Alcatel Lucent Command Line Interface Reference Guide, Version 3.4.1Feb. 09 AOS W V3.4.1 Commandline Guide
AOS-W_v3.4.1_Commandline_Reference_Guide
User Manual:
Open the PDF directly: View PDF ![]() .
.
Page Count: 1222 [warning: Documents this large are best viewed by clicking the View PDF Link!]
- AOS-W 3.4.1 Command Line Interface
- Introduction
- aaa authentication captive-portal
- aaa authentication dot1x
- aaa authentication mac
- aaa authentication mgmt
- aaa authentication stateful-dot1x
- aaa authentication stateful-dot1x clear
- aaa authentication stateful-ntlm
- aaa authentication vpn
- aaa authentication wired
- aaa authentication wispr
- aaa authentication-server internal
- aaa authentication-server ldap
- aaa authentication-server radius
- aaa authentication-server tacacs
- aaa authentication-server windows
- aaa bandwidth-contract
- aaa derivation-rules
- aaa inservice
- aaa ipv6 user add
- aaa ipv6 user clear-sessions
- aaa ipv6 user delete
- aaa ipv6 user logout
- aaa profile
- aaa query-server
- aaa radius-attributes
- aaa rfc-3576-server
- aaa server-group
- aaa sygate-on-demand
- aaa tacacs-accounting
- aaa test-server
- aaa timers
- aaa trusted-ap
- aaa user add
- aaa user clear-sessions
- aaa user delete
- aaa user fast-age
- aaa user logout
- aaa xml-api
- adp
- am
- ap enet-link-profile
- ap mesh-cluster-profile
- ap mesh-ht-ssid-profile
- ap mesh-radio-profile
- ap regulatory-domain-profile
- ap snmp-profile (deprecated)
- ap snmp-user-profile (deprecated)
- ap system-profile
- ap wipe out flash
- ap wired-ap-profile
- ap-group
- ap-name
- ap-regroup
- ap-rename
- apboot
- apflash
- apconnect
- apdisconnect
- arp
- audit-trail
- backup
- banner motd
- boot
- cellular profile
- cfgm
- clear
- clock set
- clock summer-time recurring
- clock timezone
- configure terminal
- controller-ip
- copy
- cp-bandwidth-contract
- crypto dynamic-map
- crypto ipsec
- crypto isakmp
- crypto isakmp policy
- crypto map global-map
- crypto pki
- crypto pki-import
- crypto-local ipsec-map
- crypto-local isakmp ca-certificate
- crypto-local isakmp dpd
- crypto-local isakmp key
- crypto-local isakmp permit-invalid-cert
- crypto-local isakmp server-certificate
- crypto-local isakmp xauth
- crypto-local pki
- database synchronize
- delete
- destination
- dir
- dynamic-ip
- enable
- enable secret
- encrypt
- esi group
- esi parser domain
- esi parser rule
- esi parser rule-test
- esi ping
- esi server
- exit
- export
- firewall
- firewall cp
- firewall cp-bandwidth-contract
- gateway health-check disable
- guest-access-email
- halt
- help
- hostname
- ids dos-profile
- ids general-profile
- ids impersonation-profile
- ids profile
- ids rate-thresholds-profile
- ids signature-matching-profile
- ids signature-profile
- ids unauthorized-device-profile
- interface fastethernet | gigabitethernet
- interface loopback
- interface mgmt
- interface port-channel
- interface range
- interface tunnel
- interface vlan
- interface vlan ip igmp proxy
- ip access-list eth
- ip access-list extended
- ip access-list mac
- ip access-list session
- ip access-list standard
- ip cp-redirect-address
- ip default-gateway
- ip dhcp excluded-address
- ip dhcp pool
- ip domain lookup
- ip domain-name
- ip igmp
- ip local
- ip mobile active-domain
- ip mobile domain
- ip mobile foreign-agent
- ip mobile home-agent
- ip mobile proxy
- ip mobile revocation
- ip mobile trail
- ip name-server
- ip nat
- ip ospf
- ip pppoe-max-segment-size
- ip pppoe-password
- ip pppoe-service-name
- ip pppoe-username
- ip radius
- ip route
- ipv6 access-list session
- ipv6 firewall
- lacp group
- lacp port-priority
- lacp system-priority
- lacp timeout
- license
- localip
- local-userdb add
- local-userdb del
- local-userdb export
- local-userdb fix-database
- local-userdb import
- local-userdb maximum-expiration
- local-userdb modify
- local-userdb send-to-guest
- local-userdb send-to-sponsor
- local-userdb-guest add
- local-userdb-guest del
- local-userdb-guest modify
- local-userdb-guest send-email
- location
- logging
- logging facility
- logging level
- loginsession
- logout
- mac-address-table
- masterip
- master-redundancy
- mgmt-server
- mgmt-user
- mobility-manager
- netdestination
- netservice
- network-printer
- network-storage
- ntp server
- packet-capture
- packet-capture-defaults
- page
- paging
- panic
- papi-security
- pcap
- ping
- pkt-trace
- pkt-trace-global
- pptp ip local pool
- priority-map
- process monitor
- prompt
- provision-ap
- rap-wml
- rap-wml table
- reload
- reload-peer-sc
- rename
- restore
- rf arm-profile
- rf dot11a-radio-profile
- rf dot11g-radio-profile
- rf event-thresholds-profile
- rf ht-radio-profile
- rf optimization-profile
- rft
- router mobile
- router ospf
- service
- show aaa authentication all
- show aaa authentication captive-portal
- show aaa authentication captive-portal customization
- show aaa authentication dot1x
- show aaa authentication mac
- show aaa authentication mgmt
- show aaa authentication stateful-dot1x
- show aaa authentication stateful-ntlm
- show aaa authentication vpn
- show aaa authentication wired
- show aaa authentication wispr
- show aaa authentication-server all
- show aaa authentication-server internal
- show aaa authentication-server ldap
- show aaa authentication-server radius
- show aaa authentication-server tacacs
- show aaa authentication-server windows
- show aaa tacacs-accounting
- show aaa bandwidth-contracts
- show aaa derivation-rules
- show aaa main-profile
- show aaa profile
- show aaa radius-attributes
- show aaa rfc-3576-server
- show aaa server-group
- show aaa state ap-group
- show aaa state configuration
- show aaa state debug-statistics
- show aaa state messages
- show aaa state station
- show aaa state user
- show aaa sygate-on-demand (deprecated)
- show aaa tacacs-accounting
- show aaa timers
- show aaa xml-api server
- show aaa web admin-port
- show aaa xml-api statistics
- show acl ace-table
- show acl acl-table
- show acl hits
- show adp config
- show adp counters
- show ap active
- show ap allowed-channels
- show ap ap-group
- show ap arm history
- show ap arm neighbors
- show ap arm rf-summary
- show ap arm scan-times
- show ap arm state
- show ap association
- show ap association remote
- show ap blacklist-clients
- show ap bss-table
- show ap bw-report
- show ap client status
- show ap config
- show ap coverage-holes
- show ap database
- show ap database-summary
- show ap debug association-failure
- show ap debug bss-config
- show ap debug bss-stats
- show ap debug client-mgmt-counters
- show ap debug client-stats
- show ap debug client-table
- show ap debug counters
- show ap debug datapath
- show ap debug driver-log
- show ap debug log
- show ap debug mgmt-frames
- show ap debug radio-stats
- show ap debug received-config
- show ap debug remote association
- show ap debug shaping-table
- show ap debug system-status
- show ap debug trace-addr
- show ap details
- show ap enet-link-profile
- show ap essid
- show ap ht-rates
- show ap image version
- show ap license-usage
- show ap load-balancing
- show ap mesh active
- show ap mesh debug counters
- show ap mesh debug current-cluster
- show ap mesh debug forwarding-table
- show ap mesh debug hostapd-log
- show ap mesh debug meshd-log
- show ap mesh debug provisioned-clusters
- show ap mesh neighbors
- show ap mesh tech-support
- show ap mesh topology
- show ap mesh-cluster-profile
- show ap mesh-ht-ssid-profile
- show ap mesh-radio-profile
- show ap monitor
- show ap monitor association
- show ap monitor debug
- show ap monitor stats
- show ap pcap status
- show ap profile-usage
- show ap provisioning
- show ap radio-database
- show ap remote counters
- show ap remote debug flash-config
- show ap remote debug mgmt-frames
- show ap spectrum-load-balancing
- show ap system-profile
- show ap tech-support
- show ap vlan-usage
- show ap wired-ap-profile
- show ap wmm-flow
- show ap-group
- show ap-name
- show arp
- show audit-trail
- show auth-tracebuf
- show banner
- show boot
- show cellular profile
- show clock
- show command-mapping
- show configuration
- show controller-ip
- show country
- show cp-bwcontracts
- show cpuload
- show crypto dp
- show crypto dynamic-map
- show crypto ipsec
- show crypto isakmp
- show crypto map
- show crypto pki
- show crypto-local ipsec-map
- show crypto-local isakmp
- show crypto-local pki
- show database
- show datapath
- show destination
- show dialer group
- show dir
- show dot1x ap-table
- show dot1x ap-table aes
- show dot1x ap-table dynamic-wep
- show dot1x ap-table static-wep
- show dot1x ap-table tkip
- show dot1x counters
- show dot1x supplicant-info
- show dot1x supplicant-info list-all
- show dot1x supplicant-info pmkid
- show dot1x supplicant-info statistics
- show esi groups
- show esi parser
- show esi ping
- show esi servers
- show faults
- show firewall
- show firewall-cp
- show gateway health-check
- show global-user-table count
- show-global-user-table list
- show guest-access-email
- show hostname
- show ids dos-profile
- show ids general-profile
- show ids impersonation-profile
- show ids profile
- show ids rate-thresholds-profile
- show ids signature-matching-profile
- show ids signature-profile
- show ids unauthorized-device-profile
- show image
- show interface counters
- show interface gigabitethernet
- show interface fastethernet
- show interface loopback
- show interface mgmt
- show interface port-channel
- show interface tunnel
- show interface vlan
- show inventory
- show ip access-group
- show ip access-list
- show ip cp-redirect-address
- show ip dhcp
- show ip domain-name
- show ip igmp
- show ip mobile
- show ip nat pool
- show ip ospf
- show ip pppoe-info
- show ip radius
- show ip route
- show ipc statistics app-ap
- show ipc statistics app-id
- show ipc statistics app-name
- show ipv6 access-list
- show ipv6 datapath session counters
- show ipv6 datapath session table
- show ipv6 datapath user counters
- show ipv6 datapath user table
- show ipv6 firewall
- show ipv6 mld config
- show ipv6 mld counters
- show ipv6 mld group
- show ipv6 mld interface
- show ipv6 user-table
- show keys
- show lacp
- show lacp sys-id
- show license
- show license-usage
- show localip
- show local-userdb
- show local-userdb username
- show log all
- show log ap-debug
- show log bssid-debug
- show log errorlog
- show log essid-debug
- show log network
- show log security
- show log system
- show log user
- show log user-debug
- show log wireless
- show logging
- show loginsessions
- show mac-address-table
- show master-local stats
- show master-redundancy
- show memory
- show mgmt-role
- show mgmt-users
- show netdestination
- show netservice
- show netstat
- show network-printer
- show network-storage
- show ntp peer
- show ntp servers
- show ntp status
- show packet-capture
- show packet-capture-defaults
- show papi-security
- show poe
- show port link-event
- show port monitor
- show port stats
- show port status
- show port trusted
- show port xsec
- show priority-map
- show processes
- show profile-errors
- show profile-hierarchy
- show profile-list aaa
- show profile-list ap
- show profile-list ap-group
- show profile-list ap-name
- show profile-list ids
- show profile-list rf
- show profile-list wlan
- show provisioning-ap-list
- show provisioning-params
- show rap-wml
- show references aaa authentication
- show references aaa authentication-server
- show references aaa profile
- show references aaa server-group
- show references ap
- show references guest-access-email
- show references ids
- show references papi-security
- show references rf
- show references user-role
- show references web-server
- show references wlan
- show rf arm-profile
- show rf dot11a-radio-profile
- show rf dot11g-radio-profile
- show rf event-thresholds-profile
- show rf ht-radio-profile
- show rf optimization-profile
- show rft profile
- show rft result
- show rft transactions
- show rights
- show roleinfo
- show rrm dot11k admission-capacity
- show rrm dot11k ap-channel-report
- show rrm dot11k beacon-report
- show rrm dot11k neighbor-report
- show running-config
- show session-acl-list
- show slots
- show snmp community
- show snmp inform
- show snmp trap-host
- show snmp trap-list
- show snmp trap-queue
- show snmp user-table
- show ssh
- show startup-config
- show station-table
- show storage
- show switch ip
- show switch software
- show switches
- show switchinfo
- show syscontact
- show syslocation
- show tech-support
- show telnet
- show time-range
- show trunk
- show uplink
- show usb
- show user
- show user_session_count
- show util_proc
- show version
- show vlan
- show vlan mapping
- show vlan status
- show vlan summary
- show voice call-cdrs
- show voice call-counters
- show voice call-density
- show voice call-perf
- show voice call-quality
- show voice call-stats
- show voice msg-stats
- show voice prioritization
- show voice rtcp-inactivity
- show voice statistics
- show voice trace
- show vpdn l2tp configuration
- show vpdn pptp configuration
- show vpdn pptp local pool
- show vpn-dialer
- show vrrp
- show web-server
- show wlan dot11k-profile
- show wlan edca-parameters-profile
- show wlan ht-ssid-profile
- show wlan ssid-profile
- show wlan traffic-management-profile
- show wlan virtual-ap
- show wlan voip-cac-profile
- show wms ap
- show wms channel
- show wms client
- show wms counters
- show wms general
- show wms monitor-summary
- show wms probe
- show wms rogue-ap
- show wms routers
- show wms system
- show wms wired-mac
- shutdown
- snmp-server
- spanning-tree (Global Configuration)
- spanning-tree (Configuration Interface)
- ssh
- stm
- support
- syscontact
- syslocation
- tar
- telnet
- time-range
- traceroute
- trusted
- uplink
- usb reclassify
- usb-printer
- user-role
- vlan
- vlan-name
- voip
- vpdn group l2tp
- vpdn group pptp
- vpn-dialer
- vrrp
- web-server
- whoami
- wlan dot11k-profile
- wlan edca-parameters-profile
- wlan ht-ssid-profile
- wlan ssid-profile
- wlan traffic-management-profile
- wlan virtual-ap
- wlan voip-cac-profile
- wms ap
- wms clean-db
- wms client
- wms export-class
- wms export-db
- wms general
- wms import-db
- wms reinit-db
- wms-local system
- write
- Appendix A: Command Modes

AOS-W 3.4.1
Command Line Interface
Reference Guide

www.alcatel-lucent.com
26801 West Agoura Road
Calabasas, CA 91301
AOS-W 3.4.1 Command Line Interface | Reference Guide 0510624-01 | October 2009
Copyright
© 2009 Alcatel-Lucent. All rights reserved.
Specifications in this manual are subject to change without notice.
Originated in the USA.
AOS-W, Alcatel 4308, Alcatel 4324, Alcatel 6000, Alcatel 41, Alcatel 60/61/65, Alcatel 70, and Alcatel 80 are trademarks of
Alcatel-Lucent in the United States and certain other countries.
Any other trademarks appearing in this manual are the property of their respective companies.
Legal Notice
The use of Alcatel-Lucent switching platforms and software, by all individuals or corporations, to terminate Cisco or Nortel VPN client
devices constitutes complete acceptance of liability by that individual or corporation for this action and indemnifies, in full, Alcatel-
Lucent from any and all legal actions that might be taken against it with respect to infringement of copyright on behalf of Cisco Systems
or Nortel Networks."
AOS-W 3.4.1 Command Line Interface | Reference Guide Introduction | 3
Introduction
The AOS-W command line interface (CLI) allows you to configure and manage Alcatel-Lucent switches.
The CLI is accessible from a local console connected to the serial port on the switches or through a
Telnet or Secure Shell (SSH) session from a remote management console or workstation.
What’s New In AOS-W 3.4.1
The following commands have been added in the AOS-W 3.4.1 Command Line Interface.
Modified Commands
The following commands were modified in AOS-W 3.4.1.
NOTE
Telnet access is disabled by default on Alcatel-Lucent switches. To enable Telnet access, enter the telnet cli
command from a serial connection or an SSH session, or in the WebUI navigate to the Configuration >
Management > General page.
Command Description
aaa authentication
stateful-dot1x This command configures 802.1x authentication for clients on non-Alcatel-
Lucent APs.
aaa authentication
stateful-ntlm This command configures stateful NT LAN Manager (NTLM) authentication.
aaa authentication
wispr This command configures WISPr authentication with an ISP’s WISPr RADIUS
server.
aaa authentication-
server windows
This command configures a windows server for stateful-NTLM
authentication.
apconnect This command instructs a mesh point to connect to a new parent.
clear This command clears various settings and values from your running
configuration.
lacp group Configure the per-port specific Link Aggregation Control Protocol (LACP).
lacp port-priority Configure the LACP port priority.
lacp system-priority Configure the LACP system priority.
lacp timeout Configure the timeout period for the LACP session.
show lacp View the LACP configuration status.
show lacp sys-id View the LACP system ID information
Command Parameter Change
aaa profile License requirements changed in AOS-W 3.4.1, so the sip-
authentication-role parameter now requires the Policy Enforced Firewall
license instead of the Voice Services Module license required in earlier
versions

4|Introduction AOS-W 3.4.1 Command Line Interface | Reference Guide
About this Guide
This guide describes the AOS-W command syntax. The commands in this guide are listed alphabetically.
The following information is provided for each command:
zCommand Syntax—The complete syntax of the command.
zDescription—A brief description of the command.
zSyntax—A description of the command parameters, including license requirements for specific
parameters if needed. The applicable ranges and default values, if any, are also included.
zUsage Guidelines—Information to help you use the command, including: prerequisites, prohibitions,
and related commands.
zExample—An example of how to use the command.
zCommand History—The version of AOS-W in which the command was first introduced.
Modifications and changes to the command are also noted
zCommand Information—This table describes any licensing requirements, command modes and
platforms for which this command is applicable. For more information about available licenses, see
the “Managing Software Feature Licenses” chapter in the AOS-W User Guide.
Connecting to the Switch
This section describes how to connect to the switch to use the CLI.
Serial Port Connection
The serial port is located on the front panel of the switch. Connect a terminal or PC/workstation
running a terminal emulation program to the serial port on the switch to use the CLI. Configure your
terminal or terminal emulation program to use the following communication settings.
ap-name License requirements changed in AOS-W 3.4.1, so the voip-cac-profile
parameter now requires the Policy Enforced Firewall license instead of the
Voice Services Module license required in earlier versions.
interface fastethernet |
gigabitethernet, interface
port-channel, interface
range
A new parameter, trusted {vlan <word>}, sets a range of VLANs to be
trusted. All VLANs not in the range are by default untrusted.
snmp-server A new parameter, engine-id has been added. This parameter set the
SNMP server engine ID in Hexidecimal.
show ap mesh neighbors If you include the new optional names parameter, the Portal column in the
output of this command will show AP names, (where available) rather than
BSSIDs.
vlan A new parameter, vlan range has been added. Lets the user add mulitple
VLAN IDs at once on the switch.
wlan ssid-profile New parameters, a-beacon-rate and g-beacon-rate have been added to
this command. Sets the beacon rate for 802.11a/g and should be used for
for the Distributed Antenna System (DAS) only.
Baud Rate Data Bits Parity Stop Bits Flow Control
9600 8 None 1 None
Command Parameter Change

AOS-W 3.4.1 Command Line Interface | Reference Guide Introduction | 5
Telnet or SSH Connection
Telnet or SSH access requires that you configure an IP address and a default gateway on the switch and
connect the switch to your network. This is typically performed when you run the Initial Setup on the
switch, as described in the Alcatel-Lucent Quick Start Guide. In certain deployments, you can also
configure a loopback address for the switch; see the “Deploying a Basic Alcatel-Lucent User-Centric
System” chapter in the AOS-W User Guide for more information.
Configuration changes on Master Switches
Some commands can only be issued when connected to a master switch. If you make a configuration
change on a master switch, all connected local switches will subsequently update their configurations
as well. You can manually synchronize all of the switches at any time by saving the configuration on the
master switch.
CLI Access
When you connect to the switch using the CLI, the system displays its host name followed by the login
prompt. Log in using the admin user account and the password you entered during the Initial Setup on
the switch (the password displays as asterisks). For example:
(host)
User: admin
Password: *****
When you are logged in, the user mode CLI prompt displays. For example:
(host) >
User mode provides only limited access for basic operational testing such as running ping and
traceroute.
Certain management functions are available in enable (also called “privileged”) mode. To move from
user mode to enable mode requires you to enter an additional password that you entered during the
Initial Setup (the password displays as asterisks). For example:
(host) > enable
Password: ******
When you are in enable mode, the > prompt changes to a pound sign (#):
(host) #
Configuration commands are available in config mode. Move from enable mode to config mode by
entering configure terminal at the # prompt:
(host) # configure terminal
Enter Configuration commands, one per line. End with CNTL/Z
When you are in basic config mode, (config) appears before the # prompt:
(host) (config) #
Command Help
You can use the question mark (?) to view various types of command help.
NOTE
There are several other sub- command modes that allow users to configure individual interfaces,
subinterfaces, loopback addresses, GRE tunnels and cellular profiles. For details on the prompts and the
available commands for each of these modes, see Appendix A: Command Modes on page 1219.

6|Introduction AOS-W 3.4.1 Command Line Interface | Reference Guide
When typed at the beginning of a line, the question mark lists all the commands available in your
current mode or sub-mode. A brief explanation follows each command. For example:
(host) > ?
enable Turn on Privileged commands
logout Exit this session. Any unsaved changes are lost.
ping Send ICMP echo packets to a specified IP address.
traceroute Trace route to specified IP address.
When typed at the end of a possible command or abbreviation, the question mark lists the commands
that match (if any). For example:
(host) > c?
clear Clear configuration
clock Configure the system clock
configure Configuration Commands
copy Copy Files
If more than one item is shown, type more of the keyword characters to distinguish your choice.
However, if only one item is listed, the keyword or abbreviation is valid and you can press tab or the
spacebar to advance to the next keyword.
When typed in place of a parameter, the question mark lists the available options. For example:
(host) # write ?
erase Erase and start from scratch
file Write to a file in the file system
memory Write to memory
terminal Write to terminal
<cr>
The <cr> indicates that the command can be entered without additional parameters. Any other
parameters are optional.
Command Completion
To make command input easier, you can usually abbreviate each key word in the command. You need
type only enough of each keyword to distinguish it from similar commands. For example:
(host) # configure terminal
could also be entered as:
(host) # con t
Three characters (con) represent the shortest abbreviation allowed for configure. Typing only c or co
would not work because there are other commands (like copy) which also begin with those letters. The
configure command is the only one that begins with con.
As you type, you can press the spacebar or tab to move to the next keyword. The system then attempts
to expand the abbreviation for you. If there is only one command keyword that matches the
abbreviation, it is filled in for you automatically. If the abbreviation is too vague (too few characters),
the cursor does not advance and you must type more characters or use the help feature to list the
matching commands.
Deleting Configuration Settings
Use the no command to delete or negate previously-entered configurations or parameters.
zTo view a list of no commands, type no at the enable or config prompt followed by the question
mark. For example:
(host) (config) # no?

AOS-W 3.4.1 Command Line Interface | Reference Guide Introduction | 7
zTo delete a configuration, use the no form of a configuration command. For example, the following
command removes a configured user role:
(host) (config) # no user-role <name>
zTo negate a specific configured parameter, use the no parameter within the command. For example,
the following commands delete the DSCP priority map for a priority map configuration:
(host) (config) # priority-map <name>
(host) (config-priority-map) # no dscp priority high
Saving Configuration Changes
Each Alcatel-Lucent switch contains two different types of configuration images.
zThe running config holds the current switch configuration, including all pending changes which
have yet to be saved. To view the running-config, use the following command:
(host) # show running-config
zThe startup config holds the configuration which will be used the next time the switch is rebooted.
It contains all the options last saved using the write memory command. To view the startup-config,
use the following command:
(host) # show startup-config
When you make configuration changes via the CLI, those changes affect the current running
configuration only. If the changes are not saved, they will be lost after the switch reboots. To save your
configuration changes so they are retained in the startup configuration after the switch reboots, use the
following command in enable mode:
(host) # write memory
Saving Configuration...
Saved Configuration
Both the startup and running configurations can also be saved to a file or sent to a TFTP server for
backup or transfer to another system.

8|Introduction AOS-W 3.4.1 Command Line Interface | Reference Guide
Commands That Reset the Switch or AP
If you use the CLI to modify a currently provisioned and running radio profile, those changes take place
immediately; you do not reboot the switch or the AP for the changes to affect the current running
configuration. Certain commands, however, automatically force the switch or AP to reboot. You may
want to consider current network loads and conditions before issuing these commands, as they may
cause a momentary disruption in service as the unit resets. Note also that changing the lms-ip
parameter the in an AP system profile associated with an AP group will cause all APs in that AP group
to reboot.
Command Line Editing
The system records your most recently entered commands. You can review the history of your actions,
or reissue a recent command easily, without having to retype it.
To view items in the command history, use the up arrow to move back through the list and the down
arrow key to forward. To reissue a specific command, press Enter when the command appears in the
command history. You can even use the command line editing feature to make changes to the command
prior to entering it.
Commands that reset an AP
zap-regroup
zap-rename
zapboot
zapflash
zprovision-ap reprovision
zap wired-ap-profile <profile>
forward-mode {bridge|split-
tunnel|tunnel}
zwlan virtual-ap <profile> {aaa-profile
<profile>|forward-mode {bridge|split-
tunnel|tunnel}|ssid-profile
<profile>|vlan <vlan>...}
zap system-profile <profile>
{bootstrap-threshold <number>|lms-
ip <ipaddr>|master-ip <ipaddr>}
zwlan ssid-profile <profile> {battery-
boost|deny-bcast|essid|opmode|strict-
svp|wepkey1 <key>|wepkey2
<key>|wepkey3 <key>|wepkey4
<key>|weptxkey
<index>|wmm|wmm-be-dscp <best-
effort>|wmm-bk-dscp
<background>|wmm-ts-min-inact-int
<milliseconds>|wmm-vi-dscp
<video>|wmm-vo-dscp <voice>|wpa-
hexkey <psk>|wpa-passphrase
<string>}
zwlan dotllk <profile> {bcn-
measurement-mode|dot11k-
enable|force-dissasoc}
Commands that reset a switch
zreload
zreload-peer-sc
AOS-W 3.4.1 Command Line Interface | Reference Guide Introduction | 9
The command line editing feature allows you to make corrections or changes to a command without
retyping. Table 1 lists the editing controls: To use key shortcuts, press and hold the Ctrl button while
you press a letter key.
Typographic Conventions
The following conventions are used throughout this manual to emphasize important concepts:
Table 1 Line Editing Keys
Key Effect Description
Ctrl A Home Move the cursor to the beginning of the line.
Ctrl B or the
left arrow Back Move the cursor one character left.
Ctrl D Delete Right Delete the character to the right of the cursor.
Ctrl E End Move the cursor to the end of the line.
Ctrl F or the
right arrow Forward Move the cursor one character right.
Ctrl K Delete Right Delete all characters to the right of the cursor.
Ctrl N or the
down arrow Next Display the next command in the command history.
Ctrl P or
up arrow Previous Display the previous command in the command
history.
Ctrl T Transpose Swap the character to the left of the cursor with the
character to the right of the cursor.
Ctrl U Clear Clear the line.
Ctrl W Delete Word Delete the characters from the cursor up to and
including the first space encountered.
Ctrl X Delete Left Delete all characters to the left of the cursor.
Table 2 Text Conventions
Type Style Description
Italics This style is used to emphasize important terms and to mark the
titles of books.
Boldface This style is used to emphasize command names and parameter
options when mentioned in the text.
Commands This fixed-width font depicts command syntax and examples of
commands and command output.
10 |Introduction AOS-W 3.4.1 Command Line Interface | Reference Guide
Specifying Addresses and Identifiers in Commands
This section describes addresses and other identifiers that you can reference in CLI commands.
<angle brackets> In the command syntax, text within angle brackets represents
items that you should replace with information appropriate to your
specific situation. For example:
ping <ipaddr>
In this example, you would type “ping” at the system prompt
exactly as shown, followed by the IP address of the system to
which ICMP echo packets are to be sent. Do not type the angle
brackets.
[square brackets] In the command syntax, items enclosed in brackets are optional.
Do not type the brackets.
{Item_A|Item_B} In the command examples, single items within curled braces and
separated by a vertical bar represent the available choices. Enter
only one choice. Do not type the braces or bars.
{ap-name <ap-name>}|{ipaddr
<ip-addr>}
Two items within curled braces indicate that both parameters must
be entered together. If two or more sets of curled braces are
separated by a vertical bar, like in the example to the left, enter only
one choice Do not type the braces or bars.
Table 3 Addresses and Identifiers
Address/Identifier Description
IP address For any command that requires entry of an IP address to specify a network entity,
use IPv4 network address format in the conventional dotted decimal notation (for
example, 10.4.1.258). For subnetwork addresses, specify a netmask in dotted
decimal notation (for example, 255.255.255.0).
Netmask address For subnetwork addresses, specify a netmask in dotted decimal notation (for
example, 255.255.255.0).
Media Access Control
(MAC) address For any command that requires entry of a device’s hardware address, use the
hexadecimal format (for example, 00:05:4e:50:14:aa).
Service Set Identifier
(SSID) A unique character string (sometimes referred to as a network name), consisting of
no more than 32 characters. The SSID is case-sensitive (for example, WLAN-01).
Basic Service Set
Identifier (BSSID) This entry is the unique hard-wireless MAC address of the AP. A unique BSSID
applies to each frequency— 802.11a and 802.11g—used from the AP. Use the same
format as for a MAC address.
Extended Service Set
Identifier (ESSID) Typically the unique logical name of an access point.
Table 2 Text Conventions
Type Style Description

AOS-W 3.4.1 Command Line Interface | Reference Guide Introduction | 11
Contacting Alcatel-Lucent
Fast Ethernet or Gigabit
Ethernet interface Any command that references a Fast Ethernet or Gigabit Ethernet interface requires
that you specify the corresponding port on the switch in the format <slot>/<port>:
<slot> is always 1, except when referring to interfaces on the OmniAccess 6000
switch. For the OmniAccess 6000 switch, the four slots are allocated as follows:
zSlot 0: contains a supervisor card or OmniAccess Supervisor Card III.
zSlot 1: can contain either a redundant supervisor card, OmniAccess Supervisor
Card III, or a third line card.
zSlot 2: can contain either a OmniAccess Supervisor Card III or line card
(required if slot 0 contains a supervisor card).
zSlot 3: can contain either a OmniAccess Supervisor Card III or second line card.
<port> refers to the network interfaces that are embedded in the front panel of the
OmniAccess 4302, OmniAccess 4308T, or OmniAccess 4324 switch, OmniAccess
4504/4604/4704 Multi-Service Switch, OmniAccess Supervisor Card III, or a line
card installed in the OmniAccess 6000 switch. Port numbers start at 0 from the left-
most position. Use the show port status command to obtain the interface
information currently available from a switch.
Table 4 Alcatel-Lucent Contacts
Contact Center Online
zMain Site http://www.alcatel-lucent.com/enterprise
zSupport Site https://service.esd.alcatel-lucent.com
zEmail esd.support@alcatel-lucent.com
Service & Support Contact Center Telephone
zNorth America 1-800-995-2696
zLatin America 1-877-919-9526
zEurope +33 (0) 38 855 6929
zAsia Pacific +65 6240 8484
zWorldwide 1-818-878-4507
Table 3 Addresses and Identifiers
Address/Identifier Description

12 |Introduction AOS-W 3.4.1 Command Line Interface | Reference Guide
AOS-W 3.4.1 Command Line Interface | Reference Guide aaa authentication captive-portal | 13
aaa authentication captive-portal
aaa authentication
aaa authentication captive-portal <profile>
black-list <black-list>
clone <source-profile>
default-role <role>
enable-welcome-page
guest-logon
ip-addr-in-redirection-url <ip-addr>
login-page <url>
logon-wait {cpu-threshold <percent>}|{maximum-delay <seconds>}|{minimum-delay <secs>
}
logout-popup-window
max-authentication-failures <number>
no ...
protocol-http
proxy host <ipaddr> port <port>
redirect-pause <secs>
server-group <group-name>
show-acceptable-use-policy
show-fqdn
single-session
switch-in-redirection-url <ipaddr>
sygate-on-demand-agent
use-chap
user-logon
user-vlan-in-redirection-url
welcome-page <url>
Description
This command configures a Captive Portal authentication profile.
Syntax
Parameter Description Range Default
<profile> Name that identifies an instance of the profile. The
name must be 1-63 characters. —“default”
black-list Create a black list of blocked domain Names by
specifying the domain names to be blacklisted ——
clone Name of an existing Captive Portal profile from which
parameter values are copied. ——
default-role
<role>
Role assigned to the Captive Portal user upon login.
When both user and guest logon are enabled, the
default role applies to the user logon; users logging in
using the guest interface are assigned the guest role.
—guest
enable-welcome-
page
Displays the configured welcome page before the
user is redirected to their original URL. If this option is
disabled, redirection to the web URL happens
immediately after the user logs in.
enabled/
disabled enabled
guest-logon Enables Captive Portal logon without authentication. enabled/
disabled disabled
ip-addr-in-
redirection-url
<ip-addr>
Add the IP address of a switch interface in the
redirection URL —
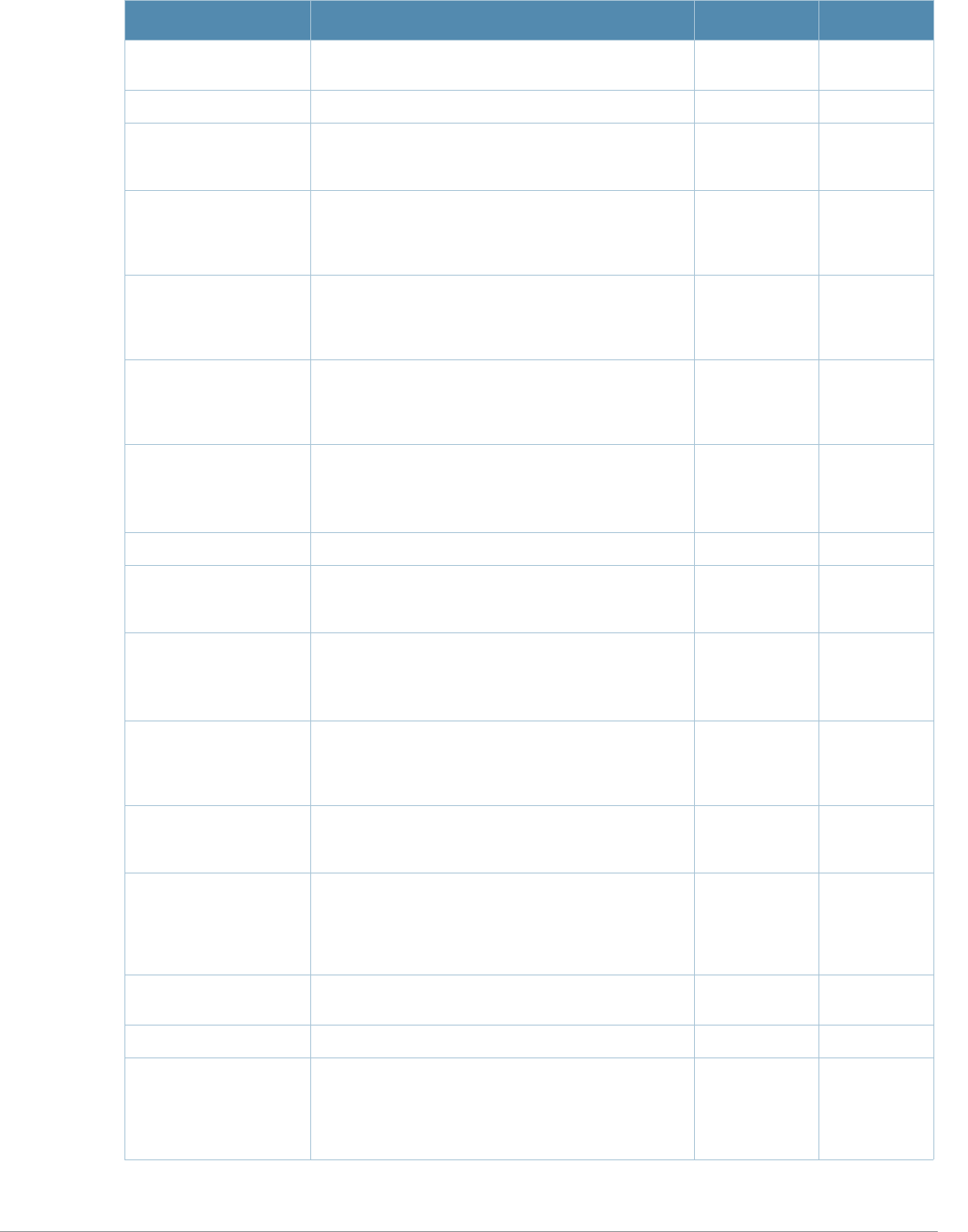
14 | aaa authentication captive-portal AOS-W 3.4.1 Command Line Interface | Reference Guide
login-page <url> URL of the page that appears for the user logon. This
can be set to any URL. —/auth/index.
html
logon-wait Configure parameters for the logon wait interval 1-100 60%
cpu-threshold
<percent>
CPU utilization percentage above which the Logon
wait interval is applied when presenting the user with
the logon page.
1-100 60%
maximum-delay
<seconds>
Maximum time, in seconds, the user will have to wait
for the logon page to pop up if the CPU load is high.
This works in conjunction with the Logon wait CPU
utilization threshold parameter.
1-10 10 seconds
minimum-delay
<secs>
Minimum time, in seconds, the user will have to wait
for the logon page to pop up if the CPU load is high.
This works in conjunction with the Logon wait CPU
utilization threshold parameter.
1-10 5 seconds
logout-popup-
window
Enables a pop-up window with the Logout link for the
user to logout after logon. If this is disabled, the user
remains logged in until the user timeout period has
elapsed or the station reloads.
enabled/
disabled enabled
max-
authentication-
failures <number>
Maximum number of authentication failures before
the user is blacklisted.
NOTE: The Wireless Intrusion Protection license
must be installed.
0-10 0
no Negates any configured parameter. — —
protocol-http Use HTTP protocol on redirection to the Captive
Portal page. If you use this option, modify the captive
portal policy to allow HTTP traffic.
enabled/
disabled disabled
(HTTPS is
used)
proxy host <ip-
addr> port <port>
Configures an IP address and port number for a
proxy server.
NOTE: This option is only available in the base
operating system.
—N/A
redirect-pause
<secs>
Time, in seconds, that the system remains in the
initial welcome page before redirecting the user to the
final web URL. If set to 0, the welcome page displays
until the user clicks on the indicated link.
1-60 10 seconds
server-group
<group-name>
Name of the group of servers used to authenticate
Captive Portal users. See “aaa server-group” on
page 57.
——
show-fqdn Allows the user to see and select the fully-qualified
domain name (FQDN) on the login page. The FQDNs
shown are specified when configuring individual
servers for the server group used with captive portal
authentication.
enabled/
disabled disabled
show-acceptable-
use-policy
Show the acceptable use policy page before the
logon page. enabled/
disabled disabled
single-session Allows only one active user session at a time. — disabled
switch-in-redir
ection-url
Sends the switch’s IP address in the redirection URL
when external captive portal servers are used. An
external captive portal server can determine the
switch from which a request originated by parsing the
‘switchip’ variable in the URL.
enabled/
disabled disabled
Parameter Description Range Default
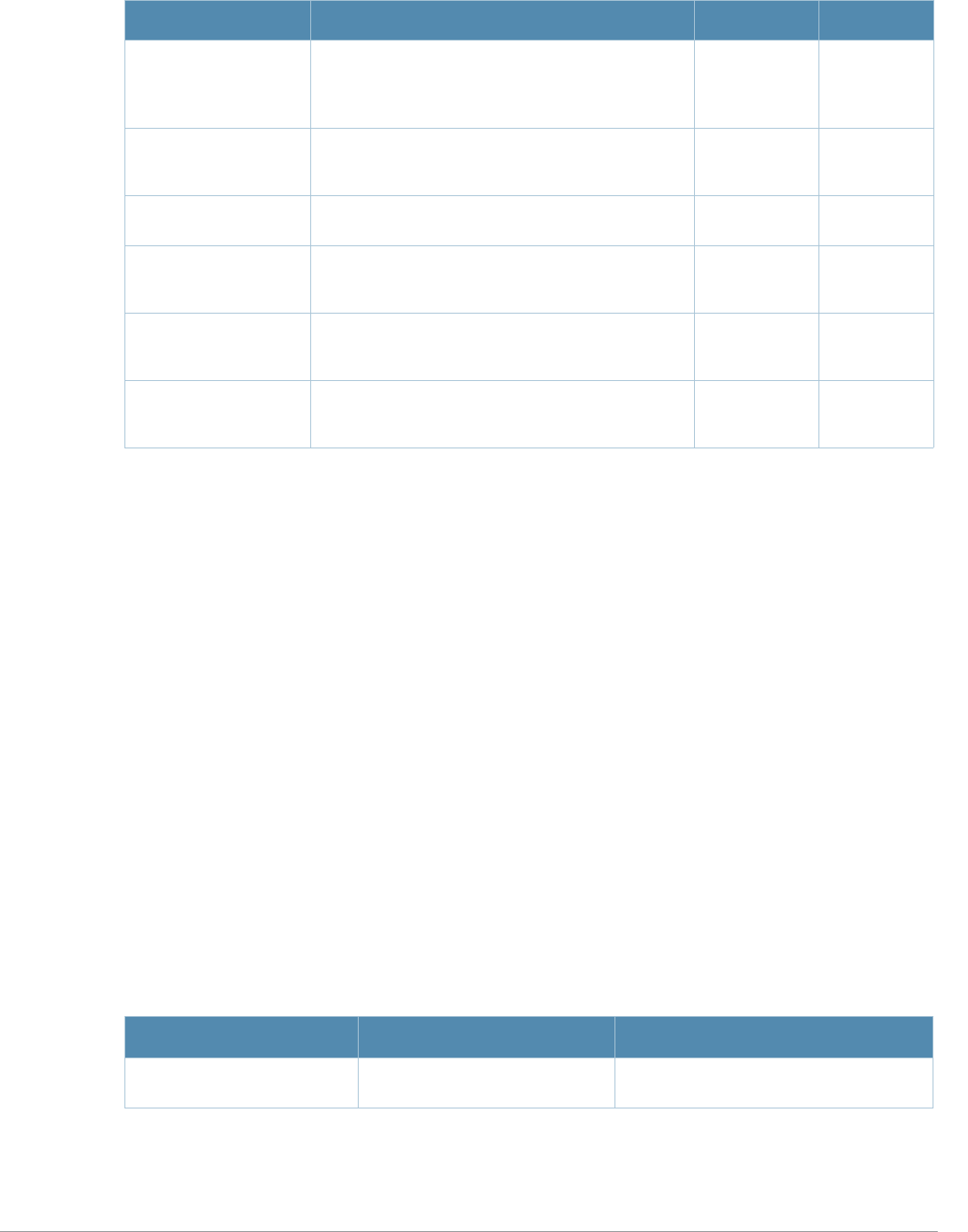
AOS-W 3.4.1 Command Line Interface | Reference Guide aaa authentication captive-portal | 15
Usage Guidelines
You can configure the Captive Portal authentication profile in the base operating system or with the Policy
Enforcement Firewall license installed. When you configure the profile in the base operating system, the
name of the profile must be entered for the initial role in the AAA profile. Also, when you configure the
profile in the base operating system, you cannot define the default-role.
Example
The following example configures a Captive Portal authentication profile that authenticates users against
the switch’s internal database. Users who are successfully authenticated are assigned the auth-guest role.
To create the auth-guest user role shown in this example, the Policy Enforcement Firewall license must be
installed in the switch.
aaa authentication captive-portal guestnet
default-role auth-guest
user-logon
no guest-logon
server-group internal
Command History
This command was introduced in AOS-W 3.0.
Command Information
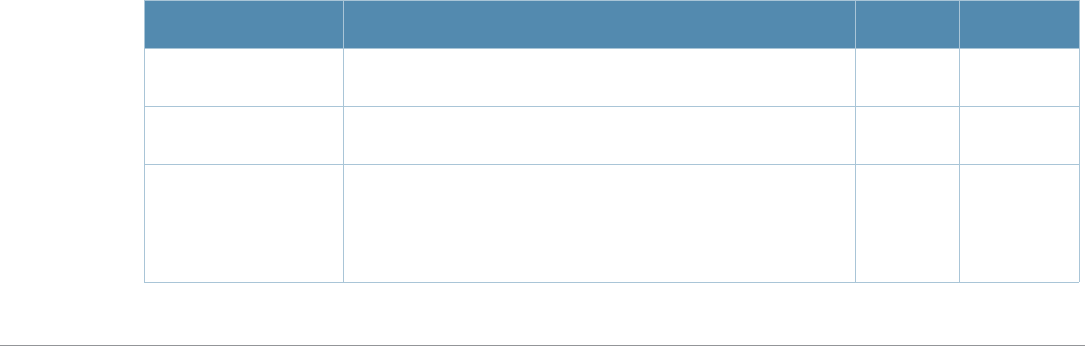
sygate-on-
demand-agent
Enables client remediation with Sygate-on-demand-
agent (SODA).
NOTE: The Policy Enforcement Firewall license must
be installed.
enabled/
disabled disabled
use-chap Use CHAP protocol. You should not use this option
unless instructed to do so by an Alcatel-Lucent
representative.
enabled/
disabled disabled (PAP
is used)
user-logon Enables Captive Portal with authentication of user
credentials. enabled/
disabled enabled
user-vlan-in-
redirection-url
<ip-addr>
Add the user VLAN in the redirection URL enabled
disabled
disabled
welcome-page <url> URL of the page that appears after logon and before
redirection to the web URL. This can be set to any
URL.
—/auth/wel-
come.html
white-list Create a white list of allowed domain Names by
specifying the domain names to be added to the
whitelist
——
Parameter Description Range Default
Platforms Licensing Command Mode
All platforms Base operating system, except for
noted parameters Config mode on master switches
16 | aaa authentication dot1x AOS-W 3.4.1 Command Line Interface | Reference Guide
aaa authentication dot1x
aaa authentication dot1x {<profile>|countermeasures}
ca-cert <certificate>
clear
clone <profile>
eapol-logoff
framed-mtu <mtu>
heldstate-bypass-counter <number>
ignore-eap-id-match
ignore-eapolstart-afterauthentication
machine-authentication blacklist-on-failure|{cache-timeout <hours>}|enable|
{machine-default-role <role>}|{user-default-role <role>}
max-authentication-failures <number>
max-requests <number>
multicast-keyrotation
no ...
opp-key-caching
reauth-max <number>
reauthentication
server {server-retry <number>|server-retry-period <seconds>}
server-cert <certificate>
termination {eap-type <type>}|enable|enable-token-caching|{inner-eap-type (eap-
gtc|eap-mschapv2)}|{token-caching-period <hours>}
timer {idrequest_period <seconds>}|{mkey-rotation-period <seconds>}|{quiet-period
<seconds>}|{reauth-period <seconds>}|{ukey-rotation-period <seconds>}|{wpa-
groupkey-delay <seconds>}|{wpa-key-period <milliseconds>}|wpa2-key-delay
<milliseconds>
tls-guest-access
tls-guest-role <role>
unicast-keyrotation
use-session-key
use-static-key
validate-pmkid
voice-aware
wep-key-retries <number>
wep-key-size {40|128}
wpa-fast-handover
xSec-mtu <mtu>
Description
This command configures the 802.1x authentication profile.
Syntax
Parameter Description Range Default
<profile> Name that identifies an instance of the profile. The name must
be 1-63 characters. —“default”
clear Clear the Cached PMK, Role and VLAN entries. This
command is available in enable mode only. ——
countermeasures Scans for message integrity code (MIC) failures in traffic
received from clients. If there are more than 2 MIC failures
within 60 seconds, the AP is shut down for 60 seconds. This
option is intended to slow down an attacker who is making a
large number of forgery attempts in a short time.
— disabled

AOS-W 3.4.1 Command Line Interface | Reference Guide aaa authentication dot1x | 17
ca-cert
<certificate>
CA certificate for client authentication. The CA certificate
needs to be loaded in the switch. ——
clone <profile> Name of an existing 802.1x profile from which parameter
values are copied. ——
eapol-logoff Enables handling of EAPOL-LOGOFF messages. — disabled
framed-mtu <MTU> Sets the framed MTU attribute sent to the authentication
server. 500-1500 1100
heldstate-
bypass-counter
<number>
(This parameter is applicable when 802.1x authentication is
terminated on the switch, also known as AAA FastConnect.)
Number of consecutive authentication failures which, when
reached, causes the switch to not respond to authentication
requests from a client while the switch is in a held state after
the authentication failure. Until this number is reached, the
switch responds to authentication requests from the client
even while the switch is in its held state.
0-3 0
ignore-eap-id-
match
Ignore EAP ID during negotiation. — disabled
ignore-eapol
start-afterauth
entication
Ignores EAPOL-START messages after authentication. — disabled
machine-authen
tication
(For Windows environments only) These parameters set
machine authentication:
NOTE: The Policy Enforcement Firewall license must be
installed.
blacklist-on
-failure
Blacklists the client if machine authentication fails. — disabled
cache-timeout
<hours>
The timeout, in hours, for machine authentication. 1-1000 24 hours (1
day)
enable Select this option to enforce machine authentication before
user authentication. If selected, either the machine-default-
role or the user-default-role is assigned to the user, depending
on which authentication is successful.
— disabled
machine-
default-role
<role>
Default role assigned to the user after completing only
machine authentication. —guest
user-default-
role <role>
Default role assigned to the user after 802.1x authentication. — guest
max-
authentication-
failures <number>
Number of times a user can try to login with wrong credentials
after which the user is blacklisted as a security threat. Set to 0
to disable blacklisting, otherwise enter a non-zero integer to
blacklist the user after the specified number of failures.
NOTE: The Wireless Intrusion Protection license must be
installed.
0-5 0 (disabled)
max-requests
<number>
Maximum number of times ID requests are sent to the client. 1-10 3
multicast-key
rotation
Enables multicast key rotation — disabled
no Negates any configured parameter. — —
Parameter Description Range Default

18 | aaa authentication dot1x AOS-W 3.4.1 Command Line Interface | Reference Guide
opp-key-caching Enables a cached pairwise master key (PMK) derived with a
client and an associated AP to be used when the client roams
to a new AP. This allows clients faster roaming without a full
802.1x authentication.
NOTE: Make sure that the wireless client (the 802.1x
supplicant) supports this feature. If the client does not support
this feature, the client will attempt to renegotiate the key
whenever it roams to a new AP. As a result, the key cached on
the switch can be out of sync with the key used by the client.
—enabled
reauth-max
<number>
Maximum number of reauthentication attempts. 1-10 3
reauthentica
tion
Select this option to force the client to do a 802.1x
reauthentication after the expiration of the default timer for
reauthentication. (The default value of the timer is 24 hours.) If
the user fails to reauthenticate with valid credentials, the state
of the user is cleared.
If derivation rules are used to classify 802.1x-authenticated
users, then the reauthentication timer per role overrides this
setting.
— disabled
reload-cert Reload Certificate for 802.1X termination. This command is
available in enable mode only. ——
server Sets options for sending authentication requests to the
authentication server group.
server-retry
<number>
Maximum number of authentication requests that are sent to
server group. 0-3 2
server-retry-
period <seconds>
Server group retry interval, in seconds. 5-65535 30 seconds
server-cert
<certificate>
Server certificate used by the switch to authenticate itself to
the client. ——
termination Sets options for terminating 802.1x authentication on the
switch.
eap-type
<type>
The Extensible Authentication Protocol (EAP) method, either
EAP-PEAP or EAP-TLS. eap-peap/
eap-tls eap-peap
enable Enables 802.1x termination on the switch. — disabled
enable-token
-caching
If you select EAP-GTC as the inner EAP method, you can
enable the switch to cache the username and password of
each authenticated user. The switch continues to
reauthenticate users with the remote authentication server,
however, if the authentication server is not available, the
switch will inspect its cached credentials to reauthenticate
users.
— disabled
inner-eap-type
eap-gtc|eap-
mschapv2
When EAP-PEAP is the EAP method, one of the following
inner EAP types is used:
EAP-Generic Token Card (GTC): Described in RFC 2284,
this EAP method permits the transfer of unencrypted
usernames and passwords from client to server. The main
uses for EAP-GTC are one-time token cards such as SecureID
and the use of LDAP or RADIUS as the user authentication
server. You can also enable caching of user credentials on the
switch as a backup to an external authentication server.
EAP-Microsoft Challenge Authentication Protocol version
2 (MS-CHAPv2): Described in RFC 2759, this EAP method is
widely supported by Microsoft clients.
eap-gtc/
eap-
mschapv2
eap-mschap
v2
Parameter Description Range Default

AOS-W 3.4.1 Command Line Interface | Reference Guide aaa authentication dot1x | 19
token-caching-
period <hours>
If you select EAP-GTC as the inner EAP method, you can
specify the timeout period, in hours, for the cached
information.
(any) 24 hours
timer Sets timer options for 802.1x authentication:
idrequest-
period
<seconds>
Interval, in seconds, between identity request retries. 1-65535 30 seconds
mkey-rotation-
period
<seconds>
Interval, in seconds, between multicast key rotation. 60-864000 1800
seconds
quiet-period
<seconds>
Interval, in seconds, following failed authentication. 1-65535 30 seconds
reauth-period
<seconds>
Interval, in seconds, between reauthentication attempts, or
specify server to use the server-provided reauthentication
period.
60-864000 86400
seconds
(1 day)
ukey-rotation-
period
<seconds>
Interval, in seconds, between unicast key rotation. 60-864000 900 seconds
wpa-groupkey
-delay
<milliseconds>
Interval, in milliseconds, between unicast and multicast key
exchanges. 0-2000 0 ms
(no delay)
wpa-key-period
<milliseconds>
Interval, in milliseconds, between each WPA key exchange. 1000-5000 3000 ms
wpa2-key-delay
<milliseconds>
Set the delay between EAP-Success and unicast key
exchange. 1-2000 0 ms
(no delay)
tls-guest-access Enables guest access for EAP-TLS users with valid
certificates. — disabled
tls-guest-role
<role>
User role assigned to EAP-TLS guest.
NOTE: The Policy Enforcement Firewall license must be
installed.
—guest
unicast-
keyrotation
Enables unicast key rotation. — disabled
use-session-key Use RADIUS session key as the unicast WEP key. — disabled
use-static-key Use static key as the unicast/multicast WEP key. — disabled
validate-pmkid When opp-key-caching is enabled, this option instructs the
switch to check the pairwise master key (PMK) ID sent by the
client. When this option is enabled, the client must send a
PMKID in the associate or reassociate frame to indicate that it
supports OKC; otherwise, full 802.1x authentication takes
place. (This feature is optional, since most clients that support
OKC do not send the PMKID in their association request.)
— disabled
voice-aware Enables rekey and reauthentication for VoWLAN clients.
NOTE: The Policy Enforced Firewall license must be installed.
—enabled
wep-key-retries
<number>
Number of times WPA/WPA2 key messages are retried. 1-5 3
wep-key-size Dynamic WEP key size, either 40 or 128 bits. 40 or 128 128 bits
wpa-fast-hand
over
Enables WPA-fast-handover. This is only applicable for
phones that support WPA and fast handover. — disabled
Parameter Description Range Default
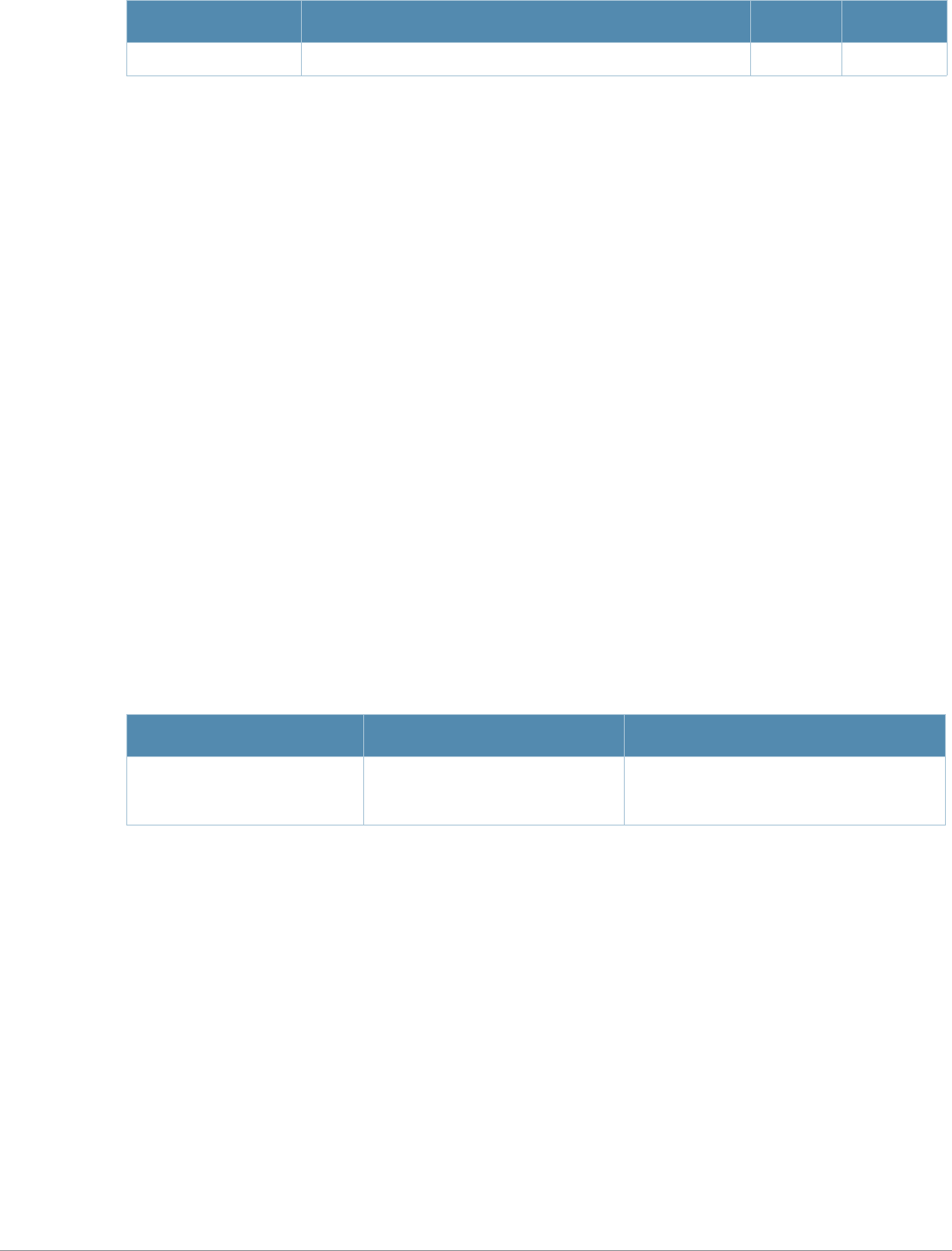
20 | aaa authentication dot1x AOS-W 3.4.1 Command Line Interface | Reference Guide
Usage Guidelines
The 802.1x authentication profile allows you to enable and configure machine authentication and 802.1x
termination on the switch (also called “AAA FastConnect”).
In the AAA profile, you specify the 802.1x authentication profile, the default role for authenticated users,
and the server group for the authentication.
Examples
The following example enables authentication of the user’s client device before user authentication. If
machine authentication fails but user authentication succeeds, the user is assigned the restricted “guest”
role:
aaa authentication dot1x dot1x
machine-authentication enable
machine-authentication machine-default-role computer
machine-authentication user-default-role guest
The following example configures an 802.1x profile that terminates authentication on the switch, where the
user authentication is performed with the switch’s internal database or to a “backend” non-802.1x server:
aaa authentication dot1x dot1x
termination enable
Command History
This command was introduced in AOS-W 3.0.
Command Information
xSec-mtu <mtu> Sets the size of the MTU for xSec. 1024-1500 1300 bytes
Parameter Description Range Default
Platforms Licensing Command Mode
All platforms Base operating system. The voice-
aware parameter requires the
Policy Enforced Firewall license
Config mode on master switches

AOS-W 3.4.1 Command Line Interface | Reference Guide aaa authentication mac | 21
aaa authentication mac
aaa authentication mac <profile>
case upper|lower
clone <profile>
delimiter {colon|dash|none}
max-authentication-failures <number>
no ...
Description
This command configures the MAC authentication profile.
Syntax
Usage Guidelines
MAC authentication profile configures authentication of devices based on their physical MAC address.
MAC-based authentication is often used to authenticate and allow network access through certain devices
while denying access to all other devices. Users may be required to authenticate themselves using other
methods, depending upon the network privileges.
Example
The following example configures a MAC authentication profile to blacklist client devices that fail to
authenticate.
aaa authentication mac mac-blacklist
max-authentication-failures 3
Command History:
Parameter Description Range Default
<profile> Name that identifies an instance of the profile. The name
must be 1-63 characters. — “default”
case The case (upper or lower) used in the MAC string sent in
the authentication request. If there is no delimiter
configured, the MAC address in lower case is sent in the
format xxxxxxxxxxxx, while the MAC address in upper
case is sent in the format XXXXXXXXXXXX.
upper|lower lower
clone <profile> Name of an existing MAC profile from which parameter
values are copied. ——
delimiter Delimiter (colon, dash, or none) used in the MAC string. colon|dash|
none none
max-
authentication-
failures <number>
Number of times a client can fail to authenticate before it is
blacklisted. A value of 0 disables blacklisting. 0-10 0 (disabled)
no Negates any configured parameter. — —
Release Modification
AOS-W 3.0 Command introduced
AOS-W 3.3.1.8 The max-authentication-failures parameter was allowed in the base operating
system. In earlier versions of AOS-W, the max-authentication-failures parameter
required the Wireless Intrusion Protection license

22 | aaa authentication mac AOS-W 3.4.1 Command Line Interface | Reference Guide
Command Information
Platforms Licensing Command Mode
All platforms Base operating system Config mode on master switches
AOS-W 3.4.1 Command Line Interface | Reference Guide aaa authentication mgmt | 23
aaa authentication mgmt
aaa authentication mgmt
default-role {guest-provisioning|location-api|network-operations|no-access|read-
only|root}
enable
no ...
server-group <group>
Description
This command configures authentication for administrative users.
Syntax
Usage Guidelines
If you enable authentication with this command, users configured with the mgmt-user command must be
authenticated using the specified server-group.
You can configure the management authentication profile in the base operating system or with the Policy
Enforcement Firewall license installed.
Example
The following example configures a management authentication profile that authenticates users against the
switch’s internal database. Users who are successfully authenticated are assigned the read-only role.
aaa authentication mgmt
default-role read-only
server-group internal
Parameter Description Range Default
default-role Select a predefined management role to assign to
authenticated administrative users: —default
default Default superuser role
guest-
provisioning
Guest provisioning role
location-api Location API role
network-
operations
Network operations role
no-access No commands are accessible for this role
read-only Read-only role
enable Enables authentication for administrative users. enabled|
disabled disabled
no Negates any configured parameter. — —
server-group
<group>
Name of the group of servers used to authenticate
administrative users. See “aaa server-group” on
page 57.
—default
24 | aaa authentication mgmt AOS-W 3.4.1 Command Line Interface | Reference Guide
Command History:
Command Information
Release Modification
AOS-W 3.0 Command introduced
AOS-W 3.2 The network-operations role was introduced.
AOS-W 3.3 The location-api-mgmt role was introduced.
Platforms Licensing Command Mode
All platforms Base operating system Config mode on master switches

AOS-W 3.4.1 Command Line Interface | Reference Guide aaa authentication stateful-dot1x | 25
aaa authentication stateful-dot1x
aaa authentication stateful-dot1x
default-role <role>
enable
no ...
server-group <group>
timeout <seconds>
Description
This command configures 802.1x authentication for clients on non-Alcatel-Lucent APs.
Syntax
Usage Guidelines
This command configures 802.1x authentication for clients on non-Alcatel-Lucent APs. The switch
maintains user session state information for these clients.
Example
The following command assigns the employee user role to clients who successfully authenticate with the
server group corp-rad:
aaa authentication stateful-dot1x
default-role employee
server-group corp-rad
Command History
This command was introduced in AOS-W 3.0.
Command Information
Parameter Description Range Default
default-role
<role>
Role assigned to the 802.1x user upon login.
NOTE: The Policy Enforcement Firewall license must
be installed.
—guest
enable Enables 802.1x authentication for clients on non-
Alcatel-Lucent APs. Use no enable to disable this
authentication.
—enabled
no Negates any configured parameter. — —
server-group
<group>
Name of the group of RADIUS servers used to
authenticate the 802.1x users. See “aaa server-group”
on page 57.
——
timeout <seconds> Timeout period, in seconds. 1-20 10 seconds
Platforms Licensing Command Mode
All platforms Base operating system Config mode on master switches
26 | aaa authentication stateful-dot1x clear AOS-W 3.4.1 Command Line Interface | Reference Guide
aaa authentication stateful-dot1x clear
aaa authentication stateful-dot1x clear
Description
This command clears automatically-created control path entries for 802.1x users on non-Alcatel-Lucent
APs.
Syntax
No parameters.
Usage Guidelines
Run this command after changing the configuration of a RADIUS server in the server group configured with
the aaa authentication stateful-dot1x command. This causes entries for the users to be created in the
control path with the updated configuration information.
Command History
This command was introduced in AOS-W 3.0.
Command Information
Platforms Licensing Command Mode
All platforms Base operating system Enable mode on master switches
AOS-W 3.4.1 Command Line Interface | Reference Guide aaa authentication stateful-ntlm | 27
aaa authentication stateful-ntlm
aaa authentication stateful-ntlm
default-role <role>
enable
server-group <server-group>
timeout <timeout>
Description
This command configures stateful NT LAN Manager (NTLM) authentication.
Syntax
Usage Guidelines
NT LAN Manager (NTLM) is a suite of Microsoft authentication and session security protocols. You can use
a stateful NTLM authentication profile to configure an Alcatel-Lucent switch to monitor the NTLM
authentication messages between clients and an authentication server. The switch can then use the
information in the Server Message Block (SMB) headers to determine the client's username and IP address,
the server IP address and the client's current authentication status. If the client successfully authenticates
via an NTLM authentication server, the switch can recognize that the client has been authentication and
assign that client a specified user role. When the user logs off or shuts down the client machine, the user
will remain in the authenticated role until the user’s authentication is aged out.
The Stateful NTLM Authentication profile requires that you specify a server group which includes the
servers performing NTLM authentication, and a default role to be assigned to authenticated users. For
details on defining a windows server used for NTLM authentication, see aaa authentication-server
windows.
Example
The following example configures a stateful NTLM authentication profile that authenticates clients via the
server group “Windows1.” Users who are successfully authenticated are assigned the “guest2” role.
aaa authentication stateful-ntlm
default-role guest2
server-group Windows1
Command History
Command introduced in AOS-W 3.4.1
Command Information
Parameter Description Range Default
default-role Select an existing role to assign to authenticated users. — guest
no Negates any configured parameter. — —
server-group
<server-group>
Name of a server group. — default
timeout <timeout> NTLM authentication request, timeout period, in seconds. 1-20 seconds 10 seconds
Platforms Licensing Command Mode
All platforms Base operating system Config mode on master switches

28 | aaa authentication vpn AOS-W 3.4.1 Command Line Interface | Reference Guide
aaa authentication vpn
aaa authentication vpn
default-role <role>
max-authentication-failures <number>
no ...
server-group <group>
Description
This command configures VPN authentication.
Syntax
Usage Guidelines
This command configures VPN authentication settings. Use the vpdn group command to enable and configure
Layer-2 Tunneling Protocol and Internet Protocol Security (L2TP/IPsec) or Point-to-Point Tunneling Protocol (PPTP)
VPN connection. (See “vpdn group l2tp” on page 1167.)
Example
The following command configures VPN authentication settings:
aaa authentication vpn
default-role employee-role-vpn
max-authentication-failures 0
server-group vpn-server-group
Command History
This command was available in AOS-W 3.0.
Command Information
Parameter Description Default
default-role
<role>
Role assigned to the VPN user upon login.
NOTE: The Policy Enforcement Firewall license must be installed.
guest
max-
authentication-
failures <number>
Maximum number of authentication failures before the user is
blacklisted. A value of 0 disables blacklisting.
NOTE: The Wireless Intrusion Protection license must be installed.
0 ((disabled)
no Negates any configured parameter. —
server-group
<group>
Name of the group of servers used to authenticate VPN users. See “aaa
server-group” on page 57.internal
Platforms Licensing Command Mode
All platforms Base operating system, except for
noted parameters Config mode on master switches
AOS-W 3.4.1 Command Line Interface | Reference Guide aaa authentication wired | 29
aaa authentication wired
aaa authentication wired
no ...
profile <aaa-profile>
Description
This command configures authentication for a client device that is directly connected to a port on the
switch.
Syntax
Usage Guidelines
This command references an AAA profile that is configured for MAC or 802.1x authentication. The port on
the switch to which the device is connected must be configured as untrusted.
Example
The following commands configure an AAA profile for dot1x authentication and a wired profile that
references the AAA profile:
aaa profile sec-wired
dot1x-default-role employee
dot1x-server-group sec-svrs
aaa authentication wired
profile sec-wired
Command History
This command was available in AOS-W 3.0.
Command Information
Parameter Description
no Negates any configured parameter.
profile <aaa-
profile>
Name of the AAA profile that applies to wired authentication. This profile must be
configured for a Layer-2 authentication, either 802.1x or MAC. See “aaa profile” on
page 50.
Platforms Licensing Command Mode
All platforms Base operating system Config mode on master switches
30 | aaa authentication wispr AOS-W 3.4.1 Command Line Interface | Reference Guide
aaa authentication wispr
aaa authentication wispr
default-role <role>
logon-wait {cpu-threshold|maximum-delay|minimum-delay}
no ...
server-group <server-group>
wispr-location-id-ac <wispr-location-id-ac>
wispr-location-id-cc <wispr-location-id-cc>
wispr-location-id-isocc <wispr-location-id-isocc>
wispr-location-id-network <wispr-location-id-network>
wispr-location-name-location <wispr-location-name-location>
wispr-location-name-operator-name <wispr-location-name-operator>
no ...
Description
This command configures WISPr authentication with an ISP’s WISPr RADIUS server.
Syntax
Usage Guidelines
Parameter Description
default-role Default role assigned to users that complete WISPr authentication.
logon-wait Configure the CPU utilization threshold that will trigger logon wait
maximum and minimum times
CPU-threshold Percentage of CPU utilization at which the maximum and minimum login
wait times are enforced. Range: 1-100%.Default: 60%.
maximum-wait If the switch’s CPU utilization has surpassed the CPU-threhold value, the
maximum-wait parameter defines the minimum number of seconds a
user will have to wait to retry a login attempt. Range: 1-10 seconds.
Default: 10 seconds.
minimum-wait If the switch’s CPU utilization has surpassed the CPU-threshold value, the
minimum-wait parameter defines the minimum number of seconds a user
will have to wait to retry a login attempt. Range: 1-10 seconds. Default: 5
seconds.
wispr-location-id-ac
<wispr-location-id-ac>
The E.164 Area Code in the WISPr Location ID.
wispr-location-id-cc
<wispr-location-id-cc>
The 1-3 digit E.164 Country Code in the WISPr Location ID.
wispr-location-id-isocc
<wispr-location-id-isocc>
The ISO Country Code in the WISPr Location ID.
wispr-location-id-network
<wispr-location-id-network>
The SSID/network name in the WISPr Location ID.
wispr-location-name-location
<wispr-location-name-location>
A name identifying the hotspot location. If no name is defined, the default
ap-name is used.
wispr-location-name-operator-
name
<wispr-location-name-operator>
A name identifying the hotspot operator.
AOS-W 3.4.1 Command Line Interface | Reference Guide aaa authentication wispr | 31
WISPr authentication allows a “smart client” to remain authenticated on the network when they roam
between Wireless Internet Service Providers, even if the wireless hotspot uses an ISP for which the client
may not have an account.
If you are hotstpot operator using WISPr authentication, and a client that has an account with your ISP
attempts to access the Internet at your hotspot, then your ISP’s WISPr AAA server authenticates that client
directly, and allows the client access on the network. If, however, the client only has an account with a
partner ISP, then your ISP’s WISPr AAA server will forward that client’s credentials to the partner ISP’s
WISPr AAA server for authentication. Once the client has been authenticated on the partner ISP, it will be
authenticated on your hotspot’s own ISP, as per their service agreements. Once your ISP sends an
authentication message to the switch, the switch assigns the default WISPr user role to that client.
AOS-W supports the following smart clients, which enable client authentication and roaming between
hotspots by embedding iPass Generic Interface Specification (GIS) redirect, proxy, authentication and
logoff messages within HTLM messages to the switch.
ziPass
zBongo
zTrustive
zweRoam
zAT&T
A WISPr authentication profile includes parameters to define RADIUS attributes, the default role for
authenticated WISPr users, maximum numbers of authenticated failures and logon wait times. The WISPr-
Location-ID sent from the switch to the WISPr RADIUS server will be the concatenation of the ISO Country
Code, E.164 Country Code, E.164 Area Code and SSID/Zone parameters configured in this profile
The parameters to define WISPr RADIUS attributes are specific to the RADIUS server your ISP uses for
WISPr authentication; contact your ISP to determine these values. You can find a list of ISO and ITU
country and area codes at the ISO and ITU web sites (www.iso.org and http://www.itu.int.)
Example
The following commands configure an WISPr authentication profile:
aaa authentication wispr
default-role authuser
max-authentication-failure 5
server-group wispr1
wispr-location-id-ac 408
wispr-location-id-cc 1
wispr-location-id-isocc us
wispr-location-id-network <wispr-location-id-network>
wispr-location-name-location <wispr-location-name-location>
wispr-location-name-operator-name <wispr-location-name-location>
Command History
This command was available in AOS-W 3.4.1.
NOTE
A Boingo smart client uses a NAS identifier in the format <CarrierID>_<VenueID> for location identification. To
support Boingo clients, you must also configure the NAS identifier parameter in the Radius server profile for the
WISPr server

32 | aaa authentication wispr AOS-W 3.4.1 Command Line Interface | Reference Guide
Command Information
Platforms Licensing Command Mode
All platforms Base operating system Config mode on master or local switches

AOS-W 3.4.1 Command Line Interface | Reference Guide aaa authentication-server internal | 33
aaa authentication-server internal
aaa authentication-server internal use-local-switch
Description
This command specifies that the internal database on a local switch be used for authenticating clients.
Usage Guidelines
By default, the internal database in the master switch is used for authentication. This command directs
authentication to the internal database on the local switch where you run the command.
Command History
This command was available in AOS-W 3.0.
Command Information
Platforms Licensing Command Mode
All platforms Base operating system Config mode on master or local switches

34 | aaa authentication-server ldap AOS-W 3.4.1 Command Line Interface | Reference Guide
aaa authentication-server ldap
aaa authentication-server ldap <server>
admin-dn <name>
admin-passwd <string>
allow-cleartext
authport <port>
base-dn <name>
clone <server>
enable
filter
host <ipaddr>
key-attribute <string>
no ...
timeout <seconds>
Description
This command configures an LDAP server.
Syntax
Parameter Description Range Default
<server> Name that identifies the server. — —
admin-dn <name> Distinguished name for the admin user who has read/
search privileges across all of the entries in the LDAP
database (the user does not need write privileges but
should be able to search the database and read attributes
of other users in the database).
——
admin-passwd
<string>
Password for the admin user. — —
allow-cleartext Allows clear-text (unencrypted) communication with the
LDAP server. enabled|
disabled disabled
authport <port> Port number used for authentication. Port 636 will be
attempted for LDAP over SSL, while port 389 will be
attempted for SSL over LDAP, Start TLS operation and
clear text.
1-65535 389
base-dn <name> Distinguished Name of the node which contains the entire
user database to use. ——
clone <server> Name of an existing LDAP server configuration from which
parameter values are copied. ——
enable Enables the LDAP server. —
filter Filter that should be applied to search of the user in the
LDAP database (default filter string is: ì(objectclass=*)î ). — (objectclas
s=)*
host <ip-addr> IP address of the LDAP server, in dotted-decimal format. — —
key-attribute
<string>
Attribute that should be used as a key in search for the
LDAP server. For Active Directory, the value is
sAMAccountName.
— sAMAccou
ntName
no Negates any configured parameter. — —
preferred-conn-
type
Preferred connection type. clear-text
ldap-s
start-tls
ldap-s
AOS-W 3.4.1 Command Line Interface | Reference Guide aaa authentication-server ldap | 35
Usage Guidelines
You configure a server before you can add it to one or more server groups. You create a server group for a
specific type of authentication (see “aaa server-group” on page 57).
Example
The following command configures and enables an LDAP server:
aaa authentication-server ldap ldap1
host 10.1.1.243
base-dn cn=Users,dc=1m,dc=corp,dc=com
admin-dn cn=corp,cn=Users,dc=1m,dc=corp,dc=com
admin-passwd abc10
key-attribute sAMAccountName
filter (objectclass=*)
enable
Command History
This command was available in AOS-W 3.0.
Command Information
timeout <seconds> Timeout period of a LDAP request, in seconds. 1-30 20 seconds
Parameter Description Range Default
Platforms Licensing Command Mode
All platforms Base operating system Config mode on master switches

36 | aaa authentication-server radius AOS-W 3.4.1 Command Line Interface | Reference Guide
aaa authentication-server radius
aaa authentication-server radius <server>
acctport <port>
authport <port>
clone <server>
enable
host <ipaddr>
key <psk>
nas-identifier <string>
nas-ip <ipaddr>
no ...
retransmit <number>
timeout <seconds>
use-md5
Description
This command configures a RADIUS server.
Syntax
Usage Guidelines
You configure a server before you can add it to one or more server groups. You create a server group for a
specific type of authentication (see “aaa server-group” on page 57).
Parameter Description Range Default
<server> Name that identifies the server. — —
acctport <port> Accounting port on the server. 1-65535 1813
authport <port> Authentication port on the server 1-65535 1812
clone <server> Name of an existing RADIUS server configuration from
which parameter values are copied. ——
enable Enables the RADIUS server.
host <ipaddr> IP address of the RADIUS server. — —
key <psk> Shared secret between the switch and the authentication
server. The maximum length is 48 bytes. ——
nas-identifier
<string>
Network Access Server (NAS) identifier to use in RADIUS
packets. ——
nas-ip <ip-addr> NAS IP address to send in RADIUS packets.
You can configure a “global” NAS IP address that the
switch uses for communications with all RADIUS servers.
If you do not configure a server-specific NAS IP, the
global NAS IP is used. To set the global NAS IP, enter the
ip radius nas-ip ipaddr command.
——
no Negates any configured parameter. — —
retransmit
<number>
Maximum number of retries sent to the server by the
switch before the server is marked as down. 0-3 3
timeout <seconds> Maximum time, in seconds, that the switch waits before
timing out the request and resending it. 1-30 5 seconds
use-md5 Use MD5 hash of cleartext password. — disabled

AOS-W 3.4.1 Command Line Interface | Reference Guide aaa authentication-server radius | 37
Example
The following command configures and enables a RADIUS server:
aaa authentication-server radius radius1
host 10.1.1.244
key qwERtyuIOp
enable
Command History
This command was available in AOS-W 3.0.
Command Information
Platforms Licensing Command Mode
All platforms Base operating system Config mode on master switches
38 | aaa authentication-server tacacs AOS-W 3.4.1 Command Line Interface | Reference Guide
aaa authentication-server tacacs
aaa authentication-server tacacs <server>
clone <server>
enable
host <ipaddr>
key <psk>
no ...
retransmit <number>
tcp-port <port>
timeout <seconds>
Description
This command configures a TACACS+ server.
Syntax
Usage Guidelines
You configure a server before you can add it to one or more server groups. You create a server group for a
specific type of authentication (see “aaa server-group” on page 57).
Example
The following command configures and enables a TACACS+ server:
aaa authentication-server tacacs tacacs1
clone default
host 10.1.1.245
key qwERtyuIOp
enable
Command History
This command was available in AOS-W 3.0.
Command Information
Parameter Description Range Default
<server> Name that identifies the server. — —
clone <server>\ Name of an existing TACACS server configuration from
which parameter values are copied. ——
enable Enables the TACACS server. —
host <ip-addr> IP address of the TACACS server. — —
key Shared secret to authenticate communication between
the TACACS+ client and server. ——
no Negates any configured parameter. — —
retransmit
<number>
Maximum number of times a request is retried. 0-3 3
tcp-port <port> TCP port used by the server. 1-65535 49
timeout <timeout> Timeout period of a TACACS request, in seconds. 1-30 20 seconds

AOS-W 3.4.1 Command Line Interface | Reference Guide aaa authentication-server tacacs | 39
Platforms Licensing Command Mode
All platforms Base operating system Config mode on master switches
40 | aaa authentication-server windows AOS-W 3.4.1 Command Line Interface | Reference Guide
aaa authentication-server windows
aaa authentication-server windows <windows_server_name>
clone <source>
enable
host <ipaddr>
Description
This command configures a windows server for stateful-NTLM authentication.
Syntax
Usage Guidelines
You must define a Windows server before you can add it to one or more server groups. You create a server
group for a specific type of authentication (see “aaa server-group” on page 57). Windows servers are used
for stateful-NTLM authentication.
Example
The following command configures and enables a windows server:
aaa authentication-server windows IAS_1
host 10.1.1.245
enable
Command History
This command was available in AOS-W 3.4.1
Command Information
Parameter Description
<windows_server_name> Name of the windows server. You will use this name when you add the
windows server to a server group.
clone <source> Name of a Windows Server from which you want to make a copy.
enable Enables the Windows server.
host <ipaddr> IP address of the Windows server.
Platforms Licensing Command Mode
All platforms Base operating system Config mode on master switches
AOS-W 3.4.1 Command Line Interface | Reference Guide aaa bandwidth-contract | 41
aaa bandwidth-contract
aaa bandwidth-contract <name> {kbits <kbits>|mbits <mbits>}
Description
This command configures a bandwidth contract.
Syntax
Usage Guidelines
You can apply a configured bandwidth contract to a user role or to a VLAN. When you apply a bandwidth
contract to a user role (see “user-role” on page 1157), you specify whether the contract applies to upstream
traffic (from the client to the switch) or downstream traffic (from the switch to the client). You can also
specify whether the contract applies to all users in a specified user role or per-user in a user role.
When you apply a bandwidth contract to a VLAN (see “interface vlan” on page 255), the contract limits
multicast traffic and does not affect other data. This is useful because an AP can only send multicast traffic
at the rate of the slowest associated client. Thus excessive multicast traffic will fill the buffers of the AP,
causing frame loss and poor voice quality. Generally, every system should have a bandwidth contract of 1
Mbps or even 700 Kbps and it should be applied to all VLANs with which users are associated, especially
those VLANs that pass through the upstream router. The exception are VLANs that are used for high speed
multicasts, where the SSID is configured without low data rates.
Example
The following command creates a bandwidth contract that limits the traffic rate to 1 Mbps:
aaa bandwidth-contract mbits 1
Command History
This command was available in AOS-W 3.0.
Command Information
Parameter Description Range
<name> Name that identifies this bandwidth contract. —
kbits <bits> Limit the traffic rate for this bandwidth contract to a specified
number of kilobits per second. 256-2000000
mbits <bits> Limit the traffic rate for this bandwidth contract to a specified
number of megabits per second. 1-2000
Platforms Licensing Command Mode
All platforms Base operating system Config mode on master switches

42 | aaa derivation-rules AOS-W 3.4.1 Command Line Interface | Reference Guide
aaa derivation-rules
aaa derivation-rules user <name>
no ...
set {role|vlan} condition <rule-type> <condition> <value> set-value {<role>|<vlan>}
[position <number>]
Description
This command configures rules by which the role or VLAN assigned to a client is derived from the client’s
association with an AP.
The Policy Enforcement Firewall must be installed for a user role to be assigned.
Syntax
Usage Guidelines
The user role can be derived from attributes from the client’s association with an AP. You configure the user
role to be derived by specifying condition rules; when a condition is met, the specified user role is assigned
to the client. You can specify more than one condition rule; the order of rules is important as the first
matching condition is applied.
User-derivation rules are executed before the client is authenticated.
Example
The following command sets the client’s user role to “guest” if the client associates to the “Guest” ESSID.
aaa derivation-rules user derive1
set role condition essid equals Guest set-value guest
Parameter Description
<name> Name that identifies this set of user derivation rules.
no Negates a configured rule.
set {role|vlan} Specify whether the action of the rule is to set the role or the VLAN.
condition Condition that should be checked to derive role/VLAN
<rule-type> Specify one of the following rule types for this user derivation rule.
zbssid: BSSID of access point.
zdhcp-option-77: Enable DHCP packet processing.
zencryption-type: Encryption method used by station.
zessid: ESSID of access point.
zlocation: user location (ap name).
zmacaddr: MAC address of user.
<condition> Specify one of the following conditions:
zcontains: Check if attribute contains the operand value.
zends-with: Check if attribute ends with the operand value.
zequals: Check if attribute equals the operand value.
znot-equals: Check if attribute is not equal to the operand value.
zstarts-with: Check if attribute starts with the operand value.
set-value
<role>|<vlan>
Specify the user role or VLAN ID to be assigned to the client if the above condition is
met.
position Position of this rule relative to other configured.
AOS-W 3.4.1 Command Line Interface | Reference Guide aaa derivation-rules | 43
Command History
This command was available in AOS-W 3.0.
Command Information
Platforms Licensing Command Mode
All platforms Base operating system. The Policy
Enforcement Firewall must be
installed for a user role to be
assigned.
Config mode on master switches
44 |aaa inservice AOS-W 3.4.1 Command Line Interface | Reference Guide
aaa inservice
aaa inservice <server-group> <server>
Description
This command designates an “out of service” authentication server to be “in service”.
Syntax
Usage Guidelines
By default, the switch marks an unresponsive authentication server as “out of service” for a period of 10
minutes (you can set a different time limit with the aaa timers dead-time command). The aaa inservice
command is useful when you become aware that an “out of service” authentication server is again available
before the dead-time period has elapsed. (You can use the aaa test-server command to test the availability
and response of a configured authentication server.)
Example
The following command sets an authentication server to be in service:
aaa inservice corp-rad rad1
Command History
This command was available in AOS-W 3.0.
Command Information
Parameter Description
<server-group> Server group to which this server is assigned.
<server> Name of the configured authentication server.
Platforms Licensing Command Mode
All platforms Base operating system Enable mode on master switches
AOS-W 3.4.1 Command Line Interface | Reference Guide aaa ipv6 user add | 45
aaa ipv6 user add
aaa ipv6 user add <ipv6addr> [authentication-method {dot1x|mac|stateful-
dot1x|vpn|web}][mac <macaddr>] [name <username>]
[profile <aaa-profile>] [role <role>]
Description
This command manually assigns a user role or other values to a specified IPv6 client.
Syntax
Usage Guidelines
This command should only be used for troubleshooting issues with a specific IPv6 client. This command
allows you to manually assign a client to a role. For example, you can create a role “debugging” that
includes a policy to mirror session packets to a specified destination for further examination, then use this
command to assign the “debugging” role to a specific client. Use the aaa ipv6 user delete command to
remove the client or device from the role.
Note that issuing this command does not affect ongoing sessions that the client may already have. For
example, if a client is in the “employee” role when you assign them to the “debugging” role, the client
continues any sessions allowed with the “employee” role. Use the aaa ipv6 user clear-sessions command
to clear ongoing sessions.
Example
The following commands create a role that logs HTTPS traffic, then assign the role to a specific IPv6 client:
ipv6 access-list session ipv6-log-https
any any svc-https permit log
user-role ipv6-web-debug
session-acl ipv6-log-https
In enable mode:
aaa ipv6 user add
2002:d81f:f9f0:1000:e409:9331:1d27:ef44
role ipv6-web-debug
Command History
This command was available in AOS-W 3.3.
Parameter Description
<ipv6addr> IPv6 address of the user to be added.
authentication-method Authentication method for the user.
dot1x 802.1x authentication.
mac MAC address of the user.
stateful-dot1x Stateful 802.1x authentication.
vpn VPN authentication
web Captive Portal authentication
mac <macaddr> Name for the user.
name <username> Name for the user.
profile <aaa-profile> AAA profile for the user.
role <role> Role for the user.

46 | aaa ipv6 user add AOS-W 3.4.1 Command Line Interface | Reference Guide
Command Information
Platforms Licensing Command Mode
All platforms Base operating system Enable mode on master switches
AOS-W 3.4.1 Command Line Interface | Reference Guide aaa ipv6 user clear-sessions | 47
aaa ipv6 user clear-sessions
aaa ipv6 user clear-sessions <ipaddr>
Description
This command clears ongoing sessions for the specified IPv6 client.
Syntax
Usage Guidelines
This command clears any ongoing sessions that the client already had before being assigned a role with the
aaa ipv6 user add command.
Example
The following command clears ongoing sessions for an IPv6 client:
aaa user clear-sessions
2002:d81f:f9f0:1000:e409:9331:1d27:ef44
Command History
This command was available in AOS-W 3.3.
Command Information
Parameter Description
<ipaddr> IPv6 address of the user.
Platforms Licensing Command Mode
All platforms Base operating system Enable mode on master switches
48 |aaa ipv6 user delete AOS-W 3.4.1 Command Line Interface | Reference Guide
aaa ipv6 user delete
aaa ipv6 user delete {<ipaddr>|all|mac <macaddr>|name <username>|role <role>}
Description
This command deletes IPv6 clients, users, or roles.
Syntax
Usage Guidelines
This command allows you to manually delete clients, users, or roles. For example, if you used to the aaa
ipv6 user add command to assign a user role to an IPv6 client, you can use this command to remove the
role assignment.
Example
The following command a role:
aaa ipv6 user delete role web-debug
Command History
This command was available in AOS-W 3.0.
Command Information
Parameter Description
<ipv6addr> IPv6 address of the client to be deleted.
all Deletes all connected IPv6 clients.
mac MAC address of the IPv6 client to be deleted.
name Name of the IPv6 client to be deleted.
role Role of the IPv6 client to be deleted.
Platforms Licensing Command Mode
All platforms Base operating system Enable mode on master switches
AOS-W 3.4.1 Command Line Interface | Reference Guide aaa ipv6 user logout | 49
aaa ipv6 user logout
aaa ipv6 user logout <ipaddr>
Description
This command logs out an IPv6 client.
Syntax
Usage Guidelines
This command logs out an authenticated IPv6 client. The client must reauthenticate.
Example
The following command logs out an IPv6 client:
aaa user logout
2002:d81f:f9f0:1000:e409:9331:1d27:ef44
Command History
This command was available in AOS-W 3.3.
Command Information
Parameter Description
<ipv6addr> IPv6 address of the client to be logged out.
Platforms Licensing Command Mode
All platforms Base operating system Enable mode on master switches

50 |aaa profile AOS-W 3.4.1 Command Line Interface | Reference Guide
aaa profile
aaa profile <profile>
authentication-dot1x <dot1x-profile>
authentication-mac <mac-profile>
clone <profile>
dot1x-default-role <role>
dot1x-server-group <group>
initial-role <role>
mac-default-role <role>
mac-server-group <group>
no ...
radius-accounting <group>
rfc-3576-server <ipaddr>
sip-authentication-role <role>
user-derivation-rules <profile>
wired-to-wireless-roam
xml-api-server <ipaddr>
Description
This command configures the authentication for a WLAN.
Syntax
Parameter Description Default
<profile> Name that identifies this instance of the profile. The name
must be 1-63 characters. “default”
authentication-dot1x
<dot1x-profile>
Name of the 802.1x authentication profile associated with
the WLAN. See “aaa authentication dot1x” on page 16.—
authentication-mac <mac-
profile>
Name of the MAC authentication profile associated with the
WLAN. See “aaa authentication mac” on page 21.—
clone <profile> Name of an existing AAA profile configuration from which
parameter values are copied. —
dot1x-default-role <role> Configured role assigned to the client after 802.1x
authentication. If derivation rules are present, the role
assigned to the client through these rules take precedence
over the default role.
NOTE: The Policy Enforcement Firewall license must be
installed.
guest
dot1x-server-group <group> Name of the server group used for 802.1x authentication.
See “aaa server-group” on page 57.—
initial-role <role> Role for unauthenticated users. logon
mac-default-role <role> Configured role assigned to the user when the device is
MAC authenticated. If derivation rules are present, the role
assigned to the client through these rules take precedence
over the default role.
NOTE: The Policy Enforcement Firewall license must be
installed.
guest
mac-server- <group> group Name of the server group used for MAC authentication. See
“aaa server-group” on page 57.—
no Negates any configured parameter. —
AOS-W 3.4.1 Command Line Interface | Reference Guide aaa profile | 51
Usage Guidelines
The AAA profile defines the user role for unauthenticated users, the default user role for MAC or 802.1x
authentication, and user derivation rules. The AAA profile contains the authentication profile and
authentication server group.
There are predefined AAA profiles available: default-dot1x, default-mac-auth, and default-open, that have
the parameter values shown in the following table.
Example
radius-accounting <group> Name of the server group used for RADIUS accounting. See
“aaa server-group” on page 57.—
rfc-3576-server <ip-addr> IP address of a RADIUS server that can send user
disconnect and change-of-authorization messages, as
described in RFC 3576, “Dynamic Authorization Extensions
to Remote Dial In User Service (RADIUS)”. See “aaa rfc-
3576-server” on page 56.
NOTE: The Policy Enforcement Firewall license must be
installed.
—
sip-authentication-role
<role>
Configured role assigned to a session initiation protocol
(SIP) client upon registration.
NOTE: The Policy Enforced Firewall license must be
installed.
guest
user-derivation-rules
<profile>
User attribute profile from which the user role or VLAN is
derived. —
wire-to-wireless-roam Keeps user authenticated when roaming from the wired side
of the network. enabled
xml-api-server <ip-addr> IP address of a configured XML API server. See “aaa xml-
api” on page 72.
NOTE: The Policy Enforcement Firewall license must be
installed.
—
Parameter Description Default
Parameter default-dot1x default-mac-
auth default-open
authentication-dot1x default N/A N/A
authentication-mac N/A default N/A
dot1x-default-role authenticated guest guest
dot1x-server-group N/A N/A N/A
initial-role logon logon logon
mac-default-role guest authenticated guest
mac-server-group default default default
radius-accounting N/A N/A N/A
rfc-3576-server N/A N/A N/A
user-derivation-rules N/A N/A N/A
wired-to-wireless roam enabled enabled enabled
52 |aaa profile AOS-W 3.4.1 Command Line Interface | Reference Guide
The following command configures an AAA profile that assigns the “employee” role to clients after they are
authenticated using the 802.1x server group “radiusnet”.
aaa profile corpnet
dot1x-default-role employee
dot1x-server-group radiusnet
Command History
Command Information
Version Description
AOS-W 3.0 Command introduced.
AOS-W 3.4.1 License requirements changed in AOS-W 3.4.1, so the sip-authentication-role
parameter now requires the Policy Enforced Firewall license instead of the Voice
Services Module license required in earlier versions.
Platforms Licensing Command Mode
All platforms Base operating system, except for
noted parameters Config mode on master switches

AOS-W 3.4.1 Command Line Interface | Reference Guide aaa query-server | 53
aaa query-server
aaa query-server <ldap-server-name> <user-name>
Description
Troubleshoot an LDAP authentication failure by verifying that the user exists in the ldap server database.
Syntax
Usage Guidelines
If the Admin-DN binds successfully but the wireless user fails to authenticate, issue this command to
troubleshoot whether the problem is with the wireless network, the switch, or the ldap server. The aaa
query-user <ldap_server_name> <username> command to makes the switch send a search query to find
the user. If that search fails in spite of the user being in the LDAP database, it is most probable that the base
DN where the search was started was not correct. In such case, it is advisable to make the base DN at the
root of the ldap tree.
Example
The example below shows part of the output for an LDAP record for the username JDOE.
Command History
This command was available in AOS-W 3.0.
Parameter Description
<ldap-server-name> Name of an LDAP server.
<user-name> Name of a user whose LDAP record you want to view.
(host) #aaa query-user eng JDOE
objectClass: top
objectClass: person
objectClass: organizationalPerson
objectClass: user
cn: John Doe
sn: Doe
userCertificate: 0\202\005\2240\202\004|\240\003\002\001\002\002\012H\011\333K
userCertificate: 0\202\005\2240\202\004|\240\003\002\001\002\002\012]\350\346F
userCertificate: 0\202\005\2240\202\004|\240\003\002\001\002\002\012\023\001\017\240
userCertificate: 0\202\005\2240\202\004|\240\003\002\001\002\002\012\031\224/\030
userCertificate: 0\202\005~0\202\004f\240\003\002\001\002\002\012\031\223\246\022
userCertificate: 0\202\005\2240\202\004|\240\003\002\001\002\002\012\037\177\374\305
givenName: JDE
distinguishedName: CN=John Doe,CN=Users,DC=eng,DC=net
instanceType: 4
whenCreated: 20060516232817.0Z
whenChanged: 20081216223053.0Z
displayName: John Doe
uSNCreated: 24599
memberOf: CN=Cert_Admins,CN=Users,DC=eng,DC=net
memberOf: CN=ATAC,CN=Users,DC=eng,DC=net
uSNChanged: 377560
department: eng
name: John Doe
...

54 | aaa query-server AOS-W 3.4.1 Command Line Interface | Reference Guide
Command Information
Platforms Licensing Command Mode
All platforms Base operating system Enable mode on master switches

AOS-W 3.4.1 Command Line Interface | Reference Guide aaa radius-attributes | 55
aaa radius-attributes
aaa radius-attributes add <attribute> <attribute-id> {date|integer|ipaddr|string}
[vendor <name> <vendor-id>]
Description
This command configures RADIUS attributes for use with server derivation rules.
Syntax
Usage Guidelines
Add RADIUS attributes for use in server derivation rules. Use the show aaa radius-attributes command
to display a list of the current RADIUS attributes recognized by the switch. To add a RADIUS attribute to
the list, use the aaa radius-attributes command.
Example
The following command adds the VSA “Alcatel-Lucent-User-Role”:
aaa radius-attributes add Alcatel-Lucent-User-Role 1 string vendor Alcatel-Lucent 14823
Command History
This command was available in AOS-W 3.0.
Command Information
Parameter Description
add <attribute>
<attribute-id>
Adds the specified attribute name (alphanumeric string), associated attribute ID
(integer), and type (date, integer, IP address, or string).
date Adds a date attribute.
integer Adds a integer attribute.
ipaddr Adds a IP address attribute.
string Adds a string attribute.
vendor (Optional) Display attributes for a specific vendor name and vendor ID.
Platforms Licensing Command Mode
All platforms Base operating system Config mode on master switches
56 | aaa rfc-3576-server AOS-W 3.4.1 Command Line Interface | Reference Guide
aaa rfc-3576-server
aaa rfc-3576-server <ipaddr>
clone <server>
key <psk>
no ...
Description
This command configures a RADIUS server that can send user disconnect and change-of-authorization
messages, as described in RFC 3576, “Dynamic Authorization Extensions to Remote Dial In User Service
(RADIUS)”.
Syntax
Usage Guidelines
The server configured with this command is referenced in the AAA profile for the WLAN (see “aaa profile”
on page 50).
Example
The following command configures an RFC 3576 server:
aaa rfc-3576-server 10.1.1.245
clone default
key asdfjkl;
Command History
This command was introduced in AOS-W 3.0.
Command Information
Parameter Description
<ipaddr> IP address of the server.
clone <server> Name of an existing RFC 3576 server configuration from which parameter values are
copied.
key <psk> Shared secret to authenticate communication between the RADIUS client and server.
no Negates any configured parameter.
Platforms Licensing Command Mode
All platforms Base operating system Config mode on master switches

AOS-W 3.4.1 Command Line Interface | Reference Guide aaa server-group | 57
aaa server-group
aaa server-group <group> allow-fail-through
auth-server <name> [match-authstring contains|equals|starts-with <string>] [match-
fqdn <string>] [position <number>] [trim-fqdn]
clone <group>
no ...
set role|vlan condition <attribute> contains|ends-with|equals|not-equals|starts-with
<string> set-value <set-value-str> [position <number>]
Description
This command allows you to add a configured authentication server to an ordered list in a server group, and
configure server rules to derive a user role, VLAN ID or VLAN name from attributes returned by the server
during authentication.
Syntax
Parameter Description Default
<group> Name that identifies the server group. The name must be 32
characters or less. —
allow-fail-through When this option is configured, an authentication failure with
the first server in the group causes the switch to attempt
authentication with the next server in the list. The switch
attempts authentication with each server in the ordered list until
either there is a successful authentication or the list of servers
in the group is exhausted.
disabled
auth-server <name> Name of a configured authentication server. —
match-authstring This option associates the authentication server with a match
rule that the switch can compare with the user/client
information in the authentication request. With this option, the
user/client information in the authentication request can be in
any of the following formats:
<domain>\<user>
<user>@<domain>
host/<pc-name>.<domain>
An authentication request is sent to the server only if there is a
match between the specified match rule and the user/client
information.You can configure multiple match rules for an
authentication server.
—
contains contains: The rule matches if the user/client information
contains the specified string.
equals The rule matches if the user/client information exactly matches
the specified string.
starts-with The rule matches if the user/client information starts with the
specified string.
match-fqdn <string> This option associates the authentication server with a
specified domain. An authentication request is sent to the
server only if there is an exact match between the specified
domain and the <domain> portion of the user information sent
in the authentication request. With this option, the user
information must be in one of the following formats:
<domain>\<user>
<user>@<domain>
—
position <number> Position of the server in the server list. 1 is the top. (last)

58 | aaa server-group AOS-W 3.4.1 Command Line Interface | Reference Guide
Usage Guidelines
You create a server group for a specific type of authentication or for accounting. The list of servers in a
server group is an ordered list, which means that the first server in the group is always used unless it is
unavailable (in which case, the next server in the list is used). You can configure servers of different types
in a server group, for example, you can include the internal database as a backup to a RADIUS server. You
can add the same server to multiple server groups. There is a predefined server group “internal” that
contains the internal database.
Example
The following command configures a server group “corp-servers” with a RADIUS server as the main
authentication server and the internal database as the backup. The command also sets the client’s user role
to the value of the returned “Class” attribute.
aaa server-group corp-servers
auth-server radius1 position 1
auth-server internal position 2
set role condition Class value-of
trim-fqdn This option causes the user information in an authentication
request to be edited before the request is sent to the server.
Specifically, this option:
removes the <domain>\ portion for user information in the
<domain>\<user> format
removes the @<domain> portion for user information in the
<user>@<domain> format
—
clone Name of an existing server group from which parameter values
are copied. —
no Negates any configured parameter. —
set role|vlan Assigns the client a user role, VLAN ID or VLAN name based on
attributes returned for the client by the authentication server.
Rules are ordered: the first rule that matches the configured
condition is applied.
VLAN IDs and VLAN names cannot be listed together.
—
condition Attribute returned by the authentication server. —
contains The rule is applied if and only if the attribute value contains the
specified string. —
ends-with The rule is applied if and only if the attribute value ends with the
specified string. —
equals The rule is applied if and only if the attribute value equals the
specified string. —
not-equals The rule is applied if and only if the attribute value is not equal
to the specified string. —
starts-with The rule is applied if and only if the attribute value begins with
the specified string. —
set-value User role or VLAN applied to the client when the rule is
matched. —
value-of Sets the user role or VLAN to the value of the attribute returned.
The user role or VLAN ID returned as the value of the attribute
must already be configured on the switch when the rule is
applied.
—
Parameter Description Default

AOS-W 3.4.1 Command Line Interface | Reference Guide aaa server-group | 59
Command History
This command was introduced in AOS-W 3.0.
Command Information
Platforms Licensing Command Mode
All platforms Base operating system Config mode on master switches
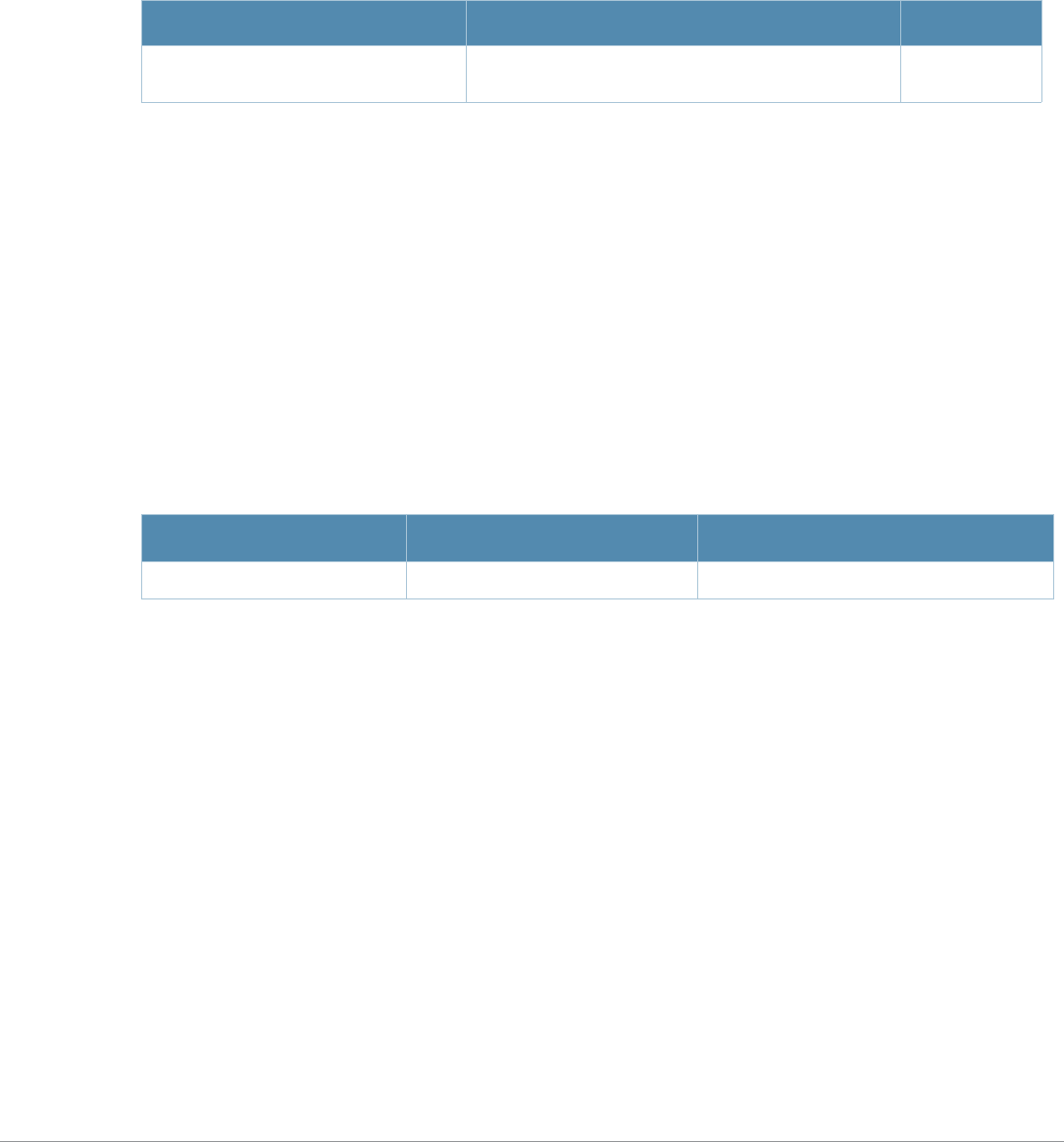
60 |aaa sygate-on-demand AOS-W 3.4.1 Command Line Interface | Reference Guide
aaa sygate-on-demand
aaa sygate-on-demand remediation-failure-role <role>
Description
This command configures the user role assigned to clients that fail Sygate On-Demand Agent (SODA)
remediation.
Syntax
Usage Guidelines
When you enable SODA client remediation in a captive portal profile, you can specify a user role to clients
that fail the remediation. The default role for such clients is the guest role.
Example
The following command assigns the logon role to users who fail remediation:
aaa sygate-on-demand remediation-failure-role logon
Command History
This command was available in AOS-W 3.0.
Command Information
Parameter Description Default
<role> User role assigned to the client upon failure of client
remediation. guest
Platforms Licensing Command Mode
All platforms Client Integrity license Config mode on master switches
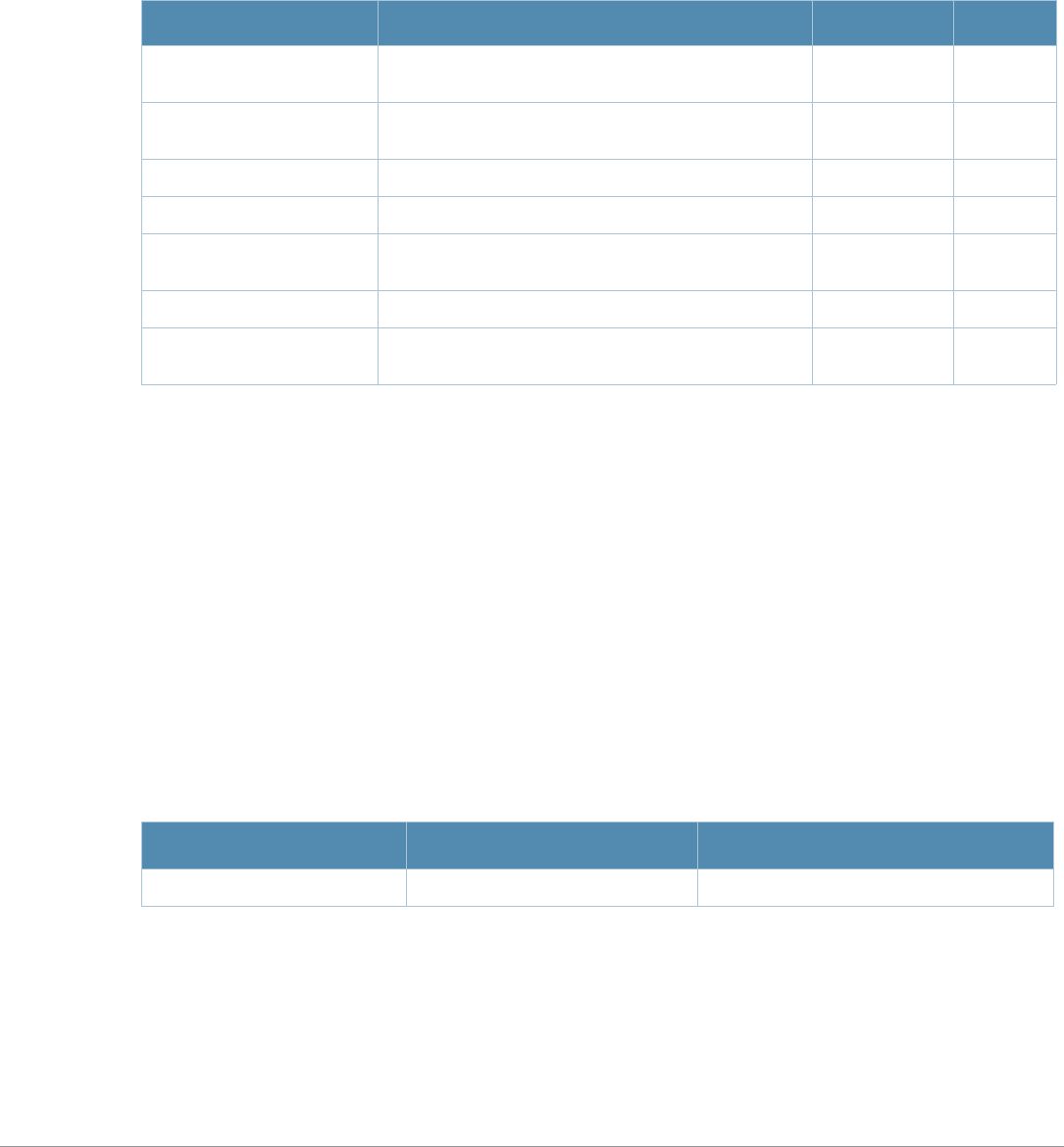
AOS-W 3.4.1 Command Line Interface | Reference Guide aaa tacacs-accounting | 61
aaa tacacs-accounting
aaa tacacs-accounting server-group <group> [command {action|all|configuration|show}]
[mode {enable|disable}]
Description
This command configures reporting of commands issued on the switch to a TACACS+ server group.
Syntax
Usage Guidelines
You must have previously configured the TACACS+ server and server group (see aaa authentication-server
tacacs on page 38 and aaa server-group on page 57).
Example
The following command enables accounting and reporting of configuration commands to the server-group
“tacacs1”:
aaa tacacs-accounting server-group tacacs1 mode enable command configuration
Command History
This command was available in AOS-W 3.0.
Command Information
Parameter Description Range Default
server-group <group> The TACACS server group to which the reporting is
sent. ——
command The types of commands that are reported to the
TACACS server group. ——
action Reports action commands only. — —
all Reports all commands. — —
configura
tion
Reports configuration commands only — —
show Reports show commands only — —
mode Enables accounting for the server group. enable/
disable disabled
Platforms Licensing Command Mode
All platforms Base operating system Config mode on master switches
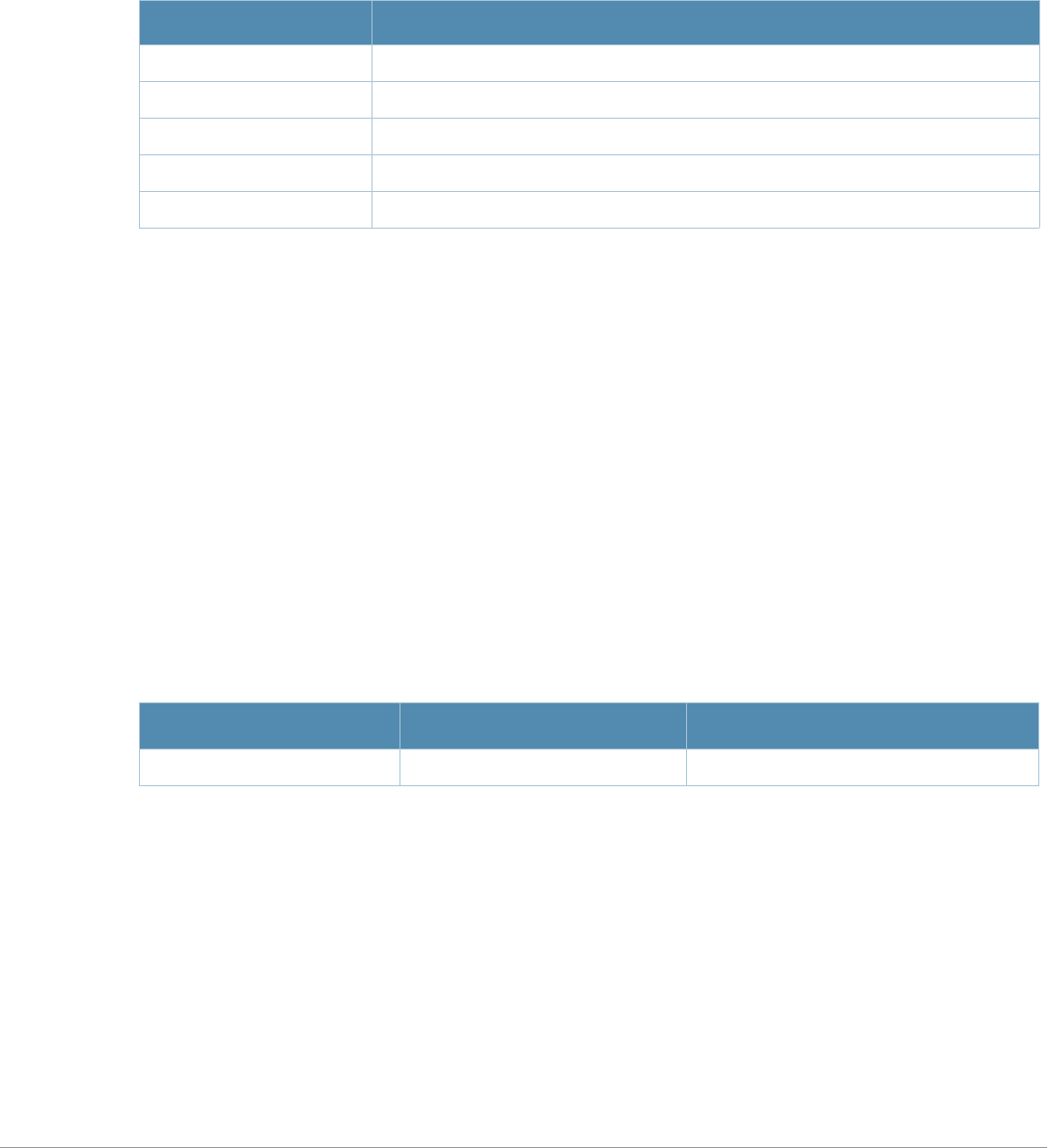
62 | aaa test-server AOS-W 3.4.1 Command Line Interface | Reference Guide
aaa test-server
aaa test-server {mschapv2|pap} <server> <username> <passwd>
Description
This command tests a configured authentication server.
Syntax
Usage Guidelines
This command allows you to check a configured RADIUS authentication server or the internal database.
You can use this command to check for an “out of service” RADIUS server.
Example
The following commands adds a user in the internal database and verifies the configuration:
local-userdb add kgreen lkjHGfds
aaa test-server pap internal kgreen lkjHGfds
Authentication successful
Command History
This command was available in AOS-W 3.0.
Command Information
Parameter Description
mschapv2 Use MSCHAPv2 authentication protocol.
pap Use PAP authentication protocol.
<server> Name of the configured authentication server.
<username> Username to use to test the authentication server.
<passwd> Password to use to test the authentication server.
Platforms Licensing Command Mode
All platforms Base operating system Config mode on master switches

AOS-W 3.4.1 Command Line Interface | Reference Guide aaa timers | 63
aaa timers
aaa timers {dead-time <minutes>|idle-timeout <number>|logon-lifetime <0-255>}
Description
This command configures the timers that you can apply to clients and servers.
Syntax
Usage Guidelines
These parameters can be left at their default values for most implementations.
Example
The following command prevents clients from timing out:
aaa timers idle-timeout 0
Command History
This command was available in AOS-W 3.0.
Related Commands
(host) (config) #show aaa timers
Parameter Description Range Default
dead-time <minutes> Maximum period, in minutes, that the switch
considers an unresponsive authentication server to
be “out of service”.
This timer is only applicable if there are two or more
authentication servers configured on the switch. If
there is only one authentication server configured,
the server is never considered out of service and all
requests are sent to the server.
If one or more backup servers are configured and a
server is unresponsive, it is marked as out of service
for the dead time; subsequent requests are sent to
the next server on the priority list for the duration of
the dead time. If the server is responsive after the
dead time has elapsed, it can take over servicing
requests from a lower-priority server; if the server
continues to be unresponsive, it is marked as down
for the dead time.
0-50 10 minutes
idle-timeout <0-255> Maximum number of minutes after which a client is
considered idle if there is no user traffic from the
client.
The timeout period is reset if there is a user traffic.
After this timeout period has elapsed, the switch
sends probe packets to the client; if the client
responds to the probe, it is considered active and the
User Idle Timeout is reset (an active client that is not
initiating new sessions is not removed). If the client
does not respond to the probe, it is removed from the
system.
To prevent clients from timing out, set the value in the
field to 0.
0-255 5 minutes
logon-lifetime Maximum time, in minutes, that unauthenticated
clients are allowed to remain logged on. 0-255 5 minutes

64 |aaa timers AOS-W 3.4.1 Command Line Interface | Reference Guide
(host) (config) #show datapath user table
Command Information
Platforms Licensing Command Mode
All platforms Base operating system Config mode on master switches
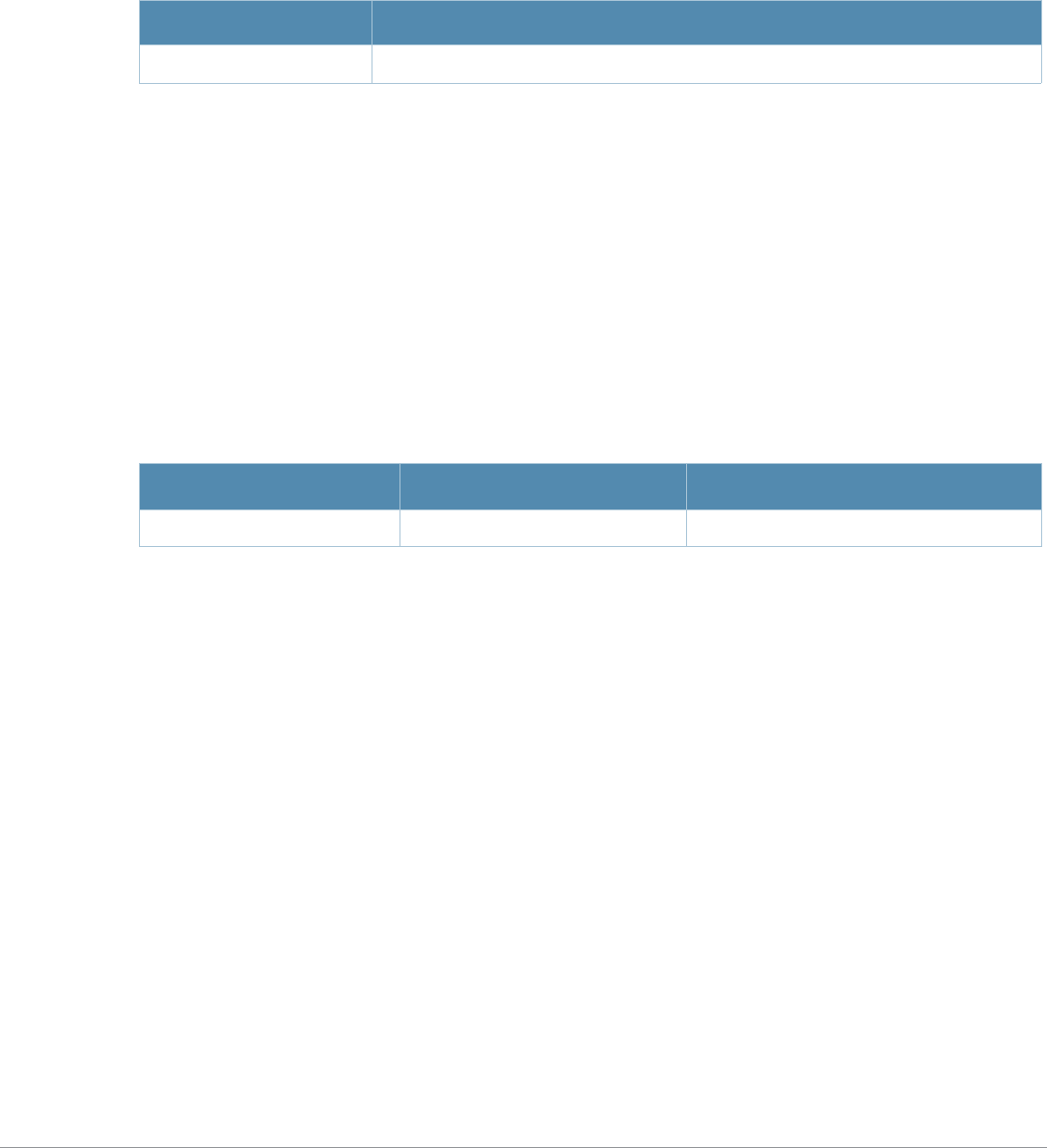
AOS-W 3.4.1 Command Line Interface | Reference Guide aaa trusted-ap | 65
aaa trusted-ap
aaa trusted-ap <macaddr>
Description
This command configures a trusted non-Alcatel-Lucent AP.
Syntax
Usage Guidelines
This command configures a non-Alcatel-Lucent AP as a trusted AP.
Example
The following configures a trusted non-Alcatel-Lucent AP:
aaa trusted-ap 00:40:96:4d:07:6e
Command History
This command was available in AOS-W 3.0.
Command Information
Parameter Description
<macaddr> MAC address of the AP
Platforms Licensing Command Mode
All platforms Base operating system Config mode on master switches

66 | aaa user add AOS-W 3.4.1 Command Line Interface | Reference Guide
aaa user add
aaa user add <ipaddr> [<number>] [authentication-method {dot1x|mac|stateful-dot1x|vpn|
web}] [mac <macaddr>] [name <username>] [profile <aaa_profile>] [role <role>]
Description
This command manually assigns a user role or other values to a specified client or device.
Syntax
Usage Guidelines
This command should only be used for troubleshooting issues with a specific client or device. This
command allows you to manually assign a client or device to a role. For example, you can create a role
“debugging” that includes a policy to mirror session packets to a specified destination for further
examination, then use this command to assign the “debugging” role to a specific client. Use the aaa user
delete command to remove the client or device from the role.
Note that issuing this command does not affect ongoing sessions that the client may already have. For
example, if a client is in the “employee” role when you assign them to the “debugging” role, the client
continues any sessions allowed with the “employee” role. Use the aaa user clear-sessions command to
clear ongoing sessions.
Example
The following commands create a role that logs HTTPS traffic, then assign the role to a specific client:
ip access-list session log-https
any any svc-https permit log
user-role web-debug
session-acl log-https
In enable mode:
aaa user add 10.1.1.236 role web-debug
Command History
Parameter Description
<ipaddr> IP address of the user to be added.
<number> Number of users to create starting with <ipaddr>.
authentication-method Authentication method for the user.
dot1x 802.1x authentication.
mac MAC authentication.
stateful-dot1x Stateful 802.1x authentication.
vpn VPN authentication.
web Captive portal authentication.
mac <macaddr> MAC address of the user.
name <username> Name for the user.
profile <aaa_profile> AAA profile for the user.
role <role> Role for the user.

AOS-W 3.4.1 Command Line Interface | Reference Guide aaa user add | 67
This command was available in AOS-W 3.0.
Command Information
Platforms Licensing Command Mode
All platforms Base operating system Enable mode on master switches
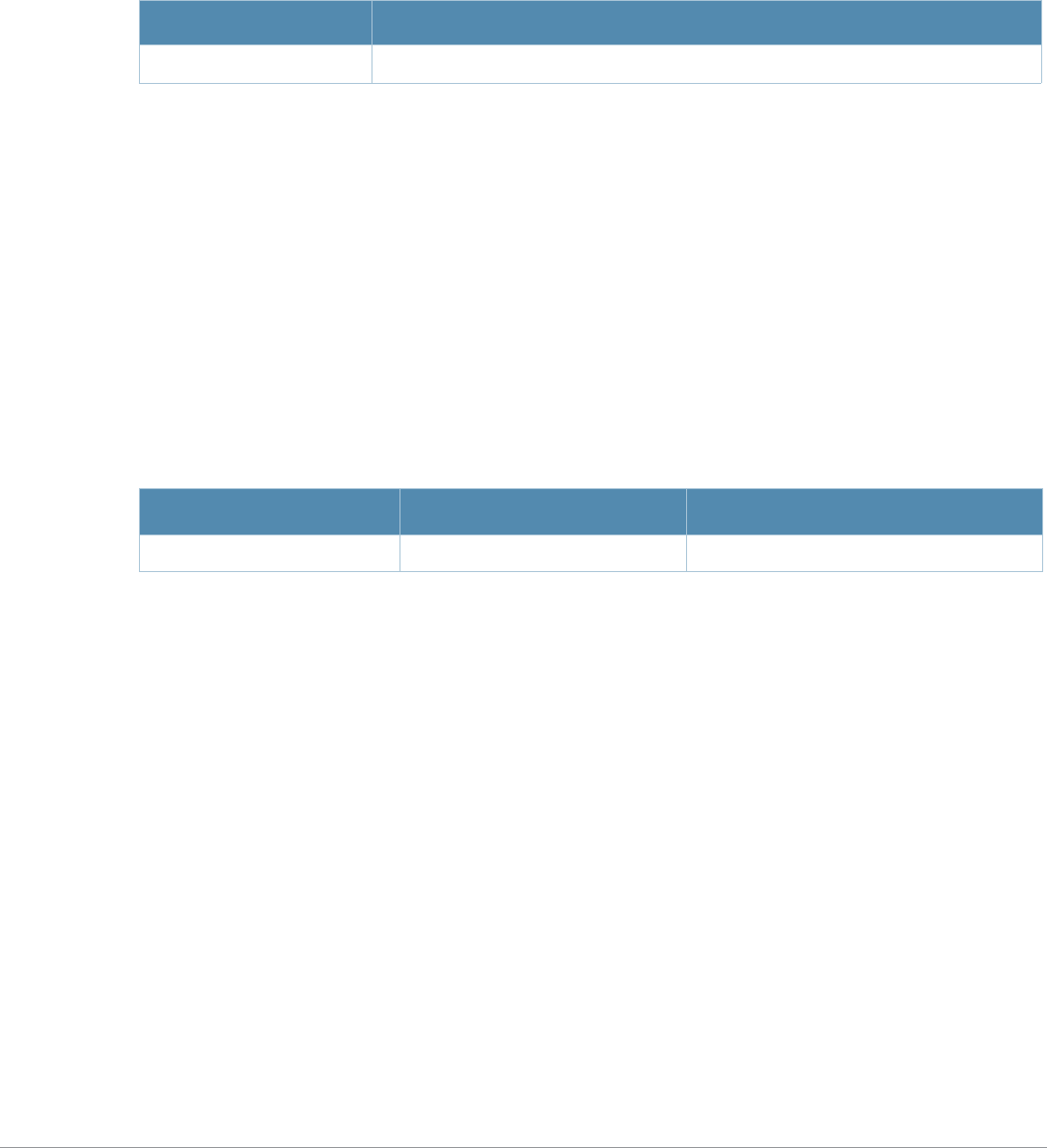
68 | aaa user clear-sessions AOS-W 3.4.1 Command Line Interface | Reference Guide
aaa user clear-sessions
aaa user clear-sessions <ipaddr>
Description
This command clears ongoing sessions for the specified client.
Syntax
Usage Guidelines
This command clears any ongoing sessions that the client already had before being assigned a role with the
aaa user add command.
Example
The following command clears ongoing sessions for a client:
aaa user clear-sessions 10.1.1.236
Command History
This command was available in AOS-W 3.0.
Command Information
Parameter Description
<ip-addr> IP address of the user.
Platforms Licensing Command Mode
All platforms Base operating system Enable mode on master switches
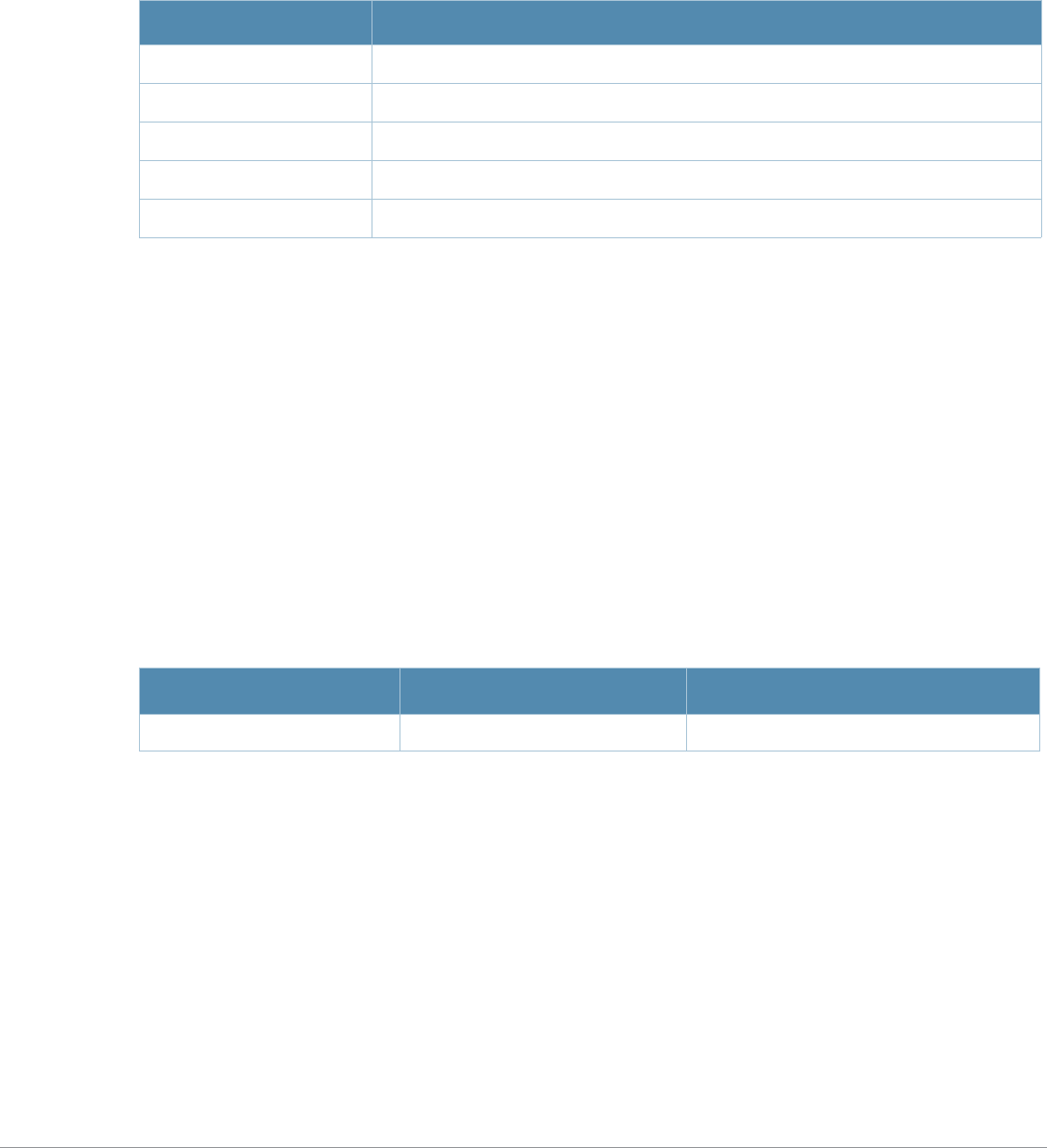
AOS-W 3.4.1 Command Line Interface | Reference Guide aaa user delete | 69
aaa user delete
aaa user delete {<ipaddr>|all|mac <macaddr>|name <username>|role <role>}
Description
This command deletes clients, users, or roles.
Syntax
Usage Guidelines
This command allows you to manually delete clients, users, or roles. For example, if you used to the aaa
user add command to assign a user role to a client, you can use this command to remove the role
assignment.
Example
The following command a role:
aaa user delete role web-debug
Command History
This command was available in AOS-W 3.0.
Command Information
Parameter Description
<ipaddr> IP address of the client to be deleted.
all Deletes all connected clients.
mac MAC address of the client to be deleted.
name Name of the client to be deleted.
role Role of the client to be deleted.
Platforms Licensing Command Mode
All platforms Base operating system Enable mode on master switches

70 | aaa user fast-age AOS-W 3.4.1 Command Line Interface | Reference Guide
aaa user fast-age
aaa user fast-age
Description
This command enables fast aging of user table entries.
Syntax
No parameters.
Usage Guidelines
When this feature is enabled, the switch actively sends probe packets to all users with the same MAC
address but different IP addresses. The users that fail to respond are purged from the system. This
command enables quick detection of multiple instances of the same MAC address in the user table and
removal of an “old” IP address. This can occur when a client (or an AP connected to an untrusted port on
the switch) changes its IP address.
Command History
This command was available in AOS-W 3.0.
Command Information
Platforms Licensing Command Mode
All platforms Base operating system Config mode on master switches
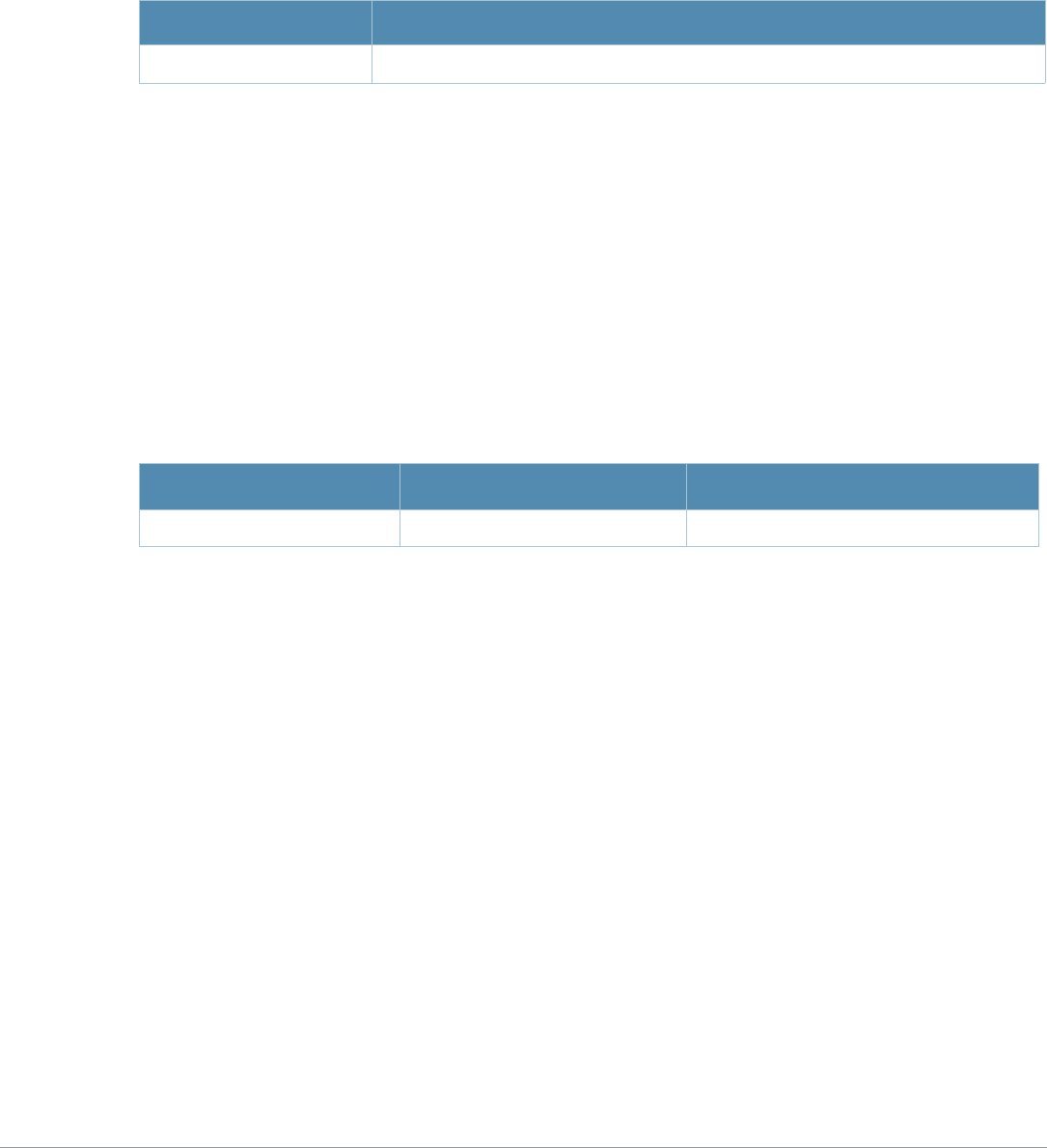
AOS-W 3.4.1 Command Line Interface | Reference Guide aaa user logout | 71
aaa user logout
aaa user logout <ipaddr>
Description
This command logs out a client.
Syntax
Usage Guidelines
This command logs out an authenticated client. The client must reauthenticate.
Example
The following command logs out a client:
aaa user logout 10.1.1.236
Command History
This command was available in AOS-W 3.0.
Command Information
Parameter Description
<ipaddr> IP address of the client to be logged out.
Platforms Licensing Command Mode
All platforms Base operating system Enable mode on master switches
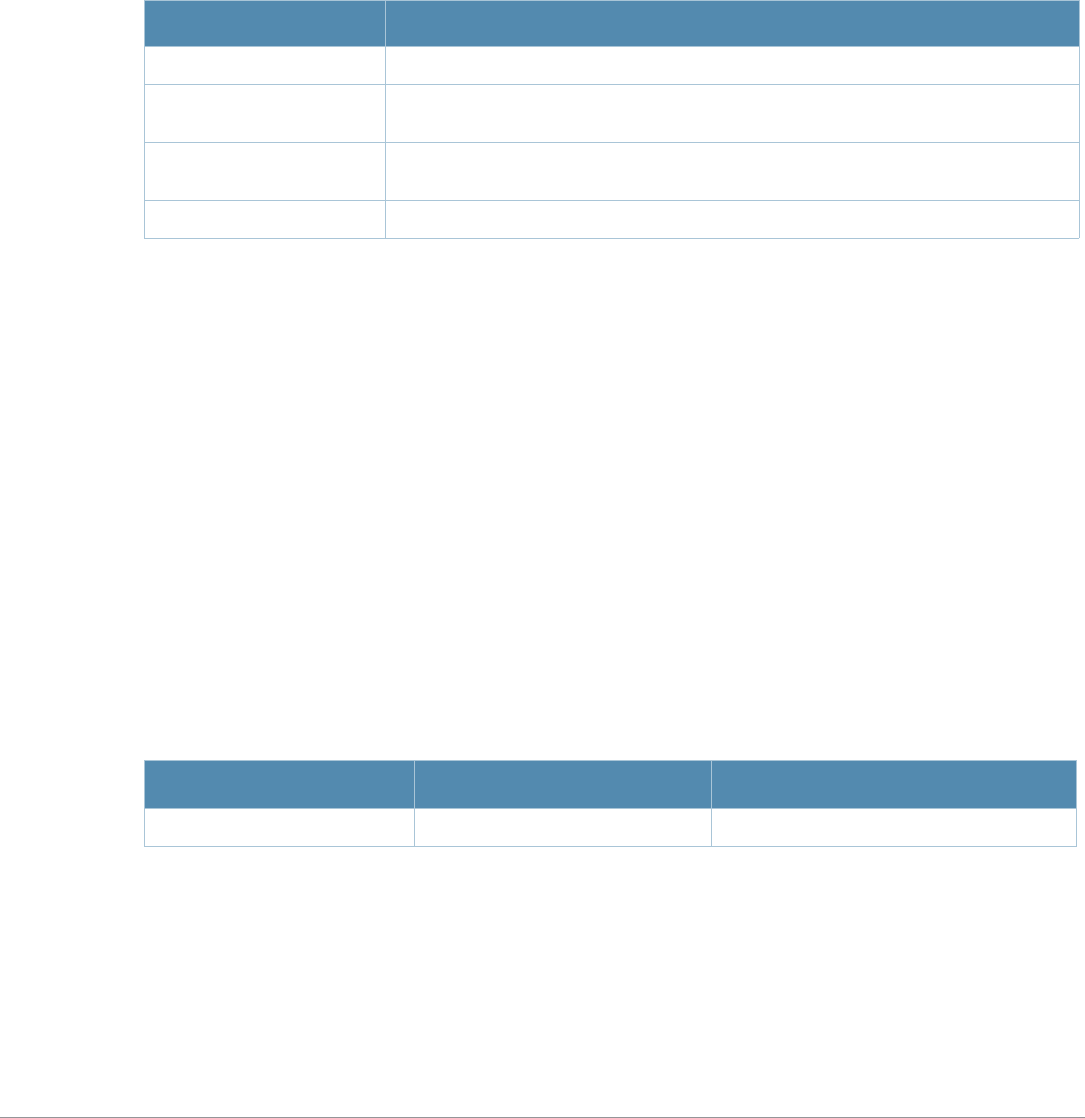
72 |aaa xml-api AOS-W 3.4.1 Command Line Interface | Reference Guide
aaa xml-api
aaa xml-api server <ipaddr>
clone <server>
key <key>
no ...
Description
This command configures an external XML API server.
Syntax
Usage Guidelines
XML API is used for authentication and subscriber management from external agents. This command
configures an external XML API server. For example, an XML API server can send a blacklist request for a
client to the switch. The server configured with this command is referenced in the AAA profile for the
WLAN (see “aaa profile” on page 50). Contact your Alcatel-Lucent representative for more information
about using the XML API.
Example
The following configures an XML API server:
aaa xml-api server 10.210.1.245
key qwerTYuiOP
Command History
This command was available in AOS-W 3.0.
Command Information
Parameter Description
server IP address of the external XML API server.
clone Name of an existing XML API server configuration from which parameter values are
copied.
key Preshared key to authenticate communication between the switch and the XML API
server.
no Negates any configured parameter.
Platforms Licensing Command Mode
All platforms Policy Enforcement Firewall license Config mode on master switches

AOS-W 3.4.1 Command Line Interface | Reference Guide adp | 73
adp
adp discovery {disable|enable} igmp-join {disable|enable} igmp-vlan <vlan>
Description
This command configures the Alcatel-Lucent Discovery Protocol (ADP).
Syntax
Usage Guidelines
Alcatel-Lucent APs send out periodic multicast and broadcast queries to locate the master switch. If the APs
are in the same broadcast domain as the master switch and ADP is enabled on the switch, the switch
automatically responds to the APs’ queries with its IP address. If the APs are not in the same broadcast
domain as the master switch, you need to enable multicast on the network. You also need to make sure that
all routers are configured to listen for IGMP join requests from the switch and can route the multicast
packets. Use the show adp config command to verify that ADP and IGMP join options are enabled on the
switch.
Example
The following example enables ADP and the sending of IGMP join requests on the switch:
adp discovery enable igmp-join enable
Command History
This command was available in AOS-W 3.0.
Command Information
Parameter Description Range Default
discovery Enables or disables ADP on the switch.enabled/
disabled enabled
igmp-join Enables or disables sending of Internet Group
Management Protocol (IGMP) join requests
from the switches.
enabled/
disabled enabled
igmp-vlan VLAN to which IGMP reports are sent. — 0 (default route
VLAN used)
Platforms Licensing Command Mode
All platforms Base operating system Config mode on master switches

74 |adp AOS-W 3.4.1 Command Line Interface | Reference Guide
AOS-W 3.4.1 Command Line Interface | Reference Guide am | 75
am
am scan <ipaddr> <channel> [bssid <bssid>]
am test <ipaddr> {suspect-rap bssid <bssid> match-type <match-type> match-method
<method>|wired-mac {add|remove {bssid <bssid>|enet-mac <enet-mac>} mac <mac>}
Description
These commands enable channel scanning or testing for the specified air monitor.
Syntax
Usage Guidelines
These commands are intended to be used with an Alcatel-Lucent AP that is configured as an air monitor.
You should not use the am test command unless instructed to do so by an Alcatel-Lucent representative.
Example
The following command sets the air monitor to scan all channels:
(host) (config) #am scan 10.1.1.244 0
Command History:
Parameter Description Range
scan IP address of the air monitor to be scanned. —
<channel> Channel to which the scanning is tuned. Set to 0 to
enable scanning of all channels. —
bssid BSSID of the air monitor. —
test IP address of the air monitor to be tested. —
suspect-rap Tests suspect-rap feature. —
match-type Match type. eth-wm | ap-wm | eth-gw-
wm
match-method Match method. equal | plus-one | minus-one
wired-mac Tests the rogue AP classification feature.
Specifies the Wired MAC table.
—
enet-mac Specifies the Ethernet MAC table. —
mac Specifies the MAC entry to add/remove from either
the Wired MAC table or the Ethernet MAC table. —
Release Modification
AOS-W 3.0 Command introduced
AOS-W 3.3.1 Support for the wired-mac and associated parameters was introduced.

76 |am AOS-W 3.4.1 Command Line Interface | Reference Guide
Command Information
Platforms Licensing Command Mode
All platforms Base operating system Enable and Config mode on master
switches
AOS-W 3.4.1 Command Line Interface | Reference Guide ap enet-link-profile | 77
ap enet-link-profile
ap enet-link-profile <profile>
clone <profile>
duplex {auto|full|half}
no ...
speed {10|100|1000|auto}
Description
This command configures an AP Ethernet link profile.
Syntax
Usage Guidelines
This command configures the duplex and speed of the Ethernet port on the AP. The configurable speed is
dependent on the port type.
Example
The following command configures the Ethernet link profile for full-duplex and 100 Mbps:
ap enet-link-profile enet
duplex full
speed 100
Command History
Command Information
Parameter Description Range Default
<profile> Name of this instance of the profile. The name must
be 1-63 characters. — “default”
clone Name of an existing Ethernet Link profile from which
parameter values are copied. ——
duplex The duplex mode of the Ethernet interface, either full,
half, or auto-negotiated. full/half/auto auto
no Negates any configured parameter. — —
speed The speed of the Ethernet interface, either 10 Mbps,
100 Mbps, 1000 Mbps (1 Gbps), or auto-negotiated. 10/100/1000/
auto auto
Release Modification
AOS-W 3.0 Command introduced
AOS-W 3.3 Support for 1000 Mbps (1 Gbps) Ethernet port speed was introduced.
Platforms Licensing Command Mode
Available on all platforms Base operating system Config mode on master switches
78 | ap mesh-cluster-profile AOS-W 3.4.1 Command Line Interface | Reference Guide
ap mesh-cluster-profile
ap mesh-cluster-profile <profile>
clone <profile>
cluster <name>
no ...
opmode [opensystem | wpa2-psk-aes]
rf-band {a | g}
wpa-hexkey <wpa-hexkey>
wpa-passphrase <wpa-passphrase>
Description
This command configures a mesh cluster profile used by mesh nodes.
Syntax
Usage Guidelines
Parameter Description Range Default
<profile> Name of this instance of the profile. The name must
be 1-63 characters. — “default”
clone Name of an existing mesh cluster profile from which
parameter values are copied. ——
cluster Indicates the mesh cluster name. The name can have
a maximum of 32 characters, and is used as the
MSSID for the mesh cluster. When you first create a
new mesh cluster profile, the profile uses the default
cluster name “Alcatel-Lucent-mesh”. Use the cluster
parameter to define a new, unique MSSID before you
assign APs or AP groups to the mesh cluster profile.
NOTE: If you want a mesh cluster to use WPA2-PSK-
AES encryption, do not use spaces in the mesh
cluster name, as this may cause errors in mesh points
associated with that mesh cluster.
To view existing mesh cluster profiles, use the CLI
command show ap mesh-cluster-profile.
—“Alcatel-
Lucent-mesh”
no Negates any configured parameter. — —
opmode Configures one of the following types of data
encryption.
zopensystem—No authentication or encryption.
zwpa2-psk-aes—WPA2 with AES encryption
using a pershared key.
Alcatel-Lucent recommends selecting wpa2-psk-aes
and using the wpa-passphrase parameter to select
a passphrase. Keep the passphrase in a safe place.
opensystem
wpa2-psk-aes
opensystem
rf-band Configures the RF band in which multiband mesh
nodes should operate:
a = 5 GHz
g = 2.4 GHz
Alcatel-Lucent recommends using 802.11a radios for
mesh deployments.
a
g
a
wpa-hexkey Configures a WPA pre-shared key. — —
wpa-passphrase Sets the WPA password that generates the PSK. — —

AOS-W 3.4.1 Command Line Interface | Reference Guide ap mesh-cluster-profile | 79
Mesh cluster profiles are specific to mesh nodes (APs configured for mesh) and provide the framework of
the mesh network. You must define and configure the mesh cluster profile before configuring an AP to
operate as a mesh node.
You can configure multiple mesh cluster profiles to be used within a mesh cluster. You must configure
different priority levels for each mesh cluster profile. See “ap-group” on page 101 or “ap-name” on page 105
for more information about priorities.
Cluster profiles, including the “default” profile, are not applied until you provision your APs for mesh.
Related Commands
To view a complete list of mesh cluster profiles and their status, use the following command:
show ap mesh-cluster-profile
To view the settings of a specific mesh cluster profile, use the following command:
show ap mesh-cluster-profile <name>
Example
The following command configures a mesh cluster profile named “cluster1” for the mesh cluster
“headquarters:”
ap mesh-cluster-profile cluster1
cluster headquarters
Command Information
Platforms Licensing Command Mode
All platforms OAW-AP80M and OAW-AP85
models require the Outdoor Mesh
Access Points license.
Config mode on master switches
80 | ap mesh-ht-ssid-profile AOS-W 3.4.1 Command Line Interface | Reference Guide
ap mesh-ht-ssid-profile
ap mesh-ht-ssid-profile <profile-name>
clone <source>
40MHz-enable
high-throughput-enable
legacy-stations
max-rx-a-mpdu-size
max-tx-a-mpdu-size
min-mpdu-start-spacing
mpdu-agg
no
short-guard-intvl-40Mhz
supported-mcs-set
Description
This command configures a mesh high-throughput SSID profile used by mesh nodes.
Syntax
Parameter Description Range Default
<profile-name> Enter the name of an existing mesh high-throughput
SSID profile to modify that profile, or enter a new
name or create a new mesh high-throughput profile.
The mesh high-throughput profile can have a
maximum of 32 characters.
To view existing high-throughput SSID radio profiles,
use the command show ap mesh-radio-profile.
default
clone <source> Copy configuration information from a source profile
into the currently selected profile
40MHz-enable Enable or disable the use of 40 MHz channels. This
parameter is enabled by default. enabled
high-throughput-
enable
Enable or disable high-throughput (802.11n) features
on this SSID. This parameter is enabled by default.
enabled
legacy-stations Allow or disallow associations from legacy (non-HT)
stations. By default, this parameter is enabled (legacy
stations are allowed).
enabled
mpdu-agg Enable or disable MAC protocol data unit (MPDU)
aggregation.
High-throughput mesh APs are able to send
aggregated MAC protocol data units (MDPUs), which
allow an AP to receive a single block
acknowledgment instead of multiple ACK signals.
This option, which is enabled by default, reduces
network traffic overhead by effectively eliminating the
need to initiate a new transfer for every MPDU.
enabled
max-tx-a-mpdu-size Maximum size of a transmitted aggregate MPDU, in
bytes. 1576 -65535 65535 bytes
max-rx-a-mpdu-size Maximum size of a received aggregate MPDU, in
bytes. 8191, 16383,
32767, 65535 65535 bytes
AOS-W 3.4.1 Command Line Interface | Reference Guide ap mesh-ht-ssid-profile | 81
Guidelines
The mesh high-throughput profile defines settings unique to 802.11n-capable, high-throughput APs. If none
of the APs in your mesh deployment are 802.11n-capable APs, you do not need to configure a high-
throughput SSID profile.
If you modify a currently provisioned and running high-throughput SSID profile, your changes take affect
immediately. You do not reboot the switch or the AP.
Related Commands
To view a complete list of mesh high-throughput SSID profiles and their status, use the following command:
(host) (config) #show ap mesh-ht-ssid-profile
To view the settings of a specific mesh radio profile, use the following command:
(host) (config) #show ap mesh-ht-ssid-profile <name>
Example
min-mpdu-start-
spacing
Minimum time between the start of adjacent MPDUs
within an aggregate MPDU, in microseconds. 0 (No restriction
on MDPU start
spacing), .25
μsec, .5 μsec, 1
μsec, 2 μsec, 4
μsec
0 usec
supported-mcs-set A list of Modulation Coding Scheme (MCS) values or
ranges of values to be supported on this SSID. The
MCS you choose determines the channel width
(20MHz vs. 40MHz) and the number of spatial
streams used by the mesh node.
The default value is 1-15; the complete set of
supported values. To specify a smaller range of
values, enter a hyphen between the lower and upper
values. To specify a series of different values,
separate each value with a comma.
Examples:
2-10
1,3,6,9,12
Range: 0-15.
1-15 1-15
short-guard-intvl-
40Mhz
Enable or disable use of short (400ns) guard interval
in 40 MHz mode.
A guard interval is a period of time between
transmissions that allows reflections from the
previous data transmission to settle before an AP
transmits data again. An AP identifies any signal
content received inside this interval as unwanted
inter-symbol interference, and rejects that data.
The 802.11n standard specifies two guard intervals:
400ns (short) and 800ns (long). Enabling a short
guard interval can decrease network overhead by
reducing unnecessary idle time on each AP. Some
outdoor deployments, may, however require a longer
guard interval. If the short guard interval does not
allow enough time for reflections to settle in your
mesh deployment, inter-symbol interference values
may increase and degrade throughput.
This parameter is enabled by default.
enabled
Parameter Description Range Default

82 | ap mesh-ht-ssid-profile AOS-W 3.4.1 Command Line Interface | Reference Guide
The following command configures a mesh high-throughput SSID profile named “HT1” and sets some non-
default settings for MAC protocol data unit (MPDU) aggregation:
(host) (config) #ap mesh-ht-ssid-profile HT1
max-rx-a-mpdu-size 32767
max-tx-a-mpdu-size 32767
min-mpdu-start-spacing .25
Command History
This command was introduced in AOS-W 3.4.
Command Information
Platforms Licensing Command Mode
All platforms OAW-AP80M and OAW-AP85
models require the Outdoor Mesh
Access Points license.
Config mode on master switches
AOS-W 3.4.1 Command Line Interface | Reference Guide ap mesh-radio-profile | 83
ap mesh-radio-profile
ap mesh-radio-profile <profile>
a-tx rates [6|9|12|18|24|36|48|54]
allowed-vlans <vlan-list>
children <children>
clone <profile>
g-tx rates [1|2|5|6|9|11|12|18|24|36|48|54]
heartbeat-threshold <count>
hop-count <hop-count>
link-threshold <count>
mesh-ht-ssid-profile
max-retries <max-retries>
mesh-mcast-opt
metric-algorithm {best-link-rssi|distributed-tree-rssi}
mpv <vlan-id>
no ...
reselection-mode {reselect-anytime|reselect-never|startup-subthreshold|
subthreshold-only}
rts-threshold <rts-threshold>
Description
This command configures a mesh radio profile used by mesh nodes.
Syntax
Parameter Description Range Default
<profile> Name of this instance of the profile. The name must
be 1-63 characters. — “default”
allowed-vlans Specify a list of VLAN IDs that can be used by a mesh
link on APs associated with this mesh radio profile
<vlan-list> A comma-separated list of VLAN IDs. You can also
specify a range of VLAN IDs using a dash (for
example, 1–4095)
a-tx rates Indicates the transmit rates for the 802.11a radio.
The AP attempts to use the highest transmission rate
to establish a mesh link. If a rate is unavailable, the
AP goes through the list and uses the next highest
rate.
6, 9, 12, 18, 24,
36, 48, 54
Mbps
6, 9, 12, 18, 24,
36, 48, 54
Mbps
children Indicates the maximum number of children a mesh
node can accept. 1-64 64
clone Name of an existing mesh radio profile from which
parameter values are copied. ——
g-tx rates Indicates the transmit rates for the 802.11b/g radio.
The AP attempts to use the highest transmission rate
to establish a mesh link. If a rate is unavailable, the
AP goes through the list and uses the next highest
rate.
1, 2, 5, 6, 9, 11,
12, 18, 24, 36,
48, 54
1, 2, 5, 6, 9, 11,
12, 18, 24, 36,
48, 54 Mbps
heartbeat-
threshold
Indicates the maximum number of heartbeat
messages that can be lost between neighboring
mesh nodes.
1-255 10
hop-count Indicates the maximum hop count from the mesh
portal. 1-32 8

84 | ap mesh-radio-profile AOS-W 3.4.1 Command Line Interface | Reference Guide
link-threshold Indicates the minimal RSSI value. If the RSSI value is
below this threshold, the link may be considered a
sub-threshold link. A sub-threshold link is a link
whose average RSSI value falls below the configured
threshold.
If this occurs, the mesh node may try to find a better
link on the same channel and cluster (only neighbors
on the same channel are considered).
The supported threshold is hardware dependent, with
a practical range of 10-90.
hardware
dependent 12
mesh-ht-ssid-
profile
High-throughput SSID Profile for the mesh feature. default
max-retries Maximum number of times a mesh node can re-send
a packet. 0-15 4 times
mesh-mcast-opt Enables or disables scanning of all active stations
currently associated to a mesh point to select the
lowest transmission rate based on the slowest
connected mesh child.
When enabled, this setting dynamically adjusts the
multicast rate to that of the slowest connected mesh
child. Multicast frames are not sent if there are no
mesh children.
Alcatel-Lucent recommends using the default value.
enabled
metric-
algorithm
Specifies the algorithm used by a mesh node to
select its parent.
Alcatel-Lucent recommends using the default value
distributed-tree-rssi.
— distributed-
tree-
rssi
best-link-
rssi
Selects the parent with the strongest RSSI,
regardless of the number of children a potential
parent has.
——
distributed-
tree-rssi
Selects the parent based on link-RSSI and node cost
based on the number of children.
This option evenly distributes the mesh points over
high quality uplinks. Low quality uplinks are selected
as a last resort.
——
mpv This parameter is experimental and reserved for
future use. 0-4094 0 (disabled)
no Negates any configured parameter. — —
reselection-mode Specifies the method used to find a better mesh link.
Alcatel-Lucent recommends using the default value
startup-subthreshold.
(see below) startup-sub
threshold
reselect-anytime Mesh points using the reselect-anytime reselection
mode perform a single topology readjustment scan
within 9 minutes of startup and 4 minutes after a link
is formed. If no better parent is found, the mesh point
returns to its original parent. This initial scan
evaluates more distant mesh points before closer
mesh points, and incurs a dropout of 5-8 seconds for
each mesh point.
After the initial startup scan is completed, connected
mesh nodes evaluate mesh links every 30 seconds. If
a mesh node finds a better uplink, the mesh node
connects to the new parent to create an improved
path to the mesh portal.
——
Parameter Description Range Default

AOS-W 3.4.1 Command Line Interface | Reference Guide ap mesh-radio-profile | 85
Usage Guidelines
Mesh radio profiles are specific to mesh nodes (APs configured for mesh) and determine the radio
frequency/channel used by mesh nodes to establish mesh links and the path to the mesh portal. You can
configure multiple radio profiles; however, you select and deploy only one radio profile per mesh cluster.
Radio profiles, including the “default” profile, are not active until you provision your APs for mesh. If you
modify a currently provisioned and running radio profile, your changes take place immediately. You do not
reboot the switch or the AP.
reselect-never Connected mesh nodes do not evaluate other mesh
links to create an improved path to the mesh portal. ——
startup-
subthreshold
Mesh points using the startup-subthreshold
reselection mode perform a single topology
readjustment scan within 9 minutes of startup and 4
minutes after a link is formed. If no better parent is
found, the mesh point returns to its original parent.
This initial startup scan evaluates more distant mesh
points before closer mesh points, and incurs a
dropout of 5-8 seconds for each mesh point. After
that time, each mesh node evaluates alternative links
if the existing uplink falls below the configured
threshold level (the link becomes a sub-threshold
link). Alcatel-Lucent recommends using this default
startup-subthreshold value.
NOTE: Starting with AOS-W 3.4.1, if a mesh point
using the startup-subthreshold mode reselects a
more distant parent because its original, closer
parent falls below the acceptable threshold, then as
long as that mesh point is connected to that more
distant parent, it will seek to reselect a parent at the
earlier distance (or less) with good link quality. For
example, if a mesh point disconnects from a mesh
parent 2 hops away and subsequently reconnects to
a mesh parent 3 hops away, then the mesh point will
continue to seek a connection to a mesh parent with
both an acceptable link quality and a distance of two
hops or less, even if the more distant parent also has
an acceptable link quality.
——
subthreshold-only Connected mesh nodes evaluate alternative links
only if the existing uplink becomes a sub-threshold
link.
NOTE: Starting with AOS-W 3.4.1, if a mesh point
using the subthreshold-only mode reselects a more
distant parent because its original, closer parent falls
below the acceptable threshold, then as long as that
mesh point is connected to that more distant parent,
it will seek to reselect a parent at the earlier distance
(or less) with good link quality. For example, if a mesh
point disconnects from a mesh parent 2 hops away
and subsequently reconnects to a mesh parent 3
hops away, then the mesh point will continue to seek
a connection to a mesh parent with both an
acceptable link quality and a distance of two hops or
less, even if the more distant parent also has an
acceptable link quality.
——
rts-threshold Defines the packet size sent by mesh nodes. Mesh
nodes transmitting frames larger than this threshold
must issue request to send (RTS) and wait for other
mesh nodes to respond with clear to send (CTS) to
begin transmission. This helps prevent mid-air
collisions.
256-2,346 2,333 bytes
Parameter Description Range Default
86 | ap mesh-radio-profile AOS-W 3.4.1 Command Line Interface | Reference Guide
Related Commands
To view a complete list of mesh radio profiles and their status, use the following command:
(host) (config) #show ap mesh-radio-profile
To view the settings of a specific mesh radio profile, use the following command:
(host) (config) #show ap mesh-radio-profile <name>
Example
The following command creates a mesh radio profile named “radio2” and associates a mesh high-
throughput profile named meshHT1:
(host) (config) #ap mesh-radio-profile radio2
mesh-ht-ssid-profile meshHT1
Command History
Command Information
Release Modification
AOS-W 3.2 Command introduced.
AOS-W 3.2.0.x, 3.3.1.x The tx-power default increased from 14 to 30 dBm.
AOS-W 3.3 The heartbeat-threshold default increased from 5 to 10 heartbeat messages.
AOS-W 3.3.2 The mesh-mcast-opt parameter was introduced.
AOS-W 3.4 The mesh-ht-ssid-profile parameter was introduced
The 11a-portal-channel, 11g-portal-channel, beacon-period and tx-power
parameters were deprecated. These settings can now be configured via the
rf dot11a-radio-profile and rf dot11g-radio-profile commands.
Platforms Licensing Command Mode
All platforms OAW-AP80M and OAW-AP85
models require the Outdoor Mesh
Access Points license.
Config mode on master switches

AOS-W 3.4.1 Command Line Interface | Reference Guide ap regulatory-domain-profile | 87
ap regulatory-domain-profile
ap regulatory-domain-profile <profile>
clone <profile>
country-code <code>
no ...
valid-11a-40mhz-channel-pair <num+|num->
valid-11a-channel <num>
valid-11g-40mhz-channel-pair <num+|num->
valid-11g-channel <num>
Description
This command configures an AP regulatory domain profile.
Syntax
Parameter Description Range Default
<profile> Name of this instance of the profile. The name must
be 1-63 characters. — “default”
clone Name of an existing regulatory domain profile from
which parameter values are copied. ——
country-code Code that represents the country in which the APs
will operate. The country code determines the 802.11
wireless transmission spectrum.
Improper country code assignment can disrupt
wireless transmissions. Most countries impose
penalties and sanctions for operators of wireless
networks with devices set to improper country
codes.
— country code
configured on
the master
switch during
initial setup
no Negates any configured parameter. — —
valid-11a-40mhz-
channel-pair
Specifies a channel pair valid for 40 MHz operation in
the regulatory domain (determined by country code)
for the
5 GHz (802.11a) frequency band.
num+: Entering a channel number with a plus (+) sign
selects a primary and secondary channel for
40 MHz mode. The number entered becomes the
primary channel and the secondary channel is
determined by increasing the primary channel
number by 4. Example: 157+ represents 157 as the
primary channel and 161 as the secondary channel.
num-: Entering a channel number with a minus (-)
sign selects a primary and secondary channel for
40 MHz mode. The number entered becomes the
primary channel and the secondary channel is
determined by decreasing the primary channel
number by 4. Example: 157- represents 157 as the
primary channel and 153 as the secondary channel.
country code determines
supported channel pairs
Note: Changing the country code
causes the valid channel lists to
be reset to the defaults for the
country.
valid-11a-
channel
Valid 802.11a channels for the country code.
num: Enter a single channel number for 20 MHz
mode of operation.
country code determines
supported channels
Note: Changing the country code
causes the valid channel lists to
be reset to the defaults for the
country.

88 | ap regulatory-domain-profile AOS-W 3.4.1 Command Line Interface | Reference Guide
Usage Guidelines
This profile configures the country code and valid channels for operation of APs. The list of valid channels
only affects the channels that may be selected by ARM or by the switch when no channel is configured.
Channels that are specifically configured in the AP radio settings profile (see rf dot11a-radio-profile on
page 414 or rf dot11g-radio-profile on page 420) must be valid for the country.
A switch shipped to certain countries, such as the U.S. and Israel, cannot terminate APs with regulatory
domain profiles that specify different country codes from the switch. For example, if a switch is designated
for the U.S., then only a regulatory domain profile with the “US” country code is valid; setting APs to a
regulatory domain profile with a different country code will result in the radios not coming up. For switches
in other countries, you can mix regulatory domain profiles on the same switch; for example, one switch can
support APs in Japan, Taiwan, China, and Singapore.
In order for an AP to boot correctly, the country code configured in the AP regulatory domain profile must
match the country code of the LMS.
Related Commands
To view the supported channels, use the show ap allowed-channels command.
AP configuration settings related to the IEEE 802.11n standard are configurable for Alcatel-Lucent’s OAW-
AP120 series access points, which are IEEE 802.11n standard compliant devices.
Examples
The following command configures the regulatory domain profile for APs in Japan:
(host) (config) #ap regulatory-domain-profile rd1
country-code JP
The following command configures a regulatory domain profile for APs in the United States and specifies
that the channel pair of 36 and 40, with 36 being the primary channel, is allowed for 40 MHz mode of
operation on the 5 GHz frequency band:
valid-11g-40mhz-
channel-pair
Specifies a channel pair valid for 40 MHz operation in
the regulatory domain (determined by country code)
for the
2.4 GHz (802.11b/g) frequency band.
num+: Entering a channel number with a plus (+) sign
selects a primary and secondary channel for
40 MHz mode. The number entered becomes the
primary channel and the secondary channel is
determined by increasing the primary channel
number by 4. Example: 1+ represents 1 as the
primary channel and 5 as the secondary channel.
num-: Entering a channel number with a minus (-)
sign selects a primary and secondary channel for
40 MHz mode. The number entered becomes the
primary channel and the secondary channel is
determined by decreasing the primary channel
number by 4. Example: 5- represents 5 as the
primary channel and 1 as the secondary channel.
country code determines
supported channel pairs
Note: Changing the country code
causes the valid channel lists to
be reset to the defaults for the
country.
valid-11g-
channel
Valid 802.11b/g channels for the country code.
num: Enter a single channel number for 20 MHz
mode of operation.
country code determines
supported channels
Note: Changing the country code
causes the valid channel lists to
be reset to the defaults for the
country.
Parameter Description Range Default

AOS-W 3.4.1 Command Line Interface | Reference Guide ap regulatory-domain-profile | 89
(host) (config) #ap regulatory-domain-profile usa1
country-code US
valid-11a-40mhz-channel-pair 36+
The following command configures a regulatory domain profile for APs in the United States and specifies
that the channel pair of 5 and 1, with 5 being the primary channel, is allowed for 40 MHz mode of operation
on the 2.4 GHz frequency band:
(host) (config) #ap regulatory-domain-profile usa1
country-code US
valid-11g-40mhz-channel-pair 5-
Command History
Command Information
Release Modification
AOS-W 3.0 Command introduced
AOS-W 3.3 Support for the IEEE 802.11n standard, including channel pairs for 40 MHz mode
of operation, was introduced
Platforms Licensing Command Mode
All platforms Base operating system Config mode on master switches

90 | ap snmp-profile (deprecated) AOS-W 3.4.1 Command Line Interface | Reference Guide
ap snmp-profile (deprecated)
Description
This command configures an SNMP profile for APs.
Command History
Version Modification
AOS-W 3.0 Command introduced
AOS-W 3.4 Command deprecated
AOS-W 3.4.1 Command Line Interface | Reference Guide ap snmp-user-profile (deprecated) | 91
ap snmp-user-profile (deprecated)
ap snmp-user-profile <profile>
auth-passwd <password>
auth-prot {md5|none|sha}
clone <profile>
no ...
priv-passwd <password>
user-name <name>
Description
This command configures an SNMPv3 user profile for APs.
Command History
Version Modification
AOS-W 3.0 Command introduced
AOS-W 3.4 Command deprecated

92 | ap system-profile AOS-W 3.4.1 Command Line Interface | Reference Guide
ap system-profile
ap system-profile <profile>
aeroscout-rtls-server ip-addr <ipaddr> port <port>
bkup-lms-ip <ipaddr>
bootstrap-threshold <number>
clone <profile>
dns-domain <domain>
double-encrypt
dump-server <server>
heartbeat-dscp <number>
keepalive-interval <seconds>
led-mode normal|off
lms-hold-down-period <seconds>
lms-ip <ipaddr>
lms-preemption
maintenance-mode
master-ip <ipaddr>
max-request-retries <number>
mtu <bytes>
native-vlan-id <vlan>
no ...
ortronics-high-temp <ortronics-high-temp>
ortronics-led-to
ortronics-low-temp <ortronics-low-temp>
ortronics-walljack
rap-dhcp-default-router <ipaddr>
rap-dhcp-dns-server <ipaddr>
rap-dhcp-lease <days>
rap-dhcp-pool-end <ipaddr>
rap-dhcp-pool-netmask <netmask>
rap-dhcp-pool-start <ipaddr>
rap-dhcp-server-id <ipaddr>
rap-dhcp-server-vlan <vlan>
request-retry-interval <seconds>
rf-band <band>
rfprotect-bkup-server <ipaddr>
rfprotect-server-ip <ipaddr>
rtls-server ip-addr <ipaddr> port <port> key <key> station-message-frequency
<seconds>
session-acl <acl>
syscontact <name>
telnet
Description
This command configures an AP system profile.
Syntax
Parameter Description Range Default
<profile> Name of this instance of the profile. The name must
be 1-63 characters. —“default”
aeroscout-rtls-
server
Enables the AP to send RFID tag information to an
AeroScout real-time asset location (RTLS) server. ——
ip-addr IP address of the AeroScout server to which location
reports are sent. ——

AOS-W 3.4.1 Command Line Interface | Reference Guide ap system-profile | 93
port Port number on the AeroScout server to which
location reports are sent. ——
bkup-lms-ip In multi-switch networks, specifies the IP address of
a backup to the IP address specified with the lms-ip
parameter.
——
bootstrap-
threshold
Number of consecutive missed heartbeats on a GRE
tunnel (heartbeats are sent once per second on each
tunnel) before an AP rebootstraps. On the switch, the
GRE tunnel timeout is 1.5 x bootstrap-threshold; the
tunnel is torn down after this number of seconds of
inactivity on the tunnel.
1-65535 8
clone Name of an existing AP system profile from which
parameter values are copied. ——
dns-domain Name of domain that is resolved by corporate DNS
servers. Use this parameter when configuring split
tunnel.
——
double-encrypt This parameter applies only to remote APs. Use
double encryption for traffic to and from a wireless
client that is connected to a tunneled SSID.
When enabled, all traffic is re-encrypted in the IPsec
tunnel. When disabled, the wireless frame is only
encapsulated inside the IPsec tunnel.
All other types of data traffic between the switch and
the AP (wired traffic and traffic from a split-tunneled
SSID) are always encrypted in the IPsec tunnel.
— disabled
dump-server (For debugging purposes.) Specifies the server to
receive a core dump generated when an AP process
crashes.
——
heartbeat-dscp DSCP value of AP heartbeats. 0-63 0
keepalive-inter
val
Time, in seconds, between keepalive messages from
the AP. 30-65535 60 seconds
led-mode The operating mode for the AP LEDs (OAW-AP120,
OAW-AP121, OAW-AP124 and OAW-AP125 only) normal
normal Display LEDs in normal mode.
off Turn off all LEDs.
lms-hold-down-
period
Time, in seconds, that the primary LMS must be
available before an AP returns to that LMS after
failover.
1-3600 600 seconds
lms-ip In multi-switch networks, specifies the IP address of
the local management switch (LMS)—the Alcatel-
Lucent switch—which is responsible for terminating
user traffic from the APs, and processing and
forwarding the traffic to the wired network. This can
be the IP address of the local or master switch.
When using redundant switchs as the LMS, set this
parameter to be the VRRP IP address to ensure that
APs always have an active IP address with which to
terminate sessions.
——
lms-preemption Automatically reverts to the primary LMS IP address
when it becomes available. — disabled
Parameter Description Range Default

94 | ap system-profile AOS-W 3.4.1 Command Line Interface | Reference Guide
maintenance-
mode
Enable or disable AP maintenance mode.
This setting is useful when deploying, maintaining, or
upgrading the network.
If enabled, APs stop flooding unnecessary traps and
syslog messages to network management systems
or network operations centers when deploying,
maintaining, or upgrading the network. The switch
still generates debug syslog messages if debug
logging is enabled.
disabled
master-ip In multi-switch networks, specifies the IP address of
the master switch. This address must be reachable
by the APs.
——
max-request-re
tries
Maximum number of times to retry AP-generated
requests, including keepalive messages. After the
maximum number of retries, the AP either tries the IP
address specified by the bkup-lms-ip (if configured)
or reboots.
1-65535 10
mtu MTU, in bytes, on the wired link for the AP. 1024-1578 —
native-vlan-id Native VLAN for bridge mode virtual APs (frames on
the native VLAN are not tagged with 802.1q tags). —1
no Negates any configured parameter. — —
ortronics-high-temp
<ortronics-high-
temp>
Temperature (in degrees Celsius) at which to
decrease transmit power on Ortronics APs. 110 C
ortronics-led-to Enable or disable the LED off timeout feature for
Ortronics APs.
Enabled
ortronics-low-temp
<ortronics-low-
temp>
Temperature (in degrees Celsius) at which to restore
configured power on Ortronics APs. 100 C
ortronics-walljack Enable or disable the wall jack on Ortronics DuoWJ
APs
Enabled
rap-dhcp-
default-router
IP address for the default DHCP router.
NOTE: The Remote AP license must be installed.
192.168.11.1
rap-dhcp-dns-
server
IP address of the DNS server.
NOTE: The Remote AP license must be installed.
192.168.11.1
rap-dhcp-lease The amount of days that the assigned IP address is
valid for the client. Specify the lease in <days>.
0 indicates the IP address is always valid; the lease
does not expire.
NOTE: The Remote AP license must be installed.
0-30 0
rap-dhcp-pool-
end
Configures a DHCP pool for remote APs. This is the
last IP address of the DHCP pool.
NOTE: The Remote AP license must be installed.
192.168.11.254
rap-dhcp-pool-
netmask
Configures a DHCP pool for remote APs. This is the
netmask used for the DHCP pool.
NOTE: The Remote AP license must be installed.
255.255.255.0
rap-dhcp-pool-
start
Configures a DHCP pool for remote APs. This is the
first IP address of the DHCP pool.
NOTE: The Remote AP license must be installed.
192.168.11.2
Parameter Description Range Default

AOS-W 3.4.1 Command Line Interface | Reference Guide ap system-profile | 95
Usage Guidelines
The AP system profile configures AP administrative operations, such as logging levels.
Example
The following command sets the LMS IP address in an AP system profile:
(host) (config) #ap system-profile local1
lms-ip 10.1.1.240
rap-dhcp-server-id IP address used as the DHCP server identifier.
NOTE: The Remote AP license must be installed.
192.168.11.1
rap-dhcp-server-
vlan
VLAN ID of the remote AP DHCP server used if the
switch is unavailable. This VLAN enables the DHCP
server on the AP (also known as the remote AP
DHCP server VLAN). If you enter the native VLAN ID,
the DHCP server is unavailable.
NOTE: The Remote AP license must be installed.
——
request-retry-
interval
Interval, in seconds, between the first and second
retries of AP-generated requests. If the configured
interval is less than 30 seconds, the interval for
subsequent retries is increased up to 30 seconds.
1-65535 10 seconds
rf-band For APs that support both a and b/g RF bands, RF
band in which the AP should operate:
zg = 2.4 GHz
za = 5 GHz
a/g g
rfprotect-bkup-
server
IP address of the backup Alcatel-Lucent RFprotect
server. The AP or AP group to which this profile
applies operates as an RFprotect sensor.
——
rfprotect-ser
ver-ip
IP address of the Alcatel-Lucent RFprotect server.
The AP or AP group to which this profile applies
operates as an RFprotect sensor.
——
rtls-server Enables the AP to send RFID tag information to an
RTLS server. ——
ip-addr IP address of the server to which location reports are
sent. ——
port Port number on the server to which location reports
are sent. ——
key Shared secret key. — —
station-message-
frequency
Indicates how often packets are sent to the server. 5-3600 30 seconds
session-acl Session ACL configured with the ip access-list
session command.
NOTE: The Policy Enforcement Firewall license must
be installed.
——
syscontact SNMP system contact information. — —
telnet Enable or disable telnet to the AP. — disabled
Parameter Description Range Default
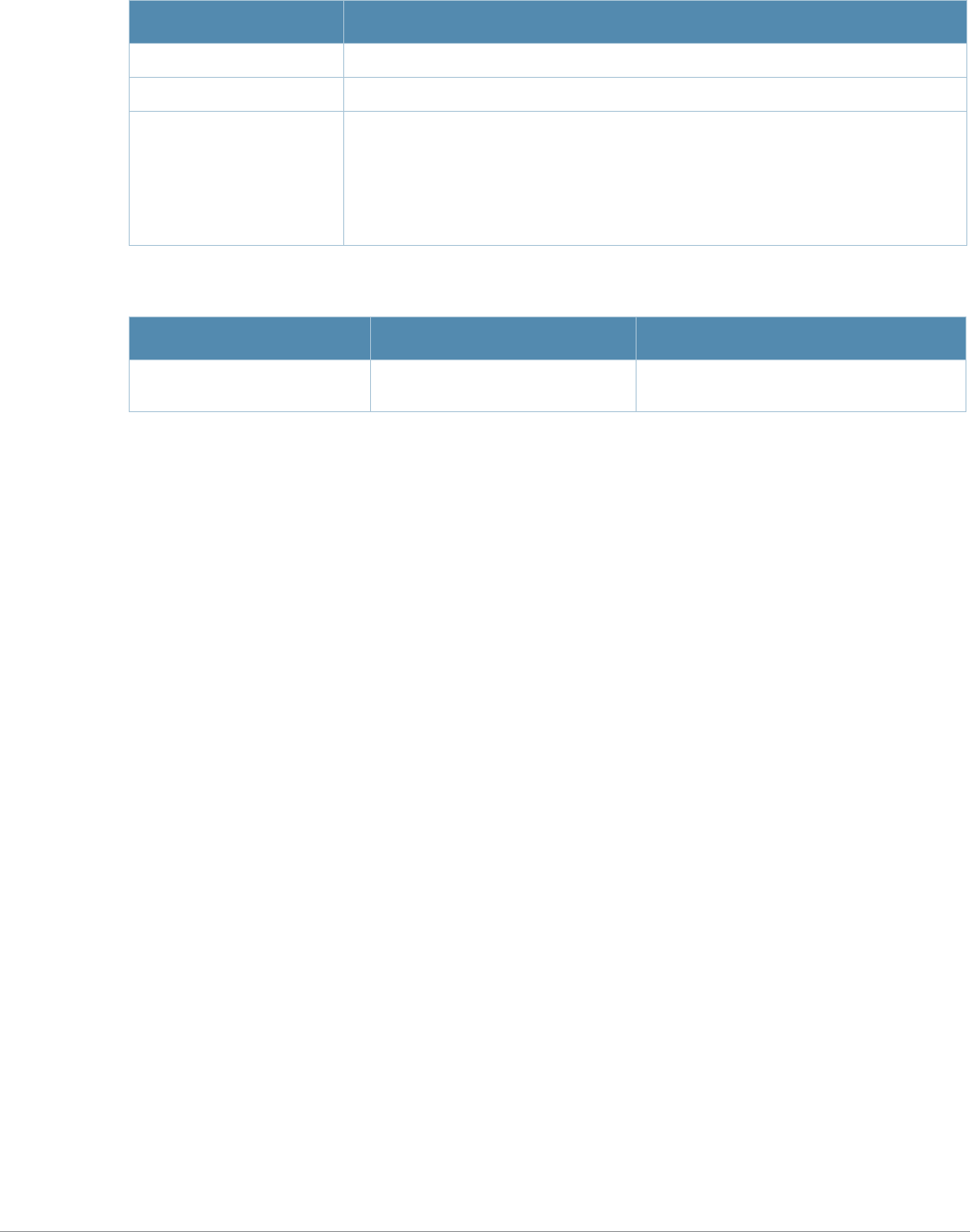
96 | ap system-profile AOS-W 3.4.1 Command Line Interface | Reference Guide
Command Information
Release Modification
AOS-W 3.0 Command introduced
AOS-W 3.2 Support for additional RTLS servers, remote AP enhancements was introduced
AOS-W 3.3.2 zMaintenance-mode parameter was introduced.
zMultiple remote AP DHCP server enhancements were introduced.
zSupport for RFprotect server and backup server configuration was introduced.
zThe mms-rtls-server parameter was deprecated in AOS-W 3.3.2. To configure the
OmniVista Mobility Manager server as an RTLS server, see “mobility-manager” on
page 351.
Platforms Licensing Command Mode
All platforms Base operating system, except for
noted parameters Config mode on master switches
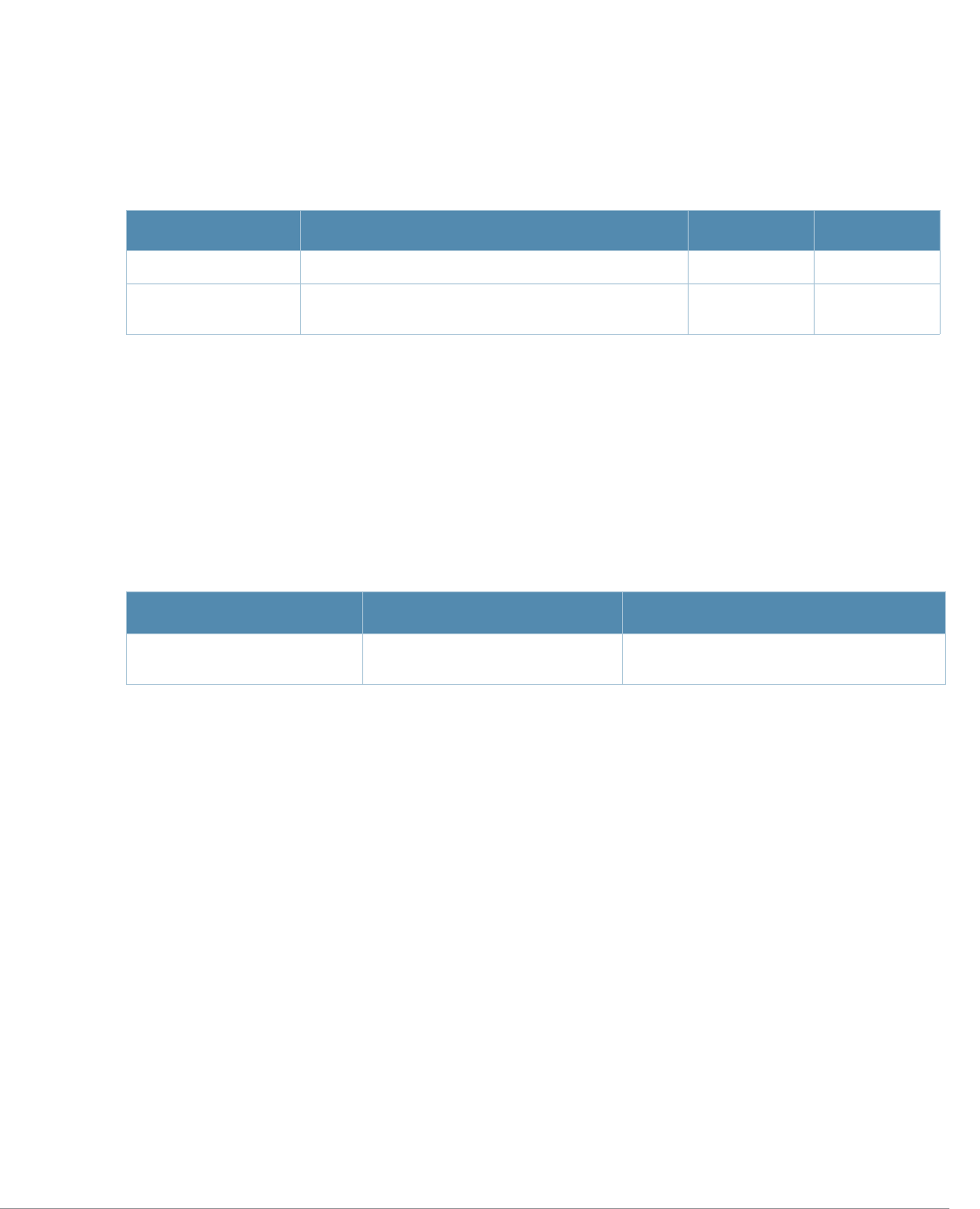
AOS-W 3.4.1 Command Line Interface | Reference Guide ap wipe out flash | 97
ap wipe out flash
ap wipe out flash
ap-name <ap-name>
ip-addr <ip-addr>
Description
Overwrite the entire AP compact flash, destroying its contents (including the current image file).
Syntax
Usage Guidelines
Use this command only under the supervision of Alcatel-Lucent technical support. If you delete the current
image in the AP’s flash memory, the AP will not function until you reload another image.
Command History
This command was introduced in AOS-W 3.3.2.
Command Information
Parameter Description Range Default
ap-name Wipe out the flash of the AP with the specified name. — —
ip-addr Wipe out the flash of the AP with the specified IP
address. ——
Platforms Licensing Command Mode
All platforms running AOS-W
3.3.2.x-FIPS or later. Base operating system Config mode on master switches

98 | ap wired-ap-profile AOS-W 3.4.1 Command Line Interface | Reference Guide
ap wired-ap-profile
ap wired-ap-profile <profile>
clone <profile>
forward-mode {bridge|split-tunnel|tunnel}
no ...
switchport access vlan <vlan>|mode {access|trunk}
trunk {allowed vlan <list>|add <list>|except <list>|remove <list>
native vlan <vlan>}
trusted
wired-ap-enable
Description
This command configures a wired AP profile.
Syntax
Usage Guidelines
This command is only applicable to Alcatel-Lucent APs that support a second Ethernet port, such as the
OAW-AP70. The wired AP profile configures the second Ethernet port (enet1) on the AP.
Parameter Description Range Default
<profile> Name of this instance of the profile. The name must
be 1-63 characters. — “default”
clone Name of an existing wired AP profile from which
parameter values are copied. ——
forward-mode Controls whether 802.11 frames are tunneled to the
switch using generic routing encapsulation (GRE),
bridged into the local Ethernet LAN (for remote APs),
or a combination thereof depending on the
destination (corporate traffic goes to the switch, and
Internet access remains local).
Only 802.1x authentication is supported when
configuring bridge or split tunnel mode.
NOTE: For split-tunnel mode, the Remote AP license
must be installed. Mesh nodes only support tunnel
mode.
bridge/split-
tunnel/tunnel tunnel
no Negates any configured parameter. — —
switchport Configures the switching mode characteristics for the
port.
access The VLAN to which the port belongs. — 1
mode The mode for the port, either access or trunk mode. access/trunk access
trunk allowed Allows multiple VLANs on the port interface. — all VLAN IDs or
VLAN names
VLAN IDs and
VLAN names
cannot be listed
together.
trunk native The native VLAN for the port (frames on the native
VLAN are not tagged with 802.1q tags). —1
trusted Sets port as either trusted or untrusted. — untrusted
wired-ap-enable Enables the wired AP. — disabled
AOS-W 3.4.1 Command Line Interface | Reference Guide ap wired-ap-profile | 99
For mesh deployments, this command is applicable to all Alcatel-Lucent APs configured as mesh nodes. If
you are using mesh to join multiple Ethernet LANs, configure and enable bridging on the mesh point
Ethernet port.
Mesh nodes only support bridge mode and tunnel mode on their wired ports (enet0 or enet1). Split tunnel
mode is not supported.
Use the bridge mode to configure bridging on the mesh point Ethernet port. Use tunnel mode to configure
secure jack operation on the mesh node Ethernet port.
When configuring the Ethernet ports on the OAW-AP70, note the following requirements:
zIf configured as a mesh portal, connect enet0 to the switch to obtain an IP address. The wired AP profile
controls enet1.Only enet1 supports secure jack operation.
zIf configured as a mesh point, the same wired AP profile will control both enet0 and enet1.
Example
The following command configures the enet1 port on the OAW-AP70 as a trunk port:
(host) (config) #ap wired-ap-profile wiredap1
switchport mode trunk
switchport trunk allowed 4,5
Command History
Command Information
Release Modification
AOS-W 3.0 Command introduced
AOS-W 3.2 Support for split tunneling was introduced
Platforms Licensing Command Mode
All platforms Base operating system, except for
noted parameters Config mode on master switches

100 | ap wired-ap-profile AOS-W 3.4.1 Command Line Interface | Reference Guide
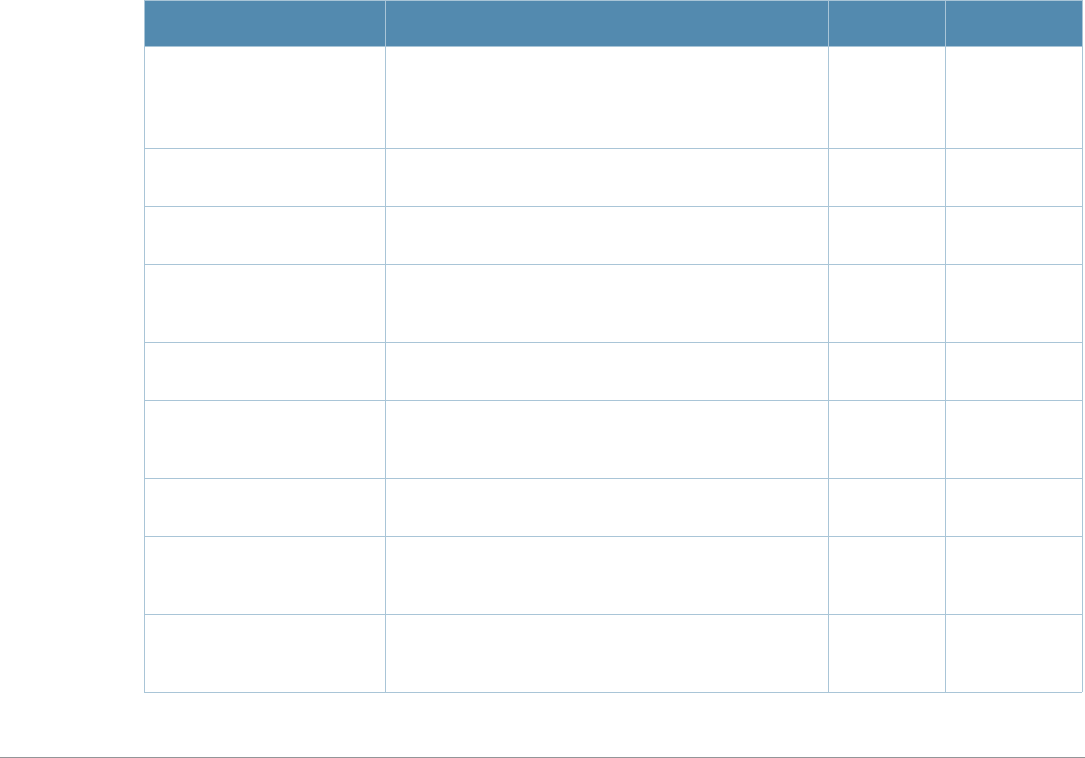
AOS-W 3.4.1 Command Line Interface | Reference Guide ap-group | 101
ap-group
ap-group <group>
ap-system-profile <profile>
clone <profile>
dot11a-radio-profile <profile>
dot11a-traffic-mgmt-profile <profile>
dot11g-radio-profile <profile>
dot11g-traffic-mgmt-profile <profile>
enet0-profile <profile>
enet1-profile <profile>
event-thresholds-profile <profile>
ids-profile <profile>
mesh-cluster-profile <profile> priority <priority>
mesh-radio-profile <profile>
no ...
regulatory-domain-profile <profile>
rf-optimization-profile <profile>
virtual-ap <profile>
voip-cac-profile <profile>
wired-ap-profile <profile>
Description
This command configures an AP group.
Syntax
Parameter Description Range Default
<group> Name that identifies the AP group. The name must be
1-63 characters.
NOTE: You cannot use quotes (“) in the AP group
name.
— “default”
ap-system-profile Configures AP administrative operations, such as
logging levels. See “ap system-profile” on page 92.— “default”
clone Name of an existing AP group from which profile
names are copied. ——
dot11a-radio-profile Configures 802.11a radio settings and load balancing
for the AP group; contains the ARM profile. See “rf
dot11a-radio-profile” on page 414.
— “default”
dot11a-traffic-mgmt-
profile
Configures bandwidth allocation. See “wlan traffic-
management-profile” on page 1194.——
dot11g-radio-profile Configures 802.11g radio settings and load balancing
for the AP group; contains the ARM profile. See “rf
dot11a-radio-profile” on page 414.
— “default”
dot11g-traffic-mgmt-
profile
Configures bandwidth allocation. See “wlan traffic-
management-profile” on page 1194.——
enet0-profile Configures the duplex and speed of the Ethernet 0
interface on the AP. See “ap enet-link-profile” on
page 77.
— “default”
enet1-profile Configures the duplex and speed of the Ethernet 1
interface on the AP. See “ap enet-link-profile” on
page 77.
— “default”

102 | ap-group AOS-W 3.4.1 Command Line Interface | Reference Guide
Usage Guidelines
AP groups are at the top of the configuration hierarchy. An AP group collects virtual AP definitions and
configuration profiles, which are applied to APs in the group.
Example
The following command configures a virtual AP profile to the “default” AP group:
(host)(config) #ap-group default
virtual-ap corpnet
Related Commands
View AP group settings using the command show ap-group.
event-thresholds-
profile
Configures Received Signal Strength Indication
(RSSI) metrics. See “rf event-thresholds-profile” on
page 426.
— “default”
ids-profile Configures Alcatel-Lucent’s Intrusion Detection
System (IDS). See “ids profile” on page 227.— “default”
mesh-cluster-profile Configures the mesh cluster profile for mesh nodes
that are members of the AP group. There is a
“default” mesh cluster profile; however, it is not
applied until you provision the mesh node. See “ap
mesh-cluster-profile” on page 78.
OAW-AP80M and OAW-AP85 models require the
Outdoor Mesh Access Points license.
— “default”
priority Configures the priority of the mesh cluster profile. If
more than two mesh cluster profiles are configured,
mesh points use this number to identify primary and
backup profile(s).
The lower the number, the higher the priority.
1-16 1
mesh-radio-profile Configures the 802.11g and 802.11a radio settings
for mesh nodes that are members of the AP group.
See “ap mesh-ht-ssid-profile” on page 80.
Commands to configure mesh for outdoor APs
require the Outdoor Mesh license.
— “default”
no Negates any configured parameter. — —
regulatory-domain-
profile
Configures the country code and valid channels. See
“ap regulatory-domain-profile” on page 87.— “default”
rf-optimization-
profile
Configure coverage hole and interference detection.
See “rf optimization-profile” on page 431.— “default”
virtual-ap One or more profiles, each of which configures a
specified WLAN. See “wlan virtual-ap” on page 1196.— “default”
voip-cac-profile Configures voice over IP (VoIP) call admission control
(CAC) options. See “wlan voip-cac-profile” on
page 1201.
The Policy Enforced Firewall license must be
installed.
— “default”
wired-ap-profile Configures the second Ethernet port (enet1) on the
AP. See “ap wipe out flash” on page 97.— “default”
Parameter Description Range Default

AOS-W 3.4.1 Command Line Interface | Reference Guide ap-group | 103
Command History:
Command Information
Release Modification
AOS-W 3.0 Command introduced
AOS-W 3.2 Support for the mesh parameters was introduced
AOS-W 3.4.1 License requirements changed in AOS-W 3.4.1, so the voip-cac-profile
parameter now requires the Policy Enforced Firewall license instead of the Voice
Services Module license required in earlier versions.
Platforms Licensing Command Mode
All platforms Base operating system, except for
noted parameters Config mode on master switches

104 | ap-group AOS-W 3.4.1 Command Line Interface | Reference Guide
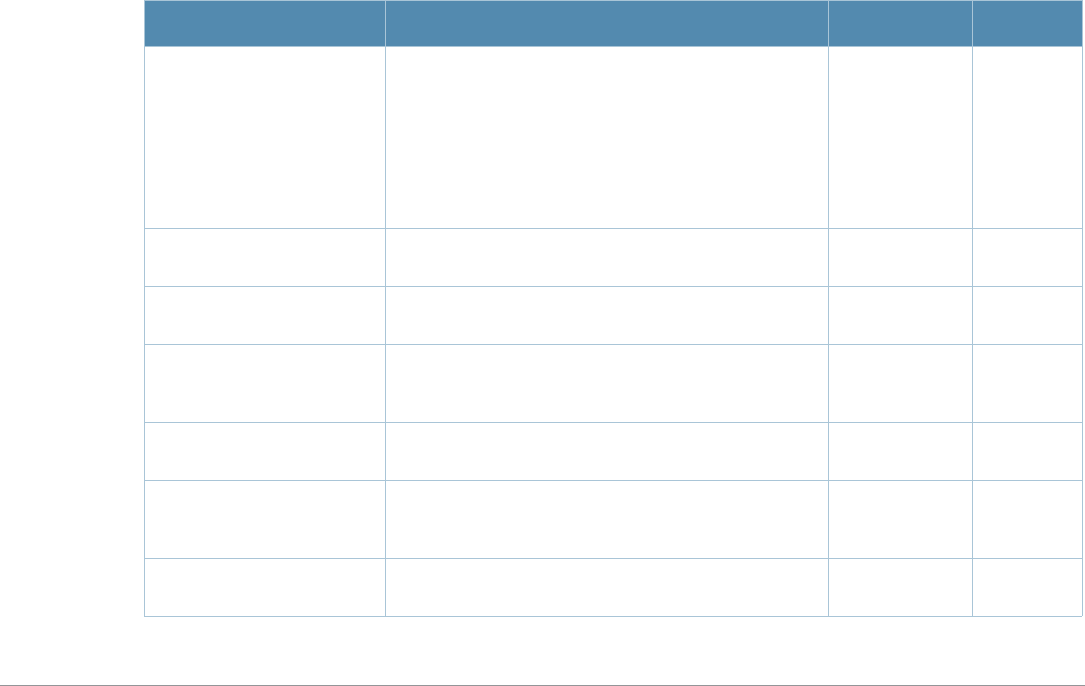
AOS-W 3.4.1 Command Line Interface | Reference Guide ap-name | 105
ap-name
ap-name <name>
ap-system-profile <profile>
clone <profile>
dot11a-radio-profile <profile>
dot11a-traffic-mgmt-profile <profile>
dot11g-radio-profile <profile>
dot11g-traffic-mgmt-profile <profile>
enet0-profile <profile>
enet1-profile <profile>
event-thresholds-profile <profile>
exclude-mesh-cluster-profile-ap <profile>
exclude-virtual-ap <profile>
ids-profile <profile>
mesh-cluster-profile <profile> priority <priority>
mesh-radio-profile <profile>
no ...
regulatory-domain-profile <profile>
rf-optimization-profile <profile>
snmp-profile <profile>
virtual-ap <profile>
voip-cac-profile <profile>
wired-ap-profile <profile>
Description
This command configures a specific AP.
Syntax
Parameter Description Range Default
<name> Name that identifies the AP. By default, an AP’s name
can either be the AP’s Ethernet MAC address, or if
the AP has been previously provisioned with an
earlier version of AOS-W, a name in the format
<building>.<floor>.<location>. The name must be 1-
63 characters.
NOTE: You cannot use quotes (“) in the AP
name.
——
ap-system-profile Configures AP administrative operations, such as
logging levels. See “ap system-profile” on page 92.— “default”
clone Name of an existing AP name from which profile
names are copied. ——
dot11a-radio-profile Configures 802.11a radio settings for the AP group;
contains the ARM profile. See “rf dot11a-radio-
profile” on page 414.
— “default”
dot11a-traffic-mgmt-
profile
Configures bandwidth allocation. See “wlan traffic-
management-profile” on page 1194.——
dot11g-radio-
profile
Configures 802.11g radio settings for the AP group;
contains the ARM profile. See “rf dot11a-radio-
profile” on page 414.
— “default”
dot11g-traffic-
mgmt-profile
Configures bandwidth allocation. See “wlan traffic-
management-profile” on page 1194.——

106 |ap-name AOS-W 3.4.1 Command Line Interface | Reference Guide
enet0-profile Configures the duplex and speed of the Ethernet 0
interface on the AP. See “ap enet-link-profile” on
page 77.
— “default”
enet1-profile Configures the duplex and speed of the Ethernet 1
interface on the AP. See “ap enet-link-profile” on
page 77.
— “default”
event-thresholds-
profile
Configures Received Signal Strength Indication
(RSSI) metrics. See “rf event-thresholds-profile” on
page 426.
— “default”
exclude-mesh-
cluster-profile-ap
Excludes the specified mesh cluster profile from this
AP.
The Secure Enterprise Mesh license must be
installed.
——
exclude-virtual-ap Excludes the specified virtual AP profiles from this
AP.
ids-profile Configures Alcatel-Lucent’s Intrusion Detection
System (IDS). See “ids profile” on page 227.— “default”
mesh-cluster-profile Configures the mesh cluster profile for the AP (mesh
node). There is a “default” mesh cluster profile;
however, it is not applied until you provision the mesh
node. See “ap mesh-cluster-profile” on page 78.
The Secure Enterprise Mesh license must be
installed.
— “default”
priority Configures the priority of the mesh cluster profile. If
more than two mesh cluster profiles are configured,
mesh points use this number to identify primary and
backup profile(s).
The lower the number, the higher the priority.
1-16 1
mesh-radio-profile Configures the 802.11g and 802.11a radio settings
for the AP (mesh node). See “ap mesh-ht-ssid-
profile” on page 80.
The Secure Enterprise Mesh license must be
installed.
— “default”
no Negates any configured parameter. — —
regulatory-domain-
profile
Configures the country code and valid channels. See
“ap regulatory-domain-profile” on page 87.— “default”
rf-optimization
-profile
Configures load balancing and coverage hole and
interference detection. See “rf optimization-profile”
on page 431.
— “default”
snmp-profile Configures SNMP-related parameters. See “ap
snmp-profile (deprecated)” on page 90.— “default”
virtual-ap One or more profiles, each of which configures a
specified WLAN. See “wlan virtual-ap” on page 1196.— “default”
voip-cac-profile Configures voice over IP (VoIP) call admission control
(CAC) options. See “wlan voip-cac-profile” on
page 1201.
The Policy Enforcement Firewall license must be
installed.
— “default”
wired-ap-profile Configures the ports for APs that are directly
attached to the switch. See “ap wipe out flash” on
page 97.
— “default”
Parameter Description Range Default

AOS-W 3.4.1 Command Line Interface | Reference Guide ap-name | 107
Usage Guidelines
Profiles that are applied to an AP group can be overridden on a per-AP name basis, and virtual APs can be
added or excluded on a per-AP name basis. If a particular profile is overridden for an AP, all parameters
from the overriding profile are used. There is no merging of individual parameters between the AP and the
AP group to which the AP belongs.
Example
The following command excludes a virtual AP profile from a specific AP:
(host) (config) #ap-name 00:0b:86:c0:cf:d8
exclude-virtual-ap corpnet
Related Commands
View AP settings using the command show ap-name.
Command History:
Command Information
Release Modification
AOS-W 3.0 Command introduced
AOS-W 3.2 Support for mesh parameters was introduced.
AOS-W 3.4.1 License requirements changed in AOS-W 3.4.1, so the voip-cac-profile
parameter now requires the Policy Enforced Firewall license instead of the Voice
Services Module license required in earlier versions.
Platforms Licensing Command Mode
All platforms Base operating system Config mode on master switches

108 |ap-name AOS-W 3.4.1 Command Line Interface | Reference Guide
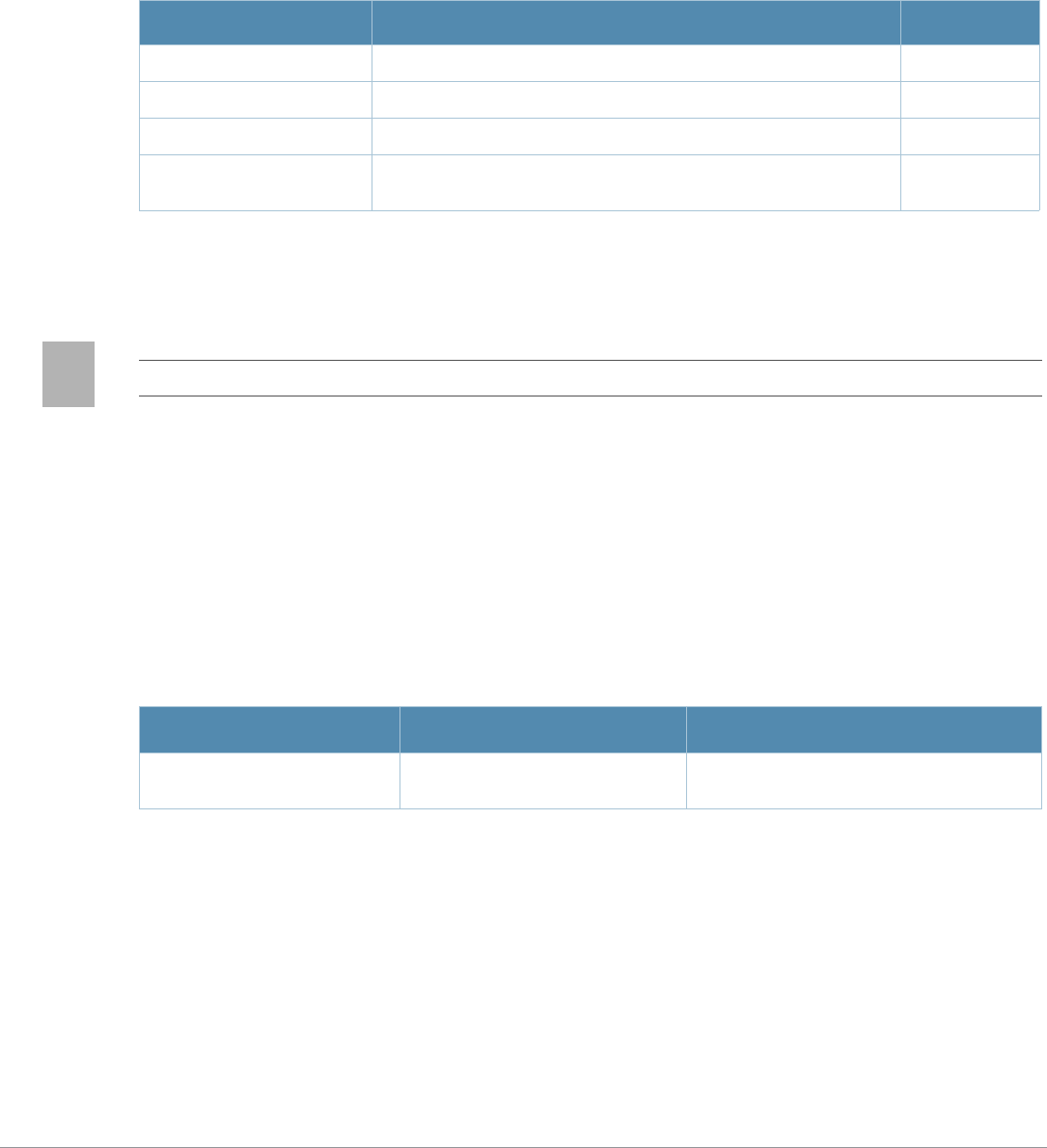
AOS-W 3.4.1 Command Line Interface | Reference Guide ap-regroup | 109
ap-regroup
ap-regroup {ap-name <name>|serial-num <num>|wired-mac <macaddr>} <group>
Description
This command moves a specified AP into a group.
Syntax
Usage Guidelines
All APs discovered by the switch are assigned to the “default” AP group. An AP can belong to only one AP
group at a time. You can move an AP to an AP group that you created with the ap-group command.
Example
The following command moves an AP to the ‘corpnet’ group:
(host)(config) #ap-regroup wired-mac 00:0f:1e:11:00:00 corpnet
Command History
This command was introduced in AOS-W 3.0.
Command Information
Parameter Description Default
ap-name Name of the AP. —
serial-num Serial number of the AP. —
wired-mac MAC address of the AP. —
<group> Name that identifies the AP group. The name must be 1-63
characters. “default”
This command automatically reboots the AP.
Platforms Licensing Command Mode
All platforms Base operating system Enable and Config mode on master
switches

110 | ap-regroup AOS-W 3.4.1 Command Line Interface | Reference Guide
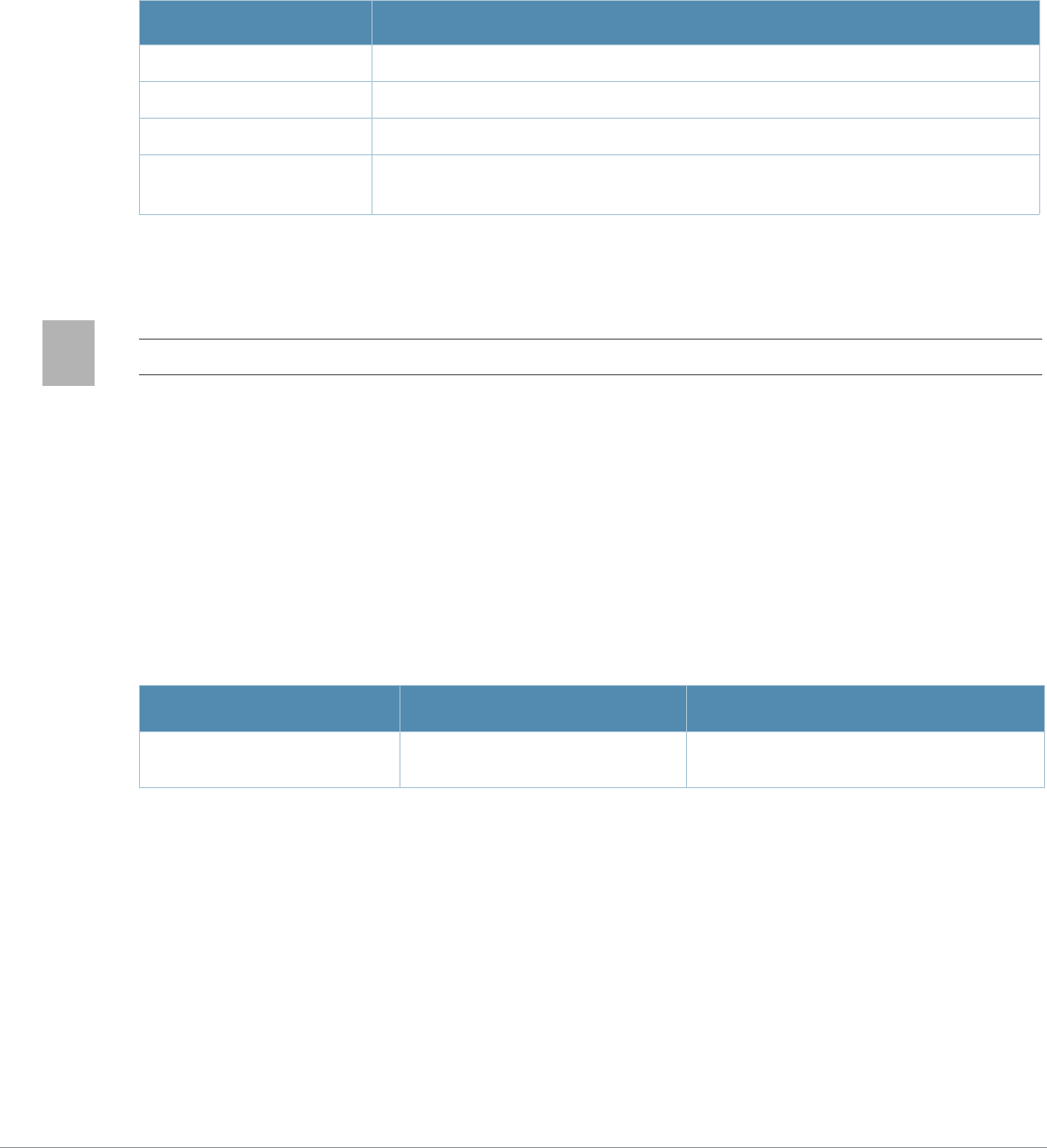
AOS-W 3.4.1 Command Line Interface | Reference Guide ap-rename | 111
ap-rename
ap-rename {ap-name <name>|serial-num <num>|wired-mac <macaddr>} <new-name>
Description
This command changes the name of an AP to the specified new name.
Syntax
Usage Guidelines
An AP name must be unique within your network.
Example
The following command renames an AP:
(host) (config) #ap-rename wired-mac 00:0f:1e:11:00:00 building3-lobby
Command History
This command was introduced in AOS-W 3.0.
Command Information
Parameter Description
ap-name Current name of the AP.
serial-num Serial number of the AP.
wired-mac MAC address of the AP.
<new-name> New name for the AP. The name must be 1-63 characters.
NOTE: You cannot use quotes (“) in the AP name.
This command automatically reboots the AP.
Platforms Licensing Command Mode
All platforms Base operating system Enable and Config mode on master
switches

112 |ap-rename AOS-W 3.4.1 Command Line Interface | Reference Guide
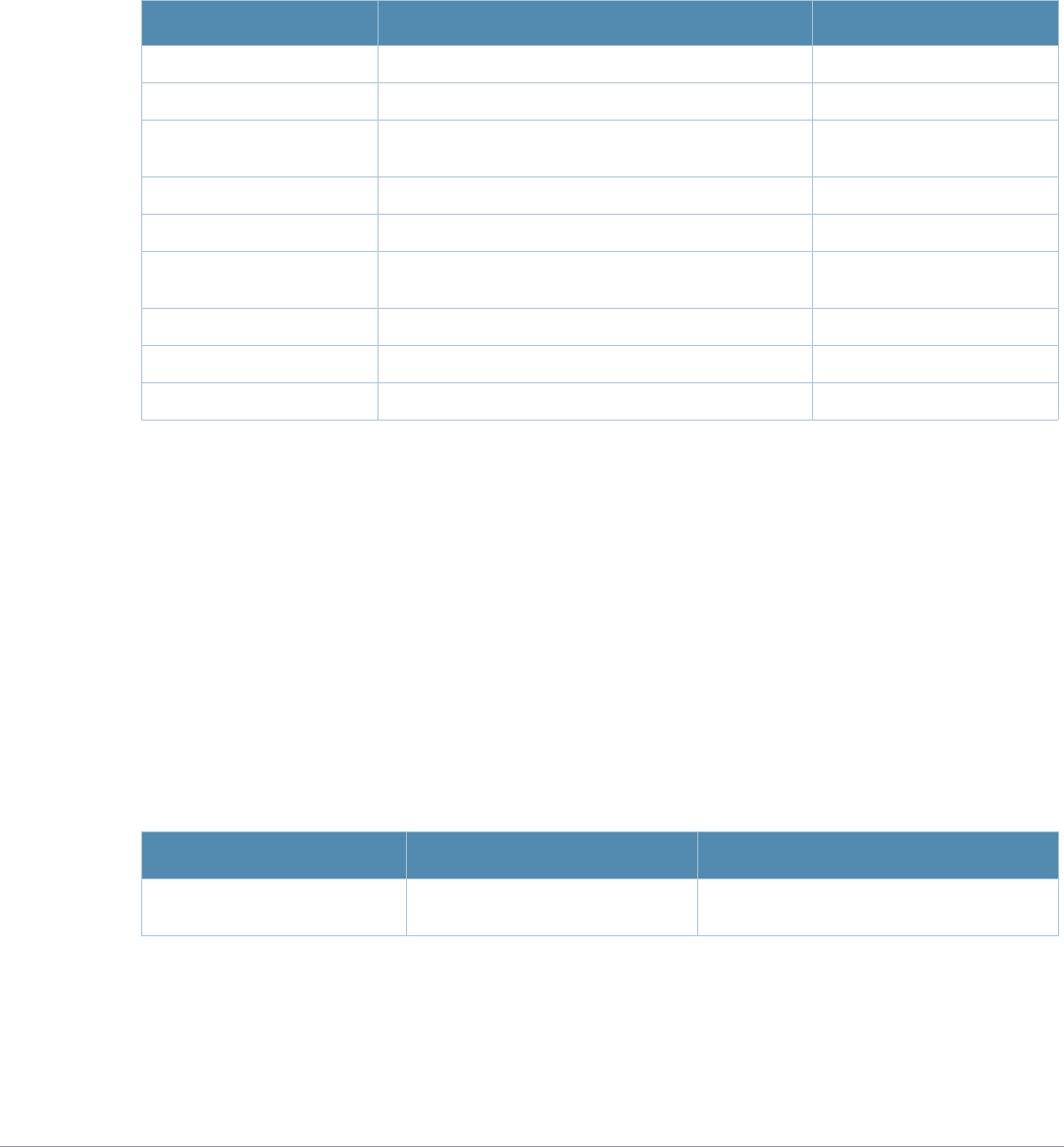
AOS-W 3.4.1 Command Line Interface | Reference Guide apboot | 113
apboot
apboot {all [global|local]|ap-group <group> [global|local]|ap-name <name>|ip-addr
<ipaddr>|wired-mac <macaddr>}
Description
This command reboots the specified APs.
Syntax
Usage Guidelines
You should not normally need to use this command as APs automatically reboot when you reprovision
them. Use this command only when directed to do so by your Alcatel-Lucent representative.
Example
The following command reboots a specific AP:
(host)(config)# apboot ap-name Building3-Lobby
Command History
This command was introduced in AOS-W 3.0.
Command Information
Parameter Description Default
all Reboot all APs. all
global Reboot APs on all switches. global
local Reboot only APs registered on this switch. This is the
default. local
ap-group Reboot APs in a specified group. ap-group
global Reboot APs on all switches. global
local Reboot only APs registered on this switch. This is the
default. local
ap-name Reboot the AP with the specified name. ap-name
ip-addr Reboot the AP at the specified IP address. ip-addr
wired-mac Reboot the AP at the specified MAC address. wired-mac
Platforms Licensing Command Mode
All platforms Base operating system Enable and Config mode on master
switches

114 | apboot AOS-W 3.4.1 Command Line Interface | Reference Guide
AOS-W 3.4.1 Command Line Interface | Reference Guide apflash | 115
apflash
apflash {ap-name <name>|ip-addr <ipaddr>|wired-mac <macaddr>} [backup-partition]
[server <ipaddr>]
Description
This command reflashes the specified AP.
Syntax
Usage Guidelines
This command directs an AP to download its image from the switch. You should not normally need to run
this command, as Alcatel-Lucent APs automatically download their images from a switch during bootup.
Example
The following command reflashes a specific AP:
(host) (config) #apflash ap-name Building3-Lobby
Command History
This command was introduced in AOS-W 3.0.
Command Information
Parameter Description
ap-name Reflash the AP with the specified name.
ip-addr Reflash the AP at the specified IP address.
wired-mac Reflash the AP at the specified MAC address.
backup-partition (OAW-AP80M only) Reflash partition two.
server IP address of the FTP server.
Platforms Licensing Command Mode
All platforms Base operating system Enable and Config modes on master
switches

116 |apflash AOS-W 3.4.1 Command Line Interface | Reference Guide
AOS-W 3.4.1 Command Line Interface | Reference Guide apconnect | 117
apconnect
apconnect {ap-name <name>|bssid <bssid>|ip-addr <ipaddr>} parent-bssid <bssid>
Description
This command instructs a mesh point to disconnect from its current parent and connect to a new parent.
Syntax
Usage Guidelines
To maintain a mesh topology created using the apconnect command, Alcatel-Lucent suggests setting the
mesh reselection-mode to reselect-never, otherwise the normal mesh reselection mechanisms could break
up the selected topology.
Example
The following command connects the mesh point “meshpoint1” to a new parent with the specified BSSID.
(host) (config) #apconnect ap-name meshpoint1 parent-bssid 00:12:6d:03:1c:f1
Related Commands
Command History
This command was introduced in AOS-W 3.4.1
Command Information
Parameter Description
ap-name <name> Specify the name of the mesh point to be connected to a new parent.
bssid <bssid> Specific the BSSID of the mesh point to be connected to a new parent.
ip-addr <ipaddr> Specific the IP address of the mesh point to be connected to a new parent.
parent-bssid <bssid> BSSID of the parent to which the mesh point should connect.
Command Description Mode
ap mesh-radio-profile
reselection-mode reselect-
never
Use this command to prevent the AP from
reselecting a new parent. Enable or Config mode
Platforms Licensing Command Mode
All platforms Base operating system Enable and Config mode on master
switches

118 | apconnect AOS-W 3.4.1 Command Line Interface | Reference Guide
AOS-W 3.4.1 Command Line Interface | Reference Guide apdisconnect | 119
apdisconnect
apdisconnect {ap-name <name>|bssid <bssid>|ip-addr <ipaddr>}
Description
This command disconnects a mesh point from its parent.
Syntax
Usage Guidelines
Each mesh point learns about the mesh portal from its parent (a mesh node that is part of the path to the
mesh portal). This command directs a mesh point to disassociate from its parent. The mesh point will
attempt to associate with another neighboring mesh node, if available. The old parent is not eligible for re-
association for 60 seconds after disconnection.
Example
The following command disconnects a specific mesh point from its parent:
(host) (config) #apdisconnect ap-name meshpoint1
Related Commands
Command History
This command was introduced in AOS-W 3.2
Command Information
Parameter Description
ap-name Specifies the name of the parent AP.
bssid Specifies the BSSID of the parent AP.
ip-addr Specifies the IP address of the parent AP.
Command Description Mode
apconnect This command connects a mesh point to a new specified parent. Enable or Config mode
Platforms Licensing Command Mode
All platforms Base operating system Enable and Config mode on master
switches

120 | apdisconnect AOS-W 3.4.1 Command Line Interface | Reference Guide
AOS-W 3.4.1 Command Line Interface | Reference Guide arp | 121
arp
arp <ipaddr> <macaddr>
Description
This command adds a static Address Resolution Protocol (ARP) entry.
Syntax
Usage Guidelines
If the IP address does not belong to a valid IP subnetwork, the ARP entry is not added. If the IP interface
that defines the subnetwork for the static ARP entry is deleted, you will be unable to use the arp command
to overwrite the entry’s current values; use the no arp command to negate the entry and then enter a new
arp command.
Example
The following command configures an ARP entry:
(host) (config) #arp 10.152.23.237 00:0B:86:01:7A:C0
Command History
This command was introduced in AOS-W 3.0.
Command Information
Parameter Description
<ipaddr> IP address of the device to be added.
<macaddr> Hardware address of the device to be added, in the format xx:xx:xx:xx:xx:xx.
Platforms Licensing Command Mode
All platforms Base operating system Config mode on master switches

122 |arp AOS-W 3.4.1 Command Line Interface | Reference Guide
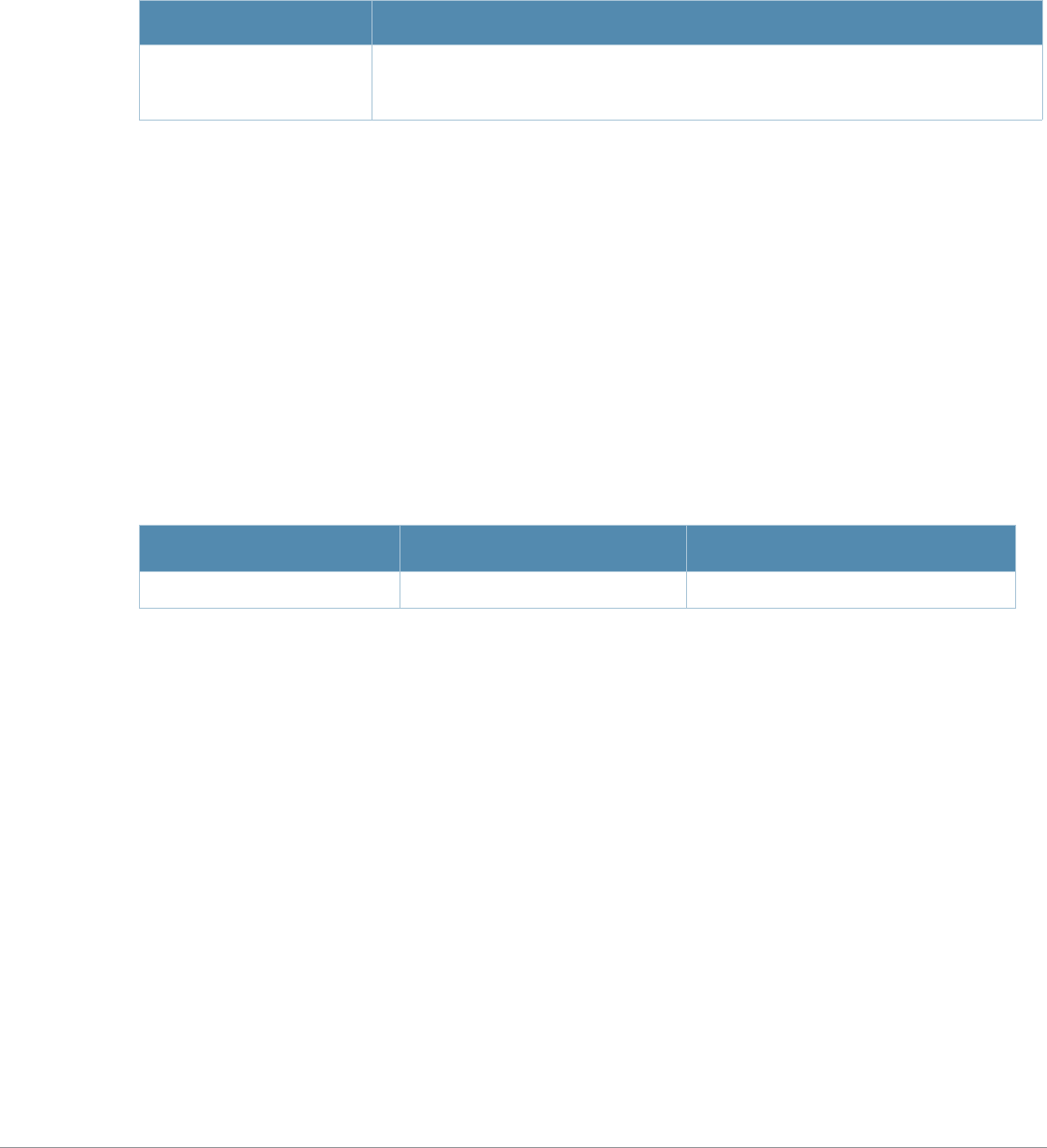
AOS-W 3.4.1 Command Line Interface | Reference Guide audit-trail | 123
audit-trail
audit-trail [all]
Description
This command enables an audit trail.
Syntax
Usage Guidelines
By default, audit trail is enabled for all commands in configuration mode. Use the show audit-trail
command to display the content of the audit trail.
Example
The following command enables an audit trail:
(host) (config) #audit-trail
Command History
This command was introduced in AOS-W 3.0.
Command Information
Parameter Description
all Enables audit trail for all commands, including enable mode commands. The audit-
trail command without this option enables audit trail for all commands in
configuration mode.
Platforms Licensing Command Mode
All platforms Base operating system Config mode on master switches

124 | audit-trail AOS-W 3.4.1 Command Line Interface | Reference Guide
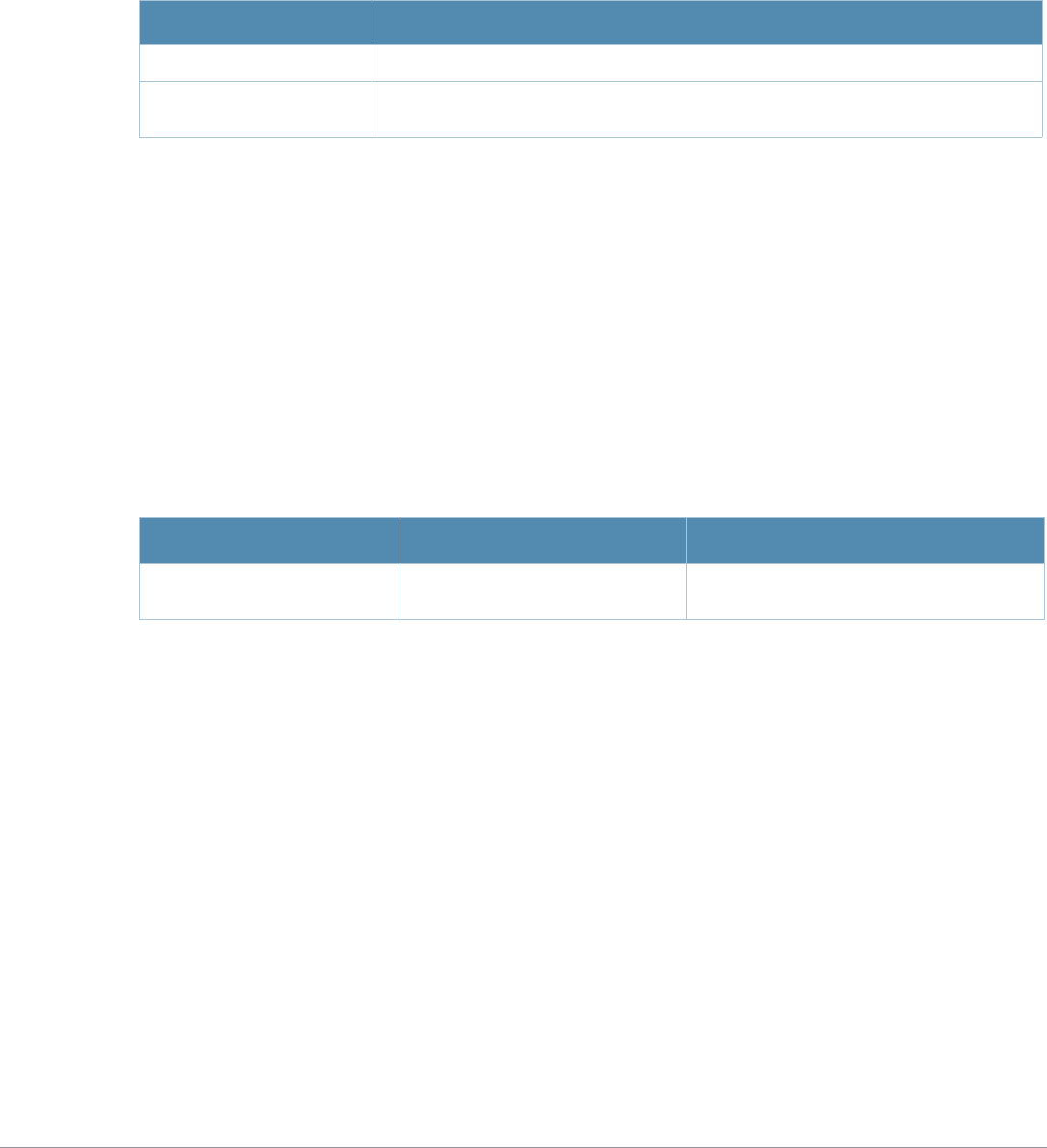
AOS-W 3.4.1 Command Line Interface | Reference Guide backup | 125
backup
backup {flash|pcmcia}
Description
This command backs up compressed critical files in flash.
Syntax
Usage Guidelines
Use the restore flash command to untar and uncompress the flashbackup.tar.gz file.
Example
The following command backs up flash directories to the flashbackup.tar.gz file:
(host)(config) #backup flash
Command History
This command was introduced in AOS-W 3.0.
Command Information
Parameter Description
flash Backs up flash directories to flashbackup.tar.gz file.
pcmcia Backs up flash images to external PCMCIA flash card. This option can only be
executed on switches that have a PCMCIA slot.
Platforms Licensing Command Mode
All platforms Base operating system Enable and Config modes on master
switches

126 |backup AOS-W 3.4.1 Command Line Interface | Reference Guide
AOS-W 3.4.1 Command Line Interface | Reference Guide banner motd | 127
banner motd
banner motd <delimiter> <textString>
Description
This command defines a text banner to be displayed at the login prompt when a user accesses the switch.
Syntax
Usage Guidelines
The banner you define is displayed at the login prompt to the switch. The banner is specific to the switch on
which you configure it. The WebUI displays the configured banner at its login prompt, but you cannot use
the WebUI to configure the banner.
The delimiter is a single character that indicates the beginning and the end of the text string in the banner.
Select a delimiter that is not used in the text string you define, because the switch ends the banner when it
sees the delimiter character repeated.
There are two ways of configuring the banner message:
zEnter a space between the delimiter and the beginning of the text string. The text can include any
character except a quotation mark (“). Use quotation marks to enclose your text if you are including
spaces (spaces are not recognized unless your text string is enclosed in quotation marks; without
quotation marks, the text is truncated at the first space). You can also use the delimiter character within
quotation marks.
zPress the Enter key after the delimiter to be placed into a mode where you can simply enter the banner
text in lines of up to 255 characters, including spaces. Quotation marks are ignored.
Example
The following example configures a banner by enclosing the text within quotation marks:
(host)(config) #banner motd * “Welcome to my switch. This switch is in the production
network, so please do not save configuration changes. Maintenance will be performed at
7:30 PM, so please log off before 7:00 PM.”*
The following example configures a banner by pressing the Enter key after the delimiter:
(host)(config) #banner motd *
Enter TEXT message [maximum of 1023 characters].
Each line in the banner message should not exceed 255 characters.
End with the character '*'.
Welcome to my switch. This switch is in the production network, so please do not save
configuration changes. Maintenance will be performed at 7:30 PM, so please log off
before 7:00 PM.*
The banner display is as follows:
Welcome to my switch. This switch is in the production network, so please do not save
configuration changes. Maintenance will be performed at 7:30 PM, so please log off
before 7:00 PM.
Parameter Description Range
<delimiter> Indicates the beginning and end of the banner text. —
<textString> The text you want displayed. up to 1023 characters

128 |banner motd AOS-W 3.4.1 Command Line Interface | Reference Guide
Command History
This command was introduced in AOS-W 1.0
Command Information
Platforms Licensing Command Mode
All platforms Base operating system Config mode on master switches
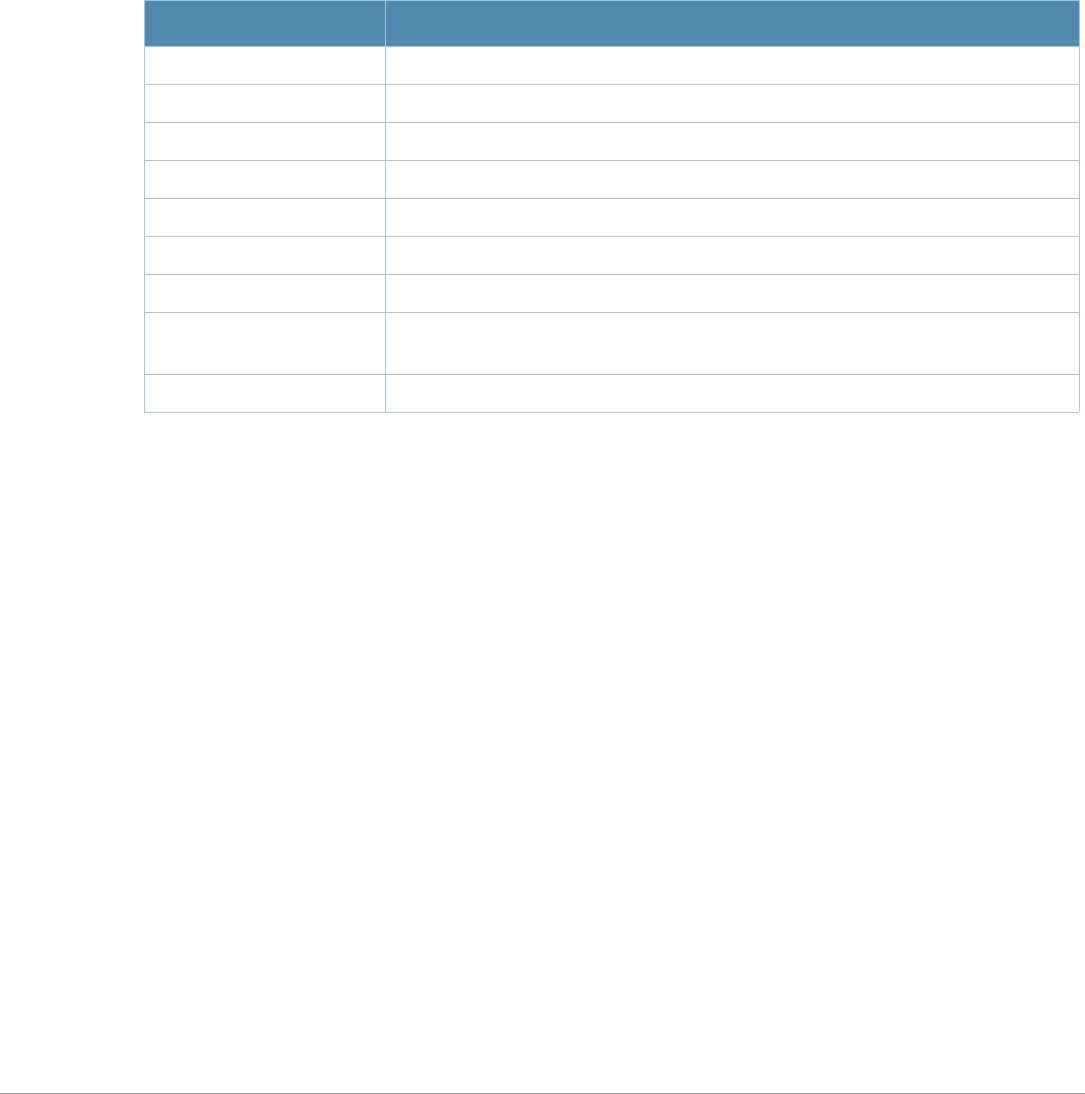
AOS-W 3.4.1 Command Line Interface | Reference Guide boot | 129
boot
boot
cf-test [fast | read-only | read-write]
config-file <filename>
system partition [0 | 1]
verbose
Description
This command configures the boot options for the switch.
Syntax
Usage Guidelines
Use the following options to control the boot behavior of the switch:
zcf-test—Test the flash during boot.
zconfig-file—Set the configuration file to use during boot.
zsystem—Specify the system partition to use during boot.
zverbose—Print extra debugging information during boot. The information is sent to the screen at boot
time. Printing the extra debugging information is disabled using the no boot verbose command.
Example
The following command uses the configuration file january-config.cfg the next time the switch boots:
boot config-file january-config.cfg
The following command uses system partition 1 the next time the switch boots:
boot system partition 1
Command History
This command was introduced in AOS-W 1.0.
Parameter Description
cf-test Sets the type of compact flash test to run when booting the switch.
fast Performs a fast test, which does not include media testing.
read-only Performs a read-only media test.
read-write Performs a read-write media test.
config-file Sets the configuration file to use when booting the switch.
<filename> Specifies the name of the configuration file from which to boot the switch.
system Specifies the system partition to use when booting the switch.
0 | 1 Indicates the partition to use as either 0 or 1.
One of the partitions is the active partition and the other is the backup.
verbose Prints extra debugging information at boot.

