197501
197501 197501
User Manual: 197501
Open the PDF directly: View PDF ![]() .
.
Page Count: 36

January,
computers
and
people
formerly
Computers
and
Automation
SNOWFLAKE
VIGNET
TE
by
Judy
Ki
ntzinger
and
Grace
C.
Hertlein
<"\
0 1 1
_r"
·./let::,
10\
'IBRAP
",
<:)T
Vo
l.
24, No. 1
IBM Versus
AT&T:
Its Meaning
To
The
User and
the
Public
-
A.
G.
W.
Biddle
The Frictional Interface
Between Computers
and Society
-
Robert
W.
Bemer
Languages Among
Computers,
Ma-
chines, Animals,
and Men
-Lawrence
M.
Clark
The Teaching
of
Com-
puter
SC
.ience:
Mas-
ter
of
Science De-
gree
-
J.
N.
Sn
yder
Nixon,
Ford, and
the
Political
Assassina
-
tions in the United
States
-Richard
E.
Sprague

MULTI-ACCESS
FORUM
"MAY
I
HAVE
YOUR CREDIT CARD NUMBER, PLEASE?"
Ed Burnett
Ed Burnett Consultant
176 Madison A venue
New York,
NY
10016
In
"The
Evolution
of
Telephone Connecting"
by
William
J.
McLoughlin,
Jr.,
published
in
the
Septem-
ber
1974
issue
of
"Computers and
People",
on
page 18,
in
the
last
sentence
appears:
One
wonders
how
long
it
will
be
before
voice
controlled
computers
will
be
saying
"May
I
have
your
credit
card
number,
please?
As
it
happens
this
is
already
in
force
in
Canada
where
the
computer
is
asking
for
data
which can be
checked
against
the
file,
such as
the
address
of
the
individual
or
the
telephone
number
of
the
indi-
vidual,
and
if
this
number
coincides,
an
order
can
then
be
placed.
If
there
is
any
fumbling,
the
com-
puter
has
also
been
trained
to
say,
"Just
a
mi
nute.
I'll
have one
of
those
fabulous
computers
known
as
a
human
clerk
get
in
touch
with
you."
This
is
now
being
done
by
Sears
and
others
up
in
Canada.
BOX NO.
vs.
P.O.
BOX NO.
Rush
Harp
Yankee Town Pond Road
Box
69
Bearsville,
NY
12409
I
am
a
consistent
admirer
of
your
philosophy
and
magazine. However,
your
"Garbage
In,
Garbage Out"
and "Computers
Don't
Make
Mistakes"
views
lead
me
to
mention a
glaring
error
which
is
consistent
with
human
beings:
Your magazine
is
addressed
wrong
to
me:
"P.O.
Box
69,"
instead
of
"Box
69".
Most box numbers
are
in
a
post
office,
for
people
who
live
and work
in
cities.
However,
not
so,
out
here
in
the
boondocks. P.O.
Box
69
is
another
party
than
I
am.
Box
69 Yankee
Town
Pond
Road
is
my
own
pet
number. Nowhere
or
at
any time does any
of
my
correspondence
say P.O. Box,
but
it
is
a
consistent
insistence
of
my
publishers
to
include
it.
I
love
your
magazine and
hate
to
have
the
copies
fall
into
other
hands,
due
to
your
error.
Keep
up
the
political
assassination
reporting.
I
am
attempting
to
spread
the
word.
Editorial Note:
Rush
Harp's
copies
are
now
addres-
sed "Box 69" and
not
"P.O.
Box
69".
We
regret
the
error.
P.S.: Computers
OFTEN
make
errorsl
--
E.C.B.
2
THE
PURPOSE
OF FORUM
• To give you,
our
readers, an
opportunity
to
discuss
ideas
that
seem
to
you important.
• To express criticism
or
comments on what
you
find
published in
our
magazine .
• To help
computer
people and
other
people discuss
significant problems related
to
computers, data
processing, and their applications and implications,
including information engineering, professional be-
havior, and the pursuit
of
truth
in input,
output,
and processing.
Your participation is cordially invited.
COMPUTER
ART
EXPOSITION
ISSUES
FOR 12 YEARS
Irene Angelico
Centre
for
Interdisciplinary Studies
Concordia
Univ.
2010 Mackay
Montreal, P.O.,
Canada
I
am
giving
a
course
on
the
relationship
of
art
and
science
in
the
twentieth
century,
and
will
de-
vote
some
time
to
computer
art.
If
you would send
me
reprints
of
the
12
annual
computer
art
exposi-
tions
(or
issues
if
reprints
are
not
available)
...
I would be most
grateful.
Editorial Note:
Reprints
are
not
available
but
back
copies
are,
and
they
may
be
ordered
from
us.
COMPUTER
ART
REPORT
Both
the
computer
art
on
the
front
cover
"Snow-
flake
Vignette"
and
the
computer
art
on
page 3 "Ap-
ple
Blossom
Vignette"
were
made
in
the
same
way
and
produced
in
two
stages.
The
first
stage
was
carried
out
by
Judy
Kintzinger,
a
student
in
a computer
art
course
in
the
summer
school
of
the
University
of
Iowa, Iowa
City.
In
the
first
stage
a
design
like
a
leaf
or
an arrow
or
a
flower
was
produced
by
com-
puter
program, and
then
repeated
in
a
rotated
pat-
tern;
then
the
entire
design,
as
a
larger
module,
was
again
repeated
in
rotation
and
recorded
on
micro-
film.
The second
stage
was
carried
out
by
Grace
C.
Hertlein,
art
editor
of
"Computers and
People,"
and
instructor
in
Judy
Kintzinger's
course.
In
the
second
stage,
the
design
was
enlarged
photographical-
ly
and
manipulated
in
various
ways
to
produce
sev-
eral
partially
overlapping
prints
with
different
de-
grees
of
lightness
and
darkness.
SECOND
INTERNATIONAL
CONFERENCE
ON
COMPUTERS
AND THE HUMANITIES -
CALL
FOR
PAPERS
AND
ART
This
conference
will
be
held
on
April
3-6,
1974,
at
the
Univ.
of
Southern
Calif.,
Los
Angeles,
CA.
Papers
are
invited
relating
to
computer
applications
in
the
humanities
(language,
literature,
music,
his-
tory,
archeology,
culture,
etc.)
and
in
the
areas
of
art
and
education.
Abstracts
should
be
sent
to:
ICCH/2,
c/o
Robert
Dilligan,
English
Dept.,
USC,
Los
Angeles,
CA
90007.
Creative
artists
in
any
field
of
art
are
invited
to
send
descriptions,
slides,
and
abstracts
to
Assoc.
Prof.
Grace
C.
Hertlein,
Computer
Science
Dept.,
Calif.
State
Univ.-Chico,
Chico,
CA
95926.
To
register
for
the
conference,
write
to
ICCH/2,
Founders
Hall
407,
USC,
Los
Angeles,
CA
90007.
COMPUTERS and PEOPLE
for
January, 1975

IA
APPLE BLOSSOM
VIGNETTE
by
Judy
Kintzinger and Grace
C.
Hertlein
COMPUTERS and PEOPLE
for
January,
1975
3
Editor and
Publisher
Assistant
Editors
Art
Editor
Software
Editor
Contributing
Editors
Vol.
24, No. 1
January, 1975
Edmund C. Berkeley
Barbara
L.
Chaffee
Linda Ladd Lovett
Neil D. Macdonald
Grace C. Hertlein
Stewart
B. Nelson
George
N.
Arnovick
John
Bennett
Moses
M.
Berlin
Andrew
D.
Booth
John
W.
Carr
III
Ted Schoeters
Richard
E.
Sprague
London
Thomas
Land
Correspondent
Advisory
Ed
Burnett
Committee James
J.
Cryan
Editorial
Offices
Advertising
Contact
Bernard
Quint
Berkeley Enterprises, Inc.
815
Washington St.
Newtonville,
MA
02160
617-332-5453
The
Publisher
Berkeley Enterprises, Inc.
815
Washington St.
Newtonville,
MA
02160
617-332-5453
"Computers
and
People,"
formerly
"Computers
and
Automation,"
is
published
monthly,
12
issues
per
year,
at
815
Washing-
ton
St.,
Newtonville,
MA
02160,
by
Berkeley
Enterprises,
I
nco
Printed
in
U.S.A.
Second
Class
Postage
paid
at
Boston,
MA,
and
addi-
tional
mailing
points.
Subscription
rates:
Un
ited
States,
$11.50
for
one
year,
$22.00
for
two
years.
Canada:
add
$1
a
year;
Mexico,
add
$6
a
year.
Else-
where:
one
year,
Swiss
francs
60;
order
through
Reliable
Information
Publishing
Company,
P.O.
Box
52,
6354
Vitznau,
Switzerland.
NOTE:
The
above
rates
do
not
include
our
publication
"The
Computer
Directory
and
Buyers'
Guide".
If
you
elect
to
re-
ceive
"The
Computer
Directory
and
Buyers'
Guide,"
please
add
$12.00
per
year
to
you,r
subscription
rate
in
U.S.
and
Canada,
and
$15.00
in
Mex
ico;
elsewhere,
the
price
of
the
Directory
is
Swiss
francs
90,
not
includ-
ing
postage
and
handling;
please
order
through
Reliable
I
nformation
Publishing
Company,
P.O.
Box
52,
6354
Vitznau,
Switzerland.
Please
address
mall
to:
Berkeley
Enter-
prises,
Inc.,
815
Washington
St.,
Newton-
ville,
MA
02160,
or
to
Berkeley
Enterprises,
I
nc.,
c/o
Reliable
I
nformation
Publishing
Co.,
P.O.
Box
52,
6354
Vitznau,
Switzerland.
Postmaster:
Please send
all
forms
3579
to
Berkeley
Enterprises,
Inc.,
815
Washing-
ton
St.,
Newtonville,
MA
02160.
©
Copyright
1975,
by
Berkeley
Enter-
prises,
Inc.
Change
of
address:
If
your
address
changes,
please
send
us
both
your
new
address
and
your
old
address
(as
it
ap-
pears
on
the
magazine
address
imprint),
and
allow
three
weeks
for
the
change
to
be
made.
4
computers
and
people
formerly Computers
and
Automation
The Computer Industry
20
IBM
Versus AT&T: Its Meaning
To
the
User and
the
Public [A]
by
A. G.
W.
Biddle, Encino, Calif.
A discussion
of
the
costly
implications
for
the
computer
industry and for users,
of
giant
monopoly
in
communication
and computing.
2
"May
I Have
Your
Credit Card
Number,
Please?" [F]
by
Ed
Burnett,
Ed
Burnett
Consultant, New York, N.Y.
Computers and SOciety
14
The Frictional Interface Between
Computers
and
Society
[A]
by
Dr.
Robert
W.
Berner, Honeywell Information Systems,
Phoenix, Ariz.
How
computers
and
society
intermesh,
sometimes
with
grinding
of
the
gears.
Computers, Language, Thought, and Communication
7 Languages Among
Computers,
Machines, Animals,
and
Men
by
Lawrence
M.
Clark, Framingham Centre, Mass.
What
is
common
and
what
is
different
among
many
kinds
of
communication
systems
that
convey infor-
mation and ideas?
6 "Can A
Computer
Be
Creative?"
by
Edmund C. Berkeley, Editor
An
argument
that
both
computers
and human beings
very
often
have
lOW-level
creativity,
and
very rarely
have high-level creativity.
Computers, Art, and the Humanities
[A]
[E]
2
Second
International Conference on Computers and
the
[F]
Humanities -Call
for
Papers and
Art
2
Computer
Art
Exposition Issues
for
12
Years [F]
by
Irene Angelico, Centre
for
Interdisciplinary
Studies,
Concordia Univ., Montreal, Canada
The
issues
of
Computers and People, formerly Computers
and Automation, which contain
computer
art.
1 Snowflake Vignette [P]
by
Judy
Kintzinger and Grace
C.
Hertlein
3 Apple Blossom Vignette [P]
by
Judy
Kintzinger
and
Grace C. Hertlein
2
Computer
Art
Report
[F]
An explanation
of
the
construction
of
the
two
vignettes.
The
Computer
Directory
and
Buyers' Guide,
1974
26
Notice
COMPUTERS
and
PEOPLE
for
January,
1975
0.
The magazine
of
the
design, applications,
and
implications
of
information processing
systems
-
and
the
pursuit
of
truth
in
input,
output,
and
processing, for
the
benefit
of
people.
Computers
and
Education
25
The
Teaching
of
Computer
Science:
Master
of
Science
Degree [A]
by
J. N.
Snyder,
Univ.
of
Illinois
at
Urbana-Champaign,
Urbana,
III.
How
one
university
is
organizing
a
curriculum
for
awarding
a
joint
degree
in
computers
and
education
Applications
of
Computers
34
Computing
and
Data
Processing
Newsletter
[C]
Cambridge,
Mass., Uses
Computer
To
Foil
School
Vandals
Braille
Computer
Terminal
Developed in
Australia
Three
Communities
in
Massachusetts
Make Savings
with
Computerized
School-Bus
Routes
Many
Radio
Music
Stations
Are
Run
by
Computer
The Profession
of
Information Engineer
and
the
Pursuit
of
Truth
27
Nixon,
Ford,
and
the
Political Assassinations in
the
[A]
United
States
by
Richard
E.
Sprague,
Hartsdale,
N.Y.
Presenting
"a
reasonable
hypothesis"
for
Gerald
Ford's
pardon
of
Richard
Nixon,
and
other
extraord
inary
events
correlated
with
that.
19
Unsettling,
Disturbing, Critical
Statement
of
policy
by
Computers
and
People
Computers, Puzzles, and Games
[F]
32
Games
and
Puzzles
for
Nimble
Minds -
and
Computers
[C]
by
Neil
Macdonald,
Assistant
Editor
ALGORITHMO
-Going
from
given
input
to
given
output
in
an
"unusual"
situation.
GIZZMO
-
Some
computational
Jabberwocky.
MAXIMDIJ -Guessing a
maxim
expressed
in digits.
NA YMAND IJ - A
systematic
pattern
among
randomness?
NUMBLES -
Deciphering
unknown
digits
from
arithmet-
ical
relations.
SIXWORDO
-Paraphrasing a passage
into
sentences
of
not
more
than
six
words
each.
Corrections
2
Box
No. vs. P.O. Box No.
[F]
by
Rush
Harp, Bearsville, N.Y.
A
human
error
corrected
for
computer
output.
Who's
Who
in
Computers
and
Data Processing
6th
Cumulative
Edition,
planned
for
1975
36
26
Notice
Entry
form
COMPUTERS and PEOPLE
for
January,
1975
Q)~~
\jQQ~~
G'0J>80&
•
Q'
~-
11-*
@
r;:[)
R-
-*
.J
'0~*r.1Q
G~~
~
\?
Q.,
II
*
*-
\)
& 0
lb
<::J
(k
\)
iG.
ANNUAL
INDEX
FOR 1974
It
is
planned
that
the
annual
index
for
the
13
issues
of
Computers and People
(including The Computer
Directory
and
Buyers' Guide,
1974)
will
be
published
early
in
1975.
If
any
subscriber
needs
an
annual
index
urgently,
before
it
is
published,
please
write
to
I
ndex
Ed
itor,
Computers and
People.
E .r-J E
'(
l
""
E
!..
t6)
,......
ev
? E
ri)fY)
'1
e~
Key
[A]
[C]
[E]
[F]
[P]
E'l.
Article
Monthly
Column
Editorial
Forum
Picture
NOTICE
*0
ON
YOUR
ADDRESS
IMPRINT
MEANS
THAT
YOUR
SUBSCRIP-
TION
INCLUDES
THE
COMPUTER
DIRECTORY.
*N
MEANS
THAT
YOUR
PRESENT SUBSCRIPTION
DOES
NOT
INCLUDE
THE
COM-
PUTER
DIRECTORY.
5
EDITORIAL
HCAN A COMPUTER
BE
CREATIVE?"
In
a
recent
discussion
a
friend
of
mine conceded
that
a
suitably
programmed computer
could
be
intelli~
gent
and a good
solver
of
problems and a very good
chess
player,
and
more
besides.
But
then
he
said:
I
subscribe
to
a
denotation
of
thought
as
in-
cluding
the
activity
which
we
generally
refer
to
as
creativity,
and
this
is
a
function
which
is
currently
denied
to
computers.
They can
do
no
more
than they
have been
told
to
do,
and
obedience
is
not
creativity.
It
is
in
the
cre-
ative
realm
that
man,
the
living
agent,
is
in-
imitable
--
thus
far.
I looked
up
defini
tions
of
"create"
and
"creati
v-
I
ty":
create:
to
bring
into
existence;
to
bring
a-
bout
a
course
of
action;
to
produce
through
imaginative
skill;
to
design,
invent,
de-
vi
se;
creative:
productive;
innovative;
formative;
constructive;
generative;
having
the
qual-
ity
of
something
created
rather
than
imita-
ted.
Then I
read
again
parts
of
a famous
essay
"Mathe-
matical
Creation"
by
the
great
mathematician,
Henri
Poincare
(1854-1912).
In
one
place
he
says:
What
is
mathematical
creation?
It
does
not
consist
in
making
new
combinations
with
mathe-
matical
entities
already
known.
Anyone
could
do
that,
but
tha
combinations
would be
infi-
nite
in
number and most
of
them
absolutely
without
interest.
To
create
consists
precise-
ly
in
not
making
useless
combinations
and
in
making
those
which
are
useful
and which
are
only
a small
minority.
Invention
is
discern-
ment,
choice.
A modern computer (which
Poincare
never
knew
a-
bout)
,can examine a
million
possible
combinations
in
less
time
than
a
human
being
can examine a
few
hundred.
Also,
it
can choose
among
the
combinations,
i;e.,
exercise
discernment,
according
to
stated
re-
qUirements,at
least
a thousand
times
faster
than
a
human
being
can.
So
the
argument,
it
seems
to
me,
reduces
to
recog-
nizing
that
there
are
really
two
kinds
of
creativity:
One
kind
we
can
call
high-level
creativity.
This
is
the
kind
that
probably
my
friend
and
Poincare
are
referring
to.
This
is
the
kind
displayed
by
an
art-
ist
who
uses
oil
colors
to
paint
a
portrait
as
good
as
Leonardo da
Vinci's
"Mona
Lisa";
or
a
musician's
use
of
a sequence
of
musical
notes
to
compose a sym-
6
phony
as
good
as
Beethoven's
5th
Symphony.
Nearly
all
human
beings
and
nearly
all
computer programs
are
unable
to
display
high-level
creativity.
But
some
do.
One
instance
of
a computer program
that
displays
high-level
creativity
is
the
checkers-
playing
program
of
Dr.
A.
L. Samuels
of
Stanford
Univ.
This
program
analyzes
checkers
situations
in
depth,
and
in
addition
learns
from
experience,
and
so
this
program has become a
checkers
champion;
it
plays
checkers
far
better
than
Dr. Samuels,
its
auth-
thor.
This
program
is
not
"obedient"
about
checkers;
it
"knows"
far
more
than
Dr. Samuels does
about
check-
ers;
it
makes
decisions
for
itself;
and
it
revises
and improves
those
decisions
in
the
light
of
experi-
ence.
Second,
there
is
ordinary
creativity.
Suppose a
kindergarten
teacher
calls
Johnny's
pictures
"crea-
tive".
Well, a computer
with
a random number
gen-
erator
and a
graphic
output
can
do
just
as
well
pro-
ducing
a
collection
of
paint
splashes.
Or suppose
a road crew
shuts
off
a
bridge
for
repairs
and
posts
signs
here
and
there
saying
"detour".
A computer
can
do
as
well
or
better
in
locating
the
signs.
A
great
many
people
and a
great
many
computer
programs can
display
ordinary
creativity.
When
a
human
being
like
Paul
Erlich
(1854-1915) makes 606
trials
for
a drug
to
cure
syphilis,
and
finds
that
No.
606 works, he
is
called
creative.
When
a
com-
puter
makes 23,793
trials
and
finds
that
the
last
one meets
best
all
the
requirements,
it
should
be
called
creative
also.
So
the
net
conclusion
to
the
argument,
it
seems
to
me,
is
thi
s :
-
ordinary
creativity
is
within
the
reach
of
a
great
many
human
beings
and a
great
many
computer programs;
high-level
creativity
is
out
of
reach
for
almost
all
human
beings
and
almost
all
com-
puter
programs;
-
the
proposed
criterion
"men
are
creative,
computers
are
not"
does
not
work,
is
not
effective,
to
distinguish
men
from computers;
- a computer can be
creative.
'
Edmund
C.
Berkeley
Editor
COMPUTERS and PEOPLE
for
January. 1975

1-
It
Languages
Among
Computers, Machines,
Animals,
and
Men
Lawrence
M.
Clark
835
Edmands Road
Framingham Centre,
Mass.
01701
"We are like fish swimming
in
an
ocean
of
natural
language.
We
are
thoroughly
immersed
in
that
ocean,
and
often
blind
and
ignorant
about
what
lies outside
of
the
part
of
the
ocean
that
we
happen to
know."
Outline
Part
1.
A Survey of Languages
1.
Telling
Computers
What
to
Do
2.
Listening
to
Computers
3.
The
Problem
of
Wrong
Instructions
4.
Artificial
Languages
for
Instructing
Computers
5.
Ordinary
Natural
Language
for
Instructing
Compu-
ters
6.
Languages
Among
Machines That
Are
Not
Computers
7.
Languages
Among
Animals
8.
Languages
Among
Men
9.
Essential
Features
of
a
Natural
Language
Part
2.
The
Designation
of Meaning
1.
Linguistic
Constraints
Upon
Thinking
2.
The
Words
for
"A
Group
of"
3.
The
Misleading
of
Thought
by
Language
4.
The
Words
for
Mathematical
Ideas
5.
How
to
Improve
the
Designation
of
Meaning
The purpose of
this
article
is
to
report
on
a
num-
ber
of
aspects
of
language,
to
discuss
some
signifi-
cant
problems of
designation
of
meaning, and
to
indi-
cate
some
probable
future
developments
in
language.
Computers
make
extensive
use
of
language
in
order
to
fulfil
their
functions;
to
place
computer
languages
in
the
perspective
of
languages
in
general
may
be
helpful.
1. Telling Computers What
to
Do
Anybody
who
approaches a computer
is
compelled
to
pay
some
attention
to
the
subject
of
language.
For
if
one
intends
to
have a computer
do
something
use-
ful,
then
one
regularly
has
to
tell
it
what
to
do
and
how
to
do
it;
and
this
requires
a system
for
giving
instructi
ons.
Now
you
yourself
can
avoid
telling
the
computer
how
to
do
it
--
by
hiring
a computer programmer,
or
buying a
software
package,
or
through
some
equivalent
process.
But
still
the
person
who
does
the
program-
ming
or
makes
the
software
has
to
learn
a system
for
instructing
the
computer, a
language.
This
requirement
implies
that
you
(or
your
sub-
stitute)
has
to
learn
a system
for
communicating
with
it.
And
a system
for
communicating
is
a
language.
So
the
subject
of
languages
in
general
is
intimately
as-
sociated
with
the
use
of
computers.
COMPUTERS and PEOPLE
for
January. 1975
2. Listening
to
a
Computer
The
computer
may
respond
to
you
with
a
single
final
answer,
or
it
may
respond
to
you
not
only
with
the
answer
but
also
with
many
intermediate
answers
and
other
pieces
of
information
besides.
In
the
case
of
access
to
a computer
through
a
time-shared
termi-
nal
or
non-shared
console,
you can
get
so
much
re-
sponse
that
you
reach
rather
full
and
adequate
two-
way
communication.
This
is
an
important
additional
dimension
of
lan-
guage;
interaction.
The
computer
says
thing-s
to
you
and you say
things
to
the
computer.
Interaction
is
far
more
satisfying
to
human
beings
--
most of
whom
love
to
talk.
To
talk
to
a computer and
to
have a
computer
talk
back
rationally
can be
thrilling.
This
experience
"turns
people
on;"
it
is
an
experience
that
helps
deprived
learners
learn.
See
the
refer-
ences
"The
Personality
of
the
Interactive
Programmed
Computer" /
2/
and "Computers
in
Inner-Ci
ty
Class-
rooms"/5/.
The
responses
of
a computer can be
of
several
styles.
The
least
useful
style
happens
when
the
computer
types
just
a questionmark
when
it
has
not
understood
something
as
an
instruction.
Then
you
wonder what you might have
said
to
the
computer
that
it
could
not
accept;
and having
come
to
some
con-
clusion,
you
try
a
new
command
on
the
computer,
to
see
if
that
works. A
much
better
response
from
the
computer happens
when
the
computer
types
"Error
21,"
say,
and
then
you look
up
error
21
in
a
numerical
list
of
errors,
find
it,
read
the
description,
rea-
lize
what you
did
that
was
wrong, and
act
differently.
A
still
better
system happens
when
the
computer
que-
ries
you,
specifying
different
possibilities
you
might have
intended,
and
asks
you
--
then
you
are
able
to
choose
among
the
possibilities,
give
the
computer a
correct
instruction,
and
proceed.
3.
The
Problem
of
Wrong Instructions
Every
now
and
then
you
find
out
that
a computer
has done
exactly
what you
told
it
to
do,
but
not
what you wanted
it
to
do.
If
you had been
talking
to
a
clerk
about
a
calcu-
lation,
the
clerk
would have
known
from
his
prior
experience
that
you
could
not
have
intended
something
that
you
said;
and so
applying
his
experience
or
gen-
eral
knowledge
or
common
sense,
he
would have changed
what you
said
to
what you meant.
Many
rather
famous
7

