port-channel, tengigabitethernet,
fortygigabitethernet) mode.
User Guidelines
This command cannot be executed on multiple ports using the interface
range command.
Example
The following example enables a Remote Monitoring (RMON) MIB history
statistics group on port 1/0/8 with the index number "1" and a polling interval
period of 2400 seconds.
console(config)#interface gigabitethernet 1/0/8
console(config-if-Gi1/0/8)#rmon collection history 1 interval 2400
rmon event
Use the rmon event command in Global Configuration mode to configure an
event. To remove an event, use the no form of this command. See also the
show rmon events
command.
Syntax
rmon event number [log] [trap
community
] [description
string
] [owner
string
]
2CSNXXX_SWUM200.book Page 1542 Tuesday, December 10, 2013 1:22 PM

RMON Commands 1543
no rmon event
number
•
number
—The event index. (Range: 1–65535)
•
log
—An entry is made in the log table for each event.
•
trap
—An SNMP trap is sent to one or more management stations.
•
community
—If an SNMP trap is to be sent, it is sent to the SNMP
community specified by this octet string. (Range: 0-127 characters)
•
description
—A comment describing this event. (Range 0-127 characters)
•
owner
—Enter a name that specifies who configured this event. If
unspecified, the name is an empty string.
Default Configuration
This command has no default configuration.
Command Mode
Global Configuration mode
User Guidelines
This command has no user guidelines.
Example
The following example configures an event with the trap index of 10.
console(config)#rmon event 10 log
rmon hcalarm
Use the rmon hcalarm to configure high capacity alarms.Use the no form of
the command to remove the alarm.
Syntax
rmon hcalarm
alarmnumber
variable
interval
{absolute | delta} rising-
threshold
value-64
[
rising-event-index
] falling-threshold
value-64
[
falling-
event-index
] [startup {rising | falling | rising-falling}] [owner
string
]
2CSNXXX_SWUM200.book Page 1543 Tuesday, December 10, 2013 1:22 PM

1544 RMON Commands
•
alarmnumber
—An alarm number that uniquely identifies the alarm entry.
(Range: 1-65536). Each entry defines a diagnostic sampler at a particular
interval for an object on the device.
•
variable
—The MIB object to monitor. May be fully qualified or relative.
Only variables that resolve to an ASN.1 primitive type of INTEGER are
allowed.
•
interval
—The interval in seconds over which the data is sampled and
compared with the rising and falling thresholds. (Range: 1– 2147483647.
The default is 1 second.)
•
absolute
—Specifies to use a fixed value for the threshold (Default value).
•
delta
—Specifies to use the difference between the current value and the
previous value.
•
rising-threshold
value-64
—Rising threshold value (−(2
63
) to 2
63
− 1)
•
rising-event-index
—Event to trigger when the rising threshold is crossed
(1–65535).
•
falling-threshold-high
value-64
—Falling threshold value (−(2
63
) to 2
63
−
1)
•
falling-event-index
—Event to trigger when the rising threshold is crossed
(1–65535).
•
startup {rising|falling|rising-falling]
—
The event that is sent when this entry is
first set to active. If the first sample after this entry is configured is greater than
or equal to the rising threshold and startup rising or startup rising-falling is
configured, a single rising event is generated. If the first sample after this entry
is configured is less than or equal to the falling threshold and startup falling or
startup rising-falling is configured then a single falling event is generated.
•
owner
string
—
Specify an owner for the alarm (string – no default).
Default Configuration
This command has no default configuration.
Command Mode
Global Configuration mode
2CSNXXX_SWUM200.book Page 1544 Tuesday, December 10, 2013 1:22 PM

RMON Commands 1545
User Guidelines
This command has no user guidelines.
Example
console(config)# rmon hcalarm 2 ifInOctets.1 30 absolute rising-threshold
high 2147483648 falling-threshold high -2147483648 startup rising owner
"dell-owner"
show rmon alarm
Use the show rmon alarm command in User EXEC mode to display alarm
configuration. Also see the
rmon alarm
command.
Syntax
show rmon alarm
number
•
number
— Alarm index. (Range: 1–65535)
Default Configuration
This command has no default configuration.
Command Mode
User EXEC mode, Configuration mode and all Configuration submodes
User Guidelines
This command has no user guidelines.
Example
The following example displays RMON 1 alarms.
console> show rmon alarm 1
Alarm 1
-------
OID: 1.3.6.1.2.1.2.2.1.10.1
Last sample Value: 878128
Interval: 30
Sample Type: delta
Startup Alarm: rising
Rising Threshold: 8700000
Falling Threshold: 78
2CSNXXX_SWUM200.book Page 1545 Tuesday, December 10, 2013 1:22 PM
1546 RMON Commands
Rising Event: 1
Falling Event: 1
Owner: CLI
The following table describes the significant fields shown in the display:
Field Description
Alarm Alarm index.
OID Monitored variable OID.
Last Sample
Value
The statistic value during the last sampling period. For example,
if the sample type is delta, this value is the difference between the
samples at the beginning and end of the period. If the sample
type is absolute, this value is the sampled value at the end of the
period.
Interval The interval in seconds over which the data is sampled and
compared with the rising and falling thresholds.
Sample Type The method of sampling the variable and calculating the value
compared against the thresholds. If the value is absolute, the
value of the variable is compared directly with the thresholds at
the end of the sampling interval. If the value is delta, the value of
the variable at the last sample is subtracted from the current
value, and the difference compared with the thresholds.
Startup Alarm The alarm that may be sent when this entry is first set. If the first
sample is greater than or equal to the rising threshold, and startup
alarm is equal to rising or rising and falling, then a single rising
alarm is generated. If the first sample is less than or equal to the
falling threshold, and startup alarm is equal falling or rising and
falling, then a single falling alarm is generated.
Rising Threshold A sampled statistic threshold. When the current sampled value is
greater than or equal to this threshold, and the value at the last
sampling interval is less than this threshold, a single event is
generated.
Falling Threshold A sampled statistic threshold. When the current sampled value is
less than or equal to this threshold, and the value at the last
sampling interval is greater than this threshold, a single event is
generated.
Rising Event The event index used when a rising threshold is crossed.
Falling Event The event index used when a falling threshold is crossed.
2CSNXXX_SWUM200.book Page 1546 Tuesday, December 10, 2013 1:22 PM

RMON Commands 1547
show rmon alarms
Use the show rmon alarms command in User EXEC mode to display the
alarms summary table.
Syntax
show rmon alarms
Default Configuration
This command has no arguments or keywords.
Command Mode
User EXEC, Privileged EXEC modes, Configuration mode and all
Configuration submodes
User Guidelines
This command has no user guidelines.
Example
The following example displays the alarms summary table:
console> show rmon alarms
Index OID Owner
----- ---------------------- -------
1 1.3.6.1.2.1.2.2.1.10.1 CLI
2 1.3.6.1.2.1.2.2.1.10.1 Manager
3 1.3.6.1.2.1.2.2.1.10.9 CLI
The following table describes the significant fields shown in the display:
Owner The entity that configured this entry.
Field Description
Index An index that uniquely identifies the entry.
OID Monitored variable OID.
Field Description
2CSNXXX_SWUM200.book Page 1547 Tuesday, December 10, 2013 1:22 PM

1548 RMON Commands
show rmon collection history
Use the show rmon collection history command in User EXEC mode to
display the requested group of statistics. Also see the
rmon collection history
command.
Syntax
show rmon collection history [{gigabitethernet unit/slot/port |
port-channel
port-channel-number
| tengigabitethernet unit/slot/port |
fortygigabitethernet unit/slot/port}]
Default Configuration
This command has no default configuration.
Command Mode
User EXEC mode, Configuration mode and all Configuration submodes
User Guidelines
The following table describes the significant fields shown in the display:
Example
The following example displays all RMON group statistics.
console> show rmon collection history
Index Interface Interval Requested Granted Owner
Owner The entity that configured this entry.
Field Description
Index An index that uniquely identifies the entry.
Interface The sampled Ethernet interface.
Interval The interval in seconds between samples.
Requested Samples The requested number of samples to be saved.
Granted Samples The granted number of samples to be saved.
Owner The entity that configured this entry.
2CSNXXX_SWUM200.book Page 1548 Tuesday, December 10, 2013 1:22 PM

RMON Commands 1549
Samples Samples
----------------------------------------------------------
1 1/0/1 30 50 50 CLI
2 1/0/1 1800 50 50 Manager
show rmon events
Use the show rmon events command in User EXEC mode to display the
RMON event table. Also see the
rmon event
command.
Syntax
show rmon events
Default Configuration
This command has no default configuration.
Command Mode
User EXEC mode, Configuration mode and all Configuration submodes
User Guidelines
The following table describes the significant fields shown in the display:
Field Description
Index An index that uniquely identifies the event.
Description A comment describing this event.
Type The type of notification that the device generates about this event.
Can have the following values: none, log, trap, log-trap. In the case
of log, an entry is made in the log table for each event. In the case of
trap, an SNMP trap is sent to one or more management stations.
Community If an SNMP trap is to be sent, it is sent to the SNMP community
specified by this octet string.
Owner The entity that configured this event.
Last time sent The time this entry last generated an event. If this entry has not
generated any events, this value is zero.
2CSNXXX_SWUM200.book Page 1549 Tuesday, December 10, 2013 1:22 PM

1550 RMON Commands
Example
The following example displays the RMON event table.
console> show rmon events
Index Description Type Community Owner Last time sent
----- ----------- ---- --------- ------ -------------------
1 Errors Log CLI Jan 18 2005 23:58:17
2 High Broadcast Log-Trap switch Manager Jan 18 2005 23:59:48
show rmon hcalarm
Use the show rmon hcalarm command to display high capacity (64-bit)
alarms configured with the
rmon hcalarm
command.
Syntax
show rmon {hcalarms | hcalarm
number
}
•
number
—The alarm index (Range: 1-65535)
Default Configuration
This command has no default configuration.
Command Modes
Privileged EXEC (all show modes)
User Guidelines
This command has no user guidelines.
Example
console#show rmon hcalarm 2
Alarm 2
----------
OID: ifInOctets.1
Last Sample Value: 0
Interval: 30
Sample Type: absolute
Startup Alarm: rising
Rising Threshold High: 2
Rising Threshold Low: 10
2CSNXXX_SWUM200.book Page 1550 Tuesday, December 10, 2013 1:22 PM

RMON Commands 1551
Rising Threshold Status: Positive
Falling Threshold High: 20
Falling Threshold Low: 10
Falling Threshold Status: Positive
Rising Event: 1
Falling Event: 2
Startup Alarm: Rising
Owner: dell-owner
console#show rmon hcalarms
Index OID Owner
----------------------------------------------
2 ifInOctets.1 dell-owner
show rmon history
Use the show rmon history command in User EXEC mode to display RMON
Ethernet Statistics history. Also see the
rmon collection history
command.
Syntax
show rmon history
index
[throughput | errors | other] [period
seconds
]
•
index
— The requested set of samples. (Range: 1–65535)
•
throughput
— Displays throughput counters.
•
errors
— Displays error counters.
•
other
— Displays drop and collision counters.
•
period
seconds
— Specifies the requested period time to display. (Range:
0–2147483647)
Default Configuration
This command has no default configuration.
Command Mode
User EXEC mode, Configuration mode and all Configuration submodes
User Guidelines
The following table describes the significant fields shown in the display:
2CSNXXX_SWUM200.book Page 1551 Tuesday, December 10, 2013 1:22 PM

1552 RMON Commands
Field Description
Time Date and Time the entry is recorded.
Octets The total number of octets of data (including those in bad packets)
received on the network (excluding framing bits but including FCS
octets).
Packets The number of packets (including bad packets) received during this
sampling interval.
Broadcast The number of good packets received during this sampling interval that
were directed to the Broadcast address.
Multicast The number of good packets received during this sampling interval that
were directed to a Multicast address. This number does not include
packets addressed to the Broadcast address.
% The best estimate of the mean physical layer network utilization on this
interface during this sampling interval, in hundredths of a percent.
CRC Align The number of packets received during this sampling interval that had a
length (excluding framing bits but including FCS octets) between 64
and 1518 octets, inclusive, but had either a bad Frame Check Sequence
(FCS) with an integral number of octets (FCS Error) or a bad FCS with
a non-integral number of octets (Alignment Error).
Undersize The number of packets received during this sampling interval that were
less than 64 octets long (excluding framing bits but including FCS
octets) and were otherwise well formed.
Oversize The number of packets received during this sampling interval that were
longer than 1518 octets (excluding framing bits but including FCS
octets) but were otherwise well formed.
Fragments The total number of packets received during this sampling interval that
were less than 64 octets in length (excluding framing bits but including
FCS octets) had either a bad Frame Check Sequence (FCS) with an
integral number of octets (FCS Error), or a bad FCS with a non-integral
number of octets (AlignmentError). It is normal for
etherHistoryFragments to increment because it counts both runts
(which are normal occurrences due to collisions) and noise hits.
2CSNXXX_SWUM200.book Page 1552 Tuesday, December 10, 2013 1:22 PM

RMON Commands 1553
Examples
The following example displays RMON Ethernet Statistics history for
"throughput" on index number 1.
console> show rmon history 1 throughput
Sample Set: 1 Owner: CLI
Interface: 1/0/1 interval: 1800
Requested samples: 50 Granted samples: 50
Maximum table size: 270
Time Octets Packets Broadcast Multicast %
-------------------- --------- ----------- ------ -------- --
09-Mar-2005 18:29:32 303595962 357568 3289 7287 19
09-Mar-2005 18:29:42 287696304 275686 2789 5878 20
The following example displays RMON Ethernet Statistics history for errors
on index number 1.
console> show rmon history 1 errors
Sample Set: 1Owner: Me
Interface: 1/0/1interval: 1800
Requested samples: 50Granted samples: 50
Maximum table size: 500 (800 after reset)
TimeCRCUndersizeOversizeFragmentsJabbers
Align
-----------------------------------------------------
09-Mar-2005110490
18:29:32
09-Mar-2005110270
18:29:42
Jabbers The number of packets received during this sampling interval that were
longer than 1518 octets (excluding framing bits but including FCS
octets), and had either a bad Frame Check Sequence (FCS) with an
integral number of octets (FCS Error) or a bad FCS with a non-integral
number of octets (Alignment Error).
Dropped The total number of events in which packets were dropped by the probe
due to lack of resources during this sampling interval. This number is
not necessarily the number of packets dropped. It is just the number of
times this condition has been detected.
Collisions The best estimate of the total number of collisions on this Ethernet
segment during this sampling interval.
Field Description
2CSNXXX_SWUM200.book Page 1553 Tuesday, December 10, 2013 1:22 PM

1554 RMON Commands
The following example displays RMON Ethernet Statistics history for "other"
on index number 1.
console> show rmon history 1 other
Sample Set: 1 Owner: Me
Interface: 1/0/1 Interval: 1800
Requested samples: 50 Granted samples: 50
Maximum table size: 270
Time Dropped Collisions
------------------- ----------- -----------
10-Mar-2005 22:06:00 3 0
10-Mar-2005 22:06:20 3 0
show rmon log
Use the show rmon log command in User EXEC mode to display the RMON
logging table.
Syntax
show rmon log [
event
]
•
event
— Event index. (Range: 1–65535)
Default Configuration
This command has no default configuration.
Command Mode
User EXEC mode, Configuration mode and all Configuration submodes
User Guidelines
The following table describes the significant fields shown in the display:
Field Description
Event An index that uniquely identifies the event.
Description A comment describing this event.
Time The time this entry was created.
2CSNXXX_SWUM200.book Page 1554 Tuesday, December 10, 2013 1:22 PM

RMON Commands 1555
Example
The following examples display the RMON logging table.
console> show rmon log
Maximum table size: 100
Event Description Time
----- ----------- --------------------
1 Errors Jan 18 2005 23:48:19
1 Errors Jan 18 2005 23:58:17
2 High Broadcast Jan 18 2005 23:59:48
console> show rmon log
Maximum table size: 100 (100 after reset)
Event Description Time
----- ----------- --------------------
1 Errors Jan 18 2005 23:48:19
1 Errors Jan 18 2005 23:58:17
2 High Broadcast Jan 18 2005 23:59:48
show rmon statistics
Use the show rmon statistics command in User EXEC mode to display the
RMON Ethernet Statistics.
Syntax
show rmon statistics {gigabitethernet unit/slot/port|
port-channel
port-
channel-number
| tengigabitethernet unit/slot/port | fortygigabitethernet
unit/slot/port}
Default Configuration
This command has no default configuration.
Command Mode
User EXEC mode, Configuration mode and all Configuration submodes
User Guidelines
The following table describes the significant fields shown in the display:
2CSNXXX_SWUM200.book Page 1555 Tuesday, December 10, 2013 1:22 PM

1556 RMON Commands
Field Description
Dropped The total number of events in which packets are dropped by the
probe due to lack of resources. This number is not always the
number of packets dropped; it is the number of times this
condition has been detected.
Octets The total number of octets of data (including those in bad
packets) received on the network (excluding framing bits but
including FCS octets).
Packets The total number of packets (including bad packets, Broadcast
packets, and Multicast packets) received.
Broadcast The total number of good packets received and directed to the
Broadcast address. This does not include Multicast packets.
Multicast The total number of good packets received and directed to a
Multicast address. This number does not include packets
directed to the Broadcast address.
CRC Align Errors The total number of packets received with a length (excluding
framing bits, but including FCS octets) of between 64 and 1518
octets, inclusive, but with either a bad Frame Check Sequence
(FCS) with an integral number of octets (FCS Error) or a bad
FCS with a non-integral number of octets (Alignment Error).
Undersize Pkts The total number of packets received less than 64 octets long
(excluding framing bits, but including FCS octets) and
otherwise well formed.
Oversize Pkts The total number of packets received longer than 1518 octets
(excluding framing bits, but including FCS octets) and
otherwise well formed.
Fragments The total number of packets received less than 64 octets in
length (excluding framing bits but including FCS octets) and
either a bad Frame Check Sequence (FCS) with an integral
number of octets (FCS Error) or a bad FCS with a non-integral
number of octets (Alignment Error).
Jabbers The total number of packets received longer than 1518 octets
(excluding framing bits, but including FCS octets), and either a
bad Frame Check Sequence (FCS) with an integral number of
octets (FCS Error) or a bad FCS with a non-integral number of
octets (Alignment Error).
2CSNXXX_SWUM200.book Page 1556 Tuesday, December 10, 2013 1:22 PM

RMON Commands 1557
Example
The following example displays RMON Ethernet Statistics for port 1/0/1.
console#show rmon statistics tengigabitethernet 1/0/1
Port: Te1/0/1
Dropped: 0
Octets: 0 Packets: 0
Broadcast: 0 Multicast: 0
CRC Align Errors: 0 Collisions: 0
Undersize Pkts: 0 Oversize Pkts: 0
Fragments: 0 Jabbers: 0
64 Octets: 0 65 - 127 Octets: 0
128 - 255 Octets: 0 256 - 511 Octets: 0
512 - 1023 Octets: 0 1024 - 1518 Octets: 0
HC Overflow Pkts: 0 HC Pkts: 0
HC Overflow Octets: 0 HC Octets: 0
Collisions The best estimate of the total number of collisions on this
Ethernet segment.
64 Octets The total number of packets (including bad packets) received
that are 64 octets in length (excluding framing bits but
including FCS octets).
65 to 127 Octets The total number of packets (including bad packets) received
that are between 65 and 127 octets in length inclusive
(excluding framing bits but including FCS octets).
128 to 255 Octets The total number of packets (including bad packets) received
that are between 128 and 255 octets in length inclusive
(excluding framing bits but including FCS octets).
256 to 511 Octets The total number of packets (including bad packets) received
that are between 256 and 511 octets in length inclusive
(excluding framing bits but including FCS octets).
512 to 1023 Octets The total number of packets (including bad packets) received
that are between 512 and 1023 octets in length inclusive
(excluding framing bits but including FCS octets).
1024 to 1518
Octets
The total number of packets (including bad packets) received
that are between 1024 and 1518 octets in length inclusive
(excluding framing bits but including FCS octets).
Field Description
2CSNXXX_SWUM200.book Page 1557 Tuesday, December 10, 2013 1:22 PM

1558 RMON Commands
HC Overflow Pkts 64 Octets: 0 HC Pkts 64 Octets: 0
HC Overflow Pkts 65 - 127 Octets: 0 HC Pkts 65 - 127 Octets: 0
HC Overflow Pkts 128 - 255 Octets: 0 HC Pkts 128 - 255 Octets: 0
HC Overflow Pkts 256 - 511 Octets: 0 HC Pkts 256 - 511 Octets: 0
HC Overflow Pkts 512 - 1023 Octets: 0 HC Pkts 512 - 1023 Octets: 0
HC Overflow Pkts 1024 - 1518 Octets: 0 HC Pkts 1024 - 1518 Octets: 0
2CSNXXX_SWUM200.book Page 1558 Tuesday, December 10, 2013 1:22 PM

SDM Templates Commands 1559
73
SDM Templates Commands
Dell Networking N2000/N3000/N4000 Series Switches
On Dell Networking devices, the total available H/W route entries are divided
statically (at compile-time) among IPV4 and IPv6 routes. If a switch is
deployed in network environments where no IPv6 routes are needed, then
H/W resources allocated for IPv6 routes are unused.
The Switch Performance Optimization feature enables the operator to
optimize resources for IPv4 only routing environments depending on the how
the switch is used in the network at runtime. The operator can choose
between Ipv4-only (where all the routing table entries are reserved for IPv4
Routes) or IPv4/IPv6 (Default) mode.
Commands in this Chapter
This chapter explains the following commands:
sdm prefer
Use the sdm prefer command in Global Configuration mode to change the
template that will be active after the next reboot. To revert to the default
template after the next reboot, use the no form of this command.
Syntax
sdm prefer {dual-ipv4-and-ipv6 |ipv4-routing} {default|data-center}
•
dual-ipv4-and-ipv6
—This keyword filters subsequent template choices to
those that support both IPv4 and IPv6. The default template sets an
nominal set of scaling parameters suitable for most situations. The data-
center template maximizes the number of ECMP next hops.
sdm prefer show sdm prefer
2CSNXXX_SWUM200.book Page 1559 Tuesday, December 10, 2013 1:22 PM

1560 SDM Templates Commands
•
ipv4-routing
—This keyword filters subsequent template choices to those
that support IPv4 and not IPv6. The default IPv4-only template maximizes
the number of IPv4 unicast routes, while limiting the number of ECMP
next hops in each route to 4. The data-center template supports increases
the number of ECMP next hops to 16 and reduces the number of routes.
Default Configuration
The system defaults to the dual IPv4 and IPv6 template.
Command Mode
Global Config
User Guidelines
SDM templates enable you to reallocate system resources to support a
different mix of features. After setting the template, you must reboot in order
for the configuration change to take effect.
If you attach a unit to a stack and its template does not match the stack’s
template, then the new unit will automatically reboot using the template
used by other stack members. To avoid the automatic reboot, you may first
set the template to the template used by existing members of the stack. Then
power off the new unit, attach it to the stack, and power it on.
The following table lists the completion messages.
show sdm prefer
Use the show sdm prefer command in Privileged EXEC mode to view the
currently active SDM template and its scaling parameters, or to view the
scaling parameters for an inactive template.
Message Type Message Description
Successful
Completion
Message
Changes to the running SDM preferences have been stored, but
cannot take effect until the next reload. Use the
show sdm
prefer
command below to see what SDM preference is currently
active.
Error Completion
Message
None
2CSNXXX_SWUM200.book Page 1560 Tuesday, December 10, 2013 1:22 PM

SDM Templates Commands 1561
Syntax
show sdm prefer {dual-ipv4-and-ipv6 |ipv4-routing} {default|data-center}
•
dual-ipv4-and-ipv6 default
—List the scaling parameters for the template
supporting IPv4 and IPv6.
•
ipv4-routing default
—List the scaling parameters for the IPv4-only
template maximizing the number of unicast routes.
•
ipv4-routing data-center
—List the scaling parameters for the IPv4-only
template supporting more ECMP next hops.
•
dual-ipv4-and-ipv6 data-center
—List the scaling parameters for the
template supporting IPv4 and IPv6 with higher scale ECMP next hops.
Default Configuration
The default template for the N4000 switch is
dual-ipv4-and-ipv6 default
. The
default template for the N3000 switch is the
dual-ipv4-and-ipv6 data-center
.
The default template for the N2000 is
dual-ipv4-and-ipv6 default
. The N2000
has limited routing functionality.
Command Mode
Privileged EXEC, Configuration mode and all Configuration submodes
User Guidelines
When invoked with no optional keywords, this command lists the currently
active template, and the template that will become active on the next reboot,
if it is different from the currently active template. If the system boots with a
non-default template, and you clear the template configuration, either using
the no sdm prefer command or by deleting the startup configuration, the
show sdm prefer command lists the default template as the next active
template. To list the scaling parameters of a specific template, use that
template’s keyword as an argument to the command.
The following table lists the completion messages.
2CSNXXX_SWUM200.book Page 1561 Tuesday, December 10, 2013 1:22 PM
1562 SDM Templates Commands
The following table explains the output parameters.
Examples
This example shows the current SDM template. The user has not changed
the next active SDM template.
console# show sdm prefer
The current template is the Dual IPv4 and IPv6 template.
ARP Entries..................................6144
IPv4 Unicast Routes..........................8160
IPv6 NDP Entries.............................2560
IPv6 Unicast Routes..........................4096
ECMP Next Hops...............................4
IPv4 Multicast Routes........................1536
Message Type Message Description
Successful
Completion
Message
Changes to the running SDM preferences have been stored, but
cannot take effect until the next reload.
Use the
show sdm prefer
command to see what SDM preference
is currently active.
Error Completion
Message
None
Parameter Description
ARP Entries The maximum number of entries in the IPv4 Address
Resolution Protocol (ARP) cache for routing interfaces.
IPv4 Unicast Routes The maximum number of IPv4 unicast forwarding table entries.
IPv6 NDP Entries The maximum number of IPv6 Neighbor Discovery Protocol
(NDP) cache entries.
IPv6 Unicast Routes The maximum number of IPv6 unicast forwarding table entries.
ECMP Next Hops The maximum number of next hops that can be installed in the
IPv4 and IPv6 unicast forwarding tables.
IPv4 Multicast
Routes
The maximum number of IPv4 multicast forwarding table
entries.
IPv6 Multicast
Routes
The maximum number of IPv6 multicast forwarding table
entries.
2CSNXXX_SWUM200.book Page 1562 Tuesday, December 10, 2013 1:22 PM

SDM Templates Commands 1563
IPv6 Multicast Routes........................512
Now the user sets the next active SDM template for optimal performance for
IPv4 routing.
console# configure
console(config)#sdm prefer ipv4-routing default
Changes to the running SDM preferences have been stored, but cannot take
effect until the next reload.
Use 'show sdm prefer' to see what SDM preference is currently active.
config# show sdm prefer
The current template is the Dual IPv4 and IPv6 template.
ARP Entries..................................6144
IPv4 Unicast Routes..........................8160
IPv6 NDP Entries.............................2560
IPv6 Unicast Routes..........................4096
ECMP Next Hops...............................4
IPv4 Multicast Routes........................1536
IPv6 Multicast Routes........................512
On the next reload, the template will be the IPv4-routing Default template.
To list the scaling parameters for the data center template, invoke the
command with the ipv4-routing data-center keywords.
config# show sdm prefer ipv4-routing data-center
Scaling parameters for the IPv4 data center template:
ARP Entries..................................6144
IPv4 Unicast Routes..........................8160
IPv6 NDP Entries.............................0
IPv6 Unicast Routes..........................0
ECMP Next Hops...............................16
IPv4 Multicast Routes........................2048
IPv6 Multicast Routes........................0
2CSNXXX_SWUM200.book Page 1563 Tuesday, December 10, 2013 1:22 PM

1564 SDM Templates Commands
2CSNXXX_SWUM200.book Page 1564 Tuesday, December 10, 2013 1:22 PM

Serviceability Tracing Packet Commands 1565
74
Serviceability Tracing Packet
Commands
Dell Networking N2000/N3000/N4000 Series Switches
Debug commands cause the output of the enabled trace to display on a serial
port or telnet console. Note that the output resulting from enabling a debug
trace always displays on the serial port. The output resulting from enabling a
debug trace displays on all login sessions for which any debug trace has been
enabled. The configuration of a debug command remains in effect the whole
login session.
The output of a debug command is always submitted to the syslog utility at a
DEBUG severity level. As such, it can be forwarded to a syslog server, stored in
the buffer log, or otherwise processed in accordance with the configuration of
the syslog utility. Configuration of console logging in the syslog utility is not
required in order to view the output of debug traces.
Debug commands are provided in the normal CLI tree. Debug settings are
not persistent and are not visible in the running configuration. To view the
current debug settings, use the show debug command.
The output of debug commands can be large and may adversely affect system
performance.
Enabling debug for all IP packets can cause a serious impact on the system
performance; therefore, it is limited by ACLs. This means debug can be
enabled for IP packets that conform to the configured ACL. This also limits
the feature availability to only when the QoS component is available. Debug
for VRRP and ARP are available on routing builds.
Commands in this Chapter
This chapter explains the following commands:
debug arp debug ip acl debug ipv6 mcache debug ospfv3
2CSNXXX_SWUM200.book Page 1565 Tuesday, December 10, 2013 1:22 PM

1566 Serviceability Tracing Packet Commands
NOTE: Debug commands are not persistent across resets.
debug arp
Use the debug arp command to enable tracing of ARP packets. Use the “no”
form of this command to disable tracing of ARP packets.
Syntax
debug arp
no debug arp
Default Configuration
ARP packet tracing is disabled by default.
Command Mode
Privileged EXEC mode.
debug
authentication
interface
debug ip mcache debug isdp debug vrrp
debug auto-voip debug ip pimdm
packet
debug lacp exception core-file
debug clear debug ip pimsm
packet
debug mldsnooping exception dump
debug console debug ip vrrp debug ospf exception protocol
debug dot1ag debug ipv6 dhcp debug ping exception switch-chip-
register
debug dot1x debug ipv6 mld debug rip show debugging
debug
igmpsnooping
debug ipv6 pimdm debug sflow show exception
debug ip dvmrp debug ipv6 pimsm debug spanning-
tree
write core
debug ip igmp
–––
2CSNXXX_SWUM200.book Page 1566 Tuesday, December 10, 2013 1:22 PM

Serviceability Tracing Packet Commands 1567
User Guidelines
There are no user guidelines for this command.
Example
console#debug arp
debug authentication interface
Use this command to enable Authentication Manager debug traces for the
interface.Use the no form of this command to set the debug trace to factory
default value.
Syntax
debug authentication
{event | all}
interface-id
no debug authentication
{event | all}
interface-id
•
event
—Traces Authentication Manager debug events.
•
all
—Enables all Authentication Manager debugs.
•
interface-id
—The interface to trace.
Default Configuration
Default value is disabled.
Command Modes
Privileged EXEC mode
User Guidelines
There are no user guidelines for this command.
Example
console# debug authentication event Gi1/0/1
console# debug authentication all Gi1/0/1
2CSNXXX_SWUM200.book Page 1567 Tuesday, December 10, 2013 1:22 PM

1568 Serviceability Tracing Packet Commands
debug auto-voip
Use the debug auto-voip command to enable Auto VOIP debug messages. se
the optional parameters to trace H323, SCCP, or SIP packets respectively. Use
the “no” form of this command to disable Auto VOIP debug messages.
Syntax
debug auto-voip [ H323 | SCCP | SIP ]
no debug auto-voip [ H323 | SCCP | SIP ]
Default Configuration
Auto VOIP tracing is disabled by default.
Command Mode
Privileged EXEC mode.
User Guidelines
There are no user guidelines for this command.
Example
console#debug auto-voip
debug clear
Use the debug clear command to disable all debug traces.
Syntax
debug clear
Default Configuration
There is no default configuration for this command.
Command Mode
Privileged EXEC mode.
2CSNXXX_SWUM200.book Page 1568 Tuesday, December 10, 2013 1:22 PM

Serviceability Tracing Packet Commands 1569
User Guidelines
There are no user guidelines for this command.
Example
console#debug clear
debug console
Use the debug console to enable the display of “debug” trace output on the
login session in which it is executed. Debug console display must be enabled
in order to view any trace output. The output of debug trace commands
appears on all login sessions for which debug console has been enabled. The
configuration of this command remains in effect for the life of the login
session. The effect of this command is not persistent across resets.
Syntax
debug console
Default Configuration
Display of debug traces is disabled by default.
Command Mode
Privileged EXEC mode.
User Guidelines
There are no user guidelines for this command.
Example
console#debug console
debug dot1ag
Use this command to enable or disable the tracing of CFM components for
events and CFM PDUs based on the type of packet for reception and
transmission.
2CSNXXX_SWUM200.book Page 1569 Tuesday, December 10, 2013 1:22 PM

1570 Serviceability Tracing Packet Commands
Syntax
debug dot1ag {all | ccm | events | lbm | lbr | ltm | ltr | pdu}
no debug dot1ag {all | ccm | events | lbm | lbr | ltm | ltr | pdu}
•
all
—Traces CCM, LBM, LBR, LTM, LTRs.
•
ccm
—Traces CCMs
•
events
—Traces CFM events
•
lbm
—Traces LBMs
•
lbr
—Traces LBRs
•
ltm
—Traces LTMs
•
ltr
—Traces LTRs
•
pdu
—Traces specific PDUs
Default Configuration
Tracing is disabled by default.
Command Modes
Privileged EXEC mode
User Guidelines
This command is only application to N4000 series switches.
Example
console#debug dot1ag all
Dot1ag CCM, LBM, LBR, LTM, LTR tracing enabled.
console#
console#debug dot1ag events
Dot1ag events tracing enabled.
console#
console#debug dot1ag ccm
2CSNXXX_SWUM200.book Page 1570 Tuesday, December 10, 2013 1:22 PM

Serviceability Tracing Packet Commands 1571
Dot1ag CCM tracing enabled.
console#
console#no debug dot1ag ccm
Dot1ag CCM tracing disabled.
debug dot1x
Use the debug dot1x command to enable dot1x packet tracing. Use the “no”
form of this command to disable dot1x packet tracing.
Syntax
debug dot1x packet [ receive | transmit ]
no debug dot1x packet [ receive | transmit ]
Default Configuration
Display of dot1x traces is disabled by default.
Command Mode
Privileged EXEC mode.
User Guidelines
There are no user guidelines for this command.
Example
console#debug dot1x packet
debug igmpsnooping
Use the debug igmpsnooping to enable tracing of IGMP Snooping packets
transmitted and/or received by the switch. IGMP Snooping should be enabled
on the device and the interface in order to monitor packets for a particular
interface.
Syntax
debug igmpsnooping packet [ receive | transmit ]
2CSNXXX_SWUM200.book Page 1571 Tuesday, December 10, 2013 1:22 PM

1572 Serviceability Tracing Packet Commands
no debug igmpsnooping packet [ receive | transmit ]
Default Configuration
Display of IGMP Snooping traces is disabled by default.
Command Mode
Privileged EXEC mode.
User Guidelines
There are no user guidelines for this command.
Example
console#debug igmpsnooping packet
debug ip acl
Use the debug ip acl command to enable debug of IP Protocol packets
matching the ACL criteria. Use the “no” form of this command to disable IP
ACL debugging.
Syntax
debug ip acl
acl
no debug ip acl
acl
•
acl
— The number of the IP ACL to debug.
Default Configuration
Display of IP ACL traces is disabled by default.
Command Mode
Privileged EXEC mode.
User Guidelines
There are no user guidelines for this command.
2CSNXXX_SWUM200.book Page 1572 Tuesday, December 10, 2013 1:22 PM

Serviceability Tracing Packet Commands 1573
Example
console#debug ip acl 1
debug ip dvmrp
Use the debug ip dvmrp to trace DVMRP packet reception and transmission.
The receive option traces only received DVMRP packets and the transmit
option traces only transmitted DVMRP packets. When neither keyword is
used in the command, all DVMRP packet traces are dumped. Vital
information such as source address, destination address, control packet type,
packet length, and the interface on which the packet is received or
transmitted is displayed on the console.
Syntax
debug ip dvmrp packet [ receive | transmit ]
no debug ip dvmrp packet [ receive | transmit ]
Default Configuration
Display of DVMRP traces is disabled by default.
Command Mode
Privileged EXEC mode.
User Guidelines
There are no user guidelines for this command.
Example
console#debug ip dvmrp packet
debug ip igmp
Use the debug ip igmp command to trace IGMP packet reception and
transmission. The receive option traces only received IGMP packets and the
transmit option traces only transmitted IGMP packets. When neither
keyword is used in the command, then all IGMP packet traces are dumped.
Vital information such as source address, destination address, control packet
2CSNXXX_SWUM200.book Page 1573 Tuesday, December 10, 2013 1:22 PM

1574 Serviceability Tracing Packet Commands
type, packet length, and the interface on which the packet is received or
transmitted is displayed on the console. Use the “no” form of this command
to disable IGMP traces.
Syntax
debug ip igmp packet [ receive | transmit ]
no debug ip igmp packet [ receive | transmit ]
Default Configuration
Display of IGMP traces is disabled by default.
Command Mode
Privileged EXEC mode.
User Guidelines
There are no user guidelines for this command.
Example
console#debug ip igmp packet
debug ip mcache
Use the debug ip mcache command for tracing MDATA packet reception and
transmission. The receive option traces only received data packets and the
transmit option traces only transmitted data packets. When neither keyword
is used in the command, then all data packet traces are dumped. Vital
information such as source address, destination address, packet length, and
the interface on which the packet is received or transmitted is displayed on
the console. Use the “no” form of this command to disable MDATA tracing.
Syntax
debug ip mcache packet [ receive | transmit ]
no debug ip mcache packet [ receive | transmit ]
Default Configuration
Display of MDATA traces is disabled by default.
2CSNXXX_SWUM200.book Page 1574 Tuesday, December 10, 2013 1:22 PM

Serviceability Tracing Packet Commands 1575
Command Mode
Privileged EXEC mode.
User Guidelines
There are no user guidelines for this command.
Example
console#debug ip mcache packet
debug ip pimdm packet
Use the debug ip pimdm packet command to trace PIMDM packet reception
and transmission. The receive option traces only received PIMDM packets
and the transmit option traces only transmitted PIMDM packets. When
neither keyword is used in the command, then all PIMDM packet traces are
dumped. Vital information such as source address, destination address,
control packet type, packet length, and the interface on which the packet is
received or transmitted is displayed on the console.
Use the no form of this command to disable debug tracing of PIMDM packet
reception and transmission.
Syntax
debug ip pimdm packet [ receive | transmit ]
no debug ip pimdm packet [ receive | transmit ]
Default Configuration
Display of PIMDM traces is disabled by default.
Command Mode
Privileged EXEC mode.
User Guidelines
There are no user guidelines for this command.
Example
console#debug ip pimdm packet
2CSNXXX_SWUM200.book Page 1575 Tuesday, December 10, 2013 1:22 PM

1576 Serviceability Tracing Packet Commands
debug ip pimsm packet
Use the debug ip pimsm command to trace PIMSM packet reception and
transmission. The receive option traces only received PIMSM packets and the
transmit option traces only transmitted PIMSM packets. When neither
keyword is used in the command, then all PIMSM packet traces are dumped.
Vital information such as source address, destination address, control packet
type, packet length, and the interface on which the packet is received or
transmitted is displayed on the console. Use the no form of this command to
disable debug tracing of PIMSM packet reception and transmission.
Syntax
debug ip pimsm packet [ receive | transmit ]
no debug ip pimsm packet [ receive | transmit ]
Default Configuration
Display of PIMSM traces is disabled by default.
Command Mode
Privileged EXEC mode.
User Guidelines
There are no user guidelines for this command.
Example
console#debug ip pimsm packet
debug ip vrrp
Use the debug ip vrrp command to enable VRRP debug protocol messages.
Use the “no” form of this command to disable VRRP debug protocol
messages.
Syntax
debug ip vrrp
no debug ip vrrp
2CSNXXX_SWUM200.book Page 1576 Tuesday, December 10, 2013 1:22 PM