130 |boot AOS-W 3.4.1 Command Line Interface | Reference Guide
Command Information
Platforms Licensing Command Mode
All platforms Base operating system Enable and Config mode on master
switches

AOS-W 3.4.1 Command Line Interface | Reference Guide cellular profile | 131
cellular profile
cellular profile <profile_name>
dialer <group>
driver acm|hso|option|sierra
import <address>
modeswitch {eject <params>}|rezero
no
priority <1-255>
serial <sernum>
tty <ttyport>
user <login> password <password>
vendor <vend_id> product <prod_id>
Description
Create new profiles to support new USB modems or to customize USB characteristics.
Syntax
Parameter Description
cellular profile <profile_name> Enter the keywords cellular profile followed by your profile name.
This command changes the configuration mode and the command
line prompt changes to:
host (config-cellular <profile_name>)#
dialer <group> Enter the keyword dialer followed by a group name to specify the
dialing parameters for the carrier. The parameters tend to be common
between service providers on the same type of network (CDMA vs.
GSM) as displayed in the show dialer group command.
driver acm|hso|option|sierra Enter the keyword driver followed by one of the driver options:
zacm: Linux ACM driver.
zhso: Option High Speed driver.
zoption: Option USB data card driver (default).
zsierra: Sierra Wireless driver.
import <address> Enter the keyword import followed by the USB device address as
displayed in the show usb command. Import retrieves the vendor/
product serial numbers from the USB device list and populates them
into the profile.
modeswitch {eject
<params>}|rezero
Enter the keyword modeswitch followed by either:
zeject followed by the CDROM device.
zrezero: Send SCSI CDROM rezero command.
Certain cellular devices must be modeswitched before the modem
switches to data mode.
no Enter the keyword no to negate the command and revert back to the
defaults.
priority <1-255> Enter the keyword priority to override the default cellular priority (100).
Range: 1 to 255.
Default: 100
serial <sernum> Enter the keyword serial followed by the USB device serial number
tty <ttyport> Enter the keyword tty followed by the Modem TTY port (i.e. ttyUSB0,
ttyACM0)
user <login> password <password> Enter the keyword user followed by your login, and then enter the
keyword password followed by your password to establish user
name authentication.
132 | cellular profile AOS-W 3.4.1 Command Line Interface | Reference Guide
Usage Guidelines
The cellular modems are plug-and-play and support most native USB modems. Cellular modems are
activated only if it is the uplink with the highest priority (see show uplink). However, new profiles can be
created using this command to support new data cards or to customize card characteristics.
Command History
Introduced in AOS-W 3.4.
Command Information
vendor <vend_id> product
<prod_id> in hex
Enter the keyword vendor followed by the vendor ID in hexadecimal
(see show usb) and then enter the keyword product followed by the
product ID listed in the show usb command.
Parameter Description
Platforms Licensing Command Mode
OmniAccess 4306 switches Base operating system Config mode on master and local switches
(config-cellular <profile_name>)

AOS-W 3.4.1 Command Line Interface | Reference Guide cfgm | 133
cfgm
cfgm {mms config {enable|disable}|set config-chunk <kbytes>|set heartbeat <seconds>|set
maximum-updates <number>|snapshot-timer <minutes>}
Description
This command configures the configuration module on the master switch.
Syntax
Usage Guidelines
By default, OmniVista Mobility Manager configuration updates on the switch are disabled to prevent any
alterations to the switch configuration. You need to explicitly enable OmniVista Mobility Manager
configuration updates for the switch to accept configuration changes from OmniVista Mobility Manager.
When OmniVista Mobility Manager configuration updates are enabled, global configuration changes can
only be done from OmniVista Mobility Manager and are not available on the master switch. You can use the
cfgm mms config disable command if the switch loses connectivity to the OmniVista Mobility Manager
and you must enter a configuration change on the master switch.
Example
The following command allows configuration updates from the OmniVista Mobility Manager:
(host)(config) #cfgm mms config enable
Command History
This command was introduced in AOS-W 3.1.
Parameter Description Range Default
mms config Permits OmniVista Mobility Manager (OmniVista
Mobility Manager) configuration updates on the
master switch. When enabled, global configuration
changes can only be done from OmniVista Mobility
Manager and are not available on the master switch.
enable|
disable disabled
set config-chunk Maximum packet size, in Kilobytes, that is sent every
second to the local switch whenever the master
switch sends a configuration to the local. If the
connection between the master and local is slow or
uneven, you can lower the size to reduce the amount
of data that needs to be retransmitted. If the
connection is very fast and stable, you can increase
the size to make the transmission more efficient.
1-100 10 Kbytes
set heartbeat Interval, in seconds, at which heartbeats are sent.
You can increase the interval to reduce traffic load. 10-300 10 seconds
set maximum-
updates
Maximum number of local switches that can be
updated at the same time with configuration
changes. You can decrease this value if you have a
busy network. You can increase this value to improve
configuration synchronization.
2-25 5
snapshot-timer Interval, in minutes, that the local switch waits for a
configuration download from the master upon bootup
or startup before loading the last snapshot
configuration.
5-60 5 minutes

134 |cfgm AOS-W 3.4.1 Command Line Interface | Reference Guide
Command Information
Platforms Licensing Command Mode
All platforms Base operating system Config mode on master switches
AOS-W 3.4.1 Command Line Interface | Reference Guide clear | 135
clear
clear
aaa
ap
arp
counters
crypto
datapath
dot1x
fault
gab-db
ip
ipc
ipv6
loginsession
master-local-entry
master-local-session
port
provisioning-ap-list
provisioning-params
rap-wml
update-counter
voice
vpdn
wms
clock
Description
This command clears various user-configured values from your running configuration.
Syntax
Parameter Description
aaa Clear all values associated with authentication profile
authentication-
server
Provide authentication server details to clear values specific to an authentication
server or all authentication server.
Parameters:
zall—clear all server statistics.
zinternal—clear internal server statistics.
zradius—clear radius server statistics.
state Clear internal status of authentication modules.
Parameters:
zconfiguration—clear all configured objects.
zdebug-statistics—clear debug statistics.
zmessages—clear authentication messages that were sent and received.
ap Clear all AP related information.
coverage-hole Clears the coverage hole details from the RF optimization plan. Coverage hole is the
area in your floor plan without any wireless signal.
mesh Clear all mesh statistics.
remote Clear all information related to remote configuration.

136 |clear AOS-W 3.4.1 Command Line Interface | Reference Guide
arp Clear all ARP table information. You can either clear all information or enter the IP
address of the ARP entry to clear a specific value.
counters Clear all interface configuration values.
fastethernet Clears configuration related to fastethernet ports.
gigabitethernet Clears configuration related to fastethernet ports.
tunnel Clears all tunnel configuration values on interface ports.
vrrp Clears all VRRP configuration values on interface ports.
datapath Clears all configuration values and statistics for the following datapath modules.
zapplication
zbridge
zbwm
zcrypto
zdma
zframe
zhardware
zip-reassembly
zmaintenance
zmessage-queue
zroute
zroute-cache
zsession
zstation
ztunnel
zuser
zwifi-reassembly
zwmm
dot1x Clears all 802.1x specific counters and supplicant statistics. Use the following
parameters:
zcounters
zsupplicant-info
fault Clears all SNMP fault configuration.
gap-db Clears global AP database. Essentially used to clear all stale AP records.
ip Clears all IP information from DHCP bindings, IGMP groups and IP mobility
configuration. Use the following parameters:
zdhcp
zigmp
zmobile
ipc Clears all interprocess communication statistics.
ipv6 Clears all IPv6 session and user statistics. Use the following parameters:
zdatapath session counters
zdatapath user counters
loginsession Clears loginsession information of a specific login session identified by the session
id.
master-local-entry Clears local switch information from the master switch LMS list. Specify the IP
address of the local switch to be removed from master switch active LMS list.
master-local-session Clear and reset master local TCP connection. Specify the IP address of either the
master or local switch.
Parameter Description
AOS-W 3.4.1 Command Line Interface | Reference Guide clear | 137
Usage Guidelines
The clear command will clear the specified parameters of their current values.
Example
The following command clears all aaa counters for all authentication servers:
(host) (config) #clear aaa authentication-server all
Command History
This command was introduced in AOS-W 3.0.
Command Information
port Clear all port statistics that includes link-event counters or all counters. Use the
following parameters:
zlink-event
zstats
provisioning-ap-list Clear AP entries from the provisioning list.
provisioning-params Clear provision parameters and reset to the default configuration parameters.
rap-wml Clear wired MAC lookup cache for a DB server.
update-counter Clear all update counter statistics.
voice Clear all voice state information. Use the following parameters:
zcall-counters
zcall-status
vpdn Clear all VPDN configuration for L2TP and PPTP tunnel. Use the following
parameters:
ztunnel l2tp id <l2tp-tunnel-id>
ztunnel pptp id <pptp-tunnel-id>
wms Clear all WLAN management commands. Use the following parameters:
zap—clear all AP related commands. Specify the BSSID of the AP.
zclient—clear all wired client related commands. Specify the MAC address of
the client.
zprobe—clear all probe information. Specify the BSSID of the probe.
zwired-mac—clear all wired MAC information. You can specify MAC of APs, or
name of an AP.
wired-mac <mac-address>
wired-mac ap-name <name of the AP>
Parameter Description
Platforms Licensing Command Mode
All platforms Base operating system Enable and Config mode on master
switches

138 |clear AOS-W 3.4.1 Command Line Interface | Reference Guide
AOS-W 3.4.1 Command Line Interface | Reference Guide clock set | 139
clock set
clock
clock set <year><month><day><time>
Description
This command sets the date and time.
Syntax
Usage Guidelines
You can configure the year, month, day, and time. You must configure all four parameters.
Specify the time using a 24-hour clock. You must specify the seconds.
Example
The following example configures the clock to January 1st of 2007, at 1:03:52 AM.
(host)(config) #clock set 2007 jan 1 1 3 52
Command History
This command was introduced in AOS-W 1.0
Command Information
Parameter Description Range
year Sets the year. Requires all 4 digits. Numeric
month Sets the month. Requires the first three letters of the month. Alphabetic
day Sets the day. 1-31
time Sets the time. Specify hours, minutes, and seconds separated by
spaces. Numeric
Platforms Licensing Command Mode
All platforms Base operating system Config mode on master switches

140 | clock summer-time recurring AOS-W 3.4.1 Command Line Interface | Reference Guide
clock summer-time recurring
clock summer-time <WORD> [recurring]
<1-4> <start day> <start month> <hh:mm>
first <start day> <start month> <hh:mm>
last <start day> <start month> <hh:mm>
<1-4> <end day> <end month> <hh:mm>
first <end day> <end month> <hh:mm>
last <end day> <end month> <hh:mm>
[<-23 - 23>]
Description
Set the software clock to begin and end daylight savings time on a recurring basis.
Syntax
Usage Guidelines
This command subtracts exactly 1 hour from the configured time.
The WORD can be any alphanumeric string, but cannot start with a colon (:). A WORD longer than five
characters is not accepted. If you enter a WORD containing punctuation, the command is accepted, but the
timezone is set to UTC.
You can configure the time to change on a recurring basis. To do so, set the week, day, month, and time
when the change takes effect (daylight savings time starts). You must also set the week, day, month, and
time when the time changes back (daylight savings time ends).
The start day requires the first three letters of the day. The start month requires the first three letters
of the month.
You also have the option to set the number of hours by which to offset the clock from UTC. This has the
same effect as the clock timezone command.
Parameter Description Range
WORD Enter the abbrivation for your time zone. For example, PDT for Pacific
Daylight Time. 3-5 characters
1-4 Enter the week number to start/end daylight savings time. For example,
enter 2 to start daylight savings time on the second week of the month. 1-4
first Enter the keyword first to have the time change begin or end on the first
week of the month. —
last Enter the keyword last to have the time change begin or end on the last
week of the month. —
start day Enter the weekday when the time change begins or ends. Sunday-
Saturday
start month Enter the month when the time change begins or ends. January-
December
hh:mm Enter the time, in hours and minutes, that the time change begins or
ends. 24 hours
-23 - 23 Hours offset from the Universal Time Clock (UTC). -23 - 23

AOS-W 3.4.1 Command Line Interface | Reference Guide clock summer-time recurring | 141
Example
The following example sets daylight savings time to occur starting at 2:00 AM on Sunday in the second week
of March, and ending at 2:00 AM on Sunday in the first week of November. The example also sets the name
of the time zone to PST with an offset of UTC - 8 hours.
clock summer-time PST recurring 2 Sun Mar 2:00 first Sun Nov 3:00 -8
Command History
This command was introduced in AOS-W 1.0
Command Information
Platforms Licensing Command Mode
All platforms Base operating system Config mode on master switches
142 |clock timezone AOS-W 3.4.1 Command Line Interface | Reference Guide
clock timezone
clock timezone <name> <-23 to 23>
Description
This command sets the timezone on the switch.
Syntax
Usage Guidelines
The name parameter can be any alphanumeric string, but cannot start with a colon (:). A time zone name
longer than five characters is not accepted. If you enter a time zone name containing punctuation, the
command is accepted, but the timezone is set to UTC.
Example
The following example configures the timezone to PST with an offset of UTC - 8 hours.
clock timezone PST -8
Command History
This command was introduced in AOS-W 1.0
Command Information
Parameter Description Range
<name> Name of the time zone. 3-5 characters
-23 to 23 Hours offset from UTC. -23 to 23
Platforms Licensing Command Mode
All platforms Base operating system Config mode on master switches

AOS-W 3.4.1 Command Line Interface | Reference Guide configure terminal | 143
configure terminal
configure terminal
Description
This command allows you to enter configuration commands.
Syntax
No Parameters.
Usage Guidelines
Upon entering this command, the enable mode prompt changes to:
(host) (config) #
To return to enable mode, enter Ctrl-Z or exit.
Example
The following command allows you to enter configuration commands:
(host) # configure terminal
Related Commands
Other commands required to configure a feature or show current settings. This may not be required for all
commands.
Command History
This command was introduced in AOS-W 3.0.
Command Information
Platforms Licensing Command Mode
All platforms Base operating system Enable mode on master switches

144 | configure terminal AOS-W 3.4.1 Command Line Interface | Reference Guide

AOS-W 3.4.1 Command Line Interface | Reference Guide controller-ip | 145
controller-ip
controller-ip [loopback|vlan <VLAN ID>]
no ...
Description
This command sets the switch IP to the loopback interface address or a specific VLAN interface address.
Syntax
Usage Guidelines
This command allows you to set the switch IP to the loopback interface address or a specific VLAN
interface address. If the switch IP command is not configured then the switch IP defaults to the loopback
interface address. If the loopback interface address is not configured then the first configured VLAN
interface address is selected. Generally, VLAN 1 is the factory default setting and thus becomes the switch
IP address.
Example
The following command sets the switch IP address to VLAN interface 6.
(host) (config) #controller-ip vlan 6
Related Commands
(host) (config) #show controller-ip
Command History
This command was introduced in AOS-W 3.4
Command Information
Parameter Description Default
loopback Sets the switch IP to the loopback interface. disabled
vlan Set the switch IP to a VLAN interface. —
VLAN ID Specifies the VLAN interface ID. —
Platform License Command Mode
Available on all platforms Base operating system Config mode on master switches

146 | controller-ip AOS-W 3.4.1 Command Line Interface | Reference Guide

AOS-W 3.4.1 Command Line Interface | Reference Guide copy | 147
copy
copy
flash: <srcfilename> {flash: <destfilename> |
scp: <scphost> <username>
<destfilename> |
tftp: <tftphost> <destfilename>} |
ftp: <ftphost> <user> <filename> system: partition {0|1} |
running-config {flash: <filename> | ftp: <ftphost> <user> <password> <filename>
[<remote-dir>] | startup-config | tftp: <tftphost> <filename>} |
scp: <scphost> <username> <filename> {flash: <destfilename>| system: partition [0|1]}|
startup-config {flash: <filename> | tftp: <tftphost> <filename>} |
system: partition {<srcpartition> 0|1} [<destpartition> 0 | 1] |
tftp: <tftphost> <filename> {flash: <destfilename> | system: partition [0|1]}
Description
This command copies files to and from the switch.
Syntax
Parameter Description
flash: Copy the contents of the switch’s flash file system, the system image, to a specified
destination.
srcfilename Full name of the flash file to be copied.
flash: Copy the file to the flash file system.
destfilename Specify the new name of the copied file.
tftp: Copy the file to a TFTP server.
tftphost Specify the IP address or hostname of the TFTP server.
ftp: Copy a file from the FTP server.
ftphost Specify the IP address or hostname of the FTP server.
user User account name required to access the FTP server.
filename Full name of the file to be copied.
0 | 1 Specify the system partition to save the file.
running-config Copy the active, running configuration to a specified destination.
flash: Copy the configuration to the flash file system.
filename Specify the new name of the copied configuration file.
ftp: Using FTP, copy the configuration to an FTP server.
ftphost Specify the IP address of the FTP server.
user User account name required to access the FTP server.
password Password required to access the FTP server.
remote-dir Specify a remote directory, if needed.
startup-config Copy the active, running configuration to the start-up configuration.
tftp: Using TFTP, copy the configuration to a TFTP server
tftphost Specify the IP address or hostname of the TFTP server.
148 |copy AOS-W 3.4.1 Command Line Interface | Reference Guide
Usage Guidelines
Use this command to save back-up copies of the configuration file to an FTP or TFTP server, or to load a
saved file from an FTP or TFTP server.
Three partitions reside on the file system flash. Totalling 256MB, the three partitions provide space to hold
the system image files (in partitions 1 and 2 which are 45MB each) and user files (in partition 3, which is
165MB). System software runs on the system partitions; the database, DHCP, startup configuration, and
logs are positioned on the user partition.
To restore a database, copy the database from the network server and import the database.
To restore a configuration file, copy the file from network server to the switch’s flash system then copy the
file from the flash system to the system configuration. This ensures that you do not accidentally overwrite
your system startup configuration file.
Example
scp: Copy an AOS-W image file or file from the flash file system using the Secure Copy
protocol. The SCP server or remote host must support SSH version 2 protocol.
scphost Specify the IP address of the SCP server or remote host.
username User account name required to access the SCP server or remote host.
filename Specify the absolute path of the filename to be copied.
flash: Copy the file to the flash file system.
destfilename Specify the new name of the copied file.
system: Copy the file to the system partition.
startup-config Copy the startup configuration to a specified flash file or to a TFTP server.
flash: Copy the file to the flash file system.
filename Specify the new name of the copied startup configuration file.
tftp: Using TFTP, copy the startup configuration to a TFTP server
tftphost Specify the IP address or hostname of the TFTP server.
system: Copy the specified system partition
srcpartition Disk partition from which to copy the system data, as either 0 or 1.
destpartition Disk partition to copy the system data to, as either 0 or 1.
tftp: Copy a file from the specified TFTP server to either the switch or another destination.
This command is typically used when performing a system restoration, or to pull a
specified file name into the wms database.
tftphost Specify the IP address or hostname of the TFTP server.
filename Full name of the file to be copied.
flash: Copy the file to the flash file system
destfilename Specify the new name of the copied file.
system Copy the file to the system partition.
Parameter Description
AOS-W 3.4.1 Command Line Interface | Reference Guide copy | 149
The following commands copy the configuration file named engineering from the TFTP server to the
switch’s flash file system and then uses that file as the startup configuration. This example assumes the
startup configuration file is named default.cfg:
(host) (config) #copy tftp: 192.0.2.0 engineering flash: default.bak
copy flash: default.bak flash: default.cfg
Command History
This command was introduced in AOS-W 1.0.
Command Information
Platforms Licensing Command Mode
All platforms Base operating system Enable and Config modes on master
switches

150 |copy AOS-W 3.4.1 Command Line Interface | Reference Guide
AOS-W 3.4.1 Command Line Interface | Reference Guide cp-bandwidth-contract | 151
cp-bandwidth-contract
cp-bandwidth-contract <name> {mbits <1..2000>}|{kbits <256..2000000>}
Description
This command configures a bandwidth contract traffic rate which can then be associated with a whitelist
session ACL.
Syntax
Example
The following example configures a bandwidth contract named “cp-rate” with a rate of 10,000Kbps.
(host)(config) #cp-bandwidth-contract cp-rate kbits 10000
Related Commands
Command History
This command was introduced in AOS-W 3.4
Command Information
Parameter Description
<name> Name of a bandwidth contract.
mbits <1..2000> Set a bandwidth rate inn mbits/seconds.
kbits <256..2000000> Set a bandwidth rate in kbits/seconds.
Command Description Mode
show cp-bwcontracts Display a list of Control Processor (CP) bandwidth
contracts for whitelist ACLs. Enable or Config modes
firewall cp This command creates a new whitelist ACL and can
associate a bandwidth contract with that ACL. Enable or Config modes
Platforms Licensing Command Mode
All platforms This command requires the PEF
license. Config mode on master switches

152 | cp-bandwidth-contract AOS-W 3.4.1 Command Line Interface | Reference Guide
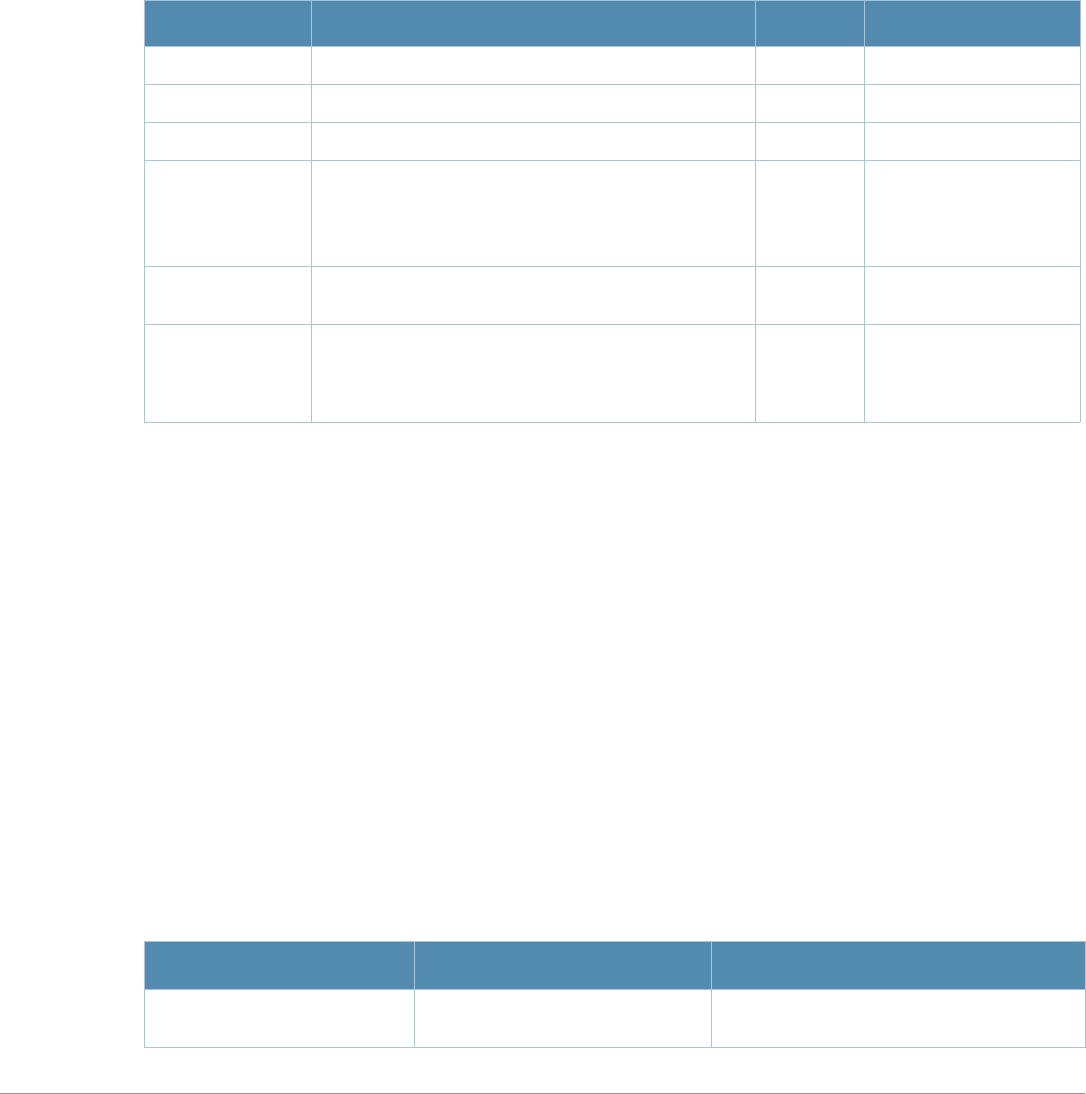
AOS-W 3.4.1 Command Line Interface | Reference Guide crypto dynamic-map | 153
crypto dynamic-map
crypto dynamic-map <name> <priority>
no ...
set puffs {group1|group2}
set security-association lifetime seconds <seconds>
set transform-set <name1> [<name2>] [<name3>] [<name4>]
Description
This command configures an existing dynamic map.
Syntax
Usage Guidelines
Dynamic maps enable IPsec SA negotiations from dynamically addressed IPsec peers. Once you have
defined a dynamic map, you can associate that map with the default global map using the command crypto
map global-map.
Example
The following command configures a dynamic map:
Command History
This command was introduced in AOS-W 3.0.
Command Information
Parameter Description Range Default
<name> Name of the map. — —
<priority> Priority of the map. 1-10000 10000
no Negates a configured parameter. — —
pfs Enables Perfect Forward Secrecy (PFS) mode. Use
one of the following:
group1: 768-bit Diffie Hellman prime modulus group
group2: 1024-bit Diffie Hellman prime modulus group
group1/
group2 disabled
seconds Configures the lifetime, in seconds, for the security
association (SA). 300-86400 no limit
transform-set Name of the transform set for this dynamic map. You
can specify up to four transform sets. You configure
transform sets with the crypto ipsec transform-set
command.
— default-transform
Platforms Licensing Command Mode
All platforms VPN Server and/or Remote AP
license Config mode on master switches
(host) (config)# crypto dynamic-map dmap1 100
set pfs group2
set security-association lifetime seconds 300
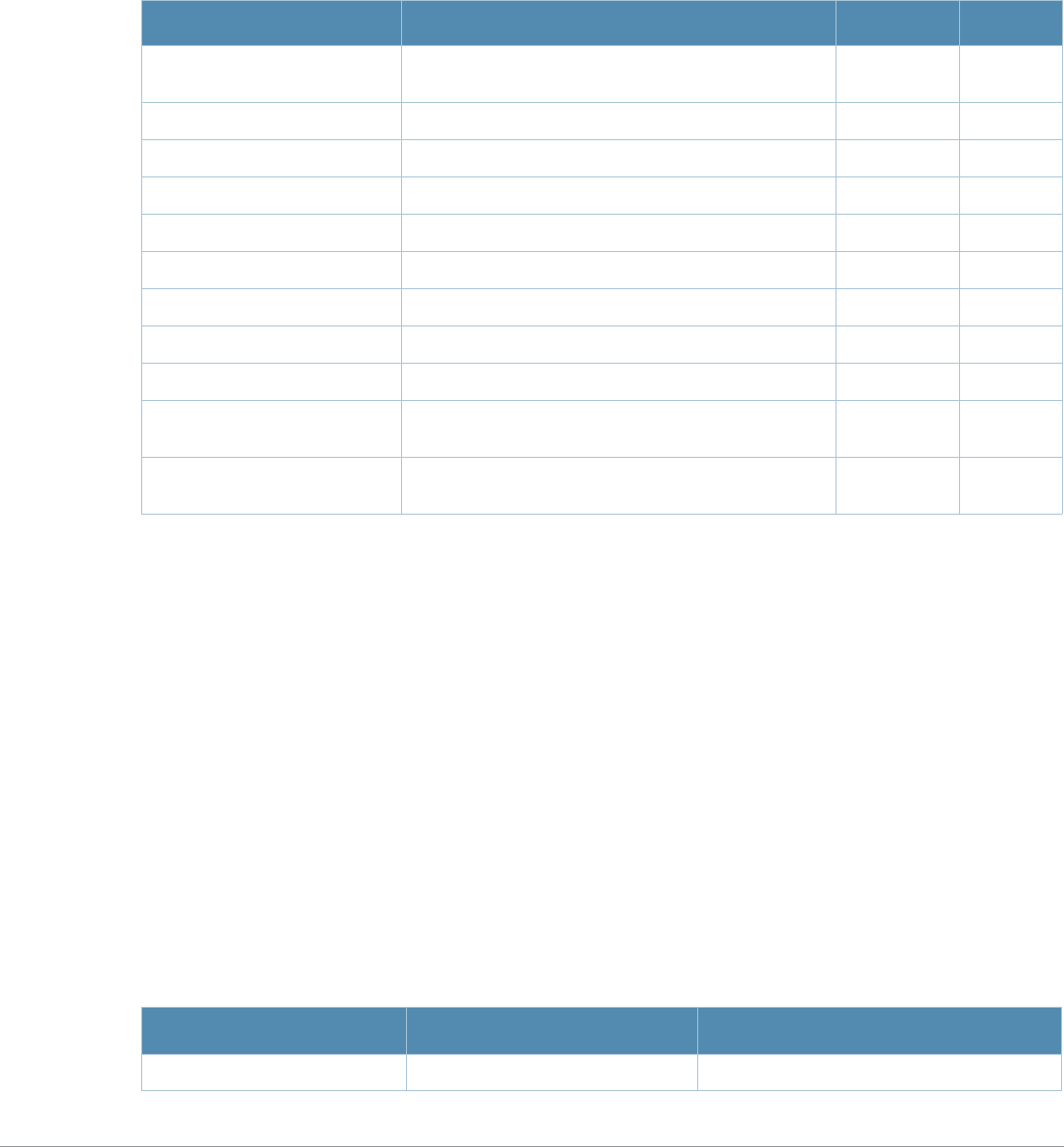
154 |crypto ipsec AOS-W 3.4.1 Command Line Interface | Reference Guide
crypto ipsec
crypto ipsec {mtu <max-mtu>}|{transform-set <transform-set-mtu> esp-3des|esp-
aes128|esp-aes192|esp-aes256|esp-des esp-md5-hmac|esp-sha-hmac}
Description
This command configures IPsec parameters.
Syntax
Usage Guidelines
Define the Maximum Transmission Unit (MTU) size allowed for network transmissions using IPsec
security, and create or edit transform sets that define a specific encryption and authentication type.
Example
The following command configures 3DES encryption and MD5 authentication for a transform set named
set1:
Command History
This command was introduced in AOS-W 3.0.
Command Information
Parameter Description Range Default
mtu Configure IPsec Maximum Transmission Unit (MTU)
parameters. ——
<max-mtu> Configure IPsec MTU. 1024-1500 1500
transform-set Create or modify a transform set. — —
<transform-set-mtu> Name of the transform set to create or modify. — —
esp-3des Use ESP with 168-bit 3DES encryption. — —
esp-aes128 Use ESP with 128-bit AES encryption. — —
esp-aes192 Use ESP with 192-bit AES encryption. — —
esp-aes256 Use ESP with 256-bit AES encryption. — —
esp-des Use ESP with 56-bit DES encryption. — —
esp-md5-hmac Use ESP with the MD5 (HMAC variant) authentication
algorithm
esp-sha-hmac Use ESP with the SHA (HMAC variant) authentication
algorithm
Platforms Licensing Command Mode
All platforms Base operating system Config mode on master switches
(host) (config)# crypto ipsec transform-set set1 esp-3des esp-md5-hmac

AOS-W 3.4.1 Command Line Interface | Reference Guide crypto isakmp | 155
crypto isakmp
crypto isakmp
{address <peer-address> netmask <mask>}|enable|disable|{groupname <name>} |
{key <keystring> address <peer-address> netmask <mask>}|
{psk-caching days <interval-days>}|
{psk-caching disable}|
{psk-caching hours <interval-hours>}|
{udpencap-behind-natdevice enable|disable}|
packet-dump
Description
This command configures Internet Key Exchange (IKE) parameters for the Internet Security Association
and Key Management Protocol (ISAKMP).
Syntax
Parameter Description
address Configure the IP address for the global group key.
<peer-address> IP address for the group key, in dotted-decimal format.
netmask Configure the IP netmask for the group key.
<mask> Subnet mask for the group key.
enable Enable IKE processing.
disable Disable IKE processing.
groupname Configure the IKE Aggressive group name. Aggressive-mode IKE is a 3-packet
IKE exchange that does not provide identity-protection, but is faster, because
fewer messages are exchanged.
<name> Name of the IKE aggressive group.
key Configure the IKE preshared key.
<keystring> Configure the value of the IKE PRE-SHARED key. The key must be between 6-64
characters long.
address Configure the IP address for the group key.
<peer-address> An IP for the group key, in dotted-decimal format.
netmask Configure the netmask for the group key IP address.
<mask> A subnet mask, in dotted-decimal format
psk-caching Configure IKE RAP PSK caching by specifying the interval of time for which the
previous PSK is valid.
If this feature is enabled, and the administrator changes the Global PSK, the
switch will accept connections from an AP using the previous PSK for the
configured time interval.
days Configure the PSK caching interval in days.
<interval-days> Caching interval.
disable Disable PSK caching. (This feature is disabled by default)
hours Configure the PSK caching interval in hours.
<interval-hours> Caching interval.
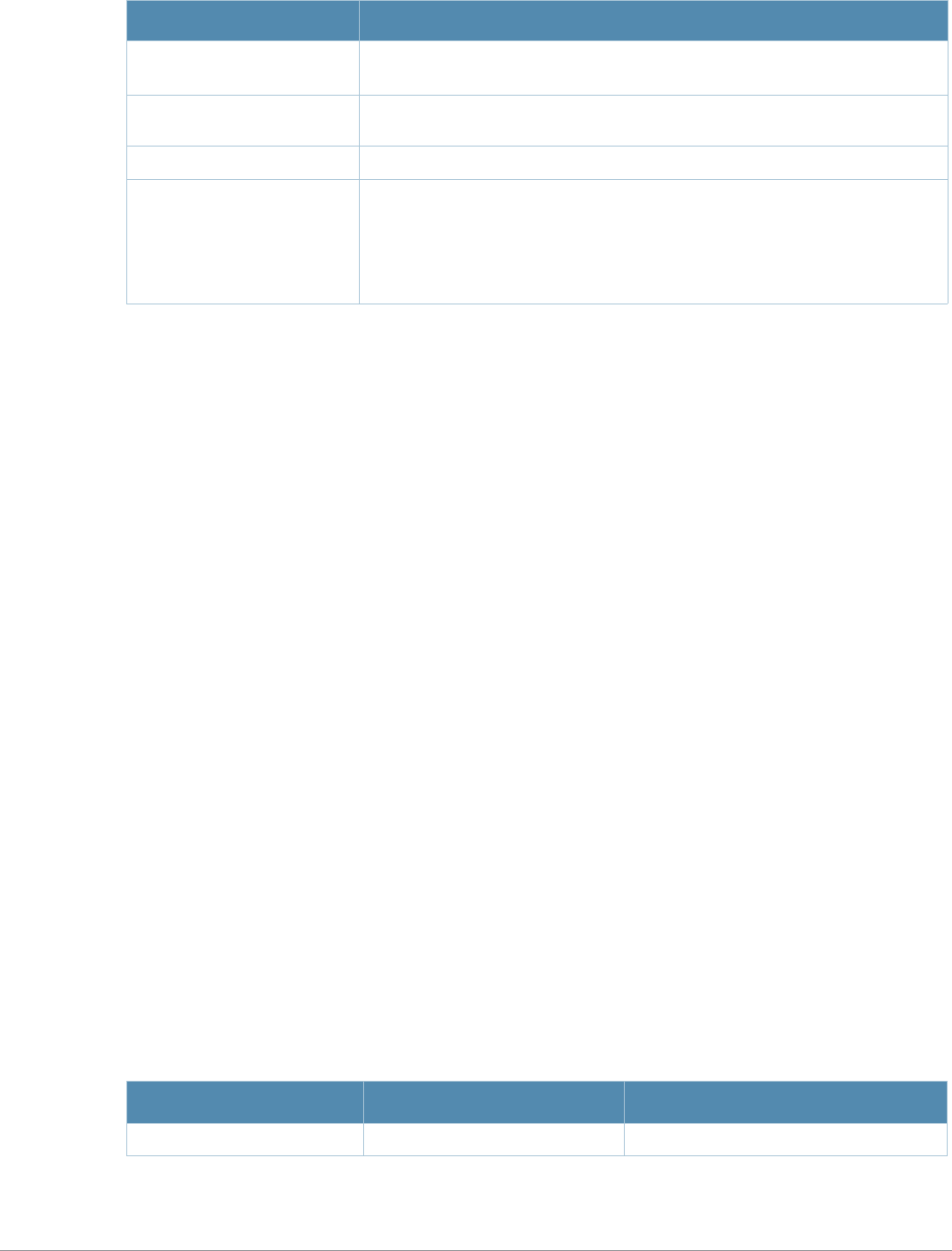
156 |crypto isakmp AOS-W 3.4.1 Command Line Interface | Reference Guide
Usage Guidelines
Preshared key (PSK)-refresh allows you to refresh the IKE PSK used by remote APs. By default, PSK-
refresh is disabled. With PSK-refresh enabled, the switch accepts connections from remote APs using the
previously configured PSK for the specified interval. After the interval elapses, that PSK expires and the
switch uses the new PSK to authenticate remote APs. If you enable and then disable PSK-refresh, the
remote AP attempts to authenticate with the currently configured global PSK only.
To enable PSK-refresh, you must:
1. Configure the amount of time in days or hours (known as the interval), to remember the previously
configured PSK used in your remote AP deployment.
NOTE: Alcatel-Lucent recommends configuring a large interval to prevent remote APs from being
unable to authenticate and connect to the network. Consider your existing PSK interval when
configuring this feature.
2. Configure the global PSK using the command crypto isakmp key. The IP address must be 0.0.0.0, and
the netmask must be 0.0.0.0.
Example
The following command configures an ISAKMP peer IP address and subnet mask. After configuring an
ISAKMP address and netmask, you will be prompted to enter the IKE preshared key.
Command History
This command was introduced in AOS-W 3.0.
Command Information
udpencap-behind-
natdevice
Configure NAT-T if switch is behind NAT device.
Only for Windows VPN Dialer
enable Enable Nat-T. (This is the recommended setting if the switch is behind a NAT
device.)
disable Disable Nat-T.
packet-dump Enable the packet dump feature to troubleshoot an IPsec tunnel establishment by
looking at the packet exchanges between the switch and the remote AP or the
other IPsec peer. The packet dump output is saved to a file named ike.pcap.
NOTE: This is a testing feature only, and should not be enabled on a production
network. To disable this feature, use the command no crypto isakmp packet-
dump.
Parameter Description
Platforms Licensing Command Mode
All platforms Base operating system Config mode on master switches
(host)(config) #crypto isakmp address 10.3.14.21 netmask 255.255.255.0
Key:*******
Re-Type Key:*******

AOS-W 3.4.1 Command Line Interface | Reference Guide crypto isakmp policy | 157
crypto isakmp policy
crypto isakmp policy
authentication pre-share|rsa-sig
encryption 3DES|AES128|AES192|AES256|DES
group 1|2
hash md5|sha
lifetime <seconds>
Description
This command configures Internet Key Exchange (IKE) policy parameters for the Internet Security
Association and Key Management Protocol (ISAKMP).
Syntax
Usage Guidelines
To define settings for a ISAKMP policy, issue the command crypto isakmp policy <priority> then press
Enter. The CLI will enter config-isakmp mode, which allows you to configure the policy authentication,
encryption, group, hash algorithm and lifetime values.
Example
Parameter Description
policy Configure an IKE policy
<priority> Specify a number from 1 to 10,000 to define a priority level for the policy. The higher
the number, the higher the priority level.
authentication Configure the IKE authentication method.
pre-share Use Pre Shared Keys for IKE authentication. This is the default authentication type.
rsa-sig Use RSA Signatures for IKE authentication.
encryption Configure the IKE encryption algorithm.
3DES Use 168-bit 3DES-CBC encryption algorithm. This is the default encryption value.
AES128 Use 128-bit AES-CBC encryption algorithm.
AES192 Use 192-bit AES-CBC encryption algorithm.
AES256 Use 256-bit AES-CBC encryption algorithm.
DES Use 56-bit DES-CBC encryption algorithm.
group Configure the IKE Diffie Hellman group.
1 Use the 768-bit Diffie Hellman prime modulus group.
2 Use the 1024-bit Diffie Hellman prime modulus group. This is the default group
setting.
hash Configure the IKE hash algorithm
md5 Use MD5 (HMAC variant) as the hash algorithm.
sha Use SHA-1 (HMAC variant) as the hash algorithm. This is the default policy
algorithm.
lifetime <seconds> Specify the lifetime of the IKE security association (SA), from 300 - 86400 seconds.
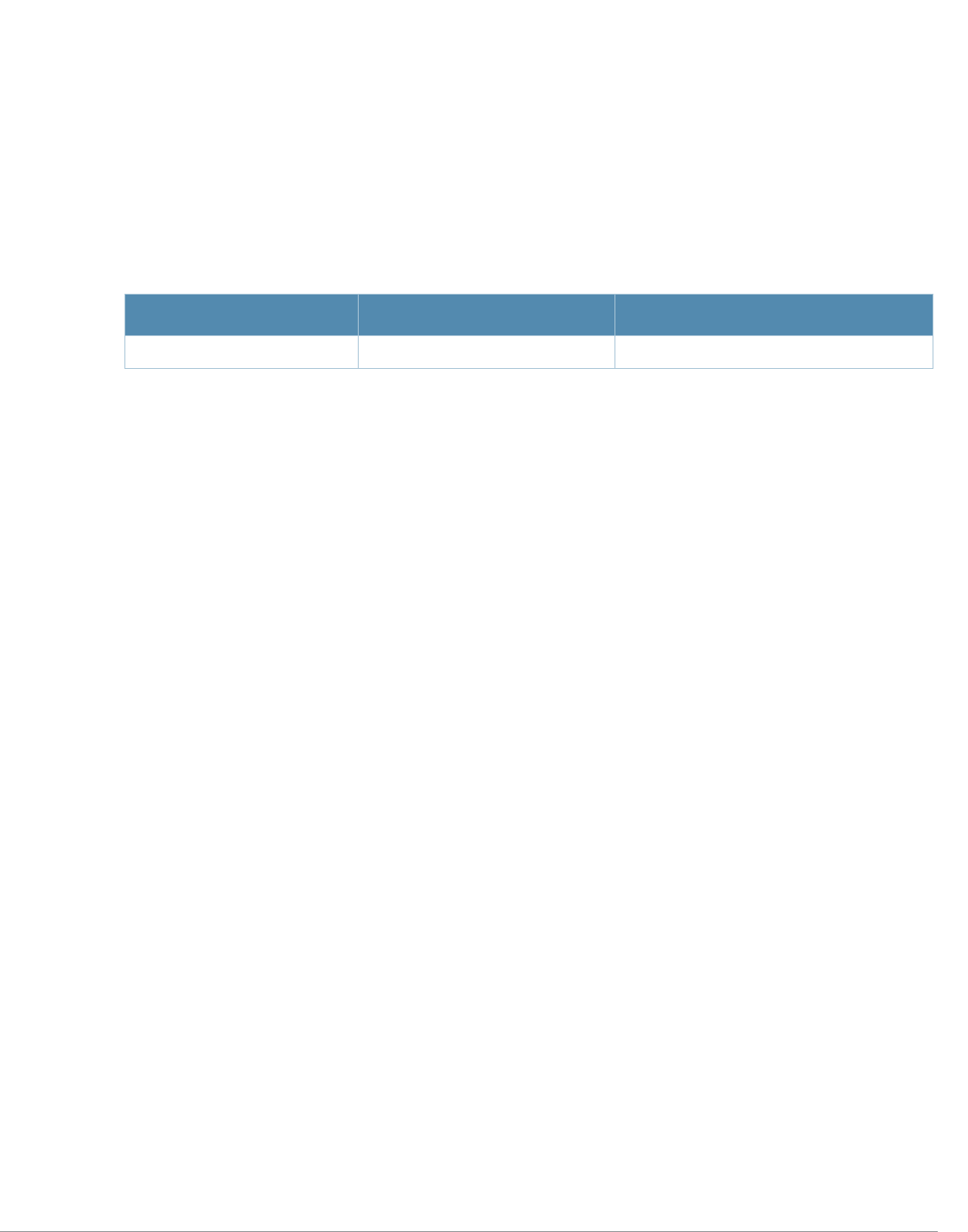
158 |crypto isakmp policy AOS-W 3.4.1 Command Line Interface | Reference Guide
The following command configures an ISAKMP peer IP address and subnet mask. After configuring an
ISAKMP address and netmask, you will be prompted to enter the IKE preshared key.
Command History
This command was introduced in AOS-W 3.0.
Command Information
Platforms Licensing Command Mode
All platforms Base operating system Config mode on master switches
(host)(config) #crypto isakmp policy1
(host)(config-isakmp) #auth rsa-sig
lifetime 86400
AOS-W 3.4.1 Command Line Interface | Reference Guide crypto map global-map | 159
crypto map global-map
crypto map global-map <map-number> ipsec-isakmp {dynamic <dynamic-map-name>}|{ipsec
<ipsec-map-name>}
Description
This command configures the default global map.
Syntax
Usage Guidelines
This command identifies the dynamic or ipsec map used as the default global map. If you have not yet
defined a dynamic or ipsec map, issue the command crypto map global-map or crypto-local ipsec-map
to define map parameters.
Example
The following command configures the global map with the dynamic map named dynamic_map_2.
Command History
This command was introduced in AOS-W 3.0
Command Information
Parameter Description
<map-number> Priority of the map.
dynamic Use a dynamic map.
<dynamic-map-name>} Name of the dynamic map.
ipsec Use a IPsec map.
<ipsec-map-name> Name of an IPsec map.
Platforms Licensing Command Mode
All platforms Base operating system Config mode on master switches
(host)(config) #crypto map global-map 2 ipsec-isakmp dynamic dynamic_map_2
160 | crypto pki AOS-W 3.4.1 Command Line Interface | Reference Guide
crypto pki
crypto pki csr key <key_val> common_name <common_val> country <country_val>
state_or_province <state> city <city_val> organization <organization_val> unit
<unit_val> email <email_val>
Description
Generate a certificate signing request (CSR) for the captive portal feature.
Syntax
Usage Guidelines
Use this command to generate a CSR for the Captive Portal feature. Display the CSR output by entering the
command show crypto pki csr. Note that this command will only generate CSR on a switch running AOS-
W 3.x or later. Earlier versions require that you generate the certificate externally.
Example
The following command configures a CSR for a user with the email address jdoe@example.com.
Command History
This command was introduced in AOS-W 3.1
Command Information
Parameter Description
key <key_val> Specify the CSR key length:1024, 2048, or 4096.
common_name <common_val> Specify a common name, e.g., www.yourcompany.com.
country <country_val> Specify a country name, e.g., US or CA.
state_or_province <state> Specify the name of a state or province.
city <city_val> Specify the name of a city.
organization <organization_val> Specify the name of an organization unit, e.g., sales.
unit <unit_val> Specify a unit value, e.g. EMEA.
email <email_val> Specify an email address, in the format name@mycompany.com.
Platforms Licensing Command Mode
All platforms Base operating system Config mode on master switches
(host)(config) #
crypto pki csr key 1024 common_name www.example.lcom country US state_or_province ca cit
organization engineering unit pubs email jdoe@example.com
AOS-W 3.4.1 Command Line Interface | Reference Guide crypto pki-import | 161
crypto pki-import
crypto pki-import {der|pem|pfx|pkcs12|pkcs7} {PublicCert|ServerCert|TrustedCA} <name>
Description
Import certificates for the captive portal feature.
Syntax
Usage Guidelines
Use this command to install a CSR for the Captive Portal feature.
Example
The following command installs a server certificate in DER format.
Command History
This command was introduced in AOS-W 3.0
Command Information
Parameter Description
der Import a certificate in DER format.
pem Import a certificate in x509 PEM format.
pfx Import a certificate in PFX format.
pkcs12 Import a certificate in PKCS12 format.
pkcs7 Import a certificate in PKCS7 format.
PublicCert Import a public certificate.
ServerCert Import a server certificate.
TrustedCA Import a trusted CA certificate.
<name> Name of a certificate.
Platforms Licensing Command Mode
All platforms Base operating system Config mode on master switches
(host)(config) #crypto pki-import der ServerCert cert_20

162 | crypto pki-import AOS-W 3.4.1 Command Line Interface | Reference Guide
AOS-W 3.4.1 Command Line Interface | Reference Guide crypto-local ipsec-map | 163
crypto-local ipsec-map
crypto-local
crypto-local ipsec-map <map> <priority>
dst-net <ipaddr> <mask>
force-natt
no ...
local-fqdn <local_id_fqdn>
peer-ip <ipaddr>
pre-connect {disable|enable}
set ca-certificate <cacert-name>
set pfs {group1|group2}
set security-association lifetime seconds <seconds>
set server-certificate <cert-name>
set transform-set <name1> [<name2>] [<name3>] [<name4>]
src-net <ipaddr> <mask>
trusted {disable|enable}
vlan <vlan>
Description
This command configures IPsec mapping for site-to-site VPN.
Syntax
Parameter Description Range Default
<map> Name of the IPsec map. — —
<priority> Priority of the entry. 1-9998 —
dst-net IP address and netmask for the destination
network. ——
force-natt Include this parameter to always enforce UDP
4500 for IKE and IPSEC. This option is disabled
by default.
——
no Negates a configured parameter. — —
local-fqdn <local_id_fqdn> If the local switch has a dynamic IP address, you
must specify the fully qualified domain name
(FQDN) of the switch to configure it as a initiator
of IKE aggressive-mode.
peer-ip <ipaddr> IP address of the peer gateway.
NOTE: If you are configuring an IPsec map for a
static-ip switch with a dynamically addressed
remote peer, you must leave the peer gateway
set to its default value of 0.0.0.0.
——
pre-connect Enables or disables pre-connection. enable/
disable disabled
set ca-certificate
<cacert-name>
User-defined name of a trusted CA certificate
installed in the switch. Use the show crypto-
local pki TrustedCA command to display the
CA certificates that have been imported into the
switch.
——
164 | crypto-local ipsec-map AOS-W 3.4.1 Command Line Interface | Reference Guide
Usage Guidelines
You can use switches instead of VPN concentrators to connect sites at different physical locations. For site-
to-site VPN between two switches, you must purchase and install VPN Server licenses on both switches.
You can configure separate CA and server certificates for each site-to-site VPN. You can also configure the
same CA and server certificates for site-to-site VPN and client VPN. Use the show crypto-local ipsec-map
command to display the certificates associated with all configured site-to-site VPN maps; use the tag
<map> option to display certificates associated with a specific site-to-site VPN map.
AOS-W supports site-to-site VPNs with two statically addressed switches, or with one static and one
dynamically addressed switch. By default, site-to-site VPN uses IKE Main-mode with Pre-Shared-Keys to
authenticate the IKE SA. This method uses the IP address of the peer, and therefore will not work for
dynamically addressed peers.
To support site-site VPN with dynamically addressed devices, you must enable IKE Aggressive-Mode with
Authentication based on a Pre-Shared-Key. The Alcatel-Lucent switch with a dynamic IP address must be
configured to be the initiator of IKE Aggressive-mode for Site-Site VPN, while the switch with a static IP
address must be configured as the responder of IKE Aggressive-mode.
Examples
The following commands configures site-to-site VPN between two switches:
(host) (config) #crypto-local ipsec-map sf-chi-vpn 100
src-net 101.1.1.0 255.255.255.0
dst-net 100.1.1.0 255.255.255.0
peer-ip 172.16.0.254
set pfs If you enable Perfect Forward Secrecy (PFS)
mode, new session keys are not derived from
previously used session keys. Therefore, if a key
is compromised, that compromised key will not
affect any previous session keys. To enable this
feature, specify one of the following Perfect
Forward Secrecy modes:
zgroup1: 768-bit Diffie Hellman prime
modulus group
zgroup2: 1024-bit Diffie Hellman prime
modulus group
group1/
group2 disabled
set security-association
lifetime seconds <seconds>
Configures the lifetime, in seconds, for the
security association (SA). 300-86400 7200
seconds
set server-certificate
<cert-name>
User-defined name of a server certificate
installed in the switch. Use the show crypto-
local pki ServerCert command to display the
server certificates that have been imported into
the switch.
——
set transform-set <name1> Name of the transform set for this IPsec map.
One transform set name is required, but you can
specify up to four transform sets. Configure
transform sets with the crypto ipsec
transform-set command.
—default-
transform
src-net <ipaddr> <mask> IP address and netmask for the source network. — —
trusted Enables or disables a trusted tunnel. enable/
disable disabled
vlan <vlan> VLAN ID. Enter 0 for the loopback. 1-4094 —
Parameter Description Range Default
AOS-W 3.4.1 Command Line Interface | Reference Guide crypto-local ipsec-map | 165
vlan 1
trusted
(host) (config) #crypto-local ipsec-map chi-sf-vpn 100
src-net 100.1.1.0 255.255.255.0
dst-net 101.1.1.0 255.255.255.0
peer-ip 172.16.100.254
vlan 1
trusted
For a dynamically addressed switch that initiates IKE Aggressive-mode for Site-Site VPN:
(host) (config)crypto-local ipsec-map <name> <priority>
src-net <ipaddr> <mask>
dst-net <ipaddr> <mask>
peer-ip <ipaddr>
local-fqdn <local_id_fqdn>
vlan <id>
pre-connect enable|disable
trusted enable
For the Pre-shared-key:
crypto-local isakmp key <key> address <ipaddr> netmask <mask>
For a static IP switch that responds to IKE Aggressive-mode for Site-Site VPN:
(host) (config)crypto-local ipsec-map <name2> <priority>
src-net <ipaddr> <mask>
dst-net <ipaddr> <mask>
peer-ip 0.0.0.0
peer-fqdn fqdn-id <peer_id_fqdn>
vlan <id>
trusted enable
For the Pre-shared-key:
crypto-local isakmp key <key> fqdn <fqdn-id>
For a static IP switch that responds to IKE Aggressive-mode for Site-Site VPN with One PSK for All FQDNs:
(host) (config)crypto-local ipsec-map <name2> <priority>
src-net <ipaddr> <mask>
peer-ip 0.0.0.0
peer-fqdn any-fqdn
vlan <id>
trusted enable
For the Pre-shared-key for All FQDNs:
crypto-local isakmp key <key> fqdn-any
Command History
This command was introduced in AOS-W 3.0.
Command Information
Platforms Licensing Command Mode
All platforms VPN and server license Config mode on master switches
166 | crypto-local isakmp ca-certificate AOS-W 3.4.1 Command Line Interface | Reference Guide
crypto-local isakmp ca-certificate
crypto-local isakmp ca-certificate <cacert-name>
Description
This command assigns the Certificate Authority (CA) certificate used to authenticate VPN clients.
Syntax
Usage Guidelines
You can assign multiple CA certificates. Use the show crypto-local isakmp ca-certificate command to
view the CA certificates associated with VPN clients.
Example
This command configures a CA certificate:
crypto-local isakmp ca-certificate TrustedCA1
Command History
This command was introduced in AOS-W 3.2.
Command Information
Parameter Description
ca-certificate User-defined name of a trusted CA certificate installed in the switch. Use the
show crypto-local pki TrustedCA command to display the CA certificates that
have been imported into the switch.
Platforms Licensing Command Mode
All platforms VPN server license is required Config mode on master switches
AOS-W 3.4.1 Command Line Interface | Reference Guide crypto-local isakmp dpd | 167
crypto-local isakmp dpd
crypto-local isakmp dpd idle-timeout <seconds> retry-timeout <seconds> retry-attempts
<number>
Description
This command configures IKE Dead Peer Detection (DPD) on the local switch.
Syntax
Usage Guidelines
DPD is enabled by default on the switch for site-to-site VPN.
Example
This command configures DPD parameters:
crypto-local isakmp dpd idle-timeout 60 retry-timeout 3 retry-attempts 5
Command History
This command was introduced in AOS-W 3.0.
Command Information
Parameter Description Range Default
idle-timeout Idle timeout, in seconds. 10-3600 22 seconds
retry-timeout Retry interval, in seconds. 2-60 2 seconds
retry-attempts Number of retry attempts. 3-10 3
Platforms Licensing Command Mode
All platforms VPN and/or Remote AP license Config mode on master and local switches
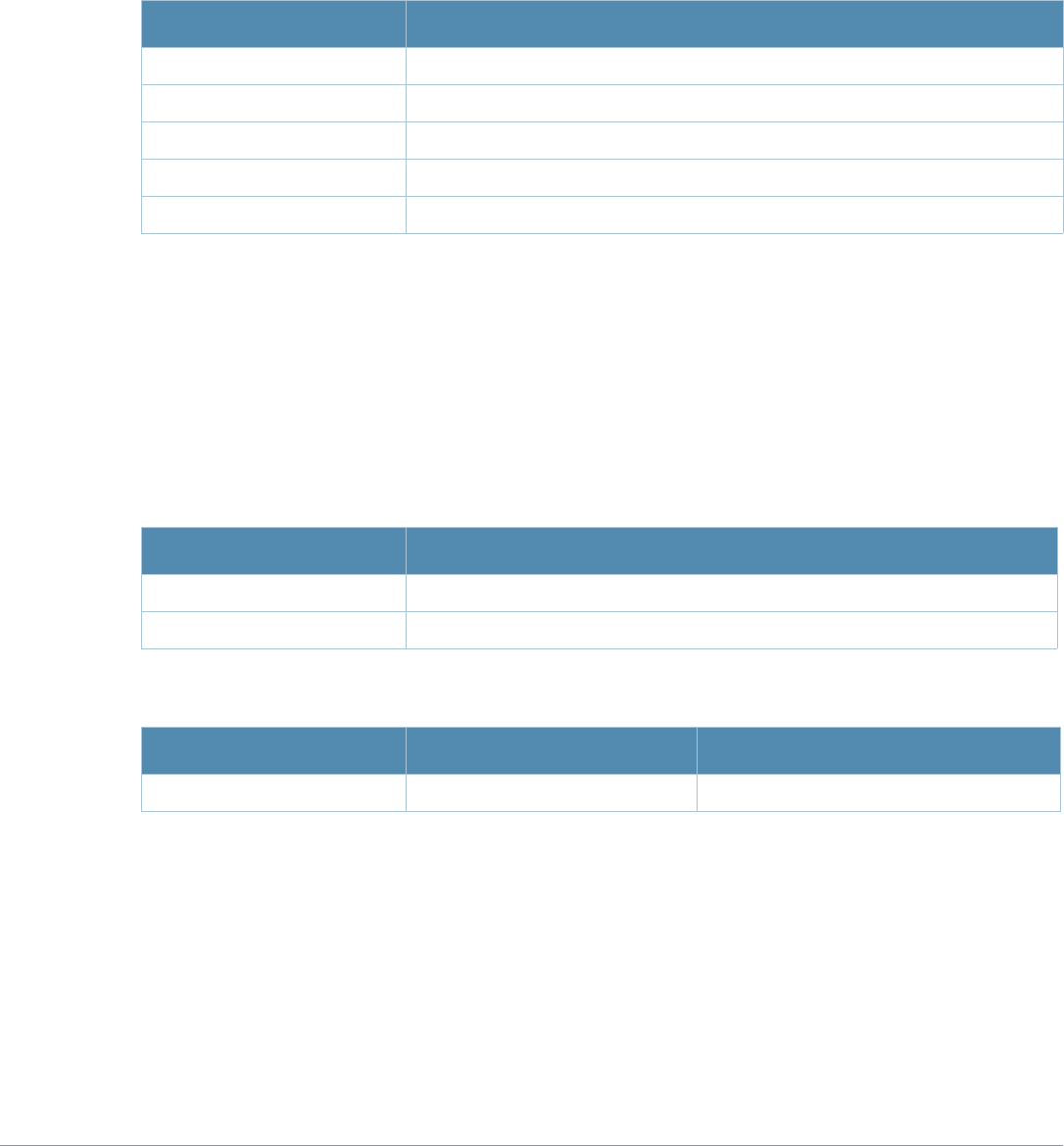
168 | crypto-local isakmp key AOS-W 3.4.1 Command Line Interface | Reference Guide
crypto-local isakmp key
crypto-local isakmp key <key> {address <peer-ipaddr> netmask <mask>}|{fqdn <ike-id-
fqdn>}|fqdn-any
Description
This command configures the IKE preshared key on the local switch for site-to-site VPN.
Syntax
Usage Guidelines
This command configures the IKE preshared key.
Example
The following command configures an IKE preshared key for site-to-site VPN:
crypto-local isakmp key R8nD0mK3y address 172.16.100.1 netmask 255.255.255.255
Command History
Command Information
Parameter Description
key <key> IKE preshared key value, between 6-64 characters.
address <peer-ipaddr> IP address for the preshared key.
netmask <mask> Netmask for the preshared key.
fqdn <ike-id-fqdn> Configure the PSK for the specified FQDN
fqdn-any Configure the PSK for any FQDN
Version Modification
AOS-W 3.0 Command introduced.
AOS-W 3.4 The fqdn and fqdn-any parameters were introduced.
Platforms Licensing Command Mode
All platforms VPN and/or Remote AP license Config mode on master and local switches

AOS-W 3.4.1 Command Line Interface | Reference Guide crypto-local isakmp permit-invalid-cert | 169
crypto-local isakmp permit-invalid-cert
crypto-local isakmp permit-invalid-cert
Description
This command allows invalid or expired certificates to be used for site-to-site VPN.
Syntax
No parameters.
Usage Guidelines
This command allows invalid or expired certificates to be used for site-to-site VPN.
Command History
This command was introduced in AOS-W 3.2.
Command Information
Platforms Licensing Command Mode
All platforms VPN and/or Remote AP license Config mode on master and local switches
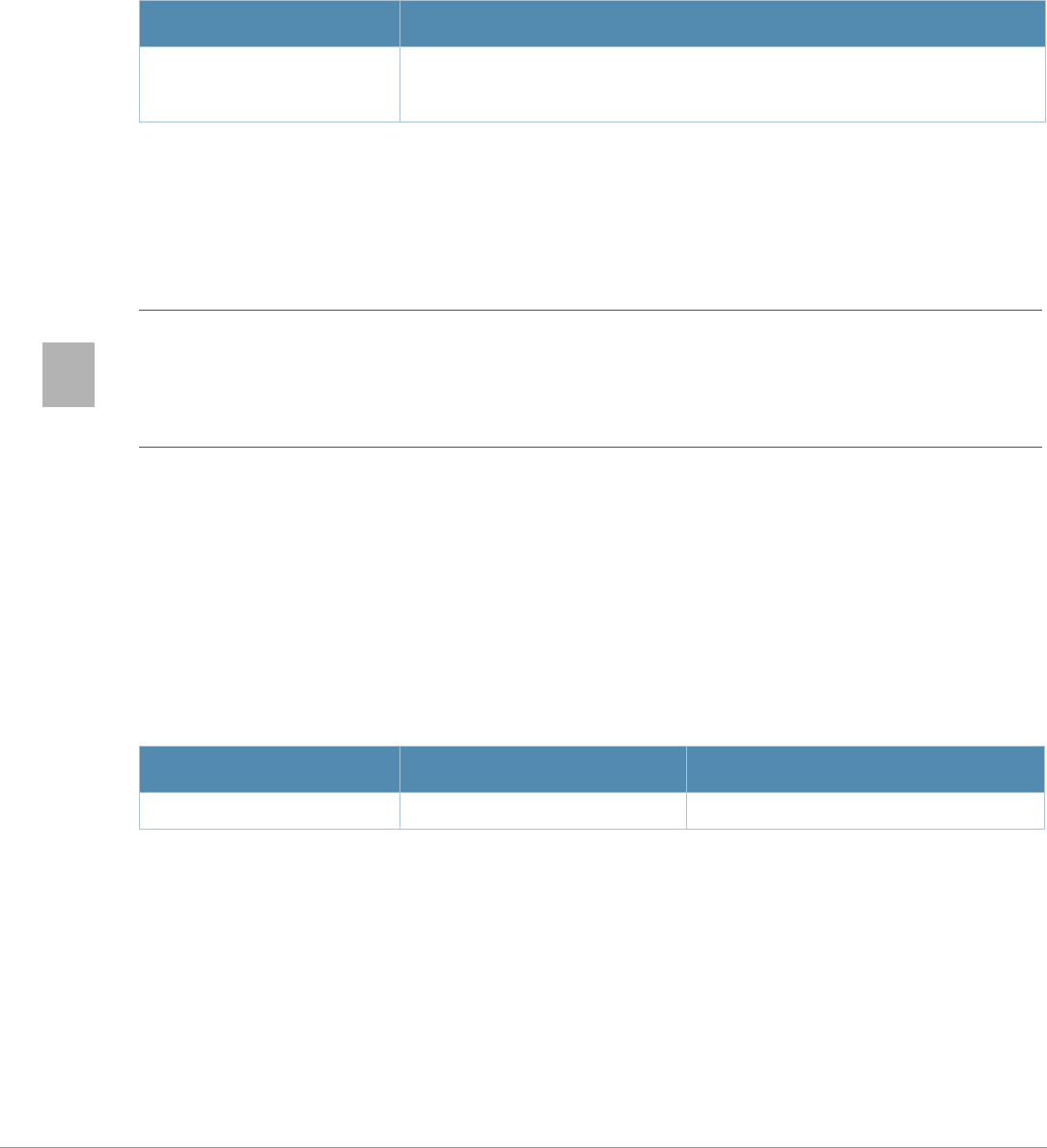
170 | crypto-local isakmp server-certificate AOS-W 3.4.1 Command Line Interface | Reference Guide
crypto-local isakmp server-certificate
crypto-local isakmp server-certificate <cert-name>
Description
This command assigns the server certificate used to authenticate the switch for VPN clients.
Syntax
Usage Guidelines
This certificate is only for VPN clients and not for site-to-site VPN clients. You can assign only one server
certificate for use with VPN clients. Use the show crypto-local isakmp server-certificate command to
view the server certificate associated with VPN clients. You must import and configure server certificates
separately on master and local switches.
Example
This command configures a server certificate:
crypto-local isakmp server-certificate ServerCert1
Command History
This command was introduced in AOS-W 3.2.
Command Information
Parameter Description
server-certifi
cate
User-defined name of a server certificate installed in the switch. Use the show
crypto-local pki ServerCert command to display the server certificates that have
been imported into the switch.
There is a default server certificate installed in the switch, however this certificate does not guarantee security for
production networks. Alcatel-Lucent strongly recommends that you replace the default certificate with a custom
certificate issued for your site or domain by a trusted CA. You can use the WebUI to generate a Certificate Signing
Request (CSR) to submit to a CA and then import the signed certificate received from the CA into the switch. For
more information, see “Managing Certificates” in the AOS-W User Guide.
Platforms Licensing Command Mode
All platforms VPN server license is required. Config mode on master and local switches
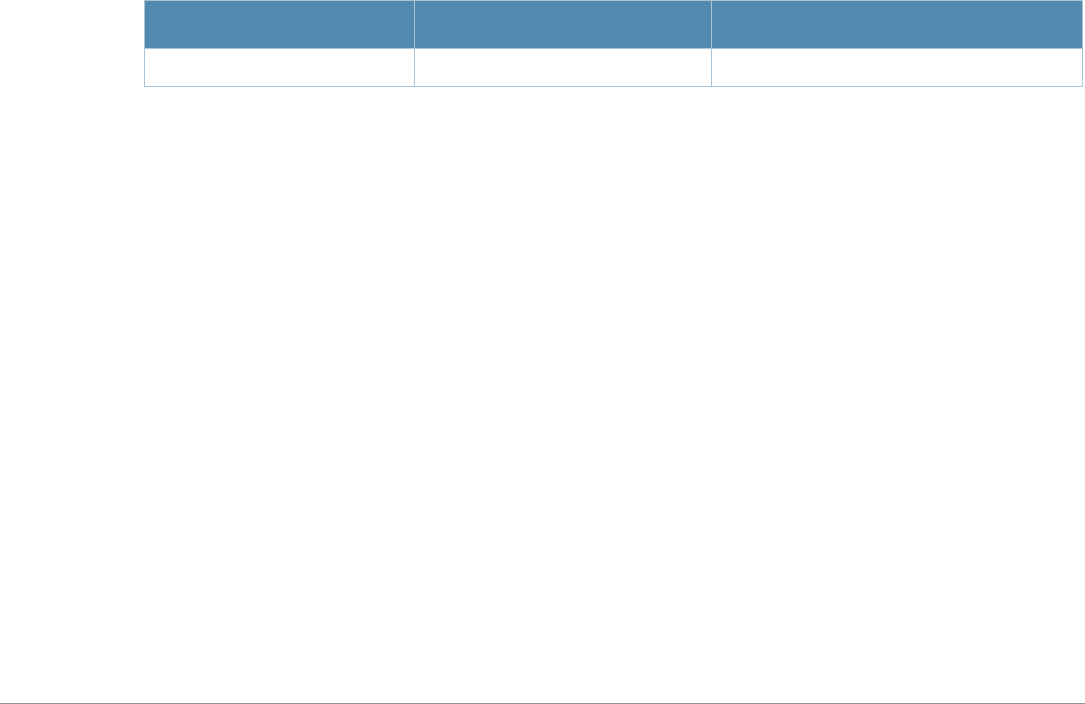
AOS-W 3.4.1 Command Line Interface | Reference Guide crypto-local isakmp xauth | 171
crypto-local isakmp xauth
crypto-local isakmp xauth
Description
This command enables IKE XAuth for VPN clients.
Syntax
No parameters.
Usage Guidelines
The no crypto-local isakmp xauth command disables IKE XAuth for VPN clients. This command only
applies to VPN clients that use certificates for IKE authentication. If you disable XAuth, then a VPN client
that uses certificates will not be authenticated using username/password. You must disable XAuth for Cisco
VPN clients using CAC Smart Cards.
Example
This command disables IKE XAuth for Cisco VPN clients using CAC Smart Cards:
no crypto-local isakmp xauth
Command History
This command was introduced in AOS-W 3.2.
Command Information
Platforms Licensing Command Mode
All platforms VPN server license is required. Config mode on master and local switches
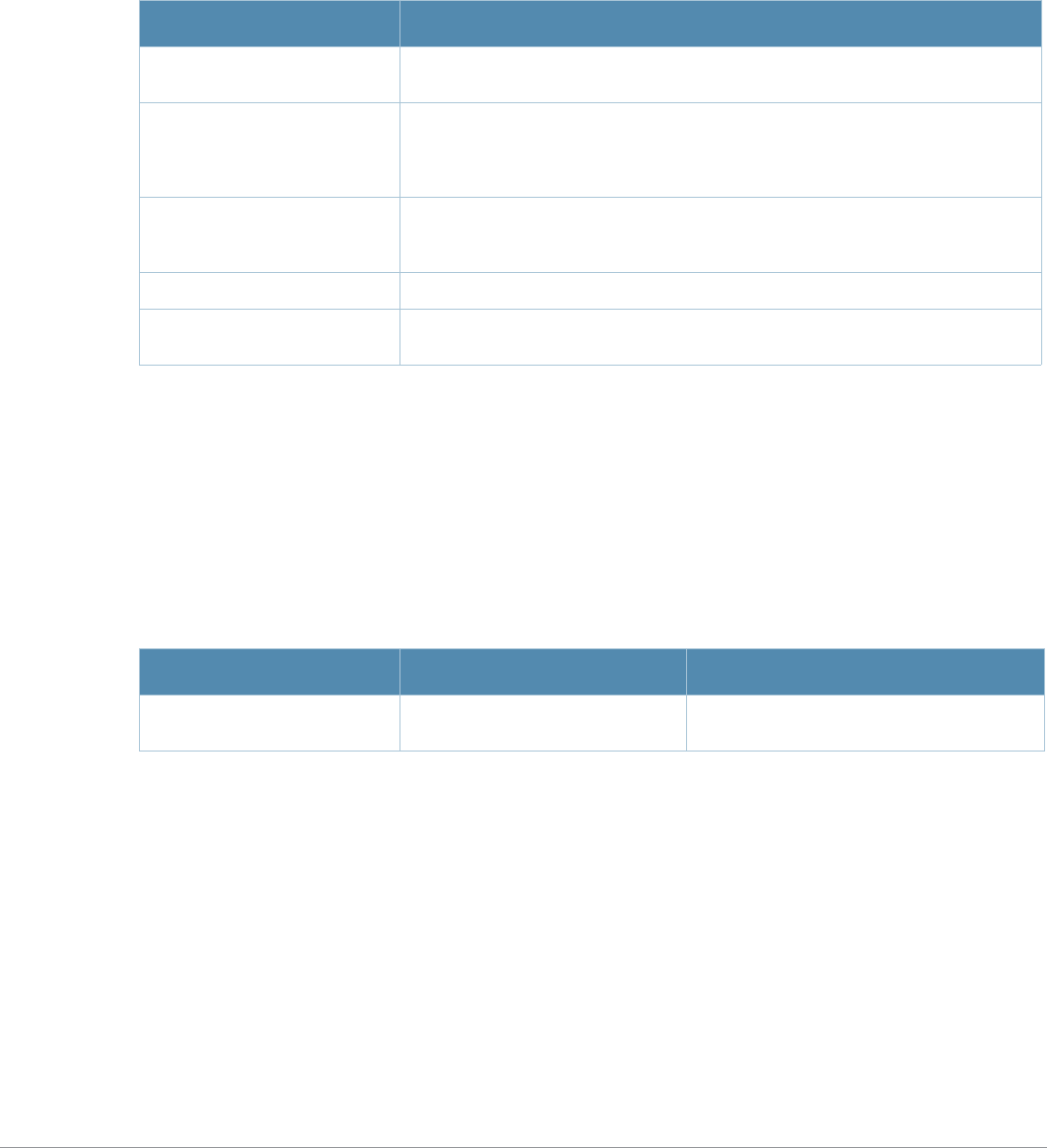
172 | crypto-local pki AOS-W 3.4.1 Command Line Interface | Reference Guide
crypto-local pki
crypto-local pki {PublicCert|ServerCert|TrustedCA} <name> <filename>
Description
This command is saved in the configuration file when you import a certificate.
Syntax
Usage Guidelines
This command in the configuration file verifies the presence of the certificate in the switch’s internal
directory structure.
Command History
This command was introduced in AOS-W 3.1.
Command Information
Parameter Description
PublicCert Public key of a certificate. This allows an application to identify an exact
certificate.
ServerCert Server certificate. This certificate must contain both a public and a private key
(the public and private keys must match). You can import a server certificate in
either PKCS12 or x509 PEM format; the certificate is stored in x509 PEM DES
encrypted format on the switch.
TrustedCA Trusted CA certificate. This can be either a root CA or intermediate CA. Alcatel-
Lucent encourages (but does not require) an intermediate CA’s signing CA to be
the switch itself.
<name> Name of the certificate.
<filename> Internal directory structure in the switch in which the imported certificate is
stored.
Platforms Licensing Command Mode
All platforms VPN server license is required. This command appears in the configuration
file after you import a certificate
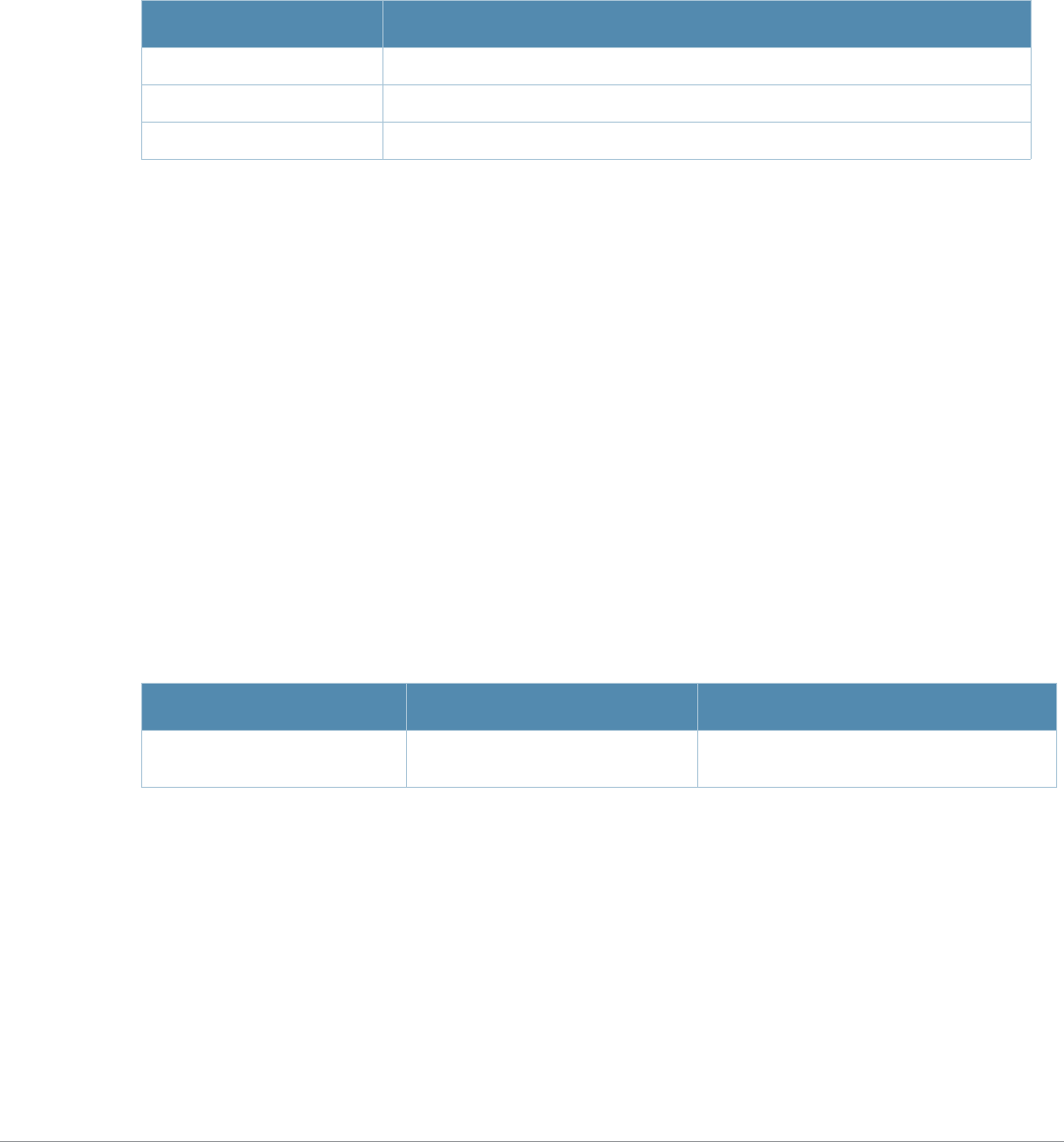
AOS-W 3.4.1 Command Line Interface | Reference Guide database synchronize | 173
database synchronize
database synchronize {[period <minutes>][rf-plan-data]}
Description
This command manually synchronizes the database between a pair of redundant master switches and
includes RF Plan data when synchronizing with standby.
Syntax
Usage Guidelines
This command takes effect immediately. If a peer is not configured, the switch displays an error message.
Use the database synchronize period command in config mode to configure the interval for automatic
database synchronization. Use the database synchronize rf-plan-data command to include RF plan data
when synchronizing in standby mode.
Example
The following commands cause the database on the active master switch to synchronize with the standby in
25 minute intervals. The synchronization includes RF plan data.
(host) (config) #database synchronize period 25
(host) (config) #database synchronize rf-plan-data
Command History
This command was introduced in AOS-W 3.0.
Command Information
Parameter Description
period Configures the interval for automatic database synchronization.
<minutes> Interval in minutes. Range is 1 — 25200 minutes.
rf-plan-data Includes the RF Plan data when synchronizing with standby mode.
Platforms Licensing Command Mode
All platforms Base operating system Enable and Config modes on master
switches

174 | database synchronize AOS-W 3.4.1 Command Line Interface | Reference Guide
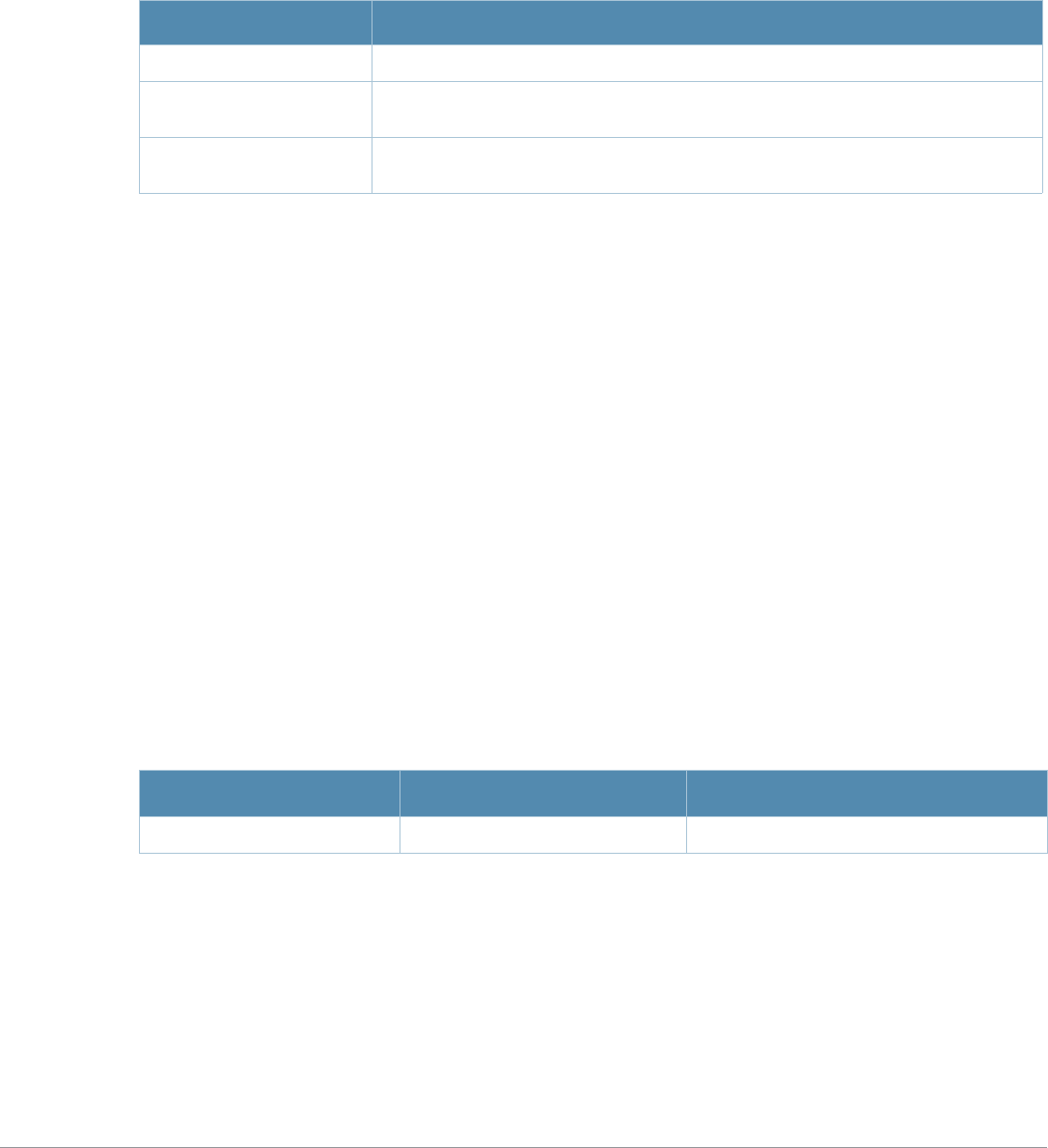
AOS-W 3.4.1 Command Line Interface | Reference Guide delete | 175
delete
delete {filename <filename>|ssh-host-addr <ipaddr>|ssh-known-hosts}
Description
This command deletes a file or RSA signature entry from flash.
Syntax
Usage Guidelines
To prevent running out of flash file space, you should delete files that you no longer need.
The copy scp command creates RSA signatures whenever it connects to a new host. These host signatures
are stored in the flash file system.
Example
The following command deletes a file:
(host) #delete filename december-config-backup.cfg
The following command deletes an RSA signature entry from flash:
(host) #delete ssh-host-addr 10.100.102.101
The following command deletes all RSA signature entries from flash:
(host) #delete ssh-known-hosts
Command History
This command was introduced in AOS-W 3.0.
Command Information
Parameter Description
filename Name of the file to be deleted.
ssh-host-addr Deletes the entry stored in flash for the RSA host signature created when you run the
copy scp command.
ssh-known -hosts Deletes all entries stored in flash for the RSA host signatures created when you run
the copy scp command.
Platforms Licensing Command Mode
All platforms Base operating system Enable mode on master switches

176 |delete AOS-W 3.4.1 Command Line Interface | Reference Guide
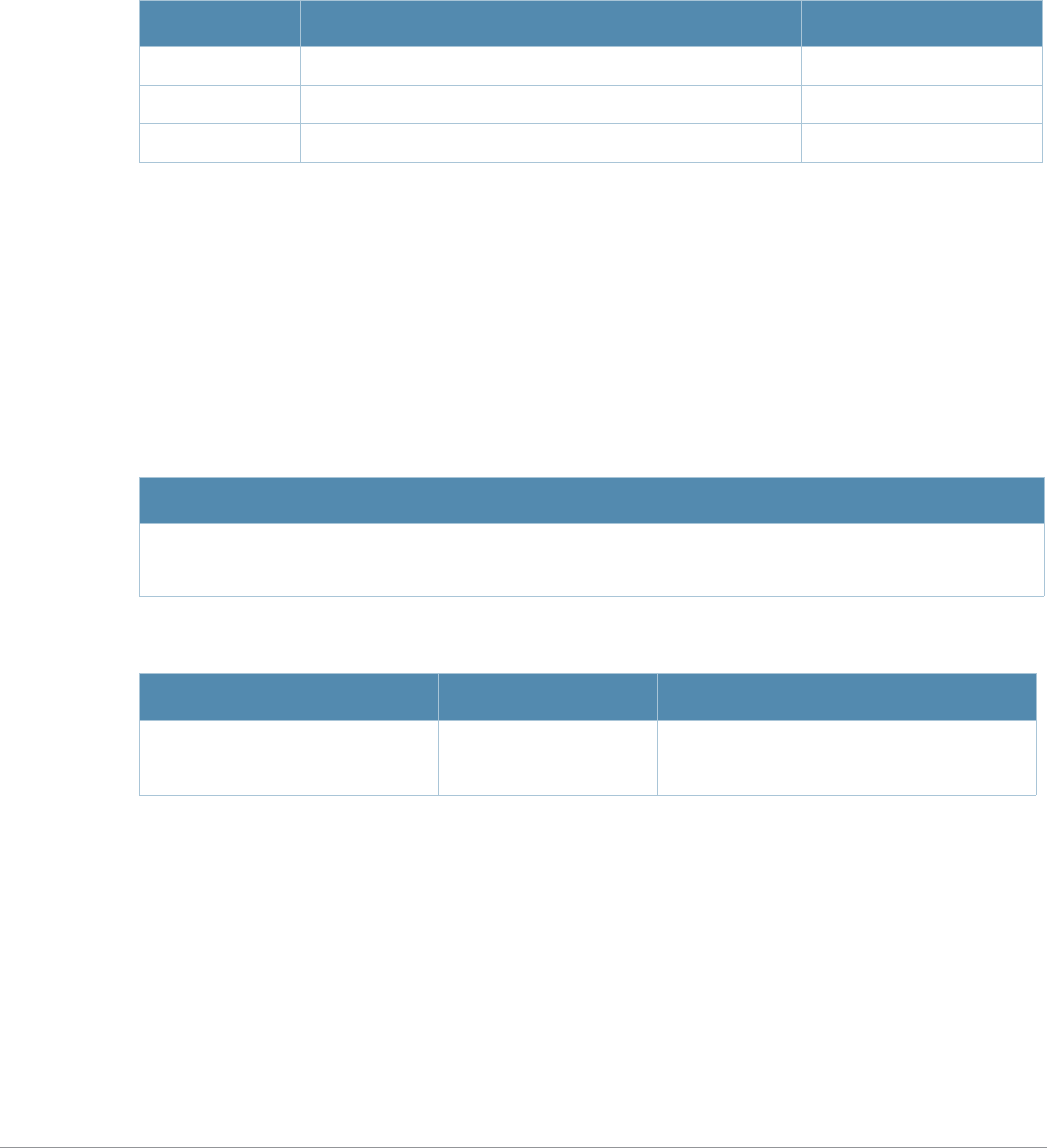
AOS-W 3.4.1 Command Line Interface | Reference Guide destination | 177
destination
destination <STRING> <A.B.C.D> [invert]
Description
This command configures the destination name and address.
Syntax
Usage Guidelines
You can configure the name and IP address of the destination. You can optionally configure the subnet, or
invert the selection.
Example
The following example configures a destination called “Home” with an IP address of 10.10.10.10.
(host) (config) #destination Home 10.10.10.10
Command History
Command Information
Parameter Description Range
STRING Destination name. Alphanumeric
A.B.C.D Destination IP address or subnet. —
invert Specifies all destinations except this one. —
Release Modification
AOS-W 1.0 Command introduced
AOS-W 3.0 Replaced with netdestination command.
Availability License Command Mode
Can be used only on the master
switch. Requires Policy
Enforcement Firewall
license
Config mode on master switches

178 | destination AOS-W 3.4.1 Command Line Interface | Reference Guide

AOS-W 3.4.1 Command Line Interface | Reference Guide dir | 179
dir
dir
Description
This command displays a list of files stored in the flash file system.
Syntax
No parameters.
Usage Guidelines
Use this command to view the system files associated with the switch.
Output from this command includes the following:
zThe first column contains ten place holders that display the file permissions.
First place holder: Displays - for a file or d for directory.
Next three place holders: Display file owner permissions: r for read access, w for write access
permissions, x for executable.
Following three place holders: Display member permissions: r for read access or x for executable.
Last three place holders: Display non-member permissions: r for read access or x for executable.
zThe second column displays the number of links the file has to other files or directories.
zThe third column displays the file owner.
zThe fourth column displays group/member information.
zThe remaining columns display the file size, date and time the file was either created or last modified,
and the file name.
Example
The following command displays the files currently residing on the system flash:
(host) #dir
The following is sample output from this command:
-rw-r--r-- 1 root root 9338 Nov 20 10:33 class_ap.csv
-rw-r--r-- 1 root root 1457 Nov 20 10:33 class_sta.csv
-rw-r--r-- 1 root root 16182 Nov 14 09:39 config-backup.cfg
-rw-r--r-- 1 root root 14174 Nov 9 2005 default-backup-11-8-05.cfg
-rw-r--r-- 1 root root 16283 Nov 9 12:25 default.cfg
-rw-r--r-- 1 root root 22927 Oct 25 12:21 default.cfg.2006-10-25_20-21-38
-rw-r--r-- 2 root root 19869 Nov 9 12:20 default.cfg.2006-11-09_12-20-22
Command History
Introduced in AOS-W 1.0
Command Information
Platform License Command Mode
Available on all platforms Available in the base operating system Enable and Config modes on
local or master switches

180 |dir AOS-W 3.4.1 Command Line Interface | Reference Guide
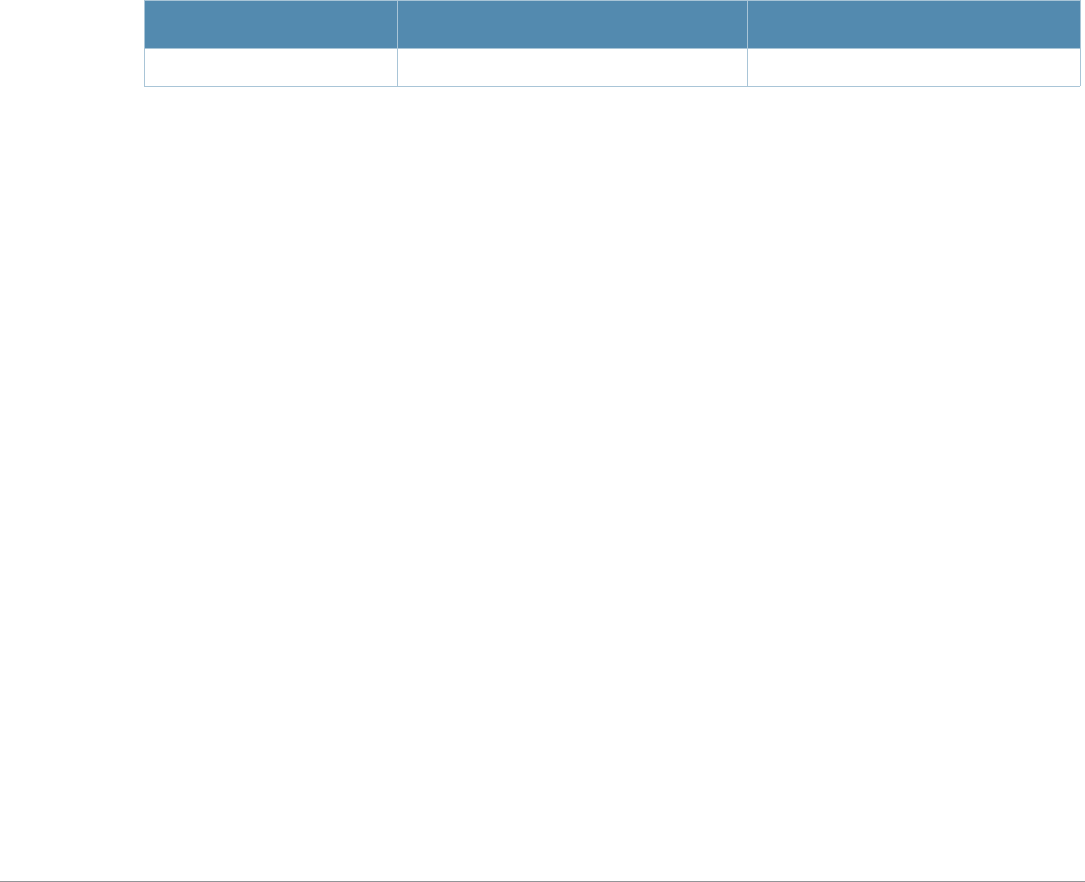
AOS-W 3.4.1 Command Line Interface | Reference Guide dynamic-ip | 181
dynamic-ip
dynamic-ip restart
Description
This command restarts the PPPoE or DHCP process.
Syntax
No parameters.
Usage Guidelines
This command can be used to renegotiate DHCP or PPPoE parameters. This can cause new addresses to be
assigned on a VLAN where the DHCP or PPPoE client is configured.
Command History
This command was introduced in AOS-W 3.0
Command Information
Platform License Command Mode
Available on all platforms Available in the base operating system Enable mode on master switches

182 |dynamic-ip AOS-W 3.4.1 Command Line Interface | Reference Guide
AOS-W 3.4.1 Command Line Interface | Reference Guide enable | 183
enable
enable
Description
This user mode command switches the switch into enable mode.
Usage Guidelines
To enter enable mode, you are prompted for the password configured during the switch’s initial setup.
Passwords display as asterisks (*) when you enter them. To change the password, use the config mode
<z_blue>“enable secret” command. If you lose or forget the enable mode password, resetting the default
admin user password also resets the enable mode password to “enable”. See the AOS-W User Guide for
more information about resetting the admin and enable mode passwords.
When you are in enable mode, the CLI prompt ends with the hash (#) character.
Example
The following example allows you to enter enable mode on the switch.
(host) >enable
Password: ******
(host) #
Command History
Command introduced in AOS-W 1.0.
Command Information
Platform License Command Mode
Available on all platforms Available in base operating system User mode on master or
local switches
184 | enable secret AOS-W 3.4.1 Command Line Interface | Reference Guide
enable secret
enable secret
Description
This config mode command allows you to change the password for enable mode.
Usage Guidelines
Use this command to change the password for enable mode. To reset the password to the factory default of
“enable”, use the no enable command.
Example
The following example allows you to change the password for enable mode.
(host) #configure terminal
Enter Configuration commands, one per line. End with CNTL/Z
(host) (config) #enable secret
Password:******
Re-Type password: ******
(host) (config) #
Command History
Command Information
The password must not contain the space and ‘?’ special characters.
Version Modification
AOS-W1.0 Command introduced
AOS-W 3.3.2 Updated with restriction of the secret phase
Platform License Command Mode
Available on all platforms Available in the base operating system Config mode on master or local
switches
AOS-W 3.4.1 Command Line Interface | Reference Guide encrypt | 185
encrypt
encrypt {disable|enable}
Description
This command allows passwords and keys to be displayed in plain text or encrypted.
Syntax
Usage Guidelines
Certain commands, such as show crypto isakmp key, display configured key information. Use the
encrypt command to display the key information in plain text or encrypted.
Example
The following command allows passwords and keys to be displayed in plain text:
(host) #encrypt disable
Command History
Introduced in AOS-W 3.0
Command Information
Parameter Description Default
disable Passwords and keys are displayed in plain text —
enable Passwords and keys are displayed encrypted enabled
Platform License Command Mode
Available on all platforms Available in the base operating system Enable mode on master or local
switches

186 |encrypt AOS-W 3.4.1 Command Line Interface | Reference Guide
AOS-W 3.4.1 Command Line Interface | Reference Guide esi group | 187
esi group
esi group <name>
esi
[no] |
[ping <attributes>] |
[server <server>]
Description
This command configures an ESI group.
Syntax
Usage Guidelines
Use the show esi group command to show ESI group information.
Example
The following command sets up the ESI group named “fortinet.”
(host) (config) #esi group fortinet
ping default
server forti_1
Command History
Introduced in AOS-W 2.5
Command Information
Parameter Description
no Negates any configured parameter.
ping Specify the name of a set of ping checking attributes defined via the command esi ping. Only
one set is allowed.
server Specify the name of a server to be added or removed from the ESI group. You define ESI servers
via the command esi server.
Platform License Command Mode
Available on all platforms Requires Policy Enforcement Firewall license Config mode on master or local
switches
188 | esi parser domain AOS-W 3.4.1 Command Line Interface | Reference Guide
esi parser domain
esi parser domain <name>
[no] |
[peer <peer-ip>] |
[server <ipaddr>]
Description
This command configures an ESI syslog parser domain.
Syntax
Usage Guidelines
The ESI parser is a generic syslog parser on the switch that accepts syslog messages from external third-
party appliances such as anti-virus gateways, content filters, and intrusion detection systems. It processes
syslog messages according to user-defined rules and takes configurable actions on the corresponding
system users.
ESI servers (see “esi server” on page 195) are configured into domains to which ESI syslog parser rules (see
“esi parser rule” on page 189) are applied.
Use the show esi parser domains command to show ESI parser domain information.
Example
The following commands configure a virus syslog parser domain named “fortinet” which contains the ESI
server “forti_1” with the trusted IP address configured using the command “esi server” on page 195.
(host) (config) #esi parser domain fortinet
server 10.168.172.3
Command History
Introduced in AOS-W 3.1.
Command Information
Parameter Description
no Negates any configured parameter
peer (Optional.) Specify the IP address of an another switch in this domain. These switches are
notified when the user cannot be found locally. This command is needed only when multiple
switches share a single ESI server
server Specify the IP address of the ESI server to which the switch listens.
Platform License Command Mode
Available on all platforms Requires Policy Enforcement Firewall
license Config mode on master or
local switches

AOS-W 3.4.1 Command Line Interface | Reference Guide esi parser rule | 189
esi parser rule
esi parser rule <rule_name>
[condition <expression>] |
[domain <name>] |
[enable]
[match {ipaddr <expression> | mac <expression> | user <expression> }] |
[no] |
[position <position>] |
[set {blacklist | role <role>} |
[test {msg <msg> | file <filename>}]
Description
This command creates or changes an ESI syslog parser rule.
Syntax
Usage Guidelines
The user creates an ESI rule by using characters and special operators to specify a pattern that uniquely
identifies a syslog message. This “condition” defines the type of message and the ESI domain to which this
message pertains. The rule contains three major fields:
zCondition: The pattern that uniquely identifies the syslog message type.
zUser: The username identifier. It can be in the form of a name, MAC address, or IP address.
zAction: The action to take when a rule match occurs.
Once a condition match occurs, no further rule-matching will be made. For the matching rule, only one
action can be defined.
Parameter Description Range Default
condition Specifies the REGEX (regular expression) pattern that uniquely
identifies the syslog. ——
domain (Optional.) Specify the ESI syslog parser domain to which this
rule applies. If not specified, the rule matches with all
configured ESI servers.
——
enables Enables this rule.
Note: The condition, user match, and set action parameters
must be configured before the rule can be enabled.
— Not enabled
match Specifies the user identifier to match, where ipaddr, mac, and
user take a REGEX pattern that uniquely identifies the user. ——
no Negates any configured parameter. — —
position Specifies the rule’s priority position. 1–32; 1
highest —
set Specifies the action to take: blacklist the user or change the
user role.
Note: The role entity should be configured before it is
accepted by the ESI rule.
——
test Test the regular expression output configured in the
esi parser rules command. You can test the expressions
against a specified syslog message, or test the expression
against a sequence of syslog messages contained in a file.
——

190 | esi parser rule AOS-W 3.4.1 Command Line Interface | Reference Guide
For more details on the character-matching operators, repetition operators, and expression anchors used to
defined the search or match target, see the External Services Interface chapter in the AOS-W User Guide.
Use the show esi parser rules command to show ESI parser rule information. Use the
show esi parser stats command to show ESI parser rule statistical information
Examples
The following command sets up the Fortigate virus rule named “forti_rule.” This rule parses the virus
detection syslog scanning for a condition match on the log_id value (log_id=) and a match on the IP address
(src=).
(host) (config) #esi parser rule forti_rule
condition “log_id=[0-9]{10}[ ]”
match ipaddr “src=(.*)[ ]”
set blacklist
domain fortinet
enable
In this example, the corresponding ESI expression is:
< Sep 26 18:30:02 log_id=0100030101 type=virus subtype=infected src=1.2.3.4 >
The following example of the test command tests a rule against a specified single syslog message.
test msg "26 18:30:02 log_id=0100030101 type=virus subtype=infected src=1.2.3.4"
< 26 18:30:02 log_id=0100030101 type=virus subtype=infected src=1.2.3.4 >
=====
Condition: Matched with rule "forti_rule"
User: ipaddr = 1.2.3.4
=====
The following example of the test command tests a rule against a file named test.log, which contains several
syslog messages.
test file test.log
< Sep 26 18:30:02 log_id=0100030101 type=virus subtype=infected src=1.2.3.4 >
==========
Condition: Matched with rule "forti_rule"
User: ipaddr = 1.2.3.4
==========
< Oct 18 10:43:40 cli[627]: PAPI_Send: To: 7f000001:8372 Type:0x4 Timed out. >
==========
Condition: No matching rule condition found
==========
< Oct 18 10:05:32 mobileip[499]: <500300> <DBUG> |mobileip| Station 00:40:96:a6:a1:
a4,
10.0.100.103: DHCP FSM received event: RECEIVE_BOOTP_REPLY current: PROXY_DHCP_NO_PROX
Y, next: PROXY_DHCP_NO_PROXY >
==========
Condition: No matching rule condition found
==========

AOS-W 3.4.1 Command Line Interface | Reference Guide esi parser rule | 191
Command History
Introduced in AOS-W 3.1
Command Information
Platform License Command Mode
Available on all platforms. Requires Policy Enforcement Firewall license. Config mode on master
and local switches
192 | esi parser rule-test AOS-W 3.4.1 Command Line Interface | Reference Guide
esi parser rule-test
esi parser rule-test
[file <filename>] |
[msg <msg>]
Description
This command allows you to test all of the enabled parser rules.
Syntax
Usage Guidelines
You can test the enabled parser rules against a syslog message input, or run the expression through a file
system composed of syslog messages. The command shows the match result as well as the user name
parsed for each message.
Example
The following command tests against a specified single syslog message.
(host) (config) #esi parser rule-test msg
"26 18:30:02 log_id=0100030101 type=virus subtype=infected src=1.2.3.4"
< 26 18:30:02 log_id=0100030101 type=virus subtype=infected src=1.2.3.4 >
=====
Condition: Matched with rule "forti_rule"
User: ipaddr = 1.2.3.4
=====
The following command tests against a file named test.log, which contains several syslog messages.
esi parser rule-test file test.log
< Sep 26 18:30:02 log_id=0100030101 type=virus subtype=infected src=1.2.3.4 >
==========
Condition: Matched with rule "forti_rule"
User: ipaddr = 1.2.3.4
==========
< Oct 18 10:43:40 cli[627]: PAPI_Send: To: 7f000001:8372 Type:0x4 Timed out. >
==========
Condition: No matching rule condition found
==========
< Oct 18 10:05:32 mobileip[499]: <500300> <DBUG> |mobileip| Station 00:40:96:a6:a1:
a4,
10.0.100.103: DHCP FSM received event: RECEIVE_BOOTP_REPLY current: PROXY_DHCP_NO_PROX
Y, next: PROXY_DHCP_NO_PROXY >
==========
Condition: No matching rule condition found
==========
Parameter Description
file Tests against a specified file containing more than one syslog message.
msg Tests against a syslog message, where <msg> is the message text.

AOS-W 3.4.1 Command Line Interface | Reference Guide esi parser rule-test | 193
Command History
Introduced in AOS-W 3.1
Command Information
Platform License Command Mode
Available on all platforms Requires Policy Enforcement Firewall license Config mode on master and
local switches
194 |esi ping AOS-W 3.4.1 Command Line Interface | Reference Guide
esi ping
esi ping <ping-name>
[frequency <seconds>] |
[no] |
[retry-count <count>] |
[timeout <seconds>] |
Description
This command specifies the ESI ping health check configuration.
Syntax
Usage Guidelines
Use the show esi ping command to show ESI ping information.
Example
The following command specifies the ping health check attributes.
(host) (config) #esi ping default
frequency 5
retry-count 2
timeout 2
Command History
Introduced in AOS-W 2.5
Command Information
Parameter Description Range Default
frequency Specifies the ping frequency in seconds. 1–65536
no Negates any configured parameter — —
retry-count Specifies the ping retry count 1–65536 2
timeout Specifies the ping timeout in seconds. 1–65536 2
Platform License Command Mode
Available on all platforms Requires Policy Enforcement Firewall license Config mode on master
and local switches
AOS-W 3.4.1 Command Line Interface | Reference Guide esi server | 195
esi server
esi server <name>
[dport <tcp-udp-port>] |
[mode {bridge | nat | route}] |
[no] |
[trusted-ip-addr <ip-addr> [health-check]] |
[trusted-port <slot/port>] |
[untrusted-ip-port <ip-addr> [health-check]] |
[untrusted-port <slot/port>]
Description
This command configures an ESI server.
Syntax
Usage Guidelines
Use the show esi server command to show ESI server information.
Example
The following command specifies the ESI server attributes.
(host) (config) #esi server forti_1
mode route
trusted-ip-addr 10.168.172.3
untrusted-ip-addr 10.168.171.3
Command History
Introduced in AOS-W 2.5.
Command Information
Parameter Description
dport Specifies the NAT destination TCP/UDP port.
mode Specifies the ESI server mode of operation: bridge, nat, or route
no Negates any configured parameter.
trusted-ip-addr Specifies the server IP address on the trusted network. As an option, you can also enable
a health check on the specified address
trusted-port Specifies the port connected to the trusted side of the ESI server; slot/port format.
untrusted-ip-addr Specifies the server IP address on the untrusted network. As an option, you can also
enable a health check on the specified address
untrusted-port Specifies the port connected to the untrusted side of the ESI server.
Platform License Command Mode
Available on all platforms Requires Policy Enforcement Firewall license Config mode on
master and local
switches

196 |esi server AOS-W 3.4.1 Command Line Interface | Reference Guide
AOS-W 3.4.1 Command Line Interface | Reference Guide exit | 197
exit
exit
Description
This command exits the current CLI mode.
Syntax
No parameters.
Usage Guidelines
Upon entering this command in a configuration sub-mode, you are returned to the configuration mode.
Upon entering this command in configuration mode, you are returned to the enable mode. Upon entering
this command in enable mode, you are returned to the user mode. Upon entering this command in user
mode, you are returned to the user login.
Example
The following sequence of exit commands return the user from the interface configuration sub-mode to
the user login:
(host) (config-if) #exit
(host) (config) #exit
(host) #exit
(host) >exit
User:
Command History
Introduced in AOS-W 3.0
Command Information
Platform License Command Mode
Available on all platforms Available in the base
operating system Available in the following command modes:
zUser
zEnable
zConfig
zConfig sub-modes

198 |exit AOS-W 3.4.1 Command Line Interface | Reference Guide
AOS-W 3.4.1 Command Line Interface | Reference Guide export | 199
export
export gap-db <filename>
Description
This command exports the global AP database to the specified file.
Syntax
Usage Guidelines
This command is intended for system troubleshooting. You should run this command only when directed to
do so by an Alcatel-Lucent support representative.
The global AP database resides on a master switch and contains information about known APs on all
switches in the system. You can view the contents of the global AP database with the show ap database
command.
Example
The following command exports the global AP database to a file:
(host) #export gap-db global-ap-db
Command History
This command was introduced in AOS-W 3.0.
Command Information
Parameter Description
<filename> Name of the file to which the global AP database is exported.
Platform License Command Mode
Available on all platforms Available in the base
operating system Enable mode on master switches.

200 |export AOS-W 3.4.1 Command Line Interface | Reference Guide

AOS-W 3.4.1 Command Line Interface | Reference Guide firewall | 201
firewall
firewall
{allow-tri-session |attack-rate {cp <rate>|ping <number>|session
<number>}|broadcast-filter-arp |cp | cp-bandwidth-contract|tcp-syn <number> |deny-
inter-user-bridging |disable-ftp-server |disable-ftp-server| disable-stateful-
h323|disable-stateful-sip |drop-ip-fragments
|enable-per-packet-logging |enforce-tcp-handshake |gre-call-id-processing
|local-valid-users|log-icmp-error|prohibit-arp-spoofing|prohibit-ip-spoofing
|prohibit-rst-replay
|session-idle-timeout <seconds> |session-mirror-destination {ip-address <ipaddr>
|port <slot>/<port>} |broadcast-filter-arp |voip-wmm-content-enforcement}
Description
This command configures firewall options on the switch.
Syntax
Parameter Description Range Default
allow-tri-session Allows three-way session when performing destination
NAT. This option should be enabled when the switch is
not the default gateway for wireless clients and the
default gateway is behind the switch. This option is
typically used for captive portal configuration.
— disabled
attack-rate Sets rates which, if exceeded, can indicate a denial of
service attack. ——
cp Rate of misbehaving user’s inbound traffic, which if
exceeded, can indicate a denial of service attack.
Recommended value is 100.
1-255 100
frames
per
second
ping Number of ICMP pings per second, which if exceeded,
can indicate a denial of service attack. Recommended
value is 4
1-255 —
session Number of TCP or UDP connection requests per
second, which if exceeded, can indicate a denial of
service attack. Recommended value is 32.
1-255 —
broadcast-filter-arp Reduces the number of broadcast packets sent to VoIP
clients, thereby improving the battery life of voice
handsets. You can enable this option for voice
handsets
in conjunction with increasing the DTIM interval on
clients.
cp See firewall cp on page 205
cp-bandwidth-contract See firewall cp-bandwidth-contract on page 207
tcp-syn Number of TCP SYN messages per second, which if
exceeded, can indicate a denial of service attack.
Recommended value is 32.
1-255 —
deny-inter-user-bridging Prevents the forwarding of Layer-2 traffic between
wired or wireless users. You can configure user role
policies that prevent Layer-3 traffic between users or
networks but this does not block Layer-2 traffic. This
option can be used to prevent traffic, such as Appletalk
or IPX, from being forwarded.
— disabled

202 |firewall AOS-W 3.4.1 Command Line Interface | Reference Guide
disable-ftp-server Disables the FTP server on the switch. Enabling this
option prevents FTP transfers.
Enabling this option could cause APs to not boot up.
You should not enable this option unless instructed to
do so by an Alcatel-Lucent representative.
— disabled
disable-stateful-h323-
processing
Disables stateful H.323 processing. — enabled
disable-stateful-sip Disables monitoring of exchanges between a voice
over IP or voice over WLAN device and a SIP server.
This option should be enabled only when thee is no
VoIP or VoWLAN traffic on the network.
— disabled
drop-ip-fragments When enabled, all IP fragments are dropped. You
should not enable this option unless instructed to do so
by an Alcatel-Lucent representative.
— disabled
enable-per-packet-logging Enables logging of every packet if logging is enabled
for the corresponding session rule. Normally, one event
is logged per session. If you enable this option, each
packet in the session is logged. You should not enable
this option unless instructed to do so by an Alcatel-
Lucent representative, as doing so may create
unnecessary overhead on the switch.
— disabled
enforce-tcp-handshake Prevents data from passing between two clients until
the three-way TCP handshake has been performed.
This option should be disabled when you have mobile
clients on the network as enabling this option will
cause mobility to fail. You can enable this option if there
are no mobile clients on the network.
— disabled
gre-call-id-processing Creates a unique state for each PPTP tunnel. You
should not enable this option unless instructed to do so
by an Alcatel-Lucent representative.
— disabled
local-valid-users Adds only IP addresses, which belong to a local
subnet, to the user-table. — disabled
log-icmp-error Logs received ICMP errors. You should not enable this
option unless instructed to do so by an Alcatel-Lucent
representative.
— disabled
prohibit-arp-spoofing Detects and prohibits arp spoofing. When this option is
enabled, possible arp spoofing attacks are logged and
an SNMP trap is sent.
— disabled
prohibit-ip-spoofing Detects IP spoofing (where an intruder sends
messages using the IP address of a trusted client).
When this option is enabled, IP and MAC addresses
are checked; possible IP spoofing attacks are logged
and an SNMP trap is sent.
— disabled
prohibit-rst-replay Closes a TCP connection in both directions if a TCP
RST is received from either direction. You should not
enable this option unless instructed to do so by an
Alcatel-Lucent representative.
— disabled
session-idle-timeout Time, in seconds, that a non-TCP session can be idle
before it is removed from the session table. You should
not modify this option unless instructed to do so by an
Alcatel-Lucent representative.
16-259 15
seconds
Parameter Description Range Default

AOS-W 3.4.1 Command Line Interface | Reference Guide firewall | 203
Usage Guidelines
This command configures global firewall options on the switch.
Example
The following command disallows forwarding of non-IP frames between users:
firewall deny-inter-user-bridging
session-mirror-
destination
Destination to which mirrored packets are sent. This
option is used only for troubleshooting or debugging.
Packets can be mirrored in multiple ACLs, so only a
single copy is mirrored if there is a match within more
than one ACL.
You can configure the following:
Ethertype to be mirrored with the Ethertype ACL mirror
option. See ip access-list eth on page 259.
IP flows to be mirrored with the session ACL mirror
option. See ip access-list session on page 265.
MAC flows to be mirrored with the MAC ACL mirror
option. See ip access-list mac on page 263.
If you configure both an IP address and a port to
receive mirrored packets, the IP address takes
precedence.
——
ip-address Configures the IP address of the mirrored destination.
Packets are encapsulated in GRE and sent to the
destination IP address.
——
port Configures the port of the mirrored destination.
Packets are forwarded to the destination port. ——
<slot> <slot> is always 1 except for the OmniAccess 6000
switch, where the slots can be 0, 1, 2, or 3. ——
<port> Number assigned to the network interface embedded
in the switch or in the line card installed in the
OmniAccess 6000 switch. Port numbers start at 0 from
the left-most position.
——
session-mirror-ipsec Configures session mirroring of all frames that are
processed by IPsec. Frames are sent to IP address
specified by the session-mirror-destination option.This
option is used only for troubleshooting or debugging.
— disabled
session-voip-timeout Idle session timeout, in seconds, for sessions that are
marked as voice sessions. If no voice packet exchange
occurs over a voice session for the specified time, the
voice session is removed.
16-300 300
seconds
broadcast-filter-arp If enabled, all broadcast ARP requests are converted to
unicast and sent directly to the client. You can check
the status of this option using the show ap active and
the show datapath tunnel command. If enabled, the
output will display the letter a in the flags column.
— disabled
wmm-voip-content-
enforcement
If traffic to or from the user is inconsistent with the
associated QoS policy for voice, the traffic is
reclassified to best effort and data path counters
incremented.
This parameter requires the Policy Enforcement
Firewall license in the switch.
— disabled
Parameter Description Range Default

204 |firewall AOS-W 3.4.1 Command Line Interface | Reference Guide
Related Commands
(host) (config) #show firewall
History
Command Information
Version Modification
AOS-W 3.0 Introduced for the first time.
AOS-W 3.2 The wmm-voip-content-enforcement parameter was introduced.
AOS-W 3.3 The session-mirror-destination parameter was modified.
AOS-W 3.3.2 The local-valid-users parameter was added.
AOS-W 3.4 The voip-proxy-arp parameter was renamed to broadcast-filter-arp and i t does
not require a Voice license.
The prohibit-arp-spoofing parameter was added.
Platform License Command Mode
Available on all platforms PEF license Config mode on master switches
AOS-W 3.4.1 Command Line Interface | Reference Guide firewall cp | 205
firewall cp
firewall cp {deny|permit} proto <IP protocol number> ports <start port number>
<last port number> [bandwidth-contract <name>]
no ...
Description
This command creates whitelist session ACLs. Whitelist ACLs consist of rules that explicitly permit or deny
session traffic from being forwarded or not to the switch. This prohibits traffic from being automatically
forwarded to the switch if it was not specifically denied in a blacklist.The maximum number of entries
allowed in the whitelist is 64.
Syntax
Usage Guidelines
This command turns the session ACL from a blacklist to a whitelist. A rule must exist that explicitly permits
the session before it is forwarded to the switch and the last rule in the list denies everything else.
Example
The following command creates a whitelist ACL that allows traffic using protocol 6 on ports 5000 through
6000 to be forwarded to the switch.
(host) (config-fw-cp) #firewall cp permit proto 6 ports 5000 6000
The following command creates a a whitelist ACL entry that denies traffic using protocol 2 on port 5000
from being forwarded to the switch:
Parameter Description Range Default
deny Specifies the entry to reject on the session ACL
whitelist — disabled
proto Indicates the protocol. — —
IP protocol number Specifies the IP protocol number that is rejected. 1-255 —
ports Port that the session traffic is using —
start port Specifies the start port 1-65535
last port Specifies the last port 1-65535
permit Specifies an entry that is allowed on the session
ACL whitelist —
proto Protocol that the session traffic is using — —
IP protocol number Specifies the IP protocol number that is allowed 1-255 —
ports Indicates the port on which session traffic is
running —
start port Specifies the starting port, in the port range, on
which session traffic is running. 1-65535
last port Specifies the last port, in the port range, on
which session traffic is running. 1-65535
bandwidth-contract <name> Specify the name of a bandwidth contract
defined via the cp-bandwidth-contract
command.
—
206 | firewall cp AOS-W 3.4.1 Command Line Interface | Reference Guide
(host) (config-fw-cp) #firewall cp deny proto 2 ports 5000 5000
Related Commands
Command History
Introduced in AOS-W 3.4
Command Information
Command Description Mode
show firewall-cp Show Control Processor (CP) whitelist ACL info. Enable or Config modes
cp-bandwidth-contract This command configures a bandwidth contract
traffic rate which can then be associated with a
whitelist session ACL.
Enable or Config modes
Platform License Command Mode
Available on all platforms PEF license Config mode on master
switches
AOS-W 3.4.1 Command Line Interface | Reference Guide firewall cp-bandwidth-contract | 207
firewall cp-bandwidth-contract
firewall cp-bandwidth-contract {auth|route|sessmirr|trusted-mcast|trusted-ucast
|untrusted-mcast|untrusted-ucast} <Rate>
Description
This command configures bandwidth contract traffic rate limits to prevent denial of service attacks.
Syntax
Usage Guidelines
This command configures firewall bandwidth contract options on the switch.
Example
The following command disallows forwarding of non-IP frames between users:
(host) (config) #firewall deny-inter-user-bridging
Related Commands
(host) (config) #show firewall
Command History
Introduced in AOS-W 3.4
Command Information
Parameter Description Range Default
auth Specifies the traffic rate limit that is forwarded to the
authentication process. 1-200 Mbps 1
route Specifies the traffic rate limit that needs ARP requests. 1-200 Mbps 1
sessmirr Specifies the session mirrored traffic forwarded to the
switch. 1-200 Mbps 1
trusted-mcast Specifies the trusted multicast traffic rate limit. 1-200 Mbps 2
trusted-ucast Specifies the trusted unicast traffic rate limit. 1-200 Mbps 80
untrusted-mcast Specifies the untrusted multicast traffic rate limit. 1-200 Mbps 2
untrusted-ucast Specifies the untrusted unicast traffic rate limit. 1-200 Mbps 10
Platform License Command Mode
Available on all platforms PEF license Config mode on master
switches

208 | firewall cp-bandwidth-contract AOS-W 3.4.1 Command Line Interface | Reference Guide
AOS-W 3.4.1 Command Line Interface | Reference Guide gateway health-check disable | 209
gateway health-check disable
gateway health-check disable
Description
Disable the gateway health check.
Usage Guidelines
The gateway health check feature can only be enabled by Alcatel-Lucent Technical Support. This command
disables the gateway health check, and should only be issued under the guidance of the support staff.
Related Commands
(host) (config) #show gateway health-check
History
Introduced in AOS-W 3.4
Command Information
Command Description Mode
show gateway health-check
Display the current status of the
gateway health-check feature This command is available in Config and
Enable mode on master and local switches
Platforms Licensing Command Mode
All platforms Base operating system Config mode on master or local switches.

210 | gateway health-check disable AOS-W 3.4.1 Command Line Interface | Reference Guide

AOS-W 3.4.1 Command Line Interface | Reference Guide guest-access-email | 211
guest-access-email
guest-access-email
smtp-port
smtp-server
no...
Description
This command configures the SMTP server which is used to send guest email. Guest email is generated
when a guest user account is created or when the Guest Provisioning user sends guest user account email a
later time.
Syntax
Usage Guidelines
As part of the guest provisioning feature, the guest-access-email command allows you to set up the SMTP
port and server that process guest provisioning email. This email process sends email to either the guest or
the sponsor whenever a guest user account is created or when the Guest Provisioning user manually sends
email from the Guest Provisioning page.
Example
The following command creates a guest-access email profile and sends guest user email through SMTP
server IP address 1.1.1.1 on port 25.
(host) (config) #guest-access-email
(host) (Guest-access Email Profile) #
(host) (Guest-access Email Profile) #smtp-port 25
(host) (Guest-access Email Profile) #smtp-server 1.1.1.1
Related Commands
(host) #show guest-access-email
(host) #local-userdb-guest add
(host) #local-userdb-guest modify
(host) #show local-userdb-guest
Command History
Parameter Description Range Default
smtp-port Identifies the SMTP port through which the guest-
access email is sent. ——
<Port number> The SMTP port number. 1–65535 25
smtp-server The SMTP server to which the switch sends the guest-
access email. ——
<IP-Address> The SMTP server’s IP address. — —
no Deletes the command configuration — —
Version Modification
AOS-W 3.4 Introduced for the first time.

212 | guest-access-email AOS-W 3.4.1 Command Line Interface | Reference Guide
Command Information
Platform License Command Mode
Available on all platforms Available in the base operating system. Config mode on master switches.

AOS-W 3.4.1 Command Line Interface | Reference Guide halt | 213
halt
halt
Description
This command halts all processes on the switch.
Syntax
No parameters.
Usage Guidelines
This command gracefully stops all processes on the switch. You should issue this command before
rebooting or shutting down to avoid interrupting processes.
Command History
Introduced in AOS-W 3.0
Command Information
Platform License Command Mode
Available on all platforms Available in the base operating system. Enable mode on master and local
switches.

214 |halt AOS-W 3.4.1 Command Line Interface | Reference Guide

AOS-W 3.4.1 Command Line Interface | Reference Guide help | 215
help
help
Description
This command displays help for the CLI.
Syntax
No parameters.
Usage Guidelines
This command displays keyboard editing commands that allow you to make corrections or changes to the a
command without retyping.
You can also enter the question mark (?) to get various types of command help:
zWhen typed at the beginning of a line, the question mark lists all commands available in the current
mode.
zWhen typed at the end of a command or abbreviation, the question mark lists possible commands that
match.
zWhen typed in place of a parameter, the question mark lists available options.
Example
The following command displays help:
(host) #help
Command History
Available in AOS-W 3.0
Command Information
Platform License Command Mode
Available on all platforms Available in the base operating
system Available in the following command modes:
zUser
zEnable
zConfig

216 |help AOS-W 3.4.1 Command Line Interface | Reference Guide
AOS-W 3.4.1 Command Line Interface | Reference Guide hostname | 217
hostname
hostname <hostname>
Description
This command changes the hostname of the switch.
Syntax
Usage Guidelines
The hostname is used as the default prompt.
You can use any alphanumeric character, punctuation, or symbol character. To use spaces, plus symbols
(+), question marks (?), or asterisks (*), enclose the text in quotes.
The default names for the following switches are:
zOmniAccess 4302 WLAN Switch: Alcatel-Lucent200
zOmniAccess 4308T WLAN Switch: Alcatel-Lucent800
zOmniAccess 4324 WLAN Switch: Alcatel-Lucent2400
zOmniAccess 6000 WLAN Switch: Alcatel-Lucent6000
zOmniAccess 4504 Multi-Service Switch: Alcatel-Lucent3200
zOmniAccess 4604 MMulti-Service Switch: Alcatel-Lucent3400
zOmniAccess 4704 Multi-Service Switch: Alcatel-Lucent3600
Example
The following example configures the switch hostname to “Switch 1”.
hostname “Switch 1”
Command History
Introduced in AOS-W 1.0
Command Information
Parameter Description Range Default
hostname The hostname of the switch 1-63 See below
Platform License Command Mode
Available on all platforms Available in the base operating system Config mode on master and
local switches

218 |hostname AOS-W 3.4.1 Command Line Interface | Reference Guide

AOS-W 3.4.1 Command Line Interface | Reference Guide ids dos-profile | 219
ids dos-profile
ids
ids dos-profile <profile>
ap-flood-inc-time <seconds>
ap-flood-quiet-time <seconds>
ap-flood-threshold <number>
assoc-rate-thresholds <number>
auth-rate-thresholds <number>
client-ht-40mhz-intol-quiet-time <seconds>
clone <profile>
deauth-rate-thresholds <number>
detect-ap-flood
detect-eap-rate-anomaly
detect-ht-40mhz-intolerance
detect-rate-anomalies
disassoc-rate-thresholds <number>
eap-rate-quiet-time <seconds>
eap-rate-threshold <number>
eap-rate-time-interval <seconds>
no ...
probe-request-rate-thresholds <number>
probe-response-rate-thresholds <number>
spoofed-deauth-blacklist
Description
This command configures traffic anomalies for denial of service (DoS) attacks.
Syntax
Parameter Description Range Default
<profile> Name that identifies an instance of the
profile. The name must be 1-63 characters. — “default”
ap-flood-inc-time Time, in seconds, during which a configured
number of fake AP beacons must be
received to trigger an alarm.
any 3600
seconds
ap-flood-quiet-time After an alarm has been triggered by a fake
AP flood, the time, in seconds, that must
elapse before an identical alarm may be
triggered.
60-360000 900
seconds
ap-flood-threshold Number of fake AP beacons that must be
received within the flood increase time to
trigger an alarm.
any 50
assoc-rate-thresholds Rate threshold for associate request frames.
auth-rate-thresholds Rate threshold for authenticate frames.
client-ht-40mhz-intol-quiet-
time
Controls the quiet time (when to stop
reporting intolerant STAs if they have not
been detected), in seconds, for detection of
802.11n 40 MHz intolerance setting.
60-360000 900
seconds
clone Name of an existing IDS DoS profile from
which parameter values are copied. ——
deauth-rate-thresholds Rate threshold for deauthenticate frames.

220 | ids dos-profile AOS-W 3.4.1 Command Line Interface | Reference Guide
Usage Guidelines
DoS attacks are designed to prevent or inhibit legitimate clients from accessing the network. This includes
blocking network access completely, degrading network service, and increasing processing load on clients
and network equipment.
detect-ap-flood Enables detection of flooding with fake AP
beacons to confuse legitimate users and to
increase the amount of processing needed
on client operating systems.
true
false
false
detect-eap-rate-anomaly Enables Extensible Authentication Protocol
(EAP) handshake analysis to detect an
abnormal number of authentication
procedures on a channel and generate an
alarm when this condition is detected.
true
false
false
detect-ht-40mhz-intolerance Enables or disables detection of 802.11n 40
MHz intolerance setting, which controls
whether stations and APs advertising 40 MHz
intolerance will be reported.
true
false
true
detect-rate-anomalies Enables detection of rate anomalies. true
false
false
disassoc-rate-thresholds Rate threshold for disassociate frames.
eap-rate-quiet-time After an EAP rate anomaly alarm has been
triggered, the time, in seconds, that must
elapse before another identical alarm may be
triggered.
60-360000 900
seconds
eap-rate-threshold Number of EAP handshakes that must be
received within the EAP rate time interval to
trigger an alarm.
any 60
eap-rate-time-interval Time, in seconds, during which the
configured number of EAP handshakes must
be received to trigger an alarm.
1-120 3 seconds
no Negates any configured parameter. — —
probe-request-rate-thresholds Rate threshold for probe request frames.
probe-response-rate-thresholds Rate threshold for probe response frames.
spoofed-deauth-blacklist Enables detection of a deauth attack initiated
against a client associated to an
Alcatel-Lucent AP. When such an attack is
detected, the client is quarantined from the
network to prevent a man-in-the-middle
attack from being successful.
true
false
false
Parameter Description Range Default
AP configuration settings related to the IEEE 802.11n standard are configurable for Alcatel-Lucent OAW-AP120
series access points, which are IEEE 802.11n standard compliant devices

AOS-W 3.4.1 Command Line Interface | Reference Guide ids dos-profile | 221
There are four predefined DoS profiles, each of which provides different levels of detection and
containment. The following describes the settings for each of the predefined profiles:
Example
The following command enables detections in the DoS profile:
(host) (config) #ids dos-profile dos1
detect-ap-flood
detect-eap-rate-anomalies
detect-rate-anomalies
spoofed-deauth-blacklist
Command History
Parameter
ids-dos-disabled ids-dos-low-setting i
ds-dos-medi
um-setting
ids-dos-high-
setting
Spoofed Deauth Blacklist false false false false
Detect AP Flood Attack false false false false
AP Flood Threshold 50 50 50 50
AP Flood Increase Time 3 seconds 3 seconds 3 seconds 3 seconds
AP Flood Detection Quiet Time 900 seconds 900 seconds 900 seconds 900 seconds
Detect EAP Rate Anomaly false false true true
EAP Rate Threshold 60 60 30 60
EAP Rate Time Interval 3 seconds 3 seconds 3 seconds 3 seconds
EAP Rate Quiet Time 900 seconds 900 seconds 900 seconds 900 seconds
Detect Rate Anomalies false false false true
Detect 802.11n 40 MHz
Intolerance Setting false true true true
Client 40 MHz Intolerance
Detection Quiet Time 900 seconds 900 seconds 900 seconds 900 seconds
Rate Thresholds for Assoc
Frames default default default default
Rate Thresholds for Disassoc
Frames default default default default
Rate Thresholds for Deauth
Frames default default default default
Rate Thresholds for Probe
Request Frames default probe-request-
response-thresholds probe-request-
response-thres
holds
probe-request-
response-thres
holds
Rate Thresholds for Probe
Response Frames default probe-request-
response-thresholds probe-request-
response-thres
holds
probe-request-
response-thres
holds
Rate Thresholds for Auth Frames default default default default
Release Modification
AOS-W 3.0 Command Introduced.
222 | ids dos-profile AOS-W 3.4.1 Command Line Interface | Reference Guide
Command Information
AOS-W 3.3 Updated with support for high-throughput IEEE 802.11n standard.
AOS-W 3.4 detect-disconnect-sta and disconnect-sta-quiet-time parameters deprecated.
Release Modification
Platform License Command Mode
Available on all platforms Requires Wireless Intrusion Protection license Config mode on master
switches

AOS-W 3.4.1 Command Line Interface | Reference Guide ids general-profile | 223
ids general-profile
ids general-profile <name>
ap-inactivity-timeout <seconds>
clone <profile>
min-pot-ap-beacon-rate <percent>
min-pot-ap-monitor-time <seconds>
no ...
signature-quiet-time <seconds>
sta-inactivity-timeout <seconds>
stats-update-interval <seconds>
wired-containment
wireless-containment
wireless-containment-debug
Description
This command configures AP attributes.
Syntax
Usage Guidelines
Parameter Description Range Default
<profile> Name that identifies an instance of the profile. The
name must be 1-63 characters. — “default”
ap-inactivity-
timeout
Time, in seconds, after which an AP is aged out. 5-36000 5 seconds
clone Name of an existing IDS general profile from which
parameter values are copied. ——
min-pot-ap-bea
con-rate
Minimum beacon rate acceptable from a potential AP,
in percentage of the advertised beacon interval. 0-100 25%
min-pot-ap-moni
tor-time
Minimum time, in seconds, a potential AP has to be
up before it is classified as a real AP. any 2 seconds
no Negates any configured parameter. — —
signature-quiet
-time
After a signature match is detected, the time to wait,
in seconds, to resume checking. 60-360000 900 seconds
sta-inactivity-
timeout
Time, in seconds, after which a station is aged out. 30-360000 60 seconds
stats-update-in
terval
Interval, in seconds, for the AP to update the switch
with statistics. This setting takes effect only if the
Alcatel-Lucent Mobility Manager is configured.
Otherwise, statistics update to the switch is disabled.
60-360000 60 seconds
wired-contain
ment
Enable containment from the wired side. — false
wireless-con
tainment
Enable containment from the wireless side. — false
wireless-con
tainment-debug
Enable debugging of containment from the wireless
side. —false
224 | ids general-profile AOS-W 3.4.1 Command Line Interface | Reference Guide
This command configures general IDS attributes. There are two predefined general IDS profiles, each of
which provides different levels of containment. The following describes the settings for each of the
predefined profiles:
Example
The following command enables containments in the general IDS profile:
(host) (config) #ids general-profile general1
wired-containment
wireless-containment
wireless-containment-debug
Command History
Introduced in AOS-W 3.0
Command Information
Parameter ids-general-disabled ids-general-high-setting
Stats Update Interval 60 seconds 60 seconds
AP Inactivity Timeout 5 seconds 5 seconds
STA Inactivity Timeout 60 seconds 60 seconds
Min Potential AP Beacon Rate 25% 25%
Min Potential AP Monitor Time 2 seconds 2 seconds
Signature Quiet Time 900 seconds 900 seconds
Wireless Containment false true
Debug Wireless Containment false false
Wired Containment false true
Platform License Command Mode
Available on all platforms Most parameters of this command are
available in the base operating system.
However, the signature-quiet
-time parameter requires the Wireless
Intrusion Protection license.
Config mode on master switches
AOS-W 3.4.1 Command Line Interface | Reference Guide ids impersonation-profile | 225
ids impersonation-profile
ids impersonation-profile <name>
beacon-diff-threshold <percent>
beacon-inc-wait-time <seconds>
clone <profile>
detect-ap-impersonation
no ...
protect-ap-impersonation
Description
This command configures anomalies for impersonation attacks.
Syntax
Usage Guidelines
A successful man-in-the-middle attack will insert an attacker into the data path between the client and the
AP. In such a position, the attacker can delete, add, or modify data, provided he has access to the
encryption keys. Such an attack also enables other attacks that can learn a client’s authentication
credentials. Man-in-the-middle attacks often rely on a number of different vulnerabilities.
There are two predefined IDS impersonation profiles, each of which provides different levels of detection.
The following describes the settings for each of the predefined profiles:
Parameter Description Range Default
<profile> Name that identifies an instance of the profile. The name
must be 1-63 characters. —“default”
beacon-diff-
threshold
Percentage increase in beacon rates that triggers an AP
impersonation event. 0-100 50%
beacon-inc-wait-time Time, in seconds, after the beacon difference threshold is
crossed before an AP impersonation event is generated. any 3 seconds
clone Name of an existing IDS impersonation profile from which
parameter values are copied. ——
detect-ap-impersonat
ion
Enables detection of AP impersonation. In AP
impersonation attacks, the attacker sets up an AP that
assumes the BSSID and ESSID of a valid AP. AP
impersonation attacks can be done for man-in-the-middle
attacks, a rogue AP attempting to bypass detection, or a
honeypot attack.
—true
no Negates any configured parameter. — —
protect-ap-impersona
tion
When AP impersonation is detected, both the legitimate
and impersonating AP are disabled using a denial of
service attack.
—false
Parameter ids-impersonation-disabled ids-impersonation-high-setting
Detect AP Impersonation false true
Protect from AP Impersonation false true
Beacon Diff Threshold 50% 50%
Beacon Increase Wait Time 3 seconds 3 seconds

226 | ids impersonation-profile AOS-W 3.4.1 Command Line Interface | Reference Guide
Example
The following command enables detections in the impersonation profile:
ids impersonation-profile mitm1
detect-ap-impersonation
Command History0
Command Information
Version Modification
AOS-W 3.0 Command Introduced
AOS-W 3.4 detect-sequence-anomaly , sequence-diff, sequence-quiet-time, sequence-time-tolerance
parameters deprecated.
Platform License Command Mode
Available on all platforms Requires Wireless Intrusion Protection
license Config mode on master switches

AOS-W 3.4.1 Command Line Interface | Reference Guide ids profile | 227
ids profile
ids profile <name>
clone <profile>
dos-profile <profile>
general-profile <profile>
impersonation-profile <profile>
no ...
signature-matching-profile <profile>
unauthorized-device-profile <profile>
Description
This command defines a set of IDS profiles.
Syntax
Usage Guidelines
This command defines a set of IDS profiles that you can then apply to an AP group (with the ap-group
command) or to a specific AP (with the ap-name command).
There are four predefined IDS profiles, each of which defines different sets of IDS profile. The following
describes the settings for each of the predefined profiles:
Parameter Description Default
<profile> Name that identifies an instance of the profile. The name
must be 1-63 characters. “default”
clone Name of an existing IDS profile from which parameter
values are copied. —
dos-profile Name of a IDS denial of service profile to be applied to
the AP group/name. See ids dos-profile on page 219.“default”
general-profile Name of an IDS general profile to be applied to the AP
group/name. See ids general-profile on page 223.“default”
impersonation-profile Name of an IDS impersonation profile to be applied to
the AP group/name. See ids impersonation-profile on
page 225.
“default”
no Negates any configured parameter. —
signature-matching-profile Name of an IDS signature matching profile to be applied
to the AP group/name. See ids
signature-matching-profile on page 231
“default”
unauthorized-device-profile Name of an IDS unauthorized device profile to be applied
to the AP group/name. See ids
unauthorized-device-profile on page 235.
“default”
Parameter ids-disabled ids-low-setting ids-medium-setting ids-high-setting
IDS General profile ids-general-disabled default default ids-general-high-
setting
IDS Signature
Matching profile default factory-default-
signatures factory-default-
signatures factory-default-
signatures
IDS DoS profile ids-dos-disabled ids-dos-low-setting ids-dos-medium-
setting ids-dos-high-set
ting

228 | ids profile AOS-W 3.4.1 Command Line Interface | Reference Guide
Example
The following command defines a set of IDS profiles:
(host) (config) #ids profile ids1
dos-profile dos1
general-profile general1
impersonation-profile mitm1
signature-matching-profile sig1
unauthorized-device-profile unauth1
Command History
Introduced in AOS-W 3.0
Command Information
IDS Impersonation
profile ids-impersonation
-disabled default default ids-impersonation
-high-setting
IDS Unauthorized
Device profile ids-unauthorized-
device-disabled default ids-unauthorized-
device-medium-
setting
ids-unauthorized-
device-high-set
ting
Parameter ids-disabled ids-low-setting ids-medium-setting ids-high-setting
Platform License Command Mode
Available on all platforms Requires Wireless Intrusion Protection
license Config mode on master
switches.

AOS-W 3.4.1 Command Line Interface | Reference Guide ids rate-thresholds-profile | 229
ids rate-thresholds-profile
ids rate-thresholds-profile <name>
channel-inc-time <seconds>
channel-quiet-time <seconds>
clone <profile>
no ...
node-quiet-time <seconds>
node-threshold <number>
node-time-interval <seconds>
Description
This command configures thresholds that are assigned to the different frame types for rate anomaly
checking.
Syntax
Usage Guidelines
A profile of this type is attached to each of the following 802.11 frame types in the IDS denial of service
profile:
zAssociation frames
zDisassociation frames
zDeauthentication frames
zProbe Request frames
zProbe Response frames
Parameter Description Range Default
<profile> Name that identifies an instance of the profile. The name
must be 1-63 characters. —“default”
channel-inc-time Time, in seconds, in which the threshold must be exceeded
in order to trigger an alarm. 0 - 360000
seconds 15
seconds
channel-quiet-time After a channel rate anomaly alarm has been triggered, the
time that must elapse before another identical alarm may be
triggered. This option prevents excessive messages in the
log file.
60-360000 900
seconds
channel-threshold Number of a specific type of frame that must be exceeded
within a specific interval in an entire channel to trigger an
alarm.
any 300
clone Name of an existing IDS rate thresholds profile from which
parameter values are copied. ——
no Negates any configured parameter. — —
node-quiet-time After a node rate anomaly alarm has been triggered, the
time, in seconds, that must elapse before another identical
alarm may be triggered. This option prevents excessive
messages in the log file.
60-360000 900
seconds
node-threshold Number of a specific type of frame that must be exceeded
within a specific interval for a particular client MAC address
to trigger an alarm.
0 -100000
frames 200
node-time-interval Time, in seconds, in which the threshold must be exceeded
in order to trigger an alarm. 1-120 15
seconds
230 |ids rate-thresholds-profile AOS-W 3.4.1 Command Line Interface | Reference Guide
zAuthentication frames
There is a predefined IDS rate thresholds profile. The following describes the settings for the predefined
profile:
Example
The following command configures frame thresholds:
(host) (config) #ids rate-thresholds-profile rate1
channel-threshold 250
node-threshold 150
Command History
Introduced in AOS-W 3.0
Command Information
Parameter probe-request-response-thresholds
Channel Increase Time 30 seconds
Channel Quiet Time 900 seconds
Channel Threshold 350
Node Time Interval 10 seconds
Node Quiet Time 900 seconds
Node Threshold 250 seconds
Platform License Command Mode
Available on all platforms Requires Wireless Intrusion Protection license Config mode on master switches
AOS-W 3.4.1 Command Line Interface | Reference Guide ids signature-matching-profile | 231
ids signature-matching-profile
ids signature-matching-profile <name>
clone <profile>
no ...
signature <profile>
Description
This command contains defined signature profiles.
Syntax
Usage Guidelines
You can include one or more predefined signature profiles or a user-defined signature profile in a signature
matching profile. The following are predefined signature profiles that are included in the signature
matching profile called “factory-default-signatures”:
Example
The following command configures a signature matching profile:
(host) (config) #ids signature-matching-profile sig1
signature Null-Probe-Response
Parameter Description Default
<profile> Name that identifies an instance of the profile. The name must be 1-63
characters. “default”
clone Name of an existing IDS signature matching profile from which parameter
values are copied. —
no Negates any configured parameter. —
signature Name of a signature profile. See <z_blue>“ids signature-profile” on page 233. —
Signature Description
AirJack Originally a suite of device drivers for 802.11(a/b/g) raw frame injection and reception. It was
intended to be used as a development tool for all 802.11 applications that need to access the
raw protocol, however one of the tools included allowed users to force off all users on an
Access Point.
ASLEAP A tool created for Linux systems that has been used to attack Cisco LEAP authentication
protocol.
Deauth-Broadcast A deauth broadcast attempts to disconnect all stations in range – rather than sending a
spoofed deauth to a specific MAC address, this attack sends the frame to a broadcast
address.
NetStumbler
Generic NetStumbler is a popular wardriving application used to locate 802.11 networks. When used
with certain NICs (such as Orinoco), NetStumbler generates a characteristic frame that can be
detected.
NetStumbler
Version 3.3.0x Version 3.3.0 of NetStumbler changed the characteristic frame slightly. This signature detects
the updated frame.
Null-Probe-Respo
nse An attack with the potential to crash or lock up the firmware of many 802.11 NICs. In this
attack, a client probe-request frame will be answered by a probe response containing a null
SSID. A number of popular NIC cards will lock up upon receiving such a probe response.

232 | ids signature-matching-profile AOS-W 3.4.1 Command Line Interface | Reference Guide
Command History
Introduced in AOS-W 3.0
Command Information
Platform License Command Mode
Available on all platforms Requires Wireless Intrusion Protection license Config mode on master
switches

AOS-W 3.4.1 Command Line Interface | Reference Guide ids signature-profile | 233
ids signature-profile
ids signature-profile <name>
bssid <macaddr>
clone <profile>
dst-mac <macaddr>
frame-type {assoc|auth|beacon|control|data|deauth|disassoc|mgmt|probe-request|
probe-response} [ssid <ssid>] [ssid-length <bytes>]
no ...
payload <pattern> [offset <number>]
seq-num <number>
src-mac <macaddr>
Description
This command configures signatures for wireless intrusion detection.
Syntax
Parameter Description Default
<profile> Name that identifies an instance of the profile. The name must be
1-63 characters. “default”
bssid BSSID field in the 802.11 frame header. —
clone Name of an existing IDS signature profile from which parameter
values are copied. —
dst-mac Destination MAC address in the 802.11 frame header. —
frame-type Type of 802.11 frame. For each type of frame, further parameters
can be specified to filter and detect only the required frames. —
assoc Association frame type
auth Authentication frame type
beacon Beacon frame type
control All control frames
data All data frames
deauth Deauthentication frame type
disassoc Disassociation frame type
mgmt Management frame type
probe-re
quest
Probe request frame type
probe-re
sponse
Probe response frame type
ssid For beacon, probe-request, and probe-response frame types,
specify the SSID as either a string or hex pattern. —
ssid-length For beacon, probe-request, and probe-response frame types,
specify the length, in bytes, of the SSID. Maximum length is 32
bytes.
—
no Negates any configured parameter. —
234 | ids signature-profile AOS-W 3.4.1 Command Line Interface | Reference Guide
Usage Guidelines
The following describes the configuration for the predefined signature profiles:
Example
The following command configures a signature profile:
(host) (config) #ids signature-profile mysig
frame-type assoc
src-mac 00:00:00:00:00:00
Command History
Introduced in AOS-W 3.0
Command Information
payload Pattern at a fixed offset in the payload of an 802.11 frame. Specify
the pattern to be matched as a string or hex pattern. Maximum
length is 32 bytes.
—
offset When a payload pattern is configured, specify the offset in the
payload where the pattern is expected to be found in the frame. —
seq-num Sequence number of the frame. —
src-mac Source MAC address in the 802.11 frame header. —
Parameter Description Default
Signature Profile Parameter Value
AirJack frame-type beacon ssid = AirJack
ASLEAP frame-type beacon ssid = asleap
Deauth-Broadcast frame-type deauth
dst-mac ff:ff:ff:ff:ff:ff
Netstumbler Generic payload offset=3 pattern=0x00601d
payload offset=6 pattern=0x0001
Netstumbler Version 3.3.0x payload offset=3 pattern=0x00601d
payload offset=12 pattern=0x000102
Null-Probe-Response frame-type probe-response ssid length = 0
Platform License Command Mode
Available on all platforms Requires Wireless Intrusion Protection license Config mode on master switches
AOS-W 3.4.1 Command Line Interface | Reference Guide ids unauthorized-device-profile | 235
ids unauthorized-device-profile
ids unauthorized-device-profile <name>
adhoc-quiet-time <seconds>
allow-well-known-mac [hsrp|iana|local-mac|vmware|vmware1|vmware2|vmware3]
cfg-valid-11a-channel <channel>
cfg-valid-11g-channel <channel>
classification
clone <profile>
detect-adhoc-network
detect-bad-wep
detect-ht-greenfield
detect-invalid-mac-oui
detect-misconfigured-ap
detect-windows-bridge
detect-wireless-bridge
mac-oui-quiet-time <seconds>
no ...
overlay-classification
privacy
protect-adhoc-network
protect-high-throughput
protect-ht-40mhz
protect-misconfigured-ap
protect-ssid
protect-valid-sta
require-wpa
rogue-containment
suspect-rogue-conf-level <level>
suspect-rogue-containment
valid-and-protected-ssid <ssid>
valid-oui <oui>
valid-wired-mac <macaddr>
wireless-bridge-quiet-time <seconds>
Description
This command configures detection of unauthorized devices, as well as rogue AP detection and
containment.
Syntax
Parameter Description Range Default
<profile> Name that identifies an instance of the profile. The name must be
1-63 characters. —“default”
adhoc-quiet-
time
Time, in seconds, that must elapse after an adhoc network detection
alarm has been triggered before another identical alarm may be
triggered.
60-3600
00 900
seconds
236 | ids unauthorized-device-profile AOS-W 3.4.1 Command Line Interface | Reference Guide
allow-well-
known-mac
Allows devices with known MAC addresses to classify rogues APs.
Depending on your network, configure one or more of the following
options for classifying rogue APs:
hsrp—Routers configured for HSRP, a Cisco-proprietary redundancy
protocol, with the HSRP MAC OUI 00:00:0c.
iana—Routers using the IANA MAC OUI 00:00:5e.
local-mac—Devices with locally administered MAC addresses
starting with 02.
vmware—Devices with any of the following VMWare OUIs: 00:0c:29,
00:05:69, or 00:50:56
vmware1—Devices with VMWare OUI 00:0c:29.
vmware2—Devices with VMWare OUI 00:05:69.
vmware3—Devices with VMWare OUI 00:50:56.
If you modify an existing configuration, the new configuration
overrides the original configuration. For example, if you configure
allow-well-known-mac hsrp and then configure
allow-well-known-mac iana, the original configuration is lost.
To add more options to the original configuration, include all of the
required options, for example: allow-well-known-mac hsrp
iana.
Use caution when configuring this command. If the neighboring
network uses similar routers, those APs might be classified as
rogues. If containment is enabled, clients attempting to associate to
an AP classified as a rogue are disconnected through a denial of
service attack.
To clear the well known MACs in the system, use the following
commands on all switches:
clear wms wired-mac
This clears all of the learned wired MAC information on the switch.
reload
This reboots the switch.
——
cfg-valid-11a-
channel
List of valid 802.11a channels that third-party APs are allowed to use. 34-165 N/A
cfg-valid-11g-
channel
List of valid 802.11b/g channels that third-party APs are allowed to
use. 1-14 N/A
classification Enable/disable rogue AP classification. A rogue AP is one that is
unauthorized and plugged into the wired side of the network. Any
other AP seen in the RF environment that is not part of the valid
enterprise network is considered to be interfering — it has the
potential to cause RF interference but it is not connected to the wired
network and thus does not represent a direct threat.
—true
clone Name of an existing IDS rate thresholds profile from which parameter
values are copied. ——
detect-adhoc-
network
Enable detection of adhoc networks. — true
detect-bad-wep Enables detection of WEP initialization vectors that are known to be
weak and/or repeating. A primary means of cracking WEP keys is to
capture 802.11 frames over an extended period of time and search
for implementations that are still used by many legacy devices.
—false
detect-ht-green
field
Enables or disables detection of high-throughput devices advertising
greenfield preamble capability. —true
detect-invalid-
mac-oui
Enables checking of the first three bytes of a MAC address, known as
the organizationally unique identifier (OUI), assigned by the IEEE to
known manufacturers. Often clients using a spoofed MAC address
do not use a valid OUI and instead use a randomly generated MAC
address. Enabling MAC OUI checking causes an alarm to be
triggered if an unrecognized MAC address is in use.
—false
Parameter Description Range Default
AOS-W 3.4.1 Command Line Interface | Reference Guide ids unauthorized-device-profile | 237
detect-miscon
figured-ap
Enables detection of misconfigured APs. An AP is classified as
misconfigured if it is classified as valid and does not meet any of the
following configurable parameters:
- valid channels
- encryption type
- list of valid AP MAC OUIs
- valid SSID list
—false
detect-windows-
bridge
Enables detection of Windows station bridging. — true
detect-wireless
-bridge
Enables detection of wireless bridging. — true
mac-oui-quiet-
time
Time, in seconds, that must elapse after an invalid MAC OUI alarm
has been triggered before another identical alarm may be triggered. 900
seconds
no Negates any configured parameter. — —
overlay-classi
fication
This option is useful when Alcatel-Lucent APs are used for monitoring
a non-Alcatel-Lucent wireless network, as it allows APs that are
plugged into the wired side of the network to be classified as
“suspected rogue” instead of “rogue”. Suspected rogue APs are not
subject to the rogue containment settings; however, if configured,
they are subject to the suspected rogue AP containment settings (see
suspect-rogue-containment).
—true
privacy Enables encryption as a valid AP configuration. — false
protect-adhoc-
network
Enables protection from adhoc networks. When adhoc networks are
detected, they are disabled using a denial of service attack. —false
protect-high-
throughput
Enables or disables protection of high-throughput (802.11n) devices. — false
protect-ht-
40mhz
Enables or disables protection of high-throughput (802.11n) devices
operating in 40 MHz mode. —false
protect-miscon
figured-ap
Enables protection of misconfigured APs. — false
protect-ssid Enables use of SSID by valid APs only. — false
protect-valid-
sta
When enabled (true), does not allow valid stations to connect to a
non-valid AP. —false
require-wpa When enabled (true), any valid AP that is not using WPA encryption is
flagged as misconfigured. —false
rogue-contain
ment
Rogue APs can be detected (see classification) but are not
automatically disabled. This option automatically shuts down rogue
APs. When this option is enabled (true), clients attempting to
associate to an AP classified as a rogue are disconnected through a
denial of service attack.
—false
suspect-rogue-
conf-level
Confidence level of suspected Rogue AP to trigger containment.
When an AP is classified as a suspected rogue AP, it is assigned a
50% confidence level. If multiple APs trigger the same events that
classify the AP as a suspected rogue, the confidence level increases
by 5% up to 95%.
In combination with suspected rogue containment, this option
configures the threshold by which containment should occur.
Suspected rogue containment occurs only when the configured
confidence level is met.
50-100 60%
Parameter Description Range Default
238 | ids unauthorized-device-profile AOS-W 3.4.1 Command Line Interface | Reference Guide
Usage Guidelines
Unauthorized device detection includes the ability to detect and disable rogue APs and other devices that
can potentially disrupt network operations.
There are three predefined unauthorized device profiles, each of which provides different levels of
detection and containment. The following describes the settings for each of the predefined profiles:
suspect-rogue-
containment
Suspected rogue APs are treated as interfering APs, thereby the
switch attempts to reclassify them as rogue APs. Suspected rogue
APs are not automatically contained. In combination with the
configured confidence level (see suspect-rogue-conf-level), this
option contains the suspected rogue APs.
—false
valid-and-pro
tected-ssid
List of valid and protected SSIDs. — —
valid-oui List of valid MAC OUIs. — —
valid-wired-mac List of MAC addresses of wired devices in the network, typically
gateways or servers. ——
wireless-bridge
-quiet-time
Time, in seconds, that must elapse after a wireless bridge alarm has
been triggered before another identical alarm may be triggered. 60-3600
00 900
seconds
Parameter Description Range Default
AP configuration settings related to the IEEE 802.11n standard are configurable for Alcatel-Lucent OAW-AP120
series access points, which are IEEE 802.11n standard compliant devices.
Parameter ids-unauthorized-
device-disabled
ids-unauthorized-device
-medium-setting
ids-unauthorized-high
-setting
Detect adhoc networks false true true
Protect from adhoc networks false false true
Detect windows bridge false true true
Detect wireless bridge false true true
Detect devices with invalid
MAC OUI false false true
MAC OUI detection quiet time 900 seconds 900 seconds 900 seconds
Adhoc network detection quiet
time 900 seconds 900 seconds 900 seconds
Wireless bridge detection quiet
time 900 seconds 900 seconds 900 seconds
Rogue AP classification false true true
Overlay rogue AP classification true true true
Valid wired MACs — — —
Rogue containment false false true
Allow well known MAC — — —
Suspected rogue containment false false false
AOS-W 3.4.1 Command Line Interface | Reference Guide ids unauthorized-device-profile | 239
Example
The following command copies the settings from the ids-unauthorized-device-disabled profile and then
enables detection and protection from adhoc networks:
ids unauthorized-device-profile unauth1
clone ids-unauthorized-device-disabled
detect-adhoc-network
protect-adhoc-network
Command History
Suspected rogue containment
confidence level 60 60 60
Protect valid stations false false true
Detect bad WEP false true true
Detect misconfigured AP false true true
Protect misconfigured AP false false true
Protect SSID false false true
Privacy false false true
Require WPA false true false
Valid 802.11g channel for
policy enforcement —— —
Valid 802.11a channel for
policy enforcement —— —
Valid MAC OUIs — — —
Valid and protected SSIDs — — —
Protect 802.11n
High-throughput Devices false false true
Protect 40 MHz 802.11n
High-throughput Devices false false true
Detect Active 802.11n
Greenfield Mode false true true
Parameter ids-unauthorized-
device-disabled
ids-unauthorized-device
-medium-setting
ids-unauthorized-high
-setting
Release Modification
AOS-W 3.0 Command introduced
AOS-W 3.3 Update with support for the high-throughput IEEE 802.11n standard. Also,
introduced allow-well-known-mac, suspect-rogue-conf-level, and
suspect-rogue-containment parameters.

240 | ids unauthorized-device-profile AOS-W 3.4.1 Command Line Interface | Reference Guide
Command Information
Platform License Command Mode
Available on all platforms Requires Wireless Intrusion Protection license Config mode on master switches
AOS-W 3.4.1 Command Line Interface | Reference Guide interface fastethernet | gigabitethernet | 241
interface fastethernet | gigabitethernet
interface
interface {fastethernet|gigabitethernet} <slot>/<port>
description <string>
duplex {auto|full|half}
ip access-group <acl> {in|out|session {vlan <vlanId>}}
no ...
poe [cisco]
port monitor {fastethernet|gigabitethernet} <slot>/<port>
priority-map <name>
shutdown
spanning-tree [cost <value>] [port-priority <value>] [portfast]
speed {10|100|auto}
switchport {access vlan <vlan>|mode {access|trunk}|
trunk {allowed vlan {<vlans>|add <vlans>|all|except <vlans>|remove <vlans>}|
native vlan <vlan>}}
trusted {vlan <word>}
xsec {point-to-point <macaddr> <key> allowed vlan <vlans> [<mtu>]|vlan <vlan>}
Description
This command configures a FastEthernet or GigabitEthernet interface on the switch.
Syntax
Parameter Description Range Default
<slot> <slot> is always 1 except for the OmniAccess 6000
WLAN Switch, where the slots can be 0, 1, 2, or 3. ——
<port> Number assigned to the network interface embedded in
the switch, or for the OmniAccess 6000 WLAN Switch, in
a line card or the OmniAccess Supervisor Card III. Port
numbers start at 0 from the left-most position.
——
description String that describes this interface. — —
duplex Transmission mode on the interface: full- or half-duplex
or auto to automatically adjust transmission. auto/full/half auto
ip access-group Applies the specified access control list (ACL) to the
interface. Use the ip access-list command to configure
an ACL.
NOTE: The Policy Enforcement Firewall license must be
installed.
——
in Applies ACL to interface’s inbound traffic. — —
out Applies ACL to interface’s outbound traffic. — —
session Applies session ACL to interface and optionally to a
selected VLAN associated with this port. ——
no Negates any configured parameter. — —
poe Enables Power-over-Ethernet (PoE) on the interface. — enabled
cisco Enables Cisco-style PoE on the interface. — disabled
port monitor Monitors another interface on the switch. — —

242 | interface fastethernet | gigabitethernet AOS-W 3.4.1 Command Line Interface | Reference Guide
priority-map Applies a priority map to the interface. Use the priority-
map command to configure a priority map which allows
you to map ToS and CoS values into high priority traffic
queues.
——
shutdown Causes a hard shutdown of the interface. — —
spanning-tree Enables spanning tree. — enabled
cost Administrative cost associated with the spanning tree. 1-65535 19 (Fast
Ethernet)
4 (Gigabit
Ethernet)
port-priority Spanning tree priority of the interface. A lower setting
brings the port closer to root port position (favorable for
forwarding traffic) than does a higher setting. This is
useful if ports may contend for root position if they are
connected to an identical bridge.
0-255 128
portfast Enables forwarding of traffic from the interface. — disabled
speed Sets the interface speed: 10 Mbps, 100 Mbps, or auto
configuration. 10|100|auto auto
switchport Sets switching mode parameters for the interface. — —
access vlan Sets the interface as an access port for the specified
VLAN. The interface carries traffic only for the specified
VLAN.
—1
mode Sets the mode of the interface to access or trunk mode
only. access|trunk access
trunk Sets the interface as a trunk port for the specified VLANs.
A trunk port carries traffic for multiple VLANs using
802.1q tagging to mark frames for specific VLANs. You
can include all VLANs configured on the switch, or add or
remove specified VLANs. Specify native to identify the
native VLAN for the trunk mode interface. Frames on the
native VLAN are not 802.1q tagged.
——
trusted Set this interface and range of VLANs to be trusted. Vlans
not included in the trusted range of VLANs will be, by
default, untrusted.
Trusted ports and VLANs are typically connected to
internal controlled networks, while untrusted ports
connect to third-party APs, public areas, or other
networks to which access controls should be applied.
When Alcatel-Lucent APs are attached directly to the
switch, set the port to be trusted.
—enabled
Parameter Description Range Default
AOS-W 3.4.1 Command Line Interface | Reference Guide interface fastethernet | gigabitethernet | 243
Usage Guidelines
Use the show port status command to obtain information about the interfaces available on the switch.
Example
The following commands configure an interface as a trunk port for a set of VLANs:
(host) (config) # interface fastethernet 1/2
(host) (config-range)# switchport mode trunk
(host) (config-range)# switchport trunk native vlan 10
(host) (config-range)# switchport trunk allowed vlan 1,10,100
The following commands configure trunk port 1/2 with test-acl session for VLAN 2.
(host) (config) # interface range fastethernet 1/2
(host) (config-range)# switchport mode trunk
(host) (config-range)# ip access-group
(host) (config-range) # ip access-group test session vlan 2
Related Commands
(host) #show interface {fastethernet|gigabitethernet} <slot>/<port>
(host) #show datapath port vlan-table <slot>/<port>
vlan <word> Sets the supplied range of VLANs as trusted. All
remaining become untrusted automatically.
For example, If you set a VLAN range as:
vlan 1-10, 100-300, 301, 305-400, 501-4094
Then all VLANs in this range are trusted and all others
become untrusted by default. You can also use the no
trusted vlan command to explicitly make an individual
VLAN untrusted. The no trusted vlan command is
additive and adds given vlans to the existing untrusted
vlan set.
However, if you execute the trusted vlan <word>
command, it overrides any earlier untrusted VLANs or a
range of untrusted VLANs and creates a new set of
trusted VLANs.
NOTE: A port supports a user VLAN range from 1-4094.
If you want to set all VLANs (1-4094) on a port as
untrusted then mark the port itself as untrusted. By
default the port and all its associated VLANs are trusted.
1-4094 —
xsec Enables and configures the Extreme Security (xSec)
protocol.
NOTE: You must purchase and install the xSec software
module license in the switch.
——
point-to-point MAC address of the switch that is the xSec tunnel
termination point, and the 16-byte shared key used to
authenticate the switches to each other. The key must be
the same on both switches.
——
allowed vlan VLANs that are allowed on the xSec tunnel. — —
mtu (Optional) MTU size for the xSec tunnel. — —
vlan xSec VLAN ID. For switch-to-switch communications,
both switches must belong to the same VLAN. 1-4094 —
Parameter Description Range Default

244 | interface fastethernet | gigabitethernet AOS-W 3.4.1 Command Line Interface | Reference Guide
Command History
Command Information
Release Modification
AOS-W 3.0 Command introduced
AOS-W 3.4 The trusted VLAN and ip access-group session vlan parameters were
introduced.
AOS-W 3.4.1 The trusted vlan <word> parameter was added.
Platforms Licensing Command Mode
All platforms This command is available in the
base operating system. The ip
access-group parameter requires
the PEF license. The xsec
parameter requires the xSec
license.
Config mode on master and local switches
AOS-W 3.4.1 Command Line Interface | Reference Guide interface loopback | 245
interface loopback
interface loopback
ip address <ipaddr>
no ...
Description
This command configures the loopback address on the switch.
Syntax
Usage Guidelines
If configured, the loopback address is used as the switch’s IP address. If you do not configure a loopback
address for the switch, the IP address assigned to VLAN 1 is used as the switch’s IP address. After you
configure or modify a loopback address, you need to reboot the switch.
Example
The following command configures a loopback address:
(host) (config) #interface loopback
ip address 10.2.22.220
Command History
This command was introduced in AOS-W 3.0
Command Information
Parameter Description
ip address Host IP address in dotted-decimal format. This address should be routable from all external
networks.
no Negates any configured parameter.
Platforms Licensing Command Mode
All platforms This command is available in the
base operating system Config mode on master and local switches
246 | interface mgmt AOS-W 3.4.1 Command Line Interface | Reference Guide
interface mgmt
interface mgmt
dhcp
ip address <ipaddr> <netmask>
no ...
shutdown
Description
This command configures the out-of-band Ethernet management port on an OmniAccess 6000 WLAN
Switch.
Syntax
Usage Guidelines
This command applies to Alcatel-Lucent Supervisor Card (SC) and OmniAccess Supervisor Card III
(OmniAccess Supervisor Card III).
Use the show interface mgmt command to view the current status of the management port.
Example
The following command configures an IP address on the management interface:
(host) (config) #interface mgmt
ip address 10.1.1.1 255.255.255.0
Platform Availability
This command is only available on the OmniAccess 6000 WLAN Switch.
Command History
This command was introduced in AOS-W 3.0
Command Information
Parameter Description
dhcp Enables DHCP on the interface.
ip address Configures an IP address and netmask on the interface.
no Negates any configured parameter.
shutdown Causes a hard shutdown of the interface.
Platforms Licensing Command Mode
OmniAccess 6000 WLAN
Switches Base operating system Config mode on master and local switches
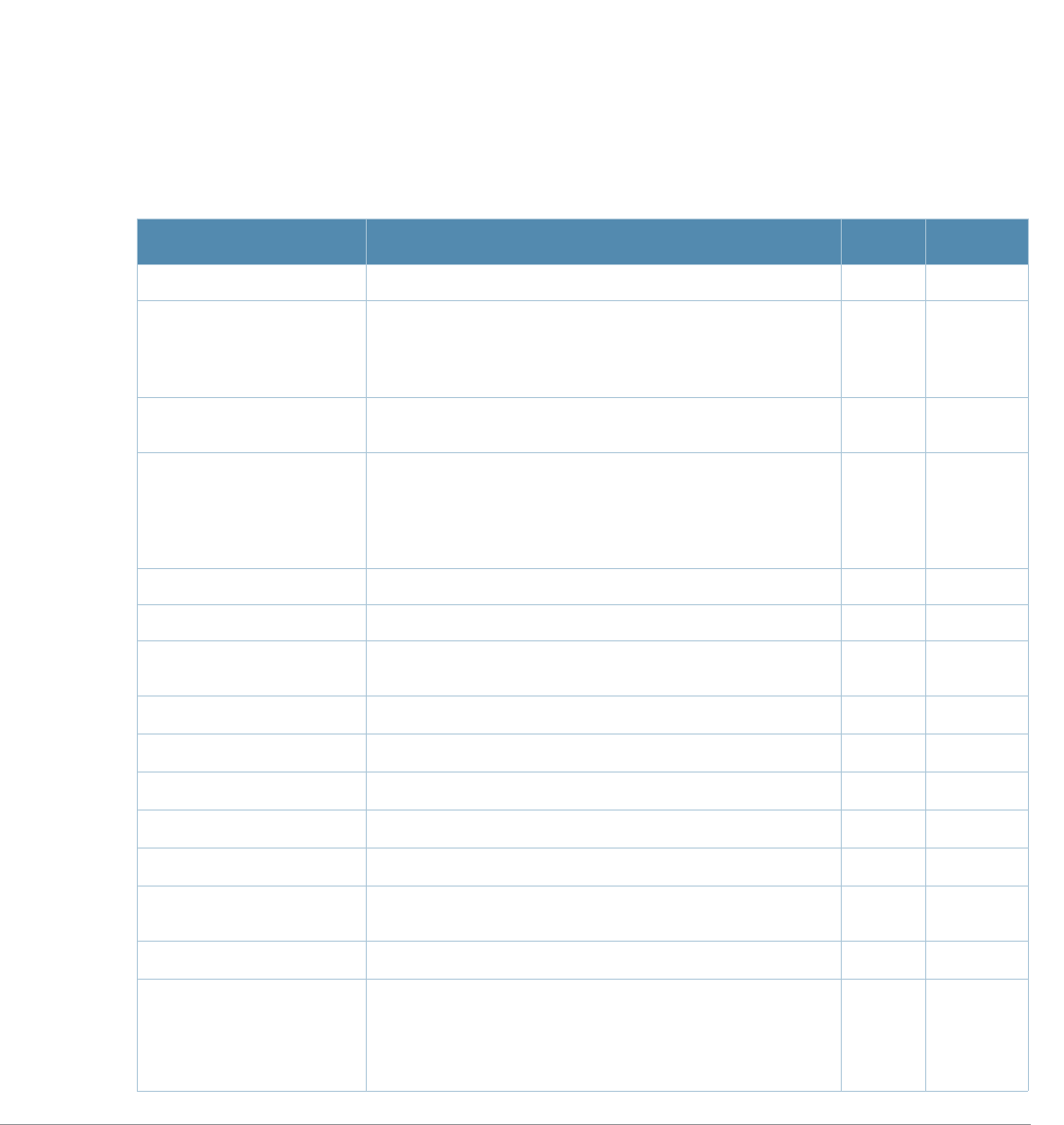
AOS-W 3.4.1 Command Line Interface | Reference Guide interface port-channel | 247
interface port-channel
interface port-channel <id>
add {fastethernet|gigabitethernet} <slot>/<port>
del {fastethernet|gigabitethernet} <slot>/<port>
ip access-group <acl> {in|out|session {vlan <vlanId>}}
no ...
shutdown
spanning-tree [portfast]
switchport {access vlan <vlan>|mode {access|trunk}|
trunk {allowed vlan {<vlans>|add <vlans>|all|except <vlans>|remove <vlans>|
native vlan <vlan>}
trusted {vlan <word>}
xsec {point-to-point <macaddr> <key> allowed vlan <vlans> [<mtu>]|vlan
<vlan>}
Description
This command configures an Ethernet port channel.
Syntax
Parameter Description Range Default
port-channel ID number for this port channel. 0-7 —
add Adds the specified FastEthernet or GigabitEthernet interface
to the port channel.
You cannot specify both FastEthernet and GigabitEthernet
interfaces for the same port channel.
——
del Deletes the specified Fastethernet or Gigabitethernet
interface to the port channel. ——
ip access-group Applies the specified access control list (ACL) to the
interface. Use the ip access-list command to configure an
ACL.
NOTE: The Policy Enforcement Firewall license must be
installed.
——
in Applies ACL to interface’s inbound traffic. — —
out Applies ACL to interface’s outbound traffic. — —
session Applies session ACL to interface and optionally to a selected
VLAN associated with this port. ——
no Negates any configured parameter. — —
shutdown Causes a hard shutdown of the interface. — —
spanning-tree Enables spanning tree. — —
portfast Enables forwarding of traffic from the interface. — —
switchport Sets switching mode parameters for the interface. — —
access vlan Sets the interface as an access port for the specified VLAN.
The interface carries traffic only for the specified VLAN. ——
mode Sets the mode of the interface to access or trunk mode only. — —
trunk Sets the interface as a trunk port for the specified VLANs. A
trunk port carries traffic for multiple VLANs using 802.1q
tagging to mark frames for specific VLANs. You can include
all VLANs configured on the switch, or add or remove
specified VLANs.
——
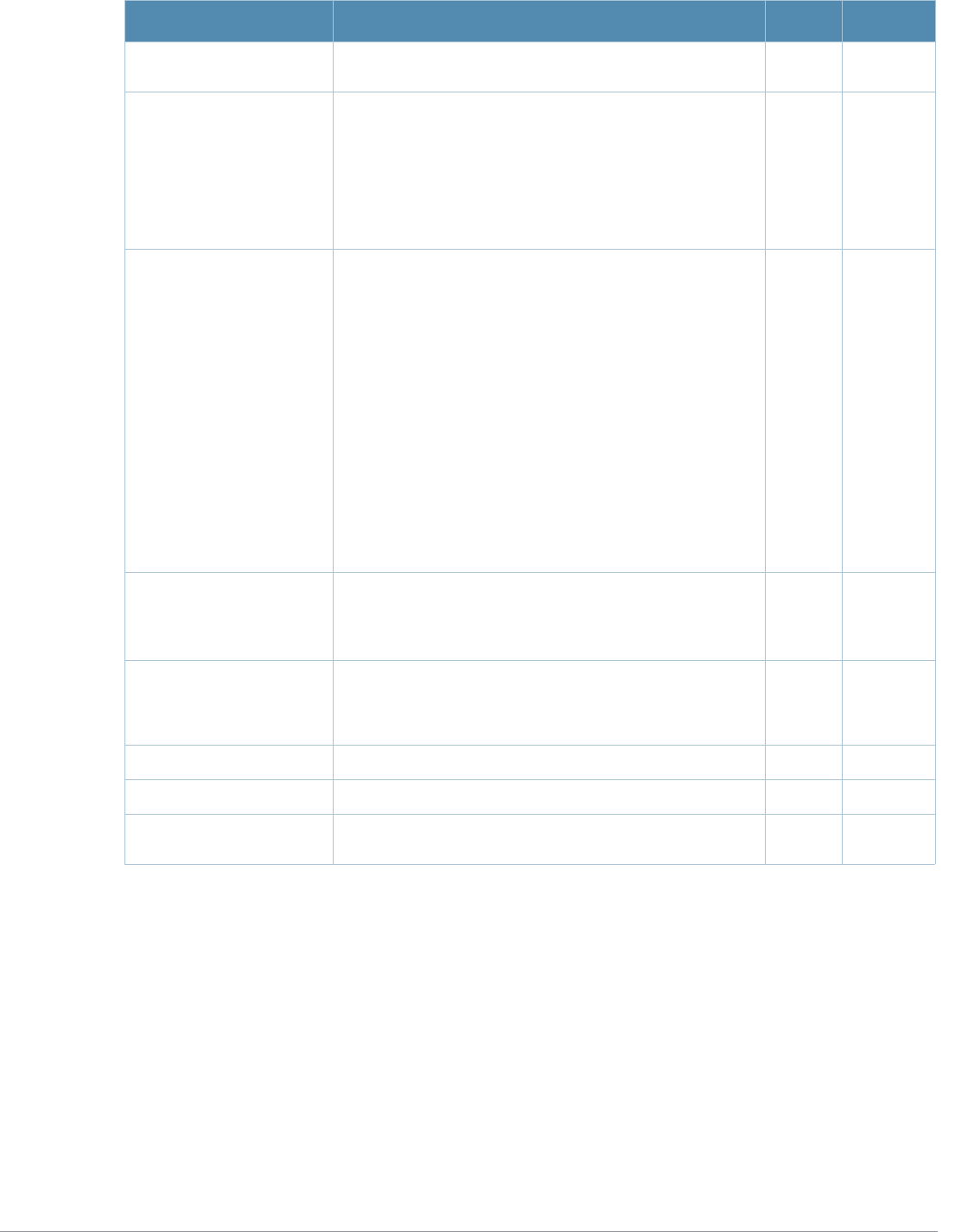
248 | interface port-channel AOS-W 3.4.1 Command Line Interface | Reference Guide
Usage Guidelines
A port channel allows you to aggregate ports on a switch. You can configure a maximum of 8 port channels
per supported switch with a maximum of 8 interfaces per port channel.
Note the following when setting up a port channel between a switch and a Cisco switch (such as a Catalyst
6500 Series Switch):
zThere must be no negotiation of the link parameters.
zThe port-channel mode on the Cisco switch must be “on”.
native Specifies the native VLAN for the trunk mode interface.
Frames on the native VLAN are not 802.1q tagged. ——
trusted Set this interface and range of VLANs to be trusted. Vlans
not included in the trusted range of VLANs will be, by
default, untrusted.
Trusted ports and VLANs are typically connected to internal
controlled networks, while untrusted ports connect to third-
party APs, public areas, or other networks to which access
controls should be applied. When Alcatel-Lucent APs are
attached directly to the switch, set the port to be trusted.
— disabled
vlan <word> Sets the supplied range of VLANs as trusted. All remaining
become untrusted automatically.
For example, If you set a VLAN range as:
vlan 1-10, 100-300, 301, 305-400, 501-4094
Then all VLANs in this range are trusted and all others
become untrusted by default. You can also use the no
trusted vlan command to explicitly make an individual VLAN
untrusted. The no trusted vlan command is additive and
adds given vlans to the existing untrusted vlan set.
However, if you execute the trusted vlan <word>
command, it overrides any earlier untrusted VLANs or a
range of untrusted VLANs and creates a new set of trusted
VLANs.
NOTE: A port supports a user VLAN range from 1-4094. If
you want to set all VLANs (1-4094) on a port as untrusted
then mark the port itself as untrusted. By default the port
and all its associated VLANs are trusted.
1-4094 —
xsec Enables and configures the Extreme Security (xSec)
protocol.
NOTE: You must purchase and install the xSec software
module license in the switch.
——
point-to-point MAC address of the switch that is the xSec tunnel
termination point, and the 16-byte shared key used to
authenticate the switches to each other. The key must be the
same on both switches.
——
allowed vlan VLANs that are allowed on the xSec tunnel. — —
mtu (Optional) MTU size for the xSec tunnel. — —
vlan xSec VLAN ID. For switch-to-switch communications, both
switches must belong to the same VLAN. 1-4094 —
Parameter Description Range Default

AOS-W 3.4.1 Command Line Interface | Reference Guide interface port-channel | 249
Example
The following command configures a port channel:
(host) (config) #interface port channel 7
add fastethernet 1/1
add fastethernet 1/2
Command History
Command Information
Release Modification
AOS-W 3.0 Command introduced
AOS-W 3.4 The trusted VLAN and ip access-group session vlan parameters were
introduced.
AOS-W 3.4.1 The trusted vlan <word> parameter was added.
Platforms Licensing Command Mode
OmniAccess 4324 and
OmniAccess 6000 WLAN
Switches, and OmniAccess
4504/4604/4704 Multi-Service
Switch
This command is available in the
base operating system. The ip
access-group parameter requires
the PEF license. The xsec
parameter requires the xSec
license.
Config mode on master and local switches
250 | interface range AOS-W 3.4.1 Command Line Interface | Reference Guide
interface range
interface range {fastethernet|gigabitethernet} <slot>/<port>-<port>
duplex {auto|full|half}
ip access-group <acl> {in|out|session {vlan <vlanId>}}
no ...
poe [cisco]
shutdown
spanning-tree [cost <value>] [port-priority <value>] [portfast]
speed {10|100|auto}
switchport {access vlan <vlan>|mode {access|trunk}|
trunk {allowed vlan {<vlans>|add <vlans>|all|except <vlans>|remove
<vlans>}|
native vlan <vlan>}}
trusted {vlan <word>}
Description
This command configures a range of FastEthernet or GigabitEthernet interfaces on the switch.
Syntax
Parameter Description Range Default
range Range of Ethernet ports in the format <slot>/<port>-
<port>. ——
duplex Transmission mode on the interface: full- or half-duplex or
auto to automatically adjust transmission. auto/full/
half auto
ip access-group Applies the specified access control list (ACL) to the
interface. Use the ip access-list command to configure an
ACL.
——
in Applies ACL to interface’s inbound traffic. — —
out Applies ACL to interface’s outbound traffic. — —
session Applies session ACL to interface and optionally to a
selected VLAN associated with this port. ——
no Negates any configured parameter. — —
poe Enables Power-over-Ethernet (PoE) on the interface. — —
cisco Enables Cisco-style PoE on the interface. — —
shutdown Causes a hard shutdown of the interface. — —
spanning-tree Enables spanning tree. — —
cost Administrative cost associated with the spanning tree. 1-65535 —
port-priority Spanning tree priority of the interface. A lower setting
brings the port closer to root port position (favorable for
forwarding traffic) than does a higher setting. This is
useful if ports may contend for root position if they are
connected to an identical bridge.
0-255
portfast Enables forwarding of traffic from the interface. — —
speed Sets the interface speed: 10 Mbps, 100 Mbps, or auto
configuration. 10|100|aut
oauto
switchport Sets switching mode parameters for the interface. — —

AOS-W 3.4.1 Command Line Interface | Reference Guide interface range | 251
Usage Guidelines
Use the show port status command to obtain information about the interfaces available on the switch.
Example
The following command configures a range of interface as a trunk port for a set of VLANs:
access vlan Sets the interface as an access port for the specified
VLAN. The interface carries traffic only for the specified
VLAN.
——
mode Sets the mode of the interface to access or trunk mode
only. ——
trunk Sets the interface as a trunk port for the specified VLANs.
A trunk port carries traffic for multiple VLANs using
802.1q tagging to mark frames for specific VLANs. You
can include all VLANs configured on the switch, or add or
remove specified VLANs. Specify native to identify the
native VLAN for the trunk mode interface. Frames on the
native VLAN are not 802.1q tagged.
——
trusted Set this interface and range of VLANs to be trusted. Vlans
not included in the trusted range of VLANs will be, by
default, untrusted.
Trusted ports and VLANs are typically connected to
internal controlled networks, while untrusted ports
connect to third-party APs, public areas, or other
networks to which access controls should be applied.
When Alcatel-Lucent APs are attached directly to the
switch, set the port to be trusted.
—enabled
vlan <word> Sets the supplied range of VLANs as trusted. All
remaining become untrusted automatically.
For example, If you set a VLAN range as:
vlan 1-10, 100-300, 301, 305-400, 501-4094
Then all VLANs in this range are trusted and all others
become untrusted by default. You can also use the no
trusted vlan command to explicitly make an individual
VLAN untrusted. The no trusted vlan command is additive
and adds given vlans to the existing untrusted vlan set.
However, if you execute the trusted vlan <word>
command, it overrides any earlier untrusted VLANs or a
range of untrusted VLANs and creates a new set of
trusted VLANs.
NOTE: A port supports a user VLAN range from 1-4094. If
you want to set all VLANs (1-4094) on a port as untrusted
then mark the port itself as untrusted. By default the port
and all its associated VLANs are trusted.
1-4094 —
Parameter Description Range Default

252 | interface range AOS-W 3.4.1 Command Line Interface | Reference Guide
interface range fastethernet 1/12-15
switchport mode trunk
switchport trunk native vlan 10
switchport trunk allowed vlan 1,10,100
Command History
Command Information
Release Modification
AOS-W 3.0 Command introduced
AOS-W 3.4 The trusted VLAN and ip access-group session vlan parameters were
introduced.
AOS-W 3.4.1 The trusted vlan <word> parameter was added.
Platforms Licensing Command Mode
All platforms Base operating system Config mode on master and local switches
AOS-W 3.4.1 Command Line Interface | Reference Guide interface tunnel | 253
interface tunnel
interface tunnel <number>
description <string>
inter-tunnel-flooding
ip address <ipaddr> <netmask>
mtu <mtu>
no ...
shutdown
trusted
tunnel checksum|destination <ipaddr>|keepalive [<interval> <retries>]|key
<key>|mode gre {<protocol>|ip}|source {<ipaddr>|loopback|vlan <vlan>}|vlan
<vlans>
Description
This command configures a tunnel interface.
Syntax
Parameter Description Range Default
tunnel Identification number for the tunnel. 1-2147483647 —
description String that describes this interface. — Tunnel
Interface
inter-tunnel-
flooding
Enables inter-tunnel flooding. — enabled
ip address IP address of the tunnel. This represents the entrance
to the tunnel. ——
mtu MTU size for the interface. — 1500
no Negates any configured parameter. — —
shutdown Causes a hard shutdown of the interface. — —
trusted Set this interface and range of VLANs to be trusted.
Vlans not included in the trusted range of VLANs will
be, by default, untrusted.
Trusted ports and VLANs are typically connected to
internal controlled networks, while untrusted ports
connect to third-party APs, public areas, or other
networks to which access controls should be applied.
When Alcatel-Lucent APs are attached directly to the
switch, set the port to be trusted.
— disabled
tunnel Configures tunneling. — mode gre
ip
checksum Enables end-to-end checksum of packets that pass
through the tunnel. — disabled
destination Destination IP address for the tunnel endpoint. — —
keepalive Enables sending of periodic keepalive frames on the
tunnel to determine the tunnel status (up or down).
You can optionally set the interval at which keepalive
frames are sent, and the number of times the frames
are resent before a tunnel is considered to be down.
— disabled
<interval> (Optional) Number of seconds at which keepalive
frames are sent. 1-86400 10
seconds
254 | interface tunnel AOS-W 3.4.1 Command Line Interface | Reference Guide
Usage Guidelines
You can configure a GRE tunnel between an Alcatel-Lucent switch and another GRE-capable device. Layer-
3 GRE tunnel type is the default (tunnel mode gre ip). You can direct traffic into the tunnel using a static
route (specify the tunnel as the next hop for a static route) or a session-based access control list (ACL).
Example
The following command configures a tunnel interface:
(host) (config) #interface tunnel 200
ip address 10.1.1.1 255.255.2550
tunnel source loopback
tunnel destination 20.1.1.242
tunnel mode gre ip
Command History
Command Information
<retries> (Optional) Number of consecutive times that the
keepalives fail before the tunnel is considered to be
down.
0-1024 3
key Key used to authenticate packets on the tunnel. 0-4294967295 —
mode gre Specifies generic route encapsulation (GRE) type. You
configure either a 16-bit protocol number (for Layer-2
tunnels) or ip (for a Layer-3 tunnel). The 16-bit protocol
number uniquely identifies a Layer-2 tunnel. The
switches at both endpoints of the tunnel must be
configured with the same protocol number.
——
source The local endpoint of the tunnel on the switch. This
can be one of the following:
zspecified IP address
zthe loopback interface configured on the switch
zspecified VLAN
——
vlan VLANs to be included in this tunnel. ——
Parameter Description Range Default
Release Modification
AOS-W 3.0 Command available
AOS-W 3.2 The keepalive parameter was introduced
Platforms Licensing Command Mode
All platforms Base operating system Config mode on master and local switches

AOS-W 3.4.1 Command Line Interface | Reference Guide interface vlan | 255
interface vlan
interface vlan <vlan>
bandwidth-contract <name>
description <string>
ip address {<ipaddr> <netmask>|dhcp-client|pppoe}|helper-address
<ipaddr>|igmp|local-proxy-arp|nat inside|{ospf area <id>}routing}
ipv6 mld [snooping]
mtu
no ...
operstate up
shutdown
Description
This command configures a VLAN interface.
Syntax
Parameter Description Range Default
vlan VLAN ID number. 1-4094 —
bandwidth-contract Name of the bandwidth contract to be applied to this
VLAN interface. When applied to a VLAN, the
contract only limits multicast traffic and does not
affect other data. Use the aaa bandwidth-contract
command to configure a bandwidth contract.
——
description String that describes this interface. — 802.1Q VLAN
ip Configures IPv4 for this interface.
address Configures the IP address for this interface, which
can be one of the following:
<ipaddr> <netmask>
dhcp-client: use DHCP to obtain the IP address
pppoe: use PPPoE to obtain the IP address
——
helper-address IP address of the DHCP server for relaying DHCP
requests for this interface. If the DHCP server is on
the same subnetwork as this VLAN interface, you do
not need to configure this parameter.
——
igmp Enables IGMP and/or IGMP snooping on this
interface. ——
local-proxy-arp Enables local proxy ARP. — —
nat inside Enables source network address translation (NAT) for
all traffic routed from this VLAN. ——
ospf Define an OSPF area. See ip ospf for complete
details on this command. ——
routing Enables layer-3 forwarding on the VLAN interface. To
disable layer-3 forwarding, you must configure the IP
address for the interface and specify no ip routing.
—(enabled)
ipv6 Configures IPv6 for this interface.
mld Enables Multicast Listener Discovery (MLD) on this
interface. ——
snooping Enables MLD snooping on this interface. — —
256 | interface vlan AOS-W 3.4.1 Command Line Interface | Reference Guide
Usage Guidelines
All ports on the switch are assigned to VLAN 1 by default. Use the interface fastethernet|gigabitethernet
command to assign a port to a configured VLAN.
Example
The following command configures a VLAN interface:
(host) (config) #interface vlan 16
ip address 10.26.1.1 255.255.255.0
ip helper-address 10.4.1.22
Command History
This command was introduced in AOS-W 3.0
Command Information
no Negates any configured parameter. — —
mtu MTU setting for the VLAN. 1024-
1500 —
operstate up Set the state of the interface to be up. — —
shutdown Causes a hard shutdown of the interface. — —
Parameter Description Range Default
Release Modification
AOS-W 3.0 Command available
AOS-W 3.3 The ipv6 parameters were introduced
AOS-W 3.4 The igmp snooping parameter was deprecated. For information on configuring
IGMP snooping in AOS-W 3.4 or later, see interface vlan ip igmp proxy on
page 257
Platforms Licensing Command Mode
All platforms Base operating system Config mode on master and local switches
AOS-W 3.4.1 Command Line Interface | Reference Guide interface vlan ip igmp proxy | 257
interface vlan ip igmp proxy
interface vlan <vlan>
ip igmp snooping|{proxy fastethernet|gigabitethernet <slot>/<port>}
Description
This command enables IGMP and/or IGMP snooping on this interface, or configures a VLAN interface for
uninterrupted streaming of multicast traffic.
Syntax
Usage Guidelines
The newer IGMP proxy feature and the older IGMP snooping feature cannot be enabled at the same time, as
both features add membership information to multicast group table. For most multicast deployments, you
should enable the IGMP Proxy feature on all VLAN interfaces to manage all the multicast membership
requirements on the switch. If IGMP snooping is configured on some of the interfaces, there is a greater
chance that multicast information transfers may be interrupted.
Example
The following example configures IGMP proxy for vlan 2. IGMP reports from the switch would be sent to
the upstream router on fastethernet port 1/3.
(host) (conf)# interface vlan 2
(conf-subif)# ip igmp proxy fastethernet 1/3
Parameter Description
snooping Enable IGMP snooping.
The IGMP protocol enables an router to discover the presence of multicast listeners
on directly-attached links. Enable IGMP snooping to limit the sending of multicast
frames to only those nodes that need to receive them.
proxy Enable IGMP on this interface.
fastethernet Enable IGMP proxy on the FastEthernet (IEEE 802.3) interface.
gigabitethernet Enable IGMP proxy on the GigabittEthernet (IEEE 802.3) interface.
<slot>/<port> Any command that references a Fast Ethernet or Gigabit Ethernet interface requires
that you specify the corresponding port on the switch in the format <slot>/<port>.
The <slot> parameter is always 1 except when referring to interfaces on the
OmniAccess 6000 switch. For the OmniAccess 6000 switch, the four slots are
allocated as follows:
z0: This slot contains a supervisor card or a OmniAccess Supervisor Card III.
z1: This slot can contain either a redundant supervisor card, OmniAccess
Supervisor Card III, or a third line card.
z2: This slot can contain either a OmniAccess Supervisor Card III or line card
(required ifslot 0 contains a supervisor card).
z3: This slot can contain either a OmniAccess Supervisor Card III or second line
card.
The <port> parameter refers to the network interfaces that are embedded in the front
panel of the OmniAccess 4302, OmniAccess 4308T or OmniAccess 4324 switch,
OmniAccess 4504/4604/4704 Multi-Service Switch, OmniAccess Supervisor Card III,
or a line card installed in the OmniAccess 6000 switch. Port numbers start at 0, from
the left-most position.
258 | interface vlan ip igmp proxy AOS-W 3.4.1 Command Line Interface | Reference Guide
Related Commands
This release of AOS-W supports version 1 of the Multicast Listener Discovery (MLD) protocol (MLDv1).
MLDv1, defined in RFC 2710, is derived from version 2 of the IPv4 Internet Group Management Protocol
(IGMPv2)
Issue the command interface vlan <vlan> ipv6 mld to enable the MLD protocol and allow an IPv6 router
to discover the presence of multicast listeners on directly-attached links. Use the CLI command interface
vlan <vlan> ipv6 mld snooping, and the IPv6 router will send multicast frames to only those nodes that
need to receive them.
Command History
This command was introduced in AOS-W 3.4
Command Information
Platforms Licensing Command Mode
All platforms Base operating system Config mode on master switches
AOS-W 3.4.1 Command Line Interface | Reference Guide ip access-list eth | 259
ip access-list eth
ip
ip access-list eth {<number>|<name>}
deny {<ethtype> [<bits>]|any} [mirror]
no ...
permit {<ethtype> [<bits>]|any} [mirror]
Description
This command configures an Ethertype access control list (ACL).
Syntax
Usage Guidelines
The Ethertype field in an Ethernet frame indicates the protocol being transported in the frame. This type of
ACL filters on the Ethertype field in the Ethernet frame header, and is useful when filtering non-IP traffic on
a physical port. This ACL can be used to permit IP frames while blocking other non-IP protocols such as IPX
or Appletalk.
If you configure the mirror option, define the destination to which mirrored packets are sent in the firewall
policy. For more information, see “firewall” on page 201.
Example
The following command configures an Ethertype ACL:
(host) (config) #ip access-list eth 200
deny 809b
Command History
Command Information
Parameter Description Range
eth Enter a name, or a number in the specified range. 200-299
deny Reject the specified packets, which can be one of the following:
Ethertype in decimal or hexadecimal (0-65535) and optional wildcard (0-65535)
any: match any Ethertype
Optionally, you can configure the mirror parameter, which mirrors packets to a
datapath or remote destination.
—
no Negates any configured parameter. —
permit Allow the specified packets, which can be one of the following:
Ethertype in decimal or hexadecimal (0-65535) and optional wildcard (0-65535)
any: match any Ethertype
Optionally, you can configure the mirror parameter, which mirrors packets to a
datapath or remote destination.
—
Release Modification
AOS-W 3.0 Command introduced
AOS-W 3.3 The mirror parameter was introduced.

260 | ip access-list eth AOS-W 3.4.1 Command Line Interface | Reference Guide
Platform License Command Mode
Available on all platforms Requires the Policy Enforcement Firewall (PEF)
license. Config mode on master
switches
AOS-W 3.4.1 Command Line Interface | Reference Guide ip access-list extended | 261
ip access-list extended
ip access-list extended {<number>|<name>}
deny <protocol> <source> <dest>
no ...
permit <protocol> <source> <dest>
Description
This command configures an extended access control list (ACL).
Syntax
Parameter Description Range
extended Enter a name, or a number in the specified range. 100-199, 2000-
2699
deny Reject the specified packets.
<protocol> Protocol, which can be one of the following:
zProtocol number between 0-255
zany: any protocol
zicmp: Internet Control Message Protocol
zigmp: Internet Gateway Message Protocol
ztcp: Transmission Control Protocol
zudp: User Datagram Protocol
—
<source> Source, which can be one of the following:
zSource address and wildcard
zany: any source
zhost: specify a single host IP address
—
<dest> Destination, which can be one of the following:
zDestination address and wildcard
zany: any destination
zhost: specify a single host IP address
—
no Negates any configured parameter. —
permit Allow the specified packets.
<protocol> Protocol, which can be one of the following:
zProtocol number between 0-255
zany: any protocol
zicmp: Internet Control Message Protocol
zigmp: Internet Gateway Message Protocol
ztcp: Transmission Control Protocol
zudp: User Datagram Protocol
—
<source> Source, which can be one of the following:
Source address and wildcard
any: any source
host: specify a single host IP address
—
<dest> Destination, which can be one of the following:
Destination address and wildcard
any: any destination
host: specify a single host IP address
—
262 | ip access-list extended AOS-W 3.4.1 Command Line Interface | Reference Guide
Usage Guidelines
Extended ACLs are supported for compatibility with router software from other vendors. This ACL permits
or denies traffic based on the source or destination IP address or IP protocol.
Example
The following command configures an extended ACL:
(host) (config) #ip access-list extended 100
deny any host 1.1.21.245 any
Command History
This command was available in AOS-W 3.0.
Command Information
Platform License Command Mode
Available on all platforms Requires the Policy Enforcement Firewall (PEF)
license Config mode on master
switches

AOS-W 3.4.1 Command Line Interface | Reference Guide ip access-list mac | 263
ip access-list mac
ip access-list mac {<number>|<name>}
deny {<macaddr>[<wildcard>]|any|host <macaddr>} [mirror]
no ...
permit {<macaddr>[<wildcard>]|any|host <macaddr>} [mirror]
Description
This command configures a MAC access control list (ACL).
Syntax
Usage Guidelines
MAC ACLs allow filtering of non-IP traffic. This ACL filters on a specific source MAC address or range of
MAC addresses.
If you configure the mirror option, define the destination to which mirrored packets are sent in the firewall
policy. For more information, see “firewall” on page 201.
Example
The following command configures a MAC ACL:
(host) (config) #ip access-list mac 700
deny 11:11:11:00:00:00
Command History
Parameter Description Range
mac Configures a MAC access list. Enter a name, or a number in the specified
range. 700-799, 1200-1299
deny Reject the specified packets, which can be the following:
MAC address and optional wildcard
any: any packets
host: specify a MAC address
Optionally, you can configure the mirror parameter, which mirrors
packets to a datapath or remote destination.
—
no Negates any configured parameter. —
permit Allow the specified packets, which can be the following:
MAC address and optional wildcard
any: any packets
host: specify a MAC address
Optionally, you can configure the mirror parameter, which mirrors
packets to a datapath or remote destination.
—
Release Modification
AOS-W 3.0 Command introduced
AOS-W 3.3 The mirror parameter was introduced.

264 | ip access-list mac AOS-W 3.4.1 Command Line Interface | Reference Guide
Command Information
Platform License Command Mode
Available on all platforms Requires Policy Enforcement Firewall
(PEF) license Config
AOS-W 3.4.1 Command Line Interface | Reference Guide ip access-list session | 265
ip access-list session
ip access-list session <name>
<source> <dest> <service> <action> [<extended action>]
no ...
Description
This command configures a session access control list (ACL).
Syntax
Parameter Description
session Enter a name for this ACL
<source> The traffic source, which can be one of the following:
alias: specify the network resource (use the netdestination command to configure aliases;
use the show netdestination command to see configured aliases)
any: match any traffic
host: specify a single host IP address
network: specify the IP address and netmask
user: represents the IP address of the user
<dest> The traffic destination, which can be one of the following:
alias: specify the network resource (use the netdestination command to configure aliases;
use the show netdestination command to see configured aliases)
any: match any traffic
host: specify a single host IP address
network: specify the IP address and netmask
user: represents the IP address of the user
<service> Network service, which can be one of the following:
IP protocol number (0-255)
name of a network service (use the show netservice command to see configured services)
any: match any traffic
tcp: specify the TCP port number (0-65535)
udp: specify the UDP port number (0-65535)
<action> Action if rule is applied, which can be one of the following:
deny: reject packets
dst-nat: perform destination NAT on packets
dual-nat: perform both source and destination NAT on packets
permit: forward packets
redirect: specify the location to which packets are redirected, which can be one of the
following:
zdatapath destination ID (0-65535)
zesi-group: specify the ESI server group configured with the esi group command
zopcode: specify the datapath destination ID (0x33, 0x34, or 0x82). Do not use this
parameter without proper guidance from Alcatel-Lucent, Inc.
tunnel: specify the ID of the tunnel configured with the interface tunnel command
src-nat: perform source NAT on packets
266 | ip access-list session AOS-W 3.4.1 Command Line Interface | Reference Guide
Usage Guidelines
Session ACLs define traffic and firewall policies on the switch. You can configure multiple rules for each
policy, with rules evaluated from top (1 is first) to bottom. The first match terminates further evaluation.
Generally, you should order more specific rules at the top of the list and place less specific rules at the
bottom of the list. The ACL ends with an implicit deny all.
Example
The following command configures a session ACL that drops any traffic from 10.0.0.0 subnetwork:
ip access-list session drop-from10
network 10.0.0.0 255.0.0.0 any any
Command History
Introduced in AOS-W 3.0
Command Information
<extended ac
tion>
Optional action if rule is applied, which can be one of the following:
blacklist: blacklist user
disable-scanning: pause ARM scanning while traffic is present. Note that you must enable
“Voice Aware Scanning” in the ARM profile for this feature to work.
dot1p-priority: specify 802.1p priority (0-7)
log: generate a log message
mirror: mirror all session packets to datapath or remote destination
If you configure the mirror option, define the destination to which mirrored packets are sent in
the firewall policy. For more information, see “firewall” on page 201.
position: specify the position of the rule (1 is first, default is last)
queue: assign flow to priority queue (high/low)
send-deny-response: if <action> is deny, send an ICMP notification to the source
time-range: specify time range for this rule (configured with time-range command)
tos: specify ToS value (0-63)
no Negates any configured parameter.
Parameter Description
Platform License Command Mode
Available on all platforms Requires Policy Enforcement
Firewall (PEF) license Config mode on master switches
AOS-W 3.4.1 Command Line Interface | Reference Guide ip access-list standard | 267
ip access-list standard
ip access-list standard {<number>|<name>}
deny {<ipaddr> <wildcard>|any|host <ipaddr>}
no ...
permit {<ipaddr> <wildcard>|any|host <ipaddr>}
Description
This command configures a standard access control list (ACL).
Syntax
Usage Guidelines
Standard ACLs are supported for compatibility with router software from other vendors. This ACL permits
or denies traffic based on the source address of the packet.
Example
The following command configures a standard ACL:
(host) (config) #ip access-list standard 1
permit host 10.1.1.244
Command History
Introduced in AOS-W 3.0
Command Information
Parameter Description Range
standard Enter a name, or a number in the specified range. 1-99, 1300-1399
deny Reject the specified packets, which can be the following:
IP address and optional wildcard
any: any packets
host: specify a host IP address
—
no Negates any configured parameter. —
permit Allow the specified packets, which can be the following:
IP address and optional wildcard
any: any packets
host: specify a host IP address
—
Platform License Command Mode
Available on all platforms Requires Policy Enforcement Firewall (PEF)
license Config mode on master
switches
268 | ip cp-redirect-address AOS-W 3.4.1 Command Line Interface | Reference Guide
ip cp-redirect-address
ip cp-redirect-address <ipaddr> | disable
Description
This command configures a redirect address for captive portal.
Syntax
Usage Guidelines
This command redirects wireless clients that are on different VLANs (from the switch’s IP address) to the
captive portal on the switch.
If you have the Policy Enforcement Firewall license installed in the switch, modify the captive portal
session ACL to permit HTTP/S traffic to the destination cp-redirect-address <ipaddr> instead of
mswitch. If you do not have the Policy Enforcement Firewall license installed in the switch, the implicit
captive-portal-profile ACL is automatically modified when you issue this command.
Example
The following command configures a captive portal redirect address:
(host) (config) #ip cp-redirect-address
Command History
Introduced in AOS-W 3.0
Command Information
Parameter Description
<ipaddr> Host address with a 32-bit netmask. This address should be routable from all external networks.
disable Disables automatic DNS resolution for captive portal.
Platform License Command Mode
Available on all platforms Available in the base operating
system Config mode on master switches
AOS-W 3.4.1 Command Line Interface | Reference Guide ip default-gateway | 269
ip default-gateway
ip default-gateway <ipaddr>|{import cell|dhcp|pppoe}|{ipsec <name>} <cost>
Description
This command configures the default gateway for the switch.
Syntax
Usage Guidelines
You can use this command to set the default gateway to the IP address of the interface on the upstream
router or switch to which you connect the switch. If you define more than one dynamic gateway type, you
must also define a cost for the route to each gateway. The switch will first attempt to obtain a gateway IP
address using the option with the lowest cost. If the switch is unable to obtain a gateway IP address, it will
then attempt to obtain a gateway IP address using the option with the next-lowest path cost.
Example
The following command configures the default gateway for the switch:
(host) (config) #ip default-gateway 10.1.1.1
Command History
Introduced in AOS-W 3.0
Command Information
Parameter Description
<ipaddr> IP address of the default gateway.
import Use a gateway IP address obtained through the cell interface, DHCP or PPPoE. The
default gateway is imported into the routing table and removed when the uplink is no
longer active.
cell Use Cell interface when available to obtain default gateway.
dhcp Use DHCP when available to obtain default gateway.
pppoe Use PPPOE when available to obtain default gateway.
ipsec <name> Define a static route using an ipsec map.
<cost> Distance metric for this route.
Platform License Command Mode
Available on all platforms Available in the base operating system Config mode on master switches
270 | ip dhcp excluded-address AOS-W 3.4.1 Command Line Interface | Reference Guide
ip dhcp excluded-address
ip dhcp excluded-address <low-ipaddr> [<high-ipaddr>]
Description
This command configures an excluded address range for the DHCP server on the switch.
Syntax
Usage Guidelines
Use this command to specifically exclude certain addresses from being assigned by the DHCP server. It is
good practice to exclude any statically assigned addresses.
Example
The following command configures an excluded address range:
ip dhcp excluded-address 192.168.1.1 192.168.1.255
Command History
Introduced in AOS-W 3.0
Command Information
Parameter Description
<low-ipaddr> Low end of range of IP addresses. For example, you can enter the IP address of the switch
so that this address is not assigned.
<high-ipaddr> High end of the range of IP addresses.
Platform License Command Mode
Available on all platforms Available in base operating system Config mode on master
switches

AOS-W 3.4.1 Command Line Interface | Reference Guide ip dhcp pool | 271
ip dhcp pool
ip dhcp pool <name>
default-router <ipaddr> ...
dns-server {<ipaddr> ... |import}
domain-name <name>
lease <days> <hours> <minutes>
netbios-name-server {<ipaddr> ... |import}
network <ipaddr> {<netmask>|<prefix>}
no ...
option <code> ip <ipaddr>
Description
This command configures a DHCP pool on the switch.
Syntax
Usage Guidelines
A DHCP pool should be created for each IP subnetwork for which DHCP services should be provided.
DHCP pools are not specifically tied to VLANs, as the DHCP server exists on every VLAN. When the switch
receives a DHCP request from a client, it examines the origin of the request to determine if it should
respond. If the IP address of the VLAN matches a configured DHCP pool, the switch answers the request.
Example
The following command configures a DHCP pool:
(host) (config) #ip dhcp pool floor1
default-router 10.26.1.1
dns-server 192.168.1.10
domain-name floor1.test.com
Parameter Description
default-router IP address of the default router for the DHCP client. The client should be on the same
subnetwork as the default router. You can specify up to eight IP addresses.
dns-server IP address of the DNS server, which can be one of the following:
<address> IP address of the DNS server. You can specify up to eight IP addresses.
import Use the DNS server address obtained through PPPoE or DHCP.
domain-name Domain name to which the client belongs.
lease The amount of time that the assigned IP address is valid for the client. Specify the lease in
<days> <hours> <minutes>.
netbios-name-
server
IP address of the NetBIOS Windows Internet Naming Service (WINS) server, which can be
one of the following:
<address> IP address of the WINS server. You can specify up to eight IP addresses.
import Use the NetBIOS name server address obtained through PPPoE or DHCP.
network Range of addresses that the DHCP server may assign to clients, in the form of <ipaddr>
and <netmask> or <ipaddr> and <prefix> (/n).
no Negates any configured parameter.
option Client-specific option code and IP address. See RFC 2132, “DHCP Options and BOOTP
Vendor Extensions”.

272 | ip dhcp pool AOS-W 3.4.1 Command Line Interface | Reference Guide
lease 0 8 0
network 10.26.1.0 255.255.255.0
Command History
Introduced in AOS-W 3.0
Command Information
Platform License Command Mode
Available on all platforms Available in the base operating system Config mode on master
switches
AOS-W 3.4.1 Command Line Interface | Reference Guide ip domain lookup | 273
ip domain lookup
ip domain lookup
Description
This command enables Domain Name System (DNS) hostname to address translation.
Syntax
There are no parameters for this command.
Usage Guidelines
This command is enabled by default. Use the no form of this command to disable.
Example
The following command enables DNS hostname translation:
(host)(config) #ip domain lookup
Command History
This command was available in AOS-W 3.0.
Command Information
Platform License Command Mode
Available on all platforms Available in the base operating system Config mode on master
switches
274 | ip domain-name AOS-W 3.4.1 Command Line Interface | Reference Guide
ip domain-name
ip domain-name <name>
Description
This command configures the default domain name.
Syntax
Usage Guidelines
The switch uses the default domain name to complete hostnames that do not contain domain names. You
must have at least one domain name server configured on the switch (see “ip name-server” on page 288).
Example
The following command configures the default domain name:
(host) (config) #ip domain-name yourdomain.com
Command History
This command was available in AOS-W 3.0.
Command Information
Parameter Description
domain-name Name used to complete unqualified host names. Do not specify the leading dot (.).
Platform License Command Mode
Available on all platforms Available in the base operating system Config mode on master
switches

AOS-W 3.4.1 Command Line Interface | Reference Guide ip igmp | 275
ip igmp
ip igmp
last-member-query-count <number>
last-member-query-interval <seconds>
query-interval <seconds>
query-response-interval <.1 seconds>
robustness-variable <2-10>
startup-query-count <number>
startup-query-interval <seconds>
version-1-router-present-timeout <seconds>
Description
This command configures Internet Group Management Protocol (IGMP) timers and counters.
Syntax
Usage Guidelines
IGMP is used to establish and manage IP multicast group membership. See RFC 3376, “Internet Group
Management Protocol, version 3” for more information.
Example
The following command configures IGMP:
(host) (config) #ip igmp
query-interval 130
Command History
This command was available in AOS-W 3.0.
Parameter Description Range Default
last-member-
query-count
Number of group-specific queries that the switch sends
before assuming that there are no local group members. —2
last-member-que
ry-interval
Maximum time, in seconds, that can elapse between
group-specific query messages. — 10 seconds
query-interval Interval, in seconds, at which the switch sends host-query
messages to the multicast group address 224.0.0.1 to
solicit group membership information.
1-1024 125 seconds
query-response-
interval
Maximum time, in .1 seconds, that can elapse between
when the switch sends a host-query message and when it
receives a response. This must be less than the query-
interval.
1-1024 100 (10
seconds)
robustness-vari
able
Increase this value to allow for expected packet loss on a
subnetwork. 2-10 2
startup-query-
count
Number of queries that the switch sends out on startup,
separated by startup-query-interval. The default is the
robustness-variable value.
—2
startup-query-
interval
Interval, in seconds, at which the switch sends general
queries on startup. The default is 1/4 of the query-interval. — 31 seconds
version-1-rou
ter-present-
timeout
Timeout, in seconds, if a version 1 IGM router is detected. — 400 seconds

276 |ip igmp AOS-W 3.4.1 Command Line Interface | Reference Guide
Command Information
Platform License Command Mode
Available on all platforms Available in the base operating system Config mode on master switches
AOS-W 3.4.1 Command Line Interface | Reference Guide ip local | 277
ip local
ip local pool <name> <start-ipaddr> [<end-ipaddr>]
Description
This command configures a local IP pool for Layer-2 Tunnel Protocol (L2TP).
Syntax
Usage Guidelines
VPN clients can be assigned IP addresses from the L2TP pool.
Example
The following command configures an L2TP pool:
(host) (config) #ip local pool 10.1.1.1 10.1.1.99
Command History
This command was available in AOS-W 3.0.
Command Information
Parameter Description
pool Name for the address pool.
<start-ipaddr> Starting IP address for the pool.
<end-ipaddr> (Optional) Ending IP address for the pool.
Platform License Command Mode
Available on all platforms This command requires the VPN Server and/
or Remote AP license. Config mode on master switches
278 | ip mobile active-domain AOS-W 3.4.1 Command Line Interface | Reference Guide
ip mobile active-domain
ip mobile
ip mobile active-domain <name>
Description
This command configures the mobility domain that is active on the switch.
Syntax
Usage Guidelines
All switches are initially part of the “default” mobility domain. If you use the “default” mobility domain, you
do not need to specify this domain as the active domain on the switch. However, once you assign a switch
to a user-defined domain, the “default” mobility domain is no longer an active domain on the switch.
Example
The following command assigns the switch to a user-defined mobility domain:
(host) (config) #ip mobile active-domain campus1
Command History
This command was available in AOS-W 3.0.
Command Information
Parameter Description
active-domain Name of the mobility domain.
Platform License Command Mode
Available on all platforms Available in the base operating system Config mode on master switches
AOS-W 3.4.1 Command Line Interface | Reference Guide ip mobile domain | 279
ip mobile domain
ip mobile domain <name>
hat <subnetwork> <mask> <vlan> <ha-ipaddr>
no ...
Description
This command configures the mobility domain on the switch.
Syntax
Usage Guidelines
You configure the HAT on a master switch; the mobility domain information is pushed to all local switches
that are managed by the same master.
HAT entries map subnetworks or VLANs and the home agents. The home agent is typically the switch’s IP
address. The home agent’s IP address must be routable; that is, all switches that belong to the same mobility
domain must be able to reach the home agent’s IP address.
The switch looks up information in the HAT to obtain the IP address of the home agent for a mobile client.
Because there can be multiple home agents on a subnetwork, the HAT can contain more than one entry for
the same subnetwork.
Example
The following command configures HAT entries:
(host) (config) #ip mobile domain default
hat 10.1.1.0 255.255.255.0 1 10.1.1.245
hat 10.1.1.0 255.255.255.0 1 10.2.1.245
hat 10.1.2.0 255.255.255.0 2 10.1.1.245
hat 10.1.3.0 255.255.255.0 3 10.1.1.245
hat 10.2.1.0 255.255.255.0 4 10.2.1.245
hat 10.2.2.0 255.255.255.0 5 10.2.1.245
hat 10.2.3.0 255.255.255.0 6 10.2.1.245
hat 10.3.1.0 255.255.255.0 7 10.3.1.245
hat 10.3.2.0 255.255.255.0 8 10.3.1.245
hat 10.3.3.0 255.255.255.0 9 10.3.1.245
Command History
This command was available in AOS-W 3.0.
Parameter Description Range
domain Name of the mobility domain. —
hat Configures a home agent table (HAT) entry. —
<subnetwork> Subnet that requires mobility service. —
<mask> Netmask for the IP address. —
<vlan> VLAN ID. The VLAN ID must be the VLAN number on the home agent
switch. 1-4094
<ha-ipaddr> IP address of the home agent. —
no Negates any configured parameter. —

280 | ip mobile domain AOS-W 3.4.1 Command Line Interface | Reference Guide
Command Information
Platform License Command Mode
Available on all platforms Available in the base operating system Config mode on master switches
AOS-W 3.4.1 Command Line Interface | Reference Guide ip mobile foreign-agent | 281
ip mobile foreign-agent
ip mobile foreign-agent {lifetime <seconds> | max-visitors <number> |
registrations {interval <msecs> | retransmits <number>}}
Description
This command configures the foreign agent for IP mobility.
Syntax
Usage Guidelines
A foreign agent is the switch which handles all mobile IP communication with a home agent on behalf of a
roaming client.
Example
The following command configures the foreign agent:
(host) (config) #ip mobile foreign-agent registration interval 10000
Command History
This command was available in AOS-W 3.0.
Command Information
Parameter Description Range Default
lifetime Requested lifetime, in seconds, as per RFC 3344, “IP
Mobility Support for IPv4”. 10-65534 180 seconds
max-visitors Maximum number of active visitors. 0-5000 5000
registrations Frequency at which re-registration messages are sent to
the home agent:
interval Retransmission interval, in milliseconds 100-10000 1000
milliseconds
retransmits Maximum number of times the foreign agent attempts
mobile IP registration message exchanges before giving
up.
0-5 3
Platform License Command Mode
Available on all platforms Available in the base operating system Config mode on master switches

282 | ip mobile home-agent AOS-W 3.4.1 Command Line Interface | Reference Guide
ip mobile home-agent
ip mobile home-agent {max-bindings <number>|replay <seconds>}
Description
This command configures the home agent for IP mobility.
Syntax
Usage Guidelines
A home agent for a mobile client is the switch where the client first appears when it joins the mobility
domain. The home agent is the single point of contact for the client when it roams.
Example
The following command configures the home agent:
(host) (config) #ip mobile home-agent replay 100
Command History
This command was available in AOS-W 3.0.
Command Information
Parameter Description Range Default
max-bindings Maximum number of mobile IP bindings. Note that there is a
license-based limit on the number of users and a one user per
binding limit in addition to unrelated users. This option is an
additional limitation to control the maximum number of roaming
users. When the limit is reached, registration requests from the
foreign agent fail which causes a mobile client to set a new
session on the visited switch, which will become its home switch.
0-5000 5000
replay Time difference, in seconds, for timestamp-based replay
protection, as described by RFC 3344, “IP Mobility Support for
IPv4”. 0 disables replay.
0-300 7 seconds
Platform License Command Mode
Available on all platforms Available in the base operating system Config mode on master switches

AOS-W 3.4.1 Command Line Interface | Reference Guide ip mobile proxy | 283
ip mobile proxy
ip mobile proxy auth-sta-roam-only | block-dhcp-release | dhcp {max-requests <number>|
transaction-hold <seconds>|transaction-timeout <seconds>}| event-threshold <number> |
log-trail | no-service-timeout <seconds> | on-association |re-home |
stale-timeout <seconds> | stand-alone-AP | trail-length <number> |trail-timeout
<seconds>
Description
This command configures the proxy mobile IP module in a mobility-enabled switch.
Syntax
Parameter Description Range Default
auth-sta-roam-
only
Allows a client to roam only if has been authenticated. If a
client has not been authenticated, no mobility service is
offered if it roams to a different VLAN or switch.
—enabled
block-dhcp-re
lease
Determines whether DHCP release packets generated from
the client should be dropped or forwarded to the DHCP server.
Blocking the packets prevents the DHCP server from
assigning the same IP address to another client until the lease
has expired.
disabled
dhcp Configures proxy DHCP
aggressive-
transaction
Terminate Proxy DHCP on aggressive Transaction ID change.
NOTE: Alcatel-Lucent recommends keeping this parameter at
the default setting:
0-65534 25
max-requests Maximum number of BOOTP packets that are allowed to be
handled during one DHCP session. 0-65534 25
transaction-
hold
Hold time, in seconds, on proxy DHCP state after completion
of DHCP transaction (DHCP ACK) was forwarded to the client.
This option ensures that late BOOTP replies reach the station
and that a retransmitted BOOTP request does not trigger a
new proxy DHCP session.
1-600 5 seconds
transaction-
timeout
Maximum time allowed for a proxy DHCP session to complete. 10-600 60 seconds
event-threshold Maximum number of mobility events (events that can trigger
mobility) handled per second. Mobility events above this
threshold are ignored. This helps to control frequent mobility
state changes when the client bounces back and forth on APs
before settling down.
1-65535 25
log-trail Enables logging at the notification level for mobile client
moves. —enabled
no-service-time
out
Time, in seconds, after which mobility service expires. If
nothing has changed from the previous state, the client is
given another bridge entry but it will have limited connectivity.
30-60000 180
seconds
on-association Mobility move detection is performed when the client
associates with the switch instead of when the client sends
packets. Enabled by default. Mobility on association can
speed up roaming and improve connectivity for devices that
do not send many uplink packets out that can trigger mobility.
Downside is security; an association is all it takes to trigger
mobility. This is irrelevant unless layer-2 security is enforced.
—enabled

284 | ip mobile proxy AOS-W 3.4.1 Command Line Interface | Reference Guide
Usage Guidelines
The proxy mobile IP module in a mobility-enabled switch detects when a mobile client has moved to a
foreign network and determines the home agent for a roaming client. The proxy mobile IP module performs
the following functions:
zDerives the address of the home agent for a mobile client from the HAT using the mobile client’s IP
address. If there is more than one possible home agent for a mobile client in the HAT, the proxy mobile
IP module uses a discovery mechanism to find the current home agent for the client.
zDetects when a mobile client has moved. Client moves are detected based on ingress port and VLAN
changes and mobility is triggered accordingly. For faster roaming convergence between AP(s) on the
same switch, it is recommended that you keep the “on-association” option enabled. This helps trigger
mobility as soon as 802.11 association packets are received from the mobile client.
Example
The following command enables re-home for voice clients:
(host) (config) #ip mobile proxy re-home
Command History
This command was available in AOS-W 3.0.
re-home Allows on-hook phones to be assigned a new home agent.
This is to load balance voice client home agents across
switches in a mobility domain.
This parameter requires that you install the Policy Enforcement
Firewall license in the switch.
—disabled
stale-timeout Number of seconds the mobility state is retained after the loss
of connectivity. This allows authentication state and mobility
information to be preserved on the home agent switch. The
default is 60 seconds but can be safely increased. Note that in
many case a station state is deleted without waiting for the
stale timeout; user delete from management, foreign agent to
foreign agent handoff, etc. (This is different from the no-
service-timeout; no-service-timeout occurs up front while the
stale-timeout begins when mobility service is provided but the
connection is disrupted for some reason.)
30-3600 60 seconds
stand-alone-AP Enables support for third party or standalone APs. When this is
enabled, broadcast packets are not used to trigger mobility
and packets from untrusted interfaces are accepted.
If mobility is enabled, you must also enable standalone AP for
the client to connect to the switch’s untrusted port. If the
switch learns wired users via the following methods, enable
standalone AP:
zThird party AP connected to the switch through the
untrusted port.
zClients connected to ENET1 on the OAW-AP70.
zWired user connected directly to the switch’s untrusted
port.
—disabled
trail-length Specifies the maximum number of entries (client moves) stored
in the user mobility trail. 1-100 30
trail-timeout Specifies the maximum interval, in seconds, an inactive
mobility trail is held. 120-86400 3600
seconds
NOTE
The re-home parameter requires the Policy Enforcement Firewall license.