stories
are
told
about
how
a computer
did
just
what
it
was
told
to
do
but
not
what
the
programmer
inten-
ded.
One
such
story
is
of
the
Mariner
space
probe
that
was
to
fly
by
Mars
and photograph
it;
but
it
missed
Mars
by
a
great
distance
because
somewhere
in
the
long
series
of
instructions
controlling
it
a hyphen had been typed
instead
of
a
space.
To
guard
against
errors
of
language,
logic,
or
human
mistake-making,
etc.,
many
common
sense
pro-
cedures
have
evolved.
For
example
in
a system
using
interactive
business
programs,
when
a
clerk
is
using
a
video
data
terminal
to
enter
orders,
on
the
screen
may
appear
something
like:
Do
you want
to
make
any changes
in
this
order?
(YIN).
Then
the
clerk
looks
over
the
figures,
compares them
with
the
incoming
purchase'order,
and
if
he
sees
nothing
wrong, he
types
N.
Then
the
screen
once more
responds:
Last
call:
are
you
really
sure
all
the
figures
here
are
right?
(YIN).
Then presumably
the
clerk
compares once more, and
if
it
still
appears
that
all
is
correct,
this
time
he has
to
type
Y.
At
that
point
and
only
then,
the
system
accepts
the
data
and
enters
the
incoming
order.
4. Artificial
Languages
for Instructing Computers
The
need
to
instruct
computers,
to
tell
them what
to
do
and
how
to
do
it,
has been
responsible
for
the
development
of
a
large
number
of
artificial
languages,
probably
more
than
2000
in
all.
At
the
beginning
of
computers,
for
example
in
1944
at
the
Harvard
Compu-
tation
Laboratory
with
the
Harvard
IBM
Automatic
Se-
quence
Controlled
Calculator
Mark
I,
it
was
necessary
to
write
instructions
in
fine
detail.
These were
sequences
of
24
ones and
zeroes
in
bottom-level
"ma-
chine
language."
These sequences of ones and
zeroes
controlled
24
corresponding
switches
at
the
tape
reading
station.
As
each
instruction
was
read
on
24
hole
paper
tape
into
the
computer,
the
machine
con-
nected
two
locations
A and B
tb
the
bus and performed
operation
C;
each
of
A,
Band
C used
eight
one's
and
zeroes.
Then
special
purpose
languages
came
into
use,
many
of
them
expressed
in
"symbolic
assembly
language."
This
would
"assemble"
a program
on
a
specific
compu-
ter,
and would
allow
the
programmer
to
designate
lo-
cations
where
particular
data
was
stored
by
using
its
symbolic
address
rather
than
its
actual
address.
Then
"general
purpose" languages were
developed,
such
as
FORTRAN
(which
was
the
first),
BASIC,
COBOL,
PLII,
APL
and a number
of
others,
and
probably
over
300
more. These
freed
the
programmer from
the
need
to
specify
particular
locations
for
the
storage
of
each
piece
of
information.
These languages
theoretically
and
often
in
practice
could
be used
without
change
from one computer
to
another.
Some
general
purpose
languages
were
developed
to
apply
to
restricted
classes
of problems, such
as:
AED,
for
Automated
Engineering
Design;
SIMSCRIPT
II,
for
large
problems
in
discrete
simulation;
COURSEWRITER,
for
computer-assisted
instruction
in
any
field
of
knowledge;
etc.
The languages
for
expressing
algorithms
(calcula-
ting
rules
and
procedures)
and
the
general
purpose
languages
for
instructing
computers have
interwoven
with
each
other.
8
5.
Ordinary Natural
Language
for
Instructing Computers
For
more
than
25
years
it
has been
widely
believed
and
maintained
that
only
rigorous,
precise,
exact
lan-
guage
could
be used
for
talking
to
computers and
that
human
beings
therefore
had
to
become inhumanly
exact
and inhumanly
logical
in
order
to
program
computers.
This
is
not
true.
About
1972
Warren
Teitelman,
then
of
Bolt
Beranek
and
Newman,
Cambridge, Mass.,
developed
a
syst~'m
DWIM
which
was
a
"front
end"
for
using
the
general
purpose
programming language
called
LISP.
LISP
is
hard
to
use
because
it
is
unusually
fussy
in
insist-
ing
on
properly
matched
pairs
of
parentheses
(mathe-
matical
parentheses
placed
around
expressions).
He
wrote
a
report
"Do
What
I
Mean:
The
Programmer's
Assistant."
He
described
a number
of
techniques
incorporated
in
the
front
end which would
"forgive"
a
human
programmer
for
his
mistakes.
It
would
either
automatically
correct
rather
transparent
mistakes,
or
query
in
regard
to
a
suggested
interpretation.
In
this
way
DWIM
would remove
much
of
the
labor
from
the
programmer,
enable
him
to
concentrate
his
atten-
tion
on
higher
level
issues,
and become markedly
more
efficient
in
his
use
of
LISP. See
Reference
14.
Work
in
understanding
ordinary
natural
language
is
going
on
at
a number
of
laboratories
including
Mass.
Inst.
of
Technology,
IBM
Corp.,
Stanford
Uni-
versity,
Xerox
Corp.,
and
elsewhere.
A
series
of
articles
on
"Computer Programming Us-
ing
Natural
Language" has been
published
in
this
magazi ne. See
Reference
/ 3 / •
The
evi
dence
of-
fered
in
these
articles
demonstrates
that
a computer
program can
take
in
a
great
variety
of
non-rigorous
instructions
(that
are
unambiguous), and produce
rigorous
instructions
from them.
Some
of
the
work
in
being
exact
in
programming
is
being
transferred
from
human
program
writing
into
human
questionnaire
answering,
which
is
easier.
IBM
Corp. has a programming language
called
RPG
II
(Re-
port
Program
Generator
Model
2).
In
this
language a
good
deal
of
the.
information
for
programming a com-
puter
to
cover
a
particular
business
application
con-
sists
of
answers
to
a
series
of
questions,
yes
or
no.
After
all
the
questions
have been answered,
the
series
of
yeses
and noes
are
put
into
the
computer
system
that
makes programs (an
RPG
II
compiler).
That
goes
to
work and produces
the
tailormade
program
that
covers
the
needs
of
the
particular
busin~ss
applica-
tion.
So
much
for
the
present
discussion
of
the
state
of computer
languages.
Let us
turn
now
to
consider-
ing
languages
in
other
areas.
6.
Languages
Among
Machines
that
Are
Not Computers
Many
machines
that
are
never
thought
of
as com-
puters
also
require
a system
for
communicating
be-
tween
the
machine and a
human
being,
and between
the
machine and
the
environment.
An
ordinary
motor
car
driven
by
an
ordinary
human
being
is
such a
ma-
chine.
It
contains
many
pieces
of
apparatus
(odome-
ter,
speedometer,
fuel
gauge,
oil
pressure
indicator,
etc.)
for
communicating
information
to
the
driver,
and
for
receiving
instructions
from
the
driver
(steer-
ing
wheel,
gear
shift
handle,
brake
pedal,
etc.)
Some
machines
act
in
complex ways
quite
indepen~
dently
of
any
human
operators.
Such machines
detect
information
(through
sensors)
and
perform
actions
that
work
on
the
environment
(through
acting
elements
COMPUTERS and PEOPLE
for
January. 1975

o
like
valves,
rods,
bells,
etc.).
They
all
contain
somewhere a
black
box
(or
more
than
one
black
box)
where
the
incoming
signals
from
sensors
are
appro-
priately
associated
with
the
outgoing
signals
to
act-
ing
elements.
Such machines
are
often
called
servomechanisms
or
automata
or
robots.
A
very
simple example
of
a
robot
is
the
heating
system
in
an
ordinary
building
--
with
its
thermostats,
pilot
flame,
valves,
relays,
etc.
A
very
complex example
of
a
robot
is
the
dial
telephone
system of North America. That
may
well
be
the
largest
and most complex
robot
ever
made.
The
languages spoken
inside
this
robot
are
sets
of
ones and
zeroes
for
some
purposes,
sets
of
tones
(as
in
the
touchtone
telephone)
for
other
purposes,
and
probably
more.
Ordinarily
in
these
languages
there
will
be
just
one word
or
expression
to
express
each
idea
or
mean-
ing
in
the
same
way
as
in
mathematics,
where
the
ex-
pression
2
is
always used
for
the
idea
two. But
when
the
dial
telephone
system
starts
talking
to
a
human
user,
it
will
translate
into
one
of
the
ordinary
na-
tural
languages,
and
utter
sounds.
For example,
now-
adays
when
I
dial
a
telephone
number
that
has been
changed,
the
system
(doubtless
a computer
connected
to
a
recording
of a
voice)
tells
me
the
digits
of
the
new
number, and a
little
later
in
the
recorded
mes-
sage
it
repeats
those
digits
once more.
7.
Languages Among Animals
Many
kinds
of
insects,
birds,
and
animals
have an
important
degree
of
language.
One
interesting
source
of
information
is
the
book "King Solomon's Ring"
by
the
Austrian
naturalist
Konrad
Lorentz.
See
refer-
ence/lO~
A
colony
of
jackdaws
that
nested
on
and
near
his
house were
able
to
do
a
fair
amount
of
com-
municating
on
a number
of
subjects.
Repeatedly
one
of
the
jackdaws,
who
was
lonely,
in
her
song seemed
to
carryon
a
soliloquy
about
"good
old
times,"
until
finally
one day
her
mate, a jackdaw
who
had been
lost
for
a long
time
from
the
colony,
returned
from
migration,
and resumed
his
relationship
with
the
colony
and
with
her.
Ants succeed
in
conveying
information
to
each
other.
The
language
appears
to
consist
of
different
chemicals
and
smells
that
convey
signals;
probably
also
the
motions
of
ant
antennae
convey
signals.
The
number
of
possible
choices
of
information
to
be
con-
veyed
is
probably
rather
small,
perhaps
no
more
than
several
dozen.
One
August I observed an
anthill
which was
eleven
feet
across,
located
near
Nyack, N.Y.
This
anthill
maintained
herds
of
aphids
on
scores
of
leaves
of
bushes a hundred
feet
distant.
The
herds
of
aphids
were
tended
by
the
ants.
There were
well
traveled
trails
in
the
deep
grass
between
the
aphid
farms and
the
anthill.
Such
organization
implies
a
system
of
communicating
information;
and any such
system
is
a
language.
Bees
undeniably
have a language
that
conveys
ideas.
Some
excellent
studies
by
the
Austrian
investigator
Karl
Von
Fritsch,
have
shown
that
bees
convey
to
other
bees
the
distance
and
the
direction
from
the
hive
of
especially
attractive
food.
He
began
his
experiments
by
setting
out
a
dish
of
scented
sugar
water
at
a
certain
distance
and
direction
from a bee
hive.
For
two
or
three
days
no
hees
found
the
dish.
Then a few bees
did
find
the
dish:
he marked them
with
paint.
Soon
a
great
many
more
bees
not
marked
with
paint
came
to
the
dish
of
sugar
water.
He
var-
ied
the
location
of
the
dish,
and
observed
the
behav-
ior
of
the
painted
bees
within
the
hive.
The
hive
COMPUTERS
and
PEOPLE
for
January, 1975
had been
made
with
a
glass
side:
he
could
watch
with
red
light
invisible
to
the
bees.
The
scout
bees
returning
to
their
hive
seemed
excited:
they
carried
out
an
elaborate
"dance,"
which
other
bees
detected
with
their
antennae.
The
dance
was
either
a round
dance,
or
else
a wagging dance:
the
number of rounds
and
the
number
of
waggings
in
an
interval
of time
in-
dicated
the
relative
distance
of
the
sugar
water.
The
direction
of
the
sugar
water
was
indicated
by
the
direction
of
the
dance
of
the
scout
bees,
in
this
way:
if
the
hive
was
horizontal,
the
direction
of
the
scout
bee's
forward motion
in
the
dance
was
the
same
as
the
direction
of
the
food:
if
the
hive
was
vertical,
then
the
direction
of
the
dance
of
the
scout
bee
was
at
an
angle
from
the
vertical
which
was
the
same
as
the
an-
gle
of
the
direction
of
the
food from
the
direction
of
the
sun.
According
to
investigators,
birds
have
learned
languages
up
to
several
hundred words: most of
this
learning
is
parroting,
utterance
without
attention
to
meaning.
The
method
of
teaching
a
bird
any words
is
affectionate
and
loving
rearing
of
the
bird
in
the
way
that
a mother
brings
up
her
young.
Occasion-
ally,
however,
the
bird
will
use
words
with
their
proper
meanings,
like
saying
"Don't
go
away"
to
the
investigator.
Monkeys
that
live
in
families
in
the
tropics
ap-
parently
use a language
consisting
of
maybe
six
to
a dozen
signals.
Wolves
that
live
in
families
and
packs have a
degree
of language
by
which
they
give
and
receive
information.
See
the
book "Never Cry
Wolf"
by
Farley
Mowat.
/12/
Chimpanzees
in
captivity,
according
to
some
in-
vestigators,
have
about
twenty words
or
signals.
A
story
is
told
that
one
scientist
having
learned
some
chimpanzee language
at
the
Yerkes
laboratory
made
himself
welcome
at
once
among
a group
of
chimpanzees
in
the
London zoo
by
talking
to
them
in
chimpanzee
language.
Chimpanzees
also
show
evidence
of
being
able
to
deal
with
nonverbal
symbols.
At
the
Yerkes
Regional
Primate
Research
Center,
Athens, Ga., a chimpanzee
named
Lana has been
"talking"
with
the
aid
of a com-
puter
and a
new
language
called
Yerkish
created
es-
pecially
for
her.
She can
make
grammatically
correct
requests
for
food and
entertainmerit
by
punching
out
sentences
on
a
special
vertical
keyboard: and she
can
"read"
in
her
language.
See
the
report
"Commu-
nication
--
Three-Way: Chimpanzee,
Man,
Computer,"
Reference/
7/.
8.
Languages Among
Man
Of
all
the
tools
of
human
beings,
language,
equip-
ment
for
communicating,
is
probably
the
most
ancient
and
the
most
indispensable.
In
order
for
the
members
of
a
species
to
work
together
in
complicated
ways,
language
is
necessary.
In
order
for
the
young
of
the
species
to
be
trained,
not
only
by
examples and
sensations,
but
also
by
ideas
and commands, language
is
necessary.
With language
the
adults
teaching
the
young
do
not
have
to
find
and
illustrate
all
the
situations
for
instruction:
some
of
the
situations
can be
dealt
with
by
words
alone.
Finally,
the
sep-
arate
items
of
language can be used
as
markers,
as
counters,
for
the
process
of
reasoning
and
thinking.
What
is
language?
Basically,
language
is
equip-
ment
for
referring
to
and
handling
all
the
ideas,
situations,
and
experiences
that
a
society
is
inter-
ested
in.
Language
deals
with
the
experiences
and
situations
that
occur
in
the
culture
of
that
society.
9

What
kind
of equipment? In
the
case
of
nearly
all
human
languages,
the
equipment
basically
consists
of
sounds
that
human
beings
can-utter
and
hear,
and
to
which meanings have been
attached
by
convention.
The
convention
is
an unspoken
general
agreement
among
the
members
of
the
society
which
is
learned
thoroughly
as
the
young
people
grow
up
in
the
society.
The
purposes
of
human
language
are:
communicating,
that
is,
conveying
ideas,
asking
questions
and
get-
ting
answers;
reasoning;
describing
strange
ideas
in
terms
of
familiar
ones;
expressing
emotions and
feel-
ings;
expressing
politeness
and ceremony.
Language
contributes
so
very
much
to
the
thinking
of
human
beings
that
we
are
seldom aware
of
all
that
it
does do. Beginning
with
our
earliest
years,
lan-
guage
teaches
us,
educates
uS,focuses
our
attention,
and
commands
us
to
deal
with
the
ideas
that
language
alludes
to.
Language
provides
hooks
for
hanging our
ideas
on, boxes
for
putting
them
in,
and
trays
for
moving them
around.
Language
is
a
mirror
of
the
thoughts
we
have, and
it
reflects
them
quite
faith-
fully
and
impartially
--
both
wh~n
we
are
right
and
wh,n
we
are
mistaken.
The
languages
actually
spoken by
the
groups
of
human
beings
allover
this
world have been
studied
to
a
considerable
extent.
An
inventory
of
them
as
of
about
1950
is
as
shown
in
Table
1.
Europe and Asia
Africa
North America
South America
Total
Table 1
. Approximate
No.
of
Languages Spoken
720
530
240
~
1730
Among
these
languages
there
is
a tremendous
va-
riety.
Many
of
them
make
neat
and
felicitous
dis-
tinctions
which
are
absent
in
English;
many
of
them
ignore
distinctions
which
are
present
in
English.
9. Essential
Features
of
a Natural Language
~mid
all
these
variations,
what
is
essential
in
a
language?
Everyone
of
the
known
languages
is
made
up
of
sounds.
The most
convenient
equipment
for
symboliz-
ing
ideas
has always been
the
sounds
that
human
be-
ings
could
utter
and
hear.
Other
languages
such
as
writing
are
secondary.
The sounds
that
occur
in
languages have been
in-
ventoried
and
studied.
There
are
perhaps
some
60
sounds and
some
60
styles
of
modifying them, making
mathematically
3600
combinations.
These
elements
are
technically
called
phones, and
the
study
of
them
phonetics.
In
anyone
language,
a
cluster
of
phones
may
be
treated
by
the
speakers
of
that
language
as
having
the
same
significance.
In
English
for
example, a
cluster
of
different
ways
for
letting
air
explode
through
the
lips
is
designated
as
"b" and
another
cluster
of
similar
sounds
is
designated
as
"p",
and
they
are
distinguished
by
speakers
of
English;
in
Dutch
this
difference
is
not
observed,
"p"
and
"b"
are
not
distinguished.
In
any language each
cluster
of
sounds
selected
by
the
language
as
significant
is
called
a phoneme,
10
and
the
study
of
them
is
called
phonemics. Phonemes
do
not
have meanings
in
themselves.
Every language can be
organized
into
phonemes.
The
number
of
phonemes
present
in
a
language
ranges
from
17
in
Tagalog,
a language
of
the
Philippines,
to
45
in
Navaho,
an
American
Indian
language
of
Ari-
zona. There
are
about
40 phonemes
in
English,
about
17
of vowel
type,
and
23
of
consonant
type.
In
every
language phonemes
are
arranged
and
as-
sembled
into
words and word
elements.
Words
and word
elements
are
technically
called
morphemes,
units
of
form; morphemes
are
those
arrangements
of
phonemes
which have meaning
in
the
language.
Every language
consists
of
a
large
set
of
words
(morphemes). A
collection
of
all
the
words (mor-
phemes)
in
a language
is
a
dictionary.
A
collection
of
all
the
meanings
represented
among
the
words
in
a language
is
a
lexicon.
Every
known
Inaguage has
at
least
5,000
words, and
English,
the
largest
lan-
guage,
contains
over
500,000 words.
Every language
recognizes
single
complete
lin-
guistic
utterances
--
which
are
often
called
sen-
tences,
although
that
term
is
not
inclusive
enough.
Every
language
has
rules
for
assembling
words and
word
elements
into
utterances.
These
rules
are
call-
ed grammar and
syntax.
Every
known
language has
in-
tricate
grammer;
some
languages have grammar
much
more
intricate
than
others.
English
has
lost
most
of
the
old
grammar
that
it
used
to
have.
This
was
a
fortunate
result
of
social
conditions
in
the
300
years
following
the
Norman
conquest
of
England
in
1066.
Every language has
the
power
to
express
a
large
part
of
any
situation
occurring
within
the
social
cuI
ture
in
which,
it
belongs.
In
addi
tion
it
has
the
power
to
create
new
expressions.
Thus
as
the
culture
of a
society
develops
and
changes,
and
new
ideas
need
to
be
referred
to,
these
new
ideas
also
may
be
expressed.
Every language summarizes
experiences
that
are
not
the
same
but
are
much
alike
into
single
words
'or
expressions
that
are,
to
the
extent
of
the
sum-
marizing,
vague. For example,
nearly
every
language
has a word
for
"the
sun";
and
all
the
different
mani-
festations
of
the
sun
at
dawn,
at
noonday,
at
sun-
set,
in
clouds,
or
in
clear
sky
are
summarized and
lumped
together
under one word,
the
word
for
"sun."
But
in
at
least
one American
Indian
language,
that
word
also
refers
to
"moon";
the
word
in
fact
means
"large
shining
heavenly
object,"
and
speakers
rely
on
the
context
to
show
which one
of
the
two
they
mean.
Every language has
devices
for
classifying
situa-
tions
and
experiences
so
that
they
can be
described
using
a
finite
number of
expressions.
The
devices
for
classifying
situations
and
experiences
vary
greatly
from language
to
language.
Some
of
the
classifications
are
obligatory
and
some
are
optional.
It
is
reasonable
to
believe
that
the
language
that
has
the
fewest
obligatory
classifications
is
the
best.
English
has
at
least
six
obligatory
classifications:
they
include
number,
gender,
case,
tense,
and
some
other
particulars.
Latin
has more. For example;
in
Latin
you
cannot
say
"Who
did
it?"
without
specifying
the
gender
of
"who" and'
the
number
of
"who."
So
there
are
four
ways
of
saying
this,
and
the
speaker
must
decide
which one
to
say.
Even
in
English
we
may
be
re-
COMPUTERS and PEOPLE
for
January, 1975
\
-;4

quired
to
specify
"animate
or
inanimate."
We
run
in-
to
the
problem
when
we
have
to
say
"who
or
what
made
this
letter?"
In
Chinese,
one does
not
have
to
spe-
cify
singular
or
plural
unless
one
desires
to.
In
Chinese,
the
word
for
"horse"
means
"horse"
or
"hor-
ses";
optional
words
tell
the
listener
whether
the
speaker
refers
to
one
or
more
horses.
Chinese
in
this
respect
is
certainly
better
than
English.
Classifications
that
make
no
difference
in
the
social
culture
of
the
people
speaking
the
langu~ge
will
not
be found.
Classifications
that
are
impor-
tant
in
their
culture
will
be
fully
worked
out.
For
example,
in
Latin
there
were two words
for
"uncle";
these
were
"atruus"
or
"avunculus"
depending
on
whe-
therthe
uncle
was
the
father's
brother
or
the
moth-
er's
brother.
But
in
English
this
distinction
is
almost
never
thought
of,
much
less
registered
in
separate
words,
because
in
our
culture
it
is
very
unimportant
whether
an
uncle
is
via
the
mother
or
the
father.
The
devices
used
for
expressing
grammar
vary
from
language
to
language.
Some
languages use
order
al-
most
to
the
exclusion
of
other
devices.
Some
use
suffixes
or
prefixes
that
tell
which terms
belong
together,
the
principle
of
concord.
For example,
Edward
Sapir,
a former
professor
of
languages
at
Yale,
gives
an example from
the
Bantu language
of
Africa.
He
says:
In
such a
sentence
as
"that
fierce
lion
who
.
came
here
is
dead,"
the
class
of
"lion,"
which
we
may
call
the
animal
class,
would
be
referred
to
by
concording
prefixes
no
less
than
six
times:
in
"that,"
in
"fierce,"
in
"lion,"
in
"who,"
in
"came" and
in
"dead."
Distinctions
which
are
considered
obligatory
in
one language
may
be
almost
missing
from
another.
For example,
the
distinction
as
to
"definite"
or
"indefini
te"
which
in
Engli
sh
we
must always
express
by
"the"
or
"a"
or
in
some
other
equivalent
way
is
missing
from
Latin~
although
Latin
does have demon-
stratives.
And
of
course
in
the
English
of
news-
paper
headlines,
this
distinction
also
disappears
as
in
"man
bi
tes
dog"
--
wri
ter
and
reader
alike
take
it
as
part
of
the
context,
to
be
reasoned
out
only
if
important.
Distinction
as
to
parts
of
speech
varies
greatly
from one language
to
another.
Most
languages
however
have
noun-like
and
verb-like
forms.
Some
languages
push
adjectives
into
verbs,
others
push them
into
nouns.
We
have
no
single
verb
for
"is
red,"
although
we
do have a
single
verb
that
means "becomes
red,"
namely
"reddens."
In
some
languages
all
adj
ecti
ves
are
verbs
in
this
fashion.
Franz
Boas, a
great
anthropologist,
said
that
some
principles
of grammar
are
the
same
allover
the
world.
He
says:
The
relational
functions
of
grammar have
cer-
tain
principles
in
common
allover
the
world.
Here belong
for
instance
the
relations
between
subject
and
predicate,
noun and
attribute,
verb
and
adverb,
and
the
relation
of
the
ex-
perience
to
the
speaker
(the
self)
and
to
others
--
that
is,
the
relation
expressed
by
the
pronouns
I,
you, and
he.
The
methods
by
means of which
these
and
other
relations
are
expressed
vary very
much,
but
they
are
neces-
sary
elements
of
every
grammar.
COMPUTERS
and
PEOPLE
for
January. 1975
Part 2.
The
Designation
of
Meaning
1. Linguistic Constraints Upon Thinking
In
spite
of
the
enormous
richness
of
developed
modern
languages,
of which
English
is
perhaps
the
best
example,
natural
language
constrains,
bends,
distorts,
that
which
we
may
want
to
say.
Sometimes
we
cannot
say what
we
want
to
say
with-
out
inventing
new
words and
new
forms
of
expression.
The
English
language
actually
adds
about
1000
to
3000
new
words,
new
uses
of
old
words, and
new
expressions
to
the
language
in
every
calendar
year.
A
fine
re-
port
on
these
words
introduced
since
1963
is
in
the
book by
Clarence
Barnhart.
See
reference/
1
/.
Edward
Sapir
(1884-1939), an American
anthropolo-
gist,
and a
professor
at
Yale
University,
linguist,
and
author,
once
wrote
as
follows,
regarding
the
important
influence
of
language
on
human
beings:
Human
beings
do
not
live
in
the
objective
world
alone,
nor
alone
in
the
world
of
social
activity
as
ordinarily
understood,
but
are
very
much
at
the
mercy of
the
particular
lan~
guage which has become
the
medium
of
expres-
sion
for
their
society.
It
is
quite
an
il-
lusion
to
imagine
that
one
adjusts
to
reality
essentially
without
the
use of language and
that
language
is
merely an
incidental
means
of
solving
specific
problems
of
communication
or
reflection.
The
fact
of
the
matter
is
that
the
"real
world"
is
to
a
large
extent
unconsciously
built
up
on
the
language
habits
of
the
group
•..•
We
see
and
hear
and
other-
wise
experience
very
largely
as
we
do
because
the
language
habits
of
our
community
predis-
pose
certain
choices
of
interpretation.
In
a
basic
sense,
human
beings
deeply
need
more
adaptable,
less
conventional
patterns
in
their
minds, so
as
to
think
better.
We
need
to
escape
limitations
from
culture,
history,
language,
propa-
ganda,
etc.
Consider
George
Orwell's
remark
in
"1984"
(published
by
Harcourt
Brace,
New
Xork,
many
editions):
The
purpose
of
Newspeak
was
not
only
to
pro-
vide
a
medium
of
expression
for
the
world-
view and
mental
habits
proper
to
the
devotees
of
Ingsoc,
but
to
make
all
other
modes
of
thought
impossible.
2.
The
Words
for
"A
Group
of"
Let
us
take
a
specific
example
of
linguistic
con-
straint.
Suppose
we
read
a
short
report,
first
in
one
style,
then
in
a second
style:
One
afternoon
in
August, John
Jones
drove
away
from
New
York
in
his
car,
surrounded
by
a
mob
of
other
cars.
Flying
overhead
was
a
drove
of
airplanes.
Soon he
overtook
a
travel-
ling
circus,
passing
a
swarm
of
elephants,
a
flock
of dogs, and a bevy
of
trucks.
As
the
sun
set,
he
saw
in
the
west
a
herd
of
rosy
red
clouds.
In
the
second
style,
here
is
the
same
report:
One
afternoon
in
August, John
Jones
drove
away
from
New
York
in
his
car,
surrounded
by
a group
of
other
cars.
Flying
overhead was a group
of
airplanes.
Soon he
overtook
a
travelling
cir-
cus,
passing
a group
of
elephants,
a group
of
dogs, and a group of
trucks.
As
the
sun
set,
11