Serviceability Tracing Packet Commands 1577
Default Configuration
Display of VRRP traces is disabled by default.
Command Mode
Privileged EXEC mode.
User Guidelines
This command has no user guidelines.
Example
console#debug ip vrrp
debug ipv6 dhcp
Use the debug ipv6 dhcp command in Privileged EXEC mode to display
debug information about DHCPv6 client activities and to trace DHCPv6
packets to and from the local DHCPv6 client. To disable debugging, use the
no form of the command.
Syntax
debug ipv6 dhcp
no debug ipv6 dhcp
Default Configuration
Debugging for the DHCP for IPv6 is disabled by default.
Command Mode
Privileged EXEC
User Guidelines
DHCPv6 client already has packet tracing. This command turns the packet
tracing on.
Examples
console#debug ipv6 dhcp
2CSNXXX_SWUM200.book Page 1577 Tuesday, December 10, 2013 1:22 PM

1578 Serviceability Tracing Packet Commands
debug ipv6 mcache
Use the debug ipv6 mcache command to trace MDATAv6 packet reception
and transmission. The receive option traces only received data packets and
the transmit option traces only transmitted data packets. When neither
keyword is used in the command, then all data packet traces are dumped.
Vital information such as source address, destination address, packet length,
and the interface on which the packet is received or transmitted is displayed
on the console.
Syntax
debug ipv6 mcache packet [ receive | transmit ]
no debug ipv6 mcache packet [ receive | transmit ]
Default Configuration
Display of MDATA traces is disabled by default.
Command Mode
Privileged EXEC mode.
User Guidelines
This command has no user guidelines.
Example
console#debug ipv6 mcache packet
debug ipv6 mld
Use the debug ipv6 mld command to trace MLD packet reception and
transmission. The receive option traces only received MLD packets and the
transmit option traces only transmitted MLD packets. When neither keyword
is used in the command, then all MLD packet traces are dumped. Vital
information such as source address, destination address, control packet type,
packet length, and the interface on which the packet is received or
transmitted is displayed on the console. Use the “no” form of this command
to disable MLD tracing.
2CSNXXX_SWUM200.book Page 1578 Tuesday, December 10, 2013 1:22 PM

Serviceability Tracing Packet Commands 1579
Syntax
debug ipv6 mld packet [ receive | transmit ]
no debug ipv6 mld packet [ receive | transmit ]
Default Configuration
Display of MLD traces is disabled by default.
Command Mode
Privileged EXEC mode.
User Guidelines
There are no user guidelines for this command.
Example
console#debug ipv6 mld packet
debug ipv6 pimdm
Use the debug ipv6 pimdm command to trace PIMDMv6 packet reception
and transmission. The receive option traces only received PIMDMv6 packets
and the transmit option traces only transmitted PIMDMv6 packets. When
neither keyword is used in the command, then all PIMDMv6 packet traces are
dumped. Vital information such as source address, destination address,
control packet type, packet length, and the interface on which the packet is
received or transmitted is displayed on the console. Use the “no” form of this
command to disable PIMDMv6 tracing.
Syntax
debug ipv6 pimdm packet [ receive | transmit ]
no debug ipv6 pimdm packet [ receive | transmit ]
Default Configuration
Display of PIMDMv6 traces is disabled by default.
2CSNXXX_SWUM200.book Page 1579 Tuesday, December 10, 2013 1:22 PM

1580 Serviceability Tracing Packet Commands
Command Mode
Privileged EXEC mode.
User Guidelines
There are no user guidelines for this command.
Example
console#debug ipv6 pimdm packet
debug ipv6 pimsm
Use the debug ipv6 pimsm command to trace PIMSMv6 packet reception
and transmission. The receive option traces only received PIMSMv6 packets
and the transmit option traces only transmitted PIMSMv6 packets. When
neither keyword is used in the command, then all PIMSMv6 packet traces are
dumped. Vital information such as source address, destination address,
control packet type, packet length, and the interface on which the packet is
received or transmitted is displayed on the console. Use the “no” form of this
command to disable PIMSMv6 tracing.
Syntax
debug ipv6 pimsm packet [ receive | transmit ]
no debug ipv6 pimsm packet [ receive | transmit ]
Default Configuration
Display of PIMSMv6 traces is disabled by default.
Command Mode
Privileged EXEC mode.
User Guidelines
There are no user guidelines for this command.
Example
console#debug ipv6 pimsm packet
2CSNXXX_SWUM200.book Page 1580 Tuesday, December 10, 2013 1:22 PM

Serviceability Tracing Packet Commands 1581
debug isdp
Use the debug isdp command to trace ISDP packet reception and
transmission. The receive option traces only received ISDP packets and the
transmit option traces only transmitted ISDP packets. When neither keyword
is used in the command, then all ISDP packet traces are dumped. Vital
information such as source address, destination address, control packet type,
packet length, and the interface on which the packet is received or
transmitted is displayed on the console. Use the “no” form of this command
to disable ISDP tracing.
Syntax
debug isdp packet [ receive | transmit ]
no debug isdp packet [ receive | transmit ]
Default Configuration
Display of ISDP traces is disabled by default.
Command Mode
Privileged EXEC mode.
User Guidelines
There are no user guidelines for this command.
Example
console#debug isdp packet
debug lacp
Use the debug lacp command to enable tracing of LACP packets received and
transmitted by the switch. Use the “no” form of this command to disable
tracing of LACP packets.
Syntax
debug lacp packet
no debug lacp packet
2CSNXXX_SWUM200.book Page 1581 Tuesday, December 10, 2013 1:22 PM

1582 Serviceability Tracing Packet Commands
Default Configuration
Display of LACP traces is disabled by default.
Command Mode
Privileged EXEC mode.
User Guidelines
There are no user guidelines for this command.
Example
console#debug lacp packet
debug mldsnooping
Use the debug mldsnooping command to trace MLD snooping packet
reception and transmission. The receive option traces only received MLD
snooping packets and the transmit option traces only transmitted MLD
snooping packets. When neither keyword is used in the command, then all
MLD snooping packet traces are dumped. Vital information such as source
address, destination address, control packet type, packet length, and the
interface on which the packet is received or transmitted is displayed on the
console. Use the “no” form of this command to disable tracing of MLD
Snooping packets.
Syntax
debug mldsnooping packet [ receive | transmit ]
no debug mldsnooping packet [ receive | transmit ]
Default Configuration
Display of MLD Snooping traces is disabled by default.
Command Mode
Privileged EXEC mode.
User Guidelines
There are no user guidelines for this command.
2CSNXXX_SWUM200.book Page 1582 Tuesday, December 10, 2013 1:22 PM

Serviceability Tracing Packet Commands 1583
Example
console#debug mldsnooping
debug ospf
Use the debug ospf command to enable tracing of OSPF packets received and
transmitted by the switch. Use the “no” form of this command to disable
tracing of OSPF packets.
Syntax
debug ospf packet
no debug ospf packet
Default Configuration
Display of OSPF traces is disabled by default.
Command Mode
Privileged EXEC mode.
User Guidelines
There are no user guidelines for this command.
Example
console#debug ospf packet
debug ospfv3
Use the debug ospfv3 command to enable tracing of OSPFv3 packets
received and transmitted by the switch. Use the “no” form of this command
to disable tracing of OSPFv3 packets.
Syntax
debug ospfv3 packet
no debug ospfv3 packet
2CSNXXX_SWUM200.book Page 1583 Tuesday, December 10, 2013 1:22 PM

1584 Serviceability Tracing Packet Commands
Default Configuration
Display of OSPFv3 traces is disabled by default.
Command Mode
Privileged EXEC mode.
User Guidelines
There are no user guidelines for this command.
Example
console#debug ospfv3 packet
debug ping
Use the debug ping command to enable tracing of ICMP echo requests and
responses. This command traces pings on the network port and on the
routing interfaces. Use the “no” form of this command to disable tracing of
ICMP echo requests and responses.
Syntax
debug ping packet
no debug ping packet
Default Configuration
Display of ICMP echo traces is disabled by default.
Command Mode
Privileged EXEC mode.
User Guidelines
There are no user guidelines for this command.
Example
The following example displays.
console#debug ping packet
2CSNXXX_SWUM200.book Page 1584 Tuesday, December 10, 2013 1:22 PM

Serviceability Tracing Packet Commands 1585
debug rip
Use the debug rip command to enable tracing of RIP requests and responses.
Use the no form of this command to disable tracing of RIP requests and
responses.
Syntax
debug rip packet
no debug rip packet
Default Configuration
Display of RIP traces is disabled by default.
Command Mode
Privileged EXEC mode.
User Guidelines
There are no user guidelines for this command.
Example
console#debug rip packet
debug sflow
Use the debug sflow command to enable sFlow debug packet trace. Use the
no form of this command to disable sFlow packet tracing.
Syntax
debug sflow packet
no debug sflow packet
Default Configuration
Display of sFlow traces is disabled by default.
2CSNXXX_SWUM200.book Page 1585 Tuesday, December 10, 2013 1:22 PM

1586 Serviceability Tracing Packet Commands
Command Mode
Privileged EXEC mode.
User Guidelines
There are no user guidelines for this command.
Example
console#debug sflow packet
debug spanning-tree
Use the debug spanning-tree command to trace spanning tree BPDU packet
reception and transmission. The receive option traces only received spanning
tree BPDUs and the transmit option traces only transmitted BPDUs. When
neither keyword is used in the command, all spanning tree BPDU traces are
dumped. Vital information such as source address, destination address,
control packet type, packet length, and the interface on which the packet is
received or transmitted is displayed on the console. Use the no form of this
command to disable tracing of spanning tree BPDUs.
Syntax
debug spanning-tree bpdu [ receive | transmit ]
no debug spanning-tree bpdu [ receive | transmit ]
Default Configuration
Display of spanning tree BPDU traces is disabled by default.
Command Mode
Privileged EXEC mode.
User Guidelines
There are no user guidelines for this command.
Example
console#debug spanning-tree bpdu
2CSNXXX_SWUM200.book Page 1586 Tuesday, December 10, 2013 1:22 PM

Serviceability Tracing Packet Commands 1587
debug vrrp
Use the debug vrrp command in Privileged EXEC mode to enable VRRP
debug protocol messages. Use the no form of this command to disable VRRP
debug protocol messages.
Syntax
debug vrrp all
no debug vrrp all
Default Configuration
The display of VRRP traces is disabled by default.
Command Mode
Privileged EXEC mode.
User Guidelines
This command has no user guidelines.
exception core-file
Use the exception core-file command to configure the core dump file name.
Use the no form of the command the reset the core file name to the default.
Syntax
exception core-file
file-name
[hostname [time-stamp] | time-stamp
[
hostname
]]
no exception core-file
•
file-name
— The file name. The maximum length is 15 characters.
Embedded blanks may not be allowed by the host file system (for example,
TFTP server) and are not recommended.
•
hostname
— Includes the switch host name in the core file name. If not
configured, uses the switch MAC address in the core file name.
•
time-stamp
—Includes the switch TOD in the core file name.
2CSNXXX_SWUM200.book Page 1587 Tuesday, December 10, 2013 1:22 PM

1588 Serviceability Tracing Packet Commands
Default Configuration
By default, the core file name has no prefix and no host name and uses the
time stamp of the switch in the core file name.
Command Modes
Global Configuration mode
User Guidelines
The configuration parameters are not validated when this command is
entered. Use the write core test command to validate the configured
parameters and that the core dump is likely to succeed.
An average core file is around 450 MB. Example copy times are as follows:
• TFTP: 13mins (different subnet)
•USB: 3 mins
Administrators should ensure that a cleanly formatted USB stick of at least
1G is used for collection of a the full core dump.
Example
This example enables core dumps to a TFTP server 10.27.9.1 reachable over
the out-of-band port. The core file is written to the dumps directory and the
name includes the host name of the switch and the switch TOD.
console(config)#exception dump tftp-server 10.27.9.1 file-path dumps
console(config)#exception core-file hostname time-stamp
console(config)#exception protocol tftp
exception dump
Use this command to configure the core dump location.
Syntax
exception dump {tftp-server
ip-address
| file-path
dir
}
no exception dump {tftp-server | file-path}
• tftp-server — The IPv4 address of a TFTP server.
•
dir
— The directory to prepend to the core file name.
2CSNXXX_SWUM200.book Page 1588 Tuesday, December 10, 2013 1:22 PM

Serviceability Tracing Packet Commands 1589
Default Configuration
Full core dumps are not enabled by default.
Command Modes
Global Configuration mode
User Guidelines
This option should only be used under the direction of Dell support
personnel.
The file-path parameter is used by both the USB and TFTP core dumps.
The TFTP server must be reachable over the out-of-band interface. Front
panel ports cannot be used for TFTP during exception processing.
Configuration parameters are not validated when the command is entered.
Use the write core test command to validate the configured parameters and
that the core dump is likely to succeed.
Example
This example enables core dumps to a TFTP server 10.27.9.1 reachable over
the out-of-band port. The core file is written to the “dumps” directory and
the name includes the host name of the switch and the switch TOD.
console(config)#exception dump tftp-server 10.27.9.1 file-path dumps
console(config)#exception core-file Core hostname time-stamp
console(config)#exception protocol tftp
exception protocol
Use the exception protocol command as directed by Dell Networking support
to enable full core dumps. Use the no form of the command to disable full
core dumps.
Syntax
exception protocol {tftp | usb | none}
no exception protocol
• tftp — Store the core dump on a TFTP server reachable on the out-of-
band port
2CSNXXX_SWUM200.book Page 1589 Tuesday, December 10, 2013 1:22 PM

1590 Serviceability Tracing Packet Commands
• usb — Store the core dump on an un-mounted USB device
• none — Core dumps are disabled
Default Configuration
Full core dumps are disabled by default.
Command Modes
Global Configuration mode
User Guidelines
The TFTP server must be reachable over the out-of-band port. Configuring a
TFTP server reachable over a front panel port is unreliable during exception
processing. This implies that core dumps on the N2000 series switches must
use the USB target.
The USB device must be plugged in at the time of the core dump trap.
The configuration parameters are not validated when the command is
entered. The administrator can use the write core test command to validate
that the configured parameters are valid and the core dump is likely to
succeed.
The file name for the core file includes options as the time stamp or
hostname as per the configured parameters.
The TFTP core dump does not support TFTPD32 or Klever Pumpkin TFTP
servers.
Example
This example enables core dumps to a TFTP server 10.27.9.1 reachable over
the out-of-band port. The core file is written to the dumps directory and the
name includes the host name of the switch and the switch TOD.
console(config)#exception dump tftp-server 10.27.9.1 file-path dumps
console(config)#exception core-file Core hostname time-stamp
console(config)#exception protocol tftp
This example enables core dumps to a USB stick. The core file is written to
the top level directory and the name includes the host name of the switch and
the switch TOD.
console(config)#exception core-file Core hostname time-stamp
2CSNXXX_SWUM200.book Page 1590 Tuesday, December 10, 2013 1:22 PM

Serviceability Tracing Packet Commands 1591
console(config)#exception protocol usb
console(config)#do dir usb
Filename Filesize Modification Time
. 16384 01/01/1970 00:00:00
.. 0 06/24/2013 17:14:30
test.bin 11 01/01/1980 00:00:00
Total Size: 1002160128
Bytes Used: 16384
Bytes Free: 1002143744
exception switch-chip-register
Use the exception switch-chip-register command to enable dumping the
switch chip registers in case of an exception. The register dump is taken only
for the master unit and not for the stack member units. Use the no form of
the command to disable dumping of the switch-chip registers.
Syntax
exception switch-chip-register
no exception switch-chip-register
Default Configuration
By default, switch register dumps are disabled.
Command Modes
Global Configuration mode
User Guidelines
This option should only be used under the direction of Dell support
personnel.
Switch registers are captured to the local file system.
show debugging
Use the show debugging command to display packet tracing configurations.
2CSNXXX_SWUM200.book Page 1591 Tuesday, December 10, 2013 1:22 PM

1592 Serviceability Tracing Packet Commands
Syntax
show debugging
no show debugging
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC mode, Configuration mode and all Configuration submodes
User Guidelines
Enabled packet tracing configurations are displayed.
Example
console#show debugging
Authentication manager all debug traces enabled on Gi1/0/1
console#
show exception
Use the show exception command to display the core dump configuration
parameters.
Syntax
show exception
Default Configuration
This command has no default configuration.
Command Modes
Privileged EXEC mode (all show modes)
User Guidelines
The default values of core dump are:
2CSNXXX_SWUM200.book Page 1592 Tuesday, December 10, 2013 1:22 PM

Serviceability Tracing Packet Commands 1593
Example
console(config)#show exception
Coredump file name............................. core
Coredump filename uses hostname................ FALSE
Coredump filename uses time-stamp.............. TRUE
TFTP server IP................................. 10.130.64.86
File path...................................... dumps
Protocol....................................... tftp
Switch-chip-register........................... TRUE
console(config)#
write core
Use the write core command to generate a core file on demand and either
reboot the switch or test the core file configuration.
Syntax
write core [test [
dest-file-name
]]
• dest-file-name — The file name used if a tftp-server is configured with the
exception dump tftp-server
command. The dest-file-name parameter
overrides the file name parameters configured with the
exception core-file
command.
Default Configuration
This command has no default configuration.
Parameter Default
Coredump file name core
Coredump filename uses hostname FALSE
Coredump filename uses time-stamp True
TFTP server IP
File path ./.
Protocol none
Switch-chip-register FALSE
2CSNXXX_SWUM200.book Page 1593 Tuesday, December 10, 2013 1:22 PM

1594 Serviceability Tracing Packet Commands
Command Modes
Privileged EXEC mode
User Guidelines
Using the write core command reboots the switch. The write core command
is useful when the device malfunctions, but has not crashed.
The write core test command is useful for validating the core dump setup. For
example, if the protocol is configured as tftp, the command write core test
communicates with the tftp server and informs the administrator if the tftp
server can be contacted. Similarly, if the protocol is configured as usb, it
mounts and unmounts the file system and then informs the administrator
regarding the status.
Example
console(config)#do write core
The system has unsaved changes.
Would you like to save them now? (y/n) n
Configuration Not Saved!
This operation will reboot the device.
Are you sure you want to create coredump? (y/n).y
----------------------------------------------------
Thu Jan 1 00:17:35 1970
[pgid:577] [pid:577] [name:(syncdb)] [signal:11]
Call Trace (depth = 3):
0xb6faf7dc
0xb6fafc60
0xb6ef742c
<188> Jan 1 00:17:36 10.27.22.174-1 General[80499188]: procmgr.c(2926) 1171
%% Application Terminated (syncdb, ID = 2, PID = 577
log_error_code osapi_crash.c 2010
Switching software SIGSEGV Handler
2CSNXXX_SWUM200.book Page 1594 Tuesday, December 10, 2013 1:22 PM

Serviceability Tracing Packet Commands 1595
This build was configured to copy this crash information to
a file.
.
.
.
(Unit 1 - Waiting to select management unit)>
Applying Global configuration, please wait ...
Applying Interface configuration, please wait ...
console>en
console#dir usb
Filename Filesize Modification Time
. 16384 01/01/1970 00:00:00
.. 0 06/24/2013 17:14:30
test.bin 11 01/01/1980 00:00:00
syncdb_hostname_1055.bin 348160 01/01/1980 00:00:00
switchdrvr_hostname_1063.bin 459640832 01/01/1980 00:00:00
Total Size: 1002160128
Bytes Used: 460029952
Bytes Free: 542130176
2CSNXXX_SWUM200.book Page 1595 Tuesday, December 10, 2013 1:22 PM

1596 Serviceability Tracing Packet Commands
2CSNXXX_SWUM200.book Page 1596 Tuesday, December 10, 2013 1:22 PM

Sflow Commands 1597
75
Sflow Commands
Dell Networking N2000/N3000/N4000 Series Switches
sFlow® is the standard for monitoring high-speed switched and routed
networks. sFlow technology is built into network equipment and gives
complete visibility into network activity, enabling effective management and
control of network resources.
The sFlow monitoring system consists of an sFlow Agent (embedded in a
switch or router or in a stand-alone probe) and a central sFlow Collector. The
sFlow Agent uses sampling technology to capture traffic statistics from the
device it is monitoring. sFlow datagrams are used to forward the sampled
traffic statistics immediately to an sFlow Collector for analysis. The traffic
samples sent to the Collector contain the source ifIndex and, for switched
packets, the destination ifIndex.
The sFlow Agent supports two forms of sampling: statistical packet-based
sampling of switched or routed Packet Flows and time-based sampling of
counters.
Commands in this Chapter
This chapter explains the following commands:
sflow destination
Use the sflow destination command to configure the sFlow collector
parameters (owner string, receiver timeout, maxdatagram, ip address and
port). Use the “no” form of this command to set receiver parameters to the
default or remove a receiver.
sflow destination show sflow agent
sflow polling show sflow destination
sflow polling (Interface Mode) show sflow polling
sflow sampling show sflow polling
sflow sampling (Interface Mode)
–
2CSNXXX_SWUM200.book Page 1597 Tuesday, December 10, 2013 1:22 PM

1598 Sflow Commands
Syntax
sflow
rcvr_index
destination {
ip-address
[
port
] | maxdatagram
size
| owner
"owner_string"
{notimeout|timeout rcvr_timeout}
no sflow
rcvr_index
destination [
ip-address
| maxdatagram | owner ]
•
rcvr_index
—The index of this sFlow Receiver (Range: 1–8).
•
ip-address
—The sFlow receiver IP address. If set to 0.0.0.0, no sFlow
datagrams will be sent.
•
size
—The maximum number of data bytes that can be sent in a single
sample datagram. The management entity should set this value to avoid
fragmentation of the sFlow datagrams. (Range: 200–9116 bytes).
•
owner_string
—The identity string for the receiver. A receiver is not
enabled until the owner string is assigned. The default is an empty string.
The identity string must be set before assigning a receiver to a sampler or
poller. (Range: 1–127 characters).
•
rcvr_timeout
—The time, in seconds, remaining before the sampler or
poller is released and stops sending samples to the receiver. Setting a value
of 0 for the timeout value permanently configures the sflow receiver. Use
the no form of the command to remove permanently configured receivers.
A management entity wanting to maintain control of the sampler is
responsible for setting a new value before the old one expires. (Range:
0–4294967295 seconds).
•
port
—The destination Layer4 UDP port for sFlow datagrams. (Range:
1–65535).
Default Configuration
No receivers are configured by default.
The default IP address is 0.0.0.0
The default maximum datagram size is 1400.
The default owner string is the empty string.
The default receiver timeout is 0.
The default destination port is 6343.
2CSNXXX_SWUM200.book Page 1598 Tuesday, December 10, 2013 1:22 PM

Sflow Commands 1599
Command Mode
Global Configuration mode.
User Guidelines
An sflow destination entry must have an owner assigned in order for polling or
sampling to be operational. The last set of command parameters are optional
in the no form of the command. Sflow commands with a timeout value
supplied do not show in the running config. Because the timer is actively
running, the command is ephemeral and is therefore not shown in the
running config. Entering an sflow command with a notimeout parameter will
cause the sflow configuration to be shown in the running config.
Example
console(config)#sflow 1 destination owner 1 timeout 2000
console(config)#sflow 1 destination maxdatagram 500
console(config)#sflow 1 destination 30.30.30.1 560
sflow polling
Use the sflow polling command to enable a new sflow poller instance for this
data source if rcvr_idx is valid. An sflow poller sends counter samples to the
receiver. Use the “no” form of this command to reset poller parameters to the
defaults.
Syntax
sflow
rcvr-index
polling {gigabitethernet | tengigabitethernet |
fortygigabitethernet}
interface-list
poll-interval
no sflow
rcvr-index
polling {gigabitethernet | tengigabitethernet |
fortygigabitethernet}
interfaces
•
rcvr-index
— The sFlow Receiver associated with the poller (Range: 1–8).
•
interface-list
— The list of interfaces to poll in unit/slot/port format.
•
poll-interval
— The sFlow instance polling interval. A poll interval of 0
disables counter sampling. A value of
n
means once in
n
seconds a counter
sample is generated. (Range: 0–86400).
2CSNXXX_SWUM200.book Page 1599 Tuesday, December 10, 2013 1:22 PM

1600 Sflow Commands
Default Configuration
There are no pollers configured by default.
The default poll interval is 0.
Command Mode
Global Configuration mode.
User Guidelines
The sflow instance must be configured using the sflow destination owner
command before this command can successfully execute.
Example
console(config)#sflow 1 polling gigabitethernet 1/0/1-10 200
sflow polling (Interface Mode)
Use the sflow polling command in Interface Mode to enable a new sflow
poller instance for this interface if rcvr_idx is valid. An sflow poller sends
counter samples to the receiver. Use the no form of this command to reset
poller parameters to the defaults.
Syntax
sflow
rcvr-index
polling
poll-interval
no sflow
rcvr-index
polling
•
rcvr-index
— The sFlow Receiver associated with the poller (Range: 1 - 8).
•
poll-interval
— The sFlow instance polling interval. A poll interval of 0
disables counter sampling. A value of n means once in n seconds a counter
sample is generated. (Range: 0 - 86400).
Default Configuration
There are no pollers configured by default.
The default poll interval is 0.
2CSNXXX_SWUM200.book Page 1600 Tuesday, December 10, 2013 1:22 PM

Sflow Commands 1601
Command Mode
Interface Configuration (Ethernet) mode
User Guidelines
This command has no user guidelines.
Example
console(config-if-Gi1/0/2)#sflow 1 polling 6055
sflow sampling
Use the sflow sampling command to enable a new sflow sampler instance for
this data source if rcvr_idx is valid. An sflow sampler collects flow samples to
send to the receiver. Use the “no” form of this command to reset sampler
parameters to the default.
Syntax
sflow
rcvr-index
sampling {gigabitethernet | tengigabitethernet |
fortygigabitethernet}
interface-list
sampling-rate
[
size
]
no sflow
rcvr-index
sampling {gigabitethernet | tengigabitethernet |
fortygigabitethernet}
interface-list
•
rcvr-index
—The sFlow Receiver for this sFlow sampler to which flow
samples are to be sent. If no receiver is configured, then no packets will be
sampled. Only active receivers can be set. If a receiver times out, then all
samplers associated with the receiver will also expire. (Range: 1–8).
•
interface-list
— The list of interfaces to poll in unit/slot/port format.
•
sampling-rate
—The statistical sampling rate for packet sampling from this
source. A value of n means that out of n incoming packets, 1 packet will be
sampled. (Range: 1024–65536).
•
size
—The maximum number of bytes that should be copied from the
sampler packet (Range: 20–256 bytes).
Default Configuration
There are no samplers configured by default.
The default is no default sampling rate.
2CSNXXX_SWUM200.book Page 1601 Tuesday, December 10, 2013 1:22 PM

1602 Sflow Commands
The default size is 128.
Command Mode
Global Configuration mode.
User Guidelines
Lower sampling numbers cause more samples to be collected and increase the
load on the CPU. Setting a sampling rate of 1024 on a large number of ports
may tax the CPU beyond it's ability to deliver the packets to the receiver.
Lowering the sampling rate (higher numerical value) will help to ensure that
all collected samples can be sent to the receiver. The sflow instance must be
configured using the sflow destination owner command before this
command can successfully execute.
Example
console(config)#sflow 1 sampling gigabitethernet 1/0/2 1500 50
sflow sampling (Interface Mode)
Use the sflow sampling command in Interface Mode to enable a new sflow
sampler instance for this data source if rcvr_idx is valid. Use the no form of
this command to reset sampler parameters to the default.
Syntax
sflow
rcvr-index
sampling
sampling-rate
[
size
]
no sflow
rcvr-index
sampling
•
rcvr-index
— The sFlow Receiver for this sFlow sampler to which flow
samples are to be sent. If no receiver is configured, then no packets will be
sampled. Only active receivers can be set. If a receiver expires, then all
samplers associated with the receiver will also expire. (Range: 1 - 8).
•
sampling-rate
— The statistical sampling rate for packet sampling from
this source. A sampling rate of 1 counts all packets. A rate of 0 disables
sampling. A value of n means that out of n incoming packets, 1 packet will
be sampled. (Range: 1024 - 65536).
•
size
— The maximum number of bytes that should be copied from the
sampler packet (Range: 20 - 256 bytes).
2CSNXXX_SWUM200.book Page 1602 Tuesday, December 10, 2013 1:22 PM

Sflow Commands 1603
Default Configuration
There are no samplers configured by default.
The default sampling rate is 0.
The default maximum header size is 128.
Command Mode
Interface Configuration (Ethernet) mode
User Guidelines
Lower sampling numbers cause more samples to be collected and increase the
load on the CPU. Setting a sampling rate of 1024 on a large number of ports
may tax the CPU beyond it's ability to deliver the packets to the receiver.
Lowering the sampling rate (higher numerical value) will help to ensure that
all collected samples can be sent to the receiver.
Example
console(config-if-Gi1/0/15)#sflow 1 sampler 1500 50
show sflow agent
Use the show sflow agent command to display the sflow agent information.
Syntax
show sflow agent
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC mode, Configuration mode and all Configuration submodes
User Guidelines
The following fields are displayed:
2CSNXXX_SWUM200.book Page 1603 Tuesday, December 10, 2013 1:22 PM
1604 Sflow Commands
Example
console#show sflow agent
sFlow Version.......................... 1.3;Dell Inc.;10.23.18.28
IP Address............................. 10.27.21.34
show sflow destination
Use the show sflow destination command to display all the configuration
information related to the sFlow receivers.
Syntax
show sflow
rcvr-index
destination
•
rcvr index
—The index of the sFlow Receiver to display (Range: 1–8).
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC mode, Configuration mode and all Configuration submodes
User Guidelines
The following fields are displayed:
sFlow Version Uniquely identifies the version and implementation of this
MIB. The version string must have the following structure: MIB
Version; Organization; Software Revision where:
MIB Version: 1.3, the version of this MIB.
Organization: Dell Corp.
Revision: 1.0
IP Address The IP address associated with this agent.
Receiver Index The sFlow Receiver associated with the sampler/poller.
Owner String The identity string for receiver, the entity making use of this
sFlowRcvrTable entry.
2CSNXXX_SWUM200.book Page 1604 Tuesday, December 10, 2013 1:22 PM

Sflow Commands 1605
Example
console(config)#show sflow 1 destination
Receiver Index................................. 1
Owner String................................... asd
Time out....................................... No Timeout
IP Address:.................................... 1.2.3.4
Address Type................................... 1
Port........................................... 6343
Datagram Version............................... 5
Maximum Datagram Size.......................... 1400
show sflow polling
Use the show sflow polling command to display the sFlow polling instances
created on the switch.
Syntax
show sflow
rcvr-index
polling [{gigabitethernet | tengigabitethernet |
fortygigabitethernet}
interface-list
]
•
rcvr-index
— The sFlow Receiver associated with the poller (Range: 1–8).
•
interface-list
— The list of interfaces to poll, in unit/slot/port format.
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC mode, Configuration mode and all Configuration submodes
User Guidelines
The following fields are displayed:
Time Out The time (in seconds) remaining before the receiver is released
and stops sending samples to sFlow receiver.
Max Datagram
Size
The maximum number of bytes that can be sent in a single sFlow
datagram.
Port The destination Layer4 UDP port for sFlow datagrams.
2CSNXXX_SWUM200.book Page 1605 Tuesday, December 10, 2013 1:22 PM

1606 Sflow Commands
Example
console# show sflow 1 polling
Poller Receiver Poller
Data Source Index Interval
----------- ------- -------
Te1/0/1 1 0
show sflow sampling
Use the show sflow sampling command to display the sFlow sampling
instances created on the switch.
Syntax
show sflow
rcvr-index
sampling [{gigabitethernet | tengigabitethernet |
fortygigabitethernet}
interface-list
]
•
rcvr-index
— The sFlow Receiver associated with the poller (Range: 1–8).
•
interface-list
— The list of interfaces on which data is sampled.
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC mode, Configuration mode and all Configuration submodes
User Guidelines
The following fields are displayed:
Poller Data
Source
The sFlowDataSource (unit/slot/port) for this sFlow sampler. This
agent will support Physical ports only.
Receiver Index The sFlowReceiver associated with this sFlow counter poller.
Poller Interval The number of seconds between successive samples of the counters
associated with this data source.
2CSNXXX_SWUM200.book Page 1606 Tuesday, December 10, 2013 1:22 PM

Sflow Commands 1607
Example
console# #show sflow 1 sampling
Sampler Receiver Packet Max Header
Data Source Index Sampling Rate Size
----------- ------- ------------- ----------
Gi1/0/1 1 0 128
Sampler Data
Source
The sFlowDataSource (unit/slot/port) for this sFlow sampler.
This agent will support Physical ports only.
Receiver Index The sFlowReceiver configured for this sFlow sampler.
Packet Sampling
Rate
The statistical sampling rate for packet sampling from this
source.
Max Header Size The maximum number of bytes that should be copied from a
sampled packet to form a flow sample.
2CSNXXX_SWUM200.book Page 1607 Tuesday, December 10, 2013 1:22 PM

1608 Sflow Commands
2CSNXXX_SWUM200.book Page 1608 Tuesday, December 10, 2013 1:22 PM

SNMP Commands 1609
76
SNMP Commands
Dell Networking N2000/N3000/N4000 Series Switches
The SNMP component provides a machine-to-machine interface for the Dell
Networking product family. This includes the ability to configure the network
device, view settings and statistics, and upload or download code or
configuration images. The agent includes a get-bulk command to reduce
network management traffic when retrieving a sequence of Management
Information Base (MIB) variables and an elaborate set of error codes for
improved reporting to the network control station. The extensible and
advanced design of the Dell Networking SNMP makes adding remote
manageability to networked devices undemanding. The agent allows a
network control station to retrieve reports from the networked device. These
reports are based upon the defined objects in the MIB. The agent queries,
reports, and sets MIB variables based upon directions from the network
control station or upon preset conditions.
Commands in this Chapter
This chapter explains the following commands:
show snmp snmp-server community-
group
snmp-server user
show snmp engineID snmp-server contact snmp-server view
show snmp filters snmp-server enable traps snmp-server v3-host
show snmp group snmp-server engineID local
–
show snmp user snmp-server filter
–
show snmp views snmp-server group
–
show trapflags snmp-server host
–
snmp-server community snmp-server location
–
2CSNXXX_SWUM200.book Page 1609 Tuesday, December 10, 2013 1:22 PM

1610 SNMP Commands
show snmp
Use the show snmp command in Privileged EXEC mode to display the SNMP
communications status.
Syntax
show snmp
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC mode, Configuration mode and all Configuration submodes
User Guidelines
This command has no user guidelines.
Example
The following example displays the SNMP communications status.
Console # show snmp
Community-StringCommunity-AccessView nameIP address
----------------------------------------------------
publicread onlyuser-viewAll
privateread writeDefault172.16.1.1
privatesuDefaultSuper172.17.1.1
Community-String Group nameIP address
-----------------------------------
publicuser-groupAll
Traps are enabled.
Authentication trap is enabled.
Version 1,2 notifications
Target Address Type Community Version UDP Filter TO Retries
Port name Sec
-------------- ------ --------- ------- ---- ------ --- -----
192.122.173.42 Trap public 2 162 filt1 15 3
192.122.173.42 Inform public 2 162 filt2 15 3
2CSNXXX_SWUM200.book Page 1610 Tuesday, December 10, 2013 1:22 PM

SNMP Commands 1611
Version 3 notifications
Target Address Type Username Security UDP Filter TO Retries
Level Port name Sec
-------------- ----- -------- -------- ---- ------ --- ------
192.122.173.42 Inform Bob Priv 162 filt31 15 3
System Contact: Robert
System Location: Marketing
show snmp engineID
Use the show snmp engineID command in Privileged EXEC mode to display
the ID of the local Simple Network Management Protocol (SNMP) engine.
Syntax
show snmp engineID
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC mode, Configuration mode and all Configuration submodes
User Guidelines
This command has no user guidelines.
Example
The following example displays the SNMP engine ID.
console# show snmp engineID
Local SNMP engineID: 08009009020C0B099C075878
show snmp filters
Use the show snmp filters command in Privileged EXEC mode to display the
configuration of filters.
Syntax
show snmp filters
filtername
2CSNXXX_SWUM200.book Page 1611 Tuesday, December 10, 2013 1:22 PM

1612 SNMP Commands
•
filtername
— Specifies the name of the filter. (Range: 1-30)
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC mode, Configuration mode and all Configuration submodes
User Guidelines
Per RFC 2573, an implicit exclude all filter is present at the beginning of
every filter list. This implicit filter is not shown in the output of this
command.
Example
The following examples display the configuration of filters with and without a
filter name specification.
console # show snmp filters
Name OID Tree Type
------------------- ---------------------------------
user-filter1 1.3.6.1.2.1.1 Included
user-filter1 1.3.6.1.2.1.1.7 Excluded
user-filter2 1.3.6.1.2.1.2.2.1.*.1 Included
console # show snmp filters user-filter1
Name OID Tree Type
------------------- ---------------------------------
user-filter1 1.3.6.1.2.1.1 Included
user-filter1 1.3.6.1.2.1.1.7 Excluded
show snmp group
Use the show snmp group command in Privileged EXEC mode to display the
configuration of groups.
Syntax
show snmp group [
groupname
]
2CSNXXX_SWUM200.book Page 1612 Tuesday, December 10, 2013 1:22 PM

SNMP Commands 1613
•
groupname
— Specifies the name of the group. (Range: 1-30)
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC mode, Configuration mode and all Configuration submodes
User Guidelines
The group name accepts any printable characters except a double quote or
question mark. Enclose the string in double quotes to include spaces within
the name. The surrounding quotes are not used as part of the name. The CLI
does not filter illegal characters and may accept entries up to the first illegal
character or reject the entry entirely.
The following table contains field descriptions.
Example
The following examples display the configuration of views.
console# show snmp group
Name Security Views
Field Description
Name Name of the group
Security
Model
SNMP model in use (v1, v2 or v3)
Security
Level
Authentication of a packet with encryption. Applicable only to SNMP
Version 3 security model.
Views
• Read–A string that is the name of the view that enables you only to
view the contents of the agent. If unspecified, all the objects except
the community-table and SNMPv3 user and access tables are
available.
• Write–A string that is the name of the view that enables you to enter
data and manage the contents of the agent.
• Notify–A string that is the name of the view that enables you to
specify an inform or a trap.
2CSNXXX_SWUM200.book Page 1613 Tuesday, December 10, 2013 1:22 PM

1614 SNMP Commands
Model Level Read Write Notify
----------------- ----- ------ -------- -------- ------
user-group V3 Auth-Priv Default "" ""
managers-group V3 NoAuth-priv Default Default ""
managers-group V3 NoAuth-priv Default "" ""
console# show snmp groups user-group
Name Security Views
Model Level Read Write Notify
----------------- ------ ------ -------- -------- -------
user-group V3 Auth-Priv Default "" ""
show snmp user
Use the show snmp user command in Privileged EXEC mode to display the
configuration of users.
Syntax
show snmp user [
username
]
•
username
— Specifies the name of the user. (Range: 1-30)
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC mode, Configuration mode and all Configuration submodes
User Guidelines
The user name accepts any printable characters except a double quote or
question mark. Enclose the string in double quotes to include spaces within
the name. The surrounding quotes are not used as part of the name. The CLI
does not filter illegal characters and may accept entries up to the first illegal
character or reject the entry entirely.
Example
The following example displays the configuration of users with the user name
specified.
2CSNXXX_SWUM200.book Page 1614 Tuesday, December 10, 2013 1:22 PM
SNMP Commands 1615
Console # show snmp user
Name Group Name Auth Priv
Meth Meth Remote Engine ID
--------------- --------------- ---- ---- -------------------
bob user-group MD5 DES 800002a20300fce3900106
john user-group SHA DES 800002a20300fce3900106
Console # show snmp users bob
Name Group Name Auth Priv
Meth Meth Remote Engine ID
--------------- --------------- ---- ---- -------------------
bob user-group MD5 DES 800002a20300fce3900106
show snmp views
Use the show snmp views command in Privileged EXEC mode to display the
configuration of views.
Syntax
show snmp views [
viewname
]
•
viewname
— Specifies the name of the view. (Range: 1-30)
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC mode, Configuration mode and all Configuration submodes
User Guidelines
This command has no user guidelines.
Example
The following examples display the configuration of views with and without a
view name specified.
console# show snmp views
Name OID Tree Type
2CSNXXX_SWUM200.book Page 1615 Tuesday, December 10, 2013 1:22 PM