AOS-W 3.4.1 Command Line Interface | Reference Guide ip mobile proxy | 285
Command Information
Platform License Command Mode
Available on all platforms Available in the base operating system. The
re-home parameter requires the Policy
Enforcement Firewall (PEF) license.
Config mode on master switches
286 | ip mobile revocation AOS-W 3.4.1 Command Line Interface | Reference Guide
ip mobile revocation
ip mobile revocation {interval <msec>|retransmits <number>
Description
This command configures the frequency at which registration revocation messages are sent.
Syntax
Usage Guidelines
A home agent or foreign agent can send a registration revocation message, which revokes registration
service for the mobile client. For example, when a mobile client roams from one foreign agent to another,
the home agent can send a registration revocation message to the first foreign agent so that the foreign
agent can free any resources held for the client.
Example
The following command configures registration revocation messages:
(host) (config) #ip mobile revocation interval 2000
Command History
This command was available in AOS-W 3.0.
Command Information
Parameter Description Range Default
interval Retransmission interval, in milliseconds. 100-10000
ms 1000 ms
retransmits Maximum number of times the home agent or foreign agent
attempts mobile IP registration/revocation message exchanges
before giving up.
0-5 3
Platform License Command Mode
Available on all platforms Available in the base operating system. Config mode on master switches
AOS-W 3.4.1 Command Line Interface | Reference Guide ip mobile trail | 287
ip mobile trail
ip mobile trail {host IP address | host MAC address}
Description
This command configures the capture of association trail for all devices.
Syntax
Usage Guidelines
A device can move from one home agent to another or between home agents. When the client makes an
association, the agent can store information about the client and registration time. The association trail can
be captured for devices even when mobility is disabled.
Example
The following command configures trail capture for a client using its IP address:
(host) (config) #ip mobile trail 1.2.3.4
Command History
This command was available in AOS-W 3.0.
Command Information
Parameter Description Default
Host IP address The IP address of the client for which the association trail is
captured. disabled
Host MAC address The MAC address of the client for which the association trail is
captured. disabled
Platform License Command Mode
Available on all platforms Available in the base operating system. Config mode on master switches
288 |ip name-server AOS-W 3.4.1 Command Line Interface | Reference Guide
ip name-server
ip name-server <ipaddr>
Description
This command configures servers for name and address resolution.
Syntax
Usage Guidelines
You can configure up to six servers using separate commands. Specify one or more servers when you
configure a default domain name (see “ip domain-name” on page 274).
Example
The following command configures a name server:
ip name-server 10.1.1.245
Command History
This command was available in AOS-W 3.0.
Command Information
Parameter Description
<ip-addr> IP address of the server.
Platform License Command Mode
Available on all platforms Available in the base operating system. Config mode on master switches
AOS-W 3.4.1 Command Line Interface | Reference Guide ip nat | 289
ip nat
ip nat pool <name> <start-ipaddr> <end-ipaddr> [<dest-ipaddr>]
Description
This command configures a pool of IP addresses for network address translation (NAT).
Syntax
Usage Guidelines
This command configures a NAT pool which you can reference in a session ACL rule (see “ip access-list
session” on page 265).
Example
The following command configures a NAT pool:
(host) (config) #ip nat pool 2net 2.1.1.1 2.1.1.125
Command History
This command was available in AOS-W 3.0.
Command Information
Parameter Description
pool Name of the NAT pool.
<start-ipaddr> IP address that defines the beginning of the range of source NAT addresses in the pool.
<end-ipaddr> IP address that defines the end of the range of source NAT addresses in the pool.
<dest-ipaddr> Destination NAT IP address.
Platform License Command Mode
Available on all platforms This command requires the Policy
Enforcement Firewall license. Config mode on master and local
switches
290 | ip ospf AOS-W 3.4.1 Command Line Interface | Reference Guide
ip ospf
ip ospf area|{authentication message-digest | cost <cost> | dead-interval <seconds> |
hello-interval <seconds> | message-digest-key <keyid> <passwd> | priority <number> |
retransmit-interval <seconds> |transmit-delay <seconds>
Description
Configure OSPF on the VLAN interface.
Syntax
Usage Guidelines
When configuring OSPF over multiple vendors, use this ip ospf cost command to ensure that all routers
use the same cost. Otherwise, OSPF may route improperly.
Related Commands
Parameter Description Range Default
area Enable OSPF on a specific interface by entering
the IP address of the router that will use OSPF.
authentication
message-digest
Enable OSPF message digest authentication. disabled
cost <cost> Change the cost associated with the OSPF traffic
on an interface. 1 to 65535 1
dead-interval
<seconds>
Set the elapse interval (seconds) since the last
hello-packet was received from the router. After
the interval elapses, the neighboring routers
declare the router dead.
1 to 65535
seconds 40
hello-interval
<seconds>
Set the elapse interval (seconds) between hello
packets sent on the interface. 1 to 65535
seconds 10
message-digest-key
<keyid> <passwd>
Enable OSPF MD5 authentication and set the key
identification and a character string password. <keyid> = 1 to
256 No default
priority <number> Set the priority number of the interface to
determine the DR. 0 to 255 1
retransmit-interval
<seconds>
Set the retransmission time between link state
advertisements for adjacencies belonging to the
interface.
NOTE: Set the time interval long enough to
prevent unnecessary retransmissions.
1 to 65535
seconds 5
transmit-delay
<seconds>
Set the elapse time before retransmitting link state
update packets on the interface. 1 to 65535
seconds 1
Command Description
show ip ospf View OSPF process on the router
show ip ospf interface View the configure OSPF interface.
AOS-W 3.4.1 Command Line Interface | Reference Guide ip ospf | 291
Command History
Command Information
Release Modification
AOS-W 3.4 Command introduced
Platforms Licensing Command Mode
All Platforms Base operating system Configuration Mode (config)
292 | ip pppoe-max-segment-size AOS-W 3.4.1 Command Line Interface | Reference Guide
ip pppoe-max-segment-size
ip pppoe-max-segment-size <mss>
Description
This command configures the maximum TCP segment size (mss), in bytes, for Point-to-Point Protocol over
Ethernet (PPPoE) data.
Syntax
Usage Guidelines
The maximum segment size for PPPoE is smaller than the normal Ethernet encapsulation size because of
the PPPoE overhead.
Example
The following command configures the PPPoE maximum TCP segment size:
(host) (config) #ip pppoe-max-segment-size 1412
Command History
This command was available in AOS-W 3.0.
Command Information
Parameter Description Range Default
<mss> Enter the keywords pppoe-max-segment-size followed by the TCP
max segment size (mss) in bytes. 128-1452 1452
Platform License Command Mode
Available on all platforms Available in the base operating system. Config mode (config) on master and
local switches
AOS-W 3.4.1 Command Line Interface | Reference Guide ip pppoe-password | 293
ip pppoe-password
ip pppoe-password <password>
Description
This command configures the PPP over Ethernet (PPPoE) password.
Syntax
Usage Guidelines
Note the following about enabling the PPPoE client on the switch:
zYou cannot enable both the DHCP and PPPoE client on the switch at the same time.
zYou can enable the PPPoE client on only one VLAN on the switch (the VLAN cannot be VLAN 1).
zYou can connect only one port in the VLAN to the uplink switch.
zAt least one interface in the VLAN must be in the up state before the PPPoE client requests an IP address
from the server.
Example
The following commands configure the PPPoE client on the switch:
(host) (config) #ip pppoe-service-name ppp2056
ip pppoe-username rudolph123
ip pppoe-password 1234567890
vlan 22
interface vlan 22
ip address pppoe
Command History
This command was available in AOS-W 3.0.
Command Information
Parameter Description
<password> Enter the keyword ip-pppoe-password followed by the PAP password configured on the
PPPoE Access Concentrator for the switch.
Platform License Command Mode
Available on all platforms Available in the base operating system. Config mode (config) on master or
local switches
294 | ip pppoe-service-name AOS-W 3.4.1 Command Line Interface | Reference Guide
ip pppoe-service-name
ip pppoe-service-name <service_name>
Description
This command configures the PPP over Ethernet (PPPoE) service name.
Syntax
Usage Guidelines
Note the following about enabling the PPPoE client on the switch:
zYou cannot enable both the DHCP and PPPoE client on the switch at the same time.
zYou can enable the PPPoE client on only one VLAN on the switch (the VLAN cannot be VLAN 1).
zYou can connect only one port in the VLAN to the uplink switch.
zAt least one interface in the VLAN must be in the up state before the PPPoE client requests an IP address
from the server.
Example
The following commands configure the PPPoE client on the switch:
(host) (config) #ip pppoe-service-name ppp2056
ip pppoe-username rudolph123
ip pppoe-password 1234567890
vlan 22
interface vlan 22
ip address pppoe
Command History
This command was available in AOS-W 3.0.
Command Information
Parameter Description
<service_name> Enter the keyword ip-pppoe-service-name followed by the PPPoE service name.
Platform License Command Mode
Available on all platforms Available in the base operating system. Config mode (config) on master and local
switches
AOS-W 3.4.1 Command Line Interface | Reference Guide ip pppoe-username | 295
ip pppoe-username
ip pppoe-username <username>
Description
This command configures the PPP over Ethernet (PPPoE) username.
Syntax
Usage Guidelines
Note the following about enabling the PPPoE client on the switch:
zYou cannot enable both the DHCP and PPPoE client on the switch at the same time.
zYou can enable the PPPoE client on only one VLAN on the switch (the VLAN cannot be VLAN 1).
zYou can connect only one port in the VLAN to the uplink switch.
zAt least one interface in the VLAN must be in the up state before the PPPoE client requests an IP address
from the server.
Example
The following commands configure the PPPoE client on the switch:
(host) (config) #ip pppoe-service-name ppp2056
ip pppoe-username rudolph123
ip pppoe-password 1234567890
vlan 22
interface vlan 22
ip address pppoe
Command History
This command was available in AOS-W 3.0.
Command Information
Parameter Description
<username> Enter the keywords ip pppoe-username followed by the PAP user name configured on
the PPPoE Access Concentrator for the switch.
Platform License Command Mode
Available on all platforms Available in the base operating system. Config mode (config) on master and
local switches

296 |ip radius AOS-W 3.4.1 Command Line Interface | Reference Guide
ip radius
ip radius {nas-ip <ipaddr>|rfc-3576-server udp-port <port>|source-interface
{loopback|vlan <vlan>}
Description
This command configures global parameters for configured RADIUS servers.
Syntax
Usage Guidelines
This command configures global RADIUS server parameters. If the aaa authentication-server radius
command configures a server-specific NAS IP, the server-specific IP address is used instead.
Example
The following command configures a global NAS IP address sent in RADIUS packets:
(host) (config) #ip radius nas-ip 192.168.1.245
Command History
This command was available in AOS-W 3.0.
Command Information
Parameter Description Range Default
nas-ip NAS IP address to send in RADIUS packets. A server-specific
NAS IP configured with the aaa authentication-server
radius command supersedes this configuration.
——
rfc-3576-server Configures the UDP port to receive requests from a RADIUS
server that can send user disconnect and change-of-authorization
messages, as described in RFC 3576, “Dynamic Authorization
Extensions to Remote Dial In User Service (RADIUS)”. See the
aaa rfc-3576-server command to configure the server.
NOTE: This parameter can only be used on the master switch.
udp-port UDP port to receive server requests. 0-65535 3799
source-inter
face
Interface for all outgoing RADIUS packets. The IP address of the
specified interface is included in the IP header of RADIUS
packets. The interface can be one of the following:
loopback The loopback interface. — —
vlan The specified VLAN. — —
Platform License Command Mode
Available on all platforms The ip radius rfc-3576-server udp-port
command requires the Policy Enforcement
Firewall (PEF) license. Other commands are
available in the base operating system.
Config mode on master and local
switches
AOS-W 3.4.1 Command Line Interface | Reference Guide ip route | 297
ip route
ip route <dest-ipaddr> <netmask> {<nexthop> [<cost>]|ipsec <map>}
Description
This command configures a static route on the switch.
Syntax
Usage Guidelines
This command configures a static route on the switch other than the default gateway. Use the ip default-
gateway command to set the default gateway to the IP address of the interface on the upstream router or
switch to which you connect the switch.
Example
The following command configures a static route:
(host) (config) #ip route 172.16.0.0 255.255.0.0 10.1.1.1
Command History
This command was available in AOS-W 3.0.
Command Information
Parameter Description
route IP address and netmask of the destination network.
<nexthop> IP address of the forwarding router.
<cost> (Optional) Cost associated with this route. You can specify a cost to prioritize routes to the
same destination. The lower the cost, the higher the priority.
ipsec Name of the IPsec map for this route.
Platform License Command Mode
Available on all platforms The ipsec parameter requires the VPN server
license. Other commands are available in the
base operating system.
Config mode on master and local
switches

298 |ip route AOS-W 3.4.1 Command Line Interface | Reference Guide
AOS-W 3.4.1 Command Line Interface | Reference Guide ipv6 access-list session | 299
ipv6 access-list session
ipv6
ipv6 access-list session <name>
<source> <dest> <service> <action> [<extended action>]
no ...
Description
This command configures a session access control list (ACL) for use with IPv6 clients.
Syntax
Parameter Description
session Enter a name for this ACL
<source> The traffic source, which can be one of the following:
zalias: specify the network resource
NOTE: This release does not support IPv6 aliases. You cannot configure an alias for an IPv6
host or network.
zany: match any traffic
zhost: specify a single host IPv6 address (for example,
2002:d81f:f9f0:1000:c7e:5d61:585c:3ab)
znetwork: specify an IPv6 address and netmask (for example, 2002:ac10:fe:: ffff:ffff:ffff::)
zuser: represents the IPv6 address of the user
<dest> The traffic destination, which can be one of the following:
zalias: specify the network resource (use the show netdestination command to see
configured aliases)
NOTE: This release does not support IPv6 aliases. You cannot configure an alias for an IPv6
host or network.
zany: match any traffic
zhost: specify a single host IPv6 address (for example,
2002:d81f:f9f0:1000:c7e:5d61:585c:3ab)
znetwork: specify an IPv6 address and netmask (for example, 2002:ac10:fe:: ffff:ffff:ffff::)
zuser: represents the IPv6 address of the user
<service> Network service, which can be one of the following:
zIP protocol number (0-255)
zname of a network service (use the show netservice command to see configured services)
NOTE: Not all network services supported with IPv4 sessions ACLs are supported for IPv6.
For example, you cannot use voice-related services (such as SIP or H323) for IPv6 session
ACLs.
zany: match any traffic
ztcp: specify the TCP port number (0-65535)
zudp: specify the UDP port number (0-65535)
<action> Action if rule is applied, which can be one of the following:
zdeny: reject packets
zpermit: forward packets
300 | ipv6 access-list session AOS-W 3.4.1 Command Line Interface | Reference Guide
Usage Guidelines
Session ACLs define traffic and firewall policies on the switch. You can configure multiple rules for each
policy, with rules evaluated from top (1 is first) to bottom. The first match terminates further evaluation.
Generally, you should order more specific rules at the top of the list and place less specific rules at the
bottom of the list. The ACL ends with an implicit deny all.
Do not use VLAN pooling if you enable IPv6 forwarding on the switch, as VLAN pooling will flood IPv6
multicast packets for all VLANs that are part of the VLAN pool. This can cause autoconfigured clients to
acquire multiple IPv6 addresses (one for each vlan in the pool) making those clients behave unpredictably.
If you need to work around this limitation, you can unicast BC/MC traffic to every station. To enable this
workaround, you must enable the wlan ssid-profile battery-boost option, and install a wlan Policy
Enforcement Firewall license.
Example
The following command configures a session ACL that permits traffic from an IPv6 subnetwork:
(host) (config) #ipv6 access-list session allow-ipv6-clients
network 2002:ac10:fe:: ffff:ffff:ffff:: any any permit
Command History
Introduced in AOS-W 3.3
Command Information
<extended ac
tion>
Optional action if rule is applied, which can be one of the following:
zblacklist: blacklist user
zdisable-scanning: pause ARM scanning while traffic is present
zdot1p-priority: specify 802.1p priority (0-7)
zlog: generate a log message
zmirror: mirror all session packets to datapath or remote destination
zposition: specify the position of the rule (1 is first, default is last)
zqueue: assign flow to priority queue (high/low)
zsend-deny-response: if <action> is deny, send an ICMP notification to the source
ztime-range: specify time range for this rule (configured with time-range command)
ztos: specify ToS value (0-63)
no Negates any configured parameter.
Platform License Command Mode
Available on all platforms Requires Policy Enforcement Firewall license Config mode on master switches

AOS-W 3.4.1 Command Line Interface | Reference Guide ipv6 firewall | 301
ipv6 firewall
ipv6 firewall
attack-rate {ping <number>|session <number>|tcp-syn <number>}
deny-inter-user-bridging |
drop-ip-fragments |
enable-per-packet-logging |
enforce-tcp-handshake |
prohibit-ip-spoofing |
prohibit-rst-replay |
session-idle-timeout <seconds> |
session-mirror-destination {ip-address <ipaddr>}|{port <slot/<port>}
Description
This command configures firewall options on the switch for IPv6 traffic.
Syntax
Parameter Description Range Default
attack-rate Sets rates which, if exceeded, can indicate a denial of service
attack.
ping Number of ICMP pings per second, which if exceeded, can
indicate a denial of service attack. Recommended value is 4 1-255 —
session Number of TCP or UDP connection requests per second, which
if exceeded, can indicate a denial of service attack.
Recommended value is 32.
1-255 —
tcp-syn Number of TCP SYN messages per second, which if exceeded,
can indicate a denial of service attack. Recommended value is
32.
1-255 —
deny-inter-user-
bridging
Prevents the forwarding of Layer-2 traffic between wired or
wireless users. You can configure user role policies that prevent
Layer-3 traffic between users or networks but this does not
block Layer-2 traffic. This option can be used to prevent
Appletalk or IPX traffic from being forwarded.
—disabled
drop-ip-frag
ments
When enabled, all IP fragments are dropped. You should not
enable this option unless instructed to do so by an Alcatel-
Lucent representative.
—disabled
enable-per-pac
ket-logging
Enables logging of every packet if logging is enabled for the
corresponding session rule. Normally, one event is logged per
session. If you enable this option, each packet in the session is
logged. You should not enable this option unless instructed to
do so by an Alcatel-Lucent representative, as doing so may
create unnecessary overhead on the switch.
—disabled
enforce-tcp-
handshake
Prevents data from passing between two clients until the three-
way TCP handshake has been performed. This option should
be disabled when you have mobile clients on the network as
enabling this option will cause mobility to fail. You can enable
this option if there are no mobile clients on the network.
—disabled
prohibit-ip-
spoofing
Detects IP spoofing (where an intruder sends messages using
the IP address of a trusted client). When this option is enabled,
IP and MAC addresses are checked; possible IP spoofing
attacks are logged and an SNMP trap is sent.
—disabled
prohibit-rst-re
play
Closes a TCP connection in both directions if a TCP RST is
received from either direction. You should not enable this
option unless instructed to do so by an Alcatel-Lucent
representative.
—disabled
302 |ipv6 firewall AOS-W 3.4.1 Command Line Interface | Reference Guide
Usage Guidelines
This command configures global firewall options on the switch for IPv6 traffic.
Example
The following command disallows forwarding of non-IP frames between IPv6 clients:
(host) (config) #ipv6 firewall deny-inter-user-bridging
Command History
Introduced in AOS-W 3.3
Command Information
session-idle-
timeout
Time, in seconds, that a non-TCP session can be idle before it
is removed from the session table. You should not modify this
option unless instructed to do so by an Alcatel-Lucent
representative.
16-259 15
seconds
session-mirror-
destination
Destination to which mirrored session packets are sent. The
destination can be either an IPv4 address or a switch port. You
configure IPv6 flows to be mirrored with the mirror option of
the ipv6 access-list session command. Use this option only
for troubleshooting or debugging.
——
ip-address
<ipaddr>
Send mirrored session packets to the specified IP address
port <slot>/
<port>
Send mirrored session packets to the specified switch port.
Parameter Description Range Default
Platform License Command Mode
Available on all platforms Available in the base operating system, except
for noted parameters Config mode on master
switches
AOS-W 3.4.1 Command Line Interface | Reference Guide lacp group | 303
lacp group
lacp group <group_number> mode {active | passive}
lacp
Description
Enable Link Aggregation Control Protocol (LACP) and configure LACP on the interface.
Syntax
Usage Guidelines
LACP is disabled by default; this command enables LACP. If the group number assigned contains static port
members, the command is rejected.
Related Command
Command History
Command Information
Parameter Description
<group_number> Enter the link aggregation group (LAG) number.
Range: 0-7
mode {active | passive} Enter the keyword mode followed by either the keyword active or passive.
zActive mode—the interface is in active negotiating state. LACP runs on any
link that is configured to be in the active state. The port in an active mode also
automatically initiates negotiations with other ports by initiating LACP
packets.
zPassive mode—the interface is not in an active negotiating state. LACP runs
on any link that is configured in a passive state. The port in a passive mode
responds to negotiations requests from other ports that are in an active state.
Ports in passive state respond to LACP packets.
Command Description
show lacp View the LACP configuration status
show lacp sys-id View the LACP system ID information
show interface port-channel View information on a specified port channel interface
Release Modification
AOS-W 3.4.1 Command introduced
Platform Licensing Command Mode
All Platforms Base operating system Configuration Interface Mode (config-if) for
Master and Local switches
304 | lacp port-priority AOS-W 3.4.1 Command Line Interface | Reference Guide
lacp port-priority
lacp port-priority <priority_value>
Description
Configure the LACP port priority.
Syntax
Usage Guidelines
Set the port priority for LACP.
Related Command
Command History
Command Information
Parameter Description
<priority_value> Enter the port-priority value. The higher the value number the lower the
priority.
Range: 1 to 65535
Default: 255
Command Description
lacp group Enable LACP and configure on the interface
lacp system-priority Set the LACP system priority
show lacp View the LACP configuration status
show lacp sys-id View the LACP system ID information
show interface port-channel View information on a specified port channel interface
Release Modification
AOS-W 3.4.1 Command introduced
Platform Licensing Command Mode
All Platforms Base operating system Configuration Interface Mode (config-if) for
Master and Local switches
AOS-W 3.4.1 Command Line Interface | Reference Guide lacp system-priority | 305
lacp system-priority
lacp system-priority <priority_value>
Description
Configure the LACP system priority.
Syntax
Usage Guidelines
Set the LACP system priority
Related Command
Command History
Command Information
Parameter Description
<priority_value> Enter the system priority value. The higher the value number the lower the priority.
Range: 1 to 65535
Default: 32768
Command Description
lacp group Enable LACP and configure on the interface
lacp port-priority Set the LACP port priority
show lacp View the LACP configuration status
show lacp sys-id View the LACP system ID information
show interface port-channel View information on a specified port channel interface
Release Modification
AOS-W 3.4.1 Command introduced
Platforms Licensing Command Mode
All Platforms Base operating system Configuration Mode (config) for Master and
Local switches
306 | lacp timeout AOS-W 3.4.1 Command Line Interface | Reference Guide
lacp timeout
lacp timeout {long | short}
Description
Configure the timeout period for the LACP session.
Syntax
Usage Guidelines
The timeout value is the amount of time that a port-channel interface waits for a LACPDU (Link
Aggregation Control Protocol data unit) from the remote system before terminating the LACP session. The
default time out value is 90 seconds (long).
Related Command
Command History
Command Information
Parameter Description
long Enter the keyword long to set the LACP session to 90 seconds. This is the
default.
short Enter the keyword short to set the LACP session to 3 seconds.
Command Description
lacp group Enable LACP and configure on the interface
show lacp View the LACP configuration status
show lacp sys-id View the LACP system ID information
show interface port-channel View information on a specified port channel interface
Release Modification
AOS-W 3.4.1 Command introduced
Platforms Licensing Command Mode
All Platforms Base operating system Configuration Interface Mode (config-if) for
Master and Local switches
AOS-W 3.4.1 Command Line Interface | Reference Guide license | 307
license
license {add <key>|del <key>|export <filename>|import <filename>|report <filename>}
Description
This command allows you to install, delete, and manage software licenses on the switch.
Syntax
Usage Guidelines
Obtain an Alcatel-Lucent software license certificate from your Alcatel-Lucent sales representative or
authorized reseller. Use the certificate ID and the system serial number to obtain a software license key
which you install in the switch.
Example
The following command adds a license key on the switch:
license add 890BobXs-cVPCb3aJ-7FbCijhZ-BuQPtuI4-RjLJW6Pl-n5K
Command History
Introduced in AOS-W 3.0
Command Information
Parameter Description
add Installs the software license key in the switch. The key is normally sent to you via email.
del Removes the software license key from the switch. The key is normally sent to you via email.
export Exports the license database on the switch to the specified file in flash.
import Replaces the license database on the switch with the specified file in flash.
The system serial numbers referenced in the imported file must match the numbers on the
switch.
report Saves a license report to the specified file in flash.
Users that are not very familiar with this procedure may wish to use the License Management page in the WebUI to
install and manage licenses on the switch.
Platform License Command Mode
Available on all platforms Available in the base operating system Enable mode on master and local
switches

308 |license AOS-W 3.4.1 Command Line Interface | Reference Guide
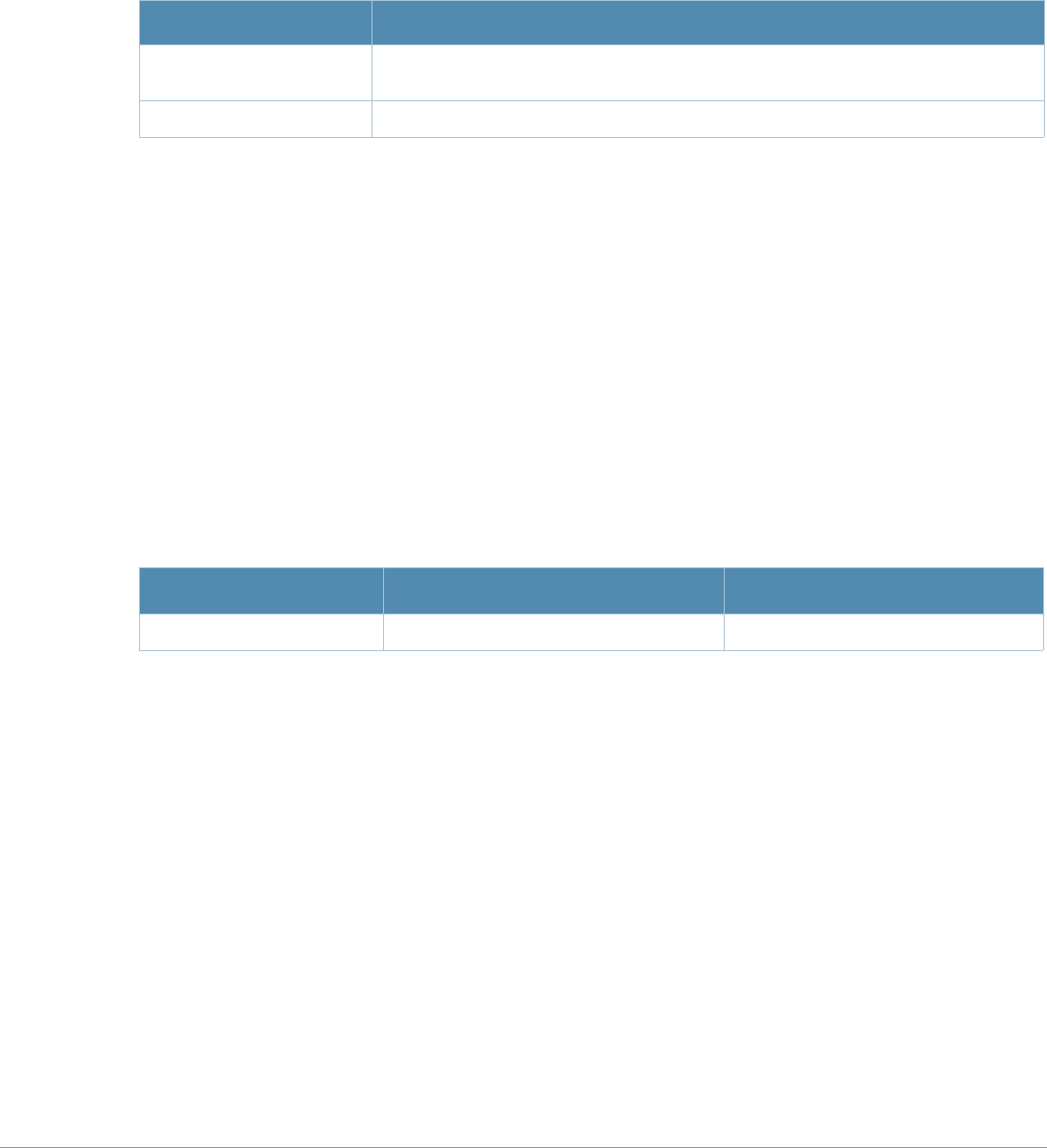
AOS-W 3.4.1 Command Line Interface | Reference Guide localip | 309
localip
localip <ipaddr> ipsec <key>
Description
This command configures the IP address and preshared key for the local switch on a master switch.
Syntax
Usage Guidelines
Use this command on a master switch to configure the IP address and preshared key for communication
with a local switch. On the local switch, use the masterip command to configure the IP address and
preshared key for the master switch.
Example
The following command configures the local switch on a master switch:
(host) (config) #localip 0.0.0.0 ipsec gw1234xyz
Command History
Introduced in AOS-W 3.0
Command Information
Parameter Description
<ipaddr> IP address of the local switch. Use the 0.0.0.0 address to configure a global
preshared key for all inter-switch communications.
ipsec Preshared key, which must be between 6-64 characters.
Platform License Command Mode
Available on all platforms Available in the base operating system Config mode on master switches

310 |localip AOS-W 3.4.1 Command Line Interface | Reference Guide
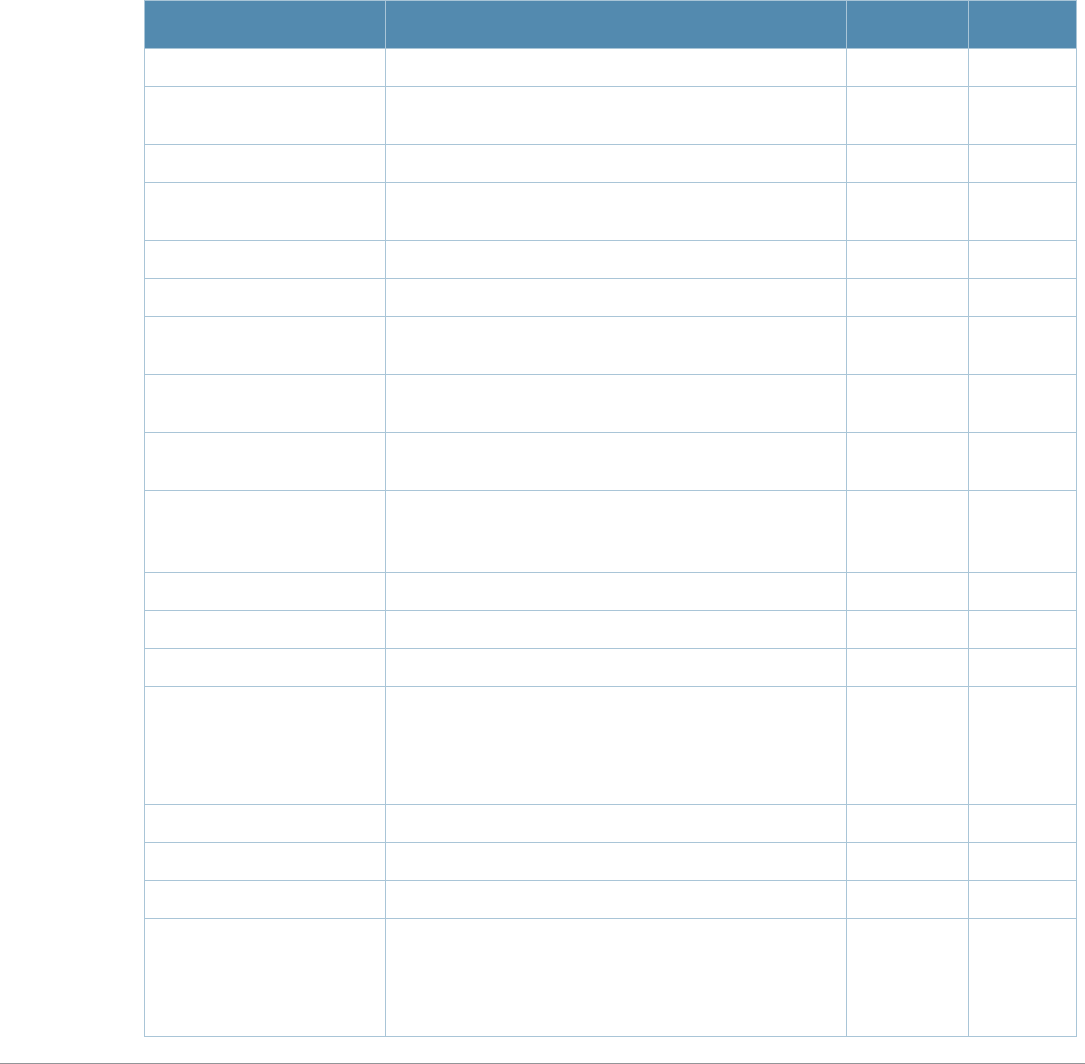
AOS-W 3.4.1 Command Line Interface | Reference Guide local-userdb add | 311
local-userdb add
localuserdb
local-userdb add {generate-username|username <name>} {generate-password|password
<passwd>} [comment <g_comments>][email <email>] [expiry {duration <minutes>|time <hh/
mm/yyy> <hh:mm>}] [guest-company <g_company>][guest-fullname <g_fullname>][guest-phone
<g-phone>][mode disable][opt-field-1 <opt1>][opt-field-2 <opt2>][opt-field-3
<opt3>][opt-field-4 <opt4>][role <role>][sponsor-dept <sp_dept>][sponsor-mail
<sp_email>][sponsor-fullname <sp_fullname>][sponsor-name <sp_name>]
[start-time <mm/dd/yyyy> <hh.mm>]
Description
This command creates a user account entry in the switch’s internal database.
Syntax
Parameter Description Range Default
generate-username Automatically generate and add a username. — —
username Add the specified username. 1 – 64
characters —
generate-password Automatically generate a password for the username. — —
password Add the specified password for the username. 6 – 128
characters —
comments Comments added to the user account. — —
email Email address for the user account. — —
expiry Expiration for the user account. If this is not set, the
account does not expire. —no
expiration
duration Duration, in minutes, for the user account. 1-
2147483647 —
time Date and time, in mm/dd/yyy and hh:mm format, that
the user account expires. ——
guest-company Name of the guest’s company.
NOTE: A guest is the person who needs guest access
to the company’s Alcatel-Lucent wireless network.
guest-fullname The guest’s full name.
guest-phone The guest’s phone number.
mode Enables or disables the user account, — Disable
opt-field-1 This category can be used for some other purpose. For
example, the optional category fields can be used for
another person, such as a “Supervisor.” You can enter
username, full name, department and Email information
into the optional fields.
——
opt-field-2 Same as opt-field-1.——
opt-field-3 Same as opt-field-1.——
opt-field-4 Same as opt-field-1.——
role Role for the user. This role takes effect when the internal
database is specified in a server group profile with a
server derivation rule. If there is no server derivation rule
configured, then the user is assigned the default role for
the authentication method.
—guest

312 | local-userdb add AOS-W 3.4.1 Command Line Interface | Reference Guide
Usage Guidelines
When you specify the internal database as an authentication server, client information is checked against
the user accounts in the internal database. You can modify an existing user account in the internal database
with the local-userdb modify command, or delete an account with the local-userdb del command.
By default, the internal database in the master switch is used for authentication. Issue the aaa
authentication-server internal use-local-switch command to use the internal database in a local
switch; you then need to add user accounts to the internal database in the local switch.
Example
The following command adds a user account in the internal database with an automatically-generated
username and password:
(host) #local-userdb add generate-username generate-password expiry duration 480
The following information is displayed when you enter the command:
GuestConnect
Username: guest4157
Password: cDFD1675
Expiration: 480 minutes
Related Commands
sponsor-dept The guest sponsor’s department name
NOTE: A sponsor is the guest's primary contact for the
visit.
——
sponsor-email The sponsor’s email address. — —
sponsor-fullname The sponsor’s full name. — —
sponsor-name The sponsor’s name. — —
start-time Date and time, in mm/dd/yyy and hh:mm format, the
guest account begins. ——
Parameter Description Range Default
Command Description Mode
show local-userdb Use this command to show the parameters
displayed in the output of this command. Enable and Config modes
show local-userdb-
guest
Use this command to show the parameters
displayed in the output of the local-userdb-
guest add command.
Enable and Config modes
mgmt-user Use the webui-cacert <certificate name>
command if you want an external authentication
server to derive the management user role. This is
helpful if there are a large number of users who need
to be authenticated.
Use the mgmt-user webui-cacert
<certificate_name> serial <number>
<username> <role> command if you want the
authentication process to use previously configured
certificate name and serial number to derive the user
role.
Config mode
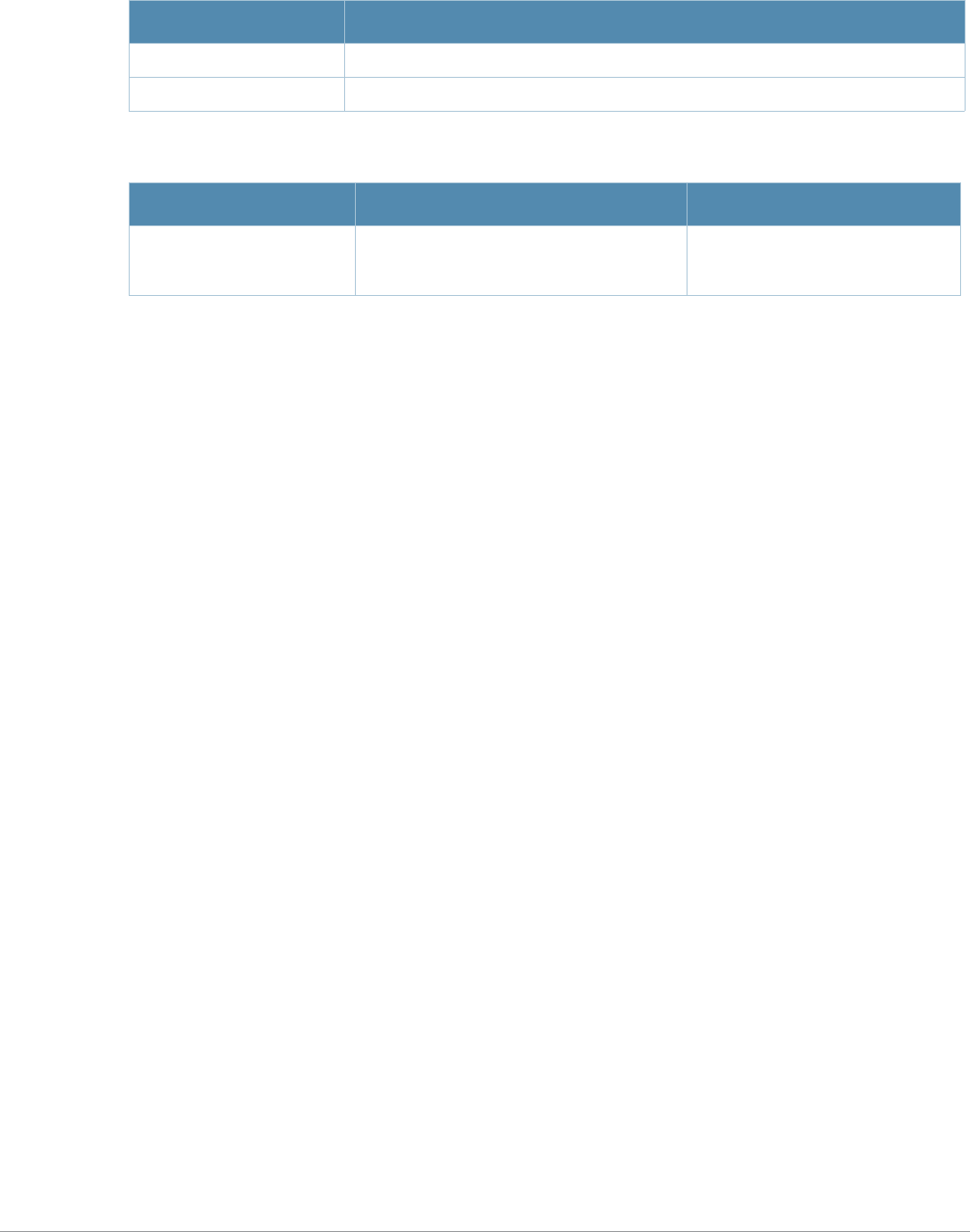
AOS-W 3.4.1 Command Line Interface | Reference Guide local-userdb add | 313
Command History
Command Information
Version Modification
AOS-W 3.0 Introduced for the first time.
AOS-W 3.4 The guest, sponsor and optional field parameters were added.
Platform License Command Mode
Available on all platforms Available in the base operating system. The
role parameter requires the Policy
Enforcement Firewall (PEF) license.
Enable mode on master switches.
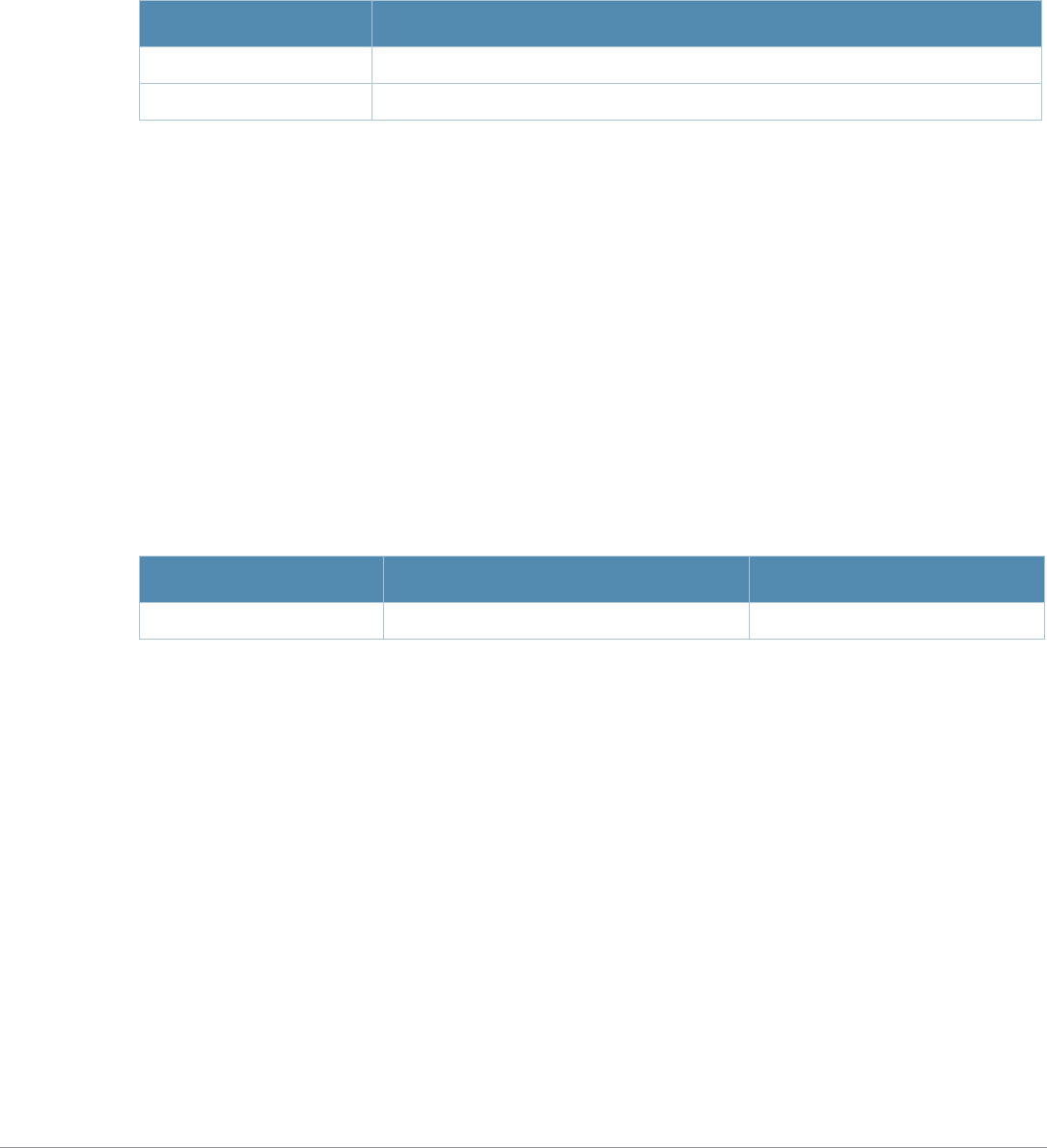
314 | local-userdb del AOS-W 3.4.1 Command Line Interface | Reference Guide
local-userdb del
local-userdb {del username <name>|del-all}
Description
This command deletes entries in the switch’s internal database.
Syntax
Usage Guidelines
User account entries created with expirations are automatically deleted from the internal database at the
specified expiration. Use this command to delete an entry before its expiration or to delete an entry that
was created without an expiration.
Example
The following command deletes a specific user account entry:
(host)#local-userdb del username guest4157
Command History
Introduced in AOS-W 3.0.
Command Information
Parameter Description
del username Deletes the user account for the specified username.
del-all Deletes all entries in the internal database.
Platform License Command Mode
Available on all platforms Available in the base operating system Enable mode on master switches.
AOS-W 3.4.1 Command Line Interface | Reference Guide local-userdb export | 315
local-userdb export
local-userdb export <filename>
Description
This command exports the internal database to a file.
Syntax
Usage Guidelines
After using this command, you can use the copy command to transfer the file from flash to another
location.
Example
The following command saves the internal database to a file:
(host)#local-userdb export jan-userdb
Command History
Introduced in AOS-W 3.0.
Command Information
Use this command with caution. It replaces the existing users with user entries from the imported file.
Parameter Description
export Saves the internal database to the specified file in flash.
Platform License Command Mode
Available on all platforms Available in the base operating system Enable mode on master switches.
316 | local-userdb fix-database AOS-W 3.4.1 Command Line Interface | Reference Guide
local-userdb fix-database
local-userdb fix-database
Description
This command deletes and reinitializes the internal database.
Syntax
No parameters.
Usage Guidelines
Before using this command, you can save the internal database with the local-userdb export command.
Command History
Introduced in AOS-W 3.0.
Command Information
Platform License Command Mode
Available on all platforms Available in the base operating system Enable mode on master switches.

AOS-W 3.4.1 Command Line Interface | Reference Guide local-userdb import | 317
local-userdb import
local-userdb import <filename>
Description
This command replaces the internal database with the specified file from flash.
Syntax
Usage Guidelines
This command replaces the contents of the internal database with the contents in the specified file. The file
must be a valid internal database file saved with the local-userdb export command.
Example
The following command imports the specified file into the internal database:
(host)#local-userdb import jan-userdb
Command History
Introduced in AOS-W 3.0.
Command Information
Parameter Description
import Replaces the internal database with the specified file.
Platform License Command Mode
Available on all platforms Available in the base operating system Enable mode on master switches.

318 | local-userdb maximum-expiration AOS-W 3.4.1 Command Line Interface | Reference Guide
local-userdb maximum-expiration
local-userdb maximum-expiration <minutes>
Description
This command configures the maximum time, in minutes, that a guest account in the internal database can
remain valid.
Syntax
Usage Guidelines
The user in the guest-provisioning role cannot create guest accounts that expire beyond the configured
maximum time. This command is not available to the user in the guest-provisioning role.
Example
The following command sets the maximum time for guest accounts in the internal database to 8 hours (480
minutes):
(host)#local-userdb maximum-expiration 480
Command History
Introduced in AOS-W 3.0.
Command Information
Parameter Description Range
maximum-expiration Maximum time, in minutes, that a guest account in the internal
database can remain valid. 1-2147483647
Platform License Command Mode
Available on all platforms Available in the base operating system Configuration mode on master
switches.
AOS-W 3.4.1 Command Line Interface | Reference Guide local-userdb modify | 319
local-userdb modify
local-userdb modify username <name> [comments <g_comments>][email <email>] [expiry
{duration <minutes>|time <hh/mm/yyy> <hh:mm>}] [guest-company <g_company>][guest-
fullname <g_fullname>][guest-phone <g-phone>][mode disable][opt-field-1 <opt1>][opt-
field-2 <opt2>][opt-field-3 <opt3>][opt-field-4 <opt4>][role <role>][sponsor-dept
<sp_dept>][sponsor-mail <sp_email>][sponsor-fullname <sp_fullname>][sponsor-name
<sp_name>][start-time <mm/dd/yyyy> <hh.mm>]
Description
This command modifies an existing user account entry in the switch’s internal database.
Syntax
Parameter Description Range Default
username Name of the existing user account entry. 1 – 64
characters —
comments Comments added to the user account. — —
email Email address for the use account. — —
expiry Expiration for the user account. If this is not set, the
account does not expire. —no
expiration
duration Duration, in minutes, for the user account. 1-
214748364
7
—
time Date and time, in mm/dd/yyy and hh:mm format, that the
user account expires. ——
guest-company Name of the guest’s company.
NOTE: A guest is the person who needs guest access to
the company’s Alcatel-Lucent wireless network.
guest-fullname The guest’s full name.
guest-phone The guest’s phone number.
mode Enables or disables the user account, — Disable
opt-field-1 This category can be used for some other purpose. For
example, the optional category fields can be used for
another person, such as a “Supervisor.” You can enter
username, full name, department and Email information
into the optional fields.
——
opt-field-2 Same as opt-field-1.——
opt-field-3 Same as opt-field-1.——
opt-field-4 Same as opt-field-1.——
role Role for the user.
The Policy Enforcement Firewall license must be installed
—guest
sponsor-dept The guest sponsor’s department name
NOTE: A sponsor is the guest's primary contact for the
visit.
——
sponsor-email The sponsor’s email address. — —
sponsor-fullname The sponsor’s full name. — —
sponsor-name The sponsor’s name. — —

320 | local-userdb modify AOS-W 3.4.1 Command Line Interface | Reference Guide
Usage Guidelines
Use the show local-userdb command to view the current user account entries in the internal database.
Example
The following command disables an existing user account in the internal database:
(host)# local-userdb modify username guest4157 mode disable
Command History
Command Information
start-time Date and time, in mm/dd/yyy and hh:mm format, the
guest account begins. ——
Parameter Description Range Default
Version Modification
AOS-W 3.0 Introduced for the first time.
AOS-W 3.4 The guest, sponsor and optional parameters were added.
Platform License Command Mode
Available on all platforms Available in the base operating system Enable mode on master switches.
AOS-W 3.4.1 Command Line Interface | Reference Guide local-userdb send-to-guest | 321
local-userdb send-to-guest
local-userdb send-to-guest
Description
This command automatically sends email to the guest when the guest user is created.
Syntax
No parameters.
Usage Guidelines
A guest is the person who needs guest access to the company’s Alcatel-Lucent wireless network. Email is
sent directly to the guest after the guest user is created. When configuring the guest provisioning feature,
the guest user is generally created by Guest Provisioning user. This is the person who is responsible for
signing in guests at your company.
\Example
(host)(config) #local-userdb send-to-guest
Command History
Introduced in AOS-W 3.4.
Command Information
Platform License Command Mode
Available on all platforms Available in the base operating system Configuration mode on master
switches.
322 | local-userdb send-to-sponsor AOS-W 3.4.1 Command Line Interface | Reference Guide
local-userdb send-to-sponsor
local-userdb send-to-sponsor
Description
This command automatically sends email to the guest’s sponsor when the guest user is created.
Syntax
No parameters.
Usage Guidelines
The sponsor is the guest's primary contact. Email is sent directly to the guest’s sponsor after the guest user
is created. When configuring the guest provisioning feature, the sponsor is generally created by the Guest
Provisioning user. This is the person who responsible for signing in guests at your company.
Example
(host)(config)#local-userdb send-to-sponsor
Command History
Introduced in AOS-W 3.4.
Command Information
Platform License Command Mode
Available on all platforms Available in the base operating system Configuration mode on master
switches.

AOS-W 3.4.1 Command Line Interface | Reference Guide local-userdb-guest add | 323
local-userdb-guest add
local-userdb-guest
local-userdb-guest add {generate-username|username <name>} {generate-password|password
<passwd>} [comment <g_comments>][email <email>] [expiry {duration <minutes>|time <hh/
mm/yyy> <hh:mm>}] [guest-company <g_company>][guest-fullname <g_fullname>][guest-phone
<g-phone>][mode disable][opt-field-1 <opt1>][opt-field-2 <opt2>][opt-field-3
<opt3>][opt-field-4 <opt4>][sponsor-dept <sp_dept>][sponsor-mail <sp_email>][sponsor-
fullname <sp_fullname>][sponsor-name <sp_name>]
[start-time <mm/dd/yyyy> <hh.mm>]
Description
This command creates a guest user in a local user database.
Syntax
Parameter Description Range Default
generate-username Automatically generate and add a guest username. — —
username Add the specified guest username. 1 – 64
characters —
generate-password Automatically generate a password for the username. — —
password Add the specified password for the username. 6 – 128
characters —
comments Comments added to the guest user account. — —
email Email address for the guest user account. — —
expiry Expiration for the user account. If this is not set, the
account does not expire. —no
expiration
duration Duration, in minutes, for the user account. 1-
2147483647 —
time Date and time, in mm/dd/yyy and hh:mm format, that
the user account expires. ——
guest-company Name of the guest’s company.
NOTE: A guest is the person who needs guest access
to the company’s Alcatel-Lucent wireless network.
guest-fullname The guest’s full name.
guest-phone The guest’s phone number.
mode Enables or disables the user account, — Disable
opt-field-1 This category can be used for some other purpose. For
example, the optional category fields can be used for
another person, such as a “Supervisor.” You can enter
username, full name, department and Email information
into the optional fields.
——
opt-field-2 Same as opt-field-1.——
opt-field-3 Same as opt-field-1.——
opt-field-4 Same as opt-field-1.——
sponsor-dept The guest sponsor’s department name.
NOTE: A sponsor is the guest's primary contact for the
visit.
——
sponsor-email The sponsor’s email address. — —
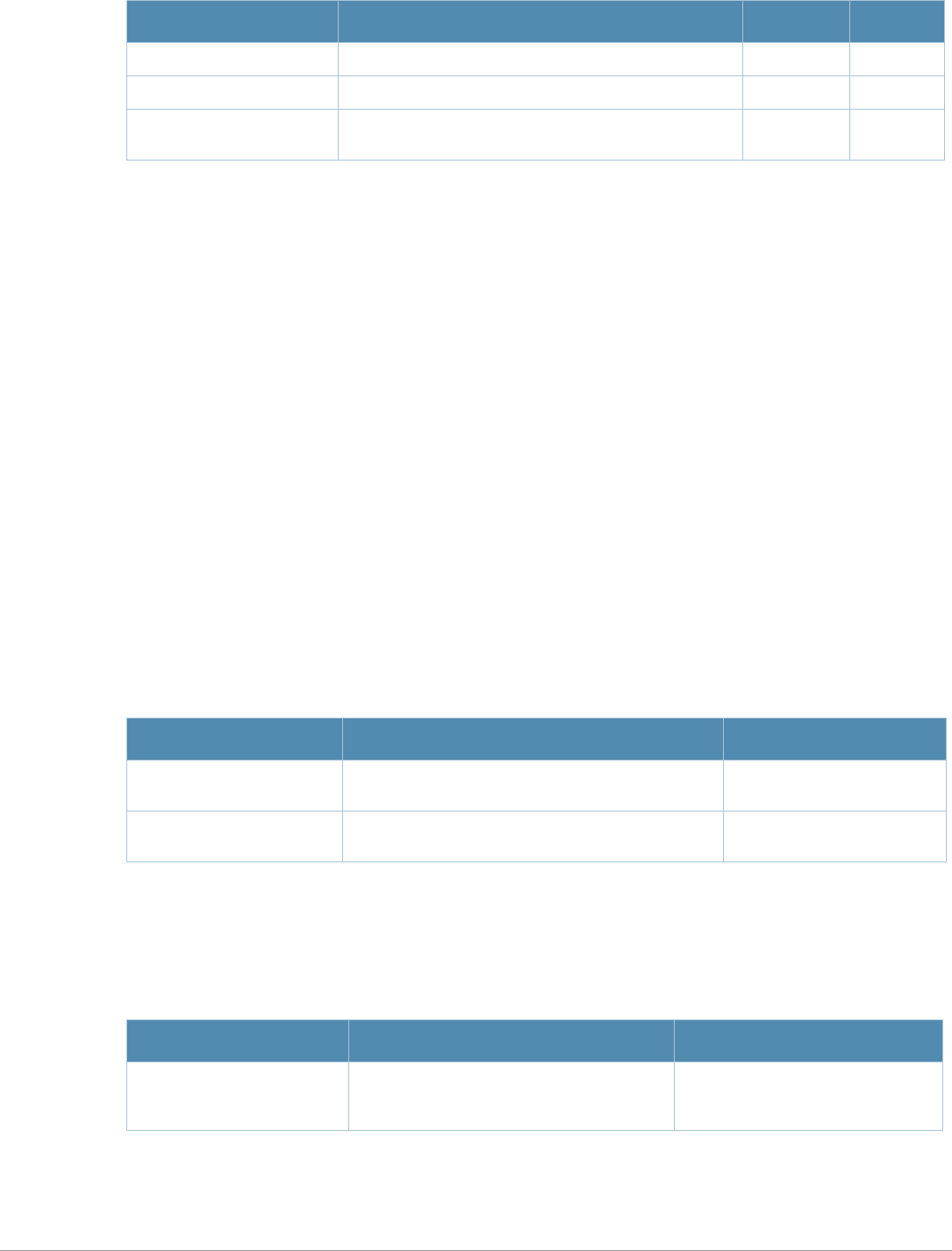
324 | local-userdb-guest add AOS-W 3.4.1 Command Line Interface | Reference Guide
Usage Guidelines
When you specify the internal database as an authentication server, client information is checked against
the user accounts in the internal database. You can modify an existing user account in the internal database
with the local-userdb-guest modify command, or delete an account with the local-userdb-guest del
command.
By default, the internal database in the master switch is used for authentication. Issue the aaa
authentication-server internal use-local-switch command to use the internal database in a local
switch; you then need to add user accounts to the internal database in the local switch.
Example
The following command adds a guest user in the internal database with an automatically-generated
username and password:
(host) #local-userdb-guest add generate-username generate-password expiry none
The following information is displayed when you enter the command:
GuestConnect
Username: guest-5433352
Password: mBgJ6764
Expiration: none
Related Commands
Command History
Introduced in AOS-W 3.4.
Command Information
sponsor-fullname The sponsor’s full name. — —
sponsor-name The sponsor’s name. — —
start-time Date and time, in mm/dd/yyy and hh:mm format, the
guest account begins. ——
Parameter Description Range Default
Command Description Mode
show local-userdb-
guest
Use this command to show the parameters
displayed in the output of this command.
Enable and Config modes
show local-userdb Use this command to show the parameters
displayed in the local-userdb command. Enable and Config modes
Platform License Command Mode
Available on all platforms Available in the base operating system. The
role parameter requires the Policy
Enforcement Firewall (PEF) license.
Enable and config modes on master
switches.

AOS-W 3.4.1 Command Line Interface | Reference Guide local-userdb-guest del | 325
local-userdb-guest del
local-userdb-guest {del username <name>|del-all}
Description
This command deletes entries in the switch’s internal database.
Syntax
Usage Guidelines
User account entries created with expirations are automatically deleted from the internal database at the
specified expiration. Use this command to delete an entry before its expiration or to delete an entry that
was created without an expiration.
Example
The following command deletes a specific user account entry:
(host) #local-userdb-guest del username guest4157
Command History
Introduced in AOS-W 3.4.
Command Information
Parameter Description
del username Deletes the user account for the specified username.
del-all Deletes all entries in the internal database.
Platform License Command Mode
Available on all platforms Available in the base operating system Enable and config modes on master
switches.
326 | local-userdb-guest modify AOS-W 3.4.1 Command Line Interface | Reference Guide
local-userdb-guest modify
local-userd-guest modify username <name> [comments <g_comments>][email <email>] [expiry
{duration <minutes>|time <hh/mm/yyy> <hh:mm>}] [guest-company <g_company>][guest-
fullname <g_fullname>][guest-phone <g-phone>][mode disable][opt-field-1 <opt1>][opt-
field-2 <opt2>][opt-field-3 <opt3>][opt-field-4 <opt4>][password <passwd][sponsor-dept
<sp_dept>][sponsor-mail <sp_email>][sponsor-fullname <sp_fullname>][sponsor-name
<sp_name>][start-time <mm/dd/yyyy> <hh.mm>]
Description
This command modifies an existing guest user entry in the switch’s internal database.
Syntax
Parameter Description Range Default
username Name of the existing user account entry. 1 – 64
characters —
comments Comments added to the user account. — —
email Email address for the use account. — —
expiry Expiration for the user account. If this is not set, the
account does not expire. —no
expiration
duration Duration, in minutes, for the user account. 1-
214748364
7
—
time Date and time, in mm/dd/yyy and hh:mm format, that the
user account expires. ——
guest-company Name of the guest’s company.
NOTE: A guest is the person who needs guest access to
the company’s Alcatel-Lucent wireless network.
guest-fullname The guest’s full name.
guest-phone The guest’s phone number.
mode Enables or disables the user account, — Disable
opt-field-1 This category can be used for some other purpose. For
example, the optional category fields can be used for
another person, such as a “Supervisor.” You can enter
username, full name, department and Email information
into the optional fields.
——
opt-field-2 Same as opt-field-1.——
opt-field-3 Same as opt-field-1.——
opt-field-4 Same as opt-field-1.——
password User’s password 1– 6
characters —
sponsor-dept The guest sponsor’s department name
NOTE: A sponsor is the guest's primary contact for the
visit.
——
sponsor-email The sponsor’s email address. — —
sponsor-fullname The sponsor’s full name. — —
sponsor-name The sponsor’s name. — —
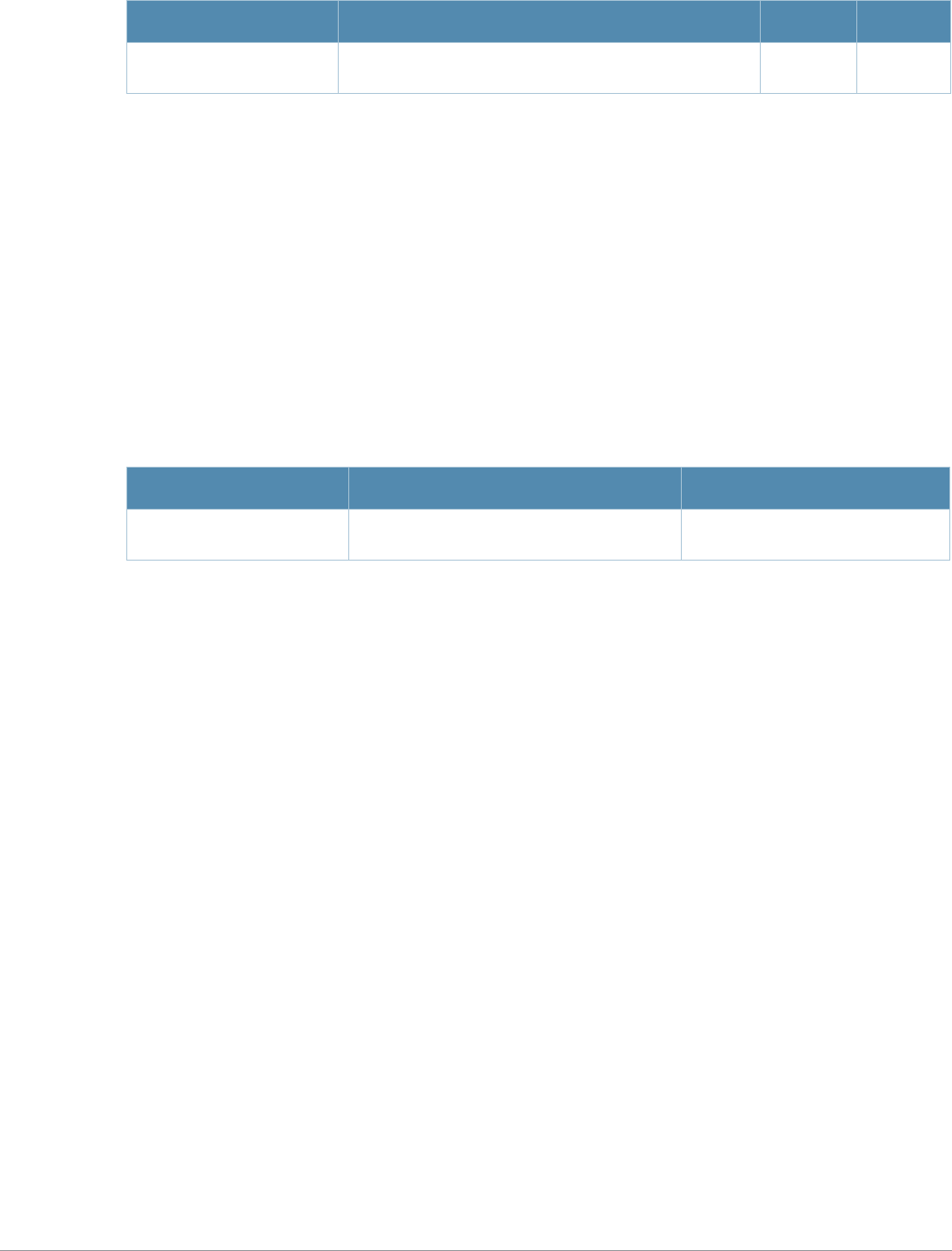
AOS-W 3.4.1 Command Line Interface | Reference Guide local-userdb-guest modify | 327
Usage Guidelines
Use the show local-userdb-guest command to view the current user account entries in the internal
database.
Example
The following command disables an guest user account in the internal database:
(host)local-userdb-guest modify username guest4157 mode disable
Command History
Introduced in AOS-W 3.4.
Command Information
start-time Date and time, in mm/dd/yyy and hh:mm format, the
guest account begins. ——
Parameter Description Range Default
Platform License Command Mode
Available on all platforms Available in the base operating system Enable and config modes on master
switches.
328 | local-userdb-guest send-email AOS-W 3.4.1 Command Line Interface | Reference Guide
local-userdb-guest send-email
local-userdb-guest send-email <username> [to-guest][to-sponsor]
Description
This command causes the switch to send email to the guest and/or sponsor any time a guest user is created.
Syntax
Usage Guidelines
This command allows the guest provisioning user or network administrator to causes the switch to send
email to the guest and/or sponsor any time a guest user is created.
Example
The following command causes the switch to send an email to the sponsor alerting them that the guest user
“Laura” was just created.
(host)# local-userdb-guest send-email Laura to-sponsor
Command History
Introduced in AOS-W 3.4.
Command Information
Parameter Description Range Default
<username> Name of the guest 1 – 64
characters —
to-guest Allows you to send email to the guest user’s address. — —
to-sponsor Allows you to send email to the sponsor’s email address. — —
Platform License Command Mode
Available on all platforms Available in the base operating system Enable mode on master switches
AOS-W 3.4.1 Command Line Interface | Reference Guide location | 329
location
location <string>
Description
This command configures the location of the switch.
Syntax
Usage Guidelines
Use this command to indicate the location of the switch. You can use a combination of numbers, letters,
characters, and spaces to create the name. To include a space in the name, use quotation marks to enclose
the text string.
To change the existing name, enter the command with a different string. To unconfigure the location, enter
“” at the prompt.
Example
The following command configures the location:
(host) (config) #location “Building 10, second floor, room 21E”
Command History
Introduced in AOS-W 3.0
Command Information
Parameter Description
location A text string that specifies the system location.
Platform License Command Mode
Available on all platforms Available in the base operating system Config mode on master switches

330 |location AOS-W 3.4.1 Command Line Interface | Reference Guide

AOS-W 3.4.1 Command Line Interface | Reference Guide logging | 331
logging
logging <ipaddr>
[ap-debug <facility>] |
[bssid-debug <facility>] |
[essid-debug <facility>] |
[network <facility>] |
[security <facility>] |
[system <facility>] |
[user <facility>] |
[user-debug <facility>] |
[wireless <facility>] |
Description
Use this command to specify the IP address of the remote logging server, as well as facility log types and
their associated facility levels.
Syntax
Usage Guidelines
The local use facilities (local0, local1, local2, local3, local4, local5, local6, and local7) are not reserved for
specific message-generating sources, and can be used for sending syslog messages. Use the show logging
command to verify that the device sends logging messages.
Example
The following command adds the remote logging server with the IP address 10.1.2.3 with a user log type
using local4.
(host) (config) #logging 10.1.2.3 user local4
Command History
Introduced in AOS-W 2.5
Parameter Description Range Default
ap-debug <facility> AP debug logs. local0 to local7 local1
bssid-debug <facility> Bssid debug logs. local0 to local7 local1
essid-debug <facility> Essid debug logs. local0 to local7 local1
network <facility> Network logs. local0 to local7 local1
security <facility> Security logs. local0 to local7 local1
system <facility> System logs. local0 to local7 local1
user <facility> User logs. local0 to local7 local1
user-debug <facility> User debug logs. local0 to local7 local1
wireless <facility> Wireless logs. local0 to local7 local1

332 | logging AOS-W 3.4.1 Command Line Interface | Reference Guide
Command Information
Platform License Command Mode
Available on all platforms Available in the base operating system Config mode on master switches
AOS-W 3.4.1 Command Line Interface | Reference Guide logging facility | 333
logging facility
logging facility <facility>
Description
Use this command to set the facility to use when logging to the remote syslog server.
Syntax
Usage Guidelines
The local use facilities (local0, local1, local2, local3, local4, local5, local6, and local7) are not reserved for
specific message-generating sources, and can be used for sending syslog messages.
Example
The following command sets the facility to local4.
(host) (config) #logging facility local4
Command History
Introduced in AOS-W 2.5
Command Information
Parameter Description Range
<facility> The facility to use when logging to a remote syslog server. local0 to local7
Platform License Command Mode
Available on all platforms Available in the base operating system Config mode on master switches

334 | logging level AOS-W 3.4.1 Command Line Interface | Reference Guide
logging level
logging level <level> <category> [process <process>] [subcat <subcategory>]
Description
Use this command to set the categories or subcategories and the severity levels of messages that are logged.
Syntax
Parameter Description
<level> The message severity level, which can be one of the following (in order of severity level):
emergencies (0) Panic conditions that occur when the system becomes unstable.
alerts (1) Any condition requiring immediate attention and correction.
critical (2) Any critical conditions, such as hard drive errors.
errors (3) Error conditions.
warnings (4) Warning messages.
notifications (5) Significant events of a non-critical and normal nature.
informational (6) Messages of general interest to system users.
debugging (7) Messages containing information for debugging purposes.
<category> Message category, which can be one of the following:
ap-debug AP troubleshooting messages. You must specify a debug value.
network Network messages.
security Security messages.
system System messages.
user User messages.
user-debug User troubleshooting messages. You must specify a MAC address.
wireless Wireless messages.
process Switch process, which can be one of the following:
aaa AAA logging
ads Anomaly detection
approc AP processes
authmgr User authentication
cfgm Configuration Manager
crypto VPN (IKE/IPsec)
cts Transport service
dbsync Database synchronization
dhcpd DHCP packets
esi External Services Interface
fpapps Layer 2 and 3 control

AOS-W 3.4.1 Command Line Interface | Reference Guide logging level | 335
Usage Guidelines
There are eight logging severity levels, each with its associated types of messages. Each level also includes
the levels below it. For example, if you set the logging level to informational (6), all messages from level 0
through level 5 (from emergencies through notifications) are also logged. The warnings severity level is set
by default for all message categories and subcategories.
Example
The following command logs critical system messages.
logging level critical system
httpd Apache
l2tp L2TP
licensemgr License manager
localdb Local database
mobileip Mobile IP
packetfilter Packet filtering of messaging and control frames
phonehome PhoneHome
pim Protocol Independent Multicast
pppoed PPPoE
pptp PPTP
processes Run-time processes
profmgr Profile Manager
publisher Publish subscribe service
rfm RF Troubleshooting Manager
snmp SNMP
stm Station management
syslogdwrap Syslogd wrap
traffic Traffic
vrrpd VRRP
wms Wireless management (master switch only)
subcat Message subcategory, which depends upon the message category specified. The
following lists the subcategories available for each message category:
zap-debug: all
znetwork: all, dhcp, mobility, packet-dump
zsecurity: aaa, all, dot1x, firewall, ike, mobility, packet-trace, vpn, webserver
zsystem: all, configuration, messages, snmp, webserver
zuser: all, captive-portal, dot1x, radius, vpn
zuser-debug: all, configuration
zwireless: all
Parameter Description

336 | logging level AOS-W 3.4.1 Command Line Interface | Reference Guide
Command History
Introduced in AOS-W 2.5
Command Information
Platform License Command Mode
Available on all platforms Available in the base operating system Config mode on master and local
switches
AOS-W 3.4.1 Command Line Interface | Reference Guide loginsession | 337
loginsession
loginsession timeout <minutes>
Description
This command configures the time a management session (via Telnet or SSH) remains active without user
activity.
Syntax
Usage Guidelines
The management user must re-login to the switch after a Telnet or SSH session times out. If you set the
timeout value to 0, sessions do not time out.
Example
The following command configures management sessions on the switch to not time out:
(host) (config) #loginsession timeout 0
Command History
This command was available in AOS-W 3.0.
Command Information
Parameter Description Range Default
timeout Number of minutes that a management session remains active
without any user activity. 5-60, 0 to
disable 15 minutes
The TCP session timeout for wireless and wired user sessions through the switch is 15 minutes; this timeout for
user sessions is not configurable.
Platform License Command Mode
Available on all platforms Requires the Policy Enforcement Firewall license Config mode on master
switches

338 | loginsession AOS-W 3.4.1 Command Line Interface | Reference Guide

AOS-W 3.4.1 Command Line Interface | Reference Guide logout | 339
logout
logout
Description
This command exits the current CLI session.
Syntax
No parameters.
Usage Guidelines
Use this command to leave the current CLI session and return to the user login.
Example
The following command exits the CLI session:
(host) >logout
User:
Command History
This command was available in AOS-W 3.0.
Command Information
Platforms Licensing Command Mode
All platforms Base operating system User mode on local or master switches

340 | logout AOS-W 3.4.1 Command Line Interface | Reference Guide
AOS-W 3.4.1 Command Line Interface | Reference Guide mac-address-table | 341
mac-address-table
mac-address-table static <macaddr> {fastethernet|gigabitethernet} <slot>/<port> vlan
<vlan>
Description
This command adds a static entry to the MAC address table.
Syntax
Usage Guidelines
The MAC address table is used to forward traffic between ports on the switch. The table includes addresses
learned by the switch. This command allows you to manually enter static addresses that are bound to
specific ports and VLANs.
Example
The following command configures a MAC address table entry:
(host) (config) #mac-address-table static 00:0b:86:f0:05:60 fastethernet 1/12 vlan 22
Command History
Available in AOS-W 3.0
Command Information
Parameter Description Range
<macaddr> Media Access Control (MAC) address, in the format xx:xx:xx:xx:xx:xx. —
<slot> <slot> is always 1 except for the OmniAccess 6000 Switch, where the
slots can be 1, 2, or 3. —
<port> Number assigned to the network interface embedded in the switch or in
the line card installed in the OmniAccess 6000 Switch. Port numbers
start at 0 from the left-most position.
vlan ID number of the VLAN. 1-4094
Platform License Command Mode
Available on all platforms Available in the base operating
system Config mode on master and local switches

342 | mac-address-table AOS-W 3.4.1 Command Line Interface | Reference Guide
AOS-W 3.4.1 Command Line Interface | Reference Guide masterip | 343
masterip
masterip <ipaddr> ipsec <key> [fqdn <fqdn>][uplink][vlan <id>]
Description
This command configures the IP address and preshared key for the master switch on a local switch.
Syntax
Usage Guidelines
Use this command on a local switch to configure the IP address and preshared key for communication with
the master switch. On the master switch, use the localip command to configure the IP address and
preshared key for a local switch.
Example
The following command configures the master switch on a local switch:
(host) (config) #masterip 10.1.1.250 ipsec gw1234567
Command History
Available in AOS-W 3.0
Command Information
Parameter Description
<ipaddr> IP address of the master switch.
ipsec <key> Preshared key, which must be between 6-64 characters.
fqdn <fqdn> The local switch’s Fully Qualified Domain Name (FQDN) used in IKE.
uplink Use the current active uplink to initiate IKE.
vlan <id> Vlan interface to initiate IKE. The switch IP address will be used if the VLAN is not specified.
Changing the IP address of the master on a local switch requires a reboot of the local switch
Platform License Command Mode
Available on all platforms Available in the base operating
system Available in Config mode on master and local
switches

344 |masterip AOS-W 3.4.1 Command Line Interface | Reference Guide

AOS-W 3.4.1 Command Line Interface | Reference Guide master-redundancy | 345
master-redundancy
master-redundancy
master-vrrp <id>
no ...
peer-ip-address <ipaddr> ipsec <key>
Description
This command associates a VRRP instance with master switch redundancy.
Syntax
Usage Guidelines
To maintain a highly redundant network, you can use a switch as a standby for the master switch. The
underlying protocol used is VRRP which you configure using the vrrp command.
Example
The following command configures VRRP for the initially preferred master switch:
(host) (config) #vrrp 22
vlan 22
ip address 10.200.22.254
priority 110
preempt
description Preferred-Master
tracking master-up-time 30 add 20
no shutdown
master-redundancy
master-vrrp 22
peer-ip-address 192.168.2.1 ipsec qwerTY012
The following shows the corresponding VRRP configuration for the peer switch.
(host) (config) #vrrp 22
vlan 22
ip address 10.200.22.254
priority 100
preempt
description Backup-Master
tracking master-up-time 30 add 20
no shutdown
master-redundancy
master-vrrp 22
peer-ip-address 192.168.22.1 ipsec qwerTY012
Parameter Description Range
master-vrrp The virtual router ID for the VRRP instance configured
with the vrrp command. 1-255
no Negates any configured parameter. —
peer-ip-address IP address of the peer switch for master redundancy. —
ipsec Preshared key used to secure communications
between the master switches. Specify a key of up to
64 bytes in length.
—

346 | master-redundancy AOS-W 3.4.1 Command Line Interface | Reference Guide
Command History
This command was introduced in AOS-W 3.0.
Command Information
Platforms Licensing Command Mode
All platforms Base operating system Config mode on master switches
AOS-W 3.4.1 Command Line Interface | Reference Guide mgmt-server | 347
mgmt-server
wlan
mgmt-server type {amp|other} primary-server <ip-addr> secondary-server <ip-addr>
Description
Register a management server with the switch by specifying the IP address of an AirWave Management
Server or any other server that should receive messages from the switch using the Application Monitoring
(AMON) protocol.
Syntax
Example
The following command defines a primary and secondary Airwave Management server.
(host) (config) #mgmt-server type amp primary-server 192.168.6.2 secondary-
server 192.168.14.38
Command History
This command was introduced in AOS-W 3.4.
Command Information
Parameter Description
amp Define an AirWave Management Server.
other
Define any other type of management server.
primary-server <ip-addr> IP address of the primary management server.
secondary-server <ip-addr> IP address of the secondary management server.
Platforms Licensing Command Mode
All platforms Base operating system. Config mode on master switches

348 |mgmt-server AOS-W 3.4.1 Command Line Interface | Reference Guide

AOS-W 3.4.1 Command Line Interface | Reference Guide mgmt-user | 349
mgmt-user
mgmt-user <username> <role> <password>
mgmt-user localauth-disable
mgmt-user ssh-pubkey client-cert <certificate> <username> <role>
mgmt-user webui-cacert <certificate_name> serial <number> <username> <role>
Description
This command configures an administrative user.
Syntax
Parameter Description Default
<username> Name of the user.
You can create a maximum of 10 management users.
NOTE: If you configure a root management user, you can use
special characters except for double-byte characters.
—
<role> Role assigned to the user. Predefined roles include:
zguest-provisioning: Allows the user to create guest accounts on
a special WebUI page.
zlocation-api-mgmt: Permits access to location API information.
You can log into the CLI; however, you cannot use any CLI
commands.
znetwork-operations: Permits access to Monitoring, Reports,
and Events pages in the WebUI. You can log into the CLI;
however, you can only use a subset of CLI commands to
monitor the switch.
zread-only: Permits access to CLI show commands or WebUI
monitoring pages only.
zroot: Permits access to all management functions on the
switch.
—
<password> NOTE: You are prompted for the <password> for this user after you
type in <role> and press Enter.
The password must have a minimum of six characters.
You can use special characters in the management user password.
The restrictions are as follows:
zYou cannot use double-byte characters
zYou cannot use the question mark (?)
zYou cannot use white space <space >
—
localauth-disable Disables authentication of management users based on the results
returned by the authentication server.
To cancel this setting, use the no form of the command:
no mgmt-user localauth-disable
To verify if authentication of local management user accounts is
enabled or disabled, use the following command:
show mgmt-user local-authentication-mode
Enabled
ssh-pubkey Configures certificate authentication of administrative users using
the CLI through SSH. —
client-cert Name of the X.509 client certificate for authenticating
administrative users using SSH. —
<username> Name of the user. —
<role> Role assigned to the authenticated user. —
webui-cacert The client certificate for authenticating administrative users using
the WebUI. —
350 |mgmt-user AOS-W 3.4.1 Command Line Interface | Reference Guide
Usage Guidelines
You can configure client certificate authentication of WebUI or SSH management users (by default, only
username/password is used). To configure certificate authentication for the WebUI or SSH, use the web-
server mgmt-auth certificate or ssh mgmt-auth public-key commands, respectively.
Use webui-cacert <certificate name> command if you want an external authentication server to derive
the management user role. This is helpful if there are a large number of users who need to be authenticated.
Or, use the if the mgmt-user webui-cacert <certificate_name> serial <number> <username> <role>
if you want the authentication process to use previously configured certificate name and serial number to
derive the user role.
Example
See the web-server and ssh command descriptions for examples of certificate and public key
authentication. The following command configures a management user and role:
(host) (config) #mgmt-user kgreen root
Password: *****
Re-Type password: *****
Command History
Command Information
<certificate_name> The CA certificate. If configured, certificate authentication and
authorization are automatically completed using an authentication
server.
—
serial Serial number of the client certificate. —
<username> Name of the user. —
<role> Role assigned to the authenticated user. —
Parameter Description Default
Release Modification
AOS-W 3.0 Command introduced
AOS-W 3.1 The ssh-pubkey and webui-cacert parameters were introduced.
AOS-W 3.2 The network-operations role was introduced.
AOS-W 3.3 The location-api-mgmt role and localauth-disable parameters were introduced.
AOS-W 3.4 The webui-cacert <certificate name> parameter had additional functionality
introduced.
Platforms Licensing Command Mode
All platforms Base operating system Config mode on master switches
AOS-W 3.4.1 Command Line Interface | Reference Guide mobility-manager | 351
mobility-manager
mobility-manager <ipaddr> user <username> <password> [interval <secs>]
[retrycount <number>] [udp-port <port>] [rtls <rtls-udp-port>] trap-version {1|2c|3}
Description
This command allows the switch to communicate with an OmniVista Mobility Manager server.
Syntax
Usage Guidelines
This command needs to be configured before the switch can communicate with the OmniVista Mobility
Manager server. This command performs three tasks:
zConfigures the IP address of the OmniVista Mobility Manager server. In previous AOS-W releases, this was
done with the mobility-server command.
zCreates an SNMP version 3 user profile with the configured <username> and <password>. This allows
SNMP SETs from the OmniVista Mobility Manager server to be received by the switch. The authentication
protocol is Secure Hash Algorithm (SHA) and Data Encryption Standard (DES) is used for encryption. If
<username> and <password> match an existing SNMP v3 user profile, the existing one is used. Otherwise, a
new profile is created.
This username and password must be used when adding this switch to the OmniVista Mobility Manager
server in the OmniVista Mobility Manager Dashboard.
zAllows SNMP traps and notifications to be sent to the OmniVista Mobility Manager server IP address, by
adding this OmniVista Mobility Manager server as a trap receiver.
zOptionally enables the OmniVista Mobility Manager server to function as a Real Time Location System
(RTLS) server to receive location information via APs from RTLS tags or other devices.
Use the show mobility-manager command to check the current status of the configured OmniVista Mobility
Manager servers.
Example
The following command configures the IP address and SNMP user profile for the OmniVista Mobility Manager
server:
(host) (config)# mobility-manager 10.2.1.245 user mms-user my-password.
Parameter Description Range Default
<ipaddr> IP address of the OmniVista Mobility Manager server. — —
user Name and SNMP password for the OmniVista
Mobility Manager server user. ——
interval Round-trip time, in seconds, to trap server. 1-65535 60 seconds
retrycount Number of retries to the OmniVista Mobility Manager
server before giving up. 1-65535 3
udp-port UDP port number for trap server. 0-65535 162
rtls UDP port number on which RSSI location data
should be received from APs. 0-65535 8000
trap-version Allows the you to specify the SNMP trap version by
the remote trap receiver. 1, 2c, or 3 3

352 | mobility-manager AOS-W 3.4.1 Command Line Interface | Reference Guide
Command History
This command was introduced in AOS-W 3.1.
Command Information
Platforms Licensing Command Mode
All platforms Base operating system Config mode on master switches
AOS-W 3.4.1 Command Line Interface | Reference Guide netdestination | 353
netdestination
netdestination <name>
host <ipaddr> [position <number>] |
invert |
network <ipaddr> <netmask> [position <number>] |
no ... |
range <start-ipaddr> <end-ipaddr> [position <number>]
Description
This command configures an alias for a network host, subnetwork, or range of addresses.
Syntax
Usage Guidelines
Aliases can simplify configuration of session ACLs, as you can use an alias when specifying the traffic
source and/or destination. Once you configure an alias, you can use it in multiple session ACLs.
Example
The following command configures an alias for an internal network:
(host) (config) #netdestination Internal
network 10.1.0.0 255.255.0.0
Command History
This command was introduced in AOS-W 3.0.
Command Information
Parameter Description Default
<name> Name for this alias. —
host Configure a single host —
invert Specifies that the inverse of the network addresses configured are used. For
example, if a network of 172.16.0.0 255.255.0.0 is configured, this parameter
specifies that the alias matches everything except this subnetwork.
—
network An IP subnetwork consisting of an IP address and netmask. —
no Negates any configured parameter. —
position Specifies the position of this network specification relative to other specifications (1 is
first, default is the last position). To view current position settings for network
destinations, use the command show netdestination network.
(last)
range A range of IP addresses consisting of sequential addresses between a lower and an
upper value. The maximum number of addresses in the range is 16. If larger ranges
are needed, convert the range into a subnetwork and use the network parameter.
—
Platforms Licensing Command Mode
All platforms Requires the Policy Enforcement
Firewall license. Config mode on master switches

354 | netdestination AOS-W 3.4.1 Command Line Interface | Reference Guide
AOS-W 3.4.1 Command Line Interface | Reference Guide netservice | 355
netservice
netservice <name> {<protocol> | tcp <port> [<port>] | udp <port> [<port>]}
[ALG <service>]
Description
This command configures an alias for network protocols.
Syntax
Usage Guidelines
Aliases can simplify configuration of session ACLs, as you can use an alias when specifying the network
service. Once you configure an alias, you can use it in multiple session ACLs.
Example
The following command configures an alias for a network service:
(host) (config) #netservice HTTP tcp 80
Command History
This command was introduced in AOS-W 3.0.
Parameter Description Range
netservice Name for this alias. —
<protocol> IP protocol number. 0-255
tcp Configure an alias for a TCP protocol
<port> TCP port number. You can specify a single port number, or define a
port range by specifying both the lower and upper port numbers. 0-65535
UDP Configure an alias for a UDP protocol
<port> UDP port number. You can specify a single port number, or define a
port range by specifying both the lower and upper port numbers. 0-65535
ALG Application-level gateway (ALG) for this alias. —
<service> Specify one of the following service types:
zdhcp: Service is DHCP
zdns: Service is DNS
zftp: Service is FTP
zh323: Service is H323
znoe: Service is Alcatel NOE
zrtsp: Service is RTSP
zsccp: Service is SCCP
zsip: Service is SIP
zsips: Service is Secure SIP
zsvp: Service is SVP
ztftp: Service is TFTP
zvocera: Service is VOCERA

356 |netservice AOS-W 3.4.1 Command Line Interface | Reference Guide
Command Information
Platforms Licensing Command Mode
All platforms Base operating system Config mode on master switches
AOS-W 3.4.1 Command Line Interface | Reference Guide network-printer | 357
network-printer
network-printer [max-clients <2-20> |
max-clients-per-host <1-20> |
max-jobs <1-1000>]
Description
This command allows you to configure client and print job for the USB printer connected to a OmniAccess
4306 series switch.
Syntax
Usage Guidelines
Use this command in the config mode.
In the enable mode, you can use the network-printer delete <printer-name> job <job-id>
command to delete print jobs in specific printer.
Command History
This command was introduced in AOS-W 3.4.
Command Information
Parameter Description
max-clients Specify the maximum number of clients that can use the printer. Currently, the
OmniAccess 4306 series supports a maximum of 20 concurrent clients.
max-clients-per-host Specify the maximum number of concurrent clients for a single host. Currently, the
OmniAccess 4306 series supports a maximum of 20 concurrent clients.
max-jobs Specify the maximum number of jobs that can be saved in the memory Currently, the
OmniAccess 4306 series switch will support a storage of 1000 jobs.
Platforms Licensing Command Mode
OmniAccess 4306 series Base operating system Config or enable mode.

358 | network-printer AOS-W 3.4.1 Command Line Interface | Reference Guide

AOS-W 3.4.1 Command Line Interface | Reference Guide network-storage | 359
network-storage
network-storage [share <share-name> ]
share [usb: disk <disk-name> <filesystem-path> mode {read-only | read-write}
no share
Description
This command allows you to perform the following operation on a network share:
zConfigure a file system path for the share–This allows users to access the share from their computer.
zRemove the share access using the no share command.
Syntax
Usage Guidelines
To access the share, you must create a filesystem path to the share. enter:
(host) (config-network-storage share)# share usb: disk <disk name> <filesystem path>
mode
Where,
disk name is the name of the disk. You can also specify the disk alias instead of the disk name.
filesystem path is the path to access the share. This path contains the partition name and the shared
folder name.
mode is the permission settings. You can either specify read-only or read-write modes.
Example
The following command associates a share to a file system path and configures the access mode.
Command History
This command was introduced in AOS-W 3.4.
Command Information
Parameter Description
share Enter a name for the share on the switch. After you enter this command, the CLI
mode will shift to operations on that share.
(host) (config-network-storage share)#share usb: disk Maxtor1TB Maxtor-Basics_Desktop-2HBADMJ4_p1/documents mode read-write
(host) (config-network-storage share)#show network-storage shares
NAS Shares
----------
Disk Name Partition Name Folder Name Share Name Share Path Share Mode Status
--------- -------------- ----------- ---------- ---------- ---------- ------
Maxtor1TB MxDocs documents Documents Maxtor-Basics_Desktop-2HBADMJ4_p1/documents Read-Write Active
Platforms Licensing Command Mode
Aruba 65x Series Base operating system Enable mode.

360 | network-storage AOS-W 3.4.1 Command Line Interface | Reference Guide
AOS-W 3.4.1 Command Line Interface | Reference Guide ntp server | 361
ntp server
ntp server <ipaddr> [iburst]
Description
This command configures a Network Time Protocol (NTP) server.
Syntax
Usage Guidelines
You can configure the switch to set its system clock using NTP by specifying one or more NTP servers.
Example
The following command configures an NTP server:
(host) (config) #ntp server 10.1.1.245
Command History
Command Information
Parameter Description Default
<ipaddr> IP address of the NTP server, in dotted-decimal format. —
iburst (Optional) This parameter causes the switch to send up to ten
queries within the first minute to the NTP server. This option is
considered “aggressive” by some public NTP servers.
disabled
Release Modification
AOS-W 1.0 Command introduced
AOS-W 3.0 The iburst parameter was introduced
Platforms Licensing Command Mode
All platforms Base operating system Config mode on master switches

362 |ntp server AOS-W 3.4.1 Command Line Interface | Reference Guide

AOS-W 3.4.1 Command Line Interface | Reference Guide packet-capture | 363
packet-capture
packet-capture [other {disable | enable}] [sysmsg {all | disable | <opcodes>]
[tcp {all | disable | <ports>}] [udp {all | disable | <ports>]]
Description
Use this command to enable or disable packet capturing and set packet capturing options for a single
packet capture session.
Syntax
Usage Guidelines
This command applies to control path packets; not datapath packets. Packets can be retrieved through the
tar log command; look for the filter.pcap file. This command activates packet capture options on the
current switch. They are not saved and applied across switches.
If you do want to enable a packet capture session without setting values that can be saved and used for
another session, use the command packet-capture. The related command packet-capture-defaults lets
you define a set of packet capture options that will run every time you enable the packet capture feature.
Example
The following command enables packet capturing for debugging a wireless WEP station doing VPN. This
example uses the following parameters and values:
zStation up/down: sysmsg opcode 30
zWEP key plumbing: sysmsg opcode 29
zDHCP: sysmsg opcode 90
zIKE: UDP port 500 and 4500
zLayer 2 Tunneling Protocol (L2TP): UDP port 1701
(host) #packet-capture sysmsg 30,29,90 udp 500,4500,1701,1812,1645
Command History
This command was introduced in AOS-W 2.3.
Parameter Description Default
other Enable or disable all other types of packets. Specify up to ten
comma-separated opcodes to capture; use all to sniff all
opcodes; use disable to bypass the all setting. All CLI ports are
always skipped.
Enabled
sysmsg Enable or disable internal messaging packets. Disabled
tcp ports Enable or disable TCP packet capturing. Specify up to ten comma-
separated ports to capture; use all to sniff all TCP ports; use
disable to bypass the all setting. All CLI ports are always
skipped.
Disabled
udp ports Enable or disable UDP packet capturing. Specify up to ten
comma-separated ports to capture; use all to sniff all UDP ports;
use disable to bypass the all setting. All CLI ports are always
skipped.
Disabled

364 | packet-capture AOS-W 3.4.1 Command Line Interface | Reference Guide
Command Information
Platforms Licensing Command Mode
All platforms Base operating system Enable mode on master switches

AOS-W 3.4.1 Command Line Interface | Reference Guide packet-capture-defaults | 365
packet-capture-defaults
packet-capture-defaults [other {disable | enable}]
[sysmsg {all | disable | <opcodes>] [tcp {all | disable | <ports>}]
[udp {all | disable | <ports>]]
Description
Use this command to enable or disable packet capturing and define a set of default packet capturing
options on the control path for debugging purposes.
Syntax
Usage Guidelines
This command applies to control path packets; not datapath packets. Packets can be retrieved through the
tar log command; look for the filter.pcap file. This command activates packet capture options on the
current switch. They are not saved and applied across switches.
Example
The following command sets the default packet capture values to debug a wireless WEP station doing VPN.
Once these default settings are defined, you can use the packet-capture command to enable packet
capturing with these values. This example uses the following parameters and values:
zStation up/down: sysmsg opcode 30
zWEP key plumbing: sysmsg opcode 29
zDHCP: sysmsg opcode 90
zIKE: UDP port 500 and 4500
zLayer 2 Tunneling Protocol (L2TP): UDP port 1701
packet-capture-defaults sysmsg 30,29,90 udp 500,4500,1701,1812,1645
Parameter Description Default
other Enable or disable all other types of packets. Specify up to ten
comma-separated opcodes to capture; use all to sniff all
opcodes; use disable to bypass the all setting. All CLI ports are
always skipped.
Enabled
sysmsg Enable or disable internal messaging packets. Disabled
tcp ports Enable or disable TCP packet capturing. Specify up to ten comma-
separated ports to capture; use all to sniff all TCP ports; use
disable to bypass the all setting. All CLI ports are always
skipped.
Disabled
udp ports Enable or disable UDP packet capturing. Specify up to ten
comma-separated ports to capture; use all to sniff all UDP ports;
use disable to bypass the all setting. All CLI ports are always
skipped.
Disabled

366 | packet-capture-defaults AOS-W 3.4.1 Command Line Interface | Reference Guide
Use the show packet-capture command to show the current action and the default values.
Command History
This command was introduced in AOS-W 2.3.
Command Information
Platforms Licensing Command Mode
All platforms Base operating system Config mode on master switches
show packet-capture
Current Active Packet Capture Actions(current switch)
=====================================================
Packet filtering TCP with 2 port(s) enabled:
2
1
Packet filtering UDP with 1 port(s) enabled:
1
Packet filtering for internal messaging opcodes disabled.
Packet filtering for all other packets disabled.
Packet Capture Defaults(across switches and reboots if saved)
============================================================
Packet filtering TCP with 2 port(s) enabled:
2
AOS-W 3.4.1 Command Line Interface | Reference Guide page | 367
page
page <length>
Description
This command sets the number of lines of text the terminal will display when paging is enabled.
Syntax
Usage Guidelines
Use this command in conjunction with the paging command to specify the number of lines of text to
display. For more information on the pause mechanism that stops the command output from printing
continuously to the terminal, refer to the command “paging” on page 369.
If you need to adjust the screen size, use your terminal application to do so.
Example
The following command sets 80 as the number of lines of text displayed:
(host) (config) #page 80
Command History
This command was introduced in AOS-W 1.0.
Command Information
Parameter Description Range
length Specifies the number of lines of text displayed. 24 - 100
Platforms Licensing Command Mode
All platforms Base operating system Config and Enable mode on master
switches

368 |page AOS-W 3.4.1 Command Line Interface | Reference Guide

AOS-W 3.4.1 Command Line Interface | Reference Guide paging | 369
paging
paging
Description
This command stops the command output from printing continuously to the terminal.
Syntax
No parameters
Usage Guidelines
By default, paging is enabled.
With paging enabled, there is a pause mechanism that stops the command output from printing
continuously to the terminal. If paging is disabled, the output prints continuously to the terminal. To disable
paging, use the no paging command. You must be in enable mode to disable paging.
The paging setting is active on a per-user session. For example, if you disable paging from the CLI, it only
affects that session. For new or existing sessions, paging is enabled by default.
You can also configure the number of lines of text displayed when paging is enabled. For more information,
refer to the command “page” on page 367.
If you need to adjust the screen size, use your terminal application to do so.
Example
The following command enables paging:
(host) (config) #paging
Command History
This command was introduced in AOS-W 1.0.
Command Information
Platforms Licensing Command Mode
All platforms Base operating system Config and Enable mode on master
switches

370 |paging AOS-W 3.4.1 Command Line Interface | Reference Guide
AOS-W 3.4.1 Command Line Interface | Reference Guide panic | 371
panic
panic {clear | info {file <filename> <symbolfile>|nvram <symbolfile>} | list {file
<filename>|nvram} | save <filename>}
Description
This command manages information created during a system crash.
Syntax
Usage Guidelines
To troubleshoot system crashes, use the panic save command to save information from NVRAM into the
specified file, then use the panic clear command to clear the information from NVRAM.
Example
The following command lists panic information in NVRAM:
(host) #panic list nvram
Command History
This command was introduced in AOS-W 3.0.
Command Information
Parameter Description
clear Removes panic information from non-volatile random access memory (NVRAM).
info Displays the content of specified panic files.
list Lists panic information in the specified file in flash or in NVRAM.
save Saves panic information from NVRAM into the specified file in flash.
Platforms Licensing Command Mode
All platforms Base operating system Enable mode on master switches

372 |panic AOS-W 3.4.1 Command Line Interface | Reference Guide
AOS-W 3.4.1 Command Line Interface | Reference Guide papi-security | 373
papi-security
papi-security
key <key>
[enhanced-security]
no...
Description
The papi-security command is used by the Alcatel-Lucent system to enforce advanced security options and
provides an enhanced level of security.
Syntax
Usage Guidelines
This command allows you to use advanced options which regulate the switch and AP communication. One
way PAPI messages are authenticated is through a shared secret key. The papi-security command lets you
configure a key on the master switch which then distributes it to other switches and APs, thus allowing
each site to have a unique key. If no key is configured, then the switch uses the default key.
When enhanced-security mode is disabled, any AP can obtain the current shared secret key.
When enhanced-security mode is enabled, an AP is not updated with the new shared secret key unless the
AP knows the previous key and the AP is updated with the new key within one hour of the key creation.
If an AP cannot be authenticated because it has the wrong key, the show ap database command displays a
“Bad key” status.
Example
This example sets a unique shared secret key called “testkey123” on the master switch.
(host) (config) #papi-security
(host) (PAPI Security Profile) #
(host) (PAPI Security Profile) #key testkey123
(host) (PAPI Security Profile) #exit
Related Commands
Alcatel-Lucent recommends that customers work closely with the Alcatel-Lucent TAC department before modifying
default settings.
Parameter Description Default
key The key authenticates the messages between
systems. —
key The key string. Range: 10–64 characters
enhanced-security Allows you to use the enhanced security mode.
This mode causes the system to reject messages
when an incorrect key is used.
disabled
no key Reverts to the default key. —
Make sure that the enhanced-security mode is disabled before installing new APs.

374 |papi-security AOS-W 3.4.1 Command Line Interface | Reference Guide
(host)(config) #show papi-security
(host)(config) #show ap database
Command History
This command was introduced in AOS-W 3.4
Command Information
Platform License Command Mode
Available on all platforms Base operating system Config mode on master switches
AOS-W 3.4.1 Command Line Interface | Reference Guide pcap | 375
pcap
pcap {raw-start <ipaddr> <target-ipaddr> <target-port> <format> [bssid <bssid>]
[channel <number>] [maxlen <maxlen>]}|{interactive <am-ip> <filter> <target-ipaddr>
<target-port> [bssid <bssid>][channel <number>]}|{clear|pause|resume|stop <am-ip> <id>
[bssid <bssid>]}
Description
These commands manage packet capture (PCAP) on Alcatel-Lucent air monitors.
Syntax
Parameter Description
raw-start Stream raw packets to an external viewer.
<ipaddr> IP address of the air monitor collecting packets.
<target-ipaddr> IP address of the client station running Wildpacket’s AiroPeek monitoring application.
<target-port> UDP port number on the client station where the captured packets are sent.
<format> Specify a number to indicate one of the following formats for captured packets:
z0 : pcap
z1 : peek
z2 : airmagnet
z3 : pcap+radio header
z4 : ppi
bssid (Optional) BSSID of the Air Monitor interface for the PCAP session.
<bssid> BSSID of the Air Monitor Interface, which is usually its MAC address.
channel (Optional) Number of a radio channel to tune into to capture packets
maxlen (Optional) Limit the length of 802.11 frames to include in the capture to a specified
maximum.
<maxlen> (Optional) Maximum number of packets to be captured.
interactive Start an interactive packet capture session.
<am-ip> IP address of the air monitor collecting packets.
<filter-spec> Packet Capture filter specification.
<target-ipaddr> IP Address of host to which the frames should be sent
<target-port> UDP Port Number to which the frames should be sent
bssid (Optional) Specify the BSSID of the Air Monitor interface for the PCAP session.
<bssid> BSSID of the Air Monitor Interface, which is usually its MAC address.
channel (Optional) Number of a radio channel to tune into to capture packets
clear Clears the packet capture session.
pause Pause a packet capture session.
resume Resume a packet capture session.
start Start a new packet capture session.
stop Stop a packet capture session.
<am-ip> IP address of the air monitor collecting packets.
376 |pcap AOS-W 3.4.1 Command Line Interface | Reference Guide
Usage Guidelines
These commands direct an Alcatel-Lucent air monitor to send packet captures to the Wildpacket’s AiroPeek
monitoring application on a remote client. The AiroPeek application listens for packets sent by the air
monitor.
The following pcap commands are available:
Before using these commands, you need to start the AiroPeek application on the client and open a capture
window for the air monitor. The AiroPeek application cannot be used to control the flow or type of packets
sent from Alcatel-Lucent air monitors.
The AiroPeek application processes all packets, however, you can apply display filters on the capture
window to control the number and type of packets being displayed. In the capture window, the time stamp
displayed corresponds to the time that the packet is received by the client and is not synchronized with the
time on the Alcatel-Lucent air monitor.
Example
The following command starts a raw packet capture session for the air monitor at 10.100.100.1 and sends
the packets to the client at 192.168.22.44 on port 604 with pcap format:
(host) (config) #pcap raw-start 10.100.100.1 192.168.22.44 604 0
Command History
<id> ID of the PCAP session.
bssid (Optional) Specify the BSSID of the Air Monitor interface for the PCAP session.
<bssid> BSSID of the Air Monitor Interface, which is usually its MAC address.
Parameter Description
Command Description
clear Clears the packet capture session.
pause Pause a packet capture session.
resume Resume a packet capture session.
start Start a new packet capture session.
stop Stop a packet capture session.
Version Change
AOS-W3.0 Command Introduced
AOS-W3.4 The maxlen parameter was introduced, and the pcap start command
deprecated.

AOS-W 3.4.1 Command Line Interface | Reference Guide pcap | 377
Command Information
Platforms Licensing Command Mode
All platforms Base operating system Enable mode on master switches

378 |pcap AOS-W 3.4.1 Command Line Interface | Reference Guide
AOS-W 3.4.1 Command Line Interface | Reference Guide ping | 379
ping
ping <ipaddress>
Description
This command sends five ICMP echo packets to the specified ip address.
Syntax<
Usage Guidelines
You can send five ICMP echo packets to a specified IP address. The switch times out after two seconds.
Example
The following example pings 10.10.10.5.
(host) >ping 10.10.10.5
The sample switch output is:
Press 'q' to abort.
Sending 5, 100-byte ICMP Echos to 10.10.10.5, timeout is 2 seconds:!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 0.408/0.5434/1.073 ms
Command History
This command was introduced in AOS-W 1.0.
Command Information
Parameter Description
<ipaddress> Destination IP Address
Platforms Licensing Command Mode
All platforms Base operating system User, Enable, and Config modes on master
switches

380 |ping AOS-W 3.4.1 Command Line Interface | Reference Guide
AOS-W 3.4.1 Command Line Interface | Reference Guide pkt-trace | 381
pkt-trace
pkt-trace acl <acl-name> {enable|disable} [trace {cptrace|pktrace} [trace-mask
<tmask>]] ]
Description
Enable packet tracing in the datapath. Use this feature only under the supervision of Alcatel-Lucent
technical support.
Syntax
Example
The following example enables packet tracing for the traffic matching the acl stateful-dot1x.
Command History
This command was introduced in AOS-W 3.4.
Command Information
Parameter Description
<acl-name> Enable packet tracing for the specified access-control list.
enable Enable packet tracing for the ACL.
disable Disable packet tracing for the ACL.
cptrace Send packet trace data into the Control Processor.
pktrace Write packet trace data in the packet.
tracemask <tmask> Specify a the trace mask. This value will be provided by Alcatel-Lucent technical
support.
Platforms Licensing Command Mode
All platforms Base operating system Enable mode on master switches
(host) #pkt-trace acl stateful-dot1x enable trace cptrace trace-mask <val>
382 | pkt-trace-global AOS-W 3.4.1 Command Line Interface | Reference Guide
pkt-trace-global
pkt-trace-global {enable|disable} [trace-mask <tmask>]
Description
Enable global packet tracing in the datapath. Use this feature only under the supervision of Alcatel-Lucent
technical support.
Syntax
Example
The following command enables the global packet tracing for all traffic.
(host) (config) #pkt-trace-global enable
Command History
This command was introduced in AOS-W 3.4.
Command Information
Parameter Description
<acl-name> Enable packet tracing for the specified access-control list.
enable Enable global packet tracing for the ACL.
disable Disable global packet tracing for the ACL.
tracemask <tmask> Specify a trace mask. Use this feature only under the supervision of Alcatel-Lucent
technical support.
Platforms Licensing Command Mode
All platforms Base operating system Enable mode on master switches
AOS-W 3.4.1 Command Line Interface | Reference Guide pptp ip local pool | 383
pptp ip local pool
pptp ip local pool <pool> <ipaddr> [<end-ipaddr>]
Description
This command configures an IP address pool for VPN users using Point-to-Point Tunneling Protocol
(PPTP).
Syntax
Usage Guidelines
If VPN is used as an access method, you specify the pool from which the user’s IP address is assigned when
the user negotiates a PPTP session. Use the show vpdn pptp local command to see the used and free
addresses in the pool.
PPTP is an alternative to IPsec that is supported by various hardware platforms. PPTP is considered to be
less secure than IPsec but also requires less configuration. You configure PPTP with the vpdn command.
Example
The following command configures an IP address pool for PPTP VPN users:
(host) (config) #pptp ip local pool pptp-pool1 172.16.18.1 172.16.18.24
Command History
This command was introduced in AOS-W 3.0.
Command Information
Parameter Description
<pool> User-defined name for the address pool.
<ipaddr> Starting IP address for the pool.
<end-ipaddr> Ending IP address for the pool.
Platforms Licensing Command Mode
All platforms Requires a VPN server license Config mode on master switches

384 | pptp ip local pool AOS-W 3.4.1 Command Line Interface | Reference Guide

AOS-W 3.4.1 Command Line Interface | Reference Guide priority-map | 385
priority-map
priority-map <name>
dot1p <priority> high
dscp <priority> high
no ...
Description
This command configures the Type of Service (ToS) and Class of Service (CoS) values used to map traffic
into high priority queues.
Syntax
Usage Guidelines
This command allows you to prioritize inbound traffic that is already tagged with 802.1p and/or IP ToS in
hardware queues. You apply configured priority maps to ports on the switch (using the interface
fastethernet or interface gigbitethernet command). This causes the switch to inspect inbound traffic on
the port; when a matching QoS tag is found, the packet or flow is mapped to the specified queue.
Example
The following commands configure a priority map and apply it to a port:
(host) (config) #priority-map pri1
dscp 4-20 high
dscp 60 high
dot1p 4-7 high
interface gigabitethernet 1/24
priority-map pri1
Command History
This command was introduced in AOS-W 3.0.
Command Information
Parameter Description Range
<name> User-defined name of the priority map. —
dot1p IEEE 802.1p priority value, or a range of values separated by a
dash (-). 0-7
dscp Differentiated Services Code Point (DSCP) priority value, or a range
of values separated by a dash (-). 0-63
no Negates any configured parameter. —
Platforms Licensing Command Mode
All platforms Base operating system Config mode on master switches

386 |priority-map AOS-W 3.4.1 Command Line Interface | Reference Guide

AOS-W 3.4.1 Command Line Interface | Reference Guide process monitor | 387
process monitor
process monitor log|restart|
Description
The process monitor validates the integrity of processes every 120 seconds. If a process does not respond
during three consecutive 120-second timeout intervals, that process is flagged as nonresponsive and the process
monitor will create a log message, restart the process or reboot the switch
Syntax
Usage Guidelines
The CLI command process monitor log enables logging for process monitoring. By default, whenever a
process does not update a required file or send a heartbeat pulse within the required time limit, the process
monitor records a critical log message, but does not restart any process. If you want the configure watchdog to
restart a process once it fails to respond, use the CLI command process monitor restart.
Example
The following changes the default process monitor behavior, so the process monitor restarts nonresponsive
processes.
(host) #process monitor restart
Related Commands
The show process monitor statistics command displays the current status of all the processes running under
the process monitor watchdog.A partial example of the output of this command is show below:
Parameter Description
log The process monitor creates a log message when a process fails to responding properly.
This is the default behavior for the process monitor
restart This parameter enables strict behavior for runtime processes.
When you enable this option, the process monitor will restart processes that fail to
responding properly.
show process monitor statistics
Process Monitor Statistics
--------------------------
Name State Restarts Timeout Value Timeout Chances
---- ----- -------- ------------- ---------------
/mswitch/bin/arci-cli-helper PROCESS_RUNNING 0 120 3
/mswitch/bin/fpcli PROCESS_RUNNING 0 120 3
/mswitch/bin/packet_filter PROCESS_RUNNING 0 120 3
/mswitch/bin/certmgr PROCESS_RUNNING 0 120 3
/mswitch/bin/dbstart PROCESS_RUNNING 0 120 3
/mswitch/bin/cryptoPOST PROCESS_RUNNING 0 120 3
/mswitch/bin/sbConsoled PROCESS_RUNNING 0 120 3
/mswitch/bin/pubsub PROCESS_RUNNING 0 120 3
/mswitch/bin/cfgm PROCESS_RUNNING 0 120 3
/mswitch/bin/syslogdwrap PROCESS_RUNNING 0 120 3
/mswitch/bin/aaa PROCESS_RUNNING 0 120 3
/mswitch/bin/fpapps PROCESS_RUNNING 0 120 3
/mswitch/bin/pim PROCESS_RUNNING 0 120 3
388 |process monitor AOS-W 3.4.1 Command Line Interface | Reference Guide
Command History
Command Information
Release Modification
AOS-W 3.4 Command introduced
AOS-W 3.4 The process restart command was deprecated.
Platforms Licensing Command Mode
All platforms Base operating system Enable mode on master switches
AOS-W 3.4.1 Command Line Interface | Reference Guide prompt | 389
prompt
prompt <prompt>
Description
This command changes the prompt text.
Syntax.
Usage Guidelines
You can use any alphanumeric character, punctuation, or symbol character. To use spaces, plus symbols
(+), question marks (?), or asterisks (*), enclose the text in quotes.
You cannot alter the parentheses that surround the prompt text, or the greater-than (>) or hash (#) symbols
that indicate user or enable CLI mode.
Example
The following example changes the prompt text to “It’s a new day!”.
(host) (config) #prompt “It’s a new day!”
(It’s a new day!) (config) #
Command History
This command was introduced in AOS-W 1.0.
Command Information
Parameter Description Range Default
prompt The prompt text displayed by the switch. 1–64 <hostname>
Platforms Licensing Command Mode
All platforms Base operating system Config mode on master switches

390 |prompt AOS-W 3.4.1 Command Line Interface | Reference Guide

AOS-W 3.4.1 Command Line Interface | Reference Guide provision-ap | 391
provision-ap
provision-ap
a-ant-bearing <bearing>
a-ant-gain <gain>
a-ant-tilt-angle <angle>
a-antenna {1|2|both}
altitude <altitude>
ap-group <group>
ap-name <name>
copy-provisioning-params {ap-name <name> | ip-addr <ipaddr>}
dns-server-ip <ipaddr>
domain-name <name>
external-antenna
fqln <name>
g-ant-bearing <bearing>
g-ant-gain <gain>
g-ant-tilt-angle <angle>
g-antenna {1|2|both}
gateway <ipaddr>
ikepsk <key>
installation default|indoor|outdoor
ipaddr <ipaddr>
latitude <location>
longitude <location>
master {<name>|<ipaddr>}
mesh-role {mesh-point|mesh-portal|none|remote-mesh-portal}
mesh-sae {sae-default|sae-disable|sae-enable}
netmask <netmask>
no ...
pap-passwd <string>
pap-user <name>
pppoe-passwd <string>
pppoe-service-name <name>
pppoe-user <name>
read-bootinfo {ap-name <name>|ip-addr <ipaddr>|wired-mac <macaddr>}
reprovision {all|ap-name <name>|ip-addr <ipaddr>|serial-num <string>|
wired-mac <macaddr>}
reset-bootinfo {ap-name <name>|ip-addr <ipaddr>|wired-mac <macaddr>}
server-ip <ipaddr>
server-name <name>
set-ikepsk-by-addr <ip-addr>
syslocation <string>
usb-dev <usb-dev>
usb-dial <usb-dial>
usb-init <usb-init>
usb-passwd <usb-passwd>
usb-tty <usb-tty>
usb-type <usb-type>
usb-user <usb-user>
Description
This command provisions or reprovisions an AP.

392 |provision-ap AOS-W 3.4.1 Command Line Interface | Reference Guide
Syntax
Parameter Description Range Default
a-ant-bearing Determines the horizontal coverage distance of the
802.11a (5GHz) antenna from True North.
From a planning perspective, the horizontal coverage
pattern does not consider the elevation or vertical
antenna pattern.
NOTE: This parameter is supported on outdoor APs
only. If you use this parameter to configure an indoor
AP, an error message is displayed.
0-360 Decimal
Degrees —
a-ant-gain Antenna gain for 802.11a (5GHz) antenna. — —
a-ant-tilt-angle Directs the angle of the 802.11a (5GHz) antenna for
optimum coverage.
Use a - (negative) value for downtilt and a + (positive)
value for uptilt.
NOTE: This parameter is supported on outdoor APs
only. If you use this parameter to configure an indoor
AP, an error message is displayed.
-90 to +90
Decimal
Degrees
—
a-antenna Antenna use for 5 GHz (802.11a) frequency band.
z1: Use antenna 1
z2: Use antenna 2
zboth: Use both antennas
1, 2, both both
altitude Altitude, in meters, of the AP.
NOTE: This parameter is supported on outdoor APs
only. If you use this parameter to configure an indoor
AP, an error message is displayed.
——
ap-group Name of the AP group to which the AP belongs. — “default”
ap-name Name for this AP. — —
copy-provisioning-
params
Initializes the provisioning-params workspace with
the current provisioning parameters of the specified
AP, The provisioning parameters of the AP must have
previously been retrieved with the read-bootinfo
option.
NOTE: This parameter can only be used on the
master switch.
——
dns-server-ip IP address of the DNS server for the AP. — —
domain-name Domain name for the AP. — —
external-anten
na
Use an external antenna with the AP. — —
fqln Fully-qualified location name (FQLN) for the AP, in the
format <APname.floor.building.campus>. ——
g-ant-bearing Determines the horizontal coverage distance of the
802.11g (2.4GHz) antenna from True North.
From a planning perspective, the horizontal coverage
pattern does not consider the elevation or vertical
antenna pattern.
NOTE: This parameter is supported on outdoor APs
only. If you use this parameter to configure an indoor
AP, an error message is displayed.
0-360 decimal
degrees —
g-ant-gain Antenna gain for 802.11g (2.4GHz) antenna. — —
AOS-W 3.4.1 Command Line Interface | Reference Guide provision-ap | 393
g-ant-tilt-angle Directs the angle of the 802.11g (2.4GHz) antenna for
optimum coverage.
Use a - (negative) value for downtilt and a + (positive)
value for uptilt.
NOTE: This parameter is supported on outdoor APs
only. If you use this parameter to configure an indoor
AP, an error message is displayed.
-90 to +90
Decimal
Degrees
—
g-antenna Antenna use for 2.4 GHz (802.11g) frequency band.
z1: Use antenna 1
z2: Use antenna 2
zboth: Use both antennas
1, 2, both both
gateway IP address of the default gateway for the AP. — —
ikepsk IKE preshared key for the AP.
NOTE: The Remote AP license must be installed.
——
installation Specify the type of installation (indoor or outdoor).
The default parameter automatically selects an
installation mode based upon the AP model type.
default
indoor
outdoor
default
ipaddr Static IP address for the AP. — —
latitude Latitude coordinates of the AP. Use the format:
Degrees, Minutes, Seconds (DMS). For example: 37
22 00 N
——
longitude Longitude coordinates of the AP. Use the DMS
format. For example: 122 02 00 W ——
master Name or IP address for the master switch. — —
mesh-role Configure the AP to operate as a mesh node. You
assign one of three roles: mesh portal, mesh point
or remote mesh point. If you select “none,” the AP
operates as a thin AP.
NOTE: OAW-AP80M and OAW-AP85 models require
the Outdoor Mesh Access Points license.
mesh-portal
mesh-point
remote-mesh-
portal
none
—
mesh-sae Enable or disable Secure Attribute Exchange (SAE)
on a mesh network. The default setting disables SAE.
If used, this feature needs to be enabled on all the
Mesh nodes (points and portals) in the network, else
there could be mesh link connectivity issues. This is a
Beta feature and recommended to be kept “disabled”
for this 3.4 release.
NOTE: OAW-AP80M and OAW-AP85 models require
the Outdoor Mesh Access Points license.
sae-default
sae-disable
sae-enable
sae-default
netmask Netmask for the IP address. — —
no Negates any configured parameter. — —
pap-passwd Password Authentication Protocol (PAP) password
for the AP.
You can use special characters in the PAP password.
Following are the restrictions:
zYou cannot use double-byte characters
zYou cannot use a tilde (~)
zYou cannot use a tick (‘)
zIf you use quotes (single or double), you must use
the backslash (\) before and after the password
NOTE: The Remote AP license must be installed.
——
Parameter Description Range Default
394 |provision-ap AOS-W 3.4.1 Command Line Interface | Reference Guide
Usage Guidelines
You do not need to provision APs before installing and using them.
The exceptions are:
pap-user PAP username for the AP.
NOTE: The Remote AP license must be installed.
——
pppoe-passwd Point-to-Point Protocol over Ethernet (PPPoE)
password for the AP.
NOTE: The Remote AP license must be installed.
——
pppoe-service-
name
PPPoE service name for the AP.
NOTE: The Remote AP license must be installed.
——
pppoe-user PPPoE username for the AP.
NOTE: The Remote AP license must be installed.
——
read-bootinfo Retrieves current provisioning parameters of the
specified AP.
NOTE: This parameter can only be used on the
master switch.
——
reprovision Provisions one or more APs with the values in the
provisioning-params workspace. To use reprovision,
you must use read-bootinfo to retrieve the current
values of the APs into the provisioning-ap-list.
NOTE: This parameter can only be used on the
master switch.
——
reset-bootinfo Restores factory default provisioning parameters to
the specified AP.
NOTE: This parameter can only be used on the
master switch.
——
server-ip IP address of the switch from which the AP boots. — —
server-name DNS name of the switch from which the AP boots. — —
set-ikepsk-by-addr Set a IKE preshared key to correspond to a specific
IP address.
syslocation User-defined description of the location of the AP. — —
usb-dev The USB device identifier.
usb-dial The dial string for the USB modem. This parameter
only needs to be specified if the default string is not
correct.
usb-init The initialization string for the USB modem. This
parameter only needs to be specified if the default
string is not correct.
usb-passwd A PPP password, if provided by the cellular service
provider
usb-tty The TTY device path for the USB modem. This
parameter only needs to be specified if the default
path is not correct.
usb-type The USB driver type.
usb-user The PPP username provided by the cellular service
provider
Parameter Description Range Default

AOS-W 3.4.1 Command Line Interface | Reference Guide provision-ap | 395
zThe OAW-AP80M and OAW-AP60, which have antenna gains that you must provision before they can be
used.
zAPs configured for mesh. You must provision the AP before you install it as a mesh node in a mesh
deployment.
Provisioned or reprovisioned values do not take effect until the AP is rebooted. APs reboot automatically
after they are successfully reprovisioned.
Provisioning a Single AP
To provision a single AP:
1. Use the read-bootinfo option to read the current information from the deployed AP you wish to
reprovision.
2. Use the show provisioning-ap-list command to see the AP to be provisioned.
3. Use the copy-provisioning-params option to copy the AP’s parameter values to the provisioning-
params workspace.
4. Use the provision-ap options to set new values. Use the show provisioning-params command to
display parameters and values in the provisioning-params workspace. Use the clear provisioning-
params command to reset the workspace to default values.
5. Use the reprovision option to provision the AP with the values in provisioning-params workspace. The
AP automatically reboots.
Provisioning Multiple APs at a Time
You can change parameter values for multiple APs at a time, however, note the following:
zYou cannot provision the following AP-specific options on multiple APs:
ap-name
ipaddr
pap-user
pap-passwd
ikepsk
If any of these options are already provisioned on the AP, their values are retained when the AP is
reprovisioned.
zThe values of the server-name, a-ant-gain, or g-ant-gain options are retained if they are not
reprovisioned.
zAll other values in the provisioning-params workspace are copied to the APs.
To provision multiple APs at the same time:
1. Use the read-bootinfo to read the current information from each deployed AP that you wish to
provision.
2. Use the copy-provisioning-params option to copy an AP’s parameter values to the provisioning-
params workspace.
Users less familiar with this process may prefer to use the Provisioning page in the WebUI to provision an AP.
The AP parameter values are written to the provisioning-ap-list. To reprovision multiple APs, the APs must be
present in the provisioning-ap-list. Use the show provisioning-ap-list command to see the APs that will be
provisioned. Use the clear provisioning-ap-list command to clear the provisioning-ap-list.

396 |provision-ap AOS-W 3.4.1 Command Line Interface | Reference Guide
3. Use the provision-ap options to set new values. Use the show provisioning-params command to
display parameters and values in the provisioning-params workspace. Use the clear provisioning-
params command to reset the workspace to default values.
4. Use the reprovision all option to provision the APs in the provisioning-ap-list with the values in
provisioning-params workspace. All APs in the provisioning-ap-list automatically reboot.
The following are useful commands when provisioning one or more APs:
zshow|clear provisioning-ap-list displays or clears the APs that will be provisioned.
zshow|clear provisioning-params displays or resets values in the provisioning-params workspace.
zshow ap provisioning shows the provisioning parameters an AP is currently using.
Example
The following commands change the IP address of the master switch on the AP:
(host) (config) #provision-ap
read-bootinfo ap-name lab103
show provisioning-ap-list
copy-provisioning-params ap-name lab103
master 10.100.102.210
reprovision ap-name lab103
Command History
Command Information
Release Modification
AOS-W 3.0 Command introduced
AOS-W 3.2 Introduced support for the mesh parameters, additional antenna parameters, and
AP location parameters.
AOS-W 3.4 Introduced support for the following parameters:
zinstallation
zmesh-sae
zset-ikepsk-by-addr
zusb-dev
zusb-dial
zusb-init
zusb-passwd
zusb-tty
zusb-type
zusb-user
Platforms Licensing Command Mode
All platforms, except for the
parameters noted in the Syntax
table.
Base operating system, except for
the parameters noted in the Syntax
table.
Config mode on master switches
AOS-W 3.4.1 Command Line Interface | Reference Guide rap-wml | 397
rap-wml
rap-wml <server-name> [ageout <period>] [cache {disable|enable}] [db-name <name>]
[ip-addr <ipaddr>] [password <password>] [type {mssql|mysql}] [user <name>]
Description
Use this command to specify the name and attributes of a MySQL or an MSSQL server.
Syntax
Usage Guidelines
Use the show rap-wml cache command to show the cache of all lookups for a database server. Use the
show rap-wml servers command to show the database server state. Use the show rap-wml wired-mac
command to show wired MAC discovered on traffic through the AP.
Example
This example configures a MySQL server and sets up associated rap-wml table attributes.
(host) (config) #rap-wml mysqlserver type mysql ip-addr 10.4.11.10 db-name
automatedtestdatabase user sa password sa
rap-wml table mysqlserver mactest_undelimited mac timestamp-column time 600
rap-wml table mysqlserver mactest_delimited mac delimiter : timestamp-column time 600
This example configures an MSSQL server and sets up associated rap-wml table attributes.
(host) (config) #rap-wml mssqlserver type mssql ip-addr 10.4.11.11 db-name
automatedtestdatabase user sa password sa
rap-wml table mssqlserver mactest_undelimited mac timestamp-column time 600
rap-wml table mssqlserver mactest_delimited mac delimiter : timestamp-column time 600
Command History
This command was introduced in AOS-W 2.0.
Command Information
Parameter Description Default
ageout (Optional) Specifies the cache ageout period, in seconds. 0
cache (Optional) Enables the cache, or disables the cache. Disabled
db-name (Optional) Specifies the name of the MySQL or MSSQL database. —
ip-addr (Optional) Specifies the IP address of the named MSSQL server. 0.0.0.0
no Negates any configured parameter. —
password (Optional) Specifies the password required for database login. —
type (Optional) Specifies the server type. —
user (Optional) Specifies the user name required for database login. —
Platforms Licensing Command Mode
All platforms Requires the Wireless Intrusion
Protection license. Config mode on master switches

398 |rap-wmltable AOS-W 3.4.1 Command Line Interface | Reference Guide
rap-wml table
rap-wml table <server-name> <table-name> <column-name> {[delimiter <char>] |
[timestamp-column <timestamp-column-name> <lookup-time>]}
Description
Use this command to specify the name and attributes of the database table to be used for lookup.
Syntax
Usage Guidelines
Use the rap-wml <servername> command to configure a MySQL or an MSSQL server, then use the rap-
wml table command to configure the associated database table for the server.
Example
This example configures a MySQL server and sets up associated rap-wml table attributes for that server.
(host) (config) #rap-wml mysqlserver type mysql ip-addr 10.4.11.10 db-name
automatedtestdatabase user sa password sa
rap-wml table mysqlserver mactest_undelimited mac timestamp-column time 600
rap-wml table mysqlserver mactest_delimited mac delimiter : timestamp-column time 600
This example configures an MSSQL server and sets up associated rap-wml table attributes for that server.
(host) (config) # rap-wml mssqlserver type mssql ip-addr 10.4.11.11 db-name
automatedtestdatabase user sa password sa
rap-wml table mssqlserver mactest_undelimited mac timestamp-column time 600
rap-wml table mssqlserver mactest_delimited mac delimiter : timestamp-column time 600
Command History
This commands was introduced in AOS-W 2.0.
Parameter Description Default
server-name Specifies the database server name (created using the rap-wml
<server-name> command. —
table-name Specifies the database table name. —
column-name Specifies the database column name with the MAC address. —
delimiter Specifies the optional delimiter character for the MAC address in
the database. No delimiter
no Negates the rap-wml table for the named server. —
timestamp-column Specify the database column name with the timestamp last seen. —
timestamp-column-nam
e
Specify the database column name with the timestamp last seen. —
lookup-time Specifies how far back—in seconds—to look for the MAC address.
Use 0 seconds to lookup everything. 0

AOS-W 3.4.1 Command Line Interface | Reference Guide rap-wml table | 399
Command Information
Platforms Licensing Command Mode
All platforms Requires the Wireless Intrusion
Protection license. Config mode on master switches

400 |rap-wmltable AOS-W 3.4.1 Command Line Interface | Reference Guide
AOS-W 3.4.1 Command Line Interface | Reference Guide reload | 401
reload
reload
Description
This command performs a reboot of the switch.
Syntax
No parameters.
Usage Guidelines
Use this command to reboot the switch if required after making configuration changes or under the
guidance of Alcatel-Lucent Networks customer support. The reload command powers down the switch,
making it unavailable for configuration. After the switch reboots, you can access it via a local console
connected to the serial port, or through an SSH, Telnet, or WebUI session. If you need to troubleshoot the
switch during a reboot, use a local console connection.
After you use the reload command, the switch prompts you for confirmation of this action. If you have not
saved your configuration, the switch returns the following message:
Do you want to save the configuration (y/n):
zEnter y to save the configuration.
zEnter n to not save the configuration.
zPress [Enter] to exit the command without saving changes or rebooting the switch.
If your configuration has already been saved, the switch returns the following message:
Do you really want to reset the system(y/n):
zEnter y to reboot the switch.
zEnter n to cancel this action.
The command will timeout if you do not enter y or n.
Example
The following command assumes you have already saved your configuration and you must reboot the
switch:
(host) (config) #reload
The switch returns the following messages:
Do you really want to reset the system(y/n): y
System will now restart!
...
Restarting system.
Command History
This command was introduced in AOS-W 1.0.
Command Information
Platforms Licensing Command Mode
All platforms Base operating system Enable and Config modes on master switches

402 |reload AOS-W 3.4.1 Command Line Interface | Reference Guide
AOS-W 3.4.1 Command Line Interface | Reference Guide reload-peer-sc | 403
reload-peer-sc
reload-peer-sc
Description
This command performs a reboot of the Supervisor Card in OmniAccess 6000 Mobility switches.
Syntax
No parameters.
Usage Guidelines
This command is supported only on switches that require the Supervisor Card (SC). The SC processes all
traffic from the line cards (LCs) and performs all management functions.
The reload-peer-sc command allows one SC to reset the other SC in a dual SC configuration. This does not
affect the SC on which the command is executed and the LCs which it controls.
After you use the reload-peer-sc command, the switch prompts you for confirmation of this action and
returns the following message:
Do you really want to reset the peer Supervisor Card(y/n):
zEnter y to reboot the peer SC.
zEnter n to cancel this action.
The command will timeout if you do not enter y or n.
Example
The following command reboots the peer SC:
reload-peer-sc
The switch returns the following messages:
Do you really want to reset the peer Supervisor Card(y/n):
Peer Supervisor Card will now restart.
Command History
This command was introduced in AOS-W 1.0.
Command Information
NOTE
This command is not applicable to the OmniAccess Supervisor Card III
Platforms Licensing Command Mode
Available only on the
OmniAccess 6000 Mobility
Switch
Base operating system Enable and Config modes on master
switches

404 | reload-peer-sc AOS-W 3.4.1 Command Line Interface | Reference Guide
AOS-W 3.4.1 Command Line Interface | Reference Guide rename | 405
rename
rename <filename> <newfilename>
Description
This command renames an existing system file.
Syntax
Usage Guidelines
Use this command to rename an existing system file on the switch. You can use a combination of numbers,
letters, and punctuation (periods, underscores, and dashes) to rename a file. The new name takes affect
immediately.
Make sure the renamed file uses the same file extension as the original file. If you change the file extension,
the file may be unrecognized by the system. For example, if you have an existing file named upgrade.log,
the new file must include the .log file extension.
You cannot rename the active configuration currently selected to boot the switch. If you attempt to rename
the active configuration file, the switch returns the following message:
Cannot rename active configuration file
To view a list of system files, and for more information about the directory contents, see “dir” on page 179.
Example
The following command changes the file named test_configuration to deployed_configuration:
(host) (config) #rename test_configuration deployed_configuration
Command History
This command was introduced in AOS-W 1.0.
Command Information
Parameter Description
filename An alphanumeric string that specifies the current name of the file on the system.
newfilename An alphanumeric string that specifies the new name of the file on the system.
Platforms Licensing Command Mode
All platforms Base operating system Eanble and Config modes on master
switches

406 |rename AOS-W 3.4.1 Command Line Interface | Reference Guide
AOS-W 3.4.1 Command Line Interface | Reference Guide restore | 407
restore
restore flash
Description
This command restores flash directories backed up to the flashbackup.tar.gz file.
Syntax
Usage Guidelines
Use the backup flash command to tar and compress flash directories to the flashbackup.tar.gz file.
Example
The following command restores flash directories from the flashbackup.tar.gz file:
(host) #restore flash
Command History
This command was introduced in AOS-W 3.0.
Command Information
Parameter Description
flash Restores flash directories from the flashbackup.tar.gz file.
Platforms Licensing Command Mode
All platforms Base operating system Enable mode on master switches

408 |restore AOS-W 3.4.1 Command Line Interface | Reference Guide
AOS-W 3.4.1 Command Line Interface | Reference Guide rf arm-profile | 409
rf arm-profile
rf
rf arm-profile <profile>
40MHz-allowed-bands {All|None|a-only|g-only}
acceptable-coverage-index <number>
active-scan (not intended for use)
assignment {disable|maintain|multi-band|single-band}
backoff-time <seconds>
client-aware
clone <profile>
error-rate-threshold <percent>
error-rate-wait-time <seconds>
free-channel-index <number>
ideal-coverage-index <number>
load-aware-scan-threshold
max-tx-power <dBm>
min-scan-time <# of scans>
min-tx-power <dBm>
mode-aware
multi-band-scan
no ...
noise-threshold <number>
noise-wait-time <seconds>
ps-aware-scan
rogue-ap-aware
scan-interval <seconds>
scan-time <milliseconds>
scanning
video-aware-scan
voip-aware-scan
Description
This command configures the Adaptive Radio Management (ARM) profile.
Syntax
Parameter Description Range Default
<profile> Name of this instance of the profile. The name must
be 1-63 characters. — “default”
40MHz-allowed- bands The specified setting allows ARM to determine if 40
MHz mode of operation is allowed on the 5 GHz or
2.4 GHz frequency band only, on both frequency
bands, or on neither frequency band.
All/None/
a-only/g-only a-only
All Allows 40 MHz channels on both the 5 GHZ (802.11a)
and 2.4 GHZ (802.11b/g) frequency bands.
None Disallows use of 40 MHz channels.
a-only Allows use of 40 MHz channels on the 5 GHZ
(802.11a) frequency band only.
g-only Allows use of 40 MHz channels on the 2.4 GHZ
(802.11b/g) frequency band only.
410 |rf arm-profile AOS-W 3.4.1 Command Line Interface | Reference Guide
acceptable-cov
erage-index
The minimal coverage that the AP should try to
achieve on its channel. The denser the AP
deployment, the lower this value should be.
This setting applies to multi-band implementations
only.
1-6 4
active-scan When the Active Scan checkbox is selected, an AP
initiates active scanning via probe request. This
option elicits more information from nearby APs, but
also creates additional management traffic on the
network. Active Scan is disabled by default, and
should not be enabled except under the direct
supervision of Alcatel-Lucent Support.
Default: disabled
disabled
assignment Activates one of four ARM channel/power
assignment modes. —single-band
(new
installations
only)
disable Disables ARM channel/power assignments.
maintain Maintains existing channel assignments.
multi-band Computes ARM assignments for both 5 GHZ
(802.11a) and 2.4 GHZ (802.11b/g) frequency bands.
single-band Computes ARM assignments for a single band.
backoff-time Time, in seconds, an AP backs off after requesting a
new channel or power. 120-3600 240
seconds
client-aware If the Client Aware option is enabled, the AP does not
change channels if there is active client traffic on that
AP. If Client Aware is disabled, the AP may change to
a more optimal channel, but this change may also
disrupt current client traffic.
—enabled
clone Name of an existing ARM profile from which
parameter values are copied. ——
error-rate-
threshold
The percentage of errors in the channel that triggers a
channel change. Recommended value is 50%. 0-100 50%
error-rate-wait
-time
Time, in seconds, that the error rate has to be at least
the error rate threshold to trigger a channel change. 1-
2,147,483,647
Recommended
Values: 1-100
30 seconds
free-channel-
index
The difference in the interference index between the
new channel and current channel must exceed this
value for the AP to move to a new channel. The
higher this value, the lower the chance an AP will
move to the new channel. Recommended value is 25.
10-40 25
ideal-coverage-
index
The coverage that the AP should try to achieve on its
channel. The denser the AP deployment, the lower
this value should be. Recommended value is 10.
2-20 10
Parameter Description Range Default
AOS-W 3.4.1 Command Line Interface | Reference Guide rf arm-profile | 411
load-aware-scan-
threshold
Load aware ARM preserves network resources
during periods of high traffic by temporarily halting
ARM scanning if the load for the AP gets too high.
The Load Aware Scan Threshold is the traffic
throughput level an AP must reach before it stops
scanning. The supported range for this setting is 0-
20000000 bytes/second. (Specify 0 to disable this
feature.)
1250000
bytes/
second
max-tx-power Maximum effective isotropic radiated power (EIRP)
from 3 to 33 dBm in 3 dBm increments. You may also
specify a special value of 127 dBm for regulatory
maximum to disable power adjustments for
environments such as outdoor mesh links. This value
takes into account both radio transmit power and
antenna gain.
Higher power level settings may be constrained by
local regulatory requirements and AP capabilities.
3, 6, 9, 12, 15,
18, 21, 24, 27,
30, 33, 127
127 dBm
min-scan-time Minimum number of times a channel must be
scanned before it is considered for assignment. The
supported range for this setting is 0-2,147,483,647
scans. Alcatel-Lucent recommends a Minimum Scan
Time between 1-20 scans.
Default: 8 scans
1-
2,147,483,647
Recommended
Values: 1-20
8 scans
min-tx-power Minimum effective isotropic radiated power (EIRP)
from 3 to 33 dBm in 3 dBm increments. You may also
specify a special value of 127 dBm for regulatory
minimum.This value takes into account both radio
transmit power and antenna gain.
Higher power level settings may be constrained by
local regulatory requirements and AP capabilities.
3, 6, 9, 12, 15,
18, 21, 24, 27,
30, 33, 127
9 dBm
mode-aware If enabled, ARM will turn APs into Air Monitors (AMs)
if it detects higher coverage levels than necessary.
This helps avoid higher levels of interference on the
WLAN. Although this setting is disabled by default,
you may want to enable this feature if your APs are
deployed in close proximity (e.g. less than 60 feet
apart).
— disabled
multi-band-scan When enabled, single-radio APs try to scan across
bands for rogue AP detection. —enabled
no Negates any configured parameter. — —
noise-threshold Maximum level of noise in a channel that triggers a
channel change (-dBm). 0-
2,147,483,647
Recommended
Values:
0-80 -dBm
75 -dBm
noise-wait-time Minimum time in seconds the noise level has to
exceed the Noise Threshold before it triggers a
channel change.
120-3600 120
seconds
ps-aware-scan When enabled, the AP will not scan if Power Save is
active. —enabled
rogue-ap-aware When enabled, the AP will try to contain off-channel
rogue APs. — disabled
Parameter Description Range Default
412 |rf arm-profile AOS-W 3.4.1 Command Line Interface | Reference Guide
Usage Guidelines
Adaptive Radio Management (ARM) is a radio frequency (RF) resource allocation algorithm that allows
each AP to determine the optimum channel selection and transmit power setting to minimize interference
and maximize coverage and throughput. This command configures an ARM profile that you apply to a radio
profile for the 5 GHz or 2.4 GHz frequency band (see “rf dot11a-radio-profile” on page 414 or “rf dot11g-
radio-profile” on page 420).
If you were running an earlier version of AOS-W with ARM disabled, ARM remains disabled when you
upgrade to the current release.
scan-interval If Scanning is enabled, the Scan Interval defines how
often the AP will leave its current channel to scan
other channels in the band.
Off-channel scanning can impact client performance.
Typically, the shorter the scan interval, the higher the
impact on performance. If you are deploying a large
number of new APs on the network, you may want to
lower the Scan Interval to help those APs find their
optimal settings more quickly. Raise the Scan Interval
back to its default setting after the APs are
functioning as desired.
0-
2,147,483,647
Recommended
Values: 0-30
10 seconds
scan-time The amount of time, in milliseconds, an AP will drift
out of the current channel to scan another channel. 50-2,147,
483,647
Recommended
Values: 50-200
110
millisecond
s
scanning The Scanning checkbox enables or disables AP
scanning across multiple channels. Disabling this
option also disables the following scanning features:
zMulti Band Scan
zRogue AP Aware
zVoip Aware Scan
zPower Save Scan
Do not disable Scanning unless you want to disable
ARM and manually configure AP channel and
transmission power.
—enabled
video-aware-scan As long as there is at least one video frame every
100 mSec the AP will reject an ARM scanning
request. Note that for each radio interface, video
frames must be defined in one of two ways:
zClassify the frame as video traffic via a session
ACL.
zEnable WMM on the WLAN’s SSID profile and
define a specific DSCP value as a video stream.
Next, create a session ACL to tag the video traffic
with the that DSCP value.
—enabled
voip-aware-scan Alcatel-Lucent’s VoIP Call Admission Control (CAC)
prevents any single AP from becoming congested
with voice calls. When you enable CAC, you should
also enable voip-aware-scan parameter in the ARM
profile, so the AP will not attempt to scan a different
channel if one of its clients has an active VoIP call.
This option requires that scanning is also enabled.
— disabled
Parameter Description Range Default
NOTE
AP configuration settings related to the IEEE 802.11n standard are configurable for Alcatel-Lucent’s OAW-AP120
series access points, which are IEEE 802.11n standard compliant devices.
AOS-W 3.4.1 Command Line Interface | Reference Guide rf arm-profile | 413
Using Adaptive Radio Management (ARM) in a Remote Network
Starting in AOS-W 3.4.1.x-rn 4.0, the ARM feature can be used by remote APs in bridge mode. Earlier
versions of AOS-W supported ARM on campus APs only.
Using Adaptive Radio Management (ARM) in a Mesh Network
When a mesh portal operates on a mesh network, the mesh portal determines the channel used by the mesh
feature. When a mesh point locates an upstream mesh portal, it will scan the regulatory domain channels
list to determine the channel assigned to it, for a mesh point always uses the channel selected by its mesh
portal. However, if a mesh portal uses an ARM profile enabled with a single-band or multi-band channel/
power assignment and the scanning feature, the mesh portal will scan the configured channel lists and the
ARM algorithm will assign the proper channel to the mesh portal.
If you are using ARM in your network, is important to note that mesh points, unlike mesh portals, do not
scan channels. This means that once a mesh point has selected a mesh portal or an upstream mesh point, it
will tune to this channel, form the link, and will not scan again unless the mesh link gets broken. This
provides good mesh link stability, but may adversely affect system throughput in networks with mesh
portals and mesh points. When ARM assigns optimal channels to mesh portals, those portals use different
channels, and once the mesh network has formed and all the mesh points have selected a portal (or
upstream mesh point), those mesh points will not be able to detect other portals on other channels that
could offer better throughput. This type of suboptimal mesh network may form if, for example, two or three
mesh points select the same mesh portal after booting, form the mesh network, and leave a nearby mesh
portal without any mesh points. Again, this will not affect mesh functionality, but may affect total system
throughput.
Example
The following command configures VoIP-aware scanning for the arm-profile named “voice-arm:”
(config) (host) #rf arm-profile voice-arm
voip-aware-scan
Command History
Command Information
Release Modification
AOS-W 3.0 Command introduced
AOS-W 3.3. Support for the high-throughput IEEE 802.11n standard was introduced
AOS-W 3.3.2 Support for the wait-time parameter was removed.
AOS-W 3.4.1 The voip-aware-scan parameter no longer requires a license, and is available in
the base OS.
Platforms Licensing Command Mode
All platforms Base operating system Enable or Config mode on master switches

414 | rf dot11a-radio-profile AOS-W 3.4.1 Command Line Interface | Reference Guide
rf dot11a-radio-profile
rf dot11a-radio-profile <profile>
arm-profile <profile>
beacon-period <milliseconds>
channel <num|num+|num->
channel-reuse {static|dynamic|disable}
channel-reuse-threshold
clone <profile>
csa
csa-count <number>
disable-arm-wids-function
dot11h
high-throughput-enable
ht-radio-profile <profile>
maximum-distance <maximum-distance>
mgmt-frame-throttle-interval <seconds>
mgmt-frame-throttle-limit <number>
mode {ap-mode|am-mode|apm-mode|sensor-mode}
no ...
radio-enable
spectrum-load-bal-domain
spectrum-load-balancing
tx-power <dBm>
Description
This command configures AP radio settings for the 5 GHz frequency band, including the Adaptive Radio
Management (ARM) profile and the high-throughput (802.11n) radio profile.
Syntax
Parameter Description Range Default
<profile> Name of this instance of the profile. The name
must be 1-63 characters. — “default”
arm-profile Configures Adaptive Radio Management (ARM)
feature. See “rf arm-profile” on page 409.— “default”
beacon-period Time, in milliseconds, between successive beacon
transmissions. The beacon advertises the AP’s
presence, identity, and radio characteristics to
wireless clients.
60 (minimum) 100
milliseconds
AOS-W 3.4.1 Command Line Interface | Reference Guide rf dot11a-radio-profile | 415
channel Channel number for the AP 802.11a/802.11n
physical layer. The available channels depend on
the regulatory domain (country). Channel number
configuration options for 20 MHz and 40 MHz
modes:
znum: Entering a channel number disables 40
MHz mode and activates 20 MHz mode for the
entered channel.
znum+: Entering a channel number with a plus
(+) sign selects a primary and secondary
channel for
40 MHz mode. The number entered becomes
the primary channel and the secondary channel
is determined by increasing the primary
channel number by 4. Example: 157+
represents 157 as the primary channel and 161
as the secondary channel.
znum-: Entering a channel number with a minus
(-) sign selects a primary and secondary
channel for
40 MHz mode. The number entered becomes
the primary channel and the secondary channel
is determined by decreasing the primary
channel number by 4. Example: 157-
represents 157 as the primary channel and 153
as the secondary channel.
NOTE: 20 MHz clients are allowed to associate
when a primary and secondary channel are
configured; however, the client will only use the
primary channel.
Depends on
regulatory
domain
—
channel-reuse When you enable the channel reuse feature, it can
operate in either of the following three modes;
static, dynamic or disable. (This feature is disabled
by default.)
zStatic mode: This mode of operation is a
coverage-based adaptation of the Clear
Channel Assessment (CCA) thresholds. In the
static mode of operation, the CCA is adjusted
according to the configured transmission
power level on the AP, so as the AP transmit
power decreases as the CCA threshold
increases, and vice versa.
zDynamic mode: In this mode, the Clear
Channel Assessment (CCA) thresholds are
based on channel loads, and take into account
the location of the associated clients. When
you set the Channel Reuse This feature is
automatically enabled when the wireless
medium around the AP is busy greater than half
the time. When this mode is enabled, the CCA
threshold adjusts to accommodate
transmissions between the AP its most distant
associated client.
zDisable mode: This mode does not support
the tuning of the CCA Detect Threshold.
enabled
disabled
enabled
Parameter Description Range Default

416 | rf dot11a-radio-profile AOS-W 3.4.1 Command Line Interface | Reference Guide
channel-reuse-
threshold
RX Sensitivity Tuning Based Channel Reuse
Threshold, in -dBm.
If the Rx Sensitivity Tuning Based Channel reuse
feature is set to static mode, this parameter
manually sets the AP’s Rx sensitivity threshold ( in
-dBm). The AP will filter out and ignore weak
signals that are below the channel threshold signal
strength.
If the value is set to zero, the feature will
automatically determine an appropriate threshold.
Depends on
regulatory
domain
—
clone Name of an existing radio profile from which
parameter values are copied. ——
csa Channel Switch Announcement (CSA), as defined
by IEEE 802.11h, allows an AP to announce that it
is switching to a new channel before it begins
transmitting on that channel.
Clients must support CSA in order to track the
channel change without experiencing disruption.
— disabled
csa-count Number of CSA announcements that are sent
before the AP begins transmitting on the new
channel.
1-16 4
disable-arm-wids-
function
Disables Adaptive Radio Management (ARM) and
Wireless IDS functions. These can be disabled if a
small increase in packet processing performance is
desired. If a radio is configured to operate in Air
Monitor mode, then these functions are always
enabled irrespective of this option. CAUTION: Use
carefully, since this effectively disables ARM and
WIDS
1-16 4
dot11h Enable advertisement of 802.11d (Country
Information) and 802.11h (TPC or Transmit Power
Control) capabilities This parameter is enabled by
default.
—enabled
high-throughput-
enable
Enables high-throughput (802.11n) features on a
radio using the 5 GHz frequency band. —enabled
ht-radio-profile Name of high-throughput radio profile to use for
configuring high-throughput support on the 5 GHz
frequency band. See “rf ht-radio-profile” on
page 429.
— “default-a”
maximum-distance Maximum distance between a client and an AP or
between a mesh point and a mesh portal, in
meters. This value is used to derive ACK and CTS
timeout times. A value of 0 specifies default
settings for this parameter, where timeouts are only
modified for outdoor mesh radios which use a
distance of 16km.
The upper limit for this parameter varies,
depending on the 20/40 MHz mode for a 5 GHz
frequency band radio:
z20MHz mode: 58km
z40MHz mode: 27km
Note that if you configure a value above the
supported maximum, the maximum supported
value will be used instead. Values below 600m will
use default settings.
0-57km
(40MHz mode)
0-27km
(20MHz mode)
0 meters
Parameter Description Range Default
AOS-W 3.4.1 Command Line Interface | Reference Guide rf dot11a-radio-profile | 417
mgmt-frame-throttle-
interval
Averaging interval for rate limiting management
frames in seconds. Zero disables rate limiting.
Note: This parameter only applies to AUTH and
ASSOC/RE-ASSOC management frames.
0-60 1 second
interval
mgmt-frame-throttle-
limit
Maximum number of management frames allowed
in each throttle interval.
NOTE: This parameter only applies to AUTH and
ASSOC/RE-ASSOC management frames.
0-999999 20 frames
per interval
mode One of the operating modes for the AP. ap-mode | am-
mode | sensor-
mode
ap-mode
ap-mode Device provides transparent, secure, high-speed
data communications between wireless network
devices and the wired LAN.
am-mode Device behaves as an air monitor to collect
statistics, monitor traffic, detect intrusions, enforce
security policies, balance traffic load, self-heal
coverage gaps, etc.
apm-mode AP monitor mode.
sensor-mode Device operates as an RFprotect managed sensor.
Changing the mode of a radio from ap-mode or
am-mode to sensor-mode or from sensor-mode to
ap-mode or am-mode causes the AP to reboot.
For a dual-radio AP, setting one radio in sensor-
mode causes both radios to behave as sensors.
no Negates any configured parameter. — —
radio-enable Enables or disables radio configuration. — enabled
spectrum-load-bal-
domain
Define a spectrum load balancing domain to
manually create RF neighborhoods.
Use this option to create RF neighborhood
information for networks that have disabled
Adaptive Radio Management (ARM) scanning and
channel assignment.
zIf spectrum load balancing is enabled in a
802.11a radio profile but the spectrum load
balancing domain is not defined, AOS-W uses
the ARM feature to calculate RF
neighborhoods.
zIf spectrum load balancing is enabled in a
802.11a radio profile and a spectrum load
balancing domain is also defined, AP radios
belonging to the same spectrum load balancing
domain will be considered part of the same RF
neighborhood for load balancing, and will not
recognize RF neighborhoods defined by the
ARM feature.
——
Parameter Description Range Default

418 | rf dot11a-radio-profile AOS-W 3.4.1 Command Line Interface | Reference Guide
Usage Guidelines
This command configures radios that operate in the 5 GHz frequency band, which includes radios utilizing
the IEEE 802.11a or IEEE 802.11n standard. Channels must be valid for the country configured in the AP
regulatory domain profile (see “ap regulatory-domain-profile” on page 87).
To view the supported channels, use the show ap allowed-channels command.
Examples
The following command configures APs to operate in AM mode for the selected dot11a-radio-profile named
“samplea:”
(host) (config) #rf dot11a-radio-profile samplea mode am-mode
The following command configures APs to operate in high-throughput (802.11n) mode on the
5 Ghz frequency band for the selected dot11a-radio profile named “samplea” and assigns a high-throughout
radio profile named “default-a:”
(host) (config) #rf dot11a-radio-profile samplea
high-throughput-enable
ht-radio-profile default-a
The following command configures a primary channel number of 157 and a secondary channel number of
161 for 40 MHz mode of operation for the selected dot11a-radio profile named “samplea:”
(host) (config) #rf dot11a-radio-profile samplea
channel <157+>
spectrum-load-
balancing
The Spectrum Load Balancing feature helps
optimize network resources by balancing clients
across channels, regardless of whether the AP or
the switch is responding to the wireless clients'
probe requests.
If enabled, the switch compares whether or not an
AP has more clients than its neighboring APs on
other channels. If an AP’s client load is at or over a
predetermined threshold as compared to its
immediate neighbors, or if a neighboring Alcatel-
Lucent AP on another channel does not have any
clients, load balancing will be enabled on that AP.
This feature is disabled by default.
NOTE: The spectrum load balancing feature
available in AOS-W 3.4.x and later releases
completely replaces the AP load balancing feature
available earlier versions of AOS-W. When you
upgrade to AOS-W 3.4.x or later, you must
manually configure the spectrum load balancing
settings, as the AP load balancing feature can no
longer be used, and any previous AP load
balancing settings will not be preserved.
— disabled
tx-power Sets the initial transmit power (dBm) on which the
AP operates, unless a better choice is available
through either calibration or from RF Plan.
This parameter can be set from 0 to 51 in .5 dBm
increments, or set to the regulatory maximum value
of 127 dBm.
Transmission power may be further limited by
regulatory domain constraints and AP capabilities.
0-51 dBm, 127
dBm 14 dBm
Parameter Description Range Default

AOS-W 3.4.1 Command Line Interface | Reference Guide rf dot11a-radio-profile | 419
Command History
Command Information
Release Modification
AOS-W 3.0 Command introduced
AOS-W 3.3.2 Introduced support for the high-throughput IEEE 802.11n standard.
AOS-W 3.4 Support for the following parameters:
zSpectrum load balancing
zSpectrum load balancing domain
zRX Sensitivity Tuning Based Channel Reuse
zRX Sensitivity Threshold
zARM/WIDS Override
AOS-W 3.4.1 The maximum-distance parameter was introduced.
Platforms Licensing Command Mode
All platforms Base operating system Config mode on master switches

420 | rf dot11g-radio-profile AOS-W 3.4.1 Command Line Interface | Reference Guide
rf dot11g-radio-profile
rf dot11g-radio-profile <profile>
arm-profile <profile>
beacon-period <milliseconds>
channel <num|num+|num->
channel-reuse {static|dynamic|disable}
channel-reuse-threshold
clone <profile>
csa
csa-count <number>
disable-arm-wids-function
dot11b-protection
dot11h
high-throughput-enable
ht-radio-profile <profile>
interference-immunity
maximum-distance <maximum-distance>
mgmt-frame-throttle-interval <seconds>
mgmt-frame-throttle-limit <number>
mode {ap-mode|am-mode|apm-mode|sensor-mode}
no ...
radio-enable
spectrum-load-bal-domain
spectrum-load-balancing
tx-power <dBm>
Description
This command configures AP radio settings for the 2.4 GHz frequency band, including the Adaptive Radio
Management (ARM) profile and the high-throughput (802.11n) radio profile.
Syntax
Parameter Description Range Default
<profile> Name of this instance of the profile. The name must
be 1-63 characters. — “default”
arm-profile Configures Adaptive Radio Management (ARM)
feature. See “rf arm-profile” on page 409.— “default”
beacon-period Time, in milliseconds, between successive beacon
transmissions. The beacon advertises the AP’s
presence, identity, and radio characteristics to
wireless clients.
60 (minimum) 100
millisecon
ds
clone Name of an existing radio profile from which
parameter values are copied. ——
csa Channel Switch Announcement (CSA), as defined by
IEEE 802.11h, allows an AP to announce that it is
switching to a new channel before it begins
transmitting on that channel.
Clients must support CSA in order to track the
channel change without experiencing disruption.
— disabled
csa-count Number of CSA announcements that are sent before
the AP begins transmitting on the new channel. 1-16 4
AOS-W 3.4.1 Command Line Interface | Reference Guide rf dot11g-radio-profile | 421
channel Channel number for the AP 802.11a/802.11n physical
layer. The available channels depend on the
regulatory domain (country). Channel number
configuration options for 20 MHz and 40 MHz
modes:
znum: Entering a channel number disables 40
MHz mode and activates 20 MHz mode for the
entered channel.
znum+: Entering a channel number with a plus (+)
sign selects a primary and secondary channel for
40 MHz mode. The number entered becomes the
primary channel and the secondary channel is
determined by increasing the primary channel
number by 4. Example: 157+ represents 157 as
the primary channel and 161 as the secondary
channel.
znum-: Entering a channel number with a minus (-)
sign selects a primary and secondary channel for
40 MHz mode. The number entered becomes the
primary channel and the secondary channel is
determined by decreasing the primary channel
number by 4. Example: 157- represents 157 as
the primary channel and 153 as the secondary
channel.
NOTE: 20 MHz clients are allowed to associate when
a primary and secondary channel are configured;
however, the client will only use the primary channel.
Depends on
regulatory
domain
—
channel-reuse When you enable the channel reuse feature, it can
operate in either of the following three modes; static,
dynamic or disable. (This feature is disabled by
default.)
zStatic mode: This mode of operation is a
coverage-based adaptation of the Clear Channel
Assessment (CCA) thresholds. In the static mode
of operation, the CCA is adjusted according to
the configured transmission power level on the
AP, so as the AP transmit power decreases as the
CCA threshold increases, and vice versa.
zDynamic mode: In this mode, the Clear Channel
Assessment (CCA) thresholds are based on
channel loads, and take into account the location
of the associated clients. When you set the
Channel Reuse This feature is automatically
enabled when the wireless medium around the
AP is busy greater than half the time. When this
mode is enabled, the CCA threshold adjusts to
accommodate transmissions between the AP its
most distant associated client.
zDisable mode: This mode does not support the
tuning of the CCA Detect Threshold.
enabled
disabled
enabled
channel-reuse-
threshold
RX Sensitivity Tuning Based Channel Reuse
Threshold, in -dBm.
If the Rx Sensitivity Tuning Based Channel reuse
feature is set to static mode, this parameter manually
sets the AP’s Rx sensitivity threshold ( in -dBm). The
AP will filter out and ignore weak signals that are
below the channel threshold signal strength.
If the value is set to zero, the feature will
automatically determine an appropriate threshold.
Depends on
regulatory
domain
—
Parameter Description Range Default
422 | rf dot11g-radio-profile AOS-W 3.4.1 Command Line Interface | Reference Guide
disable-arm-wids-
function
Disables Adaptive Radio Management (ARM) and
Wireless IDS functions. These can be disabled if a
small increase in packet processing performance is
desired. If a radio is configured to operate in Air
Monitor mode, then these functions are always
enabled irrespective of this option. CAUTION: Use
carefully, since this effectively disables ARM and
WIDS
1-16 4
dot11b-protection Enable or disable protection for 802.11b clients. This
parameter is enabled by default. Disabling this
feature may improve performance if there are no
802.11b clients on the WLAN.
WARNING: Disabling protection violates the 802.11
standard and may cause interoperability issues. If
this feature is disabled on a WLAN with 802.11b
clients, the 802.11b clients will not detect an 802.11g
client talking and can potentially transmit at the same
time, thus garbling both frames.
—enabled
dot11h Enable advertisement of 802.11d (Country
Information) and 802.11h (TPC or Transmit Power
Control) capabilities This parameter is enabled by
default.
—enabled
high-throughput-
enable
Enables high-throughput (802.11n) features on a
radio using the 2.4 GHz frequency band. —enabled
ht-radio-profile Name of high-throughput radio profile to use for
configuring high-throughput support on the 5 GHz
frequency band. See “rf ht-radio-profile” on
page 429.
— “default-a”
interference-
immunity
Set a value for 802.11 Interference Immunity. This
parameter sets the interference immunity on the 2.4
Ghz band.
The default setting for this parameter is level 2. When
performance drops due to interference from non-
802.11 interferers (such as DECT or Bluetooth
devices), the level can be increased up to level 5 for
improved performance. However, increasing the level
makes the AP slightly “deaf” to its surroundings,
causing the AP to lose a small amount of range.
The levels for this parameter are:
zLevel-0: no ANI adaptation.
zLevel-1: noise immunity only.
zLevel-2: noise and spur immunity. This is the
default setting
zLevel-3: level 2 and weak OFDM immunity.
zLevel-4: level 3 and FIR immunity.
zLevel-5: disable PHY reporting.
NOTE: Do not raise the noise immunity feature’s
default setting if the channel-reuse-threshold feature
is also enabled. A level-3 to level-5 Noise Immunity
setting is not compatible with the Channel Reuse
feature.
Level-0 - Level-
5Level-2
Parameter Description Range Default
AOS-W 3.4.1 Command Line Interface | Reference Guide rf dot11g-radio-profile | 423
maximum-distance Maximum distance between a client and an AP or
between a mesh point and a mesh portal, in meters.
This value is used to derive ACK and CTS timeout
times. A value of 0 specifies default settings for this
parameter, where timeouts are only modified for
outdoor mesh radios which use a distance of 16km.
The upper limit for this parameter varies, depending
on the 20/40 MHz mode for a 2.4GHz frequency
band radio:
z20MHz mode: 54km
z40MHz mode: 24km
Note that if you configure a value above the
supported maximum, the maximum supported value
will be used instead. Values below 600m will use
default settings.
0-24km
(40MHz mode)
0-54km
(20MHz mode)
0 meters
mgmt-frame-throttle-
interval
Averaging interval for rate limiting management
frames in seconds. Zero disables rate limiting.
Note: This parameter only applies to AUTH and
ASSOC/RE-ASSOC management frames.
0-60 1 second
interval
mgmt-frame-throttle-
limit
Maximum number of management frames allowed in
each throttle interval.
NOTE: This parameter only applies to AUTH and
ASSOC/RE-ASSOC management frames.
0-999999 20 frames
per interval
mode One of the operating modes for the AP. ap-mode | am-
mode | sensor-
mode
ap-mode
ap-mode Device provides transparent, secure, high-speed
data communications between wireless network
devices and the wired LAN.
am-mode Device behaves as an air monitor to collect statistics,
monitor traffic, detect intrusions, enforce security
policies, balance traffic load, self-heal coverage
gaps, etc.
apm-mode AP monitor mode.
sensor-mode Device operates as an RFprotect managed sensor.
Changing the mode of a radio from ap-mode or am-
mode to sensor-mode or from sensor-mode to ap-
mode or am-mode causes the AP to reboot.
For a dual-radio AP, setting one radio in sensor-mode
causes both radios to behave as sensors.
no Negates any configured parameter. — —
radio-enable Enables or disables radio configuration. — enabled
Parameter Description Range Default

424 | rf dot11g-radio-profile AOS-W 3.4.1 Command Line Interface | Reference Guide
Usage Guidelines
This command configures radios that operate in the 2.4 GHz frequency band, which includes radios utilizing
the IEEE 802.11b/g or IEEE 802.11n standard. Channels must be valid for the country configured in the AP
regulatory domain profile (see “ap regulatory-domain-profile” on page 87).
To view the supported channels, use the show ap allowed-channels command.
Examples
The following command configures APs to operate in AM mode for the selected dot11g-radio-profile named
“sampleg:”
spectrum-load-bal-
domain
Define a spectrum load balancing domain to
manually create RF neighborhoods.
Use this option to create RF neighborhood
information for networks that have disabled Adaptive
Radio Management (ARM) scanning and channel
assignment.
zIf spectrum load balancing is enabled in a
802.11g radio profile but the spectrum load
balancing domain is not defined, AOS-W uses the
ARM feature to calculate RF neighborhoods.
zIf spectrum load balancing is enabled in a
802.11g radio profile and a spectrum load
balancing domain is also defined, AP radios
belonging to the same spectrum load balancing
domain will be considered part of the same RF
neighborhood for load balancing, and will not
recognize RF neighborhoods defined by the ARM
feature.
——
spectrum-load-
balancing
The Spectrum Load Balancing feature helps optimize
network resources by balancing clients across
channels, regardless of whether the AP or the switch
is responding to the wireless clients' probe requests.
If enabled, the switch compares whether or not an AP
has more clients than its neighboring APs on other
channels. If an AP’s client load is at or over a
predetermined threshold as compared to its
immediate neighbors, or if a neighboring Alcatel-
Lucent AP on another channel does not have any
clients, load balancing will be enabled on that AP.
This feature is disabled by default.
NOTE: The spectrum load balancing feature available
in AOS-W 3.4.x and later releases completely
replaces the AP load balancing feature available
earlier versions of AOS-W. When you upgrade to
AOS-W 3.4.x or later, you must manually configure
the spectrum load balancing settings, as the AP load
balancing feature can no longer be used, and any
previous AP load balancing settings will not be
preserved.
— disabled
tx-power Sets the initial transmit power (dBm) on which the AP
operates, unless a better choice is available through
either calibration or from RF Plan.
This parameter can be set from 0 to 51 in .5 dBm
increments, or set to the regulatory maximum value
of 127 dBm.
Transmission power may be further limited by
regulatory domain constraints and AP capabilities.
0-51 dBm, 127
dBm 14 dBm
Parameter Description Range Default
AOS-W 3.4.1 Command Line Interface | Reference Guide rf dot11g-radio-profile | 425
rf dot11g-radio-profile sampleg
mode am-mode
The following command configures APs to operate in high-throughput (802.11n) mode on the
2.4 Ghz frequency band for the selected dot11g-radio profile named “sampleg” and assigns a high-
throughout radio profile named “default-g:”
rf dot11g-radio-profile sampleg
high-throughput-enable
ht-radio-profile default-g
The following command configures a primary channel number of 1 and a secondary channel number of 5
for 40 MHz mode of operation for the selected dot11g-radio profile named “sampleg:”
rf dot11g-radio-profile sampleg
channel <1+>
Command History
Command Information
Release Modification
AOS-W 3.0 Command introduced
AOS-W 3.3.2 Introduced protection for 802.11b clients and support for the high-throughput
IEEE 802.11n standard.
AOS-W 3.4 Support for the following parameters:
zSpectrum load balancing
zSpectrum load balancing domain
zRX Sensitivity Tuning Based Channel Reuse
zRX Sensitivity Threshold
zARM/WIDS Override
AOS-W 3.4.1 The maximum-distance parameter was introduced.
Platforms Licensing Command Mode
All platforms Base operating system Config mode on master switches
426 | rf event-thresholds-profile AOS-W 3.4.1 Command Line Interface | Reference Guide
rf event-thresholds-profile
rf event-thresholds-profile <profile>
bwr-high-wm <percent>
bwr-low-wm <percent>
clone <profile>
detect-frame-rate-anomalies
fer-high-wm <percent>
fer-low-wm <percent>
ffr-high-wm <percent>
ffr-low-wm <percent>
flsr-high-wm <percent>
flsr-low-wm <percent>
fnur-high-wm <percent>
fnur-low-wm <percent>
frer-high-wm <percent>
frer-low-wm <percent>
frr-high-wm <percent>
frr-low-wm <percent>
no ...
Description
This command configures the event thresholds profile.
Syntax
Parameter Description Range Default
<profile> Name of this instance of the profile. The name must
be 1-63 characters. — “default”
bwr-high-wm If bandwidth in an AP exceeds this value, a
bandwidth exceeded condition exists. The value
represents the percentage of maximum for a given
radio. (For 802.11b, the maximum bandwidth is 7
Mbps. For 802.11 a and g, the maximum is 30
Mbps.) The recommended value is 85%.
0-100 0%
bwr-low-wm After a bandwidth exceeded condition exists, the
condition persists until bandwidth drops below this
value. The recommended value is 70%.
0-100 0%
clone Name of an existing radio profile from which
parameter values are copied. ——
detect-frame-
rate-anomalies
Enable or disables detection of frame rate
anomalies. — disabled
fer-high-wm If the frame error rate (as a percentage of total
frames in an AP) exceeds this value, a frame error
rate exceeded condition exists. The recommended
value is 16%.
0-100 0%
fer-low-wm After a frame error rate exceeded condition exists,
the condition persists until the frame error rate
drops below this value. The recommended value is
8%.
0-100 0%
ffr-high-wm If the frame fragmentation rate (as a percentage of
total frames in an AP) exceeds this value, a frame
fragmentation rate exceeded condition exists. The
recommended value is 16%.
0-100 16%
AOS-W 3.4.1 Command Line Interface | Reference Guide rf event-thresholds-profile | 427
Usage Guidelines
The event threshold profile configures Received Signal Strength Indication (RSSI) metrics. When certain RF
parameters are exceeded, these events can signal excessive load on the network, excessive interference, or
faulty equipment. This profile and many of the detection parameters are disabled (value is 0) by default.
Example
The following command configures an event threshold profile:
(host) (config) #rf event-thresholds-profile et1
detect-frame-rate-anomalies
Command History
This command was introduced in AOS-W 3.0
ffr-low-wm After a frame fragmentation rate exceeded
condition exists, the condition persists until the
frame fragmentation rate drops below this value.
The recommended value is 8%.
0-100 8%
flsr-high-wm If the rate of low-speed frames (as a percentage of
total frames in an AP) exceeds this value, a low-
speed rate exceeded condition exists. This could
indicate a coverage hole. The recommended value
is 16%.
0-100 16%
flsr-low-wm After a low-speed rate exceeded condition exists,
the condition persists until the percentage of low-
speed frames drops below this value. The
recommended value is 8%.
0-100 8%
fnur-high-wm If the non-unicast rate (as a percentage of total
frames in an AP) exceeds this value, a non-unicast
rate exceeded condition exists. This value depends
upon the applications used on the network.
0-100 0%
fnur-low-wm After a non-unicast rate exceeded condition exists,
the condition persists until the non-unicast rate
drops below this value.
0-100 0%
frer-high-wm If the frame receive error rate (as a percentage of
total frames in an AP) exceeds this value, a frame
receive error rate exceeded condition exists. The
recommended value is 16%.
0-100 16%
frer-low-wm After a frame receive error rate exceeded condition
exists, the condition persists until the frame receive
error rate drops below this value. The
recommended value is 8%.
0-100 8%
frr-high-wm If the frame retry rate (as a percentage of total
frames in an AP) exceeds this value, a frame retry
rate exceeded condition exists. The recommended
value is 16%.
0-100 16%
frr-low-wm After a frame retry rate exceeded condition exists,
the condition persists until the frame retry rate
drops below this value. The recommended value is
8%.
0-100 8%
no Negates any configured parameter. — —
Parameter Description Range Default

428 | rf event-thresholds-profile AOS-W 3.4.1 Command Line Interface | Reference Guide
Command Information
Platforms Licensing Command Mode
All platforms Base operating system Config mode on master switches
AOS-W 3.4.1 Command Line Interface | Reference Guide rf ht-radio-profile | 429
rf ht-radio-profile
rf ht-radio-profile <profile>
40MHz-intolerance
clone <profile>
honor-40MHz-intolerance
no
single-chain-legacy
Description
This command configures high-throughput AP radio settings. High-throughput features use the IEEE
802.11n standard.
Syntax
Usage Guidelines
The ht-radio-profile configures high-throughput settings for networks utilizing the IEEE 802.11n standard,
which supports 40 MHZ channels and operates in both the 2.4 GHZ and 5 GHZ frequency bands.
The ht-radio-profile you wish to use must be assigned to a dot11a and/or dot11g-radio-profile. You can
assign the same profile or different profiles to the 2.4 GHZ and 5 GHZ frequency bands. See “rf dot11a-radio-
profile” on page 414 and “rf dot11g-radio-profile” on page 420.
Example
The following command configures an ht-radio-profile named “default-g” and enables 40MHz-intolerance:
(host) (config) #rf ht-radio-profile default-g
Parameter Description Range Default
<profile> Name of this instance of the profile. The name must
be 1-63 characters.
Default Options:
z“Default-a” is generally used in association with
high-throughput devices running on the 5 GHz
frequency band, see “rf dot11a-radio-profile” on
page 414.
z“Default-g” is generally used in association with
high-throughput devices running on the 2.4 GHz
frequency band, see “rf dot11g-radio-profile” on
page 420.
z“Default” is generally used when the same ht-
radio-profile is desired for use with both
frequency bands.
—default-a
default-g
default
40MHz-
intolerance
Controls whether or not APs using this radio profile
will advertise intolerance of 40 MHz operation. By
default, 40 MHz operation is allowed.
— disabled
clone Name of an existing high-throughput radio profile
from which parameter values are copied. ——
honor-40MHz-
intolerance
When enabled, the radio will stop using the 40 MHz
channels if the 40 MHz intolerance indication is
received from another AP or station.
—enabled
no Negates any configured parameter. — —
single-chain-legacy Interoperability for misbehaving legacy stations (keep
disabled unless necessary) disabled
430 | rf ht-radio-profile AOS-W 3.4.1 Command Line Interface | Reference Guide
40MHz-intolerance
Command History
Command Information
Release Modification
AOS-W 3.0 Command introduced
AOS-W 3.3.2 Support for the dsss-cck-40mhz parameter removed
AOS-W 3.4 Introduced the single-chain-legacy parameter.
Platforms Licensing Command Mode
All platforms, but operates with
IEEE 802.11n compliant
devices only
Base operating system Config mode on master switches
AOS-W 3.4.1 Command Line Interface | Reference Guide rf optimization-profile | 431
rf optimization-profile
rf optimization-profile <profile>
clone <profile>
coverage-hole-detection
detect-association-failure
detect-interference
handoff-assist
hole-detection-interval <seconds>
hole-good-rssi-threshold <number>
hole-good-sta-ageout <seconds>
hole-idle-sta-ageout <seconds>
hole-poor-rssi-threshold <number>
interference-baseline <seconds>
interference-exceed-threshold <seconds>
interference-threshold <percent>
low-rssi-threshold <number>
no ...
rssi-check-frequency <number>
rssi-falloff-wait-time <seconds>
Description
This command configures the RF optimization profile.
Syntax
Parameter Description Range Default
<profile> Name of this instance of the profile. The name must
be 1-63 characters. — “default”
clone Name of an existing optimization profile from which
parameter values are copied. ——
coverage-hole-
detection
Enables or disables coverage hole detection.
The Wireless Intrusion Protection license must be
installed.
— disabled
detect-association-
failure
Enables or disables STA association failure detection. — disabled
detect-interference Enables or disables interference detection. — disabled
handoff-assist Allows the switch to force a client off an AP when the
RSSI drops below a defined minimum threshold. — disabled
hole-detection-
interval
Time, in seconds, after a coverage hole is detected
until a coverage hole event notification is generated.
The Wireless Intrusion Protection license must be
installed.
180
seconds
hole-good-rssi-
threshold
Stations with signal strength above this value are
considered to have good coverage.
The Wireless Intrusion Protection license must be
installed.
20
hole-good-sta-ageout Time, in seconds, after which a station with good
coverage is aged out.
The Wireless Intrusion Protection license must be
installed.
30 seconds

432 | rf optimization-profile AOS-W 3.4.1 Command Line Interface | Reference Guide
Usage Guidelines
The RF optimization includes parameters for the following features:.
zCoverage hole detection looks for clients unable to associate to any AP or clients that are associating at
very low data rates or with low signal strength. These symptoms indicate areas where holes in radio
coverage exist. When the system detects such coverage holes, you are notified of the condition via the
event log.
zDetection of interference near a wireless client station or AP based on an increase in the frame retry rate
or frame receive error rate.
Example
The following command configures an RF optimization profile:
(host) (config) #rf optimization-profile opt1
coverage-hole-detection
detect-association-failure
detect-interference
Command History
hole-idle-sta-ageout Time, in seconds, after which a station in a poor
coverage area is aged out.
The Wireless Intrusion Protection license must be
installed.
90 seconds
hole-poor-rssi-
threshold
Stations with signal strength below this value will
trigger detection of a coverage hole.
The Wireless Intrusion Protection license must be
installed.
10
interference-
baseline
Time, in seconds, the air monitor should learn the
state of the link between the AP and client to create
frame retry rate (FRR) and frame receive error rate
(FRER) baselines.
30 seconds
interference-exceed-
time
Time, in seconds, the FRR or FRER exceeds the
threshold before interference is reported. 30 seconds
interference-
threshold
Percentage increase in the frame retry rate (FRR) or
frame receive error rate (FRER) before interference
monitoring begins on a given channel.
0-100 100%
low-rssi-threshold Minimum RSSI, above which deauth should never be
sent. 0
no Negates any configured parameter. — —
rssi-check-frequency Interval, in seconds, to sample RSSI. 0 seconds
rssi-falloff-wait-
time
Time, in seconds, to wait with decreasing RSSI
before deauth is sent to the client. The maximum
value is 8 seconds.
0-8 0 seconds
Parameter Description Range Default
Version Modification
AOS-W 3.0 Command introduced
AOS-W 3.4.1 Command Line Interface | Reference Guide rf optimization-profile | 433
Command Information
AOS-W 3.4 The following parameters were deprecated:
zap-lb-max-retries <number>
zap-lb-user-high-wm <percent>
zap-lb-user-low-wm <percent>
zap-lb-util-high-wm <percent>
zap-lb-util-low-wm <percent>
zap-lb-util-wait-time <seconds
zap-load-balancing
Use the command rf dot11a-radio-profile spectrum-load-balancing and
rf dot11g-radio-profile spectrum-load-balancing to enable the spectrum
load balanncing feature.
Platforms Licensing Command Mode
All platforms Base operating system Config mode on master switches
Version Modification

434 | rf optimization-profile AOS-W 3.4.1 Command Line Interface | Reference Guide

AOS-W 3.4.1 Command Line Interface | Reference Guide rft | 435
rft
rft test profile antenna-connectivity ap-name <name> [dest-mac <macaddr> [phy
{a|g}| radio {0|1}]]
rft test profile link-quality {ap-name <name> dest-mac <macaddr> [phy {a|g}|
radio {0|1}] | bssid <bssid> dest-mac <macaddr> | ip-addr <ipaddr>
dest-mac <macaddr> [phy {a|g}|radio {0|1}]}
rft test profile raw {ap-name <name> dest-mac <macaddr> [phy {a|g}|radio {0|1}]
| bssid <bssid> dest-mac <macaddr> | ip-addr <ipaddr> dest-mac <macaddr> [phy
{a|g}|radio {0|1}]}
Description
This command is used for RF troubleshooting.
Syntax
Usage Guidelines
This command can run predefined test profiles for antenna connectivity, link quality, or raw testing. You
should only run these commands when directed to do so by an Alcatel-Lucent support representative.
Command History
This command was introduced in AOS-W 3.0.
Command Information
Parameter Description Range
ap-name Name of the AP that performs the test. —
dest-mac MAC address of the client to be tested. —
phy 802.11 type, either a or g. a | g
radio Radio ID, either 0 or 1. 0 | 1
bssid BSSID of the AP that performs the test. —
ip-addr IP address of the AP that performs the test.
Platforms Licensing Command Mode
All platforms Base operating system Config mode on master switches

436 |rft AOS-W 3.4.1 Command Line Interface | Reference Guide

AOS-W 3.4.1 Command Line Interface | Reference Guide router mobile | 437
router mobile
router mobile
Description
This command enables Layer-3 (IP) mobility.
Syntax
No parameters.
Usage Guidelines
IP mobility is disabled by default on the switch. You need to use this command to enable IP mobility. This
command must be executed on all switches (master and local) that need to provide support for layer-3
roaming in a mobility domain.
You can disable IP mobility in a virtual AP profile with the wlan virtual-ap command (IP mobility is
enabled by default in a virtual AP profile).
Example
This command enables IP mobility:
(host) (config) #router mobile
Command History
Command Information
Release Modification
AOS-W 3.0 Command introduced
Platforms Licensing Command Mode
All platforms Base operating system Config mode on master switches

438 |router mobile AOS-W 3.4.1 Command Line Interface | Reference Guide
AOS-W 3.4.1 Command Line Interface | Reference Guide router ospf | 439
router ospf
router ospf {area <area-id> stub [no-summary] | router-id <rtr-id> | subnet exclude
<addr> <mask>
Description
Global OSPF configuration for the upstream router.
Syntax
Usage Guidelines
OSPFv2 is a dynamic Interior Gateway routing Protocol (IGP) based on IETF RFC 2328. The AOS-W
implementation of OSPF allows switches to deploy effectively in a Layer 3 topology. For more detailed
information, refer to the OSPF Chapter in the AOS-W User Guide.
Example
By default OSPF will advertise all the user VLAN subnet addresses in the router LSA (Link-State
Advertisement). To control the OSPF advertisement, execute the following command:
(host) (config) # router ospf subnet exclude 75.1.1.0 255.255.0.0
With the above command, any user VLAN subnet matching 75.1/16 will not be advertised in the router LSA.
To return to the default advertisement, execute the command:
(host) (config) # no router ospf subnet exclude 75.1.1.0 255.255.0.0
Related Commands
Command History
Command Information
Parameter Description
area <area-id> stub [no-summary] Set an area as a Total Stub Area. Enter the area ID in dotted
decimal format (A.B.C.D.)
router-id <rtr-id> Enter the router ID in IP address format.
subnet exclude <addr> <mask> Specify the subnet that OSPF will not advertise. Enter the subnet
and mask address in dotted decimal format (A.B.C.D).
Command Description
show ip ospf View OSPF process on the router
show ip ospf interface View the configure OSPF interface.
Release Modification
AOS-W 3.4 Command introduced
Platforms Licensing Command Mode
All Platforms Base operating system Configuration Mode (config)

440 |router ospf AOS-W 3.4.1 Command Line Interface | Reference Guide
AOS-W 3.4.1 Command Line Interface | Reference Guide service | 441
service
service [dhcp] [network-storage] [print-server]
Description
This command enables the DHCP server on the switch.
Syntax
Usage Guidelines
You can enable and configure DHCP, network-storage or print server in the switch to provide the following:
zDHCP: IP addresses to wireless clients if an external DHCP server is not available.
zNetwork-storage: To provide access to the storage devices attached to the switch.
zPrinter-server: To provide access to printers attached to the switch.
Example
The following command enables the DHCP server in the switch:
(host) (config) #service dhcp
The following command enables the NAS services in the switch:
(host) (config) #service network-storage
The following command enables the printer services in the switch:
(host) (config) #service print-server
Command History
The DHCP command was introduced in AOS-W 3.0.
The network-storage and print-server options was introduced in AOS-W 3.4
Command Information
Parameter Description Default
dhcp Enables the DHCP server disabled
network-storage Enables the NAS service disabled
print-server Enables the printer service disabled
Platforms Licensing Command Mode
All platforms Base operating system Config mode on master switches

442 | service AOS-W 3.4.1 Command Line Interface | Reference Guide

AOS-W 3.4.1 Command Line Interface | Reference Guide show aaa authentication all | 443
show aaa authentication all
show
show aaa authentication all
Description
Show authentication statistics for your switch, including authentication methods, successes and failures.
Usage Guidelines
This command displays a general overview of authentication statistics. To view authentication information for
specific profiles such as a captive-portal, MAC or 801.x authentication profile, issue the commands specific to
those features.
Example
The output of this command displays an authentication overview for your switch, including the authentication
methods used, and the numbers of successes or failures for each method. This example shows the numbers of
authentication successes and failures for a switch using TACACS+ and RADIUS authentication methods.
Command History
This command was introduced in AOS-W 3.0.
Command Information
Platforms Licensing Command Mode
All platforms Base operating system Enable or Config mode on master and local
switches
(host) #show aaa authentication all
Auth Method Statistics
----------------------
Method Success Failures
------ ------- --------
tacacs 12 2
Radius 9 1

444 | show aaa authentication captive-portal AOS-W 3.4.1 Command Line Interface | Reference Guide
show aaa authentication captive-portal
show aaa authentication captive-portal [<profile-name>]
Description
This command shows configuration information for captive portal authentication profiles.
Syntax
Usage Guidelines
Issue this command without the <profile-name> parameter to display the entire Captive Portal Authentication
profile list, including profile status and the number of references to each profile. Include a profile name to
display detailed configuration information for that profile.
If you do not yet have any captive portal authentication profiles defined, use the command aaa authentication
captive-portal to configure your captive portal profiles.
Examples
This first example shows that there are three configured captive portal profiles in the Captive Profile
Authentication Profile List. The References column lists the number of other profiles with references to a
captive portal authentication profile, and the Profile Status column indicates whether the profile is
predefined. User-defined profiles will not have an entry in the Profile Status column.
Parameter Description
<profile-name> The name of an existing captive portal authentication profile.
(host) #show aaa authentication captive-portal
Captive Portal Authentication Profile List
------------------------------------------
Name References Profile Status
---- ---------- --------------
c-portal 2
remoteuser 1
portal1 1
Total: 4
AOS-W 3.4.1 Command Line Interface | Reference Guide show aaa authentication captive-portal | 445
Include a captive portal profile name to display a complete list of configuration settings for that profile. The
example below shows settings for the captive portal profile portal1.
The output of this command includes the following parameters:
Parameter Description
Default Role Role assigned to the captive portal user upon login.
Server Group Name of the group of servers used to authenticate captive portal users.
Redirect Pause Time, in seconds, that the system remains in the initial welcome page before redirecting
the user to the final web URL. If set to 0, the welcome page displays until the user clicks
on the indicated link.
User Login Shows whether the profile has enabled or disabled captive portal with authentication of
user credentials.
Guest Login Shows whether the profile has enabled or disabled captive portal guest login without
authentication.
Logout popup window Shows whether the profile has enabled or disabled a pop-up window that allows a user to
log out. If this is disabled, the user remains logged in until the user timeout period has
elapsed or the station resets.
Use HTTP for
authentication
Shows whether the profile has enabled or disabled the ability to use the HTTP protocol to
redirect users to the captive portal page.
Login wait minimum
time
Minimum time, in seconds, the user will have to wait for the logon page to pop up if the
CPU load is high.
logon wait CPU
utilization threshold
CPU utilization percentage above which the logon wait interval is applied when directing
a captive portal user with the logon page.
Max Authentication
failures
Maximum number of authentication failures before the user is blacklisted.
Show FQDN If enabled, the user can see and select the fully-qualified domain name (FQDN) on the
captive portal login page.
Use CHAP (non-
standard)
If enabled, the captive portal profile can use the CHAP protocol.
Captive Portal Authentication Profile "portal1"
------------------------------------------------
Parameter Value
--------- -----
Default Role guest
Server Group default
Redirect Pause 10 sec
User Login Enabled
Guest Login Disabled
Logout popup window Enabled
Use HTTP for authentication Disabled
Logon wait minimum wait 5 sec
Logon wait maximum wait 10 sec
logon wait CPU utilization threshold 60%
Max Authentication failures 0
Show FQDN Disabled
Use CHAP (non-standard) Disabled
Sygate-on-demand-agent Disabled
Login page /auth/index.html
Welcome page /auth/welcome.html
Show Welcome Page Yes
Adding switch ip address in redirection URL Disabled
Allow only one active user session Disabled

446 | show aaa authentication captive-portal AOS-W 3.4.1 Command Line Interface | Reference Guide
Related Commands
Command History
This command was introduced in AOS-W 3.0.
Command Information
Sygate-on-demand-
agent
Shows whether the switch has enabled or disabled client remediation with Sygate-on-
demand-agent.
Login page URL of the page that appears for the user logon.
Welcome page URL of the page that appears after logon and before the user is redirected to the web
URL.
Command Description Mode
aaa authentication
captive-portal
Use aaa authentication captive-portal to
configure the parameters displayed in the output of
this show command.
Config mode
Platforms Licensing Command Mode
All platforms Base operating system Enable or Config mode on master or local
switches
Parameter Description
AOS-W 3.4.1 Command Line Interface | Reference Guide show aaa authentication captive-portal customization | 447
show aaa authentication captive-portal customization
show aaa authentication captive-portal customization <profile-name>
Description
Display customization settings for a captive portal profile
Syntax
Usage Guidelines
The this command shows how a captive portal profile has been customized with non-default configuration
settings. If you do not yet have any captive portal authentication profiles defined, use the command aaa
authentication captive-portal to configure your captive portal profiles
Example
The output of the following command shows how the captive portal profile c-portal has been customized. If an
individual parameter has not been changed from its default settings, its value entry will be blank.
The output of this command includes the following parameters:
Parameter Description
<profile-name> The name of an existing captive portal authentication profile.
Parameters Description
Login page design theme Indicates whether the switch is using one of the two predefined login page
designs (1 or 2) or has a custom background (3).
Login page logo image Path and filename for a custom captive portal logo. This option is only available if
the switch has a predefined login design.
Login page text Path and filename of the page that appears for the user logon.
Login policy text Path and filename of the page that displays user policy text.
Custom page background
color
Hexadecimal value for a custom background color. This option is only available if
the switch has a custom login page design theme.
Custom page background
image
Path and filename for a custom JPEG captive portal background image. This
option is only available if the switch has a custom login page design theme.
(host) #show aaa authentication captive-portal customization c-portal
Captive-Portal Customization
----------------------------
Parameter Value
--------- -----
Login page design theme 3
Login page logo image
Login page text URL/flash/upload/custom/ssu-guest-cp/logintext.html
Login policy text URL/upload/custom/ssu-guest-cp/acceptableusepolicy.html
Custom page background color
Custom page background image /upload/custom/default/auth-slider-1.gif
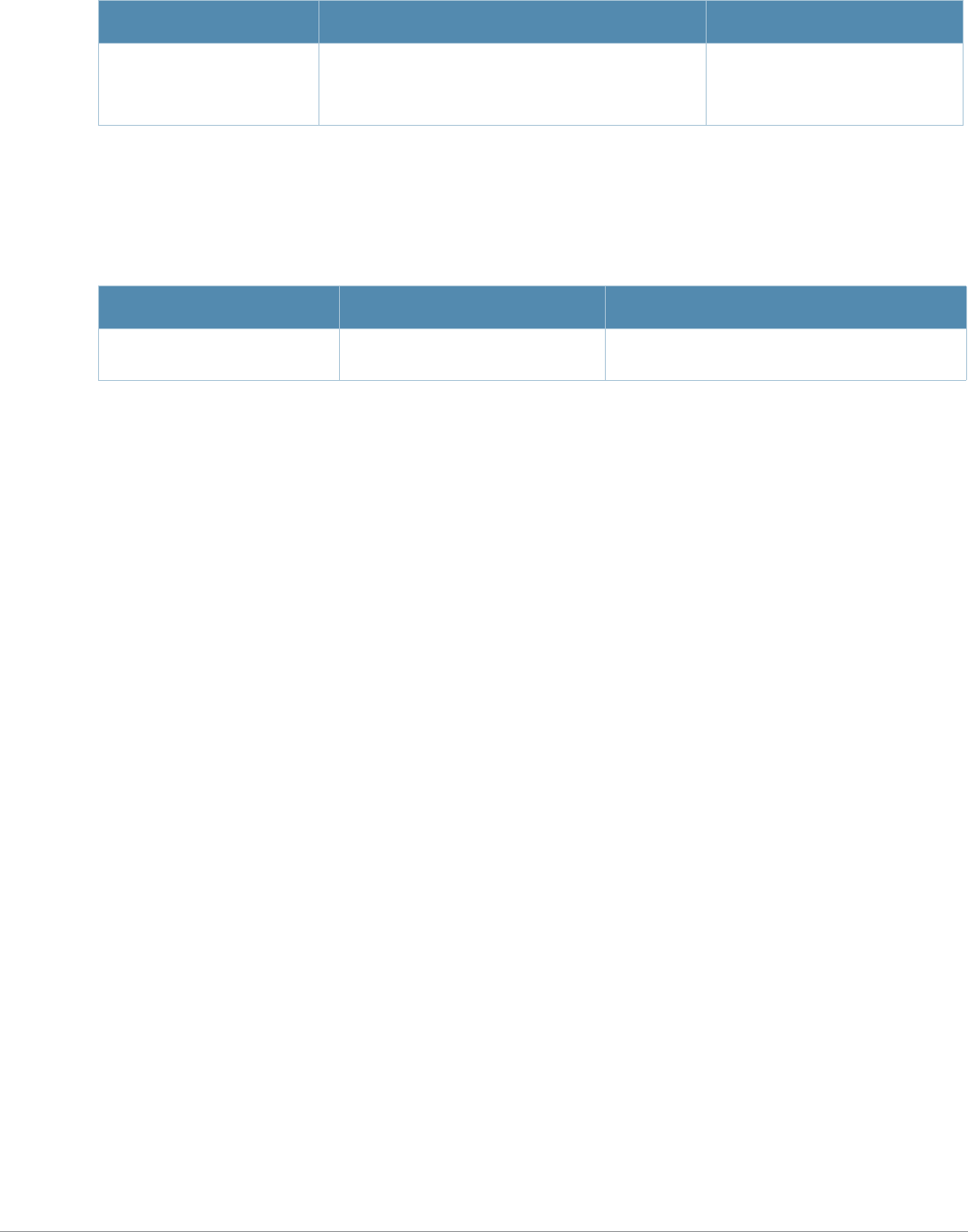
448 | show aaa authentication captive-portal customization AOS-W 3.4.1 Command Line Interface | Reference Guide
Related Commands
Command History
This command was introduced in AOS-W 3.0.
Command Information
Command Description Mode
aaa authentication
captive-portal
If you do not yet have any captive portal profiles
defined, use the command aaa authentication
captive-portal to configure your captive portal
profiles.
Config mode
Platforms Licensing Command Mode
All platforms Base operating system Enable or Config mode on master or local
switches

AOS-W 3.4.1 Command Line Interface | Reference Guide show aaa authentication dot1x | 449
show aaa authentication dot1x
show aaa authentication dot1x [<profile-name>|countermeasures]
Description
This command shows information for 802.1x authentication profiles.
Syntax
Usage Guidelines
Issue this command without the <profile-name> or countermeasures options to display the entire 802.1x
Authentication profile list, including profile status and the number of references to each profile. Include a
profile name to display detailed dot1x authentication configuration information for that profile. The
countermeasures option indicates whether the 802.1x profiles have been configured for WPA/WPS2
countermeasures. If countermeasures have not been configured, the output for this command will be blank.
Examples
The following example lists all dot1x authentication profiles. The References column lists the number of other
profiles with references to a 802.1x authentication profile, and the Profile Status column indicates whether
the profile is predefined. User-defined 802.1x profiles will not have an entry in the Profile Status column.
Parameter Description
<profile-name> The name of an existing Captive Portal authentication profile.
countermeasures Reports if WPA/WPA2 Countermeasures have been enabled for 802.1x profiles. If
enabled, the AP scans for message integrity code (MIC) failures in traffic received from
clients.
(host) #show aaa authentication dot1x
802.1X Authentication Profile List
----------------------------------
Name References Profile Status
---- ---------- --------------
default 2
default-psk 1 Predefined (editable)
dot1x 5
dot1xtest 0
Total:4

450 | show aaa authentication dot1x AOS-W 3.4.1 Command Line Interface | Reference Guide
To display a complete list of parameters for an individual profile, include the <profile> parameter. The example
below displays some of the profile details for the authentication profile pDotix.
The output of the show aaa authentication dot1x command includes the following parameters:
Parameter Value
Max authentication failures Number of times a user can try to login with wrong credentials
after which the user is blacklisted as a security threat.
Blacklisting is disabled if this parameter is set to 0.
Enforce Machine Authentication Shows if machine authentication is enabled or disabled for
Windows environments. If enabled, If enabled, either the
machine-default-role or the user-default-role is assigned to the
user, depending on which authentication is successful.
Machine Authentication: Default
Machine Role
Default role assigned to the user after completing only machine
authentication.
Machine Authentication Cache Timeout The timeout period, in hours, for machine authentication. After
this period passes, the use will have to re-authenticate.
Blacklist on Machine Authentication
Failure
If enabled, the client is blacklisted if machine authentication
fails.
Machine Authentication: Default User
Role
Default role assigned to the user after 802.1x authentication.
Interval between Identity Requests Interval, in seconds, between identity request retries
Quiet Period after Failed
Authentication
Interval, in seconds, following failed authentication.
Reauthentication Interval Interval, in seconds, between reauthentication attempts.
Use Server provided Reauthentication
Interval
If enabled, 802.1x authentication will use the server-provided
reauthentication period.
Multicast Key Rotation Time Interval Interval, in seconds, between multicast key rotations.
Unicast Key Rotation Time Interval Interval, in seconds, between unicast key rotations.
Authentication Server Retry Interval Server group retry interval, in seconds.
Authentication Server Retry Count The number of server group retries.
Framed MTU Shows the framed MTU attribute sent to the authentication
server.
(host) #show aaa authentication dot1x pDot1x
802.1X Authentication Profile "pDot1x"
--------------------------------------
Parameter Value
--------- -----
Max authentication failures 0
Enforce Machine Authentication Disabled
Machine Authentication: Default Machine Role guest
Machine Authentication Cache Timeout 24 hrs
Blacklist on Machine Authentication Failure Disabled
Machine Authentication: Default User Role guest
Interval between Identity Requests 30 sec
Quiet Period after Failed Authentication 30 sec
Reauthentication Interval 86400 sec
Use Server provided Reauthentication Interval Disabled
Multicast Key Rotation Time Interval 1800 sec
Unicast Key Rotation Time Interval 900 sec
...
AOS-W 3.4.1 Command Line Interface | Reference Guide show aaa authentication dot1x | 451
Number of times ID-Requests are
retried
Maximum number of times ID requests are sent to the client.
Maximum Number of Reauthentication
Attempts
Maximum number of reauthentication attempts.
Maximum number of times Held State
can be bypassed
Number of consecutive authentication failures which, when
reached, causes the switch to not respond to authentication
requests from a client while the switch is in a held state after the
authentication failure.
Dynamic WEP Key Message Retry Count Number of times unicast/multicast EAPOL key messages are
sent to the client.
Dynamic WEP Key Size Dynamic WEP key size, either 40 or 128 bits.
Interval between WPA/WPA2 Key
Messages
Interval, in milliseconds, between each WPA key exchange.
Delay between WPA/WPA2 Unicast Key
and Group Key Exchange
Interval, in milliseconds, between unicast and multicast key
exchanges.
WPA/WPA2 Key Message Retry Count Number of times WPA/WPA2 key messages are retried.
Multicast Key Rotation Shows if multicast key rotation is enabled or disabled.
Unicast Key Rotation Shows if unicast key rotation is enabled or disabled.
Reauthentication If enabled, this option forces the client to do a 802.1x
reauthentication after the expiration of the default timer for
reauthentication. (The default value of the timer is 24 hours.)
Opportunistic Key Caching If enabled, a cached pairwise master key (PMK) is derived with a
client and an associated AP and used when the client roams to
a new AP.
Validate PMKID Shows if the Validate PMKID feature is enabled or disabled.
When this option is enabled, the client must send a PMKID in
the associate or reassociate frame to indicate that it supports
OKC; otherwise, full 802.1x authentication takes place. (This
feature is optional, since most clients that support OKC do not
send the PMKID in their association request.)
Use Session Key If enabled, the switch will use a RADIUS session key as the
unicast WEP key.
Use Static Key If enabled, the switch will use a static key as the unicast/
multicast WEP key.
xSec MTU Shows the size of the MTU for xSec.
Termination Shows if 802.1x termination is enabled or disabled on the
switch.
Termination EAP-Type Shows the current Extensible Authentication Protocol (EAP)
method, either EAP-PEAP or EAP-TLS.
Termination Inner EAP-Type When EAP-PEAP is the EAP method, this parameter displays
the inner EAP type.
Token Caching If this feature enabled (and EAP-GTC is configured as the inner
EAP method), token caching allows the switch to cache the
username and password of each authenticated user.
Token Caching Period Timeout period, in hours, for the cached information.
CA-Certificate Name of the CA certificate for client authentication loaded in the
switch.
Parameter Value
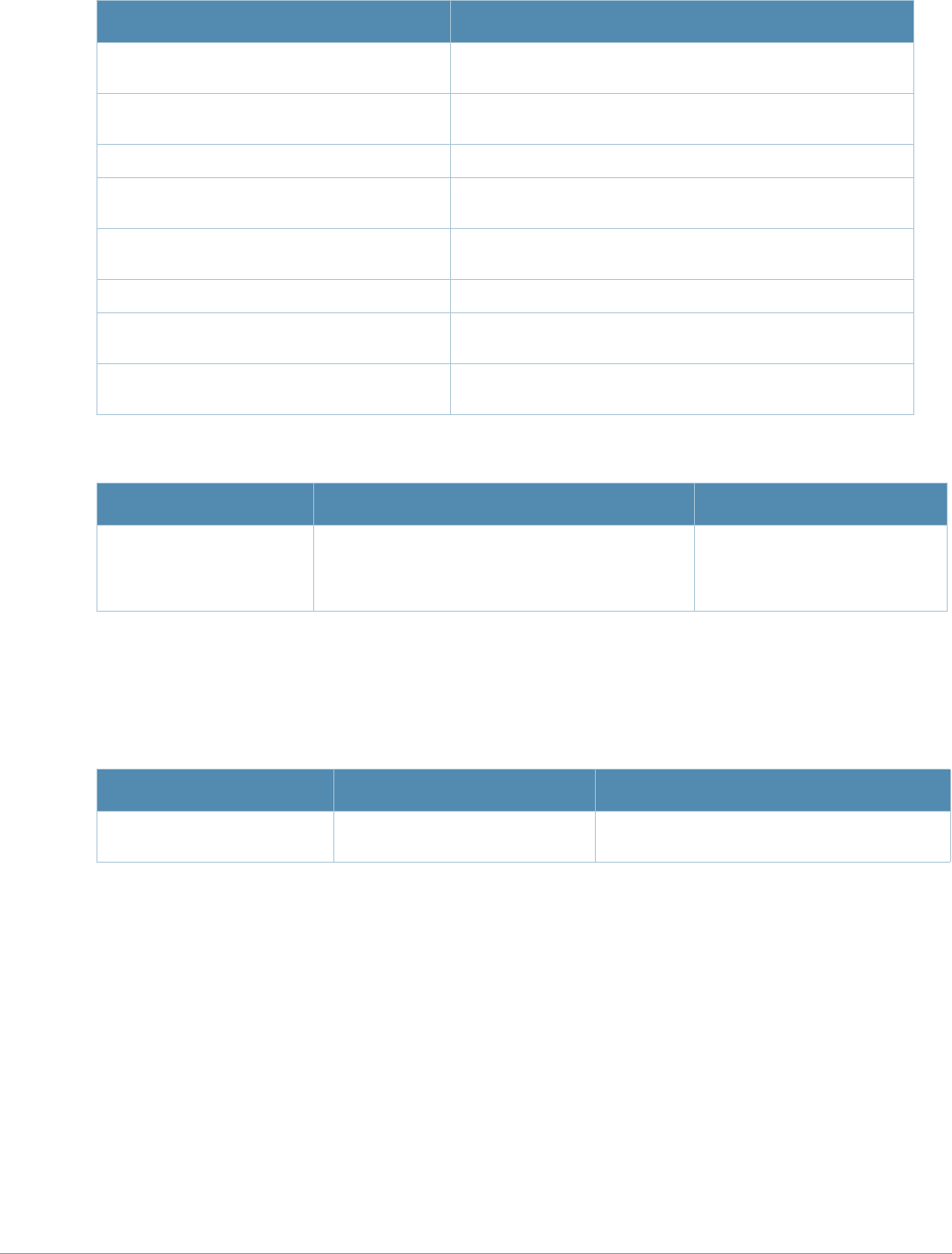
452 | show aaa authentication dot1x AOS-W 3.4.1 Command Line Interface | Reference Guide
Related Commands
Command History
This command was introduced in AOS-W 3.0.
Command Information
Server-Certificate Name of the Server certificate used by the switch to
authenticate itself to the client.
TLS Guest Access Shows if guest access for valid EAP-TLS users is enabled or
disabled.
TLS Guest Role User role assigned to EAP-TLS guest.
Ignore EAPOL-START after
authentication
If enabled, the switch ignores EAPOL-START messages after
authentication.
Handle EAPOL-Logoff Shows if handling of EAPOL-LOGOFF messages is enabled or
disabled.
Ignore EAP ID during negotiation If enabled, the switch will Ignore EAP IDs during negotiation.
WPA-Fast-Handover Shows if WPA-fast-handover is enabled or disabled. This
feature is only applicable for phones that support WPA.
Disable rekey and reauthentication
for clients on call
Shows if the rekey and reauthentication features for voice-over-
WLAN clients has been enabled or disabled.
Command Description Mode
aaa authentication
dot1x
If you do not yet have any 802.1x authentication
profiles defined, use the command aaa
authentication dot1x to configure your 802.1x
profiles.
Config mode
Platforms Licensing Command Mode
All platforms Base operating system Enable or Config mode on master or local
switches
Parameter Value

AOS-W 3.4.1 Command Line Interface | Reference Guide show aaa authentication mac | 453
show aaa authentication mac
show aaa authentication mac [<profile-name>]
Description
This command shows information for MAC authentication profiles. Issue this command without the
<profile-name> option to display the entire MAC Authentication profile list, including profile status and the
number of references to each profile. Include a profile name to display detailed MAC authentication
configuration information for that profile.
Examples
The output of the example below shows two MAC authentication profiles, default and macProfile1, which are
referenced three times by other profiles. the Profile Status columns are blank, indicating that these profiles
are both user-defined. (If a profile is predefined, the value Predefined appears in the Profile Status column.)
The following example displays configuration details for the MAC authentication profile “MacProfile1,”
including the delimiter and case used in the authentication request, and the maximum number of times a client
can fail to authenticate before it is blacklisted.
Related Commands
Command History
This command was introduced in AOS-W 3.0.
Parameter Description
<profile-name> The name of an existing MAC authentication profile.
Command Description Mode
aaa authentication
mac
Configure MAC authentication values on your
switch. Config mode
(host) #show aaa authentication mac
MAC Authentication Profile List
-------------------------------
Name References Profile Status
---- ---------- --------------
default 3
MacProfile1 3
Total:2
(host) #show aaa authentication mac MacProfile1
MAC Authentication Profile "MacProfile1"
----------------------------------------
Parameter Value
--------- -----
Delimiter colon
Case upper
Max Authentication failures 3

454 | show aaa authentication mac AOS-W 3.4.1 Command Line Interface | Reference Guide
Command Information
Platforms Licensing Command Mode
All platforms Base operating system Enable or Config mode on master or local
switches
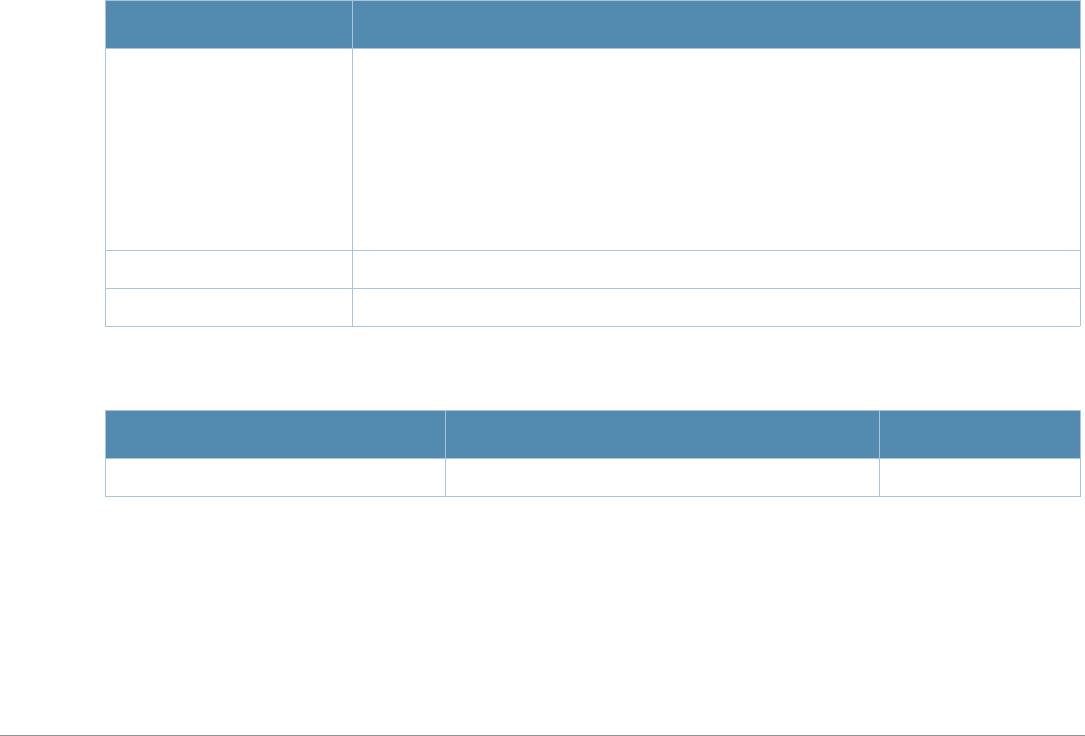
AOS-W 3.4.1 Command Line Interface | Reference Guide show aaa authentication mgmt | 455
show aaa authentication mgmt
show aaa authentication mgmt
Description
This command displays administrative user authentication information, including management authentication
roles and servers.
Usage Guidelines
Issue this command to identify the default management role assigned to authenticated administrative users, and
the name of the group of servers used to authenticate these users.
Example
The output of the following example displays management authentication information for your switch.
The output of the show aaa authentication mgmt command includes the following parameters:
Related Commands
Command History
This command was introduced in AOS-W 3.0.
Parameter Description
Default Role This parameter shows which of the following roles the switch uses for authentication
management.
zroot, the super user role (default).
zguest-provisioning, guest provisioning role.
znetwork-operations, network operator role.
zread-only, read only role.
zlocation-api-mgmt, location API management role.
zno-access, no commands are accessible.
Server Group The name of a server group.
Mode The Mode parameter indicates whether or not this feature is enabled or disabled.
Command Description Mode
aaa authentication mgmt Configure management authentication settings. Config mode
(host) #show aaa authentication mgmt
Management Authentication Profile
---------------------------------
Parameter Value
--------- -----
Default Role root
Server Group ServerGroup1
Mode Enabled

456 | show aaa authentication mgmt AOS-W 3.4.1 Command Line Interface | Reference Guide
Command Information
Platforms Licensing Command Mode
All platforms Base operating system Enable or Config mode on master or local
switches
AOS-W 3.4.1 Command Line Interface | Reference Guide show aaa authentication stateful-dot1x | 457
show aaa authentication stateful-dot1x
show aaa authentication stateful-dot1x [config-entries]
Description
This command displays configuration settings for 802.1x authentication for clients on non-Alcatel-Lucent APs.
Syntax
Usage Guidelines
Issue this command to identify the default role assigned to the 802.1x user group, name of the group of RADIUS
servers used to authenticate the 802.1x users, and the 802.1x authentication timeout period, in seconds.
Example
The output of the following example displays 802.1x authentication information for your switch.
The output of this command includes the following parameters:
When you include the config-entries parameter, the output shows the AP - Server Configuration List.
Parameter Description
config-entries Display details for the AP Server configuration list.
Parameter Description
Default Role This parameter shows which role the switch uses for 802.1x authentication management.
Server Group The name of a server group.
Timeout Timeout period for an authentication request, in seconds.
Mode The Mode parameter indicates whether or not this feature is enabled or disabled.
(host) #show aaa authentication stateful-dot1x
Stateful 802.1X Authentication Profile
--------------------------------------
Parameter Value
--------- -----
Default Role guest
Server Group newgroup2
Timeout 10 sec
Mode Enabled
(host) #show aaa authentication stateful-dot1x config-entries
AP-Server Configuration List
----------------------------
Cfg-Name AP-IP Server Shared-Secret
-------- ----- ------ -------------
cfg22 10.3.14.6 RADIUS1 secret-pwd
458 | show aaa authentication stateful-dot1x AOS-W 3.4.1 Command Line Interface | Reference Guide
The output of this command includes the following parameters:
Related Commands
Command History
This command was introduced in AOS-W 3.0.
Command Information
Parameter Description
Cfg-Name is a auto-generated name
AP-IP IP address of the AP.
Server Name of the authentication server.
Shared-Secret Shared authentication secret.
Command Description Mode
aaa authentication stateful-
dot1x
Use the command aaa authentication stateful-dot1x
to configure the settings displayed in the output of
this show command.
Config mode
Platforms Licensing Command Mode
All platforms Base operating system Enable or Config mode on master or local
switches
AOS-W 3.4.1 Command Line Interface | Reference Guide show aaa authentication stateful-ntlm | 459
show aaa authentication stateful-ntlm
show aaa authentication stateful-ntlm
Description
This command displays configuration settings for the Stateful NTLM Authentication profile. Issue this command
without the <profile-name> option to display the entire Stateful NTLM Authentication profile list, including
profile status and the number of references to each profile. Include a profile name to display detailed Stateful
NTLM authentication configuration information for that profile.
Syntax
Usage Guidelines
Issue this command to identify the default role assigned to users who have successfully authenticated the using
NT Lan Manager (NTLM) authentication protocol, the name of the group of windows servers used to
authenticate these users, and the NTLM authentication timeout period, in seconds.
Example
Examples
The output of the example below shows two stateful NTLM authentication profiles, default and
NTLMprofile1, which are each referenced one time by other profiles. the Profile Status columns are blank,
indicating that these profiles are both user-defined. (If a profile is predefined, the value Predefined appears in
the Profile Status column.)
The following example displays configuration details for the stateful NTLM authentication profile “default”.
Parameter Description
<profile-name> The name of an existing Stateful NTLM authentication profile.
(host) #show aaa authentication stateful-ntlm
Stateful NTLM Authentication Profile List
-----------------------------------------
Name References Profile Status
---- ---------- --------------
default 1
NTLMprofile1 1
Total:2
(host) #show aaa authentication stateful-ntlm default
Stateful NTLM Authentication Profile "default"
----------------------------------------------
Parameter Value
--------- -----
Default Role guest
Server Group default
Mode Disabled
Timeout 10 sec
460 | show aaa authentication stateful-ntlm AOS-W 3.4.1 Command Line Interface | Reference Guide
The output of this command includes the following parameters:
Related Commands
Command History
This command was introduced in AOS-W 3.4.1.
Command Information
Parameter Description
Default Role This parameter shows the role assigned to NTLM authenticated users.
Server Group The name of a windows server group.
Mode The Mode parameter indicates whether or not this authentication profile is enabled or
disabled.
Timeout Timeout period for an authentication request, in seconds.
Command Description
aaa authentication stateful-
ntlm
Use the command aaa authentication stateful-ntlm to configure the settings
displayed in the output of this show command.
Platforms Licensing Command Mode
All platforms Base operating system Enable or Config mode on master or local
switches
AOS-W 3.4.1 Command Line Interface | Reference Guide show aaa authentication vpn | 461
show aaa authentication vpn
show aaa authentication vpn
Description
This command displays VPN authentication settings, including authentication roles and servers.
Usage Guidelines
Issue this command to identify the default role assigned to VPN users, the name of the group of servers used to
authenticate the VPN users, and the maximum number of authentication failures allowed before the user is
blacklisted.
Example
The following example displays configuration details for VPN authentication.
The output of this command includes the following parameters:
Related Commands
Command History
This command was introduced in AOS-W 3.0.
Command Information
Parameter Description
Default Role The default role to be assigned to VPN users.
Server Group The name of the server group that performs the authentication.
Max Authentication failures Number of times a user attempted to authenticate, but failed.
Command Description Mode
aaa authentication vpn Use the command aaa authentication vpn to
configure the settings displayed in the output of this
show command.
Config mode
Platforms Licensing Command Mode
All platforms Base operating system Enable or Config mode on master or local
switches
(host) #show aaa authentication vpn
VPN Authentication Profile
--------------------------
Parameter Value
--------- -----
Default Role VPN-Role-1
Server Group default
Max Authentication failures 2

462 | show aaa authentication wired AOS-W 3.4.1 Command Line Interface | Reference Guide
show aaa authentication wired
show aaa authentication wired
Description
View wired authentication settings for a client device that is directly connected to a port onthe switch.
Usage Guidelines
This command displays the name of the AAA profile currently used for wired authentication.
Example
The following example shows the current wired profile for the switch is a profile named “secure_profile_3.”
Related Commands
Command History
This command was introduced in AOS-W 3.0.
Command Information
Command Description Mode
aaa authentication wired Use the command aaa authentication wired to
configure the settings displayed in the output of this
show command.
Config mode
Platforms Licensing Command Mode
All platforms Base operating system Enable or Config mode on master or local
switches
(host) #show aaa authentication wired
Wired Authentication Profile
----------------------------
Parameter Value
--------- -----
AAA Profile Secure_profile_3

AOS-W 3.4.1 Command Line Interface | Reference Guide show aaa authentication wispr | 463
show aaa authentication wispr
show aaa authentication wispr <profile-name)
Description
This command shows information for a WISPr authentication profiles. Issue this command without the
<profile-name> option to display the entire WISPr Authentication profile list, including profile status and the
number of references to each profile. Include a profile name to display detailed WISPr authentication
configuration information for that profile.
Examples
The output of the example below shows two WISPr authentication profiles, default and WISPR1, which are
referenced two times by other profiles. the Profile Status columns are blank, indicating that these profiles are
both user-defined. (If a profile is predefined, the value Predefined appears in the Profile Status column.)
The following example displays configuration details for the WISPr authentication profile “WISPr1”.
The output of this command includes the following parameters:
Parameter Description
<profile-name> The name of an existing MAC authentication profile.
Parameter Description
Default Role The default role to be assigned to users that have completed WISPr
authentication.
Server Group The name of the server group that performs the authentication.
(host) #show aaa authentication wispr
WISPr Authentication Profile List
-------------------------------
Name References Profile Status
---- ---------- --------------
default 2
WISPr1 2
Total:2
(host) #show aaa authentication wispr WISPr1
WISPr Authentication Profile "WISPr1"
--------------------------------------
Parameter Value
--------- -----
Default Role guest
Server Group default
Logon wait minimum wait 5 sec
Logon wait maximum wait 10 sec
logon wait CPU utilization threshold 60 %
WISPr Location-ID ISO Country Code US
WISPr Location-ID E.164 Country Code 1
WISPr Location-ID E.164 Area Code 408
WISPr Location-ID SSID/Zone Corp1
WISPr Operator Name MyCompany
WISPr Location Name Sunnyvale
464 | show aaa authentication wispr AOS-W 3.4.1 Command Line Interface | Reference Guide
Related Commands
Command History
This command was introduced in AOS-W 3.4.1.
Command Information
Logon wait minimum wait If the switch’s CPU utilization has surpassed the Login wait CPU
utilization threshold value, the Logon wait minimum wait parameter
defines the minimum number of seconds a user will have to wait to retry a
login attempt. Range: 1-10 seconds. Default: 5 seconds.
Logon wait maximum wait If the switch’s CPU utilization has surpassed thelogon wait CPU utilization
threshold value, the Logon wait maximum wait parameter defines the
maximum number of seconds a user will have to wait to retry a login
attempt. Range: 1-10 seconds. Default: 10 seconds.
WISPr Location-ID E.164 Area
Code
The E.164 Area Code in the WISPr Location ID.
WISPr Location-ID E.164 Country
Code 1
The 1-3 digit E.164 Country Code in the WISPr Location ID.
WISPr Location-ID ISO Country
Code
The ISO Country Code in the WISPr Location ID.
WISPr Location-ID SSID/Zone The SSID/network name in the WISPr Location ID.
WISPr Location Name
A name identifying the hotspot location. If no name is defined, the default
ap-name is used.
WISPr Operator Name
A name identifying the hotspot operator.
Command Description Mode
aaa authentication
wispr
Configure WISPr authentication values on your
switch. Config mode on master or local
switches.
Platforms Licensing Command Mode
All platforms Base operating system Enable or Config mode on master or local
switches
Parameter Description
AOS-W 3.4.1 Command Line Interface | Reference Guide show aaa authentication-server all | 465
show aaa authentication-server all
show aaa authentication-server all
Description
View authentication server settings for both external authentication servers and the internal switch database.
Usage Guidelines
The output of this command displays statistics for the Authentication Server Table, including the name and
address of each server, server type and configured authorization and accounting ports.
Examples
The following command shows information for the internal Authentication server, and another RADIUS server
named RADIUS-1.
The following data columns appear in the output of this command:
Command History
This command was introduced in AOS-W 3.0.
Command Information
Parameter Description
Name Name of the authentication server.
Type The type of authentication server. AOS-W supports LDAP, RADIUS and TACACS+
servers, in addition to its own local, internal authentication server.
IP addr IP address of the server, in dotted-decimal format.
AuthPort Port number used for authentication. An LDAP server uses port 636 for LDAP over SSL,
and port 389 for SSL over LDAP, Start TLS operation andclear text. The default RADIUS
authentication port is port 1812.
AcctPort Accounting port on the server. The default RADIUS accounting port is port 1813.
AcctPort Accounting port on the server.
Status Shows whether the Authentication server is enable or disabled.
Requests Number of authentication requests received by the server.
Platforms Licensing Command Mode
All platforms Base operating system Enable or Config mode on master or local
switches
(host) #show aaa authentication-server all
Auth Server Table
-----------------
Name Type IP addr AuthPort AcctPort Status Requests
---- ---- ------- -------- -------- ------ --------
Internal Local 10.168.254.221 n/a n/a Enabled 5
SMOKERAD Radius 10.4.101.123 5555 5556 Enabled 1

466 | show aaa authentication-server internal AOS-W 3.4.1 Command Line Interface | Reference Guide
show aaa authentication-server internal
show aaa authentication-server internal [statistics]
Description
View authentication server settings for the internal switch database.
Examples
The output of the command below shows that the internal authentication server has been disabled.
The following data columns appear in the output of this command:
Include the statistics parameter to display additional details for the internal server.
The following data columns appear in the output of this command:
Parameter Description
Host Name of the internal authentication server.
IP addr Address of the internal server, in dotted-decimal format.
Retries Number of retries allowed before the server stops attempting to authenticate a request.
timeout Timeout period, in seconds.
Parameter Description
PAP Requests Number of PAP requests received by the internal server.
PAP Accepts Number of PAP requests accepted by the internal server.
PAP Rejects Number of PAP requests rejected by the internal server.
MSCHAPv2 Requests Number of MSCHAPv2 requests received by the internal server.
(host) #show aaa authentication-server internal
Internal Server
---------------
Host IP addr Retries Timeout Status
---- ------- ------- ------- ------
Internal 10.168.254.221 3 5 Disabled
(host) #show aaa authentication-server internal statistics
Internal Database Server Statistics
-----------------------------------
PAP Requests 8
PAP Accepts 8
PAP Rejects 0
MSCHAPv2 Requests 0
MSCHAPv2 Accepts 0
MSCHAPv2 Rejects 0
Mismatch Response 0
Users Expired 1
Unknown Response 0
Timeouts 1
AvgRespTime (ms) 0
Uptime (d:h:m) 4:3:32
SEQ first/last/free 1,255,255
AOS-W 3.4.1 Command Line Interface | Reference Guide show aaa authentication-server internal | 467
Related Commands
Command History
This command was introduced in AOS-W 3.0.
Command Information
MSCHAPv2 Accepts Number of MSCHAPv2 requests accepted by the internal server.
MSCHAPv2 Rejects Number of MSCHAPv2 requests rejected by the internal server.
Mismatch Response Number of times the server received an authentication response to a request after
another request had been sent.
Users Expired Number of users that were deauthenticated because they stopped responding.
Unknown Response Number of times the server did not recognize the response, possibly due to internal
errors.
Timeouts Number of times that the switch timed out an authentication request.
AvgRespTime (ms) Time it takes the server to respond to an authentication request, in seconds.
Uptime (d:h:m) Time elapsed since the last server reboot.
SEQ first/last/free This internal buffer counter keeps track of the requests to the authentication server.
Command Description Mode
aaa authentication-server
internal
Issue the command aaa authentication-server
internal to use the internal database on a local
switch for authenticating clients.
Config mode
Platforms Licensing Command Mode
All platforms Base operating system Enable or Config mode on master or local
switches
Parameter Description
468 | show aaa authentication-server ldap AOS-W 3.4.1 Command Line Interface | Reference Guide
show aaa authentication-server ldap
show aaa authentication-server ldap [<ldap_server_name>]
Description
Display configuration settings for your LDAP servers.
Syntax
Examples
The output of the example below displays the LDAP server list with the names of all the LDAP servers. The
References column lists the number of other profiles that reference an LDAP server, and the Profile Status
column indicates whether the profile is predefined. User-defined profiles will not have an entry in the Profile
Status column.
Include the <ldap_server_name> parameter to display additional details for an individual server.
The output of this command includes the following parameters:
Parameter Description
<ldap_server_name> Name that identifies an LDAP server.
Parameter Description
host IP address of the LDAP server
Admin-DN Distinguished name for the admin user who has read/search privileges across all of the
entries in the LDAP database.
(host) #aaa authentication-server ldap
LDAP Server List
----------------
Name References Profile Status
---- ---------- --------------
ldap1 5
ldap2 3
ldap3 1
Total:3
(host) #show aaa authentication-server ldap ldap1
LDAP Server "ldap1"
-------------------
Parameter Value
--------- -----
Host 10.1.1.234
Admin-DN cn=corp,cn=Users,dc=1m,dc=corp,dc=com
Admin-Passwd ********
Allow Clear-Text Disabled
Auth Port 389
Base-DN cn=Users,dc=1m,dc=corp,dc=com
Filter (objectclass=*)
Key Attribute sAMAccountName
Timeout 20 sec
Mode Enabled
Preferred Connection Type ldap-s
AOS-W 3.4.1 Command Line Interface | Reference Guide show aaa authentication-server ldap | 469
Command History
This command was introduced in AOS-W 3.0.
Command Information
Admin Passwd Password for the admin user.
Allow Clear-Text If enabled, this parameter allows clear-text (unencrypted) communication with the LDAP
server.
Auth Port Port number used for authentication. Port 636 will be attempted for LDAP over SSL,
while port 389 will be attempted for SSL over LDAP, Start TLS operation and clear text.
Base-DN Distinguished Name of the node which contains the required user database.
Filter Filter that should be applied to search of the user in the LDAP database (default filter
string is: ì(objectclass=*)î ).
Key attribute Attribute that should be used as a key in search for the LDAP server.
Timeout Timeout period of a LDAP request, in seconds.
Mode Shows whether this server is Enabled or Disabled.
Preferred Connection
Type
Preferred type of connection to the server. Possible values are
zClear text
zLDAP-S
zSTART-TLS
Platforms Licensing Command Mode
All platforms Base operating system Enable or Config mode on master or local
switches
Parameter Description

470 | show aaa authentication-server radius AOS-W 3.4.1 Command Line Interface | Reference Guide
show aaa authentication-server radius
show aaa authentication-server radius [<rad_server_name>|statistics]
Description
Display configuration settings for your RADIUS servers.
Syntax
Examples
The output of the example below displays the RADIUS server list with the names of all the RADIUS servers. The
References column lists the number of other profiles that reference a RADIUS server, and the Profile Status
column indicates whether the profile is predefined. User-defined servers will not have an entry in the Profile
Status column. To view additional statistics for all RADIUS servers, include the statistics parameter.
Include the <rad_server_name> parameter to display additional details for an individual server.
The output of this command includes the following parameters:
Parameter Description
<rad_server_name> Name that identifies a RADIUS server.
Parameter Description
host IP address of the RADIUS server
Key Shared secret between the switch and the authentication server.
(host) #aaa authentication-server radius
RADIUS Server List
----------------
Name References Profile Status
---- ---------- --------------
IAS1 5
SMOKERAD 3
Total:2
(host) #show aaa authentication-server radius SMOKERAD
RADIUS Server "SMOKERAD"
------------------------
Parameter Value
--------- -----
Host 10.4.101.123
Key ********
Auth Port 5555
Acct Port 5556
Retransmits 3
Timeout 5 sec
NAS ID SMOKETEST
NAS IP N/A
Use MD5 Disabled
Mode Enabled
AOS-W 3.4.1 Command Line Interface | Reference Guide show aaa authentication-server radius | 471
Command History
This command was introduced in AOS-W 3.0.
Command Information
Acct Port Accounting port on the server.
auth port Authentication port on the server.
Retransmits Maximum number of retries sent to the server by the switch before the server is marked
as down.
Timeout Maximum time, in seconds, that the switch waits before timing out the request and
resending it.
NAS ID Network Access Server (NAS) identifier to use in RADIUS packets.
NAS IP NAS IP address to send in RADIUS packets. If you do not configure a server-specific
NAS IP, the global NAS IP is used.
Use MD5 If enabled, the RADIUS server will use a MD5 hash of cleartext password.
Mode Shows whether this server is Enabled or Disabled.
Platforms Licensing Command Mode
All platforms Base operating system Enable or Config mode on master or local
switches
Parameter Description
472 | show aaa authentication-server tacacs AOS-W 3.4.1 Command Line Interface | Reference Guide
show aaa authentication-server tacacs
show aaa authentication-server tacacs [<tacacs_server_name>]
Description
Display configuration settings for your TACACS+ servers.
Syntax
Examples
The output of the example below displays the TACACS+ server list with the names of all the TACACS+ servers.
The References column lists the number of other profiles that reference a TACACS+ server, and the Profile
Status column indicates whether the profile is predefined. User-defined profiles will not have an entry in the
Profile Status column.
Include the <tacacs_server_name> parameter to display additional details for an individual server.
The output of this command includes the following parameters:
Parameter Description
<tacacs_server_name> Name that identifies an TACACS+ server.
Parameter Description
host IP address of the TACACS+ server
Key Shared secret between the switch and the authentication server.
TCP Port TCP port used by the server.
(host) #aaa authentication-server tacacs
TACACS Server List
----------------
Name References Profile Status
---- ---------- --------------
LabAuth 5
TACACS1 3
Total:2
(host) #show aaa authentication-server tacacs tacacs1
TACACS Server "tacacs1"
---------------------
Parameter Value
--------- -----
Host 10.1.1.16
Key ********
TCP Port 49
Retransmits 3
Timeout 20 sec
Mode Enabled
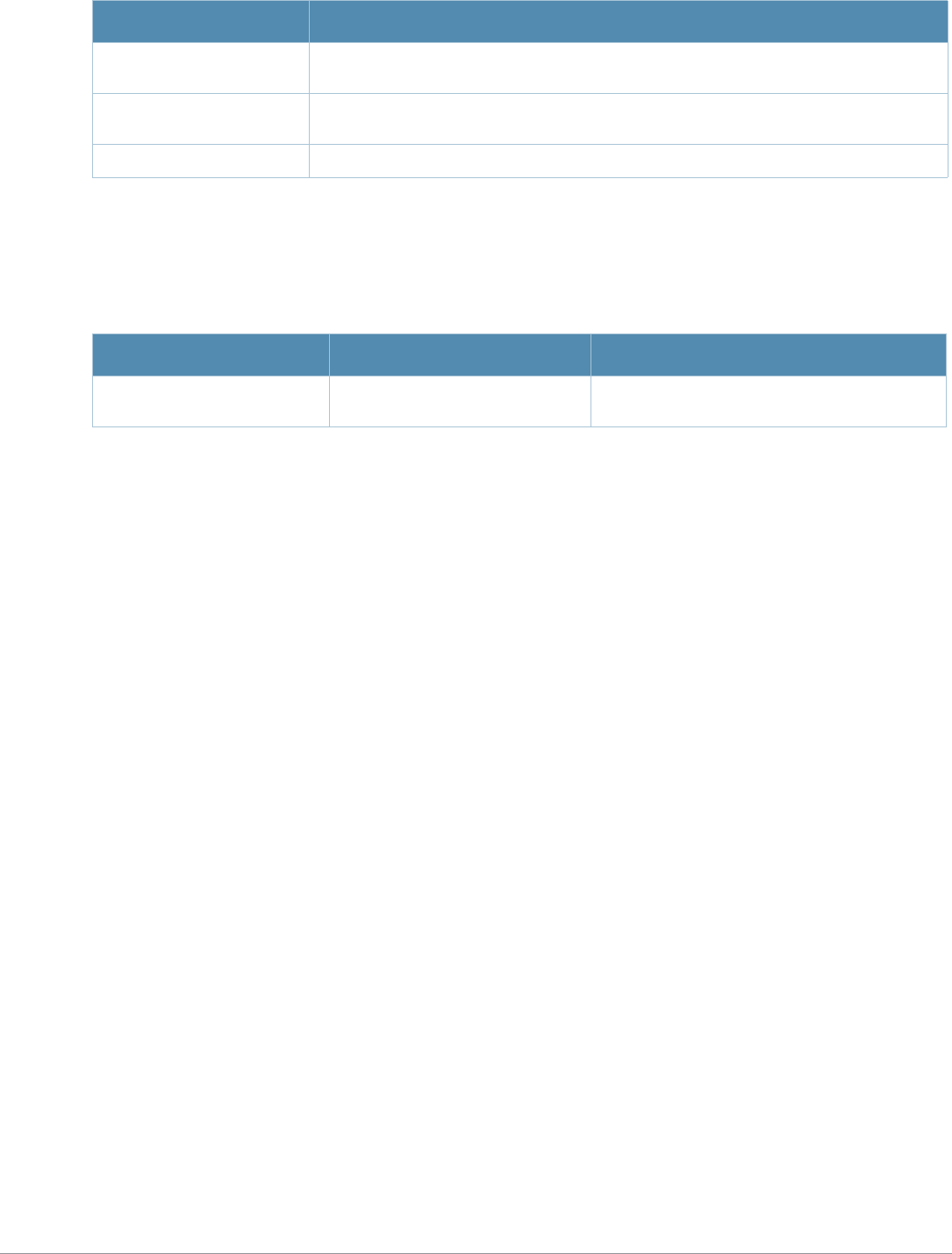
AOS-W 3.4.1 Command Line Interface | Reference Guide show aaa authentication-server tacacs | 473
Command History
This command was introduced in AOS-W 3.0.
Command Information
Retransmits Maximum number of retries sent to the server by the switch before the server is marked
as down.
Timeout Maximum time, in seconds, that the switch waits before timing out the request and
resending it.
Mode Shows whether this server is Enabled or Disabled.
Platforms Licensing Command Mode
All platforms Base operating system Enable or Config mode on master or local
switches
Parameter Description
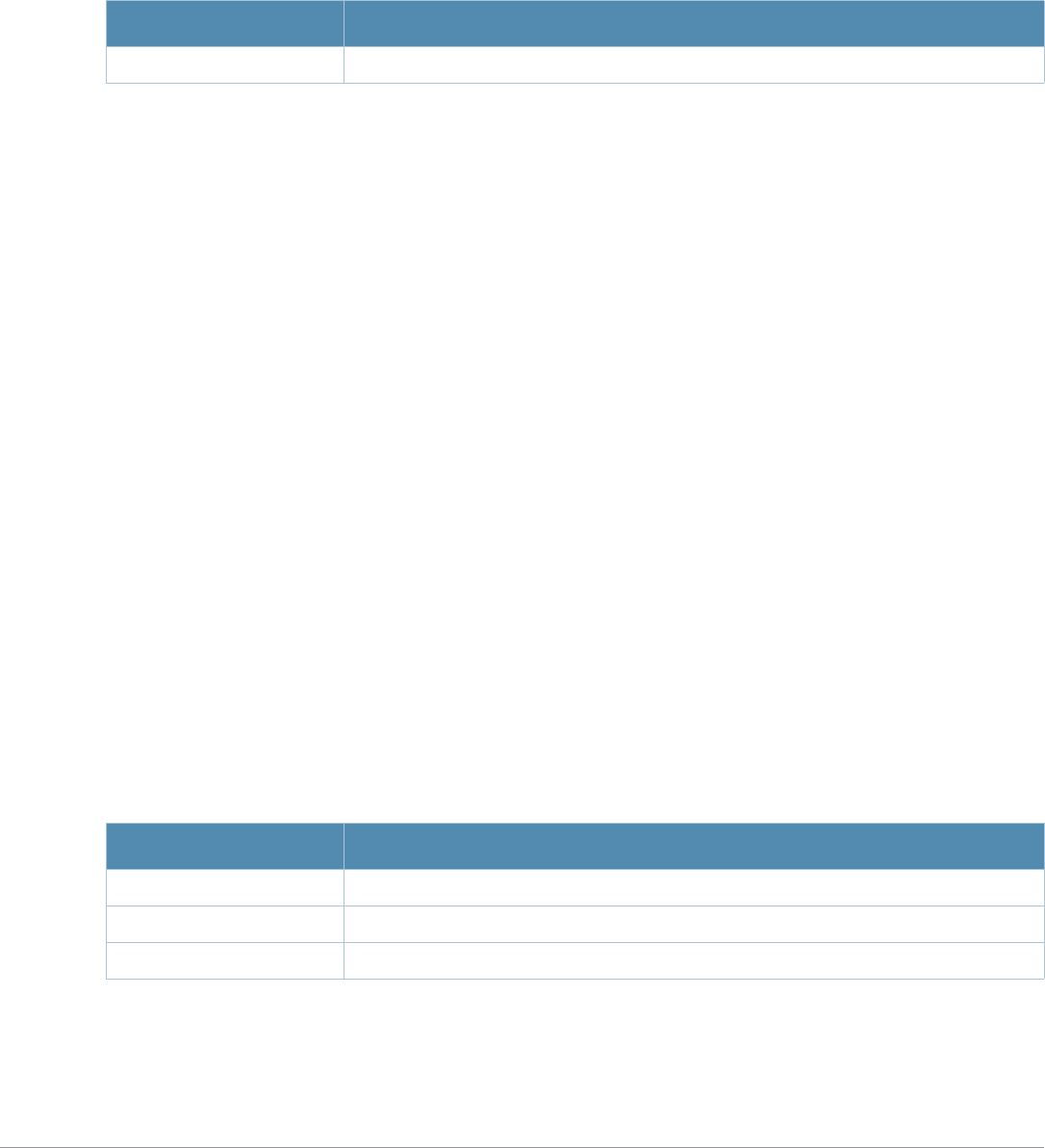
474 | show aaa authentication-server windows AOS-W 3.4.1 Command Line Interface | Reference Guide
show aaa authentication-server windows
show aaa authentication-server windows [<windows_server_name>]
Description
Display configuration settings for your Windows servers.
Syntax
Examples
The output of the example below displays the Windows server list with the names of all the Windows servers
used for NTLM authentication. The References column lists the number of other profiles that reference a
Windows server, and the Profile Status column indicates whether the profile is predefined. User-defined
profiles will not have an entry in the Profile Status column.
Include the <windows_server_name> parameter to display additional details for an individual server.
The output of this command includes the following parameters:
Command History
This command was introduced in AOS-W 3.4.1.
Parameter Description
<windows_server_name> Name that identifies a Windows server.
Parameter Description
host IP address of the Windows server
Mode Shows whether this server is Enabled or Disabled.
Windows Domain Name of the Windows domain to which this server is assigned.
(host) #aaa authentication-server tacacs
Windows Server List
----------------
Name References Profile Status
---- ---------- --------------
NTLM 1
Windows2 1
Total:2
(host) #show aaa authentication-server windows Windows2
Windows Server "windows"
------------------------
Parameter Value
--------- -----
Host 172.21.18.170
Mode Enabled
Windows Domain MyCompanyDomain