he
saw
in
the
west
a group
of
rosy
red
clouds.
In
this
example,
we
see
what happens
when
we
de-
liberately
scramble
the
customs
of
English
in
using
words
that
mean
"a
group
of,"
words
like
"mob,
drove,
swarm,
flock,
bevy,
herd."
English
contains
forty
or
fifty
such words
with
different
connotations.
For
example, "swarm"
implies
"a
group
of
bees
or
in-
sects"
and
"herd"
implies
"a
group
of
large
animals."
Of
course,
there
is
almost
no
logical
sense
in
vary-
ing
the
word meaning
"a
group
of"
depending
on
the
kind
of
thing
being
grouped.
But
as
long
as
writers
want
to
write
"good usage" and
prefer
to
obey
present
happenstance
usage
in
regard
to
words
like
these,
so
long
will
the
expression
of
logical
ideas
be
clouded,
and
thinking
be
constrained,
bent,
by
the
language
of
"good
usage."
3.
The
Misleading
of
Thought
by
Language
Benjamin Lee Whorf
(1897-1941),
a
graduate
of
Mass.
Inst.
of
Technology, worked
as
an
engineer
in
a
fire
insurance
company
in
Hartford,
Conn.;
but
a
great
deal
of
his
avocational
research
and
thinking
was
in
the
field
of language and
linguistics.
The
following
passage
is
taken
(with
minor
changes)
from
his
article
"The
Relation
of
Habitual
Thought and
Behavior
to
Language"
included
in
"Language,
Cul-
ture,
and
Personality:
Essays
in
Memory
of
Edward
Sapir,"
edited
by
Leslie
Spier,
published
by
the
Sapir
Memorial
Publication
Fund, Menasha, Wisconsin,
1941 :
((Beginning
of
Quotation))
An
accepted
pattern
of
using
words
is
often
prior
to
certain
lines
of
thinking
and forms
of
behavior.
A
man
who
assents
to
this
statement
often
sees
in
such a
statement
nothing
more
than
a
platitudinous
recognition
of
the
hypnotic
power
of
philosophical
and
learned
terminology
on
the
one hand,
or
of
catchwords,
slogans,
and
rallying
cries
on
the
other.
To
see
only
thus
far
is
to
miss
the
point
of
one
of
the
important
interconnections
which
Sapir
saw
between
language,
culture,
and
psychology.
It
is
not
so
much
in
these
special
uses
of
language
as
in
its
constant
ways
of
arranging
data
and
its
most
ordinary
everyday
analysis
of
phenomena
that
we
need
to
recognize
the
influence
it
has
on
other
activities,
cultural
and
personal.
In
the
course
of
my
professional
work
for
a
fire
insurance
company, I
undertook
the
task
of
analyzing
many
hundreds
of
reports
of
circumstances
surround-
ing
the
start
of
fires,
and
in
some
cases,
of
ex-
plosions.
My
analysis
was
directed
toward
purely
physical
conditions,
such
as
defective
wiring,
pres-
ence
or
lack
of
air
spaces
between
metal
flues
and
woodwork,
etc.,
and
the
results
were
presented
in
these
terms.
Indeed
it
was
undertaken
with
no
thought
that
any
other
significances
would
or
could
be
re-
vealed.
In due
course
it
became
evident
that
not
only
a
physical
situation
as
physics,
but
the
meaning
of
that
situation
to
people,
was
sometimes a
factor,
through
the
behavior
of
the
people,
in
the
start
of
the
fire.
And
this
factor
of
meaning
was
clearest
when
it
was
a
LINGUISTIC
MEANING,
residing
in
the
name
or
the
linguistic
description
commonly
applied
to
the
situation.
a.
Empty
Gasoline
Drums. Thus, around a
storage
of what
are
called
"gasoline
drums,"
behavior
will
tend
to
a
certain
type,
that
is,
great
care
will
be
exercised;
while
around a
storage
of
what
are
called
"empty
gasoline
drums,"
it
wi
11
tend
to
be
different
12
--
careless,
with
little
repression
of
smoking
or
of
tossing
cigarette
stubs
about.
Yet
the
"empty" drums
are
perhaps
the
more
dangerous,
since
they
contain
explosive
vapor.
Physically,
the
situation
is
hazar-
dous;
but
the
linguistic
analysis
according
to
regu-
lar
analogy
must employ
the
word
"empty,"
which
in-
evitably
suggests
lack
of
hazard.
The word "empty"
is
used
in
two
linguistic
patterns:
(1)
as
a
virtual
synonym
for
"null
and
void,
negative,
inert,"
(2)
applied
to
analysis
of
physical
situations
without
regard
to,
e.g.,
vapor,
liquid
vestiges,
or
stray
rubbish,
in
the
container.
The
situation
is
named
in
one
pattern
(2)
and
the
name
is
then
"acted
out"
or
"lived
up
to"
in
another
(1),
thi
s
being
a
gen-
eral
formula
for
the
linguistic
conditioning
of
be-
havior
into
hazardous
forms.
b.
Limestone.
In
a
wood
distillation
plant
the
metal
stills
were
insulated
with
a
covering
prepared
from
limestone
and
called
at
the
plant
"spun
lime-
stone."
After
a
period
of
use,
the
fire
below one
of
the
stills
spread
to
the
"limestone,"
which
to
everyone's
great
surprise
burned
vigorously.
Ex-
posure
to
acetic
acid
fumes from
the
stills
had
con-
verted
part
of
the
limestone
(calcium
carbonate)
to
calcium
acetate.
This
when
heated
in
a
fire
decom-
poses,
forming inflammable
acetone.
Behavior
that
tolerated
fire
close
to
the
covering
was
induced
by
use
of
the
name
"limestone,"
which
because
it
ends
in
"-stone"
implies
noncombustibi
Ii
ty.
c.
Pool
of
Water. A
tannery
discharged
waste
water
containing
animal
matter
into
an
outdoor
set-
tling
basin
partly
open.
This
situation
is
one
that
ordinarily
would be
verbalized
as
"pool
of
water."
A
workman
had
occasion
to
light
a
blowtorch
nearby,
and threw
his
match
into
the
water.
But
the
decom-
posing
waste
matter
was
evolving
gas
under
the
wood
cover,
so
that
the
setup
was
the
reverse.
of
"watery".
An
instant
flare
of
flame
ignited
the
woodwork, and
the
fire
quickly
spread
into
the
adjoining
building.
Such examples, which
could
be
greatly
multiplied,
will
suffice
to
show
how
the
cue
to
a
certain
line
of
behavior
is
often
given
by
the
analogies
of
the
linguistic
formula
in
which
the
situation
is
spoken
of,
and
by
which
to
some
degree
it
is
analyzed,
classified,
and
allotted
its
place
in
that
world
which
is
"to
a
large
extent
unconsciously
built
up
on
the
language
habits
of
the
group."
And
we
always
assume
that
the
linguistic
analysis
made
by our
group
reflects
reality
better
than
it
does.
((End
of
Quotation))
4.
The
Words for Mathematical Ideas
One
of
the
clearest
examples
of
the
need
to
break
away
from
the
restraints
of
ordinary
natural
language
is
the
development
of
mathematical
words
for
mathe-
matical
ideas.
The
special
linguistic
ways
in
which
mathematicians
talk
about
mathematics have
developed
for
more
than
2000
years.
For example,
the
formula
A
=1rr
2
is
the
mathematical
form
for
the
English
statement
The
area
of
a
circle
is
equal
to
3.1416
•••
times
the
square
of
the
radius
of
the
circle.
A formula which has had a
name
for
more
than
2000
years
is
the
Pythagorean
Theorem:
h2
= a2 +
b2
In
English
this
is:
The
area
of
the
square
constructed
on
the
hypotenuse
of
a
right-angled
triangle
is
equal
to
the
sum
of
the
areas
of
the
squares
con-
structed
on
the
base
and
on
the
altitude.
COMPUTE
RS
and PEOPLE
for
January. 1975

These
are
examples
of
the
brevity
and
perspicuity
of
mathematical
language,
which
is
a
forerunner
of
much
of
the
language used
for
describing
algorithms
to
be
used
on
computers.
Mathematics
is
very
largely
a language
that
has
three
special
properties.
First,
its
chief
subject
matter
is
certain
kinds
of
abstract
elements
--
num-
bers,
lines,
points,
etc.
--
and
the
relations
of
these
elements.
Second,
its
chief
property
is
that
it
makes use
of
very
efficient
symbols, symbols
that
one can
calculate
with
to
a
vast
extent.
Third,
its
chief
purpose
is
to
determine
necessary
consequences
from
given
assumptions.
All
these
properties
are
of
course
present
to
some
extent
in
ordinary
language.
In
ordinary
lan-
guage, you can
talk
to
some
extent
about
numbers,
lines,
points,
etc.,
and
their
relations.
In
ordi-
nary
language,
you can even
calculate
to
some
extent.
And,
using
ordinary
language,
you
are
often
interes-
ted
in
deducing
the
necessary
consequences
of
some
suppositions.
Accordingly
the
difference
between
mathematics and
ordinary
language
is
partly
a
dif-
ference
of
quality,
but
also
a
difference
of
degree.
It
is
reasonable
to
believe
that
if
you have a
de-
sirable
property
in
mathematical
language,
you
may
be
able
to
arrange
the
same
desirable
property
in
language.
We
have mentioned
calculation.
What
do
we
mean
by
it?
We
mean
that
we
can
manipulate
symbols
ac-
cording
to
rules
that
pay
little
attention
to
mean-
ings,
and
that
when
we
come
out
with
results
at
the
end
of
the
process
of
manipulation,
then
our symbols
often
apply
truthfully
to
real
situations.
People
can and
do
calculate
with
ordinary
words, even
when
they
are
not
sure
of
the
meanings
of
these
words.
Here
is
an example
taken
from "Language and
Communi-
cation"
by George
A.
Miller:
Suppose
we
learn
on
good
authority
that
all
mantelops
are
lespeads
and
that
all
lespeads
hile.
We
can
conclude
immediately
that
all
mantelops
hile,
and
that
any
grimpet
that
does
not
hile
certainly
is
not
a
mantelop.
There
may
of
course
be
lespeads
that
aren't
mantelops,
so
hiling
is
not
a
sure
sign
of
mantelopicity.
Then he
says:
The
fact
that
we
have
no
idea
what
we
are
talk-
ing
about does
not
stop
us from
talking.
We
simply
operate
on
names and
properties
accord-
ing
to
the
rules
governing
the
use
of
logical
terms.
And
he might
very
well
add, though he
did
not
say
so,
that
the
reasoning
is
perfect,
and
that
all
we
have
to
do
to
get
truthful
uses
of
the
statements
about
"mantelops,
lespeads,
hiling,
grimpets"
is
to
interpret
the
words
in
suitable
ways.
5.
How
to
Improve
the
Designation
of
Meaning
How
shall
we
improve
the
designation
of
meaning?
and
the
description
of
reality
so
that
we
can
more
faithfully
describe
it
and
deal
with
it?
Of
course
this
is
an
old
problem.
Many
people
work
on
it
both
consciously
and
unconsciously
from
time
to
time.
A
person
who
coins
a
new
and
useful
expression
is
helping
in
this
process.
In
the
United
States
some
time
in
the
1830's
the
expression
"OK"
was
coined.
No
authority
is
quite
sure
of
the
deri-
vation.
Now
the
word
is
internationally
used,
and
COMPUTERS
and
PEOPLE
for
January. 1975
everywhere
understood
and
accepted.
It
filled
a
need.
And
it
is
much
clearer
than
"yes"
and
"all
right.
"
There
is
continual
competition
in
language
be-
tween
different
expressions
for
closely
related
ideas.
The
competition
often
produces
two
words
where
there
was
just
one
before.
"Of" and
"off"
for
example
are
both
derived
from
the
same
word.
Differentiation
is
the
name
given
to
the
linguistic
process.
The
movement
for
the
liberation
of
women
has
pro-
duced
the
word "Ms." (pronounced
"miz")
so
that
a
woman
can be
addressed
politely
without
the
designa-
tion
of
whether
or
not
she
is
married.
This
is
ob-
viously
a
useful
and
democratic
improvement and
probably
is
permanent.
Correspondingly,
"spokesman"
and
"chairman"
have
sprouted
the
words
"spokesuerson"
and
"chairperson."
Whether
these
three-syllable
words
offered
in
place
of
two-syllable
words
will
survive
is
a
question;
but
the
words might
survive.
Perhaps
the
most
important
process
for
improving
the
designation
of meaning
is
paraphrasing,
trans-
lating
from one
set
of
words,
often
with
highly
colored
overtones,
into
words
that
are
much
more
neutral
and
avoid
those
overtones.
"Shit"
becomes
"excrement".
"Pigheaded
fool"
becomes
"stubborn
and
foolish
person".
"The morgue"
of
a
hospital
becomes "Ward X".
Paraphrasing
--
translating
expressions
into
other
expressions
that
"say
the
same
thing
but
say
it
better"
--
is
a key
process.
A computer can
do
paraphrasing.
When
a program
is
written
in
FORTRAN,the
computer by means
of
what
is
called
a
FOInRAN
compiler
can
paraphrase
that
program
into
a machine language program
that
will
enable
that
computer
to
solve
that
type
or
problem.
The
program
"DWIM,"
"Do
What
I Mean," mentioned
above can do
paraphrasing.
It
will
accept
many
variations
of
computer
input
from a
human
being
and
convert
them
all
into
a
single
standard
computer
in-
put.
This
is
the
early
seed of a
great
development
'in
computer
applications.
We
are
like
fish
swimming
in
an ocean of
natural
language.
We
are
thoroughly
immersed
in
that
ocean,
and
often
blind
and
ignorant
about
what
lies
outside
of
the
part
of
the
ocean
that
we
happen
to
know.
The
development of computer
paraphrasing
of
ex-
pressions,
statements
and
discourse
in
ordinary
na-
tural
language
will
take
us a long way. Like lung
fish
we
shall
climb
out
of
the
ocean, and
begin
to
obtain
a
much
greater
and more
correct
picture
of
the
world,
eventually
including
land,
atmosphere,
and
space.
REFERENCES
1.
Barnhart,
Clarence
L.,
"The
Barnhart
Dictionary
of
New
English
since
1963", Harper &
Row,
New
York,
NY,
1973, '510 pp.
2.
Berkeley,
Edmund
C.,
"The
Personali
ty
of
the
In-
teractive
Programmed Computer,"
in
"Computers and
Automation,"
Dec.,
1969
3.
Berkeley,
Edmund
C.,
Andy
Langer,
and
Casper
Ot-
ten,
"Computer Programming Using
Natural
Language,"
in
"Computers and Automation"
or
"Computers and
People":
Part
I,
Jun,
1973,
p.lO;
Part
2,
Jul,
1973,
p.18;
Part
3,
Aug,
1973,
p.28;
Part
~,
Aug,
1974,
p.2;
Part
5,
Oct,
1974,
p.30
(please
turn
to
page 19)
13

The
Frictional
Interface
Between
Computers
and
Society
Dr.
Robert
W.
Bemer
Honeywell
Information
Systems
Phoenix,
AZ
USA
For
purposes
of
this
article
I
propose
a simple
and
perhaps
novel
classification
of computer
appli-
cations
--
in
three
classes.
The
Computer
Advises
Applications
that
do
not
lead
to
decisions
affect-
ing
humans
directly
--
Examples
come
largely
from
the
field
of
numerical
computation,
the
earliest
cate-
gory
of
usage.
Computational
results
that
might
tend
to
prove
or
lead
to
a
theory;
calculations
for
spaceship
or
missile
design
(they
don't
have
to
be
built
or
launched);
programs
for
playing
games,
or
associating
payoffs
with
strategies,
etc.
We
may
term
such
computation
"advisory."
The
Computer
Proposes Decisions
Applications
with
computational
results
that
lead
to
decisions
by
humans
--
Some
of
these
can
get
very
close
to
integration
into
human
affairs.
For exam-
ple,
someone
may
be
denied
credit
or
refused
an
em-
ployment
opportunity.
It
has
turned
out,
in
much
practice,
that
the
human
decision
to
be
taken
may
be
perfunctory
or
mindless.
Nevertheless
there
is
recourse,
no
matter
how
time-consuming and
difficult
it
may
be,
and
regardless
of
what body of law
may
need
to
be
enacted
to
protect
people
in
such
circum-
stances.
The
Computer
Decides, and if
not
Countermanded
Ac~s
(the
Robot)
Applications
where
the
computer has been
previous-
ly
programmed
to
take
a
decision
and
take
an
action,
and
will
in
fact
act
unless
countermanded
in
time
--
Examples
are
online
patient
monitoring,
control
of
nuclear
power
plants,
air
traffic
control
and
col-
lision
avoidance
systems,
automatic
transportation
.
systems
(i.e.,
BART,
in
San
Francisco),
and
auto-
mobile
braking
and
antiskid
systems.
Tremendous
Increase
of
Robots
The hardware developments
of
about
the
last
three
years
leading
to
microprocessors
on
chips,
portend
a
tremendous
increase
in
the
third
class
of
applica-
tion.
And
this
is
why
we
must be
on
guard
as
to
the
propriety
and systems
aspects
of
such
applications.
Applied
to
automobiles,
such
applications
could
be
extremely
critical.
One
is
reminded
of
power-steer-
ing,
a boon
when
it
operates,
perhaps,
but
a
defi-
nite
danger
when
power
fails
or
is
turned
off.
"We
all
must
cease
to
make wrong decisions on a large scale because
mankind
can
no
longer
afford
it. Mankind's resources are
highly
limited,
and
we
can
no
longer squander
them."
-
V.
A. Trapeznikov
A
pair
of
questions
indicates
a
possible
dilemma:
Q:
Does
technology
exist
to
integrate
compu-
ter
components
very
closely
into
human
af-
fairs?
A:
Yes. For an example,
see
the
1974
US
auto-
mobiles,
which
will
not
operate
unless
seat
belts
are
fastened.
Q:
Are system
design
and good
practice
manu-
als
available
for
such a
level
of
tech-
nology,
and/or
is
suitable
indoctrination
and
education
available
in
our
educational
institutions?
A:
Emphatically
NO!
This
fact
is
frightening
enough
to
suggest
a moratorium
on
such
de-
velopments
until
we
understand
the
tool
better.
Inoperable
Robots
Consider
the
announcement
of
an
experimental
de-
vice
which
requires
matching a
certain
procedure
be-
fore
you can
start
your
automobile.
The
intent,
and
certainly
an obvious usage,
is
to
preclude
drunken
drivers
from
operating
vehicles.
But suppose
that
you
are
extremely
shaken
because
your
wife
has
just
been
killed,
and your
child
needs
to
be
taken
to
the
hospital.
Could you
start
the
car
then?
Or
consider
the
case
of
online
patient-monitoring
reported
in
Datamation magazine
of
1972
October.
The
programming
was
correct
but
the
computer
was
not
100%
reliable.
This,
as
we
know,
is
taken
care
of
by
hav-
ing
a
customer
engineer
to
fix
it.
But nobody
re-
membered
to
find
out
whether
the
customer
engineers
would always be
available
over
the
weekend, and
speedily.
As
reported,
a
patient
died
because
con-
fusion
in
the
human
system caused
the
computer
to
remain
inoperable.
Space
Effort
Experience in Overriding
Robots
Certainly
the
US
space
effort
has
gathered
ample
experience
in
the
matter
of
letting
computers
de-
cide,
when
they
are
capable
of
it,
and
of
overrid-
ing
them
sensibly
when
it
is
shown
that
they
were
programmed
incorrectly
or
without
consideration
for
all
eventualities
and
malfunctions.
We
see
many
spin-offs
from
the
space
effort
with
respect
to
products,
but
very
little
in
methodology which
could
be so
very
applicable
to
computer
usage.
Based
on
a presentation to the NordData Conference, Copenhagen, Denmark,
August
1973.
14 COMPUTERS
and
PEOPLE
for
January, 1975

:i,
t
m
o
d
d
1-
Computers
as
a
Boon
Now,
I
like
computers.
I
believe
that
they
are
presently
more
beneficial
than
harmful
to
society,
and
that
this
ratio
can be
increased
if
we
take
care-
ful
consideration
and
plan
for
their
best
and
proper
usage.
If
I were
fatalistic,
I
should
feel
that
they
have
arrived
just
in
time
to
save
us from our
enemies,
who
are
ourselves.
In
25
years
as a programmer I have
never
faced
a day
of
working
with
computers
without
pleasant
anticipation.
I
also
like
a
fire
in
the
fireplace,
but
not
ar-
son. Both
fire
and computers
are
tools
accessible
to
all
of
society
in
some
form, and
society
uses
such
basic
tools
in
many
ways,
some
deemed good and
some
bad.
Fire
was
an
early
tool,
useful
for
hollowing
out
logs
to
make
vessels,
to
make
transformations
in
food,
and
to
heat
enclosed
air.
It
was
also
used
to
burn
vegetation
and
trees,
sometimes
accidentally
(which
was
thought
bad) and sometimes
deliberately,
to
clear
for
planting
(which
was
thought
good).
Side-Effects, Unanticipated
A major
difficulty
in
analyzing
the
contribution
of
a
tool
is
the
inability
to
categorize,
in
an
ab-
solute
way,
its
uses
as
being
good
or
bad.
This
is
not
philosophical,
but
only
to
remind us
that
we
make
these
judgments
of
good and bad
in
the
narrow
context
of
our mores and
morals,
which
are
in
turn
conditioned
by
ou~
accumulated knowledge and
analy-
sis
of
the
workings of our
world.
We
have
learned
a
little
more
of
those
workings
lately,
not
because
we
sought
the
knowledge so
much
as
because
it
has
been
made
painfully
evident
to
us
that
there
is
more
or
less
coupling
between
all
the
elements
of
our
world.
I
quote
from an
interview
with
Dr.
Carl
Hammer
of
Univac,
regarding
a
conversation
with
V.
A.
Trap-
eznikov,
acting
Co-Chairman of
the
United
States
and
Russian
Joint
Commission
on
Scientific
and
Techni-
cal
Cooperation:
"He
told
me,
as
he
told
President
Nixon one day
earlier,
that
'we
all
must
cease
to
make
wrong
decisions
on
a
large
scale
because
man-
kind
can
no
longer
afford
it.
Mankind's
resources
are
highly
limited,
and
we
can
no
longer
squander
them'
•••
we
must
develop
not
only
national
but
in-
ternational
models
for
improving our
decisionmaking
processes.
Decisions
which
at
this
time
are
made
on
a
political
or
emotional
base,
neither
way
will
pro-
duce
optimal
results."
So
I
touch
on
some
bad
uses
of computers
only
to
illustrate
the
problems
to
overcome by
legislation,
education,
and
professionalism
to
make
computers
serve
us
better.
Mind-Amplifying Factor
Carl
Hammer
says
"We
have
already
built
into
our
society
a
mind-amplifying
factor
of
2000
to
one. Be-
hind
every
man,
woman,
and
child
in
this
country
(the
US),
there
stands
the
power of 2000
human
beings.
The
responsibility
of
any
data
processing
manager
of
to-
day,
of
the
computer
scientists
•••
is
so enormous
that
even I
cannot
envision
it.
It
is
the
greatest
challenge
that
has
ever
faced
mankind."
Power
it
is,
in
elemental
form. IBM's
recent
ad-
vertising
stresses
"think
of
the
computer
as
energy."
Theoretically,
the
computer
is
vast
power
at
the
COMPUTERS and PEOPLE
for
January. 1975
service
of
people,
to
be used
as
the
imagination
of
the
people
leads
it,
subject
of
course
to
limiting
legislation.
Knowledge
Power
But
let
us
not
be
lulled
by any
advertising
into
thinking
that
the
energy
is
just
like
electricity.
Computer power
is
work power,
but
it
is
also
know-
ledge
power,
of
the
kind
that
has been used
through-
out
history
for
aggrandisement
as
well
as
the
good
of
the
people.
In
a time
when
technology
stands
at
bay,
it
will
be
well
to
consider
the
dangers
of com-
puter
misuse
in
prejudicing
the
population
against
a
valuable
tool,
and
of
misuse by
corrupt
or
ignorant
officials.
There
are
no
known
instances
of computers
volun-
tarily
stopping
normal work
to
perform
illegal
acts
without
direction
by humans.
Consider
the
science
fiction
capability
of
walking
through
matter;
we
have seen
it
in
the
cinema,
usually
used
to
get
in-
to
the
bank
vault
or
perform
some
other
evil
deed.
But
in
the
cinema
it
was
a power
accorded
only
to
a
few,
being
so
technically
difficult.
Computer power
is
available
widely,
and
we
must not be
surprised
that
some
people
should
turn
it
to
their
own
ends
in
disregard
of
the
general
benefit
of
society.
Jerry Schneider: Crook, Then Security Consultant
Consider
the
case
of
Jerry
Schneider.
There
is
no
problem
with
mentioning
his
activities.
He
sent
an
abstract
of a
paper
that
he wanted
to
present
at
the
1973
National
Computer
Conference,
telling
about
how
he tapped
into
a
computerized
ordering
system
and
stole
something
like
$1
million
of
telephone
equipment
by
having
it
delivered
to
a
telephone
com-
pany van bought
at
auction.
The
computer program,
not knowing
how
to
bill
and
get
payment,
ignored
it
as
being
within
loss
limits.
When
turned
in
by
an
employee,
Schneider
spent
two
months
in
jail
and was
back
in
business
as
a computer
security
consultant
I
There
is
no
question
but
that
computer power
may
be abused by
individuals.
It
may
be so used
by
lar-
ger
entities,
such
as
corporations,
to
fool
or
de-
fraud.
It
may
be so used even by governments, how-
ever
wittingly.
Redressing the Balance
Dr. Henry Bruck of
M.I.T.
spoke
of
this
at
ACM
70,
in
a
talk
enti
tled
"To Redress
the
Balance."
His
thesis
was
that
computers,
because
of
cost
and
training
investment,
were more
likely
to
become
the
tools
of
government and
big
business
than
the
gen-
eral
public.
Countering
the
argument
that
minicom-
puters,
microcomputers,
and hand
calculators
are
available
to
individuals
at
low
cost,
he
said
that
it
was
a
fallacy
to
assume
that
this
meant
that
com-
puter
power
was
available
to
the
general
public
for
this
reason.
Shovels
for
a penny
are
useless
unless
one
knows
how
to
dig,
and has arms.
It
is
the
usage
skill
that
is
important.
He
thought
that
modifying
education
so
that
im-
parting
basic
computer
skills
(and
problem-solving
techniques)
would be
given
as
much
emphasis
as
learn-
ing
one's
own
language would be
unnecessary
over-
specialization.
Nor would
the
answer be
to
reduce
usage
by
government and
business,
for
we
have
ever
more need
for
decisionmaking
information
that
is
more
likely
to
be
accurate
and
complete,
taking
into
account
the
overall
advantage
to
people.
However,
he
saw
no
reason
why
computer
services
could
not
be
provided
to
the
citizenry
through
puhlic
institutions.
15

