Dell Data Protection Protected Workspace Administrator's Guide User Manual Administrator En Us
User Manual: Dell dell-data-protection-protected-workspace - Dell Data Protection Protected Workspace Administrator's Guide
Open the PDF directly: View PDF ![]() .
.
Page Count: 17

S
Dell Data Protection | Protected Workspace
DellDataProtection|ProtectedWorkspace
Administrator’s Guide
© 2013 Dell Inc.
Trademarks used in this text: Dell™, the DELL logo, Dell Precision™, OptiPlex™, Latitude™, and Vostro™ are trademarks of Dell Inc.
Intel®, Pentium®, Xeon®, Core™ and Celeron® are registered trademarks of Intel Corporation in the U.S. and other countries.
Microsoft® and Windows® are registered trademarks of Microsoft Corporation in the United States and/or other countries.
June 2013 Rev. A00
3
TableofContents
Section 1 – Overview and Basic Installation ........................................................................................... 5
Purpose and Intended Audience ............................................................................................................................ 5
What is Dell Data Protection | Protected Workspace? ............................................................................................. 5
System Requirements ........................................................................................................................................... 5
SupportedOperatingSystems..............................................................................................................................5
SupportedHardwarePlatforms............................................................................................................................5
MinimumSystemSpecs:.......................................................................................................................................5
RecommendedSystemSpecs:...............................................................................................................................5
ConnectivityRequirements:..................................................................................................................................5
Supported Software .............................................................................................................................................. 6
SupportedBrowsers..............................................................................................................................................6
SupportedPDFReaders.........................................................................................................................................6
SupportedDocumentPrograms............................................................................................................................6
SupportedBrowserPlugins...................................................................................................................................6
Basic Installation ......................................................................................................................................... 6
Section 2 – Enterprise End-User Deployments ....................................................................................... 7
Deploying Dell Data Protection | Protected Workspace with Software Deployment Tools .......................................... 7
ProtectedWorkspaceEXEInstallerOptions.........................................................................................................7
Connectivity requirements .................................................................................................................................... 8
ProductActivation................................................................................................................................................8
ProductUpdates....................................................................................................................................................9
Section 3 – Administration ...................................................................................................................... 10
End-User Experience .......................................................................................................................................... 10
ThreatDetection.................................................................................................................................................10
AppsTab..............................................................................................................................................................11
Administrative Preferences Override .................................................................................................................... 13
OverrideSettingsDetails.....................................................................................................................................13
Administrative Trusted Sites Override .................................................................................................................. 14
RegexPatternRecommendations.......................................................................................................................15
TrustedSitesCaution:.........................................................................................................................................15
UserTrustedSitesList.........................................................................................................................................16
Troubleshooting ................................................................................................................................................. 16
4
ManuallyTroubleshootingInstallationIssues....................................................................................................16
ManuallyTroubleshootingPost‐InstallationIssues............................................................................................16

5
Section1–OverviewandBasicInstallation
PurposeandIntendedAudience
ThisguideisintendedforITadministratorswhowillbeinstalling,deploying,andadministeringDDP|
ProtectedWorkspace.Thisguideisdesignedtohelpidentifysystemrequirements,identifypre‐
deploymenttasksandtosuggestdeploymentmethodologies.
WhatisDellDataProtection|ProtectedWorkspace?
DDP|ProtectedWorkspaceprovidesasecurewaytobrowsetheinternetbyleveragingtheexistingweb
browserinstalledonanenduserPCandallowingittoruninsidetheProtectedWorkspaceisolated
browsingenvironment(orbubble).DDP|PWalsoprotectscommondocumentssafelysuchasAdobePDFs,
MicrosoftWord,PowerPoint,andExcel.Theisolatedenvironmentkeepsunexpectedmalwarefrom
executingorinstallingonthehostmachineandisdetectedbytheDDP|PWbehaviorbasedthreat
detection.Upondetection,theisolatedenvironmentisdestroyedandacleanenvironmentisrecreatedto
ensuretheendusermachineisnotcompromised.
SystemRequirements
SupportedOperatingSystems
Windows7,32and64‐bit
SupportedHardwarePlatforms
DellOptiPlex
DellPrecision
DellLatitude
MinimumSystemSpecs:
1GBRAM
500MBfreediskspace
IntelPentiumorbetter
RecommendedSystemSpecs:
2GBRAM
500MBfreediskspace
IntelCore2Duoorbetter
ConnectivityRequirements:
Aconnectiontohttp://delllicense.invincea.com(port80)isrequiredinordertoactivatethe
productlicense.