AOS-W 3.4.1 Command Line Interface | Reference Guide show aaa authentication-server windows | 475
Command Information
Platforms Licensing Command Mode
All platforms Base operating system Enable or Config mode on master or local
switches

476 | show aaa tacacs-accounting AOS-W 3.4.1 Command Line Interface | Reference Guide
show aaa tacacs-accounting
show aaa tacacs-accounting
Description
Show configuration information for TACACS+ accounting servers.
Usage Guidelines
This command displays TACACS+ data for your switch if you have previously configured a TACACS+ server
and server group. The output includes the current TACACS+ accounting mode (enabled or disabled), and the
name of the TACACS+ server group.
Example
The output of the show aaa accounting tacacs command displays configuration information for a TACACS+
accounting server. The output of this command includes the following parameters:
Related Commands
Command History
This command was introduced in AOS-W 3.0.
Parameter Description
Mode Shows whether this server group is Enabled or Disabled.
Commands Displays the types of commands that are reported to the TACACS server group.
zaction reports action commands only.
zall reports all commands.
zconfiguration reports configuration commands only
zshow reports show commands only
Server-Group Shows whether this server is Enabled or Disabled.
Command Description Mode
aaa authentication-server tacacs Configure the TACACCS+ accounting feature. Config mode
aaa server-group Add a configured authentication server to an ordered
list in a server group, and configure server rules to
derive a user role, VLAN ID or VLAN name from
attributes returned by the server during authentication
Config mode
(host) #show aaa accounting tacacs
TACACS Accounting Configuration
-------------------------------
Parameter Value
--------- -----
Mode Enabled
Commands configuration
Server-Group tacacs1

AOS-W 3.4.1 Command Line Interface | Reference Guide show aaa tacacs-accounting | 477
Command Information
Platforms Licensing Command Mode
All platforms Base operating system Enable or Config mode on master or local
switches
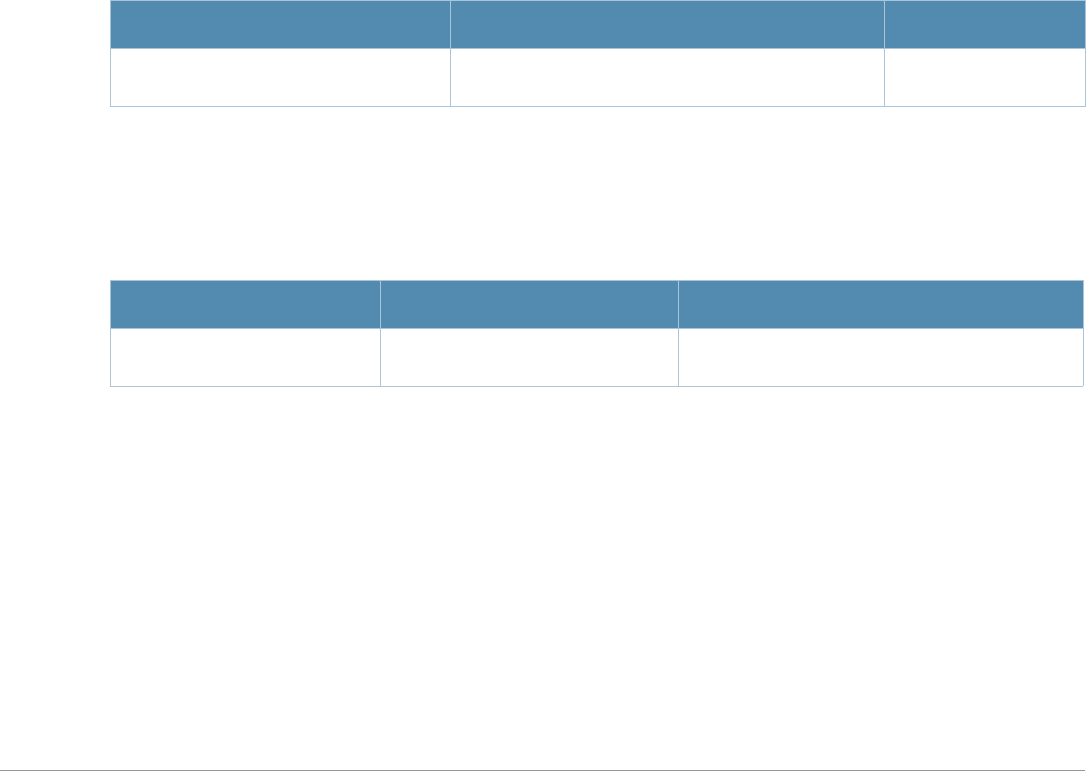
478 | show aaa bandwidth-contracts AOS-W 3.4.1 Command Line Interface | Reference Guide
show aaa bandwidth-contracts
show aaa bandwidth-contracts
Description
This command shows the contract names, ID numbers and Rate limits for your bandwidth contracts.
Example
The output of the following command shows that the bandwidth contract VLAN has a configured rate of 6
Mbps, and the contract User has a rate of 2048 Kbps.
Related Commands
Command History
This command was introduced in AOS-W 3.0.
Command Information
Command Description Mode
aaa bandwidth-contract Use this command to define contracts to limit traffic
for a user or VLAN. Config mode
Platforms Licensing Command Mode
All platforms Base operating system Enable or Config mode on master or local
switches
(host) #show aaa bandwidth-contracts
Bandwidth Contracts
-------------------
Contract Id Rate (bits/second)
-------- -- ------------------
VLAN 1 6000000
User 2 2048000
Total contracts = 2
Per-user contract total = 4096
Per-user contract usage = 0
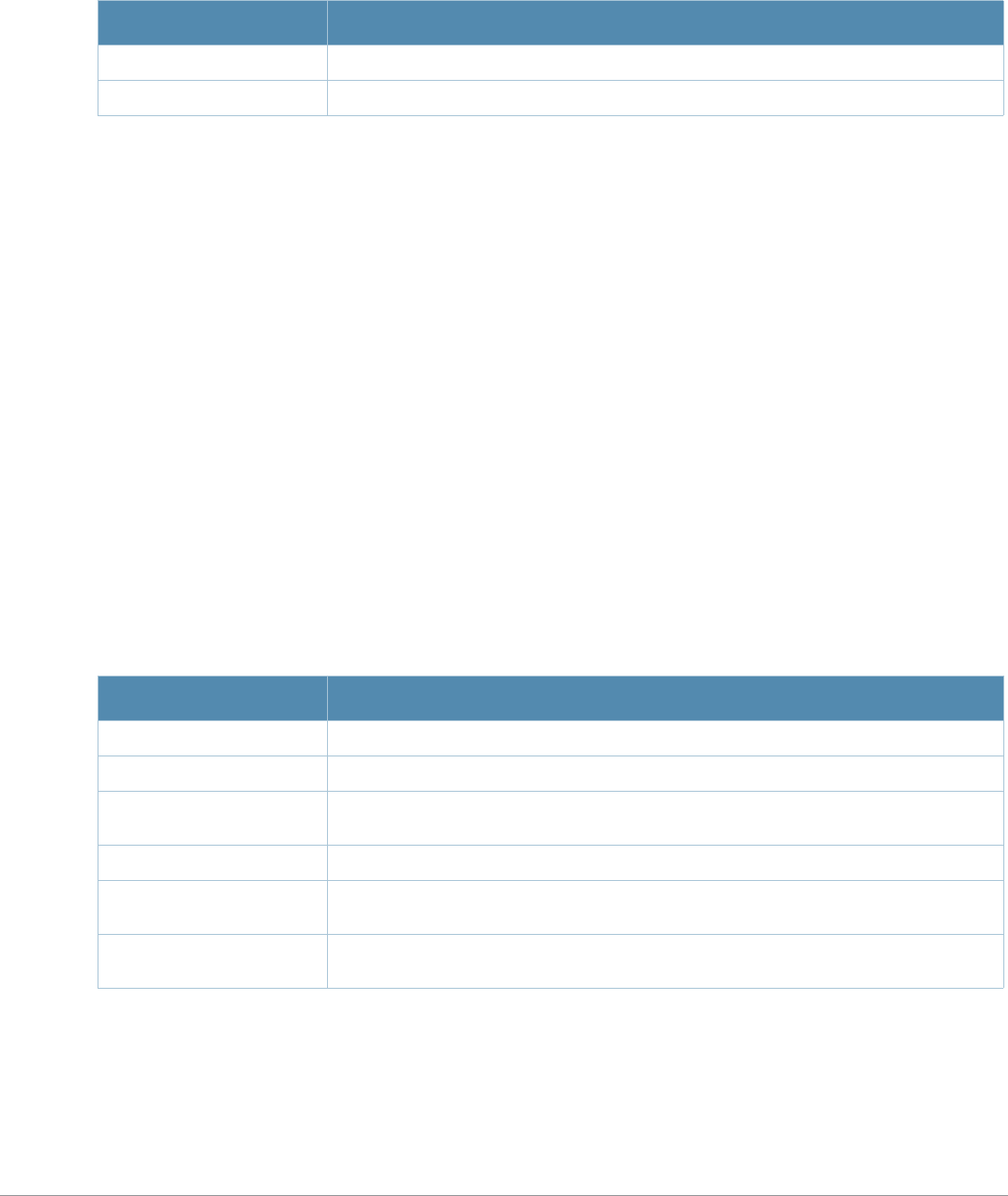
AOS-W 3.4.1 Command Line Interface | Reference Guide show aaa derivation-rules | 479
show aaa derivation-rules
show aaa derivation-rules [server-group <group-name>|user <name>]
Syntax
Description
Show derivation rules based on user information or configured for server groups.
Example
The output of the following command shows that the server group group1 has the internal database configured
as its authentication server, and that there is a single rule assigned to that group. You can omit the <group-
name> parameter to show a table of all your server groups.
The following data columns appear in the output of this command:
Parameter Description
<group-name> Name of a server group
<name> Name of a user rule group
Parameter Description
Name Name of the authentication server assigned to this server group
Inservice Specifies if the server is in service or out-of-service.
trim-FDQN If enabled, user information in an authentication request is edited before the request is
sent to the server.
match-FDQN If enabled, the authentication server is associated with a specified domain.
Priority The priority in which the rules are applied. Rules at the top of the list are applied before
rules at the bottom.
Attribute This is the attribute returned by the authentication server that is examined for Operation
and Operand match
(host) #show aaa derivation-rules server-group group1
Server Group
Name Inservice trim-FQDN match-FQDN
---- --------- --------- ----------
Internal Yes No
Server Rule Table
-----------------
Priority Attribute Operation Operand Action Value Total Hits New Hits
-------- --------- --------- ------- ------ ----- ---------- --------
1 Filter-Id equals nsFilter set vlan 111 24 0
Rule Entries: 1
480 | show aaa derivation-rules AOS-W 3.4.1 Command Line Interface | Reference Guide
To display derivation rules for a user group, include the user <name> parameter. You can also display a table
of all user rules by including the user parameter, but omitting the <name> parameter.
The following data columns appear in the output of this command:
Operation This is the match method by which the string in Operand is matched with the attribute
value returned by the authentication server.
zcontains – The rule is applied if and only if the attribute value contains the string in
parameter Operand.
zstarts-with – The rule is applied if and only if the attribute value returned starts with
the string in parameter Operand.
zends-with – The rule is applied if and only if the attribute value returned ends with the
string in parameter Operand.
zequals – The rule is applied if and only if the attribute value returned equals the string
in parameter Operand.
znot-equals – The rule is applied if and only if the attribute value returned is not equal
to the string in parameter Operand.
zvalue-of – This is a special condition. What this implies is that the role or VLAN is set
to the value of the attribute returned. For this to be successful, the role and the VLAN
ID returned as the value of the attribute selected must be already configured on the
switch when the rule is applied.
Operand This is the string to which the value of the returned attribute is matched.
Action This parameter identifies whether the rule sets a server group role (set role) or a VLAN
(set vlan).
Value Sets the user role or VLAN ID to be assigned to the client if the condition is met.
Total Hits Number of times the rule has been applied since the last server reboot.
New Hits Number of times the rule has been applied since the show aaa derivation-rules
command was last issued.
Parameter Description
Priority The priority in which the rules are applied. Rules at the top of the list are applied before
rules at the bottom.
Attribute This is the attribute returned by the authentication server that is examined for Operation
and Operand match.
Parameter Description
(host) #show aaa derivation-rules user
User Rule Table
---------------
Priority Attribute Operation Operand Action Value Total Hits New Hits
-------- --------- --------- ------- ------ ----- ---------- --------
1 location equals ap23 set role guest 56 18

AOS-W 3.4.1 Command Line Interface | Reference Guide show aaa derivation-rules | 481
Related Commands
Command History
This command was introduced in AOS-W 3.0.
Command Information
Operation This is the match method by which the string in Operand is matched with the attribute
value returned by the authentication server.
zcontains – The rule is applied if and only if the attribute value contains the string in
parameter Operand.
zstarts-with – The rule is applied if and only if the attribute value returned starts with
the string in parameter Operand.
zends-with – The rule is applied if and only if the attribute value returned ends with the
string in parameter Operand.
zequals – The rule is applied if and only if the attribute value returned equals the string
in parameter Operand.
znot-equals – The rule is applied if and only if the attribute value returned is not equal
to the string in parameter Operand.
zvalue-of – This is a special condition. What this implies is that the role or VLAN is set
to the value of the attribute returned. For this to be successful, the role and the VLAN
ID returned as the value of the attribute selected must be already configured on the
switch when the rule is applied.
Operand This is the string to which the value of the returned attribute is matched.
Action This parameter identifies whether the rule sets a server group role (set role) or a VLAN
(set vlan).
Value Sets the user role or VLAN ID to be assigned to the client if the condition is met.
Total Hits Number of times the rule has been applied since the last server reboot.
New Hits Number of times the rule has been applied since the show aaa derivation-rules
command was last issued.
Command Description Mode
aaa derivation-rules Use aaa derivation-rules to define the parameters displayed
in the output of this show command. Config mode
Platforms Licensing Command Mode
All platforms Base operating system Enable or Config mode on master or local
switches
Parameter Description
482 | show aaa main-profile AOS-W 3.4.1 Command Line Interface | Reference Guide
show aaa main-profile
show aaa main-profile summary
Description
Show a summary of all aaa profiles.
Example
The output of the show aaa main-profile summary command shows roles, server group settings, and wire-
to-wireless-roaming statistics for each AAA profile.
The following data columns appear in the output of this command:
Related Commands
Command History
This command was introduced in AOS-W 3.0.
Parameter Description
Name Name of the AAA profile.
role Role for unauthenticated users.
mac-auth Name of the server group used for MAC authentication.
dot1x-auth Name of the server group used for dot1x authentication.
rad-act Name of the server group used for RADIUS authentication.
XML-api IP address of a configured XML API server.
RFC3576 IP address of a RADIUS server that can send user disconnect and change-of-
authorization messages, as described in RFC 3576.
UDR-group Name of the user derivation rule profile.
ww-roam Shows if wired-to-wireless roaming is enabled or disabled.
Command Description Mode
aaa profile Use aaa profile define the parameters displayed in the
output of this show command. Config mode
(host) #show aaa main-profile summary
AAA Profile summary
-------------------
Name role mac-auth dot1x-auth rad-acct XML-api RFC3576 UDR-group ww-roam
---- ---- -------- ---------- -------- ------- ------- --------- ------
aaa_dot1x logon macprof2 dot1x RADIUS 10.3.1.15 10.3.15.2 Usr1 Disable
default logon macprof2 dot1x RADIUS 10.3.1.15 10.3.15.2 Usr1 Disable
defaultguest guest macprof1 default RADIUS 10.3.1.15 10.3.15.2 Usr2 Disable

AOS-W 3.4.1 Command Line Interface | Reference Guide show aaa main-profile | 483
Command Information
Platforms Licensing Command Mode
All platforms Base operating system Enable or Config mode on master or local
switches
484 | show aaa profile AOS-W 3.4.1 Command Line Interface | Reference Guide
show aaa profile
show aaa profile <profile-name>
Description
Show configuration details for an individual AAA profile.
Example
The output of the following command shows roles, servers and server group settings, and wire-to-wireless-
roaming statistics for each AAA profile.
The following data columns appear in the output of this command:
Parameter Description
Name The name of the AAA profile.
Initial Role Role for unauthenticated users.
MAC Authentication Profile Name of the MAC authentication profile.
MAC Authentication Default Role Configured role assigned to the user after MAC authentication.
MAC Authentication Server Group Name of the server group used for MAC authentication.
8021.X Authentication Profile Name of the 802.1x authentication profile.
8021.X Authentication Default Role Configured role assigned to the user after 802.1x authentication.
8021.X Authentication Server Group Name of the server group used for 802.1x authentication.
RADIUS Accounting Server Group Name of the server group used for RADIUS authentication.
XML API server IP address of a configured XML API server.
RFC 3576 server IP address of a RADIUS server that can send user disconnect and
change-of-authorization messages, as described in RFC 3576.
User derivation rules Name of the user derivation rule profile.
Wired to Wireless Roaming Shows whether Wired to Wireless Roaming is Enabled or Disabled.
(host) #show ap profile aaa_dot1x
AAA Profile "aaa_dot1x"
-----------------------
Parameter Value
--------- -----
Initial role logon
MAC Authentication Profile macprof2
MAC Authentication Default Role guest
MAC Authentication Server Group svrgrp
802.1X Authentication Profile dot1x
802.1X Authentication Default Role guest
802.1X Authentication Server Group Internal
RADIUS Accounting Server Group RADIUS
XML API server 10.3.1.15
RFC 3576 server 10.3.15.2
User derivation rules Usr1
Wired to Wireless Roaming Enabled
SIP authentication role N/A
AOS-W 3.4.1 Command Line Interface | Reference Guide show aaa profile | 485
Related Commands
Command History
This command was introduced in AOS-W 3.0.
Command Information
SIP authentication role For switchs with an installed Policy Enforcement Firewall license, this
parameter displays the configured role assigned to a session
initiation protocol (SIP) client upon registration.
Command Description Mode
aaa profile Use the command aaa profile to define AAA
profiles. Config mode
Platforms Licensing Command Mode
All platforms Base operating system Enable or Config mode on master or local
switches
Parameter Description

486 | show aaa radius-attributes AOS-W 3.4.1 Command Line Interface | Reference Guide
show aaa radius-attributes
show aaa radius-attributes
Description
Show RADIUS attributes recognized by the switch
Example
The output of the following command shows the name, currently configured value, type, vendor and RADIUS ID
for each attribute.
Related Commands
Command History
This command was introduced in AOS-W 3.0.
Command Information
Command Description Mode
aaa profile Use the command aaa profile to define AAA
profiles. Config mode
Platforms Licensing Command Mode
All platforms Base operating system Enable or Config mode on master or local
switches
(host) #show aaa radius-attributes
Dictionary
----------
Attribute Value Type Vendor Id
--------- ----- ---- ------ --
MS-CHAP-NT-Enc-PW 6 String Microsoft 311
Suffix 1004 String
Menu 1001 String
Acct-Session-Time 46 Integer
Framed-AppleTalk-Zone 39 String
Connect-Info 77 String
Acct-Ouput-Packets 48 Integer
Aruba-Location-Id 6 String Aruba 14823
Service-Type 6 Integer
Rad-Length 310 Integer
CHAP-Password 3 String
Aruba-Template-User 8 String Aruba 14823
Event-Timestamp 55 Date
Login-Service 15 Integer
Exec-Program-Wait 1039 String
Tunnel-Password 69 String
Framed-IP-Netmask 9 IP Addr
Acct-Output-Gigawords 53 Integer
MS-CHAP-CPW-2 4 String Microsoft 311
Acct-Tunnel-Packets-Lost 86 Integer
...
AOS-W 3.4.1 Command Line Interface | Reference Guide show aaa rfc-3576-server | 487
show aaa rfc-3576-server
show aaa rfc-3576-server [statistics|<udp-port>]
Description
Show configuration details for an RFC-3576 server, which is a RADIUS server that can send user disconnect and
change-of-authorization (CoA) messages, as described in RFC 3576.
Example
This first example shows that there are two configured servers in the RFC 3567 Server List. The References
column lists the number of other profiles with references to the RFC 3567 server, and the Profile Status
column indicates whether the server is predefined. User-defined servers will not have an entry in the Profile
Status column.
To view details for all RFC 3576 servers, include the statistics parameter.
The output of the show aaa rfc-3576-server statistics command includes the following parameters:
Parameter Description
Disconnect Requests Number of disconnect requests sent by the server.
Disconnect Accepts Number of disconnect requests sent by the server that were accepted by the user.
Disconnect Rejects Number of disconnect requests sent by the server that were rejected by the user.
No Secret Number of authentication requests that did not contain a RADIUS secret.
No Session ID Number of authentication requests that did not contain a session ID.
(host) #show aaa rfc-3567-server
RFC 3576 Server List
--------------------
Name References Profile Status
---- ---------- --------------
10.2.14.6 2
(host) #show aaa rfc-3576-server statistics
RADIUS RFC 3576 Statistics
--------------------------
Statistics 10.1.2.3 10.1.2.34
---------- -------- ---------
Disconnect Requests 13 3
Disconnect Accepts 12 3
Disconnect Rejects 1 0
No Secret 0 0
No Session ID 0 0
Bad Authenticator 0 0
Invalid Request 0 0
Packets Dropped 0 2
Unknown service 0 0
CoA Requests 1 0
CoA Accepts 1 0
CoA Rejects 0 0
No permission 0 0
Packets received from unknown clients: 0
Packets received with unknown request: 0
Total RFC3576 packets Received : 0
488 | show aaa rfc-3576-server AOS-W 3.4.1 Command Line Interface | Reference Guide
Related Commands
Command History
This command was introduced in AOS-W 3.0.
Command Information
Bad Authenticator Number of authentication requests that contained a missing or invalid authenticator field
in the packet.
Invalid Request Number of invalid requests.
Packets Dropped Number of packets dropped.
Unknown service Number of requests for an unknown service type.
CoA Requests Number of requests for a Change of Authorization (CoA).
CoA Accepts Number of times a CoA request was accepted.
CoA Rejects Number of times a CoA request was rejected.
No permission Number of requests for a service that has been defined, but has not been administratively
enabled.
Command Description Mode
aaa rfc-3576-server Define RFC 3576 server profiles. Config mode
Platforms Licensing Command Mode
All platforms Base operating system Enable or Config mode on master or local
switches
Parameter Description
AOS-W 3.4.1 Command Line Interface | Reference Guide show aaa server-group | 489
show aaa server-group
show aaa server-group [<group-name>|summary]
Description
Show configuration details for your AAA server groups.
Syntax
Usage Guidelines
Issue this command without the <group-name> or summary options to display the entire server group list,
including profile status and the number of references to each profile.The References column lists the number
of other profiles that reference a server group, and the Profile Status column indicates whether the server
group is predefined. User-defined server groups will not have an entry in the Profile Status column. Examples
This first example shows that there are five configured server groups
.To view additional statistics for all server groups, include the statistics parameter.
The output of the show aaa server-group summary command includes the following parameters:
Parameter Description
<group-name> The name of an existing AAA server group.
Parameter Description
name Name of an existing AAA server group.
Servers Number of servers in the group.
Rules Number of rules configured for the server group.
(host) #show aaa server-group summary
Server Group List
-----------------
Name References Profile Status
---- ---------- --------------
auth-profile-2 1
coltrane-server-group 1
default 25
group1 0
internal 0 Predefined
Total:5
(host) #show aaa server-group summary
Server Groups
-------------
Name Servers Rules hits Out-of-service
---- ------- ----- ---- --------------
auth-profile-2 1 0 0
coltrane-server-group 1 0 0
default 1 0 0
group1 1 1 0
internal 1 1 0
490 | show aaa server-group AOS-W 3.4.1 Command Line Interface | Reference Guide
To display detailed authorization, role and vlan statistics for an individual server group, include the name of the
group for which you want more information.
The output of the show aaa server-group <group-name> command includes the following parameters:
hits Number of hits for the server’s rules.
Out-of-Service Indicates whether the server is active, or out of service. Active servers may not have an
entry in the Out-of-Service column.
Parameter Description
Name Specifies if the server is in service or out-of-service.
Server-Type If enabled, user information in an authentication request is edited before the request is
sent to the server.
trim-FDQN If enabled, user information in an authentication request is edited before the request is
sent to the server.
Match-Type If the match type is authstring he authentication server associates with a match rule that
the switch can compare with the user/client information in the authentication request.
A fdqn match type associates the authentication server with a specified domain. An
authentication request is sent to the server only if there is an exact match between the
specified domain and the <domain> portion of the user information sent in the
authentication request.
Match-Op This is the match method by which the string in Match-Str is matched with the attribute
value returned by the authentication server.
zcontains – The rule is applied if and only if the attribute value contains the string in
parameter Operand.
zstarts-with – The rule is applied if and only if the attribute value returned starts with
the string in parameter Operand.
zends-with – The rule is applied if and only if the attribute value returned ends with the
string in parameter Operand.
zequals – The rule is applied if and only if the attribute value returned equals the string
in parameter Operand.
znot-equals – The rule is applied if and only if the attribute value returned is not equal
to the string in parameter Operand.
zvalue-of – This is a special condition. What this implies is that the role or VLAN is set
to the value of the attribute returned. For this to be successful, the role and the VLAN
ID returned as the value of the attribute selected must be already configured on the
switch when the rule is applied
Parameter Description
(host) #show aaa server-group summary group1
Fail Through:No
Auth Servers
------------
Name Server-Type trim-FQDN Match-Type Match-Op Match-Str
---- ----------- --------- ---------- -------- ---------
rad1 Radius No authstring equals company_eng
rad3 Radius No authstring equals company_qa
Role/VLAN derivation rules
---------------------------
Priority Attribute Operation Operand Action Value
-------- --------- --------- ------- ------ -----
1 class contains admin set role root
AOS-W 3.4.1 Command Line Interface | Reference Guide show aaa server-group | 491
Related Commands
Command History
This command was introduced in AOS-W 3.0.
Command Information
Match-Str This is the string to which the value of the returned attribute is matched.
Priority The priority in which role or VLAN derivation rules are applied. Rules at the top of the list
are applied before rules at the bottom.
Attribute For role or VLAN derivation rules, this is the attribute returned by the authentication
server that is examined for Operation and Operand match.
Operation For role or VLAN derivation rules, this is the match method by which the string in
Operand is matched with the attribute value returned by the authentication
server.
zcontains – The rule is applied if and only if the attribute value contains the string in
parameter Operand.
zstarts-with – The rule is applied if and only if the attribute value returned starts with
the string in parameter Operand.
zends-with – The rule is applied if and only if the attribute value returned ends with the
string in parameter Operand.
zequals – The rule is applied if and only if the attribute value returned equals the string
in parameter Operand.
znot-equals – The rule is applied if and only if the attribute value returned is not equal
to the string in parameter Operand.
zvalue-of – This is a special condition. What this implies is that the role or VLAN is set
to the value of the attribute returned. For this to be successful, the role and the VLAN
ID returned as the value of the attribute selected must be already configured on the
switch when the rule is applied.
Operand For role or VLAN derivation rules, this is the string to which the value of the returned
attribute is matched.
Action This parameter identifies whether the derivation rule sets a server group role (set role) or
a VLAN (set vlan).
Value Sets the user role or VLAN ID to be assigned to the client if the rule condition is met.
Command Description Mode
aaa server-group Use aaa server-group to configure the settings
displayed in the output of this show command. Config mode
Platforms Licensing Command Mode
All platforms Base operating system Enable or Config mode on master or local
switches
Parameter Description
492 | show aaa state ap-group AOS-W 3.4.1 Command Line Interface | Reference Guide
show aaa state ap-group
show aaa state ap-group
Description
Show the names and ID numbers of your AP groups
Example
This first example shows that the selected switch has two defined AP groups.
Related Commands
Command History
This command was introduced in AOS-W 3.0.
Command Information
.
Command Description Mode
aaa server-group Use aaa server-group to define the AP groups
displayed in the output of this show command Config mode
Platforms Licensing Command Mode
All platforms Base operating system Enable or Config mode on master or local
switches
(host) #show aaa state ap-group
AP Group Table
--------------
Name ID
---- --
ap1 1
ap2 2

AOS-W 3.4.1 Command Line Interface | Reference Guide show aaa state configuration | 493
show aaa state configuration
show aaa state configuration
Description
Display authentication state configuration information, including the numbers of successful and failed
authentications.
Example
This example shows authentication settings and values for a switch with no current users.
(host) #show aaa state configuration
Authentication State
--------------------
Name Value
---- -----
Switch IP 10.6.2.253
Master IP 10.100.103.253
Switch Role local
Current/Max/Total Users 129/234/4058
Current/Max/Total Stations 121/190/367550
Captive Portal Users 4
802.1x Users 119
VPN Users 0
MAC Users 0
Stateful 802.1x Users 0
Tunneled users 0
Configured user roles 21
Configured session ACL 41
Configured destinations 32
Configured services 77
Configured Auth servers 9
Auth server in service 9
Radius server timeouts 7062
Successful authentications
--------------------------
Web MAC VPN 802.1x Krb RadAcct SecureID Stateful-802.1x Management
--- --- --- ------ --- ------- -------- --------------- ----------
138 0 0 10117 0 0 0 0 0
Failed authentications
----------------------
Web MAC VPN 802.1x Krb RadAcct SecureID Stateful-802.1x Management
--- --- --- ------ --- ------- -------- --------------- ----------
48 0 0 32235 0 0 0 0 0
Idled users = 3366
Mobility = Enabled
fast age = Disabled
Bandwidth contracts = 2/1
IP takeovers = 21
Ping/SYN/Session attacks = 0/0/0
494 | show aaa state configuration AOS-W 3.4.1 Command Line Interface | Reference Guide
The output of the show aaa state configuration command includes the following parameters:
Parameter Description
Switch IP IP address of the local switch.
Master IP IP address of the master switch.
Switch Role Role assigned to the switch on which you issued the show aaa state
command.
Current/Max/Total Users Current number of users on the switch/Maximum number of users that can be
assigned to the switch at any time/Total number of users that have been
assigned to the switch since the last switch reboot.
Current/Max/Total Stations Current number of stations registered with the switch/Maximum number of
stations that can be registered with the switch at any time/Total number of
stations that have registered the switch since the last switch reboot.
Captive Portal Users Number of current users authenticated via captive portal.
802.1x Users Number of current users authenticated via 802.1x authentication.
VPN Users Number of current users authenticated via VPN authentication.
MAC Users Number of current users authenticated via MAC authentication.
Stateful 802.1x Users Number of current users authenticated via stateful 802.1x authentication.
Tunneled users Number of stations in tunneled forwarding mode, where 802.11 frames are
tunneled to the switch using generic routing encapsulation (GRE).
Configured user roles Number of configured user roles.
Configured session ACL Number of configured session ACLs.
Configured destinations Number of destinations configured using the netdestination command.
Configured services Number of service aliases configured using the netservice command.
Configured Auth servers Number of configured authentication servers.
Auth server in service Number of authentication servers currently in service.
Radius server timeouts Number of times the RADIUS server did not respond to the authentication
request.
Web Total number of captive portal authentications or authentication failures since
the last switch reset.
MAC Total number of MAC authentications or authentication failures since the last
switch reset.
VPN Total number of VPN authentications or authentication failures since the last
switch reset.
802.1x Total number of 802.1x authentications or authentication failures since the last
switch reset.
Krb Total number of Kerberos authentications or authentication failures since the
last switch reset.
RadAcct Total number of RADIUS accounting verifications or accounting failures since
the last switch reset.
SecureID Number of authentication verifications or failures using methods which use
one-time passwords. (For example, EAP-GTC being used as the inner EAP
protocol of EAP-PEAP.)
Stateful-802.1x Total number of Stateful 802.1x authentications or authentication failures since
the last switch reset.
AOS-W 3.4.1 Command Line Interface | Reference Guide show aaa state configuration | 495
Command History
This command was introduced in AOS-W 3.0.
Command Information
Management Total number of Management user authentications or authentication failures
since the last switch reset.
Idled users Total number of users that are not broadcasting data to an AP.
Mobility Shows whether the IP mobility feature has been enabled or disabled on the
switch.
fast age When the fast age feature allows the switch actively sends probe packets to all
users with the same MAC address but different IP addresses. The users that fail
to respond are purged from the system. This parameter shows if fast aging of
user table entries has been enabled or disabled.
Bandwidth contracts Number of configured bandwidth contracts on the switch.
IP takeovers Number of times a two different stations have attempted to use the same IP
address (IP spoofing).
Ping/SYN/Session attacks Number of reported ping, SYN and session attacks.
Platforms Licensing Command Mode
All platforms Base operating system Enable or Config mode on master or local
switches
Parameter Description

496 | show aaa state debug-statistics AOS-W 3.4.1 Command Line Interface | Reference Guide
show aaa state debug-statistics
show aaa state debug statistics
Description
show debug statistics for switch authentication, authorization and accounting.
Syntax
No parameters.
Example
The following example displays debug statistics for a variety of authentication errors.
The output of this command includes the following parameters:
Command History
Parameter Description
ARP Number of ARP packets sent between the datapath and the controlpath.
8021q Number of 802.1q (VLAN tag) packets sent between the datapath and the controlpath.
non-ip Number of non-ip type packets sent between the datapath and the controlpath.
zero-ip Number packets sent without an internet protocol (IP).
loopback If 1, the switch has a defined loopback address. If 0, a loopback address has not yet
been configured.
mac mismatch Number of users that were not authenticated due to MAC mismatches.
spoof Number of users that were not authenticated due to spoofed IP addresses.
drop Number of user authentication attempts that were dropped.
ncfg Number of packets sent between datapath and controlpath, where the authentication
module has not completed the initialization required to process the traffic.
idled users Number of inactive stations that are not broadcasting data to an AP.
idled users due to MAC
mismatch For internal use only.
Logon lifetime iteration Number of users deleted for lack of activity.
SIP authentication message Number of session initiation protocol (SIP) authentication messages received.
Missing auth user deletes Number of users removed from the datapath by the auth module, even without a
mapping entry in control path. This counter can help identify problems with messages
sent between the controlpath and the datapath.
(host) #show aaa state debug-statistics
user miss: ARP=47, 8021Q=5216, non-IP=0, zero-IP=0, loopback=0
user miss: mac mismatch=0, spoof=269 (74), drop=390, ncfg=0
Idled users = 3376
Idled users due to MAC mismatch = 0
Logon lifetime iterations = 4501, entries deleted = 121
SIP authentication messages received 29227, dropped 29227
Missing auth user deletes: 0

AOS-W 3.4.1 Command Line Interface | Reference Guide show aaa state debug-statistics | 497
This command was introduced in AOS-W 3.0.
Command Information
Platforms Licensing Command Mode
All platforms Base operating system Enable or Config mode on master or local or
local switches

498 | show aaa state messages AOS-W 3.4.1 Command Line Interface | Reference Guide
show aaa state messages
Description
Display numbers of authentication messages sent and received.
Syntax
No parameters.
Usage Guidelines
This command displays a general overview of authentication statistics. To view authentication information for
specific profiles such as a captive-portal, MAC or 801.x authentication profile, issue the commands specific to
those features.
Example
The output of this command displays tables of statistics for PAPI, RAW socket and Sibyte messages.
(host) #show aaa state messages
PAPI Messages
-------------
Msg ID Name Since last Read Total
------ ---- --------------- -----
5004 set master ip 2 2
7005 Set switch ip 1 1
7007 Set VLAN ip 5 5
66 delete xauth vpn users 1 1
RAW socket Messages
-------------------
Msg ID Name Since last Read Total
------ ---- --------------- -----
1 raw PAP req 188 188
33 captive portal config 11113 11113
59 TACACS ACCT config for cli 1 1
60 TACACS ACCT config for web 1 1
Sibyte Messages
---------------
Opcode Name Sent Since Last Read Sent Total Recv Since Last Read Recv Total
------ ---- -------------------- ---------- -------------------- ----------
2 bridge 21 21 0 0
4 session 4877 4877 0 0
11 ping 768 768 768 768
13 8021x 114563 114563 229126 229126
15 acl 803 803 0 0
16 ace 5519 5519 0 0
17 user 781821 781821 0 0
27 bwm 3 3 0 0
29 wkey 27109 27109 4 4
42 nat 1 1 0 0
43 user tmout 4164 4164 4160 4160
56 forw unenc 1787103 1787103 0 0
64 auth 5268 5268 5267 5267
94 aesccm key 17885 17885 0 0
111 dot1x term 196813 196813 151161 151161
114 rand 1614 1614 1612 1612
126 eapkey 1316231 1316231 2632462 2632462
114 rand 2 2 0 0
AOS-W 3.4.1 Command Line Interface | Reference Guide show aaa state messages | 499
The output of this command contains the following parameters:
Command History
This command was introduced in AOS-W 3.0.
Command Information
Parameter Description
Msg ID ID number for the message type
Name Message name
Since last Read Number of messages received since the buffer was last read.
Total Total number of message received since the switch was last reset.
opcode Code number of the message type.
Sent Since last Read Number of messages sent since the buffer was last read.
Sent Total Total number of message sent since the switch was last reset.
Recv Since last Read Number of messages received since the buffer was last read.
Recv Total Total number of message received since the switch was last reset.
Platforms Licensing Command Mode
All platforms Base operating system Enable or Config mode on master or local
switches
500 | show aaa state station AOS-W 3.4.1 Command Line Interface | Reference Guide
show aaa state station
show aaa state station <A:B:C:D:E:F>
Description
Display AAA statistics for a station.
Syntax
Example
The example below shows statistics for a station with four associated user IP addresses. The output of this
command shows station data, the AAA profiles assigned to the station, and the station’s authentication method.
Command History
This command was introduced in AOS-W 3.0.
Command Information
Parameter Description
<A:B:C:D:E:F> MAC address of a station/
Platforms Licensing Command Mode
All platforms Base operating system Enable or Config mode on master and local
switches
(host) #show aaa state station 00:21:5c:85:d0:4b
Association count = 1, User count = 4
User list = 10.1.10.10 10.6.5.168 192.168.229.1 192.168.244.1
essid: ethersphere-wpa2, bssid: 00:1a:1e:8d:5b:31 AP name/group: AL40/corp1344 PHY: a, ingress=0x10e8
(tunnel 136)
vlan default: 65, assigned: 0, current: 65 cached: 0, user derived: 0, vlan-how: 0
name: MYCOMPANY\tgonzales, role:employee (default:logon, cached:employee, dot1x:), role-how: 1, acl:51/0,
age: 00:02:50
Authentication: Yes, status: successful, method: 802.1x, protocol: EAP-MD5, server: vortex
dot1xctx:1 sap:1
Flags: mba=0
AAA prof: default-corp1344, Auth dot1x prof: default, AAA mac prof:, def role: logon
ncfg flags udr 1, mac 0, dot1x 1
Born: 1233767066 (Wed Feb 4 09:04:26 2009
AOS-W 3.4.1 Command Line Interface | Reference Guide show aaa state user | 501
show aaa state user
show aaa state user <A.B.C.D>
Description
Display statistics for an authenticated user.
Syntax
Example
The example below shows statics for a user with the IP address 10.1.10.11. The output of this command shows
user data, the user’s authentication method. and statistics for assigned roles, timers and flags.
Command History
This command was introduced in AOS-W 3.0.
Command Information
Parameter Description
<A.B.C.D> IP address of a user.
Platforms Licensing Command Mode
All platforms Base operating system Enable or Config mode on master and local
switches
(host) #show aaa state user 10.1.10.11
Name: MYCOMPANY\tsenter, IP: 10.1.10.11, MAC: 00:21:5c:85:d0:4a, Role:employee, ACL:51/0, Age: 00:01:46
Authentication: Yes, status: successful, method: 802.1x, protocol: EAP-MD5, server: vortex
Bandwidth = No Limit
Bandwidth = No Limit
Role Derivation: Default
VLAN Derivation: Matched user rule
Idle timeouts: 0, ICMP requests sent: 0, replies received: 0, Valid ARP: 0
Mobility state: Associated, HA: Yes, Proxy ARP: No, Roaming: No Tunnel ID: 0 L3 Mob: 0
Flags: internal=0, trusted_ap=0, delete=0, l3auth=0, l2=1 mba=0
Flags: innerip=0, outerip=0, guest=0, station=0, download=1, nodatapath=0
Auth fails: 0, phy_type: a-HT, reauth: 0, BW Contract: up:0 down:0, user-how: 1
Vlan default: 65, Assigned: 0, Current: 65 vlan-how: 0
Mobility Messages: L2=0, Move=0, Inter=0, Intra=0, ProxyArp=0, Flags=0x0
Tunnel=0, SlotPort=0x1018, Port=0x10e2 (tunnel 130)
Role assigned: n/a, VPN: n/a, Dot1x: Name: employee role-how: 0
Essid: ethersphere-wpa2, Bssid: 00:1a:1e:11:6b:91 AP name/group: AL31/corp1344 Phy-type: a-HT
RadAcct sessionID:n/a
RadAcct Traffic In 0/0 Out 0/0 (0:0/0:0:0:0,0:0/0:0:0:0)
Timers: arp_reply 0, spoof reply 0, reauth 0
Profiles AAA:default-corp1344, dot1x:default, mac: CP: def-role:'logon' sip-role:''
ncfg flags udr 0, mac 0, dot1x 0
Born: 1233772328 (Wed Feb 4 10:32:08 2009)
502 | show aaa sygate-on-demand (deprecated) AOS-W 3.4.1 Command Line Interface | Reference Guide
show aaa sygate-on-demand (deprecated)
show aaa sysgate-on-demand
Syntax
No parameters.
Command History
Release Modification
AOS-W 3.0 Command introduced.
AOS-W 3.4 Command deprecated.

AOS-W 3.4.1 Command Line Interface | Reference Guide show aaa tacacs-accounting | 503
show aaa tacacs-accounting
Description
Show TACACS accounting configuration.
Syntax
No parameters.
Example
The example below shows that TACACS accounting has been enabled, and that the TACACS server is in the
server group acct-server.
The output of this command includes the following parameters:
Command History
This command was introduced in AOS-W 3.0.
Command Information
Parameter Description
Mode Shows if the TACACS accounting feature is enabled or disable
Server-Group The server group that contains the active TACACS server.
Platforms Licensing Command Mode
All platforms Base operating system Enable or Config mode on master and local
switches
(host) #show aaa tacacs-accounting
TACACS Accounting Configuration
-------------------------------
Parameter Value
--------- -----
Mode Enabled
Server-Group acct-server
504 | show aaa timers AOS-W 3.4.1 Command Line Interface | Reference Guide
show aaa timers
Description
Show AAA timer values.
Syntax
No parameters
Example
The example below shows that the switch has all default timer values:
Related Commands
Command History
This command was introduced in AOS-W 3.0.
Command Information
Command Description Mode
aaa timers Use aaa timers to define the settings displayed in
the output of this show command. Config mode
Platforms Licensing Command Mode
All platforms Base operating system Enable or Config mode on master and local
switches
(host) #show aaa timers
User idle timeout = 6 minutes
Auth Server dead time = 10 minutes
Logon user lifetime = 5 minutes
AOS-W 3.4.1 Command Line Interface | Reference Guide show aaa xml-api server | 505
show aaa xml-api server
show aaa xml-api server [<server_ip>]
Description
Show a list of XML servers used for authentication, authorization and accounting.
Syntax
Example
The output of this command shows that the switch has two configured XML API servers that are each
referenced by two different AAA profiles. Note that user-defined servers will not have an entry in the Profile
Status column.
Command History
This command was introduced in AOS-W 3.0.
Command Information
Parameter Description
<server_ip> IP address of an XML API server. Include this parameter to see if a secret key is
configured for the specified server.
Platforms Licensing Command Mode
All platforms Base operating system Enable or Config mode on master and local
switches
(host) #show aaa xml-api statistics
XML API Server List
-------------------
Name References Profile Status
---- ---------- --------------
10.1.2.3 2
10.4.3.2 2

506 | show aaa web admin-port AOS-W 3.4.1 Command Line Interface | Reference Guide
show aaa web admin-port
show aaa web admin-port
Description
Show the port numbers of HTTP and HTTPS ports used for web administration.
Syntax
No parameters.
Example
The example below shows that the switch is configured to use HTTPS on port 4343, and HTTP on port 8888.
Command History
This command was introduced in AOS-W 3.0.
Command Information
Platforms Licensing Command Mode
All platforms Base operating system Enable or Config mode on master and local
switches
(host) #show aaa web admin-port
https port = 4343
http port = 8888
AOS-W 3.4.1 Command Line Interface | Reference Guide show aaa xml-api statistics | 507
show aaa xml-api statistics
show aaa xml-api statistics
Description
Display statistics for an external XML API server.
Syntax
Usage Guidelines
Issue this command to troubleshoot AAA problems and monitor usage on an XML server.
Example
The example below shows AAA statistics for an external XML server with the IP address 10.1.2.3. This
command shows the number of times that a particular event has occurred per client. The first number is the
total number of times that this event has occurred is displayed firs. The number of new events since the last
time the counters were displayed is shown in parentheses.
The output of this command includes the following parameters:
Parameter Description
<server_ip> IP address of XML API server.
Parameter Description
user_authenticate Number of users authenticated on the XML server since the last switch reboot.
user_add Number of users added to the switch’s user table.
user_delete Number of users removed from the switch’s user table.
(host) #show aaa xml-api statistics
Statistics 10.1.2.3
---------- --------
user_authenticate 0 (0)
user_add 0 (0)
user_delete 0 (0)
user_blacklist 0 (0)
user_query 0 (0)
unknown user 0 (0)
unknown role 0 (0)
unknown external agent 0 (0)
authentication failed 0 (0)
invalid command 0 (0)
invalid message authentication method 0 (0)
invalid message digest 0 (0)
missing message authentication 0 (0)
missing or invalid version number 0 (0)
internal error 0 (0)
client not authorized 0 (0)
Cant use VLAN IP 0 (0)
Invalid IP 0 (0)
Cant use Switch IP 0 (0)
missing MAC address 0 (0)
Packets received from unknown clients: 0 (0)
Packets received with unknown request: 0 (0)
Requests Received/Success/Failed : 0/0/0 (0/0/0)
508 | show aaa xml-api statistics AOS-W 3.4.1 Command Line Interface | Reference Guide
Command History
This command was introduced in AOS-W 3.0.
Command Information
user_blacklist Number of denied user association requests.
user_query Number of user queries performed.
unknown user Number of unknown users.
unknown role Number of unknown user roles.
unknown external agent Number of requests by an unknown external agent.
authentication failed Number of failed authentication requests.
invalid command Number of invalid XML commands
invalid message
authentication method Number of XML commands with an invalid authentication method (when a key is
configured on the switch).
invalid message digest Number of XML commands with an invalid digest type (when a key is configured on the
switch).
missing message
authentication Number of XML commands with an missing authentication method (when a key is
configured on the switch).
missing or invalid version
number Number of commands with a missing or invalid version number. The version number
should always be 1.0.
internal error Number of internal server errors
client not authorized Number of unauthorized clients
Cant use VLAN IP Number of time a user IP is same as the VLAN IP.
Invalid IP Number of XML commands with an invalid IP address.
Cant use Switch IP Redirection to a IP failed, possibly because the source IP has been NATted.
missing MAC address Number of XML commands with a missing MAC address.
Packets received from
unknown clients Number of packets received from unknown clients.
Packets received with
unknown request Number of packets received with unknown request
Requests Received/
Success/Failed Total number of requests received / number of successful requests / number of failed
requests
Platforms Licensing Command Mode
All platforms Base operating system Enable or Config mode on master and local
switches
Parameter Description
AOS-W 3.4.1 Command Line Interface | Reference Guide show acl ace-table | 509
show acl ace-table
show acl ace-table {ace <0-1999>}|{acl <1-2700>}
Description
Show an access list entry (ACE) table for an access control list (ACL).
Syntax
Example
The following example shows that there are eighteen access control entries for ACL 1.
Related Commands
Configure ACLs using the command ip access-list session.
Command History
This command was available in AOS-W 3.0.
Command Information
Parameter Description
ace <0-1999> Show a single ACE entry.
acl <1-2700> Show all ACE entries for a single ACL.
(host) #show acl ace-table acl 1
1020: any any 1 0-65535 0-65535 f80001:permit
1021: any any 17 0-65535 53-53 f80001:permit
1022: any any 17 0-65535 8211-8211 f80001:permit
1023: any any 17 0-65535 8200-8200 f80001:permit
1024: any any 17 0-65535 69-69 f80001:permit
1025: any any 17 0-65535 67-68 f80001:permit
1026: any any 17 0-65535 137-137 f80001:permit
1027: any any 17 0-65535 138-138 f80001:permit
1028: any any 17 0-65535 123-123 f80001:permit
1029: user 10.6.2.253 255.255.255.255 6 0-65535 443-443 f80001:permit
1030: user any 6 0-65535 80-80 d1f90,0000 f80021:permit dnat
1031: user any 6 0-65535 443-443 d1f91,0000 f80021:permit dnat
1032: any any 17 0-65535 500-500 f80001:permit
1033: any any 50 0-65535 0-65535 f80001:permit
1034: any any 17 0-65535 1701-1701 f80001:permit
1035: any any 6 0-65535 1723-1723 f80001:permit
1036: any any 47 0-65535 0-65535 f80001:permit
1037: any any 0 0-0 0-0 f180000:deny
Platforms Licensing Command Mode
All platforms Base operating system Enable and Config mode on master
switches
510 | show acl acl-table AOS-W 3.4.1 Command Line Interface | Reference Guide
show acl acl-table
show acl acl-table <1-2700>
Description
Display information for a specified access control list (ACL).
Syntax
Example
The following example displays the ACL table for the switch.
The output of this command displays the following parameters:
Parameter Description
acl-table <1-2700> Specify the number of the ACL for which you want to view information.
(host) #show acl acl-table acl 1
AclTable
--------
ACL Type ACE Index Ace Count Name Applied
--- ---- --------- --------- ---- -------
1 role 1459 18 logon 0
Total free ACE entries = 3591
Free ACE entries at the bottom = 2552
Next ACE entry to use = 1480 (table 1)
Ace entries reused 622 times
ACL count 64, tunnel acl 0
Ace entries reused 373 times
ACL count 64, tunnel acl 0
Parameter Description
ACL Number of the specified ACL
Type Shows the ACL type:
zrole: Access list is used to define a user role.
zmac: MAC ACLs allow filtering of non-IP traffic. This ACL filters on a specific
source MAC address or range of MAC addresses.
zsession: Session ACLs define traffic and firewall policies on the switch.
zether-type: This type of ACL filters on the Ethertype field in the Ethernet
frame header, and is useful when filtering non-IP traffic on a physical port.
zstandard: Standard ACLs are supported for compatibility with router
software from other vendors. This ACL permits or denies traffic based on the
source address of the packet.
ACE Index Starting index entry for the ACL’s access control entries
ACE count Number of access control entries in the ACL
Name Name of the access control list
Applied Number of times the ACL was applied to a role.
Total free ACE entries The total number of free ACE entries. This includes available ACE entries at the
bottom of the list, as well as free ACE entries in the middle of the table from
previous access list entries that were later removed.
AOS-W 3.4.1 Command Line Interface | Reference Guide show acl acl-table | 511
The following example displays the ACL table for ACL 1.
Related Commands
Configure ACLs using the command ip access-list session.
Command History
This command was available in AOS-W 3.0.
Command Information
Free ACE entries at the bottom The total number of free ACE entries at the bottom of the list.
Next ACE entry to use Ace number of the first free entry at the bottom of the list.
ACE entries reused For internal use only.
ACL count Total number of defined ACLs
Tunnel ACL Total number of defined tunnel ACLs.
Parameter Description
(host) #show acl ace-table acl 1
Acl Table
--------
ACL Type ACE Index Ace Count Name Applied
--- ---- --------- --------- ---- -------
1 role 1020 18 logon 0
Total free ACE entries = 3591
Free ACE entries at the bottom = 2991
Next ACE entry to use = 1041 (table 1)
Ace entries reused 373 times
ACL count 64, tunnel acl 0
Platforms Licensing Command Mode
All platforms Base operating system Enable and Config mode on master
switches

512 | show acl hits AOS-W 3.4.1 Command Line Interface | Reference Guide
show acl hits
show acl hits
Description
Show internal ACL hit counters.
Syntax
No parameters.
Usage Guidelines:
Issue this command to see the number of times an access control list defined a user’s role, or traffic and
firewall policies for a user session.
AOS-W 3.4.1 Command Line Interface | Reference Guide show acl hits | 513
Example
In the example below, the output of the User Role ACL Hits table is shown in two separate tables to allow
the output to fit on a single page of this document. In the actual switch command-line interface, the User
Role ACL Hits table is shown in a single, wide table.
The output of this command includes the following information:
(host) #show acl ace-table acl 1
User Role ACL Hits
------------------
Role Policy Src Dst
---- ------ --- ---
logon control any any
logon control any any
logon any any
visitor vp-control any any
visitor vp-control any any
visitor vp-access any any
visitor vp-access user mswitch-master
visitor vp-access any any
User Role ACL Hits
------------------
Service Action Dest/Opcode New Hits Total Hits Index
------- ------ ----------- -------- ---------- -----
svc-icmp permit 0 6 5052
svc-dhcp permit 0 2 5057
0 deny 0 53 5069
svc-dns permit 9 46079 4885
svc-dhcp permit 0 788 4886
svc-icmp permit 0 536 4887
svc-http permit 0 41 4889
6 9100-9100 permit 0 31 4892
Port Based Session ACL
----------------------
Policy Src Dst Service Action Dest/Opcode New Hits Total Hits Index
------ --- --- ------- ------ ----------- -------- ---------- -----
validuser 10.1.1.0 255.255.255.0 any any deny 0 214 4655
validuser any any any permit 6 2502 4656
Port ACL Hits
-------------
ACL ACE New Hits Total Hits Index
--- --- -------- ---------- -----
5 22 0 14 2382
Parameter Description
Role Name of the role assigned by the ACL.
Policy Name of the policy used by the ACL
Src The traffic source, which can be one of the following:
z<alias>: Name of a user-defined alias for a network host, subnetwork, or range
of addresses.
zany: match any traffic.
zhost: specify a single host IP address.
znetwork: specify the IP address and netmask.
zuser: represents the IP address of the user.
514 | show acl hits AOS-W 3.4.1 Command Line Interface | Reference Guide
Command History
This command was available in AOS-W 3.0.
Command Information
Dst The traffic destination, which can be one of the following:
z<alias>: Name of a user-defined alias for a network host, subnetwork, or range
of addresses.
zany: match any traffic.
zhost: specify a single host IP address.
znetwork: specify the IP address and netmask.
zuser: represents the IP address of the user.
Service Network service, which can be one of the following:
zIP protocol number (0-255)
zname of a network service (use the show netservice command to see
configured services)
zany: match any traffic
ztcp: specify the TCP port number (0-65535)
zudp: specify the UDP port number (0-65535)
Action Action if rule is applied, which can be one of the following:
zdeny: reject packets
zdst-nat: perform destination NAT on packets
zdual-nat: perform both source and destination NAT on packets
zpermit: forward packets
zredirect: specify the location to which packets are redirected
zsrc-nat: perform source NAT on packets
Dest/Opcode The datapath destination ID.
New Hits Number of ACL hits that occurred since this command was last issued.
Total Hits Total number of ACL hits recorded since the switch last reset.
Index Index number of the ACL..
ACL ACL number
ACE ACE number
New Hits Number of times the ACL was applied since this command was last issued.
Total Hits Number of times the ACL was applied since the switch was last reset.
Index Index number of the ACL..
Parameter Description
Platforms Licensing Command Mode
All platforms Base operating system Enable and Config mode on master
switches
AOS-W 3.4.1 Command Line Interface | Reference Guide show adp config | 515
show adp config
show adp config
Description
Show Alcatel-Lucent Discovery Protocol (ADP) configuration settings.
Syntax
No parameters.
Example
The following example shows that the switch has all default settings for ADP.
The output of this command includes the following parameters:
Command History
This command was available in AOS-W 3.0.
Command Information
(host) #show adp config
ADP Configuration
-----------------
key value
--- -----
discovery enable
igmp-join enable
igmp-vlan 0
Parameter Description
discovery Alcatel-Lucent APs send out periodic multicast and broadcast queries to locate
the master switch. If the APs are in the same broadcast domain as the master
switch and ADP is enabled on the switch, the switch automatically responds to
the APs’ queries with its IP address.
This command shows whether ADP is enabled or disabled on the switch.
igmp-join Shows whether the switch has enabled or disabled the sending of Internet Group
Management Protocol (IGMP) join requests.
igmp-vlan ID of the VLAN to which IGMP reports are sent. If this value is set to 0, the switch
will use the default route VLAN used.
Platforms Licensing Command Mode
All platforms Base operating system Enable or Config mode on master switches

516 | show adp counters AOS-W 3.4.1 Command Line Interface | Reference Guide
show adp counters
show adp counters
Description
Show Alcatel-Lucent Discovery Protocol (ADP) counters.
Syntax
No parameters.
Example
The following example shows the ADP counter table for the switch.
The output of this command includes the following parameters:
Command History
This command was available in AOS-W 3.0.
Command Information
(host) #show adp counters
ADP Counters
------------
key value
--- -----
IGMP Join Tx 1
IGMP Drop Tx 0
ADP Tx 0
ADP Rx 0
Parameter Description
IGMP Join Tx Number of Internet Group Management Protocol (IGMP) join requests sent by the
switch.
IGMP Drop Tx Number of Internet Group Management Protocol (IGMP) drop requests sent by
the switch.
ADP Tx Number of ADP responses sent to APs.
ADP Rx Number of multicast and broadcast queries received from APs trying to locate the
master switch.
Platforms Licensing Command Mode
All platforms Base operating system Enable or Config mode on master switches

AOS-W 3.4.1 Command Line Interface | Reference Guide show ap active | 517
show ap active
show ap active [ap-name <ap-name>|{arm-edge dot11a|dot11g|voip-
only}|dot11a|dot11g|essid <essid>|ip-addr <ip-addr>|{type access-point|air-
monitor|(sensor dot11a|dot11g|voip-only)}|voip-only
Description
Show all active APs registered to a switch.
Syntax
Example
Issue this command to displays details for all active APs.
The output of this command includes the following information:
Parameter Description
ap-name <ap-name> View data for an AP with a specified name.
arm-edge Show the state of ARM edge APs.
dot11a Show 802.11a radio information.
dot11g Show 802.11g radio information.
voip-only Show AP information filtered by associated/active VoIP clients.
essid <essid> View data for a specific ESSID (Extended Service Set Identifier). An
Extended Service Set Identifier (ESSID) is a alphanumeric name that
uniquely identifies the Service Set Identifier (SSID).
ip-addr <ip-addr> View data for an AP with a specified IP address by entering an IP
address in dotted-decimal format.
type Show AP information filtered by type of AP.
access-point Show information for Access Points only.
air-monitor Show information for Air Monitors only.
sensor Show only RFprotect Sensor information.
voip-only Show AP information filtered by associated/active VoIP clients.
(host)# show ap active
Active AP Table
---------------
Name Group IP Address 11g 11g Ch/EIRP/MaxEIRP 11a 11a Ch/EIRP/MaxEIRP AP Type Flags Uptime
Clients Clients
---- ----- ---------- ----- ------------------- ------ ---------------- ------- ----- ------
AL31 corp1344 10.6.1.202 0 AP:HT:1/8.5/33 0 AP:HT:149+/19/36 125 A 14d:11h:39m:33s
AL30 corp1344 10.6.1.203 0 AP:HT:11/8.5/33 0 AP:HT:153-/19/36 125 A 14d:11h:49m:41s
Corp1344 corp1344-AP85 10.6.14.73 0 AP:11/12.5/33 0 AP:153/12.5/36 85 14d:11h:48m:30s
AL29 corp1344 10.6.1.204 2 AP:HT:11/8.5/33 0 AP:HT:149+/19/36 125 A 14d:11h:50m:24s
AL33 corp1344 10.6.1.205 0 AP:HT:1/8.5/33 2 AP:HT:36+/16/23 125 A 14d:11h:49m:39s
AL39 corp1344 10.6.1.206 1 AP:HT:1/8.5/33 0 AP:HT:149+/19/36 125 A 14d:11h:42m:56s
Column Description
Name Name of an AP
Group The AP is associated with this AP group.
518 |show ap active AOS-W 3.4.1 Command Line Interface | Reference Guide
Command History
Introduced in AOS-W 3.0.
Command Information
IP address IP address of the AP, in dotted decimal format.
11g Clients Number of 802.11g clients using the AP.
11g Ch/EIRP/MaxEIRP 802.11g radio channel used by the AP/current effective Isotropic Radiated Power
(EIRP) /maximum EIRP.
11a Clients Number of 802.11a clients using the AP.
11a Ch/EIRP/MaxEIRP 802.11a radio channel used by the AP/current EIRP/maximum EIRP.
AP Type AP model type.
Flags This column displays any flags for this AP. The list of flag abbreviations is also
included in the output of the show ap active command.
za = Reduce ARP packets in the air
zA = Enet1 in active/standby mode
zB = Battery Boost On
zd = Drop Mcast/Bcast On or Disconnected Sensor
zD = Disconn. Extra Calls On
zE = Wired AP enabled
zK = 802.11K Enabled
zL = Client Balancing Enabled
zM = Mesh
zN = 802.11b protection disabled
zP = PPPOE
zR = Remote AP
zR- = The remote AP requires captive portal authentication. Once this
authentication is successfully completed, the R- flag changes to R.
zS = RFprotect Sensor
zU = USB modem
zX = Maintenance Mode
Uptime Number of hours, minutes and seconds since the last switch reboot or bootstrap, in
the format hours:minutes:seconds.
Platforms Licensing Command Mode
All platforms Base operating system Enable or Config mode on master switches
Column Description
AOS-W 3.4.1 Command Line Interface | Reference Guide show ap allowed-channels | 519
show ap allowed-channels
show ap allowed-channels [<ap-name>|<country-code>|<ip-addr>]
Description
This command shows configuration information for Captive portal authentication profiles.
Syntax
Usage Guidelines
Specify the country code for your switch during initial setup. Changing the country code causes the valid
channel lists to be reset to the defaults for that country.
Examples
The output of this example shows all allowed channels for the country code US.
Command History
Introduced in AOS-W 3.0.
Command Information
Parameter Description
<ap-name> Name of an AP.
<country-code> Specify a country code to display allowed channels for that country.
<ip-addr> IP address of an AP, in dotted-decimal format.
Platforms Licensing Command Mode
All platforms Base operating system Enable or Config mode on master switches
(host)# show ap allowed-channels US
Allowed Channels for Country Code "US"
--------------------------------------
PHY Type Allowed Channels
-------- ----------------
802.11g (indoor) 1 2 3 4 5 6 7 8 9 10 11
802.11a (indoor) 36 40 44 48 149 153 157 161 165
802.11g (outdoor) 1 2 3 4 5 6 7 8 9 10 11
802.11a (outdoor) 149 153 157 161 165
802.11g 40MHz (indoor) 1-5 2-6 3-7 4-8 5-9 6-10 7-11
802.11a 40MHz (indoor) 36-40 44-48 149-153 157-161
802.11g 40MHz (outdoor) 1-5 2-6 3-7 4-8 5-9 6-10 7-11
802.11a 40MHz (outdoor) 149-153 157-161
520 | show ap ap-group AOS-W 3.4.1 Command Line Interface | Reference Guide
show ap ap-group
show ap ap-group {ap-name <ap-name>|bssid <bssid>|ip-addr <ip-addr>}
Description
Show the AP group settings for an individual AP.
Syntax
Usage Guidelines
Use this command to display the contents of an AP's group profile. If you know the name of the group
whose profile settings you want to view, use the command show ap-group <profile-name>. To view a list
of all configured AP groups on your switch, use the command show ap-group.
Examples
In the example below, the output of this command lists the profiles associated with the AP group Corp13.
Related Commands
Parameter Description
ap-name <ap-name> Show data for an AP with a specific name.
bssid <bssid> Show data for a specific Basic Service Set Identifier (BSSID). An AP’s BSSID is
usually the AP’s MAC address.
ip-addr <ip-addr> Show data for an AP with a specific IP address. Enter the IP address in dotted-
decimal format.
Command Description Mode
ap-group Configure your AP groups and AP group profiles. Config mode
(host) #show ap ap-group AP2
AP group "corp13"
-------------------
Parameter Value
--------- -----
Virtual AP corp13-guest
Virtual AP corp13-ether-wpa2
Virtual AP corp13-ether-voip
Virtual AP corp13-ether-comm
802.11a radio profile default
802.11g radio profile default
Wired AP profile default
Ethernet interface 0 link profile default
Ethernet interface 1 link profile default
AP system profile corp13
VoIP Call Admission Control profile default
802.11a Traffic Management profile N/A
802.11g Traffic Management profile N/A
Regulatory Domain profile corp13-channel-profile
SNMP profile default
RF Optimization profile handoff-aggressive
RF Event Thresholds profile default

AOS-W 3.4.1 Command Line Interface | Reference Guide show ap ap-group | 521
Command History
Introduced in AOS-W 3.0.
Command Information
Platforms Licensing Command Mode
All platforms Base operating system Enable or Config mode on master switches
522 |show ap arm history AOS-W 3.4.1 Command Line Interface | Reference Guide
show ap arm history
show ap arm history {ap-name <ap-name>}|{bssid <bssid>}|{ip-addr <ip-addr>}
Description
For each interface on an AP, show the history of channel and power changes due to Adaptive Radio
Management (ARM) .
Syntax
Examples
Adaptive Radio Management (ARM) can automatically change channel and power levels based on a number
of factors such as noise levels and radio interference. The output of the show ap arm history command
shows you an AP’s channel and power changes over time, and the reason why those changes took place.
Parameter Description
ap-name <ap-name> Show ARM history for an AP with a specific name.
bssid <bssid> Show ARM history for a specific Basic Service Set Identifier (BSSID) on an AP. An
AP’s BSSID is usually the AP’s MAC address.
ip-addr <ip-addr> Show ARM history for an AP with a specific IP address. Enter the IP address in
dotted-decimal format.
(host)# #(ethersphere-lms3) #show ap arm history ap-name AP-16
Interface :wifi0
ARM History
-----------
Reason Old channel New channel Old Power New Power Last change
------ ----------- ----------- --------- --------- -----------
P- 153- 153- 12 9 3d:14h:56m:48s
P+ 153- 153- 9 12 3d:13h:44m:7s
P+ 153- 153- 12 15 3d:13h:23m:5s
P+ 153- 153- 15 18 3d:13h:16m:32s
P+ 153- 153- 18 21 3d:11h:42m:42s
P- 153- 153- 21 15 3d:8h:16m:12s
Interface :wifi1
ARM History
-----------
Reason Old channel New channel Old Power New Power Last change
------ ----------- ----------- --------- --------- -----------
P- 11 11 15 12 3d:18h:22m:28s
P+ 11 11 12 15 3d:18h:17m:27s
P- 11 11 15 12 3d:18h:9m:9s
P+ 11 11 12 15 3d:17h:48m:41s
P+ 11 11 15 18 3d:17h:44m:34s
P- 11 11 18 15 3d:17h:39m:11s
P- 11 11 15 12 3d:17h:32m:39s
P+ 11 11 12 15 3d:17h:26m:15s
I: Interference, R: Radar detection, N: Noise exceeded, E: Error threshold exceeded, INV: Invalid Channe
Containment, M: Empty Channel, P+: Increase Power, P-: Decrease Power, OFF: Turn off Radio, ON: Turn on
AOS-W 3.4.1 Command Line Interface | Reference Guide show ap arm history | 523
The output of this command includes the following information:
Command History
Introduced in AOS-W 3.0.
Command Information
Parameter Description
Reason This column displays one of the following code to indicate why the channel or power
change was made.
zI: Interference
zR: Radar detected
zN: Noise exceeded
zE: Error threshold exceeded
zINV: Invalid Channel
zG: Rogue AP Containment
zM: Empty Channel
zP+: Increase Power
zP-: Decrease Power
zOFF: Turn off Radio
zON: Turn on Radio
The Reason key appears at the bottom of the ARM History table.
Old Channel Channel number used by the AP interface before the ARM change.
New Channel Channel number used by the AP interface after the ARM change.
Old Power Power level of the AP interface before the ARM change.
New Power Power level of the AP interface after the ARM change.
Last Change Time elapsed since the change, in the format days:hours:minutes:seconds.
Platforms Licensing Command Mode
All platforms Base operating system Enable or Config mode on master or local
switches
524 | show ap arm neighbors AOS-W 3.4.1 Command Line Interface | Reference Guide
show ap arm neighbors
show ap arm neighbors {ap-name <ap-name>}|{bssid <bssid>}|{ip-addr <ip-addr>}
Description
Show the ARM settings for an AP’s neighbors.
Syntax
Examples
The output of this command shows ARM neighbor information for both the wifi1 and wifi0 interfaces on
AP ap70_1.
Command History
Introduced in AOS-W 3.0.
Command Information
Parameter Description
ap-name <ap-name> Show data for an AP with a specific name.
bssid <bssid> Show data for a specific Basic Service Set Identifier (BSSID). An AP’s BSSID is
usually the AP’s MAC address.
ip-addr <ip-addr> Show data for an AP with a specific IP address. Enter the IP address in dotted-
decimal format.
Platforms Licensing Command Mode
All platforms Base operating system Enable or Config mode on master switches
(host)# show ap arm neighbors ap70_1
Interface:wifi1
00:1b:2f:e6:1c:d0:known-interfering/SNR-1/CH-1
00:19:e3:31:55:f2:known-interfering/SNR-7/CH-1
00:1f:f3:01:4d:3f:known-interfering/SNR-1/CH-1
00:18:39:96:b4:16:known-interfering/SNR-0/CH-1
00:11:24:ec:49:05:known-interfering/SNR-0/CH-1
Interface:wifi0
00:19:7e:4d:8a:1d:known-interfering/SNR-0/CH-1
00:19:a9:ce:13:90:interfering/SNR-0/CH-4
00:19:7e:4d:80:df:known-interfering/SNR-0/CH-1
00:11:24:90:17:d4:known-interfering/SNR-0/CH-1
00:16:b6:f4:59:94:known-interfering/SNR-0/CH-1
00:14:51:6d:d1:d5:known-interfering/SNR-0/CH-1
AOS-W 3.4.1 Command Line Interface | Reference Guide show ap arm rf-summary | 525
show ap arm rf-summary
show ap arm rf-summary {ap-name <ap-name>}|{bssid <bssid>}|{ip-addr <ip-addr>}
Description
Show the state and statistics for all channels being monitored by an individual AP.
Syntax
Examples
The output of this command shows detailed information for the individual channels being monitored and
statistics for each AP interface. Use this command verify an AP’s RF health, or to determine why multiple
APs in the same area are on the same channel.
The output of this command includes the following information:
Parameter Description
ap-name <ap-name> Show channel data for an AP with a specific name.
bssid <bssid> Show channel data for a specific Basic Service Set Identifier (BSSID) on an AP. An
AP’s BSSID is usually the AP’s MAC address.
ip-addr <ip-addr> Show channel data for an AP with a specific IP address. Enter the IP address in
dotted-decimal format.
Parameter Description
channel Number of a radio channel used by the AP.
(host)# show ap arm rf-summary ap-name ap21
Channel Summary
---------------
channel retry low-speed non-unicast frag bwidth phy-err mac-err noise cov-idx intf_idx
------- ----- --------- ----------- ---- ------ ------- ------- ----- ------- --------
1 0 0 0 0 0 0 0 0 1/1 27/12//12/0
48 0 0 0 0 0 0 0 0 0/0 0/0//4/1
165 5 3 3 42 720 0 1 112 10/0 41/0//0/1
6 0 100 50 0 0 0 12 100 10/0 60/10//0/4
11 0 0 0 0 0 0 0 0 4/2 29/13//17/0
149 0 0 0 0 0 0 0 0 0/0 0/0//5/0
36 0 0 0 0 0 0 0 0 0/0 0/0//20/1
153 0 0 0 0 0 0 0 0 0/0 0/0//0/2
40 0 0 0 0 0 0 0 0 0/0 0/0//2/7
44 0 0 0 0 0 0 0 0 0/0 0/0//4/2
Interface Name :wifi0
Current ARM Assignment :165/21
Target Coverage Index :10
Covered channels a/g :0/0
Free channels a/g :7/0
ARM Edge State :enable
Last check channel/pwr :22m:12s/9m:17s
Last change channel/pwr :22m:12s/16m:55s
Next Check channel/pwr :0s/2m:41s
Interface Name :wifi1
Current ARM Assignment :6/6
TtC Id 10
526 | show ap arm rf-summary AOS-W 3.4.1 Command Line Interface | Reference Guide
Command History
Introduced in AOS-W 3.0.
Command Information
retry Number of 802.11 retry frames sent because a client failed to send an ACK.
low-speed Number of frames sent at a data rate of 18 Mbps or slower.
non-unicast The number of non-unicast frames sent on the channel.
frag Number of fragmented packets
bwidth Current bandwidth, in kbps.
phy-err Number of PHY errors on the channel.
mac-err Number of MAC errors on the channel.
noise Current noise level, in -dBm.
cov-idx The AP uses this metric to measure RF coverage. The coverage index is calculated
as x/y, where “x” is the AP’s weighted calculation of the Signal-to-Noise Ratio (SNR)
on all valid APs on a specified 802.11 channel, and “y” is the weighted calculation of
the Alcatel-Lucent APs SNR the neighboring APs see on that channel.
intf_idx The AP uses this metric to measure co-channel and adjacent channel interference.
The Interference Index is calculated as a/b//c/d, where:
zMetric value “a” is the channel interference the AP sees on its selected channel.
zMetric value “b” is the interference the AP sees on the adjacent channel.
zMetric value “c” is the channel interference the AP’s neighbors see on the
selected channel.
zMetric value “d” is the interference the AP’s neighbors see on the adjacent
channel
Interface Name Name of the fastethernet or gigabit ethernet interface
Current ARM
Assignment
Current channels assigned by the AP’s ARM profile.
Target Coverage Index Ideal value of coverage index an AP tries to achieve on its channel.
Covered channels a/g Number of channels that are currently being used by an AP’s BSSIDs.
Free channels a/g Number of channels that are available to an AP because that channel has a lower
interference index.
ARM Edge State If enabled, ARM-enabled APs on the network edge will not become Air Monitors.
Last check channel/
pwr
Time elapsed since the AP checked its channel and power settings, in
hour:minute:second format.
Last change channel/
pwr
Time elapsed since the AP changed its channel and power settings, in
hour:minute:second format.
Platforms Licensing Command Mode
All platforms Base operating system Enable or Config mode on master switches
Parameter Description

AOS-W 3.4.1 Command Line Interface | Reference Guide show ap arm scan-times | 527
show ap arm scan-times
show ap arm scan-times {ap-name <ap-name>|bssid <bssid>|ip-addr <ip-addr>}
Description
Show AM channel scan times for an individual AP.
Syntax
Examples
The output of this command shows scan times for every channel on an AP with the IP address 10.15.10.37.
Parameter Description
ap-name <ap-name> Show channel scan data for an AP with a specific name.
bssid <bssid> Show channel scan data for a specific Basic Service Set Identifier (BSSID) on an AP. An
AP’s BSSID is usually the AP’s MAC address.
ip-addr <ip-addr> Show channel scan data for an AP with a specific IP address. Enter the IP address in
dotted-decimal format.
(host)# show ap arm scan-times ip-addr 10.15.10.37
Channel Scan Time
-----------------
channel assign-time scans-attempted scans-rejected dos-scans flags timer-tick
------- ----------- --------------- -------------- --------- ----- ----------
36 8579 349 0 0 DVACT 50598
40 2365 349 0 0 DVACT 50610
44 2495 349 0 0 DVACT 50621
48 9714 349 0 0 DVACT 50656
52 0 349 0 0 DA 50643
56 0 349 0 0 DA 50655
60 0 348 0 0 DA 50519
64 0 348 0 0 DA 50530
149 5546 348 0 0 DVACT 50542
153 2310 348 0 0 DVACT 50553
157 6094 348 0 0 DVACT 50565
161 3014 348 0 0 DVACT 50576
165 10538 348 0 0 DVACT 50587
1 4194 97 0 0 DVACT 50594
2 0 97 0 0 DAC 50604
3 0 97 0 0 DAC 50615
4 0 97 0 0 DAC 50627
5 0 97 0 0 DC 50638
6 4076 97 0 0 DVACT 50656
7 0 96 0 0 DAC 50538
8 0 97 0 0 DC 50549
9 0 97 0 0 DC 50561
10 0 97 0 0 DAC 50572
11 3710 97 0 0 DVACT 50583
D: Default, V: Valid, A: AP Present, C: Reg Domain Channel, O: DOS Channel,
T:20MHZ Channel, F: 40MHz Channel, L: Reg Domain 40MHz Channel (lower), U:
Reg Domain 40MHz channel (U)
WIF Scan Time
-------------
channel last-scan-channel current-scan-channel last-dos-channel
------- ----------------- -------------------- ----------------
48 56/50655 56 0
6 6/50649 6 0

528 | show ap arm scan-times AOS-W 3.4.1 Command Line Interface | Reference Guide
The output of this command includes the following parameters:
Command History
Introduced in AOS-W 3.0.
Command Information
Parameter Description
channel A radio channel on the specified AP.
Assign-time The amount of time that an AP has been on a channel.
scans-attempted The number of times an AP has attempted to scan another channel
scans-rejected The number of times an AP attempted to scan a channel, but was unable to scan
because the scan was halted by the power save, voice aware or load aware ARM
features.
dos-scans The number of times an AP enabled with the rogue aware scanning feature had to
contain a rogue device on a channel.
flags The flags column displays additional relevant information about the channel. The
flags key appears at the bottom of the Channel Scan Time table.
timer tick Timer tick at which the last scan was attempted.
last-scan-channel The last channel scanned by the AP
current-scan-channel The AP’s current channel.
last-dos-channel The last channel that had to be contained because a rogue device was detected on
that channel.
Platforms Licensing Command Mode
All platforms Base operating system Enable or Config mode on master switches

AOS-W 3.4.1 Command Line Interface | Reference Guide show ap arm state | 529
show ap arm state
show ap arm state [ap-name <ap-name>|dot11a|dot11g|ip-addr <ip-addr>]
Description
Display Adaptive Radio Management (ARM) information for an individual AP’s neighbors, or show all
available data for any neighboring AP using an 802.11a or 802.11g radio type.
Syntax
Usage Guidelines
The output of the show ap arm state command shows 802.11a and 802.11g information for all APs. Include
an AP name or IP address to show data for just a single AP, or use the dot11a or dot11g keywords to show
data for all APs using that radio type.
Examples
The output of this command shows 802.11a information for all neighboring APs.
The output of this command includes the following information
Parameter Description
ap-name <ap-name> Show aggregate ARM Neighbor Information for a specific AP.
dot11a Show aggregate ARM Neighbor Information for all APs using an 802.11a radio.
dot11g Show aggregate ARM Neighbor Information for all APs using an 802.11g radio.
ip-addr <ip-addr> Show aggregate ARM Neighbor Information for a AP with a specific IP address by
entering its IP address in dotted-decimal format.
Column Description
Name Name of an AP.
IP address IP address of an AP.
(host)# show ap arm state
AP-AL39:10.6.1.206:48:19:23-Edge:enable
Neighbor Data
-------------
Name IP Address SNR Assignment
---- ---------- --- ----------
AL33 10.6.1.205 32 48/10
AP-AL33:10.6.1.205:48:10:23-Edge:disable
Neighbor Data
-------------
Name IP Address SNR Assignment
---- ---------- --- ----------
AL39 10.6.1.206 42 48/19
AL19 10.6.1.212 29 161/19
AL31 10.6.1.202 25 153/16
AL25 10.6.1.196 13 153/16
AL29 10.6.1.204 26 153/19
530 | show ap arm state AOS-W 3.4.1 Command Line Interface | Reference Guide
Command History
Introduced in AOS-W 3.0.
Command Information
SNR Signal-to-noise (SNR) ratio. SNR is the power ratio between an information signal
and the level of background noise.
Assignment The AP’s current channel assignment.
Platforms Licensing Command Mode
All platforms Base operating system Enable or Config mode on master switches
Column Description
AOS-W 3.4.1 Command Line Interface | Reference Guide show ap association | 531
show ap association
show ap association [ap-name <ap-name>|ap-group <ap-group>|bssid <bssid>|channel
<channel>|client-mac <client-mac>|essid <essid>|ip-addr <ip-addr>|phy {a|b|g}|voip-
only]
Description
Show the association table for an AP group or for an individual AP.
Syntax
Usage Guidelines
Use this command to check if user is connected to an AP. This command validates whether the client is
associated and indicates the last AP to which it was connected. If the flags column shows an 'A', the client is
currently associated with that AP. Alternately, if the client is not currently associated, the AP with the
smallest value of association time is the last AP used by the client.
Example
Use the show ap association client-mac command to verify that a user has associated with an AP, or to
determine last AP to which the client was connected. The output of this command in the example below
shows the association table for the client with the MAC address 00:13:fd:5c:7c:59. If the flags column in the
output of this command shows an 'A', the client associated last to that AP. Alternately, the AP with the
smallest value of association time is the last AP to which the client had associated.
In the example below, the output of this command has been broken into two separate tables to better fit this
page. In the actual output of the command, this information is shown in a single, wide table.
Parameter Description
ap-group <ap-group> Show AP associations for a specific AP group. You can also include the
channel, essid or voip-only keywords to further filter the output of this
command.
ap-name <ap-name> Show AP associations for a specific AP. You can also include the essid,
phy or voip-only keywords to further filter the output of this command.
bssid <bssid> Show the AP associations for an specific AP Basic Service Set Identifier
(BSSID). The Basic Service Set Identifier (BSSID) is usually the AP’s MAC
address.
channel <channel> Show AP associations for an individual channel by specifying the channel
for which you want to view information.
client-mac <client-mac> Show the AP associations for a specific MAC address by entering the MAC
address of a client for which you want to view association information.
essid <essid> Show AP associations for an Extended Service Set Identifier (ESSID). An
Extended Service Set Identifier (ESSID) is a alphanumeric name that
uniquely identifies the Service Set Identifier (SSID).
ip-addr <ip-addr> Show AP associations for a specific AP by entering an IP address in
dotted-decimal format. You can also include the essid, phy or voip-only
keywords to further filter the output of this command.
phy Include the phy [a|b|g] keywords to show associations for a specific 802.11
radio type, either 802.11a, 802.11b or 802.11g.
voip-only Show VoIP client information only.
532 | show ap association AOS-W 3.4.1 Command Line Interface | Reference Guide
The output of this command includes the following information:
Related Commands
Column Description
Name Name of an AP
bssid The AP Basic Service Set Identifier (BSSID)
mac MAC address of the AP
auth This column displays a y if the AP has been configured for 802.11 authorization
frame types. Otherwise, it displays an n.
assoc This column displays a y if the AP has been configured for 802.11 association frame
types. Otherwise, it displays an n.
aid 802.11 association ID. A client receives a unique 802.11 association ID when it
associates to an AP.
1-int Number of beacons in the 802.11 listen interval. There are ten beacons sent per
second, so a ten-beacon listen interval indicates a listen interval time of 1 second.
essid Name that uniquely identifies the AP’s Extended Service Set Identifier (ESSID).
vlan-id Identification number of the AP’s VLAN.
tunnel-id Identification number of the AP’s tunnel.
assoc. time Amount of time the client has associated with the AP, in the format
hours:minutes:seconds.
num assoc Number of clients associated with the AP.
flags This column displays any flags for this AP. The list of flag abbreviations is included in
the output of the show ap association command.
Command Description Mode
show ap debug association-
failure If the output of this show command indicates that a client is
not associating with an AP, use show ap debug association-
failure to determine why a client is not associated with an AP.
Config mode
(host) #show ap association client-mac 00:13:fd:5c:7c:59
Flags: W: WMM client, A: Active, R: RRM client
PHY Details: HT: High throughput; 20: 20MHz; 40: 40MHz
ss: spatial streams
Association Table
-----------------
Association Table
-----------------
-----------------
Name bssid mac auth assoc aid l-int essid
---- ----- --- ---- ----- --- ----- -----
AL12 00:1a:1e:11:5f:11 00:21:5c:50:b1:ed y y 12 10 ethersphere-wpa2
AL5 00:1a:1e:88:88:31 00:19:7d:d6:74:93 y y 6 10 ethersphere-wpa2
vlan-id tunnel-id phy assoc. time num assoc Flags
------- --------- --- ----------- --------- -----
65 0x10c4 a-HT-40sgi-2ss 35m:41s 1 WA
65 0x1072 a 24m:29s 1 WA
AOS-W 3.4.1 Command Line Interface | Reference Guide show ap association | 533
Command History
Introduced in AOS-W 3.0.
Command Information
show ap debug mgmt-frames If the output of this show command indicates that a client is
not associating with an AP, use show ap debug mgmt-
frames to determine why a client is not associated with an AP.
Config mode
Platforms Licensing Command Mode
All platforms Base operating system Enable or Config mode on master switches
Command Description Mode

534 | show ap association remote AOS-W 3.4.1 Command Line Interface | Reference Guide
show ap association remote
show ap association remote [ap-name <ap-name>|ap-group <ap-group>|bssid <bssid>|channel
<channel>|essid <essid>
Description
Display the association table for an individual AP or group of APs in bridge mode.
Syntax
Examples
The output of the command below shows the association table for clients in the AP group group1.
The output of this command includes the following information:
Parameter Description
ap-name <ap-name> Show AP associations for a specific remote AP.
ap-group <ap-group> Show AP associations for a specific group of remote APs.
bssid <bssid> Show the AP associations for an specific AP Basic Service Set Identifier (BSSID).
The Basic Service Set Identifier (BSSID) is usually the AP’s MAC address.
channel <channel> Show remote AP associations for a specific channel.
essid <essid> Show remote AP associations for an Extended Service Set Identifier (ESSID). An
Extended Service Set Identifier (ESSID) is a alphanumeric name that uniquely
identifies the Service Set Identifier (SSID).
show ap association remote ap-group group1
Flags: W: WMM client, A: Active, R: RRM client
PHY Details: HT: High throughput; 20: 20MHz; 40: 40MHz
ss: spatial streams
Association Table
-----------------
Name bssid mac auth assoc aid l-int essid vlan-id tunnel-id phy assoc.time num assoc Flags
---- ----- --- ---- ----- --- ----- ----- ------- --------- --- ---------- --------- -----
AP71 00:0b:23:c1:d6:11 00:12:6d:03:1c:f1 y y 1 10 t-lab 111 0x108e a 23s 1 A
Num Clients:1
Column Description
Name Name of an AP
bssid The AP Basic Service Set Identifier (BSSID)
mac MAC address of the AP
auth This column displays a y if the AP has been configured for 802.11 authorization
frame types. Otherwise, it displays an n.
assoc This column displays a y if the AP has been configured for 802.11 association frame
types. Otherwise, it displays an n.
aid 802.11 association ID. A client receives a unique 802.11 association ID when it
associates to an AP.
1-int Number of beacons in the 802.11 listen interval. There are ten beacons sent per
second, so a ten-beacon listen interval indicates a listen interval time of 1 second.
AOS-W 3.4.1 Command Line Interface | Reference Guide show ap association remote | 535
Command History
Introduced in AOS-W 3.0.
Command Information
essid Name that uniquely identifies the AP’s Extended Service Set Identifier (ESSID).
vlan-id Identification number of the AP’s VLAN.
tunnel-id Identification number of the AP’s tunnel.
phy The RF band in which the AP should operate:
g = 2.4 GHz
a = 5 GHz
assoc. time Amount of time the client has associated with the AP, in the format
hours:minutes:seconds.
num assoc Number of clients associated with the AP.
flags This column displays any flags for this AP. The list of flag abbreviations is included in
the output of the show ap association remote command.
Platforms Licensing Command Mode
All platforms Base operating system Enable or Config mode on master switches
Column Description

536 | show ap blacklist-clients AOS-W 3.4.1 Command Line Interface | Reference Guide
show ap blacklist-clients
show ap blacklist-clients
Description
Show a list of clients that have been denied access.
Usage Guidelines
Use the stm CLI command to add or remove users from a blacklist. Additionally, the dot1x
authentication, VPN authentication and MAC authentication profiles allow you to automatically
blacklist a client if machine authentication fails.
Examples
The output of this command shows that the switch has a single user-defined blacklisted client.
The output of this command includes the following information:
Column Description
STA MAC address of the blacklisted client.
reason The reason that the user was blacklisted.
zuser-defined: User was blacklisted due to blacklist criteria were defined by the
network administrator
zmitm-attack: Blacklisted for a man in the middle (MITM) attack; impersonating a
valid enterprise AP.
zping-flood: Blacklisted for a ping flood attack.
zsession-flood: Blacklisted for a session flood attack.
zsyn-flood: Blacklisted for a syn flood attack.
zsession-blacklist: User session was blacklisted
zIP spoofing: Blacklisted for sending messages using the IP address of a trusted
client.
zESI-blacklist: An external virus detection or intrusion detection application or
appliance blacklisted the client.
zCP-flood: Blacklisting for flooding with fake AP beacons.
zUNKNOWN: Blacklist reason unknown.
block-time (sec) Amount of time the client has been blocked, in seconds.
remaining time(sec) Amount of time remaining before the client will be allowed access to the network
again.
(host)# show ap blacklist-clients
Blacklisted Clients
-------------------
STA reason block-time(sec) remaining time(sec)
--- ------ --------------- -------------------
00:1E:37:CB:D4:52 user-defined 2480 Permanent
AOS-W 3.4.1 Command Line Interface | Reference Guide show ap blacklist-clients | 537
Related Commands
Command History
Introduced in AOS-W 3.0.
Command Information
Command Description Mode
stmadd-blacklist-client
stmremove-blacklist-client
Manually add or remove clients from a blacklist. Config mode
Platforms Licensing Command Mode
All platforms Base operating system Enable or Config mode on master switches
538 |show ap bss-table AOS-W 3.4.1 Command Line Interface | Reference Guide
show ap bss-table
show ap bss-table [ap-name <ap-name>|bssid <bssid>|essid <essid>|ip-addr <ip-addr>|port
<port>\<slot>]
Description
Show an AP’s Basic Service Set (BSS).
Syntax
Usage Guidelines
The output of the show ap bss-table command shows the Alcatel-Lucent AP BSS table for all APs. To filter
this information and view BSS table data for an individual AP or a specific port and slot number, include the
ap-name, bssid, essid, ip-addr or port keywords.
Example
The output of this command shows the BSS table for the seven active APs using the switch.
The output of this command includes the following information:
Parameter Description
ap-name <ap-name> Show the BSS table for a specific AP.
bssid <bssid> Show the BSS table for an specific AP Basic Service Set Identifier (BSSID). The
Basic Service Set Identifier (BSSID) is usually the AP’s MAC address.
essid <essid> Show the BSS table for an Extended Service Set Identifier (ESSID). An Extended
Service Set Identifier (ESSID) is a alphanumeric name that uniquely identifies the
Service Set Identifier (SSID).
ip-addr <ip-addr> Show the BSS table for a specific AP by entering an IP address in dotted-decimal
format.
port <port>/<slot> Show the BSS table for a specific port and slot on an AP. The slot and port numbers
should be separated by a forward slash (/).
show ap bss-table
Alcatel-Lucent AP BSS Table
------------------
bss ess s/p ip phy type ch/EIRP/max-EIRP cur-cl ap name in-t(s) tot-t mtu acl-state
--- --- ---- --- --- ---- ------------ ------ ------ ------ ------ --- --------
00:0b:86:cc:d8:40 corp-ap 1/3 192.0.2.0 g ap 11/16.5/33 0 3.70.17 0 50s 1500 -
00:0b:86:cc:d8:41 testbed1 1/3 192.0.2.10 g ap 11/16.5/33 1 3.70.17 0 50s 1500 -
00:0b:86:9b:49:c8 corp-ap 1/0 192.0.2.11 a ap 165/15.5/36 0 3.85.15 0 2m:0s 1578 -
00:1a:1e:81:aa:50 corp-ap 1/0 192.0.2.12 a-HT ap 44+/19/23 0 3.125.14 0 14m:0s 1578 -
00:1a:1e:81:aa:40 corp-ap 1/0 192.0.2.12 g-HT ap 6/17.5/33 0 3.125.1 0 3m:55s 1578 -
00:0b:86:cc:d8:50 corp-ap 1/3 192.0.2.14 a ap 165/19/36 0 3.70.17 0 50s 1500 -
00:0b:86:9b:49:c0 corp-ap 1/0 192.0.2.15 g ap 11/16.5/33 0 3.85.12 0 2m:0s 1578 -
Channel followed by "*" indicates channel selected due to unsupported configured channel.
Num APs:7
Num Associations:1
Column Description
bss The AP Basic Service Set Identifier (BSSID). This is usually the MAC address of the AP
ess The AP Extended Service Set Identifier (ESSID).
AOS-W 3.4.1 Command Line Interface | Reference Guide show ap bss-table | 539
Command History
Introduced in AOS-W 3.0.
Command Information
s/p The switch port used by the AP, in the format <slot>/<port>.
The <slot> number is always 1 except when referring to interfaces on the OmniAccess
6000 switch. For the OmniAccess 6000 switch, the four slots are allocated as follows:
zSlot 0: contains a supervisor card or an OmniAccess Supervisor Card III.
zSlot 1: can contain either a redundant supervisor card, OmniAccess Supervisor Card
III, or a third line card.
zSlot 2: can contain either a OmniAccess Supervisor Card III or line card (required if
zslot 0 contains a supervisor card).
zSlot 3: can contain either a OmniAccess Supervisor Card III or second line card.
The <port> number refers to the network interfaces that are embedded in the front panel
of the OmniAccess 4302, OmniAccess 4308T, or OmniAccess 4324 switch, OmniAccess
4504/4604/4704 Multi-Service Switch, OmniAccess Supervisor Card III, or a line card
installed in the OmniAccess 6000 switch. Port numbers start at 0 from the left-most
position.
ip IP address of an AP.
phy An AP radio type. Possible values are:
za—802.11a
za-HT—802.11a high throughput
zg— 802.11g
zg-HT—802.11g high throughput
type Shows whether the AP is working as an access point (AP) or air monitor (AM).
ch/EIRP/max-EIRP Radio channel used by the AP/current effective Isotropic Radiated Power (EIRP) /
maximum EIRP.
cur-cl Current number of clients on the AP.
ap name Name of the AP.
in-t(s) Number of seconds that an AP has been inactive.
tot-t An AP’s total active time, in seconds.
mtu Maximum Transmission Unit (MTU) size, in bytes. This value describes the greatest
amount of data that can be transferred in one physical frame.
acl-state An access control list (ACL) can enable or disable an AP during specific time ranges.
zDisabled: An ACL with time restrictions is currently disabled (so the AP is enabled).
zEnabled: An ACL with time restrictions is currently enabled (so the AP is disabled).
zThis data column will display a dash (-) if no ACLs are currently configured for the AP.
Platforms Licensing Command Mode
All platforms Base operating system Enable or Config mode on master switches
Column Description
540 | show ap bw-report AOS-W 3.4.1 Command Line Interface | Reference Guide
show ap bw-report
show ap bw-report {ap-name <ap-name>|bssid <bssid>|ip-addr <ip-addr>}
Description
Show the bandwidth reporting table for a specific AP.
Syntax
Examples
The output of the following command shows the Alcatel-Lucent AP bandwidth table for an AP with the IP
address 192.0.2.170.
The output of this command includes the following information for all radios on the AP:
Parameter Description
ap-name <ap-name> Show bandwidth data for an AP with a specific name.
bssid <bssid> Show bandwidth data for a specific Basic Service Set Identifier (BSSID) on an AP.
The Basic Service Set Identifier (BSSID) is usually the AP’s MAC address.
ip-addr <ip-addr> Show bandwidth data for an AP with a specific IP address by entering an IP address
in dotted-decimal format.
Column Description
Virtual AP Name of a Virtual AP
Allocated Share Maximum percentage of total bandwidth available to that Virtual AP.
Actual Share Actual percentage of total bandwidth used by a Virtual AP.
Offered Load Attempted throughput for the Virtual AP, in kbps.
Delivered Load Actual throughput for the Virtual AP, in kbps. This value may be less than the offered
load if the Virtual AP has used all its allocated bandwidth.
Average Throughput Average throughput for the virtual AP, in kbps.
show ap bw-report ip-addr 192.0.2.170
Bandwidth report for AP "AL16" radio 0
--------------------------------------
Virtual AP Allocated Share Actual Share Offered Load Delivered Load
---------- --------------- ------------ ------------ --------------
corp1344-guest 0% 0% 0 kbps 0 kbps
corp1344-ethersphere-wpa2 0% 0% 0 kbps 0 kbps
Average Throughput:0 kbps
Bandwidth report for AP "AL16" radio 1
--------------------------------------
Virtual AP Allocated Share Actual Share Offered Load Delivered Load
---------- --------------- ------------ ------------ --------------
corp1344-guest 0% 0% 0 kbps 0 kbps
corp1344-ethersphere-voip 0% 0% 0 kbps 0 kbps
corp1344-ethersphere-vocera 0% 0% 0 kbps 0 kbps
Average Throughput:0 kbps

AOS-W 3.4.1 Command Line Interface | Reference Guide show ap bw-report | 541
Command History
Introduced in AOS-W 3.0.
Command Information
Platforms Licensing Command Mode
All platforms Base operating system Enable or Config mode on master switches

542 | show ap client status AOS-W 3.4.1 Command Line Interface | Reference Guide
show ap client status
show ap client status <client-mac>
Description
Show the current status of a specific client.
Syntax
Examples
The output of the command shows the status of an individual client in the STA (station) table.
The output of this command includes the following information:
Parameter Description
<client-mac> MAC address of a client
Column Description
bssid Basic Service Set ID (BSSID) of the client.
auth This column displays a y if the AP has been configured for 802.11 authorization
frame types. Otherwise, it displays an n.
assoc This column displays a y if the AP has been configured for 802.11 association frame
types. Otherwise, it displays an n.
aid Number of beacons in the 802.11 listen interval. There are ten beacons sent per
second, so a ten-beacon listen interval indicates a listen interval time of 1 second.
l-int Number of beacons in the 802.11 listen interval. There are ten beacons sent per
second, so a ten-beacon listen interval indicates a listen interval time of 1 second.
essid Extended Service Set ID (ESSID) of the client.
vlan-id VLAN ID of the VLAN used by the client
tunnel-id Identification number for the tunnel
state If the client has been both authorized and associated, this data column will display
auth-assoc. If the client has only been authorized, this data column will display
auth.
Reason If the client failed to authenticate, this data column lists the reason code for 802.11
authentication failure
(host) #show ap client status 00:13:fd:42:32:38
STA Table
---------
bssid auth assoc aid l-int essid vlan-id tunnel-id
----- ---- ----- --- ----- ----- ------- ---------
00:1a:1e:a3:02:c9 y y 7 10 corp-wpa2 65 0x10c0
State Hash Table
----------------
bssid state reason
----- ----- ------
00:1a:1e:a3:02:c9 auth-assoc 0

AOS-W 3.4.1 Command Line Interface | Reference Guide show ap client status | 543
Command History
Introduced in AOS-W 3.0.
Command Information
Platforms Licensing Command Mode
All platforms Base operating system Enable or Config mode on master switches

544 | show ap config AOS-W 3.4.1 Command Line Interface | Reference Guide
show ap config
show ap config {ap-group <ap-group>}|{ap-name <ap-name>}|{essid <essid>}
Description
Show a large list of configuration settings for an ap-group or an individual AP.
Syntax
Examples
The example output below shows just some of the configuration settings displayed in the output of this
command.
Parameter Description
ap-group <ap-group> Display configuration settings for an AP group.
ap-name <ap-name> Display configuration settings for an AP with a specific name.
essid <essid> Display configuration settings for an AP with a specific Extended Service Set
Identifier (ESSID). An Extended Service Set Identifier (ESSID) is a alphanumeric
name that uniquely identifies the Service Set Identifier (SSID).
show ap config ap-group apgroup14
---------------------------------------------------
Parameter 802.11g 802.11a Source
--------- ------- ------- ------
LMS IP N/A N/A ap system-profile "default"
Backup LMS IP N/A N/A ap system-profile "default"
LMS Preemption Disabled Disabled ap system-profile "default"
LMS Hold-down Period 600 sec 600 sec ap system-profile "default"
Master controller IP address N/A N/A ap system-profile "default"
RF Band g g ap system-profile "default"
Double Encrypt Disabled Disabled ap system-profile "default"
Native VLAN ID 1 1 ap system-profile "default"
SAP MTU N/A N/A ap system-profile "default"
Bootstrap threshold 8 8 ap system-profile "default"
Request Retry Interval 10 sec 10 sec ap system-profile "default"
Maximum Request Retries 10 10 ap system-profile "default"
Keepalive Interval 60 sec 60 sec ap system-profile "default"
Dump Server N/A N/A ap system-profile "default"
Telnet Disabled Disabled ap system-profile "default"
FIPS enable Disabled Disabled ap system-profile "default"
SNMP sysContact N/A N/A ap system-profile "default"
RFprotect Server IP N/A N/A ap system-profile "default"
RFprotect Backup Server IP N/A N/A ap system-profile "default"
AeroScout RTLS Server N/A N/A ap system-profile "default"
Ortronics Walljack Enabled Enabled ap system-profile "default"
Ortronics LED off Time-out Enabled Enabled ap system-profile "default"
Ortronics Low Temp 100 C 100 C ap system-profile "default"
Ortronics High Temp 110 C 110 C ap system-profile "default"
RTLS Server configuration N/A N/A ap system-profile "default"
Remote-AP DHCP Server VLAN N/A N/A ap system-profile "default"
Remote-AP DHCP Server Id 192.168.11.1 192.168.11.1 ap system-profile "default"
Remote-AP DHCP Default Router 192.168.11.1 192.168.11.1 ap system-profile "default"
Remote-AP DHCP Pool Start 192.168.11.2 192.168.11.2 ap system-profile "default"
Remote-AP DHCP Pool End 192.168.11.254 192.168.11.254 ap system-profile "default"
Remote-AP DHCP Pool Netmask 255.255.255.0 255.255.255.0 ap system-profile "default"
Remote-AP DHCP Lease Time 0 days 0 days ap system-profile "default"
Heartbeat DSCP 0 0 ap system-profile "default"
Session ACL N/A N/A ap system-profile "default"
Image URL N/A N/A ap system-profile "default"
Maintenance Mode Disabled Disabled ap system-profile "default"
...
AOS-W 3.4.1 Command Line Interface | Reference Guide show ap config | 545
The output of this command includes the following parameters.
Parameter Description
LMS IP The IP address of the local management switch (LMS)—the Alcatel-Lucent
switch which is responsible for terminating user traffic from the APs, and
processing and forwarding the traffic to the wired network.
Backup LMS IP For multi-switch networks, this parameter displays the IP address of a backup
to the IP address specified with the lms-ip parameter.
LMS Preemption When this parameter is enabled, the local management switch automatically
reverts to the primary LMS IP address when it becomes available.
LMS Hold-down Period Time, in seconds, that the primary LMS must be available before an AP returns
to that LMS after failover.
Master switch IP address For multi-switch networks, this parameter displays the IP address of the master
switch.
RF Band For dual-band radios, this parameter displays the RF band in which the AP
should operate:
zg = 2.4 GHz
za = 5 GHz
Double Encrypt This parameter applies only to remote APs. Double encryption is used for traffic
to and from a wireless client that is connected to a tunneled SSID. When
enabled, all traffic is re-encrypted in the IPsec tunnel. When disabled, the
wireless frame is only encapsulated inside the IPsec tunnel.
Native VLAN ID Native VLAN for bridge mode virtual APs (frames on the native VLAN are not
tagged with 802.1q tags).
SAP MTU Maximum Transmission Unit (MTU) size, in bytes. This value describes the
greatest amount of data that can be transferred in one physical frame.
Bootstrap threshold Number of consecutive missed heartbeats on a GRE tunnel (heartbeats are sent
once per second on each tunnel) before an AP rebootstraps. On the switch, the
GRE tunnel timeout is 1.5 x bootstrap-threshold; the tunnel is torn down after
this number of seconds of inactivity on the tunnel.
Request Retry Interval Interval, in seconds, between the first and second retries of AP-generated
requests. If the configured interval is less than 30 seconds, the interval for
subsequent retries is increased up to 30 seconds.
Maximum Request Retries Maximum number of times to retry AP-generated requests, including keepalive
messages. After the maximum number of retries, the AP either reboots or tries
the IP
address specified by the backup LMS IP address (if configured).
Keepalive Interval Time, in seconds, between keepalive messages from the AP
Dump Server (For debugging purposes.) Displays the server to receive the core dump
generated if an AP process crashes.
Telnet Reports whether telnet access the AP is enabled or disabled.
SNMP sysContact SNMP system contact information.
RFprotect Server IP The IP address of the RFprotect server for this AP or group
RFprotect Backup Server
IP
The IP address of the RFprotect backup server for this AP or group
AeroScout RTLS Server Displays whether or not the AP will send RFID tag information to an AeroScout
real-time asset location (RTLS) server.
Ortronics Walljack Displays whether the external Ethernet port on the Ortronics Wi-Jack Duo AP is
enabled or disabled.
546 | show ap config AOS-W 3.4.1 Command Line Interface | Reference Guide
Ortronics LED off Time-
out
Automatically turns off the LEDs 5 minutes after the AP boots up.
Ortronics Low Temp The low-temperature threshold for the Ortronics AP. If the temperature reaches
this threshold, the maximum transmit power is restored to four.
Ortronics High Temp The high-temperature threshold for the Ortronics AP. The maximum transmit
power range is 0— 4, with a default of 4. If the AP temperature meets or
exceeds this threshold, the maximum transmit power is reduced by one until it
reaches zero.
RTLS Server configuration Displays whether or not the AP will send RFID tag information to an RTLS
server.
Remote-AP DHCP Server
VLAN
Shows the VLAN ID of the remote-AP DHCP server used when switch is
unreachable.
Remote-AP DHCP Server Id Shows the IP Address of the DHCP DNS Server.
Remote-AP DHCP Default
Router
Shows the IP Address of the DHCP Default Router.
Remote-AP DHCP Pool Start Shows the IP Address used as start of DHCP Pool.
Remote-AP DHCP Pool End Shows the IP Address used as end of DHCP Pool.
Remote-AP DHCP Pool
Netmask
Shows the netmask of DHCP Pool.
Remote-AP DHCP Lease Time Shows the length of leases, in days (0 means infinite).
Heartbeat DSCP DSCP value of AP heartbeats (0-63).
Session ACL Shows the access control list (ACL) applied on the uplink of a remote AP.
Maintenance Mode Shows if Maintenance mode is enabled or disabled. If enabled, APs stop
flooding unnecessary traps and syslog messages to network management
systems or network operations centers when deploying, maintaining, or
upgrading the network. The switch still generates debug syslog messages if
debug logging is enabled.
Radio enable Shows if the AP’s radio is enabled or disabled.
Mode Shows the operating modes for the AP.
zap-mode: Device provides transparent, secure, high-speed data
communications between wireless network devices and the wired LAN.
zam-mode: Device behaves as an air monitor to collect statistics, monitor
traffic, detect intrusions, enforce security policies, balance traffic load, self-
heal coverage gaps, etc.
High throughput enable
(radio)
Shows if high-throughput (802.11n) features on the 2.4 GHz frequency band are
enabled or disabled.
Channel Shows the channel number for the AP’s 802.11a/802.11n physical layer.
Beacon Period Shows the time, in milliseconds, between successive beacon transmissions.
The beacon advertises the AP’s presence, identity, and radio characteristics to
wireless clients.
Transmit Power Shows the current transmission power level.
Advertise 802.11d and
802.11h Capabilities
This column reports whether or not the AP will advertise its 802.11d (Country
Information) and 802.11h (TPC or Transmit Power Control) capabilities
Enable CSA Displays whether or not the AP has enabled channel switch announcements
(CSAs) for 802.11h.
Parameter Description
AOS-W 3.4.1 Command Line Interface | Reference Guide show ap config | 547
CSA Count Number of channel switch announcements that must be sent before the AP will
switch to a new channel.
Management Frame Throttle
interval
Average interval that rate limiting management frames are sent from this radio,
in seconds. If this column displays a zero (0) rate limiting is disabled for this AP.
Management Frame Throttle
Limit
Maximum number of management frames that can come from this radio in each
throttle interval.
ARM/WIDS Override Shows if Adaptive Radio Management (ARM) and Wireless IDS functions are
enabled or disabled. If a radio is configured to operate in Air Monitor mode,
then these functions are always enabled, regardless of this option.
Protection for 802.11b
Clients
Displays whether or not protection for 802.11b clients is enabled or disabled.
Assignment Displays whether or not ARM channel and power assignment has been enabled
or disabled.
Allowed bands for 40MHz
channels
Forty MHz channels may be used on the specified radio bands (802.11a or
802.11g).
Client Aware Shows if the client aware feature has been enabled or disabled for this AP. If
enabled, AP will not change channels when there are active clients.
Max Tx Power Maximum transmission power for this AP, in dBm.
Min Tx Power Minimum transmission power for this AP, in dBm.
Multi Band Scan Shows if the multi-band scan feature has been enabled or disabled on this AP. If
enabled, single-radio APs will try to scan across bands for Rogue AP detection
Rogue AP Aware Shows if the rogue AP awareness feature has been enabled or disabled on this
AP. If enabled, the AP will try to contain off-channel Rogue APs
Scan Interval This column indicates, in seconds, how often the AP will leave its current
channel to scan other channels in the band if scanning is enabled
Active Scan Displays whether or not the active scan feature is enabled.
NOTE: This option elicits more information from nearby APs, but also creates
additional management traffic on the network. Active Scan is disabled by
default, and should not be enabled except under the direct supervision of
Alcatel-Lucent Support.
Scanning Shows if scanning is enabled or disabled for this AP. If this option is disabled,
the following other options will also be disabled:
zMulti Band Scan
zRogue AP Aware
zVoip Aware Scan
zPower Save Scan
Scan Time The amount of time, in milliseconds, an AP will drift out of the current channel to
scan another channel. The supported range for this setting is 0-2,147,483,647
seconds. Alcatel-Lucent recommends a scan time between 50-200 msec.
VoIP Aware Scan Shows if VoIP aware scanning is enabled or disabled. If you use voice handsets
in the WLAN, VoIP Aware Scan should be enabled in the ARM profile so the AP
will not attempt to scan a different channel if one of its clients has an active VoIP
call. This option requires that Scanning is also enabled.
Power Save Aware Scan Shows if the power save aware scan is enabled or disabled. If enabled, the AP
will not scan a different channel if it has one or more clients and is in power save
mode.
Default: enabled
Parameter Description
548 | show ap config AOS-W 3.4.1 Command Line Interface | Reference Guide
Ideal Coverage Index The Alcatel-Lucent coverage index metric is a weighted calculation based on
the RF coverage for all Alcatel-Lucent APs and neighboring APs on a specified
channel. The Ideal Coverage Index specifies the ideal coverage that an AP
should try to achieve on its channel. The denser the AP deployment, the lower
this value should be.
Acceptable Coverage Index For multi-band implementations, the Acceptable Coverage Index specifies the
minimal coverage an AP it should achieve on its channel. The denser the AP
deployment, the lower this value should be.
Free Channel Index The current free channel index value. The Alcatel-Lucent Interference index
metric measures interference for a specified channel and its surrounding
channels. This value is calculated and weighted for all APs on those channels
(including 3rd-party APs).
An AP will only move to a new channel if the new channel has a lower
interference index value than the current channel. Free Channel Index
specifies the required difference between the two interference index values
before the AP moves to the new channel. The lower this value, the more likely it
is that the AP will move to the new channel.
Backoff Time After an AP changes channel or power settings, it waits for this backoff time
interval before it asks for a new channel/power setting.
Error Rate Threshold The minimum percentage of PHY errors and MAC errors in the channel that will
trigger a channel change.
Error Rate Wait Time Minimum time in seconds the error rate on the AP has to exceed its defined
error rate threshold before it triggers a channel change.
Noise Threshold Maximum level of noise in a channel that triggers a channel change.
Noise Wait Time Minimum time in seconds the noise level has to exceed the Noise Threshold
before it triggers a channel change on the AP.
Minimum Scan Time Minimum number of times a channel must be scanned before it is considered
for assignment. Alcatel-Lucent recommends a Minimum Scan Time between
1-20 scans.
Load aware Scan Threshold The Load Aware Scan Threshold is the traffic throughput level an AP must
reach before it stops scanning. Load aware ARM preserves network resources
during periods of high traffic by temporarily halting ARM scanning if the load for
the AP gets too high.
Mode Aware Arm Shows if the mode-aware ARM feature has been enabled or disabled for this AP.
If enabled, ARM will turn the AP into an Air Monitors (AMs) if it detects higher
coverage levels than necessary. This helps avoid higher levels of interference on
the WLAN. Although this setting is disabled by default, you may want to enable
this feature if your APs are deployed in close proximity (e.g. less than 60 feet
apart).
40 MHz intolerance The specified setting allows ARM to determine if 40 MHz mode of operation is
allowed on the 5 GHz or 2.4 GHz frequency band only, on both frequency
bands, or on neither frequency band.
Honor 40 MHz intolerance Shows if 40 MHz intolerance is enabled or disabled. If enabled, the radio will
stop using the 40 MHz channels if the 40 MHz intolerance indication is received
from another AP or station.
Legacy station workaround Shows if interoperability for misbehaving legacy stations is enabled or disabled.
ESSID Name that uniquely identifies the Extended Service Set Identifier (SSID).
Encryption Encryption type used on this AP.
DTIM Interval Shows the interval, in milliseconds, between the sending of Delivery Traffic
Indication Messages (DTIMs) in the beacon. This is the maximum number of
beacon cycles before unacknowledged network broadcasts are flushed.
Parameter Description
AOS-W 3.4.1 Command Line Interface | Reference Guide show ap config | 549
Basic Rates Lists supported 802.11a rates, in Mbps, that are advertised in beacon frames
and probe responses from this AP.
Transmit Rates Lists 802.11a rates at which the AP is allowed to send data. The actual transmit
rate depends on what the client is able to handle, based on information sent at
the time of association and on the current error/loss rate of the client.
Station Ageout Time Time, in seconds, that a client is allowed to remain idle before being aged out.
Max Transmit Attempts Maximum number of retries allowed for the AP to send a frame
RTS Threshold Wireless clients transmitting frames larger than this threshold must issue
Request to Send (RTS) and wait for the AP to respond with Clear to Send (CTS).
This helps prevent mid-air collisions for wireless clients that are not within
wireless peer range and cannot detect when other wireless clients are
transmitting.
Short Preamble Shows if a short preamble for 802.11b/g radios is enabled or disabled for this
AP. Network performance may be higher when short preamble is enabled. In
mixed radio environments, some 802.11b wireless client stations may
experience difficulty associating with the AP using short preamble. To use only
long preamble, disable short preamble. Legacy client devices that use only long
preamble generally can be updated to support short preamble.
Max Associations Maximum number of wireless clients allowed to associate to the AP
Wireless Multimedia (WMM) Shows if Wireless Multimedia (WMM) is enabled or disabled for this AP. WMM
provides prioritization of specific traffic relative to other traffic in the network
WMM TSPEC Min Inactivity
Interval
Displays the minimum inactivity time-out threshold of WMM traffic for this AP.
DSCP mapping for WMM
voice AC
Displays the DSCP value used to map WMM video traffic.
DSCP mapping for WMM
video AC
Displays the DSCP value used to map WMM voice traffic.
DSCP mapping for WMM
best-effort AC
Displays the DSCP value used to map WMM best-effort traffic
DSCP mapping for WMM
background AC
Displays the DSCP value used to map WMM background traffic.
902il Compatibility Mode Shows if 902 il compatibility mode is enabled or disabled. (This parameter only
needs to be enabled for APs with associated clients using NTT DoCoMo 902iL
phones.)
Hide SSID Shows if the feature to hide a SSID name in beacon frames is enabled or
disabled.
Deny_Broadcast Probes When a client sends a broadcast probe request frame to search for all available
SSIDs, this option controls whether or not the system responds for this SSID.
When enabled, no response is sent and clients have to know the SSID in order
to associate to the SSID. When disabled, a probe response frame is sent for this
SSID.
Local Probe Response Shows if local probe response is enabled or disabled on the AP. If this option is
enabled, the AP is responsible for sending 802.11 probe responses to wireless
clients’ probe requests. If this option is disabled, then the switch sends the
802.11 probe responses
Disable Probe Retry If disabled, the AP will not resend probes if it does not get a response.
Parameter Description
550 | show ap config AOS-W 3.4.1 Command Line Interface | Reference Guide
Battery Boost Shows if the battery boost feature is enabled or disabled for the AP. If enabled,
this feature converts multicast traffic to unicast before delivery to the client, thus
allowing you to set a longer DTIM interval. The longer interval keeps associated
wireless clients from activating their radios for multicast indication and delivery,
leaving them in power-save mode longer and thus lengthening battery life
Drop Broadcast and
Multicast
If this feature is enabled on an AP, it drops all downstream broadcast or
multicast traffic to increase battery life.
WEP Key 1 Displays the static WEP key (1 of 4).
WEP Key 2 Displays the static WEP key (2 of 4).
WEP Key 3 Displays the static WEP key (3 of 4).
WEP Key 4 Displays the static WEP key (4 of 4).
WEP Transmit Key Index Displays the key index that specifies which static WEP key is to be used.
WPA Hexkey Displays the WPA pre-shared key (PSK).
WPA Passphrase Displays the WPA passphrase with which the AP generates a pre-shared key
(PSK).
Maximum Transmit Failures Display the maximum number of transmission failures allowed before the client
gives up.
BC/MC Rate Optimization Shows if the AP has enabled or disabled scanning of all active stations currently
associated to that AP to select the lowest transmission rate for broadcast and
multicast frames. This option only applies to broadcast and multicast data
frames; 802.11 management frames are transmitted at the lowest configured
rate.
High throughput enable
(SSID)
Shows if the AP has enabled or disabled the use of its high-throughput SSID in
40 MHz mode.
40 MHz channel usage Determines if this high-throughput SSID allows high-throughput (802.11n)
stations to associate.
MPDU Aggregation Shows if the AP has enabled or disabled MAC protocol data unit (MDPU)
aggregation.
Max transmitted A-MPDU
size
Shows the maximum size, in bytes, of an A-MPDU that can be sent on the AP’s
high-throughput SSID.
Max received A-MPDU size Shows the maximum size, in bytes, of an Aggregated-MAC Packet Data Unit
(A-MPDU) that can be received on the AP’s high-throughput SSID.
Min MPDU start spacing Displays the minimum time between the start of adjacent MDPUs within an
aggregate MDPU, in microseconds.
Supported MCS set Comma-separated list of Modulation Coding Scheme (MCS) values or ranges of
values to be supported on this high-throughput SSID.
Short guard interval in
40 MHz mode
Shows if the AP has enabled or disabled use of short guard interval in 40 MHz
mode of operation.
Legacy stations Shows if the AP has enabled or disabled the legacy stations option, which
controls whether or not legacy (non-HT) stations are allowed to associate with
the AP’s SSID. By default, legacy stations are allowed to associate.
NOTE: This setting has no effect on a BSS in which HT support is not available.
Allow weak encryption Shows if the AP has enabled or disabled the weak encryption option.
The use of TKIP or WEP for unicast traffic forces the use of legacy
transmissions rates. Disabling this mode prevents the association of stations
using TKIP or WEP for unicast traffic. This mode is disabled by default.
Parameter Description
AOS-W 3.4.1 Command Line Interface | Reference Guide show ap config | 551
Virtual AP enable Wireless LAN profiles configure WLANs in the form of virtual AP profiles. This
parameter shows if the AP has enabled or disabled virtual APs.
Allowed band Shows the band(s) on which to use the virtual AP:
za—802.11a band only (5 GHz)
zg—802.11b/g band only (2.4 GHz)
zall—both 802.11a and 802.11b/g bands (5 GHz and 2.4 GHz)
VLAN Shows the VLAN(s) into which users are placed in order to obtain an IP address.
Forward mode Shows the current forward mode (bridge, split-tunnel, or tunnel) for the virtual
AP.
This parameter controls whether 802.11 frames are tunneled to the switch using
generic routing encapsulation (GRE), bridged into the local Ethernet LAN (for
remote APs), or a combination thereof depending on the destination (corporate
traffic goes to the switch, and Internet access remains local).
Only 802.1x authentication is supported when configuring bridge or split tunnel
mode.
Deny time range Shows the time range for which the AP will deny access for a virtual AP.
Mobile IP Shows if IP mobility has been enabled or disabled for the virtual AP.
HA Discovery on-
association
If enabled, all clients of a virtual-ap will received mobility service on association.
DoS Prevention Shows the status of the Dos Prevention option. If enabled, virtual APs ignore
deauthentication frames from clients. This prevents a successful deauth attack
from being carried out against the AP. This does not affect third-party APs.
Station Blacklisting Shows if the virtual AP has enabled or disabled detection of denial of service
(DoS) attacks, such as ping or SYN floods, that are not spoofed deauth attacks.
Blacklist Time Shows the number of seconds that a client will be quarantined from the network
after being blacklisted.
Authentication Failure
Blacklist Time
Shows the time, in seconds, a client is blocked if it fails repeated authentication.
If the virtual AP shows a value of 0, a blacklisted client is blocked indefinitely.
Fast Roaming Shows if the AP has enabled or disabled fast roaming.
Strict Compliance If enabled, the virtual AP denies client association requests if the AP and client
station have no common rates defined. Some legacy client stations which are
not fully 802.11-compliant may not include their configured rates in their
association requests. Such non-compliant stations may have difficulty
associating with APs unless strict compliance is disabled.
VLAN Mobility Shows if a virtual AP has enabled or disabled VLAN (Layer-2) mobility
Remote-AP Operation Shows when the virtual AP operates on a remote AP:
zalways—Permanently enables the virtual AP.
zbackup—Enables the virtual AP if the remote AP cannot connect to the
switch.
zpersistent—Permanently enables the virtual AP after the remote AP initially
connects to the switch.
zstandard—Enables the virtual AP when the remote AP connects to the
switch.
A remote AP should use always and backup for bridge SSIDs, and use
persistent and standard for 802.1x, tunneled, and split-tunneled SSIDs.
Convert Broadcast ARP
requests to unicast
If this option is enabled, all broadcast ARP requests are converted to unicast
and sent directly to the client. You can check the status of this option using the
show ap active and the show datapath tunnel command. If enabled, the
output will display the letter a in the flags column.
Parameter Description
552 | show ap config AOS-W 3.4.1 Command Line Interface | Reference Guide
Related Commands
Band Steering Shows if band-steering has been enabled or disabled for a virtual AP.
ARM’s band steering feature encourages dual-band capable clients to stay on
the 5GHz band on dual-band APs. This frees up resources on the 2.4GHz band
for single band clients like VoIP phones.
Band steering reduces co-channel interference and increases available
bandwidth for dual-band clients, because there are more channels on the 5GHz
band than on the 2.4GHz band. Dual-band 802.11n-capable clients may see
even greater bandwidth improvements, because the band steering feature will
automatically select between 40MHz or 20MHz channels in 802.11n networks.
This feature is disabled by default, and must be enabled in a Virtual AP profile.
VoIP Call Admission
Control
Shows if WiFi VoIP Call Admission Control features are enabled or disabled.
VoIP Bandwidth based CAC Shows the maximum bandwidth that can be handled by one radio, in kbps.
VoIP Call Capacity Show the number of simultaneous calls that can be handled by one radio.
VoIP Bandwidth Capacity
(kbps)
Shows the maximum bandwidth that can be handled by one radio, in kbps.
VoIP Call Handoff
Reservation
Shows the percentage of call capacity reserved for mobile VoIP clients on call.
VoIP Send SIP 100 Trying If enabled, the AP sends SIP 100 - trying messages to a call originator to
indicate that the call is proceeding. This is useful when the SIP invite may be
redirected through a number of servers before reaching the switch.
VoIP Disconnect Extra
Call
If enabled, the AP disconnects calls that exceed the high capacity threshold by
sending a deauthentication frame.
VOIP TSPEC Enforcement Shows if validation of TSPEC requests for call admission controls is enabled or
disabled.
VOIP TSPEC Enforcement
Period
Displays the maximum time for the station to start a call after the TSPEC
request.
VoIP Drop SIP Invite and
send status code (client)
Displays the status code sent to the client when a SIP Invite is dropped.
z480: Temporary Unavailable
z486: Busy Here
z503: Service Unavailable
znone: Don't send SIP status code
VoIP Drop SIP Invite and
send status code (server)
Displays the status code sent to the server when a SIP Invite is dropped.
z480: Temporary Unavailable
z486: Busy Here
z503: Service Unavailable
znone: Don't send SIP status code
Command Description Mode
ap system-profile
rf dot11g-radio-profile
rf arm-profile
rf ht-radio-profile
wlan ht-ssid-profile
wlan virtual-ap
wlan voip-cac-profile
The output of the show ap config command displays
the content of the profile settings for an individual AP or
AP group. Use the commands displayed in the column
to the left to configure these parameters.
Enable and Config
modes
Parameter Description

AOS-W 3.4.1 Command Line Interface | Reference Guide show ap config | 553
Command History
Introduced in AOS-W 3.0.
Command Information
Platforms Licensing Command Mode
All platforms Base operating system Enable or Config mode on master switches

554 | show ap coverage-holes AOS-W 3.4.1 Command Line Interface | Reference Guide
show ap coverage-holes
show ap coverage holes
Description
Show information for APs that have detected coverage holes in the wireless network.
Usage Guidelines
This command will only display coverage hole information if you have enabled coverage hole detection
using the command rf optimization-profile <profile> coverage-hole-detection. The coverage hole
detection feature requires the Wireless Intrusion Protection license.
Examples
The output of this command
The output of this command includes the following information:
Command History
Introduced in AOS-W 2.0.
Command Information
Column Description
Name Name of an AP that detected a coverage hole.
BSSID Basic Service Set Identifier (BSSID) of an AP that detected a coverage hole.
Radio The coverage hole is for this radio PHY type (a or g).
STA MAC address of the station.
RSSI The Receive Signal Strength Indicator (RSSI) value displayed in the output of this
command represents signal strength as a signal to noise ratio. For example, a value
of 30 would indicate that the power of the received signal is 30 dBm above the
signal noise threshold.
Platforms Licensing Command Mode
All platforms Wireless Intrusion Protection
license Enable or Config mode on master switches
(host) #show ap coverage-holes
Coverage Holes Detected
-----------------------
Name BSSID Radio STA RSSI
---- ----- ----- --- ----
ap12 00:1a:1e:c0:7f:fc a 00:0b:86:c7:49:94 15

AOS-W 3.4.1 Command Line Interface | Reference Guide show ap database | 555
show ap database
show ap database {group <group>|inactive|indoor|local|long|outdoor|page <page>|sensors
[disconnected]|sort-by [ap-group|ap-ip|ap-type|fqln|provisioned|status
{up|down}|switch-ip]|sort-direction[ascending|descending]|start <start> |status
{up|down]|switch <switch-ip-addr>|unprovisioned}
Description
Show the list of access points in the switch’s database.
Syntax
Parameter Description
group <group> Show data for a specified AP group.
inactive Show only local APs with no active BSSIDs or wired
AP interfaces.
indoor Show only APs that have an installation mode set to “indoor.”
local Show only APs on this switch.
long Display the following additional data columns:
zWired MAC Address,
zSerial #
zSlot/Port
zFQLN
outdoor Show only APs that have an installation mode set to “outdoor.”
page <page> Display a limited number of APs by entering the number of APs to be
displayed in the output of this command.
sensors Show only RFprotect sensors.
disconnected Show only disconnected RFprotect sensors.
sort-by Sort the output of this command by a specific data column.
ap-group Sort by AP group name.
ap-ip Sort by AP group name.
ap-type Sort by AP model.
fqln Sort by Fully Qualified Location Name (FQLN).
provisioned Sort by provisioning statistics.
status up|down If used with the sort-by keyword, status sorts the output of the
command by status type (up or down.) Otherwise, use the status
keyword to display APs with the specified status.
switch-ip Sort by switch IP address.
sort-direction Choose sort direction of AP list:.
ascending Sort AP list in ascending order by name.
descending Sort AP list in descending order by name.
start <start> Start showing the AP index at the specified index number.
status Show only APS with a given status as active or inactive.
down Show only APs that are inactive.

556 | show ap database AOS-W 3.4.1 Command Line Interface | Reference Guide
Usage Guidelines
Many of the parameters in this command can be used together to filter a large database of information
down to just the AP data you want to see. For example, you can issue the command show ap database
group <group> local status up to view a list of local APs within a specific AP group that are reporting an
up status. Include the sort-by and sort-direction keywords to specify how the data is sorted in the output
of this command.
Examples
The output of the command show ap database shows the switch’s database of information for APs in the
group default. The output also includes a description of the flag types that may appear in the Flags
column.
Related Commands
up Show only APs that are active.
switch <switch-ip-addr> Show only APs registered with a specified switch by entering a switch
IP address.
unprovisioned Show only unprovisioned APs (using modifiers).
Command Description Mode
show ap database-summary To display a more general summary overview of
the AP registered to a switch, use the command
show ap database-summary.
Enable and Config
modes
Parameter Description
show ap database group default
AP Database
-----------
Name Group AP Type IP Address Status Flags Switch IP
---- ----- ------- ---------- ------ ----- ---------
3.125.141112 default 125 192.0.2.12 Up 1h:48m:27s 10.4.97.4
3.125.142113 default 125 192.0.2.12 Up 1h:43m:6s 10.4.97.6
3.125.242115 default 125 192.0.2.13 Up 1h:41m:18s 10.4.97.10
3.60.161112 default 60 192.0.2.14 Up 1h:43m:20s 10.4.97.4
3.60.202108 default 60 192.0.2.15 Up 8h:7m:4s R 10.4.97.4
3.61.101100 default 61 192.0.2.16 Up 7h:32m:13s R 10.4.97.4
3.61.161113 default 61 192.0.2.17 Up 1h:43m:20s 10.4.97.4
3.65.101117 default 65 192.0.2.18 Up 8h:39m:7s R 10.4.97.4
3.65.121108 default 65 192.0.2.29 Up 1h:55m:14s 10.4.97.4
3.65.292112 default 65 192.0.2.32 Up 1h:43m:42s 10.4.97.10
3.70.102116 default 70 192.0.2.43 Up 8h:23m:17s R 10.4.97.4
3.70.131107 default 70 192.0.2.44 Up 1h:55m:10s 10.4.97.4
3.70.172103 default 70 192.0.2.56 Up 1h:42m:24s 10.4.97.6
3.85.152116 default 85 192.0.2.57 Up 1h:42m:56s 10.4.97.6
3.85.252117 default 85 192.0.2.58 Up 1h:43m:18s 10.4.97.10
AP-61-20 default 61 192.0.2.59 Up 21m:36s o 10.3.47.189
Flags: U = Unprovisioned; N = Duplicate name; G = No such group; L = Unlicensed
R = Remote AP; I = Inactive; X = Maintenance Mode; P = PPPoE AP
S = RFprotect Sensor; d = Disconnected Sensor; H = Using 802.11n license
M = Mesh node; Y = Mesh Recovery i = Indoor; o = Outdoor
Total APs:15

AOS-W 3.4.1 Command Line Interface | Reference Guide show ap database | 557
Command History
Introduced in AOS-W 3.0.
Command Information
Platforms Licensing Command Mode
All platforms Base operating system Enable or Config mode on master switches
558 | show ap database-summary AOS-W 3.4.1 Command Line Interface | Reference Guide
show ap database-summary
show ap database-summary
Description
Show a general summary of access point information for this switch.
Usage Guidelines
Use this command to show the current number of active APs and Air Monitors. This command is also useful
for determining how many unprovisioned APs or duplicate APs are on the network. For full details on each
AP registered to a switch, use the command show ap database.
Examples
The output of this command shows that this switch can detect a total of five APs, four up, and one down.
The output of this command includes the following information:
Command History
Introduced in AOS-W 3.0.
Command Information
show ap database-summary
(host) #show ap database-summary
AP Database Summary
-------------------
AP Mode Total Up Total Down Total Upgrading* Total Rebooting* RAP Up RAP Down RAP RAP
Upgrading* Rebooting*
------ -------- ---------- ---------------- ---------------- ------ -------- ----------- -------
Access Points 0 0 0 0 0 0 0 0
Air Monitors 0 0 0 0 0 0 0 0
Wired Access Points 0 0 0 0 0 0 0 0
Mesh Portals 0 0 0 0 0 0 0 0
Mesh Points 0 0 0 0 0 0 0 0
RFprotect Sensors 0 0 0 0 0 0 0 0
*Upgrading and Rebooting counts only reflect APs registered on this controller.
Column Description
Total Up Total number of APs with an up status.
Total Down Total number of APs with a down status.
IPSEC Up Total number of APs with an active (up) IPSEC tunnel.
IPSEC Down Total number of APs with an inactive (down) IPSEC tunnel.
Platforms Licensing Command Mode
All platforms Base operating system Enable or Config mode on master switches

AOS-W 3.4.1 Command Line Interface | Reference Guide show ap debug association-failure | 559
show ap debug association-failure
show ap debug association-failure [{ap-name <ap-name>}|{bssid <bssid>}|{client-mac
<client-mac>}|{essid <essid>}|{ip-addr <ip-addr>}]
Description
Display association failure information that can be used to troubleshoot problems on an AP.
Syntax
Usage Guidelines
Use this command to determine whether the client is associated, and identify the last AP to which it was
connected.
Example
The output of the command show ap debug association-failure displays the Association Failure Table show
below. If the Idle time column in the output of this command is a low value, reason column will describe
why association failed.
The output of this command includes the following data columns:
Parameter Description
ap-name <ap-name> Filter the Association Failure Table by AP name.
bssid <bssid> Filter the Association Failure Table by BSSID. The Basic Service Set
Identifier (BSSID) is usually the AP’s MAC address.
client-mac <client-mac> Filter the Association Failure Table to show an individual client MAC address
by entering the MAC address of a client.
essid <essid> Filter the Association Failure Table by ESSID. An Extended Service Set
Identifier (ESSID) is a alphanumeric name that uniquely identifies the Service
Set Identifier (SSID).
ip-addr <ip-addr> Filter the Association Failure Table by IP address by entering an IP address
in dotted-decimal format.
Column Description
MAC address MAC address of the client that failed to associate with an AP.
AP Name Name of an AP to which the client attempted to associate.
BSSID Basic Service Set Identifier of an AP.
ESSID Extended Service Set Identifier of an AP.
State This data column shows if the client is currently authorized or both authorized and
associated with an AP.
(host)#show ap debug association-failure
Association Failure Table
-------------------------
MAC Address AP Name BSSID ESSID State Radio Idle Time Reason
----------- ------- ----- ----- ----- ----- --------- ------
00:16:6f:09:54:3e AL29 00:1a:1e:11:6f:00 guest 802.11g 20h:39m:33s Denied; AP Going Down
00:16:6f:09:54:3e AL33 00:1a:1e:11:6e:60 guest auth 802.11g 20h:39m:33s Unspecified Failure
00:16:6f:09:54:3e AL40 00:1a:1e:8d:5b:20 guest 802.11g 20h:39m:33s Denied; Ageout
Num Association Failures:3
560 | show ap debug association-failure AOS-W 3.4.1 Command Line Interface | Reference Guide
Command History
Introduced in AOS-W 3.0.
Command Information
Radio The AP radio type.
Idle Time Amount of time that the client has been idle, in the format hours:minutes:seconds.
Reason A brief description of the reason why the client failed to associate.
Platforms Licensing Command Mode
All platforms Base operating system Enable or Config mode on master switches
Column Description

AOS-W 3.4.1 Command Line Interface | Reference Guide show ap debug bss-config | 561
show ap debug bss-config
show ap debug bss-config [ap-name <ap-name>|bssid <bssid>||essid <essid>|ip-addr <ip-
addr>|port <port>/<slot>]
Description
Show the configuration for each BSSID of an AP. This information can be used to troubleshoot problems on
an AP.
Syntax
Examples
The output of this command shows the AP configuration table for a specific BSSID.
The output of this command includes the following information:
Parameter Description
ap-name <ap-name> Filter the AP Config Table by AP name.
bssid <bssid> Filter the AP Config Table by BSSID. The Basic Service Set Identifier (BSSID) is
usually the AP’s MAC address.
essid <essid> Filter the AP Config Table by ESSID. An Extended Service Set Identifier (ESSID) is a
alphanumeric name that uniquely identifies the Service Set Identifier (SSID).
ip-addr <ip-addr> Filter the AP Config Table by IP address by entering an IP address in dotted-decimal
format.
port <port>/<slot> Filter the AP Config Table by port and slot numbers. The slot and port numbers
should be separated by a forward slash (/).
(host) #show ap debug bss-config
Alcatel-Lucent AP Config Table
---------------------
bss ess vlan ip phy type fw-mode max-cl rates tx-rates preamble mtu status wmm
--- --- ---- -- --- ---- ------- ------ ----- -------- -------- --- ------ ---
00:1a:1e:11:24:c2 cera2 66 10.6.1.203 g-HT ap tunnel 64 0x3 0xfff enable 0 enable enable
00:1a:1e:8d:5b:11 wpa2 65 10.6.1.198 a-HT ap tunnel 20 0x150 0xff0 - 0 enable enable
00:0b:86:9b:e5:60 guest 63 10.6.14.79 g ap tunnel 20 0x2 0x3fe enable 0 enable enable
00:1a:1e:97:e5:41 voip 66 10.6.1.199 g-HT ap tunnel 20 0xc 0x14c enable 0 enable enable
00:1a:1e:11:74:a1 voip 66 10.6.1.197 g-HT ap tunnel 20 0xc 0x14c enable 0 enable enable
00:1a:1e:11:5f:11 wpa2 65 10.6.1.200 a-HT ap tunnel 20 0x150 0xff0 - 0 enable enable
Column Description
bss Basic Service Set (BSS) identifier, which is usually the AP’s MAC address.
ess Extended Service Set (ESS) identifier; a user-defined name for a wireless network.
vlan The BSSID’s VLAN number.
IP The AP’s IP address.
phy One of the following 802.11 types
za
za-HT (high-throughput)
zg
zg-HT (high-throughput)
type This column shows if the BSSID is for an access point (ap) or an air monitor (am).
562 | show ap debug bss-config AOS-W 3.4.1 Command Line Interface | Reference Guide
Command History
Introduced in AOS-W 3.0.
Command Information
fw-mode The configured forward mode for the AP’s virtual AP profile.
zbridge: Bridge locally
zsplit-tunnel: Tunnel to switch or NAT locally
ztunnel: Tunnel to switch
max-cl The maximum number of clients allowed for this BSSID.
preamble Shows if short preambles are enabled for 802.11b/g radios. Network performance
may be higher when short preamble is enabled. In mixed radio environments, some
802.11b wireless client stations may experience difficulty associating with the AP
using a short preamble.
MTU Maximum Transmission Unit (MTU) size, in bytes. This value describes the greatest
amount of data that can be transferred in one physical frame.
status Shows if this BSSID is enabled or disabled.
wmm Shows if the BSSID has enabled or disabled WMM, also known as IEEE 802.11e
Enhanced Distribution Coordination Function (EDCF) WMM provides prioritization of
specific traffic relative to other traffic in the network.
Platforms Licensing Command Mode
All platforms Base operating system Enable or Config mode on master switches
Column Description
AOS-W 3.4.1 Command Line Interface | Reference Guide show ap debug bss-stats | 563
show ap debug bss-stats
show ap debug bss-stats [bssid <bssid>]
Description
Show debug and troubleshooting statistics from a specific BSSID of an AP.
Syntax
Examples
The example below shows part of the output of the command show ap debug bss-stats bssid <bssid>.
The output of this command includes the following information:
Parameter Description
bssid <bssid> Show data for a specific Basic Service Set Identifier (BSSID) on an AP. An AP’s
BSSID is usually the AP’s MAC address.
Parameter Description
Frames Rcvd For TX Number of frames received for transmission.
Tx Frames Dropped Number of transmission frames that were dropped.
Frames Transmitted Number of frames successfully transmitted.
Success With Retry Number of frames that were transmitted after being retried.
Tx Mgmt Frames Number of management frames transmitted.
Beacons Transmitted Number of beacons transmitted.
(host) #show ap debug bss-stats bssid 00:1a:1e:11:5f:11
BSSID Stats
-----------
Parameter Value
--------- -----
------------------- General Per-radio Statistics
------------------- Transmit specific Statistics
Frames Rcvd For TX 4263
Tx Frames Dropped 613
Frames Transmitted 3650
Success With Retry 0
Tx Mgmt Frames 451975
Beacons Transmitted 447712
Tx Probe Responses 4263
Tx Data Frames 0
Multicast Data 0
Tx CTS Frames 0
Dropped After Retry 613
Dropped No Buffer 0
Missed ACKs 613
Long Preamble 4263
Short Preamble 0
Tx EAPOL Frames 0
Tx 6 Mbps 3650
Tx WMM [VO] 4263
UAPSD OverflowDrop 0
------------------- Receive specific Statistics
Last SNR 0
Last ACK SNR 23
Last ACK SNR CTL0 15
Last ACK SNR CTL1 22
Last ACK SNR CTL2 15
...

564 | show ap debug bss-stats AOS-W 3.4.1 Command Line Interface | Reference Guide
Tx Probe Responses Number of transmitted probe responses.
Tx Data Frames Number of transmitted data frames.
Multicast Data Number of multicast and broadcast frames transmitted.
Tx CTS Frames Number of clear-to-sent (CTS) frames transmitted.
Dropped After Retry Number of frames dropped after an attempted retry.
Dropped No Buffer Number of frames dropped because the AP’s buffer was full.
Missed ACKs Number of missed acknowledgements (ACKs).
Long Preamble Number of frames sent with a long preamble.
Short Preamble Number of frames sent with a short preamble.
Tx EAPOL Frames Number of Extensible Authentication Protocol over LAN (EAPOL) frames
transmitted.
Tx 6 Mbps Number of frames transmitted at 6 Mbps.
Tx 9 Mbps Number of frames transmitted at 9 Mbps.
Tx 12 Mbps Number of frames transmitted at 12 Mbps.
Tx 18 Mbps Number of frames transmitted at 18 Mbps.
Tx 24 Mbps Number of frames transmitted at 24 Mbps.
Tx 36 Mbps Number of frames transmitted at 36 Mbps.
Tx 48 Mbps Number of frames transmitted at 48 Mbps.
Tx 54 Mbps Number of frames transmitted at 54 Mbps.
Tx HT 108 Mbps Number of frames transmitted at 108 Mbps.
Tx HT 120 Mbps Number of frames transmitted at 120 Mbps.
Tx HT 162 Mbps Number of frames transmitted at 162 Mbps.
Tx HT 180 Mbps Number of frames transmitted at 180 Mbps.
Tx HT 216 Mbps Number of frames transmitted at 216 Mbps.
Tx HT 240 Mbps Number of frames transmitted at 240 Mbps.
Tx HT 243 Mbps Number of frames transmitted at 243 Mbps.
Tx HT 270 Mbps Number of frames transmitted at 270 Mbps.
Tx HT 300 Mbps Number of frames transmitted at 300 Mbps.
Tx WMM Number of Wifi Multimedia (WMM) packets transmitted for the following access
categories. If the AP has not transmitted packets in a category type, this data row
will not appear in the output of the command.
Tx WMM [BE]: Best Effort
Tx WMM [BK]: Background
Tx WMM [VO]: VoIP
Tx WMM [VI]: Video
Number of Wifi Multimedia (WMM) VoIP packets transmitted.
UAPSD OverflowDrop Number of packets dropped due to Unscheduled Automatic Power Save Delivery
(U-APSD) overflow.
Last SNR The last recorded signal-to-noise ratio.
Parameter Description

AOS-W 3.4.1 Command Line Interface | Reference Guide show ap debug bss-stats | 565
Command History
Introduced in AOS-W 3.0.
Last SNR CTL0 The signal-to-noise ratio for the last received data packet on the primary (control)
channel 0. This parameter is only displayed for APs operating in 40 Mhz mode.
Last SNR CTL1 The signal-to-noise ratio for the last received data packet on the secondary (control)
channel 1. This parameter is only displayed for APs operating in 40 Mhz mode.
Last SNR CTL2 The signal-to-noise ratio for the last received data packet on the secondary (control)
channel 2. This parameter is only displayed for APs operating in 40 Mhz mode.
Last ACK SNR Signal-to-noise ratio for the last received ACK packet.
Last ACK SNR CTL0 Signal-to-noise ratio for the last received ACK packet on the primary (control)
channel 0. This parameter is only displayed for APs operating in 40 Mhz mode.
Last ACK SNR CTL1 Signal-to-noise ratio for the last received ACK packet on the primary (control)
channel 1. This parameter is only displayed for APs operating in 40 Mhz mode.
Last ACK SNR CTL2 Signal-to-noise ratio for the last received ACK packet on the primary (control)
channel 2. This parameter is only displayed for APs operating in 40 Mhz mode.
Last ACK SNR EXT0 Signal-to-noise ratio for the last received ACK packet on the secondary (extension)
channel 0. This parameter is only displayed for APs operating in 40 Mhz mode.
Last ACK SNR EXT1 Signal-to-noise ratio for the last received ACK packet on the secondary (extension)
channel 1. This parameter is only displayed for APs operating in 40 Mhz mode.
Last ACK SNR EXT2 Signal-to-noise ratio for the last received ACK packet on the secondary (extension)
channel 2. This parameter is only displayed for APs operating in 40 Mhz mode.
Frames Received Number of frames received.
Rx Data Frames Number of data frames received.
Null Data Frames Number of null data frames received.
Rx Mgmt Frames Number of management frames received.
Control Frames Number of control frames received.
Frames To Me Number of wireless frames received that are addressed to the specified BSSID.
Probe Requests Number of probe requests.
PS Poll Frames Number of Power Save poll frames
Rx 6 Mbps Number of frames received at 6 Mbps.
Rx 9 Mbps Number of frames received at 9 Mbps.
Rx 12 Mbps Number of frames received at 12 Mbps.
Rx 18 Mbps Number of frames received at 18 Mbps.
Rx 24 Mbps Number of frames received at 24 Mbps.
Rx 36 Mbps Number of frames received at 36 Mbps.
Rx 48 Mbps Number of frames received at 48 Mbps.
Rx 54 Mbps Number of frames received at 54 Mbps.
Parameter Description

566 | show ap debug bss-stats AOS-W 3.4.1 Command Line Interface | Reference Guide
Command Information
Platforms Licensing Command Mode
All platforms Base operating system Enable or Config mode on master switches
AOS-W 3.4.1 Command Line Interface | Reference Guide show ap debug client-mgmt-counters | 567
show ap debug client-mgmt-counters
show ap debug client-mgmt-counters
Description
Show the numbers of each type of message from an AP’s clients. This information can be used to
troubleshoot problems on an AP.
Examples
The output of the command
The output of this command includes the following information:
Parameter Description
Validate Client Number of times a client was validated.
AP Stats Update
Message
Number of times an AP updated its statistics with the switch.
3087 (For internal use only)
Tunnel VLAN
Membership
(For internal use only)
Update STA Tunnel
Request
(For internal use only)
Update STA Tunnel
Response
(For internal use only)
ARM Update Number of times an AP has changed its adaptive radio management (ARM) settings.
ARM Propagate (For internal use only)
ARM Neighbor Assigned (For internal use only)
(host)#show ap debug client-mgmt-counters
Counters
--------
Name Value
---- -----
Validate Client 512
AP Stats Update Message 557750
3087 6
Tunnel VLAN Membership 4493
Update STA Tunnel Request 229
Update STA Tunnel Response 229
ARM Update 808921
ARM Propagate 590567
ARM Neighbor Assigned 55396
STM SAP Down 19
AP Message 192
STA On Call Message 12164
STA Message 19750
STA SIP authenticate Message 10919
STA Deauthenticate 707
Stat Update V3 441447
VoIP CAC State Announcement 37185
Remote AP State 371330
AP Message Response 164
assoc-req 4358
assoc-resp 4358
reassoc-req 950
reassoc-resp 950
disassoc 452
deauth 5117
sapcp 351131
568 | show ap debug client-mgmt-counters AOS-W 3.4.1 Command Line Interface | Reference Guide
Command History
Introduced in AOS-W 3.0.
Command Information
STM SAP Down (For internal use only)
AP Message (For internal use only)
STA On Call Message Number of counters indicating that a station has an active phone call
STA Message (For internal use only)
STA SIP authenticate
Message
Number of messages indicating that a telephone has completed SIP registration and
authentication.
STA Deauthenticate Number of times a station sent a message to an AP to deauthenticate a client.
Stat Update V3 (For internal use only)
VoIP CAC State
Announcement
Number of times a switch announces a call admission control (CAC) state change to
the AP. Changes in CAC state could include the ability of call admission controls to
accept more or fewer calls than previously configured.
Remote AP State (For internal use only)
AP Message Response (For internal use only)
assoc-req Number of 802.11 association request management frames from the switch.
assoc-resp Number of 802.11 association responses to the switch.
reassoc-req Number of 802.11 reassociation requests to the switch.
reassoc-resp Number of 802.11 reassociation responses from the switch.
disassoc Number of 802.11 disassociation messages to the switch.
deauth Number of 802.11 deauthorization messages from the switch.
sapcp (For internal use only)
Platforms Licensing Command Mode
All platforms Base operating system Enable or Config mode on master switches
Parameter Description

AOS-W 3.4.1 Command Line Interface | Reference Guide show ap debug client-stats | 569
show ap debug client-stats
show ap debug client-stats <client-mac)
Description
Show detailed statistics about a client.
Example
The command below displays statistics for packets both received from and transmitted to the specified
client.
The output of this command includes the following information:
Parameter Description
Frames Rcvd For TX Number of frames received for transmission.
Tx Frames Dropped Number of transmission frames that were dropped.
(host) #show ap debug client-stats 00:19:7e:89:fa:e7
Station Stats
-------------
Parameter Value
--------- -----
---------------- General Per-radio Statistics
---------------- Transmit specific Statistics
Frames Rcvd For TX 22
Tx Frames Dropped 0
Frames Transmitted 22
Success With Retry 1
Tx Mgmt Frames 2
Tx Probe Responses 0
Tx Data Frames 20
Tx CTS Frames 0
Dropped After Retry 0
Dropped No Buffer 0
Missed ACKs 1
Long Preamble 22
Short Preamble 0
Tx EAPOL Frames 13
Tx 6 Mbps 15
Tx 48 Mbps 5
Tx 54 Mbps 2
Tx WMM [VO] 15
UAPSD OverflowDrop 0
---------------- Receive specific Statistics
Last SNR 31
Last SNR CTL0 28
Last SNR CTL1 25
Last SNR CTL2 22
Last ACK SNR 32
Last ACK SNR CTL0 30
Last ACK SNR CTL1 28
Last ACK SNR CTL2 21
Last ACK SNR EXT0 5
Last ACK SNR EXT1 4
Frames Received 2932
Rx Data Frames 2930
Null Data Frames 2879
Rx Mgmt Frames 1
PS Poll Frames 0
Rx 6 Mbps 14
Rx 12 Mbps 6
Rx 18 Mbps 5
Rx 24 Mbps 2
Rx 36 Mbps 13
Rx 48 Mbps 1162
Rx 54 Mbps 1730
Rx WMM [BE] 39

570 | show ap debug client-stats AOS-W 3.4.1 Command Line Interface | Reference Guide
Frames Transmitted Number of frames successfully transmitted.
Success With Retry Number of frames that were transmitted after being retried.
Tx Mgmt Frames Number of management frames transmitted.
Tx Probe Responses Number of transmitted probe responses.
Tx Data Frames Number of transmitted data frames.
Tx CTS Frames Number of clear-to-sent (CTS) frames transmitted.
Dropped After Retry Number of frames dropped after an attempted retry.
Dropped No Buffer Number of frames dropped because the AP’s buffer was full.
Missed ACKs Number of missed acknowledgements (ACKs)
Long Preamble Number of frames sent with a long preamble.
Short Preamble Number of frames sent with a short preamble.
Tx EAPOL Frames Number of Extensible Authentication Protocol over LAN (EAPOL) frames transmitted.
Tx <n> Mbps Number of frames transmitted at <n> Mbps, where <n> is a value between 6 and
300.
Tx WMM Number of Wifi Multimedia (WMM) packets transmitted for the following access
categories. If the AP has not transmitted packets in a category type, this data row
will not appear in the output of the command.
Tx WMM [BE]: Best Effort
Tx WMM [BK]: Background
Tx WMM [VO]: VoIP
Tx WMM [VI]: Video
UAPSD OverflowDrop Number of packets dropped due to Unscheduled Automatic Power Save Delivery
(U-APSD) overflow.
Last SNR The last recorded signal-to-noise ratio.
Last SNR CTL0 The signal-to-noise ratio for the last received data packet on the primary (control)
channel 0. This parameter is only displayed for APs operating in 40 Mhz mode.
Last SNR CTL1 The signal-to-noise ratio for the last received data packet on the secondary (control)
channel 1. This parameter is only displayed for APs operating in 40 Mhz mode.
Last SNR CTL2 The signal-to-noise ratio for the last received data packet on the secondary (control)
channel 2. This parameter is only displayed for APs operating in 40 Mhz mode.
Last ACK SNR Signal-to-noise ratio for the last received ACK packet.
Last ACK SNR CTL0 Signal-to-noise ratio for the last received ACK packet on the primary (control)
channel 0. This parameter is only displayed for APs operating in 40 Mhz mode.
Last ACK SNR CTL1 Signal-to-noise ratio for the last received ACK packet on the primary (control)
channel 1. This parameter is only displayed for APs operating in 40 Mhz mode.
Last ACK SNR CTL2 Signal-to-noise ratio for the last received ACK packet on the primary (control)
channel 2. This parameter is only displayed for APs operating in 40 Mhz mode.
Last ACK SNR EXT0 Signal-to-noise ratio for the last received ACK packet on the secondary (extension)
channel 0. This parameter is only displayed for APs operating in 40 Mhz mode.
Last ACK SNR EXT1 Signal-to-noise ratio for the last received ACK packet on the secondary (extension)
channel 1. This parameter is only displayed for APs operating in 40 Mhz mode.
Frames Received Number of frames received.
Parameter Description
AOS-W 3.4.1 Command Line Interface | Reference Guide show ap debug client-stats | 571
Command History
Introduced in AOS-W 3.0.
Command Information
Rx Data Frames Number of data frames received.
Null Data Frames Number of null data frames received.
Rx Mgmt Frames Number of management frames received.
PS Poll Frames Number of power save poll frames received.
Rx <n> Mbps Number of frames received at <n> Mbps, where <n> is a value between 6 and 300.
Tx WMM Number of Wifi Multimedia (WMM) packets transmitted for the following access
categories. If the AP has not transmitted packets in a category type, this data row
will not appear in the output of the command.
Tx WMM [BE]: Best Effort
Tx WMM [BK]: Background
Tx WMM [VO]: VoIP
Tx WMM [VI]: Video
Platforms Licensing Command Mode
All platforms Base operating system Enable or Config mode on master switches
Parameter Description

572 | show ap debug client-table AOS-W 3.4.1 Command Line Interface | Reference Guide
show ap debug client-table
show ap debug client-table [ap-name <ap-name>|bssid <bssid>|ip-addr <ip-addr>]
Description
Show clients associated to an AP.
Syntax
Usage Guidelines
The Tx_Rate, Rx_Rate, Last_ACK_SNR, and Last_Rx_SNR columns shown in the output of this
command display valuable troubleshooting information for clients trying to connect to a specific AP. Use
this command to verify that the transmit (Tx_Rate) and receive (Rx_Rate) rates are not too low, and that
the signal-to-noise (SNR) ratio is acceptable.
Examples
The example below shows part of the AP configuration table for a specific BSSID. Additional parameters
not displayed are described in the table below.
The output of this command includes the following information:
Parameter Description
ap-name <ap-name> Filter the AP Config Table by AP name.
bssid <bssid> Filter the AP Config Table by BSSID. The Basic Service Set Identifier (BSSID) is
usually the AP’s MAC address.
ip-addr <ip-addr> Filter the AP Config Table by IP address by entering an IP address in dotted-decimal
format.
(host) #show ap debug client-table ap-name AP12
MAC ESSID BSSID Assoc_State HT_State AID PS_State UAPSD Tx_Pkts Rx_Pkts PS_Qlen Tx_Retr
--- ----- ----- ----------- ------ --- -------- ----- ------- ------- --- ----
00:17:f2:4d:01:e2 wpa2 00:1a:1e:11:5f:11 Associated None 0x1 Awake (0,0,0,0,N/A,0) 31463 22821 0 4289
00:14:a4:25:72:6d wpa2 00:1a:1e:11:5f:11 Associated None 0x2 Awake (0,0,0,0,N/A,0) 24691 45215 0 944
00:19:7e:66:89:38 wpa2 00:1a:1e:11:5f:11 Associated None 0x4 Awake (0,0,0,0,N/A,0) 7031 24739 0 671
00:16:cf:bc:0e:ce wpa2 00:1a:1e:11:5f:11 Associated None 0x5 Awake (0,0,0,0,N/A,0) 3920 14797 0 286
00:19:7d:d6:74:93 wpa2 00:1a:1e:11:5f:11 Associated None 0x7 Awake (0,0,0,0,N/A,0) 2530 8034 0 365
UAPSD:(VO,VI,BK,BE,Max SP,Q Len)
HT Flags: A - LDPC Coding; W - 40Mhz; S - Short GI; M - Max A-MSDU
D - Delayed BA; G - Greenfield; R - Dynamic SM PS
Q - Static SM PS; N - A-MPDU disabled
Parameter Description
MAC MAC address of a client.
ESSID Extended Service Set identifier (ESSID) used by the client. An ESSID is a user-defined name for
a wireless network.
BSSID Basic Service Set identifier for the client.
Assoc_State Shows whether or not the client is currently authorized and/or associated with the AP.
HT_State Shows the client’s high-throughput (802.11n) transmission type:
znone: AP is a legacy AP that does not support the 802.11n standard.
z20Mhz: A high-throughput APs using a single 20 Mhz channel.
z40Mhz: A high-throughput APs using two 20 Mhz channels.
AOS-W 3.4.1 Command Line Interface | Reference Guide show ap debug client-table | 573
Command History
Introduced in AOS-W 3.0.
Command Information
AID 802.11 association ID. A client receives a unique 802.11 association ID when it associates to an
AP.
UAPSD This parameter shows the following values for Unscheduled Automatic Power Save Delivery
(UAPSD) in comma-separated format: VO, VI, BK, BE, Max SP, Q Len.
zVO: If 1, UAPSD is enabled for the VoIP access category. If UAPSD is disabled for this
access category, this value is 0.
zVI: If 1, UAPSD is enabled for the Video access category. If UAPSD is disabled for this
access category, this value is 0.
zBK: If 1, UAPSD is enabled for the Background access category. If UAPSD is disabled for
this access category, this value is 0.
zBE: If 1, UAPSD is enabled for the Best Effort access category. If UAPSD is disabled for this
access category, this value is 0.
zMax SP: The maximum service period is the number of frame sent per trigger packet. This
value is value can be 0, 2, 4 or 8.
zQ Len: The number of frames currently queued for the client, from 0 to 16 frames.
Tx_Pkts Number of packets transmitted by the client.
Rx_Pkts Number of packets received by the client.
PS-Qlen Power save queue length, in bytes.
Tx_Retries Number of packets that the client had to resend due to an initial transmission failure.
Platforms Licensing Command Mode
All platforms Base operating system Enable or Config mode on master switches
Parameter Description

574 | show ap debug counters AOS-W 3.4.1 Command Line Interface | Reference Guide
show ap debug counters
show ap debug counters {ap-name <ap-name>|bssid <bssid>|group <group>|ip-addr <ip-
addr>}
Description
Show AP message and reboot/bootstrap counters for an individual AP or AP group.
Syntax
Example
The output of this command can you how many times each AP has rebooted (a hard boot) or bootstrapped
(a soft boot), the number of times configuration changes were sent from the switch, and the number of
configuration changes acknowledged by that AP.
The output of this command includes the following information:
Parameter Description
ap-name <ap-name> Show debug counters for an AP with a specified name.
bssid <bssid> Show debug counters for a specific Basic Service Set Identifier (BSSID). The Basic
Service Set Identifier (BSSID) is usually the AP’s MAC address.
group <group> Show debug counters for an AP group.
ip-addr <ip-addr> Show debug counters for an AP with a specified IP address by entering an IP
address in dotted-decimal format.
Column Description
Name Name of the AP.
Group Name of the AP’s group.
IP Address IP address of the AP.
Configs sent Number of times configuration changes have been sent to the AP.
Configs Acked Number of times that the AP has acknowledged receiving a configuration change.
Bootstraps Number of times the AP restarted. Bootstraps are also known as “soft” restarts.
Reboots Number of times power to the AP cycled off and then on again. Reboots also known
as “hard” restarts.
(host) #show ap debug counters group corp1
AP Counters
-----------
Name Group IP Address Configs Configs AP Boots AP Boots Bootstraps Reboots
Sent Acked Sent Acked
---- ----- ---------- ------ ------- -------- -------- ---------- -------
AL1 corp1 10.6.1.209 1597 1597 0 0 1 0
AL10 corp1 10.6.1.198 165 165 0 0 2 1
AL12 corp1 10.6.1.200 195 195 0 0 1 0
AL15 corp1 10.6.1.197 1580 1580 0 0 1 0
AL16 corp1 10.6.1.199 73 73 0 0 1 0
AL19 corp1 10.6.1.212 8 8 0 0 1 0
Total APs :6

AOS-W 3.4.1 Command Line Interface | Reference Guide show ap debug counters | 575
Command History
Introduced in AOS-W 3.0.
Command Information
Platforms Licensing Command Mode
All platforms Base operating system Enable or Config mode on master switches

576 | show ap debug datapath AOS-W 3.4.1 Command Line Interface | Reference Guide
show ap debug datapath
show ap debug datapath {ap-group <ap-group>|ap-name <ap-name>|bssid <bssid>|ip-addr
<ip-addr>}
Description
Show datapath tunnel parameters of an AP or AP group.
Syntax
Example
The output of the following command shows datapath tunnel parameters for an AP with the IP address
192.0.2.32.
The output of this command includes the following information:
Command History
Introduced in AOS-W 3.0.
Parameter Description
ap-group <ap-group> Show data path information for a specific AP group.
ap-name <ap-name> Show data path information for an AP with a specific name.
bssid <bssid> Show data path information for a specific Basic Service Set Identifier (BSSID). The
Basic Service Set Identifier (BSSID) is usually the AP’s MAC address.
ip-addr <ip-addr> Show data path information for an AP with a specific IP address by entering an IP
address in dotted-decimal format.
(host) #show ap debug datapath 192.0.2.32
Datapath Parameters Table
-------------------------
essid encr-alg client-vlan-id tunnel-id gre-type deny-bcast num-clients
----- -------- -------------- --------- -------- ---------- -----------
guest Open 63 0x10f6 0x8300 disable 0
voip WPA2 8021X AES 66 0x1103 0x8310 disable 7
corpWPA2 PSK AES 66 0x10f1 0x8320 disable 0
guest Open 63 0x10f7 0x8200 disable 1
wpa2 WPA2 8021X AES 65 0x10be 0x8210 enable 15
Column Description
ESSID The Extended Service Set Identifier is a unique name that identifies a wireless
network
encr-alg Encryption algorithm used by the network
client-vlan-id ID of the network VLAN
tunnel-id Identification number of the AP’s tunnel.
gre-type GRE tunnel type.
deny-bcast If enabled, the AP will respond to broadcast probe requests. If disabled, the AP will
not respond to these requests.
num-clients Number of clients currently using the network.

AOS-W 3.4.1 Command Line Interface | Reference Guide show ap debug datapath | 577
Command Information
Platforms Licensing Command Mode
All platforms Base operating system Enable or Config mode on master switches
578 | show ap debug driver-log AOS-W 3.4.1 Command Line Interface | Reference Guide
show ap debug driver-log
show ap debug driver-log {ap-name <ap-name>|bssid <bssid>|ip-addr <ip-addr>}
Description
Show an AP’s driver logs.
Syntax
Usage Guidelines
Use this command to review configuration changes made since the AP was last reset.
Command History
Introduced in AOS-W 3.0.
Command Information
Parameter Description
ap-name <ap-name> Show log information for an AP with a specific name.
bssid <bssid> Show log information for a specific Basic Service Set Identifier (BSSID). The Basic
Service Set Identifier (BSSID) is usually the AP’s MAC address.
ip-addr <ip-addr> Show log information for an AP with a specific IP address by entering an IP address
in dotted-decimal format.
Platforms Licensing Command Mode
All platforms Base operating system Enable or Config mode on master switches
AOS-W 3.4.1 Command Line Interface | Reference Guide show ap debug log | 579
show ap debug log
show ap debug log {ap-group <ap-group>|ap-name <ap-name>|bssid <bssid>|ip-addr <ip-
addr>}
Description
Show an AP’s debug log.
Syntax
Usage Guidelines
An AP’s log files show configuration changes since the AP was last reset.
Command History
Introduced in AOS-W 3.0.
Command Information
Parameter Description
ap-name <ap-name> Show log information for an AP with a specific name.
bssid <bssid> Show log information for a specific Basic Service Set Identifier (BSSID). The Basic
Service Set Identifier (BSSID) is usually the AP’s MAC address.
ip-addr <ip-addr> Show log information for an AP with a specific IP address by entering an IP address
in dotted-decimal format.
Platforms Licensing Command Mode
All platforms Base operating system Enable or Config mode on master switches
580 | show ap debug mgmt-frames AOS-W 3.4.1 Command Line Interface | Reference Guide
show ap debug mgmt-frames
show ap mgmt-frames {bssid <bssid>}|{client-mac <client-mac>}|{count <count>}
Description
Show traced 802.11 management frames.
Syntax
Usage Guidelines
Use this command to determine if the client is completing an authorization/association exchange with the
client. If the client does not appear in the output of this CLI command, the client might be configured with
wrong SSID, so it cannot complete its probe-request/probe-response sequence. It is also possible that client
may be configured with shared-key authentication, which would cause 802.11 authorization to fail.
Example
The output of the command lists traced management frames for a client with the MAC address
00:23:6c:2f:9a:8, starting with the most current frame. This example shows that client attempted to associate
with an AP, was authenticated, and later logged off the network and was deauthenticated.
The output of this command includes the following information:
Parameter Description
bssid <bssid> Show management frame information for a specific Basic Service Set Identifier
(BSSID). The Basic Service Set Identifier (BSSID) is usually the AP’s MAC
address.
client-mac <client-mac> Show management frame information for a specific MAC address by entering
the MAC address of a client.
count <count> Limit the amount of management frame information displayed by specifying
number of frames to appear in the output of this command.
Host) #show ap debug mgmt-frames client-mac 00:23:6c:2f:9a:85
Traced 802.11 Management Frames
-------------------------------
Timestamp stype SA DA BSS signal Misc
--------- ----- -- -- --- ------ ----
Oct 30 11:20:19 deauth 00:23:6c:2f:9a:85 00:1a:1e:11:56:40 00:1a:1e:11:56:40 0 STA has left and is deauthenticated
Oct 30 11:04:39 assoc-resp 00:1a:1e:11:56:40 00:23:6c:2f:9a:85 00:1a:1e:11:56:40 15 Success
Oct 30 11:04:39 assoc-req 00:23:6c:2f:9a:85 00:1a:1e:11:56:40 00:1a:1e:11:56:40 0 -
Column Description
Timestamp The time the management frame was sent
stype One of the following 802.11 frame types:
auth: Authorization frame
deauth: Deauthorization frame
assoc-resp: Association response
assoc-req: Association request
SA Source MAC address.
DA Destination MAC address.
BSS Basic Service Set Identifier (BSSID) of the AP
AOS-W 3.4.1 Command Line Interface | Reference Guide show ap debug mgmt-frames | 581
Command History
Introduced in AOS-W 3.0.
Command Information
signal Signal strength as a signal to noise ratio. For example, a
value of 30 would indicate that the power of the received
signal is 30 dBm above the signal noise threshold.
Misc Additional information describing the client’s action.
Platforms Licensing Command Mode
All platforms Base operating system Enable or Config mode on master switches
Column Description

582 | show ap debug radio-stats AOS-W 3.4.1 Command Line Interface | Reference Guide
show ap debug radio-stats
show ap debug radio-stats {ap-name <ap-name>|ip-addr <ip-addr>} radio {0|1} [advanced]
Description
Show aggregate radio debug statistics of an AP.
Syntax
Example
The output of this command displays general statistics for the radio, as well as statistics for transmitted and
received frames.
If you include the advanced option at the end of the show ap debug radio-stats command, the output of
this command will include all the following parameters. If you omit the advanced option, the output will
include less information, and the data will be displayed in a different order.
Parameter Description
ap-name <ap-name> Show log information for an AP with a specific name.
ip-addr <ip-addr> Show log information for an AP with a specific IP address by entering its IP address
in dotted-decimal format.
radio {0|1} Specify the ID number of the radio for which you want to view statistics.
advanced Include this parameter to display additional radio statistics.
Parameter Description
Total Radio Resets Total number of times the radio reset.
Resets Beacon Fail Number of times the radio reset due to beacon failure.
Resets BeacQ Stuck An AP’s radio typically sends a beacon every 100 milliseconds. If beacons are not
sent at a regular interval or the radio experiences excessive noise, the beacon queue
will reset. This parameter indicates the number of queue resets.
Resets Fatal Intr Number of time the radio was reset because the AP hardware was unresponsive.
Resets RX Overrun The number of radio resets due to Receive FIFO overruns.
(host) #show ap debug radio-stats ap-name AP12 radio 1
RADIO Stats
-----------
Parameter Value
--------- -----
------------------- General Per-radio Statistics
Total Radio Resets 0
Resets Beacon Fail 0
TX Power Changes 5
Channel Changes 2
Radio Band Changes 0
Current Noise Floor 95
11g Protection 0
------------------- Transmit specific Statistics
Frames Rcvd For TX 2452151
Tx Frames Dropped 1736429
Frames Transmitted 4247212
...

AOS-W 3.4.1 Command Line Interface | Reference Guide show ap debug radio-stats | 583
Resets RF Gain Number of radio resets due to gain changes.
Resets MTU Change Number of times the radio reset due to a change in the Maximum Transmission Unit
(MTU) value.
Resets TX Timeouts Number of radio resets due to transmission timeouts (the radio doesn’t transmit a
signal within the required time frame.)
POE-Related Resets If the radio power profile drops, an OAW-AP125 may not be able to support three
transmit chains, and may drop to two chains only. This parameter displays the
number of resets due to this type of power change.
External Reset Number of times the AP has been reset because it was unplugged or its reset button
was pressed.
TX Power Changes Number of times the radio’s transmission power changed.
Channel Changes Number of times the radio’s channel changed.
Radio Band Changes Number of time the radio’s band changed.
Current Noise Floor The residual background noise detected by an AP.
NOTE: Noise seen by an AP is reported as -dBm. Therefore, a noise floor of -100
dBm is smaller (lower) than a noise floor of -50 dBm. For most environments, the
noise floor should be no greater than -80 dBm. Anything larger may indicate an
interference problem which is drowning out good signals (data) in background noise.
Avail TX Buffers An AP has a set number of buffers which it can use to buffer frames for
nonresponsive power save clients. The total number of buffer frames depends upon
the AP model type.
11g Protection This parameter shows whether 802.11g protection has been enabled or disabled.
Last TX Antenna This parameter indicates whether the last frame transmitted was sent on antenna 1
or antenna 0. This parameter can be useful for troubleshooting external antennas.
Last RX Antenna This parameter indicates whether the last frame received was via antenna 1 or
antenna 0. This parameter can be useful for troubleshooting external antennas.
Scan Requests Total number of scan requests received by the AP.
Scan Rejects Total number of scan rejected by the AP.
Load aware Scan
Rejects
Load aware ARM preserves network resources during periods of high traffic by
temporarily halting scanning if the load for the AP gets too high. The load aware
Scan Rejects parameter shows the number of times the AP has rejected a scan
because of the load aware scan feature.
PS aware Scan Rejects If the ARM power-save aware scan feature is enabled, the AP will not scan a different
channel if it has one or more clients and is in power save mode. The ps aware Scan
Rejects parameter shows the number of times the AP has rejected a scan because
of the power-save aware scan feature.
Voice aware Scan
Rejects
If you enable the VoIP Aware Scan feature in the AP’s ARM profile, the AP will not
attempt to scan a different channel if one of its clients has an active VoIP call. This
Voice aware scan Rejects parameter shows the number of times the AP has
rejected a scan because of the Voip aware scan feature.
Scan Success Number of successful scans. To view scan details, use the command show ap arm
scan-times.
EIRP The value of this parameter is the transmission power level (in dBm) + the antenna
gain value.
MAX EIRP The max EIRP depends on AP capability and the regulatory domain constraint for the
channel of operation. For example, in the US, Channels 36-48 have max EIRP of
23dBm
Parameter Description

584 | show ap debug radio-stats AOS-W 3.4.1 Command Line Interface | Reference Guide
UAPSD Flush STA Wake Number of times a client wakes from power-save mode and flushes the UAPSD
queue.
UAPSD SP Set The number of unique UAPSD Scheduled Period is started in response to UAPSD
trigger frames.
UASPD Dup Trig The number of times duplicate UAPSD trigger frames are received (i.e., retried
UAPSD triggers that were received by the AP more than once).
UAPSD Recv frame for
TX
The number of frames received for transmission over the air interface using UAPSD
UAPSD Ageout Drain The number of time UAPSD queue is drained (i.e. frames are dropped) due to ageout.
UAPSD TX proc comp The number of UAPSD frames that were successfully transmitted
UAPSD SP In prog The number of times a trigger frame was received while a Scheduled Period (SP) was
already in progress based on an earlier trigger frame.
UAPSD QOS NULL TX The number of times the AP had to respond with a QoS Null Data frame in response
to a UAPSD trigger because AP did not have Data frame queued for that client
UAPSD TX HW Queued The number of frames (Data and Null Data) that were transferred to the radio HW for
transmission, in response to UAPSD triggers.
UAPSD SP Reset The number of times the UAPSD Scheduled Period (SP) in progress is reset or
cancelled.
Frames Rcvd For TX Number of frames received for transmission.
Tx Frames Dropped Number of transmission frames that were dropped.
Frames Transmitted Number of frames successfully transmitted.
PS Unicast Number of power save unicast frames
DTIM Broadcast Number of broadcast frames with DTIM values.
Success With Retry Number of frames that were transmitted after being retried.
Tx Mgmt Frames Number of management frames transmitted.
Beacons Transmitted Number of beacons transmitted.
Tx Probe Responses Number of transmitted probe responses.
Tx Data Frames Number of transmitted data frames.
Multicast Data Number of multicast and broadcast frames transmitted.
Tx CTS Frames Number of clear-to-sent (CTS) frames transmitted.
DTIM Timeouts Number of broadcast frames with DTIM data that were not answered by a client.
Dropped After Retry Number of frames dropped after an attempted retry.
Dropped No Buffer Number of frames dropped because the AP’s buffer was full.
Dropped UAPSD Number of dropped Unscheduled Automatic Power Save Delivery (UAPSD) frames.
Missed ACKs Number of missed acknowledgement frames.
Failed Beacons Number of times a radio failed to transmit a beacon at the scheduled interval
(100ms).
Multi-Beacon Fail Number of times multiple consecutive beacons failed to transmit.
Long Preamble Number of frames sent with a long preamble.
Parameter Description

AOS-W 3.4.1 Command Line Interface | Reference Guide show ap debug radio-stats | 585
Short Preamble Number of frames sent with a short preamble.
Beacon Interrupts Number of broadcast beacons that were interrupted.
TX Interrupts Number of transmission interrupts.
FIFO Underrun The number of Receive FIFO overruns.
Allocated Desc Number of allocated transmit descriptors.
Freed Desc Number of freed transmit descriptors.
Tx EAPOL Frames Number of Extensible Authentication Protocol over LAN (EAPOL) frames transmitted
Tx AGGR Good Number of aggregated frames successfully transmitted.
Tx AGGR Unaggr Number of non-aggregate frames transmitted due to unavailability of additional
frames for aggregation at the time of transmission.
Tx <number> Mbps Number of frames transmitted at at the specificed rate (in Mbps).
Tx <number> Mbps
[Long]
Number of frames with a long preamble transmitted at at the specificed rate.
Tx <number> Mbps
[Short]
Number of frames with a short preamble transmitted at at the specificed rate.
Tx HT <number> Mbps Number of high-throughput frames transmitted at the specified rate.
Tx WMM Number of Wifi Multimedia (WMM) packets transmitted for the following access
categories. If the AP has not transmitted packets in a category type, this data row
will not appear in the output of the command.
Tx WMM [BE]: Best Effort
Tx WMM [BK]: Background
Tx WMM [VO]: VoIP
Tx WMM [VI]: Video
UAPSD OverflowDrop Number of packets dropped due to Unscheduled Automatic Power Save Delivery
(U-APSD) overflow.
TX Timeouts Number of transmission timeouts
Lost Carrier Events Number of carrier sense timeouts.
Last SNR The last recorded signal-to-noise ratio.
Last SNR CTL0 The signal-to-noise ratio for the last received data packet on the primary (control)
channel 0. This parameter is only displayed for APs operating in 40 Mhz mode.
Last SNR CTL1 The signal-to-noise ratio for the last received data packet on the secondary (control)
channel 1. This parameter is only displayed for APs operating in 40 Mhz mode.
Last SNR CTL2 The signal-to-noise ratio for the last received data packet on the secondary (control)
channel 2. This parameter is only displayed for APs operating in 40 Mhz mode.
Last SNR EXT0 Signal-to-noise ratio for the last received ACK packet on the secondary (extension)
channel 0. This parameter is only displayed for APs operating in 40 Mhz mode.
Last SNR EXT1 Signal-to-noise ratio for the last received ACK packet on the secondary (extension)
channel 1. This parameter is only displayed for APs operating in 40 Mhz mode.
Last SNR EXT2 Signal-to-noise ratio for the last received ACK packet on the secondary (extension)
channel 2. This parameter is only displayed for APs operating in 40 Mhz mode.
Last ACK SNR Signal-to-noise ratio for the last received ACK packet.
Last ACK SNR CTL0 Signal-to-noise ratio for the last received ACK packet on the primary (control)
channel 0. This parameter is only displayed for APs operating in 40 Mhz mode.
Parameter Description

586 | show ap debug radio-stats AOS-W 3.4.1 Command Line Interface | Reference Guide
Last ACK SNR CTL1 Signal-to-noise ratio for the last received ACK packet on the primary (control)
channel 1. This parameter is only displayed for APs operating in 40 Mhz mode.
Last ACK SNR CTL2 Signal-to-noise ratio for the last received ACK packet on the primary (control)
channel 2. This parameter is only displayed for APs operating in 40 Mhz mode.
Last ACK SNR EXT0 Signal-to-noise ratio for the last received ACK packet on the secondary (extension)
channel 0. This parameter is only displayed for APs operating in 40 Mhz mode.
Last ACK SNR EXT1 Signal-to-noise ratio for the last received ACK packet on the secondary (extension)
channel 1. This parameter is only displayed for APs operating in 40 Mhz mode.
Last ACK SNR EXT2 Signal-to-noise ratio for the last received ACK packet on the secondary (extension)
channel 2. This parameter is only displayed for APs operating in 40 Mhz mode.
Frames Received Number of frames received.
Good Frames Number of frames received with no errors.
Bad Frames Number of bad or error frames received.
Rx Clear 1s The percentage of time no activity was seen on the air in the last 1 second.
Rx Clear 4s The percentage of time no activity was seen on the air in the last 4 seconds.
Rx Clear 64s The percentage of time no activity was seen on the air in the last 64 seconds.
Discarded Events Number of non-802.11 events that were detected and discarded during normal
operation.
ARM Scan Frames Number of scan frames sent for the adaptive radio management (ARM) feature.
Rx Data Frames Data frames received
Null Data Frames Null data frames received
Rx Mgmt Frames Management frames received
Control Frames Control frames received.
Frames To Me Number of wireless frames received that are addressed to the specified BSSID.
Broadcast Frames Number of broadcast frames received.
Beacons Received Number of beacons received
Probe Requests Number of Probe requests received.
Rx Probe Responses Number of Probe responses received.
Rx RTS Frames Ready To Send (RTS) frames received. These frames are sent when a computer has
data to transmit.
Rx CTS Frames Clear To Send (CTS) frames received. This type of frame are used to verify that a
client is ready to receive information.
ACK Frames Number of acknowledgement frames received.
PS Poll Frames Power-Save Poll (PS-Poll) frames received. When a client exits a power-saving
mode, it transmits a PS-Poll frame to the AP to retrieve any frames buffered while it
was in power-saving mode.
Parameter Description
AOS-W 3.4.1 Command Line Interface | Reference Guide show ap debug radio-stats | 587
Command History
Introduced in AOS-W 3.0.
Command Information
CRC Errors Cyclic Redundancy Check (CRC) is a data sequence that is sent with a frame to help
verify if all the data received correctly. Possible CRC error causes include:
zHardware malfunction
zLoose or unconnected cables
zRF interference, such as overlapping access point coverage on a channel or
interfering 2.4-GHz signals from devices like microwave ovens
zand wireless handset phones
PLCP Errors Physical Layer Convergence Protocol (PLCP) errors.
Rx Frames Dropped Number of received frames that were dropped.
PHY Events The number of Physical Layer Events, that are not 802.11 packets, detected by radio
as part of its normal receive operation.
RADAR Events Number of times an AP detects a radar signature. Alcatel-Lucent APs are DFS-
compliant detects a radar signature, it will change its channel.
RX Interrupts The number of receive interrupts received by the CPU from the radio.
RX Overrun The number of Receive FIFO overruns.
Rx <number> Mbps Packets received at the specified rate (in Mbps).
Rx <number> Mbps
(Long)
Packets with a long preamble received at the specified rate.
Rx <number> Mbps
(Short)
Packets with a short preamble received at the specified rate.
Rx HT <number> Mbps Number of high-throughput packets received at the specified rate.
Rx WMM [BE] Number of Wifi Multimedia (WMM) packets received for the following access
categories. If the AP has not transmitted packets in a category type, this data row
will not appear in the output of the command.
Rx WMM [BE]: Best Effort
Rx WMM [BK]: Background
Rx WMM [VO]: VoIP
Rx WMM [VI]: Video
Platforms Licensing Command Mode
All platforms Base operating system Enable or Config mode on master switches
Parameter Description
588 | show ap debug received-config AOS-W 3.4.1 Command Line Interface | Reference Guide
show ap debug received-config
show ap debug received-config {ap-group <ap-group>|ap-name <ap-name>|bssid <bssid>|ip-
addr <ip-addr>}
Description
Show the configuration the AP downloaded from the switch.
Syntax
Example
The output of this command displays configuration information for each interface. The example below
shows only part of the output for this command. Additional parameters not displayed are described in the
table below.
Parameter Description
ap-name <ap-name> Show log information for an AP with a specific name.
bssid <bssid> Show log information for a specific Basic Service Set Identifier (BSSID). The Basic
Service Set Identifier (BSSID) is usually the AP’s MAC address.
ip-addr <ip-addr> Show log information for an AP with a specific IP address by entering an IP address
in dotted-decimal format.
(host) #show ap debug received-config ap-name AP12
Downloaded Config for WIFI 0
----------------------------
Item Value
---- -----
BSSID 00:1a:1e:11:5f:10
LMS IP 10.6.2.250
Master IP 10.100.103.2
Mode AP Mode
QBSS Probe Response Allow Access
Native VLAN ID 1
SAP MTU 1500 bytes
Heartbeat DSCP 0
High throughput enable (radio) Enabled
Channel 40-
Beacon Period 100 msec
Transmit Power 15 dBm
Advertise TPC Capability Disabled
Enable CSA Disabled
CSA Count 4
Management Frame Throttle interval 1 sec
Management Frame Throttle Limit 20
Active Scan Disabled
VoIP Aware Scan Enabled
Power Save Aware Scan Enabled
Load aware Scan Threshold 1250000 Bps
40 MHz intolerance Disabled
Honor 40 MHz intolerance Enabled
Legacy station workaround Disabled
Country Code US
ESSID guest
...

AOS-W 3.4.1 Command Line Interface | Reference Guide show ap debug received-config | 589
The output of this command includes the following information:
Parameter Description
BSSID The BSSID of the AP.
LMS IP The LMS IP is the IP address of the local switch used by the AP for client data
processing.
Master IP For environments with multiple switches, the master switch is the central
configuration and management point for all local switches.
Mode Shows the operating modes for the AP.
ap-mode: Device provides transparent, secure, high-speed data communications
between wireless network devices and the wired LAN.
am-mode: Device behaves as an air monitor to collect statistics, monitor traffic,
detect intrusions, enforce security policies, balance traffic load, self-heal coverage
gaps, etc.
QBSS Probe Response Quality-of-service BSS (QBSS).
Native VLAN ID The ID number of the Native VLAN.
SAP MTU The Maximum Transmission Unit (MTU) for the GRE tunnel.
Heartbeat DSCP DSCP value for the heartbeat traffic between the AP and the switch.
High throughput
enable (radio)
Shows if high-throughput (802.11n) features on tare enabled or disabled on the
radio.
Channel Shows the channel number for the AP’s 802.11a/802.11n physical layer.
Beacon Period Shows the time, in milliseconds, between successive beacon transmissions. The
beacon advertises the AP’s presence, identity, and radio characteristics to wireless
clients.
Transmit Power Shows the current transmission power level.
Advertise TPC
Capability
If enabled, the AP will advertise its Transmit Power Control (TPC) capability.
Enable CSA Displays whether or not the AP has enabled channel switch announcements (CSAs)
for 802.11h.
CSA Count Number of channel switch announcements that must be sent before the AP will
switch to a new channel.
Management Frame
Throttle interval
Average interval that rate limiting management frames are sent from this radio, in
seconds. If this column displays a zero (0), rate limiting is disabled for this AP.
Management Frame
Throttle Limit
Maximum number of management frames that can come from this radio in each
throttle interval.
Active Scan Displays whether or not the active scan feature is enabled.
This option elicits more information from nearby APs, but also creates additional
management traffic on the network. Active Scan is disabled by default, and should
not be enabled except under the direct supervision of Alcatel-Lucent Support.
VoIP Aware Scan Shows if VoIP aware scanning is enabled or disabled. If you use voice handsets in
the WLAN, VoIP Aware Scan should be enabled in the ARM profile so the AP will
not attempt to scan a different channel if one of its clients has an active VoIP call.
This option requires that Scanning is also enabled.
Power Save Aware Scan Shows if the power save aware scan is enabled or disabled. If enabled, the AP will
not scan a different channel if it has one or more clients and is in power save mode.
Load aware Scan
Threshold
The Load Aware Scan Threshold is the traffic throughput level an AP must reach
before it stops scanning. Load aware ARM preserves network resources during
periods of high traffic by temporarily halting ARM scanning if the load for the AP gets
too high.

590 | show ap debug received-config AOS-W 3.4.1 Command Line Interface | Reference Guide
40 MHz intolerance The specified setting allows ARM to determine if 40 MHz mode of operation is
allowed on the 5 GHz or 2.4 GHz frequency band only, on both frequency bands, or
on neither frequency band.
Honor 40 MHz
intolerance
Shows if 40 MHz intolerance is enabled or disabled. If enabled, the radio will stop
using the 40 MHz channels if the 40 MHz intolerance indication is received from
another AP or station.
Legacy station
workaround
Shows if interoperability for misbehaving legacy stations is enabled or disabled.
Country Code Display the country code for the AP. The country code specifies allowed channels for
that country.
ESSID An Extended Service Set Identifier (ESSID), for the AP.
Encryption Encryption type used on this AP.
WPA2 Pre-Auth 802.11x settings are enabled or disabled.
DTIM Interval Number of beacons that should elapse before an AP sends beacon broadcasts for
power save clients.
802.11a Basic Rates Minimum data rate required for a client to associate with the AP. For an 802.11a
radio, this value can be 6, 12 and 24 802.11 data rates. 802.11b/g radios will report
a value of 1 and 2 802.11 data rates.
802.11a Transmit
Rates
802.11 data rate at which the AP will transmit data to its clients. This value can be
6-54 for 802.11a radios, and 1-54 for 802.11b/g radios.
Station Ageout Time Number of seconds a station may be idle before it is deauthorized from an AP.
Max Transmit Attempts maximum number of times the AP will attempt to retransmit data.
RTS Threshold The minimum packet size at which the AP will issue a request-to-send (RTS) before
sending the packet.
Max Associations The maximum number of clients allowed to associated with the AP
Wireless Multimedia
(WMM)
Shows if Wireless Multimedia (WMM) is enabled or disabled for this AP. WMM
provides prioritization of specific traffic relative to other traffic in the network.
WMM TSPEC Min
Inactivity Interval
Displays the minimum inactivity time-out threshold of WMM traffic for this AP.
DSCP mapping for WMM
voice AC
Displays the DSCP value used to map WMM video traffic.
DSCP mapping for WMM
video AC
Displays the DSCP value used to map WMM voice traffic.
DSCP mapping for WMM
best-effort AC
Displays the DSCP value used to map WMM best-effort traffic
DSCP mapping for WMM
background AC
Displays the DSCP value used to map WMM background traffic.
Hide SSID Shows if the feature to hide a SSID name in beacon frames is enabled or disabled.
Deny_Broadcast Probes When a client sends a broadcast probe request frame to search for all available
SSIDs, this option controls whether or not the system responds for this SSID. When
enabled, no response is sent and clients have to know the SSID in order to associate
to the SSID. When disabled, a probe response frame is sent for this SSID.
Local Probe Response Shows if local probe response is enabled or disabled on the AP. If this option is
enabled, the AP is responsible for sending 802.11 probe responses to wireless
clients’ probe requests. If this option is disabled, then the switch sends the 802.11
probe responses
Parameter Description

AOS-W 3.4.1 Command Line Interface | Reference Guide show ap debug received-config | 591
Command History
Introduced in AOS-W 3.0.
Disable Probe Retry Shows if the AP has enabled or disabled MAC-level retries for probe response
frames. By default this parameter is enabled, which mean that MAC level retries for
probe response frames is disabled.
Maximum Transmit
Failures
Display the maximum number of transmission failures allowed before the client gives
up.
BC/MC Rate
Optimization
Shows if the AP has enabled or disabled scanning of all active stations currently
associated to that AP to select the lowest transmission rate for broadcast and
multicast frames. This option only applies to broadcast and multicast data frames;
802.11 management frames are transmitted at the lowest configured rate.
High throughput
enable (SSID)
Shows if the AP has enabled or disabled the use of its high-throughput SSID in 40
MHz mode.
40 MHz channel usage Determines if this high-throughput SSID allows high-throughput (802.11n) stations
to associate.
MPDU Aggregation Shows if the AP has enabled or disabled MAC protocol data unit (MDPU)
aggregation.
Max transmitted A-
MPDU size
Shows the maximum size, in bytes, of an A-MPDU that can be sent on the AP’s
high-throughput SSID.
Max received A-MPDU
size
Shows the maximum size, in bytes, of an Aggregated-MAC Packet Data Unit (A-
MPDU) that can be received on the AP’s high-throughput SSID.
Min MPDU start
spacing
Displays the minimum time between the start of adjacent MDPUs within an
aggregate MDPU, in microseconds.
Supported MCS set Comma-separated list of Modulation Coding Scheme (MCS) values or ranges of
values to be supported on this high-throughput SSID.
Short guard interval
in 40 MHz mode
Shows if the AP has enabled or disabled use of short guard interval in 40 MHz mode
of operation.
VLAN VLAN ID used by the SSID.
Forward mode Shows the current forward mode (bridge, split-tunnel, or tunnel) for the virtual AP.
This parameter controls whether 802.11 frames are tunneled to the switch using
generic routing encapsulation (GRE), bridged into the local Ethernet LAN (for remote
APs), or a combination thereof depending on the destination (corporate traffic goes
to the switch, and Internet access remains local).
Only 802.1x authentication is supported when configuring bridge or split tunnel
mode.
Band Steering Shows if band-steering has been enabled or disabled for a virtual AP.
ARM’s band steering feature encourages dual-band capable clients to stay on the
5GHz band on dual-band APs. This frees up resources on the 2.4GHz band for
single band clients like VoIP phones.
Band steering reduces co-channel interference and increases available bandwidth
for dual-band clients, because there are more channels on the 5GHz band than on
the 2.4GHz band. Dual-band 802.11n-capable clients may see even greater
bandwidth improvements, because the band steering feature will automatically
select between 40MHz or 20MHz channels in 802.11n networks. This feature is
disabled by default, and must be enabled in a Virtual AP profile.
Parameter Description

592 | show ap debug received-config AOS-W 3.4.1 Command Line Interface | Reference Guide
Command Information
Platforms Licensing Command Mode
All platforms Base operating system Enable or Config mode on master switches
AOS-W 3.4.1 Command Line Interface | Reference Guide show ap debug remote association | 593
show ap debug remote association
show ap debug remote association [ap-name <ap-name>|bssid <bssid>|ip-addr <ip-addr>]
Description
Show the AP association table to identify the remote clients associated to each AP.
Syntax
Usage Guidelines
Use this command to verify if a remote user is connected to an AP, and to validate the AP to which is
connected.
Example
The output of this command displays information about the remote clients associated with an AP with the
IP address 192.0.2.32.
The output of this command includes the following information:
Parameter Description
ap-group <ap-group> Show remote client associations for a specific AP group.
ap-name <ap-name> Show remote client associations for a specific AP.
bssid <bssid> Show remote client associations for an specific AP Basic Service Set Identifier
(BSSID). The Basic Service Set Identifier (BSSID) is usually the AP’s MAC address.
(host) #show ap debug remote association ip-addr 192.0.2.32
Flags: W: WMM client, A: Active, R: RRM client
PHY Details: HT: High throughput; 20: 20MHz; 40: 40MHz
<n>ss: <n> spatial streams
Association Table
-----------------
Name bssid mac auth assoc aid l-int essid vlan-id tunnel-id phy assoc. num Flags
time assoc
---- ---------------- ---------------- -- -- --- ---- ----- ---- ------ --- ----- ---- ------
AP71 00:0a:23:c1:d4:11 00:16:6d:08:1s:f1 y y 1 10 t-lab 111 0x108e a 23s 1 A
Num Clients:1
Column Description
Name Name of an AP.
bssid The AP Basic Service Set Identifier (BSSID).
mac MAC address of the AP.
auth This column displays a y if the AP has been configured for 802.11 authorization
frame types. Otherwise, it displays an n.
assoc This column displays a y if the AP has been configured for 802.11 association frame
types. Otherwise, it displays an n.
594 | show ap debug remote association AOS-W 3.4.1 Command Line Interface | Reference Guide
Command History
Introduced in AOS-W 3.0.
Command Information
aid 802.11 association ID. A client receives a unique 802.11 association ID when it
associates to an AP.
1-int Number of beacons in the 802.11 listen interval. There are ten beacons sent per
second, so a ten-beacon listen interval indicates a listen interval time of 1 second.
essid Name that uniquely identifies the AP’s Extended Service Set Identifier (ESSID).
vlan-id Identification number of the AP’s VLAN.
tunnel-id Identification number of the AP’s tunnel.
assoc. time Amount of time the client has associated with the AP, in the format
hours:minutes:seconds.
num assoc Number of clients associated with the AP.
flags This column displays any flags for this AP. The list of flag abbreviations is included in
the output of the show ap association command.
Platforms Licensing Command Mode
All platforms Base operating system Enable or Config mode on master switches
Column Description
AOS-W 3.4.1 Command Line Interface | Reference Guide show ap debug shaping-table | 595
show ap debug shaping-table
show ap debug shaping-table {ap-name <ap-name>|ip-addr <ip-addr>}
Description
Show shaping information for clients associated to an AP.
Syntax
Example
The following command shows the shaping table the an AP named ap22.
The output of this command includes the following information:
Parameter Description
ap-name <ap-name> Show shaping table information for a specific AP.
ip-addr <ip-addr> Show shaping table information for a specific AP IP address by entering its IP
address in dotted-decimal format.
Column Description
pktin Number of packets received by the AP.
pktout Number of packets sent by the AP.
pktdrop Number of packets dropped by the AP.
(host) #show ap debug shaping-table ap-name ap22
VAP station000
pktin pktout pktdrop pktqd cmn[C:O:H] drop Numcl TotCl BWmgmt
0 0 0 0 0-0-0 0-0 0-0-0 0 0
d1 d2 d3 d4 d5 d6 d7 d8 d9
0 0 0 0 0 0 0 0 0
idx tokens last-t in out drop q tx-t rx-t al-t rate
idx d1 d2 d3 d4 d5 d6 d7 d8 d9
0 0 0 0 0 0 0 0 0 0
VAP station001
pktin pktout pktdrop pktqd cmn[C:O:H] drop Numcl TotCl BWmgmt
0 8144 0 0 0-0-0 0-0 0-2-0 2 0
d1 d2 d3 d4 d5 d6 d7 d8 d9
0 0 0 0 0 0 0 0 0
idx tokens last-t in out drop q tx-t rx-t al-t rate
1 0 0 0 2966 0 0 716 0 0 0
3 0 0 0 31 0 0 8 0 0 0
idx d1 d2 d3 d4 d5 d6 d7 d8 d9
0 0 0 0 0 0 0 0 0 0
1 0 0 0 0 0 0 0 0 0
3 0 0 0 0 0 0 0 0 0

596 | show ap debug shaping-table AOS-W 3.4.1 Command Line Interface | Reference Guide
Command History
Introduced in AOS-W 3.0.
Command Information
pktqd Number of packets queued.
cmn [C:O:H] (For internal use only.)
drop Number of CCK (802.11b) and OFDM (802.11a/g) packets dropped.
Numcl Number of CCK (802.11b) and OFDM (802.11a/g) packets dropped.
TotCl Total number of clients associated with the AP
Bwmgmt This data column displays a 1 if the bandwidth management feature has been
enabled. Otherwise, it displays a 0.
d<n> (For internal use only.)
idx Association ID.
tokens This value represents the credits the station has to transmit tokens.
last-t Number of tokens that were allocated to the station last time token allocation
algorithm ran.
in Number of packets received.
out Number of packets sent.
drop Number of dropped packets.
qNumber of queued packets
tx-t Total time spent transmitting data.
rx-t Total time spent receiving data.
al-t Total time allocated for transmitting data to this station.
rate (For internal use only.)
Platforms Licensing Command Mode
All platforms Base operating system Enable or Config mode on master switches
Column Description

AOS-W 3.4.1 Command Line Interface | Reference Guide show ap debug system-status | 597
show ap debug system-status
show ap debug system-status {ap-name <ap-name>|bssid <bssid>|ip-addr <ip-addr>}
Description
Show detailed system status information for an AP.
Syntax
Usage Guidelines
The output of this command displays the following types of information for the selected AP:
The following parameters are included in the output of this command, and can help troubleshoot problems
on an AP or wireless network.
Command History
Introduced in AOS-W 3.0.
Parameter Description
ap-name <ap-name> Show system status data for an AP with a specific name.
bssid <bssid> Show system status data for a specific Basic Service Set Identifier (BSSID) on an AP.
The Basic Service Set Identifier (BSSID) is usually the AP’s MAC address.
ip-addr <ip-addr> Show system status data for an AP with a specific IP address by entering an IP
address in dotted-decimal format.
zBootstrap information zPer-radio statistics zEthernet duplex/speed settings
zDescriptor Usage zEncryption statistics zTunnel heartbeat stats
zInterface counters zAP uptime zBoot version
zMTU discovery zmemory usage zLMS information
zARP cache zKernel slab statistics zPower status
zRoute table zInterrupts zCPU type
zInterface Information
Parameter Description
The Failed column in the Descriptor
Usage section This parameter can tell you if the AP is dropping packets.
Interface Information table This parameter can tell you if the ethernet network is working properly.
This table should not show an excessive number of errors.
AP Uptime table Low values in this table can indicate problems with the wired network, or
with the AP itself.
Tunnel Heartbeat table This table can indicate the health of the underlying wired network.
Rebootstrap Information table /
Reboot Information table A large number of reboots can mean that the AP has hardware problems.

598 | show ap debug system-status AOS-W 3.4.1 Command Line Interface | Reference Guide
Command Information
Platforms Licensing Command Mode
All platforms Base operating system Enable or Config mode on master switches

AOS-W 3.4.1 Command Line Interface | Reference Guide show ap debug trace-addr | 599
show ap debug trace-addr
show ap debug trace-addr
Description
Show MAC addresses in the trace buffer.
Usage Guidelines
Use this command to troubleshoot wireless clients that are being traced for 802.11 communication
Examples
The output of the command shows the Trace List table. If no wireless clients are being traced, this table
will be empty.
Command History
Introduced in AOS-W 3.0.
Command Information
Platforms Licensing Command Mode
All platforms Base operating system Enable or Config mode on master switches
(host) #show ap debug trace-addr
Trace List
----------
MAC Address
-----------
00:1a:1e:c5:ca:b4
00:1a:1e:c5:d6:46
00:1a:1e:c5:d7:40
00:1a:1e:c5:d7:64
00:1a:1e:c5:d9:56
00:1a:1e:c5:d9:b0

600 |show ap details AOS-W 3.4.1 Command Line Interface | Reference Guide
show ap details
show ap details [advanced]{ap-name <ap-name>|bssid <bssid>|ip-addr <ip-
addr>|installation}
Description
Show detailed provisioning parameters and hardware and operating information and for a specific AP.
Syntax
Examples
The example below shows part of the output for the command show ap details ap-name <ap-name>.
Parameter Description
advanced Include the following additional data in the output of this command:
zswitch message counts
zAP group information
zVirtual AP operating information
ap-name <ap-name> Show data for a specific AP by entering the name of the AP for which you want to
display information.
bssid <bssid> Show data for an AP with the specified BSSID. The Basic Service Set Identifier
(BSSID) is usually the AP’s MAC address.
ip-addr <ip-addr> Show data for an AP with the specified IP address.
(host) # show ap details ap-name AP32
AP "AL39" Basic Information
---------------------------
Item Value
---- -----
AP IP Address 10.6.1.206
LMS IP Address 10.6.2.253
Group corp1344
Location Name N/A
Status Up
Up time 4d:12h:47m:32s
AP "AL39" Hardware Information
------------------------------
Item Value
---- -----
AP Type 125
Serial # AD0054972
Wired MAC Address 00:1a:1e:c9:17:38
Radio 0 BSSID 00:1a:1e:11:73:90
Radio 1 BSSID 00:1a:1e:11:73:80
Enet 1 MAC Address 00:1a:1e:c9:17:39
AP "AL39" Operating Information
-------------------------------
Item Value
---- -----
AP State Running
Entry created 2008-10-23 20:04:53
Last activity 2008-10-28 08:07:48
Reboots 0
Bootstraps 1
Bootstrap Threshold 7
Slot/Port 2/24

AOS-W 3.4.1 Command Line Interface | Reference Guide show ap details | 601
The output of this command includes the following information:
Column Description
AP IP Address IP address of the AP
LMS IP Address The IP address of the local management switch (LMS)—the Alcatel-Lucent
switch which is responsible for terminating user traffic from the APs, and
processing and forwarding the traffic to the wired network.
Group Name of the AP’s AP group.
Location Name Location of the AP.
Status Current status of the AP, either Up or Down.
Up time Number of hours, minutes and seconds since the last switch reboot or
bootstrap, in the format hours:minutes:seconds.
Installation AP Installation mode. The AP can be default (the factory set AP installation
type, indoor or outdoor.
AP Type AP model
Serial # Serial number for the AP
Wired MAC address MAC address of the wired interface.
Radio 0 BSSID Basic Service Set Identifier (BSSID) of the AP’s radio 0. This is usually the
radio’s MAC address.
Radio 1 BSSID Basic Service Set Identifier (BSSID) of the AP’s radio 1. This is usually the
radio’s MAC address.
Enet 1 MAC address MAC address of the AP’s ethernet port.
AP State Displays the AP’s current operational state.
Entry created Timestamp showing the time the AP registered with the switch.
Last activity Timestamp showing the last time the AP communicated with the switch. An
AP typically sends keepalive messages every minute.
Reboots Number of times power to the AP cycled off and then on again. Reboots also
known as “hard” restarts.
Bootstraps Number of times the AP restarted. Bootstraps are also known as “soft”
restarts.
Bootstrap threshold Number of consecutive missed heartbeats on a GRE tunnel (heartbeats are
sent once per second on each tunnel) before an AP rebootstraps. On the
switch, the GRE tunnel timeout is 1.5 x bootstrap-threshold; the tunnel is torn
down after this number of seconds of inactivity on the tunnel.