I
agree.
There
are
many
opportunities
for
compu-
ter
services
to
be
provided
by
municipalities
and/or
private
ventures.
One
can imagine
data
banks
that
could
serve
as
advisories
for
human
action
and
choi-
ces.
There
is
an
experiment
in
Los
Angeles where
the
computer
serves
as
a
general
counselor
for
a
multitude
of
services.
Consumerism
could
be
served
in
a
great
many
ways
--
product
safety
and
efficien-
cy,
comparative
shopping,
financing
aid
for
major
purchases,
reminders
for
preventive
maintenance,
etc.
Thus
there
are
many
ways
to
redress
the
balance
by
making computer power
really
available
to
every-
one
in
a
direct
manner and
without
having
to
learn
how
to
program. There
is
a need, however,
for
a
certain
amount
of
"computer
Ii
teracy"
in
order
to
feel
comfortable
with
such
usage.
Mystique
of
Computer
Authority
As
a
tool,
the
computer has become commonplace
with
a
rapidity
exceeded by
no
other,
even
the
auto-
mobile.
This has
caused
some
disallocation
and un-
ease,
which
the
practitioners
have
not
been
able
to
avoid.
Most
major
tools,
when
introduced,
have had
their
custodians,
and
then
their
guilds
or
profes-
sions
that,
from
gradual
experience,
added
to
the
body
of
law and
practice
those
safeguards
for
usage
that
appeared
necessary
from
gradual
occurrences
of
misuse.
This
did
not
occur
with
computers, and
perhaps
we
did
not
even use
the
time
that
was
available
to
us,
so
caught
up
were
we
with
the
mystique
and power.
Certainly
we
did
not
familiarize
people
generally
with
computers;
instead,
they
were
publicized
as
"giant
brains,"
and
the
mystique grew
into
"authori-
tativeness."
One
of
the
main problems
with
authority
is
that
it
can be blamed.
Surely
you
all
know
many
examples,
but
I
shall
add a few
to
your knowledge.
Perhaps
it
is
a worldwide phenomenon.
One
calls
the
store
that
has
made
a
mistake
in
the
bill,
the
bank
that
has
not
returned
the
cancelled
checks,
the
association
that
has
blacklisted
your
credit
--
and
the
voice
replies
"I'm
sorry,
sir,
but
we
have a com-
puter
now
•••
".
The
Allen Piano Co. Lie
The
Allen
Piano and Organ
Company
of
Phoenix
ad-
vertised
by
radio
that
its
computer had
made
a
mis-
take
in
ordering
inventory;
they
were
now
overstocked
and were
therefore
holding
a
sale.
I
wrote
the
com-
pany a
letter,
on
behalf
of
the
Association
for
Com-
puting
Machinery,
offering
to
fix
the
computer
or
program so
it
would
not
make
such a
mistake
anymore,
on
condition
that
"if
it
developed
that
a
human
was
at
fault,"
and
not
a computer,
they
would so acknow-
ledge
this
in
their
subsequent
broadcast
advertising.
Datamation magazine
followed
the
story
--
it
turned
out
that
the
Allen
Piano
and Organ
Company
DID
NOT
HAVE
a computer,
nor
did
they
use any computer
faci-
lities.
Note
the
convictions
of
the
advertisers
that
a
computer would
give
authority
to
their
spurious
claim
of
overstocking.
The
No·Apostrophe
Lie
One
Mr.
D'Unger,
not
of
the
computer community,
\vrote
to
several
companies
maintaining
mailing
lists
containing
his
name,
either
for
billing
or
solicita-
tion,
asking
them
to
please
spell
it
correctly.
Not
16
DUNGER,
and
not
D
UNGER,
and
not
Dunger
(for
those
with
lower
case
capability).
He
received
several
replies,
all
saying
that
it
was
unfortunately
impos-
sible
with
their
computer equipment.
Learning
of
this
from
his
letter
to
Computerworld, I
called
sev-
eral
of
these
data
processing
departments,
to
find
in
each
case
that
the
print
chain
was
in
fact
an
IBM
chain
that
did
have
the
apostrophe
on
it,
but
that
they
had
not
bothered
to
use
it!
It
seems
to
me
that
a man's
name
is
a
dear
possession,
and
not
one
to
be
treated
cavalierly
under
cloak
of
computer
authority.
The
Bank Lie
I once
visited
a
home
where
four
elderly
women
were
playing
bridge.
When
they
found
out
that
I
was
in
the
computer
profession
there
was
a
chorus
of
hor-
ror
stories.
Then one
brought
out a
letter
from
her
bank,
with
a
handwritten
apology from
the
teller
for
the
shortcomings
of
the
computer. I
was
on
the
spot.
To
save
face
I
called
the
bank
vice
president
to
see
what
could
be done. They
didn't
have a computer
either!
The
Authority
of
the
Computer
as an Accomplice
The
computer
is
a
convenient
means
of
implicitly
or
explicitly
covering
activities
that
run from
il-
legal
to
self-serving,
intentional
or
unintentional.
The
notorious
Equity
Funding
scandal
will
certain-
ly
become a
classic,
even though
the
exact
ways
that
it
was
perpetrated
will
take
some
time
to
discover.
We
know,
even
now,
that
it
was
a pyramiding
opera-
tion,
and
that
computers were used
to
give
authority
and
extra
layers
of
protection
from
discovery.
Many
corrective
actions
could
arise
from
the
case,
such
as
new
emphasis
on
EDP
auditing.
It
appears
that
perhaps
as
many
as
200
people
were
involved
in
col-
lusion.
The
University
of
Michigan has a
research
service
that
projects
the
effect
of
various
decisions
and
actions
upon
the
GNP
(Gross
National
Product)
and
its
growth,
with
respect
to
the
State
of
Michigan.
The
results
could
easily
be
given
in
regular
type-
written
(or
typeset)
reports,
but
they
are
not!
A
computer
printout
accompanies
the
report
to
give
it
AUTHORITY.
The
set
of
results
that
I
saw
seemed
both
spurious
and
misleading,
and
perhaps
others
could
have
detected
this
had
they
been
as
unawed
by
computers
as
I
am.
Perhaps
there
may
come
a day
when
the
US
augments
its
Environmental
Protection
Agency
with
a
Human
Pro-
tection
Agency. Then,
taking
the
lead
from
the
pres-
ent
requirement
to
make
notification
on
cigarette
packages
that
"cigarette
smoking
is
dangerous
to
your
health,"
it
could
order
that
each
computer-
printed
page be
preceded
by:
"WARNING
--
these
answers were produced by a
computer, and
could
be
hazardous
to
your
health!"
Of
course
I
am
being
facetious
about
the
overkill
which does
not
seem
to
diminish
smoking anyway,
but
I
do
recall
the
following
case.
"Sorry
General,
Three
Years
of
Wrong Answers"
Univac
was
attempting
to
sell
the
US
Army
an 1107.
The
benchmark
process
included
a
compilation
and run
of
a
certain
FORTRAN
program.
The
1107
compiler
prin-
ted
a
diagnostic
indicating
an
entry
into
the
middle
of
a
DO
loop.
The
General
in
charge
indicated
that
COMPUTERS
and
PEOPLE
for
January. 1975
I.':'
C

this
was
impossible,
as
they
had been
running
that
same
program
for
three
years,
and asked a programrner
to
examine
the
situation.
He
returned
in
a
short
whi
Ie
and
said
"Sorry,
General.
Three
years
of
wrong
answers."
The
Computer
as
a Sewage
System
A well-known
trui
sm
of computer usage
is
"Garbage
in,
Garbage
Out."
But what happens
when
we
put
per-
fectly
valid
data
in?
Can
we
get
it
out
again?
Can
someone
else
do
so?
If
it
does
come
out,
is
it
leg-
ible?
We
still
live
in
the
computer
era
where
90%
or
more
of
the
data
depends
entirely
upon
the
associa-
ted
program
to
be
turned
into
information.
The
data
description
of
COBOL
is
a
start
to
improve
this,
but
why
should
the
description
be appended
to
the
pro-
gram
rather
than
to
the
data
itself?
Do
you need a program
to
read
a book
in
the
li-
brary?
At
ACM
70, Dr. John Richardson
of
the
US
Dept.
of
Commerce
said
"Information
Conserves Re-
sources
Through
Better
Decisions,"
but
some
of
the
valuable
data
that
we
need
to
make
those
better
de-
cisions
is
not,
in
fact,
retrievable,
exchangeable,
or
digestible.
It
cannot
be
turned
into
information.
Indeed,
one
of
the
major
findings
in
the
various
studies
of
data
banks
is
that
the
sum
of
many
small
data
banks
is
not
a
large
data
bank,
at
least
not
yet,
contrary
to
the
fears
of many.
And
yet
there
are
good
as
well
as
harmful
reasons
to
consolidate
data.
If,
for
example,
the
US
Congress had
two
re-
liable
pieces
of
information
--
1)
how
much
it
was
costing
to
not
grow
cotton,
and 2)
how
much
it
was
costing
to
promote
the
use
of
cotton
--
the
very
juxtapo~ition
might
give
rise
to
some
better
deci-
sions.
The
organizing
power of
the
computer depends
completely
upon
legibility
and
interchangeability
of
data.
Incompatibility
of
Data Banks
A
classic
example
is
the
situation
that
arose
when
the
EPA
(US
Environmental
Protection
Agency)
was
formed
by
consolidation
of
several
diverse
groups,
each
with
its
own
information
systems.
When
they
tried
to
consolidate
the
data
as
well,
surely
one
of
the
main
reasons
for
the
coalescence,
they
found
out
that
data
could
not
only
not
be exchanged
be-
tween
various
components,
but
not even between
the
several
computer systems
in
the
subdivisions
of
the
agencies!
And,
of
course,
the
air
masses
travel
over
many
states,
each
state
with
its
own
computers
and
monitoring
systems,
and each computer
incapable
of
making
decisions
that
would
optimize
for
the
en-
tire
country,
much
less
the
world
--
if
that
possi-
bility
were
permitted.
Illegibility
of
Computer
Data
without
the
Program
Examples of
the
illegibility
of computer
data
without
the
program
are
countless.
Dr. Fred Whipple,
the
astronomer,
once mentioned
that
only
1%
of
his
information
from
satellite
and probe
vehicles
was
being
processed.
I
corrected
him
slightly,
to
say
"data,"
and
he
reiterated
"information."
I asked
if
anyone
could
process
the
tapes
if
the
program
were
destroyed?
He
admitted
that
it_would
be im-
possible.
"Data"
it
was.
The
Las Vegas
city
police
and county
sheriff's
department
recently
consolidated
to
form a "Metro-
poli
tan"
Force.
It
will
be
many
years
before
their
computerized
data
files
can
also
be
consolidated
to
be
of
efficient
use.
COMPUTERS and PEOPLE
for
January. 1975
Of
course
this
particular
manifestation
of
swal-
lowing
of
data
and
not
giving
it
back
to
anyone
else
could
be
largely
solved
by
using
labels
and
data
description
on
data
media, so
that
the
data
can be
self-descriptive.
Congressman Brooks
of
the
US
has
called
for
a
"declaration
of
independence
for
data."
Computer
Failure
Another
way
of
not
being
able
to
get
data
out
is
to
have
the
computer system
fail.
Integration
of
computer systems
into
human
affairs
demands extreme
reliability.
We
all
know
this,
yet
there
are
many
times
when
one
is
tempted
by
the
power
of
the
com-
puter
to
entrust
to
it
a
function
that
has
some
deadlines.
I
am
guilty
of
this
myself.
We
use
a
computer
for
text
processing
and
publication.
The
problem
is
that
we
are
forced
to
share
a computer
that
is
used
for
software
experimentation
and
new
system
software
validation,
or
for
benchmarking
in
various
configurations.
While
the
hardware
may
be
very
reliable,
newly-devEloped
software
is,
unfor-
tunately,
not
--
and
we
have
entrusted
our
total
text
to
the
disk
files.
When
difficulties
occur,
no
manual methods, however
desperate
and
strenuous,
can be employed
to
do
a
makeshift
job.
It
is
the
ultimately
perfect
job
or
none
at
all;
we
are
at
the
mercy
of
a system
that
must be
fully
operation-
al.
The
point
of
my
story
is
that
it
is
a
human
fail-
ing
to
be
optimistic
that
the
computer
will
be upl
So
one
does
not
plan
for
back-up,
duplicating
files
on
another
system,
or
batch
methods
that
work even
when
timesharing
is
down.
Now
we
cannot
even
re-
process
the
sewage.
We
have
given
the
computer
val-
id
and
useful
data
and
cannot
get
it
back
until
too
late.
Some
Actions
to
be Taken for Human
Protection
Society
long ago
learned
to
impose
minimum
re-
strictions
and
educational
or
training
requirements
upon
classes
of
workers whose
operations
affected
the
public
safety
or
welfare.
These
constraints
led
to
professions,
with
codes of
ethics
and a
store
of
recommended
practice
often
embodied
in
local
law,
such
as
building
codes.
Examinations
by
peers
is
a
prerequisite
to
practice
--
for
doctors,
lawyers,
engineers,
accountants,
ad
infinitum.
Until
now
such
restrictions
have
not
been imposed upon
the
computer community; one can
only
suppose
that
the
professions
just
mentioned
did
not
materialize
so
'abruptly
before
the
social
consciousness.
Some
public
exposure
of
malfeasances
moved
the
legislature
of
the
State
of
California
to
consider,
in
1971,
the
certification
of computer programmers
as
a
class.
This
was
given
attention
by
the
press
and,
together
with
the
fact
that
the
legislature
was
in
a quandary,
it
was
sufficient
for
assistance
to
be asked
of
AFIPS
(American
Federation
of
Infor-
mation
Processing
Societies).
AFIPS
convened a
Sys-
tem
Certification
Committee
in
1972
February.
Certification
of
Programmers
and
Handbooks
of
Good Practice
The
committee
arrived
very
quickly
at
the
con-
clusion
that
there
seemed
to
be
no
authoritative
way
to
achieve
certification.
I proposed
that
a
series
of
books
of
good
practice
should
be
conceiv-
ed and
constructed
through
AFIPS.
Thi s
proj
ect
is
now
underway.
The
first
such book
of
good
practice
is
on
confidentiality
and
security,
due
to
the
very
strong
and
justifiable
interest
in
this
topic
at
the
moment, and
is
about
to
be
field-tested.
It
is
17

largely
in
checklist
form.
As
a minor
note,
the
com-
mittee
has changed
its
name
to
"Systems Improvement,"
to
emphasize
the
fact
that
it
does
not
feel
that
any
form
of
certification
is
feasible
yet.
Reliability
of
Computers
"Reliability
for
Integration
into
Human
Affairs"
was
the
title
of
one
of
the
sessions
of
the
1973 Na-
tional
Computer Conference
in
the
US.
The
session
had a
certain
distinction.
The
other
sessions
were,
by
design,
to
reflect
a
"vertical"
or
"end
use"
or-
ientation.
Here I
deliberately
chose,
in
planning
the
program,
to
take
a
further
step,
to
see
what
as-
pects
of computer systems
design
were
common
to
many
end
uses
for
the
specific
reason
that
they
were
di-
rectly
integrated
into
human
affairs.
The
panel
included
representatives
from
air
col-
lision
avoidance
systems,
online
patient
monitoring,
online
power
plant
control,
credit
systems,
ground
transportation,
and
merchandising.
Many
of
these
applications
are
of
Type
3;
power
control
against
blackout,
for
example,
requires
a
response
faster
than
a
human
can
achieve.
Air
traffic
control
is
another;
in
the
1980's
there
are
expected
to
be 5000
people
always
in
the
air
above
Los
Angeles,
in
700
craft!
The
representative
gave
two
major
require-
ments:
-
Predictable
reliability
should be
astronomi-
cal.
-There
should
be
"bai
I-out"
capabi
li
ty
for
whenever
the
system
fails
unpredictably.
"Fire-Drills"
This
second
point
created
much
discussion;
Many
of
the
builders
of
complex
computer-controlled
sys-
tems found
that
the
people
that
ran
such systems
were seldom
able
to
practice
fixing
them.
When
they
did
fail,
they
were
not
properly
capable
of
coping.
It
was
suggested
that
holding
"fire
drills"
for
such systems
was
a
basic
element
of
good
prac-
tice.
Searching
for
other
elements
of good
practice,
it
appeared
that
none
of
the
panelists
or
their
design
teams
knew
of any
source
or
reference
book
to
use
for
reliability
aspects
of
computer
usage,
even
though
there
was
much
commonality
in
their
applica-
tions.
There
are
some
specialists
in
this
field,
such
as
Bob
Patrick,
but
no
body of knowledge
is
available
generally.
Patrick
gives
some
examples
of
bad
design:
-
One
computer
installation
had back-up
tapes
in
a
fire-proof
vault,
and
"grandfather"
tapes
inside
a mountain. But
there
was
only
one copy
of
the
"run
book"
that
told
the
op-
erator
how
to
read
the
tapes,
and
that
was
in
the
machine room, and would be
lost
in
a
fire.
- A
military
installation
had high
security,
and
was
very
protective
of
the
data.
To
en-
sure
good
readability,
the
tapes
periodically
had
the
first
20
metres
or
so
clipped.
The
problem
was
that
these
tape
strips
were thrown
away, under
custody
of
garbage
men
without
clearances,
and
they
had
not
been
erased!
$300 Million a Year
of
Computer
Crime
Donn
Parker,
who
chaired
the
above-titled
session,
is
an
authority
on
computer-related
crime.
His
es-
timate
is
that
this
now
amounts
to
$300
million
a
year,
and
will
reach
$2000
million
in
the
1980's!
18
Dick
Mills
of
the
First
National
City
Bank
says
that
the
bank has $8000
million
per
day
in
its
in-
terchange
"pipeline,"
so
that
even a
small
leak
drains
a
lot.
It
would seem
that
we
are
not
being
overcautious
in
insisting
upon
reliability
in
such
"people-sensitive"
applications.
Protective Measures Against Misuse:
Legal Measures:
Safety
Standards
There
are
many
examples
of
laws
for
involuntary
personal
protection.
Construction
workers must wear
hard
hats;
cyclists
must wear
leather
and
helmets.
These
are
occupational
protections
enforced
upon
the
individual
presumably
because
he
represents
an
in-
vestment
by
society.
The
US
Government has imposed
certain
requirements
upon
the
manufacture
of
automobiles,
i.e.,
to
be
con-
structed
so
as
to
withstand
collision
of
X
km/h
with-
out
sustaining
more
than
$Y
in
damage,
or
the
like.
The
Government has
stated
that
requiring
such
action
is
within
its
right
to
protect
the
safety
of
its
citizens.
It
seems
certain
that
the
computer has
a
direct
effect
upon
not
only
the
safety
of
our
citizens,
but
also
upon
other
rights.
It
might
thus
be
reasonable
to
demand
that
software
and
hard-
ware should
also
be
built
to
certain
standards
to
protect
these
rights.
We
are
certainly
going
to
have
to
build
computer
systems
with
facilities
for
confidentiality
and
se-
curity.
Although
there
is
no
law
on
this,
there
is
little
doubt
that
US
Government
users
will
be demand-
ing
these
features.
This
area
is
covered
comprehensively
in
"Legal
Aspects
of
Computerized
Information
Systems,"
a
US
Govt.
Report.
See
the
Honeywell Computer
Journal,
Vol. 7,
No.
1.
Voluntary
Measures:
Ombudsman
Dr. Harold Sackman, Chairman of
the
AFIPS
Commit-
tee
on
Social
Implications
of
Computers,
called
re-
cently
for
a "computer
user
society
of America."
This
was
to
be a computer
citizen's
group
active
in
social
reliability,
for
the
reason
that
the
computer
community
really
gets
to
see
the
problems
first,
and
has
the
responsibility
to
expose
the
problems
to
those
who
can
treat
them. The
ACM
owes
much
to
the
Scandinavian
creation
of
the
ombudsman;
its
ombuds-
man
program has
solved
many
problems
of
bad compu-
ter
usage.
Power
to
Audit
There
is
a growing
class
of
auditors
versed
in
data
processing,
but
we
may
have
to
take
drastic
measures
to
aid
them. There
are
many
current
ef-
forts
for
better
methods
for
software
construction.
One
hopes
that
increased
simplicity
will
lead
to
more
direct
legibility
and
auditability
of
computer
programs.
Most
programs
are
documented
poorly,
and
I
see
only
one hope
of
solution
--
the
program
spec-
ifications,
narrative
documentation,
and
operating
instructions
must be
integral!
Using a
block-struc-
tured
language
is
vital
to
constructing
auditable
software.
It
also
enables
programmed
devices
to
detect
tampering
with
the
running
programs.
Handbooks
of
Design
and
Practice
Handbooks of
design
and
practice
are
required
to
be
available
before
computing can
truly
be a
pro-
fession.
Many
computer
societies
are
in
various
stages
of
using
codes
of
practice
and
certification
COMPUTERS and PEOPLE
for
January. 1975
'."
I
"
it

ar
he
nts
on-
th-
on
d-
r
s
1d-
~r
Id
tl
j'I
..
l'
;
,I
"\
of
practitioners.
One
hopes
that
they
will
not
stop
short
of
general
certification
but
will
also
adopt
application-oriented
certification
in
joint
action
with
the
professions
of
those
applications.
We
will
have
to
equip
our systems
with
performance
measuring and
evaluation
capabilities.
Wastage
of
resources
has been
considered
an
evil
in
other
fields
before
this.
Recommendations
As
custodians
of
the
power
source
we
have
many
responsibilities.
When
I planned
the
ACM
70 Con-
ference)it
was
as
a model
for
a
National
Computer
Year, which
could
possibly
be
followed
by
an
Inter-
national
Computer Year. A
possible
list
of
goals
for
such a Year
could
be:
-
To
conscIously
put computers
in
service
for
international
goals;
to
increase
public
un-
derstanding
of
computers,
their
role
and
po-
tential;
and
to
emphasize
the
computer
as
servant
by
more humanized use and
applica-
tions.
-
To
develop
strategies
for
the
best
future
use
of
computer systems
(technological,
so-
cial,
educational,
political,
and
legisla-
ti
ve).
-
To
conserve,
and maximize
utility
of,
those
existing
and
future
intellectual
resources
known
as
data
and programs,
by
finding
how
to
utilize
them
on
mUltiple
equipment and
in
multiple
applications.
-
To
aid
~overnment,
business,
and
private
decisionmaking
by opening
up
new
and
more
complete
data
for
those
decisions,
and
to
facilitate
the
making of
those
decisions
by
reducing
the
information
volume
required
(as
opposed
to
data
volume).
-
To
plan
a
closed
cycle
for
redistributing
work
assignments
between
people
and compu-
ters,
for
re-education
prior
to
change
of
assignment,
so
that
people
can
best
fulfill
their
potential.
To
ensure
that
public
safety
and
welfare
are
considered
adequately
when
computers
are
in-
tegrated
directly
into
human
activity.
-
To
set
up
new
and broad
interdisciplinary
paths
for
exchange
of
information
among
hitherto
segregated
organizations,
and
to
foster
their
maximum
involvement
on
an
in-
ternational
scale.
-
To
plan
the
most economical and
effective
interaction
between computing systems and
other
systems such
as
communications.
Interaction Between
Computers
and
Society
It
is
not
too
soon
for
a comprehensive
examination
of
the
interaction
between computers and
our
society.
Two
papers
from
the
1973
National
Computer Conference
support
this
view
--
"The
Social
Implications
of
the
Use
of
Computers Across
National
Boundaries"
and
"A
New
NSF
Thrust
--
Computer Impact
on
Society."
NSF
is
the
National
Science
Foundation
of
the
US.
Easier
than
We
Think?
I
believe
that
it
won't
be so
difficult
for
com-
puters
and
society
to
adjust
to
each
other
if
we
re-
ally
put
our minds
to
making
it
happen.
In 1970 an
Assistant
Postmaster
General
of
the
US
observed
that
a
third
of
all
first
class
mail
is
machine-addressed,
but
only
6%
arrives
on
the
post
office
docks
in
Zipcode
order.
He
asked
why
the
computerized
address
files
could
not
be
ordered
by
COMPUTERS
and PEOPLE
for
January,
1975
Zipcode
as
well
as
any
other
way?
So
I asked
many
data
processing
departments
the
same
question.
The
answer
was
that
they
had not
thought
about
it,
and
would
just
as
soon
do
it
that
way.
It
may
be
as
simple
as
that.
o
Clark -Continued from
'page
13
4.
Carroll,
John
B.,
Editor,
"Language, Thought, and
Reali
ty:
Selected
Wri
tings
of
Benj amin Lee Whorf" ,
Technology
Press,
Mass.
Inst.
of
Technology, Cambridge,
Mass.,
1956
5.
Carter-Wooby, Amelia
R.,
"Computers
in
Inner-Ci
ty
Classrooms,"
in
"Computers and
People,"
Nov., 1974"
p.25
6.
Childe,
Gordon, "What Happened
In
History,"
Pen-
guin
Books,
Inc.,
New
York,
NY,
1943
7.
Dendy,
Larry
B.,
Ernst
von
Glasersfeld,
and
oth-
ers,
"Communication
--
Three-Way: Chimpanzee,
Man,
Computer,"
in
"Computers and Automation,"
July,
1973,
p.7
8.
Fromkin,
Victoria,
and Robert
Rodman,
"An
Intro-
duction
to
Language",
Holt,
Rinehart
and Winston,
Inc.,
New
York,
NY,
1974
9.
Lai
rd,
CharI
ton,
"The
Mi
racle
of
Language", Faw-
cett
Publications,
Greenwich,
CT,
1967, 255 pp.
10.
Lorenz,
Konrad
Z.,
"King Solomon's Ring",
Thomas
Y.
Crowell
Co.,
New
York,
NY,
1952
11.
Miller,
George
A.,
"Language and Communication",
McGraw-Hill
Book
Co.,
New
York,
NY,
1951, 298 pp.
12.
Mowat,
Farley,
"Never Cry Wolf",
Dell
Publi
shi
ng
Co.,
New
York,
NY,
1963
13.
Scott,
John
Paul,
"Animal
Behavior",
Univ.
of
Chicago
Press,
Chicago, IL, 1958
14.
Teitelman,
Warren,
'''Do
What
I Mean': The
Pro-
grammer's
Assistant,"
in
"Computers and
Automation,"
April,
1972,
p.8
U
nsettl
i
n9,
Distu
rbi
n9,
C
ritica
I . . .
Computers
and
People
(formerly
Computers
and
Automation),
believes
that
the
profession
of
information
engineer includes
not
only
competence
in
handling
information
using
computers
and
other
means,
but
also a broad
responsibility,
in a professional and engineer-
ing sense,
for:
the
reliability
and social significance
of
pertinent
in-
put
data;
the
social value and
truth
of
the
output
results.
In
the
same
way,
a bridge engineer takes a professional
responsibility
for
the
reliability
and significance
of
the
data
he
uses, and
the
safety and
efficiency
of
the
bridge
he
builds,
for
human beings
to
risk
their
lives
on.
Accordingly,
Computers
and
People publishes
from
time
to
time
articles and
other
information
related
to
socially useful
input
and
output
of
data systems
in
a broad
sense.
To
this
end we
seek
to
publish
what
is
unsettling,
disturbing,
critical
-
but
productive
of
thought
and an improved and safer planet in
which
our
children
and
later generations may have a
future,
instead
of
facing
extinction.
The
professional
information
engineer needs
to
relate his engi-
neering
to
the most
important
and most serious
problems
in
the
world
today:
war, nuclear weapons,
pollution,
the
population
explo-
sion, and
many
more.
19