1616 SNMP Commands
show trapflags
Use the show trapflags command in Privileged EXEC mode to display the
trap settings.
Syntax
show trapflags [ospf|ospfv3|captive-portal]
•
ospf
—Display OSPFv2 specific trap settings.
•
ospfv3
—Display OSPFv3 specific trap settings.
•
captive-portal
—Display captive-portal specific trap settings.
Default Configuration
There is no default configuration for this command.
Command Mode
Privileged EXEC mode, Configuration mode and all Configuration submodes
User Guidelines
This command has no user guidelines.
Example #1
console#show trapflags
Authentication Flag......................... Disable
Auto-copy-sw Flag........................... Enable
Dot1q Flag.................................. Enable
Link Up/Down Flag........................... Enable
Maclock violation Flag...................... Enable
Multiple Users Flag......................... Enable
Spanning Tree Flag.......................... Enable
VRRP trap................................... Enable
ACL Traps................................... Enable
----------- ----------------------- ---------
user-view1 1.3.6.1.2.1.1 Included
user-view1 1.3.6.1.2.1.1.7 Excluded
user-view2 1.3.6.1.2.1.2.2.1.*.1 Included
2CSNXXX_SWUM200.book Page 1616 Tuesday, December 10, 2013 1:22 PM

SNMP Commands 1617
DVMRP Traps................................. Disable
OSPFv2 Traps................................ Disable
PIM Traps................................... Disable
OSPFv3 Traps................................ Disable
FIP snooping Traps.......................... Enable
Example #2
console#show trapflags ospf
OSPF Traps:
errors:
all..............................Disabled
authentication failure...........Enabled
bad packet.......................Enabled
config error.....................Enabled
virt authentication failure .....Disabled
virt bad packet..................Disabled
virt config error................Disabled
if-rx: if-rxpacket...............Disabled
lsa: lsamaxage...................Disabled
lsaoriginate.....................Disabled
overflow: lsdboverflow...........Enabled
lsdb-approaching-overflow........Enabled
retransmit:
packets..........................Disabled
virtpackets......................Disabled
rtb: rtb-entryinfo...............Disabled
state-change:
all..............................Disabled
if state change..................Enabled
neighbor state change............Enabled
virtif state change..............Disabled
virtneighbor state change........Disabled
snmp-server community
Use the snmp-server community command in Global Configuration mode to
set up the community access string to permit access to the SNMP protocol.
To remove the specified community string, use the no form of this command.
Syntax
snmp-server community
string
{ro | rw | su} [view
view-name
][ipaddress
ipaddress
]
no snmp-server community
string
2CSNXXX_SWUM200.book Page 1617 Tuesday, December 10, 2013 1:22 PM

1618 SNMP Commands
•
string
—Permits access to the SNMP protocol. (Range: 1-20 characters)
•
ro
—Indicates read-only access.
•
rw
—Indicates read-write access.
•
su
—Indicates SNMP administrator access.
•
ipaddress
—Specifies the IP address of the management station. If no IP
address is specified, all management stations are permitted.
•
view-name
—Specifies the name of a previously defined view. For
information on views, see the User Guidelines below. (Range: 1-30
characters)
Default Configuration
No community is defined. Default to read–only access if not specified.
Command Mode
Global Configuration mode
User Guidelines
You can not specify
viewname
for su, which has an access to the whole MIB.
You can use the view name to restrict the access rights of a community string.
When it is specified:
• An internal security name is generated.
• The internal security name for SNMPv1 and SNMPv2 security models is
mapped to an internal group name.
• The internal group name for SNMPv1 and SNMPv2 security models is
mapped to a view name. If
ro
is specified, then read-view and notify-view
are mapped. If
rw
is specified, then read-view, notify-view, and write-view
are mapped.
The community name may include any printable characters except a double
quote or question mark. Enclose the string in double quotes to include spaces
within the name. The surrounding quotes are not used as part of the name.
The CLI does not filter illegal characters and may accept entries up to the
first illegal character or reject the entry entirely.
2CSNXXX_SWUM200.book Page 1618 Tuesday, December 10, 2013 1:22 PM

SNMP Commands 1619
Example
The following example configures community access string public to permit
administrative access to SNMP at an administrative station with IP address
192.168.1.20.
console(config)# snmp-server community public su ipaddress 192.168.1.20
snmp-server community-group
Use the snmp-server community-group command in Global Configuration
mode to map the internal security name for SNMP v1 and SNMP v2 security
models to the group name. To remove the specified community string, use
the no form of this command.
Syntax
snmp-server community-group
community
-
string group-name
[ipaddress
ip-
address
]
• community-string — Community string that acts like a password and
permits access to the SNMP protocol. (Range: 1-20 characters)
•
group-name —
Name of a previously defined group. The group defines the
objects available to the community. (Range: 1-30 characters)
• ip-address — Management station IP address. Default is all IP addresses.
Default Configuration
No community group is defined.
Command Mode
Global Configuration mode
User Guidelines
The
group-name
parameter can be used to restrict the access rights of a
community string. When it is specified, the software:
• Generates an internal security-name.
• Maps the internal security-name for SNMPv1 and SNMPv2 security
models to the group-name.
2CSNXXX_SWUM200.book Page 1619 Tuesday, December 10, 2013 1:22 PM

1620 SNMP Commands
Example
The following example maps a community access string dell_community to
group dell_group.
console(config)# snmp-server community-group dell_community dell_group
192.168.29.1
snmp-server contact
Use the snmp-server contact command in Global Configuration mode to set
up a system contact (sysContact) string. To remove the system contact
information, use the no form of the command.
Syntax
snmp-server contact
text
no snmp-server contact
•
text
— Character string, 0 to 160 characters, describing the system contact
information.
Default Configuration
This command has no default configuration.
Command Mode
Global Configuration mode
User Guidelines
This command has no user guidelines.
Example
The following example displays setting up the system contact point as
"Dell_Technical_Support".
console(config)# snmp-server contact Dell_Technical_Support
2CSNXXX_SWUM200.book Page 1620 Tuesday, December 10, 2013 1:22 PM

SNMP Commands 1621
snmp-server enable traps
Use the snmp-server enable traps command in Global Configuration mode to
enable sending SNMP traps globally or to enable sending individual SNMP
traps. Use the no form of this command to disable sending SNMP traps
individually or globally.
Syntax
snmp-server enable traps [acl | all | auto-copy-sw | captive-portal
cp-type
|
dot1q | dvrmp | link | maclock | multiple-users | ospf
ospftype
| ospfv3
ospfv3type
|pim |poe | snmp authentication | spanning-tree | stack |vrrp]
no snmp-server enable traps [acl | all|auto-copy-sw | captive-portal
cp-type
| dot1q | dvrmp | link | maclock| multiple-users | ospf
ospftype
| ospfv3
ospfv3type
| pim | poe | snmp authentication | spanning-tree |stack|vrrp ]
• cp-type — {all, client-auth-failure, client-connect, client-db-full, client-
disconnect}
• ospftype— {all | errors { all | authentication failure | bad packet | config
error | virt authentication failure | virt bad packet | virt config error } | lsa
{ all | lsa-maxage | lsa-originate } | overflow { all | lsdb-overflow |
lsdbapproaching- overflow } | retransmit {all | packets | virt-packets } |
state-change { all | if state change | neighbor state change | virtifstate
change | virtneighbor state change }}
• ospfv3type—{all | errors { all | bad packet | config error | virt bad packet
| virt config error } | lsa { all | lsa-maxage | lsa-originate } | overflow { all
| lsdb-overflow | lsdb-approaching-overflow } | retransmit {all | packets |
virt-packets } | state-change { all | if state change | neighbor state change
| virtif state change | virtneighbor state change }}
•
acl
—Enable traps on ACL match events.
•
all
—Enable all traps (not recommended).
•
auto-copy-sw
—Enable traps on automatic download of switch software.
•
captive-portal
—Enable captive-portal traps.
•
dot1q
—Enable traps on VLAN configuration failures.
•
dvmrp
—Enable dvmrp traps.
•
maclock
—Enable traps on MAC locking violations.
2CSNXXX_SWUM200.book Page 1621 Tuesday, December 10, 2013 1:22 PM

1622 SNMP Commands
•
ospf
—Enable OSPF event traps.
•
ospfv3
—Enable OSPFv3 event traps.
•
pim
—Enable pim traps (pim-sm and pim-dm).
•
poe
—Enable poe traps.
•
snmp authentication
—Enable snmp authentication traps.
•
spanning-tree
—Enable traps on topology changes.
•
stack
—Enable stack firmware synchronization traps.
•
vrrp
—Enable vrrp traps.
Default Configuration
SNMP authentication, link, multiple-user, spanning-tree, dot1q, mac lock
violation, and ACL traps are enabled by default.
Command Mode
Global Configuration mode.
User Guidelines
There are no user guidelines for this command.
Example
The following example displays the options for the snmp-server enable traps
command.
console(config)#snmp-server enable traps ?
aclEnable/Disable traps for Access Control Lists.
all Enable/Disable all Traps.
auto-copy-sw Enable/Disable auto copy of code if there is a version mismatch
captive-portalEnable/Disable SNMP traps for CP system events.
dot1q Enable/Disable switch level Dot1q trap flag.
dvmrp Enable/Disable traps for Distance Vector Multicast Routing Protocol.
link Enable/Disable switch level Link Up/Down trap flag.
maclock Enable/Disable switch level Maclock Violation trap flag.
multiple-usersEnable/Disable sending traps when multiple logins active.
ospfEnable/Disable OSPF Traps.
ospfv3Enable/Disable OSPFv3 Traps.
pimEnable/Disable traps for Protocol-Independent Multicast.
spanning-treeEnable/Disable sending Spanning Tree traps.
2CSNXXX_SWUM200.book Page 1622 Tuesday, December 10, 2013 1:22 PM

SNMP Commands 1623
vrrpEnable/Disable VRRP trap.
snmp-server engineID local
Use the snmpserver engineID local command in Global Configuration mode
to specify the Simple Network Management Protocol (SNMP) engine ID on
the local device.
To remove the configured engine ID, use the no form of this command.
Syntax
snmp-server engineID local {
engineid-string
| default }
no snmp-server engineID local
• engineid-string — The character string that identifies the engine ID. The
engine ID is a concatenated hexadecimal string. Each byte in hexadecimal
character strings is two hexadecimal digits. Each byte can be separated by
a period or colon. (Range: 6-32 characters)
• default — The engineID is created automatically, based on the device
MAC address.
Default Configuration
The
engineID
is not configured.
Command Mode
Global Configuration mode
User Guidelines
If you want to use SNMPv3, you need to specify an engine ID for the device.
You can specify your own ID or use a default string that is generated using the
MAC address of the device. If the SNMPv3 engine ID is deleted, or the
configuration file is erased, then SNMPv3 cannot be used. Since the
EngineID should be unique within an administrative domain, the following
guidelines are recommended:
1
For standalone devices use the default keyword to configure the Engine
ID.
2CSNXXX_SWUM200.book Page 1623 Tuesday, December 10, 2013 1:22 PM

1624 SNMP Commands
2
For stackable systems, configure your own EngineID, and verify that is
unique within your administrative domain.
Changing the value of snmpEngineID has important side-effects. A user's
password (entered on the command line) is converted to an MD5 or SHA
security digest. This digest is based on both the password and the local engine
ID. The command line password is then destroyed, as required by RFC 2274.
Because of this deletion, if the local value of engineID changes, the security
digests of SNMPv3 users will be invalid, and the users will have to be
reconfigured.
Example
The following example configures the Engine ID automatically.
console(config)# snmp-server engineID local default
snmp-server filter
Use the snmp-server filter command in Global Configuration mode to create
or update a Simple Network Management Protocol (SNMP) server filter
entry. To remove the specified SNMP server filter entry, use the no form of
this command.
Syntax
snmp-server filter
filter-name oid-tree
{included | excluded}
no snmp-server filter
filter-name
[
oid-tree
]
•
filter-name
— Specifies the label for the filter record that is being updated
or created. The name is used to reference the record. (Range: 1-30
characters.)
•
oid-tree
— Specifies the object identifier of the ASN.1 subtree to be
included or excluded from the view. To identify the subtree, specify a text
string consisting of numbers, such as
1.3.6.2.4
, or a word, such as
system
. Replace a single subidentifier with the asterisk (*) wildcard to
specify a subtree family; for example,
1.3.*.4
.
•
included
— Indicates that the filter type is included.
•
excluded
— Indicates that the filter type is excluded.
2CSNXXX_SWUM200.book Page 1624 Tuesday, December 10, 2013 1:22 PM

SNMP Commands 1625
Default Configuration
No filter entry exists.
Command Mode
Global Configuration mode
User Guidelines
An SNMP server filter identifies the objects to be included or excluded from
notifications sent to a server per RFC 2573 Section 6 "Notification Filtering."
This command can be entered multiple times for the same filter record. Later
lines take precedence when an object identifier is included in two or more
lines.
The filter name may include any printable characters except a double quote
or question mark. Enclose the string in double quotes to include spaces
within the name. The surrounding quotes are not used as part of the name.
The CLI does not filter illegal characters and may accept entries up to the
first illegal character or reject the entry entirely. Per RFC 2573, configuring a
filter adds an implicit exclude-all as the first entry in a filter record. Unless an
include statement is specified, all notifications are excluded by default.
Examples
The following example creates a filter that includes all objects in the MIB-II
system group except for sysServices (System 7) and all objects for interface 1
in the MIB-II interfaces group.
console(config)# snmp-server filter user-filter system included
console(config)# snmp-server filter user-filter system.7 excluded
console(config)# snmp-server filter user-filter ifEntry.*.1 included
snmp-server group
Use the snmp-server group command in Global Configuration mode to
configure a new Simple Management Protocol (SNMP) group or a table that
maps SNMP users to SNMP views. To remove a specified SNMP group, use
the no form of this command.
2CSNXXX_SWUM200.book Page 1625 Tuesday, December 10, 2013 1:22 PM

1626 SNMP Commands
Syntax
snmp-server group
groupname
{ v1 | v2 | v3 { noauth | auth | priv } [
notify
notifyview
] } [ context
contextname
] [ read
readview
] [ write
writeview
]
no snmp-server group
groupname
{ v1 | v2 | v3 { noauth | auth | priv } } [
context
contextname
]
•
groupname
— Specifies the name of the group. (Range: 1-30 characters.)
•
v1
— Indicates the SNMP Version 1 security model.
•
v2
— Indicates the SNMP Version 2 security model.
•
v3
— Indicates the SNMP Version 3 security model.
•
noauth
— Indicates no authentication of a packet. Applicable only to the
SNMP Version 3 security model.
•
auth
— Indicates authentication of a packet without encrypting it.
Applicable only to the SNMP Version 3 security model.
•
priv
— Indicates authentication of a packet with encryption. Applicable
only to the SNMP Version 3 security model.
•
contextname
— Provides different views of the system and provides the
user a way of specifying that context.
•
notifyview
— Defines a string that is the name of the view that enables
specifying an inform or a trap. If unspecified, nothing is defined for the
notify view. (Range: 1-30 characters.)
•
readview
— A string that is the name of the view that enables the you to
view only the contents of the agent. If unspecified, all the objects except
for the community-table and SNMPv3 user and access tables are available.
(Range: 1-30 characters.)
•
writeview
— A string that is the name of the view that enables the user to
enter data and configure the contents of the agent. If unspecified, nothing
is defined for the write view. (Range: 1-30 characters.)
Default Configuration
No group entry exists. There will be some default groups for
Read/Write/Super users. These groups cannot be deleted or modified by the
user. This command is used only to configure the user-defined groups.
2CSNXXX_SWUM200.book Page 1626 Tuesday, December 10, 2013 1:22 PM

SNMP Commands 1627
Command Mode
Global Configuration Mode
User Guidelines
View-name should be an existing view created using the snmp-server view
command. If there are multiple records with the same view-name, then the
argument specified in this command points to first view-name in the table.
Example
The following example attaches a group called user-group to SNMPv3 and
assigns to the group the privacy security level and read access rights to a view
called user-view.
console(config)# snmp-server group user-group v3 priv read user-view
snmp-server host
Use the snmp-server host command in Global Configuration mode to specify
the recipient of Simple Network Management Protocol notifications. To
remove the specified host, use the no form of this command. This command
enters the user into SNMP-host configuration mode.
Syntax
snmp-server host
host-addr
[informs [timeout
seconds
] [retries
retries
] |
traps version {1 | 2 }]] community-string [udp-port
port
] [filter
filtername
]
no snmp-server host
host-addr
{ traps | informs }
•
host-addr
—Specifies the IP address of the host (targeted recipient) or the
name of the host. (Range:1-158 characters)
•
community-string
—Specifies a password-like community string sent with
the notification operation. (Range: 1-20 characters)
•
traps
—Indicates that SNMP traps are sent to this host.
•
version 1
—Indicates that SNMPv1 traps will be used.
•
version 2
—Indicates that SNMPv2 traps will be used.
•
informs
— Indicates that SNMPv2 informs are sent to this host.
2CSNXXX_SWUM200.book Page 1627 Tuesday, December 10, 2013 1:22 PM

1628 SNMP Commands
•
seconds
—Number of seconds to wait for an acknowledgment before
resending informs. The default is 15 seconds. (Range: 1-300.)
•
retries
—Maximum number of times to resend an inform request. The
default is 3 attempts. (Range: 0-255 characters.)
•
port
—UDP port of the host to use. The default is 162. (Range: 1-65535.)
•
filtername
— A string that is the name of the filter that defines the filter
for this host. If unspecified, does not filter anything (Range: 1-30
characters.)
Default Configuration
The default configuration is 3 retries, and 15 seconds timeout. This
command is disabled by default. No notifications are sent.
If you enter this command with no keywords, the default is to send all trap
types to the host. No informs are sent to this host. If no version keyword is
present, the default is Version 1.
Command Mode
Global Configuration mode
User Guidelines
If a DNS host name is entered instead of an IP address, the switch attempts
to resolve the host name immediately using DNS. Use the
ip domain-lookup
command on page 484 and the
ip name-server
command on page 486 to
enable resolution of DNS host names.
Example
The following example enables SNMP traps for host 192.16.12.143.
console(config)# snmp-server host 192.16.12.143 Dell Networking traps v2
snmp-server location
Use the snmp-server location command in Global Configuration mode to set
the system location string. To remove the location string, use the no form of
this command.
2CSNXXX_SWUM200.book Page 1628 Tuesday, December 10, 2013 1:22 PM

SNMP Commands 1629
Syntax
snmp-server location
text
no snmp-server location
•
text
— Character string describing the system location. (Range: 1 to 255
characters.)
Default Configuration
This command has no default configuration.
Command Mode
Global Configuration mode
User Guidelines
This command has no user guidelines.
Example
The following example sets the device location as "New_York".
console(config)# snmp-server location New_York
snmp-server user
Use the snmp-server user command in Global Configuration mode to
configure a new SNMP Version 3 user. To delete a user, use the no form of this
command.
Syntax
snmp-server user
username groupname
[remote
engineid-string
] [ { auth-
md5
password
| auth-sha
password
| auth-md5-key
md5-key
| auth-sha-key
sha-key
} [priv-des
password
| priv-des-key
des-key
] ]
no snmp-server user
username
•
username
— Specifies the name of the user on the host that connects to
the agent. (Range: 1-32 characters.)
•
groupname
— Specifies the name of the group to which the user belongs.
(Range: 1-40 characters.)
2CSNXXX_SWUM200.book Page 1629 Tuesday, December 10, 2013 1:22 PM

1630 SNMP Commands
•
engineid-string
— Specifies the engine ID of the remote SNMP entity to
which the user belongs. The engine ID is a concatenated hexadecimal
string. Each byte in the hexadecimal character string is two hexadecimal
digits. The remote engine id designates the remote management station,
and should be defined to enable the device to receive acknowledgements
to "informs." (Range: 5-32 characters.)
•
auth-md5
— The HMAC-MD5-96 authentication level.
•
auth-sha
— The HMAC-SHA-96 authentication level.
•
password
— A password. (Range: 1 to 32 characters.)
• auth-
md5-key
— The HMAC-MD5-96 authentication level. Enter a
pregenerated MD5 key.
• auth-
sha-key
— The HMAC-SHA-96 authentication level. Enter a
pregenerated SHA key.
•
md5-key
— Character string
—
length 32 hex characters.
•
sha-key
— Character string
—
length 40 characters.
•
priv-des
— The CBC-DES Symmetric Encryption privacy level. Enter a
password.
•
priv-des-key
— The CBC-DES Symmetric Encryption privacy level. The
user should enter a pregenerated MD5 or SHA key depending on the
authentication level selected.
•
des-key
— The pregenerated DES encryption key. Length is determined by
authentication method selected
—
32 hex characters if MD5
Authentication is selected, 40 hex characters if SHA Authentication is
selected.
Default Configuration
No user entry exists.
Command Mode
Global Configuration mode
User Guidelines
If the SNMP local engine ID is changed, configured users will no longer be
able to connect and will need to be reconfigured.
2CSNXXX_SWUM200.book Page 1630 Tuesday, December 10, 2013 1:22 PM

SNMP Commands 1631
Example
The following example configures an SNMPv3 user "John" in group "user-
group".
console(config)# snmp-server user John user-group
snmp-server view
Use the snmp-server view command in Global Configuration mode to create
or update a Simple Network Management Protocol (SNMP) server view entry.
To delete a specified SNMP server view entry, use the no form of this
command.
Syntax
snmp-server view
view-name oid-tree
{ included | excluded }
no snmp-server view
view-name
[
oid-tree
]
•
view-name
— Specifies the label for the view record that is being created
or updated. The name is used to reference the record. (Range: 1-30
characters.)
•
oid-tree
— Specifies the object identifier of the ASN.1 subtree to be
included or excluded from the view. To identify the subtree, specify a text
string consisting of numbers, such as
1.3.6.2.4
, or a word, such as
system
. Replace a single subidentifier with the asterisk (*) wildcard to
specify a subtree family; for example
1.3.*.4
.
•
included
— Indicates that the view type is included.
•
excluded
— Indicates that the view type is excluded.
Default Configuration
A view entry does not exist.
Command Mode
Global Configuration mode
User Guidelines
This command can be entered multiple times for the same view record.
2CSNXXX_SWUM200.book Page 1631 Tuesday, December 10, 2013 1:22 PM

1632 SNMP Commands
The view name accepts any printable characters except a double quote or
question mark. Enclose the string in double quotes to include spaces within
the name. The surrounding quotes are not used as part of the name. The CLI
does not filter illegal combinations of characters on entry and may accept
entries up to the first illegal character or reject the entry entirely.
Examples
The following example creates a view that includes all objects in the MIB-II
system group except for sysServices (System 7) and all objects for interface 1
in the MIB-II interface group.
console(config)# snmp-server view user-view system included
console(config)# snmp-server view user-view system.7 excluded
console(config)# snmp-server view user-view ifEntry.*.1 included
console(config)#snmp-server view "A beautiful view!" 1.1.2.1 included
snmp-server v3-host
Use the snmp-server v3-host command in Global Configuration mode to
specify the recipient of Simple Network Management Protocol Version 3
(SNMPv3) notifications. To remove the specified host, use the no form of
this command.
Syntax
snmp-server v3-host {
ip-address
|
hostname
}
username
{traps | informs}
[noauth | auth | priv] [timeout
seconds
] [retries
retries
] [udpport
port
]
[filter
filtername
]
no snmp-server v3-host
ip-address
{traps | informs}
•
ip-address
— Specifies the IPv4 address of the host (targeted recipient).
•
hostname
— Specifies the name of the host. (Range: 1-158 characters.)
The command allows spaces in the host name when specified in double
quotes. For example, #snmp-server v3-host “host name”.
•
username
— Specifies user name used to generate the notification.
(Range: 1-30 characters.)
•
traps
— Indicates that SNMP traps are sent to this host.
•
informs
— Indicates that SNMPv2 informs are sent to this host.
•
noauth
— Specifies sending of a packet without authentication.
2CSNXXX_SWUM200.book Page 1632 Tuesday, December 10, 2013 1:22 PM

SNMP Commands 1633
•
auth
— Specifies authentication of a packet without encrypting it
•
priv
— Specifies authentication and encryption of a packet.
•
seconds
— Number of seconds to wait for an acknowledgment before
resending informs. This is not allowed for hosts configured to send traps.
The default is 15 seconds. (Range: 1-300 seconds.)
•
retries
— Maximum number of times to resend an inform request. This is
not allowed for hosts configured to send traps. The default is 3 attempts.
(Range: 0-255 retries.)
•
port
— UDP port of the host to use. The default is 162. (Range: 1-65535.)
•
filtername
— A string that is the name of the filter that define the filter for
this host. If unspecified, does not filter anything. (Range: 1-30 characters.)
Default Configuration
Default configuration is 3 retries and 15 seconds timeout.
Command Mode
Global Configuration mode
User Guidelines
The username can include any printable characters except a double quote or
question mark. Enclose the string in double quotes to include spaces within
the key. The surrounding quotes are not used as part of the key. The CLI does
not filter illegal characters but may accept entries up to the first illegal
character or reject the entry entirely.
Example
The following example identifies an SNMPv3 host.
console(config)# snmp-server v3-host 192.168.0.20
The following example shows the syntax of the no snmp-server host ip-address
command.
console(config)#no snmp-server host 1.2.3.4 ?
informs Sends SNMP informs to this host.
traps Sends SNMP traps to this host.
2CSNXXX_SWUM200.book Page 1633 Tuesday, December 10, 2013 1:22 PM

1634 SNMP Commands
2CSNXXX_SWUM200.book Page 1634 Tuesday, December 10, 2013 1:22 PM

SSH Commands 1635
77
SSH Commands
Dell Networking N2000/N3000/N4000 Series Switches
Management access to the switch is supported via telnet, SSH, or the serial
console. The Dell Networking supports secure shell (SSH) and secure sockets
layer (SSL) to help ensure the security of network transactions.
Keys and certificates can be generated externally (that is, offline) and
downloaded to the target or generated directly by the Dell Networking.
Commands in this Chapter
This chapter explains the following commands:
cryptho key generate dsa
Use the crypto key generate dsa command in Global Configuration mode to
generate DSA key pairs for your switch. A key pair is one public DSA key and
one private DSA key. Use the no form of the command to remove the
generated key from the local file system.
Syntax
crypto key generate dsa
cryptho key generate dsa ip ssh server
crypto key generate rsa key-string
crypto key pubkey-chain ssh no crypto certificate
crypto key zeroize pubkey-chain show crypto key mypubkey
crypto key zeroize {rsa|dsa} show crypto key pubkey-chain ssh
ip ssh port show ip ssh
ip ssh pubkey-auth
–
2CSNXXX_SWUM200.book Page 1635 Tuesday, December 10, 2013 1:22 PM

1636 SSH Commands
Default Configuration
DSA key pairs do not exist.
Command Mode
Global Configuration mode
User Guidelines
DSA keys are generated in pairs: one public DSA key and one private DSA
key. If your switch already has DSA keys when you issue this command, you
are warned and prompted to replace the existing keys. The keys are not saved
in the switch configuration; they are saved in the file system and the private
key is never displayed to the user. DSA keys, along with other switch
credentials, are distributed to all units in a stack on a configuration save.
Use the crypto key zeroize dsa command to remove DSA keys from the
system.
Example
The following example generates DSA key pairs.
console(config)#crypto key generate dsa
crypto key generate rsa
Use the crypto key generate rsa command in Global Configuration mode to
generate RSA key pairs. Use the no form of the command to delete the key
from the local file system.
Syntax
crypto key generate rsa
Default Configuration
RSA key pairs do not exist.
Command Mode
Global Configuration mode
2CSNXXX_SWUM200.book Page 1636 Tuesday, December 10, 2013 1:22 PM

SSH Commands 1637
User Guidelines
RSA keys are generated in pairs: one public RSA key and one private RSA key.
If your switch already has RSA keys when you issue this command, you are
warned and prompted to replace the existing keys. The keys are not saved in
the switch configuration; they are saved in the file system and the private key
is never displayed to the user. RSA keys, along with other switch credentials,
are distributed to all units in a stack on a configuration save.
Use the crypto key zeroize rsa command to remove RSA keys from the
system.
Example
The following example generates RSA key pairs.
console(config)#crypto key generate rsa
crypto key pubkey-chain ssh
Use the crypto key pubkey-chain ssh command in Global Configuration
mode to enter public key configuration mode in order to manually specify
public keys such as SSH client public keys.
Syntax
crypto key pubkey-chain ssh user-key
username
rsa/dsa
Default Configuration
By default, this command has no public keys configured.
Command Mode
Global Configuration mode
User Guidelines
This command has no user guidelines.
Example
The following example enters the SSH Public Key-chain configuration mode.
console#configure
2CSNXXX_SWUM200.book Page 1637 Tuesday, December 10, 2013 1:22 PM

1638 SSH Commands
console(config)#crypto key pubkey-chain ssh user-key bob rsa
console(config-pubkey-key)#key-string
AAAAB3NzaC1yc2EAAAADAQABAAABAQCvTnRwPWlAl4kpqIw9GBRonZQZxjHKcqKL6rMlQ+ZNXfZS
kvHG+QusIZ/76ILmFT34v7u7ChFAE+Vu4GRfpSwoQUvV35LqJJk67IOU/zfwOl1gkTwml75QR9gH
ujS6KwGN2QWXgh3ub8gDjTSqMuSn/Wd05iDX2IExQWu08licglk02LYciz+Z4TrEU/9FJxwPiVQO
jc+KBXuR0juNg5nFYsY0ZCk0N/W9a/tnkm1shRE7Di71+w3fNiOA6w9o44t6+AINEICBCCA4YcF6
zMzaT1wefWwX6f+Rmt5nhhqdAtN/4oJfce166DqVX1gWmNzNR4DYDvSzg0lDnwCAC8Qh
console(config-pubkey-key)#exit
crypto key zeroize pubkey-chain
Use the crypto key zeroize pubkey-chain command in Global Configuration
mode to erase all public key chains or the public key chain for a user.
Syntax
crypto key zeroize pubkey-chain ssh [user-key
username
]
Default Configuration
There is no default configuration for this command.
Command Mode
Global Configuration mode.
User Guidelines
This command has no user guidelines.
Example
console(config)#crypto key zeroize pubkey-chain ssh username bob
crypto key zeroize {rsa|dsa}
Use the crypto key zeroize {rsa|dsa} command in Global Configuration
mode to delete the RSA or DSA keys from the switch.
Syntax
crypto key zeroize {rsa|dsa}
2CSNXXX_SWUM200.book Page 1638 Tuesday, December 10, 2013 1:22 PM

SSH Commands 1639
Default Configuration
There is no default configuration for this command.
Command Mode
Global Configuration mode.
User Guidelines
This command has no user guidelines.
Example
console(config)#crypto key zeroize rsa
ip ssh port
Use the ip ssh port command in Global Configuration mode to specify the
TCP port to be used by the SSH server. To use the default port, use the no
form of this command.
Syntax
ip ssh port
port-number
no ip ssh port
•
port-number
— Port number for use by the SSH server.
(Range: 1025–65535)
Default Configuration
The default value is 22.
Command Mode
Global Configuration mode
User Guidelines
The SSH TCP port should not be set to a value that might conflict with other
well-known protocol port numbers used on this switch.
2CSNXXX_SWUM200.book Page 1639 Tuesday, December 10, 2013 1:22 PM

1640 SSH Commands
Example
The following example specifies the port to be used by the SSH server as
8080.
console(config)#ip ssh port 8080
ip ssh pubkey-auth
Use the ip ssh pubkey-auth command in Global Configuration mode to
enable public key authentication for incoming SSH sessions. To disable this
function, use the no form of this command.
Syntax
ip ssh pubkey-auth
no ip ssh pubkey-auth
Default Configuration
The function is disabled.
Command Mode
Global Configuration mode
User Guidelines
AAA authentication is independent from this configuration.
Example
The following example enables public key authentication for incoming SSH
sessions.
console(config)#ip ssh pubkey-auth
ip ssh server
Use the ip ssh server command in Global Configuration mode to enable the
switch to be configured from SSH. To disable this function, use the no form
of this command.
2CSNXXX_SWUM200.book Page 1640 Tuesday, December 10, 2013 1:22 PM

SSH Commands 1641
Syntax
ip ssh server
no ip ssh server
Default Configuration
The SSH server is disabled by default.
Command Mode
Global Configuration mode
User Guidelines
To generate SSH server keys, use the commands crypto key generate rsa and
crypto key generate dsa.
Example
The following example enables the switch to be configured using SSH.
console(config)#ip ssh server
key-string
Use the key-string SSH Public Key Configuration mode to specify an SSH
public key manually.
Syntax
key-string
key-string
key-string row
key-string
•
row
— To specify the SSH public key row by row.
•
key-string
— The UU-encoded DER format is the same format as the
authorized keys file used by OpenSSH.
Default Configuration
By default, the key-string is empty.
2CSNXXX_SWUM200.book Page 1641 Tuesday, December 10, 2013 1:22 PM

1642 SSH Commands
Command Mode
SSH Public Key Configuration mode
User Guidelines
Use the key-string row command to specify which SSH public key you will
configure interactively next. To complete the interactive command, you must
enter key-string row with no characters.
Examples
The following example shows how to enter a public key string for a user called
"bob."
console(config)#crypto key pubkey-chain ssh
console(config-pubkey-chain)#user-key bob rsa
console(config-pubkey-key)#key-string
AAAAB3NzaC1yc2EAAAADAQABAAABAQCvTnRwPWl
Al4kpqIw9GBRonZQZxjHKcqKL6rMlQ+
ZNXfZSkvHG+QusIZ/76ILmFT34v7u7ChFAE+
Vu4GRfpSwoQUvV35LqJJk67IOU/zfwOl1g
kTwml75QR9gHujS6KwGN2QWXgh3ub8gDjTSq
muSn/Wd05iDX2IExQWu08licglk02LYciz
+Z4TrEU/9FJxwPiVQOjc+KBXuR0juNg5nFYsY
0ZCk0N/W9a/tnkm1shRE7Di71+w3fNiOA
6w9o44t6+AINEICBCCA4YcF6zMzaT1wefWwX6f+
Rmt5nhhqdAtN/4oJfce166DqVX1gWmN
zNR4DYDvSzg0lDnwCAC8Qh
Fingerprint: a4:16:46:23:5a:8d:1d:b5:37:59:eb:44:13:b9:33:e9
console(config)#crypto key pubkey-chain ssh
console(config-pubkey-chain)#user-key bob rsa
console(config-pubkey-key)#key-string row AAAAB3Nza
console(config-pubkey-key)#key-string row C1yc2
no crypto certificate
Use the no crypto certificate command in Global Configuration mode to
display the SSH public keys of the switch.
Syntax
no crypto certificate
number
2CSNXXX_SWUM200.book Page 1642 Tuesday, December 10, 2013 1:22 PM

SSH Commands 1643
•
number
— The number of the certificate (between 1 to 2).
Default Configuration
This command has no default configuration.
Command Mode
Global Configuration mode
User Guidelines
This command has no user guidelines.
Example
console(config)#no crypto certificate 1
show crypto key mypubkey
Use the show crypto key mypubkey command in Privileged EXEC mode to
display the SSH public keys of the switch.
Syntax
show crypto key mypubkey [rsa | dsa]
•
rsa
— RSA key.
•
dsa
— DSA key.
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC mode, Configuration mode and all Configuration submodes
User Guidelines
This command has no user guidelines.
Example
The following example displays the SSH public keys on the switch.
2CSNXXX_SWUM200.book Page 1643 Tuesday, December 10, 2013 1:22 PM

1644 SSH Commands
console#show crypto key mypubkey rsa
rsa key data:
ssh-rsa AAAAB3NzaC1yc2EAAAABIwAAAQEAu7WHtjQDUygjSQXHVgyqdUby
dxUXEAiDHXcWHVr0R/ak1HDQitBzeEv1vVEToEn5ddLmRhtIgRdKUJHgBHJV
R2VaSN/WC0IK53j9re4B11AE+O3qAxwJs0KD7cTkvF9I+YdiXeOM8VE4skkw
AiyLDNVWXgNQ6iat8+8Mjth+PIo5t3HykYUCkD8B1v93nzi/sr4hHHJCdx7w
wRW3QtgXaGwYt2rdlr3x8ViAF6B7AKYd8xGVVjyJTD6TjrCRRwQHgB/BHsFr
z/Rl1SYa0vFjel/7/0qaIDSHfHqWhajYkMa4xPOtIye7oqzAOm1b76l28uTB
luBEoLQ+PKOKMiK8sQ==
Fingerprint(hex): 58:7f:5c:af:ba:d3:60:88:42:00:b0:2f:f1:5a:a8:fc
Fingerprint(bubbleBabble): xodob-liboh-heret-tiver-dyrib-godac-pynah-muzyt-
mofim-bihog-cuxyx
show crypto key pubkey-chain ssh
Use the show crypto key pubkey-chain ssh command in Privileged EXEC
mode to display SSH public keys stored on the switch.
Syntax
show crypto key pubkey-chain ssh [username
username
] [fingerprint bubble-
babble | hex]
•
username
— Specifies the remote SSH client username. (Range: 1–48
characters)
•
bubble-babble
— Fingerprints in Bubble Babble format.
•
hex
— Fingerprint in Hex format. If fingerprint is unspecified, it defaults
to Hex format.
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC mode, Configuration mode and all Configuration submodes
User Guidelines
This command has no user guidelines.
Example
The following example displays all SSH public keys stored on the switch.
2CSNXXX_SWUM200.book Page 1644 Tuesday, December 10, 2013 1:22 PM

SSH Commands 1645
console#show crypto key pubkey-chain ssh
Username Fingerprint
-------- -------------------------------------------------
bob 9A:CC:01:C5:78:39:27:86:79:CC:23:C5:98:59:F1:86
john 98:F7:6E:28:F2:79:87:C8:18:F8:88:CC:F8:89:87:C8
The following example displays the SSH public called "dana."
console#show crypto key pubkey-chain ssh username dana
Username: dana
rsa key data:
ssh-rsa AAAAB3NzaC1yc2EAAAABIwAAAIEAywqRKTRnexccxVUVTeMl+Gkh
imyUDhcTkgEfssLPMsgoXlTwzCE5+97UIIsSRKQQWR+pBNl45tCYd75LUofV
4LP6Lj1Q5Q0w5lBgiqC2MZ/iBHGSsHMAE0lpYtelZprDu4uiZHMuWezmdQp9
a1PU4jwQ22TlcfaUq3sqC3FMUoU=
Fingerprint: 2f:09:e7:6f:c9:bf:ab:04:d4:6f:a0:eb:e8:df:7a:11
show ip ssh
Use the show ip ssh command in Privileged EXEC mode to display the SSH
server configuration.
Syntax
show ip ssh
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC mode, Configuration mode and all Configuration submodes
User Guidelines
This command has no user guidelines.
Example
The following example displays the SSH server configuration.
console#show ip ssh
SSH server enabled. Port: 22
RSA key was generated.
DSA key was generated.
SSH Public Key Authentication is enabled.
Active incoming sessions:
2CSNXXX_SWUM200.book Page 1645 Tuesday, December 10, 2013 1:22 PM

1646 SSH Commands
IP Address User Name Idle Time SessionTime
------------- -------------------- -------------- --------------
10.240.1.122 John 00:00:00 00:00:08
2CSNXXX_SWUM200.book Page 1646 Tuesday, December 10, 2013 1:22 PM

