Presentation AWS Quick+Start+ +A+Practitioner+Guide+to+Securing+Your+Cloud+ +
User Manual:
Open the PDF directly: View PDF ![]() .
.
Page Count: 57

AWS Quick Start
A Practitioner’s Guide to Securing Your Cloud
(Like an Expert)
Gabe Hollombe, Senior Technical Evangelist, AWS, APAC
© 2019, Amazon Web Services, Inc. or its affiliates. All rights reserved.
Agenda: Develop your cloud security know-how
•Become familiar with the different types of AWS resources
•Quickly get up to speed with a practical overview of AWS’s identity-based
and network-based security controls
•Know how to interpret and implement AWS security controls
AWS cloud
IAM VPC
controls

© 2019, Amazon Web Services, Inc. or its affiliates. All rights reserved.
Where’s my [AWS] stuff?
© 2019, Amazon Web Services, Inc. or its affiliates. All rights reserved.

© 2019, Amazon Web Services, Inc. or its affiliates. All rights reserved.
AWS region
© 2019, Amazon Web Services, Inc. or its affiliates. All rights reserved.
AWS region
Availability Zone Availability Zone Availability Zone
© 2019, Amazon Web Services, Inc. or its affiliates. All rights reserved.
AWS region
Availability Zone Availability Zone Availability Zone
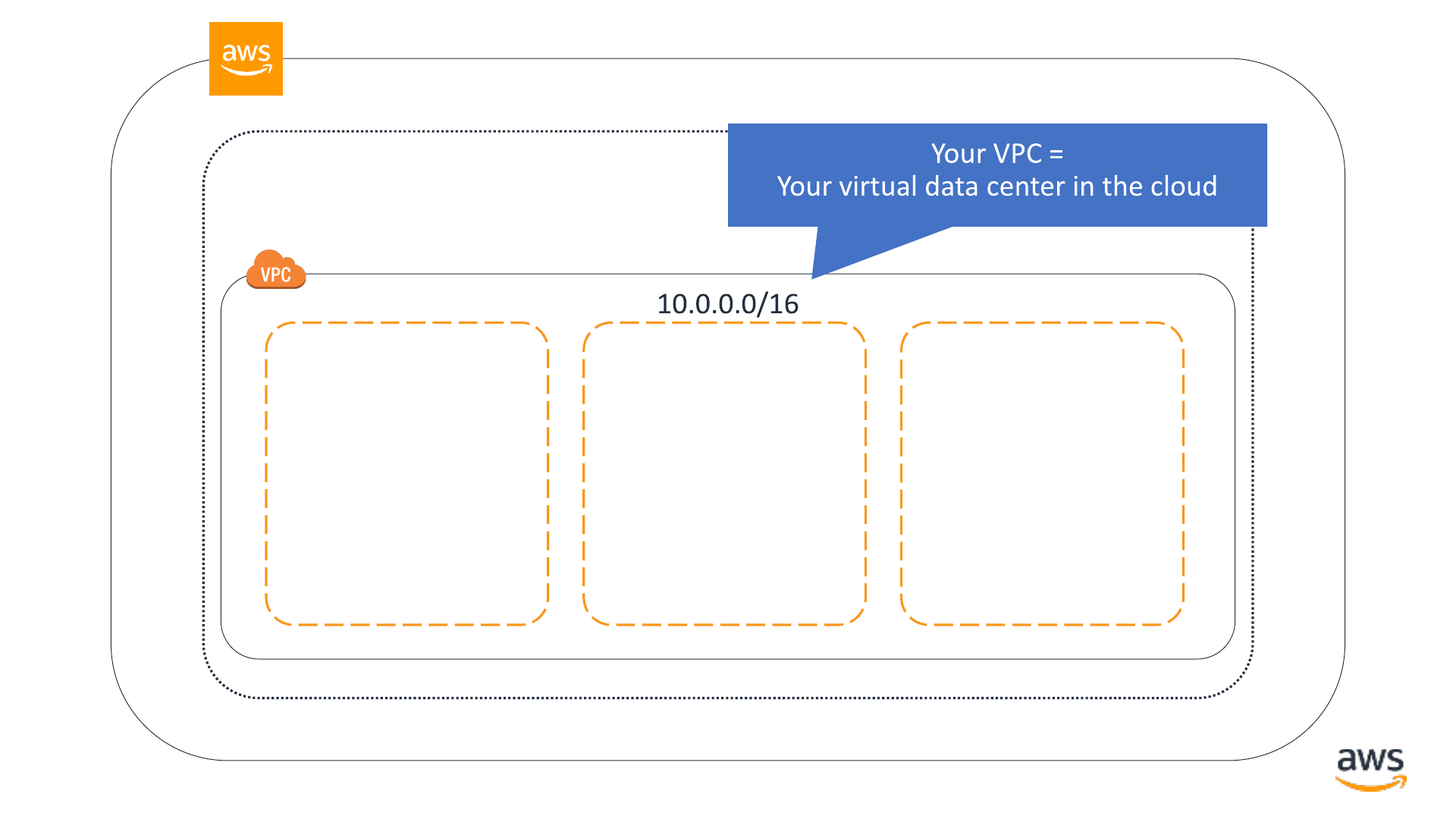
Virtual private cloud
© 2019, Amazon Web Services, Inc. or its affiliates. All rights reserved.
AWS region
Availability Zone Availability Zone Availability Zone
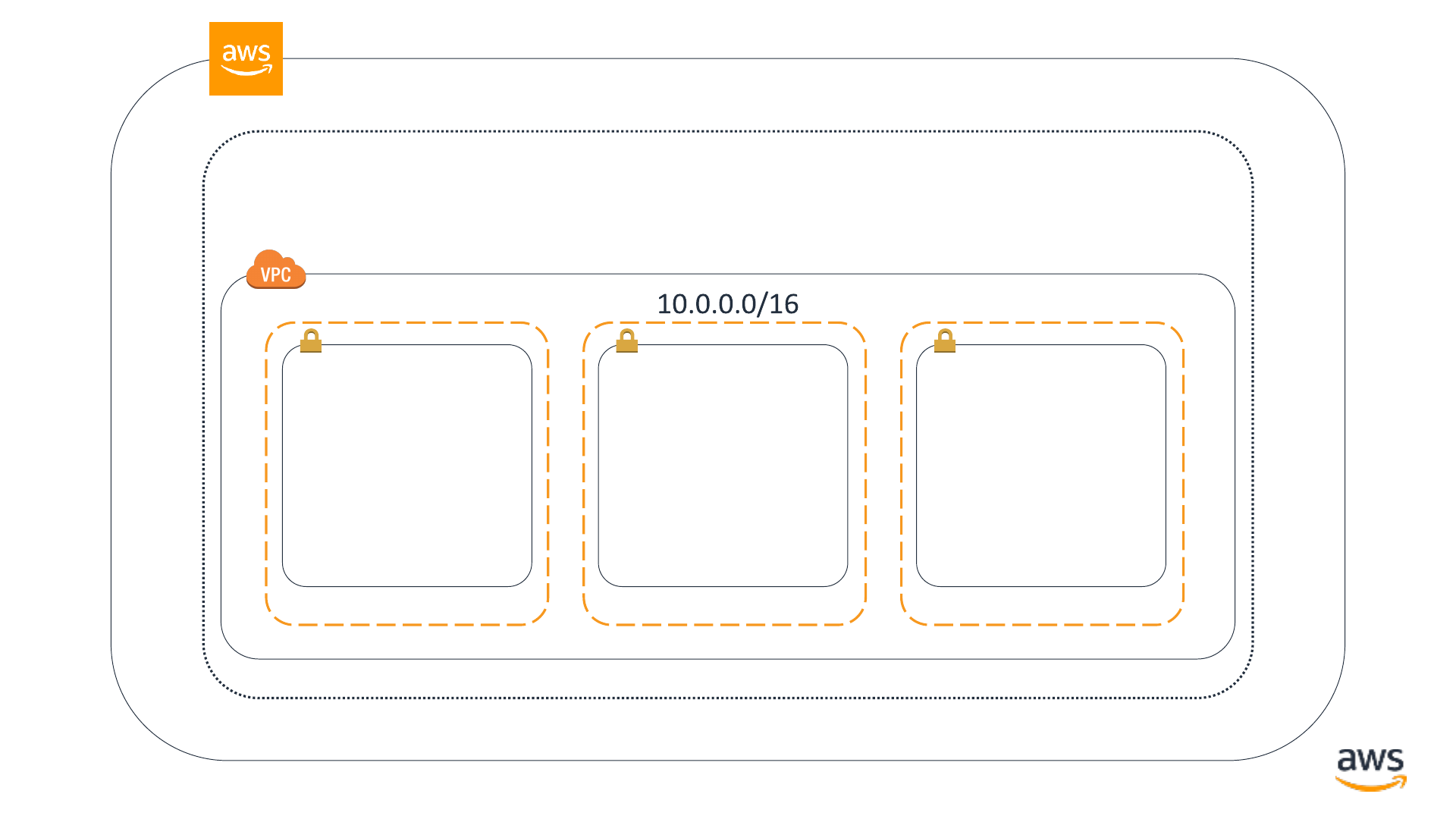
Virtual private cloud
VPC subnet VPC subnet VPC subnet
© 2019, Amazon Web Services, Inc. or its affiliates. All rights reserved.
AWS region
Availability Zone Availability Zone Availability Zone
Virtual private cloud
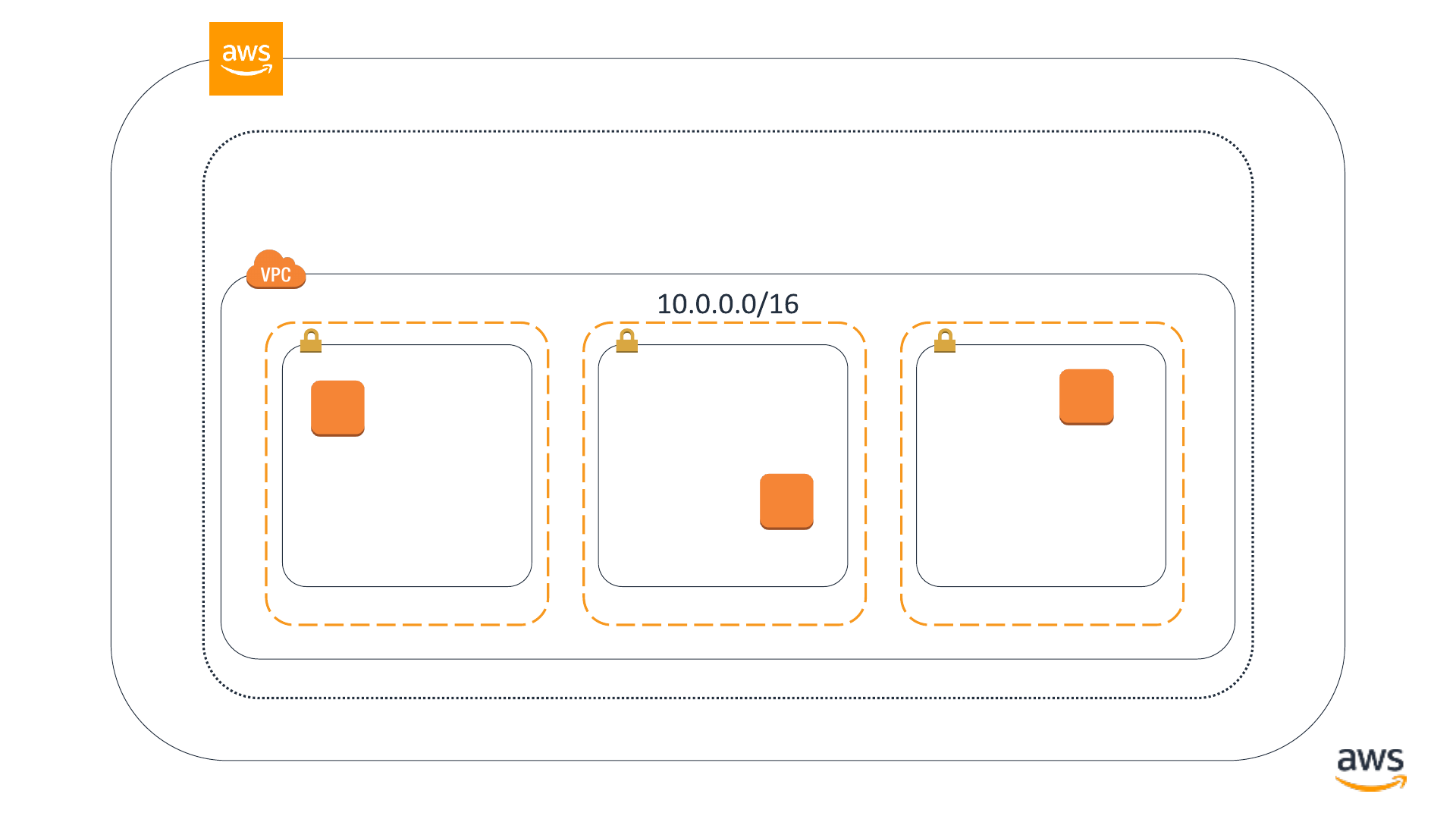
VPC subnet VPC subnet VPC subnet
EC2 instance
EC2 instance
EC2 instance
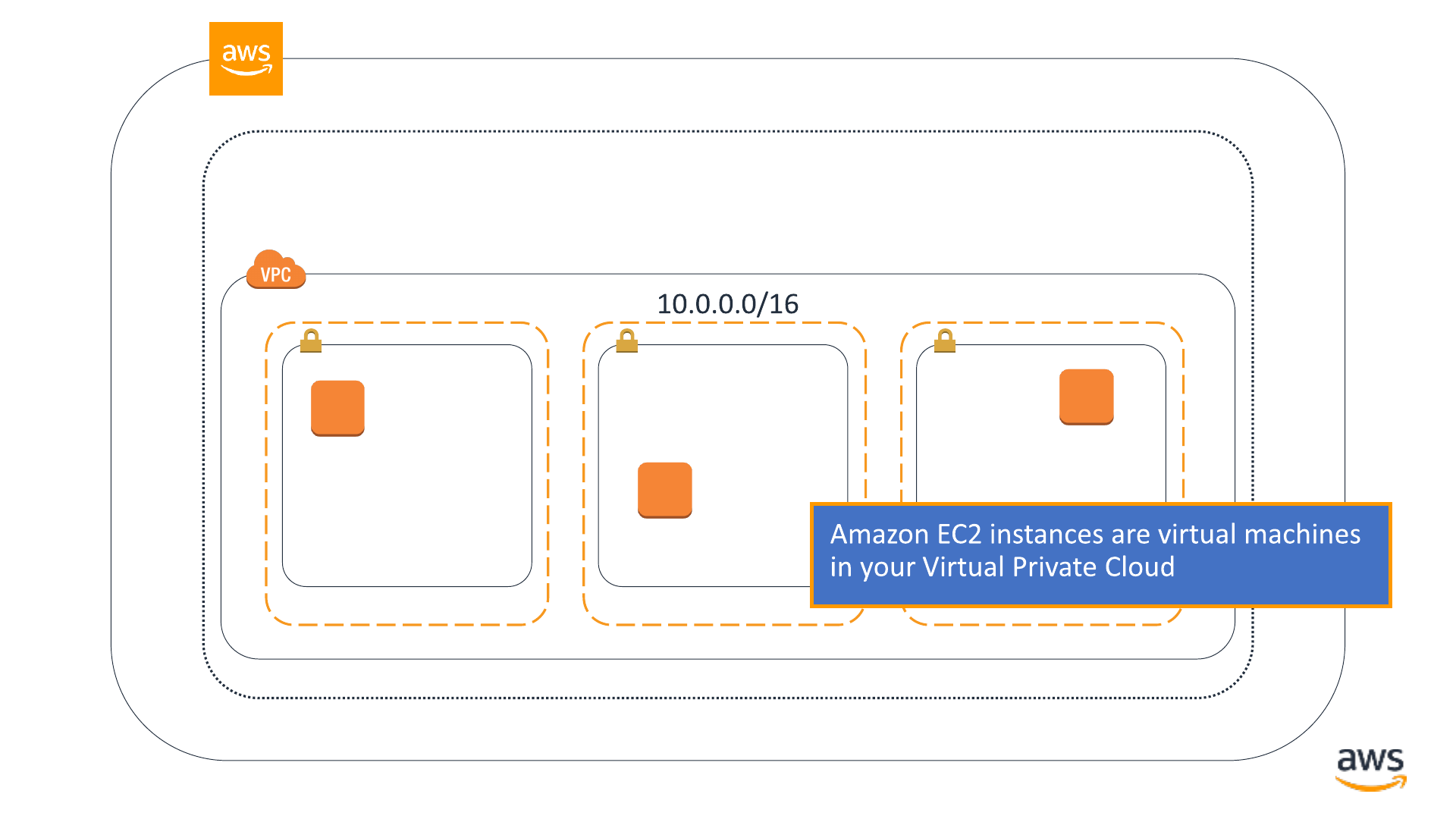
© 2019, Amazon Web Services, Inc. or its affiliates. All rights reserved.
AWS region
Availability Zone Availability Zone Availability Zone
Virtual private cloud
VPC subnet VPC subnet VPC subnet
EC2 instance
EC2 instance
EC2 instance
© 2019, Amazon Web Services, Inc. or its affiliates. All rights reserved.