IBM
Versus
AT&T:
Its Meaning To
The User And The Public
A.
G.
W.
Biddle
Executive Director
Computer Industry Association
Encino,
Calif.
91316
"Observers
now
see IBM's entry into satellite communications
as
a major threat to the computer industry. "
Based
on
an
address
to
the EDP/Telecommunications Conference
of
the National Retail Merchants Association, November, 1974.
The
subject
of
this
article
is
IBM
versus
AT&T:
Could
this
be
the
heavyweight championship
business
fight
of
the
century?
If
so,
what does
it
mean
to
the
user
and
to
the
general
public?
Unnoticed Announcement
After
the
close
of
the
stock
market
on
July
3,
1974,
the
Dow
Jones
wire
carried
a
terse
statement
datelined
Armonk,
New
York.
International
Business
Machines
Corporation
had
just
announced
it
was
pur-
chasing
controlling
interest
in
CML,
an
authorized
domestic
satellite
carrier.
The
timing
of
the
an-
nouncement
was
significant,
for
the
weekly
trade
and
business
journals
had
already
gone
to
press
and
the
business
and
financial
desks
of
the
daily
newspapers
were
closed
down
for
the
long,
4th
of
July
weekend.
It
was
hoped
that
the
move
would go
virtually
un-
noticed
and
unreported.
It
largely
was.
Initial
reactions
were mixed. A number
of
ob-
servers
felt
that
AT&T
would
at
last
face
some
major
competition
and
thus
both
the
computer and
the
com-
munications
industries
would
benefit.
However, John
DeButts,
Chairman
of
AT&T
and an outspoken
critic
of
any
competition
with
the
Bell
System,
said
that
he
had
discussed
the
IBM
move
with
the
chairman
of
IBM
and foresaw
no
problems.
The
president
of
IBM
as-
sured
the
press
that
IBM
was
"not
trying
to
put
one
over
the
left
field
fence."
Major Threat
to
the Computer
Industry
A few
--
unfortunately
a
very
few
--
observers
now
see
IBM's
entry
into
satellite
communications
as a major
threat
to
the
computer
industry,
the
com-
puter
user,
the
telephone
subscriber
and,
in
the
end,
as
a major
threat
to
our
nation.
I
include
myself
among
this select,
but
rapidly
growing group
of
vocal
dissidents.
Our
ranks
now
include
the
Department
of
Justice,
the
Federal
Trade Commission, Univac,
Fair-
child,
Western Union,
Datran,
RCA
and
others.
I
would
li
ke
to
take
thi
s
opportuni
ty
to
share
my
thoughts
and
some
of
my
deeply
felt
concerns
with
you.
Qualifications
of
This
Author
First,
however,
let
me
submit
my
qualifications
so
that
you
may
decide
whether
my
views
are
worthy
20
of
your
consideration:
- I have
spent
20
years
of
my
life
as a
specialist
in
the
development
of
marketing
and growth
strategies
for
more
than
50 major
corporations,
including
some
of
our
nation's
largest.
In
the
past
year,
I have
testified
before
six
Congressional
committees as
to
condi-
tions
in
the
computer and communications
industries.
-
And
I
am
probably
one
of
the
few
people
in
the
world
that
have
read
and
studied
the
20,000
pages
of
internal
IBM
documents,
studies
and management committee
minutes
that
have
come
to
light
as a
result
of
the
numerous
antitrust
suits
against
IBM.
-
And
just
so
you
will
have
no
doubt
about
my
biases,
I
am
told
that
I
am
very
high
on
the
"enemies"
li
st
at
Armonk
and moving
up
very
rapidly
on
AT&T's. I have
dared
to
speak
outl
Now,
let
me
give
you one man's
opinion
as
to
what
is
happening and,
perhaps
of
more
importance,
what's
in
store
for
you,
the
user
of
computers and
communications.
First
I
will
summarize and
then
come
back and
discuss
each
aspect
in
a
little
great-
er
detail.
AT&T,
Heavyweight Champion
In
one
corner
we
have
AT&T,
the
heavyweight cham-
pion
of
the
world.
It
has
revenues
of
$26
billion,
absolute
control
and ownership
of
the
communications
system,
25
percent
net
income
before
taxes,
and 14
percent
growth.
One
worker
out
of
every
80
works
for
AT&T.
AT&T
has'
failed
to
be
responsive
to
the
needs and
desires
of
the
marketplace
--
especially
in
the
areas
of
business
oriented
voice
and
data
communications.
This
certainly
comes
as
no
surprise
to
this
audience.
The
Federal
Communications Commission
has,
since
the
now
famous
Carter-phone
decision
in
1968, been
gradually
opening
up
limited,
specialized
segments
of
AT&T's
markets
to
competition
--
first
intercon-
nect
and
then
specialized
terrestrial
and
satellite
carriers.
AT&T
has
used
every
means
at
its
disposal
to
block
the
development
of
competition
and
maintain
COMPUTERS and PEOPLE
for
January. 1975
j'
,:!
'r
(,
, .~
t
s
t
w
w
i
f
i
IT
t
d
\\
9
b
I:
'Ii
C
j

at
e
y.
s
r-
r
r
t.
e
1-
/-
'
.....
its
total
monopoly power
over
all
facets
of
the
com-
munications
system.
It
has done
this
by
refusal
to
interconnect,
customer
intimidation,
and drawn
out
legal
proceedings.
At
the
moment,
it
is
losing.
AT&T,
through
its
teletype
subsidiary,
has
en-
croached upon IBM's
territory
with
the
data
speed
40
terminal.
It
has
also
started
marketing
OEM.
IBM,
The
Other
Heavyweight Champion
Now
in
the
other
corner
we
have
International
Business
Machines.
It
has revenues
of
$12
billion,
25%
net
income
before
taxes,
15%
yearly
growth, and
$4
billion
in
cash.
During most
of
the
1960s,
IBM
fell
behind
the
computer
industry
in
technology,
es-
pecially
in
the
areas
of
peripheral
products,
termi-
nals,
minicomputers and
solid
state
devices.
In
1970,
IBM
lashed
out
at
the
independent
peri-
pheral
industry
--
the
Telex's
and Memorex's
--
for
it
feared
that
the
independents
might,
in
time,
be-
come
viable
across-the-board
competitors.
And
in
the
meantime,
strategies
were
being
put
in
place
at
IBM
to
recapture
its
accustomed
7fJ'/o
share
of
EVERY
sector
of
the
computer
marketplace.
IBM's Overall
Strategy
The
elements
of
that
overall
strategy
are
now
ap-
parent.
They
include:
-
F.S.
(Future
System):
The
fourth
generation
of
computers
will
employ
up
to
four
parallel
processors,
mass
storage
and,
in
all
proba-
bility,
will
be
field
expansible.
A
signifi-
cant
amount
of
maintenance
will
be performed
by
the
user.
System
Q:
A wholly
new
software
system
utilizing
both
conventional
software
as
we
know
it
and firmware.
The
system
may
be
designed
so
that
resource
usage can be me-
tered,
with
customers charged
accordingly.
-Custom
Terminals:
A
family
of
unique,
ap-
plication-oriented
terminals
using
extensive
micro
coding,
new
IBM
de
facto
standard
pro-
tocols
and
mid-life
enhancements.
-Data
Security:
In
order
to
solve
the
data-
privacy,
security
problem,
automatic
encryp-
tion
will
probably
be
an
integral
part
of
each
element
of
the
system.
IBM
is
spending
$40
million
over 5
years
to
study
this
prob-
lem;
only
the
initial
results
will
be
in
the
public
domain.
The
design
of
the
locks
to
access
will
obviously
be
proprietary
--
no
interconnect
will
be
possible.
Satelli
te
Service:
IBM
--
preferably
in
collaboration
with
Comsat,
but
no
doubt
alone,
if
necessary
--
expects
to
have a
domestic
satellite
system
operational
within
three
or
four
years.
Geared
to
government
and
business
customers,
it
will
be
an
inte-
grated
digital
system
with
high speed
data,
voice
and image
capabilities.
Unlike
today's
systems,
it
will
not
depend upon
large
ground
stations
connected
to
the
user
through
AT&T
local
loops.
Rather.
the
system,
operating
in
the
"X"
band,
will
utilize
a
"multitude
of
customer
dedicated
antenna
and
only
a few
general-use
ground
stations."
In
essence,
each customer
wi
11
have
an
antenna
on
hi
s
roof.
COMPUTERS and PEOPLE
for
January, 1975
-
Carnation:
To
tie
it
all
together,
IBM
will
probably
soon
start
marketing
its
"3750"
electronic
switching
system
in
the
U.S. A
sophisticated
PABX,
the
3750 has been
opti-
mized
for
data
switching
but
also
has
all
of
the
features
required
for
an
integrated
com-
munication
system,
including
"direct
dialing,
tie
lines,
data
access,
signalling,
60-cycle
power,
call
directors,
satellite
connection
and
automatic
overflow
routing."
Initially
targeted
at
the
larger
user,
where
IBM
has
more
than
65%
of
the
installed
base
of
com-
puters,
Carnation
is
expected
to
contribute
$5
billion
in
revenues and
over
$1
billion
in
profit
over
the
first
five
years
of
the
program.
-Bundled
Service:
IBM's
strategy
for
the
computer/communications world
of
the
1980s
envisions
complete
end-to-end
control
of
the
total
business
voice
and
data
communications
network.
This
total
system
will
include
a
telephone
instrument
on
your
desk,
an
IBM
PBX,
IBM
terminals,
IBM
CPUs,
IBM
mass
stor-
age
devices
and
IBM
word
processors
--
all
tied
together
by
IBM
satellite.
There
will
be
relatively
few
"foreign
or
competitive
devices"
in
the
system.
IBM
will
not
dis-
close
communication
protocols
nor
electrical,
mechanical and
logical
interfaces
until
well
after
the
market
is
locked up.
In
addition,
scrambling
and
encryption
techniques
will
be
utilized
as
an
umbrella
over
the
entire
end-to-end
system.
After
all,
everyone
knows
that
the
only
secure
system
is
a
sole-source
system,
right?
-Bundled
Pricing:
The
opportunities
to
offer
full
end-to-end
service
allows
IBM
to
bundle
prices
once more.
By
submitting
a
proposal
to
you
that
"solves
your
problem
by
provid-
ing
a
solution
--
not
boxes,"
IBM
--
can as
it
has
many
times
in
the
past
--
freeze
out
any
significant
competition
that
might
de-
velop.
Loss
of
Control
of
Peripherals
I noted
earlier
that
IBM
had
lost
its
control
of
the
peripheral,
minicomputer and
terminal
markets.
I
think
the
foregoing
points
make
it
clear
that
they
are
totally
committed
to
regaining
that
control.
It's
a
beautiful
strategy.
I'm
sure
there
are
elements
of
it
I
haven't
touched on,
for
the
Telex
documents
are
now
two
years
old.
However, as you
read
the
more
than
4,000
pages
of
mihutes
of
the
top
management committee meetings
of
Messrs. Watson,
Learson,
Carey and Opel, one
thing
becomes very
clear.
They
sincerely
and
firm-
ly
believe
that
the
computer
industry
and
all
of
its
extensions
belong
to
IBM.
Trespassing
is
forbidden.
They
were
disbelieving
and shocked
that
CDC
would
dare
to
offer
a
super
computer,
better
than
anything
IBM
had
to
offer,
or
could
ever
build.
They
found
it
i"nconcei
vable
that
customers
flocked
to
Telex
and
Memorex
tape
and
disk
drives,
or
that
Sanders
was
offering
superior
terminals.
And
the
idea
that
independent
software
houses
could
increase
the
efficiency
of
an
IBM
system
by
3fJ'/o
or
more
was
pure
heresy.
Dealing
with
Upstarts
Throughout
the
four-year
period
1960-1972,
they
wrestled
with
the
problem
of
how
to
denl
with
these
21

upstarts.
An
overkill
psychology
gradually
set
in:
they
started
searching
for
techniques
that
would
make
it
impossible
for
others
to
impact IBM's growth and
profits.
The
orders
went
out:
stop
interconnection
of
non-IBM
equipment;
prevent
software
enhancement,
and
midlife
kickers;
change
standards;
lower
prices
where
competition
is
faced,
raise
them where
it
is
not;
use
object
code and micro codes wherever
pos-
sible;
scare
the
customer;
do
whatever
it
takes
--
but
take
it
all.
As
you know,
they
almost
succeeded
in
their
at-
tempts
to
put
Telex
and
Memorex
out
of
business.
Even
if
they
wind
up
paying
Telex $256
million
in
antitrust
damages, IBM's
internal
calculations
show
it
to
have been a
profitable
venture.
They were
losing
a whopping
6%
to
8%
of
their
market
overall;
they
bought
time
to
implement
their
other
strategies.
"No-No"
to
Banks
and
Wall
Street
Perhaps of even more
importance,
IBM
made
it
quite
clear
to
Wall
Street
and
the
banks
that
in-
vestment
in
a company
that
dares
to
compete
with
IBM
on
any terms
but
IBM's
is
a no-no.
The
long
range
impact
of
this
is
just
now
begin-
ning
to
show. The mere announcement of IBM's
entry
into
the
point-of-sale
market
forced
Pitney
Bowes'
withdrawal,
and I
suspect
others
are
soon
to
follow.
The
mere announcement
of
IBM's
satellite
move
has
caused
the
financial
community
to
re-evaluate
whether
additional
capital
will
be
made
available
to
the
other
terrestrial
and
satellite
carriers.
Several
will
probably
have
to
sellout
to
the
giants
if
they
are
to
survive.
In
500
IBM
Top
Meetings, Discussion
of
Responsibility
to
User:
Just
3 Times
Before
I
leave
this
subject,
I would
like
to
make
another
observation
about
the
deliberations
of IBM's
top
management,
as
reflected
in
the
Telex
documents. During
the
course
of
over
500
meetings,
each
ranging
from one
to
three
days over a
four-year
period,
IBM's
top
management
discussed
you,
the
user,
and
their
responsibility
to
you
only
three
timesl
Many
of you
in
this
audience
--
particularly
the
IBM
employees
present
and
the
loyal
IBM
customers
--
are
undoubtedly
thinking
"What
right
has he
got
to
knock
IBM?
They're
a
great
company and
they've
done
a
great
job."
To
you I
say,
I
agree.
IBM
is
prob-
ably
one
of
the
best
managed, most
aggressive
com-
panies
in
the
world
today.
It
has
made
many
valu-
able
contributions
to
the
field
of
data
processing
and
to
our
industry.
Innovations: By
Other
Suppliers,
Not
IBM
It
has
not,
as
it
otherwise
would
like
you
to
be-
lieve,
been
the
innovator
in
this
industry.
Almost
every
major advance
in
the
state
of
the
art
has
first
been developed and
brought
to
market
by
others.
IBM's
world renowned
laboratories
may
have
already
invented
the
products
you
will
be
using
in
1990
--
but
they
are
of
no
use
to
you. They
will
not
be
made
avail-
able
until
IBM
has
first
extracted
every
possible
cent
of
rental
income and
profit
from
the
equipment
it
rents
you
today.
Interconnection
Strategy:
As
Difficult
As
Possible
Instead
of
taking
a
leadership
role
in
the
de-
velopment of
standards
that
would
permit
healthy
competition
to
develop,
IBM
blocks
and
delays
at
22
both
the
national
and
international
levels.
Like
Ma
Bell,
its
monopoly
control
of
the
market depends
on
making
interconnection
with
the
system
impossible
or,
at
the
very
least,
extremely
difficult
and
cost-
ly.
Lock-Out
Techniques
AT&T
has
retained
its
absolute
monopoly power
over
the
communications market
for
more
than
ninety
years
through
four
relatively
simple
lock
out
tech-
niques:
-
Starting
with
a
patent
monopoly
of
Mr.
Bell's
invention,
AT&T
was
able
to
monopolize
the
local
exchange
market.
By
challenging
every
other
patent
in
the
courts,
it
effectively
delayed
the
development
of
competitive
in-
struments
for
15
years;
By
interconnecting
their
companies
with
Long
Lines
and
then
refusing
to
interconnect
non-
Bell
independent
companies,
it
killed
off
competition;
-
By
controlling
all
system
architecture
and
by
producing
all
of
the
equipment used
in
the
system,
it
was
able
to
prevent
the
de-
velopment
of
industry
standard
interfaces
and
thus
block
interconnection;
-
And
lastly,
by
manipulating
the
weak
and un-
sophisticated
FCC,
it
was
able
to
cast
its
anti-competitive
practices
into
bronze
in
the
tariffs
that
"regulate"
the
industry.
Monopoly Techniques
I
think
if
we
look
at
these
four
strategies
in
the
context
of
IBM,
we
will
quickly
see
some
inter-
esting
parallels
in
their
monopoly
tactics:
-
IBM
started
in
the
1920s
with
a
patent
mo-
nopoly
on
punched
card
equipment, and
it
soon
capturea
90%
of
the
market.
The
rest
it
shared
with
Remington Rand.
-
As
the
fledgling
computer
industry
developed,
devices
were needed
for
the
input
and
output
of
data.
What
would be
more
logical
than
the
punch
card
since
it
already
contained
much
of
the
user's
data?
-Remington Rand, however, under
pressure
from
IBM,
refused
to
sell
peripheral
equipment
to
the
fledgling
computer
industry;
and
IBM
would
only
sell
at
its
full
retail
price
and
then
only
after
its
own
customer's
needs had
been met.
-
Needless
to
say,
IBM
soon had
more
than
80%
of
the
installed
base
of
CPU's under
its
ab-
solute
control.
-
By
maintaining
a
separate
and
distinct
soft-
ware approach from
that
of
everyone
else
in
the
industry,
IBM
was
able
to
control
the
upward
migration
of
its
user
base.
By
con-
trolling
all
system
architecture
--
hardware
and
software
--
and
by
producing
all
of
the
equipment used
in
the
system,
it
was
able
to
prevent
the
development
of
industry
stan-
dard
interfaces
and
thus
block
interconnec-
tion.
-
And
lastly,
by
smothering
the
customer
with
tender
love
and
affection
--
lots
of
"free"
COMPUTERS
and
PEOPLE
for
January. 1975
p
a
f
u
a
a
n
p
s
t
s
s
1
f

o-
at
g
d
e
9
e
0%
v-
software
and
services
--
and by
keeping
the
DP
manager
out
of
trouble
with
his
boss,
the
user
remained
largely
unsophisticated
and
pas-
sive.
And,
the
pied
piper
led
us
down
the
road
to
Utopia.
Central Nervous
System
of
the
U.S.
Economy:
In
the
Hands
of
One
Company
We've been good
little
mice. IBM's
revenues
have
grown
15%
per
year,
compounded,
to
$12
billion.
More
than
70%
of
the
installed
base
is
still
IBM.
And
no
competitior
has been
able
to
capture
more
than
5%
of
the
market
except
by
picking
up
the
lease
base
of a
fallen
comrade.
We
have,
individually
and
collectively,
placed
the
central
nervous system of our
total
economy
in
the
hands
of
one company.
If
IBM's
field
service
or-
ganization
were
called
in
for
a two-week
refresher
or
were
unionized
and
struck,
America would
grind
to
a
total
stop.
No
bank,
airline,
trucking
company;
manufacturer,
stock
exchange
or
telephone
company
would be
able
to
function
--
because
as
each day
goes by, each one becomes more
interconnected
with
the
other
and
with
the
seven
IBM
systems
out
of
every
10 systems
in
use.
When
you
place
this
fact
in
context
with
IBM
sa-
tellites,
IBM
PABX's,
IBM
point
of
sale,
IBM
elec-
tronic
funds
transfer,
and
IBM
networks
--
the
impli-
cations
are
frightening
indeed.
Again,
the
IBM
apologi
sts
wi
11
say,
"That's
the
American system;
IBM
climbed
to
the
top
of
the
heap,
and more power
to
them."
Competitors:
Half ,Starved
for
Capital
I
say
in
response,
IBM
started
at
the
top
of
the
heap
in
the
1920s, and
since
then
it
has used
its
market power and
control
to
keep
its
competitors
half
starved
for
capital
and
its
customers
too
blin-
ded by IBM's power and IBM's image
to
find
their
way
out
of
their
cages.
It
is
said
that
ours
is
a
very
competitive
indus-
try.
I ask you,
how
competitive
is
a
race
between
Secretariat,
five
mules and 60 lame ducks?
It's
not
even fun
to
watch.
And
that
leads
me
to
my
last
and
final
point:
But
Competition
is
Healthy
Our
system
is
based
on
the
concept
that
the
forces
of
competition
will
assure
the
fullest
employment of
our
resources
for
the
good
of
the
many. Those
who
succeed
in
winning
the
game
are
rewarded
with
profits,
which
in
turn
they
can plough back
into
the
business
for
the
production
of
more
beneficial
goods.
Or
so
the
theory
goes.
What
happens
when
the
forces
of
competition
no
longer
work?
What
happens
when
the
King
of
the
Moun-
tain
can
--
through
sheer
muscle,
sophisticated
and
subtle
anti-competitive
practices
(many
hidden
under
the
guise
of
technology),
political
clout,
and monop-
oly
market
control
--
block
the
efforts
of
even
the
strongest
to
climb
the
hill?
What
happens
when
the
RCA's, General
Electrics,
Bendix's,
Honeywells,
Lit-
tons,
Philco
Fords,
Univacs and
Singers
finally
give
up
trying?
What
happens
when
the
Carters,
MCI's, Da-
trans,
Telecoms,
Storage
Technologies
and Stromberg
Carlsons
of
the
future
don't
even
get
to
try,
be-
cause
Wall
Street
and
the
bankers
have
learned
you
COMPUTERS and PEOPLE
for
January. 1975
can't
beat
IBM
or
Ma
Bell?
Monopoly
Means Higher Costs
Let
me
suggest
what I
think
will
happen.
You
will
have one
source
of
supply
for
residential
phone
service
--
AT&T
--
and your
costs
will
skyrocket.
You
will
have one
source
of
supply
for
worldwide
business
information
systems
--
voice,
data,
data
banks and word
processing,
and
all
--
IBM,
and you
will
pay
dearly.
And
your
customer
will
pay
dearly.
You
will
wish you had
the
problems
that
you have
today
--
the
problems
of
evaluating
rapidly
changing
competitive
offerings
in
communications,
terminals
and
minicomputers.
Regretfully
many
of
you
will
leave
the
pioneering
to
"the
other
guy."
History
will
probably
repeat
itself
--
you'll
tryout
what
data
processing
can
do
for
you
with
an
entry
level
System
3.
After
it's
too
late,
you
will
find
that
it
just
won't
interface
with
that
better,
less
ex-
pensive
terminal
being
offered
by
competitor
A,
or
that
you
can't
process
the
combined
results
of
your
suburban
stores
without
adding more
memory
--
IBM
memory
of
course.
And
just
as
the
402 User became
the
1401
User and
in
turn
became
the
360-50 User and
the
370-158 User, you
will
find
that
you
are
in
a
cage.
The
cost
of
conversion
to
get
out
will
be
prohibitive,
and your only
choice
will
be
to
follow
(and pay)
the
piper.
In
all
fairness,
much
of
what I have
just
said
is
equally
true
if
you
are
a
beginning
user
of
anyone's
mainframe.
The
Honeywell's,
Univac's,
and
NCR's
would love
to
offer
you
standard
interfaces
--
they
know
they
can
successfully
compete
on
price
and
per-
formance. But
if
standards
were
adopted,
they
fear
IBM
would
take
away
what
little
of
the
market
they
have.
And
IBM
fears
that
the
adoption
of
open
in-
terface
standards
would"erode
their
market
control
and
lease
base."
And
you,
ladies
and gentlemen,
are
the
victims.
Worse
yet,
you
get
it
coming and
going;
for
your
store
has
to
pass
the
cost
of
the
monopolists'
pro-
fits
on
to
the
consumer
--
and
that's
you
again.
Is
there
any wonder
as
to
why
your paycheck buys
less
each day?
Growing Resistance
by
Users
to
Higher Costs
The
National
Retail
Merchants
Association
has
made
a major
contribution
in
the
growing
resistance
to
the
misuse
of
AT&T's
monopoly power.
Ma
Bell
is
in
trouble.
People
finally
have
realized
that
the
only
so-called
"natural
monopoly"
is
the
wire,
cable
and
switching
equipment
in
the
local
service
area.
The_customer
should
be
able
to
choose and
install
any
properly
certified
terminal
he wants
on
the
end
of
that
pair
of
wires.
The
local
operating
compan-
ies
should be
able
to
procure
Long
Lines
service
from anyone
or
all
of
the
terrestrial
and
satellite
carriers
at
the
lowest
possible
cost.
The
operating
companies should be
free
to
purchase
the
equipment
they
use
in
open and
competitive
markets.
In
short,
the
telephone
monopoly should be
broken.
But
IBM
is
going
to
bail
them
out.
After
all,
how
could
a poor
little
old
restructured
Ma
Bell
com-
pete
with
a
giant
monopoly
like
IBM?
Perhaps
of
greater
significance,
IBM
will
get
the
MCIs,
Da-
trans,
Western Unions and
other
competitors
out
of
Ma
Bell's
hair,
so
that
just
the
two
of
them can
then
compete
like
proper
gentlemen
--
at
their
ac-
customed
25%
pre-tax
net
and
controlled
14%
per
year
rate
of growth.
23