Aconnectiontohttps://dellupdate.invincea.com(port443)isrequiredforproductupdates
6
SupportedSoftware
DDP|ProtectedWorkspaceleveragessoftwareinstalledonanendusermachineandrunsthatsoftware
insideanisolatedenvironment.Toensureproperfunctionalitywithintheisolatedenvironment,only
certainsoftwareandversionsaresupported.Anyunsupportedsoftwareorversionwillnotbemovedinto
theisolatedenvironmentandwillcontinuetoonlyruninthenativeinterface.
SupportedBrowsers
InternetExplorer7‐10
MozillaFirefox10‐21
SupportedPDFReaders
AdobeReader9,X,andXI
AdobeAcrobat9,XandXI
SupportedDocumentPrograms
MicrosoftWord,2010and2013
MicrosoftExcel,2010and2013
MicrosoftPowerPoint,2010and2013
SupportedBrowserPlugins
JavaRuntimeEnvironment1.6+
AdobeFlash11+
AppleQuickTime7+
MicrosoftSilverlight
BasicInstallation
DDP|ProtectedWorkspaceispackagedwithapre‐definedsetofpreferencesandconfigurationandcan
beinstalledwithoutanycustomconfiguration.Itcanbeinstalledbyfollowingthesesteps.
1. DownloadtheDDP|ProtectedWorkspaceInstaller.
2. RuntheDellSetup_<version>.exe.
3. Selecttheinstallerdefaults.
4. FinishtheDDP|ProtectedWorkspaceinstaller.
5. StartDDP|ProtectedWorkspacebydoubleclickingonthedesktopicon.

7
Section2–EnterpriseEnd‐UserDeployments
DeployingDellDataProtection|ProtectedWorkspacewithSoftwareDeploymentTools
DDP|ProtectedWorkspaceinstallationissupportedwithmanydifferentsoftwaredeploymenttools.
Currently,ProtectedWorkspaceistestedwithGPO,IBMTivoliEndpointManager(previouslyBigFix),
MicrosoftSCCMandSymantecAltiris,howeverdeploymentsshouldworkwithalldeploymenttools.
ProtectedWorkspaceEXEInstallerOptions
ThissectiondetailsoptionstobeusedforinstallingProtectedWorkspaceonend‐userPCsdirectlyorwitha
systemmanagementtool.
Silentinstallusingdefaultoptions
DellSetup_<version>.exe /S /v/qn
Silentinstallwithchangingtheinstallfolder.ExamplechangesinstallpathtoC:\TEST:
DellSetup_<version>.exe /S /v"/qn INSTALLDIR="C:\TEST"
Silentuninstall(leaveuserfiles)
DellSetup_<version>.exe /S /x /v/qn
Silentuninstall(removesuserfiles)
DellSetup_<version>.exe /S /x /v"/qn PRESERVE=\"0\""
Silentupgrade
DellSetup_<version>.exe /S /v/qn
8
Connectivityrequirements
ProductActivation
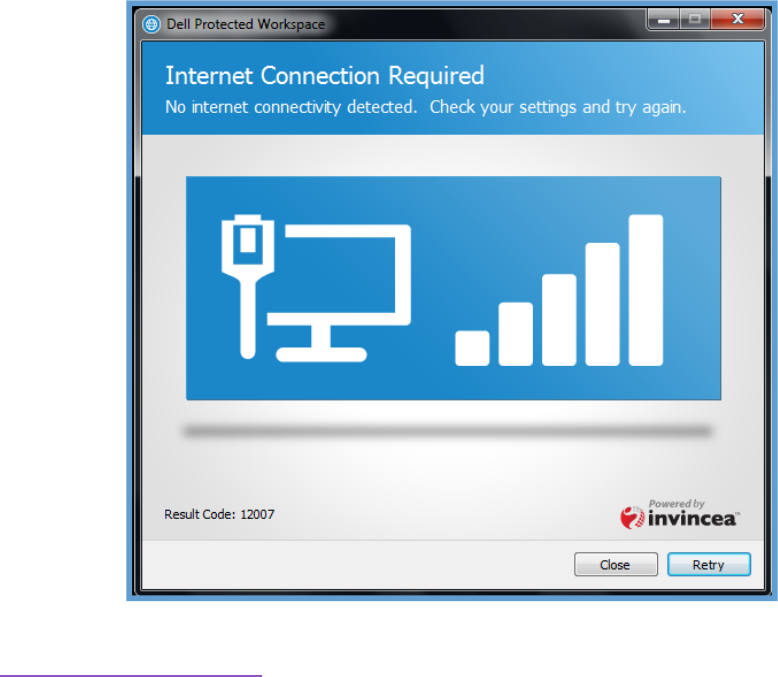
AfterinstallingDDP|ProtectedWorkspace,theproductrequiresinternetaccessinorderreachouttothe
activationservers.Ifinternetaccessisnotavailable,theproductwillasktheusertocheckthesettingsand
tryagain.