AWS region
Availability Zone Availability Zone Availability Zone
Virtual private cloud
VPC subnet VPC subnet VPC subnet
EC2 instance
EC2 instance
EC2 instance
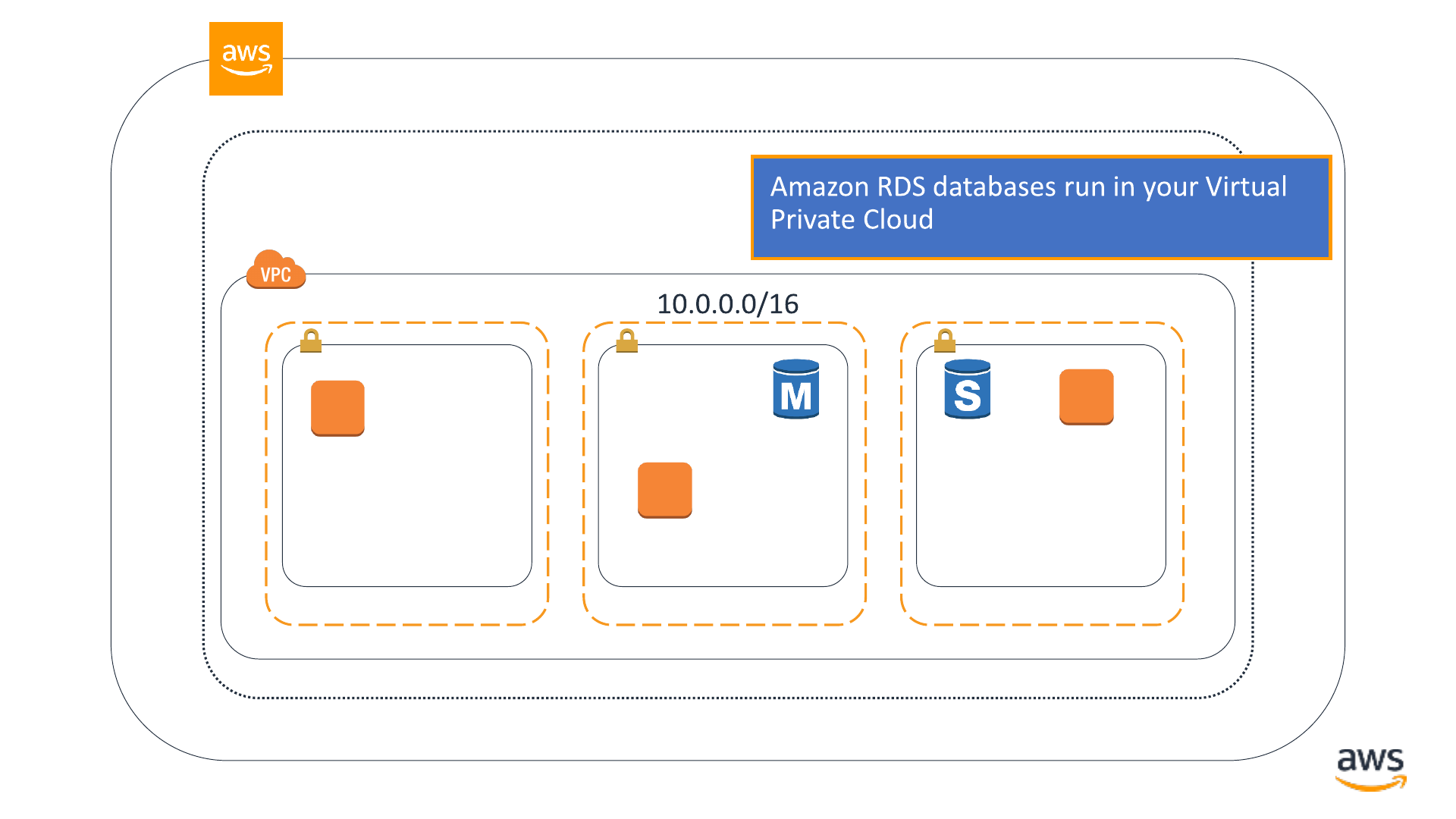
RDS DB
instance
RDS DB
instance standby
© 2019, Amazon Web Services, Inc. or its affiliates. All rights reserved.
AWS region
Availability Zone Availability Zone Availability Zone
Virtual private cloud
VPC subnet VPC subnet VPC subnet
EC2 instance
EC2 instance
EC2 instance
RDS DB
instance
RDS DB
instance standby
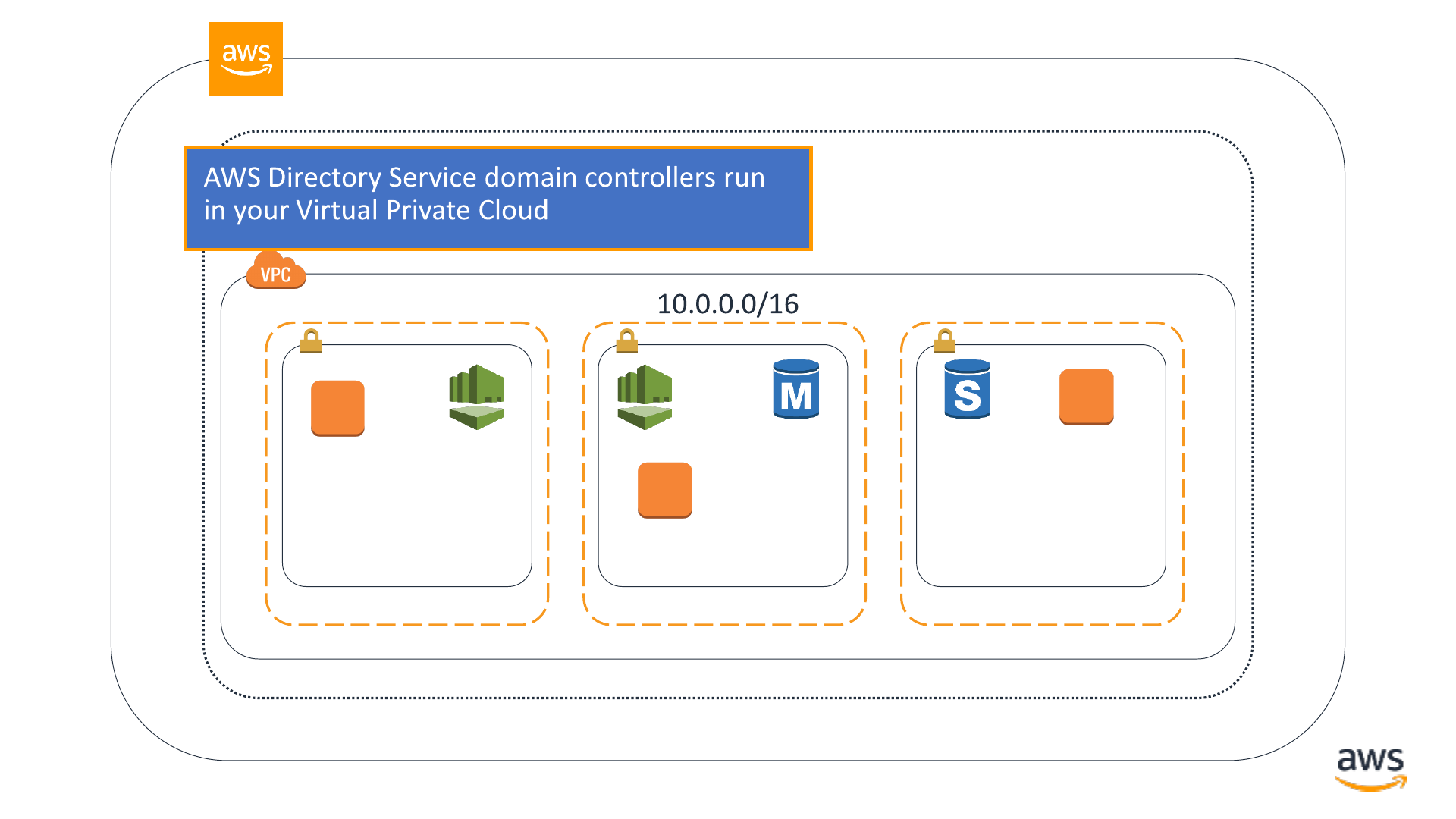
AWS Directory
Service
AWS Directory
Service
© 2019, Amazon Web Services, Inc. or its affiliates. All rights reserved.
AWS region
Availability Zone Availability Zone Availability Zone
Virtual private cloud
VPC subnet VPC subnet VPC subnet
EC2 instance
EC2 instance
EC2 instance
RDS DB
instance
RDS DB
instance standby
AWS Directory
Service
AWS Directory
Service
© 2019, Amazon Web Services, Inc. or its affiliates. All rights reserved.
AWS region
Availability Zone Availability Zone Availability Zone
Virtual private cloud
VPC subnet VPC subnet VPC subnet
EC2 instance
EC2 instance
EC2 instance
RDS DB
instance
RDS DB
instance standby
AWS Directory
Service
AWS Directory
Service
Amazon S3
bucket
Amazon SQS queue Amazon DynamoDB
table
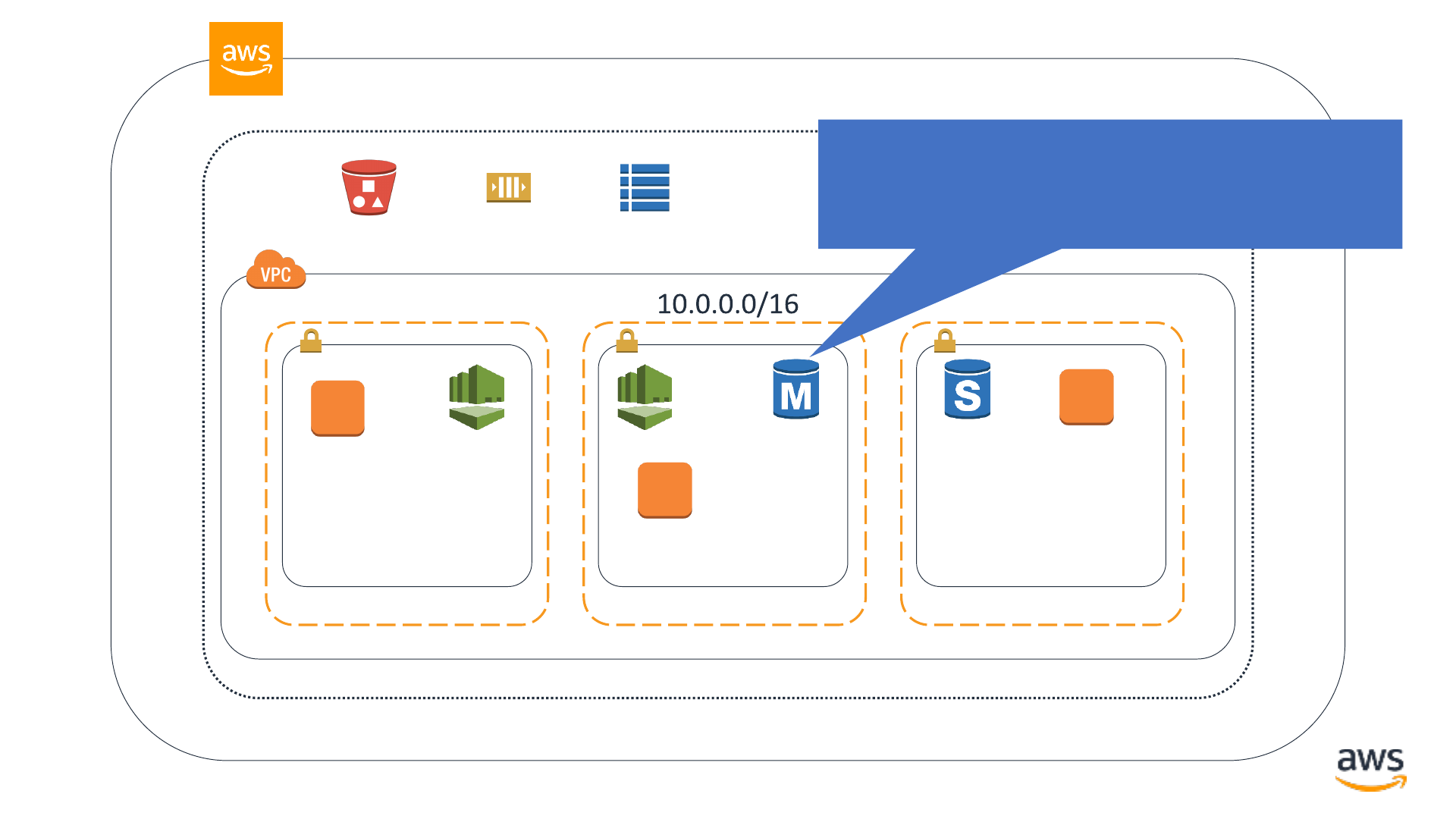
© 2019, Amazon Web Services, Inc. or its affiliates. All rights reserved.
AWS region
Availability Zone Availability Zone Availability Zone
Virtual private cloud
VPC subnet VPC subnet VPC subnet
EC2 instance
EC2 instance
EC2 instance
RDS DB
instance
RDS DB
instance standby
AWS Directory
Service
AWS Directory
Service
Amazon S3
bucket
Amazon SQS queue Amazon DynamoDB
table
$ dig mydatabase.cumxp40klozz.us-east-
2.rds.amazonaws.com +short
10.0.51.81
© 2019, Amazon Web Services, Inc. or its affiliates. All rights reserved.
AWS region
Availability Zone Availability Zone Availability Zone
Virtual private cloud
VPC subnet VPC subnet VPC subnet
EC2 instance
EC2 instance
EC2 instance
RDS DB
instance
RDS DB
instance standby
AWS Directory
Service
AWS Directory
Service
Amazon S3
bucket
Amazon SQS queue Amazon DynamoDB
table
$ dig sqs.us-east-2.amazonaws.com +short
52.95.18.51
© 2019, Amazon Web Services, Inc. or its affiliates. All rights reserved.
AWS region
Availability Zone Availability Zone Availability Zone
Virtual private cloud
VPC subnet VPC subnet VPC subnet
EC2 instance
EC2 instance
EC2 instance
RDS DB
instance
RDS DB
instance standby
AWS Directory
Service
AWS Directory
Service
Amazon S3
bucket
Amazon SQS queue Amazon DynamoDB
table
© 2019, Amazon Web Services, Inc. or its affiliates. All rights reserved.
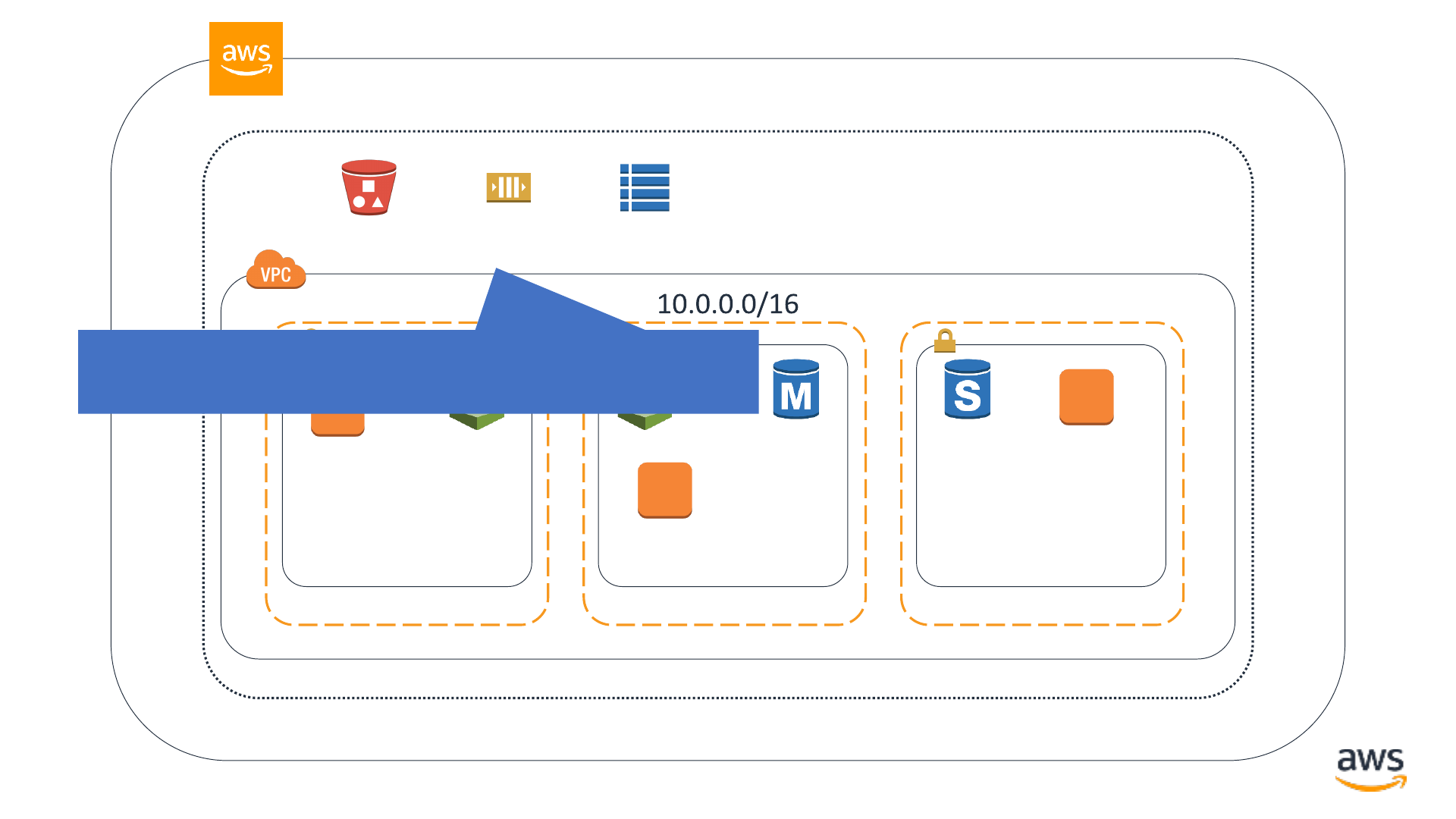
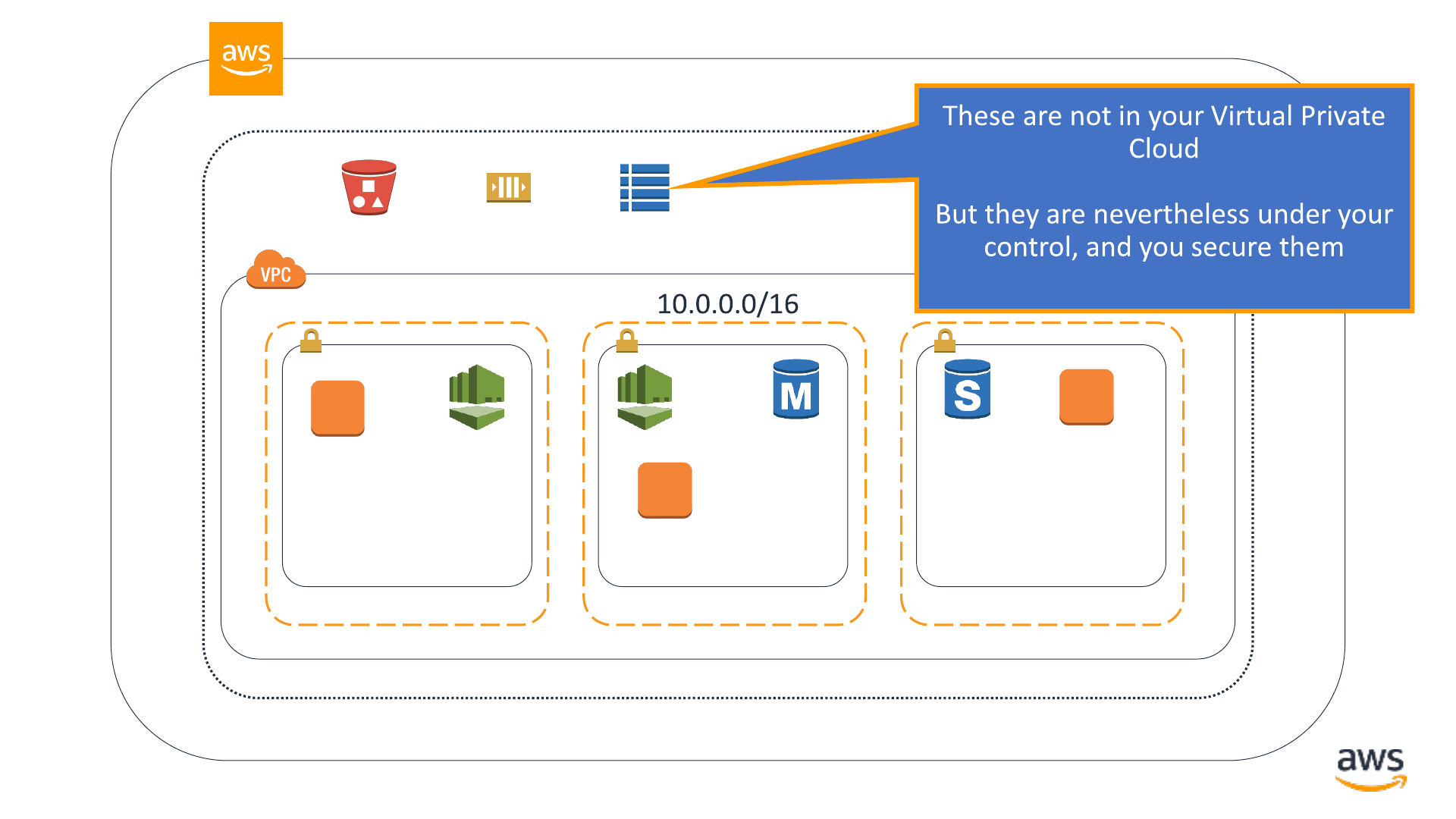
Determining a method for securing AWS resources
•If it’s in your VPC
•Identity and Access Management
(IAM) permissions
•VPC network security controls
•If it’s not in your VPC
•Identity and Access Management
(IAM) permissions

© 2019, Amazon Web Services, Inc. or its affiliates. All rights reserved.