Time
to
Stand
and
Fight Monopolies
We
think
the
time
has
come
to
stand
and
fight
on
both
fronts
--
computers and communications.
It's
time you,
the
user,
told
your
suppliers
to
grow
up
and
put
their
childish
games
aside.
It's
time you
told
the
FCC,
Congress,
AT&T
and
IBM
that
all
inter-
faces,
codes and
protocols
be
fully
disclosed
--
both
hardware and
software
--
and
that
they
must be
disclosed
early
enough
to
allow
you
to
choose between
the
compatible
and
competitive
offerings
of
at
least
three
vendors,
or
you
won't
play.
Separate
Pricing, a Key
You
should
insist
that
all
elements
of
a
product
or
service
offering
be
separately
priced.
It's
interesting
how
they
all
proclaim
that
mixed
systems
can't
be done,
yet
they
interface
overnight
when
NASA
or
some
other
significant
purchaser
man-
dates
itl
The
users
and
the
public
should ask
the
FCC
and
the
Congress
to
mandate
that
all
equipment
purchased
for
use
in
the
Nation's
communications system
--
be
it
local
service,
terrestrial
or
satellite
--
be
pro-
cured
on
an open
competitive
bid
basis.
Furthermore,
there
should
be
no
joint
or
bundled
marketing
efforts
between
CML,
IBM,
the
AT&T
operating
companies
or
Western
Electric.
All
transactions
should
be
at
arms
length.
No
strategies
intended
to
lock you,
the
user,
into
a
sole
source
system
should
be
tol-
erated.
Nor
should
anti-competitive
and
exclusion-
ary
tactics
be
permitted.
Do
these
things
and someday you
shall
be
free
--
free
to
choose
what's
best
for
you and
your
company,
not
just
what's
best
for
AT&T's
and IBM's
profit
and
loss
statements.
Retailing as an Example
of
Strong
Competitive
Business
Perhaps
I've
hit
too
hard.
If
so
forgive
me
--
but
the
National
Retail
Manufacturers
Association
is
an
audience
that
represents
one
of
the
few
re-
maInIng examples
of
the
free
enterprise
system
at
work
in
America
today.
These
firms,
whether
in
furniture,
clothing,
or
general
merchandise,
have
not
ducked under
the
pro-
tective
umbrella
of
government
regulation.
They
have
not
felt
the
palsied
hand
of
bureaucratic
regu-
lation
on
their
shoulder
as
have
our
railroads,
our
airlines,
our
trucking
industry
and our
public
utili-
ties.
They have
not
adopted
accounting
principles
that
guarantee
bankruptcy
if
there
is
the
slightest
change
in
the
status
quo.
In
the
greatest
traditions
of
the
American
free
enterprise
system,
the
retail
business
is
a
busi-
ness
in
which anyone
who
chooses
may
participate:
There
are
no
major
barriers
to
entry.
Retailers
are
free
to
succeed
--
or
to
fail
--
on
their
own
merits.
If
they
are
sensitive
to
the
needs and
desires
of
the
consumer;
if
they
give
him
or
her
what
they
perceive
to
be a
fair
value;
if
they
make
doing
business
with
them a
pleasant
experience
--
they
will
grow and
prosper
and
receive
the
re-
wards
of
a
grateful
society.
In
retailing,
the
consumer,
in
his
ultimate
wis-
dom,
is
the
final
decision
maker.
If
the
retailer
fails
to
satisfy
his
or
her
needs,
he
will
fail.
24
There
are
not
likely
to
be any
guaranteed
government
loans
to
bail
him
out;
there
is
no
government agency
to
prohibit
a
more
astute
competitor
from opening
up
across
the
street.
They
do
not
have monopoly
con-
trol
over
all
sources
of
supply
of
the
products
they
sell,
nor
can
they
dictate
style,
fashion
or
taste
all
by
themselves.
In
fact,
each day a
retailer
continues
to
prove
the
fundamental economic
principles
that
we
all
learned
in
high
school
and
college
--
lower
prices
tend
to
increase
volume and
total
profits.
It
would
seem
that
our
automobile
manufacturers
and
other
near
monopolies have
their
own
private
set
of
eco-
nomic
principles.
When
business
is
good,
they
raise
the
prices
--
when
business
is
bad,
they
raise
pri-
ces
again.
Why
does
the
consumer
put
up
with
it?
Because
there
is
no
place
else
to
go
--
there
is
no
meaningful
competition
in
the
concentrated
indus-
tries.
Crisis
The
situation
is
rapidly
approaching
crISIS
pro-
portions.
The
Arabs
are
very
conservative
inves-
tors
--
they
will
put
their
money
in
land and
in
monopolies.
After
all,
who
knows
better
the
power
of
a
Cartel?
So
they
will
largely
invest
in
the
IBMs,
AT&Ts,
General Motors and
other
corporations
dominant
in
their
respective
industries.
The
Arabs
fully
recognize
that
the
economic
importance
of each
of
those
companies
to
our
nation
and
their
large
number
of
employees
forces
the
politicians
to
see
that
the
Government
stands
behind
them
as
the
em-
ployer
and
banker
of
last
resort.
Money
invested
in
these
companies
is
as
good
or
better
than
money
invested
in
Government bonds.
Our
institutional
investors
have
also
learned
this
lesson
and
that's
why
we
have a
single
tier
market.
And
their
prophecy becomes
self-fulfilling
be-
cause
everyone below
the
Fortune
Top
Fifty
dies
for
lack
of
capital,
and
the
wisdom
underlying
the
"pru-
dent
investment"
principle
is
born
out.
11
handful
of
corporate
giants
will
then
control
the
assets
of
our
nation.
Heading
the
list
will
be our
friends
AT&T
and
IBM,
the
bluest
of
the
Blue
Chips.
Of
course,
the
unions
will
have
to
increase
their
power
in
order
to
maintain
equality,
and Government
will
have
to
grow
to
maintain
balance.
When
the
concentration
of power
is
complete,
where
do
you and I
--
the
disenfranchised
voters,
the
taxpayers
and consumers
of
our
nation
--
stand?
Please
think
about
it.
8+01:)
+0(JV"*
o
·1·
El
\l
l:)
+ 8 \7 0 +
0+-\\-\7*0
08+*VO
o
O'V
\l
o~"Vx
J::)"
V 0
COMPUTERS
and
PEOPLE
for
January, 1975

If
Ims
Ir-
1-
lal
d
t
The
Teaching
of
Computer
Science:
Master
of
Science
Degree
J.
N.
Snyder
Head
of
Department
Department
of
Computer Science
Univ.
of
Illinois
at
Urbana-Champaign
Urbana, III. 61801
Here
is
a
description
of
a
new
educational
program
being
offered
by
this
department.
We
believe
your
readers
may
be
interested.
Purpose
Computers
are
playing
an
increasingly
pervasive
role
in
our
society.
Therefore
every
educated
per-
son
should
have
some
understanding
of
the
principles
on
which
they
operate;
and
many
will
need
varying
degrees
of
skill
in
their
use.
Many
jobs
will
bring
non-computer
specialists
into
positions
where
they
should
use
computers.
Thus,
to
not
expose
today's
students
to
computers
means
giving
them poor
preparation
for
the
world
in
which
they
will
have
to
live.
The
objective
of
this
new
curriculum
is
to
pre-
pare
competent
and
well-qualified
teachers
of
com-
puter
science
for
undergraduate
colleges,
junior
colleges,
vocational-technical
colleges,
and
high
schools.
Admission Requirements
An
applicant
will
be
favorably
considered
for
admission
if
he:
holds
a
baccalaureate
or
higher
degree
equivalent
to
that
granted
by
the
University
of
Illinois,
has a
grade-point
average
of
at
least
4.0
(on a
scale
with
maximum
5.0)
for
the
last
sixty
hours
of
undergraduate
work, and has had
at
least
one
course
in
computer programming.
Applicants
with
an
~verage
below
4.0
but
above
3.75
will
be
consid-
ered
on
an
individual
basis.
The
Curriculum
The
eight
units
of
graduate
credit
required
for
the
degree
are
listed
below. A
unit
is
approximately
equal
to
four
semester
hours.
If
a
student
enters
the
program
with
only
one
course
in
computer
pro-
gramming,
he
may
have
to
take
one
or
two
undergrad-
uate
courses,
also.
1) Computer
Science
(4
units):
CS
321,
Information
Structures
or
CS
323, Machine Language and
System Programming 11
......•••....
I
unit
CS
333, Computer System
Organization
.....................
.
unit
COMPUTERS and PEOPLE
for
January. 1975
"Every
educated person
should
have some understanding
of
the principles on which computers
operate."
CS/SE
ED
357, Computer-
Assisted
Instruction
..............
1
unit
CS/~~TH
367, Computer
Application
to
Problems
in
Mathematics
........
1
unit
2)
Education
(2
units):
ED
PSYCH
311 and 312
1/2
unit
Educational
Policy
Studies
(Two
courses
selected
from
the
group 300-307)
................
1
unit
Elective
Sequence (2
units):
These
elective
courses
are
chosen
with
the
help
of
the
student's
adviser
as
a
sequence
for
specialization
in
some
area
related
to
computer
science,
dependent
on
the
student's
background and
interests.
Teaching Project
In
addition
to
the
course
requirement,
each
student
under
the
supervision
of
his
faculty
ad-
viser
is
also
required
to
complete
a
teaching
project
in
computer
science.
This
requirement
will
normally
be
fulfilled
in
connection
with
'specified
course
work
in
the
curriculum,
the
elec-
tives
or
individual
study
courses,
or
by
virtue
of
the
student's
current
or
past
employment.
Some
alternatives
(all
of
which
yield
either
course
credit
or
remuneration
for
the
student)
are:
1.
Service
as
a
teaching
assistant.
2.
Past
or
present
service
as
a
teacher
in
a
public,
secondary,
or
community
school.
3.
The
practice
being
required
for
state
certification.
4.
Preparation
of
PLATO
material
either
in
an
individual
study
course
or
as
part
of
a
CS/SE
ED
357
project.
5.
Tutoring
and/or
grading
under
special
circumstances.
25
Computer
Science Courses
CS
321
--
Information
Structures:
Lists,
trees,
and
graphs;
applications
to
string
processing
and
pattern
matching;
storage
allocation,
and
collection
of
unused
memory
space.
Prerequisite:
CS
201.
3
hours
or
1
unit.
CS
323
--
Systems Programming:
The
organization
and
structure
of
operating
systems
for
various
modes
of
computer
use
from
simple
batch
systems
to
time-sharing/multi-
processing
systems
is
discussed.
Prerequisite:
CS
201. 3
hours
or
1
unit.
CS
333
--
Computer System
Organization:
Computer system
analysis
and
design;
organ-
izational
dependence
on
computations
to
be
performed;
and speed and
cost
of
parts
and
of
overall
machines.
Prerequisite:
CS
201.
3
hours
or
1
unit.
CS/SE
ED
357
--
Computer
Applications
to
Problems
in
Mathematics:
This
course
discusses
many
problems which can
be
formulated
mathematically
and
lend
them-
selves to
computer
solution.
Problems
are
chosen from
the
following
major
areas:
applied
statistics,
in
particular
Monte
Carlo
tech-
niques
and
simulation;
combinatorics;
symbolic
algebra;
game
playing
and
decision
problems.
Prerequisite:
Junior
standing
and
CS
121
or
other
Computer
Science
100-level
programming
course;
or
the
consent
of
the
instructor.
3
hours
or
1
unit.
Financial Assistance
Many
graduate
students
in
computer
science
receive
some
financial
assistance
while
attending
the
University
of
Illinois
at
Urbana-Champaign.
Many
of
these
students
are
employed
part-time
as
teaching
or
research
assistants.
To
encourage
students
to
make
satisfactory
progress
in
their
courses
of
study,
assistantships
ordinarily
are
limited
to
one-half
time.
For
further
information
on
financial
assistance,
the
Master
of
Science
in
the
Teaching
of
Computer
Science
degree,
or
other
programs
in
computer
sci-
ence
at
the
University
of
Illinois
at
Urbana-Cham-
paign,
please
write
to
me.
0
Who's Who
in
Computers
and Data Processing
6th
Cumulative Edition, scheduled for
1975
Send us your
entry,
saying:
1. Your
name
/
2.
Home
address
/
3.
Your
organization
/
4.
Its
address
/ 5. Your
title
/
6.
Your main
interests
/
7.
Your
year
of
birth
/
8.
Your
education
and
degrees
/
9.
The
year
you
entered
the
computer
field
/ 10. Your
present
occupation
/ 11. Your
publications,
honors,
memberships, and
other
distinctions.
For
the
full
entry
form,
see
inside
the
front
cover
(page 2)
in
the
November 1974
issue.
26
Send
to:
Who's
Who
Editor,
Who's
Who
in
Com-
puters
and Data
Processing,
RFD
I,
North
Grosven-
ordale,
Conn. 06255.
THE
20th
ANNUAL
EDITION
OF
THE
COMPUTER DIRECTORY
AND
BUYERS'
GUIDE,
1974
.
..
IS
PUBLISHED - A SPECIAL 13th EDITION
of
COMPUTERS
AND
PEOPLE
The
COMPUTER DIRECTORY
AND
BUYERS' GOlDE is:
• an annual comprehensive
directory
of
the
firms which
offer
products
and
services
to
the
computing
and
data
processing
industry
.
• a basic
buyers'
guide
to
the
products
and
services avail-
able for designing, building, and using
computing
and
data processing systems.
CONTENTS (over 160
pages)
Roster
of
Organizations in Computers
and
Data Processing
Buyers' Guide
to
Products and Services
in
Computers and
Data Processi
ng
Special Geographic Roster of Organizations
in
Computers
and Data Processing
Characteristics of Digita I Computers
(14,000
entries for
380
computers
made
by
80
manufacturers)
Survey
of
Programming Languages in Business
A
Short
Guide
to
Programming Languages
Over
2600
Applications
of
Computers
and
Data Processing
Roster
of
College
and
University
Computer
Facilities
Roster
of
Computer
Associations
Roster
of
Computer
Users Groups
World
Computer
Census
Some Basic Arithmetical Tables
American
Standard
Code for Information Interchange (ASCII)
PRICE:
• U.S.A. -
$18.95
Mexico -
$21.95
Canada -
$19.95
(Prices include
$.45
postage
and
handling costs)
Elsewhere -Swiss francs
90
o
The
Directory
is
included
in
the
full annual subscription
(13 issues)
to
Computers
and
People: U.S.A.,
$23.50;
Canada,
$24.50;
Mexico,
$32.50;
elsewhere, Swiss
francs 140. (magazine address label is marked *D)
RETURNABLE
IN
7 DAYS FOR
FULL
REFUND
IF
NOT
SATISFACTORY
~
- - - - - - - - - - - (may be copied on
any
piece
of
paper! --------i
: U.S.A., Canada
and
Mexico,
to:
Berkeley Enterprises, Inc.
815
Washington St.
Newtonville,
MA
02160
I ELSEWHERE,
to:
Reliable Information Publishing
Company
P.O. Box
52
6354
Vitznau, Switzerland
, ( Yes, please send me ( ) copy(ies)
of
the
1974
Computer
I
Directory
and
Buyers'
Guide. I
I enclose: U.S.A.
Canada
__
_ Mexico
__
_
Elsewhere
______
--.-_
I
My
name
and
address
are
attached.
I'
COMPUTERS and PEOPLE
for
January. 1975

-~
NIXON, FORD, AND
THE
POLITICAL
ASSASSINATIONS IN
THE
UNITED STATES
Richard
E.
Sprague
Hartsdale,
N.
Y.
"Any
reasonable hypothesis about what
is
really going on
based on the evidence at hand, has
not
been even remotely
suggested
by
either Congress or the media."
The
Pardon
of
Nixon
Gerald
R.
Ford pardoned Richard
M.
Nixon
on
Sep-
tember
8,
1974. Thus
the
latest
act
in
a drama
that
began
in
1960,
unfolded.
Many
skeptical
U.S.
citi-
zens nodded
their
heads knowingly and assumed
Tricky
Dick had
made
his
"deal"
with
Ford,
when
he nominated
him
for
Vice
President.
Evans and
Novak\l/
assumed
that
Julie
Nixon Eisenhower
talked
Ford
into
the
par-
don
on
grounds
of
poor
Nixon
health
and
family
con-
siderations.
The
Ford
explanations
of
fears
for
Nixon's
health
didn't
seem
to
convince
very
many
news
media
people
who
saw
a seemingly
robust
ex-
president
in
San
Clemente.\2/
The pardon seemed
to
most Americans and
news
edi-
tors,
a
gross
error
in
judgment and a
total
miscar-
riage
of
justice.
Once
again,
the
United
States
as
a whole
was
fooled.
This
time,
both
Nixon and Ford
managed
to
pull
the
wool
over
the
eyes
of
the
public
and
to
narrowly
escape
revealing
what can be
called
"the
entire
rotten
crust
at
the
top
of American pow-
er."
Any
reasonable
hypothesis
about what
is
REALLY
going
on, based
on
the
evidence
at
hand, has
not
been even
remotely
suggested
by
either
Congress
or
the
media. But
here
is
a
hypothesis
which can
be·
argued
to
be
reasonable.
A Reasonable Hypothesis
A
reasonable
hypothesis
about
the
situation
lead-
ing
up
to
the
pardon,
must
begin
with
the
relation-
ship
through
the
years
between Gerald Ford and
Rich-
ard
Nixon; and
it
must go back
to
1960,
the
year
Mr.
Nixon
planned
the
overthrow
of
Castro's
Cuba.
In
1960, 'Nixon was
the
White House
action
officer
on
the
planning
for
what
turned
out
later
to
be
the
Bay
of
Pigs
invasion
of
CUba.\3/
The
Overt.hrow
of
Castro
Prior
to
that
time
Nixon had accumulated
plenty
of
reasons
to
want
Castro
overthrown.
The
anti-
Communist
attitude
was
the
reason
on
the
surface.
Underneath were
Nixon's
connections
with
the
Mafia,
and
his
friendships
and
financial
holdings
that
were
greatly
damaged
when
Castro
closed
all
the
Casinos
run
by
the
mob
in
Havana.\4/
When
Nixon and Kennedy
debated
about
Cuba
in
the
1960 campaign, Nixon
pur-
posefully
lied
to
the
American
people
about
U.S.
COMPUTERS and PEOPLE
for
January, 1975
plans
for
an
invasion.\S/
When
he
narrowly
lost
to
Kennedy,
it
created
a deep
wound
and
he
apparently
spent
much
of
the
next
three
years
planning
what
might be
called
revenge.
During
the
1960
to
1963
period
Nixon became
well
acquainted
with
a number
of
violent-tempered
or
cold-
hearted
Cubans and Americans,
both
inside
the
CIA
and
outside.
They
agreed
with
him
that
casting
out
Castro
was
highly
desirable.
One
of
these
men
was
E.
Howard
Hunt.\6/
Another
was
Bernard
Barker.\7/
A
third
was
Carlos
Prio
Soccarros.\8/
The
Cabal
In a
perhaps
separate
effort
of
their
own,
these
Nixon
cronies
and
financial
partners
became
involved
with
the
Cabal
that
murdered John
Kennedy.\9/
Wheth-
er
Nixon
was
directly
involved
in
the
Cabal's
plan-
ning
for
the
assassination
is
still
open
to
some
question,
although
one
researcher
believes
that
he
was.
\10/
There
certainly
is
substantial
evidence
that
Nixon
was
out
to
sink
Kennedy and Johnson,
at
least
politically,
and aimed
to
do
so
in
Dallas
im-
mediately
before
Kennedy
was
killed.
(See
the
sec-
tion
below
on
evidence)\ll/
At
any
rate,
whether
Nixon
was
or
was
not
direct-
ly
involved
in
planning
the
assassination
of
Presi-
dent
John F. Kennedy does
not
have
to
be
settled
here,
because
Nixon
WAS
directly
involved
in
cover-
ing
up
the
truth
about
who
did
the
deed.
Recently
revealed
evidence
from
the
Nixon-Haldeman
tapes
in-
dicates
that
Nixon
knew
the
truth
about
the
assassi-
nation
when
he
suggested
Gerald Ford
for
the
Warren
Commission.\12/
Ford
and
Nixon
The
hypothesis
then
continues
with
the
close
per-
sonal
friendship
of
Ford and Nixon
in
their
days
together
in
the
Congress,
when
both
were
strong,
ultra-conservative,
"red
white
and
blue,"
anti-
Communist,
"religious"
members
who
thought
and
talked
alike.
When
Nixon
realized
that
John Kennedy had been
killed
almost
under
his
nose
on
November 22, 1963,
in
Dallas,
Texas, by
some
of
his
Bay
of
Pigs
friends,
he
decided
to
do
everything
in
his
power
to
cover
it
up
and
to
bide
his
time
until
his
powerful
military
and
intelligence
friends
could
get
him
placed
in
the
White House.
It
took one
more
murder by
the
Cabal
27

(Robert
Kennedy)
to
get
him
there,
and
still
another
attempted
murder
to
keep
him
there
(George
Wallace).
Control Over Investigation
of
Assassinations
Control
over
the
investigations
of
these
murders
was
essential
for
Nixon and
the
Cabal.
In
order
to
guide
a
presidential
commission
away
from
the
truth,
the
closed
small
circle
of
people
who
knew
what had
happened
to
John Kennedy had
to
be
enlarged.
Allan
Dulles
was
no
problem.
He
knew
the
cause
was
an
intelligence-military
Cabal from
the
day
it
happened,
forward.
Earl
Warren
was
a
tougher
nut.
He
had
to
be
fool-
ed and
later
on,
talked
into
keeping
silent
"for
the
good
of
the
country."
Gerald Ford's Book
To
have a
ring
leader
inside
the
Warren Commission
was
critical.
It
had
to
be someone Nixon
could
real-
ly
trust.
Someone
who
had
at
least
the
appearance
of
being
honest
and
trustworthy
to
the
people.
Nixon
called
on
his
old
pal,
Gerry
Ford.
He
convinced
LBJ
that
Ford should be
on
the
Commission.\13/
Then,
the
hypothesis
continues,
that
Nixon
told
Ford
at
some
point
prior
to
January
1964
who
killed
JFK
and
why,
and he convinced Ford
that
every
effort
should
be
made
to
make
sure
Oswald
was
found
to
be
the
lone
assassin.
Ford
did
an
excellent
job.
He
not
only
steered
the
Commission
away
from
the
facts
\14/
whenever a key
witness
was
interviewed
or
an
embarrassing
situation
developed,
he
also
nailed
Oswald's
coffin
shut
personally,
by
publishing
his
own
book
on
Oswald\lS/:
"Lee Harvey Oswald
--
Por-
trait
of
The
Assassin".
This,
coming from
the
chair-
man
of
the
House
Armed
Services
Committee,
served
to
firmly
plant
in
the
minds
of
Americans
the
idea
that
there
was
no
conspiracy,
that
Oswald
was
THE
lone
assassin,
and
that
the
Warren Commission had done a
good
job.
Access
to
Power
From
the
day
Ford's
book
was
published,
Nixon and
Ford became
totally
beholden
to
each
other.
They
also
both
became
totally
beholden
to
the
members of
the
Cabal
who
were
at
or
near
the
top
of
it
or
who
were
part
of
the
small
knowledgeable
circle.
Other
members
of
what
will
henceforth
be
called
the
inner
circle,
included
J.
Edgar Hoover,
while
he
was
alive,
and Richard Helms.
Under
this
hypothesis,
no
one
could
be
permitted
to
come
into
power
in
the
White House,
or
the
CIA
or
the
Justice
Department
or
the
FBI,
unless
they
were
part
of
the
inner
circle
and
willing
to
keep
quiet
and
help
suppress
the
truth
about
the
JFK
assassina-
tion.
This
inner
circle
widened,
of
necessity,
when
Robert Kennedy
was
killed,
and Nixon became
Presi-
dent.
Both
the
people
involved
in
killing
Robert
Kennedy, and
Nixon's
top
aids
had
to
be
told
the
truth.
This
included
Haldeman,
Ehrlichman,
Kissinger,
and
possibly
others
in
the
White House, and
Mitchell.
Mitchell
also
had
the
job
of
controlling
Hoover's
successors
in
continuing
the
cover
ups.
Mitchell
was
instrumental
in
stopping
.Jim
Garrison's
investi-
gation
of
Clay
Shaw
and
the
rest
of
the
Cabal and
in
totally
discrediting
Garrison.\16/
He
was
aided
of
course,
by Richard
Helms
and
others
in
the
inner
cir-
cle
by thorough
CIA
support
in
the
Clay
Shaw
trial
cover-up
efforts.\J7/
28
Assassination
Attempt
Upon George Wallace
In
1972,
the
White House plumber
section
of
the
assassination
Cabal
decided,
perhaps
without
Nixon's
knowledge,
perhaps
with
his
approval,
to
assassinate
George
Wallace.
In
this
way, Nixon would
receive
ALL
of
the
con-
servative
vote.
Again,
the
inner
circle
grew, and
the
debts
grew. E.
Howard
Hunt and
Charles
Colson,
along
with
Tony
Ulazawicz, Donald
Segretti
and
oth-
ers,
were
in
a
position
to
make
demands
in
exchange
for
their
silence.
The
Hunt
$1
million
blackmail
threat
to
reveal
"seedy
things"
or
"hanky
panky,"
was
never
really
explainable
because
he might
talk
about
the
Watergate
or
Ellsberg
break-ins.
Three
assassinations,
(JFK,
RFK,
Wallace)
on
the
other
hand would
certainly
be worth a
cool
million
to
keep
one's
silence.
Again,
the
Haldeman-Nixon
June
23, 1972,
tapes
are
revealing.\18/
(See
later
sec-
tion
on
evidence)
The
Watergate Crisis
Now
arrives
the
Watergate
crisis.
Nixon
is
trap-
ped
by
his
own
tapes.
The
hypothesis
continues
that
discussions
with
Haldeman,
Mitchell
and
others
men-
tion
the
Kennedy
assassination
Cabal and
the
Wallace
murder
attempt.
The
Cabal and
the
inner
circle
are
suddenly
threatened
as
a
group.
The
tapes
can't
all
be
destroyed
because
too
many
Secret
Service
people
know
about them. Haldeman and Nixon manage
to
erase
one
18-1/2
minute
section
which
is
the
most
reveal-
ing
about
the
assassinations,
but
the
rest
are
still
around.
And
who
can remember
exactly
when
telephone
or
Oval
Office
conversations
may
have mentioned
the
truth
about
the
three
murders?
Succession
to
Nixon
Nixon,
sensing
again
the
need
for
a
successor
who
will
keep
quiet,
calls
on
Gerry Ford
when
Agnew
is
forced
out.
The
two
of
them, bound
inextricably
to-
gether
by
their
mutual
cover-up
of
the
assassina-
tions,
work
out
a
deal.
Nixon nominated Ford
as
Vice
President.
The
Senate,
completely
bamboozled
by
Nixon and
Ford,
did
not
ask Ford any
important
questions
about
the
assassination's
nor
his
perform-
ance
on
the
Warren Commission. They
did
ask Ford
about
his
book and he committed
perjury
two
times
befor~
the
Senate.
Nixon and Ford
agreed
that
Ford
will
keep
quiet
if
Nixon keeps
quiet,
and
that
if
necessary,
Ford
will
succeed Nixon
if
he
is
forced
to
resign,
or
be
impeached,
with
an
agreement
for
a pardon
afterward.
But,
the
most
critical
part
of
the
arrangement
is
that
those
tapes
revealing
the
truth
about
the
as-
sassinations
be
kept
out
of
circulation.
The
two
men
must keep
theiT
cover-up
going.
Each
is
now
fully
culpable.
When
the
Supreme Court
ruled
that
the
tapes
must be
turned
over,
it
was
then
time
to
implement
their
agreed-upon
strategy.
In
addition,
Jaworski,
Colson,
Mitchell,
Kissin-
ger,
Haldeman, Ehrlichman.,
the
Warren Commission,
Hunt, Helms,
Shaw
and anyone
else
in
the
inner
cir-
cle
has
to
be bought
off,
pardoned,
protected,
or
killed,
to
keep
their
silence.
Jaworski's Resignation
Leon
Jaworski
resigned
and
people
ask why.
The
real
answer
again
lies
buried
in
the
fact
that
Ja-
worski
knows
what has been
going
on.
One
way
he
knows
is
through
the
assassination
conspiracy
and
cover-up
information
passed
on
to
him
by
the
Ervin
COMPUTERS and PEOPLE
for
January, 1975