Syslog Commands 1647
78
Syslog Commands
Dell Networking N2000/N3000/N4000 Series Switches
The Dell Networking supports a centralized logging subsystem with support
for local in memory logs, crash dump logs, and forwarding messages to syslog
servers. All switch components use the logging subsystem. Components log
messages to the logging component using one of the following severity levels:
• Emergency (0): system is unusable
• Alert (1): action must be taken immediately
• Critical (2): critical conditions
• Error (3): error conditions
• Warning (4): warning conditions
• Notice(5): normal but significant conditions
• Informational(6): informational messages
• Debug(7): debug-level messages
CLI Logged to Local File and Syslog Server
The Dell Networking Command Logging component logs all command line
interface commands issued on the system. The command log messages are
stored with the other system logs and provide the system operators with a
detailed log of the commands executed.
CLI command logging is configured through any of the Dell Networking
management interfaces. When the feature is enabled, all CLI commands are
logged using the existing logging subsystems. By default, the feature is
disabled.
The CLI command logging severity is set to SEVERITY_NOTICE. The
logging severity is not modifiable by the administrator.
For example, the CLI log message for the user admin is:
<189> JAN 10 18:59:09 10.27.21.22-2 CMDLOGGER[209809328]:
cmd_logger_api.c(83) 367 %% CLI:EIA-232:----:configure
2CSNXXX_SWUM200.book Page 1647 Tuesday, December 10, 2013 1:22 PM

1648 Syslog Commands
<190> JAN 10 18:59:17 10.27.21.22-2 CLI_WEB[209809328]:
cmd_logger_api.c(260) 369 %% [CLI:----:EIA-232] Access level of user admin
has been set to 15
If enabled, the CLI command logger subsystem begins to log commands
immediately after the user is authenticated. After authentication, the CLI
generates an explicit message and invokes the command logger. The format of
the message at login is:
<189> JAN 10 18:58:56 10.27.21.22-2 CMDLOGGER[209809328]:
cmd_logger_api.c(83) 361 %% CLI:10.27.21.22:admin:User admin logged in
<190> JAN 10 18:58:56 10.27.21.22-2 CLI_WEB[209809328]:
cmd_logger_api.c(260) 362 %% [CLI:admin:10.27.21.22] User has successfully
logged in
The CLI command log subsystem also logs all user log out instances. The
format of the log message is:
<190> JAN 10 19:01:04 10.27.21.22-2 CLI_WEB[209809328]:
cmd_logger_api.c(260) 382 %% [CLI:admin:10.27.21.22] User has logged out
Commands in this Chapter
This chapter explains the following commands:
clear logging
Use the clear logging command in Privileged EXEC mode to clear messages
from the internal logging buffer.
clear logging logging facility
clear logging file logging on
description (Logging) logging protocol
level logging snmp
logging cli-command logging web-session
logging port
logging audit show logging
logging buffered show logging file
logging console show syslog-servers
–
terminal monitor
2CSNXXX_SWUM200.book Page 1648 Tuesday, December 10, 2013 1:22 PM

Syslog Commands 1649
Syntax
clear logging
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC mode
User Guidelines
This command has no user guidelines.
Example
The following example clears messages from the internal syslog message
logging buffer.
console#clear logging
Clear logging buffer [y/n]
clear logging file
Use the clear logging file command in Privileged EXEC mode to clear
messages from the logging file.
Syntax
clear logging file
Default Configuration
There is no default configuration for the command.
Command Mode
Privileged EXEC
User Guidelines
This command has no user guidelines.
2CSNXXX_SWUM200.book Page 1649 Tuesday, December 10, 2013 1:22 PM

1650 Syslog Commands
Example
The following example shows the clear logging file command and
confirmation response.
console#clear logging file
Clear logging file [y/n]
description (Logging)
Use the description command in Logging mode to describe the syslog server.
Syntax
description
description
•
description
— Sets the description of the syslog server. (Range: 1-64
characters.)
Default Configuration
This command has no default value.
Command Mode
Logging mode
User Guidelines
After entering the view corresponding to a specific syslog server, the
command can be executed to set the description of the server.
Example
The following example sets the syslog server description.
console(config-logging)#description "syslog server 1"
level
Use the level command in Logging mode to specify the severity level of syslog
messages. To reset to the default value, use the no form of the command.
Syntax
level
level
2CSNXXX_SWUM200.book Page 1650 Tuesday, December 10, 2013 1:22 PM

Syslog Commands 1651
no level
•
level
—
The severity level for syslog messages. (Range: emergency, alert, critical,
error, warning, notice, info, debug)
Default Configuration
The default value for
level
is
info.
Command Mode
Logging mode
User Guidelines
After entering the view corresponding to a specific syslog server, the
command can be executed to set the severity level for syslog messages.
Example
The following example sets the syslog message severity level to alert.
console(config-logging)#level alert
logging cli-command
Use the logging cli-command in Global Configuration mode to enable CLI
command logging.
Syntax
logging cli-command
no logging cli-command
Default Configuration
Disabled
Command Mode
Global Configuration
User Guidelines
See the CLI commands by using the
show logging
command.
2CSNXXX_SWUM200.book Page 1651 Tuesday, December 10, 2013 1:22 PM

1652 Syslog Commands
Example
console(config)#logging cli-command
console(config)#do show logging
Logging is enabled
Console Logging: level warnings. Console Messages: 384 Dropped.
Buffer Logging: level informational. Buffer Messages: 71 Logged,
File Logging: level notActive. File Messages: 385 Dropped.
CLI Command Logging : enabled
Switch Auditing : enabled
Web Session Logging : disabled
SNMP Set Command Logging : disabled
Syslog server hostname logging: informational. Messages: 0 dropped
Syslog server
a12345678901234567890123456789012345678901234567890123456789012 logging:
informational. Messages: 0 dropped
170 Messages dropped due to lack of resources.
Buffer Log:
<189> JAN 10 18:59:09 10.27.21.22-2 CMDLOGGER[209809328]:
cmd_logger_api.c(83) 367 %% CLI:EIA-232:----:configure
<190> JAN 10 18:59:17 10.27.21.22-2 CLI_WEB[209809328]:
cmd_logger_api.c(260) 369 %% [CLI:----:EIA-232] Access level of user admin
has been set to 15
<189> JAN 10 18:59:19 10.27.21.22-2 CMDLOGGER[209809328]:
cmd_logger_api.c(83) 370 %% CLI:EIA-232:----:exit
<189> JAN 10 18:59:22 10.27.21.22-2 CMDLOGGER[209809328]:
cmd_logger_api.c(83) 371 %% CLI:EIA-232:----:telnet 10.27.21.22
<189> JAN 10 18:59:27 10.27.21.22-2 TRAPMGR[209809328]: traputil.c(614) 372
%% Multiple Users: Unit: 0 Slot: 5 Port: 1
<189> JAN 10 18:59:27 10.27.21.22-2 CMDLOGGER[209809328]:
cmd_logger_api.c(83) 373 %% CLI:10.27.21.22:admin:User admin logged in
<190> JAN 10 18:59:27 10.27.21.22-2 CLI_WEB[209809328]:
cmd_logger_api.c(260) 374 %% [CLI:admin:10.27.21.22] User has successfully
logged in
<190> JAN 10 18:59:28 10.27.21.22-2 CLI_WEB[209809328]:
cmd_logger_api.c(260) 375 %% [CLI:admin:10.27.21.22] User admin logged in to
enable mode.
logging
Use the logging command in Global Configuration mode to log messages to a
syslog server. To delete the syslog server with the specified address from the
list of syslogs, use the no form of this command.
Syntax
logging {
ip-address
|
hostname
}
2CSNXXX_SWUM200.book Page 1652 Tuesday, December 10, 2013 1:22 PM

Syslog Commands 1653
no logging {
ip-address
|
hostname
}
•
ip-address
— IP address of the host to be used as a syslog server.
•
hostname
— Hostname of the host to be used as a syslog server. (Range: 1-
63 characters) The command allows spaces in the host name when
specified in double quotes. For example, #snmp-server v3-host “host
name”.
Default Configuration
No syslog servers defined.
Command Mode
Global Configuration mode
User Guidelines
Up to eight syslog servers can be used.
The Dell Dell Networking always uses the local7(23) facility in the syslog
message. Syslog messages will not exceed 96 bytes in length. Syslog messages
use the following format:
<130> JAN 01 00:00:06 0.0.0.0-1 UNKN[0x800023]: bootos.c(386) 4 %%
Event(0xaaaaaaaa)
||||||||||
|||||||||Message
|||||||||
||||||||Sequence Number
||||||||
|||||||Line Number
|||||||
||||||File Name
||||||
|||||Thread ID
|||||
||||Component Name
||||
|||Stack ID
|||
||Host IP Address
|Timestamp
PRI
2CSNXXX_SWUM200.book Page 1653 Tuesday, December 10, 2013 1:22 PM
1654 Syslog Commands
Example
The following example places the designated server in logging configuration
mode.
console(config)#logging 192.168.15.1
logging audit
Use the logging audit command to enable switch auditing. Use the no form
of the command to disable switch auditing.
Syntax
logging audit
no logging audit
PRI This consists of the facility code (see RFC 3164) multiplied by
8 and added to the severity. See below for more information on
severity.
Timestamp The system up time. For systems that use SNTP, this is UTC.
When time zones are enabled, local time will be used.
Host IP Address The IP address of the local system.
Stack ID The assigned stack ID. 1 is used for systems without stacking
capability. The top of stack is used to collect messages for the
entire stack.
Component Name Component name for the logging component. Components
must use the new APIs in order to enable identification of the
logging component. Component UNKN is substituted for
components that do not use the new logging APIs.
Thread ID The thread ID of the logging component.
File Name The name of the file containing the invoking macro.
Line Number The line number which contains the invoking macro.
Sequence Number The message sequence number for this stack component.
Sequence numbers may be skipped because of filtering but are
always monotonically increasing on a per stack member basis.
Message An informative message regarding the event.
2CSNXXX_SWUM200.book Page 1654 Tuesday, December 10, 2013 1:22 PM

Syslog Commands 1655
Default Configuration
The command default is enabled.
Command Mode
Global Configuration
Example
console(config)#logging audit
logging buffered
Use the logging buffered command in Global Configuration mode to limit
syslog messages displayed from an internal buffer based on severity. To cancel
the buffer use, use the no form of this command.
Syntax
logging buffered [
severity–level
]
no logging buffered
•
severity–level
—(Optional) The number or name of the desired severity
level. Range:
– [0 | emergencies]
– [1 | alerts]
– [2 | critical]
– [3 | errors]
– [4 | warnings]
– [5 | notifications]
– [6 | informational]
– [7 | debugging]
Default Configuration
The default value for
level
is
info.
2CSNXXX_SWUM200.book Page 1655 Tuesday, December 10, 2013 1:22 PM

1656 Syslog Commands
Command Mode
Global Configuration mode
User Guidelines
All the syslog messages are logged to the internal buffer. This command limits
the commands displayed to the user.
Example
The following example limits syslog messages collected in the internal buffer
to those of severity level "error" and above (numerically lower).
console(config)#logging buffered error
logging console
Use the logging console command in Global Configuration mode to limit
messages logged to the console based on severity. To disable logging to the
console terminal, use the no form of this command.
Syntax
logging console [
severity–level
]
no logging console
•
severity–level
—(Optional) The number or name of the desired severity
level. Range:
– [0 | emergencies]
– [1 | alerts]
– [2 | critical]
– [3 | errors]
– [4 | warnings]
– [5 | notifications]
– [6 | informational]
– [7 | debugging]
2CSNXXX_SWUM200.book Page 1656 Tuesday, December 10, 2013 1:22 PM

Syslog Commands 1657
Default Configuration
The default value for
level
is
warnings.
Command Mode
Global Configuration mode
User Guidelines
Messages at the selected level and above (numerically lower) are displayed on
the console.
Example
The following example limits messages logged to the console based on
severity level "alert".
console(config)#logging console alert
logging facility
Use the logging facility command in Global Configuration mode to
configure the facility to be used in log messages.
Syntax
logging facility
facility
no logging facility
•
facility
—The facility that will be indicated in the message. (Range: local0,
local1, local2, local3, local4, local5, local6, local7).
Default Configuration
The default value is local7.
Command Mode
Global Configuration mode
User Guidelines
This command has no user guidelines.
2CSNXXX_SWUM200.book Page 1657 Tuesday, December 10, 2013 1:22 PM

1658 Syslog Commands
Example
The following example sets the logging facility as local3.
console(config)#logging facility local3
logging file
Use the logging file command in Global Configuration mode to limit syslog
messages sent to the logging file based on severity. To cancel the buffer, use
the no form of this command.
Syntax
logging file [
severity–level-number
|
type
]
no logging file
•
severity–level
—(Optional) The number or name of the desired severity
level. Range:
– [0 | emergencies]
– [1 | alerts]
– [2 | critical]
– [3 | errors]
– [4 | warnings]
– [5 | notifications]
– [6 | informational]
– [7 | debugging]
Default Configuration
The default severity level is
error.
Command Mode
Global Configuration mode
User Guidelines
This command has no user guidelines.
2CSNXXX_SWUM200.book Page 1658 Tuesday, December 10, 2013 1:22 PM

Syslog Commands 1659
Example
The following example limits syslog messages stored in the logging file to
severity level "warning" and above (numerically lower).
console(config)#logging file warning
logging monitor
Use the logging monitor command in Global Configuration mode to enable
logging messages to telnet and SSH sessions with the default severity level.
Use the no logging monitor command to disable logging messages.
Syntax
logging monitor
severity
no logging monitor
•
severity
—(Optional) The number or name of the desired severity level.
Range:
– [0 | emergencies]
– [1 | alerts]
– [2 | critical]
– [3 | errors]
– [4 | warnings]
– [5 | notifications]
– [6 | informational]
– [7 | debugging]
Default Configuration
The default severity value is warnings. By default, logging messages are not
displayed on SSH or telnet sessions. Logging messages are displayed by
default on console sessions (serial and out-of-band ports).
Command Mode
Global Configuration mode
2CSNXXX_SWUM200.book Page 1659 Tuesday, December 10, 2013 1:22 PM

1660 Syslog Commands
User Guidelines
Messages logged to the console are filtered based on severity. Selecting a
severity level will log that severity and higher (numerically lower) level
messages.
logging on
Use the logging on command in Global Configuration mode to control error
messages logging. This command globally enables the sending of logging
messages to the currently configured locations. To disable the sending of log
messages, use the no form of this command.
Syntax
logging on
no logging on
Default Configuration
Logging is enabled.
Command Mode
Global Configuration mode
User Guidelines
The logging process controls the distribution of logging messages to the
various destinations, such as the logging buffer, logging file, or syslog server.
Logging on and off for these destinations can be individually configured using
the logging buffered, logging file, and logging
server
global configuration
commands. However, if the logging on command is disabled, no messages are
sent to these destinations. In this case, only the console will continue to
receive logging messages.
Example
The following example shows how logging is enabled.
console(config)#logging on
2CSNXXX_SWUM200.book Page 1660 Tuesday, December 10, 2013 1:22 PM

Syslog Commands 1661
logging protocol
Use this command to log messages in RFC5424 format, including time zone
and subsecond resolution time stamps. Use the no form of this command to
set the logging to the default format.
Syntax
logging protocol {
protocol-selector
}
no logging protocol
•
protocol-selector
—One of the following:
– 0 – Generate RFC3164 format messages
– 1 – Generate RFC5424 format messages
Default Configuration
Messages are logged in RFC3164 format by default.
Command Modes
Global Configuration mode.
User Guidelines
During system startup, messages are logged in RFC3164 format (e.g., in the
startup persistent log). Messages are logged in the selected format upon the
system processing the startup configuration.
The time zone must be configured for the system to generate RFC5424 log
messages with the time zone included.
The system does not support transmission of syslog messages using TLS.
Example
This example set the logging message format to RFC5424.
console(config)#logging protocol 1
This example sets the logging message format to RFC3164
console(config)#no logging protocol
The following example shows the logging format when logging protocol is set
to 0.
2CSNXXX_SWUM200.book Page 1661 Tuesday, December 10, 2013 1:22 PM

1662 Syslog Commands
console(config)#logging protocol 0
console(config)#
<190> DEC 20 20:45:20 10.130.182.151-1 USER_MGR[249300304]: user_mgr.c(1789)
5 %% User abcd Failed to login because of authentication failures
<189> DEC 20 20:45:20 10.130.182.151-1 TRAPMGR[249300304]: traputil.c(657) 6
%% Failed User Login with User ID: abcd
The following example shows the logging format when logging protocol is set
to 1.
console(config)#logging protocol 1
console(config)#
<190>1 DEC 20 20:46:20.250 10.130.182.151-1 USER_MGR[249300304]:
user_mgr.c(1789) 9 %% User xyz Failed to login because of authentication
failures
<189>1 DEC 20 20:46:20.250 10.130.182.151-1 TRAPMGR[249300304]:
traputil.c(657) 10 %% Failed User Login with User ID: xyz
The following example shows the logging format when logging protocol is set
to 1 with timezone configured on the switch.
console(config)#clock timezone +5 minutes 30 zone IST
console(config)#show clock
02:17:44 IST(UTC+5:30) Dec 21 2012
Time source is Local
console(config)#
<190>1 DEC 21 02:18:15.110+5:30 10.130.182.151-1 USER_MGR[249300304]:
user_mgr.c(1789) 13 %% User xyzt Failed to login because of authentication
failures
<189>1 DEC 21 02:18:15.110+5:30 10.130.182.151-1 TRAPMGR[249300304]:
traputil.c(657) 14 %% Failed User Login with User ID: xyzt
logging snmp
Use the logging snmp command in Global Configuration mode to enable
SNMP Set command logging. To disable, use the no form of this command.
Syntax
logging snmp
no logging snmp
2CSNXXX_SWUM200.book Page 1662 Tuesday, December 10, 2013 1:22 PM

Syslog Commands 1663
Default Configuration
Disabled.
Command Mode
Global Configuration mode
User Guidelines
To see SNMP Set command logs use the
show logging
command.
Example
console(config)#logging snmp
logging web-session
Use the logging web-session command in Global Configuration mode to
enable web session logging. To disable, use the no form of this command.
Syntax
logging web-session
no logging web-session
Default Configuration
Disabled.
Command Mode
Global Configuration mode
User Guidelines
To see web session logs use the
show logging
command.
Example
console(config)#logging web-session
<133> MAR 24 07:46:07 10.131.7.165-2 UNKN[83102768]: cmd_logger_api.c(140)
764 %% WEB:10.131.7.67:<<UNKNOWN>>:EwaSessionLookup : session[0] created
<133> MAR 24 07:46:07 10.131.7.165-2 UNKN[83102768]: cmd_logger_api.c(140)
765 %% WEB:10.131.7.67:admin:User admin logged in
2CSNXXX_SWUM200.book Page 1663 Tuesday, December 10, 2013 1:22 PM

1664 Syslog Commands
port
Use the port command in Logging mode to specify the port number of syslog
messages. To reset to the default value, use the no form of the command.
Syntax
port
port
no port
•
port
—
The port number for syslog messages. (Range: 1-65535)
Default Configuration
The default port number is 514.
Command Mode
Logging mode
User Guidelines
After entering the view corresponding to a specific syslog server, the
command can be executed to set the port number for the server.
Example
The following example sets the syslog message port to 300.
console(config-logging)#port 300
show logging
Use the show logging command in Privileged EXEC mode to display all
logging information, including auditing status and logging protocol version.
Protocol version 1 means that the messages are logged with the time zone and
time resolution up to milliseconds.
Syntax
show logging
2CSNXXX_SWUM200.book Page 1664 Tuesday, December 10, 2013 1:22 PM

Syslog Commands 1665
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC mode, Configuration mode and all Configuration submodes
User Guidelines
This command has no user guidelines.
Example
The following example displays the state of logging and the syslog messages
stored in the internal buffer.
console#show logging
Logging is enabled
Logging protocol version: 1
Console Logging: Level warnings. Messages : 1 logged, 706 ignored
Monitor Logging: disabled
Buffer Logging: Level informational. Messages : 73 logged, 634 ignored
File Logging: Level emergencies. Messages : 0 logged, 707 ignored
Switch Auditing : enabled
CLI Command Logging: disabled
Web Session Logging : disabled
SNMP Set Command Logging : disabled
Logging facility level : local7
show logging file
Use the show logging file command in Privileged EXEC mode to display the
state of logging and the syslog messages stored in the logging file.
Syntax
show logging file
Default Configuration
This command has no default configuration.
2CSNXXX_SWUM200.book Page 1665 Tuesday, December 10, 2013 1:22 PM

1666 Syslog Commands
Command Mode
Privileged EXEC mode, Configuration mode and all Configuration submodes
User Guidelines
This command has no user guidelines.
Example
The following example displays the state of logging and syslog messages
sorted in the logging file.
console#show logging file
Persistent Logging : enabled
Persistent Log Count : 1
<186> JAN 01 00:00:05 0.0.0.0-1 UNKN[268434928]: bootos.c(382) 3 %%
Event(0xaaaaaaaa)
show syslog-servers
Use the show syslog-servers command in Privileged EXEC mode to display
the syslog servers settings.
Syntax
show syslog-servers
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC mode, Configuration mode and all Configuration submodes
User Guidelines
This command has no user guidelines.
Example
The following example displays the syslog server settings.
console#show syslog-servers
2CSNXXX_SWUM200.book Page 1666 Tuesday, December 10, 2013 1:22 PM

Syslog Commands 1667
IP address Port Severity Facility Description
---------------------------------------------------------
192.180.2.275 14 Info local7 7
192.180.2.285 14 Warning local7 7
terminal monitor
Use the terminal monitor command in Privileged EXEC mode to enable the
display of system messages on the terminal for telnet and SSH sessions.
Syntax
terminal monitor
no terminal monitor
Default Configuration
The default setting is that system messages are not displayed on telnet or
SSH sessions. System messages are always displayed on console sessions
(serial or out-of-band port connections).
Command Mode
Privileged EXEC mode
User Guidelines
Use the terminal monitor command in Privileged EXEC mode enables
system messages to be displayed in a Telnet or SSH session.
Use the no terminal monitor command to disable the display of system
messages on the terminal for Telnet and SSH sessions. Use the
logging
monitor
command to display logging messages in a Telnet or SSH session.
Terminal monitor and logging monitor are enabled on console sessions by
default.
Example
This example enables the display of system messages and logging messages on
the current telnet session.
console#terminal monitor
console#configure
console(cinsfig)#logging monitor
2CSNXXX_SWUM200.book Page 1667 Tuesday, December 10, 2013 1:22 PM

1668 Syslog Commands
2CSNXXX_SWUM200.book Page 1668 Tuesday, December 10, 2013 1:22 PM

System Management Commands 1669
79
System Management Commands
Dell Networking N2000/N3000/N4000 Series Switches
This chapter explains the following commands:
asset-tag login-banner show cut-through
mode
show system
banner exec logout show hardware
profile
show system fan
banner login member show idprom
interface interface-
id
show system
temperature
banner motd motd-banner show interfaces
interface-id
show tech-support
banner motd
acknowledge
nsf show interfaces
utilization
show users
clear checkpoint
statistics
ping show memory cpu show version
clear counters
stack-ports
quit show nsf stack
connect reload show power-usage-
history
stack-port
cut-through mode service
unsupported-
transceiver
show process cpu stack-port interface
shutdown
exec-banner set description show sessions standby
exit slot show slot switch renumber
hardware profile
portmode
show banner show supported
cardtype
telnet
load-interval show checkpoint
statistics
show supported
switchtype
traceroute
locate
–
show switch update bootcode
2CSNXXX_SWUM200.book Page 1669 Tuesday, December 10, 2013 1:22 PM

1670 System Management Commands
asset-tag
Use the asset-tag command in Global Configuration mode to specify the
switch asset tag. To remove the existing asset tag, use the no form of the
command.
Syntax
asset-tag [
unit
]
tag
no asset-tag [
unit
]
•
unit
— Switch number. (Range: 1–12)
•
tag
— The switch asset tag.
Default Configuration
No asset tag is defined by default.
Command Mode
Global Configuration mode
User Guidelines
The asset-tag command accepts any printable characters for a tag name
except a double quote or question mark. Enclose the string in double quotes
to include spaces within the name. The surrounding quotes are not used as
part of the name. The CLI does not filter illegal characters and may accept
entries up to the first illegal character or reject the entry entirely.
Example
The following example specifies the switch asset tag as 1qwepot. Because the
unit parameter is not specified, the command defaults to the master switch
number.
console(config)# asset-tag 1qwepot
banner exec
Use the banner exec command to set the message that is displayed after a
successful login. Use the no form of the command to remove the set message.
2CSNXXX_SWUM200.book Page 1670 Tuesday, December 10, 2013 1:22 PM

System Management Commands 1671
Syntax
banner exec
MESSAGE
no banner exec
•
MESSAGE
— Quoted text
Default Configuration
This command has no default configuration.
Command Mode
Global Configuration
User Guidelines
The exec message may consist of multiple lines. Enter a quote to complete
the message and return to configuration mode. Up to 2000 characters may be
entered into a banner. Each line entered will consume an extra two characters
to account for the carriage return and line feed.
Example
console(config)# banner exec "banner text"
banner login
Use the banner login command to set the message that is displayed just
before the login prompt after a user has successfully connectced to the switch
and prior to the login banner. Use no banner login command to remove the
message.
Syntax
banner login
Message
no banner login
•
Message
— Quoted text
Default Configuration
This command has no default configuration.
2CSNXXX_SWUM200.book Page 1671 Tuesday, December 10, 2013 1:22 PM

1672 System Management Commands
Command Mode
Global Configuration
User Guidelines
The login banner can consist of multiple lines. Enter a quote to end the
banner text and return to the configuration prompt. Up to 2000 characters
may be entered into a banner. Each line entered will consume an extra two
characters to account for the carriage return and line feed. Different terminal
emulators will exhibit different behaviors when logging in over SSH. See the
user guidelines for
banner motd acknowledge
for some examples.
Example
console(config)# banner login "banner text"
banner motd
Use the banner motd command to set the message that is displayed prior to
logging into the switch. Use no banner motd command to remove the
message.
Syntax
banner motd
MESSAGE
no banner motd
•
MESSAGE
— Quoted text
Default Configuration
This command has no default configuration.
Command Mode
Global Configuration
User Guidelines
The motd banner can consist of multiple lines. Enter a quote to end the
banner text and return to the configuration prompt. Up to 2000 characters
may be entered into a banner. Each line entered will consume an extra two
characters to account for the carriage return and line feed.
2CSNXXX_SWUM200.book Page 1672 Tuesday, December 10, 2013 1:22 PM

System Management Commands 1673
The motd banner is usually displayed prior to logging into the switch,
although some protocols, for example SSH, may enforce different behavior.
See the user guidelines for
banner motd acknowledge
for some examples.
Example
console(config)# banner motd “IMPORTANT: There is a power shutdown at
23:00hrs today, duration 1 hr 30 minutes.”
When the MOTD banner is executed, the following displays:
IMPORTANT: There is a power shutdown at 23:00hrs today, duration 1 hr 30
minutes.
banner motd acknowledge
The banner displayed on the console must be acknowledged if banner motd
acknowledge is executed. Enter "y" or "n" to continue to the login prompt. If
"n" is entered, the session is terminated and no further communication is
allowed on that session. However, serial connection will not get terminated if
‘y’ is not entered. Use the no banner motd acknowledge command to disable
banner acknowledge.
Syntax
banner motd acknowledge
no banner motd acknowledge
Default Configuration
This command has no default configuration.
Command Mode
Global Configuration mode
User Guidelines
Various terminal emulators exhibit different behaviors with regards to the
MOTD and the acknowledge prompt, for example, TeraTerm and putty.
There are also different behaviors based upon the protocol used (SSH versus
telnet). See below for some examples where the MOTD prompt occurs either
before or after the acknowledge prompt. The banner motd in this example is
"If you need to utilize this device or otherwise make
changes to the configuration, you may contact Kevin at x911.
2CSNXXX_SWUM200.book Page 1673 Tuesday, December 10, 2013 1:22 PM

1674 System Management Commands
Please be advised this unit is under test by Kevin." and the
banner login is "Welcome to the N3024 in the Bottom Chassis -
192.168.12.190. This unit is located in A2 and is currently
under test."
SSH (putty):
login as: dellradius
If you need to utilize this device or otherwise make changes to the
configuration, you may contact Kevin at x911.
Please, be advised this unit is under test by Kevin.
dellradius@192.168.12.84's password:
Press 'y' to continue (within 30 seconds) (y/n)
Welcome to the N3024 in the Bottom Chassis - 192.168.12.190. This unit is
located in A2 and is currently under test.
N3024-C1>
SSH (Linux Terminal):
[root@kevin ~]# ssh 192.168.12.84 -l dellradius
If you need to utilize this device or otherwise make changes to the
configuration, you may contact Kevin at x911.
Please, be advised this unit is under test by Kevin.
dellradius@192.168.12.84's password:
Press 'y' to continue (within 30 seconds) (y/n)
Welcome to the N3024 in the Bottom Chassis - 192.168.12.190. This unit is
located in A2 and is currently under test.
N3024-C1>
SSH (xterm):
[root@kevin ~]# ssh 192.168.12.84 -l dellradius
If you need to utilize this device or otherwise make changes to the
configuration, you may contact Kevin at x911.
Please, be advised this unit is under test by Kevin.
dellradius@192.168.12.84's password:
Press 'y' to continue (within 30 seconds) (y/n)
Welcome to the N3024 in the Bottom Chassis - 192.168.12.190. This unit is
located in A2 and is currently under test.
N3024-C1>
2CSNXXX_SWUM200.book Page 1674 Tuesday, December 10, 2013 1:22 PM

System Management Commands 1675
Telnet:
If you need to utilize this device or otherwise make changes to the
configuration, you may contact Kevin at x911.
Press 'y' to continue (within 30 seconds) (y/n) y
Please, be advised this unit is under test by Kevin.
User:root
Password:******
Welcome to the N3024 in the Bottom Chassis - 192.168.12.190. This unit is
located in A2 and is currently under test.
N3024-C1>
Example
console(config)# banner motd “There is a power shutdown at 23:00hrs today,
duration 1 hr 30 minutes.”
console(config)# banner motd acknowledge
When the MOTD banner is executed, the following displays:
IMPORTANT: There is a power shutdown at 23:00hrs today, duration 1 hr 30
minutes.
Press ‘y’ to continue
If ‘y’ is entered, the following displays:
console >
If ‘n’ is entered, the session will get disconnected, unless it is a serial
connection.
clear checkpoint statistics
Use the clear checkpoint statistics command to clear the statistics for the
checkpointing process.
Syntax
clear checkpoint statistics
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC mode
2CSNXXX_SWUM200.book Page 1675 Tuesday, December 10, 2013 1:22 PM

1676 System Management Commands
User Guidelines
When nonstop forwarding is enabled on a stack, the stack's management unit
checkpoints operational data to the backup unit. If the backup unit takes over
as the management unit, the control plane on the new management unit uses
the checkpoint data when initializing its state. Checkpoint statistics track the
amount of data checkpointed from the management unit to the backup unit.
Example
console#clear checkpoint statistics
clear counters stack-ports
Use the clear counters stack-ports command to clear the statistics for all
stack-ports.
Syntax
clear counters stack-ports
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC mode
User Guidelines
This command resets all statistics shown by the show switch stack-ports
counters and the show switch stack-ports diag commands.
Example
console#clear counters stack-ports
connect
Use this command to connect to the serial console of a different stack
member. The connect command allows administrations that deploy terminal
servers to connect a single serial line to a stack of switches for administration
2CSNXXX_SWUM200.book Page 1676 Tuesday, December 10, 2013 1:22 PM

System Management Commands 1677
of the stack. The network administrator can use the connect command to
access the master unit serial port when presented with a “CLI unavailable
message” due to a master switchover.
Syntax
connect
unit
•
unit
—
A unit number in the stack.
Default Configuration
There is no default configuration for this command.
Command Modes
Privileged EXEC mode on stack master.
At Unit Prompt on stack member.
User Guidelines
This command is available from the Unit prompt on a member unit serial
port. The user need not be currently connected over the serial port to connect
to another unit.
The stack member being connected to must be up and running and
connected as part of the stack. This command effectively "steals" the serial
console from the target stack member. There is only one console session
allowed per stack. The "stolen" console session is not restarted and the
privilege level is not changed as a result of being "stolen." All security
mechanisms applicable to the serial port remain in place.
Example
Example 1:
To connect to a remote stack member from master.
Stack-Master#connect 2
Remote session started. Type "exit" to exit the session.
(Unit 2 - CLI unavailable - please connect to master on Unit 1)>
2CSNXXX_SWUM200.book Page 1677 Tuesday, December 10, 2013 1:22 PM

1678 System Management Commands
Example 2:
To connect to the stack master (unit 1, below) over a stack member serial
port.
(Unit 2 - CLI unavailable - please connect to master on Unit 1)>connect 1
Stack-Master#
cut-through mode
Use the cut-through mode command to enable the cut-through mode on the
switch. The mode takes effect on all ports on next reload of the switch. To
disable the cut-through mode on the switch, use the no form of this
command.
Syntax
cut-through mode
no cut-through mode
Default Configuration
This command has no default configuration.
Command Mode
Global Configuration
User Guidelines
Cut-through mode is only supported on Dell Networking N4000 series
switches. It is not supported on Dell Networking N2000/N3000 Series
switches.
Example
console(config)#cut-through mode
The mode (enable) is effective from the next reload of Switch/Stack.
exec-banner
Use the exec-banner command to enable exec banner on the console, telnet
or SSH connection. To disable, use the no form of the command.
2CSNXXX_SWUM200.book Page 1678 Tuesday, December 10, 2013 1:22 PM

System Management Commands 1679
Syntax
exec-banner
no exec-banner
•
MESSAGE
— Quoted text
Default Configuration
This command has no default configuration.
Command Mode
Line Configuration
User Guidelines
The exec banner can consist of multiple lines. Enter a quote to complete the
message and return to configuration mode.
Example
console(config-telnet)# no exec-banner
exit
Use this command to disconnect the serial connection to a remote unit.
Syntax
exit
Default Configuration
There is no default configuration for this command.
Command Modes
User EXEC mode on stack master.
Unit prompt on the stack member.
2CSNXXX_SWUM200.book Page 1679 Tuesday, December 10, 2013 1:22 PM

1680 System Management Commands
User Guidelines
This command is available in privileged exec mode on the master unit serial
port and from the Unit prompt on member unit serial ports. The user need
not be currently connected over the serial port to connect to another unit.
The stack member being connected to must be up and running and
connected as part of the stack.
Example
Example 1:
To disconnect a remote session to a stack member established from the stack
manager.
Stack-Master#connect 2
Remote session started. Type "exit" to exit the session.
(Unit 2 - CLI unavailable - please connect to master on Unit 1)>exit
Stack-Master#
Example 2:
To disconnect a remote session to the stack master established from a stack
member.
(Unit 2 - CLI unavailable - please connect to master on Unit 1)>connect 2
(Unit 2 - CLI unavailable - please connect to master on Unit 1)>
(Unit 2 - CLI unavailable - please connect to master on Unit 1)>connect 1
Stack-Master#
Stack-Master#exit
Stack-Master>exit
(Unit 2 - CLI unavailable - please connect to master on Unit 1)>
hardware profile portmode
Use the hardware profile portmode command in Interface Configuration
mode to configure a 40G port in 4x10G mode or 1x40G mode.
2CSNXXX_SWUM200.book Page 1680 Tuesday, December 10, 2013 1:22 PM

System Management Commands 1681
Use the no form of the command to return the port to the default mode
(1x40G).
Syntax
hardware profile portmode {1x40g|4x10g}
no hardware profile portmode
•
1x40g
—
Configure the port as a single 40G port using 4 lanes.
•
4x10g
—
Configure the port as four 10G ports, each on a separate lane. This
mode requires the use of a suitable 4x10G to 1x40g pigtail cable.
Default Configuration
By default, 40G ports are configured in 1x40G mode.
Command Mode
Interface Configuration mode
User Guidelines
This command is only available on the N4000 series switches. This command
can only be executed on the 40G interface. Entering this command on any of
the 4x10G interfaces (or any other 10G port) will give an error.
This command takes effect only after rebooting the switch.
hostname
Use the hostname command in Global Configuration mode to specify or
modify the switch host name. To restore the default host name, use the no
form of the command.
Syntax
hostname
name
no hostname
•
name
— The name of the host. (Range: 1–255 characters) The command
allows spaces in the host name when specified in double quotes. For
example, #snmp-server v3-host “host name”.
2CSNXXX_SWUM200.book Page 1681 Tuesday, December 10, 2013 1:22 PM

1682 System Management Commands
Default Configuration
Host name not configured.
Command Mode
Global Configuration mode
User Guidelines
The hostname may include any printable characters except a double quote or
question mark. Enclose the string in double quotes to include spaces within
the name. The surrounding quotes are not used as part of the name. The CLI
does not filter illegal characters and may truncate entries at the first illegal
character or reject the entry entirely.
Example
The following example specifies the switch host name.
console(config)# hostname Dell
initiate failover
To manually force a failover from the management unit to the backup unit in
a stack, use the initiate failover command in Stack Configuration mode.
The initiate failover command checks for stack port errors and NSF
synchronization prior to initiating failover. If stack port errors are found, or if
the NSF status is not synchronized, a message is displayed and the user is
prompted to continue or abort the operation (see example, below).
Syntax
initiate failover
Default Configuration
There is no default configuration.
Command Mode
Stack Configuration mode
2CSNXXX_SWUM200.book Page 1682 Tuesday, December 10, 2013 1:22 PM

System Management Commands 1683
User Guidelines
This command forces a warm restart of the stack. The backup unit takes over
as the new management unit without clearing the hardware state on any of
the stack members. The original management unit reboots. If the system is
not ready for a warm restart, for example because no backup unit has been
elected or one or more members of the stack do not support nonstop
forwarding, the command fails with a warning message. Use the standby
command to select a specific unit to act as the backup unit.
Examples
Example-No Stack Port Errors
console(config-stack)#initiate failover ?
<cr> Press enter to execute the command.
console(config-stack)#initiate failover
Management unit will be reloaded.
Are you sure you want to failover to the backup unit? (y/n) y
Example-Stack Port Errors
console(config-stack)#initiate failover
Warning! Stack errors detected on the following interfaces:
Interface Error Count
---------------- ----------------
Gi1/0/1 12
Gi1/0/3 22
NSF Status: Not synchronized
Stack port errors or lack of NSF synchronization may indicate a non-redundant
stack topology exists. Fail-over on a non-redundant topology may cause the
stack to split!
Management unit will be reloaded.
Are you sure you want to failover to the backup unit? (y/n)
load-interval
Use this command to load the interface utilization measurement interval.
Use the no form of this command to reset the duration to the factory default
value.
2CSNXXX_SWUM200.book Page 1683 Tuesday, December 10, 2013 1:22 PM

1684 System Management Commands
Syntax
load-interval
time
no load-interval
•
time
—
The number of seconds after which interface utilization is measured
periodically. The time has to be a multiple of 30. (Range 30-600 seconds)
Default Configuration
The default interval is 300 seconds.
Command Modes
Interface Configuration mode, Interface Range Configuration mode, Port
Channel Configuration mode, Port Channel Range Configuration mode.
User Guidelines
This command has no user guidelines.
Example
console(config-if-Gi1/0/1)#load-interval 150
locate
Use the locate command to locate a switch by LED blinking.
Syntax
locate [switch
unit
] [time
time
]
•switch
unit
—If multiple devices are stacked, you can choose which switch
to identify.
•
time
time
—LED blinking duration in seconds. Range 1-3600 seconds.
Default Configuration
Default value is 20 seconds.
Command Mode
Privileged EXEC
2CSNXXX_SWUM200.book Page 1684 Tuesday, December 10, 2013 1:22 PM