Practical introduction to IAM:
Identity and Access Management

© 2019, Amazon Web Services, Inc. or its affiliates. All rights reserved.
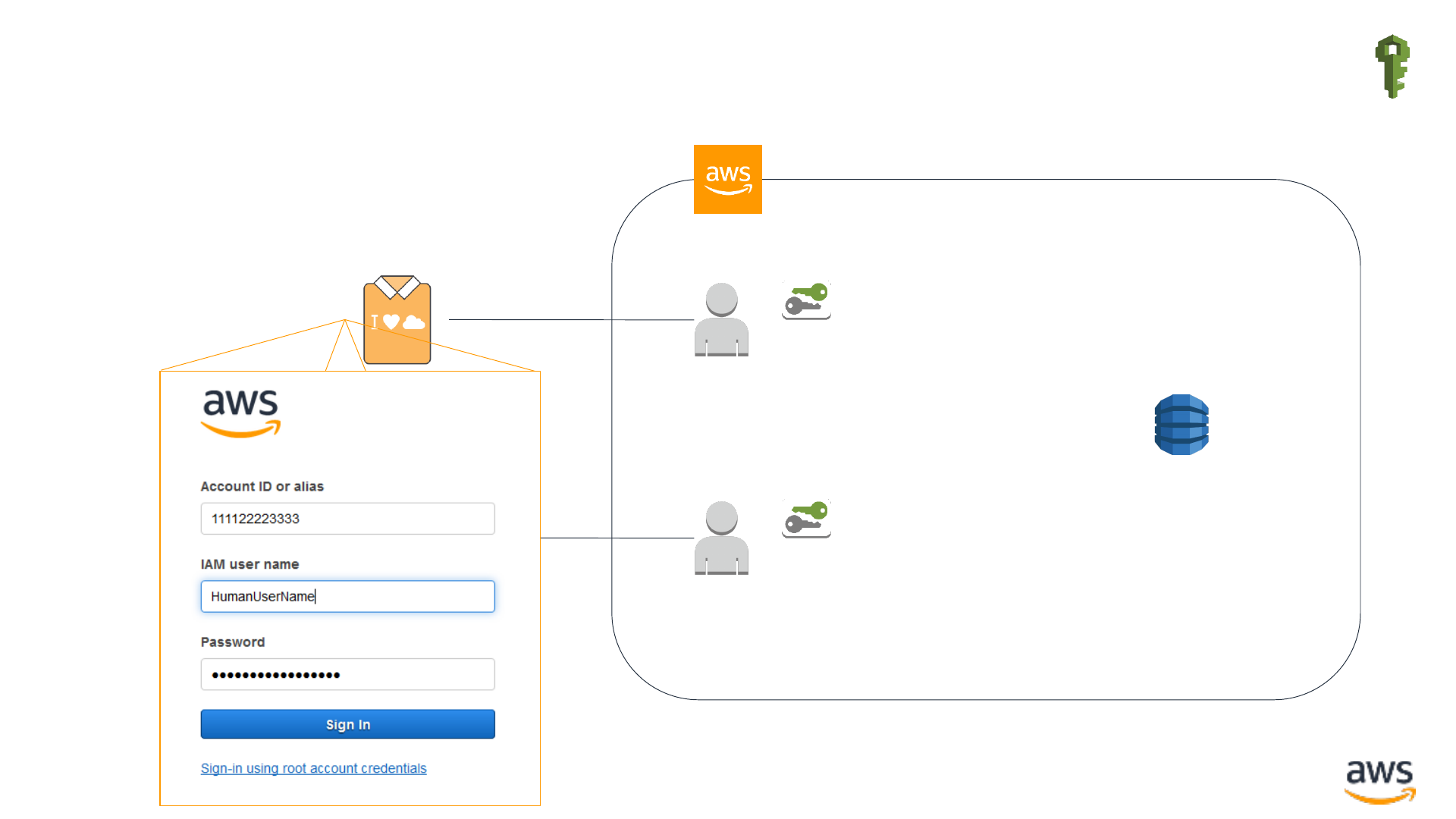
The ABCs of AWS Identity and Access
Management (IAM)
•I: Identity. IAM lets you create identities in your AWS Account who can make
authenticated requests to AWS.
•AM: Access Management. IAM is your tool for defining who has permissions to do
what to which resources in IAM.
•IAM is the AWS-wide permissions control system. So you need to know it.
IAM
© 2019, Amazon Web Services, Inc. or its affiliates. All rights reserved.
I is for Identity: Humans IAM Users
IAM
IAM user
long-term
security
credential
IAM user
long-term
security
credential
Amazon
DynamoDB
Human user
Human user
© 2019, Amazon Web Services, Inc. or its affiliates. All rights reserved.
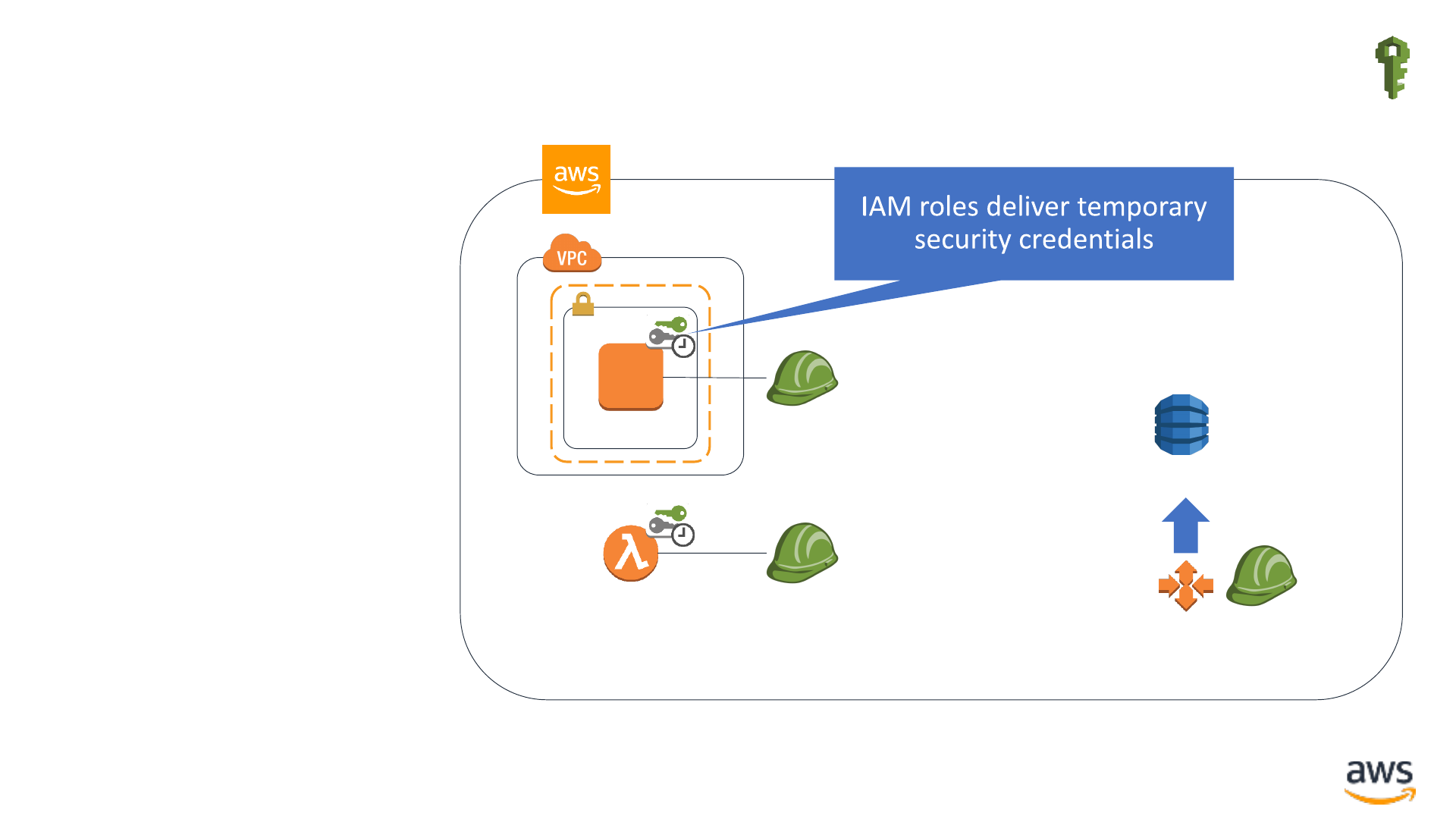
I is for Identity: Robots IAM roles
IAM
EC2 instance
Lambda
function
IAM Role
IAM Role
Amazon
DynamoDB
Application
Auto Scaling
© 2019, Amazon Web Services, Inc. or its affiliates. All rights reserved.
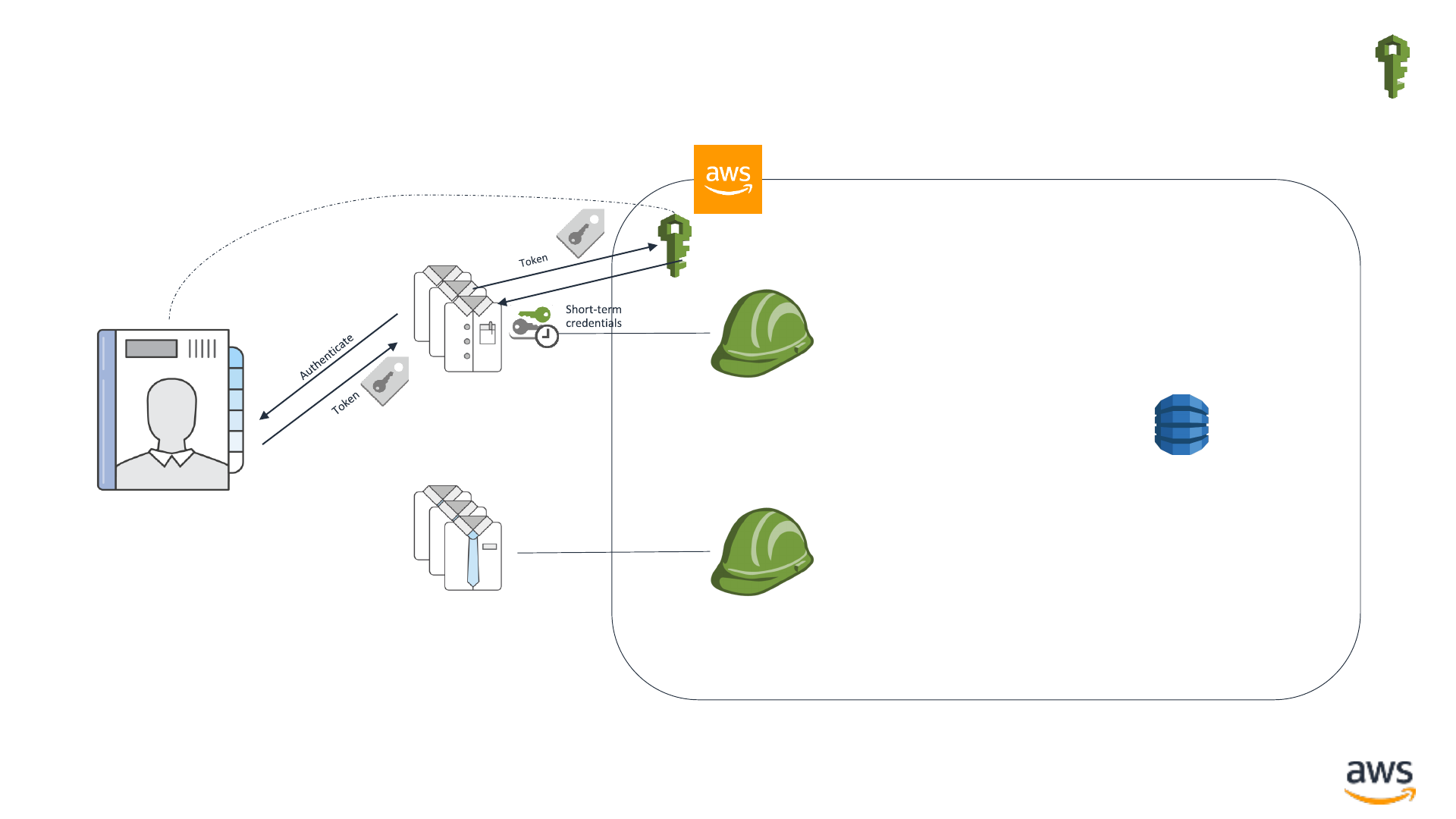
I is for Identity: Humans with external identities
Amazon
DynamoDB
Corporate identities
(analysts)
IAM Role:
Developers
Corporate identities
(developers)
IAM Role:
Analysts
IAM
Corporate
Identification
Provider
© 2019, Amazon Web Services, Inc. or its affiliates. All rights reserved.
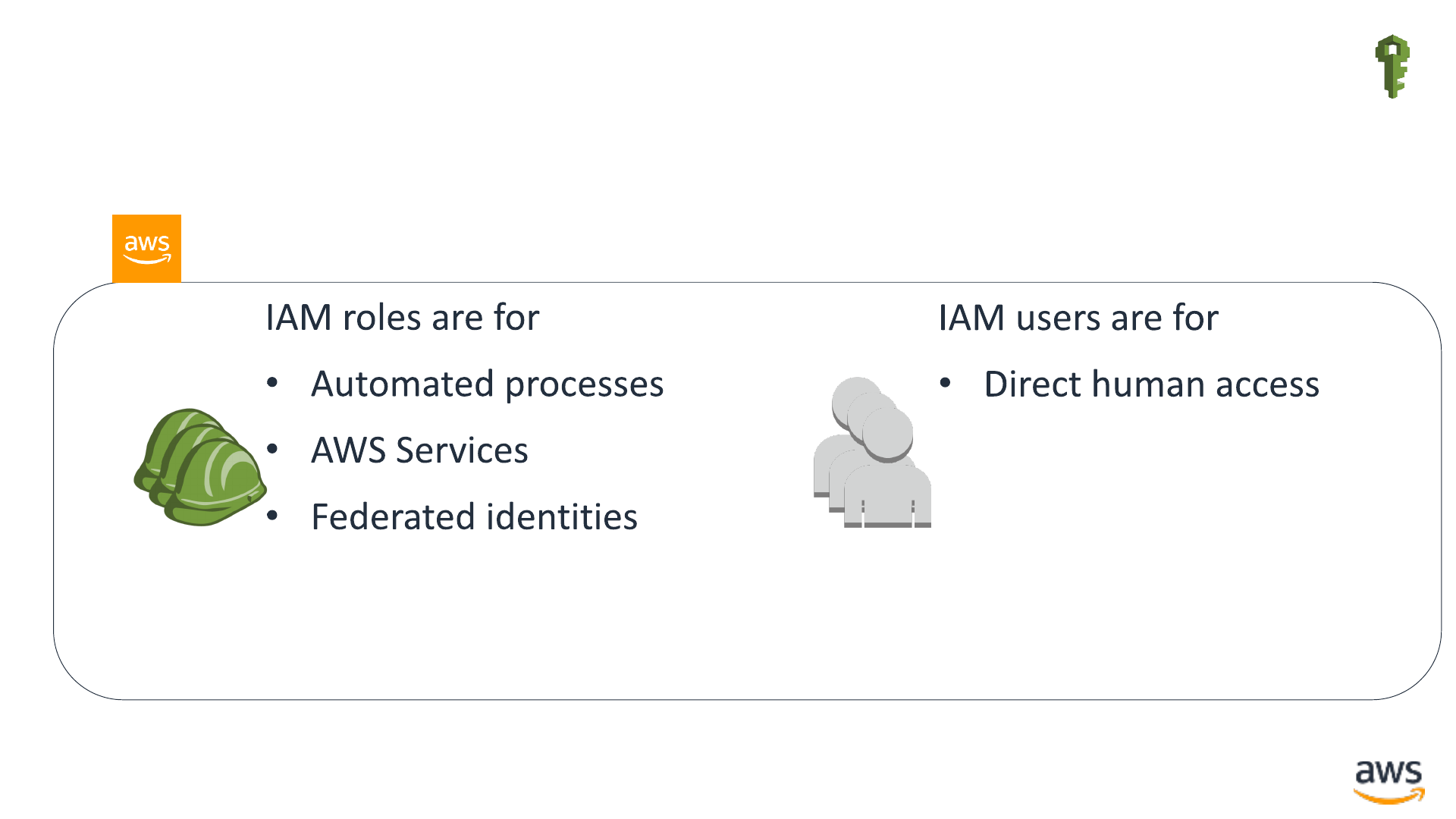
Term: IAM principal
•An IAM principal is an identity defined within an AWS Account
IAM
IAM Roles IAM Users
IAM roles authenticate using
short-lived credentials
IAM users authenticate using
long-lived credentials
© 2019, Amazon Web Services, Inc. or its affiliates. All rights reserved.