Iftheenvironmentcontainsawebproxyorotherdevice,itisimportantthataccessto
http://delllicense.invincea.combeallowedonport80.
9
ProductUpdates
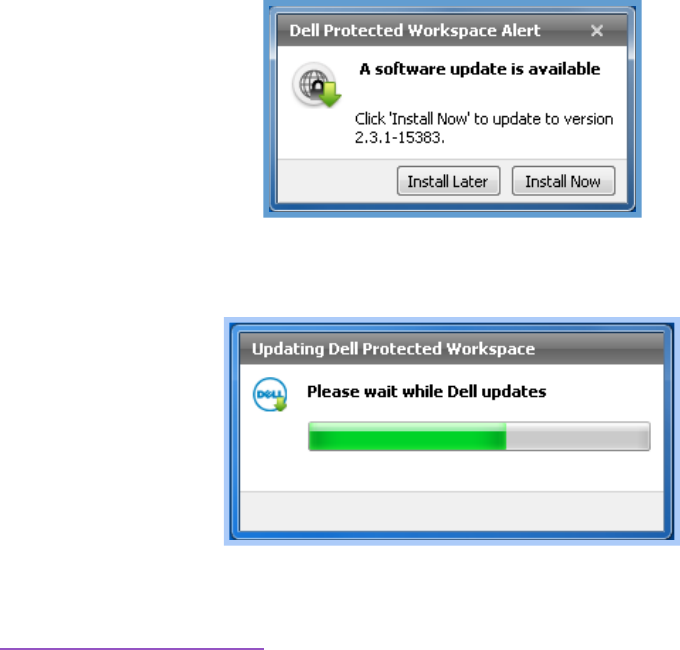
DDP|ProtectedWorkspaceisdesignedtonotifytheuserwhenanupdateisavailable.Whenanupdateis
applied,theupdatewillbedownloadedinthebackgroundwhiletheproductisrunning,andwillapply
whentheproductisrestoredorexitedandrestarted.
Duringtheupdateprocess,adialogboxwilldisplayoverthesystemtray,indicatingthattheupdateis
takingplace.
Inorderfortheautomaticupdatestooccur,itisimportantthattheproducthaveaconnectiontothe
internetandthatiftheenvironmentcontainsawebproxyorotherdevice,accessto
http://dellupdate.invincea.combeallowedonport443.
10
Section3–Administration
End‐UserExperience
ThreatDetection
DDP|ProtectedWorkspaceoffersbuiltinthreatdetectiontohelpidentifyiftheDDP|PWenvironmenthas
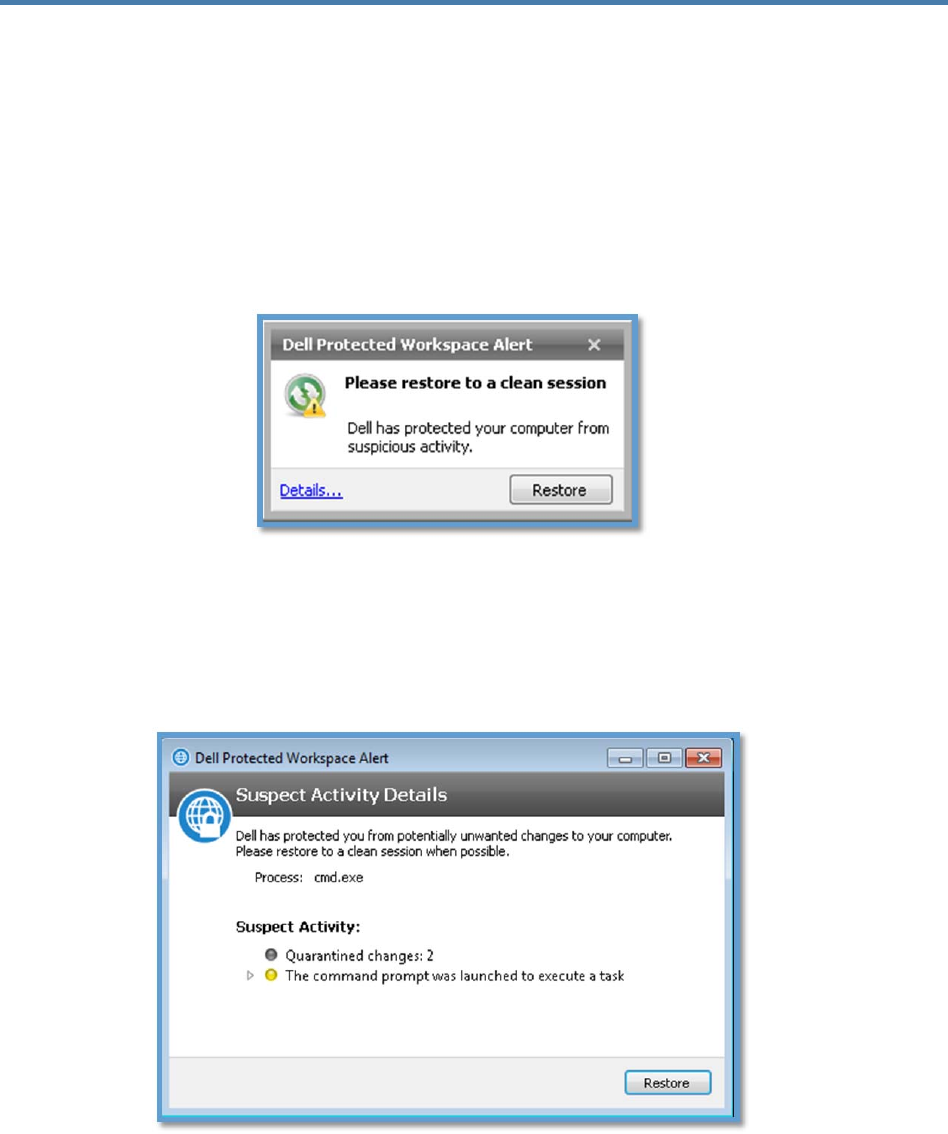
beencompromisedbyanuntrustedprocess.Whensuspiciousactivityhasbeendetected,adialogwill
displayoverthesystemtryindicatingthattheusershouldrestoretoacleansession.Itisrecommended
thattheRestorebuttonbepressedimmediatelytorestoretoacleansession,buttheuserdoeshavethe
optiontoclosethedialogboxwiththe“x”inthecornerandtocontinueusingtheproduct.Arestorecan
bedoneatalatertime.
Theusercanclickthe“Details...”linkinthebottomleftcornerofthemessagetodisplayadditionaldetails