System Management Commands 1685
User Guidelines
The LED will blink green until it times out. The user may select a new time
value while the LED is blinking. The last value selected takes effect
immediately. The locate command does not persist across reboots. This
command is not supported on Dell Networking N2000/N3000 Series series
switches.
Example
console# locate switch 1 time 555
login-banner
Use the login-banner command to enable login banner on the console, telnet
or SSH connection. To disable, use the no form of the command.
Syntax
login-banner
no login-banner
•
MESSAGE
— Quoted text
Default Configuration
This command has no default configuration.
Command Mode
Line Configuration
User Guidelines
This command has no user guidelines.
Example
console(config-telnet)# no login-banner
logout
Use this command to disconnect the serial connection to the remote unit on
the stack member.
2CSNXXX_SWUM200.book Page 1685 Tuesday, December 10, 2013 1:22 PM

1686 System Management Commands
Syntax
logout
Default Configuration
There is no default configuration for this command.
Command Modes
Unit prompt on the stack member
User Guidelines
This command is available in privileged exec mode on the master unit serial
port and from the Unit prompt on member unit serial ports. The user need
not be currently connected over the serial port to connect to another unit.
The stack member being connected to must be up and running and
connected as part of the stack.
This command is an alias for the
exit
command.
Example
(Example 1:
To disconnect a remote session to stack master established from a stack
member.
Unit 2 - CLI unavailable - please connect to master on Unit 1)>connect 1
Stack-Master#
Stack-Master#logout
(Unit 2 - CLI unavailable - please connect to master on Unit 1)>
Example 2:
To disconnect a remote session to stack master established from a stack
member.
(Unit 2 - CLI unavailable - please connect to master on Unit 1)>connect 1
Stack-Master#exit
Stack-Master>logout
(Unit 2 - CLI unavailable - please connect to master on Unit 1)>
2CSNXXX_SWUM200.book Page 1686 Tuesday, December 10, 2013 1:22 PM

System Management Commands 1687
member
Use the member command in Stack Global Configuration mode to
preconfigure a switch stack member. Execute this command on the
Management Switch. To remove a stack-member configuration from the
stack, use the no form of the command.
The no form of the command may not be used if the member is present in the stack.
Syntax
member
unit
switchindex
no member
unit
•
unit
— The switch identifier of the switch to be added or removed from
the stack. (Range: 1–12)
•
switchindex
— The index into the database of the supported switch types,
indicating the type of the switch being preconfigured. The switch index is
a 32-bit integer obtained from the
show supported switchtype
command.
Default configuration
This command has no defaults.
Command Mode
Stack Global Configuration
User Guidelines
The switch index (SID) can be obtained by executing the
show supported
switchtype
command in User Exec mode. When removing a unit from a
stack, use the no member command to remove the stack member
configuration after physically removing the unit.
Example
The following example displays how to add to stack switch number 2 with
index 1.
console(config)# stack
console(config-stack)# member 2 1
2CSNXXX_SWUM200.book Page 1687 Tuesday, December 10, 2013 1:22 PM

1688 System Management Commands
motd-banner
Use the motd-banner command to enable motd on the console, telnet or
SSH connection. To disable, use the no form of the command.
Syntax
motd-banner
no motd-banner
•
MESSAGE
— Quoted text
Default Configuration
This command has no default configuration.
Command Mode
Line Configuration
User Guidelines
This command has no user guidelines.
Example
console(config-telnet)# motd-banner
nsf
Use this command to enable non-stop forwarding. The no form of the
command will disable NSF.
Syntax
nsf
no nsf
Default Configuration
Non-stop forwarding is enabled by default.
2CSNXXX_SWUM200.book Page 1688 Tuesday, December 10, 2013 1:22 PM

System Management Commands 1689
Command Mode
Stack Global Configuration mode
User Guidelines
Nonstop forwarding allows the forwarding plane of stack units to continue to
forward packets while the control and management planes restart as a result
of a power failure, hardware failure, or software fault on the stack
management unit.
Example
console(config)#nsf
ping
Use the ping command in User EXEC mode to check the accessibility of the
desired node on the network.
Syntax
ping [ ip | ipv6 ]
ipaddress
|
hostname
[ repeat
count
] [ timeout
interval
] [
size
size
| source
sourceaddress
| loopback
loopbackaddress
|vlan
vlanid
|
tunnel
tunnelid
| out-of-band]
ping ipv6 interface { loopback
loopbackaddress
| out-of-band | vlan
vlanid
|
tunnel
tunnelid
}
ipaddress
[repeat
count
] | [timeout
interval
] | [size
size
] |
[source {
sourceaddress
| loopback
loopbackaddress
| vlan
vlanid
| tunnel
tunnelid
| out-of-band}]
•
ipaddress
— IPv4 or IPv6 address to ping (contact).
•
hostname
— Hostname to ping (contact). (Range: 1–158 characters). The
command allows spaces in the host name when specified in double quotes,
even though host names may only consist of letters, numbers and the
hyphen character.
•
count
— Number of packets to send (Range: 1–15 packets).
•
interval
— The time between Echo Requests, in seconds (Range: 1–60
seconds).
•
size
— Number of data bytes in a packet (Range: 0–13000 bytes).
•
sourceaddress
— The source IPv5 or IPv6 address for the ping.
2CSNXXX_SWUM200.book Page 1689 Tuesday, December 10, 2013 1:22 PM

1690 System Management Commands
•
loopbackaddress
— The source address from the loopback port index.
•
vlanid
— The VLAN IPv4 or IPv6 address in the transmitted packets.
•
tunnelid
— The tunnel interface IPv4 or IPv6 address in the transmitted
packets.
•
out-of-band
— The out-of-band interface IPv4 or IPv6 address in the
transmitted packets.
Default Configuration
The default count is 4.
The default interval is 3 seconds.
The default size is 0 data bytes.
It is not possible to ping from a specific interface when a VLAN is specified as
the source of the ping. The system selects the first available interface in the
VLAN from which to send the ping packets.
Command Mode
User EXEC mode, Privileged EXEC mode
User Guidelines
The local VRRP IP address is not pingable.
Examples
The following example sends an IPv4 ICMP Echo requests from VLAN 3 to
10.1.1.3
console#ping 10.1.1.3 source vlan 3
quit
Use this command to disconnect the serial connection to the remote unit on
the stack member.
Syntax
quit
2CSNXXX_SWUM200.book Page 1690 Tuesday, December 10, 2013 1:22 PM

System Management Commands 1691
Default Configuration
There is no default configuration for this command.
Command Modes
User EXEC mode, Privileged EXEC mode
User Guidelines
This command is available in privileged exec mode on the master unit serial
port and from the Unit prompt on member unit serial ports. The user need
not be currently connected over the serial port to connect to another unit.
The stack member being connected to must be up and running and
connected as part of the stack.
This command is an alias for the
exit
command.
Example
Example 1:
To disconnect a remote session to the stack master established from a stack
member.
(Unit 2 - CLI unavailable - please connect to master on Unit 1)>connect 1
Stack-Master#
Stack-Master#quit
(Unit 2 - CLI unavailable - please connect to master on Unit 1)>
Example 2:
To disconnect a remote session to the stack master established from stack
member.
(Unit 2 - CLI unavailable - please connect to master on Unit 1)>connect 1
Stack-Master#exit
Stack-Master>quit
(Unit 2 - CLI unavailable - please connect to master on Unit 1)>
reload
Use the reload command in Privileged EXEC mode to reload stack members.
The reload command checks for stack port errors prior to reloading stack
members and after the check for unsaved configuration changes. If stack port
errors are found, a message is displayed.
2CSNXXX_SWUM200.book Page 1691 Tuesday, December 10, 2013 1:22 PM

1692 System Management Commands
Syntax
reload [
stack–member–number
]
•
stack–member–number
—The stack member to be reloaded.
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC mode
User Guidelines
If no unit is specified, all units are reloaded.
Examples
Example-Reloading the Stack
The following example displays how to reload the stack.
console#reload 1
Management switch has unsaved changes.
Would you like to save them now? (y/n)n
Configuration Not Saved!
Are you sure you want to reload the switch? (y/n) y
Reloading management switch 1.
Example-Stack Port Errors
The following example shows stack port errors detected by the command.
console#reload
Management switch has unsaved changes.
Are you sure you want to continue? (y/n)
Warning! Stack port errors detected on the following interfaces:
Interface Error Count
---------------- ----------------
Gi1/0/1 12
Gi1/0/3 22
Stack port errors may indicate a non-redundant stack topology exists. Fail-
over on a non-redundant topology may cause the stack to split!
2CSNXXX_SWUM200.book Page 1692 Tuesday, December 10, 2013 1:22 PM

System Management Commands 1693
Are you sure you want to reload the stack? (y/n)
service unsupported-transceiver
Use this command to avoid the following on using an unsupported optic.
• Logging of a message.
• Generation of SNMP trap.
Use the no form of this command to set the transceiver support to the factory
default.
Syntax
service unsupported-transceiver
no service unsupported-transceiver
Default Configuration
The default configuration is to log a message along with the SNMP trap
generation on insertion or removal of an optic that is not qualified by Dell.
Command Mode
Global Configuration mode
User Guidelines
The switch logs a message and generates a trap on inserting or removing an
optics not qualified by Dell. This command suppresses the above mentioned
behavior.
Example
The following example bypasses logging of a message and trap generation on
inserting or removing an optics not qualified by Dell.
console(config)# service unsupported-transceiver
set description
Use the set description command in Stack Global Configuration mode to
associate a text description with a switch in the stack.
2CSNXXX_SWUM200.book Page 1693 Tuesday, December 10, 2013 1:22 PM

1694 System Management Commands
Syntax
set description
unit
description
•
unit
— The switch identifier. (Range: 1–12)
•
description
— The text description. (Range: 1–80 alphanumeric
characters)
Default Configuration
This command has no default configuration.
Command Mode
Stack Global Configuration mode
User Guidelines
This command has no user guidelines.
Example
The following example displays
console(config)#stack
console(config-stack)#set description 1 “unit 1"
slot
Use the slot command to configure a slot in the system. The unit/slot is the
slot identifier of the slot located in the specified unit. The
cardindex
is the
index to the database of the supported card types (see the command
show
supported cardtype
) indicating the type of card being preconfigured in the
specified slot. The card index is a 32-bit integer. If a card is currently present
in the slot that is unconfigured, the configured information will be deleted
and the slot will be reconfigured with default information for the card. The
supported card types are:
• Dell Networking N2024
• Dell Networking N2024P
• Dell Networking N2048
• Dell Networking N2048P
2CSNXXX_SWUM200.book Page 1694 Tuesday, December 10, 2013 1:22 PM

System Management Commands 1695
• Dell Networking N3024
• Dell Networking N3024F
• Dell Networking N3024P
• Dell Networking N3048
• Dell Networking N3048P
• Dell Networking N4032
• Dell Networking N4032F
• Dell Networking N4064
• Dell Networking N4064F
• Dell SFP+ Card
• Dell 10GBase-T Card
Use the no form of the command to return the unit/slot configuration to the
default value.
Syntax
slot
unit/slot
cardindex
no slot
unit/slot
•
unit/slot
— The
slot identifier of the slot.
•
cardindex
—
The index into the database of the supported card types
(see
show supported cardtype
) indicating the type of card being
preconfigured in the specified slot. The card index is a 32-bit integer.
Default Configuration
This command has no default configuration.
Command Mode
Global Configuration
User Guidelines
The card index (CID) can be obtained by executing the
show supported
cardtype
command in User EXEC mode.
2CSNXXX_SWUM200.book Page 1695 Tuesday, December 10, 2013 1:22 PM

1696 System Management Commands
Administrators may issue multiple consecutive slot commands addressing a
particular unit/slot without issuing an intervening no slot command.
Example
console(config)#slot 1/3 3
console(config)#slot 1/3 4
show banner
Use the show banner command to display banner information.
Syntax
show banner
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC, Configuration mode and all Configuration submodes
User Guidelines
This command has no user guidelines.
Example
console#show banner
Banner:Exec
Line Console...................... Enable
Line SSH.......................... Disable
Line Telnet....................... Enable
===exec=====
Banner:Login
Line Console...................... Enable
Line SSH.......................... Enable
Line Telnet....................... Disable
===login=====
Banner:MOTD
Line Console...................... Enable
2CSNXXX_SWUM200.book Page 1696 Tuesday, December 10, 2013 1:22 PM

System Management Commands 1697
Line SSH.......................... Enable
Line Telnet....................... Enable
===motd=====
show checkpoint statistics
Use the show checkpoint statistics command to display the statistics for the
checkpointing process.
Syntax
show checkpoint statistics
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC mode, Configuration mode and all Configuration submodes
User Guidelines
When nonstop forwarding is enabled on a stack, the stack's management unit
checkpoints operational data to the backup unit. If the backup unit takes over
as the management unit, the control plane on the new management unit uses
the checkpointed data when initializing its state. Checkpoint statistics track
the amount of data checkpointed from the management unit to the backup
unit.
Example
console#show checkpoint statistics
Messages Checkpointed.....................6708
Bytes Checkpointed........................894305
Time Since Counters Cleared...............3d 01:05:09
Checkpoint Message Rate...................0.025 msg/sec
Last 10-second Message Rate...............0 msg/sec
Highest 10-second Message Rate............8 msg/sec
2CSNXXX_SWUM200.book Page 1697 Tuesday, December 10, 2013 1:22 PM

1698 System Management Commands
show cut-through mode
Use the show cut-through mode command to show the cut-through mode on
the switch.
Syntax
show cut-through mode
Command Mode
Privileged EXEC, Configuration mode and all Configuration submodes
Default Configuration
This command has no default configuration.
User Guidelines
Not available on N2000 or N3000 switches.
Example
Console#show cut-through mode
Current mode : Enable
Configured mode : Disable (This mode is effective on next reload)
show hardware profile
Use the show hardware profile command in Privileged EXEC mode to display
the hardware profile information for the 40G ports. The user can optionally
specify an interface or all 40G interfaces are displayed.
Syntax
show hardware profile portmode [interface-id]
Default Configuration
This command has no default setting.
Command Mode
Privileged EXEC mode, Configuration mode and all Configuration submodes
2CSNXXX_SWUM200.book Page 1698 Tuesday, December 10, 2013 1:22 PM

System Management Commands 1699
User Guidelines
This command has no user guidelines.
Examples
console#show hardware profile portmode
Configured Running
40G Interface 10G Interfaces Mode Mode
------------- -------------- ---------- -------
Fo1/0/1 Te1/0/25-28 1x40G 4x10G
Fo1/0/2 Te1/0/29-32 1x40G 1x40G
console#show hardware profile portmode fo1/0/1
Configured Running
40G Interface 10G Interfaces Mode Mode
------------- -------------- ---------- -------
Fo1/0/1 Te1/0/25-28 1x40G 4x10G
show idprom interface interface-id
Use this command to display the optics EEPROM contents in user-readable
format.
Syntax
show idprom interface
interface-id
• interface-id—The physical interface.
Default Configuration
This command has no default configuration.
Command Modes
User EXEC, Privileged EXEC modes.
User Guidelines
This command has no user guidelines.
2CSNXXX_SWUM200.book Page 1699 Tuesday, December 10, 2013 1:22 PM

1700 System Management Commands
Example
The following example shows the optic parameters in user readable format.
console#show idprom interface tengigabitethernet 1/0/9
Type.............................. SFP+
Media............................. 10GBASE-LRM
Serial Number..................... ANF0L5J
Dell Qualified.................... Yes
The following example shows the optic parameters, but not the IDPROM
content as the entered activation code in incorrect.
console#show idprom interface tengigabitethernet 1/0/9 debug abc
Type.............................. SFP+
Media............................. 10GBASE-LRM
Serial Number..................... ANF0L5J
Dell Qualified.................... Yes
The following example shows the optic parameters along with the IDPROM
content as the user has entered correct activation code.
console#show idprom interface tengigabitethernet 1/0/9 debug D5$1kjX&2
Type.............................. SFP+
Media............................. 10GBASE-LRM
Serial Number..................... ANF0L5J
Dell Qualified.................... Yes
IDPROM content in hex format:
0 1 2 3 4 5 6 7 8 9 A B C D E F
=========================================================
0x00: 00 00 00 00 00 00 01 00 00 00 00 15 32 CE C4 B0
0x10: 34 CF 23 48 00 00 00 03 00 EA CC 70 04 23 73 C8
0x20: 32 CE BD BC 34 DE 89 50 00 00 00 01 02 2B 59 0E
0x30: 00 00 00 01 02 2B 59 0F 02 2B 59 0F 32 CE C4 50
0x40: 00 00 00 24 32 CE C3 58 34 CC 34 D4 00 00 00 00
0x50: 01 1F E1 90 00 00 00 00 00 00 00 00 00 00 00 00
0x60: 00 00 00 00 34 DE 89 50 00 00 00 00 32 CE BF 1A
0x70: 00 00 00 00 00 00 00 09 00 00 00 00 00 00 00 C6
0x80: 00 00 00 C6 00 00 00 31 00 00 00 01 00 00 00 00
0x90: 00 00 00 31 00 00 00 00 74 65 6E 67 69 67 61 62
0xA0: 69 74 65 74 68 65 72 6E 65 74 00 00 34 DE 89 50
0xB0: 00 00 00 00 00 00 00 03 00 00 00 00 34 DB BA 70
0xC0: 32 CE C4 B8 32 CE C4 20 00 00 00 03 32 CE C4 20
2CSNXXX_SWUM200.book Page 1700 Tuesday, December 10, 2013 1:22 PM

System Management Commands 1701
0xD0: 34 CE 1B 40 31 00 30 00 39 00 00 00 00 00 00 00
0xE0: 00 00 00 00 34 DE 89 50 00 00 00 00 34 DE 89 50
0xF0: 00 00 00 00 02 2D BE 00 00 00 00 00 02 2D BE 00
show interfaces advanced firmware
Use the show interfaces advanced firmware command to display the firmware
revision of the PHY for a port.
Syntax
show interfaces advanced firmware
interface
•
interface
—A 10G non-stacking physical interface.
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC, Configuration mode and all Configuration submodes
User Guidelines
This command is only applicable to 10G non-stacking interfaces.
Example
console#show interfaces advanced firmware
Port Revision Part number
-------- ----------- -----------
Te1/0/1 0x411 BCM8727
Te1/0/2 0x411 BCM8727
Te1/0/3 0x411 BCM8727
Te1/0/4 0x411 BCM8727
Te1/0/5 0x411 BCM8727
show interfaces interface-id
Use the show interfaces interface-id command to display the static and
dynamic parameters of the optics.
2CSNXXX_SWUM200.book Page 1701 Tuesday, December 10, 2013 1:22 PM

1702 System Management Commands
Syntax
show interfaces
interface-id
[transceiver [properties | detail]]
•
interface-id
—The ID for any valid physical interface.
•
properties
—Displays the optics static parameters.
•
detail
—Displays the optics static and dynamic parameters.
Default Configuration
This command has no default configuration.
Command Modes
User EXEC, Privileged EXEC modes.
User Guidelines
This command has no user guidelines.
Example
The following example shows static parameters of the optics for a given
interface.
console#show interfaces tengigabitethernet 1/0/9 transceiver properties
Type.............................. SFP+
Media............................. 10GBASE-LRM
Serial Number..................... ANF0L5J
Dell Qualified.................... Yes
The following example shows static and dynamic parameters of the optics for
a given interface.
console#show interfaces tengigabitethernet 1/0/9 transceiver detail
Type.............................. SFP+
Media............................. 10GBASE-LRM
Serial Number..................... ANF0L5J
Dell Qualified.................... Yes
Data Rate......................... 1000
Wavelength........................ 1310
Receive Power..................... -40.000
2CSNXXX_SWUM200.book Page 1702 Tuesday, December 10, 2013 1:22 PM

System Management Commands 1703
show interfaces utilization
Use this command to display interface utilization.
Syntax
show interfaces utilization [
interface-id
]
•
interface-id
—The physical or port-channel interface.
Default Configuration
There is no default configuration for this command.
Command Modes
Privileged EXEC mode
User Guidelines
This command displays the interface transmit and receive utilization in
bits/sec and packets/sec.
Example
console#show interfaces utilization
Port Interval Rx bits/s Rx packets/s Tx bits/s Tx packets/s
--------- -------- --------------- -------------- --------------- ----------
Gi1/0/1 150 52889696 103299 1968 4
Gi1/0/2 300 0 0 36175328 70654
Gi1/0/3 300 0 0 0 0
Gi1/0/4 300 0 0 0 0
Gi1/0/5 300 856 2 37785736 73799
console#show interfaces utilization gigabitethernet 1/0/1
Port Interval Rx bits/sec Rx packets/s Tx bits/s Tx packets/s
--------- -------- --------------- -------------- --------------- ----------
Gi1/0/1 150 12205152 23835 4568 8
show memory cpu
Use the show memory cpu command to check the total and available RAM
space on the switch.
2CSNXXX_SWUM200.book Page 1703 Tuesday, December 10, 2013 1:22 PM

1704 System Management Commands
Syntax
show memory cpu
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC, Configuration mode and all Configuration submodes
User Guidelines
No specific guidelines.
Example
console#show memory cpu
Total Memory........................... 262144 KBytes
Available Memory Space................. 121181 KBytes
show nsf
Use the show nsf command to show the status of non-stop forwarding.
Syntax
show nsf
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC mode, Configuration mode and all Configuration submodes
User Guidelines
There are no user guidelines for this command.
Example
console#show nsf
2CSNXXX_SWUM200.book Page 1704 Tuesday, December 10, 2013 1:22 PM

System Management Commands 1705
Administrative Status.......................... Enable
Operational Status............................. Enable
Last Startup Reason............................ Warm Auto-Restart
Time Since Last Restart........................ 0 days 16 hrs 52 mins 55 secs
Restart In Progress............................ No
Warm Restart Ready............................. Yes
Copy of Running Configuration to Backup Unit:
Status...................................... Stale
Time Since Last Copy........................ 0 days 4 hrs 53 mins 22 secs
Time Until Next Copy........................ 28 seconds
Unit NSF Support
---- -----------
1 Yes
2 Yes
3 Yes
show power-usage-history
Use the show power-usage-history command in Privileged EXEC mode to
display the history of unit power consumption for the unit specified in the
command and total stack power consumption. Historical samples are not
saved across switch reboots/reloads.
Syntax
show power-usage-history
unit-id
•
unit-id
—Stack unit for which to display the power history. Range 1-12.
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC mode, Configuration mode and all Configuration submodes
User Guidelines
There are no user guidelines for this command.
2CSNXXX_SWUM200.book Page 1705 Tuesday, December 10, 2013 1:22 PM

1706 System Management Commands
Example
console#show power-usage-history unit 1
Sampling Interval (sec)........................ 30
Total No. of Samples to Keep................... 168
Current Power Consumption (mWatts)............. 56172
Sample Time Since Power Power
No. The Sample Consumption Consumption
Was Recorded On This Unit Per Stack
(mWatts) (mWatts)
------ -------------------- ----------- -----------
3 0d:00:00:13 56172 56172
2 0d:00:00:43 56172 56172
1 0d:00:01:12 54360 54360
show process cpu
Use the show process cpu command to check the CPU utilization for each
process currently running on the switch.
Syntax
show process cpu
Command Mode
Privileged EXEC, Configuration mode and all Configuration submodes
Default Configuration
This command has no default configuration.
User Guidelines
No specific guidelines.
Example
console#show process cpu
Memory Utilization Report
status bytes
------ ----------
2CSNXXX_SWUM200.book Page 1706 Tuesday, December 10, 2013 1:22 PM

System Management Commands 1707
free 64022608
alloc 151568112
CPU Utilization:
PID Name 5 Sec 1 Min 5 Min
---------------------------------------------------------
328bb20 tTffsPTask 0.00% 0.00% 0.02%
3291820 tNetTask 0.00% 0.00% 0.01%
3295410 tXbdService 0.00% 0.00% 0.03%
347dcd0 ipnetd 0.00% 0.00% 0.01%
348a440 osapiTimer 1.20% 1.43% 1.21%
358ee70 bcmL2X.0 0.40% 0.30% 0.12%
359d2e0 bcmCNTR.0 0.80% 0.42% 0.50%
3b5b750 bcmRX 0.00% 0.13% 0.12%
3d3f6d0 MAC Send Task 0.00% 0.07% 0.10%
--More-- or (q)uit
3d48bd0 MAC Age Task 0.00% 0.00% 0.03%
40fdbf0 bcmLINK.0 0.00% 0.14% 0.46%
4884e70 tL7Timer0 0.00% 0.06% 0.02%
48a1250 osapiMonTask 0.00% 0.32% 0.17%
4969790 BootP 0.00% 0.00% 0.01%
4d71610 dtlTask 0.00% 0.06% 0.05%
4ed00e0 hapiRxTask 0.00% 0.06% 0.03%
562e810 DHCP snoop 0.00% 0.00% 0.06%
58e9bc0 Dynamic ARP Inspection 0.00% 0.06% 0.03%
62038a0 dot1s_timer_task 0.00% 0.00% 0.03%
687f360 dot1xTimerTask 0.00% 0.06% 0.07%
6e23370 radius_task 0.00% 0.00% 0.01%
6e2c870 radius_rx_task 0.00% 0.06% 0.03%
7bc9030 spmTask 0.00% 0.09% 0.01%
7c58730 ipMapForwardingTask 0.00% 0.06% 0.03%
7f6eee0 tRtrDiscProcessingTask 0.00% 0.00% 0.01%
b1516d0 dnsRxTask 0.00% 0.00% 0.01%
b194d60 tCptvPrtl 0.00% 0.06% 0.03%
b585770 isdpTask 0.00% 0.00% 0.02%
bda6210 RMONTask 0.00% 0.11% 0.11%
bdb24b0 boxs Req 0.00% 0.13% 0.10%
c2d6db0 sshd 0.00% 0.00% 0.01%
---------------------------------------------------------
--More-- or (q)uit
Total CPU Utilization 2.40% 3.62% 3.45%
2CSNXXX_SWUM200.book Page 1707 Tuesday, December 10, 2013 1:22 PM
1708 System Management Commands
show sessions
Use the show sessions command in Privileged EXEC mode to display a list of
the open telnet sessions to remote hosts.
Syntax
show sessions
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC mode, Configuration mode and all Configuration submodes
User Guidelines
This command has no user guidelines.
Example
The following example displays a list of open telnet sessions to remote hosts.
console#show sessions
User Name Connection from Idle Session Time Type
--------- --------------- -------- ------------ --------
EIA-232 00:00:00 00:07:37 Serial
admin 192.168.1.248 00:00:17 00:00:26 Telnet
admin 192.168.1.248 00:00:16 00:00:32 HTTP
console#
The following table describes the significant fields shown in the display.
Field Description
Connection Connection number
Host Remote host to which the switch is connected
through a Telnet session
Address IP address of the remote host
Port Telnet TCP port number
2CSNXXX_SWUM200.book Page 1708 Tuesday, December 10, 2013 1:22 PM

System Management Commands 1709
show slot
Use the show slot command in User EXEC mode to display information
about all the slots in the system or for a specific slot.
Syntax
show slot [
slot/port
]
Default Configuration
This command has no default configuration.
Command Mode
User EXEC, Configuration mode and all Configuration submodes
User Guidelines
The following table explains the output parameters.
If you supply a value for slot/port, the following additional information
appears as shown in the table below.
Parameter Description
Slot The slot identifier in a slot/port format.
Slot Status The slot is empty, full, or has encountered
an error.
Admin State The slot administrative mode is enabled
or disabled.
Power State The slot power mode is enabled or
disabled.
Configured Card Model Identifier The model identifier of the card
preconfigured in the slot. Model identifier
is a 32-character field used to identify a
card.
Pluggable Cards are pluggable or non-pluggable in
the slot.
2CSNXXX_SWUM200.book Page 1709 Tuesday, December 10, 2013 1:22 PM

1710 System Management Commands
Example
console>show slot
Admin Power Configured Card
Slot Status State State Model ID Pluggable
----- ------ ------- ------- -------------------------------- ---------
1/0 Full Enable Enable Dell Networking N4032 No
1/1 Empty Disable Disable Yes
show supported cardtype
Use the show supported cardtype command in User EXEC mode to display
information about all card types supported in the system. If a card index is
entered, then the command displays information about specific card types
supported in the system. Card index values are specific to each family of
products. Use the generic form (without specifying an index) to display all the
card types for a product family.
Syntax
show supported cardtype [
cardindex
]
•
cardindex
— Displays the index into the database of the supported card
types. This index is used when preconfiguring a slot.
Default Configuration
This command has no default configuration.
Parameter Description
Inserted Card Model Identifier The model identifier of the card inserted
in the slot. Model identifier is a 32-
character field used to identify a card.
This field is displayed only if the slot is
full.
Inserted Card Description The card description. This field is
displayed only if the slot is full.
Configured Card Description The description of the card preconfigured
in the slot.
2CSNXXX_SWUM200.book Page 1710 Tuesday, December 10, 2013 1:22 PM

System Management Commands 1711
Command Mode
User EXEC, Configuration mode and all Configuration submodes
User Guidelines
The CID information is used when preconfiguring cards using the slot
command.
The following table explains the output parameters.
If you supply a value for
cardindex
, the following additional information
appears as shown in the table below.
Example
console>show supported cardtype
CID Card Model ID
--- --------------------------------
1 Dell Networking N4032
2 Dell Networking N4032F
3 Dell Networking N4064
4 Dell Networking N4064F
5 Dell QSFP Card
6 Dell SFP+ Card
Parameter Description
Card Index (CID) The index into the database of the
supported card types. This index is used
when preconfiguring a slot.
Card Model Identifier The model identifier for the supported
card type.
Parameter Description
Card Type The 32-bit numeric card type for the
supported card.
Model Identifier The model identifier for the supported
card type.
Card Description The description for the supported card
type.
2CSNXXX_SWUM200.book Page 1711 Tuesday, December 10, 2013 1:22 PM
1712 System Management Commands
7 Dell 10GBase-T Card
show supported switchtype
Use the show supported switchtype command in User EXEC mode to display
information about all supported switch types.
Syntax
show supported switchtype [
switchindex
]
•
switchindex
— Specifies the index into the database of the supported
switch types, indicating the type of the switch being preconfigured. The
switch index is a 32-bit integer. (Range: 0–65535)
Default Configuration
This command has no default configuration.
Command Mode
User EXEC mode, Configuration mode and all Configuration submodes
User Guidelines
The switch SID is used when preconfiguring switches in a stack using the
member command in config-stack mode.
The following table describes the fields in the first example.
Field Description
Switch Index (SID) This field displays the index into the database of
supported switch types. This index is used when
preconfiguring a member to be added to the
stack.
Model Identifier This field displays the model identifier for the
supported switch type.
Management Preference This field indicates the management preference
value of the switch type.
Code Version This field displays the code load target identifier
of the switch type.
2CSNXXX_SWUM200.book Page 1712 Tuesday, December 10, 2013 1:22 PM

System Management Commands 1713
The following table describes the fields in the second example.
Example
The following example displays the information for supported switch types.
console#show supported switchtype
SID Switch Model ID
--- --------------------------------
1 N4032
2 N4032F
3 N4064
4 N4064F
The following example displays the format of the show supported switchtype
[
switchindex
] command.
console#show supported switchtype 1
Switch Type....................... 0xd8420001
Model Identifier.................. N4032
Switch Description................ Dell Networking N4032
Supported Cards:
Slot........................... 0
Card Index (CID)............... 1
Model Identifier............... Dell Networking N4032
Slot........................... 1
Card Index (CID)............... 5
Model Identifier............... Dell QSFP Card
Slot........................... 1
Card Index (CID)............... 6
Model Identifier............... Dell SFP+ Card
Slot........................... 1
Field Description
Switch Type This field displays the 32-bit numeric
switch type for the supported switch.
Model Identifier This field displays the model identifier for
the supported switch type.
Switch Description This field displays the description for the
supported switch type.
2CSNXXX_SWUM200.book Page 1713 Tuesday, December 10, 2013 1:22 PM

1714 System Management Commands
Card Index (CID)............... 7
Model Identifier............... Dell 10GBase-T Card
show switch
Use the show switch command in User EXEC mode to display information
about units in the stack.
The show switch command shows the configuration and status of the
stacking units, including the active and standby stack management units, the
preconfigured model identifier, the plugged in model identifier, the switch
status and the current code version. If there is a stack firmware
synchronization (SFS) operation in progress, the switch status will show as
Updating Code. Both the preconfigured switch type (as set by the member
command in stack mode) and the actual connected switch type are shown.
The show switch
unitid
command shows details of the switch configuration
including the SFS last attempt status for the specified unit.
The show switch command may show an SDM Mismatch value in the Switch
Status field. This value indicates that the unit joined the stack, but is running
a different SDM template than the management unit. This status should be
temporary; the stack unit should automatically reload using the template
running on the stack manager.
Use the show supported switchtype command to display switch SIDs.
Use the show stack-ports command to display details regarding stacking links.
Use the show switch stack-ports stack-path command to display the active
path from one stacking unit to another.
Use the show slot command to display details regarding slot configuration.
Use the show sdm prefer command to display the SDM template
configuration.
Syntax
show switch [chassis-mgmt |
stack–member–number
| stack–ports[counters
| diag | stack-path {
from-unit
|
all
}
to unit
] | stack–standby]
•
unitid
—The unit number.
•
chassis-mgmt
—Display chassis management.
2CSNXXX_SWUM200.book Page 1714 Tuesday, December 10, 2013 1:22 PM

System Management Commands 1715
•
stack–member–number
—The stack member number.
•
stack–ports
—Display summary stack-port information for all interfaces.
•
counters
—Display summary data counter information for all interfaces.
•
diag
—Display front panel stacking diagnostics for each port.
•
stack-path
—Display the active path from one stacking unit to another.
•
From-unit
—The unit from which the packets originate.
•
All
—Displays all unit paths.
•
To-unit
—The unit to which the packets are sent.
•
stack–standby
—Display the configured or automatically selected standby
unit number.
Default Configuration
This command has no default configuration.
Command Mode
User EXEC, Privileged EXEC modes, Configuration mode and all
Configuration submodes
User Guidelines
The show switch stack-ports stack-path command is useful in tracking the
path a packet may take when traversing stacking links. The command shows
active paths only, not those that may be taken after a stack failover or stack
reconvergence.
The following table describes the fields in the switch stack status example.
Unit Description
Switch This field displays the unit identifier assigned to
the switch.
Management Status This field indicates whether the switch is the
Management Switch, a stack member, or the
status is unassigned.
Switch Type This field displays the 32-bit numeric switch
type.
2CSNXXX_SWUM200.book Page 1715 Tuesday, December 10, 2013 1:22 PM

1716 System Management Commands
The additional fields in the all units example are as follows:
Preconfigured Model Identifier This field displays the model identifier for this
switch. Model Identifier is a 32-character field
assigned by the switch manufacturer to identify
the switch.
Plugged-in Model Identifier This field displays the model identifier for this
switch. Model Identifier is a 32-character field
assigned by the switch manufacturer to identify
the switch.
Switch Status This field displays the switch status. Possible
values are OK, Unsupported, Code Mismatch,
Config Mismatch, or Not Present.
Switch Description This field displays the switch description.
Detected Code Version This field displays the version of code running
on this switch. If the switch is not present and
the data is from preconfiguration, the code
version is "None."
Detected Code in Flash This field displays the version of code that is
currently stored in FLASH memory on the
switch. This code will execute after the switch is
reset. If the switch is not present and the data is
from preconfiguration, then the code version is
"None."
SFS Last Attempt Status This field displays the Stack Firmware
Synchronization status.
Serial Number This field displays the Switch serial number.
Up Time This field displays the system up time.
Unit Description
Switch This field displays the unit identifier assigned to
the switch.
Management Status This field indicates whether the switch is the
Management Switch, a stack member, or the
status is unassigned.
Unit Description
2CSNXXX_SWUM200.book Page 1716 Tuesday, December 10, 2013 1:22 PM
System Management Commands 1717
Global Status Parameters for NSF are explained as follows:
Preconfigured Model Identifier This field displays the model identifier of a
preconfigured switch ready to join the stack.
The Model Identifier is a 32-character field
assigned by the switch manufacturer to identify
the switch.
Plugged-In Model Identifier This field displays the model identifier of the
switch in the stack. Model Identifier is a 32-
character field assigned by the switch
manufacturer to identify the switch.
Switch Status This field indicates the switch status. Possible
values for this state are: OK, Unsupported,
CodeMismatch, ConfigMismatch, or
NotPresent
Code Version This field indicates the detected version of code
on this switch.
Parameter Description Range Default
NSF
Administrative
Status
Whether nonstop forwarding is
administratively enabled or disabled
Enabled
Disabled
Enabled
NSF Operational
Status
Indicates whether NSF is enabled
on the stack.
Enabled
Disabled
None
Unit Description
2CSNXXX_SWUM200.book Page 1717 Tuesday, December 10, 2013 1:22 PM
1718 System Management Commands
Last Startup
Reason
The type of activation that caused
the software to start the last time.
There are four options. “Power-On”
means that the switch rebooted.
This could have been caused by a
power cycle or an administrative
“Reload” command. “Administrative
Move” means that the administrator
issued a command for the stand-by
manager to take over. “Warm-Auto-
Restart” means that the primary
management card restarted due to a
failure, and the system executed a
nonstop forwarding failover. “Cold-
Auto-Restart” means that the
system switched from the active
manager to the backup manager and
was unable to maintain user data
traffic. This is usually caused by
multiple failures occurring close
together.
Power-On
Administrative-
Move
Warm-Auto-
Restart
Cold-Auto-
Restart
None
Time Since Last
Restart
Time since the current management
card became the active management
card. For the backup manager, the
value is set to 0d 00:00:00
Time Stamp 0d
00:00:00
Restart in progress Whether a restart is in progress. A
restart is not considered complete
until all hardware tables have been
fully reconciled.
Yes or No
Warm Restart
Ready
Whether the initial full checkpoint
has finished
Yes or No
Status Whether the running configuration
on the backup unit includes all
changes made on the management
unit.
Current or Stale
Parameter Description Range Default
2CSNXXX_SWUM200.book Page 1718 Tuesday, December 10, 2013 1:22 PM
System Management Commands 1719
Per Unit Status Parameters are explained as follows:
Examples
Example – Stack Status for the Switch
console#show switch 1
Switch............................ 1
Management Status................. Management Switch
Switch Type....................... 0xd8460001
Preconfigured Model Identifier.... N4064
Plugged-in Model Identifier....... N4064
Switch Status..................... OK
Switch Description................ Dell Networking N4064
Detected Code Version............. 6.0.0.0
Detected Code in Flash............ 6.0.0.0
SFS Last Attempt Status........... None
Serial Number..................... CN0H0F6C2829831P0023A00
Up Time........................... 3 days 1 hrs 16 mins 20 secs
Example-Stack Ports
This example displays information about the stack ports.
console#show switch stack-ports
Time Since Last
Copy
When the running configuration
was last copied from the
management unit to the backup
unit.
Time Stamp
Time Until Next
Copy
The number of seconds until the
running configuration will be copied
to the backup unit. This line only
appears when the running
configuration on the backup unit is
Stale.
0 -
L7_UNITMGR_
CONFIG_COPY
_HOLDDOWN
Parameter Description Range Default
NSF Support Whether a unit
supports NSF
Yes or No —
Parameter Description Range Default
2CSNXXX_SWUM200.book Page 1719 Tuesday, December 10, 2013 1:22 PM

1720 System Management Commands
Configured Running
Stack Stack Link Link Admin
Interface Mode Mode Status Speed (Gb/s) Status
---------------- ---------- ---------- ------------ ------------ -----------
Tw1/0/1 Stack Stack Link Down 21 Enabled
Tw1/0/2 Stack Stack Link Up 21 Disabled
Tw2/0/1 Stack Stack Link Down 21 Disabled
Tw2/0/2 Stack Stack Link Up 21 Enabled
Example – All Units in the Stack
This example displays information about all units in the stack.
console>show switch
Management Standby Preconfig Plugged-in Switch Code
SW Status Status Model ID Model ID Status Version
--- ---------- --------- ------------- ------------- ------------- ---------
1 Mgmt Sw N3048 N3048 OK 6.0.0.0
Example-Stacking Links Path
This command tracks the path a packet may take when traversing stacking
links. The command shows active paths only, not those that may be taken
after a stack failover or stack reconvergence.
console#show switch stack-ports stack-path 3 1
Packet-path from unit 3 to unit 1:
1 unit-3 port gi3/0/49 to unit-2
2 unit-2 port gi2/0/49 to unit-1
Example – Status Parameters for NSF
The show switch command is used to display which unit is the management
unit and which is the backup unit.
(nsf-stack) #show nsf
Administrative Status.......................... Enable
Operational Status............................. Enable
Last Startup Reason............................ Warm Auto-Restart
Time Since Last Restart........................ 0 days 16 hrs 52 mins 55 secs
Restart In Progress............................ No
Warm Restart Ready............................. Yes
Copy of Running Configuration to Backup Unit:
Status...................................... Stale
Time Since Last Copy........................ 0 days 4 hrs 53 mins 22 secs
2CSNXXX_SWUM200.book Page 1720 Tuesday, December 10, 2013 1:22 PM