Term: IAM policy IAM
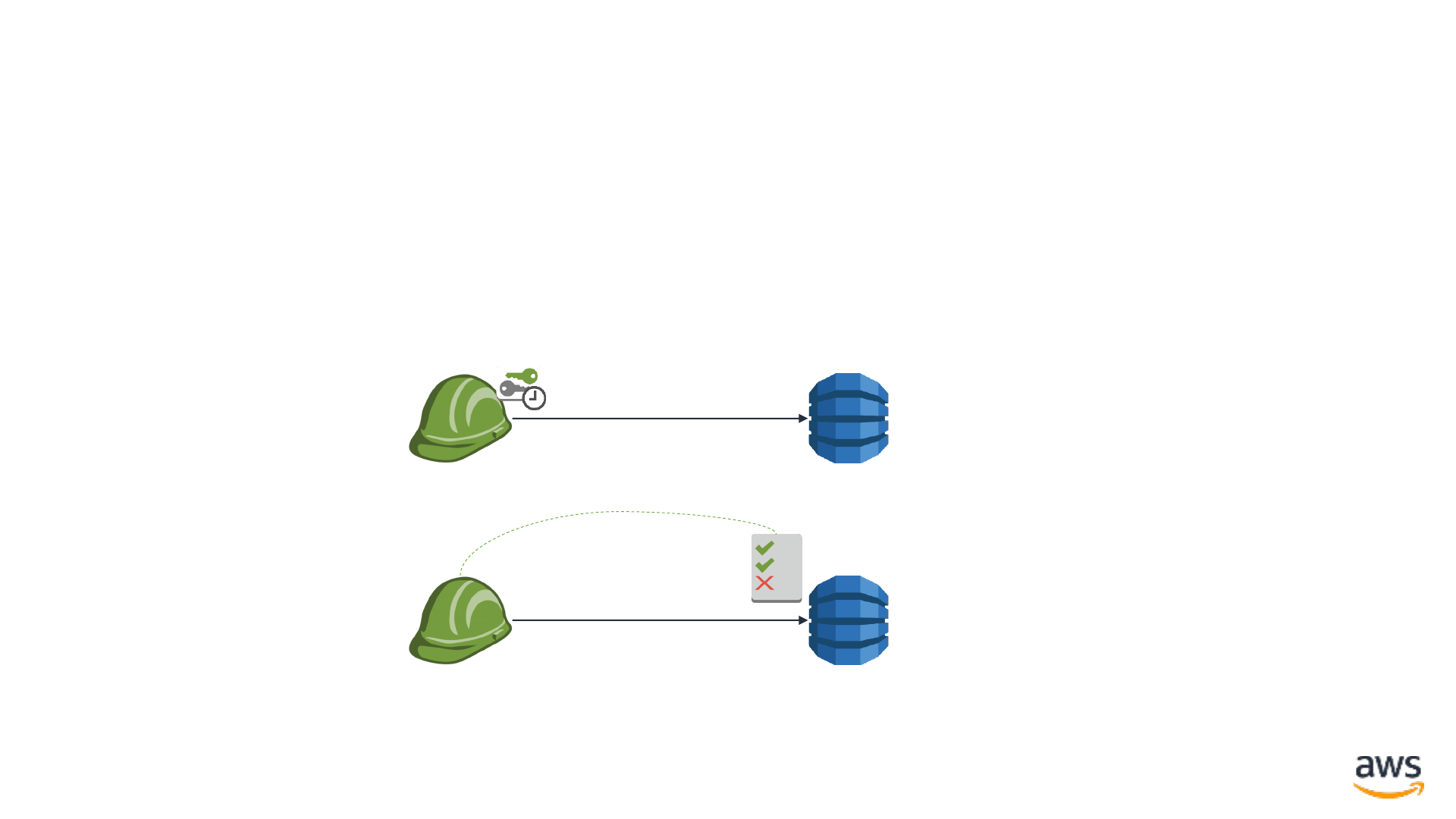
© 2019, Amazon Web Services, Inc. or its affiliates. All rights reserved.
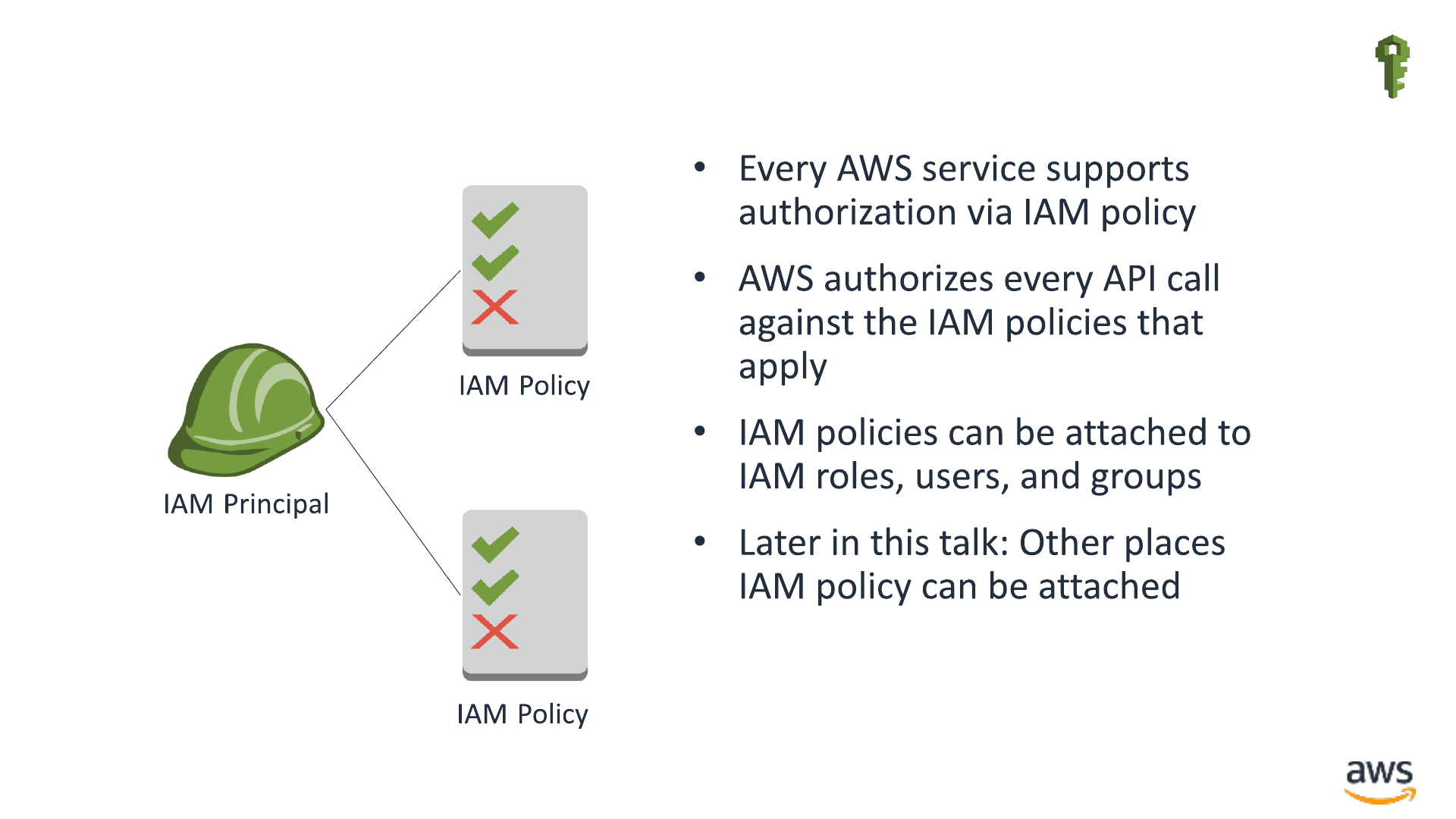
Where does IAM policy matter?
Everywhere in AWS
For an authenticated call to succeed
•The request must have a valid signature for an IAM principal
•IAM policy must specifically authorize the call
© 2019, Amazon Web Services, Inc. or its affiliates. All rights reserved.
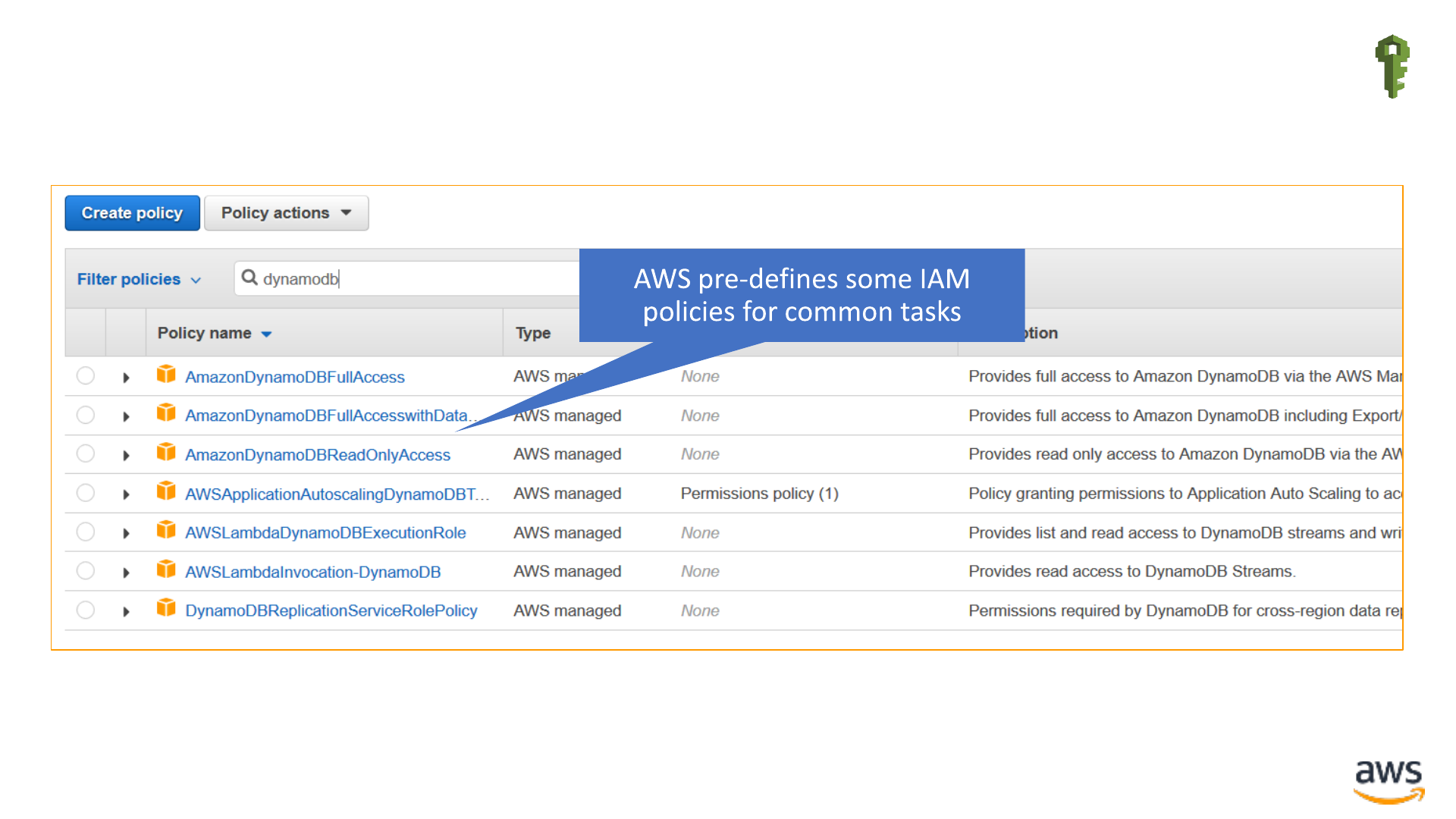
AWS-managed IAM policies IAM
© 2019 Amazon Web Services, Inc. or its affiliates. All rights reserved.
Reading an IAM policy
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": [
"dynamodb:*"
],
"Resource": "*"
}
]
}
IAM
In English: Allowed to take all
DynamoDB actions
© 2019 Amazon Web Services, Inc. or its affiliates. All rights reserved.
Writing more granular IAM Policies:
Actions
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": [
"dynamodb:BatchGetItem",
"dynamodb:GetItem",
"dynamodb:Query"
],
"Resource": "*"
}
]
}
IAM
In English: Allowed to take
only a few specific DynamoDB
actions
© 2019 Amazon Web Services, Inc. or its affiliates. All rights reserved.
Writing more granular IAM Policies:
Resource-level IAM Policies
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": [
"dynamodb:BatchGetItem",
"dynamodb:GetItem",
"dynamodb:Query",
],
"Resource": [
"arn:aws:dynamodb:us-east-2:111122223333:table/MyTableName",
"arn:aws:dynamodb:us-east-2:111122223333:table/MyTableName/index/*"
]
}
]
}
IAM
In English: Allowed to take
specific DynamoDB actions on
a specific table and its indexes

© 2019, Amazon Web Services, Inc. or its affiliates. All rights reserved.
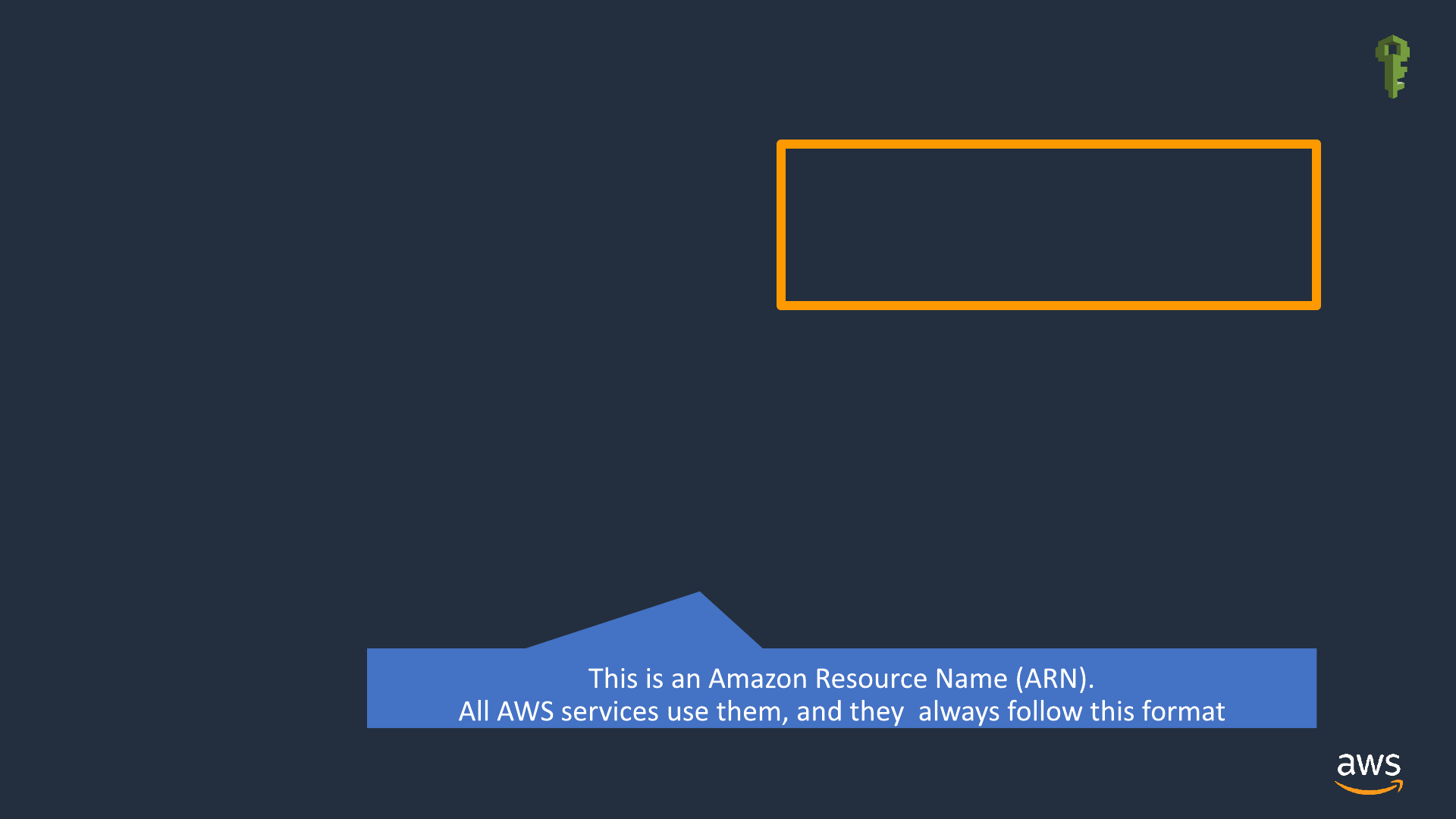
Term: Amazon Resource Name (ARN)
•Resource: A thing in AWS. Examples: S3 bucket, DynamoDB table, EC2
instance, VPC. Even IAM principals have ARNs.
•ARN: A fully-qualified name for that resource, used throughout AWS
•arn:aws:dynamodb:us-east-2:111122223333:table/MyTableName
•service region accountId service-specific name
IAM
© 2019 Amazon Web Services, Inc. or its affiliates. All rights reserved.
Writing more granular IAM policies:
Conditions
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": [
"dynamodb:*“
],
"Resource": "*",
"Condition": {
"StringEquals": {
"aws:RequestedRegion": [
"us-east-2"
]
}
}
]
}
IAM
In English: Allowed to use
DynamoDB only in the us-
east-2 region
© 2019, Amazon Web Services, Inc. or its affiliates. All rights reserved.
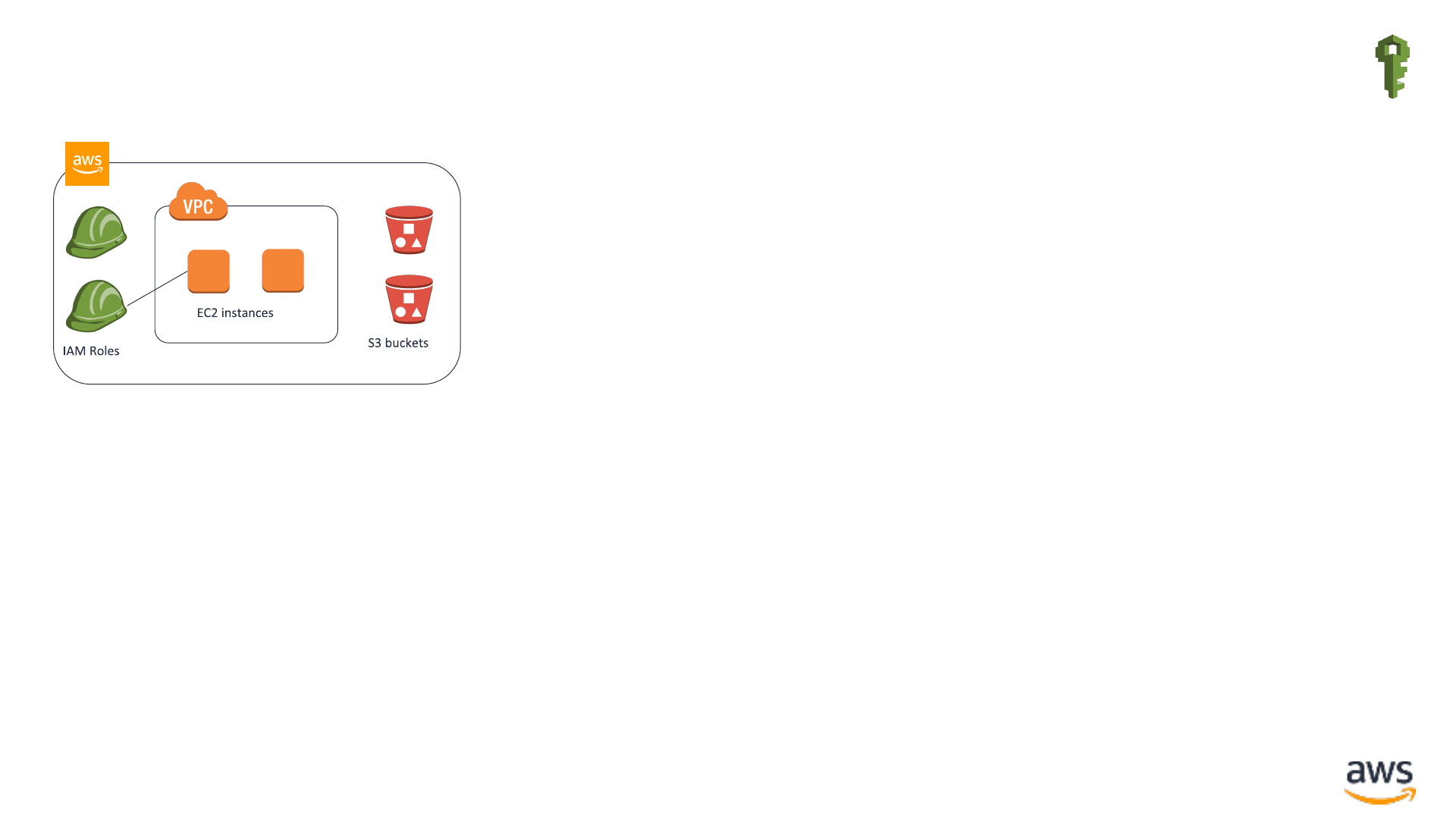
Securing AWS resources across multiple accounts IAM
© 2019, Amazon Web Services, Inc. or its affiliates. All rights reserved.