aboutthesuspiciousactivity.Thedialogwillidentifytheprocessthatwasflaggedassuspiciousandwill
alsogivedetailsaboutwhatthatprocessdidwithintheprotectedenvironment.Fromthisdialog,theuser
caneitherclosethewindowbyclickingontheXintheupperrightcorner,orcanrestorethesessionusing
therestorebutton.
11
IftheuserchoosestorestorelaterbydismissingtheSuspiciousActivitydialogtheProtectedWorkspace
icononthesystemtraywillturnreduntiltheuserrestoresDDP|ProtectedWorkspacetoacleanstate.
DDP|ProtectedWorkspaceensuresthatanythreatiscontainedwithintheprotectedenvironmentand
thattheendusersystemhasbeenprotected.
AppsTab
Atabcalledthe“Apps”tabinthepreferenceGUIallowstheuserscanusetospecifywhichprograms
withintheprotectedenvironmentwillbeusediftherearemultipleoptions(suchaswithbothInternet
ExplorerandFirefox)andwhichprogramswillactasdefaulthandlersforcertainfile(suchasAdobeReader
forPDFs).
ToaccesstheAppstab,rightclickingontheDDP|PWIconinthesystemtray,andselecting“Preferences…”
BelowisascreenshotoftheAppstab.Applicationsthathavedefinedfilehandlerswithintheprotected
environmentwilllist“ProtectedFileTypes”andwillhaveacheckboxtoenablethatapplicationasthe
handlerforthatfiletype.Forexample,ifbothAdobeReaderandAdobeAcrobatareinstalledonaclient
machine,theusercanchoosewhichwillbeusedtoopenPDFfileswiththeprotectedenvironment.The
userwillnotbeabletoselectmultipleapplicationsforthesamehandler.