System Management Commands 1721
Time Until Next Copy........................ 28 seconds
Unit NSF Support
---- -----------
1 Yes
2 Yes
3 Yes
Example – Switch Firmware Stack Status
The following example displays the Switch Firmware stack status information
for the switch.
console#show switch
Management Standby Preconfig Plugged-in Switch Code
SW Switch Status Model ID Model ID Status Version
--- ---------- --------- ------------- ------------- ------------- ---------
1 Mgmt Sw N3024 N3024 OK 6.0.0.0
2 Stack Mbr N3024 N3024 Updating Code 6.0.0.0
console#show switch 1
Switch............................ 1
Management Status................. Management Switch
Switch Type....................... 0x63400004
Preconfigured Model Identifier.... N3048P
Plugged-in Model Identifier....... N3048P
Switch Status..................... OK
Switch Description................ Dell Networking N3048P
Detected Code Version............. 6.0.0.0
Detected Code in Flash............ 6.0.0.0
SFS Last Attempt Status........... None
Serial Number..................... 13820M0230LF
Up Time........................... 0 days 3 hrs 1 mins 13 secs
Example – SDM Templates
This example shows the SDM Mismatch value in the Switch Status field.
console(config)#show switch
Management Standby Preconfig Plugged-in Switch Code
SW Status Status Model ID Model ID Status Version
--- ---------- --------- ------------- ------------- ------------- ---------
1 Mgmt Sw N4032F N4032F SDM Mismatch 10.7.14.21
2CSNXXX_SWUM200.book Page 1721 Tuesday, December 10, 2013 1:22 PM

1722 System Management Commands
show system
Use the show system command in User EXEC mode to display system
information.
Syntax
show system [
unit
]
•
unit
— The unit number.
Default Configuration
This command has no default configuration.
Command Mode
User EXEC mode, Configuration mode and all Configuration submodes
User Guidelines
This command has no user guidelines.
Example
console#show system
System Description: Dell Networking Switch
System Up Time: 0 days, 03h:02m:30s
System Contact:
System Name:
System Location:
Burned In MAC Address: 001E.C9DE.B41B
System Object ID: 1.3.6.1.4.1.674.10895.3060
System Model ID: N3048P
Machine Type: Dell Networking N3048P
System Thermal Conditions:
Unit Temperature State
(Celsius)
---- ----------- -----------
1 34 Good
Temperature Sensors:
2CSNXXX_SWUM200.book Page 1722 Tuesday, December 10, 2013 1:22 PM

System Management Commands 1723
Unit Description Temperature
(Celsius)
---- ------------------ -----------
1 MAC 33
1 PHY 34
Fans:
Unit Description Status
---- ----------- -------
1 Fan-1 Failure
1 Fan-2 Failure
Power Supplies:
Unit Description Status Average Current Since
Power Power Date/Time
(Watts) (Watts)
---- ----------- ----------- ---------- -------- -------------------
1 System OK 39.8 39.8
1 PS-1 Failure
1 PS-2 No Power N/A N/A 01/01/1970 00:00:00
USB Port Power Status:
----------------------
Device Not Present
show system fan
Use the show system fan command in User EXEC or Privileged EXEC mode
to explicitly display the fan status.
Syntax
show system fan
Default Configuration
This command has no default configuration.
Command Mode
User EXEC, Privileged EXEC, Configuration mode and all Configuration
submodes
2CSNXXX_SWUM200.book Page 1723 Tuesday, December 10, 2013 1:22 PM

1724 System Management Commands
User Guidelines
This command has no user guidelines.
Example
console>show system fan
Fans:
Unit Description Status
---- ----------- ------
1 Fan 1 OK
1 Fan 2 OK
1 Fan 3 OK
show system id
Use the show system id command in User EXEC mode to display the system
identity information.
Syntax
show system id [
unit
]
•
unit
— The unit number.
Default Configuration
This command has no default configuration.
Command Mode
User EXEC mode, Configuration mode and all Configuration submodes
User Guidelines
The tag information is on a switch by switch basis.
Example
The following example displays the system service tag information.
console#show system id
Service Tag: 13820M0230LF
Serial Number: 13820M0230LF
Asset Tag: none
Unit Service tag Serial number Asset tag
2CSNXXX_SWUM200.book Page 1724 Tuesday, December 10, 2013 1:22 PM

System Management Commands 1725
---- ------------ -------------- ------------
1 13820M0230LF 13820M0230LF none
show system power
Use the show system power command in User EXEC or Privileged EXEC
mode to display information about the system level power consumption.
Syntax
show system power
Default Configuration
This command has no default configuration.
Command Mode
User EXEC, Privileged EXEC, Configuration mode and all Configuration
submodes
User Guidelines
This command has no user guidelines.
Examples
console#show system power
Power Supplies:
Unit Description Status Average Current Since
Power Power Date/Time
(Watts) (Watts)
---- ----------- ----------- ---------- -------- -------------------
1 System OK 39.8 39.8
1 PS-1 Failure
1 PS-2 No Power N/A N/A 01/01/1970 00:00:00
2CSNXXX_SWUM200.book Page 1725 Tuesday, December 10, 2013 1:22 PM

1726 System Management Commands
show system temperature
Use the show system temperature command in User EXEC or Privileged
EXEC mode to display information about the system temperature and fan
status.
Syntax
show system temperature
Default Configuration
This command has no default configuration.
Command Mode
User EXEC, Privileged EXEC, Configuration mode and all Configuration
submodes
User Guidelines
Temperature status is indicated as per the following table:
Examples
console#show system temperature
System Thermal Conditions:
Unit Temperature State
(Celsius)
---- ----------- -----------
1 34 Good
Temperature Sensors:
Unit Description Temperature
(Celsius)
Status Degrees Celsius
Good 0-50
Medium 51-74
High 75-200
2CSNXXX_SWUM200.book Page 1726 Tuesday, December 10, 2013 1:22 PM

System Management Commands 1727
---- ------------------ -----------
1 MAC 33
1 PHY 34
show tech-support
Use the show tech-support command to display system and configuration
information for use in debugging or contacting technical support. The output
of the show tech-support command combines the output of the following
commands:
• show interfaces transceiver
• show power inline
• show switch stack-port counters
• show nsf
•show slot
• show interfaces advertise
• show interfaces advanced firmware
• show lldp remote-device all
• show interfaces counters errors
• show fiber-ports optical-transceiver
•show process cpu
• show iscsi sessions
• show ethernet cfm errors (N4000 series only)
• show power inline firmware-version
•show version
• show interfaces transceiver properties
Syntax
show tech-support
Command Mode
Privileged EXEC mode, Configuration mode and all Configuration submodes
2CSNXXX_SWUM200.book Page 1727 Tuesday, December 10, 2013 1:22 PM

1728 System Management Commands
User Guidelines
Not applicable
Default Value
Not applicable
Example
console#show tech-support
***************** Show Version ******************
Switch: 1
System Description................ Dell Networking N4032, 6.0.0.0, Linux
2.6.32.9
Machine Description............... Dell Networking Switch
System Model ID................... N4032
Machine Type...................... Dell Networking N4032
Serial Number..................... 0000
Manufacturer...................... 0xbc00
Operating System.................. Linux 2.6.32.9
Burned In MAC Address............. 0011.2233.4455
System Object ID.................. 1.3.6.1.4.1.674.10895.3042
CPU Version....................... XLP308H-B2
SOC Version....................... BCM56842_A1
HW Version........................ 3
CPLD Version...................... 17
unit active backup current-active next-active
---- ----------- ----------- -------------- --------------
1 6.0.0.0 <none> 6.0.0.0 6.0.0.0
Additional Packages............................ FASTPATH QoS
FASTPATH Multicast
FASTPATH Stacking
FASTPATH Routing
FASTPATH Data Center
***************** Show SysInfo ******************
System Location................................
System Contact.................................
2CSNXXX_SWUM200.book Page 1728 Tuesday, December 10, 2013 1:22 PM

System Management Commands 1729
System Object ID............................... 1.3.6.1.4.1.674.10895.3042
System Up Time................................. 0 days 0 hrs 14 mins 53 secs
10/100 Ethernet/802.3 interface(s)............. 1
Gig Ethernet/802.3 interface(s)................ 0
10Gig Ethernet/802.3 interface(s).............. 0
40Gig Ethernet/802.3 interface(s).............. 0
Virtual Ethernet/802.3 interface(s)............ 1
System Thermal Conditions:
--More-- or (q)uit
show users
Use the show users command in Privileged EXEC mode to display
information about the active users. The command also shows which
administrative profiles have been assigned to local user accounts and to show
which profiles are active for logged-in users.
Syntax
show users [long]
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC mode, Configuration mode and all Configuration submodes
User Guidelines
This command has no user guidelines.
Example
The following example displays a list of active users and the information
about them.
console#show users
Username Protocol Location Profile(s)
-------- -------- --------- ------------
admin Serial EIA-232 net-admin
2CSNXXX_SWUM200.book Page 1729 Tuesday, December 10, 2013 1:22 PM

1730 System Management Commands
console#show users accounts
UserName Privilege Password Password Lockout
Aging Expiry date
------- --------- -------- ------------- -------
admin 15 --- --- False
Administrative Profile(s): network-admin
user 1 --- --- False
Administrative Profile(s): network-operator
show version
Use the show version command in User EXEC mode to displays the system
version information.
Syntax
show version [
unit
]
•
unit
— The unit number.
Default Configuration
This command has no default configuration.
Command Mode
User EXEC mode, Configuration mode and all Configuration submodes
User Guidelines
This command has no user guidelines.
Example
console#show version
Machine Description............... Dell Networking Switch
System Model ID................... N4064
Machine Type...................... Dell Networking N4064
Serial Number..................... X01-64C-55
Manufacturer...................... 0xbc00
Operating System.................. Linux 2.6.32.9
Burned In MAC Address............. D067.E5C0.D19B
System Object ID.................. 1.3.6.1.4.1.674.10895.3045
CPU Version....................... XLP308H-A1
2CSNXXX_SWUM200.book Page 1730 Tuesday, December 10, 2013 1:22 PM

System Management Commands 1731
SOC Version....................... BCM56846_A1
HW Version........................ 3
CPLD Version...................... 14
unit active backup current-active next-active
---- ----------- ----------- -------------- --------------
1 6.0.0.1 5.1.0.1 6.0.0.1 5.1.0.1
console#show version 2
CPU Version....................... XLP308H-A0
SOC Version....................... BCM56842_B1
HW Version........................ 1
CPLD Version...................... 14
Unit Image 1 Image 2 Current Active Next Active
----- ------------ ------------ ----------------- -----------------
2 6.0.0.1 5.1.0.1 image1 image2
stack
Use the stack command in Global Configuration mode to set the mode to
Stack Global Config.
Syntax
stack
Default Configuration
This command has no default mode.
Command Mode
Global Configuration mode
User Guidelines
This command has no user guidelines. If not stack configuration appears in
the saved config, it is built at runtime and appears in the running config. The
operator can save the stack configuration. Stack members that do not match
the saved config after a reboot will show a config mismatch and do not join
the stack.
2CSNXXX_SWUM200.book Page 1731 Tuesday, December 10, 2013 1:22 PM

1732 System Management Commands
Example
The following example sets the mode to Stack Global Config.
console(config)#stack
console(config-stack)#
stack-port
Use the stack-port command in Stack Configuration mode to configure ports
as either Stacking ports or as Ethernet ports. This command is used to
configure Ethernet ports to operate as either stacking or Ethernet ports, or to
configure stacking modules to operate as Ethernet ports.
NOTE: This command is only valid on N4000 switches. It issues an error response if
used on the N2000 or N3000 switches.
Syntax
stack-port {fortygigabitethernet|tengigabitethernet}
unit/slot/port
{ethernet
| stack}
Default Configuration
By default, Ethernet ports are configured to operate in Ethernet mode.
Command Mode
Stack Configuration mode
User Guidelines
Once this command has been issued, the switch must be rebooted in order for
the command to take effect. Issuing multiple stack-port commands for a
single interface without intervening reboots results in undefined behavior and
is not supported. Reboot the switch and examine the output of the show
switch stack-ports command to determine the active configuration. The clear
config command does not change the stacking port mode. Only the stack-
port command can change the operating mode of the stacking port and it
only takes effect after a reboot.
The stack-port configuration mode does not appear in the running config.
Use the show switch stack-port command to display configuration and status
of stacking ports. Ports that are configured to operate as stacking ports will
2CSNXXX_SWUM200.book Page 1732 Tuesday, December 10, 2013 1:22 PM

System Management Commands 1733
show as detached in the show interfaces status command output. When
downgrading switch firmware, Ethernet ports configured as stacking revert to
Ethernet ports. It is necessary to configure the Ethernet ports as stacking on
each unit in the stack individually after a firmware downgrade.
Use the show switch command to display information regarding the switches
in a stack. Fortygigabitethernet ports are only supported on the N4000 series
switches. Redundant stacking links between any two units must operate at
the same speed. A 40G port configured in 4x10G mode is considered to be
operating at 10G speed.
Up to eight stack ports can be configured per stacking unit (four in each
direction).
The N4000 series switches support up to twelve units configured in a stack
and can utilize 10GBaseT, SFP+ or QSFP (N4000 series only) connections
for stacking. The N3000 and N2000 series switches support up to twelve unit
configured in a stack and can utilize rear panel mini-SAS ports only for
stacking.
Example
console(config-stack)#stack-port tengigabitethernet 1/0/3 stack
console(config-stack)#
stack-port interface shutdown
Use this command to enable or disable the stack port administratively. This
command is usually used to diagnose the stack in case any one of the stack
ports is exhibiting errors.
Syntax
stack-port
interface-id
shutdown
no stack-port
interface-id
shutdown
•
interface-id
—The stacking interface identifier.
Default Configuration
There no default configuration for this command.
2CSNXXX_SWUM200.book Page 1733 Tuesday, December 10, 2013 1:22 PM

1734 System Management Commands
Command Modes
Stack Configuration mode
User Guidelines
This command must be used with caution, as disabling a stack port causes
the stack to attempt to reconverge. Ensure that the stack is in an active ring
topology in order to avoid a stack split. Check the stack ports for errors and
also verify that NSF is synced before shutting down any stacking links.
Application messages will appear in the logs during stack convergence.
This command persists across reboots, therefore, administrators should use
this command with caution during stack upgrade procedures.
Example
console(config-stack)#stack-port tengigabitethernet 1/2/1 shutdown
Disabling a stack port will cause the stack to attempt to re-converge.
Application messages will appear in the logs during stack convergence.
Before shutting down a stack link, please ensure that your stack is in an
active ring topology in order to avoid a stack split. Continue? (y/n)
console(config-stack)#no stack-port twentygigbitethernet 1/0/1 shutdown
standby
Use the standby command to configure the standby in the stack. This unit
comes up as the master when the stack failover occurs. Use the no form of
this command to reset to default, in which case, a standby is automatically
selected from the existing stack units if there no preconfiguration.
Syntax
standby
unit
no standby
•
unit
— Valid unit number in the stack. (Range: 1–6 maximum. The range
is limited to the number of units available on the stack.)
2CSNXXX_SWUM200.book Page 1734 Tuesday, December 10, 2013 1:22 PM

System Management Commands 1735
Default Configuration
The default configuration is to allow the software to automatically select a
standby unit.
Command Mode
Stack Global Configuration
User Guidelines
No specific guidelines.
Examples
console(config)#stack
console(config-stack)#standby 2
switch renumber
Use the switch renumber command in Global Configuration mode to change
the identifier for a switch in the stack. Upon execution, the switch is
configured with the configuration information for the new switch, if any is
available. The old switch configuration information is retained; however, the
old switch will be
operationally detached
.
Syntax
switch
oldunit
renumber
newunit
•
oldunit
— The current switch identifier. (Range: 1–6)
•
newunit
— The updated value of the switch identifier. (Range: 1–6)
Command Mode
Global Configuration mode
User Guidelines
This command is executed on the Management Switch.
2CSNXXX_SWUM200.book Page 1735 Tuesday, December 10, 2013 1:22 PM

1736 System Management Commands
Example
The following example displays how to reconfigure switch number “1” to an
identifier of “2.”
console(config)#switch 1 renumber 2
telnet
Use the telnet command in Privileged EXEC mode to log into a host that
supports Telnet.
Syntax
telnet {
ip-address
|
hostname
} [
port
] [
keyword1......
]
•
ip-address
—Valid IP address of the destination host.
•
hostname
—Hostname of the destination host. (Range: 1–158 characters).
The command allows spaces in the host name when specified in double
quotes. For example,
console(config)#snmp-server host
"host name"
•
port
—A decimal TCP port number, or one of the keywords from the port
table in the user guidelines (see Port Table below).
•
keyword
—One or more keywords from the keywords table in the user
guidelines (see Keywords Table below).
Keywords Table
Options Description
/debug Enable telnet debugging mode.
/line Enable telnet linemode.
/localecho Enable telnet localecho.
<cr> Press ENTER to execute the command.
port
Enter the port number. Refer to the following table.
2CSNXXX_SWUM200.book Page 1736 Tuesday, December 10, 2013 1:22 PM

System Management Commands 1737
Port Table
Keyword Description Port Number
bgp Border Gateway Protocol 179
chargen Character generator 19
cmd Remote commands 514
daytime Daytime 13
discard Discard 9
domain Domain Name Service 53
echo Echo 7
exec Exec 512
finger Finger 79
ftp File Transfer Protocol 21
ftp-data FTP data connections 20
gopher Gopher 70
hostname NIC hostname server 101
ident Ident Protocol 113
irc Internet Relay Chat 194
klogin Kerberos login 543
kshell Kerberos shell 544
login Login 513
lpd Printer service 515
nntp Network News Transport Protocol 119
pim-auto-rp PIM Auto-RP 496
pop2 Post Office Protocol v2 109
pop3 Post Office Protocol v3 110
smtp Simple Mail Transport Protocol 25
sunrpc Sun Remote Procedure Call 111
syslog Syslog 514
tacacs TAC Access Control System 49
2CSNXXX_SWUM200.book Page 1737 Tuesday, December 10, 2013 1:22 PM

1738 System Management Commands
Default Configuration
port —
Telnet port (decimal 23) on the host.
Command Mode
User EXEC, Privileged EXEC mode
User Guidelines
This command has no user guidelines.
Example
Following is an example of using the telnet command to connect to
176.213.10.50.
console#telnet 176.213.10.50
Esc U sends telnet EL
traceroute
Use the traceroute command in Privileged EXEC mode to discover the IP
routes that packets actually take when traveling to their destinations.
Syntax
traceroute [ip]
ipaddress
|
hostname
[ initTtl
initTtl
] [ maxTtl
maxTtl
] [
maxFail
maxFail
] [ interval
interval
] [ count
count
] [ port
port
] [ size
size
][source {<src-ip-address>|vlan <vlan-id>|loopback <loop-id>}]
•
ipaddress
—Valid IP address of the destination host.
talk Talk 517
telnet Telnet 23
time Time 37
uucp Unix-to-Unix Copy Program 540
whois Nickname 43
www World Wide Web 80
Keyword Description Port Number
2CSNXXX_SWUM200.book Page 1738 Tuesday, December 10, 2013 1:22 PM

System Management Commands 1739
•
hostname
—Hostname of the destination host. (Range: 1–158 characters).
The command allows spaces in the host name when specified in double
quotes. For example,
console(config)#snmp-server host
"host name"
•
initTtl
—The initial time-to-live (TTL); the maximum number of router
hops between the local and remote system (Range: 0–255).
•
maxTtl
—The largest TTL value that can be used (Range:1–255).
•
maxFail
—Terminate the traceroute after failing to receive a response for
this number of consecutive probes (Range: 0–255).
•
interval
—The timeout period. If a response is not received within this
period of time, then traceroute considers that probe a failure (printing *)
and sends the next probe. If traceroute does receive a response to a probe,
then it sends the next probe immediately. (Range: 1–60 seconds).
•
count
—The number of probes to be sent at each TTL level (Range:1–10).
•
port
—The destination UDP port of the probe. This should be an unused
port on the remote destination system (Range: 1–65535).
•
size
—The size, in bytes, of the payload of the Echo Requests sent (Range:
0–39936 bytes).
•
src-ip-address
—The IPv4 source address to use in the ICMP echo request
packets.
•
vlan
—A valid VLAN interface.
•
loop-id
—A configured loopback ID
Default Configuration
The default count is 3 probes.
The default interval is 3 seconds.
The default size is 0 data bytes.
The default port is 33434.
The default initTtl is 1 hop.
The default maxTtl is 30 hops.
The default maxFail is 5 probes.
2CSNXXX_SWUM200.book Page 1739 Tuesday, December 10, 2013 1:22 PM

1740 System Management Commands
Command Mode
User Exec mode and Privileged EXEC mode
User Guidelines
Traceroute operates by sending a sequence of Internet Control Message
Protocol (ICMP) echo request packets. The time-to-live (TTL) value, is used
in determining the intermediate routers through which the packet flows
toward the destination address. Routers decrement a packet’s TTL value and
discard packets whose TTL equals 0. On discarding a packet, the router
returns an ICMP time exceeded message to the source.
Examples
The following example discovers the routes that packets will actually take
when traveling to the destination specified in the command.
(console) # traceroute 10.240.10.115 init-ttl 1 max-ttl 4 max-fail 0 interval
1 count 3 port 33434 size 43
Traceroute to 10.240.10.115, 4 hops max, 43 byte packets:
1 10.240.4.1 708 msec 41 msec 11 msec
2 10.240.10.115 0 msec 0 msec 0 msec
Hop Count = 1 Last TTL = 2 Test attempt = 6 Test Success = 6
traceroute ipv6
Use the traceroute command in Privileged EXEC mode to discover the IP
routes that packets actually take when traveling to their destinations.
Syntax
traceroute ipv6
ipv6address
|
hostname
[ initTtl
initTtl
] [ maxTtl
maxTtl
] [
maxFail
maxFail
] [ interval
interval
] [ count
count
] [ port
port
] [ size
size
][source {
src-ip-address
|vlan
vlan-id
|loopback
loop-id
}]
•
ipv6address
—
Valid IPv6 address of the destination host.
•
hostname
—
Hostname of the destination host. (Range: 1–158 characters). The
command allows spaces in the host name when specified in double quotes. For
example,
console(config)#snmp-server host "host name"
•
initTtl
—
The initial time-to-live (TTL); the maximum number of router hops
between the local and remote system (Range: 0–255). the default is 1.
2CSNXXX_SWUM200.book Page 1740 Tuesday, December 10, 2013 1:22 PM

System Management Commands 1741
•
maxTtl
—
The largest TTL value that can be used (Range:1–255). The default is
30. This must be larger or equal to the value specified in initTtl.
•
maxFail
—
Terminate the traceroute after failing to receive a response for this
number of consecutive probes (Range: 0–255).
•
interval
—
The timeout period. If a response is not received within this period of
time, then traceroute considers that probe a failure (printing *) and sends the
next probe. If traceroute does receive a response to a probe, then it sends the
next probe immediately. (Range: 1–60 seconds). The default is 3.
•
count
—
The number of probes to be sent at each TTL level (Range:1–10).
•
port
—
The destination UDP port of the probe. This should be an unused port on
the remote destination system (Range: 1–65535).
•
size
—
The size, in bytes, of the payload of the Echo Requests sent (Range:
0–
39936
bytes). The default is 0.
•
src-ip-address
—
The IPv4 source address to use in the ICMP echo request
packets.
•
vlan
—
The source VLAN over which to send the echo request.
•
loop-id
—
A configured loopback ID
Default Configuration
The default count is 3 probes.
The default interval is 3 seconds.
The default size is 0 data bytes.
The default port is 33434.
The default initTtl is 1 hop.
The default maxTtl is 30 hops.
The default maxFail is 5 probes.
Command Mode
Privileged EXEC mode.
2CSNXXX_SWUM200.book Page 1741 Tuesday, December 10, 2013 1:22 PM

1742 System Management Commands
User Guidelines
Traceroute operates by sending a sequence of Internet Control Message
Protocol (ICMP) echo request packets. The time-to-live (TTL) value, is used
in determining the intermediate routers through which the packet flows
toward the destination address. Routers decrement a packet’s TTL value and
discard packets whose TTL equals 0. On discarding a packet, the router
returns an ICMP time exceeded message to the source.
Examples
The following example discovers the routes that packets will actually take
when traveling to the destination specified in the command.
(console) # traceroute ipv6 2001::2 init-ttl 1 max-ttl 4 max-fail 0 interval
1 count 3 port 33434 size 43
Traceroute to 2001::2, 4 hops max, 43 byte packets:
1 2001::2 708 msec 41 msec 11 msec
2 2001::2 12 msec 13 msec 12 msec
3 2001::2 14 msec 9 msec 11 msec
update bootcode
Use the update bootcode command in Privileged EXEC mode to update the
bootcode on one or more switches. For each switch, the bootcode is extracted
from the active image and programmed to flash.
Syntax
update bootcode [
unit
]
•
unit
—Unit number.
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC mode
2CSNXXX_SWUM200.book Page 1742 Tuesday, December 10, 2013 1:22 PM

System Management Commands 1743
User Guidelines
It is not required to update the boot code unless directed to do so in the
release notes. Dell networking switches utilize a universal boot loader and do
not contain version specific dependencies in the boot loader. If
unit
is not
specified, all units in the stack are updated.
Example
The following example updates the bootcode on unit 2.
console#update bootcode 2
2CSNXXX_SWUM200.book Page 1743 Tuesday, December 10, 2013 1:22 PM

1744 System Management Commands
2CSNXXX_SWUM200.book Page 1744 Tuesday, December 10, 2013 1:22 PM

Telnet Server Commands 1745
80
Telnet Server Commands
Dell Networking N2000/N3000/N4000 Series Switches
The Telnet protocol (outlined in RFC 854) allows users (clients) to connect
to multiuser computers (servers) on the network. Telnet is often employed
when a user communicates with a remote login service.
Telnet is the terminal emulation protocol in the TCP/IP suite. Telnet uses
TCP as the transport protocol to initiate a connection between server and
client. After connecting, the telnet server and client enter a period of option
negotiation that determines the options each side is capable of supporting for
the connection. The connected systems can negotiate new options or
renegotiate old options at any time. In general, each end of the Telnet
connection attempts to implement all options that maximize performance
for the systems involved.
When a Telnet connection is initiated, each side of the connection is
assumed to originate and terminate at a Network Virtual Terminal, or NVT.
Therefore, the server and user hosts do not maintain information about the
characteristics of each other's terminals and terminal-handling conventions.
Telnet Client Behaviors
Different telnet clients operate differently with respect to the display of the
login banner, the MOTD banner and acknowledgements. The following
behaviors have been observed for some widely used telnet clients with a
MOTD banner configured with the following text:
If you need to utilize this device or otherwise make changes to the
configuration, you may contact the owner at x38525.
Please, be advised this unit is under test.
and a login banner configured with the following text:
Welcome to the N3024 in the Bottom Chassis - 192.168.12.190. This unit is
located in A2 and is currently under test.
Examples
1
SSH (putty):
login as: dellradius
2CSNXXX_SWUM200.book Page 1745 Tuesday, December 10, 2013 1:22 PM

1746 Telnet Server Commands
If you need to utilize this device or otherwise make changes to the
configuration, you may contact the owner at x38525.
Please, be advised this unit is under test.
dellradius@192.168.12.84's password:
Press 'y' to continue (within 30 seconds) (y/n)
Welcome to the N3024 in the Bottom Chassis - 192.168.12.190. This unit is
located in A2 and is currently under test.
N3024-C1>
2
SSH (Linux Terminal):
[root ~]# ssh 192.168.12.84 -l dellradius
If you need to utilize this device or otherwise make changes to the
configuration, you may contact the owner at x38525.
Please, be advised this unit is under test.
dellradius@192.168.12.84's password:
Press 'y' to continue (within 30 seconds) (y/n)
Welcome to the N3024 in the Bottom Chassis - 192.168.12.190. This unit is
located in A2 and is currently under test.
N3024-C1>
3
SSH (xterm):
[root ~]# ssh 192.168.12.84 -l dellradius
If you need to utilize this device or otherwise make changes to the
configuration, you may contact the owner at x38525.
Please, be advised this unit is under test.
dellradius@192.168.12.84's password:
Press 'y' to continue (within 30 seconds) (y/n)
Welcome to the N3024 in the Bottom Chassis - 192.168.12.190. This unit is
located in A2 and is currently under test.
N3024-C1>
4
Telnet:
If you need to utilize this device or otherwise make changes to the
configuration, you may contact the owner at x38525.
Press 'y' to continue (within 30 seconds) (y/n) y
Please, be advised this unit is under test.
User:root
Password:******
Welcome to the N3024 in the Bottom Chassis - 192.168.12.190. This unit is
located in A2 and is currently under test.
2CSNXXX_SWUM200.book Page 1746 Tuesday, December 10, 2013 1:22 PM

Telnet Server Commands 1747
Commands in this Chapter
This chapter explains the following commands:
ip telnet server disable
The ip telnet server disable command is used to enable/disable the Telnet
service on the switch.
Syntax
ip telnet server disable
no ip telnet server disable
Command Mode
Global Configuration
User Guidelines
No specific guidelines.
Default Value
This feature is enabled by default.
Example
console#configure
console(config)#ip telnet server disable
console(config)# no ip telnet server disable
ip telnet port
The ip telnet port command is used to configure the Telnet TCP port
number on which the switch listens for Telnet connections.
ip telnet server disable show ip telnet
ip telnet port
–
2CSNXXX_SWUM200.book Page 1747 Tuesday, December 10, 2013 1:22 PM

1748 Telnet Server Commands
Syntax
ip telnet port
port number
•
port number
— Telnet TCP port number (Range: 1025–65535)
Default Configuration
The default value for the Telnet TCP port is 23.
Command Mode
Global Configuration
User Guidelines
The Telnet server TCP port should not be set to a value that might conflict
with other well-known protocol port numbers used on this switch.
Example
console(config)#ip telnet port 1045
console(config)#no ip telnet port
show ip telnet
The show ip telnet command displays the status of the Telnet server and the
Telnet TCP port number.
Syntax
show ip telnet
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC, Configuration mode and all Configuration submodes
Example
(console)#show ip telnet
Telnet Server is Enabled. Port:23
2CSNXXX_SWUM200.book Page 1748 Tuesday, December 10, 2013 1:22 PM

Terminal Length Commands 1749
81
Terminal Length Commands
Dell Networking N2000/N3000/N4000 Series Switches
This chapter provides information about terminal length commands.
terminal length
Use the terminal length command to set the terminal length. Use the no
form of the command to reset the terminal length to the default.
Syntax
terminal length
value
no terminal length
•
value
— The length in number of lines. Range: 0–512
Default Configuration
This default value is 24.
Command Mode
Privileged EXEC mode
User Guidelines
Setting the terminal length to 0 disables paging altogether. It is
recommended that the terminal length either be set to 0 or a value larger than
4 as terminal lengths in the range of 1 to 4 may give odd output due to
prompting. The terminal length command is specific to the current session.
Logging out, rebooting or otherwise ending the current session will require
that the command be reentered. Likewise, because the terminal length
setting is specific to a session, it is never saved in the config.
Example
console#terminal length 50
2CSNXXX_SWUM200.book Page 1749 Tuesday, December 10, 2013 1:22 PM

1750 Terminal Length Commands
2CSNXXX_SWUM200.book Page 1750 Tuesday, December 10, 2013 1:22 PM

Time Ranges Commands 1751
82
Time Ranges Commands
Dell Networking N2000/N3000/N4000 Series Switches
Time ranges are used with time-based ACLs to restrict their application due
to specific time slots.
This chapter explains the following commands:
time-range
Use the time-range command in Global Configuration mode to globally
enable or disable the event notification service of the time range component.
If disabled, ACLs using time ranges are not started.
Use the optional
name
parameter to create a time range consisting of one
absolute time entry and/or one or more periodic time entries. If a time range
by this name already exists, this command enters Time-Range Configuration
mode to allow updating the time range entries.
Use the no form of the command to disable the event notifciation service.
Use the no form of this command with the optional
name
parameter to delete
a time-range identified by
name
.
Syntax
time-range [
name
]
no time-range [
name
]
•
name
—A case-sensitive alphanumeric string from 1 to 31 characters
uniquely identifying the time range. An alpha-numeric string is defined as
consisting of only alphabetic, numeric, dash, underscore, or space
characters.
Default Configuration
Time range event notification is enabled by default.
time-range periodic
absolute show time-range
2CSNXXX_SWUM200.book Page 1751 Tuesday, December 10, 2013 1:22 PM

1752 Time Ranges Commands
Command Mode
Global Configuration
User Guidelines
The CLI mode changes to Time-Range Configuration mode when you
successfully execute this command.
Example
console(config)#time-range timeRange_1
absolute
Use the absolute command in Time Range Configuration mode to add an
absolute time entry to a time range.
Use the no form of this command to delete the absolute time entry in the
time range.
Syntax
absolute {[start
time
date
] [end
time
date
]}
no absolute
•
start
time
date
—
Time and date at which the configuration that referenced the
time range is in effect. The time is expressed in a 24-hour clock, in the form of
hours:minutes. For example, 8:00 is 8:00 am and 20:00 is 8:00 pm. The date is
expressed in the format day month year. If no start time and date are specified,
the configuration statement is in effect immediately.
•
end
time
date
—
Time and date at which the configuration that referenced the
time range is no longer in effect. Same time and date format as described for the
start. The end time and date must be after the start time and date. If no end
time and date are specified, the configuration statement is in effect indefinitely.
Default Configuration
This command has no default configuration.
Command Mode
Time Range Configuration
2CSNXXX_SWUM200.book Page 1752 Tuesday, December 10, 2013 1:22 PM

Time Ranges Commands 1753
User Guidelines
Only one absolute time entry is allowed per time-range. The
time
parameter
is referenced to the currently configured time zone.
Example
console#time-range timeRange_1
console(Config-time-range)#absolute end 12:00 16 Dec 2010
periodic
Use the periodic command to add a periodic time entry to a time range. The
time
parameter is based off of the currently configured time zone. Use the no
form of this command to delete a periodic time entry from a time-range.
Syntax
periodic {
days-of-the-week
time
} to {[
days-of-the-week
]
time
}
no periodic
•
days-of-the-week
—The first occurrence of this argument is the starting
day or days from which the configuration that referenced the time range
starts going into effect. The second occurrence is the ending day or days
from which the configuration that referenced the time range is no longer
in effect. If the end days-of-the-week are the same as the start, they can be
omitted.
This argument can be any single day or combinations of days: Monday,
Tuesday, Wednesday, Thursday, Friday, Saturday, Sunday.
Other possible values are:
– daily -- Monday through Sunday
– weekdays -- Monday through Friday
– weekend -- Saturday and Sunday
– If the ending days of the week are the same as the starting days of the
week, they can be omitted.
2CSNXXX_SWUM200.book Page 1753 Tuesday, December 10, 2013 1:22 PM

1754 Time Ranges Commands
•
time
—The first occurrence of this argument is the starting hours:minutes
which the configuration that referenced the time range starts going into
effect. The second occurrence is the ending hours:minutes at which the
configuration that referenced the time range is no longer in effect.
The hours:minutes are expressed in a 24-hour clock. For example, 8:00 is
8:00 am and 20:00 is 8:00 pm.
Default Configuration
This command has no default configuration.
Command Mode
Time Range Configuration
User Guidelines
Multiple periodic entries can exist in a time range, but periodic time entries
cannot overlap each other. Periodic time entries can also coexist with an
absolute time entry in a time range.
When both periodic and absolute time entries are specified within a time
range, the periodic time entries limit the time range to only those times
specified within the periodic time range and bounded by the absolute time
range. In this case, the absolute time entry specifies the absolute start and
end dates/times and the periodic entries specify the start/stop times within
the limits of the absolute time entry dates and times.
If a periodic time entry is added to an active time-range with an existing
absolute time entry, the absolute time entry immediately becomes inactive.
For example, an administrator applies a absolute time-range configured for a
week's work hours ( 08/09-08/13 9am to 6pm) and later adds multiple
periodic entries for same days configured individually (Monday, Tuesday,
Wednesday, Thursday, Friday) but with after-work hours (9pm to 11pm) .
The administrator wants to permit/deny HTTP traffic for this time-range, but
the entire time-range is invalid due to conflicting entries. The absolute entry
is forced to inactive because the periodic entry time is not yet in effect.
Examples
console#time-range timeRange_2
console(Config-time-range)#periodic monday 00:00 to tuesday 12:30
console(Config-time-range)#periodic tuesday 13:00 to wednesday 12:00
2CSNXXX_SWUM200.book Page 1754 Tuesday, December 10, 2013 1:22 PM

Time Ranges Commands 1755
console(Config-time-range)#periodic wednesday 12:30 to thursday 20:00
console(Config-time-range)#periodic weekend 18:00 to 20:00
show time-range
Use the show time-range command in Privileged EXEC mode to display a
time range and all the absolute/periodic time entries that are defined for the
time range. The [name] parameter is used to identify a specific time range to
display. When the [name] parameter is not specified, all the time ranges
defined in the system are displayed.
Syntax
show time-range [name]
•
name
—A
specific time range to display
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC, Configuration mode and all Configuration submodes
User Guidelines
This command outputs the following.
Parameter Description
Number of Time
Ranges
Number of time ranges configured in the system.
Time Range Name Name of the time range.
Time Range Status Status of the time range(active/inactive).
Absolute start Start time and day for absolute time entry.
Absolute end End time and day for absolute time entry.
Periodic Entries Number of periodic entries in a time-range.
Periodic start Start time and day for periodic entry.
2CSNXXX_SWUM200.book Page 1755 Tuesday, December 10, 2013 1:22 PM

1756 Time Ranges Commands
Examples
console#show time-range
Admin mode: Enabled
Current number of all Time Ranges: 1
Maximum number of all Time Ranges: 100
Periodic
Time Range Name Status Entry count Absolute Entry
------------------------------ -------- ----------- --------------
t1 Active 0 Does not exist
Periodic end End time and day for periodic entry.
Parameter Description
2CSNXXX_SWUM200.book Page 1756 Tuesday, December 10, 2013 1:22 PM

USB Flash Drive Commands 1757
83
USB Flash Drive Commands
Dell Networking N2000/N3000/N4000 Series Switches
When available, a USB flash drive can be used to configure, upgrade and
provide consistency to a switching network. A USB flash drive can be plugged
in sequentially to a set of routers/switches to upgrade to newer software
versions without depending on the network to upgrade the switches with new
firmware. New switches can be preloaded with configuration prior to
deployment.
The USB Configuration Port provides access to an optional secondary storage
capability to the switch. A USB flash drive can be used to store and deploy
configurations and images from USB flash drive to the switch. A USB flash
drive can be used easily to move and copy configuration and image files from
one switch to other. Files from the switch can be copied to a USB flash device
and can be used to deploy on other switches in the network.
Validation of Files Downloaded/Uploaded from
USB Device
Image files are validated before downloading from the USB flash drive to the
switch.
Downloaded image files will be validated against the following conditions:
• File exists- Check if the file being downloaded from the USB flash drive
exists on the device.
• Valid CRC checksum.- Verify CRC for the file downloaded from the USB
flash drive to switch.
• Valid STK format - Check if the file is of type STK.
• Target device validation – Check if the file being downloaded is intended
for the target device.
2CSNXXX_SWUM200.book Page 1757 Tuesday, December 10, 2013 1:22 PM