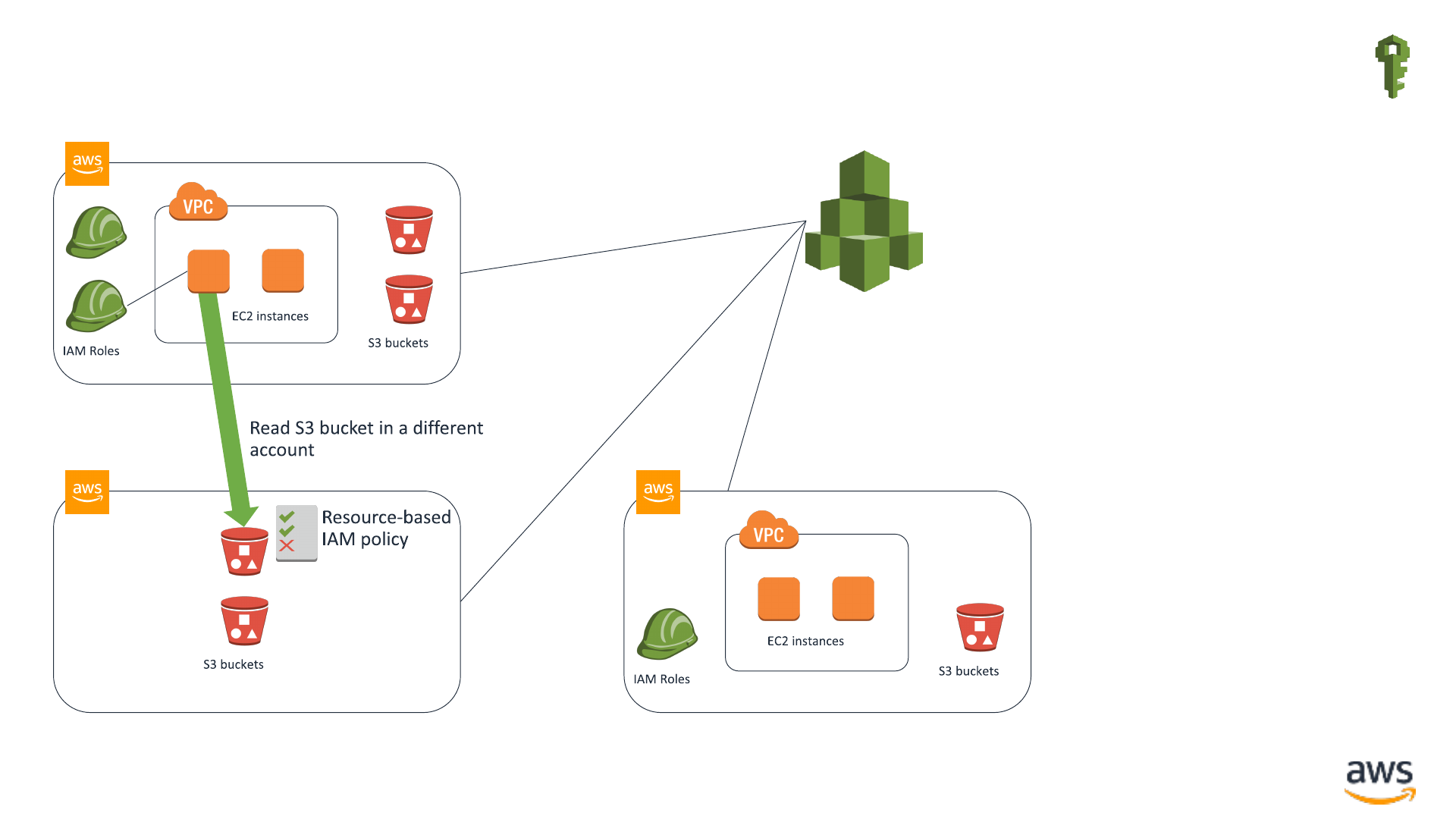
Securing AWS resources across multiple accounts
AWS
Organizations
IAM

© 2019 Amazon Web Services, Inc. or its affiliates. All rights reserved.
Example: Resource-based policy
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Principal“: {
"AWS": [ {
"arn:aws:iam::444455556666:role/MyRole"
} ],
"Action": [
"s3:GetObject"
],
"Resource": "arn:aws:s3:::my-s3-bucket/some/path/*"
}
]
}
IAM
In English: The “MyRole” IAM
Role in account 444455556666
(a different account) can read
objects from this bucket under
/some/path/
© 2019, Amazon Web Services, Inc. or its affiliates. All rights reserved.
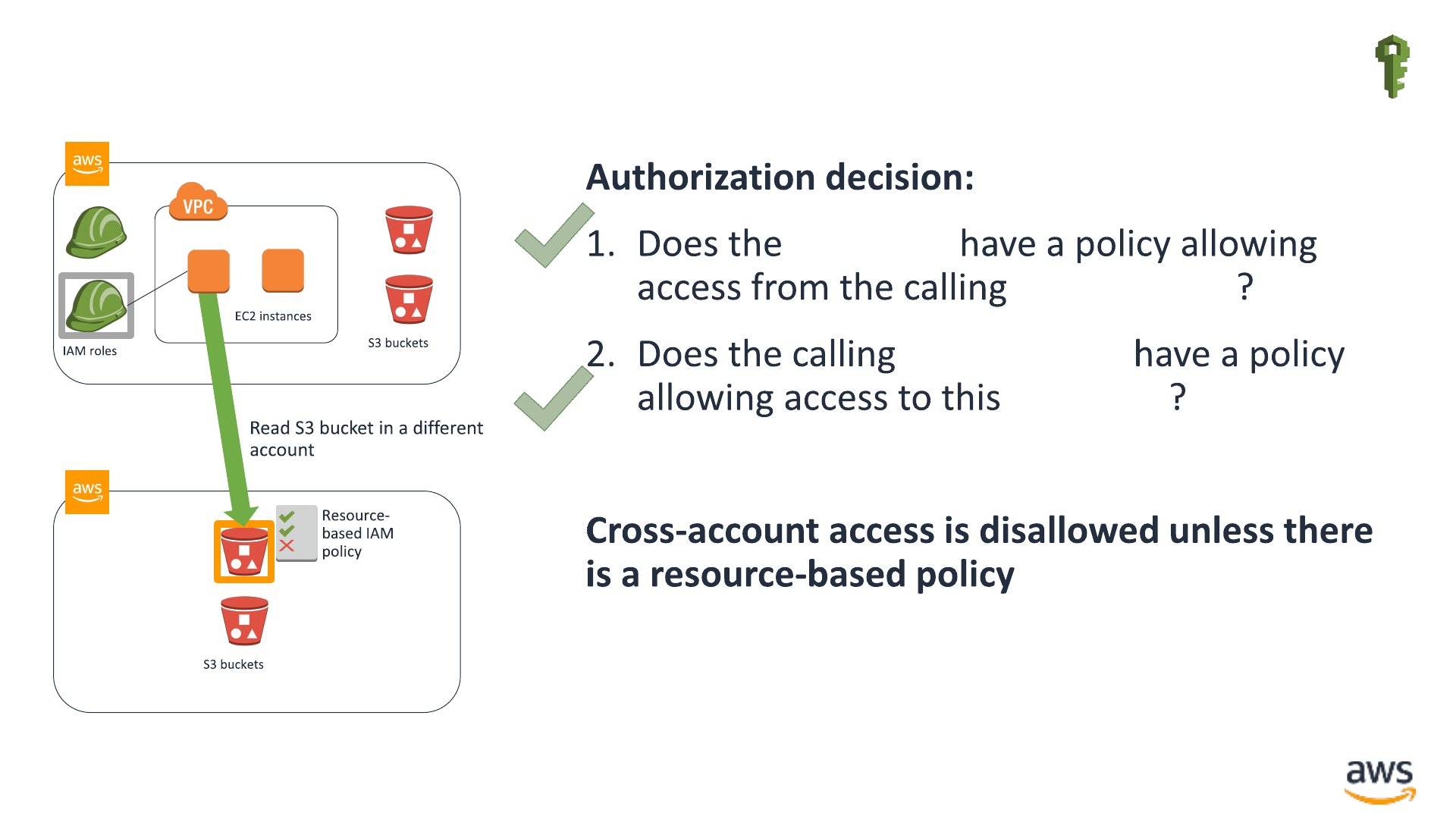
IAM Authorization of cross-account access IAM
S3 bucket
IAM principal
IAM principal
S3 bucket
© 2019, Amazon Web Services, Inc. or its affiliates. All rights reserved.
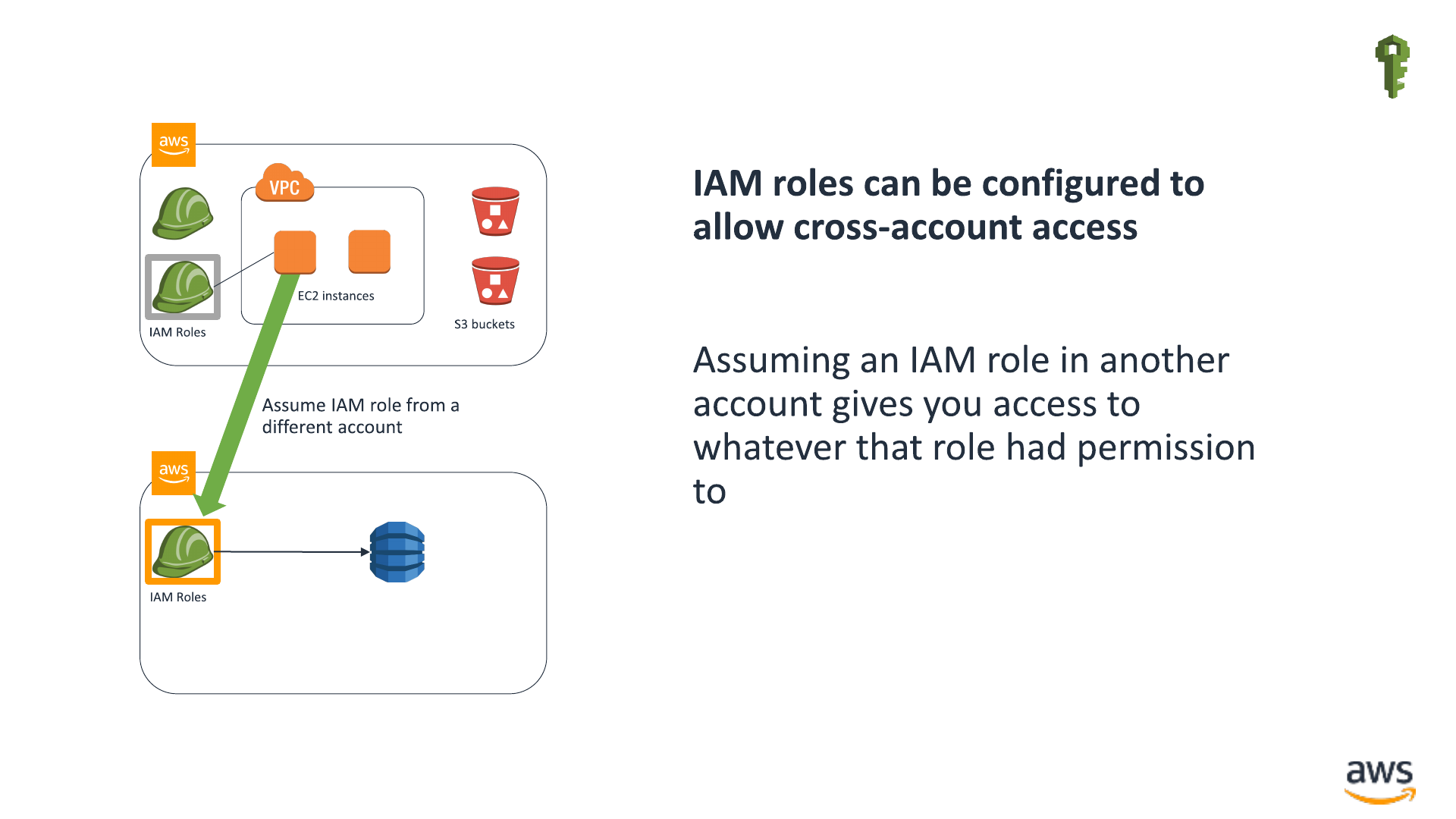
IAM authorization of cross-account access IAM
Amazon
DynamoDB
© 2019, Amazon Web Services, Inc. or its affiliates. All rights reserved.
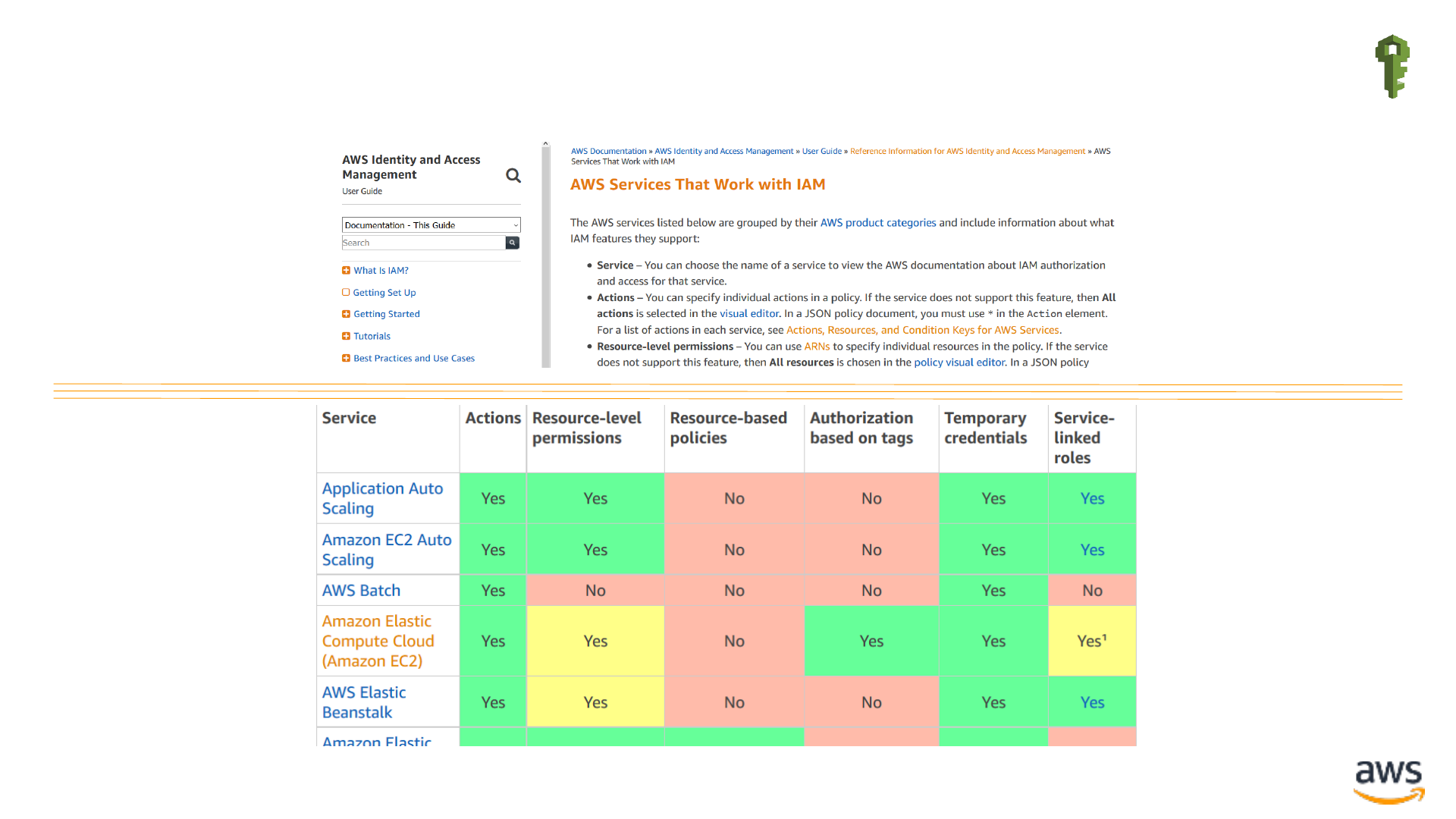
The IAM Reference IAM

© 2019, Amazon Web Services, Inc. or its affiliates. All rights reserved.