602 |show ap details AOS-W 3.4.1 Command Line Interface | Reference Guide
Slot/Port The switch port used by the AP, in the format <slot>/<port>.
The <slot> number is always 1 except when referring to interfaces on the
OmniAccess 6000 switch. For the OmniAccess 6000 switch, the four slots are
allocated as follows:
zSlot 0: contains a supervisor card or an OmniAccess Supervisor Card III.
zSlot 1: can contain either a redundant supervisor card, OmniAccess
Supervisor Card IIII, or a third line card.
zSlot 2: can contain either a OmniAccess Supervisor Card IIII or line card
(required if
zslot 0 contains a supervisor card).
zSlot 3: can contain either a OmniAccess Supervisor Card III or second line
card.
The <port> number refers to the network interfaces that are embedded in the
front panel of the OmniAccess 4302, OmniAccess 4308T, or OmniAccess
4324 switch, OmniAccess 4504/4604/4704 Multi-Service Switch,
OmniAccess Supervisor Card III, or a line card installed in the OmniAccess
6000 switch. Port numbers start at 0 from the left-most position.
High throughput Shows if high-throughput (802.11n) features are enabled or disabled.
Mode Shows the operating modes for the AP.
zAP: Device provides transparent, secure, high-speed data
communications between wireless network devices and the wired LAN.
zAM: Device behaves as an air monitor to collect statistics, monitor traffic,
detect intrusions, enforce security policies, balance traffic load, self-heal
coverage gaps, etc.
Band The RF band in which the AP should operate:
z802.11g = 2.4 GHz
z802.11a = 5 GHz
Channel Channel number for the AP 802.11a/802.11n physical layer. The available
channels depend on the regulatory domain (country).
Secondary Channel The secondary channel number for the AP. The secondary channel is a 20
MHz channel used in conjunction with the primary channel to create a 40 MHz
channel for high-throughput clients.
High-throughput capable APs use only the primary channel to communicate
with 20 MHz clients. The secondary channel is used for transmissions with 40
MHz capable high-throughput clients.
EIRP Current effective Isotropic Radiated Power (EIRP).
AP Name Name of the AP.
AP Group AP group to which the AP belongs.
Location name Fully-qualified location name (FQLN) for the AP.
SNMP sysLocation User-defined description of the location of the AP, as defined with the
command provision-ap syslocation.
Master Name or IP address for the master switch.
Gateway IP address of the default gateway for the AP.
Netmask Netmask for the AP’s IP address.
IP Addr IP address for the AP.
Dns IP IP address of the DNS server.
Domain Name Domain name used by the AP.
Server Name DNS name of the switch from which the AP boots.
Column Description

AOS-W 3.4.1 Command Line Interface | Reference Guide show ap details | 603
Server IP IP address of the switch from which the AP boots
Antenna gain for 802.11a Antenna gain for 802.11a (5GHz) antenna.
Antenna gain for 802.11g Antenna gain for 802.11g (2.4GHz) antenna.
Antenna for 802.11a Antenna use for 5 GHz (802.11a) frequency band.
z1: AP uses antenna 1
z2: AP uses antenna 2
zboth: AP uses both antennas
Antenna for 802.11g Antenna use for 2.4 GHz (802.11g) frequency band.
z1: AP uses antenna 1
z2: AP uses antenna 2
zboth: AP uses both antennas
IKE PSK The IKE pre-shared key.
PPPOE User Name Point-to-Point Protocol over Ethernet (PPPoE) user name for the AP.
PPPOE Password PPPoE password for the AP.
PPPOE Service Name PPPoE service name for the AP.
USB User Name The PPP username provided by the cellular service provider.
USB Password A PPP password, if provided by the cellular service provider.
USB Device Type The USB driver type.
USB Device Identifier The USB device identifier.
USB Dial String The dial string for the USB modem.
USB Initialization String The initialization string for the USB modem.
USB TTY device path The TTY device path for the USB modem.
Mesh Role If the mesh role is “none,” the AP is operating as a thin AP. An AP operating as
a mesh node can have one of two roles: mesh portal or mesh point.
Installation The type of installation (indoor or outdoor). The default parameter indicates
that the AOS-W automatically selects an installation mode based upon the
AP’s model type.
Latitude Latitude coordinates of the AP, in the format Degrees Minutes Seconds (DMS).
Longitude Longitude coordinates of the AP, in the format Degrees Minutes Seconds
(DMS).
Altitude Altitude, in meters, of the AP. This parameter is supported on outdoor APs
only.
Antenna bearing for
802.11a
Horizontal coverage distance of the 802.11a (5GHz) antenna from true north,
from 0-360 degrees.
NOTE: This parameter is supported on outdoor APs only. The horizontal
coverage pattern does not consider the elevation or vertical antenna pattern.
Antenna bearing for
802.11g
Horizontal coverage distance of the 802.11g (2.4GHz) antenna from true
north, from 0-360 degrees.
NOTE: This parameter is supported on outdoor APs only. The horizontal
coverage pattern does not consider the elevation or vertical antenna pattern.
Antenna tilt angle for
802.11a
The angle of the 802.11a (5GHz) antenna. This parameter can range from
between -90 degrees and 0 degrees for downtilt, and between +90 degrees
and 0 degrees for uptilt.
Column Description
604 |show ap details AOS-W 3.4.1 Command Line Interface | Reference Guide
Command History
Command Information
Antenna tilt angle for
802.11g
The angle of the 802.11g (2.4GHz) antenna. This parameter can range from
between -90 degrees and 0 degrees for downtilt, and between +90 degrees
and 0 degrees for uptilt.
Mesh SAE Enable or disable Secure Attribute Exchange (SAE) on a mesh network. The
default setting disables SAE. If used, this feature needs to be enabled on all
the Mesh nodes (points and portals) in the network, else there could be mesh
link connectivity issues. This is a Beta feature and recommended to be kept
“disabled” for 3.4 release.”
NOTE: AP80M and AP85 models require the Outdoor Mesh Access Points
license.
Release Modification
AOS-W 3.0 Command introduced
AOS-W 3.2 Introduced support for mesh parameters, additional antenna parameters, and AP
location parameters.
AOS-W 3.4 Introduced support for the following parameters:
zinstallation
zmesh-sae
zset-ikepsk-by-addr
zusb-dev
zusb-dial
zusb-init
zusb-passwd
zusb-tty
zusb-type
zusb-user
Platforms Licensing Command Mode
All platforms Base operating system Enable or Config mode on master switches
Column Description

AOS-W 3.4.1 Command Line Interface | Reference Guide show ap enet-link-profile | 605
show ap enet-link-profile
show ap enet-link-profile [<profile>]
Description
Show a list of all Ethernet Link profiles.
Usage Guidelines
Include a profile name to display details for the specified Ethernet Link Profile, or omit the <profile>
parameter to display a list of all Ethernet Link profiles.
Example
This command shows the speed of the Ethernet interface and the current duplex mode for the ethernet link
profile “default”:
The output of this command includes the following parameters:
Related Commands
Command History
Introduced in AOS-W 3.0.
Command Information
Parameter Description
Speed The speed of the Ethernet interface. This value can be either 10 Mbps, 100
Mbps, 1000 Mbps (1 Gbps), or auto (auto-negotiated).
Duplex The duplex mode of the AP’s Ethernet interface. This value can be either full,
half, or auto (auto-negotiated).
Command Description Mode
ap enet-link-profile This command configures an AP Ethernet link profile. Config mode
Platforms Licensing Command Mode
All platforms Base operating system Enable or Config mode on master switches
(host) #show ap enet-link-profile default
AP Ethernet Link profile "default"
----------------------------------
Parameter Value
--------- -----
Speed auto
Duplex auto
606 | show ap essid AOS-W 3.4.1 Command Line Interface | Reference Guide
show ap essid
show ap essid
Description
Show a Extended Service Set Identifier (ESSID) summary for the switch, including the numbers of APs and
clients associated with each ESSID.
Examples
The output of the command in the example below shows statistics for four configured ESSIDs.
The output of this command includes the following information:
Command History
Introduced in AOS-W 3.0.
Command Information
Column Description
ESSID An Extended Service Set Identifier (ESSID) is the identifying name of an 802.11
wireless network.
APs Number of APs associated with the ESSID.
VLAN(s) VLAN IDs of the VLANs for the ESSID.
Encryption The layer-2 authentication and encryption used on this ESSID to protect access and
ensure the privacy of the data transmitted to and from the network.
Platforms Licensing Command Mode
All platforms Base operating system Enable or Config mode on master switches
(host) #show ap essid
ESSID Summary
-------------
ESSID APs Clients VLAN(s) Encryption
----- --- ------- ------- ----------
vocera 21 0 66 WPA2 PSK AES
voip 23 52 66,64 WPA2 8021X AES
guest 49 6 63 Open
wpa2 26 88 65,64 WPA2 8021X AES
Num ESSID:4

AOS-W 3.4.1 Command Line Interface | Reference Guide show ap ht-rates | 607
show ap ht-rates
show ap ht-rates bssid <bssid>
Description
Show high-throughput rate information for a basic service set (BSS).
Syntax
Examples
The output of this command shows high-throughput rates for each supported MCS value. These values are
applicable to high-throughput (802.11n-capable) APs only.
The output of this command includes the following information:
Command History
Introduced in AOS-W 3.3.
Parameter Description
bssid <bssid> Show data for a specific Basic Service Set Identifier (BSSID) on an AP. An AP’s
BSSID is usually the AP’s MAC address.
Column Description
MCS A Modulation Coding Scheme (MCS) values supported on this high-throughput SSID.
Streams Number of spatial streams used by the MCS index value.
20 MHz 802.11n data rates for the MCS for 20 Mhz transmissions.
40 MHz 802.11n data rates for the MCS for 40 Mhz transmissions.
40 MHz SGI 802.11n data rates for the MCS for 40 Mhz transmissions using a short guard interval.
Host) #show ap ht-rates bssid 00:1a:1e:1e:5a:10
AP "AL12" Radio 0 BSSID 00:1a:1e:1e:5a:10 High-throughput Rates (Mbps)
----------------------------------------------------------------------
MCS Streams 20 MHz 40 MHz 40 MHz SGI
--- ------- ------ ------ ----------
0 1 6.5 13.5 15.0
1 1 13.0 27.0 30.0
2 1 19.5 40.5 45.0
3 1 26.0 54.0 60.0
4 1 39.0 81.0 90.0
5 1 52.0 108.0 120.0
6 1 58.5 121.5 135.0
7 1 65.0 135.0 150.0
8 2 13.0 27.0 30.0
9 2 26.0 54.0 60.0
10 2 39.0 81.0 90.0
11 2 52.0 108.0 120.0
12 2 78.0 162.0 180.0
13 2 104.0 216.0 240.0
14 2 117.0 243.0 270.0
15 2 130.0 270.0 300.0

608 | show ap ht-rates AOS-W 3.4.1 Command Line Interface | Reference Guide
Command Information
Platforms Licensing Command Mode
All platforms Base operating system Enable or Config mode on master switches

AOS-W 3.4.1 Command Line Interface | Reference Guide show ap image version | 609
show ap image version
show ap image version [ap-name <ap-name>|ip-addr <ip-addr>]
Description
Display an AP’s image version information.
Syntax
Usage Guidelines
By default, this command displays image version information for all APs associated with the switch. To
view image version information for a single AP, specify an AP using the ap-name or ip-addr parameters
Example
The output in the example below shows the current running image version as well as the image version
stored in the switch’s flash memory.
The output of this command includes the following information:
Parameter Description
ap-name <ap-name> View image version information for an AP with a specific name.
ip-addr <ip-addr> View image version information for an AP with a specific IP address. Enter the
address of the AP in dotted-decimal format.
(host) #show ap image version ip-addr 192.0.2.45
Access Points Image Version
---------------------------
AP Running Image Version String
-- ----------------------------
10.6.1.200 3.3.2.5 Wed Oct 22 10:46:42 PDT 2008
Flash Image Version String Matches Num Matches Num Mismatches Bad Checksums Image Load Status
---------------------------- ------- ---------- -------------- ------------- ----------------
3.3.2.5 Wed Oct 22 10:46:42 PDT 2008 Yes 3 1 0 Done
Column Description
AP Name or IP address of an AP
Running Image Version
String
String identifying the number of the image version currently running on the AP, as
well as the date on which that version was created.
Flash Image Version
String
String identifying the number of the image version in the AP’s flash memory, as well
as the date on which that version was created.
Matches If yes, the running image version matches the image version currently in the AP’s
flash memory. If no, the two image versions do not match.
Num Matches Number of times the running image version matched the flash image version after a
reboot.
Num Mismatches Number of times the running image version did not match the flash image version
after a reboot. If the images do not match, the AP will upgrade to the flash image.
Bad Checksums Number of bad checksum calculations due to an invalid or corrupted image file.
610 | show ap image version AOS-W 3.4.1 Command Line Interface | Reference Guide
Command History
Introduced in AOS-W 3.0.
Command Information
Image Load Status Current status of the AP following an upgrade.
Done: This status indicates that the switch reset after the upgrade was performed,
or the upgrade was performed after the AP first registered with the switch.
Completed: The AP was updated after it was registered to the switch, and after the
switch’s last reset. If AP shows a status of completed, it will also display the time it
took it update that AP.
In progress: The AP is currently updating its image.
Platforms Licensing Command Mode
All platforms Base operating system Enable or Config mode on master switches
Column Description
AOS-W 3.4.1 Command Line Interface | Reference Guide show ap license-usage | 611
show ap license-usage
show ap license-usage
Description
Show AP license usage information.
Examples
The output of the command below shows that switch has 82 remaining unused AP licenses.
The output of this command includes the following information:
Parameter Description
Total AP Licenses Total number of AP licenses currently available on the switch.
AP licenses used Number of AP licenses used by individual APs.
Unused AP Licenses Number of AP licenses unused and currently available.
Total RAP Licenses Total number of Remote AP (RAP) licenses currently available on the switch.
RAP licenses used Number of RAP licenses currently used by Remote APs.
Total Indoor Mesh AP
Licenses
Total number of Indoor Mesh AP (IMP) licenses currently available on the switch. The
output of this command shows information for indoor mesh licenses, even though
these licenses are not required in this version of AOS-W.
Indoor Mesh AP
Licenses Used
Number of IMP licenses currently used by Indoor Mesh APs. The output of this
command shows information for indoor mesh licenses, even though these licenses
are not required in this version of AOS-W.
Total Outdoor Mesh AP
Licenses
Total number of Outdoor Mesh AP (MAP) licenses currently available on the switch.
Outdoor Mesh AP
Licenses Used
Number of MAP licenses currently used by Outdoor Mesh APs.
Total 802.11n-120abg
Licenses
Total number of high-throughput (802.11n-capable) licenses available for 120abg
APs.
802.11n-120abg
Licenses Used
Number of high-throughput (802.11n-capable) licenses currently used by 120abg
APs
(host) #show ap license-usage
Total AP Licenses : 128
AP Licenses Used : 46
Unused AP Licenses : 82
Total RAP Licenses : 0
RAP Licenses Used : 0
Total Ortronics AP Licenses : 0
Total Indoor Mesh AP Licenses : 8
Indoor Mesh AP Licenses Used : 0
Total Outdoor Mesh AP Licenses : 8
Outdoor Mesh AP Licenses Used : 0
Total 802.11n-120abg Licenses : 0
802.11n-120abg Licenses Used : 0
Total 802.11n-121abg Licenses : 0
Total 802.11n-124abg Licenses : 0
802.11n-124abg Licenses Used : 0
Total 802.11n-125abg Licenses : 0
802.11n-125abg Licenses Used : 0
612 | show ap license-usage AOS-W 3.4.1 Command Line Interface | Reference Guide
Command History
Command Information
Total 802.11n-121abg
Licenses
Total number of high-throughput (802.11n-capable) licenses available for 121abg
APs.
802.11n-121abg
Licenses Used
Number of high-throughput (802.11n-capable) licenses currently used by 121abg
APs
Total 802.11n-124abg
Licenses
Total number of high-throughput (802.11n-capable) licenses available for 124abg
APs.
802.11n-124abg
Licenses Used
Number of high-throughput (802.11n-capable) licenses currently used by 124abg
APs
Total 802.11n-125abg
Licenses
Total number of high-throughput (802.11n-capable) licenses available for 125abg
APs.
802.11n-125abg
Licenses Used
Number of high-throughput (802.11n-capable) licenses currently used by 125abg
APs
Release Modification
AOS-W 3.0 Command Introduced.
AOS-W 3.3 The following parameters were introduced:
zTotal 802.11n-120abg Licenses
z802.11n-120abg Licenses Used
zTotal 802.11n-121abg Licenses
z802.11n-121abg Licenses Used
zTotal 802.11n-124abg Licenses
z802.11n-124abg Licenses Used
zTotal 802.11n-125abg Licenses
z802.11n-125abg Licenses Used
Platforms Licensing Command Mode
All platforms Base operating system. The output of this command varies,
according to the licenses currently installed on the switch. Enable or Config mode on
master switches
Parameter Description

AOS-W 3.4.1 Command Line Interface | Reference Guide show ap load-balancing | 613
show ap load-balancing
show ap load balancing
Description
Show the load-balancing information for each AP with load balancing enabled.
Examples
The output of the command in the example below shows details for a single AP enabled with the load-
balancing feature.
The output of this command includes the following information:
Command History
Introduced in AOS-W 3.0.
Column Description
BSS The Basic Service Set (BSS) Identifier for the AP. This is usually the APs MAC
address.
ESS The Extended Service Set (ESS) Identifier is the user-defined name of an 802.11
wireless network.
s/p The switch slot and port used by the AP, in the format <slot>/<port>.
The <slot> number is always 1 except when referring to interfaces on the
OmniAccess 6000 switch. For the OmniAccess 6000 switch, the four slots are
allocated as follows:
zSlot 0: contains a supervisor card or an OmniAccess Supervisor Card III.
zSlot 1: can contain either a redundant supervisor card, OmniAccess Supervisor
Card III, or a third line card.
zSlot 2: can contain either an OmniAccess Supervisor Card III or line card
(required if slot 0 contains a supervisor card).
zSlot 3: can contain either an OmniAccess Supervisor Card IIIor second line card.
The <port> number refers to the network interfaces that are embedded in the front
panel of the OmniAccess 4302, OmniAccess 4308T, or OmniAccess 4324 switch,
OmniAccess 4504/4604/4704 Multi-Service Mobility Switch, OmniAccess
Supervisor Card III, or a line card installed in the OmniAccess 6000 switch. Port
numbers start at 0 from the left-most position.
ip IP address of the AP
phy One of the following 802.11 types
za
za-HT (high-throughput)
zg
zg-HT (high-throughput)
chan Channel number for the AP 802.11a/802.11n physical layer. The available channels
depend on the AP’s regulatory domain (country).
cur-cl Current number of clients on the AP.
util (kbps) Current bandwidth utilization, in kbps.
(host) #show ap load-balancing
Load Balance Enabled Access Point Table
---------------------------------------
bss ess name s/p ip phy chan cur-cl util(kbps)
--- --- ---- --- -- --- ---- ------ ----------
00:0b:86:cc:8e:4e Wireless_1 mp22 2/24 10.3.148.12 a-HT 413 3 14

614 | show ap load-balancing AOS-W 3.4.1 Command Line Interface | Reference Guide
Command Information
Platforms Licensing Command Mode
All platforms Base operating system Enable or Config mode on master switches
AOS-W 3.4.1 Command Line Interface | Reference Guide show ap mesh active | 615
show ap mesh active
show ap mesh active [<mesh-cluster>|{page <page>}|{start <start>}]
Description
Show active mesh cluster APs currently registered on this switch.
Syntax
Examples
The output of this command displays a list of all active mesh points and mesh portals.
The output of this command includes the following information:
Parameter Description
<mesh-cluster> Name of a mesh cluster profile.
page <page> Limit the output of this command to a specific number of entries by entering the
number of entries you want to display.
start <start> Start displaying the index of mesh APs at a chosen index number by entering the
index number of the AP at which command output should start.
Column Description
Name Name of an AP.
Group AP group which includes the specified AP.
IP Address IP address of the AP.
BSSID Basic Service Set Identifier (BSSID) for the AP. This is usually the AP’s MAC address.
Band/Ch/EIRP/MaxEIRP The RF band in which the AP should operate (a or g)/ Radio channel used by the AP/
Current effective Isotropic Radiated Power (EIRP) /maximum EIRP
MTU Maximum Transmission Unit (MTU) size, in bytes. This value describes the greatest
amount of data that can be transferred in one physical frame.
(host) #show ap mesh active
Mesh Cluster Name: meshprofile1
------------------------------
Name Group IP Address BSSID Band/Ch/EIRP/MaxEIRP MTU Enet 0/1 Mesh Role
---- ----- ---------- ----- -------------------- --- -------- ---------
mp1 mp1 10.3.148.245 00:1a:1e:85:c0:30 802.11a/157/19/36 Off/Off Point
mp2 mp2 10.3.148.250 00:1a:1e:88:11:f0 802.11a/157/19/36 Bridge/Bridge Point
mp3 mp3 10.3.148.253 00:1a:1e:88:01:f0 802.11a/157/19/36 Bridge/Bridge Point
mpp mpp125 10.3.148.252 00:1a:1e:88:05:50 802.11a/157/19/36 1578 -/Bridge Portal
Parent #Children AP Type Uptime
------ --------- ------- ------
mp3 0 125 13d:2h:25m:19s
mpp 1 125 14d:21h:23m:49s
mp2 1 125 14d:21h:14m:55s
- 1 125 14d:19h:5m:3s
616 |show ap mesh active AOS-W 3.4.1 Command Line Interface | Reference Guide
Command History
Introduced in AOS-W 3.0.
Command Information
Enet 0/1 Shows the current mode of each wired interface.
zBridge: 802.11 frames are bridged into the local Ethernet LAN.
zTunnel: 802.11 frames are tunneled to the switch using generic routing
encapsulation (GRE).
zSplit-tunnel: 802.11 frames are either bridged into the local Ethernet LAN or
tunneled to the switch, depending upon their destination.
zOff: Interface is not available for serving clients.
If an AP has only one wired interface, the output of this command will display a dash
(-) for the unavailable port.
Mesh Role An AP operating as a mesh node can have one of two roles: mesh portal or mesh
point.
Parent If the AP is operating as a mesh point, this parameter displays the name of its parent
mesh portal. Mesh portals will display a dash (-).
#Children If the AP is operating as a mesh portal, this parameter shows the number of mesh
point children associated with that mesh portal.
AP type The AP model type.
Uptime Number of hours, minutes and seconds since the last switch reboot or bootstrap, in
the format hours:minutes:seconds.
Platforms Licensing Command Mode
All platforms This show command is available in
the base operating system.
Commands to configure the secure
enterprise mesh solution for
outdoor APs require the Outdoor
Mesh license.
Enable or Config mode on master switches
Column Description

AOS-W 3.4.1 Command Line Interface | Reference Guide show ap mesh debug counters | 617
show ap mesh debug counters
show ap mesh debug counters {ap-name <ap-name>}|{bssid <bssid>}|{ip-addr <ip-addr>}
Description
Show counters statistics for a mesh node.
Syntax
Example
The example below shows the Mesh Packet Counters table for an AP named meshpoint1. The Probe Resp,
Assoc Req, and Assoc Resp data columns show both the total number of counters and, in parenthesis, the
number of requests or responses with high-throughput information elements (HE IEs).
The output of this command includes the following information:
Parameter Description
ap-name <ap-name> Show counter statistics for an AP with a specific name.
bssid <bssid> Show counter statistics for a specific Basic Service Set Identifier (BSSID) on an AP.
An AP’s BSSID is usually the AP’s MAC address.
ip-addr <ip-addr> View counter statistics for an AP with a specific IP address. Enter the IP address of
the AP in dotted-decimal format.
(host) #show ap mesh debug counters ap-name meshpoint1
Mesh Packet Counters
--------------------
Interface Echo Sent Echo Recv Probe Req Probe Resp Assoc Req Assoc Resp Assoc Fail Link up/down Resel. Switch Other
Mgmt
--------- --------- --------- --------- ---------- --------- ---------- ---------- ------------ ------ ------ ------
Parent 68865 68755 24 8(8 HT) 3(1 HT) 3(1 HT) 1 1 - - 0
Child 68913 67373 6 8 2 2 0 1 2 0 2618886
Received Packet Statistics: Total 2890717, Mgmt 2618946 (dropped non-mesh 0), Data 271771 (dropped unassociated 1)HT: pns=8 ans=1
pnr=0 ars=0 arr=1 anr=0
Recovery Profile Usage Counters
-------------------------------
Item Value
---- -----
Enter recovery mode 0
Exit recovery mode 0
Total connections to switch 0
Mesh loop-prevention Sequence No.:1256947
Mesh timer ticks:68930
Column Description
Interface Indicates whether the mesh interface connects to a Parent AP or a Child AP. Each row of
data in the Mesh Packet Counters table shows counter values for an individual interface.
Echo Sent Number of echo packets sent.
Echo Recv Number of echo packets received.
Probe Req Number of probe request packets sent from the interface specified in the Mesh-IF
parameter.
Probe Resp Number of probe response packets sent to the interface specified in the Interface
parameter.
618 | show ap mesh debug counters AOS-W 3.4.1 Command Line Interface | Reference Guide
Command History
Introduced in AOS-W 3.0.
Command Information
Assoc Req Number of association request packets from the interface specified in the Interface
parameter.
Assoc Resp Number of association response packets from the interface specified in the Interface
parameter. This number includes valid responses and fail responses.
Assoc Fail Number of fail responses received from the interface specified in the Interface parameter.
Link up/down Number of times the link up or link down state has changed.
Resel. Number of times a mesh point attempted to reselect a different mesh portal.
Switch Number of times a mesh point successfully switched to a different mesh portal.
Other Mgmt Management frames of any type other than association and probe frames, either received
on child interface, or sent on parent interface.
Platforms Licensing Command Mode
All platforms This show command is available in
the base operating system.
Commands to configure the mesh
feature require the Mesh license.
Enable or Config mode on master switches.
Column Description
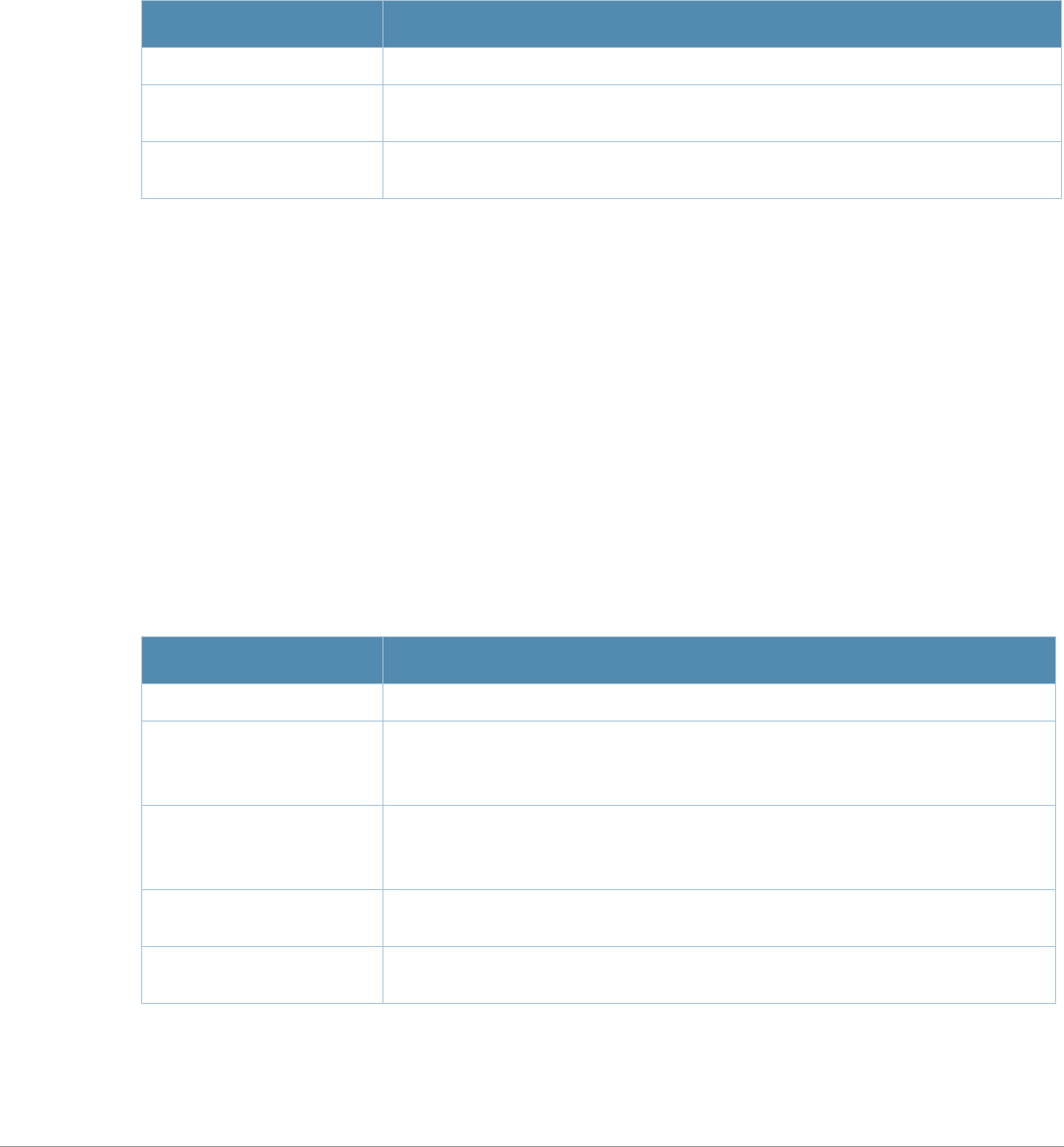
AOS-W 3.4.1 Command Line Interface | Reference Guide show ap mesh debug current-cluster | 619
show ap mesh debug current-cluster
show ap mesh debug current-cluster {ap-name <ap-name>}|{bssid <bssid>}|{ip-addr <ip-
addr>}
Description
Display information for the mesh cluster currently used by a mesh point or mesh portal.
Syntax
Examples
The output of the command below shows mesh cluster profile configuration parameters for the mesh
cluster currently used by an AP named “mp2.”
The output of this command includes the following information:
Command History
Introduced in AOS-W 3.0.
Parameter Description
ap-name <ap-name> Show mesh cluster data for an AP with a specific name.
bssid <bssid> Show mesh cluster data for a specific Basic Service Set Identifier (BSSID) on an AP.
An AP’s BSSID is usually the AP’s MAC address.
ip-addr <ip-addr> Show mesh cluster data for an AP with a specific IP address. Enter the IP address in
dotted-decimal format.
Column Description
Cluster Name Name of the mesh cluster using this profile
RF band The RF band in which the mesh point or mesh portal operates:
zg = 2.4 GHz
za = 5 GHz
Encryption Data encryption setting for the mesh cluster profile.
zopensystem—No authentication and encryption.
zwpa2-psk-aes—WPA2 with AES encryption using a preshared key.
WPA Hexkey The WPA pre-shared key (only for mesh cluster profiles using WPA2 with AES
encryption).
WPA Passphrase The WPA password that generates the preshared key (only for mesh cluster profiles
using WPA2 with AES encryption).
(host) #show ap mesh debug current-cluster ap-name mp2
AP "mp2" Current Cluster Profile: default
-----------------------------------------
Item Value
---- -----
Cluster Name smettu-mesh
RF Band a
Encryption opensystem
WPA Hexkey N/A
WPA Passphrase ********

620 | show ap mesh debug current-cluster AOS-W 3.4.1 Command Line Interface | Reference Guide
Command Information
Platforms Licensing Command Mode
All platforms This show command is available
in the base operating system.
Commands to configure the
mesh feature require the Mesh
license.
Enable or Config mode on master switches
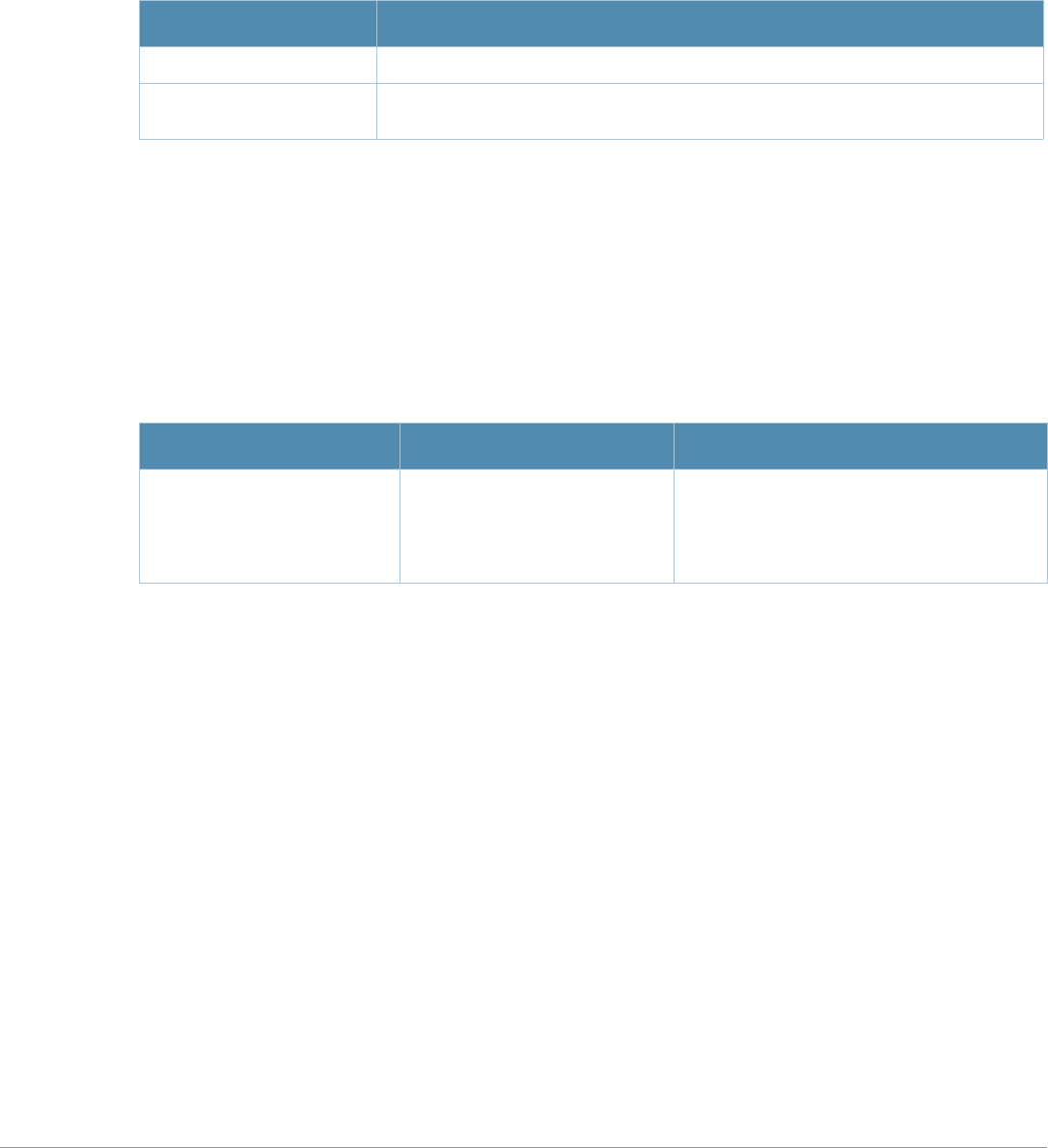
AOS-W 3.4.1 Command Line Interface | Reference Guide show ap mesh debug forwarding-table | 621
show ap mesh debug forwarding-table
show ap mesh forwarding-table {ap-name <ap-name>}|{ip-addr <ip-addr>}
Description
Show the forwarding table for a remote mesh point or remote mesh portal.
Syntax
Usage Guidelines
This is an internal technical support command. Alcatel-Lucent technical support may request that you issue
this command to help analyze and troubleshoot problems with your mesh network.
Command History
Introduced in AOS-W 3.0.
Command Information
Parameter Description
ap-name <ap-name> Show data for a remote mesh node with a specific name.
ip-addr <ip-addr> Show data for a remote mesh node with a specific IP address by entering its IP
address in dotted-decimal format.
Platforms Licensing Command Mode
All platforms This show command is available
in the base operating system.
Commands to configure the
mesh feature require the Mesh
license.
Enable or Config mode on master switches
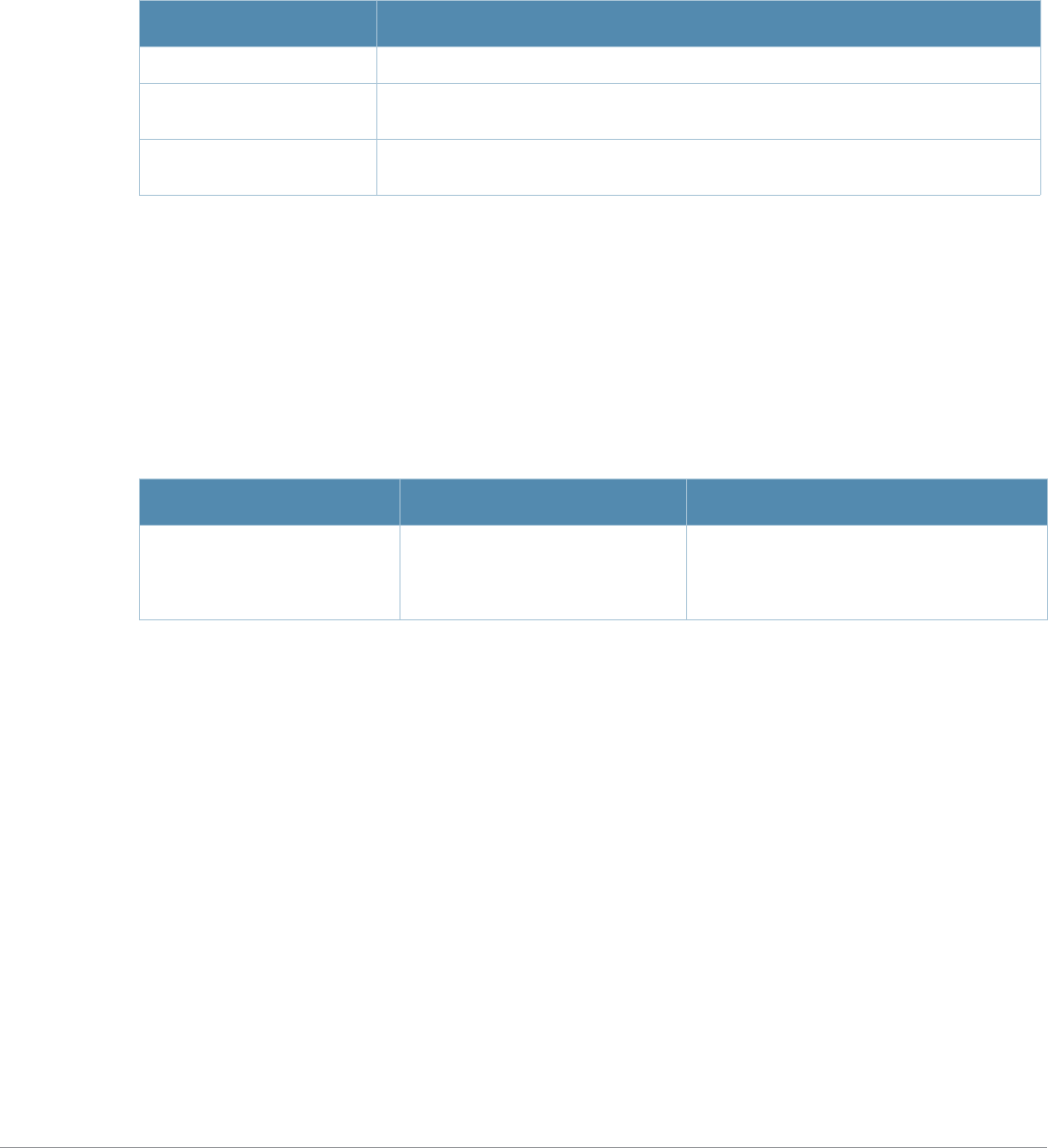
622 | show ap mesh debug hostapd-log AOS-W 3.4.1 Command Line Interface | Reference Guide
show ap mesh debug hostapd-log
show ap mesh debug hostapd-log {ap-name <ap-name>}|{bssid <bssid>}|{ip-addr <ip-addr>}
Description
Show the debug log messages for the hostapd process.
Syntax
Usage Guidelines
This is an internal technical support command. Alcatel-Lucent technical support may request that you issue
this command to help analyze and troubleshoot problems with the hostapd process or your mesh network.
Command History
Introduced in AOS-W 3.0.
Command Information
Parameter Description
ap-name <ap-name> Show data for an AP with a specific name.
bssid <bssid> Show data for a specific Basic Service Set Identifier (BSSID) on an AP. The Basic
Service Set Identifier (BSSID) is usually the AP’s MAC address.
ip-addr <ip-addr> Show data for an AP with a specific IP address by entering an IP address in dotted-
decimal format.
Platforms Licensing Command Mode
All platforms This show command is available in
the base operating system.
Commands to configure the mesh
feature require the Mesh license.
Enable or Config mode on master switches
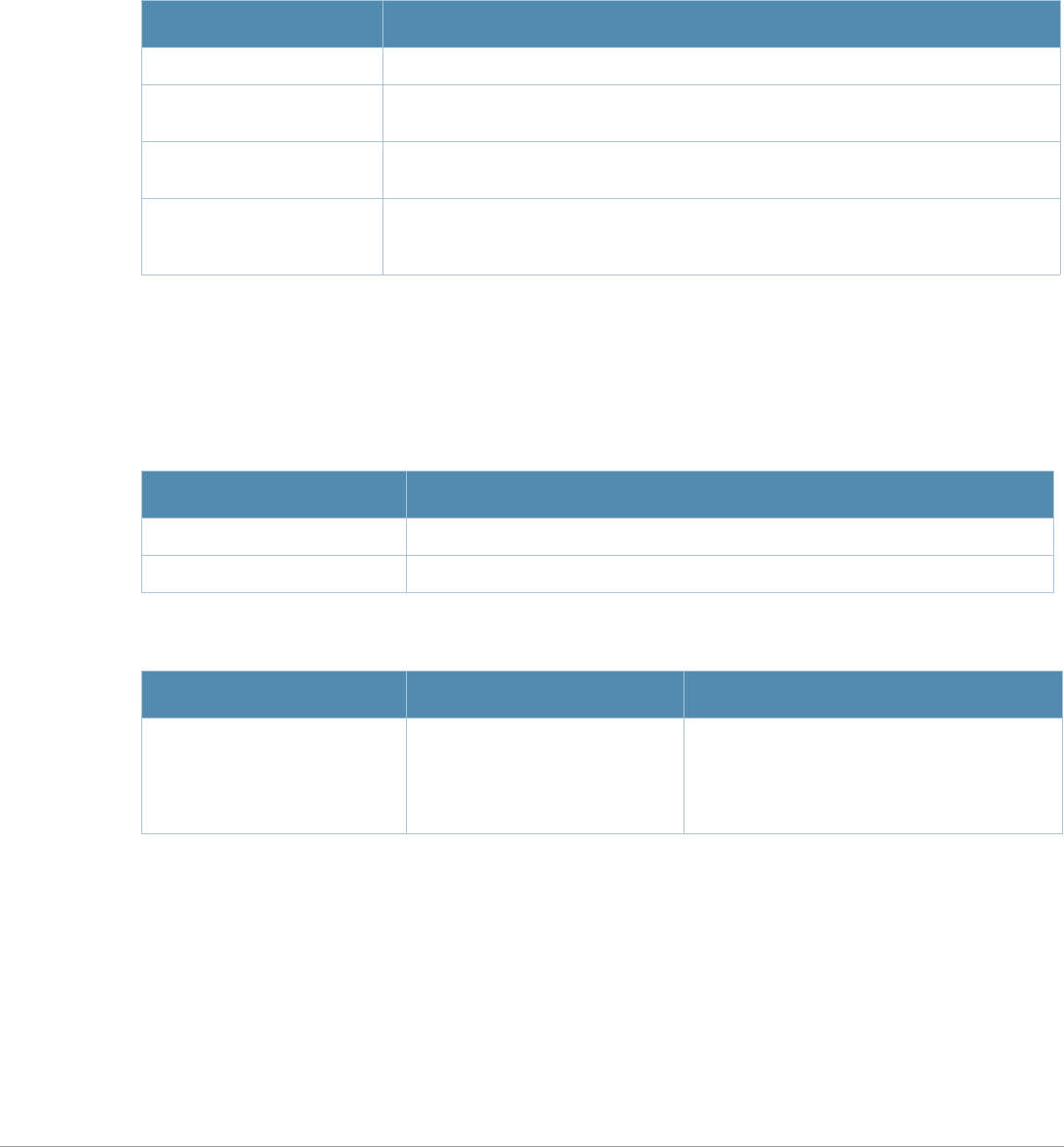
AOS-W 3.4.1 Command Line Interface | Reference Guide show ap mesh debug meshd-log | 623
show ap mesh debug meshd-log
show ap mesh debug meshd-log {ap-name <ap-name>}|{bssid <bssid>}|{ip-addr <ip-addr>}
[<page>]
Description
Show the debug log messages for the meshd process.
Syntax
Usage Guidelines
This is an internal technical support command. Alcatel-Lucent technical support may request that you issue
this command to help analyze and troubleshoot problems with the meshd process or your mesh network.
Command History
Command Information
Parameter Description
ap-name <ap-name> Show data for an AP with a specific name.
bssid <bssid> Show data for a specific Basic Service Set Identifier (BSSID) on an AP. The Basic
Service Set Identifier (BSSID) is usually the AP’s MAC address.
ip-addr <ip-addr> Show data for an AP with a specific IP address by entering an IP address in dotted-
decimal format.
<page> Display page number 0, 1 or 2, where page 0 has the newest information and page 2
has the oldest. If this parameter is omitted, this command will display all meshd log
information, oldest first.
Release Modification
AOS-W 3.0 Command introduced.
AOS-W 3.4 The page parameter was introduced.
Platforms Licensing Command Mode
All platforms This show command is available
in the base operating system.
Commands to configure the
mesh feature require the Mesh
license.
Enable or Config mode on master switches

624 | show ap mesh debug provisioned-clusters AOS-W 3.4.1 Command Line Interface | Reference Guide
show ap mesh debug provisioned-clusters
show ap mesh debug provisioned-clusters {ap-name <ap-name>}|{bssid <bssid>}|{ip-addr
<ip-addr>}
Description
Show cluster profiles provisioned on a mesh portal or mesh point.
Syntax
Example
The output of the command below shows statistics for the AP’s mesh cluster profile and recovery cluster
profile.
The output of this command displays the following information for the AP’s mesh cluster profile and
recovery cluster profiles:
Parameter Description
ap-name <ap-name> Show data for a mesh node with a specific name.
bssid <bssid> Show data for a mesh node with a specific Basic Service Set Identifier (BSSID). The
Basic Service Set Identifier (BSSID) is usually the AP’s MAC address.
ip-addr <ip-addr> Show data for a mesh node with a specific IP address by entering an IP address in
dotted-decimal format.
Column Description
Cluster Name Name of the mesh cluster using this profile
RF band The RF band in which the AP should operate:
zg = 2.4 GHz
za = 5 GHz
(host) #show ap mesh debug provisioned-clusters ap-name portal2
AP Portal Cluster Profile: mesh-cluster-profile
-------------------------------------------------
-------------------------
Parameter Value
--------- -----
Cluster Name sw-ad-GB32
RF Band a
Encryption opensystem
WPA Hexkey N/A
WPA Passphrase ********
AP "Portal" Cluster Profile: Recovery Cluster Profile
-----------------------------------------------------
Item Value
---- -----
Cluster Name Recovery-ZF-xAPl5z-g15VN
RF Band a
Encryption pa2-psk-aes
WPA Hexkey ********
WPA Passphrase N/A
AOS-W 3.4.1 Command Line Interface | Reference Guide show ap mesh debug provisioned-clusters | 625
Command History
Introduced in AOS-W 3.0.
Command Information
Encryption Data encryption setting for the mesh cluster profile.
zopensystem—No authentication and encryption.
zwpa2-psk-aes—WPA2 with AES encryption using a preshared key.
WPA Hexkey The WPA pre-shared key (only for mesh cluster profiles using WPA2 with AES
encryption).
WPA Passphrase The WPA password that generates the preshared key (only for mesh cluster profiles
using WPA2 with AES encryption).
Platforms Licensing Command Mode
All platforms This show command is available in
the base operating system.
Commands to configure the mesh
feature require the Mesh license.
Enable or Config mode on master switches
Column Description
626 | show ap mesh neighbors AOS-W 3.4.1 Command Line Interface | Reference Guide
show ap mesh neighbors
show ap mesh neighbors {ap-name <ap-name>}|{bssid <bssid>}|{ip-addr <ip-addr>} [names]
Description
Show all mesh neighbors for an AP.
Syntax
Example
In the example below, the output has been split into two tables to better fit on the page. In the actual
command-line interface, the output appears in a single, wide table. The Flags column the output of this
command indicates the high-throughput (HT) properties of the mesh node. In the example below, the string
“HT-40MHzsgi-2ss” indicates that the node uses a 40MHz channel with a short guard interval (sgi) and sends
2 spatial streams (ss).
Parameter Description
ap-name <ap-name> Show mesh neighbors for an AP with a specific name.
bssid <bssid> Show mesh neighbors for a specific Basic Service Set Identifier (BSSID) on an AP.
The Basic Service Set Identifier (BSSID) is usually the AP’s MAC address.
ip-addr <ip-addr> Show mesh neighbors for an AP with a specific IP address by entering its IP address
in dotted-decimal format.
names If you include this optional parameter, the Portal column in the output of this
command will translate the BSSIDs of mesh parent and child APs to AP names
(where available).
(host) #show ap mesh neighbors ap-name portal
Neighbor list
-------------
MAC Portal Channel Age Hops Cost Relation Flags RSSI Rate Tx/Rx
--- ------ ------- --- ---- ---- -------- ----- ---- ----------
00:0b:86:e8:09:d1 00:1a:1e:88:01:f0 157 0 1 11.00 C 3h:15m:42s - 65 54/54
00:1a:1e:88:02:91 00:1a:1e:88:01:f0 157 0 1 4.00 C 3h:35m:30s HL 59 300/300
00:0b:86:9b:27:78 Yes 157 0 0 12.00 N 3h:22m:46s - 26 -
00:0b:86:e8:09:d0 00:1a:1e:88:01:f0 157 0 1 11.00 N 3h:15m:36s - 65 -
00:1a:1e:88:02:90 00:1a:1e:88:01:f0 157+ 0 1 2.00 N 3h:35m:6s HL 59 -
A-Req A-Resp A-Fail HT-Details Cluster ID
----- ------ ------ ---------- ----------
1 1 0 Unsupported sw-ad-GB32
1 1 0 HT-40MHzsgi-2ss sw-ad-GB322
0 0 0 Unsupported mc1
0 0 0 Unsupported sw-ad-GB32
0 0 0 HT-40MHzsgi-2ss sw-ad-GB32
Total count: 5, Children: 2
Relation: P = Parent; C = Child; N = Neighbor; B = Blacklisted-neighbor
Flags: R = Recovery-mode; S = Sub-threshold link; D = Reselection backoff; F = Auth-failure; H = High Throughput; L =
AOS-W 3.4.1 Command Line Interface | Reference Guide show ap mesh neighbors | 627
The output of this command includes the following information:
Command History.
Column Description
MAC MAC address of the mesh node.
Portal By default, this column displays the BSSID of the mesh point. If you include the
optional names parameter, this column will display AP names, if available. The AP
names will include [p] (parent), or [c] (child) suffixes to indicate the role of the mesh
BSSID.
Channel Number of a radio channel used by the AP.
Age Number of seconds elapsed since the AP heard from the neighbor.
Hops Indicates the number of hops it takes traffic from the mesh node to get to the mesh
portal.
The mesh portal advertises a hop count of 0, while all other mesh nodes advertise a
cumulative count based on the parent mesh node
Cost A relative measure of the quality of the path from the AP to the switch. A lower
number indicates a better quality path, where a higher number indicates a less
favorable path (e.g, a path which may be longer or more congested than a path with
a lower value.)
For a mesh point, the path cost is the sum of the (parent path cost) + (the parent
node cost) + (the link cost).
Relation Shows the relationship between the specified AP and the AP on the neighbor list and
the amount of time that relationship has existed.
zP = Parent
zC = Child
zN = Neighbor
zB = Blacklisted-neighbor
Flags This parameter shows additional information about the mesh neighbor. The key
describing each flag appears at the bottom of the neighbor list.
RSSI The Receive Signal Strength Indicator (RSSI) value displayed in the output of this
command represents signal strength as a signal to noise ratio. For example, a value
of 30 would indicate that the power of the received signal is 30 dBm above the signal
noise threshold.
Rate Tx/Rx The rate, in Mbps, that a neighbor transmits data to or receives data from the mesh-
node specified by the command.
A-Req Number of association requests from clients
A-Resp Number of association responses from the mesh node
A-Fail Number of association failures
Cluster Name of the Mesh cluster that includes the specified AP or BSSID.
Version Modification
AOS-W 3.0 Command introduced
AOS-W 3.4.1 The names parameter was introduced. The output of this command was also
modified to include the Rate Tx/Rx column.

628 | show ap mesh neighbors AOS-W 3.4.1 Command Line Interface | Reference Guide
Command Information
Platforms Licensing Command Mode
All platforms This show command is available in
the base operating system.
Commands to configure the mesh
feature require the Mesh license.
Enable or Config mode on master switches
AOS-W 3.4.1 Command Line Interface | Reference Guide show ap mesh tech-support | 629
show ap mesh tech-support
show ap mesh tech-support ap-name <ap-name> <filename>
Description
Display all information for an AP, and save that information in a file on the switch
Syntax
Usage Guidelines
This command displays the output of the multiple mesh and debug CLI commands, then saves that data into
a report file on the switch’s flash drive, where it can be analyzed for debugging purposes. The information in
this report includes the output of the following commands:
zshow ap mesh neighbors
zshow ap mesh debug current-cluster
zshow ap mesh debug provisioned-clusters
zshow ap mesh debug counters
zshow ap mesh debug forwarding-table
zshow ap mesh debug meshd-log
zshow ap mesh debug hostapd-log
Command History
Introduced in AOS-W 3.0.
Command Information
Parameter Description
<ap-name> Name of an AP for which you want to create a report
<filename> Filename for the report created by this command. The file can only be saved in the
flash directory. If desired, you can use FTP or TFTP to copy the file to another
destination.
Platforms Licensing Command Mode
All platforms This show command is available
in the base operating system.
Commands to configure the
mesh feature require the Mesh
license.
Config mode on master switches
630 |show ap mesh topology AOS-W 3.4.1 Command Line Interface | Reference Guide
show ap mesh topology
show ap mesh topology [long] [page <page>] [start <start>]
Description
Show the mesh topology tree.
Syntax
Example
An (N) in the Mesh Role column indicates the node is 11N capable. An (N) beside the parent name in the
Parent column indicates that the mesh node’s the parent is also 11N capable.
The output of this command includes the following information:
Parameter Description
long Include the names of a mesh portal’s children in the output of this command
page <page> Limit the output of this command to a specific number of entries by entering the
number of entries you want to display.
start <start> Start displaying the mesh topology tree at a chosen index number by entering the
index number of the AP at which command output should start.
(host) #show ap mesh topology
Mesh Cluster Name: sw-ad-GB32
-----------------------------
Name Mesh Role Parent Path Cost Node Cost Link Cost Hop Count RSSI Rate Tx/Rx Last Update Uplink Age #Children
---- --------- ------ --------- --------- --------- --------- ---- ---------- ----------- ---------- ---------
ad-ap Point (N) mp3 2 0 0 1 61 300/270 6m:12s 3h:8m:7s 0
msc-1 Point mp3 2 0 0 1 64 54/54 6m:36s 2h:48m:12s 0
Total APs :2
(R): Recovery AP. (N): 11N Enabled. For Portals 'Uplink Age' equals uptime.
Column Description
Name Name of the mesh node.
Mesh Role An AP operating as a mesh node can have one of two roles: mesh portal or mesh
point.
Parent If the AP is operating as a mesh point, this parameter displays the name of its parent
mesh portal.
Path Cost A relative measure of the quality of the path from the AP to the switch. A lower
number indicates a better quality path, where a higher number indicates a less
favorable path (e.g, a path which may be longer or more congested than a path with
a lower value.)
For a mesh point, the path cost is the sum of the (parent path cost) + (the parent
node cost) + (the link cost).
Node Cost A relative measure of the quality of the node, where a lower number of is more
favorable than a higher number. This cost is related to the number of children on the
specified node.
Link Cost A relative measure of the quality of the link. For example, a more congested link will
have a higher link cost than a similar, less-congested link.
AOS-W 3.4.1 Command Line Interface | Reference Guide show ap mesh topology | 631
Command History
Command Information
Hop Count Number of hops to the mesh portal.
RSSI The Receive Signal Strength Indicator (RSSI) value displayed in the output of this
command represents signal strength as a signal to noise ratio. For example, a value
of 30 would indicate that the power of the received signal is 30 dBm above the
signal noise threshold.
Rate Tx/Rx The rate, in Mbps, that a mesh point transmits and receives at on its uplink. Note
that the rate information is only as current as indicated in the Last Update column.
Last Update Time elapsed since the mesh node last updated its statistics.
Uplink Age Time elapsed since the mesh node became active in the mesh topology.
#Children Number of children associated with a parent mesh point.
Version Modification
AOS-W 3.0 Command introduced
AOS-W 3.4.1 The output of this command was also modified to include the Rate Tx/Rx column.
Platforms Licensing Command Mode
All platforms This show command is available in
the base operating system.
Commands to configure the mesh
feature require the Mesh license.
Enable or Config mode on master switches
Column Description

632 | show ap mesh-cluster-profile AOS-W 3.4.1 Command Line Interface | Reference Guide
show ap mesh-cluster-profile
show ap mesh-cluster-profile [<profile>]
Description
Show configuration settings for a mesh cluster profile.
Syntax
Usage Guidelines
The command show ap mesh-cluster-profile displays a list of all mesh cluster profiles configured on the
switch, including the number of references to each profile and each profile’s status. Include the optional
<profile> parameter to show detailed settings for an individual mesh cluster profile.
Examples
The example below shows the configuration settings for the mesh cluster profile “meshcluster2”.
The output of this command includes the following information:
Command History
Introduced in AOS-W 3.2.
Parameter Description
<profile> Name of a mesh cluster profile
Parameter Description
Cluster Name Name of the mesh cluster using this profile
RF band The RF band in which the AP should operate:
zg = 2.4 GHz
za = 5 GHz
Encryption Data encryption setting for the mesh cluster profile.
zopensystem—No authentication and encryption.
zwpa2-psk-aes—WPA2 with AES encryption using a preshared key.
WPA Hexkey The WPA pre-shared key (only for mesh cluster profiles using WPA2 with AES
encryption).
WPA Passphrase The WPA password that generates the preshared key (only for mesh cluster profiles
using WPA2 with AES encryption).
(host) #show ap mesh-cluster-profile meshcluster2
Mesh Cluster profile "meshcluster2"
------------------------------
Parameter Value
--------- -----
Cluster Name company-mesh
RF Band a
Encryption opensystem
WPA Hexkey N/A
WPA Passphrase N/A

AOS-W 3.4.1 Command Line Interface | Reference Guide show ap mesh-cluster-profile | 633
Command Information
Platforms Licensing Command Mode
All platforms This show command is available in
the base operating system.
Commands to configure the mesh
feature require the Mesh license.
Enable or Config mode on master switches

634 | show ap mesh-ht-ssid-profile AOS-W 3.4.1 Command Line Interface | Reference Guide
show ap mesh-ht-ssid-profile
show ap mesh-ht-ssid-profile [<profile>]
Description
Show configuration settings for a mesh high-throughput Service Set Identifier (SSID) profile.
Syntax
Usage Guidelines
High-throughput APs support additional settings not available in legacy APs. A mesh high-throughput SSID
profile can enable or disable high-throughput (802.11n) features and 40 Mhz channel usage, and define
values for aggregated MAC protocol data units (MDPUs) and Modulation and Coding Scheme (MCS) ranges.
The command show ap mesh-ht-ssid-profile displays a list of all mesh high-throughput SSID profiles
configured on the switch, including the number of references to each profile and each profile’s status.
Include the optional <profile> parameter to show detailed settings for an individual mesh high-throughput
SSID profile.
Examples
The example below shows the configuration settings for the mesh high-throughput radio profile “default”.
The output of this command includes the following information:
Parameter Description
<profile> Name of a mesh high-throughput SSID profile.
Column Description
High throughput enable
(SSID)
Shows if 802.11n high-throughput features are enabled or disabled for this
profile. By default, high-throughput features are enabled.
40 MHz channel usage This parameter shows if the profile enables or disables the use of 40 MHz
channels.
(host) #show ap mesh-ht-ssid-profile default
Mesh High-throughput SSID profile "default"
-------------------------------------------
Parameter Value
--------- -----
High throughput enable (SSID) Enabled
40 MHz channel usage Enabled
MPDU Aggregation Enabled
Max transmitted A-MPDU size 65535 bytes
Max received A-MPDU size 65535 bytes
Min MPDU start spacing 0 usec
Supported MCS set 1-14
Short guard interval in 40 MHz mode Enabled
Legacy stations Allowed
Allow weak encryption Disabled
AOS-W 3.4.1 Command Line Interface | Reference Guide show ap mesh-ht-ssid-profile | 635
Command History
Introduced in AOS-W 3.4.
Command Information
MPDU Aggregation This parameter shows if the profile enables or disables MAC protocol data unit
(MPDU) aggregation.
High-throughput mesh APs are able to send aggregated MAC protocol data
units (MDPUs), which allow an AP to receive a single block acknowledgment
instead of multiple ACK signals. This option, which is enabled by default,
reduces network traffic overhead by effectively eliminating the need to initiate
a new transfer for every MPDU.
Max transmitted A-MPDU
size
Maximum size of a transmitted aggregate MPDU, in bytes.
Max received A-MPDU size Maximum size of a received aggregate MPDU, in bytes.
Min MPDU start spacing Minimum time between the start of adjacent MPDUs within an aggregate
MPDU, in microseconds.
Supported MCS set A list of Modulation Coding Scheme (MCS) values or ranges of values to be
supported on this SSID. The MCS you choose determines the channel width
(20MHz vs. 40MHz) and the number of spatial streams used by the mesh
node.
Short guard interval in 40
MHz mode
This parameter shows if the profile enables or disables use of short (400ns)
guard interval in 40 MHz mode.
A guard interval is a period of time between transmissions that allows
reflections from the previous data transmission to settle before an AP
transmits data again. An AP identifies any signal content received inside this
interval as unwanted inter-symbol interference, and rejects that data.
Legacy stations This parameter shows if the profile allows or disallows associations from
legacy (non-HT) stations.
Allow weak encryption Using TKIP or WEP encryption for unicast traffic forces legacy transmission
rates on high-throughput APs. This option is disabled by default, preventing
clients using TKIP or WEP for unicast traffic from associating with the mesh
node.
Platforms Licensing Command Mode
All platforms Base operating system Enable or Config mode on master switches
Column Description
636 | show ap mesh-radio-profile AOS-W 3.4.1 Command Line Interface | Reference Guide
show ap mesh-radio-profile
show ap mesh-radio-profile [<profile>]
Description
Show configuration settings for a mesh radio profile.
Syntax
Usage Guidelines
The radio profile determines the radio frequency/channel used only by mesh nodes to establish mesh links.
Mesh nodes operating in different cluster profiles can share the same radio profile. Conversely, mesh
portals using the same cluster profile can be assigned different mesh radio profiles to achieve frequency
separation.
The command show ap mesh-radio-profile displays a list of all mesh radio profiles configured on the
switch, including the number of references to each profile and each profile’s status. Include the optional
<profile> parameter to show detailed settings for an individual mesh radio profile.
Example
The example below shows the configuration settings for the mesh cluster profile “default”.
The output of this command includes the following information:
Parameter Description
<profile> Name of a mesh radio profile.
Parameter Description
Maximum Children The maximum number of children a mesh portal can accept.
Maximum Hop Count The maximum number of hops allowed between a mesh point and a mesh portal.
Heartbeat Threshold Indicates the maximum number of heartbeat messages that can be lost between
neighboring mesh nodes before the mesh node is considered inactive and is
dropped as a mesh neighbor.
(host) #show ap mesh-radio-profile default
Mesh Radio profile "default"
----------------------------
Parameter Value
--------- -----
Maximum Children 6
Maximum Hop Count 5
Heartbeat threshold 10
Link Threshold 12
Reselection mode reselect-anytime
Metric algorithm distributed-tree-rssi
Retry Limit 4
RTS Threshold 2333 bytes
802.11a Transmit Rates 6 9 12 18 24 36 48 54
802.11g Transmit Rates 1 2 5 6 9 11 12 18 24 36 48 54
Mesh Private Vlan 0
Allowed VLANs on mesh link 1
BC/MC Rate Optimization Enabled
Mesh High-throughput SSID Profile default
AOS-W 3.4.1 Command Line Interface | Reference Guide show ap mesh-radio-profile | 637
Command History
Command Information
Link Threshold Indicates the threshold for the lowest acceptable Receive Signal Strength Indicator
(RSSI) value. Links that drop below this threshold will have an increased link cost.
Default: 12.
Reselection Mode Specifies the one of the following methods used to find a better mesh link.
zstartup-sub-threshold: When bringing up the mesh network, mesh nodes have
3 minutes to find a better uplink. After that time, each mesh node evaluates
alternative links only if the existing uplink falls below the configured threshold
level (the link becomes a sub-threshold link). The reselection process is canceled
if the average RSSI rises on the existing uplink rises above the configured link
threshold.
zreselect-any-time: Connected mesh nodes evaluate alternative mesh links
every 30 seconds. If a mesh node finds a better uplink, the mesh node connects
to the new parent to create an improved path to the mesh portal.
zreselect-never: Connected mesh nodes do not evaluate other mesh links to
create an improved path to the mesh portal.
zsubthreshold-only: Connected mesh nodes evaluate alternative links only if the
existing uplink becomes a sub-threshold link.
Metric algorithm Algorithm used by a mesh node to select its parent.
Retry Limit Maximum number of times a mesh node can re-send a packet.
RTS Threshold The packet size sent by mesh nodes. Mesh nodes transmitting frames larger than
this threshold must issue request to send (RTS) and wait for other mesh nodes to
respond with clear to send (CTS) to begin transmission. This helps prevent mid-air
collisions.
802.11a Transmit
Rates
Indicates the transmit rates for the 802.11a radio. The AP attempts to use the
highest transmission rate to establish a mesh link. If a rate is unavailable, the AP
goes through the list and uses the next highest rate.
802.11g Transmit
Rates
Indicates the transmit rates for the 802.11g radio. The AP attempts to use the
highest transmission rate to establish a mesh link. If a rate is unavailable, the AP
goes through the list and uses the next highest rate.
Mesh Private Vlan A Vlan ID for control traffic between an RMP and mesh nodes.
BC/MC Rate
Optimization
If enabled, the mesh node will use the slowest associated mesh-point rate for
broadcast/multicast data (rather than minimum).
Mesh High-throughput
SSID Profile
The High-throughput SSID Profile associated with this mesh radio profile.
Release Modification
AOS-W 3.2 Command Introduced.
AOS-W 3.4 The 802.11g Portal channel and 802.11a Portal channel parameters were
deprecated, and the Mesh High-throughput SSID Profile parameter was
introduced.
Platforms Licensing Command Mode
All platforms Base operating system Enable or Config mode on master switches
Parameter Description
638 | show ap monitor AOS-W 3.4.1 Command Line Interface | Reference Guide
show ap monitor
show ap monitor active-laser-beams|ap-list|channel|client-list|ids-state|mesh-list|pot-
ap-list|pot-client-list|routers|wired-mac {ap-name <ap-name>}|{bssid <bssid>}|{ip-addr
<ip-addr>} {ap-bssid <ap-bssid>}|{enet-mac <enet-mac>}
Description
Show information for Alcatel-Lucent Air Monitors.
Syntax
Parameter Description
active-laser-beams Show active laser beam generators.
The output of this command shows a list of all APs that are actively performing
policy enforcement containment such as rogue containment. This command can tell
us which AP is sending out deauthorization frames, although it does not specify
which AP is being contained.
ap-list Show list of APs being monitored.
arp-cache Show ARP Cache of learned IP to MAC binding
channel Show state and stats of a specific channel.
client-list Show list of client being monitored.
ids-state Show IDS State.
mesh-list Show list of Mesh APs being monitored.
pot-ap-list Display the Potential AP table. The Potential AP table shows the following data:
zbssid: the AP’s Basic Service Set Identifier.
zchannel: The AP’s current radio channel
zphy type: The radio’s PHY type. Possible values are 802.11a, 802.11a-HT-40,
802.11b/g, 802.11b/g-HT-20.
znum-beacons: Number of beacons seen during a 10-second scan
ztot-beacons: Total number of beacons seen since the last reset.
znum-frames: Total number of frames seen since the last rest.
zmt: Monitor time; the number of timer ticks elapsed since the switch first
recognized the AP.
zat: Active time, in timer ticks.
zibss: Shows if ad-hoc BSS is enabled or disabled. It will be enabled if the bssid
has detected an ad-hoc BSS (an ibss bit in an 802.11 frame).
zrssi: The Receive Signal Strength Indicator (RSSI) value displayed in the output
of this command represents signal strength as a signal to noise ratio. For
example, a value of 30 would indicate that the power of the received signal is 30
dBm above the signal noise threshold.
pot-client-list Display the Potential client table. The Potential Client table shows the following
values:
zlast-bssid: the Last BSSID to which the client associated.
zfrom-bssid,
zto-bssid
zmt: Monitor time; the number of timer ticks elapsed since the switch first
recognized the client.
zit: Client Idle time, expressed as a number of timer ticks.
routers Show Router MAC Addresses learned. The output of this command includes the
router’s MAC address, IP address and uptime.
wired-mac Show Wired MAC Addresses learned.
ap-name <ap-name> Show data for an AP with a specific name.
AOS-W 3.4.1 Command Line Interface | Reference Guide show ap monitor | 639
Examples
The output of the command displays the Monitored AP Table, which lists all the APs monitored by a
specified AP or BSSID.
The output of this command includes the following information:
bssid <bssid> Show data for a specific Basic Service Set Identifier (BSSID) on an AP. The Basic
Service Set Identifier (BSSID) is usually the AP’s MAC address.
ip-addr <ip-addr> Show data for an AP with a specific IP address by entering its IP address in dotted-
decimal format.
ap-bssid <ap-
bssid>
Include the optional ap-bssid <ap-bssid> parameters to show how the AP is
monitoring information for another AP with a specific BSSID.
enet-mac <enet-
mac>
Include the optional enet-mac <enet-mac> parameters to show how the AP is
monitoring information for an interface with a specific ethernet MAC address.
Column Description
bssid Basic Service Set Identifier for an AP. This is usually the AP’s MAC address.
essid Extended service set identifier that names a wireless network.
chan Radio channel used by the BSSID
phy-type Radio phy type. Possible types include:
z802.11a
z802.11a-HT-40
z802.11b/g
z802.11b/g-HT-20
dos Shows if the feature to contain DoS attacks has been enabled or disabled.
mt Monitor time; the number of elapsed timer ticks since the AP first recognized the
monitored AP.
Parameter Description
(host) #show ap monitor ap-list ap-name al12
Monitored AP Table
------------------
bssid essid chan ap-type phy-type dos mt it load-balance
----- ----- ---- ------- -------- --- -- -- ------------
00:1a:1e:11:5f:02 ethersphere-vocera 6 valid 80211b/g-HT-20 disable 787272 0 disable
00:1a:1e:11:5f:00 guest 6 valid 80211b/g-HT-20 disable 787272 0 disable
00:1a:1e:11:5f:11 ethersphere-wpa2 48 valid 80211a-HT-40 disable 786835 0 disable
00:1a:1e:11:5f:10 guest 48 valid 80211a-HT-40 disable 786835 0 disable
00:1a:1e:11:5f:01 ethersphere-voip 6 valid 80211b/g-HT-20 disable 787272 0 disable
00:1a:1e:11:6e:70 guest 48 valid 80211a-HT-40 disable 18543 0 disable
00:1a:1e:11:6e:71 ethersphere-wpa2 48 valid 80211a-HT-40 disable 18543 0 disable
00:1a:1e:88:90:42 employee4a 6 unknown 80211b/g disable 3160 0 disable
00:1a:1e:88:90:41 guest4 6 unknown 80211b/g-HT-20 disable 3160 0 disable
00:1a:1e:88:90:40 employee4 6 unknown 80211b/g-HT-20 disable 3159 0 disable
00:1a:1e:8e:73:e1 guest10 6 unknown 80211b/g-HT-20 disable 941 0 disable
00:1a:1e:8e:73:e0 emplyee10 6 unknown 80211b/g-HT-20 disable 910 0 disable
00:1a:1e:8e:73:f0 emplyee10 48 unknown 80211a-HT-40 disable 252 0 disable
00:1a:1e:8e:73:f1 guest10 48 unknown 80211a-HT-40 disable 252 0 disable
00:1a:1e:8d:5b:30 guest 48 valid 80211a-HT-40 disable 189 0 disable
00:1a:1e:8d:5b:31 ethersphere-wpa2 48 valid 80211a-HT-40 disable 189 0 disable
640 | show ap monitor AOS-W 3.4.1 Command Line Interface | Reference Guide
Command History
Command Information
it AP idle time, the number of timer-ticks since the AP last saw any frames from the
monitored AP.
load-balance Shows if the load-balancing feature has been enabled on the AP.
Version Modification
AOS-W 3.0. Command introduced
AOS-W 3.4. The ap-bssid and enet-mac parameters were added to the show ap monitor
wired-mac command.
Platforms Licensing Command Mode
All platforms Base operating system Enable or Config mode on master switches
Column Description
AOS-W 3.4.1 Command Line Interface | Reference Guide show ap monitor association | 641
show ap monitor association
show ap monitor association {ap-name <ap-name>}|{bssid <bssid>}|{ip-addr <ip-addr>}
<ap-bssid>
Description
Show the association table for an Air Monitor (AM).
Syntax
Examples
The output of the command lists the MAC addresses associated with the Air Monitor BSSID.
The output of this command includes the following information:
Command History
Introduced in AOS-W 3.0.
Parameter Description
ap-name <ap-name> Show data for an AM with a specific name.
bssid <bssid> Show data for an AM with a specific Basic Service Set Identifier (BSSID). The Basic
Service Set Identifier (BSSID) is usually the AM’s MAC address.
ip-addr <ip-addr> Show data for an AM with a specific IP address by entering its IP address in dotted-
decimal format.
<ap-bssid> BSSID of an AP.
Column Description
mac MAC address associated with the Air Monitor BSSID
rsta-type Rogue station type:
zinterfering: Interfering station.
zvalid: Station is not a rogue station.
zDoS: Station may have attempted a DoS attack.
auth Displays a yes if the client has been authenticated.
phy-type The RF band in which the AP should operate:
802.11g = 2.4 GHz
802.11a = 5 GHz
(host) #show ap monitor association ap-name ap9 00:1a:1e:11:74:a1
Association Table
-----------------
mac rsta-type auth phy-type
--- --------- ---- --------
00:1d:d9:01:c4:50 valid yes 80211a
00:17:f2:4d:01:e2 valid yes 80211a
00:1f:3b:8c:28:89 valid yes 80211a
00:1d:d9:05:05:d0 valid yes 80211a
00:14:a4:25:72:6d valid yes 80211a
00:19:7d:d6:74:8d valid yes 80211a

642 | show ap monitor association AOS-W 3.4.1 Command Line Interface | Reference Guide
Command Information
Platforms Licensing Command Mode
All platforms Base operating system Enable or Config mode on master switches

AOS-W 3.4.1 Command Line Interface | Reference Guide show ap monitor debug | 643
show ap monitor debug
show ap monitor debug counters|status {ap-name <ap-name>}|{bssid <bssid>}|{ip-addr <ip-
addr>}
show ap monitor debug profile-config {ap-name <ap-name>}|{bssid <bssid>}|{ip-addr <ip-
addr>} ap-radio|ap-system|arm|event-thresholds|ids-dos|ids-general|ids-
impersonation|ids-signature-matching|ids-unauthorized-device|interference|regulatory-
domain|rf-behavior
Description
Show information for an Air Monitor’s current status, message counters, or profile settings.
Syntax
Parameter Description
counters Show Air Monitor (AM) message counters.
status Show the status of an Air Monitor.
ap-name <ap-name> Show data for an AM with a specific name.
bssid <bssid> Show data for an AM with a specific Basic Service Set Identifier (BSSID).
The Basic Service Set Identifier (BSSID) is usually the AP’s MAC address.
ip-addr <ip-addr> Show data for an AM with a specific IP address by entering its IP address
in dotted-decimal format.
profile-config Show an Air Monitor profile configuration.
ap-radio Show the Air Monitor radio configuration parameters, as defined in the
AM’s 802.11a, 802.11b, or high-throughput radio profiles.
ap-system Show an Air Monitor’s system configuration settings, as defined in it’s AP
System profile.
arm Show an Air Monitor’s Adaptive Radio Management (ARM) settings, as
defined in its current ARM profile
event-thresholds Show an Air Monitor Event Thresholds settings, as defined in its current
RF Event Thresholds profile
ids-dos Show an Air Monitor IDS DoS settings, as defined in its current IDS DoS
profile.
ids-general Show an Air Monitor IDS General Configuration settings, as defined in its
IDS General profile.
ids-impersonation Show an Air Monitor IDS Impersonation Configuration settings, as defined
in its IDS Impersonation profile.
ids-signature-matching Show an Air Monitor IDS Signature Matching configuration settings, as
defined in its IDS Signature Matching profile
ids-unauthorized-device Show an Air Monitor IDS Unauthorized Device configuration settings, as
defined in its IDS Unauthorized Device profile.
interference Show an Air Monitor’s interference configuration settings, as defined in its
current RF Optimization profile.
regulatory-domain Show an Air Monitor’s Regulatory Domain configuration settings, as
defined in its Regulatory Domain profile.
rf-behavior Show an Air Monitor RF Behavior Configuration

644 | show ap monitor debug AOS-W 3.4.1 Command Line Interface | Reference Guide
Examples
The output of the following command includes the WLAN Interface, Data Structures, WLAN Interface
Switch Status and RTLS Configuration tables for the specified AP.
(host) #show ap monitor debug status ap-name ap12
WLAN Interface
--------------
bssid scan monitor probe-type phy-type task channel pkts
----- ---- ------- ---------- -------- ---- ------- ----
00:1a:1e:11:5f:10 enable enable sap 80211a-HT-40 tuned 153 496970814
00:1a:1e:11:5f:00 enable enable sap 80211b/g-HT-20 tuned 6 391278179
Wired Interface
---------------
mac ip gw-ip gw-mac status pkts macs gw-macs tagged-pkts vlan
--- -- ----- ------ ------ ---- ---- ------- ----------- ----
00:1a:1e:c9:15:f0 192.0.2.32.200 192.0.2.32.254 00:0b:86:08:e1:00 enable 101960 2 3 103 2
Global Counters
---------------
key value
--- -----
Packets Read 888248993
Bytes Read 2819670134
Num Interrupts 681037971
Num Buffer Overflows 591393
Max PPS 16239
Cur PPS 1130
Max PPI 20
Cur PPI 2
Uptime 3323085
AP Name AL12
LMS IP 192.0.2.250
Master IP 192.0.2.253
AP Type 125
Country Code 2
Data Structures
----------------
ap sta pap psta ch msg-hash ap-l
-- --- --- ---- -- -------- ----
20 40 17 55 24 21 20
Other Parameters
-----------------
key value
--- -----
WMS on Master disabled
Stats Update Interval 60
Poll Interval 174000
Num Switches 1
Collect Stats enabled
WLAN Interface Switch Status
-----------------------------
Bssid Type Status Last-reg N-reg Last-update Next-update N-updates Last-ack
----- ---- ------ -------- ----- ----------- ----------- --------- --------
00:1a:1e:11:5f:10 local up 3321891 3821 3322965 197 10368 3322965
00:1a:1e:11:5f:00 local up 3321891 3821 3322917 187 10378 3322965
RTLS configuration
-------------------
Type Server IP Port Frequency Active
---- --------- ---- --------- ------
MMS 102.0.2.19 8000 N/A
Aeroscout 192.0.2.199 1144 N/A
RTLS 192.0.2.19 5050 30 *
AOS-W 3.4.1 Command Line Interface | Reference Guide show ap monitor debug | 645
The output of this command includes the following information:
Column Description
bssid The Basic Service Set Identifier (BSSID) for the AP. This is usually the AP’s MAC
address.
scan Indicates whether or not if active scanning is enabled on this AP.
monitor Indicates whether the AP radio is currently enabled or disabled.
probe-type This parameter displays one of the following options to show the AP is configured.
zsap: Default AP setting.
zam: AP is configured as an Air Monitor.
zm-portal: AP is configured as a Mesh portal.
zm-point: AP is configured as a Mesh point.
task This parameter displays one of the following options to show the radio’s current
task:
zscan: AP is scanning other channels.
ztuned: AP is tuned on one channel.
zlocate: AP has been asked to locate a specific AP or client.
zpcap: The AP is enabled with the Packet Capture feature.
channel The radio channel currently used by an AP’s WLAN interface.
pkts Number of packets seen on the interface.
mac MAC address for the AP’s wired interface.
ip The AP’s IP address.
gw-ip IP address for the AP’s gateway.
gw-mac MAC address for the AP’s gateway.
status Shows if the interface is currently enabled or disabled.
pkts Number of packets seen on the AP’s wired interface.
macs Number of MAC addresses in the Wired MAC table for that interface.
gw-macs Number of MAC addresses in the Wired MAC table for that interface.
tagged-pkts Number VLAN-tagged packets sent to that interface.
vlan The VLAN ID for the packets sent to that interface.
Packets read Number of packets read by the AP since it was last reset.
Bytes read Number of bytes read by the AP since it was last reset.
Num Intercepts Number of interrupts from the AP’s driver.
Num Buffer Overflows Number of times excessive traffic has filled the AP’s buffers.
Max PPS Maximum throughput rate seen on the interface, in packets per second.
Cur PPS Current throughput rate seen on the interface, in packets per second.
Max PPI Maximum interrupt rate seen on the interface, in interrupts per second.
Cur PPI Current interrupt rate seen on the interface, in interrupts per second.
Uptime Number of seconds since the AP was last reset.
LMS IP IP address of the AP’s local switch.
Master IP IP address of the AP’s master switch.
646 | show ap monitor debug AOS-W 3.4.1 Command Line Interface | Reference Guide
AP type AP model type.
Country Code The AP’s country code. Valid radio channels for your wireless network are based on
your country code. If you change the AP’s country code, the valid channels will be
reset to the defaults for the new country.
ap Number of other APs monitored by this AP.
sta Number of clients and APs seen by this AP.
pap Number of potential APs; APs which have transmitted a beacon, but have not yet
been registered.
psta Number of potential stations; AP has seen a MAC address from the station but
hasn’t yet received traffic from it.
ch Number of channel entries in the channel table.
msg-hash Number of different message types seen on the interface.
ap-l (For internal use only)
WMS on Master Indicates if the AP communicates to the wms process on a master or local switch.
enabled: Communicates with a master switch.
disabled: Communicates with a local switch only.
Stats Update Interval If the AP is collecting statistics, this value is the interval in seconds in which the AP
sends statistics to the WMS process on a switch.
Poll Interval Interval, in milliseconds, that the AP sends RSSI updates to the WMS process on a
switch.
Num Switches Number of switches to which this AP has access. If the value is 1, the AP has
access to a master or a local switch. If the value is 2, the AP has access to a master
and a local switch.
Collect Stats If enabled, the AP will collect statistics to send the WMS process on its switch.
Bssid BSSID of the radio.
Type Indicates whether the switch type is master or local.
Status If up, the AP can reach the switch. If down, the AP cannot reach the switch.
Last-reg The time the AP last registered with the WMS process.
N-reg Number of times the AP has registered with the WMS process.
Last-update The last timer tick time the AP updated the WMS process.
Next-update Interval between the last update and the next scheduled update.
N-updates Number of updates sent to the WMS process.
Last-ack Number of timer ticks since the AP received an acknowledgement from the WMS
process.
Type Type of RTLS server used by the AP, such as MMS or Aeroscout.
Server IP IP address of the RTLS server.
Port Port used by the RTLS server.
Frequency Rate, in seconds, at which RTLS messages are sent to the server.
Active Indicates if the server is active on the AP.
Column Description
AOS-W 3.4.1 Command Line Interface | Reference Guide show ap monitor debug | 647
Command History
Command Information
Version Modification
AOS-W 3.0. Command introduced
AOS-W 3.4. The tagged-pkts and vlan parameters were added to the Wired Interface table in
the output of the show ap monitor debug status command.
Platforms Licensing Command Mode
All platforms Base operating system Enable or Config mode on master switches

648 | show ap monitor stats AOS-W 3.4.1 Command Line Interface | Reference Guide
show ap monitor stats
show ap monitor stats advanced {ap-name <ap-name>}|{bssid <bssid>}|{ip-addr <ip-addr>}
client-mac <client-mac>
show ap monitor stats {ap-name <ap-name>}|{bssid <bssid>}|{ip-addr <ip-addr>} mac <mac>
Description
Show packet, signal and channel statistics for an AP or a client.
Syntax
Parameter Description
advanced Show advanced statistics for an AP or client.
ap-name <ap-name> Show statistics for an AP with a specific name.
bssid <bssid> Show data for a specific Basic Service Set Identifier (BSSID) on an AP. The Basic
Service Set Identifier (BSSID) is usually the AP’s MAC address.
ip-addr <ip-addr> Show data for an AP with a specific IP address by entering its IP address in
dotted-decimal format.
mac <mac> Show data for a specific MAC address by entering the MAC address of a client or
AP.
client-mac <client-mac> Show data for a specific client MAC address by entering the MAC address of a
client.
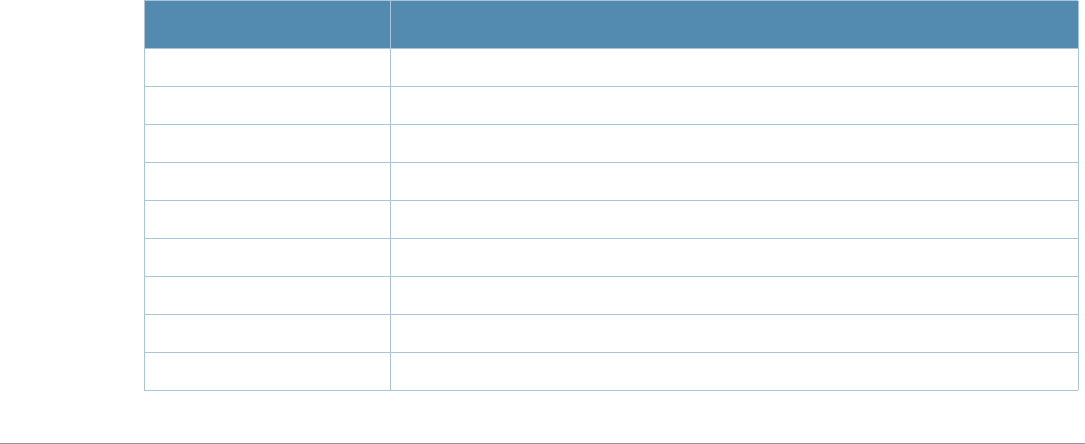
AOS-W 3.4.1 Command Line Interface | Reference Guide show ap monitor stats | 649
Example
The output of the following command shows monitoring statistics for the AP al12, and a client with the
MAC address 00:03:2a:02:6a:d7.
The output of this command includes the following information:
Column Description
retry Percent of 802.11 retry frames sent because a client failed to send an ACK.
Low-speed Percent of frames sent at a data rate of 18 Mbps or slower.
non-unicast Percent of non-unicast frames
recev-error Percent of error frames of all frames seen in the last second.
frag Rate of fragmented packets, in frames per second
bwth Current bandwidth, in bps.
avg-signal Average signal-to-noise ratio over the interval since the AP’s last reset.
Low-signal Lowest signal-to-noise ratio over the interval since the AP’s last reset.
high-signal Highest signal-to-noise ratio over the interval since the AP’s last reset.
(host) #show ap monitor stats ap-name al12 mac 00:03:2a:02:6a:d7
Aggregate Stats
---------------
retry low-speed non-unicast recv-error frag bwidth
----- --------- ----------- ---------- ---- ------
0 0 0 0 0 0
RSSI
----
avg-signal low-signal high-signal count duration (sec)
---------- ---------- ----------- ----- --------------
51 51 51 4 50
Monitored Time:6626
Last Packet Time:585500
Uptime:585502
DoS Frames
----------
tx old-tx rx old-rx
-- ------ -- ------
0 0 0 0
Interference Baseline
---------------------
FRR FRER
--- ----
17 4
Handoff Assist
--------------
rssi-index cur-signal old-cur-signal
---------- ---------- --------------
0 51 0
High Throughput Parameters
--------------------------
ht-type primary-channel sec-channel gf-supported 40mhz-intolerance
------- --------------- ----------- ------------ -----------------
none 0 0 0 0

650 | show ap monitor stats AOS-W 3.4.1 Command Line Interface | Reference Guide
Command History
Introduced in AOS-W 3.0.
Command Information
count Number of packets seen on the AP over the interval since the AP’s last reset.
Duration Time over which the AP has measured RSSI values.
tx The total number of deauthorization frames sent to this MAC address for
containment in the interval from the AP’s last reset until the current timer tick.
old-tx The total number of deauthorization frames sent to this MAC address for
containment until the previous timer tick.
rx The total number of deauthorization frames spoofing the MAC address in the
interval from the AP’s last reset until the current timer tick.
old-rx The total number of deauthorization frames sent to this MAC address for
containment until the previous timer tick.
FRR Frame retry rate, in frames per second.
FRER Frame error retry rate, in frames per second.
rssi-index This value indicates the number of consecutive timer ticks over which the value of
the Receive Signal Strength Indicator (RSSI) of the client has reduced by more than
3 units.
NOTE: This value is updated only if 'handoff-assist' is enabled in the AP’s RF
Optimization profile.
cur-signal The Receive Signal Strength Indicator (RSSI) of the most recent frame received from
the specified MAC address.
old-cur-signal The most recent Receive Signal Strength Indicator (RSSI) of the MAC which is 3
lower or 5 higher than the current RSSI.
NOTE: This value is updated only if 'handoff-assist' is enabled in the AP’s RF
Optimization profile
ht-type This parameter indicates support for the following HT types:
no: No support for high-throughput.
HT-20: Support for 20 Mhz high-throughput only.
HT-40: Support for 40 Mhz high-throughput.
primary-channel Primary radio channel.
sec-channel Secondary radio channel
gf-supported If 1, this AP supports greenfield mode. If 0, greenfield is not supported.
40mhz-intolerance Indicates whether the specified MAC address is 40 Mhz intolerant.
Platforms Licensing Command Mode
All platforms Base operating system Enable or Config mode on master switches
Column Description

AOS-W 3.4.1 Command Line Interface | Reference Guide show ap pcap status | 651
show ap pcap status
show ap pcap status {ap-name <ap-name>}|{bssid <bssid>}|{ip-addr <ip-addr>}
Description
Show the status of outstanding packet capture (pcap) sessions.
Syntax
Usage Guidelines
The Packet Capture (pcap) feature copies control path packets from the Alcatel-Lucent Control Processor,
providing visibility for packets to or from the switch.This provides a useful troubleshooting tool for
diagnosing communication problems with elements such as a Radius server. You can retrieve these packets
by issuing the command tar logs, and then viewing the file filter.pcap on the switch’s flash drive.
Example
The example below shows the Packet Capture Sessions table for an AP named AP16.
The output of this command includes the following information:
Parameter Description
ap-name <ap-name> Show data for an AP with a specific name.
bssid <bssid> Show data for a specific Basic Service Set Identifier (BSSID) on an AP. The Basic
Service Set Identifier (BSSID) is usually the AP’s MAC address.
ip-addr <ip-addr> Show data for an AP with a specific IP address by entering its IP address in dotted-
decimal format.
(host) #show ap pcap status ap-name AP16
Packet Capture Sessions
-----------------------
pcap-id filter type intf channel max-pkt-size num-pkts status url target
------- ------ ---- ---- ------- ------------ -------- ------ --- ------
1 raw 00:1a:1e:82:ab:b0 161 in-progress 10.3.9.225/5555
Column Description
pcap-id ID number of the packet capture session.
filter Packet Capture filter specification.
type A raw packet capture type indicates that the switch is streaming raw packets to an
external viewer.
intf BSSID of the interface for the PCAP session.
channel Channel used by AP to capture packets.
max-pkt-size Maximum size of all captured packets.
num-pkts Number of packets captured during the session.
status Shows the current status of the packet-capture session.
url Packet capture data can be downloaded to this URL
target IP address of the client station running Wildpacket’s AiroPeek monitoring
application

652 | show ap pcap status AOS-W 3.4.1 Command Line Interface | Reference Guide
Command History
Introduced in AOS-W 3.0.
Command Information
Platforms Licensing Command Mode
All platforms Base operating system Enable or Config mode on master switches
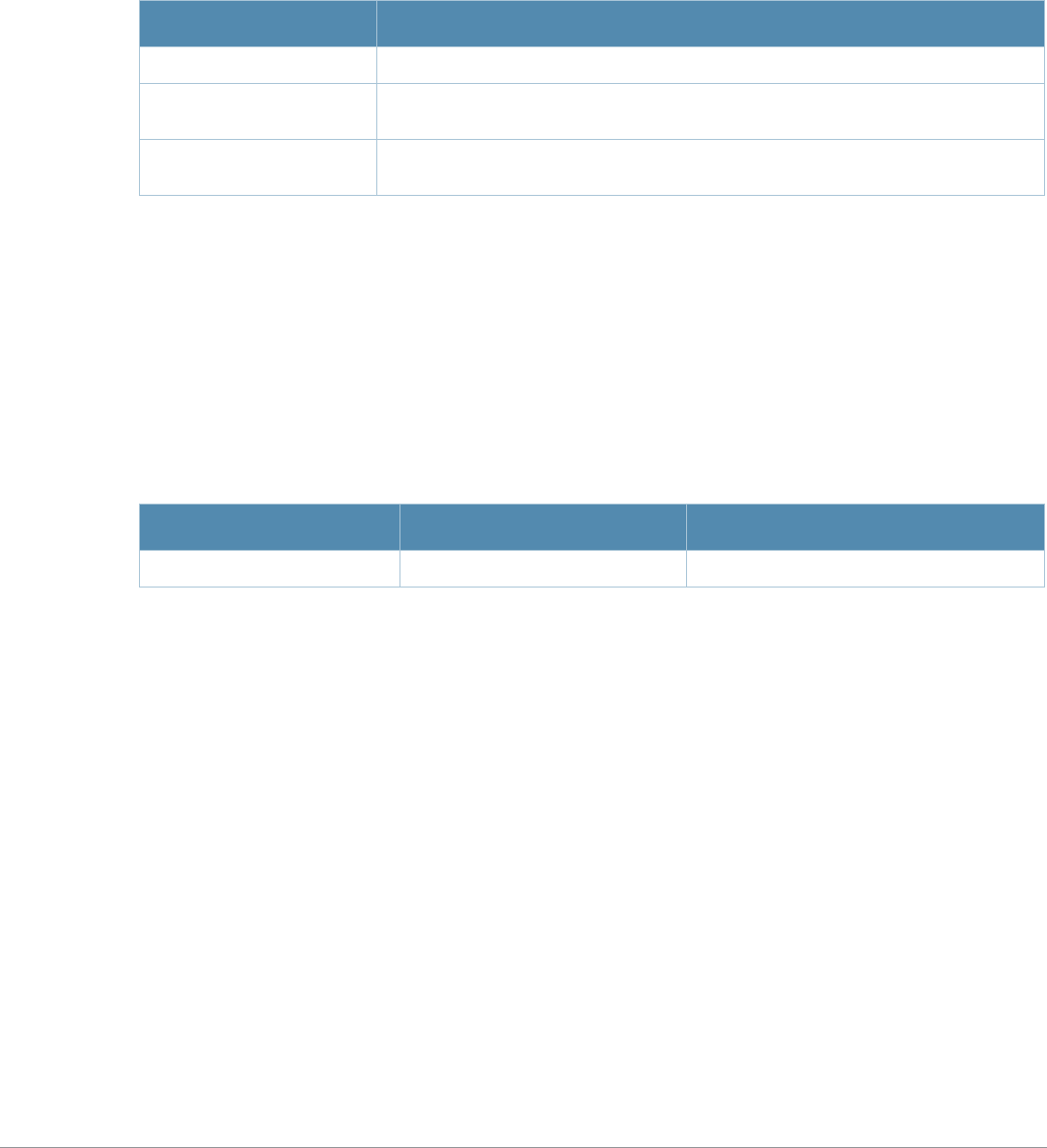
AOS-W 3.4.1 Command Line Interface | Reference Guide show ap profile-usage | 653
show ap profile-usage
show ap profile-usage {ap-name <ap-name>|bssid <bssid>|ip-addr <ip-addr>}
Description
Show a complete list of all profiles referenced by an individual AP or an AP BSSID.
Syntax
Usage Guidelines
Use this command to monitor the configuration profiles in use by an AP or a specific BSSID. The output of
this command shows the name of each profile type that is associated with the AP or BSSID, as well as the
source that associates the profile with the AP.
Command History
Introduced in AOS-W 3.0.
Command Information
Parameter Description
ap-name <ap-name> Show data for an AP with a specific name.
bssid <bssid> Show data for a specific Basic Service Set Identifier (BSSID) on an AP. The Basic
Service Set Identifier (BSSID) is usually the AP’s MAC address.
ip-addr <ip-addr> Show data for an AP with a specific IP address by entering its IP address in dotted-
decimal format.
Platforms Licensing Command Mode
All platforms Base operating system Enable or Config mode on master switches

654 | show ap provisioning AOS-W 3.4.1 Command Line Interface | Reference Guide
show ap provisioning
show ap provisioning {ap-name <ap-name>}|{bssid <bssid>}|{ip-addr <ip-addr>}
Description
Show provisioning parameters currently used by an AP.
Syntax
Parameter Description
ap-name <ap-name> Show data for an AP with a specific name.
bssid <bssid> Show data for a specific Basic Service Set Identifier (BSSID) on an AP. An AP’s
BSSID is usually the AP’s MAC address.
ip-addr <ip-addr> Show data for an AP with a specific IP address.
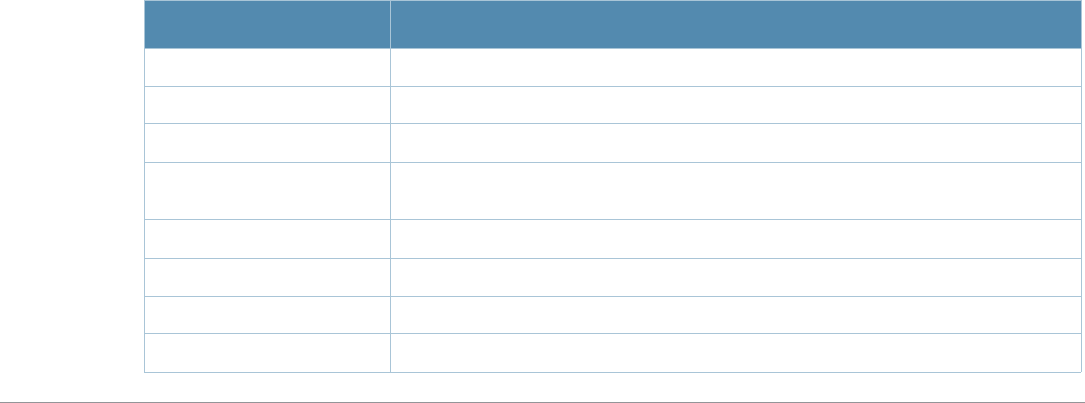
AOS-W 3.4.1 Command Line Interface | Reference Guide show ap provisioning | 655
Example
The output of this command shows that the AP named AP8 has mostly default parameters. These appear
with the value N/A.
The output of this command includes the following information:
Column Description
AP Name Name of the AP.
AP Group AP group to which the AP belongs.
Location name Fully-qualified location name (FQLN) for the AP.
SNMP sysLocation User-defined description of the location of the AP, as defined with the command
provision-ap syslocation.
Master Name or IP address for the master switch.
Gateway IP address of the default gateway for the AP.
Netmask Netmask for the AP’s IP address.
IP Addr IP address for the AP.
(host) #show ap provisioning ap-name AP8
AP "mp2" Provisioning Parameters
--------------------------------
Item Value
---- -----
AP Name mp2
AP Group mpp1
Location name N/A
SNMP sysLocation N/A
Master N/A
Gateway N/A
Netmask N/A
IP Addr N/A
DNS IP N/A
Domain Name N/A
Server Name Alcatel-Lucent-master
Server IP N/A
Antenna gain for 802.11a N/A
Antenna gain for 802.11g N/A
Antenna for 802.11a both
Antenna for 802.11g both
IKE PSK N/A
PAP User Name N/A
PAP Password N/A
PPPOE User Name N/A
PPPOE Password N/A
PPPOE Service Name N/A
USB User Name N/A
USB Password N/A
USB Device Type any
USB Device Identifier N/A
USB Dial String N/A
USB Initialization String N/A
USB TTY device path N/A
Mesh Role mesh-point
Installation default
Latitude N/A
Longitude N/A
Altitude N/A
Antenna bearing for 802.11a N/A
Antenna bearing for 802.11g N/A
Antenna tilt angle for 802.11a N/A
Antenna tilt angle for 802.11g N/A
Mesh SAE sae-default

656 | show ap provisioning AOS-W 3.4.1 Command Line Interface | Reference Guide
Dns IP IP address of the DNS server.
Domain Name Domain name used by the AP.
Server Name DNS name of the switch from which the AP boots.
Server IP IP address of the switch from which the AP boots
Antenna gain for
802.11a
Antenna gain for 802.11a (5GHz) antenna.
Antenna gain for
802.11g
Antenna gain for 802.11g (2.4GHz) antenna.
Antenna for 802.11a Antenna use for 5 GHz (802.11a) frequency band.
z1: AP uses antenna 1
z2: AP uses antenna 2
zboth: AP uses both antennas
Antenna for 802.11g Antenna use for 2.4 GHz (802.11g) frequency band.
z1: AP uses antenna 1
z2: AP uses antenna 2
zboth: AP uses both antennas
IKE PSK IKE PSK The IKE pre-shared key.
PPPOE User Name Point-to-Point Protocol over Ethernet (PPPoE) user name for the AP.
PPPOE Password PPPoE password for the AP.
PPPOE Service Name PPPoE service name for the AP.
Mesh Role If the mesh role is “none,” the AP is operating as a thin AP. An AP operating as a
mesh node can have one of two roles: mesh portal or mesh point.
Latitude Latitude coordinates of the AP, in the format Degrees Minutes Seconds (DMS).
Longitude Longitude coordinates of the AP, in the format Degrees Minutes Seconds (DMS).
Altitude Altitude, in meters, of the AP. This parameter is supported on outdoor APs
only.
Antenna bearing for
802.11a
Horizontal coverage distance of the 802.11a (5GHz) antenna from true north, from 0-
360 degrees.
NOTE: This parameter is supported on outdoor APs only. The horizontal coverage
pattern does not consider the elevation or vertical antenna pattern.
Antenna bearing for
802.11g
Horizontal coverage distance of the 802.11g (2.4GHz) antenna from true north, from
0-360 degrees.
NOTE: This parameter is supported on outdoor APs only. The horizontal coverage
pattern does not consider the elevation or vertical antenna pattern.
Antenna tilt angle
for 802.11a
The angle of the 802.11a (5GHz) antenna. This parameter can range from between -
90 degrees and 0 degrees for downtilt, and between +90 degrees and 0 degrees for
uptilt.
Antenna tilt angle
for 802.11g
The angle of the 802.11g (2.4GHz) antenna. This parameter can range from between
-90 degrees and 0 degrees for downtilt, and between +90 degrees and 0 degrees for
uptilt.
Mesh SAE Shows if the AP has enabled or disabled Secure Attribute Exchange (SAE) on a
mesh network. The default setting (sae-default) also disables SAE.
Column Description
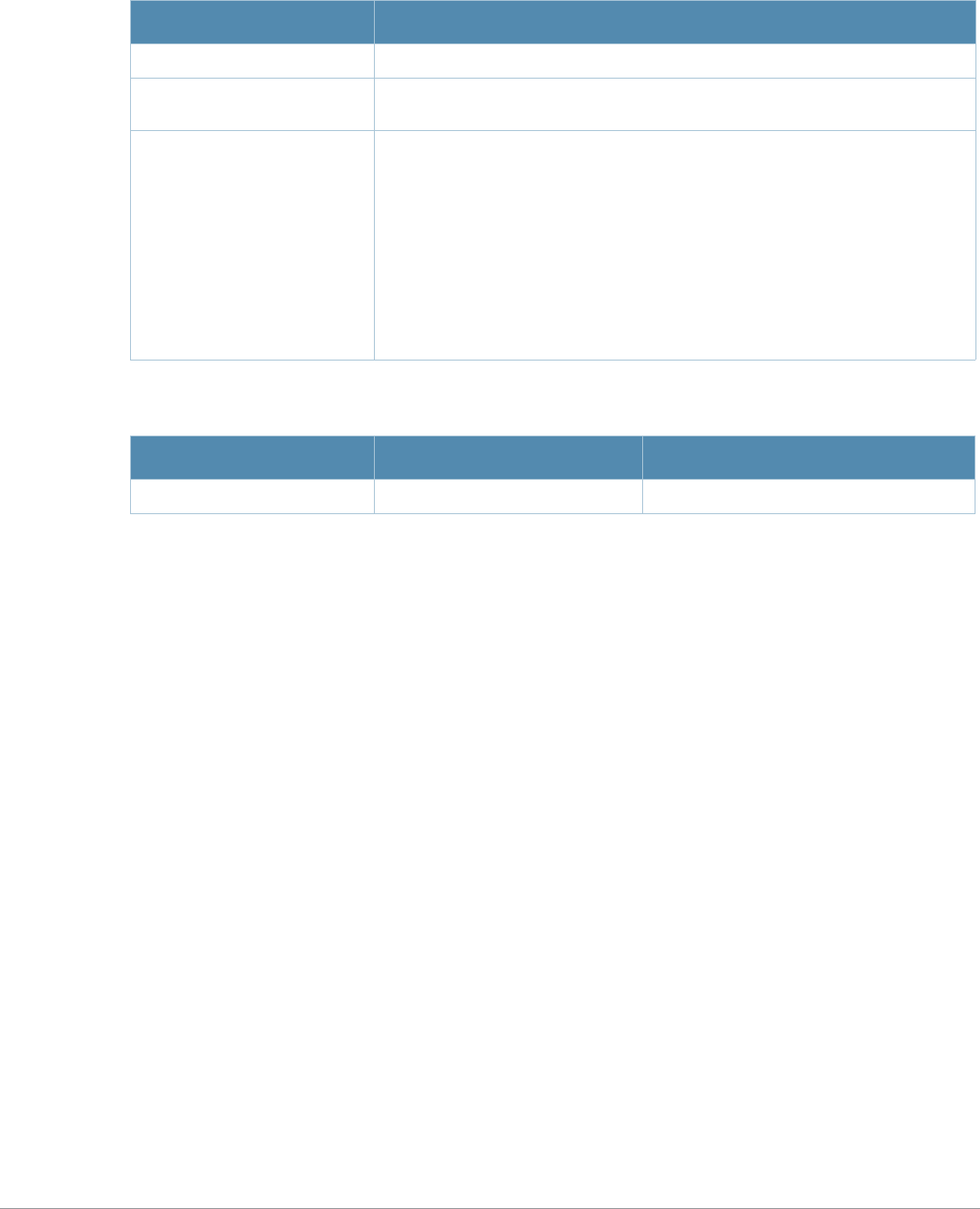
AOS-W 3.4.1 Command Line Interface | Reference Guide show ap provisioning | 657
Command History
Command Information
Release Modification
AOS-W 3.0 Command introduced
AOS-W 3.2 Introduced support for mesh parameters, additional antenna parameters, and AP
location parameters.
AOS-W 3.4 Introduced support for the following parameters:
zInstallation
zMesh SAE
zUSB User Name
zUSB Password
zUSB Device Type
zUSB Device Identifier
zUSB Dial String
zUSB Initialization String
zUSB TTY device path
Platforms Licensing Command Mode
All platforms Base operating system Enable or Config mode on master switches

658 | show ap radio-database AOS-W 3.4.1 Command Line Interface | Reference Guide
show ap radio-database
show ap radio-database [band a|g] [group <group>] [mode access-point|air-
monitor|disabled|ht|ht-40mhz|legacy|sap-monitor] [sort-by ap-group|ap-ip|ap-name|ap-
type|switch-ip] [sort-direction ascending|descending] [start <start>] [switch <switch-
ip-addr>]
Description
Show radio information for Access Points visible to this switch.
Syntax
Parameter Description
band Show only APs with a radio operating in the specified band.
aShow only APs with a radio operating in the 802.11a band (5 GHz).
gShow only APs with a radio operating in the 802.11g band (2.4 GHz).
group <group> Show only APs associated with the specified AP group
mode Show only APs with a radio operating in the specified mode.
access-point Show only APs operating as access points
air-monitor Show only APs operating as air monitors.
disabled Show only disabled APs.
ht Show only high-throughput APs.
ht-40mhz Show only 40 Mhz high-throughput APs
legacy Show only legacy (not high-throughput) APs.
sap-monitor Show only APs operating as SAP monitors
sort-by Sort the output of this command by a specific data column
ap-group Sort the output of this command by AP group name
ap-ip Sort the output of this command by AP IP address
ap-name Sort the output of this command by AP name
ap-type Sort the output of this command by AP model type.
switch-ip Sort the output of this command by switch ip address
sort-direction Select a sort direction for the output of this command
ascending Sort the output in ascending order.
descending Sort the output in descending order.
start Start displaying the output of this command at a chosen index number by entering
the index number of the AP at which command output should start.
switch <switch-ip-
addr>
Display information for APs associated with a specific switch by entering the IP
address of that switch.

AOS-W 3.4.1 Command Line Interface | Reference Guide show ap radio-database | 659
Example
The output of the command shows that the AP is aware of five other access points, three of which are
active.
The output of this command includes the following information:
Command History
Introduced in AOS-W 3.0.
Command Information
(host) #show ap radio-database
AP Radio Database
-----------------
Name Group AP Type IP Address Status Flags Switch IP 11g Mode/Chan/EIRP/Cli 11a Mode/Chan/EIRP/Cli
---- ----- ------- ---------- ------ ----- --------- ---------------------- ----------------------
mp3 default 125 10.3.129.96 Up 14h:45m:0s M 10.3.129.232 AP(HT)/10/0/0 AP(HT)/100/4/0
sw-ad-ap124-11 default 124 10.3.129.99 Up 14h:43m:18s M 10.3.129.232 AP(HT)/10/0/0 AP(HT)/100+/2/0
sw-ad-ap125-13 default 125 10.3.129.98 Up 14h:49m:36s M 10.3.129.232 AP(HT)/10/2.5/0 AP(HT)/100/4/0
sw-ad-ap65-19 default 65 10.3.129.95 Down 10.3.129.232
Flags: U = Unprovisioned; N = Duplicate name; G = No such group; L = Unlicensed
R = Remote AP; I = Inactive; X = Maintenance Mode; P = PPPoE AP; B = Built-in AP
S = RFprotect Sensor; d = Disconnected Sensor; H = Using 802.11n license
M = Mesh node; Y = Mesh Recovery
Column Description
Name Name of the AP.
Group AP group to which the AP is associated.
AP Type AP model type.
IP address IP address of the AP.
Status Current AP status. If the AP is currently up, this data column also shows the
amount of time for which the AP has been active.
Flags This column displays a letter that corresponds to some type of additional
information for the AP. The key to the list of possible flags appears at the
bottom of the output of this command.
Switch IP IP address of the AP’s switch.
11g Mode/Chan/EIRP/Cli 802.1g radio type and mode/802.11g radio channel used by the AP/current
Effective Isotropic Radiated Power (EIRP)/Number of Clients associated
with the radio
11a Mode/Chan/EIRP/Cli 802.1a radio type and mode/802.11a radio channel used by the AP/current
Effective Isotropic Radiated Power (EIRP)/Number of Clients associated
with the radio.
Platforms Licensing Command Mode
All platforms Base operating system Enable or Config mode on master switches
660 | show ap remote counters AOS-W 3.4.1 Command Line Interface | Reference Guide
show ap remote counters
show ap remote counters {ap-name <ap-name>}|{bssid <bssid>}|{ip-addr <ip-addr>}
Description
Show the numbers of message counters for Remote APs
Syntax
Examples
Use this command to determine the number of message counters recorded for each counter type seen by
the remote AP. The output of the command in the example below shows counters for Remote AP State and
VoIP CAC State Announcements.
The output of this command includes the following information:
Command History
Introduced in AOS-W 3.0.
Command Information
Parameter Description
ap-name <ap-name> Show data for an AP with a specific name.
bssid <bssid> Show data for a specific Basic Service Set Identifier (BSSID) on an AP. You must
specify an AP’s BSSID, which is usually the AP’s MAC address
ip-addr <ip-addr> Show data for an AP with a specific IP address.
Column Description
Name Name of the counter type.
Value Number of counters recorded since the AP was last reset.
Platforms Licensing Command Mode
All platforms Base operating system Enable or Config mode on master switches
(host) #show ap remote counters ap-name al22
Counters
--------
Name Value
---- -----
Remote AP State 62851
VoIP CAC State Announcement 13605
AOS-W 3.4.1 Command Line Interface | Reference Guide show ap remote debug flash-config | 661
show ap remote debug flash-config
show ap remote debug flash-config {ap-name <ap-name>|bssid <bssid>|ip-addr <ip-addr>}
acls|{vap <vap>|vaps
Description
Show the remote AP configuration stored in flash memory.
Syntax
Example
The output of this command can be used to debug problems with a remote AP. The command below shows
statistics for an AP with the IP address 192.0.2.64.
Parameter Description
ap-name <ap-name> Show debugging data for an AP with a specific name.
bssid <bssid> Show data for a specific Basic Service Set Identifier (BSSID) on an AP. The Basic
Service Set Identifier (BSSID) is usually the AP’s MAC address.
ip-addr <ip-addr> Show data for an AP with a specific IP address by entering its IP address in dotted-
decimal format.
acls Display ACLs of offline Virtual APs (VAPs).
vap <vap> Display the configuration of a specific offline VAP by entering the name of an VAP.
vaps Display the current number of offline VAPs.
(host) #show ap remote debug flash-config ip-addr 192.0.2.64 acls
Offline ACLs
------------
Item Value
---- -----
Native VLAN 1
DHCP VLAN N/A
DHCP ADDR 192.168.11.1
DHCP POOL NETMASK 255.255.255.0
DHCP POOL START 192.168.11.2
DHCP POOL END 192.168.11.254
DHCP DNS SERVER 0.0.0.0
DHCP ROUTER 192.168.11.1
DHCP DNS DOMAIN mycompany
DHCP LEASE 0
Session ACL N/A
Session ACL Name N/A
Session ACL Count N/A
Session Aces N/A
ACL 1 1
ACL 1 Name logon
ACL 1 Count 21
Aces 1 16 1 4294
...
662 |show ap remote debug flash-config AOS-W 3.4.1 Command Line Interface | Reference Guide
The output of this command includes the following information:
Command History
Introduced in AOS-W 3.0.
Command Information
Column Description
Native VLAN VLAN ID of the native VLAN.
DHCP VLAN VLAN ID of Remote AP DHCP server used when the switch is unreachable.
DHCP ADDR IP Address used as DHCP Server Identifier.
DHCP POOL NETMASK Netmask of the DHCP server pool.
DHCP POOL START IP Address used as the start of a range of addresses for a DHCP pool.
DHCP POOL END IP Address used as the end of a range of addresses for a DHCP pool.
DHCP DNS SERVER IP Address for the DHCP DNS server.
DHCP ROUTER IP Address for the DHCP default router.
DHCP DNS DOMAIN Domain name for the DHCP DNS server.
DHCP LEASE Length of DHCP DNS leases in days. If this parameter displays a zero (0) the DHCP
lease is has no defined end.
Session ACL Name of the ACL applied to the user session.
Session ACL name Name of the ACL applied to the user session.
Session ACL count Number of rules in the applied to the user session.
Session Aces A list of the individual rules in the session ACL.
ACL 1 This parameter shows the position of an individual ACL.
ACL1 Name Name of the ACL in the first position.
ACL1 Count Number of rules in the specified ACL.
ACL1 Aces A list of the individual rules in the specified ACL.
Platforms Licensing Command Mode
All platforms Base operating system Enable or Config mode on master switches

AOS-W 3.4.1 Command Line Interface | Reference Guide show ap remote debug mgmt-frames | 663
show ap remote debug mgmt-frames
show ap remote debug mgmt-frames {ap-name <ap-name>}|{bssid <bssid>|{ip-addr <ip-addr>}
[client-mac <client-mac>] [count <count>]
Description
Show traced 802.11 management frames for a remote AP.
Syntax
Examples
Use this command to debug 802,1 authentication on a remote AP. The example below shows that a client
successfully associated with the remote AP, then was later deauthenticated.
The output of this command includes the following information:
Parameter Description
ap-name <ap-name> Show debugging information for a specific AP.
bssid <bssid> Show debugging information for a specific Basic Service Set Identifier (BSSID). The
Basic Service Set Identifier (BSSID) is usually the AP’s MAC address
ip-addr Show debugging information for an AP with a specific IP address by entering its IP
address in dotted-decimal format.
client-mac Show the AP associations for a specific MAC address by entering the MAC address
of the client.
count <count> Limit the amount of information displayed by specifying number of frames to appear
in the output of this command.
(host) #show ap remote debug mgmt-frames ap-name AP32
Traced 802.11 Management Frames
-------------------------------
Timestamp stype SA DA BSS signal Misc
--------- ----- -- -- --- ------ ----
Oct 30 11:20:19 deauth 00:23:6c:2f:9a:85 00:1a:1e:11:56:40 00:1a:1e:11:56:40 0 STA has left and is deauthenticated
Oct 30 11:04:39 assoc-resp 00:1a:1e:11:56:40 00:23:6c:2f:9a:85 00:1a:1e:11:56:40 15 Success
Oct 30 11:04:39 assoc-req 00:23:6c:2f:9a:85 00:1a:1e:11:56:40 00:1a:1e:11:56:40 0 -
Column Description
Timestamp The time the management frame was sent
stype One of the following 802.11 frame types:
auth: Authorization frame
deauth: Deauthorization frame
assoc-resp: Association response
assoc-req: Association request
SA Source MAC address.
DA Destination MAC address.
BSS Basic Service Set Identifier (BSSID) of the AP
signal Signal strength as a signal to noise ratio. For example, a value of 30 would indicate
that the power of the received signal is 30 dBm above the signal noise threshold.
Misc Additional information describing the client’s action.

664 | show ap remote debug mgmt-frames AOS-W 3.4.1 Command Line Interface | Reference Guide
Command History
Introduced in AOS-W 3.0.
Command Information
Platforms Licensing Command Mode
All platforms Base operating system Enable or Config mode on master switches
AOS-W 3.4.1 Command Line Interface | Reference Guide show ap spectrum-load-balancing | 665
show ap spectrum-load-balancing
show ap spectrum-load-balancing [group <group>]
Description
Show spectrum load balancing information for an AP with this feature enabled.
Syntax
Examples
The output of the command below shows the APs currently using the spectrum load-balancing domain
default-1.
The output of this command includes the following information:
Command History
Introduced in AOS-W 3.3.2.14.
Command Information
Parameter Description
group <group> Filter this information to show only data for the specified spectrum load balancing
domain.
Column Description
Name Name of an AP
IP address AP IP address
Domain Name of the spectrum load balancing domain assigned to the AP
Assignment Current channel and power assignment for the AP.
Clients Number of clients currently using the AP.
Platforms Licensing Command Mode
All platforms Base operating system Enable or Config mode on master switches
(host) #show ap spectrum-load-balancing group default-1
Spectrum Load Balancing Group
-----------------------------
Name IP Address Domain Assignment Clients
---- ---------- ------ ---------- -------
ap121-1 192.168.151.253 default-1 149/21 3
ap124-1 192.168.151.254 default-1 48/15 3
ap125-1 192.168.151.251 default-1 44/15 2
666 | show ap system-profile AOS-W 3.4.1 Command Line Interface | Reference Guide
show ap system-profile
show ap system-profile <profile>
Description
Show an AP’s system profile settings.
Syntax
Examples
The output of the command below shows the current configuration settings for the default system profile.
The output of this command includes the following information:
Parameter Description
<profile> Name of a system profile.
Column Description
LMS IP The IP address of the local management switch (LMS)—the Alcatel-Lucent switch
which is responsible for terminating user traffic from the APs, and processing and
forwarding the traffic to the wired network.
Backup LMS IP For multi-switch networks, this parameter displays the IP address of a backup to the
IP address specified with the lms-ip parameter.
LMS Preemption When this parameter is enabled, the local management switch automatically reverts
to the primary LMS IP address when it becomes available.
LMS Hold-down Period Time, in seconds, that the primary LMS must be available before an AP returns to
that LMS after failover.
(host) #show ap system profile default
AP system profile "default"
---------------------------
Parameter Value
--------- -----
LMS IP 192.0.2.90
Backup LMS IP N/A
LMS Preemption Disabled
LMS Hold-down Period 600 sec
Master controller IP address N/A
LED operating mode (AP-12x only) normal
RF Band a
Double Encrypt Disabled
Native VLAN ID 1
SAP MTU N/A
Bootstrap threshold 7
Request Retry Interval 10 sec
Maximum Request Retries 10
Keepalive Interval 60 sec
Dump Server 192.0.2.41
Telnet Enabled
SNMP sysContact N/A
RFprotect Server IP N/A
RFprotect Backup Server IP N/A
AeroScout RTLS Server 192.0.2.32.104:1411
RTLS Server configuration N/A
Heartbeat DSCP 0
Session ACL N/A
Corporate DNS Domain N/A
Maintenance Mode Disabled

AOS-W 3.4.1 Command Line Interface | Reference Guide show ap system-profile | 667
Command History
Introduced in AOS-W 3.0.
Command Information
Master switch IP
address
For multi-switch networks, this parameter displays the IP address of the master
switch.
LED operating mode
(AP-12x only)
Displays the LED operating mode for OAW-AP120 series APs. LEDs display as
usual in the default normal operating mode, but are all turned off in off mode.
RF Band For dual-band radios, this parameter displays the RF band in which the AP should
operate:
zg = 2.4 GHz
za = 5 GHz
Double Encrypt This parameter applies only to remote APs. Double encryption is used for traffic to
and from a wireless client that is connected to a tunneled SSID. When enabled, all
traffic is re-encrypted in the IPsec tunnel. When disabled, the wireless frame is only
encapsulated inside the IPsec tunnel.
Native VLAN ID Native VLAN for bridge mode virtual APs (frames on the native VLAN are not tagged
with 802.1q tags).
SAP MTU Maximum Transmission Unit (MTU) size, in bytes. This value describes the greatest
amount of data that can be transferred in one physical frame.
Bootstrap threshold Number of consecutive missed heartbeats on a GRE tunnel (heartbeats are sent
once per second on each tunnel) before an AP rebootstraps. On the switch, the GRE
tunnel timeout is 1.5 x bootstrap-threshold; the tunnel is torn down after this number
of seconds of inactivity on the tunnel.
Dump Server (For debugging purposes.) Displays the server to receive the core dump generated if
an AP process crashes.
Telnet Reports whether telnet access the AP is enabled or disabled.
SNMP sysContact SNMP system contact information.
RFprotect Server IP The IP address of the RFprotect server for this AP or group
RFprotect Backup
Server IP
The IP address of the RFprotect backup server for this AP or group
AeroScout RTLS Server IP address of an AeroScout real-time asset location (RTLS) server.
Heartbeat DSCP DSCP value of AP heartbeats (0-63).
Session ACL Shows the access control list (ACL) applied on the uplink of a remote AP.
Corporate DNS Domain DNS name used by the corporate network.
Maintenance Mode Shows if Maintenance mode is enabled or disabled. If enabled, APs stop flooding
unnecessary traps and syslog messages to network management systems or
network operations centers when deploying, maintaining, or upgrading the network.
The switch still generates debug syslog messages if debug logging is enabled.
Platforms Licensing Command Mode
All platforms Base operating system Enable or Config mode on master switches
Column Description
668 | show ap tech-support AOS-W 3.4.1 Command Line Interface | Reference Guide
show ap tech-support
show ap tech-support ap-name <name> [<filename>]
Description
Display all information for an AP, or save that information to a file on the switch. This information can be
used by Alcatel-Lucent technical support to diagnose a problem with an AP.
Syntax
Usage Guidelines
This is an internal technical support command. Alcatel-Lucent technical support may request that you issue
this command to help analyze and troubleshoot problems with an AP or your wireless network.
Command History
Introduced in AOS-W 3.0.
Command Information
Parameter Description
<name> Name of the AP for which you want to view tech support data.
<filename> Save the output of this command into a file on the switch with the specified
filename.
Platforms Licensing Command Mode
All platforms Base operating system Enable or Config mode on master switches
AOS-W 3.4.1 Command Line Interface | Reference Guide show ap vlan-usage | 669
show ap vlan-usage
show ap vlan-usage [{ap-name <ap-name>}|{bssid <bssid>|{essid <essid>|{ip-addr <ip-
addr>}]
Description
Show the numbers of clients on each vlan.
Syntax
Examples
The output of this command displays the VLAN Usage table. Include the optional
The output of this command includes the following information:
Command History
Introduced in AOS-W 3.0.
Command Information
Parameter Description
ap-name <ap-name> Show VLAN data for an AP with a specific name.
bssid <bssid> Show VLAN data for a specific Basic Service Set Identifier (BSSID) on an AP. The
Basic Service Set Identifier (BSSID) is usually the AP’s MAC address.
essid <essid> Show VLAN data for a specific Extended Service Set Identifier (ESSID). An Extended
Service Set Identifier (ESSID) is a alphanumeric name that uniquely identifies the
Service Set Identifier (SSID).
ip-addr <ip-addr> Show VLAN data for an AP with a specific IP address by entering an IP address in
dotted-decimal format.
Column Description
VLAN ID ID number of the wireless VLAN
Clients Number of clients currently using the specified VLAN.
Platforms Licensing Command Mode
All platforms Base operating system Enable or Config mode on master switches
(host) #show ap vlan
VLAN Usage Table
----------------
VLAN ID Clients
------- -------
64 1
65 32
66 44
670 | show ap wired-ap-profile AOS-W 3.4.1 Command Line Interface | Reference Guide
show ap wired-ap-profile
show ap wired-ap-profile [<profile>]
Description
Show a list of all wired AP profiles, or display the configuration parameters in a specific wired AP profile.
Syntax
Usage Guidelines
The command show ap wired-ap-profile displays a list of all wired AP profiles, including the number of
references to each profile and the profile status. If you include the optional <profile> parameter, the
command will display detailed information for that one profile.
Example
The output of this command shows the configuration parameters for the wired AP profile “default”.
The output of this command includes the following information:
Parameter Description
<profile> Name of a wired AP profile.
Column Description
Wired AP enable Indicates whether the wired AP profile is enabled or disabled.
Forward mode The configured forward mode for the profile.
zbridge: Bridge locally
zsplit-tunnel: Tunnel to switch or NAT locally
ztunnel: Tunnel to switch
Switchport mode The profile’s switching mode.
zaccess: Set access mode characteristics of the interface.
zmode: Set trunking mode of the interface.
ztrunk: Set trunk mode characteristics of the interface.
Access mode VLAN VLAN ID of the access mode VLAN.
Trunk mode native VLAN VLAN ID of the native VLAN.
Trunk mode allowed VLANs Range of allowed VLAN IDs for the native VLAN.
(host) #show ap wired-ap-profile default
Wired AP profile "default"
--------------------------
Parameter Value
--------- -----
Wired AP enable Disabled
Forward mode tunnel
Switchport mode access
Access mode VLAN 1
Trunk mode native VLAN 1
Trunk mode allowed VLANs 1-4094
Trusted Not Trusted
Broadcast Broadcast
AOS-W 3.4.1 Command Line Interface | Reference Guide show ap wired-ap-profile | 671
Command History
Introduced in AOS-W 3.0.
Command Information
Trusted Shows if the wired port on an AP using this profile is a trusted port.
Possible values are Trusted or Not Trusted.
Broadcast If set to broadcast, the wired AP port will forward broadcast traffic. If the
parameter displays Do Not Broadcast, broadcast traffic will not be
forwarded.
Platforms Licensing Command Mode
All platforms Base operating system Enable or Config mode on master switches
Column Description
672 | show ap wmm-flow AOS-W 3.4.1 Command Line Interface | Reference Guide
show ap wmm-flow
show ap wmm-flow [{ap-name <ap-name>}|{bssid <bssid>}|{essid <essid>}|{ip-addr <ip-
addr>}] dotlla|dotllg
Description
Show the Wireless Multimedia (WMM) flow table.
Syntax
Usage Guidelines
WMM, or Wireless Multimedia Extensions, are a subset of the 802.11e standard. WMM provides for four
different types of traffic classification: voice, video, best effort, and background, with voice having the
highest priority and background the lowest. Issue the show ap wmm-flow command to view WMM flow
data for all APs. Include any of the optional parameters described in the table above to filter the table by a
specific AP, radio channel (a or g), or both an ap and radio type.
Example
The example below shows WMM flow data for all APs.
The output of this command includes the following parameters:
Parameter Description
ap-name <ap-name> View an AP with a specified name.
bssid <bssid> View data for an AP with a specific BSSID (Basic Service Set Identifier). The Basic
Service Set Identifier (BSSID) is usually the AP’s MAC address.
essid <essid> View data for a specific ESSID (Extended Service Set Identifier). An Extended
Service Set Identifier (ESSID) is a alphanumeric name that uniquely identifies the
Service Set Identifier (SSID).
ip-addr <ip-addr> View an AP with a specified IP address by entering an IP address in dotted-decimal
format.
dot11a Show the WMM flow table for a 802.11a radio.
dot11g Show the WMM flow table for a 802.11g radio.
(host) #show ap wmm-flow
WMM Flow Table
--------------
AP Name ESSID Client Description
------- ----- ------ -----------
AP125-srk NOE 00:90:7a:06:1f:5b tsid 6:prio 6:inactivity 2157352960 us:bidir:apsd:normalack:tclas prio 6 ip DIP-
192.168.101.194 DP-32514 DSCP-48:one-match
AP125-srk NOE 00:90:7a:06:1f:5b tsid 0:prio 0:inactivity 100000000 us:bidir:apsd:normalack:no-match
Num Flows:0
Column Description
AP name Name of an AP with recorded WMM flows
ESSID Extended Service Set Identifier (ESSID) of a wireless network.
Client MAC address of the client.
AOS-W 3.4.1 Command Line Interface | Reference Guide show ap wmm-flow | 673
Command History
Introduced in AOS-W 3.0.
Command Information
Description The description is a long string that includes the following information.
zTSID: The transmitting subscriber identification number. The TSID should match
the priority level for each flow.
zPriority: One of the following IEEE 802.1p priority values:
0-1 = Best Effort
2-3 = Background
4-5 = Video
6-7 = Voice
zInactivity: Tspec inactivity threshold, in microseconds.
z<country code>: AP country code, e.g. US.
zbdir: flow is bidirectional.
zapsd: flow has enabled auto power save delivery.
z<ack>: Displays the ack policy negotiated for the flow. Possible values are:
normalack
noack
blockack
resack (reserved ack)
zDIP: Destination IP address for the flow.
zDP: Destination IP Port specified in the TCLAS for flow negotiation.
zDCSP: The Differentiated Services Code Point (DSCP) priority value that
matches the flows 802.1p priority.
Platforms Licensing Command Mode
All platforms Base operating system Enable or Config mode on master switches
Column Description

674 | show ap wmm-flow AOS-W 3.4.1 Command Line Interface | Reference Guide

AOS-W 3.4.1 Command Line Interface | Reference Guide show ap-group | 675
show ap-group
show ap-group [<ap-group>]
Description
Show settings for an AP group.
Syntax
Usage Guidelines
Issue this command without the optional <ap-group> parameter to display the entire AP group list,
including profile status for each profile. Include an AP group name to display detailed configuration
information for that AP group profile.
Example
This first example shows that the switch has nine configured AP groups. The Name column lists the names
of all configured AP groups. the Profile Status column indicates whether the AP group is predefined.
(User-defined profiles will not have an entry in the Profile Status column.)
Parameter Description
<ap-group> The name of an AP group.
(host) #show ap-group
AP group List
-------------
Name Profile Status
---- --------------
corp-office
branch-office-am
corp
corp1
Corp1-AM
Corp1-AM-Ch11
Corp1-AM-Ch6
corp1-AP85
corp1-lab
Total: 9

676 | show ap-group AOS-W 3.4.1 Command Line Interface | Reference Guide
Include an AP group name to display a complete list of configuration settings for that profile. The example
below shows settings for the AP group corp1.
The output of this command includes the following parameters:
Related Commands
(host) #show ap-group corp1
AP group "corp1"
-------------------
Parameter Value
--------- -----
Virtual AP corp1-guest
Virtual AP corp1-wpa2
802.11a radio profile default
802.11g radio profile profile1-g
Wired AP profile default
Ethernet interface 0 link profile default
Ethernet interface 1 link profile default
AP system profile corp1344
VoIP Call Admission Control profile default
802.11a Traffic Management profile N/A
802.11g Traffic Management profile N/A
Regulatory Domain profile corp1344-channel-profile
SNMP profile default
RF Optimization profile handoff-aggressive
RF Event Thresholds profile default
IDS profile ids-low-setting
Mesh Radio profile default
Mesh Cluster profile N/A
Parameter Description
Virtual AP Virtual AP profile that which configures a specified WLAN.
802.11a radio profile Profile that defines 802.11a radio settings for the AP group.
802.11g radio profile Profile that defines 802.11g radio settings for the AP group.
Wired AP profile Profile that defines wired port settings for APs assigned to the AP group.
Ethernet interface 0 link profile Profile that defines the duplex and speed of the Ethernet 0 interface on the AP.
Ethernet interface 1 link profile Profile that defines the duplex and speed of the Ethernet 0 interface on the AP.
AP system profile Name of the AP system profile for the AP group.
VoIP Call Admission Control profile Name of the AP system profile for the AP group.
802.11a Traffic Management
profile Name of the 802.11a WLAN traffic management profile for the AP group.
802.11g Traffic Management
profile Name of the 802.11g WLAN traffic management profile for the AP group.
Regulatory Domain profile Name of the regulatory domain profile for the AP group.
SNMP profile Name of the SNMP profile for the AP group.
RF Optimization profile Name of the RF optimization profile for the AP group.
RF Event Thresholds profile Name of the RF event thresholds profile for the AP group.
IDS profile IDS profile for the AP group.
Mesh Radio profile Mesh radio profile assigned to the AP group.
Mesh Cluster profile Mesh cluster profile assigned to the AP group.

AOS-W 3.4.1 Command Line Interface | Reference Guide show ap-group | 677
Configure AP group settings using the command ap-group.
Command History
This command was available in AOS-W 3.0.
Command Information
Platforms Licensing Command Mode
All platforms Base operating system Enable or Config mode on master switches

678 | show ap-group AOS-W 3.4.1 Command Line Interface | Reference Guide
AOS-W 3.4.1 Command Line Interface | Reference Guide show ap-name | 679
show ap-name
show ap-name [<ap-name>]
Description
Show a list of AP names. Include the <ap-name> parameter to display detailed configuration information
for that AP.
Syntax
Example
This first example shows that the switch has eight registered APs . The Name column lists the names of
each registered AP. Note that APs are all user-defined, so they will not have an entry in the Profile Status
column.
Parameter Description
<ap-name> The name of an AP.
(host) #show ap-group
AP name List
------------
Name Profile Status
---- --------------
mp3
sw-ad-ap124-11
sw-ad-ap125-13
sw-ad-ap125-15
sw-ad-ap125-17
sw-ad-ap125-18
sw-ad-ap125-19
sw-ad-ap125-3
Total: 8
680 |show ap-name AOS-W 3.4.1 Command Line Interface | Reference Guide
Include an AP name to display a complete list of configuration settings for that AP. If the AP has default
settings, the value may appear as N/A. The AP in the example below has all default profile settings
The output of this command includes the following parameters:
(host) #show ap-group corp1
AP name "mp3"
-------------
Parameter Value
--------- -----
Virtual AP N/A
Excluded Virtual AP N/A
802.11a radio profile N/A
802.11g radio profile N/A
Wired AP profile N/A
Ethernet interface 0 link profile N/A
Ethernet interface 1 link profile N/A
AP system profile N/A
VoIP Call Admission Control profile N/A
802.11a Traffic Management profile N/A
802.11g Traffic Management profile N/A
Regulatory Domain profile N/A
RF Optimization profile N/A
RF Event Thresholds profile N/A
IDS profile N/A
Mesh Radio profile N/A
Mesh Cluster profile N/A
Excluded Mesh Cluster profile N/A
Parameter Description
Virtual AP Virtual AP profile that which configures a specified WLAN.
Excluded Virtual AP Excludes the specified mesh cluster profile from this AP.
802.11a radio profile Profile that defines 802.11a radio settings for the AP.
802.11g radio profile Profile that defines 802.11g radio settings for the AP .
Wired AP profile Profile that defines wired port settings for APs assigned to the AP .
Ethernet interface 0 link profile Profile that defines the duplex and speed of the Ethernet 0 interface on the AP.
Ethernet interface 1 link profile Profile that defines the duplex and speed of the Ethernet 0 interface on the AP.
AP system profile Name of the AP system profile for the AP.
VoIP Call Admission Control
profile Name of the AP system profile for the AP.
802.11a Traffic Management
profile Name of the 802.11a WLAN traffic management profile for the AP group.
802.11g Traffic Management
profile Name of the 802.11g WLAN traffic management profile for the AP.
Regulatory Domain profile Name of the regulatory domain profile for the AP.
RF Optimization profile Name of the RF optimization profile for the AP.
RF Event Thresholds profile Name of the RF event thresholds profile for the AP.
IDS profile IDS profile for the AP.
Mesh Radio profile Mesh radio profile assigned to the AP.
AOS-W 3.4.1 Command Line Interface | Reference Guide show ap-name | 681
Related Commands
Configure AP settings using the command ap-name.
Command History
This command was available in AOS-W 3.0.
Command Information
Mesh Cluster profile Mesh cluster profile assigned to the AP.
Excluded Mesh Cluster profile Excludes the specified mesh cluster profile from this AP.
Parameter Description
Platforms Licensing Command Mode
All platforms Base operating system Enable or Config mode on master and local
switches

682 |show ap-name AOS-W 3.4.1 Command Line Interface | Reference Guide

AOS-W 3.4.1 Command Line Interface | Reference Guide show arp | 683
show arp
show arp
Description
Show Address Resolution Protocol (ARP) entries for the switch.
Syntax
No parameters
Example
This example shows configured static ARP entries for the switch.
The output of this command includes the following parameters:
Related Commands
Add a static Address Resolution Protocol (ARP) entry using the command show arp.
Command History
This command was available in AOS-W 3.0.
Command Information
(host) #show arp
Protocol Address Hardware Address Interface
Internet 10.3.129.98 00:1A:1E:C0:80:28 vlan1
Internet 10.3.129.253 00:0B:86:42:35:80 vlan1
Internet 10.3.129.250 00:1A:92:45:DB:00 vlan1
Internet 10.3.129.99 00:1A:1E:C0:1C:60 vlan65
Internet 10.3.129.96 00:1A:1E:C0:80:1E vlan65
Internet 10.3.129.254 00:0B:86:02:EE:00 vlan1
Parameter Description
Protocol Protocol using ARP. Although the switch will most often use ARP to translate IP
addresses to Ethernet MAC addresses, ARP may also be used for other
protocols, such as Token Ring, FDDI, or IEEE 802.11, and for IP over ATM.
Address IP address of the device.
Hardware Address MAC address of the device.
Interface Interface used to send ARP requests and replies.
Platforms Licensing Command Mode
All platforms Base operating system Enable and Config mode on master and
local switches

684 |show arp AOS-W 3.4.1 Command Line Interface | Reference Guide
AOS-W 3.4.1 Command Line Interface | Reference Guide show audit-trail | 685
show audit-trail
show audit-trail {<number>]
Description
Show the switch’s audit trail log.
Syntax
Example
By default, the audit trail feature is enabled for all commands in configuration mode. The example below
shows the most recent ten audit log entries for the switch.
Related Commands
Enable or disable the audit trail feature using the command audit-trail.
Command History
This command was available in AOS-W 3.0.
Command Information
Parameter Description
<number> Start displaying the log output from the specified number of lines from the end of
the log.
(host) # show audit-trail 10
Feb 5 06:13:17 cli[1239]: USER: admin has logged in from 10.240.16.118.
Feb 5 06:20:13 cli[1239]: USER: admin connected from 10.240.16.118 has logged out.
Feb 5 06:24:37 cli[1239]: USER: admin has logged in from 10.240.16.118.
Feb 5 06:37:01 cli[1239]: USER:admin@10.3.129.250 COMMAND:<wlan virtual-ap "mp-only" no vap-enable > -- command
executed successfully
Feb 5 06:37:14 cli[1239]: USER:admin@10.3.129.250 COMMAND:<wlan virtual-ap "mp-a-only" no vap-enable > -- command
executed successfully
Feb 5 06:37:20 cli[1239]: USER:admin@10.3.129.250 COMMAND:<wlan virtual-ap "default" no vap-enable > -- command
executed successfully
Feb 5 06:37:29 cli[1239]: USER:admin@10.3.129.250 COMMAND:<wlan virtual-ap "mpp-a-only" no vap-enable > -- command
executed successfully
Feb 5 06:46:10 cli[1239]: USER:admin@10.3.129.250 COMMAND:<interface gigabitethernet "1/2" port monitor
igigabitethernet "1/1" > -- command executed successfully
Feb 5 06:57:44 cli[1239]: USER:admin@10.3.129.250 COMMAND:<ap system-profile "default" heartbeat-dscp 12 > -- command
executed successfully
Feb 5 07:05:48 cli[1239]: USER:admin@10.3.129.250 COMMAND:<wlan virtual-ap "mp-a-only" vap-enable > -- command executed
successfully
Platforms Licensing Command Mode
All platforms Base operating system Available in Enable and Config modes.
Audit trails can only be enabled on master
switches

686 | show audit-trail AOS-W 3.4.1 Command Line Interface | Reference Guide
AOS-W 3.4.1 Command Line Interface | Reference Guide show auth-tracebuf | 687
show auth-tracebuf
show auth-tracebuf [count <1-250] [failures] [mac <address>]
Description
Show the trace buffer for authentication events.
Syntax
Usage Guidelines
Use the output of this command to troubleshoot 802.1x authentication errors. Include the <address>
parameter to filter data by the MAC address of the client which is experiencing errors. This command can
tell you, for example, when 802.1x authentication completed and when keys were plumbed correctly.
Example
The example below shows the most recent ten trace buffer entries for the switch. Each row shows a
timestamp that indicates when the entry was created, the type of exchange that was made, the direction the
packet was sent, and the source and destination MAC addresses.
Command History
This command was available in AOS-W 3.0.
Parameter Description
count <1-250> limit the output of the command to the specified number of packets.
failures Filter the output of this command to display only authentication failures
mac <address> Filter the output of this command to display only information for a specified MAC
address.
(host) # show auth-buffer 10
Auth Trace Buffer
-----------------
Feb 5 08:08:29 wpa2-key2 -> 00:09:ef:05:1e:b2 00:1a:1e:97:e5:42 - 119 mic failure
Feb 5 08:08:30 wpa2-key1 <- 00:09:ef:05:1e:b2 00:1a:1e:97:e5:42 - 117
Feb 5 08:08:30 wpa2-key2 -> 00:09:ef:05:1e:b2 00:1a:1e:97:e5:42 - 119 mic failure
Feb 5 08:08:31 wpa2-key1 <- 00:09:ef:05:1e:b2 00:1a:1e:97:e5:42 - 117
Feb 5 08:08:31 station-down * 00:09:ef:05:1e:b2 00:1a:1e:97:e5:42 - -
Feb 5 08:08:31 station-up * 00:09:ef:05:1e:b2 00:1a:1e:97:e5:42 - - wpa2 psk aes
Feb 5 08:08:31 station-data-ready * 00:09:ef:05:1e:b2 00:00:00:00:00:00 66 -
Feb 5 08:08:31 wpa2-key1 <- 00:09:ef:05:1e:b2 00:1a:1e:97:e5:42 - 117
Feb 5 08:08:31 wpa2-key2 -> 00:09:ef:05:1e:b2 00:1a:1e:97:e5:42 - 119 mic failure
Feb 5 08:08:32 wpa2-key1 <- 00:09:ef:05:1e:b2 00:1a:1e:97:e5:42 - 117
Feb 5 08:08:32 wpa2-key2 -> 00:09:ef:05:1e:b2 00:1a:1e:97:e5:42 - 119 mic failure
Feb 5 08:08:33 wpa2-key1 <- 00:09:ef:05:1e:b2 00:1a:1e:97:e5:42 - 117
Feb 5 08:08:33 wpa2-key2 -> 00:09:ef:05:1e:b2 00:1a:1e:97:e5:42 - 119 mic failure
Feb 5 08:08:34 wpa2-key1 <- 00:09:ef:05:1e:b2 00:1a:1e:97:e5:42 - 117
Feb 5 08:08:34 wpa2-key2 -> 00:09:ef:05:1e:b2 00:1a:1e:97:e5:42 - 119 mic failure
Feb 5 08:08:35 wpa2-key1 <- 00:09:ef:05:1e:b2 00:1a:1e:97:e5:42 - 117
Feb 5 08:08:35 station-down * 00:09:ef:05:1e:b2 00:1a:1e:97:e5:42 - -

688 |show auth-tracebuf AOS-W 3.4.1 Command Line Interface | Reference Guide
Command Information
Platforms Licensing Command Mode
All platforms Base operating system Available in Enable or Config modes on
master or local switches

AOS-W 3.4.1 Command Line Interface | Reference Guide show banner | 689
show banner
show banner
Description
Show the current login banner
Syntax
No parameters
Usage Guidelines
Issue this command to review the banner message that appears when you first log in to the switch’s
command-line or browser interfaces.
Example
Related Commands
Configure a banner message using the command banner motd.
Command History
This command was available in AOS-W 3.0.
Command Information
(host) # show banner
This testlab switch is scheduled for maintenance starting Saturday night at 11 p.m.
Platforms Licensing Command Mode
All platforms Base operating system Config or Enable mode on master or local
switches

690 | show banner AOS-W 3.4.1 Command Line Interface | Reference Guide

AOS-W 3.4.1 Command Line Interface | Reference Guide show boot | 691
show boot
show boot
Description
Display boot parameters, including the boot partition and the configuration file to use when booting the
switch.
Syntax
No parameters.
Example
Related Commands
Configure boot parameters using the command boot.
Command History
This command was available in AOS-W 1.0.
Command Information
(host) # show boot
Config File: default.cfg
Boot Partition: PARTITION 1
Platforms Licensing Command Mode
All platforms Base operating system Config or Enable mode on master or local
switches

692 |show boot AOS-W 3.4.1 Command Line Interface | Reference Guide
AOS-W 3.4.1 Command Line Interface | Reference Guide show cellular profile | 693
show cellular profile
show cellular profile [<name>] | [factory]
Description
Display the cellular profiles and profile settings.
Syntax
Usage Guidelines
Issue this command without the <name> parameter to display configuration parameters for the entire list
of available cellular profiles. Include a profile name to display configuration information for that one
profile.
Example
The output of this command displays the Cellular Profile Table. The example below shows eight
preconfigured cellular profiles.
The output of this command includes the following parameters:
Parameter Description
<name> Enter the name of an existing cellular profile
factory Display a list of factory supported cellular profiles.
Parameters Description
Name Name of a cellular profile.
Vend Vendor ID in hexadecimal
Prod USB product ID in hexadecimal
Serial USB device serial number.
Dialer Name of a dialer group profile.
TTY Modem TTY port.
(host) #show cellular profile
Cellular Profile Table
----------------------
Name Vend Prod Serial Dialer Tty Driver Priority Modeswitch
---- ---- ---- ------ ------ --- ------ -------- ----------
Novatel_U720 1410 2110 evdo_us ttyUSB0 option default
Novatel_U727 1410 4100 evdo_us ttyUSB0 option default
Kyocera_KPC680 0c88 180a evdo_us ttyUSB0 option default
Sierra_Compass_597 1199 0023 evdo_us ttyUSB0 sierra default
Pantech_UM175 106c 3714 evdo_us ttyUSB1 option default
Sierra_USBConn_881 1199 6856 gsm_us ttyUSB0 option default
USBConn_Mercury_C885 1199 6880 gsm_us ttyUSB3 option default
Globetrotter_Icon322 0af0 d033 gsm_us ttyHS3 hso default
Default cellular priority: 100
694 | show cellular profile AOS-W 3.4.1 Command Line Interface | Reference Guide
Command History
Introduced in AOS-W 3.4.
Command Information
Driver One of the following cellular modem drivers:
zacm: Linux ACM driver.
zhso: Option High Speed driver.
zoption: Option USB data card driver (default).
zsierra: Sierra Wireless driver.
Priority Displays the cellular profile priority; profiles with the default priority of 100 will
display the word default in the Priority column
Range: 1 to 255.
Default: 100
Modeswitch One of two USB device modeswitch settings:
zeject: Eject the CDROM device.
zrezero: Send SCSI CDROM rezero command.
Parameters Description
Platforms Licensing Command Mode
600 Series Base operating system Config or Enable mode on master or local
switches
AOS-W 3.4.1 Command Line Interface | Reference Guide show clock | 695
show clock
show clock [summer-time|timezone]
Description
Display the system clock.
Syntax
Usage Guidelines
Include the optional summer-time parameter to display configured daylight savings time settings. The
timezone parameter shows the current timezone, with its time offset from Greenwich Mean Time.
Example
The output below shows the current time on the switch clock.
Related Commands
Configure clock settings using the commands clock set, clock summer-time recurring, and clock
timezone.
Command History
This command was available in AOS-W 1.0.
Command Information
Parameter Description
summer-time Show summer (daylight savings) time settings.
timezone Show the configured timezone for the switch.
(host) # show clock
Thu Feb 5 16:52:28 PST 2009
Platforms Licensing Command Mode
All platforms Base operating system Config or Enable mode on master or local
switches

696 |show clock AOS-W 3.4.1 Command Line Interface | Reference Guide
AOS-W 3.4.1 Command Line Interface | Reference Guide show command-mapping | 697
show command-mapping
show command-mapping [reverse]
Description
Show the mapping new commands to deprecated commands.
Syntax
Usage Guidelines
The syntax of many commands changed after the release of AOS-W 3.0. Use this command to display a list
of current commands and their deprecated command equivalents. Include the reverse parameter sort the
output of this table by the deprecated command syntax.
Example
The example below shows part of the output for this command. Note that a single new command may have
replaced several older commands.
Command History
This command was available in AOS-W 3.0.
Command Information
Parameter Description
reverse Sort the command map by deprecated command syntax. This command is useful
to find the current command syntax for a deprecated command.
(host) # show command-mapping
Command Map
-----------
New Command Old Command
----------- -----------
show ap active show wlan ap
show ap arm neighbors show ap arm-neighbors
show ap arm rf-summary show am rf-summary
show ap arm scan-times show am scan-times
show ap arm state show wlan arm
show ap association show stm association
show wlan client
show wlan remote-client
show ap blacklist-clients show stm dos-sta
show ap bss-table show stm connectivity
show ap client status show stm state
show ap coverage-holes show rfsm coverage-holes
show ap database show ap global-list
show sapm ap search
show ap registered
show ap debug association-failure show wlan association-failure
....
Platforms Licensing Command Mode
All platforms Base operating system Config or Enable mode on master or local
switches

698 | show command-mapping AOS-W 3.4.1 Command Line Interface | Reference Guide

AOS-W 3.4.1 Command Line Interface | Reference Guide show configuration | 699
show configuration
show configuration
Description
Show the saved configuration on the switch.
Syntax
No parameters.
Usage Guidelines
Issue this command to view the entire configuration saved on the switch, including all profiles, ACLs, and
interface settings.
Example
The example below shows part of the output for this command.
Command History
This command was available in AOS-W 1.0.
Command Information
(host) # show configuration
version 3.4
enable secret "0078b61601db950378d3d27a33c0b4d61f95b653ce9480a229"
telnet cli
prompt Lab12-800
loginsession timeout 0
hostname "sampleHost"
clock timezone PST -8
banner motd:
This switch is in Lab 12.
location "Building1.floor1"
mms config 0
controller config 1173
ip access-list eth 200
Platforms Licensing Command Mode
All platforms Base operating system Config or Enable mode on master or local
switches

700 | show configuration AOS-W 3.4.1 Command Line Interface | Reference Guide

AOS-W 3.4.1 Command Line Interface | Reference Guide show controller-ip | 701
show controller-ip
show controller-ip
Description
Show switch’s country and domain upgrade trail.
Syntax
No parameters.
Example
The output of this command shows the switch’s IP address and VLAN interface ID.
Command History
This command was available in AOS-W 3.4
Command Information
(host) # show controller-ip
Switch IP Address: 10.168.254.221
Switch IP is configured to be Vlan Interface: 1
Platforms Licensing Command Mode
All platforms Base operating system Config or Enable mode on master or local
switches

702 | show controller-ip AOS-W 3.4.1 Command Line Interface | Reference Guide
AOS-W 3.4.1 Command Line Interface | Reference Guide show country | 703
show country
show country [trail]
Description
Show switch’s country and domain upgrade trail.
Syntax
Usage Guidelines.
A switch’s country code sets the regulatory domain for the radio frequencies that the APs use. This value is
typically set during the switch’s initial setup procedure. Use this command to determine the country code
specified during setup.
Example
The output of this command shows the switch’s country, model and hardware types.
Command History
This command was available in AOS-W 1.0.
Command Information
Parameter Description
trail Display the record showing how the switch was reconfigured for it’s current
country domain when the switch hardware was upgraded.
(host) # show country
Country:US
Model:OAW-4306GW-US
Hardware:Restricted US
Platforms Licensing Command Mode
All platforms Base operating system Config or Enable mode on master or local
switches

704 | show country AOS-W 3.4.1 Command Line Interface | Reference Guide
AOS-W 3.4.1 Command Line Interface | Reference Guide show cp-bwcontracts | 705
show cp-bwcontracts
show cp-bwcontract
Description
Display a list of Control Processor (CP) bandwidth contracts for whitelist ACLs.
Syntax
No parameters.
Example
The CP bw contracts table lists the contract names, the ID number assigned to each contract, and its
defined traffic rate in bits per second.
Related Commands
Command History
This command was introduced in AOS-W 3.4
Command Information
Command Description Mode
cp-bandwidth-contract This command configures a bandwidth contract
traffic rate which can then be associated with a
whitelist session ACL.
Enable or Config modes
firewall cp This command creates a new whitelist ACL and can
associate a bandwidth contract with that ACL. Enable or Config modes
Platforms Licensing Command Mode
All platforms This command requires the PEF
license. Config mode on master switches
(host) #show cp-bwcontracts
CP bw contracts
---------------
Contract Id Rate (bits/second)
-------- -- ------------------
limit 4098 2000000000
newcontract 4097 1000000000

706 | show cp-bwcontracts AOS-W 3.4.1 Command Line Interface | Reference Guide
AOS-W 3.4.1 Command Line Interface | Reference Guide show cpuload | 707
show cpuload
show cpuload [current]
Description
Display the switch CPU load for application and system processes.
Syntax
Example
This example shows that the majority of the switch’s CPU resources are not being used by either
application (user) or system processes.
The output of this command includes the following parameters:
Command History
This command was available in AOS-W 1.0.
Command Information
Parameter Description
current Include this optional parameter at the request of Alcatel-Lucent technical support
to display additional CPU troubleshooting statistics.
(host) #show cpuload
user 6.9%, system 7.7%, idle 85.4%
Parameter Description
user Percentage of switch CPU resources used by application processes.
system Percentage of switch CPU resources used by system processes.
idle Percentage of unused switch CPU resources.
Platforms Licensing Command Mode
All platforms Base operating system Enable or Config mode on master and local
switches

708 | show cpuload AOS-W 3.4.1 Command Line Interface | Reference Guide
AOS-W 3.4.1 Command Line Interface | Reference Guide show crypto dp | 709
show crypto dp
show
show crypto dp [peer <source-ip>]
Descriptions
Displays crypto data packets.
Syntax
Usage Guidelines
Use this command to send crypto data packet information to the switch log files, or to clear a crypto ISAKMP
state associated with a specific IP address.
Examples
The command show crypto dp sends debug information to CRYTPO logs.
Related Commands
Command History
This command was introduced in AOS-W 3.0.
Command Information
Parameter Description
dp Shows crypto latest datapath packets. The output is sent to crypto logs.
peer <source-ip> Clears crypto ISAKMP state for this IP.
Command Description Mode
crypto isakmp Use this command to configure Internet Key
Exchange (IKE) parameters for the Internet Security
Association and Key Management Protocol
(ISAKMP)
Enable and Config modes
Platforms Licensing Command Mode
All platforms Base operating system Enable or Config mode on master or local
switches
(host) # show crypto
Datapath debug output sent to CRYPTO logs.
710 | show crypto dynamic-map AOS-W 3.4.1 Command Line Interface | Reference Guide
show crypto dynamic-map
show crypto dynamic-map [tag <dynamic-map-name>]
Descriptions
Displays IPsec dynamic map configurations.
Syntax
Usage Guidelines
Dynamic maps enable IPsec SA negotiations from dynamically addressed IPsec peers. Once you have defined a
dynamic map, you can associate that map with the default global map using the command crypto map global-
map.
Examples
The command show crypto dynamic-map shows IPsec dynamic map configuration.
Related Commands
Command History
This command was introduced in AOS-W 3.0.
Command Information
Parameter Description
dynamic-map IPsec dynamic maps configuration.
tag <dynamic-map-
name>
A specific dynamic map.
Command Description Mode
crypto dynamic-map Use this command to configure a dynamic map. Config mode
Platforms Licensing Command Mode
All platforms Base operating system Enable or Config mode on master or local
switches
(host) #show crypto dynamic-map
Crypto Map Template"default-dynamicmap" 10000
lifetime: [300 - 86400] seconds, no volume limit
PFS (Y/N): N
Transform sets={ default-transform }
AOS-W 3.4.1 Command Line Interface | Reference Guide show crypto ipsec | 711
show crypto ipsec
show crypto ipsec {mtu|sa[peer <peer-ip>]|transform-set [tag <transform-set-name>]}
Descriptions
Displays the current IPsec configuration on the switch.
Syntax
Usage Guidelines
The command show crypto ipsec displays the Maximum Transmission Unit (MTU) size allowed for network
transmissions using IPsec security. It also displays the transform sets that define a specific encryption and
authentication type.
Examples
The command show crypto transform-set shows the transform sets default-transform and default-ml-
transform.
Related Commands
Command History
This command was introduced in AOS-W 3.0.
Command Information
Parameter Description
mtu IPsec maximum mtu.
sa Security associations.
peer <peer-ip> IPsec security associations for a peer.
transform-set IPsec transform sets.
tag <transform-set-
name>
A specific transform set.
Command Description Mode
crypto ipsec Use this command to configure IPsec
parameters. Config mode
Platforms Licensing Command Mode
All platforms Base operating system Enable or Config mode on master or local
switches
(host) #show crypto ipsec transform-set
Transform set default-transform: { esp-3des esp-sha-hmac }
will negotiate = { Transport, Tunnel }
Transform set default-ml-transform: { esp-3des esp-sha-hmac }
will negotiate = { Transport, Tunnel }
712 | show crypto isakmp AOS-W 3.4.1 Command Line Interface | Reference Guide
show crypto isakmp
show crypto isakmp {groupname}|{key}|{policy}|{psk-caching}|{sa[peer <peer-ip>]|stats}
Descriptions
This command displays Internet Key Exchange (IKE) parameters for the Internet Security Association and Key
Management Protocol (ISAKMP).
Syntax
Usage Guidelines
Use the show crypto isakmp psk-caching command to view whether PSK caching is enabled. If it is enabled then
you can refresh the IKE PSK used by remote APs.
Examples
The command show crypto isakmp stats shows the IKE statistics.
Parameter Description
groupname Show the IKE Aggressive group name.
key Show the IKE pre-shared keys.
policy Show the IKE configured policies.
psk-caching Shows if the IKE PSK caching is enabled or disabled. This is the refresh status.
(Default is disabled.)
sa Show the security associations
peer <peer-ip> Shows crypto isakmp security associations for this IP.
stats Show the IKE statistics.
(host) #show crypto isakmp stats
Main Mode Initiator exchanges started/completed = 0/0
Main Mode Responder exchanges started/completed = 0/0
Aggr Mode Initiator exchanges started/completed = 0/0
Aggr Mode Responder exchanges started/completed = 0/0
Quick Mode Initiator exchanges started/completed = 0/0
Quick Mode Responder exchanges started/completed = 0/0
XAuth Type1 Responder exchanges started/completed = 0/0
XAuth Type2 Responder exchanges started/completed = 0/0
Mode-Config Responder exchanges started/completed = 0/0
Phase1 SAs Current/Max/Total = 0/0/0
Phase2 SAs Current/Max/Total = 0/0/0
VPN Sessions Total/RAPs/Master-Local/Redundancy = 0/0/0/0
VPN License Limits Total/Platform/Current/Violation = 16777215/16777215/0/0
Switch Role: Master
CFGM triggers: Master/Local/Redund/Failed/Total = 74682/0/0/0/74682
Redundancy changes: Master->Standby/Standby->Master = 0/0
FPAPPS TX messages: Tunnel-Up/Tunnel-Down = 0/0
FPAPPS TX messages: cfg-map-add/cfg-map-del = 0/0
FPAPPS TX messages: Peer-map-add/Peer-map-del = 0/0
FPAPPS TX messages: SwitchIP-mapadd/SwitchIP-mapdel = 0/0
FPAPPS TX messages: New-SwitchIP-map-adds = 0
Datapath To Control DPD Triggers Received = 0
DPD Initiate Reqs-Sent/Re-Sent/Replies-Rcvd/Dropped = 0/0/0/0
AOS-W 3.4.1 Command Line Interface | Reference Guide show crypto isakmp | 713
Related Commands
Command History
This command was introduced in AOS-W 3.0.
Command Information
Command Description Mode
crypto isakmp Use this command to configure Internet Key
Exchange (IKE) parameters for the Internet Security
Association and Key Management Protocol
(ISAKMP).
Config mode
Platforms Licensing Command Mode
All platforms Base operating system Enable or Config mode on master or local
switches
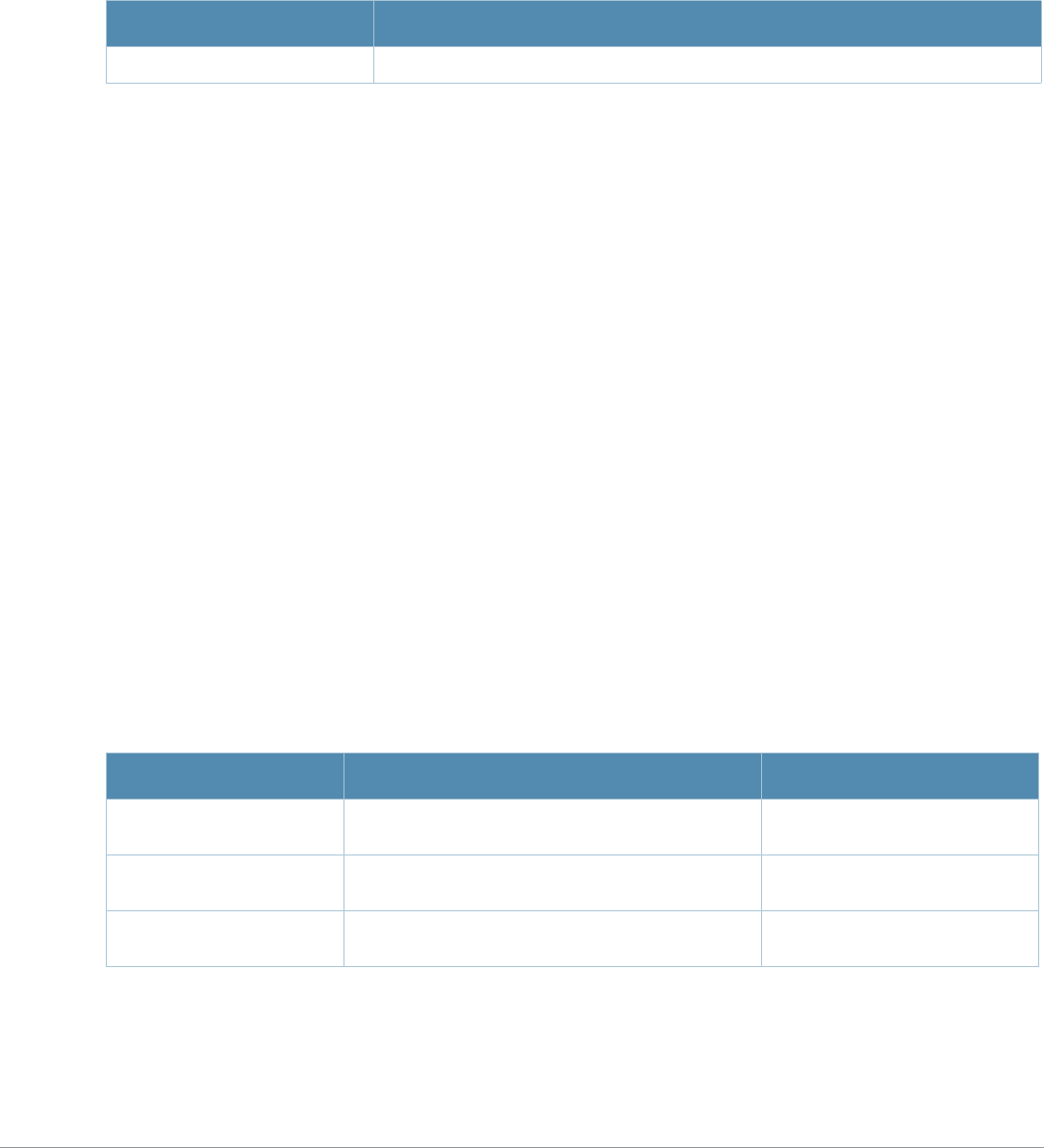
714 |show crypto map AOS-W 3.4.1 Command Line Interface | Reference Guide
show crypto map
show crypto ipsec map
Descriptions
This command displays the IPsec map configurations.
Syntax
Usage Guidelines
Use the show crypto map command to view configuration for global, dynamic and default map configurations.
Examples
The command show crypto map shows statistics for the global, dynamic and default maps.
Related Commands
Command History
This command was introduced in AOS-W 3.0.
Parameter Description
map Show the IKE Aggressive group name.
Command Description Mode
crypto map global-map Use this command to configure the default global
map. Config mode
crypto dynamic-map Use this command to configure an existing dynamic
map. Config mode
crypto map global-map Use this command to configure the default global
map. Config mode
(host) #show crypto map
Crypto Map "GLOBAL-MAP" 10000 ipsec-isakmp
Crypto Map Template"default-dynamicmap" 10000
lifetime: [300 - 86400] seconds, no volume limit
PFS (Y/N): N
Transform sets={ default-transform }
Crypto Map "default-local-master-ipsecmap" 9999 ipsec-isakmp
Crypto Map Template"default-local-master-ipsecmap" 9999
lifetime: [300 - 86400] seconds, no volume limit
PFS (Y/N): N
Transform sets={ default-ml-transform }
Peer gateway: 0.0.0.0
Interface: VLAN 0
Source network: 0.0.0.0/0.0.0.0
Destination network: 0.0.0.0/0.0.0.0
Pre-Connect (Y/N): N
Tunnel Trusted (Y/N): Y

AOS-W 3.4.1 Command Line Interface | Reference Guide show crypto map | 715
Command Information
Platforms Licensing Command Mode
All platforms Base operating system Enable or Config mode on master or local
switches

716 |show crypto pki AOS-W 3.4.1 Command Line Interface | Reference Guide
show crypto pki
show crypto pki csr
Descriptions
This command displays the certificate signing request (CSR) for the captive portal feature.
Syntax
Usage Guidelines
Use the show crypto pki command to view the CSR output.
Parameter Description
csr The certificate signing request.
AOS-W 3.4.1 Command Line Interface | Reference Guide show crypto pki | 717
Examples
The command show crypto pki shows output from the crypto pki csr command.
Related Commands
Command History
This command was introduced in AOS-W 3.0.
Command Description Mode
crypto pki Use this command to generate a certificate signing
request (CSR) for the captive portal feature. Enable mode
crypto pki-import Use this command to import certificates for the
captive portal feature. Enable mode
(host) #show crypto pki csr
Certificate Request:
Data:
Version: 0 (0x0)
Subject: C=US, ST=CA, L=Sunnyvale, O=sales, OU=EMEA,
CN=www.mycompany.com/emailAddress=myname@arubanetworks.com
Subject Public Key Info:
Public Key Algorithm: rsaEncryption
RSA Public Key: (1024 bit)
Modulus (1024 bit):
00:e6:b0:f2:95:37:d0:18:c4:ee:f7:bd:5d:96:85:
49:a3:56:63:76:ee:99:82:fe:4b:31:6c:80:25:c4:
ed:c7:9e:8e:5e:3e:a2:1f:90:62:b7:91:69:75:27:
e8:29:ba:d1:76:3c:0b:14:dd:83:3a:0c:62:f2:2f:
49:90:47:f5:2f:e6:4e:dc:c3:06:7e:d2:51:29:ec:
52:8c:40:26:de:ae:c6:a0:21:1b:ee:46:b1:7a:9b:
dd:0b:67:44:48:66:19:ec:c7:f4:24:bd:28:98:a2:
c7:6b:fb:b6:8e:43:aa:c7:22:3a:b8:ec:9a:0a:50:
c0:29:b7:84:46:70:a5:3f:09
Exponent: 65537 (0x10001)
Attributes:
a0:00
Signature Algorithm: sha1WithRSAEncryption
25:ce:0f:29:91:73:e9:cd:28:85:ea:74:7c:44:ba:b7:d0:5d:
2d:53:64:dc:ad:07:fd:ed:09:af:b7:4a:7f:14:9a:5f:c3:0a:
8a:f8:ff:40:25:9c:f4:97:73:5b:53:cd:0e:9c:d2:63:b8:55:
a5:bd:20:74:58:f8:70:be:b9:82:4a:d0:1e:fc:8d:71:a0:33:
bb:9b:f9:a1:ee:d9:e8:62:e4:34:e4:f7:8b:7f:6d:3c:70:4c:
4c:18:e0:7f:fe:8b:f2:01:a2:0f:00:49:81:f7:de:42:b9:05:
59:7c:e4:89:ed:8f:e1:3b:50:5a:7e:91:3b:9c:09:8f:b7:6b:
98:80
-----BEGIN CERTIFICATE REQUEST-----
MIIB1DCCAT0CAQAwgZMxCzAJBgNVBAYTAlVTMQswCQYDVQQIEwJDQTESMBAGA1UE
BxMJU3Vubnl2YWxlMQ4wDAYDVQQKEwVzYWxlczENMAsGA1UECxMERU1FQTEaMBgG
A1UEAxMRd3d3Lm15Y29tcGFueS5jb20xKDAmBgkqhkiG9w0BCQEWGXB3cmVkZHlA
YXJ1YmFuZXR3b3Jrcy5jb20wgZ8wDQYJKoZIhvcNAQEBBQADgY0AMIGJAoGBAOaw
8pU30BjE7ve9XZaFSaNWY3bumYL+SzFsgCXE7ceejl4+oh+QYreRaXUn6Cm60XY8
CxTdgzoMYvIvSZBH9S/mTtzDBn7SUSnsUoxAJt6uxqAhG+5GsXqb3QtnREhmGezH
9CS9KJiix2v7to5DqsciOrjsmgpQwCm3hEZwpT8JAgMBAAGgADANBgkqhkiG9w0B
AQUFAAOBgQAlzg8pkXPpzSiF6nR8RLq30F0tU2TcrQf97Qmvt0p/FJpfwwqK+P9A
JZz0l3NbU80OnNJjuFWlvSB0WPhwvrmCStAe/I1xoDO7m/mh7tnoYuQ05PeLf208
cExMGOB//ovyAaIPAEmB995CuQVZfOSJ7Y/hO1BafpE7nAmPt2uYgA==
-----END CERTIFICATE REQUEST-----

718 |show crypto pki AOS-W 3.4.1 Command Line Interface | Reference Guide
Command Information
Platforms Licensing Command Mode
All platforms Base operating system Enable or Config mode on master or local
switches
AOS-W 3.4.1 Command Line Interface | Reference Guide show crypto-local ipsec-map | 719
show crypto-local ipsec-map
show crypto-local ipsec [tag <ipsec-map-name>]
Descriptions
Displays the current IPsec map configuration on the switch.
Syntax
Usage Guidelines
The command show crypto-local ipsec displays the current IPsec configuration on the switch.
Examples
The command show crypto-local ipsec-map shows the default map configuration along with any specific
IPsec map configurations.
Related Commands
Command History
This command was introduced in AOS-W 3.4.
Parameter Description
tag <ipsec-map-name> Display a specific IPsec map.
Command Description Mode
crypto-local ipsec-map Use this command to configure IPsec mapping
for site-to-site VPN.
Config mode
(host) #show crypto-local ipsec-map
Crypto Map Template"default-local-master-ipsecmap" 9999
lifetime: [300 - 86400] seconds, no volume limit
PFS (Y/N): N
Transform sets={ default-ml-transform }
Peer gateway: 0.0.0.0
Interface: VLAN 0
Source network: 0.0.0.0/0.0.0.0
Destination network: 0.0.0.0/0.0.0.0
Pre-Connect (Y/N): N
Tunnel Trusted (Y/N): Y
Forced NAT-T (Y/N): N
Crypto Map Template"testmap" 3
lifetime: [300 - 86400] seconds, no volume limit
PFS (Y/N): N
Transform sets={ default-transform }
Peer gateway: 0.0.0.0
Interface: VLAN 0
Source network: 0.0.0.0/0.0.0.0
Destination network: 0.0.0.0/0.0.0.0
Pre-Connect (Y/N): N
Tunnel Trusted (Y/N): N
Forced NAT-T (Y/N): N

720 | show crypto-local ipsec-map AOS-W 3.4.1 Command Line Interface | Reference Guide
Command Information
Platforms Licensing Command Mode
All platforms Base operating system Enable or Config mode on master or local
switches
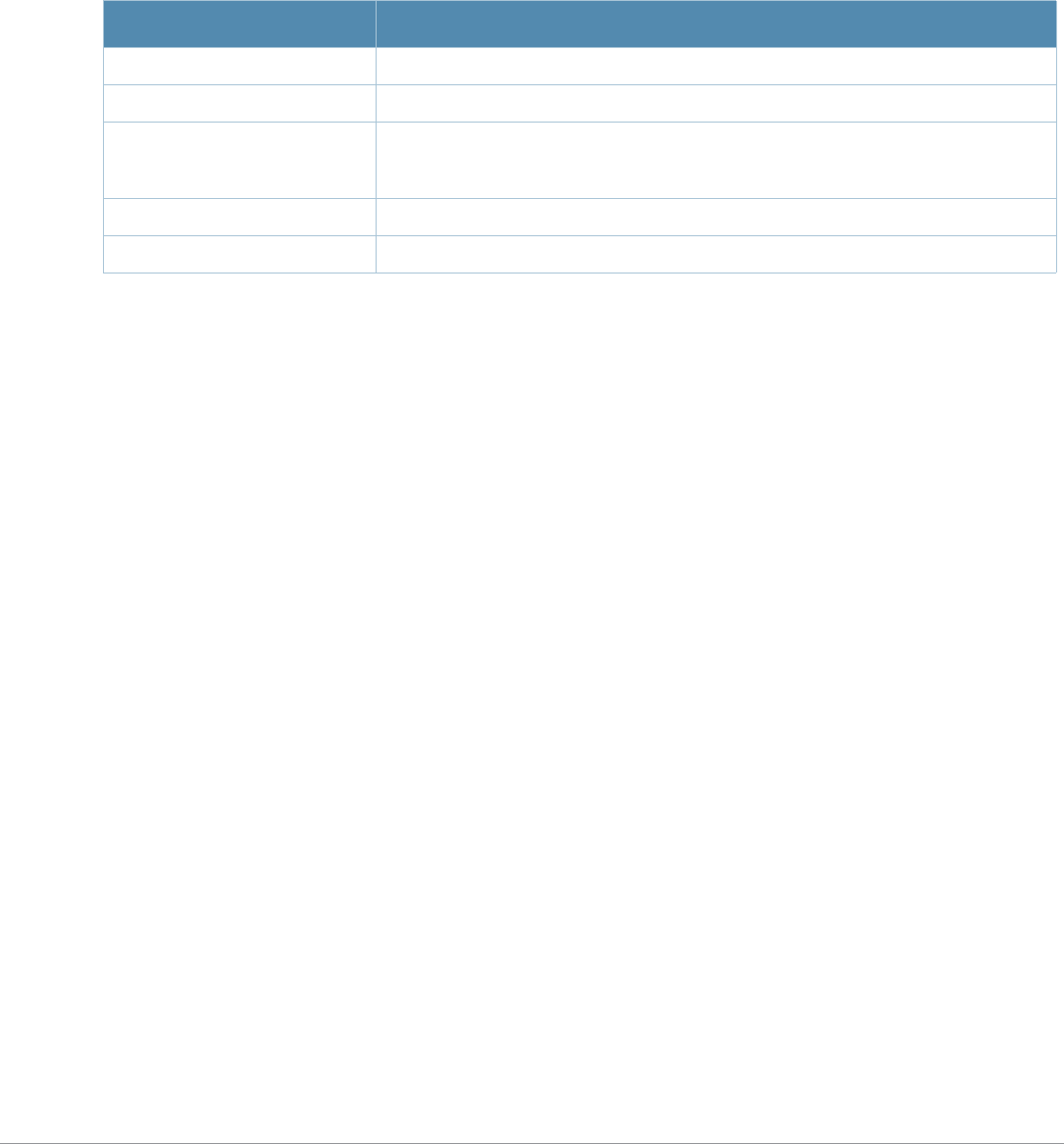
AOS-W 3.4.1 Command Line Interface | Reference Guide show crypto-local isakmp | 721
show crypto-local isakmp
show crypto isakmp {ca-certificates}|{dpd}|{key}|{server-certificate}|{xauth}
Descriptions
This command displays Internet Key Exchange (IKE) parameters for the Internet Security Association and Key
Management Protocol (ISAKMP).
Syntax
Usage Guidelines
Use the show crypto-local isakmp command to view IKE parameters.
Parameter Description
ca-certificates Shows all the Certificate Authority (CA) certificate associated with VPN clients.
dpd Shows the IKE Dead Peer Detection (DPD) configuration on the local switch.
key Shows the IKE preshared key on the local switch for site-to-site VPN. This is includes
keys configured by Fully Qualified Domain Name (FQDN) and local and global keys
configured by address.
server-certificate Shows all the IKE server certificates used to authenticate the switch for VPN clients.
xauth Shows the IKE XAuth configuration for VPN clients.
722 | show crypto-local isakmp AOS-W 3.4.1 Command Line Interface | Reference Guide
Examples
This example shows sample output for the show crypto-local ca-certificate, show crypto-local dpd, show
crypto-local key, show crypto-local server-certificate and show crypto-local xauth commands .
Related Commands
Command Description Mode
crypto-local isakmp ca-
certificate
Use this command to assign the Certificate
Authority (CA) certificate used to authenticate VPN
clients.
Config mode
crypto-local isakmp dpd Use this command to configure IKE Dead Peer
Detection (DPD) on the local switch. Config mode
crypto-local isakmp key Use this command to configure the IKE preshared
key on the local switch for site-to-site VPN. Config mode
(host) #show crypto-local isakmp ca-certificate
ISAKMP CA Certificates
-----------------------
CA certificate name Client-VPN # of Site-Site-Maps
------------------- ---------- -------------------
(host) #show crypto-local isakmp dpd
DPD is Enabled: Idle-timeout = 22 seconds, Retry-timeout = 2 seconds, Retry-attempts = 3
(host) #show crypto-local isakmp key
ISAKMP Local Pre-Shared keys configured by FQDN
------------------------------------------------
FQDN of the host Key
---------------- ---
ISAKMP Local Pre-Shared keys configured by FQDN
------------------------------------------------
FQDN of the host Key
---------------- ---
ISAKMP Local Pre-Shared keys configured by Address
---------------------------------------------------
IP address of the host Subnet Mask Length Key
---------------------- ------------------ ---
ISAKMP Global Pre-Shared keys configured by Address
----------------------------------------------------
IP address of the host Subnet Mask Length Key
---------------------- ------------------ ---
(OAW-4324) #show crypto-local isakmp server-certificate
ISAKMP Server Certificates
---------------------------
Server certificate name Client-VPN # of Site-Site-Maps
----------------------- ---------- -------------------
(host) #show crypto-local isakmp xauth
IKE XAuth Enabled
AOS-W 3.4.1 Command Line Interface | Reference Guide show crypto-local isakmp | 723
Command History
This command was introduced in AOS-W 3.4.
Command Information
crypto-local isakmp server-
certificate
Use this command to assign the server certificate
used to authenticate the switch for VPN clients. Config mode
crypto-local isakmp xauth Use this command to enable the IKE XAuth for VPN
clients. Config mode
Platforms Licensing Command Mode
All platforms Base operating system Enable or Config mode on master or local
switches
Command Description Mode
724 |show crypto-local pki AOS-W 3.4.1 Command Line Interface | Reference Guide
show crypto-local pki
show crypto pki {PublicCert|ServerCert|TrustedCA} <name> <filename>
Descriptions
This command displays imported certificate information.
Syntax
Usage Guidelines
Use the show crypto-local pki command to view the name, original filename and reference count for an
imported public, server or trusted CA certificates.
Example
This example displays information about an imported Server certificate. Both the Public and Trusted Ca
certificate parameters display similar information.
Parameter Description
PublicCert <name> Shows Public key information of a certificate. This certificate allows an application to
identify an exact certificate.
ServerCert <name> Shows Server certificate information. This certificate must contain both a public and
a private key (the public and private keys must match). You can import a server
certificate in either PKCS12 or x509 PEM format; the certificate is stored in x509
PEM DES encrypted format on the switch.
TrustedCA <name> Shows trusted CA certificate information.This certificate can be either a root CA or
intermediate CA. Alcatel-Lucent encourages (but does not require) an intermediate
CA’s signing CA to be the switch itself.
(host) (config) #show crypto-local pki serverCert
Name(total=1) Original Filename Reference Count
============== ================= ===============
sialdevice 2400a.pem 1
AOS-W 3.4.1 Command Line Interface | Reference Guide show crypto-local pki | 725
Related Commands
Command History
This command was introduced in AOS-W 3.1.
Command Information
Command Description Mode
crypto-local pki This command is saved in the configuration file and
verifies the presence of the certificate in the switch’s
internal directory structure.
Enable mode
Platforms Licensing Command Mode
All platforms VPN server license is required. Enable mode.

726 |show crypto-local pki AOS-W 3.4.1 Command Line Interface | Reference Guide

AOS-W 3.4.1 Command Line Interface | Reference Guide show database | 727
show database
show database synchronization
Description
Shows database synchronization status.
Syntax
No parameters.
Usage Guidelines
Issue this command to show the status database synchronization status.
Example
This example shows a database synchronization status.
Related Commands
Command History
Command Information
Command Description Mode
database synchronize Use this command to show the output of the
database synchronize command. Enable and Config modes
Release Modification
AOS-W 3.0 Command introduced
Platforms Licensing Command Mode
All platforms Base operating system Enable or config mode on master and local
switches
(host) #show database synchronize
Last synchronization time: Not synchronized since last reboot
Periodic synchronization is enabled and runs every 25 minutes
Synchronization includes RF plan data

728 | show database AOS-W 3.4.1 Command Line Interface | Reference Guide
AOS-W 3.4.1 Command Line Interface | Reference Guide show datapath | 729
show datapath
show
acl id <id-name> [ap-name <ap-name>|ip-addr <ip-address>]
application [ap-name <ap-name>|counters|ip-addr <ip-address>]
bridge [ap-name <ap-name>|counters|ip-addr <ip-address>|table]
bwm table
crypto counters
debug {dma counters|trace-buffers}
esi table
frame [ap-name <ap-name>|counters|ip-addr <ip-address>]
hardware {counters|statistics}
ip-reassembly [ap-name <ap-name>|counters|ip-addr <ip-address>]
lag table
maintenance counters
message-queue counters
nat [ap-name <ap-name>|counters|ip-addr <ip-address>]
port table
route [ap-name <ap-name>|counters|ip-addr <ip-address>][table]
route-cache [ap-name <ap-name>|counters|ip-addr <ip-address>|table]
services
session [ap-name <ap-name>|counters|ip-addr <ip-address>|table]
station [counters|mac <macaddr>|table]
tunnel [counters|table]
user [ap-name <ap-name>|counters|ip-addr <ip-address>|table]
utilization
vlan [ap-name <ap-name>|ip-addr <ip-address>|table]
wifi-reassembly counters
wmm counters
Descriptions
Displays system statistics for your switch.
Syntax
Parameter Description
acl id <id-name> Displays datapath statistics associated with a specified ACL. The ACL index is found
in the show rights command.
ap-name <ap-name> Name of the AP.
ip-addr <ip-address> IP address of the AP
application counters Shows application counters and errors generated by applications running on a
particular AP. These include stateful firewall application layer statistics.
ap-name <ap-name> Name of the AP.
ip-addr <ip-address> IP address of the AP.
bridge Shows bridge table entry statistics including MAC address, VLAN, assigned VLAN,
Destination and flag information for an AP.
ap-name <ap-name> Name of the AP. Shows MAC address, VLAN, assigned VLANs, destination and flags
information.
counters Shows datapath bridge table statistics such as current entries, high water mark,
maximum entries, total entries, allocation failures and max link length.
ip-addr <ip-address> IP address of the AP. Shows MAC address, VLAN, assigned VLANs, destination and
flags information.

730 | show datapath AOS-W 3.4.1 Command Line Interface | Reference Guide
table <macaddr> Displays the current high, maximum, and total number of bridge table entries for the
Alcatel-Lucent switch.
bwm table Shows bandwidth management table entry statistics such as CPU, contract, Bits/sec,
policed, available bytes, queued bytes and packets.
crypto counters Displays crypto parameter statistics including crypto, IPSEC, PPTP, WEP, TKIP,
AESCCM, WEP CRC, crypto hardware , XSEC, DOT1X and L2TP information.
debug Displays datapath debug details. These are low-level datapath details.
dma counters DMA counters are displayed.
trace-buffers Debug trace-buffer tables are displayed.
esi table Displays the contents of the datapath ESI server table entries including server, IP,
MAC, destination, VLAN, type, session and flag information.
frame counters Displays frame statistics that are received and transmitted from the datapath of the
switch.
ap-name <ap-name> Name of the AP.
ip-addr <ip-address> IP address of the AP.
hardware Displays datapath hardware counters and hardware packet statistics information.
counters Hardware counters.
statistics Hardware packet statistics.
ip-reassembly Displays the contents of the IP Reassembly statistics table.
ap-name <ap-name> Name of the AP.
counters IP reassembly counters.
ip-addr <ip-address> IP address of the AP
lag table Displays contents of the datapath link aggregation group (LAG) or port channel table.
maintenance counters Displays datapath maintenance statistics.
message-queue counters Displays statistics of messages received by a CPU from other datapath CPUs (only
CPUs that receive messages and non-zero statistics are shown).
nat Displays the contents of the datapath NAT entries table. It displays NAT pools as
configured in the datapath. Statistics include pool, SITP start, SIP end and DIP.
ap-name <ap-name> Name of AP.
counters Nat counters.
ip-addr <ip-address> IP address of the AP.
port table Displays the datapath port-vlan untrusted status and table session entries.
untrusted-vlan <slot/
port>
Show if there are untrusted vlan entries for the indicated slot and port.
vlan-table <slot/
port>
Displays the VLAN and its corresponding Session ACL for a particular slot and port.
route Displays datapath route table statistics.
ap-name <ap-name> Name of the AP.
counters Displays route table statistics such as current entries, high water mark, maximum
entries, total entries, allocation failures and max link length.
Parameter Description
AOS-W 3.4.1 Command Line Interface | Reference Guide show datapath | 731
ip-addr <ip-address> Address of IP.
table Displays route table entries such as IP, mask, gateway, cost, VLAN and flags.
verbose Displays all detailed route table entries including IP, mask, gateway, cost, VLAN, flags,
Internal VerNum Index.
route-cace Displays datapath route cache table statistics.
ap-name <ap-name> Name of the AP.
counters Displays route cache table statistics such as current entries, high water mark,
maximum entries, total entries, allocation failures and max link length.
ip-addr <ip-address> Address of IP.
table Displays route cache table entries such as IP, mask, gateway, cost, VLAN and flags.
verbose Displays all detailed route cache table entries including IP, mask, gateway, cost,
VLAN, flags, Internal VerNum Index.
services Displays the datapath services table statistics including protocol, port and service.
session Displays datapath session statistics
ap-name <ap-name> Name of AP
counters Displays counters statistics including current entries, high water mark, maximum
entries, total entries, allocation failures, duplicate entries, cross linked entries, number
of reverse entries and maximum link length.
ip-addr <ip-address> Address of IP
table Displays all the IP flows of a wireless device or Alcatel-Lucent AP. Statistics include
table entries including source IP, destination IP, protocol, SPort, DPort, Cntr, priority,
ToS, age, destination, TAge and flags.
station Displays datapath station association table statistics.
counters Display the current and high water mark amount of 802.11 associated wireless
devices on an Alcatel-Lucent switch. Values output from this command represent the
water-marks since the last boot of the switch. This is the same value obtainable from
the Num Associations output from the show stm connectivity
command.
mac <macaddr> Hardware address, in hexadecimal format.
table This command presents the Datapath Station Table Statistics detail.
Display all associated wireless devices on the Alcatel-Lucent switch with their
corresponding AP BSSID and VLAN ID.
Displays the wireless device is associated with the correct encryption type (if the
device is associated to an AP BSSID that has encryption enabled and verifies whether
the Alcatel-Lucent switch is having a problem in decrypting the wireless device’s
frames.
tunnel Displays contents of the datapath tunnel table. This command displays all the tunnels
that are terminated by the switch, including Alcatel-Lucent APs’ GRE tunnels. For
example, a GRE tunnel is created and terminated on the Alcatel-Lucent switch for
every SSID/BSSID configured on the Alcatel-Lucent AP.
counters Tunnel counters.
table Tunnel table statistics.
user Displays datapath user statistics such as current entries, pending deletes, high water
mark, maximum entries, total entries, allocation failures, invalid users and maximum
link length.
Parameter Description

732 | show datapath AOS-W 3.4.1 Command Line Interface | Reference Guide
Usage Guidelines
Use the show datapath command to display various datapath statistics for debugging purposes.
Example
In this example, the show datapath user counters command displays datapath user table statistics. .
Command History
This command was introduced in AOS-W 3.0.
Command Information
ap-name <ap-name> Name of AP.
counters User counters.
ip-addr <ip-address> IP address of the AP.
table User table statistics.
utilization Displays the current CPU utilization of all datapath CPUs.
vlan Displays VLAN table information such as VLAN memberships inside the datapath
including L@ tunnels which tunnel L2 traffic.
ap-name <ap-name> Name of the AP.
ip-addr <ip-address> IP address of AP.
table Displays VLAN number, flag, port and datapath VLAN multicast entries.
wifi-reassembly
counters
Displays wifi reassembly counters including CPU, current entries, high water-mark,
maximum entries, total entries and allocation failures.
wmm counters Displays VOIP statistics including the number of uplink and downlink resets.
Platforms Licensing Command Mode
All platforms Base operating system Enable or Config mode on master or local
switches
Parameter Description
(host) #show datapath user counters
Datapath User Table Statistics
------------------------------
Current Entries 2
Pending Deletes 0
High Water Mark 2
Maximum Entries 8191
Total Entries 143
Allocation Failures 0
Invalid Users 0
Max link length 1
AOS-W 3.4.1 Command Line Interface | Reference Guide show destination | 733
show destination
show destination <string>
Description
Display the aliases for default and user-defined network destinations.
Syntax
Example
This example displays the network destinations configured in the switch.
The output of this command includes the following parameters:
Command History
This command was available in AOS-W 1.0.
Replaced with netdestination in 3.0.
Parameter Description
string Optional parameter to view details of a specific destination alias.
Parameter Description
Position Displays the priority position of the alias.
Type The rule type of the destination alias.
IP addr The IP address configured in the alias. This can be a network address, host
address or a range.
Mask/Range Network mark or the IP address range.
(host) #show destination
controller
----------
Position Type IP addr Mask/Range
-------- ---- ------- ----------
1 host 10.16.15.1
user
----
Position Type IP addr Mask/Range
-------- ---- ------- ----------
1 network 255.255.255.255 0.0.0.0
mswitch
-------
Position Type IP addr Mask/Range
-------- ---- ------- ----------
1 host 10.16.15.1
any
---
Position Type IP addr Mask/Range
-------- ---- ------- ----------
1 network 0.0.0.0 0.0.0.0

734 |show destination AOS-W 3.4.1 Command Line Interface | Reference Guide
Command Information
Platforms Licensing Command Mode
All platforms You must have a Policy
Enforcement Firewall license to
configure or view a destination.
Enable or Config mode on master and local
switches

AOS-W 3.4.1 Command Line Interface | Reference Guide show dialer group | 735
show dialer group
crypto-local
show dialer group
Description
Display dialer group information.
Syntax
No parameters.
Usage Guidelines
Displays the Dialer Group Table with the current dialing parameters.
Example.
Command History
Introduced in AOS-W 3.4.
Command Information
Platforms Licensing Command Mode
OmniAccess 4306 switches Base operating system Config mode on master and local switches
(host) #show dialer group
Dialer Group Table
------------------
Name Init String Dial String
---- ----------- -----------
evdo_us ATQ0V1E0 ATDT#777
gsm_us AT+CGDCONT=1,"IP","ISP.CINGULAR" ATD*99#

736 | show dialer group AOS-W 3.4.1 Command Line Interface | Reference Guide
AOS-W 3.4.1 Command Line Interface | Reference Guide show dir | 737
show dir
crypto-local
show dir usb: disk <disk-name><filesystem-path>
Description
Display the list of directories in the specified disk and the filesystem path.
Syntax
Example
The command below displays the USB directory list for a device named SEGATE-HJ1235_p1.
The output of this command includes the following parameters:
Command History
This command was introduced in AOS-W 3.4.
Command Information
Parameter Description
<disk-name> Name of the USB device. If you do not know the name of the USB disk, issue the
command show usb-storage to view a list of device names.
<filesystem-path> The USB file system path.
(host) #(show dir usb: SEGATE-HJ1235_p1/docs
USB directory list
------------------
Permission Size Time Stamp Directory Name
---------- ---- -------------- --------------
drwxr-xr-x 0 May 13 09:39 samba
Parameter Description
Permission Read, write and execute permissions for the directory.
Size Size of the directory.
Time Stamp Date and time that the directory was last modified.
Directory Name Name of the directory on the USB device.
Platforms Licensing Command Mode
OmniAccess 4306 switches Base operating system Config mode on master and local switches

738 |show dir AOS-W 3.4.1 Command Line Interface | Reference Guide
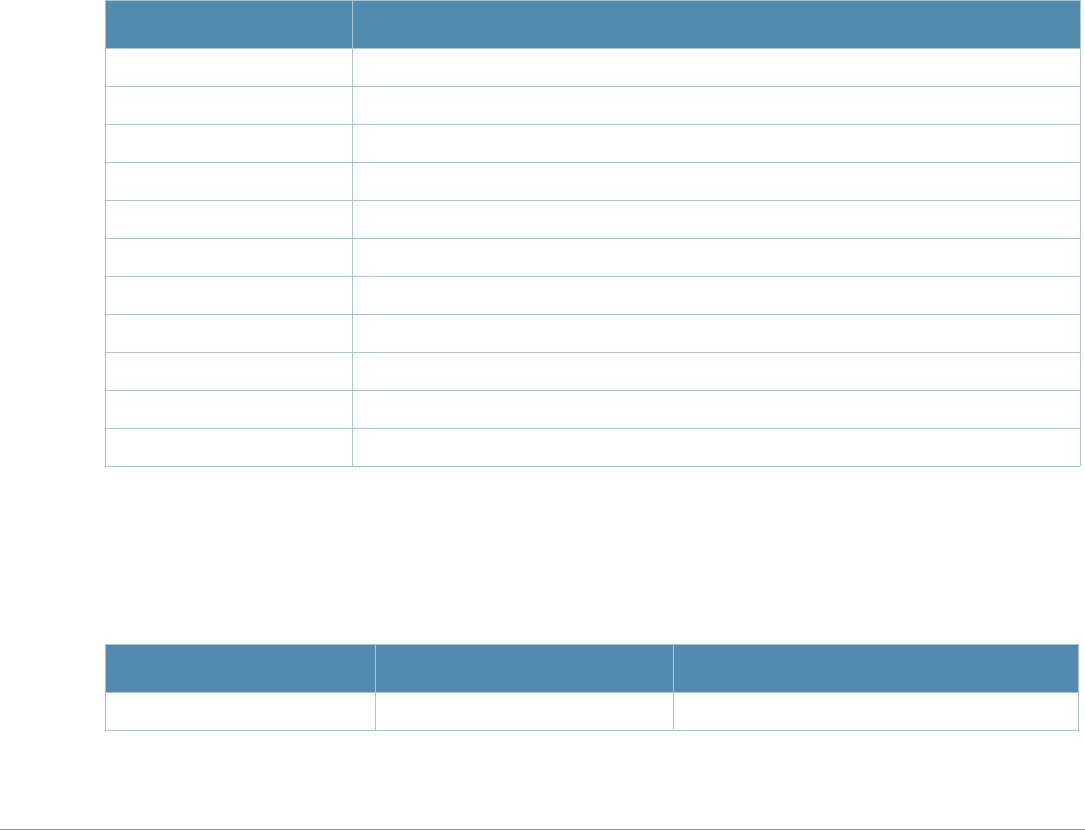
AOS-W 3.4.1 Command Line Interface | Reference Guide show dot1x ap-table | 739
show dot1x ap-table
show dot1x ap-table
Description
Shows the 802.1x AP table.
Syntax
No parameters.
Example
Issue this command to display details from the AP table.
The output of this command includes the following parameters:
Command History
This command was introduced in AOS-W 3.0.
Command Information
AP Table
--------
MAC IP Essid Type AP name Vlan Enc Stations Forwarding-Mode Profile Acl
--- -- ----- ---- ------- ---- --- -------- --------------- ------- ---
00:1a:1e:87:ff:c0 10.3.9.242 AP 00:1a:1e:c0:7f:fc 0 - 0 FORWARD_TUNNEL_80211 default/ 1
00:1a:1e:87:ff:d0 10.3.9.242 sw-pn-nokia AP 00:1a:1e:c0:7f:fc 0 WPA2-AES 0 FORWARD_TUNNEL_80211 default/default 1
00:1a:1e:82:ab:a0 10.3.9.220 AP monitor-124 0 - 0 FORWARD_TUNNEL_80211 default/ 1
00:1a:1e:82:ab:b0 10.3.9.220 AP monitor-124 0 - 0 FORWARD_TUNNEL_80211 default/ 1
00:1a:1e:87:ff:d1 10.3.9.242 sw-pn-t2 AP 00:1a:1e:c0:7f:fc 0 WPA2-PSK-AES 0 FORWARD_TUNNEL_80211 default/default 1
Num APs: 5
Parameter Description
MAC The MAC address of the AP
IP The IP address of the AP
Essid The AP’s ESSID
Type Device type
AP name Name of the AP
Vlan Number of VLANs associated with the specified AP
Enc AP’s encryption method
Stations Number of stations associated withe the specified AP
Forwarding Mode Forwarding mode used by the specified AP
Profile AP profile
Acl Number of ACLs this AP belongs to
Platforms Licensing Command Mode
All platforms Base operating system Enable or config mode on master switches
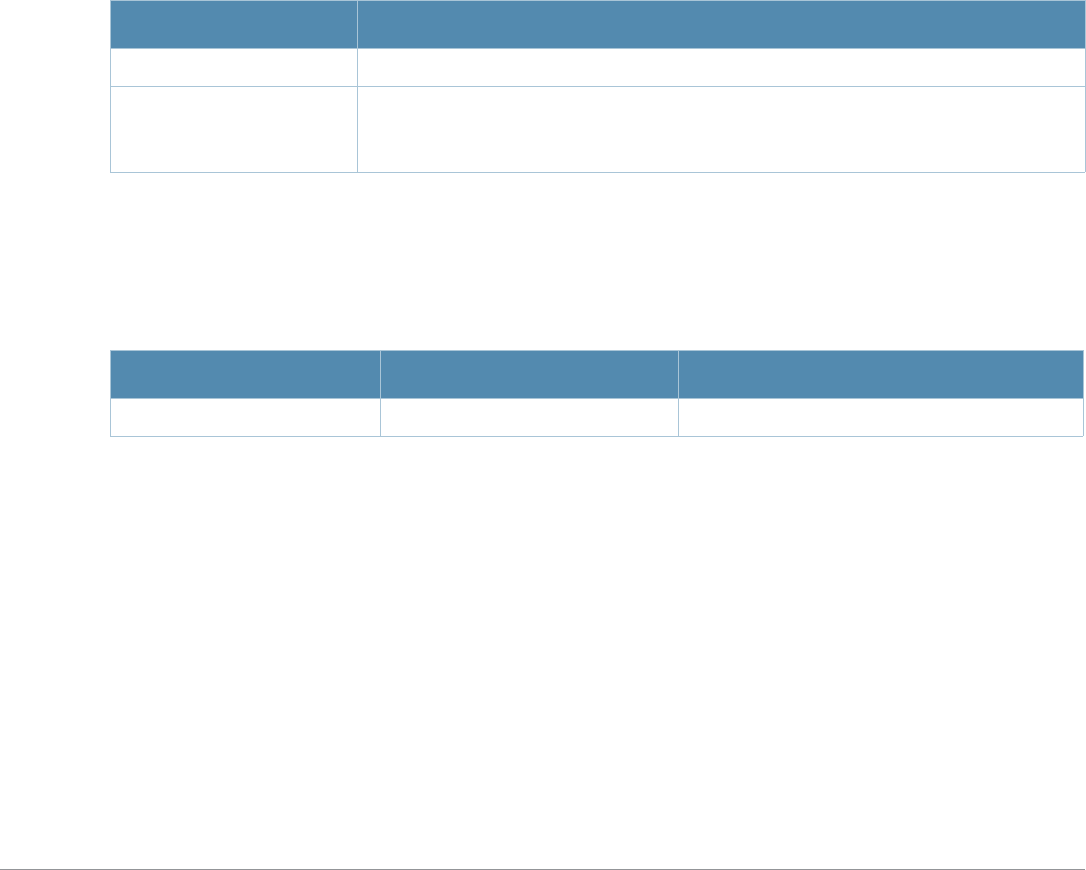
740 | show dot1x ap-table aes AOS-W 3.4.1 Command Line Interface | Reference Guide
show dot1x ap-table aes
show dot1x ap-table aes
Description
Shows the AES keys of all APs.
Syntax
No parameters.
Example
Issue this command to display AES keys of all APs.
The output of this command includes the following parameters:
Command History
This command was introduced in AOS-W 3.0.
Command Information
AP Table Showing AES Keys
-------------------------
AP-MAC GTK/Size/Slot
------ -------------
00:1a:1e:87:ff:d0 * * * * * * * */128-Bit/1
00:1a:1e:87:ff:d1 * * * * * * * */128-Bit/1
Parameter Description
AP-MAC AP MAC address
GTK/Size/Slot GTK: The group temporal key
Size: Size of the AES key
Slot: Slot number
Platforms Licensing Command Mode
All platforms Base operating system Enable or config mode on master switches
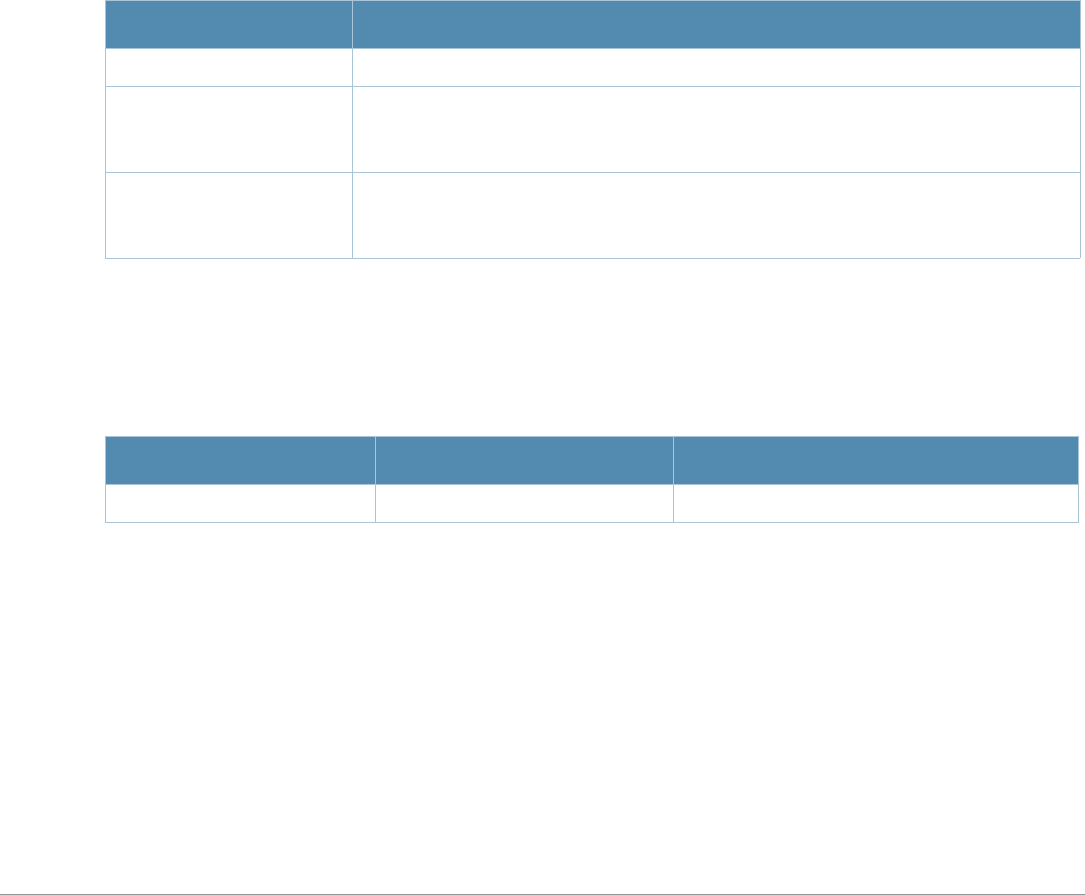
AOS-W 3.4.1 Command Line Interface | Reference Guide show dot1x ap-table dynamic-wep | 741
show dot1x ap-table dynamic-wep
show dot1x ap-table dynamic-wep
Description
Shows the dynamic WEP keys of all APs.
Syntax
No parameters.
Example
Issue this command to display dynamic keys of all APs.
The output of this command includes the following parameters:
Command History
This command was introduced in AOS-W 3.0.
Command Information
Dynamic-WEP Key Information
---------------------------
AP-MAC Key1/Size/Slot Key2/Size/Slot
------ -------------- --------------
Num APs: 0
Parameter Description
AP-MAC AP MAC address
Key1/Size/Slot Key1: The WEP key
Size: Size of the WEP key
Slot: Slot number
Key12/Size/Slot Key2: The WEP key
Size: Size of the WEP key
Slot: Slot number
Platforms Licensing Command Mode
All platforms Base operating system Enable or config mode on master switches
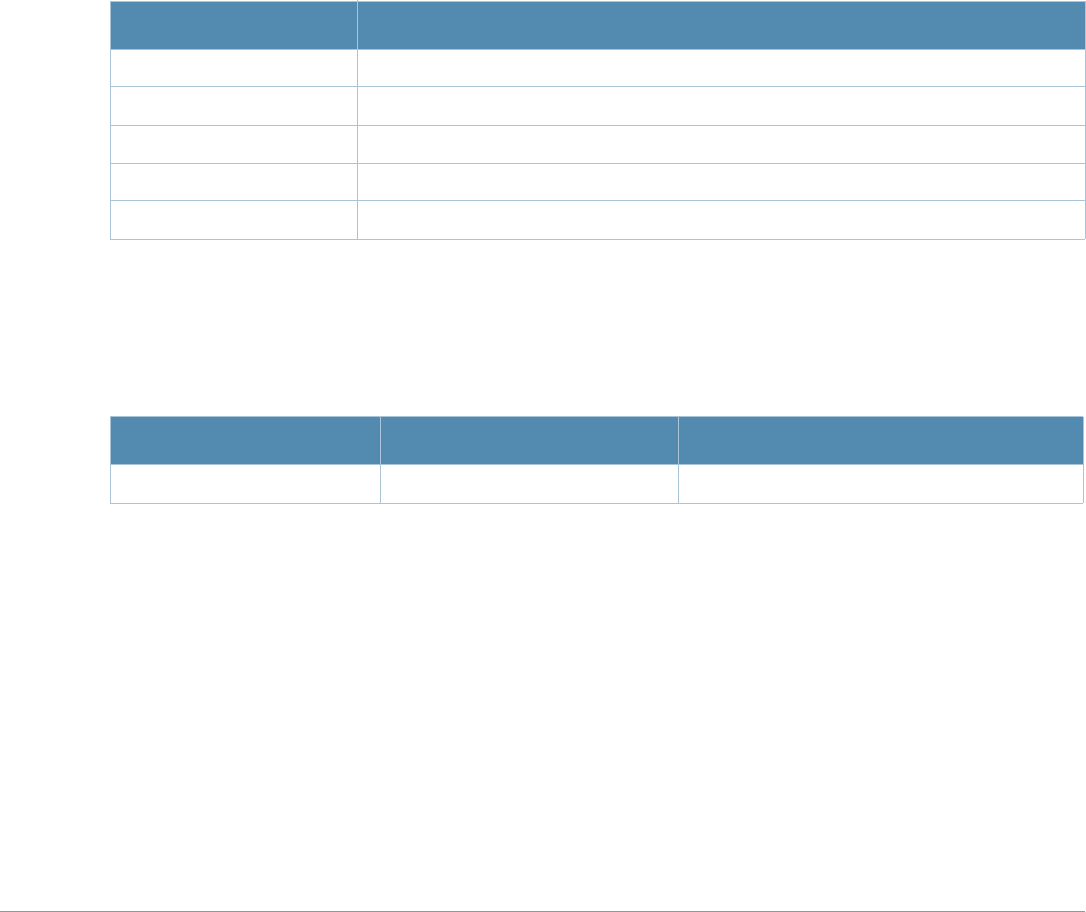
742 | show dot1x ap-table static-wep AOS-W 3.4.1 Command Line Interface | Reference Guide
show dot1x ap-table static-wep
show dot1x ap-table static-wep
Description
Shows the static WEP keys of all APs.
Syntax
No parameters.
Example
Issue this command to display the static WEP keys of all APs
The output of this command includes the following parameters:
Command History
This command was introduced in AOS-W 3.0.
Command Information
Static-WEP Key Information
--------------------------
AP-MAC Key1/Size Key2/Size Key3/Size Key3/Size
------ --------- --------- --------- ---------
Num APs: 0
Parameter Description
AP-MAC AP’s MAC address
Key1/Size WEP key 1 and its size
Key2/Size WEP key 2 and its size
Key3/Size WEP key 3 and its size
Key3/Size WEP key 3 and its size
Platforms Licensing Command Mode
All platforms Base operating system Enable or config mode on master switches
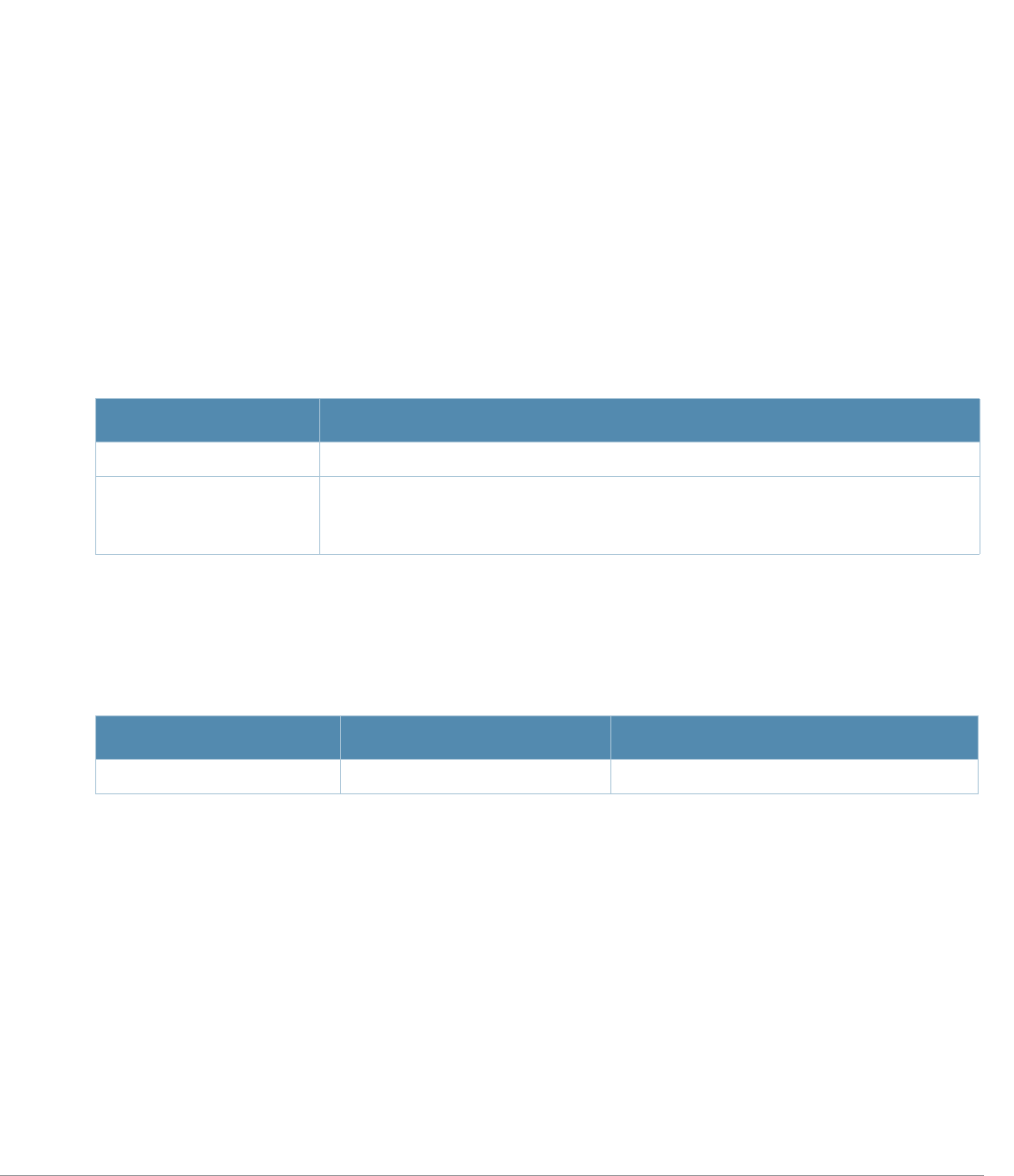
AOS-W 3.4.1 Command Line Interface | Reference Guide show dot1x ap-table tkip | 743
show dot1x ap-table tkip
show dot1x ap-table tkip
Description
Displays a table of TKIP keys on the switch.
Syntax
No parameters.
Example
Issue this command to display all TKIP keys.
The output of this command includes the following parameters:
Command History
This command was introduced in AOS-W 3.0.
Command Information
AP Table Showing TKIP Keys
--------------------------
AP-MAC GTK/Size/Slot
------ -------------
00:1a:1e:6f:e5:10 * * * * * * * */256-Bit/1
Num APs: 1
Parameter Description
AP-MAC AP MAC Address
GTK/Size/Slot GTK: The group temporal key
Size: Size of the AES key
Slot: Slot number
Platforms Licensing Command Mode
All platforms Base operating system Enable or config mode on master switches

744 | show dot1x counters AOS-W 3.4.1 Command Line Interface | Reference Guide
show dot1x counters
show dot1x counters
Description
Displays a table of dot1x counters.
Example
Issue this command to display all dot1x count information.
The output of this command includes the following parameters:
802.1x Counters
AP
Sync Request...................4
Sync Response..................3
Up.............................4
Down...........................1
Resps..........................4
Acl............................53
Station
Sync Request...................9
Sync Response..................9
Up.............................2321
Down...........................2272
Unknown........................72
EAP
RX Pkts........................4811
Dropped Pkts...................4497
TX Pkts........................5253
WPA
Message-1......................2484
Message-2......................63
Message-3......................63
Message-4......................63
Group Message-1................63
Group Message-2................63
Rx Failed......................2418
IE Mismatches..................4836
Key Exchange Failures..........602
WPA2
Message-1......................2630
Message-2......................13
Message-3......................13
Message-4......................13
Rx Failed......................2079
IE Mismatches..................4158
Key Exchange Failures..........549
Radius
Accept.........................1217
Station Deauths.................1151
Parameter Description
AP
zSync Request
zSync Response
zUp
zDown
zResps
zAcl
zNumber of sync requests sent
zNumber of sync responses sent
zNumber of times an AP has come up
zNumber of times an has gone down
zNumber of response messages sent to the AP due to an AP up message
zNumber of access control lists

AOS-W 3.4.1 Command Line Interface | Reference Guide show dot1x counters | 745
Command History
This command was introduced in AOS-W 3.0.
Command Information
Station
zSync Request
zSync Response
zUp
zDown
zUnknown
zNumber of sync requests sent to find all APs and stations that are connected
zNumber of sync responses received
zNumber of times a station (any station) connected to the AP
zNumber of times a station (any station) disconnected from the AP
zNumber of times a station attempted to start an EAP exchange before associating to
an AP. In other words, the number of times the auth module saw the start of an EAP
exchange before auth was notified that a station has associated an AP
EAP
zRX Pkts
zDropped Pkts
zTX Pkts
zNumber of EAP packets received
zNumber of EAP packets dropped (ignored) for any reason, such as bad packet,
length, EAP ID mismatch, etc.
zNumber of EAP packets sent
WPA
zMessage-1
zMessage-2
zMessage-3
zMessage-4
zGroup Message-1
zGroup Message-2
zRx Failed
zIE Mismatches
zKey Exchange
Failures
zNumber of WPA message-1s sent
zNumber of WPA message-2s sent
zNumber of WPA message-3s sent
zNumber of WPA message-4s sent
zNumber of WPA group message-1s sent
zNumber of WPA group message-2s sent
zNumber of WPA related EAP packets dropped for any reason
zNumber of WPA related EAP packets dropped because the station and switch have a
different perception of what the connection details are
zNumber of key exchange failures
WPA2
zMessage-1
zMessage-2
zMessage-3
zMessage-4
zRx Failed
zIE Mismatches
zKey Exchange
Failures
zNumber of WPA2 message-1s sent
zNumber of WPA2 message-2s sent
zNumber of WPA2 message-3s sent
zNumber of WPA2 message-4s sent
zNumber of WPA2 related EAP packets dropped for any reason
zNumber of WPA2 related EAP packets dropped because the station and switch have
a different perception of what the connection details are
zNumber of key exchange failures
Radius
z Accept zNumber of RADIUS accepts
Station Deauths Number of stations deaths
Platforms Licensing Command Mode
All platforms Base operating system Enable or config mode on master switches
Parameter Description
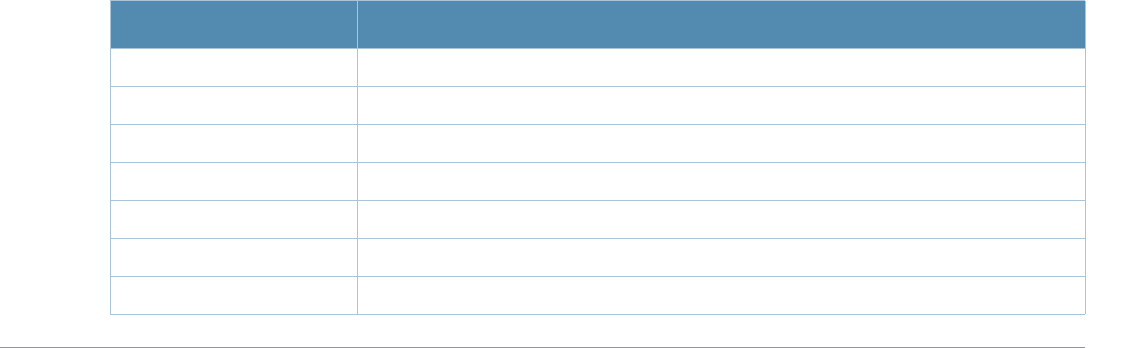
746 | show dot1x supplicant-info AOS-W 3.4.1 Command Line Interface | Reference Guide
show dot1x supplicant-info
show dot1x supplicant-info <supplicant-mac> <ap-mac>
Description
Shows the details about a specific supplicant.
Example
Issue this command to display the details about a supplicant
The output of this command includes the following parameters:
Detailed 802.1x Supplicant Information
Name CORPNETWORKS\ccutler
MAC Address 00:19:7e:a9:8e:b0
AP MAC Address 00:1a:1e:11:5f:11
Status Authentication Success
Unicast Cipher WPA2-AES
Multicast Cipher WPA2-AES
EAP-Type EAP-PEAP
Packet Statistics:
EAPOL Starts 0
EAP ID Requests 0
EAP ID Responses 0
EAPOL Logoffs from station 0
EAP pkts to the station 2
EAP pkts from station 2
Unknown EAP pkts from station 0
EAP Successes sent 0
EAP Failures sent 0
Station failed to respond 0
Station NAKs 0
Radius pkts to the server 0
Radius pkts from the server 0
Server failed to respond 0
Server rejects 0
WPA/WPA2-Key Message1 1
WPA/WPA2-Key Message2 1
WPA/WPA2-Key Message3 1
WPA/WPA2-Key Message4 1
WPA-GKey Message1 0
WPA-GKey Message2 0
ID of the last EAP request 0
Length of the last EAP request 151
ID of the last EAP response 0
Length of the last EAP response 0
ID of the last radius request 0
Length of the last radius request 0
ID of the last radius response 0
Length of the last radius response 0
Parameter Description
Name Supplicant name.
MAC Address Supplicant MAC address.
AP MAC Address AP MAC address.
Status Supplicant’s status.
Unicast Cipher Supplicant’s unicast cipher.
Multicast Cipher Supplicant’s multicast cipher.
EAP-Type Supplicant’s EAP-Type.

AOS-W 3.4.1 Command Line Interface | Reference Guide show dot1x supplicant-info | 747
EAPOL Starts Number of EAPOL starts.
EAP ID Requests Number of EAP ID requests.
EAP ID Responses Number of EAP ID responses.
EAPOL Logoffs from
station
Number of EAPOL logoffs from the station.
EAP pkts to the
station
Number of EAP packets sent to the station.
EAP pkts from station Number of EAP packets sent from the station.
Unknown EAP pkts from
station
Number of unknown EAP packets sent from the station.
EAP Successes sent Number of EAP successes sent.
EAP Failures sent Number of EAP failures sent.
Station failed to
respond
Number of times the station failed to respond.
Station NAKs Number of station negative-acknowledgement characters.
Radius pkts to the
server
Number of radius packets set to the server.
Radius pkts from the
server
Number of radius packets sent from the server.
Server failed to
respond
Number of times the server failed to respond.
Server rejects Number of times ac connection was rejected by the server.
WPA/WPA2-Key Message1 Number of WPA message-1s sent.
WPA/WPA2-Key Message2 Number of WPA message-2s sent.
WPA/WPA2-Key Message3 Number of WPA message-3s sent.
WPA/WPA2-Key Message4 Number of WPA message-4s sent.
WPA-GKey Message1 Number of WPA group message-1s sent.
WPA-GKey Message2 Number of WPA group message-2s sent.
ID of the last EAP
request
The ID of the last EAP request.
Length of the last
EAP request
The length of the last EAP request.
ID of the last EAP
response
The ID of the last EAP response.
Length of the last
EAP response
The length of the last EAP response.
ID of the last radius
request
The ID of the last radius request.
Length of the last
radius request
The length of the last radius request.
ID of the last radius
response
The ID of the last radius response.
Parameter Description
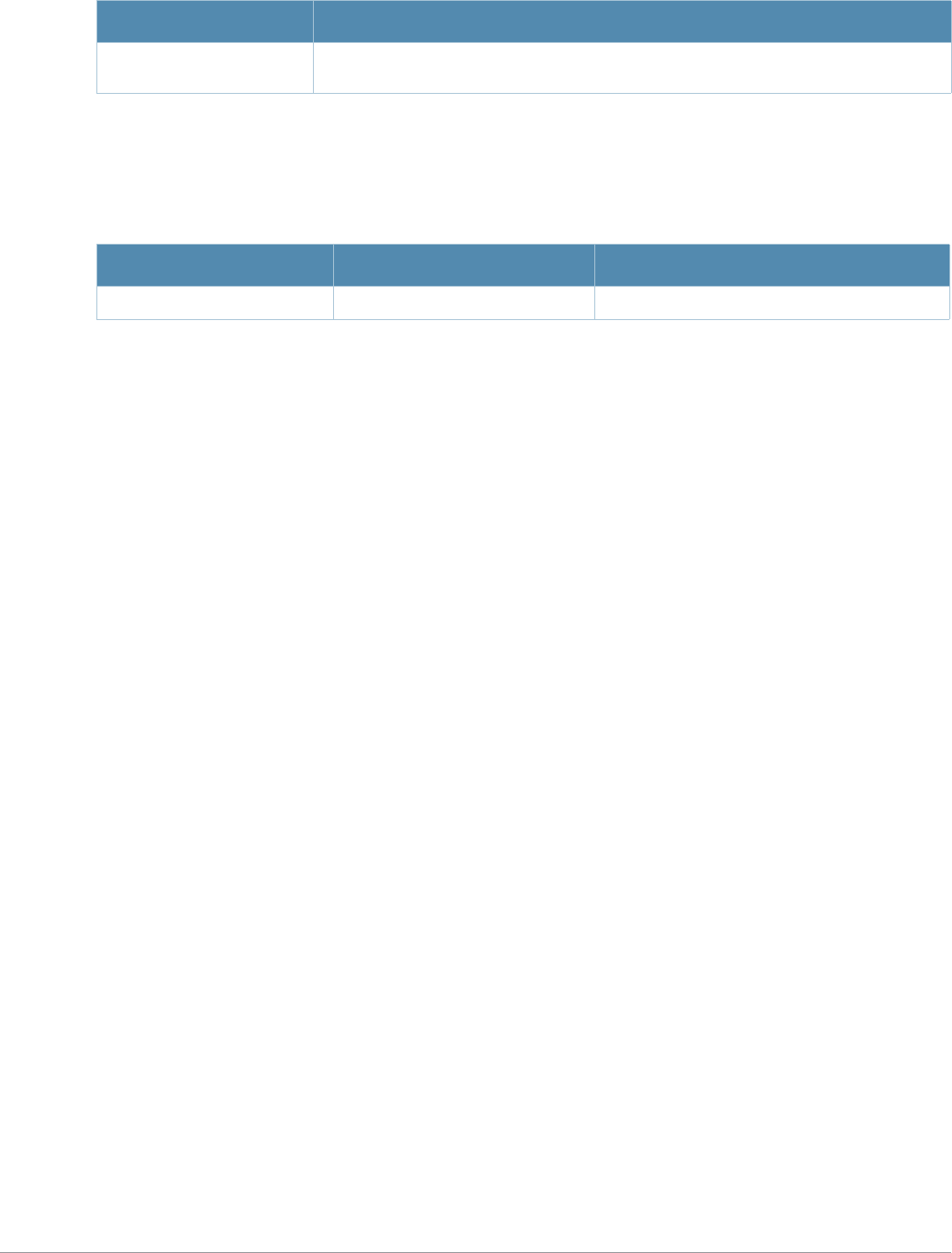
748 | show dot1x supplicant-info AOS-W 3.4.1 Command Line Interface | Reference Guide
Command History
This command was introduced in AOS-W 3.0.
Command Information
Length of the last
radius response
The length of the last radius response.
Platforms Licensing Command Mode
All platforms Base operating system Enable or config mode on master switches
Parameter Description
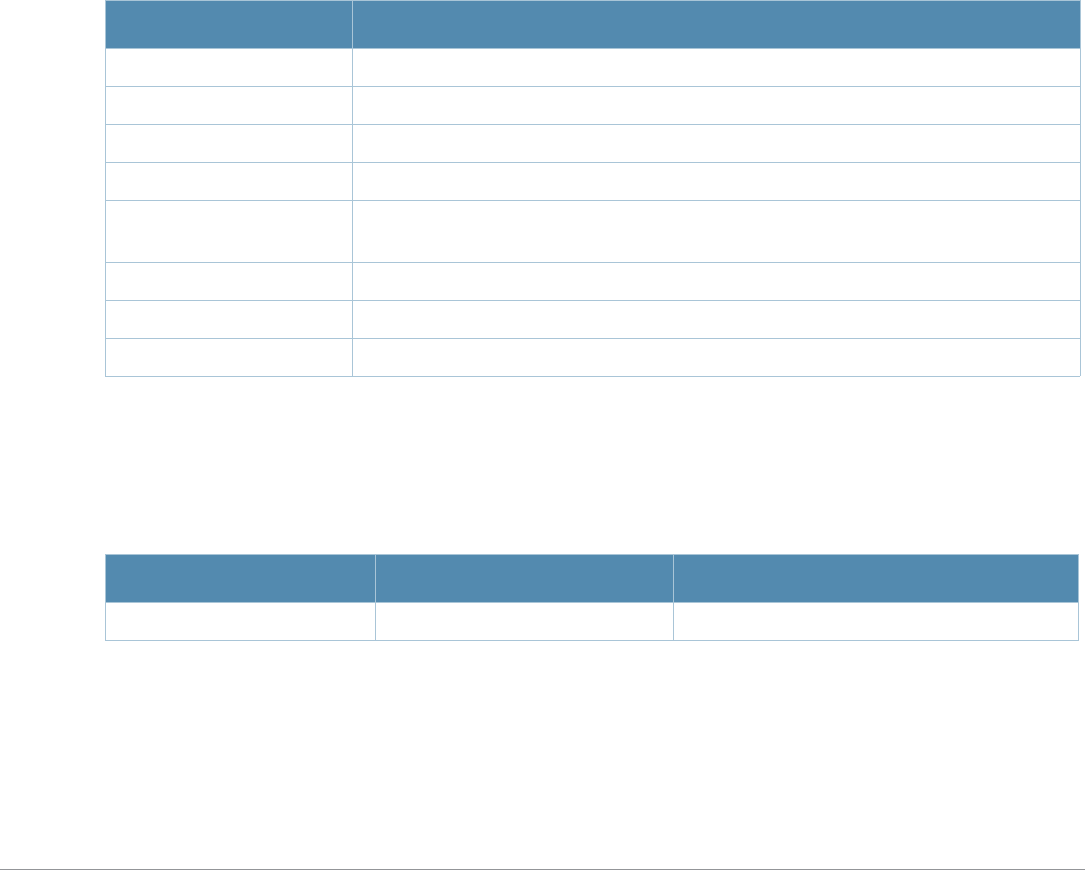
AOS-W 3.4.1 Command Line Interface | Reference Guide show dot1x supplicant-info list-all | 749
show dot1x supplicant-info list-all
show dot1x supplicant-info list all
Description
Shows all 802.1x supplicants.
Syntax
No parameters.
Example
Issue this command to display all 802.1x supplicants as well as additional relevant information.
The output of this command includes the following parameters:
Command History
This command was introduced in AOS-W 3.0.
Command Information
802.1x User Information
-----------------------
MAC Name Auth AP-MAC Enc-Key/Type Auth-Mode EAP-Type Remote
------------ -------- ---- ------ ------------------- ------------ --------- ------
00:15:00:26:f8:f5 user1 Yes 00:0b:86:8b:68:68 * * * * * * * */WPA2-AES Explicit Mode EAP-PEAP No
Station Entries: 1
Parameter Description
MAC Supplicant MAC address
Name Supplicant name
Auth Has the supplicant authenticated succesfully
AP-MAC AP MAC address
Enc-Key/Type Enc-Key: Supplicant’s encryption key
Type: Encryption type used by the supplicant
Auth-Mode Authentication mode
EAP-Type EAP type
Remote Is the supplicant remote
Platforms Licensing Command Mode
All platforms Base operating system Enable or config mode on master switches
750 | show dot1x supplicant-info pmkid AOS-W 3.4.1 Command Line Interface | Reference Guide
show dot1x supplicant-info pmkid
show dot1x supplicant-info pmkid <supplicant-mac>
Description
Shows the PMKIDs of the various stations on the switch.
Syntax
No parameters.
Example
Issue this command to display the PMKIDs of the various stations on the switch.
The output of this command includes the following parameters:
Command History
This command was introduces in AOS-W 3.0.
Command Information
PMKID Table
-----------
Mac Name AP PMKID
--- ---- -- -----
00:03:7f:bf:12:ac zoobar22 00:0b:86:a0:57:60 c2:7d:12:1a:1c:5b:40:f8:89:46:22:a5:ec:9b:fb:a6
00:03:7f:bf:12:ac zoobar22 00:0b:86:c0:04:88 bb:2d:e1:57:e1:b8:9b:a2:71:f5:98:ad:61:db:47:e7
Parameter Description
MAC Supplicant MAC address
Name Supplicant name
AP AP MAC address
PMKID Station PMKID
Platforms Licensing Command Mode
All platforms Base operating system Enable or config mode on master switches

AOS-W 3.4.1 Command Line Interface | Reference Guide show dot1x supplicant-info statistics | 751
show dot1x supplicant-info statistics
show dot1x supplicant-info statistics
Description
Shows the 802.1x statistics of the users.
Syntax
No parameters.
Example
Issue this command to display the 802.1x statistics of the users.
The output of this command includes the following parameters:
Command History
This command was introduced in AOS-W 3.0.
Command Information
802.1x Statistics
-----------------
Mac Name AP Auth-Succs Auth-Fails Auth-Tmout Re-Auths Supp-Naks UKeyRotations MKeyRotations
--- ---- -- ---------- ---------- ---------- -------- --------- ------------- -------------
00:15:00:26:f8:f5 user1 00:0b:86:8b:68:68 1 0 0 0 0 0 0
Total: 2 0 0 0 0 0 0
Station Entries: 1
Parameter Description
MAC Supplicant MAC address.
Name Supplicant name.
AP AP MAC address.
Auth-Succs Number of successful authentications.
Auth-Fails Number of authentication failures.
Auth-Tmout Number of authentication timeouts.
Re-Auths Number of reauthentications.
Supp-Naks Number of negative-acknowledgement characters sent by the supplicant.
UKeyRotations Number of unicast key rotations.
MKeyRotations Number of multicast key rotations.
Platforms Licensing Command Mode
All platforms Base operating system Enable or config mode on master switches

752 | show dot1x supplicant-info statistics AOS-W 3.4.1 Command Line Interface | Reference Guide
AOS-W 3.4.1 Command Line Interface | Reference Guide show esi groups | 753
show esi groups
show esi groups [{group-name <groupname>|{ping-name <ping-name>}]
Description
Show ESI group information.
Syntax
Usage Guidelines
The ESI parser is a mechanism for interpreting syslog messages from third party appliances such as anti-
virus gateways. Use this command to view configured ESI server groups.
Example
This example below displays the name of each configured ESI group, including its ping definitions and ESI
server.
Related Commands
Command History
This command was introduced in AOS-W 2.5.
Parameter Description
group-name <groupname> View the facility used when logging messages into the remote syslog server.
ping-name <ping-name> Enter the name of a set of ping values to how the names of ESI groups using that
set of ping attributes. Define a set of ESI ping values using the command esi
ping.
server Show the IP address of a remote logging server.
Platforms Licensing Command Mode
esi group This command configures an ESI group. Config mode on master or local switches.
esi ping This command specifies the ESI ping health check
configuration. Config mode on master or local switches.
esi server This command configures an ESI server. Config mode on master or local switches.
(host) #show esi groups
ESI Group Table
---------------
Name Tunnel ID Ping Flags Servers
---- --------- ---- ----- -------
anything 0x1042 pingset_1 C 0
cupertino 0x1043 - C 0
Flags:
C:Datapath Download complete

754 | show esi groups AOS-W 3.4.1 Command Line Interface | Reference Guide
Command Information
Platforms Licensing Command Mode
All platforms Base operating system Enable and Config mode on master or local switches.

AOS-W 3.4.1 Command Line Interface | Reference Guide show esi parser | 755
show esi parser
show esi parser domains|rules|stats
Description
Show ESI parser information.
Syntax
Usage Guidelines
The ESI parser is a generic syslog parser on the switch that accepts syslog messages from external third-
party appliances such as anti-virus gateways, content filters, and intrusion detection systems. It processes
syslog messages according to user-defined rules and takes configurable actions on the corresponding
system users.
ESI servers are configured into domains to which ESI syslog parser rules are applied.
Use the show esi parser domains command to show ESI parser domain information.
Example
The ESI Parser Domain Table in the example below shows that the switch has two ESI domains and two
ESI servers.
Related Commands
Command History
This command was introduced in AOS-W 3.1.
Parameter Description
domains Show ESI parser domain information.
rules Show ESI parser rule information.
stats Show ESI parser rule stats.
Platforms Licensing Command Mode
esi parser domain This command configures an ESI
syslog parser domain. Config mode on master or local switches.
esi parser rule This command creates or changes an
ESI syslog parser rule. Config mode on master or local switches.
esi parser rule-test This command allows you to test all
of the enabled parser rules. Config mode on master or local switches.
(host) #show esi parser domains
ESI Parser Domain Table
-----------------------
Domain ESI Servers Peer Controllers
------ ----------- ----------------
corp_domain 172.21.5.50 10.3.132.14
remote_domain 192.84.66.30
Total number of servers configured: 2

756 |show esi parser AOS-W 3.4.1 Command Line Interface | Reference Guide
Command Information
Platforms Licensing Command Mode
All platforms Base operating system Enable and Config mode on master or local switches.

AOS-W 3.4.1 Command Line Interface | Reference Guide show esi ping | 757
show esi ping
show esi ping [ping-name <ping-name>]
Description
Show settings for ESI ping health check attributes.
Syntax
Example
This example below shows that the switch has three defined sets of ping attributes.
The output of this command includes the following information:
Related Commands
Command History
This command was introduced in AOS-W 2.5.
Parameter Description
ping-name <ping-name> Include the optional ping-name <ping-name> parameters to display settings for
one specified set of ping settings.
(host) #show esi groups
ESI Ping Table
--------------
Name Frequency (sec) Timeout (sec) Retry Count ID Num Groups
---- --------------- ------------- ----------- -- ----------
ping_att1 5 2 2 0 1
ESIping 5 2 2 1 0
ESIping2 50000 2 2 2 2
Column Description
Name Name of a group of ping settings.
frequency Specifies the ping frequency in seconds.
timeout Specifies the ping timeout in seconds.
retry-count Specifies the ping retry count
ID ID number assigned to the ping attributes when that set of attributes was defined.
Num Groups Number of ESI groups to which this set of ping attributes is assigned.
Platforms Licensing Command Mode
esi ping This command specifies the ESI ping
health check configuration. Config mode on master or local switches.

758 | show esi ping AOS-W 3.4.1 Command Line Interface | Reference Guide
Command Information
Platforms Licensing Command Mode
All platforms Base operating system Enable and Config mode on master or local switches.
AOS-W 3.4.1 Command Line Interface | Reference Guide show esi servers | 759
show esi servers
show esi servers [{group-name <groupname>|{server-name <server-name>}]
Description
Show configuration information for ESI servers.
Syntax
Usage Guidelines
By default, this command displays configuration settings for all ESI servers. You can include the name of an
ESI group to view servers assigned to just that group, or specify a server name to view information for that
server only.
Example
This example below displays configuration details for the ESI server name forti_1.
The output of this command includes the following information:
Parameter Description
group-name
<groupname>
Include this optional parameter to display information for all ESI servers assigned to a
specific ESI group.
server-name
<server-name>
Specify an ESI server name to view configuration information for just that server.
(host) #show esi servers server-name forti_1
ESI Server Table
----------------
Name Trusted IP Untrusted IP Trusted s/p Untrusted s/p Group Mode NAT Port ID Flags
---- ---------- ------------ ----------- ------------- ----- ---- -------- -- -----
forti_1 10.168.173.2 10.168.171.3 -/- -/- default route 0 4 U
Flags:
C :Datapath Download complete
U :Server Up
D :Server Down
PT:Trusted Ping response outstanding
PU:Untrusted Ping response outstanding
HT:Health Check Trusted IP
HU:Health Check Untrusted IP
FT:Trusted Ping failed
FU:Untrusted Ping failed
Column Description
Name Name of the ESI server.
Trusted IP Displays the server IP address on the trusted network. As an option, you can also enable
a health check on the specified address
Untrusted IP Displays the server IP address on the untrusted network. As an option, you can also
enable a health check on the specified address
Trusted s/p Shows the slot and port connected to the trusted side of the ESI server; slot/port format.
Untrusted s/p Shows the slot and port connected to the untrusted side of the ESI server.
Group Name of the ESI group to which this server is assigned. If the server has not yet been
assigned to a group, this column will be blank.

760 | show esi servers AOS-W 3.4.1 Command Line Interface | Reference Guide
Related Commands
Command History
This command was introduced in AOS-W 2.5.
Command Information
Mode Specifies the ESI server mode of operation: bridge, nat, or route
Nat Port Displays the NAT destination TCP/UDP port.
ID ID number assigned to the server when it was first defined.
Flags This data column displays any flags associated with this server. The flag key appears
below the ESI Server Table.
Column Description
Platforms Licensing Command Mode
esi server This command configures an ESI server. Config mode on master or local switches.
Platforms Licensing Command Mode
All platforms Base operating system Enable and Config mode on master or local switches.
AOS-W 3.4.1 Command Line Interface | Reference Guide show faults | 761
show faults
show fault [history]
Description
Display a list of faults, which are any problematic conditions of the AOS-W software or hardware.
Syntax
Usage Guidelines
A switch can maintain a list of up to 100 faults. Once 100 faults have been logged, any faults arising after
that are dropped. The switch maintains a history of the last 100 faults that have cleared. Every time a new
fault clears clear, the oldest fault in the fault history is purged from the list.
Example
This example below shows all active faults the switch, including the time the fault occurred, the fault ID
number, and a description of the problem.
Parameter Description
history Include this parameter to display a history of faults cleared by the switch or the operator.
(host) #show firewall
Active Faults
-------------
Time Number Description
---- ------ -----------
2009-03-02 18:13:08 93 Authentication Server vortex is down.
2009-03-02 18:13:08 94 Authentication Server vortex is down.
2009-03-02 18:13:08 95 Authentication Server vortex is down.
2009-03-02 18:13:08 96 Authentication Server vortex is down.
2009-03-02 18:13:08 97 Authentication Server aruba-supersvr is down.
2009-03-02 18:13:08 98 All authentication servers in server group sg-auth2 are brought back in service.
2009-03-02 18:13:08 99 Authentication Server aruba-supersvr is down.
2009-03-02 18:13:08 100 All authentication servers in server group sg-auth2 are brought back in service.
2009-03-02 18:13:08 101 Authentication Server aruba-supersvr is down.
2009-03-02 18:13:08 102 All authentication servers in server group sg-auth2 are brought back in service.
2009-03-02 18:13:08 103 Authentication Server aruba-supersvr is down.
2009-03-02 18:13:08 104 All authentication servers in server group sg-auth2 are brought back in service.
2009-03-02 18:13:08 105 Authentication Server aruba-supersvr is down.
2009-03-02 18:13:08 106 All authentication servers in server group sg-auth2 are brought back in service.
2009-03-02 18:13:09 107 Authentication Server aruba-supersvr is down.
2009-03-02 18:13:09 108 All authentication servers in server group sg-auth2 are brought back in service.
2009-03-02 18:13:09 109 Authentication Server aruba-supersvr is down.
2009-03-02 18:13:09 110 All authentication servers in server group sg-auth2 are brought back in service.
2009-03-02 18:13:09 111 Authentication Server aruba-supersvr is down.
2009-03-02 18:13:09 112 All authentication servers in server group sg-auth2 are brought back in service.
2009-03-02 18:13:09 113 Authentication Server aruba-supersvr is down.
2009-03-02 18:13:09 114 All authentication servers in server group sg-auth2 are brought back in service.
2009-03-02 18:13:09 115 Authentication Server aruba-supersvr is down.
Total number of entries in the queue :23
762 | show faults AOS-W 3.4.1 Command Line Interface | Reference Guide
Related Commands
Command History
This command was introduced in AOS-W 3.0.
Command Information
Command Description Mode
clear fault <id>|all Manually clear a single fault by specifying the
fault ID number, or clear all faults by including
the all parameter.
Config mode
Platforms Licensing Command Mode
All platforms Base operating system Enable and Config mode on master or local switches.
AOS-W 3.4.1 Command Line Interface | Reference Guide show firewall | 763
show firewall
show firewall
Description
Display a list of global firewall policies.
Syntax
No parameters
Example
This example below shows all firewall policies currently configured on the switch.
The output of this command includes the following information:
(host) #show firewall
Global firewall policies
------------------------
Policy Action Rate Slot/Port
------ ------ ---- ---------
Enforce TCP handshake before allowing data Enabled
Prohibit RST replay attack Enabled
Deny all IP fragments Enabled
Prohibit IP Spoofing Enabled
Monitor ping attack Enabled 20/sec
Monitor TCP SYN attack Disabled
Monitor IP sessions attack Disabled
Deny inter user bridging Disabled
Log all received ICMP errors Disabled
Per-packet logging Disabled
Session mirror destination Disabled
Stateful SIP Processing Enabled
Allow tri-session with DNAT Enabled
Disable FTP server No
GRE call id processing Disabled
Session Idle Timeout Disabled
Broadcast-filter ARP Disabled
WMM content enforcement Disabled
Session VOIP Timeout Disabled
Stateful H.323 Processing Enabled
Stateful SCCP Processing Enabled
Only allow local subnets in user table Enabled
Monitor/police CP attacks Enabled 255/sec
Rate limit CP untrusted ucast traffic Enabled 10 Mbps
Rate limit CP untrusted mcast traffic Enabled 2 Mbps
Rate limit CP trusted ucast traffic Enabled 80 Mbps
Rate limit CP trusted mcast traffic Enabled 2 Mbps
Rate limit CP route traffic Enabled 1 Mbps
Rate limit CP session mirror traffic Enabled 1 Mbps
Rate limit CP auth process traffic Enabled 1 Mbps
Deny inter user traffic Disabled
Session mirror IPSEC Disabled
Parameter Description
Enforce TCP handshake
before allowing data
If enabled, this feature prevents data from passing between two clients until the
three-way TCP handshake has been performed. This option should be disabled
when you have mobile clients on the network as enabling this option will cause
mobility to fail. You can enable this option if there are no mobile clients on the
network.
764 | show firewall AOS-W 3.4.1 Command Line Interface | Reference Guide
Prohibit RST replay
attack
If enabled, this setting closes a TCP connection in both directions if a TCP RST is
received from either direction.
Deny all IP fragments If enabled, all IP fragments are dropped.
Prohibit IP Spoofing When this option is enabled, IP and MAC addresses are checked; possible IP
spoofing attacks are logged and an SNMP trap is sent.
Monitor ping attack If enabled, the switch monitors the number of ICMP pings per second. If this
value exceeds the maximum configured rate, the switch will register a denial of
service attack.
Monitor TCP SYN attack
If enabled, the switch monitors the number of TCP SYN messages per second. If
this value exceeds the maximum configured rate, the switch will register a denial
of service attack.
Monitor IP sessions
attack
If enabled, the switch monitors the number of TCP sessions requests per second.
If this value exceeds the maximum configured rate, the switch will register a
denial of service attack sessions.
Deny inter user
bridging
If enabled this setting prevents the forwarding of Layer-2 traffic between wired or
wireless users. You can configure user role policies that prevent Layer-3 traffic
between users or networks but this does not block Layer-2 traffic.
Log all received ICMP
errors
Shows if the switch will log received ICMP errors.
Per-packet logging If active, and logging is enabled for the corresponding session rule, this feature
logs every packet.
Session mirror
destination
Destination to which mirrored packets are sent.
Stateful SIP Processing Shows if the switch has enabled or disabled monitoring of exchanges between a
voice over IP or voice over WLAN device and a SIP server. This option should be
enabled only when thee is no VoIP or VoWLAN traffic on the network
Allow tri-session with
DNAT
Shows if the switch allows three-way session when performing destination NAT.
Disable FTP server
If active, this feature disables the FTP server on the switch.
GRE call id processing If active the switch creates a unique state for each PPTP tunnel.
Session Idle Timeout Shows if a session idle timeout interval has been defined.
Broadcast-filter ARP
If enabled, this feature reduces the number of broadcast packets sent to VoIP
clients, thereby improving the battery life of voice handsets.
WMM content enforcement If traffic to or from the user is inconsistent with the associated QoS policy for
voice, this feature reclassifies traffic to best effort and data path counters are
incremented.
Session VOIP Timeout If enabled, a idle session timeout is defined for sessions that are marked as voice
sessions.
Stateful H.323
Processing
Shows if the switch has enabled or disabled stateful H.323 processing.
Stateful SCCP
Processing
Shows if the switch has enabled or disabled stateful SCCP processing.
Only allow local
subnets in user table
If enabled, the switch only adds IP addresses which belong to a local subnet to
the user table.
Monitor/police CP
attacks
If enabled, the switch monitors the a misbehaving user’s inbound traffic rate. If
this rate is exceeded, the switch can register a denial of service attack.
Parameter Description
AOS-W 3.4.1 Command Line Interface | Reference Guide show firewall | 765
Related Commands
Command History
This command was introduced in AOS-W 3.4.
Command Information
Rate limit CP untrusted
ucast traffic
Shows the inbound traffic rate
Rate limit CP untrusted
mcast traffic
Displays the untrusted multicast traffic rate limit.
Rate limit CP trusted
ucast traffic
Displays the trusted unicast traffic rate limit.
Rate limit CP trusted
mcast traffic
Displays the trusted multicast traffic rate limit.
Rate limit CP route
traffic
Displays the traffic rate limit for traffic that needs generated ARP requests.
Rate limit CP session
mirror traffic
Displays the traffic rate limit for session mirrored traffic forwarded to the switch.
Rate limit CP auth
process traffic
Displays the traffic rate limit for traffic forwarded to the authentication process.
Deny inter user traffic If enabled, this setting disables the forwarding of Layer-2 traffic between wired or
wireless users. You can configure user role policies that prevent Layer-3 traffic
between users or networks but this does not block Layer-2 traffic.
Session mirror IPSEC If enabled, rrames are sent to IP address specified by the session-mirror-
destination option.
Parameter Description
Command Description Mode
firewall This command configures firewall options on
the switch. Config mode
firewall cp This command creates whitelist session ACLs Config mode
firewall cp-bandwidth-
contract
This command configures bandwidth contract
traffic rate limits to prevent denial of service
attacks.
Config mode
Platforms Licensing Command Mode
All platforms Base operating system Enable and Config mode on master or local switches

766 | show firewall AOS-W 3.4.1 Command Line Interface | Reference Guide

AOS-W 3.4.1 Command Line Interface | Reference Guide show firewall-cp | 767
show firewall-cp
show firewall-cp [internal]
Description
Displays the captive-portal (CP) firewall policies on the switch.
Syntax
No Parameters
Example
The output of this command shows the CP firewall policies.
Command History
This command was available in AOS-W 3.0
Command Information
(host) # show firewall-cp
CP firewall policies
--------------------
Protocol Start Port End Port Permit/Deny hits contract
-------- ---------- -------- ----------- ---- --------
6 22 22 Permit 0
6 8081 8081 Permit 0
6 8082 8082 Permit 0
6 8083 8083 Permit 0
17 1812 1812 Permit 0
17 1813 1813 Permit 0
17 67 67 Permit 0
17 68 68 Permit 0
47 1 65535 Permit 0
Platforms Licensing Command Mode
All platforms Base operating system Config or Enable mode on master or local
switches

768 | show firewall-cp AOS-W 3.4.1 Command Line Interface | Reference Guide
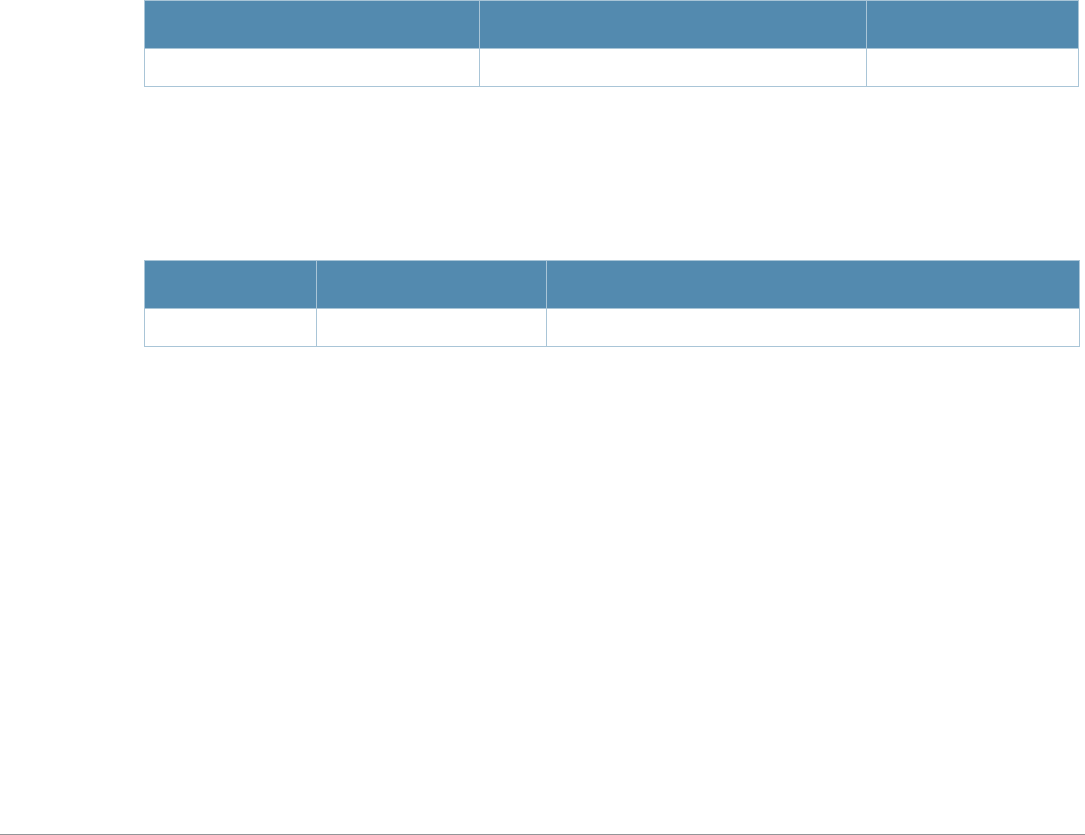
AOS-W 3.4.1 Command Line Interface | Reference Guide show gateway health-check | 769
show gateway health-check
show gateway health-check
Description
Display the current status of the gateway health-check feature.
Syntax
No parameters.
Usage Guidelines
The gateway health check feature can only be enabled by Alcatel-Lucent Technical Support.
Example
This example below shows that the gateway health-check feature has not been enabled on the switch.
Related Commands
Command History
This command was introduced in AOS-W 3.4.
Command Information
Command Description Mode
gateway health-check disable Disable the gateway health check Config mode
Platforms Licensing Command Mode
All platforms Base operating system Enable and Config mode on master or local switches
(host) #show gateway health-check
Gateway health check not enabled

770 | show gateway health-check AOS-W 3.4.1 Command Line Interface | Reference Guide

AOS-W 3.4.1 Command Line Interface | Reference Guide show global-user-table count | 771
show global-user-table count
show global-user-table
show global-user-table count
[current-switch] <IP address>
[authentication-method] {dot1x | mac | stateful-dot1x | vpn | web}
[role] <role name>
[bssid] <bssid MAC>
[essid] <essid name>
[ap-name] <AP name>
[phy-type] {a | b | g}
[age] <starting time dd:hh:mm> <ending time dd:hh:mm>
Description
This command displays a count of global user based on the specified criteria.
Syntax
Example
Issue this command to display a global user count.The output shown below is a result of the command show
global-user-table count current-switch <ip-address>.
The output includes the following parameters:
Command History
This command was introduced in AOS-W 3.4.
Parameter Description
current-switch Match IP address of the switch where the user is currently associated
authentication-method Count users matching the specified authentication method
role Count users matching the specified role
bssid Count users matching the specified BSSID
essid Count users matching the specified ESSID
ap-name Count users matching the specified AP name
phy-type Count users matching the specified Phy type
age Count users matching the specified age
Parameter Description
The number of global
users:
Total number of global users meeting the specified criteria.
Complete results.
The number of global users : 2

772 | show global-user-table count AOS-W 3.4.1 Command Line Interface | Reference Guide
Command Information
Platforms Licensing Command Mode
All platforms
Master switch only
Base operating system Enable or config mode on master switches
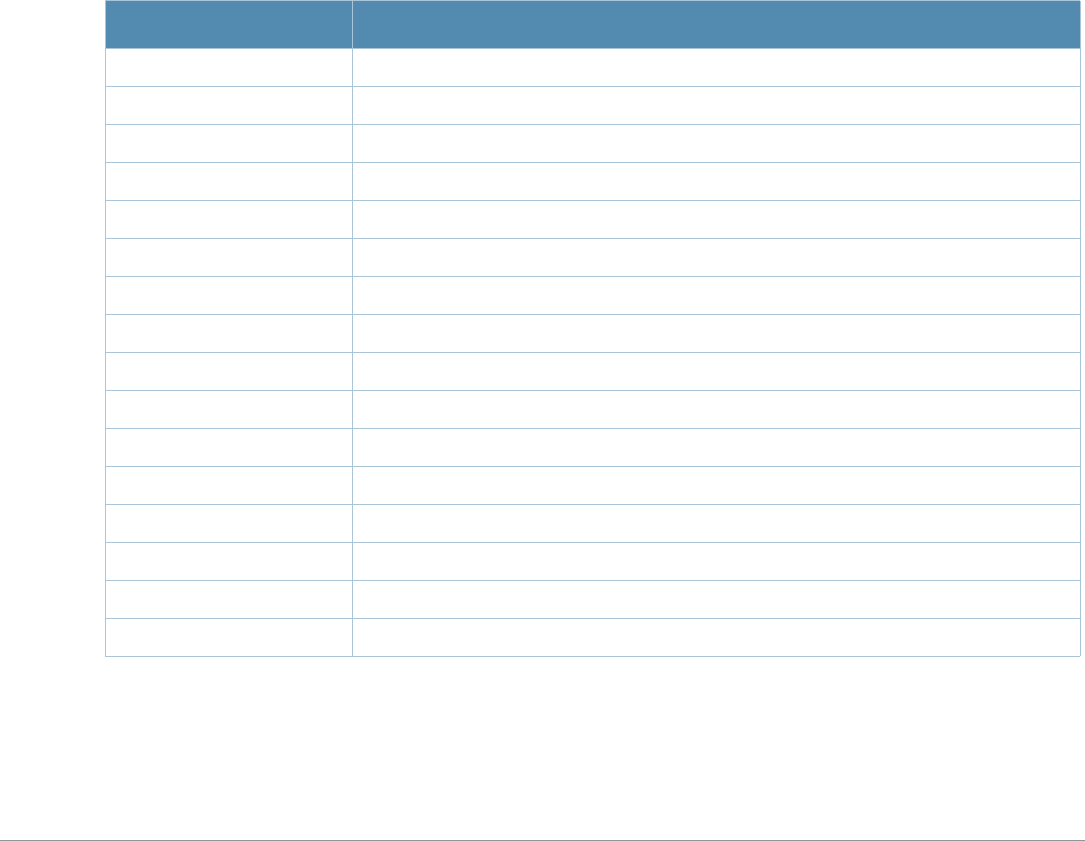
AOS-W 3.4.1 Command Line Interface | Reference Guide show-global-user-table list | 773
show-global-user-table list
show global-user-table list
[current-switch] <IP address>
[authentication-method] {dot1x | mac | stateful-dot1x | vpn | web}
[role] <role name>
[bssid] <bssid MAC>
[essid] <essid name>
[ap-name] <AP name>
[phy-type] {a | b | g}
[age] <starting time dd:hh:mm> <ending time dd:hh:mm>
[not]
[or]
[rows]
[sort] {sort_by_ap-name | sort_by_authtype | sort_by_bssid | sort_by_current-switch |
sort_by_essid | sort_by_ip | sort_by_mac | sort_by_name | sort_by_phy-type |
sort_by_role}{asc | desc}
[start]
Description
This command displays a list of current users on a specified switch.
Syntax
Parameter Description
current-switch Match IP address of the switch where the user is currently associated
authentication-method Count users matching the specified authentication method
role Count users matching the specified role
bssid Count users matching the specified BSSID
essid Count users matching the specified ESSID
ap-name Count users matching the specified AP name
phy-type Count users matching the specified Phy type
age Count users matching the specified age
current-switch Match IP address of the switch where the user is currently associated
authentication-method Count users matching the specified authentication method
role Count users matching the specified role
not Show users that do not satisfy the given criteria
or Show users that satisfy any of the given criteria
rows Number of rows to show
sort Sort the list based on a specified criteria, in ascending or descending order
start Show user table starting from a specific row

774 | show-global-user-table list AOS-W 3.4.1 Command Line Interface | Reference Guide
Example
Issue this command to display a global user count. The output shown below is a result of the command show
global-user-table list current-switch <ip-address>
The output includes the following parameters:
Command History
This command was introduced in AOS-W 3.4.
Command Information
Global Users
------------
IP MAC Name Current switch Role Age(d:h:m) Auth VPN link AP name Roaming Essid Bssid Phy Profile
---------- ------------ ------ -------------- ---- ---------- ---- -------- ------- ------- ----- ----- --- -------
1.1.1.1 7f:ff:f8:60:30:11 test11 10.3.49.100 pre-employee 00:00:00 802.1x vlan 0 Wired
1.1.1.2 7f:ff:f8:60:30:16 test12 10.3.49.100 pre-guest 00:00:00 MAC vlan 0 Wired
Complete results.
The number of global users : 2
Parameter Description
IP IP address of user
MAC MAC address of user
Name User name
Current Switch IP address of the switch where the user is currently associated
Role User role
Age User age, displayed as days : hours : minutes
Auth Authentication method used by user
VPN Link VPN link
AP name AP name
Roaming Roaming status
Essid ESSID
Bssid BSSID
Phy Phy type
Profile Profile name
Platforms Licensing Command Mode
All platforms
Master switch only
Base operating system Enable or config mode on master switches

AOS-W 3.4.1 Command Line Interface | Reference Guide show guest-access-email | 775
show guest-access-email
show guest-access-email
Description
This command shows a guest access email profile configuration.The guest access email process sends
email to either the guest or the sponsor whenever a guest user account is created or when the Guest
Provisioning user manually sends email from the Guest Provisioning page.
Syntax
No parameters.
Usage Guidelines
Issue this command to show the current guest access email profile parameters. The Parameter and Value
columns show the configured SMTP server and SMTP ports. that process guest email.
Related Commands
(host) (config) #guest-access-email smtp-port
(host) (config) #guest-access-email
(host) #local-userdb-guest add
(host) #show local-userdb-guest
Command History
This command was introduced in AOS-W 3.4.
Command Information
Platforms Licensing Command Mode
All platforms Base operating system Enable or Config mode on master or local
switches
(host) #show guest-access-email
Guest-access Email Profile
--------------------------
Parameter Value
--------- -----
SMTP Server 10.1.1.4
SMTP Port 25

776 | show guest-access-email AOS-W 3.4.1 Command Line Interface | Reference Guide

AOS-W 3.4.1 Command Line Interface | Reference Guide show hostname | 777
show hostname
show hostname
Description
Show the hostname of the switch.
Syntax
No parameters.
Example
The output of this command shows the hostname configured for the switch. A hostname can contain
alphanumeric characters, spaces, punctuation, and symbol characters.
Related Commands
Configure the switch’s hostname using the command hostname.
Command History
This command was available in AOS-W 1.0.
Command Information
(host) # show hostname
hostname is SampleHost.
Platforms Licensing Command Mode
All platforms Base operating system Available on master or local switches

778 | show hostname AOS-W 3.4.1 Command Line Interface | Reference Guide

AOS-W 3.4.1 Command Line Interface | Reference Guide show ids dos-profile | 779
show ids dos-profile
show ids dos-profile <profile-name>
Description
Show an IDS Denial Of Service (DoS) Profile
Syntax
Usage Guidelines
Issue this command without the <profile> parameter to display the entire IDS DoS profile list, including
profile status and the number of references to each profile. Include a profile name to display detailed
configuration information for that profile.
Examples
The example below shows that the switch has four configured DoS profiles.
This example displays the configuration settings for the profile ids-dos-disabled.
Parameter Description
<profile-name> Name of an IDS DoS profile.
(host) # show ids dos-profile
IDS Denial Of Service Profile List
----------------------------------
Name References Profile Status
---- ---------- --------------
default 1
ids-dos-disabled 1 Predefined
ids-dos-high-setting 1 Predefined
ids-dos-low-setting 1 Predefined
ids-dos-medium-setting 1 Predefined
(host) # show ids dos-profile ids-dos-disabled
IDS Denial Of Service Profile "ids-dos-disabled" (Predefined)
------------------------------------------------------------
Parameter Value
--------- -----
Spoofed Deauth Blacklist Disabled
Detect AP Flood Attack false
AP Flood Threshold 50
AP Flood Increase Time 3 sec
AP Flood Detection Quiet Time 900 sec
Detect EAP Rate Anomaly false
EAP Rate Threshold 60
EAP Rate Time Interval 3 sec
EAP Rate Quiet Time 900 sec
Detect Rate Anomalies false
Rate Thresholds for Assoc Frames default
Rate Thresholds for Disassoc Frames default
Rate Thresholds for Deauth Frames default
Rate Thresholds for Probe Request Frames default
Rate Thresholds for Probe Response Frames default
Rate Thresholds for Auth Frames default
Detect 802.11n 40MHz Intolerance Setting false
Client 40MHz Intolerance Detection Quiet Time 900

780 | show ids dos-profile AOS-W 3.4.1 Command Line Interface | Reference Guide
The output of this command includes the following parameters:
Related Commands
Configure IDS DoS profiles using the command ids dos-profile.
Command History
Parameter Description
Spoofed Deauth Blacklist Shows if the profile has enabled or disabled detection of a deauth
attack initiated against a client associated to an Alcatel-Lucent AP.
When such an attack is detected, the client is quarantined from the
network to prevent a man-in-the-middle attack from being successful.
Detect Ap Flood Attack Shows if the profile has enabled or disabled detection of flooding with
fake AP beacons to confuse legitimate users and to increase the
amount of processing needed on client operating systems.
AP Flood Threshold Number of fake AP beacons that must be received within the flood
increase time to trigger an alarm.
AP Flood Increase Time Time, in seconds, during which a configured number of fake AP
beacons must be received to trigger an alarm.
AP Flood Detection Quiet TIme Time, in seconds, that must elapse before an second fake AP flood
alarm may be triggered.
Detect EAP Rate Anomaly Shows if the profile has enabled or disabled Extensible Authentication
Protocol (EAP) handshake analysis to detect an abnormal number of
authentication procedures on a channel and generate an alarm when
this condition is detected.
EAP rate Threshold Number of EAP handshakes that must be received within the EAP rate
time interval to trigger an alarm.
EAP Rate TIme Interval Time, in seconds, during which the configured number of EAP
handshakes must be received to trigger an alarm.
EAP Rate Quiet Time Time, in seconds, that must elapse after an EAP rate anomaly alarm
has been triggered before another identical alarm may be triggered.
Detect Rate Anomalies Enables detection of rate anomalies.
Rate Thresholds for Assoc
Frames
Rate threshold for associate request frames.
Rate Thresholds for Disassoc
Frames
Rate threshold for disassociate frames.
Rate Thresholds for Deauth
Frames
Rate threshold for deauthenticate frames.
Rate Thresholds for Probe
Request Frames
Rate threshold for probe request frames.
Rate Thresholds for Probe
Response Frames
Rate threshold for probe response frames.
Rate Thresholds for Auth Frames Rate threshold for authenticate frames.
Detect 802.11n 40MHz
Intolerance Setting
Shows if the profile has enabled or disabled detection of 802.11n 40
MHz intolerance setting, which controls whether stations and
APs advertising 40 MHz intolerance will be reported.
Client 40MHz Intolerance
Detection Quiet Time
Seconds of quiet time when the AP stops reporting intolerant
STAs if they have not been detected).