1758 USB Flash Drive Commands
Validation for Files Uploaded from Switch to USB
Flash Drive
• Memory insufficient -Check memory availability on the USB flash drive to
upload the file.
Files downloaded from USB flash drive are not copied to RAM to perform
validations. Instead, the file is directly read from the USB flash device and
copied to buffers to perform the necessary validations.
Downloading and Uploading of Files
After the file validations are successful, the switch proceeds with downloading
of files from the USB flash device to the switch and uploading of files from
the switch to the USB flash drive. The status of file download / upload is
shown on the console. Detailed messages are logged in the system log for
further reference.
Commands in this Chapter
This chapter explains the following commands:
unmount usb
Use the unmount usb command in Privileged EXEC mode to make the USB
flash device inactive.
Syntax
unmount usb
Default Configuration
This command has no default configuration.
unmount usb dir usb
show usb
2CSNXXX_SWUM200.book Page 1758 Tuesday, December 10, 2013 1:22 PM

USB Flash Drive Commands 1759
Command Mode
Privileged EXEC
User Guidelines
Once a flash drive has been unmounted, it must be removed and reinserted in
order to be accessed again.
Example
console#unmount usb
show usb
Use the show usb command in Privileged EXEC mode to display the USB
flash device details.
Syntax
show usb device
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC
User Guidelines
The following table explains the output parameters.
Parameter Description
Device Status This field specifies the current status of device.
•
Active
if device is plugged-in and the device is recognized by
the switch.
•
Inactive
if device is not mounted.
•
Invalid
if device is not present or invalid device is plugged-in.
Manufacturer Manufacturer details
2CSNXXX_SWUM200.book Page 1759 Tuesday, December 10, 2013 1:22 PM

1760 USB Flash Drive Commands
Example
The following example is the output if the device is plugged into the USB
slot.
console#show usb device
Device Status……………………………………………… Active
Manufacturer…………………………………………………… xxxx
Serial Number………………………………………………… yyyyy
USB Version Compliance………………………… 2.0
Class Code………………………………………………………… abc
Subclass Code………………………………………………… acb
Protocol………………………………………………………………0x0
Vendor ID………………………………………………………… zzzzz
Product ID……………………………………………………… aaaaa
The following example is the output if the device is not plugged into the USB
slot.
console#show usb device
USB flash device is not plugged in.
dir usb
Use the dir usb command in Privileged EXEC mode to display the USB
device contents and memory statistics.
Serial Number Serial number of the device.
USB Version
Compliance
Version of the USB devic e.
Class Code Device Class.
Subclass Code Device SubClass.
Protocol Device Protocol.
Vendor ID Vendor specific details of device- Vendor ID.
Product ID Vendor specific details of device- Product ID.
Parameter Description
2CSNXXX_SWUM200.book Page 1760 Tuesday, December 10, 2013 1:22 PM

USB Flash Drive Commands 1761
Syntax
dir usb
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC
User Guidelines
Only the first 32 characters of the file name are displayed, even if the file
name is longer.
The following table explains the output parameters.
Example
console#dir usb
Filename Filesize Modification Time
SecureII 4096 02/25/2009 14:43:24
Documents 4096 11/27/2009 14:58:36
Stuff 4096 11/27/2009 14:59:32
Austin 4096 09/11/2010 18:43:16
running-config 819 05/13/2000 20:40:44
PC7000v20101108_1.stk 12567304 11/08/2010 16:13:54
PCM6348v10.29.16.43.stk 12444340 11/01/2010 13:55:40
Total Size: 3708858368
Bytes Used: 218435911
Bytes Free: 3490422457
Parameter Description
Filename File name
Filesize File size
Total Size USB flash device storage size.
Bytes Used Indicates size of memory used on the device.
Bytes Free Indicates size of memory free on the device.
2CSNXXX_SWUM200.book Page 1761 Tuesday, December 10, 2013 1:22 PM

1762 USB Flash Drive Commands
2CSNXXX_SWUM200.book Page 1762 Tuesday, December 10, 2013 1:22 PM

User Interface Commands 1763
84
User Interface Commands
Dell Networking N2000/N3000/N4000 Series Switches
This chapter explains the following commands:
configure terminal
Use the configure terminal command to enter global configuration mode.
This command is equivalent to the configure command with no terminal
argument.
Syntax
configure [terminal]
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC mode
Example
console#conf t
console(config)#
console#configure terminal
console(config)#
configure terminal end
do exit
enable quit
2CSNXXX_SWUM200.book Page 1763 Tuesday, December 10, 2013 1:22 PM

1764 User Interface Commands
do
Use the do command to execute commands available in Privileged EXEC
mode, Global Configuration and any config submode with command
completion. Command completion using the space bar is not available when
using this command. When in modes other than Global Configuration mode,
the do command will not appear in the list of commands shown in the help,
nor will prompting be available.
Syntax
do
line
do ?
•
line
— Command to be executed. It should be an unambiguous command
from the Privileged EXEC mode. Commands such as
configure
are
forbidden. Command line completion for the line parameter is supported.
Users may only execute commands for which they have the appropriate
privileges.
Default Configuration
This command has no default configuration.
Command Mode
All except Privileged EXEC and User EXEC modes.
User Guidelines
As per each command.
Example #1
console>en
console#configure
console(config)#interface gi1/0/1
console(config-if-Gi1/0/1)#d?
description dhcp do
dot1x duplex dvlan-tunnel
console(config-if-Gi1/0/1)#do ? ! Help from privileged EXEC level
console(config)#do ?
2CSNXXX_SWUM200.book Page 1764 Tuesday, December 10, 2013 1:22 PM

User Interface Commands 1765
arp Purge a dynamic or gateway ARP entry.
boot Select a boot image for use on the next reload.
captive-portal Manage captive portal clients.
clear Clear learned configuration or statistics.
configure Enter global Configuration mode.
copy Copy files to or from the switch.
crypto Request a crypto certificate.
debug Configure debug flags.
delete Delete a file.
dir Display directory information.
disconnect Close active remote session(s).
dot1x Initialize dot1x or re-authenticate clients.
enable Enter into user privilege mode.
erase Delete a file.
exit Exit privileged exec mode.
filedescr Set a text description for an image file.
help Display help for various special keys.
locate Blink the locator LED.
logout Exit this session. Any unsaved changes are lost.
ping Send ICMP echo packets to a specified IP address.
quit Exit this session. Any unsaved changes are lost.
release Release an in-band DHCP assigned address.
reload Reload stack or a switch in the stack.
rename Rename a file.
renew Renew an in-band DHCP assigned address.
script Manage and execute configuration scripts.
show Show configured settings and operational status.
telnet Open a telnet connection.
terminal Set per session configuration
test Test a copper port. Disable EEE modes first!.
traceroute Trace route to destination.
udld UDLD protocol commands.
unmount Flush cache and un-mount a USB device.
write Copy running configuration to startup configuration.
console(config-if-Gi1/0/1)#do a? ! Prompt/command completion from
privileged EXEC level
arp
2CSNXXX_SWUM200.book Page 1765 Tuesday, December 10, 2013 1:22 PM

1766 User Interface Commands
enable
Use the enable command in User EXEC mode to enter the Privileged EXEC
mode.
Syntax
enable
Default Configuration
The default privilege level is 15.
Command Mode
User EXEC and Privileged EXEC modes
User Guidelines
If there is no authentication method defined for enable, then a level 1 user is
not allowed to execute this command.
Example
The following example shows how to enter privileged mode.
console>enable
console#
end
Use the end command to get the CLI user control back to the privileged
execution mode or user execution mode.
Syntax
end
Default Configuration
This command has no default configuration.
Command Mode
All command modes
2CSNXXX_SWUM200.book Page 1766 Tuesday, December 10, 2013 1:22 PM

User Interface Commands 1767
User Guidelines
No specific guidelines.
Example
console(config)#end
console#end
console>
exit
Use the exit command to go to the next lower command prompt or, in User
EXEC mode, to close an active terminal session by logging off the switch.
Syntax
exit
Default Configuration
This command has no default configuration.
Command Mode
All command modes. In User EXEC mode, this command behaves identically
with the quit command.
User Guidelines
There are no user guidelines for this command.
Example
The following example changes the configuration mode from Interface
Configuration mode to User EXEC mode to the login prompt.
console(config-if-Gi1/0/1)# exit
console(config)# exit
console#exit
console>exit
User:
2CSNXXX_SWUM200.book Page 1767 Tuesday, December 10, 2013 1:22 PM

1768 User Interface Commands
quit
Use the quit command in User EXEC mode to close an active terminal
session by logging off the switch.
Syntax
quit
Default Configuration
This command has no default configuration.
Command Mode
User EXEC command mode
User Guidelines
There are no user guidelines for this command.
Example
The following example closes an active terminal session.
console>quit
2CSNXXX_SWUM200.book Page 1768 Tuesday, December 10, 2013 1:22 PM

Web Server Commands 1769
85
Web Server Commands
Dell Networking N2000/N3000/N4000 Series Switches
If enabled, the Dell Networking is manageable via industry standard web
browsers. User privilege levels are the same as for the CLI. Over 95% of the
management functions are available via the web interface, including
configuration and firmware upgrades.
Web Sessions
The HTTP protocol does not provide support for persistent connections.
Connections are constantly made and broken so there is no way to know who
is accessing the web interface or for how long they are doing so. Additionally,
with the use of basic authentication the user authorization is handled by the
client browser. This means that once entered, the user name and password are
cached in the browser and given to the server on request. Effectively, once a
user logs in to the switch, they have access until the browser closes, even
across reboots of the switch. This poses a security threat.
The Web Sessions feature makes use of cookies to control web connections,
sessions. Cookies must be enabled on the browser. The Set-Cookie directive is
sent only once at initiation of the session. With the introduction of Web
Sessions the client connections can be monitored and controlled. Web
Sessions put the authentication control in the Dell Networking instead of the
client browser resulting in a more efficient implementation that allows web
access while using Radius or TACACS+ for authentication.
The web login is implemented in the login page itself instead of a client
browser popup. Additionally, there is a logout button, always present on the
web interface. There are various commands that have been modified or added
to support Web Sessions. Similarly there are modifications to some of the
web pages. Support of SNMP configuration for Web Sessions is also available.
When the authentication method set for web login authentication is set to
TACACS+, the exec shell configuration on the TACACS+ server is used to
determine user permissions (read-only or read/ write). If the configured value
2CSNXXX_SWUM200.book Page 1769 Tuesday, December 10, 2013 1:22 PM

1770 Web Server Commands
on the server is 15, the user is given read-write permissions. Any other value is
read-only. If exec shell feature is not enabled on the server, the user is given
read-only permissions.
Commands in this Chapter
This chapter explains the following commands:
common-name
Use the common-name command in Crypto Certificate Generation or
Crypto Certificate Request mode to specify the common-name for the
switch.
Syntax
common-name
common-name
•
common-name
—Specifies the fully qualified URL or IP address of the
switch. If left unspecified, this parameter defaults to the lowest IP address
of the switch (when the certificate is generated). (Range: 1–64)
Default Configuration
This command has no default configuration.
common-name ip http secure-port
country ip http secure-server
crypto certificate generate key-generate
crypto certificate import location
crypto certificate request organization-unit
duration show crypto certificate mycertificate
ip http port show ip http server status
ip http server show ip http server secure status
ip http secure-certificate state
2CSNXXX_SWUM200.book Page 1770 Tuesday, December 10, 2013 1:22 PM

Web Server Commands 1771
Command Mode
Crypto Certification mode
User Guidelines
This command mode is entered using the crypto certificate request or crypto
certificate generate command.
Example
The following example displays how to specify the name of "router.gm.com."
console(config-crypto-cert)#common-name router.gm.com
country
Use the country command in Crypto Certificate Generation or Crypto
Certificate Request mode to specify the country.
Syntax
country
country
•
country
— Specifies the country name. (Range: 2 characters)
Default Configuration
This command has no default configuration.
Command Mode
Crypto Certificate Generation or Crypto Certificate Request mode
User Guidelines
This command mode is entered using the crypto certificate request or crypto
certificate generate command. The user can enter any two printable
characters.
Example
The following example displays how to specify the country as "us."
console(config-crypto-cert)#country us
2CSNXXX_SWUM200.book Page 1771 Tuesday, December 10, 2013 1:22 PM

1772 Web Server Commands
crypto certificate generate
Use the crypto certificate generate command in Global Configuration mode
to generate a self-signed HTTPS certificate.
Syntax
crypto certificate
number
generate
•
number
—Specifies the certificate number. (Range: 1–2)
•
generate
—Regenerates the SSL RSA key.
Default Configuration
This command has no default configuration.
Command Mode
Global Configuration mode
User Guidelines
This command is not saved in the router switch configuration; however, the
certificate and keys generated by this command are saved in the private
configuration. This saved information is never displayed to the user or backed
up to another switch. If the RSA keys do not exist, the generate parameter
must be used. To save the generated certificate and keys on the local switch
and distribute the certificate across a stack, save the configuration.
Otherwise, the certificate and keys will not be available after the next reboot.
Example
The following example generates a self-signed HTTPS certificate.
console(config)#crypto certificate 1 generate
console(config-crypto-cert)#common-name DELL
console(config-crypto-cert)#country US
console(config-crypto-cert)#Duration 3650
console(config-crypto-cert)#email no-reply@dell.com
console(config-crypto-cert)#location "Round Rock"
console(config-crypto-cert)#organization-unit "PowerConnect Networking"
console(config-crypto-cert)#organization-name "Dell, Inc."
console(config-crypto-cert)#state TX
console(config-crypto-cert)#key-generate
console(config-crypto-cert)#exit
2CSNXXX_SWUM200.book Page 1772 Tuesday, December 10, 2013 1:22 PM

Web Server Commands 1773
crypto certificate import
Use the crypto certificate import command in Global Configuration mode to
import a certificate signed by the Certification Authority for HTTPS.
Syntax
crypto certificate
number
import
•
number
— Specifies the certificate number. (Range: 1–2)
Default Configuration
This command has no default configuration.
Command Mode
Global Configuration mode
User Guidelines
Use this command to enter an external certificate (signed by the Certification
Authority) to the switch. To end the session, add a period (.) on a separate
line after the input, and press ENTER.
The imported certificate must be based on a certificate request created by the
crypto certificate request Privileged EXEC command.
If the public key found in the certificate does not match the switch's SSL RSA
key, the command fails.
This command is not saved in the router configuration; however, the
certificate imported by this command is saved in the private configuration
(which is never displayed to the user or backed up to another switch).
Example
The following example imports a certificate sighed by the Certification
Authority for HTTPS.
console(config)#crypto certificate 1 import
-----BEGIN CERTIFICATE-----
dHmUgUm9vdCBDZXJ0aWZpZXIwXDANBgkqhkiG9w0BAQEFAANLADBIAkEAp4HS
nnH/xQSGA2ffkRBwU2XIxb7n8VPsTm1xyJ1t11a1GaqchfMqqe0kmfhcoHSWr
yf1FpD0MWOTgDAwIDAQABo4IBojCCAZ4wEwYJKwYBBAGCNxQCBAYeBABDAEEw
CwR0PBAQDAgFGMA8GA1UdEwEB/wQFMAMBAf8wHQYDVR0OBBYEFAf4MT9BRD47
2CSNXXX_SWUM200.book Page 1773 Tuesday, December 10, 2013 1:22 PM

1774 Web Server Commands
ZvKBAEL9Ggp+6MIIBNgYDVR0fBIIBLTCCASkwgdKggc+ggcyGgclsZGFwOi8v
L0VByb3h5JTIwU29mdHdhcmUlMjBSb290JTIwQ2VydGlmaWVyLENOPXNlcnZl
-----END CERTIFICATE-----
Certificate imported successfully.
Issued to: router.gm.com
Issued by: www.verisign.com
Valid from: 8/9/2005 to 8/9/2005
Subject: CN= router.gm.com, 0= General Motors, C= US
Finger print: DC789788 DC88A988 127897BC BB789788
crypto certificate request
Use the crypto certificate request command in Privileged EXEC mode to
generate and display a certificate request for HTTPS. This command takes
you to Crypto Certificate Request mode.
Syntax
crypto certificate
number
request
•
number
— Specifies the certificate number. (Range: 1–2)
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC mode
User Guidelines
Use this command to export a certificate request to a Certification Authority.
The certificate request is generated in Base64-encoded X.509 format.
Before generating a certificate request, you must first generate a self-signed
certificate using the crypto certificate generate command in Global
Configuration mode in order to generate the keys. Make sure to reenter the
identical values in the certificate request fields.
After receiving the certificate from the Certification Authority, use the crypto
certificate import command in Global Configuration mode to import the
certificate into the switch. This certificate replaces the self-signed certificate.
2CSNXXX_SWUM200.book Page 1774 Tuesday, December 10, 2013 1:22 PM

Web Server Commands 1775
Use the
end
command to exit Crypto Certificate Request mode without
generating a certificate request. Use the
exit
command to exit Crypto
Certificate Request mode and generate a certificate request.
duration
Use the duration command in Crypto Certificate Generation mode to specify
the duration.
Syntax
duration
days
•
days
— Specifies the number of days a certification would be valid. If left
unspecified, the parameter defaults to 365 days. (Range: 30–3650 days)
Default Configuration
This command defaults to 365 days.
Command Mode
Crypto Certificate Generation mode
User Guidelines
This command mode is entered using the crypto certificate generate
command.
Example
The following example displays how specify a duration of 50 days that a
certification is valid.
console(config-crypto-cert)#duration 50
ip http port
Use the ip http port command in Global Configuration mode to specify the
TCP port on which the switch listens for HTTP connections. To use the
default TCP port, use the no form of this command.
2CSNXXX_SWUM200.book Page 1775 Tuesday, December 10, 2013 1:22 PM

1776 Web Server Commands
Syntax
ip http port
port-number
no ip http port
•
port-number
— Port number on which the switch HTTP server listens for
connections.. (Range: 1025–65535)
Default Configuration
This default port number is 80.
Command Mode
Global Configuration mode
User Guidelines
The HTTP TCP port should not be set to a value that might conflict with
other well-known protocol port numbers used on this switch.
Example
The following example shows how the http port number is configured to
10013.
console(config)#ip http port 10013
ip http server
Use the ip http server command in Global Configuration mode to enable the
switch to allow HTTP access to the switch. To disable this function use the
no form of this command.
Syntax
ip http server
no ip http server
Default Configuration
The default mode is enabled.
2CSNXXX_SWUM200.book Page 1776 Tuesday, December 10, 2013 1:22 PM

Web Server Commands 1777
Command Mode
Global Configuration mode
User Guidelines
This command enables HTTP access to the switch. Use the ip http secure-
server command to enable HTTPS access. It is recommended that
administrators enable HTTPS access in preference to HTTP access in order
to ensure that management activity is not snooped.
Example
The following example enables the switch to be configured from a browser.
console(config)#ip http server
ip http secure-certificate
Use the ip http secure-certificate command in Global Configuration mode to
configure the active certificate for HTTPS. To return to the default setting,
use the no form of this command.
Syntax
ip http secure-certificate
number
no ip http secure-certificate
•
number
—Specifies the certificate number. (Range: 1–2)
Default Configuration
The default value of the certificate number is 1.
Command Mode
Global Configuration mode
User Guidelines
The HTTPS certificate is generated using the crypto certificate generate
command in Global Configuration mode.
2CSNXXX_SWUM200.book Page 1777 Tuesday, December 10, 2013 1:22 PM

1778 Web Server Commands
Example
The following example configures the active certificate for HTTPS.
console(config)#ip http secure-certificate 1
ip http secure-port
Use the ip http secure-port command in Global Configuration mode to
configure a TCP port on which the switch listens for HTTPS connections. To
use the default port, use the no form of this command.
Syntax
ip http secure-port
port-number
no ip http secure-port
•
port-number
— Port number for use by the secure HTTP server. (Range:
1025–65535)
Default Configuration
This default port number is 443.
Command Mode
Global Configuration mode
User Guidelines
The HTTPS TCP port should not be set to a value that might conflict with
other well known protocol port numbers used on this switch. It is not possible
for the administrator to directly configure the port number to 443 as 443 is
out of range. Use the no form of the command to set the port number to the
default value of 443.
Example
The following example configures the HTTPS port number to 100.
console(config)#ip http secure–port 4545
2CSNXXX_SWUM200.book Page 1778 Tuesday, December 10, 2013 1:22 PM

Web Server Commands 1779
ip http secure-server
Use the ip http secure-server command in Global Configuration mode to
enable the switch to be accessed via HTTPS clients. To disable HTTPS
access,, use the no form of this command.
Syntax
ip http secure-server
no ip http secure-server
Default Configuration
The default for the switch is disabled.
Command Mode
Global Configuration mode
User Guidelines
You must import a certificate using the crypto certificate import command,
followed by the crypto certificate generate command.
Example
The following example enables the switch to be configured from a browser.
console(config)#ip http secure-server
key-generate
Use the key-generate command in Crypto Certificate Generation mode to
specify the key-generate.
Syntax
key-generate [
length
]
•
length
— Specifies the length of the SSL RSA key. If left unspecified, this
parameter defaults to 1024. (Range: 512–2048)
2CSNXXX_SWUM200.book Page 1779 Tuesday, December 10, 2013 1:22 PM

1780 Web Server Commands
Default Configuration
This command has no default configuration.
Command Mode
Crypto Certificate Generation mode
User Guidelines
This command mode is entered using the crypto certificate request
command. You must use the
key-generate
command prior to exiting the
crypto certificate request mode to properly generate a certificate request.
Example
The following example displays how to specify that you want to regenerate
the SSL RSA key 1024 byes in length.
console(config-crypto-cert)#key-generate 1024
location
Use the location command in Crypto Certificate Generation or Crypto
Certificate Request mode to specify the location or city name.
Syntax
location
location
•
location
— Specifies the location or city name. (Range: 1–64 characters)
Default Configuration
This command has no default configuration.
Command Mode
Crypto Certificate Generation or Crypto Certificate Request mode
User Guidelines
This command mode is entered using the crypto certificate request or crypto
certificate generate command.
2CSNXXX_SWUM200.book Page 1780 Tuesday, December 10, 2013 1:22 PM

Web Server Commands 1781
Example
The following example displays how to specify the city location of "austin."
console(config-crypto-cert)#location austin
organization-unit
Use the organization-unit command in Crypto Certificate Generation or
Crypto Certificate Request mode to specify the organization unit.
Syntax
organization-unit
organization-unit
•
organization-unit
— Specifies the organization-unit or department name.
(Range: 1–64 characters)
Default Configuration
This command has no default configuration.
Command Mode
Crypto Certificate Generation or Crypto Certificate Request mode
User Guidelines
This command mode is entered using the crypto certificate request or crypto
certificate generate command.
Example
The following example displays how to specify the "generalmotors"
organization-unit.
console(config-crypto-cert)#organization-unit generalmotors
show crypto certificate mycertificate
Use the show crypto certificate mycertificate command in Privileged EXEC
mode to view the SSL certificates of your switch.
Syntax
show crypto certificate mycertificate [
number
]
2CSNXXX_SWUM200.book Page 1781 Tuesday, December 10, 2013 1:22 PM

1782 Web Server Commands
•
number —
Specifies the certificate number. (Range: 1–2 digits)
Default configuration
This command has no default configuration.
Command Mode
Privileged EXEC mode, Configuration mode and all Configuration submodes
Example
The following example displays the SSL certificate of a sample switch.
console#show crypto certificate mycertificate 1
-----BEGIN CERTIFICATE-----
dHmUgUm9vdCBDZXJ0aWZpZXIwXDANBgkqhkiG9w0BAQEFAANLADBIAkEAp4HS
NnH/xQSGA2ffkRBwU2XIxb7n8VPsTm1xyJ1t11a1GaqchfMqqe0kmfhcoHSWr
yf1FpD0MWOTgDAwIDAQABo4IBojCCAZ4wEwYJKwYBBAGCNxQCBAYeBABDAEEw
CwR0PBAQDAgFGMA8GA1UdEwEB/wQFMAMBAf8wHQYDVR0OBBYEFAf4MT9BRD47
ZvKBAEL9Ggp+6MIIBNgYDVR0fBIIBLTCCASkwgdKggc+ggcyGgclsZGFwOi8v
L0VByb3h5JTIwU29mdHdhcmUlMjBSb290JTIwQ2VydGlmaWVyLENOPXNlcnZl
-----END CERTIFICATE-----
Issued by: www.verisign.com
Valid from: 8/9/2003 to 8/9/2004
Subject: CN= router.gm.com, 0= General Motors, C= US
Finger print: DC789788 DC88A988 127897BC BB789788
show ip http server status
Use the show ip http server command in User EXEC or Privileged EXEC
mode to display the HTTP server status information.
Syntax
show ip http server status
Default Configuration
This command has no default configuration.
Command Mode
User EXEC, Privileged EXEC, Configuration mode and all Configuration
submodes
2CSNXXX_SWUM200.book Page 1782 Tuesday, December 10, 2013 1:22 PM

Web Server Commands 1783
User Guidelines
This command has no user guidelines.
Example
The following example displays the HTTP server configuration.
console#show ip http server status
HTTP server enabled. Port: 80
show ip http server secure status
Use the show ip http server secure status command in User EXEC or
Privileged EXEC mode to display the HTTP secure server status information.
Syntax
show ip http server secure status
Default Configuration
This command has no default configuration.
Command Mode
User EXEC, Privileged EXEC modes, Configuration mode and all
Configuration submodes
User Guidelines
This command has no user guidelines.
Example
The following example displays an HTTPS server configuration with DH Key
exchange enabled.
console#show ip https
HTTPS server enabled. Port: 443
DH Key exchange enabled.
Certificate 1 is active
Issued by: www.verisign.com
Valid from: 8/9/2003 to 8/9/2004
Subject: CN= router.gm.com, 0= General Motors, C= US
Finger print: DC789788 DC88A988 127897BC BB789788
2CSNXXX_SWUM200.book Page 1783 Tuesday, December 10, 2013 1:22 PM

1784 Web Server Commands
Certificate 2 is inactive
Issued by: self-signed
Valid from: 8/9/2003 to 8/9/2004
Subject: CN= router.gm.com, 0= General Motors, C= US
Finger print: 1873B936 88DC3411 BC8932EF 782134BA
The following example displays the HTTPS server configuration with DH Key
exchange disabled.
console#show ip https
HTTPS server enabled. Port: 443
DH Key exchange disabled, parameters are being generated.
Certificate 1 is active
Issued by: www.verisign.com
Valid from: 8/9/2003 to 8/9/2004
Subject: CN= router.gm.com, 0= General Motors, C= US
Finger print: DC789788 DC88A988 127897BC BB789788
Certificate 2 is inactive
Issued by: self-signed
Valid from: 8/9/2003 to 8/9/2004
Subject: CN= router.gm.com, 0= General Motors, C= US
Finger print: 1873B936 88DC3411 BC8932EF 782134BA
state
Use the state command in Crypto Certificate Generation or Crypto
Certificate Request mode to specify the state or province name.
Syntax
state
state
•
state
— Specifies the state or province name. (Range: 1–64 characters)
Default Configuration
This command has no default configuration.
Command Mode
Crypto Certificate Generation or Crypto Certificate Request mode
User Guidelines
This command mode is entered using the crypto certificate request or crypto
certificate generate command.
2CSNXXX_SWUM200.book Page 1784 Tuesday, December 10, 2013 1:22 PM

Web Server Commands 1785
Example
The following example shows how to specify the state of "texas."
console(config-crypto-cert)#state texas
2CSNXXX_SWUM200.book Page 1785 Tuesday, December 10, 2013 1:22 PM