Practical introduction to Virtual Private Cloud
network security
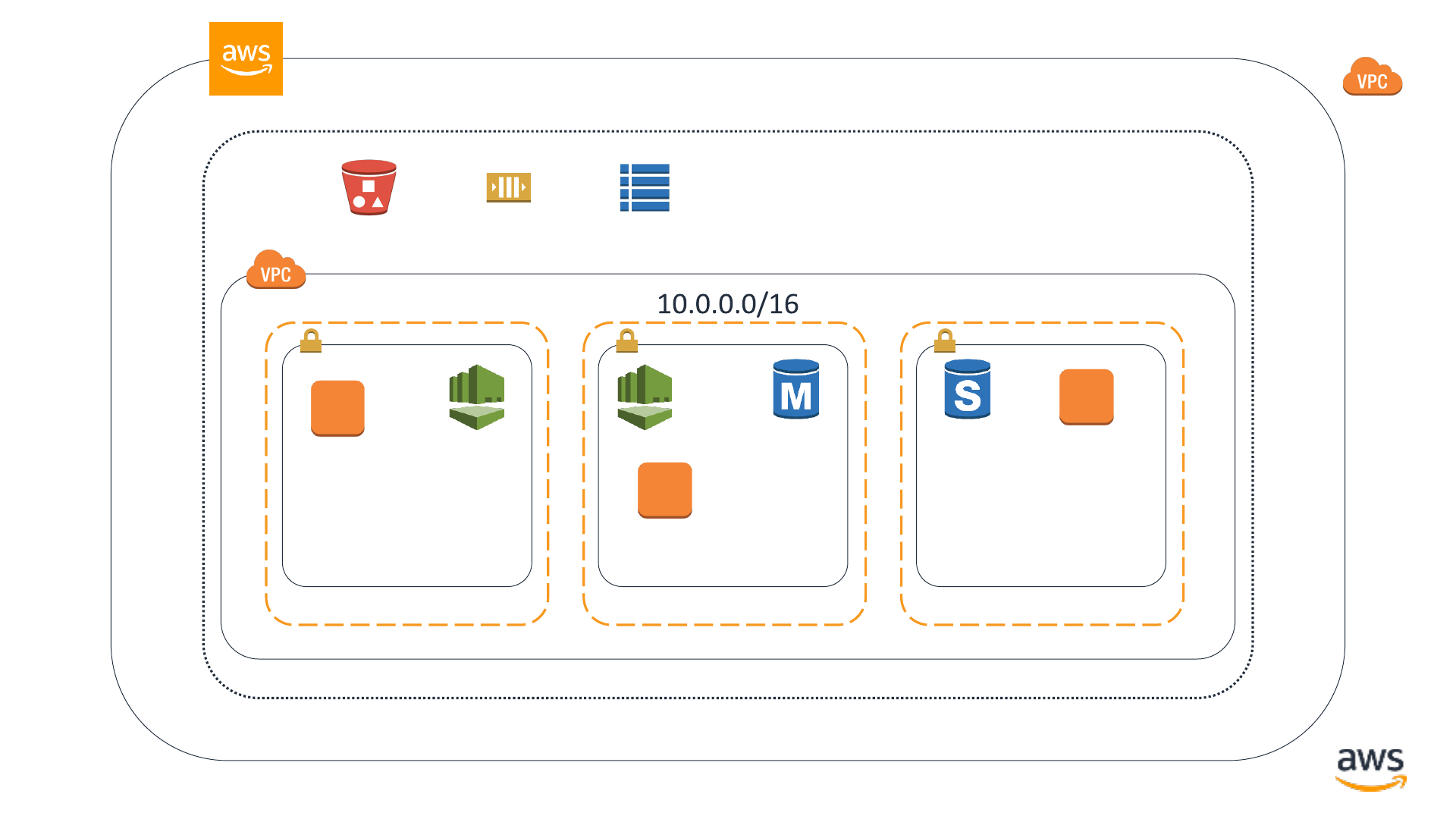
© 2019, Amazon Web Services, Inc. or its affiliates. All rights reserved.
AWS region
Availability Zone Availability Zone Availability Zone
Virtual private cloud
VPC subnet VPC subnet VPC subnet
EC2 instance
EC2 instance
EC2 instance
RDS DB
instance
RDS DB
instance standby
AWS Directory
Service
AWS Directory
Service
Amazon S3
bucket
Amazon SQS queue Amazon DynamoDB
table
© 2019, Amazon Web Services, Inc. or its affiliates. All rights reserved.
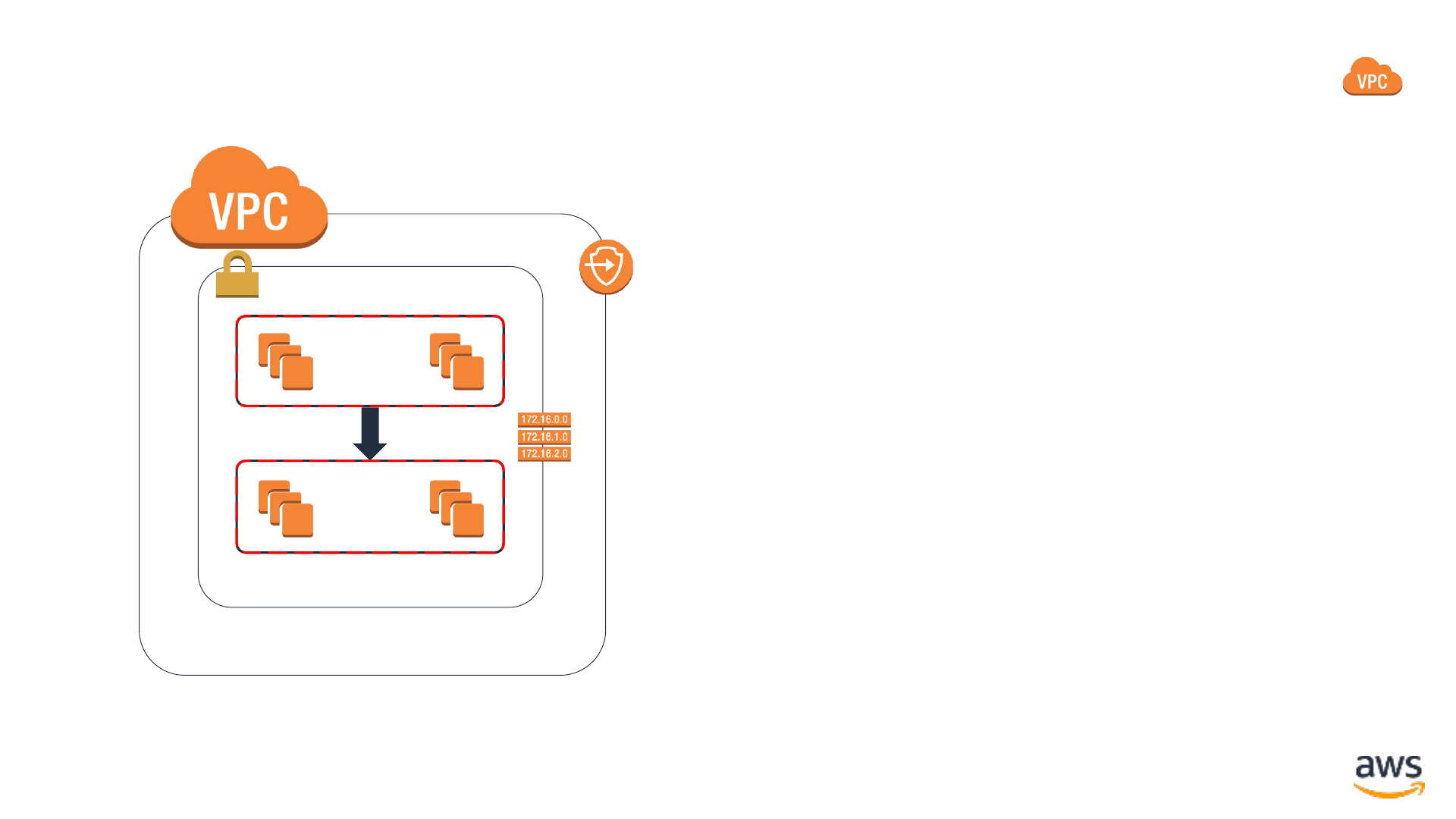
Secure connectivity with Amazon VPC
•Security Groups: Authorize
only the traffic you expect
•Routing: Route traffic headed
out of your VPC only to
expected destinations
•VPC Endpoints: Create
specific, least-privilege points
of connectivity
Virtual private cloud
VPC subnet
© 2019, Amazon Web Services, Inc. or its affiliates. All rights reserved.
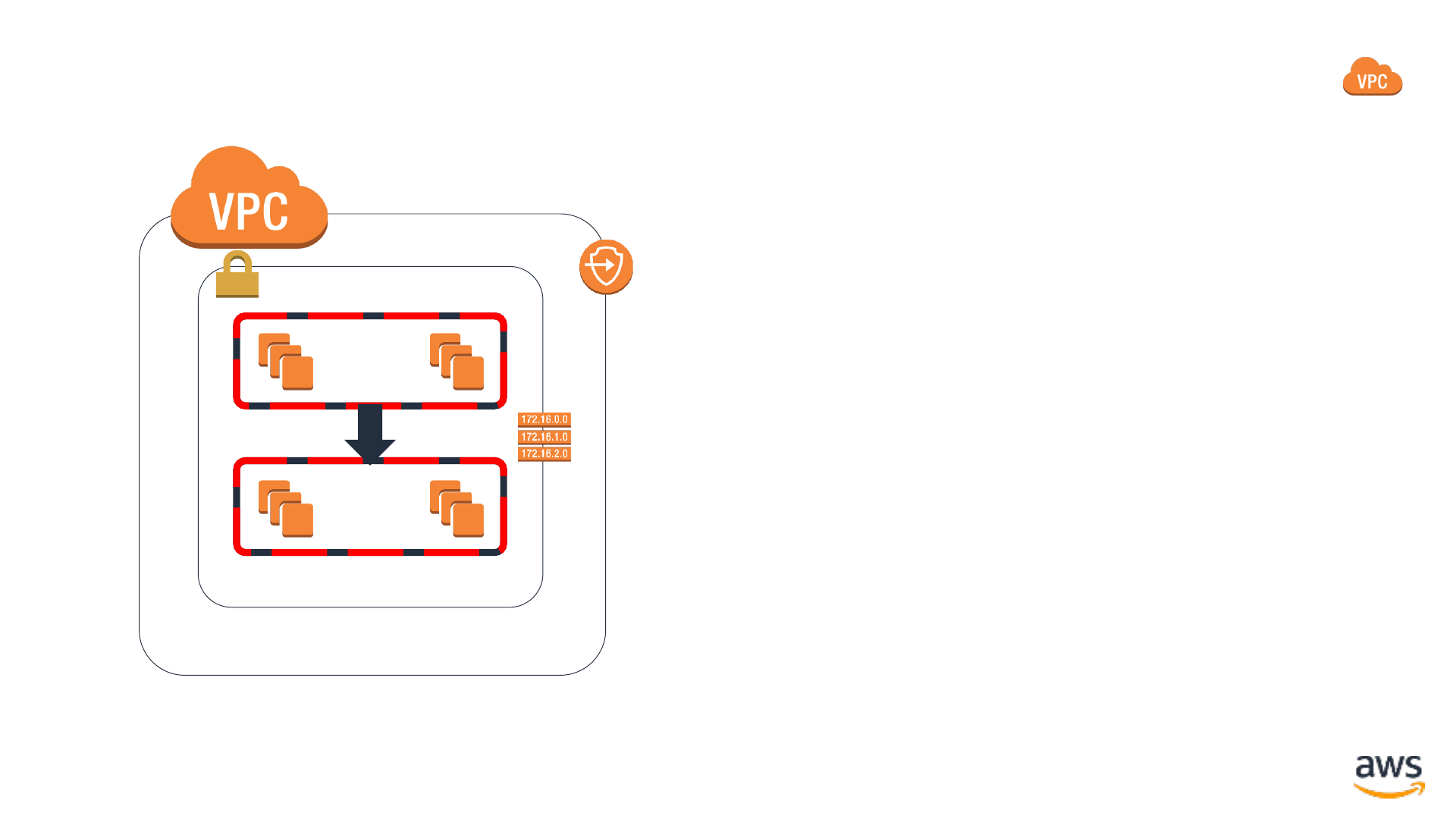
Secure connectivity with Amazon VPC
•Security Groups: Authorize
only the traffic you expect
•Routing: Route traffic headed
out of your VPC only to
expected destinations
•VPC Endpoints: Create
specific, least-privilege points
of connectivity
Virtual private cloud
VPC subnet
© 2019, Amazon Web Services, Inc. or its affiliates. All rights reserved.
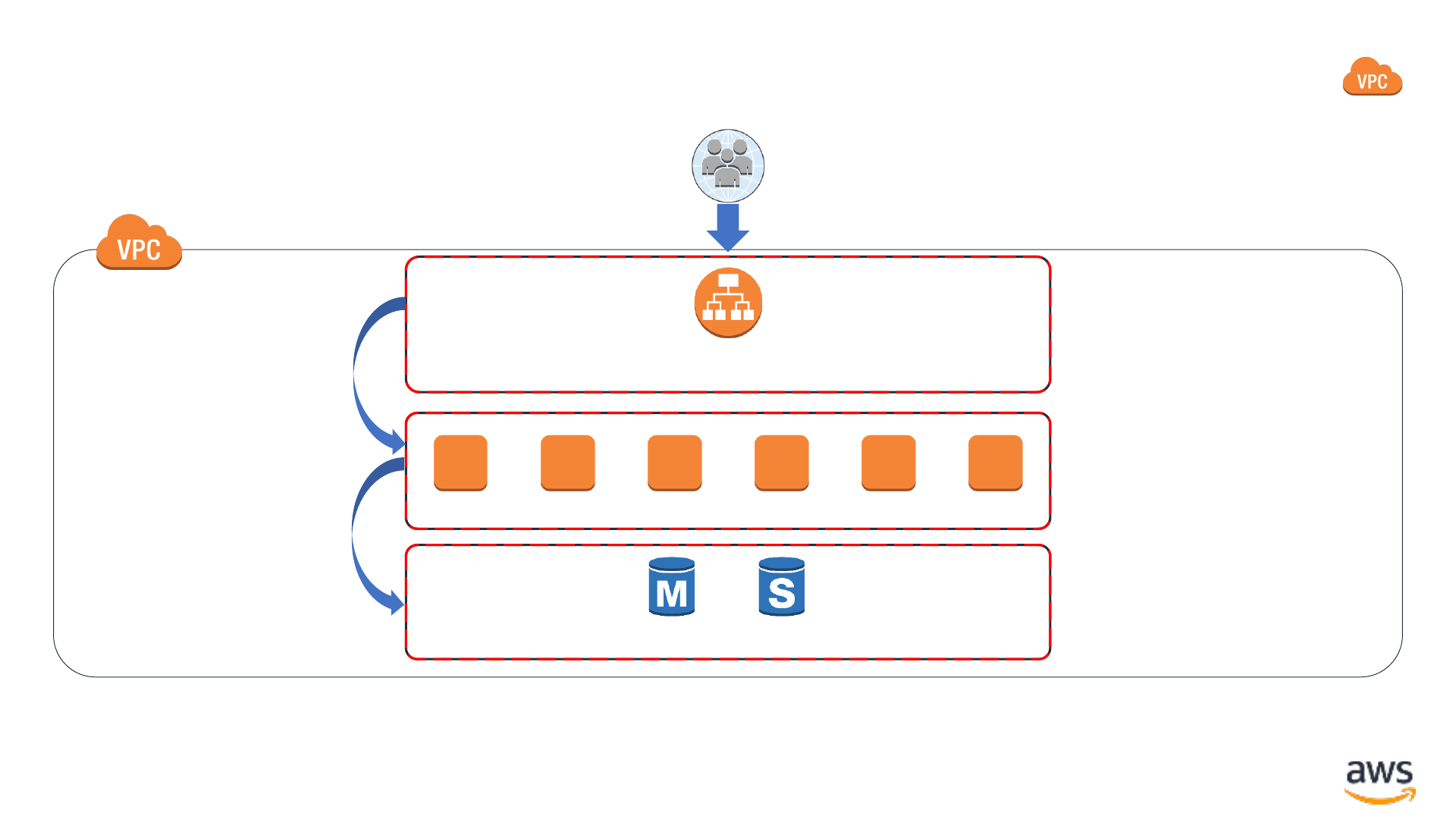
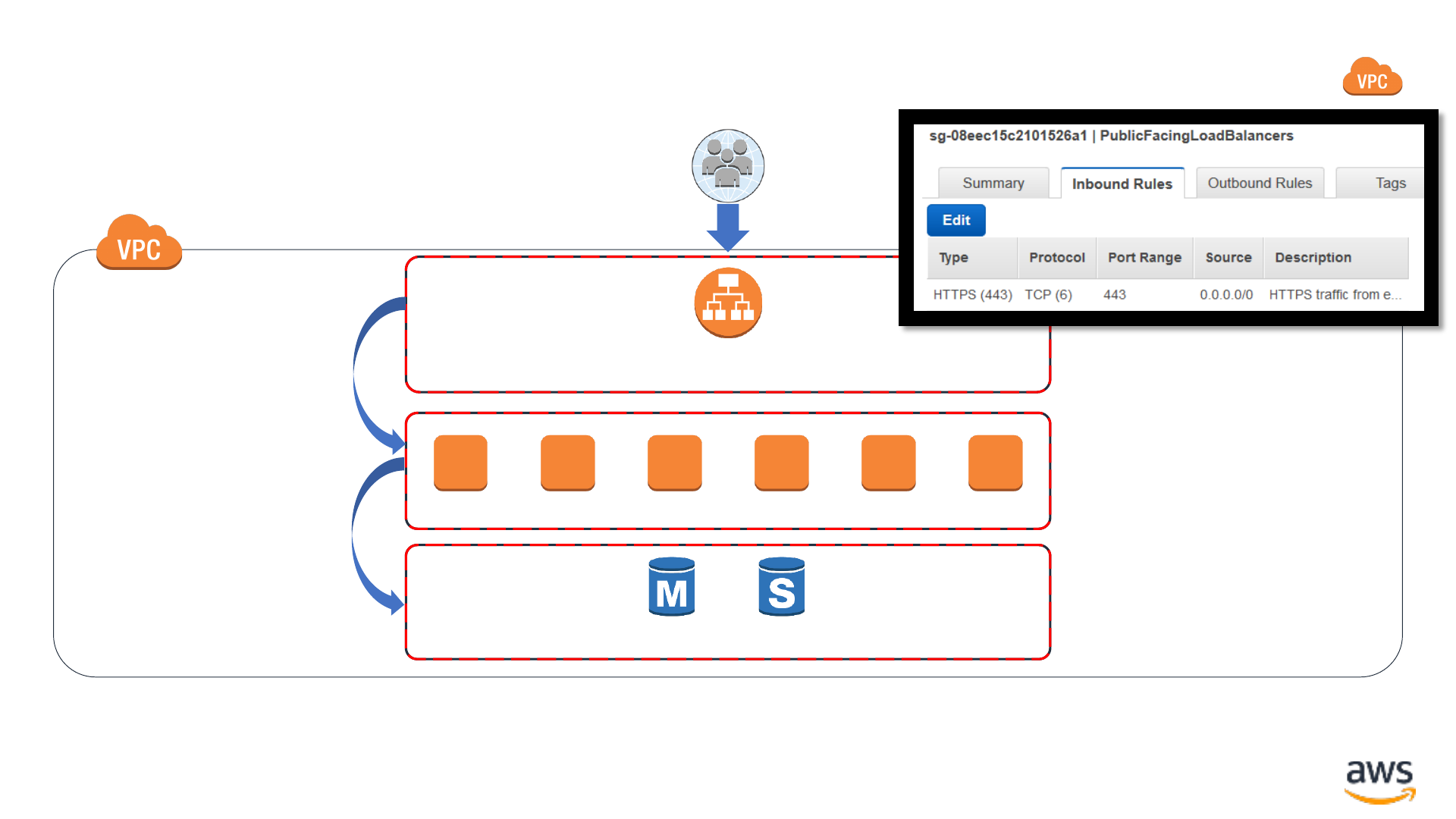
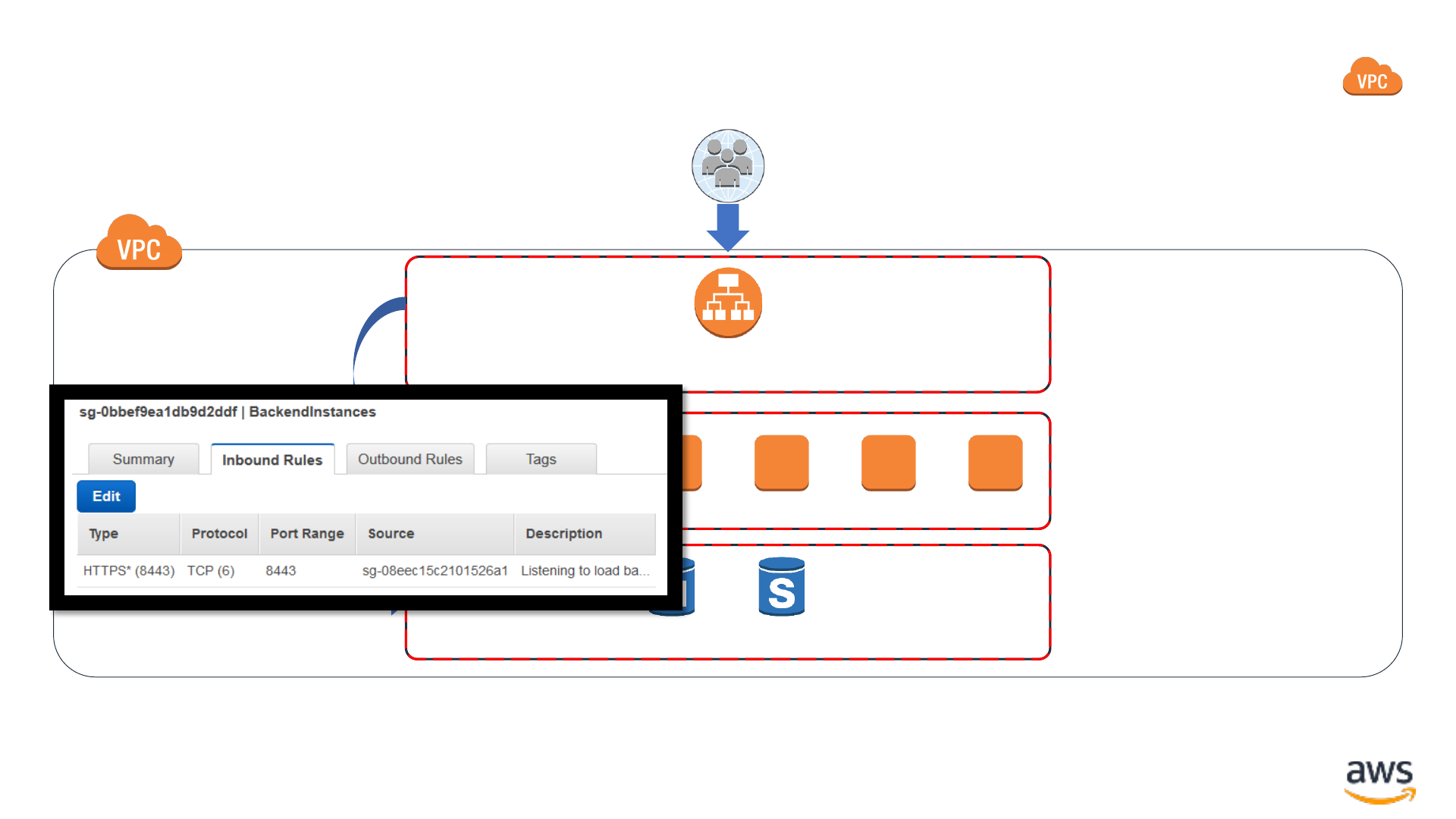
Security groups: Stateful network firewalls
Application Load
Balancer
Backend EC2 instances
RDS database
Security Group
sg-08eec15c2101526a1
Security Group
sg-0bbef9ea1db9d2ddf
Security Group
sg-0b0a4f8118aa5d450
Port 443 (HTTPS)
Port 8443 (HTTPS)
Port 3306 (MySQL)
© 2019, Amazon Web Services, Inc. or its affiliates. All rights reserved.