AOS-W 3.4.1 Command Line Interface | Reference Guide show ids dos-profile | 781
This command was available in AOS-W 3.0.
Command Information
Platforms Licensing Command Mode
All platforms Base operating system Available in Enable and Config mode on
master or local switches
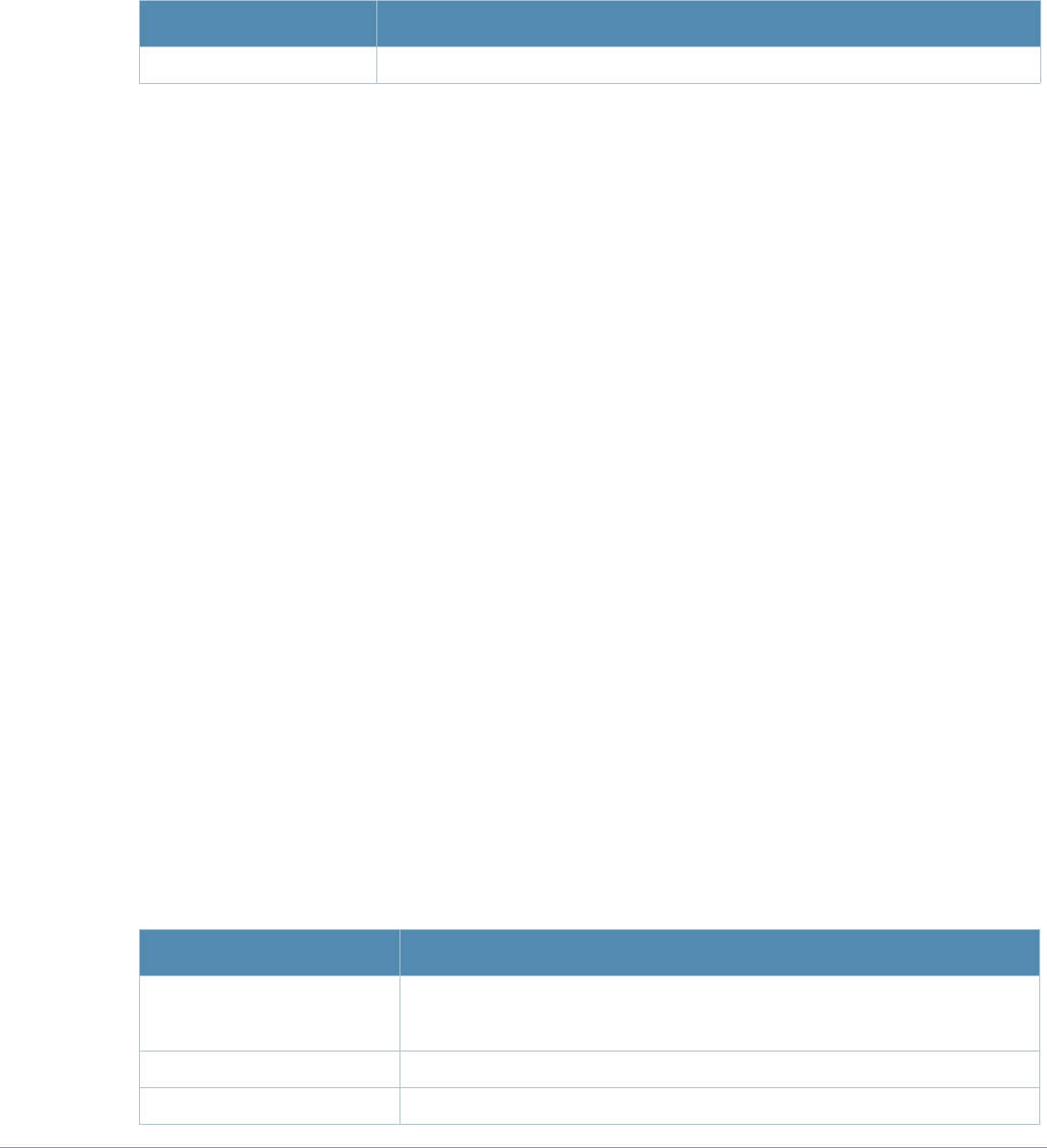
782 | show ids general-profile AOS-W 3.4.1 Command Line Interface | Reference Guide
show ids general-profile
show ids general-profile <profile-name>
Description
Show an IDS General profile.
Syntax
Usage Guidelines
Issue this command without the <profile> parameter to display the entire IDS General profile list,
including profile status and the number of references to each profile. Include a profile name to display
detailed configuration information for that profile.
Examples
The example below shows that the switch has four configured General profiles.
This example displays the configuration settings for the profile default.
The output of this command includes the following parameters:
Parameter Description
<profile-name> Name of an IDS General profile.
(host) # show ids general-profile
IDS General Profile List
------------------------
Name References Profile Status
---- ---------- --------------
default 3
ids-general-disabled 1 Predefined
ids-general-high-setting 1 Predefined
test1 0
Total:4
(host) # show ids general-profile default
IDS General Profile "default"
-----------------------------
Parameter Value
--------- -----
Stats Update Interval 60 sec
AP Inactivity Timeout 5 sec
STA Inactivity Timeout 60 sec
Min Potential AP Beacon Rate 25 %
Min Potential AP Monitor Time 3 sec
Signature Quiet Time 900 sec
Wireless Containment true
Debug Wireless Containment false
Wired Containment false
Parameter Description
Stats Update Interval Interval, in seconds, for the AP to update the switch with statistics. This setting
takes effect only if the Alcatel-Lucent Mobility Manager is configured. Otherwise,
statistics update to the switch is disabled.
AP Inactivity Timeout Time, in seconds, after which an AP is aged out.
STA Inactivity Timeout Time, in seconds, after which a station is aged out.
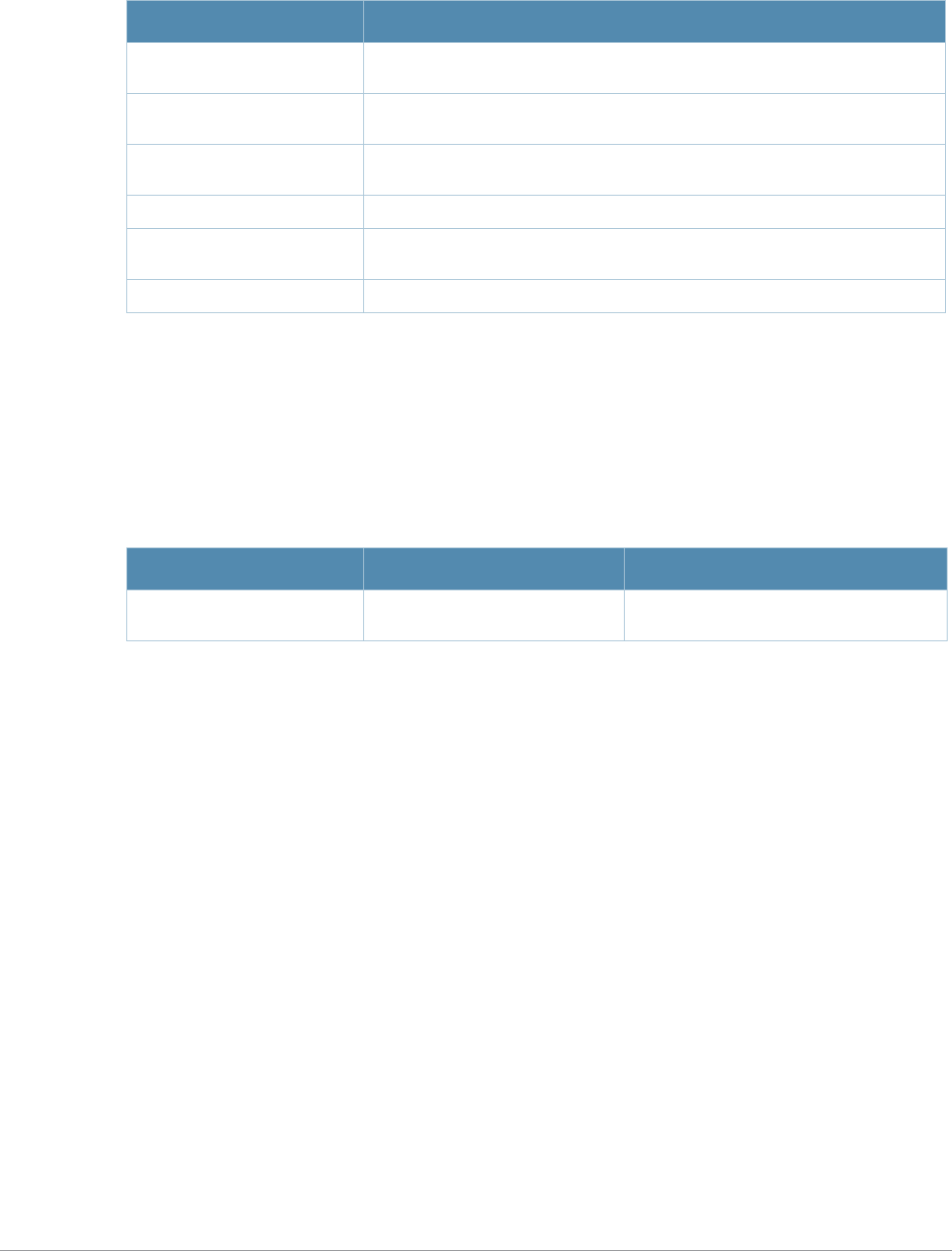
AOS-W 3.4.1 Command Line Interface | Reference Guide show ids general-profile | 783
Related Commands
Configure IDS General profiles using the command ids general-profile.
Command History
This command was available in AOS-W 3.0.
Command Information
Min Potential AP Beacon
Rate
Minimum beacon rate acceptable from a potential AP, in percentage of the
advertised beacon interval.
Min Potential AP
Monitor Time
Minimum time, in seconds, a potential AP has to be up before it is classified as a
real AP.
Signature Quiet Time After a signature match is detected, the time to wait, in seconds, to resume
checking.
Wireless Containment Shows if the profile has enabled or disabled containment from the wireless side.
Debug Wireless
Containment
Shows if the profile has enabled or disable debugging of containment from the
wireless side.
Wired Containment Shows if the profile has enabled or disable containment from the wired side.
Parameter Description
Platforms Licensing Command Mode
All platforms Base operating system Available in Enable and Config mode on
master or local switches
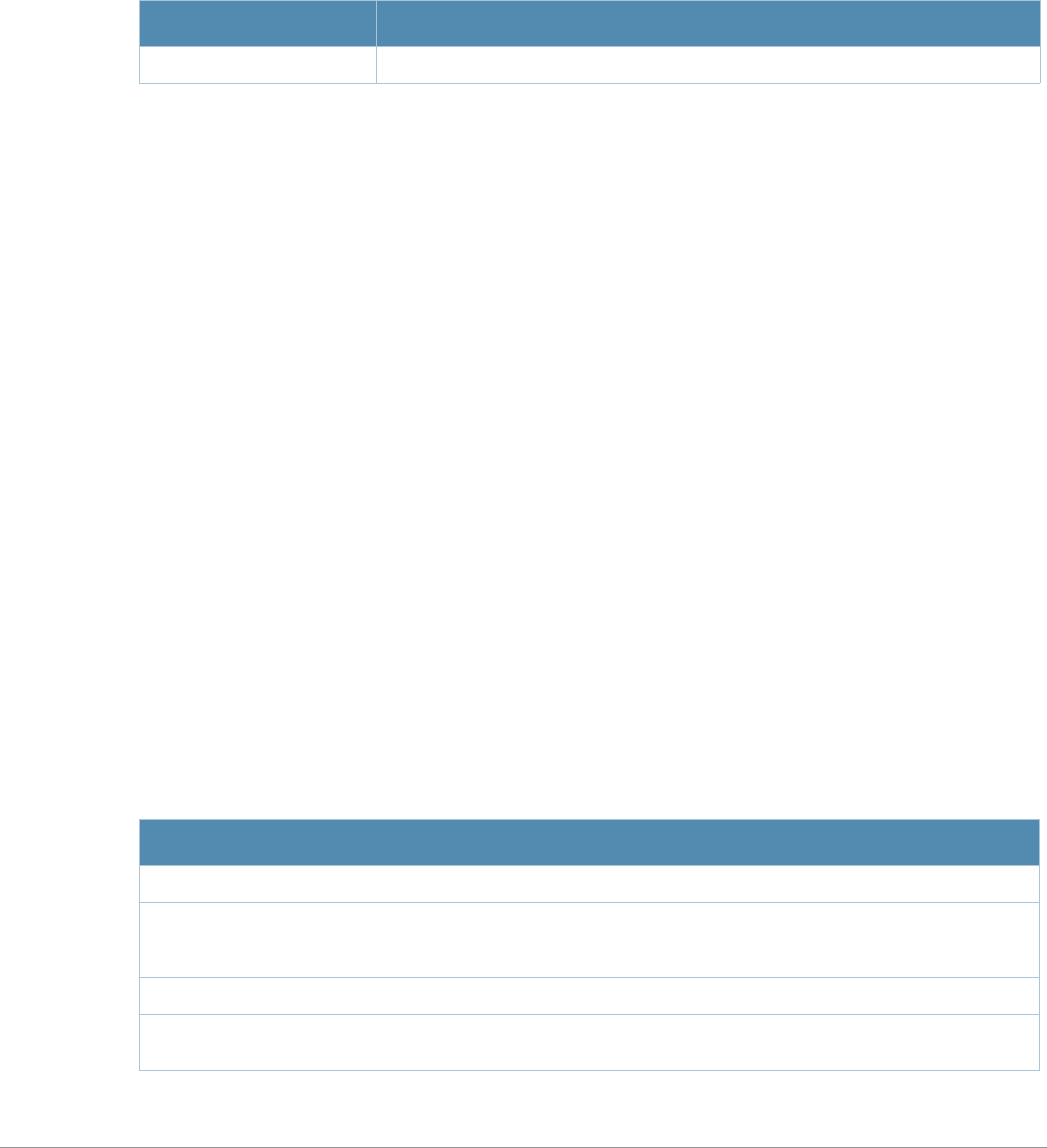
784 | show ids impersonation-profile AOS-W 3.4.1 Command Line Interface | Reference Guide
show ids impersonation-profile
show ids impersonation-profile <profile-name>
Description
Show an IDS Impersonation Profile.
Syntax
Usage Guidelines
Issue this command without the <profile> parameter to display the entire IDS Impersonation profile list,
including profile status and the number of references to each profile. Include a profile name to display
detailed configuration information for that profile.
Examples
The example below shows that the switch has three configured Impersonation profiles.
This example displays the configuration settings for the profile ids-impersonation-high-setting.
The output of this command includes the following parameters:
Parameter Description
<profile-name> Name of an IDS Impersonation profile.
(host) # show ids impersonation-profile
IDS Impersonation Profile List
------------------------------
Name References Profile Status
---- ---------- --------------
default 3
ids-impersonation-disabled 1 Predefined
ids-impersonation-high-setting 1 Predefined
Total:3
(host) # show ids impersonation-profile ids-impersonation-high-setting
IDS Impersonation Profile “ids-impersonation-high-setting” (Predefined)
-----------------------------------------------------------------------
Parameter Value
--------- -----
Detect AP Impersonation true
Protect from AP Impersonation true
Beacon Diff Threshold 50 %
Beacon Increase Wait Time 3 sec
Parameter Description
Detect AP Impersonation Shows of the profile has enabled or disabled detection of AP impersonation.
Protect from AP
Impersonation
Shows if AP impersonation is enabled or disabled for the profile. When AP
impersonation is detected, both the legitimate and impersonating AP are
disabled using a denial of service attack.
Beacon Diff Threshold Percentage increase in beacon rates that triggers an AP impersonation event.
Beacon Increase Wait
Time
Time, in seconds, after the beacon difference threshold is crossed before an AP
impersonation event is generated.
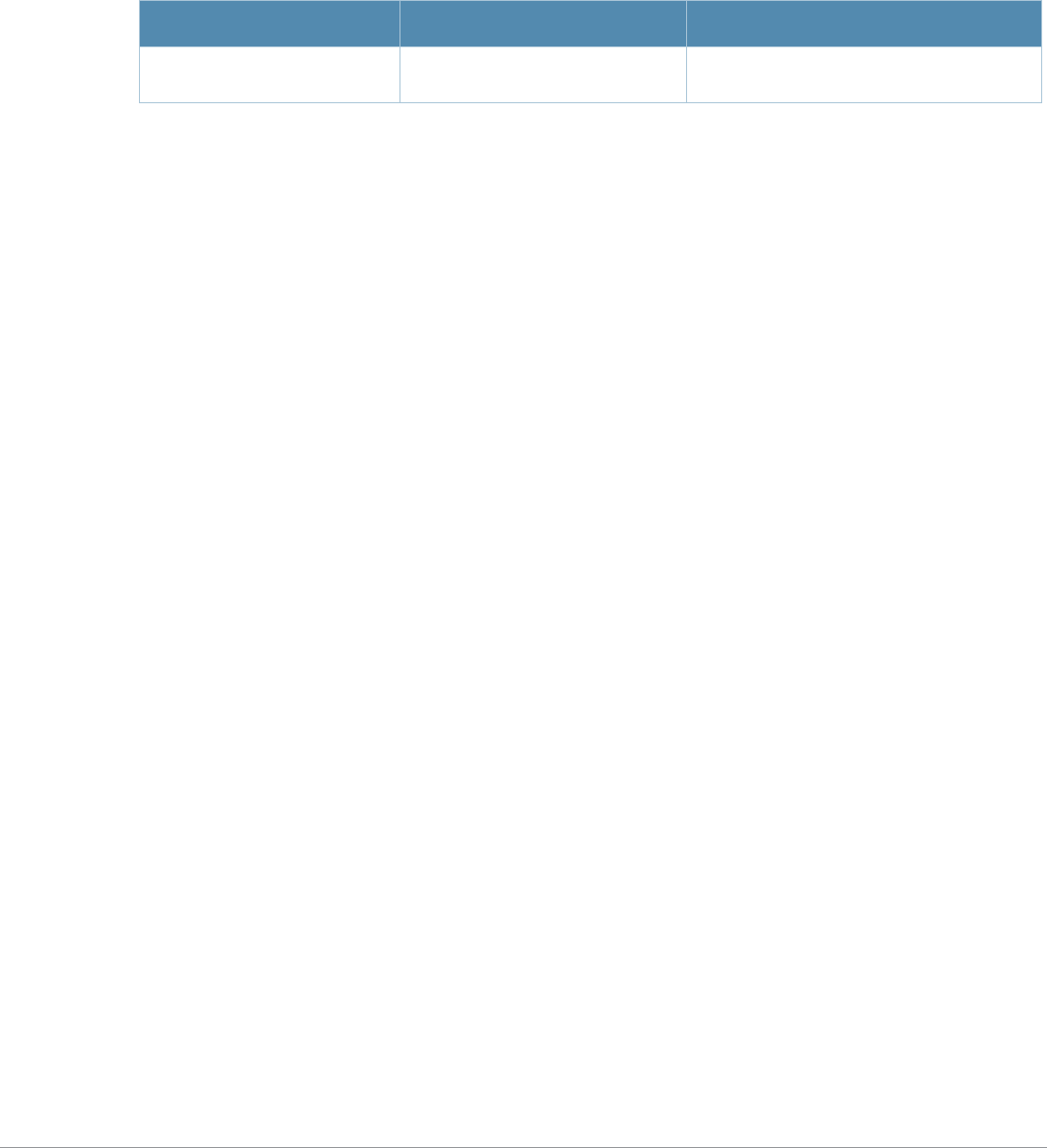
AOS-W 3.4.1 Command Line Interface | Reference Guide show ids impersonation-profile | 785
Related Commands
Configure IDS impersonation profiles using the command ids impersonation-profile.
Command History
This command was available in AOS-W 3.0.
Command Information
Platforms Licensing Command Mode
All platforms Base operating system Available in Enable and Config mode on
master or local switches
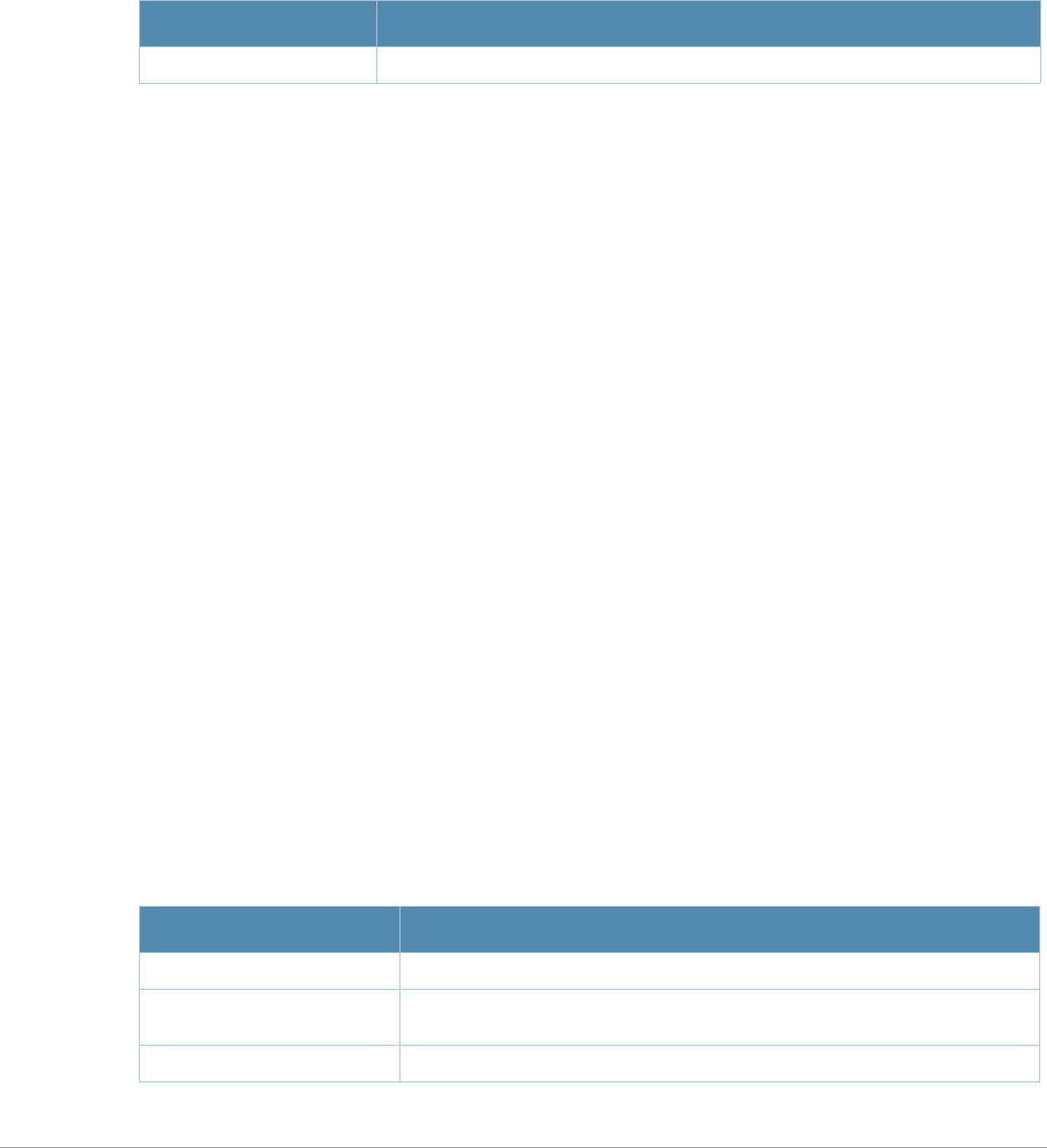
786 |show ids profile AOS-W 3.4.1 Command Line Interface | Reference Guide
show ids profile
show ids profile <profile-name>
Description
Show an IDS profile.
Syntax
Usage Guidelines
Issue this command without the <profile> parameter to display the entire IDS profile list, including profile
status and the number of references to each profile. Include a profile name to display detailed configuration
information for that profile.
Examples
The example below shows that the switch has five configured IDS Profiles.
This example displays the configuration settings for the profile ids-low-setting.
The output of this command includes the following parameters:
Parameter Description
<profile-name> Name of an IDS profile.
(host) # show ids profile
IDS Profile List
----------------
Name References Profile Status
---- ---------- --------------
default 1
ids-disabled 0 Predefined
ids-high-setting 0 Predefined
ids-low-setting 5 Predefined
ids-medium-setting 0 Predefined
Total:5
(host) # show ids profile ids-low-setting
IDS Profile "ids-low-setting" (Predefined)
------------------------------------------
Parameter Value
--------- -----
IDS General profile default
IDS Signature Matching profile factory-default-signature
IDS DOS profile ids-dos-low-setting
IDS Impersonation profile default
IDS Unauthorized Device profile default
Parameter Description
IDS General profile Name of a IDS General profile to be applied to an AP or AP group.
IDS Signature Matching
profile
Name of a IDS Signature Matching profile to be applied to an AP or AP group.
IDS DOS profile Name of a IDS Denial of Service profile to be applied to an AP or AP group.
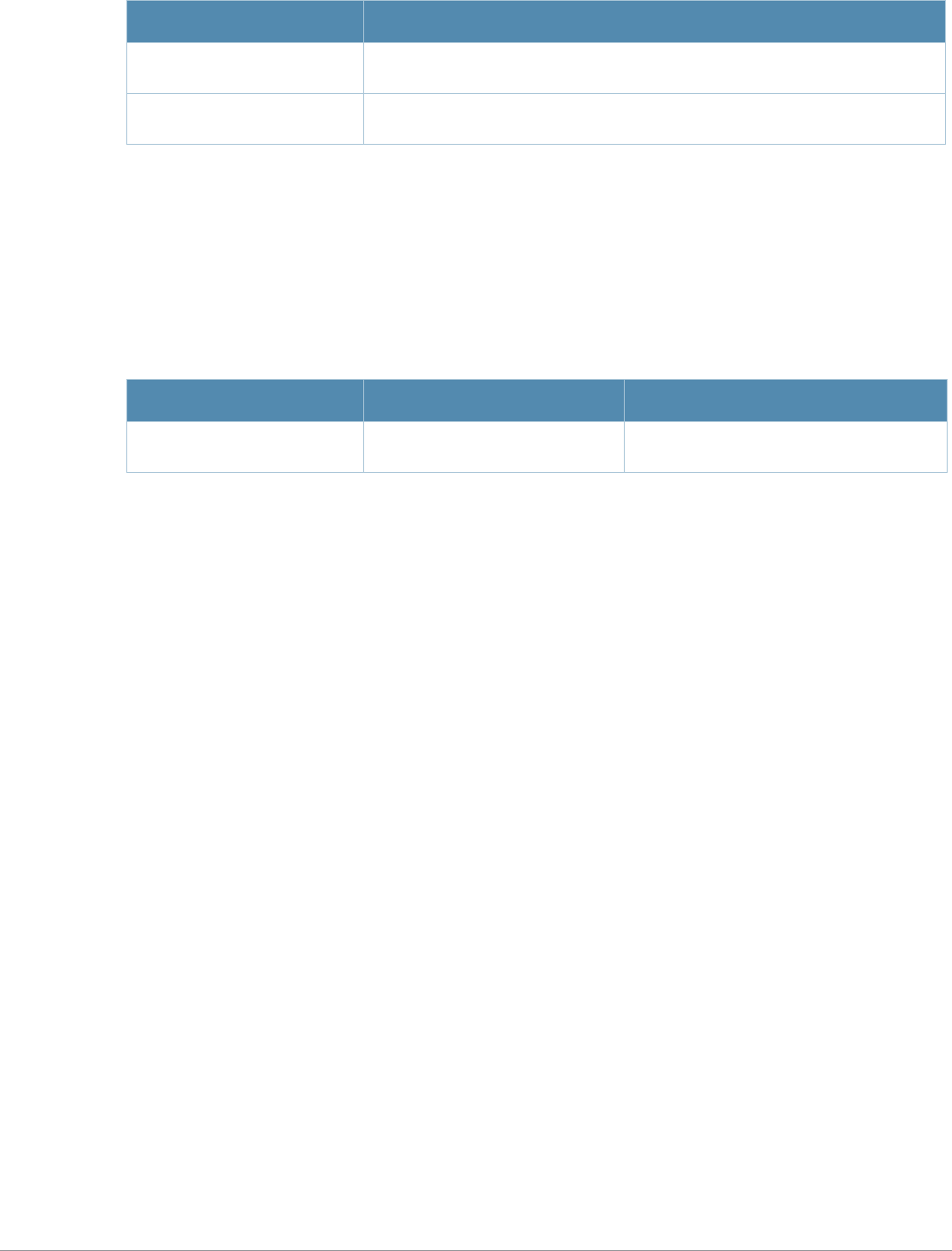
AOS-W 3.4.1 Command Line Interface | Reference Guide show ids profile | 787
Related Commands
Configure the IDS profile using the command ids profile.
Command History
This command was available in AOS-W 3.0.
Command Information
IDS Impersonation
profile
Name of a IDS Impersonation profile to be applied to an AP or AP group.
IDS Unauthorized Device
profile
Name of a IDS Unauthorized Device profile to be applied to an AP or AP group.
Parameter Description
Platforms Licensing Command Mode
All platforms Base operating system Available in Enable and Config mode on
master or local switches
788 | show ids rate-thresholds-profile AOS-W 3.4.1 Command Line Interface | Reference Guide
show ids rate-thresholds-profile
show ids rate-thresholds-profile <profile-name>
Description
Show an IDS Rate Thresholds profile.
Syntax
Usage Guidelines
Issue this command without the <profile> parameter to display the entire IDS Rate Threshold profile list,
including profile status and the number of references to each profile. Include a profile name to display
detailed configuration information for that profile.
Examples
The example below shows that the switch has eight configured IDS Rate Threshold Profiles.
This example displays the configuration settings for the profile probe-request-response-thresholds.
The output of this command includes the following parameters:.
Parameter Description
<profile-name> Name of an IDS Rate Threshold profile.
(host) # show ids rate-thresholds-profile
IDS Rate Thresholds Profile List
--------------------------------
Name References Profile Status
---- ---------- --------------
def-assoc-thresholds 1
def-auth-thresholds 1
def-deauth-thresholds 1
def-disassoc-thresholds 1
def-probe-request-thresholds 1
def-probe-response-thresholds 1
default 18
probe-request-response-thresholds 6 Predefined
Total:8
(host) # show ids rate-thresholds-profile probe-request-response-thresholds
IDS Rate Thresholds Profile "probe-request-response-thresholds" (Predefined)
----------------------------------------------------------------------------
Parameter Value
--------- -----
Channel Increase Time 30 sec
Channel Quiet Time 900 sec
Channel Threshold 350
Node Time Interval 10 sec
Node Quiet Time 900 sec
Node Threshold 250
Parameter Description
Channel Increase Time Time, in seconds, in which the threshold must be
exceeded in order to trigger an alarm.
AOS-W 3.4.1 Command Line Interface | Reference Guide show ids rate-thresholds-profile | 789
Related Commands
Configure the IDS DoS profile using the command show ids dos-profile.
Command History
This command was available in AOS-W 3.0.
Command Information
Channel Quiet Time The time that must elapse after a channel rate alarm before another identical
alarm may be triggered. This option prevents excessive messages in the log file.
Channel Threshold Number of a specific type of frame that must be exceeded within a specific
interval in an entire channel to trigger an alarm.
Node Time Interval Time, in seconds, in which the threshold must be exceeded in order to trigger an
alarm.
Node Quiet Time The time that must elapse after a node rate alarm before another identical alarm
may be triggered. This option prevents excessive messages in the log file.
Node Threshold Number of a specific type of frame that must be exceeded within a specific
interval for a particular client MAC address to trigger an alarm.
Parameter Description
Platforms Licensing Command Mode
All platforms Base operating system Available in Enable and Config mode on
master or local switches
790 | show ids signature-matching-profile AOS-W 3.4.1 Command Line Interface | Reference Guide
show ids signature-matching-profile
show ids signature-matching-profile <profile-name>
Description
Show an IDS Signature Matching profile.
Syntax
Usage Guidelines
Issue this command without the <profile> parameter to display the entire IDS Signature Matching profile
list, including profile status and the number of references to each profile. Include a profile name to display
detailed configuration information for that profile.
Examples
The example below shows that the switch has two configured Signature Matching profiles.
This example displays the configuration settings for the profile factory-default-signatures.
The output of this command includes the following parameters:
Related Commands
Configure the Signature Matching profile using the command ids signature-matching-profile.
Command History
This command was available in AOS-W 3.0.
Parameter Description
<profile-name> Name of an IDS Signature Matching profile.
(host) # show ids signature-matching-profile
IDS Signature Matching Profile List
-----------------------------------
Name References Profile Status
---- ---------- --------------
default 2
factory-default-signatures 3 Predefined
Total:2
(host) # show ids signature-matching-profile factory-default-signatures
IDS Signature Matching Profile "factory-default-signatures" (Predefined)
------------------------------------------------------------------------
Parameter Value
--------- -----
IDS Signature AirJack
IDS Signature ASLEAP
IDS Signature Deauth-Broadcast
IDS Signature Netstumbler Generic
IDS Signature Netstumbler Version 3.3.0x
IDS Signature Null-Probe-Response
Parameter Description
IDS Signature Name of a signature profile. See ids signature-profile on page 233.

AOS-W 3.4.1 Command Line Interface | Reference Guide show ids signature-matching-profile | 791
Command Information
Platforms Licensing Command Mode
All platforms Base operating system Available in Enable and Config mode on
master or local switches

792 | show ids signature-profile AOS-W 3.4.1 Command Line Interface | Reference Guide
show ids signature-profile
show ids signature-profile <profile-name>
Description
Show an IDS signature profile.
Syntax
Usage Guidelines
Issue this command without the <profile> parameter to display the entire IDS Signature profile list,
including profile status and the number of references to each profile. Include a profile name to display
detailed configuration information for that profile.
Examples
The example below shows that the switch has eight configured Signature profiles.
This example displays the configuration settings for the profile AirJack.
Parameter Description
<profile-name> Name of an IDS Signature profile.
(host) # show ids signature-profile
IDS Signature Profile List
--------------------------
Name References Profile Status
---- ---------- --------------
AirJack 1 Predefined
ASLEAP 1 Predefined
Deauth-Broadcast 1 Predefined
default 1
Netstumbler Generic 1 Predefined
Netstumbler Version 3.3.0x 1 Predefined
Null-Probe-Response 1 Predefined
sample 0
Total:8
(host) # show ids signature-profile
IDS Signature Profile "AirJack" (predefined)
---------------------------------------------
Parameter Value
--------- -----
Frame Type beacon SSID = AirJack
AOS-W 3.4.1 Command Line Interface | Reference Guide show ids signature-profile | 793
The output of this command includes the following parameters:
Related Commands
Configure the Signature profile using the command ids signature-profile.
Command History
This command was available in AOS-W 3.0.
Command Information
Parameter Description
Frame Type Type of 802.11 frame. For each type of frame, further parameters may be
included to filter and detect only the required frames.
zassoc: Association frame type.
zauth: Authentication frame type.
zbeacon: Beacon frame type.
zcontrol: All control frames.
zdata: All data frames.
zdeauth: Deauthentication frame type.
zdisassoc: Disassociation frame type.
zmgmt: Management frame type.
zprobe-request: Probe request frame type.
zprobe-response: Probe response frame type.
zssid: For beacon, probe-request, and probe-response frame types, the SSID
as either a string or hex pattern.
zssid-length: For beacon, probe-request, and probe-response frame types,
the length, in bytes, of the SSID.
payload Pattern at a fixed offset in the payload of an 802.11 frame.
sequence number Sequence number of the frame.
src- mac Source MAC address in the 802.11 frame header.
dst- mac Source MAC address in the 802.11 frame header.
bssid BSSID field in the 802.11 frame header.
Platforms Licensing Command Mode
All platforms Base operating system Available in Enable and Config mode on
master or local switches

794 | show ids unauthorized-device-profile AOS-W 3.4.1 Command Line Interface | Reference Guide
show ids unauthorized-device-profile
show ids unauthorized-device-profile <profile-name>
Description
Show an IDS Unauthorized Device Profile.
Syntax
Usage Guidelines
Issue this command without the <profile> parameter to display the entire IDS Unauthorized Device profile
list, including profile status and the number of references to each profile. Include a profile name to display
detailed configuration information for that profile.
Examples
The example below shows that the switch has four configured Unauthorized Device profiles.
Parameter Description
<profile-name> Name of an IDS Unauthorized Device profile
(host) # show ids unauthorized-device-profile
IDS Unauthorized Device Profile List
------------------------------------
Name References Profile Status
---- ---------- --------------
default 2
ids-unauthorized-device-disabled 1 Predefined
ids-unauthorized-device-high-setting 1 Predefined
ids-unauthorized-device-medium-setting 1 Predefined
Total:4
AOS-W 3.4.1 Command Line Interface | Reference Guide show ids unauthorized-device-profile | 795
This example displays the configuration settings for the profile ids-unauthorized-device-disabled.
The output of this command includes the following parameters:
(host) # show ids unauthorized-device-profile ids-unauthorized-device-disabled
IDS Unauthorized Device Profile "ids-unauthorized-device-disabled" (Predefined)
-------------------------------------------------------------------------------
Parameter Value
--------- -----
Detect Adhoc Networks false
Protect from Adhoc Networks false
Detect Windows Bridge false
Detect Wireless Bridge false
Detect Devices with an Invalid MAC OUI false
MAC OUI detection Quiet Time 900 sec
Adhoc Network detection Quiet Time 900 sec
Wireless Bridge detection Quiet Time 900 sec
Rogue AP Classification false
Overlay Rogue AP Classification true
Valid Wired MACs N/A
Allow Well Known MAC N/A
Rogue Containment false
Suspected Rogue Containment false
Suspected Rogue Containment Confidence Level 60
Protect Valid Stations false
Detect Bad WEP false
Detect Misconfigured AP false
Protect Misconfigured AP false
Protect SSID false
Privacy false
Require WPA false
Valid 802.11g channel for policy enforcement 11
Valid 802.11a channel for policy enforcement 40
Valid MAC OUIs N/A
Valid and Protected SSIDs N/A
Protect 802.11n High Throughput Devices false
Protect 40MHz 802.11n High Throughput Devices false
Detect Active 802.11n Greenfield Mode false
Parameter Description
Detect AdHoc Networks Shows if the profile has enabled or disabled detection of adhoc networks.
Protect from Adhoc
Networks
Shows if the profile has enabled or disabled protection from adhoc networks.
Detect Windows Bridge Shows if the profile has enabled or disabled detection of Windows station
bridging.
Detect Wireless Bridge Shows if the profile has enabled or disabled detection of wireless bridging.
Detect Devices with an
Invalid MAC OUI
Shows if the profile has enabled or disabled checking of the first three bytes of a
MAC address, known as the organizationally unique identifier (OUI), assigned by
the IEEE to known manufacturers.
MAC OUI detection Quiet
Time
Time, in seconds, that must elapse after an invalid MAC OUI alarm has been
triggered before another identical alarm may be triggered.
Adhoc Network detection
Quiet Time
Time, in seconds, that must elapse after an adhoc network detection alarm has
been triggered before another identical alarm may be triggered.
Wireless Bridge
detection Quiet Time
Time, in seconds, that must elapse after a wireless
bridge alarm has been triggered before another identical
alarm may be triggered.
Rogue AP Classification Shows if the profile has enabled or disabled rogue AP classification.
Overlay Rogue AP
Classification
Shows if the switch allows APs that are plugged into the wired side of the
network to be classified as “suspected rogue” instead of “rogue”.
796 | show ids unauthorized-device-profile AOS-W 3.4.1 Command Line Interface | Reference Guide
Related Commands
Configure the Unauthorized Device profile using the command ids unauthorized-device-profile.
Command History
This command was available in AOS-W 3.0.
Valid Wired MACs List of valid and protected SSIDs.
Allow Well Known MAC Shows if the profile allows devices with known MAC addresses to classify
rogue APs.
Rogue Containment Shows if the switch will automatically shut down rogue APs.
Suspected Rogue
Containment
Shows if the switch will automatically treat suspected rogue APs as interfering
APs.
Suspected Rogue
Containment Confidence
Level
Confidence level of suspected Rogue AP to trigger containment, expressed as a
percentage.
Protect Valid Stations Shows if the switch will allow valid stations to connect to a non-valid AP.
Detect Bad WEP Shows if the profile has enabled or disabled detection of WEP initialization
vectors that are known to be weak and/or repeating.
Detect Misconfigured AP Shows if the profile has enabled or disabled detection of misconfigured APs.
Protect Misconfigured
AP
Shows if the profile has enabled or disabled protection of misconfigured APs.
Protect SSID Shows if the profile has enabled or disabled use of SSID by valid APs only.
Privacy Shows if the profile has enabled or disabled encryption as a valid AP
configuration.
Require WPA Shows if the switch will flag any valid AP not using WPA as a misconfigured AP.
Valid 802.11g channel
for policy enforcement
A list of valid 802.1b/g channels that third-party APs are allowed to use.
Valid 802.11a channel
for policy enforcement
A list of valid 802.11a channels that third-party APs are allowed to use.
Valid MAC OUIs A list of valid MAC Organizationally Unique Identifiers (OUIs).
Valid and Protected
SSIDs
A list of valid and protected SSIDs.
Protect 802.11n High
Throughput Devices
Shows if the profile enables or disables protection of high-throughput (802.11n)
devices.
Protect 40MHz 802.11n
High Throughput Devices
Shows if the profile enables or disables protection of high-throughput (802.11n)
devices operating in 40 MHz mode.
Detect Active 802.11n
Greenfield Mode
Shows if the profile enables or disables detection of high-throughput devices
advertising greenfield preamble capability.
Parameter Description

AOS-W 3.4.1 Command Line Interface | Reference Guide show ids unauthorized-device-profile | 797
Command Information
Platforms Licensing Command Mode
All platforms Base operating system Available in Enable and Config mode on
master or local switches

798 | show ids unauthorized-device-profile AOS-W 3.4.1 Command Line Interface | Reference Guide
AOS-W 3.4.1 Command Line Interface | Reference Guide show image | 799
show image
show image version
Description
Show system image version information.
Syntax
No parameters.
Example
The following example shows that the switch is running AOS-W 3.4 and booting off partition 0:0.
The output of this command includes the following parameters:
Command History
This command was available in AOS-W 1.0.
Command Information
(host) #show image version
----------------------------------
Partition : 0:0 (/dev/hda1) **Default boot**
Software Version : AOS-W 3.3.2.0
Build number : 18661
Label : 18661
Built on : 2008-06-12 04:24:34 PDT
----------------------------------
Partition : 0:0 (/dev/hda1)
Software Version : AOS-W 3.3.2.0
Build number : 18661
Label : 18661
Built on : 2008-06-12 04:24:34 PDT
Parameter Description
Partition Partition number and name. The default boot partition will display a **Default
boot** notice by the partition name.
Software Version Version of AOS-W software running on the partition.
Build number Build number for the software version.
Label The label parameter can display additional information for the build. By default,
this value is the software build number.
Built on Date the software build was created.
Platforms Licensing Command Mode
All platforms Base operating system Enable and Config mode on local and
master switches

800 |show image AOS-W 3.4.1 Command Line Interface | Reference Guide
AOS-W 3.4.1 Command Line Interface | Reference Guide show interface counters | 801
show interface counters
show interface counters
Description
Displays a table of L2 interfaces counters.
Syntax
No parameters
Example
The example below shows the output of show interface counters on a Alcatel-Lucent 651.
The output of this command includes the following parameters:
Command History
This command was introduced in AOS-W 3.0.
Command Information
Parameter Description
Port Port number
InOctets Number of octets recieved through the port
InUcastPkts Number of unicast packets recieved through the port
InMcastPkts Number of multicats packets recieved through the port
InBcastPkts Number of broadcast packets recieved through the port
OutOctets Number of octets sent through the port
OutUcastPkts Number of unicast packets sent through the port
OutMcastPkts Number of multicats packets sent through the port
OutBcastPkts Number of broadcast packets sent through the port
Platforms Licensing Command Mode
All platforms Base operating system Enable or config mode on master switches
Port InOctets InUcastPkts InMcastPkts InBcastPkts
GE1/0 250559459 1664878 0 16
GE1/1 1615683022 1230973 0 16
GE1/2 204909 1511 0 16
GE1/3 2964355 22155 0 17
GE1/4 1612815178 12509415 0 228
GE1/6 23571170611 15545404 0 4
GE1/7 23562566444 15530432 8236 146
Port OutOctets OutUcastPkts OutMcastPkts OutBcastPkts
GE1/0 2504472376 2645877 8243 16770
GE1/1 169128719 820198 8243 17083
GE1/2 1881584 25785 8243 16771
GE1/3 5247669 47718 8245 16813
GE1/4 26893373267 20838930 8243 16561
GE1/6 539935348 8160008 8139 461
GE1/7 23563612641 15531317 7 336
802 | show interface gigabitethernet AOS-W 3.4.1 Command Line Interface | Reference Guide
show interface gigabitethernet
show interface gigabitethernet <slot/port>
Description
Displays information about a specified Gigabit ethernet port.
Syntax
Examples
The example below shows the output of show interface gigabitethernet 1/0.
The output of this command includes the following parameters:
Parameter Description
counters Displays L2 interface counters for the specified interface
switchport Displays L2 interface information
untrsuted-vlan Displays port member vlan untrusted status
xsec Displays xsec configuration
Parameter Description
GE 1/0 is... Displays the status of the specified port
line protocol is... Displays the status of the line protocol on the specified port
Hardware is.... Describes the hardware interface type
address is... Displays the MAC address of the hardware interface
Description The port type, name, and connector type
Encapsulation Encapsulation method assigned to this port
loopback... Displays whether or not loopback is set
Configured Configured transfer operation and speed
Negotiated Negotiated transfer operation and speed
MTU bytes MTU size of the specified port in bytes
#show interface gigabitethernet 1/0
GE 1/0 is up, line protocol is up
Hardware is Gigabit Ethernet, address is 00:0B:86:F0:33:E1 (bia 00:0B:86:F0:33:E1)
Description: GE1/0 (RJ45 Connector)
Encapsulation ARPA, loopback not set
Configured: Duplex ( AUTO ), speed ( AUTO )
Negotiated: Duplex (Full), speed (100 Mbps)
MTU 1500 bytes, BW is 100 Mbit
Last clearing of "show interface" counters 23 day 4 hr 27 min 54 sec
link status last changed 15 day 3 hr 15 min 21 sec
2049219 packets input, 112651020 bytes
Received 911909 broadcasts, 0 runts, 0 giants, 0 throttles
26 input error bytes, 0 CRC, 0 frame
906926 multicast, 1137310 unicast
185897 packets output, 58327172 bytes
0 output errors bytes, 0 deferred
0 collisions, 0 late collisions, 0 throttles
This port is TRUSTED
POE Status of the port is ON

AOS-W 3.4.1 Command Line Interface | Reference Guide show interface gigabitethernet | 803
The output of this command includes the following parameters:
BW is... Bandwidth of the link
Last clearing of
“show interface
counters”
Time since “show interface counters” was cleared
link status last
changed...
Time since “show interface counters” was cleared
Below the time, all current counters realted to the specified port are listed.
This port is... Whether or not this port is trusted
POE status of the
port is...
The POE status of the specified port
Parameter Description
Port Port number
InOctets Number of octets recieved through the port
InUcastPkts Number of unicast packets recieved through the port
InMcastPkts Number of multicats packets recieved through the port
InBcastPkts Number of broadcast packets recieved through the port
OutOctets Number of octets sent through the port
OutUcastPkts Number of unicast packets sent through the port
OutMcastPkts Number of multicats packets sent through the port
OutBcastPkts Number of broadcast packets sent through the port
Parameter Description
#show interface gigabitethernet 1/0
Port InOctets InUcastPkts InMcastPkts InBcastPkts
GE1/0 112670646 1137507 907019 4983
Port OutOctets OutUcastPkts OutMcastPkts OutBcastPkts
GE1/0 58342401 170490 104 15373
#show interface gigabitethernet 1/0 switchport
Name: GE1/0
Switchport: Enabled
Administrative mode: static access
Operational mode: static access
Administrative Trunking Encapsulation: dot1q
Operational Trunking Encapsulation: dot1q
Access Mode VLAN: 62 (VLAN0062)
Trunking Native Mode VLAN: 1 (Default)
Trunking Vlans Enabled: NONE
Trunking Vlans Active: NONE

804 | show interface gigabitethernet AOS-W 3.4.1 Command Line Interface | Reference Guide
The output of this command includes the following parameters:
The output of this command includes the following parameters:
The output of this command includes the following parameters:
Command History
This command was introduced in AOS-W 3.0.
Command Information
Parameter Description
Name Port name
Switchport Whether or not switchport is enabled
Administrative mode Administrative mode
Operational mode Operational mode
Administrative
Trunking
Encapsulation
Encapsulation method used for administrative trunking
Operational Trunking
Encapsulation
Encapsulation method used for operational trunking
Access Mode VLAN The access mode VLAN for the specified port
Trunking Native Mode
VLAN
The trunking native mode VLAN for the specified port
Trunking Vlans
Enabled
Number of trunking VLANs currently enabled
Trunking Vlans Active Number of trunking VLANs currently active
Parameter Description
Name Name of the specified port
Untrusted Vlan(s) List of untrusted VLANs
Parameter Description
xsec vlan 7 is ACTIVE This states that xsec is active on the specified port as well as the associated VLAN
Platforms Licensing Command Mode
All platforms Base operating system Enable or config mode on master switches
#show interface gigabitethernet 1/0 untrusted-vlan
Name: GE1/0
Untrusted Vlan(s)
#show interface gigabitethernet 1/1 xsec
xsec vlan 7 is ACTIVE

AOS-W 3.4.1 Command Line Interface | Reference Guide show interface fastethernet | 805
show interface fastethernet
show interface fastethernet <slot/port>
Description
Displays information about a specified fast ethernet port.
Syntax
Examples
The example below shows the output of show interface fastethernet 1/0.
The output of this command includes the following parameters:
Parameter Description
access-group Displays access groups configured on this interface
counters Displays L2 interface counters for the specified interface
switchport Displays L2 interface information
untrsuted-vlan Displays port member vlan untrusted status
xsec Displays xsec configuration
Parameter Description
FE 1/0 is... Displays the status of the specified port
line protocol is... Displays the status of the line protocol on the specified port
Hardware is.... Describes the hardware interface type
address is... Displays the MAC address of the hardware interface
Description The port type, name, and connector type
Encapsulation Encapsulation method assigned to this port
loopback... Displays whether or not loopback is set
Configured Configured transfer operation and speed
Negotiated Negotiated transfer operation and speed
MTU bytes MTU size of the specified port in bytes
FE 1/0 is up, line protocol is up
Hardware is FastEthernet, address is 00:0B:86:51:14:D1 (bia 00:0B:86:51:14:D1)
Description: fe1/0
Encapsulation ARPA, loopback not set
Configured: Duplex ( AUTO ), speed ( AUTO )
Negotiated: Duplex (Full), speed (100 Mbps)
MTU 1500 bytes, BW is 100 Mbit
Last clearing of "show interface" counters 15 day 21 hr 34 min 53 sec
link status last changed 15 day 21 hr 32 min 16 sec
1122463 packets input, 196293018 bytes
Received 661896 broadcasts, 0 runts, 0 giants, 0 throttles
0 input error bytes, 0 CRC, 0 frame
661881 multicast, 460567 unicast
191428 packets output, 97063150 bytes
0 output errors bytes, 0 deferred
0 collisions, 0 late collisions, 0 throttles
This port is TRUSTED
POE Status of the port is OFF

806 | show interface fastethernet AOS-W 3.4.1 Command Line Interface | Reference Guide
The output of this command includes the following parameters:
The output of this command includes the following parameters:
BW is... Bandwidth of the link
Last clearing of
“show interface
counters”
Time since “show interface counters” was cleared
Below the time, all current counters realted to the specified port are listed.
This port is... Whether or not this port is trusted
POE status of the
port is...
The POE status of the specified port
Parameter Description
SessionACL Session ACL name
Vlan VLAN number
Status ACL status
Parameter Description
Port Port number
InOctets Number of octets recieved through the port
InUcastPkts Number of unicast packets recieved through the port
InMcastPkts Number of multicats packets recieved through the port
InBcastPkts Number of broadcast packets recieved through the port
OutOctets Number of octets sent through the port
OutUcastPkts Number of unicast packets sent through the port
OutMcastPkts Number of multicats packets sent through the port
OutBcastPkts Number of broadcast packets sent through the port
Parameter Description
#show interface fastethernet 1/0 access-group
FE 1/0:
Port-Vlan Session ACL
---------------------
SessionACL Vlan Status
---------- ---- ------
#show interface fastethernet 1/0 counters
Port InOctets InUcastPkts InMcastPkts InBcastPkts
FE1/0 196310364 460655 661932 15
Port OutOctets OutUcastPkts OutMcastPkts OutBcastPkts
FE1/0 97074242 191401 3 72

AOS-W 3.4.1 Command Line Interface | Reference Guide show interface fastethernet | 807
The output of this command includes the following parameters:
The output of this command includes the following parameters:
Parameter Description
Name Port name
Switchport Whether or not switchport is enabled
Administrative mode Administrative mode
Operational mode Operational mode
Administrative
Trunking
Encapsulation
Encapsulation method used for administrative trunking
Operational Trunking
Encapsulation
Encapsulation method used for operational trunking
Access Mode VLAN The access mode VLAN for the specified port
Trunking Native Mode
VLAN
The trunking native mode VLAN for the specified port
Trunking Vlans
Enabled
Number of trunking VLANs currently enabled
Trunking Vlans Active Number of trunking VLANs currently active
Parameter Description
Name Name of the specified port
Untrusted Vlan(s) List of untrusted VLANs
#show interface fastethernet 1/0 switchport
Name: FE1/0
Switchport: Enabled
Administrative mode: trunk
Operational mode: trunk
Administrative Trunking Encapsulation: dot1q
Operational Trunking Encapsulation: dot1q
Access Mode VLAN: 0 ((Inactive))
Trunking Native Mode VLAN: 1 (Default)
Trunking Vlans Enabled: ALL
Trunking Vlans Active: 1-3
#show interface fastethernet 1/0 untrusted-vlan
Name: FE1/0
Untrusted Vlan(s)
#show interface fastethernet 1/1 xsec
xsec vlan 7 is ACTIVE
808 | show interface fastethernet AOS-W 3.4.1 Command Line Interface | Reference Guide
The output of this command includes the following parameters:
Command History
This command was introduced in AOS-W 3.0.
Command Information
Parameter Description
xsec vlan 7 is ACTIVE This states that xsec is active on the specified port as well as the associated VLAN
Platforms Licensing Command Mode
All platforms Base operating system Enable or config mode on master switches
AOS-W 3.4.1 Command Line Interface | Reference Guide show interface loopback | 809
show interface loopback
show interface loopback
Description
Displays information about the loopback IP interface.
Syntax
No parameters
Example
The example below shows the output of show interface loopback on a Alcatel-Lucent 651.
The output of this command includes the following parameters:
Command History
This command was introduced in AOS-W 3.0.
Command Information
Parameter Description
loopback interface
is...
Status of the loopback interface
line protocol is... Status of the line protocol on the specified port
Hardware is... Hardware interface type
address is... MAC address of the loopback interface
Internet address
is...
IP address and subnet mask of the loopback interface
Platforms Licensing Command Mode
All platforms Base operating system Enable or config mode on master switches
#show interface loopback
loopback interface is up line protocol is up
Hardware is Ethernet, address is 00:0B:86:51:14:D0
Internet address is 10.3.49.100 255.255.255.255
810 | show interface mgmt AOS-W 3.4.1 Command Line Interface | Reference Guide
show interface mgmt
show interface mgmt
Description
Displays information about mgmt interfaces.
Syntax
No parameters
Example
The example below shows the output of show interface mgmt on a Alcatel-Lucent .
he output of this command includes the following parameters:
Command History
This command was introduced in AOS-W 3.0.
Command Information
Parameter Description
mgmt is... Status of the mgmt interface
line protocol is... Status of the line protocol on the specified port
Hardware is... Describes the hardware interface type
address is... Interface’s MAC address
Internet address
is...
Interface’s IP address and subnet mask
Platforms Licensing Command Mode
Only available on a SC 1/2 or
M3 with a management port Base operating system Enable or config mode on master switches
# show interface mgmt
mgmt is up line protocol is up
Hardware is Ethernet, address is 00:0B:86:61:00:5D
Internet address is 10.4.71.10 255.255.255.0
AOS-W 3.4.1 Command Line Interface | Reference Guide show interface port-channel | 811
show interface port-channel
show interface port-channel
Description
Displays information about a specified port-channel interface.
Syntax
Example
The example below shows the output of show interface port-channel 0 on a Alcatel-Lucent .
The output of this command includes the following parameters:
Parameter Description
access-group Displays access groups configured on this interface
counters Displays L2 interface counters for the specified interface
untrsuted-vlan Displays port member vlan untrusted status
xsec Displays xsec configuration
Parameter Description
Port-Channel 0 is... Status of the specified port
line protocol is... Status of the line protocol on the specified port
Hardware is.... Hardware interface type
address is... MAC address of the hardware interface
Description The port type, name, and connector type. If the LAG is created by LACP, it is indicated as
shown in the display output above. If the LAG is created by LACP, you can not statically
add or delete any ports under that port channel. All other commands are allowed. If LACP
is not shown, then the LAG is created by static configuration.
Spanning Tree is... Spanning tree status on the specified port-channel
VLAN membership Number of VLANs the specified port-channel is associated with
Switchport priority Switchport priority of the specified port-channel
Port-Channel 0 is administratively up
Hardware is Port-Channel, address is 00:00:00:00:00:00 (bia 00:0B:86:F0:36:B1)
Description: Link Aggregate (LACP)
Spanning Tree is disabled
VLAN membership: 1
Switchport priority: 0
Member port:
Last clearing of "show interface" counters 3 day 21 hr 23 min 6 sec
link status last changed 3 day 21 hr 23 min 6 sec
0 packets input, 0 bytes
Received 0 broadcasts, 0 runts, 0 giants, 0 throttles
0 input error bytes, 0 CRC, 0 frame
0 multicast, 0 unicast
0 packets output, 0 bytes
0 output errors bytes, 0 deferred
0 collisions, 0 late collisions, 0 throttles
Port-Channel 0 is NOT TRUSTED
812 |show interface port-channel AOS-W 3.4.1 Command Line Interface | Reference Guide
The output of this command includes the following parameters:
The output of this command includes the following parameters:
Last clearing of
“show interface
counters”
Time since “show interface counters” was cleared
Below the time, all current counters realted to the specified port are listed.
Port-channel 0 is... Whether or not this port-channel is trusted
Parameter Description
SessionACL Session ACL name
Vlan VLAN number
Status ACL status
Parameter Description
PC Port number
InOctets Number of octets recieved through the port
InUcastPkts Number of unicast packets recieved through the port
InMcastPkts Number of multicats packets recieved through the port
InBcastPkts Number of broadcast packets recieved through the port
OutOctets Number of octets sent through the port
OutUcastPkts Number of unicast packets sent through the port
OutMcastPkts Number of multicats packets sent through the port
OutBcastPkts Number of broadcast packets sent through the port
Parameter Description
#show interface port-channel 0 access-group
Port-Channel 0:
Port-Vlan Session ACL
---------------------
SessionACL Vlan Status
---------- ---- ------
#show interface port-channel 0 counters
Port InOctets InUcastPkts InMcastPkts InBcastPkts
PC 0: 0 0 0 0
Port OutOctets OutUcastPkts OutMcastPkts OutBcastPkts
PC 0: 0 0 0 0
AOS-W 3.4.1 Command Line Interface | Reference Guide show interface port-channel | 813
The output of this command includes the following parameters:
The output of this command includes the following parameters:
Command History
Command Information
Parameter Description
Name Name of the specified port
Untrusted Vlan(s) List of untrusted VLANs
Parameter Description
xsec vlan 7 is ACTIVE This states that xsec is active on the specified port as well as the associated VLAN
Release Modification
AOS-W 3.4.1 Modified to display LACP when applicable
AOS-W 3.0. Introduced
Platforms Licensing Command Mode
All platforms Base operating system Enable or config mode on master switches
#show interface port-channel 0 untrusted-vlan
Name: FE1/0
Untrusted Vlan(s)
#show interface port-channel 0 xsec
xsec vlan 7 is ACTIVE

814 | show interface tunnel AOS-W 3.4.1 Command Line Interface | Reference Guide
show interface tunnel
show interface tunnel
Description
Displays information about tunnel interfaces.
Syntax
No parameters
Example
The example below shows the output of show interface tunnel.
he output of this command includes the following parameters:
Command History
This command was introduced in AOS-W 3.0.
Parameter Description
Tunnel 2000 is... Status of the specified tunnel
line protocol is... Displays the status of the line protocol on the specified tunnel
Description Description of the specified interface
Internet address
is...
IP address and subnet mask of the specified interface
Source IP address of the tunnel’s source
Destination IP address of the tunnel’s source
Tunnel mtu is set
to...
Size of the specified tunnel’s MTU
Tunnel is an... Description of the specified tunnel
Tunnel is... Whether or not the specified tunnel is trusted
Inter tunnel flooding
is...
Status of inter tunnel flooding on the specified tunnel
Tunnel keepalive
is...
Status of tunnel keepalive on the specified tunnel
#show interface tunnel 2000
Tunnel 2000 is up line protocol is up
Description: Tunnel Interface
Internet address is 3.3.3.1 255.255.255.0
Source 192.168.203.1
Destination 192.168.202.1
Tunnel mtu is set to 1100
Tunnel is an IP GRE TUNNEL
Tunnel is Trusted
Inter Tunnel Flooding is enabled
Tunnel keepalive is disabled

AOS-W 3.4.1 Command Line Interface | Reference Guide show interface tunnel | 815
Command Information
Platforms Licensing Command Mode
All platforms Base operating system Enable or config mode on master switches
816 | show interface vlan AOS-W 3.4.1 Command Line Interface | Reference Guide
show interface vlan
show interface vlan
Description
Displays information about a specified VLAN interface.
Syntax
No parameters
Example
The example below shows the output of show interface vlan 1on a Alcatel-Lucent 651.
The output of this command includes the following parameters:
Parameter Description
VLAN1 is... Status of the specified VLAN
line protocol is... Displays the status of the line protocol on the specified port
Hardware is... Describes the hardware interface type
Interface address
is...
Displays the MAC address of the hardware interface
Description Description of the specified VLAN
Internet address
is...
IP address and subnet mask of the specified VLAN
Routing interface
is...
Status of the routing interface
Forwarding mode is... Status of the forwarding mode
Directed broadcast
is...
Displays whether or not directed broadcast is enabled
Encapsulation Encapsulation type
loopback... Loopback status
MTU MTU size of the specified port in bytes
Last clearing of
“show interface
counters”
Time since “show interface counters” was cleared
link status last
changed
Time since link status llast changed
#show interface vlan 1
VLAN1 is up line protocol is up
Hardware is CPU Interface, Interface address is 00:0B:86:51:14:D0 (bia 00:0B:86:51:14:D0)
Description: 802.1Q VLAN
Internet address is 10.3.49.50 255.255.255.0
Routing interface is enable, Forwarding mode is enable
Directed broadcast is disabled
Encapsulation 802, loopback not set
MTU 1500 bytes
Last clearing of "show interface" counters 15 day 22 hr 35 min 32 sec
link status last changed 15 day 22 hr 32 min 55 sec
Proxy Arp is disabled for the Interface
AOS-W 3.4.1 Command Line Interface | Reference Guide show interface vlan | 817
Command History
This command was introduced in AOS-W 3.0.
Command Information
Proxy ARP is... Status of proxy ARP on the specified interface
Platforms Licensing Command Mode
All platforms Base operating system Enable or config mode on master switches
Parameter Description

818 | show interface vlan AOS-W 3.4.1 Command Line Interface | Reference Guide

AOS-W 3.4.1 Command Line Interface | Reference Guide show inventory | 819
show inventory
show inventory
Description
Displays hardware inventory of the switch.
Syntax
No parameters
Example
Issue this command to display the hardware component inventory of the switch.
Supervisor Card slot : 1
Mobility Processor : FPGA Rev 0x30030920
Mobility Processor Assembly# : 2010027B
Mobility Processor Serial# : F00488202
SC Assembly# : 2010032B (Rev:02.00)
SC Serial# : FP0001470 (Date:07/01/24)
SC Model# : M3mk1
Mgmt Port HW MAC Addr : 00:0B:86:F0:23:02
HW MAC Addr : 00:0B:86:01:C5:00 to 00:0B:86:01:C5:7
FXPLD Version : (Rev: 20)
PEER Supervisor Card : Absent
Line Card 0 : Absent
Line Card 1 : Not accessible from this SC
Line Card 2 : Present
Line Card 2 FPGA : LCCI Rev 0x6
Line Card 2 Switch Chip : Broadcom 56308 Rev 0x3
Line Card 2 Mez Card : Present
Line Card 2 SPOE : Present
Line Card 2 Sup Card 0 : Absent
Line Card 2 Sup Card 1 : Present ( Active )
Line Card 2 Assembly# : 2000001C (Rev:03.00) (24FE+2GE)
Line Card 2 Serial# : C00000277 (Date:02/22/05)
Line Card 2 SPOE Assembly# : 2000020B (Rev:01.00) (SPOE-2)
Line Card 2 SPOE Serial# : FP0000100
Line Card 2 MEZZ Assembly# : 2000002A (Rev:01.00)
Line Card 2 MEZZ Serial# : S00000540
Line Card 3 : Present
Line Card 3 FPGA : LCCI Rev 0x6
Line Card 3 Switch Chip : Broadcom 56308 Rev 0x3
Line Card 3 Mez Card : Present
Line Card 3 SPOE : Present
Line Card 3 Sup Card 0 : Absent
Line Card 3 Sup Card 1 : Present ( Active )
Line Card 3 Assembly# : 2000001C (Rev:03.00) (24FE+2GE)
Line Card 3 Serial# : C00007293 (Date:09/27/05)
Line Card 3 SPOE Assembly# : 2000003B (Rev:02.00) (SPOE-1)
Line Card 3 SPOE Serial# : S00001750
Line Card 3 MEZZ Assembly# : 2000002A (Rev:01.00)
Line Card 3 MEZZ Serial# : C00007172
FAN 0 : OK, Speed High
FAN 1 : OK, Speed High
FAN 2 : OK, Speed High
Fan Tray Assembly# : 2000007C (Rev:01.00)
Fan Tray Serial# : C00013879 (Date:12/18/04)
Back Plane Assembly# : 2000006B (Rev:01.00)
Back Plane Serial# : A00000250 (Date:12/18/04)
Power Supply type : Power One (400W)
Power Supply 0 : OK (400W)
Power Supply 1 : FAILED
Power Supply 2 : Absent
M3mk1 Card Temperatures : M3mk1 card 47 C
: CPU 47 C
AMP Card Temperatures : Processor Card 41 C
: Mobility Processor 56 C
M3mk1 Card Voltages : M3mk1 5000mV 5010 mV
: M3mk1 3300mV 3340 mV
: M3mk1 2500mV 2432 mV
: M3mk1 1800mV 1790 mV
: M3mk1 1500mV 1490 mV
: M3mk1 1250mV 1260 mV
: M3mk1 1200mV 1200 mV
: M3mk1 IBC 12000mV 11815 mV
: M3mk1 CPU Fan Speed 6887 RPMs
: M3mk1 CPU CORE 1200mV 1080 mV
: M3mk1 XGMII VTT 750mV 750 mV
: M3mk1 VTT0(a&b) 900mV 900 mV
: M3mk1 VTT1(c&d) 900mV 900 mV
: AMP 3300mV 3320 mV
: AMP 2500mV 2480 mV
: AMP 1800mV 1800 mV
: AMP 1500mV 1500 mV
: AMP BCM 1200mV 1200 mV
: AMP FPGA 1200mV(1) 1200 mV
: AMP FPGA 1200mV(2) 1200 mV

820 | show inventory AOS-W 3.4.1 Command Line Interface | Reference Guide
The output includes the following parameters:
The output of this command will vary between switches.
Parameter Description
Supervisor Card Slot Supervisor card slot number
Mobility Processor Revision of the image downloaded to the FPGA. This can change if a newer image is
included in a newer release.
Mobility Processor
Assembly#
Assembly number of the mobility processor. This only applies to M3 cards.
Mobility Processor
Serial#
Serial number of the mobility processor. This only applies to M3 cards.
SC Assembly# Assembly number of the supervisor card.
SC Serial# Serial number of the supervisor card.
SC Model# Model number of the supervisor card.
Mgmt Port HW MAC
Address
MAC address of the mgmt port
HW MAC Address MAC address
FXPLD Version Revision of programmable logic device on supervisor card.
PEER Supervisor Card States whether or not a PEER supervisor card is present.
Line Card <slot
number>
States whether or not a line card is present in the specified slot
Line Card <slot
number> FPGA
Name/type of FPGA associated with the specified line card slot
Line Card <slot
number> Switch Chip
Name/type of switch card associated with the specified line card slot
Line Card <slot
number> Mez Card
States whether or not a mezzanine card is present in the specified slot
Line Card <slot
number> SPOE
States whether or not a SPOE card is present in the specified slot
Line Card <slot
number> Sup Card 0
States whether or not a supervisor card 0 is present in the specified slot
Line Card <slot
number> Sup Card 1
States whether or not a supervisor card 1 is present in the specified slot
Line Card <slot
number> Assembly#
Assembly number of the line card in the specified slot
Line Card <slot
number> Serial#
Serial number of the line card in the specified slot
Line Card <slot
number> SPOE
Assembly#
Assembly number of SPOE line card in the specified slot
Line Card <slot
number> SPOE Serial#
Serial number of SPOE line card in the specified slot
AOS-W 3.4.1 Command Line Interface | Reference Guide show inventory | 821
Command History
This command was introduced in AOS-W 1.0.
Command Information
Line Card <slot
number> MEZZ
Assembly#
Assembly number of the mezzanine card in the specified slot
Line Card <slot
number> MEZZ Serial#
Serial number of the mezzanine card in the specified slot
FAN <Fan number>Status of the specified fan
Fan Tray Assembly# Assembly number of the fan tray
Fan Tray Serial# Serial number of fan tray
Back Plane Assembly# Assembly number of the back plane
Back Plane Serial# Serial number of the back plane
Power Supply Type Power supply type
Power Supply <power
supply number>
Power supply status
M3mk1 Card
Temperatures
zM3mk1 card
zCPU
zThe temperature from the sensor on the supervisor card
zThe temperature from the CPU die
AMP Card Temperatures
zProcessor Card
zMobility Processor
zThe temperature from the sensor on the Mobility Processor card
zThe temperature from the FPGA die
M3mk1 Card Voltages This parameter displays to columns of voltages for many components displayed
previously by this command. The voltage displayed in the right column should match the
corresponding value in the left column, generally with +/- 5%.
Platforms Licensing Command Mode
All platforms Base operating system Enable or config mode on master switches
Parameter Description

822 | show inventory AOS-W 3.4.1 Command Line Interface | Reference Guide
AOS-W 3.4.1 Command Line Interface | Reference Guide show ip access-group | 823
show ip access-group
show ip access-group
Description
Display access control lists (ACLs) configured for each port on the switch.
Syntax
No parameters.
Examples
The example below shows part of the output of this command. If a port does not have a defined session
ACL, the Port-Vlan Session ACL table will be blank.
The output of this command includes the following parameters:
Related Commands
Command History
Command Information
(host) # show ip access-group
FE 1/0:
Rx access list 200 is applied
session access list User14 is applied
Port-Vlan Session ACL
---------------------
SessionACL Vlan Status
---------- ---- ------
coltrane 22 configured
Parameter Description
Session ACL Name of the ACL applied to the interface.
VLAN If the ACL was applied to a VLAN associated with this port, this column will show the VLAN ID.
Status Shows whether or not the session ACL is configured.
Command Description
interface fastethernet | gigabitethernet ip access-
group.Configure an access group for an
interface.
Release Modification
AOS-W 3.0 Command introduced
AOS-W 3.4 The VLAN output parameters was introduced.
Platforms Licensing Command Mode
All platforms Base operating system Available in Config or Enable mode on
master or local switches
824 | show ip access-list AOS-W 3.4.1 Command Line Interface | Reference Guide
show ip access-list
show ip access-list {brief|<string>}
Description
Display a table of all configured access control lists (ACLs), or show details for a specific ACL.
Syntax
Examples
The example below shows general information for all ACLs in the Access List table.
The output of this command includes the following parameters:
Parameter Description
brief Display a table of information for all ACLs.
<string> Specify the name of a single ACL to display detailed information on that ACL.
(Host) #show ip access-list brief
Access list table
-----------------
Name Type Use Count Roles
---- ---- --------- -----
200 eth
33 standard
allowall session 2 trusted-ap default-vpn-role
ap-acl session 2 rap_role ap-role
captiveportal session 4 coltrane-logon wizardtest-logon test-logon logon
control session 7 ap-role coltrane-logon wizardtest-logon guest stateful test-logo
cplogout session 1 guest
default session
guest session
log-https session
srcnat session
stateful-dot1x session 2 stateful-dot1x logon
stateful-kerberos session
validuser session 1 test-24325
Parameter Description
Name Name of an access-control list (ACL).
Type Shows that the ACL is one of the following ACL policy types:
zEthertype
zStandard
zSession
zMAC
zExtended
Use Count Number of rules defined in the ACL.
Roles Names of user roles associated with the ACL.

AOS-W 3.4.1 Command Line Interface | Reference Guide show ip access-list | 825
Include the name of a specific ACL to show detailed configuration information for that ACL.
The output of this command may include some or all of the following parameters:
(Host)# show ip access-list stateful-dot1x
ip access-list session stateful-dot1x
stateful-dot1x
--------------
Priority Source Destination Service Action TimeRange Log Expired Queue TOS 8021P Blacklist Mirror DisScan
-------- ------ ----------- ------- ------ ---------- --- ------- ------ --- ----- --------- ------- -------
1 any any svc-dns permit Low
2 any any svc-dhcp permit Low
3 any 127.0.0.1 udp 1812 redirect Low
Parameter Description
Priority Name of an access-control list (ACL).
Source The traffic source, which can be one of the following:
zalias: The network resource (use the netdestination command to configure aliases; use the
show netdestination command to see configured aliases)
zany: Matches any traffic.
zhost: A single host IP address.
znetwork: The IP address and netmask.
zuser: The IP address of the user.
Destination The traffic destination, which can be one of the following:
zalias: The network resource (use the netdestination command to configure aliases; use the
show netdestination command to see configured aliases)
zany: Matches any traffic.
zhost: A single host IP address.
znetwork: An IP address and netmask.
zuser: The IP address of the user.
Service Network service, which can be one of the following:
zAn IP protocol number (0-255).
zThe name of a network service (use the show netservice command to see configured services).
zany: Matches any traffic.
ztcp: A TCP port number (0-65535).
zudp: A UDP port number (0-65535).
Action Action if rule is applied, which can be one of the following:
deny: Reject packets.
dst-nat: Perform destination NAT on packets.
dual-nat: Perform both source and destination NAT on packets.
permit: Forward packets.
redirect: Specify the location to which packets are redirected, which can be one of the following:
zDatapath destination ID (0-65535).
zesi-group: Specify the ESI server group configured with the esi group command
zopcode: Specify the datapath destination ID (0x33, 0x34, or 0x82). Do not use this parameter
without proper guidance from Alcatel-Lucent, Inc.
tunnel: Specify the ID of the tunnel configured with the interface tunnel command.
src-nat: Perform source NAT on packets.
Timerange Any defined time range for this rule.
Log Shows if the rule was configured to generate a log message when the rule is applied.
Expired Shows if the rule has expired.
Queue Shows if the rule assigns a matching flow to a priority queue (high/low).
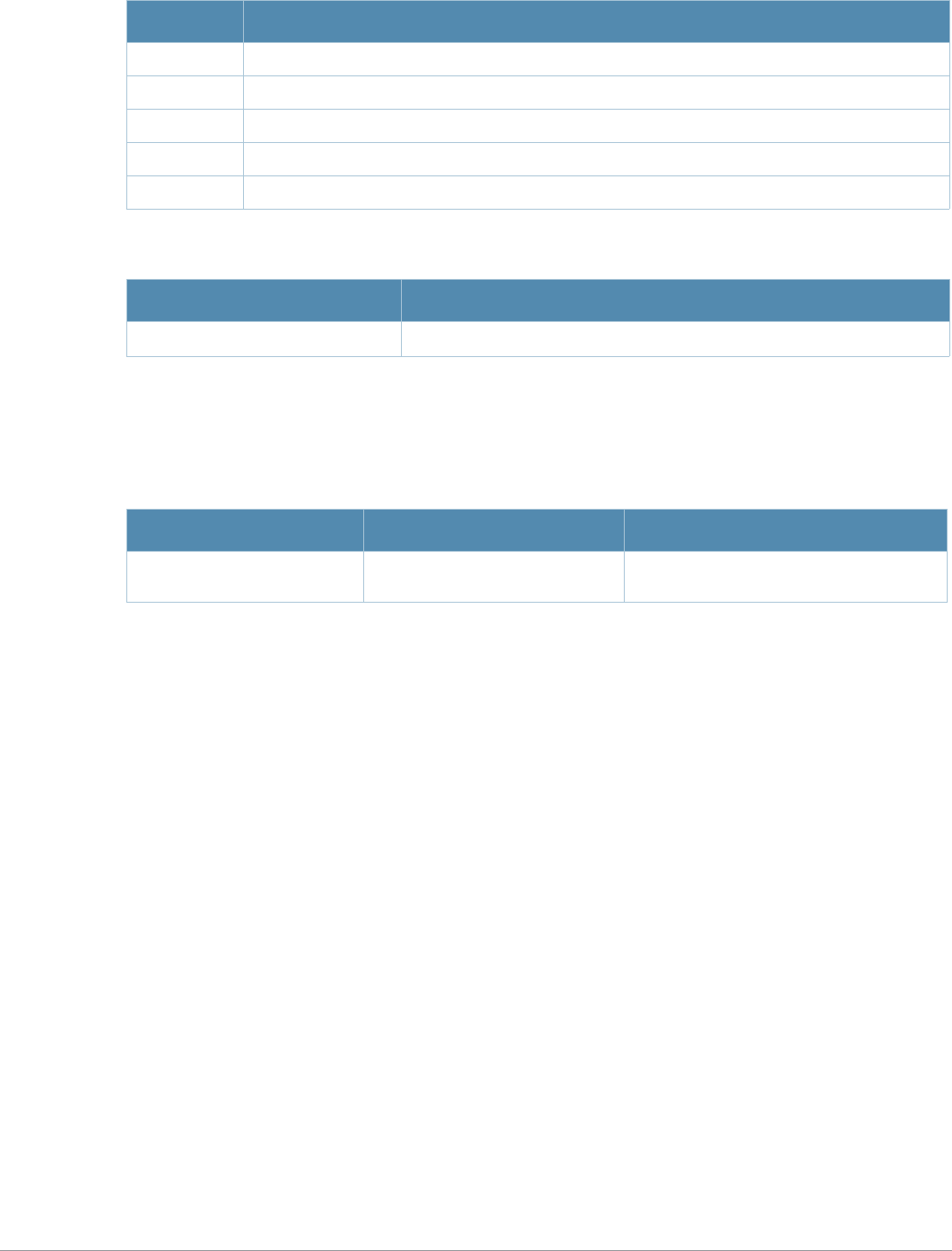
826 | show ip access-list AOS-W 3.4.1 Command Line Interface | Reference Guide
Related Commands
Command History
Introduced in AOS-W 3.0.
Command Information
Tos Specifies the configured ToS value (0-63)
8021.p 802.11p priority level applied by the rule (0-7).
Blacklist Shows if the rule should blacklist any matching user.
Mirror Shows if the rule was configured to mirror all session packets to datapath or remote destination.
DisScan Shows if the rule was configured to pause ARM scanning while traffic is present.
Parameter Description
Command Description
ip access-list session Configure an access list for an interface.
Platforms Licensing Command Mode
All platforms Base operating system Available in Config or Enable mode on
master or local switches
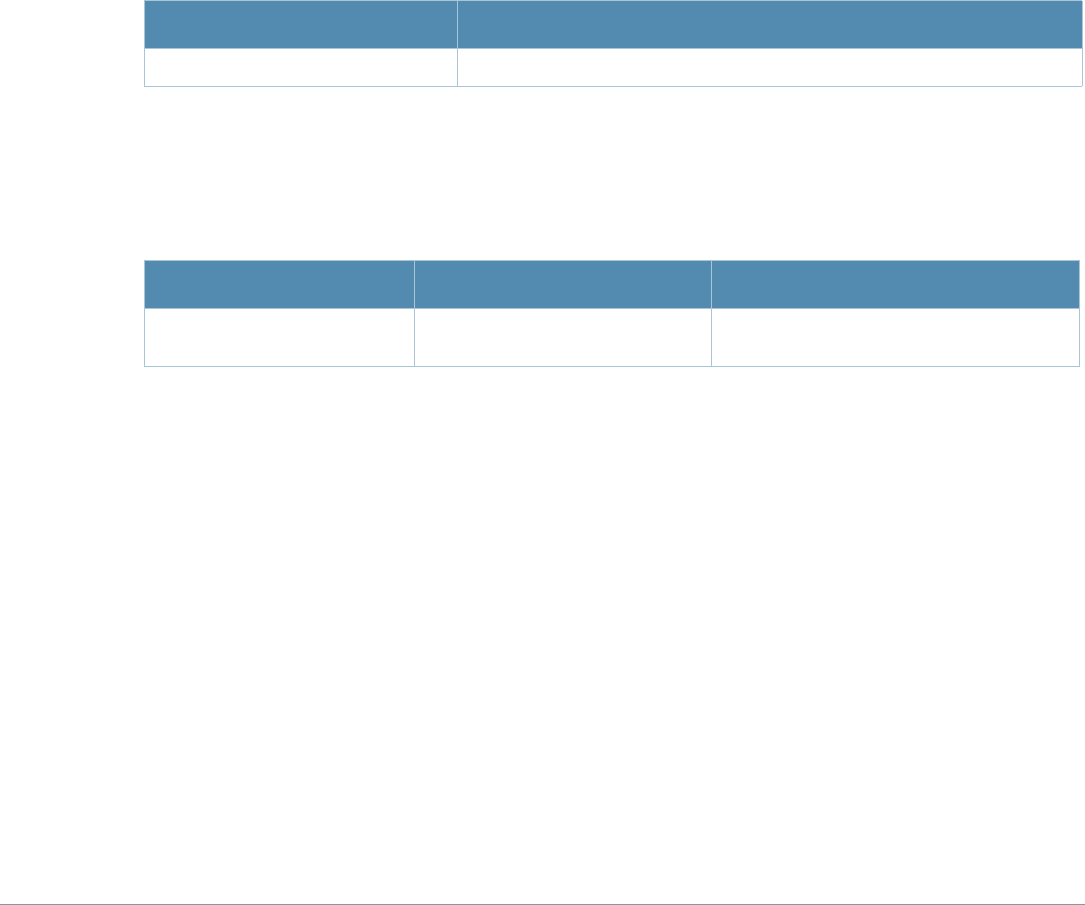
AOS-W 3.4.1 Command Line Interface | Reference Guide show ip cp-redirect-address | 827
show ip cp-redirect-address
show ip cp-redirect-address
Description
Show the captive portal automatic redirect IP address.
Syntax
No parameters.
Examples
The example below shows the IP address to which captive portal users are automatically directed.
Related Commands
Command History
Introduced in AOS-W 3.0.
Command Information
(host) # show ip cp-redirect-address
Captive Portal redirect Address... 10.3.63.11
Command Description
ip cp-redirect-address This command configures a redirect address for captive portal.
Platforms Licensing Command Mode
All platforms Base operating system Available in Config or Enable mode on
master or local switches
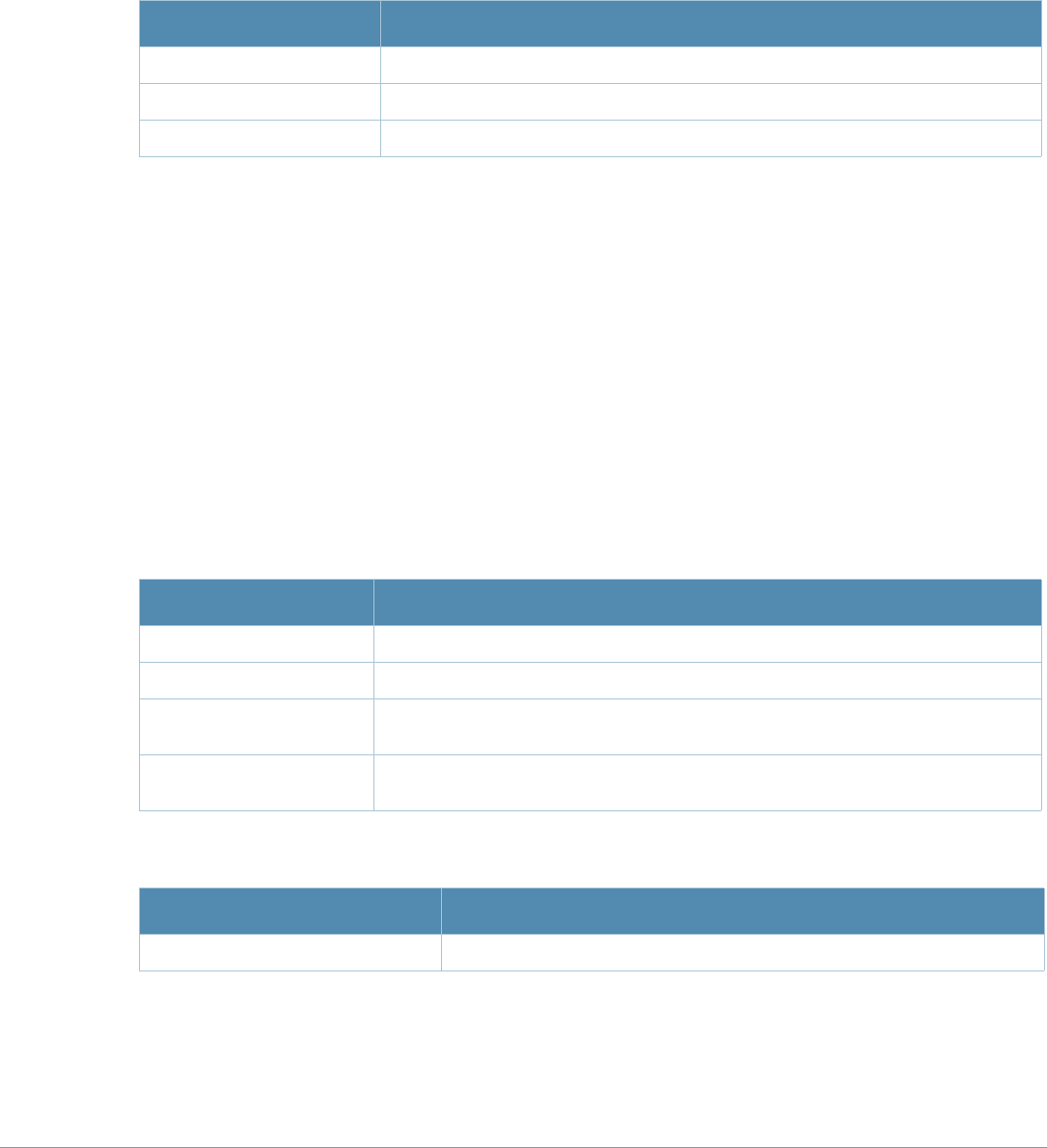
828 |show ip dhcp AOS-W 3.4.1 Command Line Interface | Reference Guide
show ip dhcp
show ip dhcp {binding|database|statistics}
Description
Show DHCP Server Settings.
Syntax
Examples
The example below shows DHCP statistics for two configured networks.
The output of this command includes the following parameters:
Related Commands
Command History
Introduced in AOS-W 3.0.
Parameter Description
binding Show DHCP server bindings.
database Show DHCP server settings.
statistics Show DHCP pool statistics.
(host) # show ip dhcp statistics
Network Name 172.19.42.0/24
Free leases 137
Active leases 115
Expired leases 0
Abandoned leases 0
Network Name 10.14.86.0/24
Free leases 126
Active leases 126
Expired leases 0
Abandoned leases 0
Parameter Description
Network Name Range of addresses that the DHCP server may assign to clients.
Free leases Number of available DHCP leases.
Expired leases Number of leases that have expired because they have extended past their valid
lease period.
Abandoned leases Number of abandoned leases. Abandoned leases will not be reassigned unless there
are no free leases available.
Command Description
ip dhcp pool This command configures a DHCP pool on the switch.

AOS-W 3.4.1 Command Line Interface | Reference Guide show ip domain-name | 829
show ip domain-name
show ip domain-name
Description
Show the full domain name and server.
Syntax
No parameters.
Examples
The example below shows that the IP domain lookup feature is enabled, but that no DNS server has been
configured on the switch.
Related Commands
Command History
Introduced in AOS-W 3.0.
Command Information
(host) #show ip domain-name
IP domain lookup: Enabled
IP Host.Domain name: MyCompany2400.
No DNS server configured
Command Description
ip domain lookup This command enables Domain Name System (DNS) hostname to address translation.
ip domain-name This command configures the default domain name.
ip dhcp pool This command configures a DHCP pool on the switch.
Platforms Licensing Command Mode
All platforms Base operating system Available in Config or Enable mode on
master or local switches

830 |show ip igmp AOS-W 3.4.1 Command Line Interface | Reference Guide
show ip igmp
show ip igmp config|counters|{group maddr <maddr>}|{interface [vlan <vlan>]}|{proxy-
group vlan <vlan>}|{proxy-mobility-group maddr <maddr>}|proxy-mobiity-stats|proxy-stats
Description
Display Internet Group Management Protocol (IGMP) timers and counters.
Syntax
Examples
The example below displays the IGMP interface table for all VLANs on the switch.
Parameter Description
config Show the current IGMP configuration
counters Display a list counters for the following IGMP queries:
zreceived-total
zreceived-queries
zreceived-v1-reports
zreceived-v2-reports
zreceived-leaves
zreceived-unknown-types
zlen-errors
zchecksum-errors
znot-vlan-dr
ztransmitted-queries
zforwarded
group maddr <maddr> Show IGMP group information
interface vlan <vlan> Show IGMP interface information
proxy-group vlan <vlan> Show IGMP proxy group information for a specific interface.
proxy-mobility-group
maddr <maddr>
Display the IGMP proxy group information stored for mobile clients which are
away from the switch.
proxy-mobiity-stats Display the most important messages exchanged between the mobility process
and the IGMP proxy.
proxy-stats Display the number of messages transmitted and received by the IGMP proxy
on the upstream interface
(host) # show ip igmp interface vlan 2
IGMP Interface Table
--------------------
VLAN Addr Netmask MAC Address IGMP Snooping Querier Destination IGMP Proxy
---- ---- ------- ----------- ---- -------- ------- ----------- -----------
64 10.6.4.252 255.255.255.0 00:0b:86:01:99:00 disabled disabled 10.6.4.252 CP disabled
65 10.6.5.252 255.255.255.0 00:0b:86:01:99:00 disabled disabled 10.6.5.252 CP disabled
1 10.6.2.252 255.255.255.0 00:0b:86:01:99:00 disabled disabled 10.6.2.252 CP disabled
66 10.6.6.252 255.255.255.0 00:0b:86:01:99:00 disabled disabled 10.6.6.252 CP disabled
63 10.6.3.252 255.255.255.0 00:0b:86:01:99:00 disabled disabled 10.6.3.252 CP disabled
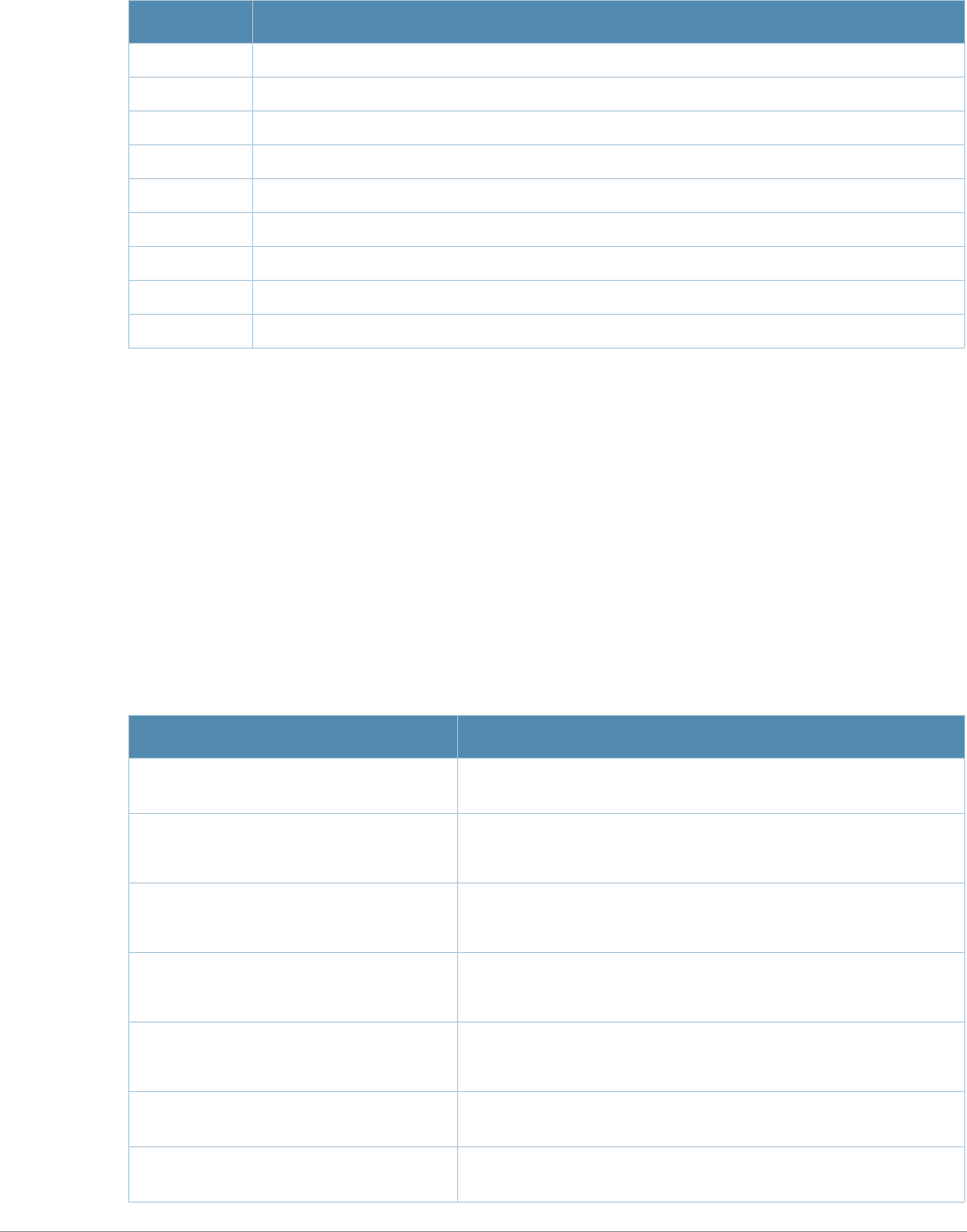
AOS-W 3.4.1 Command Line Interface | Reference Guide show ip igmp | 831
The output of this command includes the following parameters:
The following example displays the current IGMP configuration settings for the switch.
The output of this command includes the following parameters:
Parameter Description
VLAN A VLAN ID number.
Addr IP address of a VLAN router.
Netmask Subnet mask for the IP address.
MAC Address MAC destination address.
IGMP Shows if IGMP proxy is enabled or disabled.
Snooping Shows if IGMP snooping is enabled or disabled.
Querier IP address of an IGMP querier.
Destination Traffic destination.
IGMP Proxy Shows if IGMP proxy.
(host) #show ip igmp config
IGMP Config
-----------
Name Value
---- -----
robustness-variable 2
query-interval 125
query-response-interval 100
startup-query-interval 31
startup-query-count 2
last-member-query-interval 10
last-member-query-count 2
version-1-router-present-timeout 400
Parameter Description
robustness-variable This variable is increased from its default level of 2 to allow for
expected packet loss on a subnetwork.
query-interval Interval, in seconds, at which the switch sends host-query messages
to the multicast group address 224.0.0.1 to solicit group membership
information.
query-response-interval Maximum time, in .1 second intervals, that can elapse between when
the switch sends a host-query message and when it receives a
response. This must be less than the query-interval.
startup-query-count Number of queries that the switch sends out on startup, separated
by startup-query-interval. The default setting is the value of the
robustness-variable parameter.
startup-query-interval Interval, in seconds, at which the switch sends general queries on
startup. The default value of this parameter is 1/4 of the query-
interval.
last-member-query-count Number of group-specific queries that the switch sends before
assuming that there are no local group members.
last-member-query-interval Maximum time, in seconds, that can elapse between group-specific
query messages.

832 |show ip igmp AOS-W 3.4.1 Command Line Interface | Reference Guide
Related Commands
Command History
Introduced in AOS-W 3.0.
Command Information
version-1-router-present-timeout Timeout, in seconds, if the switch detects a version 1 IGM router.
Parameter Description
Command Description
ip igmp This command configures Internet Group Management Protocol (IGMP) timers and counters.
Platforms Licensing Command Mode
All platforms Base operating system Available in Config or Enable mode on master switches.

AOS-W 3.4.1 Command Line Interface | Reference Guide show ip mobile | 833
show ip mobile
show ip mobile
active-domains
binding [<host-ip>|<host-macaddr>|brief]
domain [<name>]
global
hat
host [<host-ip>|<host-macaddr>|brief]
packet-trace [<count>]
remote <host-ip>|<host-macaddr>
trace <ip-addr>|<mac-addr>|{force <ip-addr>|<mac-addr>}
traffic dropped|foreign-agent|home-agent|proxy|proxy-dhcp
trail <host-ip>|<host-macaddr>
tunnel
visitor [<host-ip>|<host-macaddr>|brief]
Description
Display statistics and configuration information for the mobile protocol.
Syntax
Parameter Description
active domains IP mobility domains active on this switch
binding Display a list of Home Agent Bindings
[<host-ip>] Filter the Home Agent Bindings list to display data for a specific host IP address.
[<host-macaddr>] Filter the Home Agent Bindings list to display data for a specific host MAC
address.
[brief] Limit the output of this command to show just two lines of data.
domain [<name>] Display subnet, VLAN and home agent information for all mobility domains, or
specify a mobility domain name to view data for that domain only.
global View the current Mobility Agents global configuration
hat Display the Active Home Agent table.
host Display a list of Mobile IP hosts.
[<host-ip>] Filter the Mobile Host List to display data for a specific host IP address.
[<host-macaddr>] Filter the Mobile Host List to display data for a specific host MAC address.
[brief] Limit the output of this command to show just two lines of data.
packet-trace [<count>] Packet trace between Datapath-Mobility
remote <host-ip>|<host-
macaddr>
Display Mobile IP remote host(s)
trace Show if the Mobile IP feature will poll remote switches for mobility status of
station
<ip-addr> Host IP address
<mac-addr> Host MAC address
force <ip-addr>|<mac-
addr>
Show if the Mobile IP feature will poll remote switches for mobility status of
station.

834 |show ip mobile AOS-W 3.4.1 Command Line Interface | Reference Guide
Examples
The example below lists mobility domains configured on the switch, and shows information for any subnets
defined on these domains.
The output of this command includes the following parameters:
traffic Display mobile IP protocol statistics for:
zProxy DHCP
zProxy Mobile IP
zHome Agent Registrations
zForeign Agent Registrations
zRegistration Revocations
dropped Show only counters for dropped mobility traffic.
foreign-agent Show only mobile IP foreign agent statistics.
A foreign agent is the switch which handles all mobile IP communication with a
home agent on behalf of a roaming client.
home-agent Show only mobile IP home agent statistics.
A home agent for a mobile client is the switch where the client first appears
when it joins the mobility domain.
proxy Show only counters for mobile IP proxy traffic.
proxy-dhcp Show only counters for mobile IP proxy DHCP traffic.
trail <host-ip>|<host-
macaddr>
Show the mobile IP roaming trail by entering a host’s IP or MAC address.
tunnel Show the Mobile Tunnel Table for IPIP Tunnels.
visitor Display a list of mobile nodes visiting a foreign agent.
[<host-ip>] Filter the Foreign Agent Visitor list to display data for a specific host IP
adddress.
[<host-macaddr>] Filter the Foreign Agent Visitor list to display data for a specific host MAC
adddress.
[brief] Limit the output of this command to show just two lines of data.
Parameter Description
(host) #show ip mobile domain
Mobility Domains:, 2 domain(s)
------------------------------
Domain name default
Home Agent Table, 0 subnet(s)
Domain name newdomain
Home Agent Table, 2 subnet(s)
subnet mask VlanId Home Agent
--------------- --------------- ------ ---------------
10.2.124.76 255.255.255.255 1 10.4.62.2
172.21.5.50 255.255.255.255 1 10.4.62.2
Parameter Description
subnet Subnet configured for the IP mobility service.
mask Subnet mask
VLAN ID VLAN ID of the VLAN used by the subnet.

AOS-W 3.4.1 Command Line Interface | Reference Guide show ip mobile | 835
Use the show ip mobile host command to track mobile users.
The output of this command includes the following parameters:
Related Commands
Command History
Command introduced in AOS-W 3.0.
Command Information
Home Agent IP address of the home agent or mobility agent.
Parameter Description
(host) #show ip mobile host
Mobile Host List, 1 host(s)
---------------------------
00:40:96:a6:a1:a4 10.0.100.194
Roaming Status: Home Switch/Home VLAN, Service time 0 days 00:06:47
Home VLAN 100 on network 10.0.100.0/24
DHCP lease for corporate-240 at Thu Sep 21 15:11:44 2006 for 7200 secs from 10.3.26.1
Parameter Description
<mac-addr> <ip-addr> MAC and IP addresses of the host
Roaming Status Displays how long the host has used its current switch and VLAN.
Home VLAN VLAN ID, IP address and subnet of the home VLAN.
DHCP lease Displays the amount of time the station has had its current DHCP lease.
Command Description
ip mobile active-domain This command configures the mobility domain that is active on the switch.
ip mobile domain This command configures the mobility domain on the switch.
ip mobile foreign-agent This command configures the foreign agent for IP mobility.
ip mobile home-agent This command configures the home agent for IP mobility.
ip mobile proxy
This command configures the proxy mobile IP module in a mobility-enabled
switch
.
ip mobile revocation This command configures the frequency at which registration revocation
messages are sent.
ip mobile trail This command configures the capture of association trail for all devices.
Platforms Licensing Command Mode
All platforms Base operating system Available in Config or Enable mode on
master or local switches

836 | show ip nat pool AOS-W 3.4.1 Command Line Interface | Reference Guide
show ip nat pool
show ip nat pool
Description
Display pools of IP addresses for network address translation (NAT.
Syntax
No parameters
Examples
The example below shows the current NAT pool configuration on the switch.
The output of this command includes the following parameters:
Related Commands
Command History
This command was available in AOS-W 3.0.
Command Information
(host) # show ip nat pools
NAT Pools
---------
Name Start IP End IP DNAT IP
---- -------- --------- -------
2net 2.1.1.1 2.1.1.125
Parameter Description
Name Name of the NAT pool.
Start IP IP address that defines the beginning of the range of source NAT addresses in the pool.
End IP IP address that defines the end of the range of source NAT addresses in the pool.
DNAT IP Destination NAT IP address, if defined.
Command Description
ip nat This command configures a pool of IP addresses for network address translation (NAT).
Platforms Licensing Command Mode
All platforms Though this command is available in the operating system, you
must have a Policy Enforcement Firewall license to configure a
NAT pool.
Available in Config or Enable
mode on master or local
switches
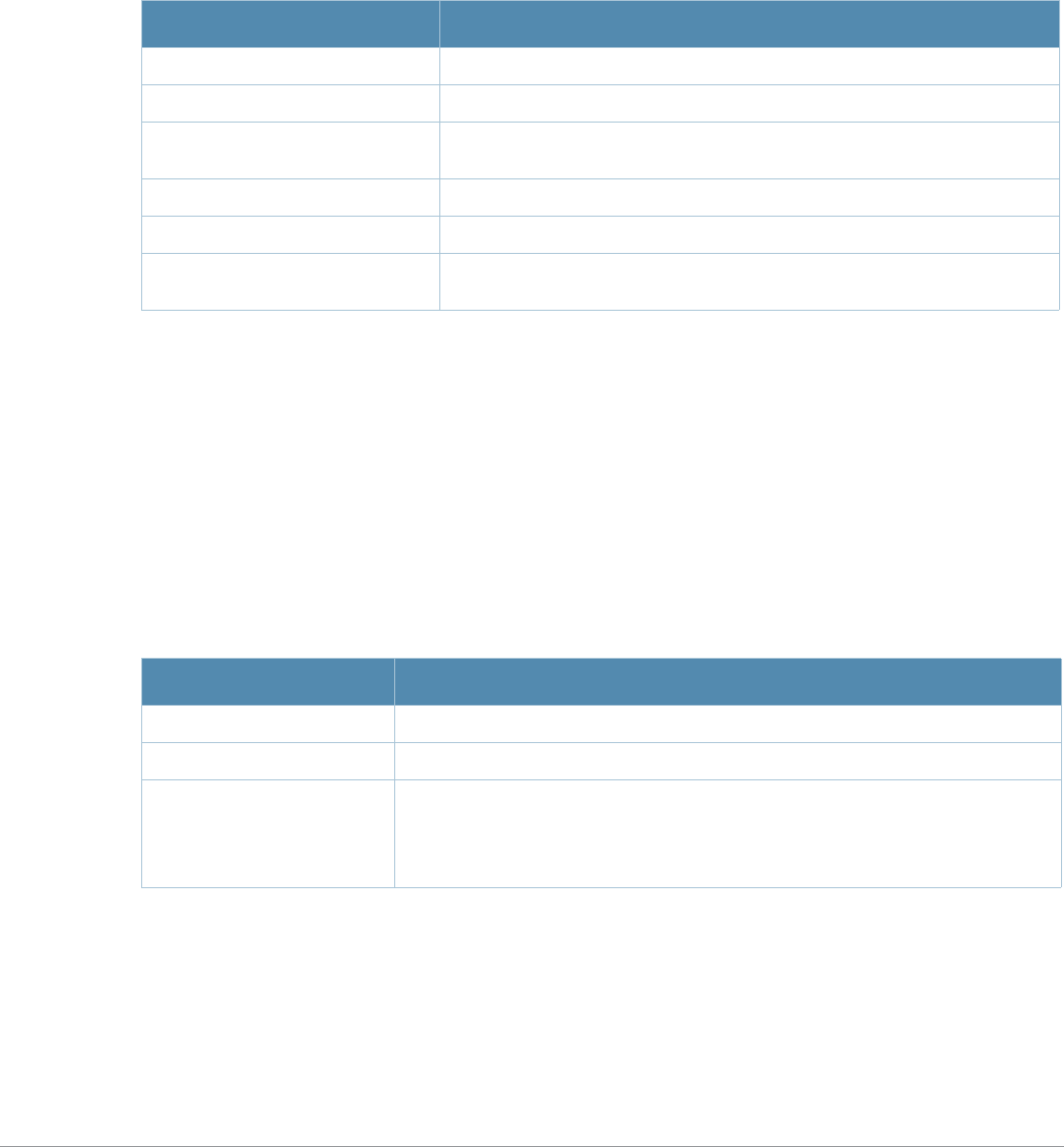
AOS-W 3.4.1 Command Line Interface | Reference Guide show ip ospf | 837
show ip ospf
show ip ospf [database]|[debug route]|[interface tunnel|vlan <id>]|[neighbor]|
[redistribute]|[subnet]
Description
Display statistics and configuration information for the Open Shortest Path First (OSPF) routing protocol.
Syntax
Example
If you issue this command without any of the optional parameters described in the table above, the show ip
ospf command will display general router and area settings for the OSPF.
The output of this command includes the following parameters.
Parameter Description
database Show database information for the OSPF protocol.
debug route Show debugging information for OSPF routes.
interface tunnel|vlan <id> Display the status of OSPF on an individual interface by specifying a tunnel
or VLAN ID number.
neighbor Display data for OSPF neighboring routers.
redistribute Display OSPF route distribution information.
subnet Display the subnets manually added to the Subnet Exclude List via the
router ospf subnet exclude <addr> <mask> command.
(host) (config-subif)# show ip ospf
OSPF is currently running with Router ID 123.45.110.200
Number of areas in this router is 1
Area 10.1.1.0
Number of interfaces in this area is 2
Area is totally stub area
SPF algorithm executed 0 times
Parameter Description
OSPF Router ID Verifies that OSPF is running and the router ID that OSPF is running on.
Number of areas List the number of areas configured in the router.
Area Displays the Area ID followed by:
znumber of interfaces in the area
zindicates if the area is a totally stub area
znumber of times the SPF algorithm has been executed

838 |show ip ospf AOS-W 3.4.1 Command Line Interface | Reference Guide
To display OSPF settings for an individual interface, you must specify a VLAN or tunnel ID number. The
example below displays part of the output of the show ip ospf interface vlan command.
The output may include some or all of the following parameters.
(host) # show ip ospf interface vlan 10
Vlan 3 is up, line protocol is up
Internet Address 3.3.3.1, Mask 255.255.255.0, Area 10.1.1.1
Router ID 10.4.131.227, Network Type BROADCAST, Cost: 1
Transmit Delay is 1 sec, State WAIT, Priority 1
Designated Router id 0.0.0.0, Interface Address 3.3.3.1
Backup designated Router id 0.0.0.0, Interface Address 3.3.3.1
Timer intervals configured, Hello 10, Dead 40, Retransmit 5
Neighbor Count is 0
Tx Stat: Hellos 1 DbDescr 0 LsReq 0 LsUpdate 0 LsAck 0 Pkts 1
Rx Stat: Hellos 0 DbDescr 0 LsReq 0 LsUpdate 0 LsAck 0 Pkts 0
DisCd 0 BadVer 0 BadNet 0 BadArea 0 BadDstAdr 0 BadAuType 0
BadAuth 0 BadNeigh 0 BadPckType 0 BadVirtLink 0
...
Parameter Description
Vlan <number> Identifies that the interface type and ID are up and functional.
Internet Address Internet address, network mask, and area assigned to the interface.
Router ID Displays the router ID, that the network type is Broadcast, and the cost value.
Transmit Delay Details of the transmit delay, state, and priority.
Designated Router Details of the designated router ID and interface address.
Backup Designated Router ID Details of the backup router ID and interface address.
Timer intervals configured Details of elapse time intervals for Hello, Dead, Transmit (wait), and retransmit.
Neighbor Count Details the number of neighbors and adjacent neighbors.
Tx Stat Counters and statistics for transmitted data.
zHellos: Number of transmitted hello packets. These packets are sent every
hello interval.
zDbDescr: Number of transmitted database description packets.
zLsReq: Number of transmitted link state request packets.
zLsUpdate: Number of transmitted link state update packets.
zLsAck: Number of transmitted link state acknowledgment packets
zPkts: Total number of transmitted packets.
Rx Stat Counters and statistics for received data.
zHellos: Number of received hello packets. These packets are sent every
hello interval.
zDbDescr: Number of received database description packets.
zLsReq: Number of received link state request packets.
zLsUpdate: Number of received link state update packets.
zLsAck: Number of received link state acknowledgment packets
zPkts: Total number of received packets.
DisCd Number of received packets that are discarded.
BadVer Number of received packets that have bad OSPF version number.
BadNet Number of received packets that belong to different network than the local
interface.
BadArea Number of received packets that belong to different area than the local
interface.
BadDstAdr Number of received packets that have wrong destination address.
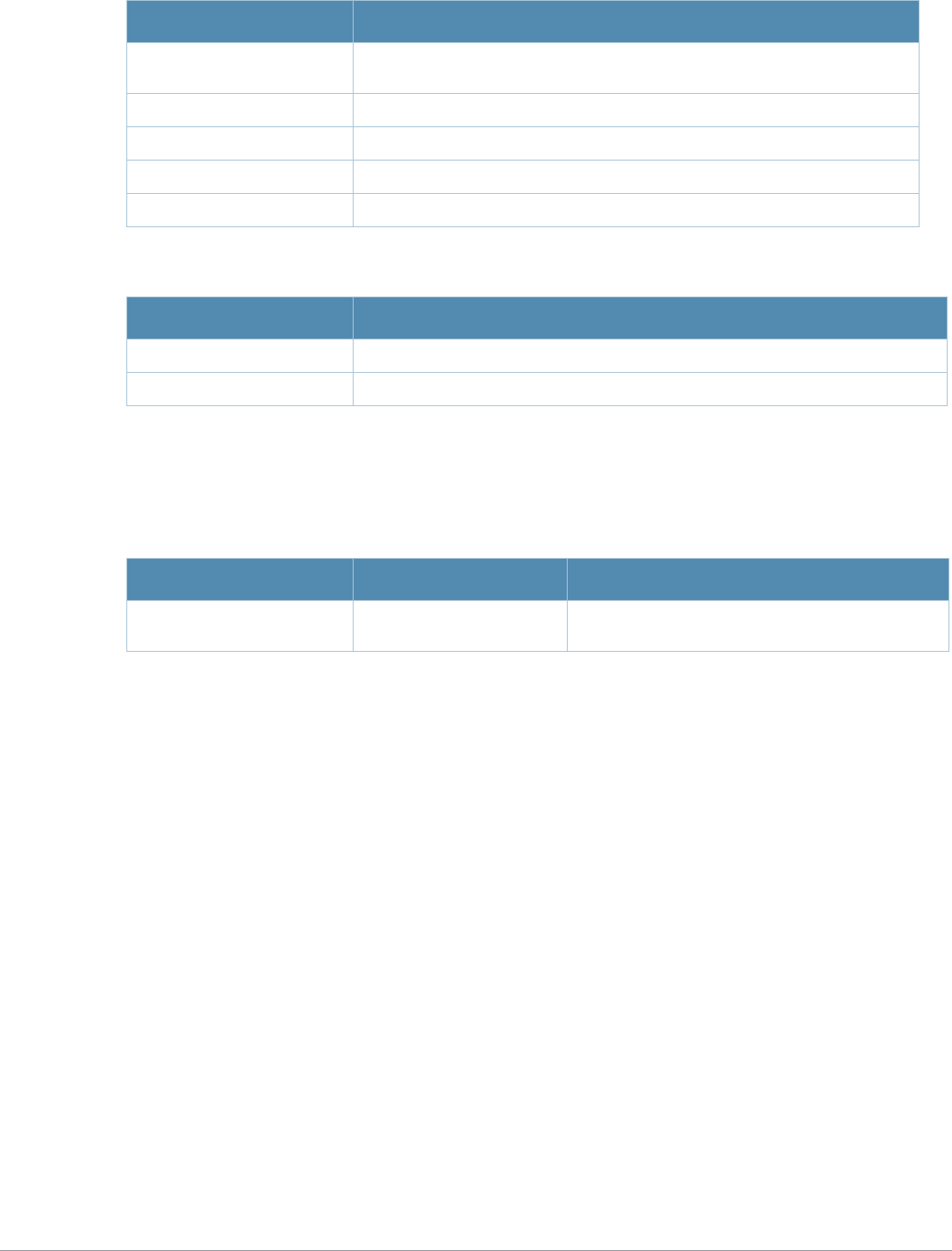
AOS-W 3.4.1 Command Line Interface | Reference Guide show ip ospf | 839
Related Commands
Command History
Introduced in AOS-W 3.4.
Command Information
BadAuType Number of received packets that have different authentication type than the
local interface.
BadAuth Number of received packets where authentication failed.
BadNeigh Number of received packets which didn’t have a valid neighbor.
BadPckType Number of received packets that have wrong OSPF packet type.
BadVirtLink Number of received packets that didn’t match have a valid virtual link.
Parameter Description
Command Description
ip ospf Configure OSPF on the interface
router ospf Configure OSPF on the router
Platforms Licensing Command Mode
All platforms Base operating system Available in Config or Enable mode on master or
local switches
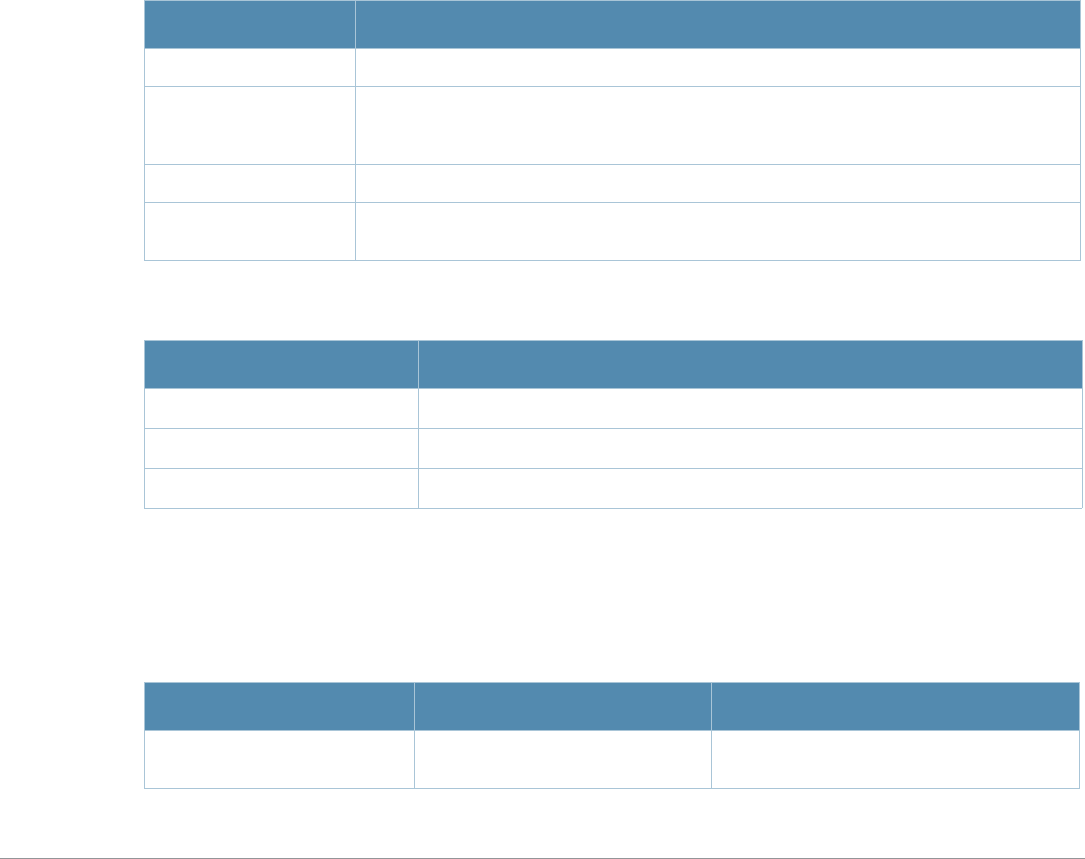
840 | show ip pppoe-info AOS-W 3.4.1 Command Line Interface | Reference Guide
show ip pppoe-info
show ip pppoe-info
Description
Display configuration settings for Point-to-Point Protocol over Ethernet (PPPoE).
Syntax
No parameters.
Examples
The example below shows the current PPPoE configuration.
The output of this command includes the following parameters:
Related Commands
Command History
Introduced in AOS-W 3.0.
Command Information
(host) #show ip pppoe-info
PPPoE username: rudolph123
PPPoE password: <HIDDEN>
PPPoE service name: ppp2056
PPPoE VLAN: 22
Parameter Description
PPPoE username PAP username configured on the PPPoE access concentrator.
PPPoE password If this parameter displays the word <HIDDEN>, a PAP password is configured on the
PPPoE access concentrator. If this parameter is <NONE>, there is no PPOE password
configured.
PPPoE service name PPPoE service name.
PPPoE VLAN VLAN configured to use PPPoE to obtain an IP address via the command interface vlan
<id> ip address pppoe.
Command Description
ip pppoe-password This command configures the PPP over Ethernet (PPPoE) password.
ip pppoe-service-name This command configures the PPP over Ethernet (PPPoE) service name.
ip pppoe-username This command configures the PPP over Ethernet (PPPoE) username.
Platforms Licensing Command Mode
All platforms Base operating system Available in Config or Enable mode on
master or local switches
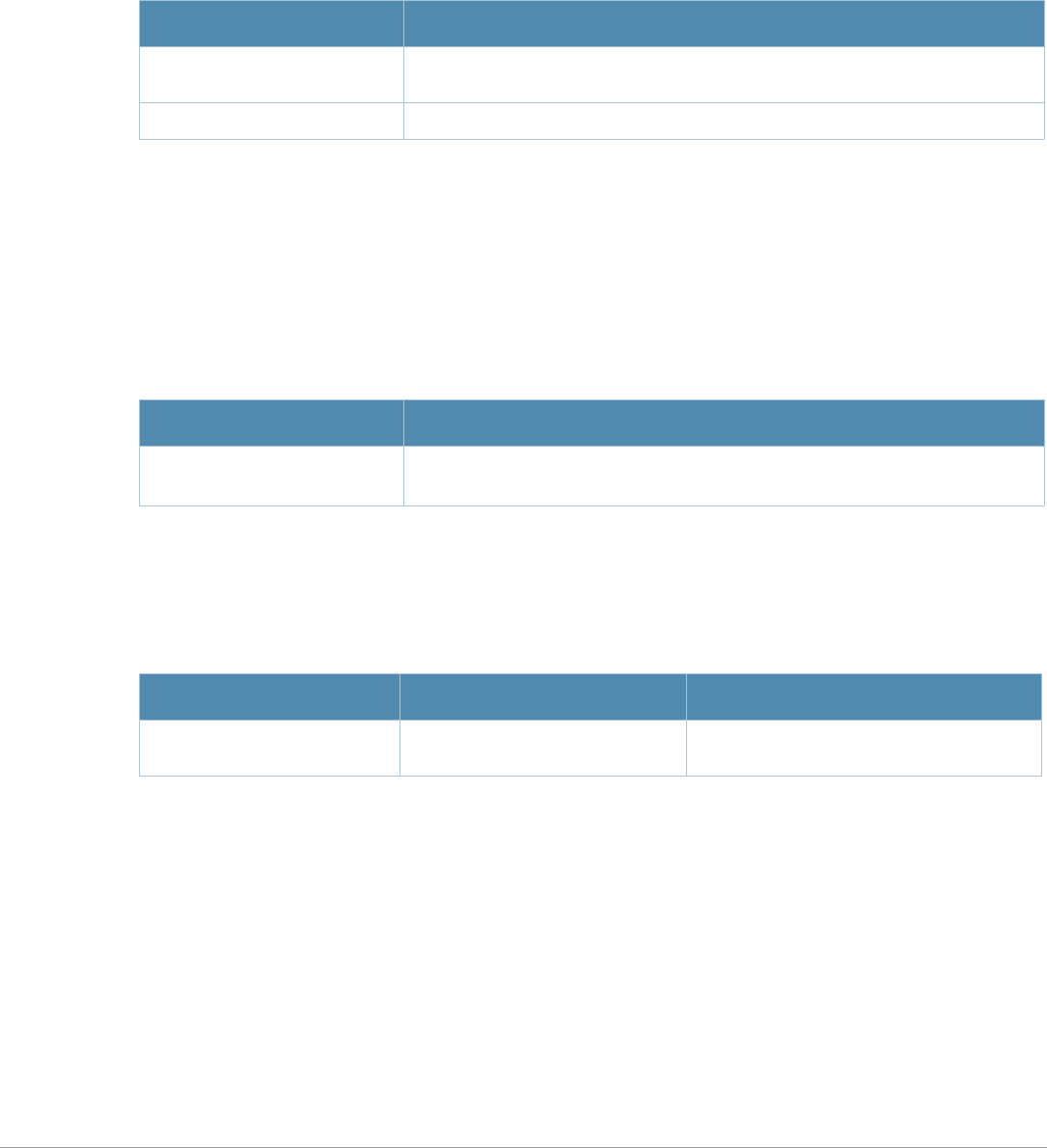
AOS-W 3.4.1 Command Line Interface | Reference Guide show ip radius | 841
show ip radius
show ip radius nas-ip|source-interface
Description
Display global parameters for configured RADIUS servers.
Syntax
Examples
The example below shows the RADIUS client NAS IP address.
Related Commands
Command History
Introduced in AOS-W 3.0.
Command Information
Command Description
nas-ip Show the Network Access Server (NAS) IP address attribute sent in outgoing
RADIUS requests
source-interface Show the source address of outgoing RADIUS requests
(host) #show ip radius nas-ip
RADIUS client NAS IP address = 10.168.254.221
Command Description
ip radius This command configures global parameters for configured RADIUS
servers.
Platforms Licensing Command Mode
All platforms Base operating system Available in Config or Enable mode on
master or local switches

842 | show ip route AOS-W 3.4.1 Command Line Interface | Reference Guide
show ip route
show ip route [static]
Description
View the Alcatel-Lucent switch routing table.
Syntax
Usage Guidelines
This command displays static routes configured on the switch via the ip route command. Use the ip
default-gateway command to set the default gateway to the IP address of the interface on the upstream
router or switch to which you connect the switch.
Examples
The example below shows the ip address of routers and the VLANs to which they are connected.
Related Commands
Command History
Introduced in AOS-W 3.0.
Command Information
Command Description
static Include this optional parameter to display only static routes.
(host) #show ip route
Codes: C - connected, O - OSPF, R - RIP, S - static
M - mgmt, U - route usable, * - candidate default
Gateway of last resort is 10.6.2.254 to network 0.0.0.0
S* 0.0.0.0/0 [1/0] via 10.6.2.254*
C 10.9.2.0 is directly connected, VLAN1
C 10.9.3.0 is directly connected, VLAN63
C 10.9.4.0 is directly connected, VLAN64
C 10.9.5.0 is directly connected, VLAN65
C 10.9.6.0 is directly connected, VLAN66
C 0.0.0.0 is directly connected, Tunnel 1
C 10.100.103.253 is an ipsec map default-local-master-ipsecmap
Command Description
ip radius This command configures global parameters for configured RADIUS servers.
Platforms Licensing Command Mode
All platforms Base operating system Available in Config or Enable mode on
master or local switches
AOS-W 3.4.1 Command Line Interface | Reference Guide show ipc statistics app-ap | 843
show ipc statistics app-ap
show ipc statistics app-ap {am|sapd|sta} {ap-name <ap-name>}|{bssid <bssid>}|{ip-addr
<ip-addr>}
Description
Display Inter Process Communication (IPC) statistics for a specific AP or BSSID.
Syntax
Usage Guidelines
Issue this command at the request of Alcatel-Lucent support to troubleshoot application errors.
Example
The following example shows IPC statistics for the SAPD process on an AP named mpp125.
The output of this command includes the following data columns:
Parameter Description
am Show IPC statistics for an air monitor.
sapd Show IPC statistics for the SAPD process.
stm Show IPC statistics for station management communications.
ap-name <ap-name> Show IPC statistics for an AP with a specific name.
bssid <bssid> Show IPC statistics for a specific Basic Service Set Identifier (BSSID). An AP’s
BSSID is usually the AP’s MAC address.
ip-addr <ip-addr> Show IPC statistics for an AP with a specific IP address. Enter the IP address in
dotted-decimal format.
(host) #show ipc statistics app-ap sapd ap-name mpp125
Local Statistics
To application Tx Msg Tx Blk Tx Ret Tx Fail Rx Ack Rx Msg Rx Drop Rx Err Tx Ack
MESH 3 0 1 0 3 1 1 0 1
RF Client 1 0 0 0 1 1 0 0 1
STM 1 0 0 0 1 0 0 0 0
Nanny 1 0 0 0 1 0 0 0 0
Remote Statistics
To application Tx Msg Tx Blk Tx Ret Tx Fail Rx Ack Rx Msg Rx Drop Rx Err Tx Ack
AMAPI CLI Client 0 0 0 0 0 1 0 0 1
STM 248 0 0 0 0 248 0 0 0
Allocated Buffers 0
Static Buffers 1
Static Buffer Size 1444
Parameter Description
Tx Msg Number of transmitted messages.
Tx Blk Number of blocking messages transmitted.
Tx Ret Number of transmitted messages that were returned.
Tx Fail Number of failure messages that were transmitted.
844 | show ipc statistics app-ap AOS-W 3.4.1 Command Line Interface | Reference Guide
Command History
This command was available in AOS-W 1.0.
Command Informationh
Rx Ack Number of received acknowledgements.
Rx Msg Number of received messages.
Rx Drop Number of received messages that were dropped.
Rx Err Number of received messages with errors.
Tx Ack Number of transmitted acknowledgements.
Allocated Buffers Number of allocated buffers for IPC messages.
Static Buffers Number of static buffers for IPC messages.
Static Buffer Size Size of the static buffer.
Parameter Description
Platforms Licensing Command Mode
All platforms Base operating system Enable and Config mode on local and
master switches
AOS-W 3.4.1 Command Line Interface | Reference Guide show ipc statistics app-id | 845
show ipc statistics app-id
show ipc statistics app-id <app-id>
Description
Display Inter Process Communication (IPC) statistics for a specific AP or BSSID.
Syntax
Usage Guidelines
Issue this command at the request of Alcatel-Lucent support to troubleshoot application errors.
Command History
This command was available in AOS-W 1.0.
Command Information
Parameter Description
<app-id> Application ID number. This number must be obtained from Alcatel-Lucent
support.
Platforms Licensing Command Mode
All platforms Base operating system Enable and Config mode on local and
master switches
846 | show ipc statistics app-name AOS-W 3.4.1 Command Line Interface | Reference Guide
show ipc statistics app-name
show ipc statistics app-name <name>
Description
Display Inter Process Communication (IPC) statistics for a specific application.
Syntax
Example
The following example shows IPC statistics for the STM process.
Parameter Description
<name> One of the following application names:
zaaa: Administrator Authentication
zads: Anomaly Detection
zauthmgr: User Authentication
zcertmgr: Certificate Manager
zcfgm: Config Manager
zcts: Transport Service
zdbsync: Database Synchronization
zdhcp: DHCP Server
zesi: Server Load Balancing
zfpapps: Layer 2,3 control
zhttpd: HTTPD
zike: IKE Daemon
zl2tp: L2TP
zlicensemgr: License Manager
zmobileip: Mobile IP
zntp: NTP Daemon
zpim: Protocol Independent Multicast
zpktfilter: Packet Filter
zpptp: PPTP
zprofmgr: Profile Manager
zpublisher: Publish subscribe service
zresolver: Resolver
zsnmp: SNMP agent
zstm: Station Management
(host) #show ipc statistics app-name stm
Local Statistics
To application Tx Msg Tx Blk Tx Ret Tx Fail Rx Ack Rx Msg Rx Drop Rx Err Tx Ack
AMAPI Web Client 0 0 0 0 0 34405 0 0 34405
Layer2/3 233098 1 0 0 233095 12 0 0 12
Authentication Se 1076236 0 0 0 1076236 0 0 0 0
Authentication 54494 7448 54 1 54050 468811 0 0 0
Publisher 4 0 0 0 4 2 52 0 2
AMAPI CLI Client 1 0 0 0 1 702 0 0 702
Profile Manager 1 1 0 0 1 0 0 0 0
Mobile IP 1120303 0 0 0 1076236 1 0 0 0
Syslog Manager 2 2 0 0 2 0 0 0 0
WMS 0 0 0 0 0 19 0 0 19
PIM 2 1 0 0 2 1 1 0 1
Configuration Man 2 1 0 0 2 13 0 0 12
License Manager 1 1 0 0 1 0 0 0 0
Datapath 3281237 66425 1 0 1907552 1382289 104 6 0
Nanny 1 0 0 0 0 0 0 0 0
Remote Statistics
To application Tx Msg Tx Blk Tx Ret Tx Fail Rx Ack Rx Msg Rx Drop Rx Err Tx Ack
WMS 59 0 0 0 59 0 0 0 0
STM 54983 0 0 0 0 1527435 0 0 0
Allocated Buffers 0
Static Buffers 4
Static Buffer Size 1400
AOS-W 3.4.1 Command Line Interface | Reference Guide show ipc statistics app-name | 847
The output of this command includes the following data columns:
Command History
This command was available in AOS-W 3.0.
Command Information
Parameter Description
Tx Msg Number of transmitted messages.
Tx Blk Number of blocking messages transmitted.
Tx Ret Number of transmitted messages that were returned.
Tx Fail Number of failure messages that were transmitted.
Rx Ack Number of received acknowledgements.
Rx Msg Number of received messages.
Rx Drop Number of received messages that were dropped.
Rx Err Number of received messages with errors.
Tx Ack Number of transmitted acknowledgements.
Allocated Buffers Number of allocated buffers for IPC messages.
Static Buffers Number of static buffers for IPC messages.
Static Buffer Size Size of the static buffer.
Platforms Licensing Command Mode
All platforms Base operating system Enable or Config mode on master or local
switches

848 | show ipc statistics app-name AOS-W 3.4.1 Command Line Interface | Reference Guide
AOS-W 3.4.1 Command Line Interface | Reference Guide show ipv6 access-list | 849
show ipv6 access-list
show ipv6 access-list [<string> | brief]
Description
Displays IPv6 access list configured in the switch.
Syntax
Example
This example displays the session access control list details.
The output of this command includes the following parameters:
Command History
This command was available in AOS-W 3.3.
Parameter Description
string To view details of a specific ACL.
brief To view a summary of all IPv6 ACLs.
Parameter Description
Name Name of the IPv6 ACL.
Type Type of ACL rule.
Use Count Number of times impacted.
Roles Roles using the ACL.
(host) #show ipv6 access-list brief
Access list table
-----------------
Name Type Use Count Roles
---- ---- --------- -----
v6-allowall session 2 default-vpn-role authenticated
v6-dhcp-acl session 1 guest
v6-dns-acl session 1 guest
v6-http-acl session 1 guest
v6-https-acl session 1 guest
v6-icmp-acl session 1 guest
v6-logon-control session 1 logon
(host) #show ipv6 access-list v6-allowall
ipv6 access-list session v6-allowall
v6-allowall
-----------
Priority Source Destination Service Action TimeRange Log Expired Queue TOS 8021P Blacklist
Mirror DisScan
-------- ------ ----------- ------- ------ --------- --- ------- ----- --- ----- --------- -
---- -------
1 any any any permit Low

850 | show ipv6 access-list AOS-W 3.4.1 Command Line Interface | Reference Guide
Command Information
Platforms Licensing Command Mode
All platforms Base operating system Enable or Config mode on master and local
switches
AOS-W 3.4.1 Command Line Interface | Reference Guide show ipv6 datapath session counters | 851
show ipv6 datapath session counters
show ipv6 datapath session counters
Description
Displays datapath session table statistics.
Example
This example displays the session counter statistics.
The output of this command includes the following parameters:
Command History
This command was available in AOS-W 1.0.
Command Information
Parameter Description
Current Entries Number of session entries in the datapath table.
High Water Mark The maximum number of session since the switch uptime.
Maximum Entries The maximum limit for session entries.
Total Entries The total number of session entries.
Allocation Failures The number of datapath sessions that could not be established.
Duplicate Entries The total number of duplicate session entries.
No Reverse Entries The total number of sessions that does not have reverse entries.
Platforms Licensing Command Mode
All platforms Base operating system Enable or Config mode on master and local
switches
(host) #show datapath session counters
Datapath Session Table Statistics
---------------------------------
Current Entries 7
High Water Mark 167
Maximum Entries 65535
Total Entries 37287
Allocation Failures 0
Duplicate Entries 0
Cross linked Entries 0
No Reverse Entries 0
Max link length 2

852 | show ipv6 datapath session table AOS-W 3.4.1 Command Line Interface | Reference Guide
show ipv6 datapath session table
show ipv6 datapath session table <IPv6 Address>
Description
Displays current IPv6 session on the switch.
Syntax
Example
This example displays the session access control list details.
The output of this command includes the following parameters:
Parameter Description
<IPv6 IP Address> Optional parameter. If specified, displays IPv6 datapath session table for that IP
address. By defaults, displays session table for all IPv6 addresses.
(host) #show ipv6 datapath session
Datapath Session Table Statistics
---------------------------------
Current Entries 45
High Water Mark 47
Maximum Entries 524287
Total Entries 9098
Allocation Failures 0
Duplicate Entries 0
Cross linked Entries 0
No Reverse Entries 0
Max link length 0
Datapath Session Table Entries
------------------------------
Flags: F - fast age, S - src NAT, N - dest NAT
D - deny, R - redirect, Y - no syn
H - high prio, P - set prio, T - set ToS
C - client, M - mirror, V - VOIP
I - Deep inspect, U - Locally destined
Source IP Destination IP Prot SPort DPort Cntr Prio ToS Age Destination Flags
--------- -------------- ---- ----- ----- ---- ---- --- --- ----------- -----
2003:d81f:f9f0:1001:617c:9151:6d25:f754 2003:d81f:f9f0:1001::3 58 3951 32768 0 0 0 1 tunnel 13 FYCI
2003:d81f:f9f0:1001:617c:9151:6d25:f754 2003:d81f:f9f0:1001::3 58 3950 32768 0 0 0 1 tunnel 13 FYCI
Parameter Description
Source IP The source IP address of the datapath.
Destination IP The destination IP address of the datapath.
Prot Denotes the protocol number.
SPort Source port of the datapath.
DPort Destination port of the datapath.
ToS Specifies the type of service.
AOS-W 3.4.1 Command Line Interface | Reference Guide show ipv6 datapath session table | 853
Command History
This command was available in AOS-W 3.0.
Command Information
Age Age of the session in seconds.
Destination Destination slot of the switch.
Platforms Licensing Command Mode
All platforms Base operating system Enable or Config mode on master and local
switches
Parameter Description
854 | show ipv6 datapath user counters AOS-W 3.4.1 Command Line Interface | Reference Guide
show ipv6 datapath user counters
show ipv6 datapath user counters
Description
Displays datapath user table statistics.
Example
This example displays the user table statistics for IPv6 users.
Command History
This command was available in AOS-W 3.0.
Command Information
Platforms Licensing Command Mode
All platforms Base operating system Enable or Config mode on master and local
switches
(host) #show ipv6 datapath user counters
Datapath User Table Statistics
------------------------------
Current Entries 0
Pending Deletes 0
High Water Mark 0
Maximum Entries 2047
Total Entries 0
Allocation Failures 0
Invalid Users 0
Max link length 0

AOS-W 3.4.1 Command Line Interface | Reference Guide show ipv6 datapath user table | 855
show ipv6 datapath user table
show ipv6 datapath user table
Description
Displays ipv6 datapath user table entries.
Example
This example displays the user table entries in the datapath.
The output of this command includes the following parameters:
Command History
This command was available in AOS-W 3.0.
Command Information
(host) #show ipv6 datapath user table
Datapath User Table Entries
---------------------------
Flags: P - Permanent, W - WEP, T- TKIP, V - ProxyArp for User, A - ProxyARP to User, N - VPN
IP MAC ACLs Contract Location Age Sessions Flags
-- --- ---- -------- -------- --- --------- -----
fe80::216:ceff:fe2c:b485 00:16:CE:2C:B4:85 1/0 0/0 1 28 0/65535 W
2003:d81f:f9f0:1001:617c:9151:6d25:f754 00:16:CE:2C:B4:85 1/0 0/0 1 0 0/65535 W
Parameter Description
IP IP address of the user (client).
MAC MAC address of the user (client).
ACLs The access control list assigned to the user.
Contract Bandwidth contract.
Location This value refers to the AP-group of the IPv6 client. Use the show aaa state ap-
group to get the AP group and the location ID mapping.
Age Total time connected to the switch.
Sessions Number of active sessions.
Platforms Licensing Command Mode
All platforms Base operating system Enable or Config mode on master and local
switches

856 | show ipv6 firewall AOS-W 3.4.1 Command Line Interface | Reference Guide
show ipv6 firewall
show ipv6 firewall
Example
This example displays the status of all firewall configurations.
The output of this command includes the following parameters:
Parameter Description
Monitor ping attack Displays status on monitoring ICMP pings, frequency (in seconds) at which the
attacks are monitored and the port on which the monitoring is configured.
Monitor TCP SYN attack Status on monitoring TCP SYN messages, frequency (in seconds) at which the
attacks are monitored and the port on which the monitoring is configured.
Monitor IPv6 sessions
attack
Status on TCP and UDP connection requests, in seconds) at which the attacks are
monitored and the port on which the monitoring is configured.
Deny inter user
bridging
Status on Layer-2 traffic forwarding between wired and wireless users, frequency (in
seconds) at which the messages are monitored and the port on which the monitoring
is configured.
Deny all IPv6 fragments Status on IPv6 fragments to be dropped.
Per-packet logging Status on packet logging for the corresponding session rule.
Enforce TCP handshake
before allowing data
Status on TCP handshake between two clients.
Prohibit RST replay
attack
Status on a TCP connections in both directions.
Session Idle Timeout Status on TCP session idle timeout.
Session mirror
destination
Status on mirrored session packet traffic.
Prohibit IPv6 Spoofing Status on IP spoofing. When this option is enabled, IP and MAC addresses are
checked; possible IP spoofing attacks are logged and an SNMP trap is sent.
Enable IPv6 Stateful
Firewall
Status of IPv6 firewall.
(host) #show ipv6 firewall
Global IPv6 firewall policies
-----------------------------
Policy Action Rate Slot/Port
------ ------ ---- ---------
Monitor ping attack Disabled
Monitor TCP SYN attack Disabled
Monitor IPv6 sessions attack Disabled
Deny inter user bridging Disabled
Deny all IPv6 fragments Disabled
Per-packet logging Disabled
Enforce TCP handshake before allowing data Disabled
Prohibit RST replay attack Disabled
Session Idle Timeout Disabled
Session mirror destination Disabled
Prohibit IPv6 Spoofing Disabled
Enable IPv6 Stateful Firewall Disabled

AOS-W 3.4.1 Command Line Interface | Reference Guide show ipv6 firewall | 857
Command History
This command was available in AOS-W 3.0.
Command Information
Platforms Licensing Command Mode
All platforms Base operating system Enable or Config mode on master and local
switches
858 | show ipv6 mld config AOS-W 3.4.1 Command Line Interface | Reference Guide
show ipv6 mld config
show ipv6 mld config
Description
Displays Multicast Listener Discover (MLD) configuration details.
Example
This example displays the current MLD configuration values.
The output of this command includes the following parameters:
Command History
This command was available in AOS-W 3.3.
Command Information
Parameter Description
robustness-variable Denotes the value that is used to calculate the timeout value of a MLD client.
query-interval Denotes the time interval at which the MLD query is sent.
query-response-interval Denotes the time interval during the MLD query response should be received.
startup-query-interval Denotes the time interval between successive MLD queries during startup.
startup-query-count Number of times queries are sent during startup.
last-member-query-interval Denotes the time interval between successive MLD queries after the last member
has left the MLD group.
last-member-query-count Number of times queries are sent after the last member has left the MLD group.
Platforms Licensing Command Mode
All platforms Base operating system Enable or Config mode on master and local
switches
(host) #show ipv6 mld config
MLD Config
----------
Name Value
---- -----
robustness-variable 2
query-interval 125
query-response-interval 100
startup-query-interval 31
startup-query-count 2
last-member-query-interval 10
last-member-query-count 2
AOS-W 3.4.1 Command Line Interface | Reference Guide show ipv6 mld counters | 859
show ipv6 mld counters
show ipv6 mld counters
Description
Displays the statistics of MLD.
Example
This example displays the MLD statistics for the following values.
The output of this command includes the following parameters:
Command History
This command was available in AOS-W 3.3.
Parameter Description
received-total The total number of MLD messages.
received-queries The total number of MLD queries.
received-v1-reports The total number of MLD v1 reports received.
received-leaves The total number of MLD v1 leave messages received.
received-unknown-types The total number of unrecognized messages received.
len-errors The total number of error message where the length check has failed.
checksum-errors The total number of error message where the checksum has failed.
not-vlan-dr The number of messages received for which the current switch is not the designated
router.
transmitted-queries The total number of transmitted MLD queries.
forwarded The total number of MLD messages forwarded.
(host) #show ipv6 mld counters
MLD Statistics
--------------
Name Value
---- -----
received-total 0
received-queries 0
received-v1-reports 0
received-leaves 0
received-unknown-types 0
len-errors 0
checksum-errors 0
not-vlan-dr 0
transmitted-queries 0
forwarded 0

860 | show ipv6 mld counters AOS-W 3.4.1 Command Line Interface | Reference Guide
Command Information
Platforms Licensing Command Mode
All platforms Base operating system Enable or Config mode on master and local
switches
AOS-W 3.4.1 Command Line Interface | Reference Guide show ipv6 mld group | 861
show ipv6 mld group
show ipv6 mld group
Example
This example displays MLD group details.
The output of this command includes the following parameters:
Command History
This command was available in AOS-W 3.3.
Command Information
Parameter Description
Group Name of MLD groups.
Members Number of members in an MLD group.
Platforms Licensing Command Mode
All platforms Base operating system Enable or Config mode on master and local
switches
(host) #show ipv6 mld group
MLD Group Table
---------------
Group Members
----- -------
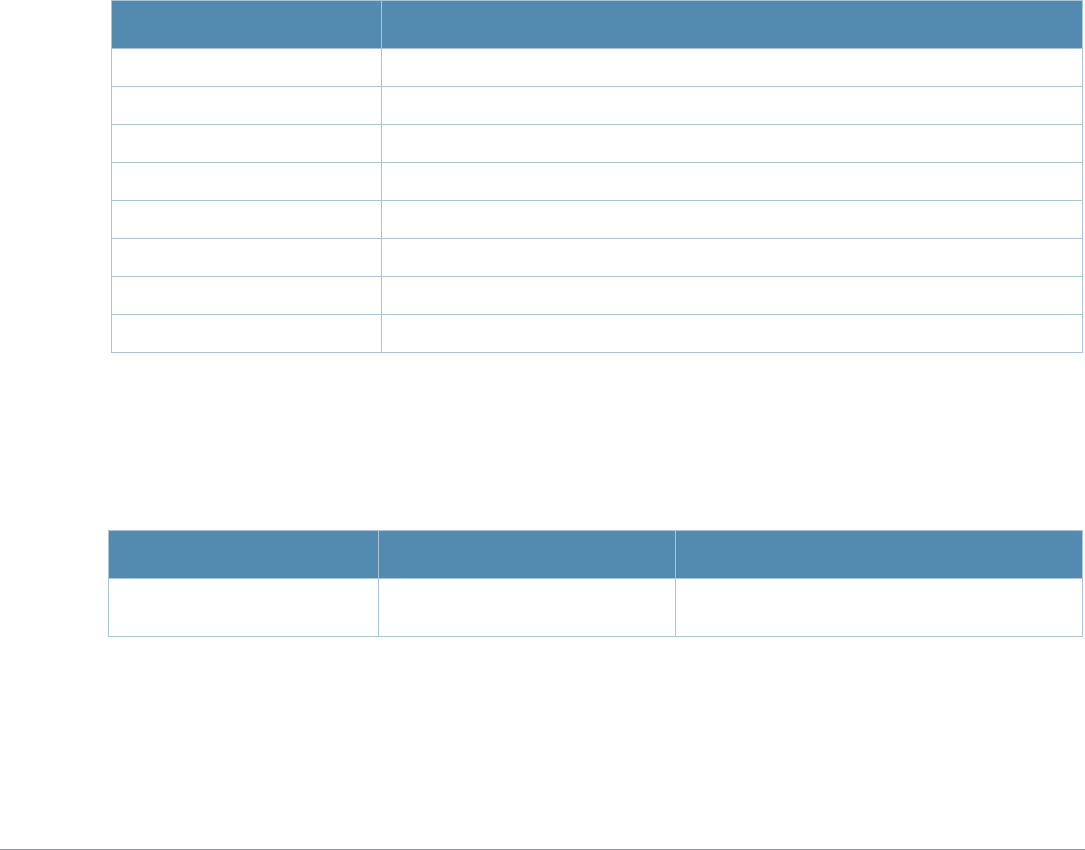
862 |show ipv6 mld interface AOS-W 3.4.1 Command Line Interface | Reference Guide
show ipv6 mld interface
show ipv6 mld interface
Example
This example displays MLD status on VLANs. To view details for a specific VLAN, you can specify the VLAN ID.
The output of this command includes the following parameters:
Command History
This command was available in AOS-W 3.3.
Command Information
Parameter Description
VLAN Denotes the VLAN ID.
Addr IP address of the VLAN interface.
Netmask Network mask of the VLAN interface IP address.
MAC Address MAC address of VLAN interface.
MLD Status of MLD.
Snooping Status of MLD snooping.
Querier IPv6 address of the MLD querier for the VLAN.
Destination Denotes the destination of the MLD messages.
Platforms Licensing Command Mode
All platforms Base operating system Enable or Config mode on master and local
switches
(host) #show ipv6 mld interface
MLD Interface Table
-------------------
VLAN Addr Netmask MAC Address MLD Snooping Querier Destination
---- ---- ------- ----------- --- -------- ------- -----------
224 10.224.224.1 255.255.255.0 00:0b:86:f0:20:20 disabled disabled :: CP
1 10.15.44.10 255.255.255.0 00:0b:86:f0:20:20 disabled disabled :: CP
50 156.1.50.1 255.255.255.0 00:0b:86:f0:20:20 disabled disabled :: CP
211 211.1.1.1 255.255.255.0 00:0b:86:f0:20:20 disabled disabled :: CP
51 156.1.51.1 255.255.255.0 00:0b:86:f0:20:20 disabled disabled :: CP
999 99.1.1.2 255.255.255.0 00:0b:86:f0:20:20 disabled disabled :: CP
7 7.7.7.1 255.255.255.0 00:0b:86:f0:20:20 disabled disabled :: CP
170 192.170.1.1 255.255.255.0 00:0b:86:f0:20:20 disabled disabled :: CP

AOS-W 3.4.1 Command Line Interface | Reference Guide show ipv6 user-table | 863
show ipv6 user-table
show ipv6 user-table [authentication-method {dot1x | mac | stateful-dot1x | vpn | web} |
bssid <bssid> |
debug {rows | unique} |
essid <essid-name> |
internal {rows} |
ip <IPv6-address> |
location <ap-group-name> |
mac <mac-address> |
mobile {bindings | rows | unique | visitors} |
name <user-name> |
phy-type {a | b} |
role <role-name> |
rows |
station |
verbose ]
Description
Displays IPv6 user table entries. You can filter the output based on various parameters are described in table.
Syntax
Parameter Description
authentication-method Displays entries in the IPv6 user-table that matches the following authentication
methods:
zdot1x
zmac
zstateful-mac
zvpn
zweb
bssid Displays entries in the IPv6 user-table that are associated to the specified BSSID.
debug Displays entries in the IPv6 user-table that are in debug mode.
essid Displays entries in the IPv6 user-table that are associated to the specified ESSID.
internal Displays internal IPv6 users.
ip Displays IPv6 users that match the specified IPv6 IP address.
location This value refers to the AP-group of the IPv6 client. Use the show aaa state ap-
group to get the AP group and the location ID mapping.
mac Displays users with the specified MAC address.
mobile Displays list of mobile users in the IPv6 user table. The following filters are available for
this parameter:
zbindings—list of users that have moved away from the current switch.
zrows—displays entries that match the specified row number.
zunique—displays unique entries in the IPv6 user-table.
zvisitors—displays users that have associated with the current switch.
name Displays IPv6 user table entries that match the specified name.
phy-type Displays IPv6 user table entries that match a or b phy-type.
role Displays IPv6 user table entries that match the specified role.

864 | show ipv6 user-table AOS-W 3.4.1 Command Line Interface | Reference Guide
Example
This example displays dot1x authenticate users in IPv6 user table.
The output of this command includes the following parameters:
Command History
This command was available in AOS-W 3.3.
Command Information
rows Displays specific rows in the IPv6 user table. Enter the starting row number and the
number of rows to be displayed.
station Displays the station table information for the IPv6 user table entries.
verbose Displays the complete IPv6 user table with all details.
Parameter Description
(host) show ipv6 user-table authentication-method dot1x
Users
-----
IP MAC Name Role Age(d:h:m) Auth VPN link AP name
Roaming Essid/Bssid/Phy Profile
---------- ------------ ------ ---- ---------- ---- -------- ------
- ------- --------------- -------
fe80::216:ceff:fe2c:b485 00:16:ce:2c:b4:85 Wing-A logon 00:00:06 802.1x
00:0b:86:c1:0e:8c Wireless Wing-A/00:0b:86:90:e8:c0/g default-dot1x
2003:d81f:f9f0:1001:617c:9151:6d25:f754 00:16:ce:2c:b4:85 Wing-A logon 00:00:06 802.1x
00:0b:86:c1:0e:8c Wireless Wing-A/00:0b:86:90:e8:c0/g default-dot1x
Parameter Description
IP IP address of the client in that row that authenticating using dot1x
MAC MAC address of the client.
Name Name of the client.
Role The role assigned to the client.
Age (d:h:m) Total time that client is connected to switch.
Auth Authentication type.
AP name Name of the AP associated with the client.
Roaming Current roaming status of the client.
Essid/Bssid/Phy ESSID/BSSID/Phy to which the client is associated.
Profile Displays the aaa profile.
Platforms Licensing Command Mode
All platforms Base operating system Enable or Config mode on master and local
switches

AOS-W 3.4.1 Command Line Interface | Reference Guide show keys | 865
show keys
show keys {all]
Description
Show whether optional keys and features are enabled or disabled on the switch.
Syntax
Example
The following example shows the status of all optional keys and features on the switch.
Parameter Description
all Include this optional parameter to display the status of all optional keys and features. If this
parameter is omitted, the output will display the status of the most commonly used features and
keys.
(host) #show keys all
Licensed Features
-----------------
Feature Status
------- ------
Access Points 48
Remote Access Points 48
External Servers 0
xSec Users 0
CIM Users 0
Ortronics Access Points 48
Contexts 0
Outdoor Mesh Access Points 48
3rd-party Remote APs 0
Wireless Intrusion Protection Module Unlimited
Policy Enforcement Firewall Module Unlimited
Voice Service Module Unlimited
VPN Server Module Unlimited
xSec Module Unlimited
Indoor Mesh Access Points 48
120abg Upgrade 0
121abg Upgrade 0
124abg Upgrade 0
125abg Upgrade 0
WLAN Switch ENABLED
Wireless Intrusion Protection ENABLED
RF Director ENABLED
Policy Enforcement Firewall ENABLED
Remote APs ENABLED
External Services Interface ENABLED
Client Integrity Module ENABLED
Auto Radio Resource Alloc ENABLED
Adaptive Radio Management ENABLED
VPN Server ENABLED
Wired 802.1X ENABLED
Secure Access ENABLED
Wired Grid Points ENABLED
xSec Module ENABLED
MMC AP ENABLED
Netgear AP DISABLED
Voice Services Module ENABLED
Remote AP VPN Termination DISABLED
Ortronics AP ENABLED
Mesh Point APs ENABLED
Location API DISABLED
Mesh Visualization DISABLED
AP Developers Module ENABLED
Power Over Ethernet ENABLED
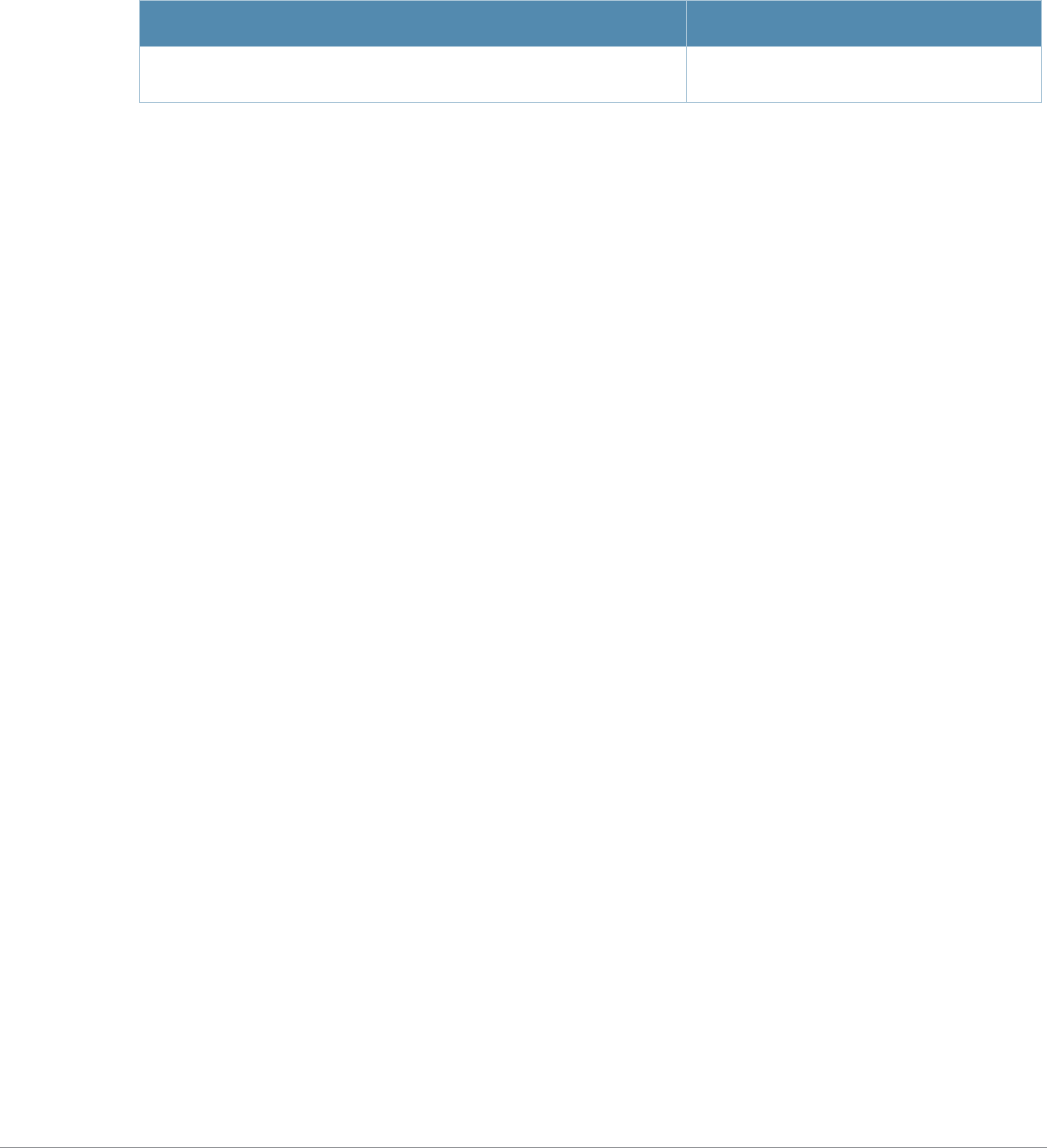
866 |show keys AOS-W 3.4.1 Command Line Interface | Reference Guide
Related Commands
To view the license usage database (including the license key strings) use the command show license.
Command History
This command was available in AOS-W 1.0.
Command Information
Platforms Licensing Command Mode
All platforms Base operating system Enable and Config mode on local and
master switches

AOS-W 3.4.1 Command Line Interface | Reference Guide show lacp | 867
show lacp
show lacp <group_number> {counters | internal | neighbor}
Description
View the LACP configuration status.
Syntax
Example
The port uses the group number +1 as its “actor admin key”. By default, all the ports use the long timeout
value (90 seconds).
When a port, in a LAG, is misconnected (that is, the partner device is different than the other ports or the
neighborship timesouts or can not exchange LACPDUs with the partner), the port status is displayed as
“DOWN” (see the following example).
The “counters” option allows you to view LACP received (Rx) traffic, transmitting (Tx) traffic, data units
(DU) received and transmitted by port.
Parameter Description
<group_number> Enter the Link aggregation group number.
Range: 0-7
counters Enter the keyword counters to view the LACP traffic.
internal Enter the keyword internal to view the LACP internal information.
neighbor Enter the keyword neighbor to view the LACP neighbor information.
(Host)#show lacp 0 neighbor
Flags: S - Device is requesting Slow LACPDUs
F - Device is requesting fast LACPDUs
A - Device is in active mode P - Device is in passive mode
Partner's information
---------------------
Port Flags Pri OperKey State Num Dev Id
---- ----- ---- ------- ----- ---- ----------------
FE 1/1 SA 1 0x10 0x45 0x5 00:0b:86:51:1e:70
FE 1/2 SA 1 0x10 0x45 0x6 00:0b:86:51:1e:70
(Host)#show lacp 0 internal
Flags: S - Device is requesting Slow LACPDUs
F - Device is requesting fast LACPDUs
A - Device is in active mode P - Device is in passive mode
Port Flags Pri AdminKey OperKey State Num Status
---- ----- ---- -------- -------- ----- ---- -------
FE 1/1 SA 1 0x1 0x1 0x45 0x2 DOWN
FE 1/2 SA 1 0x1 0x1 0x45 0x3 UP
(Host)#show lacp 0 counters
Port LACPDUTx LACPDURx MarkrTx MarkrRx MrkrRspTx MrkrRspRx
---- -------- -------- ------- -------- --------- ---------
FE 1/1 10 10 0 0 0 0
FE 1/2 12 12 0 0 0 0
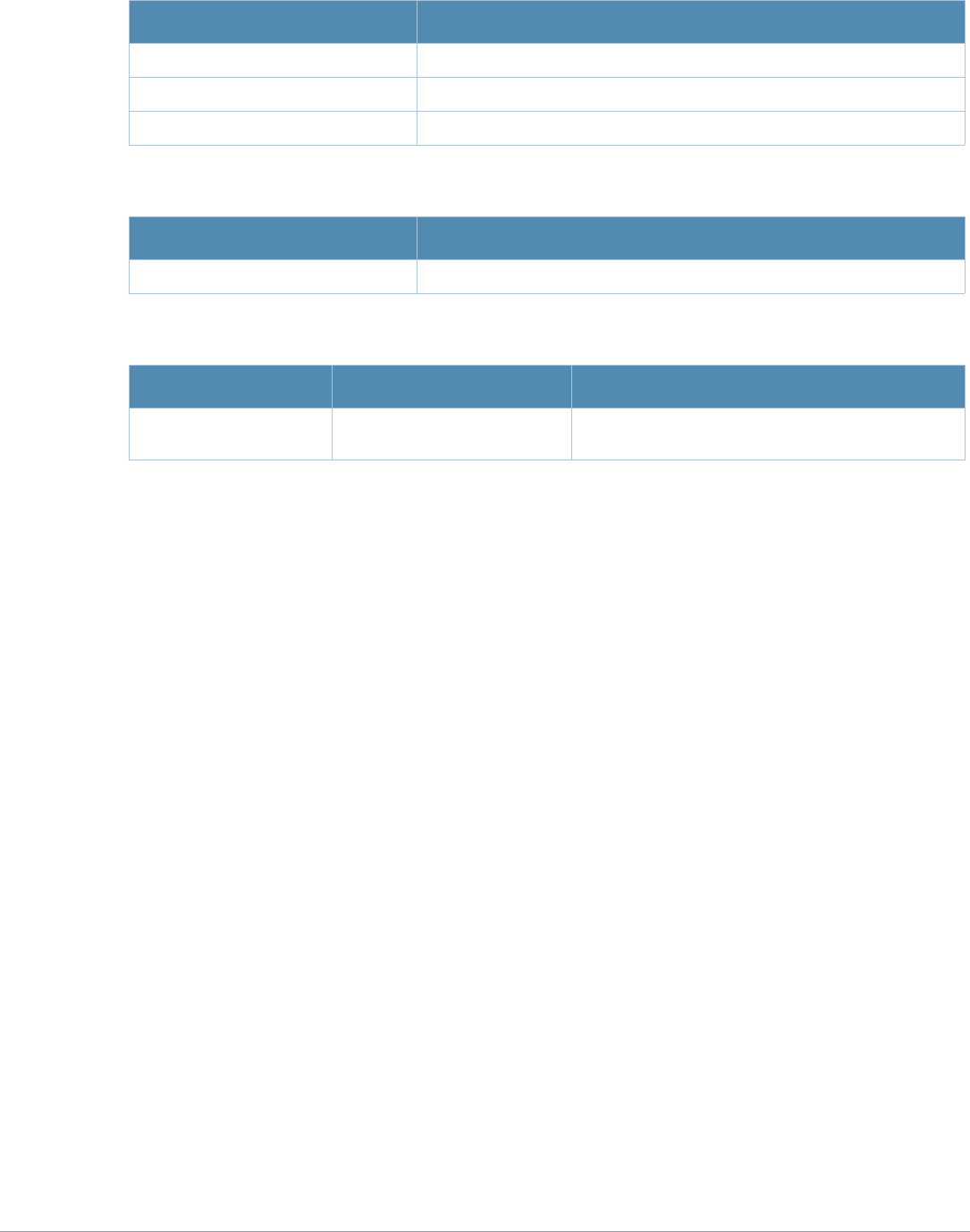
868 |show lacp AOS-W 3.4.1 Command Line Interface | Reference Guide
Related Command
Command History
Command Information
Command Description
lacp group Enable LACP and configure on the interface
show interface port-channel View information on a specified port-channel interface
show lacp sys-id View the LACP system ID information
Release Modification
AOS-W 3.4.1 Command introduced
Platform Licensing Command Mode
All Platforms Base operating system Enable and Configuration modes for Master and
Local switches

AOS-W 3.4.1 Command Line Interface | Reference Guide show lacp sys-id | 869
show lacp sys-id
show lacp sys-id
Description
View the LACP system MAC address and port priority.
Example
This command returns the port priority and the MAC address (comma separated). In the example below,
the port priority is the default value 32768 followed by the MAC address 00:0B:86:40:37:C0
Related Command
Command History
Command Information
Command Description
lacp group Enable LACP and configure on the interface
lacp port-priority Configure the LACP port priority
show lacp View the LACP configuration status
show interface port-channel View information on a specified port channel interface
Release Modification
AOS-W 3.4.1 Command introduced
(Host)#show lacp sys-id
32768,00:0B:86:40:37:C0
Platform Licensing Command Mode
All Platforms Base operating system Enable and Configuration modes (config) for
Master and Local switch

870 | show lacp sys-id AOS-W 3.4.1 Command Line Interface | Reference Guide
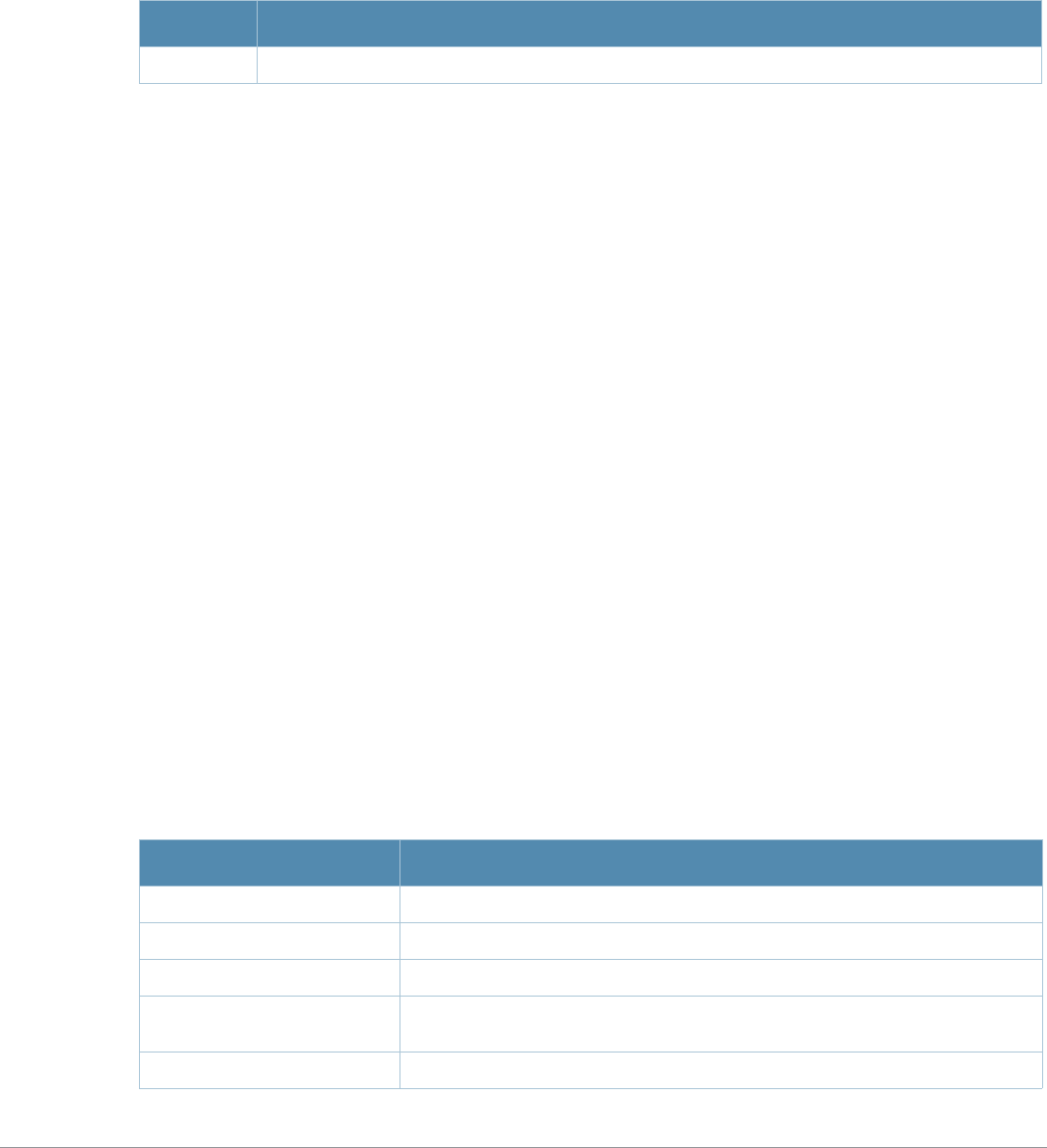
AOS-W 3.4.1 Command Line Interface | Reference Guide show license | 871
show license
show license [limits]
Description
Show the license database.
Syntax
Example
The following example shows the license database. Note that the verbose parameter has been omitted, so
the output shows only part of each license key.
The output of this command includes the following data columns:
Parameter Description
limits Include this optional parameter to show the limits for currently installed licenses.
(host) #(smettu) #show license
License Table
-------------
Key Installed Expires Flags Service Type
--- --------- ------- ----- ------------
JJZEDAkm-YoZvGL3m-Z/c67mMV-3tYi9... 2008-10-30 Never 125abg Upgrade: 512
11:07:59
n6uk2sVB-6NfQiwQy-8rH+OG9C-CvHKl... 2008-10-30 Never E MMC AP
11:09:47
NJ1tKkgC-oC0vI1eK-c6ChDkEf-gM8ZG... 2008-10-30 Never E Client Integrity Module
11:10:08
OgsSu4gS-iekszbY8-7vaBO7KV-ZmITZ... 2008-10-30 Never E Policy Enforcement Firewall
11:10:17
rZ0mXhHS-IhUrdzel-MbrAhX2X-A6Que... 2008-10-30 Never E Access Points: 512
11:10:26
sSnw4Q5z-k0wfxsUf-1hjVVZH0-OHJdQ... 2008-10-30 Never E VPN Server
11:10:35
VaJPCZcT-OIkc10rA-RUbhPhbV-C7u0q... 2008-10-30 Never E External Services Interface
11:10:46
/VLs3jgM-05bYeD41-W/NECd/u-X+HLQ... 2008-10-30 Never 124abg Upgrade: 512
11:10:56
vnJoGAWU-FLt1+YQh-eYwRENxP-F8icI... 2008-10-30 Never E AP Developers Module
11:11:05
VuXpnSEa-TFtkxq2q-+mWq5A32-Di74y... 2008-10-30 Never E External Services Interface
11:11:17
xw0Y2oR6-cqTr9nQn-72eIHxyr-pSVtz... 2008-10-30 Never E Wireless Intrusion Protection
11:11:30
...
Parameter Description
Key License key string.
Installed Date and time that the license key was installed on the switch.
Expires Expiration date for the key, if applicable.
Flags This column displays additional information for the license key. The key
describing each flag letter key appears at the bottom of the license table.
Service Type Name of the feature or option enabled by the license key.
872 |show license AOS-W 3.4.1 Command Line Interface | Reference Guide
Related Commands
To view additional statistics for license key usage, use the command show keys.
Command History
Command Information
Release Modification
AOS-W1.0 Command introduced.
AOS-W 3.4 Verbose parameter was deprecated. This command now displays the entire
license key by default.
Platforms Licensing Command Mode
All platforms Base operating system Config mode on local and master switches
AOS-W 3.4.1 Command Line Interface | Reference Guide show license-usage | 873
show license-usage
show license-usage ap|user|vpn|xsec
Description
Display license usage information.
Syntax
Example
This example below the total available AP licenses and the number of licenses currently in use.
The output of this command includes the following information:
Parameter Description
ap Show AP license usage information.
user Show Policy Enforcement Firewall (PEF) user license usage.
vpn Show VPN server module license usage.
xsec Show Extreme Security (xSec) user and tunnel license usage.
Parameter Description
Total AP Licenses Total number of AP licenses currently available on the switch.
AP licenses used Number of AP licenses used by individual APs.
Unused AP Licenses Number of AP licenses unused and currently available.
Total RAP Licenses Total number of Remote AP (RAP) licenses currently available on the switch.
RAP licenses used Number of RAP licenses currently used by Remote APs.
Total Indoor Mesh AP
Licenses
Total number of Indoor Mesh AP (IMP) licenses currently available on the switch. The
output of this command shows information for indoor mesh licenses, even though
these licenses are not required in this version of AOS-W.
(host) #(ethersphere-lms3) #show license-usage ap
Total AP Licenses : 128
AP Licenses Used : 47
Unused AP Licenses : 81
Total RAP Licenses : 0
RAP Licenses Used : 0
Total Ortronics AP Licenses : 0
Total Indoor Mesh AP Licenses : 8
Indoor Mesh AP Licenses Used : 0
Total Outdoor Mesh AP Licenses : 8
Outdoor Mesh AP Licenses Used : 0
Total 802.11n-120abg Licenses : 0
802.11n-120abg Licenses Used : 0
Total 802.11n-121abg Licenses : 0
Total 802.11n-124abg Licenses : 0
802.11n-124abg Licenses Used : 0
Total 802.11n-125abg Licenses : 0
802.11n-125abg Licenses Used : 0

874 | show license-usage AOS-W 3.4.1 Command Line Interface | Reference Guide
Command History
Command Information
Indoor Mesh AP
Licenses Used
Number of IMP licenses currently used by Indoor Mesh APs. The output of this
command shows information for indoor mesh licenses, even though these licenses
are not required in this version of AOS-W.
Total Outdoor Mesh
AP Licenses
Total number of Outdoor Mesh AP (MAP) licenses currently available on the switch.
Outdoor Mesh AP
Licenses Used
Number of MAP licenses currently used by Outdoor Mesh APs.
Total 802.11n-120abg
Licenses
Total number of high-throughput (802.11n-capable) licenses available for 120abg APs.
802.11n-120abg
Licenses Used
Number of high-throughput (802.11n-capable) licenses currently used by 120abg APs
Total 802.11n-121abg
Licenses
Total number of high-throughput (802.11n-capable) licenses available for 121abg APs.
802.11n-121abg
Licenses Used
Number of high-throughput (802.11n-capable) licenses currently used by 121abg APs
Total 802.11n-124abg
Licenses
Total number of high-throughput (802.11n-capable) licenses available for 124abg APs.
802.11n-124abg
Licenses Used
Number of high-throughput (802.11n-capable) licenses currently used by 124abg APs
Total 802.11n-125abg
Licenses
Total number of high-throughput (802.11n-capable) licenses available for 125abg APs.
802.11n-125abg
Licenses Used
Number of high-throughput (802.11n-capable) licenses currently used by 125abg APs
Release Modification
AOS-W 3.0 Command Introduced.
AOS-W 3.3 The following parameters were introduced in the output of show license-usage ap.
zTotal 802.11n-120abg Licenses
z802.11n-120abg Licenses Used
zTotal 802.11n-121abg Licenses
z802.11n-121abg Licenses Used
zTotal 802.11n-124abg Licenses
z802.11n-124abg Licenses Used
zTotal 802.11n-125abg Licenses
z802.11n-125abg Licenses Used
Platforms Licensing Command Mode
All platforms Base operating system. The output of this command varies,
according to the licenses currently installed on the switch. Enable or Config mode on
master switches
Parameter Description

AOS-W 3.4.1 Command Line Interface | Reference Guide show localip | 875
show localip
show localip
Description
Displays the IP address and VPN shared key between master and local.
Syntax
No parameters.
Example
The output of this command shows the switch’s IP address and shared key between master and local
switches.
Command History
This command was available in AOS-W 3.0
Command Information
(host) # show localip
Local Switches configured by Local Switch IP
---------------------------------------------
Switch IP address of the Local Key
------------------------------ ---
0.0.0.0 ********
Platforms Licensing Command Mode
All platforms Base operating system Config or Enable mode on master or local
switches

876 | show localip AOS-W 3.4.1 Command Line Interface | Reference Guide
AOS-W 3.4.1 Command Line Interface | Reference Guide show local-userdb | 877
show local-userdb
show local-userdb {[maximum-expiration][start <offset> page <page_size]}
Description
Shows information about user’s accounts in the local user database.
Syntax
Usage Guidelines
Issue this command without any parameters to display a general overview of user’s accounts in the database.
Use the maximum-expiration parameter to show how long the account is valid for in minutes. Use the start
<offset> page <page_size> parameters to control which user account records in the database display initially
and the number of account records displayed on a page.
Example
This example shows the basic summary of a user accounts in the database.
The output of this command includes the following parameters:
Parameter Description
maximum-expiration How long the account is valid, in minutes, in the internal database.
<offset> The user account record’s location (by number) as it is listed in the database.
<page_size> The number of user account records that display on one page.
Parameter Description
Name Name of the user.
Password The user’s password.
Role Role for the user. This role takes effect when the internal database is specified in a server
group profile with a server derivation rule. If there is no server derivation rule configured,
then the user is assigned the default role for the authentication method.
E-mail Shows the email address of the user account.
Enabled Shows whether the account is enabled or disabled.
Expiry Shows the expiration date for the user account. If this is not set, the account does not
expire.
(host) #show local-userdb maximum-expiration start 5 page 4
local-userdb maximum-expiration 90
User Summary
------------
Name Password Role E-Mail Enabled Expiry Status Sponsor-Name Grantor-Name
---- -------- ---- ------ ------- ------ ------ ------------ ------------
guest-0657984 ******** guest Yes Active admin
guest-8330301 ******** guest Yes Active admin
guest-5433352 ******** guest Yes Active admin
guest-3469360 ******** guest Yes Active admin
User Entries: 11
878 | show local-userdb AOS-W 3.4.1 Command Line Interface | Reference Guide
Related Commands
Command History
Command Information
Status Shows whether the profile has enabled or disabled the ability to use the HTTP protocol to
redirect users to the captive portal page.
Sponsor-Name Shows the sponsor’s name.
Grantor-Name Shows the grantor’s name.
User Entries Shows the number of user accounts in the database.
Command Description Mode
local-userdb add Use this command to configure the parameters
displayed in the output of this show command. Enable and Config modes
local-userdb-guest
add
Use this command to configure parameters for a
guest user account. Enable and Config modes
Release Modification
AOS-W 3.0 Command introduced
AOS-W 3.4 The Expiry, Status, Sponsor-name and Grantor-name were introduced.
Platforms Licensing Command Mode
All platforms Base operating system Enable or config mode on master and local
switches
Parameter Description
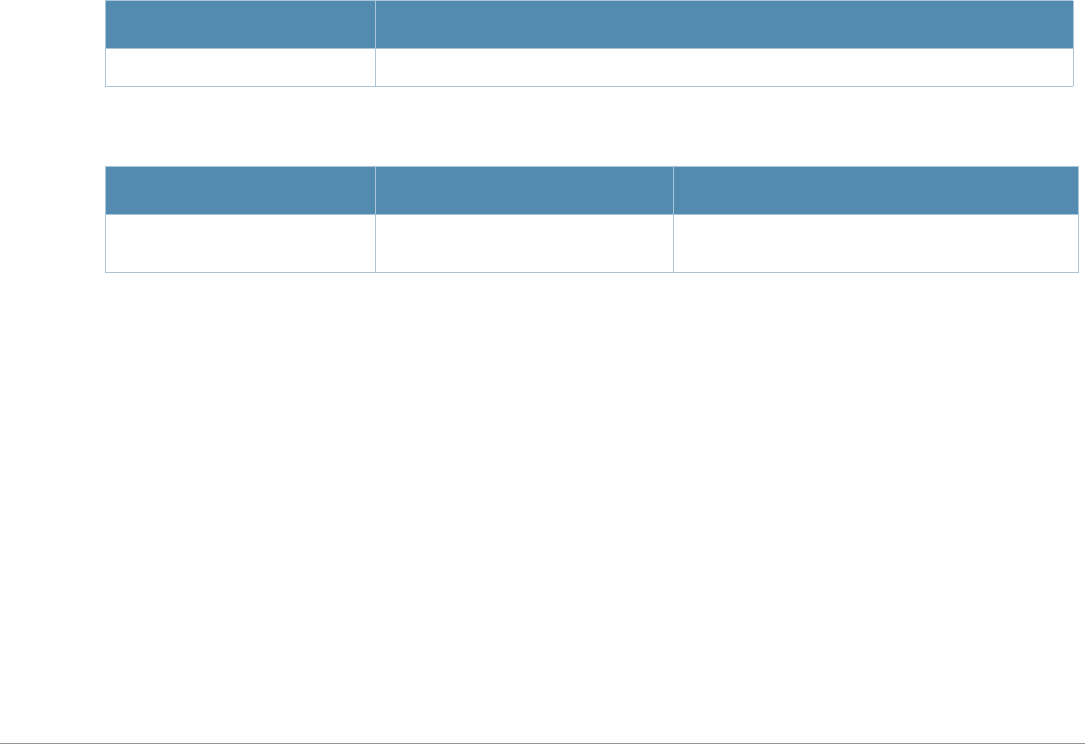
AOS-W 3.4.1 Command Line Interface | Reference Guide show local-userdb username | 879
show local-userdb username
show local-userdb username <name>
Description
Shows information about specific user account in the internal switch database.
Usage Guidelines
Issue this command to display an overview of a particular user account in the database.
Example
This example shows the basic summary of a user account Paula in the database.
Command History
Command Information
Release Modification
AOS-W 3.0 Command introduced
Platforms Licensing Command Mode
All platforms Base operating system Enable or config mode on master and local
switches
(host) #show local-userdb username Paula
User Summary
------------
Name Password Role E-Mail Enabled Expiry Status Sponsor-Name Grantor-Name
---- -------- ---- ------ ------- ------ ------ ------------ ------------
paula ******** guest Yes Inactive admin
User Entries: 1

880 | show local-userdb username AOS-W 3.4.1 Command Line Interface | Reference Guide

AOS-W 3.4.1 Command Line Interface | Reference Guide show log all | 881
show log all
show log all [<number>]
Description
Show the switch’s full log.
Syntax
Example
This example shows the most ten recent log entries for the switch.
Command History
This command was introduced in AOS-W 3.4.
Command Information
Parameter Description
<number> Start displaying the log output from the specified number of lines from the end of
the log.
(host) #show log all 10
Mar 3 13:26:20 localdb[567]: <133006> <ERRS> |localdb| User admin Failed Authentication
Mar 3 13:26:20 localdb[567]: <133006> <ERRS> |localdb| User admin Failed Authentication
Mar 3 13:26:20 localdb[567]: <133019> <ERRS> |localdb| User admin was not found in the database
Mar 3 13:26:20 localdb[567]: <133019> <ERRS> |localdb| User admin was not found in the database
Mar 3 13:46:54 fpcli: USER: admin connected from 10.100.100.66 has logged out.
Mar 3 13:57:53 fpcli: USER: admin has logged in from 10.100.100.66.
Mar 3 13:57:53 localdb[567]: <133006> <ERRS> |localdb| User admin Failed Authentication
Mar 3 13:57:53 localdb[567]: <133006> <ERRS> |localdb| User admin Failed Authentication
Mar 3 13:57:53 localdb[567]: <133019> <ERRS> |localdb| User admin was not found in the database
Mar 3 13:57:53 localdb[567]: <133019> <ERRS> |localdb| User admin was not found in the database
Platforms Licensing Command Mode
All platforms Base operating system Available in Enable and Config modes.
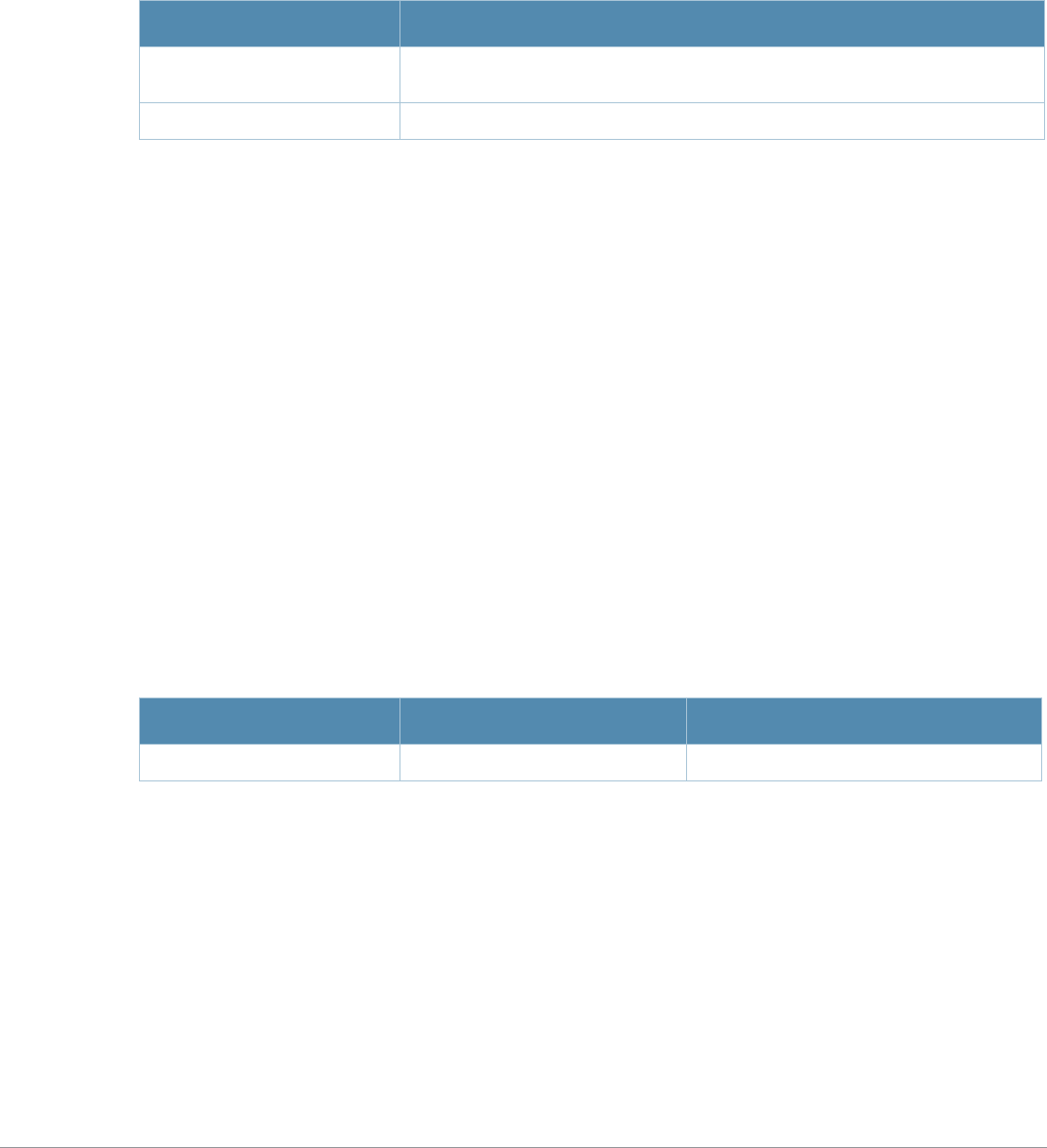
882 | show log ap-debug AOS-W 3.4.1 Command Line Interface | Reference Guide
show log ap-debug
show log ap-debug{[<number>][all]}
Description
Show the switch’s AP debug logs.
Syntax
Example
This example shows the ten most recent AP debug logs for the switch.
Command History
This command was available in AOS-W 3.0.
Command Information
Parameter Description
<number> Start displaying the log output from the specified number of lines from the end of
the log.
all Shows all the AP debug logs for the switch.
(host) #show log ap-debug 10
Feb 17 16:47:11 KERNEL(1.1.1@10.3.49.253): vap_device_event: dev aruba001 (0:1) is down
Feb 17 16:47:11 KERNEL(1.1.1@10.3.49.253): vap_device_event: dev aruba001 (0:1) has been unregistere
d
Feb 17 16:47:11 KERNEL(1.1.1@10.3.49.253): vap_device_event: dev aruba001 (0:1) has been registered
Feb 17 16:47:12 KERNEL(1.1.1@10.3.49.253): vap_device_event: dev aruba001 (0:1) is up
Feb 17 17:05:47 KERNEL(1.1.1@10.3.49.253): vap_device_event: dev aruba001 (0:1) is down
Feb 17 17:05:47 KERNEL(1.1.1@10.3.49.253): vap_device_event: dev aruba001 (0:1) has been unregistere
d
Feb 17 17:29:37 KERNEL(1.1.1@10.3.49.253): vap_device_event: dev aruba001 (0:1) has been registered
Feb 17 17:29:37 KERNEL(1.1.1@10.3.49.253): vap_device_event: dev aruba001 (0:1) is up
Feb 27 17:02:24 KERNEL(1.1.1@10.3.49.253): vap_device_event: dev aruba002 (0:2) is down
Feb 27 17:02:24 KERNEL(1.1.1@10.3.49.253): vap_device_event: dev aruba002 (0:2) has been unregistere
Platforms Licensing Command Mode
All platforms Base operating system Available in Enable and Config modes.
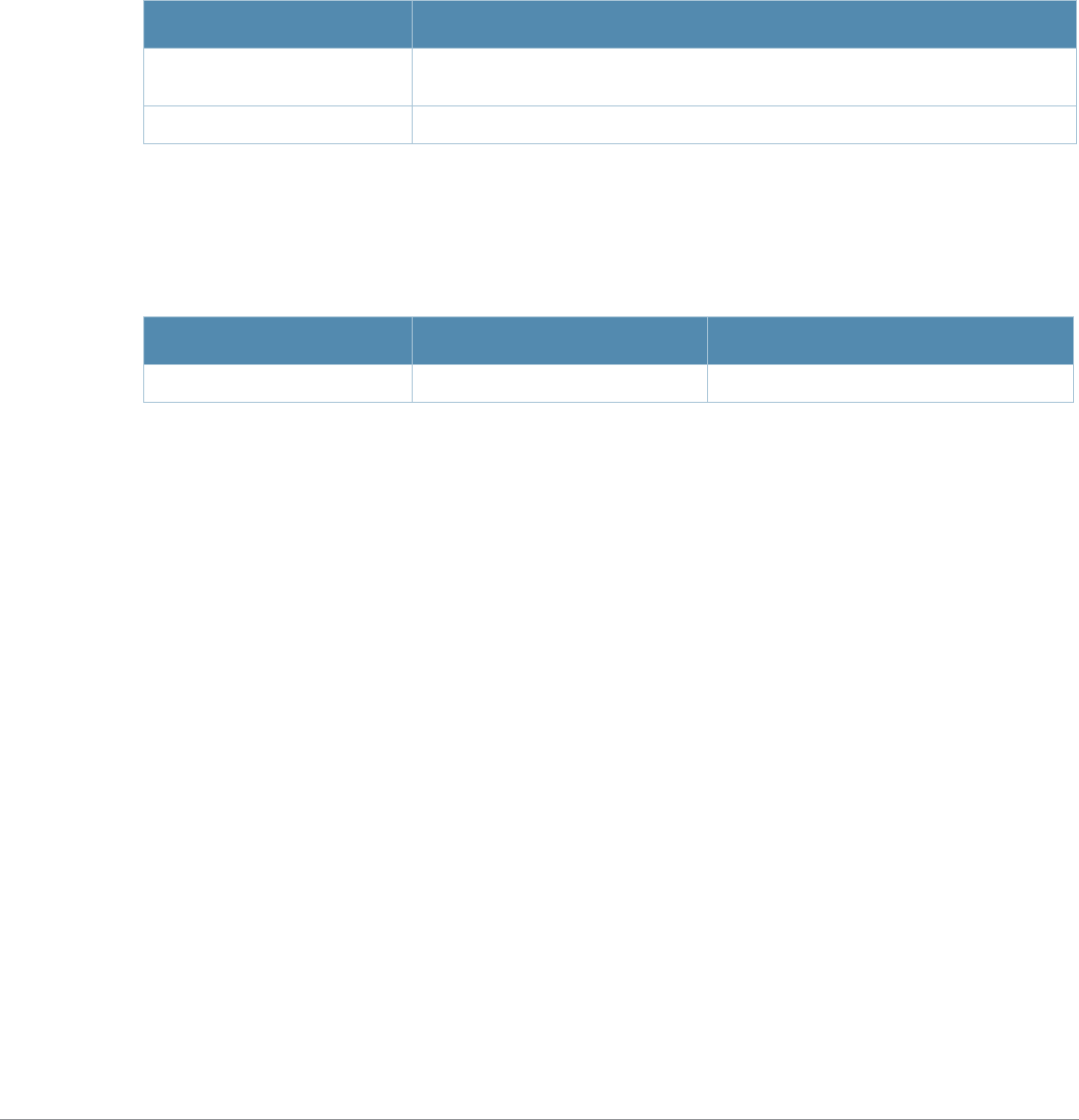
AOS-W 3.4.1 Command Line Interface | Reference Guide show log bssid-debug | 883
show log bssid-debug
show log bssid-debug{[<number>][all]}
Description
Show the switch’s Bssid debug logs.
A Basic Service Set Identifier (BSSID) uniquely defines each wireless client and Wireless Broadband
Router.
Syntax
Command History
This command was available in AOS-W 3.0.
Command Information
Parameter Description
<number> Start displaying the log output from the specified number of lines from the end of
the log.
all Shows all the Bssid debug logs for the switch.
Platforms Licensing Command Mode
All platforms Base operating system Available in Enable and Config modes
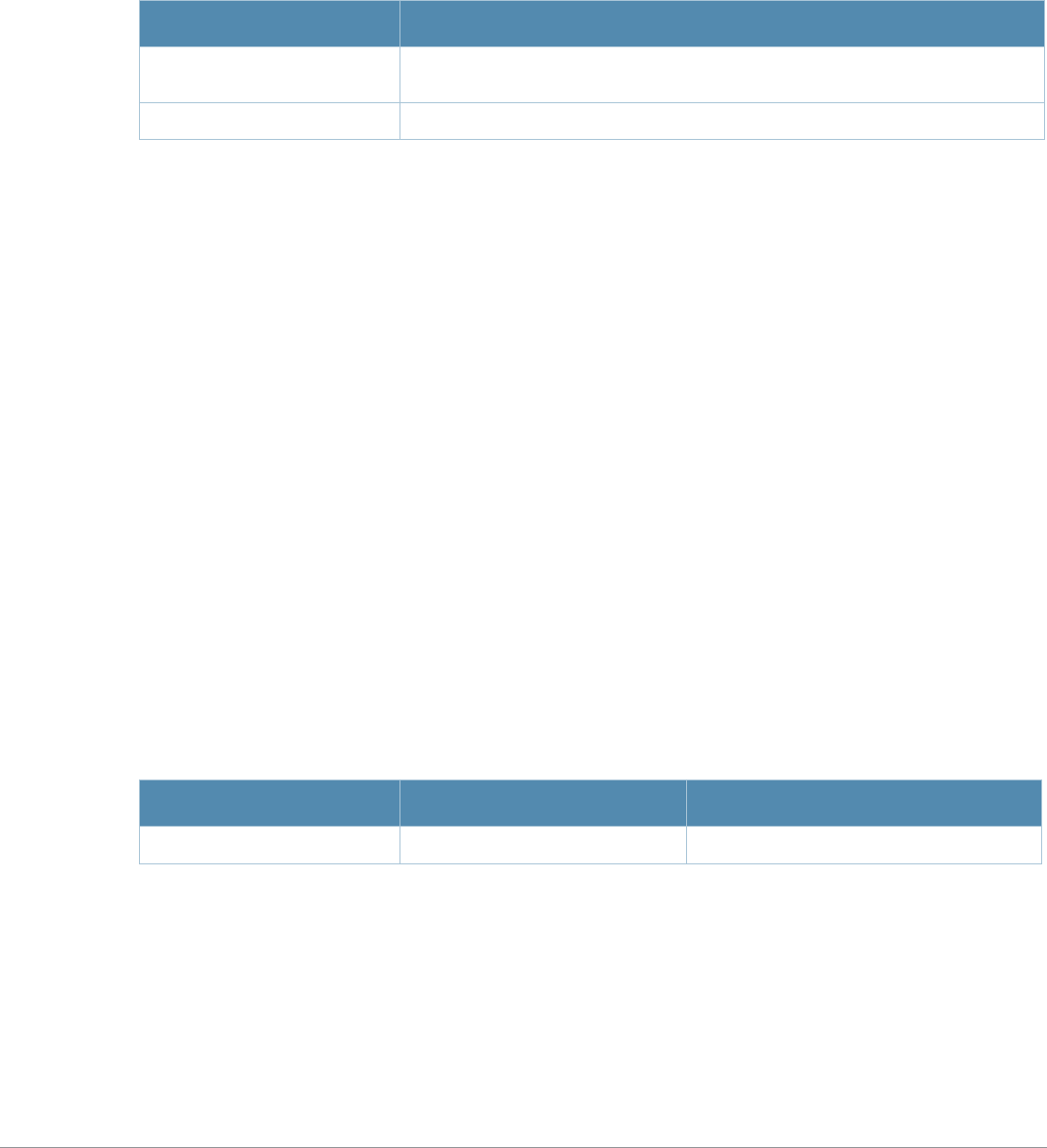
884 | show log errorlog AOS-W 3.4.1 Command Line Interface | Reference Guide
show log errorlog
show log errorlog{[<number>][all]}
Description
Show the switch’s system errors and other critical information.
Syntax
Example
This example shows the ten most recent system log errors.
Command History
This command was available in AOS-W 3.0.
Command Information
Parameter Description
<number> Start displaying the log output from the specified number of lines from the end of
the log.
all Shows all the error logs for the switch.
(host) #show log errorlog 10
Mar 5 10:30:34 <sapd 106007> <ERRS> |AP 1.1.1@10.3.49.253 sapd| AM 00:0b:86:a2:e7:40: Rogue AP detected
dnh-blah, BSSID 00:0b:86:b5:86:c0, Wired MAC 00:0b:86:02:ee:00, and IP 10.3.49.254
Mar 5 10:31:39 <sapd 404080> <ERRS> |AP 1.1.1@10.3.49.253 sapd| AM 00:0b:86:a2:e7:40: ADHOC network det
00:13:ce:45:91:a0, BSSID 02:13:ce:2d:37:50, ESSID adhoc_ap70 Channel 11 and RSSI 22
Mar 5 10:32:12 <sapd 106007> <ERRS> |AP 1.1.1@10.3.49.253 sapd| AM 00:0b:86:a2:e7:40: Rogue AP detected
dnh-blah, BSSID 00:0b:86:b5:86:c0, Wired MAC 00:0b:86:02:ee:00, and IP 10.3.49.254
Mar 5 10:32:46 <sapd 106007> <ERRS> |AP 1.1.1@10.3.49.253 sapd| AM 00:0b:86:a2:e7:40: Rogue AP detected
dnh-blah, BSSID 00:0b:86:b5:86:c0, Wired MAC 00:0b:86:02:ee:00, and IP 10.3.49.254
Mar 5 10:40:32 <localdb 133019> <ERRS> |localdb| User admin was not found in the database
Mar 5 10:40:32 <localdb 133006> <ERRS> |localdb| User admin Failed Authentication
Mar 5 10:41:10 <sapd 106007> <ERRS> |AP 1.1.1@10.3.49.253 sapd| AM 00:0b:86:a2:e7:40: Rogue AP detected
rlo-open, BSSID 00:0b:86:c9:9e:20, Wired MAC 00:00:00:00:00:00, and IP 0.0.0.0
Mar 5 10:41:31 <sapd 106007> <ERRS> |AP 1.1.1@10.3.49.253 sapd| AM 00:0b:86:a2:e7:40: Rogue AP detected
QA_MARORA_VOCERA, BSSID 00:0b:86:c9:9e:21, Wired MAC 00:0b:86:02:ee:00, and IP 10.3.49.254
Mar 5 10:48:01 <sapd 404080> <ERRS> |AP 1.1.1@10.3.49.253 sapd| AM 00:0b:86:a2:e7:40: ADHOC network det
00:13:ce:45:d9:4d, BSSID 02:13:ce:28:40:48, ESSID adhoc_ap70 Channel 11 and RSSI 8
Mar 5 11:04:21 <sapd 404080> <ERRS> |AP 1.1.1@10.3.49.253 sapd| AM 00:0b:86:a2:e7:40: ADHOC network det
00:13:ce:45:d9:4d, BSSID 02:13:ce:2d:37:50, ESSID adhoc_ap70 Channel 11 and RSSI 9
Platforms Licensing Command Mode
All platforms Base operating system Available in Enable and Config modes.
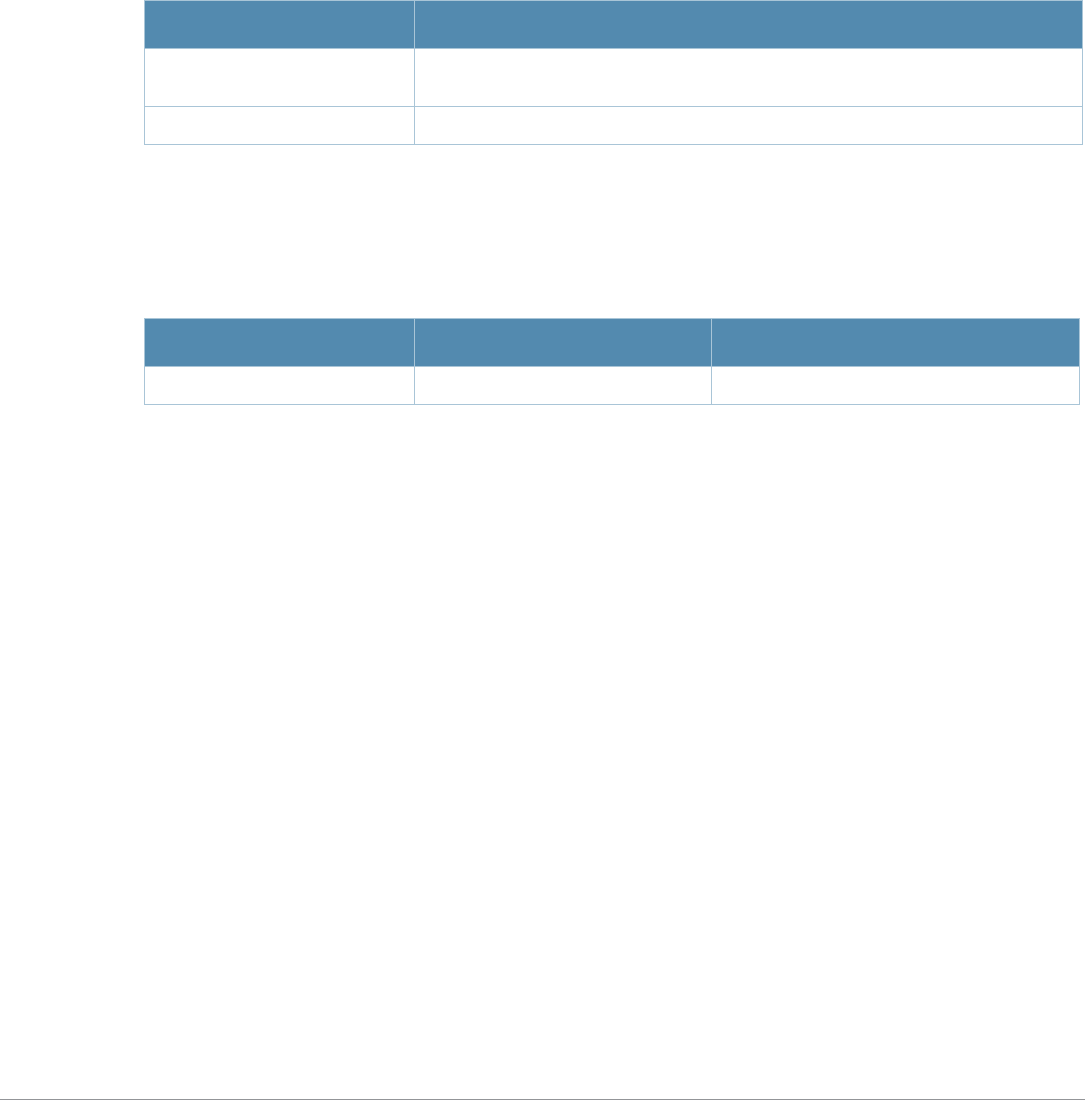
AOS-W 3.4.1 Command Line Interface | Reference Guide show log essid-debug | 885
show log essid-debug
show log essid-debug{[<number>][all]}
Description
Show the switch’s Essid debug logs.
An Extended Service Set Identifier (ESSID) is used to identify the wireless clients and Wireless Broadband
Routers in a WLAN. All wireless clients and Wireless Broadband Routers in the WLAN must use the same
ESSID.
Syntax
Command History
This command was available in AOS-W 3.0.
Command Information
Parameter Description
<number> Start displaying the log output from the specified number of lines from the end of
the log.
all Shows all the Essid debug logs for the switch.
Platforms Licensing Command Mode
All platforms Base operating system Available in Enable and Config modes.
886 | show log network AOS-W 3.4.1 Command Line Interface | Reference Guide
show log network
show log network{[<number>][all]}
Description
Show the switch’s system network errors.
Syntax
Example
This example shows the switch’s recent network log errors.
Command History
This command was available in AOS-W 3.0.
Command Information
Parameter Description
<number> Start displaying the log output from the specified number of lines from the end of
the log.
all Shows all the network logs for the switch.
(host) #show log network all
Feb 17 14:47:14 :209801: <WARN> |fpapps| Physical link down: port 1/1
Feb 17 14:48:04 :209801: <WARN> |fpapps| Physical link down: port 1/1
Platforms Licensing Command Mode
All platforms Base operating system Available in Enable and Config modes.
AOS-W 3.4.1 Command Line Interface | Reference Guide show log security | 887
show log security
show log security{[<number>][all]}
Description
Show the switch’s security logs.
Syntax
Example
This example shows the switch’s last seven security logs.
Command History
This command was available in AOS-W 3.0.
Command Information
Parameter Description
<number> Start displaying the log output from the specified number of lines from the end of
the log.
all Shows all the security logs for the switch.
(host) #show log security 7
Mar 5 11:53:43 :124004: <DBUG> |authmgr| Local DB auth failed for user admin, error (User not found in
Mar 5 11:53:43 :124003: <INFO> |authmgr| Authentication result=Authentication failed(1), method=Managem
server=Internal, user=10.100.100.66
Mar 5 11:53:43 :124004: <DBUG> |authmgr| Auth server 'Internal' response=1
Mar 5 11:53:43 :125027: <DBUG> |aaa| mgmt-auth: admin, failure, , 0
Mar 5 11:53:43 :125024: <NOTI> |aaa| Authentication Succeeded for User admin, Logged in from 10.100.100
Connecting to 10.3.49.100 port 22 connection type SSH
Mar 5 11:53:58 :103060: <DBUG> |ike| ipc.c:ipc_get_cfgm_role:2826 Sending REQUEST for CFGM Role
Mar 5 11:53:58 :103060: <DBUG> |ike| ipc.c:get_local_cfg_trigger_ike:2653 IKE got trigger from CFGM : s
Platforms Licensing Command Mode
All platforms Base operating system Available in Enable and Config modes.
888 | show log system AOS-W 3.4.1 Command Line Interface | Reference Guide
show log system
show log system{[<number>][all]}
Description
Show the switch’s system logs.
Syntax
Example
This example shows the switch’s last ten system logs.
Command History
This command was available in AOS-W 3.0.
Command Information
Parameter Description
<number> Start displaying the log output from the specified number of lines from the end of
the log.
all Shows all the system logs for the switch.
(host) #show log system 10
Mar 5 11:55:59 :316073: <DBUG> |wms| Received New AP Message: AP 00:0b:86:b5:87:c2 Status 1 Num-WM 0
Mar 5 11:55:59 :316083: <DBUG> |wms| mysql: UPDATE ap_table SET ssid='qa-abu-customerissue', current_ch
type='generic-ap', ibss='no', phy_type='80211g', rap_type='interfering', match_mac='00:00:00:00:00:00',
power_level='255', status='up' WHERE id='71575' ;
Mar 5 11:55:59 :316029: <DBUG> |wms| Sending message to Probe: IP:10.3.49.253 Msg-Type:PROBE_RAP_TYPE
00:0b:86:b5:87:c2 Type:1
Mar 5 11:55:59 :316036: <DBUG> |wms| Received New STA Message: MAC 00:0b:86:b5:87:c2 Status 0
Mar 5 11:55:59 :316032: <DBUG> |wms| STA Probe: ADD Probe 00:0b:86:a2:e7:40 for STA 00:0b:86:b5:87:c2
Mar 5 11:56:00 :399814: <DBUG> |fpapps| PoE: RAN THRU ITERATION 2
Mar 5 11:56:00 :326001: <DBUG> |AP 1.1.1@10.3.49.253 sapd| AM: am_read_bss_data_stats: radio 0: pktsIn
bytesIn 0 bytesOut 0
Mar 5 11:56:00 :326001: <DBUG> |AP 1.1.1@10.3.49.253 sapd| AM: am_read_bss_data_stats: radio 0: pktsIn 0
bytesIn 0 bytesOut 18143486
Mar 5 11:56:01 :326001: <DBUG> |AP 1.1.1@10.3.49.253 sapd| AM: MPPS 2722 CPPS 338 PKTS 452036609 BYTES 2
334327351
Mar 5 11:56:02 :399814: <DBUG> |fpapps| PoE: Evaluating port 1/5 rv is 0 and crv is 1
state :3
Platforms Licensing Command Mode
All platforms Base operating system Available in Enable and Config modes.
AOS-W 3.4.1 Command Line Interface | Reference Guide show log user | 889
show log user
show log user{[<number>][all]}
Description
Show the switch’s user logs.
Syntax
Example
This example shows the switch’s last ten user logs.
Command History
This command was available in AOS-W 3.0.
Command Information
Parameter Description
<number> Start displaying the log output from the specified number of lines from the end of
the log.
all Shows all the user logs for the switch.
(host) #show log user 10
Mar 5 13:29:57 :501083: <WARN> |stm| Probe request: 00:0b:86:cd:1a:00: Invalid Station MAC address from
00:0b:86:a2:e7:40-1.1.1
Mar 5 13:32:08 :501083: <WARN> |stm| Probe request: 00:0b:86:cd:1a:00: Invalid Station MAC address from
00:0b:86:a2:e7:40-1.1.1
Mar 5 13:36:41 :501083: <WARN> |stm| Probe request: 00:0b:86:cd:1a:00: Invalid Station MAC address from
00:0b:86:a2:e7:40-1.1.1
Mar 5 13:38:42 :501083: <WARN> |stm| Probe request: 00:0b:86:cd:1a:00: Invalid Station MAC address from
00:0b:86:a2:e7:40-1.1.1
Mar 5 13:40:41 :501083: <WARN> |stm| Probe request: 00:0b:86:cd:1a:00: Invalid Station MAC address from
00:0b:86:a2:e7:40-1.1.1
Mar 5 13:42:51 :501083: <WARN> |stm| Probe request: 00:0b:86:cd:1a:00: Invalid Station MAC address from
00:0b:86:a2:e7:40-1.1.1
Mar 5 13:47:03 :501083: <WARN> |stm| Probe request: 00:0b:86:cd:1a:00: Invalid Station MAC address from
00:0b:86:a2:e7:40-1.1.1
Mar 5 13:49:07 :501083: <WARN> |stm| Probe request: 00:0b:86:cd:1a:00: Invalid Station MAC address from
00:0b:86:a2:e7:40-1.1.1
Mar 5 13:53:08 :501083: <WARN> |stm| Probe request: 00:0b:86:cd:1a:00: Invalid Station MAC address from
00:0b:86:a2:e7:40-1.1.1
Mar 5 13:55:14 :501083: <WARN> |stm| Probe request: 00:0b:86:cd:1a:00: Invalid Station MAC address from
00:0b:86:a2:e7:40-1.1.1
Platforms Licensing Command Mode
All platforms Base operating system Available in Enable and Config modes.
890 | show log user-debug AOS-W 3.4.1 Command Line Interface | Reference Guide
show log user-debug
show log user-debug{[<number>][all]}
Description
Show the switch’s user debug logs.
Syntax
Example
This example shows the switch’s last ten user debug logs.
Command History
This command was available in AOS-W 3.0.
Command Information
Parameter Description
<number> Start displaying the log output from the specified number of lines from the end of
the log.
all Shows all the user debug logs for the switch.
(host) #show log user-debug 10
Mar 5 13:57:24 :501090: <DBUG> |stm| Probe response: 00:18:f8:ab:77:a4: AP 10.3.49.253-00:0b:86:a2:e7:4
Mar 5 13:57:24 :501090: <DBUG> |stm| Probe response: 00:18:f8:ab:77:a4: AP 10.3.49.253-00:0b:86:a2:e7:4
Mar 5 13:58:26 :501082: <DBUG> |stm| Probe request: 00:18:f8:ab:77:a4: AP 10.3.49.253-00:0b:86:a2:e7:40
Mar 5 13:58:26 :501085: <DBUG> |stm| Probe request: 00:18:f8:ab:77:a4: AP 10.3.49.253-00:0b:86:a2:e7:40
Mar 5 13:58:26 :501090: <DBUG> |stm| Probe response: 00:18:f8:ab:77:a4: AP 10.3.49.253-00:0b:86:a2:e7:4
Mar 5 13:58:26 :501090: <DBUG> |stm| Probe response: 00:18:f8:ab:77:a4: AP 10.3.49.253-00:0b:86:a2:e7:4
Mar 5 13:58:27 :501082: <DBUG> |stm| Probe request: 00:18:f8:ab:77:a4: AP 10.3.49.253-00:0b:86:a2:e7:40
Mar 5 13:58:27 :501085: <DBUG> |stm| Probe request: 00:18:f8:ab:77:a4: AP 10.3.49.253-00:0b:86:a2:e7:40
Mar 5 13:58:27 :501090: <DBUG> |stm| Probe response: 00:18:f8:ab:77:a4: AP 10.3.49.253-00:0b:86:a2:e7:4
Mar 5 13:58:27 :501090: <DBUG> |stm| Probe response: 00:18:f8:ab:77:a4: AP 10.3.49.253-00:0b:86:a2:e7:4
Platforms Licensing Command Mode
All platforms Base operating system Available in Enable and Config modes.
AOS-W 3.4.1 Command Line Interface | Reference Guide show log wireless | 891
show log wireless
show log wireless{[<number>][all]}
Description
Show the switch’s wireless logs.
Syntax
Example
This example shows the switch’s last ten wireless logs.
Command History
This command was available in AOS-W 3.0.
Command Information
Parameter Description
<number> Start displaying the log output from the specified number of lines from the end of
the log.
all Shows all the wireless logs for the switch.
(host) #show log wireless 10
Mar 5 13:59:31 :404003: <WARN> |AP 1.1.1@10.3.49.253 sapd| AM 00:0b:86:a2:e7:40: Interfering AP detected
cp-psk and BSSID 00:0b:86:8b:70:20
Mar 5 13:59:35 :404003: <WARN> |AP 1.1.1@10.3.49.253 sapd| AM 00:0b:86:a2:e7:40: Interfering AP detected
BSSID 00:0b:86:c0:06:83
Mar 5 13:59:38 :404003: <WARN> |AP 1.1.1@10.3.49.253 sapd| AM 00:0b:86:a2:e7:40: Interfering AP detected
BSSID 00:0b:86:c0:06:85
Mar 5 13:59:41 :404003: <WARN> |AP 1.1.1@10.3.49.253 sapd| AM 00:0b:86:a2:e7:40: Interfering AP detected
BSSID 00:0b:86:89:f9:42
Mar 5 13:59:41 :404003: <WARN> |AP 1.1.1@10.3.49.253 sapd| AM 00:0b:86:a2:e7:40: Interfering AP detecte
SANJAY-OSUWIRELESS and BSSID 00:0b:86:89:f9:40
Mar 5 13:59:44 :404003: <WARN> |AP 1.1.1@10.3.49.253 sapd| AM 00:0b:86:a2:e7:40: Interfering AP detecte
SANJAY-OSUVOICE and BSSID 00:0b:86:8c:fb:c0
Mar 5 13:59:44 :404003: <WARN> |AP 1.1.1@10.3.49.253 sapd| AM 00:0b:86:a2:e7:40: Interfering AP detecte
Google and BSSID 00:0b:86:4f:82:c0
Mar 5 13:59:47 :404003: <WARN> |AP 1.1.1@10.3.49.253 sapd| AM 00:0b:86:a2:e7:40: Interfering AP detecte
SANJAY-OSUVOICE and BSSID 00:0b:86:89:f9:41
Mar 5 13:59:50 :404003: <WARN> |AP 1.1.1@10.3.49.253 sapd| AM 00:0b:86:a2:e7:40: Interfering AP detected
BSSID 00:0b:86:c0:06:86
Mar 5 13:59:50 :404003: <WARN> |AP 1.1.1@10.3.49.253 sapd| AM 00:0b:86:a2:e7:40: Interfering AP detected
dnh-blah and BSSID 00:0b:86:60:b8:80
Platforms Licensing Command Mode
All platforms Base operating system Available in Enable and Config modes.

892 | show log wireless AOS-W 3.4.1 Command Line Interface | Reference Guide

AOS-W 3.4.1 Command Line Interface | Reference Guide show logging | 893
show logging
show logging facility|server|{level [verbose]}
Description
the IP address of the remote logging server, as well as facility log types and their associated facility levels.
Syntax
Usage Guidelines
The AOS-W logging levels follow syslog convention:
zlevel 7: Emergency
zlevel 6: Alert
zlevel 5: Critical
zlevel 4: Errors.
zlevel 3: Warning
zlevel 2:Notices
zlevel 1:Informational
zlevel 0: Debug
The default logging level is leve1 1. You can change this setting via the logging command.
Example
This example below displays defined logging levels for each logging facility.
This example below displays the IP address of a remote log server. If a remote log server has not yet been
defined, this command will not display any output.
Parameter Description
facility View the facility used when logging messages into the remote syslog server.
server Show the IP address of a remote logging server.
level [verbose] Show logging levels at which the messages are logged. Include the optional verbose
parameter to display additional data for logging subcategories and processes.
(host) #show logging level
LOGGING LEVELS
--------------
Facility Level
-------- -----
network warnings
security warnings
system warnings
user warnings
wireless warnings
(host) #show logging server
Remote Server: 10.4.114.12
894 | show logging AOS-W 3.4.1 Command Line Interface | Reference Guide
Related Commands
Command History
This command was introduced in AOS-W 2.5.
Command Information
Command Description Mode
logging Use this command to specify the IP address of the remote
logging server, as well as facility log types and their
associated facility levels.
Config mode on master and local
switches
Platforms Licensing Command Mode
All platforms Base operating system Enable and Config mode on master or local switches

AOS-W 3.4.1 Command Line Interface | Reference Guide show loginsessions | 895
show loginsessions
show loginsessions
Description
Displays the current administrator login sessions statistics.
Syntax
No parameters.
Example
Issue this command to display the admin login session statistics.
The output includes the following parameters:
Command History
This command was introduced in AOS-W 3.0.
Command Information
Parameter Description
ID Sessions identification number
User Name Administrator’s user name
User Role Administrator’s role
Connection From The IP address from which the administrator is connecting
Idle Time Amount of time the user has been idle
Session Time Total time the session has been open
Platforms Licensing Command Mode
All platforms Base operating system Enable or config mode on master switches
Session Table
-------------
ID User Name User Role Connection From Idle Time Session Time
-- --------- --------- --------------- --------- ------------
1 admin root 10.100.102.43 00:00:00 00:27:59

896 | show loginsessions AOS-W 3.4.1 Command Line Interface | Reference Guide

AOS-W 3.4.1 Command Line Interface | Reference Guide show mac-address-table | 897
show mac-address-table
show mac-address-table
Description
Displays a MAC forwarding table.
Syntax
No parameters.
Example
Issue this command to display the MAC forwarding table.
The output includes the following parameters:
Command History
This command was introduced in AOS-W 1.0.
Command Information
Parameter Description
Dynamic Address Count Count of dynamic addresses currently associated with the switch
Static Address (User-
defined) Count
Count of static, user-defined addresses associated with the switch
System Self Address
Count
Number of self system addresses
Total MAC Addresses Total number of MAC addresses associated with the switch
Maximum MAC Addresses Maximum number of MAC addresses
Destination Address Destination MAC address
Address Type Destination address type
VLAN Associated VLAN
Destination Port Destination port
Platforms Licensing Command Mode
All platforms Base operating system Enable or config mode on master switches
Dynamic Address Count: 0
Static Address (User-defined) Count: 0
System Self Address Count: 0
Total MAC Addresses : 6
Maximum MAC addresses : 6
MAC Address Table
------------------
Destination Address Address Type VLAN Destination Port
------------------- ------------ ---- ----------------
00:0b:86:00:00:00 Mgmt 1 vlan 1
00:0b:86:f0:05:60 Mgmt 1 vlan 1
00:0b:86:00:00:00 Mgmt 62 vlan 62
00:0b:86:f0:05:60 Mgmt 62 vlan 62
00:0b:86:00:00:00 Mgmt 4095 vlan 4095
00:0b:86:f0:05:60 Mgmt 4095 vlan 4095

898 | show mac-address-table AOS-W 3.4.1 Command Line Interface | Reference Guide
AOS-W 3.4.1 Command Line Interface | Reference Guide show master-local stats | 899
show master-local stats
show master-local stats [<ip-addr>] [<page>]
Description
Display statistics for communication between master and local switches.
Syntax
Usage Guidelines
By default, master and Local switchs exchange heartbeat messages every 10 seconds. These "Heartbeats" a
include configuration timestamp. If a master switch has later timestamp than the local switch, the state of
the local switch changes from ‘Update Successful’ to ‘Update Required’.
Example
This example below shows statistics for all communications between the master and local switch.
The output of this command includes the following data columns:
Command History
This command was introduced in AOS-W 3.0.
Parameter Description
<ip-addr> Include the IP address of a switch to display statistics that switch only.
<page> Start displaying the output of this command at the specified page number.
(host) #show master-local stats
Missed -> HB Resp from Master
-----------------------------
IP Address HB Req HB Resp Total Missed Last Sent Missed Peer Reset Cfg Terminate Last Synced
---------- ------ ------- ------------ ---------------- ---------- ------------- -----------
10.6.2.252 194721 194208 926 0 105 1 Thu Feb 26 21:12:04 2009
Parameter Description
IP Address IP address of the local switch.
HB Req Heartbeat requests sent from the local switch.
HB Resp Heartbeat responses sent from the master switch.
Total Missed Total number of heartbeats that were not received by the local switch.
Last Sent Missed This counter will increment if switch misses the last heartbeat from the peer
switch. This counter will keep on incrementing until the heartbeat message is
received from peer.
Peer Reset The number of times the connection to peer is been reset. The connection could
reset due to network connectivity problems or when the peer switch reboots.
Cfg Terminate Number of times the switch has failed to upgrade to a new configuration
Last Synced Timestamp showing the last time the local switch synched its configuration from
the master switch.