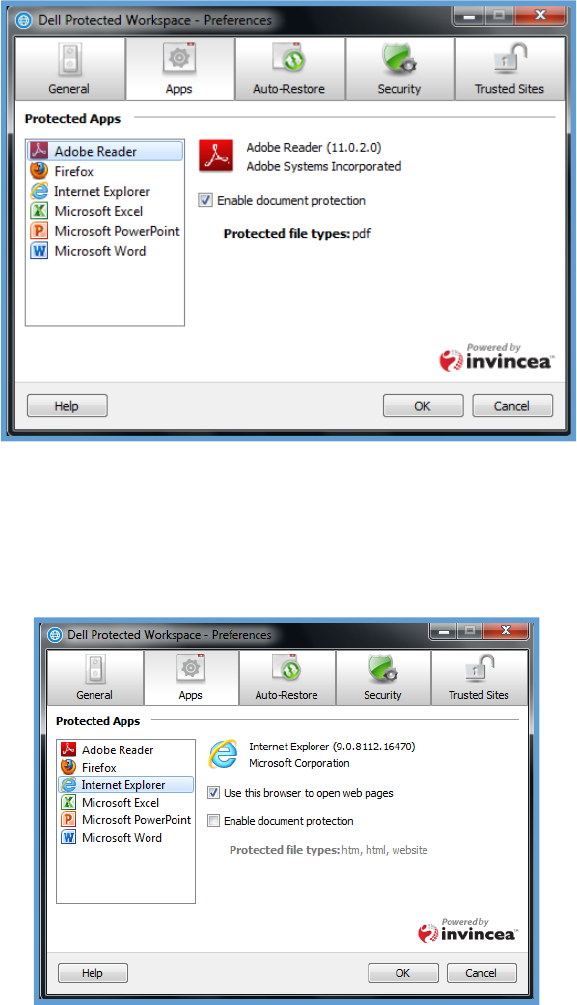
12
Additionally,fromtheAppstab,userswillbeabletoselectwhichbrowserwillbeusedtoopenwebpages
bydefaultwithintheprotectedenvironment.Theusercanselect“Usethisbrowsertoopenwebpages”
foreitherInternetExplorerorFirefox.
13
AdministrativePreferencesOverride
Insomeorganizations,administratorsmaywanttodisabletheabilityforDDP|ProtectedWorkspacefrom
reachingouttotheDDP|PWserversforsoftwareupdates,errorreportingandthreatdetectionreporting.
TheseoptionscanbedisabledbyaddinganoverridefileoneachPC.Itisrecommendedthattheseoptions
notbeusedunlessabsolutelynecessary.
TheoverridefileisasimpleXMLfilethatcanbecreatedinNotepadorasimilartexteditor.Createafile
withthename“preferences.xml”andcopythefollowingtextintoit:
<?xml version="1.0" encoding="UTF-8" ?>
<preferences ver="3">
<error_report enabled="false" />
<software_update enabled="false" interval="daily" user_modifiable="false" />
<send_threat_reports enabled="false" prompt="false" />
</preferences>
Oncethisfileiscreated,itneedstobeplacedontoeachPCthatneedstheoverride.Thelocationforthis
fileneedstobe:
C:\ProgramData\Invincea\Enterprise\Admin
Oncethisfileisinplace,start(orrestart)theDDP|ProtectedWorkspaceproductandtheseoverrideswill
takeeffect.
OverrideSettingsDetails
<error_reportenabled="false"/>
Theerror_reportoptiondisablestheabilityforDDP|ProtectedWorkspaceproducttosenderrorreports
whenaproducterroroccurs.Whenanerrorwindowisdisplayedthe“Submit”willbedisabled.
<software_updateenabled="false"interval="daily"user_modifiable="false"/>
Thesoftware_updateoptiondisablestheabilityforDDP|ProtectedWorkspaceproducttoautomatically
applycriticalupdatestotheproduct.Thesecriticalupdatesallowforerrorstobecorrectastheyare
reportedandshouldbeallowedtoensurethatlatestcriticalupdatesarealwaysapplied.