Security groups: Stateful network firewalls
Application Load
Balancer
Backend EC2 instances
RDS database
Security Group
sg-08eec15c2101526a1
Security Group
sg-0bbef9ea1db9d2ddf
Security Group
sg-0b0a4f8118aa5d450
Port 443 (HTTPS)
Port 8443 (HTTPS)
Port 3306 (MySQL)
© 2019, Amazon Web Services, Inc. or its affiliates. All rights reserved.
Security groups: Stateful network firewalls
Application Load
Balancer
Backend EC2 instances
RDS database
Security Group
sg-08eec15c2101526a1
Security Group
sg-0bbef9ea1db9d2ddf
Security Group
sg-0b0a4f8118aa5d450
Port 443 (HTTPS)
Port 8443 (HTTPS)
Port 3306 (MySQL)
© 2019, Amazon Web Services, Inc. or its affiliates. All rights reserved.
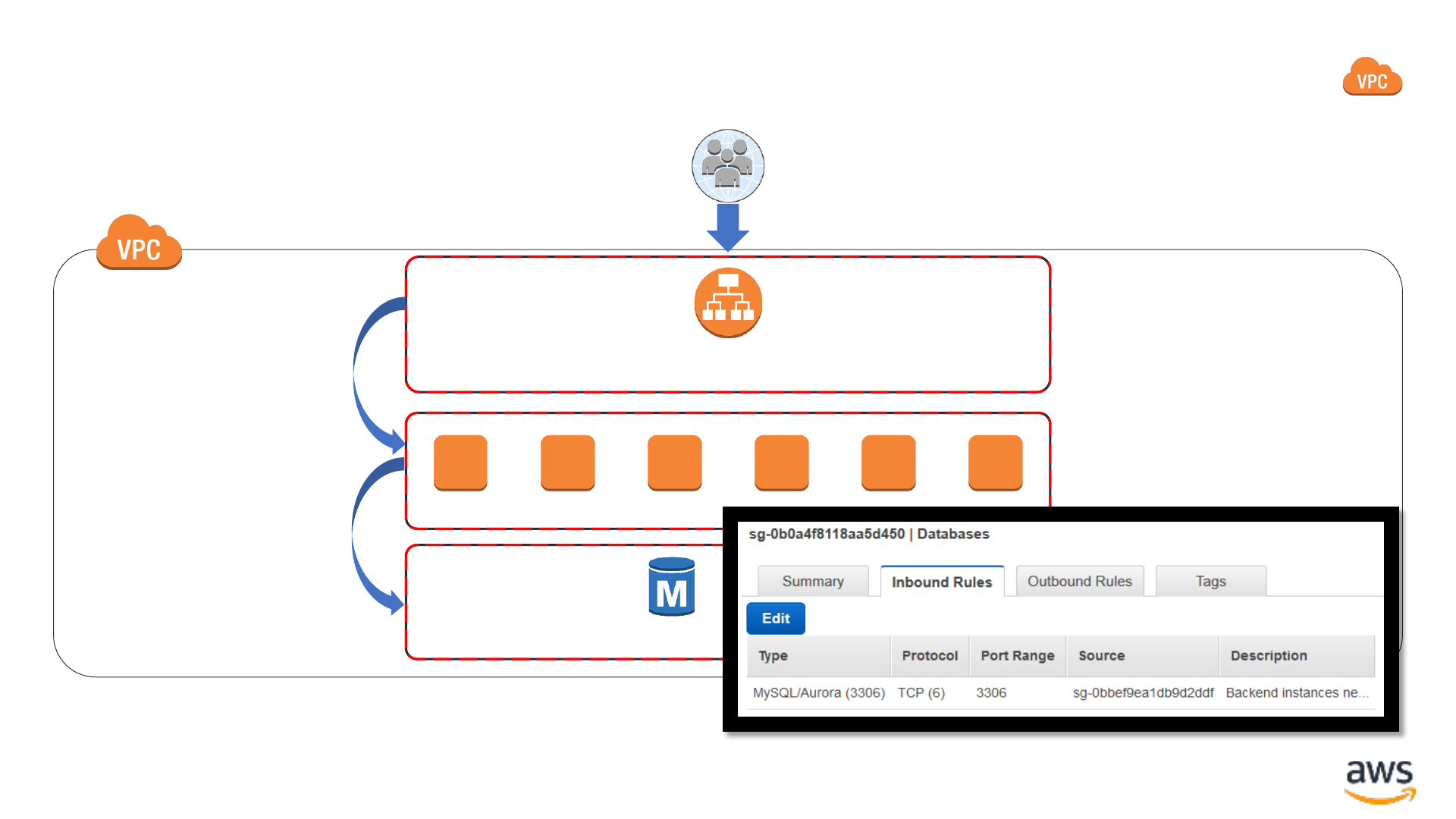
Security Groups: Stateful network firewalls
Application Load
Balancer
Backend EC2 instances
RDS database
Security Group
sg-08eec15c2101526a1
Security Group
sg-0bbef9ea1db9d2ddf
Security Group
sg-0b0a4f8118aa5d450
Port 443 (HTTPS)
Port 8443 (HTTPS)
Port 3306 (MySQL)
© 2019, Amazon Web Services, Inc. or its affiliates. All rights reserved.
Secure connectivity with Amazon VPC
•Security Groups: Authorize
only the traffic you expect
•Routing: Route traffic headed
out of your VPC only to
expected destinations
•VPC Endpoints: Create
specific, least-privilege points
of connectivity
Virtual private cloud
VPC subnet
© 2019, Amazon Web Services, Inc. or its affiliates. All rights reserved.
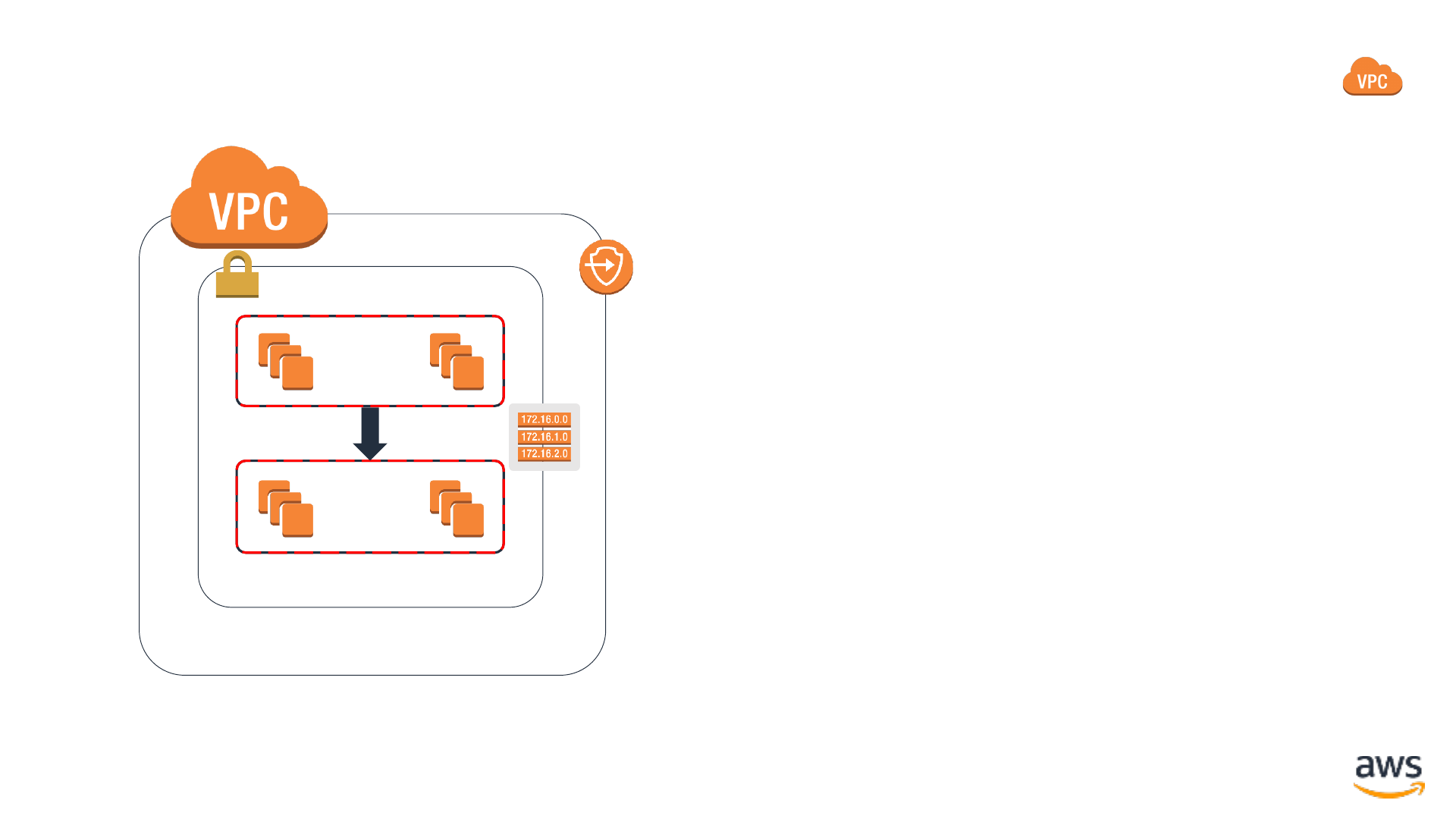
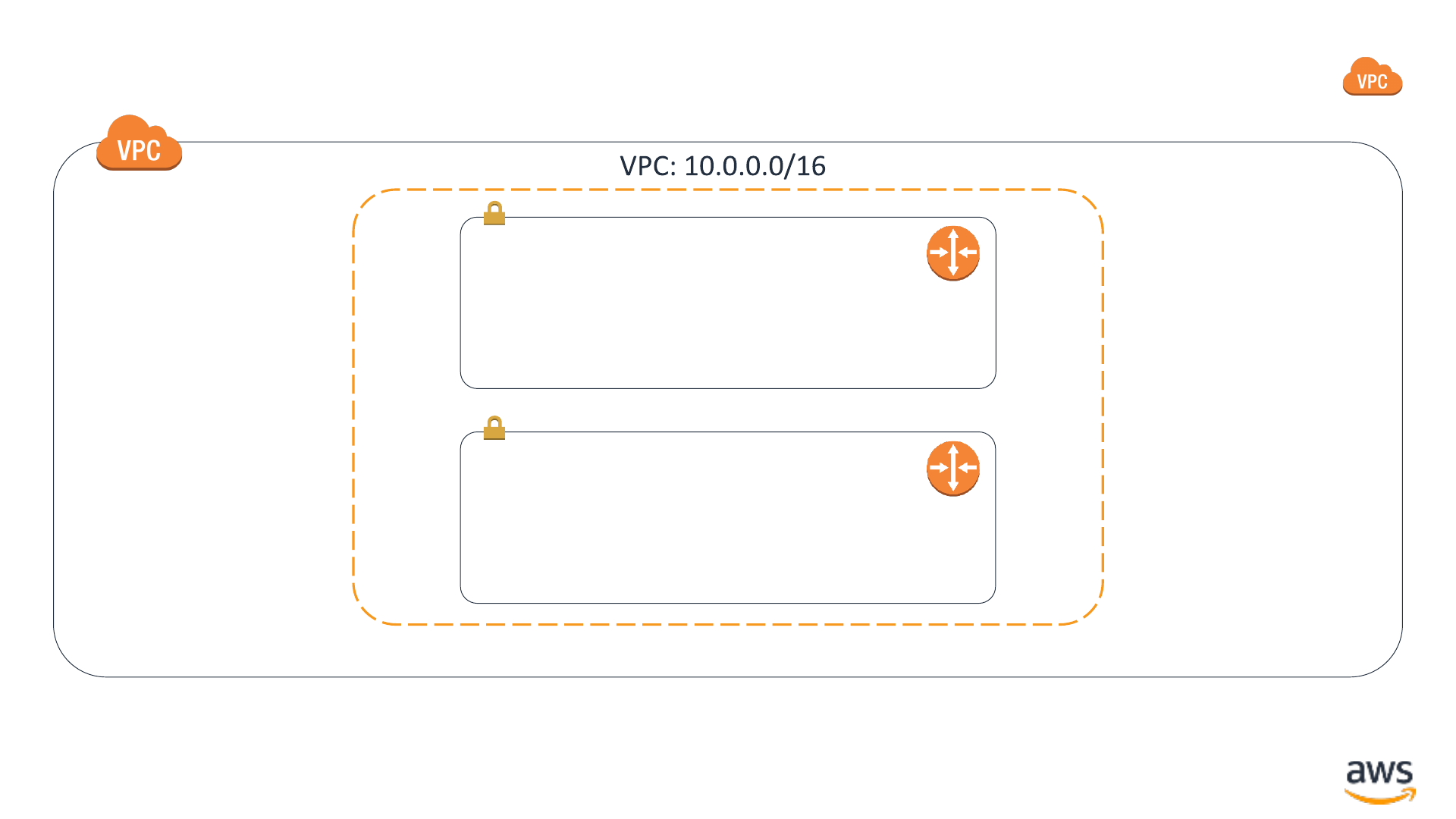
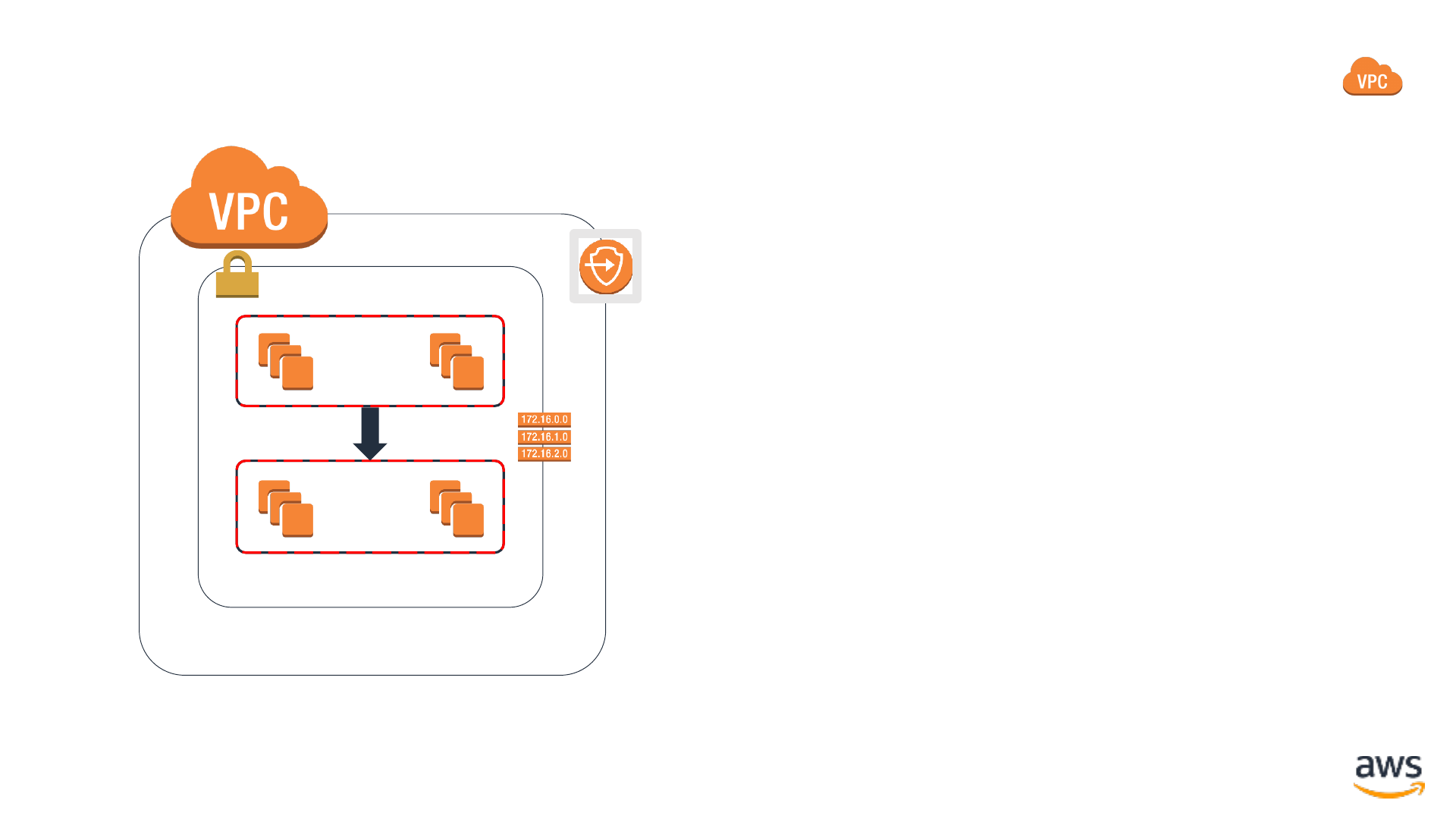
Routing for least-privilege connectivity
Availability Zone Availability Zone Availability Zone
VPC subnet: 10.0.1.0/24
VPC subnet: 10.0.51.0/24
VPC subnet: 10.0.2.0/24
VPC subnet: 10.0.52.0/24
VPC subnet: 10.0.3.0/24
VPC subnet: 10.0.53.0/24
© 2019, Amazon Web Services, Inc. or its affiliates. All rights reserved.