900 | show master-local stats AOS-W 3.4.1 Command Line Interface | Reference Guide
Command Information
Platforms Licensing Command Mode
All platforms Base operating system Enable and Config mode on master or local switches.
AOS-W 3.4.1 Command Line Interface | Reference Guide show master-redundancy | 901
show master-redundancy
show master-redundancy
Description
Display the master switch redundancy configuration.
Syntax
No parameters.
Example
This example below shows the current master redundancy configuration, including the ID number of the
master VRRP virtual router and the IP address of the peer switch for master redundancy.
Related Commands
Command History
This command was introduced in AOS-W 3.0.
Command Information
(host) #show master-redundancy
Master redundancy configuration:
VRRP Id 2 current state is MASTER
Peer's IP Address is 2.1.1.4
Command Description
master-redundancy This command associates a VRRP instance with master switch redundancy.
vrrp This command configures the Virtual Router Redundancy Protocol (VRRP).
Platforms Licensing Command Mode
All platforms Base operating system Enable and Config mode on master switches.

902 | show master-redundancy AOS-W 3.4.1 Command Line Interface | Reference Guide

AOS-W 3.4.1 Command Line Interface | Reference Guide show memory | 903
show memory
show memory [ap {meshd|rfd|sapd} {ap-name <ap-name>}|{bssid <bssid>}|{ip-addr <ip-addr>}]
|[auth|cfgm|dbsync|fpapps|fpcli|isakmpd|l2tpd|mobileip|ospf|pim|pptpd|profmgr|slb
|snmpd|stm|udbserver|wms]
Description
Show the amounts of free and available memory on the switch, or include a process name to show memory
information for a process on the AP or switch.
Syntax
Parameter Description
ap Show memory information for a process running on a specific AP.
meshd Display memory information for the meshd process on the specified AP.
rfd Display memory information for the rfd process on the specified AP.
sapd Display memory information for the rfd process on the specified AP.
ap-name <ap-name> Display memory information for an AP with the specified AP name.
bssid <bssid> Display memory information for an AP with the specified BSSID.
ip-addr <ip-addr> Display memory information for an AP with the specified IP address.
auth Display memory information for the auth process on the switch.
cfgm Display memory information for the cfgm process on the switch.
dbsync Display memory information for the dbsync process on the switch.
fpapps Display memory information for the fpapps process on the switch.
fpcli Display memory information for the fpcli process on the switch.
isakmpd Display memory information for the isakmpd process on the switch.
l2tpd Display memory information for the l2tpd process on the switch.
mobileip Display memory information for the mobileip process on the switch.
ospf Display memory information for the ospf process on the switch.
pim Display memory information for the pim process on the switch.
pptpd Display memory information for the pptpd process on the switch.
profmgr Display memory information for the profmgr process on the switch.
slb Display memory information for the slb process on the switch.
apsnmpd Display memory information for the apsnmpd process on the switch.
stm Display memory information for the auth process on the switch.
udbserver Display memory information for the udbserver process on the switch.
wms Display memory information for the wms process on the switch.
904 | show memory AOS-W 3.4.1 Command Line Interface | Reference Guide
Usage Guidelines
Include the name of a process to show memory information for that process. Use this command under the
supervision of Alcatel-Lucent technical support to help debug process errors.
Example
The command show memory displays, in Kilobytes, the total memory on the switch, the amount of memory
currently being used, and the amount of free memory.
Include the name of a process to show memory statistics for that process. The example below shows
memory statistics for mobileip.
The output of this command includes the following columns:
Command History
(host) # show memory
Memory (Kb): total: 256128, used: 162757, free: 93371
(host) # show memory mobileip
Type Num Allocs Size Allocs Total Allocs Total Size
default 92 145622 441 241087
PC Allocs Size
0x1000be14 1 64
0x10016cb0 1 41000
0x10021604 1 80
0x10032e34 1 24
0x30019a24 1 2200
0x30019bd8 1 41000
0x30019bf0 1 41000
0x30019c28 1 11263
0x3001b134 2 1967
0x300326b8 9 72
0x30032738 4 64
0x3019dfdc 1 44
0x3019ee60 3 48
0x3019ef18 1 784
0x301b63bc 13 312
0x301b6470 10 200
0x301b648c 10 920
0x301b7614 3 36
0x301b7770 8 128
0x301bd460 3 60
Column Description
Type The show memory command currently shows information for predefined
processes only, so this column always displays the parameter default.
Num Alloc Current number of memory allocations.
Size Allocs Total size of all memory allocations, in bytes.
Total Allocs Maximum number of allocations used throughout in the life of the process.
Total Size Maximum size of allocations used throughout in the life of the process, in bytes.
PC Program counter: the address of a memory allocation. (For internal use only.)
Allocs Number of memory allocations at that program counter. (For internal use only.)
Size Size of all memory allocations at that program counter. (For internal use only.)

AOS-W 3.4.1 Command Line Interface | Reference Guide show memory | 905
This command was available in AOS-W 3.0.
Command Information
Platforms Licensing Command Mode
All platforms Base operating system Config or Enable mode on master or local
switches

906 | show memory AOS-W 3.4.1 Command Line Interface | Reference Guide
AOS-W 3.4.1 Command Line Interface | Reference Guide show mgmt-role | 907
show mgmt-role
show mgmt-role
Description
This command allows the user to view a list of management role configurations.
Syntax
No parameters.
Example
Issue this command to display a list of management user roles.
The output includes the following parameters:
Command History
This command was introduced in AOS-W 1.0.
Command Information
Parameter Description
ROLE Name of the management user role
DESCRIPTION Description of the management user role
Platforms Licensing Command Mode
All platforms Base operating system Enable or config mode on master switches
Management User Roles
---------------------
ROLE DESCRIPTION
---- -----------
root Super user role
read-only Read only commands
network-operations network-operations
guest-provisioning guest-provisioning
location-api-mgmt location-api-mgmt
no-access Default role, no commands are accessible for this role
location-api-mgmt location-api-mgmt

908 | show mgmt-role AOS-W 3.4.1 Command Line Interface | Reference Guide
AOS-W 3.4.1 Command Line Interface | Reference Guide show mgmt-users | 909
show mgmt-users
show mgmt-users [ <username> |
local-authentication-mode <username> |
ssh-pubkey <username> |
webui-cacert <username> ]
Description
Displays list of management users on the switch and also details of each management users.
Syntax
Syntax
Example
The output of this command shows the number of management users in the switch.
Command History
This command was available in AOS-W 3.3.2
Command Information
Parameter Description
username To view details of a specific management user.
local-authentication-mode Status of local-authentication mode.
ssh-pubkey Number of management users using the ssh-pubkey.
webui-cacert Number of management users using web CA certificates.
(host) # show mgmt-user
Management User Table
---------------------
USER PASSWD ROLE STATUS
---- ------ ---- ------
admin ***** root ACTIVE
Platforms Licensing Command Mode
All platforms Base operating system Config or Enable mode on master or local
switches

910 | show mgmt-users AOS-W 3.4.1 Command Line Interface | Reference Guide
AOS-W 3.4.1 Command Line Interface | Reference Guide show netdestination | 911
show netdestination
show netdestination <netdestination name>
Description
Displays network destination information.
Syntax
No parameters.
Example
Issue this command to display all netdestination configured on this switch. The output shown displays
information for all configuration netdestinations. To display additional detailed information for an
individual netdestinations, include the name of the netdestination at the end of the command.
The output includes the following parameters:
Command History
This command was introduced in AOS-W 3.0.
Parameter Description
Position Network destination position
Type Network destination type
IP addr IP address of the network destination
Mask/Range Network destination subnet mask and range
(host) #show destination
controller
----------
Position Type IP addr Mask/Range
-------- ---- ------- ----------
1 host 10.16.15.1
user
----
Position Type IP addr Mask/Range
-------- ---- ------- ----------
1 network 255.255.255.255 0.0.0.0
mswitch
-------
Position Type IP addr Mask/Range
-------- ---- ------- ----------
1 host 10.16.15.1
any
---
Position Type IP addr Mask/Range
-------- ---- ------- ----------
1 network 0.0.0.0 0.0.0.0

912 | show netdestination AOS-W 3.4.1 Command Line Interface | Reference Guide
Command Information
Platforms Licensing Command Mode
All platforms You must have a Policy
Enforcement Firewall license to
configure or view a netdestination.
Enable or config mode on master switches
AOS-W 3.4.1 Command Line Interface | Reference Guide show netservice | 913
show netservice
show netservice [<string>]
Description
Show network services
Syntax
Usage guidelines
Issue this command without the optional <string> parameter to view a complete table of network services
on the switch. Include the <string> parameter to display settings for a single network service only.
Example
The following example shows the protocol type, ports and application-level gateway (ALG) for the DHCP
service.
Related Commands
To configure an alias for network protocols, use the command netservice.
Command History
This command was available in AOS-W 1.0.
Command Information
Parameter Description
<string> Name of a network service.
(host) #show netservice svc-dhcp
Services
--------
Name Protocol Ports ALG
---- -------- ----- ---
svc-dhcp udp 67 68
Platforms Licensing Command Mode
All platforms Base operating system Enable and Config mode on local and
master switches

914 | show netservice AOS-W 3.4.1 Command Line Interface | Reference Guide
AOS-W 3.4.1 Command Line Interface | Reference Guide show netstat | 915
show netstat
show netstat [stats]
Description
Show current active network connections.
Syntax
Usage guidelines
Issue this command without the optional stats parameter to view a complete table of active network
connections. Include the stats parameter to display aggregate statistics for IP, ICMP, TCP and UDP
protocols.
Parameter Description
<string> Show network statistics, filtered by protocol type.
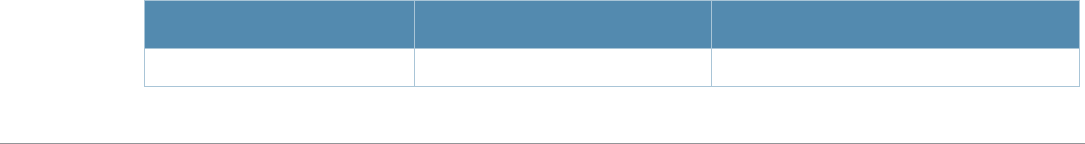
916 | show netstat AOS-W 3.4.1 Command Line Interface | Reference Guide
Example
The following example shows incoming and outgoing packet statistics for the switch.
Related Commands
To configure an alias for network protocols, use the command netservice.
Command History
This command was available in AOS-W 1.0.
Command Information
(host) #show netstat stats
Ip:
1084012095 total packets received
2 with invalid headers
3 forwarded
426940 incoming packets discarded
932097114 incoming packets delivered
1004595164 requests sent out
52847 fragments dropped after timeout
201323411 reassemblies required
50179757 packets reassembled ok
53204 packet reassembles failed
136827034 fragments created
Icmp:
1969625 ICMP messages received
5 input ICMP message failed.
ICMP input histogram:
destination unreachable: 1752058
timeout in transit: 1684
redirects: 70805
echo requests: 145073
echo replies: 5
249806 ICMP messages sent
0 ICMP messages failed
ICMP output histogram:
destination unreachable: 51944
time exceeded: 52796
redirect: 2
echo replies: 145064
Tcp:
3 active connections openings
0 passive connection openings
0 failed connection attempts
0 connection resets received
2 connections established
1006383 segments received
1147229 segments send out
9603 segments retransmitted
0 bad segments received.
2568 resets sent
Udp:
928478757 packets received
40767 packets to unknown port received.
426937 packet receive errors
910267627 packets sent
Platforms Licensing Command Mode
All platforms Base operating system Config mode on local and master switches
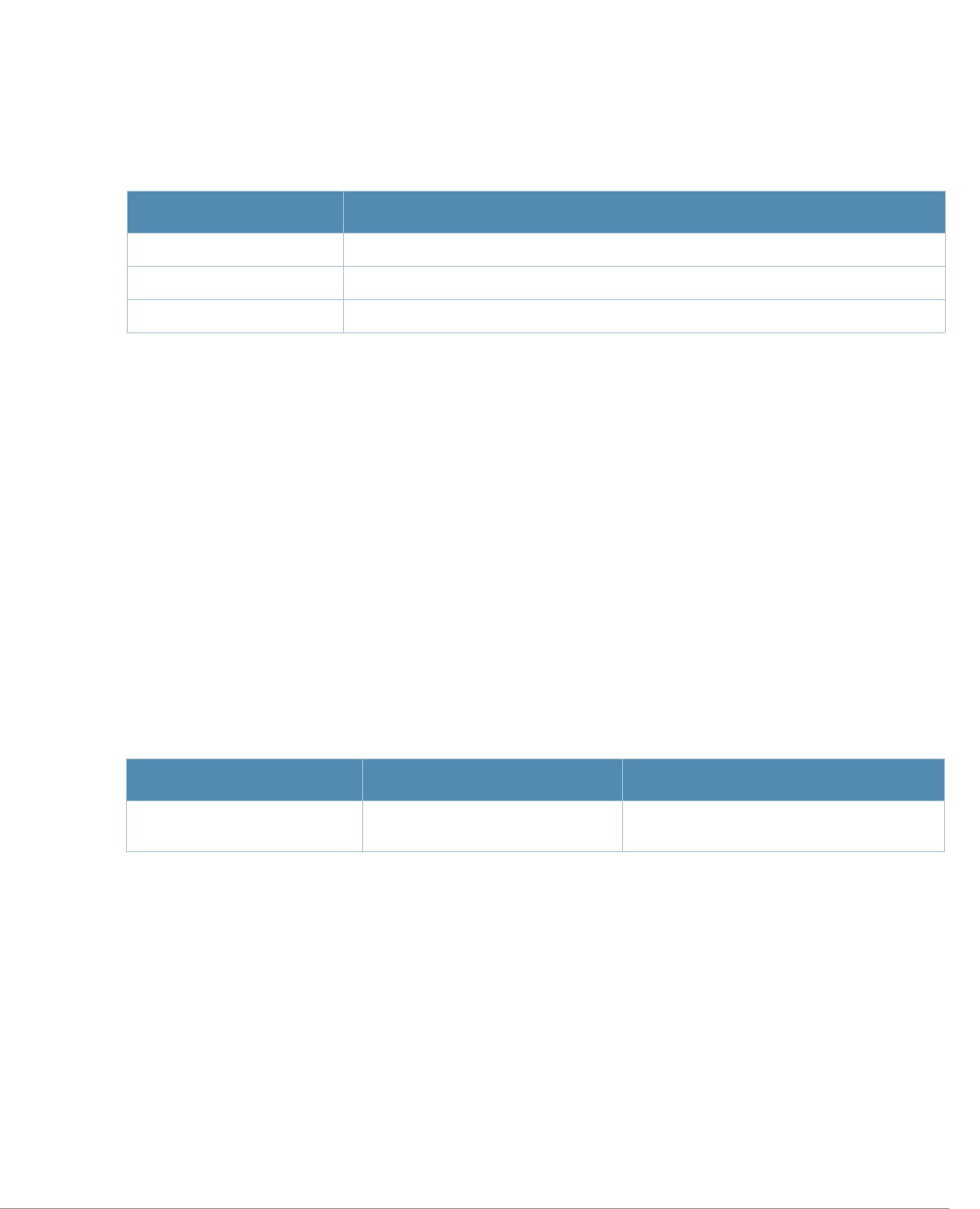
AOS-W 3.4.1 Command Line Interface | Reference Guide show network-printer | 917
show network-printer
show network-printer [config | job <printer-name> | status]
Description
Displays configuration, job status details, and printer status of USB printers connected to a OmniAccess
4306 series switch.
Syntax
Example
The output of this command shows the status of all printers connected to the switch.
Command History
This command was available in AOS-W 3.4
Command Information
Parameter Description
config Displays the configuration details of the printer service on the switch.
job Displays the list of job in queue in all printers connected to the switch.
status Displays the status of all printers connected to the switch.
(host) #show network-printer status
Networked Printer Status
------------------------
Printer Name Printer Alias Status Comment
------------ ------------- ------ -------
usblp_Hewlett-Packard_HP_Color_LaserJet_CP3505_CNBJ8B1003 HPLJ_P3005 idle enabled
usblp_HP_Officejet_Pro_L7500_MY872231FX HPOJ_L7500 idle enabled
Platforms Licensing Command Mode
OmniAccess 4306 series
switch Base operating system Enable mode

918 | show network-printer AOS-W 3.4.1 Command Line Interface | Reference Guide

AOS-W 3.4.1 Command Line Interface | Reference Guide show network-storage | 919
show network-storage
show network-storage [ files opened |
shares {<file-system-path> | disk |
status |
users {disk <disk-name>} ]
Description
Displays details about the USB storage device connect to a OmniAccess 4306 series switch.
Syntax
Example
The output of this command shows the status of all printers connected to the switch.
Command History
This command was available in AOS-W 3.4
Command Information
Parameter Description
files opened Displays the list of opened files in the USB storage device connected to the switch.
shares Displays the list of shares that are created in the USB storage device. This option provides the
following details:
zname of the share
zname of the disk by alias.
zthe folder associated with the share,
zthe access mode
status Displays the status of the storage service on the switch.
users Displays the list of users by IP address, connected share name and connection time.
(host) #show network-storage users
NAS Users
---------
Share Name Machine Connected at
---------- ------- ------------
Documents 192.168.1.4 Fri Apr 21 14:28:59 2009
Documents 192.168.1.5 Fri Apr 21 14:17:09 2009
Platforms Licensing Command Mode
OmniAccess 4306 series
switch Base operating system Enable mode

920 | show network-storage AOS-W 3.4.1 Command Line Interface | Reference Guide
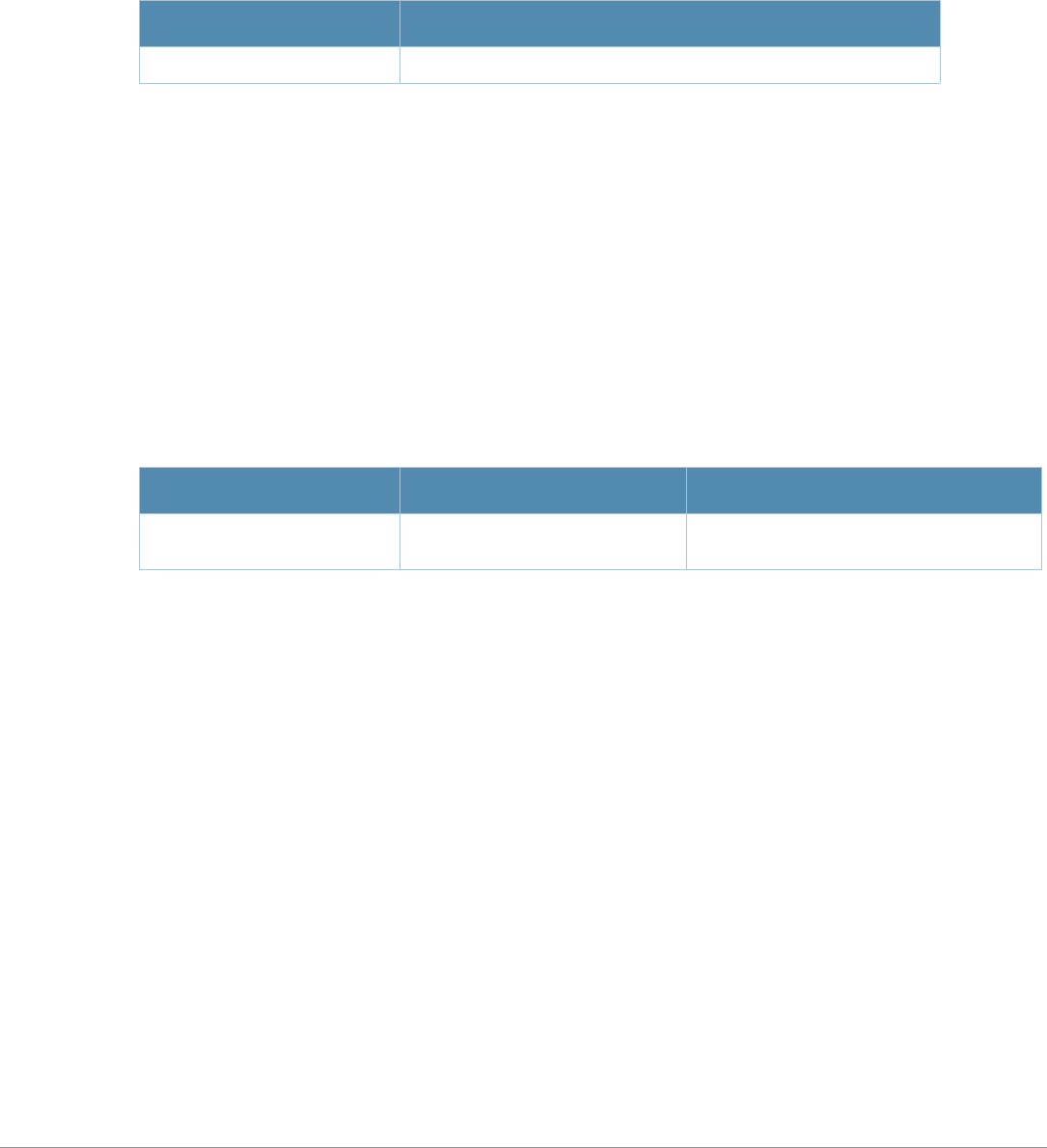
AOS-W 3.4.1 Command Line Interface | Reference Guide show ntp peer | 921
show ntp peer
show ntp peer <a.b.c.d>
Description
Show NTP peer information.
Syntax
Usage guidelines
The show ntp peer command is used for NTP server troubleshooting, and should only be used under the
supervision of Alcatel-Lucent technical support. Issue the show ntp servers command to view basic
settings for currently configured NTP servers.
Related Commands
To configure an NTP server, use the command ntp server.
Command History
This command was available in AOS-W 3.0.
Command Information
Parameter Description
<a.b.c.d> IP address of an NTP peer
Platforms Licensing Command Mode
All platforms Base operating system Enable and Config mode on local and
master switches
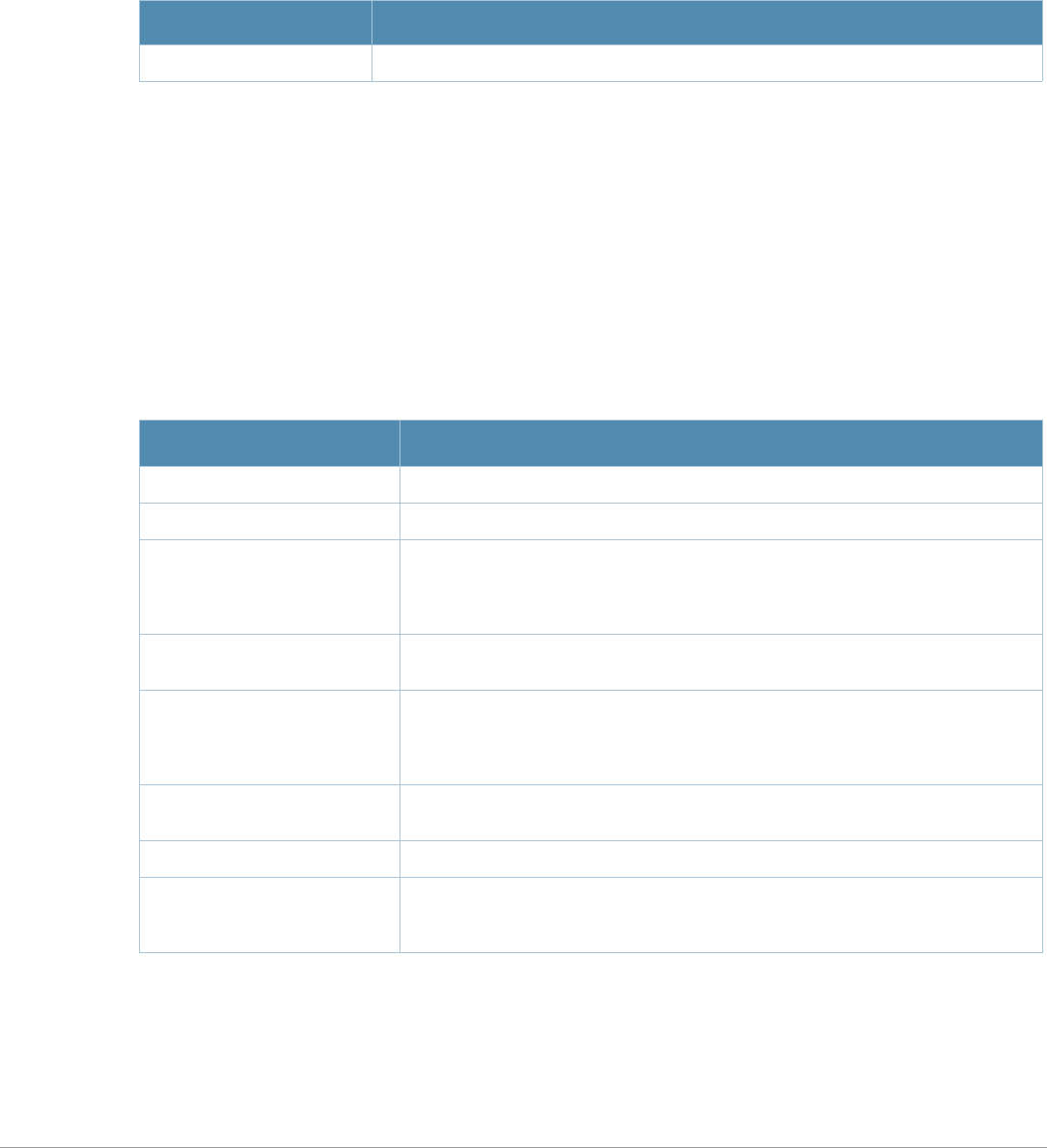
922 | show ntp servers AOS-W 3.4.1 Command Line Interface | Reference Guide
show ntp servers
show rft servers [brief]
Description
Show information for Network TIme Protocol (NTP) servers.
Syntax
Example
The following example shows values for the primary and backup NTP servers. The primary server is
marked with an asterisk (*) and the backup server is marked with an equals sign (=). Note that a backup
server will not display delay, offset or dispersion data, as it is not currently in use.
The output of this command includes the following parameters:
Related Commands
To configure an NTP server, use the command ntp server.
Command History
Parameter Description
brief Display only the IP address of the defined NTP servers.
(host) #show ntp servers
remote local st poll reach delay offset disp
=======================================================================
=10.4.0.21 10.6.2.253 16 1024 0 0.00000 0.000000 0.00000
*10.1.1.250 10.6.2.253 2 1024 377 0.00081 -0.010376 0.03040
Parameter Description
remote IP address of the remote NTP server defined using the cli command ntp server.
local IP address of the local clock.
st NTP uses hierarchical levels of clock sources, or strata, and assigns each layer a
number starting with zero at the root. The st column in the output of this
command represents the number of servers between the configured NTP server
and the root reference clock.
poll Interval, in seconds, between the local NTP server’s attempt to poll the remote
NTP server.
reach An index that measures whether or not the remote NTP server could be reached
at eight most recent polling intervals. If the NTP server has just been configured
and hasn’t yet been polled successfully, the value will be zero (0). A value of 377
indicates that the last eight poll queries were successful.
delay Delay, in seconds, between the time that the local clock polls the NTP server and
the NTP server returns a reply.
offset The difference in time, in seconds, between the local clock and the NTP server.
disp Dispersion represents the maximum error of the local clock relative to the
reference clock, and is a measurement of the time server and network quality.
Lower dispersion values are preferred over higher dispersion values.

AOS-W 3.4.1 Command Line Interface | Reference Guide show ntp servers | 923
This command was available in AOS-W 3.0.
Command Information
Platforms Licensing Command Mode
All platforms Base operating system Enable and Config mode on local and
master switches
924 | show ntp status AOS-W 3.4.1 Command Line Interface | Reference Guide
show ntp status
show ntp status
Description
Show information for a NTP server.
Syntax
No parameters.
Example
The following example shows values for the primary NTP server.
The output of this command includes the following parameters:
(host) #show ntp status
system uptime: 7594
time since reset: 7594
bad stratum in packet: 0
old version packets: 113
new version packets: 0
unknown version number: 0
bad packet format: 0
packets processed: 110
bad authentication: 0
packets rejected: 0
system peer: 10.1.1.250
system peer mode: client
leap indicator: 00
stratum: 3
precision: -18
root distance: 0.03236 s
root dispersion: 0.06728 s
reference ID: [10.1.1.250]
reference time: cd45b701.bcbc05d5 Tue, Feb 17 2009 14:21:53.737
system flags: auth monitor ntp kernel stats
jitter: 0.005020 s
stability: 0.866 ppm
broadcastdelay: 0.003998 s
authdelay: 0.000000 s
Parameter Description
system uptime The number of seconds the local NTP server has been associated with the
switch.
time since reset The number of seconds since the last time the local NTP server was restarted.
bad stratum in packet The number of NTP packets with a corrupted stratum bit.
old version packets Number of packets that match the previous NTP version. A version number is in
every NTP packet.
new version packets Number of packets that match the current NTP version.
unknown version number Number of packets with an unknown NTP version.
bad packet format Number of NTP packets dropped due to an invalid packet format.
packets processed Number of NTP packets received and processed by the switch.
bad authentication Number of NTP packets that failed to be authenticated.
AOS-W 3.4.1 Command Line Interface | Reference Guide show ntp status | 925
Related Commands
To configure an NTP server, use the command ntp server.
Command History
This command was available in AOS-W 3.0.
Command Information
packets rejected Number of NTP packets rejected because they had an invalid format.
system peer The IP address of the peer NTP server.
system peer mode The peer mode of this remote association:
zSymmetric Active
zSymmetric Passive
zClient
zServer
zBroadcast
leap indicator This parameter indicates whether or not a leap-second should be inserted or
removed at the end of the last day of the current month.
z00 no warning
z01 +1 second (following minute has 61 seconds)
z10 -1 second (following minute has 59 seconds)
stratum The stratum level of the peer
precision The advertised precision of the switch. This value can range from -4 and -20,
inclusive.
root distance Total round trip delay to the stratum 1 reference clock.
root dispersion Total dispersion to the stratum 1 reference clock. This value is a cumulative
measure of all errors associated with the network hops and servers between the
NTP server and its stratum 1 server.
reference ID IP address of the remote NTP server
reference time Time when the local system clock was last set or corrected, in NTP timestamp
format.
system flags This parameter displays any flags configured for this NTP entity.
jitter The average magnitude of jitter between several time queries.
stability The average magnitude of offset between several time queries
broadcastdelay The broadcast delay of this NTP server association, in seconds.
authdelay The authentication delay of this NTP server association, in seconds.
Parameter Description
Platforms Licensing Command Mode
All platforms Base operating system Enable and Config mode on local and
master switches

926 | show ntp status AOS-W 3.4.1 Command Line Interface | Reference Guide

AOS-W 3.4.1 Command Line Interface | Reference Guide show packet-capture | 927
show packet-capture
show packet-capture
Description
Displays packet capture status on the switch.
Syntax
No Parameters
Example
The output of this command shows the packet capture configuration details.
Command History
This command was available in AOS-W 3.3.2
Command Information
(host) # show packet-capture
Current Active Packet Capture Actions(current switch)
=====================================================
Packet filtering TCP with 1 port(s) enabled:
2
Packet filtering UDP with 1 port(s) enabled:
5
Packet filtering for internal messaging opcodes disabled.
Packet filtering for all other packets enabled.
Packet Capture Defaults(across switches and reboots if saved)
============================================================
Packet filtering TCP with 1 port(s) enabled:
2
Packet filtering UDP with 1 port(s) enabled:
5
Packet filtering for internal messaging opcodes disabled.
Packet filtering for all other packets enabled.
Platforms Licensing Command Mode
All platforms Base operating system Config or Enable mode on master or local
switches

928 | show packet-capture AOS-W 3.4.1 Command Line Interface | Reference Guide
AOS-W 3.4.1 Command Line Interface | Reference Guide show packet-capture-defaults | 929
show packet-capture-defaults
show packet-capture-defaults
Description
Displays the status of default packet capture options.
Syntax
No Parameters
Example
The output of this command shows packet capture status.
Command History
This command was available in AOS-W 3.3.2
Command Information
(host) # show packet-capture-defaults
Current Active Packet Capture Actions(current switch)
=====================================================
Packet filtering for TCP ports disabled.
Packet filtering for UDP ports disabled.
Packet filtering for internal messaging opcodes disabled.
Packet filtering for all other packets disabled.
Packet Capture Defaults(across switches and reboots if saved)
============================================================
Packet filtering for TCP ports disabled.
Packet filtering for UDP ports disabled.
Packet filtering for internal messaging opcodes disabled.
Packet filtering for all other packets disabled.
Platforms Licensing Command Mode
All platforms Base operating system Config or Enable mode on master or local
switches

930 | show packet-capture-defaults AOS-W 3.4.1 Command Line Interface | Reference Guide
AOS-W 3.4.1 Command Line Interface | Reference Guide show papi-security | 931
show papi-security
show papi-security
Description
This command shows a configured papi-security profile.
Syntax
Usage Guidelines
Issue this command to show the a selected papi-security profile configuration. The papi-security
command is used by the Alcatel-Lucent system to enforce advanced security options and provides an
enhanced level of security.
The Parameter column displays the PAPI Key and Enhanced security mode parameters. The Value column
displays a Papi key value (encrypted) and indicates whether the Enhanced security mode is enabled or
disabled. If an AP cannot be authenticated because it has the wrong key, the show ap database command
displays a “Bad key” status.
.
Related Commands
Use the command papi-security to configure a papi-security profile.
Command History
This command was introduced in AOS-W 3.4.
Command Information
Parameter Description Range Default
PAPI Key The key string. The key authenticates the
messages between systems. Range: 10–64
characters —
Enhanced security
mode
Indicates if the enhanced security mode is
enabled or disabled. This mode causes the
system to reject messages when an incorrect key
is used.
— disabled
Platforms Licensing Command Mode
All platforms Base operating system Enable or config mode on master or local
switches
(host) #show papi-security
PAPI Security Profile
---------------------
Parameter Value
--------- -----
PAPI Key ********
Enhanced security mode Enabled

932 | show papi-security AOS-W 3.4.1 Command Line Interface | Reference Guide
AOS-W 3.4.1 Command Line Interface | Reference Guide show poe | 933
show poe
show poe [slot/port]
Description
Displays the PoE status of all or a specific port on the switch.
Syntax
No Parameters
Example
The output of this command shows the PoE status of port 10 in slot 1.
Command History
This command was available in AOS-W 3.0
Command Information
(host) # show poe 1/10
PoE Status
----------
Port Status Voltage(mV) Current(mA) Power (mW)
---- ------ ----------- ----------- ----------
FE 1/10 Off N/A N/A N/A
Platforms Licensing Command Mode
All platforms Base operating system Config or Enable mode on master or local
switches

934 |show poe AOS-W 3.4.1 Command Line Interface | Reference Guide
AOS-W 3.4.1 Command Line Interface | Reference Guide show port link-event | 935
show port link-event
show port link-event
Description
Displays the link status on each of the port on the switch.
Syntax
No Parameters
Example
The output of this command shows the link status on all ports in the switch.
Command History
This command was available in AOS-W 3.3.2
Command Information
(host) # show port link-event
Slot/Port UP DOWN Slot/Port UP DOWN
--------- -- ---- --------- -- ----
2 / 0 0 0 2 / 1 0 0
2 / 2 0 0 2 / 3 1 1
2 / 4 0 0 2 / 5 0 0
2 / 6 0 0 2 / 7 1 1
2 / 8 0 0 2 / 9 0 0
2 / 10 10 9 2 / 11 2 1
2 / 12 1 0 2 / 13 0 0
2 / 14 1 0 2 / 15 6 5
2 / 16 5 4 2 / 17 9 8
2 / 18 1 0 2 / 19 5 4
2 / 20 0 0 2 / 21 4 4
2 / 22 2 2 2 / 23 9 9
2 / 24 0 0 2 / 25 0 0
3 / 0 24 23 3 / 1 0 0
3 / 2 0 0 3 / 3 0 0
3 / 4 1 0 3 / 5 1 0
3 / 6 0 0 3 / 7 0 0
3 / 8 94 94 3 / 9 0 0
3 / 10 0 0 3 / 11 5886 5886
3 / 12 49751 49750 3 / 13 50 49
3 / 14 2589 2588 3 / 15 228 227
3 / 16 2 1 3 / 17 2423 2423
3 / 18 8245 8244 3 / 19 5098 5098
3 / 20 74 73 3 / 21 2 2
3 / 22 1 0 3 / 23 0 0
3 / 24 0 0 3 / 25 0 0
Platforms Licensing Command Mode
All platforms Base operating system Config or Enable mode on master or local
switches
936 | show port monitor AOS-W 3.4.1 Command Line Interface | Reference Guide
show port monitor
show port monitor
Description
Displays the list of ports that are configured to be monitored.
Syntax
No Parameters
Example
The output of this command shows the link status on all ports in the switch.
Command History
This command was available in AOS-W 3.3.2
Command Information
(host) # show port monitor
Monitor Port Port being Monitored
------------ --------------------
FE 1/10 FE 1/20
Platforms Licensing Command Mode
All platforms Base operating system Config or Enable mode on master or local
switches

AOS-W 3.4.1 Command Line Interface | Reference Guide show port stats | 937
show port stats
show port status
Description
Displays the activity statistics on each of the port on the switch.
Syntax
No Parameters
Example
The output of this command shows the link status on all ports in the switch.
Command History
This command was available in AOS-W 3.3.2
Command Information
(host) # #show port stats
Port Statistics
---------------
Port PacketsIn PacketsOut BytesIn BytesOut InputErrorBytes OutputErrorBytes CRCErrors
---- --------- ---------- ------- -------- --------------- ---------------- ---------
...
...
FE1/4 0 0 0 0 0 0 0
FE1/5 0 0 0 0 0 0 0
FE1/6 0 0 0 0 0 0 0
FE1/7 0 0 0 0 0 0 0
FE1/8 0 0 0 0 0 0 0
FE1/9 0 0 0 0 0 0 0
FE1/10 0 2041530 0 296644355 0 0 0
FE1/11 0 0 0 0 0 0 0
FE1/12 0 0 0 0 0 0 0
FE1/13 0 0 0 0 0 0 0
FE1/14 0 3 0 138 0 0 0
FE1/15 0 0 0 0 0 0 0
FE1/16 2937495 1861880 582814945 244607030 32 0 2
FE1/17 0 0 0 0 0 0 0
FE1/18 591066 1220117 67049881 143261677 0 0 0
FE1/19 0 0 0 0 0 0 0
FE1/20 1205264 836266 211330696 85313659 80 0 5
FE1/21 0 0 0 0 0 0 0
FE1/22 0 0 0 0 0 0 0
...
...
Platforms Licensing Command Mode
All platforms Base operating system Config or Enable mode on master or local
switches
938 | show port status AOS-W 3.4.1 Command Line Interface | Reference Guide
show port status
show port status
Description
Displays the status of all ports on the switch.
Syntax
No Parameters
Example
The output of this command shows the status of all ports in the switch.
Command History
This command was available in AOS-W 3.3.2
Command Information
(host) # show port status
Port Status
-----------
Slot-Port PortType adminstate operstate poe Trusted SpanningTree PortMode
--------- -------- ---------- --------- --- ------- ------------ --------
1/0 FE Enabled Up Enabled Yes Forwarding Access
1/1 FE Enabled Down Enabled Yes Disabled Access
1/2 FE Enabled Down Enabled Yes Disabled Access
1/3 FE Enabled Down Enabled Yes Disabled Access
1/4 FE Enabled Down Enabled Yes Disabled Access
1/5 FE Enabled Down Enabled Yes Disabled Access
1/6 FE Enabled Down Enabled Yes Disabled Access
1/7 FE Enabled Down Enabled Yes Disabled Access
1/8 FE Enabled Down Enabled Yes Disabled Access
1/9 FE Enabled Down Enabled Yes Disabled Access
1/10 FE Enabled Down Enabled Yes Disabled Access
1/11 FE Enabled Down Enabled Yes Disabled Access
1/12 FE Enabled Down Enabled Yes Disabled Access
1/13 FE Enabled Down Enabled Yes Disabled Access
1/14 FE Enabled Down Enabled Yes Disabled Access
1/15 FE Enabled Down Enabled Yes Disabled Access
1/16 FE Enabled Up Enabled Yes Forwarding Access
...
...
...
Platforms Licensing Command Mode
All platforms Base operating system Config or Enable mode on master or local
switches

AOS-W 3.4.1 Command Line Interface | Reference Guide show port trusted | 939
show port trusted
show port trusted
Description
Displays the list of ports configured with trusted profiles.
Syntax
No Parameters
Example
The output of this command shows the list of ports with trusted profile.
Command History
This command was available in AOS-W 3.3.2
Command Information
(host) # show port trusted
FE 1/0
FE 1/1
FE 1/2
FE 1/3
FE 1/4
FE 1/5
FE 1/6
FE 1/7
FE 1/8
FE 1/9
FE 1/10
FE 1/11
FE 1/12
FE 1/13
FE 1/14
FE 1/15
FE 1/16
FE 1/17
FE 1/18
FE 1/19
FE 1/20
FE 1/21
FE 1/22
FE 1/23
GE 1/24
GE 1/25
Platforms Licensing Command Mode
All platforms Base operating system Config or Enable mode on master or local
switches
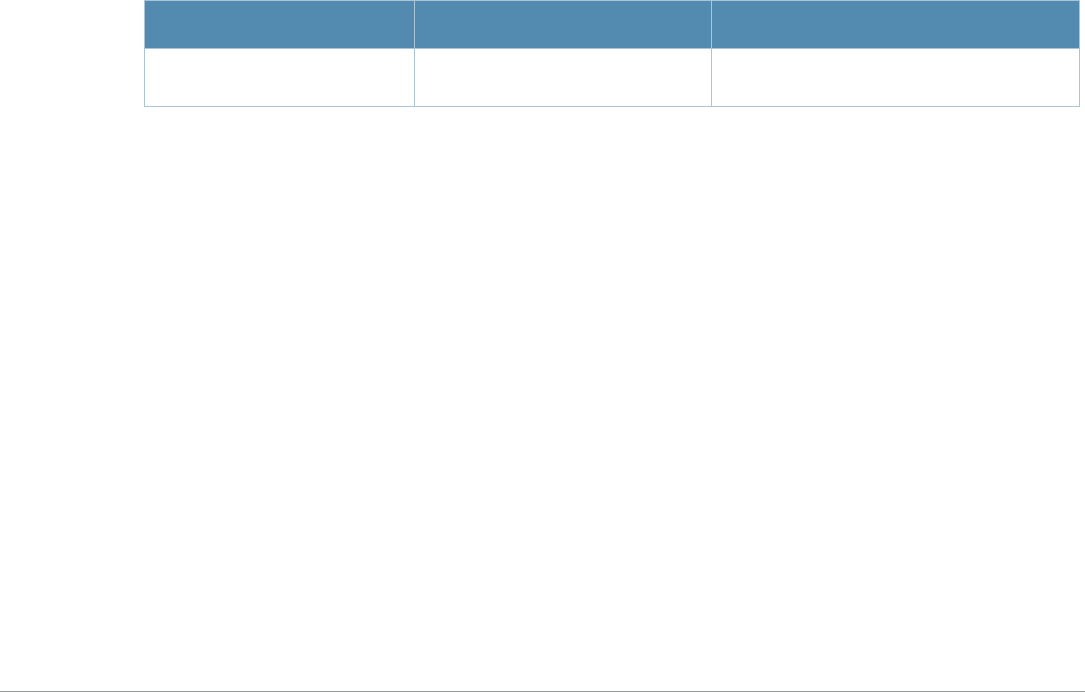
940 |show port xsec AOS-W 3.4.1 Command Line Interface | Reference Guide
show port xsec
show port xsec
Description
Displays the list of xSec enabled ports.
Syntax
No Parameters
Example
The output of this command shows the list of xSec enabled ports.
Command History
This command was available in AOS-W 3.3.2
Command Information
(host) # #show port xsec
Xsec Ports
----------
Interface xsec vlan state
--------- --------- -----
Platforms Licensing Command Mode
All platforms Base operating system Config or Enable mode on master or local
switches
AOS-W 3.4.1 Command Line Interface | Reference Guide show priority-map | 941
show priority-map
show priority-map
Description
Displays the list of priority maps on a interface.
Syntax
No Parameters
Example
The output of this command shows the priority maps configured on all interfaces.
Command History
This command was available in AOS-W 3.0
Command Information
(host) # show priority-map
Priority Map
-------------
ID Name DSCP-TOS DOT1P-COS
-- ---- -------- ---------
1 my-map 4-20,60 4-7
Platforms Licensing Command Mode
All platforms Base operating system Config or Enable mode on master or local
switches

942 |show priority-map AOS-W 3.4.1 Command Line Interface | Reference Guide
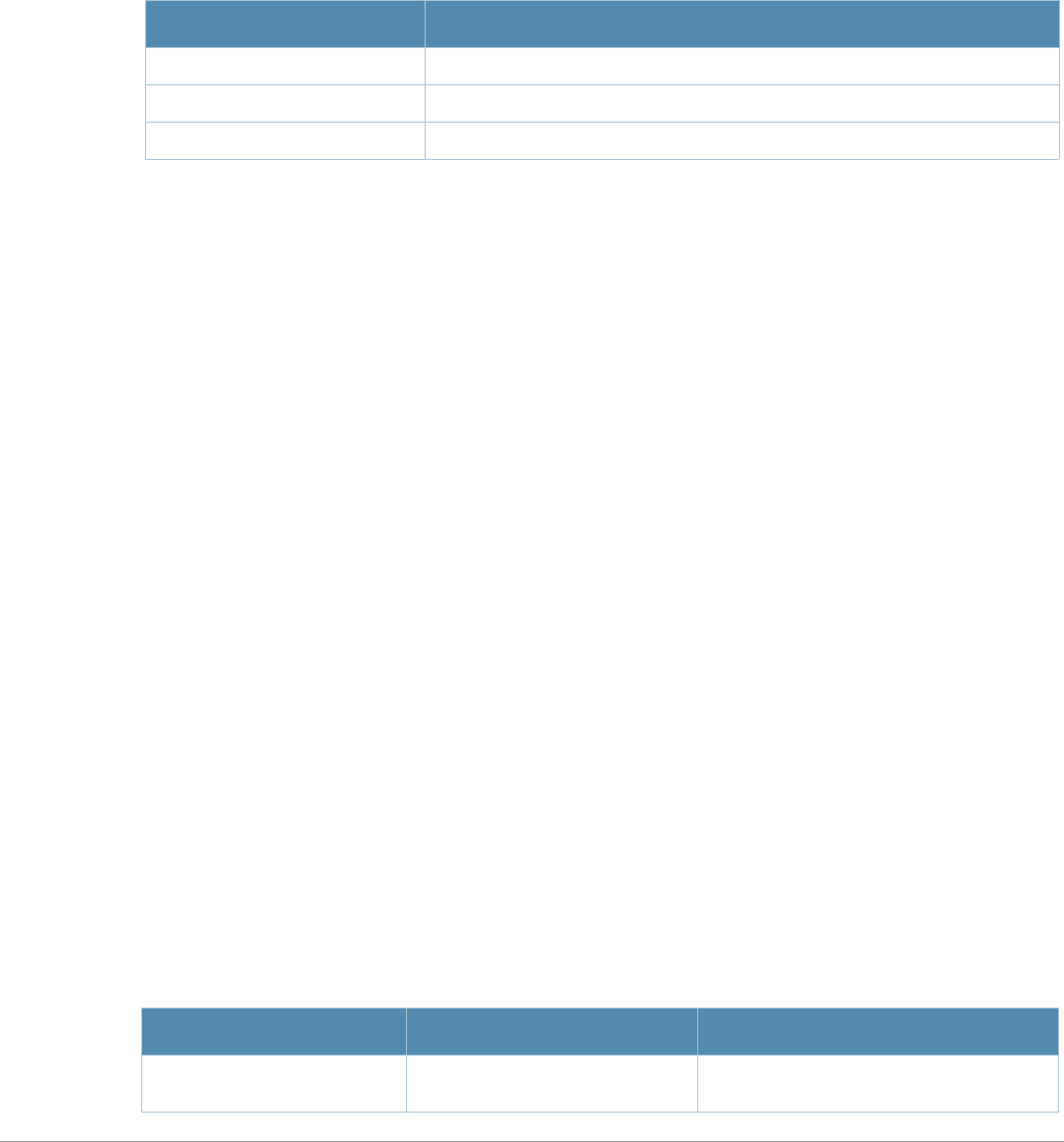
AOS-W 3.4.1 Command Line Interface | Reference Guide show processes | 943
show processes
show processes [sort-by {cpu | memory}]
Description
Displays the list of all process running on the switch. You can sort the list either by CPU intensive or
memory intensive processes.
Syntax
Example
The output of this command shows list of processes sorted by CPU usage.
Command History
This command was available in AOS-W 3.0
Command Information
Parameter Description
sort-by To add sort filter to the output
cpu This will sort output based on CPU usage.
memory This will sort output based on memory usage.
(host) # show priority-map
%CPU S PID PPID VSZ RSS F NI START TIME EIP CMD
3.7 S 595 517 20908 12184 040 0 Apr24 03:39:04 303a4fa8 /mswitch/bin/fpapps
0.2 S 12354 410 1028 296 000 0 02:13 00:00:00 30087fa8 sleep 10
0.1 S 536 441 12012 7264 040 0 Apr24 00:09:08 100e4a74 /mswitch/mysql/libexec/mysqld --basedir=/m
datadir=/var/
0.0 S 2 1 0 0 040 0 Apr24 00:00:00 00000000 [keventd]
0.0 S 4 0 0 0 040 0 Apr24 00:00:00 00000000 [kswapd]
0.0 S 6 0 0 0 040 0 Apr24 00:00:00 00000000 [kupdated]
0.0 S 57 1 0 0 040 0 Apr24 00:00:00 00000000 [kjournald]
0.0 S 67 1 1036 424 000 0 Apr24 00:00:00 30087fa8 /bin/sh /mswitch/bin/syslogd_start
0.0 S 1 0 1028 384 100 0 Apr24 00:00:12 30087fa8 init
0.0 S 397 1 1732 804 100 0 Apr24 00:00:00 30152fa8 /mswitch/bin/nanny /mswitch/bin/nanny_list
0.0 S 399 397 14140 10172 100 0 Apr24 00:00:16 303c8fa8 /mswitch/bin/arci-cli-helper
0.0 S 402 1 768 268 040 0 Apr24 00:00:00 30060fa8 /sbin/tftpd -s -l -u nobody /mswitch/sap
0.0 S 69 67 1404 752 100 0 Apr24 00:01:27 300d3fa8 /mswitch/bin/syslogd -x -r -n -m 0 -f /msw
syslog.conf
0.0 S 407 397 3100 1028 100 0 Apr24 00:00:00 302a0fa8 /mswitch/bin/packet_filter
0.0 S 408 397 4296 1340 100 0 Apr24 00:00:00 30339fa8 /mswitch/bin/certmgr
0.0 R 3 0 0 0 040 19 Apr24 00:00:01 00000000 [ksoftirqd_CPU0]
0.0 S 453 397 700 284 000 0 Apr24 00:01:20 30087fa8 /mswitch/bin/msgHandler -g
0.0 S 468 397 1236 492 100 0 Apr24 00:00:00 300f8fa8 /mswitch/bin/pubsub
0.0 S 484 397 18456 14064 100 0 Apr24 00:00:19 303c8fa8 /mswitch/bin/cfgm
Platforms Licensing Command Mode
All platforms Base operating system Config or Enable mode on master or local
switches

944 |show processes AOS-W 3.4.1 Command Line Interface | Reference Guide
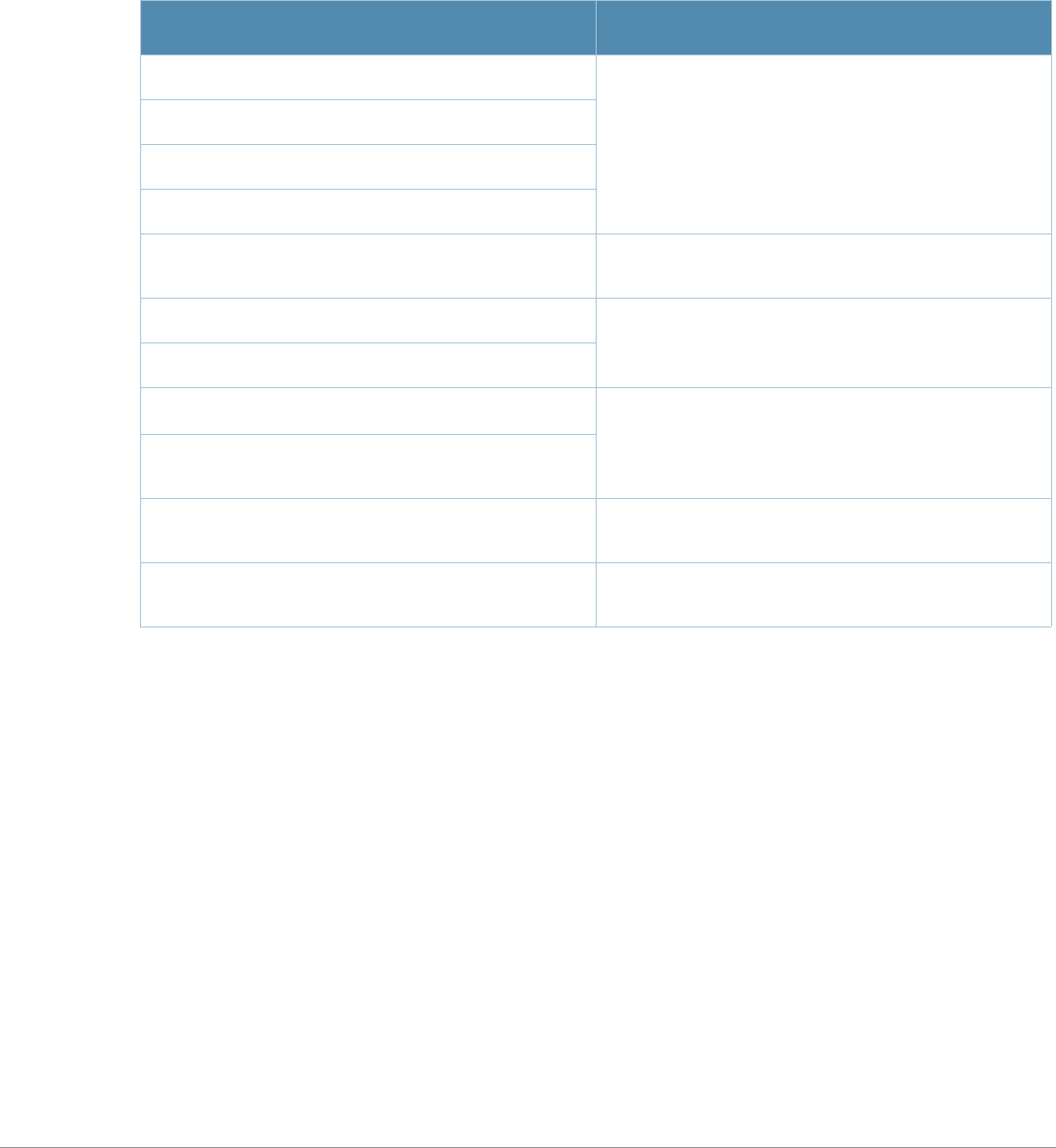
AOS-W 3.4.1 Command Line Interface | Reference Guide show profile-errors | 945
show profile-errors
show profile-errors
Description
Displays the list of invalid user-created profiles. The following are the list of some profile errors:
Syntax
No Parameters
Example
The output of this command shows list of profiles that are invalid and also displays the error in those
profiles. In this example, the VLAN 1000 that is mapped to virtual-ap test-vap does not exist.
Table 1 List of Profile Errors
Error Name Description
Named VLAN [named_VLAN] is removed These errors are displayed if a virtual AP profile is
configure with a VLAN that does not exist.
Named VLAN [named_VLAN] is not mapped
Named VLAN [named_VLAN] is invalid
VLAN [x] does not exist
Server group is invalid This error is displayed if a aaa profile is configured an
invalid server group.
User derivation rule is invalid This error is displayed if a user role in a aaa profile is
invalid.
User role is invalid
Controller country code is undefined These errors are displayed, if your switch is not set to
the correct country code or if the country code specified
in a WLAN profile does not match the switch’s country
code.
Country [country_name] does not match controller
country [country_name]
Opmode requires WPA key This message is displayed if a SSID profile is configured
without a WPA key.
WARNING: if weptxkey = [x], wepkey[x] must be
set in order to use static WEP This message is displayed if a SSID profile is configured
to use a static WEP and the WEP is not configured.
(host) #show profile-errors
Invalid Profiles
----------------
Profile Error
------- -----
wlan virtual-ap "test-vap" VLAN 1000 does not exist

946 | show profile-errors AOS-W 3.4.1 Command Line Interface | Reference Guide
Command History
This command was available in AOS-W 3.0
Command Information
Platforms Licensing Command Mode
All platforms Base operating system Config or Enable mode on master or local
switches

AOS-W 3.4.1 Command Line Interface | Reference Guide show profile-hierarchy | 947
show profile-hierarchy
show profile-hierarchy
Description
Displays the profile hierarchy template.
Syntax
No Parameters
Example
The output of this command shows how profiles relate to each other, and how some higher-level profiles
reference other lower-level profiles.
(host) # show profile-hierarchy
ap-group
wlan virtual-ap
aaa profile
aaa authentication mac
aaa server-group
aaa authentication dot1x
aaa xml-api server
aaa rfc-3576-server
wlan ssid-profile
wlan edca-parameters-profile station
wlan edca-parameters-profile ap
wlan ht-ssid-profile
rf dot11a-radio-profile
rf arm-profile
rf ht-radio-profile
rf dot11g-radio-profile
rf arm-profile
rf ht-radio-profile
ap wired-ap-profile
ap enet-link-profile
ap system-profile
wlan voip-cac-profile
wlan traffic-management-profile
ap regulatory-domain-profile
ap snmp-profile
ap snmp-user-profile
rf optimization-profile
rf event-thresholds-profile
ids profile
ids general-profile
ids signature-matching-profile
ids signature-profile
ids dos-profile
ids rate-thresholds-profile
ids impersonation-profile
ids unauthorized-device-profile
ap mesh-radio-profile
ap mesh-ht-ssid-profile

948 | show profile-hierarchy AOS-W 3.4.1 Command Line Interface | Reference Guide
Command History
This command was available in AOS-W 3.0
Command Information
Platforms Licensing Command Mode
All platforms Base operating system Config or Enable mode on master or local
switches
AOS-W 3.4.1 Command Line Interface | Reference Guide show profile-list aaa | 949
show profile-list aaa
show profile-list aaa [{authentication [captive-portal | dot1x | mac | stateful-ntlm |
wispr]} |{authentication-server [ldap | radius | tacacs | windows]} | {profile} | {rfc-
3576-server} | {server-group} | {xml-api}]
Description
Displays the list of aaa profiles.
Syntax
Example
The output of this command shows list of aaa profiles that use captive-portal authentication.
Command History
This command was available in AOS-W 3.0
Command Information
Parameter Description
authentication List of aaa authentication profiles.
captive-portal Captive portal authentication profiles.
dot1x 802.1x authentication profiles.
mac MAC authentication profiles.
stateful-ntlm Stateful-NTLM authentication profiles.
wispr WISPr authentication profiles.
authentication-server List of aaa authentication servers
ldap List of servers using LDAP for AAA authentication.
radius List of servers using RADIUS for AAA authentication.
tacacs List of servers using TACACS+ for AAA authentication.
windows List of Windows servers used for AAA authentication.
profile Displays the aaa profile details.
rfc-3576-server Displays IP address of RADIUS servers that use RFC 3576 specification to
exchange authorization messages.
server-group List of server group used for RADIUS accounting.
xml-api List of servers configured in an external XML API server.
(host) # show profile-list aaa authentication captive-portal
Captive Portal Authentication Profile List
------------------------------------------
Name References Profile Status
---- ---------- --------------
default 1

950 | show profile-list aaa AOS-W 3.4.1 Command Line Interface | Reference Guide
Platforms Licensing Command Mode
All platforms Base operating system Config or Enable mode on master or local
switches

AOS-W 3.4.1 Command Line Interface | Reference Guide show profile-list ap | 951
show profile-list ap
show profile-list ap [ enet-link-profile | mesh-cluster-profile |
mesh-ht-ssid-profile | mesh-radio-profile | regulatory-domain-profile |
snmp-profile | snmp-user-profile | system-profile | wired-ap-profile ]
Description
Displays the list of AP profiles.
Syntax
Example
The output of this command shows list of profiles that are invalid and also displays the error in those
profiles.
Command History
This command was available in AOS-W 3.0
Command Information
Parameter Description
enet-link-profile Display a list of AP ethernet link profiles.
mesh-cluster-profile Display a list of mesh cluster profiles used by mesh nodes.
mesh-ht-ssid-profile Display a list of mesh high-throughput SSID profiles used by mesh nodes.
mesh-radio-profile Display a list of mesh radio profiles used by mesh nodes.
regulatory-domain-profile Display a list of AP regulatory profiles.
snmp-profile Display a list of SNMP profiles.
snmp-user-profile Display a list of SNMPv3 user profiles.
system-profile Display a list of AP system profiles.
wired-ap-profile Display a list ofwired AP profiles.
(host) # show profile-list aaa authentication captive-portal
Captive Portal Authentication Profile List
------------------------------------------
Name References Profile Status
---- ---------- --------------
default 1
Platforms Licensing Command Mode
All platforms Base operating system Config or Enable mode on master or local
switches

952 | show profile-list ap-group AOS-W 3.4.1 Command Line Interface | Reference Guide
show profile-list ap-group
show profile-list ap-group
Description
Displays the status of AP groups profiles in the switch.
Syntax
No Parameters
Example
The output of this command shows the status of AP group profiles in the switch.
Command History
This command was available in AOS-W 3.0
Command Information
(host) # show profile-list ap-group
AP group List
-------------
Name Profile Status
---- --------------
default
Total:1
Platforms Licensing Command Mode
All platforms Base operating system Config or Enable mode on master or local
switches

AOS-W 3.4.1 Command Line Interface | Reference Guide show profile-list ap-name | 953
show profile-list ap-name
show profile-list ap-name
Description
Displays the status of AP profiles in the switch.
Syntax
No Parameters
Example
The output of this command shows status of AP profiles in the switch.
Command History
This command was available in AOS-W 3.0
Command Information
(host) # show profile-list ap-name
AP name List
------------
Name Profile Status
---- --------------
Total:0
Platforms Licensing Command Mode
All platforms Base operating system Config or Enable mode on master or local
switches
954 | show profile-list ids AOS-W 3.4.1 Command Line Interface | Reference Guide
show profile-list ids
show profile-list ids [dos-profile | general-profile | impersonation-profile |
profile | rate-thresholds-profile | signature-matching-profile |
signature-profile | unauthorized-device-profile ]
Description
Displays the status of all IDS profiles in the switch.
Syntax
Example
The output of this command shows a list of all IDS DoS profiles.
Command History
This command was available in AOS-W 3.0
Command Information
Parameter Description
dos-profile Display a list of IDS DoS profiles.
general-profile Display a list of IDS generate profiles.
impersonation-profile Display a list IDS impersonation profile.
profile Display a list of IDS profiles.
rate-thresholds-profile Display a list of IDS rate threshold profiles.
signature-matching-profile Display a list of IDS signature-matching profiles.
signature-profile Display a list of IDS signature profiles.
unauthorized-device-profile Display a list of IDS unauthorized device profiles.
(host) # show profile-list ids dos-profile
IDS Denial Of Service Profile List
----------------------------------
Name References Profile Status
---- ---------- --------------
default 1
ids-dos-disabled 1 Predefined
ids-dos-high-setting 1 Predefined
ids-dos-low-setting 1 Predefined
ids-dos-medium-setting 1 Predefined
Total:5
Platforms Licensing Command Mode
All platforms Base operating system Config or Enable mode on master or local
switches
AOS-W 3.4.1 Command Line Interface | Reference Guide show profile-list rf | 955
show profile-list rf
show profile-list rf [ arm-profile | dot11a-radio-profile | dot11g-radio-profile |
event-thresholds-profile | ht-radio-profile | optimization-profile ]
Description
Displays the status of all radio profiles.
Syntax
Example
The output of this command shows status of ARM profile.
Command History
This command was available in AOS-W 3.0
Command Information
Parameter Description
arm-profile Details of Adaptive Radio Management (ARM) Profile.
dot11a-radio-profile Details of AP radio settings for the 5GHz frequency band, including the
ARM profile and the high-throughput (802.11n) radio profile.
dot11g-radio-profile Details of AP radio settings for the 2.4 GHz frequency band, including the
ARM profile and the high-throughput (802.11n) radio profile.
event-thresholds-profile Details of events thresholds profile.
ht-radio-profile Details of high-throughput AP radio settings
optimization-profile Details of the RF optimization profile
(host) # show profile-list rf arm-profile
Adaptive Radio Management (ARM) profile List
--------------------------------------------
Name References Profile Status
---- ---------- --------------
default 2
Total:1
Platforms Licensing Command Mode
All platforms Base operating system Config or Enable mode on master or local
switches

956 | show profile-list wlan AOS-W 3.4.1 Command Line Interface | Reference Guide
show profile-list wlan
show profile-list wlan [ dotllk-profile | edca-parameters-profile | ht-ssid-profile |
ssid-profile | traffic-management-profile | virtual-ap | voip-cac-profile | wmm-
traffic-management-profile]
Description
Displays the status of WLAN profiles on the switch.
Syntax
Example
The output of this command shows that the switch has a single ARM profile, “default”.
Command History
This command was available in AOS-W 3.0
Command Information
Parameter Description
dot11k-profile Show a list of all 802.11K Profiles
edca-parameters-profile Show a list of all enhanced distributed channel access (EDCA) profile for
APs or for clients (stations)
ht-ssid-profile Show a list of all high-throughput SSID profile.s
traffic-management-profile Show a list of all traffic management profiles.
virtual-ap Show a list of all the virtual AP profiles.
voip-cac-profile Show a list of all voice over IP (VoIP) call admission control (CAC) profiles
wmm-traffic-management-
profile
Show a list of all WMM traffic management profiles.
(host) # show profile-list rf arm-profile
Adaptive Radio Management (ARM) profile List
--------------------------------------------
Name References Profile Status
---- ---------- --------------
default 2
Total:1
Platforms Licensing Command Mode
All platforms Base operating system Config or Enable mode on master or local
switches
AOS-W 3.4.1 Command Line Interface | Reference Guide show provisioning-ap-list | 957
show provisioning-ap-list
show provisioning-ap-list
Description
Displays the list of all APs that are in queue to be provisioned by the admin.
Syntax
No Parameters
Command History
This command was available in AOS-W 3.4
Command Information
Platforms Licensing Command Mode
All platforms Base operating system Config or Enable mode on master or local
switches

958 |show provisioning-ap-list AOS-W 3.4.1 Command Line Interface | Reference Guide

AOS-W 3.4.1 Command Line Interface | Reference Guide show provisioning-params | 959
show provisioning-params
show provisioning-params
Description
Displays the list of parameters and the values used to provision the APs.
Syntax
No Parameters
Example
The output of this command shows list of all provisioning parameters and their values.
(host) # show provisioning-params
AP provisioning
---------------
Parameter Value
--------- -----
AP Name N/A
AP Group default
Location name N/A
SNMP sysLocation N/A
Master N/A
Gateway N/A
Netmask N/A
IP Addr N/A
DNS IP N/A
Domain Name N/A
Server Name N/A
Server IP N/A
Antenna gain for 802.11a N/A
Antenna gain for 802.11g N/A
Use external antenna No
Antenna for 802.11a both
Antenna for 802.11g both
IKE PSK N/A
PAP User Name N/A
PAP Password N/A
PPPOE User Name N/A
PPPOE Password N/A
PPPOE Service Name N/A
USB User Name N/A
USB Password N/A
USB Device Type any
USB Device Identifier N/A
USB Dial String N/A
USB Initialization String N/A
USB TTY device path N/A
Mesh Role none
Installation default
Latitude N/A
Longitude N/A
Altitude N/A
Antenna bearing for 802.11a N/A
Antenna bearing for 802.11g N/A
Antenna tilt angle for 802.11a N/A
Antenna tilt angle for 802.11g N/A

960 | show provisioning-params AOS-W 3.4.1 Command Line Interface | Reference Guide
Command History
This command was available in AOS-W 3.0
Command Information
Platforms Licensing Command Mode
All platforms Base operating system Config or Enable mode on master or local
switches

AOS-W 3.4.1 Command Line Interface | Reference Guide show rap-wml | 961
show rap-wml
show rap-wml [cache <server-name> | server | wired-mac <bssid-of-AP> ]
Description
Displays the name and attributes of a MySQL database or a MySQL server.
Syntax
Example
The output of this command shows status of all database servers.
Command History
This command was available in AOS-W 3.0
Command Information
Parameter Description
cache Displays the cache of all lookups for a database server
servers Displays the database server state.
wired-mac Displays the wired MAC discovered on traffic through the AP
(host) # #show rap-wml servers
WML DB Servers
--------------
name ip type user password db-name cache ageout(sec) in-service
---- -- ---- ---- -------- ------- ----- ----------- ----------
WML DB Tables
-------------
server db table column timestamp-column lookup-time(sec) delimiter query-count
------ -- ----- ------ ---------------- ---------------- --------- -----------
Mesh SAE sae-default
Platforms Licensing Command Mode
All platforms Base operating system Config or Enable mode on master or local
switches

962 | show rap-wml AOS-W 3.4.1 Command Line Interface | Reference Guide

AOS-W 3.4.1 Command Line Interface | Reference Guide show references aaa authentication | 963
show references aaa authentication
crypto-local
show references aaa authentication {captive-portal <profile-name>}|{dot1x <profile-
name>}|{mac <profile-name>}|mgmt|stateful-dot1x|{stateful-ntlm <profile-
name>}|vpn|wired|{wispr {profile-name>} [page <number>] [start <number>]
Description
Show AAA profile references.
Syntax
Example
Use this command to show where a specified AAA profile has been applied. The output of the example
shown below indicates that the aaa profile default-dot1x contains a single reference to the 802.1x
authentication profile default.
Parameter Description
captive-portal <profile-name> Show the number of references to a captive-portal profile.
dot1x <profile-name> Show the number of references to a 802.1x authentication profile.
mac <profile-name> Show the number of references to a MAC authentication profile.
mgmt <profile-name> Show the number of references to a management authentication
profile.
stateful-dot1x Show the number of references to the stateful 802.1X authentication
profile.
stateful-ntlm <profile-name> Show the number of references to the specified stateful NTLM
authentication profile.
vpn Show the number of references to VPN authentication.
wired Show the number of references to wired authentication.
wired Show the number of references to a wispr authentication.
wispr <profile-name> Show the number of references to the specified WISPr authentication
profile.
page <number> Include this optional parameter to limit output of this command to the
specified number of items.
start <number> Include this optional parameter to start displaying the output of this
command at the specified index number.
(host) #show references aaa authentication dot1x default
References to 802.1X Authentication Profile "default"
-----------------------------------------------------
Referrer Count
-------- -----
aaa profile "default-dot1x" authentication-dot1x 1
Total References:1

964 | show references aaa authentication AOS-W 3.4.1 Command Line Interface | Reference Guide
Command History.
Command Information
Version Modification
AOS-W 3.0 Command introduced
AOS-W 3.4.1 The stateful-ntlm and wispr parameters were introduced.
Platforms Licensing Command Mode
Available on all platforms Base operating system Config mode on master and local switches

AOS-W 3.4.1 Command Line Interface | Reference Guide show references aaa authentication-server | 965
show references aaa authentication-server
crypto-local
show references aaa authentication-server {ldap <ladp-server-name>}|{radius <radius-
server-name>}|{tacacs <tacacs-server-name>} [page <number>] [start <number>]
Description
Display information about AAA authentication servers.
Syntax
Example
Issue this command to show the AAA server groups that include references to the specified server. The
example below shows that two server groups, default and rad, each include a single reference to the
radius server rad01.
Command History
This command was introduced in AOS-W 3.0.
Command Information
Parameter Description
ldap <ladp-server-name> Show the number of server groups that include references to the
specified LDAP server.
radius <radius-server-name> Show the number of server groups that include references to the
specified RADIUS server.
tacacs <radius-server-name> Show the number of server groups that include references to the
specified TACACS server.
page <number> Include this optional parameter to limit output of this command to the
specified number of items.
start <number> Include this optional parameter to start displaying the output of this
command at the specified index number.
Platforms Licensing Command Mode
Available on all platforms Base operating system Config mode on master and local switches
(host) #show references aaa authentication-server radius rad01
References to RADIUS Server "rad01"
-----------------------------------
Referrer Count
-------- -----
aaa server-group "default" server_group 1
aaa server-group "rad" server_group 1
Total References:2
966 | show references aaa profile AOS-W 3.4.1 Command Line Interface | Reference Guide
show references aaa profile
crypto-local
show references aaa profile <profile-name>
Description
Show references to an AAA Profile.
Syntax
Example
Issue this command to show the wlan virtual AP profiles that include references to the specified AAA
profile. The example below shows that seven different virtual AP profiles include a single reference to the
AAA profile default.
Command History
This command was introduced in AOS-W 3.0.
Command Information
Parameter Description
profile <profile-name> Name of an AAA profile for which you want to view references.
Platforms Licensing Command Mode
Available on all platforms Base operating system Config mode on master and local switches
(host) #References to AAA Profile "default"
-----------------------------------
Referrer Count
-------- -----
wlan virtual-ap "1.0.0_corporateHQ-wpa2" aaa-profile 1
wlan virtual-ap "110.0.corporateHQ-wpa2" aaa-profile 1
wlan virtual-ap "default" aaa-profile 1
wlan virtual-ap "corporateHQ-vocera" aaa-profile 1
wlan virtual-ap "corporateHQ-voip-wpa2" aaa-profile 1
wlan virtual-ap "Test123" aaa-profile 1
wlan virtual-ap "branch12" aaa-profile 1
Total References:7
AOS-W 3.4.1 Command Line Interface | Reference Guide show references aaa server-group | 967
show references aaa server-group
crypto-local
show references aaa server-group <sg-name> [page] [start]}
Description
Show references to a server group.
Syntax
Example
.Issue this command to display a list of AAA profiles that include references to the specified server group.
Command History
This command was introduced in AOS-W 3.0.
Command Information
Parameter Description
server-group <sg-name> Name of the server group for which you want to show references
page <number> Include this optional parameter to limit output of this command
to the specified number of items.
start <number> Include this optional parameter to start displaying the output of
this command at the specified index number.
Platforms Licensing Command Mode
Available on all platforms Base operating system Config mode on master and local switches
(host) #show references aaa server-group default
References to Server Group "default"
------------------------------------
Referrer Count
-------- -----
aaa profile "aircorp-office-ssid" mac-server-group 1
aaa profile "amigopod-guest" mac-server-group 1
aaa profile "default" mac-server-group 1
aaa profile "default-airwave-office" mac-server-group 1
aaa profile "defaultcorporate" mac-server-group 1
aaa profile "defaultcorporate-no-okc" mac-server-group 1
aaa profile "defaultcorporate-okc" mac-server-group 1
aaa profile "default-dot1x" mac-server-group 1
aaa profile "default-India" mac-server-group 1
aaa profile "default-india-hotel" mac-server-group 1
aaa profile "default-India-split" mac-server-group 1
aaa profile "voip-psk" mac-server-group 1
aaa profile "default-dot1x-psk" mac-server-group 1
aaa profile "default-mac-auth" mac-server-group 1
aaa profile "default-open" mac-server-group 1
aaa profile "default-xml-api" mac-server-group 1
Total References:16

968 | show references ap AOS-W 3.4.1 Command Line Interface | Reference Guide
show references ap
crypto-local
show references ap
enet-link-profile <profile-name>
mesh-cluster-profile <profile-name>
mesh-ht-ssid-profile <profile-name>
mesh-radio-profile <profile-name>
regulatory-domain-profile <profile-name>
system-profile <profile-name>
wired-ap-profile <profile-name>
page <number>
start <number>
Description
Show the number of references to a specific AP profile.
Syntax
Parameter Description
enet-link-profile
<profile-name>
Show AP groups that include a references to this ethernet link profile.
mesh-cluster-profile
<profile-name>
Show AP groups that include a references to this mesh cluster profile.
mesh-ht-ssid-profile
<profile-name>
Show AP groups that include a references to this mesh high-throughput
SSID profile.
mesh-radio-profile
<profile-name>
Show AP groups that include a references to this mesh radio profile.
regulatory-domain-profile
<profile-name>
Show AP groups that include a references to this regulatory domain profile.
system-profile <profile-
name>
Show AP groups that include a references to this system profile.
wired-ap-profile <profile-
name>
Show AP groups that include a references to this wired AP profile.
page <number> Include this optional parameter to limit output of this command to the
specified number of items.
start <number> Include this optional parameter to start displaying the output of this
command at the specified index number.

AOS-W 3.4.1 Command Line Interface | Reference Guide show references ap | 969
Example
The example below shows that 10 different AP groups include links to the AP ethernet link profile Default.
These 10 AP groups reference the Default ethernet link profile for both their ethernet 0 and ethernet 1
interfaces, for a total of 20 references altogether.
Command History
This command was introduced in AOS-W 3.0.
Command Information
Platforms Licensing Command Mode
Available on all platforms Base operating system Config mode on master and local switches
(host)#show references ap enet-link-profile default
References to AP Ethernet Link profile "default"
------------------------------------------------
Referrer Count
-------- -----
ap-group "10.0.0" enet0-profile 1
ap-group "10.0.0" enet1-profile 1
ap-group "corp" enet0-profile 1
ap-group "corp" enet1-profile 1
ap-group "Corp_AM_Ch1" enet0-profile 1
ap-group "Corp_AM_Ch1" enet1-profile 1
ap-group "Corp_AM_Ch6" enet0-profile 1
ap-group "Corp_AM_Ch6" enet1-profile 1
ap-group "corpTest" enet0-profile 1
ap-group "corpTest" enet1-profile 1
ap-group "default" enet0-profile 1
ap-group "default" enet1-profile 1
ap-group "India_Local" enet0-profile 1
ap-group "India_Local" enet1-profile 1
ap-group "ops" enet0-profile 1
ap-group "ops" enet1-profile 1
ap-group "voip-test" enet0-profile 1
ap-group "voip-test" enet1-profile 1
ap-group "voip-test-nokia" enet0-profile 1
ap-group "voip-test-nokia" enet1-profile 1
Total References:20
970 | show references guest-access-email AOS-W 3.4.1 Command Line Interface | Reference Guide
show references guest-access-email
crypto-local
show references guest-access-email [page <number>] [start <number>]
Description
Show references to the global guest access email profile.
Syntax
Example
Command History
This command was introduced in AOS-W 3.0.
Command Information
Parameter Description
page <number> Include this optional parameter to limit output of this command to the
specified number of items.
start <number> Include this optional parameter to start displaying the output of this
command at the specified index number.
Platforms Licensing Command Mode
Available on all platforms Base operating system Config mode on master and local switches
(host) #show references guest-access-email
References to Guest-access Email Profile
----------------------------------------
Referrer Count
-------- -----
Total References:0
AOS-W 3.4.1 Command Line Interface | Reference Guide show references ids | 971
show references ids
crypto-local
show references ids
dos-profilegeneral-profile
general-profile
impersonation-profile
profile
rate-thresholds-profile
signature-matching-profile
signature-profile
unauthorized-device-profile
Description
Displays IDS profile references.
Syntax
Command History
This command was introduced in AOS-W 3.0.
Command Information
Parameter Description
dos-profilegeneral-profile Show references to an IDS Denial Of Service Profile
general-profile Show references to an IDS General Profile
impersonation-profile Show references to an IDS Impersonation Profile
profile Show references to an IDS Profile
rate-thresholds-profile Show references to an IDS Rate Thresholds Profile
signature-matching-profile Show references to an IDS Signature Matching Profile
signature-profile Show references to an IDS Signature Profile
unauthorized-device-
profile
Show references to an IDS Signature Profile
Platforms Licensing Command Mode
Available on all platforms Base operating system Config mode on master and local switches
972 | show references papi-security AOS-W 3.4.1 Command Line Interface | Reference Guide
show references papi-security
crypto-local
show references papi-security [page <number>] [start <number>]
Description
Show references to a PAPI security profile.
Syntax
Example
Command History
This command was introduced in AOS-W 3.4.
Command Information
Parameter Description
page <number> Include this optional parameter to limit output of this command to the
specified number of items.
start <number> Include this optional parameter to start displaying the output of this
command at the specified index number.
Platforms Licensing Command Mode
Available on all platforms Base operating system Config mode on master and local switches
(host) #show references papi-security
References to PAPI Security Profile
-----------------------------------
Referrer Count
-------- -----
Total References:0
AOS-W 3.4.1 Command Line Interface | Reference Guide show references rf | 973
show references rf
crypto-local
show references rf
dot11a-radio-profile <profile-name>
dot11g-radio-profile <profile-name>
event-thresholds-prof <profile-name>
ht-radio-profile <profile-name>
optimization-profile <profile-name>
Description
Show RF profile references.
Syntax
Command History
This command was introduced in AOS-W 3.0.
Command Information
Parameter Description
dot11a-radio-profile Show references to a 802.11a radio profile
dot11g-radio-profile Show references to a 802.11g radio profile
event-thresholds-prof Show references to an RF Event Thresholds Profile
ht-radio-profile Show references to a High-throughput radio profile
optimization-profile Show references to an RF Optimization Profile
Platforms Licensing Command Mode
Available on all platforms Base operating system Config mode on master and local switches
974 | show references user-role AOS-W 3.4.1 Command Line Interface | Reference Guide
show references user-role
crypto-local
show references user-role <role_name>
Description
Show access rights for user role.
Syntax
Example
Command History
This command was introduced in AOS-W 3.0.
Command Information
Parameter Description
<role_name> The role name assigned to a user.
Platforms Licensing Command Mode
Available on all platforms Base operating system Config mode on master and local switches
(host) #show references user-role guest
References to User Role "guest"
-------------------------------
aaa profile "airwave-office-ssid" mac-default-role
aaa profile "amigopod-guest" mac-default-role
aaa profile "corp1344-voip" mac-default-role
aaa profile "default" mac-default-role
aaa profile "default-airwave-office" mac-default-role
aaa profile "default-corp1344" mac-default-role
aaa profile "default-corp1344-no-okc" mac-default-role
aaa profile "default-corp1344-okc" mac-default-role
aaa profile "default-dot1x" mac-default-role
aaa profile "default-dot1x-psk" mac-default-role
aaa profile "default-dot1x-psk" dot1x-default-role
aaa profile "default-India" mac-default-role
aaa profile "default-india-hotel" mac-default-role
AOS-W 3.4.1 Command Line Interface | Reference Guide show references web-server | 975
show references web-server
crypto-local
show references web-server [page <number>] [start <number>]
Description
Show the Web server configuration references.
Syntax
Example
Command History
This command was introduced in AOS-W 3.0.
Command Information
Parameter Description
page <number> Include this optional parameter to limit output of this command to the
specified number of items.
start <number> Include this optional parameter to start displaying the output of this
command at the specified index number.
Platforms Licensing Command Mode
Available on all platforms Base operating system Config mode on master and local switches
(host) #show references web-server
References to Web Server Configuration
--------------------------------------
Referrer Count
-------- -----
Total References:0

976 | show references wlan AOS-W 3.4.1 Command Line Interface | Reference Guide
show references wlan
crypto-local
show references wlan
dot11k-profile <profile-name>
edca-parameters-profile <profile-name>
ht-ssid-profile <profile-name>
ssid-profile <profile-name>
traffic-management-pr <profile-name>
virtual-ap <profile-name>
voip-cac-profile <profile-name>
Description
Shows WLAN profile references.
Syntax
Example
Command History
This command was introduced in AOS-W 3.0.
Command Information
Parameter Description
dot11k-profile <profile-name> Shows references to a 802.11K profile.
edca-parameters-profile <profile-
name>
Shows references to an EDCA parameters profile.
ht-ssid-profile <profile-name> Shows references to a high-throughput SSID profile.
ssid-profile <profile-name> Shows references to an SSID management profile.
traffic-management-pr <profile-name> Shows references to a traffic management profile.
virtual-ap <profile-name> Shows references to a virtual AP profile.
voip-cac-profile <profile-name> Shows references to a VOIP Call Admission Control profile.
Platforms Licensing Command Mode
Available on all platforms Base operating system Config mode on master and local switches
(host) #show references web-server
References to Web Server Configuration
--------------------------------------
Referrer Count
-------- -----
Total References:0

AOS-W 3.4.1 Command Line Interface | Reference Guide show rf arm-profile | 977
show rf arm-profile
show rf arm-profile [<profile>]
Description
Show an Adaptive Radio Management (ARM) profile.
Syntax
Usage Guidelines
Issue this command without the <profile> parameter to display the entire ARM profile list, including
profile status and the number of references to each profile. Include a profile name to display detailed
configuration information for that profile.
Examples
The example below shows that the switch has five configured ARM profiles. The References column lists
the number of other profiles with references to the ARM profile, and the Profile Status column indicates
whether the profile is predefined. User-defined profiles will not have an entry in the Profile Status column.
Parameter Description
<profile> Name of an ARM profile.
(host) # show rf arm-profile
Adaptive Radio Management (ARM) profile List
--------------------------------------------
Name References Profile Status
---- ---------- --------------
airwave 2
default 4
default-AP85 2
no-scanning 1
Wireless-rf-profile 1
Total:5

978 |show rf arm-profile AOS-W 3.4.1 Command Line Interface | Reference Guide
This example displays the configuration settings for the profile Wireless_rf_profile.
The output of this command includes the following parameters:
(host) #show rf arm-profile default
Adaptive Radio Management (ARM) profile "test"
----------------------------------------------
Parameter Value
--------- -----
Assignment disable
Allowed bands for 40MHz channels a-only
Client Aware Enabled
Max Tx Power 30 dBm
Min Tx Power 9 dBm
Multi Band Scan Enabled
Rogue AP Aware Disabled
Scan Interval 10 sec
Active Scan Disabled
Scanning Enabled
Scan Time 110 msec
VoIP Aware Scan Disabled
Video Aware Scan Enabled
Power Save Aware Scan Enabled
Ideal Coverage Index 10
Acceptable Coverage Index 4
Free Channel Index 25
Backoff Time 240 sec
Error Rate Threshold 50 %
Error Rate Wait Time 30 sec
Noise Threshold 75 -dBm
Noise Wait Time 120 sec
Minimum Scan Time 8 sec
Load aware Scan Threshold 1250000 Bps
Parameter Description
Assignment Displays the current ARM channel/power assignment mode.
Allowed bands for 40MHz
channels Shows if 40 MHz mode of operation is allowed on the 5 GHz (802.11a) or 2.4 GHz
(802.11b/g) frequency band only, on all frequency bands, or on neither frequency
band.
Client Aware Shows if the client aware feature is enabled or disabled. When enabled, the AP
does not change channels when there are active clients.
Max Tx Power The highest transmit power levels for the AP, from 0-30 dBm in 3 dBm
increments. Higher power level settings may be constrained by local regulatory
requirements and AP capabilities. In the event that an AP is configured for a Max
Tx Power setting it cannot support, this value will be reduced to the highest
supported power setting.
Min Tx Power The lowest transmit power levels for the AP, from 0-30 dBm, in 3 dBm
increments. Note that power settings will not change if the Assignment option is
set to disabled or maintain.
Multi Band Scan If enabled, single-radio APs will try to scan across bands for rogue AP detection.
Rogue AP Aware If enabled, Alcatel-Lucent APs may change channels to contain off-channel rogue
APs with active clients. This security features allows APs to change channels
even if the Client Aware setting is disabled.
This setting is disabled by default, and should only be enabled in high-security
environments where security requirements are allowed to consume higher levels
of network resources. You may prefer to receive Rogue AP alerts via SNMP traps
or syslog events.
AOS-W 3.4.1 Command Line Interface | Reference Guide show rf arm-profile | 979
Command History
This command was available in AOS-W 3.0.
Command Information
Scan Interval If Scanning is enabled, the Scan Interval defines how often the AP will leave its
current channel to scan other channels in the band.
Off-channel scanning can impact client performance. Typically, the shorter the
scan interval, the higher the impact on performance. If you are deploying a large
number of new APs on the network, you may want to lower the Scan Interval to
help those APs find their optimal settings more quickly. Raise the Scan Interval
back to its default setting after the APs are functioning as desired.
Active Scan If enabled, the AP initiates active scanning via probe request. This option elicits
more information from nearby APs, but also creates additional management
traffic on the network. Active Scan is disabled by default, and should not be
enabled except under the direct supervision of Alcatel-Lucent Support.
Scanning Shows if the AP has enabled or disabled AP scanning of other channels.
Scan Time The amount of time, in milliseconds, an AP will drift out of the current channel to
scan another channel.
VoIP Aware Scan Shows if Alcatel-Lucent’s VoIP Call Admission Control (CAC) prevents any single
AP from becoming congested with voice calls. If CAC is enabled, you should also
enable VoIP Aware Scan in the ARM profile, so the AP will not attempt to scan a
different channel if one of its clients has an active VoIP call.
Power Save Aware Scan When enabled, the AP will not scan if Power Save is active.
Video Aware Scan If Video Aware Scan is enabled in the ARM profile, the AP will not attempt to scan
a different channel if one of its clients has an active video session.
Ideal Coverage Index The coverage that the AP should try to achieve on its channel. The denser the AP
deployment, the lower this value should be.
Acceptable Coverage Index The minimal coverage that the AP should try to achieve on its channel. The
denser the AP deployment, the lower this value should be.
Free Channel Index The difference in the interference index between the new channel and current
channel must exceed this value for the AP to move to a new channel. The higher
this value, the lower the chance an AP will move to the new channel.
Backoff Time Time, in seconds, an AP backs off after requesting a new channel or power level.
Error Rate Threshold The percentage of errors in the channel that triggers a channel change.
Error Rate Wait Time Time, in seconds, that the error rate has to maintain or surpass the error rate
threshold before it triggers a channel change.
Noise Threshold Maximum level of noise (in -dBm) in a channel that triggers a channel change.
Noise Wait Time Time, in seconds, the noise has to be high to trigger a channel change.
Minimum Scan Time Time, in seconds, that a channel must be scanned before it is considered for
assignment.
Load aware Scan Threshold The traffic throughput level an AP must reach before it stops scanning, in bytes/
second. A value of 0 to disables this feature.
Mode Aware Arm If enabled, ARM will turn APs into Air Monitors (AMs) if it detects higher coverage
levels than necessary. This helps avoid higher levels of interference on the WLAN.
Although this setting is disabled by default, you may want to enable this feature if
your APs are deployed in close proximity (e.g. less than 60 feet apart).
Parameter Description

980 |show rf arm-profile AOS-W 3.4.1 Command Line Interface | Reference Guide
Platforms Licensing Command Mode
All platforms Base operating system Enable and Config mode on local and
master switches

AOS-W 3.4.1 Command Line Interface | Reference Guide show rf dot11a-radio-profile | 981
show rf dot11a-radio-profile
show rf dot11a-radio-profile [<profile>]
Description
Show an 802.11a Radio profile.
Syntax
Usage Guidelines
Issue this command without the <profile> parameter to display the entire 802.11a Radio profile list,
including profile status and the number of references to each profile. Include a profile name to display
detailed configuration information for that profile.
Examples
The example below shows that the switch has three configured 802.11a Radio profiles. The References
column lists the number of other profiles with references to the 802.11a Radio profile, and the Profile
Status column indicates whether the profile is predefined. User-defined profiles will not have an entry in
the Profile Status column.
This example displays the configuration settings for the profile default.
Parameter Description
<profile> Name of an 802.11a profile.
(host) # show rf dot11a-radio-profile
802.11a radio profile List
--------------------------
Name References Profile Status
---- ---------- --------------
default 18
default-AP85 1
test 1
Total:3
(host) # show rf dot11a-radio-profile default
802.11a radio profile "default"
-------------------------------
Parameter Value
--------- -----
Radio enable Enabled
Mode ap-mode
High throughput enable (radio) Enabled
Channel 157+
Beacon Period 100 msec
Transmit EIRP 15 dBm
Advertise 802.11d and 802.11h Capabilities Enabled
Spectrum load balancing Disabled
RX Sensitivity Tuning Based Channel Reuse dynamic
RX Sensitivity Threshold 0 -dBm
Enable CSA Disabled
CSA Count 4
Management Frame Throttle interval 1 sec
Management Frame Throttle Limit 20
ARM/WIDS Override Enabled
Adaptive Radio Management (ARM) Profile default
High-throughput Radio Profile default-a
982 | show rf dot11a-radio-profile AOS-W 3.4.1 Command Line Interface | Reference Guide
The output of this command includes the following parameters:
Parameter Description
Radio enable Shows if the AP has enabled or disabled transmissions on this radio band.
Mode Access Point operating mode. Available options are:
zam-mode: Air Monitor mode
zap-mode: Access Point mode
zapm-mode: Access Point Monitor mode
zsensor-mode: RFprotect sensor mode
High throughput enable (radio) Name of a high-throughput profile referenced by this 802.11a radio profile.
A high-throughput profile manages 40 Mhz tolerance settings, and controls
whether or not APs using this profile will advertise intolerance of 40 MHz
operation. (This option is disabled by default, allowing 40 MHz operation.)
A high-throughput profile also determines whether an AP radio using the profile
will stop using the 40 MHz channels surrounding APs or stations advertise 40
Mhz intolerance. This option is enabled by default.
Channel Channel number for the AP 802.11a/802.11n physical layer.
Beacon Period Time, in milliseconds, between successive beacon transmissions. The beacon
advertises the AP’s presence, identity, and radio characteristics to wireless
clients
Transmit EIRP Maximum transmit power (EIRP) in dBm from 0 to 51 in .5 dBm increments.
Further limited by regulatory domain constraints and AP capabilities.
Advertise 802.11d and 802.11h
Capabilities If enabled, the radio advertises its 802.11d (Country Information) and 802.11h
(Transmit Power Control) capabilities.
Spectrum load balancing The Spectrum load balancing feature helps optimize network resources by
balancing clients across channels, regardless of whether the AP or the switch is
responding to the wireless clients' probe requests.
If enabled, the switch compares whether or not an AP has more clients than its
neighboring APs on other channels. If an AP’s client load is at or over a
predetermined threshold as compared to its immediate neighbors, or if a
neighboring Alcatel-Lucent AP on another channel does not have any clients,
load balancing will be enabled on that AP. This feature is disabled by default.
RX Sensitivity Tuning Based
Channel Reuse Shows if the channel reuse feature’s current operating mode, static, dynamic or
disable.
zStatic: This mode of operation is a coverage-based adaptation of the Clear
Channel Assessment (CCA) thresholds. In the static mode of operation, the
CCA is adjusted according to the configured transmission power level on the
AP, so as the AP transmit power decreases as the CCA threshold increases,
and vice versa.
zDynamic: In this mode, the Clear Channel Assessment (CCA) thresholds are
based on channel loads, and take into account the location of the associated
clients. When you set the Channel Reuse This feature is automatically
enabled when the wireless medium around the AP is busy greater than half
the time. When this mode is enabled, the CCA threshold adjusts to
accommodate transmissions between the AP its most distant associated
client.
zDisable: This mode does not support the tuning of the CCA Detect
Threshold.
RX Sensitivity Threshold If the Rx Sensitivity Tuning Based Channel reuse feature is set to static mode, this
parameter manually sets the AP’s Rx sensitivity threshold (-dBm). The AP will
filter out and ignore weak signals that are below the channel threshold signal
strength. For example, if the RX sensitivity threshold was set to -65 dBm, the AP
would ignore signals with a strength from -1 dBM to -64 dBm. If the value is set
to zero, the feature will automatically determine an appropriate threshold.
AOS-W 3.4.1 Command Line Interface | Reference Guide show rf dot11a-radio-profile | 983
Command History
Command Information
Enable CSA Shows if Channel Switch Announcements (CSAs) are enabled or disabled. CSAs,
as defined by IEEE 802.11h, enable an AP to announce that it is switching to a
new channel before it begins transmitting on that channel. This allows clients that
support CSA to transition to the new channel with minimal downtime.
CSA Count Number of channel switch announcements that must be sent prior to switching to
a new channel. The default CSA count is 4 announcements.
Management Frame Throttle
Interval Averaging interval for rate limiting mgmt frames from this radio, in seconds. A
management frame throttle interval of 0 seconds disables rate limiting.
Management Frame Throttle
Limit Maximum number of management frames that can come in from this radio in
each throttle interval.
ARM/WIDS Override If enabled, this option disables Adaptive Radio Management (ARM) and Wireless
IDS functions and slightly increases packet processing performance. If a radio is
configured to operate in Air Monitor mode, then the ARM/WIDS override
functions are always enabled, regardless of whether or not this check box is
selected.
Adaptive Radio Management
(ARM) Profile Name of an Adaptive Radio Management profile associated with this 802.11a
profile.
High-throughput Radio Profile Name of a High Throughput Radio profile associated with this 802.11a profile.
Parameter Description
Release Modification
AOS-W 3.0 Command introduced.
AOS-W 3.3.2 Introduced support for the high-throughput IEEE 802.11n standard.
AOS-W 3.4 Support for the following parameters:
zSpectrum load balancing
zRX Sensitivity Tuning Based Channel Reuse
zRX Sensitivity Threshold
zARM/WIDS Override
Platforms Licensing Command Mode
All platforms Base operating system Enable and Config mode on local and
master switches

984 | show rf dot11g-radio-profile AOS-W 3.4.1 Command Line Interface | Reference Guide
show rf dot11g-radio-profile
show rf dot11g-radio-profile [<profile>]
Description
Show an 802.11g Radio profile.
Syntax
Usage Guidelines
Issue this command without the <profile> parameter to display the entire 802.11g profile list, including
profile status and the number of references to each profile. Include a profile name to display detailed
configuration information for that profile.
Examples
The example below shows that the switch has four configured 802.11g profiles. The References column
lists the number of other profiles with references to the 802.11g profile, and the Profile Status column
indicates whether the profile is predefined. User-defined profiles will not have an entry in the Profile
Status column.
Parameter Description
<profile> Name of a 802.11g profile.
(host) # show rf arm-profile
Adaptive Radio Management (ARM) profile List
--------------------------------------------
Name References Profile Status
---- ---------- --------------
airwave 4
default 4
no-scanning 1
nokia-rf-profile 1
Total:4
AOS-W 3.4.1 Command Line Interface | Reference Guide show rf dot11g-radio-profile | 985
This example displays the configuration settings for the profile airwave.
The output of this command includes the following parameters:
(host) # show rf dot11g-radio-profile default
802.11g radio profile "default"
-------------------------------
Parameter Value
--------- -----
Radio enable Enabled
Mode ap-mode
High throughput enable (radio) Enabled
Channel 1
Beacon Period 100 msec
Transmit EIRP 20 dBm
Advertise 802.11d and 802.11h Capabilities Enabled
Spectrum load balancing Disabled
RX Sensitivity Tuning Based Channel Reuse disable
RX Sensitivity Threshold 0 -dBm
Non 802.11 Interference Immunity Level-2
Enable CSA Disabled
CSA Count 4
Management Frame Throttle interval 1 sec
Management Frame Throttle Limit 20
ARM/WIDS Override Enabled
Protection for 802.11b Clients Enabled
Adaptive Radio Management (ARM) Profile default-AP85
High-throughput Radio Profile default-g
Parameter Description
Radio enable Shows if the AP has enabled or disabled transmissions on this radio band.
Mode Access Point operating mode. Available options are:
zam-mode: Air Monitor mode
zap-mode: Access Point mode
zapm-mode: Access Point Monitor mode
zsensor-mode: RFprotect sensor mode
High throughput enable (radio) Name of a high-throughput profile referenced by this 802.11a radio profile.
A high-throughput profile manages 40 Mhz tolerance settings, and controls
whether or not APs using this profile will advertise intolerance of 40 MHz
operation. (This option is disabled by default, allowing 40 MHz operation.)
A high-throughput profile also determines whether an AP radio using the profile
will stop using the 40 MHz channels surrounding APs or stations advertise 40
Mhz intolerance. This option is enabled by default.
Channel Channel number for the AP 802.11a/802.11n physical layer.
Beacon Period Time, in milliseconds, between successive beacon transmissions. The beacon
advertises the AP’s presence, identity, and radio characteristics to wireless
clients
Transmit EIRP Maximum transmit power (EIRP) in dBm from 0 to 51 in .5 dBm increments.
Further limited by regulatory domain constraints and AP capabilities.
Advertise 802.11d and 802.11h
Capabilities If enabled, the radio advertises its 802.11d (Country Information) and 802.11h
(Transmit Power Control) capabilities.
986 | show rf dot11g-radio-profile AOS-W 3.4.1 Command Line Interface | Reference Guide
Spectrum load balancing The Spectrum load balancing feature helps optimize network resources by
balancing clients across channels, regardless of whether the AP or the switch is
responding to the wireless clients' probe requests.
If enabled, the switch compares whether or not an AP has more clients than its
neighboring APs on other channels. If an AP’s client load is at or over a
predetermined threshold as compared to its immediate neighbors, or if a
neighboring Alcatel-Lucent AP on another channel does not have any clients,
load balancing will be enabled on that AP. This feature is disabled by default.
RX Sensitivity Tuning Based
Channel Reuse Shows if the channel reuse feature’s current operating mode, static, dynamic or
disable.
zStatic: This mode of operation is a coverage-based adaptation of the Clear
Channel Assessment (CCA) thresholds. In the static mode of operation, the
CCA is adjusted according to the configured transmission power level on the
AP, so as the AP transmit power decreases as the CCA threshold increases,
and vice versa.
zDynamic: In this mode, the Clear Channel Assessment (CCA) thresholds are
based on channel loads, and take into account the location of the associated
clients. When you set the Channel Reuse This feature is automatically
enabled when the wireless medium around the AP is busy greater than half
the time. When this mode is enabled, the CCA threshold adjusts to
accommodate transmissions between the AP its most distant associated
client.
zDisable: This mode does not support the tuning of the CCA Detect
Threshold.
RX Sensitivity Threshold If the Rx Sensitivity Tuning Based Channel reuse feature is set to static mode, this
parameter manually sets the AP’s Rx sensitivity threshold (-dBm). The AP will
filter out and ignore weak signals that are below the channel threshold signal
strength. For example, if the RX sensitivity threshold was set to -65 dBm, the AP
would ignore signals with a strength from -1 dBM to -64 dBm. If the value is set
to zero, the feature will automatically determine an appropriate threshold.
Non 802.11 Interference
Immunity Show the current value for 802.11 Interference Immunity on the 2.4 Ghz band.
The default setting for this parameter is level 2. When performance drops due to
interference from non-802.11 interferers (such as DECT or Bluetooth devices),
the level can be increased up to level 5 for improved performance. However,
increasing the level makes the AP slightly “deaf” to its surroundings, causing the
AP to lose a small amount of range.
The levels for this parameter are:
zLevel-0: no ANI adaptation.
zLevel-1: noise immunity only.
zLevel-2: noise and spur immunity.
zLevel-3: level 2 and weak OFDM immunity.
zLevel-4: level 3 and FIR immunity.
zLevel-5: disable PHY reporting.
Enable CSA Shows if Channel Switch Announcements (CSAs) are enabled or disabled. CSAs,
as defined by IEEE 802.11h, enable an AP to announce that it is switching to a
new channel before it begins transmitting on that channel. This allows clients that
support CSA to transition to the new channel with minimal downtime.
CSA Count Number of channel switch announcements that must be sent prior to switching to
a new channel. The default CSA count is 4 announcements.
Management Frame Throttle
Interval Averaging interval for rate limiting mgmt frames from this radio, in seconds. A
management frame throttle interval of 0 seconds disables rate limiting.
Management Frame Throttle
Limit Maximum number of management frames that can come in from this radio in
each throttle interval.
Parameter Description
AOS-W 3.4.1 Command Line Interface | Reference Guide show rf dot11g-radio-profile | 987
Command History
Command Information
ARM/WIDS Override If enabled, this option disables Adaptive Radio Management (ARM) and Wireless
IDS functions and slightly increases packet processing performance. If a radio is
configured to operate in Air Monitor mode, then the ARM/WIDS override
functions are always enabled, regardless of whether or not this check box is
selected.
Protection for 802.11b Clients Shows if the profile has enabled or disabled protection for 802.11b clients.
Adaptive Radio Management
(ARM) Profile Name of an Adaptive Radio Management profile associated with this 802.11a
profile.
High-throughput Radio Profile Name of a High Throughput Radio profile associated with this 802.11a profile.
Parameter Description
Release Modification
AOS-W 3.0 Command introduced
AOS-W 3.3.2 Introduced protection for 802.11b clients and support for the high-throughput
IEEE 802.11n standard
AOS-W 3.4 Support for the following parameters:
zSpectrum load balancing
zRX Sensitivity Tuning Based Channel Reuse
zRX Sensitivity Threshold
zARM/WIDS Override
Platforms Licensing Command Mode
All platforms Base operating system Enable and Config mode on local and
master switches

988 | show rf event-thresholds-profile AOS-W 3.4.1 Command Line Interface | Reference Guide
show rf event-thresholds-profile
show rf event-thresholds-profile [<profile>]
Description
Show an Event Thresholds profile.
Syntax
Usage Guidelines
Issue this command without the <profile> parameter to display the entire Event Thresholds profile list,
including profile status and the number of references to each profile. Include a profile name to display
detailed configuration information for that profile.
Examples
The example below shows that the switch has two configured Event Thresholds profiles. The References
column lists the number of other profiles with references to the Event Thresholds profile, and the Profile
Status column indicates whether the profile is predefined. User-defined profiles will not have an entry in
the Profile Status column.
This example displays the configuration settings for the profile default.
Parameter Description
<profile> name of an Event Thresholds profile
(host) # show rf event-thresholds-profile
RF Event Thresholds Profile List
--------------------------------
Name References Profile Status
---- ---------- --------------
default 6
event1 2
Total: 2
(host) # show rf event-thresholds-profile default
RF Event Thresholds Profile "default"
-------------------------------------
Parameter Value
--------- -----
Detect Frame Rate Anomalies Disabled
Bandwidth Rate High Watermark 0 %
Bandwidth Rate Low Watermark 0 %
Frame Error Rate High Watermark 0 %
Frame Error Rate Low Watermark 0 %
Frame Fragmentation Rate High Watermark 16 %
Frame Fragmentation Rate Low Watermark 8 %
Frame Low Speed Rate High Watermark 16 %
Frame Low Speed Rate Low Watermark 8 %
Frame Non Unicast Rate High Watermark 0 %
Frame Non Unicast Rate Low Watermark 0 %
Frame Receive Error Rate High Watermark 16 %
Frame Receive Error Rate Low Watermark 8 %
Frame Retry Rate High Watermark 16 %
Frame Retry Rate Low Watermark 8 %
AOS-W 3.4.1 Command Line Interface | Reference Guide show rf event-thresholds-profile | 989
The output of this command includes the following parameters:
Command History
This command was available in AOS-W 3.0.
Command Information
Parameter Description
Detect Frame Rate Anomalies Shows of the profile enables or disables detection of frame rate anomalies.
Bandwidth Rate High
Watermark If bandwidth in an AP exceeds this value, it triggers a bandwidth exceeded
condition. The value represents the percentage of maximum for a given radio.
(For 802.11b, the maximum bandwidth is 7 Mbps. For 802.11 a and g, the
maximum is 30 Mbps.) The recommended value is 85%.
Bandwidth Rate Low
Watermark If an AP triggers a bandwidth exceeded condition, the condition persists until
bandwidth drops below this value.
Frame Error Rate High
Watermark If the frame error rate (as a percentage of total frames in an AP) exceeds this
value, it triggers a frame error rate exceeded condition.
Frame Error Rate Low
Watermark If an AP triggers a frame error rate exceeded condition, the condition persists
until the frame error rate drops below this value.
Frame Fragmentation Rate
High Watermark If the frame fragmentation rate (as a percentage of total frames in an AP) exceeds
this value, it triggers a frame fragmentation rate exceeded condition.
Frame Fragmentation Rate Low
Watermark If an AP triggers a frame fragmentation rate exceeded condition, the condition
persists until the frame fragmentation rate drops below this value.
Frame Low Speed Rate High
Watermark If the rate of low-speed frames (as a percentage of total frames in an AP) exceeds
this value, it triggers a low-speed rate exceeded condition.
Frame Low Speed Rate Low
Watermark After a low-speed rate exceeded condition exists, the condition persists until
the percentage of low-speed frames drops below this value.
Frame Non Unicast Rate High
Watermark If the non-unicast rate (as a percentage of total frames in an AP) exceeds this
value, it triggers a non-unicast rate exceeded condition. This value depends
upon the applications used on the network.
Frame Non Unicast Rate Low
Watermark If an AP triggers a non-unicast rate exceeded condition, the condition persists
until the non-unicast rate drops below this value.
Frame Receive Error Rate High
Watermark If the frame receive error rate (as a percentage of total frames in an AP) exceeds
this value, it triggers a frame receive error rate exceeded condition.
Frame Receive Error Rate Low
Watermark If an AP triggers a frame receive error rate exceeded condition, the condition
persists until the frame receive error rate drops below this value.
Frame Retry Rate High
Watermark If the frame retry rate (as a percentage of total frames in an AP) exceeds this
value, it triggers a frame retry rate exceeded condition.
Frame Retry Rate Low
Watermark If an AP triggers a frame retry rate exceeded condition exists, the condition
persists until the frame retry rate drops below this value.
Platforms Licensing Command Mode
All platforms Base operating system Enable and Config mode on local and
master switches
990 | show rf ht-radio-profile AOS-W 3.4.1 Command Line Interface | Reference Guide
show rf ht-radio-profile
show rf ht-radio-profile [<profile>]
Description
Show a High-throughput Radio profile.
Syntax
Usage Guidelines
Issue this command without the <profile> parameter to display the entire High-throughput Radio profile
list, including profile status and the number of references to each profile. Include a profile name to display
detailed configuration information for that profile.
Examples
The example below shows that the switch has five configured High-throughput Radio profiles. The
References column lists the number of other profiles with references to the High-throughput Radio profile,
and the Profile Status column indicates whether the profile is predefined and editable, and if that
predefined profile has been changed from its default settings. User-defined profiles will not have an entry in
the Profile Status column.
This example displays the configuration settings for the predefined profile default-a.
The output of this command includes the following parameters:
Parameter Description
<profile> Name of a High-throughput Radio profile.
(host) # show rf ht-radio-profile
High-throughput radio profile List
----------------------------------
Name References Profile Status
---- ---------- --------------
default 0
default-a 8 Predefined (editable)
default-g 3 Predefined (changed)
legacystation 1
test 1
Total:5
(host) #show rf ht-radio-profile default-a
High-throughput radio profile "default-a" (Predefined (editable))
-----------------------------------------------------------------
Parameter Value
--------- -----
40 MHz intolerance Disabled
Honor 40 MHz intolerance Enabled
Legacy station workaround Disabled
Parameter Description
40 MHz intolerance Shows whether or not APs using this radio profile will advertise intolerance of 40
MHz operation. By default, 40 MHz operation is allowed.
Honor 40 MHz intolerance If this parameter is enabled, the radio will stop using the 40 MHz channels if the
40 MHz intolerance indication is received from another AP or station.
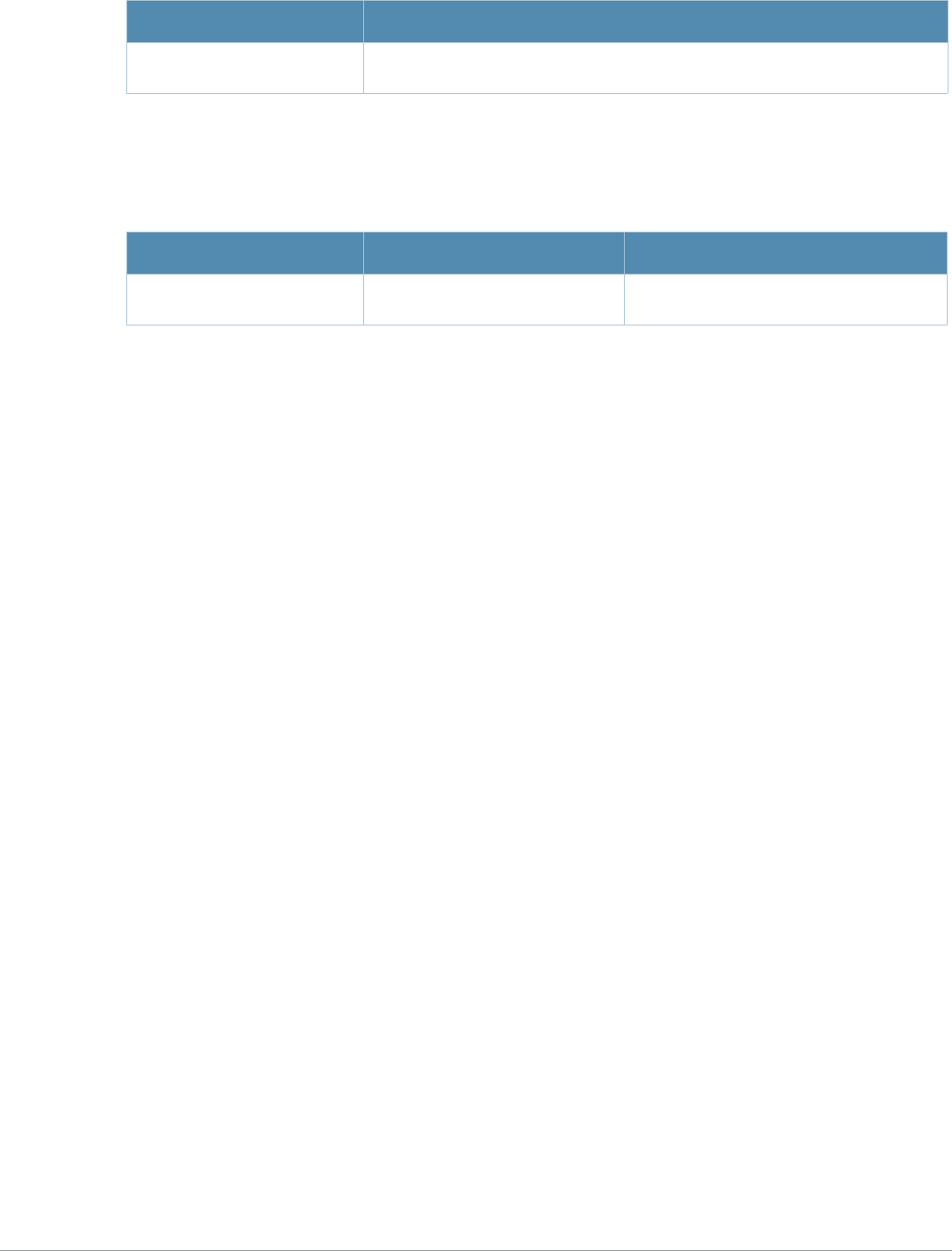
AOS-W 3.4.1 Command Line Interface | Reference Guide show rf ht-radio-profile | 991
Command History
This command was available in AOS-W 3.0.
Command Information
Legacy station workaround Shows if the profile enables interoperability for misbehaving legacy stations. This
parameter is disabled by default.
Parameter Description
Platforms Licensing Command Mode
All platforms Base operating system Enable and Config mode on local and
master switches

992 | show rf optimization-profile AOS-W 3.4.1 Command Line Interface | Reference Guide
show rf optimization-profile
show rf optimization-profile [<profile>]
Description
Show an Optimization profile.
Syntax
Usage Guidelines
Issue this command without the <profile> parameter to display the entire Optimization profile list,
including profile status and the number of references to each profile. Include a profile name to display
detailed configuration information for that profile.
Examples
The example below shows that the switch has two configured Optimization profiles. The References
column lists the number of other profiles with references to the Optimization profile, and the Profile
Status column indicates whether the profile is predefined. User-defined profiles will not have an entry in
the Profile Status column.
This example displays the configuration settings for the profile profile2.
Parameter Description
<profile> name of an ARM profile
(host) # show rf optimization-profile
RF Optimization Profile List
----------------------------
Name References Profile Status
---- ---------- --------------
default 6
profile2 1
Total:2
(host) #show rf optimization-profile profile2
RF Optimization Profile "profile2"
---------------------------------
Parameter Value
--------- -----
Station Handoff Assist Disabled
Detect Association Failure Disabled
Coverage Hole Detection Disabled
Hole Good RSSI Threshold 20
Hole Good Station Ageout 30 sec
Hole Detection Interval 180 sec
Hole Idle Station Ageout 90 sec
Hole Poor RSSI Threshold 10
Detect interference Disabled
Interference Threshold 90 %
Interference Threshold Exceed Time 25 sec
Interference Baseline Time 25 sec
RSSI Falloff Wait Time 0 sec
Low RSSI Threshold 0
RSSI Check Frequency 0 sec
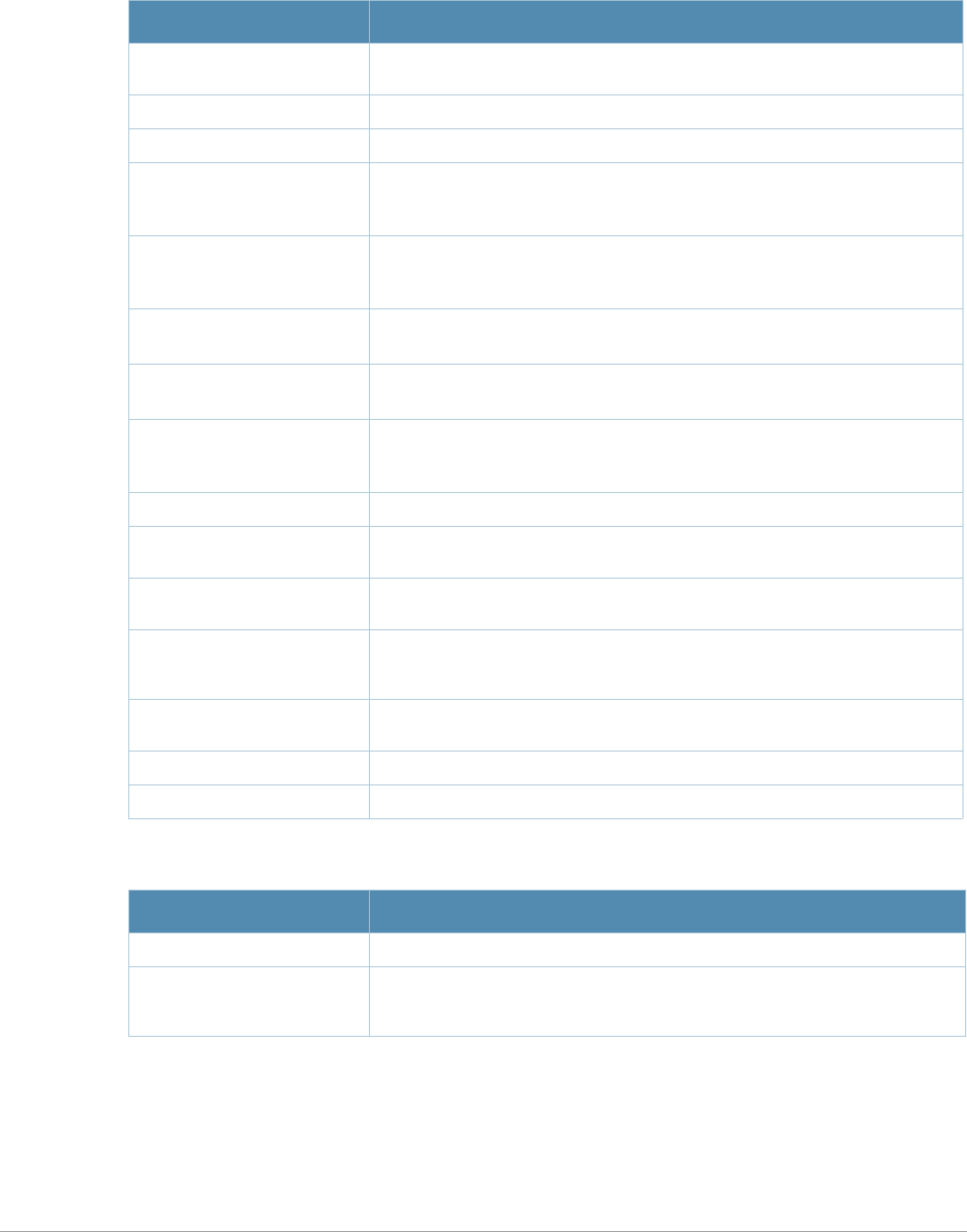
AOS-W 3.4.1 Command Line Interface | Reference Guide show rf optimization-profile | 993
The output of this command includes the following parameters:
Command History
This command was available in AOS-W 3.0.
Parameter Description
Station Handoff Assist If enabled, this parameter allows the switch to force a client off an AP when the
RSSI drops below a defined minimum threshold.
Detect Association Failure Shows if the profile enables or disables STA association failure detection.
Coverage Hole Detection Shows if the profile enables or disables coverage hole detection.
Hole Good RSSI Threshold Time, in seconds, after a coverage hole is detected until a coverage hole event
notification is generated.
The Wireless Intrusion Protection license must be installed.
Hole Good Station Ageout Stations with signal strength above this value are considered to have good
coverage.
The Wireless Intrusion Protection license must be installed.
Hole Detection Interval Time, in seconds, after which a station with good coverage is aged out.
The Wireless Intrusion Protection license must be installed.
Hole Idle Station Ageout Time, in seconds, after which a station in a poor coverage area is aged out.
The Wireless Intrusion Protection license must be installed.
Hole Poor RSSI Threshold Stations with signal strength below this value will trigger detection of a coverage
hole.
The Wireless Intrusion Protection license must be installed.
Detect interference Enables or disables interference detection.
Interference Threshold Percentage increase in the frame retry rate (FRR) or frame receive error rate
(FRER) before interference monitoring begins on a given channel.
Interference Threshold Exceed
Time Time, in seconds, the FRR or FRER exceeds the threshold before interference is
reported.
Interference Baseline Time Time, in seconds, the air monitor should learn the state of the link between the AP
and client to create frame retry rate (FRR) and frame receive error rate (FRER)
baselines.
RSSI Falloff Wait Time Time, in seconds, to wait with decreasing RSSI before a deauthorization message
is sent to the client. The maximum value is 8 seconds.
Low RSSI Threshold Minimum RSSI above which deauthorization messages should never be sent.
RSSI Check Frequency Interval, in seconds, to sample RSSI.
Version Modification
AOS-W 3.0 Base operating system
AOS-W 3.4 Output parameters displaying load balancing status were removed. You can now
view the status of the load balancing feature via the commands show rf
dot11a-radio-profile and show rf dot11g-radio-profile.

994 | show rf optimization-profile AOS-W 3.4.1 Command Line Interface | Reference Guide
Command Information
Platforms Licensing Command Mode
All platforms Base operating system Enable and Config mode on local and
master switches
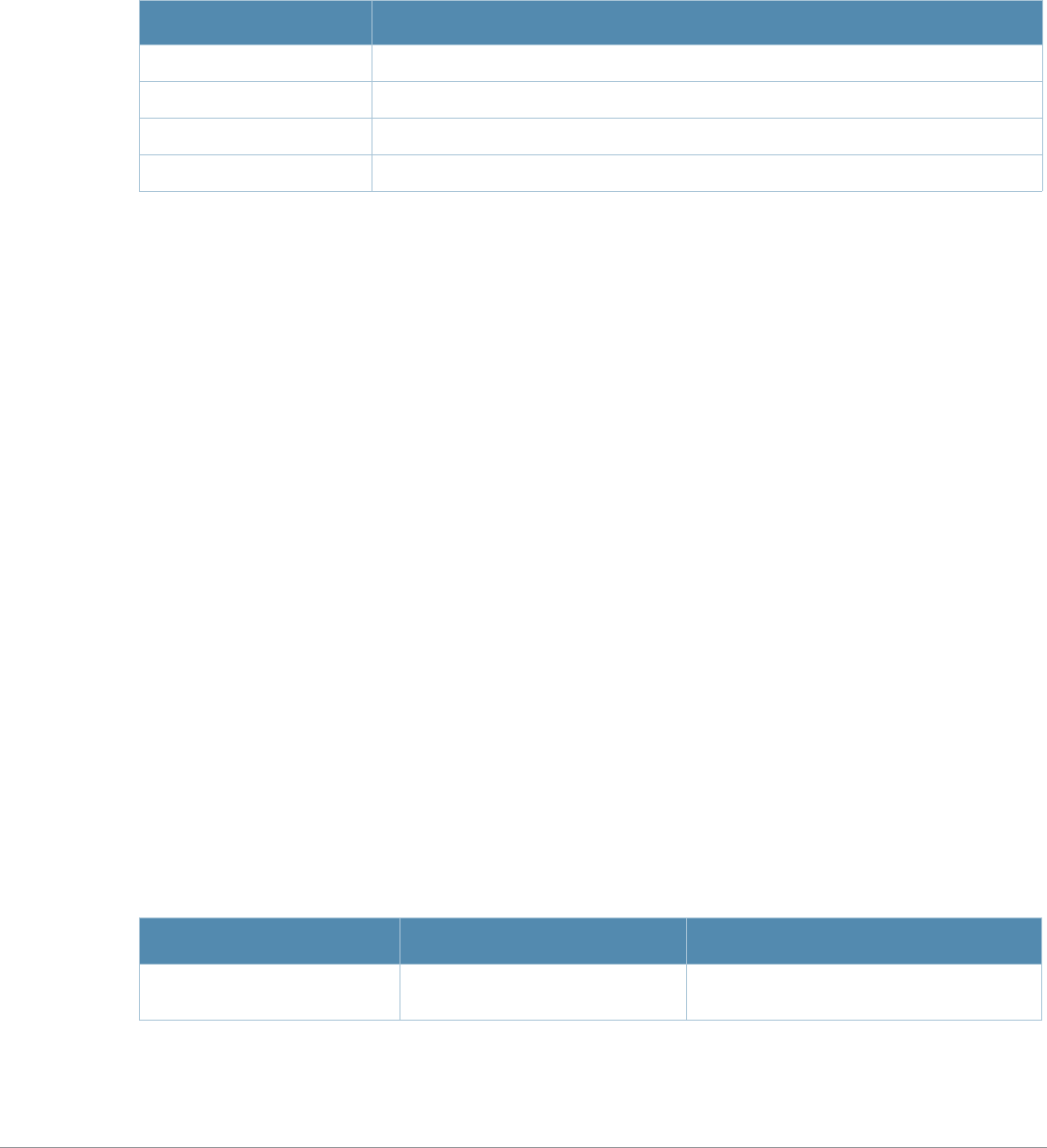
AOS-W 3.4.1 Command Line Interface | Reference Guide show rft profile | 995
show rft profile
show rft profile {all|antenna-connectivity|link-quality|raw}
Description
Show parameters for the predefined RF test profiles.
Syntax
Usage guidelines
The rft command is used for RF troubleshooting, and should only be used under the supervision of Alcatel-
Lucent technical support. Issue the show rft profile command to view the profiles used for these RF tests.
Example
The following example shows the testing parameters for the predefined link-quality RF test profile.
Related Commands
To view the results of an RF test, use the command show rft result.
Command History
This command was available in AOS-W 3.0.
Command Information
Parameter Description
all Show all predefined profiles.
antenna-connectivity Show configured parameters for the predefined Antenna Connectivity test profile.
link-quality Show configured parameters for the predefined Link Quality test profile.
raw Show configured parameters for the predefined RAW test profile.
(host) #show rft profile link-quality
Profile LinkQuality: Built-in profile
--------------------------------------
Parameter Value
--------- -----
Antenna 1 and/or 2
Frame Type Null Data
Num Packets 100 for each data-rate
Packet Size 1500
Num Retries 0
Data Rate All rates are tried
Platforms Licensing Command Mode
All platforms Base operating system Enable and Config mode on local and
master switches
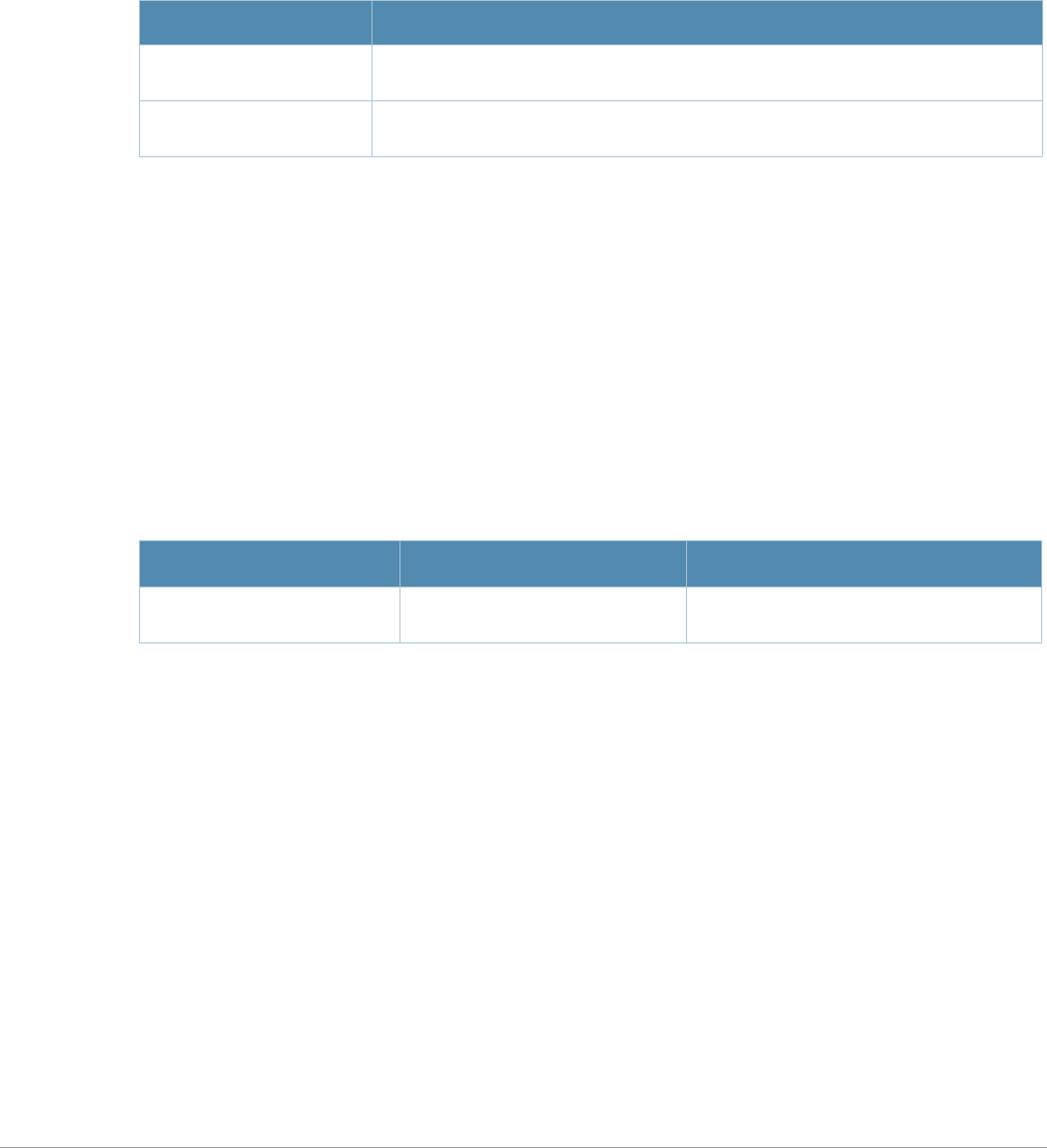
996 |show rft result AOS-W 3.4.1 Command Line Interface | Reference Guide
show rft result
show rft result all|{trans-id <trans-id>}
Description
Show the results of an RF test.
Syntax
Usage guidelines
The rft command is used for RF troubleshooting, and should only be used under the supervision of Alcatel-
Lucent technical support.
Related Commands
To view a list of the most recent transaction IDs for each test type, use the command show rft
transactions.
Command History
This command was available in AOS-W 3.0.
Command Information
Parameter Description
all Show the most recent test result for each test type (antenna-connectivity, link-quality
or raw).
trans-id <trans-id> Each RF test is assigned a transaction ID. Include the trans-id <trans-id>
parameters to show the test result for a specific transaction ID.
Platforms Licensing Command Mode
All platforms Base operating system Enable and Config mode on local and
master switches
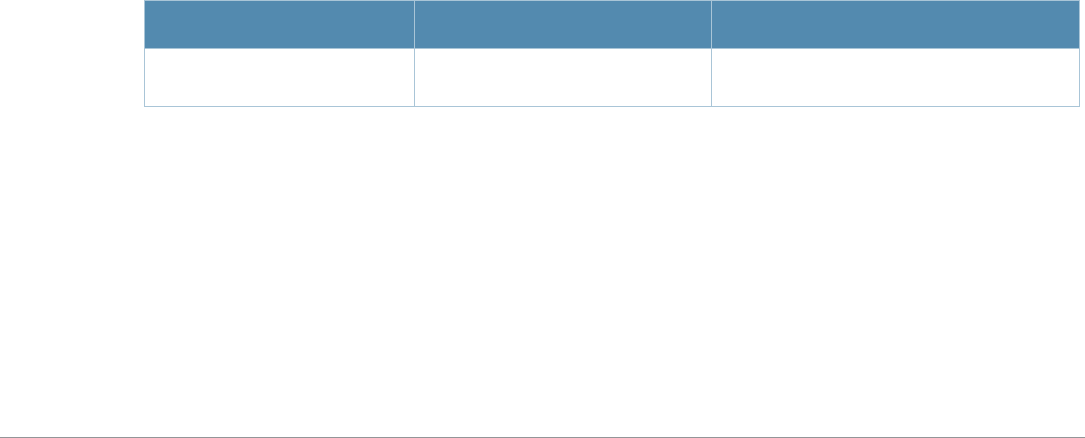
AOS-W 3.4.1 Command Line Interface | Reference Guide show rft transactions | 997
show rft transactions
show rft transactions
Description
Show transaction IDs of RF tests.
Syntax
No parameters.
Usage guidelines
The rft command is used for RF troubleshooting, and should only be used under the supervision of Alcatel-
Lucent technical support. Issue the show rft transaction command to view the transaction IDs for the
most recent test of each test type.
Example
The following example shows the transaction IDs for the latest RAW, link-quality and antenna-connectivity
tests.
Related Commands
Use transaction IDs with the command show rft result to view results for individual RF tests.
Command History
This command was available in AOS-W 3.0.
Command Information
(host) #show rft transactions
RF troubleshooting transactions
-------------------------------
Profile Transaction ID
------- --------------
RAW 2001
LinkQuality 2101
AntennaConnectivity 1801
Platforms Licensing Command Mode
All platforms Base operating system Enable and Config mode on local and
master switches

998 | show rft transactions AOS-W 3.4.1 Command Line Interface | Reference Guide
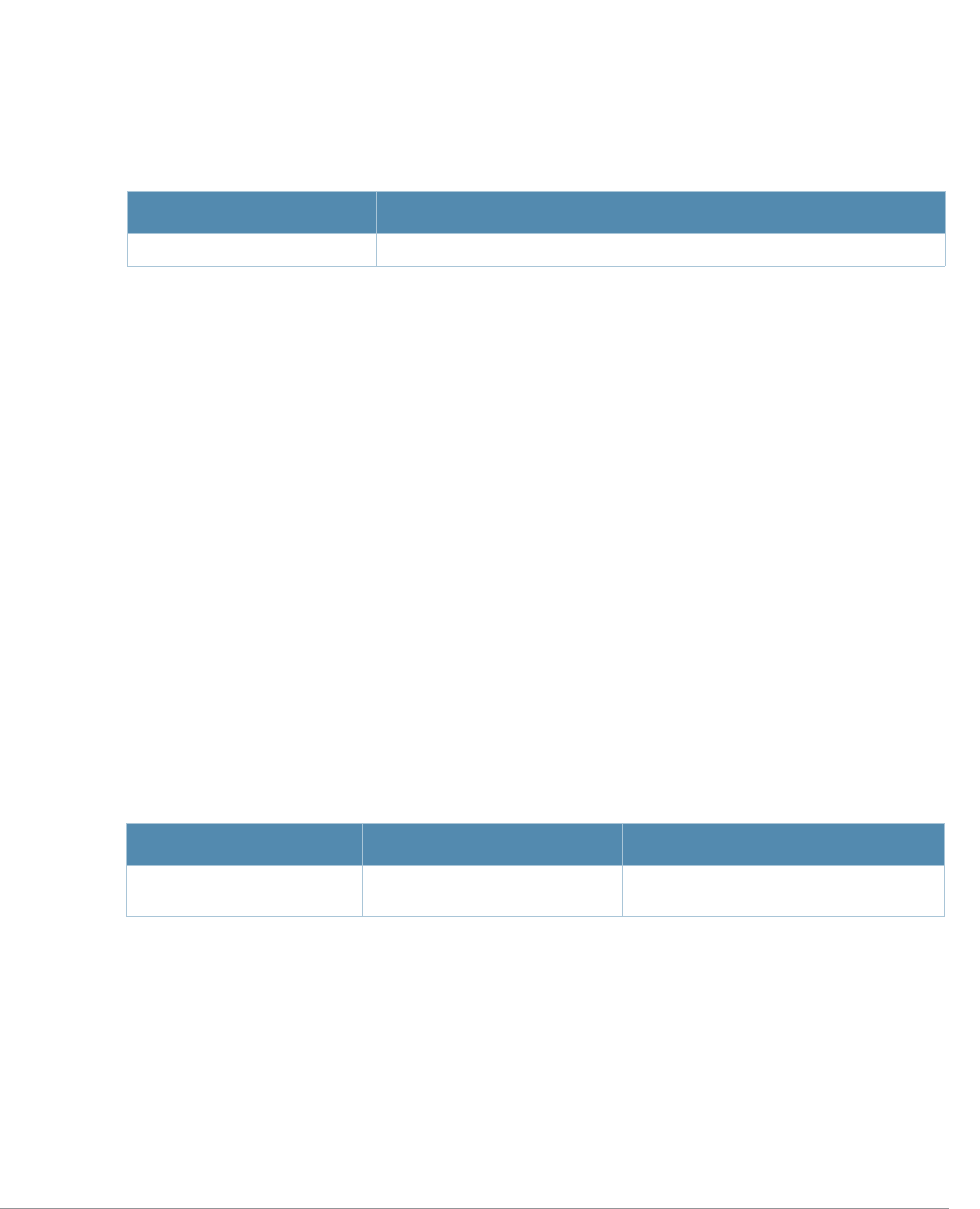
AOS-W 3.4.1 Command Line Interface | Reference Guide show rights | 999
show rights
show rights [<name-of-a-role>]
Description
Displays the list of user roles in the roles table with high level details of role policies. To view role policies
of a specific role specify the role name.
Syntax
Example
The output of this command shows the list of roles in the role table.
Command History
This command was available in AOS-W 3.0
Command Information
Parameter Description
name-of-a-role Enter the role name to view its policy details.
(host) # show rights
RoleTable
---------
Name ACL Bandwidth ACL List Type
---- --- --------- -------- ----
ap-role 4 Up: No Limit,Dn: No Limit control/,ap-acl/ System
authenticated 39 Up: No Limit,Dn: No Limit allowall/,v6-allowall/ User
default-vpn-role 37 Up: No Limit,Dn: No Limit allowall/,v6-allowall/ User
guest 3 Up: No Limit,Dn: No Limit http-acl/,https-acl/,dhcp-acl/User
guest-logon 6 Up: No Limit,Dn: No Limit logon-control/,captiveportal/ User
logon 1 Up: No Limit,Dn: No Limit logon-control/,captiveportal/ User
stateful-dot1x 5 Up: No Limit,Dn: No Limit System
voice 38 Up: No Limit,Dn: No Limit sip-acl/,noe-acl/,svp-acl/,vocera-acl/ User
Platforms Licensing Command Mode
All platforms Base operating system Config or Enable mode on master or local
switches

1000 |show rights AOS-W 3.4.1 Command Line Interface | Reference Guide

AOS-W 3.4.1 Command Line Interface | Reference Guide show roleinfo | 1001
show roleinfo
show roleinfo
Description
Displays the role of the switch.
Syntax
No Parameters
Example
The output of this command shows the role of the switch.
Command History
This command was available in AOS-W 3.0
Command Information
(host) # show roleinfo
switchrole:master
Platforms Licensing Command Mode
All platforms Base operating system Config or Enable mode on master or local
switches

1002 | show roleinfo AOS-W 3.4.1 Command Line Interface | Reference Guide
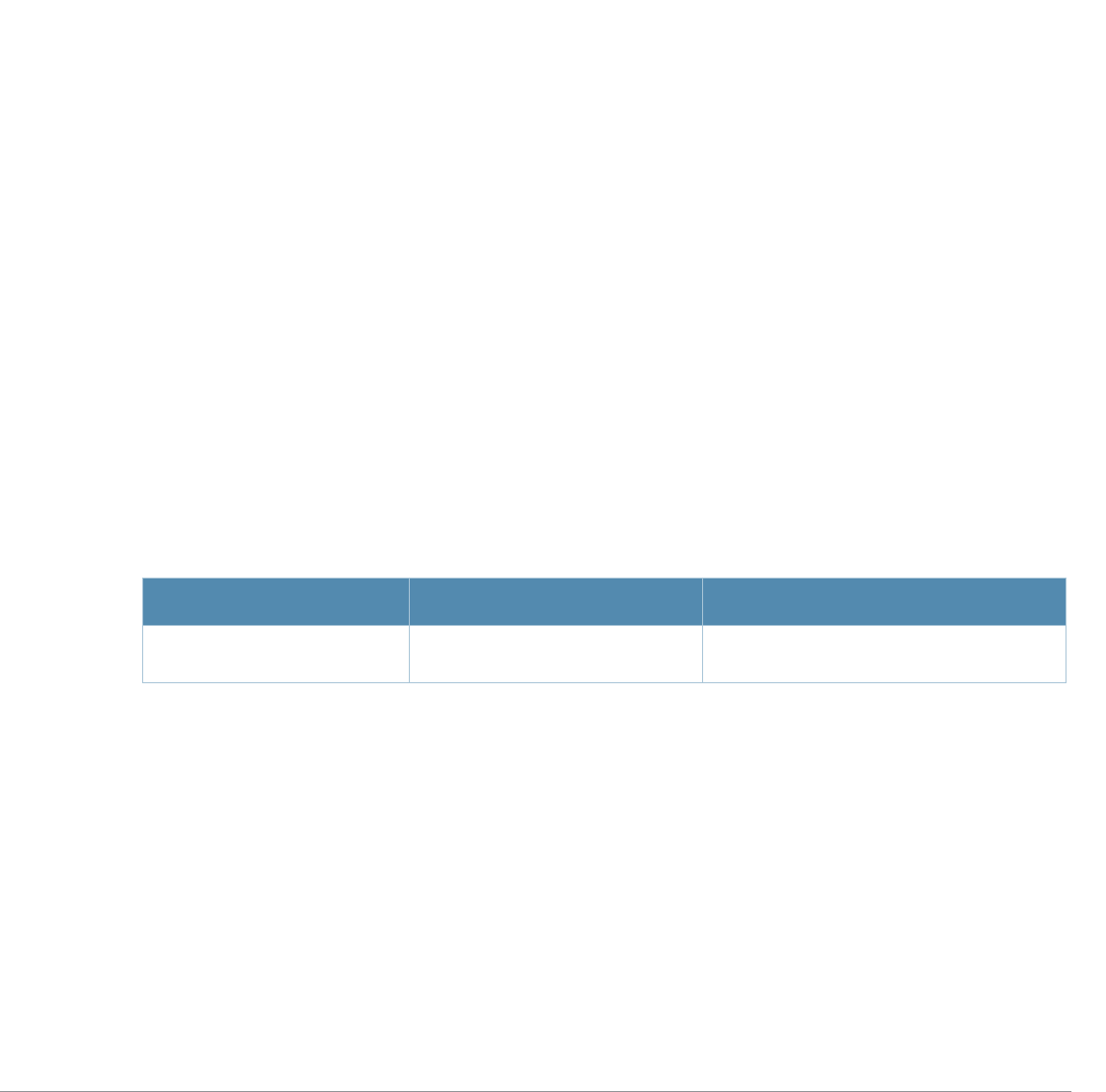
AOS-W 3.4.1 Command Line Interface | Reference Guide show rrm dot11k admission-capacity | 1003
show rrm dot11k admission-capacity
show rrm dot11k admission-capacity
Description
Displays the available admission capacity for voice traffic on an APs.
Syntax
No Parameters
Example
The output of this command shows the available admission capacity for voice traffic on all APs.
Command History
This command was available in AOS-W 3.4
Command Information
(host) # show rrm dot11k admission-capacity
802.11K Available Admission Capacity for Voice
----------------------------------------------
Flags: B: Bandwidth based CAC, C: Call-count based CAC
D: CAC Disabled, E: CAC Enabled
AP Name IP Address Freq Band Chan Total Available Flags
------- ---------- --------- ---- ----- --------- -----
r-wing-94 10.16.12.247 5 GHz 40 31250 0 EC
r-wing-94 10.16.12.247 2.4 GHz 11 31250 0 EC
Num APs:2
Platforms Licensing Command Mode
All platforms Base operating system Config or Enable mode on master or local
switches
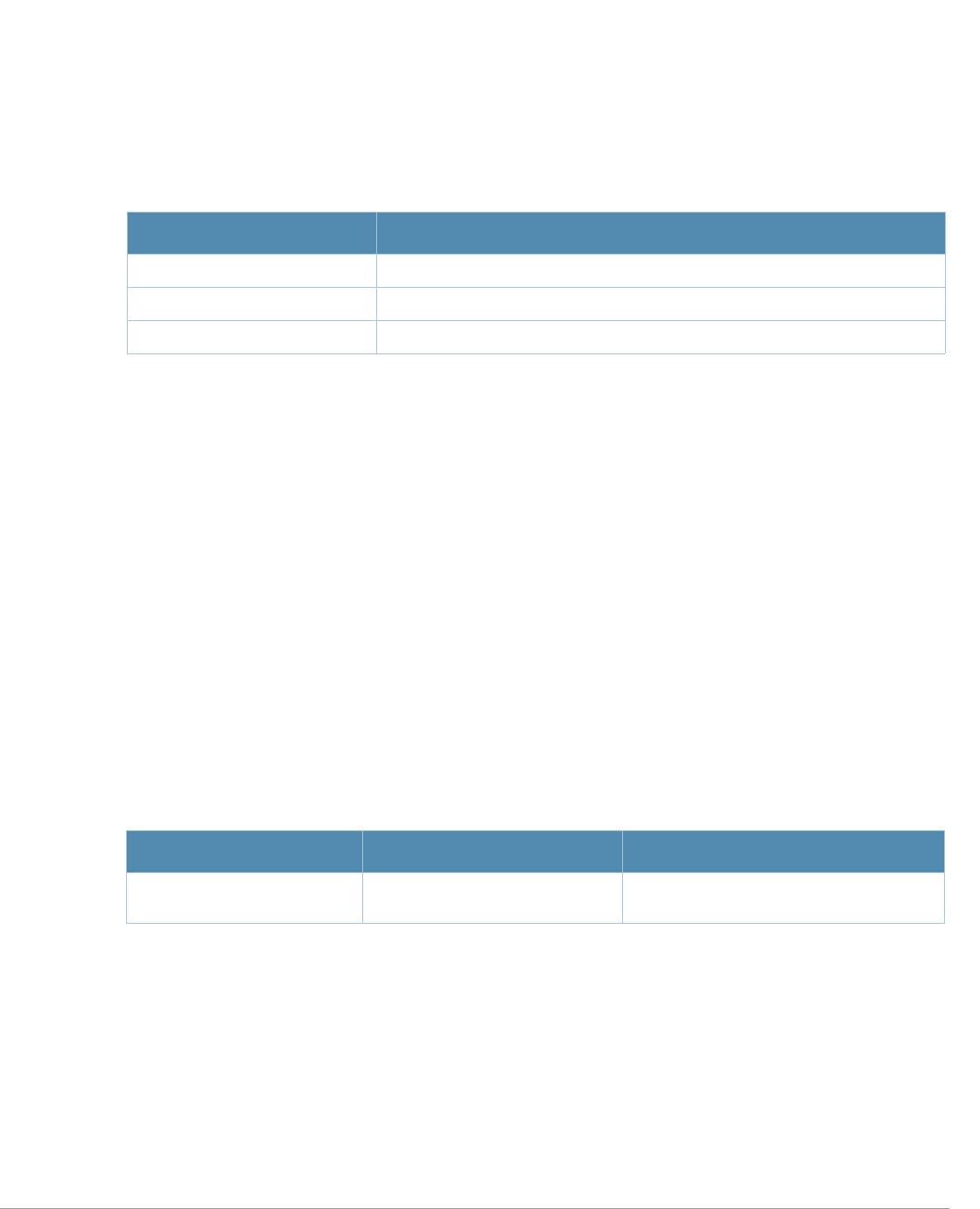
1004 | show rrm dot11k ap-channel-report AOS-W 3.4.1 Command Line Interface | Reference Guide
show rrm dot11k ap-channel-report
show rrm dot11k ap-channel-report [ap-name <name-of-an-ap> |
bssid <bssid-of-an-ap> | ip-addr <ip-address-of-an-ap>]
Description
Displays the channel information gathered by the AP. You can either specify an ap-name, bssid or ip-
address of an AP to see more details.
Syntax
Example
The output of this command shows the channel information for r-wing-94:94.
Command History
This command was available in AOS-W 3.4
Command Information
Parameter Description
ap-name Enter the name of the AP.
bssid Enter the BSSID address of the AP.
ip-addr Enter the IP address of the AP.
(host) # show rrm dot11k ap-channel-report ap-name r-wing-94
802.11K AP Channel Report Details
----------------------------------
Freq Band Channel List
--------- ------------
2.4 GHz 11,
5 GHz 36, 40, 157, 161, 165,
Num Entries:2
Platforms Licensing Command Mode
All platforms Base operating system Config or Enable mode on master or local
switches
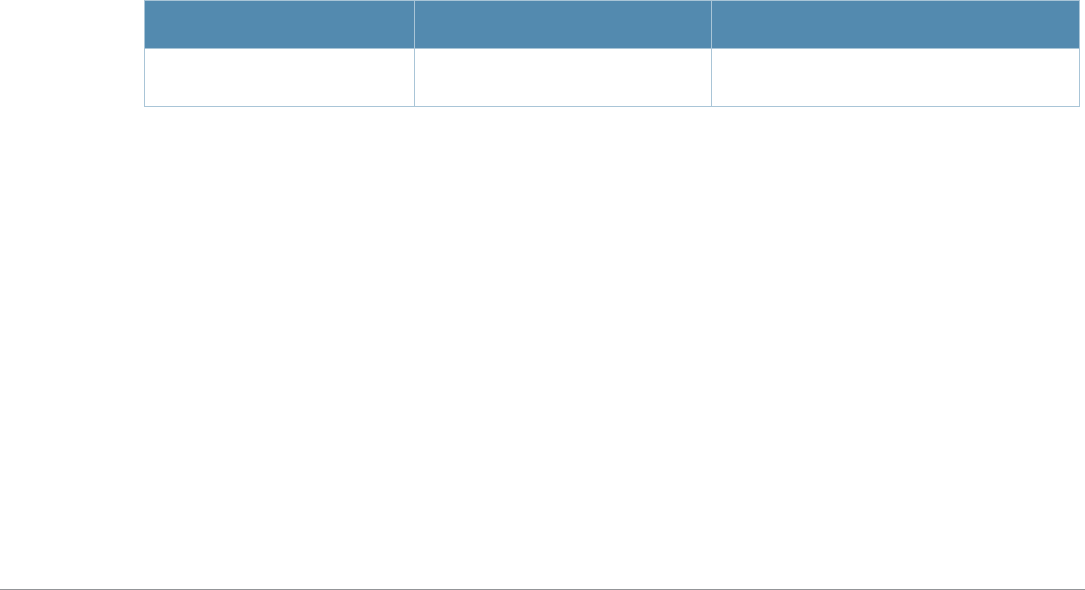
AOS-W 3.4.1 Command Line Interface | Reference Guide show rrm dot11k beacon-report | 1005
show rrm dot11k beacon-report
show rrm dot11k beacon-report
Description
Displays the beacon report information sent by a client to its AP.
Syntax
No Parameters
Example
The output of this command shows the beacon report for the client 00:1f:6c:7a:d4:fd.
Command History
This command was available in AOS-W 3.4
Command Information
(host) # show rrm dot11k beacon-report station-mac 00:1f:6c:7a:d4:fd
802.11K Beacon Report Details
--------------------------------------------------
Channel BSSID Reg Class Antenna ID Meas. Mode
---------- ------- ------------ ------------- ----------------
1 00:0b:86:6d:3e:40 0 1 Bcn Table
Num Elements:1
Platforms Licensing Command Mode
All platforms Base operating system Config or Enable mode on master or local
switches
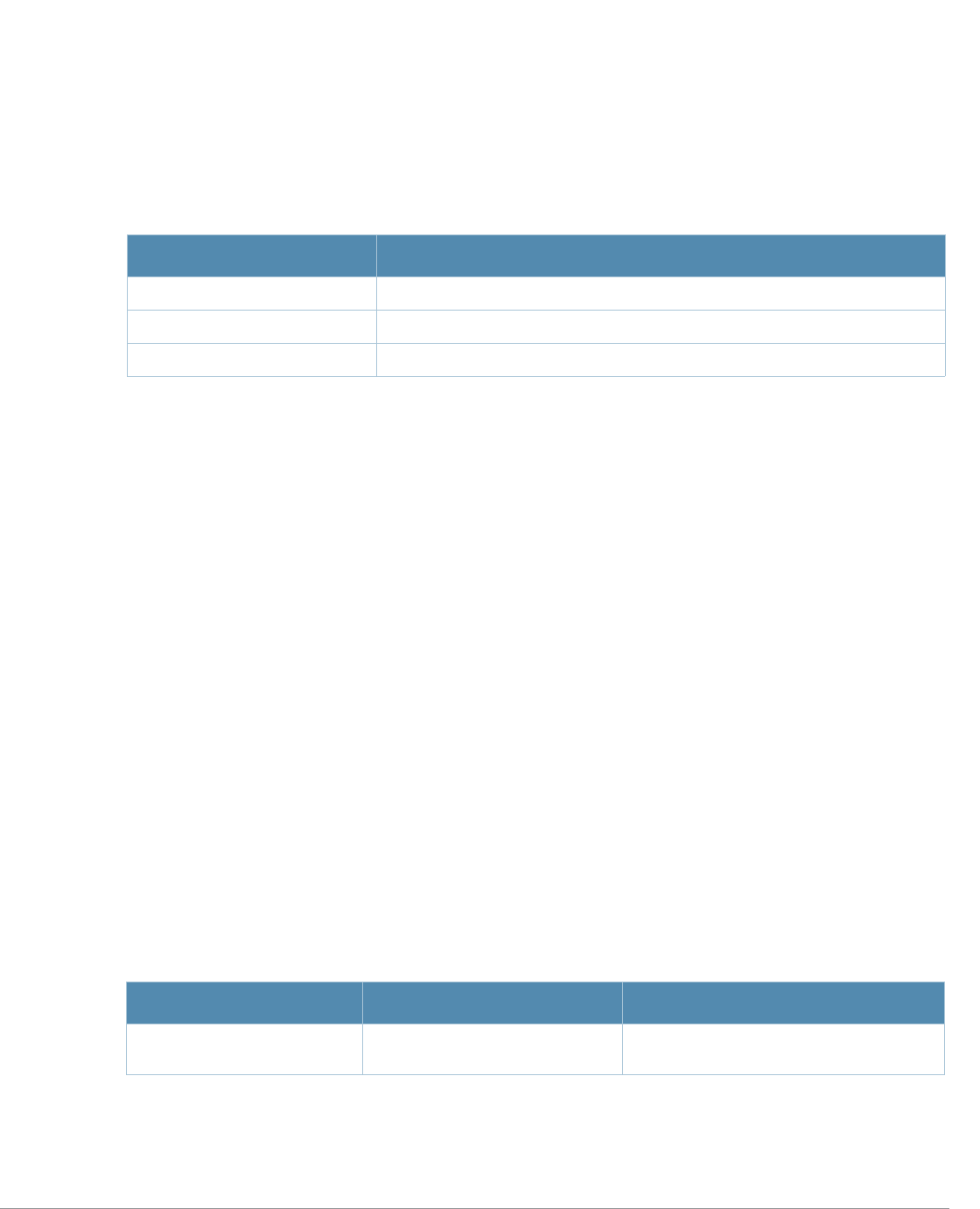
1006 | show rrm dot11k neighbor-report AOS-W 3.4.1 Command Line Interface | Reference Guide
show rrm dot11k neighbor-report
show rrm dot11k neighbor-report [ap-name <name-of-an-ap> [essid] |
bssid <bssid-of-an-ap> | ip-addr <ip-address-of-an-ap>]
Description
Displays the neighbor information for a particular AP. If the AP name or the AP’s IP address is specified, the
user can optionally specify the ESSID to get the neighbor information. If the ESSID is not specified, the
command will display the neighbor information for all the Virtual AP's configured on the AP.
Syntax
Example
The output of this command shows the neighbor information for r-wing-94.
Command History
This command was available in AOS-W 3.4
Command Information
Parameter Description
ap-name Enter the name of the AP.
bssid Enter the BSSID address of the AP.
ip-addr Enter the IP address of the AP.
(host) # show rrm dot11k neighbor-report ap-name r-wing-94
802.11K Neighbor Report Details
-------------------------------
Flags: S: Spectrum Management, Q: QoS, A: APSD, R: Radio Measurement
ESSID BSSID Channel Reachability Security Authenticator Preference Flags
----- ----- ------- ------------ -------- ------------- ---------- -----
r-wing-voice 00:0b:86:6d:3e:30 165 Reachable Same Same 1 SR
r-wing-voice 00:0b:86:6d:3e:20 1 Reachable Same Same 1 SR
r-wing-data 00:0b:86:6d:3e:40 6 Reachable Same Same 1 SR
r-wing-data 00:0b:86:6d:4e:41 153 Reachable Same Same 1 SR
Num Entries:4
Platforms Licensing Command Mode
All platforms Base operating system Config or Enable mode on master or local
switches
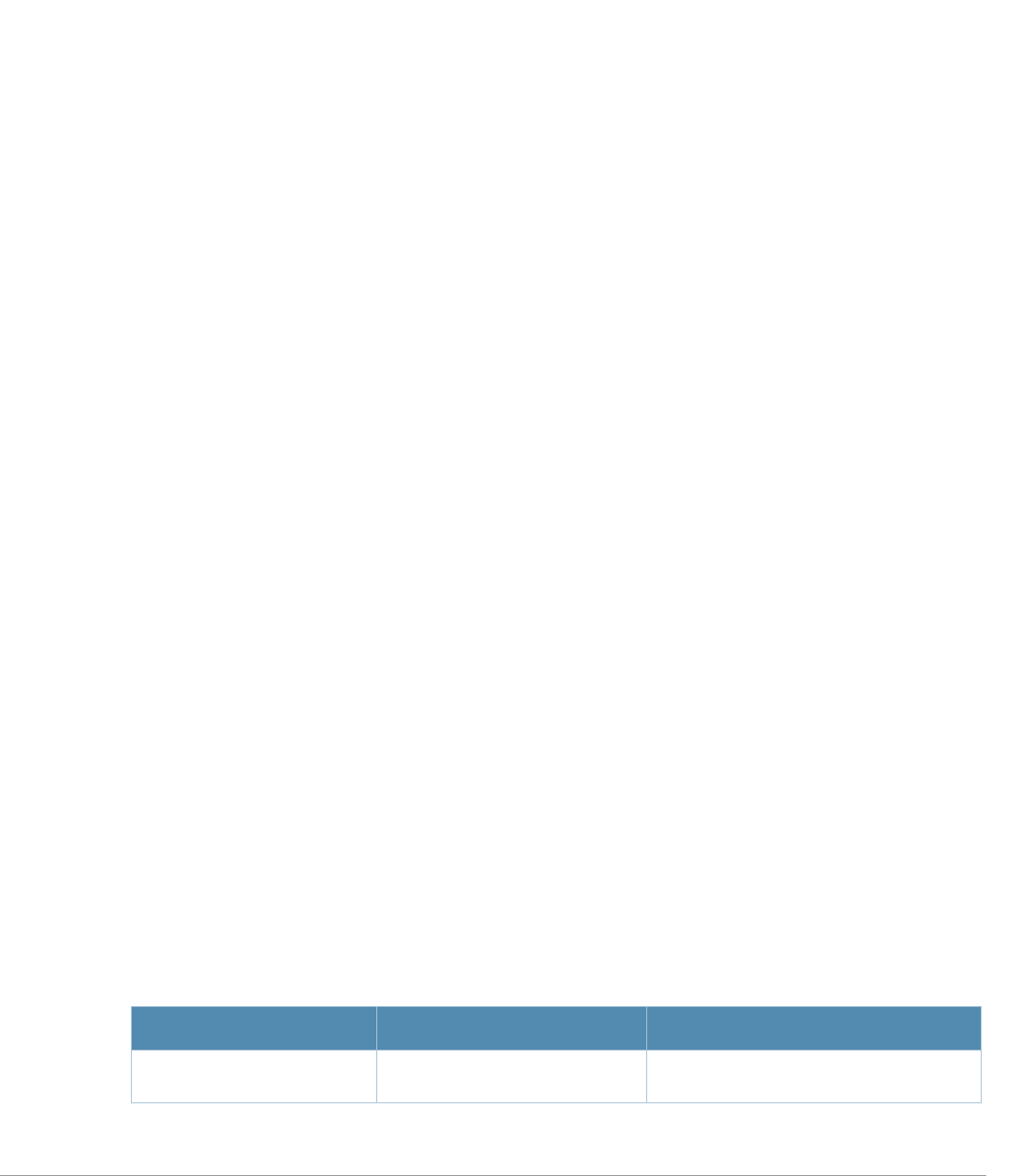
AOS-W 3.4.1 Command Line Interface | Reference Guide show running-config | 1007
show running-config
show running-config
Description
Displays the current switch configuration, including all pending changes which are yet to be saved.
Syntax
No Parameters
Example
The output of this command shows the available admission capacity for voice traffic on all APs.
Command History
This command was available in AOS-W 3.0
Command Information
(host) # show running-config
version 3.4
enable secret "******"
telnet soe
loginsession timeout 0
hostname "vjoshi-2400"
clock timezone PST -8
location "Building1.floor1"
mms config 0
controller config 986
ip access-list eth validuserethacl
permit any
!
netservice svc-netbios-dgm udp 138
netservice svc-snmp-trap udp 162
netservice svc-https tcp 443
netservice svc-dhcp udp 67 68 alg dhcp
netservice svc-smb-tcp tcp 445
netservice svc-ike udp 500
netservice svc-l2tp udp 1701
...
...
...
netservice svc-bootp udp 67 69
netservice svc-snmp udp 161
netservice svc-v6-dhcp udp 546 547
netservice svc-icmp 1
--More-- (q) quit (u) pageup (/) search (n) repeat
Platforms Licensing Command Mode
All platforms Base operating system Config or Enable mode on master or local
switches

1008 | show running-config AOS-W 3.4.1 Command Line Interface | Reference Guide
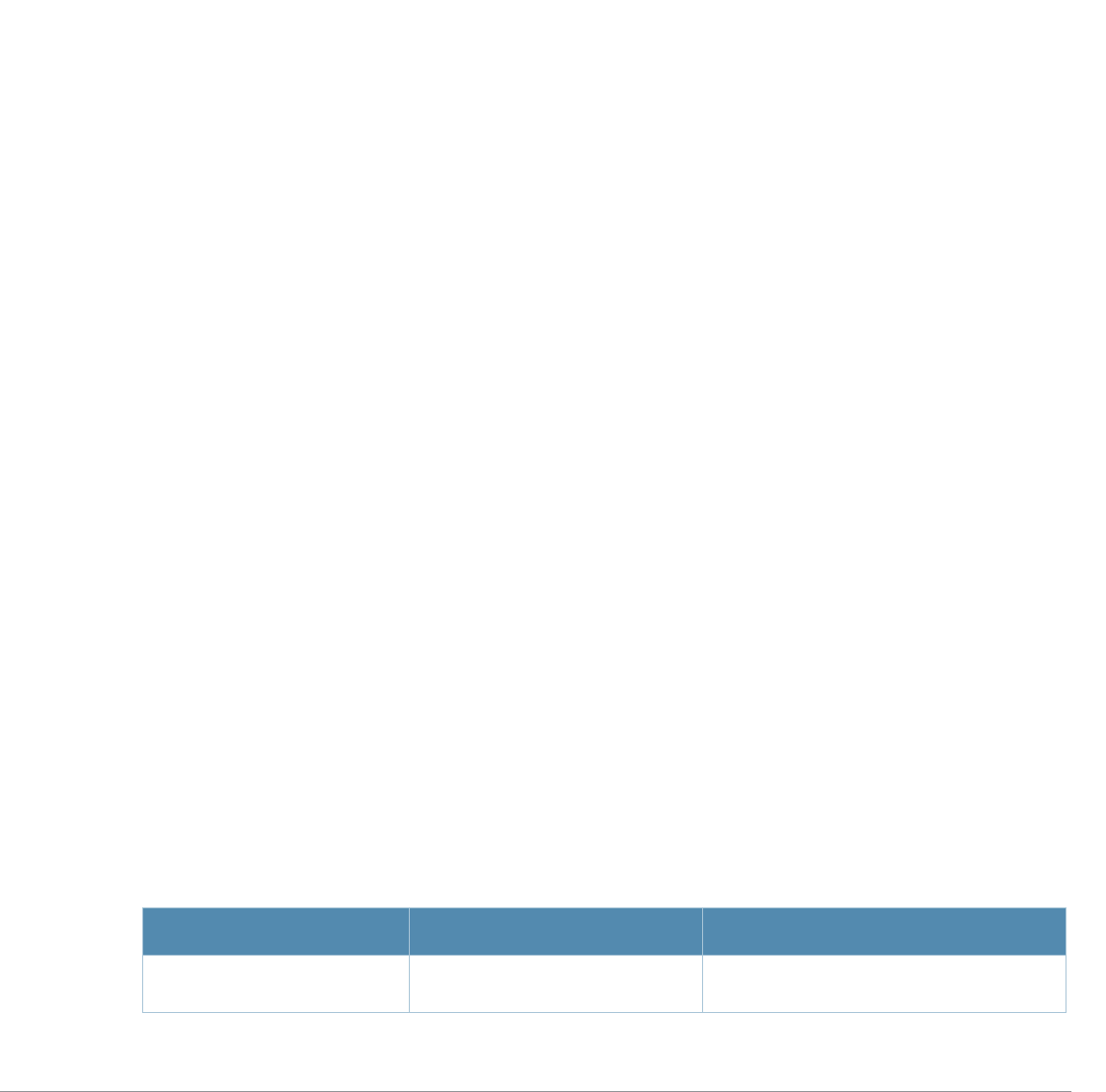
AOS-W 3.4.1 Command Line Interface | Reference Guide show session-acl-list | 1009
show session-acl-list
show session-acl-list
Description
Displays the list of configured session ACLs in the switch.
Syntax
No Parameters
Example
The output of this command shows the session ACLs in the switch.
Command History
This command was available in AOS-W 3.4
Command Information
(host) # show session-access-list
v6-icmp-acl
allow-diskservices
control
validuser
v6-https-acl
vocera-acl
icmp-acl
v6-dhcp-acl
captiveportal
v6-dns-acl
allowall
test
sip-acl
https-acl
...
...
...
v6-http-acl
dhcp-acl
http-acl
stateful-dot1x
ap-acl
svp-acl
noe-acl
stateful-kerberos
v6-logon-control
h323-acl
Platforms Licensing Command Mode
All platforms Base operating system Config or Enable mode on master or local
switches

1010 | show session-acl-list AOS-W 3.4.1 Command Line Interface | Reference Guide

AOS-W 3.4.1 Command Line Interface | Reference Guide show slots | 1011
show slots
show slots
Description
Displays the list of slots in the switch, including the status and card type.
Syntax
No Parameters
Example
The output of this command shows slot details on the switch.
Command History
This command was available in AOS-W 3.4
Command Information
(host) # show slots
Slots
------
Slot Status Card Type
---- ------ ---------
1 Present A2400
Platforms Licensing Command Mode
All platforms Base operating system Config or Enable mode on master or local
switches

1012 |show slots AOS-W 3.4.1 Command Line Interface | Reference Guide

AOS-W 3.4.1 Command Line Interface | Reference Guide show snmp community | 1013
show snmp community
show snmp community
Description
Displays the SNMP community string details.
Syntax
No Parameters
Example
The output of this command shows slot details on the switch.
Command History
This command was available in AOS-W 3.0
Command Information
(host) # show snmp community
SNMP COMMUNITIES
----------------
COMMUNITY ACCESS VERSION
--------- ------ -------
public READ_ONLY V1, V2c
Platforms Licensing Command Mode
All platforms Base operating system Config or Enable mode on master or local
switches

1014 |show snmp inform AOS-W 3.4.1 Command Line Interface | Reference Guide
show snmp inform
show snmp inform
Description
Displays the length of SNMP inform queue.
Syntax
No Parameters
Example
The output of this command shows slot details on the switch.
Command History
This command was available in AOS-W 3.0
Command Information
(host) # show snmp inform stats
Inform queue size is 100
SNMP INFORM STATS
-----------------
HOST PORT INFORMS-INQUEUE OVERFLOW TOTAL INFORMS
---- ---- --------------- -------- -------------
Platforms Licensing Command Mode
All platforms Base operating system Config or Enable mode on master or local
switches

AOS-W 3.4.1 Command Line Interface | Reference Guide show snmp trap-host | 1015
show snmp trap-host
show snmp trap-host
Description
Displays the configured SNMP trap hosts.
Syntax
No Parameters
Example
The output of this command shows details of a SNMP trap host.
Command History
This command was available in AOS-W 3.0
Command Information
(host) # show snmp trap-hosts
SNMP TRAP HOSTS
---------------
HOST VERSION SECURITY NAME PORT TYPE TIMEOUT RETRY
---- ------- ------------- ---- ---- ------- -----
10.16.14.1 SNMPv2c public 162 Trap N/A N/A
Platforms Licensing Command Mode
All platforms Base operating system Config or Enable mode on master or local
switches

1016 |show snmp trap-list AOS-W 3.4.1 Command Line Interface | Reference Guide
show snmp trap-list
show snmp trap-list
Description
Displays the list of SNMP traps.
Syntax
No Parameters
Example
The output of this command shows the list of SNMP traps and the status.
Command History
This command was available in AOS-W 3.0
Command Information
(host) # show snmp trap-list
SNMP TRAP LIST
--------------
TRAP-NAME CONFIGURABLE ENABLE-STATE
--------- ------------ ------------
authenticationFailure Yes Enabled
coldStart Yes Enabled
linkDown Yes Enabled
linkUp Yes Enabled
warmStart Yes Enabled
wlsxAPBssidEntryChanged Yes Enabled
wlsxAPEntryChanged Yes Enabled
wlsxAPImpersonation Yes Enabled
wlsxAPInterferenceCleared Yes Enabled
wlsxAPInterferenceDetected Yes Enabled
wlsxAPRadioAttributesChanged Yes Enabled
wlsxAPRadioEntryChanged Yes Enabled
wlsxAccessPointIsDown Yes Enabled
wlsxAccessPointIsUp Yes Enabled
wlsxAdhocNetwork Yes Enabled
wlsxAdhocNetworkBridgeDetected Yes Enabled
wlsxAdhocNetworkBridgeDetectedAP Yes Enabled
...
...
...
...
wlsxFanOK Yes Enabled
wlsxFanTrayInserted Yes Enabled
--More-- (q) quit (u) pageup (/) search (n) repeat
Platforms Licensing Command Mode
All platforms Base operating system Config or Enable mode on master or local
switches

AOS-W 3.4.1 Command Line Interface | Reference Guide show snmp trap-queue | 1017
show snmp trap-queue
show snmp trap-queue
Description
Displays the list of SNMP traps in queue.
Syntax
No Parameters
Example
The output of this command shows the list of SNMP traps sent to host.
Command History
This command was available in AOS-W 3.0
Command Information
(host) # show snmp trap-queue
2009-04-29 00:47:40 An AP/AM 00:0b:86:cd:cc:14, radio 2 at Location 00:0b:86:cd:cc:14 and channel 1, det
interfering access point (BSSID 00:e0:fc:18:b5:35, SSID WA1003A). More information can be obtained from
10.16.15.1/screens/wmsi/reports.html?mode=ap&bssid=00:e0:fc:18:b5:35.
2009-04-29 00:49:01 An AP/AM 00:0b:86:cd:cc:14, radio 2 at Location 00:0b:86:cd:cc:14 and channel 10, de
interfering access point (BSSID 00:1a:1e:a8:2d:a0, SSID l-wing-94). More information can be obtained fro
10.16.15.1/screens/wmsi/reports.html?mode=ap&bssid=00:1a:1e:a8:2d:a0.
2009-04-29 00:49:19 An AP/AM 00:0b:86:cd:cc:14, radio 2 at Location 00:0b:86:cd:cc:14 and channel 1, det
interfering access point (BSSID 00:e0:fc:18:b5:35, SSID WA1003A). More information can be obtained from
10.16.15.1/screens/wmsi/reports.html?mode=ap&bssid=00:e0:fc:18:b5:35.
2009-04-29 00:49:20 An AP/AM 00:0b:86:cd:cc:14, radio 2 at Location 00:0b:86:cd:cc:14 and channel 1, det
interfering access point (BSSID 00:0b:86:5c:d8:e0, SSID r-wing-94). More information can be obtained fro
10.16.15.1/screens/wmsi/reports.html?mode=ap&bssid=00:0b:86:5c:d8:e0.
2009-04-29 00:49:31 An AP/AM 00:0b:86:cd:cc:14, radio 1 at Location 00:0b:86:cd:cc:14 and channel 36, de
interfering access point (BSSID 00:1a:1e:8d:dc:20, SSID ). More information can be obtained from http://
screens/wmsi/reports.html?mode=ap&bssid=00:1a:1e:8d:dc:20.
2009-04-29 00:50:15 An AP/AM 00:0b:86:cd:cc:14, radio 2 at Location 00:0b:86:cd:cc:14 and channel 1, det
interfering access point (BSSID 00:e0:fc:18:b5:35, SSID WA1003A). More information can be obtained from
10.16.15.1/screens/wmsi/reports.html?mode=ap&bssid=00:e0:fc:18:b5:35.
--More-- (q) quit (u) pageup (/) search (n) repeat
Platforms Licensing Command Mode
All platforms Base operating system Config or Enable mode on master or local
switches
1018 | show snmp user-table AOS-W 3.4.1 Command Line Interface | Reference Guide
show snmp user-table
show snmp user-table [user <username> auth-prot [sha | md5] <value> priv-prot [aes |
des] <value>]
Description
Displays the list of SNMP user profile for a specified username.
Syntax
Example
The output of this command shows the list of SNMP traps sent to host.
Command History
This command was available in AOS-W 3.0
Command Information
Parameter Description
auth-prot Authentication protocol for the user, either HMAC-MD5-98 Digest Authentication Protocol (MD5)
or HMAC-SHA-98 Digest Authentication Protocol (SHA), and the password for use with the
designated protocol.
priv-prot Privacy protocol for the user, either Advanced Encryption Standard (AES) or CBC-DES
Symmetric Encryption Protocol (DES), and the password for use with the designated protocol.
(host) # show snmp user-table
SNMP USER TABLE
---------------
USER AUTHPROTOCOL PRIVACYPROTOCOL FLAGS
---- ------------ --------------- -----
Sam SHA AES
fire SHA AES
Platforms Licensing Command Mode
All platforms Base operating system Config or Enable mode on master or local
switches
AOS-W 3.4.1 Command Line Interface | Reference Guide show ssh | 1019
show ssh
show ssh
Description
Displays the SSH configuration details.
Syntax
No Parameters
Example
The output of this command shows SSH configuration details.
Command History
This command was available in AOS-W 3.0
Command Information
(host) # show ssh
SSH Settings:
-------------
DSA Enabled
Mgmt User Authentication Method username/password
Platforms Licensing Command Mode
All platforms Base operating system Config or Enable mode on master or local
switches

1020 | show ssh AOS-W 3.4.1 Command Line Interface | Reference Guide
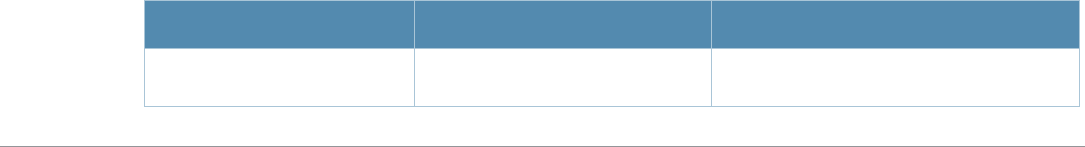
AOS-W 3.4.1 Command Line Interface | Reference Guide show startup-config | 1021
show startup-config
show startup-config
Description
Displays the configuration which will be used the next time the switch is rebooted. It contains all the
options last saved using the write memory command. Any unsaved changes are not included.
Syntax
No Parameters
Example
The output of this command shows slot details on the switch.
Command History
This command was available in AOS-W 3.0
Command Information
(host) # show startup-config
version 3.4
enable secret "608265290155fb924578f15b12670a75a37045cbdf62fb0d3a"
telnet cli
telnet soe
loginsession timeout 30
hostname "FirstFloor2400"
clock timezone PST -8
location "Building1.floor1"
mms config 0
controller config 22
ip access-list eth validuserethacl
permit any
!
netservice svc-snmp-trap udp 162
netservice svc-dhcp udp 67 68
netservice svc-smb-tcp tcp 445
netservice svc-https tcp 443
netservice svc-ike udp 500
netservice svc-l2tp udp 1701
netservice svc-syslog udp 514
...
...
...
netservice svc-msrpc-udp udp 135 139
netservice svc-ssh tcp 22
netservice svc-http-proxy1 tcp 3128
--More-- (q) quit (u) pageup (/) search (n) repeat
Platforms Licensing Command Mode
All platforms Base operating system Config or Enable mode on master or local
switches

1022 | show startup-config AOS-W 3.4.1 Command Line Interface | Reference Guide

AOS-W 3.4.1 Command Line Interface | Reference Guide show station-table | 1023
show station-table
show station-table [mac <mac_address>]
Description
Displays the internal station table entries and also details of a station table entry.
Syntax
No Parameters
Example
The output of this command shows details of an entry in the station table.
Command History
This command was available in AOS-W 3.0
Command Information
(host) # show station-table mac 00:1f:6c:7a:d4:fd
Association Table
-----------------
BSSID IP Essid AP name Phy Age
--------------- ----------- ------- ------- --- ---
00:0b:86:6d:3e:30 10.15.20.252 sam - a 01:03:41
Platforms Licensing Command Mode
All platforms Base operating system Config or Enable mode on master or local
switches

1024 |show station-table AOS-W 3.4.1 Command Line Interface | Reference Guide

AOS-W 3.4.1 Command Line Interface | Reference Guide show storage | 1025
show storage
show storage
Description
Displays the storage information on the switch.
Syntax
No Parameters
Example
The output of this command shows the storage details on the switch.
Command History
This command was available in AOS-W 3.0
Command Information
(host) # show storage
Filesystem Size Used Available Use% Mounted on
/dev/root 57.0M 54.6M 2.3M 96% /
none 70.0M 2.0M 68.0M 3% /tmp
/dev/hda3 149.7M 9.3M 132.6M 7% /flash
Platforms Licensing Command Mode
All platforms Base operating system Config or Enable mode on master or local
switches

1026 |show storage AOS-W 3.4.1 Command Line Interface | Reference Guide

AOS-W 3.4.1 Command Line Interface | Reference Guide show switch ip | 1027
show switch ip
show switch ip
Description
Displays the IP address of the switch and VLAN ID.
Syntax
No Parameters
Example
The output of this command shows the IP address and VLAN ID of the switch.
Command History
This command was available in AOS-W 3.0
Command Information
(host) # show switch ip
Switch IP Address: 10.16.15.1
Switch IP is from Vlan Interface: 1
Platforms Licensing Command Mode
All platforms Base operating system Config or Enable mode on master or local
switches

1028 | show switch software AOS-W 3.4.1 Command Line Interface | Reference Guide
show switch software
show switch software
Description
Displays the details of the software running in the switch.
Syntax
No Parameters
Example
The output of this command shows the details of software running in the switch.
Command History
This command was available in AOS-W 3.0
Command Information
(host) # show switch software
Alcatel-Lucent Operating System-Wireless.
AOS-W (MODEL: OAW-651-US), Version 3.4.0.0
Website: http://www.alcatel.com/enterprise
All Rights Reserved (c) 2005-2009, Alcatel-Lucent.
Compiled on 2009-05-31 at 21:59:21 PDT (build 21443) by p4build
ROM: System Bootstrap, Version CPBoot 1.0.0.0 (build 21083)
Built: 2009-04-06 20:51:16
Built by: p4build@re_client_21083
Switch uptime is 23 hours 15 minutes 4 seconds
Reboot Cause: User reboot.
Supervisor Card
Processor XLS 408 (revision A1) with 907M bytes of memory.
32K bytes of non-volatile configuration memory.
256M b t f S i C d S t fl h ( d l NAND 256MB)
Platforms Licensing Command Mode
All platforms Base operating system Config or Enable mode on master or local
switches

AOS-W 3.4.1 Command Line Interface | Reference Guide show switches | 1029
show switches
show switches [all | state {complete | incomplete | inprogress | required} |
summary ]
Description
Displays the details of switches connected to the master switch including the master switch.
Syntax
Example
The output of this command lists all switches connected to the master switch including the master switch.
Command History
This command was available in AOS-W 3.0
Command Information
Parameter Description
all List of all switches.
state Configuration status of all switches.
summary Status of all switches connected to the master.
(host) # show switches all
All Switches
------------
IP Address Name Location Type Version Status Configuration State Config Sync Tim
---------- ---- -------- ---- ------- ------ ------------------- ---------------
10.16.12.1 r-wing-94 Building1.floor1 master 3.4.0.0 up UPDATE SUCCESSFUL 0
Platforms Licensing Command Mode
All platforms Base operating system Config or Enable mode on master or local
switches

1030 | show switches AOS-W 3.4.1 Command Line Interface | Reference Guide
AOS-W 3.4.1 Command Line Interface | Reference Guide show switchinfo | 1031
show switchinfo
show switchinfo
Description
Displays the latest and complete summary of switch details including role, last configuration change,
hostname, reason for last reboot.
Syntax
No Parameters
Example
The output of this command lists all switches connected to the master switch including the master switch.
Command History
This command was available in AOS-W 3.0
Command Information
(host) # show switchinfo
Hostname is TechPubs
Location not configured
System Time:Fri Jun 5 09:54:06 PST 2009
Alcatel-Lucent Operating System-Wireless.
AOS-W (MODEL: OAW-651-US), Version 3.4.0.0
Website: http://www.alcatel.com/enterprise
All Rights Reserved (c) 2005-2009, Alcatel-Lucent.
Compiled on 2009-05-31 at 21:59:21 PDT (build 21443) by p4build
.........
.........
.........
Internet address is 172.16.0.254 255.255.255.0
Routing interface is enable, Forwarding mode is enable
Directed broadcast is disabled
Encapsulation 802, loopback not set
MTU 1500 bytes
Last clearing of "show interface" counters 0 day 23 hr 24 min 30 sec
link status last changed 0 day 23 hr 20 min 54 sec
Proxy Arp is disabled for the Interface
Switchrole:local
masterip:192.168.68.217
IKE PSK: 4e17d3529044f984c727db19636f133a
Configuration Changed since last save
No crash information available.
Reboot Cause: User reboot.
Platforms Licensing Command Mode
All platforms Base operating system Config or Enable mode on master or local
switches

1032 |show switchinfo AOS-W 3.4.1 Command Line Interface | Reference Guide

AOS-W 3.4.1 Command Line Interface | Reference Guide show syscontact | 1033
show syscontact
show syscontact
Description
Displays the contact information for support.
Syntax
No Parameters
Example
The output of this command shows the contact information for technical support.
Command History
This command was available in AOS-W 3.1
Command Information
(host) # show syscontact
admin@mycompany.com
Platforms Licensing Command Mode
All platforms Base operating system Config or Enable mode on master or local
switches

1034 | show syscontact AOS-W 3.4.1 Command Line Interface | Reference Guide

AOS-W 3.4.1 Command Line Interface | Reference Guide show syslocation | 1035
show syslocation
show syslocation
Description
Displays the location details of the switch.
Syntax
No Parameters
Example
The output of this command location of the switch.
Command History
This command was available in AOS-W 3.1
Command Information
(host) # show syslocation
Building 1, Floor 1
Platforms Licensing Command Mode
All platforms Base operating system Config or Enable mode on master or local
switches

1036 | show syslocation AOS-W 3.4.1 Command Line Interface | Reference Guide
AOS-W 3.4.1 Command Line Interface | Reference Guide show tech-support | 1037
show tech-support
show tech-support
Description
Displays all information about the switch required for technical support purposes.
Syntax
No Parameters
Command History
This command was available in AOS-W 3.1
Command Information
Platforms Licensing Command Mode
All platforms Base operating system Config or Enable mode on master or local
switches

1038 | show tech-support AOS-W 3.4.1 Command Line Interface | Reference Guide

AOS-W 3.4.1 Command Line Interface | Reference Guide show telnet | 1039
show telnet
show telnet
Description
Displays the status of telnet access using command line interface (CLI) or serial over ethernet (SOE) to the
switch.
Syntax
No Parameters
Example
The output of this command shows the status of CLI and SOE access to the switch.
Command History
This command was available in AOS-W 3.0
Command Information
(host) # show telnet
telnet cli is enabled
telnet soe is enabled
Platforms Licensing Command Mode
All platforms Base operating system Config or Enable mode on master or local
switches

1040 |show telnet AOS-W 3.4.1 Command Line Interface | Reference Guide
AOS-W 3.4.1 Command Line Interface | Reference Guide show time-range | 1041
show time-range
show time-range [<string>|summary]
Description
Displays the list of time range configured in the system and rules affected by the time range.
Syntax
No Parameters
Example
The output of this command shows the absolute time range details
Command History
This command was available in AOS-W 3.0
Command Information
(host) # show time-range
Time-Range monitoring, Absolute
-------------------------------
StartDate Start-time EndDate End-time Applied
--------- ---------- ------- -------- -------
4/29/2009 23:00 4/30/2009 12:00 No
Platforms Licensing Command Mode
All platforms Base operating system Config or Enable mode on master or local
switches

1042 |show time-range AOS-W 3.4.1 Command Line Interface | Reference Guide

AOS-W 3.4.1 Command Line Interface | Reference Guide show trunk | 1043
show trunk
show trunk
Description
Displays the list of trunk ports on the switch.
Syntax
No Parameters
Example
The output of this command shows details of a trunk port.
Command History
This command was available in AOS-W 3.0
Command Information
(host) # show trunk
Trunk Port Table
-----------------
Port Vlans Allowed Vlans Active Native Vlan
---- ------------- ------------ -----------
FE2/12 1,613,615-617,632-633,636-640,667-668 1,613,615-617,632-633,636-640,667-668 1
Platforms Licensing Command Mode
All platforms Base operating system Config or Enable mode on master or local
switches

1044 | show trunk AOS-W 3.4.1 Command Line Interface | Reference Guide
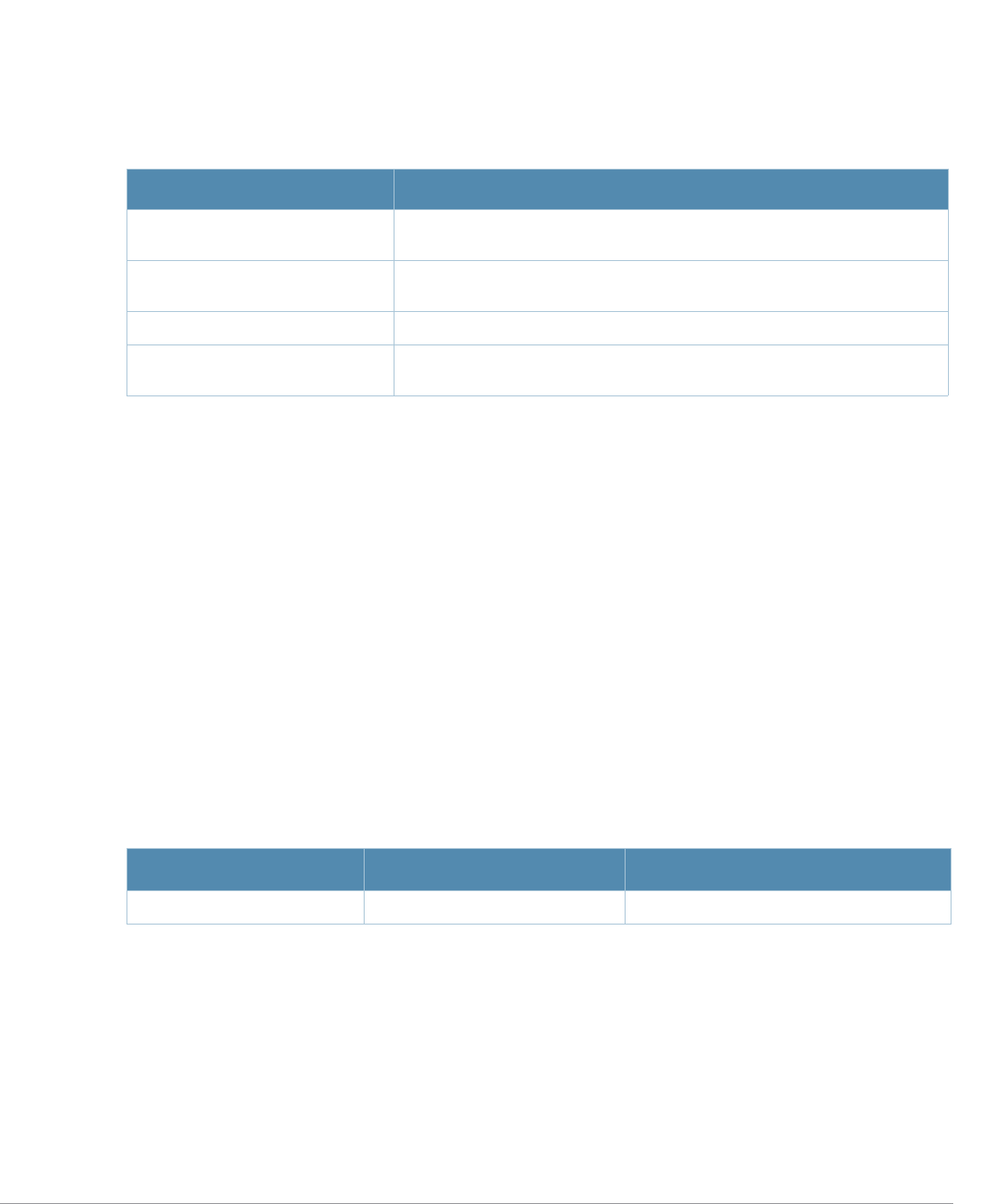
AOS-W 3.4.1 Command Line Interface | Reference Guide show uplink | 1045
show uplink
crypto-local
show uplink [config|{connection <link_id>}|signal|{stats <link_id}]
Description
Displays uplink configuration details on an OmniAccess 4306 series switch.
Syntax
Example
The output of this command displays the switch uplink status .
Command History
Introduced in AOS-W 3.4.
Command Information
Parameter Description
config Enter the keyword config to display the uplink manager, the default wired
priority and default cellular priority
connection Enter the keyword connection followed by the uplink ID number to display
the connection details.
signal Enter the keyword signal to display the cellular uplink signal strength.
stats Enter the keyword stats followed by the uplink ID number to display the
statistical information on the designated uplink.
Platforms Licensing Command Mode
OmniAccess 4306 switches Base operating system Config mode on master and local switches
(host) ##show uplink
Uplink Manager: Enabled
Uplink Management Table
-----------------------
Id Uplink Type Properties Priority State Status
-- ----------- ---------- ------- ----- ------
1 Wired vlan 1 200 Initializing Waiting for link
2 Cellular Novatel_U727 100 Standby Ready

1046 | show uplink AOS-W 3.4.1 Command Line Interface | Reference Guide
AOS-W 3.4.1 Command Line Interface | Reference Guide show usb | 1047
show usb
crypto-local
show usb [cellular|ports|test|verbose]
Description
Display detailed USB device information.
Syntax
Examples
The USB Device table, in the example below, displays the USB port is in the 'Device Ready' state, meaning
that the port has passed the diagnostic test and is ready to send and receive data.
Below is an example of the show usb verbose display output (partial).
Command History
Introduced in AOS-W 3.4.
Command Information
Parameter Description
cellular Enter the keyword cellular to display cellular devices.
ports Enter the keyword ports to display detailed TTY port information such as
signal strength.
test Enter the keyword test to test the USB TTY ports.
NOTE: Testing an invalid modem port may cause the switch to “hang”. To
resolve this, unplug and re-plug the modem.
verbose Enter the keyword verbose to display detailed USB information including
serial number and USB type.
Platforms Licensing Command Mode
OmniAccess 4306 switches Base operating system Config mode on master and local switches
(host) (config-cellular new_modem)# show usb
USB Device Table
----------------
Address Product Vendor ProdID Serial Type Profile State
------- ------- ------ ------ ------ ---- ------- -----
18 Novatel Wireless CDMA 1410 4100 091087843891000 Cellular new_modem Device ready
(host) #show usb verbose
...
T: Bus=01 Lev=02 Prnt=02 Port=00 Cnt=01 Dev#= 3 Spd=12 MxCh= 0
D: Ver= 1.10 Cls=00(>ifc ) Sub=00 Prot=00 MxPS=64 #Cfgs= 1
P: Vendor=1410 ProdID=4100 Rev= 0.00
S: Manufacturer=Novatel Wireless Inc.
S: Product=Novatel Wireless CDMA
S: SerialNumber=091087843891000
C:* #Ifs= 5 Cfg#= 1 Atr=a0 MxPwr=500mA
...

1048 | show usb AOS-W 3.4.1 Command Line Interface | Reference Guide

AOS-W 3.4.1 Command Line Interface | Reference Guide show user | 1049
show user
show user
authentication-method {[dot1x][mac][stateful-dot1x][vpn][web]}[rows <NUMBER>
<NUMBER>]
bssid <A:B:C:D:E:F> rows <NUMBER> <NUMBER>
essid <STRING> rows <NUMBER> <NUMBER>
internal rows <NUMBER> <NUMBER>
ip <A.B.C.D> rows <NUMBER> <NUMBER>
location b.f.l rows <NUMBER> <NUMBER>
mac <A:B:C:D:E:F>
mobile {[bindings][visitors]} [rows <NUMBER> <NUMBER>]
name <STRING>
phy-type {[a]|[b]}[rows <NUMBER> <NUMBER>]
role <STRING> rows <NUMBER> <NUMBER>
rows <NUMBER> <NUMBER>
Description
Displays detailed information about the switch’s connection in regards to mobility state and statistics,
authentication statistics, VLAN assignment method, AP datapath tunnel info, radius accounting statistics,
user name, user-role derivation method, datapath session flow entries, and 802.11 association state and
statistics. The show user command allows you to filter specific information by parameter.
Syntax
Parameter Description
authentication-method Authentication method used for the device.
dot1x Number of users to create starting with <ipaddr>.
mac Authentication method.
stateful-dot1x 802.1x authentication.
vpn MAC authentication.
web Stateful 802.1x authentication.
rows <NUMBER> <NUMBER> Displays the log output from the specified number of rows from the end of
the log and the total number of rows to display.
bssid <A:B:C:D:E:F> BSSID address of the device.
essid <STRING> ESSID of the device.
internal rows <NUMBER>
<NUMBER>
Displays the log output from the specified number of rows from the end of
the log and the total number of rows to display
ip <A.B.C.D> IP address of user.
location b.f.l Displays the building, floor and location of the device.
mac <A:B:C:D:E:F> MAC address .
mobile Mobile users.
bindings Users that have moved away.
visitors Users that are visitors.
name <STRING> User’s name.
phy-type 801.11 type
1050 | show user AOS-W 3.4.1 Command Line Interface | Reference Guide
Usage Guidelines
Use the show user command to show detailed output (which matches the switch output of user statistics)
and includes the entire output of show user-table, mobility state and statics, authentication statistics, VLAN
assignment method, AP datapath tunnel information, radius accounting statistics, user-role derivation
method, datapath session flow entries and 802.11 association state and statistics.
Example
This example displays users currently in the employee role. The output of this command is split into two
tables in this document, however it appears in one table in the CLI.
The output of this command includes the following information:
aMatches PHY type a.
gMatches PHY type b or g.
role <STRING> User role such as employee, visitor and so on.
rows <NUMBER> <NUMBER> Displays the output from the specified number of rows from the end of the
log and the total number of rows to display
rows <NUMBER> <NUMBER> Displays the output from the specified number of rows from the end of the
log and the total number of rows to display
Parameter Description
Column Description
IP IP address of the device.
MAC MAC address of the device.
Name User’s name of the device.
Role User’s assigned role.
Age(d:h:m) Age of the user’s current session, in the format days:hours:minutes.
Auth Authentication method.
(host) (config) show user role employee
Users
-----
IP MAC Name Role Age(d:h:m) Auth VPN link AP name
---------- ------------ ------ ---- ---------- ---- -------- -------
192.168.160.1 00:23:6c:80:3d:bc madisonl employee 01:05:50 802.1x 1263
10.100.105.100 00:05:4e:45:5e:c8 ARUBANETWORKS employee 00:02:22 802.1x wlan-qa-cage
10.100.105.102 00:14:a5:30:c2:7f pdedhia employee 01:20:09 802.1x 2198
10.100.105.97 00:1b:77:c4:a2:fa ARUBANETWORKS employee 00:02:18 802.1x 2198
10.100.105.109 00:21:5c:02:16:bb myao employee 00:05:40 802.1x 1109
Users
-----
Roaming Essid/Bssid/Phy Profile
------- --------------- -------
Associated ethersphere-wpa2/00:1a:1e:85:d3:b1/a-HT default
Associated ethersphere-wpa2/00:1a:1e:6f:e5:51/a default
Associated ethersphere-wpa2/00:1a:1e:87:ef:f1/a default
Associated ethersphere-wpa2/00:1a:1e:87:ef:f1/a default
Associated ethersphere-wpa2/00:1a:1e:85:c2:11/a-HT default
AOS-W 3.4.1 Command Line Interface | Reference Guide show user | 1051
Command History
This command was introduced in AOS-W 3.0.
Command Information
VPN link Shows if the user is connected via a VPN link.
AP name Name of the AP.
Roaming Roaming type.
Essid/Bssid/Phy The Extended Service Set Identifier (ESSID), unique hard-wireless MAC address of
the AP (BSSID), and the 802.11 (PHY) type.
Profile Profile assigned to the device.
Column Description
Platforms Licensing Command Mode
All platforms Base operating system Available in Enable and Config modes.

1052 | show user AOS-W 3.4.1 Command Line Interface | Reference Guide

AOS-W 3.4.1 Command Line Interface | Reference Guide show user_session_count | 1053
show user_session_count
show user_session_count
Description
Show the number of users using an ESSID for different time intervals.
Syntax
No parameters.
Usage Guidelines
Issue this command to show the numbers of users using each configured ESSID for the following time
intervals:
Example
The example below shows that 95 users on the guest ESSID have been using that ESSID for between 120
and 239 minutes, and that 22 users have been using that ESSID for 240 minutes or longer.
Command History
This command was available in AOS-W 3.0.
Command Information
z1-4 minutes
z5-14 minutes
z15-29 minutes
z30-49 minutes
z50-119 minutes
z120-239 minutes
z240 minutes and longer
(host) #show user_session_count
User Session Count
------------------
ESSID Time Bucket Number of Users
----- ----------- ---------------
guest 1 8
guest 5 1
guest 15 2
guest 30 1
guest 60 1
guest 120 96
guest 240 22
companySSID-voip 1 0
companySSID-voip 5 0
companySSID-voip 15 0
companySSID-voip 30 0
companySSID-voip 60 1
companySSID-voip 120 43
companySSID-voip 240 46
Platforms Licensing Command Mode
All platforms Base operating system Enable and Config mode on local and
master switches

1054 | show user_session_count AOS-W 3.4.1 Command Line Interface | Reference Guide

AOS-W 3.4.1 Command Line Interface | Reference Guide show util_proc | 1055
show util_proc
show util_proc guest-email counters
Description
Show counters for the guest email process.
Syntax
No parameters.
Usage Guidelines
As part of guest provisioning, the guest access email feature allows you to define the SMTP port and server
that processes guest provisioning email. This server sends email to the guest or the sponsor when a guest
user manually sends email from the Guest Provisioning page, or when a user creates a guest account.
Example
The output of this command shows the numbers of guest emails received, sent and dropped since the
switch was last reset.
Related Commands
To configure SMTP servers and server ports for guest email, use the command guest-access-email.
Command History
This command was available in AOS-W 1.0.
Command Information
(host) #show util_proc guest-email counters
Guest Email Counters
--------------------
Name Value
---- -----
Email Received 14
Email Sent 3
Email Dropped 0
Platforms Licensing Command Mode
All platforms Base operating system Enable and Config mode on local and
master switches

1056 | show util_proc AOS-W 3.4.1 Command Line Interface | Reference Guide
AOS-W 3.4.1 Command Line Interface | Reference Guide show version | 1057
show version
show version
Description
Show the system software version.
Syntax
No parameters.
Example
The output of this command in this example shows that the switch is a OmniAccess 4302 model running
AOS-W version 3.4.0.0.
The output of this command includes the following information
Command History
This command was available in AOS-W 1.0.
Command Information
(host) #show version
Alcatel-Lucent Operating System-Wireless.
AOS-W (MODEL: OAW-4302-US), Version 3.4.0.0
Website: http://www.alcatel.com/enterprise
All Rights Reserved (c) 2005-2009, Alcatel-Lucent.
Compiled on 2008-12-17 at 22:52:36 PST (build 20263) by p4build
ROM: System Bootstrap, Version CPBoot 1.2.11 (Sep 13 2005 - 17:39:11)
Switch uptime is 41 days 8 hours 57 minutes 18 seconds
Reboot Cause: User reboot.
Supervisor Card
Processor 16.20 (pvr 8081 1014) with 256M bytes of memory.
32K bytes of non-volatile configuration memory.
256M bytes of Supervisor Card System flash (model=CF 256MB).
Parameter Description
Model Switch model type.
Version Version of AOS-W software.
ROM System bootstrap version.
Switch Uptime Switch uptime (time elapsed since the last switch reset.
Reboot Cause Reason the switch was last rebooted.
Supervisor Card Details for the switch’s internal supervisor card.
Platforms Licensing Command Mode
All platforms Base operating system Enable and Config mode on local and
master switches

1058 |show version AOS-W 3.4.1 Command Line Interface | Reference Guide
AOS-W 3.4.1 Command Line Interface | Reference Guide show vlan | 1059
show vlan
show vlan <id>
Description
This command shows a configured VLAN interface number, description and associated ports.
Syntax
Usage Guidelines
Issue this command to show the a selected VLAN configuration. The VLAN column lists the VLAN ID. The
Description column provides the VLAN name or number and the Ports column shows the VLAN’s
associated ports.
Related Commands
(host) (config) #vlan
(host) (config) #vlan-name
Command History
This command was introduced in AOS-W 3.0.
Command Information
Parameter Description Range Default
<id> Identification number for the VLAN. 1-4094 1
Platforms Licensing Command Mode
All platforms Base operating system Enable or config mode on master or local
switches
(host) #show vlan
VLAN CONFIGURATION
------------------
VLAN Description Ports
---- ----------- -----
1 Default FE2/0-7 FE2/9-23 GE2/24-25 FE3/0-23 GE3/24-25 Pc0-7
3 VLAN0003 FE2/2
4 VLAN0004 FE2/2
200 VLAN0200 FE2/2
201 VLAN0201 FE2/2
202 VLAN0202 FE2/2
203 VLAN0203 FE2/2
204 VLAN0204 FE2/2
1060 | show vlan mapping AOS-W 3.4.1 Command Line Interface | Reference Guide
show vlan mapping
show vlan mapping
Description
This command shows a configured VLAN name, its pool status and the VLAN IDs assigned to the pool.
Syntax
Usage Guidelines
Issue this command to show the a selected VLAN configuration. The VLAN Name column displays the
name of the VLAN pool. The Pool Status column indicates if the pool is enabled or disabled. The VLAN
IDs column lists the VLANs that are part of the pool. .
Related Commands
(host) (config) #vlan
(host) (config) #vlan-name
Command History
This command was introduced in AOS-W 3.0.
Command Information
Parameter Description Range Default
<id> Identification number for the VLAN. 1-4094 1
Platforms Licensing Command Mode
All platforms Base operating system Enable or config mode on master or local
switches
(host) #show vlan mapping
VLAN Name Pool Status VLAN IDs
--------- ----------- --------
mypool Enabled 65,210
mypool2 Enabled 212,256

AOS-W 3.4.1 Command Line Interface | Reference Guide show vlan status | 1061
show vlan status
show vlan status <id>
Description
This command shows the current status of all VLANs on the switch.
Syntax
This command has no parameters.
Usage Guidelines
Issue this command to show the status of VLANs on the switch.The VLAN ID column displays the VLAN ID
name or number. The IP Address column provides the VLAN’s IP address. The Adminstate column
indicates if the VLAN is enabled or disabled. The Operstate column indicates if the VLAN is currently up
and running. The PortCount column shows how many ports are associated with the VLAN. The Nat
Inside column displays whether source Nat is enabled for the VLAN interface. If Nat is enabled, all the
traffic passing through this VLAN interface is the source natted to the outgoing interface’s IP address..
Related Commands
(host) (config) #vlan
(host) (config) #vlan-name
Command History
This command was introduced in AOS-W 3.0.
Command Information
Platforms Licensing Command Mode
All platforms Base operating system Enable or config mode on master or local
switches
(host) #show vlan status
Vlan Status
-----------
VlanId IPAddress Adminstate Operstate PortCount Nat Inside
------ --------- ---------- --------- --------- ----------
1 10.168.254.221/255.255.255.252 Enabled Up 5 Disabled
2 unassigned/unassigned Enabled Down 2 Disabled
4 unassigned/unassigned Enabled Down 1 Disabled
25 unassigned/unassigned Enabled Down 1 Disabled
212 10.168.212.2/255.255.255.0 Enabled Down 2 Disabled
213 10.168.213.2/255.255.255.0 Enabled Down 2 Disabled
1170 10.3.132.14/255.255.255.0 Enabled Up 2 Disabled
1062 | show vlan summary AOS-W 3.4.1 Command Line Interface | Reference Guide
show vlan summary
show vlan summary
Description
This command shows the number of existing VLANs.
Syntax
Usage Guidelines
Issue this command to show the number of existing VLANs on the switch.
Related Commands
(host) (config) #vlan
(host) (config) #vlan-name
Command History
This command was introduced in AOS-W 3.0.
Command Information
Parameter Description
Number of existing VLANs The number of existing VLANs on the switch.
Platforms Licensing Command Mode
All platforms Base operating system Enable or config mode on master or local
switches
(host) #show vlan summary
Number of existing VLANs :13

AOS-W 3.4.1 Command Line Interface | Reference Guide show voice call-cdrs | 1063
show voice call-cdrs
show voice call-cdrs [bssid <value> | count <number> | detail | essid <value> |
extn <value> | ip <ip-address> | proto {sip | svp | noe | sccp | vocera | h323}
| sta <mac-address> ]
Description
Displays detailed call records of voice client.
Syntax
Example
The output of this command shows detailed call records filtered by SIP protocol and limited to 5 entries.
Command History
This command was available in AOS-W 3.3.1
Parameter Description
bssid Filter records based on BSSID of voice clients.
count Specify the number of records to be displayed by entering a number.
detail Include this parameter to display the following additional data columns for each
call record.
zReason
zCodec
zBand
zSetup Time(sec)
zRe-Assoc Initial-BSSID
zInitial-ESSID
zInitial-AP Name
essid Filter records based on ESSID of voice clients.
extn View detailed records for a particular extension number.
ip View detailed records of voice client using its IP address.
proto View detailed records filtered on protocol.
sta View detailed records filtered on MAC address.
(host) # show voice call-cdrs proto sip count 5
Voice Client(s) CDRs
--------------------
CDR Id Client IP Client Name ALG Dir Called/Calling Party Status Dur(sec) Orig time R-value
------ --------- ----------- --- --- -------------------- ------ -------- --------- -------
85 10.15.86.243 6210 sip IC 6201 SUCC 48 Apr 29 12:35:39 NA
84 10.15.86.252 6201 sip OG 6210 SUCC 48 Apr 29 12:35:39 NA
83 10.15.86.243 6210 sip OG 6201 SUCC 37 Apr 29 12:29:19 NA
82 10.15.86.252 6201 sip IC 6210 SUCC 37 Apr 29 12:29:19 NA
81 10.15.86.243 6210 sip OG 6201 SUCC 46 Apr 29 12:03:55 NA
Num CDRS:5

1064 | show voice call-cdrs AOS-W 3.4.1 Command Line Interface | Reference Guide
Command Information
Platforms Licensing Command Mode
All platforms Base operating system Config or Enable mode on master or local
switches
AOS-W 3.4.1 Command Line Interface | Reference Guide show voice call-counters | 1065
show voice call-counters
show voice call-counters
Description
Displays outgoing, incoming and terminated call counter details.
Syntax
No Parameters
Example
The output of this command shows call counter statitics.
Command History
This command was available in AOS-W 3.3.1
Command Information
(host) # show voice call-counters
System Wide Voice Call Counters
-------------------------------
Total Call Originated Call Terminated Active Success Failed Blocked Aborted
----- --------------- --------------- ------ ------- ------ ------- -------
86 45 41 1 70 11 0 4
Platforms Licensing Command Mode
All platforms Base operating system Config or Enable mode on master or local
switches

1066 | show voice call-density AOS-W 3.4.1 Command Line Interface | Reference Guide
show voice call-density
show voice call-density [bssid <value> | essid <value> | extn <value> |
ip <ip-address> | proto <protocol>]
Description
Displays voice call density report during a time period.
Syntax
No Parameters
Example
The output of this command shows call density report filtered on SIP protocol.
Command History
This command was available in AOS-W 3.0
Command Information
(host) # show voice call-counters
VoIP Call Density Report for protocol 'sip'
-------------------------------------------
Sample Time Orig Term Active Succ Fail Blocked Aborted R-Value
----------- ---- ---- ------ ---- ---- ------- ------- -------
Apr 29 14:42:16 0 0 0 0 0 0 0 NA
Apr 29 14:40:00 0 0 0 0 0 0 0 NA
Apr 29 14:30:00 0 0 0 0 0 0 0 NA
Apr 29 14:20:00 0 0 0 0 0 0 0 NA
Apr 29 14:10:00 0 0 0 0 0 0 0 NA
Apr 29 14:00:00 0 0 0 0 0 0 0 NA
Apr 29 13:50:00 0 0 0 0 0 0 0 NA
Apr 29 13:40:00 0 0 0 0 0 0 0 NA
Apr 29 13:30:00 0 0 0 0 0 0 0 NA
...
...
...
Apr 29 06:20:00 0 0 0 0 0 0 0 NA
Apr 29 06:10:00 0 0 0 0 0 0 0 NA
Apr 29 06:00:00 0 0 0 0 0 0 0 NA
Apr 29 05:50:00 0 0 0 0 0 0 0 NA
Apr 29 05:40:00 0 0 0 0 0 0 0 NA
--More-- (q) quit (u) pageup (/) search (n) repeat
Platforms Licensing Command Mode
All platforms Base operating system Config or Enable mode on master or local
switches
AOS-W 3.4.1 Command Line Interface | Reference Guide show voice call-perf | 1067
show voice call-perf
show voice call-perf [bssid <value> | essid <value> | extn <value> |
ip <ip_address> | proto <value>
Description
Displays voice call quality over a period of time.
Syntax
No Parameters
Example
The output of this command shows call performance report for extension 6210.
Command History
This command was available in AOS-W 3.3.1
Command Information
(host) # show voice call-counters
VoIP Call Performance Report for Client '6210'
----------------------------------------------
Sample Time Delay(ms) AP-Switch Delay(ms) Jitter Packet Loss R-Value MOS Band
----------- --------- ------------------- ------ ----------- ------- --- ----
May 1 14:30:11 0.00 0.00 0.000 0.00 0.00 NA NA
May 1 14:30:00 0.00 0.00 0.000 0.00 0.00 NA NA
May 1 14:20:00 0.00 0.00 0.000 0.00 0.00 NA NA
May 1 14:10:00 0.00 0.00 0.000 0.00 0.00 NA NA
May 1 14:00:00 0.00 0.00 0.000 0.00 0.00 NA NA
May 1 13:50:00 0.00 0.00 0.000 0.00 0.00 NA NA
May 1 13:40:00 0.00 0.00 0.000 0.00 0.00 NA NA
May 1 13:30:00 0.00 0.00 0.000 0.00 0.00 NA NA
...
...
...
May 1 09:10:00 0.00 0.00 0.000 0.00 0.00 NA NA
May 1 09:00:00 0.00 0.00 0.000 0.00 0.00 NA NA
May 1 08:50:00 0.00 0.00 0.000 0.00 0.00 NA NA
May 1 08:40:00 0.00 0.00 0.000 0.00 0.00 NA NA
May 1 08:30:00 0.00 0.00 0.000 0.00 0.00 NA NA
--More-- (q) quit (u) pageup (/) search (n) repeat
Platforms Licensing Command Mode
All platforms Base operating system Config or Enable mode on master or local
switches
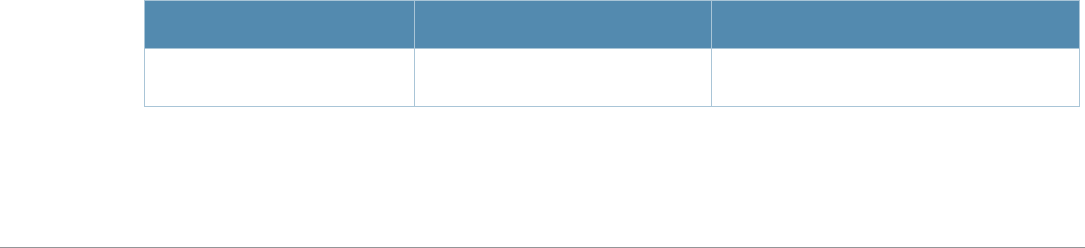
1068 | show voice call-quality AOS-W 3.4.1 Command Line Interface | Reference Guide
show voice call-quality
show voice call-quality [bssid <value> | essid <value> | extn <value> |
ip <ip_address> | proto <value>
Description
Displays voice call quality for each call over a period of time.
Syntax
No Parameters
Example
The output of this command shows call quality report for calls made by extension 6210.
Command History
This command was available in AOS-W 3.3.1
Command Information
(host) # show voice call-counters
Voice Client(s) Call Quality Reports
------------------------------------
Client(IP) Client(MAC) Client(Name) ALG Orig Time Direction Called/Calling Party Duration Codec
Delay Jitter Pkt Loss R-Value Band BSSID ESSID AP Name
---------- ----------- ------------ --- --------- --------- -------------------- -------- -----
----- ------ -------- ------- ---- ----- ----- -------
10.15.86.243 00:03:2a:01:ba:61 6210 sip Apr 30 13:09:28 IC 6009 6 G729
NA NA NA NA NA 00:0b:86:6d:3e:20 raja1 AP-70-862
10.15.86.243 00:03:2a:01:ba:61 6210 sip Apr 30 13:03:14 IC 6009 5 G729
NA NA NA NA NA 00:0b:86:6d:3e:20 raja1 AP-70-862
10.15.86.243 00:03:2a:01:ba:61 6210 sip Apr 30 12:53:17 IC 6009 103 G711
9.190 1.310 0.093 91 GREEN 00:0b:86:6d:3e:20 raja1 AP-70-862
10.15.86.243 00:03:2a:01:ba:61 6210 sip Apr 30 12:40:39 IC 6202 751 G729
0.000 0.000 0.273 NA NA 00:0b:86:6d:3e:20 raja1 AP-70-862
...
...
...
10.15.86.243 00:03:2a:01:ba:61 6210 sip Apr 29 15:09:52 OG 6201 223 G729
0.000 0.000 1.003 NA NA 00:0b:86:e6:e0:80 raja1 RAP-70-862
10.15.86.243 00:03:2a:01:ba:61 6210 sip Apr 29 15:00:28 OG 6201 69 G729
0.000 0.000 3.376 NA NA 00:0b:86:e6:e0:80 raja1 RAP-70-862
10.15.86.243 00:03:2a:01:ba:61 6210 sip Apr 29 12:35:39 IC 6201 48 G729
0.000 0.000 0.347 NA NA 00:0b:86:e6:e0:80 raja1 RAP-70-862
--More-- (q) quit (u) pageup (/) search (n) repeat
Platforms Licensing Command Mode
All platforms Base operating system Config or Enable mode on master or local
switches
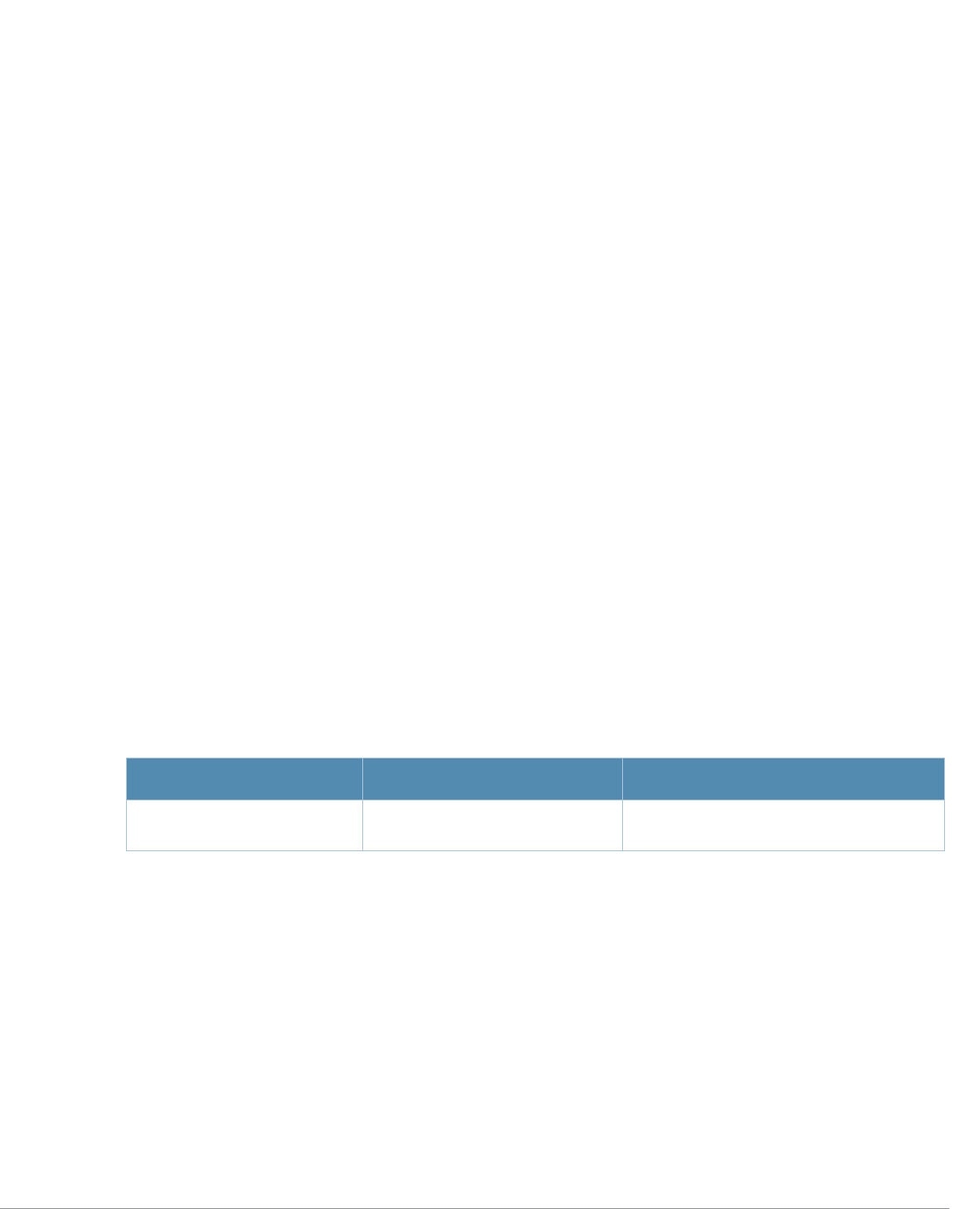
AOS-W 3.4.1 Command Line Interface | Reference Guide show voice call-stats | 1069
show voice call-stats
show voice call-stats [bssid <value> | cip <client-ip-address> | essid <value> |
extn <value> | ip <ip_address> | proto <value> | sta <value>]
Description
Displays voice call statistics for each client.
Syntax
No Parameters
Example
The output of this command shows call quality report for calls made by extension 6210.
Command History
This command was available in AOS-W 3.3.1
Command Information
(host) # show voice call-stats
Voice Client(s) Call Statistics
-------------------------------
Client IP Client MAC Client Name ALG Originated Terminated Active Failed Success Blocked Aborted
Duration R-Value Band
--------- ---------- ----------- --- ---------- ---------- ------ ------ ------- ------- -------
-------- ------- ----
10.15.86.248 00:1f:6c:7a:d4:fd 6005 sccp 3 2 0 0 5 0 0
20489.0/2.0/4173.0 93.00/79.00/89.00 GREEN
10.15.86.247 00:1f:6c:7a:d5:f8 6002 sccp 2 3 0 0 4 0 1
57709.0/2.0/11616.8 93.00/71.00/87.00 GREEN
Num Clients:2
Platforms Licensing Command Mode
All platforms Base operating system Config or Enable mode on master or local
switches
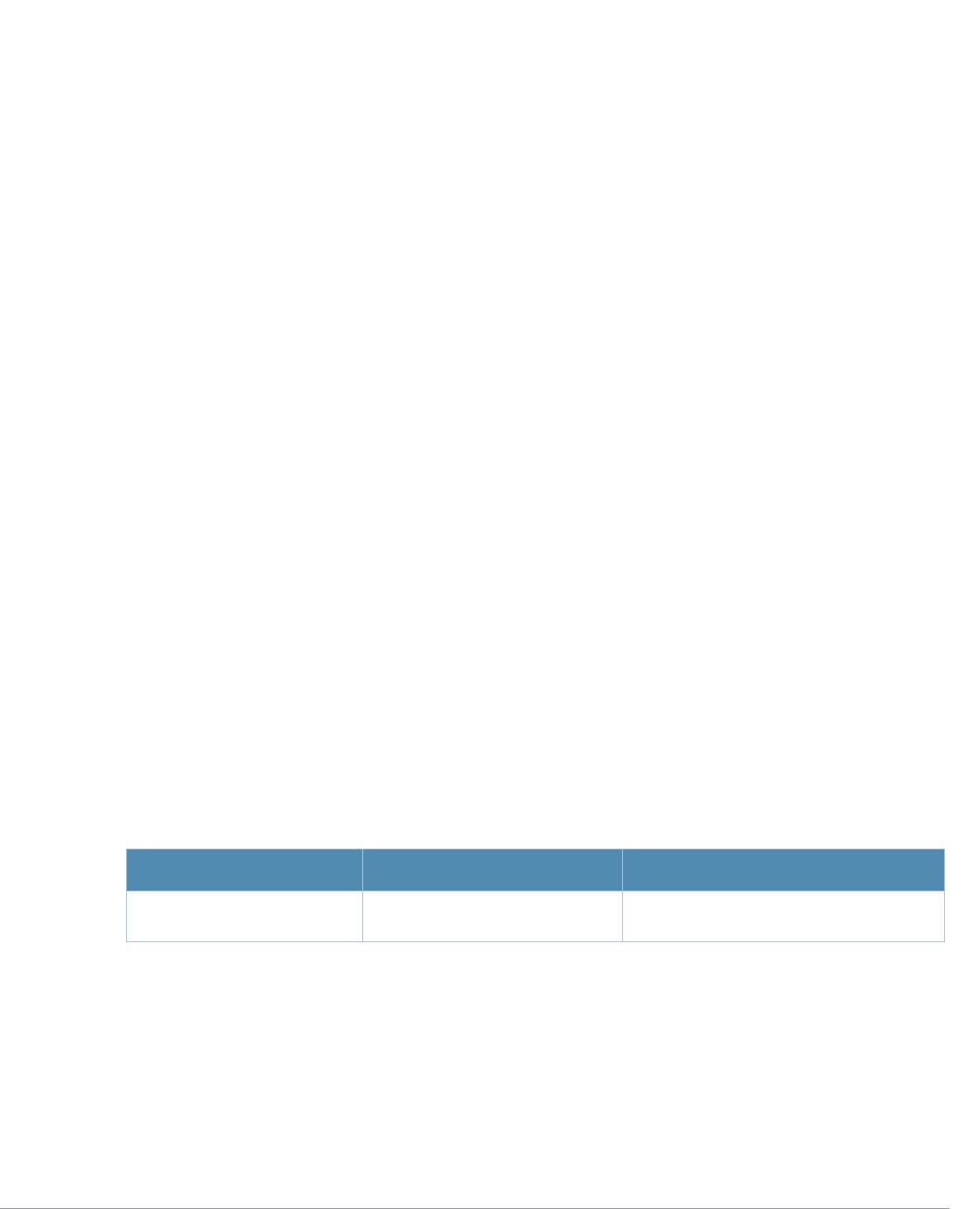
1070 |show voice msg-stats AOS-W 3.4.1 Command Line Interface | Reference Guide
show voice msg-stats
show voice msg-stats
[sccp { bssid <value> | cip <client-ip-address> | essid <value> | ip <ip_address> |
sta <client-MAC-address> } | sip { bssid <value> | cip <client-ip-address> | essid
<value> | ip <ip_address> | sta <client-MAC-address> } ]
Description
Displays voice message counters for each call using either the SCCP or SIP protocol.
Syntax
No Parameters
Example
The output of this command shows voice message statistics for essid sam filtered on SCCP protocol.
Command History
This command was available in AOS-W 3.3.1
Command Information
(host) # show voice msg-stats sccp essid sam
SCCP Voice Client(s) Msg Statistics
-----------------------------------
Client Name Client IP AP Name BSSID ESSID Register Register Ack Unregister Unregister Ack
Keepalive Keepalive Ack OpenRecvChannel OpenRecvChannel Ack StartMedia CloseRecvChannel StopMedia OffHook
OnHook Ringing Connected Busy Hold Transfer Invalid
----------- --------- ------- ----- ----- -------- ------------ ---------- -------------- -
-------- ------------- --------------- ------------------- ---------- ---------------- --------- ------- ----
-- ------- --------- ---- ---- -------- -------
6005 10.15.86.248 AP-70-862 00:0b:86:6d:3e:30 sam 43 5 1 2 5950
6185 7 4 6 7 6 5 17 2 8
0 0 0 0
6002 10.15.86.247 AP-70-862 00:0b:86:6d:3e:30 sam 39 6 2 2 5936
6048 4 4 4 7 6 4 18 3 4
0 0 0 0
Num Clients:2
Platforms Licensing Command Mode
All platforms Base operating system Config or Enable mode on master or local
switches

AOS-W 3.4.1 Command Line Interface | Reference Guide show voice prioritization | 1071
show voice prioritization
show voice prioritization
Description
Displays the status of voice prioritization.
Syntax
No Parameters
Example
The output of this command shows the status of voice prioritization.
Command History
This command was available in AOS-W 3.3.1
Command Information
(host) # show voice prioritization
Voice Prioritization:disable
Platforms Licensing Command Mode
All platforms Base operating system Config or Enable mode on master or local
switches
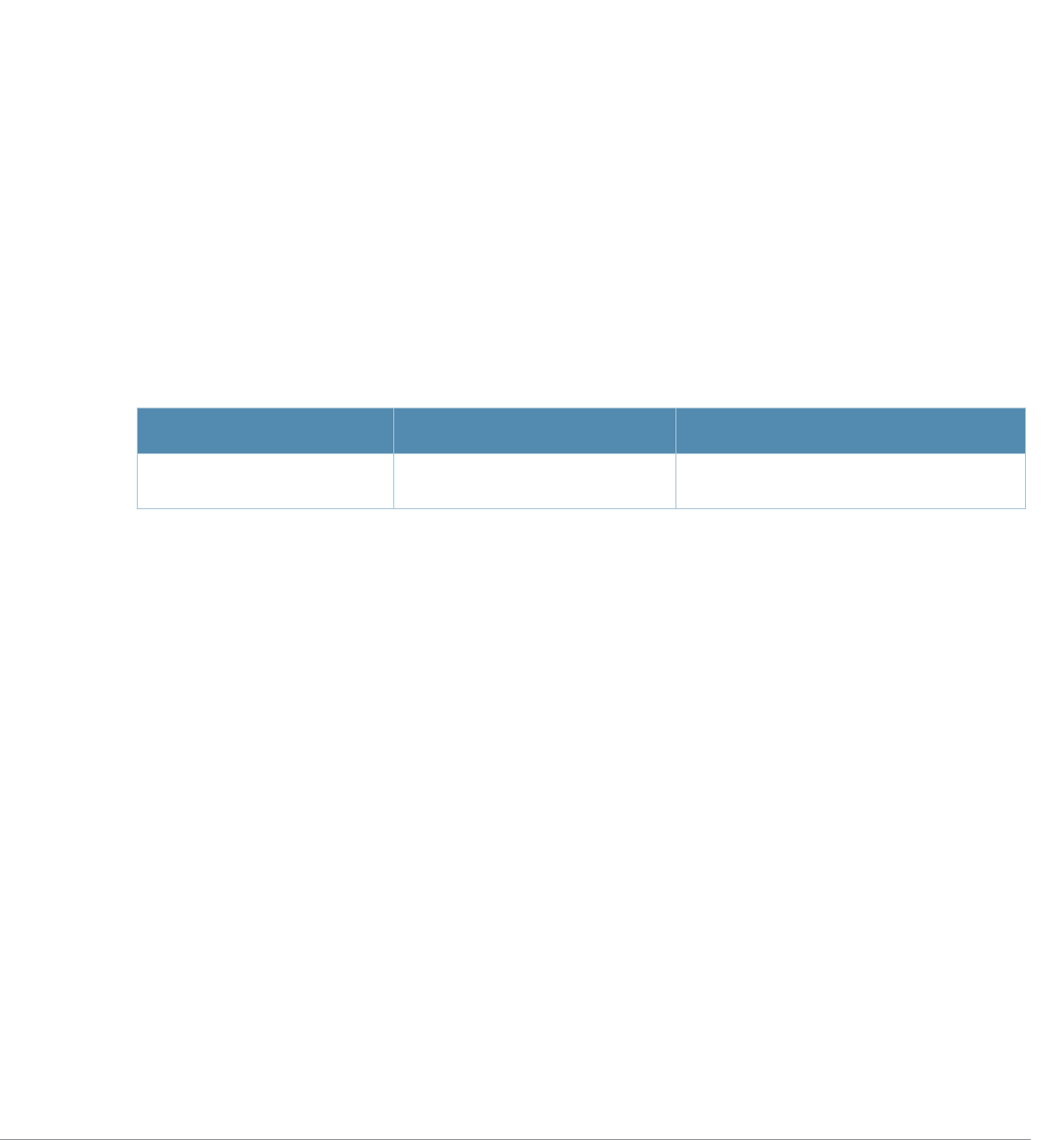
1072 | show voice rtcp-inactivity AOS-W 3.4.1 Command Line Interface | Reference Guide
show voice rtcp-inactivity
show voice rtcp-inactivity
Description
Displays the status of RTCP protocol.
Syntax
No parameters
Example
The output of this command shows the status of RTCP protocol.
Command History
This command was available in AOS-W 3.3.1
Command Information
(host) # #show voice rtcp-inactivity
Voice rtcp-inactivity:disable
Platforms Licensing Command Mode
All platforms Base operating system Config or Enable mode on master or local
switches
AOS-W 3.4.1 Command Line Interface | Reference Guide show voice statistics | 1073
show voice statistics
show voice statistics [ cac | tspec-enforcement ]
Description
Displays the CAC and TSPEC enforced voice statistics.
Syntax
No parameters
Example
The output of this command shows statistics for TSPEC enforced calls.
Command History
This command was available in AOS-W 3.3.1
Command Information
(host) # show voice statistics tspec-enforcement
TSPEC Enforcement statistics
----------------------------
Name Value
---- -----
TSPEC ADDTS Request 16
TSPEC accepted 16
TSPEC denied due to CAC 0
TSPEC enforcement timer events 2
Calls established within enforcement period 0
TSPEC deleted after enforcement period 1
Platforms Licensing Command Mode
All platforms Base operating system Config or Enable mode on master or local
switches
1074 | show voice trace AOS-W 3.4.1 Command Line Interface | Reference Guide
show voice trace
show voice trace [ sccp {count <value> | ip <ip_address> | mac <mac_address>} |
sip {count <value> | ip <ip_address> | mac <mac_address>} ]
Description
Displays the signalling message trace details for all clients.
Syntax
No parameters
Example
The output of this command shows signalling message trace.
Command History
This command was available in AOS-W 3.3.1
Command Information
(host) # #show voice trace sccp count 10
SCCP Voice Client(s) Message Trace
----------------------------------
Sender Name Client(MAC) Client(IP) Event Time Direction Msg
----------- ----------- ---------- ---------- --------- ---
6005 00:1f:6c:7a:d4:fd 10.15.86.248 May 1 15:40:48 Server-To-Client Keepalive Ack
6005 00:1f:6c:7a:d4:fd 10.15.86.248 May 1 15:40:48 Client-To-Server Keepalive
6002 00:1f:6c:7a:d5:f8 10.15.86.247 May 1 15:40:45 Server-To-Client Keepalive Ack
6002 00:1f:6c:7a:d5:f8 10.15.86.247 May 1 15:40:45 Client-To-Server Keepalive
6005 00:1f:6c:7a:d4:fd 10.15.86.248 May 1 15:40:40 Server-To-Client Display Prompt
6005 00:1f:6c:7a:d4:fd 10.15.86.248 May 1 15:40:40 Server-To-Client Clear Notify
6005 00:1f:6c:7a:d4:fd 10.15.86.248 May 1 15:40:40 Server-To-Client Clear Pri Notify
6005 00:1f:6c:7a:d4:fd 10.15.86.248 May 1 15:40:40 Server-To-Client Clear Pri Notify
6002 00:1f:6c:7a:d5:f8 10.15.86.247 May 1 15:40:40 Server-To-Client Display Prompt
6002 00:1f:6c:7a:d5:f8 10.15.86.247 May 1 15:40:40 Server-To-Client Clear Notify
Num of Rows:10
Platforms Licensing Command Mode
All platforms Base operating system Config or Enable mode on master or local
switches

AOS-W 3.4.1 Command Line Interface | Reference Guide show vpdn l2tp configuration | 1075
show vpdn l2tp configuration
show vpdn l2tp configuration
Description
Displays the VPN L2TP tunnel configuration.
Syntax
No Parameters
Example
The output of this command shows the L2TP tunnel configuration.
Command History
This command was available in AOS-W 3.0
Command Information
(host) # show vpdn l2tp configuration
Enabled
Hello timeout: 30 seconds
DNS primary server: 10.16.15.1
DNS secondary server: 10.16.14.1
WINS primary server: 0.0.0.0
WINS secondary server: 0.0.0.0
PPP client authentication methods:
PAP
IP LOCAL POOLS:
vpnpool: 10.16.15.150 - 10.16.15.160
Platforms Licensing Command Mode
All platforms Base operating system Config or Enable mode on master or local
switches

1076 | show vpdn pptp configuration AOS-W 3.4.1 Command Line Interface | Reference Guide
show vpdn pptp configuration
show vpdn pptp configuration
Description
Displays the PPTP configuration on the switch.
Syntax
No Parameters
Example
The output of this command shows the L2TP tunnel configuration.
Command History
This command was available in AOS-W 3.0
Command Information
(host) # show vpdn pptp configuration
Enabled
Hello timeout: 30 seconds
DNS primary server: 10.15.1.1
DNS secondary server: 10.15.1.200
WINS primary server: 0.0.0.0
WINS secondary server: 0.0.0.0
PPP client authentication methods:
MSCHAP
MSCHAPv2
MPPE Configuration
128 bit encryption enabled
IP LOCAL POOLS
Platforms Licensing Command Mode
All platforms Base operating system Config or Enable mode on master or local
switches

AOS-W 3.4.1 Command Line Interface | Reference Guide show vpdn pptp local pool | 1077
show vpdn pptp local pool
show vpdn pptp local pool <pool_name>
Description
Displays the IP address pool for VPN users using Point-to-Point Tunneling Protocol.
Syntax
No Parameters
Example
The output of this command shows the all IP address pools for VPN users.
Command History
This command was available in AOS-W 3.0
Command Information
(host) # show vpdn pptp local pool
IP addresses used in pool localgroup
0 IPs used - 11 IPs free - 11 IPs configured
Platforms Licensing Command Mode
All platforms Base operating system Config or Enable mode on master or local
switches

1078 | show vpdn pptp local pool AOS-W 3.4.1 Command Line Interface | Reference Guide

AOS-W 3.4.1 Command Line Interface | Reference Guide show vpn-dialer | 1079
show vpn-dialer
show vpn-dialer <dialer_name>
Description
Displays the VPN dialer configuration for users using VPN dialers.
Syntax
No Parameters
Example
The output of this command shows the VPN dialer configuration for remoteUsers.
Command History
This command was available in AOS-W 3.0
Command Information
(host) # show vpn-dialer remoteUser
remoteUser
----------
Attribute Value
--------- -----
PPTP disabled
L2TP enabled
DNETCLEAR disabled
WIREDNOWIFI disabled
PAP enabled
CHAP enabled
MSCHAP enabled
MSCHAPV2 enabled
CACHE-SECURID disabled
IKESECS 4000
IKEENC 3DES
IKEGROUP ONE
IKEHASH MD5
IKEAUTH PRE-SHARE
IKEPASSWD ********
IPSECSECS 4000
IPSECGROUP GROUP1
IPSECENC ESP-3DES
IPSECAUTH ESP-MD5-HMAC
SECURID_NEWPINMODE disabled
Platforms Licensing Command Mode
All platforms Base operating system Config or Enable mode on master or local
switches

1080 | show vpn-dialer AOS-W 3.4.1 Command Line Interface | Reference Guide

AOS-W 3.4.1 Command Line Interface | Reference Guide show vrrp | 1081
show vrrp
show vrrp <vrid>
Description
Displays the list of all VRRP configuration on the switch. To view a specific VRRP configuration, specify the
VRID number.
Syntax
No Parameters
Example
The output of this command shows the VRRP configuration enabled in one of the floors of the building.
Command History
Command Information
(host) # show vrrp
Virtual Router 2:
Description Floor-1 Settings
Admin State DOWN, VR State INIT
IP Address 10.15.1.10, MAC Address 00:00:5e:00:01:02, vlan 1
Priority 2, Advertisement 10 sec, Preemption Enable
Auth type PASSWORD, Auth data: 123456
tracking type is master-up-time, duration 500 minutes, value 3
tracking type is vrrp-master-state, vrid 10, value 1
tracking type is vlan, vlanid 1, subtract value 3
tracking type is interface, fastethernet 1/1, subtract value 3
tracked priority 2
Version Modification
AOS-W 1.0 Command introduced
AOS-W 3.3 The tracking interface and tracking vlan parameters were introduced.
AOS-W 3.3.2 The add option was removed from the tracking interface and tracking vlan
parameters.
Platforms Licensing Command Mode
All platforms Base operating system Config or Enable mode on master or local
switches

1082 |show vrrp AOS-W 3.4.1 Command Line Interface | Reference Guide

AOS-W 3.4.1 Command Line Interface | Reference Guide show web-server | 1083
show web-server
show web-server
Description
Displays the configuration of the switch’s web server.
Syntax
No Parameters
Example
The output of this command shows the web-server configuration.
Command History
This command was available in AOS-W 3.0
Command Information
(host) # show web-server
Web Server Configuration
------------------------
Parameter Value
--------- -----
Cipher Suite Strength high
SSL/TLS Protocol Config sslv3 tlsv1
Switch Certificate default
Captive Portal Certificate default
Management user's WebUI access method username/password
User session timeout <30-3600> (seconds) 900
Maximum supported concurrent clients <25-400> 25
Platforms Licensing Command Mode
All platforms Base operating system Config or Enable mode on master or local
switches

1084 | show web-server AOS-W 3.4.1 Command Line Interface | Reference Guide
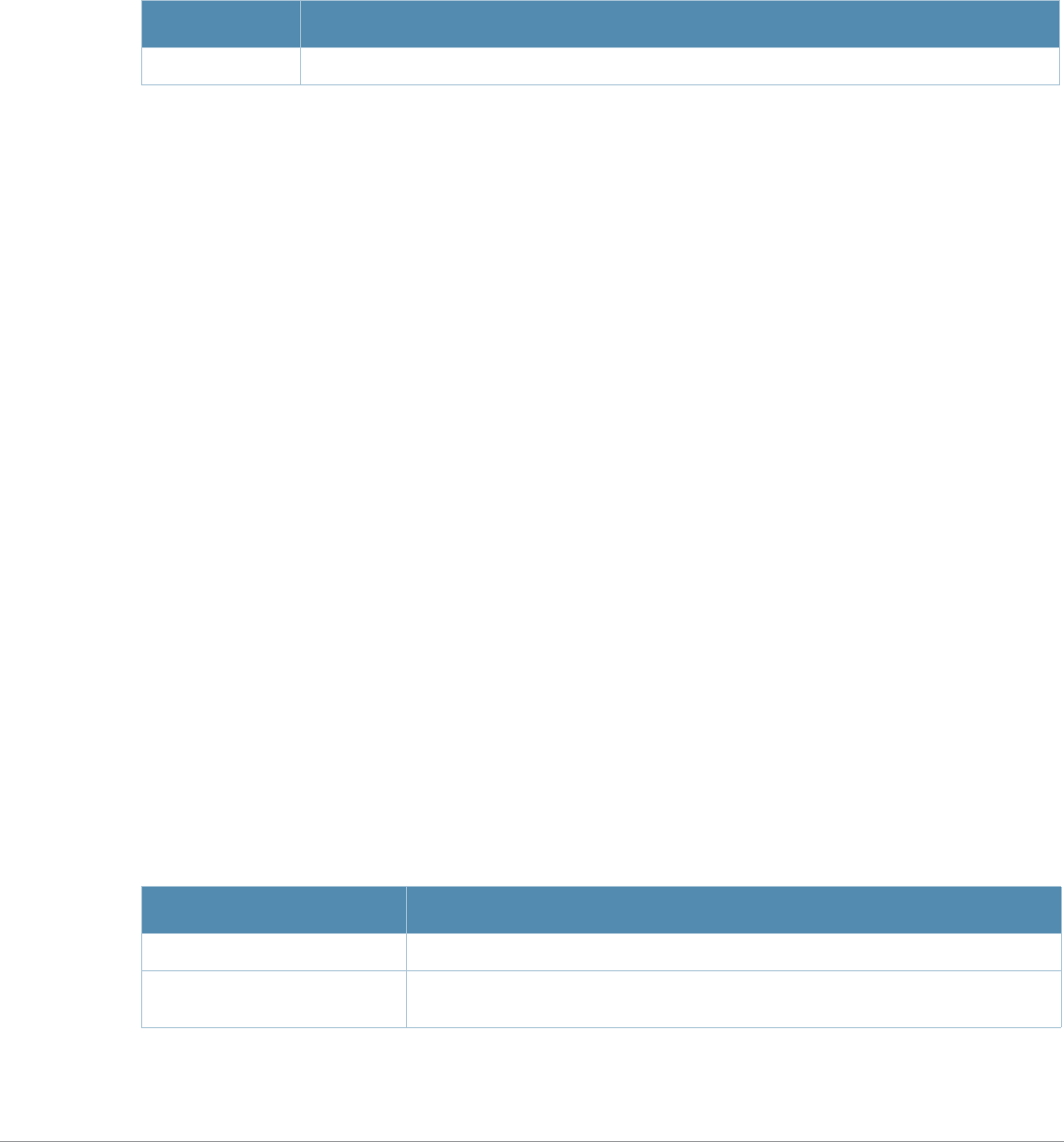
AOS-W 3.4.1 Command Line Interface | Reference Guide show wlan dot11k-profile | 1085
show wlan dot11k-profile
show wlan dot11k-profile [<profile>]
Description
Show a list of all 802.11k profiles, or display detailed configuration information for a specific 802.11k
profile.
Syntax
Usage Guidelines
Issue this command without the <profile> parameter to display the entire ARM profile list, including profile
status and the number of references to each profile. Include a profile name to display detailed configuration
information for that profile.
Examples
The example below shows that the switch has two configured 802.11k profiles. The References column
lists the number of other profiles with references to the 802.11k profile, and the Profile Status column
indicates whether the profile is predefined. (User-defined profiles will not have an entry in the Profile Status
column.)
The following example shows configuration settings defined for the profile 11kprofile2.
The output of this command includes the following data columns:
Parameter Description
<profile> Name of an 802.11k profile.
(host) #show wlan dot11k-profile
802.11K Profile List
--------------------
Name References Profile Status
---- ---------- --------------
default 8
11kprofile2 1
Total: 2
(host) #show wlan dot11k-profile default
802.11K Profile "11kprofile2"
-------------------------
Parameter Value
--------- -----
Advertise 802.11K Capability Enabled
Forcefully disassociate on-hook voice clients Disabled
Measurement Mode for Beacon Reports beacon-table
Parameter Description
Advertise 802.11K Capability Shows if the profile has enabled or disabled the 802.11K feature.
Forcefully disassociate on-
hook voice clients If enabled, the AP may forcefully disassociate “on-hook” voice clients (clients that
are not on a call) after period of inactivity.
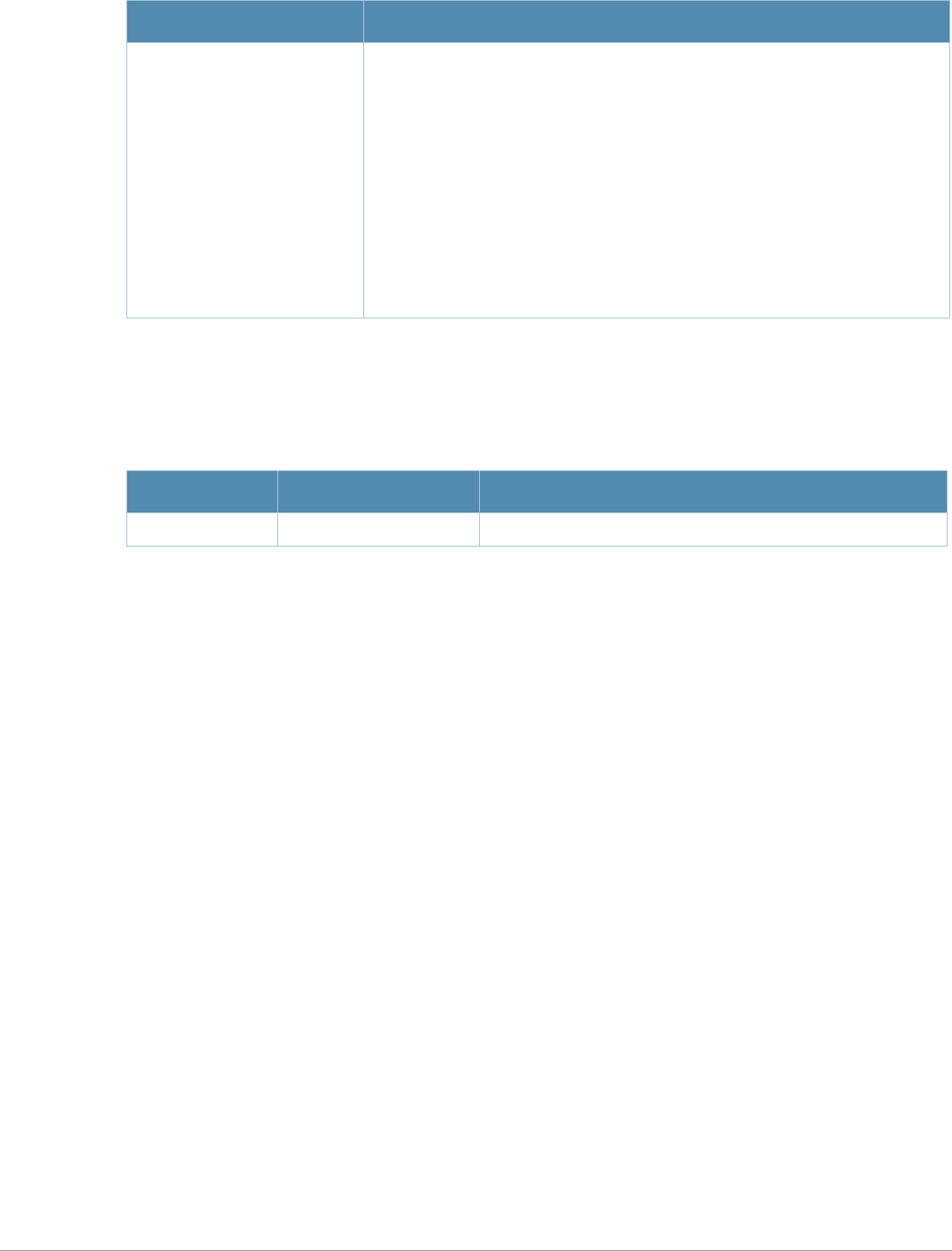
1086 | show wlan dot11k-profile AOS-W 3.4.1 Command Line Interface | Reference Guide
Command History
This command was introduced in AOS-W 3.0.
Command Information
Measurement Mode for Beacon
Reports Shows the profile’s beacon measurement mode:
z
active
:
In this mode, the client sends a probe request to the broadcast
destination address on all supported channels, sets a measurement duration
timer, and, at the end of the measurement duration, compiles all received
beacons or probe response with the requested SSID and BSSID into a
measurement report.
zbeacon-table: In this mode, the client measures beacons and returns a report
with stored beacon information for any supported channel with the requested
SSID and BSSID. The client does not perform any additional measurements.
This is the default beacon measurement mode.
zpassive: In this mode, the client sets a measurement duration timer, and, at
the end of the measurement duration, compiles all received beacons or probe
response with the requested SSID and BSSID into a measurement report.
Parameter Description
Platforms Licensing Command Mode
All platforms Base operating system Enable and Config mode on master or local switches.
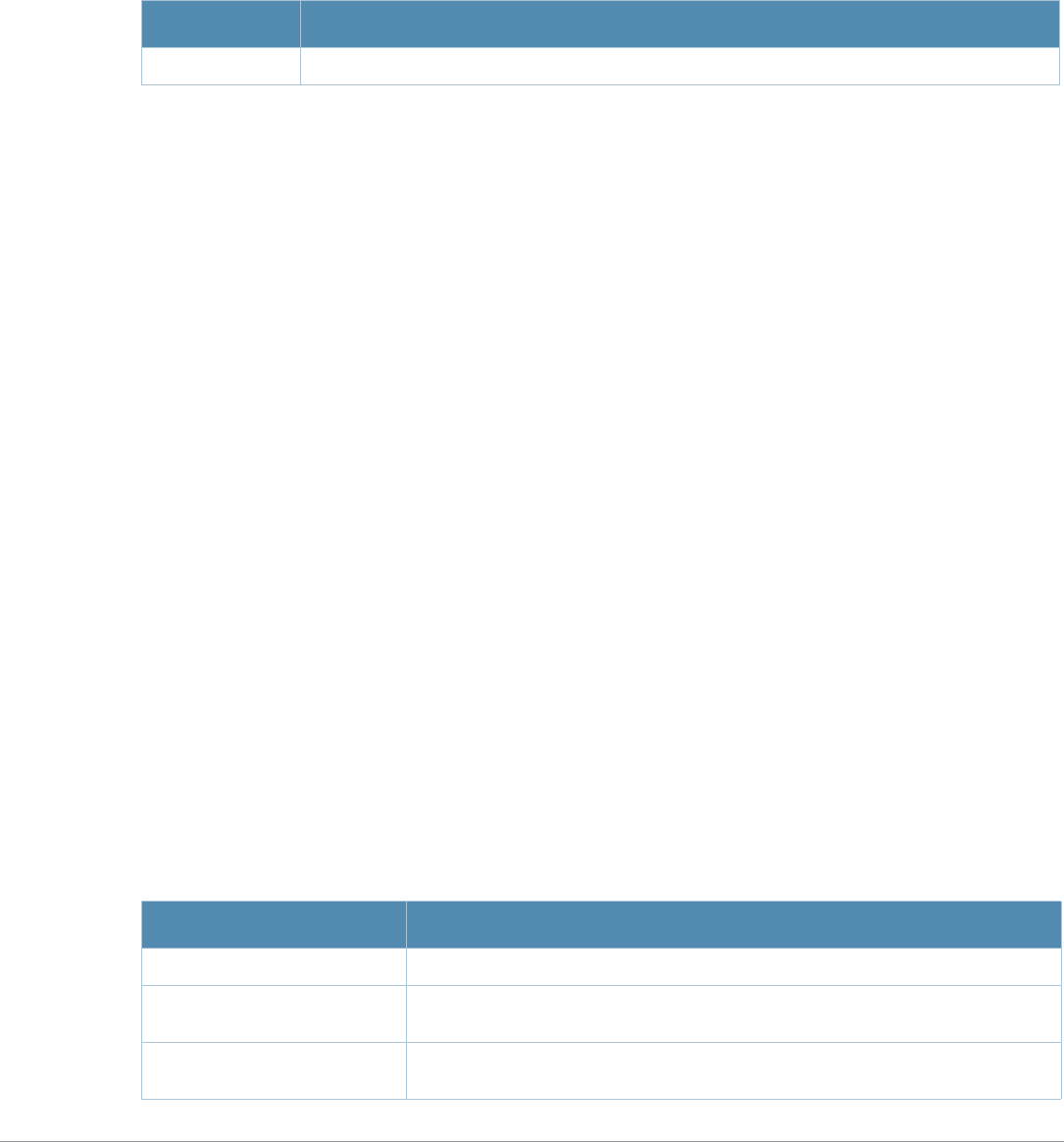
AOS-W 3.4.1 Command Line Interface | Reference Guide show wlan edca-parameters-profile | 1087
show wlan edca-parameters-profile
show wlan edca-parameters-profile ap|station [<profile>]
Description
Display an Enhanced Distributed Channel Access (EDCA) profile for APs or for clients (stations). EDCA
profiles are specific either to APs or clients.
Syntax
Usage Guidelines
Issue this command without the <profile> parameter to display a EDCA Parameters profile list, including
profile status and the number of references to each profile. Include a profile name to display detailed
configuration information for that profile.
Examples
The example below shows that the switch has three EDCA Parameters profiles configured for stations. The
References column lists the number of other profiles with references to the EDCA Parameters profile, and
the Profile Status column indicates whether the profile is predefined. (User-defined profiles will not have
an entry in the Profile Status column.)
The following example shows configuration settings defined for the profile station-corp1.
The output of this command includes the following data columns:
Parameter Description
<profile> Name of a EDCA Parameters profile.
(host) #show wlan edca-parameters-profile station
EDCA Parameters profile (Station) List
---------------------------------
Name References Profile Status
---- ---------- --------------
station-corp1 3
station-corp2 1
testprofile 0
Total:3
(host) #show wlan edca-parameters-profile ap station-corp1
EDCA Parameters
---------------
AC ECWmin ECWmax AIFSN TXOP ACM
-- ------ ------ ----- ---- ---
Best-effort 4 6 3 0 0
Background 4 10 7 0 0
Video 3 4 1 94 0
Voice 2 3 1 47 0
Parameter Description
AC Name of an Access channel queue (Best-effort, Background, Video or Voice).
ECWmin The exponential (n) value of the minimum contention window size, as expressed
by 2n-1. A value of 4 computes to 24-1 = 15.
ECWmax The exponential (n) value of the maximum contention window size, as expressed
by 2n-1. A value of 4 computes to 24-1 = 15.