<send_threat_reportsenabled="false"prompt="false"/>
Thesend_threat_reportsoptiondisablestheabilityforDDP|ProtectedWorkspaceproducttoreport
homewhenasuspiciousactivityisdetected.Thesereportshelptoensurethattheproductdetectionis
workingcorrectlyandisnottriggeringalertswhennoactualthreatispresent.
14
AdministrativeTrustedSitesOverride
BydesigntheDDP|ProtectedWorkspaceproductrunstheusersnativewebbrowserswithinanisolated
environment.Thisisolatedenvironmentkeepstheuser’sPCsafefrommaliciouscontentbutcanalso
causesomeinteroperabilityissueswithcertainwebsites.Ifthesewebsitesarebusinesscriticaland
trusted,theusershavetheabilitytomanuallytrustthemlocally.Bytrustingthem,thesesiteswillbe
openedwithinthenativebrowseriftheURLisbrowsedtointheprotectedenvironment.
Asanaddedconvenience,administratorshavetheabilitytoapplyanoverridefilethataddsasetoftrusted
siteswithoutanyuserinteraction.
TheoverridefileisasimpleTXTfilethatcanbecreatedinNotepadorasimilartexteditor.Createafile
withthename“trustedsites.txt”
Oncethisfileiscreated,itneedstobeplacedontoeachPCthatneedstheoverride.Thelocationforthis
fileneedstobe:
C:\ProgramData\Invincea\Enterprise\Admin
Oncethisfileisinplace,start(orrestart)theDDP|ProtectedWorkspaceproductandtheseoverrideswill
takeeffect.
TheformatofthetrustedURLsneedstobeinREGEXformat.Thefollowingsectionoutlineshowtocreate
URLsinthecorrectformat.
HerearesomeexamplesofcorrectlyformattedURLs.Thepoundsign(#)indicatesafilecomment:
#The following lines designate trusted sites/domains
^https?://([^/]*\.)*adobe\.com/.*
^https?://([^/]*\.)*acrobat\.com/.*
^https?://([^/]*\.)*webex\.com/.*
^https?://([^/]*\.)*dell\.com/.*
^https://internal\.dell\.com:8080/.*
^ftp://dell/.*
Theproductperformsalinebylineexaminationofthetrustedsites.txtfileandstopsatthefirstmatch.The
followingsectionoutlinessomepossibleentriesintothetrustedsites.txtfileandwhattheresulting
outcomewouldbe.
^ftp://dell/.*
Theaboveentrywouldmatchanythingthatstartswithftp://dell/andwouldallowanyadditionaltextafter
thelast/.
^https?://([^/]*\.)*dell\.com/.*
Theaboveentrywouldmatchanythingthatstartswith“http://”or“https://”,endswith“.dell.com/”and
allowsanysubdomainsofdell.com.[^/]*isanythingthatdoesn’tcontaina“/”so“dell.com”mustshow
upinthebaseportionoftheURL.Inotherwords,thiswillmatchhttp://anything.dell.com/*,butwillnot
matchhttp://fakedell.com/*orhttp://anything.com/?imageurl=fake.dell.com/*.
15
^https://internal\.dell\.com:8080/.*
Theaboveentrywillmatchtheexactsiteandportspecifiedandanythingthatfollows.
ToaddlocalIPsubnets,usethefollowingformat:
^https://192\.168\.1\.*(:\d{1,5})?/.*
TheaboveentrywillmatchanyURLthatuseshttporhttps,andisaccessedwitha192.168.1.xsubnetIP
address.ItalsoallowsforanyporttobeusedonthisURL.
ItisimportanttonotethattrustedsitesisnotabletodoDNSlookups.Therefore,trustingaspecificsubnet
ofaddressesdoesnottrusttheirassociatedDNSnames.IfDNSnamesneedtobeusedforthetrustedsite
list,eachDNSnamemustbelistedout.
^https://([^/]*\.)*sharepoint\.*
^https://([^/]*\.)*myinternalserver\.*
RegexPatternRecommendations
Belowaresomeregexpatternsthatcanbeusedtocreatecustomentries.
“^”Beginningoftheline.
“?”Matchzeroor1ofthepreviouscharacter
“$”Endoftheline.
“\.”Periodcharacter.(A“.”matchesanycharacter.)
“.*”Matchanynumber(zeroormore)ofanycharacters.
untrusted=Un‐matchtheregexinsteadofmatch.
“[^/]*”Matchanynumberofanycharactersexcept“/”.