Routing for least-privilege connectivity
Availability Zone
VPC subnet: 10.0.2.0/24
VPC subnet: 10.0.52.0/24
© 2019, Amazon Web Services, Inc. or its affiliates. All rights reserved.
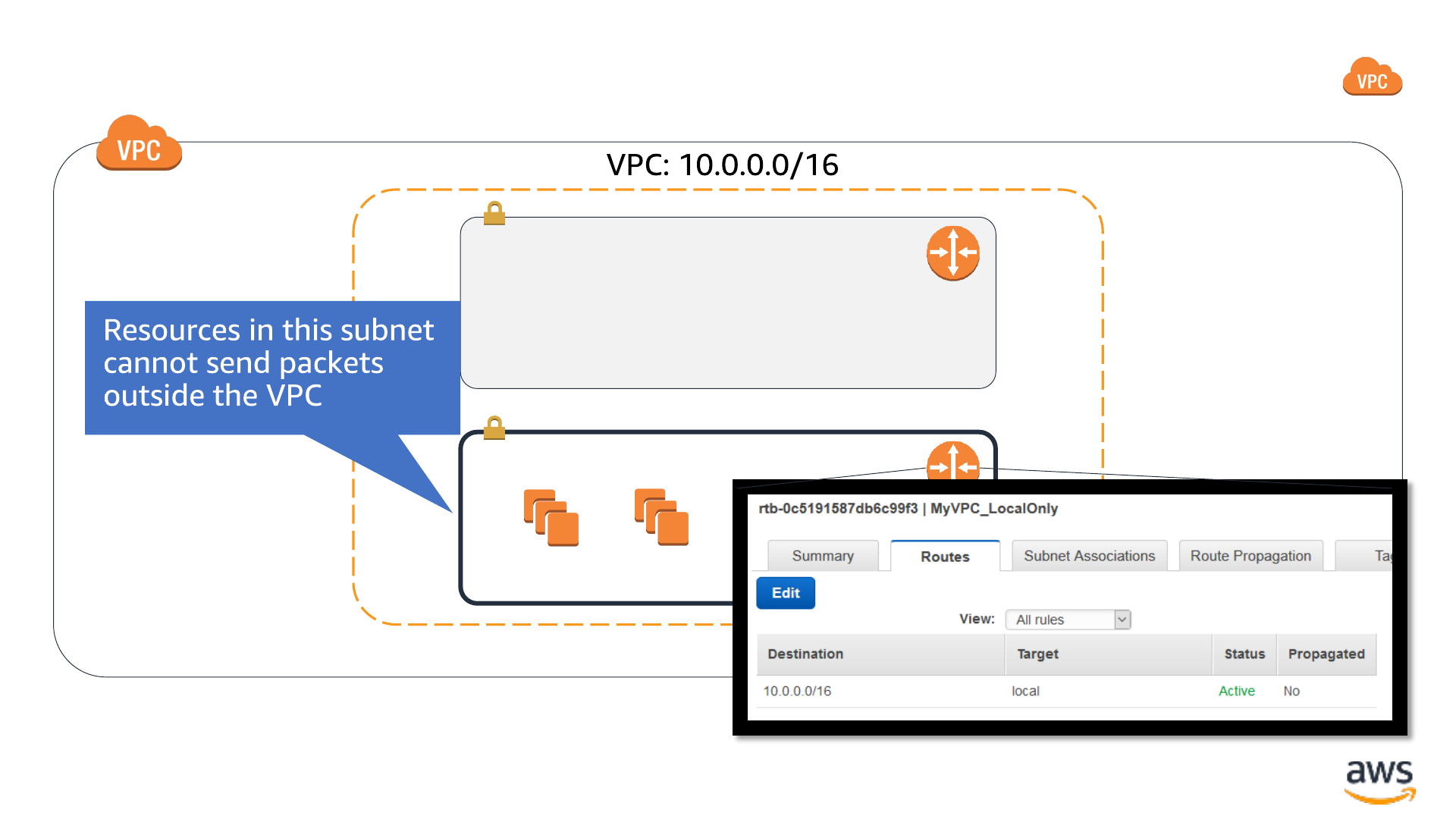
Routing: No outbound connectivity
Availability Zone
VPC Subnet: 10.0.2.0/24
VPC Subnet: 10.0.52.0/24
AWS Elasticache
- Redis
EC2 instances
© 2019, Amazon Web Services, Inc. or its affiliates. All rights reserved.
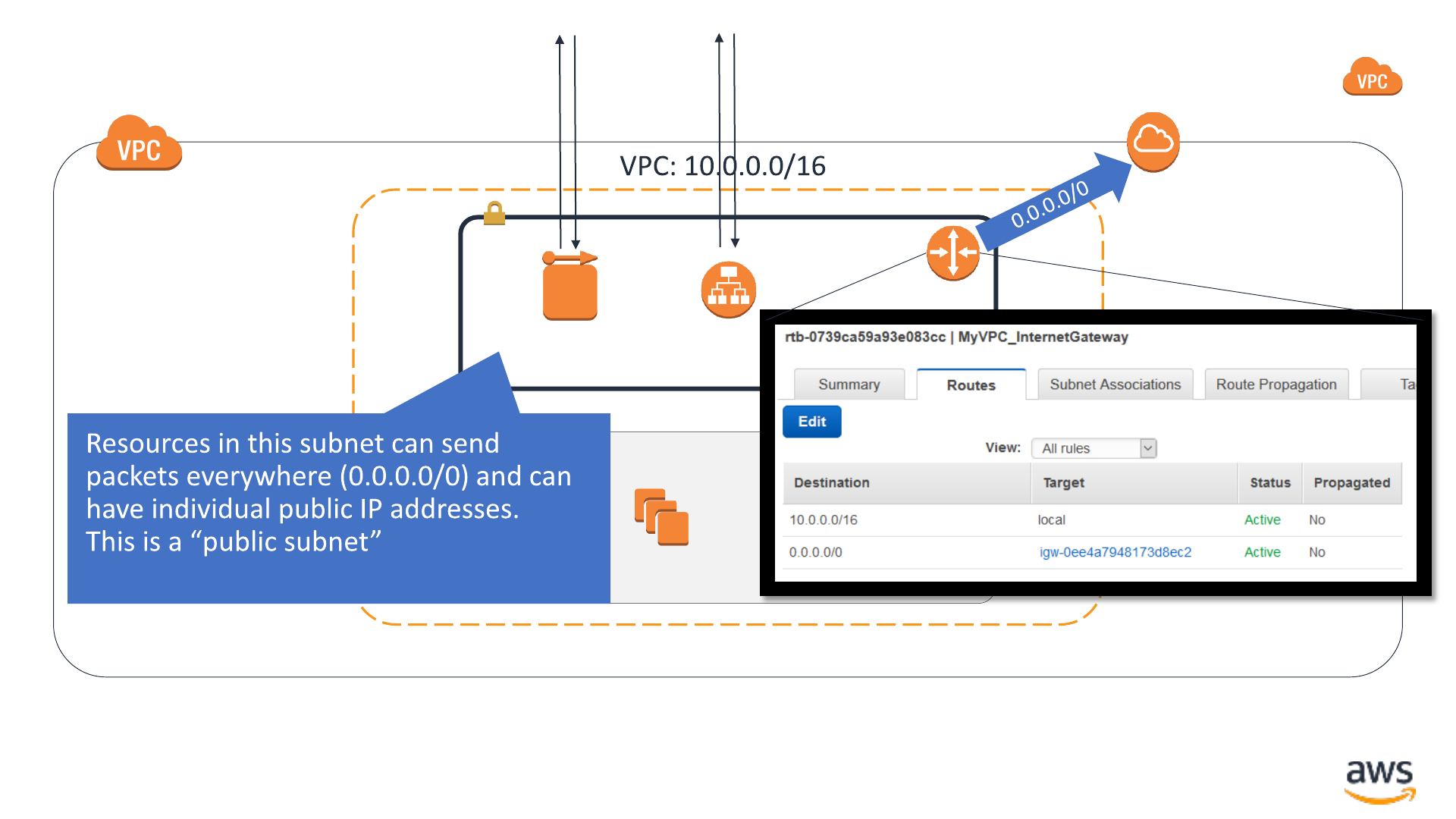
Routing: Full internet connectivity
Availability Zone
VPC subnet: 10.0.2.0/24
VPC subnet: 10.0.52.0/24
AWS Elasticache -
Redis
EC2 instances
Application Load
Balancer
Public-facing EC2
instance
Internet
gateway
Public IP address
© 2019, Amazon Web Services, Inc. or its affiliates. All rights reserved.
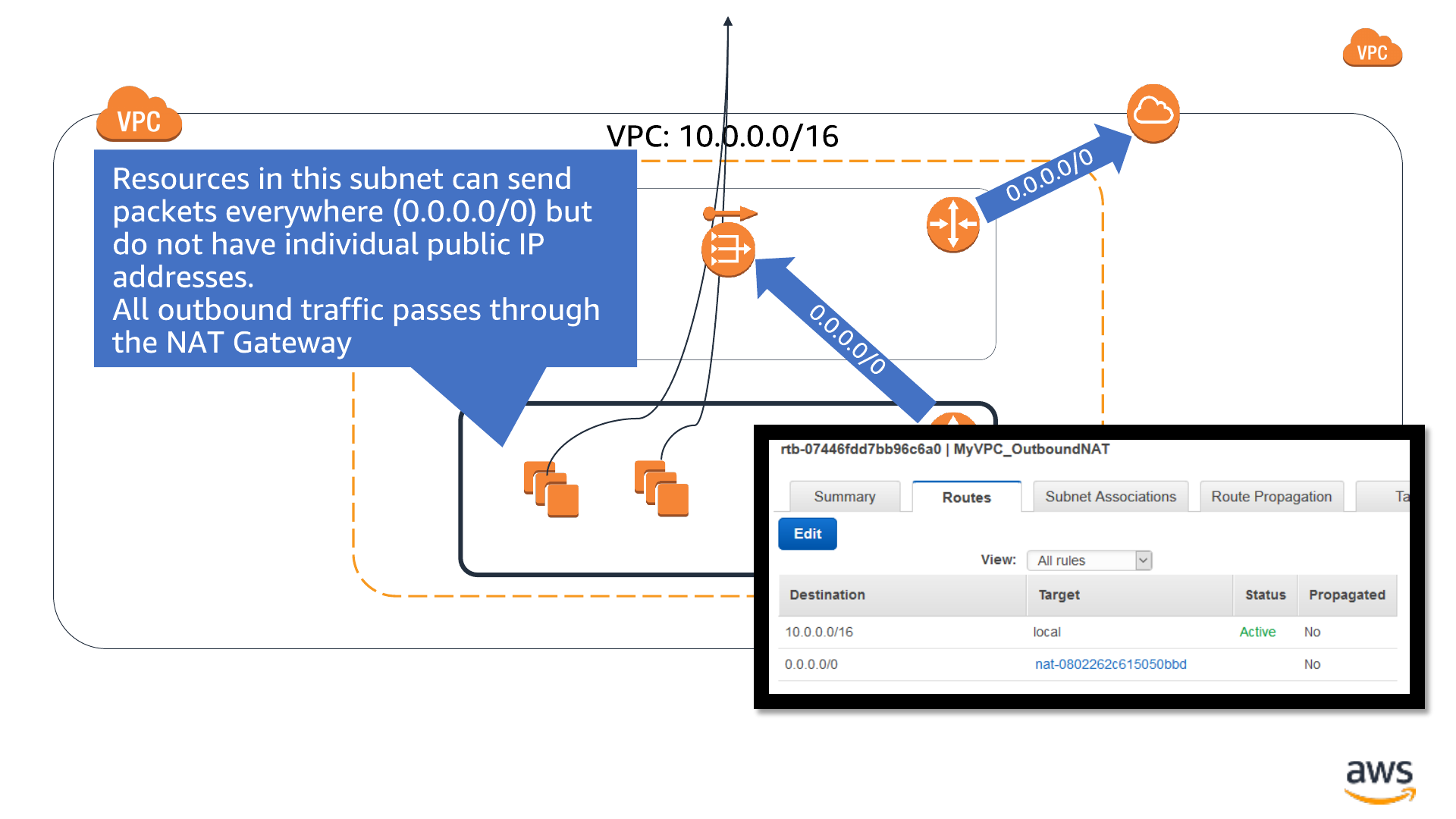
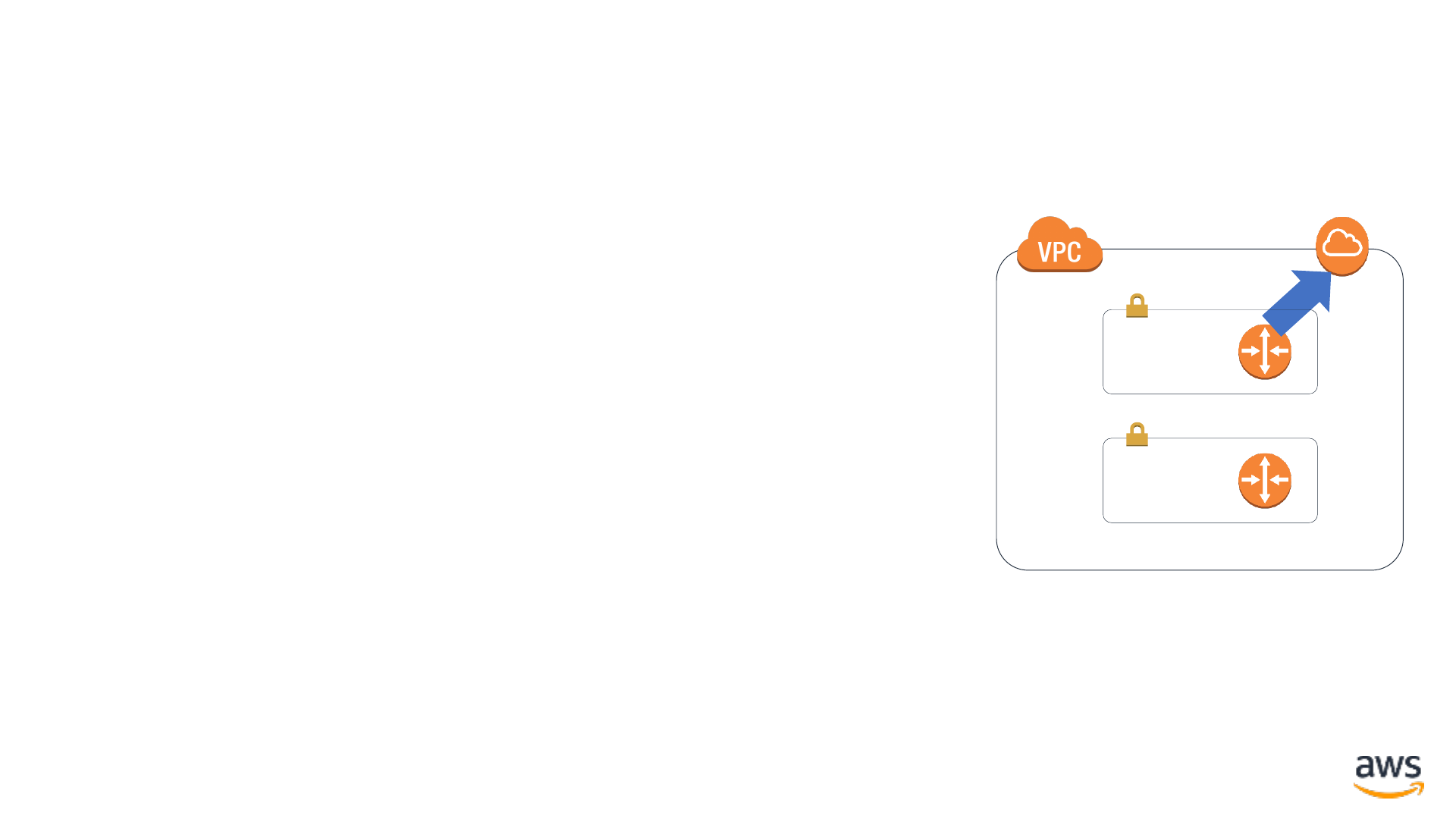
Routing: Outbound-only internet connectivity
Availability Zone
VPC Subnet: 10.0.2.0/24
VPC Subnet: 10.0.52.0/24
AWS Elasticache
- Redis
EC2 instances
Internet
gateway
Public IP
address
VPC NAT
gateway
© 2019, Amazon Web Services, Inc. or its affiliates. All rights reserved.
Routing for least privilege: Summary
•AWS offers a variety of routing options
•Determine the different routing needs of
different parts of your workload, and put
them in different subnets
•Have only the routes you need in each
subnet.
© 2019, Amazon Web Services, Inc. or its affiliates. All rights reserved.
Secure connectivity with Amazon VPC
•Security Groups: Authorize
only the traffic you expect
•Routing: Route traffic headed
out of your VPC only to
expected destinations
•VPC Endpoints: Create
specific, least-privilege points
of connectivity
Virtual private cloud
VPC subnet
© 2019, Amazon Web Services, Inc. or its affiliates. All rights reserved.
What we didn’t talk about
•Encryption
•Visibility and detective controls
•Higher-level security services
VPC Flow logs

© 2019, Amazon Web Services, Inc. or its affiliates. All rights reserved.
Thank You
Gabe Hollombe, AWS
Twitter & LinkedIn: @gabehollombe
© 2019, Amazon Web Services, Inc. or its affiliates. All rights reserved.

© 2019, Amazon Web Services, Inc. or its affiliates. All rights reserved.
Thank You for Attending AWS Quick Start
We hope you found it interesting! A kind reminder to complete the survey.
Let us know what you thought of today’s event and how we can improve
the event experience for you in the future.
aws-apac-marketing@amazon.com
twitter.com/AWSCloud
facebook.com/AmazonWebServices
youtube.com/user/AmazonWebServices
slideshare.net/AmazonWebServices
twitch.tv/aws