1088 | show wlan edca-parameters-profile AOS-W 3.4.1 Command Line Interface | Reference Guide
Command History
This command was introduced in AOS-W 3.1.
Command Information
AIFSN Arbitrary inter-frame space number.
TXOP Transmission opportunity, in units of 32 microseconds.
ACM If this column displays a 1, the profile has enabled mandatory admission control.
If this column displays a 0, the profile has disabled this feature.
Parameter Description
Platforms Licensing Command Mode
All platforms This show command is available in the base operating
system, but the switch must have the Policy Enforcement
Firewall license in order to configure EDCA Parameter Profiles.
Enable and Config mode on
master or local switches
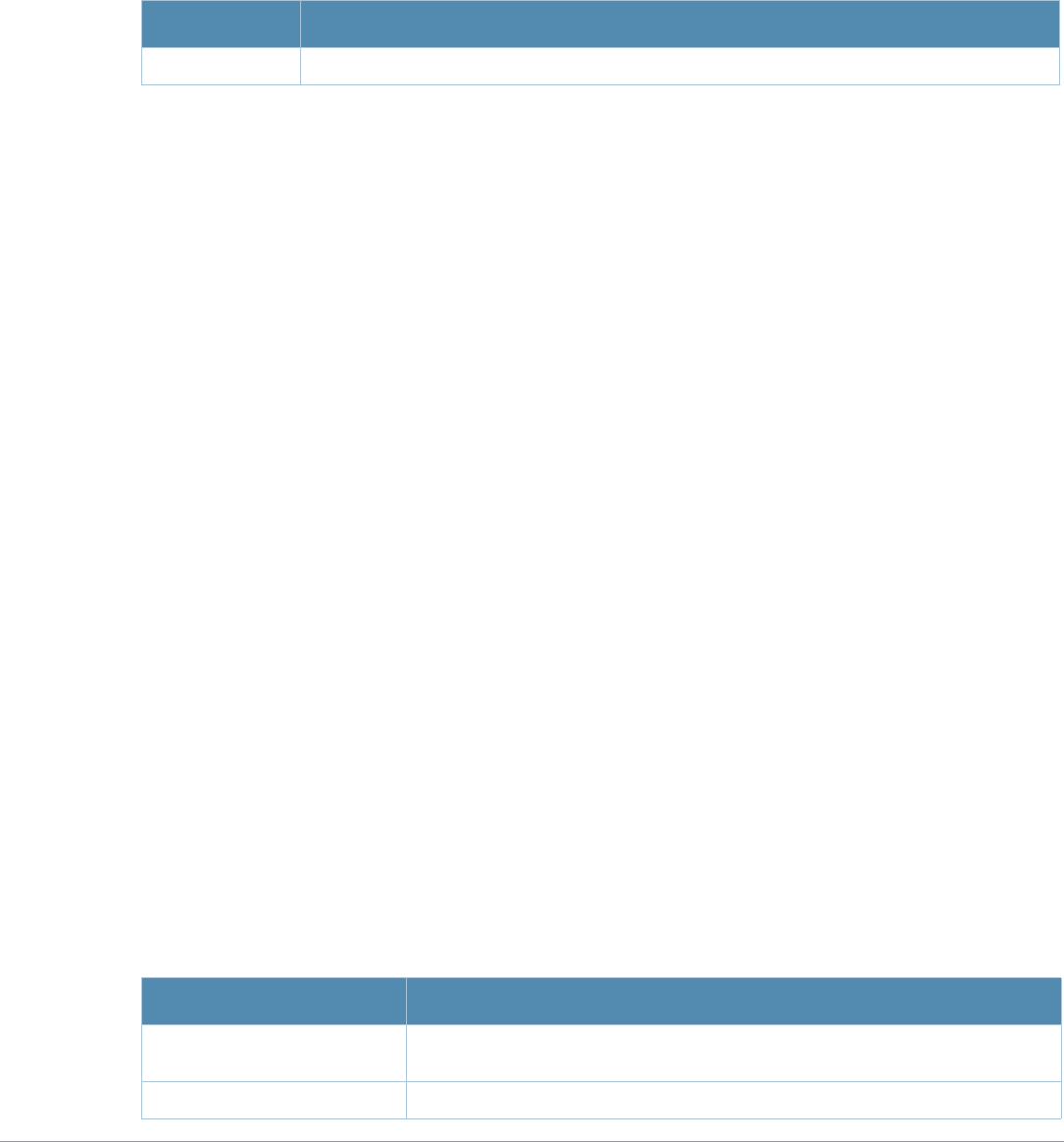
AOS-W 3.4.1 Command Line Interface | Reference Guide show wlan ht-ssid-profile | 1089
show wlan ht-ssid-profile
show wlan ht-ssid-profile [<profile>]
Description
Show a list of all High-throughput SSID profiles, or display detailed configuration information for a specific
High-throughput SSID profile.
Syntax
Usage Guidelines
Issue this command without the <profile> parameter to display the entire High-throughput SSID profile list,
including profile status and the number of references to each profile. Include a profile name to display
detailed configuration information for that profile.
Examples
The example below shows that the switch has two configured High-throughput SSID profiles. The
References column lists the number of other profiles with references to the High-throughput SSID profile,
and the Profile Status column indicates whether the profile is predefined. (User-defined profiles will not
have an entry in the Profile Status column.)
The following example shows configuration settings defined for the profile default2.
The output of this command includes the following data columns:
Parameter Description
<profile> Name of a High-throughput SSID profile.
(host) #show wlan ht-ssid-profile
High-throughput SSID profile List
---------------------------------
Name References Profile Status
---- ---------- --------------
HT-profile1 16
default2 1
Total:2
(host) #show wlan ht-ssid-profile default
High-throughput SSID profile "default"
--------------------------------------
Parameter Value
--------- -----
High throughput enable (SSID) Enabled
40 MHz channel usage Enabled
MPDU Aggregation Enabled
Max transmitted A-MPDU size 65535 bytes
Max received A-MPDU size 65535 bytes
Min MPDU start spacing 0 usec
Supported MCS set 0-15
Short guard interval in 40 MHz mode Enabled
Legacy stations Allowed
Allow weak encryption Disabled
Parameter Description
High throughput enable
(SSID)
Shows if the profile enables or disables high-throughput (802.11n) features.
40 MHz channel usage Shows if the profile enables or disables the use of 40 MHz channels.
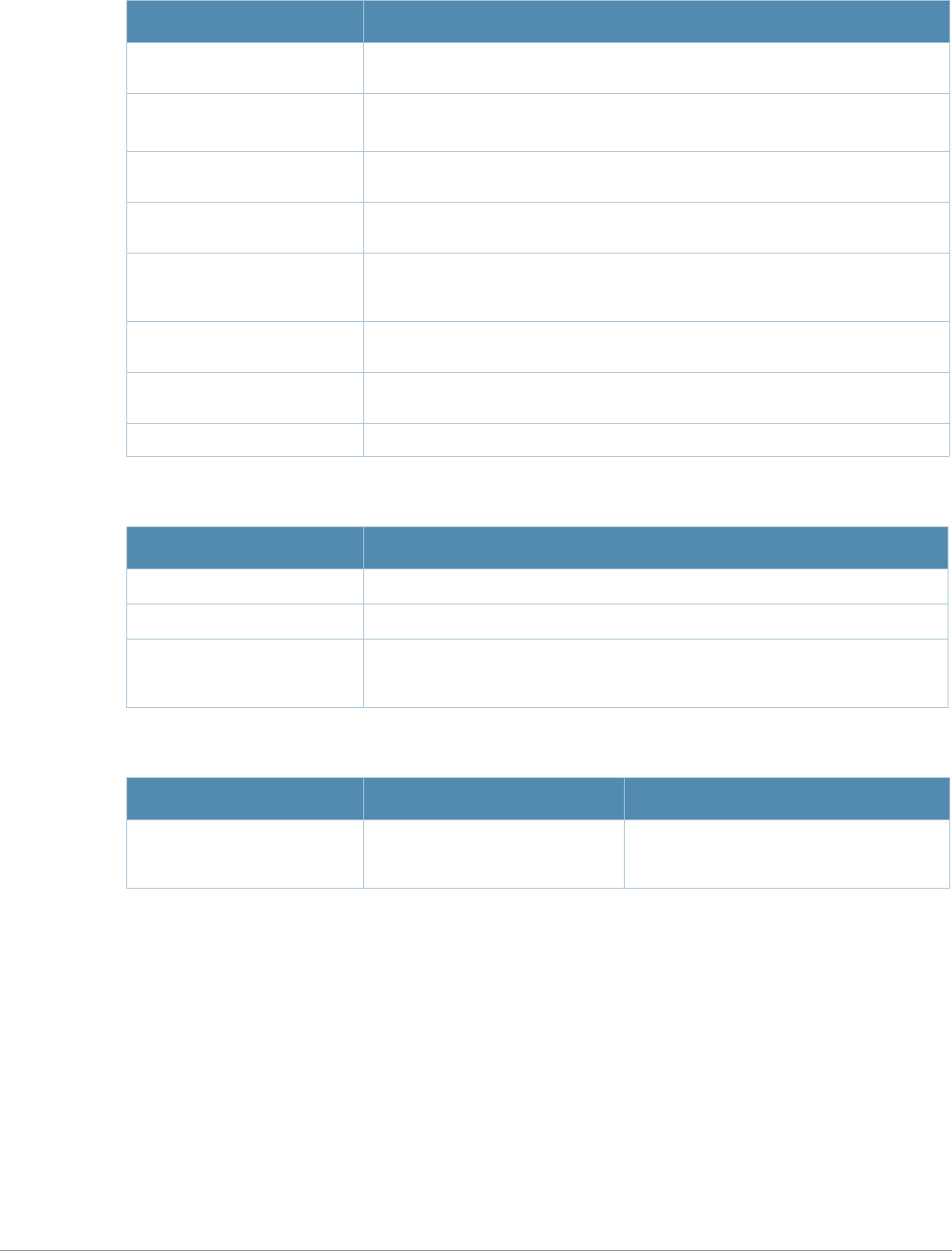
1090 | show wlan ht-ssid-profile AOS-W 3.4.1 Command Line Interface | Reference Guide
Command History
Command Information
MPDU Aggregation Shows if the profile enables or disables MAC protocol data unit (MPDU)
aggregation.
Max transmitted A-MPDU
size
Configured maximum size of a transmitted aggregate MPDU, in bytes.
Max received A-MPDU
size
Configured maximum size of a received aggregate MPDU, in bytes.
Min MPDU start spacing Configured minimum time between the start of adjacent MPDUs within an
aggregate MPDU, in microseconds.
Supported MCS set Displays a list of Modulation Coding Scheme (MCS) values or ranges of values to
be supported on this SSID. The MCS you choose determines the channel width
(20MHz vs. 40MHz) and the number of spatial streams used by the mesh node.
Short guard interval in
40 MHz mode
Shows if the profile enables or disables use of short (400ns) guard interval in 40
MHz mode.
Legacy stations Allow or disallow associations from legacy (non-HT) stations. By default, this
parameter is enabled (legacy stations are allowed).
Allow weak encryption Shows if the profile enables or disables the use of TKIP or WEP for unicast traffic.
Parameter Description
Version Description
AOS-W 3.3 Command introduced
AOS-W 3.3.1 The legacy-stations parameter was introduced
AOS-W 3.3.2 De-aggregation of MAC Service Data Units (A-MSDUs) on the OmniAccess 4504/
4604/4704 and the OmniAccess Supervisor Card III (OmniAccess Supervisor
Card III) was introduced
Platforms Licensing Command Mode
All platforms but operates with
IEEE 802.11n compliant
devices only
Base operating system Config mode on master switches

AOS-W 3.4.1 Command Line Interface | Reference Guide show wlan ssid-profile | 1091
show wlan ssid-profile
show wlan ssid-profile [<profile>]
Description
Show a list of all SSID profiles, or display detailed configuration information for a specific SSID profile.
Syntax
Usage Guidelines
Issue this command without the <profile> parameter to display the entire SSID profile list, including profile
status and the number of references to each profile. Include a profile name to display detailed configuration
information for that profile.
Examples
The example below shows that the switch has six configured SSID profiles. The References column lists
the number of other profiles with references to the SSIDs profile, and the Profile Status column indicates
whether the profile is predefined. (User-defined profiles will not have an entry in the Profile Status column.)
Parameter Description
<profile> Name of an SSID profile.
(host) #show wlan ssid-profile
SSID Profile List
-----------------
Name References Profile Status
---- ---------- --------------
coltrane-ssid-profile 1
corp1-ssid-profile 3
Remote 1
Secure-Profile2 0
test-ssid-profile 1
wizardtest-ssid-profile 1
Total:6
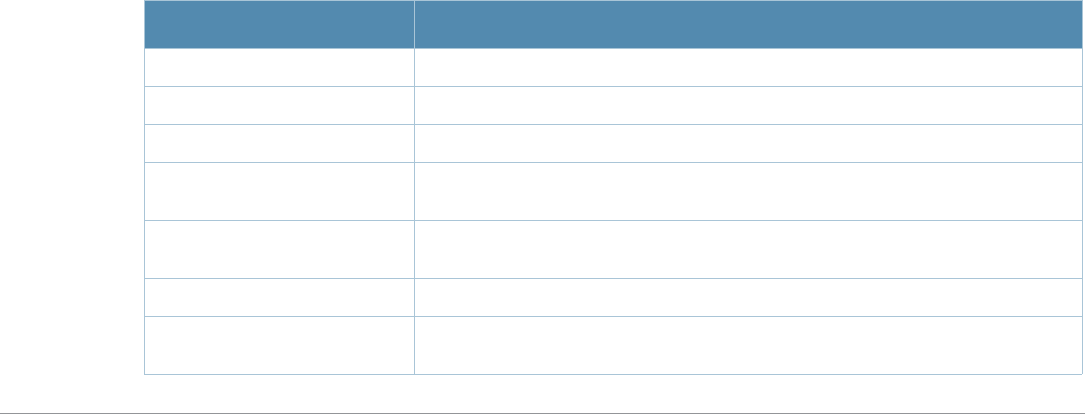
1092 | show wlan ssid-profile AOS-W 3.4.1 Command Line Interface | Reference Guide
The following example shows configuration settings defined for the SSID Profile Remote.
The output of this command includes the following data columns:
(host) #show wlan ssid-profile remote
SSID Profile "Remote"
---------------------
Parameter Value
--------- -----
SSID enable Enabled
ESSID remoteoffice
Encryption opensystem
DTIM Interval 1 beacon periods
802.11a Basic Rates 6 12 24
802.11a Transmit Rates 6 9 12 18 24 36 48 54
802.11g Basic Rates 1 2
802.11g Transmit Rates 1 2 5 6 9 11 12 18 24 36 48 54
Station Ageout Time 1000 sec
Max Transmit Attempts 8
RTS Threshold 2333 bytes
Short Preamble Enabled
Max Associations 64
Wireless Multimedia (WMM) Disabled
Wireless Multimedia U-APSD (WMM-UAPSD) Powersave Enabled
WMM TSPEC Min Inactivity Interval 0 msec
DSCP mapping for WMM voice AC 56
DSCP mapping for WMM video AC 40
DSCP mapping for WMM best-effort AC 24
DSCP mapping for WMM background AC 8
902il Compatibility Mode Disabled
Hide SSID Disabled
Deny_Broadcast Probes Disabled
Local Probe Response Enabled
Disable Probe Retry Enabled
Battery Boost Disabled
WEP Key 1 N/A
WEP Key 2 N/A
WEP Key 3 N/A
WEP Key 4 N/A
WEP Transmit Key Index 1
WPA Hexkey N/A
WPA Passphrase N/A
Maximum Transmit Failures 0
EDCA Parameters Station profile N/A
EDCA Parameters AP profile N/A
BC/MC Rate Optimization Disabled
Strict Spectralink Voice Protocol (SVP) Disabled
High-throughput SSID Profile default
Parameter Description
SSID Shows of the profile has enabled or disabled this SSID
ESSID Name that uniquely identifies the Service Set Identifier (SSID).
Encryption The layer-2 authentication and encryption type used on this ESSID.
DTIM Interval The interval, in milliseconds, between the sending of Delivery Traffic Indication
Messages (DTIMs) in the beacon.
802.11a Basic Rates List of supported 802.11a rates, in Mbps, that are advertised in beacon frames
and probe responses.
802.11a Transmit Rates Set of 802.11a rates at which the AP is allowed to send data.
802.11g Basic Rates List of supported 802.11b/g rates, in Mbps, that are advertised in beacon frames
and probe responses.
AOS-W 3.4.1 Command Line Interface | Reference Guide show wlan ssid-profile | 1093
802.11g Transmit Rates Set of 802.11b/g rates at which the AP is allowed to send data.
Station Ageout Time Time, in seconds, that a client is allowed to remain idle before being aged out.
Max Transmit Attempts Maximum transmission failures allowed before the client gives up.
RTS Threshold Wireless clients transmitting frames larger than this defined threshold must issue
Request to Send (RTS) and wait for the AP to respond with Clear to Send (CTS).
Short Preamble Shows if the profile enables or disables short preamble for 802.11b/g radios
Max Associations Maximum number of wireless clients for the AP
Wireless Multimedia
(WMM)
Shows if the profile enables or disables WMM, also known as IEEE 802.11e
Enhanced Distribution Coordination Function (EDCF)
Wireless Multimedia U-
APSD (WMM-UAPSD)
Powersave
Shows if the profile enables or disables Wireless Multimedia (WMM) UAPSD
powersave.
WMM TSPEC Min
Inactivity Interval
Specifies the minimum inactivity time-out threshold of WMM traffic.
DSCP mapping for WMM
voice AC
DSCP value used to map WMM voice traffic.
DSCP mapping for WMM
video AC
DSCP value used to map WMM video traffic.
DSCP mapping for WMM
best-effort AC
DSCP value used to map WMM best-effort traffic.
DSCP mapping for WMM
background AC
DSCP value used to map WMM background traffic.
902il Compatibility
Mode
(For clients using NTT DoCoMo 902iL phones only) When enabled, the switch
does not drop packets from the client if a small or old initialization vector value is
received.
Hide SSID Shows if the profile enables or disables hiding of the SSID name in beacon
frames.
Deny_Broadcast Probes When a client sends a broadcast probe request frame to search for all available
SSIDs, this option controls whether or not the system responds for this SSID.
When enabled, no response is sent and clients have to know the SSID in order to
associate to the SSID. When disabled, a probe response frame is sent for this
SSID
Local Probe Response Shows if the profile enables or disables local probe response on the AP. If this
option is enabled, the AP is responsible for sending 802.11 probe responses to
wireless clients’ probe requests. If this option is disabled, then the switch sends
the 802.11 probe responses
Disable Probe Retry Shows if the profile enables or disables battery MAC level retries for probe
response frames.
Battery Boost If enabled, this feature converts multicast traffic to unicast before delivery to the
client, thus allowing you to set a longer DTIM interval.
WEP Key 1 Displays the Static WEP key associated with this key index.
WEP Key 2 Displays the Static WEP key associated with this key index.
WEP Key 3 Displays the Static WEP key associated with this key index.
WEP Key 4 Displays the Static WEP key associated with this key index.
WEP Transmit Key Index Show the key index that specifies which static WEP key is to be used
Parameter Description

1094 | show wlan ssid-profile AOS-W 3.4.1 Command Line Interface | Reference Guide
Command History
This command was introduced in AOS-W 3.0.
Command Information
WPA Hexkey WPA pre-shared key (PSK).
WPA Passphrase WPA passphrase used to generate a pre-shared key (PSK).
Maximum Transmit
Failures
Maximum transmission failures allowed before the client gives up.
EDCA Parameters Station
profile
Name of the enhanced distributed channel access (EDCA) Station profile that
applies to this SSID.
EDCA Parameters AP
profile
Name of the enhanced distributed channel access (EDCA) AP profile that applies
to this SSID.
BC/MC Rate Optimization Shows if the profile enables or disables scanning of all active stations currently
associated to an AP to select the lowest transmission rate for broadcast and
multicast frames. This option only applies to broadcast and multicast data
frames; 802.11 management frames are transmitted at the lowest configured rate
Strict Spectralink
Voice Protocol (SVP)
Shows if the profile enables or disables strict Spectralink Voice Protocol (SVP).
High-throughput SSID
Profile
Name of the high-throughput SSID profile associated with this SSID profile.
Parameter Description
Platforms Licensing Command Mode
All platforms Base operating system Enable and Config mode on master or local switches.
AOS-W 3.4.1 Command Line Interface | Reference Guide show wlan traffic-management-profile | 1095
show wlan traffic-management-profile
show wlan traffic-management-profile [<profile>]
Description
Show a list of all traffic management profiles, or display detailed configuration information for a specific
traffic management profile.
Syntax
Usage Guidelines
Issue this command without the <profile> parameter to display the entire Traffic Management profile list,
including profile status and the number of references to each profile. Include a profile name to display
detailed configuration information for that profile.
Examples
The example below shows that the switch has three configured Traffic Management profiles. The
References column lists the number of other profiles with references to the Traffic Management profile,
and the Profile Status column indicates whether the profile is predefined. (User-defined profiles will not
have an entry in the Profile Status column.)
The following example shows configuration settings defined for the profile mgmt1.
The output of this command includes the following data columns:
Parameter Description
<profile> Name of a Traffic Management profile.
(host) #show wlan
Traffic management profile List
-------------------------------
Name References Profile Status
---- ---------- --------------
mgmt1 1
mgmt3 0
mgmt4 2
Total: 3
(host) #show wlan traffic-management-profile mgmt1
Traffic management profile "default"
------------------------------------
Parameter Value
--------- -----
Proportional BW Allocation N/A
Report interval 5 min
Station Shaping Policy default-access
Parameter Description
Proportional BW
Allocation
Minimum bandwidth, as a percentage of available bandwidth, allocated to an
SSID when there is congestion on the wireless network. An SSID can use all
available bandwidth if no other SSIDs are active.
Report interval Number of minutes between bandwidth usage reports.
1096 | show wlan traffic-management-profile AOS-W 3.4.1 Command Line Interface | Reference Guide
Command History
This command was introduced in AOS-W 3.0.
Command Information
Station Shaping Policy Shows which of three possible Station Shaping policies is configured on the
profile.
zdefault-access: Traffic shaping is disabled, and client performance is
dependent on MAC contention resolution. This is the default traffic shaping
setting.
zfair-access: Each client gets the same airtime, regardless of client capability
and capacity. This option is useful in environments like a training facility or
exam hall, where a mix of 802.11a/g, 802.11g and 802.11n clients need equal
to network resources, regardless of their capabilities. The bw-alloc parameter
of a traffic management profile allows you to set a minimum bandwidth to be
allocated to a virtual AP profile when there is congestion on the wireless
network.You must set traffic shaping to fair-access to use this bandwidth
allocation value for an individual virtual AP.
zpreferred-access: High-throughput (802.11n) clients do not get penalized
because of slower 802.11a/g or 802.11b transmissions that take more air time
due to lower rates. Similarly, faster 802.11a/g clients get more access than
802.11b clients.
Parameter Description
Platforms Licensing Command Mode
All platforms Base operating system Enable and Config mode on master or local switches.
AOS-W 3.4.1 Command Line Interface | Reference Guide show wlan virtual-ap | 1097
show wlan virtual-ap
show wlan virtual-ap [<profile>]
Description
Show a list of all Virtual AP profiles, or display detailed configuration information for a specific Virtual AP
profile.
Syntax
Usage Guidelines
Issue this command without the <profile> parameter to display the entire Virtual AP profile list, including
profile status and the number of references to each profile. Include a profile name to display detailed
configuration information for that profile.
Examples
The example below shows that the switch has six configured Virtual AP profiles. The References column
lists the number of other profiles with references to the Virtual AP profile, and the Profile Status column
indicates whether the profile is predefined. (User-defined profiles will not have an entry in the Profile Status
column.)
Parameter Description
<profile> Name of a Virtual AP profile
(host) #show wlan virtual-ap
Virtual AP profile List
-----------------------
Name References Profile Status
---- ---------- --------------
coltrane-vap-profile 1
default 2
MegTest 1
Remote 1
test-vap-profile 1
wizardtest-vap-profile 1
Total: 6
1098 | show wlan virtual-ap AOS-W 3.4.1 Command Line Interface | Reference Guide
The following example shows configuration settings defined for the profile wizardtest-vap-profile.
The output of this command includes the following data columns:
(host) #show wlan virtual-ap test-vap-profile
Virtual AP profile "wizardtest-vap-profile"
----------------------------
Parameter Value
--------- -----
Virtual AP enable Enabled
Allowed band all
AAA Profile default
802.11K Profile default
SSID Profile default
VLAN N/A
Forward mode tunnel
Deny time range N/A
Mobile IP Enabled
HA Discovery on-association Disabled
DoS Prevention Enabled
Station Blacklisting Enabled
Blacklist Time 3600 sec
Authentication Failure Blacklist Time 3600 sec
Fast Roaming Disabled
Strict Compliance Enabled
VLAN Mobility Disabled
Remote-AP Operation standard
Drop Broadcast and Multicast Disabled
Convert Broadcast ARP requests to unicast Enabled
Band Steering Disabled
Parameter Description
Virtual AP enable Shows if the profile enables or disables the virtual AP.
Allowed band The band(s) on which to use the virtual AP:
za—802.11a band only (5 GHz)
zg—802.11b/g band only (2.4 GHz)
zall—both 802.11a and 802.11b/g bands (5 GHz and 2.4 GHz)
AAA Profile Name of the AAA profile associated with this virtual AP.
802.11K Profile Name of an 802.11k profile associated with this virtual AP.
SSID Profile Name of an SSID profile associated with this virtual AP.
VLAN The VLAN(s) into which users are placed in order to obtain an IP address.
Forward mode Forwarding mode defined on the profile:
zbridge mode
zsplit-tunnel mode
ztunnel mode
The forwarding mode controls whether 802.11 frames are tunneled to the switch
using generic routing encapsulation (GRE), bridged into the local Ethernet LAN
(for remote APs), or a combination thereof depending on the destination
(corporate traffic goes to the switch, and Internet access remains local).
Deny time range Time range for which the AP will deny access.
Mobile IP Shows if the profile has enabled or disabled IP mobility.
HA Discovery on-
association
If enabled, all clients of a virtual-ap will received mobility service on association.
DoS Prevention If enabled, APs ignore deauthentication frames from clients. This prevents a
successful deauth attack from being carried out against the AP. This does not
affect third-party APs.
AOS-W 3.4.1 Command Line Interface | Reference Guide show wlan virtual-ap | 1099
Command History
This command was introduced in AOS-W 3.0.
Command Information
Station Blacklisting Shows if the profile has enabled or disabled detection of denial of service (DoS)
attacks, such as ping or SYN floods, that are not spoofed deauth attacks.
Blacklist Time Number of seconds that a client is quarantined from the network after being
blacklisted.
Authentication Failure
Blacklist Time
Time, in seconds, a client is blocked if it fails repeated authentication. An
authentication failure blacklist time of 0 blocks failed users indefinitely.
Fast Roaming Shows if the AP has enabled or disabled fast roaming.
Strict Compliance If enabled, the AP denies client association requests if the AP and client station
have no common rates defined. Some legacy client stations which are not fully
802.11-compliant may not include their configured rates in their association
requests. Such non-compliant stations may have difficulty associating with APs
unless strict compliance is disabled.
VLAN Mobility Shows if the AP has enabled or disabled VLAN (Layer-2) mobility.
Remote-AP Operation Shows how the virtual AP operates on a remote AP:
zalways: Permanently enables the virtual AP.
zbackup: Enables the virtual AP if the remote AP cannot connect to the switch.
zpersistent: Permanently enables the virtual AP after the remote AP initially
connects to the switch.
zstandard: Enables the virtual AP when the remote AP connects to the switch.
Drop Broadcast and
Multicast
If enabled, the virtual AP will filter out broadcast and multicast traffic in the air.
Convert Broadcast ARP
requests to unicast
If enabled, all broadcast ARP requests are converted to unicast and sent directly
to the client
Band Steering If enabled, ARM’s band steering feature encourages dual-band capable clients to
stay on the 5GHz band on dual-band APs. This frees up resources on the 2.4GHz
band for single band clients like VoIP phones.
Parameter Description
Platforms Licensing Command Mode
All platforms Base operating system Enable and Config mode on master or local switches.
1100 | show wlan voip-cac-profile AOS-W 3.4.1 Command Line Interface | Reference Guide
show wlan voip-cac-profile
show wlan voip-cac-profile [<profile>]
Description
Show a list of all VoIP Call Admission Control profiles, or display detailed configuration information for a
specific VoIP Call Admission Control profile.
Syntax
Usage Guidelines
Issue this command without the <profile> parameter to display the entire VoIP Call Admission Control
profile list, including profile status and the number of references to each profile. Include a profile name to
display detailed configuration information for that profile.
Examples
The example below shows that the switch has three configured VoIP Call Admission Control profiles. The
References column lists the number of other profiles with references to the VoIP Call Admission Control
profile, and the Profile Status column indicates whether the profile is predefined. (User-defined profiles
will not have an entry in the Profile Status column.)
The following example shows configuration settings defined for the profile QAlab-voip.
Parameter Description
<profile> Name of a VoIP Call Admission Control profile
(host) #show wlan voip-cac-profile
VoIP Call Admission Control profile List
----------------------------------------
Name References Profile Status
---- ---------- --------------
corp-voip 6
kgtest 0
QAlab-voip 1
Total:3
(host) #show wlan voip-cac-profile
VoIP Call Admission Control profile "QAlab-voip"
---------------------------------------------
Parameter Value
--------- -----
VoIP Call Admission Control Disabled
VoIP Bandwidth based CAC Disabled
VoIP Call Capacity 10
VoIP Bandwidth Capacity (kbps) 2000
VoIP Call Handoff Reservation 20 %
VoIP Send SIP 100 Trying Enabled
VoIP Disconnect Extra Call Disabled
VOIP TSPEC Enforcement Disabled
VOIP TSPEC Enforcement Period 1 sec
VoIP Drop SIP Invite and send status code (client) 486
VoIP Drop SIP Invite and send status code (server) 486
AOS-W 3.4.1 Command Line Interface | Reference Guide show wlan voip-cac-profile | 1101
The output of this command includes the following data columns:
Command History
This command was introduced in AOS-W 3.0.
Command Information
Parameter Description
VoIP Call Admission Control Shows if the profile enables or disables WiFi VoIP Call Admission
Control features.
VoIP Bandwidth based CAC Shows the desired call admission control (CAC) Mechanism:
zDisable - CAC is based on Call Counts
zEnable - CAC should be based on Bandwidth.
VoIP Call Capacity Number of simultaneous calls that can be handled by one radio.
VoIP Bandwidth Capacity (kbps) The maximum bandwidth that can be handled by one radio, in kbps.
VoIP Call Handoff Reservation Percentage of call capacity reserved for mobile VoIP clients on call.
VoIP Send SIP 100 Trying Shows if the profile enables or disables sending of SIP 100 - trying
messages to a call originator to indicate that the call is proceeding.
VoIP Disconnect Extra Call If enabled, the switch disconnects calls that exceed the high capacity
threshold by sending a deauthentication frame.
VOIP TSPEC Enforcement Shows if the profile enables or disables validation of TSPEC requests for
CAC.
VOIP TSPEC Enforcement Period Maximum time for the station to start the call after the TSPEC request
VoIP Drop SIP Invite and send
status code (client)
Display the status code sent back to the client if the profile is configured
to drop a SIP Invite:
z480: Temporary Unavailable
z486: Busy Here
z503: Ser vice Unavailable
znone: Don't send SIP status code
VoIP Drop SIP Invite and send
status code (server)
Display the status code sent back to the server if the profile is
configured to drop a SIP Invite:
z480: Temporary Unavailable
z486: Busy Here
z503: Ser vice Unavailable
znone: Don't send SIP status code
Platforms Licensing Command Mode
All platforms Base operating system Enable and Config mode on master or local switches.

1102 | show wlan voip-cac-profile AOS-W 3.4.1 Command Line Interface | Reference Guide
AOS-W 3.4.1 Command Line Interface | Reference Guide show wms ap | 1103
show wms ap
show wms ap {<bssid>}|{list [mon-mac <mon-mac> bssid <bssid>}|{stats [mon-mac <mon-mac>
bssid <bssid>}
Description
Display information for APs currently monitored by the AOS-W Wireless Management System (WMS).
Syntax
Usage Guidelines
The WMS feature periodically sends statistics that it has collected for APs and Probes to the WMS process.
When WMS receives an event message from an AM, it will save the event information along with the BSSID of
the AP that generated the event in the WMS database. When WMS receives statistics from the AM, it updates its
state, and the database.
Examples
The command show wms ap <bssid> displays a list of AP MAC addresses and the BSSIDs seen by each AP.
The output of this command includes the following information:
Parameter Description
<bssid> Enter the AP’s BSSID number in hexadecimal format (XX:XX:XX:XX:XX:XX).
list Show the AP Tree Table for all APs.
mon-mac <mon-mac> Show the AP Tree Table for an AP with the specified MAC address.
bssid <bssid> Show the AP Tree Table for an AP with the specified BSSID.
stats Show the AP Tree Table for all APs.
mon-mac <mon-mac> Show the AP Tree Table for an AP with the specified MAC address.
bssid <bssid> Show the AP Tree Table for an AP with the specified BSSID.
(host)# show wms ap 00:1a:1e:88:01:e0
AP Info
-------
BSSID SSID Channel Type RAP_Type Status Match MAC Ageout HT-Type HT-Sec-Chan
----- ---- ------- ---- -------- ------ --------- ------ ------- -----------
00:1a:1e:88:01:e0 sw-ad 11 soft-ap valid up 00:00:00:00:00:00 -1
Probe Info
----------
MAC IP Name Type Status AP Type
--- -- ---- ---- ------ -------
00:1a:1e:88:02:80 10.3.129.94 ad-ap125-13 soft-ap up 125
00:1a:1e:88:01:e0 10.3.129.96 mp3 soft-ap up 125
00:1a:1e:81:c6:00 10.3.129.99 ad-ap124-11 soft-ap down 124
00:0b:86:8a:15:20 10.3.129.93 sap61-1-6 soft-ap down 65
Column Description
BSSID Basic Service Set Identifier for the AP. This is usually the AP’s MAC address.
SSID The Service Set Identifier that identifies a wireless network.
Channel Channel used by the AP’s radio.
1104 | show wms ap AOS-W 3.4.1 Command Line Interface | Reference Guide
The example below shows received and transmitted data statistics for each BSSID seen by a monitoring AP.
Type A WMS AP type can be one of the following:
zsoft-ap: an Alcatel-Lucent Access Point (AP).
zair-monitor: An Alcatel-Lucent Air Monitor (AM).
RAP_Type Indicates one of the following Rogue AP types:
zValid (not a rogue AP)
zInterfering
zRogue
zSuspected Rogue
zDisabled Rogue
zUnclassified
zKnown Interfering
Status If up, the AP is active. If down (or no information is shown) the AP is inactive.
Match MAC MAC address of a wired device that helped identify the AP as a rogue. If the AP has not
been identified as a rogue, this column will display the MAC address 00:00:00:00:00:00.
Ageout An ageout time is the time, in minutes, that the client must remain unseen by any probes
before it is eliminated from the database. If this column displays a -1, the client has not
yet aged out. Any other number indicates the number of minutes since the client has
passed its ageout interval.
HT-type The type of high-throughput traffic sent by the AP:
zHT-20mhz: The AP radio uses a single 20 mHz channel
zHT-40mhz: The AP radio uses a 40 MHz channel pair comprised of two adjacent 20
MHz channels.
HT-Sec-Chan Secondary channel used for 40 MHz high-throughput transmissions.
MAC MAC address of a probe that can see the specified AP.
IP IP address of a probe that can see the specified AP.
Name Name of the probe.
Type Displays the probe type: A WMS probe can be one of the following:
zsoft-ap: an Alcatel-Lucent Access Point (AP).
zair-monitor: An Alcatel-Lucent Air Monitor (AM).
Status If up, the AP is active. If down (or no information is shown) the AP is inactive.
AP Type AP model type.
Column Description
(host)# show wms ap stats
AP Stats Table
----------------
Monitor-MAC BSSID RSSI TxPkt RxPkt TxByte RxByte HTRates-Rx
----------- ----- ---- ----- ----- ------ ------ ----------
00:0b:86:c1:af:20 00:0b:86:9a:f2:00 12 1575675 65 173239998 9340 0
00:0b:86:c1:af:20 00:0b:86:9a:f2:08 12 1560559 0 162297938 0 0
00:0b:86:c1:be:56 00:0b:86:9b:e5:60 12 1683013 4188 184400159 257583 0
00:0b:86:c1:be:56 00:0b:86:9b:e5:68 12 1580152 105 164216336 1470 0
00:0b:86:c2:0a:98 00:0b:86:a0:a9:80 48 1608023 40596 166962148 568386 0
00:0b:86:c2:1c:08 00:0b:86:a1:c0:80 42 1587097 26236 164904668 453196 0
00:0b:86:c2:1c:38 00:0b:86:a1:c3:80 42 1573040 20511 174536514 654024 0
00:0b:86:c2:3e:a9 00:0b:86:a3:ea:90 48 1588204 34179 165017293 897431 0
00:0b:86:c4:0f:3c 00:0b:86:c0:f3:d0 48 1571202 14258 174338376 351148 0
00:0b:86:c4:4d:06 00:0b:86:c4:d0:70 48 1598423 56198 182267018 3805826 0
00:1a:1e:c0:88:82 00:1a:1e:88:88:30 18 1717310 247532 394461405 14998234 8
00:1a:1e:c0:88:82 00:1a:1e:88:88:20 18 1092023 114722 242006054 2442917 10
00:1a:1e:c0:88:88 00:1a:1e:88:88:90 36 1783226 485620 460219125 27781583 16
AOS-W 3.4.1 Command Line Interface | Reference Guide show wms ap | 1105
The output of this command includes the following information:
Command History
This command was introduced in AOS-W 3.0
Command Information
Column Description
Monitor-MAC MAC address of an AP.
BSSID Basic Service Set Identifier of a station.
RSSI Received Signal Strength Indicator for the station, as seen by the AP.
txPkt Number of transmitted packets.
RxPkt Number of received packets.
TxByte Number of transmitted bytes.
RxByte Number of received bytes.
HTRates-Rx Number of bytes received at high-throughput rates.
Platforms Licensing Command Mode
All platforms Base operating system Config mode on master switches
1106 | show wms channel AOS-W 3.4.1 Command Line Interface | Reference Guide
show wms channel
show wms channel stats
Description
Display per-channel statistics for monitored APs.
Syntax
No parameters.
Example
This example shows per-channel statistics for monitored APs.
The output of this command includes the following information:
Column Description
Monitor-MAC MAC address of an AP.
Channel 802.11 radio channel.
NumAP Number of other APs seen on the specified channel.
NumSta Number stations seen on the specified channel.
TotalPkt Number of received packets.
TotalByte Number of received bytes.
Noise Current noise level.
(host) #show wms channel stats
Channel Stats Table
---------------------
Monitor-MAC Channel NumAP NumSta TotalPkt TotalByte Noise
----------- ------- ----- ------ -------- --------- -----
00:0b:86:c1:af:20 1 1 0 5228276 613640650 97
00:0b:86:c1:af:20 6 1 0 1355 168764 0
00:0b:86:c1:af:20 11 8 0 5880 1040338 0
00:0b:86:c1:af:20 36 0 0 2 28 0
00:0b:86:c1:af:20 40 0 0 2 112 0
00:0b:86:c1:af:20 44 0 0 50 903 0
00:0b:86:c1:af:20 48 0 0 23 544 0
00:0b:86:c1:af:20 149 1 0 27094 557579 0
00:0b:86:c1:af:20 153 3 0 4648662 544817261 99
00:0b:86:c1:af:20 165 1 0 1655 200349 0
00:0b:86:c1:be:56 1 43 4 14446324 1959058619 0
00:0b:86:c1:be:56 6 8 1 14168505 1955474600 96
00:0b:86:c1:be:56 11 72 1 180553 23987119 0
00:0b:86:c1:be:56 36 53 0 14716 1022825 0
00:0b:86:c1:be:56 40 8 0 3033 501568 0
00:0b:86:c1:be:56 44 3 0 1453 217596 0
00:0b:86:c1:be:56 48 4 0 5330 1067660 0
00:0b:86:c1:be:56 149 0 0 609279 72205247 105
00:0b:86:c1:be:56 153 1 0 7615369 779579648 0
00:0b:86:c1:be:56 165 1 0 4238 486121 0
00:0b:86:c2:0a:98 40 4 0 4247 434512 0
00:0b:86:c2:0a:98 48 5 0 4052 420436 0
00:0b:86:c2:0a:98 149 4 0 6548323 732910481 104
00:0b:86:c2:1c:08 40 3 0 4613 478188 0
00:0b:86:c2:1c:08 48 4 0 6235436 658263321 103
00:0b:86:c2:1c:08 149 5 0 18904 803078 0

AOS-W 3.4.1 Command Line Interface | Reference Guide show wms channel | 1107
Command History
This command was introduced in AOS-W 3.0
Command Information
Platforms Licensing Command Mode
All platforms Base operating system Config mode on master switches
1108 | show wms client AOS-W 3.4.1 Command Line Interface | Reference Guide
show wms client
show wms client <mac>|{list}|{probe <mac>}|{stats [mon-mac <mon-mac> mac <mac>]}
Description
Display a list of client information for the clients that can be seen by monitoring APs.
Syntax
Example
The AP Info table in the example below shows that the client is associated to an AP with the BSSID
00:0b:86:cd:86:a0. The Probe info table shows the MAC addresses of three other APs that can see the client.
The output of this command includes the following information:
Parameter Description
<mac> Show statistics for a client with the specified MAC address, including the BSSID of the AP
to which that client is currently associated, and the MAC addresses of other monitoring
APs that can see that client.
list Show statistics for all monitored clients.
probe <mac> Specify a client’s MAC address to show the BSSIDs of all probes that can see that client.
stats Show the STA stats table, which displays data for all clients seen by each monitoring AP.
mon-mac <mon-mac>
mac <mac>
Enter a monitoring AP’s MAC address (<mon-mac>) and the MAC address of a client
(<mac>) to show data for traffic received from and sent to a specific client as seen by a
specific AP.
Column Description
MAC MAC address of the client
Type Station type (valid, interfering, or disabled rogue client )
Status If up, the client is active. If down (or no information is shown) the client is inactive.
(host) #show wms client 00:0e:35:29:9b:28
STA Info
--------
MAC Type Status Ageout
--- ---- ------ ------
00:0e:35:29:9b:28 valid up -1
AP Info
-------
BSSID SSID Channel Type RAP_Type Status Match MAC Ageout
----- ---- ------- ---- -------- ------ --------- ------
00:0b:86:cd:86:a0 MySSiD 11 soft-ap valid up 00:00:00:00:00:00 -1
Probe Info
----------
MAC IP Name Type Status Name AP Type
--- -- ---- ---- ------ ---- -------
00:0b:86:a2:2b:50 192.168.2.10 0 soft-ap up LeftAP 61
00:0b:86:ad:94:40 192.168.2.5 0 soft-ap up 1.1.1 61
00:0b:86:cd:86:a0 192.168.2.4 0 soft-ap up CEO 70
AOS-W 3.4.1 Command Line Interface | Reference Guide show wms client | 1109
Command History
This command was introduced in AOS-W 3.0
Command Information
ageout An ageout time is the time, in minutes, that the client must remain unseen by any probes
before it is eliminated from the database. If this column displays a -1, the client has not
yet aged out. Any other number indicates the number of minutes since the client has
passed its ageout interval.
BSSID BSSID of the AP to which the client is associated.
SSID Extended service set identifier (ESSID) of the BSSID.
RAP_Type Indicates one of the following Rogue AP types:
zValid (not a rogue AP)
zInterfering
zRogue
zDisabled Rogue
zSuspected Rogue
zUnclassified
zKnown Interfering
Status If up, the AP is active. If down (or no information is shown) the AP is inactive.
Match MAC MAC address of a wired device that helped identify the AP as a rogue. If the AP has not
been identified as a rogue, this column will display the MAC address 00:00:00:00:00:00.
Ageout An ageout time is the time, in minutes, that the client must remain unseen by any probes
before it is eliminated from the database. If this column displays a -1, the client has not
yet aged out. Any other number indicates the number of minutes since the client has
passed its ageout interval.
MAC MAC address of a WMS probe.
IP IP address of a WMS probe.
Type A WMS AP type can be one of the following:
zsoft-ap: an Alcatel-Lucent Access Point (AP).
zair-monitor: An Alcatel-Lucent Air Monitor (AM).
Status If up, the probe is active. If down (or no information is shown) the probe is inactive.
Name Name of the probe. If a name has not been defined for the probe, this column may display
a zero (0).
AP type Model type of the probe.
Platforms Licensing Command Mode
All platforms Base operating system Config mode on master switches
Column Description
1110 | show wms counters AOS-W 3.4.1 Command Line Interface | Reference Guide
show wms counters
show wms counters [debug|event]
Description
Show WMS event and debug counters. If you omit the optional debug and events parameters, the show wms
counters command will display wms debug and events counters in a single table.
Syntax
Usage Guidelines
This command displays counters for database entries, messages and data structures. The counters displayed
will vary for each switch; if the switch does not have an entry for a particular counter type, it will not appear in
the output of this command
Example
This example shows part of the output of the command show wms counters.
Command History
This command was introduced in AOS-W 3.0
Command Information
Parameter Description
debug Show show debug counters only
events Show events counters only. If you omit the debug and events parameters, the show wms
counters will display debug and events counters in a single table.
Platforms Licensing Command Mode
All platforms Base operating system Config mode on master switches
(host) #show wms counters
Counters
--------
Name Value
---- -----
DB Reads 288268
DB Writes 350870
Probe Table DB Reads 2477
Probe Table DB Writes 952
AP Table DB Reads 143992
AP Table DB Writes 138867
STA Table DB Reads 40404
STA Table DB Writes 99687
Probe STA Table DB Reads 101352
Probe STA Table DB Writes 117566
Probe Register 2476
Probe State Update 37077
Set RAP Type 42552
Set RAP Type Conf Level 152
...

AOS-W 3.4.1 Command Line Interface | Reference Guide show wms general | 1111
show wms general
show wms general
Description
Display general statistics for the wms configuration.
Syntax
No parameters
Example
This example shows per-channel statistics for all monitored APs.
The output of this command includes the following information:
Column Description
poll-interval Interval, in milliseconds, for communication between the switch and Alcatel-Lucent AMs.
The switch contacts the AM at this interval to download AP to station associations,
update policy configuration changes, and download AP and station statistics.
poll-retries Maximum number of failed polling attempts before the polled AM is considered to be
down.
ap-ageout-interval Time, in minutes, that an AP must remain unseen by any probes before it is deleted from
the database.
sta-ageout-interval Time, in minutes, that an client must unseen by any probes before it is deleted from the
database.
learn-ap Enables “learning” of non-Alcatel-Lucent APs.
persistent-known-
interfering
If enabled, APs that are marked as known interfering from being aged out.
propagate-wired-MACs Shows if the switch has enabled or disabled the propagation of the gateway wired MACs.
stat-update Shows if the switch has enabled or disabled WMS statistics updates in the database.
(host) #show wms general
General Attributes
------------------
Key Value
--- -----
poll-interval 176000
poll-retries 2
ap-ageout-interval 30
sta-ageout-interval 30
learn-ap enable
persistent-known-interfering disable
propagate-wired-macs enable
stat-update enable
collect-stats enable
classification-server-ip 10.4.151.19
rtls-port 0
wms-on-master disable
use-db disable
calc-poll-interval 176000
Switch IP 10.6.2.253
Is Master enable
1112 | show wms general AOS-W 3.4.1 Command Line Interface | Reference Guide
Command History
This command was introduced in AOS-W 3.0
Command Information
collect-stats If enabled, if the master switch will collect up to 25,000 statistic entries for monitored APs
and clients.
classification-
server-ip
IP address of an AMP (Airwave Management Platform) that will perform Rogue AP
classification. If there is a classification server defined, the wms-on-master and use-db
parameters will be disabled.
rtls-port Port number on the RTLS server to which WMS statistics should be sent.
wms-on-master The WMS process is enabled on the master switch.
use-db Shows if WMS data is updated to the database on the master switch.
calc-poll-interval Interval (in milliseconds) specifies the frequency with which an AP sends updates about
monitored APs and monitored clients to the switch. By default it uses the configured
poll-interval value. If the # of deployed radios is more than 30, the calc-poll-interval is
computed as 2000*number-of-radios.
Switch IP IP address of the switch.
Is Master If enabled, the switch is a master switch. Otherwise, it is defined as a local switch.
Platforms Licensing Command Mode
All platforms Base operating system Config mode on master switches
Column Description
AOS-W 3.4.1 Command Line Interface | Reference Guide show wms monitor-summary | 1113
show wms monitor-summary
show wms channel stats
Description
Display the numbers of different AP and client types monitored over the last 5 minutes, 1 hour, and since the
switch was last reset.
Syntax
No parameters.
Usage Guidelines
The WLAN management system (WMS) on the switch monitors wireless traffic to detect any new AP or wireless
client station that tries to connect to the network. When an AP or wireless client is detected, it is classified and
its classification is used to determine the security policies which should be enforced on the AP or client. Use the
show wms monitor-summary command to view a quick summary of each classified AP and client type
currently on the network.
If AP learning is enabled (with the wms general command), non-Alcatel-Lucent APs connected on the same
wired network as Alcatel-Lucent APs are classified as valid APs. If AP learning is disabled, a non-Alcatel-Lucent
AP is classified as an unsecure or suspect-unsecure AP.
Example
This example shows that the switch currently has 144 valid APs and 32 active valid clients, and verifies that the
switch currently aware of a single disabled rogue AP.
Command History
This command was introduced in AOS-W 3.0
Command Information
Platforms Licensing Command Mode
All platforms Base operating system Config mode on master switches
(host) #show wms monitor-summary
WMS Monitor Summary
-------------------
Last 5 Min Last Hour All
- ---------- --------- ---
Valid APs 0 0 144
Interfering APs 0 0 0
Rogue APs 0 0 0
Disabled Rogue APs 0 0 1
Unclassified APs 0 0 0
Known Interfering APs 0 0 0
Suspected Rogue APs 0 0 0
Valid Clients 0 0 32
Interfering Clients 0 0 0
Disabled Rogue Clients 0 0 0
1114 | show wms probe AOS-W 3.4.1 Command Line Interface | Reference Guide
show wms probe
show wms probe
Description
Display detailed information for a list of WMS probes.
Syntax
No parameters
Example
This example shows the Probe List table for WMS probes.
The output of this command includes the following information:
(host) #show wms probe
Probe List
----------
Monitor Eth MAC BSSID PHY Type IP LMS IP Scan Status Updates Reqs Stats Type
--------------- ----- -------- -- ------ ---- ------ ------- ---- ----- ----
00:0b:86:cd:11:64 00:0b:86:51:16:48 80211A 10.13.11.19 10.6.2.250 No Up 1893 0 11544 soft-ap
00:1a:1e:c2:2c:c4 00:1a:1e:a2:cc:40 80211G 10.6.1.220 10.6.2.250 Yes Up 940 1 40796 air-monitor
00:0b:86:c1:be:56 00:0b:86:9b:e5:60 80211G 10.6.14.79 10.6.2.250 No Up 927 0 30711 soft-ap
00:0b:86:c4:4d:06 00:0b:86:c4:d0:70 80211A 10.6.14.78 10.6.2.250 No Up 926 0 11339 soft-ap
00:1a:1e:c2:30:80 00:1a:1e:a3:08:00 80211G 10.6.1.235 10.6.2.250 Yes Up 1425 0 26171 air-monitor
00:1a:1e:c2:2c:ba 00:1a:1e:a2:cb:a0 80211G 10.6.1.231 10.6.2.250 Yes Up 971 1 21005 air-monitor
00:1a:1e:c9:16:f0 00:1a:1e:11:6f:10 80211AHT-40mhz 10.6.1.204 10.6.2.250 No Up 969 0 17813 soft-ap
00:1a:1e:c9:16:b8 00:1a:1e:11:6b:90 80211AHT-40mhz 10.6.1.202 10.6.2.250 No Up 945 0 27800 soft-ap
00:1a:1e:c9:16:e6 00:1a:1e:11:6e:70 80211AHT-40mhz 10.6.1.205 10.6.2.250 No Up 946 0 26671 soft-ap
00:1a:1e:c9:17:38 00:1a:1e:11:73:90 80211AHT-40mhz 10.6.1.206 10.6.2.250 No Up 962 0 22186 soft-ap
00:1a:1e:c9:16:f4 00:1a:1e:11:6f:40 80211GHT-20mhz 10.6.1.209 10.6.2.250 No Up 958 0 18246 soft-ap
00:0b:86:c1:af:20 00:0b:86:9a:f2:00 80211G 10.6.14.73 10.6.2.250 No Up 977 0 13786 soft-ap
00:0b:86:cd:ce:ce 00:0b:86:5c:ec:e8 80211A 10.13.11.196 10.6.2.250 No Up 730 0 11548 soft-ap
00:0b:86:c7:47:bc 00:0b:86:f4:7b:c0 80211G 10.6.1.238 10.6.2.250 Yes Up 951 0 40260 air-monitor
00:0b:86:c4:0f:3c 00:0b:86:c0:f3:d0 80211A 172.30.171.2 10.6.2.250 No Up 927 0 11369 soft-ap
Column Description
Monitor Eth MAC Ethernet MAC address of a probe.
BSSID Probe Radio BSSID.
PHY Type Radio PHY type:
z802.11A
z802.11AHT-40Mbps
z802.11AHT-20Mbps
z802.11G
z802,11GHT-20Mbps
IP IP address of the AP.
LMS IP IP address of the AP’s local switch.
Scan Shows if the Air Monitor is performing scanning.
Status If the scan column displays a status of Up, the AP or AM is active
Updates Number of updates the AP or AM sent to the WMS database since the switch was last
reset.
Reqs Number of database update requests that have not yet been added into the database.
Stats Total number of statistics updates sent to the database.
AOS-W 3.4.1 Command Line Interface | Reference Guide show wms probe | 1115
Command History
This command was introduced in AOS-W 3.0
Command Information
Type A WMS AP type can be one of the following:
zsoft-ap: an Alcatel-Lucent Access Point (AP).
zair-monitor: An Alcatel-Lucent Air Monitor (AM).
Platforms Licensing Command Mode
All platforms Base operating system Config mode on master switches
Column Description
1116 | show wms rogue-ap AOS-W 3.4.1 Command Line Interface | Reference Guide
show wms rogue-ap
show wms rogue-ap <mac>
Description
Display statistics for APs classified as rogues APs.
Syntax
Example
The output of this command shows statistics for a suspected Rogue AP, including how it was classified as a
suspected rogue.
The output of this command includes the following information:
Parameter Description
<mac> MAC address of a rogue AP.
Column Description
BSSID BSSID of the suspected rogue AP.
SSID The rogue AP’s Extended service set identifier.
Channel Channel used by a radio on the rogue AP.
Type Indicates if the AP is an Alcatel-Lucent AP, a Cisco AP, or an AP from any other
manufacturer (generic AP).
RAP Type Type of rogue AP,
zSuspect-unsecure: AP has not been confirmed as a rogue AP.
zunsecure: AP has been confirmed as a rogue AP
(host) #show wms rogue-ap 00:0b:86:d4:ca:12
Suspect Rogue AP Info
---------------------
Key Value
--- -----
BSSID 00:0b:86:d4:ca:12
SSID aruba-voip
Channel 36
Type generic-ap
RAP Type suspect-unsecure
Confidence Level 55%
Status up
Match Type Base-BSSID-Override
Match MAC 00:0b:86:c5:4c:a0
Match IP 1.1.1.249
Match AM Aruba802.11n
Match Method Exact-Match
Suspect Match Types Base-BSSID-Override Base-BSSID-Override
Helper AP BSSID 00:0b:86:d4:ca:10
Match Time Sun Jul 27 13:08:16 2008
Match MAC Seen at APs
---------------------
AP-name
-------
ap-O44
AOS-W 3.4.1 Command Line Interface | Reference Guide show wms rogue-ap | 1117
Command History
This command was introduced in AOS-W 3.0
Command Information
Status Shows if the AP is active (up) or inactive (down).
Match Type Describes how the AP was classified as a rogue.
zEth-Wired-MAC: An Alcatel-Lucent AP or AM detected that a single MAC address
was in both the Ethernet Wired-Mac table and a non-valid AP wired-Mac table.
zAP-Wired-MAC: An interfering AP is marked as rogue when the Alcatel-Lucent AP
finds a MAC address in one of its valid AP wired-mac table and in an interfering AP
wired-mac table. You can enable or disable the AP-Wired-MAC matching method
using the CLI command ids unauthorized-device-profile overlay-classi
fication.
zConfig-Wired-MAC: This type of classification occurs when an Alcatel-Lucent AP or
AM detects a match between a wired MAC table and a pre-defined MAC address that
has manually defined via the command ids unauthorized-device-profile valid-
wired-mac.
zExternal-Wired-MAC: This type of classification occurs when an Alcatel-Lucent AP or
AM detects a match between a wired MAC table entry and a pre-defined MAC
address manually defined in the rap-wml table.
zBase-BSSID-Override: If an Alcatel-Lucent AP is detected as rogue, then all virtual
APs on the particular rogue are marked as rogue using Base-BSSID-Override match
type.
zManual: An AP is manually defined as a rogue by via the command wms ap <bssid>
mode unsecure.
zEMS: An AP is manually defined as a rogue by via the Element Management System
Match MAC MAC address of a wired device that helped identify the AP as a rogue. If the AP has not
been identified as a rogue, this column will display the MAC address 00:00:00:00:00:00.
Match IP IP address of a wired device that helped identify the AP as a rogue.
Match AM Alcatel-Lucent Air Monitor that reporting seeing the rogue AP.
Match Method This variable indicates the type of match.
Suspect Match Types Describes how an AP was classified as a suspected rogue AP.
Helper Ap BSSID BSSID of the AP or AM that helped classify a rogue AP.
AP name Names of APs that are able to see the specified MAC address.
Match Time Time the AP was identified as a rogue AP.
Platforms Licensing Command Mode
All platforms Base operating system Config mode on master switches
Column Description
1118 | show wms routers AOS-W 3.4.1 Command Line Interface | Reference Guide
show wms routers
show wms routers <mac>
Description
Show Learned Router Mac Information for WMS APs.
Syntax
Usage Guidelines
This command displays the MAC addresses of devices that have been determined to be routers by the listed
APs. This output of this command will be blank if there is not any broadcast/multicast activity in an AP's subnet.
Example
In the example below, a single WMS AP has learned MAC information for four different routers.
Command History
This command was introduced in AOS-W 3.0
Command Information
Column Description
<mac> MAC address of a probe that can see the router.
Platforms Licensing Command Mode
All platforms Base operating system Config mode on master switches
(host) #show wms routers
Router Mac 00:08:00:00:11:12 is Seen by APs
-------------------------------------------
AP-Name
-------
AP32
Router Mac 00:08:00:00:11:29 is Seen by APs
-------------------------------------------
AP-Name
-------
AP32
Router Mac 00:08:00:00:11:57 is Seen by APs
-------------------------------------------
AP-Name
-------
AP32
Router Mac 00:08:00:00:11:6e is Seen by APs
-------------------------------------------
AP-Name
-------
AP32
AOS-W 3.4.1 Command Line Interface | Reference Guide show wms system | 1119
show wms system
show wms system
Description
Show the WMS system configuration and system state.
Syntax
No parameters.
Example
This example shows the WMS System Configuration and System State tables.
The output of this command includes the following information:
Command History
This command was introduced in AOS-W 3.0
Column Description
Max Threshold The maximum number of table entries allowed. If this table displays a zero (0), there is no
configured limit.
NOTE: If a configured maximum limit has reached, the switch will not create new WMS
entries for monitored APs and monitored stations. If new APs are deployed after this limit is
reached, those APs will not be marked as 'valid', which will impair the effectiveness of the
Adaptive Radio Management feature. If there are new Rogue APs in the network, they will not
be classified as a rogue.
Current Threshold Current number of table entries.
Total AP Count Total number of statistics entries for monitored APs in the AP table.
Total STA Count Total number of statistics entries for monitored stations in the Station table.
MAX RB-tree Count Maximum number of entries allowed in the statistics.
Total Tree Count Total number of entries currently in the statistics tree. If this limit has been reached, the switch
will not add entries with the RSSI information for APs, monitored APs and monitored clients
that are seen by them. This can negatively affect the RF Plan application.
Poll Count (Max) Current and maximum poll counts.
(host) #show wms system
System Configuration
--------------------
Key Value
--- -----
max-threshold 30000
System State
-------------
Key Value
--- -----
Max Threshold 30000
Current Threshold 28470
Total AP Count 27153
Total STA Count 3294
MAX RB-tree Count 50000
Total Tree Count 50000
Poll Count (Max) 10(365)

1120 | show wms system AOS-W 3.4.1 Command Line Interface | Reference Guide
Command Information
Platforms Licensing Command Mode
All platforms Base operating system Config mode on master switches
AOS-W 3.4.1 Command Line Interface | Reference Guide show wms wired-mac | 1121
show wms wired-mac
show wms wired-mac [{<mac>}|{ap-name <ap-name>}]
Description
Show a table of gateway wired addresses. This command can display a list of APs aware of a specific gateway
MAC address, or list the wired MAC addresses known to a single AP.
Syntax
Example
This example shows that the AP Corp-AP125-AM is aware of four different gateway wired MAC addresses.
Command History
This command was introduced in AOS-W 3.0
Command Information
Column Description
<mac> Specify a wired MAC address to display a list of APs that are aware of this wired MAC.
ap-name <ap-name> Specify the IP address of an AP to list the wired MAC addresses of which it is aware.
Platforms Licensing Command Mode
All platforms Base operating system Config mode on master switches
(host) #show wms wired-mac ap-name Corp-AP125-AM
Learned Wired Macs for AP: Corp-AP125-AM
----------------------------------------------
Wired-Mac
---------
00:0b:86:41:01:20
00:0b:86:60:2e:ac
00:0b:86:40:1e:60
00:0b:86:08:e1:00

1122 | show wms wired-mac AOS-W 3.4.1 Command Line Interface | Reference Guide
AOS-W 3.4.1 Command Line Interface | Reference Guide shutdown | 1123
shutdown
shutdown all
Description
This command disables all interfaces on the switch.
Usage Guidelines
This command stops all traffic through the physical ports on the switch. The console port remains active.
Use this command only when you have physical access to the switch, so that you can continue to manage
using the console port.
To shut down an individual interface, tunnel, or VLAN, use the shutdown option within the interface
command. To restore the ports, use the no shutdown command.
Example
The following example shuts down all physical interfaces on the switch.
(host) (config)#shutdown all
Command History
This command was introduced in AOS-W 1.0.
Command Information
Platforms Licensing Command Mode
All platforms Base operating system Config mode on master or local switches

1124 | shutdown AOS-W 3.4.1 Command Line Interface | Reference Guide
AOS-W 3.4.1 Command Line Interface | Reference Guide snmp-server | 1125
snmp-server
snmp-server
community <string>
enable trap
engine-id
host <ipaddr> version {1 <name> udp-port <port>}|2c|{3 <name>} [inform] [interval
<seconds>] [retrycount <number>] [udp-port <port>]}
inform queue-length <size>
stats
trap enable|disable|{source <ipaddr>}
user <name> [auth-prot {md5|sha} <password>] [priv-prot {AES|DES} <password>]
Description
This command configures SNMP parameters.
Syntax
Parameter Description Range Default
community Sets the read-only community string. — —
enable trap Enables sending of SNMP traps to the configured host. — disabled
engine-id Sets the SNMP server engine ID as a hexadecimal number. 24
characters
maximum
—
host Configures the IP address of the host to which SNMP traps are
sent. This host needs to be running a trap receiver to receive and
interpret the traps sent by the switch.
——
version Configures the SNMP version and security string for notification
messages. ——
inform Sends SNMP inform messages to the configured host. — disabled
inform Specifies the length for the SNMP inform queue. 100-350 250
stats Allows file-based statistics collection for OmniVista Mobility
Manager. The switch generates a file that contains statistics data
used by OmniVista Mobility Manager to display information in
chart and graph formats.
File-based statistics collection is transparent to the user and
increases the efficiency of transferring information between the
switch and OmniVista Mobility Manager.
enabled
trap Source IP address of SNMP traps. — disabled
disable Disables an SNMP trap. You can get a list of valid trap names
using the show snmp trap-list command. ——
enable Enables an SNMP trap. — —
source The IP address of the destination to which the trap is sent. — —
interval Estimated round trip time to this host. 60
seconds
retrycount Number of times that SNMP inform messages are attempted to
be sent to the host before giving up. 3
udp-port The port number to which notification messages are sent. — 162
1126 |snmp-server AOS-W 3.4.1 Command Line Interface | Reference Guide
Usage Guidelines
This command configures SNMP on the switch only. You configure SNMP-related information for APs in an
SNMP profile which you apply to an AP group or to a specific AP. To configure SNMP hostname, contact,
and location information for the switch, use the hostname, syscontact, and syslocation commands.
Example
The following command configures an SNMP trap receiver:
(host) (config) #snmp-server host 191.168.1.1 version 2c 12345678
Command History
Command Information
user Configures an SNMPv3 user profile for the specified username. — —
auth-prot Authentication protocol for the user, either HMAC-MD5-98 Digest
Authentication Protocol (MD5) or HMAC-SHA-98 Digest
Authentication Protocol (SHA), and the password for use with the
designated protocol.
MD5/SHA SHA
priv-prot Privacy protocol for the user, either Advanced Encryption
Standard (AES) or CBC-DES Symmetric Encryption Protocol
(DES), and the password for use with the designated protocol.
AES/DES DES
Parameter Description Range Default
Release Modification
AOS-W 3.0 Command introduced
AOS-W 3.3.1 The stats parameter was introduced
Platforms Licensing Command Mode
All platforms Base operating system Config mode on master switches
AOS-W 3.4.1 Command Line Interface | Reference Guide spanning-tree (Global Configuration) | 1127
spanning-tree (Global Configuration)
spanning-tree
[forward-time <value> | hello-time <value> | max-age <value> | priority <value>]
Description
This command is the global configuration for the Rapid Spanning Tree Protocol (RSTP). See spanning-tree
(Configuration Interface) for details on the RSTP (config-if) command.
Syntax
Usage Guidelines
This command configures the global RSTP settings on the switch and is backward compatible with past
versions of AOS-W using STP.
By default, all interfaces and ports on the switch run RSTP as specified in 802.1w and 802.1D. The default
RSTP values can be used for most implementations.
Use the no spanning-tree command to disable RSTP.
Example
The following command sets the time a port spends in the listening and learning state to 3 seconds:
spanning-tree forward-time 3
The following command sets the time the root bridge waits to transmit BPDUs to 4 seconds:
spanning-tree hello-time 4
The following command sets the time the root bridge waits to receive a hello packet to 30 seconds:
spanning-tree max-age 30
RSTP is backward compatible with STP and is enabled by default. For ease of use, this command uses the
spanning tree keyword.
Parameter Description Range Default
forward-time Specifies the time, in seconds, the port spends
in the listening and learning state. During this
time, the port waits to forward data packets.
4-30 15 seconds
hello-time Specifies the time, in seconds, between each
bridge protocol data unit (BPDU) transmitted by
the root bridge.
1-10 2 seconds
max-age Specifies the time, in seconds, the root bridge
waits to receive a hello packet before changing
the STP topology.
6-40 20 seconds
priority Set the priority of a bridge to make it more or
less likely to become the root bridge. The bridge
with the lowest value has the highest priority.
When configuring the priority, remember the
following:
The highest priority bridge is the root bridge.
The highest priority value is 0 (zero).
0-65535 32768
1128 | spanning-tree (Global Configuration) AOS-W 3.4.1 Command Line Interface | Reference Guide
The following command sets the bridge priority to 10, making it more likely to become the root bridge:
spanning-tree priority 10
Command History
Command Information
Release Modification
AOS-W 3.4 Upgraded STP to RSTP with full backward compatibility
AOS-W 1.0 Introduced the Spanning Tree Protocol (STP)
Platforms Licensing Command Mode
All platforms Base operating system Configuration (config)

AOS-W 3.4.1 Command Line Interface | Reference Guide spanning-tree (Configuration Interface) | 1129
spanning-tree (Configuration Interface)
spanning-tree [cost <value> | point-to-point | port-priority <value> | portfast]
Description
Alcatel-Lucent’s RSTP implementation interoperates with both PVST (Per VLAN Spanning Tree 802.1D) and
Rapid-PVST (802.1w) implementation on industry-standard router/switches. Syntax
Usage Guidelines
Alcatel-Lucent supports global instances of STP and RSTP only. Therefore, the ports on industry-standard
routers/switches must be on the default or untagged VLAN for interoperability with Alcatel-Lucent switchs.
AOS-W supports RSTP on the following interfaces:
zFastEthernet IEEE 802.3—fastethernet
zGigabitethernet IEEE 802.3—gigabitethernet
zPort Channel ID—port-channel
In addition to port state changes, RSTP introduces port roles for all the interfaces (see Table 1).
RSTP is backward compatible with STP and is enabled by default. For clarity, this RSTP command uses the
spanning tree keyword.
Parameter Description Range Default
cost <value> Enter the RSTP path cost. Use the cost
values to determine the most favorable
path to a particular destination: the
lower the cost, the better the path
1 - 65536 Default: Based on Interface type:
zFast Ethernet 10Mbs—100
zFast Ethernet 100Mbs—19
z1Gigabit Ethernet—4
z10 Gigabit Ethernet—2
point-to-point Set the interface to a point-to-point n/a Enabled
port-priority
<value>
Change the RSTP priority. 0 - 255 128
portfast Change from blocking to forwarding n/a Disabled
Table 1 Port Role Descriptions
RSTP (802.1w)
Port Role Description
Root The port that receives the best BPDU on a bridge.
Designated The port can send the best BPDU on the segment to which it is connected.
Alternate The port offers an alternate path, in the direction of root bridge, to that provided by bridge’s
root port.
Backup The port acts as a backup for the path provided by a designated port in the direction of the
spanning tree.
1130 | spanning-tree (Configuration Interface) AOS-W 3.4.1 Command Line Interface | Reference Guide
Example
The RSTP default values are adequate for most implementation. Use caution when making changes to the
spanning tree values.
(host) (config-if) #spanning-tree cost 345
(host) (config-if) #spanning-tree point-to-point ?
(host0) (config-if) #spanning-tree portfast ?
Related Commands
spanning-tree (Global Configuration) on page 1127
Command History
Command Information
Release Modification
AOS-W 3.4 Upgraded STP to RSTP with full backward compatibility.
AOS-W 1.0 Introduced the Spanning Tree Protocol (STP).
Platforms Licensing Command Mode
All platforms Base operating system Configuration Interface (config-if)
AOS-W 3.4.1 Command Line Interface | Reference Guide ssh | 1131
ssh
ssh disable_dsa | mgmt-auth {public-key [username/password] | username/password
[public-key]}
Description
This command configures SSH access to the switch.
Syntax
Usage Guidelines
Public key authentication is supported using a X.509 certificate issued to the management client. If you
specify public-key authentication, you need to load the client X.509 certificate into the switch and configure
certificate authentication for the management user with the mgmt-user ssh-pubkey command.
Example
The following commands configure SSH access using public key authentication only:
(host) (config) #ssh mgmt-auth public-key
mgmt-user ssh-pubkey client-cert ssh-pubkey cli-admin root
Command History
Command Information
Parameter Description Default
disable_dsa Disables DSA authentication for SSH. Only RSA authentication is
used. —
mgmt-auth Configures authentication method for the management user. You
can specify username/password only, public key only, or both
username/password and public key.
username/
password
Version Modification
AOS-W 3.0 Command introduced
AOS-W 3.1 The mgmt-auth parameter was introduced
Platforms Licensing Command Mode
All platforms Base operating system Config mode on master switches

1132 |ssh AOS-W 3.4.1 Command Line Interface | Reference Guide
AOS-W 3.4.1 Command Line Interface | Reference Guide stm | 1133
stm
stm add-blacklist-client <macaddr> | kick-off-sta <macaddr> <bssid>| remove-blacklist-
client <macaddr> | start-trace <macaddr> | stop-trace <macaddr>
Description
This command is used to manually control the blacklisting of clients.
Syntax
Usage Guidelines
When you blacklist a client, the client is not allowed to associate with any AP in the network. If the client is
connected to the network when you blacklist it, a deauthentication message is sent to force the client to
disconnect. The blacklisted client is blacklisted for the duration specified in the virtual AP profile.
Example
The following command blacklists a client:
(host) #stm add-blacklist-client 00:01:6C:CC:8A:6D
Command History
This command was introduced in AOS-W 1.0.
Command Information
Parameter Description
add-blacklist-client MAC address of the client to be added to the denial of service list.
kick-off-sta MAC address of the client to disassociated.
<macaddr> MAC address from which the client is to be blacklisted.
<bssid> BSSID from which the client is to be blacklisted.
remove-blacklist-client MAC address of the client to remove from the denial of service list.
start-trace Client or BSSID on which to start tracing.
stop-trace Client or BSSID on which to stop tracing.
Platforms Licensing Command Mode
All platforms Base operating system Enable mode on master or local switches

1134 |stm AOS-W 3.4.1 Command Line Interface | Reference Guide
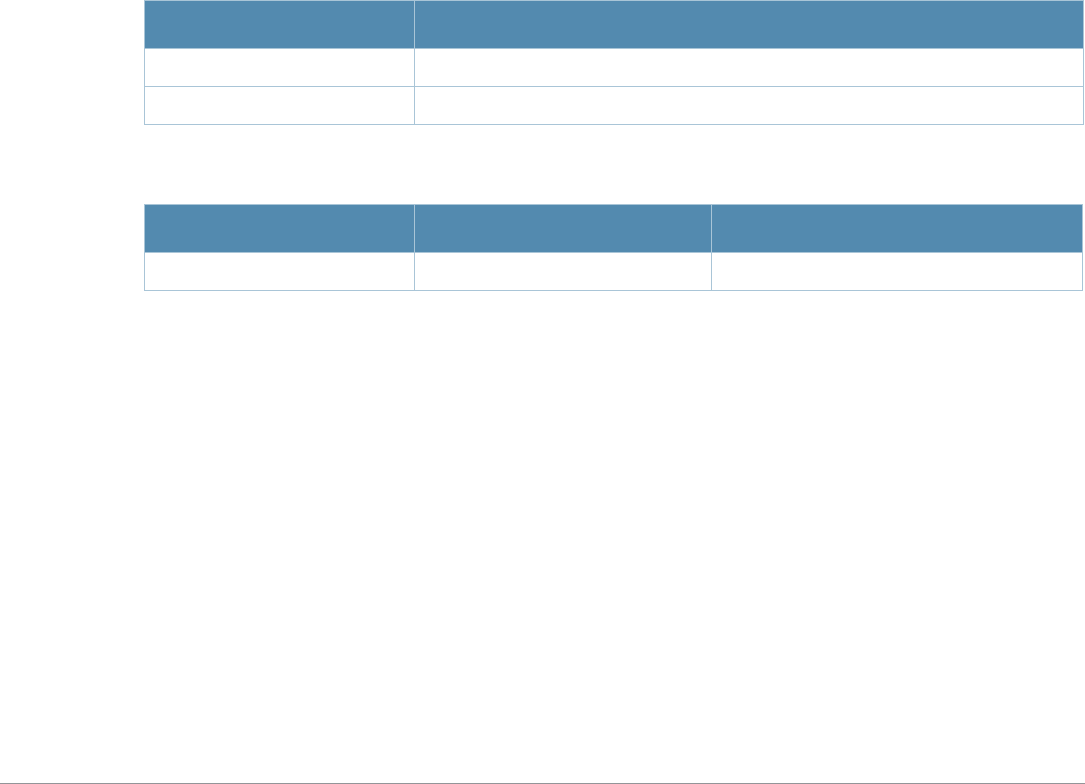
AOS-W 3.4.1 Command Line Interface | Reference Guide support | 1135
support
support
Description
This command, which should be used only in conjunction with Alcatel-Lucent customer support, is for
switch debugging purposes only.
Syntax
No parameters.
Usage Guidelines
This command is used by Alcatel-Lucent customer support for debugging the switch. Do not use this
command without the guidance of Alcatel-Lucent customer support.
In AOS-W 2.4 and 2.5, this command was named secret.
Example
The following command allows Alcatel-Lucent customer support to debug the switch:
(host) #support
Command History
Command Information
Version Modification
AOS-W 2.4 Command introduced as the secret command
AOS-W 3.1 Command renamed to support
Platforms Licensing Command Mode
All platforms Base operating system Enable mode on master switches

1136 | support AOS-W 3.4.1 Command Line Interface | Reference Guide
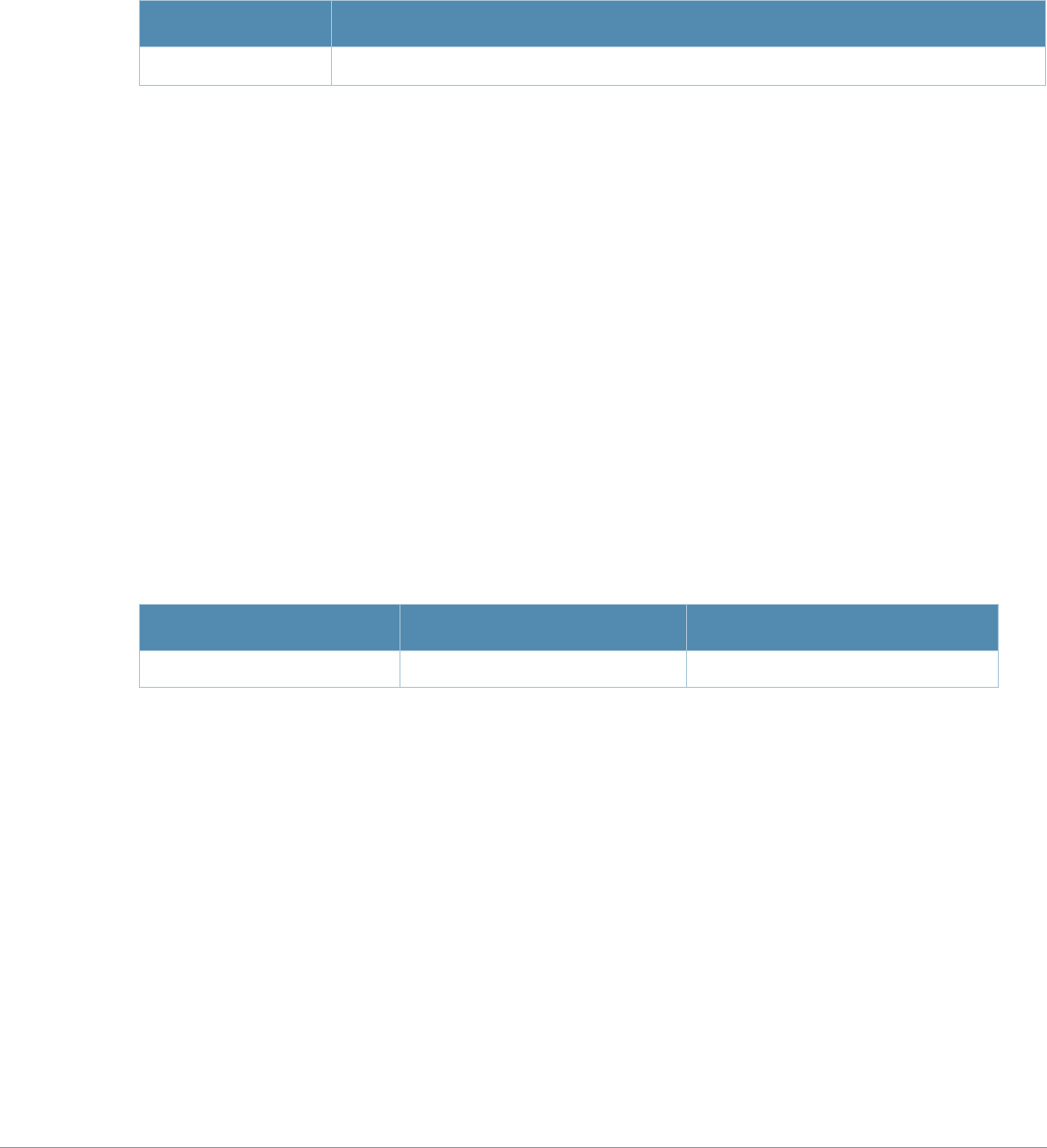
AOS-W 3.4.1 Command Line Interface | Reference Guide syscontact | 1137
syscontact
syscontact <syscontact>
Description
This command configures the name of the system contact for the switch.
Syntax
Usage Guidelines
Use this command to enter the name of the person who acts as the system contact or administrator for the
switch. You can use a combination of numbers, letters, characters, and spaces to create the name. To
include a space in the name, use quotation marks to enclose the alphanumeric string. For example, to create
the system contact name Lab Technician 1, enter “Lab Technician 1” at the prompt.
To change the existing name, enter the command with a different string. The new name takes affect
immediately. To unconfigure the name, enter “” at the prompt.
Example
The following command defines LabTechnician as the system contact name:
(host) (config) #syscontact LabTechnician
Command History
This command was introduced in AOS-W 3.1.
Command Information
Parameter Description
syscontact An alphanumeric string that specifies the name of the system contact.
Platforms Licensing Command Mode
All platforms Base operating system Config mode on master switches

1138 |syscontact AOS-W 3.4.1 Command Line Interface | Reference Guide
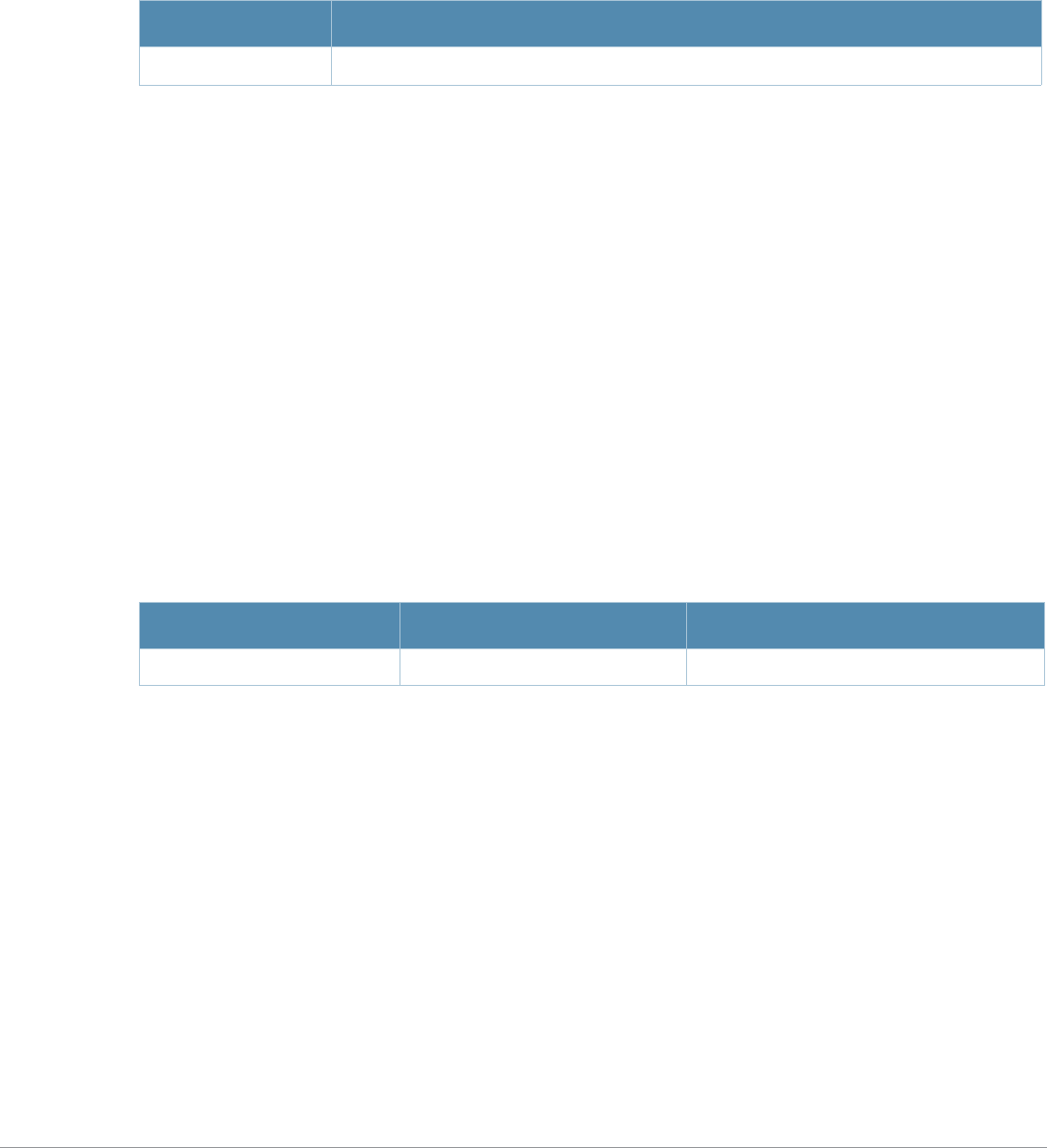
AOS-W 3.4.1 Command Line Interface | Reference Guide syslocation | 1139
syslocation
syslocation <syslocation>
Description
This command configures the name of the system location for the switch.
Syntax
Usage Guidelines
Use this command to indicate the location of the switch. You can use a combination of numbers, letters,
characters, and spaces to create the name. To include a space in the name, use quotation marks to enclose
the text string.
To change the existing name, enter the command with a different string. To unconfigure the location, enter
“” at the prompt.
Example
The following command defines SalesLab as the location for the switch:
(host) # syslocation “Building 10, second floor, room 21E”
syscontact LabTechnician
Command History
This command was introduced in AOS-W 3.1.
Command Information
Parameter Description
syslocation An alphanumeric string that specifies the name of the system location.
Platforms Licensing Command Mode
All platforms Base operating system Config mode on master switches

1140 |syslocation AOS-W 3.4.1 Command Line Interface | Reference Guide
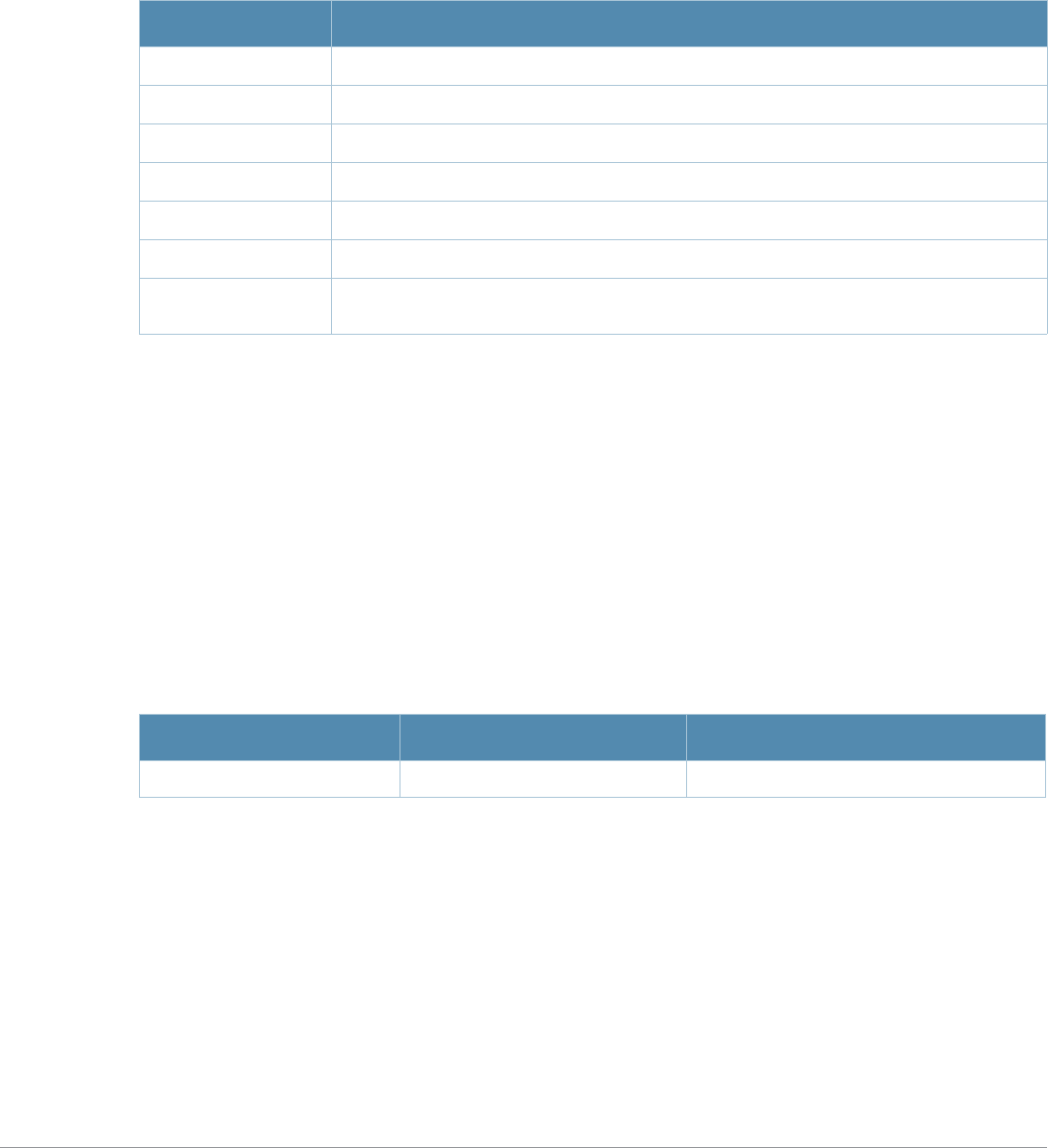
AOS-W 3.4.1 Command Line Interface | Reference Guide tar | 1141
tar
tar clean {crash|flash|logs}| crash | flash | logs [tech-support]
Description
This command archives a directory.
Syntax
Usage Guidelines
This command creates archive files in Unix tar file format.
Example
The following command creates the log.tar file with technical support information:
tar logs tech-support
Command History
The command was introduced in AOS-W 3.0
Command Information
Parameter Description
clean Removes a tar file
crash Removes crash.tar
flash Removes flash.tar.gz
logs Removes logs.tar
crash Archives the crash directory to crash.tar. A crash directory must exist.
flash Archives and compresses the /flash directory to flash.tar.gz.
logs Archives the logs directory to log.tar. Optionally, technical support information can be
included.
Platforms Licensing Command Mode
All platforms Base operating system Enable mode on master switches

1142 |tar AOS-W 3.4.1 Command Line Interface | Reference Guide
AOS-W 3.4.1 Command Line Interface | Reference Guide telnet | 1143
telnet
telnet {cli|soe}
Description
Enable telnet to the switch or to an AP through the switch.
Syntax
Usage Guidelines
Use the cli option to enable telnet to the switch.
Use the soe option to enable telnet using the SoE protocol. This allows you to remotely manage an AP
directly connected to the switch.
Example
The following example enables telnet to the switch using the CLI.
(host) (config) #telnet cli
Command History
The command was introduced in AOS-W 1.0
Command Information
Parameter Description Default
cli Enable telnet using the CLI. Disabled
soe Enable telnet using Serial over Ethernet (SoE). Disabled
Platforms Licensing Command Mode
All platforms Base operating system Config mode on master switches

1144 |telnet AOS-W 3.4.1 Command Line Interface | Reference Guide

AOS-W 3.4.1 Command Line Interface | Reference Guide time-range | 1145
time-range
time-range <name> absolute [end <mm/dd/yyyy> <hh:mm>]|[start <mm/dd/yyyy> <hh:mm>]
time-range <name> periodic
Daily <hh:mm> to <hh:mm>
Friday <hh:mm> to <hh:mm>
Monday <hh:mm> to <hh:mm>
Saturday <hh:mm> to <hh:mm>
Sunday <hh:mm> to <hh:mm>
Thursday <hh:mm> to <hh:mm>
Tuesday <hh:mm> to <hh:mm>
Wednesday <hh:mm> to <hh:mm>
Weekday <hh:mm> to <hh:mm>
Weekend <hh:mm> to <hh:mm>
no ...
Description
This command configures time ranges.
Syntax
Usage Guidelines
You can use time ranges when configuring session ACLs. Once you configure a time range, you can use it in
multiple session ACLs.
Example
The following command configures a time range for daytime working hours:
(host) (config) #time-range working-hours periodic
weekday 7:30 to 18:00
Command History
The command was introduced in AOS-W 3.0.
Command Information
Parameter Description
<name> Name of this time range. You can reference this name in other commands.
absolute Specifies an absolute time range, with a specific start and/or end time and date.
periodic Specifies a recurring time range. Specify the start and end time and Daily, Weekday,
Weekend, or the day of the week.
no Negates any configured parameter.
Platforms Licensing Command Mode
All platforms Base operating system Config mode on master switches

1146 |time-range AOS-W 3.4.1 Command Line Interface | Reference Guide
AOS-W 3.4.1 Command Line Interface | Reference Guide traceroute | 1147
traceroute
traceroute <ipaddr>
Description
Trace the route to the specified IP address.
Syntax
Usage Guidelines
Use this command to identify points of failure in your network.
Example
The following command traces the route to the device identified by the IP address 10.1.2.3.
(host) (config) #traceroute 10.1.2.3
Command History
The command was introduced in AOS-W 2.0.
Command Information
Parameter Description
<ipaddr> The destination IP address.
Platforms Licensing Command Mode
All platforms Base operating system User, Enable, and Config modes on local or
master switches

1148 | traceroute AOS-W 3.4.1 Command Line Interface | Reference Guide
AOS-W 3.4.1 Command Line Interface | Reference Guide trusted | 1149
trusted
trusted all
Description
This command makes all physical interfaces on the switch trusted ports.
Syntax
Usage Guidelines
Trusted ports are typically connected to internal controlled networks. Untrusted ports connect to third-
party APs, public areas, or any other network to which the switch should provide access control. When
Alcatel-Lucent APs are attached directly to the switch, set the connecting port to be trusted.
By default, all ports on the switch are treated as trusted. You can use the interface fastethernet or
interface gigabitethernet commands to make individual ports trusted.
Example
The following command makes all ports trusted:
(host) (config) #trusted all
Command History
The command was introduced in AOS-W 2.0.
Command Information
Parameter Description
all Makes all ports on the switch trusted.
Platforms Licensing Command Mode
All platforms Base operating system Config mode on master switches

1150 |trusted AOS-W 3.4.1 Command Line Interface | Reference Guide
AOS-W 3.4.1 Command Line Interface | Reference Guide uplink | 1151
uplink
crypto-local
uplink {cellular priority <prior>}|disable|enable|{wired priority <prior>}|{wired
vlan <id>}
Description
Manage and configure the uplink network connection on the OmniAccess 4306 switches.
Syntax
Usage Guidelines
The OmniAccess 4306 switches supports multiple 3G cellular uplinks in addition to its standard wired ports,
providing redundancy in the event of a connection failure. If an OmniAccess 4306’s wired link cannot access
the internet, the switch can fail over to a secondary cellular link and continue routing traffic.
Command History
This command was introduced in AOS-W 3.4.
Command Information
Parameter Description Range
cellular priority <prior> Set the priority of the cellular uplink. By default, the cellular
uplink is a lower priority than the wired uplink; making the
wired link the primary link and the cellular link the secondary or
backup link.
Configuring the cellular link with a higher priority than your
wired link priority will set your cellular link as the primary
switch link.
1-255
enable Enable the uplink manager. —
disable Disable the uplink manager. —
wired priority <prior> Set the priority of the wired uplink. Each uplink type has an
associated priority; wired ports having the highest priority by
default.
1-255
wired vlan <id> Define the VLAN identification (ID) of the uplink VLAN. 1-4094
Platforms Licensing Command Mode
OmniAccess 4306 switches Base operating system Config mode on master and local switches

1152 |uplink AOS-W 3.4.1 Command Line Interface | Reference Guide
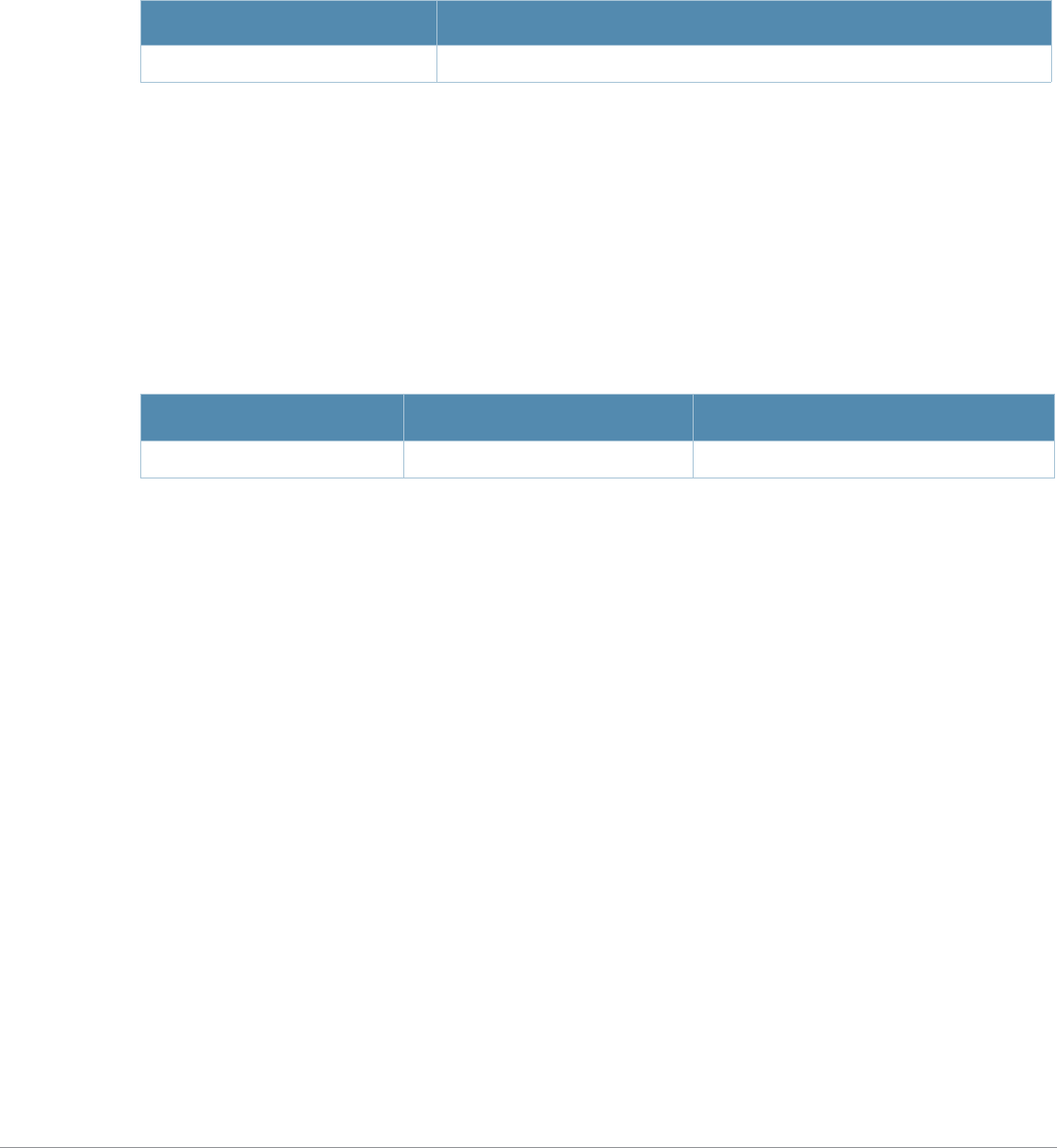
AOS-W 3.4.1 Command Line Interface | Reference Guide usb reclassify | 1153
usb reclassify
crypto-local
usb reclassify <address>
Description
Disconnect and reclassify an USB device.
Syntax
Usage Guidelines
There's no way to power off an USB port on the OmniAccess 4306 switch, but you can re-initialize the
device using the usb reclassify command. This command removes the modem from the USB device list,
then detects it via the USB table.
Command History
Introduced in AOS-W 3.4.
Command Information
Parameter Description
<address> USB device address from the show usb command.
Platforms Licensing Command Mode
OmniAccess 4306 switches Base operating system Config mode on master and local switches

1154 | usb reclassify AOS-W 3.4.1 Command Line Interface | Reference Guide
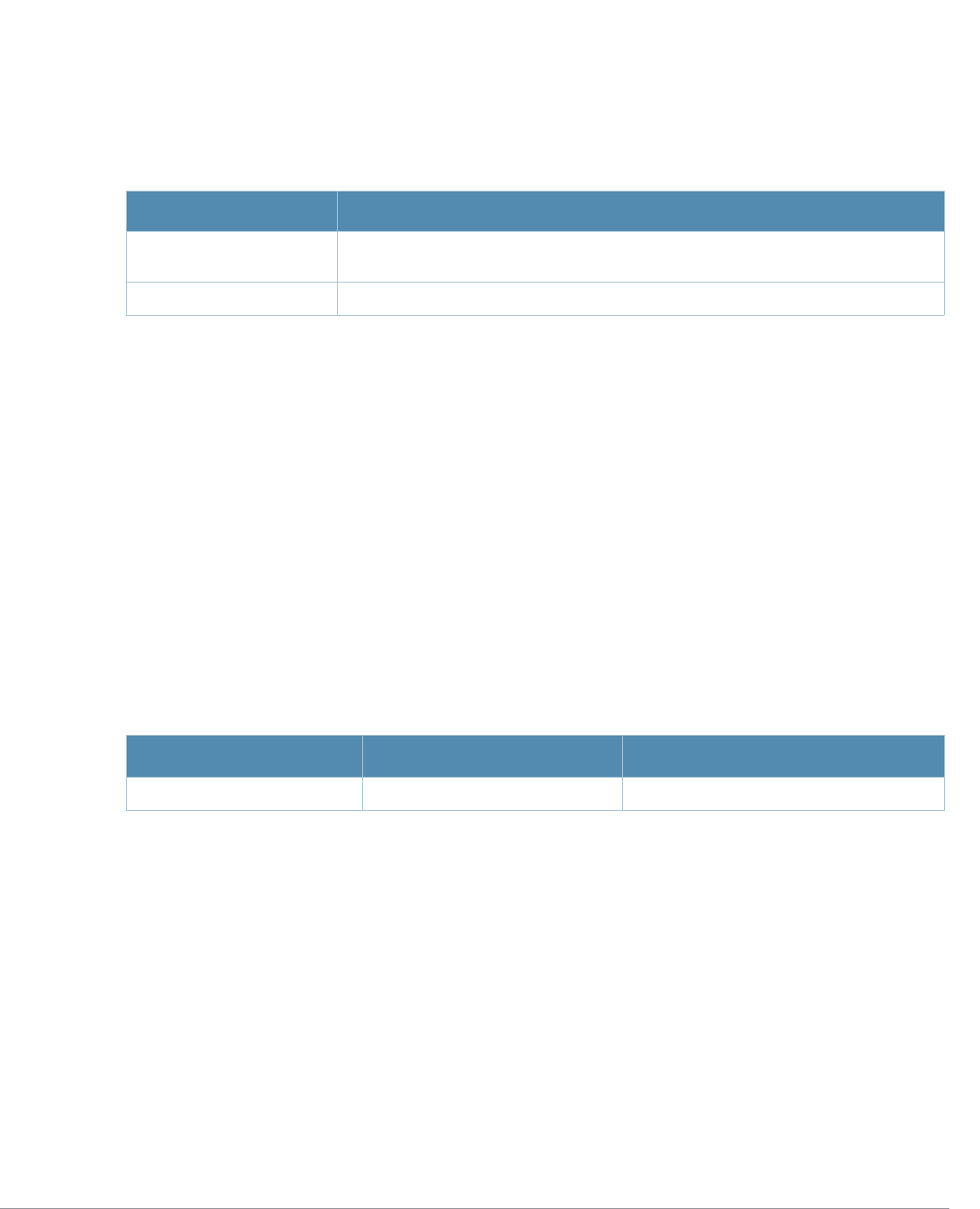
AOS-W 3.4.1 Command Line Interface | Reference Guide usb-printer | 1155
usb-printer
usb-printer [printer <printer-name> alias <alias-name>]
Description
This command allows you to provide an alias to a USB printer connected to a Alcatel-Lucent OAW-AP65
series switch.
Syntax
Example
The following command creates an alias for a printer:
(host) usb-printer printer usblp_HP_Officejet_Pro_L7500_MY872231FX alias HPOJ_L7500
(host) #show network-printer status
Networked Printer Status
------------------------
Printer Name Printer Alias Status Comment
------------ ------------- ------ -------
usblp_Hewlett-Packard_HP_Color_LaserJet_CP3505_CNBJ8B1003 HPLJ_P3005 idle enabled
usblp_HP_Officejet_Pro_L7500_MY872231FX HPOJ_L7500 idle enabled
Command History
This command was introduced in AOS-W 3.4.
Command Information
Parameter Description
printer Enter the default printer name. To get the default printer name use the show
network-printer status command.
alias Enter a new alias name for the printer.
Platforms Licensing Command Mode
OmniAccess 4306 series Base operating system Enable mode.

1156 |usb-printer AOS-W 3.4.1 Command Line Interface | Reference Guide
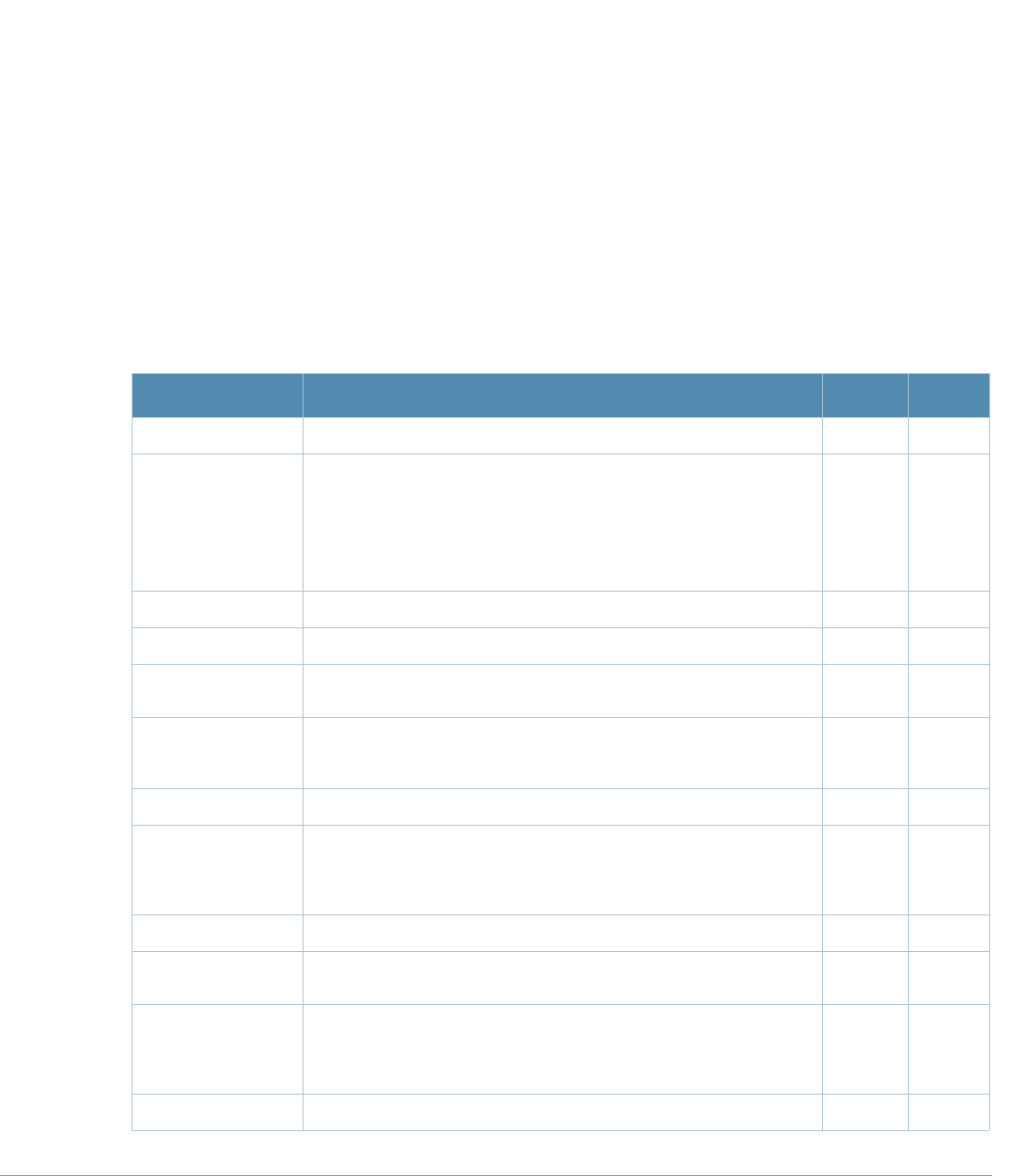
AOS-W 3.4.1 Command Line Interface | Reference Guide user-role | 1157
user-role
user-role <name>
access-list {eth|mac|session} <acl> [ap-group <group>] [position <number>]
bw-contract <name> [per-user] {downstream|upstream}
captive-portal <profile>
dialer <name>
ipv6 session-acl <string>
max-sessions <number>
no ...
pool {l2tp|pptp} <name>
reauthentication-interval <minutes>
session-acl <acl> [ap-group <group>] [position <number>]
stateful-ntlm <ntlm_profile_name>
vlan {VLAN ID|VLAN name}
wispr <wispr_profile_name>
Description
This command configures a user role.
Syntax
Parameter Description Range Default
<name> Name of the user role. — —
access-list Type of access control list (ACL) to be applied:
eth: Ethertype ACL, configured with the ip access-list eth
command.
mac: MAC ACL, configured with the ip access-list mac command.
session: Session ACL, configured with the ip access-list session
command.
——
<acl> Name of the configured ACL.
ap-group (Optional) AP group to which this ACL applies. — —
position (Optional) Position of this ACL relative to other ACLs that you can
configure for the user role. 1 is the top. — (last)
bandwidth-con
tract
Name of a bandwidth contract or rate limiting policy configured with
the aaa bandwidth-contract command. The bandwidth contract
must be applied to either downstream or upstream traffic.
——
downstream Applies the bandwidth contract to traffic from the switch to the client. — —
per-user Specifies that bandwidth contract is assigned on a per-user basis
instead of a per-role basis. For example, if two users are active on
the network and both are part of the same role with a 500 Kbps
bandwidth contract, then each user is able to use up to 500 Kbps.
—(per role)
upstream Applies the bandwidth contract to traffic from the client to the switch. — —
captive-portal Name of the captive portal profile configured with the aaa
authentication captive-portal command. ——
dialer If VPN is used as an access method, name of the VPN dialer
configured with the vpn-dialer command. The user can login using
captive portal and download the dialer. The dialer is a Windows
application that configures the VPN client.
——
max-sessions Maximum number of datapath sessions per user in this role. 0-65535 65535

1158 | user-role AOS-W 3.4.1 Command Line Interface | Reference Guide
Usage Guidelines
Every client in an Alcatel-Lucent user-centric network is associated with a user role. All wireless clients
start in an initial role. From the initial role, clients can be placed into other user roles as they pass
authentication.
Example
The following command configures a user role:
(host) (config) #user-role new-user
dialer default-dialer
pool pptp-pool-1
Command History
no Negates any configured parameter. — —
ipv6 session-
acl <string>
Specify a session ACL for IPV6 users.
pool If VPN is used as an access method, specifies the IP address pool
from which the user’s IP address is assigned:
l2tp: When a user negotiates a Layer-2 Tunneling Protocol (L2TP)/
IPsec session, specifies an address pool configured with the ip local
pool command.
pptp: When a user negotiates a Point-to-Point Tunneling Protocol
(PPTP) session, specifies an address pool configured with the pptp
ip local pool command.
——
<name> Name of the L2TP or PPTP pool to be applied. — —
reauthentica
tion-interval
Interval, in minutes, after which the client is required to
reauthenticate. 0-4096, 0
to disable 0
(disable
d)
session-acl Session ACL configured with the ip access-list session command. — —
ap-group (Optional) AP group to which this ACL applies. — —
position (Optional) Position of this ACL relative to other ACLs that you can
configure for the user role. 1 is the top. — (last)
stateful-ntlm Apply stateful NTLM authentication to the specified user role
vlan Identifies the VLAN ID or VLAN name to which the user role is
mapped. This parameters works only when using Layer-2
authentication such as 802.1x or MAC address, ESSID, or encryption
type role mapping because these authentications occur before an IP
address is assigned. If a user authenticates using a Layer-3
mechanism such as VPN or captive portal this parameter has no
effect.
NOTE: VLAN IDs and VLAN names cannot be listed together.
——
wispr Apply WISPr authentication to the specified user role.
Parameter Description Range Default
Version Modification
AOS-W 3.0 Command introduced
AOS-W 3.4.1 The stateful-ntlm and wispr parameters were introduced.

AOS-W 3.4.1 Command Line Interface | Reference Guide user-role | 1159
Command Information
Platforms Licensing Command Mode
All platforms This command requires the Policy
Enforcement Firewall license. Config mode on master switches

1160 | user-role AOS-W 3.4.1 Command Line Interface | Reference Guide
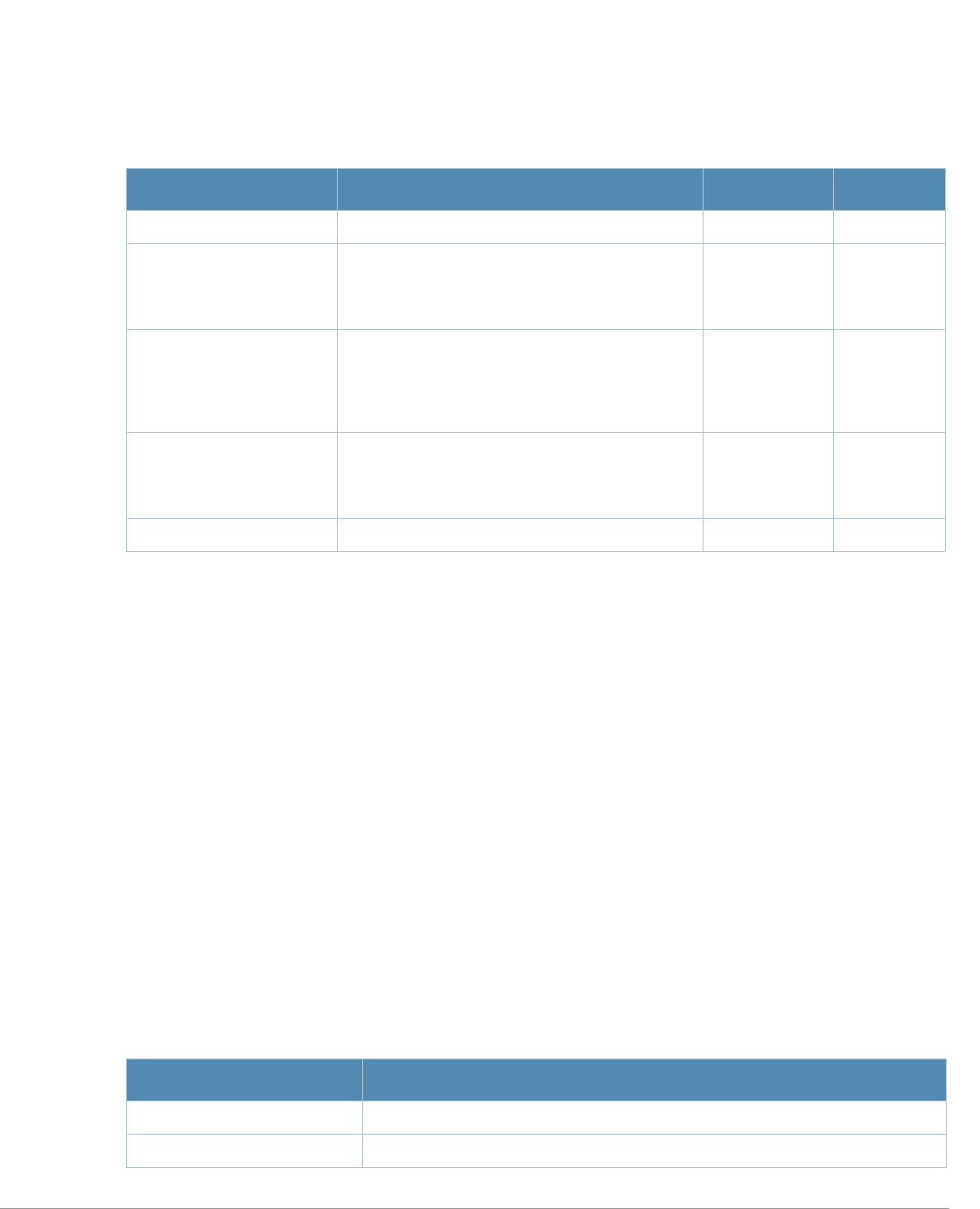
AOS-W 3.4.1 Command Line Interface | Reference Guide vlan | 1161
vlan
vlan {<id> [<description>]| [<name>][<vlan-ids>]|range <word>}
Description
This command creates a VLAN ID or a range of VLAN IDs on the switch.
Syntax
Usage Guidelines
Use the interface vlan command to configure the VLAN interface, including an IP address. Use the
vlan-name command to create a named VLAN to set up a VLAN pool. A VLAN pool consists of a set of
VLAN IDs which are grouped together to efficiently manage multi-switch networks from a single location.
Example
The following command creates VLAN ID 27 with the description myvlan on the switch.
(host) (config) #vlan 27 myvlan
The following command associates the VLAN IDs 5, 12 and 100 with VLAN guestvlan on the switch.
vlan guestvlan 5,12,100
The following command creates VLAN IDs 200-300, 302, 303-400.
(host) (config) #vlan range 200-300,302, 303-400
Related Commands
(host) (config) #show vlan
Command History
Parameter Description Range Default
<id> Identification number for the VLAN. 2-4094 1
<description> Description of a VLAN ID. 1-32 characters;
cannot begin
with a numeric
character
VLAN000x,
where x is the
ID number.
<name> (Optional) Identification name of the VLAN. The
VLAN name was created using the vlan-name
command.
1-32 characters;
a name cannot
begin with a
numeric
character
VLAN<id>
<vlan-ids> (Optional) List of VLAN IDs that are associated
with this VLAN. If two or more IDs are listed, the
VLAN needs to specified first as a VLAN pool
using the vlan-name command.
Existing VLAN
IDs 1
range <word> Creates a range or multiple VLAN IDs at once. 2-4094 —
Release Modification
AOS-W 3.0 Command available.
AOS-W 3.4 vlan-ids option available.
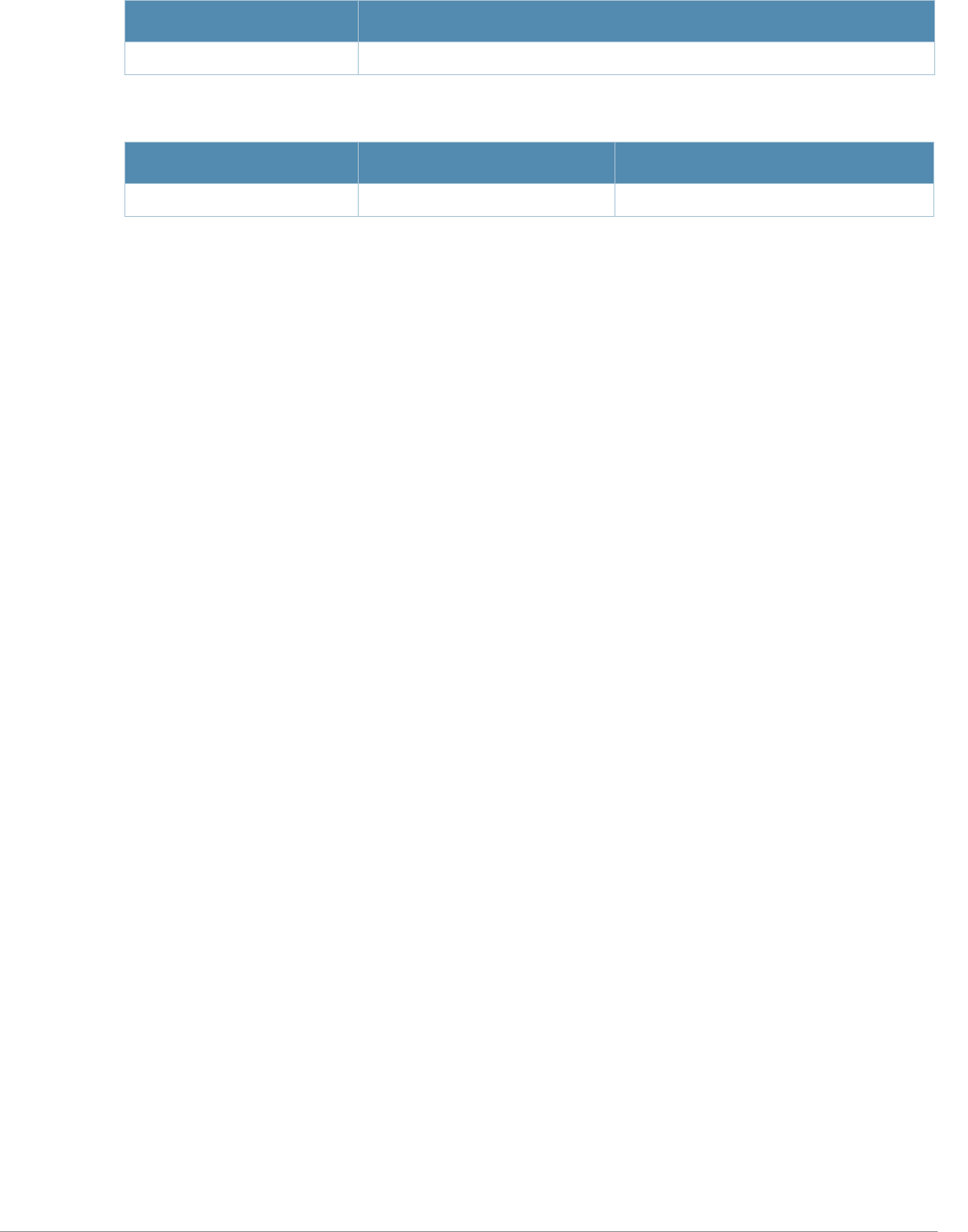
1162 |vlan AOS-W 3.4.1 Command Line Interface | Reference Guide
Command Information
AOS-W 3.4.1 vlan range option available.
Platforms Licensing Command Mode
All platforms Base operating system Config mode on master switches
Release Modification
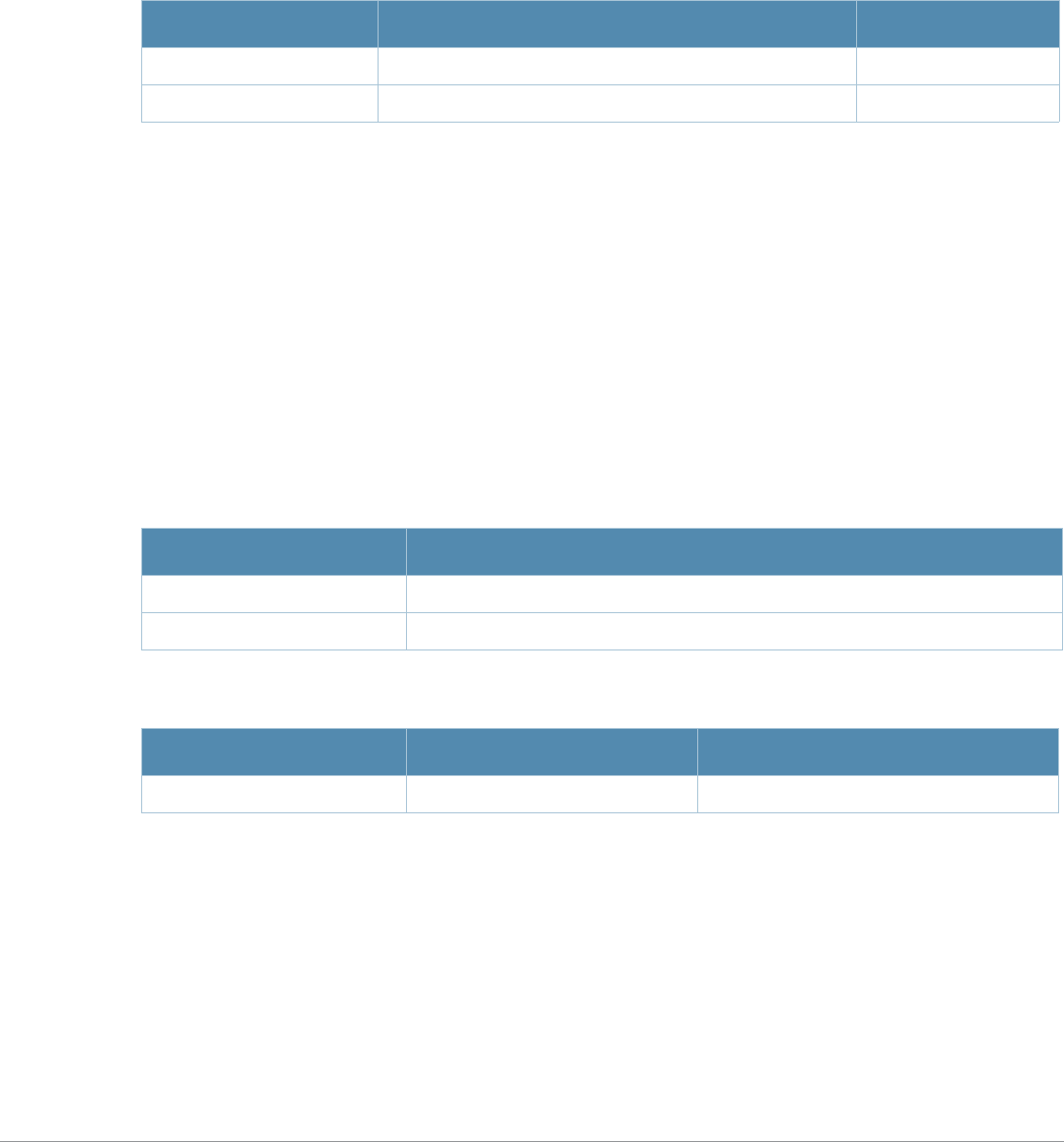
AOS-W 3.4.1 Command Line Interface | Reference Guide vlan-name | 1163
vlan-name
vlan-name <name> [pool]
Description
This command creates a named VLAN on the switch and can enable it as a pool. A named VLAN needs to be
first created to assign one or a pool of VLAN IDs to that name.
Syntax
Usage Guidelines
Create a named VLAN so you can set up a VLAN pool. A VLAN pool consists of a set of VLAN IDs which are
grouped together to efficiently manage multi-switch networks from a single location.
Example
The following command creates a VLAN pool named mytest on the switch:
vlan-name mytest pool
Related Commands
(host) (config) #show vlan
Command History
Command Information
Parameter Description Range
<name> Name for the VLAN. 1–32 characters
[pool] (Optional) Sets the named VLAN to be a pool. —
Version Modification
AOS-W 3.0 Command introduced.
AOS-W 3.4 the pool parameter was introduced.
Platforms Licensing Command Mode
All platforms Base operating system Config mode on master switches

1164 | vlan-name AOS-W 3.4.1 Command Line Interface | Reference Guide
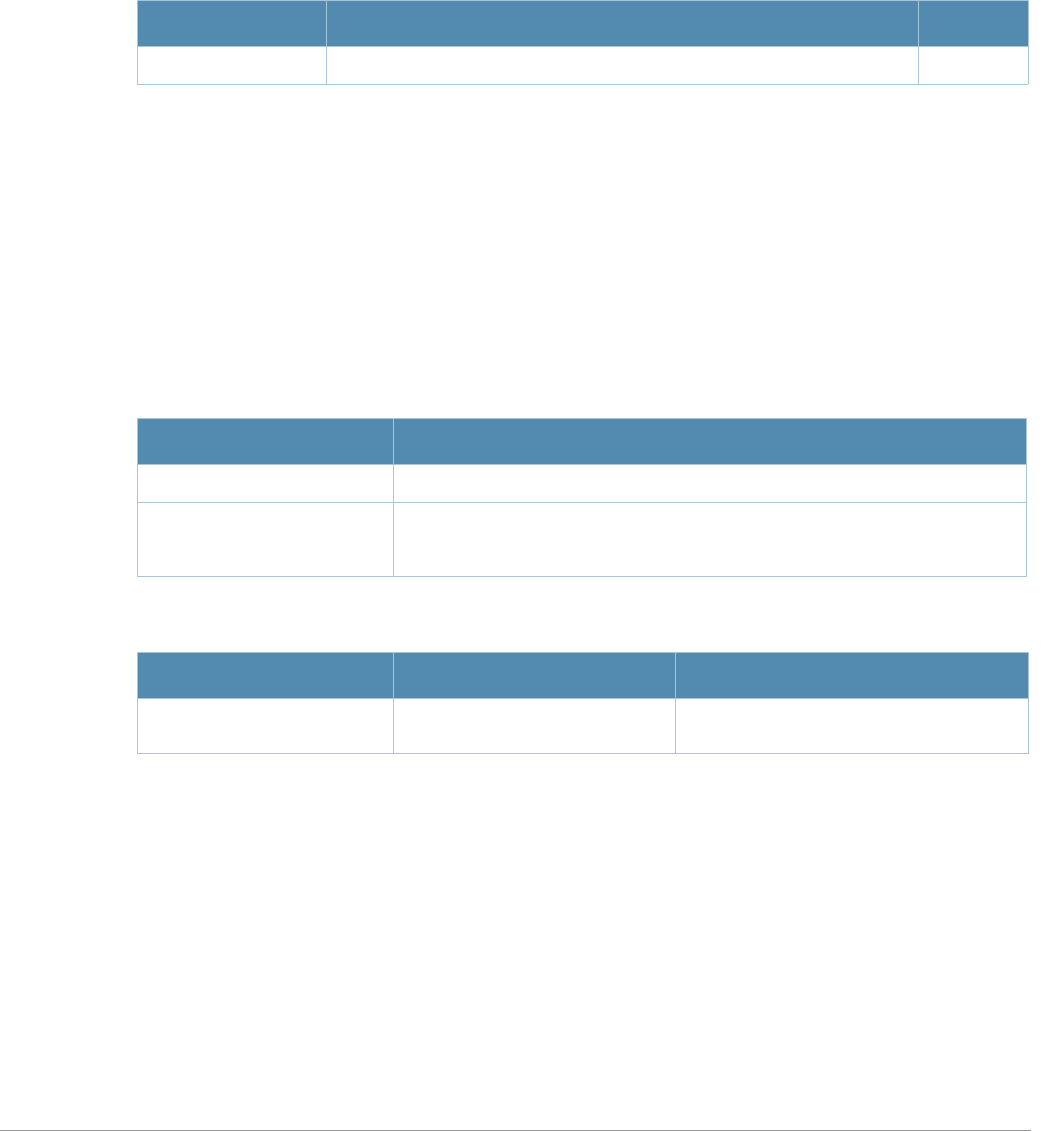
AOS-W 3.4.1 Command Line Interface | Reference Guide voip | 1165
voip
voip [prioritization {disable|enable}]
Description
This command enables Voice over IP (VoIP) traffic prioritization.
Syntax
Usage Guidelines
This command allows VoIP traffic to be automatically assigned to the high-priority queue. When this
command is enabled, you do not need to configure a session ACL to place voice traffic into the high-priority
queue.
Example
The following command enables VoIP traffic prioritization:
(host) (config) #voip prioritization
Command History
Command Information
Parameter Description Default
prioritization Allows voice traffic to be assigned automatically to the high priority queue. disabled
Version Description
AOS-W 3.0 Command introduced.
AOS-W 3.4.1 License requirements changed in AOS-W 3.4.1, so the command now requires
the Policy Enforced Firewall license instead of the Voice Services Module license
required in earlier versions.
Platforms Licensing Command Mode
All platforms This command requires the Policy
Enforcement Firewall license Config mode on master switch

1166 |voip AOS-W 3.4.1 Command Line Interface | Reference Guide

AOS-W 3.4.1 Command Line Interface | Reference Guide vpdn group l2tp | 1167
vpdn group l2tp
vpdn group l2tp
client configuration {dns|wins} <ipaddr1> [<ipaddr2>]
disable|enable
l2tp tunnel hello <seconds>
no ...
ppp authentication {CACHE-SECURID|CHAP|EAP|MSCHAP|MSCHAPv2|PAP}
ppp securid cache <minutes>
Description
This command configures an L2TP/IPsec VPN connection.
Syntax
Usage Guidelines
L2TP/IPsec relies on the PPP connection process to perform user authentication and protocol
configuration. You specify the protocol used for PPP authentication and whether SecureID tokens are
cached on the switch. Client addresses are assigned from a pool configured with the ip local pool
command.
Parameter Description Range Default
client
configuration
Configures parameters for the remote clients. — —
dns Configures a primary and optional secondary DNS server. — —
wins Configures a primary and optional secondary WINS server. — —
disable|enable Disables or enables termination of L2TP clients. — enabled
l2tp tunnel
hello
Configures L2TP tunneling hello timeout, in seconds. 10-1440 60 seconds
no Negates any configured parameter. — —
ppp
authentication
Enables the protocols for PPP authentication. This list should
match the L2TP configuration configured with the vpn-dialer
command on the switch.
——
CACHE-SECUR
ID
The switch caches Secure ID tokens so that the user does not
need to reauthenticate each time a network connection is lost. ——
CHAP Use CHAP with PPP authentication. — —
EAP Use EAP-TLS with PPP authentication. Specify this protocol
for Windows IPsec VPN clients that use Common Access Card
(CAC) Smart Cards that contain user information and digital
certificates.
——
MSCHAP Use MSCHAP with PPP authentication. — —
MSCHAPv2 Use MSCHAPv2 with PPP authentication. This is the default
for L2TP ——
PAP Use PAP with PPP authentication. — —
ppp securid If CACHE-SECURID is configured for PPP authentication, this
specifies the time, in minutes, that the token is cached. 15-10080 1440 minutes

1168 | vpdn group l2tp AOS-W 3.4.1 Command Line Interface | Reference Guide
Example
The following command configures virtual private dial-in networking:
(host) (coinfig) #vpdn group l2tp
ppp authentication PAP
client configuration dns 10.1.1.2
client configuration wins 10.1.1.2
Command History
The command was introduced in AOS-W 3.0.
Command Information
Platforms Licensing Command Mode
All platforms This command requires the VPN
Server and/or Remote AP license Config mode on master switches

AOS-W 3.4.1 Command Line Interface | Reference Guide vpdn group pptp | 1169
vpdn group pptp
vpdn group pptp
client configuration {dns|wins} <ipaddr1> [<ipaddr2>]
disable|enable
no ...
ppp authentication {MSCHAP|MSCHAPv2}
pptp echo <seconds>
Description
This command configures a PPTP VPN connection.
Syntax
Usage Guidelines
PPTP connections require user-level authentication through a PPP authentication protocol (MSHCAPv2 is
the currently-supported method.) Client addresses are assigned from a pool configured with the pptp
command.
Example
The following command configures virtual private dial-in networking:
vpdn group pptp
ppp authentication MSCHAPv2
client configuration dns 10.1.1.2
Parameter Description Range Default
client configuration Configures parameters for the
remote clients. ——
dns Configures a primary and optional
secondary DNS server. ——
wins Configures a primary and optional
secondary WINS server. ——
disable|enable Disables or enables termination of
PPTP clients. —enabled
no Negates any configured parameter. — —
ppp authentication Enables the protocols for PPP
authentication. This list should
match the PPTP configuration
configured with the vpn-dialer
command on the switch.
——
MSCHAP Use MSCHAP with PPP
authentication. ——
MSCHAPv2 Use MSCHAPv2 with PPP
authentication. This is the default
for L2TP
——
pptp echo Time, in seconds, that the switch
waits for a PPTP echo response
from the client before considering
the client to be down. The client is
disconnected if it does not
respond within this interval.
10-300 60 seconds

1170 | vpdn group pptp AOS-W 3.4.1 Command Line Interface | Reference Guide
client configuration wins 10.1.1.2
Command History
The command was introduced in AOS-W 3.0.
Command Information
Platforms Licensing Command Mode
All platforms This command requires the VPN
Server license Config mode on master switches
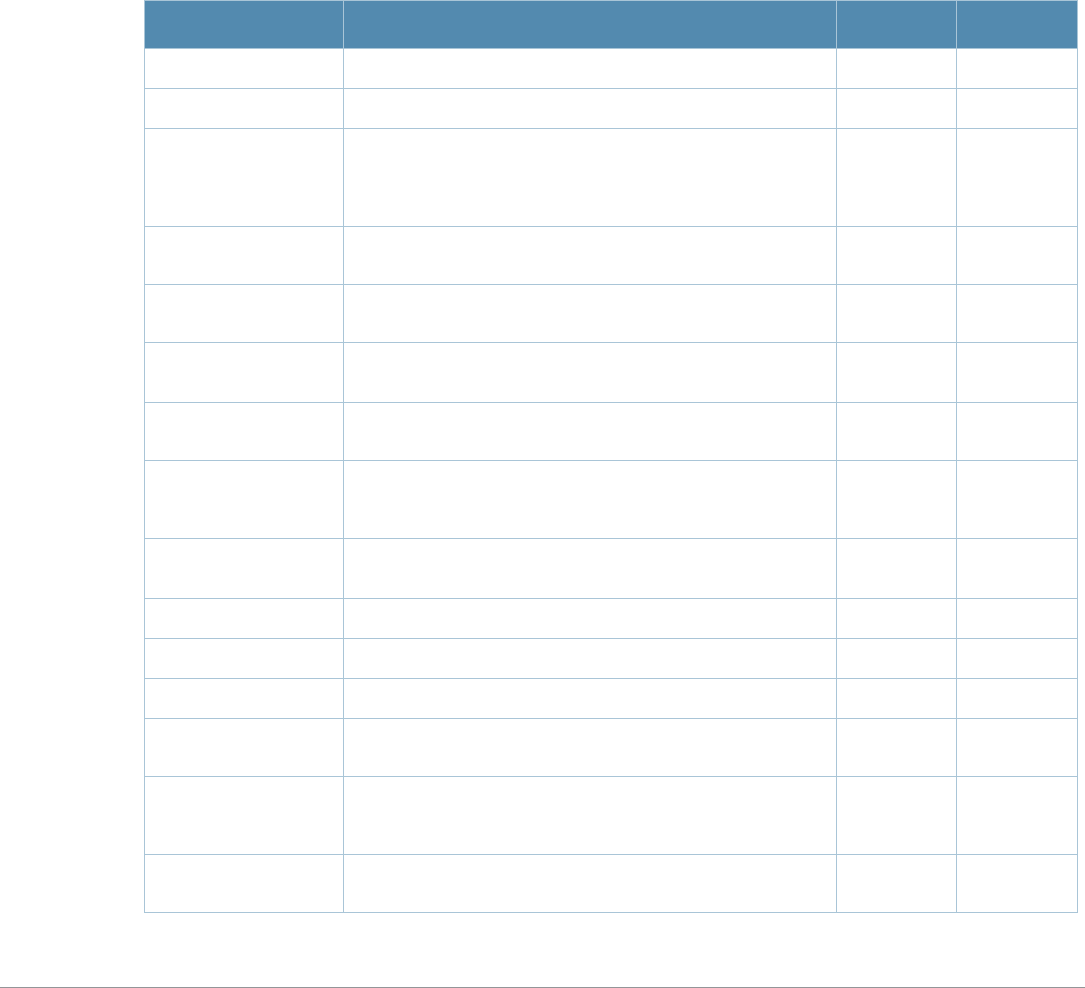
AOS-W 3.4.1 Command Line Interface | Reference Guide vpn-dialer | 1171
vpn-dialer
vpn-dialer <name>
enable dnetclear|l2tp|pptp|securid_newpinmode|wirednowifi
ike {authentication {pre-share <key>|rsa-sig}|encryption {3des|des}|
group {1|2}|hash {md5|sha}|lifetime [<seconds>]}
ipsec {encryption {esp-3des|esp-des}|hash {esp-md5-hmac|esp-sha-hmac}|
lifetime [<seconds>]|pfs {group1|group2}}
no {enable...|ipsec...|ppp...}
ppp authentication {cache-securid|chap|mschap|mschapv2|pap}
Description
This command configures the VPN dialer.
Syntax
Parameter Description Range Default
<name> Name that identifies this VPN dialer configuration. — —
enable Enables dialer operations: — —
dnetclear Enables “split tunneling” functionality so that traffic
destined for the internal network is tunneled while traffic for
the Internet is not. This option is not recommended for
security reasons.
— disabled
l2tp Allows the dialer to negotiate a Layer-2 Tunneling Protocol
(L2TP)/IPsec tunnel with the switch. —enabled
pptp Allows the dialer to negotiate a Point-to-Point Tunneling
Protocol (PPTP) with the switch. — disabled
securid_new
pinmode
Supports SecurID new and next pin mode. — disabled
wirednowifi Allows the dialer to detect when a wired network
connection is in use, and shuts down the wireless interface. — disabled
ike Configures internet key exchange (IKE) protocol. This
configuration must match the IKE policy configured with the
crypto isakmp policy command on the switch.
——
authentica
tion
Specifies whether preshared keys or RSA signatures are
used for IKE authentication. pre-share |
rsa-sig pre-share
encryption Specifies the IKE encryption protocol, either DES or 3DES. 3des | des 3des
group Specifies the Diffie-Hellman group, either 1 or 2. 1 | 2 2
hash Specifies the HASH algorithm, ether SHA or MD5. md5 | sha sha
lifetime Specifies how long an IKE security association lasts, in
seconds. 300-86400 28800
seconds
ipsec Configures IPsec. This configuration must match the IPsec
parameters configured with the crypto dynamic-map and
crypto ipsec commands on the switch.
——
encryption Specifies the encryption type for IPsec, either DES or
3DES. esp-3des |
esp-des esp-3des
1172 | vpn-dialer AOS-W 3.4.1 Command Line Interface | Reference Guide
Usage Guidelines
A VPN dialer is a Windows application that configures a Windows client for use with the VPN services in the
switch. When VPN is used as an access method, a user can login using captive portal and download a VPN
dialer. You can customize a VPN dialer for a user role configured with the user-role command. After the
user authenticates via captive portal, a link appears to allow download of the VPN dialer if a dialer is
configured for the user role.
Example
The following command configures a VPN dialer:
(host) (config) #vpn-dialer default-dialer
ike authentication pre-share f00xYz123BcA
Command History
The command was introduced in AOS-W 3.0.
Command Information
hash Specifies the hash algorithm used by IPsec, either MD5 or
SHA. esp-md5-
hmac | esp-
sha- hmac
esp-sha-
hmac
lifetime Specifies how long an IPsec security association lasts, in
seconds. 300-86400 7200
seconds
pfs Specifies the IPsec Perfect Forward Secrecy (PFS) mode,
either group 1 or group 2. group1 |
group2 group2
no Negates any configured parameter. — —
ppp authentica
tion
Enables the protocols for PPP authentication. This list
should match the L2TP or PPTP configuration configured
with the vpdn command on the switch.
——
cache-secur
id
The switch caches Secure ID tokens so that the user does
not need to reauthenticate each time a network connection
is lost.
— disabled
chap Use CHAP with PPP authentication. — enabled
mschap Use MSCHAP with PPP authentication. — enabled
mschapv2 Use MSCHAPv2 with PPP authentication. — enabled
pap Use PAP with PPP authentication. — enabled
Parameter Description Range Default
Platforms Licensing Command Mode
All platforms This command requires the VPN
Server license. Config mode on master switches

AOS-W 3.4.1 Command Line Interface | Reference Guide vrrp | 1173
vrrp
vrrp <id>
advertise <interval>
authentication <password>
description <text>
ip address <ipaddr>
no...
preempt
priority <level>
shutdown
tracking interface {fastethernet <slot>/<port>|gigabitethernet <slot>/<port>}
{sub <value>}
tracking master-up-time <duration> add <value>
tracking vlan <vlanid> {sub <value>}
tracking vrrp-master-state <vrid> add <value>
vlan <vlanid>
Description
This command configures the Virtual Router Redundancy Protocol (VRRP).
Syntax
Parameter Description Range Default
id Number that uniquely identifies the VRRP instance, also
known as the VRID. This number should match the
VRID on the other member of the redundant pair.
For ease in administration, you should configure this
with the same value as the VLAN ID.
After you configure the VRID, the command platform
enters VRRP mode. From here, you can access the
remaining VRRP commands.
1-255 —
advertise Specifies the time, in seconds, between successive
VRRP advertisements sent by the current master.
Alcatel-Lucent recommends that you use the default
value.
1-60 seconds 1 second
(1s=1000ms)
authentication Configure an optional password of up to eight
characters to be used to authenticate VRRP peers in
their advertisements.
The password must be the same on both members of
the redundant pair.
The password is sent in plain-text and therefore should
not be treated as a security measure. Rather, the
purpose of the password is to guard against
misconfigurations in the event that other VRRP devices
exist on the same network.
8 characters —
description Configure an optional text string to describe the VRRP
instance. 1-80 characters —

1174 | vrrp AOS-W 3.4.1 Command Line Interface | Reference Guide
ip address Configure the virtual IP address that will be owned by
the elected VRRP master. Use the same IP address on
each member of the redundant pair.
This IP address will be redundant - it will be active on
the VRRP master, and will become active on the VRRP
backup in the event that the VRRP master fails.
The IP address must be unique; the IP address cannot
be the loopback address of the switch. Only IPv4
address formats are supported.
——
no Negates all configured VRRP parameters. — —
preempt Preempt mode allows a switch to take over the role of
master if it detects a lower priority switch currently
acting as master.
Alcatel-Lucent recommends that you use the default
setting to avoid excessive interruption to users or
“flapping” if a problematic switch is cycling up and
down.
— disabled
priority Defines the priority level of the VRRP instance for the
switch. This value is used in the election mechanism for
the master.
A higher number specifies a higher priority.
The default priority setting is adequate for most
networks.
100 1-255
shutdown Administratively shutdown VRRP. When down, VRRP is
not active, although the switch maintains the
configuration information.
To start the VRRP instance, use no shutdown.
—enabled
(VRRP is
down)
tracking
interface
Configures VRRP tracking based on Layer-2 interface
state transitions. You can configure this on Fast
Ethernet or Gigabit Ethernet interfaces.
You can track a combined maximum of 16 VLAN and
Layer-2 interfaces.
——
<slot> <slot> is always 1 except for the OmniAccess 6000
switch, where the slots can be 0, 1, 2, or 3. ——
<port> Number assigned to the network interface embedded in
the switch or in the line card installed in the
OmniAccess 6000 switch. Port numbers start at 0 from
the left-most position.
——
sub Decreases the priority of the VRRP instance by the
specified amount. When the interface comes up again,
the value is restored to the previous priority level.
The combined priority and tracking vales cannot
exceed 255.
If the priority value exceeds 255, the switch displays an
error message.
0-255 —
tracking
master-up-time
duration
Monitors how long the switch has been master for the
VRRP instance. 0-1440 minutes —
tracking
master-up-time
add
Instructs the switch to add the specified value to the
existing priority level.
The combined priority and tracking values cannot
exceed 255.
If the priority value exceeds 255, the switch displays an
error message similar to the following:
Error: Vrrp 30 priority + tracking value exceeds 255
0-255 —
Parameter Description Range Default

AOS-W 3.4.1 Command Line Interface | Reference Guide vrrp | 1175
Usage Guidelines
Use this command to set parameters for VRRP on the switch. The default VRRP parameters can be left for
most implementations.
You can use a combination of numbers, letters, and characters to create the authentication password and
the VRRP description. To include a space in the password or description, enter quotation marks around the
string. For example, to create the password Floor 1, enter “Floor 1” at the prompt.
To change the existing password or description, enter the command with a different string. The new
password or description takes affect immediately.
To unconfigure the existing password or description, enter ““ at the prompt. If you update the password on
one switch, you must update the password on the redundant member pair.
Interface Tracking
You can track multiple VRRP instances to prevent asymmetric routing and dynamically change the VRRP
master to adapt to changes in the network. VRRP interface tracking can alter the priority of the VRRP
instance based on the state of a particular VLAN or Layer-2 interface. The priority of the VRRP instance can
increase or decrease based on the operational state of the specified interface. For example, interface
transitions (up/down events) can trigger a recomputation of the VRRP priority, which can change the VRRP
master depending on the resulting priority. You can track a combined maximum of 16 interfaces.
Example
The following command configures a priority of 105 for VRRP ID (VRID) 30:
tracking vlan Configures VRRP tracking based on VLAN state
transitions.
You can track a combined maximum of 16 VLAN and
Layer-2 interfaces.
——
sub Decreases the priority of the VRRP instance by the
specified amount. When the VLAN comes up again, the
value is restored to the previous priority level.
The combined priority and tracking values cannot
exceed 255.
If the priority value exceeds 255, the switch displays an
error message.
0-255 —
vrrp-master-
state
Specifies the VRID to use for tracking the state of the
VRRP master switch. 1-255 —
vrrp-master-
state add
Instructs the switch to add the specified value to the
existing priority level.
The combined priority and tracking values cannot
exceed 255.
If the priority value exceeds 255, the switch displays an
error message similar to the following:
Error: Vrrp 30 priority + tracking value exceeds 255
0-255 —
vlan Specifies the VLAN ID of the VLAN on which VRRP will
run. 1-4094 —
Parameter Description Range Default
You must enable preempt mode to allow a switch to take over the role of master if it detects a lower
priority switch currently acting as master
1176 | vrrp AOS-W 3.4.1 Command Line Interface | Reference Guide
(host) (config) #vrrp 30
priority 105
The following commands configure VLAN interface tracking and assumes the following:
zYou have two switchs, a primary and a backup.
zThe configuration highlights the parameters for interface tracking. You may have other parameters
configured for VRRP.
If VLAN 20 goes down, VRRP 20 automatically fails over, VRRP 10 and VRRP 30 would drop their priority to
95, causing a failover to the backup switch. Once VLAN 20 comes back up, the primary switch restores the
VRRP priority to 105 for all VRRP IDs and resumes the master VRRP role.
Command History
Command Information
Primary Configuration Backup Configuration
vrrp 10
vlan 10
ip address 10.200.22.254
priority 105
preempt
tracking vlan 20 sub 10
vrrp 20
vlan 20
ip address 10.200.22.254
preempt
priority 105
tracking vlan 10 sub 10
vrrp 30
vlan 30
ip address 10.200.22.254
preempt
priority 105
tracking vlan 20 sub 10
vrrp 10
vlan 10
ip address 10.200.22.254
priority 100
preempt
tracking vlan 20 sub 10
vrrp 20
vlan 20
ip address 10.200.22.254
preempt
priority 100
tracking vlan 10 sub 10
vrrp 30
vlan 30
ip address 10.200.22.254
preempt
priority 100
tracking vlan 20 sub 10
Version Modification
AOS-W 1.0 Command introduced
AOS-W 3.3 The tracking interface and tracking vlan parameters were introduced.
AOS-W 3.3.2 The add option was removed from the tracking interface and tracking vlan
parameters.
Platforms Licensing Command Mode
All platforms Base operating system Config mode on master and local switches

AOS-W 3.4.1 Command Line Interface | Reference Guide web-server | 1177
web-server
web-server
captive-portal-cert <name>
ciphers {high|low|medium}
mgmt-auth [certificate] [username/password]
no ...
ssl-protocol [sslv2] [sslv3] [tlsvl]
session-timeout <session-timeout>
switch-cert <name>
Description
This command configures the switch’s web server.
Syntax
Usage Guidelines
There is a default server certificate installed in the switch, however this certificate does not guarantee
security in production networks. Alcatel-Lucent strongly recommends that you replace the default
certificate with a custom certificate issued for your site by a trusted Certificate Authority (CA). See the
AOS-W User Guide for more information about how to generate a Certificate Signing Request (CSR) to
submit to a CA and how to import the signed certificate received from the CA into the switch. After
importing the signed certificate into the switch, use the web-server command to specify the certificate for
captive portal or WebUI access. If you need to specify a different certificate for captive portal or WebUI
access, use the no command to revert back to the default certificate before you specify the new certificate
(see the Example section).
Parameter Description Range Default
captive-portal-
cert
Name of the server certificate associated with captive portal.
Use the show crypto-local pki ServerCert command to
see the server certificates installed in the switch.
—default
ciphers Configures the strength of the cipher suite:
high: encryption keys larger than 128 bits
low: 56 or 64 bit encryption keys
medium: 128 bit encryption keys
high, low,
medium high
mgmt-auth Authentication method for the management user; you can
choose to use either username/password or certificates, or
both username/password and certificates.
username/
password,
certificate
username/
password
no Negates any configured parameter. — —
session-timeout
<session-
timeout>
Specifies the amount of time after which the WebUI session
times out and requires login for continued access. 30-3600
seconds 900
seconds
ssl-protocol Secure Sockets Layer (SSL) or Transport Layer Security
(TLS) protocol version used for securing communication with
the web server:
SSLv3
TLSv1
sslv3, tlsv1 sslv3, tlsv1
switch-cert Name of the server certificate associated with WebUI
access. Use the show crypto-local pki ServerCert
command to see the server certificates installed in the
switch.
—default
1178 | web-server AOS-W 3.4.1 Command Line Interface | Reference Guide
You can use client certificates to authenticate management users. If you specify certificate authentication,
you need to configure certificate authentication for the management user with the mgmt-user webui-
cacert command.
Example
The following commands configure WebUI access with client certificates only, and specify the server
certificate for the switch:
(host) (config) #web-server mgmt-auth certificate
switch-cert ServerCert1
mgmt-user webui-cacert serial 1111111 web-admin root
To specify a different server certificate, use the no command to revert back to the default certificate before
you specify the new certificate:
(host) (config) #web-server mgmt-auth certificate
switch-cert ServerCert1
no switch-cert
switch-cert ServerCert2
Command History
Command Information
Version Modification
AOS-W 3.0 Command introduced
AOS-W 3.1 The mgmt-auth parameter was introduced.
AOS-W 3.2 The captive-portal-cert parameter was introduced.
Platforms Licensing Command Mode
All platforms The web-server ciphers and
web-server ssl-protocol
commands require the PEF license
Config mode on master switches

AOS-W 3.4.1 Command Line Interface | Reference Guide whoami | 1179
whoami
whoami
Description
This command displays information about the current user logged into the switch.
Syntax
No parameters.
Usage Guidelines
Use this command to display the name and role of the user who is logged into the switch for this session.
Example
The following command displays information about the user logged into the switch:
(host) #whoami
Command History
This command was available in AOS-W 1.0.
Command Information
Platforms Licensing Command Mode
All platforms Base operating system Enable and Config modes on master and
local switches

1180 |whoami AOS-W 3.4.1 Command Line Interface | Reference Guide

AOS-W 3.4.1 Command Line Interface | Reference Guide wlan dot11k-profile | 1181
wlan dot11k-profile
wlan
wlan dotllk <profile>
bcn-measurement-mode {active|beacon-table|passive}
clone <profile>
dot11k-enable
force-disassoc
no ...
Description
Configure a 802.11k radio profile.
Syntax
Parameter Description Default
<profile> Name of this instance of the profile. The name must be 1-63
characters. “default”
bcn-measurement-mode
Configures an active, beacon-table or passive beacon measurement
mode for the profile. beacon-table
active
Enables
active
beacon measurement mode.
In this mode, the client
sends a probe request to the broadcast destination address on all
supported channels, sets a measurement duration timer, and, at the
end of the measurement duration, compiles all received beacons or
probe response with the requested SSID and BSSID into a
measurement report.
NOTE: If the station doesn't support active measurement mode, it
returns a Beacon Measurement Report with the Incapable bit set in
the Measurement Report Mode field.
—
beacon-table
Enables
beacon-table
beacon measurement mode.
In this mode, the
client measures beacons and returns a report with stored beacon
information for any supported channel with the requested SSID and
BSSID. The client does not perform any additional measurements.
This is the default beacon measurement mode.
NOTE: If a station doesn't support beacon-table able measurement
mode, it returns a Beacon Measurement Report with the Incapable bit
set in the Measurement Report Mode field.
—
passive Enables passive beacon measurement mode. In this mode, the client
sets a measurement duration timer, and, at the end of the
measurement duration, compiles all received beacons or probe
response with the requested SSID and BSSID into a measurement
report.
NOTE: If a station doesn't support passive measurement mode, it
returns a Beacon Measurement Report with the Incapable bit set in
the Measurement Report Mode field.
—
clone <profile> Copy settings from another specified 802.11k profile. —
dot11k-enable Enables the 802.11K feature. This feature is disabled by default. Disabled
1182 | wlan dot11k-profile AOS-W 3.4.1 Command Line Interface | Reference Guide
Usage Guidelines
In a 802.11k network, if the AP with the strongest signal is reaches its maximum capacity, clients may
connect to an underutilized AP with a weaker signal. A 802.11k profile can assigned to each virtual AP.
Example
The following command enable the 802.11k feature on the 802.11k profile:
(host) (config) #wlan dot11k-profile default
(host) (802.11K Profile "default") #dot11k-enable
Command History
This command was introduced in AOS-W 3.4.
Command Information
force-dissasoc This feature allows the AP to forcefully disassociate “on-hook” voice
clients (clients that are not on a call) after period of inactivity.
Without the forced disassociation feature, if an AP has reached its call
admission control limits and an on-hook voice client wants to start a
new call, that client may be denied. If forced disassociation is enabled,
those clients can associate to a neighboring AP that can fulfil their
QoS requirements.
This feature is disabled by default.
Disabled
no Negates or removes any configured parameter
Parameter Description Default
Platforms Licensing Command Mode
All platforms Base operating system. Config mode on master switches
AOS-W 3.4.1 Command Line Interface | Reference Guide wlan edca-parameters-profile | 1183
wlan edca-parameters-profile
wlan
wlan edca-parameters-profile {ap|station} <profile>
{background | best-effort | video | voice}
[acm][aifsn <number>] [ecw-max <exponent> [ecw-min <exponent>] [txop <number>]
[clone <profile>
Description
This command configures an enhanced distributed channel access (EDCA) profile for APs or for clients
(stations).
Syntax
Usage Guidelines
EDCA profiles are specific either to APs or clients. You apply an EDCA profile to a specific SSID profile. use
this command only under the guidance of your Alcatel-Lucent representative.
The following are the default values configured for APs:
Parameter Description Range Default
<profile> Name of this instance of the profile. The name must be 1-63
characters. —“default”
background Configures the background queue. — —
best-effort Configures the best-effort queue. — —
video Configures the video queue. — —
voice Configures the voice queue. — —
acm Specifies mandatory admission control. The client reserves the
access category through traffic specification (TSPEC) signaling.
Enter 1 to enable, 0 to disable.
0, 1 0 (disabled)
aifsn Arbitrary inter-frame space number. 1-15 0
ecw-max The exponential (n) value of the maximum contention window
size, as expressed by 2n-1. A value of 4 computes to 24-1 = 15. 1-15 0
ecw-min The exponential (n) value of the minimum contention window size,
as expressed by 2n-1. A value of 4 computes to 24-1 = 15. 0-15 0
txop Transmission opportunity, in units of 32 microseconds. Divide the
desired transmission duration by 32 to determine the value to
configure. For example, for a transmission duration of 3008
microseconds, enter 94 (3008/32).
0-2047 0
clone Name of an existing EDCA profile from which parameter values
are copied. ——
Access Category ecw-min ecw-max aifsn txop acm
best-effort4630No
background41070No
video 34194No
voice 23147No
1184 | wlan edca-parameters-profile AOS-W 3.4.1 Command Line Interface | Reference Guide
The following are the default values configured for clients:
Example
The following command configures an EDCA profile for APs:
(host) (config) #wlan edca-parameters-profile ap edca1
best-effort ecw-min 15 ecw-max 15 aifsn 15 txop 100 acm 1
Command History
This command was introduced in AOS-W 3.1.
Command Information
Access Category ecw-min ecw-max aifsn txop acm
best-effort41030No
background41070No
video 34294No
voice 23247No
Version Description
AOS-W 3.1 Command introduced.
AOS-W 3.4.1 License requirements changed in AOS-W 3.4.1, so the command now requires
the Policy Enforced Firewall license instead of the Voice Services Module license
required in earlier versions.
Platforms Licensing Command Mode
All platforms Policy Enforced Firewall license Config mode on master switches
AOS-W 3.4.1 Command Line Interface | Reference Guide wlan ht-ssid-profile | 1185
wlan ht-ssid-profile
wlan ht-ssid-profile <profile>
40MHz-enable
allow-weak-encryption
clone <profile>
high-throughput-enable
legacy-stations
max-rx-a-mpdu-size {8191|16383|32767|65535}
max-tx-a-mpdu-size <bytes>
min-mpdu-start-spacing {0|.25|.5|1|2|4|8|16}
mpdu-agg
no...
short-guard-intvl-40MHz
supported-mcs-set <mcs-list>
Description
This command configures a high-throughput SSID profile.
Syntax
Parameter Description Range Default
<profile> Name of this instance of the profile. The name must be 1-63
characters. —“default”
40MHz-
enable
Enables or disables the use of this high-throughput SSID in 40 MHz
mode. —enabled
allow-weak-
encryption
Enabling the use of TKIP or WEP for unicast traffic disables A-MPDU
aggregation but allows the association to proceed. Disabling this
prevents stations using TKIP or WEP for unicast traffic from associating
at all. It is disabled by default.
—disabled
clone Name of an existing high-throughput SSID profile from which
parameter values are copied. ——
high-
throughput-
enable
Determines if this high-throughput SSID allows high-throughput
(802.11n) stations to associate.
Enabling high-throughput in an ht-ssid-profile enables Wi-Fi
Multimedia (WMM) base features for the associated SSID.
—enabled
legacy-
stations
Controls whether or not legacy (non-HT) stations are allowed to
associate with this SSID. By default, legacy stations are allowed to
associate.
This setting has no effect on a BSS in which HT support is not
available.
—enabled
max-rx-a-
mpdu-
size
Controls the maximum size, in bytes, of an Aggregated-MAC Packet
Data Unit (A-MPDU) that can be received on this high-throughput SSID. 8191/
16383/
32767/
65535
65535
8191 Maximum size of 8191 bytes.
16383 Maximum size of 16383 bytes.
32767 Maximum size of 32767 bytes.
65535 Maximum size of 65535 bytes.
max-tx-a-
mpdu-
size
Controls the maximum size, in bytes, of an A-MPDU that can be sent
on this high-throughput SSID. 1576-
65535 65535

1186 | wlan ht-ssid-profile AOS-W 3.4.1 Command Line Interface | Reference Guide
Usage Guidelines
The ht-ssid-profile configures the high-throughput SSID.
De-aggregation of MAC Service Data Units (A-MSDUs) is supported on the OmniAccess 4504/4604/4704
switch and the OmniAccess Supervisor Card III (OmniAccess Supervisor Card III) with a maximum frame
transmission size of 4k bytes; however, this feature is always enabled and is not configurable. Aggregation
is not currently supported.
Example
The following command configures the maximum size of a received aggregate MDPU to be 8191 bytes for
the high-throughput SSID named “htcorpnet:”
(host) (config) #wlan ht-ssid-profile htcorpnet
max-rx-a-mpdu-size 8191
Command History
min-mpdu-
start-
spacing
Minimum time between the start of adjacent MDPUs within an
aggregate MDPU in microseconds. 0/.25/.5/1/
2/4/8/16 0
0No restriction on MDPU start spacing.
.25 Minimum time of .25 μsec.
.5 Minimum time of .5 μsec.
1Minimum time of 1 μsec.
2Minimum time of 2 μsec.
4Minimum time of 4 μsec.
8Minimum time of 8 μsec.
16 Minimum time of 16 μsec.
mpdu-agg Enables or disables MAC protocol data unit (MDPU) aggregation. — enabled
no Negates any configured parameter. — —
short-
guard-
intvl-40MHz
Enables or disables use of short guard interval in 40 MHz mode of
operation. enabled
supported-
mcs-
set
Comma-separated list of Modulation Coding Scheme (MCS) values or
ranges of values to be supported on this high-throughput SSID. 0-15 0-15
Parameter Description Range Default
NOTE
AP configuration settings related to the IEEE 802.11n standard are configurable for Alcatel-Lucent OAW-AP120
series access points, which are IEEE 802.11n standard compliant devices.
Version Description
AOS-W 3.3 Command introduced
AOS-W 3.3.1 The legacy-stations parameter was introduced
AOS-W 3.4.1 Command Line Interface | Reference Guide wlan ht-ssid-profile | 1187
Command Information
AOS-W 3.3.2 De-aggregation of MAC Service Data Units (A-MSDUs) on the OmniAccess 4504/
4604/4704 and the OmniAccess Supervisor Card III (OmniAccess Supervisor
Card III) was introduced
Platforms Licensing Command Mode
All platforms but operates with
IEEE 802.11n compliant
devices only
Base operating system Config mode on master switches
Version Description
1188 | wlan ssid-profile AOS-W 3.4.1 Command Line Interface | Reference Guide
wlan ssid-profile
wlan ssid-profile <profile>
902il-compatibility-mode
a-basic-rates <mbps>
a-beacon-rate
a-tx-rates <mbps>
ageout <seconds>
battery-boost
clone <profile>
deny-bcast
disable-probe-retry
dtim-period <milliseconds>
edca-parameters-profile {ap|station} <profile>
essid <name>
g-basic-rates <mbps>
g-beacon-rate
g-tx-rates <mbps>
hide-ssid
ht-ssid-profile <profile>
local-probe-response
max-clients <number>
max-retries <number>
max-tx-fail <number>
mcast-rate-opt
no ...
opmode {dynamic-wep opensystem static-wep wpa-aes wpa-psk-aes wpa-psk-tkip wpa-tkip
wpa2-aes wpa2-psk-aes wpa2-psk-tkip wpa2-tkip xSec}
rts-threshold <number>
short-preamble
ssid-enable
strict-svp
wepkey1 <key>
wepkey2 <key>
wepkey3 <key>
wepkey4 <key>
weptxkey <index>
wmm
wmm-be-dscp <best-effort>
wmm-bk-dscp <background>
wmm-ts-min-inact-int <milliseconds>
wmm-vi-dscp <video>
wmm-vo-dscp <voice>
wpa-hexkey <psk>
wpa-passphrase <string>
Description
This command configures an SSID profile.
Syntax
Parameter Description Range Default
<profile> Name of this instance of the profile. The name must be 1-63
characters. — “default”
AOS-W 3.4.1 Command Line Interface | Reference Guide wlan ssid-profile | 1189
902il-
compatibility-
mode
(For clients using NTT DoCoMo 902iL phones only) When
enabled, the switch does not drop packets from the client if a
small or old initialization vector value is received. (When TKIP or
AES is used for encryption and TSPEC is enabled, the phone
resets the value of the initialization vector after add/delete
TSPEC.)
NOTE: The Policy Enforced Firewall license must be installed.
—disabled
a-basic-rates List of supported 802.11a rates, in Mbps, that are advertised in
beacon frames and probe responses. 6, 9, 12,
18, 24,
36, 48,
54 Mbps
6, 12, 24
Mbps
a-beacon-rate Sets the beacon rate for 802.11a (use for Distributed Antenna
System (DAS) only). Using this parameter in normal operation may
cause connectivity problems.
default,
6, 9, 12,
18,24,36,
48,54
Mbps
minimum
valid rate
a-tx-rates Set of 802.11a rates at which the AP is allowed to send data. The
actual transmit rate depends on what the client is able to handle,
based on information sent at the time of association and on the
current error/loss rate of the client.
6, 9, 12,
18, 24,
36, 48,
54 Mbps
6, 9, 12,
18, 24, 36,
48, 54
Mbps
ageout Time, in seconds, that a client is allowed to remain idle before
being aged out. 1000
seconds
battery-boost Converts multicast traffic to unicast before delivery to the client,
thus allowing you to set a longer DTIM interval. The longer interval
keeps associated wireless clients from activating their radios for
multicast indication and delivery, leaving them in power-save
mode longer and thus lengthening battery life.
NOTE: The Policy Enforced Firewall license must be installed.
—disabled
clone Name of an existing SSID profile from which parameter values are
copied. ——
deny-bcast When a client sends a broadcast probe request frame to search
for all available SSIDs, this option controls whether or not the
system responds for this SSID. When enabled, no response is
sent and clients have to know the SSID in order to associate to
the SSID. When disabled, a probe response frame is sent for this
SSID.
—disabled
disable-probe-
retry
Enable or disable battery MAC level retries for probe response
frames. By default this parameter is enabled, which mean that
MAC level retries for probe response frames is disabled.
Enabled
dtim-period Specifies the interval, in milliseconds, between the sending of
Delivery Traffic Indication Messages (DTIMs) in the beacon. This is
the maximum number of beacon cycles before unacknowledged
network broadcasts are flushed. When using wireless clients that
employ power management features to sleep, the client must
revive at least once during the DTIM period to receive broadcasts.
1
edca-parameters
-profile
Name of the enhanced distributed channel access (EDCA) profile
that applies to this SSID.
NOTE: This profile requires the Policy Enforced Firewall license in
the switch. Configure this parameter only under the guidance of
your Alcatel-Lucent representative.
——
ap|sta Assigns the specified EDCA profile to AP or station (client). — —
essid Name that uniquely identifies the Service Set Identifier (SSID). The
SSID can be up to 31 characters. —“aruba-
ap”
Parameter Description Range Default

1190 | wlan ssid-profile AOS-W 3.4.1 Command Line Interface | Reference Guide
g-basic-rates List of supported 802.11b/g rates that are advertised in beacon
frames and probe responses. 1, 2, 5, 6,
9, 11, 12,
18, 24,
36, 48,
54 Mbps
1, 2 Mbps
g-beacon-rate Sets the beacon rate for 802.11g (use for Distributed Antenna
System (DAS) only). Using this parameter in normal operation may
cause connectivity problems.
default,
1,2,5, 6
9, 11, 12,
18, 24,
36, 48,
54 Mbps
minimum
valid rate
g-tx-rates Set of 802.11b/g rates at which the AP is allowed to send data.
The actual transmit rate depends on what the client is able to
handle, based on information sent at the time of association and
on the current error/loss rate of the client.
1, 2, 5, 6,
9, 11, 12,
18, 24,
36, 48,
54 Mbps
1, 2, 5, 6,
9, 11, 12,
18, 24, 36,
48, 54
Mbps
hide-ssid Enables or disables hiding of the SSID name in beacon frames.
Note that hiding the SSID does very little to increase security. —disabled
ht-ssid-profile Name of high-throughput SSID profile to use for configuring high-
throughput support. See “wlan ht-ssid-profile” on page 1185.— “default”
local-probe-re
sponse
Enable or disable local probe response on the AP. If this option is
enabled, the AP is responsible for sending 802.11 probe
responses to wireless clients’ probe requests. If this option is
disabled, then the switch sends the 802.11 probe responses.
—enabled
max-clients Maximum number of wireless clients for the AP. 0-256 64
max-retries Maximum number of retries allowed for the AP to send a frame. 0-15 4
max-tx-fail Maximum transmission failures allowed before the client gives up. 0
mcast-rate-opt Enables or disables scanning of all active stations currently
associated to an AP to select the lowest transmission rate for
broadcast and multicast frames. This option only applies to
broadcast and multicast data frames; 802.11 management frames
are transmitted at the lowest configured rate.
NOTE: Do not enable this parameter unless instructed to do so by
your Alcatel-Lucent representative.
—disabled
no Negates any configured parameter. — —
opmode The layer-2 authentication and encryption to be used on this
ESSID to protect access and ensure the privacy of the data
transmitted to and from the network.
(see
following
)
opensyste
m
dynamic-wep WEP with dynamic keys.
opensystem No authentication and encryption.
static-wep WEP with static keys.
wpa-aes WPA with AES encryption and dynamic keys using 802.1x.
wpa-psk-aes WPA with AES encryption using a preshared key.
wpa-psk-tkip WPA with TKIP encryption using a preshared key.
wpa-tkip WPA with TKIP encryption and dynamic keys using 802.1x.
wpa2-aes WPA2 with AES encryption and dynamic keys using 802.1x.
wpa2-psk-aes WPA2 with AES encryption using a preshared key.
Parameter Description Range Default
AOS-W 3.4.1 Command Line Interface | Reference Guide wlan ssid-profile | 1191
wpa2-psk-
tkip
WPA2 with TKIP encryption using a preshared key.
wpa2-tkip WPA2 with TKIP encryption and dynamic keys using 802.1x.
wpa-psk-aes WPA with AES encryption using a preshared key.
wpa2-psk-
tkip
WPA2 with TKIP encryption using a preshared key.
wpa2-tkip WPA2 with TKIP encryption and dynamic keys using 802.1x.
xSec Encryption and tunneling of Layer-2 traffic between the switch
and wired or wireless clients, or between switches. To use xSec
encryption, you must use a RADIUS authentication server. For
clients, you must install the Funk Odyssey client software.
Requires installation of the xSec license. For xSec between
switches, you must install an xSec license in each switch.
rts-threshold Wireless clients transmitting frames larger than this threshold
must issue Request to Send (RTS) and wait for the AP to respond
with Clear to Send (CTS). This helps prevent mid-air collisions for
wireless clients that are not within wireless peer range and cannot
detect when other wireless clients are transmitting.
2333
bytes
short-preamble Enables or disables short preamble for 802.11b/g radios. Network
performance may be higher when short preamble is enabled. In
mixed radio environments, some 802.11b wireless client stations
may experience difficulty associating with the AP using short
preamble. To use only long preamble, disable short preamble.
Legacy client devices that use only long preamble generally can
be updated to support short preamble.
—enabled
ssid-enable Enables/disables this SSID. — enabled
strict-svp Enable Strict Spectralink Voice Protocol (SVP) — disabled
wepkey1 -
wepkey4
Static WEP key associated with the key index. Can be 10 or 26
hex characters in length. ——
weptxkey Key index that specifies which static WEP key is to be used. Can
be 1, 2, 3, or 4. 1, 2, 3, 4 1
wmm Enables or disables WMM, also known as IEEE 802.11e
Enhanced Distribution Coordination Function (EDCF). WMM
provides prioritization of specific traffic relative to other traffic in
the network.
—disabled
wmm-be-dscp DSCP value used to map WMM best-effort traffic. 0-255 24
wmm-bk-dscp DSCP used to map WMM background traffic. 0-255 8
wmm-ts-min-in
act-int
Specifies the minimum inactivity time-out threshold of WMM
traffic. This setting is useful in environments where low inactivity
interval time-outs are advertised, which may cause unwanted
timeouts.
0-
3,600,00
0
0
millisecon
ds
wmm-uapsd Enable Wireless Multimedia (WMM) UAPSD powersave. — enabled
wmm-vi-dscp DSCP used to map WMM video traffic. 0-255 40
wmm-vo-dscp DSCP used to map WMM voice traffic. 0-255 56
wpa-hexkey WPA pre-shared key (PSK). — —
wpa-passphrase WPA passphrase with which to generate a pre-shared key (PSK). — —
Parameter Description Range Default
1192 | wlan ssid-profile AOS-W 3.4.1 Command Line Interface | Reference Guide
Usage Guidelines
The SSID profile configures the SSID.
Default WMM mappings exist for all SSIDs. After you customize an WMM mapping and apply it to the SSID,
the switch overwrites the default mapping values and uses the user-configured values.
Multicast Rate Optimization
The Multicast Rate Optimization feature dynamically selects the rate for sending broadcast/multicast
frames on any BSS. This feature determines the optimal rate for sending broadcast and multicast frames
based on the lowest of the unicast rates across all associated clients.
When the Multicast Rate Optimization option (mcast-rate-opt) is enabled, the switch scans the list of all
associated stations in that BSS and finds the lowest transmission rate as indicated by the rate adaptation
state for each station. If there are no associated stations in the BSS, it selects the lowest configured rate as
the transmission rate for broadcast and multicast frames.
This feature is disabled by default. Multicast Rate Optimization applies to broadcast and multicast frames
only. 802.11 management frames are not affected by this feature and will be transmitted at the lowest
configured rate.
Example
The following command configures an SSID for WPA2 AES authentication:
(host) (config) #wlan ssid-profile corpnet
ssid Corpnet
opmode wpa2-aes
Command History
NOTE
AP configuration settings related to the IEEE 802.11n standard are configurable for Alcatel-Lucent’s OAW-AP120
series access points, which are IEEE 802.11n standard compliant devices.
NOTE
The Multicast Rate Optimization feature should only be enabled on a BSS where all associated stations are sending
or receiving unicast data. If there is no unicast data to or from a particular station, then the rate adaptation state
may not accurately reflect the current sustainable transmission rate for that station. This could result in a higher
packet error rate for broadcast/multicast packets at that station.
Release Modification
AOS-W 3.0 Command introduced
AOS-W 3.2 The wmm-ts-min-inact-int parameter was introduced.The wpa2-preauth
parameter was removed,
AOS-W 3.3 Support for the high-throughput IEEE 802.11n standard was introduced including
the ht-ssid-profile parameter and various rate changes.
AOS-W 3.3.1 Support for configurable WMM AC mapping was introduced including the wmm-
be-dscp, wmm-bk-dscp, wmm-vi-dscp, and wmm-vo-dscp parameters.
AOS-W 3.4 The deny-bcast and disable-probe-retry parameters were introduced. The
drop-mcast parameter was deprecated.
AOS-W 3.4.1 License requirements changed in AOS-W 3.4.1, so the command now requires
the Policy Enforced Firewall license instead of the Voice Services Module license
required in earlier versions.

AOS-W 3.4.1 Command Line Interface | Reference Guide wlan ssid-profile | 1193
Command Information
Platforms Licensing Command Mode
All platforms Base operating system except for
the noted parameters Config mode on master switches
1194 | wlan traffic-management-profile AOS-W 3.4.1 Command Line Interface | Reference Guide
wlan traffic-management-profile
wlan traffic-management-profile <profile>
bw-alloc virtual-ap <virtual-ap> share <percent>
clone <profile>
no ...
report-interval <minutes>
shaping-policy default-access|fair-access|preferred-access
Description
This command configures a traffic management profile.
Syntax
Parameter Description Range Default
<profile> Name of this instance of the profile. The name must
be 1-63 characters. — “default”
bw-alloc Minimum bandwidth, as a percentage of available
bandwidth, allocated to an SSID when there is
congestion on the wireless network. An SSID can use
all available bandwidth if no other SSIDs are active.
virtual-ap Name of the virtual AP profile which pertains to the
SSID. ——
share Percentage of available bandwidth allocated to this
SSID. 0-100 —
clone Name of an existing traffic management profile from
which parameter values are copied. ——
no Negates any configured parameter. — —
report-interval Number of minutes between bandwidth usage
reports. 5 minutes
shaping-policy Define Station Shaping Policy This feature has the
following three options:
zdefault-access: Traffic shaping is disabled, and
client performance is dependent on MAC
contention resolution. This is the default traffic
shaping setting.
zfair-access: Each client gets the same airtime,
regardless of client capability and capacity. This
option is useful in environments like a training
facility or exam hall, where a mix of 802.11a/g,
802.11g and 802.11n clients need equal to
network resources, regardless of their
capabilities. The bw-alloc parameter of a traffic
management profile allows you to set a minimum
bandwidth to be allocated to a virtual AP profile
when there is congestion on the wireless
network.You must set traffic shaping to fair-
access to use this bandwidth allocation value for
an individual virtual AP.
zpreferred-access: High-throughput (802.11n)
clients do not get penalized because of slower
802.11a/g or 802.11b transmissions that take
more air time due to lower rates. Similarly, faster
802.11a/g clients get more access than 802.11b
clients.
default-access
fair-access
preferred-
access
default-
access

AOS-W 3.4.1 Command Line Interface | Reference Guide wlan traffic-management-profile | 1195
Usage Guidelines
The traffic management profile allows you to allocate bandwidth to SSIDs. When you enable the band-
steering feature, an AP keeps track of all BSSIDs active on a radio, all clients connected to the BSSID, and
802.11a/g, 802.11b, or 802.11n capabilities of each client. Every sampling period, airtime is allocated to each
client, giving it opportunity to get and receive traffic. The specific amount of airtime given to an individual
client is determined by;
zClient capabilities (802.11a/g, 802.11b or 802.11n)
zAmount of time the client spent receiving data during the last sampling period
zNumber of active clients in the last sampling period
zActivity of the current client in the last sampling period
The bw-alloc parameter of a traffic management profile allows you to set a minimum bandwidth to be
allocated to a virtual AP profile when there is congestion on the wireless network.You must set traffic
shaping to fair-access to use this bandwidth allocation value for an individual virtual AP.
Example
The following command configures a traffic management profile that allocates bandwidth to the corpnet
virtual AP:
(host) (config) #wlan traffic-management-profile best
bw-alloc virtual-ap corpnet share 75
Command History
This command was introduced in AOS-W 3.0. The mode parameters were introduced in AOS-W 3.2.
Command Information
Platforms Licensing Command Mode
All platforms Base operating system on master
switches Config mode on master switches
1196 | wlan virtual-ap AOS-W 3.4.1 Command Line Interface | Reference Guide
wlan virtual-ap
wlan virtual-ap <profile>
aaa-profile <profile>
allowed-band <band>...
auth-failure-blacklist-time <seconds>
band-steering
blacklist
blacklist-time <seconds>
broadcast-filter
broadcast-filter-arp
clone <profile>
deny-time-range <range>
dos-prevention
dot11k-profile
fast-roaming
forward-mode {bridge|split-tunnel|tunnel}
ha-disc-onassoc
mobile-ip
no ...
rap-operation {always|backup|persistent|standard}
ssid-profile <profile>
strict-compliance
vap-enable
dynamic-mcast-optimization
dynamic-mcast-optimization-threshold
vlan <vlan>...
vlan-mobility
wmm-traffic-management-profile
Description
This command configures a virtual AP profile.
Syntax
Parameter Description Range Default
<profile> Name of this instance of the profile. The name must
be 1-63 characters. — “default”
aaa-profile Name of the AAA profile that applies to this virtual AP. — “default”
allowed-band The band(s) on which to use the virtual AP:
a—802.11a band only (5 GHz)
g—802.11b/g band only (2.4 GHz)
all—both 802.11a and 802.11b/g bands
(5 GHz and 2.4 GHz)
a/g/all all
auth-failure-
blacklist-time
Time, in seconds, a client is blocked if it fails
repeated authentication. 0 blocks indefinitely. 0
AOS-W 3.4.1 Command Line Interface | Reference Guide wlan virtual-ap | 1197
band-steering ARM’s band steering feature encourages dual-band
capable clients to stay on the 5GHz band on dual-
band APs. This frees up resources on the 2.4GHz
band for single band clients like VoIP phones.
Band steering reduces co-channel interference and
increases available bandwidth for dual-band clients,
because there are more channels on the 5GHz band
than on the 2.4GHz band. Dual-band 802.11n-
capable clients may see even greater bandwidth
improvements, because the band steering feature will
automatically select between 40MHz or 20MHz
channels in 802.11n networks. This feature is
disabled by default, and must be enabled in a Virtual
AP profile.
Starting with AOS-W 3.4.1, the band steering feature
supports both campus APs and remote APs that
have a virtual AP profile set to tunnel, split-tunnel or
bridge forwarding mode. Note, however, that if a
campus or remote APs has virtual AP profiles
configured in bridge or split-tunnel forwarding mode
but no virtual AP in tunnel mode, those APs will
gather information about 5G-capable clients
independently and will not exchange this information
with other APs that also have bridge or split-tunnel
virtual APs only.
The Band Steering feature will not work unless the
you use the enable the "Local Probe Response"
parameter in the Wireless LAN SSID profile for the
SSID that requires band steering. You can enable the
local probe response parameter using the CLI
command wlan ssid-profile <profile> local-probe-
response.
— disabled
blacklist Enables detection of denial of service (DoS) attacks,
such as ping or SYN floods, that are not spoofed
deauth attacks.
—enabled
blacklist-time Number of seconds that a client is quarantined from
the network after being blacklisted. 3600
seconds (1
hour)
broadcast-filter Filter out broadcast and multicast traffic in the air. — disabled
broadcast-filter-arp If enabled, all broadcast ARP requests are converted
to unicast and sent directly to the client. You can
check the status of this option using the show ap
active and the show datapath tunnel command. If
enabled, the output will display the letter a in the
flags column.
— disabled
clone Name of an existing traffic management profile from
which parameter values are copied. ——
deny-time-range Specify the name of the time range for which the AP
will deny access. Time ranges can be defined using
the CLI command time-range.
——
dos-prevention If enabled, APs ignore deauthentication frames from
clients. This prevents a successful deauth attack
from being carried out against the AP. This does not
affect third-party APs.
— disabled
dot11k-profile Name of an 802.11k profile to be associated with this
VAP. —default
Parameter Description Range Default
1198 | wlan virtual-ap AOS-W 3.4.1 Command Line Interface | Reference Guide
dynamic-mcast-
optimization
Enable/Disable dynamic multicast optimization. This
parameter can only be enabled on a switch with a
PEF license.
disabled
dynamic-mcast-
optimization-
threshold
Maximum number of high-throughput stations in a
multicast group beyond which dynamic multicast
optimization stops.
forward-mode Controls whether 802.11 frames are tunneled to the
switch using generic routing encapsulation (GRE),
bridged into the local Ethernet LAN (for remote APs),
or a combination thereof depending on the
destination (corporate traffic goes to the switch, and
Internet access remains local).
Select one of the following forward modes:
zTunnel: 802.11 frames are tunneled to the switch
using generic routing encapsulation (GRE).
zBridge: 802.11 frames are bridged into the local
Ethernet LAN (for remote APs). An AP in bridge
mode supports only the 802.1x authentication
type.
zSplit-Tunnel: 802.11 frames are either tunneled
or bridged, depending on the destination
(corporate traffic goes to the switch, and Internet
access remains local). An AP in split-tunnel mode
supports only the 802.1x authentication type and
requires a Remote AP license.
NOTE: Virtual APs in bridge or split-tunnel mode
using static WEP should use key slots 2-4 on the
switch . Key slot 1 should only be used with Virtual
APs in tunnel mode.
bridge/
split-
tunnel/
tunnel
tunnel
ha-disc-onassoc If enabled, all clients of a virtual-ap will receive
mobility service on association. — disabled
mobile-ip Enables or disables IP mobility for this virtual AP. — enabled
multi-association Enables or disables multi-association for this virtual
AP. When enabled, this feature allows a station to be
associated to multiple APs. If this feature is disabled,
when a station moves to new AP it will be
deauthorized by the AP to which it was previously
connected, deleting station context and flushing key
caching information.
— disabled
no Negates any configured parameter. — —
rap-operation Configures when the virtual AP operates on a remote
AP:
always—Permanently enables the virtual AP.
backup—Enables the virtual AP if the remote AP
cannot connect to the switch.
persistent—Permanently enables the virtual AP after
the remote AP initially connects to the switch.
standard—Enables the virtual AP when the remote
AP connects to the switch.
Use always and backup for bridge SSIDs.
Use persistent and standard for 802.1x, tunneled,
and split-tunneled SSIDs.
The Remote AP license must be installed.
always/
backup/
persistent/
standard
standard
ssid-profile Name of the SSID profile that applies to this virtual
AP. — “default”
Parameter Description Range Default
AOS-W 3.4.1 Command Line Interface | Reference Guide wlan virtual-ap | 1199
Usage Guidelines
Wireless LAN profiles configure WLANs in the form of virtual AP profiles. A virtual AP profile contains an
SSID profile which defines the WLAN and an AAA profile which defines the authentication for the WLAN.
You can configure and apply multiple instances of virtual AP profiles to an AP group or to an individual AP.
A named VLAN can be deleted although it is configured in a virtual AP profile. If this occurs the virtual AP
profiles becomes invalid. If the named VLAN is added back later the virtual AP becomes valid again.
Example
The following command configures a virtual AP:
wlan virtual-ap corpnet
vlan 1
aaa-profile corpnet
Command History.
strict-compli
ance
If enabled, the AP denies client association requests
if the AP and client station have no common rates
defined. Some legacy client stations which are not
fully 802.11-compliant may not include their
configured rates in their association requests. Such
non-compliant stations may have difficulty
associating with APs unless strict compliance is
disabled.
— disabled
vap-enable Enable or disable the virtual AP. — enabled
vlan The VLAN(s) into which users are placed in order to
obtain an IP address. Enter VLANs as a comma-
separated list of existing VLAN IDs or VLAN names. A
mixture of names and numeric IDs are not allowed.
1
vlan-mobility Enable or disable VLAN (Layer-2) mobility. — disabled
wmm-traffic-
management-profile
Specify the WMM Traffic Management Profile to be
associated with this Virtual AP Profile. —__
Parameter Description Range Default
Release Modification
AOS-W 3.0 Command introduced
AOS-W 3.2 Support for the split tunneling option and the rap-operation parameter was
introduced.
AOS-W 3.3 In support of the IEEE 802.11n standard, a change to the allowed-band parameter
was introduced.
AOS-W 3.3.2 zSupport for the ha-disc-onassoc parameter was introduced.
zThe band-steering parameter was introduced but is not a released feature in
AOS-W 3.3.2. Do not use band-steering without proper guidance from
Alcatel-Lucent.
zSupport for the voip-proxy-arp parameter was introduced.
AOS-W 3.4 The voip-proxy-arp parameter was renamed to broadcast-filter-arp and i t does
not require a Voice license.
The fast-roaming parameter was renamed to multi-association.

1200 | wlan virtual-ap AOS-W 3.4.1 Command Line Interface | Reference Guide
Command Information
Platforms Licensing Command Mode
All platforms Base operating system, except for
the noted parameters. Config mode on master switches

AOS-W 3.4.1 Command Line Interface | Reference Guide wlan voip-cac-profile | 1201
wlan voip-cac-profile
wlan voip-cac-profile <profile>
bandwidth-cac
bandwidth-capacity <bandwidth-capacity>
call-admission-control
call-capacity
call-handoff-reservation <percent>
clone <profile>
disconnect-extra-call
no ...
send-sip-100-trying
send-sip-status-code client|server <code>
wmm_tspec_enforcement
wmm_tspec_enforcement_period <seconds>
Description
This command configures a voice over iP (VoIP) call admission control (CAC) profile.
Syntax
Parameter Description Range Default
<profile> Name of this instance of the profile. The name must
be 1-63 characters. — “default”
bandwidth-cac Select the desired call admission control (CAC)
Mechanism:
zDisable - CAC is based on Call Counts
zEnable - CAC should be based on Bandwidth.
— disabled
bandwidth-capacity Define the maximum bandwidth that can be handled
by one radio, in kbps. The default value is 2000 kbps
(2 Mbps)
——
<bandwidth-capacity> Maximum bandwidth that can be handled by one
radio, in kbps. The default value is 2000 kbps (2
Mbps)
1-600000 2000
call-admission-
control
Enables or disables WiFi VoIP Call Admission Control
features. — disabled
call-capacity Number of simultaneous calls that can be handled by
one radio. 0-8000 10
call-handoff-
reservation
Percentage of call capacity reserved for mobile VoIP
clients on call. 0-100 20%
clone Name of an existing VoIP CAC profile from which
parameter values are copied. ——
disconnect-ex
tra-call
Disconnects calls that exceed the high capacity
threshold by sending a deauthentication frame. — disabled
no Negates any configured parameter. — —
send-sip-100-
trying
Enables sending of SIP 100 - trying messages to a
call originator to indicate that the call is proceeding.
This is useful when the SIP invite may be redirected
through a number of servers before reaching the
switch.
—enabled
1202 | wlan voip-cac-profile AOS-W 3.4.1 Command Line Interface | Reference Guide
Usage Guidelines
The VoIP CAC profile prevents any single AP from becoming congested with voice calls.
Example
The following command enables VoIP CAC:
(host) (config) #wlan voip-cac-profile cac1
call-admission-control
disconnect-extra-call
Command History
Command Information
send-sip-status-code
client|server <code>
Use this parameter with the client or server options
to drop a SIP Invite and send status code back to the
client or server. You must also include one of the
following codes:
z480: Temporary Unavailable
z486: Busy Here
z503: Ser vice Unavailable
znone: Don't send SIP status code
—486
wmm_tspec_en
forcement Enables validation of TSPEC requests for CAC. — disabled
wmm_tspec_en
forcement_
period
Maximum time for the station to start the call after the
TSPEC request. 1-100 1 second
Parameter Description Range Default
Version Change
AOS-W 3.0 Command introduced
AOS-W 3.4 The following parameters were deprecated:
zactive-load-balancing
zhigh-threshold-capacity
znoe-call-capacity
zsccp-call-capacity
zsvp-call-capacity
zvocera-call-capacity
The following parameters were introduced:
zbandwidth-cac
zbandwidth-capacity
zcall-capacity
AOS-W 3.4.1 License requirements changed in AOS-W 3.4.1, so the command now requires
the Policy Enforced Firewall license instead of the Voice Services Module license
required in earlier versions.
Platforms Licensing Command Mode
All platforms Policy Enforced Firewall license Config mode on master switches

AOS-W 3.4.1 Command Line Interface | Reference Guide wlan voip-cac-profile | 1203

1204 | wlan voip-cac-profile AOS-W 3.4.1 Command Line Interface | Reference Guide

AOS-W 3.4.1 Command Line Interface | Reference Guide wms ap | 1205
wms ap
wms ap <bssid> mode {dos|interfering|known-interfering|suspect-unsecure|unsecure|valid}
Description
This command allows you to classify an AP into one of several categories.
Syntax
Usage Guidelines
If AP learning is enabled (with the wms general learn-ap enable command), non-Alcatel-Lucent APs
connected on the same wired network as Alcatel-Lucent APs are classified as valid APs. If AP learning is
disabled, a non-Alcatel-Lucent AP is classified as an unsecure or suspect-unsecure AP.
Example
The following command classifies an interfering AP as a known-interfering AP:
(host) #wms ap 01:00:00:00:00:00 mode known-interfering
Command History
This command was introduced in AOS-W 3.0.
Command Information
Parameter Description
<bssid> BSSID of the AP.
mode Classify the AP into one of the following categories.
dos Enables denial of service for this AP. Any clients connected to this AP are disconnected.
interfering An AP seen in the RF environment but is not connected to the wired network.
known-
interfering
An interfering AP whose BSSID is known.
suspect-
unsecure
A suspected rogue AP that is plugged into the wired side of the network but may not be an
unauthorized device. Automatic shutdown of rogue APs does not apply to these devices.
unsecure A rogue AP that is unauthorized and is plugged into the wired side of the network. You can
configure automatic shutdown of rogue APs in the IDS unauthorized device detection
profile.
valid An AP that is part of the enterprise providing WLAN service.
Platforms Licensing Command Mode
All platforms Base operating system Enable mode on master switches
1206 |wms clean-db AOS-W 3.4.1 Command Line Interface | Reference Guide
wms clean-db
wms clean-db
Description
This command deletes the WMS database.
Syntax
Usage Guidelines
This command deletes all entries from the WMS database. Do not use this command unless instructed to do
so by an Alcatel-Lucent representative.
Example
The following command cleans the WMS database:
(host) #wms clean-db
WMS Database will be deleted. Do you want to proceed with this action [y/n]:
Command History
This command was introduced in AOS-W 3.0.
Command Information
Parameter Description
clean-db Cleans the WMS database.
Platforms Licensing Command Mode
All platforms Base operating system Enable mode on master switches
AOS-W 3.4.1 Command Line Interface | Reference Guide wms client | 1207
wms client
wms client <macaddr> mode {dos|interfering|valid}
Description
This command allows you to classify a wireless client into one of several categories.
Syntax
Usage Guidelines
AOS-W can automatically determine client classification based on client behavior, but this command allows
you to explicitly classify a client. The classification of a client is used in certain policy enforcement
features. For example, if protect-valid-sta is enabled in the IDS Unauthorized Device Profile, then clients
that are classified as valid cannot connect to non-valid APs.
Example
The following command classifies a client as valid:
(host) #wms client 00:00:A4:34:C9:B3 mode valid
Command History
This command was introduced in AOS-W 3.0.
Command Information
Parameter Description
client MAC address of the client.
mode Classify the client into one of the following categories:
dos Enables denial of service to this client.
interfering A client seen in the RF environment that is outside of the enterprise.
valid A client that is part of the enterprise.
Platforms Licensing Command Mode
All platforms Base operating system Enable mode on master switches
1208 |wms export-class AOS-W 3.4.1 Command Line Interface | Reference Guide
wms export-class
wms export-class <filename>
Description
This command exports classification information into a file.
Syntax
Usage Guidelines
This command writes classification data into comma separated values (CSV) files—one for APs and one for
clients. You can import these files into the Alcatel-Lucent Mobility Manager system.
Example
The following command exports classification data into an AP and a client file:
(host) #wms export-class class
Exported data to class_ap.csv and class_sta.csv
Command History
This command was introduced in AOS-W 3.0.
Command Information
Parameter Description
<filename> Name of the file into which you want to export classification information
Platforms Licensing Command Mode
All platforms Base operating system Enable mode on master switches
AOS-W 3.4.1 Command Line Interface | Reference Guide wms export-db | 1209
wms export-db
wms export-db <filename>
Description
This command exports the WMS database to a specified file.
Syntax
Usage Guidelines
The file is exported as an ASCII text file. If you have configured the switch for operation with the Alcatel-
Lucent OmniVista Mobility Manager (OmniVista Mobility Manager), this command will fail and an error will
be returned.
Example
The following command exports the WMS database to a file:
(host) #wms export-db database
Exported WMS DB to database
Command History
This command was introduced in AOS-W 3.0.
Command Information
Parameter Description
<filename> Name of the file into which you want to export the database. The filename plus any
extensions must be no longer than 32 characters and may contain only keyboard
characters.
Platforms Licensing Command Mode
All platforms Base operating system Enable mode on master switches

1210 |wms general AOS-W 3.4.1 Command Line Interface | Reference Guide
wms general
wms general ap-ageout-interval <minutes> | collect-stats {disable|enable} |
learn-ap {enable|disable} | persistent-known-interfering {enable|disable} |
poll-interval <milliseconds> |poll-retries <number> | propagate-wired-macs
{enable|disable} | sta-ageout-interval <minutes> | stat-update
{enable|disable}
Description
This command configures the WLAN management system (WMS).
Syntax
Usage Guidelines
By default, non-Alcatel-Lucent APs that are connected on the same wired networks as Alcatel-Lucent APs
are classified as “rogue” APs. Enabling AP learning classifies non-Alcatel-Lucent APs as “valid” APs.
Typically, you would want to enable AP learning in environments with large numbers of existing non-
Alcatel-Lucent APs and leave AP learning enabled until all APs in the network have been detected and
classified as valid. Then, disable AP learning and reclassify any unknown APs as interfering.
Example
The following command enables AP learning:
(host) #wms general learn-ap enable
To disable AP learning:
(host) #wms general learn-ap disable
Parameter Description Range Default
ap-ageout-inter
val
Time, in minutes, that an AP remains unseen by any
probes before it is deleted from the database. 0 to disable 30 minutes
collect-stats Enables collection of statistics (up to 25,000 entries) on the
master switch for monitored APs and clients. This only
applies when OmniVista Mobility Manager is not
configured.
enable|
disable disabled
learn-ap Enables “learning” of non-Alcatel-Lucent APs. enable|
disable disabled
persistent-known
-interfering
Enables APs that are marked as known interfering from
being aged out. enable|
disable disabled
poll-interval Interval, in milliseconds, for communication between the
switch and Alcatel-Lucent AMs. The switch contacts the
AM at this interval to download AP to station associations,
update policy configuration changes, and download AP
and station statistics.
(any) 60000
milliseconds
(1 minute)
poll-retries Maximum number of failed polling attempts before the
polled AM is considered to be down. (any) 2
propagate-wired-
macs
Enables the propagation of the gateway wired MAC
information. enable|
disable enabled
sta-ageout-in
terval
Time, in minutes, that a client remains unseen by any
probes before it is deleted from the database. 0 to disable 30 minutes
stat-update Enables statistics updating in the database. enable|
disable enabled

AOS-W 3.4.1 Command Line Interface | Reference Guide wms general | 1211
Command History
This command was introduced in AOS-W 3.0.
Command Information
Platforms Licensing Command Mode
All platforms Base operating system Config mode on master switches
1212 |wms import-db AOS-W 3.4.1 Command Line Interface | Reference Guide
wms import-db
wms import-db <filename>
Description
This command imports the specified file into the WMS database.
Syntax
Usage Guidelines
The imported file replaces the WMS database. The imported file must be a valid WMS database file that you
previously exported using the wms export-db command.
Example
The following command imports the WMS database from a file:
(host) #wms import-db database
Command History
This command was introduced in AOS-W 3.0.
Command Information
Parameter Description
<filename> Name of the file into which you want to import into the database. The filename plus any
extensions must be no longer than 32 characters and may contain only keyboard
characters.
Platforms Licensing Command Mode
All platforms Base operating system Enable mode on master switches

AOS-W 3.4.1 Command Line Interface | Reference Guide wms reinit-db | 1213
wms reinit-db
wms reinit-db
Description
This command reinitializes the WMS database to its factory defaults.
Syntax
No parameters.
Usage Guidelines
When you use this command, there is no automatic backup of the current database. If an OmniVista
Mobility Manager server is configured on the switch (see “mobility-manager” on page 351), this command
will fail and return an error.
Example
The following command reinitializes the WMS database:
(host) #wms reinit-db
WMS Database will be re-initialized. Do you want to proceed with this action [y/n ]:
Command History
This command was introduced in AOS-W 3.0.
Command Information
Platforms Licensing Command Mode
All platforms Base operating system Enable mode on master switches

1214 | wms reinit-db AOS-W 3.4.1 Command Line Interface | Reference Guide
AOS-W 3.4.1 Command Line Interface | Reference Guide wms-local system | 1215
wms-local system
wms-local system max-threshold <max-threshold>
Description
This command defines local WMS system settings for the maximum number of APs and client stations.
Syntax
Usage Guidelines
Use this command with caution. Increasing the limit will cause an increase in usage in the memory by WMS.
In general, each entry will consume about 500 bytes of memory. If the setting is bumped up by 2000, then it
will cause an increase in WMS memory usage by 1MB
Example
The following command sets the maximum number of APs and stations at 500.
Command History
This command was introduced in AOS-W 3.3.2.
Command Information
Parameter Description
<max-threshold> Set the max threshold for the total number of APs and Stations. This value can be any 32-
bit number.
Platforms Licensing Command Mode
All platforms Base operating system Config mode on master switches
host) (config)# wms-local system max-threshold 500

1216 | wms-local system AOS-W 3.4.1 Command Line Interface | Reference Guide

AOS-W 3.4.1 Command Line Interface | Reference Guide write | 1217
write
write {erase [all] | memory | terminal}
Description
This command saves the running configuration to memory or displays the running configuration on the
screen. This command can also be used to erase the running configuration and return the switch to factory
defaults.
Syntax
Usage Guidelines
Configuration changes made using the CLI affect only the current session. You must save your changes for
them to be retained across system reboots. Changes are lost if the system reboots before saving the
changes. To save your configuration changes, use the write memory command.
If you use the write erase command, the license key management database on the switch is not affected.
If you use the write erase all command, all databases on the switch are deleted, including the license
key management database. If you reset the switch to the factory default configuration, perform the Initial
Setup as described in the Alcatel-Lucent Quick Start Guide.
If you use the write terminal command, all of the commands used to configure the switch appear on
the terminal. If paging is enabled, there is a pause mechanism that stops the output from printing
continuously to the terminal. To navigate through the output, use any of the commands displayed at the
bottom of the output, as described in below. If paging is disabled, the output prints continuously to the
terminal. For more information about the paging command, see “paging” on page 369..
Example
The following command saves your changes so they are retained after a reboot:
(host) #write memory
The following command deletes the running configuration and databases and returns the switch to the
factory default settings:
Parameter Description
erase Erases the running system configuration file. Rebooting the switch resets it to the factory
default configuration. If you specify all, the configuration and all data in the switch
databases (including the license, WMS, and internal databases) are erased.
memory Saves the current system configuration to memory. Any configuration changes made
during this session will be made permanent.
terminal Displays the current system configuration.
Key Description
Q Exit the display.
U Page up through the output.
spacebar Page down through the output.
/ Enter a text string to search for.
N Repeat the text string to search for.

1218 |write AOS-W 3.4.1 Command Line Interface | Reference Guide
(host) #write erase
Command History
This command was introduced in AOS-W 1.0.
Command Information
Platforms Licensing Command Mode
All platforms Base operating system Enable and Config modes

AOS-W 3.4.1 Command Line Interface | Reference Guide Appendix A: Command Modes | 1219
Appendix A:
Command Modes
The AOS-W command-line interface offers different levels of user access by differentiating between
different command modes.
When you first log in to the CLI, you start your session in User mode, which provides only limited
access for basic operational testing. You must enter an additional password to access Enable mode,
which allows you to issue show commands run certain management functions. Configuration
commands can only be issued in Config mode. You can access Config mode by entering configure
terminal at the command prompt. You can exit your current command mode and return to a lower-level
command mode at any time by entering exit at the command prompt.
The following sections describes how to access each command mode, the command prompt for each
mode, and links to its available commands.
User mode
You always begin a CLI session in user mode, the command mode with the lowest level of user access.
The command prompt for a user mode session is a greater-than (>) symbol:
(host) >
The following commands are available in user mode.
zenable
zexit
zhelp
zlogout
zping
ztraceroute

1220 | Appendix A: Command Modes AOS-W 3.4.1 Command Line Interface | Reference Guide
Enable Mode
To move from user mode to enable mode, you must enter the command enable, press Enter, then
enter config mode password that was defined during the switch’s initial setup process. (The default
password is enable.) Users in enable mode may return to user mode at any time by entering the
command exit.
The command prompt for a CLI session in enable mode is a pound (#) symbol:
(host) #
The following commands are available in enable mode.
Config Mode
To move from enable mode to config mode, enter the command config terminal. Users in config mode
may return to enable mode at any time by entering the command exit.
When you are in config mode, (config) appears before the # prompt:
(host) (config) #
The following commands are available in basic config mode.
zaaa authentication dot1x clear|
|reload-cert
zaaa authentication stateful-dot1x
clear
zaaa inservice
zaaa ipv6 user add
zaaa ipv6 user clear-sessions
zaaa ipv6 user clear-sessions
zaaa ipv6 user delete
zaaa ipv6 user logout
zaaa query-server
zaaa test-server
zaaa user add
zaaa user clear-sessions
zaaa user delete
zaaa user logout
zam
zap wipe out flash
zap-regroup
zap-rename
zapboot
zapdisconnect
zapflash
zaudit-trail
zbackup
zboot
zclock
zconfigure terminal
zcopy
zcrypto isakmp packet-dump
zcrypto pki
zcrypto pki-import
zdatabase synchronize
zdelete
zdir
zdynamic-ip
zencrypt
zexit
zexport
zhalt
zhelp
zlicense
zlocaluserdb
zlocal-userdb-guest
zpacket-capture
zpage
zpaging
zpanic
zpcap
zping
zreload
zreload-peer-sc
zrename
zrestore
zrft
zshow
zstm
zsupport
ztar
ztraceroute
zusb reclassify
zwhoami
zwms ap
zwms clean-db
zwms client
zwms export-class
zwms export-db
zwms import-db
zwms reinit-db
zwrite

AOS-W 3.4.1 Command Line Interface | Reference Guide Appendix A: Command Modes | 1221
zaaa authentication
zaaa bandwidth-contract
zaaa derivation-rules
zaaa inservice
zaaa ipv6 user add
zaaa derivation-rules
zaaa derivation-rules
zaaa profile
zaaa radius-attributes
zaaa rfc-3576-server
zaaa server-group
zaaa sygate-on-demand
zaaa tacacs-accounting
zaaa timers
zaaa user fast-age
zaaa xml-api
zadp
zam
zap enet-link-profile
zap mesh-cluster-profile
zap mesh-ht-ssid-profile
zap regulatory-domain-profile
zap regulatory-domain-profile
zap snmp-profile (deprecated)
zap regulatory-domain-profile
zap system-profile
zap wipe out flash
zap-group
zap-regroup
zap-rename
zapboot
zapdisconnect
zapflash
zarp
zbackup
zbanner motd
zboot
zcellular profile
zcfgm
zclock
zcontroller-ip
zcrypto dynamic-map
zcrypto ipsec
zcrypto isakmp
zcrypto map global-map
zcrypto-local
zdestination
zesi
zexit
zfirewall
zgateway health-check disable
zguest-access-email
zhelp
zhostname
zids
zinterface
zip
zipv6
zlacp
zlocaluserdb
zlocalip
zlocation
zlogging
zloginsession
zmac-address-table
zmaster-redundancy
zmasterip
zmgmt-server
zmgmt-user
zmobility-manager
zmux-address
zmux-loop-prevention
znetdestination
znetservice
zntp server
zpacket-capture-defaults
zpapi-security
zping
zpkt-trace
zpkt-trace-global
zpptp ip local pool
zpriority-map
zprocess monitor
zprompt
zprovision-ap
zrap-wml
zrf
zrouter mobile
zservice
zshutdown
zspanning-tree
zssh
zsyscontact
zsyslocation
ztelnet
ztime-range
ztraceroute
ztrusted
zuplink
zuser-role
zvlan
zvlan-name
zvoip
zvpdn group l2tp
zvpn-dialer
zvrrp
zweb-server
zwhoami
zwlan
zwms general
zwms-local system

1222 | Appendix A: Command Modes AOS-W 3.4.1 Command Line Interface | Reference Guide
Configuration Sub-modes
Some config mode commands can enter you into a sub-mode with a limited number of available
commands specific to that mode. When you are in a configuration sub-mode, the (config) that appears
before the command prompt will change to indicate your current mode; e.g (config-if) for config-
interface mode, and (config-tunnel) for config-tunnel mode.
You can exit a sub-command mode and return to the basic configuration mode at any time by entering
the exit command.