1786 Web Server Commands
2CSNXXX_SWUM200.book Page 1786 Tuesday, December 10, 2013 1:22 PM
Appendix A: List of Commands
A
aaa accounting dot1x default start-stop . . . . . . . . . . . . . . . . . . . . . . . 701
aaa authentication dot1x default . . . . . . . . . . . . . . . . . . . . . . . . . . . . 220
aaa authentication enable . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 221
aaa authentication login . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 223
aaa authorization . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 224
aaa authorization network default radius . . . . . . . . . . . . . . . . . . . . . . 227
aaa ias-user username . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 227
aaa new-model . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 228
absolute . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1752
accounting . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 702
acct-port . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 703
action . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 545
add . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 547
admin-profile . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 251
area default-cost (Router OSPF) . . . . . . . . . . . . . . . . . . . . . . . . . . . 1196
area default-cost (Router OSPFv3) . . . . . . . . . . . . . . . . . . . . . . . . . 1278
area nssa (Router OSPF) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1196
area nssa (Router OSPFv3) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1279
area nssa default-info-originate (Router OSPF Config) . . . . . . . . . 1198
area nssa default-info-originate (Router OSPFv3 Config) . . . . . . . 1280
area nssa no-redistribute . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1199, 1281
area nssa no-summary . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1200, 1282
area nssa translator-role . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1200, 1283
area nssa translator-stab-intv . . . . . . . . . . . . . . . . . . . . . . . . . . 1201, 1284
area range (Router OSPF) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1202
area range (Router OSPFv3) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1285
area stub . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1205, 1286
area stub no-summary . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1206, 1287
area virtual-link . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1206, 1287
area virtual-link authentication . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1209
area virtual-link dead-interval . . . . . . . . . . . . . . . . . . . . . . . . . 1210, 1289
area virtual-link hello-interval . . . . . . . . . . . . . . . . . . . . . . . . . 1211, 1290
area virtual-link retransmit-interval . . . . . . . . . . . . . . . . . . . . 1212, 1291
area virtual-link transmit-delay . . . . . . . . . . . . . . . . . . . . . . . . 1213, 1292
arp . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 920
2CSNXXX_SWUM200.book Page 1787 Tuesday, December 10, 2013 1:22 PM
arp access-list . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 345
arp cachesize . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 921
arp dynamicrenew . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 922
arp purge . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 923
arp resptime . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 924
arp retries . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 925
arp timeout . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 925
asset-tag . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1670
assign-queue . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 639
authentication enable . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 858
authentication order . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 859
authentication priority . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 859
authentication restart . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 860
authentication timeout . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1397
authorization . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 229
auth-port . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 704
auto-cost . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1213
auto-summary . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1341
B
bandwidth . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1214
banner exec . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1670
banner login . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1671
banner motd . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1672
banner motd acknowledge . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1673
block . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1402
boot auto-copy-sw . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1388
boot auto-copy-sw allow-downgrade . . . . . . . . . . . . . . . . . . . . . . . . . 1389
boot host autoreboot . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1390
boot host autosave . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1390
boot host dhcp . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1391
boot host retrycount . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1392
boot system . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1458
bootfile . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 935
bootpdhcprelay maxhopcount . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1031
bootpdhcprelay minwaittime . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1032
C
capability opaque . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1215
captive-portal . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1397
2CSNXXX_SWUM200.book Page 1788 Tuesday, December 10, 2013 1:22 PM
captive-portal client deauthenticate . . . . . . . . . . . . . . . . . . . . . . . . . 1410
channel-group . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 593
class . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 639
class-map . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 640
class-map rename . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 641
classofservice dot1p-mapping . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 642
classofservice ip-dscp-mapping . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 643
classofservice traffic-class-group . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 899
classofservice trust . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 646
clear (IAS) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 229
clear arp-cache . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 926
clear arp-cache management . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 927
clear authentication authentication-history . . . . . . . . . . . . . . . . . . . . 862
clear authentication statistics . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 861
clear captive-portal users . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1414
clear checkpoint statistics . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1675
clear config . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1459
clear counters . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 372
clear counters stack-ports . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1676
clear dhcp l2relay statistics interface . . . . . . . . . . . . . . . . . . . . . . . . . 322
clear dot1x authentication–history . . . . . . . . . . . . . . . . . . . . . . . . . . . 874
clear green-mode statistics . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 434
clear gvrp statistics . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 443
clear host . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 478
clear ip address-conflict-detect . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 478
clear ip arp inspection statistics . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 346
clear ip dhcp binding . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 935
clear ip dhcp conflict . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 936
clear ip dhcp snooping binding . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 330
clear ip dhcp snooping statistics . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 331
clear ip helper statistics . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1033
clear ip mroute . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1138
clear ip ospf . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1216
clear ip ospf stub-router . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1217
clear ipv6 dhcp . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 959
clear ipv6 dhcp snooping binding . . . . . . . . . . . . . . . . . . . . . . . . . . . . 975
clear ipv6 neighbors . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1082
clear ipv6 statistics . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1083
clear isdp counters . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 301
2CSNXXX_SWUM200.book Page 1789 Tuesday, December 10, 2013 1:22 PM
clear isdp table . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 302
clear lldp remote-data . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 552
clear lldp statistics . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 553
clear logging . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1648
clear logging email statistics . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 365
clear logging file . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1649
clear mac address-table . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 280
clear power inline statistics . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1535
clear priority-flow-control statistics . . . . . . . . . . . . . . . . . . . . . . . . . . 912
clear spanning-tree detected-protocols . . . . . . . . . . . . . . . . . . . . . . . . 731
clear vpc statistics . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 607
client-identifier . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 937
client-name . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 937
clock summer-time date . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1447
clock summer-time recurring . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1446
clock timezone hours-offset . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1444
common-name . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1770
compatible rfc1583 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1217
configuration . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1402
conform-color . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 647
connect . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1676
copy . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1460
cos-queue min-bandwidth . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 649
cos-queue random-detect . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 650
cos-queue strict . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 652
country . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1771
crypto certificate generate . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1772
crypto certificate import . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1773
crypto certificate request . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1774
crypto key generate dsa . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1635
crypto key generate rsa . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1636
crypto key pubkey-chain ssh . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1637
crypto key zeroize {rsa|dsa} . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1638
crypto key zeroize pubkey-chain . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1638
cut-through mode . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1678
D
datacenter-bridging . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 889
dcb enable . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 554
2CSNXXX_SWUM200.book Page 1790 Tuesday, December 10, 2013 1:22 PM
deadtime . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 705
debug aaa accounting . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 705
debug arp . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1566
debug authentication interface . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1567
debug auto-voip . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1568
debug cfm . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 428
debug clear . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1568
debug console . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1569
debug dhcp packet . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 326
debug dot1ag . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1569
debug dot1x . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1571
debug igmpsnooping . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1571
debug ip acl . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1572
debug ip dvmrp . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1573
debug ip igmp . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1573
debug ip mcache . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1574
debug ip pimdm packet . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1575
debug ip pimsm packet . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1576
debug ip vrrp . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1576
debug ipv6 dhcp . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1577
debug ipv6 mcache . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1578
debug ipv6 mld . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1578
debug ipv6 pimdm . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1579
debug ipv6 pimsm . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1580
debug isdp . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1581
debug lacp . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1581
debug mldsnooping . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1582
debug ospf . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1583
debug ospfv3 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1583
debug ping . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1584
debug rip . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1585
debug sflow . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1585
debug spanning-tree . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1586
debug udld . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 789
debug vpc . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 608
debug vrrp . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1587
default-information originate (Router OSPF Configuration) . . . . 1218
default-information originate (Router OSPFv3 Configuration) . . . 1292
default-information originate (Router RIP Configuration) . . . . . . 1342
2CSNXXX_SWUM200.book Page 1791 Tuesday, December 10, 2013 1:22 PM
default-metric . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1219, 1293, 1343
default-router . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 938
delete . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1465
delete backup-config . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1466
delete backup-image . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1466
delete startup-config . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1467
deny (management) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1496
deny | permit (IP ACL) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 261
deny | permit (IPv6 ACL) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 498
deny | permit (Mac-Access-List-Configuration) . . . . . . . . . . . . . . . . 266
depends-on . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 547
description . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 373
description (Administrative Profile Config) . . . . . . . . . . . . . . . . . . . . 251
description (Logging) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1650
dhcp l2relay (Global Configuration) . . . . . . . . . . . . . . . . . . . . . . . . . 312
dhcp l2relay (Interface Configuration) . . . . . . . . . . . . . . . . . . . . . . . . 312
dhcp l2relay circuit-id . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 313
dhcp l2relay remote-id . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 314
dhcp l2relay trust . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 314
dhcp l2relay vlan . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 315
diffserv . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 653
dir . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1467
dir usb . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1760
distance ospf . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1220, 1294
distance rip . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1344
distribute-list out . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1221, 1344
dns-server (IP DHCP Pool Config) . . . . . . . . . . . . . . . . . . . . . . . . . . 939
dns-server (IPv6 DHCP Pool Config) . . . . . . . . . . . . . . . . . . . . . . . . . 960
do . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1764
domain-name (IP DHCP Pool Config) . . . . . . . . . . . . . . . . . . . . . . . 940
domain-name (IPv6 DHCP Pool Config) . . . . . . . . . . . . . . . . . . . . . 960
dos-control firstfrag . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1479
dos-control icmp . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1479
dos-control l4port . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1480
dos-control sipdip . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1481
dos-control tcpflag . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1482
dos-control tcpfrag . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1482
dot1x dynamic-vlan enable . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 845
dot1x guest-vlan . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 875
2CSNXXX_SWUM200.book Page 1792 Tuesday, December 10, 2013 1:22 PM
dot1x initialize . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 846
dot1x mac-auth-bypass . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 847
dot1x max-req . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 848
dot1x max-users . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 849
dot1x port-control . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 849
dot1x re-authenticate . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 851
dot1x reauthentication . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 851
dot1x system-auth-control . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 852
dot1x system-auth-control monitor . . . . . . . . . . . . . . . . . . . . . . . . . . 853
dot1x timeout guest-vlan-period . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 853
dot1x timeout quiet-period . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 854
dot1x timeout re-authperiod . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 855
dot1x timeout server-timeout . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 856
dot1x timeout tx-period . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 857
dot1x unauth-vlan . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 875
drop . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 653
duplex . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 374
duration . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1775
dvlan-tunnel ethertype . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 797
E
enable . . . . . . . . . . . . . . . . . . . . . . . 1222, 1295, 1345, 1398, 1403, 1766
enable authentication . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 230
enable password . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 231
enable password encrypted . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1516
encapsulation . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1047
end . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1766
erase . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1468
ethernet cfm cc level . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 417
ethernet cfm domain . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 416
ethernet cfm mep active . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 420
ethernet cfm mep archive-hold-time . . . . . . . . . . . . . . . . . . . . . . . . . 420
ethernet cfm mep enable . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 419
ethernet cfm mep level . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 418
ethernet cfm mip level . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 421
exception core-file . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1587
exception dump . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1588
exception protocol . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1589
exception switch-chip-register . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1591
2CSNXXX_SWUM200.book Page 1793 Tuesday, December 10, 2013 1:22 PM
exec-banner . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1678
exec-timeout . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1489
exit . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1679, 1767
exit (mst) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 732
exit-overflow-interval . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1223, 1296
external-lsdb-limit . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1224, 1297
F
feature vpc . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 609
filedescr . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1469
flowcontrol receive . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 374
G
garp timer . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 444
gmrp enable . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1004
green-mode eee . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 433
green-mode eee-lpi-history . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 434
green-mode energy-detect . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 432
group . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1404
gvrp enable (global) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 445
gvrp enable (interface) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 446
gvrp registration-forbid . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 447
gvrp vlan-creation-forbid . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 448
H
hardware profile portmode . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1680
hardware-address . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 940
hashing-mode . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 595
history . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1490
history size . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1491
host . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 941
hostname . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1681
hostroutesaccept . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1346
http port . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1399
https port . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1399
I
initiate failover . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1682
instance (mst) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 732
interface . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 375, 1404
interface loopback . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1133
interface port-channel . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 594
2CSNXXX_SWUM200.book Page 1794 Tuesday, December 10, 2013 1:22 PM
interface range . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 376
interface range port-channel . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 594
interface range vlan . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 800
interface tunnel . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1358
interface vlan . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 799
ip access-group . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 268
ip access-list . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 260
ip address . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1047
ip address (Out-of-Band) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 479
ip address dhcp (Interface Config) . . . . . . . . . . . . . . . . . . . . . . . . . . . 481
ip address-conflict-detect run . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 481
ip arp inspection filter . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 347
ip arp inspection limit . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 347
ip arp inspection trust . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 348
ip arp inspection validate . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 349
ip arp inspection vlan . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 350
ip default-gateway . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 483
ip dhcp bootp automatic . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 942
ip dhcp conflict logging . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 943
ip dhcp excluded-address . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 943
ip dhcp ping packets . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 944
ip dhcp pool . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 932
ip dhcp relay information check . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1033
ip dhcp relay information check-reply . . . . . . . . . . . . . . . . . . . . . . . 1034
ip dhcp relay information option . . . . . . . . . . . . . . . . . . . . . . . . . . . 1035
ip dhcp relay information option-insert . . . . . . . . . . . . . . . . . . . . . . 1036
ip dhcp snooping . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 331
ip dhcp snooping binding . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 332
ip dhcp snooping database . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 333
ip dhcp snooping database write-delay . . . . . . . . . . . . . . . . . . . . . . . . 334
ip dhcp snooping limit . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 335
ip dhcp snooping log-invalid . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 336
ip dhcp snooping trust . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 337
ip dhcp snooping verify mac-address . . . . . . . . . . . . . . . . . . . . . . . . . 338
ip domain-lookup . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 484
ip domain-name . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 484
ip dvmrp . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 995
ip dvmrp metric . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 996
ip helper enable . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1040
2CSNXXX_SWUM200.book Page 1795 Tuesday, December 10, 2013 1:22 PM
ip helper-address (global configuration) . . . . . . . . . . . . . . . . . . . . . . 1037
ip helper-address (interface configuration) . . . . . . . . . . . . . . . . . . . 1038
ip host . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 485
ip http authentication . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 232
ip http port . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1775
ip http secure-certificate . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1777
ip http secure-port . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1778
ip http secure-server . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1779
ip http server . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1776
ip https authentication . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 233
ip icmp echo-reply . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1483
ip icmp error-interval . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1484
ip igmp last-member-query-count . . . . . . . . . . . . . . . . . . . . . . . . . . 1009
ip igmp last-member-query-interval . . . . . . . . . . . . . . . . . . . . . . . . . 1009
ip igmp mroute-proxy . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1010
ip igmp proxy-service . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1021
ip igmp proxy-service reset-status . . . . . . . . . . . . . . . . . . . . . . . . . . . 1022
ip igmp proxy-service unsolicited-report-interval . . . . . . . . . . . . . . 1023
ip igmp query-interval . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1011
ip igmp query-max-response-time . . . . . . . . . . . . . . . . . . . . . . . . . . 1012
ip igmp robustness . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1013
ip igmp snooping (global) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 454
ip igmp snooping (VLAN) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 456
ip igmp snooping querier . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 468
ip igmp snooping querier election participate . . . . . . . . . . . . . . . . . . 469
ip igmp snooping querier query-interval . . . . . . . . . . . . . . . . . . . . . . . 470
ip igmp snooping querier timer expiry . . . . . . . . . . . . . . . . . . . . . . . . 471
ip igmp snooping querier version . . . . . . . . . . . . . . . . . . . . . . . . . . . . 472
ip igmp snooping report-suppression . . . . . . . . . . . . . . . . . . . . . . . . . 462
ip igmp snooping unregistered floodall . . . . . . . . . . . . . . . . . . . . . . . 463
ip igmp snooping vlan groupmembership-interval . . . . . . . . . . . . . . 460
ip igmp snooping vlan immediate-leave . . . . . . . . . . . . . . . . . . . . . . . 459
ip igmp snooping vlan last-member-query-interval . . . . . . . . . . . . . . 461
ip igmp snooping vlan mcrtrexpiretime . . . . . . . . . . . . . . . . . . . . . . . 462
ip igmp snooping vlan mrouter . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 464
ip igmp startup-query-count . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1014
ip igmp startup-query-interval . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1014
ip igmp version . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1015
ip irdp . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1333
2CSNXXX_SWUM200.book Page 1796 Tuesday, December 10, 2013 1:22 PM
ip irdp holdtime . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1335
ip irdp maxadvertinterval . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1336
ip irdp minadvertinterval . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1337
ip irdp multicast . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1338
ip irdp preference . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1338
ip local-proxy-arp . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 928
ip mroute . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1140
ip multicast boundary . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1140
ip multicast ttl-threshold . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1142
ip multicast-routing . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1141
ip name-server . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 486
ip netdirbcast . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1049
ip ospf area . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1225
ip ospf authentication . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1225
ip ospf cost . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1226
ip ospf database-filter all out . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1227
ip ospf dead-interval . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1228
ip ospf hello-interval . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1228
ip ospf mtu-ignore . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1229
ip ospf network . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1230
ip ospf priority . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1231
ip ospf retransmit-interval . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1232
ip ospf transmit-delay . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1233
ip pim . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1143
ip pim bsr-border . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1144
ip pim bsr-candidate . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1145
ip pim dense-mode . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1146
ip pim dr-priority . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1146
ip pim hello-interval . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1147
ip pim join-prune-interval . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1148
ip pim rp-address . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1149
ip pim rp-candidate . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1150
ip pim sparse-mode . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1150
ip pim ssm . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1151
ip policy route-map . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1049
ip proxy-arp . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 928
ip redirects . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1485
ip rip . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1347
ip rip authentication . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1347
2CSNXXX_SWUM200.book Page 1797 Tuesday, December 10, 2013 1:22 PM
ip rip receive version . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1348
ip rip send version . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1349
ip route . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1050
ip route default . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1051
ip route distance . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1053
ip routing . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1053
ip ssh port . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1639
ip ssh pubkey-auth . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1640
ip ssh server . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1640
ip telnet port . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1747
ip telnet server disable . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1747
ip unreachables . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1485
ip verify binding . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 531
ip verify source . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 529
ip verify source port-security . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 531
ip vrrp . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1366
ip vrrp accept-mode . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1382
ipv6 access-list . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 504
ipv6 access-list rename . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 504
ipv6 address . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1083
ipv6 address (Interface Config) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 487
ipv6 address (OOB Port) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 488
ipv6 address dhcp . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 489
ipv6 dhcp pool . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 961
ipv6 dhcp relay . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 962
ipv6 dhcp server . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 963
ipv6 dhcp snooping log-invalid . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 982
ipv6 dhcp snooping trust . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 983
ipv6 dhcp snooping verify mac-address . . . . . . . . . . . . . . . . . . . . . . . 983
ipv6 enable . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1085
ipv6 enable (Interface Config) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 490
ipv6 enable (OOB Config) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 491
ipv6 gateway (OOB Config) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 491
ipv6 hop-limit . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1086
ipv6 host . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1086
ipv6 icmp error-interval . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1486
IPv6 Limitations & Restrictions . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1081
ipv6 mld host-proxy . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1088
ipv6 mld host-proxy reset-status . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1089
2CSNXXX_SWUM200.book Page 1798 Tuesday, December 10, 2013 1:22 PM
ipv6 mld host-proxy unsolicit-rprt-interval . . . . . . . . . . . . . . . . . . . 1090
ipv6 mld last-member-query-count . . . . . . . . . . . . . . . . . . . . . . . . . 1087
ipv6 mld last-member-query-interval . . . . . . . . . . . . . . . . . . . . . . . . 1088
ipv6 mld query-interval . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1090
ipv6 mld query-max-response-time . . . . . . . . . . . . . . . . . . . . . . . . . 1091
ipv6 mld snooping (Global) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 514
ipv6 mld snooping listener-message-suppression . . . . . . . . . . . . . . . . 511
ipv6 mld snooping querier . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 521
ipv6 mld snooping querier (VLAN mode) . . . . . . . . . . . . . . . . . . . . . 522
ipv6 mld snooping querier address . . . . . . . . . . . . . . . . . . . . . . . . . . . 523
ipv6 mld snooping querier election participate . . . . . . . . . . . . . . . . . 523
ipv6 mld snooping querier query-interval . . . . . . . . . . . . . . . . . . . . . . 524
ipv6 mld snooping querier timer expiry . . . . . . . . . . . . . . . . . . . . . . . 525
ipv6 mld snooping vlan groupmembership-interval . . . . . . . . . . . . . 510
ipv6 mld snooping vlan immediate-leave . . . . . . . . . . . . . . . . . . . . . . 510
ipv6 mld snooping vlan last-listener-query-interval . . . . . . . . . . . . . . 512
ipv6 mld snooping vlan mcrtexpiretime . . . . . . . . . . . . . . . . . . . . . . . 513
ipv6 mld snooping vlan mrouter . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 514
ipv6 nd dad attempts . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1092
ipv6 nd managed-config-flag . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1093
ipv6 nd ns-interval . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1093
ipv6 nd other-config-flag . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1094
ipv6 nd prefix . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1095
ipv6 nd ra-interval . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1096
ipv6 nd ra-lifetime . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1097
ipv6 nd reachable-time . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1098
ipv6 nd suppress-ra . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1099
ipv6 ospf . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1297
ipv6 ospf area . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1298
ipv6 ospf cost . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1299
ipv6 ospf dead-interval . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1300
ipv6 ospf hello-interval . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1300
ipv6 ospf mtu-ignore . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1301
ipv6 ospf network . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1302
ipv6 ospf priority . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1303
ipv6 ospf retransmit-interval . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1304
ipv6 ospf transmit-delay . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1305
ipv6 pim (VLAN Interface config) . . . . . . . . . . . . . . . . . . . . . . . . . . 1168
ipv6 pim bsr-border . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1169
2CSNXXX_SWUM200.book Page 1799 Tuesday, December 10, 2013 1:22 PM
ipv6 pim bsr-candidate . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1170
ipv6 pim dense-mode . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1171
ipv6 pim dr-priority . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1171
ipv6 pim hello-interval . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1172
ipv6 pim join-prune-interval . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1173
ipv6 pim register-threshold . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1173
ipv6 pim rp-address . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1174
ipv6 pim rp-candidate . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1175
ipv6 pim sparse-mode . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1176
ipv6 pim ssm . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1176
ipv6 route . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1099
ipv6 route distance . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1101
ipv6 router ospf . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1305
ipv6 traffic-filter . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 505
ipv6 unicast-routing . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1101
ipv6 unreachables . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1487
ipv6 verify binding . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 984
ipv6 verify source . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 985
iscsi aging time . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 536
iscsi cos . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 537
iscsi enable . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 539
iscsi target port . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 540
isdp advertise-v2 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 302
isdp enable . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 303
isdp holdtime . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 304
isdp timer . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 304
K
key . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 706, 772
key encrypted . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 707, 772
key-generate . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1779
key-string . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1641
L
lacp port-priority . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 596
lacp system-priority . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 597
lacp timeout . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 598
lease . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 945
level . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1650
line . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1491
2CSNXXX_SWUM200.book Page 1800 Tuesday, December 10, 2013 1:22 PM
link-dependency group . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 546
lldp dcbx port-role . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 893
lldp dcbx version . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 890
lldp med . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 554
lldp med confignotification . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 555
lldp med faststartrepeatcount . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 555
lldp med transmit-tlv . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 556
lldp notification . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 557
lldp notification-interval . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 557
lldp receive . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 558
lldp timers . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 559
lldp tlv-select dcbxp . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 891
lldp transmit . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 560
lldp transmit-mgmt . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 561
lldp transmit-tlv . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 561
load-interval . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1683
locale . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1405
locate . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1684
location . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1780
log adjacency-changes . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1233
logging . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1652
logging audit . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1654
logging buffered . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1655
logging cli-command . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1651
logging console . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1656
logging email . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 358
logging email from-addr . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 362
logging email logtime . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 363
logging email message-type subject . . . . . . . . . . . . . . . . . . . . . . . . . . 363
logging email message-type to-addr . . . . . . . . . . . . . . . . . . . . . . . . . . 361
logging email test message-type . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 364
logging email urgent . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 359
logging facility . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1657
logging file . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1658
logging monitor . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1659
logging on . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1660
logging protocol . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1661
logging snmp . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1662
logging traps . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 360
2CSNXXX_SWUM200.book Page 1801 Tuesday, December 10, 2013 1:22 PM
logging web-session . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1663
login authentication . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 235
login-banner . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1685
logout . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1685
M
mac access-group . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 270
mac access-list extended . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 271
mac access-list extended rename . . . . . . . . . . . . . . . . . . . . . . . . . . . . 272
mac address-table aging-time . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 281
mac address-table multicast forbidden address . . . . . . . . . . . . . . . . . 282
mac address-table static . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 283
macro apply . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1431
macro description . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1433
macro global apply . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1429
macro global description . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1431
macro global trace . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1430
macro name . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1428
macro trace . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1432
mail-server ip-address | hostname . . . . . . . . . . . . . . . . . . . . . . . . . . . 366
management access-class . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1497
management access-list . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1498
mark cos . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 654
mark ip-dscp . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 655
mark ip-precedence . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 655
match class-map . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 656
match cos . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 657
match destination-address mac . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 658
match dstip . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 659
match dstip6 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 659
match dstl4port . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 660
match ethertype . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 661
match ip address . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1054
match ip dscp . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 662
match ip precedence . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 663
match ip tos . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 664
match ip6flowlbl . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 662
match length . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1056
match mac-list . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1057
2CSNXXX_SWUM200.book Page 1802 Tuesday, December 10, 2013 1:22 PM
match protocol . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 665
match source-address mac . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 666
match srcip . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 667
match srcip6 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 667
match srcl4port . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 668
match vlan . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 669
maximum-paths . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1236, 1306
max-metric router-lsa . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1234
member . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1687
mirror . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 670
mode dvlan-tunnel . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 801
monitor capture . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 377
monitor capture (Privileged Exec) . . . . . . . . . . . . . . . . . . . . . . . . . . . 382
monitor session . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 628
motd-banner . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1688
msgauth . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 708
mvr . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 576
mvr group . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 576
mvr immediate . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 580
mvr mode . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 577
mvr querytime . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 578
mvr type . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 581
mvr vlan . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 579
mvr vlan group . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 582
N
name (Captive Portal) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1406
name (mst) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 734
name (RADIUS server) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 708
name (VLAN Configuration) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 802
netbios-name-server . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 946
netbios-node-type . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 947
network . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 947
network area . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1237
next-server . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 948
no clock summer-time . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1448
no clock timezone . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1445
no crypto certificate . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1642
no user . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1415
2CSNXXX_SWUM200.book Page 1803 Tuesday, December 10, 2013 1:22 PM
nsf . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1238, 1307, 1688
nsf helper . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1239, 1308
nsf helper strict-lsa-checking . . . . . . . . . . . . . . . . . . . . . . . . . . 1239, 1309
nsf restart-interval . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1240, 1309
O
option . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 949
organization-unit . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1781
P
passive-interface . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1242, 1310
passive-interface default . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1241, 1311
password (aaa IAS User Configuration) . . . . . . . . . . . . . . . . . . . . . . . 236
password (Line Configuration) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 237
password (Mail Server Configuration Mode) . . . . . . . . . . . . . . . . . . . 368
password (User EXEC) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 238
passwords aging . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1506
passwords history . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1506
passwords lock-out . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1507
passwords min-length . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1508
passwords strength exclude-keyword . . . . . . . . . . . . . . . . . . . . . . . . 1515
passwords strength max-limit consecutive-characters . . . . . . . . . . . 1513
passwords strength max-limit repeated-characters . . . . . . . . . . . . . 1513
passwords strength minimum character-classes . . . . . . . . . . . . . . . . 1514
passwords strength minimum lowercase-letters . . . . . . . . . . . . . . . . 1510
passwords strength minimum numeric-characters . . . . . . . . . . . . . 1511
passwords strength minimum special-characters . . . . . . . . . . . . . . . 1512
passwords strength minimum uppercase-letters . . . . . . . . . . . . . . . 1510
passwords strength-check . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1509
peer-detection enable . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 610
peer-keepalive destination . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 611
peer-keepalive enable . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 612
periodic . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1753
permit (management) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1499
permit ip host mac host . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 351
ping . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1689
ping ethernet cfm . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 422
ping ipv6 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1102
ping ipv6 interface . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1103
police-simple . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 670
2CSNXXX_SWUM200.book Page 1804 Tuesday, December 10, 2013 1:22 PM
police-single-rate . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 672
police-two-rate . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 673
policy-map . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 674
port . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 773, 1664
port (Mail Server Configuration Mode) . . . . . . . . . . . . . . . . . . . . . . . 367
port security . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 284
port security max . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 285
port-channel local-preference . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 599
port-channel min-links . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 600
power inline . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1526
power inline detection . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1527
power inline high-power . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1527
power inline limit . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1528
power inline management . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1529
power inline powered-device . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1533
power inline priority . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1533
power inline reset . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1534
power inline usage-threshold . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1535
prefix-delegation . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 965
primary . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 709
priority . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 710, 774
priority-flow-control mode . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 910
priority-flow-control priority . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 911
private-vlan . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 832
protocol . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1406
protocol group . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 803
protocol vlan group . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 804
protocol vlan group all . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 805
Q
quit . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1768
R
radius-server attribute 4 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 711
radius-server deadtime . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 712
radius-server host . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 713
radius-server key . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 714
radius-server key encrypted . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 715
radius-server retransmit . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 715
radius-server source-ip . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 716
2CSNXXX_SWUM200.book Page 1805 Tuesday, December 10, 2013 1:22 PM
radius-server timeout . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 717
random-detect exponential-weighting-constant . . . . . . . . . . . . . . . . 678
random-detect queue-parms . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 675
rate-limit cpu . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1105
redirect . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 678, 1407
redirect-url . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1407
redistribute . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1242, 1312, 1350
release dhcp . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 324
reload . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1691
remote-span . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 630
rename . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1470
renew dhcp . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 325
retransmit . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 718
revision (mst) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 735
rmon alarm . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1539
rmon collection history . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1541
rmon event . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1542
rmon hcalarm . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1543
role priority . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 614
route-map . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1058
router ospf . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1244
router rip . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1351
router-id . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1244, 1312
rule . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 252
S
script apply . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1451
script delete . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1452
script list . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1453
script show . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1453
script validate . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1454
sdm prefer . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1559
security . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 366
service . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 417
service dhcp . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 953
service dhcpv6 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 966
service unsupported-transceiver . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1693
service-acl input . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 273
service-policy . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 679
2CSNXXX_SWUM200.book Page 1806 Tuesday, December 10, 2013 1:22 PM
session-timeout . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1408
set description . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1693
set interface null0 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1059
set ip default next-hop . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1060
set ip next-hop . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1061
set ip precedence . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1062
sflow destination . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1597
sflow polling . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1599
sflow polling (Interface Mode) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1600
sflow sampling . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1601
sflow sampling (Interface Mode) . . . . . . . . . . . . . . . . . . . . . . . . . . . 1602
show aaa ias-users . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 238
show aaa servers . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 718
show aaa statistics . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 239
show access-lists interface . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 274
show accounting methods . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 721
show admin-profiles . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 253
show admin-profiles brief . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 254
show arp . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 929
show arp access-list . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 351
show authentication . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 862
show authentication methods . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 240
show authenticaton authentication-history . . . . . . . . . . . . . . . . . . . . 863
show authenticaton statistics . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 864
show authorization methods . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 241
show auto-copy-sw . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1393
show backup-config . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1470
show banner . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1696
show boot . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1393
show bootvar . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1471
show captive-portal . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1400
show captive-portal client status . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1410
show captive-portal configuration . . . . . . . . . . . . . . . . . . . . . . . . . . . 1420
show captive-portal configuration client status . . . . . . . . . . . . . . . . 1411
show captive-portal configuration interface . . . . . . . . . . . . . . . . . . . 1421
show captive-portal configuration locales . . . . . . . . . . . . . . . . . . . . . 1422
show captive-portal configuration status . . . . . . . . . . . . . . . . . . . . . 1423
show captive-portal interface client status . . . . . . . . . . . . . . . . . . . . 1412
show captive-portal interface configuration status . . . . . . . . . . . . . 1413
2CSNXXX_SWUM200.book Page 1807 Tuesday, December 10, 2013 1:22 PM
show captive-portal status . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1401
show captive-portal user . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1415
show checkpoint statistics . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1697
show class-map . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 680
show classofservice dot1p-mapping . . . . . . . . . . . . . . . . . . . . . . . . . . 682
show classofservice ip-dscp-mapping . . . . . . . . . . . . . . . . . . . . . . . . . 683
show classofservice traffic-class-group . . . . . . . . . . . . . . . . . . . . . . . . 906
show classofservice trust . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 685
show cli modes . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 255
show clock . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1448
show copper-ports tdr . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1521
show crypto certificate mycertificate . . . . . . . . . . . . . . . . . . . . . . . . 1781
show crypto key mypubkey . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1643
show crypto key pubkey-chain ssh . . . . . . . . . . . . . . . . . . . . . . . . . . 1644
show cut-through mode . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1698
show debugging . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1591
show dhcp l2relay agent-option vlan . . . . . . . . . . . . . . . . . . . . . . . . . . 319
show dhcp l2relay all . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 316
show dhcp l2relay circuit-id vlan . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 320
show dhcp l2relay interface . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 316
show dhcp l2relay remote-id vlan . . . . . . . . . . . . . . . . . . . . . . . . . . . . 321
show dhcp l2relay stats interface . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 317
show dhcp l2relay subscription interface . . . . . . . . . . . . . . . . . . . . . . 318
show dhcp l2relay vlan . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 319
show dhcp lease . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 326
show diffserv . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 686
show diffserv service brief . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 688
show diffserv service interface . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 686
show diffserv service interface port-channel . . . . . . . . . . . . . . . . . . . . 687
show dos-control . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1487
show dot1x . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 865
show dot1x advanced . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 876
show dot1x authentication-history . . . . . . . . . . . . . . . . . . . . . . . . . . . 866
show dot1x clients . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 868
show dot1x interface . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 870
show dot1x interface statistics . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 871
show dot1x users . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 873
show dvlan-tunnel . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 806
show dvlan-tunnel interface . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 807
2CSNXXX_SWUM200.book Page 1808 Tuesday, December 10, 2013 1:22 PM
show ethernet cfm domain . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 424
show ethernet cfm errors . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 424
show ethernet cfm maintenance-points local . . . . . . . . . . . . . . . . . . 425
show ethernet cfm maintenance-points remote . . . . . . . . . . . . . . . . 426
show ethernet cfm statistics . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 427
show exception . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1592
show fiber-ports optical-transceiver . . . . . . . . . . . . . . . . . . . . . . . . . 1522
show gmrp configuration . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1005
show green-mode . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 439
show green-mode eee-lpi-history interface . . . . . . . . . . . . . . . . . . . . . 440
show green-mode interface-id . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 435
show gvrp configuration . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 448
show gvrp error-statistics . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 450
show gvrp statistics . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 451
show hardware profile . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1698
show hosts . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 492
show idprom interface interface-id . . . . . . . . . . . . . . . . . . . . . . 385, 1699
show interfaces advanced firmware . . . . . . . . . . . . . . . . . . . . . . . . . . 1701
show interfaces advertise . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 385
show interfaces configuration . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 387
show interfaces cos-queue . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 689
show interfaces counters . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 388
show interfaces description . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 391
show interfaces detail . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 392
show interfaces interface-id . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1701
show interfaces loopback . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1134
show interfaces port-channel . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 601
show interfaces priority-flow-control . . . . . . . . . . . . . . . . . . . . . . . . . 913
show interfaces random-detect . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 691
show interfaces status . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 393
show interfaces switchport . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 808
show interfaces traffic-class-group . . . . . . . . . . . . . . . . . . . . . . . . . . . 907
show interfaces transceiver . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 396, 398
show interfaces tunnel . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1358
show interfaces utilization . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1703
show ip access-lists . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 275
show ip address-conflict . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 493
show ip arp inspection . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 352
show ip arp inspection vlan . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 354
2CSNXXX_SWUM200.book Page 1809 Tuesday, December 10, 2013 1:22 PM
show ip brief . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1063
show ip dhcp binding . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 954
show ip dhcp conflict . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 955
show ip dhcp global configuration . . . . . . . . . . . . . . . . . . . . . . . . . . . 955
show ip dhcp pool . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 956
show ip dhcp relay . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1042
show ip dhcp server statistics . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 956
show ip dhcp snooping . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 338
show ip dhcp snooping binding . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 339
show ip dhcp snooping database . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 340
show ip dhcp snooping interfaces . . . . . . . . . . . . . . . . . . . . . . . . . . . . 341
show ip dhcp snooping statistics . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 342
show ip dvmrp . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 997
show ip dvmrp interface . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 998
show ip dvmrp neighbor . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 998
show ip dvmrp nexthop . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 999
show ip dvmrp prune . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1000
show ip dvmrp route . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1000
show ip helper statistics . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1043
show ip helper-address . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 494, 1041
show ip http server secure status . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1783
show ip http server status . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1782
show ip igmp . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1016
show ip igmp groups . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1017
show ip igmp interface . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1017
show ip igmp interface stats . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1019
show ip igmp membership . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1018
show ip igmp proxy-service . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1024
show ip igmp proxy-service groups . . . . . . . . . . . . . . . . . . . . . . . . . . 1025
show ip igmp proxy-service groups detail . . . . . . . . . . . . . . . . . . . . . 1026
show ip igmp proxy-service interface . . . . . . . . . . . . . . . . . . . . . . . . 1025
show ip igmp snooping . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 456
show ip igmp snooping groups . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 457
show ip igmp snooping mrouter . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 458
show ip igmp snooping querier . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 473
show ip interface . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1064
show ip irdp . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1339
show ip mcast mroute static . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1157
show ip mroute . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1154
2CSNXXX_SWUM200.book Page 1810 Tuesday, December 10, 2013 1:22 PM
show ip mroute group . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1155
show ip mroute source . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1156
show ip multicast . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1152
show ip multicast interface . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1154
show ip ospf . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1245
show ip ospf abr . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1251
show ip ospf area . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1252
show ip ospf asbr . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1254
show ip ospf database . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1254
show ip ospf database database-summary . . . . . . . . . . . . . . . . . . . . 1257
show ip ospf interface . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1259
show ip ospf interface brief . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1261
show ip ospf interface stats . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1262
show ip ospf neighbor . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1262
show ip ospf range . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1266
show ip ospf statistics . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1267
show ip ospf stub table . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1269
show ip ospf traffic . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1270
show ip ospf virtual-link . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1272
show ip ospf virtual-links brief . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1273
show ip pim . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1157
show ip pim boundary . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1153
show ip pim bsr-router . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1158
show ip pim interface . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1159
show ip pim neighbor . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1161
show ip pim rp hash . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1162
show ip pim rp mapping . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1163
show ip policy . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1065
show ip protocols . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1066
show ip rip . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1352
show ip rip interface . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1353
show ip rip interface brief . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1354
show ip route . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1070
show ip route preferences . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1072
show ip route summary . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1073
show ip source binding . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 534
show ip ssh . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1645
show ip telnet . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1748
show ip traffic . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1074
2CSNXXX_SWUM200.book Page 1811 Tuesday, December 10, 2013 1:22 PM
show ip verify source . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 533
show ip vlan . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1075
show ip vrrp interface . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1382
show ipv6 access-lists . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 507
show ipv6 brief . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1107
show ipv6 dhcp . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 967
show ipv6 dhcp binding . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 967
show ipv6 dhcp interface (Privileged EXEC) . . . . . . . . . . . . . . . . . . . 970
show ipv6 dhcp interface (User EXEC) . . . . . . . . . . . . . . . . . . . . . . . 968
show ipv6 dhcp interface out-of-band statistics . . . . . . . . . . . . . . . . . 495
show ipv6 dhcp pool . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 973
show ipv6 dhcp snooping . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 986
show ipv6 dhcp snooping binding . . . . . . . . . . . . . . . . . . . . . . . . . . . . 987
show ipv6 dhcp snooping database . . . . . . . . . . . . . . . . . . . . . . . . . . . 988
show ipv6 dhcp snooping interfaces . . . . . . . . . . . . . . . . . . . . . . . . . . 989
show ipv6 dhcp snooping statistics . . . . . . . . . . . . . . . . . . . . . . . . . . . 989
show ipv6 dhcp statistics . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 973
show ipv6 interface . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1107
show ipv6 interface management statistics . . . . . . . . . . . . . . . . . . . 1110
show ipv6 interface out-of-band . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 496
show ipv6 mld groups . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1111
show ipv6 mld interface . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1114
show ipv6 mld snooping . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 515
show ipv6 mld snooping groups . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 517
show ipv6 mld snooping mrouter . . . . . . . . . . . . . . . . . . . . . . . . . . . . 519
show ipv6 mld snooping querier . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 526
show ipv6 mld traffic . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1122
show ipv6 mld-proxy . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1116
show ipv6 mld-proxy groups . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1118
show ipv6 mld-proxy groups detail . . . . . . . . . . . . . . . . . . . . . . . . . . 1119
show ipv6 mld-proxy interface . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1121
show ipv6 mroute . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1180
show ipv6 mroute group . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1182
show ipv6 mroute source . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1183
show ipv6 neighbors . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1123
show ipv6 ospf . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1313
show ipv6 ospf abr . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1317
show ipv6 ospf area . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1318
show ipv6 ospf asbr . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1319
2CSNXXX_SWUM200.book Page 1812 Tuesday, December 10, 2013 1:22 PM
show ipv6 ospf border-routers . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1319
show ipv6 ospf database . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1320
show ipv6 ospf database database-summary . . . . . . . . . . . . . . . . . . 1322
show ipv6 ospf interface . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1323
show ipv6 ospf interface brief . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1324
show ipv6 ospf interface stats . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1325
show ipv6 ospf interface vlan . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1326
show ipv6 ospf neighbor . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1327
show ipv6 ospf range . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1329
show ipv6 ospf stub table . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1329
show ipv6 ospf virtual-link brief . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1331
show ipv6 ospf virtual-links . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1330
show ipv6 pim . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1177
show ipv6 pim interface . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1184
show ipv6 pim neighbor . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1185
show ipv6 pim rp mapping . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1186
show ipv6 pim rphash . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1186
show ipv6 route . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1124
show ipv6 route preferences . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1125
show ipv6 route summary . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1126
show ipv6 source binding . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 990
show ipv6 traffic . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1127
show ipv6 verify . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 991
show ipv6 verify source . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 992
show ipv6 vlan . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1129
show iscsi . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 542
show iscsi sessions . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 543
show isdp . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 305
show isdp entry . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 306
show isdp interface . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 307
show isdp neighbors . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 308
show isdp traffic . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 309
show lacp . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 602
show line . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1492
show link-dependency . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 548
show lldp . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 562
show lldp dcbx . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 895
show lldp interface . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 563
show lldp local-device . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 564
2CSNXXX_SWUM200.book Page 1813 Tuesday, December 10, 2013 1:22 PM
show lldp med . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 565
show lldp med interface . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 566
show lldp med local-device detail . . . . . . . . . . . . . . . . . . . . . . . . . . . . 567
show lldp med remote-device . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 568
show lldp remote-device . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 570
show lldp statistics . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 571
show lldp tlv-select . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 894
show logging . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1664
show logging email statistics . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 364
show logging file . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1665
show mac address-table . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 287
show mac address-table address . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 287
show mac address-table count . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 288
show mac address-table dynamic . . . . . . . . . . . . . . . . . . . . . . . . . . . . 289
show mac address-table interface . . . . . . . . . . . . . . . . . . . . . . . . . . . . 290
show mac address-table multicast . . . . . . . . . . . . . . . . . . . . . . . . . . . . 285
show mac address-table static . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 291
show mac address-table vlan . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 292
show mail-server . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 369
show management access-class . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1501
show management access-list . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1502
show memory cpu . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1703
show monitor capture . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 397
show monitor session . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 631
show mvr . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 583
show mvr interface . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 585
show mvr members . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 584
show mvr traffic . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 587
show nsf . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1704
show parser macro . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1433
show passwords configuration . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1516
show passwords result . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1518
show policy-map . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 691
show policy-map interface . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 692
show port protocol . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 811
show ports security . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 293
show ports security addresses . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 294
show power inline . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1536
show power inline firmware-version . . . . . . . . . . . . . . . . . . . . . . . . . 1537
2CSNXXX_SWUM200.book Page 1814 Tuesday, December 10, 2013 1:22 PM
show power-usage-history . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1705
show process cpu . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1706
show radius statistics . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 721
show rmon alarm . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1545
show rmon alarms . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1547
show rmon collection history . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1548
show rmon events . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1549
show rmon hcalarm . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1550
show rmon history . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1551
show rmon log . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1554
show rmon statistics . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1555
show route-map . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1076
show routing heap summary . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1078
show running-config . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1472
show sdm prefer . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1560
show service-acl interface . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 274
show service-policy . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 693
show sessions . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1708
show sflow agent . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1603
show sflow destination . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1604
show sflow polling . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1605
show sflow sampling . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1606
show slot . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1709
show snmp . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1610
show snmp engineID . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1611
show snmp filters . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1611
show snmp group . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1612
show snmp user . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1614
show snmp views . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1615
show sntp configuration . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1436
show sntp server . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1437
show sntp status . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1438
show spanning-tree . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 735
show spanning-tree summary . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 740
show spanning-tree vlan . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 741
show startup-config . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1473
show statistics . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 398
show statistics port-channel . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 604
show statistics switchport . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 401
2CSNXXX_SWUM200.book Page 1815 Tuesday, December 10, 2013 1:22 PM
show storm-control . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 403
show supported cardtype . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1710
show supported switchtype . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1712
show switch . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1714
show switchport protected . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 410
show switchport voice . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 298
show syslog-servers . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1666
show system . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1722
show system fan . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1723
show system id . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1724
show system internal pktmgr . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 410
show system power . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1725
show system temperature . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1726
show tacacs . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 774
show tech-support . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1727
show time-range . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1755
show trapflags . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1616
show udld . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 787
show usb . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1759
show users . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1729
show users accounts . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 242
show users login-history . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 243
show version . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1730
show vlan . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 812
show vlan association mac . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 813
show vlan association subnet . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 814
show vlan private-vlan . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 833
show vlan remote-span . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 633
show voice vlan . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 838
show vpc . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 615
show vpc brief . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 616
show vpc consistency-features . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 619
show vpc consistency-parameters . . . . . . . . . . . . . . . . . . . . . . . . . . . . 618
show vpc peer-keepalive . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 619
show vpc role . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 620
show vpc statistics . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 621
show vrrp . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1376
show vrrp interface . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1378
show vrrp interface brief . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1380
2CSNXXX_SWUM200.book Page 1816 Tuesday, December 10, 2013 1:22 PM
show vrrp interface stats . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1381
shutdown . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 403
slot . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1694
snmp-server community . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1617
snmp-server community-group . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1619
snmp-server contact . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1620
snmp-server enable traps . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1621
snmp-server engineID local . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1623
snmp-server filter . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1624
snmp-server group . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1625
snmp-server host . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1627
snmp-server location . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1628
snmp-server user . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1629
snmp-server v3-host . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1632
snmp-server view . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1631
sntp . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 953
sntp authenticate . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1439
sntp authentication-key . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1440
sntp broadcast client enable . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1441
sntp client poll timer . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1441
sntp server . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1442
sntp trusted-key . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1443
sntp unicast client enable . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1444
source-ip . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 725
spanning-tree . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 743
spanning-tree auto-portfast . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 743
spanning-tree backbonefast . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 744
spanning-tree bpdu flooding . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 745
spanning-tree bpdu-protection . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 746
spanning-tree cost . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 747
spanning-tree disable . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 748
spanning-tree forward-time . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 749
spanning-tree guard . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 750
spanning-tree loopguard . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 750
spanning-tree max-age . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 751
spanning-tree max-hops . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 752
spanning-tree mode . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 753
spanning-tree mst configuration . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 754
spanning-tree mst cost . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 755
2CSNXXX_SWUM200.book Page 1817 Tuesday, December 10, 2013 1:22 PM
spanning-tree mst port-priority . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 756
spanning-tree mst priority . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 757
spanning-tree portfast . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 758
spanning-tree portfast bpdufilter default . . . . . . . . . . . . . . . . . . . . . . 759
spanning-tree portfast default . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 759
spanning-tree port-priority . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 760
spanning-tree port-priority (Interface Configuration) . . . . . . . . . . . . 760
spanning-tree priority . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 762
spanning-tree tcnguard . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 763
spanning-tree transmit hold-count . . . . . . . . . . . . . . . . . . . . . . . . . . . 763
spanning-tree uplinkfast . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 764
spanning-tree vlan . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 765
spanning-tree vlan forward-time . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 766
spanning-tree vlan hello-time . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 767
spanning-tree vlan max-age . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 768
spanning-tree vlan priority . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 769
spanning-tree vlan root . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 769
speed . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 404, 1493
split-horizon . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1354
stack . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1731
stack-port . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1732
stack-port interface shutdown . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1733
standby . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1734
state . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1784
storm-control broadcast . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 406
storm-control multicast . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 406
storm-control unicast . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 407
switch renumber . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1735
switchport access vlan . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 815
switchport forbidden vlan . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 816
switchport general acceptable-frame-type tagged-only . . . . . . . . . . . 817
switchport general allowed vlan . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 817
switchport general ingress-filtering disable . . . . . . . . . . . . . . . . . . . . 818
switchport general pvid . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 819
switchport mode . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 820
switchport mode private-vlan . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 831
switchport private-vlan . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 830
switchport protected . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 408
switchport protected name . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 409
2CSNXXX_SWUM200.book Page 1818 Tuesday, December 10, 2013 1:22 PM
switchport trunk . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 821
switchport voice detect auto . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 300
system jumbo mtu . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 412
T
tacacs-server host . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 775
tacacs-server key . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 776
tacacs-server key encrypted . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 777
tacacs-server timeout . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 778
telnet . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1736
terminal length . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1749
terminal monitor . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1667
test copper-port tdr . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1523
timeout . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 726, 778
time-range . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1751
timers pacing flood . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1273
timers pacing lsa-group . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1274
timers spf . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1275
traceroute . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1738
traceroute ethernet cfm . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 423
traceroute ipv6 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1129, 1740
traffic-class-group max-bandwidth . . . . . . . . . . . . . . . . . . . . . . . . . . . 901
traffic-class-group min-bandwidth . . . . . . . . . . . . . . . . . . . . . . . . . . . 902
traffic-class-group strict . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 903
traffic-class-group weight . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 905
traffic-shape . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 694
tunnel destination . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1359
tunnel mode ipv6ip . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1360
tunnel source . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1361
U
udld enable (Global Config) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 783
udld enable (Interface Config) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 786
udld message time . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 785
udld port . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 787
udld reset . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 784
udld timeout interval . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 785
unmount usb . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1758
update bootcode . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1742
usage . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 726
2CSNXXX_SWUM200.book Page 1819 Tuesday, December 10, 2013 1:22 PM
user group . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1416, 1424
user group moveusers . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1424
user group name . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1425
user name . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1418
user password . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1419
user session-timeout . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1419
user-logout . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1417
username . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 244
username (Mail Server Configuration Mode) . . . . . . . . . . . . . . . . . . 368
username unlock . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 246
V
verification . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1409
vlan . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 823
vlan association mac . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 824
vlan association subnet . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 825
vlan makestatic . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 825
vlan priority . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 695
vlan protocol group . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 826
vlan protocol group add protocol . . . . . . . . . . . . . . . . . . . . . . . . . . . . 827
vlan protocol group name . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 828
vlan protocol group remove . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 829
voice vlan . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 836
voice vlan (Interface) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 836
voice vlan data priority . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 837
vpc . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 622
vpc domain . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 623
vpc peer-link . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 624
vrrp accept-mode . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1366
vrrp authentication . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1367
vrrp description . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1368
vrrp ip . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1369
vrrp mode . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1370
vrrp preempt . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1371
vrrp priority . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1372
vrrp timers advertise . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1372
vrrp timers learn . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1373
vrrp track interface . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1374
vrrp track ip route . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1375
2CSNXXX_SWUM200.book Page 1820 Tuesday, December 10, 2013 1:22 PM

www.dell.com | support.dell.com
Printed in the U.S.A.
2CSNXXX_SWUM200.book Page 1 Tuesday, December 10, 2013 1:22 PM
2CSNXXX_SWUM200.book Page 2 Tuesday, December 10, 2013 1:22 PM