d
n-
t
r
Committee and Cox. A second
way
is
through
his
own
involvement
in
1964
in
the
JFK
cover-up.
In
any
case
he
will
have
to
be
taken
care
of.
Jaworski
could
be a problem, even though he
help-
ed
with
the
JFK
cover-up
from
the
beginning.
19/
Hunt
has
already
been
taken
care
of
by
getting
him out
of
jail,
buying
him
a
large
estate
in
Florida,
and
pay-
ing
him
a
lot
of
money.\20/
Helms
can be
counted
on.
Kissinger
may
have been a problem,
but
he
agreed
fi-
nally.
His
wiretaps
were
likely
ordered
to
find
out
who
knew
about
the
assassinations.
Hoover
is
dead.
Clay
Shaw
was
murdered.\21/
Out
of
the
Warren
Com-
mission,
Warren
is
dead.
Boggs
was
killed.
Dulles
is
dead.
LBJ
is
dead.
Richard
Russell
is
dead.
John
Sherman Cooper
was
bought
off
by
giving
him an
impor-
tant
ambassadorship.
John
J.
McCloy
is
too
old
to
worry
about,
and
of
course
Ford
is
O.K.
That
leaves
Colson,
Mitchell,
Haldeman, and
Ehr-
lichman,
plus
some
other
small
fry.
The
Nixon-Ford
strategy
as
planned
with
these
men,
must have
in-
volved
pardons
for
all
of
them
in
exchange
for
their
silence,
especially
Haldeman and
Mitchell
because
they
not
only
knew
what happened
to
JFK,
but
took
overt
actions
to
cover-up.
(Haldeman
erased
the
18-1/2
minutes
of
tape
and
Mitchell
nailed
Jim Gar-
rison.)
The
pardons
may
have
to
wait
until
the
trial
is
over,
but
they
are
agreed
to
in
advance.
New Members
of
the
Inner Circle
Newer
members
of
the
inner
circle
may
cause
some
problems.
They
all
have
to
know
the
truth
by
now.
Rockefeller
and Alex Haig must
know
and have
agreed
to
silence.
William
Colby,
William
Saxbe, and
Clar-
ence
Kelly
know
because
of
their
access
to
the
re-
cords;
so
they
must have
agreed
to
cover-up
continu-
ance.
Of
extreme
importance
is
Saxbe's
and
Kelly's
con-
trol
of
the
new
trial
and
hearing
coming
up
for
Sir-
han
B.
Sirhan
and
possibly
an
investigation
of
Arthur
Bremer. Also Ford and
his
cronies
in
the
House must
knock
out
any
efforts
by Henry
B.
Gonzalez
of
Texas
to
start
a
new
House Committee
investigation
of
the
JFK
assassination.
Haig seems
to
have been bought
off
by
promising
him
a top
NATO
post
in
exchange
for
his
silence.
In
this
hypothesis,
Gerald
Ford
is
stuck.
He
must
remain committed
to
the
Cabal and
to
Nixon. What-
ever
assassination
the
Cabal
may
undertake
in
1976,
he must
close
his
eyes
to
it,
and
continue
covering
up.
Ted
Kennedy, George McGovern, and Eugene McCarthy
would have had
very
little
chance
of
surviving
the
situation
if
they
showed
election
promise
in
1976.
Also
the
tapes
must be
controlled
and
edited
at
all
costs.
Nixon
no
doubt
required
help
in
listening
to
the
tapes
after
Haldeman
left
and
sorting
out
those
in
which
assassinations
and
cover-ups
were
discussed.
General Haig
was
logically
the
man
he
selected
to
do
this
dirty
work.
It
is
almost
certain
that
no
tapes
could
be
turned
over
to
Judge
Sirica
or
to
Jaworski
with
any
assassination
references
left
on
them.
One
of
the
tapes
demanded by
Jaworski
had such
referen-
ces.
This
is
the
recording
made
on
June 23, 1972,
in
which Nixon and Haldeman
are
discussing
Watergate,
just
six
days
after
the
break
in.
The
Nixon
transcript
of
that
tape
turned
over
to
Judge
Sirica
upon
orders
of
the
Supreme
Court,
shows
many
sections
labelled
unintelligible.
It
is
a
near
certainty
from
three
parts
of
the
discussion
that
COMPUTERS and PEOPLE
for
January. 1975
day,
that
the
critical
sections
were
edited
out
by
Nixon and
General
Haig
prior
to
turning
them
over
to
Sirica
and
prior
to
making a
transcript.
Judge
Sirica
is
the
only
person
in
the
chain
of
possession
of
that
tape
who
could
be
counted
on
to
make
a
scien-
tific
analysis
of
the
tape
to
see
whether
it
was
tampered
with
before
he
received
it.
The
hypothesis
would be confirmed
if
erasures
or
noise
superimposed
on
sections
of
that
tape
were found by such an
analy-
si
s.
With
regard
to
the
rest
of
Nixon's
tapes
which
are
still
in
Gerald
Ford's
possession
and
control,
there
may
be
many
references
to
assassinations
and
cover-ups.
Rather
than
go
through
all
of
them and
edit
or
erase
the
critical
material,
it
is
much
more
likely
that
Ford
will
either
turn
them
over
to
Nixon
for
total
destruction,
or
sit
on
them
forever
without
letting
anyone
not
in
the
"inner
circle"
hear
them.
The
Evidence
for
This Hypothesis
The
evidence
supporting
this
hypothesis
is
as
follows:
1.
Nixon
was
White House
action
officer·on
Cuban
in-
vasion
plans
1960. Source: "Compulsive
Spy,"
Tad
Szulc,
Viking
Press,
1974
2.
Nixon
was
in
contact
with
Hunt, and
others
dur-
ing
Bay
of
Pigs
planning.
Source:
Nixon,
Bay
of
Pigs
&
Watergate
--
R.
E. Sprague,
C&A
--
January,
1973
3.
Nixon
lied
to
the
American
people
by
his
own
ad-
mission
about
the
Bay
of
Pigs
during
his
TV
de-
bates
with
Kennedy
in
1960.
Source:
"Six
Cri-
ses"
by
Richard
M.
Nixon
4.
Nixon
was
linked
financially
to
the
Mafia and
the
Cuban
Casino
operations
before
Castro
took
over.
Source:
"Nixon and
the
Mafia,"
Jeff
Gerth,
Sundance, December, 1972
5.
Nixon
was
acquainted
with
Hunt,
Barker,
Martinez,
Sturgis,
Carlos
Prio
Soccarros,
and
other
Water-
gate
people
and
anti
Castro
people
in
Florida,
and
was
financially
linked
with
Barker,
Martinez,
and
Soccarros.
Source:
"Nixon &
the
Mafia" and
"Nixon,
Bay
of
Pigs
& Watergate"
6.
Hunt,
Barker,
Sturgis
&
Soccarros
were
connected
with
the
assassination
Cabal
in
the
murder
of
JFK.
Source:
R.
Sprague
--
several
articles
lately.
CIA
article,
Nixon
Bay
of
Pigs
article,
Bullets
or
Ballots
7.
Nixon
was
in
Dallas
for
three
days
including
the
morning
of
the
assassination.
He
was
trying
to
stir
up
trouble
for
Kennedy.
Source:
Warren
Commission
Exhibits
--
Vol. 23, Pages 941-943
8.
Nixon went
to
Dallas
under
false
pretenses.
There
was
no
Board
meeting
of
the
Pepsi
Cola
Company
as
he
announced
his
law
firm
had
to
attend.
Source:
Pepsi
Cola Co.
list
of board
meetings.
Corporate
Records
9.
Nixon
did
not
admit
being
in
Dnllas
on
the
day
Kennedy
was
shot
and
did
not
revenl
the
true
rea-
son
for
his
trip.
lie
held
two
press
conferences
on
the
two
days
before
the
assassination
subtly
attacking
both
Kennedy and Johnson and
emphasiz-
ing
the
Democratic
political
problems
in
Texas.
Source: Warren Commission
Exhibits
--
Vol. XXII,
Pages 941-943
29

10. Research
indicates
that
Nixon
either
knew
in
ad-
vance about
the
Cabal's
plans,
or
learned
about
them soon
after
the
assassination.
Source:
Trow-
bridge
Ford,
"Letter
to
House
Commi
ttee
on
the
Judiciary,"
Holy Cross
College,
Worcester,
Mass.
June,
1974.
11. Nixon proposed
to
Lyndon Johnson
that
Gerald
Ford
serve
on
the
Warren Commission.
Source:
Trowbridge
Ford,
"Letter
to
Judiciary
Committee"
12. Ford
led
the
Commission
cover-up
by
controlling
the
questioning
of
key
witnesses
and
by
several
other
means.
Source:
Trowbridge Ford, Holy
Cross
College,
Worcester,
Mass.
"Letter
to
Ju-
diciary
Committee"
13. Ford
helped
plant
the
idea
that
Oswald
was
the
only
assassin
and
that
there
was
no
conspiracy,
firmly
in
the
minds
of
the
American
public
by
publi
shing
HIS
OWN
BOOK,
and
ti
tling
it,
"Lee
Harvey Oswald
--
Portrait
of
THE
Assassin".
Source:
Ford's
book, "Lee Harvey Oswald
--
Por-
trait
of
The
Assassin"
14. Ford
purposefully
covered
up
the
conspiracy
of
the
Cabal
in
the
JFK
assassination
and
also
cov-
ered
up
the
fact
that
Oswald
was
a
paid
informer
for
the
FBI.
He
did
this
by
dismissing
the
sub-
ject
in
his
book
as
worthless
rumor and by
keep-
ing
the
executive
sessions
of
the
Commission
where Oswald's
FBI
informer
status
was
discussed,
classified
Top
Secret.
Sources:
Ford's
book;
The
Assassination
of
President
Kennedy
--
Declas-
sification
of
Relevant
Documents from
the
Nation-
al
Archives;
R.
E. Sprague
--
Computers & Auto-
mation,
October,
1971'
15. Ford
continued
the
cover-up
of
his
assassination
cover-up
when
he
was
questioned
before
being
con-
firmed by
the
Senate
as
Vice
President.
He
lied
under
oath
two
times
to
the
Senate
Committee,
thus
committing
perjury.
He
stated
that
he had
written
his
book about Oswald
with
no
access
to
classified
documents.
He
lied
about
this
be-
cause
his
book used
classified
documents
about
Oswald's
FBI
informer
status.
He
lied
when
he
said
that
the
book
was
titled,
"Lee Harvey Os-
wald
--
Portrait
of
an
Assassin."
This
was
sig-
nificant
in
1973
because
the
public
by
then
had
become
very
skeptical
about
a
lone
assassin.
By
changing one word
in
the
title,
Ford
made
the
book
seem
a
little
less
like
what
it
actually
was;
an
effort
to
make
Oswald seem
to
be
the
lone
assassin.
Source:
Ford's
book;
Ford's
testimony
before
the
Senate
Committee.
16.
Jaworski
aided
in
the
JFK
cover-up
by
sitting
on
evidence
of
conspiracy
accumulated by Waggoner
Carr,
Texas
Attorney
General,
whom
he
represen-
ted
in
liaison
with
the
Warren Commission. _
He
also
stopped
the
critical
testimony
of
Jack
Ruby
when
he
was
testifying
before
the
Warren
Commis-
sion,
and
diverted
attention
away
from Ruby's
intent
to
reveal
the
conspiracy
to
kill
both
Kennedy and Oswald.
Sources:
Dr.
Tuteur,
psy-
chiatrist
who
interviewed
Ruby
in
his
jail
cell.
"Psychiatric
Examination
of
Jack
Ruby"
Mental
Health,
April,
1974, Vol. 58
#2,
Washington,
D.C.;
Trowbridge Ford,
"Letter
to
the
Judiciary
Com-
mittee"
17.
Nixon became
President
in
1968
only
because
Rdb-
ert
Kennedy
was
killed
by
a
conspiracy,
involv-
ing
the
Cabal and
the
CIA.
Nixon
was
well
aware
of
the
conspiracy
whether
or
not
he approved of
it
in
advance.
Sources:
Investigation
by
Wil-
30
liam
Turner
and John
Christian
and
FBI
Report
on
RFK
assassination.
18. John
Mitchell
and
J.
Edgar Hoover,
joined
Nixon
and
the
lower
level
members
of
the
Cabal
in
cov-
ering
up
the
RFK
murder
conspiracy.
They
classi-
fied
the
evidence
Top
Secret
and murdered
sev-
eral
witnesses,
plus
controlling
the
Judge
in
the
Sirhan
trial,
the
District
Attorney
and
ihe
Chief
of
Police
in
Los
Angeles
during
and
after
the
trial.
They
still
control
these
people
plus
the
Los
Angeles County Board
of
Supervisors.
Clarence
Kelley
is
now
also
involved.
Sources:
Same
as
above,
plus
L.A. County Board Meeting
minutes and
Baxter
Ward
hearings.
19. With knowledge
of
Nixon and
the
Cabal,
the
plumb-
ers
group
ordered
the
assassination
of
George
Wallace
in
1972,
to
insure
Nixon's
election
by
picking
up
Wallace's
vote.
(About 18%-in
the
polls).
Source:
Investigation
by
Committee
to
Investigate
Assassinations
and
by
William
Turn-
er,
1973-74.
20.
J.
Edgar Hoover and
Richard
Helms
were aware
of
who
killed
John Kennedy and Robert Kennedy and
helped
cover-up
both
conspiracies.
Sources:
a.
Richard E. Sprague,
"RFK
Articles
on
Conspir-
acy,"
Computers & Automation,
Oct.
1970,
Sept.
1972;
b.
Victor
Marchettis's
public
statements
--
December, 1973
--
about;
c.
Richard
Helm's
and Admiral
Taylor's
covering
up
Clay Shaws'
CIA
connections
and paying
his
lawyers.
21. John
Mitchell
controlled
the
trial
of
Clay
Shaw
and
the
Garrison
investigation
and
discredited
Garrison
by framing
him
in
a
New
Orleans
gamb-
ling
case.
Source:
"The Framing of Jim
Garri-
son,"
Richard
E.
Sprague, Computers & Automation,
December, 1973.
22. Nixon and Haldeman
discussed
the
assassination
of John Kennedy,
the
conspiracy,
Hunt's
involve-
ment,
the
possibility
that
Hunt might
talk,
the
cover-up,
the
Bay
of
Pigs
relationship
between
Nixon, Hunt and
the
other
Cabal members, and
the
briefing
Nixon might have
to
give
anyone
running
against
him
in
1972, about
these
matters
of
"Na-
tional
Security."
Source:
Tape
transcript
--
Nixon and Haldeman
--
June 23, 1972.
The
major-
ity
of
the
tape
was
transcribed
as
being
unin-
telligible.
But Nixon mentions Hunt
possibly
revealing
"Hanky Panky,"
that
we
were not
in-
volved
in
OURSELVES.
He
was
referring
to
Halde-
man,
Nixon and Co.
All
of
the
actions
so
far
revealed
in
Watergate
would
not
fit
that
descrip-
tion.
The
assassinations
of
JFK,
RFK,
and Wal-
lace
were
undoubtedly
what Nixon
was
talking
a-
bout.
Nixon
also
says
to
Haldeman
when
discussing
Hunt
and Watergate and
the
other
Watergate
men,
"It
all
goes back
to
the
Bay
of
Pigs,
you know."
Then
several
"unintelligible"
statements
appear
in
Nixon's
edited
transcript.
Finally,
Nixon
tells
Haldeman he
may
have
to
"burden"
the
Demo-
cratic
candidate,
whoever
it
may
be,
by
briefing
him
on
those
matters
of
"National
Security"
on
which he
was
briefed
by
Johnson.
The
context
in
which
thi
s
appears,
surrounded
by
"unintelli-
gible"
remarks,
indicates
Nixon
was
talking
about
matters
which would be
very
embarrassing
and
would have
to
be
kept
secret
at
all
.costs.
This
is
the
tape
that
was
probably
edited
and
erased
partly
by Nixon and Haig.
COMPUTERS and PEOPLE for January,
HI7S