TrustedSitesCaution:
BeawarethatthewholeURLstringispassedtoDDP|ProtectedWorkspaceandmatchedagainstthislist.
Slightvariationsinsyntaxcanmakeadifferencebetweenmatchingandmatchinginthewayyouintend.As
anexample,theURL:
http://www.dell.com$
isnotsafeandwouldnotmatch.Itwouldnotmatchbecauseatrailing“/”isoftenaddedbyWindows
beforetheURLispassedtoapplications.Itisnotsafebecausethisstringcouldbepartoftheparametersof
anURLandnotthewebsiteyouintended.
.*www.dell.com.*
matchesif“www.dell.com”appearsanywhereintheURL,notjustastheaddress‐suchasmatching
http://www.fakesite.com/spoofsite=http://www.dell.com/
16
UserTrustedSitesList
FromDDP|ProtectedWorkspace,auserhastheabilitytotrustsiteslocally.Thesesiteswillbeaddedto
thebeginningofthelistofsitesprovidedwithinanadministrativeoverridefile.Forexample,ifanadmin
truststhefollowing:
^https://([^/]*\.)*sharepoint\.*
^https://([^/]*\.)*myinternalserver\.*
Andausertrusts:
google.com
yahoo.com
ThenthefulllistoftrustedsitesforthisPCwillincludeallofthesitesoutlined:
^https?://([^/]*\.)*google\.com/.*
^https?://([^/]*\.)*yahoo\.com/.*
^https://([^/]*\.)*sharepoint\.*
^https://([^/]*\.)*myinternalserver\.*
Troubleshooting
ManuallyTroubleshootingInstallationIssues
TherearetwologfilesthataregeneratedduringtheinstallationofDDP|ProtectedWorkspacethatcan
offerinsightastowhyaninstallationmayhavefailed.
ThefirstfileistheMSIoutputfile.Iftheinstallerisrunmanuallyviathestandardexecutable,thisfilewill
becreatedintheC:\Windows\Tempdirectory.ThelogfilenamewillbeInvEnterpriseMSI.log.Thisfilewill
providedetailsonfailuresthathappenedduringpre‐checks,suchasdiskspace,memoryorothersystem
requirements.
ThesecondfileistheDDP|ProtectedWorkspaceinstallerfile.Itwillbelocatedinthesamedirectoryas
theMSIfile,andwillbenamedInvEnterpriseInstall.log.Thislogwillprovideindicationoffailuresduring
theinstallationandconfigurationprocess.AnyerrorswillbetaggedincapitalletterswiththewordERROR
orFATALafterthedateandtimestamp.AnylinethatistaggedwithDEBUG,TRACEorINFOcanbe
ignored.
ManuallyTroubleshootingPost‐InstallationIssues
Therearethreelogfilesthatareprimarilyusedtoidentifyissuespost‐installation.
ThefirstfileisthelogfilefortheDDP|ProtectedWorkspaceServiceandisnamedInvProtectSvc.log.This
isagloballogfilethatlogsinformationacrossalluseraccounts.Thefirstlocationis:
C:\Windows\Temp\Invincea\
Thislogprovidesinformationabouttheapplicationsthatwedetectduringstartup(suchastheversionifIE,
AdobeReader,Java,Flash,etc.)andwhatlocationsofthehostsystemareaccessiblebytheisolated
environmentornot.
17
Aswiththeinstallerlogfiles,errorswillbenotedatERRORorFATALafterthedateandtimestamp.
2012‐05‐0208:04:33,203ERRORInv.MC.TCPConnection‐[5864]SSLHandshakeerror:Anexisting
connectionwasforciblyclosedbytheremotehost
ThesecondfileisthelogfilefortheinstanceofDDP|ProtectedWorkspacerunningunderausercontext.
Thisfileisnamedinv.logandislocatedintheusersAppDatafolder.EachuseronasinglePCwillhavean
inv.logfile.Thisfilewillhelpidentifyifthereareunsupportedversionsofanapplicationinstalled,or
communicationissueswithneededresources.
Whileloggedinastheuserhavingissues,thelogfilecanbefoundatthisaddressonallOSs:
%APPDATA%\Invincea\Enterprise\inv.log
Again,anyerrorswillbemarkedwithERRORorFATALafterthetimeanddatestamp.
2012‐05‐2212:48:59,157ERRORInv.TaskMgr‐Error:TimeoutwhenperformingRestore,Wait
forGuestConnect