23. Nixon and
Mitchell
discussed
the
assassinations
and
the
attempt
to
assassinate
George
Wallace.
These
discussions
probably
occurred
mostly
on
Nixon's
Potomac
yacht,
but
some
could
be
on
the
tapes.
Mitchell
executed
orders
to
suppress
the
truth
about
these
events.
Source:
a.
Article
by
Martha
Mitchell,
McCall's
magazine, September,
197~,
with
Mrs. George
Wallace,
discussing
Nixon
and plumbers
hiring
Arthur
Bremer;
b.
Public
statements
by
Martha
Mitchell
to
Helen
Scott,
U.P.I.,
Spring,
1973,
concerning
conversations
Nixon and
Mitchell
had
on
Nixon's
yacht,
about
dirty
things.
24.
Gerald
Ford
now
has
possession
of
the
most
criti-
cal
tapes
when
assassinations
and
cover-up
were
discussed.
He
will
not
let
go
of
them
or
he
will
give
them
to
Nixon. Source:
News
stories
about
White House
keeping
the
Nixon
tapes,
August and
September, 1974.
25.
Jaworski
can be
counted
on
to
keep
the
assassi-
nation
material
under wraps even
after
his
resig-
nation.
He
is
already
well
aware of
the
evidence
of
conspiracy
and
cover-up
in
all
three
cases.
(JFK,
RFK,
Wallace).
Source:
Discussions
and
meetings
between
this
author
and
Watergate
Sen-
ate
Committee
staff.
Assassination
evidence
has
been
in
Ervin
Committee and
Jaworski's
possession
since
the
summer
of
1973. The
fact
that
Jaworski
has
not
introduced
any
of
it
is
indicative
that
it
will
remain
secret.
His
resignation
would
seem
to
be
connected
in
some
way
with
the
"deal"
between Nixon and
Ford.
It
remains
to
be
seen
whether
Henry Ruth,
the
new
Prosecutor,
can
be
controlled
in
the
same
manner.
26. Hunt has been
taken
care
of
and
will
keep
silent.
He
is
out
of
jail
and
living
on
a
beautiful
$100,000
estate
in
Florida
with
plenty
of
money,
across
the
street
from
his
Bay
of
Pigs
friend,
Manuel Artime.
Source:
Washington Watch news-
letter,
and
correspondence
from
Tristram
Coffin
--
August 10, 1974.
27. Clay
Shaw
was
murdered by
the
Cabal,
undoubtedly
to
keep him from
talking,
now
that
the
truth
about
his
CIA
position
has been
revealed
by
Vic-
tor
Marchetti.
He
was
embalmed
quickly
before
the
coroner
could
determine
the
cause
of
death.
Evidence
indicates
he
was
killed
somewhere
else
and
then
brought
to
his
own
apartment
where
he
was
found
dead.
Source:'
New
Orleans
County
Coroner's
statement
and
eye-witnesses
who
were
Shaw's
neighbors.
Zodiac
News
Service,
August,
1974.
28. Hale Boggs, Warren Commission
member
was
possi-
bly
killed
by
the
Cabal.
Boggs'
airplane
dis-
appeared
in
Alaska.
No
trace
of
it
was
ever
found and
no
explanation
of
how
the
plane
could
have
crashed
has
ever
been
given.
Mrs. Boggs
has
expressed
doubts
about
it
being
an
accident.
Source:
News
Stories
--
1972-73.
29. Four
of
the
seven Warren Commission members have
died:
Warren,
Dulles,
Russell
and Boggs.
Of
the
remaining
members, Ford
is
President,
John
J.
McCloy
is
retired
and
living
in
Connecticut
and John Sherman Cooper
is
the
new
Ambassador
to
East
Germany.
30.
Richard
Russell,
Hale Boggs and Cooper
believed
there
was
a
conspiracy
in
the
JFK
assassination.
Russell
and Boggs
both
said
so
publicly.
They
are
dead.
Cooper
has
said
so
privately.
COMPUTERS and PEOPLE
for
January. 1975
31.
Haldeman
erased
18-1/2
minutes
of
a
taped
dis-
cussion
with
Nixon. This
tape
undoubtedly
con-
tained
"National
Security"
matters.
The
fact
that
Haldeman
did
the
erasing
can
easily
be
de-
termined
by
tracing
the
trail
of
possession
of
the
tape
from
the
day
it
was
taken
out
of
the
vault
to
the
day
the
gap
was
discovered.
Halde-
man
had
the
tape
with
the
recorder
alone
for
nearly
48
hours.
No
one
else,
including
Nixon,
had
the
tape
alone
long enough
to
do
the
erasing.
32.
Ford and
the
"inner
circle"
contemplated
pardons
for
Mitchell,
Haldeman, Ehrlichman and
possibly
others
who
know
the
number one
secret.
Source:
News
Stories
September
9-11,
1974.
After
public
and
private
outcries
stopped
this
maneuver
by
Ford,
alternate
arrangements
will
have
to
be
made
to
keep them
all
quiet.
33.
Ford's
statements
to
the
sub-committee
of
the
House
Judiciary
Committee
concerning
his
pardon
of
Nixon dodged
the
real
issue.
Only
Elizabeth
Holtzman asked
questions
coming
close
to
the
~l
secret.
When
she asked about a
prior
agreement,
Ford
said,
"I
have
made
no
deal,
there
was
no
deal,
since
I became Vice
President."
Those
last
few words were
not
reported
by
the
press,
but
a
large
number
of
Americans watched and
heard
him say them.
Of
course
he spoke
truth-
fully
because
the
"deal"
was
made
BEFORE
he
be-
came
Vice
President.
Footnotes
1.
Evans &
Novak
column
--
September 12, 1974
2.
Paris
Herald
Tribune
--
September 12, 1974
3.
"Compulsive
Spy,"
Tad
Szulc,
Viking
Press,
1974
~.
"Nixon and
the
Mafia,"
Jeff
Gerth,
Sundance,
De-
cember. 1972.
5.
"Six
Crises",
Richard
M.
Nixon
6.
"Compulsive Spy"
7.
"Nixon and
the
Mafia"
8.
"Nixon,
Bay
of
Pigs
&
Watergate"
--
R.
E.
Sprague,
Computers and Automation,
January,
1973
9.
"Nixon,
Bay
of
Pigs
&
Watergate"
--
R.
E. Sprague,
Computers and Automation,
January,
1973
10. Trowbridge Ford, Holy Cross
College,
several
pa-
pers
and
articles
11. Warren Commission
Hearings
&
Exhibits
--
Vol. 23,
Pages 941-943
12. Nixon
Transcript
of
June 23, 1972,
tape
--
N.Y.
Times,
Aug.
6,
1974
13. Trowbridge Ford
--
Article
on
Gerald
Ford &
War-
ren
Commission
14. Trowbridge Ford
--
Artiale
on
Gerald
Ford & War-
ren
Commission
15. Gerald Ford
--
"Lee Harvey Oswald
Portrait
of
the
Assassin"
16. "The Framing
of
Jim
Garrison,"
R.
E. Sprague,
Computers and Automation, December, 1973
17. "The
CIA
and
the
Kennedy
Assassination"
--
Un-
published
article
by
R.
E. Sprague
18. Nixon
tape,
June
23, 1972
19. Warren Commission
Exhibits
--
Testimony
of
Jack
Ruby, Vol.
V,
Pages 181-213 and Vol.
XIV,
Pa-
ges
504-571. Also Trowbridge Ford
article
on
Jaworski
20. Washington
Watch
and
Triss
Coffin
letter,
August
10, 1974
21. Zodiac
News
Service
release
~-
August 20, 1974
31
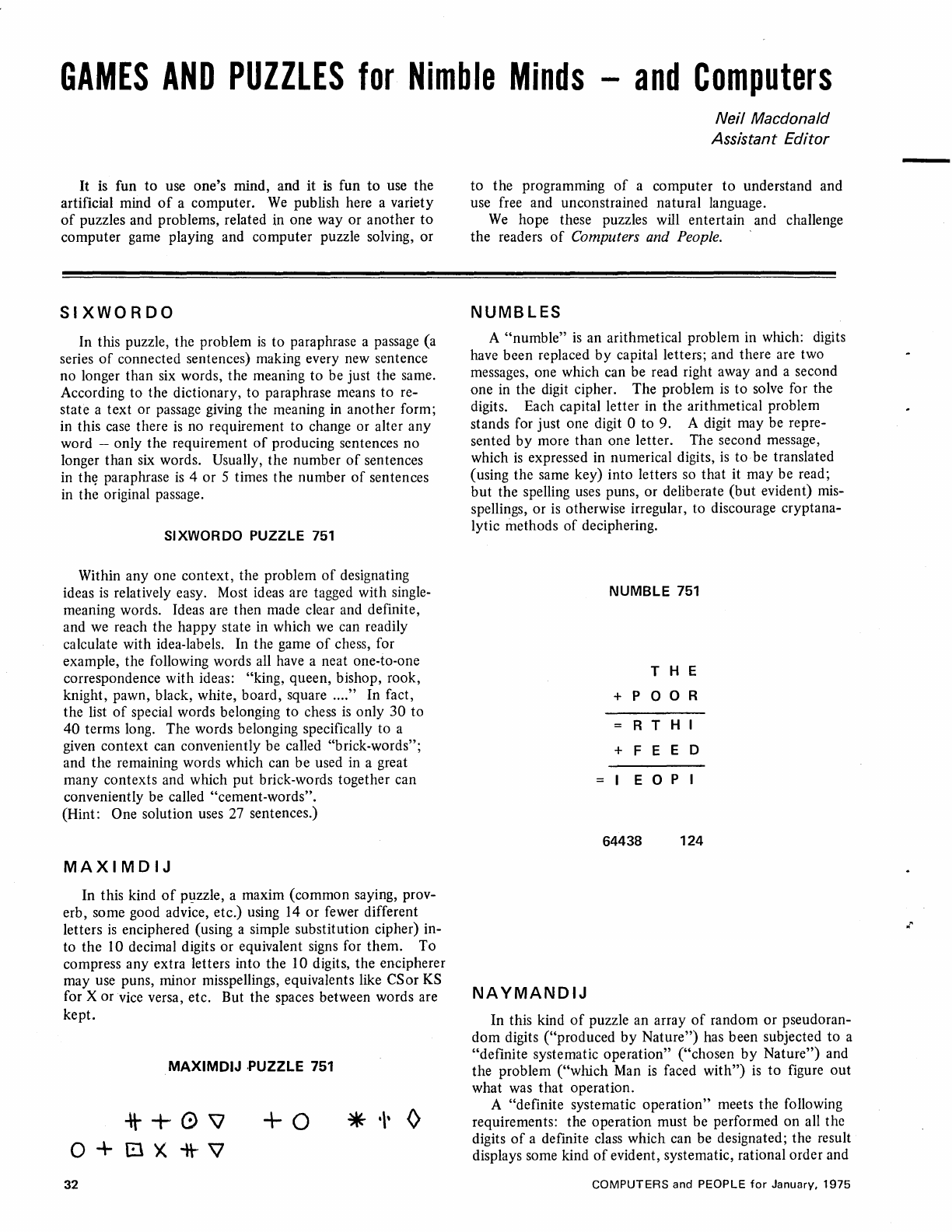
GAMES
AND
PUZZLES
for
Nimble
Minds
and
Computers
It
is fun
to
use one's mind, and it
is
fun
to
use the
artificial mind
of
a computer.
We
publish here a variety
of
puzzles and problems, related in one way or another
to
computer game playing and computer puzzle solving,
or
SIXWORDO
In this puzzle, the problem
is
to paraphrase a passage (a
series
of
connected sentences) making every new sentence
no longer than six words, the meaning
to
be just the same.
According to the dictionary, to paraphrase means
to
re-
state a text or passage giving the meaning in another form;
in this case there
is
no requirement to change or alter any
word -only the requirement
of
producing sentences no
longer than six words. Usually, the number
of
sentences
in
th~
paraphrase
is
4
or
5 times the number
of
sentences
in the original passage.
SIXWORDO PUZZLE
751
Within
anyone
context, the problem
of
designating
ideas
is
relatively easy. Most ideas are tagged with single-
meaning words. Ideas are then made clear and definite,
and we reach the happy state in which
we
can readily
calculate with idea-labels. In the game
of
chess, for
example, the following words all have a neat one-to-one
correspondence with ideas: "king, queen, bishop, rook,
knight, pawn, black, white, board, square ....
" In fact,
the list
of
special words belonging to chess
is
only
30
to
40
terms long. The words belonging specifically to a
given context can conveniently be called "brick-words";
and the remaining words which can be used in a great
many contexts and which
put
brick-words together can
conveniently be called "cement-words".
(Hint: One solution uses 27 sentences.)
MAXIMDIJ
In this kind
of
p~zzle,
a maxim (common saying, prov-
erb, some good advice, etc.) using 14
or
fewer different
letters
is
enciphered (using a simple substitution cipher) in-
to
the
10 decimal digits
or
equivalent signs for them. To
compress any extra letters into the 10 digits, the encipherer
may use puns, minor misspellings, equivalents like CSor
KS
for X or vice versa, etc. But the spaces between words are
kept.
MAXIMDIJ
.PUZZLE 751
+0
32
Neil Macdonald
Assistant Editor
to
the programming
of
a computer
to
understand and
use free and unconstrained natural language.
We
hope these puzzles will entertain and challenge
the readers
of
Computers and People. '
NUMBLES
A
"numb
Ie"
is
an arithmetical problem in which: digits
have been replaced
by
capital letters; and there are two
messages, one which can be read right away and a second
one in the digit cipher. The problem
is
to
solve for the
digits. Each capital letter in the arithmetical problem
stands for just one digit 0 to 9. A digit may be repre-
sented
by
more than one letter. The second message,
which
is
expressed in numerical digits,
is
to
be translated
(using the same key) into letters so
that
it may be read;
but
the spelling uses puns,
or
deliberate
(but
evident) mis-
spellings, or
is
otherwise irregular, to discourage cryptana-
lytic methods
of
deciphering.
NAYMANDIJ
NUMBLE
751
THE
+ P 0 0 R
R T H I
+
FEE
D
E 0 P
64438 124
In
this kind
of
puzzle an array
of
random
or
pseudoran-
dom
digits ("produced
by
Nature")
has been subjected
to
a
"definite systematic operation" ("chosen
by
Nature")
and
the problem
("which
Man
is
faced
with")
is
to
figure
out
what was
that
operation.
A "definite systematic
operation"
meets the following
requirements: the operation must be performed on all the
digits
of
a definite class which can be designated; the result
displays some kind
of
evident, systematic, rational order and
COMPUTERS
and PEOPLE
for
January,
1975
-
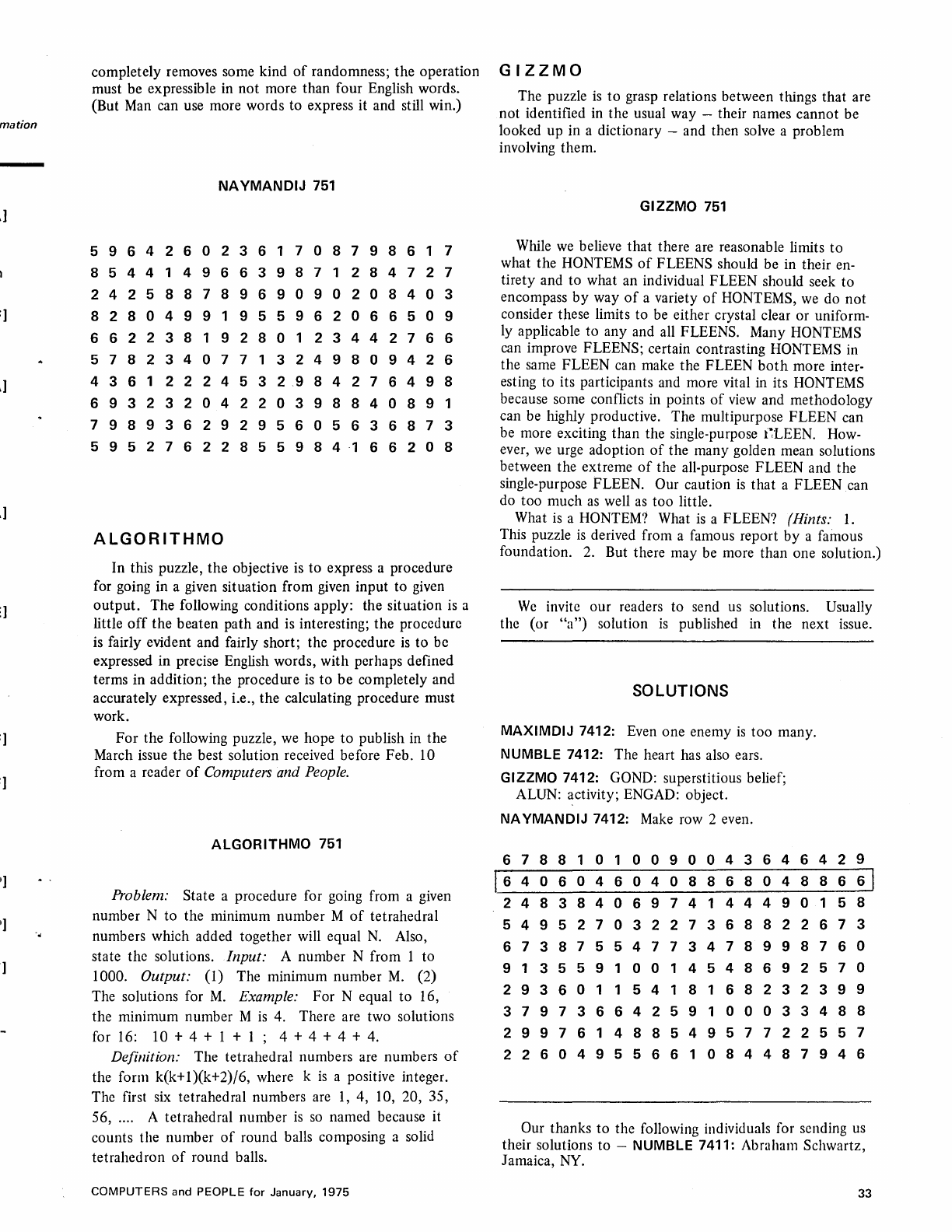
mation
~
]
~]
~
]
]
completely removes some kind
of
randomness;
the
operation
must be expressible in
not
more than four English words.
(But Man can use more words
to
express it and still win.)
NA YMANDIJ
751
5
964
260 236
1 7 0 8 7
986
1 7
8 5
441
496
6 3 9
871
2 8 4 7 2 7
2 4 2 5 8
878
9 6 9 0 9 0 2 0 8 4 0 3
8 2 8 0 4 9 9 1 9 5 5 9 6
206
650
9
6
622
381
928
0 1 2 3 4 4 2 7 6 6
578
234
077
1
324
9 8 0 9 4 2 6
4 3 6 1 2 2 2 4 5 3
29
8 4 2 7 6 4 9 8
693
2 3
204
2 2 0 3 9 8
840
891
798
9 3 6 2 9
295
605
6 3
687
3
5 9 5 2 7 6 2 2 8 5 5 9 8 4
-1
6 6 2 0 8
ALGORITHMO
In this puzzle,
the
objective is
to
express a procedure
for going in a given situation from given input to given
output.
The following conditions apply: the situation
is
a
little
off
the
beaten path and is interesting; the procedure
is fairly evident and fairly short; the procedure
is
to be
expressed in precise English words, with perhaps defined
terms in addition; the procedure is
to
be
completely and
accurately expressed, i.e.,
the
calculating procedure must
work.
For
the following puzzle, we hope
to
publish in the
March issue the best solution received before Feb. 10
from a reader
of
Computers and People.
ALGORITHMO 751
Problem: State a procedure for going from a given
number N
to
the minimum number M
of
tetrahedral
numbers which added together will equal
N.
Also,
state the solutions.
Input:
A number N from 1
to
1000. Output: (1) The minimum number
M.
(2)
The solutions for
M.
Example: For N equal
to
16,
the minimum number M
is
4. There are two solutions
for 16: 10 + 4 + 1 + 1 ; 4 + 4 + 4 + 4.
Definition: The tetrahedral numbers are numbers
of
the form k(k+
l)(k+2)/6,
where k
is
a positive integer.
The first six tetrahedral numbers are
1,
4, 10, 20, 35,
56, .... A tetrahedral number
is
so
named because
it
counts the number
of
round balls composing a solid
tetrahedron
of
round balls.
COMPUTERS and PEOPLE
for
January, 1975
G I
ZZMO
The puzzle
is
to
grasp relations between things
that
are
not
identified in the usual way -their names cannot be
looked up in a dictionary -and then solve a problem
involving them.
GIZZMO
751
While
we
believe
that
there are reasonable limits
to
what the HONTEMS
of
FLEENS should be in their en-
tirety and to what an individual FLEEN should seek
to
encompass
by
way
of
a variety
of
HONTEMS, we do
not
consider these limits
to
be either crystal clear or uniform-
ly applicable
to
any and all FLEENS. Many HONTEMS
can improve FLEENS; certain contrasting HONTEMS in
the same FLEEN can make the FLEEN
both
more inter-
esting to its participants and more vital in its HONTEMS
because some conflicts in points
of
view and methodology
can be highly productive. The multipurpose FLEEN can
be more exciting
than
the single-purpose
l~LEEN.
How-
ever,
we
urge adoption
of
the many golden mean solutions
between the extreme
of
the all-purpose FLEEN and the
single-purpose FLEEN. Our caution
is
that
a FLEEN
can
do too much
as
well
as
too
little.
What is a HONTEM? What
is
a FLEEN? (Hints:
1.
This puzzle
is
derived from a famous report
by
a famous
foundation. 2. But there may be more than one solution.)
We
invite
our
readers
to
send us solutions. Usually
the (or
"a")
solution
is
published in the next issue.
SOLUTIONS
MAXIMDIJ
7412: Even one enemy
is
too many.
NUMBLE 7412: The heart has also ears.
GIZZMO 7412: GOND: superstitious belief;
ALUN: activity; ENGAD: object.
NAYMANDIJ 7412: Make row 2 even.
6 7 8 8 1 0 0 0 9 0 0 4 3 6 4 6 4 2 9
164
0 6 0 4
604
0
886
8 0 4 8 8 6 6 I
2 4 8 3
840
6 9
741
444
901
5 8
5 4 9 5 2 7 0 3 2 2 7 3 6 8 8 2
267
3
6 7 3 8 7
554
7 7 3 4
789
9 8 7 6 0
9 1 3 5 5 9 1
001
454
869
2 5 7 0
2 9 3
601
154
1 8 1 6 8
232
399
3 7 9 7 3
664
259
1
000
334
8 8
2 9 9 7 6 1 4 8 8 5 4
957
7 2
255
7
2 2 6 0 4 9 5
566
1
084
4 8 7
946
Our thanks
to
the following individuals for sending
us
their solutions
to
-NUMBLE 7411: Abraham Schwartz,
Jamaica, NY.
33
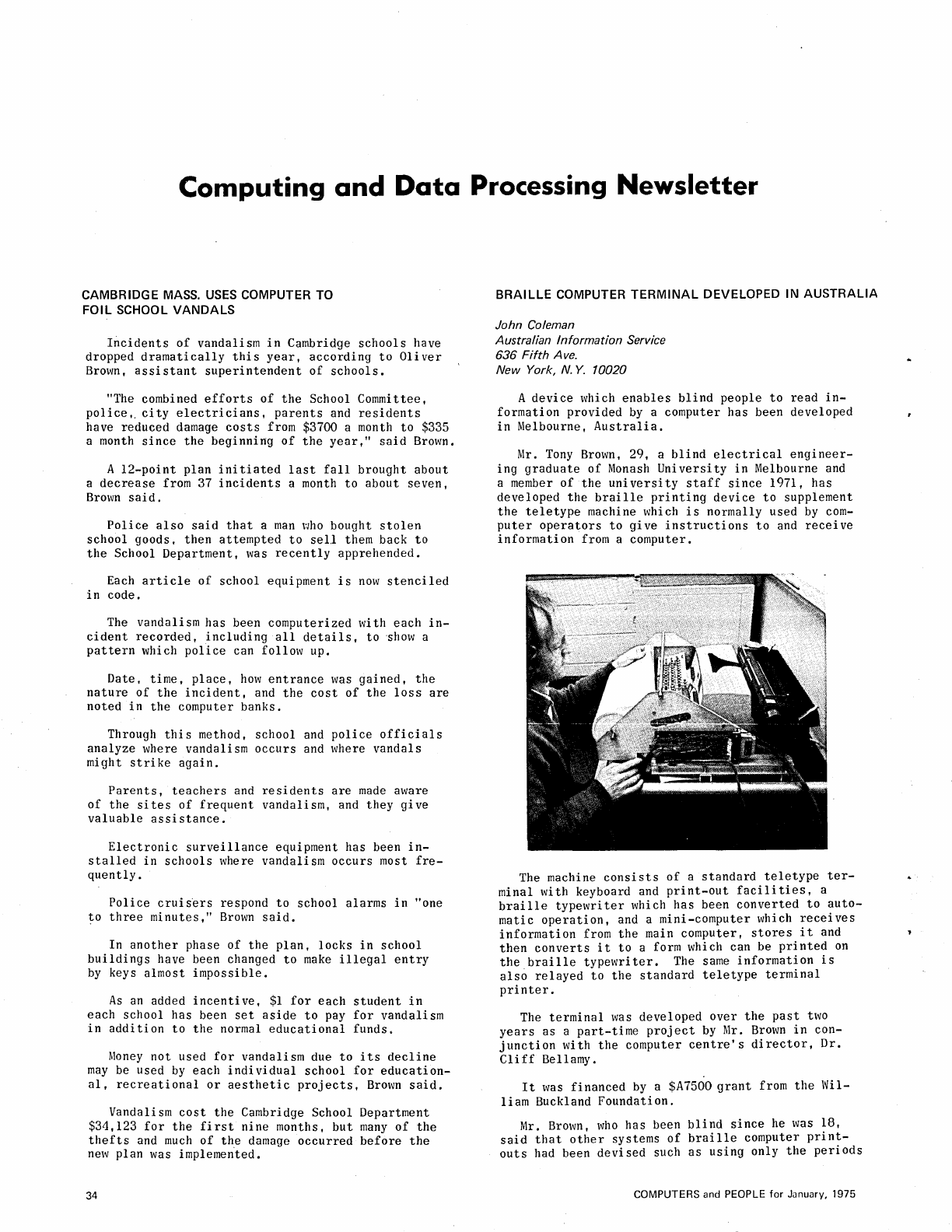
Computing
and
Data
Processing
Newsletter
CAMBRIDGE MASS.
USES
COMPUTER
TO
FOIL SCHOOL
VANDALS
Incidents
of
vandalism
in
Cambridge
schools
have
dropped
dramatically
this
year,
according
to
Oliver
Brown,
assistant
superintendent
of
schools.
"The combined
efforts
of
the
School Committee,
police
..
ci
ty
electricians,
parents
and
residents
have reduced damage
costs
from $3700 a month
to
$335
a month
since
the
beginning
of
the
year,"
said
Brown.
A
l2-point
plan
initiated
last
fall
brought
about
a
decrease
from 37
incidents
a month
to
about
seven,
Brown
said.
Police
also
said
that
a
man
who
bought
stolen
school
goods,
then
attempted
to
sell
them back
to
the
School Department,
was
recently
apprehended.
Each
article
of
school equipment
is
now
stenciled
in
code.
The
vandalism
has been
computerized
with
each
in-
cident
recorded,
including
all
details,
to
~how
a
pattern
which
police
can
follow
up.
Date,
time,
place,
how
entrance
was
gained,
the
nature
of
the
incident,
and
the
cost
of
the
loss
are
noted
in
the
computer
banks.
Through
this
method,
school
and
police
officials
analyze
where vandalism
occurs
and where
vandals
might
strike
again.
Parents,
teachers
and
residents
are
made
aware
of
the
sites
of
frequent
vandalism,
and
they
give
valuable
assistance.
Electronic
surveillance
equipment has been
in-
stalled
in
schools
where
vandalism
occurs
most
fre-
quently.
Police
cruisers
respond
to
school alarms
in
"one
to
three
minutes,"
Brown
said.
In
another
phase
of
the
plan,
locks
in
school
buildings
have been changed
to
make
illegal
entry
by
keys
almost
impossible.
As
an
added
incentive,
$1
for
each
student
in
each
school
has been
set
aside
to
pay
for
vandalism
in
addition
to
the
normal
educational
funds.
Money
not
used
for
vandalism
due
to
its
decline
may
be used
by
each
individual
school
for
education-
al,
recreational
or
aesthetic
projects,
Brown
said.
Vandalism
cost
the
Cambridge School Department
$34,123
for
the
first
nine
months,
but
many
of
the
thefts
and
much
of
the
damage
occurred
before
the
new
plan
was
implemented.
34
BRAILLE
COMPUTER
TERMINAL
DEVELOPED IN
AUSTRALIA
John Coleman
Australian
Information
Service
636
Fifth
Ave.
New York,
N.
Y.
10020
A
device
which
enables
blind
people
to
read
in-
formation
provided
by
a computer has been developed
in
Melbourne,
Australia.
Mr.
Tony
Brown, 29, a
blind
electrical
engineer-
ing
graduate
of
Monash
University
in
Melbourne and
a
member
of
the
university
staff
since
1971, has
developed
the
braille
printing
device
to
supplement
the
teletype
machine which
is
normally used
by
com-
puter
operators
to
give
instructions
to
and
receive
information
from a computer.
The
machine
consists
of
a
standard
teletype
ter-
minal
with
keyboard and
print-out
facilities,
a
braille
typewriter
which
has
been
converted
to
auto-
matic
operation,
and a
mini-computer
which
receives
information
from
the
main computer,
stores
it
and
then
converts
it
to
a form which can be
printed
on
the
braille
typewriter.
The
same
information
is
also
relayed
to
the
standard
teletype
terminal
printer.
The
terminal
was
developed
over
the
past
two
years
as a
part-time
project
by
Mr.
Brown
in
con-
junction
with
the
computer
centre's
director,
Dr.
Cli
ff
Bellamy.
It
was
financed
by
a $A7500
grant
from
the
Wil-
liam
Buckland
Foundation.
Mr.
Brown,
who
has been
blind
since
he
was
18,
said
that
other
systems
of
braille
computer
print-
outs
had been
devised
such
as
using
only
the
periods
COMPUTERS and PEOPLE
for
January. 1975

on
a
standard
printer;
but
that
these
tended
to
be
difficult
to
program and
to
read.
The
new
terminal
designed
and
built
by
the
compu-
ter
centre
combines
great
flexibility
with
high
qual-
ity
of
output.
The
prototype
model
will
undergo
some
refinement
and
then
it
will
be
tested
by
other
blind
computer
programmers and
with
other
computers.
THREE COMMUNITIES IN MASSACHUSETTS
MAKE
SAVINGS
WITH COMPUTERIZED SCHOOL-BUS ROUTES
Massachusetts
school
transportation
costs,
which
last
year
topped $55
million,
have been
forced
sharp-
ly
upward
this
year
by
inflationary
pressures
--
such
as
higher
vehicle
cost~
increased
oil
prices
and
ris-
ing
bus
drivers'
salaries
--
not
to
mention
extra
court-ordered
busing
in
Boston and
Springfield.
But
computerized
bus
routing
has
chopped more
than
$100,000 from 1974
school
transportation
budg-
ets
in
Braintree,
Brockton and
Taunton.
School
officials
in
those
communities
hired
con-
sultants
to
survey
local
traffic
patterns,
locations
of
students'
homes
and
school
destinations,
then
de-
veloped
plans
for
more
efficient
use
of
school
buses.
"The
consultants
did
everything
we
asked and
more,"
said
Taunton School
Supt.
Edward
Aleixo.
Aleixo
said
57
buses
formerly
were used
to
cover
87
routes
in
the
city.
Now
there
are
nine
more
routes
but
only
33
buses.
Taunton's
savings
may
have been augmented
by
com-
petition
among
four
bus companies
for
a
share
of
the
contract.
Each
route
was
bid
separately.
Long
said
the
consultants
proposed
several
alter-
nate
busing
programs
for
Brockton.
"We
decided
not
to
adopt
staggered
school
closing
hours,"
Long
said,
"but
wi
th more
efficient
scheduling
we
cut
our
trans-
portation
budget
about
8
percent
last
year."
In
Taunton,
the
cutback
in
the
number
of
buses
required
adjustment
of
school
starting
times.
The
high
school
classes
start
at
8
a.m.,
middle school
at
8:30
and
elementary
grades
at
9.
In
these
and
other
communities
with
recently
re-
vamped
schedules,
school
officials
report
there
were
some
parental
complaints
during
the
early
weeks of
school.
Longer bus
routes
or
double
bus
trips
forced
some
students
to
leave
home
earlier
than
in
past
years.
Younger
children
on
an
early
bus
may
tire
more
easily
than
older
students,
and
they
need
extra
su-
pervision
if
they
arrive
at
school
20 minutes
or
more
before
classes
begin.
As
more
children
are
assigned
to
each
bus,
dis~
ciplinary
problems
may
increase,
and
safety
analysts
may
become concerned
about
standees.
"If
you're
going
to
save
this
much
money, some-
thing
has
got
to
give
somewhere,"
said
Braintree's
School Committee
chairman,
Mrs. John Grabosky,
who
added
that
Braintree's
busing
costs
dropped from
$368,000
in
1973
to
approximately
$253,600
this
year.
COMPUTERS
and
PEOPLE
for
January, 1975
Consultants'
fees
depend
on
the
size
of
the
school
system and
the
extent
of
services
required
by
the
school
committee.
Among
the
consultants
which
offer
computerized
bus
routing
are:
LKB
Systems
of
Syosset,
NoY.; Program-
med
Transportation
of
Penfield,
N.Y.; Westinghouse
Learning
Corp.,
of
Waltham; and
Educational
Coordi-
nates,
of
Princeton,
N.J.
Leo P. Turo,
director
of
the
state
Board
of
Educa-
tion's
school
management
services,
is
skeptical
about
paying
private
consultants
for
bus
scheduling.
Turo
said
his
office
assists
public
schools
with
scheduling,
contracts,
safety
and
other
busing
prob-
lems
--
all
without
cost
to
the
school
system.
Hull
School
Supt.
Richard
Charlton
said
Turo's
department
helped
his
community
write
specifications
for
its
transportation
contract
but
did
not
restruc-
ture
bus
routes.
Some
school
officials
reject
use
of
consultants,
contending
that
local
school
bus
coordinators
know
their
community and
its
transportation
problems
bet-
ter
than
any
outside
consultant
could
in
a few weeks.
One
school
official
disagreed.
"I
don't
think
we
could
have done
as
well
by
ourselves."
Brockton's
Girard
Long
said:
"Most
routes
were
set
up
years
ago and
only
changed
when
buses
became
overcrowded.
No
one
in
the
school
department
has
time
to
plot
the
location
of
every
student's
home.
If
some
company
is
equipped
to
do
this
and can save
us money,
why
not
take
advantage
of
it?"
MANY
RADIO MUSIC STATIONS ARE RUN BY COMPUTER
A
current
development
is
the
automated
radio
station
run
by
computer. According
to
Broadcast
Magazine,
more
than
half
the
FM
radio
stations
in
the
country
are
now
completely
automated,
with
more
scheduled
to
take
that
route
in
the
near
future.
This
magazine
also
reports
that
automation
is
making
gradual
inroads
in
the
AM
market.
Here's
how
a system works. A
station
hires
a
programming
company
and
tells
it
what
type
of
for-
mat
is
desired
--
adult
rock,
beautiful
music,
top-
40,
etc.
The
programming company
then
chooses
the
actual
music
to
be
played
and
the
order
the
songs
are
to
be
played
in,
based
on
what
has
been
success-
ful
for
other
stations
with
the
same
format.
The
songs
are
taped
and
sent
to
the
station,
where
they
are
simply
put
into
the
computer and
played
one
af-
ter
another
automatically.
At
some
stations,
even
the
commercials
are
taped
beforehand.
Then
all
a
station
has
to
do
is
to
key-
punch
an
order
to
the
computer
telling
it
when
to
use
a
certain
commercial.
It's
done
without
a
sin-
gle
human
being
ever
having
to
touch
the
tape.
One
general
manager
stressed
cost
as
a major
ad-
vantage
of
the
automated
systems.
"One
or
two
an-
nouncers
to
tape
your
commercials,
a
couple
of
people
to
be
with
the
computer
24
hours
a
day,
and
there's
your
broadcasting
staff."
To
people
who
complain
that
an
automated
station
has a "canned" sound,
he
replies,
"These days
the
computers
are
so
sophisticated
that
unless
wo
toll
people
we're
automated,
they'd
never
know."
35

The
6th
cumulative
edition
of
ttWHO'S
·WHO
IN
COMPUTERS
AND
DATA
PROCESSING"
is due to
be
published in 1975
•
Send
us
your
order at the special prepublication price
of
$34.50
(Price after publication
will
be
$40.00) \
..
:,
The most essential components in computers and
data processing are PEOPLE -who are they?
what do
they
do? where do
they
do it?
~
..
"Who's Who in Computers and Data Processing" is
par-
ticularly useful for:
"Who's Who in Computers and Data Processing" is
jointly
published
by
Quadrangle/The New York Times
Book Co. and
"Computers
and People" (Berkeley
Enter-
prises Inc.)
This publication
is
based
on
"never ceasing" data gath-
ering
about
computer
professionals carried
out
for more
than
10 years
by
"Computers
and People" (formerly
"Computers
and
Automation").
Our files contain inform-
ation
on
more
than
17,000
computer
professionals.
Personnel managers
Libraries
Conference planners
1-
- - - - - - (may
be
copied on any piece
of
paper)-
- - - - - - - - - -
_.
WHO'S WHO
IN
COMPUTERS
AND
DATA
PROCESSING I
815
Washington St., Newtonville, Mass.
02160
Directors
of
computer
installations
Suppliers to the
computer
industry
Executive search organizations
Prospective authors
Prospective speakers
...
anyone who needs
to
keep up with the important people
in
the field.
Each
computer
professional has a capsule biography
detailing: last name; first name and middle initial
(if
any); occupation; year
of
birth; university education
and degrees; year entered the computer field; main
interests; job title; organization and its address; pub-
lications, honors and memberships; home address.
We
are confident
that
you
will find
the
subscription will
repay you
many
times over. In fact, one day when this
wealth
of
material gives
you
the
inside track
with
some-
one
important
to
you,
you'll find
the
information
PRICELESS:
the
most essential
component
in EDP
is
CAPABLE PEOPLE.
YES,
please
enroll me
as
a subscriber
to
Who's Who
in Computers and
Data
Processing
as
follows:
I enclose
$34.50
prepublication price
for
the
1975
cumulative
"Who's
Who"
when published.
I can't
wait
for
a number
of
months.
Please
send
me
the
last cumulative
edition,
and 3 updating
supplements. I enclose $34.50.
Both.
I enclose $69.00.
RETURNABLE
IN
10
DAYS
FOR
FULL
REFUND
IF
NOT
SATISFACTORY
Name
______________________________________
___
Tit
I
e-
________________________________________
_
Organization
__________________________________
_
Address
______________________________________
_
City
_______________
State &
Zip,
_______________
_
Your
Signature P.O. No.
__
_
(if
company order)
I
SI