Guide To Industrial Control System (ICS) Security Systems SecurityãNIST SP.800 82R2ããJPCERTåè¨
Guide%20to%20Industrial%20Control%20Systems%20(ICS)%20Security%E3%80%90NIST%20SP.800-82R2%E3%80%91%E3%80%90JPCERT%E5%92%8C%E8%A8
User Manual:
Open the PDF directly: View PDF ![]() .
.
Page Count: 490 [warning: Documents this large are best viewed by clicking the View PDF Link!]
- Executive Summary
- ã¨ã°ã¼ã¯ãã£ããµããªã¼
- 1.ãIntroduction
- 1.ãã¯ããã«
- 2.ãOverview of Industrial Control Systems
- 2.ãç£æ¥ç¨å¶å¾¡ã·ã¹ãã ã®æ¦è¦
- 2.1ãç£æ¥ç¨å¶å¾¡ã·ã¹ãã ã®é²å
- 2.2 ICS Industrial Sectors and Their Interdependencies
- 2.2ãICSã®ç£æ¥é¨éã¨ãã®ç¸äºä¾åæ§
- 2.3 ICS Operation and Components
- 2.3ãICSã®æä½åã³ã³ã³ãã¼ãã³ã
- 2.3.1 ICS System Design Considerations
- 2.3.1ãICSã®ã·ã¹ãã è¨è¨ä¸ã®èæ ®äºé
- 2.3.2 SCADA Systems
- 2.3.2ãSCADA
- 2.3.3 Distributed Control Systems
- 2.3.3ãåæ£å¶å¾¡ã·ã¹ãã
- 2.3.4 Programmable Logic Controller Based Topologies
- 2.3.4ãããã°ã©ã å¯è½è«çã³ã³ããã¼ã©ãã¼ã¹ã®ãããã¸ã¼
- 2.4 Comparing ICS and IT Systems Security
- 2.4ãICSã·ã¹ãã ã¨ITã·ã¹ãã ã®ã»ãã¥ãªãã£æ¯è¼
- 2.5 Other Types of Control Systems
- 2.5ãå¥ç¨®ã®å¶å¾¡ã·ã¹ãã
- 3.ãICS Risk Management and Assessment
- 3.ãICSã®ãªã¹ã¯ç®¡çã¨ãªã¹ã¯è©ä¾¡
- 3.1ããªã¹ã¯ç®¡ç
- 3.2 Introduction to the Risk Management Process
- 3.2ããªã¹ã¯ç®¡çããã»ã¹ã®ç´¹ä»
- 3.3 Special Considerations for Doing an ICS Risk Assessment
- 3.3ãICSãªã¹ã¯è©ä¾¡ã®å®æ½ã«éãã¦ã®ç¹å¥ãªèæ
®äºé
- 3.3.1ãICSæ å ±ã»ãã¥ãªãã£ãªã¹ã¯è©ä¾¡ã«ãããå®å ¨æ§
- 3.3.2 Potential Physical Impacts of an ICS Incident
- 3.3.3 Impact of Physical Disruption of an ICS Process
- 3.3.2ãICSã¤ã³ã·ãã³ãã«ããç©ççå½±é¿ã®å¯è½æ§
- 3.3.3ãICSããã»ã¹ã®ç©ççä¸æã«ããå½±é¿
- 3.3.4 Incorporating Non-digital Aspects of ICS into Impact Evaluations
- 3.3.4ãICSã®éãã¸ã¿ã«é¢ãå½±é¿è©ä¾¡ã«å«ãã
- 3.3.5 Incorporating the Impact of Safety Systems
- 3.3.6 Considering the Propagation of Impact to Connected Systems
- 3.3.5ãå®å ¨ã·ã¹ãã ã®å½±é¿ãå«ãã
- 3.3.6ãæ¥ç¶ã·ã¹ãã ã¸ã®å½±é¿æ³¢åã«å¯¾ããèæ ®
- 4.ãICS Security Program Development and Deployment
- 4.ãICSã»ãã¥ãªãã£ããã°ã©ã ã®éçºåã³å±é
- 4.1 Business Case for Security
- 4.1.1 Benefits
- 4.1ãã»ãã¥ãªãã£ã®äºæ¥äºä¾
- 4.1.1ã便ç
- 4.2 Build and Train a Cross-Functional Team
- 4.3 Define Charter and Scope
- 4.2ãæ©è½æ¨ªæãã¼ã ã®çµæã»æè²è¨ç·´
- 4.3ãæ²ç« åã³é©ç¨ç¯å²ã®æ確å
- 4.4 Define ICS-specific Security Policies and Procedures
- 4.5 Implement an ICS Security Risk Management Framework
- 4.4ãICSåºæã®ã»ãã¥ãªãã£ããªã·ã¼åã³æé ã®æ確å
- 4.5ãICSã»ãã¥ãªãã£ãªã¹ã¯ç®¡çä½å¶ã®å®è¡
- 4.5.1 Categorize ICS Systems and Networks Assets
- 4.5.2 Select ICS Security Controls
- 4.5.1ãICSã·ã¹ãã ã¨ãããã¯ã¼ã¯è³ç£ã®åé¡
- 4.5.2ãICSã»ãã¥ãªãã£ç®¡çã®é¸æ
- 4.5.3 Perform Risk Assessment
- 4.5.4 Implement the Security Controls
- 4.5.3ããªã¹ã¯è©ä¾¡å®æ½
- 4.5.4ãã»ãã¥ãªãã£ç®¡çã®å®è£
- 5.ãICS Security Architecture
- 5.ãICSã»ãã¥ãªãã£ã¢ã¼ããã¯ãã£
- 5.1ããããã¯ã¼ã¯ã®åå²ã¨åé¢
- 5.2 Boundary Protection
- 5.2å¢çã®ä¿è·
- 5.3 Firewalls
- 5.3ããã¡ã¤ã¢ã¦ã©ã¼ã«
- 5.4 Logically Separated Control Network
- 5.4ãè«ççã«åé¢ãããå¶å¾¡ãããã¯ã¼ã¯
- 5.5 Network Segregation
- 5.5ããããã¯ã¼ã¯ã®åé¢
- 5.5.1ããã¥ã¢ã«ãã¼ã ï¾ï¾ã³ã³ãã¥ã¼ã¿/ãã¥ã¢ã«ãããã¯ã¼ã¯ã¤ã³ã¿ãã§ã¼ã¹ã«ã¼ãï¼NICï¼
- 5.5.2ãä¼æ¥ãããã¯ã¼ã¯ã¨å¶å¾¡ãããã¯ã¼ã¯éã®ãã¡ã¤ã¢ã¦ã©ã¼ã«
- 5.5.3 Firewall and Router between Corporate Network and Control Network
- 5.5.3ä¼æ¥ãããã¯ã¼ã¯ã¨å¶å¾¡ãããã¯ã¼ã¯éã®ãã¡ã¤ã¢ã¦ã©ã¼ã«ã¨ã«ã¼ã¿
- 5.5.4 Firewall with DMZ between Corporate Network and Control Network
- 5.5.4ãä¼æ¥ãããã¯ã¼ã¯ã¨å¶å¾¡ãããã¯ã¼ã¯éã®DMZä»ããã¡ã¤ã¢ã¦ã©ã¼ã«
- 5.5.5 Paired Firewalls between Corporate Network and Control Network
- 5.5.5ãä¼æ¥ãããã¯ã¼ã¯ã¨å¶å¾¡ãããã¯ã¼ã¯éã®ãã¢ã¼ããã¡ã¤ã¢ã¦ã©ã¼ã«
- 5.5.6 Network Segregation Summary
- 5.6 Recommended Defense-in-Depth Architecture
- 5.6ãæ¨å¥¨å¤å±¤é²å¾¡ã¢ã¼ããã¯ãã£
- 5.7 General Firewall Policies for ICS
- 5.7ãICSã®å ¨è¬çãã¡ã¤ã¢ã¦ã©ã¼ã«ããªã·ã¼
- 5.8 Recommended Firewall Rules for Specific Services
- 5.8ãç¹å®ãµã¼ãã¹ã®æ¨å¥¨ãã¡ã¤ã¢ã¦ã©ã¼ã«ã«ã¼ã«
- 5.8.1 Domain Name System (DNS)
- 5.8.2 Hypertext Transfer Protocol (HTTP)
- 5.8.3 FTP and Trivial File Transfer Protocol (TFTP)
- 5.8.4 Telnet
- 5.8.1ãé ååã·ã¹ãã ï¼DNSï¼
- 5.8.2ããã¤ãã¼ããã¹ã転éãããã³ã«ï¼HTTPï¼
- 5.8.3ãFTPåã³ããªãã¢ã«ãã¡ã¤ã«è»¢éãããã³ã«ï¼TFTPï¼
- 5.8.4ããã«ãããï¼Telnetï¼
- 5.8.5 Dynamic Host Configuration Protocol (DHCP)
- 5.8.6 Secure Shell (SSH)
- 5.8.7 Simple Object Access Protocol (SOAP)
- 5.8.8 Simple Mail Transfer Protocol (SMTP)
- 5.8.9 Simple Network Management Protocol (SNMP)
- 5.8.5ãåçãã¹ãæ§æãããã³ã«ï¼DHCPï¼
- 5.8.6ãã»ãã¥ã¢ã·ã§ã«ï¼SSH)
- 5.8.7ãã·ã³ãã«ãªãã¸ã§ã¯ãã¢ã¯ã»ã¹ãããã³ã«ï¼SOAPï¼
- 5.8.8ãã·ã³ãã«ã¡ã¼ã«è»¢éãããã³ã«ï¼SMTPï¼
- 5.8.9ãã·ã³ãã«ãããã¯ã¼ã¯ç®¡çãããã³ã«ï¼SNMPï¼
- 5.8.10 Distributed Component Object Model (DCOM)
- 5.8.11 SCADA and Industrial Protocols
- 5.9 Network Address Translation (NAT)
- 5.9ããããã¯ã¼ã¯ã¢ãã¬ã¹å¤æï¼NATï¼
- 5.10 Specific ICS Firewall Issues
- 5.10ãICSãã¡ã¤ã¢ã¦ã©ã¼ã«åºæã®åé¡
- 5.11 Unidirectional Gateways
- 5.12 Single Points of Failure
- 5.13 Redundancy and Fault Tolerance
- 5.11ãåæ¹åæ§ã²ã¼ãã¦ã§ã¤
- 5.12ãåä¸é害ç¹
- 5.13ãåé·æ§ã¨ãã©ã¼ã«ããã¬ã©ã³ã¹
- 5.14 Preventing Man-in-the-Middle Attacks
- 5.14ã人ãä»å¨ããæ»æã®é²æ¢
- 5.15 Authentication and Authorization
- 5.15ãèªè¨¼ã¨æ¨©éä»ä¸
- 5.15.1 ICS Implementation Considerations
- 5.16 Monitoring, Logging, and Auditing
- 5.17 Incident Detection, Response, and System Recovery
- 5.16ãç£è¦ããã®ã³ã°åã³ç£æ»
- 5.17ãã¤ã³ã·ãã³ãæ¤ç¥ã対å¿åã³ã·ã¹ãã 復æ§
- 6.ã Applying Security Controls to ICS
- 6. ICSã¸ã®ã»ãã¥ãªãã£å¯¾çã®é©ç¨
- 6.1ãç£æ¥ç¨å¶å¾¡ã·ã¹ãã ç¨ãªã¹ã¯ç®¡çä½å¶ã®å®æ½
- 6.1.1 Step 1: Categorize Information System
- 6.1.1ãæé 1ï¼æ å ±ã·ã¹ãã ã®åé¡
- 6.1.2 Step 2: Select Security Controls
- 6.1.2ãæé 2ï¼ã»ãã¥ãªãã£å¯¾çã®é¸æ
- 6.1.3 Step 3: Implement Security Controls
- 6.1.4 Step 4: Assess Security Controls
- 6.1.5 Step 5: Authorize Information System
- 6.1.3ãæé 3ï¼ã»ãã¥ãªãã£å¯¾çã®å®è£
- 6.1.4ãæé 4ï¼ã»ãã¥ãªãã£å¯¾çã®è©ä¾¡
- 6.1.5ãæé 5ï¼æ å ±ã·ã¹ãã ã®è¨±å¯
- 6.1.6 Step 6: Monitor Security Controls
- 6.2 Guidance on the Application of Security Controls to ICS
- 6.2ãICSã¸ã®ã»ãã¥ãªãã£å¯¾çã®é©ç¨ã«ä¿ãã¬ã¤ãã³ã¹
- 6.2.1 Access Control
- 6.2.1ãã¢ã¯ã»ã¹å¶å¾¡
- 6.2.1.1 Role-based Access Control (RBAC)
- 6.2.1.1ãå½¹å²ã«åºã¥ãã¢ã¯ã»ã¹å¶å¾¡ï¼RBACï¼
- 6.2.1.2 Web Servers
- 6.2.1.3 Virtual Local Area Network (VLAN)
- 6.2.1.2ãã¦ã§ããµã¼ã
- 6.2.1.3ãä»®æ³LANï¼VLANï¼
- 6.2.1.4 Dial-up Modems
- 6.2.1.4ããã¤ã¢ã«ã¢ããã¢ãã
- 6.2.1.5 Wireless
- 6.2.1.5ãã¯ã¤ã¤ã¬ã¹
- 6.2.2 Awareness and Training
- 6.2.3 Audit and Accountability
- 6.2.2ãæèåã³è¨ç·´
- 6.2.3ãç£æ»åã³èª¬æ責任
- 6.2.4 Security Assessment and Authorization
- 6.2.5 Configuration Management
- 6.2.4ãã»ãã¥ãªãã£è©ä¾¡åã³æ¨©éä»ä¸
- 6.2.5ãæ§æ管ç
- 6.2.6 Contingency Planning
- 6.2.6ãä¸æ¸¬äºæ è¨ç»
- 6.2.7 Identification and Authentication
- 6.2.7ãèå¥åã³èªè¨¼
- 6.2.7.1 Password Authentication
- 6.2.7.1ããã¹ã¯ã¼ãèªè¨¼
- 6.2.7.2 Challenge/response Authentication
- 6.2.7.2ããã£ã¬ã³ã¸/ã¬ã¹ãã³ã¹èªè¨¼
- 6.2.7.3 Physical Token Authentication
- 6.2.7.3ãç©ççãã¼ã¯ã³èªè¨¼
- 6.2.7.4 Smart Card Authentication
- 6.2.7.4ãã¹ãã¼ãã«ã¼ãèªè¨¼
- 6.2.7.5 Biometric Authentication
- 6.2.7.5ããã¤ãªã¡ããªãã¯èªè¨¼
- 6.2.8 Incident Response
- 6.2.8ãã¤ã³ã·ãã³ã対å¿
- 6.2.9 Maintenance
- 6.2.10 Media Protection
- 6.2.9ãä¿å®
- 6.2.10ãã¡ãã¤ã¢ä¿è·
- 6.2.11 Physical and Environmental Protection
- 6.2.11ãç©çç°å¢ä¸ã®ä¿è·ï¼PEï¼
- 6.2.12 Planning
- 6.2.12ããã©ã³ãã³ã°
- 6.2.13 Personnel Security
- 6.2.13ã人å¡ã®ã»ãã¥ãªãã£
- 6.2.14 Risk Assessment
- 6.2.15 System and Services Acquisition
- 6.2.14ããªã¹ã¯è©ä¾¡
- 6.2.15ãã·ã¹ãã åã³ãµã¼ãã¹ã®åå¾
- 6.2.16 System and Communications Protection
- 6.2.16ãã·ã¹ãã åã³éä¿¡ä¿è·
- 6.2.16.1 Encryption
- 6.2.16.1ãæå·å
- 6.2.17 System and Information Integrity
- 6.2.17ãã·ã¹ãã åã³æ å ±ã®ä¿å ¨
- 6.2.18 Program Management
- 6.2.19 Privacy Controls
- 6.2.18ãããã°ã©ã 管ç
- 6.2.19ããã©ã¤ãã·ã¼ç®¡ç
- 6.1ãç£æ¥ç¨å¶å¾¡ã·ã¹ãã ç¨ãªã¹ã¯ç®¡çä½å¶ã®å®æ½
- Appendix AâAcronyms and Abbreviations
- ä»é²Aãé åèªåã³ç¥èª
- Appendix BâGlossary of Terms
- ä»é²Bãç¨èªé
- Appendix CâThreat Sources, Vulnerabilities, and Incidents
- ä»é²C ãè å¨æºãèå¼±æ§åã³ã¤ã³ã·ãã³ã
- Appendix DâCurrent Activities in Industrial Control System Security
- ä»é²D ãç£æ¥ç¨å¶å¾¡ã·ã¹ãã ã»ãã¥ãªãã£ã«ãããç¾å¨ã®æ´»å
- Appendix EâICS Security Capabilities and Tools
- ä»é²EãICSã»ãã¥ãªãã£æ©è½åã³ãã¼ã«
- Appendix FâReferences
- Appendix GâICS Overlay
- ä»é²Gã ICSãªã¼ãã¼ã¬ã¤

NIST Special Publication 800-82
Revision 2
Guide to Industrial Control
Systems (ICS) Security
Supervisory Control and Data Acquisition (SCADA) Systems, Distributed Control Systems (DCS),
and Other Control System Configurations such as Programmable Logic Controllers (PLC)
Keith Stouffer
Victoria Pillitteri
Suzanne Lightman
Marshall Abrams
Adam Hahn
This publication is available free of charge from:
http://dx.doi.org/10.6028/NIST.SP.800-82r2
é¦è¨³ï¼
ä¸è¬ç¤¾å£æ³äºº JPCERT ã³ã¼ãã£ãã¼ã·ã§ã³ã»ã³ã¿ã¼
Japan Computer Emergency
Response Team Coordination
Center
é»åç½²åè
: Japan Computer Emergency Response
Team Coordination Center
DN : c=JP, st=Tokyo, l=Chiyoda-ku,
email=office@jpcert.or.jp, o=Japan Computer
Emergency Response Team Coordination Center,
cn=Japan Computer Emergency Response Team
Coordination Center
æ¥ä» : 2016.04.12 09:20:04 +09'00'

NIST SP800-82
第2ç
ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼
ã»ãã¥ãªãã£ã¬ã¤ã
SCADAãDCSãPLC ãã®ä»ã®å¶å¾¡ã·ã¹ãã è¨å®
Keith Stouffer
Victoria Pillitteri
Suzanne Lightman
Marshall Abrams
Adam Hahn
æ¬åºçç©ã¯æ¬¡ã®ãµã¤ãããç¡æã§å
¥æå¯è½ï¼
http://dx.doi.org/10.6028/NIST.SP.800-82r2

NIST Special Publication 800-82
Revision 2
Guide to Industrial Control Systems
(ICS) Security
Supervisory Control and Data Acquisition (SCADA) systems, Distributed Control Systems (DCS), and
other control system configurations such as Programmable Logic Controllers (PLC)
Keith Stouffer
Intelligent Systems Division
Engineering Laboratory
Victoria Pillitteri
Suzanne Lightman
Computer Security Division
Information Technology Laboratory
Marshall Abrams
The MITRE Corporation
Adam Hahn
Washington State University
This publication is available free of charge from:
http://dx.doi.org/10.6028/NIST.SP.800-82r2
May 2015
U.S. Department of Commerce
Penny Pritzker, Secretary
National Institute of Standards and Technology
Willie May, Under Secretary of Commerce for Standards and Technology and Director

NISTSP800-82
第2ç
ç£æ¥ç¨å¶å¾¡ã·ã¹ãã (ICS)
ã»ãã¥ãªãã£ã¬ã¤ã
SCADAãDCSãPLCããã®ä»ã®å¶å¾¡ã·ã¹ãã ã®è¨å®
Keith Stouffer
ã¨ã³ã¸ãã¢ãªã³ã°ç 究æ(EL)
ã¤ã³ããªã¸ã§ã³ãã·ã¹ãã ãã£ãã¸ã§ã³
Victoria Pillitteri
Suzanne Lightman
æ
å ±æè¡ç 究æ(ITL)
ã³ã³ãã¥ã¼ã¿ã»ãã¥ãªãã£ãã£ãã¸ã§ã³
Marshall Abrams
MITRE 社
Adam Hahn
ã¯ã·ã³ãã³å·ç«å¤§å¦
æ¬åºçç©ã¯æ¬¡ã®ãµã¤ãããç¡æã§å
¥æå¯è½ï¼
http://dx.doi.org/10.6028/NIST.SP.800-82r2
2015 å¹´5æ
ç±³å½ååç
é·å® Penny Pritzker
ååçæ¨æºæè¡æ
å½æ¬¡å®
ç±³å½å½ç«æ¨æºæè¡ç 究æ æé·
Willie May

SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
v
Authority
This publication has been developed by NIST to further its statutory responsibilities under the Federal
Information Security Modernization Act (FISMA) of 2014, 44 U.S.C. § 3541 et seq., Public Law (P.L.)
113-283. NIST is responsible for developing information security standards and guidelines, including
minimum requirements for federal information systems, but such standards and guidelines shall not apply
to national security systems without the express approval of appropriate federal officials exercising policy
authority over such systems. This guideline is consistent with the requirements of the Office of
Management and Budget (OMB) Circular A-130, Section 8b(3), Securing Agency Information Systems, as
analyzed in Circular A-130, Appendix IV: Analysis of Key Sections. Supplemental information is provided
in Circular A-130, Appendix III, Security of Federal Automated Information Resources.
Nothing in this publication should be taken to contradict the standards and guidelines made mandatory and
binding on federal agencies by the Secretary of Commerce under statutory authority. Nor should these
guidelines be interpreted as altering or superseding the existing authorities of the Secretary of Commerce,
Director of the OMB, or any other federal official. This publication may be used by nongovernmental
organizations on a voluntary basis and is not subject to copyright in the United States. Attribution would,
however, be appreciated by NIST.
National Institute of Standards and Technology Special Publication 800-82, Revision 2 Natl. Inst.
Stand. Technol. Spec. Publ. 800-82, Rev. 2, 247 pages (May 2015)
This publication is available free of charge from
:http://dx.doi.org/10.6028/NIST.SP.800-82r2
CODEN: NSPUE2
Certain commercial entities, equipment, or materials may be identified in this document in order to describe
an experimental procedure or concept adequately. Such identification is not intended to imply
recommendation or endorsement by NIST, nor is it intended to imply that the entities, materials, or
equipment are necessarily the best available for the purpose.
There may be references in this publication to other publications currently under development by NIST in
accordance with its assigned statutory responsibilities. The information in this publication, including
concepts and methodologies, may be used by federal agencies even before the completion of such
companion publications. Thus, until each publication is completed, current requirements, guidelines, and
procedures, where they exist, remain operative. For planning and transition purposes, federal agencies may
wish to closely follow the development of these new publications by NIST.
Organizations are encouraged to review all draft publications during public comment periods and provide
feedback to NIST. All NIST Computer Security Division publications, other than the ones noted above, are
available at http://csrc.nist.gov/publications.
Comments on this publication may be submitted to:
National Institute of Standards and Technology
Attn: Computer Security Division, Information Technology Laboratory
100 Bureau Drive (Mail Stop 8930) Gaithersburg, MD 20899-8930
Electronic Mail: nist800-82rev2comments@nist.gov

SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
vi
æ¬ææ¸ã«ã¤ãã¦
æ¬åºçç©ã¯ã2014 å¹´é£é¦æ
å ±ã»ãã¥ãªãã£è¿ä»£åæ³ï¼FISMAï¼44 U.S.C. § 3541 åã³ä¸è¬æ³
ï¼P.L.ï¼113-283 ã«åºã¥ããç±³å½å½ç«æ¨æºæè¡ç 究æï¼NISTï¼ããã®æ³ç責åãéè¡ããããã«
ä½æããã
NIST ã¯ãé£é¦æ
å ±ã·ã¹ãã ã®æä½éã®è¦ä»¶äºé
ãå«ãã æ
å ±ã»ãã¥ãªãã£æ¨æºåã³ã¬ã¤ãã©ã¤
ã³ãä½æãã責åããããããã®ãããªæ¨æºåã³ã¬ã¤ãã©ã¤ã³ã¯ãå½å®¶å®å
¨ä¿éã«ä¿ããã·ã¹ã
ã ã«ããã¦ã¯ãé£é¦å½å±ã«ããå½è©²ã·ã¹ãã ã«å¯¾ããããªã·ã¼æ¨©éãè¡ä½¿ããæ示çæ¿èªããªã
ãã°é©ç¨ãããªããæ¬ã¬ã¤ãã©ã¤ã³ã¯ãè¡æ¿ç®¡çäºç®å±ï¼OMBï¼éé A-130ã8b(3)æ¡ããæ¿åº
æ©é¢æ
å ±ã·ã¹ãã ã®ä¿å
¨ãï¼éé A-130 ä»é² IVã主è¦æ¡æã®åæãã«è¨è¼ï¼ã®è¦ä»¶ã«ä¸è´ããã
è£è¶³æ
å ±ã¯ãéé A-130 ä»é² IIIãé£é¦èªååæ
å ±ãªã½ã¼ã¹ã®ã»ãã¥ãªãã£ãã«è¨è¼ããã¦ããã
æ¬åºçç©ã®ãããªãè¨è¿°ããååé·å®ã®æ³ç権éã«ããé£é¦æ¿åºæ©é¢ã«é©ç¨ãããæ¨æºåã³ã¬ã¤
ãã©ã¤ã³ãå¦å®ãããã®ã§ã¯ãªããã¾ãã¬ã¤ãã©ã¤ã³ã¯ãååé·å®ãè¡æ¿ç®¡çäºç®å±é·å®ãã¾ã
ã¯ãã®ä»é£é¦å½å±ã®æ¢åã®æ¨©éã«å¤æ´ãå ãããã代æ¿ãããã®ã¨è§£éãã¦ã¯ãªããªãã
æ¬åºçç©ã¯ãæ¿åºä»¥å¤ã®çµç¹ãä»»æã«ä½¿ç¨ãããã¨ãã§ããç±³å½ã«ãããèä½æ¨©ã®å¯¾è±¡ã¨ãªããª
ãããNIST ã¯èä½æ¨©ã®å¸°å±ãæè¨ãããã¨ã«æè¬ããã
ç±³å½å½ç«æ¨æºæè¡ç 究æï¼NISTï¼SP800-82 第2çã
Natl. Inst. Stand. Technol. Spec. Publ. 800-82, Rev. 2, 247 ãã¼ã¸ï¼2015 å¹´5æï¼
æ¬åºçç©ã¯æ¬¡ã®ãµã¤ãããå
¥æå¯è½(ç¡æ)
ï¼http://dx.doi.org/10.6028/NIST.SP.800-82r2
CODEN:NSPUE2
æ¬ææ¸ã§ã¯ãç¹å®ãããå¶å©å£ä½åãè£
ç½®åã¯è³æã¯ãå®é¨çãªæé åã¯æ¦å¿µãé©åã«èª¬æããã
ãã®ãã®ã§ããããããã£ã¦ãNIST ã«ããæ¨å¥¨ãä¿è¨¼ãããã®ã§ã¯ãªããå½è©²å¶å©å£ä½ãè£
ç½®å
ã¯è³æãããã®ç®çã«é¢ãã¦å¾ãããæè¯ã®ãã®ã§ãããã¨ãæå³ãããã®ã§ããªãã
æ¬åºçç©ã§ã¯ãNIST ããã®è² è¨ãããæ³ç責åã«å¾ã£ã¦ç¾å¨ä½æä¸ã®ä»ã®åºçç©ãåç
§ããå ´å
ããããæ¬åºçç©ã®æ¦å¿µãæ¹æ³è«ãå«ãæ
å ±ã¯ãåè¿°ã®é¢é£åºçç©ã®å®æåã§ãã£ã¦ããé£é¦æ¿åº
æ©é¢ã使ç¨ããå ´åãããããã£ã¦ãååºçç©ãå®æããã¾ã§ã¯ãç¾å¨ã®å¿
é è¦ä»¶ãã¬ã¤ãã©ã¤ã³
åã³æé ãåå¨ããå ´åããããã¯å¼ãç¶ãæå¹ã§ãããé£é¦æ¿åºæ©é¢ã¯è¨ç»ä½æã¨ç§»è¡ã®ç®çã¨
ãã¦ãNIST ã«ãããããæ°è¦åºçç©ã®ä½æç¶æ³ã確èªããããã
åçµç¹ã¯ããããªãã¯ã³ã¡ã³ãã®å
¬åæéä¸ã«ãå
¨ã¦ã®å
¬éãã©ããææ¸ãé²è¦§ããã³ã¡ã³ãã NIST
ã«æ示ãããããå
¨ã¦ã® NIST ã³ã³ãã¥ã¼ã¿ã»ãã¥ãªãã£ãã£ãã¸ã§ã³ã®åºçç©ã¯ãä¸è¨ã®ãã®
ãé¤ãã
http://csrc.nist.gov/publications
ããå
¥æã§ããã
æ¬åºçç©ã«é¢ããæè¦ã¯ã以ä¸ã®å®å
ã«æåºããããã
Attnï¼Computer Security Division, Information Technology Laboratory
100 Bureau Drive (Mail Stop 8930) Gaithersburg, MD 20899-8930
é»åã¡ã¼ã«ï¼nist800-82rev2comments@nist.gov
SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
vii
Reports on Computer Systems Technology
The Information Technology Laboratory (ITL) at the National Institute of Standards and Technology
(NIST) promotes the U.S. economy and public welfare by providing technical leadership for the Nationâs
measurement and standards infrastructure. ITL develops tests, test methods, reference data, proof of
concept implementations, and technical analyses to advance the development and productive use of
information technology. ITLâs responsibilities include the development of management, administrative,
technical, and physical standards and guidelines for the cost-effective security and privacy of other than
national security-related information in federal information systems. The Special Publication 800-series
reports on ITLâs research, guidelines, and outreach efforts in information system security, and its
collaborative activities with industry, government, and academic organizations.
Abstract
This document provides guidance on how to secure Industrial Control Systems (ICS), including
Supervisory Control and Data Acquisition (SCADA) systems, Distributed Control Systems (DCS), and
other control system configurations such as Programmable Logic Controllers (PLC), while addressing their
unique performance, reliability, and safety requirements. The document provides an overview of ICS and
typical system topologies, identifies typical threats and vulnerabilities to these systems, and provides
recommended security countermeasures to mitigate the associated risks.
Keywords
Computer security; distributed control systems (DCS); industrial control systems (ICS); information
security; network security; programmable logic controllers (PLC); risk management; security controls;
supervisory control and data acquisition (SCADA) systems
SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
viii
ã³ã³ãã¥ã¼ã¿ã·ã¹ãã æè¡ã«é¢ããã¬ãã¼ã
ç±³å½å½ç«æ¨æºæè¡ç 究æï¼NISTï¼ã®æ
å ±æè¡ç 究æï¼ITLï¼ã¯ãå½ã®è¨æ¸¬åã³åºæºã¤ã³ãã©ã«é¢
ããæè¡ççµ±çãå³ããã¨ã«ãããç±³å½ã®çµæ¸ã»å
Œ
±ç¦ç¥ãä¿é²ãã¦ãããITL ã¯è©¦é¨ã試é¨æ³ã
åºæºãã¼ã¿ãæ¦å¿µã®å®è¨¼åã³æè¡è§£æã®éçºãé²ããæ
å ±æè¡ã®éçºã¨çç£çå©ç¨ãä¿é²ãã¦ã
ããITL ã®è²¬åã«ã¯ãé£é¦æ
å ±ã·ã¹ãã ã«ãããå½ã®ã»ãã¥ãªãã£é¢é£æ
å ±ä»¥å¤ã®ãè²»ç¨å¹æã®
é«ãã»ãã¥ãªãã£åã³ãã©ã¤ãã·ã¼ã«é¢ããéå¶ã管çãæè¡åã³ç©ççåºæºã»ã¬ã¤ãã©ã¤ã³ã®
ä½æãå«ã¾ãããSP800 ã·ãªã¼ãºã¯ãITL ã®ç 究ãã¬ã¤ãã©ã¤ã³åã³æ
å ±ã·ã¹ãã ã»ãã¥ãªãã£
ã«ãããå
Œ
±ç¦ç¥ã«åããåçµä¸¦ã³ã«ç£å®å¦ã¨ã®é£æºã«é¢ããå ±åæ¸ã§ããã
æé²
æ¬ææ¸ã¯ãSCADAãDCSãPLC ãã®ä»ã®å¶å¾¡ã·ã¹ãã è¨å®ãå«ãç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã®
ä¿å
¨æ¹æ³ã«é¢ããã¬ã¤ãã³ã¹ã§ããããã®ç¬ç¹ãªæ§è½ã»ä¿¡é ¼æ§ã»å®å
¨æ§è¦ä»¶ã«ã¤ãã¦åãä¸ããã
ICS ã®æ¦è¦ã¨å
¸åçãªã·ã¹ãã ãããã¸ã¼ãè¿°ã¹ããããã·ã¹ãã ã¸ã®ä¸è¬çãªè
å¨ã¨èå¼±æ§ã
æããã«ããé¢ä¿ãããªã¹ã¯ãæ¸ããããã®ã»ãã¥ãªãã£å¯¾çã«ã¤ãã¦æè¨ããã
ãã¼ã¯ã¼ã
ã³ã³ãã¥ã¼ã¿ã»ãã¥ãªãã£ãDCSãICSãæ
å ±ã»ãã¥ãªãã£ããããã¯ã¼ã¯ã»ãã¥ãªãã£ã
PLCããªã¹ã¯ç®¡çãã»ãã¥ãªãã£å¯¾çãSCADA
SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
ix
Acknowledgments for Revision 2
The authors gratefully acknowledge and appreciate the significant contributions from individuals and
organizations in the public and private sectors, whose thoughtful and constructive comments improved the
overall quality, thoroughness, and usefulness of this publication. A special acknowledgement to Lisa Kaiser,
Department of Homeland Security, the Department of Homeland Security Industrial Control System Joint
Working Group (ICSJWG), and Office of the Deputy Undersecretary of Defense for Installations and
Environment, Business Enterprise Integration Directorate staff, Daryl Haegley and Michael Chipley, for
their exceptional contributions to this publication.
Acknowledgments for Previous Versions
The original authors, Keith Stouffer, Joe Falco, and Karen Scarfone of NIST, wish to thank their colleagues
who reviewed drafts of the original version of the document and contributed to its technical content. The
authors would particularly like to acknowledge Tim Grance, Ron Ross, Stu Katzke, and Freemon Johnson
of NIST for their keen and insightful assistance throughout the development of the document. The authors
also gratefully acknowledge and appreciate the many contributions from the public and private sectors
whose thoughtful and constructive comments improved the quality and usefulness of the publication. The
authors would particularly like to thank the members of ISA99. The authors would also like to thank the
UK National Centre for the Protection of National Infrastructure (CPNI)) for allowing portions of the Good
Practice Guide on Firewall Deployment for SCADA and Process Control Network to be used in the
document as well as ISA for allowing portions of the ISA-62443 Standards to be used in the document.
Note to Readers
This document is the second revision to NIST SP 800-82, Guide to Industrial Control Systems (ICS)
Security. Updates in this revision include:
Updates to ICS threats and vulnerabilities.
Updates to ICS risk management, recommended practices, and architectures.
Updates to current activities in ICS security.
Updates to security capabilities and tools for ICS.
Additional alignment with other ICS security standards and guidelines.
New tailoring guidance for NIST SP 800-53, Revision 4 security controls including the
introduction of overlays.
An ICS overlay for NIST SP 800-53, Revision 4 security controls that provides tailored security
control baselines for Low, Moderate, and High impact ICS.

SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
x
第2çã«é¢ããè¬è¾
æ¬ææ¸ã®èè
ãã¯ãå®æ°ã®å人åã³çµç¹ããå¤å¤§ã®è²¢ç®ããã£ããã¨ãèªããããã«è¬æã表ã
ãããã®ç¤ºåã«å¯ã¿å»ºè¨çãªæè¦ã«ãããæ¬åºçç©ã®å
¨ä½çãªè³ªãå
æ¬æ§åã³æç¨æ§ãåä¸ããã
ç¹ã« Lisa Kaiserï¼å½åå®å
¨ä¿éçï¼ãå½åå®å
¨ä¿éçã® Industrial Control System Joint Working
Group (ICSJWG)åã³ Office of the Deputy Undersecretary of Defense for Installations and Environmentã
Business Enterprise Integration Directorate ã®è·å¡ãDaryl Haegley åã³ Michael Chipley ã«å¯¾ãã¦ãã
ãããã®ç¹å¥ãªè²¢ç®ã«è¬è¾ã表ãããã®ã§ããã
æ§çã«é¢ããè¬è¾
æ§çã®èè
ã§ãã NIST ã®Keith StoufferãJoe Falco åã³ Karen Scarfone ã¯ãæ¬ææ¸ã®åæ¡ãç²¾æ»
ãããã®æè¡çå
容ã«å¯ä¸ããåå諸æ°ã«è¬æã表ãããèè
ã¯ç¹ã«ãNIST ã®Tim GranceãRon
RossãStu Katzke åã³ Freemon Johnson ã«å¯¾ããææ¸ã®ä½æå
¨è¬ã«ãããéãæ´å¯ãä¸ãã¦ããã
ãã¨ã«è¬æã表ãããã¾ããå®æ°ããå¤å¤§ã®è²¢ç®ãããã示åã«å¯ã¿å»ºè¨çãªæè¦ã«ããåºçç©
ã®è³ªã¨æç¨æ§ãåä¸ãããã¨ã«ãè¬æã表ãããã¨ããã ISA99 ã®ã¡ã³ãã¼ã«ã¯æè¬ãã¦ããã
ã¾ããSCADA åã³ããã»ã¹å¶å¾¡ãããã¯ã¼ã¯ã®ãã¡ã¤ã¢ã¦ã©ã¼ã«ã«ä¿ãé©æ£è¦ç¯ã¬ã¤ããã®ä¸
é¨ãæ¬ææ¸ã§å©ç¨ããã¦ãããè±å½ã¤ã³ãã©ã¹ãã©ã¯ãã£é²è·ã»ã³ã¿ã¼ï¼CPNIï¼åã³ ISA-
62443 è¦æ ¼ãåæ§ã«å©ç¨ããã¦ããã ISA ã«å¯¾ãã¦ããè¬æã表ããã
èªè
ã¸ã®æ³¨è¨
æ¬ææ¸ã¯ NIST SP 800-82ãGuide to Industrial Control Systems (ICS) Securityï¼ç£æ¥ç¨å¶å¾¡ã·ã¹ãã
ã»ãã¥ãªãã£ã¬ã¤ããã®ç¬¬ 2çã§ãããæ´æ°å
容ã¯ä»¥ä¸ã®ã¨ããã
ICS ã®è
å¨ã¨èå¼±æ§ã«é¢ããæ¹è¨
ICS ãªã¹ã¯ç®¡çãæ¨å¥¨è¦ç¯ããã³ã¢ã¼ããã¯ãã£ã«é¢ããæ¹è¨
ICS ã»ãã¥ãªãã£ã«ãããç¾å¨ã®æ´»åã«é¢ããæ¹è¨
ICS ã®ã»ãã¥ãªãã£æ§è½ã¨ãã¼ã«ã«é¢ããæ¹è¨
ä»ã® ICS ã»ãã¥ãªãã£åºæºããã³ã¬ã¤ãã©ã¤ã³ã¨ã®è£è¶³èª¿æ´
ãªã¼ãã¼ã¬ã¤ã®ç´¹ä»ãå«ã NIST SP 800-53 ã®æ°ã¬ã¤ãã³ã¹ç¬¬ 4çã»ãã¥ãªãã£å¯¾ç
ä½ã»ä¸ã»é«ã¤ã³ãã¯ã ICS ã«åã£ãã»ãã¥ãªãã£ç®¡ççã®ãã¼ã¹ã©ã¤ã³ãä¸ãã¦ã
ãNIST SP 800-53 第4çã®ã»ãã¥ãªãã£ç®¡ççã«å¯¾å¿ãã ICS ãªã¼ãã¼ã¬ã¤
æ¬ææ¸ã¯ãè±èªçã®åå
¸ã«æ²¿ã£ã¦å¯¾è¨³ããããåªãã¦ãã¾ãããå®å
¨æ§ãæ£ç¢ºæ§ã
ä¿è¨¼ãããã®ã§ã¯ããã¾ãããæ¬ææ¸ã«è¨è¼ããã¦ããæ
å ±ããçããæ失ã¾ãã¯
æ害ã«å¯¾ãã¦ãJPCERT/CC ã¯è²¬ä»»ãè² ããã®ã§ã¯ããã¾ããã
SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
xi
Table of Contents
Executive Summary .............................................................................................................................. 1
ã¨ã°ã¼ã¯ãã£ããµããªã¼ ......................................................................................................................... 2
1. Introduction ..................................................................................................................................... 9
1.1 Purpose and Scope ................................................................................................................................... 9
1.2 Audience ................................................................................................................................................... 9
1. ã¯ããã« .......................................................................................................................................... 10
1.1 ç®çåã³é©ç¨ç¯å² ................................................................................................................................. 10
1.2 対象è
................................................................................................................................................... 10
1.3 Document Structure ................................................................................................................................ 11
1.3 ææ¸ã®æ§æ ............................................................................................................................................ 12
2. Overview of Industrial Control Systems .................................................................................... 13
2.1 Evolution of Industrial Control Systems ................................................................................................... 13
2. ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ã®æ¦è¦............................................................................................................. 14
2.1 ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ã®é²å ................................................................................................................... 14
2.2 ICS Industrial Sectors and Their Interdependencies ............................................................................... 15
2.2.1 Manufacturing Industries ............................................................................................................. 15
2.2.2 Distribution Industries .................................................................................................................. 15
2.2.3 Differences between Manufacturing and Distribution ICS ............................................................ 15
2.2.4 ICS and Critical Infrastructure Interdependencies ....................................................................... 15
2.2 ICS ã®ç£æ¥é¨éã¨ãã®ç¸äºä¾åæ§ ......................................................................................................... 16
2.2.1 製é æ¥ç .................................................................................................................................... 16
2.2.2 é
éæ¥ç .................................................................................................................................... 16
2.2.3 製é ICS ã¨é
é ICS ã®ç¸é ...................................................................................................... 16
2.2.4 ICS ã¨éè¦ã¤ã³ãã©ã®ç¸äºä¾åæ§ ............................................................................................. 16
2.3 ICS Operation and Components ............................................................................................................. 17
2.3 ICS ã®æä½åã³ã³ã³ãã¼ãã³ã ............................................................................................................ 18
2.3.1 ICS System Design Considerations ............................................................................................. 19
2.3.1 ICS ã®ã·ã¹ãã è¨è¨ä¸ã®èæ
®äºé
............................................................................................. 20
2.3.2 SCADA Systems .......................................................................................................................... 21
2.3.2 SCADA ...................................................................................................................................... 22
2.3.3 Distributed Control Systems ........................................................................................................ 31
2.3.3 åæ£å¶å¾¡ã·ã¹ãã ..................................................................................................................... 32
2.3.4 Programmable Logic Controller Based Topologies...................................................................... 35
2.3.4 ããã°ã©ã å¯è½è«çã³ã³ããã¼ã©ãã¼ã¹ã®ãããã¸ã¼ ............................................................ 36
2.4 Comparing ICS and IT Systems Security ................................................................................................ 39
2.4 ICS ã·ã¹ãã 㨠IT ã·ã¹ãã ã®ã»ãã¥ãªãã£æ¯è¼.................................................................................. 40
2.5 Other Types of Control Systems ............................................................................................................. 45
2.5 å¥ç¨®ã®å¶å¾¡ã·ã¹ãã ............................................................................................................................. 46
3. ICS Risk Management and Assessment..................................................................................... 49
3.1 Risk Management ................................................................................................................................... 49
3. ICS ã®ãªã¹ã¯ç®¡çã¨ãªã¹ã¯è©ä¾¡ ...................................................................................................... 50
3.1 ãªã¹ã¯ç®¡ç ............................................................................................................................................ 50
3.2 Introduction to the Risk Management Process ........................................................................................ 51
3.2 ãªã¹ã¯ç®¡çããã»ã¹ã®ç´¹ä» ................................................................................................................... 52
3.3 Special Considerations for Doing an ICS Risk Assessment .................................................................... 55
3.3.1 Safety within an ICS Information Security Risk Assessment ....................................................... 55
3.3 ICS ãªã¹ã¯è©ä¾¡ã®å®æ½ã«éãã¦ã®ç¹å¥ãªèæ
®äºé
............................................................................... 56
SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
xii
3.3.1 ICS æ
å ±ã»ãã¥ãªãã£ãªã¹ã¯è©ä¾¡ã«ãããå®å
¨æ§ .................................................................... 56
3.3.2 Potential Physical Impacts of an ICS Incident ............................................................................. 57
3.3.3 Impact of Physical Disruption of an ICS Process ......................................................................... 57
3.3.2 ICS ã¤ã³ã·ãã³ãã«ããç©ççå½±é¿ã®å¯è½æ§ ........................................................................... 58
3.3.3 ICS ããã»ã¹ã®ç©ççä¸æã«ããå½±é¿ ...................................................................................... 58
3.3.4 Incorporating Non-digital Aspects of ICS into Impact Evaluations ............................................... 59
3.3.4 ICS ã®éãã¸ã¿ã«é¢ãå½±é¿è©ä¾¡ã«å«ãã .................................................................................. 60
3.3.5 Incorporating the Impact of Safety Systems ................................................................................ 61
3.3.6 Considering the Propagation of Impact to Connected Systems ................................................... 61
3.3.5 å®å
¨ã·ã¹ãã ã®å½±é¿ãå«ãã.................................................................................................... 62
3.3.6 æ¥ç¶ã·ã¹ãã ã¸ã®å½±é¿æ³¢åã«å¯¾ããèæ
® .................................................................................. 62
4. ICS Security Program Development and Deployment .............................................................. 63
4. ICS ã»ãã¥ãªãã£ããã°ã©ã ã®éçºåã³å±é ................................................................................ 64
4.1 Business Case for Security ..................................................................................................................... 65
4.1.1 Benefits ................................................................................................................................................ 65
4.1 ã»ãã¥ãªãã£ã®äºæ¥äºä¾ ...................................................................................................................... 66
4.1.1 便ç ................................................................................................................................................... 66
4.1.2 Potential Consequences .............................................................................................................. 67
4.1.2 çãå¾ãçµæ............................................................................................................................. 68
4.1.3 Resources for Building Business Case ........................................................................................ 69
4.1.4 Presenting the Business Case to Leadership .............................................................................. 69
4.1.3 äºæ¥äºä¾ä½æã®ããã®ãªã½ã¼ã¹ ................................................................................................ 70
4.1.4 äºæ¥äºä¾ãçµç¹ã®é·ã«æ示ãã ................................................................................................ 70
4.2 Build and Train a Cross-Functional Team ............................................................................................... 71
4.3 Define Charter and Scope ....................................................................................................................... 71
4.2 æ©è½æ¨ªæãã¼ã ã®çµæã»æè²è¨ç·´ ........................................................................................................ 72
4.3 æ²ç« åã³é©ç¨ç¯å²ã®æ確å ................................................................................................................... 72
4.4 Define ICS-specific Security Policies and Procedures ............................................................................ 73
4.5 Implement an ICS Security Risk Management Framework ..................................................................... 73
4.4 ICS åºæã®ã»ãã¥ãªãã£ããªã·ã¼åã³æé ã®æ確å ............................................................................ 74
4.5 ICS ã»ãã¥ãªãã£ãªã¹ã¯ç®¡çä½å¶ã®å®è¡.............................................................................................. 74
4.5.1 Categorize ICS Systems and Networks Assets ........................................................................... 75
4.5.2 Select ICS Security Controls ....................................................................................................... 75
4.5.1 ICS ã·ã¹ãã ã¨ãããã¯ã¼ã¯è³ç£ã®åé¡ .................................................................................. 76
4.5.2 ICS ã»ãã¥ãªãã£ç®¡çã®é¸æ .................................................................................................... 76
4.5.3 Perform Risk Assessment ........................................................................................................... 77
4.5.4 Implement the Security Controls .................................................................................................. 77
4.5.3 ãªã¹ã¯è©ä¾¡å®æ½ ......................................................................................................................... 78
4.5.4 ã»ãã¥ãªãã£ç®¡çã®å®è£
........................................................................................................... 78
5. ICS Security Architecture ............................................................................................................ 79
5.1 Network Segmentation and Segregation ................................................................................................. 79
5. ICS ã»ãã¥ãªãã£ã¢ã¼ããã¯ã㣠.................................................................................................. 80
5.1 ãããã¯ã¼ã¯ã®åå²ã¨åé¢ ................................................................................................................... 80
5.2 Boundary Protection ................................................................................................................................ 83
5.2 å¢çã®ä¿è· .............................................................................................................................................. 84
5.3 Firewalls .................................................................................................................................................. 85
5.3 ãã¡ã¤ã¢ã¦ã©ã¼ã« ................................................................................................................................. 86
5.4 Logically Separated Control Network ...................................................................................................... 89
5.4 è«ççã«åé¢ãããå¶å¾¡ãããã¯ã¼ã¯ ................................................................................................. 90
5.5 Network Segregation ............................................................................................................................... 91
5.5.1 Dual-Homed Computer/Dual Network Interface Cards (NIC) ...................................................... 91
5.5.2 Firewall between Corporate Network and Control Network ......................................................... 91
SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
xiii
5.5 ãããã¯ã¼ã¯ã®åé¢ ............................................................................................................................. 92
5.5.1 ãã¥ã¢ã«ãã¼ã ï¾ï¾ã³ã³ãã¥ã¼ã¿/ãã¥ã¢ã«ãããã¯ã¼ã¯ã¤ã³ã¿ãã§ã¼ã¹ã«ã¼ãï¼NICï¼ .......... 92
5.5.2 ä¼æ¥ãããã¯ã¼ã¯ã¨å¶å¾¡ãããã¯ã¼ã¯éã®ãã¡ã¤ã¢ã¦ã©ã¼ã«.................................................. 92
5.5.3 Firewall and Router between Corporate Network and Control Network ....................................... 95
5.5.3 ä¼æ¥ãããã¯ã¼ã¯ã¨å¶å¾¡ãããã¯ã¼ã¯éã®ãã¡ã¤ã¢ã¦ã©ã¼ã«ã¨ã«ã¼ã¿ ...................................... 96
5.5.4 Firewall with DMZ between Corporate Network and Control Network ......................................... 97
5.5.4 ä¼æ¥ãããã¯ã¼ã¯ã¨å¶å¾¡ãããã¯ã¼ã¯éã® DMZ ä»ããã¡ã¤ã¢ã¦ã©ã¼ã« ................................. 98
5.5.5 Paired Firewalls between Corporate Network and Control Network .......................................... 101
5.5.5 ä¼æ¥ãããã¯ã¼ã¯ã¨å¶å¾¡ãããã¯ã¼ã¯éã®ãã¢ã¼ããã¡ã¤ã¢ã¦ã©ã¼ã« ................................. 102
5.5.6 Network Segregation Summary ................................................................................................. 103
5.6 Recommended Defense-in-Depth Architecture ..................................................................................... 103
5.5.6 ãããã¯ã¼ã¯åé¢ã®ã¾ã¨ã ..................................................................................................... 104
5.6 æ¨å¥¨å¤å±¤é²å¾¡ã¢ã¼ããã¯ã㣠............................................................................................................. 104
5.7 General Firewall Policies for ICS ........................................................................................................... 105
5.7 ICS ã®å
¨è¬çãã¡ã¤ã¢ã¦ã©ã¼ã«ããªã·ã¼............................................................................................ 106
5.8 Recommended Firewall Rules for Specific Services ............................................................................. 109
5.8 ç¹å®ãµã¼ãã¹ã®æ¨å¥¨ãã¡ã¤ã¢ã¦ã©ã¼ã«ã«ã¼ã« .................................................................................... 110
5.8.1 Domain Name System (DNS) .................................................................................................... 111
5.8.2 Hypertext Transfer Protocol (HTTP) .......................................................................................... 111
5.8.3 FTP and Trivial File Transfer Protocol (TFTP) ........................................................................... 111
5.8.4 Telnet ......................................................................................................................................... 111
5.8.1 é ååã·ã¹ãã ï¼DNSï¼ ........................................................................................................ 112
5.8.2 ãã¤ãã¼ããã¹ã転éãããã³ã«ï¼HTTPï¼ .......................................................................... 112
5.8.3 FTP åã³ããªãã¢ã«ãã¡ã¤ã«è»¢éãããã³ã«ï¼TFTPï¼ ........................................................ 112
5.8.4 ãã«ãããï¼Telnetï¼ ............................................................................................................. 112
5.8.5 Dynamic Host Configuration Protocol (DHCP)........................................................................... 113
5.8.6 Secure Shell (SSH) .................................................................................................................... 113
5.8.7 Simple Object Access Protocol (SOAP) .................................................................................... 113
5.8.8 Simple Mail Transfer Protocol (SMTP) ...................................................................................... 113
5.8.9 Simple Network Management Protocol (SNMP) ........................................................................ 113
5.8.5 åçãã¹ãæ§æãããã³ã«ï¼DHCPï¼ .................................................................................... 114
5.8.6 ã»ãã¥ã¢ã·ã§ã«ï¼SSH) ........................................................................................................... 114
5.8.7 ã·ã³ãã«ãªãã¸ã§ã¯ãã¢ã¯ã»ã¹ãããã³ã«ï¼SOAPï¼ ........................................................... 114
5.8.8 ã·ã³ãã«ã¡ã¼ã«è»¢éãããã³ã«ï¼SMTPï¼ ............................................................................. 114
5.8.9 ã·ã³ãã«ãããã¯ã¼ã¯ç®¡çãããã³ã«ï¼SNMPï¼ .................................................................. 114
5.8.10 Distributed Component Object Model (DCOM) ........................................................................ 115
5.8.11 SCADA and Industrial Protocols .............................................................................................. 115
5.9 Network Address Translation (NAT) ...................................................................................................... 115
5.8.10 åæ£ã³ã³ãã¼ãã³ããªãã¸ã§ã¯ãã¢ãã«ï¼DCOMï¼ ............................................................ 116
5.8.11 SCADA åã³ç£æ¥ç¨ãããã³ã« ............................................................................................. 116
5.9 ãããã¯ã¼ã¯ã¢ãã¬ã¹å¤æï¼NATï¼ .................................................................................................. 116
5.10 Specific ICS Firewall Issues ................................................................................................................ 117
5.10.1 Data Historians ........................................................................................................................ 117
5.10.2 Remote Support Access .......................................................................................................... 117
5.10.3 Multicast Traffic ........................................................................................................................ 117
5.10 ICS ãã¡ã¤ã¢ã¦ã©ã¼ã«åºæã®åé¡ .................................................................................................... 118
5.10.1 ãã¼ã¿ãã¹ããªã¢ã³ .............................................................................................................. 118
5.10.2 é éãµãã¼ãã·ã¹ãã .......................................................................................................... 118
5.10.3 ãã«ããã£ã¹ããã©ãã£ãã¯................................................................................................ 118
5.11 Unidirectional Gateways ..................................................................................................................... 119
5.12 Single Points of Failure ....................................................................................................................... 119
5.13 Redundancy and Fault Tolerance ...................................................................................................... 119
5.11 åæ¹åæ§ã²ã¼ãã¦ã§ã¤ ...................................................................................................................... 120
SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
xiv
5.12 åä¸éå®³ç¹ ........................................................................................................................................ 120
5.13 åé·æ§ã¨ãã©ã¼ã«ããã¬ã©ã³ã¹ ....................................................................................................... 120
5.14 Preventing Man-in-the-Middle Attacks ................................................................................................ 121
5.14 人ãä»å¨ããæ»æã®é²æ¢ .................................................................................................................. 122
5.15 Authentication and Authorization ......................................................................................................... 125
5.15 èªè¨¼ã¨æ¨©éä»ä¸ ................................................................................................................................ 126
5.15.1 ICS Implementation Considerations ................................................................................................. 127
5.16 Monitoring, Logging, and Auditing ....................................................................................................... 127
5.17 Incident Detection, Response, and System Recovery ........................................................................ 127
5.15.1 ICS å®è£
ä¸ã®èæ
®äºé
........................................................................................................... 128
5.16 ç£è¦ããã®ã³ã°åã³ç£æ» .................................................................................................................. 128
5.17 ã¤ã³ã·ãã³ãæ¤ç¥ã対å¿åã³ã·ã¹ãã å¾©æ§ ...................................................................................... 128
6. Applying Security Controls to ICS ........................................................................................... 129
6.1 Executing the Risk Management Framework Tasks for Industrial Control Systems ............................. 129
6. ICS ã¸ã®ã»ãã¥ãªãã£å¯¾çã®é©ç¨ ...................................................................................... 130
6.1 ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ç¨ãªã¹ã¯ç®¡çä½å¶ã®å®æ½ .................................................................................... 130
6.1.1 Step 1: Categorize Information System ..................................................................................... 131
6.1.1 æé 1ï¼æ
å ±ã·ã¹ãã ã®åé¡ .................................................................................................. 132
6.1.2 Step 2: Select Security Controls ................................................................................................ 135
6.1.2 æé 2ï¼ã»ãã¥ãªãã£å¯¾çã®é¸æ ........................................................................................... 136
6.1.3 Step 3: Implement Security Controls ......................................................................................... 137
6.1.4 Step 4: Assess Security Controls............................................................................................... 137
6.1.5 Step 5: Authorize Information System ....................................................................................... 137
6.1.3 æé 3ï¼ã»ãã¥ãªãã£å¯¾çã®å®è£
........................................................................................... 138
6.1.4 æé 4ï¼ã»ãã¥ãªãã£å¯¾çã®è©ä¾¡ ........................................................................................... 138
6.1.5 æé 5ï¼æ
å ±ã·ã¹ãã ã®è¨±å¯ .................................................................................................. 138
6.1.6 Step 6: Monitor Security Controls .............................................................................................. 139
6.2 Guidance on the Application of Security Controls to ICS ...................................................................... 139
6.1.6 æé 6ï¼ã»ãã¥ãªãã£å¯¾çã®ç£è¦ ........................................................................................... 140
6.2 ICS ã¸ã®ã»ãã¥ãªãã£å¯¾çã®é©ç¨ã«ä¿ãã¬ã¤ãã³ã¹ .......................................................................... 140
6.2.1 Access Control........................................................................................................................... 143
6.2.1 ã¢ã¯ã»ã¹å¶å¾¡........................................................................................................................... 144
6.2.2 Awareness and Training ............................................................................................................ 153
6.2.3 Audit and Accountability ............................................................................................................ 153
6.2.2 æèåã³è¨ç·´........................................................................................................................... 154
6.2.3 ç£æ»åã³èª¬æ責任 ................................................................................................................... 154
6.2.4 Security Assessment and Authorization .................................................................................... 157
6.2.5 Configuration Management ....................................................................................................... 157
6.2.4 ã»ãã¥ãªãã£è©ä¾¡åã³æ¨©éä»ä¸ .............................................................................................. 158
6.2.5 æ§æ管ç .................................................................................................................................. 158
6.2.6 Contingency Planning ................................................................................................................ 159
6.2.6 ä¸æ¸¬äºæ
è¨ç»........................................................................................................................... 160
6.2.7 Identification and Authentication ................................................................................................ 165
6.2.7 èå¥åã³èªè¨¼........................................................................................................................... 166
6.2.8 Incident Response ..................................................................................................................... 177
6.2.8 ã¤ã³ã·ãã³ãå¯¾å¿ ................................................................................................................... 178
6.2.9 Maintenance .............................................................................................................................. 181
6.2.10 Media Protection ...................................................................................................................... 181
6.2.9 ä¿å® ......................................................................................................................................... 182
6.2.10 ã¡ãã¤ã¢ä¿è·......................................................................................................................... 182
6.2.11 Physical and Environmental Protection ................................................................................... 183
6.2.11 ç©çç°å¢ä¸ã®ä¿è·ï¼PEï¼ ..................................................................................................... 184
SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
xv
6.2.12 Planning ................................................................................................................................... 189
6.2.12 ãã©ã³ãã³ã°......................................................................................................................... 190
6.2.13 Personnel Security ................................................................................................................... 191
6.2.13 人å¡ã®ã»ãã¥ãªã㣠.............................................................................................................. 192
6.2.14 Risk Assessment ..................................................................................................................... 193
6.2.15 System and Services Acquisition ............................................................................................. 193
6.2.14 ãªã¹ã¯è©ä¾¡ ............................................................................................................................ 194
6.2.15 ã·ã¹ãã åã³ãµã¼ãã¹ã®åå¾................................................................................................ 194
6.2.16 System and Communications Protection ................................................................................. 195
6.2.16 ã·ã¹ãã åã³éä¿¡ä¿è· .......................................................................................................... 196
6.2.16.1 Encryption ............................................................................................................................. 197
6.2.16.1 æå·å ................................................................................................................................ 198
6.2.17 System and Information Integrity ............................................................................................. 203
6.2.17 ã·ã¹ãã åã³æ
å ±ã®ä¿å
¨ ....................................................................................................... 204
6.2.18 Program Management ............................................................................................................. 209
6.2.19 Privacy Controls ....................................................................................................................... 209
6.2.18 ããã°ã©ã 管ç ..................................................................................................................... 210
6.2.19 ãã©ã¤ãã·ã¼ç®¡ç ................................................................................................................. 210
List of Apendix
Appendix AâAcronyms and Abbreviations ......................................................................................................... 213
ä»é² A é åèªåã³ç¥èª ..................................................................................................................................... 214
Appendix BâGlossary of Terms ......................................................................................................................... 219
ä»é² B ç¨èªé .................................................................................................................................................... 220
Appendix CâThreat Sources, Vulnerabilities, and Incidents .............................................................................. 255
ä»é² C è
å¨æºãèå¼±æ§åã³ã¤ã³ã·ãã³ã ........................................................................................................ 256
Appendix DâCurrent Activities in Industrial Control System Security ................................................................. 283
ä»é² D ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ã»ãã¥ãªãã£ã«ãããç¾å¨ã®æ´»å ....................................................................... 284
Appendix EâICS Security Capabilities and Tools ............................................................................................... 315
ä»é² E ICS ã»ãã¥ãªãã£æ©è½åã³ãã¼ã« ......................................................................................................... 316
Appendix FâReferences .................................................................................................................................... 323
Appendix GâICS Overlay ................................................................................................................................... 341
ä»é² G ICS ãªã¼ãã¼ã¬ã¤ ................................................................................................................................. 342
List of Figure
Figure 2-1. ICS Operation ..................................................................................................................................... 19
å³2-1.ICS ã®åä½ .................................................................................................................................................. 20
Figure 2-2. SCADA System General Layout ......................................................................................................... 23
å³2-2.SCADA ã®å
¨è¬ã¬ã¤ã¢ã¦ã .......................................................................................................................... 24
Figure 2-3. Basic SCADA Communication Topologies .......................................................................................... 25
å³2-3. åºæ¬ç SCADA éä¿¡ãããã¸ã¼ .............................................................................................................. 26
Figure 2-4. Large SCADA Communication Topology ............................................................................................ 27
å³2-4. 大è¦æ¨¡ SCADA éä¿¡ãããã¸ã¼ .............................................................................................................. 28
Figure 2-5. SCADA System Implementation Example (Distribution Monitoring and Control) ................................ 29
å³2-5. SCADA ã®å®è£
ä¾ï¼åæ£ç£è¦ã»å¶å¾¡ï¼ ..................................................................................................... 30
Figure 2-6. SCADA System Implementation Example (Rail Monitoring and Control) ............................................ 31
å³2-6. SCADA ã®å®è£
ä¾ï¼åè»ç£è¦ã»å¶å¾¡ï¼ ....................................................................................................... 32
Figure 2-7. DCS Implementation Example ............................................................................................................ 35
å³2-7.DCS ã®å®è£
ä¾ ............................................................................................................................................. 36
Figure 2-8. PLC Control System Implementation Example ................................................................................... 37
å³2-8. PLC å¶å¾¡ã·ã¹ãã ã®å®è£
ä¾ ....................................................................................................................... 38
SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
xvi
Figure 3-1. Risk Management Process Applied Across the Tiers .......................................................................... 51
å³3-1.å
¨æ®µéã«ã¾ããããªã¹ã¯ç®¡çããã»ã¹ ....................................................................................................... 52
Figure 5-1. Firewall between Corporate Network and Control Network ................................................................. 93
å³5-1.ä¼æ¥ãããã¯ã¼ã¯ã¨å¶å¾¡ãããã¯ã¼ã¯éã®ãã¡ã¤ã¢ã¦ã©ã¼ã« ................................................................... 94
Figure 5-2. Firewall and Router between Corporate Network and Control Network .............................................. 95
å³5-2.ä¼æ¥ãããã¯ã¼ã¯ã¨å¶å¾¡ãããã¯ã¼ã¯éã®ãã¡ã¤ã¢ã¦ã©ã¼ã«ã¨ã«ã¼ã¿ ..................................................... 96
Figure 5-3. Firewall with DMZ between Corporate Network and Control Network ................................................. 97
å³5-3.ä¼æ¥ãããã¯ã¼ã¯ã¨å¶å¾¡ãããã¯ã¼ã¯éã® DMZ ä»ããã¡ã¤ã¢ã¦ã©ã¼ã« ................................................... 98
Figure 5-4. Paired Firewalls between Corporate Network and Control Network .................................................. 101
å³5-4.ä¼æ¥ãããã¯ã¼ã¯ã¨å¶å¾¡ãããã¯ã¼ã¯éã®ãã¢ã¼ããã¡ã¤ã¢ã¦ã©ã¼ã« ................................................... 102
Figure 5-5. CSSP Recommended Defense-In-Depth Architecture ...................................................................... 105
å³5-5.CSSP ã®æ¨å¥¨å¤å±¤é²å¾¡ã¢ã¼ããã¯ã㣠..................................................................................................... 106
Figure 6-1. Risk Management Framework Tasls ................................................................................................. 131
å³6-1.ãªã¹ã¯ç®¡çä½å¶æ¥å .................................................................................................................................. 132
Figure C-1. ICS-CERT Reported Incidents by Year ............................................................................................ 275
å³C-1. ICS-CERT ã«å±åºã®ãã£ã年度å¥ã¤ã³ã·ãã³ãä»¶æ° .............................................................................. 276
Figure G-1 Detailed Overlay Control Specifications Illustrated ............................................................................ 365
å³G-1 詳細ãªã¼ãã¼ã¬ã¤ç®¡çä»æ§ã®èª¬æ ........................................................................................................... 366
List of Tables
Table 2-1. Summary of IT System and ICS Differences ........................................................................................ 43
表2-1.IT ã·ã¹ãã 㨠ICS ã®ç¸éç¹ ........................................................................................................................ 44
Table 3-1. Categories of Non-Digital ICS Control Components ............................................................................. 59
表3-1. éãã¸ã¿ã« ICS å¶å¾¡ã³ã³ãã¼ãã³ãã®ã«ãã´ãªã¼ .................................................................................... 60
Table 6-1. Possible Definitions for ICS Impact Levels Based on ISA99 .............................................................. 133
表6-1. ISA99 ã«åºã¥ã ICS å½±é¿ã¬ãã«ã®å®ç¾© .................................................................................................... 134
Table 6-2. Possible Definitions for ICS Impact Levels Based on Product Produced, Industry and Security
Concerns ............................................................................................................................................................. 135
表6-2. çç£ç©ãç£æ¥åã³ã»ãã¥ãªãã£é¢å¿äºã«åºã¥ã ICS ã¸ã®å½±é¿ã¬ãã«ã®å®ç¾© .......................................... 136
Table C-1. Threats to ICS .................................................................................................................................... 255
表C-1. ICS ã®è
å¨ ............................................................................................................................................... 256
Table C-2. Policy and Procedure Vulnerabilities and Predisposing Conditions ................................................... 261
表C-2. ããªã·ã¼åã³æé ã®èå¼±æ§åã³å¼±ç¹ã¨ãªãç¶æ
..................................................................................... 262
Table C-3. Architecture and Design Vulnerabilities and Predisposing Conditions ............................................... 265
Table C-4. Configuration and Maintenance Vulnerabilities and Predisposing Conditions ................................... 265
表C-3.ã¢ã¼ããã¯ãã£åã³è¨è¨ä¸ã®èå¼±æ§åã³å¼±ç¹ã¨ãªãç¶æ
........................................................................ 266
表C-4.æ§æåã³ä¿å®ä¸ã®èå¼±æ§åã³å¼±ç¹ã¨ãªãç¶æ
.......................................................................................... 266
Table C-5. Physical Vulnerabilities and Predisposing Conditions ........................................................................ 269
表C-5.ç©ççèå¼±æ§åã³å¼±ç¹ã¨ãªãç¶æ
............................................................................................................ 270
Table C-6. Software Development Vulnerabilities and Predisposing Conditions ................................................. 271
Table C-7. Communication and Network Configuration Vulnerabilities and Predisposing Conditions ................. 271
表C-6.ã½ããã¦ã¨ã¢éçºä¸ã®èå¼±æ§åã³å¼±ç¹ã¨ãªãç¶æ
................................................................................... 272
表C-7.éä¿¡åã³ãããã¯ã¼ã¯æ§æä¸ã®èå¼±æ§åã³å¼±ç¹ã¨ãªãç¶æ
.................................................................... 272
Table C-8. Example Adversarial Incidents ........................................................................................................... 273
表C-8. æ»æã¤ã³ã·ãã³ãã®ä¾ ............................................................................................................................ 274
Table G-1 Security Control Baselines .................................................................................................................. 345
表G-1 ã»ãã¥ãªãã£ç®¡çãã¼ã¹ã©ã¤ã³ ............................................................................................................ 346

SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
1
Executive Summary
This document provides guidance for establishing secure industrial control systems (ICS). These ICS,
which include supervisory control and data acquisition (SCADA) systems, distributed control systems
(DCS), and other control system configurations such as Programmable Logic Controllers (PLC) are often
found in the industrial control sectors. ICS are typically used in industries such as electric, water and
wastewater, oil and natural gas, transportation, chemical, pharmaceutical, pulp and paper, food and
beverage, and discrete manufacturing (e.g., automotive, aerospace, and durable goods.) SCADA systems
are generally used to control dispersed assets using centralized data acquisition and supervisory control.
DCS are generally used to control production systems within a local area such as a factory using
supervisory and regulatory control. PLCs are generally used for discrete control for specific applications
and generally provide regulatory control. These control systems are vital to the operation of the U.S. critical
infrastructures that are often highly interconnected and mutually dependent systems. It is important to note
that approximately 90 percent of the nation's critical infrastructures are privately owned and operated.
Federal agencies also operate many of the ICS mentioned above; other examples include air traffic control
and materials handling (e.g., Postal Service mail handling.) This document provides an overview of these
ICS and typical system topologies, identifies typical threats and vulnerabilities to these systems, and
provides recommended security countermeasures to mitigate the associated risks.
Initially, ICS had little resemblance to traditional information technology (IT) systems in that ICS were
isolated systems running proprietary control protocols using specialized hardware and software. Many ICS
components were in physically secured areas and the components were not connected to IT networks or
systems. Widely available, low-cost Internet Protocol (IP) devices are now replacing proprietary solutions,
which increases the possibility of cybersecurity vulnerabilities and incidents. As ICS are adopting IT
solutions to promote corporate business systems connectivity and remote access capabilities, and are being
designed and implemented using industry standard computers, operating systems (OS) and network
protocols, they are starting to resemble IT systems. This integration supports new IT capabilities, but it
provides significantly less isolation for ICS from the outside world than predecessor systems, creating a
greater need to secure these systems. The increasing use of wireless networking places ICS
implementations at greater risk from adversaries who are in relatively close physical proximity but do not
have direct physical access to the equipment. While security solutions have been designed to deal with
these security issues in typical IT systems, special precautions must be taken when introducing these same
solutions to ICS environments. In some cases, new security solutions are needed that are tailored to the ICS
environment.
Although some characteristics are similar, ICS also have characteristics that differ from traditional
information processing systems. Many of these differences stem from the fact that logic executing in ICS
has a direct effect on the physical world. Some of these characteristics include significant risk to the health
and safety of human lives and serious damage to the environment, as well as serious financial issues such
as production losses, negative impact to a nationâs economy, and compromise of proprietary information.
ICS have unique performance and reliability requirements and often use operating systems and applications
that may be considered unconventional to typical IT personnel. Furthermore, the goals of safety and
efficiency sometimes conflict with security in the design and operation of control systems.
ICS cybersecurity programs should always be part of broader ICS safety and reliability programs at both
industrial sites and enterprise cybersecurity programs, because cybersecurity is essential to the safe and
reliable operation of modern industrial processes. Threats to control systems can come from numerous
sources, including hostile governments, terrorist groups, disgruntled employees, malicious intruders,
complexities, accidents, and natural disasters as well as malicious or accidental actions by insiders. ICS
security objectives typically follow the priority of availability and integrity, followed by confidentiality.

SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
2
ã¨ã°ã¼ã¯ãã£ããµããªã¼
æ¬ææ¸ã¯ãã»ãã¥ã¢ãªç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ãæ§ç¯ããããã®ã¬ã¤ãã³ã¹ã¨ãªããSCADAã
DCSãPLC ãã®ä»ã®å¶å¾¡ã·ã¹ãã è¨å®ãå«ãã ããã ICS ã¯ãç£æ¥ç¨å¶å¾¡æ¥çã«ããè¦ããããICS
ã¯ä¸è¬çã«é»æ°ãä¸ä¸æ°´ãç³æ²¹ã»ã¬ã¹ã輸éãåå¦ãå»è¬åããã«ãã»è£½ç´ãé£åã»é£²æåã³çµç«è£½
é ï¼èªåè»ãèªç©ºå®å®ãèä¹
æ¶è²»è²¡çï¼æ¥çã§å©ç¨ããã¦ãããSCADA ã¯ãéä¸ãã¼ã¿åå¾ç£è¦å¶
御ã«ãããåæ£åãããè³ç£ãå¶å¾¡ããããã«ãé常使ç¨ãããDCS ã¯ããã¼ã«ã«ã¨ãªã¢å
ã«ããå·¥
å ´çã®çç£ã·ã¹ãã ããç£è¦ã»è¦å¶å¶å¾¡ã«ããå¶å¾¡ããããã«ãé常使ç¨ãããPLC ã¯ãç¹æ®ç¨éã§
ã®é¢æ£å¶å¾¡ã«é常使ç¨ããè¦å¶å¶å¾¡ãé常è¡ãããã®ãããªå¶å¾¡ã·ã¹ãã ã¯ãé«åº¦ã«é£æºã»ç¸äºä¾å
ããã·ã¹ãã ã¨ãªããç±³å½ã®éè¦ã¤ã³ãã©ã®éå¶ã«ç·è¦ãªå½¹å²ãæããã¦ãããå½ã®éè¦ã¤ã³ãã©ã®
ããã 90%ã¯ãç§ä¼æ¥ãä¿æãéå¶ãã¦ããç¹ã«æ³¨æãã¹ãã§ãããé£é¦æ¿åºæ©é¢ãåè¿°ã® ICS ã®å¤
ããéå¶ãã¦ãããããã®ã»ãã«ãèªç©ºäº¤é管å¶ãç©æµå¦çï¼éµä¾¿ç©ã®åæ±çï¼ãªã©ããããæ¬ææ¸
ã§ã¯ãã®ãã㪠ICS ã®æ¦è¦åã³ä¸è¬çãªã·ã¹ãã ãããã¸ã¼ã«ã¤ãã¦ç¤ºããã·ã¹ãã ã«ã¨ã£ã¦ã®ä¸è¬
çãªè
å¨ã¨èå¼±æ§ãç¹å®ããé¢é£ãªã¹ã¯ãä½æ¸ããããã®æ¨å¥¨ã»ãã¥ãªãã£å¯¾çãæ示ããã
åæã® ICS ã¯ãç¹æ®ãªãã¼ãã¦ã¨ã¢ã¨ã½ããã¦ã¨ã¢ã使ç¨ãã¦å°ç¨å¶å¾¡ãããã³ã«ãå®è¡ããé絶ã
ããã·ã¹ãã ã ã£ããããå¾æ¥ã®æ
å ±æè¡ï¼ITï¼ã·ã¹ãã ã¨ã¯é¡ä¼¼ç¹ãã»ã¨ãã©ãªãã£ããICS ã³ã³
ãã¼ãã³ãã®å¤ãã¯ç©ççã«å®å
¨ãªã¨ãªã¢å
ã«ç½®ãããIT ãããã¯ã¼ã¯ãã·ã¹ãã ã«æ¥ç¶ããã¦ããª
ãã£ããæ¨ä»ãåºãå©ç¨å¯è½ãªä½ã³ã¹ãã®ã¤ã³ã¿ã¼ããããããã³ã«ï¼IPï¼ããã¤ã¹ãå°ç¨ã½ãªã¥ã¼
ã·ã§ã³ã«åã£ã¦ä»£ããã¤ã¤ãããã¨ããããµã¤ãã¼ã»ãã¥ãªãã£ã®èå¼±æ§ãã¤ã³ã·ãã³ããçããè
ç¶æ§ãé«ã¾ã£ã¦ãããICS ã¯IT ã½ãªã¥ã¼ã·ã§ã³ãæ¡ç¨ãã¦ãä¼æ¥ãã¸ãã¹ã·ã¹ãã ã¸ã®æ¥ç¶æ§ããªã¢
ã¼ãã¢ã¯ã»ã¹è½åãé«ããã¾ããæ¥çæ¨æºã³ã³ãã¥ã¼ã¿ããªãã¬ã¼ãã£ã³ã°ã·ã¹ãã ï¼OSï¼åã³ãã
ãã¯ã¼ã¯ãããã³ã«ã使ç¨ãã¦è¨è¨ã»å®è£
ãããããã«ãªã£ã¦ããããã®ãã ICS ã¯æ¬¡ç¬¬ã« IT ã·ã¹
ãã ã¨é¡ä¼¼æ§ãæã¤ããã«ãªã£ã¦ããããã®ãããªçµ±ååã¯æ°ã㪠IT è½åããµãã¼ããããããã
以åã®ã·ã¹ãã ã«æ¯ã¹ãã¨ãå¤çããã®é絶æ§ãæ ¼æ®µã«å£ããããã»ãã¥ãªãã£ã®å¿
è¦æ§ãå¢ããã¯
ã¤ã¤ã¬ã¹ãããã¯ã¼ã¯ã®å©ç¨åº¦ãé«ã¾ãã«ã¤ãã¦ãç©ççã«è¿ãå ´æã«ããããè£
ååã¸ã®ç´æ¥çãª
ç©ççã¢ã¯ã»ã¹ã¯ã§ããªãå¤æµã«ãã ICS å®è£
ãªã¹ã¯ãå¢å¤§ãããã»ãã¥ãªãã£ã½ãªã¥ã¼ã·ã§ã³ã¯ã
ä¸è¬ç㪠IT ã·ã¹ãã ã«ãããã»ãã¥ãªãã£åé¡ãæ±ãããã«ã§ãã¦ããã®ã§ãICS ç°å¢ã«æã¡è¾¼ãå ´
åã«ã¯ç¹å¥ãªæ³¨æãæ¬ ãããªããå ´åã«ãã£ã¦ã¯ããã® ICS ç°å¢ã«ç¹åããæ°ããã»ãã¥ãªãã£ã½ãª
ã¥ã¼ã·ã§ã³ãå¿
è¦ã¨ãªãã
ããã¤ãã®ç¹å¾´ã¯ä¼¼ã¦ãã¦ããICS ã«ã¯å¾æ¥ã®æ
å ±å¦çã·ã¹ãã ã¨ã¯ç°ãªãç¹å¾´ããããããããé
ãã®å¤ãã¯ãICS ã§å®è¡ãããè«çãå®ä¸çã«ç´æ¥çãªå½±é¿ãåã¼ãã¨ããäºå®ããçãããã®ã§ã
ããããããç¹æ§ã®ä¸ã«ã¯ã人ã®å¥åº·ãå®å
¨ã«å¯¾ããæ·±å»ãªãªã¹ã¯ãé大ãªç°å¢ç ´å£ã®ã»ããçç£é
ä½æ¸ãå½å®¶çµæ¸ã¸ã®æªå½±é¿ãç§å¯æ
å ±ã®æ¼æ´©ã¨ãã£ãé大ãªè²¡ååé¡ãå«ã¾ãã¦ãããICS ã®æ§è½å
ã³ä¿¡é ¼æ§è¦ä»¶ã¯ç¬ç¹ã§ãæ®éã® IT é¢ä¿è
ã«ã¯å¥ç°ã«è¦ãã OS ãã¢ããªã±ã¼ã·ã§ã³ã使ç¨ãããã¨ã
å¤ããæ´ã«å®å
¨æ§ã¨å¹çæ§ã®ç®æ¨ã¯ãå¶å¾¡ã·ã¹ãã ã®è¨è¨ã»éç¨ä¸ãã»ãã¥ãªãã£ã¨ç«¶åããå ´åã
ããã
ãµã¤ãã¼ã»ãã¥ãªãã£ã¯ãç¾ä»£ã®ç£æ¥å·¥ç¨ãå®å
¨ãã¤é«ãä¿¡é ¼æ§ããã£ã¦éç¨ããä¸ã§ä¸å¯æ¬ ã§ãã
ãã¨ãããICS ãµã¤ãã¼ã»ãã¥ãªãã£ããã°ã©ã ã¯ãç£æ¥ç¾å ´ã«ããã¦ãä¼æ¥ãµã¤ãã¼ã»ãã¥ãªãã£
ããã°ã©ã ã«ããã¦ãã常ã«ããåºç¯ãª ICS ã®å®å
¨æ§ã»ä¿¡é ¼æ§ããã°ã©ã ã®ä¸é¨ã¨ãªãã¹ãã§ããã
å¶å¾¡ã·ã¹ãã ã«å¯¾ããè
å¨ã®æºã¯å¤å²ã«ããããæµæãæã¤æ¿åºããããªã¹ãã°ã«ã¼ããä¸æºãæ±ã
ãå¾æ¥å¡ãæªæãæã¤ä¾µå
¥è
ãè¤éæ§ãäºæ
ãèªç¶ç½å®³ãå
é¨é¢ä¿è
ã®æå³çåã¯å¶çºçè¡çºçãã
ããICS ã»ãã¥ãªãã£ã®ç®çã¯ãä¸è¬çã«å¯ç¨æ§ã¨å®å
¨æ§ãåªå
äºé
ã¨ããæ©å¯æ§ãããã«ç¶ãã
SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
3
Possible incidents an ICS may face include the following:
ï¼ Blocked or delayed flow of information through ICS networks, which could disrupt ICS operation.
ï¼ Unauthorized changes to instructions, commands, or alarm thresholds, which could damage, disable,
or shut down equipment, create environmental impacts, and/or endanger human life.
ï¼ Inaccurate information sent to system operators, either to disguise unauthorized changes, or to cause
the operators to initiate inappropriate actions, which could have various negative effects.
ï¼ ICS software or configuration settings modified, or ICS software infected with malware, which could
have various negative effects.
ï¼ Interference with the operation of equipment protection systems, which could endanger costly and
difficult-to-replace equipment.
ï¼ Interference with the operation of safety systems, which could endanger human life.
Major security objectives for an ICS implementation should include the following:
ï¼ Restricting logical access to the ICS network and network activity. This may include using
unidirectional gateways, a demilitarized zone (DMZ) network architecture with firewalls to prevent
network traffic from passing directly between the corporate and ICS networks, and having separate
authentication mechanisms and credentials for users of the corporate and ICS networks. The ICS
should also use a network topology that has multiple layers, with the most critical communications
occurring in the most secure and reliable layer.
ï¼ Restricting physical access to the ICS network and devices. Unauthorized physical access to
components could cause serious disruption of the ICSâs functionality. A combination of physical
access controls should be used, such as locks, card readers, and/or guards.
ï¼ Protecting individual ICS components from exploitation. This includes deploying security patches
in as expeditious a manner as possible, after testing them under field conditions; disabling all unused
ports and services and assuring that they remain disabled; restricting ICS user privileges to only those
that are required for each personâs role; tracking and monitoring audit trails; and using security
controls such as antivirus software and file integrity checking software where technically feasible to
prevent, deter, detect, and mitigate malware.
ï¼ Restricting unauthorized modification of data. This includes data that is in transit (at least across
the network boundaries) and at rest.
ï¼ Detecting security events and incidents. Detecting security events, which have not yet escalated into
incidents, can help defenders break the attack chain before attackers attain their objectives. This
includes the capability to detect failed ICS components, unavailable services, and exhausted resources
that are important to provide proper and safe functioning of the ICS.
ï¼ Maintaining functionality during adverse conditions. This involves designing the ICS so that each
critical component has a redundant counterpart. Additionally, if a component fails, it should fail in a
manner that does not generate unnecessary traffic on the ICS or other networks, or does not cause
another problem elsewhere, such as a cascading event. The ICS should also allow for graceful
degradation such as moving from "normal operation" with full automation to "emergency operation"
with operators more involved and less automation to "manual operation" with no automation.
SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
4
ICS ãç´é¢ãå¾ãã¤ã³ã·ãã³ãã«ã¯æ¬¡ã®ãããªãã®ãããã
ï¼ ICS ãããã¯ã¼ã¯çµç±æ
å ±ã®é®æåã¯é
延ãICS ã®éç¨ä¸æã«è³ããããªãã
ï¼ å½ä»¤ãã³ãã³ãåã¯ã¢ã©ã¼ã é¾å¤ã®ç¡æå¤æ´ãè£
ååã®é害ãæ
éè¥ããã¯é®æãç°å¢ã¸ã®
å½±é¿åã¯äººå½ã¸ã®å±éºãçããããªãã
ï¼ ç¡æå¤æ´ã®é è½åã¯æä½å¡ã«èª¤æä½ãè¡ããããã¨ãç®çã¨ãããã·ã¹ãã ãªãã¬ã¼ã¿ã¸ã®
誤æ
å ±ééãæ§ã
ãªæªå½±é¿ãçããããªãã
ï¼ ICS ã½ããã¦ã¨ã¢è¥ããã¯è¨å®ã®å¤æ´å㯠ICS ã½ããã¦ã¨ã¢ã®ãã«ã¦ã¨ã¢ææãæ§ã
ãªæªå½±
é¿ãçããããªãã
ï¼ è£
ååä¿è·è£
ç½®ã¨ã®å¹²æ¸ãé«é¡ã§æè£
å°é£ãªè£
ååãå±éºç¶æ
ã«ç½®ããããªãã
ï¼ å®å
¨è£
ç½®ã®éç¨ã«å¯¾ããå¹²æ¸ã人å½ãå±éºã«ããããããªãã
ICS å®è£
ã®ä¸»ãªã»ãã¥ãªãã£ä¸ã®éæç®æ¨ã«ã¯ä»¥ä¸ãå«ããã¹ãã ã
ï¼ ICS ãããã¯ã¼ã¯ã¸ã®è«ççãªã¢ã¯ã»ã¹ã¨ãããã¯ã¼ã¯ä¸ã®æ´»åã®å¶éãããã«ã¯ä¼æ¥ãã
ãã¯ã¼ã¯ã¨ICS ãããã¯ã¼ã¯éã®ç´æ¥çãªãããã¯ã¼ã¯ãã©ãã£ãã¯ãé²æ¢ããä¼æ¥ãã
ãã¯ã¼ã¯åã³ ICS ãããã¯ã¼ã¯ã¦ã¼ã¶åãã«ãç¬ç«ããèªè¨¼ã¡ã«ããºã ã¨èªè¨¼æ
å ±ãæã¤
ä¸æ¹åæ§ã²ã¼ãã¦ã§ã¤ãéæ¦è£
å°å¸¯ï¼DMZï¼ã®ãã¡ã¤ã¢ã¦ã©ã¼ã«ä»ããããã¯ã¼ã¯ã¢ã¼ã
ãã¯ãã£ã®å©ç¨ãå«ã¾ãããã¾ã ICS ã¯ãæãã»ãã¥ã¢ã§ä¿¡é ¼æ§ã®é«ãã¬ã¤ã¤ã¼ã§æéè¦
éä¿¡ãè¡ãããã«ãã¬ã¤ã¤ã¼ãããã¯ã¼ã¯ãããã¸ã¼ãå©ç¨ãã¹ãã§ããã
ï¼ ICS ãããã¯ã¼ã¯åã³ããã¤ã¹ã¸ã®ç©ççã¢ã¯ã»ã¹å¶éãã³ã³ãã¼ãã³ãã¸ã®ä¸æ£ãªç©çã¢
ã¯ã»ã¹ã¯ãICS ã®æ©è½ã«é大ãªä¸æããããããããªããæ½é ãã«ã¼ããªã¼ãã¼ãè¦åå¡ç
ã®ç©çã¢ã¯ã»ã¹å¶å¾¡ãä½µç¨ãã¹ãã§ããã
ï¼ åã
ã® ICS ã³ã³ãã¼ãã³ãã®æªç¨é²æ¢ãããã«ã¯æ¬¡ã®å
容ãå«ã¾ãããã»ãã¥ãªãã£ããã
ããã£ã¼ã«ãæ¡ä»¶ä¸ã§è©¦é¨å¾ãã§ããã ãè¿
éã«å±éããã使ç¨ãã¦ããªããã¼ãåã³ãµã¼
ãã¹ãå
¨ã¦ä½¿ç¨ä¸è½ã«ãã使ç¨ä¸è½ç¶æ
ãä¿ãããããã«ãããICS ã¦ã¼ã¶æ¨©éã®ä»ä¸ãã
å½¹å²ä¸å¿
è¦ã¨ãã人å¡ã«éå®ãããç£æ»è¨¼è·¡ã®è¿½è·¡åã³ç£è¦ãæè¡çã«å®è¡å¯è½ãªå ´åãã¢
ã³ãã¦ã¤ã«ã¹ã½ããã¦ã¨ã¢ããã¡ã¤ã«æ´åæ§ç¢ºèªã½ããã¦ã¨ã¢çã®ã»ãã¥ãªãã£ç®¡çãå©ç¨
ãããã«ã¦ã¨ã¢ãäºé²ã»ææ¢ã»æ¤åºã»ç·©åããã
ï¼ ãã¼ã¿ã®ç¡æå¤æ´å¶éãããã«ã¯éä¿¡ä¸ã®ãã¼ã¿ï¼å°ãªãã¨ããããã¯ã¼ã¯å¢çãè¶ããã
ã®ï¼åã³éæ¢ãã¼ã¿ãå«ã¾ããã
ï¼ ã»ãã¥ãªãã£ä¸ã®ã¤ãã³ãåã³ã¤ã³ã·ãã³ãã®æ¤åºãã¾ã ã¤ã³ã·ãã³ãã«ã¯è³ããªãã»ãã¥
ãªãã£ã¤ãã³ããæ¤åºã§ããã°ãé²å¾¡å´ã¯ãæ»æå´ã®ç®çéæåã«æ»æé£éãæã¡åããã¨
ãã§ãããããã«ã¯ ICS ãé©æ£ãã¤å®å
¨ãªæ©è½ãçºæ®ããä¸ã§éè¦ãªãICS ã³ã³ãã¼ãã³ã
ã®é害ã使ç¨ä¸è½ã®ãµã¼ãã¹åã³æ¯æ¸ãããªã½ã¼ã¹ãæ¤åºããè½åãå«ã¾ããã
ï¼ æªæ¡ä»¶ä¸ã§ã®æ©è½ä¿æãããã«ã¯åéè¦ã³ã³ãã¼ãã³ãã«åé·æ§ãæããã ICS è¨è¨ãé¢ä¿
ãã¦ãããã¾ããããã³ã³ãã¼ãã³ãã«é害ãåºãå ´åã§ããICS ãã®ä»ã®ãããã¯ã¼ã¯ã«
ä¸è¦ã®ãã©ãã£ãã¯ãçãããããé£éã¤ãã³ããªã©å¥ã®åé¡ãæ´¾çããã¦ã¯ãªããªããã¾
ãICS ã¯ãæ©è½ãä½ä¸ããå ´åã§ãã£ã¦ããå
¨èªåã®ãæ£å¸¸é転ãããæä½å¡ãå ãã£ã
åèªåã®ãç·æ¥é転ãã¸ã次ãã§å®å
¨ãªãæåé転ãã¸ã¨æ©è½ãå¾ã
ã«ä½ä¸ããã°ã¬ã¼ã¹ã
ã«ãã°ã©ãã¼ã·ã§ã³ã«ãªã£ã¦ããã¹ãã§ããã
SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
5
ï¼ Restoring the system after an incident. Incidents are inevitable and an incident response plan is
essential. A major characteristic of a good security program is how quickly the system can be
recovered after an incident has occurred.
To properly address security in an ICS, it is essential for a cross-functional cybersecurity team to share
their varied domain knowledge and experience to evaluate and mitigate risk to the ICS. The cybersecurity
team should consist of a member of the organizationâs IT staff, control engineer, control system operator,
network and system security expert, a member of the management staff, and a member of the physical
security department at a minimum. For continuity and completeness, the cybersecurity team should consult
with the control system vendor and/or system integrator as well. The cybersecurity team should coordinate
closely with site management (e.g., facility superintendent) and the companyâs Chief Information Officer
(CIO) or Chief Security Officer (CSO), who in turn, accepts complete responsibility and accountability for
the cybersecurity of the ICS, and for any safety incidents, reliability incidents, or equipment damage caused
directly or indirectly by cyber incidents. An effective cybersecurity program for an ICS should apply a
strategy known as âdefense-in-depth,â layering security mechanisms such that the impact of a failure in any
one mechanism is minimized. Organizations should not rely on âsecurity by obscurity.â
In a typical ICS this means a defense-in-depth strategy that includes:
ï¼ Developing security policies, procedures, training and educational material that applies specifically to
the ICS.
ï¼ Considering ICS security policies and procedures based on the Homeland Security Advisory System
Threat Level, deploying increasingly heightened security postures as the Threat Level increases.
ï¼ Addressing security throughout the lifecycle of the ICS from architecture design to procurement to
installation to maintenance to decommissioning.
ï¼ Implementing a network topology for the ICS that has multiple layers, with the most critical
communications occurring in the most secure and reliable layer.
ï¼ Providing logical separation between the corporate and ICS networks (e.g., stateful inspection
firewall(s) between the networks, unidirectional gateways).
ï¼ Employing a DMZ network architecture (i.e., prevent direct traffic between the corporate and ICS
networks).
ï¼ Ensuring that critical components are redundant and are on redundant networks.
ï¼ Designing critical systems for graceful degradation (fault tolerant) to prevent catastrophic cascading
events.
ï¼ Disabling unused ports and services on ICS devices after testing to assure this will not impact ICS
operation.
ï¼ Restricting physical access to the ICS network and devices.
ï¼ Restricting ICS user privileges to only those that are required to perform each personâs job (i.e.,
establishing role-based access control and configuring each role based on the principle of least
privilege).
ï¼ Using separate authentication mechanisms and credentials for users of the ICS network and the
corporate network (i.e., ICS network accounts do not use corporate network user accounts).
SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
6
ï¼ ã¤ã³ã·ãã³ãå¾ã®ã·ã¹ãã 復æ§ãã¤ã³ã·ãã³ãã¯é¿ããããªãã®ã§ãã¤ã³ã·ãã³ã対å¦è¨ç»
ãä¸å¯æ¬ ã¨ãªããåªããã»ãã¥ãªãã£ããã°ã©ã ã®ä¸»è¦ãªç¹å¾´ã¯ãã¤ã³ã·ãã³ãçºçå¾ãã·
ã¹ãã ãã©ãã ãè¿
éã«å¾©æ§ã§ãããã¨ããç¹ã«ããã
ICS ã«ããã¦ã»ãã¥ãªãã£ãé©æ£ã«ç¢ºä¿ããã«ã¯ãæ©è½æ¨ªæåãµã¤ãã¼ã»ãã¥ãªãã£ãã¼ã ãå¤
æ§ãªåéã®ç¥èã»çµé¨ãå
±æãåããICS ã®ãªã¹ã¯ãè©ä¾¡ã»ç·©åãããã¨ãä¸å¯æ¬ ã¨ãªãããµã¤
ãã¼ã»ãã¥ãªãã£ãã¼ã ã®æ§æã¯ãæä½ã§ãçµç¹ã® IT è¦å¡ãå¶å¾¡ã¨ã³ã¸ãã¢ãå¶å¾¡ã·ã¹ãã ãª
ãã¬ã¼ã¿ããããã¯ã¼ã¯åã³ã·ã¹ãã ã»ãã¥ãªãã£å°éå¡ãçµå¶ã«é¢ããè¦å¡åã³ç©ççã»ãã¥
ãªãã£é¨éè¦å¡ã¨ãã¹ãã§ãããç¶ç¶æ§ã¨å®å
¨æ§ã確ä¿ããããããµã¤ãã¼ã»ãã¥ãªãã£ãã¼ã
ã¯ãå¶å¾¡ã·ã¹ãã ã®ãã³ãã¼ãã·ã¹ãã ã¤ã³ãã°ã¬ã¼ã¿ã¨ãåè°ãã¹ãã§ãããã¾ãç¾å ´ç®¡çè
ï¼æ½è¨è²¬ä»»è
çï¼ã®ã»ããICS ã®ãµã¤ãã¼ã»ãã¥ãªãã£ãå®å
¨ä¸ã®ã¤ã³ã·ãã³ããä¿¡é ¼æ§ä¸ã®ã¤
ã³ã·ãã³ãåã¯ãµã¤ãã¼ã¤ã³ã·ãã³ãã«ããç´æ¥ã»éæ¥ã«çããè£
ååã®æ害ã«å
¨è²¬ä»»ãè² ãä¼
æ¥ã®æé«æ
å ±è²¬ä»»è
ï¼CIOï¼åã¯æé«ã»ãã¥ãªãã£è²¬ä»»è
ï¼CSOï¼ã¨ãå¯æ¥ã«é£æºãåãã¹ãã§
ãããICS ã®å¹æçãªãµã¤ãã¼ã»ãã¥ãªãã£ããã°ã©ã ã¯ãå¤å±¤é²å¾¡ï¼defense-in-depthï¼ãã¨ã
ã¦ç¥ãããæ¦ç¥ãã¤ã¾ããããã¡ã«ããºã ã®é害ã®å½±é¿ãæå°éã«é£ãæ¢ãããããã¬ã¤ã¤ãªã³
ã°ã»ãã¥ãªãã£ã¡ã«ããºã ãé©ç¨ãã¹ãã§ãããçµç¹ã¯ãææ§ãªã»ãã¥ãªãã£ãã«ä¾åãã¹ãã§
ãªãã
ãã®ãã¨ã¯ãä¸è¬ç㪠ICS ã§ã¯ä»¥ä¸ã®å
容ãå«ãã å¤å±¤é²å¾¡æ¦ç¥ãæå³ããã
ï¼ ICS ã«ç¹åãã¦é©ç¨ãããã»ãã¥ãªãã£ããªã·ã¼ãæé åã³æè²è¨ç·´è³æã®ä½æ
ï¼ å½åå®å
¨ä¿éã¢ããã¤ã¶ãªã¼ã·ã¹ãã è
å¨ã¬ãã«ã«åºã¥ã ICS ã»ãã¥ãªãã£ããªã·ã¼åã³æ
é ã®æ¤è¨ãè
å¨ã¬ãã«ã®ä¸æã«è¿½éãã¦æ®µéçã«é«ã¾ãã»ãã¥ãªãã£æ
å¢ã®ä¿æ
ï¼ ã¢ã¼ããã¯ãã£è¨è¨ãã調éãè¨ç½®ãä¿å®ãå»æ£ã¾ã§ãICS ã®å
¨ã©ã¤ããµã¤ã¯ã«ãéããã»
ãã¥ãªãã£ã®èæ
®
ï¼ æãã»ãã¥ã¢ã§ä¿¡é ¼æ§ã®é«ãã¬ã¤ã¤ã¼ã§æéè¦éä¿¡ãè¡ãããã«ãã¬ã¤ã¤ã¼ICS ãããã¯ã¼
ã¯ãããã¸ã¼ã®å®è£
ï¼ ä¼æ¥ãããã¯ã¼ã¯ã¨ ICS ãããã¯ã¼ã¯éã®è«ççåå²ï¼ãããã¯ã¼ã¯éãä¸æ¹åæ§ã²ã¼ãã¦
ã§ã¤éã®ã¹ãã¼ããã«ã¤ã³ã¹ãã¯ã·ã§ã³ãã¡ã¤ã¢ã¦ã©ã¼ã«ãªã©ï¼
ï¼ DMZ ãããã¯ã¼ã¯ã¢ã¼ããã¯ãã£ã®æ¡ç¨ï¼ä¼æ¥ãããã¯ã¼ã¯ã¨ ICS ãããã¯ã¼ã¯éã®ç´æ¥
ãã©ãã£ãã¯ãé²æ¢ï¼
ï¼ éè¦ã³ã³ãã¼ãã³ãã®åé·åã¨åé·æ§ãããã¯ã¼ã¯ä¸ã§ã®ä½¿ç¨
ï¼ å£æ»
çãªé£éã¤ãã³ããé²ãã°ã¬ã¼ã¹ãã«ãã°ã©ãã¼ã·ã§ã³ï¼ãã©ã¼ã«ããã¬ã©ã³ãï¼ãå
ããéè¦ã·ã¹ãã ã®è¨è¨
ï¼ ICS ã®éç¨ã«å½±é¿ããªããã¨ãæ¤è¨¼ããä¸ã§ãICS ããã¤ã¹ä¸ã®ä¸ä½¿ç¨ãã¼ãåã³ãµã¼ãã¹
ã使ç¨ä¸è½ã«ãããã¨
ï¼ ICS ãããã¯ã¼ã¯åã³ããã¤ã¹ã¸ã®ç©ççã¢ã¯ã»ã¹å¶éã
ï¼ å人ã®æ¥åãè¡ãããã«å¿
è¦ãª ICS ã¦ã¼ã¶æ¨©éã«éå®ããã権éã®ä»ä¸ï¼å½¹å²ã«åºã¥ãã¢ã¯
ã»ã¹å¶å¾¡ã¨æå°æ¨©éååã«åºã¥ãå½¹å²æ§æï¼
ï¼ ICS ãããã¯ã¼ã¯åã³ä¼æ¥ãããã¯ã¼ã¯ã¦ã¼ã¶åãã®ç¬ç«ããèªè¨¼ã¡ã«ããºã ã¨èªè¨¼æ
å ±ã®
使ç¨ï¼ICS ãããã¯ã¼ã¯ã¢ã«ã¦ã³ãã«ä¼æ¥ãããã¯ã¼ã¯ã¦ã¼ã¶ã®ã¢ã«ã¦ã³ãã使ç¨ããªãï¼

SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
7
ï¼ Using modern technology, such as smart cards for Personal Identity Verification (PIV).
ï¼ Implementing security controls such as intrusion detection software, antivirus software and file
integrity checking software, where technically feasible, to prevent, deter, detect, and mitigate the
introduction, exposure, and propagation of malicious software to, within, and from the ICS.
ï¼ Applying security techniques such as encryption and/or cryptographic hashes to ICS data storage and
communications where determined appropriate.
ï¼ Expeditiously deploying security patches after testing all patches under field conditions on a test
system if possible, before installation on the ICS.
ï¼ Tracking and monitoring audit trails on critical areas of the ICS.
ï¼ Employing reliable and secure network protocols and services where feasible.
The National Institute of Standards and Technology (NIST), in cooperation with the public and private
sector ICS community, has developed specific guidance on the application of the security controls in NIST
Special Publication (SP) 800-53 Revision 4, Security and Privacy Controls for Federal Information
Systems and Organizations [22], to ICS.
While many controls in Appendix F of NIST SP 800-53 are applicable to ICS as written, many controls
require ICS-specific interpretation and/or augmentation by adding one or more of the following to the
control:
ï§ ICS Supplemental Guidance provides organizations with additional information on the
application of the security controls and control enhancements in Appendix F of NIST SP 800-53
to ICS and the environments in which these specialized systems operate. The Supplemental
Guidance also provides information as to why a particular security control or control
enhancement may not be applicable in some ICS environments and may be a candidate for
tailoring (i.e., the application of scoping guidance and/or compensating controls). ICS
Supplemental Guidance does not replace the original Supplemental Guidance in Appendix F of
NIST SP 800-53.
ï§ ICS Enhancements (one or more) that provide enhancement augmentations to the original control
that may be required for some ICS.
ï§ ICS Enhancement Supplemental Guidance that provides guidance on how the control
enhancement applies, or does not apply, in ICS environments.
The most successful method for securing an ICS is to gather industry recommended practices and engage in
a proactive, collaborative effort between management, the controls engineer and operator, the IT
organization, and a trusted automation advisor. This team should draw upon the wealth of information
available from ongoing federal government, industry groups, vendor and standards organizational activities
listed in Appendix Dâ.
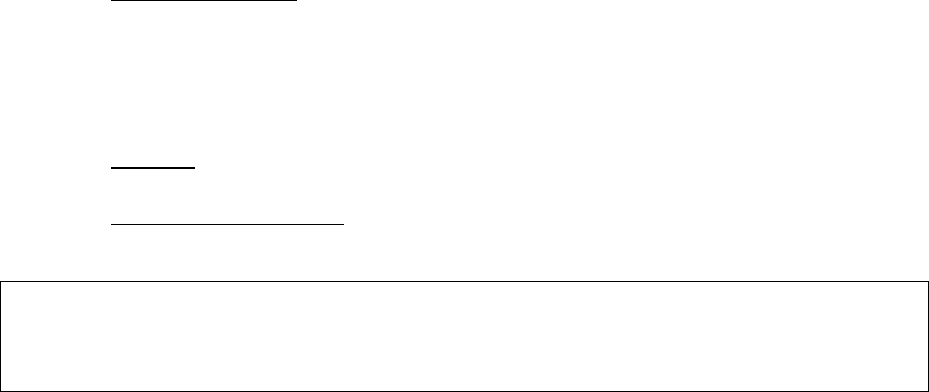
SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
8
ï¼ èº«å証æï¼PIVï¼ç¨ã¹ãã¼ãã«ã¼ããªã©ææ°æè¡ã®ä½¿ç¨
ï¼ æè¡çã«å®è¡å¯è½ãªå ´åãICS ã«å
¥ããICS ããåºããããã³ ICS å
ã«ãããã«ã¦ã¨ã¢ã®å°
å
¥ã»æé²ã»ä¼æãäºé²ã»ææ¢ã»æ¤åºã»ç·©åããããã®ä¾µå
¥æ¤ç¥ã½ããã¦ã¨ã¢ãã¢ã³ãã¦ã¤ã«
ã¹ã½ããã¦ã¨ã¢ããã¡ã¤ã«æ´åæ§ç¢ºèªã½ããã¦ã¨ã¢çã«ããã»ãã¥ãªãã£ç®¡ç
ï¼ é©å½ã§ããã°ãICS ãã¼ã¿ã¹ãã¬ã¼ã¸åã³éä¿¡ã¸ã®æå·ååã¯æå·å¦çããã·ã¥çã»ãã¥ãª
ãã£æè¡ã®é©ç¨
ï¼ ICS ã¸ã®ã¤ã³ã¹ãã¼ã«åã«å¯è½ã§ããã°ããã£ã¼ã«ãæ¡ä»¶ä¸ã§è©¦é¨è£
ç½®ã«ããæ¤è¨¼ããã»ã
ã¥ãªãã£ãããã®è¿
éãªå±é
ï¼ ICSéè¦é åã§ã®ç£æ»è¨¼è·¡ã®è¿½è·¡åã³ç£è¦
ï¼ å®è¡å¯è½ãªãä¿¡é ¼æ§ã®é«ãã»ãã¥ã¢ãªãããã¯ã¼ã¯ãããã³ã«åã³ãµã¼ãã¹ã®æ¡ç¨
ç±³å½æ¨æºæè¡å±ï¼NISTï¼ã¯å®æ° ICS å
±åä½ã®ååãå¾ã¦ãNISTSPï¼SPï¼800-53 第4çãé£é¦æ
å ±ã·ã¹ãã ã»çµç¹ã®ã»ãã¥ãªãã£ã»ãã©ã¤ãã·ã¼ç®¡çã[22]ã«è¨è¼ããã ICS ã¸ã®ã»ãã¥ãªãã£
管çã®é©ç¨ã«é¢ãã¦ãå
·ä½çãªã¬ã¤ãã³ã¹ãä½æããã
NIST SP 800-53 ã®ä»é² Fã«è¨è¼ãããå¶å¾¡ã®å¤ãã¯ãè¨è¿°ã©ãã ICS ã«é©ç¨å¯è½ã§ã¯ãããã大
æµã¯ ICS ç¹æã®è§£éãå¿
è¦ã§ã以ä¸ã«ç¤ºããã®ãå°ãªãã¨ã 1ã¤è¿½å ããå¿
è¦ãããã
ï§ ICS è£è¶³ã¬ã¤ãã³ã¹ãNIST SP 800-53 ã®ä»é² Fã«è¨è¼ãããã»ãã¥ãªãã£ç®¡çåã³
管çæ¡å¼µããICS åã³ãããå°ç¨ã·ã¹ãã ã®å®è¡ç°å¢ã«é©ç¨ããããã®è£è¶³æ
å ±ã
示ããã¾ããICS ç°å¢ã«ãã£ã¦ã¯ç¹å®ã®ã»ãã¥ãªãã£ç®¡çã管çæ¡å¼µãé©ç¨ã§ããã
調æ´ãå¿
è¦ã¨ãªãçç±ã«ã¤ãã¦ã示ãï¼ã¹ã³ã¼ãã³ã°ã¬ã¤ãã³ã¹åã¯è£å®å¶å¾¡ã®é©
ç¨ï¼ãICS è£è¶³ã¬ã¤ãã³ã¹ã¯ãNIST SP 800-53 ã®ä»é² Fã«ãããªãªã¸ãã«ã®è£è¶³ã¬
ã¤ãã³ã¹ã«ä»£ãããã®ã§ã¯ãªãã
ï§ ICS æ¡å¼µï¼1ã¤åã¯è¤æ°ï¼ãICSã«ãã£ã¦ã¯å¿
è¦ã¨ãªãå
ã
ã®å¶å¾¡ã«æ¡å¼µãå
ããã
ï§ ICS æ¡å¼µè£è¶³ã¬ã¤ãã³ã¹ãICS ç°å¢ã«ããã¦ç®¡çæ¡å¼µé©ç¨ã®å¯å¦ã«ã¤ãã¦
示ãã
ICS
ã®ã»ãã¥ãªãã£ç¢ºä¿ã«æãææã®ä¸ããæ¹æ³ã¯ãæ¥çã®æ¨å¥¨è¦ç¯ãèç©ããå¹¹é¨ãå¶å¾¡ã¨ã³
ã¸ãã¢åã³æä½å¡ãIT çµç¹ä¸¦ã³ã«ä¿¡ç¨ã®ããããªã¼ãã¡ã¼ã·ã§ã³ã¢ããã¤ã¶ã¼éã§ãç©æ¥µçã«å
調ãã¦åãçµããã¨ã§ããããã®ãã¼ã ã¯ãé£é¦æ¿åºãæ¥çã°ã«ã¼ãããã³ãã¼åã³ä»é² Dã«æ²
è¼ããã¦ããè¦æ ¼å£ä½ããã®è±å¯ãªæ
å ±ãå©ç¨ãã¹ãã§ããã

SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
9
1. Introduction
1.1 Purpose and Scope
The purpose of this document is to provide guidance for
securing industrial control systems (ICS), including
supervisory control and data acquisition (SCADA)
systems, distributed control systems (DCS), and other
systems performing control functions. The document
provides a notional overview of ICS, reviews typical
system topologies and architectures, identifies known
threats and vulnerabilities to these systems, and provides
recommended security countermeasures to mitigate the
associated risks. Additionally, it presents an ICS-tailored
security control overlay, based on NIST SP 800-53 Rev. 4
[22], to provide a customization of controls as they apply
to the unique characteristics of the ICS domain. The body
of the document provides context for the overlay, but the
overlay is intended to stand alone.
ICS are found in many industries such as electric, water
and wastewater, oil and natural gas, chemical,
pharmaceutical, pulp and paper, food and beverage, and
discrete manufacturing (e.g., automotive, aerospace, and
durable goods). Because there are many different types of
ICS with varying levels of potential risk and impact, the
document provides a list of many different methods and
techniques for securing ICS. The document should not be
used purely as a checklist to secure a specific system.
Readers are encouraged to perform a risk-based
assessment on their systems and to tailor the
recommended guidelines and solutions to meet their
specific security, business and operational requirements.
The range of applicability of the basic concepts for
securing control systems presented in this document
continues to expand.
1.2 Audience
This document covers details specific to ICS. Readers of
this document should be acquainted with general computer
security concepts, and communication protocols such as
those used in networking. The document is technical in
nature; however, it provides the necessary background to
understand the topics that are discussed.

SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
10
1. ã¯ããã«
1.1 ç®çåã³é©ç¨ç¯å²
æ¬ææ¸ã®ç®çã¯ãç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã®ã»
ãã¥ãªãã£ã確ä¿ããããã®ã¬ã¤ãã³ã¹ã示ãã
ã¨ã«ãããICS ã«ã¯ SCADAãDCSããã®ä»ã®å¶å¾¡
ã·ã¹ãã ãå«ã¾ãããæ¬ææ¸ã§ã¯ãã®ãã㪠ICS
ã®æ¦å¿µã«ã¤ãã¦æ¦è¦ã示ããä¸è¬çãªã·ã¹ãã ã
ããã¸ã¼ã¨ã¢ã¼ããã¯ãã£ã«ã¤ãã¦èå¯ããã·ã¹
ãã ã«å¯¾ããæ¢ç¥ã®è
å¨ã¨èå¼±æ§ãç¹å®ããé¢é£
ãªã¹ã¯ãä½æ¸ããããã®æ¨å¥¨ã»ãã¥ãªãã£å¯¾çã
æ示ãããã¾ããNIST SP 800-53 æ¹è¨ 4 [22]ã«
å¾ããICS åãã«èª¿æ´ãããã»ãã¥ãªãã£
管çãªã¼ãã¼ã¬ã¤ãæ示ãã管çã ICS é å
ã®ç¬ç¹ãªç¹å¾´ã«é©ç¨ããéã®ã«ã¹ã¿ãã¤ãºã«ã¤ã
ã¦ç¤ºãã
ææ¸ã¯ãªã¼ãã¼ã¬ã¤ã®å
容ãæ示ãããããªã¼ã
ã¼ã¬ã¤ã¯ããèªä½ãç¬ç«ãããã®ã§ããã
ICS ã¯é»æ°ãä¸ä¸æ°´ãç³æ²¹ã»ã¬ã¹ãåå¦ãå»è¬åã
ãã«ãã»è£½ç´ãé£åã»é£²æåã³çµç«è£½é ï¼èªåè»ã
èªç©ºå®å®ãèä¹
æ¶è²»è²¡çï¼æ¥çã§å©ç¨ããã¦ããã
ãªã¹ã¯ã¬ãã«ããã®å½±é¿ãä¸æ§ã§ãªã種ã
ã® ICS
ããããããæ¬ææ¸ã§ã¯ ICS ã»ãã¥ãªãã£ã®æ¹æ³
ã¨æè¡ã®ãªã¹ãã示ããæ¬ææ¸ã¯ãç¹å®ã®ã·ã¹ã
ã ã»ãã¥ãªãã£ã確ä¿ããããã®åãªããã§ãã¯
ãªã¹ãã¨ãã¦ä½¿ç¨ãã¹ãã§ãªãã
èªè
ã¯ã使ç¨ãã¦ããã·ã¹ãã ã«é¢ãã¦ããªã¹ã¯
ã«ç«èããè©ä¾¡ãè¡ããæ¨å¥¨ããã¦ããã¬ã¤ãã©
ã¤ã³åã³ã½ãªã¥ã¼ã·ã§ã³ãåºæã®ã»ãã¥ãªãã£ã
æ¥åããã³éç¨ä¸ã®è¦ä»¶ã«åãããã«èª¿æ´ãã¹ã
ã§ãããæ¬ææ¸ã«ç¤ºãããå¶å¾¡ã·ã¹ãã ã®ã»ãã¥
ãªãã£ç¢ºä¿ã«é¢ããåºæ¬æ¦å¿µã®é©ç¨ç¯å²ã¯ãä»å¾
ãå¼ãç¶ãæ¡å¤§ããã
1.2 対象è
æ¬ææ¸ã«ã¯ ICS ã«ç¹æã®è©³ç´°ãªäºé
ã網ç¾
ããã¦
ãããèªè
ã¯ãä¸è¬çãªã³ã³ãã¥ã¼ã¿ã»ãã¥ãªã
ã£æ¦å¿µããã³ãããã¯ã¼ã¯ã§ä½¿ç¨ãããéä¿¡ãã
ãã³ã«ã«éãã¦ããã¹ãã§ãããæ¬ææ¸ã®å
容ã¯ã
ãã®æ§è³ªä¸æè¡çã§ã¯ããããè¨è¿°ããã¦ããè«
é¡ãç解ããããã«å¿
è¦ãªèæ¯ããæ示ããã
大統é å½ä»¤
13636
ãéè¦ã¤ã³ãã©ã¹ã
ã©ã¯ãã£ã®ãµã¤ãã¼ã»ãã¥ãªãã£æ¹
åãã¨ã®é¢ä¿
ç±³å½ã®å½å®¶åã³çµæ¸å®å
¨ä¿éã¯ãé«ã
ä¿¡é ¼æ§ããã£ã¦éè¦ã¤ã³ãã©ãæ©è½ã
ããã¨ã«ããã£ã¦ããã大統é å½ä»¤
13636ãéè¦ã¤ã³ãã©ã¹ãã©ã¯ãã£ã®
ãµã¤ãã¼ã»ãã¥ãªãã£æ¹åã[82]ã¯
NIST ã«å¯¾ãã¦ãé¢ä¿è
ã¨ååããéè¦
ã¤ã³ãã©ã¸ã®ãµã¤ãã¼ãªã¹ã¯ãæ¸ãã
ããã®èªçºçæ çµã¿ï¼ãã¬ã¼ã ã¯ã¼
ã¯ï¼ãæ§ç¯ããããå½ãã¦ããããµã¤
ãã¼ã»ãã¥ãªãã£ãã¬ã¼ã ã¯ã¼ã¯
ï¼CSFï¼[83]ã¯è¦æ ¼ãã¬ã¤ãã©ã¤ã³åã³
æè¯è¦ç¯ãããªããéè¦ã¤ã³ãã©ã®ä¿
è·ãä¿é²ããããã®ãã¬ã¼ã ã¯ã¼ã¯
ã¯ãåªå
çã§æè»æ§ããããå復å¯è½
ã§ããã©ã¼ãã³ã¹æ¬ä½ã®ãè²»ç¨å¹æã®
é«ãåçµã«ãããéè¦ã¤ã³ãã©ã®ææ
è
åã³éç¨è
ãä¼æ¥ç§å¯ãå人æ
å ±å
ã³äººæ¨©ãä¿è·ãã¤ã¤ããµã¤ãã¼ã»ãã¥
ãªãã£é¢é£ãªã¹ã¯ã管çã§ããããã«
æ¯æ´ãããæåã® CSFã¯2014 å¹´2æ
ã«çºè¡¨ãããå¤æ§ãªé¨éã種ã
ã®éç¨
ç°å¢ã«é©ç¨ã§ããã ãã®æè»æ§ãåã
ããå½å®¶ã¬ãã«ã®ãã¬ã¼ã ã¯ã¼ã¯ã¨ãª
ã£ãããã® CSF ã¯ãé¢ä¿è
ããã®æ
å ±
ãåºã«ä½æãããå¤ç¨®å¤æ§ãªé¨éã«ã
ããæ¢åæ¥åãããã®ãã¬ã¼ã ã¯ã¼ã¯
å
ã§å©ç¨ã§ããããã«ããã
ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ã®ãµã¤ãã¼ã»ãã¥
ãªãã£è¦æ ¼ãã¬ã¤ãã©ã¤ã³åã³è¦ç¯ã
æ´»ç¨ãã¦ãçµç¹ã®ãªã¹ã¯ç®¡çããã°ã©
ã ã¨ã®é¢ä¿ã§ CSF ã®æ©è½ãæ¤è¨ããã
ã¨ãã§ããã
SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
11
The intended audience is varied and includes the following:
ï¼ Control engineers, integrators, and architects who design or implement secure ICS.
ï¼ System administrators, engineers, and other information technology (IT) professionals who administer,
patch, or secure ICS.
ï¼ Security consultants who perform security assessments and penetration testing of ICS.
ï¼ Managers who are responsible for ICS.
ï¼ Senior management who are trying to understand implications and consequences as they justify and
apply an ICS cybersecurity program to help mitigate impacts to business functionality.
ï¼ Researchers and analysts who are trying to understand the unique security needs of ICS.
ï¼ Vendors that are developing products that will be deployed as part of an ICS.
1.3 Document Structure
The remainder of this guide is divided into the following major sections:
ï¼ Section 2 provides an overview of ICS including a comparison between ICS and IT systems.
ï¼ Section 3 provides a discussion of ICS risk management and assessment.
ï¼ Section 4 provides an overview of the development and deployment of an ICS security program to
mitigate the risk of the vulnerabilities identified in Appendix C.
ï¼ Section 5 provides recommendations for integrating security into network architectures typically
found in ICS, with an emphasis on network segregation practices.
ï¼ Section 6 provides a summary of the management, operational, and technical controls identified in
NIST Special Publication 800-53, Security and Privacy Controls for Federal Information Systems and
Organizations, and provides initial guidance on how these security controls apply to ICS.
The guide also contains several appendices with supporting material, as follows:
ï¼ Appendix Aâ provides a list of acronyms and abbreviations used in this document.
ï¼ Appendix Bâ provides a glossary of terms used in this document.
ï¼ Appendix Câ provides a list of ICS threats, vulnerabilities and incidents.
ï¼ Appendix Dâ provides a list of ICS security activities.
ï¼ Appendix Eâ provides a list of ICS security capabilities and tools
ï¼ Appendix Fâ provides a list of references used in the development of this document.
ï¼ Appendix Gâ provides an ICS overlay, listing security controls, enhancements, and supplemental
guidance that apply specifically to ICS.
SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
12
ææã®å¯¾è±¡ã¯å¤å²ã«ããããã以ä¸ãå«ãã
ï¼ ã»ãã¥ã¢ãª ICS ã®è¨è¨åã¯å®è£
ã«é¢ããå¶å¾¡ã¨ã³ã¸ãã¢ãã¤ã³ãã°ã¬ã¼ã¿åã³è¨è¨è
ï¼ ICS ã®ç®¡çããããã¾ãã¯ã»ãã¥ãªãã£ã«æºããã·ã¹ãã 管çè
ãã¨ã³ã¸ãã¢ãã®ä» IT å°é
å¡
ï¼ ICS ã®ã»ãã¥ãªãã£è©ä¾¡åã³ãããã¬ã¼ã·ã§ã³ã»ãã¹ããè¡ãã»ãã¥ãªãã£ã³ã³ãµã«ã¿ã³ã
ï¼ ICS æ
å½å¹¹é¨
ï¼ äºæ¥æ©è½ã¸ã®å½±é¿ãç·©åãã ICS ãµã¤ãã¼ã»ãã¥ãªãã£ããã°ã©ã ã®æ¿èªã»é©ç¨ãè¡ãéã«ã
ãã®æå³ã¨çµæã®ç解ã«åªããä¸ç´ç®¡çè·
ï¼ ICS ç¬ç¹ã®ã»ãã¥ãªãã£ãã¼ãºã®ç解ã«åªããç 究è
åã³ã¢ããªã¹ã
ï¼ ICS ã®ä¸é¨ã¨ãã¦å±éããã製åã®éçºã«å½ãããã³ãã¼
1.3 ææ¸ã®æ§æ
æ¬ã¬ã¤ãã®ãã以éã®é¨åã¯ã以ä¸ã®ã»ã¯ã·ã§ã³ã«å¤§å¥ãããã
ï¼ ã»ã¯ã·ã§ã³ 2ï¼ICS ã·ã¹ãã 㨠IT ã·ã¹ãã ã®æ¯è¼çãICS ã®æ¦è¦ã示ãã
ï¼ ã»ã¯ã·ã§ã³ 3ï¼ICS ã®ãªã¹ã¯ç®¡çã¨ãªã¹ã¯è©ä¾¡ã«ã¤ãã¦èª¬æããã
ï¼ ã»ã¯ã·ã§ã³ 4ï¼ä»é² Cã§æããã«ããã¦ããèå¼±æ§ãªã¹ã¯ãç·©åãããICS ã»ãã¥ãªãã£ã
ãã°ã©ã ã®éçºã»å±éã«ã¤ãã¦æ¦è¦ã示ãã
ï¼ ã»ã¯ã·ã§ã³ 5ï¼ICS ã®ä¸è¬çãªãããã¯ã¼ã¯ã¢ã¼ããã¯ãã£ã«ã»ãã¥ãªãã£ãçµã¿è¾¼ãä¸ã§
ã®æ¨å¥¨äºé
ã示ããç¹ã«ãããã¯ã¼ã¯éé¢è¦ç¯ã«ã¤ãã¦ç¹çããã
ï¼ ã»ã¯ã·ã§ã³ 6ï¼NISTSP800-53ãé£é¦æ
å ±ã·ã¹ãã ã»çµç¹ã®ã»ãã¥ãªãã£ã»ãã©ã¤ãã·ã¼ç®¡
çãã«å®ãã管çã»éç¨ã»æè¡å¶å¾¡ãã¨ãã¾ã¨ãããã®ãããªã»ãã¥ãªãã£ç®¡çã ICS ã«
é©ç¨ããæ¹æ³ã«ã¤ãã¦åæã®ã¬ã¤ãã³ã¹ã示ãã
ã¾ãæ¬ã¬ã¤ãã«ã¯ãè£è¶³è³æãæä¾ãã以ä¸ã®ä»é²ãå«ã¾ããã
ï¼ ä»é² Aâæ¬æ¸ã§ä½¿ç¨ããé åèªåã³ç¥èªã®ãªã¹ã
ï¼ ä»é² Bâæ¬æ¸ã§ä½¿ç¨ããç¨èªé
ï¼ ä»é² CâICS ã®è
å¨ãèå¼±æ§åã³ã¤ã³ã·ãã³ããªã¹ã
ï¼ ä»é² DâICS ã»ãã¥ãªãã£æ´»åãªã¹ã
ï¼ ä»é² EâICS ã»ãã¥ãªãã£è½åã»ãã¼ã«ãªã¹ã
ï¼ ä»é² Fâæ¬æ¸ã®ä½ææã«ä½¿ç¨ããåèæç®ãªã¹ã
ï¼ ä»é² GâICS ã«ç¹åãã¦é©ç¨ãããã»ãã¥ãªãã£ç®¡çãæ¡å¼µåã³è£è¶³ã¬ã¤ãã³ã¹ãªã¹ããæ²
è¼ãã ICS ãªã¼ãã¼ã¬ã¤

SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
13
2. Overview of Industrial Control Systems
Industrial control system (ICS) is a general term that encompasses several types of control systems,
including supervisory control and data acquisition (SCADA) systems, distributed control systems (DCS),
and other control system configurations such as Programmable Logic Controllers (PLC) often found in the
industrial sectors and critical infrastructures. An ICS consists of combinations of control components (e.g.,
electrical, mechanical, hydraulic, pneumatic) that act together to achieve an industrial objective (e.g.,
manufacturing, transportation of matter or energy). The part of the system primarily concerned with
producing the output is referred to as the process. The control part of the system includes the specification
of the desired output or performance. Control can be fully automated or may include a human in the loop.
Systems can be configured to operate open-loop, closed-loop, and manual mode. In open-loop control
systems the output is controlled by established settings. In closed-loop control systems, the output has an
effect on the input in such a way as to maintain the desired objective. In manual mode the system is
controlled completely by humans. The part of the system primarily concerned with maintaining
conformance with specifications is referred to as the controller (or control). A typical ICS may contain
numerous control loops, Human Machine Interfaces (HMIs), and remote diagnostics and maintenance tools
built using an array of network protocols. ICS control industrial processes are typically used in electrical,
water and wastewater, oil and natural gas, chemical, transportation, pharmaceutical, pulp and paper, food
and beverage, and discrete manufacturing (e.g., automotive, aerospace, and durable goods) industries.
ICS are critical to the operation of the U.S. critical infrastructures that are often highly interconnected and
mutually dependent systems. It is important to note that approximately 85 percent of the nation's critical
infrastructures are privately owned and operated1. Federal agencies also operate many of the industrial
processes mentioned above as well as air traffic control. This section provides an overview of SCADA,
DCS, and PLC systems, including typical topologies and components. Several diagrams are presented to
depict the network topology, connections, components, and protocols typically found on each system to
facilitate the understanding of these systems. These examples only attempt to identify notional topology
concepts. Actual implementations of ICS may be hybrids that blur the line between DCS and SCADA
systems. Note that the diagrams in this section do not focus on securing ICS. Security architecture and
security controls are discussed in Section 5 and Section 6 of this document respectively.
2.1 Evolution of Industrial Control Systems
Many of todayâs ICS evolved from the insertion of IT capabilities into existing physical systems, often
replacing or supplementing physical control mechanisms. For example, embedded digital controls replaced
analog mechanical controls in rotating machines and engines. Improvements in cost-and performance have
encouraged this evolution, resulting in many of todayâs âsmartâ technologies such as the smart electric grid,
smart transportation, smart buildings, and smart manufacturing. While this increases the connectivity and
criticality of these systems, it also creates a greater need for their adaptability, resilience, safety, and
security.
Engineering of ICS continues to evolve to provide new capabilities while maintaining the typical long
lifecycles of these systems. The introduction of IT capabilities into physical systems presents emergent
behavior that has security implications. Engineering models and analysis are evolving to address these
emergent properties including safety, security, privacy, and environmental impact interdependencies.
1 http://www.dhs.gov/critical-infrastructure-sector-partnerships (last updated April 2014)

SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
14
2. ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ã®æ¦è¦
ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã¨ã¯ãæ°ç¨®ã®å¶å¾¡ã·ã¹ãã ãå
æ¬ããæ±ç¨çãªç¨èªã§ãããã«ã¯å
種ç£æ¥é¨éãéè¦ã¤ã³ãã©ã§ä½¿ç¨ããã¦ãã SCADAãDCSãPLCããã®ä»ã®å¶å¾¡ã·ã¹ãã ã®è¨
å®ãå«ã¾ãããICS ã¯ç£æ¥ä¸ã®ç®çï¼ç©åãã¨ãã«ã®ã¼ã®çç£ã»è¼¸éçï¼ãéæããããã«ä½µç¨
ãããå¶å¾¡ç¨ã³ã³ãã¼ãã³ãï¼é»æ°ã»æ©æ¢°ã»æ²¹å§ã»ç©ºæ°çï¼ãçµã¿åããã£ã¦æ§æããã¦ããã
ç¹ã«åºåãç£ã¿åºãã·ã¹ãã ã®ä¸é¨ãããã»ã¹ã¨å¼ã¶ãã·ã¹ãã ã®å¶å¾¡é¨åã«ã¯ãææã®åºåå
ã¯ããã©ã¼ãã³ã¹ã®ä»æ§ãå«ã¾ãããå¶å¾¡ã¯å®å
¨èªååãå¯è½ã§ãã«ã¼ãä¸ã«äººéãå«ã¾ããå ´
åããããã·ã¹ãã ã¯ãªã¼ãã³ã«ã¼ããã¯ãã¼ãºãã«ã¼ãåã³æåã¢ã¼ãã®ãããã«ãè¨å®å¯è½
ã§ããããªã¼ãã³ã«ã¼ãå¶å¾¡ã·ã¹ãã ã§ã¯ãåºåã¯è¨å®ããå
容ã«å¾ã£ã¦å¶å¾¡ããããã¯ãã¼ãº
ãã«ã¼ãå¶å¾¡ã·ã¹ãã ã§ã¯ãææã®ç®çãç¶æããããã«ãåºåãå
¥åã«å½±é¿ãåã¼ããæåã¢
ã¼ãã§ã¯ã人éãå
¨é¢çã«ã·ã¹ãã ãå¶å¾¡ãããç¹ã«ä»æ§ãç¶æãããã¨ããã·ã¹ãã ã®ä¸é¨ã
ã³ã³ããã¼ã©ï¼åã¯å¶å¾¡ï¼ã¨å¼ã¶ãä¸è¬ç㪠ICS ã«ã¯ãå¤æ§ãªãããã¯ã¼ã¯ãããã³ã«ã使ç¨ã
ã¦æ§ç¯ããã種ã
ã®å¶å¾¡ã«ã¼ãããã³ãã·ã³ã¤ã³ã¿ãã§ã¼ã¹ï¼HMIï¼åã³ãªã¢ã¼ã診æä¿å®ãã¼
ã«ãå«ã¾ãããICS ã®å¶å¾¡ç¨ç£æ¥ããã»ã¹ã¯ãä¸è¬ã«é»æ°ãä¸ä¸æ°´ãç³æ²¹ã天ç¶ã¬ã¹ãåå¦ã輸
éãå»è¬åããã«ãã»è£½ç´ãé£åã»é£²æåã³çµç«è£½é ï¼èªåè»ãèªç©ºå®å®ãèä¹
æ¶è²»è²¡çï¼æ¥ç
ã§å©ç¨ããã¦ããã
ICS ã¯ãé«åº¦ã«é£æºã»ç¸äºä¾åããã·ã¹ãã ã¨ãªãå ´åãå¤ããç±³å½ã®éè¦ã¤ã³ãã©ã®éå¶ã«ç·
è¦ãªå½¹å²ãæããã¦ãããå½ã®éè¦ã¤ã³ãã©ã®ããã 85%ã¯ãç§ä¼æ¥ãä¿æãéå¶ãã¦ããç¹ã«
注æãã¹ãã§ããã2é£é¦æ¿åºæ©é¢ã¯ãä¸è¨ã®ç£æ¥ç¨ããã»ã¹ã®ã»ãèªç©ºäº¤é管å¶ã§ãå¤ãã®ç£
æ¥ç¨ããã»ã¹ãéç¨ãã¦ããããã®ã»ã¯ã·ã§ã³ã§ã¯ãä¸è¬çãªãããã¸ã¼ãã³ã³ãã¼ãã³ããå«
ããSCADAãDCS åã³ PLC ã·ã¹ãã ã«ã¤ãã¦æ¦è¦ã示ãããããã·ã¹ãã ã«å¯¾ããç解ã容æ
ã«ãããããåã·ã¹ãã ã®ä¸è¬çãªãããã¯ã¼ã¯ãããã¸ã¼ãæ¥ç¶ãã³ã³ãã¼ãã³ãåã³ããã
ã³ã«ãå³ç¤ºããããã®ãããªä¾ã¯ãåã«æ½è±¡çãªãããã¸ã¼æ¦å¿µãæããã«ããããã®ãã®ã§ã
ããICS ã®å®éã®å®è£
ã¯ãã¤ããªããã§ãDCS ã¨SCADA ã®å¢çãææ§ã§ãããæ¬ã»ã¯ã·ã§ã³ã®
å³ã¯ãICS ã®ã»ãã¥ãªãã£ã«ç¹åãããã®ã§ã¯ãªããã»ãã¥ãªãã£ã¢ã¼ããã¯ãã£åã³ã»ãã¥ãª
ãã£ç®¡çã«ã¤ãã¦ã¯ãã»ã¯ã·ã§ã³ 5ã¨ã»ã¯ã·ã§ã³ 6ã§åãä¸ããã
2.1 ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ã®é²å
ä»æ¥ã® ICS ã®å¤ãã¯ãIT è½åãæ¢åã®ç©çã·ã¹ãã ã«æ¿å
¥ããã¨ããããé²åãã¦ãããç©çå¶
御ã¡ã«ããºã ã«ä»£ãããã®ãè£å®ãããã®ãå¤ããä¾ãã°ãçµè¾¼ãã¸ã¿ã«å¶å¾¡ã¯ãå転å¼æ©æ¢°ã
ã¨ã³ã¸ã³ã®ã¢ããã°å¼æ©æ¢°å¶å¾¡ã«åã£ã¦ä»£ãã£ããã³ã¹ãããã©ã¼ãã³ã¹ã®æ¹åããã®é²åãä¿
ããã¹ãã¼ãé
é»ç¶²ãã¹ãã¼ã輸éãã¹ãã¼ã建è¨ãã¹ãã¼ã製é çãä»æ¥ã®ãã¹ãã¼ãããã¯
ããã¸ã¼ãããããããããã«ããããããã·ã¹ãã ã®æ¥ç¶æ§ãéè¦æ§ãå¢ããã ãã§ãªããã
ã®é©å¿æ§ãå復åãå®å
¨æ§åã³ã»ãã¥ãªãã£ã«å¯¾ããå¤å¤§ãªéè¦ããåµåºããã
ICS ã®ã¨ã³ã¸ãã¢ãªã³ã°ã¯å¼ãç¶ãé²åãã¦ãããæ°ããªè½åãä»ä¸ããä¸æ¹ããããã·ã¹ãã
ã®æ¦ãã¦é·ãã©ã¤ããµã¤ã¯ã«ãç¶æãã¦ãããIT è½åãç©çã·ã¹ãã ã«å°å
¥ãããã¨ã¯ãã»ãã¥
ãªãã£ä¸ã®æå³ãæã¤æ°ããªè¡åã¨ãªã£ã¦ãããã¨ã³ã¸ãã¢ãªã³ã°ã¢ãã«åã³åæã¯é²åã®éä¸
ã«ãããå®å
¨æ§ãã»ãã¥ãªãã£ããã©ã¤ãã·ã¼ãç°å¢å½±é¿ã¨ãã£ãç¸äºä¾åæ§ã®ããæ°ããªå±æ§
ãåãä¸ããããã«ãªã£ã¦ããã
2 http://www.dhs.gov/critical-infrastructure-sector-partnerships (æçµæ´æ° 2014 å¹´4æ)
SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
15
2.2 ICS Industrial Sectors and Their Interdependencies
Control systems are used in many different industrial sectors and critical infrastructures, including
manufacturing, distribution, and transportation.
2.2.1 Manufacturing Industries
Manufacturing presents a large and diverse industrial sector with many different processes, which can be
categorized into process-based and discrete-based manufacturing.
The process-based manufacturing industries typically utilize two main processes [1]:
ï¼ Continuous Manufacturing Processes. These processes run continuously, often with transitions to
make different grades of a product. Typical continuous manufacturing processes include fuel or steam
flow in a power plant, petroleum in a refinery, and distillation in a chemical plant.
ï¼ Batch Manufacturing Processes. These processes have distinct processing steps, conducted on a
quantity of material. There is a distinct start and end step to a batch process with the possibility of
brief steady state operations during intermediate steps. Typical batch manufacturing processes include
food manufacturing.
The discrete-based manufacturing industries typically conduct a series of steps on a single device to create
the end product. Electronic and mechanical parts assembly and parts machining are typical examples of this
type of industry.
Both process-based and discrete-based industries utilize the same types of control systems, sensors, and
networks. Some facilities are a hybrid of discrete and process-based manufacturing.
2.2.2 Distribution Industries
ICS are used to control geographically dispersed assets, often scattered over thousands of square kilometers,
including distribution systems such as water distribution and wastewater collection systems, agricultural
irrigation systems, oil and natural gas pipelines, electrical power grids, and railway transportation systems.
2.2.3 Differences between Manufacturing and Distribution ICS
While control systems used in manufacturing and distribution industries are very similar in operation, they
are different in some aspects. Manufacturing industries are usually located within a confined factory or
plant-centric area, when compared to geographically dispersed distribution industries. Communications in
manufacturing industries are usually performed using local area network (LAN) technologies that are
typically more reliable and high speed as compared to the long-distance communication wide-area
networks (WAN) and wireless/RF (radio frequency) technologies used by distribution industries. The ICS
used in distribution industries are designed to handle long-distance communication challenges such as
delays and data loss posed by the various communication media used. The security controls may differ
among network types.
2.2.4 ICS and Critical Infrastructure Interdependencies
The U.S. critical infrastructure is often referred to as a âsystem of systemsâ because of the
interdependencies that exist between its various industrial sectors as well as interconnections between
business partners [8] [9]. Critical infrastructures are highly interconnected and mutually dependent in
SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
16
2.2 ICS ã®ç£æ¥é¨éã¨ãã®ç¸äºä¾åæ§
å¶å¾¡ã·ã¹ãã ã¯è£½é ãç©æµã輸éçã種ã
ã®ç£æ¥é¨éã§ä½¿ç¨ãããéè¦ãªã¤ã³ãã©ã¨ãªã£ã¦ããã
2.2.1 製é æ¥ç
ä¸å£ã«è£½é ã¨ãã£ã¦ããå¤ç¨®å¤æ§ãªé¨éã«æ§ã
ãªããã»ã¹ããããããã»ã¹ä¸»ä½ã®è£½é ã¨çµç«ä¸»
ä½ã®è£½é ã«å¤§å¥ãããã
ããã»ã¹ä¸»ä½ã®è£½é æ¥çã¯ãä¸è¬çã«æ¬¡ã® 2ã¤ã®ä¸»è¦ããã»ã¹ãå©ç¨ãã[1]ã
ï¼ ç¶ç¶è£½é ããã»ã¹ãç¶ç¶çã«å®æ½ãããããã»ã¹ã§ãã°ã¬ã¼ããç°ãªãåä¸ã®è£½åã«ç§»è¡ã
ããã¨ãå¤ããä¸è¬çãªç¶ç¶è£½é ããã»ã¹ã«ã¯ãçºé»æã®çæãè¸æ°ã®æµãã製油æã®ç³æ²¹ã
åå¦ãã©ã³ãã®è¸ç液ãå«ã¾ããã
ï¼ ããã製é ããã»ã¹ã大éã®è³æã«å¯¾ãã¦ãæ確ã«åãããã¹ããããããªããããããã
ã»ã¹ã«ã¯æ確ãªéå§ã¹ãããã¨çµäºã¹ããããããããã®ä¸éã«ããã¦ã¯çãå®å¸¸ç¶æ
ã®æ¥
åãè¡ãããå ´åããããä¸è¬çãªããã製é ããã»ã¹ã«ã¯é£å製é ãå«ã¾ããã
çµç«ä¸»ä½ã®è£½é æ¥çã¯ãä¸è¬ã«åä¸ã®ããã¤ã¹ã§ä¸é£ã®ã¹ããããå®è¡ããæçµè£½åãçã¿åºãã
é»åé¨åã»æ©æ¢°é¨åã®çµç«ãé¨åã®å·¥ä½ãªã©ã¯ãã®å
¸åã§ããã
ããã»ã¹ä¸»ä½ã®æ¥çãçµç«ä¸»ä½ã®æ¥çããå種ã®å¶å¾¡ã·ã¹ãã ãã»ã³ãµåã³ãããã¯ã¼ã¯ã使ç¨
ãããæ½è¨ã«ãã£ã¦ã¯ã両æ¹ã®è£½é ãåæã«è¡ãæãããã
2.2.2 é
éæ¥ç
ICS ã¯å°ççã«åæ£ããè³ç£ã®ç®¡çã«ä½¿ç¨ãããã¨ãã«ã¯ç¯å²ãæ°åãã平米ã«ããªããã¨ãã
ããä¾ãã°ä¸ä¸æ°´éãçæ¼ãç³æ²¹ã»å¤©ç¶ã¬ã¹ãã¤ãã©ã¤ã³ãéé»ç¶²ãééçã§ããã
2.2.3 製é ICS ã¨é
é ICS ã®ç¸é
製é æ¥çã¨é
éæ¥çã®å¶å¾¡ã·ã¹ãã ã®æ¥åã¯ã¨ã¦ãããä¼¼ã¦ããããç°ãªãé¢ãããã¤ãããã
製é æ¥çã¯ãé常ééãããå·¥å ´ããã©ã³ãä¸å¿ã®é åå
ã«ããã®ã«å¯¾ããé
éæ¥çã¯å°ççã«
åæ£ãã¦ããã製é æ¥çã®é信㯠LAN ãå©ç¨ãã¦é常è¡ããããããã¯é
éæ¥çãå©ç¨ããé·è·
é¢ã® WAN åã³ç¡ç· RF æè¡ã«æ¯ã¹ã¦ãä¸è¬ã«ä¿¡é ¼æ§ãé度ã«ãåªãããé
éæ¥çã® ICS ã¯ãå©ç¨
ãã種ã
ã®éä¿¡ã¡ãã£ã¢ã«èµ·å ããé
延ããã¼ã¿åªå¤±ã¨ãã£ãé·è·é¢éä¿¡ã®è«¸åé¡ã«å¯¾å¦ã§ãã
ããã«è¨è¨ããããã»ãã¥ãªãã£ç®¡çã¯ããããã¯ã¼ã¯ã®ç¨®é¡ã«å¿ãã¦ç°ãªãã
2.2.4 ICS ã¨éè¦ã¤ã³ãã©ã®ç¸äºä¾åæ§
ç±³å½ã®éè¦ã¤ã³ãã©ã¯ããããè¤æ°ã®ã·ã¹ãã ãããªãã·ã¹ãã ãã¨å¼ã°ããããçç±ã¯å¤ç¨®å¤
æ§ãªæ¥çã»é¨éãç¸äºã«ä¾åãåãããã¸ãã¹ãã¼ããã¼å士ãç¸äºã«é¢ããåã£ã¦ããããã§
ãã[8] [9]ãéè¦ã¤ã³ãã©ã¯ãç©ççã«ãå¤æ°ã®æ
å ±ã»éä¿¡æè¡é¢ã§ããé«åº¦ã«ç¸äºé£æºãã
è¤éã«ç¸äºä¾åãåã£ã¦ããã
SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
17
complex ways, both physically and through a host of information and communications technologies. An
incident in one infrastructure can directly and indirectly affect other infrastructures through cascading and
escalating failures.
Both the electrical power transmission and distribution grid industries use geographically distributed
SCADA control technology to operate highly interconnected and dynamic systems consisting of thousands
of public and private utilities and rural cooperatives for supplying electricity to end users. Some SCADA
systems monitor and control electricity distribution by collecting data from and issuing commands to
geographically remote field control stations from a centralized location. SCADA systems are also used to
monitor and control water, oil and natural gas distribution, including pipelines, ships, trucks, and rail
systems, as well as wastewater collection systems.
SCADA systems and DCS are often networked together. This is the case for electric power control centers
and electric power generation facilities. Although the electric power generation facility operation is
controlled by a DCS, the DCS must communicate with the SCADA system to coordinate production output
with transmission and distribution demands.
Electric power is often thought to be one of the most prevalent sources of disruptions of interdependent
critical infrastructures. As an example, a cascading failure can be initiated by a disruption of the microwave
communications network used for an electric power transmission SCADA system. The lack of monitoring
and control capabilities could cause a large generating unit to be taken offline, an event that would lead to
loss of power at a transmission substation. This loss could cause a major imbalance, triggering a cascading
failure across the power grid. This could result in large area blackouts that could potentially affect oil and
natural gas production, refinery operations, water treatment systems, wastewater collection systems, and
pipeline transport systems that rely on the grid for electric power.
2.3 ICS Operation and Components
The basic operation of an ICS is shown in Figure 2-1 [2]. Some critical processes may also include safety
systems. Key components include the following:
A typical ICS contains numerous control loops, human interfaces, and remote diagnostics and maintenance
tools built using an array of network protocols on layered network architectures. A control loop utilizes
sensors, actuators, and controllers (e.g., PLCs) to manipulate some controlled process. A sensor is a device
that produces a measurement of some physical property and then sends this information as controlled
variables to the controller. The controller interprets the signals and generates corresponding manipulated
variables, based on a control algorithm and target set points, which it transmits to the actuators. Actuators
such as control valves, breakers, switches, and motors are used to directly manipulate the controlled
process based on commands from the controller.
Operators and engineers use human interfaces to monitor and configure set points, control algorithms, and
to adjust and establish parameters in the controller. The human interface also displays process status
information and historical information. Diagnostics and maintenance utilities are used to prevent, identify,
and recover from abnormal operation or failures.
Sometimes these control loops are nested and/or cascading âwhereby the set point for one loop is based on
the process variable determined by another loop. Supervisory-level loops and lower-level loops operate
continuously over the duration of a process with cycle times ranging on the order of milliseconds to
minutes.
SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
18
ããã¤ã³ãã©ã®ã¤ã³ã·ãã³ãã¯ãé£éãé害ã®ã¨ã¹ã«ã¬ã¼ã·ã§ã³ãéãã¦ãä»ã®ã¤ã³ãã©ã«ãç´
æ¥ã»éæ¥ã«å½±é¿ãåã¼ãã
éé»ã»é
é»æ¥çã§ã¯ãããããå°ççåæ£ SCADA å¶å¾¡æè¡ã使ç¨ãã¦ãã¨ã³ãã¦ã¼ã¶ã«é»æ°ãä¾
給ããããã«ãæ°åãã®å®æ°å
Œ
±äºæ¥è
åã³å°æ¹ååçµåãããªããé«åº¦ã«ç¸äºé£æºããåçã·
ã¹ãã ãéç¨ãã¦ãããé éå¶å¾¡ã¹ãã¼ã·ã§ã³ã«å¯¾ãã¦ä¸ãæããã³ãã³ããçºè¡ãã¦ãã¼ã¿ã
åéããé
é»ãç£è¦ã»å¶å¾¡ãã¦ãã SCADA ããããã¾ããã¤ãã©ã¤ã³ãè¹è¶ããã©ãã¯ãééã
ä¸æ°´éçãæ°´ã»ç³æ²¹ã»å¤©ç¶ã¬ã¹ã®é
éãç£è¦ã»å¶å¾¡ãã SCADA ãããã
SCADA ã¨DCS ã¯ãããã¯ã¼ã¯åããã¦ãããã¨ãå¤ããé»åå¶å¾¡ã»ã³ã¿ã¼ã¨çºé»æ½è¨ããã®ä¸ä¾
ã§ãããçºé»æ½è¨ã¯ DCS ã§å¶å¾¡ãããããDCS ã¯SCADA ã¨éä¿¡ãè¡ããéé»ã»é
é»éè¦ã«å¿ãã¦
çç£åºåã調æ´ããªããã°ãªããªãã
é»åã¯ãç¸äºä¾åãåã£ãéè¦ã¤ã³ãã©ã®å´©å£ããããããæãæ®åããã½ã¼ã¹ã®ä¸ã¤ã¨èãã
ãã¦ãããä¸ä¾ã¨ãã¦ãéé» SCADA ç¨ã®ãã¤ã¯ãæ³¢é信網ãå´©å£ããã°ãé£éé害ã®å¼ãéã¨ãª
ãå¾ããç£è¦ã»å¶å¾¡è½åã®æ¬ å¦ã¯ã大åçºé»è£
ç½®ããªãã©ã¤ã³ã«ããå¤é»æã®é»ååªå¤±ã«è³ãã
ããªããããããåªå¤±ã«ãã大ããªä¸åè¡¡ãçããé»å網å
¨ä½ã®é£éé害ã®å¼ãéã¨ãªãããã®
çµæåºååé»ãçããé»å網ã«ä¾åããç³æ²¹ã»å¤©ç¶ã¬ã¹çç£ã製油ææ¥åãæ°´å¦çã·ã¹ãã ãä¸
æ°´éåã³ãã¤ãã©ã¤ã³æ¬éã·ã¹ãã ã«ãå½±é¿ãåºããã
2.3 ICS ã®æä½åã³ã³ã³ãã¼ãã³ã
ICS ã®åºæ¬æä½ãå³ 2-1 ã«ç¤ºã[2]ãéè¦ããã»ã¹ã«ãã£ã¦ã¯ãå®å
¨ã·ã¹ãã ãå«ãããã®ãã
ãããã¼ã³ã³ãã¼ãã³ãã¯ä»¥ä¸ã®ã¨ããã
ä¸è¬ç㪠ICS ã«ã¯æ°å¤ãã®å¶å¾¡ã«ã¼ãããã¥ã¼ãã³ã¤ã³ã¿ãã§ã¼ã¹ã®ã»ããã¬ã¤ã¤ã¼ããããã¯
ã¼ã¯ã¢ã¼ããã¯ãã£ã¼ã®å¤æ§ãªãããã¯ã¼ã¯ãããã³ã«ãå©ç¨ãã¦ä½æãããªã¢ã¼ã診æã»ä¿å®
ãã¼ã«ãå«ã¾ãããå¶å¾¡ã«ã¼ãã¯ã»ã³ãµãã¢ã¯ãã¥ã¨ã¼ã¿åã³ã³ã³ããã¼ã©ï¼PLC çï¼ã使ç¨ã
ã¦ãå¶å¾¡ããã»ã¹ã®ããã¤ããæä½ãããã»ã³ãµã¯ç¹å®ã®ç©çç¹æ§ãè¨æ¸¬ãããã®æ
å ±ãå¶å¾¡å¤
æ°ã¨ãã¦ã³ã³ããã¼ã©ã«éä¿¡ããããã¤ã¹ã§ãããã³ã³ããã¼ã©ã¯ä¿¡å·ã解éããå¶å¾¡ã¢ã«ã´ãª
ãºã ã¨ç®æ¨è¨å®ç¹ãåºã«å¯¾å¿ããæä½å¤æ°ãçæããã¢ã¯ãã¥ã¨ã¼ã¿ã«éä¿¡ãããã¢ã¯ãã¥ã¨ã¼
ã¿ã¯ãã«ãããã¬ã¼ã«ãã¹ã¤ãããã¢ã¼ã¿çã®ãã¨ã§ãã³ã³ããã¼ã©ããã®ã³ãã³ãã«å¾ã£ã¦å¶
御ããã»ã¹ãç´æ¥æä½ããã
æä½å¡åã³ã¨ã³ã¸ãã¢ã¯ãã¥ã¼ãã³ã¤ã³ã¿ãã§ã¼ã¹ãå©ç¨ããè¨å®ç¹ãå¶å¾¡ã¢ã«ã´ãªãºã ãç£
è¦ã»è¨å®ããã³ã³ããã¼ã©ã®ãã©ã¡ã¼ã¿ã調æ´ã»è¨å®ããã
ã¾ããã¥ã¼ãã³ã¤ã³ã¿ãã§ã¼ã¹ã¯ããã»ã¹ã®ã¹ãã¼ã¿ã¹æ
å ±åã³å±¥æ´æ
å ±ã表示ããã診æã»ä¿
å®ã¦ã¼ãã£ãªãã£ã¯ãç°å¸¸æä½ãé害ã®é²æ¢ãç¹å®åã³å復ã«å©ç¨ãããã
ãã®ãããªå¶å¾¡ã«ã¼ãã¯ãã¹ããã«ã¹ã±ã¼ãã«ãªã£ã¦ãããã¨ãããããã®å ´åãããã«ã¼ãã®
è¨å®ç¹ã¯å¥ã®ã«ã¼ãã«ãã決ã¾ãããã»ã¹å¤æ°ã«ä¾åãããç£è¦ã¬ãã«ã®ã«ã¼ãã¨ä½ã¬ãã«ã«ã¼
ã㯠1ã¤ã®ããã»ã¹ä¸ç¶ç¶çã«æ©è½ãããµã¤ã¯ã«æéã¯ããªç§ããååä½ã¾ã§ã¨ãªãã
SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
19
Figure 2-1. ICS Operation
To support subsequent discussions, this section defines key ICS components that are used in control and
networking. Some of these components can be described generically for use in SCADA systems, DCS and
PLCs, while others are unique to one. The Glossary of Terms in Appendix Bâ contains a more detailed
listing of control and networking components. Additionally, Figure 2-5 and Figure 2-6 show SCADA
implementation examples; Figure 2-7 shows a DCS implementation example and Figure 2-8 shows a PLC
implementation example that incorporates these components.
2.3.1 ICS System Design Considerations
While Section 2.3 introduced the basic components of an ICS, the design of an ICS, including whether a
SCADA, DCS, or PLC-based topologies are used depends on many factors. This section identifies key
factors that drive design decisions regarding the control, communication, reliability, and redundancy
properties of the ICS. Because these factors heavily influence the design of the ICS, they will also help
determine the security needs of the system.
ï¼ Control Timing Requirements. ICS processes have a wide range of time-related requirements,
including very high speed, consistency, regularity, and synchronization. Humans may not be able to
reliably and consistently meet these requirements; automated controllers may be necessary. Some
systems may require the computation to be performed as close to the sensor and actuators as possible
to reduce communication latency and perform necessary control actions on time.
SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
20
å³2-1.ICS ã®åä½
以å¾ã®èª¬æã®ä¾¿å®ä¸ããã®ã»ã¯ã·ã§ã³ã§ã¯å¶å¾¡åã³ãããã¯ã¼ã¯ã§ä½¿ç¨ãã ICS ã®ãã¼ã³ã³ãã¼
ãã³ãã«ã¤ãã¦æããã«ãããSCADAãDCS åã³ PLC ã§æ±ç¨çã«ç¨ãããã®ãããã°ãã©ãã 1
ã¤ã«ç¹åãã¦ãããã®ããããä»é² Bã®ç¨èªéã«ã¯ãå¶å¾¡ã³ã³ãã¼ãã³ãåã³ãããã¯ã¼ã¯ã³ã³
ãã¼ãã³ãã®è©³ç´°ãªãªã¹ãããããã¾ãå³ 2-5 ã¨å³ 2-6 ã«ã¯ SCADAãå³ 2-7 ã«ã¯ DCSãå³ 2-8 ã«
ã¯PLC ã®å®è£
ä¾ããããã示ããããããã³ã³ãã¼ãã³ããçµã¿è¾¼ã¾ãã¦ããã
2.3.1 ICS ã®ã·ã¹ãã è¨è¨ä¸ã®èæ
®äºé
ã»ã¯ã·ã§ã³ 2.3 ã«ã¯ ICS ã®åºæ¬ã³ã³ãã¼ãã³ããICS ã®è¨è¨ãç´¹ä»ããã¦ãããSCADAãDCSã
PLC ã®ãããã«åºã¥ããããã¸ã¼ã使ç¨ãã¹ããã¯ãå¤ãã®è¦å ã«ä¾åããç¹ã説æããã¦ããã
ãã®ã»ã¯ã·ã§ã³ã§ã¯ãICS ã®å¶å¾¡ãéä¿¡ãä¿¡é ¼æ§åã³åé·ç¹æ§ã«é¢ããè¨è¨ä¸ã®éè¦è¦å ãæã
ãã«ãããããããè¦å 㯠ICS ã®è¨è¨ã«å¤§ããå½±é¿ãããããã·ã¹ãã ã®ã»ãã¥ãªãã£éè¦ãå¤
å®ããä¸ã§ãå½¹ç«ã¤ã
ï¼ å¶å¾¡ã®ã¿ã¤ãã³ã°è¦ä»¶ãICS ã®ããã»ã¹ã«ã¯ãé«éæ§ãä¸è²«æ§ãè¦åæ§ãåææ§çãåºç¯ãª
æéé¢é£ã®è¦ä»¶ãããã人éã¯ããããè¦ä»¶ã«å¯¾ãã¦ãé«ãä¿¡é ¼æ§ã¨ä¸è²«æ§ããã£ã¦å¿ãã
ãã¨ã¯ã§ããªããããèªåã³ã³ããã¼ã©ãå¿
è¦ã¨ãªããã·ã¹ãã ã«ãã£ã¦ã¯ãéä¿¡ã®å¾
ã¡æ
éãç縮ããå¿
è¦ãªå¶å¾¡åä½ãæéã©ããã«è¡ããããã»ã³ãµã¨ã¢ã¯ãã¥ã¨ã¼ã¿ãã§ããã
ãè¿ã¥ãã¦è¨ç®ãè¡ãå¿
è¦ãçããã
ãã¥ã¼ãã³ã»ãã·ã³
ã¤ã³ã¿ãã§ã¼ã¹ï¼HMIï¼ ãªã¢ã¼ã診æã»ä¿å®
è¨å®ç¹ãå¶å¾¡ã¢ã«ã´ãªãºã ã
ãã©ã¡ã¼ã¿å¶ç´ã
ããã»ã¹ãã¼ã¿
æä½å¤æ°
ã¢ã¯ãã¥ã¨ã¼ã¿
ããã»ã¹å
¥å
ã³ã³ããã¼ã©
å¶å¾¡ãããããã»ã¹
妨害
å¶å¾¡å¤æ°
ã»ã³ãµ
ããã»ã¹åºå
SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
21
ï¼ Geographic Distribution. Systems have varying degrees of distribution, ranging from a small system
(e.g., local PLC-controlled process) to large, distributed systems (e.g., oil pipelines, electric power
grid). Greater distribution typically implies a need for wide area (e.g., leased lines, circuit switching,
and packet switching) and mobile communication.
ï¼ Hierarchy. Supervisory control is used to provide a central location that can aggregate data from
multiple locations to support control decisions based on the current state of the system. Often a
hierarchical/centralized control is used to provide human operators with a comprehensive view of the
entire system.
ï¼ Control Complexity. Often control functions can be performed by simple controllers and preset
algorithms. However, more complex systems (e.g., air traffic control) require human operators to
ensure that all control actions are appropriate to meet the larger objectives of the system.
ï¼ Availability. The systemâs availability (i.e., reliability) requirements are also an important factor in
design. Systems with strong availability/up-time requirements may require more redundancy or
alternate implementations across all communication and control.
ï¼ Impact of Failures. The failure of a control function could incur substantially different impacts across
domains. Systems with greater impacts often require the ability to continue operations through
redundant controls, or the ability to operate in a degraded state. The design needs to address these
requirements.
ï¼ Safety. The systemâs safety requirements area also an important factor in design. Systems must be
able to detect unsafe conditions and trigger actions to reduce unsafe conditions to safe ones. In most
safety-critical operations, human oversight and control of a potentially dangerous process is an
essential part of the safety system.
2.3.2 SCADA Systems
SCADA systems are used to control dispersed assets where centralized data acquisition is as important as
control [3] [4]. These systems are used in distribution systems such as water distribution and wastewater
collection systems, oil and natural gas pipelines, electrical utility transmission and distribution systems, and
rail and other public transportation systems. SCADA systems integrate data acquisition systems with data
transmission systems and HMI software to provide a centralized monitoring and control system for
numerous process inputs and outputs. SCADA systems are designed to collect field information, transfer it
to a central computer facility, and display the information to the operator graphically or textually, thereby
allowing the operator to monitor or control an entire system from a central location in near real time. Based
on the sophistication and setup of the individual system, control of any individual system, operation, or task
can be automatic, or it can be performed by operator commands.
Typical hardware includes a control server placed at a control center, communications equipment (e.g.,
radio, telephone line, cable, or satellite), and one or more geographically distributed field sites consisting of
Remote Terminal Units (RTUs) and/or PLCs, which controls actuators and/or monitors sensors. The
control server stores and processes the information from RTU inputs and outputs, while the RTU or PLC
controls the local process. The communications hardware allows the transfer of information and data back
and forth between the control server and the RTUs or PLCs. The software is programmed to tell the system
what and when to monitor, what parameter ranges are acceptable, and what response to initiate when
parameters change outside acceptable values. An Intelligent Electronic Device (IED), such as a protective
relay, may communicate directly to the control server, or a local RTU may poll the IEDs to collect the data
and pass it to the control server. IEDs provide a direct interface to control and monitor equipment and
sensors. IEDs may be directly polled and controlled by the control server and in most
SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
22
ï¼ å°ççãªåæ£ãã·ã¹ãã ã®åæ£ã®ç¨åº¦ã¯ãå°è¦æ¨¡ãªã·ã¹ãã ï¼ãã¼ã«ã« PLC å¶å¾¡ããã»ã¹
çï¼ãã大è¦æ¨¡ãªåæ£ã·ã¹ãã ï¼ç³æ²¹ãã¤ãã©ã¤ã³ãé»å網çï¼ã¾ã§å¤å²ã«ããããåæ£ã®
ç¨åº¦ã大ãããªãã°ãé常åºåã«ãªãï¼åç·ãªã¼ã¹ãåè·¯åæ¿ããã±ããåæ¿çï¼ã移åé
ä¿¡ãå¿
è¦ã¨ãªãã
ï¼ é層ãç£è¦å¶å¾¡ãå©ç¨ãã¦ãè¤æ°æå¨å°ã®ãã¼ã¿ãä¸ãæããåéããã·ã¹ãã ã®ç¾ç¶ã«åº
ã¥ãã¦å¶å¾¡ã®æ±ºå®ã«å½¹ç«ã¦ããã¨ãã§ãããé層ã»éä¸ç®¡çãå©ç¨ãã¦ãã·ã¹ãã å
¨ä½ãå
æ¬çã«è¦ãªãã人éãæä½ãè¡ããã¨ãå¤ãã
ï¼ å¶å¾¡ã®è¤éæ§ãå¶å¾¡ã¯åç´ãªã³ã³ããã¼ã©ã¨ããªã»ããã¢ã«ã´ãªãºã ã§è¡ããããã¨ãå¤ãã
ããããããè¤éãªã·ã¹ãã ï¼èªç©ºäº¤é管å¶çï¼ã§ã¯ãå
¨ã¦ã®å¶å¾¡è¡çºãé©æ£ã§ããã大ã
ãªã·ã¹ãã ç®æ¨ã«åè´ããããããæä½å¡ãå¿
è¦ã¨ãªãã
ï¼ å¯ç¨æ§ãã·ã¹ãã ã®å¯ç¨æ§ï¼ããªãã¡ä¿¡é ¼æ§ï¼è¦ä»¶ããè¨è¨ã«ãããéè¦è¦å ã¨ãªããé«ã
å¯ç¨æ§/ã¢ããã¿ã¤ã è¦ä»¶ãæã£ãã·ã¹ãã ã«ã¯ãéä¿¡åã³å¶å¾¡å
¨è¬ãéãã¦ãã£ããã®åé·
æ§ã代æ¿å®è£
ãå¿
è¦ã¨ãªãã
ï¼ é害ã®å½±é¿ãå¶å¾¡æ©è½ã®é害ã¯ãããªãå¤æ§ãªå½±é¿ãå
¨é åã«ãããããããªããå½±é¿åº¦ã®
大ããã·ã¹ãã ã«ã¯ãåé·å¶å¾¡ãéåç¶æ
ã§ã®éç¨è½åãéãã¦ãéç¨ãç¶ç¶ããè½åãæ±
ãããããã¨ãå¤ããè¨è¨ã§ã¯ããããè¦ä»¶ãèæ
®ã«å
¥ããå¿
è¦ãããã
ï¼ å®å
¨æ§ãã·ã¹ãã ã®å®å
¨æ§è¦ä»¶ãè¨è¨ã®éè¦è¦ç´ ã¨ãªããä¸å®å
¨ç¶æ
ãæ¤ç¥ãã¦ãå®å
¨ç¶æ
ã«è¿ã¥ãããã¨ãæ±ãããããæãå®å
¨æ§ãæ±ããããéç¨ã§ã¯ãæ½å¨çã«å±éºãªããã»ã¹
ã«å¯¾ãã人éã®ç£è¦ã»å¶å¾¡ãå®å
¨æ§ã·ã¹ãã ã®ä¸å¯æ¬ é¨åã¨ãªãã
2.3.2 SCADA
SCADA ã¯ãéä¸ãã¼ã¿åå¾ãå¶å¾¡ã¨åæ§ã«éè¦ãªå ´åã«ãåæ£åãããè³ç£ãå¶å¾¡ããããã«ä½¿
ç¨ãã[3] [4]ãä¸ä¸æ°´éãç³æ²¹ã»å¤©ç¶ã¬ã¹ãã¤ãã©ã¤ã³ãéé»ã»é
é»ã·ã¹ãã ãééãã®ä»ã®
å
Œ
±è¼¸éã¨ãã£ãé
éã·ã¹ãã ã«ä½¿ç¨ããã¦ãããSCADA ã¯ããã¼ã¿åå¾ã·ã¹ãã ããã¼ã¿éä¿¡
ã·ã¹ãã ããã³ HMI ã½ããã¦ã¨ã¢ã¨çµ±åããå¤æ°ã®ããã»ã¹ã®ã¤ã³ãããã¨ã¢ã¦ããããã®ãã
ã®éä¸çç£è¦ã»å¶å¾¡ã·ã¹ãã ã¨ãªããSCADA ã¯ãç¾å ´ã®æ
å ±ãåéãã¦ä¸å¤®ã³ã³ãã¥ã¼ã¿æ½è¨ã¸
転éããæ
å ±ãå³å½¢ãããã¹ãå½¢å¼ã§æä½å¡ã«è¡¨ç¤ºããã·ã¹ãã å
¨ä½ãã»ã¨ãã©ãªã¢ã«ã¿ã¤ã ã«
ä¸ãæããç£è¦ã»å¶å¾¡ã§ããããã«ãããåã
ã®ã·ã¹ãã ãæ´ç·´åãã¦è¨å®ãããã¨ã«ããã
åã
ã®ã·ã¹ãã ãåä½åã¯ã¿ã¹ã¯ãèªååãããããªãã¬ã¼ã¿ã®ã³ãã³ãã§å®è¡ããããããã¨
ãã§ããã
ä¸è¬çãªãã¼ãã¦ã¨ã¢ã¨ãã¦ã¯ãã³ã³ããã¼ã«ã»ã³ã¿ã¼ã«è¨ç½®ãããã³ã³ããã¼ã«ãµã¼ããéä¿¡
è£
ç½®ï¼ç¡ç·ãé»è©±åç·ãã±ã¼ãã«ããµãã©ã¤ãçï¼ã®ã»ããé é端æ«è£
ç½®ï¼RTUï¼å㯠PLC ã§æ§
æãããï¼ãæåã¯è¤æ°ã®å°ççã«åæ£ãããç¾å ´ãå«ã¾ããã¢ã¯ãã¥ã¨ã¼ã¿ãã»ã³ãµãç£è¦ã
ããã³ã³ããã¼ã«ãµã¼ãã¯ãRTU ã®å
¥åºåæ
å ±ãä¿åã»å¦çããRTU å㯠PLC ã¯ãã¼ã«ã«ããã»
ã¹ãå¶å¾¡ãããéä¿¡ãã¼ãã¦ã¨ã¢ã¯ãã³ã³ããã¼ã«ãµã¼ã㨠RTU å㯠PLC éã®æ
å ±è»¢éã¨ãã¼ã¿
ã®éåä¿¡ãå®ç¾ãããã½ããã¦ã¨ã¢ã¯ããã°ã©ã å¯è½ã§ãç£è¦å¯¾è±¡ã¨ææãåå
¥ãããããã©ã¡
ã¼ã¿ã®ç¯å²ããã©ã¡ã¼ã¿ãç¯å²ãé¸è±ããå ´åã«åãã¹ã対å¦ã決å®ãããä¿è·ãªã¬ã¼çã®ã¤ã³
ããªã¸ã§ã³ãé»åããã¤ã¹ï¼IEDï¼ãç´æ¥ã³ã³ããã¼ã«ãµã¼ãã¨éä¿¡ãè¡ããããã¼ã«ã« RTU ã
IED ã«ãã¼ãªã³ã°ãã¦ãã¼ã¿ãåéãããããã³ã³ããã¼ã«ãµã¼ãã«æ¸¡ããIED ã¯ãè£
åååã³
ã»ã³ãµã®å¶å¾¡ã»ç£è¦ã®ç´æ¥çãªã¤ã³ã¿ãã§ã¼ã¹ã¨ãªããã¾ãã³ã³ããã¼ã«ãµã¼ãããç´æ¥ãã¼ãª
ã³ã°ã¨å¶å¾¡ãåããã»ã¨ãã©ã®å ´åãã³ã³ããã¼ã«ã»ã³ã¿ã¼ããç´æ¥æ示ãåããã« IED ãæä½
ãããã¼ã«ã«ããã°ã©ãã³ã°ãæããã
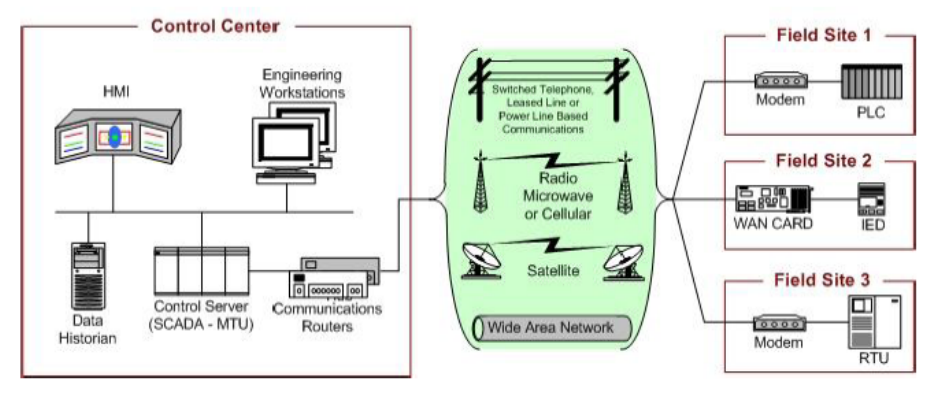
SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
23
cases have local programming that allows for the IED to act without direct instructions from the control
center. SCADA systems are usually designed to be fault-tolerant systems with significant redundancy built
into the system. Redundancy may not be a sufficient countermeasure in the face of malicious attack.
Figure 2-2 shows the components and general configuration of a SCADA system. The control center
houses a control server and the communications routers. Other control center components include the HMI,
engineering workstations, and the data historian, which are all connected by a LAN. The control center
collects and logs information gathered by the field sites, displays information to the HMI, and may generate
actions based upon detected events. The control center is also responsible for centralized alarming, trend
analyses, and reporting. The field site performs local control of actuators and monitors sensors (Note that
sensors and actuators are only shown in Figure 2-5). Field sites are often equipped with a remote access
capability to allow operators to perform remote diagnostics and repairs usually over a separate dial up
modem or WAN connection. Standard and proprietary communication protocols running over serial and
network communications are used to transport information between the control center and field sites using
telemetry techniques such as telephone line, cable, fiber, and radio frequency such as broadcast, microwave
and satellite.
SCADA communication topologies vary among implementations. The various topologies used, including
point-to-point, series, series-star, and multi-drop [5], are shown in Figure 2-3.
Point-to-point is functionally the simplest type; however, it is expensive because of the individual channels
needed for each connection. In a series configuration, the number of channels used is reduced; however,
channel sharing has an impact on the efficiency and complexity of SCADA operations. Similarly, the
series-star and multi-drop configurationsâ use of one channel per device results in decreased efficiency and
increased system complexity.
Figure 2-2. SCADA System General Layout
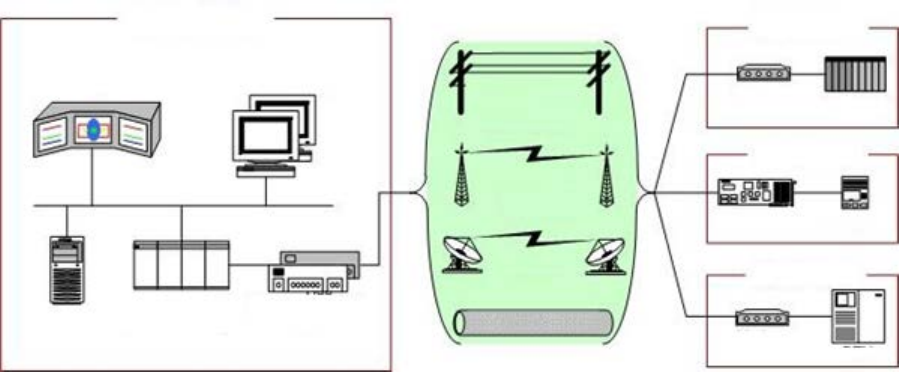
SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
24
é常ãSCADA ã¯ããã©ã¼ã«ããã¬ã©ã³ãã·ã¹ãã ã§ãç¸å½ã®åé·æ§ãçµè¾¼ã¾ãã¦ãããåé·æ§
ã¯ãæªæããæ»æã«å¯¾ãã¦ã¯ååãªå¯¾çã«ãªãå¾ãªããã¨ãããã
å³2-2 ã¯SCADA ã®ã³ã³ãã¼ãã³ãã¨å
¨ä½æ§æã示ããã³ã³ããã¼ã«ã»ã³ã¿ã¼ã«ã¯ãã³ã³ããã¼ã«
ãµã¼ãã¨éä¿¡ã«ã¼ã¿ãè¨ç½®ããããã³ã³ããã¼ã«ã»ã³ã¿ã¼ã®ãã®ä»ã®ã³ã³ãã¼ãã³ãã«ã¯ HMIã
ã¨ã³ã¸ãã¢ãªã³ã°ã¯ã¼ã¯ã¹ãã¼ã·ã§ã³åã³ãã¼ã¿ãã¹ããªã¢ã³ãå«ã¾ããã¿ãª LAN ã§ç¹ãã£ã¦ã
ããã³ã³ããã¼ã«ã»ã³ã¿ã¼ã¯ãç¾å ´ãµã¤ããåéããæ
å ±ãåéã»è¨é²ããHMI ã«è¡¨ç¤ºããæ¤ç¥
ããã¤ãã³ãã«å¿ãã¦ã¢ã¯ã·ã§ã³ãçæãããã¾ãéä¸ã¢ã©ã¼ã ããã¬ã³ãåæåã³å ±åãæ
å½
ãããç¾å ´ãµã¤ãã¯ã¢ã¯ãã¥ã¨ã¼ã¿ã®ãã¼ã«ã«å¶å¾¡ãè¡ããã»ã³ãµãç£è¦ããï¼ã»ã³ãµåã³ã¢ã¯
ãã¥ã¨ã¼ã¿ã¯å³ 2-5 ã«ã®ã¿ç¤ºãããï¼ãç¾å ´ãµã¤ãã¯ãæä½å¡ããªã¢ã¼ã診æãä¿®çãè¡ããã
ãã«ãªã¢ã¼ãã¢ã¯ã»ã¹è½åãåãããã®ãå¤ããé常ã¯ç¬ç«ãããã¤ã¢ã«ã¢ããã¢ãã ã WAN æ¥
ç¶ãå©ç¨ãã¦ãããã·ãªã¢ã«éä¿¡åã³ãããã¯ã¼ã¯éä¿¡ã§ä½¿ç¨ããæ¨æºãããã³ã«åã³å°ç¨ãã
ãã³ã«ã¯ãã³ã³ããã¼ã«ã»ã³ã¿ã¼ã¨ç¾å ´ãµã¤ãéã§ã®æ
å ±éä¿¡ã«å©ç¨ããããã®éä¿¡ã¯ãé»è©±å
ç·ãã±ã¼ãã«ããã¡ã¤ãã¼ãç¡ç·å¨æ³¢æ°ï¼ããã¼ããã£ã¹ãããã¤ã¯ãæ³¢ããµãã©ã¤ãçï¼ã¨ã
ã£ããã¬ã¡ããªæè¡ãå©ç¨ãã¦è¡ãã
SCADA éä¿¡ãããã¸ã¼ã¯ãå®è£
ã«ãã£ã¦æ§ã
ã«ç°ãªã£ã¦ããã2å°ç¹éãã·ãªã¼ãºãã·ãªã¼ãºã¹
ã¿ã¼ããã«ããããã[5]çã®ãå©ç¨ãããæ§ã
ãªãããã¸ã¼ãå³ 2-3 ã«ç¤ºãã
2å°ç¹éã¯æ©è½çã«æãåç´ã§ããããæ¥ç¶ãã¨ã«ããããã®ãã£ã³ãã«ãå¿
è¦ã§ãããã¨ãã
ã³ã¹ãé«ã«ãªããã·ãªã¼ãºæ§æã§ã¯ããã£ã³ãã«æ°ãå°ãªãã¦ãããããã£ã³ãã«ãå
±æããã
ããSCADA ã®åä½ã®å¹çã¨è¤éãã«å½±é¿ããã
åæ§ã«ã·ãªã¼ãºã¹ã¿ã¼åã³ãã«ãããããæ§æã§ã¯ãããã¤ã¹ãã¨ã« 1ãã£ã³ãã«ã使ç¨ããã
ããå¹çãä½ä¸ããã·ã¹ãã ãè¤éã«ãªãã
å³2-2.SCADA ã®å
¨è¬ã¬ã¤ã¢ã¦ã
ã³ã³ããã¼ã«
ã»ã³ã¿ã¼
HMI
ã¨ã³ã¸ãã¢ãªã³ã°
ã¯ã¼ã¯ã¹ãã¼ã·ã§ã³
ãã¼ã¿
ãã¹ããªã¢ã³
å¶å¾¡ãµã¼ã
ï¼
SCADA-MTU
ï¼
éä¿¡ã«ã¼ã¿
åæ¿é»è©±ããªã¼ã¹
åç·åã¯é»åç·
å©ç¨éä¿¡
ãã¤ã¯ãæ³¢ç¡ç·
åã¯ã»ã«ã©ã¼
è¡æ
WAN
ç¾å ´ãµã¤ã 1
ã¢ãã PLC
ç¾å ´ãµã¤ã 2
WAN ã«ã¼ã IED
ã¢ãã RTU
ç¾å ´ãµã¤ã 3
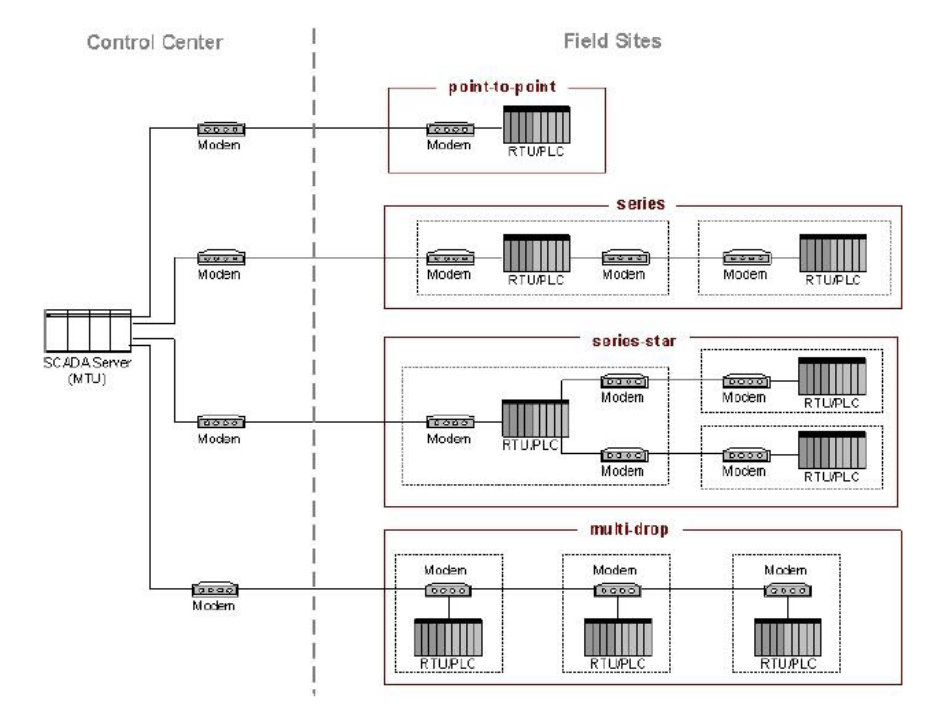
SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
25
The four basic topologies Figure 2-3 can be further augmented using dedicated devices to manage
communication exchanges as well as message switching and buffering. Large SCADA systems containing
hundreds of RTUs often employee a sub-control server to alleviate the burden on the primary server. This
type of topology is shown in Figure 2-4.
Figure 2-5 shows an example of a SCADA system implementation. This particular SCADA system consists
of a primary control center and three field sites. A second backup control center provides redundancy in the
event of a primary control center malfunction. Point-to-point connections are used for all control center to
field site communications, with two connections using radio telemetry. The third field site is local to the
control center and uses the WAN for communications. A regional control center resides above the primary
control center for a higher level of supervisory control. The corporate network has access to all control
centers through the WAN, and field sites can be accessed remotely for troubleshooting and maintenance
operations. The primary control center polls field devices for data at defined intervals (e.g., 5 seconds, 60
seconds) and can send new set points to a field device as required. In addition to polling and issuing high-
level commands, the control server also watches for priority interrupts coming from field site alarm
systems.
Figure 2-3. Basic SCADA Communication Topologies
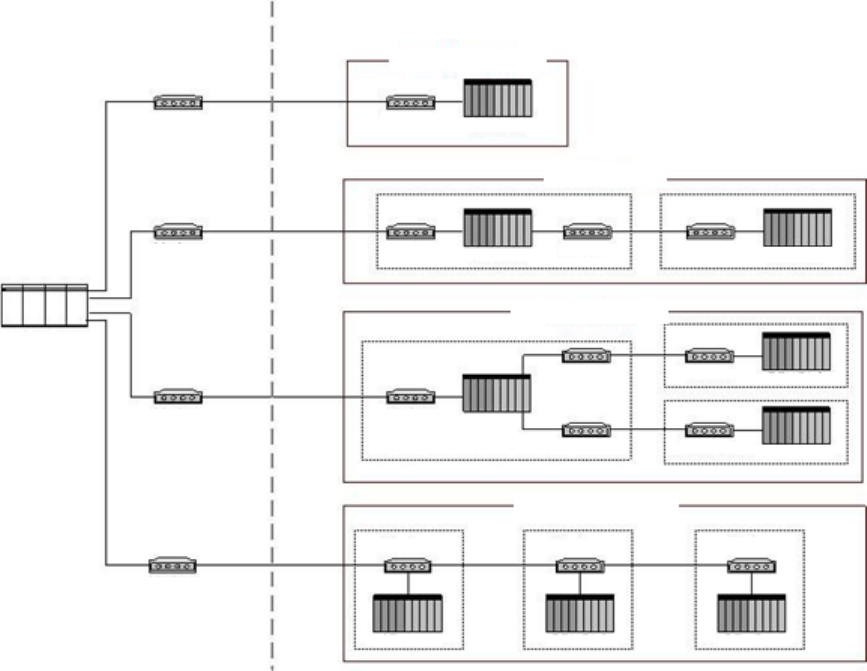
SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
26
å³2-3 ã®4ã¤ã®åºæ¬ãããã¸ã¼ã¯ãå°ç¨ããã¤ã¹ã使ç¨ãã¦æ´ã«å¢ãããé信交æãã¡ãã»ã¼ã¸
åæ¿ããããã¡ãªã³ã°ã管çãããã¨ãã§ãããæ°ç¾ã® RTU ãæã¤å¤§è¦æ¨¡ SCADA ã¯ããµãã³
ã³ããã¼ã«ãµã¼ããæ¡ç¨ãããã©ã¤ããªãµã¼ãã®è² è·ã軽æ¸ãã¦ãããã¨ãå¤ãããã®ç¨®ã®ãã
ãã¸ã¼ã¯å³ 2-4 ã«ç¤ºãã
å³2-5 ã¯SCADA ã®å®è£
ä¾ã§ããããã®ç¹æ®ãª SCADA ã¯ããã©ã¤ããªã³ã³ããã¼ã«ã»ã³ã¿ã¼ã¨ 3ã¤
ã®ç¾å ´ãµã¤ãã§æ§æãããã2çªç®ã®ããã¯ã¢ããã³ã³ããã¼ã«ã»ã³ã¿ã¼ã¯ããã©ã¤ããªã³ã³ã
ãã¼ã«ã»ã³ã¿ã¼ãä¸å
·åãèµ·ããã¦ããå ´åã«åé·æ§ãçºæ®ããã2å°ç¹éæ¥ç¶ã¯ãå
¨ã¦ã®ã³ã³
ããã¼ã«ã»ã³ã¿ã¼ã¨ç¾å ´ãµã¤ãéã®éä¿¡ã«ä½¿ç¨ããç¡ç·ãã¬ã¡ããªã«ããæ¥ç¶ã 2ã¤ã«ãªã£ã¦ã
ãã3çªç®ã®ç¾å ´ãµã¤ãã¯ã³ã³ããã¼ã«ã»ã³ã¿ã¼ã«å¯¾ãã¦ãã¼ã«ã«ã§ãWAN æ¥ç¶ãå©ç¨ãããå°
åã³ã³ããã¼ã«ã»ã³ã¿ã¼ã¯ãã©ã¤ããªã³ã³ããã¼ã«ã»ã³ã¿ã¼ã®ä¸ä½ã«ãããããé«ä½ã®ç£è¦å¶å¾¡
ãè¡ããä¼æ¥ãããã¯ã¼ã¯ã¯ WAN çµç±ã§ã³ã³ããã¼ã«ã»ã³ã¿ã¼ã«ã¢ã¯ã»ã¹ããç¾å ´ãµã¤ãã¯ããª
ã¢ã¼ãã¢ã¯ã»ã¹ã«ãããã©ãã«ã·ã¥ã¼ãã£ã³ã°ã¨ä¿å®ä½æ¥ãè¡ããããã«ãªã£ã¦ããããã©ã¤ã
ãªã³ã³ããã¼ã«ã»ã³ã¿ã¼ã¯ãæå®ãããééï¼5ç§ã60 ç§çï¼ã§ç¾å ´ã®ããã¤ã¹ã«ãã¼ã¿ã®ãã¼
ãªã³ã°ãè¡ããå¿
è¦ã«å¿ãã¦æ°ããªè¨å®ç¹ãç¾å ´ã®ããã¤ã¹ã«éä¿¡ããããã¼ãªã³ã°ã¨ãã¤ã¬ã
ã«ã³ãã³ãã®çºè¡ã«å ãã¦ãã³ã³ããã¼ã«ãµã¼ãã¯ãç¾å ´ãµã¤ãã®ã¢ã©ã¼ã ã·ã¹ãã ããéãã
ãåªå
ä¸æã®ç£è¦ãè¡ãã
å³2-3. åºæ¬ç SCADA éä¿¡ãããã¸ã¼
ã³ã³ããã¼ã«ã»ã³ã¿ã¼
ç¾å ´ãµã¤ã
ã¢ãã
ã¢ãã
ã¢ãã
ã¢ãã
ã¢ãã
ã¢ãã
ã¢ãã
ã¢ãã ã¢ãã ã¢ãã
ã¢ãã
ã¢ãã
ã¢ãã
ã¢ãã
ã¢ãã
ã¢ãã
SCADA ãµã¼ã
ï¼MTUï¼
2å°ç¹é
RTU/PLC
RTU/PLC RTU/PLC
RTU/PLC
RTU/PLC
RTU/PLC
RTU/PLC RTU/PLC RTU/PLC
ã·ãªã¼ãº
ã·ãªã¼ãºã¹ã¿ã¼
ãã«ããããã
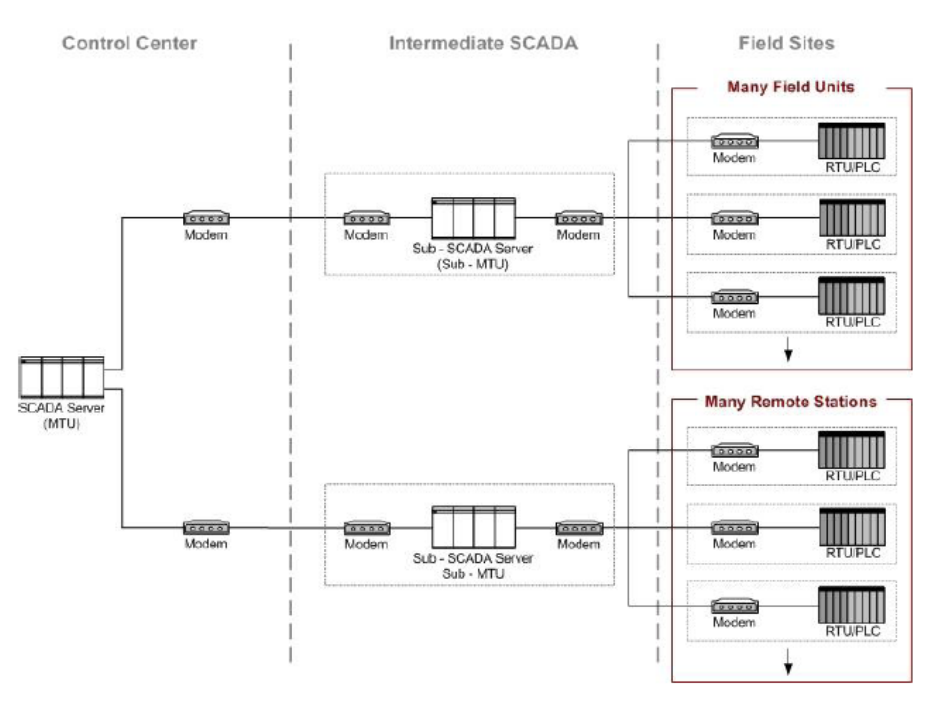
SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
27
Figure 2-4. Large SCADA Communication Topology
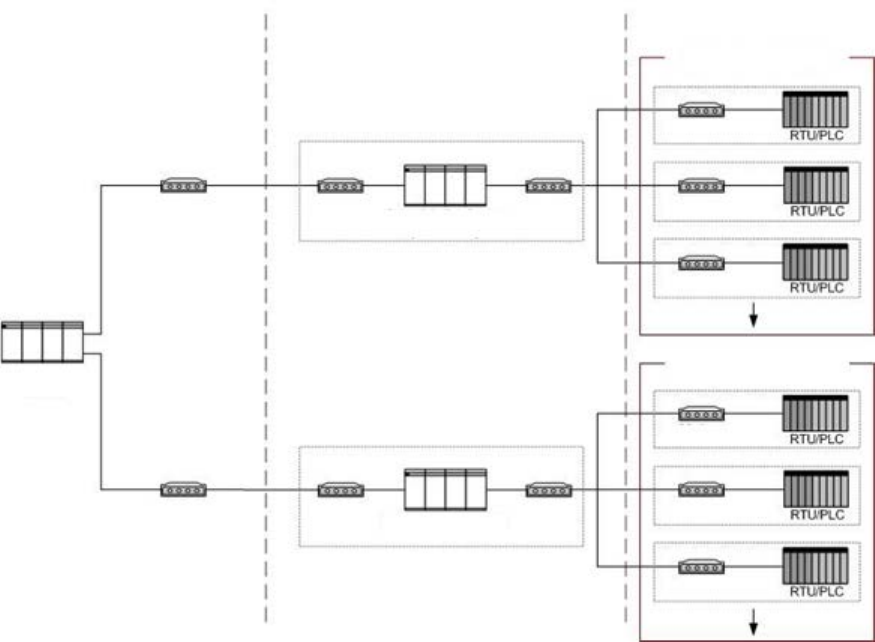
SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
28
å³2-4. 大è¦æ¨¡ SCADA éä¿¡ãããã¸ã¼
ã³ã³ããã¼ã«ã»ã³ã¿ã¼
ç¾å ´ãµã¤ã
ã¢ãã ã¢ãã
ã¢ãã
ã¢ãã
ã¢ãã
SCADA ãµã¼ã
ï¼MTUï¼
å¤æ°ã®ãã£ã¼ã«ãè£
ç½®
å¤æ°ã®é éã¹ãã¼ã·ã§ã³
ä¸é SCADA
SCADA
ãµã¼ã
ï¼ãµã MTUï¼
ã¢ãã ãµã
SCADA
ãµã¼ã
ï¼ãµã MTUï¼
ã¢ãã
ã¢ãã
ã¢ãã
ã¢ãã
ã¢ãã
ã¢ãã
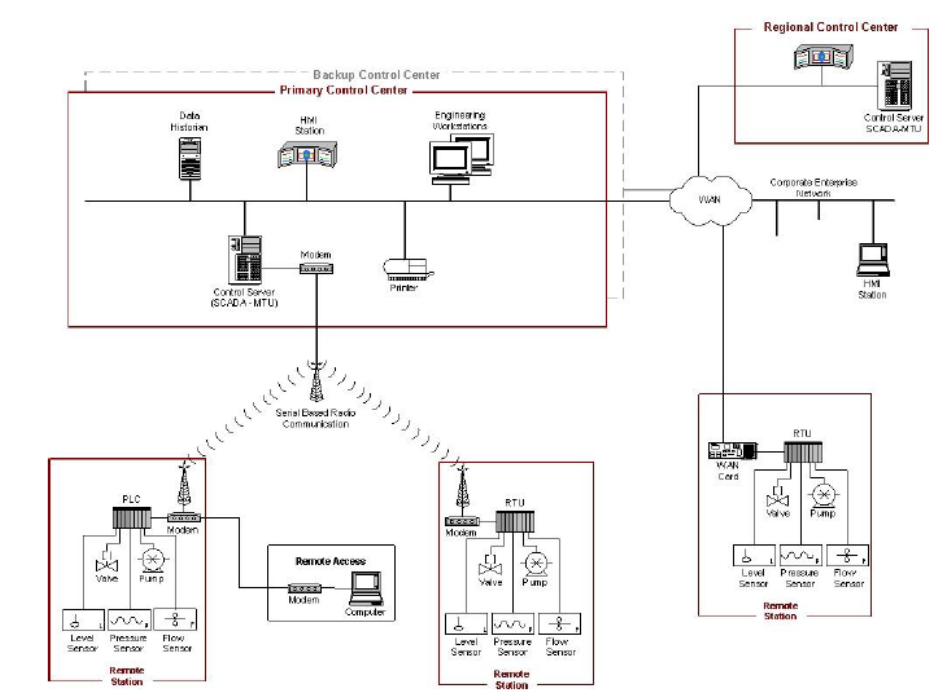
SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
29
Figure 2-5. SCADA System Implementation Example (Distribution Monitoring and Control)
Figure 2-6 shows an example implementation for rail monitoring and control. This example includes a rail
control center that houses the SCADA system and three sections of a rail system. The SCADA system polls
the rail sections for information such as the status of the trains, signal systems, traction electrification
systems, and ticket vending machines. This information is also fed to operator consoles at the HMI station
within the rail control center. The SCADA system also monitors operator inputs at the rail control center
and disperses high-level operator commands to the rail section components. In addition, the SCADA
system monitors conditions at the individual rail sections and issues commands based on these conditions
(e.g., stopping a train to prevent it from entering an area that has been determined to be flooded or occupied
by another train based on condition monitoring).
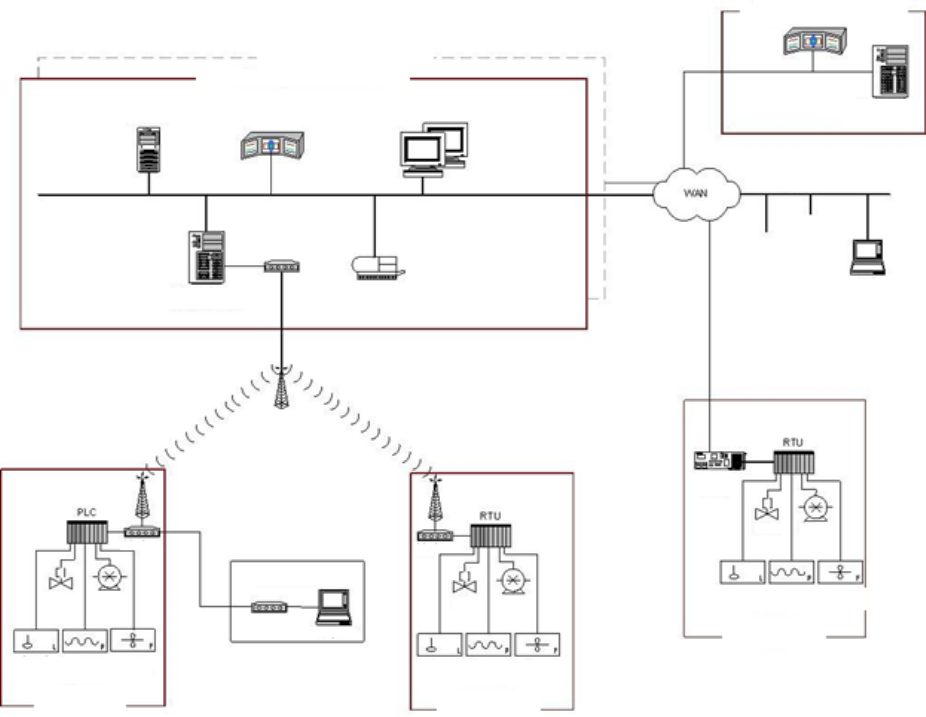
SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
30
å³2-5. SCADA ã®å®è£
ä¾ï¼åæ£ç£è¦ã»å¶å¾¡ï¼
å³2-6 ã¯ãééç£è¦ã»å¶å¾¡ã®å®è£
ä¾ã§ããããã®ä¾ã§ã¯ãSCADA ã¨ééã·ã¹ãã ã® 3ã»ã¯ã·ã§ã³
ãæããééå¶å¾¡ã»ã³ã¿ã¼ãå«ã¾ãããSCADA ã¯ééã®ã»ã¯ã·ã§ã³ã«å¯¾ããåè»ã®ç¶æ
ãä¿¡å·è£
ç½®ãç½å¼å¸¯é»è£
ç½®ãä¹è»å¸è²©å£²æ©çã®æ
å ±ã®ãã¼ãªã³ã°ãè¡ãããã®æ
å ±ã¯ãééå¶å¾¡ã»ã³ã¿ã¼
å
ã«ãã HMI ã¹ãã¼ã·ã§ã³ã®æä½å¡ã³ã³ã½ã¼ã«ã«ãä¾çµ¦ããããã¾ã SCADA ã¯ãééå¶å¾¡ã»ã³ã¿
ã¼ã«ãããæä½å¡ã®å
¥åæ
å ±ãç£è¦ããä¸ä½ã®æä½å¡ã³ãã³ããééã»ã¯ã·ã§ã³ã³ã³ãã¼ãã³ã
ã«çºè¡ãããå ãã¦ãåã
ã®ééã»ã¯ã·ã§ã³ã«ãããç¶æ
ãç£è¦ããããã«å¿ãã¦ã³ãã³ããçº
è¡ããï¼ç¶æ
ç£è¦ã«åºã¥ãã洪水ã¨å¤å®ãããå°åºãã»ãã®åè»ãããå°åºã«é²å
¥ããªãããã«
åè»ãåæ¢ããããªã©ï¼ã
ããã¯ã¢ããã³ã³ããã¼ã«ã»ã³ã¿ã¼
ãã¼ã¿ãã¹ããªã¢ã³
ããªã³ã¿
HMI ã¹ãã¼ã·ã§ã³
ä¼æ¥ãããã¯ã¼ã¯
ã·ãªã¢ã«ãã¼ã¹
ç¡ç·éä¿¡
ãã©ã¤ããªã³ã³ããã¼ã«ã»ã³ã¿ã¼
ã¨ã³ã¸ãã¢ãªã³ã°ã¯ã¼
ã¯ã¹ãã¼ã·ã§ã³
ã¢ãã
WAN
Card
å°åã³ã³ããã¼ã«ã»ã³ã¿ã¼
å¶å¾¡ãµã¼ã
ï¼SCADA-MTUï¼
ã¢ãã
é é
ã¹ãã¼ã·ã§ã³
ãã«ã ãã³ã
ã¬ãã«
ã»ã³ãµ
æµé
ã»ã³ãµ
å§å
ã»ã³ãµ
ãªã¢ã¼ãã¢ã¯ã»ã¹
ã¢ãã ã³ã³ãã¥ã¼ã¿
å¶å¾¡ãµã¼ã
ï¼SCADA-MTUï¼
HMI ã¹ãã¼ã·ã§ã³
é é
ã¹ãã¼ã·ã§ã³
ãã«ã ãã³ã
ã¬ãã«
ã»ã³ãµ
æµé
ã»ã³ãµ
å§å
ã»ã³ãµ
é é
ã¹ãã¼ã·ã§ã³
ãã«ã ãã³ã
ã¬ãã«
ã»ã³ãµ
æµé
ã»ã³ãµ
å§å
ã»ã³ãµ
ã¢ãã
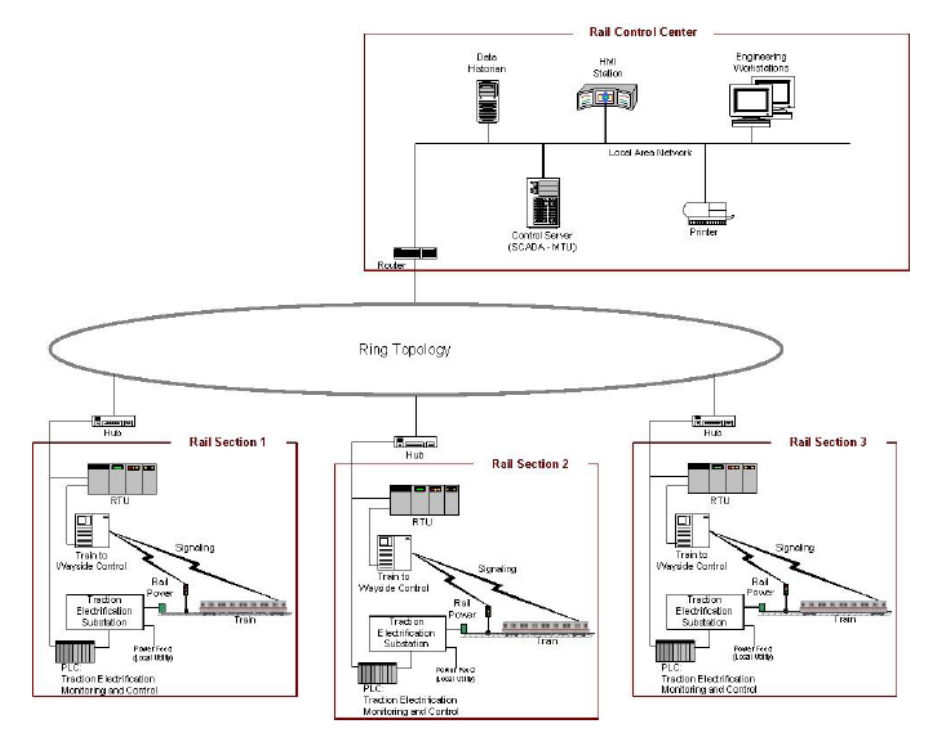
SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
31
Figure 2-6. SCADA System Implementation Example (Rail Monitoring and Control)
2.3.3 Distributed Control Systems
DCS are used to control production systems within the same geographic location for industries such as oil
refineries, water and wastewater treatment, electric power generation plants, chemical manufacturing plants,
automotive production, and pharmaceutical processing facilities. These systems are usually process control
or discrete part control systems.
DCS are integrated as a control architecture containing a supervisory level of control overseeing multiple,
integrated sub-systems that are responsible for controlling the details of a localized process. A DCS uses a
centralized supervisory control loop to mediate a group of localized controllers that share the overall tasks
of carrying out an entire production process [6]. Product and process control are usually achieved by
deploying feedback or feedforward control loops whereby key product and/or process conditions are
automatically maintained around a desired set point. To accomplish the desired product and/or process
tolerance around a specified set point, specific process controllers, or more capable PLCs, are employed in
the field and are tuned to provide the desired tolerance as well as the rate of self-correction during process
upsets. By modularizing the production system, a DCS reduces the impact of a single fault on the
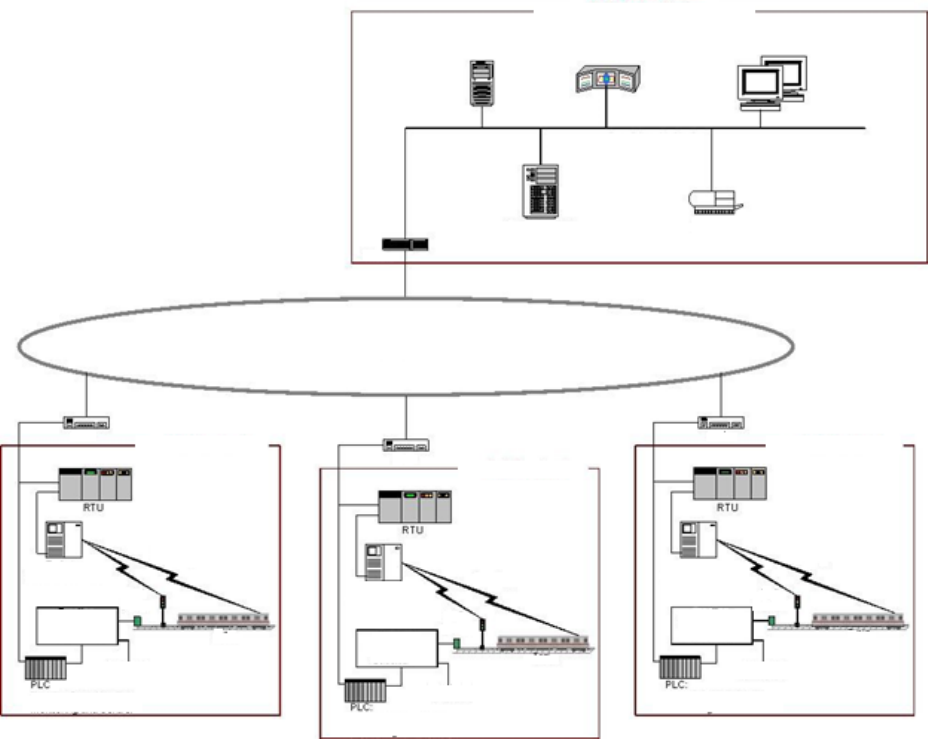
SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
32
å³2-6. SCADA ã®å®è£
ä¾ï¼åè»ç£è¦ã»å¶å¾¡ï¼
2.3.3 åæ£å¶å¾¡ã·ã¹ãã
DCS ã¯å°ççã«åãå ´æã«ããçç£ã·ã¹ãã ã®å¶å¾¡ã«ä½¿ç¨ãããç³æ²¹ç²¾è£½ãä¸ä¸æ°´éå¦çãçºé»
æãåå¦ãã©ã³ããèªåè»çç£ãå»è¬åå¦çæ½è¨çãå«ã¾ããããã®ãããªã·ã¹ãã ã¯ãé常ã
ãã»ã¹å¶å¾¡ã·ã¹ãã ãåå¥é¨åå¶å¾¡ã·ã¹ãã ã§ããã
DCS ã¯ãå±å¨ããã»ã¹ã®ç´°é¨ãå¶å¾¡ããè¤æ°ã®çµ±åãµãã·ã¹ãã ã«å¯¾ãããç£è¦ã¬ãã«ã§ã®å¶å¾¡
ãå«ããå¶å¾¡ã¢ã¼ããã¯ãã£ã¨ãã¦çµ±åããããDCS ã¯éä¸ç£è¦ã»å¶å¾¡ã«ã¼ããå©ç¨ãã¦ãçç£
ããã»ã¹å
¨ä½ã®å®è¡ã«é¢ããå
¨ã¿ã¹ã¯ãå
±æããå±å¨ã³ã³ããã¼ã©ã® 1ã°ã«ã¼ãã仲ä»ãã[6]ã
製åã»ããã»ã¹å¶å¾¡ã¯ãé常ãã£ã¼ãããã¯/ãã£ã¼ããã©ã¯ã¼ãå¶å¾¡ã«ã¼ããå±éãã¦è¡ãã
éè¦ãªè£½åãããã»ã¹ã®ç¶æ
ã¯ãææã®è¨å®ç¹ä»è¿ã«èªåçã«ä¿ããããææã®è£½åãããã»ã¹
ã®è¨±å®¹èª¤å·®ãæå®ãããè¨å®ç¹ä»è¿ã«ä¿ã¤ãããç¹æ®ããã»ã¹ã³ã³ããã¼ã©åã¯ããé«æ§è½ã®
PLC ãç¾å ´ã«æ¡ç¨ãã¦èª¿æ´ããããã»ã¹ä¸èª¿æã«ææã®è¨±å®¹èª¤å·®å
ã«åã¾ãããã«ããããèªå·±
è£æ£çãè¨å®ããããã¦ãããçç£ã·ã¹ãã ãã¢ã¸ã¥ã¼ã«åãããã¨ã§ãDCS ã¯ãåä¸ã®é害ã
ã·ã¹ãã å
¨ä½ã«ä¸ããå½±é¿ãæ¸ããã
ééã³ã³ããã¼ã«ã»ã³ã¿ã¼
LAN
ãã¼ã¿ãã¹ããªã¢ã³ HMI ã¹ãã¼ã·ã§ã³ ä¼æ¥ã¯ã¼ã¯ã¹ãã¼ã·ã§ã³
å¶å¾¡ãµã¼ã
SCADA MTU
ããªã³ã¿
ã«ã¼ã¿
ãªã³ã°åãããã¸ã¼
ééã»ã¯ã·ã§ã³ 1
Hub
沿ç·å¶å¾¡åè»
ä¿¡å·çºä¿¡
ç½å¼å¸¯é»ãµã
ã¹ãã¼ã·ã§ã³
ééé»å
åè»
給é»ï¼å°å
é»åä¼ç¤¾ï¼
ç½å¼å¸¯é»
ç£è¦å¶å¾¡
ééã»ã¯ã·ã§ã³ 2
Hub
沿ç·å¶å¾¡åè»
ä¿¡å·çºä¿¡
ç½å¼å¸¯é»ãµã
ã¹ãã¼ã·ã§ã³
ééé»å
åè»
給é»ï¼å°å
é»åä¼ç¤¾ï¼
ç½å¼å¸¯é»
ç£è¦å¶å¾¡
ééã»ã¯ã·ã§ã³ 3
Hub
沿ç·å¶å¾¡åè»
ä¿¡å·çºä¿¡
ç½å¼å¸¯é»ãµã
ã¹ãã¼ã·ã§ã³
ééé»å
åè»
給é»ï¼å°å
é»åä¼ç¤¾ï¼
ç½å¼å¸¯é»
ç£è¦å¶å¾¡
SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
33
overall system. In many modern systems, the DCS is interfaced with the corporate network to give business
operations a view of production.
An example implementation showing the components and general configuration of a DCS is depicted in
Figure 2-7. This DCS encompasses an entire facility from the bottom-level production processes up to the
corporate or enterprise layer. In this example, a supervisory controller (control server) communicates to its
subordinates via a control network. The supervisor sends set points to and requests data from the distributed
field controllers. The distributed controllers control their process actuators based on control server
commands and sensor feedback from process sensors.
Figure 2-7 gives examples of low-level controllers found on a DCS system. The field control devices
shown include a PLC, a process controller, a single loop controller, and a machine controller. The single
loop controller interfaces sensors and actuators using point-to-point wiring, while the other three field
devices incorporate fieldbus networks to interface with process sensors and actuators. Fieldbus networks
eliminate the need for point-to-point wiring between a controller and individual field sensors and actuators.
Additionally, a fieldbus allows greater functionality beyond control, including field device diagnostics, and
can accomplish control algorithms within the fieldbus, thereby avoiding signal routing back to the PLC for
every control operation. Standard industrial communication protocols designed by industry groups such as
Modbus and Fieldbus [7] are often used on control networks and fieldbus networks.
In addition to the supervisory-level and field-level control loops, intermediate levels of control may also
exist. For example, in the case of a DCS controlling a discrete part manufacturing facility, there could be an
intermediate level supervisor for each cell within the plant. This supervisor would encompass a
manufacturing cell containing a machine controller that processes a part and a robot controller that handles
raw stock and final products. There could be several of these cells that manage field-level controllers under
the main DCS supervisory control loop.
SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
34
æè¿ã®ã·ã¹ãã ã«ã¯ãDCS ã¨ä¼æ¥ãããã¯ã¼ã¯ã®ã¤ã³ã¿ãã§ã¼ã¹ã確ä¿ãã¦ãäºæ¥æ¥åã«çç£ç
ãªè¦³ç¹ãä»ä¸ãã¦ãããã®ãå°ãªããªãã
å³2-7 ã¯ãã³ã³ãã¼ãã³ã㨠DCS ã®ä¸è¬çãªæ§æã®ä¾ã示ãããã® DCS ã§ã¯ãçç£ããã»ã¹ã®åº
辺ããä¼æ¥å±¤ã«è³ãå
¨ã¦ã®æ½è¨ãåãããã¦ããããã®ä¾ã§ã¯ãç£è¦ã³ã³ããã¼ã©ï¼å¶å¾¡ãµã¼
ãï¼ãå¶å¾¡ãããã¯ã¼ã¯ãä»ãã¦ãå¾å±å±¤ã¨éä¿¡ãè¡ãããã«ãªã£ã¦ãããã¹ã¼ãã¼ãã¤ã¶ã¯ã
åæ£ãã£ã¼ã«ãã³ã³ããã¼ã©ã¸ã®è¨å®ç¹ã¨ããããã®è¦æ±ãéä¿¡ãããåæ£ã³ã³ããã¼ã©ã¯ãå¶
御ãµã¼ãã®ã³ãã³ãåã³ããã»ã¹ã»ã³ãµããã®ã»ã³ãµãã£ã¼ãããã¯ãåºã«ãããã»ã¹ã¢ã¯ãã¥
ã¨ã¼ã¿ãå¶å¾¡ããã
å³2-7 ã¯ãDCS ã·ã¹ãã ã«è¦ãããä½ã¬ãã«ã³ã³ããã¼ã©ã®ä¾ã§ããããã£ã¼ã«ãã³ã³ããã¼ã©
ããã¤ã¹ã«ã¯ãPLCãããã»ã¹ã³ã³ããã¼ã©ãåä¸ã«ã¼ãã³ã³ããã¼ã©åã³ãã·ã³ã³ã³ããã¼ã©
ãé
ç½®ããã¦ãããåä¸ã«ã¼ãã³ã³ããã¼ã©ã¯ã2å°ç¹éé
ç·ã«ããã»ã³ãµã¨ã¢ã¯ãã¥ã¨ã¼ã¿ã®
ã¤ã³ã¿ãã§ã¼ã¹ã¨ãªãããã以å¤ã® 3種é¡ã®ããã¤ã¹ã¯ããã£ã¼ã«ããã¹ãããã¯ã¼ã¯ã使ç¨ã
ã¦ãããã»ã¹ã»ã³ãµã¨ã¢ã¯ãã¥ã¨ã¼ã¿ã®ã¤ã³ã¿ãã§ã¼ã¹ã確ä¿ãã¦ããããã£ã¼ã«ããã¹ããã
ã¯ã¼ã¯ã«ã¯ãã³ã³ããã¼ã©ã¨åã
ã®ãã£ã¼ã«ãã»ã³ãµãã¢ã¯ãã¥ã¨ã¼ã¿éã® 2å°ç¹éé
ç·ãä¸è¦
ã§ãããã¾ããã£ã¼ã«ããã¹ã¯ããã£ã¼ã«ãããã¤ã¹ã®è¨ºæãªã©ãå¶å¾¡ä»¥ä¸ã®æ©è½ãçºæ®ããã»
ãããã£ã¼ã«ããã¹å
ã§å¶å¾¡ã¢ã«ã´ãªãºã ãå®ç¾ããå¶å¾¡æä½ã®ãã³ã«ä¿¡å·ã PLC ã«è¿ãå¿
è¦ã
ãªããå¶å¾¡ãããã¯ã¼ã¯ããã£ã¼ã«ããã¹ãããã¯ã¼ã¯ã§ã¯ãModbus and Fieldbus [7]çã®æ¥
çã°ã«ã¼ããè¨è¨ããæ¨æºçãªéä¿¡ãããã³ã«ãå¤ç¨ãããã
ç£è¦ã¬ãã«åã³ãã£ã¼ã«ãã¬ãã«ã§ã®å¶å¾¡ã«ã¼ãã®ã»ãã«ãä¸éã¬ãã«ã®å¶å¾¡ããããä¾ãã°ã
é¨åçµç«è£½é æ½è¨ãå¶å¾¡ãã DCS ã®å ´åããã©ã³ãå
ã®ã»ã«ãã¨ã«ä¸éã¬ãã«ã®ã¹ã¼ãã¼ãã¤ã¶
ãé
ç½®ãããã¨ãããããã®ã¹ã¼ãã¼ãã¤ã¶ã¯è£½é ã»ã«ãå
å«ãã製é ã»ã«ã«ã¯ï¼é¨åãå¦çã
ãï¼ãã·ã³ã³ã³ããã¼ã©ã¨ï¼åæå¨åº«ã¨æçµè£½åãæ±ãï¼ããããã³ã³ããã¼ã©ãå«ã¾ãããã
ã®ãããªã»ã«ãããã¤ããããã®ããããåã»ã«ã¯ã¡ã¤ã³ DCS ç£è¦å¶å¾¡ã«ã¼ãã®ä¸ã§ããã£ã¼ã«
ãã¬ãã«ã®ã³ã³ããã¼ã©ã管çããã
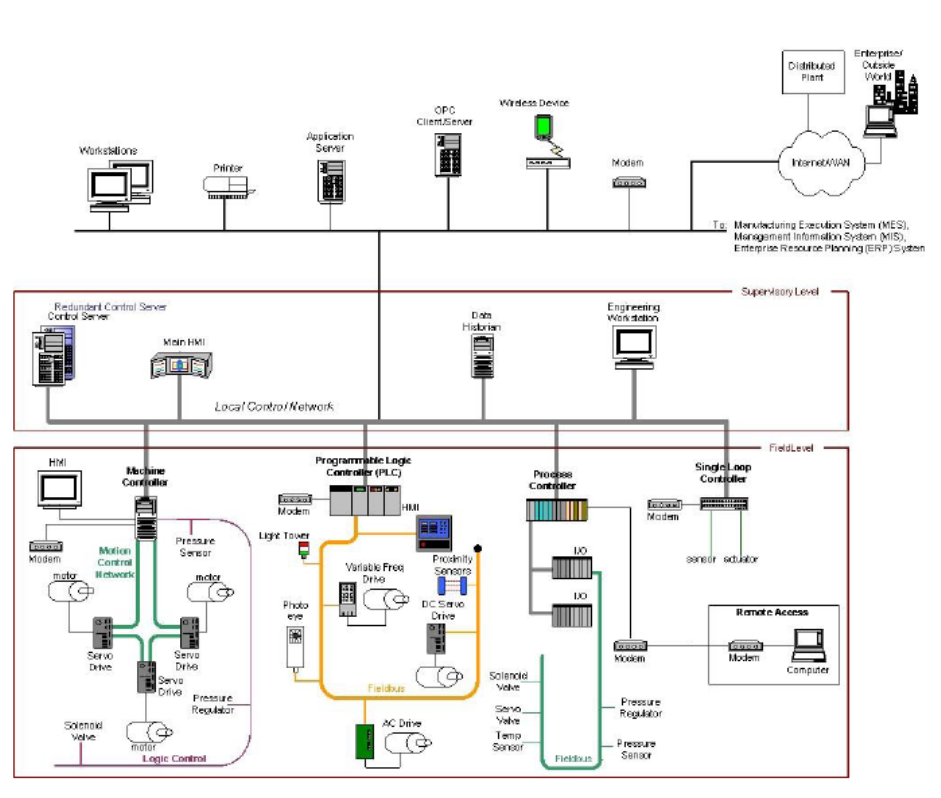
SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
35
Figure 2-7. DCS Implementation Example
2.3.4 Programmable Logic Controller Based Topologies
PLCs are used in both SCADA and DCS systems as the control components of an overall hierarchical
system to provide local management of processes through feedback control as described in the sections
above. In the case of SCADA systems, they may provide the same functionality of RTUs. When used in
DCS, PLCs are implemented as local controllers within a supervisory control scheme.
In addition to PLC usage in SCADA and DCS, PLCs are also implemented as the primary controller in
smaller control system configurations to provide operational control of discrete processes such as
automobile assembly lines and power plant soot blower controls These topologies differ from SCADA and
DCS in that they generally lack a central control server and HMI and, therefore, primarily provide closed-
loop control without direct human involvement. PLCs have a user-programmable memory for storing
instructions for the purpose of implementing specific functions such as I/O control, logic, timing, counting,
three mode proportional-integral-derivative (PID) control, communication, arithmetic, and data and file
processing.
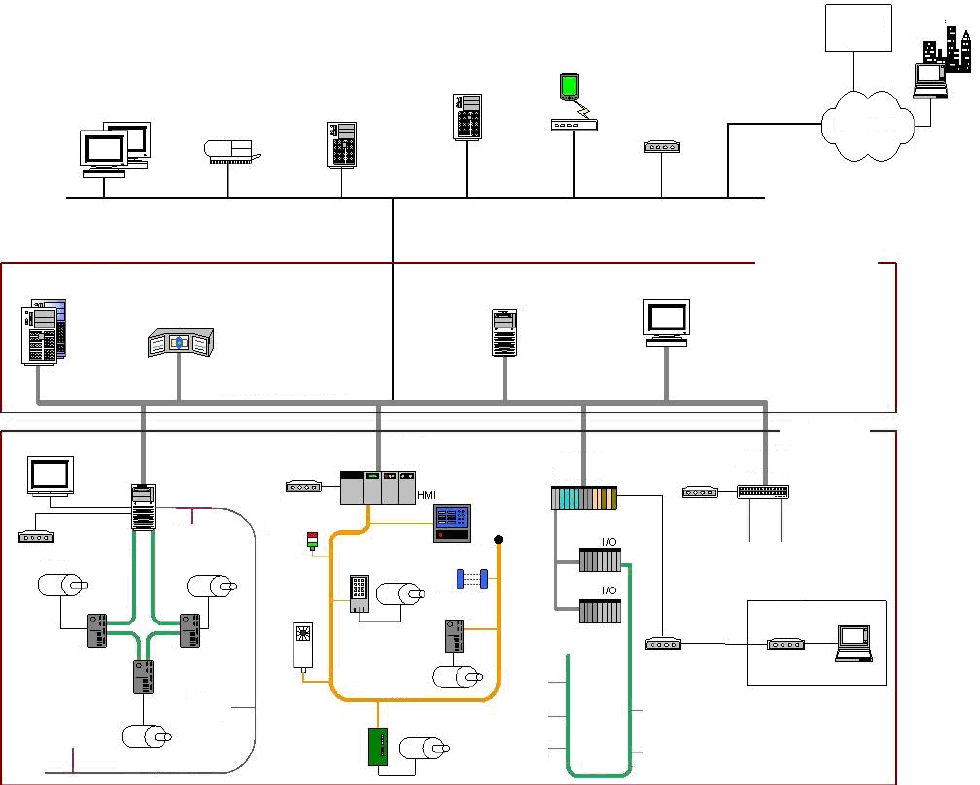
SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
36
å³2-7.DCS ã®å®è£
ä¾
2.3.4 ããã°ã©ã å¯è½è«çã³ã³ããã¼ã©ãã¼ã¹ã®ãããã¸ã¼
PLC ã¯SCADA ã¨DCS ã®ä¸¡ã·ã¹ãã ã«ããã¦ãé層ã·ã¹ãã å
¨ä½ã®å¶å¾¡ã³ã³ãã¼ãã³ãã¨ãã¦ä½¿ç¨
ãããåè¿°ã®ã¨ããããã£ã¼ãããã¯å¶å¾¡ãéãã¦ããã»ã¹ã®ãã¼ã«ã«ç®¡çãè¡ããSCADA ã®å ´
åãRTU ã¨åæ§ã®æ©è½ãçºæ®ãããDCS ã§ä½¿ç¨ãããå ´åãPLC ã¯ç£è¦ã»å¶å¾¡ã«ããããã¼ã«ã«
ã³ã³ããã¼ã©ã¨ãã¦å®è£
ãããã
SCADA ã¨DCS ã§ä½¿ç¨ãããã»ããPLC ã¯ããå°è¦æ¨¡ã®å¶å¾¡ã·ã¹ãã æ§æã«ããããã©ã¤ããªã³ã³
ããã¼ã©ã¨ãã¦ãå©ç¨ãããèªåè»çµç«ã©ã¤ã³çã®çµç«ããã»ã¹ãçºé»æã®ç
¤ç
ããã¢ã¼ã®å¶å¾¡
ãªã©ãæä½ãå¶å¾¡ãããSCADA ãDCS ã¨ã®ãããã¸ã¼ã®éãã¯ãä¸è¬ã«ä¸å¤®å¶å¾¡ãµã¼ã㨠HMI ã
ãªããã¨ã§ããã®ãã人éã®ç´æ¥çãªä»å¨ãªãã«ã主ã«ã¯ãã¼ãºãã«ã¼ãå¶å¾¡ãè¡ã£ã¦ããã
PLC ã«ã¯ã¦ã¼ã¶ãããã°ã©ã å¯è½ãªã¡ã¢ãªããããI/O å¶å¾¡ãè«çãã¿ã¤ãã³ã°ãã«ã¦ã³ããæ¯
ä¾ã»ç©åã»å¾®åï¼PIDï¼3ã¢ã¼ãå¶å¾¡ãéä¿¡ãæ¼ç®ããã¼ã¿ããã¡ã¤ã«ã®å¦ççã®å
·ä½çãªæ©è½
ãå®è£
ããããã®å½ä»¤ãæ ¼ç´ããã
ã¯ã¼ã¯ã¹ãã¼ã·ã§ã³
ããªã³ã¿
ã¢ããªã±ã¼ã·ã§ã³
ãµã¼ã
æ¥åç¨ã¯ã©ã¤ã¢ã³ã
/ãµã¼ã ç¡ç·ããã¤ã¹
ã¢ãã
åæ£
ãã©ã³ã
ã¤ã³ã¿ã¼ããã
/WAN
ä¼æ¥ã®å¤é¨ä¸ç
åé·å¶å¾¡ãµã¼ã
å¶å¾¡ãµã¼ã ã¡ã¤ã³ HMI
ãã¼ã«ã«ã³ã³ããã¼ã«
ãããã¯ã¼ã¯
ãã¼ã¿ãã¹ããªã¢ã³ ä¼æ¥ã¯ã¼ã¯ã¹ãã¼ã·ã§ã³
ç£è¦ã¬ãã«
çç£å®è¡ã·ã¹ãã ï¼MESï¼ã管ç
æ
å ±ã·ã¹ãã ï¼MISï¼ãä¼æ¥è³æºè¨
ç»ï¼ERPï¼ã·ã¹ãã ã¸
ç£è¦ã¬ãã«
HMI
ãã·ã³
ã³ã³ããã¼ã©
ããã°ã©ããã«è«ç
ã³ã³ããã¼ã©ï¼
PLC
ï¼
ã¢ãã
ã¢ãã
ã¢ã¼ã¿ ã¢ã¼ã¿
ãµã¼ãé§å
ãµã¼ãé§å
ãµã¼ãé§å
ã½ã¬ãã¤ããã«ã AC é§å
è«çå¶å¾¡
ã¢ã¼ã·ã§ã³å¶å¾¡
ãããã¯ã¼ã¯
å§åã»ã³ãµ
å§å
ã¬ã®ã¥ã¬ã¼ã¿
ã¢ã¼ã¿
ã¿ã¯ã¼ç¹ç¯
æå
å¯å¤å¨æ³¢æ°é§å
DC
ãµã¼ã
é§å
è¿æ¥ã»ã³ãµ
ãã£ã¼ã«ããã¹
ã»ã³ãµ ã¢ã¯ãã¥ã¨ã¼ã¿
ã¢ãã ã¢ãã
ããã»ã¹
ã³ã³ããã¼ã©
ã½ã¬ãã¤ã
ãã«ã
ãµã¼ããã«ã
温度ã»ã³ãµ
å§åã¬ã®ã¥ã¬ã¼ã¿
å§åã»ã³ãµ
ãªã¢ã¼ãã¢ã¯ã»ã¹
ã³ã³ãã¥ã¼ã¿
ã¢ãã
åã«ã¼ã
ã³ã³ããã¼ã©
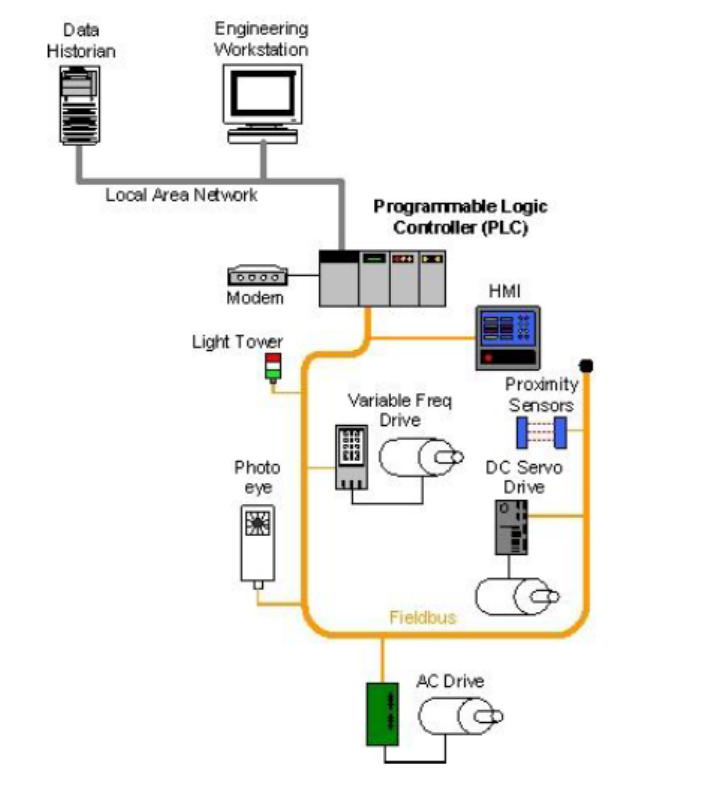
SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
37
Figure 2-8 shows control of a manufacturing process being performed by a PLC over a fieldbus network.
The PLC is accessible via a programming interface located on an engineering workstation, and data is
stored in a data historian, all connected on a LAN.
Figure 2-8. PLC Control System Implementation Example
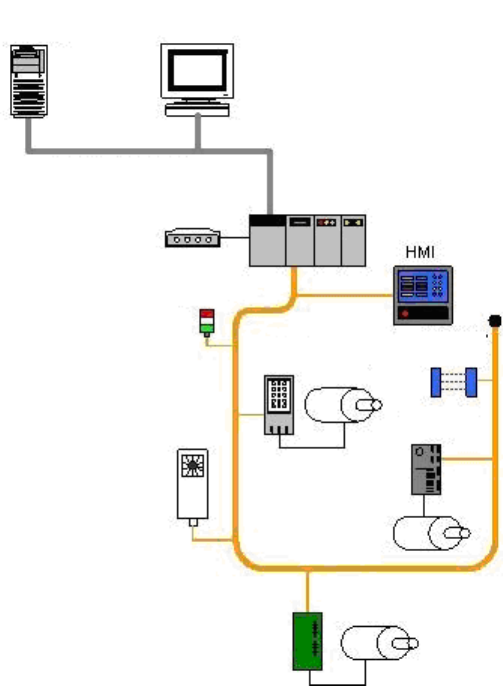
SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
38
å³2-8 ã¯ããã£ã¼ã«ããã¹ãããã¯ã¼ã¯çµç±ã§ PLC ãå®æ½ãã製é ããã»ã¹å¶å¾¡ã示ãã
PLC ã«ã¯ã¨ã³ã¸ãã¢ãªã³ã°ã¯ã¼ã¯ã¹ãã¼ã·ã§ã³ä¸ã®ããã°ã©ãã³ã°ã¤ã³ã¿ãã§ã¼ã¹ãä»ãã¦ã¢ã¯
ã»ã¹ã§ãããã¼ã¿ã¯ãã¹ããªã¢ã³ã«ä¿ç®¡ãããå
¨ã¦ LAN ã§æ¥ç¶ããã¦ããã
å³2-8. PLC å¶å¾¡ã·ã¹ãã ã®å®è£
ä¾
ãã£ã¼ã«ããã¹
PLC
ã¢ãã
AC
é§å
ã¿ã¯ã¼ç¹ç¯
æå
å¯å¤å¨æ³¢æ°é§å
DC
ãµã¼ã
é§å
è¿æ¥ã»ã³ãµ
LAN
ãã¼ã¿ãã¹ããªã¢ã³
ã¨ã³ã¸ãã¢ãªã³ã°
ã¯ã¼ã¯ã¹ãã¼ã·ã§ã³
SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
39
2.4 Comparing ICS and IT Systems Security
ICS control the physical world and IT systems manage data. ICS have many characteristics that differ from
traditional IT systems, including different risks and priorities. Some of these include significant risk to the
health and safety of human lives, serious damage to the environment, and financial issues such as
production losses, and negative impact to a nationâs economy. ICS have different performance and
reliability requirements, and also use operating systems and applications that may be considered
unconventional in a typical IT network environment. Security protections must be implemented in a way
that maintains system integrity during normal operations as well as during times of cyber attack [17].
Initially, ICS had little resemblance to IT systems in that ICS were isolated systems running proprietary
control protocols using specialized hardware and software. Widely available, low-cost Ethernet and
Internet Protocol (IP) devices are now replacing the older proprietary technologies, which increases the
possibility of cybersecurity vulnerabilities and incidents. As ICS are adopting IT solutions to promote
corporate connectivity and remote access capabilities, and are being designed and implemented using
industry standard computers, operating systems (OS) and network protocols, they are starting to resemble
IT systems. This integration supports new IT capabilities, but it provides significantly less isolation for ICS
from the outside world than predecessor systems, creating a greater need to secure these systems. While
security solutions have been designed to deal with these security issues in typical IT systems, special
precautions must be taken when introducing these same solutions to ICS environments. In some cases, new
security solutions are needed that are tailored to the ICS environment.
The environments in which ICS and IT systems operate are constantly changing. The environments of
operation include, but are not limited to: the threat space; vulnerabilities; missions/business functions;
mission/business processes; enterprise and information security architectures; information technologies;
personnel; facilities; supply chain relationships; organizational governance/culture;
procurement/acquisition processes; organizational policies/procedures; organizational assumptions,
constraints, risk tolerance, and priorities/trade-offs).
The following lists some special considerations when considering security for ICS:
ï¼ Timeliness and Performance Requirements. ICS are generally time-critical, with the criterion for
acceptable levels of delay and jitter dictated by the individual installation. Some systems require
reliable, deterministic responses. High throughput is typically not essential to ICS. In contrast, IT
systems typically require high throughput, and they can typically withstand some level of delay and
jitter. For some ICS, automated response time or system response to human interaction is very critical.
Some ICS are built on real-time operating systems (RTOS), where real-time refers to timeliness
requirements. The units of real-time are very application dependent and must be explicitly stated.
ï¼ Availability Requirements. Many ICS processes are continuous in nature. Unexpected outages of
systems that control industrial processes are not acceptable. Outages often must be planned and
scheduled days or weeks in advance. Exhaustive pre-deployment testing is essential to ensure high
availability (i.e., reliability) for the ICS. Control systems often cannot be easily stopped and started
without affecting production. In some cases, the products being produced or equipment being used is
more important than the information being relayed. Therefore, the use of typical IT strategies such as
rebooting a component, are usually not acceptable solutions due to the adverse impact on the
requirements for high availability, reliability and maintainability of the ICS. Some ICS employ
redundant components, often running in parallel, to provide continuity when primary components are
unavailable.
SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
40
2.4 ICS ã·ã¹ãã 㨠IT ã·ã¹ãã ã®ã»ãã¥ãªãã£æ¯è¼
ICS ã¯ç©ççä¸çãå¶å¾¡ããIT ã·ã¹ãã ã¯ãã¼ã¿ã管çãããICS ã¯å¾æ¥ã® IT ã·ã¹ãã ã¨ã¯ç°
ãªãç¹å¾´ãå¤ãããªã¹ã¯ãåªå
度ãç°ãªããä¸ã«ã¯äººã®å¥åº·ãå®å
¨ã«å¤§ããªãªã¹ã¯ã¨ãªããç°å¢
ãæãªããçç£åªå¤±çã®è²¡æ¿åé¡ã¨ãªããå½å®¶çµæ¸ã«æªå½±é¿ãåã¼ããã®ããããICS ã®æ§è½å
ã³ä¿¡é ¼æ§è¦ä»¶ã¯ç°ãªã£ã¦ãããæ®éã® IT ãããã¯ã¼ã¯ç°å¢ã§ã¯å¥ç°ã«è¦ãã OS ãã¢ããªã±ã¼ã·
ã§ã³ã使ç¨ãããã»ãã¥ãªãã£ã®ä¿è·ã¯ãæ£å¸¸éç¨æã«ããµã¤ãã¼æ»æã®éã«ãã·ã¹ãã ä¿å
¨ã
ç¶æã§ããããã«å®è£
ããªããã°ãªããªãã[17]
å½å ICS ã¯ãç¹æ®ãªãã¼ãã¦ã¨ã¢ã¨ã½ããã¦ã¨ã¢ã使ç¨ãã¦å°ç¨å¶å¾¡ãããã³ã«ãå®è¡ããé絶
ãããã·ã¹ãã ã ã£ããããIT ã·ã¹ãã ã¨ã¯é¡ä¼¼ç¹ãã»ã¨ãã©ãªãã£ããæ¨ä»ãåºãå©ç¨å¯è½
ãªä½ã³ã¹ãã®ã¤ã¼ãµããããã¤ã³ã¿ã¼ããããããã³ã«ï¼IPï¼ããã¤ã¹ãæ§å¼ã®å°ç¨æè¡ã«åã£
ã¦ä»£ããã¤ã¤ãããã¨ããããµã¤ãã¼ã»ãã¥ãªãã£ã®èå¼±æ§ãã¤ã³ã·ãã³ããçããèç¶æ§ãé«
ã¾ã£ã¦ãããICS ã¯IT ã½ãªã¥ã¼ã·ã§ã³ãæ¡ç¨ãã¦ãä¼æ¥ã®æ¥ç¶æ§ããªã¢ã¼ãã¢ã¯ã»ã¹è½åãä¿
é²ãã¦ãããã¾ããæ¥çæ¨æºã³ã³ãã¥ã¼ã¿ããªãã¬ã¼ãã£ã³ã°ã·ã¹ãã ï¼OSï¼åã³ãããã¯ã¼ã¯
ãããã³ã«ã使ç¨ããããã«è¨è¨ã»å®è£
ãããããã«ãªã£ã¦ããããã®ãã ICS ã¯æ¬¡ç¬¬ã« IT ã·
ã¹ãã ã¨é¡ä¼¼æ§ãæã¤ããã«ãªã£ã¦ããããã®ãããªçµ±ååã¯æ°ã㪠IT è½åããµãã¼ããããã
ãã以åã®ã·ã¹ãã ã«æ¯ã¹ãã¨ãå¤çããã®é絶æ§ãæ ¼æ®µã«å£ããããã»ãã¥ãªãã£ã®å¿
è¦æ§ã
å¢ãã
ã»ãã¥ãªãã£ã½ãªã¥ã¼ã·ã§ã³ã¯ãä¸è¬ç㪠IT ã·ã¹ãã ã«ãããã»ãã¥ãªãã£åé¡ãæ±ãããã«
ã§ãã¦ããããããããåãã½ãªã¥ã¼ã·ã§ã³ã ICS ç°å¢ã«æã¡è¾¼ãå ´åã«ã¯ç¹å¥ãªæ³¨æãæ¬ ãã
ãªããå ´åã«ãã£ã¦ã¯ããã® ICS ç°å¢ã«ç¹åããæ°ããã»ãã¥ãªãã£ã½ãªã¥ã¼ã·ã§ã³ãå¿
è¦ã¨ãª
ãã
ICS ã·ã¹ãã 㨠IT ã·ã¹ãã ã®åä½ç°å¢ã¯çµ¶ããå¤åãã¦ãããä¾ãã°ãè
å¨ç©ºéãèå¼±æ§ãä»»
åã»ãã¸ãã¹æ©è½ãä»»åã»ãã¸ãã¹ããã»ã¹ãä¼æ¥ã»æ
å ±ã»ãã¥ãªãã£ã¢ã¼ããã¯ãã£ãæ
å ±æ
è¡ã人äºãæ½è¨ããµãã©ã¤ãã§ã¼ã³ã®é¢ä¿ãçµç¹ã®ã¬ããã³ã¹/ã«ã«ãã£ã¼ã調éã»åå¾ããã»
ã¹ãçµç¹ã®æ¹éã»æé ãçµç¹ã®åæäºé
ãå¶ç´ããªã¹ã¯è¨±å®¹åº¦ãåªå
度/ãã¬ã¼ããªãçãããã
ICS ã®ã»ãã¥ãªãã£ãæ¤è¨ããéã®ç¹å¥ãªèæ
®äºé
ã以ä¸ã«åæããã
ï¼ é©ææ§è¦ä»¶ã¨æ§è½è¦ä»¶ãICS ã¯ç·æ¥ãè¦ãããã®ãå¤ããé
延ãã¸ãã¿ã¼ã®è¨±å®¹åº¦åºæºã
åã
ã®è£
ç½®ã«å¿ãã¦å®ãããã¦ãããä¿¡é ¼æ§ã®é«ã決å®è«çå¿çãæ±ããã·ã¹ãã ãããã
é«ãã¹ã«ã¼ãããã¯ä¸è¬ã« ICS ã«ã¯å¿
é ã§ãªããå対㫠IT ã·ã¹ãã ã§ã¯é常ãé«ãã¹ã«ã¼ã
ãããæ±ããããããç¨åº¦ã®é
延ãã¸ãã¿ã¼ã¯è¨±å®¹ãããããã種㮠ICS ã§ã¯ã人ã®ç¸äºä½
ç¨ã«å¯¾ããèªåå¿çæéãã·ã¹ãã å¿çã¯é常ã«éè¦ã¨ãªãããªã¢ã«ã¿ã¤ã ãªãã¬ã¼ãã£ã³
ã°ã·ã¹ãã ï¼RTOSï¼ä¸ã«æ§ç¯ããã ICS ããããããã§ãããªã¢ã«ã¿ã¤ã ãé©ææ§è¦ä»¶ã¨
ãªãããªã¢ã«ã¿ã¤ã ã®åä½ã¯ã¢ããªã±ã¼ã·ã§ã³ã«ä¾åããæ示çã«ç¤ºãå¿
è¦ãããã
ï¼ å¯ç¨æ§è¦ä»¶ãICS ããã»ã¹ã®å¤ãã¯ããã®æ§è³ªä¸ç¶ç¶çã§ãããç£æ¥ããã»ã¹ãå¶å¾¡ãã¦ã
ãã·ã¹ãã ã®äºå®å¤ã®åæ¢ã¯åãå
¥ãããããã®ã§ã¯ãªããåæ¢ã®å¤ãã¯ãæ°æ¥åã¯æ°é±é
åã«ãããããè¨ç»ã»äºå®ããããã®ã§ãªããã°ãªããªããICS ã®é«ãå¯ç¨æ§ï¼ããªãã¡ä¿¡
é ¼æ§ï¼ã確ä¿ããã«ã¯ãå¾¹åºçãªå±éå試é¨ã®å®æ½ãä¸å¯æ¬ ã¨ãªããçç£ã«å½±é¿ãåã¼ãã
ã¨ãªããå¶å¾¡ã·ã¹ãã ã®åæ¢ã»éå§ã容æã«å®è¡ã§ãããã¨ã¯å°ãªããçç£ä¸ã®è£½åã使ç¨
ä¸ã®è£
ååã®æ¹ããä¼éããæ
å ±ãããéè¦ã¨ããã±ã¼ã¹ãããããããã£ã¦ãã³ã³ãã¼ã
ã³ãã®ãªãã¼ãã¨ãã£ãä¸è¬ç㪠IT æ¦ç¥ã®å©ç¨ã¯ãICS ã®é«ãå¯ç¨æ§ã»ä¿¡é ¼æ§ã»ä¿å®æ§è¦ä»¶
ã«æªå½±é¿ãåã¼ããããé常åãå
¥ãããã解決çã¨ã¯ãªããªããICS ã§ã¯åé·ã³ã³ãã¼ã
ã³ããæ¡ç¨ãã¦åæéç¨ãããã¨ãå¤ãããã©ã¤ããªã³ã³ãã¼ãã³ããå©ç¨ã§ããªãå ´åã®
ç¶ç¶æ§ã確ä¿ãã¦ããã
SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
41
ï¼ Risk Management Requirements. In a typical IT system, data confidentiality and integrity are
typically the primary concerns. For an ICS, human safety and fault tolerance to prevent loss of life or
endangerment of public health or confidence, regulatory compliance, loss of equipment, loss of
intellectual property, or lost or damaged products are the primary concerns. The personnel responsible
for operating, securing, and maintaining ICS must understand the important link between safety and
security. Any security measure that impairs safety is unacceptable.
ï¼ Physical Effects. ICS field devices (e.g., PLC, operator station, DCS controller) are directly
responsible for controlling physical processes. ICS can have very complex interactions with physical
processes and consequences in the ICS domain that can manifest in physical events. Understanding
these potential physical effects often requires communication between experts in control systems and
in the particular physical domain.
ï¼ System Operation. ICS operating systems (OS) and control networks are often quite different from IT
counterparts, requiring different skill sets, experience, and levels of expertise. Control networks are
typically managed by control engineers, not IT personnel. Assumptions that differences are not
significant can have disastrous consequences on system operations.
ï¼ Resource Constraints. ICS and their real time OSs are often resource-constrained systems that do not
include typical contemporary IT security capabilities. Legacy systems are often lacking resources
common on modern IT systems. Many systems may not have desired features including encryption
capabilities, error logging, and password protection. Indiscriminate use of IT security practices in ICS
may cause availability and timing disruptions. There may not be computing resources available on ICS
components to retrofit these systems with current security capabilities. Adding resources or features
may not be possible.
ï¼ Communications. Communication protocols and media used by ICS environments for field device
control and intra-processor communication are typically different from most IT environments, and
may be proprietary.
ï¼ Change Management. Change management is paramount to maintaining the integrity of both IT and
control systems. Unpatched software represents one of the greatest vulnerabilities to a system.
Software updates on IT systems, including security patches, are typically applied in a timely fashion
based on appropriate security policy and procedures. In addition, these procedures are often automated
using server-based tools. Software updates on ICS cannot always be implemented on a timely basis.
These updates need to be thoroughly tested by both the vendor of the industrial control application and
the end user of the application before being implemented. Additionally, the ICS owner must plan and
schedule ICS outages days/weeks in advance. The ICS may also require revalidation as part of the
update process. Another issue is that many ICS utilize older versions of operating systems that are no
longer supported by the vendor. Consequently, available patches may not be applicable. Change
management is also applicable to hardware and firmware. The change management process, when
applied to ICS, requires careful assessment by ICS experts (e.g., control engineers) working in
conjunction with security and IT personnel.
ï¼ Managed Support. Typical IT systems allow for diversified support styles, perhaps supporting
disparate but interconnected technology architectures. For ICS, service support is sometimes via a
single vendor, which may not have a diversified and interoperable support solution from another
vendor. In some instances, third-party security solutions are not allowed due to ICS vendor license and
service agreements, and loss of service support can occur if third party applications are installed
without vendor acknowledgement or approval.
SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
42
ï¼ ãªã¹ã¯ç®¡çè¦ä»¶ãä¸è¬ç㪠IT ã·ã¹ãã ã§ã¯ãé常ãã¼ã¿ã®æ©å¯æ§ã¨ä¿å
¨ã主è¦é¢å¿äºã¨ãªãã
ICS ã§ã¯ã人å½ã®åªå¤±ãå
¬è¡è¡çã»å½æ°ã®ä¿¡é ¼ã®å±æ©ãéµæ³ãè£
ååã®æ失ãç¥ç財ç£ã®æ
失ã製åã®æ害ãé²æ¢ããããã®äººçå®å
¨æ§ã¨ãã©ã¼ã«ããã¬ã©ã³ã¹ã主è¦é¢å¿äºã§ããã
ICS ã®éç¨ã»ã»ãã¥ãªãã£ã»ä¿å®æ
å½è
ã¯ãå®å
¨æ§ã¨ã»ãã¥ãªãã£ã®éè¦ãªé¢ä¿ãç解ããª
ããã°ãªããªãããããªãã»ãã¥ãªãã£å¯¾çããå®å
¨æ§ãé»å®³ããã®ã§ããã°åãå
¥ããã
ãªãã
ï¼ ç©ççå½±é¿ãICS ã®ãã£ã¼ã«ãããã¤ã¹ï¼PLCããªãã¬ã¼ã¿ã¹ãã¼ã·ã§ã³ãDCS ã³ã³ããã¼
ã©çï¼ã¯ãç©ççããã»ã¹ãç´æ¥å¶å¾¡ãã¦ãããICS ã¨ç©ççããã»ã¹ã¨ã®ç¸äºä½ç¨ã¯æ¥µã
ã¦è¤éã§ãICS é åã«ãããçµæã¯ç©ççã¤ãã³ãã¨ãã¦æããã«ãªãããã®ãããªç©çç
å½±é¿ãç解ããã«ã¯ãå¶å¾¡ã·ã¹ãã ã®å°éå¡ã¨ç¹å®ã®ç©ççé åã®å°éå¡å士ã®ã³ãã¥ãã±
ã¼ã·ã§ã³ãå¿
è¦ã¨ãªãå ´åãå¤ãã
ï¼ ã·ã¹ãã éç¨ãICS ã®OS ã¨å¶å¾¡ãããã¯ã¼ã¯ã¯ãIT ã®å ´åã¨å
¨ãç°ãªããã¨ãå¤ããæ±ã
ãããã¹ãã«ãçµé¨ãå°éç¥èã¬ãã«ãç°ãªããå¶å¾¡ãããã¯ã¼ã¯ã¯ãé常ãIT è·å¡ã§ã¯ãª
ãå¶å¾¡ã¨ã³ã¸ãã¢ã管çãã¦ããã大ããªéãã¯ãªãã¨ããèªèã§ããã¨ãã·ã¹ãã éç¨ã«
æ²æ¨ãªçµæãæããããªãã
ï¼ ãªã½ã¼ã¹ã®å¶ç´ãICS ã¨ãã®ãªã¢ã«ã¿ã¤ã OS ã¯ãªã½ã¼ã¹å¶ç´ã®ããã·ã¹ãã ã§ãããã¨ãå¤
ããããã«ã¯æè¿ã®ä¸è¬çãªã»ãã¥ãªãã£æ©è½ã¯å«ã¾ããªããã¬ã¬ã·ã¼ã·ã¹ãã ã«ã¯ãæè¿
ã®IT ã·ã¹ãã ã¨å
±éã®ãªã½ã¼ã¹ããªããæå·åæ©è½ãã¨ã©ã¼ãã°ããã¹ã¯ã¼ãä¿è·ã¨ãã£ã
æã¾ããæ©è½ãä»ãã¦ããªãã·ã¹ãã ãå¤ããICS ã«ããã IT ã»ãã¥ãªãã£ã®è¦ç¯ãè¦å¢ãª
ã使ç¨ããã¨ãå¯ç¨æ§ãã¿ã¤ãã³ã°ã«åé¡ãèµ·ããããªãããã®ãããªã·ã¹ãã ã«ç¾è¡ã®ã»
ãã¥ãªãã£æ©è½ãä»ä¸ããICS ã³ã³ãã¼ãã³ãã«å©ç¨ã§ããã³ã³ãã¥ã¼ãã£ã³ã°ãªã½ã¼ã¹ã¯
ãªãã§ãããããªã½ã¼ã¹ãæ©è½ã®è¿½å ã¯ã§ããªãã
ï¼ éä¿¡ããã£ã¼ã«ãããã¤ã¹ã®å¶å¾¡ãããã»ããµå
éä¿¡ç¨ã« ICS ç°å¢ã§ä½¿ç¨ãããéä¿¡ããã
ã³ã«åã³ã¡ãã£ã¢ã¯ã大æµã® IT ç°å¢ã¨ã¯ç°ãªãå°ç¨ã®ãã®ãå¤ãã
ï¼ ç®¡çå¤æ´ã管çå¤æ´ã¯ IT ã·ã¹ãã ã¨å¶å¾¡ã·ã¹ãã ã®ä¿å
¨ã«èè¦ã§ãããããããå½ã¦ã¦ããª
ãã½ããã¦ã¨ã¢ã¯ãã·ã¹ãã ã«ã¨ã£ã¦æãèå¼±ãªç¹ã® 1ã¤ã¨ãªããIT ã·ã¹ãã ã«ãããã»ã
ã¥ãªãã£ãããçã®ã½ããã¦ã¨ã¢æ´æ°ã¯ãé©æ£ãªã»ãã¥ãªãã£ããªã·ã¼ã¨æé ã«å¾ã£ã¦ãã¿
ã¤ã ãªã¼ã«è¡ããããã¾ãããããæé ã¯ããµã¼ããã¼ã¹ã®ãã¼ã«ã使ç¨ãã¦èªååããã¦
ããå ´åãå¤ããICS ã§ã®ã½ããã¦ã¨ã¢æ´æ°ã¯ãå¿
ãããã¿ã¤ã ãªã¼ã«è¡ãããããã§ã¯ãª
ããæ´æ°ã®å®è¡åã«ãç£æ¥ç¨å¶å¾¡ã¢ããªã±ã¼ã·ã§ã³ãã³ãã¼ã¨ã¢ããªã±ã¼ã·ã§ã³ã®ã¨ã³ãã¦
ã¼ã¶åæ¹ã«ããå¾¹åºçãªè©¦é¨ãå¿
è¦ã¨ãªããã¾ã ICS ææè
ã¯æ°æ¥ããæ°é±éåã«ãããã
ããåæ¢ã®è¨ç»ã»äºå®ãç«ã¦ãªããã°ãªããªããã¾ãæ´æ°ããã»ã¹ã®ä¸ç°ã¨ãã¦ãåæ¤è¨¼ã
å¿
è¦ã¨ãªããå¥ã®åé¡ã¨ãã¦ããã³ãã¼ããµãã¼ããæã¡åã£ã OS ã®æ§ãã¼ã¸ã§ã³ã使ç¨
ãã ICS ãå¤ããã¨ãæããããããã®çµæãå
¥æå¯è½ãªããããé©ç¨ã§ããªããã¨ã«ãªãã
管çå¤æ´ã¯ããã¼ãã¦ã¨ã¢ããã¡ã¼ã ã¦ã¨ã¢ã«ãå½ã¦ã¯ã¾ããå¤æ´ç®¡çã®ããã»ã¹ã ICS ã«
é©ç¨ããå ´åã¯ãICS å°éå¡ï¼å¶å¾¡ã¨ã³ã¸ãã¢çï¼ãã»ãã¥ãªãã£è·å¡ã IT è·å¡ã¨é£æºãã¦ã
æ
éã«è©ä¾¡ãè¡ãå¿
è¦ãããã
ï¼ ç®¡çãµãã¼ããä¸è¬ç㪠IT ã·ã¹ãã ã§ã¯ç¨®ã
ã®ãµãã¼ãã¹ã¿ã¤ã«ãèªããããç°ãªã£ã¦ã¯ã
ã¦ãç¸äºé£æ¥ããæè¡ã¢ã¼ããã¯ãã£ããµãã¼ããã¦ãããICS ã§ã¯ããµã¼ãã¹ãµãã¼ãã
ãã³ãã¼1社ãæ
å½ããã»ãã®ãã³ãã¼ããã®å¤æ§ã§ç¸äºéç¨æ§ã®ãããµãã¼ãã½ãªã¥ã¼ã·
ã§ã³ãå¾ãããªããã¨ããããã¾ã ICS ãã³ãã¼ã®ã©ã¤ã»ã³ã¹ã»ãµã¼ãã¹å¥ç´ã«ããããµã¼
ããã¼ãã£ã®ã»ãã¥ãªãã£ã½ãªã¥ã¼ã·ã§ã³ãèªããããªãå ´åãããããã³ãã¼ã®è¨±å¯ãå¾
ãã«ãµã¼ããã¼ãã£ã®ã¢ããªã±ã¼ã·ã§ã³ãã¤ã³ã¹ãã¼ã«ããã¨ããµã¼ãã¹ãµãã¼ãã解ç´ã«
ãªããã¨ãããå¾ãã

SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
43
ï¼ Component Lifetime. Typical IT components have a lifetime on the order of 3 to 5 years, with
brevity due to the quick evolution of technology. For ICS where technology has been developed in
many cases for very specific use and implementation, the lifetime of the deployed technology is often
in the order of 10 to 15 years and sometimes longer.
ï¼ Component Location. Most IT components and some ICS are located in business and commercial
facilities physically accessible by local transportation. Remote locations may be utilized for backup
facilities. Distributed ICS components may be isolated, remote, and require extensive transportation
effort to reach. Component location also needs to consider necessary physical and environmental
security measures.
Table 2-1 summarizes some of the typical differences between IT systems and ICS.
Table 2-1. Summary of IT System and ICS Differences
Category
Information Technology System
Industrial Control System
Performance
Requirements
Non-real-time
Response must be consistent
High throughput is demanded
High delay and jitter may be
acceptable
Less critical emergency
interaction
Tightly restricted access control
can be implemented to the degree
necessary for security
Real-time
Response is time-critical
Modest throughput is acceptable
High delay and/or jitter is not acceptable
Response to human and other emergency interaction
is critical
Access to ICS should be strictly controlled, but should
not hamper or interfere with human-machine
interaction
Availability
(Reliability)
Requirements
Responses such as rebooting are
acceptable
Availability deficiencies can often
be tolerated, depending on the
systemâs operational requirements
Responses such as rebooting may not be acceptable
because of process availability requirements
Availability requirements may necessitate redundant
systems
Outages must be planned and scheduled days/weeks
in advance
High availability requires exhaustive pre-deployment
testing
Risk Management
Requirements
Manage data
Data confidentiality and integrity is
paramount
Fault tolerance is less important â
momentary downtime is not a
major risk
Major risk impact is delay of
business operations
Control physical world
Human safety is paramount, followed by protection of
the process
Fault tolerance is essential, even momentary
downtime may not be acceptable
Major risk impacts are regulatory non-compliance,
environmental impacts, loss of life, equipment, or
production
System Operation Systems are designed for use with
typical operating systems
Upgrades are straightforward with
the availability of automated
deployment tools
Differing and possibly proprietary operating systems,
often without security capabilities built in
Software changes must be carefully made, usually by
software vendors, because of the specialized control
algorithms and perhaps modified hardware and
software involved
Resource
Constraints
Systems are specified with
enough resources to support the
addition of third-party applications
such as security solutions
Systems are designed to support the intended
industrial process and may not have enough memory
and computing resources to support the addition of
security capabilities
SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
44
ï¼ ã³ã³ãã¼ãã³ãã®å¯¿å½ãä¸è¬ã« IT ã³ã³ãã¼ãã³ãã®å¯¿å½ã¯ 3ï½5å¹´ã§ãæè¡é²æ©ã®éããã
çå½ã§ãããå¤ãã®å ´åã極ãã¦ç¹æ®ãªä½¿ç¨ã¨å®è£
ãç®æãã¦æè¡éçºããã ICS ã§ã¯ã寿
å½ã¯ 10ï½15 å¹´ã§ãå ´åã«ãã£ã¦ã¯ãã以ä¸ã«ãªãã
ï¼ ã³ã³ãã¼ãã³ãã®æå¨å ´æãã»ã¨ãã©ã® IT ã³ã³ãã¼ãã³ãåã³ãã種㮠ICS ã³ã³ãã¼ãã³ã
ã¯ãå°å
ã®äº¤éæ©é¢ãå©ç¨ãã¦ç©ççã«ç«å
¥å¯è½ãªäºæ¥ã»åç¨æ½è¨ã«ç½®ããã¦ãããé éå°
ã¯ããã¯ã¢ããæ½è¨ã¨ãã¦ä½¿ç¨ããããåæ£ ICS ã³ã³ãã¼ãã³ãã¯é絶ãããé¢ãã¦ããã
ãã交éã«ããªãã®å´åãå¿
è¦ã¨ãªããã¾ãã³ã³ãã¼ãã³ãã®æå¨å ´æã¯ãç©ççã»ç°å¢ç
ã»ãã¥ãªãã£å¯¾çãèæ
®ããå¿
è¦ãããã
表2-1 ã¯ãIT ã·ã¹ãã 㨠ICS ã¨ã®ä¸è¬çãªç¸éãåãã¾ã¨ãããã®ã§ããã
表2-1.IT ã·ã¹ãã 㨠ICS ã®ç¸éç¹
ã«ãã´ãª
æ
å ±ï¼
IT
ï¼ã·ã¹ãã
ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼
ICS
ï¼
æ§è½è¦ä»¶ ãªã¢ã«ã¿ã¤ã ä¸è¦
å¿çã¯ä¸è²«ãã¦ãããã¨
ãã¤ã¹ã«ã¼ãããå¿
é
大ããªé
延ã¨ã¸ãã¿ã¼ã¯è¨±å®¹
éè¦ãªç·æ¥ç¸äºä½ç¨ãå°ãªããã¨
ã»ãã¥ãªãã£ã«å¿
è¦ãªç¨åº¦ã«å³æ ¼
ãªã¢ã¯ã»ã¹å¶éãå®è£
ã§ãããã¨
ãªã¢ã«ã¿ã¤ã
å¿çã¯ç·æ¥ãè¦ãã
ä¸ç¨åº¦ã®ã¹ã«ã¼ãããã§å¯
大ããªé
延ãã¸ãã¿ã¼ã¯ä¸å¯
人ãã®ä»ã®ç·æ¥ç¸äºä½ç¨ã¸ã®å¿çãéè¦
ICS ã¸ã®ã¢ã¯ã»ã¹ã¯å³éã«å¶éããããããã³
ãã·ã³ã¤ã³ã¿ãã§ã¼ã¹ãé»å®³ã»å¹²æ¸ããªã
å¯ç¨æ§ï¼ä¿¡é ¼
æ§ï¼ç¨ä»¶
ãªãã¼ãçã®å¿çã¯å¯
å¯ç¨æ§ã®æ¬ ç¹ã¯ã·ã¹ãã ã®éç¨è¦
件ã«å¿ãã¦è¨±å®¹ããããã¨ãå¤ã
ããã»ã¹ã®å¯ç¨æ§è¦ä»¶ã«ãããªãã¼ãçã®å¿ç
ã¯ä¸å¯
å¯ç¨æ§è¦ä»¶ããåé·ã·ã¹ãã ãå¿
è¦ã¨ãªãå ´å
ãã
åæ¢ã¯æ°æ¥åã¯æ°é±éåã«ãããããè¨ç»ã»äº
å®
é«å¯ç¨æ§è¦ä»¶ã«ããå¾¹åºçãªå±éå試é¨ãå¿
è¦
ãªã¹ã¯ç®¡çè¦ä»¶ ãã¼ã¿ã管ç
ãã¼ã¿ã®æ©å¯æ§ã¨ä¿å
¨ãèè¦
ãã©ã¼ã«ããã¬ã©ã³ã¹ã¯ãã»ã©é
è¦ã§ãªãï¼ç¬æã®ãã¦ã³ã¿ã¤ã ã¯
é大ãªã¹ã¯ã§ãªãï¼
é大ãªãªã¹ã¯å½±é¿ã¯æ¥åã®é
延
ç©çä¸çã®å¶å¾¡
人ã®å®å
¨ãèè¦ãããã»ã¹ã®ä¿è·ã¯ãã®æ¬¡
ãã©ã¼ã«ããã¬ã©ã³ã¹ãä¸å¯æ¬ ãç¬æã®ãã¦ã³
ã¿ã¤ã ãä¸å¯
é大ãªãªã¹ã¯å½±é¿ã¯æ³ä»¤ä¸å±¥è¡ãç°å¢ã¸ã®å½±
é¿ã人å½ã»è£
ååã»çç£åªå¤±
ã·ã¹ãã éç¨ ã·ã¹ãã ã¯ä¸è¬ç OS ä¸ã§ä½¿ç¨
ã¢ããã°ã¬ã¼ãã¯èªåå±éãã¼ã«
ãå©ç¨ããã®ã§å®¹æ
ã¾ã¡ã¾ã¡ã§å°ç¨ã® OS ã使ç¨ããå ´åãããã»ã
ã¥ãªãã£æ©è½ã¯ãªããã¨ãå¤ã
å°ç¨å¶å¾¡ã¢ã«ã´ãªãºã ã¨ä¿®æ£æ¸ã¿ãã¼ãã¦ã¨ã¢/
ã½ããã¦ã¨ã¢ãé¢ä¿ãããããã½ããã¦ã¨ã¢å¤
æ´ã¯æ
éãè¦ããé常ãã³ãã¼ãæ
å½
ãªã½ã¼ã¹ã®å¶ç´ ã·ã¹ãã ã¯ã»ãã¥ãªãã£ã½ãªã¥ã¼
ã·ã§ã³çã®è¿½å ãµã¼ããã¼ãã£ã¢
ããªã±ã¼ã·ã§ã³ã«å¯¾å¿ããååãª
ãªã½ã¼ã¹ãé©ç¨
ã·ã¹ãã ã¯ææã®ç£æ¥ããã»ã¹ã«å¯¾å¿ãããã
ã«ã§ãã¦ããã追å ã»ãã¥ãªãã£æ©è½ã«å¯¾å¿ã
ãååãªã¡ã¢ãªãæ¼ç®ãªã½ã¼ã¹ã¯ãªã

SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
45
Category
Information Technology System
Industrial Control System
Communications Standard communications
protocols
Primarily wired networks with
some localized wireless
capabilities
Typical IT networking practices
Many proprietary and standard communication
protocols
Several types of communications media used
including dedicated wire and wireless (radio and
satellite)
Networks are complex and sometimes require the
expertise of control engineers
Change
Management
Software changes are applied in a
timely fashion in the presence of
good security policy and
procedures. The procedures are
often automated.
Software changes must be thoroughly tested and
deployed incrementally throughout a system to ensure
that the integrity of the control system is maintained.
ICS outages often must be planned and scheduled
days/weeks in advance. ICS may use OSs that are no
longer supported
Managed Support
Allow for diversified support styles
Service support is usually via a single vendor
Component
Lifetime
Lifetime on the order of 3 to 5
years
Lifetime on the order of 10 to 15 years
Components
Location
Components are usually local and
easy to access
Components can be isolated, remote, and require
extensive physical effort to gain access to them
In summary, the operational and risk differences between ICS and IT systems create the need for increased
sophistication in applying cybersecurity and operational strategies. A cross-functional team of control
engineers, control system operators and IT security professionals needs to work closely to understand the
possible implications of the installation, operation, and maintenance of security solutions in conjunction
with control system operation. IT professionals working with ICS need to understand the reliability impacts
of information security technologies before deployment. Some of the OSs and applications running on ICS
may not operate correctly with commercial-off-the-shelf (COTS) IT cybersecurity solutions because of
specialized ICS environment architectures.
2.5 Other Types of Control Systems
Although this guide provides guidance for securing ICS, other types of control systems share similar
characteristics and many of the recommendations from this guide are applicable and could be used as a
reference to protect such systems against cybersecurity threats. For example, although many building,
transportation, medical, security and logistics systems use different protocols, ports and services, and are
configured and operate in different modes than ICS, they share similar characteristics to traditional ICS
[18]. Examples of some of these systems and protocols include:
Other Types of Control Systems
ï¼ Advanced Metering Infrastructure.
ï¼ Building Automation Systems.
ï¼ Building Management Control Systems.
ï¼ Closed-Circuit Television (CCTV) Surveillance Systems.
ï¼ CO2 Monitoring.
ï¼ Digital Signage Systems.
ï¼ Digital Video Management Systems.
ï¼ Electronic Security Systems.
ï¼ Emergency Management Systems.
SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
46
ã«ãã´ãª æ
å ±ï¼ITï¼ã·ã¹ãã ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼
éä¿¡ æ¨æºéä¿¡ãããã³ã«
ãã©ã¤ããªæç·ãããã¯ã¼ã¯ã§å±
æçã«ç¡ç·æ©è½ãã
ä¸è¬ç IT ãããã¯ã¼ã¯è¦ç¯
å¤æ°ã®å°ç¨ã»æ¨æºéä¿¡ãããã³ã«
å°ç¨æç·ã»ç¡ç·ï¼ç¡ç·åã³ãµãã©ã¤ãï¼ãå«ã
æ°ç¨®ã®éä¿¡ã¡ãã£ã¢ãå©ç¨
ãããã¯ã¼ã¯ã¯è¤éã§ãå¶å¾¡ã¨ã³ã¸ãã¢ã®å°é
ç¥èãå¿
è¦ã¨ãããã¨ãã
管çå¤æ´ ã½ããã¦ã¨ã¢å¤æ´ã¯è¯å¥½ãªã»ãã¥
ãªãã£ããªã·ã¼ã»æé ã«å¾ãã¿ã¤
ã ãªã¼ã«å®æ½ãæé ã¯èªååãã
ã¦ãããã¨ãå¤ãã
ã½ããã¦ã¨ã¢å¤æ´ã¯ãã·ã¹ãã å
¨ä½ãéãã¦å¾¹
åºçã«è©¦é¨ã»å±éããå¶å¾¡ã·ã¹ãã ãä¿å
¨ãã
ãããã«ãããICS åæ¢ã®å¤ãã¯ãæ°æ¥åã¯æ°é±
éåã«ãããããè¨ç»ã»äºå®ãå¿
è¦ããµãã¼ã
ãçµäºãã OS ã使ç¨ãã¦ããå ´åãã
管çãµãã¼ã å¤æ§ãªãµãã¼ãã¹ã¿ã¤ã«ãã ãµã¼ãã¹ãµãã¼ãã¯é常 1æ¥è
ã®ã¿
ã³ã³ãã¼ãã³ã
ã®å¯¿å½
3å¹´ï½5å¹´ 10 å¹´ï½15 å¹´
ã³ã³ãã¼ãã³ã
ã®æå¨å ´æ
é常ãã¼ã«ã«æå¨ã§ãã¢ã¯ã»ã¹ã
容æ
ã³ã³ãã¼ãã³ãã¯é絶ãããé éå°ã«ãããã¢
ã¯ã»ã¹ã«ã¯ããªãã®ç©ççå´åãå¿
è¦
è¦ç´ããã¨ãICS ã·ã¹ãã 㨠IT ã·ã¹ãã éã«ã¯ãéç¨åã³ãªã¹ã¯ã®éãããããã¨ãããæ´ç·´
ããããµã¤ãã¼ã»ãã¥ãªãã£ã¨éç¨æ¦ç¥ãé©ç¨ããå¿
è¦ãçãããå¶å¾¡ã¨ã³ã¸ãã¢ãå¶å¾¡ã·ã¹ã
ã æä½å¡åã³ IT ã»ãã¥ãªãã£å°éå¡ãããªãæ©è½æ¨ªæãã¼ã ã¯ãç·å¯ã«é£æºãã¦ãã»ãã¥ãªã
ã£ã½ãªã¥ã¼ã·ã§ã³ã®å°å
¥ãéç¨åã³ä¿å®ãããããå¾ãæå³ããå¶å¾¡ã·ã¹ãã ã®éç¨ã¨ã®å
¼ãå
ãã§ç解ããå¿
è¦ããããICS ã§ä½æ¥ãè¡ã IT å°éå¡ã¯å±éåã«ãæ
å ±ã»ãã¥ãªãã£æè¡ã®ä¿¡
é ¼æ§å½±é¿ã«ã¤ãã¦ç解ãã¦ããå¿
è¦ããããICS ä¸ã§å®è¡ãã OS ãã¢ããªã±ã¼ã·ã§ã³ã®ä¸ã«ã¯ã
ç¹æ®ãª ICS ç°å¢ã¢ã¼ããã¯ãã£ã«èµ·å ãã¦ãæ°çï¼COTSï¼IT ãµã¤ãã¼ã»ãã¥ãªãã£ã½ãªã¥ã¼ã·
ã§ã³ã®æ£å¸¸ãªåä½ãã§ããªããã®ãããã
2.5 å¥ç¨®ã®å¶å¾¡ã·ã¹ãã
æ¬æ¸ã§ã¯ ICS ã®ã»ãã¥ãªãã£ã確ä¿ããããã®ã¬ã¤ãã³ã¹ã示ãããå¥ç¨®ã®å¶å¾¡ã·ã¹ãã ã§ãå
±
éã®ç¹å¾´ããããæ¬æ¸ã®æ¨å¥¨äºé
ã®å¤ãã¯é©ç¨å¯è½ã§ããµã¤ãã¼ã»ãã¥ãªãã£è
å¨ãããããã
ã·ã¹ãã ãä¿è·ããéã®åèæ¸ã¨ãã¦æ´»ç¨å¯è½ã§ãããä¾ãã°ããã«ã輸éãå»çãã»ãã¥ãªã
ã£ããã¸ã¹ãã£ãã¯çã®ã·ã¹ãã ã®å¤ãã¯ä½¿ç¨ãããããã³ã«ããã¼ãåã³ãµã¼ãã¹ãç°ãªãã
ICS ã¨ã¯ç°ãªãã¢ã¼ãã§è¨å®ããéç¨ããã¦ããããä¼çµ±ç㪠ICS ã¨å
±éã®ç¹å¾´ãæã£ã¦ãã
[18]ãããããã·ã¹ãã ããããã³ã«ã®ä¾ã以ä¸ã«ç¤ºãã
å¥ç¨®ã®å¶å¾¡ã·ã¹ãã
ï¼ ææ°è¨éã¤ã³ãã©ã¹ãã©ã¯ãã£
ï¼ ãã«ãªã¼ãã¡ã¼ã·ã§ã³ã·ã¹ãã
ï¼ ãã«ç®¡çå¶å¾¡ã·ã¹ãã
ï¼ CCTV ãµã¼ãã¤ã©ã³ã¹ã·ã¹ãã
ï¼ CO2 ç£è¦
ï¼ ãã¸ã¿ã«æ¨èã·ã¹ãã
ï¼ ãã¸ã¿ã«ãããªç®¡çã·ã¹ãã
ï¼ é»åã»ãã¥ãªãã£ã·ã¹ãã
ï¼ ç·æ¥ç®¡çã·ã¹ãã

SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
47
ï¼ Energy Management Systems.
ï¼ Exterior Lighting Control Systems.
ï¼ Fire Alarm Systems.
ï¼ Fire Sprinkler Systems.
ï¼ Interior Lighting Control Systems.
ï¼ Intrusion Detection Systems.
ï¼ Physical Access Control Systems.
ï¼ Public Safety/Land Mobile Radios.
ï¼ Renewable Energy Geothermal Systems.
ï¼ Renewable Energy Photo Voltaic Systems.
ï¼ Shade Control Systems.
ï¼ Smoke and Purge Systems.
ï¼ Vertical Transport System (Elevators and Escalators).
ï¼ Laboratory Instrument Control Systems.
ï¼ Laboratory Information Management Systems (LIMS).
Protocols/Ports and Services
ï¼ Modbus: Master/Slave - Port 502.
ï¼ BACnet3: Master/Slave - Port 47808.
ï¼ LonWorks/LonTalk4: Peer to Peer - Port 1679.
ï¼ DNP3: Master/Slave â Port 19999 when using Transport Layer Security (TLS), Port 20000 when not
using TLS.
ï¼ IEEE 802.x - Peer to Peer.
ï¼ ZigBee - Peer to Peer.
ï¼ Bluetooth â Master/Slave.
The security controls provided in Appendix Gâ of this guide are general and flexible enough be used to
evaluate other types of control systems, but subject matter experts should review the controls and tailor
them as appropriate to address the uniqueness of other types of control systems. There is no âone size fits
all,â and the risks may not be the same, even within a particular group. For example, a building has many
different sub-systems such as building automation, fire alarm, physical access control, digital signage,
CCTV, etc. Critical life safety systems such as the fire alarm and physical access control systems may drive
the impact level to be a âHigh,â while the other systems will usually be âLow.â An organization might
decide to evaluate each sub-system individually, or decide to use an aggregated approach. The control
systems evaluation should be coupled to the Business Impact, Contingency Plan, and Incident Response
Plan to ensure organizational critical functions and operations can be recovered and restored as defined by
the organizations Recovery Time Objectives.
3 http://www.bacnet.org/
4 http://en.wikipedia.org/wiki/LonWorks

SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
48
ï¼ ã¨ãã«ã®ã¼ç®¡çã·ã¹ãã
ï¼ è¡ç¯å¶å¾¡ã·ã¹ãã
ï¼ ç«ç½å ±ç¥ã·ã¹ãã
ï¼ æ¶ç«ç¨ã¹ããªã³ã¯ã©ã¼ã·ã¹ãã
ï¼ å±å
ç¯å¶å¾¡ã·ã¹ãã
ï¼ ä¾µå
¥æ¤ç¥ã·ã¹ãã
ï¼ ç©ççç«å
¥ç®¡çã·ã¹ãã
ï¼ å
¬è¡å®å
¨/é¸ä¸ç§»åç¡ç·
ï¼ åçã¨ãã«ã®ã¼å°ç±ã·ã¹ãã
ï¼ åçã¨ãã«ã®ã¼å¤ªé½å
çºé»ã·ã¹ãã
ï¼ ã·ã§ã¼ãå¶å¾¡ã·ã¹ãã
ï¼ æç
ã·ã¹ãã
ï¼ éç´è¼¸éã·ã¹ãã ï¼ã¨ã¬ãã¼ã¿/ã¨ã¹ã«ã¬ã¼ã¿ï¼
ï¼ å®é¨å®¤è¨å¨å¶å¾¡ã·ã¹ãã
ï¼ å®é¨å®¤æ
å ±ç®¡çã·ã¹ãã ï¼LIMSï¼
ãããã³ã«/ãã¼ãåã³ãµã¼ãã¹
ï¼ Modbus:ãã¹ã¿ã¼/ã¹ã¬ã¼ã - ãã¼ã 502
ï¼ BACnet5:ãã¹ã¿ã¼/ã¹ã¬ã¼ã - ãã¼ã 47808
ï¼ LonWorks/LonTalk6ãã¢ãã¼ã㢠- ãã¼ã 1679
ï¼ DNP3:ãã©ã³ã¹ãã¼ã層ã»ãã¥ãªãã£ï¼TLSï¼ä½¿ç¨æãã¹ã¿ã¼/ã¹ã¬ã¼ã â ãã¼ã 19999
TLS ä¸ä½¿ç¨æãã¼ã 20000
ï¼ IEEE 802.x - ãã¢ãã¼ãã¢
ï¼ ZigBee - ãã¢ãã¼ãã¢.
ï¼ Bluetooth â ãã¹ã¿ã¼/ã¹ã¬ã¼ã
æ¬æ¸ã®ä»é² Gã«è¨è¼ãããã»ãã¥ãªãã£ç®¡çã¯ãä¸è¬çã§æè»æ§ããããããå¥ç¨®ã®å¶å¾¡ã·ã¹ã
ã ã®è©ä¾¡ã«ãå©ç¨ã§ããããããããã®ä¸»é¡ã®å°é家ã¯ãã®å¶å¾¡ãç²¾æ»ããè¦ããã°èª¿æ´ãå ã
ã¦ãå¥ç¨®ã·ã¹ãã ã®ç¬èªæ§ãæ¤è¨ãã¹ãã§ãããç¹å®ã®ã°ã«ã¼ãå
ã§ãã£ã¦ããå
¨ã¦ã«é©åãã
ãããªã¼ãµã¤ãºãã®ãããªãã®ã¯åå¨ããããªã¹ã¯ãåãã§ã¯ãªããä¾ãã°ããã«ã«ã¯ãã«ãªã¼
ãã¡ã¼ã·ã§ã³ãç«ç½å ±ç¥å¨ãç©ççç«å
¥ç®¡çããã¸ã¿ã«æ¨èãCCTV çã®å¤ç¨®å¤æ§ãªãµãã·ã¹ã
ã ãåå¨ãããç«ç½å ±ç¥å¨ãç©ççç«å
¥ç®¡çã·ã¹ãã ã®ãããªéè¦ãªçå½å®å
¨ã·ã¹ãã ã¯ãå½±é¿
ã¬ãã«ããé«ãã¨ãã¹ãã§ããã®ä»ã®ã·ã¹ãã ã¯é常ãä½ãã¨ãªãããçµç¹ã¯ããããã®ãµãã·
ã¹ãã ã®åå¥è©ä¾¡ãè¡ããã決å®ãããããã¯éç´çãªã¢ããã¼ããåããã¨ã決å®ã§ãããã
å¶å¾¡ã·ã¹ãã ã®è©ä¾¡ã¯ãäºæ¥å½±é¿ä¸æ¸¬äºæ
è¨ç»ãã¤ã³ã·ãã³ã対å¿è¨ç»ã®ä¸é¨ã«å«ãã¦ãçµç¹ã®
éè¦æ©è½ã確ä¿ããã°ãçµç¹ã®ç®æ¨å¾©æ§æéã©ããã«æ¥åãå復ã»å¾©æ§ãããã¨ãã§ããã
5 http://www.bacnet.org/
6 http://en.wikipedia.org/wiki/LonWorks

SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
49
3. ICS Risk Management and Assessment
3.1 Risk Management
Organizations manage risk every day in meeting their business objectives. These risks may include
financial risk, risk of equipment failure, and personnel safety risk, to name just a few. Organizations must
develop processes to evaluate the risks associated with their business and to decide how to deal with those
risks based on organizational priorities and both internal and external constraints. This management of risk
is conducted as an interactive, ongoing process as part of normal operations. Organizations that use ICS
have historically managed risk through good practices in safety and engineering. Safety assessments are
well established in most sectors and are often incorporated into regulatory requirements. Information
security risk management is an added dimension that can be complementary. The risk management process
and framework outlined in this section can be applied to any risk assessment including both safety and
information security.
A risk management process should be employed throughout an organization, using a three-tiered approach
to address risk at the (i) organization level; (ii) mission/business process level; and (iii) information system
level (IT and ICS). The risk management process is carried out seamlessly across the three tiers with the
overall objective of continuous improvement in the organizationâs risk-related activities and effective inter-
tier and intra-tier communication among all stakeholders having a shared interest in the mission/business
success of the organization.
This section focuses primarily on ICS considerations at the information system level, however, it is
important to note that the risk management activities, information, and artifacts at each tier impact and
inform the other tiers. Section 6 extends the concepts presented here to the control family level and
provides ICS-specific recommendations to augment security control families. Throughout the following
discussion of risk management, ICS considerations will be highlighted and the impact that these
considerations have on the risk management process will be discussed.
For more information on multi-tiered risk management and the risk management process, refer to NIST
Special Publication 800-39, Managing Information Security Risk: Organization, Mission and Information
System View [20]. NIST Special Publication 800-37 Revision 1, Guide for Applying the Risk Management
Framework to Federal Information Systems: A Security Life Cycle Approach [21], provides guidelines for
applying the Risk Management Framework to federal information systems to include conducting the
activities of security categorization,7 security control selection and implementation, security control
assessment, information system authorization,8 and security control monitoring. NIST Special Publication
800-30, Guide for Conducting Risk Assessments, provides a step-by-step process for organizations on: (i)
how to prepare for risk assessments; (ii) how to conduct risk assessments; (iii) how to communicate risk
assessment results to key organizational personnel; and (iv) how to maintain the risk assessments over time
[79].
7 FIPS 199 provides security categorization guidance for non-national security systems [15]. CNSS Instruction 1253 provides similar guidance for national security systems.
8 Security authorization is the official management decision given by a senior organizational official to
authorize operation of an information system and to explicitly accept the risk to organizational operations
and assets, individuals, other organizations, and the Nation based on the implementation of an agreed-upon
set of security controls.

SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
50
3. ICS ã®ãªã¹ã¯ç®¡çã¨ãªã¹ã¯è©ä¾¡
3.1 ãªã¹ã¯ç®¡ç
çµç¹ã¯ããã®äºæ¥ç®çãéæãããããæ¥ã
ãªã¹ã¯ã管çãã¦ããããããããªã¹ã¯ã«ã¯è²¡æ¿ä¸
ã®ãªã¹ã¯ãè£
ååé害ã«ãããªã¹ã¯ã人ã®å®å
¨ã«é¢ãããªã¹ã¯ãªã©ããããçµç¹ã¯ããã»ã¹ãç
å®ãã¦ãäºæ¥ã«é¢ä¿ãããªã¹ã¯ãè©ä¾¡ããçµç¹ã®åªå
äºé
ãçµç¹å
å¤ã®å¶ç´äºé
ãåºã«ããªã¹ã¯
ã¸ã®å¯¾å¦æ³ã決å®ããªããã°ãªããªãããã®ãªã¹ã¯ç®¡çã¯ãæ£è¦æ¥åã®ä¸ç°ã¨ãã¦ãç¸äºä½ç¨ç
ãªç¾è¡ããã»ã¹ã¨ãã¦å®æ½ããããICS ã使ç¨ããçµç¹ã¯æ´å²çã«ãå®å
¨æ§ã¨ã¨ã³ã¸ãã¢ãªã³ã°
ã«ãããåªè¯è¦ç¯ãéãã¦ããªã¹ã¯ã管çãã¦ãããå®å
¨æ§è©ä¾¡ã¯ã»ã¨ãã©ã®é¨éã§ç¢ºç«ããã¦
ãããè¦å¶ä¸ã®è¦ä»¶ã«çãè¾¼ã¾ãã¦ãããã¨ãå¤ããæ
å ±ã»ãã¥ãªãã£ã®ãªã¹ã¯ç®¡çã¯ãè£è¶³ç
ãªä»å ç次å
ã®ãã®ã§ããããã®ã»ã¯ã·ã§ã³ã§ç¥è¿°ãããªã¹ã¯ç®¡çã®ããã»ã¹ã¨æ çµã¿ã¯ãå®å
¨
æ§åã³æ
å ±ã»ãã¥ãªãã£ãå«ããããããªã¹ã¯è©ä¾¡ã«å¿ç¨ã§ããã
ãªã¹ã¯ç®¡çã®ããã»ã¹ã¯ãçµç¹å
¨ä½ãéãã¦ã(1)çµç¹ã¬ãã«ã(2)ä»»å/äºæ¥ããã»ã¹ã¬ãã«ã(3)
æ
å ±ã·ã¹ãã ã¬ãã«ï¼IT åã³ ICSï¼ãã¨ãã 3段æ§ãã®ã¢ããã¼ãã§æ¡ç¨ãã¹ãã§ããããªã¹ã¯
管çããã»ã¹ã¯ãçµç¹ã®ä»»å/äºæ¥ã«å
±éã®é¢å¿ãæ±ãé¢ä¿è
éã«ããã¦ãçµç¹ã®ãªã¹ã¯é¢é£æ´»
ååã³å段ééã»å段éå
ã®å¹æçãªéä¿¡ã絶ããæ¹åããã¨ããå
¨ä½çãªç®çãæã£ã¦ã3ã¤
ã®æ®µéã«ããã£ã¦ã·ã¼ã ã¬ã¹ã«è¡ãããã
ãã®ã»ã¯ã·ã§ã³ã§ã¯ä¸»ã«ãæ
å ±ã·ã¹ãã ã¬ãã«ã§ã® ICS ã®èæ
®äºé
ã«æ³¨ç®ããããå段éã«ãã
ããªã¹ã¯ç®¡çæ´»åãæ
å ±åã³æç£ããä»ã®æ®µéã«å½±é¿ã¨æ
å ±ããããããã¨ã«æ³¨æãã¹ãã§ããã
ã»ã¯ã·ã§ã³ 6ã§ã¯ãããã§ç´¹ä»ããæ¦å¿µãæ´ã«å¶å¾¡ç³»åã¬ãã«ã«æ¡å¼µããã»ãã¥ãªãã£å¯¾çç³»å
ãå¢ããããã® ICS ç¹æã®æ¨å¥¨äºé
ãæ示ããããã以éã®ãªã¹ã¯ç®¡çã«é¢ããè«è°ãéãã¦ã
ICS ã®èæ
®äºé
ã«ã¤ãã¦ç¹çããããããèæ
®äºé
ããªã¹ã¯ç®¡çããã»ã¹ã«åã¼ãå½±é¿ã«ã¤ãã¦
èå¯ããã
å¤æ®µéãªã¹ã¯ç®¡çã¨ãªã¹ã¯ç®¡çããã»ã¹ã®è©³ç´°ã«ã¤ãã¦ã¯ãNISTSP800-39ãæ
å ±ã»ãã¥ãªãã£ãª
ã¹ã¯ã®ç®¡çï¼çµç¹ãä»»ååã³æ
å ±ã·ã¹ãã æ¦èª¬ã[20]ãåç
§ã®ãã¨ãNISTSP800-37 æ¹è¨ 1ãé£é¦
æ
å ±ã·ã¹ãã ã¸ã®ãªã¹ã¯ç®¡çä½ç³»é©ç¨ã¬ã¤ãï¼ã»ãã¥ãªãã£ã©ã¤ããµã¤ã¯ã«ã¢ããã¼ãã[21]ã¯ã
ãªã¹ã¯ç®¡çä½ç³»ãé£é¦æ
å ±ã·ã¹ãã ã«é©ç¨ããéã®ã¬ã¤ãã©ã¤ã³ã¨ãªããã®ã§ãã»ãã¥ãªãã£åº
å9ãã»ãã¥ãªãã£ç®¡çã®é¸æã»å®è£
ãã»ãã¥ãªãã£ç®¡çã®è©ä¾¡ãæ
å ±ã·ã¹ãã ã®èªå¯ 10åã³ã»
ãã¥ãªãã£ç®¡çã®ç£è¦ã¨ãã£ã諸活åã®å®æ½è¦é ãçãè¾¼ã¾ãã¦ãããNISTSP800-30ããªã¹ã¯è©
価ã¬ã¤ããã¯ã(1)ãªã¹ã¯è©ä¾¡ã®æºåè¦é ã(2) ãªã¹ã¯è©ä¾¡ã®å®æ½è¦é ã(3)çµç¹è¦äººã¸ã®ãªã¹ã¯è©
価çµæã®ä¼éè¦é ã(4) ãªã¹ã¯è©ä¾¡ã®çµæçç¶æè¦é ã«ã¤ãã¦ãçµç¹ã®ããã»ã¹ã段éå¥ã«èª¬æ
ãã¦ãã[79]ã
9 FIPS 199 ã¯ãå½ä»¥å¤ã®ã»ãã¥ãªãã£ã·ã¹ãã ã«é¢ããã»ãã¥ãªãã£åºåã®ã¬ã¤ãã³ã¹ã¨ãªã[15]ãCNSS å½ä»¤ 1253 ã¯ãå½
ã®ã»ãã¥ãªãã£ã·ã¹ãã ã«é¢ããå種ã®ã¬ã¤ãã³ã¹ã
10 ã»ãã¥ãªãã£èªå¯ã¯ãçµç¹ã®é«å®ã«ããå
¬çãªç®¡ç決å®ã§ãæ
å ±ã·ã¹ãã ã®éç¨ãèªå¯ããçµç¹ã®éå¶ã»è³ç£ãå人ãä»ã®
çµç¹åã³å½å®¶ã«å¯¾ãããªã¹ã¯ããåæãããã»ãã¥ãªãã£å¯¾çã®å®è£
ã«åºã¥ãã¦ãæ示çã«è¨±å®¹ãããã®ã§ããã
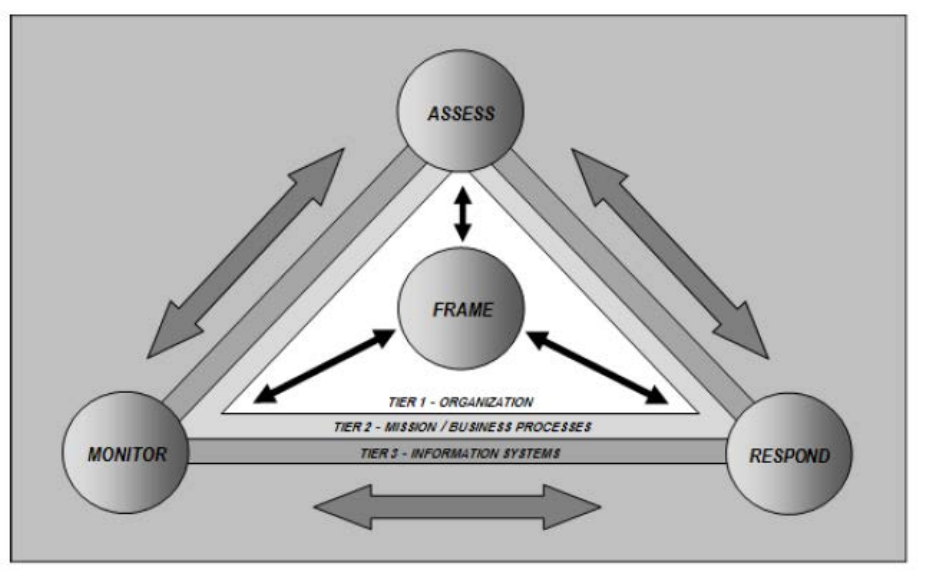
SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
51
3.2 Introduction to the Risk Management Process
As shown in Figure 3-1, the risk management process has four components: framing, assessing, responding
and monitoring. These activities are interdependent and often occur simultaneously within an organization.
For example, the results of the monitoring component will feed into the framing component. As the
environment in which organizations operate is always changing, risk management must be a continuous
process where all components have on-going activities. It is important to remember that these components
apply to the management of any risk whether information security, physical security, safety or financial.
Figure 3-1. Risk Management Process Applied Across the Tiers
The framing component in the risk management process consists of developing a framework for the risk
management decisions to be made. The level of risk that an organization is willing to accept is its risk
tolerance [21, p.6].
The framing component should include review of existing documentation, such as prior risk assessments.
There may be related activities; such as community wide disaster management planning that also should be
considered since they impact the requirements that a risk assessment must consider.
SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
52
3.2 ãªã¹ã¯ç®¡çããã»ã¹ã®ç´¹ä»
å³3-1 ã«ç¤ºãããã«ããªã¹ã¯ç®¡çããã»ã¹ã«ã¯ãæ§æ³ãè©ä¾¡ã対å¿ãç£è¦ã® 4ã¤ã®è¦ç´ ãããã
ããã諸活åã¯ç¸äºä¾åãã¦ãããåãçµç¹å
ã§åæã«çãããã¨ãå¤ããä¾ãã°ãç£è¦ã®çµ
æãæ§æ³ã«åæ ããããçµç¹ãç½®ãããç°å¢ã¯çµ¶ããå¤åãã¦ããããããªã¹ã¯ç®¡çã¯ç¶ç¶ç
ãªããã»ã¹ã§ã4ã¤ã®è¦ç´ ãã©ããé²è¡ä¸ã§ãªããã°ãªããªããåè¦ç´ ã¯ãæ
å ±ã»ãã¥ãªãã£ã
ç©ççã»ãã¥ãªãã£ãå®å
¨ã財æ¿ã®å¥ãåããããããããªã¹ã¯ã®ç®¡çã«å½ã¦ã¯ã¾ããã¨ãé
è¨ããã®ã¯èè¦ã§ããã
å³3-1.å
¨æ®µéã«ã¾ããããªã¹ã¯ç®¡çããã»ã¹
ãªã¹ã¯ç®¡çããã»ã¹ã«ãããæ§æ³ã¯ãä¸ãã¹ããªã¹ã¯ç®¡çä¸ã®æ±ºå®ã«é¢ããä½ç³»ãçå®ããã
ã¨ã«ãããçµç¹ãåãå
¥ãããããªã¹ã¯ã¬ãã«ããªã¹ã¯ãã¬ã©ã³ã¹ã§ãã[21, p.6]ã
ãã®æ§æ³ã«ã¯ã以åã®ãªã¹ã¯è©ä¾¡æ¸ãªã©æ¢åææ¸ã®ç²¾æ»ãå«ããã¹ãã§ãããé¢é£æ´»åããã
å¾ãããä¾ãã°ãå
±åä½å
ã®ç½å®³ç®¡çè¨ç»ãªã©ãããªã¹ã¯è©ä¾¡ã§æ¤è¨ãè¦ãã諸è¦ä»¶ã«å½±é¿ã
ããããèæ
®ã«å«ããã¹ãã§ããã
è©ä¾¡
ç£è¦
æ§æ³
対å¿
段é
1 â
çµç¹
段é
2 â
ä»»å
/
äºæ¥ããã»ã¹
段é
3 â
æ
å ±ã·ã¹ãã

SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
53
ICS-specific Recommendations and Guidance
For operators of ICS, safety is the major consideration that directly affects decisions on how systems are
engineered and operated. Safety can be defined as âfreedom from conditions that can cause death, injury,
occupational illness, damage to or loss of equipment or property, or damage to the environment.â116 Part of
the framing component for an ICS organization is determining how these requirements interact with
information security. For example, if safety requirements conflict with good security practice, how will the
organization decide between the two priorities? Most ICS operators would answer that safety is the main
consideration â the framing component makes such assumptions explicit so that there is agreement
throughout the process and the organization.
Another major concern for ICS operators is the availability of services provided by the ICS. The ICS may
be part of critical infrastructure (for example, water or power systems), where there is a significant need for
continuous and reliable operations. As a result, ICS may have strict requirements for availability or for
recovery. Such assumptions should be developed and stated in the framing component. Otherwise, the
organization may make risk decisions that result in unintended consequences on those who depend on the
services provided.
The physical operating environment is another aspect of risk framing that organizations should consider
when working with ICS. ICS often have specific environmental requirements (e.g., a manufacturing
process may require precise temperature), or they may be tied to their physical environment for operations.
Such requirements and constraints should be explicitly stated in the framing component so that the risks
arising from these constraints can be identified and considered.
Assessing risk requires that organizations identify their threats and vulnerabilities, the harm that such
threats and vulnerabilities may cause the organization and the likelihood that adverse events arising from
those threats and vulnerabilities may actually occur.
ICS-specific Recommendations and Guidance
The DHS National Cybersecurity & Communications Integration Center (NCCIC)12 serves as a centralized
location where operational elements involved in cybersecurity and communications reliance are
coordinated and integrated. The Industrial Control Systems Cyber Emergency Response Team (ICS-
CERT)13 collaborates with international and private sector Computer Emergency Response Teams
(CERTs) to share control systems-related security incidents and mitigation measures. ICS-CERT works to
reduce risks within and across all critical infrastructure sectors by partnering with law enforcement
agencies and the intelligence community and coordinating efforts among Federal, state, local, and tribal
governments and control systems owners, operators, and vendors.
When assessing the potential impact to an organizationâs mission from a potential ICS incident, it is
important to incorporate the effect on the physical process/system, impact on dependent systems/processes,
and impact on the physical environment among other possibilities. In addition, the potential impact on
safety should always be considered.
11 MIL-STD-882E,
Standard Practice â System Safety
, Department of Defense (DoD), May 11, 2012,
https://acc.dau.mil/CommunityBrowser.aspx?id=683694
12 http://www.dhs.gov/about-national-cybersecurity-communications-integration-center
13 https://ics-cert.us-cert.gov/

SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
54
ICS åºæã®æ¨å¥¨äºé
åã³ã¬ã¤ãã³ã¹
ICS æä½å¡ã«ã¨ã£ã¦å®å
¨ã¯ãã·ã¹ãã ã®è¨ç»ã»å®è¡è¦é ã®æ±ºå®ã«ç´æ¥å½±é¿ããé大èæ
®äºé
ã§ã
ããå®å
¨ã¯ãæ»äº¡ãè² å·ãè·æ¥ç
ãè£
ååã»è³ç£ã®æ害ã»åªå¤±ãç°å¢ç ´å£ãçããç¶æ
ããå
ã
ã¦ãããã¨ãã¨å®ç¾©ã§ãã 14ãICS çµç¹ã®æ§æ³é¨åã¯ããã®ãããªè¦ä»¶ã¨æ
å ±ã»ãã¥ãªãã£ã¨ã®
ç¸äºä½ç¨è¦é ãå¤å®ãããã¨ã«ãããä¾ãã°ãå®å
¨è¦ä»¶ãã»ãã¥ãªãã£ã®é©æ£è¦ç¯ã¨ç¸å®¹ããªã
å ´åãçµç¹ã¯ 2ã¤ã®åªå
課é¡ã®éã§ã©ã®ãããªæ±ºå®ãè¡ãã®ãã大æ¹ã® ICS æä½å¡ã¯ãå®å
¨ã主
è¦ãªèæ
®äºé
ã ã¨çããããæ§æ³ã¯ããã®ãããªåæäºé
ãæ確ã«ãã¦ãããã»ã¹ã¨çµç¹å
¨ä½ã
éãã¦åæãå½¢æããã
ICS æä½å¡ã«ã¨ã£ã¦ããã 1ã¤ã®é大é¢å¿äºé
ã¯ãICS ãæä¾ãããµã¼ãã¹ã®å¯ç¨æ§ã§ãããICS
ã¯éè¦ã¤ã³ãã©ã®ä¸é¨ã§ãããã¨ãããï¼ä¾ãã°æ°´éãé»æ°ã·ã¹ãã ï¼ããã®å ´åãç¶ç¶çã§ä¿¡
é ¼æ§ã®é«ãéç¨ã«å¯¾ããéè¦ã¯æ¥µãã¦å¤§ããããã®çµæãICS ã¯å¯ç¨æ§ã¨å復ã«å¯¾ããè¦ä»¶ãå³
æ ¼ã«ãªããããããåæäºé
ãçå®ããæ§æ³ã«è¨è¼ãã¹ãã§ãããããããªãã¨ãçµç¹ã¯ãªã¹ã¯
ã®ãã決å®ãä¸ãããããå
ã§ãæä¾ããããµã¼ãã¹ã«ä¾åãã¦ãã人ã
ã«æãã¬çµæãããã
ããã¨ã«ãªãã
ç©ççåä½ç°å¢ã¯ãICS ã使ç¨ããå ´åã«çµç¹ãèæ
®ãã¹ãããã 1ã¤ã®é¢ã§ãããICS ã«ã¯ç¹
æ®ãªç°å¢è¦ä»¶ãå¤ãï¼è£½é ããã»ã¹ã§ã®æ£ç¢ºãªæ¸©åº¦è¦ä»¶ãªã©ï¼ãç©ççãªåä½ç°å¢ã«ææããã¦
ãããã¨ããããããããè¦ä»¶ãå¶ç´äºé
ãæ§æ³ã«æè¨ããå¶ç´äºé
ããçãããªã¹ã¯ãç¹å®
ããé
æ
®ã§ããããã«ãã¹ãã§ããã
ãªã¹ã¯ãè©ä¾¡ããéã«ã¯ãçµç¹ã®è
å¨ã¨èå¼±æ§ãããã«ãã£ã¦çµç¹ã被ãæ害ãããããè
å¨ã¨
èå¼±æ§ã«ããããããããæ害äºè±¡ãå®éã«çããå
¬ç®ãæããã«ãããã¨ãå¿
è¦ã¨ãªãã
ICS åºæã®æ¨å¥¨äºé
åã³ã¬ã¤ãã³ã¹
DHS å½å®¶ãµã¤ãã¼ã»ãã¥ãªãã£éä¿¡çµ±åã»ã³ã¿ã¼(NCCIC)15ã¯éä¸æå¨å°ã¨ãã¦æ©è½ãããµã¤ã
ã¼ã»ãã¥ãªãã£ã¨éä¿¡ã®ä¿¡é ¼æ§ã«é¢ããéç¨è¦ç´ ã¯ããã§èª¿æ´ãããçµ±ååããã¦ãããç£æ¥ç¨
å¶å¾¡ã·ã¹ãã ãµã¤ãã¼ç·æ¥å¯¾å¿ãã¼ã (ICS-CERT)16ã¯ãæµ·å¤åã³æ°éã®ã³ã³ãã¥ã¼ã¿ç·æ¥å¯¾å¿ã
ã¼ã (CERT)ã¨é£æºãã¦ãå¶å¾¡ã·ã¹ãã é¢é£ã®ã»ãã¥ãªãã£ã¤ã³ã·ãã³ãã¨ç·©å対çãå
±æãã¦
ãããICS-CERT ã¯è¡æ¿å½å±ãæ
å ±çµç¹ã¨ã®é£æºãé£é¦ã»å·ã»å°æ¹ã»è«¸é¨æèªæ²»ä½ã®ã»ãå¶å¾¡ã·
ã¹ãã ææè
ããã³ãã¼ã¨ã®ååãéãã¦ãããããéè¦ã¤ã³ãã©é¨éã«é¢ãããªã¹ã¯åæ¸ã«åª
ãã¦ããã
ICS ã¤ã³ã·ãã³ããçããå ´åã«çµç¹ã®ä»»åã«åã¶å½±é¿åº¦ãè©ä¾¡ããéãã¨ãããç©ççããã»
ã¹/ã·ã¹ãã ã¸ã®å½±é¿ãå¾å±ã·ã¹ãã /ããã»ã¹ã¸ã®å½±é¿åã³ç©ççç°å¢ã¸ã®å½±é¿ãå«ãããã¨ã
èè¦ã§ãããå ãã¦ãå®å
¨æ§ã«ä¸ãå¾ãå½±é¿ã常ã«èæ
®ã«å
¥ããã¹ãã§ããã
14 MIL-STD-882E,
Standard Practice â System Safety
, å½é²ç·ç (DoD), May 11, 2012,
https://acc.dau.mil/CommunityBrowser.aspx?id=683694
15 http://www.dhs.gov/about-national-cybersecurity-communications-integration-center
16 https://ics-cert.us-cert.gov/

SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
55
The responding component is based on the concept of a consistent organization-wide response to the
identification of risk. Response to identification of risk (as opposed to the response to an incident) requires
that organizations first identify possible courses of actions to address risk, evaluate those possibilities in
light of the organizationâs risk tolerance and other considerations determined during the framing step, and
choose the best alternative for the organization. The response component includes the implementation of
the chosen course of action to address the identified risk: acceptance, avoidance, mitigation, sharing,
transfer, or any combination of those options17.
ICS-specific Recommendations and Guidance
For ICS, available risk responses may be constrained by system requirements, potential adverse impact on
operations, or even regulatory compliance regimes. An example of risk sharing is when utilities enter into
agreements to âloanâ line workers in an emergency, which reduces the duration of the effect of an incident
to acceptable levels.
Monitoring is the fourth component of the risk management activities. Organizations must monitor risk on
an on-going basis including: the implementation of chosen risk management strategies; the changes in the
environment that may affect the risk calculation; and, the effectiveness and efficiency of risk reduction
activities. The activities in the monitoring component impact all the other components.
3.3 Special Considerations for Doing an ICS Risk Assessment
The nature of ICS means that when an organization does a risk assessment, there may be additional
considerations that do not exist when doing a risk assessment of a traditional IT system. Because the impact
of a cyber incident in an ICS may include both physical and digital effects, risk assessments need to
incorporate those potential effects. This section will provide a more in-depth examination of the following:
ï¼ Impacts on safety and use of safety assessments.
ï¼ Physical impact of a cyber incident on an ICS, including the larger physical environment; effect on the
process controlled, and the physical effect on the ICS itself.
ï¼ The consequences for risk assessments of non-digital control components within an ICS.
3.3.1 Safety within an ICS Information Security Risk Assessment
The culture of safety and safety assessments is well established within the majority of the ICS user
community. Information security risk assessments should be seen as complementary to such assessments
though the assessments may use different approaches and cover different areas. Safety assessments are
concerned primarily with the physical world. Information security risk assessments primarily look at the
digital world. However, in an ICS environment, the physical and the digital are intertwined and significant
overlap may occur.
It is important that organizations consider all aspects of risk management for safety (e.g., risk framing, risk
tolerances), as well as the safety assessment results, when carrying out risk assessments for information
security. The personnel responsible for the information security risk assessment must be able
17 For additional information on accepting, avoiding, mitigating, sharing, or transferring risk, refer to NIST
Special Publication 800-39 [20].

SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
56
対å¿ã¯ãçµç¹å
¨ä½ãéãã¦é¦å°¾ä¸è²«ããå½¢ã§ãªã¹ã¯ã®ç¹å®ã«åãçµãã¨ããèãæ¹ã«åºã¥ãã¦ã
ãããªã¹ã¯ã®ç¹å®ã¸ã®å¯¾å¿ã¯ï¼ã¤ã³ã·ãã³ãã¸ã®å¯¾å¿ã¨ã¯ç°ãªãï¼ãã¾ããªã¹ã¯ã«å¯¾ãã¦çµç¹ã
åãå¾ãè¡åæ¹éãè¦æ¥µããæ§æ³ã¹ãããã§å¤å®ãããçµç¹ã®ãªã¹ã¯ãã¬ã©ã³ã¹ãã®ä»ã®èæ
®äº
é
ã«ç
§ããã¦ãåãå¾ãåè¡åæ¹éãè©ä¾¡ããæåçãé¸æãããã¨ãæ±ããããã対å¿ã«ã¯ã
é¸å®ããè¡åæ¹éãå®è¡ãã¦ãç¹å®æ¸ã¿ã®ãªã¹ã¯ã«å¯¾å¦ãããã¨ãå«ã¾ããããã«ã¯å容ãåé¿ã
ç·©åãå
±æã転å«åã¯ãããã®çµåãããã 18ã
ICS åºæã®æ¨å¥¨äºé
åã³ã¬ã¤ãã³ã¹
ICS ã§ã¯ãå©ç¨ã§ãããªã¹ã¯å¯¾å¿ã¯ã·ã¹ãã è¦ä»¶ãéç¨ã«æªå½±é¿ãåºãå¯è½æ§åã¯è¦å¶ã¸ã®ã³ã³
ãã©ã¤ã¢ã³ã¹å½¢æ
ã«ããå¶ç´ãããå ´åãããããªã¹ã¯å
±æã®ä¸ä¾ã¨ãã¦ãç·æ¥æã«å
Œ
±ä¼æ¥ã
å´åè
ããåºåããããå¥ç´ãç· çµããããã«ãã£ã¦ã¤ã³ã·ãã³ãã®å½±é¿æéãå容ã¬ãã«ã¾ã§
ç縮ãããã±ã¼ã¹ãæããããã
ç£è¦ã¯ãªã¹ã¯ç®¡çã® 4çªç®ã®è¦ç´ ã¨ãªããçµç¹ã¯ãªã¹ã¯ãç¶ç¶çã«ç£è¦ããªããã°ãªããªããã
ããã«ã¯é¸å®ãããªã¹ã¯ç®¡çæ¦ç¥ã®å®è¡ããªã¹ã¯ç®å®ã«å½±é¿ããç°å¢ã®å¤ååã³ãªã¹ã¯åæ¸æ´»å
ã®å¹æã»å¹çãå«ã¾ãããç£è¦ã«ããã諸活åã¯ä»ã®å
¨ã¦ã®è¦ç´ ã«å½±é¿ããã
3.3 ICS ãªã¹ã¯è©ä¾¡ã®å®æ½ã«éãã¦ã®ç¹å¥ãªèæ
®äºé
ICS ã®æ§è³ªä¸ãçµç¹ããªã¹ã¯è©ä¾¡ãè¡ãéã«ã¯ãå¨æ¥ã® IT ã·ã¹ãã ã®ãªã¹ã¯è©ä¾¡å®æ½æã«ã¯åå¨
ããªãè£è¶³çãªèæ
®äºé
ãããå¾ããã¨ã§ãããICS ã«ããããµã¤ãã¼ã¤ã³ã·ãã³ãã®å½±é¿ã«ã¯ã
ç©ççå½±é¿ã¨ãã¸ã¿ã«å¹æã®ä¸¡æ¹ãããããããªã¹ã¯è©ä¾¡ã«ã¯ãã®ãããªå½±é¿ã®å¯è½æ§ãå«ãã
å¿
è¦ãããããã®ã»ã¯ã·ã§ã³ã§ã¯ã以ä¸ã«ã¤ãã¦æ´ã«æ·±ãèå¯ããã
ï¼ å®å
¨æ§ã¸ã®å½±é¿åã³å®å
¨æ§è©ä¾¡ã®ä½¿ç¨
ï¼ ãµã¤ãã¼ã¤ã³ã·ãã³ãã ICS ã«ä¸ããå½±é¿ãããã«ã¯ãã大è¦æ¨¡ãªç©çç°å¢ã管çãããã
ãã»ã¹ã¸ã®å½±é¿åã³ ICS ãã®ãã®ã¸ã®ç©ççå½±é¿ãå«ã¾ããã
ï¼ ICS å
ã®éãã¸ã¿ã«å¶å¾¡ã³ã³ãã¼ãã³ããªã¹ã¯è©ä¾¡çµæ
3.3.1 ICS æ
å ±ã»ãã¥ãªãã£ãªã¹ã¯è©ä¾¡ã«ãããå®å
¨æ§
大é¨åã® ICS ã¦ã¼ã¶å
±å社ä¼ã§ã¯ãå®å
¨æ§ãå®å
¨æ§è©ä¾¡ã®æåãå®çãã¦ãããæ
å ±ã»ãã¥ãªã
ã£ãªã¹ã¯è©ä¾¡ã¯ã種ã
ã®ã¢ããã¼ããå©ç¨ãæ§ã
ãªåéã対象ã¨ãã¦ã¯ããããããã¾ã§ãå®å
¨
æ§è©ä¾¡ã®è£å®ã¨è¦ãªãã¹ãã§ãããå®å
¨æ§è©ä¾¡ã¯ã主ã«ç©ççãªä¸çã対象ã«ãã¦ãããæ
å ±ã»
ãã¥ãªãã£ãªã¹ã¯è©ä¾¡ã§ã¯ã主ã«ãã¸ã¿ã«ä¸çãé¢å¿ã®å¯¾è±¡ã¨ãªããããã ICS ç°å¢ã§ã¯ãç©ç
ä¸çããã¸ã¿ã«ä¸çãäºãã«å
¥ãçµãã§ãããªãéãªãåã£ã¦ããå ´åãããã
æ
å ±ã»ãã¥ãªãã£ã®ãªã¹ã¯è©ä¾¡ãè¡ãå ´åãçµç¹ã¯ãå®å
¨ã«é¢ãããªã¹ã¯ç®¡çã®ããããé¢ï¼ãª
ã¹ã¯ã®æ§æ³ããªã¹ã¯ãã¬ã©ã³ã¹çï¼ã®ã»ããå®å
¨æ§è©ä¾¡ã®çµæãèæ
®ã«å
¥ãããã¨ãèè¦ã§ããã
æ
å ±ã»ãã¥ãªãã£ãªã¹ã¯è©ä¾¡æ
å½è
ã¯ã
18 ãªã¹ã¯ã®å容ãåé¿ãç·©åãå
±æåã¯è»¢å«ã®è©³ç´°ã¯ NIST ç¹å¥åºçç© 800-39 [20]ãåç
§ã®ãã¨ã
SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
57
to identify and communicate identified risks that could have safety implications. Conversely, the personnel
charged with safety assessments must be familiar with the potential physical impacts and their likelihood
developed by the information security risk assessment process.
3.3.2 Potential Physical Impacts of an ICS Incident
Evaluating the potential physical damage from a cyber incident should incorporate: i) how an incident
could manipulate the operation of sensors and actuators to impact the physical environment; ii) what
redundant controls exist in the ICS to prevent an impact; and iii) how a physical incident could emerge
based on these conditions. A physical impact could negatively impact the surrounding world through
multiple means, including the release of hazardous materials (e.g., pollution, crude oil), damaging kinetic
forces (e.g., explosions), and exposure to energy sources (e.g., electricity, steam). The physical incident
could negatively impact the ICS and supporting infrastructure, the various processes performed by the ICS,
or the larger physical environment. An evaluation of the potential physical impacts should include all parts
of an ICS, beginning with evaluating the potential impacts on the set of sensor and actuators. Each of these
domains will be further explored below.
Evaluating the impact of a cyber incident on the physical environment should focus on potential damage to
human safety, the natural environment, and other critical infrastructures. Human safety impacts should be
evaluated based on whether injury, disease, or death is possible from a malfunction of the ICS. This should
incorporate any previously performed safety impact assessments performed by the organization regarding
both employees and the general public. Environmental impacts also may need to be addressed. This
analysis should incorporate any available environmental impact assessments performed by the organization
to determine how an incident could impact natural resources and wildlife over the short or long term. In
addition, it should be noted that ICS may not be located within a single, controlled location and can be
distributed over a wide physical area and exposed to uncontrolled environments. Finally, the impact on the
physical environment should explore the extent to which an incident could damage infrastructures external
to the ICS (e.g., electric generation/delivery, transportation infrastructures, and water services).
3.3.3 Impact of Physical Disruption of an ICS Process
In addition to the impact on the physical environment, the risk assessment should also evaluate potential
effects to the physical process performed by the ICS under consideration, as well as other systems. An
incident that impacts the ICS and disrupts the dependent process may cause cascading impacts into other
related ICS processes and the general publicâs dependence on the resulting products and services. Impact to
related ICS processes could include both systems and processes within the organization (e.g., a
manufacturing process that depends on the process controlled by the system under consideration) or
systems and processes external to the organization (e.g., a utility selling generated energy to a nearby plant).
A cyber incident can also negatively impact the physical ICS under consideration. This type of impact
primarily includes the physical infrastructure of the plant (e.g., tanks, valves, motors), along with both the
digital and non-digital control mechanisms (e.g., cables, PLCs, pressure gauge). Damage to the ICS or
physical plant may cause either short or long term outages depending on the degree of the incident. An
example of a cyber incident impacting the ICS is the Stuxnet malware, which caused physical damage to
the centrifuges as well as disrupting dependent processes.
SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
58
ç¹å®ããããªã¹ã¯ã§å®å
¨ä¸ã®æå³ããããã®ãæããã«ãã¦ãä¼éã§ããªããã°ãªããªããå対
ã«å®å
¨æ§è©ä¾¡æ
å½è
ã¯ãæ
å ±ã»ãã¥ãªãã£ãªã¹ã¯è©ä¾¡ããã»ã¹ã«ããçºçããå¯è½æ§ã®ããç©ç
çå½±é¿ã¨ãã®å
¬ç®ã«ã¤ãã¦ç²¾éãã¦ããªããã°ãªããªãã
3.3.2 ICS ã¤ã³ã·ãã³ãã«ããç©ççå½±é¿ã®å¯è½æ§
ãµã¤ãã¼ã¤ã³ã·ãã³ãã«ããçãå¾ãç©ççæ害ã®è©ä¾¡ã«ã¯æ¬¡ã®ãã®ãå«ã¾ããã(1)ã¤ã³ã·ãã³
ããã»ã³ãµåã³ã¢ã¯ãã¥ã¨ã¼ã¿ã®åä½ãã©ã®ããã«æä½ãã¦ç©ççç°å¢ã«å½±é¿ãåã¼ããã(2)å½±
é¿ãé²ãããã®ã©ã®ãããªåé·å¶å¾¡ã ICS ã«ãããã(3)ãã®ãããªæ¡ä»¶ä¸ã§ç©ççã¤ã³ã·ãã³ã
ã¯ã©ã®ããã«çããããç©ççå½±é¿ã¯å¨å²ã®ä¸çã«æ§ã
ãªæ段ã§æªå½±é¿ãåã¼ããããªãããã
ãã«ã¯å±éºç©ã®æ¾åºï¼æ±æãåæ²¹çï¼ãéååã«ããæå·ï¼ççºçï¼ãã¨ãã«ã®ã¼æºã¸ã®æé²
ï¼é»æ°ãè¸æ°çï¼ãªã©ããããç©ççã¤ã³ã·ãã³ãã¯ãICS åã³æ¯æ´ã¤ã³ãã©ãICS ãå®æ½ãã
å¤æ§ãªããã»ã¹åã¯ãã大è¦æ¨¡ã®ç©çç°å¢ã«æªå½±é¿ãä¸ããããªããå¯è½æ§ã®ããç©ççå½±é¿ã®
è©ä¾¡ã«ã¯ ICS ã®ããããé¨åãå«ããã¾ãã»ã³ãµã»ã¢ã¯ãã¥ã¨ã¼ã¿ã»ããã¸ã®å½±é¿ã®å¯è½æ§ãã
éå§ãã¹ãã§ããããããé åã®åé¨åã«ã¤ãã¦ã¯è©³ããå¾è¿°ããã
ç©çç°å¢ã«ä¸ãããµã¤ãã¼ã¤ã³ã·ãã³ãã®å½±é¿è©ä¾¡ã¯ã人çå®å
¨ãèªç¶ç°å¢ãã®ä»éè¦ã¤ã³ã
ã©ã«ä¸ãå¾ãæ害ãéè¦ãã¹ãã§ããã人çå®å
¨ã¸ã®å½±é¿ã¯ãICS ã®é害ããè² å·ã»ç¾ç
ã»æ»
亡ãçãããå¦ããåºã«è©ä¾¡ãã¹ãã§ãããããã«ã¯ä»¥åçµç¹ãå¾æ¥å¡ã¨ä¸è¬å½æ°ã«é¢ãã¦å®
æ½ããå®å
¨æ§å½±é¿è©ä¾¡ãå«ããã¹ãã§ãããç°å¢å½±é¿ãåãä¸ããå¿
è¦ããããããã®åæã«
ã¯ãã¤ã³ã·ãã³ããçæçã»é·æçã«å¤©ç¶è³æºãéççç©ã«ä¸ããå½±é¿ãå¤å®ããããã«çµç¹
ãå®æ½ããç°å¢å½±é¿è©ä¾¡ããå©ç¨ã§ããã°å«ããã¹ãã§ãããå ãã¦ãICS ã¯ç®¡çãããä¸ã
æã«é
ç½®ããã¦ããããåºç¯ãªå°åã«åæ£ãã管çããã¦ããªãç°å¢ã«æããã¦ããå ´åãã
ããã¨ã«ãçæãã¹ãã§ãããæå¾ã«ãç©çç°å¢ã¸ã®å½±é¿ã¯ãã¤ã³ã·ãã³ãã ICS ã®å¤é¨ã«ã
ãã¤ã³ãã©ã«ã©ã®ç¨åº¦ã®æ害ãä¸ãããã調æ»ãã¹ãã§ããï¼çºé»ã»éé»ã輸éã¤ã³ãã©ãæ°´
éäºæ¥çï¼ã
3.3.3 ICS ããã»ã¹ã®ç©ççä¸æã«ããå½±é¿
ç©çç°å¢ã¸ã®å½±é¿ã«å ãã¦ããªã¹ã¯è©ä¾¡ã§ã¯ ICS ãå®è¡ããèæ
®å¯¾è±¡ã®ç©çããã»ã¹ã¨ä»ã®ã·
ã¹ãã ã¸ã®å½±é¿ãè©ä¾¡ãã¹ãã§ããã
ICS ã«å½±é¿ãä¸ãå¾å±ããã»ã¹ãä¸æãããã¤ã³ã·ãã³ãã¯ãä»ã® ICS é¢é£ããã»ã¹ãããã
ãçãã製åã»ãµã¼ãã¹ã«ä¾åãã¦ããå½æ°ã«ãé£éçãªå½±é¿ãåã¼ããããªããé¢é£ ICS ã
ãã»ã¹ã¸ã®å½±é¿ã«ã¯ãçµç¹å
ã®ã·ã¹ãã åã³ããã»ã¹ï¼èæ
®ä¸ã®ã·ã¹ãã ã«å¶å¾¡ãããããã»
ã¹ã«ä¾åãã¦ãã製é ããã»ã¹çï¼åã¯çµç¹å¤ã®ã·ã¹ãã åã³ããã»ã¹ï¼çç£ããã¨ãã«ã®ã¼
ãè¿é£ã®ãã©ã³ãã«å£²ãå
Œ
±äºæ¥ä½çï¼ãå«ã¾ãå¾ãã
ãµã¤ãã¼ã¤ã³ã·ãã³ãã¯ãèæ
®ä¸ã®ç©çç ICS ã«ãæªå½±é¿ãä¸ããããã®ç¨®ã®å½±é¿ã«ã¯ä¸»ã¨ã
ã¦ãã©ã³ãã®ç©ççã¤ã³ãã©ï¼ã¿ã³ã¯ããã«ããã¢ã¼ã¿çï¼ããã¸ã¿ã«/éãã¸ã¿ã«å¶å¾¡ã¡ã«
ããºã ï¼ã±ã¼ãã«ãPLCãå§åã²ã¼ã¸çï¼ãå«ã¾ãããICS ãç©ççãã©ã³ãã¸ã®æ害ã¯ãã¤ã³
ã·ãã³ãã®ç¨åº¦ã«å¿ãã¦çæåã¯é·æã®åæ¢ã«è³ããããªããICS ã«å½±é¿ãããµã¤ãã¼ã¤ã³ã·
ãã³ãã®ä¸ä¾ã¨ã㦠Stuxnet ãã«ã¦ã¨ã¢ããããé å¿åé¢æ©ãç©ççã«æå·ããå¾å±ããã»ã¹
ãä¸æãããã

SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
59
3.3.4 Incorporating Non-digital Aspects of ICS into Impact Evaluations
The impacts on the ICS cannot be adequately determined by focusing only on the digital aspects of the
system, as there are often non-digital mechanisms available that provide fault tolerance and prevent the ICS
from acting outside of acceptable parameters. Therefore, these mechanisms may help reduce any negative
impact that a digital incident on the ICS might have and must be incorporated into the risk assessment
process. For example, ICS often have non-digital control mechanisms that can prevent the ICS from
operating outside of a safe boundary, and thereby limit the impact of an attack (e.g., a mechanical relief
pressure valve). In addition, analog mechanisms (e.g., meters, alarms) can be used to observe the physical
system state to provide operators with reliable data if digital readings are unavailable or corrupted. Table 3-
1 provides a categorization of non-digital control mechanisms that could be available to reduce the impact
of an ICS incident.
Table 3-1. Categories of Non-Digital ICS Control Components
System Type
Description
Analog Displays or Alarms Non-digital mechanisms that measure and display the state of the physical system
(e.g., temperature, pressure, voltage, current) and can provide the operator with
accurate information in situations when digital displays are unavailable or
corrupted. The information may be provided to the operator on some non-digital
display (e.g., thermometers, pressure gauges) and through audible alarms.
Manual Control
Mechanisms
Manual control mechanisms (e.g., manual valve controls, physical breaker
switches) provide operators with the ability to manually control an actuator without
relying on the digital control system. This ensures that an actuator can be
controlled even if the control system is unavailable or compromised.
Analog Control Systems
Analog control systems use non-digital sensors and actuators to monitor and
control a physical process. These may be able to prevent the physical process
from entering an undesired state in situations when the digital control system is
unavailable or corrupted. Analog controls include devices such as regulators,
governors, and electromechanical relays.
Determination of the potential impact that a cyber incident may have on the ICS should incorporate
analysis of all non-digital control mechanisms and the extent to which they can mitigate potential negative
impacts to the ICS. There are multiple considerations when considering the possible mitigation effects of
non-digital control mechanisms, such as:
ï¼ Non-digital control mechanisms may require additional time and human involvement to perform
necessary monitoring or control functions and these efforts may be substantial. For example, such
mechanisms may require operators to travel to a remote site to perform certain control functions. Such
mechanisms may also depend on human response times, which may be slower than automated
controls.
ï¼ Manual and analog systems may not provide monitoring or control capabilities with the same degree
of accuracy and reliability as the digital control system. This may present risk if the primary control
system is unavailable or corrupted due to reduced quality, safety, or efficiency of the system. For
example, a digital/numeric protection relay provides more accuracy and reliable detection of faults
than analog/static relays, therefore, the system maybe more likely to exhibit a spurious relay tripping
if the digital relays are not available.

SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
60
3.3.4 ICS ã®éãã¸ã¿ã«é¢ãå½±é¿è©ä¾¡ã«å«ãã
ãã©ã¼ã«ããã¬ã©ã³ã¹ãçºæ®ããICS ã許容ãã©ã¡ã¼ã¿ãé¸è±ããªãããã«é²æ¢ã§ããéãã¸
ã¿ã«ã¡ã«ããºã ãå©ç¨ã§ããã®ã§ãã·ã¹ãã ã®ãã¸ã¿ã«é¢ã«ã®ã¿æ³¨ç®ãã¦ããã¨ãICS ã¸ã®å½±
é¿ãé©æ£ã«å¤å®ãããã¨ãã§ããªãããããã£ã¦ããã®ãããªã¡ã«ããºã ã¯ãICS ä¸ã®ãã¸ã¿
ã«ã¤ã³ã·ãã³ãã«èµ·å ããæªå½±é¿ãæ¸ããããããªã¹ã¯è©ä¾¡ããã»ã¹ã«çµã¿è¾¼ãå¿
è¦ãããã
ä¾ãã°ãICS ã«ã¯éãã¸ã¿ã«å¶å¾¡ã¡ã«ããºã ãæã¤ãã®ãå¤ããICS ãå®å
¨éçãè¶
ããªããã
ã«ãã¦ãæ»æã®å½±é¿ãå¶éãã¦ããï¼æ©æ¢°å¼ã®å§åãªãªã¼ããã«ãçï¼ãã¾ãã¢ããã°ã¡ã«ã
ãºã ï¼ã¡ã¼ã¿ãã¢ã©ã¼ã çï¼ã使ç¨ãã¦ãã·ã¹ãã ã®ç©ççãªç¶æ
ã観å¯ãããã¸ã¿ã«è¡¨ç¤ºã®
å©ç¨ä¸è½ã»ä¸ææã«ãä¿¡é ¼ã§ãããã¼ã¿ãæä½å¡ã«æ示ãããã¨ãã§ããã表 3-1 ã¯ãICS ã¤
ã³ã·ãã³ãã®å½±é¿ãæ¸ãããéãã¸ã¿ã«å¶å¾¡ã¡ã«ããºã ã®åºåã§ããã
表3-1. éãã¸ã¿ã« ICS å¶å¾¡ã³ã³ãã¼ãã³ãã®ã«ãã´ãªã¼
ã·ã¹ãã ã®ç¨®é¡
å
容
ã¢ããã°ãã£ã¹ãã¬ã¤åã¯
ã¢ã©ã¼ã
ç©ççã·ã¹ãã ã®ç¶æ
ï¼æ¸©åº¦ãå§åãé»å§ãé»æµçï¼ãè¨æ¸¬ã»è¡¨ç¤ºãããã¸ã¿ã«ã
ã£ã¹ãã¬ã¤ã®å©ç¨ä¸è½ã»ä¸ææã«æ£ç¢ºãªç¶æ³æ
å ±ãæä½å¡ã«æä¾ã§ããéãã¸ã¿ã«
ã¡ã«ããºã ãæ
å ±ã¯éãã¸ã¿ã«ãã£ã¹ãã¬ã¤ï¼æ¸©åº¦è¨ãå§åè¨çï¼ãé³å£°ã¢ã©ã¼ã
ã«ããæä½å¡ã«æä¾ããã
æåå¶å¾¡ã¡ã«ããºã æåå¶å¾¡ã¡ã«ããºã ï¼æåãã«ãå¶å¾¡ãç©ççãã¬ã¼ã«ã¹ã¤ããçï¼ãããã°ãæ
ä½å¡ã¯ãã¸ã¿ã«å¶å¾¡ã·ã¹ãã ã«ä¾åãããã¨ãªãã¢ã¯ãã¥ã¨ã¼ã¿ãæã§æä½ã§ã
ãããã®ããå¶å¾¡ã·ã¹ãã ãå©ç¨ä¸è½ã»ä¸èª¿ã§ãã¢ã¯ãã¥ã¨ã¼ã¿ãå¶å¾¡ã§ããã
ã¢ããã°å¶å¾¡ã·ã¹ãã
ã¢ããã°å¶å¾¡ã·ã¹ãã ã¯éãã¸ã¿ã«ã»ã³ãµã¨ã¢ã¯ãã¥ã¨ã¼ã¿ã使ç¨ãã¦ãç©çãã
ã»ã¹ãç£è¦ã»å¶å¾¡ããããã®ãããã¸ã¿ã«å¶å¾¡ã·ã¹ãã ãå©ç¨ä¸è½ã»ä¸ææã§ãã
ç©çããã»ã¹ã好ã¾ãããªãç¶æ
ã«é¥ããªãã§ãããã¢ããã°å¶å¾¡ã«ã¯ã¬ã®ã¥ã¬ã¼
ã¿ãã¬ããã¼ãé»åæ©æ¢°å¼ãªã¬ã¼çã®ããã¤ã¹ãããã
ãµã¤ãã¼ã¤ã³ã·ãã³ãã ICS ã«ä¸ãå¾ãå½±é¿åº¦ã®å¤å®ã«ã¯ãå
¨ã¦ã®éãã¸ã¿ã«å¶å¾¡ã¡ã«ããº
ã ã®åæã¨ããããã ICS ã¸ã®æªå½±é¿ãç·©åã§ããç¨åº¦ãçãè¾¼ãã¹ãã§ãããéãã¸ã¿ã«
å¶å¾¡ã¡ã«ããºã ã«ãããã®ãããªç·©åå¹æãæ¤è¨ããéã«ã¯ã次ã®ãããªèæ
®äºé
ãããã
ï¼ éãã¸ã¿ã«å¶å¾¡ã¡ã«ããºã ãå¿
è¦ãªç£è¦åã¯å¶å¾¡æ©è½ãçºæ®ããã«ã¯ãä½åã®æéã¨äººã®é¢
ä¸ãä¸å¯æ¬ ã§ããããããªãã®ç¨åº¦ã«ãªããã¨ããããä¾ãã°ãæä½å¡ãé æ¹ã®ç¾å ´ã¾ã§åº
åãã¦ããã種ã®å¶å¾¡ãè¡ããªããã°ãªããªãå ´åããããã¾ã人ã«ãã対å¿æéãããã
ãããèªåå¶å¾¡ã«æ¯ã¹ãã¨é
ããªãã
ï¼ æååã³ã¢ããã°ã·ã¹ãã ã®ç£è¦åã¯å¶å¾¡è½åã¯ããã¸ã¿ã«å¶å¾¡ã·ã¹ãã ã»ã©ã®ç²¾åº¦ãä¿¡é ¼
æ§ã«ã¯åã°ãªããã¨ããããã·ã¹ãã ã®å質ãå®å
¨æ§åã¯å¹çãä½ä¸ãã¦ããã©ã¤ããªå¶å¾¡
ã·ã¹ãã ãå©ç¨ä¸è½ãä¸æã«ãªã£ãå ´åã«ãããã¯ãªã¹ã¯ã¨ãªãå¾ããä¾ãã°ããã¸ã¿ã«/æ°
å¤ä¿è·ãªã¬ã¼ã¯ãã¢ããã°/ã¹ã¿ãã£ãã¯ãªã¬ã¼ãããé害æ¤ç¥ç²¾åº¦ãä¿¡é ¼æ§ãé«ãã®ã§ãã
ã¸ã¿ã«ãªã¬ã¼ãå©ç¨ã§ããªãã¨ãã·ã¹ãã ã¯ãªã¬ã¼ã®çä¼¼ããªãããçãããããªãã
SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
61
3.3.5 Incorporating the Impact of Safety Systems
Safety systems may also reduce the impact of a cyber incident to the ICS. Safety systems are often
deployed to perform specific monitoring and control functions to ensure the safety of people, the
environment, process, and ICS. While these systems are traditionally implemented to be fully redundant
with respect to the primary ICS, they may not provide complete redundancy from cyber incidents,
specifically from a sophisticated attacker. The impact of the implemented security controls on the safety
system should be evaluated to determine that they do not negatively impact the system.
3.3.6 Considering the Propagation of Impact to Connected Systems
Evaluating the impact of an incident must also incorporate how the impact from the ICS could propagate to
a connected ICS or physical system. An ICS may be interconnected with other systems, such that failures in
one system or process can easily cascade to other systems either within or external to the organization.
Impact propagation could occur due to both physical and logical dependencies. Proper communication of
the results of risk assessments to the operators of connected or interdependent systems and processes is one
way to mitigate such impacts.
Logical damage to an interconnected ICS could occur if the cyber incident propagated to the connected
control systems. An example could be if a virus or worm propagated to a connected ICS and then impacted
that system. Physical damage could also propagate to other interconnected ICS. If an incident impacts the
physical environment of an ICS, it may also impact other related physical domains. For example, the
impact could result in a physical hazard which degrades nearby physical environments. Additionally, the
impact could also degrade the common shared dependencies (e.g., power supply), or result in a shortage of
material needed for a later stage in an industrial process.
SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
62
3.3.5 å®å
¨ã·ã¹ãã ã®å½±é¿ãå«ãã
å®å
¨ã·ã¹ãã ã§ã¯ãICS ã«ä¸ãããµã¤ãã¼ã¤ã³ã·ãã³ãã®å½±é¿ãæ¸ããå®å
¨ã·ã¹ãã ã¯äººã»ç°
å¢ã»ããã»ã¹ã»ICS ã®å®å
¨ã確ä¿ããããã«ãç¹æ®ãªç£è¦ã»å¶å¾¡æ©è½ç¨ã«å±éããããã¨ãå¤
ããããããã·ã¹ãã ã§ã¯ããã©ã¤ã㪠ICS ã«é¢ãã¦ã¯å¾æ¥å®å
¨ãªåé·æ§ã確ä¿ããã¦ãã
ä¸æ¹ãç¹ã«å·§å¦ãªæ»æè
ããã®ãµã¤ãã¼ã¤ã³ã·ãã³ãã«é¢ãã¦ã¯å®å
¨ãªåé·æ§ããªããå®è£
ãããã»ãã¥ãªãã£ç®¡çãå®å
¨ã·ã¹ãã ã«ä¸ããå½±é¿ã®è©ä¾¡ã¯ãã·ã¹ãã ã¸ã®æªå½±é¿ã®æç¡
ãå¤å®ãã¹ãã§ããã
3.3.6 æ¥ç¶ã·ã¹ãã ã¸ã®å½±é¿æ³¢åã«å¯¾ããèæ
®
ã¤ã³ã·ãã³ãã®å½±é¿ãè©ä¾¡ããéã«ã¯ãICS ããã®å½±é¿ããæ¥ç¶ãããå¥ã® ICS ãç©ççã·ã¹ã
ã ã«ã©ã®ç¨åº¦æ³¢åãããã¨ããç¹ãå«ããªããã°ãªããªãã1ã¤ã® ICS ã¯ãããã¤ãã®ã·ã¹ãã
ã¨é£æ¥ããã¦ããå ´åããããããã·ã¹ãã åã¯ããã»ã¹ã®é害ãçµç¹å
å¤ã®ä»ã®ã·ã¹ãã ã«å®¹
æã«é£éãããã¨ããããå½±é¿ã®æ³¢åã¯ãç©ççå¾å±é¢ä¿ã¨è«ççå¾å±é¢ä¿ã®åæ¹ã«èµ·å ãã¦ç
ãå¾ããããããå½±é¿ãç·©åãã 1ã¤ã®æ¹æ³ã¯ããªã¹ã¯è©ä¾¡ã®çµæãé£æ¥åã¯ç¸äºä¾åããã·ã¹
ãã åã³ããã»ã¹ã®æä½å¡ã«é©åã«ä¼ãããã¨ã§ããã
é£æ¥ ICS ã®è«ççæ害ã¯ããµã¤ãã¼ã¤ã³ã·ãã³ããé£æ¥å¶å¾¡ã·ã¹ãã ã«æ³¢åããå ´åã«çãå¾ãã
ã¦ã¤ã«ã¹ãã¯ã¼ã ãé£æ¥ ICS ã«æ³¢åãã次ãã§ã·ã¹ãã ã«å½±é¿ãä¸ããå ´åããã®ä¸ä¾ã§ããã
ç©ççæ害ãå¥ã®é£æ¥ ICS ã«æ³¢åãå¾ããããã¤ã³ã·ãã³ãã ICS ã®ç©çç°å¢ã«å½±é¿ããå ´åã
ä»ã®é¢é£ç©çé åã«ãå½±é¿ãåã¼ãå¾ããä¾ãã°ãå½±é¿ã«ããç©ççå±å®³ãçãããããé£æ¥ã®
ç©çç°å¢ãå£åãããå ´åããã®ä¸ä¾ã§ããã
ã¾ãå½±é¿ã¯å
±éçãªå
±æå¾å±é¢ä¿ï¼é»æºçï¼ããå£åãããç£æ¥ããã»ã¹ã®å¾ç¶æ®µéã§å¿
è¦ã¨ãª
ãè³æã«ä¸è¶³ããããäºæ
ã«ããªãå¾ãã

SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
63
4. ICS Security Program Development and Deployment
Section 2 addresses critical operational differences between ICS and IT systems, and Section 3 addresses
risk management. This section combines these two concerns by addressing how organizations should
develop and deploy an ICS security program. ICS security plans and programs should be consistent and
integrated with existing IT security experience, programs, and practices, but must account for the specific
requirements and characteristics of ICS technologies and environments. Organizations should review and
update their ICS security plans and programs regularly to reflect changes in technologies, operations,
standards, and regulations, as well as the security needs of specific facilities.
This section provides an overview of the development and deployment of an ICS security program. Section
4.1 describes how to establish a business case for an ICS security program, including suggested content for
the business case. Sections 4.2 through 4.5 discuss the development of a comprehensive ICS security
program and provide information on several major steps in deploying the program. Information on specific
security controls that might be implemented as part of the security program is provided in Section 6.
Effectively integrating security into an ICS requires defining and executing a comprehensive program that
addresses all aspects of security, ranging from identifying objectives to day-to-day operation and ongoing
auditing for compliance and improvement. An ICS information security manager with appropriate scope,
responsibility, and authority must be identified. This section describes the basic process for developing a
security program, including the following:
ï¼ Develop a business case for security.
ï¼ Build and train a cross-functional team.
ï¼ Define charter and scope.
ï¼ Define specific ICS policies and procedures.
ï¼ Implement an ICS Security Risk Management Framework.
o Define and inventory ICS assets.
o Develop security plan for ICS Systems.
o Perform a risk assessment.
o Define the mitigation controls.
ï¼ Provide training and raise security awareness for ICS staff.
More detailed information on the various steps is provided in ISA-62443-2-1 Security for Industrial
Automation and Control Systems: Establishing an Industrial Automation and Control Systems Security
Program [34].
The commitment to a security program begins at the top. Senior management must demonstrate a clear
commitment to information security. Information security is a business responsibility shared by all
members of the enterprise and especially by leading members of the business, process, and management
teams. Information security programs with adequate funding and visible, top-level support from
organization leaders are more likely to achieve compliance, function more smoothly, and have greater
success than programs that lack that support.

SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
64
4. ICS ã»ãã¥ãªãã£ããã°ã©ã ã®éçºåã³å±é
ã»ã¯ã·ã§ã³ 2ã§ã¯ ICS ã·ã¹ãã 㨠IT ã·ã¹ãã ã®éç¨ä¸ã®å¤§ããªéãããã»ã¯ã·ã§ã³ 3ã§ã¯ãªã¹
ã¯ç®¡çã«ã¤ãã¦åãä¸ããããã®ã»ã¯ã·ã§ã³ã§ã¯ãçµç¹ã¯ããã« ICS ã»ãã¥ãªãã£ããã°ã©ã ã
çå®ãã¦å±éãã¹ããã«ã¤ãã¦èå¯ããããã 2ã¤ã®é¢å¿äºãé¢é£ã¥ãããICS ã»ãã¥ãªãã£ã®
è¨ç»åã³ããã°ã©ã ã¯é¦å°¾ä¸è²«ããæ¢åã® IT ã»ãã¥ãªãã£çµé¨ã»ããã°ã©ã ã»è¦ç¯ã¨ä¸ä½åã
ã¦ããã¹ãã§ããããICS æè¡ã»ç°å¢ã®ç¹æ®è¦ä»¶åã³ç¹æ§ãåãä¸ãã¦ããªããã°ãªããªããçµ
ç¹ã¯ãICS ã»ãã¥ãªãã£ã®è¨ç»åã³ããã°ã©ã ãå®æçã«è¦ç´ãã¦æ´æ°ããæè¡ã»éç¨ã»è¦æ ¼ã»
è¦åã®å¤æ´ç¹ã®ã»ããç¹æ®æ½è¨ã®ã»ãã¥ãªãã£éè¦ãåæ ãã¹ãã§ããã
ãã®ã»ã¯ã·ã§ã³ã§ã¯ãICS ã»ãã¥ãªãã£ããã°ã©ã ã®éçºåã³å±éã«ã¤ãã¦æ¦èª¬ãããã»ã¯ã·ã§
ã³4.1 ã§ã¯ãICS ã»ãã¥ãªãã£ããã°ã©ã ã«é¢ããäºæ¥ã®ãå
容æ¡ãå«ããæ§ç¯ä¾ã«ã¤ãã¦ç¤ºãã
4.2ï½4.5 ã§ã¯ãå
æ¬ç㪠ICS ã»ãã¥ãªãã£ããã°ã©ã ã®éçºã«ã¤ãã¦åä¸ãããããå±éããã
ãã®å¤§ã¾ããªæé ãããã¤ã示ããã»ãã¥ãªãã£ããã°ã©ã ã®ä¸ç°ã¨ãã¦å®è£
ãããç¹å®ã®ã»ã
ã¥ãªãã£ç®¡çã«ã¤ãã¦ã¯ãã»ã¯ã·ã§ã³ 6ã§åãä¸ããã
ICS ã«ã»ãã¥ãªãã£ãå¹æçã«çµã¿è¾¼ãã«ã¯ãæ¥å¸¸æ¥åã®ç®çããã³ã³ãã©ã¤ã¢ã³ã¹ã»æ¹åã«é¢
ããç£æ»ã¾ã§ãå¤å²ã«ãããã»ãã¥ãªãã£ã®ããããé¢ã網ç¾
ããå
æ¬çãªããã°ã©ã ãè¨è¨ã
ã¦å®è¡ãããã¨ãå¿
è¦ã¨ãªããé©æ£ãªç¯å²ã責任åã³æ¨©éãæãã ICS æ
å ±ã»ãã¥ãªãã£ç®¡çè
ãæ確ã«ããªããã°ãªããªãããã®ã»ã¯ã·ã§ã³ã§ã¯ã以ä¸ãå«ãã»ãã¥ãªãã£ããã°ã©ã éçºã«
é¢ããåºæ¬ããã»ã¹ã«ã¤ãã¦èª¬æããã
ï¼ ã»ãã¥ãªãã£ã®ãã¸ãã¹äºä¾ä½æ
ï¼ æ©è½æ¨ªæãã¼ã ã®çµæã»æè²è¨ç·´
ï¼ æ²ç« åã³é©ç¨ç¯å²ã®æ確å
ï¼ å
·ä½ç㪠ICS ã®æ¹éåã³æé ã®æ確å
ï¼ ICS ã»ãã¥ãªãã£ãªã¹ã¯ç®¡çä½å¶ã®å®è¡
o ICS è³ç£ã®ç¹å®åã³æç´°å
o ICS ã·ã¹ãã ã»ãã¥ãªãã£è¨ç»çå®
o ãªã¹ã¯è©ä¾¡å®æ½
o ç·©å対çã®æ確å
ï¼ ICS ã¹ã¿ããã®è¨ç·´åã³ã»ãã¥ãªãã£æèã®å¼·å
種ã
ã®æé ã«é¢ãã詳細ã¯ãISA-62443-2-1ãå·¥æ¥ãªã¼ãã¡ã¼ã·ã§ã³å¶å¾¡ã·ã¹ãã ã®ã»ãã¥ãªã
ã£ï¼å·¥æ¥ãªã¼ãã¡ã¼ã·ã§ã³å¶å¾¡ã·ã¹ãã ã»ãã¥ãªãã£ããã°ã©ã ã®æ§ç¯ã[34]ã«è¨è¼ããã¦ããã
ã»ãã¥ãªãã£ããã°ã©ã ã¸ã®å¯¾å¿ã¯çµç¹ã®ãããããå§ã¾ããä¸ç´ç®¡çè
ã¯ãæ
å ±ã»ãã¥ãªãã£
ã¸ã®æ確ãªå¯¾å¿ãæããã«ããªããã°ãªããªããæ
å ±ã»ãã¥ãªãã£ã¯ä¼æ¥ã®å
¨ç¤¾å¡ãå
±æãã¦ã
ãä»äºä¸ã®è²¬åã§ããããç¹ã«äºæ¥ãããã»ã¹åã³ç®¡çãã¼ã ã®æå°è
ã¯ããè¨ãããååãªè³
éããã¦ããããçµç¹ã®ãããã¬ãã«ã®å¯è¦åãããæ¯æ´ãåããæ
å ±ã»ãã¥ãªãã£ããã°ã©ã
ã¯ããããå¾ãããªãããã°ã©ã ã«æ¯ã¹ã¦ãã³ã³ãã©ã¤ã¢ã³ã¹ãéæããããã¹ã ã¼ãºã«æ©è½ãã
ãã大ããªæåã¨ãªãå
¬ç®ãé«ããªãã
SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
65
Whenever a new system is being designed and installed, it is imperative to take the time to address security
throughout the lifecycle, from architecture to procurement to installation to maintenance to
decommissioning. There are serious risks in deploying systems to production based on the assumption that
they will be secured later. If there is insufficient time and resources to secure the system properly before
deployment, it is unlikely that there will be sufficient time and resources later to address security.
Designing and implementing a new system is quite rare. It is much more common to improve, expand, or
update an existing system. Everything in this section, indeed in this document, applies to managing the risk
of existing ICS. Building an ICS Security Program and applying it to existing systems is much more
complex and challenging.
4.1 Business Case for Security
The first step in implementing an information security program for ICS is to develop a compelling business
case for the unique needs of the organization. The business case should capture the business concerns of
senior management while being founded in the experience of those who are already dealing with many of
the same risks. The business case provides the business impact and financial justification for creating an
integrated information security program. It should include detailed information about the following:
ï¼ Benefits, including improved control system reliability and availability, of creating an integrated
security program.
ï¼ Prioritized potential costs and damage scenarios if an information security program for the ICS is not
implemented.
ï¼ High-level overview of the process required to implement, operate, monitor, review, maintain, and
improve the information security program.
ï¼ Costs and resources required to develop, implement and maintain the security program.
Before presenting the business case to management, there should be a well-thought-out and developed
security implementation and cost plan. For example, simply requesting a firewall is insufficient.
4.1.1 Benefits
Responsible risk management policy mandates that the threat to the ICS should be measured and monitored
to protect the interests of employees, the public, shareholders, customers, vendors, society, and the nation.
Risk analysis enables costs and benefits to be weighed so that informed decisions can be made on
protective actions. In addition to reducing risks, exercising due-diligence and displaying responsibility also
helps organizations by:
ï¼ Improving control system safety, reliability and availability.
ï¼ Improving employee morale, loyalty, and retention.
ï¼ Reducing community concerns.
ï¼ Increasing investor confidence.
ï¼ Reducing legal liabilities.
ï¼ Meeting regulatory requirements.
ï¼ Enhancing the corporate image and reputation.
ï¼ Helping with insurance coverage and cost.
ï¼ Improving investor and banking relations.
SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
66
æ°ããã·ã¹ãã ãè¨è¨ã»å°å
¥ããå ´åã¯å¸¸ã«ãã¢ã¼ããã¯ãã£ãã調éãå°å
¥ãä¿å®ãå»æ£ã«è³
ãã¾ã§ãã©ã¤ããµã¤ã¯ã«å
¨ä½ãè¦éããã»ãã¥ãªãã£ã«ã¤ãã¦èå¯ããæéãåãåãããã¨ã
èè¦ã§ãããã»ãã¥ãªãã£ã¯å¾ã§èããã¨ãã£ãæ³å®ã«åºã¥ãã¦ãã·ã¹ãã ãçç£ç¾å ´ã«å±éã
ããã¨ã«ã¯é大ãªãªã¹ã¯ããããå±éåã«ã·ã¹ãã ã»ãã¥ãªãã£ããã£ãã確ä¿ããããã®æé
ã¨ãªã½ã¼ã¹ããªããã°ãå±éå¾ã«ãããè¦ãã ããã¨ãªã©ãã¼ã¤ããªãã
æ°è¦ã«ã·ã¹ãã ãè¨è¨ãã¦å®è£
ãããã¨ã¯ã¾ãã§ãããæ¢åã®ã·ã¹ãã ãæ¹è¯ãæ¡å¼µåã¯æ´æ°
ããå ´åãã¯ããã«å¤ãããã®ã»ã¯ã·ã§ã³ã®å
¨ã¦ãã¨ãããããæ¬æ¸ã®å
¨ã¦ã®é¨åããæ¢å
ICS ã®ãªã¹ã¯ç®¡çã«è©²å½ãããICS ã»ãã¥ãªãã£ããã°ã©ã ãæ§ç¯ãã¦ãæ¢åã·ã¹ãã ã«é©ç¨
ããã®ã¯ã¯ããã«è¤éã§èª²é¡ãå¤ãã
4.1 ã»ãã¥ãªãã£ã®äºæ¥äºä¾
ICS ã®æ
å ±ã»ãã¥ãªãã£ããã°ã©ã ãå®è£
ãã第 1ã¹ãããã¯ãçµç¹ç¹æã®ãã¼ãºã«å¯¾å¿ãã
å¼·åãªäºæ¥äºä¾ãä½æãããã¨ã§ãããäºæ¥äºä¾ã¯ãåæ§ã®ãªã¹ã¯ãå¤åã«æ±ã£ããã¨ãã
ãè
ã®éå»ã®çµé¨ã«æ ¹ããã¤ã¤ããä¸ç´ç®¡çè
ã®äºæ¥ã¸ã®é¢å¿äºãã¨ããã¦ããã¹ãã§ããã
äºæ¥äºä¾ã¯ãçµ±åæ
å ±ã»ãã¥ãªãã£ããã°ã©ã ãä½æããä¸ã§ãäºæ¥ã¸ã®å½±é¿ãä¸ããè³é
æ åºã®çç±ã¨ãªãã以ä¸ã«é¢ãã詳細ãªæ
å ±ã網ç¾
ãã¹ãã§ããã
ï¼ å¶å¾¡ã·ã¹ãã ã®ä¿¡é ¼æ§ã»å¯ç¨æ§ã®åä¸ãªã©ãçµ±åã»ãã¥ãªãã£ããã°ã©ã ãä½æãããã¨ã«
ããå¾ããã便ç
ï¼ ICS ã®æ
å ±ã»ãã¥ãªãã£ããã°ã©ã ãå®è£
ããªãå ´åã«çãå¾ãåªå
çµè²»åã³æ害
ï¼ æ
å ±ã»ãã¥ãªãã£ããã°ã©ã ã®å®è£
ã»éç¨ã»ç£è¦ã»è¦ç´ãã»ä¿å®ã»æ¹åã«è¦ããããã»ã¹ã®ã
é«ã¬ãã«ã®æ¦è¦
ï¼ ã»ãã¥ãªãã£ããã°ã©ã ã®éçºã»å®è£
ã»ä¿å®ã«è¦ããçµè²»åã³ãªã½ã¼ã¹
äºæ¥äºä¾ãçµå¶é£ã«æ示ããåã«ãã»ãã¥ãªãã£ã®å®è£
ã»çµè²»è¨ç»ãæ
éã«ç·´ãä¸ãã¦ä½æ
ãã¹ãã§ãããä¾ãã°ãåã«ãã¡ã¤ã¢ã¦ã©ã¼ã«ãè¦æ±ããã ãã§ã¯ä¸ååã§ããã
4.1.1 便ç
ãã£ãããããªã¹ã¯ç®¡çæ¹éã¯ãICS ã«å¯¾ããè
å¨ãè¨æ¸¬ã»ç£è¦ãã¦ãå¾æ¥å¡ã»å½æ°ã»æ ªä¸»ã»é¡§
客ã»ãã³ãã¼ã»ç¤¾ä¼ã»å½ã®å©çãå®ããã¨ã義åã¥ãã¦ããããªã¹ã¯åæã«ããã³ã¹ã/便çã®
æ¯è¼èéãè¡ããã¨ãã§ããæ
å ±ãåºã«ä¿è·å¯¾çã«é¢ãã決å®ãä¸ããã¨ãã§ããããªã¹ã¯åæ¸
ã«å ãã以ä¸ã«å¯¾ããå½ç¶ã®åªååã³è²¬ä»»ã示ããã¨ãçµç¹ã®çã¨ãªãã
ï¼ å¶å¾¡ã·ã¹ãã ã®å®å
¨æ§ã»ä¿¡é ¼æ§ã»å¯ç¨æ§ã®åä¸
ï¼ å¾æ¥å¡ã®å£«æ°ã»å¿ èª å¿ã»å¤ç¶æ欲ã®åä¸
ï¼ å
±åä½æ¸å¿µäºé
ã®ç·©å
ï¼ æè³å®¶ã®ä¿¡é ¼æã®å¢å¼·
ï¼ æ³ç責任ã®è»½æ¸
ï¼ æ³çè¦ä»¶ã®éµå®
ï¼ ä¼æ¥ã¤ã¡ã¼ã¸ã»å声ã®æ¡å¤§
ï¼ ä¿éºéã»çµè²»ã«ããææ¸
ï¼ æè³å®¶ã»éè¡ã¨ã®é¢ä¿æ¹å
SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
67
A strong safety and information security management program is fundamental to a sustainable business
model.
Improved control systems security and control system specific security policies can potentially enhance
control system reliability and availability. This also includes minimizing unintentional control system
information security impacts from inappropriate testing, policies, and misconfigured systems.
4.1.2 Potential Consequences
The importance of secure systems should be further emphasized as business reliance on interconnectivity
increases. Denial of Service (DoS) attacks and malware (e.g., worms, viruses) have become all too
common and have already impacted ICS. Cyber attacks can have significant physical and consequential
impacts. Risk management is addressed in Section 3. The major categories of impacts are as follows:
ï¼ Physical Impacts. Physical impacts encompass the set of direct consequences of ICS failure. The
potential effects of paramount importance include personal injury and loss of life. Other effects
include the loss of property (including data) and potential damage to the environment.
ï¼ Economic Impacts. Economic impacts are a second-order effect from physical impacts ensuing from
an ICS incident. Physical impacts could result in repercussions to system operations, which in turn
inflict a greater economic loss on the facility, organization, or others dependent on the ICS.
Unavailability of critical infrastructure (e.g., electrical power, transportation) can have economic
impact far beyond the systems sustaining direct and physical damage These effects could negatively
impact the local, regional, national, or possibly global economy.
ï¼ Social Impacts. Another second-order effect, the consequence from the loss of national or public
confidence in an organization, is many times overlooked. It is, however, a very real consequence that
could result from an ICS incident.
The program to control such risks is addressed in Section 3. Note that items in this list are not independent.
In fact, one can lead to another. For example, release of hazardous material can lead to injury or death.
Examples of potential consequences of an ICS incident are listed below:
ï¼ Impact on national securityâfacilitate an act of terrorism.
ï¼ Reduction or loss of production at one site or multiple sites simultaneously.
ï¼ Injury or death of employees.
ï¼ Injury or death of persons in the community.
ï¼ Damage to equipment.
ï¼ Release, diversion, or theft of hazardous materials.
ï¼ Environmental damage.
ï¼ Violation of regulatory requirements.
ï¼ Product contamination.
ï¼ Criminal or civil legal liabilities.
ï¼ Loss of proprietary or confidential information.
ï¼ Loss of brand image or customer confidence.
Undesirable incidents of any sort detract from the value of an organization, but safety and security incidents
can have longer-term negative impacts than other types of incidents on all stakeholdersâemployees,
shareholders, customers, and the communities in which an organization operates.
The list of potential business consequences needs to be prioritized to focus on the particular business
consequences that senior management will find the most compelling. The highest priority items shown in
SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
68
ãã¸ãã¹ã¢ãã«ãæç¶ãããã«ã¯ããã£ããããå®å
¨æ§ã»æ
å ±ã»ãã¥ãªãã£ç®¡çããã°ã©ã
ãä¸å¯æ¬ ã§ããã
å¶å¾¡ã·ã¹ãã ã®ã»ãã¥ãªãã£åã³å¶å¾¡ã·ã¹ãã ç¹æã®ã»ãã¥ãªãã£æ¹éãæ¹åããã°ãå¶å¾¡ã·ã¹
ãã ã®ä¿¡é ¼æ§ã»å¯ç¨æ§ãåä¸ããå¾ããããã«ã¯ä¸é©åãªè©¦é¨ãæ¹éåã³èª¤è¨å®ãããã·ã¹ãã
ããçãããå¶å¾¡ã·ã¹ãã æ
å ±ã»ãã¥ãªãã£ã¸ã®æ³å®å¤ã®å½±é¿ã極åæãããã¨ãå«ã¾ããã
4.1.2 çãå¾ãçµæ
ã»ãã¥ã¢ãªã·ã¹ãã ãéè¦ãªãã¨ã¯ãäºæ¥ãç¸äºæ¥ç¶ã«ã¾ãã¾ãä¾åããããã«ãªã£ã¦ãããã¨
ãããæããã§ããããµã¼ãã¹å¦¨å®³ï¼DoSï¼æ»æããã«ã¦ã¨ã¢ï¼ã¯ã¼ã ãã¦ã¤ã«ã¹çï¼ã®åå¨ã¯
常æ
ã«ãªã£ã¦ãããICS ã«ãå½±é¿ãåãã§ããããµã¤ãã¼æ»æã¯ç©ççãªå½±é¿ãæ³¢åçãªå½±é¿ã
大ããããªã¹ã¯ç®¡çã«ã¤ãã¦ã¯ã»ã¯ã·ã§ã³ 3ã§åãä¸ãããå½±é¿ã¯ä»¥ä¸ã®ããã«å¤§å¥ãããã
ï¼ ç©ççå½±é¿ãããã«ã¯ ICS é害ã«ããç´æ¥ã®çµæãå«ã¾ãããææªã®çµæã¨ãã¦äººã®è² å·ã
æ»äº¡ãçãå¾ãããã®ã»ãè³ç£ã®åªå¤±ï¼ãã¼ã¿çï¼ãç°å¢ç ´å£çãããã
ï¼ çµæ¸çå½±é¿ããã㯠ICS ã¤ã³ã·ãã³ãã«èµ·å ããç©ççå½±é¿ããæ´¾çããäºæ¬¡çå½±é¿ã§ãã·
ã¹ãã éç¨ã«å½±é¿ãåã¼ãããã®çµææ½è¨ãçµç¹ãã®ä» ICS ã«ä¾åãããã®ã«å¯¾ããæ´ã«å¤§
ããªçµæ¸çæ失ããããããéè¦ã¤ã³ãã©ï¼é»åã輸éçï¼ãå©ç¨ä¸è½ã«ãªãã¨ãã·ã¹ãã
ã®ç´æ¥ã®ç©ççæ害ãã¯ããã«è¶ããçµæ¸çå½±é¿ãçããããã®çµæãå°å
ãå°åãå½å®¶ã
ããã«ã¯ä¸ççµæ¸ã«æªå½±é¿ãåã³ãããªãã
ï¼
社ä¼çå½±é¿ãããã¯å¥ã®äºæ¬¡çå½±é¿ã§ãçµç¹ã«å¯¾ããå½æ°ã®ä¿¡é ¼æã失ãããçµæçãããã
è¦éããã«ãããã¡ã§ãããããããICS ã¤ã³ã·ãã³ãããçããå®ã«ç¾å®çãªçµæã§ããã
ãã®ãããªãªã¹ã¯ã管çããããã®ããã°ã©ã ã«ã¤ãã¦ã¯ã»ã¯ã·ã§ã³ 3ã§åãä¸ããããã®
ãªã¹ãä¸ã®é
ç®ã¯ãããããç¬ç«ãã¦ããã®ã§ã¯ãªãããããããããã®ãå¥ã®ãã®ãå°ã
ãã¨ããããä¾ãã°ãå±éºç©ã®æ¾åºã¯è² å·ãæ»äº¡äºæ
ã«ã¤ãªãããICS ã¤ã³ã·ãã³ãããçã
å¾ãçµæã以ä¸ã«ä¾ç¤ºããã
ï¼ å½å®¶å®å
¨ä¿éã¸ã®å½±é¿âããè¡çºãå©é·ãã
ï¼ 1ãæåã¯è¤æ°åæãµã¤ãã«ãããçç£ã®æ¸å°ã»åªå¤±
ï¼ å¾æ¥å¡ã®è² å·ã»æ»äº¡
ï¼ å
±åä½æ§æå¡ã®è² å·ã»æ»äº¡
ï¼ è£
ååã®æ害
ï¼ å±éºç©ã®æ¾åºã»æµç¨ã»çé£
ï¼ ç°å¢ç ´å£
ï¼ æ³çè¦ä»¶ã®ä¾µå®³
ï¼ è£½åã®æ±æ
ï¼ åæ³åã¯æ°æ³ä¸ã®è²¬ä»»
ï¼ å°æã»ç§å¯æ
å ±ã®åªå¤±
ï¼ ãã©ã³ãã¤ã¡ã¼ã¸ã»é¡§å®¢ã®ä¿¡ç¨ã®åªå¤±
ã©ã®ãããªç¨®é¡ã®ãã®ã§ãããæã¾ãããªãã¤ã³ã·ãã³ãã¯çµç¹ã®ä¾¡å¤ãæ¸ããããå®å
¨ã
ã»ãã¥ãªãã£ãé¢ä¿ããã¤ã³ã·ãã³ãã¯ããã以å¤ã®ã¤ã³ã·ãã³ãã«æ¯ã¹ã¦ãããé·æçãª
æªå½±é¿ãå¾æ¥å¡ãæ ªä¸»ã顧客åã³çµç¹ãå±ããå
±åä½ãå«ããå
¨ã¦ã®é¢ä¿è
ã«æããããã
å¯è½æ§ã®ããäºæ¥çµæã®ãªã¹ããããäºæ¥çµæã®åªå
度ãæ¤è¨ããä¸ç´ç®¡çè
ãç¹ã«å½±é¿åº¦ã
大ããã¨æãããã®ã«æ³¨åããå¿
è¦ããããåªå
çãªäºæ¥çµæãªã¹ãã®æåªå
é
ç®ã

SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
69
the list of prioritized business consequences should be evaluated to obtain an estimate of the annual
business impact, preferably but not necessarily in financial terms.
The Sarbanes-Oxley Act requires corporate leaders to sign off on compliance with information accuracy
and protection of corporate information.19 Also, the demonstration of due diligence is required by most
internal and external audit firms to satisfy shareholders and other organization stakeholders. By
implementing a comprehensive information security program, management is exercising due diligence.
4.1.3 Resources for Building Business Case
Significant resources for information to help form a business case can be found in external resources in
other organizations in similar lines of businessâeither individually or in information sharing exchanges,
trade and standards organizations, consulting firmsâand internal resources in related risk management
programs or engineering and operations. External organizations can often provide useful tips as to what
factors most strongly influenced management to support their efforts and what resources within their
organizations proved most helpful. For different industries, these factors may be different, but there may be
similarities in the roles that other risk management specialists can play. Appendix Dâ provides a list and
short description of some of the current activities in ICS security.
Internal resources in related risk management efforts (e.g., information security, health, safety and
environmental risk, physical security, business continuity) can provide tremendous assistance based on
their experience with related incidents in the organization. This information is helpful from the standpoint
of prioritizing threats and estimating business impact. These resources can also provide insight into which
managers are focused on dealing with which risks and, thus, which managers might be the most appropriate
or receptive to serving as a champion. Internal resources in control systems engineering and operations can
provide insight into the details of how control systems are deployed within the organization, such as the
following:
ï¼ How networks are typically partitioned and segregated.
ï¼ What remote access connections are generally employed.
ï¼ How high-risk control systems or safety instrumented systems are typically designed.
ï¼ What security countermeasures are commonly used.
4.1.4 Presenting the Business Case to Leadership
Section 3 describes a three-tiered approach that addresses risk at the: (i) organization level; (ii)
mission/business process level; and (iii) information system level. The risk management process is carried
out seamlessly across the three tiers with the overall objective of continuous improvement in the
organizationâs risk-related activities and effective inter-tier and intra-tier communication among all
stakeholders having a shared interest in the mission/business success of the organization.
It is critical for the success of the ICS security program that organization level management buy into and
participate in the ICS security program. Tier 1 organization level management that encompasses both IT
and ICS operations has the perspective and authority to understand and take responsibility for the risks.
The Tier 1 business leadership will be responsible for approving and driving information security policies,
assigning security roles and responsibilities, and implementing the information security program across the
organization. Funding for the entire program can usually be done in phases. While some
19 More information on the Sarbanes-Oxley Act, and a copy of the act itself, can be found at
http://www.sec.gov/about/laws.shtml.

SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
70
è©ä¾¡ãã¦ãå¹´éäºæ¥å½±é¿è¦ç©ãä½æãã¹ãã§ãããè¦ç©ã¯è²¡åçãªè¦³ç¹ããè¡ãã®ãæã¾ãã
ãã義åã§ã¯ãªãã
Sarbanes-Oxley æ³ã¯ãæ
å ±ã®æ£ç¢ºæ§ã¨ä¼æ¥æ
å ± 20ã®ä¿è·éµå®ã«é¢ãã¦ãä¼æ¥è²¬ä»»è
ã«ç½²åã義
åã¥ãã¦ãããã¾ãã»ã¨ãã©ã®å
å¤ç£æ»æ³äººã«å¯¾ãã¦ãç¶ãã¹ãåªåãå¾æ³¨ãã¦æ ªä¸»ãã®ä»çµ
ç¹é¢ä¿è
ãæºè¶³ãããããæ±ãã¦ãããå
æ¬çæ
å ±ã»ãã¥ãªãã£ããã°ã©ã ãæ½è¡ãããã¨ã§ã
çµå¶é£ã¯ãããã¹ãåªåãå¾æ³¨ãã¦ãããã¨ã«ãªãã
4.1.3 äºæ¥äºä¾ä½æã®ããã®ãªã½ã¼ã¹
äºæ¥äºä¾ã®æ§ç¯ã«å½¹ç«ã¤ããªãã®ãªã½ã¼ã¹ãå¤é¨åæ¥çµç¹ã®ãªã½ã¼ã¹ã«ãããä¾ãã°åã
ã®ä¼æ¥ã
åã¯æ
å ±å
±æ交æãåå¼çµç¹åã³è¦æ ¼çµç¹ãã³ã³ãµã«ã¿ã³ãä¼æ¥ãªã©ã®ã»ããé¢é£ãªã¹ã¯ç®¡çã
ãã°ã©ã ãã¨ã³ã¸ãã¢ãªã³ã°ãæ¥åã¨ãã£ãå
é¨ãªã½ã¼ã¹ãããå©ç¨ã§ãããå¤é¨çµç¹ã¯ãçµå¶
é£ã®åçµã«æã大ããªå½±é¿ãä¸ããè¦å ã«ã¤ãã¦ãã¾ãçµç¹å
ã®ã©ã®ãªã½ã¼ã¹ãæãå½¹ç«ã£ãã
ã¨ãã£ãç¹ã«é¢ãã¦ãæç¨ãªãã³ããä¸ãã¦ããããã¨ãå¤ããæ¥çãç°ãªãã°ããããè¦å ã
ç°ãªãããä»ã®ãªã¹ã¯ç®¡çæ
å½è
ãæããå½¹å²ã«ã¯å
±éç¹ããããä»é² Dã«ã¯ãICS ã»ãã¥ãªã
ã£ã«ãããç¾å¨ã®æ´»åã®ããã¤ããç°¡åã«ç´¹ä»ãããªã¹ããããã
é¢ä¿ãããªã¹ã¯ç®¡çã®åçµï¼æ
å ±ã»ãã¥ãªãã£ãè¡çãå®å
¨ã»ç°å¢ãªã¹ã¯ãç©ççã»ãã¥ãªãã£ã
äºæ¥ç¶ç¶çï¼ã«ãããå
é¨ãªã½ã¼ã¹ã¯ãçµç¹ã®é¢é£ã¤ã³ã·ãã³ãã§ã®çµé¨ãåºã«ã大ããªå©ãã¨
ãªãããã®æ
å ±ã¯ãè
å¨ã®åªå
ä»ãã¨äºæ¥å½±é¿ã®è¦ç©ã®è¦³ç¹ããå½¹ç«ã¤ããããããªã½ã¼ã¹ãæ´»
ç¨ããã°ãã©ã®ç®¡çè
ãã©ã®ãªã¹ã¯ã«å¯¾å¿ãã¦ããããã¾ãã©ã®ç®¡çè
ãæ¨é²è
ã¨ãã¦ç¸å¿ãã
ãã対å¿åãããããå¤æãããã¨ãã§ããããå¶å¾¡ã·ã¹ãã ã¨ã³ã¸ãã¢ãªã³ã°æ¥åã®å
é¨ãªã½
ã¼ã¹ãæ´»ç¨ããã°ã以ä¸ã®ãããªãçµç¹ã¸ã®å¶å¾¡ã·ã¹ãã ã®è©³ç´°ãªå±éæ¹æ³ãå¤æãããã¨ãã§
ããã
é»åã¡ã¼ã«
ï¼ ãããã¯ã¼ã¯ã®ä¸è¬çãªåºç»ã»åå²æ¹æ³
ï¼ ä¸è¬çã«æ¡ç¨ãããªã¢ã¼ãã¢ã¯ã»ã¹æ¥ç¶
ï¼ é«ãªã¹ã¯å¶å¾¡ã·ã¹ãã åã¯å®å
¨è¨è£
ã·ã¹ãã ã®ä¸è¬çè¨è¨
ï¼ å
±éçã«ä½¿ç¨ããã»ãã¥ãªãã£å¯¾ç
4.1.4 äºæ¥äºä¾ãçµç¹ã®é·ã«æ示ãã
ã»ã¯ã·ã§ã³ 3ã§ã¯æ¬¡ã® 3ã¬ãã«ã§ã®ãªã¹ã¯ã«å¯¾å¿ãã 3段éã®åçµã«ã¤ãã¦èª¬æãããï¼1ï¼çµ
ç¹ã¬ãã«ãï¼2ï¼ä»»åã»äºæ¥ããã»ã¹ã¬ãã«ã(3)æ
å ±ã·ã¹ãã ã¬ãã«ããªã¹ã¯ç®¡çããã»ã¹ã¯ã
çµç¹ã®ä»»åã»äºæ¥ã®æåã«å
±éã®é¢å¿ãæ±ãé¢ä¿è
éã«ããã¦ãçµç¹ã®ãªã¹ã¯é¢é£æ´»ååã³å段
ééã»å段éå
ã®å¹æçãªã³ãã¥ãã±ã¼ã·ã§ã³ã絶ããæ¹åããã¨ããå
¨ä½çãªç®çãæã£ã¦ã
3ã¤ã®æ®µéã«ããã£ã¦ã·ã¼ã ã¬ã¹ã«è¡ãããã
ICS ã»ãã¥ãªãã£ããã°ã©ã ãæåãããã«ã¯çµç¹ã¬ãã«ã§çµå¶é£ãåããã°ã©ã ã«ç´å¾ãã¦ã
åå ãããã¨ãèè¦ã§ãããIT åã³ ICS æ¥ååæ¹ãå
å«ãã第 1段éã®çµç¹ã¬ãã«çµå¶é£ã«ã¯ã
ãªã¹ã¯ãç解ã責任ãå¼ãåããè¦éãã¨æ¨©éãããã
第1段éã®äºæ¥ã®ãªã¼ãã¼ã¯ãæ
å ±ã»ãã¥ãªãã£ããªã·ã¼ãæ¿èªã»æ¨é²ããã»ãã¥ãªãã£ã®å½¹å²
ã¨è²¬ä»»ãä»ä¸ããæ
å ±ã»ãã¥ãªãã£ããã°ã©ã ãçµç¹å
¨ä½ã«ããã£ã¦å®è¡ãã責åãè² ãããã
ã°ã©ã å
¨ä½ã¸ã®è³éæ åºã¯ãé常ãã§ã¼ãºãã¨ã«è¡ãã
20 Sarbanes-Oxley æ³ã®è©³ç´°åã³å
¥æã¯æ¬¡ã® URL ãåç
§ã®ãã¨ãhttp://www.sec.gov/about/laws.shtml.
SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
71
funding may be required to start the information security activity, additional funding can be obtained later
as the security vulnerabilities and needs of the program are better understood and additional strategies are
developed. Additionally, the costs (both direct and indirect) should be considered for retrofitting the ICS
for security vs. addressing security to begin with.
Often, a good approach to obtain management buy-in to address the problem is to ground the business case
in a successful actual third-party example. The business case should present to management that the other
organization had the same problem and then present that they found a solution and how they solved it. This
will often prompt management to ask what the solution is and how it might be applicable to their
organization.
4.2 Build and Train a Cross-Functional Team
It is essential for a cross-functional information security team to share their varied domain knowledge and
experience to evaluate and mitigate risk in the ICS. At a minimum, the information security team should
consist of a member of the organizationâs IT staff, a control engineer, a control system operator, security
subject matter experts, and a member of the enterprise risk management staff. Security knowledge and
skills should include network architecture and design, security processes and practices, and secure
infrastructure design and operation. Contemporary thinking that both safety and security are emergent
properties of connected systems with digital control suggests including a safety expert. For continuity and
completeness, the information security team should also include the control system vendor and/or system
integrator.
The information security team should report directly to the information security manager at the
mission/business process or organization tier, who in turn reports to the mission/business process manager
(e.g., facility superintendent) or enterprise information security manager (e.g., the companyâs CIO/CSO),
respectively. Ultimate authority and responsibility rests in the Tier 1 risk executive function that provides a
comprehensive, organization-wide approach to risk management. The risk executive function works with
the top management to accept a level of residual risk and accountability for the information security of the
ICS. Management level accountability will help ensure an ongoing commitment to information security
efforts.
While the control engineers will play a large role in securing the ICS, they will not be able to do so without
collaboration and support from both the IT department and management. IT often has years of security
experience, much of which is applicable to ICS. As the cultures of control engineering and IT are often
significantly different, their integration will be essential for the development of a collaborative security
design and operation.
4.3 Define Charter and Scope
The information security manager should establish policy that defines the guiding charter of the
information security organization and the roles, responsibilities, and accountabilities of system owners,
mission/business process managers, and users. The information security manager should decide upon and
document the objective of the security program, the business organizations affected, all the computer
systems and networks involved, the budget and resources required, and the division of responsibilities. The
scope can also address business, training, audit, legal, and regulatory requirements, as well as timetables
and responsibilities. The guiding charter of the information security organization is a constituent of the
information security architecture which is part of the enterprise architecture, as discussed in Section 3.
SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
72
æ
å ±ã»ãã¥ãªãã£æ´»åãéå§ããã¨ãã«ããç¨åº¦ã®è³éããããã追å è³éã¯ãã»ãã¥ãªãã£
ã®èå¼±æ§ã¨ããã°ã©ã ã®å¿
è¦æ§ãããæ確ã«ãªãã追å æ¦ç¥ãçå®ããå¾ã§å¾ããã¨ãã§ããã
ã¾ãã³ã¹ãï¼ç´æ¥è²»ã»éæ¥è²»ï¼ã¯ãICS ã¸ã®ã»ãã¥ãªãã£å®è£
ã¨éå§æã®ã»ãã¥ãªãã£ã¨ãè
æ
®ãã¦æ±ºããã¹ãã§ããã
çµå¶é£ãåé¡ã«é¢ããããã«ããããã®åçµã¨ãã¦ãäºæ¥äºä¾ãæåãã第ä¸è
ã®å®ä¾ã«å£ã
ã¨ä¸æãè¡ããã¨ãå¤ããäºæ¥äºä¾ã¯çµå¶é£ã«å¯¾ããä»ã®çµç¹ã§ãåãåé¡ãæ±ãããã¨ã解
決çãè¦ãã ããããã«è§£æ±ºãããã示ãã¹ãã§ããããããããã¨ã§çµå¶é£ã¯ããã®è§£æ±ºç
ã¯ä½ããèªåãã¡ã®çµç¹ã«ã©ãå¿ç¨ã§ããã®ããåããã¨ãã§ããããã«ãªãã
4.2 æ©è½æ¨ªæãã¼ã ã®çµæã»æè²è¨ç·´
æ©è½æ¨ªæåæ
å ±ã»ãã¥ãªãã£ãã¼ã ãå¤æ§ãªåéã®ç¥èã»çµé¨ãå
±æãåããICS ã®ãªã¹ã¯ã
è©ä¾¡ã»ç·©åãããã¨ãä¸å¯æ¬ ã¨ãªããæ
å ±ã»ãã¥ãªãã£ãã¼ã ã®æ§æã¯ãå°ãªãã¨ãçµç¹ã® IT
è·å¡ãå¶å¾¡ã¨ã³ã¸ãã¢ãå¶å¾¡ã·ã¹ãã æä½å¡ãã»ãã¥ãªãã£åé¡æ
å½è
åã³ä¼æ¥ã®ãªã¹ã¯ç®¡ç
è·å¡ãå«ããã¹ãã§ãããã»ãã¥ãªãã£ã®ç¥èã»ã¹ãã«ã«ã¯ããããã¯ã¼ã¯ã¢ã¼ããã¯ãã£ã»
è¨è¨ãã»ãã¥ãªãã£ããã»ã¹ã»è¦ç¯åã³ã»ãã¥ã¢ãªã¤ã³ãã©ã»æ¥åãå«ããã¹ãã§ãããå®å
¨
ã¨ã»ãã¥ãªãã£ã¯ãã¸ã¿ã«å¶å¾¡ãåããæ¥ç¶ã·ã¹ãã ã®æ°ããç¹å¾´ã§ããã¨ããæè¿ã®èãæ¹
ã«ã¯ãå®å
¨ã®ã¨ãã¹ãã¼ããå«ãããã¨ã示åããã¦ãããç¶ç¶æ§ã¨å®å
¨æ§ã確ä¿ããããã
æ
å ±ã»ãã¥ãªãã£ãã¼ã ã«ã¯ãå¶å¾¡ã·ã¹ãã ã®ãã³ãã¼ãã·ã¹ãã ã¤ã³ãã°ã¬ã¼ã¿ããå«ãã
ã¹ãã§ããã
æ
å ±ã»ãã¥ãªãã£ãã¼ã ã«ã¯ãä»»åã»äºæ¥ããã»ã¹åã¯çµç¹ã¬ãã«ã®æ
å ±ã»ãã¥ãªãã£ç®¡ç
è
ã«ç´æ¥å ±åãä¸ããã¹ãã§ã次ãã§å管çè
ã¯ãããããä»»åã»äºæ¥ããã»ã¹ç®¡çè
ï¼æ½
è¨ç£ç£çï¼åã¯ä¼æ¥æ
å ±ã»ãã¥ãªãã£ç®¡çè
ï¼CIO/CSO çï¼ã«å ±åãããæçµçãªæ¨©éã¨è²¬ä»»
ã¯ããªã¹ã¯ç®¡çã«å¯¾ãã¦å
¨ä½çãçµç¹å
¨ä½ã«ãããåçµãè¡ãã第 1段éã«ããããªã¹ã¯æ
å½å½¹å¡ã«ããããªã¹ã¯æ
å½å½¹å¡ã¯ãçµå¶ã®ãããã¨é£æºãã¦ãICS ã®æ
å ±ã»ãã¥ãªãã£ã«é¢ã
ãæ®ãã®ãªã¹ã¯ã¬ãã«ã¨èª¬æ責任ãåãå
¥ãããçµå¶é£ã¬ãã«ã®èª¬æ責任ã¯ãæ
å ±ã»ãã¥ãª
ãã£ã¸ã®åçµã«å¯¾ãã¦è¡ããã¦ãã姿å¢ã確åºãããã®ã«ããã®ã«å½¹ç«ã¤ã
å¶å¾¡ã¨ã³ã¸ãã¢ã¯ ICS ã®ã»ãã¥ãªãã£ç¢ºä¿ã«å¤§ããªå½¹å²ãæããããIT é¨éã¨çµå¶é£ããã®å
åã»æ¯æ´ããªããã°åã¾ããªããIT ã«ãããã»ãã¥ãªãã£ã®çµé¨ã¯æ°å¹´ã«åã¶ãã¨ãå¤ããã
ãã®å¤§é¨å㯠ICS ã«ãå¿ç¨ã§ãããå¶å¾¡ã¨ã³ã¸ãã¢ã¨ IT ã®æåã¯ãããã大ããç°ãªããã
ååçãªã»ãã¥ãªãã£ã®è¨è¨ã»å®æ½ãå®æããã«ã¯ä¸¡è
ã®ä¸ä½åãä¸å¯æ¬ ã¨ãªãã
4.3 æ²ç« åã³é©ç¨ç¯å²ã®æ確å
æ
å ±ã»ãã¥ãªãã£ç®¡çè
ã¯ãæ
å ±ã»ãã¥ãªãã£ã®çµç¹ãã·ã¹ãã ææè
ãä»»åã»äºæ¥ããã»ã¹
管çè
åã³ã¦ã¼ã¶ã®å½¹å²ã»è²¬ä»»ã»èª¬æ責任ãæ確ã«ãããæéã¨ãªãæ²ç« ãå®ããã¹ãã§ããã
æ
å ±ã»ãã¥ãªãã£ç®¡çè
ã¯ãã»ãã¥ãªãã£ããã°ã©ã ã®ç®çãå½±é¿ãåããäºæ¥çµç¹ãé¢ä¿ã
ãå
¨ã¦ã®ã³ã³ãã¥ã¼ã¿ã·ã¹ãã ã¨ãããã¯ã¼ã¯ãå¿
è¦ãªäºç®ã¨ãªã½ã¼ã¹åã³è²¬ä»»ã®åæ
ãæã
ãã«ãã¦ãææ¸åãã¹ãã§ããã
ã¾ãããã«ã¯äºæ¥ãè¨ç·´ãç£æ»ãæ³çè¦ä»¶åã³äºå®è¡¨ã¨è²¬ä»»ãå«ã¾ãããæ
å ±ã»ãã¥ãªãã£
çµç¹ã®æéã¨ãªãæ²ç« ã¯ãã»ã¯ã·ã§ã³ 3ã§èª¬æããä¼æ¥ã¢ã¼ããã¯ãã£ã®ä¸é¨ããªãæ
å ±ã»
ãã¥ãªãã£ã¢ã¼ããã¯ãã£ãæ§æããè¦ç´ ã¨ãªãã
SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
73
There may already be an information security program in place or being developed for the organizationâs
IT business systems. The ICS information security manager should identify which existing practices to
leverage and which practices are specific to the control system. In the long run, it will be easier to get
positive results if the team can share resources with others in the organization that have similar objectives.
4.4 Define ICS-specific Security Policies and Procedures
Policies and procedures are at the root of every successful security program. Wherever possible, ICS-
specific security policies and procedures should be integrated with existing operational/management
policies and procedures. Policies and procedures help to ensure that security protection is both consistent
and current to protect against evolving threats. Appendix C cites a lack of security policy as an important
vulnerability. Appendix Gâ, the ICS overlay, contains many ICS information security policy
recommendations. After an information security risk analysis has been performed, the information security
manager should examine existing security policies to see if they adequately address the risks to the ICS. If
needed, existing policies should be revised or new policies created.
As discussed in Section 3, Tier 1 management is responsible for developing and communicating the risk
tolerance of the organizationâthe level of risk the organization is willing to acceptâwhich allows the
information security manager to determine the level of risk mitigation that should be taken to reduce
residual risk to acceptable levels. The development of the security policies should be based on a risk
assessment that will set the security priorities and goals for the organization so that the risks posed by the
threats are mitigated sufficiently. Procedures that support the policies need to be developed so that the
policies are implemented fully and properly for the ICS. Security procedures should be documented, tested,
and updated periodically in response to policy, technology, and threat changes.
4.5 Implement an ICS Security Risk Management Framework
From an abstract viewpoint, the management of ICS risks is another risk added to the list of risks
confronting an organization (e.g., financial, safety, IT, environmental). In each case, managers with
responsibility for the mission or business process establish and conduct a risk management program in
coordination with top managementâs risk executive function. NIST Special Publication 800-39, Managing
Information Security RiskâOrganization, Mission, and Information System View [20], is the foundation of
such a risk management program. Just like the other mission/business process areas, the personnel
concerned with ICS apply their specialized subject matter knowledge to establishing and conducting ICS
security risk management and to communicating with enterprise management to support effective risk
management across all the enterprise. NIST Special Publication 800-37, Guide for Applying the Risk
Management Framework to Federal Information Systems [21], introduces the risk management framework
which addresses the process of implementing the framework. The following sections summarize this
process and apply the RMF to an ICS environment.
The RMF process includes a set of well-defined risk-related tasks that are to be carried out by selected
individuals or groups within well-defined organizational roles (e.g., risk executive [function], authorizing
official, authorizing official designated representative, chief information officer, senior information security
officer, enterprise architect, information security architect, information owner/steward, information system
owner, common control provider, information system security officer, and security control assessor). Many
risk management roles have counterpart roles defined in the routine system development life cycle
processes. RMF tasks are executed concurrently with or as part of system development life cycle processes,
taking into account appropriate dependencies.
SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
74
æ¢ã«çµç¹ã® IT äºæ¥ã·ã¹ãã ã«é¢ããæ
å ±ã»ãã¥ãªãã£ããã°ã©ã ãæ½è¡ããã¦ããããä½æä¸
ã¨ããå ´åããããICS æ
å ±ã»ãã¥ãªãã£ç®¡çè
ã¯ãæ¢åã®è¦ç¯ã§æ´»ç¨ã§ãããã®ã¨ãå¶å¾¡ã·
ã¹ãã ã«åºæã®è¦ç¯ã¨ãç¹å®ãã¹ãã§ãããé·ãç®ã§è¦ãã°ãçµç¹ã§åæ§ã®ç®çãæã£ããã¼
ã å士ããªã½ã¼ã¹ãå
±æãåããã¨ã§ãããçµæãå¾ããããªãã
4.4 ICS åºæã®ã»ãã¥ãªãã£ããªã·ã¼åã³æé ã®æ確å
ããªã·ã¼ã¨æé ã¯ãããããã»ãã¥ãªãã£ããã°ã©ã ãæåã«å°ãè¦ã§ãããå¯è½ã§ããã°ã
ICS åºæã®ã»ãã¥ãªãã£ããªã·ã¼ã¨æé ãæ¢åã®æ¥å/管çããªã·ã¼åã³æé ã¨ä¸ä½åãã¹ã
ã§ãããããªã·ã¼ã¨æé ã¯ãé²åããè
å¨ã«å¯¾ãã¦ãã»ãã¥ãªãã£ä¿è·ãä¸è²«æ§ã¨ææ°æ§ã
åãããã®ã«ããä¸ã§å½¹ç«ã¤ãä»é² Cã«ã¯ãã»ãã¥ãªãã£ããªã·ã¼ã®æ¬ å¦ãé大ãªèå¼±æ§ã¨
ãã¦è¨åãã¦ãããä»é² Gã®ICS ãªã¼ãã¼ã¬ã¤ã«ã¯ãæ°ã
ã® ICS æ
å ±ã»ãã¥ãªãã£ããªã·ã¼
ã«é¢ããæ¨å¥¨äºé
ãå«ã¾ãã¦ãããæ
å ±ã»ãã¥ãªãã£ã®ãªã¹ã¯åæãå®æ½å¾ãæ
å ±ã»ãã¥ãª
ãã£ç®¡çè
ã¯æ¢åã®ã»ãã¥ãªãã£ããªã·ã¼ãæ¤è¨¼ããICS ã¸ã®ãªã¹ã¯ããã£ããåãä¸ããã
ã¦ããã確èªãã¹ãã§ãããå¿
è¦ã§ããã°ãæ¢åã®ã»ãã¥ãªãã£ããªã·ã¼ãæ¹æ£ããããä½
ãç´ãã¹ãã§ããã
ã»ã¯ã·ã§ã³ 3ã§è¿°ã¹ãã¨ããã第 1段éã®çµå¶é£ã¯çµç¹ã®ãªã¹ã¯ãã¬ã©ã³ã¹ãçå®ãã¦ä¼éã
ã責任ãæããããªã¹ã¯ãã¬ã©ã³ã¹ã¨ã¯çµç¹ãåãå
¥ãå¯è½ãªã¬ãã«ã®ãªã¹ã¯ããããããã
åºã«æ
å ±ã»ãã¥ãªãã£ç®¡çè
ã¯ãæ®ãã®ãªã¹ã¯ãå容ã¬ãã«ã«ã¾ã§ç·©åããããã®ãªã¹ã¯ã¬ã
ã«ç·©åçã決ãããã¨ãã§ãããã»ãã¥ãªãã£ããªã·ã¼ã®çå®ã¯ããªã¹ã¯è©ä¾¡ã«åºã¥ããããª
ã¹ã¯è©ä¾¡ã¯çµç¹ã®ã»ãã¥ãªãã£åªå
度ã¨ç®æ¨ãè¨å®ããè
å¨ããããããªã¹ã¯ãååç·©åã§ã
ãããã«ãããããªã·ã¼ãæ¯ããæé ã¯ãããªã·ã¼ã ICS ã«å¯¾ãã¦ååãã¤é©æ£ã«å®æ½ã§ãã
ããã«çå®ããå¿
è¦ããããã»ãã¥ãªãã£æé ã¯ããªã·ã¼ãæè¡åã³è
å¨ã®å¤åã«å¯¾å¿ãã¦ã
ææ¸åããæ¤è¨¼ããå®æçã«æ´æ°ãã¹ãã§ããã
4.5 ICS ã»ãã¥ãªãã£ãªã¹ã¯ç®¡çä½å¶ã®å®è¡
æ½è±¡çãªã¨ããæ¹ãããã°ãICS ãªã¹ã¯ã®ç®¡çã¯ãçµç¹ãç´é¢ãããªã¹ã¯ãªã¹ãï¼è²¡æ¿ãå®å
¨ã
ITãç°å¢çï¼ã«è¿½å ãããä»å çãªã¹ã¯ã¨ãããããããã®å ´åããä»»åãäºæ¥ããã»ã¹ã«è²¬
ä»»ãæãã管çè
ã¯ãçµå¶ãããã®ãªã¹ã¯æ
å½å½¹å¡ã¨å調ãã¦ããªã¹ã¯ç®¡çããã°ã©ã ãçå®
ãå®è¡ãããNIST ç¹å¥åºçç© 800-39ãæ
å ±ã»ãã¥ãªãã£ãªã¹ã¯ã®ç®¡çï¼çµç¹ãä»»åããã³æ
å ±ã·ã¹ãã ã®ç²¾æ»ã[20]ã¯ããã®ãããªãªã¹ã¯ç®¡çããã°ã©ã ã®åºæ¬ã§ãããä»ã®ä»»åã»äºæ¥
ããã»ã¹åéã¨åæ§ãICS ã«é¢ãã人å¡ã¯ããããã®å°éç¥èããICS ã»ãã¥ãªãã£ãªã¹ã¯ç®¡
çã®çå®ããä¼æ¥çµå¶é£ã¨é£æºãã¦å
¨ç¤¾çãã¤å¹æçãªãªã¹ã¯ç®¡çã®æ¯æ´ã«é©ç¨ãããNIST ç¹
å¥åºçç© 800-37ãé£é¦æ
å ±ã·ã¹ãã ã«ãªã¹ã¯ç®¡çä½å¶ãé©ç¨ããããã®ã¬ã¤ãã [21]ã¯ããª
ã¹ã¯ç®¡çä½å¶ã«ã¤ãã¦èª¬æããä½å¶æ§ç¯ããã»ã¹ãåãä¸ãã¦ãããç¶ãã»ã¯ã·ã§ã³ã§ã¯ãã
ã®ããã»ã¹ãè¦ç´ããICS ç°å¢ã¸ã®ãªã¹ã¯ç®¡çä½å¶ï¼RMFï¼ã®é©ç¨ã説æããã
RMF ããã»ã¹ã«ã¯ãæ確åãããçµç¹çå½¹å²ï¼ãªã¹ã¯æ
å½å½¹å¡ã許å¯æ¨©è
ã許å¯æ¨©è
ãæåã
ã代表è
ãæé«æ
å ±è²¬ä»»è
ãæ
å ±ã»ãã¥ãªãã£ä¸»ä»»ãä¼æ¥è¨è¨è
ãæ
å ±ã»ãã¥ãªãã£è¨è¨è
ã
æ
å ±ææè
/å·äºãæ
å ±ã·ã¹ãã ææè
ãå
±éå¶å¾¡ãããã¤ããæ
å ±ã·ã¹ãã ã»ãã¥ãªãã£æ
å½è
ãã»ãã¥ãªãã£ç®¡çæ»å®è
çï¼ã®ç¯å²å
ã§é¸ã°ããå人ãã°ã«ã¼ããéè¡ãã¹ããæ確å
ããããªã¹ã¯é¢é£ä½æ¥ãå«ã¾ãã¦ããããªã¹ã¯ç®¡çä¸ã®å½¹å²ã®å¤ãã«ã¯ãæ常çãªã·ã¹ãã é
çºã©ã¤ããµã¤ã¯ã«ããã»ã¹ã§æããã«ããã¦ãããã®ã«ç¸å½ããå½¹å²ãå«ã¾ãããRMF ä½æ¥ã¯ã
é©æ£ãªç¸äºä¾åãèæ
®ã«å
¥ããä¸ã§ãã·ã¹ãã éçºã©ã¤ããµã¤ã¯ã«ããã»ã¹ã¨åæã«ãåã¯ã
ã®ä¸é¨ã¨ãã¦å®æ½ããã
SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
75
Organizations may also wish to consult ISA-62443-2-1, Security for Industrial Automation and Control
Systems: Establishing an Industrial Automation and Control Systems Security Program, which describes
another view of the elements contained in a cybersecurity management system for use in the industrial
automation and control systems environment [34]. It provides guidance on how to meet the requirements
described for each element. Sections 4 through 6 correspond most closely to NIST SP 800-39; other
sections correspond to other NIST Special Publications and to the ICS overlay in Appendix Gâ of this
document. All of these guidance documents recognize that one size does not fit all; rather, domain
knowledge should be applied in tailoring or adapting the guidance to the specific organization.
4.5.1 Categorize ICS Systems and Networks Assets
The information security team should define, inventory, and categorize the applications and computer
systems within the ICS, as well as the networks within and interfacing to the ICS. The focus should be on
systems rather than just devices, and should include PLCs, DCS, SCADA, and instrument-based systems
that use a monitoring device such as an HMI. Assets that use a routable protocol or are dial-up accessible
should be documented. The team should review and update the ICS asset list annually and after each asset
addition or removal.
There are several commercial enterprise IT inventory tools that can identify and document all hardware and
software resident on a network. Care must be taken before using these tools to identify ICS assets; teams
should first conduct an assessment of how these tools work and what impact they might have on the
connected control equipment. Tool evaluation may include testing in similar, non-production control
system environments to ensure that the tools do not adversely impact the production systems. Impact could
be due to the nature of the information or the volume of network traffic. While this impact may be
acceptable in IT systems, it may not be acceptable in an ICS.
An automated management system for inventory (e.g., Computerized Maintenance Management System
(CMMS), Computer Aided Facility Management System (CAFM), Building Information Model (BIM),
Geospatial Information System (GIS), Construction-Operations Building information exchange data
(COBie, Building Automation Management information exchange (BAMie), Sustainment Management
Systems (SMS) Builder) allows an organization to keep an accurate account of what is on the system for
security reasons and budgetary reasons as well.
4.5.2 Select ICS Security Controls
The security controls selected based on the security categorization of the ICS are documented in the
security plan to provide an overview of the security requirements for the ICS information security program
and describes the security controls in place or planned for meeting those requirements. The development of
security plans is addressed in NIST Special Publication 800-18 Revision 1, Guide for Developing Security
Plans for Federal Information Systems [19]. The security plan can be one document, or it can be the set of
all documents addressing the security concerns for a system and the plans for countering these concerns. In
addition to security controls, NIST Special Publication 800-53 Revision 4, Security and Privacy Controls
for Federal Information Systems and Organizations [20], provides a set of information security program
management (PM) controls that are typically implemented at the organization level and not directed at
individual organizational information systems. This section addresses how an organization establishes and
carries out these program management controls.
The successful implementation of security controls for organizational information systems depends on the
successful implementation of organization-wide program management controls. The manner in which
organizations implement the program management controls depends on specific organizational
characteristics including, for example, the size, complexity, and mission/business requirements of the
SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
76
ISA-62443-2-1ãç£æ¥ãªã¼ãã¡ã¼ã·ã§ã³åã³å¶å¾¡ã·ã¹ãã ã®ã»ãã¥ãªãã£ï¼ç£æ¥ãªã¼ãã¡ã¼ã·
ã§ã³åã³å¶å¾¡ã·ã¹ãã ã®ã»ãã¥ãªãã£ããã°ã©ã ã®æ§ç¯ã[34]ã¯ãç£æ¥ãªã¼ãã¡ã¼ã·ã§ã³åã³
å¶å¾¡ã·ã¹ãã ç°å¢ç¨ã®ãµã¤ãã¼ã»ãã¥ãªãã£ç®¡çã·ã¹ãã ã«å¯¾ããå¥ã®è¦æ¹ãç´¹ä»ãã¦ããã
åèã«ãããã¨ãã§ããããè¦ç´ ãã¨ã«è¦ä»¶ãæºè¶³ããããã®æ¹æ³ã«ã¤ãã¦ãæéãè¨è¼ãã
ã¦ãããã»ã¯ã·ã§ã³ 4ï½6ã¯NIST SP 800-39 ã«ã»ã¼å¯¾å¿ãã¦ãããä»ã®ã»ã¯ã·ã§ã³ã¯ãã以å¤
ã®NIST ç¹å¥åºçç©åã³æ¬æ¸ä»é² Gã®ICS ãªã¼ãã¼ã¬ã¤ã«å¯¾å¿ãã¦ããããããã¬ã¤ãã³ã¹æ
æ¸ã¯ã©ããã¿ãªãä¸ã¤ã®ãµã¤ãºã§å
¨ã¦ã«ãã£ãããããããªãã®ã¯ãªãã¨è¿°ã¹ã¦ããããããã
ããåéã®ç¥è¦ãå¿ç¨ãã¦ãã¬ã¤ãã³ã¹ãç¹å®ã®çµç¹ã«é©å¿ãããã¹ãã§ããã
4.5.1 ICS ã·ã¹ãã ã¨ãããã¯ã¼ã¯è³ç£ã®åé¡
æ
å ±ã»ãã¥ãªãã£ãã¼ã ã¯ãICS å
ã®ã¢ããªã±ã¼ã·ã§ã³åã³ã³ã³ãã¥ã¼ã¿ã·ã¹ãã 並ã³ã« ICS
å
åã³ ICS ã¨é£æ¥ãããããã¯ã¼ã¯ãå®ç¾©ããç®é²ãä½æããåé¡ãã¹ãã§ãããããã¤ã¹ã®
ã¿ãªããã·ã¹ãã ã«é
æ
®ããPLCsãDCSãSCADAããã®ä» HMI çã®ç£è¦ããã¤ã¹ã使ç¨ããè¨å¨
主ä½ã®ã·ã¹ãã ãå«ããã¹ãã§ãããã«ã¼ãã£ã³ã°ãããã³ã«ã使ç¨ããè³ç£ããã¤ã¢ã«ã¢ã
ãã§ã¢ã¯ã»ã¹ããè³ç£ã¯ææ¸åãã¹ãã§ããããã¼ã 㯠ICS è³ç£ãªã¹ããå¹´ã«ä¸åº¦ãã¾ã追å
ãåé¤ããããã³ã«è¦ç´ãã¦æ´æ°ãã¹ãã§ããã
ãããã¯ã¼ã¯ã«å¸¸é§ãã¦ããå
¨ã¦ã®ãã¼ãã¦ã¨ã¢/ã½ããã¦ã¨ã¢ãèå¥ãã¦è¨é²ã§ãããå¸è²©
ã®ä¼æ¥ IT ã¤ã³ãã³ããªã¼ãã¼ã«ãããã¤ãããããããããã¼ã«ã使ç¨ã㦠ICS è³ç£ãèå¥
ããåã«æ³¨æãå¿
è¦ã¨ãªãããã¼ã ã¯ã¾ããã¼ã«ã®åãã¨ãæ¥ç¶ãããå¶å¾¡è£
ååã«åã¶å½±
é¿ã調ã¹ãã¹ãã§ããããã¼ã«ãè©ä¾¡ããã«ã¯ãé¡ä¼¼ã®éçç£ç°å¢ã«ããã試é¨ãè¡ããç
ç£ã·ã¹ãã ã«ã¯æªå½±é¿ããªããã¨ã確èªããã¨ãããå½±é¿ã¯ãæ
å ±ã®æ§è³ªããããã¯ã¼ã¯ã
ã©ãã£ãã¯éã«èµ·å ãããã¨ããããããããå½±é¿ã¯ IT ã·ã¹ãã ã§ã¯è¨±å®¹ã§ãã¦ããICS ã§
ã¯åãå
¥ããããªããã¨ãããã
ã¤ã³ãã³ããªã¼ç¨èªå管çã·ã¹ãã ï¼ã³ã³ãã¥ã¼ã¿ä¿å®ç®¡çã·ã¹ãã [CMMS]ãã³ã³ãã¥ã¼ã¿æ´
ç¨æ½è¨ç®¡çã·ã¹ãã [CAFM]ããã«æ
å ±ã¢ãã«[BIM]ãå°ç空éæ
å ±ã·ã¹ãã [GIS]ã建è¨ä½æ¥ã
ã«æ
å ±äº¤æãã¼ã¿[COBie]ããã«ãªã¼ãã¡ã¼ã·ã§ã³ç®¡çæ
å ±äº¤æ[BAMie]ãæç¶ç®¡çã·ã¹ãã
[SMS]ãã«ãã¼çï¼ã¯ã»ãã¥ãªãã£ç®çã¨äºç®ç®çã§ã·ã¹ãã ä¸ã«ãããã®ãæ£ç¢ºã«ææ¡ãã
ãã¨ãã§ããã
4.5.2 ICS ã»ãã¥ãªãã£ç®¡çã®é¸æ
ICS ã®ã»ãã¥ãªãã£åé¡ã«å¾ã£ã¦é¸æããã»ãã¥ãªãã£ç®¡çã¯ãã»ãã¥ãªãã£è¨ç»æ¸ã«è¨é²ã
ããICS æ
å ±ã»ãã¥ãªãã£ããã°ã©ã ã®ã»ãã¥ãªãã£è¦ä»¶ã®æ¦è¦ã示ããè¦ä»¶ãéµå®ãããã
ã«æ½è¡ä¸åã¯è¨ç»ä¸ã®ã»ãã¥ãªãã£ç®¡çã«ã¤ãã¦èª¬æãä¸ãããã»ãã¥ãªãã£è¨ç»æ¸ã®ä½æã«
ã¤ãã¦ã¯ãNIST ç¹å¥åºçç© 800-18 æ¹è¨ç¬¬ 1çãé£é¦æ
å ±ã·ã¹ãã ç¨ã»ãã¥ãªãã£è¨ç»æ¸ã®ä½
æã¬ã¤ãã[19]ã§åãä¸ãããã¦ãããã»ãã¥ãªãã£è¨ç»æ¸ã¯ä¸åã®ææ¸ã§ããããã·ã¹ãã
ã®ã»ãã¥ãªãã£ä¸ã®èª²é¡ã¨ãã®å¯¾å¦è¨ç»ãåããå
¨ææ¸ã®ä¸é¨ã§ãã£ã¦ããããã»ãã¥ãªãã£
管çã«å ãã¦ãNIST ç¹å¥åºçç© 800-53 æ¹è¨ç¬¬ 4çãé£é¦æ
å ±ã·ã¹ãã ã»çµç¹ç¨ã»ãã¥ãªã
ã£ã»ãã©ã¤ãã·ã¼ç®¡çã[20]ã«ã¯ãä¸è¬ã«çµç¹ã¬ãã«ã§å®è£
ãããåã
ã®çµç¹æ
å ±ã·ã¹ãã ã«
ã¯ãªãæ
å ±ã»ãã¥ãªãã£ããã°ã©ã 管çï¼PMï¼å¶å¾¡ã«ã¤ãã¦åãä¸ãããã¦ããããã®ã»ã¯ã·
ã§ã³ã§ã¯ãããã°ã©ã 管çå¶å¾¡ã®æ§ç¯åã³å®æ½è¦é ã«ã¤ãã¦åãä¸ããã
çµç¹ã®æ
å ±ã·ã¹ãã ç¨ã»ãã¥ãªãã£ç®¡çãé¦å°¾ããå®è£
ã§ãããã©ããã¯ãçµç¹å
¨ä½ã«ããã
ããã°ã©ã 管çå¶å¾¡ãé¦å°¾ããå®è£
ã§ãããã©ããã«ããã£ã¦ãããããã°ã©ã 管çå¶å¾¡ã®å®
è£
æ¹æ³ã¯ãããããã®ä¼æ¥ã®è¦æ¨¡ãè¤éæ§ãä»»åã»äºæ¥è¦ä»¶ã¨ãã£ãä¼æ¥ã®æ§æ ¼ã«å·¦å³ãããã
SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
77
respective organizations. The program management controls complement the security controls and focus on
the programmatic, organization-wide information security requirements that are independent of any
particular information system and are essential for managing information security programs. Organizations
document program management controls in the information security program plan. The organization-wide
information security program plan supplements the individual security plans developed for each
organizational information system. Together, the security plans for the individual information systems and
the information security program cover the totality of security controls employed by the organization.
4.5.3 Perform Risk Assessment
Because every organization has a limited set of resources, organizations should assess the impacts to
organizational operations (i.e., mission, functions, image, and reputation), organizational assets, individuals,
other organizations, and the Nation (e.g., using FIPS 199 [15] or a more granular approach). As discussed
in Section 3, organizations can experience the consequences/impact of adverse events at the individual ICS
system level (e.g., failing to perform as required), at the mission/business process level (e.g., failing to fully
meet mission/business objectives), and at the organizational level (e.g., failing to comply with legal or
regulatory requirements, damaging reputation or relationships, or undermining long-term viability). An
adverse event can have multiple consequences and different types of impact, at different levels, and in
different time frames. NIST SP 800-53 [22] and the ICS overlay in Appendix Gâ incorporate baseline
security controls that derive from this determination of impact.
The organization may perform a detailed risk assessment for the highest impact systems and assessments
for lower impact systems as deemed prudent and as resources allow. The risk assessment will help identify
any weaknesses that contribute to information security risks and mitigation approaches to reduce the risks.
Risk assessments are conducted multiple times during a systemâs life cycle. The focus and level of detail
varies according to the systemâs maturity.
4.5.4 Implement the Security Controls
Organizations should analyze the detailed risk assessment and the impacts to organizational operations (i.e.,
mission, functions, image, and reputation), organizational assets, individuals, other organizations, and the
Nation, and prioritize selection of mitigation controls. Organizations should focus on mitigating risk with
the greatest potential impact. Security control implementation is consistent with the organizationâs
enterprise architecture and information security architecture.
The controls to mitigate a specific risk may vary among types of systems. For example, user authentication
controls might be different for ICS than for corporate payroll systems and e-commerce systems. The ICS
information security manager should document and communicate the selected controls, along with the
procedures for using the controls. Some risks may be identified that can be mitigated by âquick fixâ
solutionsâlow-cost, high-value practices that can significantly reduce risk. Examples of these solutions are
restricting Internet access and eliminating email access on operator control stations or consoles.
Organizations should identify, evaluate, and implement suitable quick fix solutions as soon as possible to
reduce security risks and achieve rapid benefits. The Department of Energy (DOE) has a â21 Steps to
Improve Cyber Security of SCADA Networksâ [33] document that could be used as a starting point to
outline specific actions to increase the security of SCADA systems and other ICS.
SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
78
ããã°ã©ã 管çå¶å¾¡ã¯ã»ãã¥ãªãã£ç®¡çãè£å®ãããã®ã§ãç¹å®ã®æ
å ±ã·ã¹ãã ããç¬ç«ããã
æ
å ±ã»ãã¥ãªãã£ããã°ã©ã ã®ç®¡çã«ä¸å¯æ¬ ãªãããã°ã©ã ã«å¾ã£ãå
¨çµç¹çæ
å ±ã»ãã¥ãªãã£
è¦ä»¶ã«ç¦ç¹ãå½ã¦ã¦ããã
çµç¹ã¯ãããã°ã©ã 管çå¶å¾¡ãæ
å ±ã»ãã¥ãªãã£ããã°ã©ã è¨ç»æ¸ã®ä¸ã«è¨è¼ãããå
¨çµç¹ç
æ
å ±ã»ãã¥ãªãã£ããã°ã©ã è¨ç»æ¸ã¯ãåçµç¹ã®æ
å ±ã·ã¹ãã ç¨åå¥ã»ãã¥ãªãã£è¨ç»æ¸ãè£
å®ãããåæã«åã
ã®æ
å ±ã·ã¹ãã ç¨ã»ãã¥ãªãã£è¨ç»æ¸ã¨æ
å ±ã»ãã¥ãªãã£ããã°ã©ã ã¯ã
çµç¹ãæ¡ç¨ããã»ãã¥ãªãã£ç®¡çãå
¨ä½çã«ç¶²ç¾
ããã
4.5.3 ãªã¹ã¯è©ä¾¡å®æ½
ã©ã®çµç¹ã«ãããç¨åº¦ã®ãªã½ã¼ã¹ããããããçµç¹ã¯çµç¹æ¥åã¸ã®å½±é¿ï¼ä»»åãæ©è½ãã¤ã¡ã¼
ã¸ãè©å¤çï¼ãçµç¹ã®è³ç£ãå人ãä»ã®çµç¹ãå½ã«å¯¾ããå½±é¿ãè©ä¾¡ãã¹ãã§ãã
ï¼FIPS199[15]ãã®ä»ã®ã¢ããã¼ãã使ç¨ï¼ãã»ã¯ã·ã§ã³ 3ã§èª¬æããããã«ãçµç¹ã¯åã
ã®
ICS ã·ã¹ãã ã¬ãã«ã§ï¼è¦ä»¶ä¸å±¥è¡çï¼ãä»»åã»äºæ¥ããã»ã¹ã¬ãã«ã§ï¼ä»»åã»äºæ¥ç®çã®ä¸
å®å
¨ãªéè¡çï¼ãçµç¹ã¬ãã«ã§ï¼æ³çè¦ä»¶ã®ä¸å±¥è¡ãè©å¤ã»é¢ä¿ã®æ¯æãé·æçå®ç¾æ§ã®é»å®³
çï¼ãæ害äºè±¡ã®çµæã»å½±é¿ã被ããã¨ããããæ害äºè±¡ãããããçµæã¯ç¨®ã
ãããå¤æ§ãª
å½±é¿ãæ§ã
ãªã¬ãã«ãæé帯ã§çãããã¨ããããNIST SP 800-53[22]åã³ä»é² Gã®ICS ãªã¼
ãã¼ã¬ã¤ã«ã¯ããã®å½±é¿å¤å®ããå¾ãåºæ¬ã¨ãªãã»ãã¥ãªãã£ç®¡çãåãä¸ãããã¦ããã
çµç¹ã¯é©åã¨èããããå ´åããªã½ã¼ã¹ã®è¨±ãç¯å²ã§ãæ大ã®å½±é¿ãåããã·ã¹ãã ã«ã¯è©³ç´°
ãªãªã¹ã¯è©ä¾¡ãè¡ããæ¯è¼çå½±é¿ã®å°ãªãã·ã¹ãã ã«ãè©ä¾¡ãè¡ããã¨ãã§ããããªã¹ã¯è©ä¾¡
ã¯ãæ
å ±ã»ãã¥ãªãã£ã®ãªã¹ã¯ã«å¯ä¸ããå¼±ç¹ã¨ããªã¹ã¯ç·©åçãè¦æ¥µããã®ã«å½¹ç«ã¤ããªã¹
ã¯è©ä¾¡ã¯ã·ã¹ãã ã®ã©ã¤ããµã¤ã¯ã«æéä¸ãä½åº¦ãè¡ããéç¹ã¨è©³ç´°ã¬ãã«ã¯ã·ã¹ãã ã®å®æ
度ã«å¿ãã¦ç°ãªãã
4.5.4 ã»ãã¥ãªãã£ç®¡çã®å®è£
çµç¹ã¯è©³ç´°ãªãªã¹ã¯è©ä¾¡ã¨ãçµç¹æ¥åï¼ä»»åãæ©è½ãã¤ã¡ã¼ã¸ãè©å¤çï¼ãçµç¹è³ç£ãå人ã
ä»ã®çµç¹ãå½ã«å¯¾ããå½±é¿ãåæããç·©åçã®é¸å®ãåªå
ä»ããã¹ãã§ãããã¾ãæ大ã®å½±
é¿ããããããªãªã¹ã¯ã®ç·©åã«æ³¨åãã¹ãã§ãããã»ãã¥ãªãã£ç®¡çã®å®è£
ã¯ãçµç¹ã®ä¼æ¥
ã¢ã¼ããã¯ãã£åã³æ
å ±ã»ãã¥ãªãã£ã¢ã¼ããã¯ãã£ã¨æ´åããã
ç¹å®ã®ãªã¹ã¯ã®ç·©åçã¯ãã·ã¹ãã ã®ç¨®é¡ã«å¿ãã¦ç°ãªããä¾ãã°ãICS ã§ã®ã¦ã¼ã¶èªè¨¼ç®¡ç
ã¯ãä¼æ¥ã®çµ¦ä¸æ¯æã·ã¹ãã ã eã³ãã¼ã¹ã·ã¹ãã ã¨ã¯ç°ãªããICS æ
å ±ã»ãã¥ãªãã£ç®¡çè
ã¯ãé¸ãã 対çã¨ãã®ä½¿ç¨æé ã«ã¤ãã¦è¨é²ããä¼éãã¹ãã§ããããè¿
éè£ä¿®ãã½ãªã¥ã¼ã·
ã§ã³ãã¤ã¾ããªã¹ã¯ã大å¹
ã«æ¸ãããä½ã³ã¹ãã§é«ä¾¡å¤ãªè¦ç¯ã«ããç·©åå¯è½ãªãªã¹ã¯ãæã
ãã«ãªããã¨ããããããããã½ãªã¥ã¼ã·ã§ã³ã®ä¾ã¨ãã¦ãæä½å¡å¶å¾¡ã¹ãã¼ã·ã§ã³ãã³ã³ã½
ã¼ã«ã¸ã®ã¤ã³ã¿ã¼ãããã¢ã¯ã»ã¹ã®å¶éãé»åã¡ã¼ã«ã¢ã¯ã»ã¹ã®æé¤ãªã©ããããçµç¹ã¯ã»ã
ã¥ãªãã£ãªã¹ã¯ãæ¸ãããããã«ä¾¿çãå¾ãããããã«ãé©æ£ãªè¿
éè£ä¿®çã®èå¥ã»è©ä¾¡ã»å®
è£
ãå¯åçéããã«è¡ãã¹ãã§ãããã¨ãã«ã®ã¼çï¼DOEï¼ã«ã¯ãSCADA ãããã¯ã¼ã¯ã®ãµã¤ã
ã¼ã»ãã¥ãªãã£ãæ¹åãã 21 ã®ã¹ãããã[33]ããããSCADA ã·ã¹ãã ãã®ä» ICS ã®å
·ä½çã»
ãã¥ãªãã£åä¸çãèããã¹ã¿ã¼ãã£ã³ã°ãã¤ã³ãã¨ãã¦ä½¿ç¨ãããã¨ãã§ããã

SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
79
5. ICS Security Architecture
When designing a network architecture for an ICS deployment, it is usually recommended to separate the
ICS network from the corporate network. The nature of network traffic on these two networks is different:
Internet access, FTP, email, and remote access will typically be permitted on the corporate network but
should not be allowed on the ICS network. Rigorous change control procedures for network equipment,
configuration, and software changes may not be in place on the corporate network. If ICS network traffic is
carried on the corporate network, it could be intercepted or be subjected to DoS or Man-in-the-Middle
attacks [5.14]. By having separate networks, security and performance problems on the corporate network
should not be able to affect the ICS network.
Practical considerations, such as cost of ICS installation or maintaining a homogenous network
infrastructure, often mean that a connection is required between the ICS and corporate networks. This
connection is a significant security risk and should be protected by boundary protection devices. If the
networks must be connected, it is strongly recommended that only minimal (single if possible) connections
be allowed and that the connection is through a firewall and a DMZ. A DMZ is a separate network segment
that connects directly to the firewall. Servers containing the data from the ICS that needs to be accessed
from the corporate network are put on this network segment. Only these systems should be accessible from
the corporate network. With any external connections, the minimum access should be permitted through the
firewall, including opening only the ports required for specific communication. The following sections
elaborate on these architectural considerations. The ICS-CERT recommended practices working group
provides additional guidance as recommended practices21.
5.1 Network Segmentation and Segregation
This section addresses partitioning the ICS into security domains and separating the ICS from other
networks, such as the corporate network, and presents illustrative security architecture. Operational risk
analysis should be performed to determine critical parts of each ICS network and operation and help define
what parts of the ICS need to be segmented. Network segmentation involves partitioning the network into
smaller networks. For example, one large ICS network is partitioned into multiple ICS networks, where the
partitioning is based on factors such as management authority, uniform policy and level of trust, functional
criticality, and amount of communications traffic that crosses the domain boundary. Network segmentation
and segregation is one of the most effective architectural concepts that an organization can implement to
protect its ICS. Segmentation establishes security domains, or enclaves, that are typically defined as being
managed by the same authority, enforcing the same policy, and having a uniform level of trust.
Segmentation can minimize the method and level of access to sensitive information, ICS communication
and equipment configuration, and can make it significantly more difficult for a malicious cyber adversary
and can contain the effects of non-malicious errors and accidents. A practical consideration in defining a
security domain is the amount of communications traffic that crosses the domain boundary, because
domain protection typically involves examining boundary traffic and determining whether it is permitted.
The aim of network segmentation and segregation is to minimize access to sensitive information for those
systems and people who donât need it, while ensuring that the organization can continue to operate
effectively. This can be achieved using a number of techniques and technologies depending on the
networkâs architecture and configuration.
21 ICS-CERT recommended practices may be found at http://ics-cert.us-cert.gov/Recommended-Practices.

SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
80
5. ICS ã»ãã¥ãªãã£ã¢ã¼ããã¯ãã£
ICS å±éã®ãããã¯ã¼ã¯ã¢ã¼ããã¯ãã£ãè¨è¨ããéã«ã¯ãICS ãããã¯ã¼ã¯ãä¼æ¥ãããã¯ã¼
ã¯ããåãé¢ããã¨ã常ã«æ¨å¥¨ãããã両è
ã«ããããããã¯ã¼ã¯ãã©ãã£ãã¯ã®æ§è³ªã¯ç°ãªãã
ä¼æ¥ãããã¯ã¼ã¯ã§ã¯ã¤ã³ã¿ã¼ãããã¢ã¯ã»ã¹ãFTPãé»åã¡ã¼ã«åã³ãªã¢ã¼ãã¢ã¯ã»ã¹ãé常
許å¯ããã¦ããããICS ãããã¯ã¼ã¯ã§ã¯è¨±å¯ãã¹ãã§ãªãããããã¯ã¼ã¯è£
ååãæ§æåã³ã½
ããã¦ã¨ã¢å¤æ´ã«é¢ããå³æ ¼ãªå¤æ´ç®¡çæé ã¯ãä¼æ¥ãããã¯ã¼ã¯ã§ã¯å®æ½ãããªããICS ãã
ãã¯ã¼ã¯ãä¼æ¥ãããã¯ã¼ã¯ã¨ä¸ç·ã«ããã¨ãååãããã DoS ã人ãä»å¨ããæ»æã«ããã
ããããªã[5.14]ããããã¯ã¼ã¯ãåãé¢ããã¨ã§ãä¼æ¥ãããã¯ã¼ã¯ã®æ§è½ãåé¡ãçãã¦ãã
ICS ãããã¯ã¼ã¯ã«ã¯å½±é¿ãåã°ãªãã
ICS ã®è¨ç½®ã³ã¹ããå質ãªãããã¯ã¼ã¯ã¤ã³ãã©ã®ä¿å®ã³ã¹ãã¨ãã£ãç¾å®çãªèæ
®ã®çµæã
ICS ãããã¯ã¼ã¯ã¨ä¼æ¥ãããã¯ã¼ã¯ãæ¥ç¶ãããã¨ãããããããã®ãããªæ¥ç¶ã«ã¯å¤§ããªã»
ãã¥ãªãã£ãªã¹ã¯ããããå¢çä¿è·ããã¤ã¹ã§ä¿è·ãã¹ãã§ããã両ãããã¯ã¼ã¯ãæ¥ç¶ããå ´
åãæ¥ç¶ãæå°éï¼å¯è½ãªãã·ã³ã°ã«ï¼ã«ã¨ã©ãããã¡ã¤ã¢ã¦ã©ã¼ã«ã¨ DMZ ãè¨ãããã¨ãå¼·
ãæ¨å¥¨ããããDMZ ã¯å¥åã®ãããã¯ã¼ã¯ã»ã°ã¡ã³ãã§ããã¡ã¤ã¢ã¦ã©ã¼ã«ã«ç´æ¥æ¥ç¶ãããã
ICS ããã®ãã¼ã¿ãæã£ã¦ãããµã¼ãã§ãä¼æ¥ãããã¯ã¼ã¯ããæ¥ç¶ãããã®ã«ã¤ãã¦ã¯ããã®
ãããã¯ã¼ã¯ã»ã°ã¡ã³ãã«ç½®ããä¼æ¥ãããã¯ã¼ã¯ããæ¥ç¶å¯è½ãªã®ã¯ããã®ãããªã·ã¹ãã ã®
ã¿ã¨ãã¹ãã§ãããã©ã®ãããªå¤é¨æ¥ç¶ã§ãããæå°éã®ã¢ã¯ã»ã¹ã®ã¿ãã¡ã¤ã¢ã¦ã©ã¼ã«çµç±ã§
許å¯ããç¹å®ã®æ¥ç¶ã«å¿
è¦ãªãã¼ãã®ã¿éæ¾ãã¹ãã§ãããç¶ãã»ã¯ã·ã§ã³ã§ã¯ããã®ãããªã¢
ã¼ããã¯ãã£ä¸ã®èæ
®äºé
ã詳ããåãä¸ãããICS-CERT æ¨å¥¨è¦ç¯ä½æ¥ã°ã«ã¼ãã¯ãæ¨å¥¨è¦ç¯
ã¨ãã¦ä»å çãªã¬ã¤ãã³ã¹ãæä¾ãã¦ããã22
5.1 ãããã¯ã¼ã¯ã®åå²ã¨åé¢
ãã®ã»ã¯ã·ã§ã³ã§ã¯ãICS ã®ã»ãã¥ãªãã£é åã¸ã®åºç»åã¨ãä¼æ¥ãããã¯ã¼ã¯çä»ã®ãããã¯
ã¼ã¯ããã® ICS ã®åé¢ã«ã¤ãã¦èª¬æããã»ãã¥ãªãã£ã¢ã¼ããã¯ãã£ã®ä¾ã示ããæ¥åä¸ã®ãªã¹
ã¯åæãå®æ½ããå ICS ãããã¯ã¼ã¯åã³æ¥åã®éè¦é¨åãå¤å¥ããåå²ãã¹ã ICS é¨ä½ã®æ確
åãæ¯æ´ããããããã¯ã¼ã¯ã®åå²ã«ã¯ããããã¯ã¼ã¯ãããå°ãããããã¯ã¼ã¯ã«åºç»ããã
ã¨ãå«ã¾ãããä¾ãã°ã大ã㪠ICS ãããã¯ã¼ã¯ãè¤æ°ã® ICS ãããã¯ã¼ã¯ã«åºç»åããããåº
ç»ã¯çµå¶é£ã®æ¨©éãçµ±ä¸çãªããªã·ã¼åã³ä¿¡é ¼ã¬ãã«ãæ©è½ä¸ã®éè¦åº¦ãé åå¢çãè¶ããéä¿¡
ãã©ãã£ãã¯éã¨ãã£ãè¦å ãåºã«ããããããã¯ã¼ã¯ã®åå²ã¨åé¢ã¯ãçµç¹ããã® ICS é²è·ã®
ããã«å®è£
ã§ããæãå¹æçãªã¢ã¼ããã¯ãã£æ¦å¿µã® 1ã¤ã§ãããåå²ã«ãã£ã¦ã»ãã¥ãªãã£ã¢
ã¼ããã¯ãã£é åãã¤ã¾ãé£ã³å°ãã§ããããããã¯åãããªã·ã¼ãæ½è¡ããçµ±ä¸ãããä¿¡é ¼ã¬
ãã«ãæã¤åä¸ã®æ¨©éã«ãã管çããããã®ã¨ãä¸è¬ã«å®ç¾©ããã¦ãããåå²ã«ããè¦æ³¨ææ
å ±ã
ICS éä¿¡ãåã³è£
ååè¨å®ã¸ã®ã¢ã¯ã»ã¹æ¹æ³ãã¬ãã«ãæå°éã«æããæªæãããµã¤ãã¼æ»æã
èããå°é£ã«ããæªæã«ãããªãé誤ãäºæ
ã®å½±é¿ãå°ãè¾¼ãããã¨ãã§ãããã»ãã¥ãªãã£é
åãæ確ã«ããéã®ç¾å®çãªèæ
®äºé
ã¨ãã¦ãé åå¢çãè¶ããéä¿¡ãã©ãã£ãã¯éããããã¨
ããã®ã¯ãé åã®ä¿è·ã«ã¯ãé常å¢çãã©ãã£ãã¯ã®æ¤è¨¼ã¨è¨±å¯ã®æç¡ã«å¯¾ããå¤å®ãé¢ä¿ãã¦
ããããã§ããã
ãããã¯ã¼ã¯åå²ã»åé¢ã®ä¸»ç¼ã¯ãå¿
è¦ã¨ãã¦ããªãã·ã¹ãã ã人ãè¦æ³¨ææ
å ±ã«ã¢ã¯ã»ã¹ãã
ã®ãæå°éã«æããä¸æ¹ã§ãçµç¹ã®åæ»ãªæ¥åéè¡ã確ä¿ãããã¨ã«ãããããã¯ããããã¯ã¼
ã¯ã¢ã¼ããã¯ãã£åã³æ§æã«å¿ãã¦ã種ã
ã®ææ³ãæè¡ãé§ä½¿ãããã¨ã§éæãããã
22 ICS-CERT æ¨å¥¨ã®è¦ç¯ã«ã¤ãã¦ã¯ãå³è¨ã®ãã¼ã¸ãåç
§ã®ãã¨ãhttp://ics-cert.us-cert.gov/Recommended-Practices.
SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
81
Traditionally, network segmentation and segregation is implemented at the gateway between domains. ICS
environments often have multiple well-defined domains, such as operational LANs, control LANs, and
operational DMZs, as well as gateways to non-ICS and less trustworthy domains such as the Internet and
the corporate LANs. When insider attacks, social engineering, mobile devices, and other vulnerabilities and
predisposing conditions discussed in Appendix Câ are considered, protecting domain gateways is prudent
and worth considering.
Network segregation involves developing and enforcing a ruleset controlling which communications are
permitted through the boundary. Rules typically are based on source and destination identity and the type or
content of the data being transferred.
When implementing network segmentation and segregation correctly you are minimizing the method and
level of access to sensitive information. This can be achieved using a variety of technologies and methods.
Depending on the architecture and configuration of your network, some of the common technologies and
methods used include:
ï¼ Logical network separation enforced by encryption or network device-enforced partitioning.
o Virtual Local Area Networks (VLANS).
o Encrypted Virtual Private Networks (VPNs) use cryptographic mechanisms to separate traffic
combined on one network.
o Unidirectional gateways restrict communications between connections to a single direction,
therefore, segmenting the network.
ï¼ Physical network separation to completely prevent any interconnectivity of traffic between domains.
ï¼ Network traffic filtering which can utilize a variety of technologies at various network layers to
enforce security requirements and domains.
o Network layer filtering that restricts which systems are able to communicate with others on the
network based on IP and route information.
o Stateâbased filtering that restricts which systems are able to communicate with others on the
network based on their intended function or current state of operation.
o Port and/or protocol level filtering that restricts the number and type of services that each system
can use to communicate with others on the network.
o Application filtering that commonly filters the content of communications between systems at the
application layer. This includes application-level firewalls, proxies, and content-based filter.
Some vendors are making products to filter ICS protocols at the application level which they market as
ICS firewalls.
Regardless of the technology chosen to implement network segmentation and segregation, there are four
common themes that implement the concept of defense-in-depth by providing for good network
segmentation and segregation:
ï¼ Apply technologies at more than just the network layer. Each system and network should be
segmented and segregated, where possible, from the data link layer up to and including the application
layer.
ï¼ Use the principles of least privilege and needâtoâknow. If a system doesnât need to communicate
with another system, it should not be allowed to. If a system needs to talk only to another system on a
specific port or protocol and nothing elseâor it needs to transfer a limited set of labeled or fixed-
format data, it should be restricted as such.
SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
82
å¾æ¥ãããã¯ã¼ã¯ã®åå²ã»åé¢ã¯ãé åéã®ã²ã¼ãã¦ã§ã¤ã«å®è£
ããããICS ç°å¢ã¯ãæ¥åç¨
LANã管çç¨ LANãæ¥åç¨ DMZãé ICS ã¸ã®ã²ã¼ãã¦ã§ã¤ãã¤ã³ã¿ã¼ããããä¼æ¥ LAN çä¿¡é ¼æ§
ã®ä½ãé åã¸ã®ã²ã¼ãã¦ã§ã¤ã¨ãã£ããæ確ã«å®ç¾©ãããè¤æ°ã®é åãæã¤ãã®ãå¤ããä»é²
Cã§åãä¸ãããã¦ããã¤ã³ãµã¤ãã¼æ»æãã½ã¼ã·ã£ã«ã¨ã³ã¸ãã¢ãªã³ã°ãã¢ãã¤ã«ããã¤ã¹
ãã®ä»ã®èå¼±æ§åã³å¼±ç¹ã¨ãªãç¶æ
ã«ã¤ãã¦æ¤è¨ããå ´åãé åã²ã¼ãã¦ã§ã¤ãé²è·ãããã¨
ã¯å
å®ã§ãããæ¤è¨ã«å¤ããã
ãããã¯ã¼ã¯ã®åå²ã«ã¯ãå¢çãè¶ãã¦ãããéä¿¡ã管çããè¦åãçå®ããå®è¡ãããã¨ã
å«ã¾ãããè¦åã¯ãéä¿¡ãã¼ã¿ã®çºä¿¡å
ã»çä¿¡å
IDã種é¡åã¯å
容ãåºã«ããã
ãããã¯ã¼ã¯ã®åå²ã»åé¢ãé©æ£ã«å®è£
ããã°ãè¦æ³¨ææ
å ±ã¸ã®ã¢ã¯ã»ã¹æ¹æ³ãã¬ãã«ãæå°
éã«æãããã¨ã«ãªããããã¯å¤æ§ãªæè¡ãæ¹æ³ãç¨ãããã¨ã§å®ç¾ããããããã¯ã¼ã¯ã®ã¢
ã¼ããã¯ãã£åã³æ§æã«å¿ãã¦ãå
±éã«ç¨ããããæè¡ã»æ¹æ³ã¨ãã¦æ¬¡ã®ãããªãã®ãããã
ï¼ æå·ååã¯ãããã¯ã¼ã¯ããã¤ã¹ã«ããåºç»åã«ããå®è¡ãããè«çãããã¯ã¼ã¯åé¢
o ä»®æ³ LANï¼VLANSï¼
o æå·åä»®æ³ãã©ã¤ãã¼ããããã¯ã¼ã¯ï¼VPNsï¼ã¯æå·ã¡ã«ããºã ã使ç¨ãã¦ã
ãããããã¯ã¼ã¯ä¸ã®ãã©ãã£ãã¯ã®çµåãåé¢ãã
o åæ¹åã²ã¼ãã¦ã§ã¤ã¯æ¥ç¶ç¹éã®éä¿¡ãä¸æ¹åã«å¶éãã¦ããããã¯ã¼ã¯ãåå²
ãã
ï¼ ç©ççãããã¯ã¼ã¯åé¢ã¯é åéã®ãã©ãã£ãã¯ã®ç¸äºé£æ¥ãå
¨ã¦é²æ¢ãã
ï¼ ãããã¯ã¼ã¯ãã©ãã£ãã¯ãã£ã«ã¿ãªã³ã°ã¯å¤æ§ãªæè¡ã種ã
ã®ãããã¯ã¼ã¯å±¤ã§ä½¿ç¨ãã
ã»ãã¥ãªãã£è¦ä»¶åã³é åãæ½è¡ãã
o ãããã¯ã¼ã¯å±¤ãã£ã«ã¿ãªã³ã°ã¯ãIP åã³ã«ã¼ãæ
å ±ãåºã«ããããã¯ã¼ã¯ä¸ã®
ä»ã®ã·ã¹ãã ã¨äº¤ä¿¡å¯è½ãªã·ã¹ãã ãå¶éãã
o ç¶æ
ãã¼ã¹ãã£ã«ã¿ãªã³ã°ã¯ãç®çã¨ããæ©è½ãåä½ã®ç¾ç¶ãåºã«ããããã¯ã¼ã¯
ä¸ã®ä»ã®ã·ã¹ãã ã¨äº¤ä¿¡å¯è½ãªã·ã¹ãã ãå¶éãã
o ãã¼ãåã¯ãããã³ã«ã¬ãã«ãã£ã«ã¿ãªã³ã°ã¯ããããã¯ã¼ã¯ä¸ã®ä»ã®ã·ã¹ã
ã ã¨äº¤ä¿¡ããããã«ã·ã¹ãã ã使ç¨ã§ãããµã¼ãã¹ã®æ°ã¨ç¨®é¡ãå¶éãã
o ã¢ããªã±ã¼ã·ã§ã³ãã£ã«ã¿ãªã³ã°ã¯é常ãã·ã¹ãã éã®äº¤ä¿¡å
容ãã¢ããªã±ã¼ã·
ã§ã³å±¤ã§ãã£ã«ã¿ãªã³ã°ãããã¢ããªã±ã¼ã·ã§ã³ã¬ãã«ã®ãã¡ã¤ã¢ã¦ã©ã¼ã«ãã
ããã·åã³ã³ã³ãã³ããã¼ã¹ã®ãã£ã«ã¿ã¼ãå«ã¾ããã
ãã³ãã¼ã«ãã£ã¦ã¯ã製åã ICS ãããã³ã«ãã¢ããªã±ã¼ã·ã§ã³ã¬ãã«ã§ãã£ã«ã¿ãªã³ã°ã
ãããã«ãªã£ã¦ãããããã ICS ãã¡ã¤ã¢ã¦ã©ã¼ã«ã¨ãã¦è²©å£²ãã¦ããã
ãããã¯ã¼ã¯åå²ã»åé¢ã®ããã«é¸ãã æè¡ã¨ã¯ãããããªããè¯å¥½ãªãããã¯ã¼ã¯åå²ã»
åé¢ãå
·åãããã¨ã§ãå¤å±¤é²å¾¡æ¦å¿µãå®è£
ãã次㮠4ã¤ã®å
±éçãªãã¼ããããã
ï¼ ãããã¯ã¼ã¯å±¤ä»¥å¤ã«ãæè¡ãé©ç¨ãããå¯è½ã§ããã°ããã¼ã¿ãªã³ã¯å±¤ããã¢ããªã±ã¼ã·
ã§ã³å±¤ã¾ã§ã·ã¹ãã ãã¨ã«ãããã¯ã¼ã¯ãã¨ã«åå²ã»åé¢ãã¹ãã§ããã
ï¼ æå°æ¨©éã®ååã¨ç¥ãå¿
è¦ã®ååãé©ç¨ãããä»ã®ã·ã¹ãã ã¨ã®éä¿¡ãä¸è¦ã§ããã°ãä¸è¨±
å¯ã¨ãã¹ãã§ãããä»ã®ã·ã¹ãã ã¨ç¹å®ã®ãã¼ãããããã³ã«ã§ã®ã¿äº¤ä¿¡ããå ´åãåã¯é
å®ãããã©ãã«ã®ãã¼ã¿ã»ãããåºå®æ§å¼ã®ãã¼ã¿ã®ã¿ãéä¿¡ããå ´åããã®ããã«å¶éã
ã¹ãã§ããã

SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
83
ï¼ Separate information and infrastructure based on security requirements. This may include using
different hardware or platforms based on different threat and risk environments in which each system
or network segment operates. The most critical components require more strict isolation from other
components. In addition to network separation, the use of virtualization could be employed to
accomplish the required isolation.
ï¼ Implement whitelisting23 instead of blacklisting; that is, grant access to the known good, rather than
denying access to the known bad. The set of applications that run in ICS is essentially static, making
whitelisting more practical. This will also improve an organizationâs capacity to analyze log files.
5.2 Boundary Protection
Boundary protection devices control the flow of information between interconnected security domains to
protect the ICS against malicious cyber adversaries and non-malicious errors and accidents. Transferring
information between systems representing different security domains with different security policies
introduces risk that such transfers violate one or more domain security policies. Boundary protection
devices are key components of specific architectural solutions that enforce specific security policies.
Organizations can isolate ICS and business system components performing different missions and/or
business functions. Such isolation limits unauthorized information flows among system components and
also provides the opportunity to deploy greater levels of protection for selected components. Separating
system components with boundary protection mechanisms provides the capability for increased protection
of individual components and more effective control of information flows between those components.
Boundary protection controls include gateways, routers, firewalls, guards, network-based malicious code
analysis and virtualization systems, intrusion detection systems (networked and host-based), encrypted
tunnels, managed interfaces, mail gateways, and unidirectional gateways (e.g., data diodes). Boundary
protection devices determine whether data transfer is permitted, often by examining the data or associated
metadata.
Network and ICS security architects must decide which domains are to be permitted direct communication,
the policies governing permitted communication, the devices to be used to enforce the policy, and the
topology for provisioning and implementing these decisions, which are typically based on the trust
relationship between domains. Trust involves the degree of control that the organization has over the
external domain (e.g., another domain in the same organization, a contracted service provider, the Internet).
Boundary protection devices are arranged in accordance with organizational security architecture. A
common architectural construct is the demilitarized zones (DMZ), a host or network segment inserted as a
âneutral zoneâ between security domains. Its purpose is to enforce the ICS domainâs information security
policy for external information exchange and to provide external domains with restricted access while
shielding the ICS domain from outside threats.
Additional architectural considerations and functions that can be performed by boundary protection devices
for inter-domain communications include:
23 A whitelist is a list or register of those that are being provided a particular privilege, service, mobility,
access or recognition. Only those on the list will be accepted, approved or recognized (i.e., permitted).
Whitelisting is the reverse of blacklisting, the practice of identifying those that are denied, unrecognized,
or ostracized (i.e., prohibited).

SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
84
ï¼ ã»ãã¥ãªãã£è¦ä»¶ã«åºã¥ããæ
å ±ã¨ã¤ã³ãã©ãåé¢ãããããã«ã¯ã種ã
ã®è
å¨ãåã·ã¹ã
ã åã¯ãããã¯ã¼ã¯ã»ã°ã¡ã³ããåä½ãããªã¹ã¯ç°å¢ã«å¾ã£ã¦ãç°ãªããã¼ãã¦ã¨ã¢ããã©
ãããã¼ã ã使ç¨ãããã¨ãå«ã¾ãããæéè¦ã³ã³ãã¼ãã³ãã¯ãä»ã®ã³ã³ãã¼ãã³ããã
ããå³æ ¼ã«åé¢ããå¿
è¦ãããããããã¯ã¼ã¯ã®åé¢ã«å ãã¦ãå¿
è¦ãªåé¢ãå®ç¾ãããã
ã«ä»®æ³åãç¨ãããã¨ãã§ããã
ï¼ ãã©ãã¯ãªã¹ãã§ã¯ãªããã¯ã¤ããªã¹ã 24ãå®è¡ãããã¤ã¾ããæ¢ç¥ã®æªã«ã¢ã¯ã»ã¹ãæå¦
ããã®ã§ã¯ãªããæ¢ç¥ã®è¯ã«ã¢ã¯ã»ã¹ã許å¯ãããICS ã§å®è¡ããã¢ããªã±ã¼ã·ã§ã³ã»ãã
ã¯åºæ¬çã«éçã§ããããããã¯ã¤ããªã¹ããããç¾å®çã§ãããããã«ããçµç¹ã®ãã°ã
ã¡ã¤ã«åæè½åãåä¸ããã
5.2 å¢çã®ä¿è·
å¢çã®ä¿è·ããã¤ã¹ã¯ãé£æ¥ãããã»ãã¥ãªãã£é åéã®æ
å ±ã®æµããå¶å¾¡ããICS ãæªæãã
ãµã¤ãã¼æ»æãæªæã®ãªãé誤ã»äºæ
ããä¿è·ãããå¥ã®ã»ãã¥ãªãã£ããªã·ã¼ãæã£ãã»ãã¥
ãªãã£é åã®ç°ãªãã·ã¹ãã éã§æ
å ±éä¿¡ãããã¨ã¯ãé åã®ã»ãã¥ãªãã£ããªã·ã¼ãå°ãªãã¨
ãä¸ã¤ã¯ç¯ãã¨ãããªã¹ã¯ãæã¡è¾¼ã¾ãããå¢çä¿è·ããã¤ã¹ã¯ãç¹å®ã®ã»ãã¥ãªãã£ããªã·ã¼
ãæ½è¡ããç¹å®ã®ã¢ã¼ããã¯ãã£ã½ãªã¥ã¼ã·ã§ã³ã®éè¦ã³ã³ãã¼ãã³ãã§ããã
çµç¹ã¯ ICS ã¨ãå¥ã®ä»»åãäºæ¥æ©è½ãæããã¦ããäºæ¥ã·ã¹ãã ã³ã³ãã¼ãã³ããåé¢ãããã¨
ãã§ãããåé¢ãããã¨ã§ãã·ã¹ãã ã³ã³ãã¼ãã³ãéã®æªè¨±å¯æ
å ±ã®æµããå¶éããé¸å®ãã
ã³ã³ãã¼ãã³ãã«ããé«ã¬ãã«ã®ä¿è·ãä¸ãããå¢çä¿è·ã¡ã«ããºã ãåããã·ã¹ãã ã³ã³ãã¼
ãã³ããåé¢ãããã¨ã§ãåã
ã®ã³ã³ãã¼ãã³ãã®ä¿è·è½åãåä¸ãããããã³ã³ãã¼ãã³ãé
ã®æ
å ±ã®æµããããå¹æçã«å¶å¾¡ãããã¨ãã§ããã
å¢çä¿è·å¶å¾¡ã«ã¯ãã²ã¼ãã¦ã§ã¤ãã«ã¼ã¿ããã¡ã¤ã¢ã¦ã©ã¼ã«ãã¬ã¼ãããããã¯ã¼ã¯ãã¼ã¹ã®
æªæããã³ã¼ã解æã»ä»®æ³åã·ã¹ãã ãä¾µå
¥æ¤ç¥ã·ã¹ãã ï¼ãããã¯ã¼ã¯åã³ãã¹ããã¼ã¹ï¼ã
æå·åãã³ãã«ã管çã¤ã³ã¿ãã§ã¼ã¹ãã¡ã¼ã«ã²ã¼ãã¦ã§ã¤åã³åæ¹åã²ã¼ãã¦ã§ã¤ï¼ãã¼ã¿ã
ã¤ãªã¼ãçï¼ãå«ã¾ãããå¢çä¿è·ããã¤ã¹ã¯ããã¼ã¿åã¯é¢é£ã¡ã¿ãã¼ã¿ãæ¤è¨¼ãããã¨ã§ã
ãã¼ã¿éä¿¡ã許å¯ããã¦ãããã©ãããå¤å®ããã
ãããã¯ã¼ã¯åã³ ICS ã»ãã¥ãªãã£ã®è¨è¨è
ã¯ãç´æ¥äº¤ä¿¡ã許å¯ãã¹ãé åã許å¯ããã交信ã
çµ±å¶ããããªã·ã¼ãããªã·ã¼ã®å®è¡ç¨ããã¤ã¹ã決å®ããé常ããã¡ã¤ã³éã®ä¿¡é ¼é¢ä¿ãåºã«ã
ãããã®ãããªæ±ºå®ã®æºåã»å®è£
ãããã¸ã¼ã決å®ããªããã°ãªããªããä¿¡é ¼ã«ã¯ãçµç¹ãå¤é¨
é åï¼åãçµç¹å
ã®å¥é åãå§è¨ãµã¼ãã¹ãããã¤ããã¤ã³ã¿ã¼ãããçï¼ã«å¯¾ãã¦æããå¶å¾¡
ã®ç¨åº¦ãé¢ä¿ããã
å¢çä¿è·ããã¤ã¹ã¯ãçµç¹ã®ã»ãã¥ãªãã£ã¢ã¼ããã¯ãã£ã«å¾ã£ã¦é
ç½®ãããå
±éçãªã¢ã¼ãã
ã¯ãã£æ§æã¯ãéæ¦è£
å°å¸¯ï¼DMZï¼ããã¹ãåã¯ã»ãã¥ãªãã£é åéã«ãä¸ç«å°å¸¯ãã¨ãã¦æ¿
å
¥ããããããã¯ã¼ã¯ã»ã°ã¡ã³ãã¨ãªããç®çã¯ãå¤é¨ã¨ã®æ
å ±äº¤æç¨ ICS é åæ
å ±ã»ãã¥ãªã
ã£ããªã·ã¼ãæ½è¡ããICS é åãå¤é¨è
å¨ããã·ã¼ã«ããã¤ã¤ãå¤é¨é åã«ã¢ã¯ã»ã¹å¶éã課ã
ããã¨ã«ããã
é åé交信ç¨å¢çä¿è·ããã¤ã¹ã«ããå®æ½å¯è½ãªä»å çãªã¢ã¼ããã¯ãã£ã®èæ
®äºé
åã³æ©è½ã«
ã¯æ¬¡ã®ãã®ãããã
24 ãã¯ã¤ããªã¹ãã¨ã¯ãç¹å®ã®æ¨©éããµã¼ãã¹ã移åãã¢ã¯ã»ã¹åã¯èªèãä»ä¸ããã人å¡ã®ç»é²ãªã¹ããããããªã¹ãã«
æ²è¼ããã¦ããè
ã®ã¿ãå容ãæ¿èªåã¯èªèï¼è¨±å¯ï¼ãããããã¯ã¤ããªã¹ãã¯ãã©ãã¯ãªã¹ãã®å対ã§ãå¾è
ã¯æå¦ã
éèªèåã¯è¿½æ¾ï¼ç¦æ¢ï¼ãããè
ãèå¥ãããã¨ãããã
SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
85
ï¼ Denying communications traffic by default and allowing communications traffic by exception (i.e.,
deny all, permit by exception). A deny-all, permit-by-exception communications traffic policy ensures
that only those connections which are approved are allowed. This is known as a white-listing policy.
ï¼ Implementing proxy servers that act as an intermediary for external domainsâ requesting information
system resources (e.g., files, connections, or services) from the ICS domain. External requests
established through an initial connection to the proxy server are evaluated to manage complexity and
to provide additional protection by limiting direct connectivity.
ï¼ Preventing the unauthorized exfiltration of information. Techniques include, for example, deep packet
inspection firewalls and XML gateways. These devices verify adherence to protocol formats and
specification at the application layer and serve to identify vulnerabilities that cannot be detected by
devices operating at the network or transport layers. The limited number of formats, especially the
prohibition of free form text in email, eases the use of such techniques at ICS boundaries.
ï¼ Only allowing communication between authorized and authenticated source and destinations address
pairs by one or more of the organization, system, application, and individual.
ï¼ Extending the DMZ concept to other separate subnetworks is useful, for example, in isolating ICS to
prevent adversaries from discovering the analysis and forensics techniques of organizations.
ï¼ Enforcing physical access control to limit authorized access to ICS components.
ï¼ Concealing network addresses of ICS components from discovery (e.g., network address not
published or entered in domain name systems), requiring prior knowledge for access.
ï¼ Disabling control and troubleshooting services and protocols, especially those employing broadcast
messaging, which can facilitate network exploration.
ï¼ Configuring boundary protection devices to fail in a predetermined state. Preferred failure states for
ICS involve balancing multiple factors including safety and security.
ï¼ Configuring security domains with separate network addresses (i.e., as disjoint subnets).
ï¼ Disabling feedback (e.g., non-verbose mode) to senders when there is a failure in protocol validation
format to prevent adversaries from obtaining information.
ï¼ Implementing one-way data flow, especially between different security domains.
ï¼ Establishing passive monitoring of ICS networks to actively detect anomalous communications and
provide alerts.
5.3 Firewalls
Network firewalls are devices or systems that control the flow of network traffic between networks
employing differing security postures. In most modern applications, firewalls and firewall environments are
discussed in the context of Internet connectivity and the UDP/IP protocol suite. However, firewalls have
applicability in network environments that do not include or require Internet connectivity. For example,
many corporate networks employ firewalls to restrict connectivity to and from internal networks servicing
more sensitive functions, such as the accounting or human resource departments. Firewalls can
SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
86
ï¼ ããã©ã«ãã§éä¿¡ãã©ãã£ãã¯ãæ絶ããä¾å¤çã«éä¿¡ãã©ãã£ãã¯ã許å¯ããï¼å
¨ã¦æ絶
ããä¾å¤ã®ã¿è¨±å¯ï¼ãå
¨ã¦æ絶ãä¾å¤ã®ã¿è¨±å¯ã®éä¿¡ãã©ãã£ãã¯ããªã·ã¼ã¯ãæ¿èªæ¸ã¿ã®
æ¥ç¶ã ãã許å¯ãããããã«ãããããã¯ãã¯ã¤ããªã¹ãããªã·ã¼ã¨ãã¦ç¥ããã¦ããã
ï¼ ãããã·ãµã¼ããå®è£
ããå¤é¨é åãã ICS é åã¸ã®æ
å ±ã·ã¹ãã ãªã½ã¼ã¹ï¼ãã¡ã¤ã«ãæ¥
ç¶ããµã¼ãã¹çï¼è¦æ±ã仲ä»ãããããããã·ãµã¼ãã¸ã®æåã®æ¥ç¶ãéãã¦ç¢ºç«ãããå¤
é¨è¦æ±ã¯ãè¤éæ§ã管çããç´æ¥æ¥ç¶ãå¶éãããã¨ã§ä»å çãªä¿è·ãä¸ããããã«è©ä¾¡ã
åããã
ï¼ è¨±å¯ããã¦ããªãæ
å ±ãããæãããã¨ãé²æ¢ãããä¾ãã°ããã£ã¼ããã±ããã¤ã³ã¹ãã¯
ã·ã§ã³ãã¡ã¤ã¢ã¦ã©ã¼ã«ãXMLãã²ã¼ãã¦ã§ã¤çã®æè¡ãããããããããã¤ã¹ã¯ããã
ãã³ã«å½¢å¼ã¨ä»æ§ã®æ´åæ§ãã¢ããªã±ã¼ã·ã§ã³å±¤ã§æ¤è¨¼ãããããã¯ã¼ã¯å±¤ããã©ã³ã¹ãã¼
ã層ã§åä½ããããã¤ã¹ã«ã¯æ¤åºã§ããªãèå¼±æ§ãç¹å®ãããå½¢å¼ã®æ°ãéå®ããã¦ããã
ç¹ã«é»åã¡ã¼ã«ã«ãããèªç±ãã©ã¼ãããã¯ç¦ãããã¦ããããããã®ãããªæè¡ã ICS
å¢çã§ä½¿ç¨ããã®ã¯å®¹æã§ããã
ï¼ çµç¹ãã·ã¹ãã ãã¢ããªã±ã¼ã·ã§ã³åã³å人㮠1ã¤åã¯è¤æ°ã®æ¿èªã»èªè¨¼æ¸ã¿ã½ã¼ã¹ã¨å®å
ã¢ãã¬ã¹ã®ãã¢éã§ã®ã¿äº¤ä¿¡ã許å¯ããã
ï¼ DMZ ã®æ¦å¿µãã»ãã®åé¢ãµããããã¯ã¼ã¯ã«æ¡å¼µããã®ã¯æç¨ã§ãä¾ãã°ãICS ãéé¢ã
ãéã«ãæ»æå´ãçµç¹ã®åæãææ»æè¡ãè¦ãã ããªãããã«ã§ããã
ï¼ ç©ççã¢ã¯ã»ã¹å¶å¾¡ãå®æ½ãã¦ãICS ã³ã³ãã¼ãã³ãã¸ã®ã¢ã¯ã»ã¹è¨±å¯ãå¶éããã
ï¼ ICS ã³ã³ãã¼ãã³ãã®ãããã¯ã¼ã¯ã¢ãã¬ã¹ãåãããªãããã«é è½ãï¼å
¬éããªãããã¡
ã¤ã³åã·ã¹ãã ã«å
¥ããªããªã©ï¼ãäºåã®ç¥èããªããã°ã¢ã¯ã»ã¹ã§ããªãããã«ããã
ï¼ ç®¡çãµã¼ãã¹ããã©ãã«ã·ã¥ã¼ãã£ã³ã°ãµã¼ãã¹åã³ãããã³ã«ã使ç¨ä¸è½ã«ãããç¹ã«ã
ããã¯ã¼ã¯æ¢æ»ã容æã«ã§ããããã¼ããã£ã¹ãã¡ãã»ã¼ã¸ã使ç¨ãã¦ãããã®ã«ã¤ãã¦è¨
ããã
ï¼ å¢çä¿è·ããã¤ã¹ã決ããããç¶æ
ã§æ©è½ããªããªãããã«è¨å®ãããICS ã«å¯¾ããæ
æã®
æ©è½ä¸è½ç¶æ
ã¯ãå®å
¨æ§ã¨ã»ãã¥ãªãã£ç種ã
ã®è¦å éã§ãã©ã³ã¹ãåããã¨ãé¢ä¿ããã
ï¼ ã»ãã¥ãªãã£é åã«ç¬ç«ãããããã¯ã¼ã¯ã¢ãã¬ã¹ãè¨å®ããï¼å
¨ãå¥ã®ãµããããçï¼ã
ï¼ ãããã³ã«ã®å¦¥å½æ§æ¤è¨¼å½¢å¼ã«ä¸åãããå ´åãéä¿¡å´ã«ãã£ã¼ãããã¯ãéããªãï¼éå
é·ã¢ã¼ãçï¼ããã«ãã¦ãæ»æå´ãæ
å ±ãå¾ãããªãããã
ï¼ åæ¹åã®ãã¼ã¿ããã¼ãç¹ã«å¥ã
ã®ã»ãã¥ãªãã£é åéã«å®è£
ããã
ï¼ ICS ãããã¯ã¼ã¯ãããã·ãç£è¦ãã¦ãç°å¸¸äº¤ä¿¡ãç©æ¥µçã«æ¤åºããã¢ã©ã¼ããçºããã
5.3 ãã¡ã¤ã¢ã¦ã©ã¼ã«
ãã¡ã¤ã¢ã¦ã©ã¼ã«ã¯ãå¥ã
ã®ã»ãã¥ãªãã£ç¶æ
ã«ãããããã¯ã¼ã¯éã§ããããã¯ã¼ã¯ãã©ã
ã£ãã¯ã®æµããå¶å¾¡ããããã¤ã¹åã¯ã·ã¹ãã ã®ãã¨ã§ãããã»ã¨ãã©ã®æ°ããã¢ããªã±ã¼ã·
ã§ã³ã§ã¯ããã¡ã¤ã¢ã¦ã©ã¼ã«åã³ãã¡ã¤ã¢ã¦ã©ã¼ã«ç°å¢ã¯ãã¤ã³ã¿ã¼ãããæ¥ç¶ã UDP/IP ã
ããã³ã«ã¹ã¤ã¼ãã¨ã®é¢ä¿ã§è¨åãããããã ããã¡ã¤ã¢ã¦ã©ã¼ã«ã¯ãã¤ã³ã¿ã¼ãããæ¥ç¶ã
å«ã¾ãªããåã¯å¿
è¦ã¨ããªããããã¯ã¼ã¯ç°å¢ã«ãé©ç¨å¯è½ã§ãããä¾ãã°ãå¤ãã®ä¼æ¥ãã
ãã¯ã¼ã¯ã§ã¯ãã¡ã¤ã¢ã¦ã©ã¼ã«ã使ç¨ãã¦ãä¼è¨ã人äºé¨éçãç§å¿ãè¦ããæ©è½ãæãã社
å
ãããã¯ã¼ã¯ã¸ã®æ¥ç¶ãå¶éãã¦ãããæ´ã«ãã¡ã¤ã¢ã¦ã©ã¼ã«ã¯ã
SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
87
further restrict ICS inter-subnetwork communications between functional security subnets and devices. By
employing firewalls to control connectivity to these areas, an organization can prevent unauthorized access
to the respective systems and resources within the more sensitive areas. There are three general classes of
firewalls:
ï¼ Packet Filtering Firewalls. The most basic type of firewall is called a packet filter. Packet filter
firewalls are essentially routing devices that include access control functionality for system addresses
and communication sessions. The access control is governed by a set of directives collectively referred
to as a rule set. In their most basic form, packet filters operate at layer 3 (network) of the Open
Systems Interconnection (OSI), ISO/IEC 7498 model. This type of firewall checks basic information
in each packet, such as IP addresses, against a set of criteria before forwarding the packet. Depending
on the packet and the criteria, the firewall can drop the packet, forward it, or send a message to the
originator. This type of firewall can offer a high level of security, but could result in overhead and
delay impacts on network performance.
ï¼ Stateful Inspection Firewalls. Stateful inspection firewalls are packet filters that incorporate added
awareness of the OSI model data at layer 4 (transport). Stateful inspection firewalls filter packets at
the network layer, determine whether session packets are legitimate, and evaluate the contents of
packets at the transport layer (e.g., TCP, UDP) as well. Stateful inspection keeps track of active
sessions and uses that information to determine if packets should be forwarded or blocked. It offers a
high level of security and good performance, but it may be more expensive and complex to administer.
Additional rule sets for ICS applications may be required.
ï¼ Application-Proxy Gateway Firewalls. This class of firewalls examines packets at the application
layer and filters traffic based on specific application rules, such as specified applications (e.g.,
browsers) or protocols (e.g., FTP). Firewalls of this type can be very effective in preventing attacks on
the remote access and configuration services provided by ICS components. They offer a high level of
security, but could have overhead and delay impacts on network performance, which can be
unacceptable in an ICS environment. NIST SP 800-41 Revision 1, Guidelines on Firewalls and
Firewall Policy [85], provides general guidance for the selection of firewalls and the firewall policies.
In an ICS environment, firewalls are most often deployed between the ICS network and the corporate
network [34]. Properly configured, they can greatly restrict undesired access to and from control system
host computers and controllers, thereby improving security. They can also potentially improve a control
networkâs responsiveness by removing non-essential traffic from the network. When properly designed,
configured, and maintained, dedicated hardware firewalls can contribute significantly to increasing the
security of todayâs ICS environments.
Firewalls provide several tools to enforce a security policy that cannot be accomplished locally on the
current set of process control devices available in the market, including the ability to:
ï¼ Block all communications with the exception of specifically enabled communications between devices
on the unprotected LAN and protected ICS networks. Blocking can be based on, for example, source
and destination IP address pairs, services, ports, state of the connection, and specified applications or
protocols supported by the firewall. Blocking can occur on both inbound and outbound packets, which
is helpful in limiting high-risk communications such as email.
ï¼ Enforce secure authentication of all users seeking to gain access to the ICS network. There is
flexibility to employ varying protection levels of authentication methods including simple passwords,
complex passwords, multi-factor authentication technologies, tokens, biometrics and smart cards.
Select the particular method based upon the vulnerability of the ICS network to be protected, rather
than using the method that is available at the device level.
SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
88
æ©è½çãªã»ãã¥ãªãã£ãµããããã¨ããã¤ã¹éã® ICS ãµããããé交信ãå¶éããããã¡ã¤ã¢ã¦
ã©ã¼ã«ãæ¡ç¨ãã¦ããããã¨ãªã¢ã¸ã®æ¥ç¶ã管çããã°ãçµç¹ã¯ããæ©å¯åº¦ã®é«ãã¨ãªã¢å
ã®ã·
ã¹ãã ããªã½ã¼ã¹ã¸ã®ä¸æ£ã¢ã¯ã»ã¹ãé²æ¢ã§ããããã¡ã¤ã¢ã¦ã©ã¼ã«ã¯æ¬¡ã® 3ã¤ã«å¤§å¥ã§ããã
ï¼ ãã±ãããã£ã«ã¿ãªã³ã°ãã¡ã¤ã¢ã¦ã©ã¼ã«ãæããã¼ã·ãã¯ãªã¿ã¤ãã®ãã¡ã¤ã¢ã¦ã©ã¼ã«ã
ãã±ãããã£ã«ã¿ã¨å¼ã°ããããã±ãããã£ã«ã¿ãã¡ã¤ã¢ã¦ã©ã¼ã«ã¯ãåºæ¬çã«ã«ã¼ãã£ã³
ã°ããã¤ã¹ã§ãã·ã¹ãã ã¢ãã¬ã¹ã¨äº¤ä¿¡ã»ãã·ã§ã³ã®ã¢ã¯ã»ã¹å¶å¾¡æ©è½ãæã¤ãã¢ã¯ã»ã¹å¶
御ã¯ãã«ã¼ã«ã»ããã¨ç·ç§°ãããä¸å¼ã®æ令ã«ããå¶å¾¡ããããæããã¼ã·ãã¯ãªå½¢æ
ã§ã¯ã
ãã±ãããã£ã«ã¿ã¯ ISO/IEC 7498 ã¢ãã«ããªã¼ãã³ã·ã¹ãã é£æ¥ï¼OSIï¼ã®ã¬ã¤ã¤ã¼3ï¼ã
ããã¯ã¼ã¯ï¼ã§åä½ããããã®ã¿ã¤ãã®ãã¡ã¤ã¢ã¦ã©ã¼ã«ã¯ããã±ããã転éããåã«ãå
ãã±ããä¸ã® IP ã¢ãã¬ã¹çã®åºæ¬æ
å ±ãåºæºã«ç
§ããã¦ãã§ãã¯ããããã±ããã¨åºæºã«
å¿ãã¦ããã¡ã¤ã¢ã¦ã©ã¼ã«ã¯ãã±ããã®ããããã転éãè¡ãã»ããã¡ãã»ã¼ã¸ãçºä¿¡è
ã«
éãããã®ã¿ã¤ãã®ãã¡ã¤ã¢ã¦ã©ã¼ã«ã¯ãã»ãã¥ãªãã£ã®ã¬ãã«ã¯é«ããããªã¼ãã¼ããã
ãé
延ãçãããããã¯ã¼ã¯ããã©ã¼ãã³ã¹ã«å½±é¿ãä¸ãããã¨ãããã
ï¼ ã¹ãã¼ããã«ã¤ã³ã¹ãã¯ã·ã§ã³ãã¡ã¤ã¢ã¦ã©ã¼ã«ããã㯠OSI ã¢ãã«ãã¼ã¿ã®è¿½å 注æäºé
ãã¬ã¤ã¤ã¼4ï¼ãã©ã³ã¹ãã¼ãï¼ã«çµã¿è¾¼ãã ãã±ãããã£ã«ã¿ã§ããããã±ãããããã
ã¯ã¼ã¯ã¬ã¤ã¤ã¼ã§ãã£ã«ã¿ãªã³ã°ããã»ãã·ã§ã³ãã±ããã®é©æ ¼æ§ãå¤å®ãããã±ããå
容
ããã©ã³ã¹ãã¼ãã¬ã¤ã¤ã¼ï¼TCPãUDP çï¼ã§ãè©ä¾¡ãããã¹ãã¼ããã«ã¤ã³ã¹ãã¯ã·ã§
ã³ã¯ã¢ã¯ãã£ãã»ãã·ã§ã³ã追跡ãããã®æ
å ±ãåºã«ãã±ããã®è»¢éåã¯ãããã¯ãå¤å®ã
ããã»ãã¥ãªãã£ã®ã¬ãã«ã¯é«ãããã©ã¼ãã³ã¹ãè¯å¥½ã§ããããé«ä¾¡ã§ç®¡çè
ã«ã¨ã£ã¦è¤
éã¨ãªããICS ã¢ããªã±ã¼ã·ã§ã³ã®ä»å çãªã«ã¼ã«ã»ãããå¿
è¦ã«ãªããã¨ãããã
ï¼ ã¢ããªã±ã¼ã·ã§ã³ã»ãããã·ã²ã¼ãã¦ã§ã¤ãã¡ã¤ã¢ã¦ã©ã¼ã«ããã®ã¯ã©ã¹ã®ãã¡ã¤ã¢ã¦ã©ã¼
ã«ã¯ããã±ãããã¢ããªã±ã¼ã·ã§ã³å±¤ã§æ¤è¨¼ããç¹å®ã®ã¢ããªã±ã¼ã·ã§ã³ï¼ãã©ã¦ã¶ã¼çï¼
ããããã³ã«ï¼FTP çï¼ã¨ãã£ãç¹å®ã¢ããªã±ã¼ã·ã§ã³ã«ã¼ã«ã«å¾ã£ã¦ãã©ãã£ãã¯ããã£
ã«ã¿ãªã³ã°ããããã®ã¿ã¤ãã®ãã¡ã¤ã¢ã¦ã©ã¼ã«ã¯ããªã¢ã¼ãã¢ã¯ã»ã¹ãICS ã³ã³ãã¼ã
ã³ããæä¾ããè¨å®ãµã¼ãã¹ã«å¯¾ããæ»æã®äºé²ã«æ¥µãã¦å¹æããããã»ãã¥ãªãã£ã®ã¬ã
ã«ã¯é«ããããªã¼ãã¼ããããé
延ãçãããããã¯ã¼ã¯ããã©ã¼ãã³ã¹ã«å½±é¿ãä¸ããã
ã¨ããããããICS ç°å¢ã§ã¯åãå
¥ããããªãå ´åããããNIST SP800-41 æ¹è¨ç¬¬ 1çãã
ã¡ã¤ã¢ã¦ã©ã¼ã«åã³ãã¡ã¤ã¢ã¦ã©ã¼ã«ããªã·ã¼ã¬ã¤ãã©ã¤ã³ã[85]ã«ã¯ããã¡ã¤ã¢ã¦ã©ã¼ã«
åã³ãã¡ã¤ã¢ã¦ã©ã¼ã«ããªã·ã¼ãé¸å®ããããã®ä¸è¬çã¬ã¤ãã³ã¹ãããã
ICS ç°å¢ã§ã¯ããã¡ã¤ã¢ã¦ã©ã¼ã«ã¯ ICS ãããã¯ã¼ã¯ã¨ä¼æ¥ãããã¯ã¼ã¯éã«å¤ç¨ããã¦ãã
[34]ãæ£ããè¨å®ããã°ãå¶å¾¡ã·ã¹ãã ã®ãã¹ãã³ã³ãã¥ã¼ã¿ã¨ã³ã³ããã¼ã©éã®ä¸æ£ã¢ã¯ã»
ã¹ãèããå¶éããã»ãã¥ãªãã£ãæ¹åãããã¾ãä¸è¦ãªãã©ãã£ãã¯ããããã¯ã¼ã¯ããé¤
å»ãããããå¶å¾¡ãããã¯ã¼ã¯ã®å¿çæ度ãæ¹åãããã¨ããããè¨è¨ã»è¨å®ã»ä¿å®ãé©æ£ã§
ããã°ãå°ç¨ã®ãã¼ãã¦ã¨ã¢ãã¡ã¤ã¢ã¦ã©ã¼ã«ã¯ãä»æ¥ã® ICS ç°å¢ã®ã»ãã¥ãªãã£åä¸ã«å¤§ã
ãè²¢ç®ããã
ãã¡ã¤ã¢ã¦ã©ã¼ã«ã¯ããã¤ããã¼ã«ãæä¾ãã¦ã»ãã¥ãªãã£ããªã·ã¼ãæ½è¡ãããããã®ãã
ãªã»ãã¥ãªãã£ããªã·ã¼ã¯ãç¾å¨å
¥æå¯è½ãªå¸è²©ã®ããã»ã¹å¶å¾¡ããã¤ã¹ã«å¯¾ãã¦ãã¼ã«ã«ã§
å®ç¾ã§ããªããã®ã§ããã次ã®ãããªæ©è½ãæããã
ï¼ ä¿è·ããã¦ããªã LAN ä¸ã®ããã¤ã¹ã¨ä¿è·ããã ICS ãããã¯ã¼ã¯ä¸ã®ããã¤ã¹éã§ç¹ã«
許å¯ããããã®ãé¤ããå
¨ã¦ã®äº¤ä¿¡ããããã¯ããããããã¯ã¯ã½ã¼ã¹åã³å®å
ã® IP ã¢ã
ã¬ã¹ãã¢ããµã¼ãã¹ããã¼ããæ¥ç¶ç¶æ
ããã¡ã¤ã¢ã¦ã©ã¼ã«ã許å¯ããç¹å®ã®ã¢ããªã±ã¼ã·
ã§ã³åã¯ãããã³ã«ã«å¾ã£ã¦è¡ãããããã¯ã¯çä¿¡ãã±ããã§ãéä¿¡ãã±ããã§ãçãããã
ãã㯠eã¡ã¼ã«çã®é«ãªã¹ã¯éä¿¡ãå¶éããä¸ã§å½¹ç«ã¤ã
ï¼ ICS ãããã¯ã¼ã¯ã«ã¢ã¯ã»ã¹ãããã¨ããå
¨ã¦ã®ã¦ã¼ã¶èªè¨¼ãã»ãã¥ã¢ã«ãããèªè¨¼æ¹æ³ã«
ã¯åç´ãªãã¹ã¯ã¼ããè¤éãªãã¹ã¯ã¼ããè¤åè¦ç´ èªè¨¼æè¡ããã¼ã¯ã³ãçç©è¨æ¸¬å¦ãã¹ã
ã¼ãã«ã¼ãçãããã種ã
ã®ä¿è·ã¬ãã«ãæè»ã«æ¡ç¨ã§ããã
ããã¤ã¹ã¬ãã«ã§å©ç¨ã§ããæ¹æ³ã使ç¨ããã®ã§ã¯ãªããä¿è·ãã¹ã ICS ãããã¯ã¼ã¯ã®
èå¼±æ§ãåºã«ãç¹å®ã®æ¹æ³ãé¸å®ããã
SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
89
ï¼ Enforce destination authorization. Users can be restricted and allowed to reach only the nodes on the
control network necessary for their job function. This reduces the potential of users intentionally or
accidentally gaining access to and control of devices for which they are not authorized, but adds to the
complexity for on-the-job-training or cross-training employees.
ï¼ Record information flow for traffic monitoring, analysis, and intrusion detection.
ï¼ Permit the ICS to implement operational policies appropriate to the ICS but that might not be
appropriate in an IT network, such as prohibition of less secure communications like email, and
permitted use of easy-to-remember usernames and group passwords.
ï¼ Be designed with documented and minimal (single if possible) connections that permit the ICS
network to be severed from the corporate network, should that decision be made, in times of serious
cyber incidents.
Other possible deployments include using either host-based firewalls or small standalone hardware
firewalls in front of, or running on, individual control devices. Using firewalls on an individual device basis
can create significant management overhead, especially in change management of firewall configurations,
however this practice will also simplify individual configuration rulesets.
There are several issues that must be addressed when deploying firewalls in ICS environments, particularly
the following:
ï¼ The possible addition of delay to control system communications.
ï¼ The lack of experience in the design of rule sets suitable for industrial applications. Firewalls used to
protect control systems should be configured so they do not permit either incoming or outgoing traffic
by default. The default configuration should be modified only when it is necessary to permit
connections to or from trusted systems to perform authorized ICS functions.
Firewalls require ongoing support, maintenance, and backup. Rule sets need to be reviewed to make sure
that they are providing adequate protection in light of ever-changing security threats. System capabilities
(e.g., storage space for firewall logs) should be monitored to make sure that the firewall is performing its
data collection tasks and can be depended upon in the event of a security violation. Real-time monitoring of
firewalls and other security sensors is required to rapidly detect and initiate response to cyber incidents.
5.4 Logically Separated Control Network
The ICS network should, at a minimum, be logically separated from the corporate network on physically
separate network devices. Based on the ICS network configuration, additional separation needs to be
considered for Safety Instrumented Systems and Security Systems (e.g., physical monitoring and access
controls, doors, gates, cameras, VoIP, access card readers) that are often either part of the ICS network or
utilize the same communications infrastructure for remote sites. When enterprise connectivity is required:
ï¼ There should be documented and minimal (single if possible) access points between the ICS network
and the corporate network. Redundant (i.e., backup) access points, if present, must be documented.
ï¼ A stateful firewall between the ICS network and corporate network should be configured to deny all
traffic except that which is explicitly authorized.
ï¼ The firewall rules should at a minimum provide source and destination filtering (i.e., filter on media
access control [MAC] address), in addition to TCP and User Datagram Protocol (UDP) port filtering
and Internet Control Message Protocol (ICMP) type and code filtering.
SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
90
ï¼ å®å
ã®è¨±å¯ãã¦ã¼ã¶ã¯ãèªåã®æ¥åã«å¿
è¦ãªå¶å¾¡ãããã¯ã¼ã¯ä¸ã®ãã¼ãã«ããå°éã§ããª
ãããã«å¶éãåãããããã«ããã¦ã¼ã¶ãã許å¯ããã¦ããªãããã¤ã¹ã«ãæ
æåã¯å¶ç¶
ã«ã¢ã¯ã»ã¹ãã¦å¶å¾¡ãè¡ãå¯è½æ§ã¯æ¸ãããOJT ã交差è¨ç·´ä¸ã®å¾æ¥å¡ã«ã¯è¤éããå¢ãã
ï¼ ãã©ãã£ãã¯ç£è¦ã解æåã³ä¾µå
¥æ¤ç¥ã®ããã®æ
å ±ã®æµãã®è¨é²ã
ï¼ IT ãããã¯ã¼ã¯ã«ã¯é©åããªãããICS ã«ã¯é©åããæ¥åããªã·ã¼ã ICS ãå®æ½ãããã¨ã
許å¯ãããä¾ãã°é»åã¡ã¼ã«çã®ã»ãã¥ãªãã£ã®ä½ãéä¿¡ãè¦ããããã¦ã¼ã¶åãã°ã«ã¼ã
ãã¹ã¯ã¼ãã®ä½¿ç¨ãç¦æ¢ãããªã©ã
ï¼ æ·±å»ãªãµã¤ãã¼ã¤ã³ã·ãã³ãã®éã«æ±ºå®ãããã°ãICS ãããã¯ã¼ã¯ãä¼æ¥ãããã¯ã¼ã¯ã
ãåæã§ãããææ¸åãããæä½éã®ï¼ã§ããã° 1ã¤ã®ã¿ï¼æ¥ç¶ã«ããã
ãã®ä»å¯è½ãªå±éã¨ãã¦ã¯ããã¹ããã¼ã¹ã®ãã¡ã¤ã¢ã¦ã©ã¼ã«ããå°åã®ã¹ã¿ã³ãã¢ãã¼ã³ã
ã¼ãã¦ã¨ã¢ãã¡ã¤ã¢ã¦ã©ã¼ã«ãåã
ã®å¶å¾¡ããã¤ã¹ã®åé¢ã«åã¯ããããããã¤ã¹ä¸ã«é
ç½®ã
ã¦ä½¿ç¨ããæ¡ããããåã
ã®ããã¤ã¹ã«ãã¡ã¤ã¢ã¦ã©ã¼ã«ã使ç¨ããã¨ãç¹ã«ãã¡ã¤ã¢ã¦ã©ã¼
ã«è¨å®ã®äº¤æ管çã«ãããªãã®ç®¡çãªã¼ãã¼ããããçããããåã
ã®è¨å®ã«ã¼ã«ã»ãããç°¡
ç´ åãããã¨ã«ããªãã
ICS ç°å¢ã«ãã¡ã¤ã¢ã¦ã©ã¼ã«ãå±éããéã«ã¯ãç¹ã«æ¬¡ã®ãããªèæ
®ãã¹ãåé¡ãããã¤ãã
ãã
ï¼ å¶å¾¡ã·ã¹ãã ã®éä¿¡ã«é
延ãå ããå¯è½æ§
ï¼ ç£æ¥ç¨éã«åã£ãã«ã¼ã«ã»ããã®èæ¡ã«ãããçµé¨ã®æ¬ å¦ãå¶å¾¡ã·ã¹ãã ã®ä¿è·ã«ä½¿ç¨ãã
ãã¡ã¤ã¢ã¦ã©ã¼ã«ã®è¨å®ã¯ãçä¿¡ãã©ãã£ãã¯ãéä¿¡ãã©ãã£ãã¯ãããã©ã«ãã§è¨±å¯ããª
ãããã«ãã¹ãã§ãããããã©ã«ãè¨å®ã®å¤æ´ã¯ãä¿¡é ¼ããã¦ããã·ã¹ãã ã¨ã®æ¥ç¶ã許å¯
ãã¦ã許å¯ããã ICS æ©è½ãå®æ½ããå¿
è¦ãããå ´åã®ã¿ã«ãã¹ãã§ããã
ãã¡ã¤ã¢ã¦ã©ã¼ã«ã¯ã絶ãããµãã¼ãã»ä¿å®ã»ããã¯ã¢ãããå¿
è¦ã¨ããã絶ããå¤åããè
å¨ã¨ãã観ç¹ããããã£ããä¿è·ã確ä¿ã§ããããã«ãã«ã¼ã«ã»ãããè¦ç´ãå¿
è¦ããããã·
ã¹ãã ã®è½åï¼ãã¡ã¤ã¢ã¦ã©ã¼ã«ãã°ã®ã¹ãã¬ã¼ã¸å®¹éçï¼ãç£è¦ãã¦ããã¡ã¤ã¢ã¦ã©ã¼ã«ã
ãã¼ã¿åéä½æ¥ãç¶è¡ã§ããããã«ããã»ãã¥ãªãã£éåäºæ
ãçãã¦ãä¿¡é ¼æ§ãä¿ãããã
ãã«ãã¹ãã§ããããã¡ã¤ã¢ã¦ã©ã¼ã«ãã®ä»ã®ã»ãã¥ãªãã£ã»ã³ãµã¯ããªã¢ã«ã¿ã¤ã ã§ç£è¦ãã
ãµã¤ãã¼ã¤ã³ã·ãã³ããæ¤ç¥ãã¦å³å¿ã§ããããã«ããªããã°ãªããªãã
5.4 è«ççã«åé¢ãããå¶å¾¡ãããã¯ã¼ã¯
å°ãªãã¨ã ICS ãããã¯ã¼ã¯ã¯ãç©ççã«åé¢ããããããã¯ã¼ã¯ããã¤ã¹ä¸ã®ä¼æ¥ãããã¯ã¼
ã¯ãããè«ççã«åé¢ããã¦ããã¹ãã§ãããICS ãããã¯ã¼ã¯è¨å®ãåºã«ãä»å çãªåé¢ãå®
å
¨è¨è£
ã·ã¹ãã ã¨ã»ãã¥ãªãã£ã·ã¹ãã ï¼ç©ççç£è¦ã¢ã¯ã»ã¹å¶å¾¡ããã¢ãã²ã¼ããã«ã¡ã©ã
VoIPãç«å
¥ã«ã¼ããªã¼ãã¼çï¼åãã«æ¤è¨ããå¿
è¦ãããããããã·ã¹ãã ã¯ãICS ãããã¯ã¼
ã¯ã®ä¸é¨ããªãããåãéä¿¡ã¤ã³ãã©ãé éãµã¤ãç¨ã«ä½¿ç¨ãã¦ãããã¨ãå¤ããä¼æ¥ã®æ¥ç¶ã
å¿
è¦ãªå ´åã
ï¼ ææ¸åãããæä½éã®ï¼ã§ããã° 1ã¤ã®ã¿ï¼ã¢ã¯ã»ã¹ãã¤ã³ãã ICS ãããã¯ã¼ã¯ã¨ä¼æ¥ã
ããã¯ã¼ã¯éã«ããã¹ãã§ãããåé·ï¼ããã¯ã¢ããï¼ã¢ã¯ã»ã¹ãã¤ã³ããããã°ãææ¸å
ããªããã°ãªããªãã
ï¼ ICS ãããã¯ã¼ã¯ã¨ä¼æ¥ãããã¯ã¼ã¯éã®ã¹ãã¼ããã«ãã¡ã¤ã¢ã¦ã©ã¼ã«ã¯ãæ示çã«è¨±å¯
ããããã®ä»¥å¤ãä¸åã®ãã©ãã£ãã¯ãæ絶ããããã«è¨å®ããã
ï¼ TCP åã³ã¦ã¼ã¶ãã¼ã¿ã°ã©ã ãããã³ã«ï¼UDPï¼ãã¼ããã£ã«ã¿ãªã³ã°ãã¤ã³ã¿ã¼ãããå¶
御ã¡ãã»ã¼ã¸ãããã³ã«ï¼ICMPï¼ã¿ã¤ãã»ã³ã¼ããã£ã«ã¿ãªã³ã°ã«å ãã¦ããã¡ã¤ã¢ã¦ã©
ã¼ã«ã«ã¼ã«ã¯å°ãªãã¨ãã½ã¼ã¹åã³å®å
ãã£ã«ã¿ãªã³ã°ï¼ã¡ãã£ã¢ã¢ã¯ã»ã¹å¶å¾¡[MAC]ã¢ã
ã¬ã¹ã§ã®ãã£ã«ã¿ãªã³ã°ï¼ãè¡ãã¹ãã§ããã
SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
91
An acceptable approach to enabling communication between an ICS network and a corporate network is to
implement an intermediate DMZ network. The DMZ should be connected to the firewall such that specific
(restricted) communication may occur between only the corporate network and the DMZ, and the ICS
network and the DMZ. The corporate network and the ICS network should not communicate directly with
each other. This approach is described in Sections 5.5.4 and 5.5.5. Additional security may be obtained by
implementing a Virtual Private Network (VPN) between the ICS and external networks.
5.5 Network Segregation
ICS networks and corporate networks can be segregated to enhance cybersecurity using different
architectures. This section describes several possible architectures and explains the advantages and
disadvantages of each. Please note that the intent of the diagrams in Section 5.5 is to show the placement of
firewalls to segregate the network. Not all devices that would be typically found on the control network or
corporate network are shown. Section 5.6 provides guidance on a recommended defense-in-depth
architecture.
5.5.1 Dual-Homed Computer/Dual Network Interface Cards (NIC)
Dual-homed computers can pass network traffic from one network to another. A computer without proper
security controls could pose additional threats. To prevent this, no systems other than firewalls should be
configured as dual-homed to span both the control and corporate networks. All connections between the
control network and the corporate network should be through a firewall. This configuration provides no
security improvement and should not be used to bridge networks (e.g., ICS and corporate networks).
5.5.2 Firewall between Corporate Network and Control Network
By introducing a simple two-port firewall between the corporate and control networks, as shown in Figure
5-1, a significant security improvement can be achieved. Properly configured, a firewall significantly
reduces the chance of a successful external attack on the control network.
Unfortunately, two issues still remain with this design. First, if the data historian resides on the corporate
network, the firewall must allow the data historian to communicate with the control devices on the control
network. A packet originating from a malicious or incorrectly configured host on the corporate network
(appearing to be the data historian) would be forwarded to individual PLCs/DCS.
SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
92
ICS ãããã¯ã¼ã¯ã¨ä¼æ¥ãããã¯ã¼ã¯éã®äº¤ä¿¡ãå¯è½ã«ããåãå
¥ããããã¢ããã¼ãã¯ãä¸é
DMZ ãããã¯ã¼ã¯ãå®è£
ãããã¨ã§ãããDMZ ã¯ãã¡ã¤ã¢ã¦ã©ã¼ã«ã«æ¥ç¶ãããä¼æ¥ãããã¯
ã¼ã¯ã¨ DMZ éåã³ ICS ãããã¯ã¼ã¯ã¨ DMZ éã§ã®ã¿ç¹å®ã®ï¼å¶éãããï¼äº¤ä¿¡ãçãããã
ã«ãããä¼æ¥ãããã¯ã¼ã¯ã¨ ICS ãããã¯ã¼ã¯éã§ã¯ç´æ¥äº¤ä¿¡ãçããªãããã«ãã¹ãã§ããã
ãã®ã¢ããã¼ãã¯ã»ã¯ã·ã§ã³ 5.5.4 åã³ 5.5.5 ã§èª¬æãããVPN ãICS ãããã¯ã¼ã¯ã¨å¤é¨ããã
ã¯ã¼ã¯éã«å®è£
ããã°ãæ´ã«ã»ãã¥ãªãã£ãé«ã¾ãã
5.5 ãããã¯ã¼ã¯ã®åé¢
ICS ãããã¯ã¼ã¯ã¨ä¼æ¥ãããã¯ã¼ã¯ãåé¢ããå¥ã
ã®ã¢ã¼ããã¯ãã£ã使ç¨ãã¦ãµã¤ãã¼ã»
ãã¥ãªãã£ãé«ãããã¨ãã§ããããã®ã»ã¯ã·ã§ã³ã§ã¯ãããã¤ãå¯è½ãªã¢ã¼ããã¯ãã£ã«ã¤
ãã¦åãä¸ããããããã®å©ç¹ã»æ¬ ç¹ã説æãããã»ã¯ã·ã§ã³ 5.5 ã®å³ã®æå³ã¯ããã¡ã¤ã¢ã¦
ã©ã¼ã«ã®é
ç½®ã«ãããããã¯ã¼ã¯ã®åé¢ã示ããã¨ã«ããç¹ã«çæãããããå¶å¾¡ãããã¯ã¼
ã¯ãä¼æ¥ãããã¯ã¼ã¯ä¸ã«é常ããããã¤ã¹ããå¿
ãããå
¨ã¦ç¤ºããã¦ããªããã»ã¯ã·ã§ã³
5.6 ã§ã¯ãæ¨å¥¨ãããå¤å±¤é²å¾¡ã¢ã¼ããã¯ãã£ã®ã¬ã¤ãã³ã¹ã示ãã
5.5.1 ãã¥ã¢ã«ãã¼ã ï¾ï¾ã³ã³ãã¥ã¼ã¿/ãã¥ã¢ã«ãããã¯ã¼ã¯ã¤ã³ã¿ãã§ã¼ã¹ã«ã¼ã
ï¼NICï¼
ãã¥ã¢ã«ãã¼ã ï¾ï¾ã³ã³ãã¥ã¼ã¿ã¯ããããã¯ã¼ã¯ãã©ãã£ãã¯ããããããã¯ã¼ã¯ããå¥ã®ã
ããã¯ã¼ã¯ã¸ééãããããã£ããããã»ãã¥ãªãã£å¯¾çã®ãªãã³ã³ãã¥ã¼ã¿ã§ã¯ãè
å¨ãå¢
å ããããããé²ãã«ã¯ãå¶å¾¡ãããã¯ã¼ã¯ã§ãä¼æ¥ãããã¯ã¼ã¯ã§ãããã¡ã¤ã¢ã¦ã©ã¼ã«ä»¥
å¤ã®ã·ã¹ãã ããã¥ã¢ã«ãã¼ã ï¾ï¾ã«è¨å®ãããã¨ã§ãããå¶å¾¡ãããã¯ã¼ã¯ã¨ä¼æ¥ãããã¯ã¼
ã¯éã®å
¨ã¦ã®æ¥ç¶ã¯ããã¡ã¤ã¢ã¦ã©ã¼ã«çµç±ã¨ãã¹ãã§ããããã®è¨å®ã§ã»ãã¥ãªãã£ãåä¸
ãããã¨ã¯ãªãããããã¯ã¼ã¯éã®ããªãã¸ã«ä½¿ç¨ãã¹ãã§ãªãï¼ICS ãããã¯ã¼ã¯ã¨ä¼æ¥ã
ããã¯ã¼ã¯çï¼ã
5.5.2 ä¼æ¥ãããã¯ã¼ã¯ã¨å¶å¾¡ãããã¯ã¼ã¯éã®ãã¡ã¤ã¢ã¦ã©ã¼ã«
å³5-1 ã®ããã«ã両ãããã¯ã¼ã¯éã«åç´ãª 2ãã¼ããã¡ã¤ã¢ã¦ã©ã¼ã«ãè¨ç½®ãããã¨ã§ãã
ãªãã»ãã¥ãªãã£ãåä¸ãããé©æ£ã«è¨å®ããã°ãã¡ã¤ã¢ã¦ã©ã¼ã«ã¯ãå¶å¾¡ãããã¯ã¼ã¯ã«å¯¾
ããå¤é¨æ»æãæåããå¯è½æ§ã大å¹
ã«æ¸ããã
æ®å¿µãªãããã®è¨è¨ã«ã¯ 2ã¤ã®åé¡ããããã¾ãããã¼ã¿ãã¹ããªã¢ã³ãä¼æ¥ãããã¯ã¼ã¯ã«
常é§ãã¦ããå ´åããã¡ã¤ã¢ã¦ã©ã¼ã«ã¯ããã¼ã¿ãã¹ããªã¢ã³ãå¶å¾¡ãããã¯ã¼ã¯ä¸ã®å¶å¾¡ã
ãã¤ã¹ã¨äº¤ä¿¡ããã®ã許å¯ããªããã°ãªããªããæªæãããã¹ããä¼æ¥ãããã¯ã¼ã¯ä¸ã®è¨å®
ã«ä¸åãããï¼ãã¼ã¿ãã¹ããªã¢ã³ã®ããã«è¦ããï¼ãã¹ãããã®ãã±ããã¯ãåã
ã®
PLCs/DCS ã«è»¢éãããã
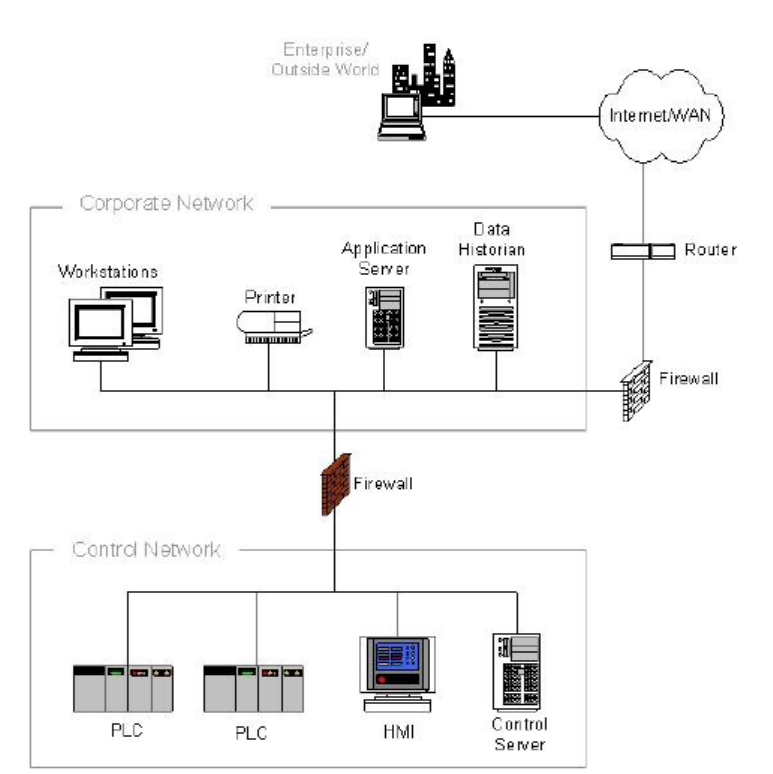
SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
93
Figure 5-1. Firewall between Corporate Network and Control Network
If the data historian resides on the control network, a firewall rule must exist that allows all hosts from the
enterprise to communicate with the historian. Typically, this communication occurs at the application layer
as Structured Query Language (SQL) or Hypertext Transfer Protocol (HTTP) requests. Flaws in the
historianâs application layer code could result in a compromised historian. Once the historian is
compromised, the remaining nodes on the control network are vulnerable to a worm propagating or an
interactive attack.
Another issue with having a simple firewall between the networks is that spoofed packets can be
constructed that can affect the control network, potentially permitting covert data to be tunneled in allowed
protocols. For example, if HTTP packets are allowed through the firewall, then Trojan horse software
accidentally introduced on an HMI or control network laptop could be controlled by a remote entity and
send data (such as captured passwords) to that entity, disguised as legitimate traffic.
In summary, while this architecture is a significant improvement over a non-segregated network, it requires
the use of firewall rules that allow direct communications between the corporate network and control
network devices. This can result in possible security breaches if not very carefully designed and monitored
[35].
SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
94
å³5-1.ä¼æ¥ãããã¯ã¼ã¯ã¨å¶å¾¡ãããã¯ã¼ã¯éã®ãã¡ã¤ã¢ã¦ã©ã¼ã«
ãã¼ã¿ãã¹ããªã¢ã³ãå¶å¾¡ãããã¯ã¼ã¯ä¸ã«å¸¸é§ãã¦ããå ´åãå
¨ã¦ã®ãã¹ããä¼æ¥å´ãããã¹
ããªã¢ã³ã«éä¿¡ã§ãããã¡ã¤ã¢ã¦ã©ã¼ã«è¦åããªããã°ãªããªããä¸è¬ã«ãã®éä¿¡ã¯ãSQL åã¯
HTTP è¦æ±ã¨ãã¦ã¢ããªã±ã¼ã·ã§ã³å±¤ã§çããããã¹ããªã¢ã³ã®ã¢ããªã±ã¼ã·ã§ã³å±¤ã³ã¼ãã«ä¸
åãããã¨ããã¹ããªã¢ã³ã®æ©è½ãä½ä¸ããããããªãã¨ãå¶å¾¡ãããã¯ã¼ã¯ã®æ®ãã®ãã¼ãã
ã¯ã¼ã ã®ä¼æãã¤ã³ã¿ã©ã¯ãã£ãæ»æã«å¯¾ãã¦èå¼±ã«ãªãã
ãããã¯ã¼ã¯éã«åç´ãã¡ã¤ã¢ã¦ã©ã¼ã«ãè¨ç½®ããããä¸ã¤ã®åé¡ç¹ã¯ããªããã¾ããã±ããã
çæãããå¶å¾¡ãããã¯ã¼ã¯ã«å½±é¿ãåã¼ããç§å¯ãã¼ã¿ã許å¯ããããããã³ã«ã§ãã³ãã«ã
ããå¯è½æ§ããããä¾ãã° HTTP ãã±ããã®ééããã¡ã¤ã¢ã¦ã©ã¼ã«ãã許å¯ãããã¨ãHMI ã
å¶å¾¡ãããã¯ã¼ã¯ã©ãããããã«å¶ç¶å
¥ãè¾¼ãã ããã¤ã®æ¨é¦¬ãå¤é¨å£ä½ã«é éæä½ãããæ£å¸¸
ãªãã©ãã£ãã¯ãè£
ã£ã¦ããã¼ã¿ï¼ææãããã¹ã¯ã¼ãçï¼ãå½è©²å£ä½ã«éä¿¡ããããã¨ã«ãªãã
ã¾ã¨ãã¨ãã¦ããã®ã¢ã¼ããã¯ãã£ã¯éåé¢ãããã¯ã¼ã¯ãããªãæ¹åããä¸æ¹ã§ãä¼æ¥ããã
ã¯ã¼ã¯ããã¤ã¹ã¨å¶å¾¡ãããã¯ã¼ã¯ããã¤ã¹éã®ç´æ¥äº¤ä¿¡ã許å¯ããã¨ãããã¡ã¤ã¢ã¦ã©ã¼ã«è¦
åã使ç¨ããªããã°ãªããªãããã®çµæãè¨è¨ã¨ç£è¦ãããªãæ
éã«è¡ããªãã¨ãã»ãã¥ãªãã£
侵害ãçãããã¨ã«ãªãã
ä¼æ¥ãããã¯ã¼ã¯
ã¯ã¼ã¯ã¹ãã¼ã·ã§ã³
ã¢ããªã±ã¼ã·ã§ã³
ãµã¼ã
ãã¼ã¿
ãã¹ããªã¢ã³
ã¤ã³ã¿ã¼ããã/WAN
ããªã³ã¿
ã«ã¼ã¿
ãã¡ã¤ã¢ã¦ã©ã¼ã«
å¶å¾¡ãããã¯ã¼ã¯
ãã¡ã¤ã¢ã¦ã©ã¼ã«
PLC PLC
å¶å¾¡ãµã¼ã
ä¼æ¥/å¤ç
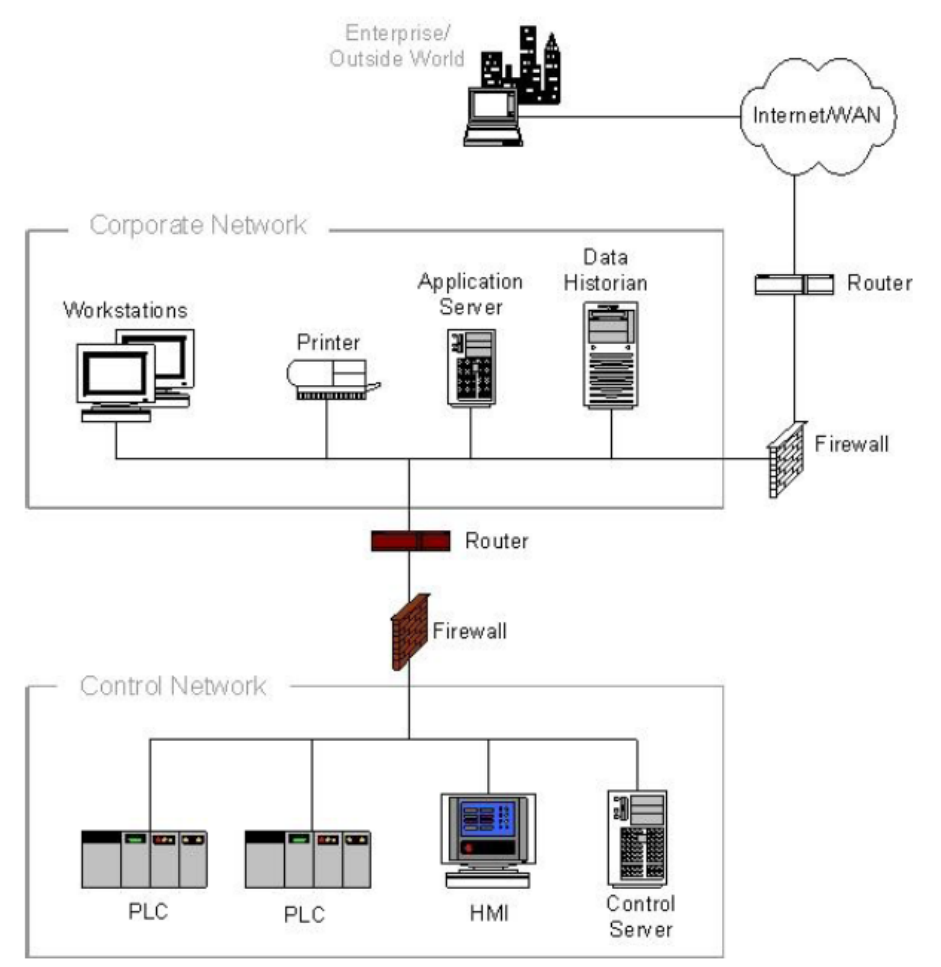
SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
95
5.5.3 Firewall and Router between Corporate Network and Control Network
A slightly more sophisticated design, shown in Figure 5-2, is the use of a router/firewall combination. The
router sits in front of the firewall and offers basic packet filtering services, while the firewall handles the
more complex issues using either stateful inspection or proxy techniques. This type of design is very
popular in Internet-facing firewalls because it allows the faster router to handle the bulk of the incoming
packets, especially in the case of DoS attacks, and reduces the load on the firewall. It also offers improved
defense-in-depth because there are two different devices an adversary must bypass [35].
Figure 5-2. Firewall and Router between Corporate Network and Control Network
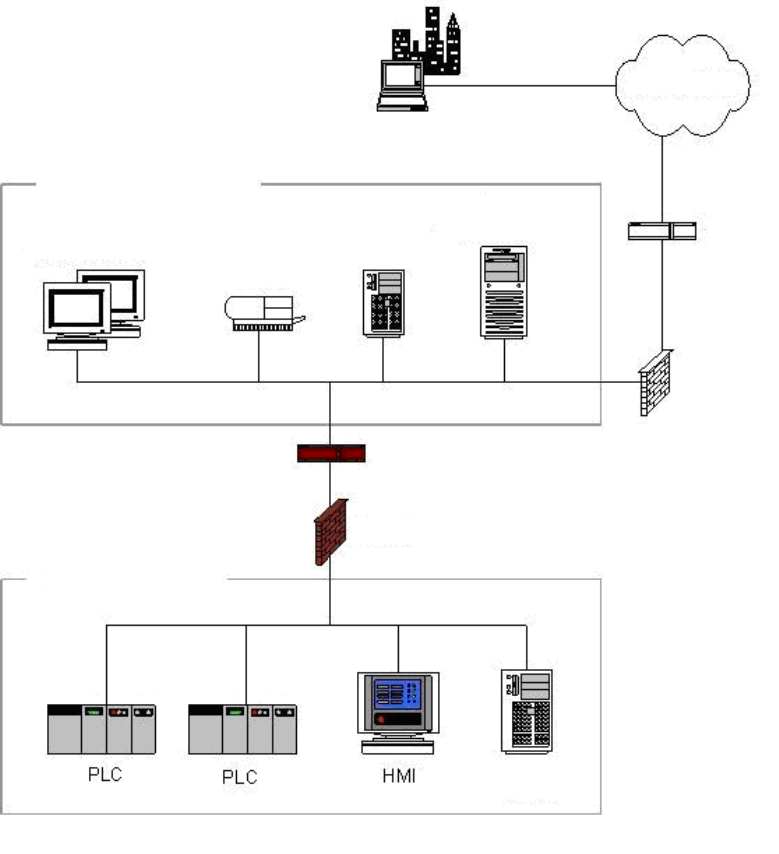
SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
96
5.5.3 ä¼æ¥ãããã¯ã¼ã¯ã¨å¶å¾¡ãããã¯ã¼ã¯éã®ãã¡ã¤ã¢ã¦ã©ã¼ã«ã¨ã«ã¼ã¿
å³5-2 ã¯ããæ´ç·´ãããè¨è¨ã§ãã«ã¼ã¿ã¨ãã¡ã¤ã¢ã¦ã©ã¼ã«ãä½µç¨ãã¦ãããã«ã¼ã¿ããã¡ã¤ã¢
ã¦ã©ã¼ã«ã®åé¢ã«æ®ãããã±ããã®åºæ¬çãã£ã«ã¿ãªã³ã°ãè¡ããããã¡ã¤ã¢ã¦ã©ã¼ã«ã¯ã¹ãã¼
ããã«ã¤ã³ã¹ãã¯ã·ã§ã³åã¯ãããã·æè¡ãç¨ãã¦ããè¤éãªåé¡ã®å¦çã«å½ããããããã®ç¨®
ã®è¨è¨ã¯ã¤ã³ã¿ã¼ãããã«é¢ãããã¡ã¤ã¢ã¦ã©ã¼ã«ã§ã¯ããä¸è¬çã§ããããããé«éãªã«ã¼ã¿
ã«å¤§éã®çä¿¡ãã±ãããå¦çããã¦ãç¹ã« DoS æ»æã®å ´åã«åãããã¡ã¤ã¢ã¦ã©ã¼ã«ã¸ã®è² è·
ãæ¸ããããã§ãããã¾ãæ»æå´ã¯ 2種ã®ããã¤ã¹ãééããªããã°ãªããªããããå¤å±¤é²å¾¡ã
æ¹åããã[35]ã
å³5-2.ä¼æ¥ãããã¯ã¼ã¯ã¨å¶å¾¡ãããã¯ã¼ã¯éã®ãã¡ã¤ã¢ã¦ã©ã¼ã«ã¨ã«ã¼ã¿
ä¼æ¥ãããã¯ã¼ã¯
ã¯ã¼ã¯ã¹ãã¼ã·ã§ã³
ã¢ããªã±ã¼ã·ã§ã³
ãµã¼ã
ãã¼ã¿
ãã¹ããªã¢ã³
ã¤ã³ã¿ã¼ããã/WAN
ããªã³ã¿
ã«ã¼ã¿
ãã¡ã¤ã¢ã¦ã©ã¼ã«
å¶å¾¡ãããã¯ã¼ã¯
ã«ã¼ã¿
PLC
PLC
å¶å¾¡ãµã¼ã
ä¼æ¥/å¤ç
ãã¡ã¤ã¢ã¦ã©ã¼ã«
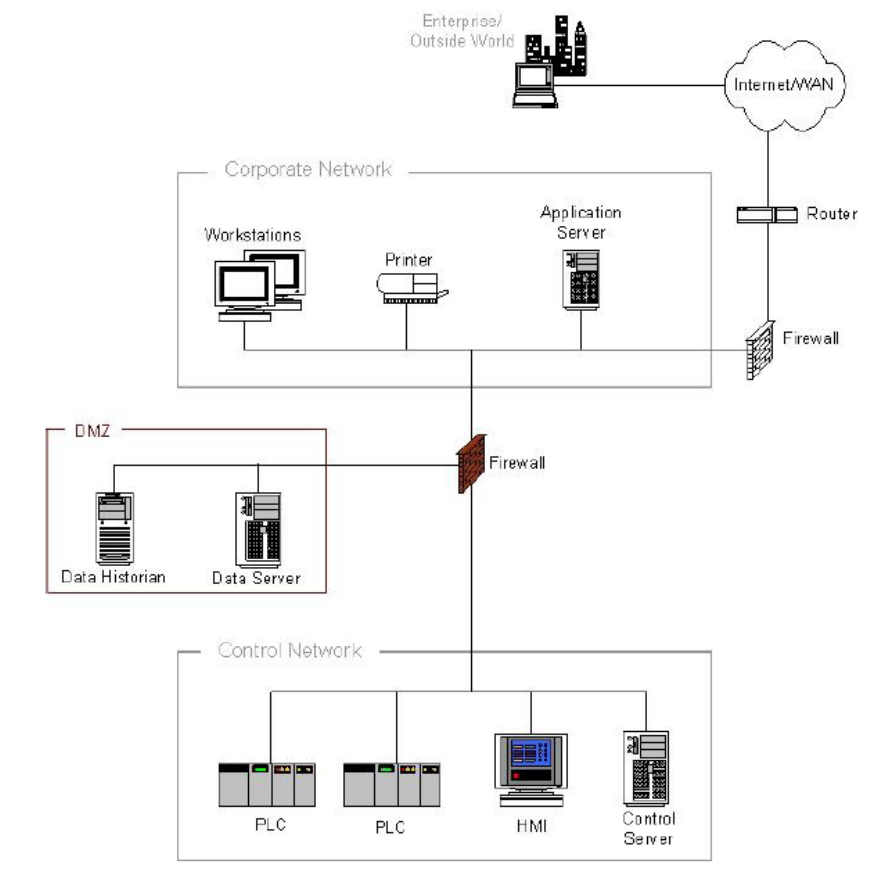
SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
97
5.5.4 Firewall with DMZ between Corporate Network and Control Network
A significant improvement is the use of firewalls with the ability to establish a DMZ between the corporate
and control networks. Each DMZ holds one or more critical components, such as the data historian, the
wireless access point, or remote and third party access systems. In effect, the use of a DMZ-capable
firewall allows the creation of an intermediate network.
Creating a DMZ requires that the firewall offer three or more interfaces, rather than the typical public and
private interfaces. One of the interfaces is connected to the corporate network, the second to the control
network, and the remaining interfaces to the shared or insecure devices such as the data historian server or
wireless access points on the DMZ network. Implementing continuous ingress and egress traffic monitoring
on the DMZ is recommended. Additionally, firewall rulesets that only permit connections between the
control network and DMZ that are initiated by control network devices are recommended. Figure 5-3
provides an example of this architecture.
Figure 5-3. Firewall with DMZ between Corporate Network and Control Network
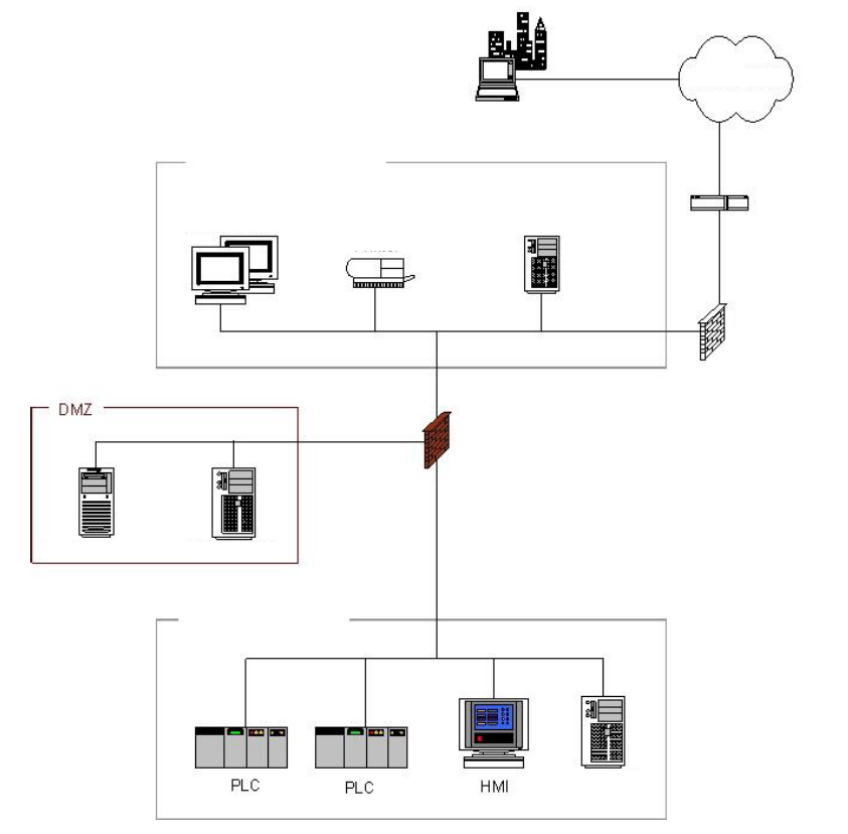
SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
98
5.5.4 ä¼æ¥ãããã¯ã¼ã¯ã¨å¶å¾¡ãããã¯ã¼ã¯éã® DMZ ä»ããã¡ã¤ã¢ã¦ã©ã¼ã«
ä¼æ¥ãããã¯ã¼ã¯ã¨å¶å¾¡ãããã¯ã¼ã¯éã« DMZ ãè¨ç½®ã§ãããã¡ã¤ã¢ã¦ã©ã¼ã«ã使ç¨ããã°ã
ããªãã®æ¹åã¨ãªããå DMZ ã¯ãã¼ã¿ãã¹ããªã¢ã³ãã¯ã¤ã¢ã¬ã¹ã¢ã¯ã»ã¹ãã¤ã³ãããªã¢ã¼ã
ã¢ã¯ã»ã¹ã·ã¹ãã ããµã¼ããã¼ãã£ã¢ã¯ã»ã¹ã·ã¹ãã çã1ååã¯è¤æ°ã®éè¦ã³ã³ãã¼ãã³ã
ãæãããå®éã« DMZ è½åã®ãããã¡ã¤ã¢ã¦ã©ã¼ã«ã使ç¨ããã°ãä¸éãããã¯ã¼ã¯ãæ§ç¯ã§
ããã
DMZ ãè¨ç½®ããã«ã¯ããã¡ã¤ã¢ã¦ã©ã¼ã«ãé常ã®ãããªãã¯ã»ãã©ã¤ãã¼ãã¤ã³ã¿ãã§ã¼ã¹ã§
ã¯ãªãã3ã¤ä»¥ä¸ã®ã¤ã³ã¿ãã§ã¼ã¹ãåãã¦ãããã¨ãå¿
é ã¨ãªãããã® 1ã¤ã¯ä¼æ¥ãããã¯
ã¼ã¯ã«æ¥ç¶ããã2ã¤ç®ã¯å¶å¾¡ãããã¯ã¼ã¯ã«ããã以å¤ã®ã¤ã³ã¿ãã§ã¼ã¹ã¯ãã¼ã¿ãã¹ããª
ã¢ã³ãµã¼ãã DMZ ãããã¯ã¼ã¯ä¸ã®ã¯ã¤ã¢ã¬ã¹ã¢ã¯ã»ã¹ãã¤ã³ãçãå
±æåã¯ã»ãã¥ãªãã£ã®
ä½ãããã¤ã¹ã«æ¥ç¶ããããDMZ ã®çä¿¡ã»éä¿¡ãã©ãã£ãã¯ãé£ç¶çã«ç£è¦ã§ããããã«å®è£
ãããã¨ãè¦ãããããã¾ããã¡ã¤ã¢ã¦ã©ã¼ã«ã«ã¼ã«ã»ããã¯ãå¶å¾¡ãããã¯ã¼ã¯ããã¤ã¹ã
éå§ãããå¶å¾¡ãããã¯ã¼ã¯ã¨ DMZ éã®æ¥ç¶ã許å¯ãããã®ãæ¨å¥¨ãããã
å³5-3 ã«ãã®ã¢ã¼ããã¯ãã£ã®ä¾ã示ãã
å³5-3.ä¼æ¥ãããã¯ã¼ã¯ã¨å¶å¾¡ãããã¯ã¼ã¯éã® DMZ ä»ããã¡ã¤ã¢ã¦ã©ã¼ã«
ä¼æ¥ãããã¯ã¼ã¯
ã¯ã¼ã¯ã¹ãã¼ã·ã§ã³
ã¢ããªã±ã¼ã·ã§ã³
ãµã¼ã
ãã¼ã¿ãã¹ããªã¢ã³
ã¤ã³ã¿ã¼ããã/WAN
ããªã³ã¿
ã«ã¼ã¿
ãã¡ã¤ã¢ã¦ã©ã¼ã«
å¶å¾¡ãããã¯ã¼ã¯
å¶å¾¡ãµã¼ã
ä¼æ¥/å¤ç
ãã¡ã¤ã¢ã¦ã©ã¼ã«
ãã¼ã¿ãµã¼ã
SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
99
By placing corporate-accessible components in the DMZ, no direct communication paths are required from
the corporate network to the control network; each path effectively ends in the DMZ. Most firewalls can
allow for multiple DMZs, and can specify what type of traffic may be forwarded between zones. As Figure
5-3 shows, the firewall can block arbitrary packets from the corporate network from entering the control
network, and can also regulate traffic from the other network zones including the control network. With
well-planned rule sets, a clear separation can be maintained between the control network and other
networks, with little or no traffic passing directly between the corporate and control networks.
If a patch management server, an antivirus server, or other security server is to be used for the control
network, it should be located directly on the DMZ. Both functions could reside on a single server. Having
patch management and antivirus management dedicated to the control network allows for controlled and
secure updates that can be tailored for the unique needs of the ICS environment. It may also be helpful if
the antivirus product chosen for ICS protection is not the same as the antivirus product used for the
corporate network. For example, if a malware incident occurs and one antivirus product cannot detect or
stop the malware, it is somewhat likely that another product may have that capability.
The primary security risk in this type of architecture is that if a computer in the DMZ is compromised, then
it can be used to launch an attack against the control network via application traffic permitted from the
DMZ to the control network. This risk can be greatly reduced if a concerted effort is made to harden and
actively patch the servers in the DMZ and if the firewall ruleset permits only connections between the
control network and DMZ that are initiated by control network devices. Other concerns with this
architecture are the added complexity and the potential increased cost of firewalls with several ports. For
more critical systems, however, the improved security should more than offset these disadvantages [35].
SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
100
ä¼æ¥å´ããã¢ã¯ã»ã¹å¯è½ãªã³ã³ãã¼ãã³ãã DMZ å
ã«é
ç½®ãããã¨ã§ãä¼æ¥ãããã¯ã¼ã¯ãã
å¶å¾¡ãããã¯ã¼ã¯ã¸ã®ç´æ¥çãªéä¿¡çµè·¯ã¯ä¸è¦ã¨ãªããåçµè·¯ã¯ DMZ ã§ãã£ããå®çµãããè¤
æ°ã® DMZ ãåãããã¡ã¤ã¢ã¦ã©ã¼ã«ãå¤ããã¾ã¼ã³éã§è»¢éã許ããããã©ãã£ãã¯ã®ç¨®é¡ã
æå®ã§ããããã«ãªã£ã¦ãããå³ 5-3 ã«ç¤ºãããããã«ããã¡ã¤ã¢ã¦ã©ã¼ã«ã¯ãä¼æ¥ãããã¯
ã¼ã¯ããæ¥ãä¸å®ã®ãã±ãããå¶å¾¡ãããã¯ã¼ã¯ã«é²å
¥ããã®ããããã¯ããå¶å¾¡ãããã¯ã¼
ã¯ãå«ããä»ã®ãããã¯ã¼ã¯ã¾ã¼ã³ããæ¥ããã©ãã£ãã¯ã®è¦å¶ãè¡ããããè¨ç»ãããã«ã¼
ã«ã»ãããæã¤ãã¨ã§ãå¶å¾¡ãããã¯ã¼ã¯ã¨ä»ã®ãããã¯ã¼ã¯éã®æ確ãªåé¢ãå¯è½ã«ãªãã
ä¼æ¥ãããã¯ã¼ã¯ã¨å¶å¾¡ãããã¯ã¼ã¯éã«ã¯ã»ã¨ãã©åã¯å
¨ããã©ãã£ãã¯ãå¾æ¥ããªããã
ã«ãªãã
å¶å¾¡ãããã¯ã¼ã¯ã«ããã管çãµã¼ããã¢ã³ãã¦ã¤ã«ã¹ãµã¼ããã®ä»ã®ã»ãã¥ãªã㣠ãµã¼ã
ã使ç¨ããå ´åãç´æ¥ DMZ ã«é
ç½®ãã¹ãã§ããããããã®æ©è½ã 1ã¤ã®ãµã¼ãã«å¸¸é§ã§ããã
å¶å¾¡ãããã¯ã¼ã¯å°ç¨ã®ããã管çåã³ã¢ã³ãã¦ã¤ã«ã¹ç®¡çãæã¦ã°ãICS ç°å¢ç¹æã®ãã¼ãº
ã«ãã£ããããå¶å¾¡ãããã»ãã¥ã¢ãªæ´æ°ãå¯è½ã«ãªããã¾ããICS ã®ä¿è·ç¨ã«é¸å®ããã¢ã³
ãã¦ã¤ã«ã¹è£½åã¨ä¼æ¥ãããã¯ã¼ã¯ç¨ã®è£½åãéã£ã¦ããã°ããããå½¹ç«ã¤ãä¾ãã°ããã«ã¦
ã¨ã¢ã¤ã³ã·ãã³ããèµ·ãã¦ãããã¢ã³ãã¦ã¤ã«ã¹è£½åã§ã¯æ¤ç¥ã»åæ¢ä¸è½ã ã£ãã¨ãã¦ããå¥
ã®è£½åã«ãã®è½åãããå ´åãããã
ãã®ç¨®ã®ã¢ã¼ããã¯ãã£ã«ããã主ãªã»ãã¥ãªãã£ãªã¹ã¯ã¯ãDMZ ã§ããã³ã³ãã¥ã¼ã¿ã®æ§è½
ãä½ä¸ããå ´åã«ããããå©ç¨ãã¦ãDMZ ããå¶å¾¡ãããã¯ã¼ã¯ã¸è¨±å¯ããã¦ããã¢ããªã±ã¼
ã·ã§ã³ãã©ãã£ãã¯çµç±ã§ãå¶å¾¡ãããã¯ã¼ã¯ã¸ã®æ»æãçºåãããã¨ã§ãããDMZ å
ã®ãµã¼
ãã®æèæ§ãé«ãç©æ¥µçã«ããããå½ã¦ãåçµããããã¡ã¤ã¢ã¦ã©ã¼ã«ã®ã«ã¼ã«ã»ããããå¶
御ãããã¯ã¼ã¯ããã¤ã¹ãéå§ãããå¶å¾¡ãããã¯ã¼ã¯ã¨ DMZ éã®æ¥ç¶ã ãã許å¯ããããã«
ããã°ããã®ãªã¹ã¯ã¯èããæ¸ãããã®ã¢ã¼ããã¯ãã£ã«é¢ãããã®ä»ã®æ¸å¿µææã¨ãã¦ã¯ã
è¤éããå¢ããã¨ã¨ãè¤æ°ã®ãã¼ããæã¤ãã¡ã¤ã¢ã¦ã©ã¼ã«ãã³ã¹ãé«ã«ãªããã¨ã§ãããã
ãããããéè¦ãªã·ã¹ãã ã§ã¯ãã»ãã¥ãªãã£ã®åä¸ã¯ããããæ¬ ç¹ãè£ã£ã¦ä½ããã[35]ã
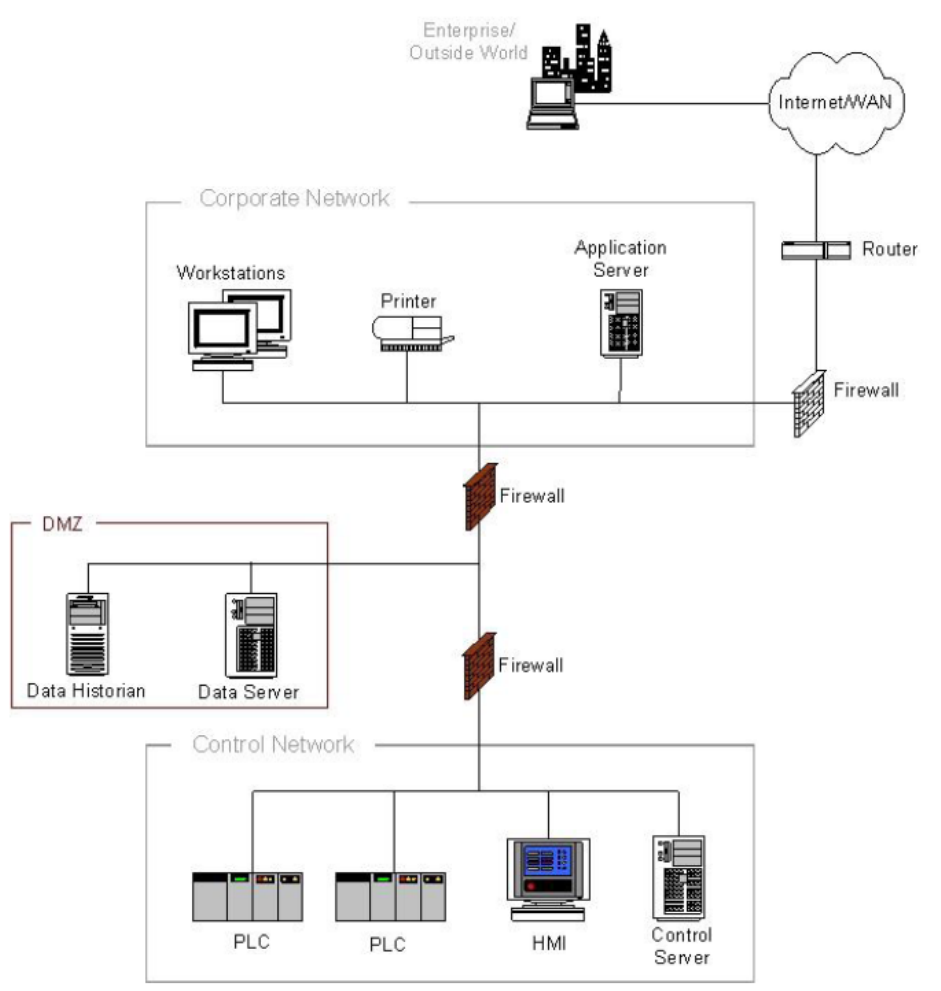
SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
101
5.5.5 Paired Firewalls between Corporate Network and Control Network
A variation on the firewall with a DMZ solution is to use a pair of firewalls positioned between the
corporate and ICS networks, as shown in Figure 5-4. Common servers such as the data historian are
situated between the firewalls in a DMZ-like network zone sometimes referred to as a Manufacturing
Execution System (MES) layer. As in the architectures described previously, the first firewall blocks
arbitrary packets from proceeding to the control network or the shared historians. The second firewall can
prevent unwanted traffic from a compromised server from entering the control network, and prevent control
network traffic from impacting the shared servers.
Figure 5-4. Paired Firewalls between Corporate Network and Control Network
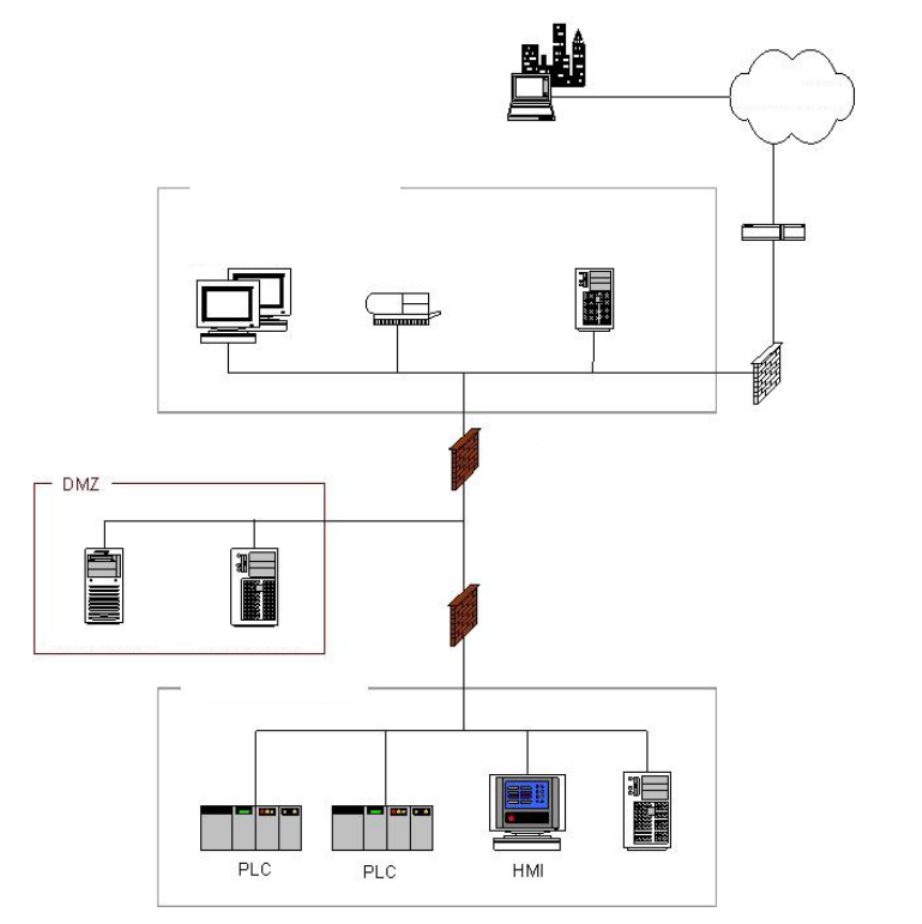
SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
102
5.5.5 ä¼æ¥ãããã¯ã¼ã¯ã¨å¶å¾¡ãããã¯ã¼ã¯éã®ãã¢ã¼ããã¡ã¤ã¢ã¦ã©ã¼ã«
DMZ ä»ããã¡ã¤ã¢ã¦ã©ã¼ã«ã½ãªã¥ã¼ã·ã§ã³ã®ããªã¨ã¼ã·ã§ã³ã¨ãã¦ãå³ 5-4 ã«ç¤ºãããã«ãã
ã¡ã¤ã¢ã¦ã©ã¼ã«ããã¢ã«ãã¦ä¼æ¥ãããã¯ã¼ã¯ã¨ ICS ãããã¯ã¼ã¯éã«é
ç½®ããæ¹æ³ããããã
ã¼ã¿ãã¹ããªã¢ã³ã®ãããªå
±éãµã¼ãã¯ãçç£å®æ½ã·ã¹ãã ï¼MESï¼ã¬ã¤ã¤ã¼ã¨å¼ã°ãã DMZ
ã«ä¼¼ããããã¯ã¼ã¯ã¾ã¼ã³å
ã®ãã¡ã¤ã¢ã¦ã©ã¼ã«ã¨ãã¡ã¤ã¢ã¦ã©ã¼ã«ã®éã«é
ç½®ããããåè¿°ã®
ã¢ã¼ããã¯ãã£ã¨åæ§ãæåã®ãã¡ã¤ã¢ã¦ã©ã¼ã«ã¯ãä¸å®ã®ãã±ãããå¶å¾¡ãããã¯ã¼ã¯ãå
±æ
ãã¹ããªã¢ã³ã¸è¡ããªãããã«ãããã¯ããã2çªç®ã®ãã¡ã¤ã¢ã¦ã©ã¼ã«ã¯ãæ§è½ãä½ä¸ãããµ
ã¼ãããã®ä¸è¦ã®ãã©ãã£ãã¯ãå¶å¾¡ãããã¯ã¼ã¯ã¸é²å
¥ããªãããã«ããå¶å¾¡ãããã¯ã¼ã¯ã
ã©ãã£ãã¯ãå
±æãµã¼ãã«å½±é¿ããªãããã«ããã
å³5-4.ä¼æ¥ãããã¯ã¼ã¯ã¨å¶å¾¡ãããã¯ã¼ã¯éã®ãã¢ã¼ããã¡ã¤ã¢ã¦ã©ã¼ã«
ä¼æ¥ãããã¯ã¼ã¯
ã¯ã¼ã¯ã¹ãã¼ã·ã§ã³
ã¢ããªã±ã¼ã·ã§ã³
ãµã¼ã
ãã¼ã¿ãã¹ããªã¢ã³
ã¤ã³ã¿ã¼ããã/WAN
ããªã³ã¿
ã«ã¼ã¿
ãã¡ã¤ã¢ã¦ã©ã¼ã«
å¶å¾¡ãããã¯ã¼ã¯
å¶å¾¡ãµã¼ã
ä¼æ¥/å¤ç
ãã¡ã¤ã¢ã¦ã©ã¼ã«
ãã¼ã¿ãµã¼ã
ãã¡ã¤ã¢ã¦ã©ã¼ã«

SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
103
If firewalls from two different manufacturers are used, then this solution may offer an advantage. It also
allows the control group and the IT group to have clearly separated device responsibility because each can
manage a firewall on its own, if the decision is made within the organization to do so. The primary
disadvantage with two-firewall architectures is the increased cost and management complexity. For
environments with stringent security requirements or the need for clear management separation, this
architecture has some strong advantages.
5.5.6 Network Segregation Summary
In summary, dual-homed computers generally not provide suitable isolation between control networks and
corporate networks. The two-zone solutions (no DMZ) are not recommended because they provide only
weak protection. If used, they should only be deployed with extreme care. The most secure, manageable,
and scalable control network and corporate network segregation architectures are typically based on a
system with at least three zones, incorporating one or more DMZs.
5.6 Recommended Defense-in-Depth Architecture
A single security product, technology or solution cannot adequately protect an ICS by itself. A multiple
layer strategy involving two (or more) different overlapping security mechanisms, a technique also known
as defense-in-depth, is desired so that the impact of a failure in any one mechanism is minimized. A
defense-in-depth architecture strategy includes the use of firewalls, the creation of demilitarized zones,
intrusion detection capabilities along with effective security policies, training programs, incident response
mechanisms and physical security. In addition, an effective defense-in-depth strategy requires a thorough
understanding of possible attack vectors on an ICS. These include:
ï¼ Backdoors and holes in network perimeter.
ï¼ Vulnerabilities in common protocols.
ï¼ Attacks on field devices.
ï¼ Database attacks.
ï¼ Communications hijacking and âman-in-the-middleâ attacks.
ï¼ Spoofing attacks.
ï¼ Attacks on privileged and/or shared accounts.
Figure 5-5 shows an ICS defense-in-depth architecture strategy that has been developed by the DHS
Control Systems Security Program (CSSP) NCCIC/ICS-CERT Recommended Practices committee25 as
described in the Control Systems Cyber Security: Defense in Depth Strategies [36] document. Additional
supporting documents that cover specific issues and associated mitigations are also included on the site.
The Control Systems Cyber Security: Defense in Depth Strategies document provides guidance and
direction for developing defense-in-depth architecture strategies for organizations that use control system
networks while maintaining a multi-tiered information architecture that requires:
ï¼ Maintenance of various field devices, telemetry collection, and/or industrial-level process systems.
ï¼ Access to facilities via remote data link or modem.
ï¼ Public facing services for customer or corporate operations.
25 Information on the CSSP Recommended Practices is located at http://ics-cert.us-cert.gov/Recommended-
Practices

SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
104
ç°ãªãäºã¤ã®ã¡ã¼ã«ã¼ã®ãã¡ã¤ã¢ã¦ã©ã¼ã«ãä½µç¨ããã¨ããã®ã½ãªã¥ã¼ã·ã§ã³ã«ã¯å©ç¹ãããã
ã¾ãå¶å¾¡ã°ã«ã¼ãåã³ IT ã°ã«ã¼ãã®ããã¤ã¹æ
å½åºåãæ確ã«ã§ãããçç±ã¯ãçµç¹ã®æ±ºå®ã
ä¸ãããã°ããããããèªåã®ãã¡ã¤ã¢ã¦ã©ã¼ã«ã管çã§ããããã§ãããäºéãã¡ã¤ã¢ã¦ã©ã¼
ã«ã¢ã¼ããã¯ãã£ã®ä¸»ãªæ¬ ç¹ã¯ãã³ã¹ãé«ã«ãªã管çãè¤éã«ãªããã¨ã§ãããå³æ ¼ãªã»ãã¥ãª
ãã£è¦ä»¶ã®ããç°å¢ãæ確ãªç®¡çã®åé¢ãæ±ããããç¶æ³ã§ã¯ããã®ã¢ã¼ããã¯ãã£ã¯å¤§ããªå©
ç¹ãããã
5.5.6 ãããã¯ã¼ã¯åé¢ã®ã¾ã¨ã
ã¾ã¨ãã¨ãã¦ãç·ãã¦äºéãã¼ã ã³ã³ãã¥ã¼ã¿ã¯ãå¶å¾¡ãããã¯ã¼ã¯ã¨ä¼æ¥ãããã¯ã¼ã¯éã®å
é¢ããã£ããè¡ãããã®ã§ã¯ãªãã2ã¾ã¼ã³ã½ãªã¥ã¼ã·ã§ã³ï¼DMZ ãªãï¼ã¯ãä¿è·ã«å¼±ç¹ããã
ããæ¨å¥¨ã§ããªãã使ç¨ããå ´åã¯ãç´°å¿ã®æ³¨æãæã£ã¦å±éãã¹ãã§ãããå¶å¾¡ãããã¯ã¼ã¯
ã¨ä¼æ¥ãããã¯ã¼ã¯ãåé¢ããããã®æãã»ãã¥ã¢ã§ã管çããããã¹ã±ã¼ã©ãã«ãªåé¢ã¢ã¼ã
ãã¯ãã£ã¯ãé常 1ã¤åã¯è¤æ°ã® DMZ ãæã£ãæä½3ã¤ã®ã¾ã¼ã³ãæããã·ã¹ãã ãåºèª¿ã¨ã
ãã
5.6 æ¨å¥¨å¤å±¤é²å¾¡ã¢ã¼ããã¯ãã£
åä¸ã®ã»ãã¥ãªãã£è£½åãæè¡åã¯ã½ãªã¥ã¼ã·ã§ã³ã®ã¿ã§ ICS ããã£ããä¿è·ãããã¨ã¯ä¸å¯è½
ã§ãããå¤å±¤é²å¾¡æè¡ã¨ãã¦ãç¥ããã¦ãã 2ã¤ä»¥ä¸ã®ç°ç¨®éç³ã»ãã¥ãªãã£ã¡ã«ããºã ãç¨ã
ããã«ãã¬ã¤ã¤ã¼æ¦ç¥ã¯ã1ã¤ã®ã¡ã«ããºã ã«é害ãåºã¦ãããã®å½±é¿ãæå°ã«é£ãæ¢ãããã
ããæã¾ãããå¤å±¤é²å¾¡ã¢ã¼ããã¯ãã£æ¦ç¥ã«ã¯ããã¡ã¤ã¢ã¦ã©ã¼ã«ã®ä½¿ç¨ãéæ¦è£
å°å¸¯ãä¾µå
¥
æ¤ç¥æ©è½ãå¹æçãªã»ãã¥ãªãã£ããªã·ã¼ãè¨ç·´è¨ç»ãã¤ã³ã·ãã³ã対å¿ã¡ã«ããºã åã³ç©çç
ã»ãã¥ãªãã£ã®æ§ç¯ãå«ã¾ãããå ãã¦ãå¹æçãªå¤å±¤é²å¾¡æ¦ç¥ãè¬ããã«ã¯ãICS ã«å¯¾ãã¦æ»
æå¯è½ãªãã¯ã¿ã¼ãååã«ç解ãããã¨ãæ±ãããããããã«ã¯ä»¥ä¸ãå«ã¾ããã
ï¼ ãããã¯ã¼ã¯å¨è¾ºã®ããã¯ãã¢åã³ãã¼ã«
ï¼ å
±éãããã³ã«ã®èå¼±æ§
ï¼ ãã£ã¼ã«ãããã¤ã¹ã«å¯¾ããæ»æ
ï¼ ãã¼ã¿ãã¼ã¹ã«å¯¾ããæ»æ
ï¼ éä¿¡ãã¤ã¸ã£ãã¯åã³ã人ãä»å¨ãããæ»æ
ï¼ ãªããã¾ãæ»æ
ï¼ æ¨©éã¢ã«ã¦ã³ãåã¯å
±éã¢ã«ã¦ã³ãã«å¯¾ããæ»æ
å³5-5 ã¯ããå¶å¾¡ã·ã¹ãã ã®ãµã¤ãã¼ã»ãã¥ãªãã£ï¼å¤å±¤é²å¾¡æ¦ç¥ã[36]ã«è¨è¿°ããã¦ãã DHS
å¶å¾¡ã·ã¹ãã ã»ãã¥ãªãã£ããã°ã©ã ï¼CSSP) /ICS-CERT æ¨å¥¨è¦ç¯å§å¡ä¼ 26ã«ããéçºãããã
ICS ã®å¤å±¤é²å¾¡ã¢ã¼ããã¯ãã£æ¦ç¥ã示ããå
·ä½çãªåé¡ç¹ãé¢é£ç·©åçã«é¢ããä»å çãªæ ¹æ
ææ¸ããµã¤ãã«ããã
ãå¶å¾¡ã·ã¹ãã ã®ãµã¤ãã¼ã»ãã¥ãªãã£ï¼å¤å±¤é²å¾¡æ¦ç¥ãã«ã¯ãå¶å¾¡ã·ã¹ãã ãããã¯ã¼ã¯ã使
ç¨ãã以ä¸ãå¿
è¦ã¨ããå¤æ®µéæ
å ±ã¢ã¼ããã¯ãã£ãç¶æãã¦ããçµç¹åãã«ãå¤å±¤é²å¾¡ã¢ã¼ã
ãã¯ãã£æ¦ç¥ãçå®ããããã®æéã¨æ示ãè¨è¼ããã¦ããã
ï¼ ç¨®ã
ã®ãã£ã¼ã«ãããã¤ã¹ããã¬ã¡ããªåéåã¯ç£æ¥ã¬ãã«ããã»ã¹ã·ã¹ãã ã®ä¿å®
ï¼ é éãã¼ã¿ãªã³ã¯ãã¢ãã çµç±ã«ããæ½è¨ã¸ã®ã¢ã¯ã»ã¹
ï¼ é¡§å®¢ã»ä¼æ¥æ¥åç¨å
Œ
±ãµã¼ãã¹
26 CSSP æ¨å¥¨è¦ç¯ã«é¢ããæ
å ±ã¯æ¬¡ã® URL ããå
¥æã§ãããhttp://ics-cert.us-cert.gov/Recommended-Practices
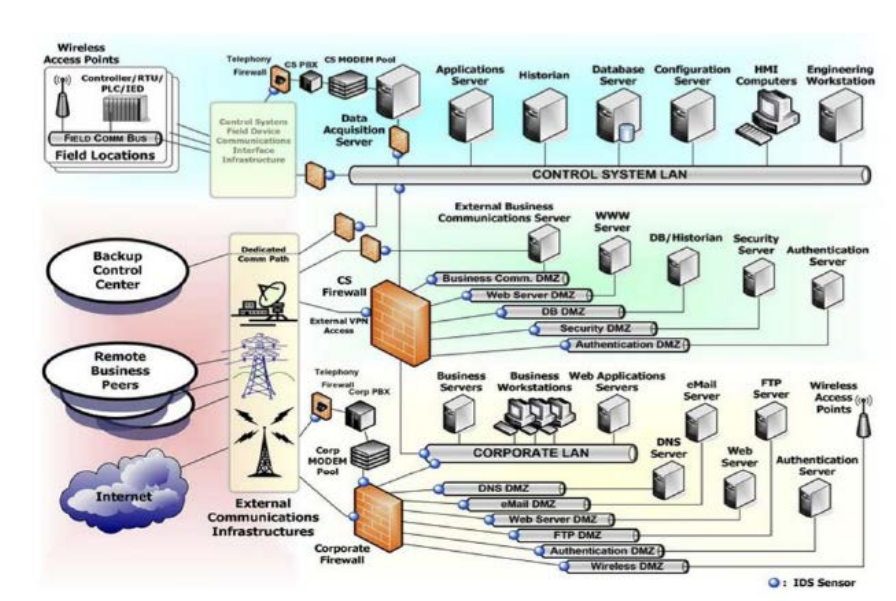
SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
105
This strategy includes firewalls, the use of demilitarized zones and intrusion detection capabilities
throughout the ICS architecture. The use of several demilitarized zones in Figure 5-5 provides the added
capability to separate functionalities and access privileges and has proved to be very effective in protecting
large architectures comprised of networks with different operational mandates. Intrusion detection
deployments apply different rule-sets and signatures unique to each domain being monitored.
Figure 5-5. CSSP Recommended Defense-In-Depth Architecture
5.7 General Firewall Policies for ICS
Once the defense-in-depth architecture is in place, the work of determining exactly what traffic should be
allowed through the firewalls begins. Configuring the firewalls to deny all except for the traffic absolutely
required for business needs is every organizationâs basic premise, but the reality is much more difficult.
Exactly what does âabsolutely required for businessâ mean and what are the security impacts of allowing
that traffic through? For example, many organizations considered allowing SQL traffic through the firewall
as required for business for many data historian servers. Unfortunately, the SQL vulnerability was also the
target for the Slammer worm [Table C-8. Example Adversarial Incidents]. Many important protocols used
in the industrial world, such as HTTP, FTP, OPC/DCOM, EtherNet/IP, and Modbus/TCP, have significant
security vulnerabilities.
The remaining material in this section summarizes some of the key points from the Centre for the
Protection of National Infrastructureâs (CPNI) Firewall Deployment for SCADA and Process Control
Networks: Good Practice Guide [35].
When installing a single two-port firewall without a DMZ for shared servers (i.e., the architecture described
in Section 5.5.2), particular care needs to be taken with the rule design. At a minimum, all rules
SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
106
ãã®æ¦ç¥ã«ã¯ãICS ã¢ã¼ããã¯ãã£å
¨ä½ãéãã¦ããã¡ã¤ã¢ã¦ã©ã¼ã«ãéæ¦è£
å°å¸¯åã³ä¾µå
¥æ¤ç¥
æ©è½ã®ä½¿ç¨ãå«ã¾ãããå³ 5-5 ã®è¤æ°éæ¦è£
å°å¸¯ã®ä½¿ç¨ã¯ãæ©è½ã¨ã¢ã¯ã»ã¹æ¨©éãåããããã®
ä»å çãªå¯¾çã§ã種ã
ã®æ¥åãæ
ãè¤æ°ãããã¯ã¼ã¯ãããªã大è¦æ¨¡ã¢ã¼ããã¯ãã£ã®ä¿è·ã«é
常ã«å¹æã®ãããã¨ãåãã£ã¦ãããä¾µå
¥æ¤ç¥ã®å±éã¯ãå¥ã
ã®ã«ã¼ã«ã»ããã¨ç£è¦ããé åã
ã¨ã«ä¸æã®ç½²åãé©ç¨ããã
å³5-5.CSSP ã®æ¨å¥¨å¤å±¤é²å¾¡ã¢ã¼ããã¯ãã£
5.7 ICS ã®å
¨è¬çãã¡ã¤ã¢ã¦ã©ã¼ã«ããªã·ã¼
å¤å±¤é²å¾¡ã¢ã¼ããã¯ãã£ãæ½è¡ãããªãã次ã«ãã¡ã¤ã¢ã¦ã©ã¼ã«ã§è¨±å¯ãããã©ãã£ãã¯ãæ確
ã«æ±ºããä½æ¥ãå§ã¾ããäºæ¥ã«çµ¶å¯¾å¿
è¦ãªãã©ãã£ãã¯ä»¥å¤ã¯å
¨ã¦æ絶ããããã«ãã¡ã¤ã¢ã¦ã©
ã¼ã«ãè¨å®ãããã¨ã¯ãã©ã®ä¼æ¥ã§ãåºæ¬ã§ããããç¾å®ã¯ã¯ããã«é£ããã
ãäºæ¥ã«çµ¶å¯¾å¿
è¦ãã¨ã¯ä½ãæå³ããã®ãããã®ãã©ãã£ãã¯ãééãããã¨ã©ããªã»ãã¥ãªã
ã£ä¸ã®å½±é¿ãåºãã®ããä¾ãã°ãå¤ãã®çµç¹ã§ã¯ãäºæ¥ä¸å¤æ°ã®ãã¼ã¿ãã¹ããªã¢ã³ãµã¼ãã«å¿
è¦ãªãã¨ãããSQL ãã©ãã£ãã¯ã®ãã¡ã¤ã¢ã¦ã©ã¼ã«ééãæ¤è¨ãããæ®å¿µãªãããSQL ã®èå¼±
æ§ãã¹ã©ãã¼ã¯ã¼ã ã®æ¨çã ã£ã[表C-8.æ»æã¤ã³ã·ãã³ãã®ä¾]ãHTTPãFTPãOPC/DCOMã
EtherNet/IPãModbus/TCP çãç£æ¥çã§ä½¿ç¨ããã¦ããéè¦ãããã³ã«ã®å¤ãã«ã¯ã大ããªã»ã
ã¥ãªãã£ä¸ã®èå¼±æ§ãããã
ãã®ã»ã¯ã·ã§ã³ã®æ®ãã®é¨åã§ã¯ãå½å®¶ã¤ã³ãã©ä¿è·ã»ã³ã¿ã¼ï¼CPNIï¼ã®ãSCADA åã³ããã»
ã¹å¶å¾¡ãããã¯ã¼ã¯ç¨ãã¡ã¤ã¢ã¦ã©ã¼ã«å±éï¼é©æ£è¦ç¯ã¬ã¤ãã[35]ããéè¦ãã¤ã³ããããã¤
ãè¦ç´ããã
å
±æãµã¼ãï¼ã»ã¯ã·ã§ã³ 5.5.2 ã®ã¢ã¼ããã¯ãã£çï¼ç¨ã« DMZ ãªãã®åä¸ 2ãã¼ããã¡ã¤ã¢ã¦ã©
ã¼ã«ãè¨ç½®ããå ´åãã«ã¼ã«ã®æ¤è¨ã«ã¯ç¹ã«æ³¨æãè¦ãããå°ãªãã¨ãã©ã®ã«ã¼ã«ã
ã¯ã¤ã¢ã¬ã¹ã¢ã¯ã»ã¹ãã¤ã³ã
å¤é¨éä¿¡ã¤ã³ãã©
ã³ã³ããã¼ã©
/RTU/PLC/IED
ãã£ã¼ã«ãå
±éãã¹
ãã£ã¼ã«ãã®å ´æ
é»è©±éä¿¡ãã¡ã¤ã¢
ã¦ã©ã¼ã«
CS PBX
CS
ã¢ãã ãã¼ã«
ããã¯ã¢ããå¶å¾¡
ã»ã³ã¿ã¼
é éäºæ¥ãã¢
ã¤ã³ã¿ã¼ããã
å¶å¾¡ã·ã¹ãã
ãã£ã¼ã«ãã
ãã¤ã¹
éä¿¡ã¤ã³ã¿
ãã§ã¼ã¹
ã¤ã³ãã©
å°ç¨å
±éçµè·¯
ãã¼ã¿
åå¾ãµã¼ã
ã¢ããªã±ã¼ã·ã§
ã³ãµã¼ã
ãã¹ããªã¢ã³
ãã¼ã¿ãã¼ã¹ãµ
ã¼ã
è¨å®ãµã¼ã
HMI
ã³ã³ãã¥ã¼ã¿
ã¨ã³ã¸ãã¢ãªã³ã°
ã¯ã¼ã¯ã¹ãã¼ã·ã§ã³
å¶å¾¡ã·ã¹ãã
LAN
å¤é¨äºæ¥éä¿¡
ãµã¼ã
WWW
ãµã¼ã
DB/
ãã¹ããªã¢ã³
ã»ãã¥ãªãã£
ãµã¼ã
èªè¨¼ãµã¼ã
äºæ¥å
±é
DMZ
Web
ãµã¼ã
DMZ
DB DMZ
ã»ãã¥ãªã㣠DMZ
èªè¨¼ DMZ
ä¼æ¥
LAN
äºæ¥ãµã¼ã
äºæ¥ã¯ã¼ã¯
ã¹ãã¼ã·ã§ã³
Web
ã¢ããªã±ã¼
ã·ã§ã³ãµã¼ã
e
ã¡ã¼ã«
ãµã¼ã
FTP
ãµã¼ã
ã¯ã¤ã¢ã¬ã¹
ã¢ã¯ã»ã¹
ãã¤ã³ã
èªè¨¼ãµã¼ã
Web
ãµã¼ã
DNS
ãµã¼ã
DNS DMZ
e
ã¡ã¼ã«
DMZ
Web
ãµã¼ã
DMZ
FTP DMZ
èªè¨¼
DMZ
ã¯ã¤ã¤ã¬ã¹
DMZ
IDS
ã»ã³ãµ
é»è©±éä¿¡ãã¡ã¤ã¢
ã¦ã©ã¼ã«
CS
ãã¡ã¤ã¢
ã¦ã©ã¼ã«
å¤é¨
VPN
ã¢ã¯ã»ã¹
ä¼æ¥
PBX
ä¼æ¥ã¢ãã
ãã¼ã«
ä¼æ¥
ãã¡ã¤ã¢ã¦ã©ã¼ã«
SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
107
should be stateful rules that are both IP address and port (application) specific. The address portion of the
rules should restrict incoming traffic to a very small set of shared devices (e.g., the data historian) on the
control network from a controlled set of addresses on the corporate network. Allowing any IP addresses on
the corporate network to access servers inside the control network is not recommended. In addition, the
allowed ports should be carefully restricted to relatively secure protocols such as Hypertext Transfer
Protocol Secure (HTTPS). Allowing HTTP, FTP, or other unsecured protocols to cross the firewall is a
security risk due to the potential for traffic sniffing and modification. Rules should be added to deny hosts
outside the control network from initiating connections with hosts on the control network. Rules should
only allow devices internal to the control network the ability to establish connections outside the control
network.
On the other hand, if the DMZ architecture is being used, then it is possible to configure the system so that
no traffic will go directly between the corporate network and the control network. With a few special
exceptions (noted below), all traffic from either side can terminate at the servers in the DMZ. This allows
more flexibility in the protocols allowed through the firewall. For example, Modbus/TCP might be used to
communicate from the PLCs to the data historian, while HTTP might be used for communication between
the historian and enterprise clients. Both protocols are inherently insecure, yet in this case they can be used
safely because neither actually crosses between the two networks. An extension to this concept is the idea
of using âdisjointâ protocols in all control network to corporate network communications. That is, if a
protocol is allowed between the control network and DMZ, then it is explicitly not allowed between the
DMZ and corporate network. This design greatly reduces the chance of a worm such as Slammer actually
making its way into the control network, because the worm would have to use two different exploits over
two different protocols.
One area of considerable variation in practice is the control of outbound traffic from the control network,
which could represent a significant risk if unmanaged. One example is Trojan horse software that uses
HTTP tunneling to exploit poorly defined outbound rules. Thus, it is important that outbound rules be as
stringent as inbound rules.
Example outbound rules include:
ï¼ Outbound traffic through the control network firewall should be limited to essential communications
only and should be limited to authorized traffic originating from DMZ servers.
ï¼ All outbound traffic from the control network to the corporate network should be source and
destination-restricted by service and port.
In addition to these rules, the firewall should be configured with outbound filtering to stop forged IP
packets from leaving the control network or the DMZ. In practice this is achieved by checking the source
IP addresses of outgoing packets against the firewallâs respective network interface address. The intent is to
prevent the control network from being the source of spoofed (i.e., forged) communications, which are
often used in DoS attacks. Thus, the firewalls should be configured to forward IP packets only if those
packets have a correct source IP address for the control network or DMZ networks. Finally, Internet access
by devices on the control network should be strongly discouraged.
SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
108
IP ã¢ãã¬ã¹ã¨ãã¼ãï¼ã¢ããªã±ã¼ã·ã§ã³ï¼ã«åºæã®ã¹ãã¼ããã«ã«ã¼ã«ã«ãã¹ãã§ãããã«ã¼
ã«ã®ã¢ãã¬ã¹é¨ä½ã¯ãä¼æ¥ãããã¯ã¼ã¯ã®ç®¡çãããã¢ãã¬ã¹ã»ããããæ¥ããã©ãã£ãã¯ãã
å¶å¾¡ãããã¯ã¼ã¯ä¸ã®ããå°ã»ããã®å
±æããã¤ã¹ï¼ãã¼ã¿ãã¹ããªã¢ã³çï¼ã«éå®ãããä¼
æ¥ãããã¯ã¼ã¯ä¸ã® IP ã¢ãã¬ã¹ãå¶å¾¡ãããã¯ã¼ã¯å
ã®ãµã¼ãã«ã¢ã¯ã»ã¹ã§ããããã«ããã®
ã¯è¦ããããªããã¾ãã許å¯ãããã¼ãã¯ç¨å¿ã®ãããHTTPS çã®æ¯è¼çã»ãã¥ã¢ãªãããã³
ã«ã«éå®ãã¹ãã§ãããHTTPãFTP ãã®ä»ã»ãã¥ã¢ã§ãªããããã³ã«ããã¡ã¤ã¢ã¦ã©ã¼ã«ãè¶
ããã®ã¯ããã©ãã£ãã¯ã®ã¹ãããã£ã³ã°ãå¤æ´ã®ãããããããããã»ãã¥ãªãã£ãªã¹ã¯ã¨
ãªããå¶å¾¡ãããã¯ã¼ã¯å¤ã®ãã¹ããå¶å¾¡ãããã¯ã¼ã¯ä¸ã®ãã¹ãã«æ¥ç¶ã§ããªãããã«ã«ã¼
ã«ã追å ãã¹ãã§ãããå¶å¾¡ãããã¯ã¼ã¯å
ã®ããã¤ã¹ã ããå¶å¾¡ãããã¯ã¼ã¯ã®å¤ã«æ¥ç¶ã§
ããã«ã¼ã«ã«ãã¹ãã§ããã
å対ã«ãDMZ ã¢ã¼ããã¯ãã£ã使ç¨ãã¦ããå ´åã¯ããã©ãã£ãã¯ãä¼æ¥ãããã¯ã¼ã¯ã¨å¶å¾¡
ãããã¯ã¼ã¯éã§ç´æ¥å¾æ¥ããªãããã«ã·ã¹ãã è¨å®ãããã¨ãã§ãããç¹å¥ãªå ´åãé¤ãã¦
ï¼ä¸è¨åç
§ï¼ããããã®å´ããã®ãã©ãã£ãã¯ã DMZ å
ã®ãµã¼ãã§çµäºãããã¨ã¯ã§ããªãã
ããã«ãããã¡ã¤ã¢ã¦ã©ã¼ã«ãééå¯è½ãªãããã³ã«ã®æè»æ§ãåä¸ãããä¾ãã°ãPLCs ã
ããã¼ã¿ãã¹ããªã¢ã³ã¸ã®éä¿¡ã« Modbus/TCP ã使ç¨ããHTTP ã¯ãã¹ããªã¢ã³ã¨ä¼æ¥ã¯ã©ã¤ã¢
ã³ãéã®éä¿¡ã«ä½¿ç¨ã§ãããã©ã¡ãã®ãããã³ã«ãæ¬æ¥ã»ãã¥ã¢ã§ã¯ãªããããã®å ´å㯠2ã¤
ã®ãããã¯ã¼ã¯ãè¶ãããã¨ããªããããå®å
¨ã«ä½¿ç¨ã§ããããã®æ¦å¿µãæ·è¡ãããã®ããå¥
種ããããã³ã«ãå
¨ã¦ã®å¶å¾¡ãããã¯ã¼ã¯ã¨ä¼æ¥ãããã¯ã¼ã¯éä¿¡ã«ä½¿ç¨ããã¨ããèãæ¹ã§
ãããã¤ã¾ãããããããã³ã«ãå¶å¾¡ãããã¯ã¼ã¯ã¨ DMZ éã§è¨±å¯ããããDMZ ã¨ä¼æ¥ããã
ã¯ã¼ã¯éã§ã¯æ示çã«è¨±å¯ããªãã¨ãããã®ã§ããããã®è¨è¨ã¯ã¹ã©ãã¼ã®ãããªã¯ã¼ã ãå¶
御ãããã¯ã¼ã¯ã«ä¾µå
¥ããæ©ä¼ãèããæ¸ããããããã¯ãã®ã¯ã¼ã ã 2種é¡ã®ãããã³ã«ã
å©ç¨ããªããã°ãªããªãããã§ããã
ããªãã®ããªã¨ã¼ã·ã§ã³ãããã®ãå¶å¾¡ãããã¯ã¼ã¯ããã®éä¿¡ãã©ãã£ãã¯ã®å¶å¾¡ã§ã管ç
ãè¡ãå±ããªãã¨å¤§ããªãªã¹ã¯ã¨ãªãããã®ä¸ä¾ãããã¤ã®æ¨é¦¬ã§ãHTTP ãã³ããªã³ã°ã使ãã
å®ç¾©ã«ä¸åãããéä¿¡ã«ã¼ã«ã欺ãããããã£ã¦ãéä¿¡ã«ã¼ã«ã¯çä¿¡ã«ã¼ã«åæ§ã«å³æ ¼ã§ãªã
ãã°ãªããªãã
以ä¸ã¯éä¿¡ã«ã¼ã«ã®ä¾ã§ããã
ï¼ å¶å¾¡ãããã¯ã¼ã¯ãã¡ã¤ã¢ã¦ã©ã¼ã«ãè¶ããéä¿¡ãã©ãã£ãã¯ã¯ãä¸å¯æ¬ ãªéä¿¡ã®ã¿ã«éå®ãã
ã¾ã DMZ ãµã¼ãããã®è¨±å¯ããããã©ãã£ãã¯ã®ã¿ã«éå®ãã¹ãã§ããã
ï¼ å¶å¾¡ãããã¯ã¼ã¯ããä¼æ¥ããã¯ã¯ã¼ã¯ã¸ã®å
¨ã¦ã®éä¿¡ãã©ãã£ãã¯ã¯ããµã¼ãã¹ã¨ãã¼ã
ã«ããã½ã¼ã¹åã³å®å
å¶éãè¨ããã¹ãã§ããã
ãããã®ã«ã¼ã«ã«å ãã¦ããã¡ã¤ã¢ã¦ã©ã¼ã«ã®è¨å®ã¯éä¿¡ãã£ã«ã¿ãããã¦ãå½ã® IP ãã±ãã
ãå¶å¾¡ãããã¯ã¼ã¯ã DMZ ããå¤ã«åºãªãããã«ãã¹ãã§ãããå®éã«ã¯ãéä¿¡ãã±ããã®ã½
ã¼ã¹ IP ã¢ãã¬ã¹ãããã¡ã¤ã¢ã¦ã©ã¼ã«ã®åãããã¯ã¼ã¯ã¤ã³ã¿ãã§ã¼ã¹ã¢ãã¬ã¹ã«ç
§ããã¦ã
ã§ãã¯ãããã¨ã§ãããè¡ã£ã¦ãããç®çã¯ãå¶å¾¡ãããã¯ã¼ã¯ã欺çï¼æ¬ä¼¼ï¼éä¿¡ã®ã½ã¼ã¹ã«
ãªããªãããã«ãããã¨ã§ããããã㯠DoS æ»æã§å¤ç¨ãããããã®ããã«ãã¡ã¤ã¢ã¦ã©ã¼ã«
ã¯ãå¶å¾¡ãããã¯ã¼ã¯ã DMZ ãããã¯ã¼ã¯ã® IP ã¢ãã¬ã¹ãæ£ããå ´åã«ã®ã¿ãIP ãã±ããã転
éããããã«è¨å®ãã¹ãã§ãããæå¾ã«ãå¶å¾¡ãããã¯ã¼ã¯ä¸ã®ããã¤ã¹ã«ããã¤ã³ã¿ã¼ããã
ã¢ã¯ã»ã¹ã¯ãæ¯éã¨ããããã¹ãã§ããã
SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
109
In summary, the following should be considered as recommended practice for general firewall rule sets:
ï¼ The base rule set should be deny all, permit none.
ï¼ Ports and services between the control network environment and the corporate network should be
enabled and permissions granted on a specific case-by-case basis. There should be a documented
business justification with risk analysis and a responsible person for each permitted incoming or
outgoing data flow.
ï¼ All âpermitâ rules should be both IP address and TCP/UDP port specific, and stateful if appropriate.
ï¼ All rules should restrict traffic to a specific IP address or range of addresses.
ï¼ Traffic should be prevented from transiting directly from the control network to the corporate network.
All traffic should terminate in the DMZ.
ï¼ Any protocol allowed between the control network and DMZ should explicitly NOT be allowed
between the DMZ and corporate networks (and vice-versa).
ï¼ All outbound traffic from the control network to the corporate network should be source and
destination-restricted by service and port.
ï¼ Outbound packets from the control network or DMZ should be allowed only if those packets have a
correct source IP address that is assigned to the control network or DMZ devices.
ï¼ Control network devices should not be allowed to access the Internet.
ï¼ Control networks should not be directly connected to the Internet, even if protected via a firewall.
ï¼ All firewall management traffic should be carried on either a separate, secured management network
(e.g., out of band) or over an encrypted network with multi-factor authentication. Traffic should also
be restricted by IP address to specific management stations.
ï¼ All firewall policies should be tested periodically.
ï¼ All firewalls should be backed up immediately prior to commissioning.
These should be considered only as guidelines. A careful assessment of each control environment is
required before implementing any firewall rule sets.
5.8 Recommended Firewall Rules for Specific Services
Beside the general rules described above, it is difficult to outline all-purpose rules for specific protocols.
The needs and recommended practices vary significantly between industries for any given protocol and
should be analyzed on an organization-by-organization basis. The Industrial Automation Open Networking
Association (IAONA) offers a template for conducting such an analysis [37], assessing each of the
protocols commonly found in industrial environments in terms of function, security risk, worst case impact,
and suggested measures. Some of the key points from the IAONA document are summarized in this section.
The reader is advised to consult this document directly when developing rule sets.
SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
110
ã¾ã¨ãã¨ãã¦ãå
¨è¬çãªãã¡ã¤ã¢ã¦ã©ã¼ã«ã®ã«ã¼ã«ã»ããç¨æ¨å¥¨è¦ç¯ã¨ãã¦ã次ã®ç¹ãèæ
®ãã¹
ãã§ããã
ï¼ ã«ã¼ã«ã»ããã®åºæ¬ã¯å
¨ã¦æ絶ãä½ã許å¯ããªãã§ããã
ï¼ å¶å¾¡ãããã¯ã¼ã¯ç°å¢ã¨ä¼æ¥ãããã¯ã¼ã¯éã®ãã¼ãåã³ãµã¼ãã¹ã使ç¨å¯è½ã«ãã許å¯ã¯
ã±ã¼ã¹ãã¤ã±ã¼ã¹ã§ä¸ããã¹ãã§ãããããããäºæ¥çç±æ¸ã¨ãã¦ææ¸åãããªã¹ã¯åæå
ã³è¨±å¯ããçä¿¡ã»éä¿¡ãã¼ã¿ããã¼ã®è²¬ä»»è
ã¨ã¨ãã«è¨é²ããã
ï¼ å
¨ã¦ã許å¯ãã«ã¼ã«ã¯ãIP ã¢ãã¬ã¹åã³ TCP/UDP ãã¼ãåºæã«ããå¿
è¦ãªãã¹ãã¼ããã«
ã¨ããã
ï¼ å
¨ã¦ã®ã«ã¼ã«ã¯ããã©ãã£ãã¯ãç¹å®ã® IP ã¢ãã¬ã¹åã¯ã¢ãã¬ã¹ç¯å²ã«éå®ãã¹ãã§ããã
ï¼ ãã©ãã£ãã¯ã¯ãå¶å¾¡ãããã¯ã¼ã¯ããä¼æ¥ãããã¯ã¼ã¯ã¸ç´æ¥éä¿¡ãããªãããã«ãã¹ã
ã§ãããå
¨ã¦ã®ãã©ãã£ãã¯ã¯ DMZ ã§çµäºãã¹ãã§ããã
ï¼ å¶å¾¡ãããã¯ã¼ã¯ã¨ DMZ éã§è¨±å¯ããããããã³ã«ã¯ãDMZ ã¨ä¼æ¥ãããã¯ã¼ã¯éï¼ãã®
éæ¹åãï¼ã§ã¯æ示çã«è¨±å¯ããªãããã«ãã¹ãã§ããã
ï¼ å¶å¾¡ãããã¯ã¼ã¯ããä¼æ¥ããã¯ã¯ã¼ã¯ã¸ã®å
¨ã¦ã®éä¿¡ãã©ãã£ãã¯ã¯ããµã¼ãã¹ã¨ãã¼ã
ã«ããã½ã¼ã¹åã³å®å
å¶éãè¨ããã¹ãã§ããã
ï¼ å¶å¾¡ãããã¯ã¼ã¯å㯠DMZ ããã®éä¿¡ãã±ããã¯ãå¶å¾¡ãããã¯ã¼ã¯å㯠DMZ ããã¤ã¹
ã«å²ãå½ã¦ãããã½ã¼ã¹ IP ã¢ãã¬ã¹ãæ£ããå ´åã«ã®ã¿è¨±å¯ãã¹ãã§ããã
ï¼ å¶å¾¡ãããã¯ã¼ã¯ããã¤ã¹ã®ã¤ã³ã¿ã¼ãããã¢ã¯ã»ã¹ã¯è¨±å¯ãã¹ãã§ãªãã
ï¼ å¶å¾¡ãããã¯ã¼ã¯ã¯ããã¡ã¤ã¢ã¦ã©ã¼ã«ã§ä¿è·ããã¦ãã¦ããç´æ¥ã¤ã³ã¿ã¼ãããã«æ¥ç¶ã
ã¹ãã§ãªãã
ï¼ å
¨ã¦ã®ãã¡ã¤ã¢ã¦ã©ã¼ã«ç®¡çãã©ãã£ãã¯ã¯ãå¥åã®ãã»ãã¥ã¢ç®¡çãããã¯ã¼ã¯ï¼ãã³ã
å¤çï¼åã¯å¤è¦ç´ èªè¨¼ãåããæå·åãããã¯ã¼ã¯ã¸ç¶ãã¹ãã§ãããã¾ããã©ãã£ãã¯ã¯ã
IP ã¢ãã¬ã¹ã«ããç¹å®ã®ç®¡çã¹ãã¼ã·ã§ã³ã«éå®ãã¹ãã§ããã
ï¼ å
¨ã¦ã®ãã¡ã¤ã¢ã¦ã©ã¼ã«ããªã·ã¼ã¯ãå®æçã«æ¤è¨¼ãã¹ãã§ããã
ï¼ å
¨ã¦ã®ãã¡ã¤ã¢ã¦ã©ã¼ã«ã¯ã試é転ãè¡ãç´åã«ããã¯ã¢ãããã¹ãã§ããã
以ä¸ã¯ããã¾ã§ãæéã¨ãã¦æ¤è¨ãã¹ããã®ã§ããããã¡ã¤ã¢ã¦ã©ã¼ã«ã«ã¼ã«ã»ãããå®æ½
ããåã«ãåå¶å¾¡ç°å¢ãæ
éã«è©ä¾¡ããå¿
è¦ãããã
5.8 ç¹å®ãµã¼ãã¹ã®æ¨å¥¨ãã¡ã¤ã¢ã¦ã©ã¼ã«ã«ã¼ã«
ä¸è¨ã®å
¨è¬ã«ã¼ã«ã«å ãã¦ãç¹å®ã®ãããã³ã«ç¨ã«æ±ç¨çãªã«ã¼ã«ã決ããã®ã¯é£ãããç¹å®ã®
ãããã³ã«ã«é¢ãããã¼ãºã¨æ¨å¥¨è¦ç¯ã¯ãæ¥çã«ãã£ã¦ã¾ã¡ã¾ã¡ã§ãçµç¹ãã¨ã«åæãã¹ãã§ã
ããç£æ¥ãªã¼ãã¡ã¼ã·ã§ã³ãªã¼ãã³ãããã¯ã¼ãã³ã°åä¼ï¼IAONAï¼ã¯ããã®ãããªåæãè¡
ãããã®ã²ãªå½¢ãæä¾ãã¦ãã[37]ãç£æ¥ç°å¢ã§ä½¿ç¨ããä¸è¬çãªãããã³ã«ãæ©è½ãã»ãã¥ãª
ãã£ãªã¹ã¯ãææªäºæ
ã®å½±é¿åã³å¯¾çã®è¦³ç¹ããåå¥ã«è©ä¾¡ãã¦ãããIAONA ææ¸ã®éè¦ç¹ã®
ããã¤ããè¦ç´ãããã®ããã®ã»ã¯ã·ã§ã³ã§åãä¸ãããèªè
ã¯ãã«ã¼ã«ã»ãããçå®ããéã«
ç´æ¥ãã®ææ¸ã調ã¹ãããæ¨å¥¨ããã
SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
111
5.8.1 Domain Name System (DNS)
Domain Name System (DNS) is primarily used to translate between domain names and IP addresses. For
example, a DNS could map a domain name such as control.com to an IP address such as 192.168.1.1. Most
Internet services rely heavily on DNS, but its use on the control network is relatively rare at this time. In
most cases there is little reason to allow DNS requests out of the control network to the corporate network
and no reason to allow DNS requests into the control network. DNS requests from the control network to
DMZ should be addressed on a case-by-case basis. Local DNS or the use of host files is recommended.
5.8.2 Hypertext Transfer Protocol (HTTP)
HTTP is the protocol underlying Web browsing services on the Internet. Like DNS, it is critical to most
Internet services. It is seeing increasing use on the plant floor as well as an all-purpose query tool.
Unfortunately, it has little inherent security, and many HTTP applications have vulnerabilities that can be
exploited. HTTP can be a transport mechanism for many manually performed attacks and automated
worms.
In general, HTTP should not be allowed to cross from the public/corporate to the control network.
If web-based technologies are absolutely required, the following best practices should be applied:
ï¼ Control access to web-based services on the physical or network layer using white-listing;
ï¼ Apply access control to both source and destination;
ï¼ Implement authorization to access the service on the application layer (instead of physical or network-
layer checks);
ï¼ Implement service using only the necessary technologies (e.g., scripts are used only if they are
required);
ï¼ Check service according to known application security practices;
ï¼ Log all attempts of service usage ; and
ï¼ Use HTTPS rather than HTTP, and only for specific authorized devices.
5.8.3 FTP and Trivial File Transfer Protocol (TFTP)
FTP and Trivial File Transfer Protocol (TFTP) are used for transferring files between devices. They are
implemented on almost every platform including many SCADA systems, DCS, PLCs, and RTUs, because
they are very well known and use minimum processing power. Unfortunately, neither protocol was created
with security in mind; for FTP, the login password is not encrypted, and for TFTP, no login is required at
all. Furthermore, some FTP implementations have a history of buffer overflow vulnerabilities. As a result,
all TFTP communications should be blocked, while FTP communications should be allowed for outbound
sessions only or if secured with additional token-based multi-factor authentication and an encrypted tunnel.
More secure protocols, such as Secure FTP (SFTP) or Secure Copy (SCP), should be employed whenever
possible.
5.8.4 Telnet
The telnet protocol defines an interactive, text-based communications session between a client and a host. It
is used mainly for remote login and simple control services to systems with limited resources or to systems
with limited needs for security. It is a severe security risk because all telnet traffic, including passwords, is
unencrypted, and it can allow a remote individual considerable control over a device. It is recommended to
use the Secure Shell (SSH) protocol [5.8.6] for remote administration. Inbound telnet
SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
112
5.8.1 é ååã·ã¹ãã ï¼DNSï¼
é ååã·ã¹ãã ï¼DNSï¼ã¯ã主ã¨ãã¦é åå㨠IP ã¢ãã¬ã¹éã®ç¿»è¨³ã«ä½¿ç¨ãããä¾ãã°ãDNS
ã¯
control.com
ã¨ããé ååã
192.168.1.1
ã¨ãã IP ã¢ãã¬ã¹ã¨ãã¦ãããããã
大æµã®ã¤ã³ã¿ã¼ããããµã¼ãã¹ã¯ DNS ã«å¤§ããä¾åãã¦ããããå¶å¾¡ãããã¯ã¼ã¯ã§ã®ä½¿ç¨ã¯
ä»ã®ã¨ããæ¯è¼çå°ãªããã»ã¨ãã©ã®å ´åãå¶å¾¡ãããã¯ã¼ã¯ããä¼æ¥ãããã¯ã¼ã¯ã¸ã® DNS
è¦æ±ã許å¯ããçç±ã¯ãªããå¶å¾¡ãããã¯ã¼ã¯ã¸ã® DNS è¦æ±ã許å¯ããçç±ããªããå¶å¾¡ãã
ãã¯ã¼ã¯ãã DMZ ã¸ã® DNS è¦æ±ã¯ãã±ã¼ã¹ãã¤ã±ã¼ã¹ã§æ±ãã¹ãã§ããããã¼ã«ã« DNS ãã
ã¹ããã¡ã¤ã«ã®ä½¿ç¨ãæ¨å¥¨ãããã
5.8.2 ãã¤ãã¼ããã¹ã転éãããã³ã«ï¼HTTPï¼
HTTP ã¯ã¤ã³ã¿ã¼ãããä¸ã® Web é²è¦§ãµã¼ãã¹ãããã³ã«ã§ãããDNS ã¨åæ§ãã»ã¨ãã©ã®ã¤ã³
ã¿ã¼ããããµã¼ãã¹ã«ã¨ã£ã¦éè¦ã§ããããã©ã³ãã®ç¾å ´ãæ±ç¨ã¯ã¨ãªãã¼ã«ã§ã®ä½¿ç¨ãå¢ã
ã¦ããã
æ®å¿µãªããã»ãã¥ãªãã£ããã£ãããã¦ããããHTTP ã¢ããªã±ã¼ã·ã§ã³ã®å¤ãã«ã¯æªç¨ããã
èå¼±æ§ããããHTTP ã¯ãæåæ»æãèªåã¯ã¼ã ã®å¤ãã§éä¿¡ã¡ã«ããºã ã«ãªãã
ç·ã㦠HTTP ã¯ãå
¬é/ä¼æ¥ãããã¯ã¼ã¯ããå¶å¾¡ãããã¯ã¼ã¯ã¸å
¥ããã¹ãã§ãªããã¦
ã§ããã¼ã¹æè¡ãã©ããã¦ãå¿
è¦ã¨ãªãå ´åã次ã®ãããªæè¯è¦ç¯ãé©ç¨ãã¹ãã§ããã
ï¼ ãã¯ã¤ããªã¹ãã使ç¨ããç©ççåã¯ãããã¯ã¼ã¯ã¬ã¤ã¤ã¼ä¸ã®ã¦ã§ããã¼ã¹ãµã¼ãã¹ã¸ã®
å¶å¾¡ã¢ã¯ã»ã¹
ï¼ ã½ã¼ã¹åã³å®å
ã®åæ¹ã«ã¢ã¯ã»ã¹å¶å¾¡ãé©ç¨
ï¼ ã¢ããªã±ã¼ã·ã§ã³å±¤ã®ãµã¼ãã¹ã¸ã®ã¢ã¯ã»ã¹ã許å¯ï¼ç©ççåã¯ãããã¯ã¼ã¯ã¬ã¤ã¤ã¼ãã§
ãã¯ã§ãªãï¼
ï¼ å¿
é æè¡ã®ã¿ã使ç¨ãã¦ãµã¼ãã¹ãå®è£
ï¼ã¹ã¯ãªããã¯å¿
è¦ãªå ´åã®ã¿ä½¿ç¨ï¼
ï¼ æ¢ç¥ã®ã¢ããªã±ã¼ã·ã§ã³ã»ãã¥ãªãã£è¦ç¯ã«å¾ã£ã¦ãµã¼ãã¹ããã§ãã¯
ï¼ ãµã¼ãã¹ãå©ç¨ãããã¨ãã試ã¿ãå
¨ã¦è¨é²
ï¼ HTTP ã®ä»£ããã« HTTPS ã使ç¨ãã許å¯ãããç¹å®ããã¤ã¹ã®ã¿ã¨ãã
5.8.3 FTP åã³ããªãã¢ã«ãã¡ã¤ã«è»¢éãããã³ã«ï¼TFTPï¼
FTP ã¨TFTP ã¯ããã¤ã¹éã§ã®ãã¡ã¤ã«ã®ããåãã«ä½¿ããããç¥å度ãé«ããå¦çãã¯ã¼ãæ
å°ã§æ¸ããããSCADA ã·ã¹ãã ãDCSãPLCsãRTUs çã»ã¨ãã©å
¨ã¦ã®ãã©ãããã¼ã ã«å®è£
ããã¦ãããæ®å¿µãªãããã©ããã»ãã¥ãªãã£ãèãã¦ä½ããã¦ã¯ããªããFTP ã®ãã°ã¤ã³ãã¹
ã¯ã¼ãã¯æå·åããã¦ããããTFTP ã§ã¯ãã°ã¤ã³ã®å¿
è¦ãããªããæ´ã«å®è£
ããã FTP ã«ãã£
ã¦ã¯ããããã¡ããªã¼ãã¼ããã¼ããã¨ããèå¼±æ§ããã£ãããã®çµæãTFTP éä¿¡ã¯å
¨ã¦ãã
ãã¯ãã¹ãã§ãFTP éä¿¡ã«ã¤ãã¦ã¯éä¿¡ã»ãã·ã§ã³ã®ã¿ãåã¯ä»å çãªãã¼ã¯ã³ãã¼ã¹ã®å¤è¦ç´
èªè¨¼åã³æå·åãã³ãã«ã§ã»ãã¥ãªãã£ã確ä¿ãããã®ã®ã¿è¨±å¯ãã¹ãã§ãããå¯è½ã§ããã°å¸¸
ã«ãã»ãã¥ã¢ FTPï¼SFTPï¼ãã»ãã¥ã¢ã³ãã¼ã¨ãã£ãããã»ãã¥ãªãã£ã®é«ããããã³ã«ãæ¡
ç¨ãã¹ãã§ããã
5.8.4 ãã«ãããï¼Telnetï¼
ãã«ããããããã³ã«ã¯ãã¯ã©ã¤ã¢ã³ãã¨ãã¹ãéã®ã¤ã³ã¿ã©ã¯ãã£ããªããã¹ããã¼ã¹ã®éä¿¡
ã»ãã·ã§ã³ãå®ç¾©ããã主ã«ãªã½ã¼ã¹ã®éãããã·ã¹ãã ãã»ãã¥ãªãã£éè¦ã®ä½ãã·ã¹ãã ã¸
ã®é éãã°ã¤ã³åã³åç´ãªç®¡çãµã¼ãã¹ç¨ã«ä½¿ç¨ããããå
¨ã¦ã®ãã«ããããã©ãã£ãã¯ã¯ãã¹
ã¯ã¼ããå«ãã¦æå·åããã¦ããªããããã»ãã¥ãªãã£ãªã¹ã¯ã¯é大ã§ãé éå°ã«ããå人ãã
ãã¤ã¹ãããªãã®ç¨åº¦å¶å¾¡ã§ãã¦ãã¾ãã
SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
113
sessions from the corporate to the control network should be prohibited unless secured with token-based
multi-factor authentication and an encrypted tunnel. Outbound telnet sessions should be allowed only over
encrypted tunnels (e.g., VPN) to specific authorized devices.
5.8.5 Dynamic Host Configuration Protocol (DHCP)
DHCP is used on IP networks for dynamically distributing network configuration parameters, such as IP
addresses for interfaces and services. The base DHCP includes no mechanism for authenticating servers
and clients. Rogue DHCP servers can provide incorrect information to clients. Unauthorized clients can
gain access to server and cause exhaustion of available resources (e.g., IP addresses). To prevent this, it is
recommended to use static configuration instead of dynamic address allocation, which should be the typical
configuration for ICS devices. If dynamic allocation is necessary, it is recommended to enable DHCP
snooping to defend against rogue DHCP servers, Address Resolution Protocol (ARP) and IP spoofing. The
DHCP servers should be placed in the same network segment as configured equipment (e.g., on the router).
DHCP relaying is not recommended.
5.8.6 Secure Shell (SSH)
SSH allows remote access to a device. It provides secure authentication and authorization based on
cryptography. If remote access is required to the control network, SSH is recommended as the alternative to
telnet, rlogin, rsh, rcp and other insecure remote access tools.
5.8.7 Simple Object Access Protocol (SOAP)
SOAP is an XML-based format syntax to exchange messages. Traffic flows related to SOAP-based
services should be controlled at the firewall between corporate and ICS network segments. If these services
are necessary, deep-packet inspection and/or application layer firewalls should be used to restrict the
contents of messages.
5.8.8 Simple Mail Transfer Protocol (SMTP)
SMTP is the primary email transfer protocol on the Internet. Email messages often contain malware, so
inbound email should not be allowed to any control network device. Outbound SMTP mail messages from
the control network to the corporate network are acceptable to send alert messages.
5.8.9 Simple Network Management Protocol (SNMP)
SNMP is used to provide network management services between a central management console and
network devices such as routers, printers, and PLCs. Although SNMP is an extremely useful service for
maintaining a network, it is very weak in security. Versions 1 and 2 of SNMP use unencrypted passwords
to both read and configure devices (including devices such as PLCs), and in many cases the passwords are
well known and cannot be changed. Version 3 is considerably more secure but is still limited in use. SNMP
V1 & V2 commands both to and from the control network should be prohibited unless they are over a
separate, secured management network, whereas SNMP V3 commands may be able to be sent to the ICS
using the security features inherent to V3.
SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
114
é é管çã«ã¯ã»ãã¥ã¢ã·ã§ã«ï¼SSHï¼ãããã³ã«[5.8.6]ã使ç¨ããããæ¨å¥¨ãããä¼æ¥ãããã¯
ã¼ã¯ããå¶å¾¡ãããã¯ã¼ã¯ã¸ã®çä¿¡ãã«ãããã»ãã·ã§ã³ã¯ããã¼ã¯ã³ãã¼ã¹ã®å¤è¦ç´ èªè¨¼åã³
æå·åãã³ãã«ã§ã»ãã¥ãªãã£ã確ä¿ããã¦ããªããã°ãç¦æ¢ãã¹ãã§ãããéä¿¡ãã«ãããã¯ã
許å¯ãããç¹å®ã®ããã¤ã¹ã«å¯¾ãã¦ãæå·åãã³ãã«ï¼VPN çï¼ã§ã®ã¿è¨±å¯ãã¹ãã§ããã
5.8.5 åçãã¹ãæ§æãããã³ã«ï¼DHCPï¼
DHCP ã¯ãä¾ãã° IP ã¢ãã¬ã¹ãã¤ã³ã¿ãã§ã¼ã¹ããµã¼ãã¹ã¸å²ãå½ã¦ããªã©ãIP ãããã¯ã¼ã¯
ä¸ã§ãããã¯ã¼ã¯æ§æãã©ã¡ã¼ã¿ãåçã«å²ãå½ã¦ãã¨ãã«ä½¿ç¨ãããåºæ¬ç㪠DHCP ã«ã¯ãµã¼
ãã¨ã¯ã©ã¤ã¢ã³ãã®èªè¨¼ã¡ã«ããºã ããªãããã¼ã° DHCP ãµã¼ãã¯ä¸æ£ç¢ºãªæ
å ±ãã¯ã©ã¤ã¢ã³ã
ã«æä¾ãããæªè¨±å¯ã®ã¯ã©ã¤ã¢ã³ãããµã¼ãã«ã¢ã¯ã»ã¹ãã¦ãå©ç¨å¯è½ãªãªã½ã¼ã¹ï¼IP ã¢ãã¬ã¹
çï¼ãæ¯æ¸ããããã¨ãããããããé²ãã«ã¯ãåçãªã¢ãã¬ã¹å²å½ã§ã¯ãªãéçæ§æã«ããã
ã¨ãæ¨å¥¨ãããICS ããã¤ã¹ã§ã¯ãããä¸è¬çãªæ§æã¨ãªãã¹ãã§ãããåçå²å½ãå¿
è¦ãªå ´åã
DHCP ã¹ãã¼ãã³ã°ã使ç¨å¯è½ã«ãããã¼ã° DHCPãã¢ãã¬ã¹è§£æ±ºãããã³ã«ï¼ARPï¼åã³IP è©
称ãé²æ¢ãããã¨ãæ¨å¥¨ããããDHCP ãµã¼ãã¯ãæ§æè£
ååã¨åããããã¯ã¼ã¯ã»ã°ã¡ã³ã
ï¼ã«ã¼ã¿ä¸çï¼å
ã«é
ç½®ãã¹ãã§ãããDHCP ãªã¬ã¼ã¯æ¨å¥¨ã§ããªãã
5.8.6 ã»ãã¥ã¢ã·ã§ã«ï¼SSH)
SSH ã¯ããã¤ã¹ã¸ã®ãªã¢ã¼ãã¢ã¯ã»ã¹ãå¯è½ã«ãããã»ãã¥ã¢ãªèªè¨¼ãè¡ããæå·æ³ã«åºã¥ãã¦
許å¯ãä¸ãããå¶å¾¡ãããã¯ã¼ã¯ã¸ã®ãªã¢ã¼ãã¢ã¯ã»ã¹ãå¿
è¦ãªå ´åããã«ããããrãã°ã¤ã³ã
rshãrcp ãã®ä»ã®ã»ãã¥ã¢ã§ãªããªã¢ã¼ãã¢ã¯ã»ã¹ãã¼ã«ã«ä»£ã㦠SSH ã®ä½¿ç¨ãæ¨å¥¨ãããã
5.8.7 ã·ã³ãã«ãªãã¸ã§ã¯ãã¢ã¯ã»ã¹ãããã³ã«ï¼SOAPï¼
SOAP ã¯ãã¡ãã»ã¼ã¸äº¤æç¨ã® XML ãã¼ã¹å½¢å¼ã®ã·ã³ã¿ãã¯ã¹ã§ãããSOAP ãã¼ã¹ãµã¼ãã¹ã«
é¢é£ãããã©ãã£ãã¯ããã¼ã¯ãä¼æ¥åã³ ICS ãããã¯ã¼ã¯ã»ã°ã¡ã³ãéã®ãã¡ã¤ã¢ã¦ã©ã¼ã«ã§
å¶å¾¡ãã¹ãã§ããããã®ãããªãµã¼ãã¹ãå¿
è¦ãªå ´åããã£ã¼ããã±ããã¤ã³ã¹ãã¯ã·ã§ã³åã¯
ã¢ããªã±ã¼ã·ã§ã³å±¤ãã¡ã¤ã¢ã¦ã©ã¼ã«ã使ç¨ãã¦ãã¡ãã»ã¼ã¸å
容ãå¶éãã¹ãã§ããã
5.8.8 ã·ã³ãã«ã¡ã¼ã«è»¢éãããã³ã«ï¼SMTPï¼
SMTP ã¯ã¤ã³ã¿ã¼ãããã§ã®ä¸»è¦ãªé»åã¡ã¼ã«è»¢éãããã³ã«ã§ãããé»åã¡ã¼ã«ã¡ãã»ã¼ã¸ã«
ã¯ãã«ã¦ã¨ã¢ãå«ã¾ãã¦ãããã¨ãå¤ããããçä¿¡é»åã¡ã¼ã«ã¯ããããªãå¶å¾¡ãããã¯ã¼ã¯ã
ãã¤ã¹ã«ãéããã¹ãã§ãªããå¶å¾¡ãããã¯ã¼ã¯ããä¼æ¥ãããã¯ã¼ã¯ã¸ã®éä¿¡ SMTP ã¡ã¼ã«ã¡
ãã»ã¼ã¸ã¯ãã¢ã©ã¼ãã¡ãã»ã¼ã¸ã®éä¿¡æã«è¨±å¯ãããã
5.8.9 ã·ã³ãã«ãããã¯ã¼ã¯ç®¡çãããã³ã«ï¼SNMPï¼
SNMP ã¯ãä¸å¤®ç®¡çã³ã³ã½ã¼ã«ã¨ãããã¯ã¼ã¯ããã¤ã¹ï¼ã«ã¼ã¿ãããªã³ã¿ãPLCs çï¼éã®ãã
ãã¯ã¼ã¯ç®¡çãµã¼ãã¹ãæä¾ããããã«ä½¿ç¨ãããSNMP ã¯ãããã¯ã¼ã¯ã®ä¿å®ã«ã¯æ¥µãã¦ä¾¿å©
ãªãµã¼ãã¹ã§ããããã»ãã¥ãªãã£ã極ãã¦å¼±ããSNMP ã®ãã¼ã¸ã§ã³ 1ã¨2ã§ã¯ãèªåããã
ãã¤ã¹ï¼PLCs çï¼è¨å®ãæå·åããã¦ããªããã¹ã¯ã¼ãã使ç¨ãã¦ãããå¤ãã®å ´åãã¹ã¯ã¼
ããããç¥ããã¦ãããå¤æ´ãã§ããªãããã¼ã¸ã§ã³ 3ã§ã¯ããªãã»ãã¥ã¢ã«ãªã£ã¦ãããã
使ç¨ããã¦ããæ°ã¯å°ãªãã
å¶å¾¡ãããã¯ã¼ã¯ã¨ã® SNMP ãã¼ã¸ã§ã³ 1ã¨2ã®ã³ãã³ãã¯ãå¥åã®ã»ãã¥ã¢ãªç®¡çãããã¯ã¼
ã¯ä»¥å¤ã§ã¯ç¦æ¢ã¨ãã¹ãã§ããã¼ã¸ã§ã³ 3ã®ã³ãã³ãã¯åºæã®ã»ãã¥ãªãã£æ©è½ã使ç¨ã㦠ICS
ã«éä¿¡ã§ããã

SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
115
5.8.10 Distributed Component Object Model (DCOM)
DCOM is the underlying protocol for OLE for Process Control (OPC). It utilizes Microsoftâs Remote
Procedure Call (RPC) service which, when not patched, has many vulnerabilities. These vulnerabilities
were the basis for the Blaster worm27 exploits. In addition, OPC, which utilizes DCOM, dynamically opens
a wide range of ports (1024 to 65535) that can be extremely difficult to filter at the firewall. This protocol
should only be allowed between control network and DMZ networks and explicitly blocked between the
DMZ and corporate network. Also, users are advised to restrict the port ranges used by making registry
modifications on devices using DCOM.
5.8.11 SCADA and Industrial Protocols
SCADA and industrial protocols, such as Modbus/TCP, EtherNet/IP, IEC 61850, ICCP and DNP328, are
critical for communications to most control devices. Unfortunately, many of these protocols were designed
without security built in and do not typically require any authentication to remotely execute commands on a
control device. These protocols should only be allowed within the control network and not allowed to cross
into the corporate network.
5.9 Network Address Translation (NAT)
Network address translation (NAT) is a service where IP addresses used on one side of a network device
can be mapped to a different set on the other side on an as-needed basis. It was originally designed for IP
address reduction purposes so that an organization with a large number of devices that occasionally needed
Internet access could get by with a smaller set of assigned Internet addresses.
To do this, most NAT implementations rely on the premise that not every internal device is actively
communicating with external hosts at a given moment. The firewall is configured to have a limited number
of outwardly visible IP addresses. When an internal host seeks to communicate with an external host, the
firewall remaps the internal IP address and port to one of the currently unused, more limited, public IP
addresses, effectively concentrating outgoing traffic into fewer IP addresses. The firewall must track the
state of each connection and how each private internal IP address and source port was remapped onto an
outwardly visible IP address/port pair. When returning traffic reaches the firewall, the mapping is reversed
and the packets forwarded to the proper internal host.
For example, a control network device may need to establish a connection with an external, non-control
network host (for instance, to send a critical alert email). NAT allows the internal IP address of the
initiating control network host to be replaced by the firewall; subsequent return traffic packets are
remapped back to the internal IP address and sent to the appropriate control network device. More
specifically, if the control network is assigned the private subnet 192.168.1.xxx and the Internet network
expects the device to use the corporate assigned addresses in the range 192.6.yyy.zzz, then a NAT firewall
will substitute (and track) a 192.6.yyy.zzz source address into every outbound IP packet generated by a
control network device.
Producer-consumer protocols, such as EtherNet/IP and Foundation Fieldbus, are particularly troublesome
because NAT does not support the multicast-based traffic that these protocols need to offer their full
services.
27 http://en.wikipedia.org/wiki/Blaster_%28computer_worm%29
28 15 IEEE 1815-2012,
IEEE Standard for Electric Power Systems CommunicationsâDistributed Network Protocol
(DNP3)
,) incorporates DNP3 Secure Authentication version 5 (DNP3-SAv5) which provides strong application
layer authentication with remote security credential management. See
https://standards.ieee.org/findstds/standard/1815-2012.html.

SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
116
5.8.10 åæ£ã³ã³ãã¼ãã³ããªãã¸ã§ã¯ãã¢ãã«ï¼DCOMï¼
DCOM ã¯ããã»ã¹å¶å¾¡ç¨ OLEï¼OPCï¼ã®åºæ¬ãããã³ã«ã§ããããã¤ã¯ãã½ããã®é éæç¶ã
å¼ã³åºãï¼RPCï¼ãµã¼ãã¹ã使ç¨ããããããã¯ããããå½ã¦ãªãã¨èå¼±æ§ãå¤ãããã®ãããª
èå¼±æ§ã¯ããã©ã¹ã¿ã¼ã¯ã¼ã 29ã®æ¨çã¨ãªã£ããã¾ã DCOM ãå©ç¨ãã OPC ã¯ãå¤æ§ãªãã¼ã
ãåçã«éãããï¼1024ï½65535)ããã¡ã¤ã¢ã¦ã©ã¼ã«ã§ã®ãã£ã«ã¿ãªã³ã°ã極ãã¦å°é£ã¨ãªãã
ãã®ãããã³ã«ã¯ãå¶å¾¡ãããã¯ã¼ã¯ã¨ DMZ éã§ã®ã¿è¨±å¯ãã¹ãã§ãDMZ ã¨ä¼æ¥ãããã¯ã¼ã¯
éã§ã¯æ示çã«ãããã¯ãã¹ãã§ãããã¾ãã¦ã¼ã¶ã¯ãDCOM 使ç¨ããã¤ã¹ã®ã¬ã¸ã¹ããªå¤æ´
æã«ä½¿ç¨ãããã¼ãã®ç¯å²ãéå®ããã®ãããã
5.8.11 SCADA åã³ç£æ¥ç¨ãããã³ã«
Modbus/TCPãEtherNet/IPãIEC 61850ãICCPãDNP330çã® SCADA åã³ç£æ¥ç¨ãããã³ã«ã¯ãã»
ã¨ãã©ã®å¶å¾¡ããã¤ã¹ã¸ã®éä¿¡ã«ã¨ã£ã¦èè¦ã§ãããæ®å¿µãªãããããã®ãããã³ã«ã®å¤ãã¯ã
ã»ãã¥ãªãã£ãèæ
®ã«å
¥ããã«è¨è¨ããã¦ãããå¶å¾¡ããã¤ã¹ä¸ã§ã³ãã³ããé éå®è¡ããéã«ã
é常èªè¨¼ãå¿
è¦ã¨ããªãããã®ãããªãããã³ã«ã¯å¶å¾¡ãããã¯ã¼ã¯å
ã§ã®ã¿è¨±å¯ããä¼æ¥ãã
ãã¯ã¼ã¯ã¸ã®é²å
¥ã¯è¨±å¯ãã¹ãã§ãªãã
5.9 ãããã¯ã¼ã¯ã¢ãã¬ã¹å¤æï¼NATï¼
ãããã¯ã¼ã¯ã¢ãã¬ã¹å¤æï¼NATï¼ãµã¼ãã¹ã¯ããããã¯ã¼ã¯ããã¤ã¹ã®ä¸æ¹ã®å´ã§ä½¿ç¨ãã¦ã
ãIP ã¢ãã¬ã¹ããå¿
è¦ã®é½åº¦ãä»æ¹ã®å´ã«ããããããå
ã
ã®è¨è¨ç®çã¯ãæã
ã¤ã³ã¿ã¼ãã
ãã¢ã¯ã»ã¹ãå¿
è¦ã¨ãªãå¤éã®ããã¤ã¹ãæããçµç¹ããå°æ°ã®å²å½ã¤ã³ã¿ã¼ãããã¢ãã¬ã¹ã§
æ¸ãããã« IP ã¢ãã¬ã¹ãæ¸ãããã¨ã«ãã£ãã
ãã®ããã»ã¨ãã©ã® NAT å®è£
ã§ã¯ãå
¨ã¦ã®ç¤¾å
ããã¤ã¹ããããç¬éã«å¤é¨ãã¹ãã¨æ´»çºã«äº¤
ä¿¡ããããã§ã¯ãªãã¨ããåæã«ç«ã£ã¦ããããã¡ã¤ã¢ã¦ã©ã¼ã«ã®è¨å®ã¯ãå¤é¨ããè¦ãã IP
ã¢ãã¬ã¹ã®æ°ãéå®ãããããã«è¡ãã社å
ãã¹ãã社å¤ãã¹ãã¨äº¤ä¿¡ããéããã¡ã¤ã¢ã¦ã©ã¼
ã«ã¯ãå
é¨ IP ã¢ãã¬ã¹ã¨ãã¼ããç¾å¨ä½¿ç¨ãã¦ããªãæ´ã«éå®ããããããªã㯠IP ã¢ãã¬ã¹ã«
ãªãããããéä¿¡ãã©ãã£ãã¯ãããå°æ°ã® IP ã¢ãã¬ã¹ã«å¹æçã«éçµãããããã¡ã¤ã¢ã¦ã©
ã¼ã«ã¯ãããããã®æ¥ç¶ã®ç¶æ
ã¨ãåãã©ã¤ãã¼ãå
é¨ IP ã¢ãã¬ã¹åã³ã½ã¼ã¹ãã¼ãããå¤é¨
ããè¦ãã IP ã¢ãã¬ã¹/ãã¼ãã®ãã¢ã«ã©ããªãããããããã追跡ããªããã°ãªããªããæ»ã
ãã©ãã£ãã¯ããã¡ã¤ã¢ã¦ã©ã¼ã«ã«éããã¨ããããã³ã°ãå転ãããã±ãããæ£ãã社å
ãã¹
ãã«è»¢éãããã
ä¾ãã°ãå¶å¾¡ãããã¯ã¼ã¯ããã¤ã¹ã¯ãå¤é¨ã®éå¶å¾¡ãããã¯ã¼ã¯ãã¹ãã¨æ¥ç¶ã確ç«ããå¿
è¦
ãçãããã¨ãããï¼éè¦ã¢ã©ã¼ãé»åã¡ã¼ã«ã®éä¿¡ãªã©ï¼ãNAT ã¯ãéå§å¶å¾¡ãããã¯ã¼ã¯
ãã¹ãã®å
é¨ IP ã¢ãã¬ã¹ããã¡ã¤ã¢ã¦ã©ã¼ã«ã«ããç½®æãããããã«ãããã®å¾ã®æ»ããã©ã
ã£ãã¯ãã±ããã¯ãå
é¨ IP ã¢ãã¬ã¹ã«ãªããããããæ£ããå¶å¾¡ãããã¯ã¼ã¯ããã¤ã¹ã«éã
ãããå
·ä½çã«è¨ãã¨ãå¶å¾¡ãããã¯ã¼ã¯ã«ãã©ã¤ãã¼ããµãããã 192.168.1.xxx ãå²ãå½ã¦
ãããã¤ã³ã¿ã¼ããããããã¯ã¼ã¯ã¯ããã¤ã¹ã 192.6.yyy.zzz ã®ç¯å²ã®ä¼æ¥å²å½ã¢ãã¬ã¹ã使ç¨
ããããã«äºæ³ãã¦ããã¨ããããã®å ´åãNAT ãã¡ã¤ã¢ã¦ã©ã¼ã«ã¯ã192.6.yyy.zzz ã½ã¼ã¹ã¢ã
ã¬ã¹ããå¶å¾¡ãããã¯ã¼ã¯ããã¤ã¹ãçæããå
¨ã¦ã®çºä¿¡ IP ãã±ããã«ç½®æï¼ãã¦è¿½è·¡ï¼ããã
EtherNet/IP ãFoundation Fieldbus ã¨ãã£ãçç£è
ã»æ¶è²»è
ãããã³ã«ã¯ãã¨ãããåé¡ãå¤ãã
ã¨ããã®ã¯ããããã®ãããã³ã«ãååãªãµã¼ãã¹ãæä¾ããããã«å¿
è¦ã¨ãããã«ããã£ã¹ã
ãã¼ã¹ã®ãã©ãã£ãã¯ã« NAT ã対å¿ãã¦ããªãããã§ããã
29 http://en.wikipedia.org/wiki/Blaster_%28computer_worm%29
30 IEEE 1815-2012ãé»åã·ã¹ãã éä¿¡ç¨ IEEE è¦æ ¼-åæ£ãããã¯ã¼ã¯ãããã³ã«ï¼DNP3ï¼ãã¯ãDNP3 ã»ãã¥ã¢èªè¨¼ãã¼ã¸
ã§ã³ 5ï¼DNP3-SAv5ï¼ãçµã¿è¾¼ãã§ãããé éã»ãã¥ãªãã£ä¿¡é ¼æ§ç®¡çã«å¼·åãªã¢ããªã±ã¼ã·ã§ã³å±¤èªè¨¼ãä»ä¸ããã次
ã®URL ãåç
§ã®ãã¨ãhttps://standards.ieee.org/findstds/standard/1815-2012.html.
SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
117
In general, while NAT offers some distinct advantages, its impact on the actual industrial protocols and
configuration should be assessed carefully before it is deployed. Furthermore, certain protocols are
specifically broken by NAT because of the lack of direct addressing. For example, OPC requires special
third-party tunneling software to work with NAT.
5.10 Specific ICS Firewall Issues
In addition to the issues with firewalls and ICS already discussed, there are some additional problems that
need to be examined in more detail. The rest of this section discusses three specific areas of concern: the
placement of data historians, remote access for ICS support, and multicast traffic.
5.10.1 Data Historians
The existence of shared control network/corporate network servers such as data historians and asset
management servers can have a significant impact on firewall design and configuration. In three-zone
systems the placement of these servers in a DMZ is relatively straightforward, but in two-zone designs the
issues become complex. Placing the historian on the corporate side of the firewall means that a number of
insecure protocols, such as Modbus/TCP or DCOM, must be allowed through the firewall and that every
control device reporting to the historian is exposed to the corporate side of the network. On the other hand,
putting the historian on the control network side means other equally questionable protocols, such as HTTP
or SQL, must be allowed through the firewall, and there is now a server accessible to nearly everyone in the
organization sitting on the control network.
In general, the best solution is to avoid two-zone systems (no DMZ) and use a three-zone design, placing
the data collector in the control network and the historian component in the DMZ.
5.10.2 Remote Support Access
Another issue for ICS firewall design is user and/or vendor remote access into the control network. Any
users accessing the control network from remote networks should be required to authenticate using an
appropriately strong mechanism such as token-based authentication. While it is possible for the controls
group to set up their own remote access system with multi-factor authentication on the DMZ, in most
organizations it is typically more efficient to use existing systems set up by the IT department. In this case a
connection through the firewall from the IT remote access server is needed.
Remote support personnel connecting over the Internet or via dialup modems should use an encrypted
protocol, such as running a corporate VPN connection client, application server, or secure HTTP access,
and authenticate using a strong mechanism, such as a token based multi-factor authentication scheme, in
order to connect to the general corporate network. Once connected, they should be required to authenticate
a second time at the control network firewall using a strong mechanism, such as a token based multi-factor
authentication scheme, to gain access to the control network. Proxy servers can also provide additional
capabilities for securing remote support access.
5.10.3 Multicast Traffic
Most industrial producer-consumer (or publisher-subscriber) protocols operating over Ethernet, such as
EtherNet/IP and Foundation Fieldbus HSE, are IP multicast-based. The first advantage of IP multicasting is
network efficiency; by not repeating the data transmission to the multiple destinations, a significant
reduction in network load can occur. The second advantage is that the sending host need not be concerned
with knowing every IP address of every destination host listening for the broadcast information. The third,
and perhaps most important for industrial control purposes, is that a single multicast message offers
SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
118
å
¨ä½ã¨ãã¦ãNAT ã«ã¯ããã¤ãæ確ãªå©ç¹ãããããå±éããã«å
ç«ã£ã¦ãå®éã®ç£æ¥ç¨ãã
ãã³ã«åã³æ§æã«ä¸ããå½±é¿ãæ
éã«è©ä¾¡ãã¹ãã§ãããæ´ã«ç¹å®ã®ãããã³ã«ã¯ãç´æ¥ã®ã¢ã
ã¬ãã·ã³ã°ããªããããNAT ã«ããç ´å£ããããä¾ãã° OPC ã¯ãNAT ã¨å
±ç¨ããããã«ã¯ãµã¼
ããã¼ãã£ã®ç¹æ®ãã³ããªã³ã°ã½ããã¦ã¨ã¢ãå¿
é ã¨ãªãã
5.10 ICS ãã¡ã¤ã¢ã¦ã©ã¼ã«åºæã®åé¡
ããã¾ã§è¦ã¦ãããã¡ã¤ã¢ã¦ã©ã¼ã«ã¨ ICS ã«é¢ããåé¡ã«å ãã¦ãæ´ã«è©³ããèå¯ãã¹ãåé¡ã
ããããã®ã»ã¯ã·ã§ã³ã®æ®ãã®é¨åã§ã¯ããã¼ã¿ãã¹ããªã¢ã³ã®é
ç½®ãICS ãµãã¼ãã®ããã®ãª
ã¢ã¼ãã¢ã¯ã»ã¹ããã«ããã£ã¹ããã©ãã£ãã¯ã¨ãã 3ã¤ã®ç¹å®åéã«ã¤ãã¦èå¯ããã
5.10.1 ãã¼ã¿ãã¹ããªã¢ã³
ãã¼ã¿ãã¹ããªã¢ã³ãè³ç£ç®¡çãµã¼ãã¨ãã£ãå
±æå¶å¾¡/ä¼æ¥ãããã¯ã¼ã¯ãµã¼ãã®åå¨ã¯ãã
ã¡ã¤ã¢ã¦ã©ã¼ã«ã®è¨è¨ãæ§æã«å¤§ããªå½±é¿ãåã¼ããã¨ãããã3ã¾ã¼ã³ã·ã¹ãã ã§ã¯ãããã
ãµã¼ãã DMZ ã«é
ç½®ããã®ã¯æ¯è¼çåç´æå¿«ã ãã2ã¾ã¼ã³è¨è¨ã§ã¯åé¡ãè¤éã«ãªãããã¹
ããªã¢ã³ããã¡ã¤ã¢ã¦ã©ã¼ã«ã®ä¼æ¥å´ã«ç½®ãã¨ãããã¨ã¯ãModbus/TCP ãDCOM ã¨ãã£ãã»ã
ã¥ã¢ã§ãªãå¤æ°ã®ãããã³ã«ããã¡ã¤ã¢ã¦ã©ã¼ã«ã«å
¥ãã®ã許ããã¨ã«ãªãããã¹ããªã¢ã³ã®ä¸
ã«ããå
¨ã¦ã®å¶å¾¡ããã¤ã¹ããããã¯ã¼ã¯ã®ä¼æ¥å´ã«ããããããã¨ã«ãªããå対ã«ããã¹ããª
ã¢ã³ãå¶å¾¡ãããã¯ã¼ã¯å´ã«ç½®ãã°ãHTTP ãSQL ã¨ãã£ãåæ§ã«åé¡ã®å¤ããããã³ã«ããã¡
ã¤ã¢ã¦ã©ã¼ã«ã«å
¥ãã®ã許ããã¨ã«ãªããå¶å¾¡ãããã¯ã¼ã¯ä¸ã«ãããµã¼ãã«ãçµç¹ã®ã»ã¼å
¨å¡
ãã¢ã¯ã»ã¹ã§ãããã¨ã«ãªã£ã¦ãã¾ãã
ç·ãã¦æåã®ã½ãªã¥ã¼ã·ã§ã³ã¯ã2ã¾ã¼ã³ã·ã¹ãã ï¼DMZ ãªãï¼ãé¿ã㦠3ã¾ã¼ã³ã·ã¹ãã ã使
ç¨ãããã¼ã¿ã³ã¬ã¯ã¿ã¯å¶å¾¡ãããã¯ã¼ã¯å
ã«ããã¹ããªã¢ã³ã³ã³ãã¼ãã³ã㯠DMZ å
ã«é
ç½®
ãããã¨ã§ããã
5.10.2 é éãµãã¼ãã·ã¹ãã
ICS ãã¡ã¤ã¢ã¦ã©ã¼ã«è¨è¨ã®å¥ã®åé¡ã¯ãã¦ã¼ã¶åã¯ãã³ãã¼ãå¶å¾¡ãããã¯ã¼ã¯ã«ãªã¢ã¼ãã¢
ã¯ã»ã¹ãããã¨ã§ãããé éãããã¯ã¼ã¯ããå¶å¾¡ãããã¯ã¼ã¯ã«ã¢ã¯ã»ã¹ããã¦ã¼ã¶ã¯ããã¼
ã¯ã³ãã¼ã¹èªè¨¼çã®å¼·åãªã¡ã«ããºã ã使ç¨ãã¦ãèªè¨¼ã義åã¥ããã¹ãã§ãããå¶å¾¡ã°ã«ã¼ã
ãDMZ ã«å¤è¦ç´ èªè¨¼æ©è½ã®ä»ããç¬èªã®ãªã¢ã¼ãã¢ã¯ã»ã¹ã·ã¹ãã ãè¨ç½®ããã®ã¯å¯è½ã§ãã
ããã»ã¨ãã©ã®çµç¹ã§ã¯ãIT é¨éãè¨ç½®ããæ¢åã·ã¹ãã ãå©ç¨ããæ¹ãå¹ççã§ããããã®å ´
åãIT ãªã¢ã¼ãã¢ã¯ã»ã¹ãµã¼ããããã¡ã¤ã¢ã¦ã©ã¼ã«ãçµç±ããæ¥ç¶ãå¿
è¦ã¨ãªãã
ã¤ã³ã¿ã¼ãããåã¯ãã¤ã¢ã«ã¢ããã¢ãã çµç±ã§æ¥ç¶ããé éãµãã¼ãè¦å¡ã¯ãä¼æ¥ VPN æ¥ç¶
ã¯ã©ã¤ã¢ã³ããã¢ããªã±ã¼ã·ã§ã³ãµã¼ããã»ãã¥ã¢ HTTP ã¢ã¯ã»ã¹çãå®è¡ããæå·ãããã³ã«
ã使ç¨ããæ±ç¨ä¼æ¥ãããã¯ã¼ã¯ã«ã¢ã¯ã»ã¹ããããããã¼ã¯ã³ãã¼ã¹å¤è¦ç´ èªè¨¼çã®å¼·åãªã¡
ã«ããºã ã使ç¨ãã¦èªè¨¼ãè¡ãã¹ãã§ãããæ¥ç¶ãããªããå¶å¾¡ãããã¯ã¼ã¯ãã¡ã¤ã¢ã¦ã©ã¼ã«
ã«ããã¦ããã¼ã¯ã³ãã¼ã¹å¤è¦ç´ èªè¨¼çã®å¼·åãªã¡ã«ããºã ã使ç¨ãã¦å度èªè¨¼ãæ±ãã¦ããã
å¶å¾¡ãããã¯ã¼ã¯ã¸ã®ã¢ã¯ã»ã¹ã許å¯ãã¹ãã§ããããããã·ãµã¼ããé éãµãã¼ãã¢ã¯ã»ã¹ã®
ã»ãã¥ãªãã£ãæ´ã«åä¸ãããã
5.10.3 ãã«ããã£ã¹ããã©ãã£ãã¯
EtherNet/IP ãFoundation Fieldbus HSE ãªã©ã¤ã¼ãµãããä¸ã§æ©è½ããã»ã¨ãã©ã®çç£è
ã»æ¶è²»è
ï¼åã¯çºè¡è
ã»è³¼èªè
ï¼ãããã³ã«ã¯ IP ãã«ããã£ã¹ããã¼ã¹ã§ãããIP ãã«ããã£ã¹ãã£ã³
ã°ã®æ大ã®å©ç¹ã¯ãããã¯ã¼ã¯å¹çã«ããããã¼ã¿éä¿¡ãè¤æ°ã®å®å
ã«ç¹°ãè¿ãå¿
è¦ããªãããã
ãããã¯ã¼ã¯è² è·ãèããæ¸ãã2ã¤ç®ã®å©ç¹ã¯ãéä¿¡ãã¹ãããããã¼ããã£ã¹ãæ
å ±ããªã¹
ãã³ã°ãã¦ããå
¨ã¦ã®å®å
ãã¹ãã® IP ã¢ãã¬ã¹ãç¥ãå¿
è¦ããªããã¨ã§ããã
SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
119
far better capabilities for time synchronization between multiple control devices than multiple unicast
messages.
If the source and destinations of a multicast packet are connected with no intervening routers or firewalls
between them, the multicast transmission is relatively seamless. However, if the source and destinations are
not on the same LAN, forwarding the multicast messages to a destination becomes more complicated. To
solve the problem of multicast message routing, hosts need to join (or leave) a group by informing the
multicast router on their network of the relevant group ID through the use of the Internet Group
Management Protocol (IGMP). Multicast routers subsequently know of the members of multicast groups
on their network and can decide whether or not to forward a received multicast message onto their network.
A multicast routing protocol is also required. From a firewall administration perspective, monitoring and
filtering IGMP traffic becomes another series of rule sets to manage, adding to the complexity of the
firewall.
Another firewall issue related to multicasting is the use of NAT. A firewall performing NAT that receives a
multicast packet from an external host has no reverse mapping for which internal group ID should receive
the data. If IGMP-aware, it could broadcast it to every group ID it knows about, because one of them will
be correct, but this could cause serious issues if an unintended control packet were broadcast to a critical
node. The safest action for the firewall to take is to drop the packet. Thus, multicasting is generally
considered NAT-unfriendly.
5.11 Unidirectional Gateways
Hardware-enforced unidirectional gateways (e.g., data diodes) are increasingly deployed at the boundary
between ICS and IT networks, as well as between Safety Instrumented System networks and control
networks. Unidirectional gateways are a combination of hardware and software. The hardware permits data
to flow from one network to another, but is physically unable to send any information at all back into the
source network. The software replicates databases and emulates protocol servers and devices.
5.12 Single Points of Failure
Single points of failure can exist at any level of the ANSI/ISO stack. An example is PLC control of safety
interlocks. Because security is usually being added to the ICS environment, an evaluation should be done to
identify potential failure points and a risk assessment done to evaluate each pointâs exposure. Remediation
methods can then be postulated and evaluated and a ârisk versus rewardâ determination made and design
and implementation done.
5.13 Redundancy and Fault Tolerance
ICS components or networks that are classified as critical to the organization have high availability
requirements. One method of achieving high availability is through the use of redundancy. Additionally, if
a component fails, it should fail in a manner that does not generate unnecessary traffic on the ICS, or does
not cause another problem elsewhere, such as a cascading event.
The control system should have the ability to execute an appropriate fail-safe process upon the loss of
communications with the ICS or the loss of the ICS itself. The organization should define what "loss of
communications" means (e.g., 500 milliseconds, 5 seconds, 5 minutes, etc. without communications). The
organization should then, based on potential consequences, define the appropriate fail-safe process for their
industry.
SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
120
3ã¤ç®ã¯ãããããç£æ¥ç¨å¶å¾¡ç®çã§ã¯æãéè¦ã¨æãããããè¤æ°å¶å¾¡ããã¤ã¹éã®æéåæã«
ã¨ã£ã¦ã1ã¤ã®ãã«ããã£ã¹ãã¡ãã»ã¼ã¸ã®æ¹ãè¤æ°ã®ã¦ããã£ã¹ãã¡ãã»ã¼ã¸ãããã¯ããã«åª
ãã¦ãããã¨ã§ããã
ãã«ããã£ã¹ããã±ããã®ã½ã¼ã¹ã¨å®å
ã仲ä»ã«ã¼ã¿ããã¡ã¤ã¢ã¦ã©ã¼ã«ãªãã§æ¥ç¶ããã¦ããå ´
åããã«ããã£ã¹ãéä¿¡ã¯ç¸å¯¾çã«ã·ã¼ã ã¬ã¹ã§ããããã ããã½ã¼ã¹ã¨å®å
ãåã LAN ä¸ã«ãª
ãå ´åããã«ããã£ã¹ãã¡ãã»ã¼ã¸ã®å®å
転éã¯è¤éã«ãªãããã«ããã£ã¹ãã¡ãã»ã¼ã¸ã«ã¼ãã£
ã³ã°ã®åé¡ã解決ããã«ã¯ãåãã¹ãã 1ã¤ã®ã°ã«ã¼ãã«å å
¥ï¼åã¯é¢è±ï¼ãããã¨ã§ããããã
ãè¡ãã«åãã¹ãã®ãããã¯ã¼ã¯ä¸ã®ãã«ããã£ã¹ãã«ã¼ã¿ã«ãã¤ã³ã¿ã¼ãããã°ã«ã¼ã管çãã
ãã³ã«ï¼IGMPï¼ãä»ãã¦ãå½è©²ã°ã«ã¼ã ID ãéç¥ãããåãã«ããã£ã¹ãã«ã¼ã¿ã¯ãããããã®
ãããã¯ã¼ã¯ä¸ã®ãã«ããã£ã¹ãã°ã«ã¼ãã¡ã³ãã¼ã«ã¤ãã¦ç¥ããåä¿¡ãããã«ããã£ã¹ãã¡ãã»
ã¼ã¸ããããã¯ã¼ã¯ã«è»¢éãããã©ããã決å®ããããã«ããã£ã¹ãã«ã¼ãã£ã³ã°ãããã³ã«ãå¿
è¦ã¨ãªãããã¡ã¤ã¢ã¦ã©ã¼ã«ç®¡çã®è¦³ç¹ããããã°ãIGMP ãã©ãã£ãã¯ã®ç£è¦åã³ãã£ã«ã¿ãªã³
ã°ã¯ã管çãã¹ãå¥ã®ã«ã¼ã«ã»ããã¨ãªãããã¡ã¤ã¢ã¦ã©ã¼ã«ããã£ããè¤éã«ããã
ãã«ããã£ã¹ãã£ã³ã°ã«é¢é£ããå¥ã®ãã¡ã¤ã¢ã¦ã©ã¼ã«ã®åé¡ã¯ NAT ã®ä½¿ç¨ã§ãããNAT ãå®è¡
ãããã¡ã¤ã¢ã¦ã©ã¼ã«ã§ãå¤é¨ãã¹ãããã®ãã«ããã£ã¹ããã±ãããåä¿¡ãããã®ã«ã¯ãªãã¼ã¹
ãããã³ã°ããªããããã«ã¤ãã¦ã¯å
é¨ã°ã«ã¼ã ID ããã¼ã¿ãåä¿¡ãã¹ãã§ãããIGMP ãèªèã
ã¦ããã°ãæ¢ç¥ã®ã°ã«ã¼ã ID å
¨ã¦ã«ããã¼ããã£ã¹ãããããã®çç±ã¯ããã®ãã¡ã® 1ã¤ãæ£ãã
ã¦ããæå³ããªãå¶å¾¡ãã±ãããéè¦ãã¼ãã«ããã¼ããã£ã¹ããããã¨ã大ããªåé¡ã«ãªãå¯è½
æ§ãããããã§ããããã¡ã¤ã¢ã¦ã©ã¼ã«ãåãå¾ãæãå®å
¨ãªçã¯ããã±ããããããããããã¨
ã§ããããã£ã¦ããã«ããã£ã¹ãã£ã³ã°ã¯ç·ã㦠NAT ã¨ç¸æ§ãæªãã¨ã¿ãªãããã
5.11 åæ¹åæ§ã²ã¼ãã¦ã§ã¤
ãã¼ãã¦ã¨ã¢ã§å¼·å¶ããåæ¹åæ§ã²ã¼ãã¦ã§ã¤ï¼ãã¼ã¿ãã¤ãªã¼ãçï¼ã¯ãICS ãããã¯ã¼ã¯ã¨
IT ãããã¯ã¼ã¯éããå®å
¨è¨è£
ã·ã¹ãã ãããã¯ã¼ã¯ã¨å¶å¾¡ãããã¯ã¼ã¯éã®å¢çã«ã¾ãã¾ãå±
éãããããã«ãªã£ã¦ãããåæ¹åæ§ã²ã¼ãã¦ã§ã¤ã¯ãã¼ãã¦ã¨ã¢ã¨ã½ããã¦ã¨ã¢ãçµã¿åãã
ããã®ã§ããããã¼ãã¦ã¨ã¢ã¯ãã¼ã¿ãä¸æ¹ã®ãããã¯ã¼ã¯ããä»æ¹ã®ãããã¯ã¼ã¯ã¸æµããã®
ã許å¯ããããã½ã¼ã¹ãããã¯ã¼ã¯ã«æ
å ±ãè¿ããã¨ã¯ç©ççã«ä¸å¯è½ã§ãããã½ããã¦ã¨ã¢ã¯
ãã¼ã¿ãã¼ã¹ãè¤è£½ãã¦ããããã³ã«ãµã¼ãåã³ããã¤ã¹ãã¨ãã¥ã¬ã¼ãããã
5.12 åä¸é害ç¹
åä¸é害ç¹ã¯ãANSI/ISO ã¹ã¿ãã¯ã®ã©ã®ã¬ãã«ã«ããããä¸ä¾ã¯å®å
¨ã¤ã³ã¿ã¼ããã¯ã® PLC å¶
御ã§ãããã»ãã¥ãªãã£ã¯é常 ICS ç°å¢ã«è¿½å ããã¦ãããã®ãªã®ã§ãè©ä¾¡ãè¡ã£ã¦é害ã¨ãªã
å¾ãç¹ãæããã«ãããªã¹ã¯è©ä¾¡ãè¡ã£ã¦åç¹ã®ã¨ã¯ã¹ãã¼ã¸ã£ãæ»å®ããã
次ãã§å¯¾å¦æ¹æ³ãæ³å®ãã¦è©ä¾¡ããããªã¹ã¯å¯¾å ±é
¬ããå¤å®ããè¨è¨ã»å®è£
ãè¡ãã
5.13 åé·æ§ã¨ãã©ã¼ã«ããã¬ã©ã³ã¹
çµç¹ã«ã¨ã£ã¦éè¦ã¨åé¡ããã ICS ã³ã³ãã¼ãã³ãããããã¯ã¼ã¯ã«ã¯ãé«ãå¯ç¨æ§è¦ä»¶ã課ã
ãããé«ãå¯ç¨æ§ãå®ç¾ãã 1ã¤ã®æ¹æ³ã¯ãåé·æ§ã®å©ç¨ã§ãããã¾ããããã³ã³ãã¼ãã³ãã«
é害ãåºãå ´åã§ããICS ã«ä¸è¦ã®ãã©ãã£ãã¯ãçãããããé£éã¤ãã³ããªã©å¥ã®åé¡ãæ´¾
çããã¦ã¯ãªããªãã
å¶å¾¡ã·ã¹ãã ã¯ãICS ã¨ã®éä¿¡åªå¤±æå㯠ICS ãã®ãã®ã®åªå¤±æã«ãé©åãªãã§ã¼ã«ã»ã¼ããã
ã»ã¹ãå®è¡ã§ããè½åãåãã¦ããã¹ãã§ãããçµç¹ã¯ãéä¿¡åªå¤±ãã®æå³ãæããã«ãã¹ãã§
ããï¼éä¿¡é絶㧠500 ããªç§ã5ç§ã5åçï¼ã次ãã§çãå¾ãçµæãåºã«ãç£æ¥ç¨ã®é©æ£ãªã
ã§ã¼ã«ã»ã¼ãããã»ã¹ãæããã«ãã¹ãã§ããã
SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
121
Backups should be performed using the âbackup-in-depthâ approach, with layers of backups (e.g., local,
facility, disaster) that are time-sequenced such that rapid recent local backups are available for immediate
use and secure backups are available to recover from a massive security incident. A mixture of
backup/restore approaches and storage methods should be used to ensure that backups are rigorously
produced, securely stored, and appropriately accessible for restoration.
5.14 Preventing Man-in-the-Middle Attacks
A man-in-the-middle attack requires knowledge of the protocol being manipulated. The Address Resolution
Protocol (ARP) man-in-the-middle attack is a popular method for an adversary to gain access to the
network flow of information on a target system. This is performed by attacking the network ARP cache
tables of the controller and the workstation machines. Using the compromised computer on the control
network, the adversary poisons the ARP tables on each host and informs them that they must route all their
traffic through a specific IP and hardware address (i.e., the adversaryâs machine). By manipulating the ARP
tables, the adversary can insert their machine between the two target machines and/or devices.
The ARP man-in-the-middle attack works by initiating gratuitous ARP commands to confuse each host (i.e.,
ARP poisoning). These ARP commands cause each of the two target hosts to use the MAC address of the
adversary as the address for the other target host. When a successful man-in-the-middle attack is performed,
the hosts on each side of the attack are unaware that their network data is taking a different route through
the adversaryâs computer.
Once an adversary has successfully inserted their machine into the information stream, they now have full
control over the data communications and could carry out several types of attacks. One possible attack
method is the replay attack. In its simplest form, captured data from the control/HMI is modified to
instantiate activity when received by the device controller. Captured data reflecting normal operations in
the ICS could be played back to the operator as required. This would cause the operatorâs HMI to appear to
be normal and the attack will go unobserved. During this replay attack the adversary could continue to send
commands to the controller and/or field devices to cause an undesirable event while the operator is unaware
of the true state of the system.
Another attack that could be carried out with the man-in-the-middle attack is sending false messages to the
operator, and could take the form of a false negative or a false positive. This may cause the operator to take
an action, such as flipping a breaker, when it is not required, or it may cause the operator to think
everything is fine and not take an action when an action is required. The adversary could send commands to
the operatorâs console indicating a system change, and when the operator follows normal procedures and
attempts to correct the problem, the operatorâs action could cause an undesirable event. There are variations
of the modification and replay of control data which could impact the operations of the system.
Protocol manipulation and the man-in-the-middle attack are among the most popular ways to manipulate
insecure protocols, such as those found in control systems. However, there are mitigation techniques [38]
that can be applied to secure the systems through MAC address locking, static tables, encryption,
authentication, and monitoring.
ï¼ MAC Address Locking - The ARP man-in-the-middle attack requires the adversary to be connected
to the local network or have control of a local computer on the network. Port security, also called
MAC address locking, is one method to secure the physical connection at the end of each port on a
network switch. High-end corporate class network switches usually have some kind of option for
MAC address locking. MAC address locking is very effective against a rogue individual looking to
physically plug into the internal network. Without port security, any open network jack on the wall
SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
122
ããã¯ã¢ããã¯ãå¤å±¤ããã¯ã¢ãããã¢ããã¼ãã«ãããæç³»åé ã«ãªã£ãããã¯ã¢ãã層ï¼ã
ã¼ã«ã«ãæ½è¨ãç½å®³çï¼ã«å¯¾ãã¦å®æ½ããæ¥éã«è¡ãããæè¿ã®ãã¼ã«ã«ããã¯ã¢ãããããã«
使ç¨ã§ããããã«ããã»ãã¥ã¢ãªããã¯ã¢ããã大è¦æ¨¡ãªã»ãã¥ãªãã£ã¤ã³ã·ãã³ããã復帰ã
ãéã«å©ç¨ã§ããããã«ãããããã¯ã¢ãã/復å
ã¨ã¹ãã¬ã¼ã¸æ³ã¨ãä½µç¨ãã¦ãããã¯ã¢ãã
ãå³æ ¼ã«ä½æãããå®å
¨ã«ä¿ç®¡ãããé©åã«å¾©å
ã§ããããã«ããã
5.14 人ãä»å¨ããæ»æã®é²æ¢
人ãä»å¨ããæ»æã¯ãæä½ ä¸ã®ãããã³ã«ã«å¯¾ããç¥èãå¿
é ã¨ãªããå®å
解決ãããã³ã«
ï¼ARPï¼ã®äººãä»å¨ããæ»æã¯ãæ»æå´ãæ¨çã·ã¹ãã ä¸ã®æ
å ±ã®æµãã«ã¢ã¯ã»ã¹ããããã®
ããããæ¹æ³ã§ããããããè¡ãã«ã¯ãã³ã³ããã¼ã©åã³ã¯ã¼ã¯ã¹ãã¼ã·ã§ã³ãã·ã³ã®ãã
ãã¯ã¼ã¯ ARP ãã£ãã·ã¥ãã¼ãã«ãæ»æãããå¶å¾¡ãããã¯ã¼ã¯ä¸ã®æ§è½ãä½ä¸ããã³ã³ã
ã¥ã¼ã¿ãå©ç¨ãã¦ãæ»æå´ã¯åãã¹ãä¸ã® ARP ãã¼ãã«ãæ»ããå
¨ã¦ã®ãã©ãã£ãã¯ãç¹å®
ã®IP åã³ãã¼ãã¦ã¨ã¢ã¢ãã¬ã¹ï¼æ»æå´ã®ãã·ã³ï¼ã«éãããæ示ãããæ»æå´ã¯ ARP ãã¼
ãã«ãæä½ãã¦ã2å°ã®æ¨çãã·ã³éåã¯ããã¤ã¹éã«èªãã®ãã·ã³ãæ¿å
¥ããã
ARP ã®äººãä»å¨ããæ»æã¯ãä½è¨ãª ARP ã³ãã³ããçºè¡ãã¦ãåãã¹ããæ··ä¹±ããããã¨ã§æ©
è½ããï¼ARP ãã¤ãºãã³ã°ï¼ããã®ãã㪠ARP ã³ãã³ãã¯ã2å°ã®æ¨çãã¹ãã®ãã®ãã®ã«ã
æ»æå´ã® MAC ã¢ãã¬ã¹ãä»ã®æ¨çãã¹ãç¨ã®ã¢ãã¬ã¹ã¨ãã¦ä½¿ç¨ããããã«ä»åããã人ãä»
å¨ããæ»æãæåããã¨ãæ»æã®ä¸¡å´ã®ãã¹ããæ°ã¥ããªããã¡ã«ããããã¯ã¼ã¯ãã¼ã¿ãå¥
çµè·¯ããã©ã£ã¦æ»æå´ã®ã³ã³ãã¥ã¼ã¿ã«æµããã
æ»æå´ãèªãã®ãã·ã³ãé¦å°¾ããæ
å ±çµè·¯ã«æ¿å
¥ããã¨ããã¼ã¿éä¿¡ãå
¨é¢çã«å¶å¾¡ã§ãã
種ã
ã®æ»æãä»æããããããã«ãªãããã® 1ã¤ããªãã¬ã¼æ»æã§ãããæãåç´ãªå½¢æ
ã¯ã
å¶å¾¡/HMI ããææãããã¼ã¿ãæ¹å¤ãã¦ãããã¤ã¹ã³ã³ããã¼ã©ããããåä¿¡ããã¨ãã«è¡å
ãèµ·ããããã«ãããã®ã§ãããICS ã«ãããæ£å¸¸ãªæ¥åãåæ ããææãã¼ã¿ã¯ãå¿
è¦ã«å¿
ãã¦æä½å¡ã«ãã¬ã¤ããã¯ããããããã«ããæä½å¡ã® HMI ã¯è¦ããä¸æ£å¸¸ã«è¦ããæ»æã¯çº
è¦ããªãããã®ãªãã¬ã¼æ»æä¸ã«ãæ»æå´ã¯ã³ã³ããã¼ã©åã¯ãã£ã¼ã«ãããã¤ã¹ã«ã³ãã³ã
ãéãç¶ããæ害äºè±¡ãçãããããã¨ãã§ããããæä½å¡ã¯ã·ã¹ãã ã®å®æ
ã«æ°ã¥ããªãã
人ãä»å¨ããæ»æã®å¥ã®ãã®ã¨ãã¦ãå½ã®ã¡ãã»ã¼ã¸ãæä½å¡ã«éããæ¬ä¼¼é°æ§åã¯æ¬ä¼¼é½æ§
ã®å½¢æ
ãåããã®ãããããã®ããæä½å¡ã¯ããã¬ã¼ã«ã¼ãè½ã¨ãã¨ãã£ãä¸è¦ãªå¯¾å¿ãåã£
ãããéã«å¿
è¦ãªå¯¾å¿ãåããªããã°ãªããªãã®ã«ãå
¨ã¦è¯å¥½ã¨æãè¾¼ãã§ä½ãããªãã¨ãã£
ããã¨ãçãããæ»æå´ã¯æä½å¡ã®ã³ã³ã½ã¼ã«ã«ãã·ã¹ãã ã®å¤æ´ã示ãã³ãã³ããéããæ
ä½å¡ãé常æé ã«å¾ã£ã¦åé¡ãä¿®æ£ãããã¨ããã¨ããããå
ã§æ害äºè±¡ãçºçãããã·ã¹ã
ã ã®åä½ã«å½±é¿ããå¶å¾¡ãã¼ã¿ã®å¤æ´åã³ãªãã¬ã¼ã«ã¯ç¨®ã
ã®ããªã¨ã¼ã·ã§ã³ãããã
ãããã³ã«æä½ã¨äººãä»å¨ããæ»æã¯ãå¶å¾¡ã·ã¹ãã ã§è¦ããããã®ã®ãã¡ãã»ãã¥ã¢ã§ãªãã
ããã³ã«ãæä½ããæ¹æ³ã¨ãã¦æããã使ç¨ãããæ¹æ³ã® 1ã¤ã§ãããããã MAC ã¢ãã¬ã¹ã
ãã¯ãã¹ã¿ãã£ãã¯ãã¼ãã«ãæå·åãèªè¨¼åã³ç£è¦ãéãã¦ãã·ã¹ãã ãã»ãã¥ã¢ã«ãããã
ã®ç·©åæè¡ããã[38]ã
ï¼ MAC ã¢ãã¬ã¹ãã㯠- ARP ã®äººãä»å¨ããæ»æã§ã¯ãæ»æå´ããã¼ã«ã«ãããã¯ã¼ã¯ã«æ¥
ç¶ãããããã¯ã¼ã¯ä¸ã®ãã¼ã«ã«ã³ã³ãã¥ã¼ã¿ãå¶å¾¡ãããã¨ãå¿
è¦ã¨ãªããMAC ã¢ãã¬
ã¹ããã¯ã¨ãå¼ã°ãããã¼ãã»ãã¥ãªãã£ã¯ããããã¯ã¼ã¯ã¹ã¤ããä¸ã®åãã¼ã端ã«ãã
ãç©ççæ¥ç¶ãã»ãã¥ã¢ã«ããæ¹æ³ã§ããããã¤ã¨ã³ãä¼æ¥ã¯ã©ã¹ãããã¯ã¼ã¯ã¹ã¤ããã«
ã¯ãé常 MAC ã¢ãã¬ã¹ããã¯ç¨ã®ãªãã·ã§ã³ãããã¤ãç¨æããã¦ãããMAC ã¢ãã¬ã¹
ããã¯ã¯ãå
é¨ãããã¯ã¼ã¯ã¸ã®ç©ççãã©ã°ã¤ã³ãç®è«ãå人ã«å¯¾ãã¦æ¥µãã¦æå¹ã§ããã
ãã¼ãã»ãã¥ãªãã£ããªãå ´åãå£é¢ã®ãªã¼ãã³ãããã¯ã¼ã¯ã¸ã£ãã¯ãå©ç¨ãã¦ã
SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
123
could be used as an avenue onto the corporate network. Port security locks a specific MAC address to
a specific port on a managed switch. If the MAC address does not match, the communication link is
disabled and the intruder will not be able to achieve their goal. Some of the more advanced switches
have an auto resetting option, which will reset the security measure if the original MAC is returned to
the port.
Although port security is not attacker proof, it does add a layer of added security to the physical
network. It also protects the local network from employees plugging un-patched and out-of-date
systems onto the protected network. This reduces the number of target computers a remote adversary
can access. These security measures not only protect against attacks from external networks but
provide added physical protection as well.
ï¼ Static Tables â An ICS network that stays relatively static could attempt to implement statically coded
ARP tables. Most operating systems have the capability to statically code all of the MAC addresses
into the ARP table on each computer. Statically coding the ARP tables on each computer prevents the
adversary from changing them by sending ARP reply packets to the victim computer. While this
technique is not feasible on a large and/or dynamic corporate network, the limited number of hosts on
an ICS network could be effectively protected this way.
ï¼ Encryption - As a longer-term solution, systems should be designed to include encryption between
devices in order to make it very difficult to reverse engineer protocols and forge packets on control
system networks. Encrypting the communications between devices would make it nearly impossible to
perform this attack. Protocols that provide strong authentication also provide resilience to man-in-the-
middle attacks. The impact of encryption on network and operational performance needs to be
considered.
ï¼ Authentication - Protocols with strong authentication provide resilience to man-in-the-middle attacks.
ï¼ Monitoring - Monitoring for ARP poisoning provides an added layer of defense. There are several
programs available (e.g., ARPwatch) that can monitor for changing MAC addresses through the ARP
packets.
SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
124
ä¼æ¥ãããã¯ã¼ã¯ã¸ä¾µå
¥ãããã¨ãã§ããããã¼ãã»ãã¥ãªãã£ã¯ã管çãããã¹ã¤ãã
ä¸ã®ç¹å®ãã¼ãã«ç¹å® MAC ã¢ãã¬ã¹ãããã¯ãããMAC ã¢ãã¬ã¹ãåããªãã¨ãéä¿¡ãªã³
ã¯ã使ç¨ä¸è½ã«ãªããä¾µå
¥è
ã¯ç®çãéãããã¨ãã§ããªããããé²åããã¹ã¤ããã§ã¯ã
èªåãªã»ãããªãã·ã§ã³ããããå
ã® MAC ããã¼ãã«æ»ãã¨ãã»ãã¥ãªãã£å¯¾çããªã»ã
ããããããã«ãªã£ã¦ããã
ãã¼ãã»ãã¥ãªãã£ã¯ãæ»æãå¯ãä»ããªãããã§ã¯ãªãããç©çãããã¯ã¼ã¯ã«ã»ãã¥
ãªãã£ã®ã¬ã¤ã¤ã¼ã追å ãããã®ã¨ãªããã¾ãå¾æ¥å¡ããããã®å½ãã£ã¦ããªãæ§å¼ã·ã¹
ãã ã§ãä¿è·ããããããã¯ã¼ã¯ã«æ¥ç¶ããå ´åã«ããã¼ã«ã«ãããã¯ã¼ã¯ãä¿è·ããã
ããã«ããé éæ»æã§ã¢ã¯ã»ã¹ã§ããæ¨çã³ã³ãã¥ã¼ã¿ã®æ°ãæ¸ããããããã»ãã¥ãªã
ã£å¯¾çã¯ãå¤é¨ãããã¯ã¼ã¯ããã®æ»æããä¿è·ããã ãã§ãªããç©ççä¿è·ãå¢ããã
ã¨ã«ããªãã
ï¼ ã¹ã¿ãã£ãã¯ãã¼ãã« - æ¯è¼çéç㪠ICS ãããã¯ã¼ã¯ã¯ãéçã«ã³ã¼ãã£ã³ã°ããã ARP
ãã¼ãã«ãå®è£
ãããã¨ãããã»ã¨ãã©ã® OS ã«ã¯ãå
¨ã¦ã® MAC ã¢ãã¬ã¹ãåã³ã³ãã¥ã¼
ã¿ã® ARP ãã¼ãã«ã«éçã«ã³ã¼ãã£ã³ã°ããè½åãåãã£ã¦ãããåã³ã³ãã¥ã¼ã¿ã® ARP
ãã¼ãã«ã¸ã®éçã³ã¼ãã£ã³ã°ãè¡ããã¨ã«ãããæ»æå´ã¯ãARP ãªãã©ã¤ãã±ãããæ¨
çã³ã³ãã¥ã¼ã¿ã«éä¿¡ãã¦ããã¼ãã«ãå¤æ´ãããã¨ãã§ããªããªãããã®æè¡ã¯ã大è¦æ¨¡
ãªåã¯åçãªä¼æ¥ãããã¯ã¼ã¯ã§ã¯å®ç¾ã§ããªãããICS ãããã¯ã¼ã¯ä¸ã®éå®çãªæ°ã®ã
ã¹ããªãããã®æ¹æ³ã§æå¹ã«ä¿è·ã§ããã
ï¼ æå·å - ããé·æçãªã½ãªã¥ã¼ã·ã§ã³ã¨ãã¦ããããã³ã«ã®ãªãã¼ã¹ã¨ã³ã¸ãã¢ãªã³ã°ãå¶
御ã·ã¹ãã ãããã¯ã¼ã¯ä¸ã®ãã±ããã®å½é ãå°é£ã«ãããããããã¤ã¹éã®æå·åãè¨è¨
ã«å«ããã¹ãã§ãããããã¤ã¹éã®éä¿¡ãæå·åããã°ããã®æ»æãã»ã¼ä¸å¯è½ã«ãªããå¼·
åãªèªè¨¼ãè¡ããããã³ã«ã¯ã人ãä»å¨ããæ»æã«å¯¾ããæè»æ§ãä»ä¸ãããæå·åã«ãã
ãããã¯ã¼ã¯ãæ¥åããã©ã¼ãã³ã¹ã¸ã®å½±é¿ãæ¤è¨ããå¿
è¦ãããã
ï¼ èªè¨¼ - å¼·åãªèªè¨¼ã¡ã«ããºã ãæã¤ãããã³ã«ã¯ã人ãä»å¨ããæ»æã«å¯¾ããæè»æ§ãä»ä¸
ããã
ï¼ ç£è¦ - ARP ãã¤ãºãã³ã°ã®ç£è¦ã«ããé²å¾¡å±¤ãåããªããARP ãã±ããã®ä¸ã§çµ¶ããå¤åã
ãMAC ã¢ãã¬ã¹ãç£è¦ã§ããããã°ã©ã ãããã¤ãããï¼ARP ã¦ã©ããçï¼ã

SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
125
5.15 Authentication and Authorization
An ICS may contain a large number of systems, each of which must be accessed by a variety of users.
Performing the authentication and authorization of these users presents a challenge to the ICS. Managing
these userâs accounts can be problematic as employees are added, removed, and as their roles change. As
the number of systems and users grow, the process of managing these accounts becomes more complicated.
The authentication of a user or system is the process of verifying the claimed identity. Authorization, the
process of granting the user access privileges, is determined by applying policy rules to the authenticated
identity and other relevant information31. Authorization is enforced by some access control mechanism.
The authentication process can be used to control access to both systems (e.g. HMIs, field devices, SCADA
servers) and networks (e.g., remote substations LANs).
Authentication and authorization can be performed either in a distributed or centralized approach. With
distributed authentication and authorization, every system performs these steps on their own. Each system
is responsible for storing its own set of user accounts, credentials, and roles and performing the
identification and authentication of the user. This approach typically does not require any additional
infrastructure. However, this approach is problematic in that it does not scale well as the size of the system
increases. For example, if a user leaves the organization, the corresponding user account must be removed
from each system individually.
In contrast to the distributed approach, centralized authentication and authorization systems are commonly
used to manage larger number of users and accounts. A centralized approach utilizes some central
authentication system (e.g., Microsoft Active Directory, Lightweight Directory Access Protocol (LDAP) to
store all accounts and manage the authentication and authorization of all individuals and systems. An
authentication protocol (e.g., Kerberos, RADIUS, TACACS+) is then used to communicate data between
the authentication server and the system performing authentication.
While a centralized approach provides substantially improved scalability, it also presents numerous
additional concerns that may impact its use in ICS environments. The following considerations apply:
ï¼ Authentication servers create a single system that is responsible for managing all system accounts and
must be highly secured.
ï¼ The authentications server system requires high availability because its failure may prevent users from
authenticating to a system during an emergency. Redundancy may be required.
ï¼ Some clients may cache user credentials locally to ensure that users can still be authenticated in the
absence of the server. Caching may only be available for users that have recently authenticated.
Caching also introduces complications for revocation.
ï¼ Networks used to support the authentication protocol must be reliable and secure to ensure
authentication attempts are not hindered.
31 In general, authorization to perform a set of operations is determined by evaluating attributes associated
with the subject, object, requested operations, and, in some cases, environment conditions against policy,
rules, or relationships that describe the allowable operations for a given set of attributes. For further
information see NIST SP 800-162,
Guide to Attribute Based Access Control (ABAC) Definition and
Considerations
, at http://nvlpubs.nist.gov/nistpubs/specialpublications/NIST.sp.800-162.pdf

SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
126
5.15 èªè¨¼ã¨æ¨©éä»ä¸
ICS ã«ã¯å¤æ°ã®ã·ã¹ãã ãå«ã¾ããå ´åããããå¤ç¨®å¤æ§ãªã¦ã¼ã¶ãããããã«ã¢ã¯ã»ã¹ã§ã
ãªããã°ãªããªãããããã¦ã¼ã¶ã®èªè¨¼ã¨è¨±å¯ãè¡ãã®ã¯ ICS ã«ã¨ã£ã¦éè·ã¨ãªããå¾æ¥å¡ã®
追å ãåé¤ã¨å½¹å²ã®å¤åã«ä¼´ããã¦ã¼ã¶ã¢ã«ã¦ã³ãã®ç®¡çãç
©éã«ãªããã·ã¹ãã ã¨ã¦ã¼ã¶ã®
æ°ãå¢ããã«ã¤ãã¦ãã¢ã«ã¦ã³ã管çã®ããã»ã¹ãã©ãã©ãè¤éåããã
ã¦ã¼ã¶åã¯ã·ã¹ãã ã®è¨±å¯ã¯ãããããã主張ãã ID ãæ¤è¨¼ããããã»ã¹ã§ããã権éä»ä¸
ã¯ãã¦ã¼ã¶ã«ã¢ã¯ã»ã¹æ¨©ãä¸ããããã»ã¹ã§ã権éãåãã ID ãã®ä»é¢é£æ
å ± 32ã«ããªã·ã¼
è¦åãé©ç¨ãã¦å¤å®ãããã権éä»ä¸ã¯ä½ããã®ã¢ã¯ã»ã¹å¶å¾¡ã¡ã«ããºã ã«ããå®è¡ãããã
権éä»ä¸ããã»ã¹ãå©ç¨ãã¦ãã·ã¹ãã ï¼HMIsããã£ã¼ã«ãããã¤ã¹ãSCADA ãµã¼ãçï¼ã¨ã
ããã¯ã¼ã¯ï¼é éãµãã¹ãã¼ã·ã§ã³ LAN çï¼ã®ä¸¡æ¹ã¸ã®ã¢ã¯ã»ã¹ãå¶å¾¡ã§ããã
èªè¨¼ã¨æ¨©éä»ä¸ã¯ãåæ£ã¢ããã¼ãã§ãéä¸ã¢ããã¼ãã§ãè¡ããã¨ãã§ãããåæ£èªè¨¼ã»æ¨©
éä»ä¸ãå©ç¨ããã¨ãåã·ã¹ãã ããããã®æé ãç¬èªã«è¡ããåã·ã¹ãã ã¯ããããã®è²¬ä»»
ã§ã¦ã¼ã¶ã¢ã«ã¦ã³ããèªè¨¼æ
å ±åã³å½¹å²ãä¿ç®¡ããã¦ã¼ã¶ã®èå¥ã¨æ¨©éä»ä¸ãè¡ããé常ãã
ã®ã¢ããã¼ãã«ã¯ã»ãã®ã¤ã³ãã©ãä¸è¦ã§ããããã ããã·ã¹ãã ã®å¢å¤§ã«ä¼´ãã¹ã±ã¼ã©ããª
ãã£ã«åé¡ããããä¾ãã°ãããã¦ã¼ã¶ãé社ããå ´åãã¦ã¼ã¶ã¢ã«ã¦ã³ããããããã®ã·ã¹
ãã ããåé¤ããªããã°ãªããªãã
åæ£ã¢ããã¼ãã¨ã¯å¯¾ç
§çã«ãéä¸èªè¨¼ã»æ¨©éä»ä¸ã·ã¹ãã ã¯ãä¸è¬ã«ãã大è¦æ¨¡ãªã¦ã¼ã¶
åã³ã¢ã«ã¦ã³ãã®ç®¡çã«ä½¿ç¨ããããéä¸ã¢ããã¼ãã¯ç¹å®ã®ä¸å¤®èªè¨¼ã·ã¹ãã ï¼Microsoft
Active Directoryã Lightweight Directory Access Protocol[LDAP]çï¼ã使ç¨ãã¦å
¨ã¦ã®
ã¢ã«ã¦ã³ããä¿ç®¡ããå
¨ã¦ã¼ã¶ã»å
¨ã·ã¹ãã ã®èªè¨¼ã¨æ¨©éä»ä¸ã管çããã次ãã§æ¨©éä»ä¸
ãããã³ã«ï¼KerberosãRADIUSãTACACS+çï¼ã使ç¨ãã¦èªè¨¼ãµã¼ãã¨èªè¨¼å®æ½ã·ã¹ãã éã§
ãã¼ã¿éä¿¡ãè¡ãã
éä¸ã¢ããã¼ãã§ã¯ã¹ã±ã¼ã©ããªãã£ãããªãåä¸ããåé¢ãICS ç°å¢ã§ä½¿ç¨ããå ´åã®å½±é¿
ã«ã¤ãã¦ã¯ä¸å®ãå¤ãã次ã®ãããªè¦èæ
®äºé
ãããã
ï¼ èªè¨¼ãµã¼ããåä¸ã·ã¹ãã ãåµåºãããããå
¨ã¦ã®ã·ã¹ãã ã¢ã«ã¦ã³ãã管çããé«åº¦ã«ã»
ãã¥ã¢ã§ãªããã°ãªããªãã
ï¼ èªè¨¼ãµã¼ãã·ã¹ãã ã¯ãæ
éããã¨ç·æ¥æã§ãã¦ã¼ã¶ã¯ã·ã¹ãã èªè¨¼ãã§ããªããªãããã
é«ãå¯ç¨æ§ãæ±ãããããåé·æ§ãå¿
è¦ã¨ãªããã
ï¼ ã¯ã©ã¤ã¢ã³ãã«ãã£ã¦ã¯ãã¦ã¼ã¶ã®èªè¨¼æ
å ±ããã¼ã«ã«ã§ãã£ãã·ã¥ãããµã¼ãããªãã¦ã
ã¦ã¼ã¶ãèªè¨¼ã§ããããã«ãã¦ããããã£ãã·ã³ã°ã¯ãæè¿èªè¨¼ããã¦ã¼ã¶ã«ããå©ç¨ã§ã
ãªãããã£ãã·ã³ã°ã¯åæ¶ãè¤éã«ããã
ï¼ èªè¨¼ãããã³ã«ããµãã¼ãããããã®ãããã¯ã¼ã¯ã¯ä¿¡é ¼æ§ãé«ãã»ãã¥ã¢ã§ãèªè¨¼ã®è©¦ã¿
ã妨ããããªãããã«ããªããã°ãªããªãã
32 ç·ãã¦ä¸é£ã®æä½ãããããã®æ¨©éä»ä¸ã¯ã主ä½ã対象ãæ±ãã¦ããæä½å
容ã«é¢ä¿ããå±æ§ãè©ä¾¡ãã¦å¤å®ããããå ´
åã«ãã£ã¦ã¯ãç¹å®ã®å±æ§ã«é¢ãã¦è¨±å¯ããæä½å
容ãè¦å®ããããªã·ã¼ãè¦ååã¯é¢ä¿ã«ç
§ããã¦ãç°å¢æ¡ä»¶ãè©ä¾¡ã
å¤å®ããã詳細ã¯æ¬¡ã® URL ã«ãã NIST SP 800-162ãå±æ§ã«åºã¥ãã¢ã¯ã»ã¹å¶å¾¡ï¼ABACï¼å®ç¾©åã³èæ
®ããåç
§ã®ãã¨ã
http://nvlpubs.nist.gov/nistpubs/specialpublications/NIST.sp.800-162.pdf

SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
127
5.15.1 ICS Implementation Considerations
While centralized authentication and authorization servers are commonly used in an IT environment, there
are many challenges to integrating them into ICS. While authentication servers and protocols integrate with
many commodity IT products (e.g., Microsoft Windows, Linux, Oracle), often ICS may utilize their own
application-specific accounts and authentication mechanisms that were not designed to interface with third
party servers and protocols. This limits the adoption of such mechanism in an ICS environment. Older
network devices and most field devices do not support any mechanisms to integrated with a centralized
authentication system.
5.16 Monitoring, Logging, and Auditing
The security architecture of an ICS must also incorporate mechanisms to monitor, log, and audit activities
occurring on various systems and networks. Monitoring, logging, and auditing activities are imperative to
understanding the current state of the ICS, validating that the system is operating as intended, and that no
policy violations or cyber incidents have hindered the operation of the system. Network security monitoring
is valuable to characterize the normal state of the ICS, and can provide indications of compromised systems
when signature-based technologies fail. Additionally, strong system monitoring, logging, and auditing is
necessary to troubleshoot and perform any necessary forensic analysis of the system33.
5.17 Incident Detection, Response, and System Recovery
Incidents are inevitable and incident detection, response, and system recovery plans are essential. Major
characteristics of a good security program are how soon after an incident has occurred that the incident can
be detected and how quickly a system can be recovered after an incident has been detected. Incident
response in ICS is closely aligned to disaster recovery, specifically to address the stringent uptime
requirements of ICS. Incident Responders must be trained for ICS-specific scenarios, as normal methods
of recovering IT systems may not apply to ICS.
33 For further information see NIST SP 800-94,
Guide to Intrusion Detection and Prevention Systems (IDPS)
[55].

SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
128
5.15.1 ICS å®è£
ä¸ã®èæ
®äºé
éä¸èªè¨¼ãµã¼ãåã³éä¸æ¨©éä»ä¸ãµã¼ãã¯ãIT ç°å¢ã§ã¯æ®éã«å©ç¨ããã¦ããããICS ã«ä¸¡è
ã
çµã¿è¾¼ãã®ã¯åé¡ãå¤ããèªè¨¼ãµã¼ãåã³ãããã³ã«ã¯å¤ãã®å¸è²© IT 製åï¼Microsoft Windowsã
LinuxãOracle çï¼ãçµã¿è¾¼ãããICS ã§ã¯ç¬èªã®ã¢ããªã±ã¼ã·ã§ã³åºæã®ã¢ã«ã¦ã³ãã¨èªè¨¼ã¡ã«
ããºã ã使ç¨ãããã¨ãå¤ãããããã¯ãµã¼ããã¼ãã£ã®ãµã¼ãåã³ãããã³ã«ã¨é£æºãããã
ã«ã¯ã§ãã¦ããªãããã®ãã ICS ç°å¢ã§ã¯ããããã¡ã«ããºã ã®æ¡ç¨ã«éçããããæ§åã®ãã
ãã¯ã¼ã¯ããã¤ã¹ãã»ã¨ãã©ã®ãã£ã¼ã«ãããã¤ã¹ã¯ãéä¸èªè¨¼ã·ã¹ãã ã«çµã¿è¾¼ããã¡ã«ããº
ã ã«å¯¾å¿ãã¦ããªãã
5.16 ç£è¦ããã®ã³ã°åã³ç£æ»
ICS ã®ã»ãã¥ãªãã£ã¢ã¼ããã¯ãã£ã«ã¯ã種ã
ã·ã¹ãã ããããã¯ã¼ã¯ãç£è¦ããã°åã³ç£æ»ã§
ããã¡ã«ããºã ãçµã¿è¾¼ã¾ãã¦ããªããã°ãªããªããç£è¦ããã®ã³ã°åã³ç£æ»æ´»å㯠ICS ã®ç¾ç¶
ãç解ããã·ã¹ãã ãäºå®ã©ãã稼åãã¦ãããæ¤è¨¼ããã·ã¹ãã ã®åä½ã妨害ãããããªããª
ã·ã¼éåããµã¤ãã¼ã¤ã³ã·ãã³ãããªããã¨ãæ¤è¨¼ããããã«ä¸å¯æ¬ ã§ããããããã¯ã¼ã¯ã»ã
ã¥ãªãã£ç£è¦ã¯ãICS ã®æ£å¸¸ç¶æ
ã®ç¹å¾´ãæ確åããããã«è²´éã§ãç½²åãã¼ã¹ã®æè¡ã«é害ã
åºãã¨ãã«ãã·ã¹ãã æ§è½ãä½ä¸ããå
åãæ示ã§ãããã¾ãããã©ãã«ã·ã¥ã¼ãã£ã³ã°ãè¡ãã
ã·ã¹ãã 34ã®å¿
è¦ãªèª¿æ»åæãè¡ãã«ã¯ãå¼·åãªã·ã¹ãã ç£è¦ããã®ã³ã°åã³ç£æ»ãå¿
è¦ã§ããã
5.17 ã¤ã³ã·ãã³ãæ¤ç¥ã対å¿åã³ã·ã¹ãã 復æ§
ã¤ã³ã·ãã³ãã¯é¿ããããªãã®ã§ãã¤ã³ã·ãã³ãæ¤ç¥ã対å¿åã³ã·ã¹ãã 復æ§è¨ç»ãä¸å¯æ¬ ã¨ãª
ããåªç§ãªã»ãã¥ãªãã£ããã°ã©ã ã®ä¸»ãªç¹å¾´ã¯ãã¤ã³ã·ãã³ãçºçæã«ããã«ç´ æ©ãæ¤ç¥ãã
æ¤ç¥å¾ããã«è¿
éã«ã·ã¹ãã ã復æ§ã§ãããã«ãããICS ã«ãããã¤ã³ã·ãã³ã対å¿ã¯ãç½å®³å¾©
æ§ã¨å¯æ¥ã«é£æºããç¹ã« ICS ã®å³æ ¼ãªã¢ããã¿ã¤ã è¦ä»¶ã«ã¤ãã¦æ¤è¨ãããIT ã·ã¹ãã ã®é常ã®
復æ§æ¹æ³ã¯ ICS ã«ã¯å½ã¦ã¯ã¾ããªããããã¤ã³ã·ãã³ã対å¿è
ã®è¨ç·´ã¯ãICS åºæã®ã·ããªãªã«
沿ã£ã¦å®æ½ããªããã°ãªããªãã
34 詳細㯠NIST SP 800-94ãä¾µå
¥æ¤ç¥é²æ¢ã·ã¹ãã ï¼IDPSï¼ã[55]ãåç
§ã®ãã¨ã

SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
129
6. Applying Security Controls to ICS
A single security product or technology cannot adequately protect an ICS. Securing an ICS is based on a
combination of effective security policies and a properly configured set of security controls. The selection
and implementation of security controls to apply to an ICS can have major implications on the operations,
so it is critical to consider:
ï¼ Which security controls are needed to adequately mitigate risk to an acceptable level that supports the
organizational missions and business functions?
ï¼ Have the selected security controls been implemented or is there a realistic implementation plan in
place?
ï¼ What is the required level of assurance that the selected security controls are implemented correctly,
operating as intended, and producing a desired outcome?
As identified in Section 3, the questions should be answered in the context of an effective, organization-
wide risk management process and cybersecurity strategy that identifies, mitigates (as necessary), and
continuously monitors risks to its ICS. An effective cybersecurity strategy for an ICS should apply defense-
in-depth, a technique of layering security mechanisms so that the impact of a failure in any one mechanism
is minimized. Use of such a strategy is explored within the security control discussions and their
applications to ICS that follow.
6.1 Executing the Risk Management Framework Tasks for Industrial Control
Systems
The following describes the process of applying the Risk Management Framework (RMF) to ICS. The
process includes a brief description of each activity and identifies supporting NIST documents. The
following steps, while shown sequentially, can be implemented in a different order to be consistent with
established management and system development life cycle processes [21].

SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
130
6. ICS ã¸ã®ã»ãã¥ãªãã£å¯¾çã®é©ç¨
åä¸ã®ã»ãã¥ãªãã£è£½åãæè¡ã§ã¯ãICS ããã£ããä¿è·ãããã¨ã¯ã§ããªããICS ã®ã»ãã¥ãª
ãã£ç¢ºä¿ã¯ãæå¹ãªã»ãã¥ãªãã£ããªã·ã¼ã¨æ§æã®è¡ãå±ããã»ãã¥ãªãã£å¯¾çãåºèª¿ã¨ããã
ICS ã«é©ç¨ããã»ãã¥ãªãã£å¯¾çã®é¸å®ã¨å®è£
ã¯ãæ¥åã¨å¯æ¥ãªé¢ä¿ãæã¤ããã以ä¸ã«ã¤ãã¦
è¯ãæ¤è¨ãããã¨ãèè¦ã§ããã
ï¼ ãªã¹ã¯ã許容ã§ããã¬ãã«ã¾ã§ç·©åããçµç¹ã®ä»»åã¨äºæ¥æ©è½ãæ¯æ´ã§ããããã«ããã«ã¯
ã©ã®ã»ãã¥ãªãã£å¯¾çãå¿
è¦ãã
ï¼ é¸å®ããã»ãã¥ãªãã£å¯¾çã¯å®è¡ãããããããã¨ãç¾å®çãªå®è¡è¨ç»ããããã
ï¼ é¸å®ããã»ãã¥ãªãã£å¯¾çãäºå®ã©ããæ£ããå®è¡ããææã®çµæãå¾ãã«ã¯ã©ã®ç¨åº¦ã®ä¿
証ã¬ãã«ãå¿
è¦ãã
ã»ã¯ã·ã§ã³ 3ã§æ確ã«ããããã«ãä¸è¨ã®è³ªåã«å¯¾ããçãã¯ãæå¹ãªçµç¹å
¨ä½ã®ãªã¹ã¯ç®¡çã
ãã»ã¹ã¨ãçµç¹ã® ICS ãªã¹ã¯ãç¹å®ããå¿
è¦ã«å¿ãã¦ç·©åããç¶ç¶çã«ç£è¦ãããµã¤ãã¼ã»ãã¥
ãªãã£æ¦ç¥ã«ç
§ããã¦æ示ãããã¹ãã§ãããICS ã®å¹æçãªãµã¤ãã¼ã»ãã¥ãªãã£æ¦ç¥ã¯ãå¤
層é²å¾¡ã¨ãã¦ç¥ãããã¬ã¤ã¤ãªã³ã°ã»ãã¥ãªãã£ã¡ã«ããºã æè¡ãé©ç¨ããããã¡ã«ããºã ã®é
害ã®å½±é¿ãæå°éã«é£ãæ¢ããããããã«ãã¹ãã§ããããã®ãããªæ¦ç¥ã®ä½¿ç¨ã¯ãã»ãã¥ãªã
ã£ç®¡çã«é¢ããè°è«ã¨ãã®å¾ã® ICS ã¸ã®é©ç¨ã®ä¸ã§çå®ãããã
6.1 ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ç¨ãªã¹ã¯ç®¡çä½å¶ã®å®æ½
ãªã¹ã¯ç®¡çä½å¶ï¼RMFï¼ã ICS ã«é©ç¨ããããã®ããã»ã¹ã以ä¸ã«è¨è¿°ãããããããã®æ´»åã«
対ããæ¦è¦ã¨ NIST ã®æ ¹æ ææ¸ã示ããæé ãé çªã«ç¤ºãããçå®ããã管çã»ã·ã¹ãã éçºã©
ã¤ããµã¤ã¯ã«ããã»ã¹[21]ã«å¾ã£ã¦ãé åºãå¤ãã¦å®æ½ãã¦ããã¾ããªãã
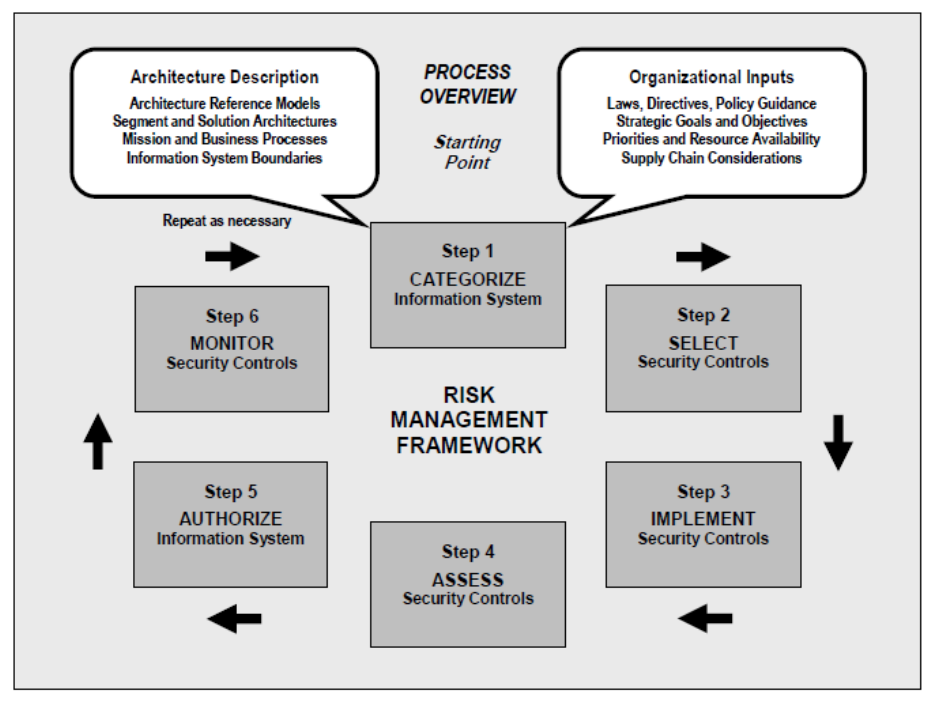
SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
131
Figure 6-1. Risk Management Framework Tasls
6.1.1 Step 1: Categorize Information System
The first activity in the RMF is to categorize the information and information system according to potential
impact of loss. For each information type and information system under consideration, the three FISMA-
defined security objectivesâconfidentiality, integrity, and availabilityâare associated with one of three
levels of potential impact should there be a breach of security. It is important to remember that for an ICS,
availability is generally the greatest concern.
The standards and guidance for this categorization process can be found in FIPS 199 [15] and NIST SP
800-60 [25], respectively. NIST is in the process of updating NIST SP 800-60 to provide additional
guidance on the categorization of ICS.
SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
132
å³6-1.ãªã¹ã¯ç®¡çä½å¶æ¥å
6.1.1 æé 1ï¼æ
å ±ã·ã¹ãã ã®åé¡
RMF ã®ç¬¬ 1æ©ã¯ãåªå¤±æã®å½±é¿ã«å¿ãã¦ãæ
å ±ã¨æ
å ±ã·ã¹ãã ãåé¡ãããã¨ã§ãããæ¤è¨ä¸
ã®æ
å ±ã®ç¨®é¡ã¨æ
å ±ã·ã¹ãã ãã¨ã«ãFISMA ã®å®ç¾©ã«ããæ©å¯æ§ã»å®å
¨æ§ã»å¯ç¨æ§ã¨ãã 3ã¤
ã®ã»ãã¥ãªãã£ç®æ¨ããã»ãã¥ãªãã£éåããã£ãå ´åã® 3ã¬ãã«ã®ãã¡ã®ããããã«é¢é£ã¥ã
ããããICS ã§ã¯ç·ãã¦å¯ç¨æ§ãæ大ã®é¢å¿äºã¨ãªãç¹ãéè¨ããã®ã¯èè¦ã§ããã
ãã®åé¡ããã»ã¹ã®åºæºã¨ã¬ã¤ãã³ã¹ã¯ããããã FIPS 199[15]㨠NIST SP 800-60 [25]ã«ããã
NIST ã§ã¯ NIST SP 800-60 ãæ¹è¨ä¸ã§ãICS ã®åé¡ã«é¢ããè£è¶³çãªã¬ã¤ãã³ã¹ãæä¾ããäºå®
ã§ããã
ã¢ã¼ããã¯ãã£ã®èª¬æ
ã¢ã¼ããã¯ãã£åºæºã¢ãã«ã»ã°
ã¡ã³ãåã³ã½ãªã¥ã¼ã·ã§ã³
ã¢ã¼ããã¯ãã£ä»»åã»äºæ¥ãã
ã»ã¹æ
å ±ã·ã¹ãã ã®å¢ç
çµç¹ã®å
¥å
æ³å¾ãæ示æ¸ãããªã·ã¼
ã¬ã¤ãã³ã¹ã®æ¦ç¥çç®æ¨ã»ç®æ¨åª
å
é ä½åã³ãªã½ã¼ã¹å¯ç¨æ§ãµãã©
ã¤
ãã§ã¼ã³ã«å¯¾ããèæ
®äºé
æé
1
ï¼
æ
å ±ã·ã¹ãã ã®åé¡
æé
6
ï¼
ã»ãã¥ãªãã£å¯¾çã®ç£è¦
æé
5
ï¼
æ
å ±ã·ã¹ãã ã®è¨±å¯
æé
4
ï¼
ã»ãã¥ãªãã£å¯¾çã®è©ä¾¡
æé
3
ï¼
ã»ãã¥ãªãã£å¯¾çã®å®æ½
æé
2
ï¼
ã»ãã¥ãªãã£å¯¾çã®é¸å®
ãªã¹ã¯
管çä½å¶
ããã»ã¹ã®æ¦è¦
éå§ç¹
å¿
è¦ã«å¿ãã¦ç¹°ãè¿ã

SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
133
The following ICS example is taken from FIPS 199 [15]:
ICS-specific Recommendations and Guidance
A power plant contains a SCADA system controlling the distribution of electric power for a large military
installation. The SCADA system contains both real-time sensor data and routine administrative
information. The management at the power plant determines that: (i) for the sensor data being acquired by
the SCADA system, there is no potential impact from a loss of confidentiality, a high potential impact from
a loss of integrity, and a high potential impact from a loss of availability; and (ii) for the administrative
information being processed by the system, there is a low potential impact from a loss of confidentiality, a
low potential impact from a loss of integrity, and a low potential impact from a loss of availability. The
resulting security categories, SC, of these information types are expressed as:
SC sensor data = {(confidentiality, NA), (integrity, HIGH), (availability, HIGH)},
and
SC administrative information = {(confidentiality, LOW), (integrity, LOW), (availability, LOW)}.
The resulting security category of the information system is initially expressed as:
SC SCADA system = {(confidentiality, LOW), (integrity, HIGH), (availability, HIGH)},
representing the high water mark or maximum potential impact values for each security objective from the
information types resident on the SCADA system. The management at the power plant chooses to increase
the potential impact from a loss of confidentiality from low to moderate, reflecting a more realistic view of
the potential impact on the information system should there be a security breach due to the unauthorized
disclosure of system-level information or processing functions. The final security category of the
information system is expressed as:
SC SCADA system = {(confidentiality, MODERATE), (integrity, HIGH), (availability, HIGH)}.
FIPS 199 specifies that information systems be categorized as low-impact, moderate-impact, or high-
impact for the security objectives of confidentiality, integrity, and availability. Possible definitions for low,
moderate, and high levels of security based on impact for ICS based on ISA99 are provided in Table 6-1.
Possible definitions for ICS impact levels based on product produced, industry and security concerns are
provided in Table 6-2.
Table 6-1. Possible Definitions for ICS Impact Levels Based on ISA99
Impact Category
Low-Impact
Moderate-Impact
High-Impact
Injury Cuts, bruises requiring
first aid
Requires hospitalization Loss of life or limb
Financial Loss
$1,000
$100,000
Millions
Environmental Release Temporary damage Lasting damage Permanent damage, off-
site damage
Interruption of
Production
Minutes Days Weeks
Public Image
Temporary damage
Lasting damage
Permanent damage
SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
134
以ä¸ã® ICS ã®ä¾ã¯ãFIPS 199[15]ããæç²ãããã®ã§ããã
ICS åºæã®æ¨å¥¨äºé
åã³ã¬ã¤ãã³ã¹
ããçºé»æã«ã¯ã大è¦æ¨¡è»äºæ½è¨ã¸ã®é
é»ãå¶å¾¡ãã SCADA ã·ã¹ãã ãè¨ç½®ããã¦ããã
SCADA ã·ã¹ãã ã«ã¯ãªã¢ã«ã¿ã¤ã ã»ã³ãµãã¼ã¿ã¨å®å¸¸ã®ç®¡çæ
å ±ãå«ã¾ãããçºé»æã®çµå¶é£
ã¯ä»¥ä¸ã®ã¨ããå¤å®ãã¦ãããï¼1ï¼SCADA ã·ã¹ãã ã§åå¾ããã»ã³ãµãã¼ã¿ã«ã¤ãã¦ã¯ãæ©å¯
æ§ã失ããã¦ãå½±é¿ã¯ãªããå®å
¨æ§ã失ãããã¨ããªãã®å½±é¿ããããå¯ç¨æ§ã失ãããã¨ããª
ãã®å½±é¿ããããï¼2ï¼ã·ã¹ãã ãå¦çãã管çæ
å ±ã«ã¤ãã¦ã¯ãæ©å¯æ§ã失ããã¦ãå½±é¿ã¯å°
ãªããå®å
¨æ§ã失ããã¦ãå½±é¿ã¯å°ãªããå¯ç¨æ§ã失ããã¦ãå½±é¿ã¯å°ãªãããã®ãããªæ
å ±ã®
種é¡ã«åºã¥ãçµæãã»ãã¥ãªãã£åé¡ï¼SCï¼ã¯æ¬¡ã®å¼ã§è¡¨ããã¨ãã§ããã
SC ã»ã³ãµãã¼ã¿ = {(æ©å¯æ§ãNA), (å®å
¨æ§, HIGH), (å¯ç¨æ§, HIGH)}ãã¾ã
SC 管çæ
å ± = {(æ©å¯æ§ãLOW), (å®å
¨æ§, LOW), (å¯ç¨æ§, LOW)}ã
æ
å ±ã·ã¹ãã ã«åºã¥ãã»ãã¥ãªãã£åé¡ã¯å½å
SC SCADA ã·ã¹ãã = {(æ©å¯æ§ãLOW), (å®å
¨æ§, HIGH), (å¯ç¨æ§, HIGH)}ã§ã
SCADA ã·ã¹ãã ã«å¸¸é§ããæ
å ±ã®ç¨®é¡ã«åºã¥ãã»ãã¥ãªãã£ç®æ¨ãã¨ã®å½±é¿å¤ã¯ã大åã¯æ大
å½±é¿åº¦ã示ãã¦ãããçºé»æã®çµå¶é£ã®é¸æã¯ãæ©å¯æ§ã失ãããã¨ãã®å½±é¿åº¦ãä½ããä¸ã«ãã
ä¸ä¸ã·ã¹ãã ã¬ãã«åã¯å¦çæ©è½ã®æ¼æ´©ã«ããã»ãã¥ãªãã£éåãçããéã«ãæ
å ±ã·ã¹ãã ã¸
ã®å½±é¿ãããç¾å®çã«ã¨ãããããã«ãããæçµçãªæ
å ±ã·ã¹ãã ã«åºã¥ãã»ãã¥ãªãã£åé¡ã¯
SC SCADA ã·ã¹ãã = {(ä¿¡é ¼æ§ãMODERATE), (å®å
¨æ§, HIGH), (å¯ç¨æ§, HIGH)}ã¨ãªã£ãã
FIPS 199 ã§ã¯ãæ©å¯æ§ã»å®å
¨æ§ã»å¯ç¨æ§ã®ã»ãã¥ãªãã£ç®æ¨ã«é¢ããæ
å ±ã·ã¹ãã ã®åé¡ãä½å½±
é¿åº¦ãä¸å½±é¿åº¦ãé«å½±é¿åº¦ã¨å®ãã¦ããã ISA99 ã«å¾ã£ã ICS ã¸ã®å½±é¿ã«åºã¥ããã»ãã¥ãªãã£
ã¬ãã«ä½ã»ä¸ã»é«ã®å®ç¾©ã表 6-1 ã«ç¤ºããçç£ç©ãç£æ¥åã³ã»ãã¥ãªãã£é¢å¿äºã«åºã¥ãã ICS
ã¸ã®å½±é¿ã¬ãã«ã®å®ç¾©ã表 6-2 ã«ç¤ºãã
表6-1. ISA99 ã«åºã¥ã ICS å½±é¿ã¬ãã«ã®å®ç¾©
å½±é¿åº¦åé¡
ä½
ä¸
é«
è² å· å¿æ¥å¦ç½®ãè¦ããåã
å·ãææ²
å
¥é¢ãå¿
è¦ çå½ã»åè¢ã®åªå¤±
ééçåªå¤± $1,000 $100,000 æ°ç¾ä¸
ç°å¢æ¾åº ä¸æçãã¡ã¼ã¸ é·æçãã¡ã¼ã¸ æ°¸ç¶çãã¡ã¼ã¸ãç¾
å ´å¤ã®ãã¡ã¼ã¸
çç£ä¸æ å æ¥ é±
å½æ°ã®ã¤ã¡ã¼ã¸ ä¸æçãã¡ã¼ã¸ é·æçãã¡ã¼ã¸ æ°¸ç¶çãã¡ã¼ã¸
SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
135
Table 6-2. Possible Definitions for ICS Impact Levels Based on Product Produced, Industry and
Security Concerns
Impact Category
Low-Impact
Moderate-Impact
High-Impact
Product Produced ï½¥ Non-hazardous
materials or products
ï½¥ Non-ingested
consumer products
ï½¥ Some hazardous
products or steps
during production
ï½¥ High amount of
proprietary
information
ï½¥ Critical infrastructure (e.g.,
electricity)
ï½¥ Hazardous materials
ï½¥ Ingested products
Industry Examples ï½¥ Plastic injection
molding
ï½¥ Warehouse
applications
ï½¥ Automotive metal
industries
ï½¥ Pulp and paper
ï½¥ Semiconductors
ï½¥ Utilities
ï½¥ Petrochemical
ï½¥ Food and beverage
ï½¥ Pharmaceutical
Security Concerns ï½¥ Protection against
minor injuries
ï½¥ Ensuring uptime
ï½¥ Protection against
moderate injuries
ï½¥ Ensuring uptime
ï½¥ Capital investment
ï½¥ Protection against major
injuries/loss of life
ï½¥ Ensuring uptime
ï½¥ Capital investment
ï½¥ Trade secrets
ï½¥ Ensuring basic social services
ï½¥
Regulatory compliance
6.1.2 Step 2: Select Security Controls
This framework activity includes the initial selection of minimum security controls planned or in place to
protect the information system based on a set of requirements. FIPS 200 documents a set of minimum-
security requirements covering 18 security-related areas with regard to protecting the confidentiality,
integrity, and availability of federal information systems and the information processed, stored, and
transmitted by those systems [16]. Additional information on each of the 18 security control families is in
Section 6.2.
The baseline controls are the starting point for the security control selection process and chosen based on
the security category and associate impact level of information systems determined in Step 1.
To address the need for developing community-wide and specialized sets of security controls for
information systems and organizations, the concept of overlays is introduced. An overlay is a fully
specified set of security controls, control enhancements, and supplemental guidance derived from the
application of tailoring guidance to security control baselines described in NIST SP 800-53.
In general, overlays are intended to reduce the need for ad hoc tailoring of baselines by organizations
through the selection of a set of controls and control enhancements that more closely correspond to
common circumstances, situations, and/or conditions. However, the use of overlays does not in any way
preclude organizations from performing further tailoring (i.e., overlays can also be subject to tailoring) to
reflect organization-specific needs, assumptions, or constraints. For further information on creating
overlays, refer to SP 800-53, Section 3.3 and Appendix I.
Appendix Gâ includes an ICS-specific overlay of applicable NIST SP 800-53 controls that provide
tailored baselines for low-impact, moderate-impact, and high-impact ICS. These tailored baselines can be
utilized as starting specifications and recommendations that can be applied to specific ICS by responsible
personnel. As discussed in earlier sections, the use of an overlay does not in any way preclude
organizations from performing further tailoring to add or remove controls and control enhancements (i.e.,
overlays can also be subject to tailoring) to reflect organization-specific needs, assumptions, or constraints.

SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
136
表6-2. çç£ç©ãç£æ¥åã³ã»ãã¥ãªãã£é¢å¿äºã«åºã¥ã ICS ã¸ã®å½±é¿ã¬ãã«ã®å®ç¾©
ã«ãã´ãª
ä½
ä¸
é«
çç£ç© ⢠å±éºç©ã»ç£ç©ä»¥
å¤
⢠éæååæ¶è²»
財
⢠çç£æã«ããç¨åº¦ã®å±
éºç£ç©ã»æé
⢠å¤éã®å°ææ
å ±
⢠éè¦ã¤ã³ãã©ï¼é»æ°
çï¼
⢠å±éºç©
⢠æååç£ç©
ç£æ¥ä¾ ⢠ãã©ã¹ãã
ã¯å°åºæå½¢
⢠å庫ã¢
ããª
⢠è»ä¸¡éå±æ¥ç
⢠ãã«ã製ç´
⢠åå°ä½
⢠å
Œ
±äºæ¥
⢠ç³æ²¹åå¦
⢠é£å飲æ
⢠è¬å¤
ã»ãã¥ãªãã£
é¢å¿äº
⢠軽å·äºé²
⢠稼å確ä¿
⢠ä¸ç¨åº¦ã®è² å·äº
é²
⢠稼å確ä¿
⢠è³æ¬æè³
⢠éå·ã»æ»äº¡äºé²
⢠稼å確ä¿
⢠è³æ¬æè³
⢠åå¼ä¸ã®ç§å¯
⢠åºæ¬ç社ä¼ç¦ç¥ã®ç¢º
ä¿
â¢
æ³ä»¤éµå®
6.1.2 æé 2ï¼ã»ãã¥ãªãã£å¯¾çã®é¸æ
ãã®æ çµã§ã®æ´»åã«ã¯ãä¸é£ã®è¦ä»¶ã«åºã¥ãæ
å ±ã·ã¹ãã ãä¿è·ããããã®è¨ç»ä¸åã¯å®æ½ä¸
ã®æä½éã®ã»ãã¥ãªãã£å¯¾çã®åæé¸æãè¡ããã¨ãå«ã¾ãããFIPS200 ã«ã¯ã18 ã®ã»ãã¥ãª
ãã£é¢é£åéã網ç¾
ããä¸é£ã®æä½ã»ãã¥ãªãã£è¦ä»¶ãè¨é²ããã¦ãããé£é¦æ
å ±ã·ã¹ãã ã®
æ©å¯æ§ã»å®å
¨æ§ã»å¯ç¨æ§ã®ä¿è·ãããããã·ã¹ãã ãå¦çã»ä¿ç®¡ã»éä¿¡ããæ
å ±ã«ã¤ãã¦åã
ä¸ãããã¦ãã[16]ã18 ã®ã»ãã¥ãªãã£å¯¾çåéã«é¢ããä»å çãªæ
å ±ã¯ã»ã¯ã·ã§ã³ 6.2 ã§å
ãä¸ããã
ãã¼ã¹ã©ã¤ã³å¶å¾¡ã¯ãã»ãã¥ãªãã£å¯¾çé¸å®ããã»ã¹ã®éå§ç¹ã¨ãªããã»ãã¥ãªãã£åé¡ã¨æ
é 1ã§å¤å®ãããæ
å ±ã·ã¹ãã ã®å½±é¿åº¦ã«åºã¥ãã¦é¸æãããã
æ
å ±ã·ã¹ãã åã³çµç¹åãã«ãå
±åä½å
¨ä½ã®å°ç¨ã»ãã¥ãªãã£å¯¾çãçå®ããå¿
è¦ããããª
ã¼ãã¼ã¬ã¤æ¦å¿µãå°å
¥ããã¦ããããªã¼ãã¼ã¬ã¤ã¯ãå®å
¨ã«ç¹åããã»ãã¥ãªãã£å¯¾çã管
çæ¡å¼µåã³è£è¶³ã¬ã¤ãã³ã¹ã§ãNIST SP 800-53 ã«è¨è¼ããã¦ããã»ãã¥ãªãã£å¯¾çãã¼ã¹ã©
ã¤ã³ç¨ã¬ã¤ãã³ã¹ããçãããã®ã§ããã
ä¸è¬ã«ãªã¼ãã¼ã¬ã¤ã¯ãå
±éçãªç°å¢ãç¶æ³ã»ç¶æ
ã«ç·å¯ã«å¯¾å¿ããä¸é£ã®å¶å¾¡ã»å¶å¾¡æ¡å¼µã
é¸æãããã¨ã§ãçµç¹ã«ãããã®å ´ãã®ãã®ãã¼ã¹ã©ã¤ã³èª¿æ´ã®å¿
è¦æ§ãæ¸ãããã¨ãç®çã§
ããããã ããªã¼ãã¼ã¬ã¤ãå©ç¨ãã¦ããçµç¹åºæã®å¿
è¦ã»åæã»å¶ç´ã«å¯¾å¿ããããããã
以ä¸ã®èª¿æ´ãå
¨ãä¸è¦ã«ãªãããã§ã¯ãªãï¼ã¤ã¾ããªã¼ãã¼ã¬ã¤ã¯èª¿æ´å¯è½ï¼ããªã¼ãã¼ã¬ã¤
ã®ä½æã«ã¤ãã¦ã¯ãSP 800-53 ã®ã»ã¯ã·ã§ã³ 3.3 ã¨ä»é² Iãåç
§ã®ãã¨ã
ä»é² Gã«ã¯ãä»é² Gã«ã¯ãä½ã»ä¸ã»é«å½±é¿åº¦ ICS ã«èª¿æ´æ¸ã¿ãã¼ã¹ã©ã¤ã³ã示ããã該å½ãã
NIST SP 800-53 å¶å¾¡ã®åºæãªã¼ãã¼ã¬ã¤ãå«ã¾ãã¦ããã ããã調æ´æ¸ã¿ãã¼ã¹ã©ã¤ã³ã¯ã
責任è
ãåºæã® ICS ã«é©ç¨å¯è½ãªå½åã®ä»æ§æ¸åã³æ¨å¥¨äºé
ã¨ãã¦å©ç¨ã§ãããåè¿°ã®éãã
ãªã¼ãã¼ã¬ã¤ãå©ç¨ãã¦ããçµç¹åºæã®å¿
è¦ã»åæã»å¶ç´ã«å¯¾å¿ããããããã以ä¸ã®èª¿æ´ã
å ãã¦ãå¶å¾¡ã»å¶å¾¡æ¡å¼µã®è¿½å ã»åé¤ãè¡ããããªèª¿æ´ãå
¨ãä¸è¦ã«ãªãããã§ã¯ãªãï¼ã¤ã¾
ããªã¼ãã¼ã¬ã¤ã¯èª¿æ´å¯è½ï¼ã
SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
137
Additionally, ICS owners can take advantage of the ability to tailor the initial baselines presented in the
Appendix Gâ Overlay when it is not possible or feasible to implement specific security controls contained
in the baselines. However, all tailoring activity should, as its primary goal, focus on meeting the intent of
the original security controls whenever possible or feasible. For example, in situations where the ICS
cannot support, or the organization determines it is not advisable to implement particular security controls
or control enhancements in an ICS (e.g., performance, safety, or reliability are adversely impacted), the
organization provides a complete and convincing rationale for how the selected compensating controls
provide an equivalent security capability or level of protection for the ICS and why the related baseline
security controls could not be employed. If the ICS cannot support the use of automated mechanisms, the
organization employs non-automated mechanisms or procedures as compensating controls in accordance
with the general tailoring guidance in Section 3.3 of NIST SP 800-53. Compensating controls are not
exceptions or waivers to the baseline controls; rather, they are alternative safeguards and countermeasures
employed within the ICS that accomplish the intent of the original security controls that could not be
effectively employed. Organizational decisions on the use of compensating controls are documented in the
security plan for the ICS.
6.1.3 Step 3: Implement Security Controls
This activity involves the implementation of security controls in new or legacy information systems. The
security control selection process described in this section can be applied to ICS from two different
perspectives: (i) new development; and (ii) legacy.
For new development systems, the security control selection process is applied from a requirements
definition perspective since the systems do not yet exist and organizations are conducting initial security
categorizations. The security controls included in the security plans for the information systems serve as a
security specification and are expected to be incorporated into the systems during the development and
implementation phases of the system development life cycle.
In contrast, for legacy information systems, the security control selection process is applied from a gap
analysis perspective when organizations are anticipating significant changes to the systems (e.g., during
major upgrades, modifications, or outsourcing). Since the information systems already exist, organizations
in all likelihood have completed the security categorization and security control selection processes
resulting in the establishment of previously agreed-upon security controls in the respective security plans
and the implementation of those controls within the information systems.
6.1.4 Step 4: Assess Security Controls
This activity determines the extent to which the security controls in the information system are effective in
their application. NIST SP 800-53A provides guidance for assessing security controls initially selected
from NIST SP 800-53 to ensure that they are implemented correctly, operating as intended, and producing
the desired outcome with respect to meeting the security requirements of the system. To accomplish this,
NIST SP 800-53A provides expectations based on assurance requirements defined in NIST SP 800-53 for
characterizing the expectations of security assessments by FIPS 199 impact level.
6.1.5 Step 5: Authorize Information System
This activity results in a management decision to authorize the operation of an information system and to
explicitly accept the risk to agency operations, agency assets, or individuals based on the implementation of
an agreed-upon set of security controls.
SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
138
ã¾ã ICS ææè
ã¯ããã¼ã¹ã©ã¤ã³ã«å«ã¾ããç¹å®ã®ã»ãã¥ãªãã£å¯¾çã®å®æ½ãä¸å¯è½ã®å ´åãä»
é²Gã®ãªã¼ãã¼ã¬ã¤ã«ç¤ºãããå½åãã¼ã¹ã©ã¤ã³ã®èª¿æ´æ©è½ãå©ç¨ãããã¨ãã§ããããã ãå
¨
ã¦ã®èª¿æ´æ´»åã¯ãã®ä¸»ããç®æ¨ã¨ãã¦ãå¯è½ãªå ´åã«ã¯å¿
ãå
ã
ã®ã»ãã¥ãªãã£å¯¾çã®æå³ã«å¾
ãããã«ãã¹ãã§ãããä¾ãã°ãICS ã対å¿ãã¦ããªãå ´åãåã¯ç¹å®ã®ã»ãã¥ãªãã£å¯¾çã管
çæ¡å¼µã ICS ã§å®æ½ããã®ãå¾çã§ãªãã¨å¤æããå ´åï¼ããã©ã¼ãã³ã¹ãå®å
¨æ§ãä¿¡é ¼æ§ãä½
ä¸ãããªã©ï¼ãçµç¹ã¯ã代ããã«é¸ãã 管ççãã©ã®ããã« ICS ã«åçã®ã»ãã¥ãªãã£è½åãä¿
è·ã¬ãã«ãçºæ®ãããããªããã¼ã¹ã©ã¤ã³ã»ãã¥ãªãã£å¯¾çãæ¡ç¨ã§ããªããã«ã¤ãã¦ãååç´
å¾ã®ããæ ¹æ ã示ããICS ãèªåã¡ã«ããºã ã®ä½¿ç¨ã«å¯¾å¿ãã¦ããªãå ´åãNIST SP 800-53 ã»ã¯
ã·ã§ã³ 3.3.ã®ä¸è¬ç調æ´ã¬ã¤ãã³ã¹ã«å¾ããçµç¹ã¯éèªåã¡ã«ããºã ãæé ã代æ¿ç®¡çã¨ãã¦æ¡
ç¨ããã
代æ¿ç®¡çã¯ãã¼ã¹ã©ã¤ã³ç®¡çã®ä¾å¤ãæ¾æ£ã§ã¯ãªãã代æ¿ã®å®å
¨çåã³å¯¾çã¨ã㦠ICS å
ã§æ¡
ç¨ãããæå¹å©ç¨ã§ããªãå
ã
ã®ã»ãã¥ãªãã£å¯¾çã®ç®çãæããã代æ¿ç®¡çãå©ç¨ããçµç¹
ã®æ±ºå®ã¯ãICS ã®ã»ãã¥ãªãã£è¨ç»æ¸ã«è¨é²ããã
6.1.3 æé 3ï¼ã»ãã¥ãªãã£å¯¾çã®å®è£
ãã®æ´»åã¯ãã»ãã¥ãªãã£å¯¾çãæ°è¦åã¯ã¬ã¬ã·ã¼æ
å ±ã·ã¹ãã ã«å®è£
ãããã¨ãé¢ä¿ããã
ãã®ã»ã¯ã·ã§ã³ã§èª¬æããã»ãã¥ãªãã£å¯¾çé¸å®ããã»ã¹ã¯ãï¼1ï¼æ°è¦éçºãï¼2ï¼ã¬ã¬ã·ã¼
ã¨ãã 2ã¤ã®è¦³ç¹ãã ICS ã«é©ç¨ãããã¨ãã§ããã
æ°è¦éçºã·ã¹ãã ã§ã¯ãã»ãã¥ãªãã£å¯¾çé¸å®ããã»ã¹ã¯ãã·ã¹ãã ã¯ã¾ã åå¨ãã¦ãããã
çµç¹ã¯æåã®ã»ãã¥ãªãã£åé¡ãå®æ½ãã¤ã¤ãããããè¦ä»¶å®ç¾©ã®è¦³ç¹ããé©ç¨ããããæ
å ±
ã·ã¹ãã ã®ã»ãã¥ãªãã£è¨ç»æ¸ã«å«ã¾ããã»ãã¥ãªãã£å¯¾çã¯ãã»ãã¥ãªãã£ä»æ§æ¸ã¨ãªãã
ã®ã§ãã·ã¹ãã éçºã©ã¤ããµã¤ã¯ã«æ®µéã§ãã·ã¹ãã ã«çµã¿è¾¼ã¾ãããã¨ãæå¾
ãããã
対ç
§çã«ã¬ã¬ã·ã¼æ
å ±ã·ã¹ãã ã§ã¯ãã»ãã¥ãªãã£å¯¾çã®é¸å®ããã»ã¹ã¯ãçµç¹ãããªãã®
ã·ã¹ãã å¤æ´ãäºæããå ´åï¼å¤§ããããªæ´æ°ãå¤æ´ãå¤æ³¨çï¼ãæ ¼å·®åæã®è¦³ç¹ããé©ç¨
ããããæ
å ±ã·ã¹ãã ã¯æ¢ã«åå¨ãã¦ããããçµç¹ã¯ããããèç¶æ§ã«ããã¦ã»ãã¥ãªãã£
ã®åé¡ã¨ã»ãã¥ãªãã£å¯¾çé¸å®ããã»ã¹ãå®æ½æ¸ã¿ã§ãããåã»ãã¥ãªãã£è¨ç»æ¸ã®ä¸ã§å
ææ¸ã¿ã®ã»ãã¥ãªãã£å¯¾çãçå®ãããããããæ
å ±ã·ã¹ãã ã§å®è£
ããã¦ããã
6.1.4 æé 4ï¼ã»ãã¥ãªãã£å¯¾çã®è©ä¾¡
ãã®æ´»åã¯ãæ
å ±ã·ã¹ãã ä¸ã®ã»ãã¥ãªãã£å¯¾çããããããã®ç¨éã«ããã¦ã©ãã»ã©æå¹ã§
ããããå¤å®ãããNIST SP 800-53A ã§ã¯ãã»ãã¥ãªãã£å¯¾çãé©æ£ã«å®è£
ããäºå®ã©ããã«
åä½ãããã·ã¹ãã ã®ã»ãã¥ãªãã£è¦ä»¶ã«ããªã£ãææã®çµæãå¾ããããNIST SP 800-53 ã
ãé¸ãã ã»ãã¥ãªãã£å¯¾çãè©ä¾¡ããããã®ã¬ã¤ãã³ã¹ã示ããã¦ããããããå®ç¾ããããã
NIST SP 800-53A ã«ã¯ãFIPS199 ã®å½±é¿ã¬ãã«ã«å¾ã£ãã»ãã¥ãªãã£è©ä¾¡äºæ³ãç¹å¾´ä»ããã
NIST SP 800-53 ã§å®ç¾©ãããä¿è¨¼è¦ä»¶ã«åºã¥ããæå¾
ã«ã¤ãã¦è¨è¿°ããã¦ããã
6.1.5 æé 5ï¼æ
å ±ã·ã¹ãã ã®è¨±å¯
ãã®æ´»åã®çµæãçµå¶é£ã®æ±ºå®ã¨ãªããæ
å ±ã·ã¹ãã ã®ç¨¼åã許å¯ããåæãããã»ãã¥ãªã
ã£å¯¾çã®å®è£
ãåºèª¿ã¨ãã¦ãçµç¹æ¥åã»è³ç£ã»äººå¡ã¸ã®ãªã¹ã¯ãæ示çã«åãå
¥ãããã¨ã«ãª
ãã
SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
139
6.1.6 Step 6: Monitor Security Controls
This activity continuously tracks changes to the information system that may affect security controls and
assesses control effectiveness. NIST SP 800-137 provides guidance on information security continuous
monitoring [21].
6.2 Guidance on the Application of Security Controls to ICS
Because todayâs ICS are often a combination of legacy systems, often with a planned life span of twenty to
thirty years, or a hybrid of legacy systems augmented with newer hardware and software that are
interconnected to other systems, it is often difficult or infeasible to apply some of the security controls
contained in NIST SP 800-53. While many controls in Appendix F of NIST SP 800-53 are applicable to
ICS as written, several controls did require ICS-specific interpretation and/or augmentation. Appendix I of
NIST SP 800-53 provides an example overlay template and additional information on each section of the
overlay.
The NIST SP 800-53 controls are organized into 18 families; each family contains security controls related
to the general security topic of the family. Security controls may involve aspects of policy, oversight,
supervision, manual processes, actions by individuals, or automated mechanisms implemented by
information systems/devices. The 18 security-related areas discussed in the following sections are:
ï¼ Access Control (AC): the process of granting or denying specific requests for obtaining and using
information and related information processing services for physical access to areas within the
information system environment.
ï¼ Awareness and Training (AT): policies and procedures to ensure that all information system users
are given appropriate security training relative to their usage of the system and that accurate training
records are maintained.
ï¼ Audit and Accountability (AU): independent review and examination of records and activities to
assess the adequacy of system controls, to ensure compliance with established policies and operational
procedures, and to recommend necessary changes in controls, policies, or procedures.
ï¼ Security Assessment and Authorization (CA): assurance that the specified controls are implemented
correctly, operating as intended, and producing the desired outcome.
ï¼ Contingency Planning (CP): policies and procedures designed to maintain or restore business
operations, including computer operations, possibly at an alternate location, in the event of
emergencies, system failures, or disaster.
ï¼ Configuration Management (CM): policies and procedures for controlling modifications to
hardware, firmware, software, and documentation to ensure the information system is protected
against improper modifications prior to, during, and after system implementation.
ï¼ Identification and Authentication (IA): the process of verifying the identity of a user, process, or
device, through the use of specific credentials (e.g., passwords, tokens, biometrics), as a prerequisite
for granting access to resources in an IT system.
ï¼ Incident Response (IR): policies and procedures pertaining to incident response training, testing,
handling, monitoring, reporting, and support services.
ï¼ Maintenance (MA): policies and procedures to manage all maintenance aspects of an information
system.
SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
140
6.1.6 æé 6ï¼ã»ãã¥ãªãã£å¯¾çã®ç£è¦
ãã®æ´»åã¯ãã»ãã¥ãªãã£å¯¾çã«å½±é¿ããæ
å ±ã·ã¹ãã ã®å¤æ´ã追跡ãã管çã®å¹ææ§ãè©
価ãããNIST SP 800-137 ã«ãæ
å ±ã»ãã¥ãªãã£ã®å¸¸ç¶ç£è¦ã«ä¿ãã¬ã¤ãã³ã¹ããã[21]ã
6.2 ICS ã¸ã®ã»ãã¥ãªãã£å¯¾çã®é©ç¨ã«ä¿ãã¬ã¤ãã³ã¹
ä»æ¥ã® ICS ã¯ãäºæ³å¯¿å½ã 20ï½30 å¹´ã®ã¬ã¬ã·ã¼ã·ã¹ãã ãä»ã®ã·ã¹ãã ã¸é£æ¥ãããæ¯è¼ç
æ°ãããã¼ãã¦ã¨ã¢/ã½ããã¦ã¨ã¢ã§å¼·åãããã¬ã¬ã·ã¼ã·ã¹ãã ãä½µç¨ãã¦ãããããNIST
SP 800-53 ã®ã»ãã¥ãªãã£å¯¾çãé©ç¨ããã®ã¯å°é£åã¯ä¸å¯è½ãªå ´åãå¤ããNIST SP 800-53
ã®ä»é² Fã«è¨è¼ããã管ççã®å¤ãã¯ãè¨è¿°ã©ãã ICS ã«é©ç¨å¯è½ã§ã¯ããããICS ç¹æã®è§£
éãè£å¼·ãå¿
è¦ãªãã®ãå°ãªããªããNIST SP 800-53 ã®ä»é² Iã«ã¯ããªã¼ãã¼ã¬ã¤ãã³ãã¬
ã¼ãã®ä¾ãããªã¼ãã¼ã¬ã¤ã®åã»ã¯ã·ã§ã³ã«é¢ããè£è¶³æ
å ±ãããã
NIST SP 800-53 ã®ç®¡çç㯠18 ã®åéã«ã¾ã¨ããããååéã¯ããããã®å
¨è¬çã»ãã¥ãªãã£
ãã¼ãã«é¢ä¿ããã»ãã¥ãªãã£å¯¾çã«ã¤ãã¦åãä¸ãã¦ãããã»ãã¥ãªãã£å¯¾çã«ã¯ããªã·ã¼ã
æå°ãç£ç£ãæåããã»ã¹ãå人ã®è¡åãæ
å ±ã·ã¹ãã /ããã¤ã¹ãå®è£
ããèªåã¡ã«ããºã
ã®æ§ç¸ãå«ã¾ããããç¶ãã»ã¯ã·ã§ã³ã§èª¬æãã 18 ã®ã»ãã¥ãªãã£é¢é£åéã¯ä»¥ä¸ã®ã¨ããã
ï¼ ã¢ã¯ã»ã¹å¶å¾¡ï¼ACï¼ï¼æ
å ±ã·ã¹ãã ç°å¢ä¸ã®ã¨ãªã¢ã«ç©ççã«ã¢ã¯ã»ã¹ãã¦ãæ
å ±åã³é¢
é£æ
å ±å¦çãµã¼ãã¹ãåå¾ã»å©ç¨ããããã®æ示çè¦æ±ã許å¯ãããæ絶ãããã¨ãããã
ã»ã¹ã
ï¼ æèåã³è¨ç·´ï¼ATï¼ï¼å
¨ã¦ã®æ
å ±ã·ã¹ãã ã¦ã¼ã¶ãã·ã¹ãã å©ç¨ã«é¢ããé©æ£ãªã»ãã¥ãª
ãã£è¨ç·´ãåããæ£ç¢ºãªè¨ç·´è¨é²ãä¿æããããã®ããªã·ã¼åã³æé ã
ï¼ ç£æ»åã³èª¬æ責任ï¼AUï¼ï¼ã·ã¹ãã å¶å¾¡ã®å¦¥å½æ§ãè©ä¾¡ããè¦å®ã®ããªã·ã¼åã³æ¥åæé
ãéµå®ãããå¶å¾¡ã»ããªã·ã¼ã»æé ã«å¿
è¦ãªå¤æ´ãæ¨å¥¨ããããã®è¨é²åã³æ´»åã«å¯¾ããç¬
ç«ã®å¯©æ»ã»æ¤è¨¼ã
ï¼ ã»ãã¥ãªãã£è©ä¾¡åã³æ¨©éä»ä¸ï¼CAï¼ï¼æå®ã®å¶å¾¡ãäºå®ã©ããæ£ããå®è¡ããææã®çµ
æãå¾ãããã®ä¿è¨¼ã
ï¼ ä¸æ¸¬äºæ
è¨ç»ï¼CPï¼ï¼ç·æ¥æã»ã·ã¹ãã é害æã»ç½å®³æã«ä»£æ¿å°ãªã©ã§ã³ã³ãã¥ã¼ã¿ãæ
ä½ãããªã©ãæ¥åãç¶æã»å¾©æ§ããããã®ããªã·ã¼åã³æé ã
ï¼ æ§æ管çï¼CMï¼ï¼ãã¼ãã¦ã¨ã¢ã»ãã¡ã¼ã ã¦ã¨ã¢ã»ã½ããã¦ã¨ã¢ã»ææ¸ã¸ã®å¤æ´ã管çãã
ã·ã¹ãã å®è£
åã»ä¸ã»å¾ã®ä¸é©åãªæ¹å¤ããæ
å ±ã·ã¹ãã ãä¿è·ããããã®ããªã·ã¼åã³æ
é ã
ï¼ èå¥åã³èªè¨¼ï¼IAï¼ï¼IT ã·ã¹ãã ä¸ã®ãªã½ã¼ã¹ã¸ã®ã¢ã¯ã»ã¹è¨±å¯ã®åæã¨ãã¦ãç¹å®ã®èª
証æ
å ±ï¼ãã¹ã¯ã¼ãããã¼ã¯ã³ããã¤ãªã¡ããªã¯ã¹çï¼ã«ããã¦ã¼ã¶ã»ããã»ã¹ã»ããã¤ã¹
ã®ID ãæ¤è¨¼ããããã»ã¹ã
ï¼ ã¤ã³ã·ãã³ã対å¿ï¼IRï¼ï¼ã¤ã³ã·ãã³ã対å¿è¨ç·´ã»è©¦é¨ã»å¦çã»ç£è¦ã»å ±åã»æ¯æ´ãµã¼ãã¹
ã«ä¿ãããªã·ã¼åã³æé ã
ï¼ ä¿å®ï¼MAï¼ï¼æ
å ±ã·ã¹ãã ã®ããããä¿å®é¢ã管çããããã®ããªã·ã¼åã³æé ã

SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
141
ï¼ Media Protection (MP): policies and procedures to ensure secure handling of media. Controls cover
access, labeling, storage, transport, sanitization, destruction, and disposal.
ï¼ Physical and Environmental Protection (PE): policies and procedures addressing physical,
transmission, and display access control as well as environmental controls for conditioning (e.g.,
temperature, humidity) and emergency provisions (e.g., shutdown, power, lighting, fire protection).
ï¼ Planning (PL): development and maintenance of a plan to address information system security by
performing assessments, specifying and implementing security controls, assigning security levels, and
responding to incidents.
ï¼ Personnel Security (PS): policies and procedures for personnel position categorization, screening,
transfer, penalty, and termination; also addresses third-party personnel security.
ï¼ Risk Assessment (RA): the process of identifying risks to operations, assets, or individuals by
determining the probability of occurrence, the resulting impact, and additional security controls that
would mitigate this impact.
ï¼ System and Services Acquisition (SA): allocation of resources for information system security to be
maintained throughout the systems life cycle and the development of acquisition policies based on risk
assessment results including requirements, design criteria, test procedures, and associated
documentation.
ï¼ System and Communications Protection (SC): mechanisms for protecting both system and data
transmission components.
ï¼ System and Information Integrity (SI): policies and procedures to protect information systems and
their data from design flaws and data modification using functionality verification, data integrity
checking, intrusion detection, malicious code detection, and security alert and advisory controls.
ï¼ Program Management (PM): provides security controls at the organizational rather than the
information-system level.
Additionally, Appendix J of NIST SP 800-53 Rev. 4 includes a catalog of Privacy Controls. Privacy
controls are the administrative, technical, and physical safeguards employed within organizations to protect
and ensure the proper handling of personally identifiable information (PII).35 The 8 privacy control families
are each aligned with the Fair Information Practice Principles (FIPPS),36 which are designed to build public
trust in an organizationâs privacy practices and to help organizations avoid tangible costs and intangible
damages stemming from privacy incidents.
35 OMB Memorandum 07-16 defines PII as âinformation which can be used to distinguish or trace an individualâs
identity such as their name, social security number, biometric records, etc., alone, or when combined with
other personal or identifying information which is linked or linkable to a specific individual, such as date
and place of birth, motherâs maiden name, etc.â [86]. OMB Memorandum 10-22 reaffirmed this definition [87].
NIST Special Publication 800-122 defines PII as âany information about an individual [that is] maintained
by an agency, including: (i) any information that can be used to distinguish or trace an individualâs
identity, such as name, social security number, date and place of birth, motherâs maiden name, or biometric
records; and (ii) any other information that is linked or linkable to an individual, such as medical,
educational, financial, and employment informationâ [88].
36 The FIPPs are widely accepted in the United States and internationally as a general framework for privacy
and are reflected in other federal and international laws and policies. In a number of organizations, FIPPs
serve as the basis for analyzing privacy risks and determining appropriate mitigation strategies. The
Federal Enterprise Architecture Security and Privacy Profile (FEA-SPP) also provided information and
materials in development of the privacy controls [89].

SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
142
ï¼ ã¡ãã¤ã¢ä¿è·ï¼MPï¼ï¼ã¡ãã¤ã¢ã®ã»ãã¥ã¢ãªåæ±ããè¡ãããã®ããªã·ã¼åã³æé ã管ç
çã¯ãã¢ã¯ã»ã¹ã»ã©ãã«ã»ã¹ãã¬ã¼ã¸ã»è¼¸éã»ãµãã¿ã¤ãºã»ç ´æ£ã»å»æ£ã対象ã¨ããã
ï¼ ç©çç°å¢ä¸ã®ä¿è·ï¼PEï¼ï¼èª¿ç¯ï¼æ¸©åº¦ã湿度çï¼åã³ç·æ¥è£
ç½®ï¼åæãé»åãç
§æãé²ç«
çï¼ã®ç©ççãéä¿¡ã表示ã¢ã¯ã»ã¹å¶å¾¡åã³ç°å¢å¶å¾¡ã«é¢ããããªã·ã¼åã³æé ã
ï¼ ãã©ã³ãã³ã°ï¼PLï¼ãè©ä¾¡ã®å®æ½ãã»ãã¥ãªãã£ç®¡çã®æå®ã»å®æ½ãã»ãã¥ãªãã£ã¬ãã«
ã®å²å½åã³ã¤ã³ã·ãã³ã対å¿ã«ãããæ
å ±ã·ã¹ãã ã»ãã¥ãªãã£ã«é¢ããè¨ç»æ¸ã®ä½æã»ç¶
æã
ï¼ äººå¡ã®ã»ãã¥ãªãã£ï¼PSï¼ï¼äººå¡ã®é
ç½®åé¡ãé¸æã転å±ãç½°ååã³çµäºã«é¢ããããªã·ã¼
åã³æé ã§ããµã¼ããã¼ãã£è·å¡ã®ã»ãã¥ãªãã£ãå«ããã
ï¼ ãªã¹ã¯è©ä¾¡ï¼RAï¼ï¼çºç確çããã®å½±é¿ãå½±é¿ãç·©åããããã®ä»å çã»ãã¥ãªãã£å¯¾ç
ã®å¤å®ãéããæ¥åã»è³ç£ã»äººå¡ã«å¯¾ãããªã¹ã¯èå¥ããã»ã¹ã
ï¼ ã·ã¹ãã åã³ãµã¼ãã¹ã®åå¾ï¼SAï¼ï¼ã·ã¹ãã ã®ã©ã¤ããµã¤ã¯ã«æéãéãã¦ç¶æãã¹ã
æ
å ±ã·ã¹ãã ã»ãã¥ãªãã£ã«å¯¾ãããªã½ã¼ã¹å²å½ã¨ãè¦ä»¶ã»è¨è¨åºæºã»è©¦é¨æé ã»é¢é£ææ¸
ãå«ãããªã¹ã¯è©ä¾¡çµæã«åºã¥ãåå¾ããªã·ã¼çå®ã
ï¼ ã·ã¹ãã åã³éä¿¡ä¿è·ï¼SCï¼ï¼ã·ã¹ãã ã¨ãã¼ã¿éä¿¡ã³ã³ãã¼ãã³ãã¨ãä¿è·ããããã®
ã¡ã«ããºã ã
ï¼ ã·ã¹ãã åã³æ
å ±ã®ä¿å
¨ï¼SIï¼ï¼æ©è½æ¤è¨¼ã»ãã¼ã¿ä¿å
¨ãã§ãã¯ã»ä¾µå
¥æ¤ç¥ã»æªè³ªã³ã¼ãæ¤
ç¥ã»ã»ãã¥ãªãã£ã¢ã©ã¼ãå§å管çã使ç¨ããè¨è¨ã®æ¬ é¥ããã¼ã¿æ¹å¤ããæ
å ±ã·ã¹ãã ã
ãã¼ã¿ãä¿è·ããããã®ããªã·ã¼åã³æé ã
ï¼ ããã°ã©ã 管çï¼PMï¼ï¼æ
å ±ã·ã¹ãã ã¬ãã«ã§ã¯ãªãçµç¹ã¬ãã«ã§ã®ã»ãã¥ãªãã£å¯¾çã
è¡ãã
以ä¸ã«å ãã¦ãNIST SP 800-53 æ¹è¨ç¬¬ 4çã®ä»é² Jã«ã¯ãã©ã¤ãã·ã¼ç®¡ççã®ã«ã¿ãã°ãæ²è¼ã
ãã¦ããããã©ã¤ãã·ã¼ç®¡ççã¯ãå人ãç¹å®å¯è½ãªæ
å ±ï¼PIIï¼ã«å¯¾ããä¿è·ã¨é©æ£ãªåæ±ã
確ä¿ããããã«çµç¹å
ã§æ¡ç¨ããã管çä¸ã®æè¡çã»ç©ççå®å
¨å¯¾çã§ããã37ãã©ã¤ãã·ã¼ç®¡
çã® 8åéãããããå
¬æ£æ
å ±è¦ç¯ååï¼FIPPSï¼ã«æ´åãã¦ããã38çµç¹ã®ãã©ã¤ãã·ã¼è¦ç¯
ã«å¯¾ããå½æ°ã®ä¿¡é ¼ãé¸æãããã©ã¤ãã·ã¼ã¤ã³ã·ãã³ãããçããæå½¢ã®çµè²»ãç¡å½¢ã®æ害ã®
åé¿ãç®æãã¦ããã
37 OMB è¦æ¸ 07-16 ã¯PII ããæ°åã社ä¼ä¿éçªå·ããã¤ãªã¡ããªãã¯è¨é²çãåç¬ã§ãåã¯èªçæ¥ãåºçå°ã
æ¯è¦ªã®æ§å§çç¹å®ã®å人ã«çµã³ã¤ããçµã³ã¤ãããããã®ä»ã®å人è¥ããã¯ã¯èº«åæ
å ±ã¨çµã¿åããã¦ãå
人ã®èº«åãå¤å¥åã¯è¿½è·¡ã§ããæ
å ±ãã¨å®ç¾©ãã¦ãã[86]ãOMB è¦æ¸ 10-22 ã¯ãã®å®ç¾©ã追èªãã¦ãã[87]ã
NIST SP800-122 ã¯PII ããããæ©é¢ãä¿æãã¦ããå人ã«é¢ããæ
å ±ã§ãï¼1ï¼æ°åã社ä¼ä¿éçªå·ãèª
çæ¥ãåºçå°ãæ¯è¦ªã®æ§å§ããã¤ãªã¡ããªãã¯è¨é²çãå人ã®èº«åãå¤å¥åã¯è¿½è·¡ã§ããæ
å ±åã³ï¼2ï¼å»
çãæè²ã財æ¿ãå°±æ¥æ
å ±çãå人ã«çµã³ã¤ããçµã³ã¤ãããããã®ä»ã®æ
å ±ãã¨å®ç¾©ãã¦ãã[88]ã
38 FIPPs ã¯ãä¸è¬çãªãã©ã¤ãã·ã¼åºç¤ã¨ãã¦ãç±³å½ã§ãä¸ççã«ãåºãåãå
¥ãããã¦ãããä»ã®é£é¦åã³
ä¸ççæ³å¾ãããªã·ã¼ã«åæ ããã¦ãããFIPPs ã¯ãå¤ãã®çµç¹ã§ãã©ã¤ãã·ã¼ãªã¹ã¯ã®åæãé©åãªç·©å
çå¤å®æã®æ ¹æ ã¨ãªã£ã¦ãããé£é¦ä¼æ¥ã¢ã¼ããã¯ãã£ã»ãã¥ãªãã£ãã©ã¤ãã·ã¼ãããã¡ã¤ã«ï¼FEA-
SPPï¼ã«ããã©ã¤ãã·ã¼ç®¡çãçå®ããããã®æ
å ±ãè³æã示ããã¦ãã[89]ã
SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
143
Sections 6.2.1 through 6.2.19 introduce each of the SP 800-53 control families and privacy controls,
provide background information on the control family, as well as any ICS guidance and implementation
considerations for ICS owners. ICS-specific recommendations and guidance, if available, is provided in an
outlined box for each section. Much of the ICS-specific guidance was derived from ISA-62443 [34] and the
EPRI report: Supervisory Control and Data Acquisition (SCADA) Systems Security Guide [62].
6.2.1 Access Control
The security controls that fall within the NIST SP 800-53 Access Control (AC) family provide policies and
procedures for specifying the use of system resources by only authorized users, programs, processes, or
other systems. This family specifies controls for managing information system accounts, including
establishing, activating, modifying, reviewing, disabling, and removing accounts. Controls cover access
and flow enforcement issues such as separation of duties, least privilege, unsuccessful login attempts,
system use notification, previous logon notification, concurrent session control, session lock, and session
termination. There are also controls to address the use of portable and remote devices and personally owned
information systems to access the information system as well as the use of remote access capabilities and
the implementation of wireless technologies. Access can take several forms, including viewing, using, and
altering specific data or device functions.
Supplemental guidance for the AC controls can be found in the following documents:
ï¼ NIST SP 800-63 provides guidance on remote electronic authentication [53].
ï¼ NIST SP 800-48 provides guidance on wireless network security with particular emphasis on the IEEE
802.11b and Bluetooth standards 0.
ï¼ NIST SP 800-97 provides guidance on IEEE 802.11i wireless network security [64].
ï¼ FIPS 201 provides requirements for the personal identity verification of federal employees and
contractors [65].
ï¼ NIST SP 800-96 provides guidance on PIV card to reader interoperability [66].
ï¼ NIST SP 800-73 provides guidance on interfaces for personal identity verification [49].
ï¼ NIST SP 800-76 provides guidance on biometrics for personal identity verification [50].
ï¼ NIST SP 800-78 provides guidance on cryptographic algorithms and key sizes for personal identity
verification [67].
If the new federal Personal Identity Verification (PIV) is used as an identification token, the access control
system should conform to the requirements of FIPS 201 and NIST SP 800-73 and employ either
cryptographic verification or biometric verification. When token-based access control employs
cryptographic verification, the access control system should conform to the requirements of NIST SP 800-
78. When token-based access control employs biometric verification, the access control system should
conform to the requirements of NIST SP 800-76.
Access control technologies are filter and blocking technologies designed to direct and regulate the flow of
information between devices or systems once authorization has been determined. The following sections
present several access control technologies and their use with ICS.
SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
144
ã»ã¯ã·ã§ã³ 6.2.1ï½6.2.19 ã§ã¯ãSP 800-53 ã®ããããã®ç®¡çåéã¨ãã©ã¤ãã·ã¼ç®¡çã示ããã
å¶å¾¡åéã®èæ¯æ
å ±ã®ã»ããICS ææè
åãã® ICS ã¬ã¤ãã³ã¹ã¨å®è£
ä¸ã®èæ
®äºé
ã説æããã¦
ãããICS åºæã®æ¨å¥¨äºé
ã¨ã¬ã¤ãã³ã¹ãå©ç¨å¯è½ãªå ´åã¯ãåã»ã¯ã·ã§ã³ã®å²ã¿ã«ç¤ºãããã
ICS åºæã®ã¬ã¤ãã³ã¹ã¯å¤§åã ISA-62443 [34]ã¨EPRI å ±åæ¸ãSCADA ã·ã¹ãã ã»ãã¥ãªãã£ã¬
ã¤ãã[62]ãåºã«ãã¦ããã
6.2.1 ã¢ã¯ã»ã¹å¶å¾¡
NIST SP 800-53 ã®ã¢ã¯ã»ã¹å¶å¾¡ï¼ACï¼ãã¡ããªã«é¢ããã»ãã¥ãªãã£å¯¾çã«ã¯ã許å¯ãããã¦
ã¼ã¶ãããã°ã©ã ãããã»ã¹ãã®ä»ã·ã¹ãã ã®ã¿ã«ããã·ã¹ãã ãªã½ã¼ã¹ã®å©ç¨ã«ã¤ãã¦è¦å®
ããããã®ããªã·ã¼åã³æé ã示ããã¦ããããã®ãã¡ããªã¯ãã¢ã«ã¦ã³ãã®è¨å®ã»ä½¿ç¨é
å§ã»å¤æ´ã»è¦ç´ãã»ä½¿ç¨ç¦æ¢ã»åé¤çãæ
å ±ã·ã¹ãã ã®ã¢ã«ã¦ã³ãã管çããããã®æ¹æ³ãè¦
å®ããã管ççã¯ãä»»åã®åãåããæä½ç¹æ¨©ããã°ã¤ã³ã®å¤±æãã·ã¹ãã å©ç¨éç¥ã以åã®
ãã°ãªã³éç¥ã並è¡ã»ãã·ã§ã³ç®¡çãã»ãã·ã§ã³ããã¯ãã»ãã·ã§ã³çµäºçãã¢ã¯ã»ã¹ã¨ãã
ã¼ã®å®è¡åé¡ã網ç¾
ãã¦ãããã¾ããã¼ã¿ãã«ããã¤ã¹ãé éããã¤ã¹åã³å人ä¿æã®æ
å ±ã·
ã¹ãã ã«ããæ
å ±ã·ã¹ãã ã¸ã®ã¢ã¯ã»ã¹ã®ã»ãããªã¢ã¼ãã¢ã¯ã»ã¹æ©è½ãã¯ã¤ã¤ã¬ã¹æè¡ã®å®
è£
ã«é¢ãã管ççãåãä¸ãã¦ãããã¢ã¯ã»ã¹ã«ã¯é²è¦§ã使ç¨ãç¹å®ãã¼ã¿ãããã¤ã¹æ©è½ã®
å¤æ´ã¨ãã£ãããã¤ãã®å½¢æ
ãããã
AC 管çã®è£è¶³çã¬ã¤ãã³ã¹ã以ä¸ã®ææ¸ã«æ²è¼ããã¦ããã
ï¼ NIST SP 800-63ï¼é éé»åèªè¨¼ã«ä¿ãã¬ã¤ãã³ã¹[53]
ï¼ NIST SP 800-48ï¼IEEE 802.11b åã³ Bluetooth è¦æ ¼ 0ãéç¹ã¨ããã¯ã¤ã¤ã¬ã¹ãããã¯ã¼ã¯ã»
ãã¥ãªãã£ã«ä¿ãã¬ã¤ãã³ã¹
ï¼ NIST SP 800-97ï¼IEEE 802.11i ã¯ã¤ã¤ã¬ã¹ãããã¯ã¼ã¯ã»ãã¥ãªãã£ã«ä¿ãã¬ã¤ãã³ã¹[64]
ï¼ FIPS 201ï¼é£é¦è·å¡åã³å¥ç´å¾æ¥å¡ã®å人身å
確èªã«ä¿ãè¦ä»¶[65]
ï¼ NIST SP 800-96ï¼PIV ã«ã¼ãã¨ãªã¼ãã¼ã®ç¸äºéç¨ã«ä¿ãã¬ã¤ãã³ã¹[66]
ï¼ NIST SP 800-73ï¼å人身å
確èªã¤ã³ã¿ãã§ã¼ã¹ã«ä¿ãã¬ã¤ãã³ã¹[49]
ï¼ NIST SP 800-76ï¼å人身å
確èªãã¤ãªã¡ããªã¯ã¹ã«ä¿ãã¬ã¤ãã³ã¹[50]
ï¼ NIST SP 800-78ï¼å人身å
確èªã®æå·ã¢ã«ã´ãªãºã åã³ãã¼ãµã¤ãºã«ä¿ãã¬ã¤ãã³ã¹[67]
æ°ããé£é¦å人身å
確èªï¼PIVï¼ãèå¥ãã¼ã¯ã³ã¨ãã¦ä½¿ç¨ãã¦ããå ´åãã¢ã¯ã»ã¹å¶å¾¡ã·ã¹
ãã 㯠FIPS 201 åã³ NIST SP 800-73 ã®è¦ä»¶ã«å¾ããæå·ç¢ºèªåã¯ãã¤ãªã¡ããªãã¯ç¢ºèªã
æ¡ç¨ãã¹ãã§ããããã¼ã¯ã³ãã¼ã¹ã®ã¢ã¯ã»ã¹å¶å¾¡ãæå·ç¢ºèªãæ¡ç¨ãã¦ããå ´åãã¢ã¯ã»
ã¹å¶å¾¡ã·ã¹ãã 㯠NIST SP 800-78 ã®è¦ä»¶ã«å¾ãã¹ãã§ããããã¼ã¯ã³ãã¼ã¹ã®ã¢ã¯ã»ã¹å¶å¾¡
ããã¤ãªã¡ããªãã¯ç¢ºèªãæ¡ç¨ãã¦ããå ´åãã¢ã¯ã»ã¹å¶å¾¡ã·ã¹ãã 㯠NIST SP 800-76 ã®è¦
件ã«å¾ãã¹ãã§ããã
ã¢ã¯ã»ã¹å¶å¾¡æè¡ã¯ã権éä»ä¸ã®ç¢ºå®å¾ã«ãããã¤ã¹éåã¯ã·ã¹ãã éã§ã®æ
å ±ã®æµããè¦
å¶ããããã®ãã£ã«ã¿ã¨ãããã¯æè¡ã§ãããç¶ãã»ã¯ã·ã§ã³ã§ã¯ãããã¤ãã®ã¢ã¯ã»ã¹å¶
御æè¡ã¨ ICS ã§ã®ä½¿ç¨ã«ã¤ãã¦ç¤ºãã
SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
145
6.2.1.1 Role-based Access Control (RBAC)
RBAC is a technology that has the potential to reduce the complexity and cost of security administration in
networks with large numbers of intelligent devices. Under RBAC, security administration is simplified
through the use of roles, hierarchies, and constraints to organize user access levels. RBAC reduces costs
within an organization because it accepts that employees change roles and responsibilities more frequently
than the duties within roles and responsibilities.
ICS-specific Recommendations and Guidance
RBAC can be used to provide a uniform means to manage access to ICS devices while reducing the cost of
maintaining individual device access levels and minimizing errors. RBAC should be used to restrict ICS
user privileges to only those that are required to perform each personâs job (i.e., configuring each role
based on the principle of least privilege). The level of access can take several forms, including viewing,
using, and altering specific ICS data or device functions.
RBAC tools can set, modify, or remove authorizations in applications, but they do not replace the
authorization mechanism; they do not check and authenticate users every time a user wants to access an
application. RBAC tools offer interfaces to authorization mechanisms for most current platforms in the IT
arena. However, legacy ICS systems or specialized ICS equipment may require development of specialized
interface software. This issue is a large problem for ICS that use a number of proprietary operating systems
or customized operating system implementations and interfaces.
SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
146
6.2.1.1 å½¹å²ã«åºã¥ãã¢ã¯ã»ã¹å¶å¾¡ï¼RBACï¼
RBAC ã¯ãå¤æ°ã®ã¤ã³ããªã¸ã§ã³ã¹ããã¤ã¹ã使ç¨ãããããã¯ã¼ã¯ã®è¤éãã¨ã»ãã¥ãªãã£
対çã³ã¹ããæ¸ãããæè¡ã§ãããRBAC ã®ä¸ã§ã¯ãå½¹å²ãé層åã³ã¦ã¼ã¶ã¢ã¯ã»ã¹ã¬ãã«ç®¡
çã®å¶ç´ãå©ç¨ãã¦ãã»ãã¥ãªãã£å¯¾çãç°¡ç´ åããããRBAC ã§ã¯ãå¾æ¥å¡ã®å½¹å²ã»è²¬ä»»å
ã§ã®ä»»åå¤æ´ããããå½¹å²ã»è²¬ä»»ã®å¤æ´ãããé »ç¹ã«åãå
¥ããã®ã§ãçµç¹å
ã®ã³ã¹ããæ¸
ãã
ICS åºæã®æ¨å¥¨äºé
åã³ã¬ã¤ãã³ã¹
RBAC ãå©ç¨ããã°ãåã
ã®ããã¤ã¹ã¢ã¯ã»ã¹ã¬ãã«ã®ç¶æã«è¦ããã³ã¹ããæ¸ãããã¨ã©ã¼ã
æå°éã«æãã¤ã¤ãICS ããã¤ã¹ã¸ã®ä¸æ§ã®ã¢ã¯ã»ã¹ç®¡çæ段ãæä¾ã§ãããICS ã¦ã¼ã¶æ¨©éã®
ä»ä¸ãæ¥åä¸å¿
è¦ã¨ãã人å¡ã«éå®ããããã« RBAC ãå©ç¨ãã¹ãã§ããï¼æå°æ¨©éååã«åºã¥
ãå½¹å²æ§æï¼ãã¢ã¯ã»ã¹ã¬ãã«ã«ã¯é²è¦§ã使ç¨ãç¹å® ICS ãã¼ã¿ãããã¤ã¹æ©è½ã®å¤æ´ã¨ãã£ã
ããã¤ãã®å½¢æ
ãããã
RBAC ãã¼ã«ã¯ãã¢ããªã±ã¼ã·ã§ã³ã«ããã権éä»ä¸ãè¨å®ã»å¤æ´ã»åé¤ã§ãããã権éä»ä¸ã¡
ã«ããºã ã®ä»£è¡ã¯ããªããã¤ã¾ããã¦ã¼ã¶ãã¢ããªã±ã¼ã·ã§ã³ã¸ã®ã¢ã¯ã»ã¹ãæ±ãããã³ã«ãã
ã§ãã¯ãèªè¨¼ãè¡ããã¨ã¯ãªããRBAC ãã¼ã«ã¯ãIT åéã«ãããã»ã¨ãã©ã®ç¾è¡ãã©ãããã¼
ã åãã«ã権éä»ä¸ã¡ã«ããºã ã®ã¤ã³ã¿ãã§ã¼ã¹ãæä¾ãã¦ããããã ãã¬ã¬ã·ã¼ICS ã·ã¹ãã
ãç¹æ® ICS è£
ååã«ã¯ãç¹æ®ã¤ã³ã¿ãã§ã¼ã¹ã½ããã¦ã¨ã¢ã®éçºãå¿
è¦ã¨ãªãå ´åãããããã®
åé¡ã¯ãå¤æ°ã®ç¬èª OS ãã«ã¹ã¿ã OS ã®å®è£
åã³ã¤ã³ã¿ãã§ã¼ã¹ãå©ç¨ãã¦ãã ICS ã§å¤§ããª
åé¡ã¨ãªãã
SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
147
6.2.1.2 Web Servers
Web and Internet technologies are being added to a wide variety of ICS products because they make
information more accessible and products more user-friendly and easier to configure remotely. However,
they may also add cyber risks and create new security vulnerabilities that need to be addressed.
ICS-specific Recommendations and Guidance
SCADA and historian software vendors typically provide Web servers as a product option so that users
outside the control room can access ICS information. In many cases, software components such as ActiveX
controls or Java applets must be installed or downloaded onto each client machine accessing the Web
server. Some products, such as PLCs and other control devices, are available with embedded Web, FTP,
and email servers to make them easier to configure remotely and allow them to generate email notifications
and reports when certain conditions occur. When feasible, use HTTPS rather than HTTP, use SFTP or SCP
rather than FTP, block inbound FTP and email traffic, etc. Security appliances (or gateways) are beginning
to appear with application proxies able to examine Web, FTP, and email traffic to block attacks and prevent
downloading of ActiveX® controls or Java® applets.
Unless there is substantial benefit to connecting ICSs to the Internet, the systems are best left not
connected.
6.2.1.3 Virtual Local Area Network (VLAN)
VLANs divide physical networks into smaller logical networks to increase performance, improve
manageability, and simplify network design. VLANs are achieved through configuration of Ethernet
switches. Each VLAN consists of a single broadcast domain that isolates traffic from other VLANs. Just as
replacing hubs with switches reduces collisions, using VLANs limits the broadcast traffic, as well as
allowing logical subnets to span multiple physical locations. There are two categories of VLANs:
ï¼ Static, often referred to as port-based, where switch ports are assigned to a VLAN so that it is
transparent to the end user.
ï¼ Dynamic, where an end device negotiates VLAN characteristics with the switch or determines the
VLAN based on the IP or hardware addresses.
Although more than one IP subnet may coexist on the same VLAN, the general recommendation is to use a
one-to-one relationship between subnets and VLANs. This practice requires the use of a router or multi-
layer switch to join multiple VLANs. Many routers and firewalls support tagged frames so that a single
physical interface can be used to route between multiple logical networks.
VLANs are not typically deployed to address host or network vulnerabilities in the way that firewalls or
IDS are deployed. However, when properly configured, VLANs do allow switches to enforce security
policies and segregate traffic at the Ethernet layer. Properly segmented networks can also mitigate the risks
of broadcast storms that may result from port scanning or worm activity.
Switches have been susceptible to attacks such as MAC spoofing, table overflows, and attacks against the
spanning tree protocols, depending on the device and its configuration. VLAN hopping, the ability for an
attack to inject frames to unauthorized ports, has been demonstrated using switch spoofing or double-
encapsulated frames. These attacks cannot be conducted remotely and require local physical access to the
switch. A variety of features such as MAC address filtering, port-based authentication using IEEE 802.1x,
SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
148
6.2.1.2 ã¦ã§ããµã¼ã
ã¦ã§ãæè¡åã³ã¤ã³ã¿ã¼ãããæè¡ã¯ãæ
å ±ã¸ã®ã¢ã¯ã»ã¹ã便å©ã«ãªããã¦ã¼ã¶ã«ã¨ã£ã¦è£½å
ã使ãããããªããé éè¨å®ã容æã«ãªããããå¤ç¨®å¤æ§ãª ICS 製åã«è¿½å ãããããã«ãªã£
ã¦ãããããããµã¤ãã¼ãªã¹ã¯ãé«ã¾ããæ°ããªã»ãã¥ãªãã£ä¸ã®èå¼±æ§ãçãã対å¿ãå¿
è¦
ã¨ãªãã
ICS åºæã®æ¨å¥¨äºé
åã³ã¬ã¤ãã³ã¹
SCADA ããã¹ããªã¢ã³ã½ããã¦ã¨ã¢ã®ãã³ãã¼ã¯ãé常ãã¦ã§ããµã¼ãã製åãªãã·ã§ã³ã® 1ã¤ã¨ãã¦æ
ä¾ããå¶å¾¡å®¤ã®å¤ã«ããã¦ã¼ã¶ã ICS æ
å ±ã«ã¢ã¯ã»ã¹ã§ããããã«ãã¦ãããå¤ãã®å ´åãActiveX ã³ã³ã
ãã¼ã«ã Java ã¢ãã¬ããã¨ãã£ãã½ããã¦ã¨ã¢ã³ã³ãã¼ãã³ãããã¦ã§ããµã¼ãã«ã¢ã¯ã»ã¹ããã¯ã©ã¤ã¢ã³
ããã·ã³ã«ã¤ã³ã¹ãã¼ã«åã¯ãã¦ã³ãã¼ãããªããã°ãªããªããPLC ãã®ä»ã®å¶å¾¡ããã¤ã¹çã®è£½åã«ã¯ã
ã¦ã§ããµã¼ããFTP ãµã¼ãåã³é»åã¡ã¼ã«ãµã¼ããçµã¿è¾¼ã¾ãã¦ãããé éè¨å®ã容æã§ãç¹å®ã®äºæ
ãç
ããå ´åã«ã¯ãé»åã¡ã¼ã«éç¥ãã¬ãã¼ããçæã§ããããã«ãªã£ã¦ãããå¯è½ã§ããã° HTTP ã§ã¯ãªã
HTTPS ããFTP ã§ã¯ãªã SFTP å㯠SCP ã使ç¨ããçä¿¡ FTP ãé»åã¡ã¼ã«ãã©ãã£ãã¯çã¯ãããã¯ããã
ã¦ã§ããFTP åã³é»åã¡ã¼ã«ãã©ãã£ãã¯ãæ¤æ»ãã¦ãæ»æããããã¯ããActiveX®ã³ã³ããã¼ã«ã Java®
ã¢ãã¬ããã®ãã¦ã³ãã¼ããé²æ¢ã§ããã»ãã¥ãªãã£è£
ç½®ï¼åã¯ã²ã¼ãã¦ã§ã¤ï¼ã®ä»ããã¢ããªã±ã¼ã·ã§ã³
ãããã·ãåºå§ãã¦ããã
ICS
ãã¤ã³ã¿ã¼ãããæ¥ç¶ãããã¨ã®ç¸å½ã®å©çããªãããããã·ã¹ãã ãéæ¥ç¶ã¨ããã®ãæåã§ããã
6.2.1.3 ä»®æ³ LANï¼VLANï¼
VLAN ã¯ãç©çãããã¯ã¼ã¯ãããå°ããªè«çãããã¯ã¼ã¯ã«åå²ããããã©ã¼ãã³ã¹ã¨ç®¡ç
æ§ãæ¹åãããããã¯ã¼ã¯è¨è¨ãç°¡ç´ åãããVLAN ã¯Ethernet ã¹ã¤ããã®è¨å®ã«ããå®ç¾ã
ããå VLAN ã¯ããã©ãã£ãã¯ãä»ã® VLAN ããéé¢ããåä¸ã®ããã¼ããã£ã¹ãé åã§æ§æã
ããããããã¹ã¤ããã«ä»£ããã¨ç«¶åãæ¸ãããã«ãVLAN ã使ç¨ããã°ããã¼ããã£ã¹ãã
ã©ãã£ãã¯ãå¶éãããè«çãµãããããè¤æ°ã®ç©ççãªå ´æã«ã¾ãããããã«ã§ãããVLAN
ã«ã¯æ¬¡ã® 2種é¡ãããã
ï¼ éç VLANï¼ãã¼ããã¼ã¹ã¨å¼ã°ãããã¨ãå¤ããã¹ã¤ãããã¼ãã VLAN ã«å²ãå½ã¦ã
ããã¨ã³ãã¦ã¼ã¶ã«ééã§ããã
ï¼ åç VLANï¼ã¨ã³ãããã¤ã¹ãã¹ã¤ãã㨠VLAN ç¹æ§ã«ã¤ãã¦ãã´ã·ã¨ã¼ãããããIP ã¢
ãã¬ã¹åã¯ãã¼ãã¦ã¨ã¢ã¢ãã¬ã¹ã«åºã¥ã㦠VLAN ãå¤å®ããã
è¤æ°ã® IP ãµãããããåã VLAN ä¸ã«å
±åãããããµãããã㨠VLAN éã§ä¸å¯¾ä¸ã®é¢ä¿ãå©
ç¨ãããã¨ãä¸è¬çã«æ¨å¥¨ãããããã®è¦ç¯ã«ã¯ãè¤æ° VLAN ã«è·æ
ããããã®ã«ã¼ã¿åã¯ã
ã«ãã¬ã¤ã¤ã¼ã¹ã¤ãããå¿
é ã¨ãªããã«ã¼ã¿ããã¡ã¤ã¢ã¦ã©ã¼ã«ã®å¤ãã¯ãã¿ã°ä»ããã¬ã¼ã
ã«å¯¾å¿ãã¦ããã1ã¤ã®ç©çã¤ã³ã¿ãã§ã¼ã¹ãå©ç¨ãã¦ãè¤æ°ã®è«çãããã¯ã¼ã¯éã§çµè·¯æ
å®ãããã¨ãã§ããã
VLAN ã¯ããã¡ã¤ã¢ã¦ã©ã¼ã«ã IDS ã¨åããããªå±éæ¹æ³ã§ããã¹ãããããã¯ã¼ã¯ã®èå¼±æ§
ã«å¯¾å¦ããããã«å±éããããã¨ã¯ãã¾ããªãããããæ£ããè¨å®ããã¨ãVLAN ã¯ã¹ã¤ãã
ãæ¥ç¶ããªã·ã¼ãæ½è¡ãããã©ãã£ãã¯ã Ethernet 層ã§åé¢ãããã¨ãã§ããããã£ããå
é¢ããããããã¯ã¼ã¯ã¯ããã¼ãã¹ãã£ãã³ã°ãã¯ã¼ã ã«ããçããããã¼ããã£ã¹ãã¹ãã¼
ã ã®ãªã¹ã¯ãç·©åã§ããã
ã¹ã¤ããã¯ãããã¤ã¹ã¨ãã®è¨å®ã«å¿ãã¦ãMAC å½è£
ããã¼ãã«ãªã¼ãã¼ããã¼ãã¹ããã³ã°
ããªã¼ãããã³ã«æ»æçã®æ»æã«å¼±ããæ»æå´ããã¬ã¼ã ãæªè¨±å¯ãã¼ãã«æ³¨å
¥ãã VLAN ãã
ãã³ã°ã¯ãã¹ã¤ããå½è£
ãäºéã«ãã»ã«ãã¬ã¼ã ã使ç¨ãããã¨ãåãã£ã¦ããããã®ãããª
æ»æã¯é éæä½ãã§ãããã¹ã¤ããã¸ã®ãã¼ã«ã«ã®ç©çã¢ã¯ã»ã¹ãå¿
è¦ã¨ãªããMAC ã¢ãã¬ã¹
ãã£ã«ã¿ãªã³ã°ãIEEE 802.1
x
ãå©ç¨ãããã¼ããã¼ã¹ã®èªè¨¼çã®å¤æ§ãªæ©è½ãã

SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
149
and specific vendor recommended practices can be used to mitigate these attacks, depending on the device
and implementation.
ICS-specific Recommendations and Guidance
VLANs have been effectively deployed in ICS networks, with each automation cell assigned to a single
VLAN to limit unnecessary traffic flooding and allow network devices on the same VLAN to span multiple
switches [34].
6.2.1.4 Dial-up Modems
ICS systems have stringent reliability and availability requirements. When there is a need to troubleshoot
and repair, the technical resources may not be physically located at the control room or facility. Therefore,
ICS often use modems to enable vendors, system integrators, or control engineers maintaining the system
to dial in and diagnose, repair, configure, and perform maintenance on the network or component. While
this allows easy access for authorized personnel, if the dial-up modems are not properly secured, they can
also provide backdoor entries for unauthorized use.
Dial-up often uses remote control software that gives the remote user powerful (administrative or root)
access to the target system. Such software usually has security options that should be carefully reviewed
and configured.
ICS-specific Recommendations and Guidance
ï¼ Consider using callback systems when dial-up modems are installed in an ICS. This ensures that a
dialer is an authorized user by having the modem establish the working connection based on the
dialerâs information and a callback number stored in the ICS approved authorized user list.
ï¼ Ensure that default passwords have been changed and strong passwords are in place for each modem.
ï¼ Physically identify modems in use to the control room operators.
ï¼ Configure remote control software to use unique user names and passwords, strong authentication,
encryption if determined appropriate, and audit logs. Use of this software by remote users should be
monitored on an almost real-time frequency.
ï¼ If feasible, disconnect modems when not in use or consider automating this disconnection process by
having modems disconnect after being on for a given amount of time. It should be noted that
sometimes modem connections are part of the legal support service agreement with the vendor (e.g.,
24x7 support with 15 minute response time). Personnel should be aware that disconnecting/removing
the modems may require that contracts be renegotiated.

SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
150
ãã³ãã¼ãæ¨å¥¨ããç¹å®ã®è¦ç¯ãå©ç¨ãã¦ãããã¤ã¹ãå®è£
ã«å¿ãã¦ãããããæ»æãç·©åã§ã
ãã
ICS åºæã®æ¨å¥¨äºé
åã³ã¬ã¤ãã³ã¹
VLAN ã¯ICS ãããã¯ã¼ã¯ã«æå¹ã«å±éããã¦ãããåãªã¼ãã¡ã¼ã·ã§ã³ã»ã«ã 1ã¤ã® VLAN ã«
å²ãå½ã¦ã¦ä¸è¦ãªãã©ãã£ãã¯ã®æ´ªæ°´ãå¶éããåã VLAN ä¸ã®ãããã¯ã¼ã¯ããã¤ã¹ãè¤æ°
ã¹ã¤ããã«ã¾ãããããã«ãã¦ãã
[34]
ã
6.2.1.4 ãã¤ã¢ã«ã¢ããã¢ãã
ICS ã·ã¹ãã ã®ä¿¡é ¼æ§åã³å¯ç¨æ§ã«ã¯å³æ ¼ãªè¦ä»¶ã課ãããããã©ãã«ã·ã¥ã¼ãã£ã³ã°ãä¿®ç
ãå¿
è¦ã¨ãªãå ´åãå¶å¾¡å®¤ãå¶å¾¡æ½è¨ã«æè¡ãªã½ã¼ã¹ãç©ççã«åå¨ããªããã¨ãããã
ãã£ã¦ ICS ã§ã¯ãã·ã¹ãã ä¿å®ãæ
å½ãããã³ãã¼ãã·ã¹ãã ã¤ã³ãã°ã¬ã¼ã¿åã¯å¶å¾¡ã¨ã³
ã¸ãã¢ãã¢ãã ã使ç¨ãã¦ãã¤ã¢ã«ã¤ã³ãããããã¯ã¼ã¯ãæ§æã®è¨ºæãä¿®çãè¨å®åã³ä¿
å®ãè¡ããããã«ãããã¨ãå¤ãããããããã¨ã§æ¨©éãä¸ããããè·å¡ã®ã¢ã¯ã»ã¹ã容æ
ã«ãªãåé¢ããã¤ã¢ã«ã¢ããã¢ãã ã®ã»ãã¥ãªãã£ããã£ãã確ä¿ããã¦ããªãã¨ãä¸æ£ä½¿
ç¨ãããããããã¯ãã¢ä¾µå
¥ã許ããã¨ã«ããªããããªãã
ãã¤ã¢ã«ã¢ããã§ã¯ãé éã¦ã¼ã¶ã«ç®æ¨ã·ã¹ãã ã¸ã®ä¸ä½ï¼ç®¡çè
å㯠rootï¼ã¢ã¯ã»ã¹æ¨©ãä¸
ããé éå¶å¾¡ã½ããã¦ã¨ã¢ã使ç¨ãããã¨ãå¤ããé常ãã®ãããªã½ããã¦ã¨ã¢ã«ã¯ãæ
éã«
ç²¾æ»ãã¦è¨å®ãã¹ãã»ãã¥ãªãã£ãªãã·ã§ã³ãä»ãã¦ããã
ICS åºæã®æ¨å¥¨äºé
åã³ã¬ã¤ãã³ã¹
ï¼ ICS ã«ãã¤ã¢ã«ã¢ããã¢ãã ãè¨ç½®ããã¦ããå ´åãã³ã¼ã«ããã¯ã·ã¹ãã ã®å©ç¨ãæ¤è¨ã
ãããããå©ç¨ããã¨ãã¢ãã 㯠ICS ãèªå¯ããèªå®ã¦ã¼ã¶ãªã¹ãã«ä¿åããã¦ããçºå¼
è
æ
å ±ã¨ã³ã¼ã«ããã¯çªå·ãåºã«æå¹ãªæ¥ç¶ã確ç«ãããããçºå¼è
ã¯ç¢ºå®ã«èªå®ã¦ã¼ã¶ã¨
ãªãã
ï¼ ã¢ãã ãã¨ã«å¿
ãããã©ã«ãã®ãã¹ã¯ã¼ããå¤æ´ããå¼·åãªãã¹ã¯ã¼ããè¨å®ããã
ï¼ ä½¿ç¨ä¸ã®åã¢ãã ãå¶å¾¡å®¤ãªãã¬ã¼ã¿ã«ç©ççã«èå¥ã§ããããã«ããã
ï¼ é éå¶å¾¡ã½ããã¦ã¨ã¢ãè¨å®ããä¸æã®ã¦ã¼ã¶åã¨ãã¹ã¯ã¼ããå¼·åãªèªè¨¼ãå¿
è¦ã§ããã°
æå·åãç£æ»ãã°ã使ç¨ã§ããããã«ãããé éã¦ã¼ã¶ã«ããæ¬ã½ããã¦ã¨ã¢ã®ä½¿ç¨ããã»
ã¼ãªã¢ã«ã¿ã¤ã ã§ç£è¦ãã¹ãã§ããã
ï¼ å¯è½ã§ããã°ä¸ä½¿ç¨æã«ã¯ã¢ãã ãåæããããä¸å®æéãªã³ã«ãªã£ã¦ããå ´åã«ã¯ãªãã«
ãããããªåæããã»ã¹ã®èªååãæ¤è¨ãããã¢ãã æ¥ç¶ã¯ããã³ãã¼ã¨ã®æ³çãªãµãã¼ã
ãµã¼ãã¹å¥ç´ã®ä¸é¨ã«å«ã¾ãã¦ããå ´åãããç¹ãéè¨ãã¹ãã§ããï¼15 å対å¿ã§ã®å¹´ä¸
ç¡ä¼ãµãã¼ããªã©ï¼ãè·å¡ã¯ãã¢ãã ã®åæãæ¤å»ãè¡ãã«ã¯ãå¥ç´ä¸åè°ãå¿
è¦ã¨ãªãã
ã¨ãèªèãã¹ãã§ããã

SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
151
6.2.1.5 Wireless
The use of wireless within an ICS is a risk-based decision that has to be determined by the organization.
Generally, wireless LANs should only be deployed where health, safety, environmental, and financial
implications are low. NIST SP 800-48 and SP 800-97 provide guidance on wireless network security.
ICS-specific Recommendations and Guidance
Wireless LANs
ï¼ Prior to installation, a wireless survey should be performed to determine antenna location and strength
to minimize exposure of the wireless network. The survey should take into account the fact that
attackers can use powerful directional antennas, which extend the effective range of a wireless LAN
beyond the expected standard range. Faraday cages and other methods are also available to minimize
exposure of the wireless network outside of the designated areas.
ï¼ Wireless usersâ access should utilize IEEE 802.1x authentication using a secure authentication
protocol (e.g., Extensible Authentication Protocol [EAP] with TLS [EAP-TLS]) that authenticates
users via a user certificates or a Remote Authentication Dial In User Service (RADIUS) server.
ï¼ The wireless access points and data servers for wireless worker devices should be located on an
isolated network with documented and minimal (single if possible) connections to the ICS network.
ï¼ Wireless access points should be configured to have a unique service set identifier (SSID), disable
SSID broadcast, and enable MAC filtering at a minimum.
ï¼ Wireless devices, if being utilized in a Microsoft Windows ICS network, should be configured into a
separate organizational unit of the Windows domain.
ï¼ Wireless device communications should be encrypted and integrity-protected. The encryption must
not degrade the operational performance of the end device. Encryption at OSI Layer 2 should be
considered, rather than at Layer 3 to reduce encryption latency. The use of hardware accelerators to
perform cryptographic functions should also be considered.
For mesh networks, consider the use of broadcast key versus public key management implemented at OSI
Layer 2 to maximize performance. Asymmetric cryptography should be used to perform administrative
functions, and symmetric encryption should be used to secure each data stream as well as network control
traffic. An adaptive routing protocol should be considered if the devices are to be used for wireless
mobility. The convergence time of the network should be as fast as possible supporting rapid network
recovery in the event of a failure or power loss. The use of a mesh network may provide fault tolerance thru
alternate route selection and pre-emptive fail-over of the network.
Wireless field networks
The ISA10039 Committee is working to establish standards, recommended practices, technical reports, and
related information that will define procedures for implementing wireless systems in the automation and
control environment with a focus on the field level (e.g., IEEE 802.15.4). Guidance is directed towards
those responsible for the complete life cycle including the designing, implementing, on-going maintenance,
scalability or managing industrial automation and control systems, and applies to users, system integrators,
practitioners, and control systems manufacturers and vendors.
39 Additional information on ISA100 at: http://www.isa.org/isa100.

SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
152
6.2.1.5 ã¯ã¤ã¤ã¬ã¹
ICS å
ã§ã®ã¯ã¤ã¤ã¬ã¹ã®å©ç¨ã¯ããªã¹ã¯ã«åºã¥ã決å®äºé
ã§ãããçµç¹ã決å®ããªããã°ãªããª
ããä¸è¬ã«ã¯ã¤ã¤ã¬ã¹ LAN ã¯ãå¥åº·ã»å®å
¨ã»ç°å¢ã»è²¡æ¿ä¸ã®å¶ç´ãå°ãªãå ´åã«ã®ã¿å±éãã¹
ãã§ãããNIST SP 800-48 åã³ SP 800-97 ã«ã¯ãã¯ã¤ã¤ã¬ã¹ãããã¯ã¼ã¯æ¥ç¶ã«ä¿ãã¬ã¤ãã³ã¹
ãããã
ã¯ã¤ã¤ã¬ã¹ LAN ã«ä¿ã ICS åºæã®æ¨å¥¨äºé
åã³ã¬ã¤ãã³ã¹
ï¼ è¨ç½®åã«ç¡ç·ç¶æ
ã調æ»ããã¢ã³ããä½ç½®ã¨å¼·åº¦ãå¤å®ããã¯ã¤ã¤ã¬ã¹ãããã¯ã¼ã¯ã®é²åº
度ãæå°éã«ãããæ»æå´ãå©ç¨ããå¼·åæåæ§ã¢ã³ããã¯ãã¯ã¤ã¤ã¬ã¹ LAN ã®æå¹è·é¢
ããæ¨æºçãªäºæ³è·é¢ãè¶
ãã¦å»¶ä¼¸ã§ãããã¨ã念é ã«ç½®ãã¦èª¿æ»ãè¡ãã¹ãã§ããããã¡
ã©ãã¼ç®±ãã®ä»ã®æ段ãå©ç¨ãã¦ãææã®ã¨ãªã¢å¤ã«ã¯ã¿åºãã¯ã¤ã¤ã¬ã¹ãããã¯ã¼ã¯ã®é²
åºåº¦ãæå°ã«æããã
ï¼ ã¯ã¤ã¤ã¬ã¹ã¦ã¼ã¶ã®ã¢ã¯ã»ã¹ã¯ãã¦ã¼ã¶è¨¼ææ¸åã¯é éèªè¨¼ãã¤ã¢ã«ã¤ã³ã¦ã¼ã¶ãµã¼ãã¹
ï¼RADIUSï¼ãµã¼ããä»ãã¦ã¦ã¼ã¶èªè¨¼ãè¡ããã»ãã¥ã¢ãªãããã³ã«ï¼TLS ä»ãæ¡å¼µèªè¨¼
ãããã³ã«[EAP-TLS]çï¼ã使ç¨ãã IEEE802.1xèªè¨¼ãå©ç¨ãã¹ãã§ããã
ï¼ ã¯ã¤ã¤ã¬ã¹ã¢ã¯ã»ã¹ãã¤ã³ãåã³ã¯ã¤ã¤ã¬ã¹ã¯ã¼ã«ããã¤ã¹ç¨ãã¼ã¿ãµã¼ãã¯ãICS ããã
ã¯ã¼ã¯æ¥ç¶ãæå°éã«ãï¼ã§ããã° 1ã¤ã®ã¿ï¼ãææ¸åãããé絶ãããã¯ã¼ã¯ä¸ã«ç½®ãã¹
ãã§ããã
ï¼ ã¯ã¤ã¤ã¬ã¹ã¢ã¯ã»ã¹ãã¤ã³ãã¯ããµã¼ãã¹ã»ããèå¥åï¼SSIDï¼ãä¸æã«ããSSID ããã¼
ããã£ã¹ãã使ç¨ç¦æ¢ãæå°éã® MAC ãã£ã«ã¿ãªã³ã°ã使ç¨å¯è½ã«è¨å®ãã¹ãã§ããã
ï¼ ã¯ã¤ã¤ã¬ã¹ããã¤ã¹ã Microsoft Windows ICS ãããã¯ã¼ã¯ã§ä½¿ç¨ããå ´åãWindows é å
ã®å¥ã®çµç¹ã¦ãããã«è¨å®ãã¹ãã§ããã
ï¼ ã¯ã¤ã¤ã¬ã¹ããã¤ã¹éä¿¡ã¯ãæå·åãã¦ä¿å
¨ãã¹ãã§ãããæå·åã«ãããã¨ã³ãããã¤ã¹
ã®åä½ããã©ã¼ãã³ã¹ãä½ä¸ãã¦ã¯ãªããªããæå·åã®å¾
ã¡æéãç縮ãããããOSI ã¬ã¤
ã¤ã¼3ã§ã¯ãªãã¬ã¤ã¤ã¼2ã§ã®æå·åãèæ
®ãã¹ãã§ãããã¾ãæå·é¢æ°ãå®è¡ãããã¼ã
ã¦ã¨ã¢å éå¨ã®å©ç¨ãèæ
®ãã¹ãã§ããã
ã¡ãã·ã¥ãããã¯ã¼ã¯ã§ã¯ãããã©ã¼ãã³ã¹ãæ大ã«ä¸ãããããOSI ã¬ã¤ã¤ã¼2ã«å®è£
ã
ããããã¼ããã£ã¹ããã¼å¯¾å
¬ééµç®¡çã®ä½¿ç¨ãæ¤è¨ãããé対称æå·ãå©ç¨ãã¦ç®¡çæ©è½
ãå®æ½ãã対称æå·ãå©ç¨ãã¦åãã¼ã¿ã¹ããªã¼ã ã¨ãããã¯ã¼ã¯å¶å¾¡ãã©ãã£ãã¯ã®ã»ã
ã¥ãªãã£ã確ä¿ãã¹ãã§ãããããã¤ã¹ãã¯ã¤ã¤ã¬ã¹ç§»åç®çã§ä½¿ç¨ããå ´åã¯ãæé©çµè·¯
æå®ãããã³ã«ã®å©ç¨ãèæ
®ãã¹ãã§ãããé害æãé»ååªå¤±æã®ãããã¯ã¼ã¯å復ãæ©ã
ãããããããã¯ã¼ã¯ã®åææéã¯ã§ããã ãçããã¹ãã§ãããã¡ãã·ã¥ãããã¯ã¼ã¯ã
使ç¨ãããã¨ã§ã代æ¿çµè·¯é¸å®ã¨å
è¡çãã§ã¤ã«ãªã¼ãã¼ãéãã¦ããã©ã¼ã«ããã¬ã©ã³ã¹
ãå¾ããããã
ã¯ã¤ã¤ã¬ã¹ãã£ã¼ã«ããããã¯ã¼ã¯
ãã£ã¼ã«ãã¬ãã«ï¼IEEE 802.15.4 çï¼ã«ç¹åãããªã¼ãã¡ã¼ã·ã§ã³åã³å¶å¾¡ç°å¢ã«ãããã¯ã¤ã¤
ã¬ã¹ã·ã¹ãã ã®æé ãå®ãããããISA 10040å§å¡ä¼ã¯è¦æ ¼ãæ¨å¥¨è¦ç¯ãæè¡ã¬ãã¼ãåã³é¢é£æ
å ±ã®çå®ã«åãã¦ä½æ¥ä¸ã§ãããç£æ¥ãªã¼ãã¡ã¼ã·ã§ã³åã³å¶å¾¡ã·ã¹ãã ã®è¨è¨ãå®è£
ãä¿å®ã
ã¹ã±ã¼ã©ããªãã£ã管ççã®ã©ã¤ããµã¤ã¯ã«æ
å½è
åãã«ã¬ã¤ãã³ã¹ãæ示ããã¦ãããã¦ã¼
ã¶ãã·ã¹ãã ã¤ã³ãã°ã¬ã¼ã¿ãå®æ½æ
å½è
åã³å¶å¾¡ã·ã¹ãã ã®ã¡ã¼ã«ã¼/ãã³ãã¼ã«é©ç¨ãã
ãã
40 ISA100 ã«é¢ãã追å æ
å ±ã次㮠URL ã«ãããhttp://www.isa.org/isa100.

SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
153
6.2.2 Awareness and Training
The security controls that fall within the NIST SP 800-53 Awareness and Training (AT) family provide
policy and procedures for ensuring that all users of an information system are provided basic information
system security awareness and training materials before authorization to access the system is granted.
Personnel training must be monitored and documented.
Supplemental guidance for the AT controls can be found in the following documents:
ï¼ NIST SP 800-50 provides guidance on security awareness training [61].
ï¼ NIST SP 800-100 provides guidance on information security governance and planning [27].
ICS-specific Recommendations and Guidance
For the ICS environment, this must include control system-specific information security awareness and
training for specific ICS applications. In addition, an organization must identify, document, and train all
personnel having significant ICS roles and responsibilities. Awareness and training must cover the physical
process being controlled as well as the ICS.
Security awareness is a critical part of ICS incident prevention, particularly when it comes to social
engineering threats. Social engineering is a technique used to manipulate individuals into giving away
private information, such as passwords. This information can then be used to compromise otherwise secure
systems.
Implementing an ICS security program may bring changes to the way in which personnel access computer
programs, applications, and the computer desktop itself. Organizations should design effective training
programs and communication vehicles to help employees understand why new access and control methods
are required, ideas they can use to reduce risks, and the impact on the organization if control methods are
not incorporated. Training programs also demonstrate managementâs commitment to, and the value of, a
cybersecurity program. Feedback from staff exposed to this type of training can be a valuable source of
input for refining the charter and scope of the security program.
6.2.3 Audit and Accountability
An audit is an independent review and examination of records and activities to assess the adequacy of
system controls, to ensure compliance with established policies and operational procedures, and to
recommend necessary changes in controls, policies, or procedures. The security controls that fall within the
NIST SP 800-53 Audit and Accountability (AU) family provide policies and procedures for generating
audit records, their content, capacity, and retention requirements. The controls also provide safeguards to
react to problems such as an audit failure or audit log capacity being reached. Audit data should be
protected from modification and be designed with non-repudiation capability.
Supplemental guidance for the AU controls can be found in the following documents:
ï¼ NIST SP 800-61 provides guidance on computer security incident handling and audit log retention
[59].

SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
154
6.2.2 æèåã³è¨ç·´
NIST SP 800-53 ã®æèåã³è¨ç·´ï¼ATï¼ãã¡ããªã«å«ã¾ããã»ãã¥ãªãã£å¯¾çã«ã¯ãã·ã¹ãã ã¸
ã®ã¢ã¯ã»ã¹æ¨©éãä»ä¸ããåã«ãæ
å ±ã·ã¹ãã ã®å
¨ã¦ã¼ã¶ã«åºæ¬çãªã·ã¹ãã ã»ãã¥ãªãã£ã«
対ããæèã»è¨ç·´è³æãè¡ã渡ãããã«ããããã®ããªã·ã¼åã³æé ãå®ãããã¦ããã
è¨ç·´ã¯ç£è¦ã¨ææ¸åãæ±ããããã
AT 管çã®è£è¶³çã¬ã¤ãã³ã¹ã以ä¸ã®ææ¸ã«æ²è¼ããã¦ããã
ï¼ NIST SP 800-50ï¼ã»ãã¥ãªãã£æèè¨ç·´ã«ä¿ãã¬ã¤ãã³ã¹[61]
ï¼ NIST SP 800-100ï¼æ
å ±ã»ãã¥ãªãã£ã¬ããã³ã¹åã³ãã©ã³ãã³ã°ã«ä¿ãã¬ã¤ãã³ã¹[27]
ICS åºæã®æ¨å¥¨äºé
åã³ã¬ã¤ãã³ã¹
ICS ç°å¢ã§ã¯ãç¹å®ã® ICS ç¨éã«é¢ããå¶å¾¡ã·ã¹ãã åºæã®æ
å ±ã»ãã¥ãªãã£æèã»è¨ç·´ãå«ã
ãªããã°ãªããªããã¾ãçµç¹ã¯ãICS ã«å¤§ããªå½¹å²ã¨è²¬ä»»ãæãã¦ããè·å¡å
¨ã¦ãç¹å®ããè¨é²
ããè¨ç·´ããªããã°ãªããªããæèã»è¨ç·´ã¯ãå¶å¾¡ãããç©ççããã»ã¹ã¨ ICS ã«ã¤ãã¦åãä¸
ããªããã°ãªããªãã
ã»ãã¥ãªãã£æèã¯ãICS ã¤ã³ã·ãã³ãã®äºé²ãç¹ã«ã½ã¼ã·ã£ã«ã¨ã³ã¸ãã¢ãªã³ã°è
å¨ã«é¢ã
ã¦ãICS ã®èè¦ãªä¸é¨ã§ãããã½ã¼ã·ã£ã«ã¨ã³ã¸ãã¢ãªã³ã°ã¨ã¯ãå人ãæä½ãã¦ãã¹ã¯ã¼ãç
ã®å人æ
å ±ãå¼ãåºãæè¡ã®ãã¨ã§ãããå¼ãåºããæ
å ±ãå©ç¨ãã¦ãã·ã¹ãã ã®ã»ãã¥ãªãã£
ãä½ä¸ããããã¨ãã§ããã
ICS ã»ãã¥ãªãã£ããã°ã©ã ãå®æ½ãããã¨ã§ãè·å¡ã«ããã³ã³ãã¥ã¼ã¿ããã°ã©ã ãã¢ããªã±
ã¼ã·ã§ã³åã³ã³ã³ãã¥ã¼ã¿ãã¹ã¯ããããã®ãã®ã®å©ç¨æ¹æ³ãå¤ãããã¨ãã§ãããçµç¹ã¯å¹æ
çãªè¨ç·´ããã°ã©ã ã¨ä¼éæ段ãèæ¡ãã¦ãæ°ããªã¢ã¯ã»ã¹ã»ç®¡çè¦é ãå¿
è¦ãªçç±ããªã¹ã¯ã
æ¸ããããã®ã¢ã¤ãã£ã¢ã管çè¦é ãå®ãããªãå ´åã®çµç¹ã¸ã®å½±é¿ã«ã¤ãã¦å¾æ¥å¡ãç解ã§ã
ãããã«ãã¹ãã§ãããã¾ãè¨ç·´ããã°ã©ã ã§ã¯ããµã¤ãã¼ã»ãã¥ãªãã£ããã°ã©ã ã«å¯¾ããçµ
å¶é£ã®å¼·ãé¢å¿ã¨ãããã°ã©ã ã®ä¾¡å¤ãå®è¨¼ããã被è¨ç·´è
ããã®ãã£ã¼ãããã¯ã¯ãã»ãã¥ãª
ãã£ããã°ã©ã ã®æ²ç« åã³é©ç¨ç¯å²ãæ¹åããããã®è²´éãªè³ã¨ãªãã
6.2.3 ç£æ»åã³èª¬æ責任
ç£æ»ã¯ã·ã¹ãã å¶å¾¡ã®å¦¥å½æ§ãè©ä¾¡ããè¦å®ã®ããªã·ã¼åã³æ¥åæé ãéµå®ãããå¶å¾¡ã»ã
ãªã·ã¼ã»æé ã«å¿
è¦ãªå¤æ´ãæ¨å¥¨ããããã®è¨é²åã³æ´»åã«å¯¾ããç¬ç«ã®å¯©æ»ã»æ¤è¨¼ã§ããã
NIST SP 800-53 ã®ç£æ»åã³èª¬æ責任ï¼AUï¼ãã¡ããªã«å«ã¾ããã»ãã¥ãªãã£å¯¾çã§ã¯ãç£æ»
è¨é²ãå
容ãè½ååã³ä¿æè¦ä»¶ã«ä¿ãããªã·ã¼åã³æé ãå®ãã¦ãããã¾ãç£æ»ã®ä¸åãç£
æ»è¨é²è½åãéçã«éããéã®åé¡ã«å¯¾å¦ããããã®å¯¾çãå®ãããã¦ããããç£æ»ãã¼ã¿
ã¯æ¹å¤ã§ããªãããã«ä¿è·ããå¦èªä¸è½ã®ãã®ã¨ãã¦çå®ãã¹ãã§ããã
AU 管çã®è£è¶³çã¬ã¤ãã³ã¹ã以ä¸ã®ææ¸ã«æ²è¼ããã¦ããã
ï¼ NIST SP 800-61ï¼ã³ã³ãã¥ã¼ã¿ã»ãã¥ãªãã£ã¤ã³ã·ãã³ãã®å¦çåã³ç£æ»è¨é²ã®ä¿æã«ä¿ã
ã¬ã¤ãã³ã¹[59]

SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
155
ï¼ NIST SP 800-92 provides guidance on log management (including audit logs) [68].
ï¼ NIST SP 800-100 provides guidance on information security governance and planning [27].
ICS-specific Recommendations and Guidance
It is necessary to determine that the system is performing as intended. Periodic audits of the ICS should be
performed to validate the following items:
ï¼ The security controls present during system validation testing (e.g., factory acceptance testing and site
acceptance testing) are still installed and operating correctly in the production system.
ï¼ The production system is free from security compromises and provides information on the nature and
extent of compromises as feasible, should they occur.
ï¼ The management of change program is being rigorously followed with an audit trail of reviews and
approvals for all changes.
The results from each periodic audit should be expressed in the form of performance against a set of
predefined and appropriate metrics to display security performance and security trends. Security
performance metrics should be sent to the appropriate stakeholders, along with a view of security
performance trends.
Traditionally, the primary basis for audit in IT systems has been recordkeeping. Using appropriate tools
within an ICS environment requires extensive knowledge from an IT professional familiar with the ICS,
critical production and safety implications for the facility. Many of the process control devices that are
integrated into the ICS have been installed for many years and do not have the capability to provide the
audit records described in this section. Therefore, the applicability of these more modern tools for auditing
system and network activity is dependent upon the capabilities of the components in the ICS.
The critical tasks in managing a network in an ICS environment are ensuring reliability and availability to
support safe and efficient operation. In regulated industries, regulatory compliance can add complexity to
security and authentication management, registry and installation integrity management, and all functions
that can augment an installation and operational qualification exercise. Diligent use of auditing and log
management tools can provide valuable assistance in maintaining and proving the integrity of the ICS from
installation through the system life cycle. The value of these tools in this environment can be calculated by
the effort required to re-qualify or otherwise retest the ICS where the integrity due to attack, accident, or
error is in question. The system should provide reliable, synchronized time stamps in support of the audit
tools.
Monitoring of sensors, logs, Intrusion Detection Systems (IDS), antivirus, patch management, policy
management software, and other security mechanisms should be done on a real-time basis where feasible.
A first-line monitoring service would receive alarms, do rapid initial problem determination and take action
to alert appropriate facility personnel to intervene.
System auditing utilities should be incorporated into new and existing ICS projects. These auditing utilities
should be tested (e.g., off-line on a comparable ICS) before being deployed on an operational ICS. These
tools can provide tangible records of evidence and system integrity. Additionally, active log management
utilities may actually flag an attack or event in progress and provide location and tracing information to
help respond to the incident [34].

SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
156
ï¼ NIST SP 800-92ï¼è¨é²ç®¡çï¼ç£æ»è¨é²ãå«ãï¼ã«ä¿ãã¬ã¤ãã³ã¹[68]
ï¼ NIST SP 800-100ï¼æ
å ±ã»ãã¥ãªãã£ã¬ããã³ã¹åã³ãã©ã³ãã³ã°ã«ä¿ãã¬ã¤ãã³ã¹[27]
ICS åºæã®æ¨å¥¨äºé
åã³ã¬ã¤ãã³ã¹
ã·ã¹ãã ãäºå®ã©ããã«ç¨¼åãã¦ãããå¤å®ããå¿
è¦ããããICS ã®å®æçç£æ»ãè¡ãã次ã®
ç¹ãæ¤è¨¼ãã¹ãã§ããã
ï¼ ã·ã¹ãã ã®å¦¥å½æ§æ¤è¨¼ï¼å·¥å ´ã®æ¤ååã³ç¾å ´ã§ã®æ¤åçï¼æã«ãã£ãã»ãã¥ãªãã£å¯¾çãã
ã®ã¾ã¾è¨ç½®ãããçç£ã·ã¹ãã ã§æ£å¸¸ã«ç¨¼åãã¦ããã
ï¼ çç£ã·ã¹ãã ã«ã»ãã¥ãªãã£ä¸ã®æ§è½ä½ä¸ããªããæ§è½ä½ä¸ãçããå ´åã«ã¯ãå¯è½ã§ãã
ã°ãã®æ§è³ªãç¨åº¦ã«ã¤ãã¦æ
å ±ãæä¾ããã
ï¼ ããã°ã©ã å¤æ´ã®ç®¡çã¯ãå
¨ã¦ã®å¤æ´å
容ã®å¯©æ»ã»æ¿èªç£æ»è¨¼è·¡ã«å¾ã£ã¦éµå®ããã¦ããã
åå®æç£æ»ã®çµæã¯ãäºåã«å®ããããé©æ£ãªè©ä¾¡åºæºã«ç
§ããã¦æ績ã®å½¢ã§è¨è¼ããã»ã
ã¥ãªãã£ããã©ã¼ãã³ã¹ã¨ã»ãã¥ãªãã£ååã¨ã示ãã¹ãã§ãããã»ãã¥ãªãã£ããã©ã¼ã
ã³ã¹è©ä¾¡åºæºã¯ãã»ãã¥ãªãã£ååã«é¢ããæè¦ã¨ã¨ãã«ãé¢ä¿è
ã«éè´ãã¹ãã§ããã
ä¼çµ±çã« IT ã·ã¹ãã ã«ãããç£æ»ã®åºæ¬ã¯ãè¨é²ç®¡çã«ãã£ããICS ç°å¢ã§é©æ£ãªãã¼ã«ã
使ç¨ããã«ã¯ãICS ã«éããæ½è¨ã«é¢ããéè¦çç£ã»å®å
¨æ§ã®å¶ç´ãç解ãã IT å°éå¡ã®åº
ç¯ãªç¥è¦ãå¿
è¦ã¨ãªããICS ã«çµã¿è¾¼ã¾ããããã»ã¹å¶å¾¡ããã¤ã¹ã®å¤ãã¯ãä½å¹´ãåã«è¨ç½®
ããããã®ã»ã¯ã·ã§ã³ã§è¿°ã¹ãç£æ»è¨é²ã®æä¾è½åããªãããããã£ã¦ãç£æ»ã·ã¹ãã åã³ã
ããã¯ã¼ã¯æ´»åç¨ã®ãããææ°ãã¼ã«ã®é©ç¨ã¯ãICS ã³ã³ãã¼ãã³ãã®è½åã«å·¦å³ãããã
ICS ç°å¢ã«ããããããã¯ã¼ã¯ç®¡çã®éè¦ã¿ã¹ã¯ã¯ãä¿¡é ¼æ§ã¨å¯ç¨æ§ã確ä¿ãã¦ãå®å
¨ã§å¹ç
çãªæ¥åãæ¯ãããã¨ã«ãããè¦å¶ãåããæ¥çã§ã¯ãè¦å¶ãéµå®ãããã¨ã§ã»ãã¥ãªãã£
ã¨èªè¨¼ç®¡çã帳簿åã³æ½è¨ã®å®å
¨æ§ç®¡çãæ½è¨åã³æ¥åé©æ ¼æ§æ¼ç¿ãå¼·åããããã®ããã
ãæ©è½ãè¤éã«ãªããç£æ»ã»è¨é²ç®¡çãã¼ã«ãå©æ´»ç¨ãããã¨ã§ãã¤ã³ã¹ãã¼ã«ããã©ã¤ã
ãµã¤ã¯ã«å
¨è¬ãéãã¦ãICS ãä¿å®ãå®å
¨æ§ãå®è¨¼ããä¸ã§ãè²´éãªå©ããå¾ããããICS ç°
å¢ã«ãããããããã¼ã«ã®ä¾¡å¤ã¯ãæ»æã»å®è¡ã»é誤çã«ããå®å
¨æ§ãçåè¦ãããå ´åã«
å¿
è¦ã¨ãªããé©æ ¼æ§ã®ååå¾ã ICS ã®åæ¤æ»ã¨ãã£ãå´åã«ç
§ããã¦è¨ç®ã§ããããã·ã¹ã
ã ã¯ç£æ»ãã¼ã«ã«å¯¾å¿ãã¦ãä¿¡é ¼æ§ã®é«ãåæã¿ã¤ã ã¹ã¿ã³ããåãã¦ããã¹ãã§ããã
ã»ã³ãµããã°ãä¾µå
¥æ¤ç¥ã·ã¹ãã ï¼IDSï¼ãã¢ã³ãã¦ã¤ã«ã¹ãããã管çãããªã·ã¼ç®¡çã½
ããã¦ã¨ã¢ãã®ä»ã®ã»ãã¥ãªãã£ã¡ã«ããºã ã¯ãå¯è½ã§ããã°ãªã¢ã«ã¿ã¤ã ã§å®è¡ã§ããã¹
ãã§ãããæåç·ã®ç£è¦ãµã¼ãã¹ã¯ã¢ã©ã¼ã ãåé ããåæã®åé¡å¤å¥ãè¿
éã«è¡ãã該å½
æ½è¨è·å¡ã対å¦ããããã«ã¢ã¯ã·ã§ã³ãèµ·ããã
ã·ã¹ãã ç£æ»ã¦ã¼ãã£ãªãã£ãæ°è¦åã³æ¢å ICS ããã¸ã§ã¯ãã«çµã¿è¾¼ãã¹ãã§ãããã¦ã¼ãã£
ãªãã£ã¯ã稼åä¸ã® ICS ã«å±éããåã«ã試é¨ãè¡ãã¹ãã§ããï¼åçã® ICS ã§ã®ãªãã©ã¤ã³è©¦
é¨ï¼ãããããã¼ã«ã¯ã証æ åã³ã·ã¹ãã ã®å®å
¨æ§ã«é¢ããæå½¢ã®è¨é²ãæä¾ã§ãããã¾ãã¢ã¯
ãã£ããã°ç®¡çã¦ã¼ãã£ãªãã£ã¯ãé²è¡ä¸ã®æ»æãäºè±¡ã«ãã©ã°ãç«ã¦ãä½ç½®ã¨è¿½è·¡æ
å ±ãæä¾
ãã¦ãã¤ã³ã·ãã³ãã¸ã®å¯¾å¿ãå©ãã
[34]
ã
SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
157
There should be a method for tracing all console activities to a user, either manually (e.g., control
room sign in) or automatic (e.g., login at the application and/or OS layer). Policies and procedures for
what is logged, how the logs are stored (or printed), how they are protected, who has access to the logs
and how/when are they reviewed should be developed. These policies and procedures will vary with
the ICS application and platform. Legacy systems typically employ printer loggers, which are
reviewed by administrative, operational, and security staff. Logs maintained by the ICS application
may be stored at various locations and may or may not be encrypted.
6.2.4 Security Assessment and Authorization
The security controls that fall within the NIST SP 800-53 Assessment and Authorization (CA) family
provide the basis for performing periodic assessments and providing certification of the security controls
implemented in the information system to determine if the controls are implemented correctly, operating as
intended, and producing the desired outcome to meet the system security requirements. A senior
organizational official is responsible for accepting residual risk and authorizing system operation. These
steps constitute accreditation. In addition, all security controls should be monitored on an ongoing basis.
Monitoring activities include configuration management and control of information system components,
security impact analysis of changes to the system, ongoing assessment of security controls, and status
reporting.
Supplemental guidance for the CA controls can be found in the following documents:
ï¼ NIST SP 800-53A provides guidance on security control assessments [23].
ï¼ NIST SP 800-37 provides guidance defining the information system boundary and security
certification and accreditation of the information system [21].
ï¼ NIST SP 800-100 provides guidance on information security governance and planning [27].
6.2.5 Configuration Management
Configuration management policy and procedures are used to control modifications to hardware, firmware,
software, and documentation to ensure that the information system is protected against improper
modifications prior to, during, and after system implementation. The security controls that fall within the
NIST SP 800-53 Configuration Management (CM) family provide policy and procedures for establishing
baseline controls for information systems. Controls are also specified for maintaining, monitoring, and
documenting configuration control changes. There should be restricted access to configuration settings, and
security settings of IT products should be set to the most restrictive mode consistent with ICS operational
requirements.
Supplemental guidance for the CM controls can be found in the following documents:
ï¼ NIST SP 800-70 provides guidance on configuration settings for IT products [26].
ï¼ NIST SP 800-100 provides guidance on information security governance and planning [27].
ï¼ NIST SP 800-128 provides guidance on implementation of a security-focused configuration
management program [80].
SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
158
æåï¼å¶å¾¡å®¤ã¸ã®ç«å
¥ç½²åçï¼åã¯èªåï¼ã¢ããªã±ã¼ã·ã§ã³ã OS ã¸ã®ãã°ã¤ã³çï¼ã«ãããã
ãã¦ã¼ã¶ã®å
¨ã¦ã®ã³ã³ã½ã¼ã«æ´»åã«å¯¾ãã追跡æ¹æ³ãæã¤ã¹ãã§ãããè¨é²å
容ãè¨é²ã®ä¿ç®¡
ï¼åã¯ããªã³ãï¼æ¹æ³ãä¿è·è¦é ãè¨é²ã¸ã®ã¢ã¯ã»ã¹ä»¶ä¿æè
ãè¨é²ã®å¤æ´æ¹æ³ã»ææã«é¢ãã
ããªã·ã¼åã³æé ãä½æãã¹ãã§ãããããªã·ã¼åã³æé ã¯ãICS ã®ç¨éåã³ãã©ãããã¼ã ã«
ããç°ãªããã¬ã¬ã·ã¼ã·ã¹ãã ã§ã¯ããªã³ã¿ãã¬ã¼ãé常ãæ¡ç¨ãã¦ããã管çãæ¥ååã³ã»ã
ã¥ãªãã£è·å¡ãç®ãéãã¦ãããICS ã¢ããªã±ã¼ã·ã§ã³ãç¶æãããã°ã¯ã種ã
ã®å ´æã«ä¿ç®¡ã
ããæå·åããã¦ãããã®ãããã°ãããã¦ããªããã®ãããã
6.2.4 ã»ãã¥ãªãã£è©ä¾¡åã³æ¨©éä»ä¸
NIST SP 800-53 ã®ã»ãã¥ãªãã£è©ä¾¡åã³æ¨©éä»ä¸ï¼CAï¼ãã¡ããªã«å«ã¾ããã»ãã¥ãªãã£å¯¾
çã¯ãå®æçè©ä¾¡ãè¡ããæ
å ±ã·ã¹ãã ã«å®è£
ããã¦ããã»ãã¥ãªãã£å¯¾çã®è¨¼ææ¸ã交ä»ã
ãæ ¹æ ãå®ãã¦ãããããã«å¾ã管çãé©æ§ã«è¡ãããäºå®ã©ããã«ç¨¼åããã·ã¹ãã ã»ãã¥
ãªãã£è¦ä»¶ã«åè´ããçµæã«ãªã£ã¦ãããã©ãããå¤å®ã§ãããçµç¹ã®å¹¹é¨ã¯æ®çãªã¹ã¯ãå
ãå
¥ããã·ã¹ãã ã®ç¨¼åã許å¯ãã責任ãæããããã®ãããªæé ãèªå®ãæ§æãããã¾ãã
å
¨ã¦ã®ã»ãã¥ãªãã£å¯¾çã¯ç¶ç¶çã«ç£è¦ãã¹ãã§ãããç£è¦æ´»åã«ã¯æ
å ±ã·ã¹ãã ã³ã³ãã¼ã
ã³ãã®è¨å®ç®¡çãã·ã¹ãã å¤æ´ã®ã»ãã¥ãªãã£å½±é¿åæãé²å±ä¸ã®ã»ãã¥ãªãã£å¯¾çã®è©ä¾¡å
ã³ç¾ç¶å ±åãå«ã¾ããã
CA 管çã®è£è¶³çã¬ã¤ãã³ã¹ã以ä¸ã®ææ¸ã«æ²è¼ããã¦ããã
ï¼ NIST SP 800-53Aï¼ã»ãã¥ãªãã£å¯¾çè©ä¾¡ã«ä¿ãã¬ã¤ãã³ã¹[23]
ï¼ NIST SP 800-37ï¼æ
å ±ã·ã¹ãã å¢çåã³æ
å ±ã·ã¹ãã ã»ãã¥ãªãã£è¨¼æã»èªå®ã®å®ç¾©ã«ä¿ã
ã¬ã¤ãã³ã¹[21]
ï¼ NIST SP 800-100ï¼æ
å ±ã»ãã¥ãªãã£ã¬ããã³ã¹åã³ãã©ã³ãã³ã°ã«ä¿ãã¬ã¤ãã³ã¹[27]
6.2.5 æ§æ管ç
æ§æ管çããªã·ã¼åã³æé ã«å¾ãããã¼ãã¦ã¨ã¢ã»ãã¡ã¼ã ã¦ã¨ã¢ã»ã½ããã¦ã¨ã¢ã»ææ¸ã¸
ã®å¤æ´ã管çããã·ã¹ãã å®è£
åã»ä¸ã»å¾ã®ä¸é©åãªæ¹å¤ããæ
å ±ã·ã¹ãã ãä¿è·ããã
NIST SP 800-53 ã®æ§æ管çï¼CMï¼ãã¡ããªã«å«ã¾ããã»ãã¥ãªãã£å¯¾çã«ã¯ãæ
å ±ã·ã¹ãã
ã®ãã¼ã¹ã©ã¤ã³ç®¡çãçå®ããããã®ããªã·ã¼åã³æé ãå®ãããã¦ãããæ§æ管çã®å¤æ´
ãç¶æã»ç£è¦ã»è¨é²ããããã®ç®¡çããããæ§æè¨å®ã¸ã®ã¢ã¯ã»ã¹ã¯å¶éãããIT 製åã®ã»
ãã¥ãªãã£è¨å®ã¯ãICS æ¥åè¦ä»¶ã«å¾ãæãå³æ ¼ãªã¢ã¼ãã«è¨å®ãã¹ãã§ããã
CM 管çã®è£è¶³çã¬ã¤ãã³ã¹ã以ä¸ã®ææ¸ã«æ²è¼ããã¦ããã
ï¼ NIST SP 800-70ï¼IT 製åã®æ§æè¨å®ã«ä¿ãã¬ã¤ãã³ã¹[26]
ï¼ NIST SP 800-100ï¼æ
å ±ã»ãã¥ãªãã£ã¬ããã³ã¹åã³ãã©ã³ãã³ã°ã«ä¿ãã¬ã¤ãã³ã¹[27]
ï¼ NIST SP 800-128 ã«ãã»ãã¥ãªãã£éè¦æ§æ管çããã°ã©ã ã«ä¿ãã¬ã¤ãã³ã¹[80]ã

SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
159
ICS-specific Recommendations and Guidance
A formal change management program should be established and procedures used to insure that all
modifications to an ICS network meet the same security requirements as the original components identified
in the asset evaluation and the associated risk assessment and mitigation plans. Risk assessment should be
performed on all changes to the ICS network that could affect security, including configuration changes,
the addition of network components, and installation of software. Changes to policies and procedures may
also be required. The current ICS network configuration and device configurations must always be known
and documented.
6.2.6 Contingency Planning
Contingency plans are designed to maintain or restore business operations, including computer operations,
possibly at an alternate location, in the event of emergencies, system failures, or disaster. The security
controls that fall within the NIST SP 800-53 Contingency Planning (CP) family provide policies and
procedures to implement a contingency plan by specifying roles and responsibilities, and assigning
personnel and activities associated with restoring the information system after a disruption or failure. Along
with planning, controls also exist for contingency training, testing, and plan update, and for backup
information processing and storage sites.
Supplemental guidance for the CP controls can be found in the following documents:
ï¼ NIST SP 800-34 provides guidance on contingency planning [52].
ï¼ NIST SP 800-100 provides guidance on information security governance and planning [27].
ICS-specific Recommendations and Guidance
Contingency plans should cover the full range of failures or problems that could be caused by cyber
incidents. Contingency plans should include procedures for restoring systems from known valid backups,
separating systems from all non-essential interferences and connections that could permit cybersecurity
intrusions, and alternatives to achieve necessary interfaces and coordination. Employees should be trained
and familiar with the contents of the contingency plans. Contingency plans should be periodically reviewed
with employees responsible for restoration of the ICS, and tested to ensure that they continue to meet their
objectives. Organizations also have business continuity plans and disaster recovery plans that are closely
related to contingency plans. Because business continuity and disaster recovery plans are particularly
important for ICS, they are described in more detail in the sections to follow.
6.2.6.1 Business Continuity Planning
Business continuity planning addresses the overall issue of maintaining or reestablishing production in the
case of an interruption. These interruptions may take the form of a natural disaster (e.g., hurricane, tornado,
earthquake, flood), an unintentional man-made event (e.g., accidental equipment damage, fire or explosion,
operator error), an intentional man-made event (e.g., attack by bomb, firearm or vandalism, attacker or
virus), or an equipment failure. From a potential outage perspective, this may involve typical time spans of
days, weeks, or months to recover from a natural disaster, or minutes or hours to recover from a malware
infection or a mechanical/electrical failure. Because there is often a separate discipline
that deals with reliability and electrical/mechanical maintenance, some organizations choose to define
business continuity in a way that excludes these sources of failure. Because business continuity also deals
primarily with

SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
160
ICS
åºæã®æ¨å¥¨äºé
åã³ã¬ã¤ãã³ã¹
æ£è¦ã®å¤æ´ç®¡çããã°ã©ã ãçå®ããICS ãããã¯ã¼ã¯ã¸ã®å
¨ã¦ã®å¤æ´å
容ããè³ç£è©ä¾¡è¨ç»
æ¸åã³é¢é£ãªã¹ã¯è©ä¾¡ã»ç·©åè¨ç»æ¸ã«ç¹å®ãããå½åã®ã³ã³ãã¼ãã³ãã¨åãã»ãã¥ãªãã£
è¦ä»¶ã«åè´ããããã«æé ãè¡ä½¿ããªããã°ãªããªãããªã¹ã¯è©ä¾¡ã¯ãã»ãã¥ãªãã£ã«å½±é¿
ãã ICS ãããã¯ã¼ã¯ã¸ã®å
¨ã¦ã®å¤æ´ã«å¯¾ãã¦è¡ãã¹ãã§ãããã«ã¯æ§æå¤æ´ããããã¯ã¼
ã¯ã³ã³ãã¼ãã³ãã®è¿½å ãã½ããã¦ã¨ã¢ã®ã¤ã³ã¹ãã¼ã«ãå«ã¾ãããããªã·ã¼åã³æé ã®å¤
æ´ãå¿
è¦ã¨ãªããç¾å¨ã® ICS ãããã¯ã¼ã¯æ§æã¨ããã¤ã¹æ§æã¯å¸¸ã«ç¥ããããè¨é²ããã¦
ããªããã°ãªããªãã
6.2.6 ä¸æ¸¬äºæ
è¨ç»
ç·æ¥æ対å¿è¨ç»ã¯ãç·æ¥æã»ã·ã¹ãã é害æã»ç½å®³æã«ä»£æ¿å°ãªã©ã§ã³ã³ãã¥ã¼ã¿ãæä½ã
ããªã©ãæ¥åãç¶æã»å¾©æ§ããããã«ä½æãããã NIST SP 800-53 ã®ä¸æ¸¬äºæ
è¨ç»ï¼CPï¼ã
ã¡ããªã«å«ã¾ããã»ãã¥ãªãã£å¯¾çã¯ãå½¹å²ã¨è²¬ä»»ãå®ããä¸æã»æ
éå¾ã®æ
å ±ã·ã¹ãã ã®
復æ§ã«é¢é£ãã人å¡ã»æ´»åãå²ãå½ã¦ã¦ãä¸æ¸¬äºæ
è¨ç»ãå®è¡ããããã®ããªã·ã¼åã³æé
ãå®ãã¦ããã
ãã©ã³ãã³ã°ã®ã¿ãªããã管çã¯ãä¸æ¸¬äºæ
対å¦è¨ç·´ã試é¨ãè¨ç»ã®æ´æ°ãããã¯ã¢ããæ
å ±
å¦çã»ä¿ç®¡ãµã¤ãã«ã¤ãã¦ãåãä¸ãã¦ããã
CP 管çã®è£è¶³çã¬ã¤ãã³ã¹ã以ä¸ã®ææ¸ã«æ²è¼ããã¦ããã
ï¼ NIST SP 800-34ï¼ä¸æ¸¬äºæ
è¨ç»ã®ç«æ¡ã«ä¿ãã¬ã¤ãã³ã¹[52]
ï¼ NIST SP 800-100ï¼æ
å ±ã»ãã¥ãªãã£ã¬ããã³ã¹åã³ãã©ã³ãã³ã°ã«ä¿ãã¬ã¤ãã³ã¹[27]
ICS
åºæã®æ¨å¥¨äºé
åã³ã¬ã¤ãã³ã¹
ç·æ¥æ対å¿è¨ç»ã¯ããµã¤ãã¼ã¤ã³ã·ãã³ãã«ããçãå¾ãããããé害ãåé¡ã«ã¤ãã¦åãä¸ã
ãã¹ãã§ãããç·æ¥æ対å¿è¨ç»ã«ã¯ãæ¢ç¥ã®æå¹ããã¯ã¢ããããã·ã¹ãã ã復æ§ãããµã¤ãã¼
ã»ãã¥ãªãã£ä¾µå
¥ã許ãéè¦ã§ãªãå
¨ã¦ã®å¹²æ¸ã»æ¥ç¶ããã·ã¹ãã ãåé¢ããããã®ããªã·ã¼å
ã³æé ã®ã»ããå¿
è¦ãªã¤ã³ã¿ãã§ã¼ã¹ã»èª¿æ´ãå®ç¾ããããã®ä»£æ¿æ¹æ³ãå«ããã¹ãã§ãããå¾
æ¥å¡ã¯è¨ç·´ãåããä¸æ¸¬äºæ
è¨ç»ã®å
容ã«ç²¾éãã¦ããã¹ãã§ãããè¨ç»æ¸ã¯ãICS ã®å¾©æ§æ
å½
è
ã¨ã¨ãã«å®æçã«è¦ç´ãã常ã«ç®çã«åè´ãã¦ããã試é¨ãè¡ãã¹ãã§ãããçµç¹ã¯ãç·æ¥æ
対å¿è¨ç»ã¨å¯æ¥ãªé¢ãããæã¤äºæ¥ç¶ç¶è¨ç»æ¸ã¨ç½å®³å¾©æ§è¨ç»æ¸ãä¿æããã両è¨ç»æ¸ã¯ç¹ã«
ICS ã«ã¨ã£ã¦éè¦ã§ãããããç¶ãã»ã¯ã·ã§ã³ã§è©³è¿°ããã
6.2.6.1 äºæ¥ç¶ç¶è¨ç»
äºæ¥ç¶ç¶è¨ç»ã®ç«æ¡ã§ã¯ãä¸ææã®çç£ã®ç¶æåã¯åéã«é¢ããå
¨è¬çãªåé¡ãåãä¸ããã
ä¸æã«ã¯èªç¶ç½å®³ï¼ããªã±ã¼ã³ããã«ãã¼ããå°éã洪水çï¼ã人çºçãªäºæããªãäºè±¡ï¼å¶
çºçãªè£
ååã®æ害ãç«ç½ã»ççºãæä½ãã¹çï¼ã人çºçãªæ
æã®äºè±¡ï¼çå¼¾ãéå¨ã»ç ´å£è¡
çºã«ããæ»æãæ»æè
ã»ã¦ã¤ã«ã¹çï¼ãè£
ååã®æ
éãªã©ããããææ¥åæ¢ã®è¦³ç¹ããããã¨ã
èªç¶ç½å®³ããã®å¾©æ§ã«ã¯ä¸è¬ã«æ¥ã»é±ã»æåä½ã®æéãè¦ãããã«ã¦ã¨ã¢ææãæ©æ¢°ã»é»åç
æ
éã®å ´åã¯åã»æéåä½ã¨ãªãã
SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
161
that deals with reliability and electrical/mechanical maintenance, some organizations choose to define
business continuity in a way that excludes these sources of failure. Because business continuity also deals
primarily with the long-term implications of production outages, some organizations also choose to place a
minimum interruption limit on the risks to be considered. For the purposes of ICS cybersecurity, it is
recommended that neither of these constraints be made. Long-term outages (disaster recovery) and short-
term outages (operational recovery) should both be considered. Because some of these potential
interruptions involve man-made events, it is also important to work collaboratively with the physical
security organization to understand the relative risks of these events and the physical security
countermeasures that are in place to prevent them. It is also important for the physical security organization
to understand which areas of a production site house data acquisition and control systems that might have
higher-level risks.
Before creating a business continuity plan (BCP) to deal with potential outages, it is important to specify
the recovery objectives for the various systems and subsystems involved based on typical business needs.
There are two distinct types of objectives: system recovery and data recovery. System recovery involves
the recovery of communication links and processing capabilities, and it is usually specified in terms of a
Recovery Time Objective (RTO). This is defined as the time required to recover the required
communication links and processing capabilities. Data recovery involves the recovery of data describing
production or product conditions in the past and is usually specified in terms of a Recovery Point Objective
(RPO). This is defined as the longest period of time for which an absence of data can be tolerated.
Once the recovery objectives are defined, a list of potential interruptions should be created and the recovery
procedure developed and described. For most of the smaller scale interruptions, repair and replace activities
based on a critical spares inventory will prove adequate to meet the recovery objectives. When this is not
true, contingency plans need to be developed. Due to the potential cost and importance of these
contingency plans, they should be reviewed with the managers responsible for business continuity planning
to verify that they are justified. Once the recovery procedures are documented, a schedule should be
developed to test part or all of the recovery procedures. Particular attention must be paid to the verification
of backups of system configuration data and product or production data. Examples of system configuration
data include computer configuration backups, application configuration backups, operational control limits,
control bands and setpoints for pre-incident operation for all ICS programmable equipment. Not only
should these be tested when they are produced, but the procedures followed for their storage should also be
reviewed periodically to verify that the backups are kept in environmental conditions that will not render
them unusable and that they are kept in a secure location, so they can be quickly obtained by authorized
individuals when needed.
SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
162
ä¿¡é ¼æ§ãé»æ°ã»æ©æ¢°ã®ä¿å®ã«é¢ããå¥ã®è¦åãå¤åã«ãããããçµç¹ã«ãã£ã¦ã¯ãã®ãããªæ
é
åå ãæé¤ããä¸ã§äºæ¥ç¶ç¶ãå®ãã¦ããã¨ããããããäºæ¥ç¶ç¶ã¯ã主ã«é·æçãªææ¥åæ¢ã®
å¶ç´ãæ±ããããèæ
®ãã¹ããªã¹ã¯ã«æçä¸æéçãè¨å®ãã¦ããçµç¹ããããICS ãµã¤ãã¼ã»
ãã¥ãªãã£ã®ç®çä¸ããã®ãããªå¶ç´äºé
ã¯è¨ããªããã¨ãè¦ãããããé·æææ¥åæ¢ï¼ç½å®³å¾©
æ§ï¼ã¨çæææ¥åæ¢ï¼æ¥å復æ§ï¼ã®ä¸¡æ¹ãæ¤è¨ãã¹ãã§ããããã®ãããªä¸æã«ã¯äººçºçãªäºè±¡
ãå«ã¾ãããããç©ççã»ãã¥ãªãã£çµç¹ã¨é£æºãã¦ãããããäºè±¡ã®ç¸å¯¾çãªã¹ã¯ã¨ãããã
é²æ¢ããããã«è¬ãããã¦ããç©ççã»ãã¥ãªãã£å¯¾çã«ã¤ãã¦ç解ãããã¨ãèè¦ã§ãããã¾
ãç©ççã»ãã¥ãªãã£çµç¹ããçç£ç¾å ´ã®ã©ãã«é«ãªã¹ã¯ã®ãã¼ã¿åå¾ã»å¶å¾¡ã·ã¹ãã ãããã
ãææ¡ãã¦ãããã¨ãèè¦ã§ããã
ææ¥åæ¢ãåãä¸ããäºæ¥ç¶ç¶è¨ç»æ¸ï¼BCPï¼ãä½æããåã«ãä¸è¬çãªäºæ¥ãã¼ãºã«åºã¥ãã
種ã
ã®ã·ã¹ãã ã»ãµãã·ã¹ãã ã®å¾©æ§å¯¾è±¡ãæå®ãããã¨ãèè¦ã§ããã復æ§å¯¾è±¡ã¯ã·ã¹ãã
ã¨ãã¼ã¿ã® 2種é¡ã§ãããã·ã¹ãã 復æ§ã¯ãéä¿¡ãªã³ã¯ã¨å¦çæ©è½ã®å¾©æ§ãé¢ä¿ããé常ãç®
æ¨å¾©æ§æéï¼RTOï¼ã¨ãã¦å®ãããã¦ãããããã¯å¿
é éä¿¡ãªã³ã¯åã³å¦çæ©è½ã復æ§ããã
ãã®æéã¨ãã¦å®ç¾©ãããããã¼ã¿å¾©æ§ã¯ãéå»ã®çç£åã¯è£½åç¶æ
ãè¨è¿°ãããã¼ã¿ã®å¾©æ§
ãé¢ä¿ããé常ãç®æ¨å¾©æ§æç¹ï¼RPOï¼ã¨ãã¦å®ãããã¦ãããããã¯ãã¼ã¿ããªãã¦ã許容
ã§ããæé·æéã¨ãã¦å®ç¾©ãããã
復æ§å¯¾è±¡ãå®ãããªããä¸æå¯è½æ§ãªã¹ããä½æãã復æ§æé ãä½æãè¨è¿°ãã¹ãã§ããã大
æµã®å°è¦æ¨¡ä¸æã§ã¯ãéè¦è£ç¨åå¨åº«ã«åºã¥ãä¿®çã»äº¤æã§å¾©æ§å¯¾è±¡ã«åå対å¿ã§ããããã
ãå½ã¦ã¯ã¾ããªãå ´åã«ã¯ãç·æ¥æ対å¿è¨ç»ãä½æããå¿
è¦ããããç·æ¥æ対å¿è¨ç»ã®ã³ã¹ã
ã¨éè¦æ§ãããç·æ¥æ対å¿è¨ç»ã¯äºæ¥ç¶ç¶ãã©ã³ãã³ã°æ
å½ç®¡çè
ã¨ã¨ãã«è¦ç´ãããã®å¦¥å½
æ§ãæ¤è¨¼ãã¹ãã§ããã復æ§æé ãææ¸åãããªãã復æ§æé ã®ä¸é¨åã¯å
¨é¨ã®è©¦é¨ãè¡ãã
ãã®ã¹ã±ã¸ã¥ã¼ã«ãç«ã¦ãã¹ãã§ãããã·ã¹ãã æ§æãã¼ã¿åã³è£½åã»çç£ãã¼ã¿ã®ããã¯ã¢
ããæ¤è¨¼ã«ã¯ãç¹ã«æ³¨æãæããªããã°ãªããªããã·ã¹ãã æ§æãã¼ã¿ã®ä¾ã¨ãã¦ãã³ã³ãã¥
ã¼ã¿æ§æããã¯ã¢ãããã¢ããªã±ã¼ã·ã§ã³æ§æããã¯ã¢ãããæ¥åä¸ã®ç®¡çéçãå
¨ã¦ã® ICS
ããã°ã©ã å¯è½è£
ååã®ã¤ã³ã·ãã³ãåã®ç®¡çç¯å²ã»è¨å®ç¹çããããããã¯ã¢ããã¯ä½æã®
é½åº¦è©¦é¨ãè¡ãã ãã§ãªãããããã®ä¿åæé ãå®æçã«è¦ç´ãã¦ãããã¯ã¢ãããç°å¢æ¡ä»¶
ã«é©åãã¦å©ç¨å¯è½ã§ãã»ãã¥ã¢ãªå ´æã«ä¿ç®¡ãããå¿
è¦ãªå ´åã«ã¯æ¨©éã®ãã人å¡ãããã«
å
¥æã§ããããã«ãªã£ã¦ãããæ¤è¨¼ããã

SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
163
6.2.6.2 Disaster Recovery Planning
A disaster recovery plan (DRP) is a documented process or set of procedures to recover and protect an IT
infrastructure in the event of a disaster. The DRP, ordinarily documented in written form, specifies
procedures an organization is to follow in the event of a disaster. It is a comprehensive statement of
consistent actions to be taken before, during and after a disaster. The disaster could be natural,
environmental or man-made. Man-made disasters could be intentional or unintentional.
ICS-specific Recommendations and Guidance
A DRP is essential to continued availability of the ICS. The DRP should include the following items:
ï¼ Required response to events or conditions of varying duration and severity that would activate the
recovery plan.
ï¼ Procedures for operating the ICS in manual mode with all external electronic connections severed
until secure conditions can be restored.
ï¼ Roles and responsibilities of responders.
ï¼ Processes and procedures for the backup and secure storage of information.
ï¼ Complete and up-to-date logical network diagram.
ï¼ Personnel list for authorized physical and cyber access to the ICS.
ï¼ Communication procedure and list of personnel to contact in the case of an emergency including ICS
vendors, network administrators, ICS support personnel, etc.
ï¼ Current configuration information for all components.
ï¼ Schedule for exercising the DRP.
The plan should also indicate requirements for the timely replacement of components in the case of an
emergency. If possible, replacements for hard-to-obtain critical components should be kept in inventory.
The security plan should define a comprehensive backup and restore policy. In formulating this policy, the
following should be considered:
ï¼ The speed at which data or the system must be restored. This requirement may justify the need for a
redundant system, spare offline computer, or valid file system backups.
ï¼ The frequency at which critical data and configurations are changing. This will dictate the frequency
and completeness of backups.
ï¼ The safe onsite and offsite storage of full and incremental backups.
ï¼ The safe storage of installation media, license keys, and configuration information.
ï¼ Identification of individuals responsible for performing, testing, storing, and restoring backups.

SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
164
6.2.6.2 ç½å®³å¾©æ§è¨ç»
ç½å®³å¾©æ§è¨ç»ï¼DRPï¼ã¯ãç½å®³æã« IT ã¤ã³ãã©ã復æ§ãä¿è·ããããã®ææ¸åãããããã»ã¹
åã¯æé ã§ãããDRP ã¯é常ææ¸åãããç½å®³æã«çµç¹ãåãæé ãå®ãããç½å®³åã»ä¸ã»å¾ã«
åãã¹ãä¸è²«ããè¡åã«ã¤ãã¦ãå
æ¬çã«è¨è¿°ãããç½å®³ã¯èªç¶ç°å¢ã®å ´åãããã°ã人çºçãª
ãã®ãããã人çºç½å®³ã¯æ
æåã¯å¶çºã«ããçããã
ICS åºæã®æ¨å¥¨äºé
åã³ã¬ã¤ãã³ã¹
DRP ã¯ãICS ã®å¯ç¨æ§ãä¿æããããã«ä¸å¯æ¬ ã§ãããDRP ã«ã¯ä»¥ä¸ãå«ããã¹ãã§ããã
ï¼ å¾©æ§è¨ç»æ¸ãçºåãããäºè±¡åã¯ç¶æ
ã®æéã¨é大æ§ã«å¿ãã¦æ±ãããã対å¿
ï¼ å¤é¨ã¸ã®é»åæ¥ç¶ãå
¨ã¦æãããä¸ã§ãã»ãã¥ã¢ãªç¶æ
ã«å¾©æ§ããã¾ã§ãæåã¢ã¼ã㧠ICS
ã稼åãããããã®æé
ï¼ å¯¾å¿è
ã®å½¹å²ã¨è²¬ä»»
ï¼ æ
å ±ã®ããã¯ã¢ããã¨ã»ãã¥ã¢ãªä¿åãè¡ãããã®ããã»ã¹ã¨æé
ï¼ å®å
¨ãªææ°ã®è«çãããã¯ã¼ã¯å³
ï¼ ICS ã¸ã®ç«å
¥åã³ãµã¤ãã¼ã¢ã¯ã»ã¹æ¨©éã®ãã人å¡ãªã¹ã
ï¼ ç·æ¥æã®éä¿¡æé åã³é£çµ¡ç¸æã®ãªã¹ãï¼ICS ãã³ãã¼ããããã¯ã¼ã¯ç®¡çè
ãICS ãµãã¼
ãè¦å¡çãå«ããï¼
ï¼ å
¨ã¦ã®ã³ã³ãã¼ãã³ãã®ææ°æ§ææ
å ±
ï¼ DRP æ¼ç¿ã¹ã±ã¸ã¥ã¼ã«
è¨ç»æ¸ã«ã¯ãç·æ¥æã®ã³ã³ãã¼ãã³ããé©æ交æããããã®è¦ä»¶ãå«ããã¹ãã§ãããã§ããã°
å
¥æå°é£ãªéè¦ã³ã³ãã¼ãã³ãã®ä»£æ¿åã¯ãå¨åº«ããã¦ããã¹ãã§ããã
ã»ãã¥ãªãã£è¨ç»æ¸ã¯ãå
æ¬çãªããã¯ã¢ããåã³å¾©æ§ããªã·ã¼ãå®ããã¹ãã§ãããããªã·ã¼
ã®çå®ã«å½ãã£ã¦ã¯ã次ã®ç¹ãèæ
®ã«å
¥ããã¹ãã§ããã
ï¼ ãã¼ã¿åã¯ã·ã¹ãã ã®å¾©æ§ã«è¦ããé度ããã®è¦ä»¶ããããã¨ããåé·ã·ã¹ãã ãã¹ãã¢ã®
ãªãã©ã¤ã³ã³ã³ãã¥ã¼ã¿åã¯æå¹ãã¡ã¤ã«ã·ã¹ãã ããã¯ã¢ãããå¿
è¦ã¨ãããã
ï¼ éè¦ãã¼ã¿åã³æ§æå¤æ´ã®é »åº¦ãããã«ããããã¯ã¢ããã®é »åº¦ãå®å
¨æ§ã決ã¾ãã
ï¼ å
¨é¢ããã¯ã¢ããåã³å·®åããã¯ã¢ããã®å®å
¨ãªãªã³ãµã¤ãåã³ãªããµã¤ãä¿ç®¡
ï¼ ã¤ã³ã¹ãã¼ã«ã¡ãã£ã¢ãã©ã¤ã»ã³ã¹ãã¼åã³è¨å®æ
å ±ã®å®å
¨ãªä¿ç®¡
ï¼ ããã¯ã¢ããã®å®æ½ã»è©¦é¨ã»ä¿ç®¡ã»å¾©æ§æ
å½è
ã®ç¹å®
SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
165
6.2.7 Identification and Authentication
Authentication describes the process of positively identifying potential network users, hosts, applications,
services, and resources using a combination of identification factors or credentials. The result of this
authentication process then becomes the basis for permitting or denying further actions (e.g., when an
automatic teller machine asks for a PIN). Based on the authentication determination, the system may or
may not allow the potential user access to its resources. Authorization is the process of determining who
and what should be allowed to have access to a particular resource; access control is the mechanism for
enforcing authorization. Access control is described in Section 6.2.1.
There are several possible factors for determining the authenticity of a person, device, or system, including
something you know, something you have or something you are. For example, authentication could be
based on something known (e.g., PIN number or password), something possessed (e.g., key, dongle, smart
card), something you are such as a biological characteristic (e.g., fingerprint, retinal signature), a location
(e.g., Global Positioning System [GPS] location access), the time a request is made, or a combination of
these attributes. In general, the more factors that are used in the authentication process, the more robust the
process will be. When two or more factors are used, the process is known generically as multi-factor
authentication.
The security controls that fall within the NIST SP 800-53 Identification and Authentication (IA) family
provide policy and guidance for the identification and authentication of users of and devices within the
information system. These include controls to manage identifiers and authenticators within each technology
used (e.g., tokens, certificates, biometrics, passwords, key cards).
Supplemental guidance for the IA controls can be found in the following documents:
ï¼ NIST SP 800-63 provides guidance on remote electronic authentication [53].
ï¼ NIST SP 800-73 provides guidance on interfaces for personal identity verification [49].
ï¼ NIST SP 800-76 provides guidance on biometrics for personal identity verification [50].
ï¼ NIST SP 800-100 provides guidance on information security governance and planning [27].
ICS-specific Recommendations and Guidance
Computer systems in ICS environments typically rely on traditional passwords for authentication. Control
system suppliers often supply systems with default passwords. These passwords are factory set and are
often easy to guess or are changed infrequently, which creates additional security risks. Also, protocols
currently used in ICS environments generally have inadequate or no network service authentication. There
are now several forms of authentication available in addition to traditional password techniques being used
with ICS. Some of these, including password authentication, are presented in the following sections with
discussions regarding their use with ICS.
SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
166
6.2.7 èå¥åã³èªè¨¼
èªè¨¼ã¯ããããã¯ã¼ã¯ã¦ã¼ã¶ããã¹ããã¢ããªã±ã¼ã·ã§ã³ããµã¼ãã¹åã³ãªã½ã¼ã¹ãèå¥è¦ç´
ãèªè¨¼æ
å ±ãçµã¿åããã¦ãè½åçã«èå¥ããããã»ã¹ã§ãããèªè¨¼ããã»ã¹ã®çµæãã次ã®
ã¢ã¯ã·ã§ã³ã許å¯ãããæ絶ãããã®æ ¹æ ã¨ãªãï¼ATM ã®PIN è¦æ±æçï¼ãèªè¨¼å¤å®ã«åºã¥ãã
ã·ã¹ãã ã¯ã¦ã¼ã¶ã®ãªã½ã¼ã¹ã¸ã®ã¢ã¯ã»ã¹ã許å¯åã¯æ絶ããã権éä»ä¸ã¨ã¯ãç¹å®ã®ãªã½ã¼
ã¹ã«ã¢ã¯ã»ã¹ã許ããã主ä½ãå¤å®ããããã»ã¹ã®ãã¨ã§ãã¢ã¯ã»ã¹å¶å¾¡ã¨ã¯æ¨©éä»ä¸ãè¡ã
ã¡ã«ããºã ããããã¢ã¯ã»ã¹å¶å¾¡ã«ã¤ãã¦ã¯ã»ã¯ã·ã§ã³ 6.2.1 ã§èª¬æããã
å人ãããã¤ã¹åã¯ã·ã¹ãã ã®æ£å½æ§ãå¤å®ããè¦ç´ ãããã¤ããããå人ãç¥ã£ã¦ããã
ã¨ãæã£ã¦ãããã®åã¯ä½è
ã§ããããªã©ã§ãããä¾ãã°ãèªè¨¼ã¯æ¢ç¥ã®äºæï¼PIN çªå·ãã
ã¹ã¯ã¼ãçï¼ãææç©ï¼ãã¼ããã³ã°ã«ãã¹ãã¼ãã«ã¼ãçï¼ãçç©å¦çç¹å¾´çã®å人æ
å ±
ï¼æç´ã網èç
§åçï¼ãå ´æï¼å
¨å°ç測ä½ã·ã¹ãã [GPS]ä½ç½®ã¢ã¯ã»ã¹çï¼ãè¦æ±æå»åã¯ã
ããå±æ§ãä½µç¨ãã¦è¡ããããç·ãã¦ãèªè¨¼ããã»ã¹ã§å©ç¨ããè¦ç´ ãå¢ããã°å¢ããã»ã©ã
ããã»ã¹ã¯å¼·åã«ãªãã2ã¤ä»¥ä¸ã®è¦ç´ ãå©ç¨ããããã»ã¹ã¯å¤è¦ç´ èªè¨¼ã¨ãã¦ç¥ããã¦ããã
NIST SP 800-53 ã®èå¥åã³èªè¨¼ï¼IAï¼ãã¡ããªã«å«ã¾ããã»ãã¥ãªãã£å¯¾çã¯ãæ
å ±ã·ã¹ã
ã ã«ãããã¦ã¼ã¶åã³ããã¤ã¹ã®èå¥åã³èªè¨¼ã«ä¿ãããªã·ã¼åã³ã¬ã¤ãã³ã¹ãå®ãã¦ããã
使ç¨ãããåæè¡ï¼ãã¼ã¯ã³ã証ææ¸ããã¤ãªã¡ããªã¯ã¹ããã¹ã¯ã¼ãããã¼ã«ã¼ãçï¼ã§ã®
èå¥åã³èªè¨¼ã®ç®¡çãå«ã¾ãã¦ããã
IA 管çã®è£è¶³çã¬ã¤ãã³ã¹ã以ä¸ã®ææ¸ã«æ²è¼ããã¦ããã
ï¼ NIST SP 800-63ï¼é éé»åèªè¨¼ã«ä¿ãã¬ã¤ãã³ã¹[53]
ï¼ NIST SP 800-73ï¼å人身å
確èªã¤ã³ã¿ãã§ã¼ã¹ã«ä¿ãã¬ã¤ãã³ã¹[49]
ï¼ NIST SP 800-76ï¼å人身å
確èªãã¤ãªã¡ããªã¯ã¹ã«ä¿ãã¬ã¤ãã³ã¹[50]
ï¼ NIST SP 800-100ï¼æ
å ±ã»ãã¥ãªãã£ã¬ããã³ã¹åã³ãã©ã³ãã³ã°ã«ä¿ãã¬ã¤ãã³ã¹[27]
ICS
åºæã®æ¨å¥¨äºé
åã³ã¬ã¤ãã³ã¹
ICS ç°å¢ã«ãããã³ã³ãã¥ã¼ã¿ã·ã¹ãã ã¯ãä¸è¬ã«ä¼çµ±çãªèªè¨¼ãã¹ã¯ã¼ãã«ä¾åãã¦ãããå¶
御ã·ã¹ãã ãµãã©ã¤ã¤ã¯ãããã©ã«ãã®ãã¹ã¯ã¼ããè¨å®ãã¦ã·ã¹ãã ãä¾çµ¦ãããã¨ãå¤ãã
ãã¹ã¯ã¼ãã¯å·¥å ´ã§è¨å®ãããç°¡åã«æ¨æ¸¬ã§ãããã®ãå¤ããæ»
å¤ã«å¤æ´ãããªããã¨ãããã»
ãã¥ãªãã£ãªã¹ã¯ã¨ãªããã¾ãç¾å¨ ICS ç°å¢ã§å©ç¨ããã¦ãããããã³ã«ã®ãããã¯ã¼ã¯ãµã¼ã
ã¹èªè¨¼ã¯ãç·ãã¦ä¸é©åã§ãããå
¨ããªããç¾å¨ã§ã¯ãICS ã§å©ç¨ãããä¼çµ±çãªãã¹ã¯ã¼ãæ
è¡ã«å ãã¦ãããã¤ãã®èªè¨¼å½¢æ
ãããããã¹ã¯ã¼ãèªè¨¼ãå«ãããããã®ããã¤ãã ICS ã§å©
ç¨ãããã¨ã«ã¤ãã¦ãç¶ãã»ã¯ã·ã§ã³ã§èª¬æããã

SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
167
6.2.7.1 Password Authentication
Password authentication technologies determine authenticity based on testing for something the device or
human requesting access should know, such as a PIN number or password. Password authentication
schemes are thought of as the simplest and most common forms of authentication.
Password vulnerabilities can be reduced by using an active password checker that prohibits weak, recently
used, or commonly used passwords. Another weakness is the ease of third-party eavesdropping. Passwords
typed at a keyboard are easily observed or recorded, especially in areas where adversaries could plant tiny
wireless cameras or keystroke loggers. Network service authentication often transmits passwords as
plaintext (unencrypted), allowing any network capture tool to expose the passwords.
ICS-specific Recommendations and Guidance
One problem with passwords unique to the ICS environment is that a userâs ability to recall and enter a
password may be impacted by the stress of the moment. During a major crisis when human intervention is
critically required to control the process, an operator may panic and have difficulty remembering or
entering the password and either be locked out completely or be delayed in responding to the event. If the
password has been entered wrong and the system has a limit on allowed wrong password entries, the
operator may be locked out permanently until an authorized employee can reset the account. Biometric
identifiers may have similar drawbacks. Organizations should carefully consider the security needs and the
potential ramifications of the use of authentication mechanisms on these critical systems.
In situations where the ICS cannot support, or the organization determines it is not advisable (e.g.,
performance, safety, or reliability are adversely impacted), to implement authentication mechanisms in an
ICS, the organization uses compensating controls, such as rigorous physical security controls (e.g., control
center keycard access for authorized users) to provide an equivalent security capability or level of
protection for the ICS. This guidance also applies to the use of session lock and session termination in an
ICS.
Special consideration must be made when pushing down policies based on login password authentication
within the ICS environment. Without an exclusion list based on machine identification (ID), non-operator
logon can result in policies being pushed down such as auto- logoff timeout and administrator password
replacement that can be detrimental to the operation of the system.
Some ICS operating systems make setting secure passwords difficult, as the password size is very small
and the system allows only group passwords at each level of access, not individual passwords. Some
industrial (and Internet) protocols transmit passwords in plaintext, making them susceptible to interception.
In cases where this practice cannot be avoided, it is important that users have different (and unrelated)
passwords for use with encrypted and non-encrypted protocols.
The following are general recommendations and considerations with regards to the use of passwords.
ï¼ The length, strength, and complexity of passwords should balance security and operational ease of
access within the capabilities of the software and underlying OS.
ï¼ Passwords should have appropriate length and complexity for the required security. In particular, they
should not be able to be found in a dictionary or contain predictable sequences of numbers or letters.

SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
168
6.2.7.1 ãã¹ã¯ã¼ãèªè¨¼
ãã¹ã¯ã¼ãèªè¨¼æè¡ã¯ãã¢ã¯ã»ã¹ãæ±ãã¦ããããã¤ã¹ã人ãç¥ã£ã¦ããã¹ãæ
å ±ï¼PIN çªå·ã
ãã¹ã¯ã¼ãçï¼ãæ¤è¨¼ãã¦æ£å½æ§ãå¤å®ããæè¡ã§ããããã¹ã¯ã¼ãèªè¨¼æ³ã¯ãèªè¨¼ã®æãåç´
ãã¤æ
£ç¨çãªå½¢ã¨è¦ãªããã¦ããã
ãã¹ã¯ã¼ãã®èå¼±æ§ã¯ãåç´ãªãã®ãæè¿ä½¿ç¨ãããã®ããã使ç¨ããããã®ãç¦æ¢ããã¢ã¯ã
ã£ããã¹ã¯ã¼ããã§ãã«ã¼ãå©ç¨ãããã¨ã§æ¸ãããã¨ãã§ãããå¥ã®å¼±ç¹ã¯ããµã¼ããã¼ãã£
ã容æã«ååã§ãããã¨ã§ããããã¼ãã¼ãã§ã¿ã¤ããããã¹ã¯ã¼ãã¯ãç¹ã«æ»æå´ãå°åã¯ã¤
ã¤ã¬ã¹ã«ã¡ã©ããã¼ã¹ããã¼ã¯ãã¬ã¼ãè¨ç½®ããå ´æã§ã¯ã容æã«è¦³å¯åã¯è¨é²ã§ãããããã
ã¯ã¼ã¯ãµã¼ãã¹èªè¨¼ã¯ããã¹ã¯ã¼ããå¹³æï¼æå·åãªãï¼ã§éä¿¡ãããã¨ãå¤ãããããã¯ã¼ã¯
ãã£ããã£ãã¼ã«ãããã°ãã¹ã¯ã¼ããé²è¦ãã¦ãã¾ãã
ICS åºæã®æ¨å¥¨äºé
åã³ã¬ã¤ãã³ã¹
ICS ã«ä¸æã®ãã¹ã¯ã¼ãã使ç¨ããåé¡ç¹ã¯ãã¦ã¼ã¶ããã¹ã¯ã¼ããæãåºãã¦å
¥åããè½å
ã¯ããã®ã¨ãã®ã¹ãã¬ã¹ã«å½±é¿ããããã¨ã«ãããå±æ©ã®éã«ãããã»ã¹ã®å¶å¾¡ã«äººã®å¯¾å¿ãæ¯
éã¨ãå¿
è¦ã¨ãããå ´åãæä½å¡ããããã¯ã«é¥ãããã¹ã¯ã¼ããæãåºããã«ãã°ã¤ã³ã§ããª
ãã£ããã対å¿ãé
ããããããã¨ããããééã£ããã¹ã¯ã¼ããå
¥åããã·ã¹ãã ã«ééãã
ã¹ã¯ã¼ãã®å
¥åå¶éãããå ´åããã®æä½å¡ã¯ã権éã®ããå¾æ¥å¡ãã¢ã«ã¦ã³ãããªã»ãããã
ã¾ã§ããã£ã¨ãã°ã¤ã³ã§ããªããªãããã¤ãªã¡ããªãã¯èå¥åã«ãåæ§ã®æ¬ é¥ããããçµç¹ã¯ã
ã»ãã¥ãªãã£ãã¼ãºã¨éè¦ã·ã¹ãã ã«ãããèªè¨¼ã¡ã«ããºã ã®å©ç¨ã«é¢ããåé¡ã«ã¤ãã¦æ
éã«
æ¤è¨ãã¹ãã§ããã
ICS ã対å¿ãã¦ããããå㯠ICS ã¸ã®èªè¨¼ã¡ã«ããºã ã®å®è£
ãä¸é©åã¨å¤æããå ´åï¼ããã©ã¼
ãã³ã¹ãå®å
¨æ§ãä¿¡é ¼æ§ãä½ä¸ãããªã©ï¼ãçµç¹ã¯å³æ ¼ãªç©ççã»ãã¥ãªãã£å¯¾ççã®ä»£æ¿ç®¡ç
ãå©ç¨ãã¦ï¼å¶å¾¡ã»ã³ã¿ã¼ã¸ã®ã権éã®ããã¦ã¼ã¶ã«ãããã¼ã«ã¼ããå©ç¨ããç«å
¥çï¼ãICS
ã®åçã®ã»ãã¥ãªãã£æ©è½åã¯ä¿è·ã¬ãã«ã確ä¿ããããã®ã¬ã¤ãã³ã¹ã¯ãICS ã®ã»ãã·ã§ã³ã
ãã¯åã³ã»ãã·ã§ã³çµäºã«ãå½ã¦ã¯ã¾ãã
ICS ç°å¢ã§ã®ãã°ã¤ã³ãã¹ã¯ã¼ãèªè¨¼ãåºã«ãããªã·ã¼ãå¼ãä¸ããå ´åã¯ãç¹å¥ãªèæ
®ãè¦ã
ãããã·ã³ ID ã«åºã¥ãæé¤ãªã¹ãããªãå ´åãæä½å¡ä»¥å¤ã®ãã°ãªã³ã¯ãã·ã¹ãã ã®åä½ãæª
åãããèªåãã°ãªãã¿ã¤ã ã¢ã¦ãã管çè
ãã¹ã¯ã¼ãã®ç½®æã¨ãã£ããããªã·ã¼ã®å¼ãä¸ãã
çãå¾ãã
ICS ã®OS ã«ãã£ã¦ã¯ããã¹ã¯ã¼ããµã¤ãºãçããåã¬ãã«ã§ã®ã¢ã¯ã»ã¹æãã·ã¹ãã ãå人ã
ã¹ã¯ã¼ãã§ã¯ãªãã°ã«ã¼ããã¹ã¯ã¼ãã®ã¿åãä»ããããã«ãªã£ã¦ãããããã»ãã¥ã¢ãªãã¹ã¯
ã¼ãè¨å®ãå°é£ã§ãããç¹å®ã®ç£æ¥ç¨ï¼åã³ã¤ã³ã¿ã¼ãããï¼ãããã³ã«ã¯ããã¹ã¯ã¼ããå¹³æ
ã§éä¿¡ããããååãããããããã®è¦ç¯ã®å©ç¨ãé¿ããããªãå ´åãã¦ã¼ã¶ã¯å¥ã®ï¼ç¡é¢ä¿
ãªï¼ãã¹ã¯ã¼ããæã¡ãæå·åãããã³ã«åã³éæå·åãããã³ã«ã§å©ç¨ãããã¨ãèè¦ã§ã
ãã
以ä¸ã¯ãã¹ã¯ã¼ãã®å©ç¨ã«é¢ããä¸è¬çãªæ¨å¥¨äºé
åã³èæ
®äºé
ã§ããã
ï¼ ãã¹ã¯ã¼ãã®é·ãã強度åã³è¤éãã¯ãã½ããã¦ã¨ã¢åã³ä½¿ç¨ OS ã®è½åå
ã§ãã»ãã¥ãªã
ã£ã¨ã¢ã¯ã»ã¹ããããã®ãã©ã³ã¹ãåãã¹ãã§ããã
ï¼ ãã¹ã¯ã¼ãã®é·ãã¨è¤éãã¯ãå¿
è¦ãªã»ãã¥ãªãã£ã«è¦åã£ããã®ã¨ãã¹ãã§ãããç¹ã«è¾
æ¸ã«è¼ã£ã¦ããç¨èªããæ°åãæåã®é åºãäºæ³å¯è½ãªãã®ã¯ä½¿ç¨ãã¹ãã§ãªãã

SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
169
ï¼ Passwords should be used with care on operator interface devices such as control consoles on critical
processes. Using passwords on these consoles could introduce potential safety issues if operators are
locked out or delayed access during critical events. Physical security should supplement operator
control consoles when password protection is not feasible.
ï¼ The keeper of master passwords should be a trusted employee, available during emergencies. Any
copies of the master passwords must be stored in a very secure location with limited access.
ï¼ The passwords of privileged users (such as network technicians, electrical or electronics technicians
and management, and network designers/operators) should be most secure and be changed frequently.
Authority to change master passwords should be limited to trusted employees. A password audit
record, especially for master passwords, should be maintained separately from the control system.
ï¼ In environments with a high risk of interception or intrusion (such as remote operator interfaces in a
facility that lacks local physical security access controls), organizations should consider
supplementing password authentication with other forms of authentication such as multi-factor
authentication using biometric or physical tokens.
ï¼ For user authentication purposes, password use is common and generally acceptable for users logging
directly into a local device or computer. Passwords should not be sent across any network unless
protected by some form of FIPS-approved encryption or salted cryptographic hash specifically
designed to prevent replay attacks. It is assumed that the device used to enter a password is connected
to the network in a secure manner.
ï¼ For network service authentication purposes, passwords should not be passed as plain text. There are
more secure alternatives available, such as challenge/response or public key authentication.
6.2.7.2 Challenge/response Authentication
Challenge/response authentication requires that both the service requester and service provider know a
âsecretâ code in advance. When service is requested, the service provider sends a random number or string
as a challenge to the service requester. The service requester uses the secret code to generate a unique
response for the service provider. If the response is as expected, it proves that the service requester has
access to the âsecretâ without ever exposing the secret on the network.
Challenge/response authentication addresses the security vulnerabilities of traditional password
authentication. When passwords (hashed or plain) are sent across a network, a portion of the actual âsecretâ
itself is being sent, giving the secret to the remote device performs authentication. Therefore, traditional
password exchange always suffers the risk of discovery or replay. Because the secret is known in advance
and never sent in challenge/response systems, the risk of discovery is eliminated. If the service provider can
never send the same challenge twice, and the receiver can detect all duplications, the risks of network
capture and replay attacks are eliminated.

SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
170
ï¼
éè¦ããã»ã¹ã®å¶å¾¡ã³ã³ã½ã¼ã«çãæä½å¡ã¤ã³ã¿ãã§ã¼ã¹ããã¤ã¹ã§ã¯ããã¹ã¯ã¼ãã注æ
æ·±ã使ç¨ãã¹ãã§ããããã®ãããªã³ã³ã½ã¼ã«ä¸ã§ã®ãã¹ã¯ã¼ãã®ä½¿ç¨ã¯ãç·æ¥æã«æä½å¡
ããã°ã¤ã³ã§ãããåã¯å¯¾å¿ãé
ããå ´åã«ãå®å
¨ä¸ã®åé¡ãçèµ·ããããã¹ã¯ã¼ãä¿è·ã
å©ç¨ã§ããªãå ´åãç©ççã»ãã¥ãªãã£ã¯æä½å¡å¶å¾¡ã³ã³ã½ã¼ã«ãè£å®ãããã®ã¨ãªãã
ï¼ ãã¹ã¿ã¼ãã¹ã¯ã¼ãã®ä¿ç®¡è
ã¯ãç·æ¥æã«é£çµ¡ãä»ãä¿¡é ¼ã®ç½®ããå¾æ¥å¡ã¨ãã¹ãã§ããã
ãã¹ã¿ã¼ãã¹ã¯ã¼ãã®åããä½æããå ´åã¯ãç«å
¥ãå¶éãããå®å
¨ãªå ´æã«ä¿ç®¡ããªãã
ã°ãªããªãã
ï¼ ç¹æ¨©ã¦ã¼ã¶ï¼ãããã¯ã¼ã¯æè¡è
ãé»æ°ã»é»åæ師ã»ç®¡çè
ããããã¯ã¼ã¯è¨è¨è
ã»æä½å¡
çï¼ã®ãã¹ã¯ã¼ãã¯ã»ãã¥ã¢ã§ãé »ç¹ã«å¤æ´ãã¹ãã§ããããã¹ã¿ã¼ãã¹ã¯ã¼ãã®å¤æ´æ¨©é
ã¯ä¿¡é ¼ã®ç½®ããå¾æ¥å¡ã«éå®ãã¹ãã§ããããã¹ã¯ã¼ãç£æ»è¨é²ãç¹ã«ãã¹ã¿ã¼ãã¹ã¯ã¼ã
ç¨ã¯ãå¶å¾¡ã·ã¹ãã ããç¬ç«ãã¦ä¿ç®¡ãã¹ãã§ããã
ï¼ åååã¯ä¾µå
¥ãªã¹ã¯ã®é«ãç°å¢ï¼ãã¼ã«ã«ã®ç©ççã»ãã¥ãªãã£ç«å
¥å¶éã®ãªãæ½è¨ã«ãã
ãé éæä½å¡ã¤ã³ã¿ãã§ã¼ã¹çï¼ã§ã¯ãçµç¹ã¯ããã¤ãªã¡ããªãã¯ãç©ççãã¼ã¯ã³ãå©ç¨
ããå¤è¦ç´ èªè¨¼çãå¥å½¢æ
ã®è£è¶³çãã¹ã¯ã¼ãèªè¨¼ãèæ
®ãã¹ãã§ããã
ï¼ ã¦ã¼ã¶èªè¨¼ç®çã§ã¯ããã¹ã¯ã¼ãã®å©ç¨ã¯ä¸è¬çã§ãã¦ã¼ã¶ãç´æ¥ãã¼ã«ã«ããã¤ã¹ãã³ã³
ãã¥ã¼ã¿ã«ãã°ã¤ã³ããæ¹æ³ã¨ãã¦åºãåãå
¥ãããã¦ãããç¹å®ã®å½¢æ
ã® FIPS æ¿èªæå·
åã¯ãªãã¬ã¼æ»æé²æ¢ç¨ã½ã«ãä½µç¨æå·å¦çããã·ã¥ã§ä¿è·ããã¦ããªãå ´åããã¹ã¯ã¼ã
ããããã¯ã¼ã¯ãè¶ãã¦éä¿¡ãã¹ãã§ãªãããã¹ã¯ã¼ãå
¥åããã¤ã¹ã¯ãã»ãã¥ã¢ãªæ¹æ³ã§
ãããã¯ã¼ã¯æ¥ç¶ããã¦ãããã¨ãåæã§ããã
ï¼ ãããã¯ã¼ã¯ãµã¼ãã¹èªè¨¼ç®çã§ã¯ããã¹ã¯ã¼ããå¹³æã§æ¸¡ãã¹ãã§ãªããããã以å¤ã«
ãããã£ã¬ã³ã¸/ã¬ã¹ãã³ã¹èªè¨¼ãå
¬ééµèªè¨¼çã®ã»ãã¥ã¢ãªä»£æ¿æ段ãããã
6.2.7.2 ãã£ã¬ã³ã¸/ã¬ã¹ãã³ã¹èªè¨¼
ãã£ã¬ã³ã¸/ã¬ã¹ãã³ã¹èªè¨¼ã¯ããµã¼ãã¹ã®è¦æ±å´ã¨æä¾å´ãåãã£ã¦ãç§å¯ã®ãã³ã¼ããç¥ã£
ã¦ããªããã°ãªããªãããµã¼ãã¹è¦æ±ãããã¨ããµã¼ãã¹ãããã¤ãã¯ã©ã³ãã ãªæ°åãæåå
ããã£ã¬ã³ã¸ã¨ãã¦è¦æ±è
ã«éä¿¡ãããè¦æ±è
ã¯ç§å¯ã³ã¼ãã使ç¨ãã¦ãä¸æã®ã¬ã¹ãã³ã¹ãã
ããã¤ãåãã«çæãããã¬ã¹ãã³ã¹ãæå¾
ã©ããã ã¨ãè¦æ±è
ã¯ããç§å¯ãããããã¯ã¼ã¯ä¸
ã«ããããã¨ãªããç§å¯ã¸ã®ã¢ã¯ã»ã¹æ¨©ãæã£ã¦ãããã¨ã«ãªãã
ãã£ã¬ã³ã¸/ã¬ã¹ãã³ã¹èªè¨¼ã¯ãä¼çµ±çãªãã¹ã¯ã¼ãèªè¨¼ã®ã»ãã¥ãªãã£ä¸ã®èå¼±æ§ã«å¯¾å¿ãã
ãã®ã¨ãªãããããã¯ã¼ã¯ãè¶ãã¦ãã¹ã¯ã¼ãï¼ããã·ã¥ååã¯å¹³æï¼ãéä¿¡ãããå ´åãå®é
ã®ãç§å¯ããã®ãã®ãéä¿¡ãããç§å¯ãé éããã¤ã¹ã«ä¸ãããã¨ã§èªè¨¼ãè¡ãããããããã£
ã¦ãä¼çµ±çãªãã¹ã¯ã¼ã交æã«ã¯ã常ã«é²è¦åã¯ãªãã¬ã¼ã®ãªã¹ã¯ãã¤ãã¾ã¨ãããã£ã¬ã³ã¸/
ã¬ã¹ãã³ã¹ã·ã¹ãã ã§ã¯ç§å¯ã¯äºåã«ç¥ããããéä¿¡ãããªããããé²è¦ãªã¹ã¯ã¯æé¤ãããã
ãµã¼ãã¹ãããã¤ããåããã£ã¬ã³ã¸ãäºåº¦éããã¨ãã§ããªããã°ãåä¿¡è
ãå
¨ã¦ã®è¤è£½ãæ¢
ç¥ãã¦ãããããã¯ã¼ã¯ãã£ããã£ã¨ãªãã¬ã¼æ»æã®ãªã¹ã¯ã¯æé¤ãããã
SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
171
ICS-specific Recommendations and Guidance
For User Authentication, the direct use of challenge/response authentication may not be feasible for control
system due to the possible latency that may be introduced in the necessary fast dynamics required for
access to a control system or industrial network. For Network Service Authentication, the use of
challenge/response authentication is preferable to more traditional password or source identity
authentication schemes.
Challenge/response authentication provides more security than encrypted passwords for user authentication
across a network. Managing master encryption algorithms and master passwords becomes increasing more
complex as more parties are involved in the security processes and is an important consideration in the
robustness of the security scheme.
6.2.7.3 Physical Token Authentication
Physical or token authentication is similar to password authentication, except that these technologies
determine authenticity by testing for secret code or key produced by a device or token the person requesting
access has in their possession, such as security tokens or smart cards. Increasingly, private keys are being
embedded in physical devices such as USB dongles. Some tokens support single-factor authentication only,
so that simply having possession of the token is sufficient to be authenticated. Others support multi-factor
authentication that requires knowledge of a PIN or password in addition to possessing the token.
The primary vulnerability that token authentication addresses is easily duplicating a secret code or sharing
it with others. It eliminates the all-too-common scenario of a password to a âsecureâ system being left on
the wall next to a PC or operator station. The security token cannot be duplicated without special access to
equipment and supplies.
A second benefit is that the secret within a physical token can be very large, physically secure, and
randomly generated. Because it is embedded in metal or silicon, it does not have the same risks that
manually entered passwords do. If a security token is lost or stolen, the authorized user loses access, unlike
traditional passwords that can be lost or stolen without notice.
Common forms of physical/token authentication include:
ï¼ Traditional physical lock and keys.
ï¼ Security cards (e.g., magnetic, smart chip, optical coding).
ï¼ Radio frequency devices in the form of cards, key fobs, or mounted tags.
ï¼ Dongles with secure encryption keys that attach to the USB, serial, or parallel ports of computers.
ï¼ One-time authentication code generators (e.g., key fobs).
For single-factor authentication, the largest weakness is that physically holding the token means access is
granted (e.g., anyone finding a set of lost keys now has access to whatever they open). Physical/token
authentication is more secure when combined with a second form of authentication, such as a memorized
PIN used along with the token.
SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
172
ICS åºæã®æ¨å¥¨äºé
åã³ã¬ã¤ãã³ã¹
ã¦ã¼ã¶èªè¨¼ã«é¢ãã¦ãå¶å¾¡ã·ã¹ãã ã§ã¯ãã£ã¬ã³ã¸/ã¬ã¹ãã³ã¹èªè¨¼ã®ç´æ¥çãªä½¿ç¨ã¯ä¸å¯è½ã
ããããªããã¨è¨ãã®ã¯ãå¶å¾¡ã·ã¹ãã åã¯ç£æ¥ç¨ãããã¯ã¼ã¯ã¸ã®ã¢ã¯ã»ã¹ã«å¿
è¦ã¨ãããé«
éãã¤ããã¯ã¹ã§ã¯ãå¾
ã¡æéãçããããªãããã§ããããããã¯ã¼ã¯ãµã¼ãã¹èªè¨¼ã§ã¯ãã
ã£ã¬ã³ã¸/ã¬ã¹ãã³ã¹èªè¨¼ã®ä½¿ç¨ã¯ãä¼çµ±çãªãã¹ã¯ã¼ãæ¹å¼ãã½ã¼ã¹èå¥èªè¨¼æ¹å¼ãããæã¾
ããã
ãããã¯ã¼ã¯ãè¶ããã¦ã¼ã¶èªè¨¼ã§ã¯ããã£ã¬ã³ã¸/ã¬ã¹ãã³ã¹èªè¨¼ã®ã»ãã¥ãªãã£ã¯æå·ãã¹
ã¯ã¼ããããå¼·ãããã¹ã¿ã¼æå·ã¢ã«ã´ãªãºã åã³ãã¹ã¿ã¼ãã¹ã¯ã¼ãã®ç®¡çã¯ãã»ãã¥ãªãã£
ããã»ã¹ã«é¢ä¿ããå½äºè
ãå¢ããã«ã¤ãã¦ãã¾ãã¾ãè¤éã«ãªã£ã¦ãããã»ãã¥ãªãã£ä½å¶ã®
å
ç¢æ§ã«ãããéè¦ãªèæ
®äºé
ã§ããã
6.2.7.3 ç©ççãã¼ã¯ã³èªè¨¼
ç©ççåã¯ãã¼ã¯ã³èªè¨¼ã¯ãã¹ã¯ã¼ãèªè¨¼ã«ä¼¼ã¦ããããéãã¯ã¢ã¯ã»ã¹è¦æ±è
ãæã£ã¦ã
ãããã¤ã¹ããã¼ã¯ã³ï¼ã»ãã¥ãªãã£ãã¼ã¯ã³ãã¹ãã¼ãã«ã¼ãï¼ãçæããç§å¯ã³ã¼ãã
ãã¼ãæ¤è¨¼ãã¦èªè¨¼ãå¤å¥ããç¹ã«ãããã¾ãã¾ã USB ãã³ã°ã«çã®ç©ççããã¤ã¹ã«ãã©
ã¤ãã¼ããã¼ãåãè¾¼ã¾ããããã«ãªã£ã¦ãããåè¦ç´ èªè¨¼ã«ãã対å¿ãã¦ããªããã¼ã¯ã³
ãããããã¼ã¯ã³ãæã£ã¦ãããããã°èªè¨¼ã«ååã¨ãããã¨ã§ããããã¼ã¯ã³ã®ä¿æã«å
ãã¦ãPIN ããã¹ã¯ã¼ããè¦æ±ããå¤è¦ç´ èªè¨¼ã«å¯¾å¿ãããã®ãããã
ãã¼ã¯ã³èªè¨¼ã®ä¸»ãªèå¼±æ§ã¯ãç§å¯ã³ã¼ãã®è¤è£½ã容æãªãã¨ã¨ä»äººã¨ã®å
±æãå¯è½ãªãã¨ã§
ããããã¼ã¯ã³ã使ãã°ããã»ãã¥ã¢ãªãã·ã¹ãã ã®ãã¹ã¯ã¼ãã PC ãæä½å¡ã¹ãã¼ã·ã§ã³
ã®è¿ãã«æ¸ãã¨ã©ãã¦ãããããªãããããã·ããªãªã¯ãªããªããã»ãã¥ãªãã£ãã¼ã¯ã³ã®è¤
製ã¯ãè£
ååããµãã©ã¤åã¸ã®ç¹å¥ãªã¢ã¯ã»ã¹æ¨©ããªããã°ã§ããªãã
2ã¤ç®ã®å©ç¹ã¯ãç©ççãã¼ã¯ã³å
é¨ã®ç§å¯ã¯ãµã¤ãºã大ãããç©ççã«ã»ãã¥ã¢ã§ãã©
ã³ãã çæããããéå±ãã·ãªã³ã³ã«åãè¾¼ã¾ãã¦ãããããããã¥ã¢ã«æä½ã§ãã¹ã¯ã¼
ããå
¥åãããããªãªã¹ã¯ã¯ãªããã»ãã¥ãªãã£ãã¼ã¯ã³ããªãããå ´åãçã¾ããå ´åã
ã¦ã¼ã¶ã¯ã¢ã¯ã»ã¹æ¨©ã失ããããã¯æ°ã¥ããªããã¡ã«ãªããããçã¾ããããããã¹ã¯ã¼
ãã¨ã®éãã§ããã
ç©çç/ãã¼ã¯ã³èªè¨¼ã®å
±éå½¢æ
ã¨ãã¦æ¬¡ã®ãã®ãããã
ï¼ ä¼çµ±çãªç©çããã¯ã¨ãã¼
ï¼ ã»ãã¥ãªãã£ã«ã¼ãï¼ç£æ°ãã¹ãã¼ãããããå
ã³ã¼ãã£ã³ã°çï¼
ï¼ ã«ã¼ãããã¼ãã©ãåã¯åä»ãã¿ã°çã®ç¡ç·å¨æ³¢æ°ããã¤ã¹
ï¼ USBãã³ã³ãã¥ã¼ã¿ã®ã·ãªã¢ã«åã¯ãã©ã¬ã«ãã¼ãã«åãä»ããã»ãã¥ã¢ãªæå·éµä»ããã³
ã°ã«
ï¼ ã¯ã³ã¿ã¤ã èªè¨¼ã³ã¼ãã¸ã§ãã¬ã¼ã¿ï¼ãã¼ãã©ãçï¼
åè¦ç´ èªè¨¼ã®æ大ã®å¼±ç¹ã¯ããã¼ã¯ã³ãç©ççã«ä¿æãã¦ããã°ã¢ã¯ã»ã¹ã§ãããã¨ã«ãã
ï¼éµæã®æ¾å¾è
ã¯ä»äººã®å®¶ã«èªç±ã«åºå
¥ãã§ããï¼ãç©çç/ãã¼ã¯ã³èªè¨¼ã¯ãå¥å½¢æ
ã®èªè¨¼ã¨
ä½µç¨ããã¨ã»ãã¥ãªãã£ãåä¸ããï¼è¨æ¶ãã PIN ã¨ã®ä½µç¨ãªã©ï¼ã

SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
173
ICS-specific Recommendations and Guidance
Multi-factor authentication is an accepted good practice for access to ICS applications from outside the ICS
firewall.
Physical/token authentication has the potential for a strong role in ICS environments. An access card or
other token can be an effective form of authentication for computer access, as long as the computer is in a
secure area (e.g., once the operator has gained access to the room with appropriate secondary
authentication, the card alone can be used to enable control actions).
6.2.7.4 Smart Card Authentication
Smart cards are similar to token authentication, but can provide additional functionality. Smart cards can be
configured to run multiple on-board applications to support building access, computer dual-factor or triple-
factor authentication and cashless vending on a single card, while also acting as the company photo ID for
the individual.
Typically, smart cards come in a credit card size form-factor that can be printed, embossed, and
individually personalized. Smart cards can be customized, individualized, and issued in-house or
outsourced to service providers who typically issue hundreds of thousands of cards per day.
Smart cards enhance software-only solutions, such as password authentication, by offering an additional
authentication factor and removing the human element in memorizing complex secrets. They also:
ï¼ Isolate security-critical computations, involving authentication, digital signatures, and key exchange
from other parts of the system that do not have a need to know.
ï¼ Enable portability of credentials and other private information between multiple computer systems.
ï¼ Provide tamper-resistant storage for protecting private keys and other forms of personal information.
The majority of issues are logistical around issuing the cards, particularly to replace lost or stolen cards.
ICS-specific Recommendations and Guidance
Although smart cards are relatively inexpensive and offer useful functionality in an industrial control
system context, their implementation must be done within the overall security context of the plant. The
necessary identification of individuals, issuance of cards, revocation should compromise be suspected, and
the assignment of authorizations to authenticated identities, represents a significant initial and on-going
challenge. In some cases corporate IT or other resources may be available to assist in the deployment of
smart card and public key based infrastructures.
If smart cards are implemented in an industrial control setting, provisions for management of lost or
damaged cards should be considered, as well as the costs to incorporate a respective access control system
and provide a management process for card distribution and retrieval.

SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
174
ICS åºæã®æ¨å¥¨äºé
åã³ã¬ã¤ãã³ã¹
å¤è¦ç´ èªè¨¼ã¯ãICS ãã¡ã¤ã¢ã¦ã©ã¼ã«å¤ãã ICS ã¢ããªã±ã¼ã·ã§ã³ã«ã¢ã¯ã»ã¹ããéã®åãå
¥ã
ãããåªè¯è¦ç¯ã§ããã
ç©çç/ãã¼ã¯ã³èªè¨¼ã¯ãICS ç°å¢ã§å¤§ããªå½¹å²ãæããå¯è½æ§ããããã¢ã¯ã»ã¹ã«ã¼ããã®ä»ã®
ãã¼ã¯ã³ã¯ãã³ã³ãã¥ã¼ã¿ãã»ãã¥ã¢ãªã¨ãªã¢ã«ããéããã³ã³ãã¥ã¼ã¿ã¸ã®å¹æçãªèªè¨¼å½¢æ
ã§ããï¼æä½å¡ã 2ã¤ç®ã®é©æ£ãªèªè¨¼ãçµã¦å®¤å
ã«ç«ã¡å
¥ãã¨ãå¶å¾¡è¡çºãè¡ãã«ã¯ã«ã¼ãã®ã¿
ã¨ãªãï¼ã
6.2.7.4 ã¹ãã¼ãã«ã¼ãèªè¨¼
ã¹ãã¼ãã«ã¼ãã¯ãã¼ã¯ã³èªè¨¼ã«ä¼¼ã¦ããããä»å çãªæ©è½ããããã¹ãã¼ãã«ã¼ãã¯ãè¤æ°
ã®ãªã³ãã¼ãã¢ããªã±ã¼ã·ã§ã³ãå®è¡ãã¦ã建ç©ã¸ã®ç«å
¥ãã³ã³ãã¥ã¼ã¿ã® 2éè¦ç´ å㯠3é
è¦ç´ èªè¨¼åã³ 1æã®ã«ã¼ãã§ã®ãã£ãã·ã¥ã¬ã¹è²©å£²ã«å¯¾å¿ã§ããããã«è¨å®å¯è½ã§ãä¼æ¥ã®å
çä»ãåäººç¨ ID ã«ã¼ãã¨ãã¦ã使ç¨ã§ããã
ä¸è¬ã«ã¹ãã¼ãã«ã¼ãã¯ã¯ã¬ã¸ããã«ã¼ããµã¤ãºã§ãå°åã»ã¨ã³ãã¹ã»åå¥åãå¯è½ã§ããã
ã«ã¹ã¿ãã¤ãºãå人å¥ã®åå¥åãå¯è½ã§ãçµç¹å
ã§çºè¡ã§ããã»ããæ°åä¸ã®ã«ã¼ããæ¯æ¥çº
è¡ãã¦ãããµã¼ãã¹ãããã¤ãã«å¤æ³¨ãããã¨ãã§ããã
ã¹ãã¼ãã«ã¼ãã¯ãä»å çãªèªè¨¼è¦ç´ ãæä¾ããè¤éãªç§å¯ãè¦ããã¨ãã人çè¦å ãæé¤ã
ããã¨ã«ããããã¹ã¯ã¼ãèªè¨¼çã®ã½ããã¦ã¨ã¢ã®ã¿ã«ä¾åããã½ãªã¥ã¼ã·ã§ã³ãæ¡å¼µããã
ã¾ã次ã®ãããªç¹å¾´ãããã
ï¼ ã»ãã¥ãªãã£ã®éè¦ãªæ¼ç®ãä¾ãã°èªè¨¼ããã¸ã¿ã«ç½²åãç¥ãå¿
è¦ã®ãªãã·ã¹ãã ã®ä»ã®é¨
ä½ããã®ãã¼äº¤æã®éé¢
ï¼ è¤æ°ã³ã³ãã¥ã¼ã¿ã·ã¹ãã éã§ã®èªè¨¼æ
å ±ãã®ä»å人æ
å ±ã®ãã¼ã¿ããªãã£ã®å®ç¾
ï¼ ãã©ã¤ãã¼ããã¼ãã®ä»ã®å人æ
å ±ã®æ¹å¤é²æ¢ä¿ç®¡
åé¡ã®å¤§åã¯ãã«ã¼ãçºè¡ã«é¢ããæ¥åçãªå
容ã§ãç¹ã«ã«ã¼ãã®ç´å¤±ã»çé£ãå¤ãã
ICS åºæã®æ¨å¥¨äºé
åã³ã¬ã¤ãã³ã¹
ã¹ãã¼ãã«ã¼ãã¯æ¯è¼çå®ä¾¡ã§ãç£æ¥ç¨å¶å¾¡ã·ã¹ãã ã«ããã¦ä¾¿å©ãªæ©è½ãçºæ®ãããããã®å®
è£
ã¯ããã©ã³ãã®å
¨ä½çãªã»ãã¥ãªãã£ãèæ
®ããä¸ã§è¡ããªããã°ãªããªããå¿
è¦ãªå人è
å¥ãã«ã¼ãçºè¡ãåæ¶ã«ãããã¤ãã¹è¦ç´ ãèæ
®ã«å
¥ãããªããèªè¨¼æ¸ã¿å人ã«å¯¾ãã権éã®ä»
ä¸ã¯ãå½åã«ããã以å¾ã大ããªèª²é¡ã¨ãªããå ´åã«ãã£ã¦ã¯ãä¼æ¥ IT ãã®ä»ã®ãªã½ã¼ã¹ãå©
ç¨ãã¦ãã¹ãã¼ãã«ã¼ãã¨å
¬ééµãã¼ã¹ã®ã¤ã³ãã©ãå±éããè³ã¨ã§ãããã
ã¹ãã¼ãã«ã¼ããç£æ¥ç¨å¶å¾¡ç°å¢ã«å®è£
ããå ´åãç´å¤±ã»æ¯æã«ã¼ãã®ç®¡çè¦å®ãããããã®ã¢
ã¯ã»ã¹å¶å¾¡ã·ã¹ãã ã®çµè¾¼ã¿ã«è¦ããã³ã¹ããæ¤è¨ããã«ã¼ãé
å¸ã»ååã®ç®¡çããã»ã¹ãå®ã
ãã¹ãã§ããã
SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
175
6.2.7.5 Biometric Authentication
Biometric authentication technologies determine authenticity by determining presumably unique biological
characteristics of the human requesting access. Usable biometric features include finger minutiae, facial
geometry, retinal and iris signatures, voice patterns, typing patterns, and hand geometry.
Like physical tokens and smart cards, biometric authentication enhances software-only solutions, such as
password authentication, by offering an additional authentication factor and removing the human element
in memorizing complex secrets. In addition, because biometric characteristics are unique to a given
individual, biometric authentication addresses the issues of lost or stolen physical tokens and smart cards.
Noted issues with biometric authentication include:
ï¼ Distinguishing a real object from a fake (e.g., how to distinguish a real human finger from a silicon-
rubber cast of one or a real human voice from a recorded one).
ï¼ Generating type-I and type-II errors (the probability of rejecting a valid biometric image, and the
probability of accepting an invalid biometric image, respectively). Biometric authentication devices
should be configured to the lowest crossover between these two probabilities, also known as the
crossover error rate.
ï¼ Handling environmental factors such as temperature and humidity to which some biometric devices
are sensitive.
ï¼ Addressing industrial applications where employees may have on safety glasses and/or gloves and
industrial chemicals may impact biometric scanners.
ï¼ Retraining biometric scanners that occasionally âdriftâ over time. Human biometric traits may also
shift over time, necessitating periodic scanner retraining.
ï¼ Requiring face-to-face technical support and verification for device training, unlike a password that
can be given over a phone or an access card that can be handed out by a receptionist.
ï¼ Denying needed access to the control system because of a temporary inability of the sensing device to
acknowledge a legitimate user.
ï¼ Being socially acceptable. Users consider some biometric authentication devices more acceptable than
others. For example, retinal scans may be considered very low on the scale of acceptability, while
thumb print scanners may be considered high on the scale of acceptability. Users of biometric
authentication devices will need to take social acceptability for their target group into consideration
when selecting among various biometric authentication technologies.
ICS-specific Recommendations and Guidance
Biometric devices make a useful secondary check versus other forms of authentication that can become lost
or borrowed. Using biometric authentication in combination with token-based access control or badge-
operated employee time clocks increases the security level. A possible application is in a control room that
is environmentally controlled and physically secured [34].
Biometrics can provide a valuable authentication mechanism, but need to be carefully assessed for
industrial applications because physical and environmental issues within the installation environment may
need to be restructured for reliable authorized authentication. The exact physical and environmental
properties of an installation should be coordinated with a system vendor or manufacturer.
SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
176
6.2.7.5 ãã¤ãªã¡ããªãã¯èªè¨¼
ãã¤ãªã¡ããªãã¯èªè¨¼æè¡ã¯ãã¢ã¯ã»ã¹è¦æ±ããå人ã®ãå人ã«åºæã¨èãããã¦ããçç©
å¦çç¹å¾´ãå¤å¥ãã¦èªè¨¼ãå¤å®ãããå©ç¨ã§ãããã¤ãªã¡ããªãã¯ç¹æ§ã«ã¯æç´ãé¡ã®è¼ªéã
網èåã³å
彩ç¹æ§ãé³å£°ãã¿ã¼ã³ãã¿ã¤ãã³ã°ãã¿ã¼ã³ãæã®è¼ªéçãããã
ç©ççãã¼ã¯ã³ãã¹ãã¼ãã«ã¼ãã¨åæ§ããã¤ãªã¡ããªãã¯èªè¨¼ã¯ãä»å çãªèªè¨¼è¦ç´ ãæ
ä¾ããè¤éãªç§å¯ãè¦ããã¨ãã人çè¦å ãæé¤ãããã¨ã«ããããã¹ã¯ã¼ãèªè¨¼çã®ã½ã
ãã¦ã¨ã¢ã®ã¿ã«ä¾åããã½ãªã¥ã¼ã·ã§ã³ãå¼·åãããã¨ãã§ãããã¾ããçç©å¦çç¹å¾´ã¯ç¹
å®ã®å人ã«åºæã§ãããã¨ããããã¤ãªã¡ããªãã¯èªè¨¼ã¯ãç©ççãã¼ã¯ã³ãã¹ãã¼ãã«ã¼
ãã®ç´å¤±ã»çé£åé¡ã«å¯¾å¿ãããã®ã¨ãªãã
ãã¤ãªã¡ããªãã¯èªè¨¼ã«ã¤ãã¦ç¥ããã¦ããåé¡ã«ã¯æ¬¡ã®ãããªãã®ãããã
ï¼ å®ç©ã¨å½ç©ã®åºå¥ï¼äººã®æã¨ååãããã·ãªã³ã³è£½ã®æãå®éã®çºå£°ã¨é²é³ãã声ã®åºå¥æ¹
æ³ï¼
ï¼ ã¿ã¤ã 1ã¨ã©ã¼ã¨ã¿ã¤ã 2ã¨ã©ã¼ã®çæï¼æå¹ãªãã¤ãªã¡ããªãã¯ç»åãæ絶ãã確çãç¡
å¹ãªãã¤ãªã¡ããªãã¯ç»åãåãå
¥ãã確çï¼ããã¤ãªã¡ããªãã¯èªè¨¼ããã¤ã¹ã¯ãããã
2ã¤ã®ç¢ºçã®éã®æä½ã®ã¯ãã¹ãªã¼ãã¼ã«è¨å®ãããã¹ãã§ãã¯ãã¹ãªã¼ãã¼èª¤å·®çã¨ãã¦
ãç¥ãããã
ï¼ ç¹å®ã®ãã¤ãªã¡ããªãã¯ããã¤ã¹ãææã«åå¿ãã温度ã»æ¹¿åº¦çã®ç°å¢å åã®å¦ç
ï¼ å¾æ¥å¡ãå®å
¨ã´ã¼ã°ã«ãã°ãã¼ããçç¨ããå·¥æ¥ç¨åå¦ç©è³ªããã¤ãªã¡ããªãã¯ã¹ãã£ãã¼
ã«å½±é¿ããç£æ¥ç¨ã¢ããªã±ã¼ã·ã§ã³ã®å¦ç
ï¼ çµæçã«ãããªããããããã¤ãªã¡ããªãã¯ã¹ãã£ãã¼ã®åè¨ç·´ã人ã®ãã¤ãªã¡ããªãã¯ç¹
æ§ã¯çµæçã«å¤åãããããã¹ãã£ãã¼ã®å®æçåè¨ç·´ãå¿
è¦ã«ãªãã
ï¼ 1対1ã®æè¡æ¯æ´ã¨ããã¤ã¹è¨ç·´ã®æ¤è¨¼ãå¿
è¦ãåä»ä¿ããé»è©±ã§æãããããã¹ã¯ã¼ããã
æ渡ãå¯è½ãªã¢ã¯ã»ã¹ã«ã¼ãã¨ç°ãªãã
ï¼ é©æ ¼ã¦ã¼ã¶ãèªç¥ããæ¤ç¥ããã¤ã¹ã®ä¸æçä¸èª¿ã«ããå¶å¾¡ã·ã¹ãã ã¸ã®ã¢ã¯ã»ã¹æå¦
ï¼ ç¤¾ä¼ã®åå
¥ãæ
å¢ããã¤ãªã¡ããªãã¯èªè¨¼ã«å¯¾ããã¦ã¼ã¶ã®å容度ã¯ããã¤ã¹ã«ããã°ãã¤
ãããããä¾ãã°ãå容度ã¯ç¶²èã¹ãã£ã³ã®å ´åä½ãã親æã®ããªã³ãã¹ãã£ãã¼ã¯é«ãã
å¤æ§ãªãã¤ãªã¡ããªãã¯æè¡ã®ä¸ãããããããé¸æããéããã¤ãªã¡ããªãã¯èªè¨¼ããã¤
ã¹ã¦ã¼ã¶ã¯ã対象ã°ã«ã¼ãã«å¯¾ãã社ä¼ã®å容度ãèæ
®ã«å
¥ããå¿
è¦ãããã
ICS
åºæã®æ¨å¥¨äºé
åã³ã¬ã¤ãã³ã¹
ãã¤ãªã¡ããªãã¯ããã¤ã¹ã¯ãç´å¤±ããã貸åãããã§ããä»ã®å½¢æ
ã®èªè¨¼ã«å¯¾ãã¦ãæç¨ãª
å¯æ¬¡çãã§ãã¯ãã§ããããã¼ã¯ã³ãã¼ã¹ã®ã¢ã¯ã»ã¹å¶å¾¡ãããã¸ææ¥ããå¾æ¥å¡ã®ã¿ã¤ã ã¬
ã³ã¼ãã¨ä½µç¨ããã°ãã»ãã¥ãªãã£ã¬ãã«ãåä¸ãããèããããç¨éã¨ãã¦ãç°å¢çã«å¶å¾¡
ããç©ççãªã»ãã¥ãªãã£ã確ä¿ããã¦ããå¶å¾¡å®¤ããã[34]ã
ãã¤ãªã¡ããªã¯ã¹ã¯è²´éãªèªè¨¼ã¡ã«ããºã ã¨ãªãããä¿¡é ¼æ§ã®é«ãèªè¨¼ãå¾ãã«ã¯è¨ç½®ç°å¢ã®
ç©çã»ç°å¢åé¡ã解決ããå¿
è¦ããããããç£æ¥ç¨éã¨ãã¦ã¯æ
éãªè©ä¾¡ãè¦ãããè¨ç½®ã®æ£
確ãªç©çã»ç°å¢ç¹æ§ã«ã¤ãã¦ãã·ã¹ãã ãã³ãã¼ãã¡ã¼ã«ã¼ã¨èª¿æ´ãã¹ãã§ããã

SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
177
6.2.8 Incident Response
An incident response plan is documentation of a predetermined set of instructions or procedures to detect,
respond to, and limit consequences of incidents against an organizationâs information systems. Response
should be measured first and foremost against the âservice being provided,â not just the system that was
compromised. If an incident is discovered, there should be a quick risk assessment performed to evaluate
the effect of both the attack and the options to respond. For example, one possible response option is to
physically isolate the system under attack. However, this may have such a dire impact on the service that it
is dismissed as not viable.
The security controls that fall within the NIST SP 800-53 Incident Response (IR) family provide policies
and procedures for incident response monitoring, handling, and reporting. The handling of a security
incident includes preparation, detection and analysis, containment, eradication, and recovery. Controls also
cover incident response training for personnel and testing the incident response capability for an
information system.
Supplemental guidance for the IR controls can be found in the following documents:
ï¼ NIST SP 800-61 provides guidance on incident handling and reporting [59].
ï¼ NIST SP 800-83 provides guidance on malware incident prevention and handling [60].
ï¼ NIST SP 800-100 provides guidance on information security governance and planning [27] .
ICS-specific Recommendations and Guidance
Regardless of the steps taken to protect an ICS, it is always possible that it may be compromised by an
intentional or unintentional incident. The following symptoms can arise from normal network problems,
but when several symptoms start to appear, a pattern may indicate the ICS is under attack and may be
worth investigating further. If the adversary is skilled, it may not be very obvious that an attack is
underway.
The symptoms of an incident could include any of the following:
ï¼ Unusually heavy network traffic.
ï¼ Out of disk space or significantly reduced free disk space.
ï¼ Unusually high CPU usage.
ï¼ Creation of new user accounts.
ï¼ Attempted or actual use of administrator-level accounts.
ï¼ Locked-out accounts.
ï¼ Account in-use when the user is not at work.
ï¼ Cleared log files.
ï¼ Full log files with unusually large number of events.

SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
178
6.2.8 ã¤ã³ã·ãã³ã対å¿
ã¤ã³ã·ãã³ã対å¿è¨ç»æ¸ã¯ãçµç¹ã®æ
å ±ã·ã¹ãã ã«å¯¾ããã¤ã³ã·ãã³ãã®çµæãæ¤ç¥ãã対å¿
ããå±éããããã®äºåã«æ±ºããããä¸é£ã®æ示åã¯æé ãææ¸åãããã®ã§ããã対å¿ã¯ã
ã¾ãè¨æ¸¬ãããã¨ãããã¦ãæä¾ä¸ã®ãµã¼ãã¹ãã«å¯¾ãã¦è¡ããã®ã§ãããæ§è½ãä½ä¸ããã·
ã¹ãã ã ãã«è¡ãã®ã§ã¯ãªããã¤ã³ã·ãã³ããçºè¦ããããªããè¿
éã«ãªã¹ã¯è©ä¾¡ãè¡ããæ»
æã®å½±é¿ã¨å¯¾å¿ãªãã·ã§ã³ã®ä¸¡æ¹ãè©ä¾¡ãããä¾ãã°ã対å¿ãªãã·ã§ã³ã®ä¸ä¾ã¨ãã¦ãæ»æã
ããã·ã¹ãã ãç©ççã«é絶ãããã¨ãã§ãããããã ããã®å¯¾å¿ã ã¨ããµã¼ãã¹ã«æ·±å»ãªå½±
é¿ãåã¶ãããå®è¡ä¸è½ã¨ä¸è¹´ãããã
NIST SP 800-53 ã®ã¤ã³ã·ãã³ã対å¿ï¼IRï¼ãã¡ããªã«å«ã¾ããã»ãã¥ãªãã£å¯¾çã«ã¯ãã¤ã³
ã·ãã³ã対å¿ã®ç£è¦ãå¦çåã³å ±åã®ããã®ããªã·ã¼åã³æé ãå®ãããã¦ãããã»ãã¥ãªã
ã£ã¤ã³ã·ãã³ãã®å¦çã«ã¯ãæºåãæ¤åºã»åæãå°ãè¾¼ããæ ¹çµ¶åã³å¾©æ§ãå«ã¾ããã管çç
ãè·å¡ã®ã¤ã³ã·ãã³ã対å¿è¨ç·´åã³æ
å ±ã·ã¹ãã ã®ã¤ã³ã·ãã³ã対å¿è½å試é¨ãå«ãã
IR 管çã®è£è¶³çã¬ã¤ãã³ã¹ã以ä¸ã®ææ¸ã«æ²è¼ããã¦ããã
ï¼ NIST SP 800-61ï¼ã¤ã³ã·ãã³ãå¦çåã³å ±åã«ä¿ãã¬ã¤ãã³ã¹[59]
ï¼ NIST SP 800-83ï¼ãã«ã¦ã¨ã¢ã¤ã³ã·ãã³ãé²æ¢åã³å¦çã«ä¿ãã¬ã¤ãã³ã¹[60]
ï¼ NIST SP 800-100ï¼æ
å ±ã»ãã¥ãªãã£ã¬ããã³ã¹åã³ãã©ã³ãã³ã°ã«ä¿ãã¬ã¤ãã³ã¹[27]
ICS
åºæã®æ¨å¥¨äºé
åã³ã¬ã¤ãã³ã¹
ICS ã®ä¿è·æé ã¨ã¯ç¡é¢ä¿ã«ãæ
æåã¯å¶çºçãªã¤ã³ã·ãã³ãã«ãã ICS ã®æ§è½ãä½ä¸ããå ´
åããããæ£å¸¸ãªãããã¯ã¼ã¯åé¡ã¨ãã¦ä»¥ä¸ã®ãããªå¾´åãè¦ãããããããã¤ãã®å¾´åã
åºå§ãããªããICS ãæ»æããã¦ãããã¨ã示ããã¿ã¼ã³ã§ããã調æ»ãè¡ãã«å¤ãããæ»æ
å´ãå·§å¦ã ã¨ãæ»æä¸ã§ãããã¨ãæ確ã«ã¯ãªããªãã
ã¤ã³ã·ãã³ãã®å¾´åã«ã¯æ¬¡ã®ãããªãã®ãããã
ï¼ ãããã¯ã¼ã¯ãã©ãã£ãã¯ãç°å¸¸ã«éã
ï¼ ãã£ã¹ã¯å®¹éããªãåã¯ç©ºã容éãèããå°ãªã
ï¼ CPU å©ç¨çãç°å¸¸ã«é«ã
ï¼ æ°è¦ã¦ã¼ã¶ã¢ã«ã¦ã³ããä½æããã¦ãã
ï¼ ç®¡çè
ã¬ãã«ã¢ã«ã¦ã³ãã使ç¨åã¯ä½¿ç¨ãããã¨ãã形跡ããã
ï¼ ã¢ã«ã¦ã³ããããã¯ã¢ã¦ãããã
ï¼ ãã®ã¦ã¼ã¶ãä¸å¨ãªã®ã«ã¢ã«ã¦ã³ãã使ç¨ããã¦ãã
ï¼ ãã°ãã¡ã¤ã«ãã¯ãªã¢ããã¦ãã
ï¼ ãã°ãã¡ã¤ã«ãä¸æ¯ã§ã¤ãã³ãæ°ãç°å¸¸ã«å¤ã

SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
179
ï¼
Antivirus or IDS alerts.
ï¼ Disabled antivirus software and other security controls.
ï¼ Unexpected patch changes.
ï¼ Machines connecting to outside IP addresses.
ï¼ Requests for information about the system (social engineering attempts).
ï¼ Unexpected changes in configuration settings.
ï¼ Unexpected system shutdown.
To minimize the effects of these intrusions, it is necessary to plan a response. Incident response planning
defines procedures to be followed when an intrusion occurs. NIST SP 800-61 Revision 2, Computer
Security Incident Handling Guide [59], provides guidance on incident response planning, which might
include the following items:
ï¼ Classification of Incidents. The various types of ICS incidents should be identified and classified as
to potential impact so that a proper response can be formulated for each potential incident.
ï¼ Response Actions. There are several responses that can be taken in the event of an incident. These
range from doing nothing to full system shutdown (although full shutdown of an ICS is a highly
unlikely response). The response taken will depend on the type of incident and its effect on the ICS
system and the physical process being controlled. A written plan documenting the types of incidents
and the response to each type should be prepared. This will provide guidance during times when there
might be confusion or stress due to the incident. This plan should include step-by-step actions to be
taken by the various organizations. If there are reporting requirements, these should be noted as well
as where the report should be made and phone numbers to reduce reporting confusion.
ï¼ Recovery Actions. The results of the intrusion could be minor, or the intrusion could cause many
problems in the ICS. Risk analysis should be conducted to determine the sensitivity of the physical
system being controlled to failure modes in the ICS. In each case, step-by-step recovery actions should
be documented so that the system can be returned to normal operations as quickly and safely as
possible. Recovery actions for an intrusion that affects operation of the ICS will closely align with the
system's Disaster Recovery Plan, and should take into account the planning and coordination already
established.
During the preparation of the incident response plan, input should be obtained from the various
stakeholders including operations, engineering, IT, system support vendors, management, organized labor,
legal, and safety. These stakeholders should also review and approve the plan.

SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
180
ï¼
ã¢ã³ãã¦ã¤ã«ã¹ã¢ã©ã¼ãåã¯
IDS
ã¢ã©ã¼ããåºã¦ãã
ï¼ ã¢ã³ãã¦ã¤ã«ã¹ã½ããã¦ã¨ã¢ãã®ä»ã®ã»ãã¥ãªãã£å¯¾çãç¡å¹ã«ãªã£ã¦ãã
ï¼ äºå®å¤ã®ãããå¤æ´ããªããã¦ãã
ï¼ ãã·ã³ãå¤é¨ IP ã¢ãã¬ã¹ã«æ¥ç¶ããã¦ãã
ï¼ ã·ã¹ãã ã«é¢ããæ
å ±è«æ±ããã£ãï¼ã½ã¼ã·ã£ã«ã¨ã³ã¸ãã¢ãªã³ã°ã®ãããã¿ï¼
ï¼ æ§æã®è¨å®ã«äºå®å¤ã®å¤æ´ããªããã¦ãã
ï¼ äºå®å¤ã®ã·ã¹ãã é®æããã£ã
ãã®ãããªä¾µå
¥ã®å½±é¿ãæå°éã«é£ãæ¢ããããã対å¿ãè¨ç»ããå¿
è¦ããããã¤ã³ã·ãã³
ã対å¿è¨ç»ã®ç«æ¡ã§ã¯ãä¾µå
¥ããã£ãéã«åãã¹ãæé ãå®ãããNIST SP 800-61 æ¹è¨ç¬¬2
çãã³ã³ãã¥ã¼ã¿ã»ãã¥ãªãã£ã¤ã³ã·ãã³ãã®å¦çã[59]ã«ã¯ãã¤ã³ã·ãã³ã対å¿è¨ç»ã®ç«
æ¡ã«ä¿ãã¬ã¤ãã³ã¹ã示ããã¦ããã以ä¸ã®é
ç®ãå«ã¾ãã¦ããã
ï¼
ã¤ã³ã·ãã³ãã®åºåã
種ã
ã® ICS ã¤ã³ã·ãã³ããèå¥ããå½±é¿åº¦ãåºåããã¤ã³ã·ãã³ãã
ã¨ã«é©æ£ãªå¯¾å¿ãåããããã«ãã¹ãã§ããã
ï¼
対å¿è¡åã
ã¤ã³ã·ãã³ãããããéã«ã¯ãåãå¾ã対å¿ãããã¤ããããä½ãããªããã¨ã
ãã·ã¹ãã ã®å
¨é¢é®æã¾ã§ããï¼ãã¡ãããICS ã®å
¨é¢é®æã¯ã»ã¼ããããã«ãªã対å¿ã§ã¯
ããï¼ã対å¿ã¯ã¤ã³ã·ãã³ãã®ã¿ã¤ããICS ã·ã¹ãã ã¸ã®å½±é¿åã³å¶å¾¡ä¸ã«ç©çããã»ã¹ã«
å¿ãã¦åããããã¤ã³ã·ãã³ãã®ã¿ã¤ãã¨åã¿ã¤ãã¸ã®å¯¾å¿ãè¨é²ããè¨ç»æ¸ãç¨æãã¹ã
ã§ããããããããã¨ãã¤ã³ã·ãã³ãã«ããæ··ä¹±ãã¹ãã¬ã¹ä¸ã«ãã£ã¦ãã¬ã¤ãã³ã¹ã¨ãª
ããè¨ç»æ¸ã«ã¯ãå¤æ§ãªçµç¹ãåãã¹ã段éãã¨ã®è¡åãå«ããã¹ãã§ãããå ±åè¦ä»¶ãã
ãã°ãå ±åå
ã®ã»ããå ±åæã®æ··ä¹±ãå°ãªãããããé»è©±çªå·ã¨ã¨ãã«ãè¦ä»¶ãè¨è¼ãã¦ã
ãã
ï¼
復æ§å¯¾çã
ä¾µå
¥ã®çµæãåãã«è¶³ããªããã¨ãããã°ãICS ã«å¤ãã®åé¡ãçãããããã¨
ãããããªã¹ã¯åæãè¡ããICS ã®æ
éæ
æ§ã«å½±é¿ãåããå¶å¾¡ä¸ã®ç©çã·ã¹ãã ã®æ度ã
å¤å®ããããããã®å ´åãã段éãã¨ã®å¾©æ§å¯¾çãææ¸åããã§ããã ãè¿
éãã¤å®å
¨ã«ã·
ã¹ãã ãæ£å¸¸æ¥åã«å¾©å¸°ã§ããããã«ãããICS ã®ç¨¼åã«å½±é¿ããä¾µå
¥ã¸ã®å¾©æ§å¯¾çã¯ãã·
ã¹ãã ã®ç½å®³å¾©æ§è¨ç»æ¸ã¨å¯æ¥ã«é£æºããæ¢ã«ãªããããã©ã³ãã³ã°ã調æ´äºé
ãèæ
®ã«å
¥
ããã¹ãã§ããã
ã¤ã³ã·ãã³ã対å¿è¨ç»æ¸ãæºåããéã«ã¯ãéç¨ãã¨ã³ã¸ãã¢ãªã³ã°ãITãã·ã¹ãã ãµãã¼ãã
ã³ãã¼ãçµå¶æãçµåå´åè
ãæ³å¾ãå®å
¨çã®é¢ä¿è
ããå¹
åºãæè¦ãèãã¹ãã§ãããã¾ãã
ããé¢ä¿è
ã¯ãè¨ç»æ¸ã®å¯©æ»ã»æ¿èªã«ãé¢ããã¹ãã§ããã

SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
181
6.2.9 Maintenance
The security controls that fall within the NIST SP 800-53 Maintenance (MA) family provide policy and
procedure for performing routine and preventative maintenance on the components of an information
system. This includes the usage of maintenance tools (both local and remote) and management of
maintenance personnel.
Supplemental guidance for the MA controls can be found in the following documents:
ï¼ NIST SP 800-63 provides guidance on electronic authentication for remote maintenance [53].
ï¼ NIST SP 800-100 provides guidance on information security governance and planning [27].
6.2.10 Media Protection
The security controls that fall within the NIST SP 800-53 Media Protection (MP) family provide policies
and procedures for limiting the access to media to authorized users. Controls also exist for labeling media
for distribution and handling requirements, as well as storage, transport, sanitization (removal of
information from digital media), destruction, and disposal of the media.
Supplemental guidance for the MP controls can be found in the following documents:
ï¼ NIST SP 800-88 provides guidance on appropriate sanitization equipment, techniques, and procedures
[78].
ï¼ NIST SP 800-100 provides guidance on information security governance and planning [27].
ICS-specific Recommendations and Guidance
Media assets include removable media and devices such as floppy disks, CDs, DVDs and USB memory
sticks, as well as printed reports and documents. Physical security controls should address specific
requirements for the safe and secure maintenance of these assets and provide specific guidance for
transporting, handling, and erasing or destroying these assets. Security requirements could include safe
storage from loss, fire, theft, unintentional distribution, or environmental damage.
If an adversary gains access to backup media associated with an ICS, it could provide valuable data for
launching an attack. Recovering an authentication file from the backups might allow an adversary to run
password cracking tools and extract usable passwords. In addition, the backups typically contain machine
names, IP addresses, software version numbers, usernames, and other data useful in planning an attack.
The use of any unauthorized CDs, DVDs, floppy disks, USB memory sticks, or similar removable media
on any node that is part of or connected to the ICS should not be permitted in order to prevent the
introduction of malware or the inadvertent loss or theft of data. Where the system components use
unmodified industry standard protocols, mechanized policy management software can be used to enforce
media protection policy.

SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
182
6.2.9 ä¿å®
NIST SP 800-53 ã®ä¿å®ï¼MAï¼ãã¡ããªã«å«ã¾ããã»ãã¥ãªãã£å¯¾çã¯ãæ
å ±ã·ã¹ãã ã³ã³ãã¼
ãã³ãã®æ常æ´åã¨äºé²æ´åã«ä¿ãããªã·ã¼åã³æé ãå®ãã¦ãããããã«ã¯æ´åãã¼ã«ï¼ã
ã¼ã«ã«ã¨é éï¼ã®å©ç¨åã³æ´åè¦å¡ã®ç®¡çãå«ã¾ããã
MA 管çã®è£è¶³çã¬ã¤ãã³ã¹ã以ä¸ã®ææ¸ã«æ²è¼ããã¦ããã
ï¼ NIST SP 800-63ï¼é éä¿å®ã®é»åèªè¨¼ã«ä¿ãã¬ã¤ãã³ã¹[53]
ï¼ NIST SP 800-100ï¼æ
å ±ã»ãã¥ãªãã£ã¬ããã³ã¹åã³ãã©ã³ãã³ã°ã«ä¿ãã¬ã¤ãã³ã¹[27]
6.2.10 ã¡ãã¤ã¢ä¿è·
NIST SP 800-53 ã®ã¡ãã¤ã¢ä¿è·ï¼MPï¼ãã¡ããªã«å«ã¾ããã»ãã¥ãªãã£å¯¾çã«ã¯ãã¡ãã£ã¢ã¸
ã®ã¢ã¯ã»ã¹ã許å¯ãåããã¦ã¼ã¶ã ãã«å¶éããããã®ããªã·ã¼åã³æé ãå®ãããã¦ããã
管çã«ã¯ãé
å¸è¦ä»¶åã³å¦çè¦ä»¶ç¨ã®ã¡ãã£ã¢ã®ã©ããªã³ã°ã®ã»ããã¡ãã£ã¢ã®ä¿ç®¡ã輸éã
ãµãã¿ã¤ãºï¼ãã¸ã¿ã«ã¡ãã£ã¢ããã®æ
å ±åé¤ï¼ãç ´å£ãç ´æ£ãå«ã¾ããã
MP 管çã®è£è¶³çã¬ã¤ãã³ã¹ã以ä¸ã®ææ¸ã«æ²è¼ããã¦ããã
ï¼ NIST SP 800-88ï¼é©åãªãµãã¿ã¤ãºè£
ååãæè¡åã³æé ã«ä¿ãã¬ã¤ãã³ã¹[78]
ï¼ NIST SP 800-100ï¼æ
å ±ã»ãã¥ãªãã£ã¬ããã³ã¹åã³ãã©ã³ãã³ã°ã«ä¿ãã¬ã¤ãã³ã¹[27]
ICS
åºæã®æ¨å¥¨äºé
åã³ã¬ã¤ãã³ã¹
ã¡ãã£ã¢è³ç£ã«ã¯ããããã¼ãã£ã¹ã¯ãCDãDVDãUSB ã¡ã¢ãªã¹ãã£ãã¯çã®åãå¤ãå¯è½
ã¡ãã£ã¢åã³ããã¤ã¹ã®ã»ãå°å·ç©ããããç©ççã»ãã¥ãªãã£å¯¾çã§ã¯ããããè³ç£ã®å®å
¨
ãã¤ã»ãã¥ã¢ãªä¿å®è¦ä»¶ãåãä¸ãããããã®è¼¸éãå¦çåã³æ¶å»åã¯ç ´å£ã«ä¿ãå
·ä½çãªã¬
ã¤ãã³ã¹ã容æãã¹ãã§ãããã»ãã¥ãªãã£è¦ä»¶ã«ã¯ãç´å¤±ã»ç«ç½ã»çé£ã»æ³å®å¤ã®é
å¸ã»ç°
å¢è¢«å®³ããã®å®å
¨ãªä¿åãå«ãããã¨ãã§ããã
æ»æå´ã ICS é¢é£ã®ããã¯ã¢ããã¡ãã£ã¢ã«ã¢ã¯ã»ã¹ããã¨ãè²´éãªãã¼ã¿ãæ»æã«å©ç¨ãã
ãå¯è½æ§ããããæ»æå´ã¯ããã¯ã¢ããããèªè¨¼ãã¡ã¤ã«ãå復ãã¦ããã¹ã¯ã¼ã解æãã¼ã«
ãå®è¡ãããã¹ã¯ã¼ããæãåããã¨ãã§ãããã¾ãããã¯ã¢ããã«ã¯é常ããã·ã³åãIP ã¢
ãã¬ã¹ãã½ããã¦ã¨ã¢ã®ãã¼ã¸ã§ã³çªå·ãã¦ã¼ã¶åãã®ä»æ»æã«å½¹ç«ã¤ãã¼ã¿ãå
¥ã£ã¦ããã
ICS ã®ä¸é¨å㯠ICS ã«æ¥ç¶ããããã¼ãä¸ã®è¨±å¯ããã¦ããªã CDãDVDãããããã¼ãã£ã¹
ã¯ãUSB ã¡ã¢ãªã¹ãã£ãã¯çã®åãå¤ãå¯è½ã¡ãã£ã¢ã®ä½¿ç¨ã¯ããã«ã¦ã¨ã¢åã¯æ³å®å¤ã®ãã¼ã¿
åªå¤±ã»çé£ãäºé²ããããã«è¨±å¯ãã¹ãã§ãªããã·ã¹ãã ã³ã³ãã¼ãã³ããæªä¿®æ£ã®æ¥çæ¨æºã
ããã³ã«ã使ç¨ããå ´åãããªã·ã¼ç®¡çã½ããã¦ã¨ã¢ãå©ç¨ãã¦ã¡ãã£ã¢ä¿è·ããªã·ã¼ãæ½è¡ã
ããã¨ãã§ããã

SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
183
6.2.11 Physical and Environmental Protection
The security controls that fall within the NIST SP 800-53 Physical and Environmental Protection (PE)
family provide policy and procedures for all physical access to an information system including designated
entry/exit points, transmission media, and display media. These include controls for monitoring physical
access, maintaining logs, and handling visitors. This family also includes controls for the deployment and
management of emergency protection controls such as emergency shutdown of the IT system, backup for
power and lighting, controls for temperature and humidity, and protection against fire and water damage.
Supplemental guidance for the PE controls can be found in the following documents:
ï¼ NIST SP 800-46 provides guidance on telecommuting and broadband communication security [51].
ï¼ NIST SP 800-100 provides guidance on information security governance and planning [27].
Physical security measures are designed to reduce the risk of accidental or deliberate loss or damage to
plant assets and the surrounding environment. The assets being safeguarded may be physical assets such as
tools and plant equipment, the environment, the surrounding community, and intellectual property,
including proprietary data such as process settings and customer information. The deployment of physical
security controls is often subject to environmental, safety, regulatory, legal, and other requirements that
must be identified and addressed specific to a given environment. The subject of deploying physical
security controls is vast and needs to be specific to the type of protection needed.
ICS-specific Recommendations and Guidance
The physical protection of the cyber components and data associated with the ICS must be addressed as
part of the overall security of a plant. Security at many ICS facilities is closely tied to plant safety. A
primary goal is to keep people out of hazardous situations without preventing them from doing their job or
carrying out emergency procedures. Physical security controls are any physical measures, either active or
passive, that limit physical access to any information assets in the ICS environment. These measures are
employed to prevent many types of undesirable effects, including:
ï¼ Unauthorized physical access to sensitive locations.
ï¼ Physical modification, manipulation, theft or other removal, or destruction of existing systems,
infrastructure, communications interfaces, personnel, or physical locations.
ï¼ Unauthorized observation of sensitive informational assets through visual observation, note taking,
photographs, or other means.
ï¼ Prevention of unauthorized introduction of new systems, infrastructure, communications interfaces, or
other hardware.
ï¼ Prevention of unauthorized introduction of devices intentionally designed to cause hardware
manipulation, communications eavesdropping, or other harmful impact.
Gaining physical access to a control room or control system components often implies gaining logical
access to the process control system as well. Likewise, having logical access to systems such as main
servers and control room computers allows an adversary to exercise control over the physical process.

SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
184
6.2.11 ç©çç°å¢ä¸ã®ä¿è·ï¼PEï¼
NIST SP 800-53 ã®ç©çç°å¢ä¸ã®ä¿è·ï¼PEï¼ãã¡ããªã«å«ã¾ãã¦ããã»ãã¥ãªãã£å¯¾çã«ã¯ãæ
å ±
ã·ã¹ãã ã¸ã®ããããç©ççç«å
¥ã«ä¿ãããªã·ã¼åã³æé ãå®ãããã¦ãããæå®ãããå
¥éå ´
ç¹ãéä¿¡åªä½ã表示åªä½ã«ã¤ãã¦è¨è¿°ããã¦ãããç©ççç«å
¥ã®ç£è¦ãè¨é²ã®ç¶æãæ¥è¨ªè
ã®å
æ±ã«é¢ãã管çãå«ã¾ãã¦ãããã¾ããã®ãã¡ããªã«ã¯ãç·æ¥ä¿è·å¯¾çã®å±éåã³ç®¡çã«é¢ãã
対çãå«ã¾ããIT ã·ã¹ãã ã®ç·æ¥é®æãé»åã»ç
§æã®ããã¯ã¢ããã温度ã»æ¹¿åº¦ç®¡çãç«ç½ã»æ°´
害対ççã«ã¤ãã¦åãä¸ãã¦ããã
PE 管çã®è£è¶³çã¬ã¤ãã³ã¹ã以ä¸ã®ææ¸ã«æ²è¼ããã¦ããã
ï¼ NIST SP 800-46ï¼å¨å®
å¤ååã³ããã¼ããã³ãéä¿¡ã«ä¿ãã¬ã¤ãã³ã¹[51]
ï¼ NIST SP 800-100ï¼æ
å ±ã»ãã¥ãªãã£ã¬ããã³ã¹åã³ãã©ã³ãã³ã°ã«ä¿ãã¬ã¤ãã³ã¹[27]
ç©ççã»ãã¥ãªãã£å¯¾çã¯ããã©ã³ãè³ç£ãå¨è¾ºç°å¢ã«å¯¾ããå¶çºçåã¯æ
æã®åªå¤±ã»æ害ãªã¹
ã¯ã軽æ¸ããããã®ãã®ã§ãããä¿è·å¯¾è±¡ãããã®ã¯ããã¼ã«ã»ãã©ã³ãè£
ååãç°å¢ãå¨è¾ºå
±
åä½ãç¥ç財ç£ï¼ããã»ã¹è¨å®ã顧客æ
å ±ã¨ãã£ãå°æãã¼ã¿ï¼çã®ç©ççè³ç£ã対象ã§ããã
ç©ççã»ãã¥ãªãã£å¯¾çã®å±éã¯ç°å¢ãå®å
¨æ§ãè¦å¶ãæ³å¾ãã®ä»ç¹å®ã®ç°å¢ã«åºæã®è¦ä»¶ã«ã
ãå·¦å³ããããã¨ãå¤ããç©ççã»ãã¥ãªãã£å¯¾çã®å±é対象ã¯åºç¯ã§ãå¿
è¦ã¨ãããä¿è·ã®ã¿
ã¤ãã«ç¹åããå¿
è¦ãããã
ICS åºæã®æ¨å¥¨äºé
åã³ã¬ã¤ãã³ã¹
ãµã¤ãã¼ã³ã³ãã¼ãã³ãåã³ ICS é¢é£ãã¼ã¿ã®ç©ççä¿è·ã¯ããã©ã³ãå
¨ä½ã®ã»ãã¥ãªãã£ã®ä¸
ç°ã¨ãã¦æ¤è¨ããªããã°ãªããªããå¤ãã® ICS æ½è¨ã®ã»ãã¥ãªãã£ã¯ããã©ã³ãã®å®å
¨æ§ã¨å¯æ¥
ã«çµã³ã¤ãã¦ããã主ãªç®æ¨ã¯ãå¾æ¥å¡ãè·åãç·æ¥æé ãéè¡ããã®ã妨ãããã¨ãªããå±éº
ç¶æ
ã«ã¯ç½®ããªããã¨ã«ãããç©ççã»ãã¥ãªãã£å¯¾çã¯ãè½åçåã¯ååçãªç©çç対çã§ã
ICS ç°å¢ã«ãããæ
å ±è³ç£ã¸ã®ç©ççç«å
¥ãå¶éããããã®ãããªå¯¾çãæ¡ç¨ãããã¨ã§ã次ã®
ãããªæã¾ãããªã種ã
ã®å½±é¿ãé²ããã¨ãã§ããã
ï¼ æ³¨æãè¦ããå ´æã¸ã®ç¡æç«å
¥
ï¼ æ¢åã·ã¹ãã ãã¤ã³ãã©ãéä¿¡ã¤ã³ã¿ãã§ã¼ã¹ãè·å¡åã¯å ´æã®ç©ççå¤æ´ãæä½ãçé£ã
ã®ä»ã®é¤å»åã¯ç ´å£
ï¼ è¦èªãã¡ã¢ãåçãã®ä»ã®æ段ã«ããè¦æ³¨ææ
å ±è³ç£ã®ç¡æåµå¯
ï¼ æ°è¦ã·ã¹ãã ãã¤ã³ãã©ãéä¿¡ã¤ã³ã¿ãã§ã¼ã¹ãã®ä»ãã¼ãã¦ã¨ã¢ã®ç¡æå°å
¥
ï¼ ãã¼ãã¦ã¨ã¢æä½ãéä¿¡ååãã®ä»æ害影é¿ãæå³ããããã¤ã¹ã®ç¡æå°å
¥
å¶å¾¡å®¤ãå¶å¾¡ã·ã¹ãã ã³ã³ãã¼ãã³ãã¸ã®ç«å
¥ã¯ãããã»ã¹å¶å¾¡ã·ã¹ãã ã¸ã®è«çã¢ã¯ã»ã¹ãå¯
è½ã«ãªããã¨ãå¤ããåæ§ã«ãã¡ã¤ã³ãµã¼ããå¶å¾¡å®¤ã®ã³ã³ãã¥ã¼ã¿çã®ã·ã¹ãã ã¸ã®è«çã¢ã¯
ã»ã¹ãå¾ãããã°ãæ»æå´ã¯ç©çããã»ã¹ãå¶å¾¡ã§ããããã«ãªãã

SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
185
If computers are readily accessible, and they have removable media drives (e.g., floppy disks, compact
discs, external hard drives) or USB ports, the drives can be fitted with locks or removed from the
computers and USB ports disabled. Depending on security needs and risks, it might also be prudent to
disable or physically protect power buttons to prevent unauthorized use. For maximum security, servers
should be placed in locked areas and authentication mechanisms (such as keys) protected. Also, the
network devices on the ICS network, including switches, routers, network jacks, servers, workstations, and
controllers, should be located in a secured area that can only be accessed by authorized personnel. The
secured area should also be compatible with the environmental requirements of the devices.
A defense-in-depth solution to physical security should include the following attributes:
ï¼ Protection of Physical Locations. Classic physical security considerations typically refer to a ringed
architecture of layered security measures. Creating several physical barriers, both active and passive,
around buildings, facilities, rooms, equipment, or other informational assets, establishes these physical
security perimeters. Physical security controls meant to protect physical locations include fences, anti-
vehicle ditches, earthen mounds, walls, reinforced barricades, gates, or other measures. Most
organizations include this layered model by preventing access to the plant first by the use of fences,
guard shacks, gates, and locked doors.
ï¼ Access Control. Access control systems should ensure that only authorized people have access to
controlled spaces. An access control system should be flexible. The need for access may be based on
time (day vs. night shift), level of training, employment status, work assignment, plant status, and a
myriad of other factors. A system must be able to verify that persons being granted access are who
they say they are (usually using something the person has, such as an access card or key; something
they know, such as a personal identification number (PIN); or something they are, using a biometric
device). Access control should be highly reliable, yet not interfere with the routine or emergency
duties of plant personnel. Integration of access control into the process system allows a view into not
only security access, but also physical and personnel asset tracking, dramatically accelerating response
time in emergencies, helping to direct individuals to safe locations, and improving overall
productivity. Within an area, access to network and computer cabinets should be limited to only those
who have a need, such as network technicians and engineers, or computer maintenance staff.
Equipment cabinets should be locked and wiring should be neat and within cabinets. Consider keeping
all computers in secure racks and using peripheral extender technology to connect human-machine
interfaces to the racked computers.
Access Monitoring Systems. Access monitoring systems include still and video cameras, sensors, and
various types of identification systems. Examples of these systems include cameras that monitor
parking lots, convenience stores, or airline security. These devices do not specifically prevent access
to a particular location; rather, they store and record either the physical presence or the lack of
physical presence of individuals, vehicles, animals, or other physical entities. Adequate lighting
should be provided based on the type of access monitoring device deployed.
Access Limiting Systems. Access limiting systems may employ a combination of devices to
physically control or prevent access to protected resources. Access limiting systems include both
active and passive security devices such as fences, doors, safes, gates, and guards. They are often
coupled with identification and monitoring systems to provide role-based access for specific
individuals or groups of individuals.
ï¼ People and Asset Tracking. Locating people and vehicles in a large installation is important for
safety reasons, and it is increasingly important for security reasons as well. Asset location
technologies can be used to track the movements of people and vehicles within the plant, to ensure
that they stay in authorized areas, to identify personnel needing assistance, and to support emergency
response.

SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
186
ã³ã³ãã¥ã¼ã¿ã¸ã®ã¢ã¯ã»ã¹ã容æã§ãåãå¤ãå¯è½ã¡ãã£ã¢ãã©ã¤ãï¼ããããã¼ãã£ã¹ã¯ã
CD
ãå¤
ä»ããã¼ããã£ã¹ã¯çï¼å㯠USB ãã¼ããä»ãã¦ããå ´åããã©ã¤ããããã¯ãããã³ã³ãã¥ã¼ã¿ã
ãåãå¤ããUSB ãã¼ããç¡å¹ã«ãããã¨ãã§ãããã»ãã¥ãªãã£ä¸ã®ãã¼ãºåã³ãªã¹ã¯ã«å¿ãã¦ã
é»æºãã¿ã³ãç¡æã§æä½ã§ããªãããã«ã使ç¨ä¸è½ã«ãããç©ççã«ä¿è·ããã®ããããã»ãã¥ãªã
ã£ãæ大åããããããµã¼ãã¯éµã®ãããã¨ãªã¢ã«ç½®ããèªè¨¼ã¡ã«ããºã ï¼ãã¼çï¼ãä¿è·ãã¹ãã§
ãããã¾ã ICS ãããã¯ã¼ã¯ä¸ã®ãããã¯ã¼ã¯ããã¤ã¹ï¼ã¹ã¤ãããã«ã¼ã¿ããããã¯ã¼ã¯ã¸ã£ã
ã¯ããµã¼ããã¯ã¼ã¯ã¹ãã¼ã·ã§ã³ãã³ã³ããã¼ã©çï¼ã¯ã許å¯ãããè·å¡ããç«ã¡å
¥ããã¨ã®ã§ããª
ãã»ãã¥ã¢ãªå ´æã«ç½®ãã¹ãã§ãããã»ãã¥ã¢ãªå ´æã¯ãããã¤ã¹ã®ç°å¢è¦ä»¶ã«ãé©åãã¦ããã¹ã
ã§ããã
ç©ççã»ãã¥ãªãã£ã®å¤å±¤é²å¾¡ã½ãªã¥ã¼ã·ã§ã³ã¯ã次ã®ãããªå±æ§ãå«ãã§ããã¹ãã§ããã
ï¼
å ´æã®ä¿è·ã
æ¢æã®ç©ççã»ãã¥ãªãã£ã§ã¯ãèæ
®äºé
ã¨ãã¦é常å¤éã»ãã¥ãªãã£å¯¾çã®
ãªã³ã°ã¢ã¼ããã¯ãã£ã«è¨åãã¦ããã建ç©ãæ½è¨ãé¨å±ãè£
ååãã®ä»æ
å ±è³ç£ã®å¨ãã«
è½åçã»ååçç©çããªã¢ã¼ãè¨ç½®ããç©ççã»ãã¥ãªãã£å¢çãæ§ç¯ãããå ´æãä¿è·ã
ãããã®ç©ççã»ãã¥ãªãã£å¯¾çã«ã¯ãã§ã³ã¹ãè»æ¢ãæºãåçããå£ãããªã±ã¼ããã²ã¼
ããã®ä»ãããã大æµã®çµç¹ã§ã¯ãã¾ããã§ã³ã¹ãã¬ã¼ããã³å¾
æ©æãã²ã¼ãåã³æ½é ãã¢
ã«ãããã©ã³ãã¸ã®ç«å
¥ãé²ããã¨ã§ããã®å¤éã¢ãã«ãåãè¾¼ãã§ããã
ï¼
ç«å
¥ç®¡çã
ç«å
¥ç®¡çã·ã¹ãã ã¯ã許å¯ãåãã人å¡ã ãã管ç空éã«ç«ã¡å
¥ããã¨ãã§ãã
ããã«ãã¹ãã§ãããç«å
¥ç®¡çã·ã¹ãã ã¯æè»æ§ãåãã¦ããã¹ãã§ãããç«å
¥ã®å¿
è¦æ§ã¯
æéï¼æ¥ä¸ã»å¤éã·ããå¤åï¼ãè¨ç·´ã¬ãã«ãéç¨å½¢æ
ãå½¹è·ããã©ã³ãã®ç¶æ
ãã®ä»å¤ç¨®
å¤æ§ãªè¦å ã§çãããã·ã¹ãã ã¯ãç«å
¥è¨±å¯ãåãã人å¡ãèªããã©ãèªç§°ãã¦ããã確èª
ã§ããªããã°ãªããªãï¼é常ãç«å
¥ã«ã¼ããéµçã®ææç©ãå人èå¥çªå·[PIN]çä½ããã®
ç¥èããã¤ãªã¡ããªãã¯ããã¤ã¹ã«ããå人æ
å ±çãå©ç¨ããï¼ãç«å
¥ç®¡çã¯é«ãä¿¡é ¼æ§ã
æã¤ã¹ãã§ãããããã©ã³ãè·å¡ã®æ常任åãç·æ¥ä»»åã妨ãã¦ã¯ãªããªããç«å
¥ç®¡çãã
ãã»ã¹ã·ã¹ãã ã«åãè¾¼ãã°ãã»ãã¥ãªãã£ã¢ã¯ã»ã¹ã®ã¿ãªãããç©ççã»äººçè³ç£ã®è¿½è·¡
ãå¯è½ã«ãªããç·æ¥æã®å¯¾å¿æéãèããç縮ãããå¾æ¥å¡ãå®å
¨ãªå ´æã¸èªå°ããå©ãã¨
ãªããå
¨ä½çãªçç£æ§ãé«ãããã¨ãã§ãããã¨ãªã¢å
ã§ã¯ããããã¯ã¼ã¯ãã³ã³ãã¥ã¼ã¿
ãã£ããããã¸ã®ã¢ã¯ã»ã¹ã¯ããããã¯ã¼ã¯æ師ã»ã¨ã³ã¸ãã¢ãã³ã³ãã¥ã¼ã¿ä¿å®è¦å¡çã
å¿
è¦ãªäººå¡ã®ã¿ã«å¶éããããè£
ååãã£ããããã¯æ½é ããé
ç·ãæ´çãã¦ãã£ãããã
å
ã«ç´ããã¹ãã§ãããå
¨ã¦ã®ã³ã³ãã¥ã¼ã¿ãå®å
¨ãªã©ãã¯ã«ç´ããå¨è¾ºå»¶é·æè¡ãå©ç¨ã
ã¦ãã©ãã¯ã®ã³ã³ãã¥ã¼ã¿ã«ãã³ãã·ã³ã¤ã³ã¿ãã§ã¼ã¹ãæ¥ç¶ããã
ç«å
¥ç£è¦ã·ã¹ãã
ãç«å
¥ç£è¦ã·ã¹ãã ã«ã¯ãããªã«ã¡ã©ãã»ã³ãµåã³å¤æ§ãªèå¥ã·ã¹ãã ã
å«ã¾ãããã·ã¹ãã ã«ã¯é§è»å ´ãã³ã³ããã¨ã³ã¹ã¹ãã¢ãèªç©ºä¼ç¤¾ã®ã»ãã¥ãªãã£ç£è¦ç¨ã®
ã«ã¡ã©ãå«ã¾ããããããããã¤ã¹ã¯ç¹å®ã®å ´æã¸ã®ç«å
¥ãé²ãã®ã§ã¯ãªããå人ãè»ä¸¡ã
åç©ãã®ä»ç©ä½ã®åå¨ã®æç¡ãä¿åãè¨é²ãããç£è¦ããã¤ã¹ã®ç¨®é¡ã«å¿ãã¦é©åãªç
§æã
åããã¹ãã§ããã
ç«å
¥å¶éã·ã¹ãã
ãç«å
¥å¶éã·ã¹ãã ã¯ãä¿è·ãªã½ã¼ã¹ãç©ççã«ç®¡çããããã¤ã¹åã¯ä¿
è·ãªã½ã¼ã¹ã¸ã®ã¢ã¯ã»ã¹ãé²æ¢ããããã¤ã¹ãä½µç¨ãããç«å
¥å¶éã·ã¹ãã ã«ã¯ããã§ã³
ã¹ããã¢ãé庫ãã²ã¼ããç£è¦çã®è½åçã»ååçã»ãã¥ãªãã£ããã¤ã¹ãå«ã¾ãããè
å¥ã»ç£è¦ã·ã¹ãã ã¨é£åãããã¨ãå¤ããç¹å®ã®å人ãã°ã«ã¼ãã«å½¹å²ã«å¿ããã¢ã¯ã»ã¹ã
ä¸ããã
ï¼
人å¡ã»è³ç£ã®è¿½è·¡ã
åºå¤§ãªç£æ¥æ½è¨ã§ã¯ãå®å
¨ä¸ã®çç±ãã人ãè»ä¸¡ãè¦ã¤ãåºããã¨ãé
è¦ã§ãã»ãã¥ãªãã£ä¸ã®çç±ãããã¾ãã¾ãéè¦ã«ãªã£ã¦ããããã©ã³ãå
ã§ã®äººãè»ä¸¡ã®
移åã追跡ã§ããè³ç£ä½ç½®æ¨å®æè¡ã使ç¨ããã°ã許å¯ã¨ãªã¢å
ã«ã¨ã©ã¾ããæ¯æ´ãå¿
è¦ã¨
ãã¦ããè·å¡ãèå¥ããç·æ¥å¯¾å¿ãæ¯æ´ã§ããã

SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
187
ï¼ Environmental Factors. In addressing the security needs of the system and data, it is important to
consider environmental factors. For example, if a site is dusty, systems should be placed in a filtered
environment. This is particularly important if the dust is likely to be conductive or magnetic, as in the
case of sites that process coal or iron. If vibration is likely to be a problem, systems should be
mounted on rubber bushings to prevent disk crashes and wiring connection problems. In addition, the
environments containing systems and media (e.g., backup tapes, floppy disks) should have stable
temperature and humidity. An alarm to the process control system should be generated when
environmental specifications such as temperature and humidity are exceeded.
ï¼ Environmental Control Systems. Heating, ventilation, and air conditioning (HVAC) systems for
control rooms must support plant personnel during normal operation and emergency situations, which
could include the release of toxic substances. Fire systems must be carefully designed to avoid causing
more harm than good (e.g., to avoid mixing water with incompatible products). HVAC and fire
systems have significantly increased roles in security that arise from the interdependence of process
control and security. For example, fire prevention and HVAC systems that support industrial control
computers need to be protected against cyber incidents.
ï¼ Power. Reliable power for the ICS is essential, so an uninterruptible power supply (UPS) should be
provided. If the site has an emergency generator, the UPS battery life may only need to be a few
seconds; however, if the site relies on external power, the UPS battery life may need to be hours. It
should be sized, at a minimum, so that the system can be shutdown safely.
6.2.11.1 Control Center/Control Room
ICS-specific Recommendations and Guidance
Providing physical security for the control center/control room is essential to reduce the potential of many
threats. Control centers/control rooms frequently have consoles continuously logged onto the primary
control server, where speed of response and continual view of the plant is of utmost importance. These
areas will often contain the servers themselves, other critical computer nodes, and sometimes plant
controllers. It is essential that access to these areas be limited to authorized users only, using authentication
methods such as smart or magnetic identity cards or biometric devices. In extreme cases, it may be
considered necessary to make the control center/control room blast-proof, or to provide an offsite
emergency control center/control room so that control can be maintained if the primary control
center/control room becomes uninhabitable.
6.2.11.2 Portable Devices
ICS-specific Recommendations and Guidance
Computers and computerized devices used for ICS functions (such as PLC programming) should never be
allowed to leave the ICS area. Laptops, portable engineering workstations and handhelds (e.g., 375 HART
communicator) should be tightly secured and should never be allowed to be used outside the ICS network.
Antivirus and patch management should be kept current.

SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
188
ï¼
ç°å¢è¦å ã
ã·ã¹ãã åã³ãã¼ã¿ã®ã»ãã¥ãªãã£ãã¼ãºãæ¤è¨ããä¸ã§ãç°å¢è¦å ãèæ
®ã«å
¥
ãããã¨ãèè¦ã§ãããä¾ãã°ãç¾å ´ãã»ããã£ã½ãå ´åããã£ã«ã¿ãå°å
¥ããç°å¢ã«ã·ã¹
ãã ãè¨ç½®ãã¹ãã§ãããç¹ã«ç³çãéã®å¦çç¾å ´ã®ããã«ã塵è¥ã«å°é»æ§ãç£æ§ãããå ´
åã«ã¯ç¹ã«éè¦ã¨ãªããæ¯åãåé¡ã«ãªãããã§ããã°ãã·ã¹ãã ãã©ãã¼ããã·ã³ã°ä¸ã«
æ®ãä»ãããã£ã¹ã¯ã¯ã©ãã·ã¥ãé
ç·æ¥ç¶ã®åé¡ãäºé²ãã¹ãã§ãããã¾ãã·ã¹ãã ã¨ã¡ã
ã£ã¢ï¼ããã¯ã¢ãããã¼ããããããã¼ãã£ã¹ã¯çï¼ãããç°å¢ã§ã¯ã温度ã»æ¹¿åº¦ãä¸å®ã«
ä¿ã¤ã¹ãã§ãããããã»ã¹å¶å¾¡ã·ã¹ãã ã®ã¢ã©ã¼ã ã¯ã温度ã»æ¹¿åº¦ã¨ãã£ãç°å¢ä»æ§ãéç
ãè¶
ããã¨ãã«çºçãã¹ãã§ããã
ï¼
ç°å¢å¶å¾¡ã·ã¹ãã ã
å¶å¾¡å®¤ã®ææ¿ææ°ç©ºèª¿ï¼HVACï¼ã·ã¹ãã ã¯ãæ£å¸¸ææ¥æåã³ç·æ¥äºæ
æã«ãã©ã³ãè·å¡ãæ¯æ´ã§ããªããã°ãªãããããã«ã¯æ¯ç©ã®æåºãå«ã¾ãããé²ç«è£
ç½®ã®
è¨è¨ã¯æ
éã«è¡ããå©ç¹ãããæ¬ ç¹ã大ãããªããªãããã«ããªããã°ãªããªãï¼æ°´ã¨ç¸å®¹
ããªãç©è³ªã®æ··ååé¿çï¼ã
ããã»ã¹å¶å¾¡ã¨ã»ãã¥ãªãã£ã®ç¸äºä¾åæ§ã«ãããHVAC ã·ã¹ãã ã¨é²ç«è£
ç½®ãã»ãã¥ãªã
ã£ã§æããå½¹å²ã¯èããå¢å¤§ãã¦ãããä¾ãã°ãç£æ¥ç¨å¶å¾¡ã³ã³ãã¥ã¼ã¿ã«å¯¾å¿ããé²ç«è£
置㨠HVAC ã·ã¹ãã ã¯ããµã¤ãã¼ã¤ã³ã·ãã³ãããå®ãå¿
è¦ãããã
ï¼
é»æºã
ICS ã«ã¯ä¿¡é ¼æ§ã®é«ãé»æºãä¸å¯æ¬ ãªãããç¡åé»é»æºè£
ç½®ï¼UPSï¼ãè£
åãã¹ãã§
ãããç¾å ´ã«ç·æ¥ç¨ã®çºé»æ©ãããå ´åãUPS ã®ããããªå¯¿å½ã¯æ°ç§ç¨åº¦ã§ããããå¤é¨
é»æºã«ä¾åãã¦ããå ´åã¯ãæ°æéãããªããã°ãªããªããå°ãªãã¨ã大ãããå®ãã¦ãã·
ã¹ãã ãå®å
¨ã«é®æã§ããããã«ãã¹ãã§ããã
6.2.11.1 ã³ã³ããã¼ã«ã»ã³ã¿ã¼/å¶å¾¡å®¤
ICS
åºæã®æ¨å¥¨äºé
åã³ã¬ã¤ãã³ã¹
種ã
ã®è
å¨ã®å¯è½æ§ãæ¸ãããããã³ã³ããã¼ã«ã»ã³ã¿ã¼/å¶å¾¡å®¤ã®ç©ççã»ãã¥ãªãã£ã®ç¢ºä¿
ãä¸å¯æ¬ ã§ãããã³ã³ããã¼ã«ã»ã³ã¿ã¼/å¶å¾¡å®¤ã«ã¯ããã©ã¤ããªå¶å¾¡ãµã¼ãã«å¸¸ç¶çã«æ¥ç¶ã
ã¦ããã³ã³ã½ã¼ã«ãããå ´åãå¤ãã対å¿é度ã¨ãã©ã³ããç¶ç¶çã«è¦ããã¨ã極ãã¦éè¦ã§
ããããµã¼ããã®ä»ã®éè¦ã³ã³ãã¥ã¼ã¿ãã¼ããããå ´åãå¤ããã¨ãã«ã¯ãã©ã³ãã³ã³ãã
ã¼ã©ããããã³ã³ããã¼ã«ã»ã³ã¿ã¼/å¶å¾¡å®¤ã¸ã®ç«å
¥ã¯ãã¹ãã¼ãã«ã¼ããç£æ°ã«ã¼ãããã¤ãª
ã¡ããªãã¯ããã¤ã¹çãå©ç¨ãã許å¯ãåããã¦ã¼ã¶ã«éå®ãããã¨ãèè¦ã§ããã極端ãªå ´
åãã³ã³ããã¼ã«ã»ã³ã¿ã¼/å¶å¾¡å®¤ãé²çä»æ§ã«ãããããªããµã¤ãã®ç·æ¥ç¨ã³ã³ããã¼ã«ã»ã³
ã¿ã¼/å¶å¾¡å®¤ãç¨æãã¦ããã©ã¤ããªã®ã³ã³ããã¼ã«ã»ã³ã¿ã¼/å¶å¾¡å®¤ã®ç«å
¥ä¸è½æã«å¶å¾¡ãç¶è¡
ã§ãããããªæ¤è¨ãå¿
è¦ã«ãªããã
6.2.11.2 ãã¼ã¿ãã«ããã¤ã¹
ICS
åºæã®æ¨å¥¨äºé
åã³ã¬ã¤ãã³ã¹
ICS æ©è½ç¨ã«å©ç¨ããã³ã³ãã¥ã¼ã¿åã³ã³ã³ãã¥ã¼ã¿ããã¤ã¹ï¼PLC ããã°ã©ãã³ã°çï¼ã¯ãICS
ã¨ãªã¢ããæ¬åºãã¦ã¯ãªããªããã©ãããããããã¼ã¿ãã«ã¨ã³ã¸ãã¢ãªã³ã°ã¯ã¼ã¯ã¹ãã¼ã·ã§
ã³åã³ãã³ããã«ãï¼375 HART ã³ãã¥ãã±ã¼ã¿çï¼ã®ã»ãã¥ãªãã£ã¯å³æ ¼ã«ããICS ãããã¯
ã¼ã¯å¤ã§ã¯ä½¿ç¨ãã¹ãã§ãªããã¢ã³ãã¦ã¤ã«ã¹åã³ãããã®ç®¡çãææ°ç¶æ
ã«ä¿ã¤ã¹ãã§ããã

SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
189
6.2.11.3 Cabling
ICS-specific Recommendations and Guidance
Cabling design and implementation for the control network should be addressed in the cybersecurity plan.
Unshielded twisted pair communications cable, while acceptable for the office environment, is generally
not suitable for the plant environment due to its susceptibility to interference from magnetic fields, radio
waves, temperature extremes, moisture, dust, and vibration. Industrial RJ-45 connectors should be used in
place of other types of twisted pair connectors to provide protection against moisture, dust and vibration.
Fiber-optic cable and coaxial cable are often better network cabling choices for the control network because
they are immune to many of the typical environmental conditions including electrical and radio frequency
interference found in an industrial control environment. Cable and connectors should be color-coded and
labeled so that the ICS and IT networks are clearly delineated and the potential for an inadvertent cross-
connect is reduced. Cable runs should be installed so that access is minimized (i.e., limited to authorized
personnel only) and equipment should be installed in locked cabinets with adequate ventilation and air
filtration.
6.2.12 Planning
A security plan is a formal document that provides an overview of the security requirements for an
information system and describes the security controls in place or planned for meeting those requirements.
The security controls that fall within the NIST SP 800-53 Planning (PL) family provide the basis for
developing a security plan. These controls also address maintenance issues for periodically updating a
security plan. A set of rules describes user responsibilities and expected behavior regarding information
system usage with provision for signed acknowledgement from users indicating that they have read,
understand, and agree to abide by the rules of behavior before authorizing access to the information system.
Supplemental guidance for the PL controls can be found in the following documents:
ï¼ NIST SP 800-18 provides guidance on preparing rules of behavior [19].
ï¼ NIST SP 800-100 provides guidance on information security governance and planning [27].
ICS-specific Recommendations and Guidance
A security plan for an ICS should build on appropriate existing IT security experience, programs, and
practices. However, the critical differences between IT and ICS addressed in Section 2.4 will influence how
security will be applied to the ICS. A forward-looking plan is needed to provide a method for continuous
security improvements. Whenever a new system is being designed and installed, it is imperative to take the
time to address security throughout the lifecycle, from architecture to procurement to installation to
maintenance to decommissioning. ICS security is a rapidly evolving field requiring the security planning
process to constantly explore emerging ICS security capabilities as well as new threats that are identified
by organizations such as the ICS-CERT.

SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
190
6.2.11.3 ã±ã¼ãã«é
ç·
ICS
åºæã®æ¨å¥¨äºé
åã³ã¬ã¤ãã³ã¹
å¶å¾¡ãããã¯ã¼ã¯ç¨ã±ã¼ãã«é
ç·ã®è¨è¨åã³å®è£
ã¯ããµã¤ãã¼ã»ãã¥ãªãã£è¨ç»æ¸ã®ä¸ã§åãä¸
ããã¹ãã§ãããéä¿¡ç¨ã®ã·ã¼ã«ãã®ãªãæã対ç·ã¯ããªãã£ã¹ç°å¢ã§ã¯åãå
¥ããããããé
常ãã©ã³ãç°å¢ã§ã¯ç£å ´ãç¡ç·å¨æ³¢æ°ã温度ã®å¯æã湿æ°ã塵è¥åã³æ¯åã«ããå¹²æ¸ãåããã
ãããä¸åãã§ããã湿æ°ã»å¡µè¥ã»æ¯å対çã¨ãã¦ãç£æ¥ç¨ RJ-45 ã³ãã¯ã¿ããã®ä»ã®æã対ç·
ã³ãã¯ã¿ã®ä»£ããã«ä½¿ç¨ãã¹ãã§ãããå
ã±ã¼ãã«åã³å軸ã±ã¼ãã«ã¯ãç£æ¥ç¨å¶å¾¡ç°å¢ã«ãã
ããé»æ°ã»ç¡ç·å¨æ³¢æ°å¹²æ¸çã®ç°å¢æ¡ä»¶ã®å¤ãã«å½±é¿ãåããªããããå¶å¾¡ãããã¯ã¼ã¯ç¨ã®é
ç·é¸æè¢ã¨ãã¦è¯ãå ´åãå¤ããã±ã¼ãã«åã³ã³ãã¯ã¿ã«ã¯ã«ã©ã¼ã³ã¼ãã¨ã©ãã«ãä»ããICS
ãããã¯ã¼ã¯ã¨ IT ãããã¯ã¼ã¯ã®èå¥ãæ確ã«ãããã£ãã交差é
ç·ããªãããã«ãã¹ãã§ã
ããé
ç·ã¯ãé
ç·ã¸ã®ã¢ã¯ã»ã¹ãæå°ã§æ¸ãããã«è¡ãï¼è¨±å¯ãããè·å¡ã®ã¿ï¼ãè£
ååã¯æ½é
ã§ãããã£ããããã«åç´ããææ°ã¨ç©ºæ°æ¿¾éãè¡ãã
6.2.12 ãã©ã³ãã³ã°
ã»ãã¥ãªãã£è¨ç»æ¸ã¯ãæ
å ±ã·ã¹ãã ã®ã»ãã¥ãªãã£è¦ä»¶ãæ¦èª¬ããæ£å¼ææ¸ã§ããã®è¦ä»¶
ãæºè¶³ããå®æ½ä¸åã¯è¨ç»ä¸ã®ã»ãã¥ãªãã£å¯¾çã«ã¤ãã¦è¨è¿°ãããNIST SP 800-53 ãã©ã³
ãã³ã°ï¼PLï¼ãã¡ããªã«ã¯ãã»ãã¥ãªãã£è¨ç»æ¸ãä½æããããã®æ ¹æ ã示ããã¦ããã管
ççã«ã¯ãã»ãã¥ãªãã£è¨ç»æ¸ãå®æçã«æ´æ°ããããã®ä¿å®åé¡ãå«ã¾ãããä¸é£ã®è¦å
ã¯ãæ
å ±ã·ã¹ãã ã®å©ç¨ã«é¢ããã¦ã¼ã¶ã®è²¬ä»»ã¨æå¾
ãããè¡åã«ã¤ãã¦èª¬æããæ
å ±ã·ã¹
ãã ã¸ã®ã¢ã¯ã»ã¹è¨±å¯ãå¾ãåã«ãã¦ã¼ã¶ãè¡åè¦åãèªã¿ãç解ããéµå®ããæ¨ã®ç½²åå
¥
ãåææ¸ãä»ãã¦ããã
PL 管çã®è£è¶³çã¬ã¤ãã³ã¹ã以ä¸ã®ææ¸ã«æ²è¼ããã¦ããã
ï¼ NIST SP 800-18ï¼è¡åè¦åã®ä½æã«ä¿ãã¬ã¤ãã³ã¹[19]
ï¼ NIST SP 800-100ï¼æ
å ±ã»ãã¥ãªãã£ã¬ããã³ã¹åã³ãã©ã³ãã³ã°ã«ä¿ãã¬ã¤ãã³ã¹[27]
ICS
åºæã®æ¨å¥¨äºé
åã³ã¬ã¤ãã³ã¹
ICS ã®ã»ãã¥ãªãã£è¨ç»æ¸ã¯ã該å½ããæ¢åã® IT ã»ãã¥ãªãã£çµé¨ãããã°ã©ã åã³è¦ç¯ãåºæ¬
ã¨ãããã»ã¯ã·ã§ã³ 2.4 ã§èª¬æãã IT ã¨ICS ã®éè¦ãªç¸éã¯ãICS ã¸ã®ã»ãã¥ãªãã£é©ç¨æ¹æ³ã«
å½±é¿ããã絶ããã»ãã¥ãªãã£ãæ¹åãã¦ããã®æ¹æ³ã示ããããååããªè¨ç»æ¸ãå¿
è¦ã¨ãª
ããæ°ããã·ã¹ãã ãè¨è¨ã»å°å
¥ããå ´åã¯å¸¸ã«ãã¢ã¼ããã¯ãã£ãã調éãå°å
¥ãä¿å®ãå»æ£
ã«è³ãã¾ã§ãã©ã¤ããµã¤ã¯ã«å
¨ä½ãè¦éããã»ãã¥ãªãã£ã«ã¤ãã¦èå¯ããæéãåãåããã
ã¨ãèè¦ã§ãããICS ã»ãã¥ãªãã£ã¯æ¥éã«é²å±ä¸ã®åéã§ãã»ãã¥ãªãã£ã®ãã©ã³ãã³ã°ãã
ã»ã¹ã§ã¯ãICS ã»ãã¥ãªãã£ã®æ°èæ©è½ã¨ãICS-CERT ãªã©ã®æ©é¢ã«ããç¹å®ãããæ°ããè
å¨
ã絶ããæ¢ç´¢ãããã¨ãæ±ããããã
SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
191
6.2.13 Personnel Security
The security controls that fall within the NIST SP 800-53 Personnel Security (PS) family provide policies
and procedures to reduce the risk of human error, theft, fraud, or other intentional or unintentional misuse
of information systems.
Supplemental guidance for the PS controls can be found in the following documents:
ï¼ NIST SP 800-35 provides guidance on information technology security services [44].
ï¼ NIST SP 800-73 provides guidance on interfaces for personal identity verification [49].
ï¼ NIST SP 800-76 provides guidance on biometrics for personal identity verification [50].
ï¼ NIST SP 800-100 provides guidance on information security governance and planning [27].
Personnel security measures are meant to reduce the possibility and risk of human error, theft, fraud, or
other intentional or unintentional misuse of informational assets. There are three main aspects to personnel
security:
ï¼ Hiring Policies. This includes pre-employment screening such as background checks, the interview
process, employment terms and conditions, complete job descriptions and detailing of duties, terms
and condition of employment, and legal rights and responsibilities of employees or contractors.
ï¼ Organization Policies and Practices. These include security policies, information classification,
document and media maintenance and handling policies, user training, acceptable usage policies for
organization assets, periodic employee performance reviews, appropriate background checks, and any
other policies and actions that detail expected and required behavior of organization employees,
contractors, and visitors. Organization policies to be enforced should be written down and readily
available to all workers through an employee handbook, distributed as email notices, located in a
centralized resource area, or posted directly at a workerâs area of responsibility.
ï¼ Terms and Conditions of Employment. This category includes job and position responsibilities,
notification to employees of terminable offenses, disciplinary actions and punishments, and periodic
employee performance reviews.
ICS-specific Recommendations and Guidance
Positions should be categorized with a risk designation and screening criteria, and individuals filling a
position should be screened against this criteria as well as complete an access agreement before being
granted access to an information system. Personnel should be screened for the critical positions controlling
and maintaining the ICS.
Additionally, training programs should be carefully developed to ensure that each employee has received
training relevant and necessary to his job functions. Further, ensure that the employees have demonstrated
their competence in their job functions.
SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
192
6.2.13 人å¡ã®ã»ãã¥ãªãã£
NIST SP 800-53 ã®äººå¡ã®ã»ãã¥ãªãã£ï¼PSï¼ãã¡ããªã«å«ã¾ããã»ãã¥ãªãã£å¯¾çã¯ã人çé
誤ãçé£ãè©æ¬ºãã®ä»æ
æåã¯ä¸ä½çºã«ããæ
å ±ã·ã¹ãã ã®èª¤ç¨ãæ¸ããããã®ããªã·ã¼åã³
æé ãå®ãã¦ããã
PS 管çã®è£è¶³çã¬ã¤ãã³ã¹ã以ä¸ã®ææ¸ã«æ²è¼ããã¦ããã
ï¼ NIST SP 800-35ï¼æ
å ±æè¡ã»ãã¥ãªãã£ãµã¼ãã¹ã«ä¿ãã¬ã¤ãã³ã¹[44]
ï¼ NIST SP 800-73ï¼å人身å
確èªã¤ã³ã¿ãã§ã¼ã¹ã«ä¿ãã¬ã¤ãã³ã¹[49]
ï¼ NIST SP 800-76ï¼å人身å
確èªãã¤ãªã¡ããªã¯ã¹ã«ä¿ãã¬ã¤ãã³ã¹[50]
ï¼ NIST SP 800-100ï¼æ
å ±ã»ãã¥ãªãã£ã¬ããã³ã¹åã³ãã©ã³ãã³ã°ã«ä¿ãã¬ã¤ãã³ã¹[27]
人å¡ã®ã»ãã¥ãªãã£å¯¾çã¯ã人çé誤ãçé£ãè©æ¬ºãã®ä»æ
æåã¯ä¸ä½çºã«ããæ
å ±è³ç£ã®
誤ç¨æ©ä¼ãæ¸ããããã®ãã®ã§ããã人å¡ã®ã»ãã¥ãªãã£ã«ã¯æ¬¡ã® 3ã¤ã®é¢ãããã
ï¼ éç¨ããªã·ã¼ãããã«èæ¯èª¿æ»ãé¢æ¥ããã»ã¹çã®éç¨åã®ã¹ã¯ãªã¼ãã³ã°ãéç¨å¥ç´ãè·
åæç´°ãéç¨æ¡ä»¶ãå¾æ¥å¡ã»è«è² æ¥è
ã®æ³ç権å©ã¨è²¬åãå«ã¾ããã
ï¼ çµç¹ã®ããªã·ã¼åã³è¦ç¯ãããã«å«ã¾ããã®ã¯ã»ãã¥ãªãã£ããªã·ã¼ãæ
å ±åºåãææ¸åã³
ã¡ãã£ã¢ã®ç¶æåã³åæ±ããªã·ã¼ãã¦ã¼ã¶è¨ç·´ãçµç¹è³ç£ã®åãå
¥ããããå©ç¨ããªã·ã¼ã
å¾æ¥å¡å®æå¤åè©å®ãé¢é£ããèæ¯èª¿æ»ãã®ä»å¾æ¥å¡ã»è«è² æ¥è
ã»æ¥è¨ªè
ã®æå¾
ã»ç¾©åè¡å
ã詳述ããããªã·ã¼åã³è¡çºã§ãããæ½è¡ãã¹ãçµç¹ã®ããªã·ã¼ã¯æ¸é¢ã«ããå¾æ¥å¡ãã³ã
ããã¯ãéãã¦å
¨å¡ã容æã«å©ç¨ã§ããé»åã¡ã¼ã«éç¥ã§é
å¸ãããéä¸ãªã½ã¼ã¹ã¨ãªã¢ã«
ç½®ãããåã¯å¾æ¥å¡ã®æ
å½ã¨ãªã¢ã«æ²ç¤ºãã¹ãã§ããã
ï¼ éç¨æ¡ä»¶ãããã«ã¯è·ååã³å½¹è·ã®è²¬åãå¾æ¥å¡ã«å¯¾ããå¥ç´è§£é¤ã¨ãªãéåã®éç¥ãæ²ç½°
åã³å®æå¤åè©å®ãå«ã¾ããã
ICS
åºæã®æ¨å¥¨äºé
åã³ã¬ã¤ãã³ã¹
å½¹è·ã¯ãªã¹ã¯æå®åã³é¸æåºæºã§åé¡ãããå½¹è·ã«å°±ãå人ã¯ãã®åºæºã«ç
§ããã¦é¸æããã
æ
å ±ã·ã¹ãã ã¸ã®ã¢ã¯ã»ã¹æ¨©ãå¾ãåã«ã¢ã¯ã»ã¹åææ¸ãä½æãã¹ãã§ãããICS ã®å¶å¾¡åã³
ä¿å®ãæ
å½ããéè¦å½¹è·ã«å°±ãè·å¡ã¯é¸æãã¹ãã§ããã
ã¾ãæ
éã«è¨ç·´ããã°ã©ã ãä½æããåå¾æ¥å¡ãè·ä½ã«å¿ããè¨ç·´ãåããããããã«ãã¹
ãã§ãããæ´ã«å¾æ¥å¡ãè·åã«ãããé©æ§ãå®è¨¼ã§ããããã«ããã
SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
193
6.2.14 Risk Assessment
The security controls that fall within the NIST SP 800-53 Risk Assessment (RA) family provide policy and
procedures to develop, distribute, and maintain a documented risk assessment policy that describes purpose,
scope, roles, responsibilities, and compliance as well as policy implementation procedures. An information
system and associated data is categorized based on the security objectives and a range of risk levels. A risk
assessment is performed to identify risks and the magnitude of harm that could result from the unauthorized
access, use, disclosure, disruption, modification, or destruction of an information system and data. Also
included in these controls are mechanisms for keeping risk assessments up-to-date and performing periodic
testing and vulnerability assessments.
Supplemental guidance for the RA controls can be found in the following documents:
ï¼ NIST SP 800-30 provides guidance on conducting risk assessments and updates [79].
ï¼ NIST SP 800-39 provides guidance on risk management at all organizational levels [20].
ï¼ NIST SP 800-40 provides guidance on handling security patches [40].
ï¼ NIST SP 800-115 provides guidance on network security testing [41].
ï¼ NIST SP 800-60 provides guidance on determining security categories for information types [25].
ï¼ NIST SP 800-100 provides guidance on information security governance and planning [27].
ICS-specific Recommendations and Guidance
Organizations must consider the potential consequences resulting from an incident on an ICS. Well-defined
policies and procedures lead to mitigation techniques designed to thwart incidents and manage the risk to
eliminate or minimize the consequences. The potential degradation of the physical plant, economic status,
or stakeholder/national confidence could justify mitigation.
For an ICS, a very important aspect of the risk assessment is to determine the value of the data that is
flowing from the control network to the corporate network. In instances where pricing decisions are
determined from this data, the data could have a very high value. The fiscal justification for mitigation has
to be derived by comparing the mitigation cost to the effects of the consequence. However, it is not
possible to define a one-size-fits-all set of security requirements. A very high level of security may be
achievable but undesirable in many situations because of the loss of functionality and other associated
costs. A well-thought-out security implementation is a balance of risk versus cost. In some situations the
risk may be safety, health, or environment-related rather than purely economic. The risk may result in an
unrecoverable consequence rather than a temporary financial setback
6.2.15 System and Services Acquisition
The security controls that fall within the NIST SP 800-53 System and Services Acquisition (SA) family
provide the basis for developing policies and procedures for acquisition of resources required to adequately
protect an information system. These acquisitions are based on security requirements and security
specifications. As part of the acquisition procedures, an information system is managed using a system
development life cycle methodology that includes information security considerations. As part of
acquisition, adequate documentation must be maintained on the information system and constituent
components.

SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
194
6.2.14 ãªã¹ã¯è©ä¾¡
NIST SP 800-53 ã®ãªã¹ã¯è©ä¾¡ï¼RAï¼ãã¡ããªã«å«ã¾ããã»ãã¥ãªãã£å¯¾çã«ã¯ãç®çãé©ç¨
ç¯å²ãå½¹å²ã責任ãã³ã³ãã©ã¤ã¢ã³ã¹åã³ããªã·ã¼å®æ½æé ãè¨è¿°ãããªã¹ã¯è©ä¾¡ããªã·ã¼æ
æ¸ãä½æã»é
å¸ã»ä¿æããããã®ããªã·ã¼åã³æé ãå®ãããã¦ãããæ
å ±ã·ã¹ãã åã³é¢é£
ãã¼ã¿ã¯ãã»ãã¥ãªãã£ç®æ¨åã³ãªã¹ã¯ã¬ãã«ã®ç¯å²ãåºã«åé¡ãããããªã¹ã¯è©ä¾¡ã¯ãªã¹ã¯
ã¨ãä¸æ£ã¢ã¯ã»ã¹ãå©ç¨ãæ¼æ´©ã妨害ãæ¹å¤åã¯æ
å ±ã·ã¹ãã ã»ãã¼ã¿ã®ç ´å£ããçãå¾ãæ
害ã®è¦æ¨¡ãæããã«ããããã«å®æ½ãããã¾ããªã¹ã¯è©ä¾¡ãææ°ç¶æ
ã«ä¿ã¡ãå®æçæ¤è¨¼åã³
èå¼±æ§è©ä¾¡ãå®æ½ããããã®ã¡ã«ããºã ããã®ç®¡çã§åãä¸ããã
RA 管çã®è£è¶³çã¬ã¤ãã³ã¹ã以ä¸ã®ææ¸ã«æ²è¼ããã¦ããã
ï¼ NIST SP 800-30ï¼ãªã¹ã¯è©ä¾¡ã®å®æ½åã³æ´æ°ã«ä¿ãã¬ã¤ãã³ã¹[79]
ï¼ NIST SP 800-39ï¼ããããçµç¹ã¬ãã«ã«ããããªã¹ã¯ç®¡çã«ä¿ãã¬ã¤ãã³ã¹[20]
ï¼ NIST SP 800-40ï¼ã»ãã¥ãªãã£ãããã®åæ±ã«ä¿ãã¬ã¤ãã³ã¹[40]
ï¼ NIST SP 800-115ï¼ãããã¯ã¼ã¯ã»ãã¥ãªãã£ã®è©¦é¨ã«ä¿ãã¬ã¤ãã³ã¹[41]
ï¼ NIST SP 800-60ï¼æ
å ±ç¨®é¡ã®ã»ãã¥ãªãã£åé¡å¤å®ã«ä¿ãã¬ã¤ãã³ã¹[25]
ï¼ NIST SP 800-100ï¼æ
å ±ã»ãã¥ãªãã£ã¬ããã³ã¹åã³ãã©ã³ãã³ã°ã«ä¿ãã¬ã¤ãã³ã¹[27]
ICS
åºæã®æ¨å¥¨äºé
åã³ã¬ã¤ãã³ã¹
çµç¹ã¯ ICS ä¸ã®ã¤ã³ã·ãã³ãããçãå¾ãçµæãæ¤è¨ããªããã°ãªããªãããã£ããå®ç¾©ãã
ãããªã·ã¼åã³æé ã¯ãã¤ã³ã·ãã³ããé»æ¢ãããªã¹ã¯ã管çãã¦çµæãæé¤åã¯æå°éã«é£
ãæ¢ããããã®ç·©åæè¡ã«éããããã©ã³ããçµæ¸ç¶æ
åã¯å©å®³é¢ä¿è
ã»å½æ°ã®ä¿¡é ¼æãä½ä¸
ãããã¨ãããç·©åçã¯æ¯éã¨ãå¿
è¦ã¨ãªãã
ICS ã«ããããªã¹ã¯è©ä¾¡ã®æ¥µãã¦éè¦ãªä¸é¢ã¯ãå¶å¾¡ãããã¯ã¼ã¯ããä¼æ¥ãããã¯ã¼ã¯ã¸æµ
ãããã¼ã¿ã®ä¾¡å¤ãå¤å®ãããã¨ã§ãããä¾ãã°ããã®ãã¼ã¿ãåºã«ä¾¡æ ¼ã決å®ããå ´åãã
ã¼ã¿ã¯æ¥µãã¦é«ã価å¤ãæã¤ãç·©åãæ£å½åããä¼è¨ä¸ã®çç±ã¯ãç·©åã«è¦ããã³ã¹ãã¨çµæ
ããçããå½±é¿ã®æ¯è¼ããå¼ãåºããªããã°ãªããªããã¨ã¯è¨ãã1ã¤ã§å
¨ã¦ã«é©åãããã
ãªã»ãã¥ãªãã£è¦ä»¶ãå®ç¾©ãããã¨ã¯ä¸å¯è½ã§ãããé«ã¬ãã«ã®ã»ãã¥ãªãã£ã¯éæå¯è½ã§ã¯
ããããæ©è½ã失ãããã®ä»é¢é£ã³ã¹ããããããã¨ããã大æµã¯æã¾ãããªããããæ¤è¨ã
ããã»ãã¥ãªãã£ã¯ããªã¹ã¯ã¨ã³ã¹ãã®ãã©ã³ã¹ãåãã¦ãããããå ´åããªã¹ã¯ã¯ç´ç²ãªçµ
æ¸ããããå®å
¨ãå¥åº·åã¯ç°å¢é¢é£ã¨ãªãããªã¹ã¯ã¯ãä¸æçãªè²¡æ¿ä¸ã®å¤±æã¨ãããããå
ãè¿ãã®ã¤ããªãçµæãæããã¨ãããã
6.2.15 ã·ã¹ãã åã³ãµã¼ãã¹ã®åå¾
NIST SP 800-53 ã®ã·ã¹ãã åã³ãµã¼ãã¹ã®åå¾ï¼SAï¼ãã¡ããªã«å«ã¾ããã»ãã¥ãªãã£å¯¾ç
ã«ã¯ãæ
å ±ã·ã¹ãã ãå®ãããã«å¿
è¦ã¨ããããªã½ã¼ã¹ã®åå¾ã«ä¿ãããªã·ã¼åã³æé ã®çå®
æ ¹æ ã示ããã¦ãããåå¾ã¯ãã»ãã¥ãªãã£è¦ä»¶åã³ã»ãã¥ãªãã£ä»æ§æ¸ã«åºã¥ããåå¾æé
ã®ä¸ç°ã¨ãã¦ãæ
å ±ã·ã¹ãã ã¯ãæ
å ±ã»ãã¥ãªãã£ã®èæ
®äºé
ãå«ããã·ã¹ãã éçºã©ã¤ããµ
ã¤ã¯ã«æ¹æ³è«ãå©ç¨ãã¦ç®¡çããããåå¾ã®ä¸ç°ã¨ãã¦ãæ
å ±ã·ã¹ãã åã³æ§æã³ã³ãã¼ãã³
ãã«é¢ããææ¸ãä¿æããªããã°ãªããªãã
SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
195
The SA family also addresses outsourced systems and the inclusion of adequate security controls by
vendors as specified by the supported organization. Vendors are also responsible for configuration
management and security testing for these outsourced information systems.
Supplemental guidance for the SA controls can be found in the following documents:
ï¼ NIST SP 800-23 provides guidance on the acquisition and use of tested/evaluated information
technology products [42].
ï¼ NIST SP 800-27 provides guidance on engineering principles for information system security [43].
ï¼ NIST SP 800-35 provides guidance on information technology security services [44].
ï¼ NIST SP 800-36 provides guidance on the selection of information security products [45].
ï¼ NIST SP 800-64 provides guidance on security considerations in the system development life cycle
[46].
ï¼ NIST SP 800-65 provides guidance on integrating security into the capital planning and investment
control process [47].
ï¼ NIST SP 800-70 provides guidance on configuration settings for information technology products [26].
ï¼ NIST SP 800-100 provides guidance on information security governance and planning [27].
ICS-specific Recommendations and Guidance
The security requirements of an organization outsourcing the management and control of all or some of its
information systems, networks, and desktop environments should be addressed in a contract agreed
between the parties. External suppliers that have an impact on the security of the organization must be held
to the same security policies and procedures to maintain the overall level of ICS security. Security policies
and procedures of second and third-tier suppliers should also be in compliance with corporate cybersecurity
policies and procedures in the case that they impact ICS security.
DHS has developed a procurement language document [48] for specifying security requirements when
procuring new systems or maintaining existing systems.
6.2.16 System and Communications Protection
The security controls that fall within the NIST SP 800-53 System and Communications Protection (SC)
family provide policy and procedures for protecting systems and data communications components.
Supplemental guidance for the SC controls can be found in the following documents:
ï¼ NIST SP 800-28 provides guidance on active content and mobile code [69].
ï¼ NIST SP 800-52 provides guidance on Transport Layer Security (TLS) Implementations [70].
ï¼ NIST SP 800-56 provides guidance on cryptographic key establishment [71].
ï¼ NIST SP 800-57 provides guidance on cryptographic key management [72].
SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
196
SA ãã¡ããªã§ã¯å¤æ³¨ã·ã¹ãã ãããµãã¼ããåããçµç¹ãæå®ãããã³ãã¼ã«ããã»ãã¥ãªã
ã£å¯¾çã®åãè¾¼ã¿ã«ã¤ãã¦ãåãä¸ãã¦ããããã³ãã¼ã¯ããã®ãããªå¤æ³¨æ
å ±ã·ã¹ãã ã®æ§æ
管çåã³ã»ãã¥ãªãã£è©¦é¨ã«ã責任ãè² ãã
SA 管çã®è£è¶³çã¬ã¤ãã³ã¹ã以ä¸ã®ææ¸ã«æ²è¼ããã¦ããã
ï¼ NIST SP 800-23ï¼è©¦é¨ã»è©ä¾¡æ¸ã¿æ
å ±æè¡è£½åã®åå¾åã³å©ç¨ã«ä¿ãã¬ã¤ãã³ã¹[42]
ï¼ NIST SP 800-27ï¼æ
å ±ã·ã¹ãã ã»ãã¥ãªãã£ã®ã¨ã³ã¸ãã¢ãªã³ã°ååã«ä¿ãã¬ã¤ãã³ã¹[43]
ï¼ NIST SP 800-35ï¼æ
å ±æè¡ã»ãã¥ãªãã£ãµã¼ãã¹ã«ä¿ãã¬ã¤ãã³ã¹[44]
ï¼ NIST SP 800-36ï¼æ
å ±ã»ãã¥ãªãã£è£½åã®é¸å®ã«ä¿ãã¬ã¤ãã³ã¹[45]
ï¼ NIST SP 800-64ï¼ã·ã¹ãã éçºã©ã¤ããµã¤ã¯ã«ã«ãããã»ãã¥ãªãã£èæ
®äºé
ã«ä¿ãã¬ã¤ã
ã³ã¹[46]
ï¼ NIST SP 800-65ï¼è³æ¬è¨ç»åã³æè³ç®¡çããã»ã¹ã¸ã®ã»ãã¥ãªãã£çµ±åã«ä¿ãã¬ã¤ãã³ã¹
[47]
ï¼ NIST SP 800-70ï¼æ
å ±æè¡è£½åã®æ§æè¨å®ã«ä¿ãã¬ã¤ãã³ã¹[26]
ï¼ NIST SP 800-100ï¼æ
å ±ã»ãã¥ãªãã£ã¬ããã³ã¹åã³ãã©ã³ãã³ã°ã«ä¿ãã¬ã¤ãã³ã¹[27]
ICS åºæã®æ¨å¥¨äºé
åã³ã¬ã¤ãã³ã¹
æ
å ±ã·ã¹ãã ããããã¯ã¼ã¯åã³ãã¹ã¯ãããç°å¢ã®å
¨é¨åã¯ä¸é¨ã®ç®¡çã»å¯¾çãå¤æ³¨ããé
ã®ã»ãã¥ãªãã£è¦ä»¶ã¯ã両å½äºè
éã®å¥ç´æ¸ã§åãä¸ããã¹ãã§ãããçµç¹ã®ã»ãã¥ãªãã£ã«
å½±é¿ãä¸ãã社å¤ãµãã©ã¤ã¤ã¯ãICS ã»ãã¥ãªãã£ã®å
¨ä½ã¬ãã«ãç¶æããããã®åãã»ãã¥
ãªãã£ããªã·ã¼åã³æé ã«å¾ããªããã°ãªããªããå«è«ã以éã®ãµãã©ã¤ã¤ã®ã»ãã¥ãªãã£ã
ãªã·ã¼åã³æé ããICS ã»ãã¥ãªãã£ã«å½±é¿ããå ´åã¯ãä¼æ¥ã®ãµã¤ãã¼ã»ãã¥ãªãã£ããªã·
ã¼åã³æé ãéµå®ãã¹ãã§ããã
DHS ã¯ãæ°è¦ã·ã¹ãã 調éåã¯æ¢åã·ã¹ãã ä¿å®ã®éã®ã»ãã¥ãªãã£è¦ä»¶ãå®ããããã®èª¿
éè¨èªææ¸[48]ãä½æããã
6.2.16 ã·ã¹ãã åã³éä¿¡ä¿è·
NIST SP 800-53 ã®ã·ã¹ãã åã³éä¿¡ä¿è·ï¼SCï¼ãã¡ããªã«å«ã¾ããã»ãã¥ãªãã£å¯¾çã«ã¯ãã·
ã¹ãã åã³ãã¼ã¿éä¿¡ã³ã³ãã¼ãã³ããä¿è·ããããã®ããªã·ã¼åã³æé ãå®ãããã¦ããã
SC 管çã®è£è¶³çã¬ã¤ãã³ã¹ã以ä¸ã®ææ¸ã«æ²è¼ããã¦ããã
ï¼ NIST SP 800-28ï¼ã¢ã¯ãã£ãã³ã³ãã³ãåã³ã¢ãã¤ã«ã³ã¼ãã«ä¿ãã¬ã¤ãã³ã¹[69]
ï¼ NIST SP 800-52ï¼ãã©ã³ã¹ãã¼ãã¬ã¤ã¤ã¼ã»ãã¥ãªãã£ï¼TLSï¼ã®å®è£
ã«ä¿ãã¬ã¤ãã³ã¹[70]
ï¼ NIST SP 800-56ï¼æå·éµã®è¨å®ã«ä¿ãã¬ã¤ãã³ã¹[71]
ï¼ NIST SP 800-57ï¼æå·éµã®ç®¡çã«ä¿ãã¬ã¤ãã³ã¹[72]

SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
197
ï¼ NIST SP 800-58 provides guidance on security considerations for VoIP technologies [73].
ï¼ NIST SP 800-63 provides guidance on remote electronic authentication [53].
ï¼ NIST SP 800-77 provides guidance on IPsec VPNs [74].
6.2.16.1 Encryption
Encryption is the cryptographic transformation of data (called plaintext) into a form (called ciphertext) that
conceals the dataâs original meaning to prevent it from being known or used. If the transformation is
reversible, the corresponding reversal process is called decryption, which is a transformation that restores
encrypted data to its original state [75].
ICS-specific Recommendations and Guidance
Before deploying encryption, first determine if encryption is an appropriate solution for the specific ICS
application, because authentication and integrity are generally the key security issues for ICS applications.
Other cryptographic solutions such as cryptographic hashes should also be considered.
The use of encryption within an ICS environment could introduce communications latency due to the
additional time and computing resources required to encrypt, decrypt, and authenticate each message. For
ICS, any latency induced from the use of encryption, or any other security technique, must not degrade the
operational performance of the end device or system. Before deploying encryption within an ICS
environment, solutions should go through extensive performance testing. Encryption at OSI Layer 2 should
be considered, rather than at Layer 3 to reduce encryption latency.
In addition, encrypted messages are often larger than unencrypted messages due to one or more of the
following:
ï¼ Additional checksums to reduce errors.
ï¼ Protocols to control the cryptography.
ï¼ Padding (for block ciphers).
ï¼ Authentication procedures.
ï¼ Other required cryptographic processes.
Cryptography also introduces key management issues. Sound security policies require periodic key
changes. This process becomes more difficult as the geographic size of the ICS increases, with extensive
SCADA systems being the most severe example. Because site visits to change keys can be costly and slow,
it is useful to be able to change keys remotely.
If cryptography is selected, the most effective safeguard is to use a complete cryptographic system
approved by the NIST/ Communications Security Establishment (CSE) Cryptographic Module Validation
Program (CMVP)41. Within this program standards are maintained to ensure that cryptographic systems
were studied carefully for weaknesses by a wide range of experts, rather than being developed by a few
engineers in a single organization. At a minimum, certification makes it probable that:
ï¼ Some method (such as counter mode) will be used to ensure that the same message does not
41 Information on the CMVP can be found on the CMVP web site http://csrc.nist.gov/cryptval/cmvp.htm.

SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
198
ï¼ NIST SP 800-58ï¼VoIP æè¡ã®ã»ãã¥ãªãã£èæ
®äºé
ã«ä¿ãã¬ã¤ãã³ã¹[73]
ï¼ NIST SP 800-63ï¼é éé»åèªè¨¼ã«ä¿ãã¬ã¤ãã³ã¹[53]
ï¼ NIST SP 800-77ï¼IPsec VPNs ã«ä¿ãã¬ã¤ãã³ã¹[74]
6.2.16.1 æå·å
æå·åã¨ã¯ãã¼ã¿ï¼å¹³æã¨å¼ã°ããï¼ãæå·å¤æãã¦ãããå½¢æ
ï¼æå·æã¨å¼ã°ããï¼ã«ããã
ã¨ã§ããã¼ã¿ã®åºã®æå³ãç§å¿ããç¥ããããå©ç¨ããããã§ããªãããã«ãããå¤æãéå¤æ
ãå¯è½ãªå ´åããã®ããã»ã¹ã¯å¾©å·ã¨å¼ã°ããæå·åããããã¼ã¿ãå
ã®ç¶æ
ã«æ»ã[75]ã
ICS åºæã®æ¨å¥¨äºé
åã³ã¬ã¤ãã³ã¹
èªè¨¼ã¨å®å
¨æ§ã¯ãç·ã㦠ICS ç¨éã§ã¯ä¸»è¦ãªã»ãã¥ãªãã£åé¡ã¨ãªããããæå·åãè¡ãåã«ã
ã¾ããããç¹å®ã® ICS ç¨éã«é©ããã½ãªã¥ã¼ã·ã§ã³ãã©ãããå¤å®ãããæå·å¦çããã·ã¥çã
ãã®ä»ã®æå·ã½ãªã¥ã¼ã·ã§ã³ã«ã¤ãã¦ãèæ
®ãã¹ãã§ããã
ICS ç°å¢ã§æå·ã使ç¨ããã¨ãåã¡ãã»ã¼ã¸ã®æå·ã復å·åã³èªè¨¼ã«ä»å çãªæéã¨è¨ç®ãªã½ã¼
ã¹ãè¦ãããããéä¿¡ã®å¾
ã¡æéãçããå ´åããããICS ã§ã¯ãæå·ã®ä½¿ç¨åã¯ä»ã®ã»ãã¥ãª
ãã£æè¡ããçããå¾
ã¡æéã¯ãã¨ã³ãããã¤ã¹ãã·ã¹ãã ã®éç¨ããã©ã¼ãã³ã¹ãä½ä¸ããã¦
ã¯ãªããªããICS ç°å¢ã§æå·ãå±éããåã«ãå¾¹åºçãªããã©ã¼ãã³ã¹è©¦é¨ãè¡ãã¹ãã§ããã
æå·åã®å¾
ã¡æéãç縮ãããããOSI ã¬ã¤ã¤ã¼3ã§ã¯ãªãã¬ã¤ã¤ã¼2ã§ã®æå·åãèæ
®ãã¹ã
ã§ããã
ã¾ã以ä¸ã«æããçç±ãããæå·ã¡ãã»ã¼ã¸ã¯å¹³æã¡ãã»ã¼ã¸ãã大ãããªããã¨ãå¤ãã
ï¼ ã¨ã©ã¼ãæ¸ããããã®ä»å çãªãã§ãã¯ãµã
ï¼ æå·åãå¶å¾¡ããããã®ãããã³ã«
ï¼ ããã£ã³ã°ï¼ãããã¯æå·ç¨ï¼
ï¼ èªè¨¼æé
ï¼ ä»ã®å¿
é æå·åããã»ã¹
æå·åã«ã¯éµç®¡çã®åé¡ãçãããå¥å
¨ãªã»ãã¥ãªãã£ããªã·ã¼ã«ã¯å®æçãªéµã®å¤æ´ãå¿
é ã§
ããããã®ããã»ã¹ã¯ãICS ã®å°ççãªè¦æ¨¡ãæ¡å¤§ããã¨ãã£ããé£ãããªããå
¸åä¾ã大è¦æ¨¡
SCADA ã·ã¹ãã ã§ãããç¾å ´ã«åºåãã¦ãã¼å¤æ´ãè¡ãã®ã¯ã³ã¹ãã¨æéãããããããé é
æä½ã便å©ã§ããã
æå·åã®å°å
¥ãé¸æãããªããæãå¹æçãªå®å
¨å¯¾çã¯ã ã«ããéä¿¡å®å
¨ä¿éå±ï¼CSEï¼ã®æå·
ã¢ã¸ã¥ã¼ã«å¦¥å½æ§æ¤è¨¼ããã°ã©ã ï¼CMVPï¼42ãæ¿èªããå®å
¨ãªæå·åã¢ã¸ã¥ã¼ã«ãå©ç¨ããã
ã¨ã§ããããã®ããã°ã©ã ã§ã¯ãæå·åã·ã¹ãã ã¯åä¸çµç¹ã®å°æ°ã¨ã³ã¸ãã¢ã«éçºãå§ããã®
ã§ã¯ãªããåºç¯ãªå°é家ããã®å¼±ç¹ãæ
éã«èª¿æ»ããããã«åºæºãå®ãã¦ãããå°ãªãã¨ãèªå®
æ¸ã¯ä»¥ä¸ã®å¯è½æ§ãèªãã¦ããã
ï¼ ç¹å®ã®æ¹æ³ï¼ã«ã¦ã³ã¿ã¼ã¢ã¼ãçï¼ãå©ç¨ãã¦ãåãã¡ãã»ã¼ã¸ãæ¯ååãå¤ãçæããªã
ããã«ããã
42 CMVP ã«é¢ããæ
å ±ã¯æ¬¡ã® CMVP ãµã¤ãã«ãããhttp://csrc.nist.gov/cryptval/cmvp.htm.
訳注)æãå½ã§ã¯ãFIPS140-2 ã«èµ·æºãæ㤠JIS X 19790 ã«åºã¥ãæå·ã¢ã¸ã¥ã¼ã«è©¦é¨åã³èªè¨¼å¶åº¦ããIPA ã»ãã¥ãªãã£ã»ã³
ã¿ã¼ãéç¨ãã¦ãã(http://www.ipa.go.jp/security/jcmvp/index.html

SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
199
generate the same value each time.
ï¼ ICS messages are protected against replay and forging.
ï¼ Key management is secure throughout the life cycle of the key.
ï¼ The system is using an effective random number generator.
ï¼ The entire system has been implemented securely.
Even then, the technology is effective only if it is an integral part of an effectively enforced information
security policy. American Gas Association (AGA) report 12-1 [5] contains an example of such a security
policy. While it is directed toward a natural gas SCADA system, many of its policy recommendations
could apply to any ICS.
For an ICS, encryption can be deployed as part of a comprehensive, enforced security policy. Organizations
should select cryptographic protection based on a risk assessment and the identified value of the
information being protected and ICS operating constraints. Specifically, a cryptographic key should be long
enough so that guessing it or determining it through analysis takes more effort, time, and cost than the
value of the protected asset.
The encryption hardware should be protected from physical tampering and uncontrolled electronic
connections. Assuming cryptography is the appropriate solution, organizations should select cryptographic
protection with remote key management if the units being protected are so numerous or geographically
dispersed that changing keys is difficult or expensive.
Use separate plaintext and ciphertext ports unless the network absolutely requires the restriction to pass
both plaintext and ciphertext through each port.
Use only modules that can be certified to comply with a standard, such as FIPS 140-2 [90] through the
Cryptographic Module Validation Program (CMVP).
6.2.16.2 Virtual Private Network (VPN)
One method of encrypting communication data is through a VPN, which is a private network that operates
as an overlay on a public infrastructure, so that the private network can function across a public network.
The most common types of VPN technologies implemented today are:
ï¼ Internet Protocol Security (IPsec). IPsec is a set of standards defined by IETF to govern the secure
communications of data across public networks at the IP layer. IPsec is included in many current
operating systems. The intent of the standards is to guarantee interoperability across vendor platforms;
however, the reality is that the determination of interoperability of multi-vendor implementations
depends on specific implementation testing conducted by the end-user organization. IPsec supports
two encryption modes: transport and tunnel. Transport mode encrypts only the data portion (payload)
of each packet, but leaves the header untouched. The more secure tunnel mode adds a new header to
each packet and encrypts both the original header and the payload. On the receiving side, an IPsec-
compliant device decrypts each packet. The protocol has been continually enhanced to address
specific requirements, such as extensions to the protocol to address individual user authentication and
NAT device transversal. These extensions are typically vendor-specific and can lead to interoperability
issues primarily in host-to-security gateway environments. NIST SP 800-77 provides guidance on
IPsec VPNs [74].

SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
200
ï¼ ICS ã¡ãã»ã¼ã¸ããªãã¬ã¼ã欺çããä¿è·ãããã
ï¼ ãã¼ç®¡çããã¼ã®ã©ã¤ããµã¤ã¯ã«ä¸ã»ãã¥ã¢ã«ãªãã
ï¼ ã·ã¹ãã ãå¹æçãªä¹±æ°çºçå¨ã使ç¨ããã
ï¼ ã·ã¹ãã å
¨ä½ãã»ãã¥ã¢ã«å®è£
ãããã
ããã§ããã®æè¡ãå¹æçã§ããããã«ã¯ããããæå¹ã«å®æ½ããã¦ããæ
å ±ã»ãã¥ãªãã£ããª
ã·ã¼ã®ä¸å¯æ¬ ãªä¸é¨ã«ãªã£ã¦ããå ´åã®ã¿ã§ãããç±³å½ã¬ã¹åä¼ï¼AGAï¼å ±åæ¸12-1[5]ã«ã¯ã
ãã®ãããªã»ãã¥ãªãã£ããªã·ã¼ã®ä¸ä¾ãè¼ã£ã¦ããã天ç¶ã¬ã¹ SCADA ã·ã¹ãã åãã®ãã®ã§
ã¯ãããããã®ããªã·ã¼æ¨å¥¨äºé
ã®å¤ãã¯ã©ã® ICS ã«ãå½ã¦ã¯ã¾ãã
ICS ã§ã¯ãæå·åã¯å
æ¬çãªã»ãã¥ãªãã£æ½è¡ã®ä¸ç°ã¨ãã¦å±éå¯è½ã§ãããçµç¹ã¯ããªã¹ã¯è©
価ãä¿è·ãããæ
å ±ã®ä¾¡å¤åã³ ICS æ¥åã®å¶ç´äºé
ãåºã«ãæå·åä¿è·ãé¸æãã¹ãã§ãããç¹
ã«æå·éµã¯ååé·ããã解æã«ããæ¨æ¸¬ã»å¤å¥ã«è¦ããå´åã»æéã»ã³ã¹ãããä¿è·ãããè³ç£
価å¤ã«è¦åããªãããã«ãã¹ãã§ããã
æå·åãã¼ãã¦ã¨ã¢ã¯ãç©ççæ¹ç«ã管çå¤ã®é»åæ¥ç¶ããä¿è·ãã¹ãã§ãããæå·åããµãã
ããã½ãªã¥ã¼ã·ã§ã³ã§ããã¨ã¿ãªããªããä¿è·ããé¨ç½²ãå¤ãå°ççã«åæ£ãã¦ãã¦ãã¼å¤æ´ã
å°é£ã»å²é«ã«ãªãå ´åãçµç¹ã¯é éãã¼ç®¡çã®å¯è½ãªæå·åä¿è·ãé¸æãã¹ãã§ããã
ãããã¯ã¼ã¯ãå¹³æãæå·æãåãã¼ããã渡ããã¨ã絶対çã«å¶éãã¦ããã®ã§ãªããã°ãå¹³
æãã¼ãã¨æå·æãã¼ããåé¢ãã¦ä½¿ç¨ããã
æå·ã¢ã¸ã¥ã¼ã«å¦¥å½æ§æ¤è¨¼ããã°ã©ã ï¼CMVPï¼ãéãã¦ãFIPS 140-2 [90]çã®è¦æ ¼ã«é©åãã
ã¢ã¸ã¥ã¼ã«ã®ã¿ã使ç¨ããã
6.2.16.2 ä»®æ³ãã©ã¤ãã¼ããããã¯ã¼ã¯ï¼VPNï¼
éä¿¡ãã¼ã¿ãæå·åãã 1ã¤æ¹æ³ã¯ VPN ãçµç±ãããã¨ã§ãããVPN ã¯å
¬éã¤ã³ãã©ä¸ã®ãªã¼
ãã¼ã¬ã¤ã¨ãã¦æ©è½ãããã©ã¤ãã¼ããããã¯ã¼ã¯ã¯å
¬éãããã¯ã¼ã¯ã¨ã®éã§ç¨¼åãããä»æ¥
å®è£
ããã¦ããæãä¸è¬ç㪠VPN æè¡ã«ã¯ä»¥ä¸ãããã
ï¼ ã¤ã³ã¿ã¼ããããããã³ã«ã»ãã¥ãªãã£ï¼IPSecï¼ãIPSec ã¯IETF ãå®ç¾©ããè¦æ ¼ã§ãIP ã¬
ã¤ã¤ã¼ã«ãããå
¬éãããã¯ã¼ã¯ãè¶ãã¦ãã»ãã¥ã¢ãªãã¼ã¿éä¿¡ãå¶å¾¡ãããIPSec ã¯ç¾
è¡OS ã®å¤ãã«çµã¿è¾¼ã¾ãã¦ããããã®è¦æ ¼ã®ç®çã¯ããã³ãã¼ãã©ãããã¼ã éã®ç¸äºé
ç¨æ§ãä¿å®ãããã¨ã«ããããã ãç¾å®ã«ã¯ãè¤æ°ãã³ãã¼å®è£
éã®ç¸äºéç¨æ§ã®å¤å®ã¯ã
ã¨ã³ãã¦ã¼ã¶çµç¹ãè¡ãåå¥ã®å®è£
試é¨ã«å·¦å³ããããIPSec ã¯ããã©ã³ã¹ãã¼ãã¨ãã³ã
ã«ã¨ãã 2ã¤ã®æå·ã¢ã¼ãã«å¯¾å¿ãã¦ããããã©ã³ã¹ãã¼ãã¢ã¼ãã¯ãåãã±ããã®ãã¼ã¿
é¨åï¼ãã¤ãã¼ãï¼ã®ã¿ãæå·åãããããã¼ã¯ãã®ã¾ã¾ã«ãããããã»ãã¥ã¢ãªãã³ãã«
ã¢ã¼ãã¯ãåãã±ããã«æ°ãããããã¼ãä»ããå
ã®ãããã¼ã¨ãã¤ãã¼ããã¨ãã«æå·å
ãããåä¿¡å´ã§ã¯ãIPSec ã«é©åããããã¤ã¹ãåãã±ããã復å·ããããããã³ã«ã¯ç¶ç¶
çã«æ¡å¼µãããç¹å®ã®è¦ä»¶ã«ã対å¿ããããã«ãªã£ã¦ãããåã
ã®ã¦ã¼ã¶èªè¨¼åã³ NAT ã
ãã¤ã¹æ¨ªæã«å¯¾å¿ãããããã³ã«æ¡å¼µããã®ä¸ã«å«ã¾ããããã®ãããªæ¡å¼µã¯ä¸è¬ã«ãã³ã
ã¼åºæã®ãã®ã§ãããããç¹ã«ãã¹ãããã»ãã¥ãªãã£ã²ã¼ãã¦ã§ã¤ç°å¢ã«ããã¦ãç¸äºé
ç¨æ§ã®åé¡ç¹ã¨ãªããNIST SP 800-77 ã«ã¯ãIPsec VPN ã«ä¿ãã¬ã¤ãã³ã¹[74]ãããã
SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
201
ï¼ Secure Sockets Layer (SSL). SSL provides a secure channel between two machines that encrypts the
contents of each packet. The IETF made slight modifications to the SSL version 3 protocol and
created a new protocol called Transport Layer Security (TLS). The terms âSSLâ and âTLSâ are often
used interchangeably, and this document generically uses the SSL terminology. SSL is most often
recognized for securing HTTP traffic; this protocol implementation is known as HTTP Secure
(HTTPS). However, SSL is not limited to HTTP traffic; it can be used to secure many different
application layer programs. SSL-based VPN products have gained acceptance because of the market
for âclientlessâ VPN products. These products use standard Web browsers as clients, which have built-
in SSL support. The âclientlessâ term means that there is no need to install or configure third-party
VPN âclientâ software on usersâ systems. NIST SP 800-52 provides guidance on SSL configuration
[70].
ï¼ Secure Shell (SSH). SSH is a command interface and protocol for securely gaining access to a remote
computer. It is widely used by network administrators to remotely control Web servers and other types
of servers. The latest version, SSH2, is a proposed set of standards from the IETF. Typically, SSH is
deployed as a secure alternative to a telnet application. SSH is included in most UNIX distributions,
and is typically added to other platforms through a third-party package.
ICS-specific Recommendations and Guidance
VPNs are most often used in the ICS environment to provide secure access from an untrusted network to
the ICS control network. Untrusted networks can range from the Internet to the corporate LAN. Properly
configured, VPNs can greatly restrict access to and from control system host computers and controllers,
thereby improving security. They can also potentially improve control network responsiveness by removing
unauthorized non-essential traffic from the intermediary network.
Other possible deployments include using either host-based or mini-standalone security gateways, either
interposed before or running on individual control devices. This technique of implementing VPNs on an
individual device basis can have significant administration overhead.
VPN devices used to protect control systems should be thoroughly tested to verify that the VPN technology
is compatible with the application and that implementation of the VPN devices does not unacceptably
affect network traffic characteristics.

SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
202
ï¼ ã»ãã¥ã¢ã½ã±ããã¬ã¤ã¤ã¼ï¼SSLï¼ãSSL ã¯2å°ã®ãã·ã³éã«ã»ãã¥ã¢ãªçµè·¯ãä¸ããåã
ã±ããã®å
容ãæå·åãããIETF ã¯SSL ãè¥å¹²æ¹ä¿®ã㦠SSL ãã¼ã¸ã§ã³ 3ã¨ãããã©ã³ã¹
ãã¼ãã¬ã¤ã¤ã¼ã»ãã¥ãªãã£ï¼TLSï¼ãæ°è¦ãããã³ã«ã¨ãã¦ä½æããããSSLãã¨
ãTLSãã¯ãç¨èªã¨ãã¦äºæçã«ä½¿ããããã¨ãå¤ããæ¬æ¸ã§ã¯å
¨è¬çã« SSL ã®ç¨èªãç¨ã
ããSSL ã¯HTTP ãã©ãã£ãã¯ãã»ãã¥ã¢ã«ããæè¡ã¨ãã¦ããç¥ããã¦ããããã®ããã
ã³ã«å®è£
㯠HTTP ã»ãã¥ã¢ï¼HTTPSï¼ã¨ãã¦ç¥ããã¦ãããããã SSL ã¯HTTP ãã©ãã£
ãã¯ã«éå®ãããªããå¤æ§ãªã¢ããªã±ã¼ã·ã§ã³å±¤ããã°ã©ã ãã»ãã¥ã¢ã«ããããã«å©ç¨ã
ãããSSL ãã¼ã¹ã® VPN 製åã¯ãã¯ã©ã¤ã¢ã³ãã¬ã¹ãVPN 製åå¸å ´ã®ããã§ãåãå
¥ãã
ãã¦ããããããã製åã§ã¯ãSSL ãµãã¼ããå
èµãããæ¨æºçã¦ã§ããã©ã¦ã¶ã¼ãã¯ã©ã¤
ã¢ã³ãã¨ãã¦å©ç¨ããããã¯ã©ã¤ã¢ã³ãã¬ã¹ãã¨ã¯ããµã¼ããã¼ãã£ã® VPNãã¯ã©ã¤ã¢ã³
ããã½ããã¦ã¨ã¢ãã¦ã¼ã¶ã·ã¹ãã ã«ã¤ã³ã¹ãã¼ã«åã¯è¨å®ããå¿
è¦ããªãã¨ããæå³ã§ã
ããNIST SP 800-52 ã«ã¯ãSSL ã®è¨å®ã«ä¿ãã¬ã¤ãã³ã¹[70]ãããã
ï¼ ã»ãã¥ã¢ã·ã§ã«ï¼SSH)ãSSH ã¯ãé éã³ã³ãã¥ã¼ã¿ã¸ã®ã»ãã¥ã¢ãªã¢ã¯ã»ã¹ãå¾ãããã®
ã³ãã³ãã¤ã³ã¿ãã§ã¼ã¹åã³ãããã³ã«ã§ãããã¦ã§ããµã¼ããã®ä»ã®ãµã¼ããé éæä½ã
ããããåºããããã¯ã¼ã¯ç®¡çè
ã«å©ç¨ããã¦ãããææ°ãã¼ã¸ã§ã³ã® SSH2 ãæ°ããè¦æ ¼
ã¨ãã¦ãIETF ããæå±ããã¦ãããä¸è¬ã« SSH ã¯ããã«ãããã«ä»£ããã»ãã¥ã¢ãªä»£æ¿æ
段ã¨ãã¦å±éããã¦ãããSSH ã¯ã»ã¨ãã©ã® UNIX ãã£ã¹ããªãã¥ã¼ã·ã§ã³ã«çµã¿è¾¼ã¾ãã¦
ãããé常ããµã¼ããã¼ãã£ããã±ã¼ã¸ãéãã¦ãä»ã®ãã©ãããã¼ã ã«ã追å ããã¦ããã
ICS
åºæã®æ¨å¥¨äºé
åã³ã¬ã¤ãã³ã¹
VPN ã¯ãä¿¡é ¼ã®ç½®ããªããããã¯ã¼ã¯ãã ICS å¶å¾¡ãããã¯ã¼ã¯ã¸ã»ãã¥ã¢ã«ã¢ã¯ã»ã¹ããã
ããICS ç°å¢ã§å©ç¨ããããã¨ãå¤ããä¿¡é ¼ã®ç½®ããªããããã¯ã¼ã¯ã¨ã¯ãã¤ã³ã¿ã¼ãããã
ãä¼æ¥ LAN ã¾ã§å¤å²ã«ããããæ£ããè¨å®ããã°ãVPN ã¯å¶å¾¡ã·ã¹ãã ã®ãã¹ãã³ã³ãã¥ã¼
ã¿ããã³ã³ã³ããã¼ã©ã¨ã®ã¢ã¯ã»ã¹ãèããå¶éããã»ãã¥ãªãã£ãæ¹åãããã¾ãæªè¨±å¯ã®
ä¸è¦ãã©ãã£ãã¯ãåªä»ãããã¯ã¼ã¯ããé¤å»ãããã¨ã§ãå¶å¾¡ãããã¯ã¼ã¯ã®å¿çæ度ãæ¹
åã§ããã
ãã®ä»å¯è½ãªå±éã¨ãã¦ã¯ããã¹ããã¼ã¹åã¯å°åã®ã¹ã¿ã³ãã¢ãã¼ã³ã»ãã¥ãªãã£ã²ã¼
ãã¦ã§ã¤ãåã
ã®å¶å¾¡ããã¤ã¹ã®åé¢ã«åã¯é£ç¶ã§é
ç½®ãã¦ä½¿ç¨ããæ¡ããããåã
ã®ã
ãã¤ã¹ãã¨ã« VPN ãå®è£
ãããã®æè¡ã¯ã管çãªã¼ãã¼ãããã大ãããªãã
å¶å¾¡ã·ã¹ãã ã®ä¿è·ã«ä½¿ç¨ãã VPN ããã¤ã¹ã¯ãå¾¹åºçã«è©¦é¨ãè¡ããVPN æè¡ãã¢ããªã±ã¼
ã·ã§ã³ã«é©åãã¦ãããã¨ãVPN ããã¤ã¹ã®å®è£
ã«ãããããã¯ã¼ã¯ãã©ãã£ãã¯ç¹æ§ã許容
é度ãè¶
ãã¦å½±é¿ãããªããã¨ã確èªãã¹ãã§ããã
SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
203
6.2.17 System and Information Integrity
Maintaining system and information integrity assures that sensitive data has not been modified or deleted in
an unauthorized and undetected manner. The security controls that fall within the NIST SP 800-53 System
and Information Integrity (SI) family provide policies and procedures for identifying, reporting, and
correcting information system flaws. Controls exist for malicious code detection, spam and spyware
protection, and intrusion detection, although they may not be appropriate for all ICS applications. Also
provided are controls for receiving security alerts and advisories, and the verification of security functions
on the information system. In addition, there are controls within this family to detect and protect against
unauthorized changes to software and data, provide restrictions to data input and output, and check for the
accuracy, completeness, and validity of data as well as handle error conditions, although they may not be
appropriate for all ICS applications.
Supplemental guidance for the SI controls can be found in the following documents:
ï¼ NIST SP 800-40 provides guidance on security patch installation [40].
ï¼ NIST SP 800-94 provides guidance on Intrusion Detection and Prevention (IDP) Systems [55].
ï¼ NIST SP 800-100 provides guidance on information security governance and planning [27].
ICS-specific Recommendations and Guidance
Controls exist for malicious code detection, spam and spyware protection, and intrusion detection, although
they may not be appropriate for all ICS applications. ICS-specific recommendations and guidance for these
controls are included in Sections Error! Reference source not found.and 0.
SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
204
6.2.17 ã·ã¹ãã åã³æ
å ±ã®ä¿å
¨
ã·ã¹ãã åã³æ
å ±ä¿å
¨ãç¶æãããã¨ã«ãããè¦æ³¨æãã¼ã¿ãæ¹å¤ããããç¡æã§æ°ã¥ããªã
ãã¡ã«åé¤ããããããªãã¨ããªããªããNIST SP 800-53 ã®ã·ã¹ãã åã³æ
å ±ã®ä¿å
¨ï¼SIï¼ã
ã¡ããªã«å«ã¾ããã»ãã¥ãªãã£å¯¾çã«ã¯ãæ
å ±ã·ã¹ãã ã®æ¬ é¥ãèå¥ããå ±åããæ¯æ£ããã
ãã®ããªã·ã¼åã³æé ãå®ãããã¦ãããå
¨ã¦ã® ICS ç¨éã«é©åããããã§ã¯ãªãããæªæã
ãã³ã¼ãã®æ¤åºãã¹ãã åã³ã¹ãã¤ã¦ã¨ã¢ä¿è·åã³ä¾µå
¥æ¤ç¥ã®ããã®å¯¾çããããã¾ãã»ãã¥
ãªãã£ã¢ã©ã¼ããå§åãåããããã®å¯¾çããæ
å ±ã·ã¹ãã ä¸ã®ã»ãã¥ãªãã£æ©è½ã®æ¤è¨¼å¯¾ç
ããããå ãã¦ãå
¨ã¦ã® ICS ç¨éã«é©åããããã§ã¯ãªããããã®ãã¡ããªã§ã¯ãã½ããã¦ã¨
ã¢ããã¼ã¿ã¸ã®ç¡æå¤æ´ãæ¤åºã»é²æ¢ããããã®å¯¾çããã¼ã¿å
¥åºåãå¶éããããã®å¯¾çã
ãã¼ã¿ã®æ£ç¢ºæ§ã»å®å
¨æ§ã»å¦¥å½æ§ã確èªããããã®å¯¾çãã¨ã©ã¼ç¶æ
ãå¦çããããã®å¯¾çã
ããã
SI 管çã®è£è¶³çã¬ã¤ãã³ã¹ã以ä¸ã®ææ¸ã«æ²è¼ããã¦ããã
ï¼ NIST SP 800-40ï¼ã»ãã¥ãªãã£ãããã®ã¤ã³ã¹ãã¼ã«ã«ä¿ãã¬ã¤ãã³ã¹[40]
ï¼ NIST SP 800-94ï¼ä¾µå
¥æ¤ç¥åã³é²æ¢ã«ä¿ãã¬ã¤ãã³ã¹[55]
ï¼ NIST SP 800-100ï¼æ
å ±ã»ãã¥ãªãã£ã¬ããã³ã¹åã³ãã©ã³ãã³ã°ã«ä¿ãã¬ã¤ãã³ã¹[27]
ICS
åºæã®æ¨å¥¨äºé
åã³ã¬ã¤ãã³ã¹
å
¨ã¦ã® ICS ç¨éã«é©åããããã§ã¯ãªãããæªæããã³ã¼ãã®æ¤åºãã¹ãã åã³ã¹ãã¤ã¦ã¨ã¢ä¿
è·åã³ä¾µå
¥æ¤ç¥ã®ããã®å¯¾çããããããã対çã«é¢ãã ICS åºæã®æ¨å¥¨äºé
åã³ã¬ã¤ãã³ã¹ã
ã»ã¯ã·ã§ã³ Error!Reference source not found.and 0ã«ããã

SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
205
6.2.17.1 Virus and Malicious Code Detection
Antivirus and malware code detection products evaluate files on a computerâs storage devices against an
inventory of known malware signature files. If one of the files on a computer matches the profile of a
known virus, the virus is removed through a disinfection process (e.g., quarantine, deletion) so it cannot
infect other local files or communicate across a network to infect other files. Antivirus software can be
deployed on workstations, servers, firewalls and handheld devices.
ICS-specific Recommendations and Guidance
Antivirus tools only function effectively when installed, configured, running full-time, and maintained
properly against the state of known attack methods and payloads. While antivirus tools are common
security practice in IT computer systems, their use with ICS may require adopting special practices
including compatibility checks, change management issues, and performance impact metrics. These special
practices should be utilized whenever new signatures or new versions of antivirus software are installed.
Major ICS vendors recommend and even support the use of particular antivirus tools. In some cases,
control system vendors may have performed regression testing across their product line for supported
versions of a particular antivirus tool and also provide associated installation and configuration
documentation. There is also an effort to develop a general set of guidelines and test procedures focused on
ICS performance impacts to fill the gaps where ICS and antivirus vendor guidance is not available [56].
Generally:
ï¼
Windows, Unix, Linux systems, etc. used as consoles, engineering workstations, data historians, HMIs
and general purpose SCADA and backup servers can be secured just like commercial IT equipment:
install push- or auto-updated antivirus and patch management software with updates distributed via an
antivirus server and patch management server located inside the process control network and auto-
updated from the IT network.
ï¼ Follow vendor recommendations on all other servers and computers (DCS, PLC, instruments) that
have time-dependent code, modified or extended the operating system or any other change that makes
it different from any standard PC that one could buy at an office supply or computer store. Expect the
vendor to make periodic maintenance releases that include security patches.
6.2.17.2 Intrusion Detection and Prevention
Intrusion detection systems (IDS) monitor events on a network, such as traffic patterns, or a system, such as
log entries or file accesses, so that they can identify an intruder breaking into or attempting to break into a
system [57]. IDS ensure that unusual activity such as new open ports, unusual traffic patterns, or changes to
critical operating system files is brought to the attention of the appropriate security personnel.
The two most commonly used types of IDS are:
ï¼ Network-Based IDS. These systems monitor network traffic and generate alarms when they identify
traffic that they deem to be an attack.

SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
206
6.2.17.1 ã¦ã¤ã«ã¹åã³æªæããã³ã¼ãã®æ¤åº
ã¦ã¤ã«ã¹åã³æªæããã³ã¼ãã®æ¤åºè£½åã¯ãã³ã³ãã¥ã¼ã¿ã®ã¹ãã¬ã¼ã¸ããã¤ã¹ä¸ã«ãããã¡ã¤
ã«ããæ¢ç¥ã®ãã«ã¦ã¨ã¢ã·ã°ããã£ãã¡ã¤ã«ã®ç®é²ã«ç
§ããã¦è©ä¾¡ãããã³ã³ãã¥ã¼ã¿ä¸ã®ãã¡
ã¤ã«ã® 1ã¤ãæ¢ç¥ã®ã¦ã¤ã«ã¹ã®ãããã¡ã¤ã«ã«åè´ããã¨ããã®ã¦ã¤ã«ã¹ã¯æ¶æ¯ããã»ã¹ï¼æ¤ç«ã
åé¤çï¼ãéãã¦æé¤ãããä»ã®ãã¼ã«ã«ãã¡ã¤ã«ããããã¯ã¼ã¯ãè¶ããä»ã®ãã¡ã¤ã«ã¸ã®æ
æåã失ããã¢ã³ãã¦ã¤ã«ã¹ã½ããã¦ã¨ã¢ã¯ã¯ã¼ã¯ã¹ãã¼ã·ã§ã³ããµã¼ãããã¡ã¤ã¢ã¦ã©ã¼ã«å
ã³ãã³ããã«ãããã¤ã¹ã«å±éã§ããã
ICS åºæã®æ¨å¥¨äºé
åã³ã¬ã¤ãã³ã¹
ã¢ã³ãã¦ã¤ã«ã¹ãã¼ã«ã¯ã¤ã³ã¹ãã¼ã«ãããè¨å®ããã常æå®è¡ãããæ£ããç¶æããã¦ããå ´
åã«ã®ã¿ãæ¢ç¥ã®æ»ææ¹æ³åã³ãã¤ãã¼ãç¶æ
ã«å¯¾ãã¦æå¹ã«æ©è½ãããIT ã³ã³ãã¥ã¼ã¿ã·ã¹ã
ã ã§ã¯ä¸è¬çãªã»ãã¥ãªãã£è¦ç¯ã¨ãªã£ã¦ããããICS ã§ä½¿ç¨ããã«ã¯ãæ´åæ§ãã§ãã¯ã管ç
å¤æ´åé¡ãããã©ã¼ãã³ã¹å½±é¿è©ä¾¡åºæºçã®ç¹å¥ãªè¦ç¯ãæ¡ç¨ããå¿
è¦ãããããã®ãããªç¹å¥
è¦ç¯ã¯ãã¢ã³ãã¦ã¤ã«ã¹ã½ããã¦ã¨ã¢ã®æ°è¦ã·ã°ããã£ãæ°ãã¼ã¸ã§ã³ãã¤ã³ã¹ãã¼ã«ããã¨ã
ã«ã¯å¿
ãæ¡ç¨ãã¹ãã§ããã
大æ ICS ãã³ãã¼ã¯ãç¹å®ã®ã¢ã³ãã¦ã¤ã«ã¹ãã¼ã«ã®ä½¿ç¨ãæ¨å¥¨ãããµãã¼ããè¡ã£ã¦ãããå ´
åã«ãã£ã¦ã¯ãå¶å¾¡ã·ã¹ãã ãã³ãã¼ã¯ã製åç³»åå
¨ä½ã®ãªã°ã¬ãã·ã§ã³è©¦é¨ãè¡ããç¹å®ã®ã¢
ã³ãã¦ã¤ã«ã¹ãã¼ã«ã®åãã¼ã¸ã§ã³ã®å¯¾å¿ç¶æ³ãæ¤è¨¼ãã¦ãããã¨ããããé¢ä¿ããã¤ã³ã¹ãã¼
ã«åã³è¨å®ã«é¢ããææ¸ãæä¾ãã¦ãããã¾ã ICS ã¢ã³ãã¦ã¤ã«ã¹ãã³ãã¼ã¬ã¤ãã³ã¹ããªãå ´
åã«ã¯ãä¸è¶³ãè£ããããICS ããã©ã¼ãã³ã¹ã®å½±é¿ã«ç¹åããæ±ç¨çãªã¬ã¤ãã©ã¤ã³åã³è©¦é¨
æé ã®ä½æã«ãåãçµãã§ãã[56]ã
ä¸è¬çã«ã
ï¼ ã³ã³ã½ã¼ã«ãã¨ã³ã¸ãã¢ãªã³ã°ã¯ã¼ã¯ã¹ãã¼ã·ã§ã³ããã¼ã¿ãã¹ããªã¢ã³ãHMIãæ±ç¨
SCADA åã³ããã¯ã¢ãããµã¼ãã¨ãã¦å©ç¨ãã WindowsãUnixãLinux ã·ã¹ãã çã¯ãå¸
販㮠IT è£
åååæ§ã«ã»ãã¥ã¢ã«ãããã¨ãå¯è½ã§ããããã®å ´åãããã·ã¥å¼åã¯èªåæ´
æ°å¼ã®ã¢ã³ãã¦ã¤ã«ã¹åã³ããã管çã½ããã¦ã¨ã¢ãã¤ã³ã¹ãã¼ã«ããï¼æ´æ°ã¯ããã»ã¹å¶
御ãããã¯ã¼ã¯å
ã«ããã¢ã³ãã¦ã¤ã«ã¹ãµã¼ãåã³ããã管çãµã¼ãçµç±ã§é
å¸ãããIT
ãããã¯ã¼ã¯ããèªåæ´æ°ãããï¼ã
ï¼ æéä¾åã³ã¼ããæã¡ãOS ãæ¹ä¿®ã»æ¡å¼µãããããã®ä»ã®å¤æ´ãå ãã¦ãå¸è²©ã®æ¨æº PC ã¨
ã¯ç°ãªã£ã¦ããä¸è¨ä»¥å¤ã®å
¨ã¦ã®ã³ã³ãã¥ã¼ã¿ï¼DCSãPLCãã¤ã³ã¹ãã«ã¡ã³ãï¼ã«ã¤ãã¦
ã¯ããã³ãã¼ã®æ¨å¥¨äºé
ã«å¾ãããã³ãã¼ãå®æçã«ã»ãã¥ãªãã£ãããã®å
¥ã£ãä¿å®ãªãª
ã¼ã¹ãæä¾ãããã¨ãæå¾
ããã
6.2.17.2 ä¾µå
¥æ¤ç¥åã³é²æ¢
ä¾µå
¥æ¤ç¥ã·ã¹ãã ï¼IDSï¼ã¯ããã©ãã£ãã¯ãã¿ã¼ã³çã®ãããã¯ã¼ã¯ã¤ãã³ãããã°é
ç®ãã
ã¡ã¤ã«ã¢ã¯ã»ã¹çã®ã·ã¹ãã ãç£è¦ããã·ã¹ãã ã«å
¥ãè¾¼ãä¾µå
¥è
ãã·ã¹ãã ã«å
¥ãè¾¼ããã¨ã
ãä¾µå
¥è
ãè¦æ¥µãããã¨ãã§ãã[57]ãIDS ã¯ããã¼ãã®æ°è¦éè¨ãé常ã¨ç°ãªããã©ãã£ãã¯
ãã¿ã¼ã³ãéè¦ãª OS ãã¡ã¤ã«ã¸ã®å¤æ´ã¨ãã£ãæ®æ®µã¨éãæ´»åãã»ãã¥ãªãã£æ
å½è·å¡ã®æ³¨æ
ãå¼ãããã«ããã
IDS ã使ç¨ããä¸è¬çãªç¨®é¡ã¯æ¬¡ã® 2ã¤ã§ããã
ï¼ ãããã¯ã¼ã¯ãã¼ã¹ IDSãã·ã¹ãã ã¯ãããã¯ã¼ã¯ãã©ãã£ãã¯ãç£è¦ãã¦ãæ»æã¨è¦ãªã
ãããã©ãã£ãã¯ãç¹å®ããã¨ã¢ã©ã¼ã ãçºããã

SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
207
ï¼ Host-Based IDS. This software monitors one or more types of characteristics of a system, such as
application log file entries, system configuration changes, and access to sensitive data on a system and
responds with an alarm or countermeasure when a user attempts to breach security.
ICS-specific Recommendations and Guidance
An effective IDS deployment typically involves both host-based and network-based IDS. In the current ICS
environment, network-based IDS are most often deployed between the control network and the corporate
network in conjunction with a firewall; host-based IDS are most often deployed on the computers that use
general-purpose OSs or applications such as HMIs, SCADA servers, and engineering workstations.
Properly configured, an IDS can greatly enhance the security management teamâs ability to detect attacks
entering or leaving the system, thereby improving security. They can also potentially improve a control
networkâs efficiency by detecting non-essential traffic on the network. However, even when IDS are
implemented, security staff can primarily recognize individual attacks, as opposed to organized patterns of
attacks over time. Network security monitoring and an understanding of the normal state of the ICS
network can help distinguish attacks from transient conditions, and both trigger and provide information
into events that are outside the normal state.
Current IDS and IPS products are effective in detecting and preventing well-known Internet attacks, but
until recently they have not addressed ICS protocol attacks. IDS and IPS vendors are beginning to develop
and incorporate attack signatures for various ICS protocols such as Modbus, DNP3, and ICCP [58].
6.2.17.3 Patch Management
Patches are additional pieces of code that have been developed to address specific problems or flaws in
existing software. Vulnerabilities are flaws that can be exploited, enabling unauthorized access to IT
systems or enabling users to have access to greater privileges than authorized.
A systematic approach to managing and using software patches can help organizations to improve the
overall security of their IT systems in a cost-effective way. Organizations that actively manage and use
software patches can reduce the chances that the vulnerabilities in their IT systems can be exploited; in
addition, they can save time and money that might be spent in responding to vulnerability-related incidents.
NIST SP 800-40 Revision 3 [40] provides guidance for organizational security managers who are
responsible for designing and implementing security patch and vulnerability management programs and for
testing the effectiveness of the programs in reducing vulnerabilities. The guidance is also useful to system
administrators and operations personnel who are responsible for applying and testing patches and for
deploying solutions to vulnerability problems.
ICS-specific Recommendations and Guidance
Applying patches to OS components creates another situation where significant care should be exercised in
the ICS environment. Patches should be adequately tested (e.g., off-line on a comparable ICS) to determine
the acceptability of side effects. Regression testing is advised. It is not uncommon for patches to have an
adverse effect on other software. A patch may remove a vulnerability, but it can

SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
208
ï¼ ãã¹ããã¼ã¹ IDSããã®ã½ããã¦ã¨ã¢ã¯ãã¢ããªã±ã¼ã·ã§ã³ãã°ãã¡ã¤ã«ã¨ã³ããªãã·ã¹ã
ã è¨å®å¤æ´ãã·ã¹ãã ä¸ã®è¦æ³¨æãã¼ã¿ã¸ã®ã¢ã¯ã»ã¹ã¨ãã£ãã·ã¹ãã ç¹æ§ã¿ã¤ãã 1ã¤ã
è¤æ°ç£è¦ãã¦ãã¦ã¼ã¶ãã»ãã¥ãªãã£éåãããããã¨ãã¢ã©ã¼ã åã¯å¯¾çããã£ã¦å¯¾å¿ã
ãã
ICS
åºæã®æ¨å¥¨äºé
åã³ã¬ã¤ãã³ã¹
å¹æç㪠IDS ã®å±éã«ã¯ãé常ãã¹ããã¼ã¹ã¨ãããã¯ã¼ã¯ãã¼ã¹ã® IDS ãã¨ãã«å«ã¾ããã
ç¾å¨ã® ICS ç°å¢ã§ã¯ããããã¯ã¼ã¯ãã¼ã¹ IDS ã¯ãå¶å¾¡ãããã¯ã¼ã¯ã¨ãã¡ã¤ã¢ã¦ã©ã¼ã«çµç±
ã®ä¼æ¥ãããã¯ã¼ã¯ã¨ã®éã§å±éããããã¨ãå¤ããä¸æ¹ãã¹ããã¼ã¹ IDS ã¯ãæ±ç¨ OS ã
HMIãSCADA ãµã¼ããã¨ã³ã¸ãã¢ãªã³ã°ã¯ã¼ã¯ã¹ãã¼ã·ã§ã³çã®ã¢ããªã±ã¼ã·ã§ã³ã使ç¨ãã
ã³ã³ãã¥ã¼ã¿ã§å±éããããã¨ãå¤ããæ£ããè¨å®ããã°ãIDS ã¯ã»ãã¥ãªãã£ãã¼ã ã®è½å
ãèããåä¸ãããã·ã¹ãã ã¸ã®ä¾µå
¥ã»éåºãæ¤ç¥ããã»ãã¥ãªãã£ãæ¹åãããã¾ãããã
ã¯ã¼ã¯ä¸ã®ä¸è¦ãªãã©ãã£ãã¯ãæ¤åºãã¦ãå¶å¾¡ãããã¯ã¼ã¯ã®å¹çãæ¹åã§ããããã ã
IDS ãå®è£
ããå ´åã§ããã»ãã¥ãªãã£è¦å¡ã¯ãçµæçãªæ»æã®çµç¹çãã¿ã¼ã³ã¨ã¯å対ã«ã
åã
ã®æ»æãèªèã§ããããããã¯ã¼ã¯ã»ãã¥ãªãã£ç£è¦åã³ ICS ãããã¯ã¼ã¯ã®æ£å¸¸ç¶æ
ã«
対ããç解ãããã°ãé渡çç¶æ
ããã®æ»æãè¦æ¥µããæ£å¸¸ç¶æ
ãé¸è±ããã¤ãã³ãã«å¯¾ãã¦
ããªã¬ã¼ã¨æ
å ±ãçºä¿¡ãããããªãã
ç¾å¨ã® IDS åã³ IPS 製åã¯ãè¯ãç¥ãããã¤ã³ã¿ã¼ãããæ»æã®æ¤ç¥ã»é²æ¢ã«å¹æãããããæ
è¿ã«ãªãã¾ã§ ICS ãããã³ã«æ»æã«ã¯å¯¾å¿ãã¦ããªãã£ããIDS åã³ IPS ãã³ãã¼ã¯ãModbusã
DNP3
åã³
ICCP
çã®å¤æ§ãª
ICS
ãããã³ã«ã®æ»æã·ã°ããã£ãéçºããçµã¿è¾¼ã¿ã¤ã¤ãã
[58]
ã
6.2.17.3 ããã管ç
ãããã¯ã³ã¼ãã®è¿½å ãã¼ã¹ã§ãæ¢åã½ããã¦ã¨ã¢ã®åé¡ãæ¬ é¥ã«å¯¾å¿ããããã«éçºãããã
èå¼±æ§ã¯æªç¨å¯è½ãªæ¬ é¥ã§ãIT ã·ã¹ãã ã¸ã®ä¸æ£ã¢ã¯ã»ã¹ãå¯è½ã«ããã¦ã¼ã¶ã«ä»ä¸ããã¦ã
ã以ä¸ã®æ¨©éãä¸ããã
ã½ããã¦ã¨ã¢ããããä½ç³»çã«ç®¡çã»å©ç¨ããåçµããããã¨ã§ãçµç¹ã¯è²»ç¨å¹æã®é«ãæ¹æ³
ã§ãIT ã·ã¹ãã å
¨ä½ã®ã»ãã¥ãªãã£ãæ¹åã§ãããã½ããã¦ã¨ã¢ããããç©æ¥µçã«ç®¡çã»å©
ç¨ããçµç¹ã§ã¯ãIT ã·ã¹ãã ã®èå¼±æ§ãæªç¨ãããå¯è½æ§ãæ¸ããã¾ãèå¼±æ§ã«é¢ä¿ããã¤
ã³ã·ãã³ã対å¿ã«è¦ããæéã¨ã³ã¹ããç¯ç´ã§ããã
NIST SP 800-40 第3ç[40]ã«ã¯ãã»ãã¥ãªãã£ãããã®è¨è¨ã»å®è£
ãèå¼±æ§ç®¡çããã°ã©ã
åã³èå¼±æ§è»½æ¸ããã°ã©ã ã®å¹ææ§æ¤è¨¼ãæ
å½ããã»ãã¥ãªãã£ç®¡çè
åãã®ã¬ã¤ãã³ã¹ãã
ãããã®ã¬ã¤ãã³ã¹ã¯ããããã®é©ç¨ã¨è©¦é¨ãèå¼±æ§åé¡ã®ã½ãªã¥ã¼ã·ã§ã³å±éãæ
å½ããã·
ã¹ãã 管çè
ãè·å¡ã«ãå½¹ç«ã¤ã
ICS
åºæã®æ¨å¥¨äºé
åã³ã¬ã¤ãã³ã¹
OS ã³ã³ãã¼ãã³ãã¸ã®ãããé©ç¨ã¯ãICS ç°å¢ã§ã¯ç¹ã«æ
éãæãã¹ãå¥ã®ç¶æ³ãçãããã
ããã®è©¦é¨ã¯ååã«è¡ãï¼åçã® ICS ç°å¢ã§ãªãã©ã¤ã³ã§ï¼ãå¯æ¬¡çå½±é¿ã®è¨±å®¹åº¦ãå¤å®ãã¹
ãã§ããããªã°ã¬ãã·ã§ã³è©¦é¨ãæ¨å¥¨ããããããããä»ã®ã½ããã¦ã¨ã¢ã«æªå½±é¿ãåã¼ãã
ã¨ã¯çãããªãããããã¯èå¼±æ§ããªããããã

SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
209
also introduce a greater risk from a production or safety perspective. Patching the vulnerability may also
change the way the OS or application works with control applications, causing the control application to
lose some of its functionality. Another issue is that many ICS utilize older versions of operating systems
that are no longer supported by the vendor. Consequently, available patches may not be applicable.
Organizations should implement a systematic, accountable, and documented ICS patch management
process for managing exposure to vulnerabilities.
Once the decision is made to deploy a patch, there are other tools that automate this process from a
centralized server and with confirmation that the patch has been deployed correctly. Consider separating
the automated process for ICS patch management from the automated process for non-ICS applications.
Patching should be scheduled to occur during planned ICS outages.
6.2.18 Program Management
The security controls that fall within the NIST SP 800-53 Program Management (PM) focus on the
organization-wide information security requirements that are independent of any particular information
system and are essential for managing information security programs.
Organizations document program management controls in the information security program plan. The
organization-wide information security program plan supplements the individual security plans developed
for each organizational information system. In addition to documenting the information security program
management controls, the security program plan provides a vehicle for the organization, in a central
repository, to document all security controls that have been designated as common controls (i.e., security
controls inherited by organizational information systems).
6.2.19 Privacy Controls
Protecting the privacy of personally identifiable information (PII)43 collected, used, maintained, shared, and
disposed of by programs and information systems is critical given the advances in information technologies
and applications of those technologies. Effective privacy for individuals depends on the safeguards
employed within the organizational information systems that are processing, storing, and transmitting PII.
Organizations cannot have effective privacy without a foundation of information security. However,
privacy is more than security and includes, for example, the principles of transparency, notice, and choice.
The privacy controls focus on information privacy as a value distinct from, but highly interrelated with,
information security. The privacy controls are based on the Fair Information Practice Principles (FIPPs)
embodied in the Privacy Act of 1974, Section 208 of the E-Government Act of 2002, and related Office of
Management and Budget (OMB) guidance. The FIPPs are designed to build public trust in an
organizationâs privacy practices and to help organizations avoid tangible costs and intangible damages
stemming from privacy incidents.
43 OMB Memorandum 07-16 defines PII as âinformation which can be used to distinguish or trace an individualâs
identity such as their name, social security number, biometric records, etc., alone, or when combined with
other personal or identifying information which is linked or linkable to a specific individual, such as date
and place of birth, motherâs maiden name, etc.â [86]. OMB Memorandum 10-22 reaffirmed this definition [87].
NIST Special Publication 800-122 defines PII as âany information about an individual [that is] maintained
by an agency, including: (i) any information that can be used to distinguish or trace an individualâs
identity, such as name, social security number, date and place of birth, motherâs maiden name, or biometric
records; and (ii) any other information that is linked or linkable to an individual, such as medical,
educational, financial, and employment informationâ [88].

SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
210
çç£ãå®å
¨æ§ã®è¦³ç¹ããã¯ããã大ããªãªã¹ã¯ã«ãªãå ´åããããèå¼±æ§ã«ããããå½ã¦ãã¨ã
OS ãã¢ããªã±ã¼ã·ã§ã³ã¨å¶å¾¡ã¢ããªã±ã¼ã·ã§ã³ã®é£åæ¹æ³ãå¤ãããå¶å¾¡ã¢ããªã±ã¼ã·ã§ã³ã®
æ©è½ã失ããããã¨ããããå¥ã®åé¡ã¨ãã¦ããã³ãã¼ããµãã¼ããæã¡åã£ã OS ã®æ§ãã¼ã¸
ã§ã³ã使ç¨ãã ICS ãå¤ããã¨ãæããããããã®çµæãå
¥æå¯è½ãªããããé©ç¨ã§ããªããã¨
ã«ãªããçµç¹ã¯èå¼±æ§ã®é²åºã管çãããããä½ç³»çã§èª¬æã®ã¤ããææ¸åããã ICS ããã管
çããã»ã¹ãå®è¡ãã¹ãã§ããã
ãããã®å±éã決å®ãããªããéä¸åãµã¼ããããã®ããã»ã¹ãèªååããããããæ£ããå±é
ããããã¨ã確èªã§ããå¥ã®ãã¼ã«ããããICS ããã管çã®èªååããã»ã¹ããICS 以å¤ã®ã¢
ããªã±ã¼ã·ã§ã³ã®èªååããã»ã¹ããåé¢ãããã¨ãæ¤è¨ããããããã®é©ç¨ã¯ãè¨ç»ããã
ICS ã®ææ¥åæ¢æã«è¡ãããã«äºå®ãã¹ãã§ããã
6.2.18 ããã°ã©ã 管ç
NIST SP 800-53 ã®ããã°ã©ã 管çï¼PMï¼ã«å«ã¾ãã¦ããã»ãã¥ãªãã£å¯¾çã¯ãç¹å®ã®æ
å ±ã·ã¹
ãã ããç¬ç«ãããæ
å ±ã»ãã¥ãªãã£ããã°ã©ã ã®ç®¡çã«ä¸å¯æ¬ ãªãå
¨çµç¹çæ
å ±ã»ãã¥ãªãã£
è¦ä»¶ã«ç¦ç¹ãå½ã¦ã¦ããã
çµç¹ã¯ãããã°ã©ã 管çå¶å¾¡ãæ
å ±ã»ãã¥ãªãã£ããã°ã©ã è¨ç»æ¸ã®ä¸ã«è¨è¼ãããå
¨çµç¹çæ
å ±ã»ãã¥ãªãã£ããã°ã©ã è¨ç»æ¸ã¯ãåçµç¹ã®æ
å ±ã·ã¹ãã ç¨åå¥ã»ãã¥ãªãã£è¨ç»æ¸ãè£å®ã
ããæ
å ±ã»ãã¥ãªãã£ããã°ã©ã 管ç対çã®ææ¸åã«å ãã¦ãã»ãã¥ãªãã£ããã°ã©ã è¨ç»æ¸ã¯ã
å
±é管çï¼çµç¹ã®æ
å ±ã·ã¹ãã ãç¶æ¿ãã¦ããã»ãã¥ãªãã£å¯¾çï¼ã¨ãã¦æå®ããã¦ããå
¨ã¦ã®
ã»ãã¥ãªãã£å¯¾çãææ¸åããæ段ãéä¸ä¿ç®¡å ´æã«ç¨æããã
6.2.19 ãã©ã¤ãã·ã¼ç®¡ç
æ
å ±æè¡ã®é²æ©ããã®æè¡ã®é©ç¨ãèæ
®ããã¨ãããã°ã©ã åã³æ
å ±ã·ã¹ãã ãåéã»å©ç¨ã»ç¶
æã»å
±æã»å»æ£ããå人ãç¹å®å¯è½ãªæ
å ±ï¼PIIï¼44ã®ãã©ã¤ãã·ã¼ä¿è·ã¯éè¦ã§ãããå¹æçãª
å人ãã©ã¤ãã·ã¼ã¯ãPII ãå¦çã»ä¿ç®¡ã»è»¢éããçµç¹ã®æ
å ±ã·ã¹ãã ã§æ¡ç¨ããã¦ããå®å
¨å¯¾
çã«å·¦å³ããããæ
å ±ã»ãã¥ãªãã£ã®åºç¤ã確ç«ããã¦ããªãçµç¹ã«ã¯ãå¹æçãªãã©ã¤ãã·ã¼
ã¯ãªããã¨ã¯è¨ãããã©ã¤ãã·ã¼ã¯ã»ãã¥ãªãã£ä»¥ä¸ã®ãã®ã§ãããä¾ãã°éææ§ãéç¥åã³é¸
æã®ååãå«ã¾ããã
ãã©ã¤ãã·ã¼ç®¡çã¯ãæ
å ±ã»ãã¥ãªãã£ã¨ã®é¢ä¿ã¯å¼·ããã®ã®ãããã¨ã¯å¥ã®ä¾¡å¤ã¨ãã¦ã®ãã©
ã¤ãã·ã¼æ
å ±ãéç¹ã¨ããããã©ã¤ãã·ã¼ç®¡çã¯ããã©ã¤ãã·ã¼æ³ï¼1974 å¹´ï¼ã®å
¬æ£æ
å ±è¦ç¯
ååï¼FIPPsï¼ãé»åæ¿åºæ³ï¼2002 å¹´ï¼ç¬¬ 208 æ¡åã³é¢ä¿ããè¡æ¿äºç®ç®¡çå±ï¼OMBï¼ã¬ã¤ãã³
ã¹ãæ ¹æ ã¨ãã¦ãããFIPPs ã¯ãçµç¹ã®ãã©ã¤ãã·ã¼è¦ç¯ã«å¯¾ããå½æ°ã®ä¿¡é ¼ãé¸æãããã©ã¤
ãã·ã¼ã¤ã³ã·ãã³ãããçããæå½¢ã®çµè²»ãç¡å½¢ã®æ害ã®åé¿ãç®æãã¦ããã
44 OMB è¦æ¸ 07-16 ã¯PII ããæ°åã社ä¼ä¿éçªå·ããã¤ãªã¡ããªãã¯è¨é²çãåç¬ã§ãåã¯èªçæ¥ãåºçå°ãæ¯è¦ªã®æ§å§ç
ç¹å®ã®å人ã«çµã³ã¤ããçµã³ã¤ãããããã®ä»ã®å人è¥ããã¯èº«åæ
å ±ã¨çµã¿åããã¦ãå人ã®èº«åãå¤å¥åã¯è¿½è·¡ã§ã
ãæ
å ±ãã¨å®ç¾©ãã¦ãã[86]ãOMB è¦æ¸ 10-22 ã¯ãã®å®ç¾©ã追èªãã¦ãã[87]ãNIST SP800-122 ã¯PII ãããæ©é¢ãä¿æ
ãã¦ããå人ã«é¢ããæ
å ±ã§ãï¼1ï¼æ°åã社ä¼ä¿éçªå·ãèªçæ¥ãåºçå°ãæ¯è¦ªã®æ§å§ããã¤ãªã¡ããªãã¯è¨é²çãå
人ã®èº«åãå¤å¥åã¯è¿½è·¡ã§ããæ
å ±åã³ï¼2ï¼å»çãæè²ã財æ¿ãå°±æ¥æ
å ±çãå人ã«çµã³ã¤ããçµã³ã¤ãããããã®ä»
ã®æ
å ±ãã¨å®ç¾©ãã¦ãã[88]ã
SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
211
Privacy controls are the administrative, technical, and physical safeguards employed within organizations
to protect and ensure the proper handling of PII. There are eight privacy control families with each family
aligning with one of the FIPPs. The privacy control families can be implemented at the organization,
department, agency, component, office, program, or information system level. The privacy controls are
structured in a similar manner to the information system security controls in Appendix F of NIST SP 800-
53.
The Privacy Appendix of NIST SP 800-53, Rev. 4 [22], provides a structured set of privacy controls, based
on international standards and best practices to help organizations enforce requirements derived from
federal privacy legislation, policies, regulations, directives, standards, and guidance. Additionally, it
establishes a linkage and relationship between privacy and security controls for purposes of enforcing
respective privacy and security requirements that may overlap in concept and in implementation within
federal information systems, programs, and organizations.
The privacy controls are intended primarily for use by an organizationâs Senior Agency Official for Privacy
(SAOP)/Chief Privacy Officer (CPO) when working with program managers, information system
developers, and information security personnel to determine how best to incorporate effective privacy
protections and practices within those programs and/or systems. These controls facilitate the organizationâs
efforts to comply with privacy requirements affecting those programs and/or systems that collect, use,
maintain, share, or dispose of PII. This promotes closer cooperation between privacy and security officials
within the federal government to help achieve the objectives of senior leaders/executives in enforcing the
requirements in federal privacy legislation, policies, regulations, directives, standards, and guidance.
The 8 privacy control families include:
ï¼ Authority and Purpose (AP).
ï¼ Accountability, Audit, and Risk Management (AR).
ï¼ Data Quality and Integrity (DI).
ï¼ Data Minimization and Retention (DM).
ï¼ Individual Participation and Redress (IP).
ï¼ Security (SE).
ï¼ Transparency (TR).
ï¼ Use Limitation (UL).
SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
212
ãã©ã¤ãã·ã¼ç®¡çã¯ãPII ã«å¯¾ããä¿è·ã¨é©æ£ãªåæ±ã確ä¿ããããã«çµç¹å
ã§æ¡ç¨ããã管ç
ä¸ã®æè¡çã»ç©ççå®å
¨å¯¾çã§ããããã©ã¤ãã·ã¼ç®¡çã® 8ãã¡ããªãããããã® FIPPS ã«æ´å
ãã¦ããããã©ã¤ãã·ã¼ç®¡çåéã¯ãçµç¹ã»é¨ç½²ã»æ©é¢ã»ã³ã³ãã¼ãã³ãããªãã£ã¹ãããã°ã©
ã åã¯æ
å ±ã·ã¹ãã ã¬ãã«ã§å®æ½ã§ããããã©ã¤ãã·ã¼ç®¡çã¯ãNIST SP 800- 53 ä»é² Fã«ããæ
å ±ã·ã¹ãã ã®ã»ãã¥ãªãã£å¯¾çã¨åæ§ã®æ¹æ³ã§æ§ç¯ãããã
NIST SP 800-53 æ¹è¨ç¬¬4ç[22]ã«ã¯ãå½éè¦æ ¼åã³é©æ§è¦ç¯ã«åºã¥ãã¦æ§ç¯ããããã©ã¤ãã·
ã¼ç®¡çããããçµç¹ãé£é¦ãã©ã¤ãã·ã¼æ³ãæ¿çãè¦åãå½ä»¤ãè¦æ ¼åã³ã¬ã¤ãã³ã¹ããçã
ãè¦ä»¶ãå®æ½ããå©ãã¨ãªããã¾ããé£é¦æ
å ±ã·ã¹ãã ãããã°ã©ã åã³çµç¹å
ã§æ¦å¿µä¸ãå®
æ½ä¸ãéãªãåãããã©ã¤ãã·ã¼è¦ä»¶ã¨ã»ãã¥ãªãã£è¦ä»¶ãæ½è¡ããä¸ã§ããã©ã¤ãã·ã¼ç®¡ç
ã¨ã»ãã¥ãªãã£å¯¾çã®çµã³ã¤ããé¢ä¿ã«ã¤ãã¦ãè¨è¿°ãã¦ããã
ãã©ã¤ãã·ã¼ç®¡çã®ç®çã¯ã主ã«çµç¹ã®ãã©ã¤ãã·ã¼æ
å½ä¸ç´å®åï¼SAOPï¼/ãã©ã¤ãã·ã¼æ
å½
主任ï¼CPOï¼ãããã°ã©ã 管çè
ãæ
å ±ã·ã¹ãã éçºè
åã³æ
å ±ã»ãã¥ãªãã£è·å¡ã¨ååããé
ã«ãå¹æçãªãã©ã¤ãã·ã¼ä¿è·ã»è¦ç¯ããããããã°ã©ã ãã·ã¹ãã ã«çµã¿è¾¼ãæåã®æ¹æ³ã®
å¤å®ã«ä½¿ç¨ãããã¨ã«ããããã®ãããªç®¡çã«ãã£ã¦ãPII ãåéã»å©ç¨ã»ç¶æã»å
±æã»å»æ£
ããããã°ã©ã ãã·ã¹ãã ã«å½±é¿ãä¸ãããã©ã¤ãã·ã¼è¦ä»¶éµå®ã«å¯¾ããçµç¹ã®åçµã容æã«
ãªããããã«ããé£é¦æ¿åºã®ãã©ã¤ãã·ã¼æ
å½è
ã¨ã»ãã¥ãªãã£æ
å½è
éã®é£æºãç·å¯ã«ãªãã
å¹¹é¨ãé£é¦ãã©ã¤ãã·ã¼æ³ãæ¿çãè¦å¶ãæ令ãè¦æ ¼åã³ã¬ã¤ãã³ã¹ã®è¦ä»¶ãæ½è¡ãã¦ç®æ¨ã
éæã§ããããã«ããã
8ã¤ã®ãã©ã¤ãã·ã¼ç®¡çåéã¯æ¬¡ã®ã¨ããã
ï¼ æ¨©éåã³ç®çï¼APï¼
ï¼ èª¬æ責任ãç£æ»åã³ãªã¹ã¯ç®¡çï¼ARï¼
ï¼ ãã¼ã¿å質åã³å®å
¨æ§ï¼DIï¼
ï¼ ãã¼ã¿ã®æå°ååã³ä¿æï¼DMï¼
ï¼ å人ã®åå åã³è³ åï¼IPï¼
ï¼ ã»ãã¥ãªãã£ï¼SEï¼
ï¼ éææ§ï¼TRï¼
ï¼ ä½¿ç¨éçï¼ULï¼

SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
213
Appendix AâAcronyms and Abbreviations
Selected acronyms and abbreviations used in the Guide to Industrial Control Systems (ICS) Security are
defined below.
AC Alternating Current
ACL Access Control List
AGA American Gas Association
API American Petroleum Institute
ARP Address Resolution Protocol
BCP Business Continuity Plan
CIDX Chemical Industry Data Exchange
CIGRE International Council on Large Electric Systems
CIP Critical Infrastructure Protection
CMVP Cryptographic Module Validation Program
COTS Commercial Off-the-Shelf
CPNI Centre for the Protection of National Infrastructure
CPU Central Processing Unit
CSE Communications Security Establishment
CSRC Computer Security Resource Center
CSSC Control System Security Center
CVE Common Vulnerabilities and Exposures
DCOM Distributed Component Object Model
DCS Distributed Control System(s)
DETL Distributed Energy Technology Laboratory
DHS Department of Homeland Security
DMZ Demilitarized Zone
DNP3 DNP3 Distributed Network Protocol (published as IEEE 1815)
DNS Domain Name System
DOE Department of Energy
DoS Denial of Service
DRP Disaster Recovery Plan
EAP Extensible Authentication Protocol
EMS Energy Management System
EPRI Electric Power Research Institute
ERP Enterprise Resource Planning
FIPS Federal Information Processing Standards
FISMA Federal Information Security Modernization Act
FTP File Transfer Protocol
GAO Government Accountability Office
GPS Global Positioning System
HMI Human-Machine Interface
HSPD Homeland Security Presidential Directive
HTTP Hypertext Transfer Protocol

SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
214
ä»é² A é åèªåã³ç¥èª
ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ãã§ä½¿ç¨ãã主ãªé åèªåã³ç¥èªã®å®ç¾©ã¯ä»¥ä¸ã®
ã¨ããã
AC 交æµ
ACL ã¢ã¯ã»ã¹å¶å¾¡ãªã¹ã
AGA ç±³å½ã¬ã¹åä¼
API ç±³å½ç³æ²¹åä¼
ARP ã¢ãã¬ã¹è§£æ±ºãããã³ã«
BCP äºæ¥ç¶ç¶è¨ç»æ¸
CIDX
åå¦æ¥çãã¼ã¿äº¤æ
CIGRE å½é大é»åã·ã¹ãã ä¼è°
CIP éè¦ã¤ã³ãã©ä¿è·
CMVP æå·ã¢ã¸ã¥ã¼ã«å¦¥å½æ§æ¤è¨¼ããã°ã©ã
COTS æ°çå
CPNI å½å®¶ã¤ã³ãã©ä¿è·ã»ã³ã¿ã¼
CPU ä¸å¤®æ¼ç®è£
ç½®
CSE éä¿¡ã»ãã¥ãªãã£å±
CSRC ã³ã³ãã¥ã¼ã¿ã»ãã¥ãªãã£ãªã½ã¼ã¹ã»ã³ã¿ã¼
CSSC å¶å¾¡ã·ã¹ãã ã»ãã¥ãªãã£ã»ã³ã¿ã¼
CVE å
±éèå¼±æ§æé²
DCOM åæ£åã³ã³ãã¼ãã³ããªãã¸ã§ã¯ãã¢ãã«
DCS åæ£å¶å¾¡ã·ã¹ãã
DETL åæ£ã¨ãã«ã®ã¼æè¡ç 究æ
DHS å½åå®å
¨ä¿éç
DMZ éæ¦è£
å°å¸¯
DNP3 DNP3 åæ£ãããã¯ã¼ã¯ãããã³ã«ï¼IEEE 1815 ã¨ãã¦çºè¡)
DNS é ååã·ã¹ãã
DOE
ã¨ãã«ã®ã¼ç
DoS ãµã¼ãã¹å¦¨å®³
DRP ç½å®³å¾©æ§è¨ç»æ¸
EAP æ¡å¼µå¯è½èªè¨¼ãããã³ã«
EMS ã¨ãã«ã®ã¼ç®¡çã·ã¹ãã
EPRI é»åç 究æ
ERP ä¼æ¥è³æºè¨ç»
FIPS é£é¦æ
å ±å¦çè¦æ ¼
FISMA é£é¦æ
å ±ã»ãã¥ãªãã£å¼·åæ³
FTP ãã¡ã¤ã«è»¢éãããã³ã«
GAO æ¿åºèª¬æ責任å±
GPS ã°ãã¼ãã«ãã¸ã·ã§ãã³ã°ã·ã¹ãã
HMI ãã³ãã·ã³ã¤ã³ã¿ãã§ã¼ã¹
HSPD å½åå®å
¨ä¿é大統é å½ä»¤
HTTP ãã¤ãã¼ããã¹ã転éãããã³ã«
SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
215
HTTPS Hypertext Transfer Protocol Secure
HVAC Heating, Ventilation, and Air Conditioning
I/O Input/Output
I3P Institute for Information Infrastructure Protection
IACS Industrial Automation and Control System
IAONA Industrial Automation Open Networking Association
ICCP Inter-control Center Communications Protocol
ICMP Internet Control Message Protocol
ICS Industrial Control System(s)
ICS-CERT Industrial Control Systems - Cyber Emergency Response Team
IDS Intrusion Detection System
IEC International Electrotechnical Commission
IED Intelligent Electronic Device
IEEE Institute of Electrical and Electronics Engineers
IETF Internet Engineering Task Force
IGMP Internet Group Management Protocol
INL Idaho National Laboratory
IP Internet Protocol
IPS Intrusion Prevention System
IPsec Internet Protocol Security
ISA International Society of Automation
ISID Industrial Security Incident Database
ISO International Organization for Standardization
IT Information Technology
ITL Information Technology Laboratory
LAN Local Area Network
MAC Media Access Control
MES Manufacturing Execution System
MIB Management Information Base
MTU Master Terminal Unit (also Master Telemetry Unit)
NAT Network Address Translation
NCCIC National Cybersecurity and Communications Integration Center
NCSD National Cyber Security Division
NERC North American Electric Reliability Council
NFS Network File System
NIC Network Interface Card
NISCC National Infrastructure Security Coordination Centre
NIST National Institute of Standards and Technology
NSTB National SCADA Testbed
OLE Object Linking and Embedding
OMB Office of Management and Budget
OPC OLE for Process Control
OS Operating System
OSI Open Systems Interconnection
SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
216
HTTPS ãã¤ãã¼ããã¹ã転éãããã³ã«ã»ãã¥ã¢
HVAC
å·ææ¿ç©ºèª¿è¨å
I/O å
¥åºå
I3P æ
å ±ã¤ã³ãã©ä¿è·åä¼
IACS ç£æ¥ç¨ãªã¼ãã¡ã¼ã·ã§ã³å¶å¾¡ã·ã¹ãã
IAONA
ç£æ¥ãªã¼ãã¡ã¼ã·ã§ã³ãªã¼ãã³ãããã¯ã¼ã¯ã¢ã½ã·ã¨ã¼ã·ã§ã³
ICCP å¶å¾¡éã»ã³ã¿ã¼éä¿¡ãããã³ã«
ICMP ã¤ã³ã¿ã¼ãããã³ã³ããã¼ã«ã¡ãã»ã¼ã¸ãããã³ã«
ICS
ç£æ¥ç¨å¶å¾¡ã·ã¹ãã
ICS-CERT ç£æ¥ç¨å¶å¾¡ã·ã¹ãã - ãµã¤ãã¼ç·æ¥å¯¾å¿ãã¼ã
IDS
ä¾µå
¥æ¤ç¥ã·ã¹ãã
IEC å½éé»æ°æè¡å§å¡ä¼
IED ã¤ã³ããªã¸ã§ã³ãé»åæ©å¨
IEEE é»æ°é»åæè¡è
åä¼
IETF ã¤ã³ã¿ã¼ãããã¨ã³ã¸ãã¢ãªã³ã°ã¿ã¹ã¯ãã©ã¼ã¹
IGMP ã¤ã³ã¿ã¼ãããã°ã«ã¼ã管çãããã³ã«
INL
ã¢ã¤ããå½ç«ç 究æ
IP ã¤ã³ã¿ã¼ããããããã³ã«
IPS ä¾µå
¥é²æ¢ã·ã¹ãã
IPsec ã¤ã³ã¿ã¼ããããããã³ã«ã»ãã¥ãªãã£
ISA å½éãªã¼ãã¡ã¼ã·ã§ã³åä¼
ISID ç£æ¥ã»ãã¥ãªãã£ã¤ã³ã·ãã³ããã¼ã¿ãã¼ã¹
ISO å½éæ¨æºåæ©æ§
IT æ
å ±æè¡
ITL æ
å ±æè¡ç 究æ
LAN ãã¼ã«ã«ã¨ãªã¢ãããã¯ã¼ã¯
MAC ã¡ãã£ã¢ã¢ã¯ã»ã¹å¶å¾¡
MES çç£å®è¡ã·ã¹ãã
MIB 管çæ
å ±ãã¼ã¹
MTU ãã¹ã¿ã¼ç«¯æ«è£
ç½®ï¼ãã¹ã¿ã¼ãã¬ã¡ããªè£
ç½®ã¨ãããï¼
NAT ãããã¯ã¼ã¯ã¢ãã¬ã¹å¤æ
NCCIC ç±³å½ãµã¤ãã¼ã»ãã¥ãªãã£éä¿¡çµ±åã»ã³ã¿ã¼
NCSD ç±³å½ãµã¤ãã¼ã»ãã¥ãªãã£é¨
NERC åç±³é»åä¿¡é ¼åº¦åè°ä¼
NFS ãããã¯ã¼ã¯ãã¡ã¤ã«ã·ã¹ãã
NIC ãããã¯ã¼ã¯ã¤ã³ã¿ãã§ã¼ã¹ã«ã¼ã
NISCC ç±³å½ã¤ã³ãã©ã»ãã¥ãªãã£èª¿æ´ã»ã³ã¿ã¼
NIST ç±³å½æ¨æºæè¡å±
NSTB ç±³å½ SCADA ãã¹ãããã
OLE ãªãã¸ã§ã¯ãã®ãªã³ã¯ã¨åãè¾¼ã¿
OMB 管çäºç®å±
OPC ããã»ã¹å¶å¾¡ç¨ OLE
OS ãªãã¬ã¼ãã£ã³ã°ã·ã¹ãã
OSI ãªã¼ãã³ã·ã¹ãã ç¸äºæ¥ç¶
SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
217
PCII Protected Critical Infrastructure Information
PDA Personal Digital Assistant
PIN Personal Identification Number
PID Proportional â Integral - Derivative
PIV Personal Identity Verification
PLC Programmable Logic Controller
PP Protection Profile
PPP Point-to-Point Protocol
R&D Research and Development
RADIUS Remote Authentication Dial In User Service
RBAC Role-Based Access Control
RFC Request for Comments
RMA Reliability, Maintainability, and Availability
RMF Risk Management Framework
RPC Remote Procedure Call
RPO Recovery Point Objective
RTO Recovery Time Objective
RTU Remote Terminal Unit (also Remote Telemetry Unit)
SC Security Category
SCADA Supervisory Control and Data Acquisition
SCP Secure Copy
SFTP Secure File Transfer Protocol
SIS Safety Instrumented System
SMTP Simple Mail Transfer Protocol
SNL Sandia National Laboratories
SNMP Simple Network Management Protocol
SP Special Publication
SPP-ICS System Protection Profile for Industrial Control Systems
SQL Structured Query Language
SSH Secure Shell
SSID Service Set Identifier
SSL Secure Sockets Layer
TCP Transmission Control Protocol
TCP/IP Transmission Control Protocol/Internet Protocol
TFTP Trivial File Transfer Protocol
TLS Transport Layer Security
UDP User Datagram Protocol
UPS Uninterruptible Power Supply
US-CERT United States Computer Emergency Readiness Team
USB Universal Serial Bus
VFD Variable Frequency Drive
VLAN Virtual Local Area Network
VPN Virtual Private Network
WAN Wide Area Network
XML Extensible Markup Language
SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
218
PCII ä¿è·ãããéè¦ã¤ã³ãã©æ
å ±
PDA æºå¸¯æ
å ±ç«¯æ«
PIN å人èå¥çªå·
PID æ¯ä¾ã»ç©åã»å¾®å
PIV å人ã®èº«å
確èª
PLC ããã°ã©ããã«è«çå¶å¾¡è£
ç½®
PP ä¿è·ãããã¡ã¤ã«
PPP ãã¤ã³ããã¼ãã¤ã³ããããã³ã«
R&D ç 究éçº
RADIUS é éèªè¨¼ãã¤ã¢ã«ã¤ã³ã¦ã¼ã¶ãµã¼ãã¹
RBAC å½¹å²ãã¼ã¹ã¢ã¯ã»ã¹å¶å¾¡
RFC ã³ã¡ã³ãè¦æ±ï¼ãªã¯ã¨ã¹ã ãã©ã¼ ã³ã¡ã³ãï¼
RMA ä¿¡é ¼æ§ã»ä¿å®æ§ã»å¯ç¨æ§
RMF ãªã¹ã¯ç®¡çä½å¶
RPC é éæé å¼åºã
RPO ç®æ¨å¾©æ§ç¹
RTO ç®æ¨å¾©æ§æé
RTU é é端æ«è£
ç½®ï¼é éãã¬ã¡ããªè£
ç½®ã¨ãããï¼
SC ã»ãã¥ãªãã£åé¡
SCADA ç£è¦å¶å¾¡ãã¼ã¿åå¾ï¼ã¹ãã£ãï¼
SCP ã»ãã¥ã¢ã³ãã¼
SFTP ã»ãã¥ã¢ãã¡ã¤ã«è»¢éãããã³ã«
SIS å®å
¨è¨è£
ã·ã¹ãã
SMTP ã·ã³ãã«ã¡ã¼ã«è»¢éãããã³ã«
SNL ãµã³ãã£ã¢å½ç«ç 究æ
SNMP ã·ã³ãã«ãããã¯ã¼ã¯ç®¡çãããã³ã«
SP ç¹å¥åºçç©
SPP-ICS ç£æ¥å¶å¾¡ã·ã¹ãã ç¨ã·ã¹ãã ä¿è·ãããã¡ã¤ã«
SQL æ§é åç
§ä¼è¨èª
SSH ã»ãã¥ã¢ã·ã§ã«
SSID ãµã¼ãã¹ã»ããèå¥å
SSL ã»ãã¥ã¢ã½ã±ããã¬ã¤ã¤ã¼
TCP éä¿¡å¶å¾¡ãããã³ã«
TCP/IP éä¿¡å¶å¾¡ãããã³ã«/ã¤ã³ã¿ã¼ããããããã³ã«
TFTP ããªãã¢ã«ãã¡ã¤ã«è»¢éãããã³ã«
TLS ãã©ã³ã¹ãã¼ã層ã»ãã¥ãªãã£
UDP ã¦ã¼ã¶ãã¼ã¿ã°ã©ã ãããã³ã«
UPS ç¡åé»é»æºè£
ç½®
US-CERT ç±³å½ã³ã³ãã¥ã¼ã¿ç·æ¥æå³å¿ãã¼ã
USB ã¦ããã¼ãµã«ã·ãªã¢ã«ãã¹
VFD å¯å¤å¨æ³¢æ°é§å
VLAN ä»®æ³ LAN
VPN ä»®æ³ãã©ã¤ãã¼ããããã¯ã¼ã¯
WAN åºåãããã¯ã¼ã¯
XML æ¡å¼µãã¼ã¯ã¢ããè¨èª

SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
219
Appendix BâGlossary of Terms
Selected terms used in the Guide to Industrial Control Systems (ICS) Security are defined below. Source
References for certain definitions are listed at the end of this appendix.
Alternating Current Drive
Synonymous with Variable Frequency Drive (VFD).
SOURCE: NIST IR 6859 [2]
Access Control List (ACL)
A mechanism that implements access control for a system resource by
enumerating the identities of the system entities that are permitted to
access the resources.
SOURCE: RFC 4949 [75]
Accreditation
The official management decision given by a senior agency official to
authorize operation of an information system and to explicitly accept the
risk to agency operations (including mission, functions, image, or
reputation), agency assets, or individuals, based on the implementation of
an agreed-upon set of security controls.
SOURCE: NIST SP 800-53 [22]
Actuator
A device for moving or controlling a mechanism or system. It is operated
by a source of energy, typically electric current, hydraulic fluid pressure,
or pneumatic pressure, and converts that energy into motion. An actuator
is the mechanism by which a control system acts upon an environment.
The control system can be simple (a fixed mechanical or electronic
system), software-based (e.g. a printer driver, robot control system), or a
human or other agent.
Alarm
A device or function that signals the existence of an abnormal condition
by making an audible or visible discrete change, or both, so as to attract
attention to that condition.
SOURCE: ANSI/ISA-5.1-2009
Antivirus Tools
Software products and technology used to detect malicious code, prevent
it from infecting a system, and remove malicious code that has infected
the system.
Application Server
A computer responsible for hosting applications to user workstations.
Attack
An attempt to gain unauthorized access to system services, resources, or
information, or an attempt to compromise system integrity, availability,
or confidentiality.
SOURCE: CNSSI-4009

SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
220
ä»é² B ç¨èªé
ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼
ICS
ï¼ã»ãã¥ãªãã£ã¬ã¤ã
ã§ä½¿ç¨ãã主ãªç¨èªã®å®ç¾©ã¯ä»¥ä¸ã®ã¨ãããã
ãã¤ãã®å®ç¾©ã«ã¤ãã¦ã¯ãæ¬ä»é²ã®æ«å°¾ã«ãã®åºå
¸ãæ²è¼ããã¦ããã
Alternating Current Driveï¼
交æµé§å
å¯å¤å¨æ³¢æ°é§åï¼
VFDï¼ã¨å義
åºå
¸ï¼
NIST IR 6859 [2]
Access Control List (ACL)ï¼
ã¢ã¯ã»ã¹å¶å¾¡ãªã¹ã
ãªã½ã¼ã¹ã¸ã®ã¢ã¯ã»ã¹ã許å¯ãããã·ã¹ãã å®ä½ã®ä¸è´ç¹ãåæãã
ãã¨
ã«ããã·ã¹ãã ãªã½ã¼ã¹ã¸ã®ã¢ã¯ã»ã¹å¶å¾¡ãè¡ãã¡ã«ããºã ã
åºå
¸ï¼
RFC 4949 [75]
Accreditationï¼èªå®
åæãããã»ãã¥ãªãã£
対ç
ã®å®è£
ã«åºã¥ããæ
å ±ã·ã¹ãã ã®éç¨ã
èªå¯ãã
æ¿åºæ©é¢ã®æ¥åï¼ä»»åãæ©è½ãã¤ã¡ã¼ã¸ãè©å¤çï¼ã
æ¿åºæ©
é¢ã®
è³ç£åã¯å人ã®ãªã¹ã¯ãæ示çã«åãå
¥ããããæ¿åºæ©é¢
ã®ä¸ç´
å®å
ãä¸ãå
¬ç管ç決å®ã
åºå
¸ï¼
NIST SP 800-53 [22]
Actuatorï¼ã¢ã¯ãã¥ã¨ã¼ã¿
æ©æ§åã¯ã·ã¹ãã ãåããåã¯å¶å¾¡ããããã®ããã¤ã¹ãä¸è¬ã«é»
æµãæ²¹å§ã空æ°å§çã®ã¨ãã«ã®ã¼æºã§ä½åãããã®ã¨ãã«ã®ã¼ãéå
ã«å¤ãããã¢ã¯ãã¥ã¨ã¼ã¿ã¯ãå¶å¾¡ã·ã¹ãã ãç°å¢ã«åããããæ©æ§
ã§ãããå¶å¾¡ã·ã¹ãã ã¯åç´ã§ï¼åºå®æ©æ§ãé»åã·ã¹ãã ï¼ãã½ãã
ã¦ã¨ã¢
ãã¼ã¹ï¼ããªã³ã¿ãã©ã¤ã
ãããããå¶å¾¡ã·ã¹ãã çï¼ã人ã
ã®ä»ã«ããã
Alarmï¼ã¢ã©ã¼ã
ç°å¸¸ç¶æ
ãç¥ãããããã¤ã¹åã¯æ©è½ã§ãé³ãè¦è¦çå¤åã«ããç°å¸¸
ç¶æ
ã«æ³¨æãå¼ãã
åºå
¸ï¼
ANSI/ISA-5.1-2009
Ant
ivirus Tools
ï¼
ã¢ã³ãã¦ã¤ã«ã¹ãã¼ã«
ã½ããã¦ã¨ã¢
製ååã³æè¡ã§ãæªæããã³ã¼ããæ¤åºãã¦ã·ã¹ãã ã¸
ã®ææãé²ããææãã¦ããå ´åã«ã¯æªæããã³ã¼ããæé¤ããã
Application Serverï¼
ã¢ããªã±ã¼ã·ã§ã³ãµã¼ã
ã¦ã¼ã¶ã¯ã¼ã¯ã¹ãã¼ã·ã§ã³ã«ã¢ããªã±ã¼ã·ã§ã³ããã¹ãã£ã³ã°ããã³
ã³ãã¥ã¼ã¿ã
Attackï¼æ»æ
ã·ã¹ãã ãµã¼ãã¹ããªã½ã¼ã¹è¥ããã¯æ
å ±ã«ç¡æã§ã¢ã¯ã»ã¹ãããã¨
ãããããã¿åã¯ã·ã¹ãã ã®
å®å
¨æ§ãå¯ç¨æ§è¥ããã¯æ©å¯æ§ãä½ä¸ã
ãããã¨ãããããã¿ã
åºå
¸ï¼
CNSSI-4009
SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
221
Authentication
Verifying the identity of a user, process, or device, often as a prerequisite
to allowing access to resources in an information system.
SOURCE: NIST SP 800-53 [22]
Authorization
The right or a permission that is granted to a system entity to access a
system resource.
SOURCE: RFC 4949 [75]
Backdoor
An undocumented way of gaining access to a computer system. A
backdoor is a potential security risk.
Batch Process
A process that leads to the production of finite quantities of material by
subjecting quantities of input materials to an ordered set of processing
activities over a finite time using one or more pieces of equipment.
SOURCE: ANSI/ISA-88.01-1995
Broadcast
Transmission to all devices in a network without any acknowledgment by
the receivers.
SOURCE: IEC/PAS 62410
Buffer Overflow
A condition at an interface under which more input can be placed into a
buffer or data holding area than the capacity allocated, overwriting other
information. Adversaries exploit such a condition to crash a system or to
insert specially crafted code that allows them to gain control of the system.
SOURCE: NIST SP 800-28 [69]
Certification
A comprehensive assessment of the management, operational, and
technical security controls in an information system, made in support of
security accreditation, to determine the extent to which the controls are
implemented correctly, operating as intended, and producing the desired
outcome with respect to meeting the security requirements for the system.
SOURCE: NIST SP 800-37 [21]
Clear Text
Information that is not encrypted.
Communications Router
A communications device that transfers messages between two networks.
Common uses for routers include connecting a LAN to a WAN, and
connecting MTUs and RTUs to a long-distance network medium for
SCADA communication.
Confidentiality
Preserving authorized restrictions on information access and disclosure,
including means for protecting personal privacy and proprietary
information.
SOURCE: NIST SP 800-53 [22]
SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
222
Authenticationï¼èªè¨¼
ã¦ã¼ã¶ãããã»ã¹åã¯ããã¤ã¹ã®åä¸æ§ãæ¤è¨¼ãããã¨ã§ãæ
å ±ã·ã¹
ãã ä¸ã®ãªã½ã¼ã¹ã¸ã®åæã¨ãªããã¨ãå¤ãã
åºå
¸ï¼
NIST SP 800-53 [22]
Authorizationï¼æ¨©éä»ä¸
ã·ã¹ãã ã®å®å¨è
ãã·ã¹ãã ãªã½ã¼ã¹ã«ã¢ã¯ã»ã¹ããããã«ä¸ããã
ã権å©åã¯è¨±å¯ã
åºå
¸ï¼
RFC 4949 [75]
Backdoorï¼ããã¯ãã¢
ã³ã³ãã¥ã¼ã¿ã·ã¹ãã ã¸ã®ã¢ã¯ã»ã¹ãå¾ãä¸æ£ãªæ¹æ³ãããã¯ãã¢ã¯
ã»ãã¥ãªãã£ãªã¹ã¯ã¨ãªãã
Batch Processï¼
ãããããã»ã¹
大éã®å
¥åç©ã
1
ã¤åã¯è¤æ°ã®è£
ååãç¨ãã¦ãããæéãããã¦é
çªã«ä¸é£ã®å¦çã«ããããã¨ã«ãããéå®ãããéã«ããããã»ã¹ã
åºå
¸ï¼
ANSI/ISA-88.01-1995
Broadcastï¼
ããã¼ããã£ã¹ã
ãããã¯ã¼ã¯å
ã®å
¨ã¦ã®ããã¤ã¹ã«ã
åãæå´ã®äºè§£ãå¾ããã¨ãªã
éä¿¡ãããã¨ã
åºå
¸ï¼
IEC/PAS 62410
Bu
ffer Overflow
ï¼
ãããã¡ãªã¼ãã¼ããã¼
å²ãå½ã¦ããã容éãè¶
ãã¦å
¥åããããã¡åã¯ãã¼ã¿ä¿æé åã«ç½®
ãããä»ã®æ
å ±ãä¸æ¸ããã
ã¤ã³ã¿ãã§ã¼ã¹ã®ç¶æ
ã
æ»æå´ã¯ãã®ãããªç¶æ
ãå©ç¨ãã¦ãã·ã¹ãã ãã¯ã©ãã·ã¥ãããç¹
æ®ã³ã¼ããæ¿å
¥ãã¦ã·ã¹ãã ã®å¶å¾¡ãå¾ããã¨ãã§ããã
åºå
¸ï¼
NIST SP 800-28 [69]
Certificationï¼è¨¼æ
ã»ãã¥ãªãã£èªå®ãæ¯æ´ããããã«è¡ãæ
å ±ã·ã¹ãã ã®ç®¡çãéç¨å
ã³æè¡ä¸ã®
ã»ãã¥ãªãã£å¯¾çã«å¯¾ããå
æ¬çè©ä¾¡ã§ãã³ã³ãã
ã¼ã«ã
ã©ã®ç¨åº¦é©æ£ã«å®è£
ããã¦ããããäºå®ã©ããã«ç¨¼åãã¦ããããã·
ã¹ãã ã»ãã¥ãªãã£è¦ä»¶ã«åè´ããçµæã«ãªã£ã¦ãããå¤å®ããã
åºå
¸ï¼
NIST SP 800-37 [21]
Clear Textï¼å¹³æ
æå·åããã¦ããªãæ
å ±ã
Communications Routerï¼
éä¿¡ã«ã¼ã¿
2
ã¤ã®ãããã¯ã¼ã¯éã§ã¡ãã»ã¼ã¸ã転éããéä¿¡ããã¤ã¹ãã«ã¼ã¿
ã®ä¸è¬çãªä½¿ç¨æ¹æ³ã¨ãã¦ã
LAN ã¨WAN ã®æ¥ç¶ããSCADA éä¿¡ç¨
ã®
MTU åã³ RTU ã¨é è·é¢ãããã¯ã¼ã¯åªä½ã®æ¥ç¶ãããã
Confidentialityï¼æ©å¯æ§
æ
å ±ã®å©ç¨åã³æ¼æ´©ã«å
¬èªã®å¶éã課ããã¨ã§ãå人æ
å ±åã³å°ææ
å ±ãä¿è·ããæ段ãå«ã¾ããã
åºå
¸ï¼
NIST SP 800-53 [22]
SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
223
Configuration (of a system or
device)
Step in system design; for example, selecting functional units, assigning
their locations, and defining their interconnections.
SOURCE: IEC/PAS 62409
Configuration Control
Process for controlling modifications to hardware, firmware, software,
and documentation to ensure the information system is protected against
improper modifications before, during, and after system implementation.
SOURCE: CNSSI-4009
Continuous Process
A process that operates on the basis of continuous flow, as opposed to
batch, intermittent, or sequenced operations.
Control Algorithm
A mathematical representation of the control action to be performed.
SOURCE: The Automation, Systems, and Instrumentation Dictionary
Control
The part of the ICS used to perform the monitoring and control of the
physical process. This includes all control servers, field devices, actuators,
sensors, and their supporting communication systems.
Control Center
An equipment structure or group of structures from which a process is
measured, controlled, and/or monitored.
SOURCE: ANSI/ISA-51.1-1979
Control Loop
A control loop consists of sensors for measurement, controller hardware
such as PLCs, actuators such as control valves, breakers, switches and
motors, and the communication of variables. Controlled variables are
transmitted to the controller from the sensors. The controller interprets the
signals and generates corresponding manipulated variables, based on set
points, which it transmits to the actuators. Process changes from
disturbances result in new sensor signals, identifying the state of the
process, to again be transmitted to the controller.
Control Network
Those networks of an enterprise typically connected to equipment that
controls physical processes and that is time or safety critical. The control
network can be subdivided into zones, and there can be multiple separate
control networks within one enterprise and site.
SOURCE: ISA99 [34]
Control Server
A controller that also acts as a server that hosts the control software that
communicates with lower-level control devices, such as Remote Terminal
Units (RTUs) and Programmable Logic Controllers (PLCs), over an ICS
network. In a SCADA system, this is often called a SCADA server, MTU,
or supervisory controller.
SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
224
Configuration (of a system
or device)ï¼
ï¼ã·ã¹ãã åã¯ããã¤ã¹
ã®ï¼æ§æ
ã·ã¹ãã è¨è¨ã«ä»å
¥ãããã¨ãä¾ãã°ãæ©è½ã¦ãããã®é¸å®ãå ´æã®
å²å½ããããã®ç¸äºæ¥ç¶çã
åºå
¸ï¼
IEC/PAS 62409
Configuration Controlï¼
æ§æ管ç
ã·ã¹ãã å®è£
åã»ä¸ã»å¾ã®ä¸é©åãªæ¹å¤ããæ
å ±ã·ã¹ãã ãä¿è·ãã
ãã
ã«ããã¼ãã¦ã¨ã¢ã»ãã¡ã¼ã ã¦ã¨ã¢ã»ã½ããã¦ã¨ã¢ã»ææ¸ã¸ã®å¤
æ´ã管çããããã»ã¹ã
åºå
¸ï¼
CNSSI-4009
Continuous Processï¼
ç¶ç¶ããã»ã¹
ç¶ç¶çãªæµããåºæ¬ã¨ããæä½ããã»ã¹ã§ãããããéæ¬ åã¯ä¸é£æ
ä½ã®å対ã
Control Algorithmï¼
å¶å¾¡ã¢ã«ã´ãªãºã
å®æ½ãã¹ãå¶å¾¡è¡çºã®æ°å¦ç表ç¾ãåºå
¸ï¼ãªã¼ãã¡ã¼ã·ã§ã³ã»ã·ã¹ã
ã ã»è¨è£
äºå
¸
Controlï¼å¶å¾¡
ç©çããã»ã¹ã®ç£è¦åã³å¶å¾¡ãè¡ãããã«ç¨ãã
ICS ã®ä¸é¨ãå
¨ã¦ã®
å¶å¾¡ãµã¼ãããã£ã¼ã«ãããã¤ã¹ãã¢ã¯ãã¥ã¨ã¼ã¿ã
ã»ã³ãµ
åã³ãã
ãã®æ¯æ´éä¿¡ã·ã¹ãã ãå«ãã
Control Centerï¼
å¶å¾¡ã»ã³ã¿ã¼
1
ã¤åã¯ä¸ç¾¤ã®è£
ååæ§é ä½ã§ãããããããã»ã¹ãè¨æ¸¬ããå¶å¾¡
ããç£è¦ããã
åºå
¸ï¼
ANSI/ISA-51.1-1979
Control Loopï¼
å¶å¾¡ã«ã¼ã
å¶å¾¡ã«ã¼ãã¯è¨æ¸¬
ã»ã³ãµãå¶å¾¡ãã¼ãã¦ã¨ã¢ï¼PLC
çï¼ãã¢ã¯ãã¥ã¨
ã¼ã¿ï¼å¶å¾¡å¼ããã¬ã¼ã«ãã¹ã¤ãããã¢ã¼ã¿çï¼åã³å¤æ°ã®éä¿¡ã§æ§
æããããå¶å¾¡å¤æ°ã¯
ã»ã³ãµ
çµç±ã§ã³ã³ããã¼ã©ã«è»¢éããããã³ã³
ããã¼ã©ã¯ä¿¡å·ã解éããè¨å®ç¹ãåºã«å¯¾å¿ããæä½å¤æ°ãçæãã
ã¢ã¯ãã¥ã¨ã¼ã¿ã«éä¿¡ããã
妨害ã®çµæããã»ã¹ãå¤æ´ãããã¨ã
ã»ã³ãµä¿¡å·ãå¤ãããããã»ã¹
ç¶æ
ãèå¥ãã¦ãå度ã³ã³ããã¼ã©ã«éä¿¡ããã
Control Networkï¼
å¶å¾¡ãããã¯ã¼ã¯
ãã®ãããªä¼æ¥ãããã¯ã¼ã¯ã¯ãä¸è¬ã«ç©çããã»ã¹ãã»ããããè£
ååã«æ¥ç¶ãããæéãå®å
¨æ§ã®ç¹ã§éè¦
ã§ãããå¶å¾¡ãããã¯ã¼ã¯
ã¯ã¾ã¼ã³ã«åãããã¾ã¼ã³ãã¨ã«
1ã¤ã®ä¼æ¥åã¯ç¾å ´å
ã«å¥ã
ãªè¤æ°
ã®å¶å¾¡ãããã¯ã¼ã¯ãåå¨ããã
åºå
¸ï¼
ISA99 [34]
Control Serverï¼
å¶å¾¡ãµã¼ã
ãµã¼ãã¨ãã¦æ©è½ããã³ã³ããã¼ã©ã§ã
ICS ãããã¯ã¼ã¯ä¸ã§ä¸ä½ã¬
ãã«ã®ããã¤ã¹ï¼
RTUãPLC çï¼ã¨ã®éä¿¡ãè¡ãå¶å¾¡ã½ããã¦ã¨ã¢
ã
ãã¹ãããã
SCADA ã·ã¹ãã ã§ã¯ SCADA ãµã¼ããMTU åã¯ç£è¦ã³
ã³ããã¼ã©ã¨å¼ã°ãããã¨ãå¤ãã
SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
225
Control system
A system in which deliberate guidance or manipulation is used to achieve
a prescribed value for a variable. Control systems include SCADA, DCS,
PLCs and other types of industrial measurement and control systems.
Controlled Variable
The variable that the control system attempts to keep at the set point value.
The set point may be constant or variable.
SOURCE: The Automation, Systems, and Instrumentation Dictionary
Controller
A device or program that operates automatically to regulate a controlled
variable.
SOURCE: ANSI/ISA-51.1-1979
Cycle Time
The time, usually expressed in seconds, for a controller to complete one
control loop where sensor signals are read into memory, control
algorithms are executed, and corresponding control signals are transmitted
to actuators that create changes the process resulting in new sensor
signals.
SOURCE: The Automation, Systems, and Instrumentation Dictionary
Data Diode
A data diode (also referred to as a unidirectional gateway, deterministic
one-way boundary device or unidirectional network) is a network
appliance or device allowing data to travel only in one direction.
Database
A repository of information that usually holds plant-wide information
including process data, recipes, personnel data, and financial data.
SOURCE: NIST IR 6859 [2]
Data Historian
A centralized database supporting data analysis using statistical process
control techniques.
DC Servo Drive
A type of drive that works specifically with servo motors. It transmits
commands to the motor and receives feedback from the servo motor
resolver or encoder.
SOURCE: NIST IR 6859 [2]
SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
226
Control Systemï¼
å¶å¾¡ã·ã¹ãã
ããå¤æ°ã®äºå®å¤ãå®ç¾ããããã«ãè¨ç»çãªã¬ã¤ãã³ã¹åã¯æä½ã
å©ç¨ããã·ã¹ãã ãå¶å¾¡ã·ã¹ãã ã«ã¯
SCADAãDCSãPLC ãã®ä»ã®
ç£æ¥ç¨è¨æ¸¬å¶å¾¡
ä»æ§ãããã
Controlled Variableï¼
å¶å¾¡å¤æ°
å¶å¾¡ã·ã¹ãã ãè¨å®ç¹ãç¶æãããã¨ããå¤æ°ãè¨å®ç¹ã¯å®æ°åã¯å¤
æ°ã¨ãªãã
åºå
¸ï¼
ãªã¼ãã¡ã¼ã·ã§ã³ã»ã·ã¹ãã ã»è¨è£
äºå
¸
Controllerï¼
ã³ã³ããã¼ã©
å¶å¾¡å¤æ°ãèªåçã«èª¿æ´ããããã¤ã¹åã¯ããã°ã©ã ãåºå
¸ï¼
ANSI/ISA
-51.1-1979
Cycle Timeï¼
ãµã¤ã¯ã«æé
ã³ã³ããã¼ã©ã
1
ã¤ã®å¶å¾¡ã«ã¼ããå®äºããããã®ãé常ç§åä½ã§ç¤º
ãããæéã§ã
ã»ã³ãµ
ä¿¡å·ãã¡ã¢ãªã«èªã¿è¾¼ã¾ããå¶å¾¡ã¢ã«ã´ãªãºã
ãå®è¡ããã対å¿ããå¶å¾¡ä¿¡å·ãã¢ã¯ãã¥ã¨ã¼ã¿ã«éããã¦ããã»ã¹
ãå¤æ´ããæ°ããª
ã»ã³ãµä¿¡å·ãçããã
åºå
¸ï¼
ãªã¼ãã¡ã¼ã·ã§ã³ã»ã·ã¹ãã ã»è¨è£
äºå
¸
Data Diodeï¼
ãã¼ã¿ãã¤ãªã¼ã
ãã¼ã¿ãã¤ãªã¼ãï¼åæ¹åã²ã¼ãã¦ã§ã¤ã決å®è«çä¸æ¹éè¡å¢çãã
ã¤ã¹åã¯åæ¹åãããã¯ã¼ã¯ã¨ãå¼ã°ããï¼ã¯ãããã¯ã¼ã¯æ©å¨åã¯
ããã¤ã¹ã§ããã¼ã¿ãä¸æ¹åã«æµããããã«ããã
Databaseï¼
ãã¼ã¿ãã¼ã¹
æ
å ±ãèãããããã®ã§ãé常ããã»ã¹ãã¼ã¿ãã¬ã·ãã人äºãã¼
ã¿ãä¼è¨ãã¼ã¿çã®ãã©ã³ãå
¨ä½ã®æ
å ±ãèç©ããã¦ããã
åºå
¸ï¼
NIST IR 6859 [2]
Data Histo
rian
ï¼
ãã¼ã¿ãã¹ããªã¢ã³
éä¸ãã¼ã¿ãã¼ã¹ã§ãéçããã»ã¹ç®¡ç
æè¡
ãç¨ãã¦ãã¼ã¿è§£æãè¡
ãã
DC Servo Driveï¼
ç´æµãµã¼ãé§å
ç¹ã«ãµã¼ãã¢ã¼ã¿ã§ä½åããé§åã®ç¨®é¡ãã³ãã³ããã¢ã¼ã¿ã«éä¿¡
ãããµã¼ãã¢ã¼ã¿
ãªã¾ã«ã
åã¯ã¨ã³ã³ã¼ããããã£ã¼ãããã¯ãåä¿¡
ããã
åºå
¸ï¼
NIST IR 6859 [2]
SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
227
Demilitarized Zone
(DMZ)
An interface on a routing firewall that is similar to the interfaces found on
the firewallâs protected side. Traffic moving between the DMZ and other
interfaces on the protected side of the firewall still goes through the firewall
and can have firewall protection policies applied.
SOURCE: SP 800-41 [85]
A host or network segment inserted as a âneutral zoneâ between an
organizationâs private network and the Internet.
SOURCE: SP 800-45 [91]
Perimeter network segment that is logically between internal and external
networks. Its purpose is to enforce the internal networkâs Information
Assurance policy for external information exchange and to provide external,
untrusted sources with restricted access to releasable information while
shielding the internal networks from outside attacks.
SOURCE: CNSSI-4009
Denial of Service (DoS)
The prevention of authorized access to a system resource or the delaying of
system operations and functions.
SOURCE: RFC 4949 [75]
Diagnostics
Information concerning known failure modes and their characteristics. Such
information can be used in troubleshooting and failure analysis to help
pinpoint the cause of a failure and help define suitable corrective measures.
SOURCE: The Automation, Systems, and Instrumentation Dictionary
Disaster Recovery Plan
(DRP)
A written plan for processing critical applications in the event of a major
hardware or software failure or destruction of facilities.
SOURCE: NIST SP 800-34 [52]
Discrete Process
A type of process where a specified quantity of material moves as a unit
(part or group of parts) between work stations and each unit maintains its
unique identity.
SOURCE: The Automation, Systems, and Instrumentation Dictionary
Distributed Control System
(DCS)
In a control system, refers to control achieved by intelligence that is
distributed about the process to be controlled, rather than by a centrally
located single unit.
SOURCE: The Automation, Systems, and Instrumentation Dictionary
Distributed Plant
A geographically distributed factory that is accessible through the Internet
by an enterprise.
SOURCE: NIST IR 6859 [2]
SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
228
Demilitarized Zone
(DMZ)ï¼
éæ¦è£
å°å¸¯
ã«ã¼ãã£ã³ã°ãã¡ã¤ã¢ã¦ã©ã¼ã«ä¸ã®
ã¤ã³ã¿ãã§ã¼ã¹ã§ããã¡ã¤ã¢ã¦ã©
ã¼ã«ã®ä¿è·å´ã®
ã¤ã³ã¿ãã§ã¼ã¹ã«ä¼¼ã¦ãããDMZ ã¨ãã¡ã¤ã¢ã¦ã©ã¼
ã«ã®ä¿è·å´ã«ããå¥ã®
ã¤ã³ã¿ãã§ã¼ã¹éã®ãã©ãã£ãã¯ã¯ããã¡ã¤ã¢
ã¦ã©ã¼ã«ãééãããã¡ã¤ã¢ã¦ã©ã¼ã«ä¿è·ããªã·ã¼ãé©ç¨ãããã
åºå
¸ï¼
SP 800-41 [85]
ãä¸ç«å°å¸¯ãã¨ãã¦çµç¹ã®ãã©ã¤ãã¼ããããã¯ã¼ã¯ã¨ã¤ã³ã¿ã¼ãã
ãéã«æ¿å
¥ããããã¹ãåã¯ãããã¯ã¼ã¯ã»ã°ã¡ã³ãã
åºå
¸ï¼
SP 800-45 [91]
å
é¨ãããã¯ã¼ã¯ã¨å¤é¨ãããã¯ã¼ã¯ã®éã«è«ççã«ããå¨è¾ºããã
ã¯ã¼ã¯ã»ã°ã¡ã³ããç®çã¯ãå¤é¨ã¨ã®æ
å ±äº¤æç¨å
é¨ãããã¯ã¼ã¯ã®
æ
å ±ä¿è¨¼ããªã·ã¼ãæ½è¡ããå
é¨ãããã¯ã¼ã¯ãå¤é¨è
å¨ããã·ã¼ã«
ããã¤ã¤ãå¤é¨ã®ä¿¡é ¼ã®ç½®ããªãè¦æ±ã½ã¼ã¹ã«ããæ
å ±ã¸ã®ã¢ã¯ã»
ã¹
ã«å¶éã課ãããã¨ã«ããã
åºå
¸ï¼
CNSSI-4009
Denial of Service (DoS)ï¼
ãµã¼ãã¹å¦¨å®³
ã·ã¹ãã ãªã½ã¼ã¹ã¸ã®å
¬èªã¢ã¯ã»ã¹ã妨ãåã¯ã·ã¹ãã ã®éç¨åã³æ©
è½ãé
ããããã¨ã
åºå
¸ï¼
RFC 4949 [75]
Diagnosticsï¼è¨ºæ
æ¢ç¥ã®é害æ
æ§åã³ãã®ç¹å¾´ã«é¢ããæ
å ±ããã®ãããªæ
å ±ã¯ãã©ã
ã«ã·ã¥ã¼ãã£ã³ã°ãæ
é解æã«ä½¿ç¨ã§ããåå ãé©æ£ãªå¯¾çãå²ãåº
ãå©ãã¨ãªãã
åºå
¸ï¼
ãªã¼ãã¡ã¼ã·ã§ã³ã»ã·ã¹ãã ã»è¨è£
äºå
¸
Disaster Recovery Plan
(DRP)ï¼ç½å®³å¾©æ§è¨ç»æ¸
大è¦æ¨¡ãª
ãã¼ãã¦ã¨ã¢/ã½ããã¦ã¨ã¢é害ãæ½è¨ç ´å£ã®éã«éè¦äºé
ãå¦çããããã®ææ¸ã
åºå
¸ï¼
NIST SP 800-34 [52]
Discrete Processï¼
é¢æ£ããã»ã¹
æå®éã®ææãããåä½ï¼ãã¼ãåã¯ãã¼ãã°ã«ã¼ãï¼ã¨ãã¦ã¯ã¼ã¯
ã¹ãã¼ã·ã§ã³éã移åããååä½ããã®åºæã®ã¢ã¤ãã³ãã£ãã£ãä¿
æããããã»ã¹ã®ç¨®é¡ãåºå
¸ï¼ãªã¼ãã¡ã¼ã·ã§ã³ã»ã·ã¹ãã ã»è¨è£
äº
å
¸
Distributed Control System
(DCS)ï¼
åæ£å¶å¾¡ã·ã¹ãã
å¶å¾¡ã·ã¹ãã ã«ãã£ã¦ãä¸å¤®ã«ç½®ããã
1ã¤ã®è£
ç½®ã§ã¯ãªããå¶å¾¡ã
ãããã»ã¹ã«ã¤ãã¦åæ£ãããã¤ã³ããªã¸ã§ã³ã¹ã«ãã£ã¦è¡ãããå¶
御ããããåºå
¸ï¼ãªã¼ãã¡ã¼ã·ã§ã³ã»ã·ã¹ãã ã»è¨è£
äºå
¸
Distributed Plantï¼
åæ£ãã©ã³ã
ä¼æ¥ãã¤ã³ã¿ã¼ããããéãã¦ã¢ã¯ã»ã¹ã§ãã
å°ç
çã«åæ£ãããå·¥
å ´ã
åºå
¸ï¼
NIST IR 6859 [2]
SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
229
Disterbance
An undesired change in a variable being applied to a system that tends to
adversely affect the value of a controlled variable.
SOURCE: ANSI/ISA-51.1-1979
Domain
An environment or context that includes a set of system resources and a set
of system entities that have the right to access the resources as defined by a
common security policy, security model, or security architecture. See
Security Domain.
SOURCE: CNSSI-4009; SP 800-53 [22]; SP 800-37 [21]
Domain Controller
A server responsible for managing domain information, such as login
identification and passwords.
SOURCE: NIST IR 6859 [2]
Encryption
Cryptographic transformation of data (called âplaintextâ) into a form (called
âciphertextâ) that conceals the dataâs original meaning to prevent it from
being known or used. If the transformation is reversible, the corresponding
reversal process is called âdecryption,â which is a transformation that
restores encrypted data to its original state.
SOURCE: RFC 4949 [75]
Enterprise
An organization that coordinates the operation of one or more processing
sites.
SOURCE: ANSI/ISA-88.01-1995
Enterprise Resource
Planning (ERP) System
A system that integrates enterprise-wide information including human
resources, financials, manufacturing, and distribution as well as connects the
organization to its customers and suppliers.
Extensible Markup
Language (XML)
A specification for a generic syntax to mark data with simple, human-
readable tags, enabling the definition, transmission, validation, and
interpretation of data between applications and between organizations.
Fault Tolerant
Of a system, having the built-in capability to provide continued, correct
execution of its assigned function in the presence of a hardware and/or
software fault.
Field Device
Equipment that is connected to the field side on an ICS. Types of field
devices include RTUs, PLCs, actuators, sensors, HMIs, and associated
communications.
Field Site
A subsystem that is identified by physical, geographical, or logical
segmentation within the ICS. A field site may contain RTUs, PLCs,
actuators, sensors, HMIs, and associated communications.
SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
230
Disturbanceï¼æ¹ä¹±
å¶å¾¡ãããå¤æ°å¤ã«æªå½±é¿ãä¸ããããã·ã¹ãã ã«å ããããæã¾ã
ããªãå¤æ°ã®å¤æ´ã
åºå
¸ï¼
ANSI/ISA-51.1-1979
Domainï¼é å
ã·ã¹ãã ãªã½ã¼ã¹åã³å
±éæ¥ç¶ããªã·ã¼ãæ¥ç¶ã¢ãã«åã¯
æ¥ç¶ã¢ã¼ã
ãã¯ãã£ã®è¦å®ã©ãããªã½ã¼ã¹ã¸
ã®ã¢ã¯ã»ã¹æ¨©ãæã¤ã·ã¹ãã å®ä½ã
å«ã
ç°å¢åã¯ã³ã³ããã¹ããã»ãã¥ãªãã£é åãåç
§ã
åºå
¸ï¼
CNSSI-4009; SP 800-53 [22]; SP 800-37 [21]
Domain Controllerï¼
é åã³ã³ããã¼ã©
ãã°ã¤ã³èå¥ããã¹ã¯ã¼ãã¨ãã£ãé åæ
å ±ã管çãããµã¼ãã
åºå
¸ï¼
NIST IR 6859 [2]
Encryptionï¼æå·å
æå·å¤æã¯ãã¼ã¿ï¼å¹³æã¨å¼ã°ããï¼ãæå·å¤æãã¦ãããå½¢æ
ï¼æ
å·æã¨å¼ã°ããï¼ã«ãããã¨ã§ããã¼ã¿ã®
å
ã®æå³ãç§å¿ããç¥ãã
ããå©ç¨ããããã§ããªãããã«ãããå¤æãéå¤æãå¯è½ãªå ´åã
ãã®ããã»ã¹ã¯å¾©å·ã¨å¼ã°ããæå·åããããã¼ã¿ãå
ã®ç¶æ
ã«æ»
ãã
åºå
¸ï¼
RFC 4949 [75]
Enterpriseï¼ä¼æ¥
1
ã¤ã¾ãã¯ãã以ä¸ã®å¦çç¾å ´ã®éç¨ã調æ´ããçµç¹ã
åº
å
¸ï¼ANSI/ISA-88.01-1995
Enterprise Resource
Planning (ERP) Systemï¼
ä¼æ¥è³æºè¨ç»ã·ã¹ãã
人çè³æºã財æ¿ãçç£ãæµéçã®å
¨ä¼æ¥çæ
å ±ãä¸ä½åããçµç¹ãã
ã®é¡§å®¢ã
ãµãã©ã¤ã¤ã«æ¥ç¶ããã·ã¹ãã ã
Extensible Markup
Language (XML)ï¼
æ¡å¼µãã¼ã¯ã¢ããè¨èª
ãã¼ã¿ãåç´ã§äººãèªããã¿ã°ãä»ãã¦è¨è¿°ããæ±ç¨æ§æä»æ§ã§ãã¢
ããªã±ã¼ã·ã§ã³éåã³çµç¹éã§ã®
ãã¼ã¿ã®
å®ç¾©ãéä¿¡ã妥å½æ§æ¤è¨¼å
ã³è§£éãå¯è½ã«ããã
Fault To
lerant
ï¼
ãã©ã¼ã«ããã¬ã©ã³ã
ã·ã¹ãã ã§ã
ãã¼ãã¦ã¨ã¢åã³ã½ããã¦ã¨ã¢ãæ
éããã¨ãã§ããå²
ãå½ã¦ãããæ©è½ãç¶ç¶ãã¦æ£ããå®è¡ã§ãã
ãçµã¿è¾¼ã¿ã®è½åã
Field Deviceï¼
ãã£ã¼ã«ãããã¤ã¹
ICS
ã®ãã£ã¼ã«ãå´ã«æ¥ç¶ãããè£
ååã種é¡ã¨ã㦠RTUãPLCãã¢
ã¯ãã¥ã¨ã¼ã¿ã
ã»ã³ãµãHMI åã³é¢é£éä¿¡æ©å¨ãããã
Field Siteï¼
ãã£ã¼ã«ããµã¤ã
ICS
å
ã®ç©ççãå°ççåã¯è«ççåºç»ã«ããèå¥ããããµãã·ã¹ã
ã ããã£ã¼ã«ããµã¤ãã«ã¯
RTUãPLCãã¢ã¯ãã¥ã¨ã¼ã¿ãã»ã³ãµã
HMI
åã³é¢é£éä¿¡æ©å¨ãããã
SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
231
Fieldbus
A digital, serial, multi-drop, two-way data bus or communication path or
link between low-level industrial field equipment such as sensors,
transducers, actuators, local controllers, and even control room devices. Use
of fieldbus technologies eliminates the need of point-to-point wiring
between the controller and each device. A protocol is used to define
messages over the fieldbus network with each message identifying a
particular sensor on the network.
File Transfer Protocol (FTP)
FTP is an Internet standard for transferring files over the Internet. FTP
programs and utilities are used to upload and download Web pages,
graphics, and other files between local media and a remote server which
allows FTP access.
SOURCE: API 1164
Firewall
An inter-network gateway that restricts data communication traffic to and
from one of the connected networks (the one said to be âinsideâ the
firewall) and thus protects that networkâs system resources against threats
from the other network (the one that is said to be âoutsideâ the firewall).
SOURCE: RFC 4949 [75]
An inter-network connection device that restricts data communication
traffic between two connected networks. A firewall may be either an
application installed on a general-purpose computer or a dedicated platform
(appliance), which forwards or rejects/drops packets on a network.
Typically firewalls are used to define zone borders. Firewalls generally
have rules restricting which ports are open. SOURCE: ISA-62443-1-1 [34]
Human-Machine Interface
(HMI)
The hardware or software through which an operator interacts with a
controller. An HMI can range from a physical control panel with buttons
and indicator lights to an industrial PC with a color graphics display
running dedicated HMI software.
SOURCE: NIST IR 6859 [2]
Software and hardware that allows human operators to monitor the state of
a process under control, modify control settings to change the control
objective, and manually override automatic control operations in the event
of an emergency. The HMI also allows a control engineer or operator to
configure set points or control algorithms and parameters in the controller.
The HMI also displays process status information, historical information,
reports, and other information to operators, administrators, managers,
business partners, and other authorized users. Operators and engineers use
HMIs to monitor and configure set points, control algorithms, send
commands, and adjust and establish parameters in the controller. The HMI
also displays process status information and historical information.
Identification
The process of verifying the identity of a user, process, or device, usually as
a prerequisite for granting access to resources in an IT system.
SOURCE: NIST SP 800-47 [92]
SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
232
Fieldbusï¼ãã£ã¼ã«ããã¹
ã»ã³ãµ
ããã©ã³ã¹ãã¥ã¼ãµãã¢ã¯ãã¥ã¨ã¼ã¿ããã¼ã«ã«ã³ã³ããã¼
ã©ãå¶å¾¡å®¤ããã¤ã¹çã®ä½ã¬ãã«ç£æ¥ç¨ãã£ã¼ã«ãè£
ååéã®ãã¸ã¿
ã«ã
ã·ãªã¢ã«ã
ãã«ããããããåæ¹åãã¼ã¿ãã¹ãéä¿¡çµè·¯åã¯ãª
ã³ã¯ããã£ã¼ã«ããã¹æè¡ãå©ç¨ããã¨ãã³ã³ããã¼ã©ã¨åããã¤ã¹
éã§ã®
2
å°ç¹éé
ç·ã®å¿
è¦ããªããªãããããã³ã«ã使ç¨ãã¦ãã£ã¼
ã«ããã¹ãããã¯ã¼ã¯ä¸ã®ã¡ãã»ã¼ã¸ãå®ç¾©ããåã¡ãã»ã¼ã¸ã¯ãã
ãã¯ã¼ã¯ä¸ã®ç¹å®ã®
ã»ã³ãµã§èå¥ããã
File Transfer Protocol
(FT
P)
ï¼
ãã¡ã¤ã«è»¢éãããã³ã«
ã¤ã³ã¿ã¼ãããä¸ã§ãã¡ã¤ã«ã転éããã¤ã³ã¿ã¼ãããè¦æ ¼ã
FTP ã
ãã°ã©ã åã³ã¦ã¼ãã£ãªãã£ã使ç¨ãã¦ãã¦ã§ããã¼ã¸ãã°ã©ãã£ã
ã¯ãã®ä»ã®ãã¡ã¤ã«ããã¼ã«ã«ã¡ãã£ã¢ã¨
FTP ã¢ã¯ã»ã¹ã許å¯ãã
é éãµã¼ãã§ã¢ãããã¼ã
/ãã¦ã³ãã¼ãããã
åºå
¸ï¼
API 1164
Firewallï¼
ãã¡ã¤ã¢ã¦ã©ã¼ã«
ãããã¯ã¼ã¯éã²ã¼ãã¦ã§ã¤ã§ãæ¥ç¶ããããããã¯ã¼ã¯ï¼ãã¡ã¤ã¢
ã¦ã©ã¼ã«ã®ãä¸ãã«ããï¼éã§ã®ãã¼ã¿éä¿¡ãã©ãã£ãã¯ãå¶éãã
å½è©²ãããã¯ã¼ã¯ã®ã·ã¹ãã ãªã½ã¼ã¹ãä»ã®ãããã¯ã¼ã¯ï¼ãã¡
ã¤ã¢
ã¦ã©ã¼ã«ã®ãå¤ãã«ããï¼ããã®è
å¨ããå®ãã
åºå
¸ï¼
RFC 4949 [75]
æ¥ç¶ããã
2ã¤ã®ãããã¯ã¼ã¯éã§ãã¼ã¿éä¿¡ãã©ãã£ãã¯ãå¶éã
ããããã¯ã¼ã¯é
æ¥ç¶ããã¤ã¹ããã¡ã¤ã¢ã¦ã©ã¼ã«ã¯ãæ±ç¨ã³ã³ãã¥
ã¼ã¿åã¯å°ç¨ãã©ãããã¼ã ï¼æ©å¨ï¼ã«ã¤ã³ã¹ãã¼ã«ãããã¢ããªã±
ã¼ã·ã§ã³ã§ããããã¯ã¼ã¯ä¸ã®ãã±ããã転éåã¯æ絶
/ããããã
ããä¸è¬ã«ãã¡ã¤ã¢ã¦ã©ã¼ã«ã¯ã¾ã¼ã³å¢çãå®ããã®ã«ä½¿ç¨ãããã
ã¡ã¤ã¢ã¦ã©ã¼ã«ã¯ã©ã®ãã¼ããéæ¾ããããå¶éããã
åº
å
¸ï¼ISA-62443-1-1 [34]
Human
-Machine Interface
(HMI)ï¼
ãã³ãã·ã³ã¤ã³ã¿ãã§ã¼ã¹
æä½å¡ãã³ã³ããã¼ã©ã¨ç¸äºä½ç¨ãè¡ãããã«ä½¿ç¨ãããã¼ãã¦ã¨ã¢
åã¯
ã½ããã¦ã¨ã¢
ããã¿ã³ãã¤ã³ã¸ã±ã¼ã¿ã©ã¤ãã®ä»ããç©ççå¶å¾¡
ããã«ãããã«ã©ã¼ã°ã©ãã£ãã¯ãã£ã¹ãã¬ã¤ã®ä»ããå°ç¨
HMI ã½
ããã¦ã¨ã¢
ãå®è¡ããç£æ¥ç¨ PC ã¾ã§å¤æ§ã§ããã
åºå
¸ï¼
NIST IR 6859 [2]
æä½å¡ãå¶å¾¡ä¸ã®ããã»ã¹ç¶æ
ãç£è¦ããå¶å¾¡è¨å®ãå¤ãã¦å¶å¾¡å¯¾è±¡
ãå¤æ´ããç·æ¥æã«èªåå¶å¾¡é転ãæåã«å¤æ´ã§ãã
ã½ããã¦ã¨ã¢å
ã³
ãã¼ãã¦ã¨ã¢ãå¶å¾¡ã¨ã³ã¸ãã¢ãæä½å¡ã¯ãã³ã³ããã¼ã©ã®è¨å®ç¹
åã¯å¶å¾¡ã¢ã«ã´ãªãºã åã³ãã©ã¡ã¼ã¿ãå¤æ´ãããã¨ãã§ãããã¾ã
HMI
ã¯ããã»ã¹ç¶æ
ãå±¥æ´æ
å ±ãã¬ãã¼ããã®ä»ã®æ
å ±ãæä½å¡ã管
çè
ãããã¼ã¸ã£ããã¸ãã¹ãã¼ããã¼ãã®ä»è¨±å¯ãããã¦ã¼ã¶ã«è¡¨
示ãããæä½å¡åã³ã¨ã³ã¸ãã¢ã¯
HMI ãå©ç¨ããè¨å®ç¹ãç£è¦ã»è¨
å®ããã¢ã«ã´ãªãºã ãå¶å¾¡ãã
ã³ãã³ããéä¿¡ããã³ã³ããã¼ã©ã®ã
ã©ã¡ã¼ã¿ã調æ´ã»è¨å®ãããã¾ã
HMI ã¯ããã»ã¹ã®ã¹ãã¼ã¿ã¹æ
å ±
åã³å±¥æ´æ
å ±ã表示ããã
Identificationï¼èå¥
ã¦ã¼ã¶ãããã»ã¹åã¯ããã¤ã¹ã®åä¸æ§ãæ¤è¨¼ããããã»ã¹ã§ãé常
IT
ã·ã¹ãã ä¸ã®ãªã½ã¼ã¹ã¸ã®ã¢ã¯ã»ã¹ä»ä¸ã®åæã¨ãªãã
åºå
¸ï¼
NIST SP 800-47 [92]
SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
233
Incident
An occurrence that actually or potentially jeopardizes the confidentiality,
integrity, or availability of an information system or the information the
system processes, stores, or transmits or that constitutes a violation or
imminent threat of violation of security policies, security procedures, or
acceptable use policies
SOURCE: FIPS 200 [16]; SP 800-53 [22]
Industrial Control System
(ICS)
General term that encompasses several types of control systems, including
supervisory control and data acquisition (SCADA) systems, distributed
control systems (DCS), and other control system configurations such as
Programmable Logic Controllers (PLC) often found in the industrial sectors
and critical infrastructures. An ICS consists of combinations of control
components (e.g., electrical, mechanical, hydraulic, pneumatic) that act
together to achieve an industrial objective (e.g., manufacturing,
transportation of matter or energy).
Information Security
Program Plan
Formal document that provides an overview of the security requirements for
an organization-wide information security program and describes the
program management controls and common controls in place or planned for
meeting those requirements.
SOURCE: NIST SP 800-53 [22]
Input/Output (I/O)
A general term for the equipment that is used to communicate with a
computer as well as the data involved in the communications.
SOURCE: The Automation, Systems, and Instrumentation Dictionary
Insider
An entity inside the security perimeter that is authorized to access system
resources but uses them in a way not approved by those who granted the
authorization.
SOURCE: RFC 4949 [75]
Integrity
Guarding against improper information modification or destruction, and
includes ensuring information non-repudiation and authenticity.
SOURCE: NIST SP 800-53 [22]
Intelligent Electronic Device
(IED)
Any device incorporating one or more processors with the capability to
receive or send data/control from or to an external source (e.g., electronic
multifunction meters, digital relays, controllers).
SOURCE: AGA 12 [5]
Internet
The single interconnected world-wide system of commercial, government,
educational, and other computer networks that share the set of protocols
specified by the Internet Architecture Board (IAB) and the name and
address spaces managed by the Internet Corporation for Assigned Names
and Numbers (ICANN). SOURCE: RFC 4949 [75]
SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
234
Incidentï¼ã¤ã³ã·ãã³ã
æ
å ±ã·ã¹ãã åã¯ã·ã¹ãã ãå¦çãä¿ç®¡è¥ããã¯éä¿¡ããæ
å ±ã®
æ©å¯
æ§ã
å®å
¨æ§è¥ããã¯å¯ç¨æ§ãç¾å®ã«åã¯å¯è½æ§ã¨ãã¦å±éºã«é¥ããäº
象åã¯æ¥ç¶ããªã·ã¼ãæ¥ç¶æé è¥ããã¯
妥å½ãªä½¿ç¨ããªã·ã¼ã«éåã
ãããç´ã¡ã«éåããããªäºè±¡ã
åºå
¸ï¼
FIPS 200 [16]; SP 800-53 [22]
Industrial Control System
(ICS)ï¼
ç£æ¥ç¨å¶å¾¡ã·ã¹ãã
ï¼
ICS
ï¼
æ°ç¨®ã®å¶å¾¡ã·ã¹ãã ãå
æ¬ããæ±ç¨çãªç¨èªã§ãããã«ã¯
å種ç£æ¥é¨
éãéè¦ã¤ã³ãã©ã§ä½¿ç¨ããã¦ãã
SCADAãDCSãPLCããã®ä»ã®
å¶å¾¡ã·ã¹ãã ã®è¨å®
ãå«ã¾ãããICS ã¯ç£æ¥ä¸ã®ç®çï¼ç©åãã¨ãã«
ã®ã¼ã®çç£ã»è¼¸éçï¼ãéæããããã«ä½µç¨ãããå¶å¾¡ç¨ã³ã³ãã¼ã
ã³ãï¼é»æ°ã»æ©æ¢°ã»æ²¹å§ã»ç©ºæ°çï¼ãçµã¿åããã£ã¦æ§æããã¦ã
ãã
Information Security
Program Planï¼
æ
å ±ã»ãã¥ãªãã£ããã°ã©
ã è¨ç»æ¸
å
¨çµç¹çæ
å ±ã»ãã¥ãªãã£ããã°ã©ã ã®ã»ãã¥ãªãã£è¦ä»¶ã«ã¤ãã¦æ¦
説ããè¦ä»¶ãæºè¶³ããããã«å®æ½ä¸åã¯è¨ç»ä¸ã®ããã°ã©ã 管ç対ç
åã³å
±é管ç
ã«ã¤ãã¦è¨è¿°ããæ£å¼ææ¸ã
åºå
¸ï¼
NIST SP 800-53 [22]
Input/Output (I/O)ï¼å
¥åºå
ã³ã³ãã¥ã¼ã¿ã¨éä¿¡ããããã®è£
åååã³éä¿¡ã«å«ã¾ãããã¼ã¿ã示
ãä¸è¬ç¨èªã
åºå
¸ï¼
ãªã¼ãã¡ã¼ã·ã§ã³ã»ã·ã¹ãã ã»è¨è£
äºå
¸
Insiderï¼ã¤ã³ãµã¤ãã¼
ã»ãã¥ãªãã£å¢çå
ã«ãã¦ã·ã¹ãã ãªã½ã¼ã¹ã¸ã®ã¢ã¯ã»ã¹ã許ããã¦
ãããã許å¯ããã以å¤ã®æ¹æ³ã§ä½¿ç¨ããå®å¨è
ã
åºå
¸ï¼
RFC 4949 [75]
Integrityï¼å®å
¨æ§
ä¸æ£ãªæ
å ±ã®æ¹å¤åã¯ç ´å£ãé²ããã¨ã§ãæ
å ±ã®å¦èªé²æ¢åã³æ£å½æ§
ã確ä¿ããã
åºå
¸ï¼
NIST SP 800-53 [22]
Intelligent Electronic Device
(IED)ï¼
ã¤ã³ããªã¸ã§ã³ãé»åæ©å¨
1
ã¤åã¯è¤æ°ã®ããã»ã¹ãçµã¿è¾¼ãã ããã¤ã¹ã§ãå¤é¨ã½ã¼ã¹ã¨ã®é
ã§ãã¼ã¿
/å¶å¾¡ãéåä¿¡ããè½åãæã¤ï¼é»åå¤æ©è½ã¡ã¼ã¿ããã¸ã¿
ã«ãªã¬ã¼ãã³ã³ããã¼ã©çï¼ã
åºå
¸ï¼
AGA 12 [5]
Internetï¼ã¤ã³ã¿ã¼ããã
ç£å®å¦ãã®ä»ã®ãããã¯ã¼ã¯ã
1
ã¤ã«é£æ¥ããä¸ççã·ã¹ãã ã§ãã¤
ã³ã¿ã¼ãããã¢ã¼ããã¯ãã£å§å¡ä¼ï¼
IABï¼ãæå®ãããããã³ã«å
ã³
ICANN ã管çããåååã³ã¢ãã¬ã¹ç©ºéãå
±æãããåºå
¸ï¼RFC
4949 [75]
SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
235
Intrusion Determination
System (IDS)
A security service that monitors and analyzes network or system events for
the purpose of finding, and providing real-time or near real-time warning of,
attempts to access system resources in an unauthorized manner.
SOURCE: RFC 4949 [75]
Intrusion Prevention System
(IPS)
A system that can detect an intrusive activity and can also attempt to stop
the activity, ideally before it reaches its targets.
Jitter
The time or phase difference between the data signal and the ideal clock.
Key Logger
A program designed to record which keys are pressed on a computer
keyboard used to obtain passwords or encryption keys and thus bypass other
security measures.
Light Tower
A device containing a series of indicator lights and an embedded controller
used to indicate the state of a process based on an input signal.
SOURCE: NIST IR 6859 [2]
Local Area Network (LAN)
A group of computers and other devices dispersed over a relatively limited
area and connected by a communications link that enables any device to
interact with any other on the network.
Machine Controller
A control system/motion network that electronically synchronizes drives
within a machine system instead of relying on synchronization via
mechanical linkage.
Maintenance
Any act that either prevents the failure or malfunction of equipment or
restores its operating capability.
SOURCE: The Automation, Systems, and Instrumentation Dictionary
Malware
Software or firmware intended to perform an unauthorized process that will
have adverse impact on the confidentiality, integrity, or availability of an
information system. A virus, worm, Trojan horse, or other code-based entity
that infects a host. Spyware and some forms of adware are also examples of
malicious code (malware).
SOURCE: NIST SP 800-53 [22]
Management Controls
The security controls (i.e., safeguards or countermeasures) for an
information system that focus on the management of risk and the
management of information security.
SOURCE: NIST SP 800-18 [19]
Manipulated Variable
In a process that is intended to regulate some condition, a quantity or a
condition that the control alters to initiate a change in the value of the
regulated condition.
SOURCE: The Automation, Systems, and Instrumentation Dictionary
SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
236
Intrusion Detection System
(ID
S)
ï¼
ä¾µå
¥æ¤ç¥ã·ã¹ãã
ã·ã¹ãã ãªã½ã¼ã¹ã«ç¡æã§ã¢ã¯ã»ã¹ãããããã¿ãçºè¦ãããªã¢ã«ã¿
ã¤ã åã¯ã»ã¼ãªã¢ã«ã¿ã¤ã ã§è¦åããããã«ããããã¯ã¼ã¯åã¯ã·ã¹
ãã ã¤ãã³ããç£è¦ã»åæããã»ãã¥ãªãã£ãµã¼ãã¹ã
åºå
¸ï¼
RFC 4949 [75]
Intrusion Prevention System
(IPS)ï¼
ä¾µå
¥é²æ¢ã·ã¹ãã
ä¾µå
¥æ´»åãæ¤ç¥ããå¯è½ã§ããã°ç®æ¨ã«éããåã«æ´»åãããããã
ãã¨ãã§ããã·ã¹ãã ã
Jitterï¼ã¸ãã¿ã¼
ãã¼ã¿ä¿¡å·ã¨çæ³
çã¯ããã¯éã®æéå·®åã¯ãã§ã¼ãºã
Key Loggerï¼ãã¼ãã¬ã¼
ãã¹ã¯ã¼ãã
æå·éµ
ãåå¾ããä»ã®ã»ãã¥ãªãã£æ段ãè¿åãããã
ã«ãã³ã³ãã¥ã¼ã¿ã®ãã¼ãã¼ãã§æ¼ããããã¼ãè¨é²ããããã°ã©
ã ã
Light Towerï¼ã©ã¤ãã¿ã¯ã¼
å
¥åä¿¡å·ã«åºã¥ãã¦ããã»ã¹ç¶æ
ã表示ãããä¸é£ã®ã¤ã³ã¸ã±ã¼ã¿ã©
ã¤ãã¨çµè¾¼ã¿ã³ã³ããã¼ã©ãåããããã¤ã¹ã
åºå
¸ï¼
NIST IR 6859 [2]
Local Area Network
(LAN)ï¼
ãã¼ã«ã«ã¨ãªã¢ãããã¯ã¼
ã¯
æ¯è¼çéå®ãããã¨ãªã¢å
ã«åæ£ããéä¿¡ãªã³ã¯ã§æ¥ç¶ãããããã
ãããããã¯ã¼ã¯ä¸ã§é£åããã³ã³ãã¥ã¼ã¿ãã®ä»ã®ããã¤ã¹ã°ã«ã¼
ãã
Machine Controllerï¼
ãã·ã³ã³ã³ããã¼ã©
ãã·ã³ã·ã¹ãã å
ã®ãã©ã¤ãããæ©æ¢°å¼ãªã³ã¯çµç±ã®åæã«ä¾åã
ããé»åçã«åæããå¶å¾¡ã·ã¹ãã
/ã¢ã¼ã·ã§ã³ãããã¯ã¼ã¯ã
Maintenanceï¼ä¿å®
è£
ååã®æ
éåã¯ä¸å
·åãé²æ¢åã¯ç¨¼åç¶æ
ã«å復ããè¡çºã
åºå
¸ï¼
ãªã¼ãã¡ã¼ã·ã§ã³ã»ã·ã¹ãã ã»è¨è£
äºå
¸
Malwareï¼ãã«ã¦ã¨ã¢
æ
å ±ã·ã¹ãã ã®
æ©å¯æ§ãå®å
¨æ§åã¯å¯ç¨æ§ã«æªå½±é¿ããä¸æ£ã¢ã¯ã»ã¹
ãè¡ãããã®
ã½ããã¦ã¨ã¢åã¯ãã¡ã¼ã ã¦ã¨ã¢ãã¦ã¤ã«ã¹ãã¯ã¼ã ã
ããã¤ã®æ¨é¦¬ãã®ä»ã³ã¼ããã¼ã¹ã®ãã®ããã¹ããææãããã
ã¹ã
ã¤ã¦ã¨ã¢
ãããã¤ãã®å½¢æ
ã®ã¢ãã¦ã§ã¢ãæªæããã³ã¼ãï¼ãã«ã¦ã¨
ã¢
ï¼ã®ä¾ã§ããã
åºå
¸ï¼
NIST SP 800-53 [22]
Management Controlsï¼
管ç対ç
ãªã¹ã¯ç®¡çåã³æ
å ±ã»ãã¥ãªãã£ç®¡çã«ç¹åããæ
å ±ã·ã¹ãã ã®ã»ã
ã¥ãªãã£
対çï¼å®å
¨çåã¯å¯¾çï¼ã
åºå
¸ï¼
NIST SP 800-18 [19]
Manipulated Variableï¼
æä½ãããå¤æ°
ç¹å®ã®ç¶æ
ã調æ´ããããã®ããã»ã¹ã«ããã¦ã調æ´æ¸ã¿ç¶æ
ã®å¤ã
å¶å¾¡ãå¤æ´ããã¨ãã®éåã¯ç¶æ
ãåºå
¸ï¼ãªã¼ãã¡ã¼ã·ã§ã³ã»ã·ã¹ã
ã ã»è¨è£
äºå
¸
SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
237
Manufacturing Execution
System (MES)
A system that uses network computing to automate production control and
process automation. By downloading recipes and work schedules and
uploading production results, a MES bridges the gap between business and
plant-floor or process-control systems.
SOURCE: NIST IR 6859 [2]
Master Terminal Unit
(MTU)
See Control Server.
Modem
A device used to convert serial digital data from a transmitting terminal to a
signal suitable for transmission over a telephone channel to reconvert the
transmitted signal to serial digital data for the receiving terminal.
SOURCE: NIST IR 6859 [2]
Motion Control Network
The network supporting the control applications that move parts in
industrial settings, including sequencing, speed control, point-to-point
control, and incremental motion.
SOURCE: The Automation, Systems, and Instrumentation Dictionary
Network Interface Card
(NIC)
A circuit board or card that is installed in a computer so that it can be
connected to a network.
Object Linking and
Embedding (OLE) for
Process Control (OPC)
A set of open standards developed to promote interoperability between
disparate field devices, automation/control, and business systems.
Operating System
An integrated collection of service routines for supervising the sequencing
of programs by a computer. An operating system may perform the functions
of input/output control, resource scheduling, and data management. It
provides application programs with the fundamental commands for
controlling the computer.
SOURCE: The Automation, Systems, and Instrumentation Dictionary
Operational Controls
The security controls (i.e., safeguards or countermeasures) for an
information system that are primarily implemented and executed by people
(as opposed to systems).
SOURCE: NIST SP 800-18 [19]
Password
A string of characters (letters, numbers, and other symbols) used to
authenticate an identity or to verify access authorization.
Phishing
Tricking individuals into disclosing sensitive personal information by
claiming to be a trustworthy entity in an electronic communication (e.g.,
internet web sites).
SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
238
Manufacturing Execution
System (MES)ï¼
çç£å®è¡ã·ã¹ãã
ãããã¯ã¼ã¯ã³ã³ãã¥ã¼ãã£ã³ã°ãå©ç¨ãã¦çç£å¶å¾¡åã³ããã»ã¹ã®
èªååãè¡ãã·ã¹ãã ãã¬ã·ãã¨ä½æ¥ã¹ã±ã¸ã¥ã¼ã«ããã¦ã³ãã¼ã
ããçç£çµæãã¢ãããã¼ããããã¨ã«ããã
MES ã¯äºæ¥ã·ã¹ãã
ã¨ãã©ã³ãç¾å ´ã·ã¹ãã åã¯ããã»ã¹å¶å¾¡ã·ã¹ãã éã®ã®ã£ãããå
ããã
åºå
¸ï¼
NIST IR 6859 [2]
Master
Terminal Unit
(MTU)ï¼
ãã¹ã¿ã¼ç«¯æ«è£
ç½®
å¶å¾¡ãµã¼ããåç
§ã
Modemï¼ã¢ãã
é信端æ«ããã®ã·ãªã¢ã«ãã¸ã¿ã«ãã¼ã¿ãé»è©±ç¶²éä¿¡ã«é©ããä¿¡å·ã«
å¤æããå信端æ«ã«ã¯ã·ãªã¢ã«ãã¸ã¿ã«ãã¼ã¿ã«åå¤æããããã®ã
ãã¤ã¹ã
åºå
¸ï¼
NIST IR 6859 [2]
Motion
Control Network
ï¼
åä½å¶å¾¡ãããã¯ã¼ã¯
ç£æ¥ç°å¢ã«ããã¦ãã¼ããåããå¶å¾¡ã¢ããªã±ã¼ã·ã§ã³ã«å¯¾å¿ããã
ããã¯ã¼ã¯ã§ãåä½ã«ã¯ã·ã¼ã±ã³ã·ã³ã°ãé
度å¶å¾¡ã2ç¹éå¶å¾¡ãå·®
ååä½çãããã
åºå
¸ï¼
ãªã¼ãã¡ã¼ã·ã§ã³ã»ã·ã¹ãã ã»è¨è£
äºå
¸
Network Interface Card
(NIC)ï¼ãããã¯ã¼ã¯ã¤ã³
ã¿ãã§ã¼ã¹ã«ã¼ã
ã³ã³ãã¥ã¼ã¿ã«è¨ç½®ãããåè·¯åºæ¿åã¯ã«ã¼ãã§ãã³ã³ãã¥ã¼ã¿ãã
ããã¯ã¼ã¯ã«æ¥ç¶ããã
Object Linking and
Embedding (OLE) for
Process Control (OPC)ï¼
ããã»ã¹å¶å¾¡ç¨
OLE
ç°ç¨®ãã£ã¼ã«ãããã¤ã¹éããªã¼ãã¡ã¼ã·ã§ã³
/å¶å¾¡éåã³äºæ¥ã·ã¹
ãã éã®ç¸äºéç¨æ§ãä¿é²ããããã«éçº
ããããªã¼ãã³è¦æ ¼ã
Operating Systemï¼
ãªãã¬ã¼ãã£ã³ã°ã·ã¹ãã
ã³ã³ãã¥ã¼ã¿ã«ããããã°ã©ã ã®ã·ã¼ã±ã³ã·ã³ã°ãç£è¦ããã
å®å¸¸ãµ
ã¼ãã¹ã®éåä½ãå
¥åºåå¶å¾¡ããªã½ã¼ã¹ã¹ã±ã¸ã¥ã¼ãªã³ã°åã³ãã¼ã¿
管çãè¡ããã³ã³ãã¥ã¼ã¿ãå¶å¾¡ããããã®æ©è½ã³ãã³ããã¢ããªã±
ã¼ã·ã§ã³ããã°ã©ã ã«æä¾ããã
åºå
¸ï¼
ãªã¼ãã¡ã¼ã·ã§ã³ã»ã·ã¹ãã ã»è¨è£
äºå
¸
Operational Controlsï¼
éç¨å¶å¾¡
主ã«äººéï¼ã·ã¹ãã ã§ã¯ãªãï¼ãå®è£
ãå®è¡ããæ
å ±ã·ã¹ãã ã®ã»ã
ã¥ãªãã£
対çï¼å®å
¨çåã¯å¯¾çï¼ã
åºå
¸ï¼
NIST SP 800-18 [19]
Passwordï¼ãã¹ã¯ã¼ã
身åãèªè¨¼åã¯ã¢ã¯ã»ã¹æ¨©éã確èªããããã®æååï¼æåãæ°åã
ã®ä»è¨å·ï¼ã
Phishingï¼ãã£ãã·ã³ã°
é»åéä¿¡
ï¼ã¤ã³ã¿ã¼ãããã¦ã§ããµã¤ãçï¼ã«ããã¦ä¿¡é ¼ã§ããå®ä½
ã§ããã¨ä¸»å¼µãããã¨ã«ããã欺ãã¦å人æ
å ±ãé示ããããã¨ã
SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
239
Photo Eye
A light sensitive sensor utilizing photoelectric control that converts a light
signal into an electrical signal, ultimately producing a binary signal based
on an interruption of a light beam.
SOURCE: NIST IR 6859 [2]
Plant
The physical elements necessary to support the physical process. This can
include many of the static components not controlled by the ICS; however,
the operation of the ICS may impact the adequacy, strength, and durability
of the plantâs components.
Port
The entry or exit point from a computer for connecting communications or
peripheral devices.
SOURCE: The Automation, Systems, and Instrumentation Dictionary
Port Scanning
Using a program to remotely determine which ports on a system are open
(e.g., whether systems allow connections through those ports).
SOURCE: NIST SP 800-61 [59]
Predisposing Condition
A condition that exists within an organization, a mission/business
process, enterprise architecture, or information system including its
environment of operation, which contributes to (i.e., increases or
decreases) the likelihood that one or more threat events, once
initiated, will result in undesirable consequences or adverse impact to
organizational operations and assets, individuals, other organizations,
or the Nation.
SOURCE: SP 800-30 [79]
Pressure Regulator
A device used to control the pressure of a gas or liquid.
SOURCE: NIST IR 6859 [2]
Pressure Sensor
A sensor system that produces an electrical signal related to the pressure
acting on it by its surrounding medium. Pressure sensors can also use
differential pressure to obtain level and flow measurements.
SOURCE: NIST IR 6859 [2]
Printer
A device that converts digital data to human-readable text on a paper
medium.
SOURCE: NIST IR 6859 [2]
Process Controller
A type of computer system, typically rack-mounted, that processes sensor
input, executes control algorithms, and computes actuator outputs.
SOURCE: NIST IR 6859 [2]
SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
240
Photo Eyeï¼ãã©ãã¢ã¤
å
ä¿¡å·ãé»åä¿¡å·ã«å¤æããå
é»åå¶å¾¡ãå©ç¨
ããæå
ã»ã³ãµ
ã§ãå
ç·ãä¸æãã¦ãã¤ããªä¿¡å·ãçæããã
åºå
¸ï¼
NIST IR 6859 [2]
Plantï¼ãã©ã³ã
ç©çããã»ã¹ãæ¯ããããã®ç©çè¦ç´ ã
ICS ã§å¶å¾¡ãããªãå¤ãã®é
çã³ã³ãã¼ãã³ããå«ã¾ãå¾ããã
ICS ã®éç¨ã¯ãã©ãããã¼ã ã³ã³
ãã¼ãã³ãã®é©åæ§ã強度åã³èä¹
æ§ã«å½±é¿ããã
Portï¼ãã¼ã
ã³ã³ãã¥ã¼ã¿ãéä¿¡æ©å¨åã¯å¨è¾ºããã¤ã¹ã«æ¥ç¶ããããã®åºå
¥å£ã¨
ãªãç¹ã
åºå
¸
ï¼ãªã¼ãã¡ã¼ã·ã§ã³ã»ã·ã¹ãã ã»è¨è£
äºå
¸
Port Scanningï¼
ãã¼ãã¹ãã£ãã³ã°
ããã°ã©ã ãå©ç¨ãã¦éæ¾ããã¦ãããã¼ãï¼ããããã·ã¹ãã ã«æ¥
ç¶ã§ãããï¼ãå¤å®ãããã¨ã
åºå
¸ï¼
NIST SP 800-61 [59]
Predisposing Conditionï¼
ç´ å çç¶æ
çµç¹ãä»»åã»äºæ¥ãä¼æ¥ã¢ã¼ããã¯ãã£åã¯æ
å ±ã·ã¹ãã å
ã«åå¨ã
ãç¶æ
ã®ãã¨ã§ããã£ããçºåããã¨ãçµç¹ã®éå¶åã³è³ç£ãå人ã
ä»ã®çµç¹åã¯å½ã«æªå½±é¿ãä¸ããè
å¨äºè±¡ã«å¯ä¸ï¼å¢æ¸ï¼ããéç¨ç°
å¢ãå«ã¾ããã
åºå
¸ï¼
SP 800-30 [79]
Pressure Regulatorï¼
å§åã¬ã®ã¥ã¬ã¼ã¿
ã¬ã¹åã¯æ¶²ä½ã®å§åãå¶å¾¡ããããã¤ã¹ãåºå
¸ï¼
NIST IR 6859 [2]
Pressure Sensorï¼
å§åã»ã³ãµ
å¨è¾ºåªä½ããåããå§åã«é¢ããé»æ°ä¿¡å·ãçºçãã
ã»ã³ãµã·ã¹ã
ã ãå§å
ã»ã³ãµã¯å·®å§ãå©ç¨ãã¦ã¬ãã«åã³æµéã®è¨æ¸¬ãè¡ãã
åº
å
¸ï¼NIST IR 6859 [2]
Printerï¼ããªã³ã¿
ãã¸ã¿ã«ãã¼ã¿ã人ãèªããç´ã®ããã¹ãã«å¤æããããã¤ã¹ãåº
å
¸ï¼
NIST IR 6859 [2]
Process Controllerï¼
ããã»ã¹ã³ã³ããã¼ã©
é常ã©ãã¯ã«è¨ç½®ããã
1種ã®ã³ã³ãã¥ã¼ã¿ã·ã¹ãã ã§ãã»ã³ãµå
¥å
ãå¦çããå¶å¾¡ã¢ã«ã´ãªãºã ãå®è¡ããã¢ã¯ãã¥ã¨ã¼ã¿åºåãè¨ç®ã
ãã
åºå
¸ï¼
NIST IR 6859 [2]
SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
241
Programmable Logic
Controller
(PLC)
A solid-state control system that has a user-programmable memory for
storing instructions for the purpose of implementing specific functions such
as I/O control, logic, timing, counting, three mode (PID) control,
communication, arithmetic, and data and file processing.
SOURCE: The Automation, Systems, and Instrumentation Dictionary
A small industrial computer originally designed to perform the logic
functions executed by electrical hardware (relays, switches, and mechanical
timer/counters). PLCs have evolved into controllers with the capability of
controlling complex processes, and they are used substantially in SCADA
systems and DCS. PLCs are also used as the primary controller in smaller
system configurations. PLCs are used extensively in almost all industrial
processes.
Protocol
A set of rules (i.e., formats and procedures) to implement and control some
type of association (e.g., communication) between systems.
SOURCE: RFC 4949 [75]
Protocol Analyzer
A device or software application that enables the user to analyze the
performance of network data so as to ensure that the network and its
associated hardware/software are operating within network specifications.
SOURCE: The Automation, Systems, and Instrumentation Dictionary
Proximity Sensor
A non-contact sensor with the ability to detect the presence of a target
within a specified range. SOURCE: NIST IR 6859 [2]
Proxy Server
A server that services the requests of its clients by forwarding those requests
to other servers.
SOURCE: CNSSI-4009
Real-Time
Pertaining to the performance of a computation during the actual time that
the related physical process transpires so that the results of the computation
can be used to guide the physical process.
SOURCE: NIST IR 6859 [2]
Redundant Control Server
A backup to the control server that maintains the current state of the control
server at all times.
SOURCE: NIST IR 6859 [2]
Relay
An electromechanical device that completes or interrupts an electrical circuit
by physically moving conductive contacts. The resultant motion can be
coupled to another mechanism such as a valve or breaker.
SOURCE: The Automation, Systems, and Instrumentation Dictionary
SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
242
Pr
ogrammable Logic
Controller (PLC)ï¼
ããã°ã©ããã«è«çå¶å¾¡è£
ç½®
ã½ãªããã¹ãã¼ãå¶å¾¡ã·ã¹ãã ã§ãã¦ã¼ã¶ãããã°ã©ã å¯è½ãªã¡ã¢ãª
ãããã
I/O å¶å¾¡ãè«çãã¿ã¤ãã³ã°ãã«ã¦ã³ãã3ã¢ã¼ãï¼PIDï¼ã®
å¶å¾¡ãéä¿¡ãæ¼ç®ããã¼ã¿ããã¡ã¤ã«ã®å¦ççã®å
·ä½çãªæ©è½ãå®è£
ããããã®å½ä»¤ãæ ¼ç´ããã
åºå
¸ï¼
ãªã¼ãã¡ã¼ã·ã§ã³ã»ã·ã¹ãã ã»è¨è£
äºå
¸
å
ã
ã¯é»æ°ç
ãã¼ãã¦ã¨ã¢ï¼ãªã¬ã¼ãã¹ã¤ããåã³æ©æ¢°çã¿ã¤ãã¼/
ã«ã¦ã³ã¿ã¼ï¼ã«ããå®è¡ãããè«çæ©è½ãå®è¡ããããã«è¨è¨ããã
å°åã®ç£æ¥ç¨ã³ã³ãã¥ã¼ã¿ãè¤éãªããã»ã¹ã®å¶å¾¡è½åãæã£ãã³ã³
ããã¼ã©ã«é²åãã
SCADA ã·ã¹ãã åã³ DCS ã§å¤ç¨ããããã¾ãã
ããå°åã®ã·ã¹ãã æ§æä¸ã§
ãã©ã¤ããª
ã³ã³ããã¼ã©ã¨ãã¦ãå©ç¨ã
ãã¦ããã
PLC
ã¯ã»ã¨ãã©å
¨ã¦ã®ç£æ¥ããã»ã¹ã§åºç¯ã«å©ç¨ãããã
Protocolï¼ãããã³ã«
ã·ã¹ãã éã®ãã種ã®é¢ä¿ï¼éä¿¡çï¼ãå®è¡ãå¶å¾¡ããããã®ä¸é£ã®
è¦åï¼å½¢å¼åã³æé ï¼ã
åºå
¸ï¼
RFC 4949 [75]
Protocol Analyzerï¼
ãããã³ã«åæå¨
ãããã¯ã¼ã¯åã³é¢é£
ãã¼ãã¦ã¨ã¢/ã½ããã¦ã¨ã¢ããããã¯ã¼ã¯ä»
æ§å
ã§åä½ããããã«ãã¦ã¼ã¶ããããã¯ã¼ã¯ãã¼ã¿ã®ããã©ã¼ãã³
ã¹ãåæã§ããããã«ããããã¤ã¹ã¾ãã¯
ã½ããã¦ã¨ã¢ã
åºå
¸ï¼
ãªã¼ãã¡ã¼ã·ã§ã³ã»ã·ã¹ãã ã»è¨è£
äºå
¸
Proximity Sensorï¼
è¿æ¥ã»ã³ãµ
ç®æ¨å¤ãæå®ç¯å²ã«ãããã¨ãæ¤åºã§ããéæ¥è§¦å
ã»ã³ãµã
åºå
¸ï¼
NIST IR 6859 [2]
Proxy Serverï¼
ãããã·ãµã¼ã
ã¯ã©ã¤ã¢ã³ãããã®è¦æ±ãä»ã®ãµã¼ãã«è»¢éãããµã¼ãã
åºå
¸ï¼
CNSSI-4009
Real
-Time
ï¼ãªã¢ã«ã¿ã¤ã
è¨ç®ã«é¢ä¿ããç©çããã»ã¹ãçºçãã¦ãè¨ç®çµæãç©çããã»ã¹ã®
å¶å¾¡ã«å©ç¨ã§ããå®æéè¨ç®ãããã
åºå
¸ï¼
NIST IR 6859 [2]
Redundant Control
Serverï¼
åé·å¶å¾¡ãµã¼ã
å¶å¾¡ãµã¼ãã®ããã¯ã¢ããã§ãå¶å¾¡ãµã¼ãã®ç¾å¨ã®ç¶æ
ã常æä¿æã
ãã
åºå
¸ï¼
NIST IR 6859 [2]
Relayï¼ãªã¬ã¼
æ¥ç¹ãç©ççã«åããã¦é»æ°åè·¯ãæ¥ç¶åã¯ä¸æ
ããé»åæ©æ¢°å¼ãã
ã¤ã¹ããã®çµæçããéåã¯ããã«ãããã¬ã¼ã«ã¨ãã£ãå¥ã®ããã¤
ã¹ã«é£æºããã
åºå
¸ï¼
ãªã¼ãã¡ã¼ã·ã§ã³ã»ã·ã¹ãã ã»è¨è£
äºå
¸
SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
243
Remote Access
Access by users (or information systems) communicating external to an
information system security perimeter.
SOURCE: NIST SP 800-53 [22]
Remote Access Point
Distinct devices, areas and locations of a control network for remotely
configuring control systems and accessing process data. Examples include
using a mobile device to access data over a LAN through a wireless access
point, and using a laptop and modem connection to remotely access an ICS
system.
Remote Diagnostics
Diagnostics activities conducted by individuals communicating external to
an information system security perimeter.
Remote Maintenance
Maintenance activities conducted by individuals communicating external to
an information system security perimeter.
Remote Terminal Unit
(RTU)
A computer with radio interfacing used in remote situations where
communications via wire is unavailable. Usually used to communicate with
remote field equipment. PLCs with radio communication capabilities are
also used in place of RTUs.
Special purpose data acquisition and control unit designed to support DCS
and SCADA remote stations. RTUs are field devices often equipped with
network capabilities, which can include wired and wireless radio interfaces
to communicate to the supervisory controller. Sometimes PLCs are
implemented as field devices to serve as RTUs; in this case, the PLC is often
referred to as an RTU.
Resource Starvation
A condition where a computer process cannot be supported by available
computer resources. Resource starvation can occur due to the lack of
computer resources or the existence of multiple processes that are competing
for the same computer resources.
Risk
The level of impact on agency operations (including mission, functions,
image, or reputation), agency assets, or individuals resulting from the
operation of an information system, given the potential impact of a threat
and the likelihood of that threat occurring.
SOURCE: NIST SP 800-30 [79]
Risk Assessment
The process of identifying risks to agency operations (including mission,
functions, image, or reputation), agency assets, or individuals by
determining the probability of occurrence, the resulting impact, and
additional security controls that would mitigate this impact. Part of risk
management, synonymous with risk analysis. Incorporates threat and
vulnerability analyses.
SOURCE: NIST SP 800-30 [79]
SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
244
Remote Accessï¼
ãªã¢ã¼ãã¢ã¯ã»ã¹
æ
å ±ã·ã¹ãã ã®ã»ãã¥ãªãã£å¨è¾ºå¤ããéä¿¡ãè¡ãã¦ã¼ã¶ï¼åã¯æ
å ±
ã·ã¹ãã
ï¼ã®ã¢ã¯ã»ã¹ã
åºå
¸ï¼
NIST SP 800-53 [22]
Remote Access
Point
ï¼
ãªã¢ã¼ãã¢ã¯ã»ã¹ç¹
å¶å¾¡ã·ã¹ãã ãé éè¨å®ããããã»ã¹ãã¼ã¿ã«ã¢ã¯ã»ã¹ããããã®å¶
御ãããã¯ã¼ã¯ã®æ確ãªããã¤ã¹ãã¨ãªã¢åã³å ´æãä¾ãã°ã¢ãã¤ã«
ããã¤ã¹ãå©ç¨ãã¦ãã¯ã¤ã¤ã¬ã¹ã¢ã¯ã»ã¹ç¹ãã
LAN çµç±ã®ãã¼ã¿
ã¢ã¯ã»ã¹ãã©ãããããåã³ã¢ãã ãå©ç¨ãã
ICS ã·ã¹ãã ã¢ã¯ã»ã¹
ãããã
Remote Diagnosticsï¼
ãªã¢ã¼ã診æ
æ
å ±ã·ã¹
ãã ã»ãã¥ãªãã£å¨è¾ºå¤ããå人ãè¡ã診ææ´»åã
Remote Maintenanceï¼
é éä¿å®
æ
å ±ã·ã¹ãã ã»ãã¥ãªãã£å¨è¾ºå¤ããå人ãè¡ãä¿å®æ´»åã
Remote Terminal Unit
(
RTU)
ï¼
é é端æ«è£
ç½®
æç·éä¿¡ãå©ç¨ã§ããªãé éç°å¢ã§ä½¿ç¨ããç¡ç·
ã¤ã³ã¿ãã§ã¼ã¹
ä»ã
ã³ã³ãã¥ã¼ã¿ãé常
ã
é éãã£ã¼ã«ãè£
ååã¨ã®éä¿¡ã«ä½¿ç¨ãããç¡
ç·éä¿¡æ©è½ä»ã
PLC ãRTU ã®ä»£ããã«ä½¿ç¨ãããã
DCS
åã³ SCADA é éã¹ãã¼ã·ã§ã³ããµãã¼ãããããã®ç¹æ®ç®çã§
ã®ãã¼ã¿åå¾å¶å¾¡è£
ç½®ã
RTU ã¯ãç£è¦ã³ã³
ããã¼ã©ã¨ã®éä¿¡ç¨æç·ã»
ç¡ç·
ã¤ã³ã¿ãã§ã¼ã¹çããããã¯ã¼ã¯æ©è½ãè£
åãã¦ããå ´åãå¤
ãã
PLC ã¯ãã£ã¼ã«ãããã¤ã¹ã¨ãã¦å®è£
ãã RTU ã¨ãã¦å©ç¨ãã
ããã¨ãããã
PLC ã¯RTU ã¨å¼ã°ãããã¨ãå¤ãã
Resource Starvationï¼
ãªã½ã¼ã¹æ¯æ¸
å©ç¨å¯è½ãªã³ã³ãã¥ã¼ã¿ãªã½ã¼ã¹ã§ã¯ã³ã³ãã¥ã¼ã¿ããã»ã¹ããµãã¼
ãã§ããªãç¶æ
ãã³ã³ãã¥ã¼ã¿ãªã½ã¼ã¹ã®æ¬ ä¹åã¯åãã³ã³ãã¥ã¼ã¿
ãªã½ã¼ã¹ããããè¤æ°ããã»ã¹ã®ç«¶åã«ããçãããã¨ãããã
Riskï¼ãªã¹ã¯
è
å¨ã®æ½å¨çå½±é¿åã³å½è©²è
å¨ãçããèç¶æ§ã«éã¿ãæ
å ±ã·ã¹ãã
ã®éç¨ããçãã
æ¿åºæ©é¢ã®æ¥åï¼ä»»åãæ©è½ãã¤ã¡ã¼ã¸ãè©å¤
çï¼ã
æ¿åºæ©é¢ã®è³ç£åã¯å人ã¸ã®å½±é¿åº¦ã
åºå
¸ï¼
NIST SP 800-30 [79]
Risk Assessmentï¼
ãªã¹ã¯è©ä¾¡
çºç確çããã®å½±é¿ãå½±é¿ãç·©åããããã®ä»å çã»ãã¥ãªãã£å¯¾ç
ã®å¤å®ãéãã
æ¿åºæ©é¢ã®
æ¥åï¼ä»»åãæ©è½ãã¤ã¡ã¼ã¸ãè©å¤çï¼ã
è³ç£åã¯å人ã«å¯¾ãããªã¹ã¯èå¥ããã»ã¹ããªã¹ã¯ç®¡çã®ä¸é¨ã§ããª
ã¹ã¯åæã¨å義ãè
å¨åæåã³èå¼±æ§åæãåãå
¥ããã
åºå
¸
ï¼NIST SP 800-30 [79]
SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
245
Risk Management
The process of managing risks to organizational operations (including
mission, functions, image, reputation), organizational assets, individuals,
other organizations, and the Nation, resulting from the operation of an
information system, and includes: (i) the conduct of a risk assessment; (ii)
the implementation of a risk mitigation strategy; and (iii) employment of
techniques and procedures for the continuous monitoring of the security
state of the information system.
SOURCE: FIPS 200, Adapted [16]
Risk Management
Framework
The Risk Management Framework (RMF), presented in NIST SP 800-37,
provides a disciplined and structured process that integrates information
security and risk management activities into the system development life
cycle.
SOURCE: SP 800-37 [21]
Router
A computer that is a gateway between two networks at OSI layer 3 and that
relays and directs data packets through that inter-network. The most
common form of router operates on IP packets.
SOURCE: RFC 4949 [75]
Router Flapping
A router that transmits routing updates alternately advertising a destination
network first via one route, then via a different route.
Safety Instrumented System
(SIS)
A system that is composed of sensors, logic solvers, and final control
elements whose purpose is to take the process to a safe state when
predetermined conditions are violated. Other terms commonly used include
emergency shutdown system (ESS), safety shutdown system (SSD), and
safety interlock system (SIS).
SOURCE: ANSI/ISA-84.00.01
SCADA Server
The device that acts as the master in a SCADA system.
SOURCE: NIST IR 6859 [2]
Security Audit
Independent review and examination of a systemâs records and activities to
determine the adequacy of system controls, ensure compliance with
established security policy and procedures, detect breaches in security
services, and recommend any changes that are indicated for
countermeasures.
SOURCE: ISO/IEC 7498
Security Controls
The management, operational, and technical controls (i.e., safeguards or
countermeasures) prescribed for an information system to protect the
confidentiality, integrity, and availability of the system and its information.
SOURCE: FIPS PUB 199 [15]
SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
246
Risk Managementï¼
ãªã¹ã¯ç®¡ç
æ
å ±ã·ã¹ãã ã®éç¨ããçãããçµç¹ã®éå¶ï¼ä»»åãæ©è½ãã¤ã¡ã¼
ã¸ãè©å¤çï¼åã³è³ç£ãå人ãä»ã®çµç¹åã¯å½ã¸ã®ãªã¹ã¯ã管çãã
ããã»ã¹ã§ã以ä¸ãå«ããï¼
1ï¼ãªã¹ã¯è©ä¾¡ã®å®æ½ãï¼2
ï¼ãªã¹ã¯ç·©å
çã®å®æ½ãï¼
3ï¼æ
å ±ã·ã¹ãã ã®ã»ãã¥ãªãã£ç¶æ
ã常ç¶ç£è¦ããã
ãã®
æè¡åã³æé ã®æ¡ç¨ã
åºå
¸ï¼
FIPS 200, Adapted [16]
Risk Management
Frameworkï¼
ãªã¹ã¯ç®¡çä½å¶
NIST SP 800
-37 ã«ç¤ºããããªã¹ã¯ç®¡çä½å¶ï¼RMF
ï¼ã¯ãæ
å ±ã»ãã¥ãª
ãã£æ´»åã¨ãªã¹ã¯ç®¡çæ´»åãã·ã¹ãã éçºã©ã¤ããµã¤ã¯ã«ã«çµ±ååã
ãããã®çµ±å¶ã®åããçµç¹åãããããã»ã¹ã¨å®ãã¦ããã
åºå
¸ï¼
SP 800-37 [21]
Routerï¼ã«ã¼ã¿
OSI
ã¬ã¤ã¤ã¼3ã§ã®ãããã¯ã¼ã¯ã¨ãã¼ã¿ããã±ã¼ã¸ãä¸ç¶æåãã
ãããã¯ã¼ã¯éã®ã²ã¼ãã¦ã§ã¤ã¨ãªãã³ã³ãã¥ã¼ã¿ãæãä¸è¬çãªå½¢
æ
ã®ã«ã¼ã¿ã¯
IP ãã±ããã§åä½ããã
åºå
¸ï¼
RFC 4949 [75]
Router Flappingï¼
ã«ã¼ã¿ãã©ããã³ã°
çµè·¯æ´æ°ã交äºã«éä¿¡ããã«ã¼ã¿ã
å®å
ãããã¯ã¼ã¯ãã¾ã
ããçµè·¯
ã§åºå
ãã次ãã§å¥çµè·¯ã§è¡ãã
Safety Instrumented System
(SIS)ï¼å®å
¨è¨è£
ã·ã¹ãã
ã»ã³ãµããã¸ãã¯ã½ã«ãã¼åã³æçµå¶å¾¡ã¨ã¬ã¡ã³ãã§æ§æãããã·ã¹
ãã ã§ãç®çã¯äºãå®ããããæ¡ä»¶ããé¸è±ããéã«ãããã»ã¹ãå®
å
¨ç¶æ
ã«æ»ããã¨ã«ãããä¸è¬ã«ä½¿ç¨ããããã®ä»ã®ç¨èªã¨ãã¦ç·æ¥
é®æã·
ã¹ãã ï¼ESSï¼ãå®å
¨é®æã·ã¹ãã ï¼SSDï¼ãå®å
¨é£åã·ã¹ã
ã ï¼
SISï¼çãããã
åºå
¸ï¼
ANSI/ISA-84.00.01
SCADA Serverï¼
SCADA ãµã¼ã
SCADA
ã·ã¹ãã ã§ãã¹ã¿ã¼ã¨ãªãããã¤ã¹ã
åºå
¸ï¼
NIST IR 6859 [2]
Security Auditï¼
ã»ãã¥ãªãã£ç£æ»
ã·ã¹ãã å¶å¾¡ã®é©åæ§ãå¤å®ããè¦å®ã®ã»ãã¥ãªãã£ããªã·ã¼åã³æ
é ã®éµå®ã確ä¿ããã»ãã¥ãªãã£ãµã¼ãã¹éåãæ¤åºãã対çã¨ãã¦
示åãããå¤æ´
å
容ãå§åããããã®ã·ã¹ãã ã®è¨é²åã³æ´»åã«å¯¾ã
ãç¬ç«çãªå¯©æ»åã³æ¤è¨¼ã
åºå
¸ï¼
ISO/IEC 7498
Security Controlsï¼
ã»ãã¥ãªãã£å¯¾ç
ã·ã¹ãã ã¨ãã®æ
å ±ã®
æ©å¯æ§ãå®å
¨æ§
åã³å¯ç¨æ§ãä¿è·ããããã®æ
å ±ã·ã¹ãã ç¨ç®¡çã»éç¨ã»æè¡å¯¾çï¼å®å
¨çã対ææ段çï¼ã
åºå
¸ï¼
FIPS PUB 199 [15]
SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
247
Security Plan
Formal document that provides an overview of the security requirements for
the information system and describes the security controls in place or
planned for meeting those requirements.
SOURCE: NIST SP 800-53 [22]
Security Policy
Security policies define the objectives and constraints for the security
program. Policies are created at several levels, ranging from organization or
corporate policy to specific operational constraints (e.g., remote access). In
general, policies provide answers to the questions âwhatâ and âwhyâ
without dealing with âhow.â Policies are normally stated in terms that are
technology-independent.
SOURCE: ISA99
Sensor
A device that produces a voltage or current output that is representative of
some physical property being measured (e.g., speed, temperature, flow).
SOURCE: The Automation, Systems, and Instrumentation Dictionary
A device that measures a physical quantity and converts it into a signal
which can be read by an observer or by an instrument. A sensor is a device,
which responds to an input quantity by generating a functionally related
output usually in the form of an electrical or optical signal.
Servo Valve
An actuated valve whose position is controlled using a servo actuator.
SOURCE: NIST IR 6859 [2]
Set Point
An input variable that sets the desired value of the controlled variable. This
variable may be manually set, automatically set, or programmed.
SOURCE: The Automation, Systems, and Instrumentation Dictionary
Simple Network
Management Protocol
(SNMP)
A standard TCP/IP protocol for network management. Network
administrators use SNMP to monitor and map network availability,
performance, and error rates. To work with SNMP, network devices utilize a
distributed data store called the Management Information Base (MIB). All
SNMP-compliant devices contain a MIB which supplies the pertinent
attributes of a device. Some attributes are fixed or âhard-codedâ in the MIB,
while others are dynamic values calculated by agent software running on the
device.
SOURCE: API 1164
Single Loop Controller
A controller that controls a very small process or a critical process.
SOURCE: NIST IR 6859 [2]
Social Engineering
An attempt to trick someone into revealing information (e.g., a password)
that can be used to attack systems or networks.
SOURCE: NIST SP 800-61 [59]
SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
248
Security Planï¼
ã»ãã¥ãªãã£è¨ç»æ¸
æ
å ±ã·ã¹ãã ã®ã»ãã¥ãªãã£è¦ä»¶ãæ¦èª¬ããæ£å¼ææ¸ã§ããã®è¦ä»¶ã
æºè¶³ããå®æ½ä¸åã¯è¨ç»ä¸ã®ã»ãã¥ãªãã£
対çã«ã¤ãã¦è¨è¿°ããã
ã®ã
åºå
¸ï¼
NIST SP 800-53 [22]
Security Policyï¼
ã»ãã¥ãªãã£ããªã·ã¼
ã»ãã¥ãªãã£ããªã·ã¼ã¯ã»ãã¥ãªãã£ããã°ã©ã ã®ç®çã¨å¶ç´äºé
ã
å®ç¾©ãããããªã·ã¼ã¯
ããã¤ãã®ã¬ãã«ã§ä½æãããçµç¹åã¯ä¼æ¥ã
ãªã·ã¼ããå
·ä½çãªéç¨ä¸ã®å¶ç´äºé
ï¼
ãªã¢ã¼ãã¢ã¯ã»ã¹çï¼ã¾ã§ã
ããç·ã
ã¦ããªã·ã¼ã¯ãä½ããã¨ãããªããã«ã¯çãããããã©ã®ã
ãã«ãã¨ãã質åã«ã¯çãã¦ããªããé常
ãæè¡ã¨ã¯ç¡é¢ä¿ã®ç¨èªã§
è¨è¿°ãããã
åºå
¸ï¼
ISA99
Sensorï¼ã»ã³ãµ
è¨æ¸¬ä¸ã®ç©çç¹æ§ï¼é度ã温度ãæµéçï¼ã表ããé»å§åã¯é»æµåºå
ãçºçãããããã¤ã¹ã
åºå
¸ï¼
ãªã¼ãã¡ã¼ã·ã§ã³ã»ã·ã¹ãã ã»è¨è£
äºå
¸
ç©ççéãè¨æ¸¬ãã¦ä¿¡å·ã«å¤æããããã¤ã¹ã§ãä¿¡å·ã¯è¦³å¯è
ãè¨å¨
ã§èªã¿åããã¨ãã§ãããæ©è½çã«é¢ããã®ããåºåããé常
ã
é»æ°
åã¯å
å¦ä¿¡å·ã¨ãã¦çæãããã¨ã«ãããå
¥åã«å¯¾å¿ããããã¤ã¹ã
Servo Val
ve
ï¼
ãµã¼ããã«ã
ãµã¼ãã¢ã¯ãã¥ã¨ã¼ã¿ã使ç¨ãã¦ä½ç½®ãå¶å¾¡ããä½åå¼ã
åºå
¸ï¼
NIST IR 6859 [2]
Set Pointï¼è¨å®ç¹
å¶å¾¡å¤æ°ã®ææã®å¤ãè¨å®ããå
¥åå¤æ°ããã®å¤æ°ã¯
ããã¥ã¢ã«æ
ä½
ãèªåãããã°ã©ã åã®ãããã«ãã£ã¦ãè¨å®å¯è½ã§ããã
åºå
¸ï¼
ãªã¼ãã¡ã¼ã·ã§ã³ã»ã·ã¹ãã ã»è¨è£
äºå
¸
Simple Network
Management Protocol
(SNMP)ï¼
ã·ã³ãã«ãããã¯ã¼ã¯ç®¡ç
ãããã³ã«
ãããã¯ã¼ã¯ç®¡çç¨
æ¨æº TCP/IP ãããã³ã«ããããã¯ã¼ã¯ç®¡çè
ã¯
ãã®ãããã³ã«ã使ç¨ãã¦ãããã¯ã¼ã¯ã®å¯ç¨æ§ãããã©ã¼ãã³ã¹å
ã³ã¨ã©ã¼çãç£è¦ããã
SNMP ã«å¯¾å¿ãã¦ããããã¯ã¼ã¯ããã¤ã¹ã¯
管çæ
å ±ãã¼ã¹ï¼
MIBï¼ã¨å¼ã°ããåæ£ãã¼ã¿ã¹ãã¢ã使ç¨ãããå
¨
ã¦ã®
SNMP é©åããã¤ã¹ã¯ MIB ãæã£ã¦ãããããã¤ã¹ã®é¢é£å±æ§
ãä¾çµ¦ãããããå±æ§ã¯
MIB ã«åºå®åã¯ããã¼ãã³ã¼ãããããã¾
ããããã®ã¯ããã¤ã¹ã§å®è¡ä¸ã®ã¨ã¼ã¸ã§ã³ãã«ããè¨ç®ãããåç
å¤ã¨ãªãã
åºå
¸ï¼
API 1164
Single Loop Controllerï¼
åä¸ã«ã¼ãã³ã³ããã¼ã©
極ãã¦å°ããªããã»ã¹åã¯éè¦ããã»ã¹ãå¶å¾¡ããã³ã³ããã¼ã©ãåº
å
¸ï¼
NIST IR 6859 [2]
Social Engineeringï¼
ã½ã¼ã·ã£ã«ã¨ã³ã¸ãã¢ãªã³
ã°
ã·ã¹ãã ããããã¯ã¼ã¯ã®æ»æã«ä½¿ç¨ããããã人ã欺ãã¦æ
å ±ï¼ã
ã¹ã¯ã¼ãçï¼ãæ¼æ´©ããããããã¿ã
åºå
¸ï¼
NIST SP 800-61 [59]
SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
249
Solenoid Value
A valve actuated by an electric coil. A solenoid valve typically has two
states: open and closed.
SOURCE: NIST IR 6859 [2]
Spyware
Software that is secretly or surreptitiously installed onto an information
system to gather information on individuals or organizations without their
knowledge; a type of malicious code.
SOURCE: NIST SP 800-53 [22]
Statistical Process Control
(SPC)
The use of statistical techniques to control the quality of a product or
process.
SOURCE: The Automation, Systems, and Instrumentation Dictionary
Steady State
A characteristic of a condition, such as value, rate, periodicity, or amplitude,
exhibiting only negligible change over an arbitrarily long period of time.
SOURCE: ANSI/ISA-51.1-1979
Supervisory Control
A term that is used to imply that the output of a controller or computer
program is used as input to other controllers. See Control Server
SOURCE: The Automation, Systems, and Instrumentation Dictionary
Supervisory Control and
Data Acquisition (SCADA)
A generic name for a computerized system that is capable of gathering and
processing data and applying operational controls over long distances.
Typical uses include power transmission and distribution and pipeline
systems. SCADA was designed for the unique communication challenges
(e.g., delays, data integrity) posed by the various media that must be used,
such as phone lines, microwave, and satellite. Usually shared rather than
dedicated.
SOURCE: The Automation, Systems, and Instrumentation Dictionary
System Security Plan
Formal document that provides an overview of the security requirements for
a system and describes the security controls in place or planned for meeting
those requirements.
SOURCE: NIST SP 800-18, Adapted [19]
Technical Controls
The security controls (i.e., safeguards or countermeasures) for an
information system that are primarily implemented and executed by the
information system through mechanisms contained in the hardware,
software, or firmware components of the system.
SOURCE: NIST SP 800-18 [19]
Temperature Sensor
A sensor system that produces an electrical signal related to its temperature
and, as a consequence, senses the temperature of its surrounding medium.
SOURCE: NIST IR 6859 [2]
SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
250
Solenoid Valveï¼
ã½ã¬ãã¤ããã«ã
é»æ°ã³
ã¤ã«ã§ä½åããå¼ãé常ãéãã¨ãéãã® 2ã¤ã®ç¶æ
ãããã
åºå
¸ï¼
NIST IR 6859 [2]
Spywareï¼ã¹ãã¤ã¦ã¨ã¢
æ°ã¥ãããã«å人åã¯çµç¹ã®æ
å ±ãåéãããããç§å¯è£ã«åã¯ä¸æ£
ã«æ
å ±ã·ã¹ãã ã«åãä»ãããã
ã½ããã¦ã¨ã¢ã§ãæªæããã³ã¼ãã®
1
種ã
åºå
¸ï¼
NIST SP 800-53 [22]
Statistical Process Control
(SPC)ï¼
çµ±è¨çããã»ã¹ç®¡ç
製ååã¯ããã»ã¹ã®å質ã管çããããã®çµ±è¨
æè¡ã®ä½¿ç¨ã
åºå
¸ï¼ãªã¼ãã¡ã¼ã·ã§ã³ã»ã·ã¹ãã ã»è¨è£
äºå
¸
Steady Stateï¼å®å¸¸ç¶æ
å¤ãçãå¨æãè¦æ¨¡çã®ç¶æ
ç¹æ§ããããä»»æã®é·æéã«ãããå¤å
ãç¡è¦ã§ãããã¨ã
åºå
¸ï¼
ANSI/ISA-51.1-1979
Supervisory Controlï¼
ç£è¦å¶å¾¡
ã³ã³ããã¼ã©åã¯ã³ã³ãã¥ã¼ã¿ããã°ã©ã ã®åºåãä»ã®ã³ã³ããã¼ã©
ã®å
¥åã¨ãã¦ä½¿ç¨ããã¦ãããã¨ã示ãç¨èªãå¶å¾¡ãµã¼ããåç
§
åºå
¸ï¼
ãªã¼ãã¡ã¼ã·ã§ã³ã»ã·ã¹ãã ã»è¨è£
äºå
¸
Supervi
sory Control and
Data Acquisition
(SCADA)ï¼
ç£è¦å¶å¾¡ãã¼ã¿åå¾
é·è·é¢ã®ãã¼ã¿åéå¦çã¨éç¨å¶å¾¡ãè¡ããã³ã³ãã¥ã¼ã¿å¶å¾¡ã·ã¹ã
ã ã®æ±ç¨çãªå称ãéé
é»åã³ãã¤ãã©ã¤ã³çã«ããå©ç¨ããããé»
話åç·ããã¤ã¯ãæ³¢ã人工è¡æçã§ä½¿ç¨ãããå¤æ§ãªåªä½ã«ç¹æã®é
ä¿¡åé¡ï¼é
延ããã¼ã¿æ´åæ§çï¼ã«å¯¾å¿ãã¦è¨è¨ããããé常å°ç¨ã§
ã¯ãªãå
±æããããã¨ãå¤ãã
åºå
¸ï¼
ãªã¼ãã¡ã¼ã·ã§ã³ã»ã·ã¹ãã ã»è¨è£
äºå
¸
System Security Planï¼
ã·ã¹ãã ã»ãã¥ãªãã£è¨ç»
æ¸
ã·ã¹ãã ã»
ãã¥ãªãã£è¦ä»¶ã®æ¦è¦ã示ããè¦ä»¶ãéµå®ããããã«æ½è¡
ä¸åã¯è¨ç»ä¸ã®ã»ãã¥ãªãã£
対çã«ã¤ãã¦èª¬æããæ£å¼ææ¸ã
åºå
¸
ï¼NIST SP 800-18, Adapted [19]
Technical Controlsï¼
æè¡å¶å¾¡
ã·ã¹ãã ã®
ãã¼ãã¦ã¨ã¢ãã½ããã¦ã¨ã¢åã¯ãã¡ã¼ã ã¦ã¨ã¢
ã³ã³ãã¼
ãã³ãã«å«ã¾ããã¡ã«ããºã ãéãã¦ã主ã«æ
å ±ã·ã¹ãã ã«ããå®è£
ããå®æ½ãããæ
å ±ã·ã¹ãã ç¨ã®ã»ãã¥ãªãã£å¯¾çï¼å®å
¨çåã¯å¯¾æ
æ段ï¼ã
åºå
¸ï¼
NIST SP 800-18 [19]
Temperature Sensorï¼
温度ã»ã³ãµ
温度ã«é¢ããé»æ°ä¿¡å·ãçºçããããã®çµæå¨è¾ºåªä½ã®æ¸©åº¦ãæ¤ç¥ã
ã
ã»ã³ãµã·ã¹ãã ã
åºå
¸ï¼
NIST IR 6859 [2]
SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
251
Threat
Any circumstance or event with the potential to adversely impact agency
operations (including mission, functions, image, or reputation), agency
assets, or individuals through an information system via unauthorized
access, destruction, disclosure, modification of information, and/or denial of
service.
SOURCE: NIST SP 800-53 [22]
Threat Event
An event or situation that has the potential for causing undesirable
consequences or impact.
SOURCE: SP 800-30 [79]
Threat Source
The intent and method targeted at the intentional exploitation of a
vulnerability or a situation and method that may accidentally trigger a
vulnerability. Synonymous with Threat Agent.
SOURCE: FIPS 200 [16]; SP 800-53 [22]; SP 800-53A [23]; SP 800-37
[21]
Transmission Control
Protocol (TCP)
TCP is one of the main protocols in TCP/IP networks. Whereas the IP
protocol deals only with packets, TCP enables two hosts to establish a
connection and exchange streams of data. TCP guarantees delivery of data
and also guarantees that packets will be delivered in the same order in which
they were sent.
SOURCE: API 1164
Trojan Horse
A computer program that appears to have a useful function, but also has a
hidden and potentially malicious function that evades security mechanisms,
sometimes by exploiting legitimate authorizations of a system entity that
invokes the program.
SOURCE: RFC 4949 [75]
Unauthorized Access
A person gains logical or physical access without permission to a network,
system, application, data, or other resource.
SOURCE: NIST SP 800-61 [59]
Unidirectional Gateway
Unidirectional gateways are a combination of hardware and software. The
hardware permits data to flow from one network to another, but is
physically unable to send any information at all back into the source
network. The software replicates databases and emulates protocol servers
and devices.
Valve
An in-line device in a fluid-flow system that can interrupt flow, regulate the
rate of flow, or divert flow to another branch of the system.
SOURCE: The Automation, Systems, and Instrumentation Dictionary
Variable Frequency Drive
(VFD)
A type of drive that controls the speed, but not the precise position, of a
non-servo, AC motor by varying the frequency of the electricity going to
that motor. VFDs are typically used for applications where speed and power
are important, but precise positioning is not.
SOURCE: NIST IR 6859 [2]
SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
252
Threatï¼è
å¨
ä¸æ£ã¢ã¯ã»ã¹
ãç ´å£ãé示ãæ
å ±ã®æ¹å¤åã¯ãµã¼ãã¹å¦¨å®³ãéãã¦ã
æ¿åºæ©é¢ã®
æ¥åï¼ä»»åãæ©è½ãã¤ã¡ã¼ã¸ãè©å¤çï¼ãæ¿åºæ©é¢ã®è³ç£
åã¯å人ã«æªå½±é¿ãåã¼ããããªãç¶æ³åã¯äºè±¡ã
åºå
¸ï¼
NIST SP 800-53 [22]
Threat Eventï¼è
å¨äºè±¡
æã¾ãããªãçµæãå½±é¿ãçããããªãäºè±¡åã¯ç¶æ³ã
åºå
¸ï¼
SP 800-30 [79]
Threat Sourceï¼è
å¨æº
èå¼±æ§åã¯ç¶æ³åã³æ¹æ³ãæ
æã«å©ç¨ãããã¨ãããããææåã³æ¹
æ³ã§ãå¶çºçã«èå¼±æ§ãçããããåå ã¨ãªãå¾ããè
å¨ã¨ã¼ã¸ã§ã³
ãã¨å義ã
åºå
¸ï¼
FIPS 200 [16]; SP 800-53 [22]; SP 800-53A [23]; SP 800-37 [21]
Transmission Control
Protocol (TCP)ï¼
éä¿¡å¶å¾¡ãããã³ã«
TCP/IP
ãããã¯ã¼ã¯ã«ããã主ãªãããã³ã«ã® 1ã¤ãIP ãããã³ã«
ããã±ããå¦çã ããªã®ã«å¯¾ãã
TCP ã¯2
å°ã®ãã¹ããæ¥ç¶ã確ç«ã
ã¦ãã¼ã¿ã¹ããªã¼ã ã交æã§ããããã«ããããã¼ã¿ã®é
éãä¿è¨¼
ãããã±ãããéä¿¡é ã«å±ãããã«ã§ããã
åºå
¸ï¼
API 1164
Trojan Horseï¼
ããã¤ã®æ¨é¦¬
ã³ã³ãã¥ã¼ã¿ããã°ã©ã ã§ã便å©ãªæ©è½ãæã¤ããé ããæªæããæ©
è½ããããããã°ã©ã ãèµ·åããã·ã¹ãã å®å¨è
ã®
é©æ ¼æ§ãå©ç¨ã
ã¦ãã»ãã¥ãªãã£æ©æ§ã«ä¾µå
¥ããã
åºå
¸ï¼
RFC 4949 [75]
Unauthorized Accessï¼
ä¸æ£ã¢ã¯ã»ã¹
ãããã¯ã¼ã¯ãã·ã¹ãã ãã¢ããªã±ã¼ã·ã§ã³ããã¼ã¿ãã®ä»ã®ãªã½ã¼
ã¹ã«ã人ã許å¯ãªãè«ççåã¯ç©ççã¢ã¯ã»ã¹ãããã¨ã
åºå
¸ï¼
NIST SP 800-61 [59]
Unidirectional Gatewayï¼
åæ¹åã²ã¼ãã¦ã§ã¤
åæ¹åæ§ã²ã¼ãã¦
ã§ã¤ã¯ãã¼ãã¦ã¨ã¢ã¨ã½ããã¦ã¨ã¢ãçµã¿åããã
ãã®ã§ããã
ãã¼ãã¦ã¨ã¢ã¯ãã¼ã¿ãä¸æ¹ã®ãããã¯ã¼ã¯ããä»æ¹ã®
ãããã¯ã¼ã¯ã¸æµããã®ã許å¯ããããã½ã¼ã¹ãããã¯ã¼ã¯ã«æ
å ±ã
è¿ããã¨ã¯ç©ççã«ä¸å¯è½ã§ããã
ã½ããã¦ã¨ã¢ã¯ãã¼ã¿ãã¼ã¹ãè¤
製ãã¦ããããã³ã«ãµã¼ãåã³ããã¤ã¹ãã¨ãã¥ã¬ã¼ãããã
Valveï¼ãã«ãï¼å¼ï¼
æµä½ã·ã¹ãã ä¸ã®ã¤ã³ã©ã¤ã³ããã¤ã¹ã§ãæµããé®æããæµéã調ç¯
ããã·ã¹ãã ä¸ã§ã®æµãã®æ¹åãå¤ãããã¨ãã§ããã
åºå
¸ï¼ãªã¼ãã¡ã¼ã·ã§ã³ã»ã·ã¹ãã ã»è¨è£
äºå
¸
Variable Frequenc
y Drive
(VFD)ï¼å¯å¤å¨æ³¢æ°é§å
ã¢ã¼ã¿ã¸ã®é»æ°å¨æ³¢æ°ãå¤ãããã¨ã«ãããéãµã¼ãåã®äº¤æµã¢ã¼ã¿
ã®é度ãå¶å¾¡ããé§åã®
1種ã§ã精確ãªä½ç½®ã¯å¶å¾¡ã§ããªããä¸è¬ã«
é度ã¨é»åãéè¦ããã精確ãªä½ç½®ã¯éè¦ã§ãªãç¨éã«å©ç¨ãããã
åºå
¸ï¼
NIST IR 6859 [2]
SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
253
Virtual Private Network
(VPN)
A restricted-use, logical (i.e., artificial or simulated) computer network that
is constructed from the system resources of a relatively public, physical
(i.e., real) network (such as the Internet), often by using encryption (located
at hosts or gateways), and often by tunneling links of the virtual network
across the real network.
SOURCE: RFC 4949 [75]
Virus
A hidden, self-replicating section of computer software, usually malicious
logic, that propagates by infecting (i.e., inserting a copy of itself into and
becoming part of) another program. A virus cannot run by itself; it requires
that its host program be run to make the virus active.
SOURCE: RFC 4949 [75]
Virus Definitions
Predefined signatures for known malware used by antivirus detection
algorithms.
Vulnerability
Weakness in an information system, system security procedures, internal
controls, or implementation that could be exploited or triggered by a threat
source.
SOURCE: NIST SP 800-53 [22]
Whitelist
A list of discrete entities, such as hosts or applications that are known to be
benign and are approved for use within an organization and/or information
system.
SOURCE: SP 800-128 [80]
Wide Area Network (WAN)
A physical or logical network that provides data communications to a larger
number of independent users than are usually served by a local area
network (LAN) and that is usually spread over a larger geographic area than
that of a LAN.
SOURCE: API 1164
Wireless Device
Any device that can connect to an ICS network via radio or infrared waves,
usually to collect or monitor data, but also in some cases to modify control
set points.
Workstation
A computer used for tasks such as programming, engineering, and design.
SOURCE: NIST IR 6859 [2]
Worm
A computer program that can run independently, can propagate a complete
working version of itself onto other hosts on a network, and may consume
computer resources destructively.
SOURCE: RFC 4949 [75]
SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
254
Virtual Private Network
(VPN)ï¼
ä»®æ³ãã©ã¤ãã¼ããããã¯
ã¼ã¯
éå®çã«ä½¿ç¨ãããè«ççï¼äººå·¥çåã¯æ¨¡æ¬çï¼ã³ã³ãã¥ã¼ã¿ã¼ãã
ãã¯ã¼ã¯ã§ãæ¯è¼çå
¬éãããç©ççï¼ç¾å®çï¼ãããã¯ã¼ã¯ï¼ã¤ã³
ã¿ã¼ãããçï¼ããæ§ç¯ãããæå·åãå©ç¨ãããã¨ãå¤ãï¼ãã¹ã
åã¯ã²ã¼ãã¦ã§ã¤ã§ï¼ãä»®æ³ãããã¯ã¼ã¯ãªã³ã¯ãå®ãããã¯ã¼ã¯ã«
ãã³ããªã³ã°ãããã¨ãå¤ãã
åºå
¸ï¼
RFC 4949 [75]
Virusï¼ã¦ã¤ã«ã¹
ã³ã³ãã¥ã¼ã¿ã¼
ã½ããã¦ã¨ã¢
ã®é ããèªå·±è¤è£½ã»ã¯ã·ã§ã³ã§ãé常æª
æãããã¸ãã¯ã§ãããä»ã®ããã°ã©ã ãææãããï¼ã³ãã¼ãæ¿å
¥
ãã¦èªåãããã°ã©ã ã®ä¸é¨ã¨ãªãï¼ãã¨ã§å¢æ®ãããã¦ã¤ã«ã¹ã¯ã
ãèªä½ã§å®è¡ãããã¨ã¯ã§ããããã¹ãããã°ã©ã ã«ãã£ã¦ã¢ã¯ãã£
ãã«ãããå¿
è¦ãããã
åºå
¸ï¼
RFC 4949 [75]
Virus Definitionsï¼
ã¦ã¤ã«ã¹å®ç¾©
ã¢ã³ãã¦ã¤ã«ã¹æ¤ç¥ã¢ã«ã´ãªãºã ã§ä½¿ç¨ãããæ¢ç¥ã®
ãã«ã¦ã¨ã¢ã®äº
åå®ç¾©ã·ã°ããã£ã
Vulnerabilityï¼èå¼±æ§
æ
å ±ã·ã¹ãã ãã·ã¹ãã ã»ãã¥ãªãã£æé ãå
é¨å¶å¾¡å
ã¯å®è£
ã«ãã
ãå¼±ç¹ã§ãè
å¨æºã«ããå©ç¨åã¯èµ·åãããã
åºå
¸ï¼
NIST SP 800-53 [22]
Whitelistï¼ãã¯ã¤ããªã¹ã
åè¯ã§ãããã¨ãç¥ããã¦ãããçµç¹åã¯æ
å ±ã·ã¹ãã ä¸ã§ãå©ç¨ã
許å¯ããã¦ãããã¹ããã¢ããªã±ã¼ã·ã§ã³çã®åå¥å®ä½
ãªã¹ãã
åºå
¸ï¼
SP 800-128 [80]
Wide Area Network
(WAN)ï¼
åºåãããã¯ã¼ã¯
é常
ãLAN ãµã¼ãã¹ãããã¦ã¼ã¶æ°ãå¤ããããåºåã«ã¾ããã£ã¦
ãã¼ã¿éä¿¡ãµã¼ãã¹ãè¡ãç©ççåã¯è«ççãããã¯ã¼ã¯ã
åºå
¸ï¼
API 1164
Wireless Deviceï¼
ã¯ã¤ã¤ã¬ã¹ããã¤ã¹
é常
ããã¼ã¿ã®åéåã¯ç£è¦ãç®çã«ç¡ç·åã¯èµ¤å¤ç·ã§ ICS ãããã¯
ã¼ã¯ã«æ¥ç¶ã§ããããã¤ã¹ã§ãå¶å¾¡è¨å®ç¹ã®å¤æ´ã«ä½¿ç¨ãããã¨ãã
ãã
Workstationï¼
ã¯ã¼ã¯ã¹ãã¼ã·ã§ã³
ããã°ã©ãã³ã°ãã¨ã³ã¸ãã¢ãªã³ã°ãè¨è¨çã®ã¿ã¹ã¯ã«ä½¿ç¨ããã³ã³
ãã¥ã¼ã¿ã
åºå
¸ï¼
NIST IR 6859 [2]
Wormï¼ã¯ã¼ã
ç¬ç«ãã¦å®è¡ã§ããã³ã³ãã¥ã¼ã¿ããã°ã©ã ã§ãèªåèªèº«ã®å®å
¨ãªå
ä½ãã¼ã¸ã§ã³ãä»ã®ãã¹ãä¸ã«ä¼æãããã³ã³ãã¥ã¼ã¿ãªã½ã¼ã¹ãç ´
å£çã«æ¶è²»ããã
åºå
¸ï¼
RFC 4949 [75]

SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
255
Appendix CâThreat Sources, Vulnerabilities, and Incidents
Several terms are used to describe the inter-related concepts of threat, threat source, threat event, and
incident. A threat is any circumstance or event with the potential to adversely impact organizational
operations (including mission, functions, image, or reputation), organizational assets, individuals, other
organizations, or the Nation through an information system via unauthorized access, destruction, disclosure,
modification of information, and/or denial of service. Threats have some intent or method that may exploit
of a vulnerability through either intentional or unintentional means, this intent or method referred to as the
threat source. A vulnerability is a weakness in an information system (including an ICS), system security
procedures, internal controls, or implementation that could be exploited or triggered by a threat source. A
threat event is an event or situation that has the potential for causing undesirable consequences or impact.
When a threat event occurs it becomes an incident that actually or potentially jeopardizes the
confidentiality, integrity, or availability of an information system or the information the system processes,
stores, or transmits or that constitutes a violation or imminent threat of violation of security policies,
security procedures, or acceptable use policies. This section will explore ICS-specific threat sources,
vulnerabilities, and incidents.
Threat Sources
Threats to ICS can come from numerous sources, which can be classified as adversarial, accidental,
structural, and environmental. Table C-1 lists and defines known threats sources to ICS. It is necessary to
create a risk management strategy for the ICS that protects the system against these possible threat sources.
The threat source must be well understood in order to define and implement adequate protection. For
example, environmental events (e.g. floods, earthquakes) are well understood, but may vary in their
magnitude, frequency, and their ability to compound other interconnected events. However, adversarial
threats depend on the resources available to the adversary and the emergence of previously unknown
vulnerabilities or attacks.
Table C-1. Threats to ICS
Type of Threat Source
Description
Characteristics
ADVERSARIAL
- Individual
- Outsider
- Insider
- Trusted Insider
- Privileged Insider
- Group
- Ad hoc
- Established
- Organization
- Competitor
- Supplier
- Partner
- Customer
- Nation-State
Individuals, groups, organizations, or states that
seek to exploit the organizationâs dependence on
cyber resources (e.g., information in electronic
form, information and communications
technologies, and the communications and
information-handling capabilities provided by
those technologies)
Capability, Intent, Targeting
ACCIDENTAL
- User
- Privileged User/Administrator
Erroneous actions taken by individuals in the
course of executing their everyday
responsibilities.
Range of effects
SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
256
ä»é² C è
å¨æºãèå¼±æ§åã³ã¤ã³ã·ãã³ã
è
å¨ãè
å¨æºãè
å¨äºè±¡åã³ã¤ã³ã·ãã³ãã®ç¸äºã«é¢é£ãåã£ãæ¦å¿µã示ãã®ã«ããã¤ãã®ç¨èª
ãç¨ãããããè
å¨ã¨ã¯ãä¸æ£ã¢ã¯ã»ã¹ãç ´å£ãé示ãæ
å ±ã®æ¹å¤åã¯ãµã¼ãã¹å¦¨å®³ã«ãããæ
å ±ã·ã¹ãã ãéãã¦ãçµç¹æ¥åï¼ä»»åãæ©è½ãã¤ã¡ã¼ã¸ãè©å¤çï¼ãçµç¹è³ç£ãå人ãä»ã®çµç¹
åã¯å½ã«æªå½±é¿ãåã¼ããããªãç¶æ³åã¯äºè±¡ããããè
å¨ã«ã¯ãæ
æåã¯æå³ããªãæ段ã§è
å¼±æ§ãå©ç¨ããææåã¯æ¹æ³ãããããã®ææåã¯æ¹æ³ãè
å¨æºã¨ãããèå¼±æ§ã¨ã¯æ
å ±ã·ã¹ã
ã ï¼ICS ãå«ãï¼ãã·ã¹ãã ã»ãã¥ãªãã£æé ãå
é¨å¶å¾¡åã¯å®è£
ã«ãããå¼±ç¹ã§ãè
å¨æºã«ã
ãå©ç¨åã¯èµ·åããããè
å¨äºè±¡ã¯ãæã¾ãããªãçµæãå½±é¿ãçããããªãäºè±¡åã¯ç¶æ³ãã
ããè
å¨äºè±¡ãçèµ·ããã¨ã¤ã³ã·ãã³ãã¨ãªããã¤ã³ã·ãã³ãã¯ãæ
å ±ã·ã¹ãã åã¯ã·ã¹ãã ã
å¦çã»ä¿ç®¡ã»éä¿¡ããæ
å ±ã®æ©å¯æ§ã»å®å
¨æ§ã»å¯ç¨æ§ãå®éã«å±éºã«é¥ãããããã®å¯è½æ§ãã
ããã¾ãã»ãã¥ãªãã£ããªã·ã¼ãã»ãã¥ãªãã£æé åã¯åãå
¥ããããããªã·ã¼ã®ä½¿ç¨ã®éåå
ã¯ç´ã¡ã«éåã¨ãªãè
å¨ãæ§æããããã®ã»ã¯ã·ã§ã³ã§ã¯ãICS åºæã®è
å¨æºãèå¼±æ§åã³ã¤ã³
ã·ãã³ãã«ã¤ãã¦èª¬æããã
è
å¨æº
ICS ã®è
å¨ã«ã¯å¤æ§ãªèµ·æºããããæµæ§ãå¶çºæ§ãæ§é æ§åã³ç°å¢æ§ã«åé¡ã§ããã表 C-1 ã¯ã
ICS ã®æ¢ç¥ã®è
å¨ã¨ãã®å®ç¾©ã示ããã·ã¹ãã ããã®ãããªè
å¨æºããå®ããããICS ãªã¹ã¯ç®¡
çæ¦ç¥ãçå®ããå¿
è¦ãããããã£ããä¿è·ã§ãããããè
å¨æºãååç解ããªããã°ãªããªãã
ä¾ãã°ãç°å¢çäºè±¡ï¼æ´ªæ°´ãå°éçï¼ã«ã¤ãã¦ã¯ããç解ã§ãã¦ãããã®ãã°ããã¥ã¼ããé »åº¦
åã³ä»ã®é¢é£äºè±¡ã¨è¤åããã¨ãã®æ½å¨åã¯ä¸æ§ã§ãªãããããæµæ§è
å¨ã¯ãæµãå©ç¨ã§ãããª
ã½ã¼ã¹ã¨ã以åç¥ããã¦ããèå¼±æ§åã¯æ»æã®åºç¾ã«ä¾åããã
表C-1. ICS ã®è
å¨
è
å¨æºã®ç¨®é¡
å
容
ç¹å¾´
æµæ§
- å人
- é¨å¤è
- ã¤ã³ãµã¤ãã¼
- ä¿¡é ¼ã®ç½®ããã¤ã³ãµã¤ãã¼
- 権éã®ããã¤ã³ãµã¤ãã¼
- ã°ã«ã¼ã
- ã¢ãããã¯
- 常å¤
- çµç¹
- 競åç¸æ
- ãµãã©ã¤ã¤
- ãã¼ããã¼
- 顧客
-
å½ã»å·
çµç¹ã®ãµã¤ãã¼ãªã½ã¼ã¹ï¼é»åæ
å ±ãæ
å ±ã»éä¿¡æè¡ããããæè¡ã«ããæä¾ãã
ãéä¿¡ã»æ
å ±å¦çè½åçï¼ã¸ã®ä¾åæ§ãå©
ç¨ãããã¨ããããå人ãã°ã«ã¼ããçµç¹
åã¯å½
è½åãææãç®æ¨é¸å®
å¶çºæ§
- ã¦ã¼ã¶
-
ç¹æ¨©ã¦ã¼ã¶
/
管çè
å人ãæ¥å¸¸æ¥åãæããéã®é誤è¡çº
å½±é¿ç¯å²

SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
257
Type of Threat Source
Description
Characteristics
STRUCTURAL
- Information Technology (IT) Equipment
- Storage
- Processing
- Communications
- Display
- Sensor
- Controller
- Environmental Controls
- Temperature/Humidity Controls
- Power Supply
- Software
- Operating System
- Networking
- General-Purpose Application
- Mission-Specific Application
Failures of equipment, environmental controls, or
software due to aging, resource depletion, or
other circumstances which exceed expected
operating parameters.
Range of effects
ENVIRONMENTAL
- Natural or man-made disaster
- Fire
- Flood/Tsunami
- Windstorm/Tornado
- Hurricane
- Earthquake
- Bombing
- Overrun
- Unusual Natural Event (e.g., sunspots)
- Infrastructure Failure/Outage
- Telecommunications
- Electrical Power
Natural disasters and failures of critical
infrastructures on which the organization
depends, but which are outside the control of the
organization.
Note: Natural and man-made disasters can also
be characterized in terms of their severity and/or
duration. However, because the threat source
and the threat event are strongly identified,
severity and duration can be included in the
description of the threat event (e.g., Category 5
hurricane causes extensive damage to the
facilities housing mission-critical systems, making
those systems unavailable for three weeks).
Range of effects
Vulnerabilities and Predisposing Conditions
This section addresses vulnerabilities and predisposing conditions that may be found in typical ICS.
Vulnerabilities are weaknesses in information systems, system procedures, controls, or implementations the
can be exploited by a threat source. Predisposing conditions are properties of the organization,
mission/business process, architecture, or information systems that contribute to the likelihood of a threat
event. The order of these vulnerabilities and predisposing conditions does not necessarily reflect any
priority in terms of likelihood of occurrence or severity of impact. Additionally, the vulnerabilities and
predisposing conditions identified in this section should not be considered a complete list; it should also not
be assumed that these issues are found within every ICS.
SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
258
è
å¨æºã®ç¨®é¡
å
容
ç¹å¾´
æ§é ç
- æ
å ±æè¡ï¼ITï¼è£
åå
- ã¹ãã¬ã¼ã¸
- å¦ç
- éä¿¡
- ãã£ã¹ãã¬ã¤
- ã»ã³ãµ
- ã³ã³ããã¼ã©
- ç°å¢å¶å¾¡
- 温度ã»æ¹¿åº¦å¶å¾¡
- é»æº
- ã½ããã¦ã¨ã¢
- ãªãã¬ã¼ãã£ã³ã°ã·ã¹ãã
- ãããã¯ã¼ãã³ã°
- æ±ç¨ã¢ããªã±ã¼ã·ã§ã³
-
ä»»ååºæã¢ããªã±ã¼ã·ã§ã³
çµå¹´ããªã½ã¼ã¹ä¸è¶³ãã®ä»ã®ç¶æ³ã«ããäºæ³é転
ãã©ã¡ã¼ã¿ãè¶
ããè£
ååãç°å¢å¶å¾¡åã¯ã½ãã
ã¦ã¨ã¢ã®é害
å½±é¿ç¯å²
ç°å¢ç
- èªç¶ã»äººçºç½å®³
- ç«ç½
- 洪水ã»æ´¥æ³¢
- æ´é¢¨ã»ãã«ãã¼ã
- ããªã±ã¼ã³
- å°é
- çç ´
- ãªã¼ãã¼ã©ã³
- ç°å¸¸å¤©ç¶ç¾è±¡ï¼å¤ªé½é»ç¹çï¼
- ã¤ã³ãã©é害/åæ¢
- ç¡ç·éä¿¡
-
é»å
èªç¶ç½å®³åã³çµç¹ãä¾åããéè¦ã¤ã³ãã©ã®é害
ã§ãçµç¹ã®å¶å¾¡å¤ã®ãã®
注ï¼èªç¶ã»äººçºç½å®³ã¯é大æ§ã¨æéã«ããç¹å¾´ã¥
ããããããããè
å¨æºåã³è
å¨äºè±¡ã¯ç¹å®ãã
ã¦ããã®ã§ãé大æ§ã¨æéã¯ãè
å¨äºè±¡ä¸ã«å«ã
ãããï¼ä¾ãã°ã«ãã´ãªã¼5ã®ããªã±ã¼ã³ã¯ãä»»
åã«ä¸å¯æ¬ ãªã·ã¹ãã ã®ããæ½è¨ã«ç大ãªè¢«å®³ã
ä¸ããã·ã¹ãã ã 3é±é使ç¨ä¸è½ã«ãªãï¼ã
å½±é¿ç¯å²
èå¼±æ§åã³å¼±ç¹ã¨ãªãç¶æ
ãã®ã»ã¯ã·ã§ã³ã§ã¯ãä¸è¬ç㪠ICS ã«ãããã¡ãªèå¼±æ§ã¨å¼±ç¹ã¨ãªãç¶æ
ã«ã¤ãã¦åãä¸ããã
èå¼±æ§ã¯æ
å ±ã·ã¹ãã ãã·ã¹ãã æé ãå¶å¾¡åã¯å®è£
ã«ãããå¼±ç¹ã§ãè
å¨æºã«ããå©ç¨ããã
ãããå¼±ç¹ã¨ãªãç¶æ
ã¨ã¯ãçµç¹ãä»»åã»äºæ¥ããã»ã¹ãã¢ã¼ããã¯ãã£åã¯æ
å ±ã·ã¹ãã ã®ç¹
æ§ã§ãè
å¨äºè±¡ãçããå
¬ç®ãé«ããããã®ãããªèå¼±æ§ã¨å¼±ç¹ã¨ãªãç¶æ
ã¯ãçºçã®å
¬ç®ã¨å½±
é¿ã®é大æ§ã®ç¹ã§å¿
ãããåªå
ã¥ããããããã§ã¯ãªããã¾ãããã®ã»ã¯ã·ã§ã³ã§åãä¸ããã
ã®ãå
¨ã¦ã¨ããããã§ããªããéã«ã©ã® ICS ã«ãããããå¿
ãããã¨ãããã®ã§ããªãã

SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
259
The vulnerabilities and predisposing conditions are grouped according to where they existâsuch as in the
organizationâs policy and procedures, or the inadequacy of security mechanisms implemented in hardware,
firmware, and software. The former are referred to as being in the organization and the latter as being in the
system. Understanding the source of vulnerabilities and predisposing conditions can assist in determining
optimal mitigation strategies. The groups of vulnerabilities used in this appendix are:
ï¼ Policy and Procedure.
ï¼ Architecture and Design.
ï¼ Configuration and Maintenance.
ï¼ Physical.
ï¼ Software Development.
ï¼ Communication and Network.
Deeper analysis may uncover that causes and observations may not be one-to-one; that is, some underlying
causes may exhibit multiple symptoms and some symptoms may come from more than one cause. SP 800-
53 contains a taxonomy of security controls, or countermeasures, to mitigate vulnerabilities and
predisposing conditions. These are categorized in families, where each family contains security controls
related to the general security topic of the family. While the families and controls from 800-53 provide a
more complete overview of the potential vulnerabilities and predisposing conditions within in an ICS, this
section briefly reviews those issues known to be common within ICS.
Any given ICS will usually exhibit a subset of the identified vulnerabilities, but may also contain additional
vulnerabilities and predisposing conditions unique to the particular ICS implementation that do not appear
in this appendix. Specific current information on ICS vulnerabilities can be researched at the Industrial
Control System Computer Emergency Response Team (ICS-CERT) Web site.45
Some vulnerabilities and predisposing conditions can be mitigated; others can only be accepted and
controlled by appropriate countermeasures, but will result in some residual risk to the ICS. For example,
some existing policies and procedures may be changed with a level of effort that the organization considers
acceptable; others are more expeditiously dealt with by instituting additional policies and procedures.
Vulnerabilities in products and services acquired from outside the organization are rarely under the direct
control of the organization. Changes may be influenced by market forces, but this is a slow and indirect
approach. Instead, the organization may change predisposing conditions to reduce the likelihood that a
systemic vulnerability will be exploited.
Policy and Procedure Vulnerabilities and Predisposing Conditions
Vulnerabilities and predisposing conditions are often introduced into the ICS because of incomplete,
inappropriate, or nonexistent security policy, including its documentation, implementation guides (e.g.,
procedures), and enforcement. Management support of security policy and procedures is the cornerstone of
any security program. Organization security policy can reduce vulnerabilities by mandating and enforcing
proper conduct. Written policy and procedures are mechanisms for informing staff and stakeholders of
decisions about behavior that is beneficial to the organization. From this perspective, policy is an
educational and instructive way to reduce vulnerabilities. Enforcement is partner to policy, encouraging
people to do the ârightâ thing. Various forms of corrective action are the usual consequences
45 http://ics-cert.us-cert.gov.http://ics-cert.us-cert.gov..

SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
260
èå¼±æ§ã¨å¼±ç¹ã¨ãªãç¶æ
ã¯ãã©ãã«ãããã«å¿ãã¦ã°ã«ã¼ãåãã§ãããä¾ãã°ãçµç¹ã®ããªã·
ã¼åã³æé ããã¼ãã¦ã¨ã¢ããã¡ã¼ã ã¦ã¨ã¢ãã½ããã¦ã¨ã¢ã®ã»ãã¥ãªãã£ã¡ã«ããºã ã®ä¸åç
ã§ãããåè
ã¯çµç¹ãå¾è
ã¯ã·ã¹ãã ã«ããã¨ãããã¨ã«ãªããèå¼±æ§ã¨å¼±ç¹ã¨ãªãç¶æ
ã®èµ·æº
ãç解ããã¨ãæé©ã®ç·©åçã決ãããããªãããã®ä»é²ã§ä½¿ç¨ããèå¼±æ§ã®ã°ã«ã¼ãã¯ä»¥ä¸ã®
ã¨ããã
ï¼ ããªã·ã¼åã³æé
ï¼ ã¢ã¼ããã¯ãã£åã³è¨è¨
ï¼ æ§æåã³ä¿å®
ï¼ ç©çé¢
ï¼ ã½ããã¦ã¨ã¢éçº
ï¼ éä¿¡åã³ãããã¯ã¼ã¯
æ·±ãåæããã¨ãåå ã¨è¦³å¯çµæã 1対1ã§ãªããã¨ãåãããã¤ã¾ããç¹å®ã®æ ¹æ¬åå ããè¤
æ°ã®å¾´åãçããç¹å®ã®å¾´åã¯è¤æ°ã®åå ããçãã¦ãããSP 800-53 ã«ã¯ã»ãã¥ãªãã£å¯¾çã®
åé¡ãè¨ãæããã°èå¼±æ§ã¨å¼±ç¹ã¨ãªãç¶æ
ãç·©åãã対çãè¼ãããã¦ããããã¡ããªå¥ã«å
é¡ãããåãã¡ããªã«ã¯ãã®ãã¡ããªã®å
¨è¬çã»ãã¥ãªãã£åé¡ã«é¢ããã»ãã¥ãªãã£å¯¾çãå«
ã¾ãã¦ããã800-53 ã®ç³»åã¨ç®¡çã¯ãICS å
ã®èå¼±æ§ã¨å¼±ç¹ã¨ãªãç¶æ
ã«é¢ããããå®æ度ã®é«
ãæ¦èª¬ãããããã®ã»ã¯ã·ã§ã³ã§ã¯ãICS ã«å
±éçãªåé¡ãæçã«æ¯ãè¿ãã
ã©ã® ICS ã§ãé常æããã«ãªã£ã¦ããèå¼±æ§ã®ä¸é¨ãé²åãã¦ããããç¹å®ã® ICS å®è£
ã«åºæã®ã
ãã®ä»é²ã§ã¯åãä¸ãããã¦ããªãèå¼±æ§ã¨å¼±ç¹ã¨ãªãç¶æ
ããããICS ã®èå¼±æ§ã«é¢ããç¹å®
ã®ç¾è¡æ
å ±ãç£æ¥ç¨å¶å¾¡ã·ã¹ãã ã³ã³ãã¥ã¼ã¿ç·æ¥æ対å¿ãã¼ã ï¼ICS-CERTï¼ã®ãµã¤ãã«ã
ã46ã
ããã¤ãã®èå¼±æ§ã¨å¼±ç¹ã¨ãªãç¶æ
ã¯ç·©åã§ããããã®ä»ã«ã¤ãã¦ã¯ã許容ãããé©å½ãªå¯¾çã§
管çãããããªãããICS ã®æ®çãªã¹ã¯ã¨ãªããä¾ãã°ãæ¢åããªã·ã¼åã³æé ã¯ãçµç¹ã許容
ã§ããããã¬ãã«ã®åçµã§å¤æ´ããããã®ãããã°ãè£è¶³çãªããªã·ã¼åã³æé ãå¶å®ãã¦ãã
ã£ã¨è¿
éã«å¦çã§ãããã®ãããã
çµç¹å¤ããåå¾ãã製åããµã¼ãã¹ã®èå¼±æ§ã¯ãçµç¹ã®ç´æ¥ã®ç®¡çä¸ã«ç½®ããããã¨ã¯ã¾ããªãã
å¤æ´ã¯å¸å ´åã«å½±é¿ãããããç·©æ
¢ã§éæ¥çã§ããã代ããã«ãçµç¹ã¯å¼±ç¹ã¨ãªãç¶æ
ãå¤ãã¦ã
ã·ã¹ãã ã®èå¼±æ§ãã¤ãããå¯è½æ§ãä½ããããã¨ãã§ãããã
ããªã·ã¼åã³æé ã®èå¼±æ§åã³å¼±ç¹ã¨ãªãç¶æ
èå¼±æ§åã³å¼±ç¹ã¨ãªãç¶æ
ã¯ãã»ãã¥ãªãã£ããªã·ã¼ã®ä¸åãä¸é©ååã¯æ¬ å¦ã«ãã ICS ã«æã¡
è¾¼ã¾ãããã¨ãå¤ããä¾ãã°ææ¸ãå®æ½ã¬ã¤ãï¼æé çï¼ãæ½è¡çã§ãããã»ãã¥ãªãã£åã³æ
é ã«å¯¾ããçµå¶é£ã«ããæ¯æ´ã¯ãããããã»ãã¥ãªãã£ããã°ã©ã ã®åå°ã¨ãªããçµç¹ã®ã»ãã¥
ãªãã£ããªã·ã¼ã¯ãé©æ£ãªè¡åã義åã¥ãã¦æ½è¡ãããã¨ã§ãèå¼±æ§ãæ¸ãããã¨ãã§ãããæ¸
é¢ã«ããããªã·ã¼åã³æé ã¯ãè·å¡åã³é¢ä¿è
ã«ãçµç¹ã®å©çã¨ãªãè¡åã«é¢ãã決å®äºé
ãç¥
ããããã¡ã«ããºã ã¨ãªãããã®è¦³ç¹ãããããªã·ã¼ã¯èå¼±æ§ãæ¸ããããã®æè²çã»æè¨çæ¹
æ³ã¨ãªããæ½è¡ã¯ããªã·ã¼ã®ããã¼ããã¼ãã§ããããæ£ããããã¨ãè¡ããã人ã奨å±ããã
å¤æ§ãªå½¢æ
ã®æ¯æ£å¦ç½®ã¯ãããªã·ã¼åã³æé ãéµå®ãã¦ããªãè·å¡ã«å¯¾ãã¦é常ãé©ç¨ãããã
46 http://ics-cert.us-cert.gov.http://ics-cert.us-cert.gov.

SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
261
to personnel not following policy and procedures. Policies should be explicit about the consequences to
individuals or organizations that do not conform.
There is usually a complex policy and procedure environment that includes laws and regulations,
overlapping jurisdictions and spheres of influence, economics, custom, and history. The larger enterprise is
often subdivided into organizational units that should work together to reduce vulnerabilities. The scope
and hierarchical relationship among policies and procedures needs to be managed for maximum
effectiveness.
Certain controls in SP 800-53 and the ICS overlay in Appendix Gâ specify responsibilities and
requirements for the organization, while others focus on the capabilities and operation of the various
systems within the organization. For example, the control AC-6, Least Privilege, states âThe organization
employs the principle of least privilege, allowing only authorized accesses for users (or processes acting on
behalf of users) which are necessary to accomplish assigned tasks in accordance with organizational
missions and business functions.â The organization has to make decisions that get codified in policy and
procedures. Some resulting artifacts, such as job descriptions that include roles, responsibilities, and
authority, remain in a form suitable for people, while other artifacts, such as attributes, privileges, and
access control rules, are implemented in IT.
Note that the ICS overlay follows SP 800-53 in employing the term âorganizationâ very flexibly so that its
guidance can be used by all sizes of organizational entities up and down an organization chart. Specific
organizations should be identified, starting with the organization responsible for issuing and maintaining
the policy or procedure.
Table C-2 presents examples of observed policy and procedure vulnerabilities for ICS.
Table C-2. Policy and Procedure Vulnerabilities and Predisposing Conditions
Vulnerability
Description
Inadequate security policy for the ICS Vulnerabilities are often introduced into ICS due to inadequate policies or the
lack of policies specifically for control system security. Every countermeasure
should be traceable to a policy. This ensures uniformity and accountability.
Policy must include portable and mobile devices used with ICS.
No formal ICS security training and awareness
program
A documented formal security training and awareness policy and program is
designed to keep staff up to date on organizational security policies and
procedures as well as threats, industry cybersecurity standards, and
recommended practices. Without training on specific ICS policies and
procedures, staff cannot be expected to maintain a secure ICS environment.
Absent or deficient ICS equipment implementation
guidelines
Equipment implementation guidelines should be kept up to date and readily
available. These guidelines are an integral part of security procedures in the
event of an ICS malfunction.
Lack of administrative mechanisms for security policy
enforcement
Staff responsible for enforcing security should be held accountable for
administering documented security policies and procedures.
Inadequate review of the effectiveness of the ICS
security controls
Procedures and schedules should exist to determine the extent to which the
security program and its constituent controls are implemented correctly,
operating as intended, and producing the desired outcome with respect to
meeting the security requirements for the ICS. The examination is sometimes
called an âaudit,â âevaluation,â or âassessment.â Policy should address the
stage of the life-cycle, purpose, technical expertise, methodology, and level
of independence.
SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
262
ããªã·ã¼ã¯ãéµå®ãã¦ããªãå人åã¯çµç¹ã«å¯¾ããçµæã«é¢ãã¦æ示çã§ããã¹ãã§ããã
æ³è¦ãå
å«ããå½±é¿ãçµæ¸ãç¿æ
£åã³æ´å²ã®ç®¡è½åã³ç¯å²ãéãªãåããè¤éãªããªã·ã¼åã³æ
é ç°å¢ã常ã«åå¨ããã大ä¼æ¥ã¯ãèå¼±æ§ãæ¸ããããã«ååã§ããçµç¹åä½ã«ç´°ååãããã
ã¨ãå¤ããããªã·ã¼åã³æé éã®ç¯å²ã¨é層çé¢ä¿ã管çãã¦ãæ大ã®å¹æãä¸ããã¹ãã§ããã
SP 800-53 åã³ä»é² Gã®ICS ãªã¼ãã¼ã¬ã¤ã«å«ã¾ãã¦ããç¹å®ã®ç®¡çã«ã¯ã責任ã¨çµç¹è¦ä»¶ãè¨
è¼ããã¦ãããã¾ãå¥ãªãã®ã¯çµç¹å
ã®å¤æ§ãªã·ã¹ãã ã®è½åã¨éç¨ãéç¹ã«ãªã£ã¦ãããä¾ã
ã°ã管ç AC-6 æå°æ¨©éã«ã¯ããçµç¹ã¯æå°æ¨©éã®ååãæ¡ç¨ããçµç¹ã®ä»»åã»äºæ¥ä¸ã®æ©è½ã«
å¿ãã¦å²ãå½ã¦ãããä»äºãéè¡ããã®ã«å¿
è¦ãªã¦ã¼ã¶ï¼åã¯ãã®ä»£ããã¨ãªãããã»ã¹ï¼ã ã
ã«ã¢ã¯ã»ã¹æ¨©éãä¸ãããã¨ãããçµç¹ã¯æ±ºå®ããªããã°ãªããã決å®äºé
ã¯ããªã·ã¼åã³æé
ã«æè¨ãããããã®çµæã¯ãä¾ãã°å½¹å²ã»è²¬ä»»ã»æ¨©éãæè¨ããè·åæç´°æ¸ã¨ãªããè·å¡ã«é©ã
ãå½¢æ
ãåããã®ãããã°ãå±æ§ã»ç¹æ¨©ã»ã¢ã¯ã»ã¹å¶å¾¡è¦åã®ããã«ãIT ã«ããã¦å®æ½ãããã
ã®ãããã
ICS ãªã¼ãã¼ã¬ã¤ã¯ SP 800-53 ã«æºæ ãã¦ããçµç¹ãã¨ããèªã極ãã¦æè»ã«ç¨ãã¦ããããã
ãã®ã¬ã¤ãã³ã¹ã¯ãçµç¹ã®å¤§å°æ§ã
ãªé¨ç½²ã§ä½¿ç¨ã§ãããã¾ãããªã·ã¼åã¯æé ã®çºåºã»ç¶æã
æ
å½ããçµç¹ãç®åãã«ãç¹å®ã®çµç¹ãæããã«ãã¹ãã§ããã
表C-2 ã¯ã観å¯ããã¦ãã ICS ç¨ããªã·ã¼åã³æé ã®èå¼±æ§ã示ãã
表C-2. ããªã·ã¼åã³æé ã®èå¼±æ§åã³å¼±ç¹ã¨ãªãç¶æ
èå¼±æ§
å
容
ICS ç¨ã»ãã¥ãªãã£ããªã·ã¼ã®ä¸å ç¹ã«å¶å¾¡ã·ã¹ãã ã®ã»ãã¥ãªãã£ã«é¢ããããªã·ã¼ã®ä¸ååã¯æ¬ å¦ãããICS
ã«èå¼±æ§ãå
¥ãè¾¼ããã¨ãå¤ããããããã®å¯¾çã¯ããªã·ã¼ããåºã¦ããã¹
ãã§ãããããã«ããçµ±ä¸æ§ã¨èª¬æ責任ã確ä¿ããããããªã·ã¼ã¯æºè¡/ã¢ã
ã¤ã«ããã¤ã¹ãå«ããªããã°ãªããªãã
æ£è¦ã® ICS ã»ãã¥ãªãã£è¨ç·´ã»æè
ããã°ã©ã è¨ç»ã®æ¬ å¦
ææ¸åãããæ£è¦ã®ã»ãã¥ãªãã£è¨ç·´ã»æèããªã·ã¼è¨ç»ã¯ã常ã«ææ°ã®ã»
ãã¥ãªãã£ããªã·ã¼ã»æé ãè
å¨ãç£æ¥ç¨ãµã¤ãã¼ã»ãã¥ãªãã£è¦æ ¼åã³æ¨
奨è¦ç¯ãè·å¡ã«ç¥ããããããã«ãããå
·ä½ç㪠ICS ããªã·ã¼åã³æé ããª
ããã°ãè·å¡ã« ICS ç°å¢ã®ã»ãã¥ãªãã£ãç¶æã§ããã¨æå¾
ãããã¨ã¯ã§ã
ãªãã
ICS è£
ååå®è£
ã¬ã¤ãã©ã¤ã³ã®æ¬ å¦
åã¯æ¬ é¥
è£
å
åå®è£
ã¬ã¤ãã©ã¤ã³ã¯ææ°ç¶æ
ã«ä¿ã¡ãããã«å©ç¨ã§ããã¹ãã§ããã
ã¬ã¤ãã©ã¤ã³ã¯ãICS é害ã®éã«ã»ãã¥ãªãã£æé ã®ä¸å¯æ¬ ãªä¸é¨ã¨ãªãã
ã»ãã¥ãªãã£ããªã·ã¼ãæ½è¡ãã管
çæ©æ§ã®æ¬ å¦
ã»ãã¥ãªãã£ã®æ½è¡æ
å½è·å¡ã¯ãææ¸åãããã»ãã¥ãªãã£ããªã·ã¼åã³æ
é ã®ç®¡çã«èª¬æ責任ãæããã
ICS ã»ãã¥ãªãã£å¯¾çã®å¹ææ§ã«å¯¾
ããè¦ç´ãã®ä¸å
ã»ãã¥ãªãã£ããã°ã©ã ã¨ãã®å¯¾çãã©ã®ç¨åº¦é©æ£ã«å®æ½ããã¦ããããäº
å®ã©ãã稼åãã¦ããããææã®çµæãããããã¦ãããããICS ã»ãã¥ãª
ãã£è¦ä»¶ã®éæã¨ãã観ç¹ã§å¤å®ããæé åã³ã¹ã±ã¸ã¥ã¼ã«ãå®ããã¹ãã§
ããããã®æ¤è¨¼ããç£æ»ãããè©ä¾¡ï¼evaluationï¼ãåã¯ãè©ä¾¡
ï¼assessmentï¼ãã¨å¼ã¶ãã¨ããããããªã·ã¼ã¯ã©ã¤ããµã¤ã¯ã«ã®æ®µéãç®
çãæè¡ç¥è¦ãæ¹æ³è«åã³ç¬ç«ã¬ãã«ãåãä¸ããã¹ãã§ããã

SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
263
Vulnerability
Description
No ICS-specific contingency plan A contingency plan should be prepared, tested and available in the
event of a major hardware or software failure or destruction of
facilities. Lack of a specific plan for the ICS could lead to extended
downtimes and production loss.
Lack of configuration management policy Lack of policy and procedures for ICS configuration change
management can lead to unmanageable and highly vulnerable
inventory of hardware, firmware, and software.
Lack of adequate access control policy Access control enforcement depends of policy the correctly models
roles, responsibilities, and authorizations. The policy model must
enable the way the organization functions.
Lack of adequate authentication policy Authentication policies are needed to define when authentication
mechanisms (e.g., passwords, smart cards) must be used, how
strong they must be, and how they must be maintained. Without
policy, systems might not have appropriate authentication controls,
making unauthorized access to systems more likely. Authentication
policies should be developed as part of an overall ICS security
program taking into account the capabilities of the ICS and its
personnel to handle more complex passwords and other
mechanisms.
Inadequate incident detection and response
plan and procedures
Incident detection and response plans, procedures, and methods are
necessary for rapidly detecting incidents, minimizing loss and
destruction, preserving evidence for later forensic examination,
mitigating the weaknesses that were exploited, and restoring ICS
services. Establishing a successful incident response capability
includes continually monitoring for anomalies, prioritizing the
handling of incidents, and implementing effective methods of
collecting, analyzing, and reporting data.
Lack of redundancy for critical components Lack of redundancy in critical components could provide single point
of failure possibilities
System Vulnerabilities and Predisposing Conditions
Security controls must clearly identify the systems to which they apply. Systems range widely in size,
scope, and capability. At the small end of the spectrum, a system may be an individual hardware or
software product or service. At the other end of the spectrum we find large complex systems, systems-of-
systems, and networks, all of which incorporate hardware architecture and software framework (including
application frameworks), where the combination supports the operation of the ICS.
System vulnerabilities can occur in the hardware, firmware, and software used to build the ICS. Sources of
vulnerabilities include design flaws, development flaws, misconfigurations, poor maintenance, poor
administration, and connections with other systems and networks. Many of the controls in the SP 800-53
and the ICS overlay in Appendix Gâ specify what the system must do to mitigate these vulnerabilities.
The potential vulnerabilities and predisposing conditions commonly found within ICS systems are
categorized with the following tables:
ï¼ Table C-3. Architecture and Design Vulnerabilities and Predisposing Conditions.
ï¼ Table C-4. Configuration and Maintenance Vulnerabilities and Predisposing Conditions.
ï¼ Table C-5. Physical Vulnerabilities and Predisposing Conditions.

SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
264
èå¼±æ§
å
容
ICS åºæã®ç·æ¥æ対å¿è¨ç»ã®æ¬ å¦ ç·æ¥æ対å¿è¨ç»ãä½æããæ¤è¨¼ãã大è¦æ¨¡ãªãã¼ãã¦ã¨ã¢åã¯ã½ããã¦ã¨ã¢
é害æãæ½è¨ç ´å£æã«å©ç¨ã§ããããã«ãã¹ãã§ãããICS ã®å
·ä½çè¨ç»æ¸
ããªãã¨ããã¦ã³ã¿ã¤ã ãçç£æ失ãæ¡å¤§ããããªãã
æ§æ管çããªã·ã¼ã®æ¬ å¦ ICS æ§æ管çããªã·ã¼åã³æé ã®æ¬ å¦ã¯ããã¼ãã¦ã¨ã¢ããã¡ã¼ã ã¦ã¨ã¢å
ã³ã½ããã¦ã¨ã¢ã®ç®¡çã§ããªã大ããªèå¼±æ§ã«ã¤ãªããã
é©æ£ãªã¢ã¯ã»ã¹å¶å¾¡ããªã·ã¼ã®æ¬ å¦ ã¢ã¯ã»ã¹å¶å¾¡ã®æ½è¡ã¯ãããªã·ã¼ã®æ£ããã¢ãã«å½¹å²ã責任åã³æ¨©éä»ä¸ã«
ããã£ã¦ãããããªã·ã¼ã¢ãã«ã¯ãçµç¹ãæ©è½ããããã®æ¹æ³ãå®ç¾ããªã
ãã°ãªããªãã
é©æ£ãªèªè¨¼ããªã·ã¼ã®æ¬ å¦ èªè¨¼ã¡ã«ããºã ï¼ãã¹ã¯ã¼ããã¹ãã¼ãã«ã¼ãçï¼ãå©ç¨ããéã«ãèªè¨¼ã
ãªã·ã¼ã¯ã¡ã«ããºã ã®å¼·åº¦åã³ç¶ææ¹æ³ãæããã«ããå¿
è¦ããããããªã·
ã¼ããªããã°ãã·ã¹ãã ã¯é©æ£ãªèªè¨¼ç®¡çãã§ãããç¡é§ã¢ã¯ã»ã¹ã許ãã
ã¨ã«ãªããèªè¨¼ããªã·ã¼ã¯ãå
¨ä½ç㪠ICS ã»ãã¥ãªãã£ããã°ã©ã ã®ä¸ç°ã¨
ãã¦ä½æããICS ã®è½åã¨ãããè¤éãªãã¹ã¯ã¼ããã®ä»ã®ã¡ã«ããºã ãæ±
ãè·å¡ã®è½åã¨ãèæ
®ã«å
¥ããã¹ãã§ããã
ã¤ã³ã·ãã³ãæ¤ç¥ã»å¯¾å¿è¨ç»æ¸åã³
æé ã®ä¸å
ã¤ã³ã·ãã³ãæ¤ç¥ã»å¯¾å¿è¨ç»æ¸ãæé åã³æ¹æ³ã¯ã¤ã³ã·ãã³ãã®è¿
éãªæ¤
ç¥ãæ失ã»ç ´å£ã®å±éãå¾æ¥å¿
è¦ã¨ãªã調æ»æ¤è¨¼ç¨è¨¼æ ã®ä¿åãå©ç¨ããã
å¼±ç¹ã®ç·©ååã³ ICS ãµã¼ãã¹ã®å¾©æ§ãè¡ãä¸ã§å¿
è¦ã§ãããæå¹ãªã¤ã³ã·ã
ã³ã対å¿è½åã«ã¯ãç°å¸¸ã«å¯¾ããç¶ç¶ç£è¦ãã¤ã³ã·ãã³ãå¦çã®åªå
ã¥ãã
å¹æçãªãã¼ã¿åéã»åæã»å ±åæ¹æ³ã®å®æ½ãå«ã¾ããã
éè¦ã³ã³ãã¼ãã³ãã®åé·æ§ã®æ¬ å¦
éè¦ã³ã³ãã¼ãã³ãã®åé·æ§ã®æ¬ å¦ã¯ãåä¸é害ç¹ã¨ãªããããªãã
ã·ã¹ãã ã®èå¼±æ§åã³å¼±ç¹ã¨ãªãç¶æ
ã»ãã¥ãªãã£å¯¾çã§ã¯ãé©ç¨å¯¾è±¡ã¨ãªãã·ã¹ãã ãç¹å®ããªããã°ãªããªããã·ã¹ãã ã®è¦æ¨¡ã
ç¯å²åã³è½åã¯å¤ç¨®å¤æ§ã§ãããæå°ã·ã¹ãã ã¯ãåã
ã®ãã¼ãã¦ã¨ã¢è¥ããã¯ã½ããã¦ã¨ã¢è£½
ååã¯ãµã¼ãã¹ã§ããããå対ã«æ大ã·ã¹ãã ã¯ã大è¦æ¨¡è¤åã·ã¹ãã ãã·ã¹ãã ä¸ã«ã·ã¹ãã
ã®ãããã®åã³ãããã¯ã¼ã¯ã§ããããã¯ãã¼ãã¦ã¨ã¢ã¢ã¼ããã¯ãã£åã³ã½ããã¦ã¨ã¢ãã¬ã¼
ã ã¯ã¼ã¯ï¼ã¢ããªã±ã¼ã·ã§ã³ãã¬ã¼ã ã¯ã¼ã¯çï¼ãå«ã¿ãããããä¸ä½ã¨ãªã£ã¦ ICS ã®éç¨ãæ¯
ããã
ã·ã¹ãã èå¼±æ§ã¯ ICS ãæ§ç¯ãããã¼ãã¦ã¨ã¢ããã¡ã¼ã ã¦ã¨ã¢åã³ã½ããã¦ã¨ã¢ã§çãå¾ãã
èå¼±æ§ã®åå ã«ã¯è¨è¨ä¸ã®æ¬ é¥ãéçºä¸ã®æ¬ é¥ãè¨å®ãã¹ãä¿å®ã®ä¸åã管çã®ä¸ååã³ä»ã®ã·
ã¹ãã ããããã¯ã¼ã¯ã¸ã®æ¥ç¶çããããSP 800-53 åã³ä»é² Gã®ICS ãªã¼ãã¼ã¬ã¤ã«å«ã¾ãã¦
ãã管çã®å¤ãã¯ããã®ãããªèå¼±æ§ãç·©åããããã«ã·ã¹ãã ãè¡ããªããã°ãªããªãäºæã
è¦å®ãã¦ããã
ICS ã§ä¸è¬çã«è¦ãããèå¼±æ§åã³å¼±ç¹ã¨ãªãç¶æ
ã以ä¸ã®è¡¨ã«åé¡ããã
ï¼ è¡¨C-3.ã¢ã¼ããã¯ãã£åã³è¨è¨ä¸ã®èå¼±æ§åã³å¼±ç¹ã¨ãªãç¶æ
ï¼ è¡¨C-4.æ§æåã³ä¿å®ä¸ã®èå¼±æ§åã³å¼±ç¹ã¨ãªãç¶æ
ï¼ è¡¨C-5.ç©ççèå¼±æ§åã³å¼±ç¹ã¨ãªãç¶æ

SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
265
ï¼ Table C-6. Software Development Vulnerabilities and Predisposing Conditions.
ï¼ Table C-7. Communication and Network Configuration Vulnerabilities and Predisposing Conditions.
Table C-3. Architecture and Design Vulnerabilities and Predisposing Conditions
Vulnerability
Description
Inadequate incorporation of
security into architecture and
design.
Incorporating security into the ICS architecture, design must start with budget, and
schedule of the ICS. The security architecture is part of the Enterprise Architecture. The
architectures must address the identification and authorization of users, access control
mechanism, network topologies, and system configuration and integrity mechanisms.
Insecure architecture
allowed to evolve
The network infrastructure environment within the ICS has often been developed and
modified based on business and operational requirements, with little consideration for
the potential security impacts of the changes. Over time, security gaps may have been
inadvertently introduced within particular portions of the infrastructure. Without
remediation, these gaps may represent backdoors into the ICS.
No security perimeter
defined
If the ICS does not have a security perimeter clearly defined, then it is not possible to
ensure that the necessary security controls are deployed and configured properly. This
can lead to unauthorized access to systems and data, as well as other problems.
Control networks used for
non-control traffic
Control and non-control traffic have different requirements, such as determinism and
reliability, so having both types of traffic on a single network makes it more difficult to
configure the network so that it meets the requirements of the control traffic. For
example, non-control traffic could inadvertently consume resources that control traffic
needs, causing disruptions in ICS functions.
Control network services not
within the control network
Where IT services such as Domain Name System (DNS), and Dynamic Host
Configuration Protocol (DHCP) are used by control networks, they are often
implemented in the IT network, causing the ICS network to become dependent on the IT
network that may not have the reliability and availability requirements needed by the
ICS.
Inadequate collection of
event data history
Forensic analysis depends on collection and retention of sufficient data. Without proper
and accurate data collection, it might be impossible to determine what caused a security
incident to occur. Incidents might go unnoticed, leading to additional damage and/or
disruption. Regular security monitoring is also needed to identify problems with security
controls, such as misconfigurations and failures.
Table C-4. Configuration and Maintenance Vulnerabilities and Predisposing Conditions
Vulnerability
Description
Hardware, firmware, and
software not under
configuration management.
The organization doesnât know what it has, what versions it has, where they are, or what
their patch status is, resulting in an inconsistent, and ineffective defense posture. A
process for controlling modifications to hardware, firmware, software, and
documentation should be implemented to ensure an ICS is protected against inadequate
or improper modifications before, during, and after system implementation. A lack of
configuration change management procedures can lead to security oversights,
exposures, and risks. To properly secure an ICS, there should be an accurate listing of
the assets in the system and their current configurations. These procedures are critical
to executing business continuity and disaster recovery plans.
SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
266
ï¼ è¡¨C-6.ã½ããã¦ã¨ã¢éçºä¸ã®èå¼±æ§åã³å¼±ç¹ã¨ãªãç¶æ
ï¼ è¡¨C-7.éä¿¡åã³ãããã¯ã¼ã¯æ§æä¸ã®èå¼±æ§åã³å¼±ç¹ã¨ãªãç¶æ
表C-3.ã¢ã¼ããã¯ãã£åã³è¨è¨ä¸ã®èå¼±æ§åã³å¼±ç¹ã¨ãªãç¶æ
èå¼±æ§
å
容
ã¢ã¼ããã¯ãã£åã³è¨è¨ã¸ã®ã»ãã¥
ãªãã£çµè¾¼ã¿ä¸ã®ä¸å
ã»ãã¥ãªãã£ã ICS ã¢ã¼ããã¯ãã£ã«çµã¿è¾¼ãéãäºç®åã³ ICS ã®ã¹ã±ã¸ã¥
ã¼ã«ããè¨è¨ãéå§ããªããã°ãªããªããã»ãã¥ãªãã£ã¢ã¼ããã¯ãã£ã¯ä¼
æ¥ã¢ã¼ããã¯ãã£ã®ä¸é¨ã¨ãªããã¢ã¼ããã¯ãã£ã¯ã¦ã¼ã¶ã®èå¥ã»èªè¨¼ãã¢
ã¯ã»ã¹å¶å¾¡ã¡ã«ããºã ããããã¯ã¼ã¯ãããã¸ã¼åã³ã·ã¹ãã æ§æã»å®å
¨æ§
ã¡ã«ããºã ãåãä¸ããªããã°ãªããªãã
æ´ã«é²è¡ããããªã»ãã¥ã¢ã§ãªãã¢
ã¼ããã¯ãã£
ICS å
ã®ãããã¯ã¼ã¯ã¤ã³ãã©ç°å¢ã¯ãäºæ¥ã»éç¨ä¸ã®è¦ä»¶ãåºã«éçºã»æ¹
ä¿®ããã¦ãããã¨ãå¤ããå¤æ´å
容ãã»ãã¥ãªãã£ã«åã¼ãå½±é¿ã¯ãã¾ãè
æ
®ããã¦ããªããæéã®çµéã¨ã¨ãã«ãæ³å®å¤ã®ã»ãã¥ãªãã£ã®ã£ãããã¤
ã³ãã©ã®ç¹å®é¨ä½ã«çãããã¨ãããã対çãåããã«ããã¨ããã®ãããª
ã®ã£ããã
ICS
ã®ããã¯ãã¢ã«ãªããã¨ãããã
ã»ãã¥ãªãã£å¢çãæªå®ç¾© ICS ã®ã»ãã¥ãªãã£å¨è¾ºã®å®ç¾©ãæããã§ãªãã¨ãå¿
è¦ãªã»ãã¥ãªãã£å¯¾ç
ã®å±éã»è¨å®ãæ£ããå®æ½ã§ããªãããã®ããã·ã¹ãã ããã¼ã¿ã¸ã®ä¸æ£ã¢
ã¯ã»ã¹ã許ããä»ã®åé¡ãçºçããããªãã
å¶å¾¡ãããã¯ã¼ã¯ãå¶å¾¡ä»¥å¤ã®ãã©
ãã£ãã¯ã«ä½¿ç¨
決å®è«ãä¿¡é ¼æ§çãå¶å¾¡ãã©ãã£ãã¯ã¨éå¶å¾¡ãã©ãã£ãã¯ã®è¦ä»¶ã¯ç°ãªã
ãããåæ¹ã 1ã¤ã®ãããã¯ã¼ã¯ã§ä½¿ç¨ããã¨ãå¶å¾¡ãã©ãã£ãã¯è¦ä»¶ãé
æããããã®ãããã¯ã¼ã¯è¨å®ãé£ãããªããä¾ãã°éå¶å¾¡ãã©ãã£ãã¯
ã¯ãå¶å¾¡ãã©ãã£ãã¯ãå¿
è¦ã¨ãããªã½ã¼ã¹ãæ³å®å¤ã«æ¶è²»ãããã¨ãã
ãã
ICS
æ©è½ã®ä¸æãæããã¨ãããã
å¶å¾¡ãããã¯ã¼ã¯ãµã¼ãã¹ãå¶å¾¡ã
ããã¯ã¼ã¯å
ã«ãªã
å¶å¾¡ã·ã¹ãã ã«é ååã·ã¹ãã ï¼DNSï¼ãåçãã¹ãæ§æãããã³ã«
ï¼DHCPï¼çã® IT ãµã¼ãã¹ãå©ç¨ãã¦ããå ´åããµã¼ãã¹ã¯ IT ãããã¯ã¼
ã¯å
ã«å®è£
ããã¦ãããã¨ãå¤ããããICS ãããã¯ã¼ã¯ã ICS ã®ä¿¡é ¼æ§å
ã³å¯ç¨æ§è¦ä»¶ã«æºããªã
IT
ãããã¯ã¼ã¯ã«ä¾åããçµæã«ãªãã
ã¤ãã³ããã¼ã¿ãã¹ããªã¢ã³åéã®
ä¸å
調æ»åæã¯ååãªãã¼ã¿åéã»ä¿æã«ä¾åãããé©æ£ãã¤æ£ç¢ºãªãã¼ã¿ã®å
éããªããã°ãã»ãã¥ãªãã£ã¤ã³ã·ãã³ãã®çºççç±ãå¤å¥ã§ããªããã¤ã³
ã·ãã³ãã«æ°ã¥ãããæ害ãä¸æãæ¡å¤§ããããªããè¨å®ãã¹ãé害çãã»
ãã¥ãªãã£å¯¾çã®åé¡ç¹ãè¦æ¥µãããããå®æçãªã»ãã¥ãªãã£ç£è¦ãå¿
è¦
ã¨ãªãã
表C-4.æ§æåã³ä¿å®ä¸ã®èå¼±æ§åã³å¼±ç¹ã¨ãªãç¶æ
èå¼±æ§
å
容
ãã¼ãã¦ã¨ã¢/ãã¡ã¼ã ã¦ã¨ã¢/ã½ã
ãã¦ã¨ã¢ãæ§æ管çå¤ã«ãã
ä½ã使ç¨ãã¦ããããã©ã®ãã¼ã¸ã§ã³ããã©ãã«ãããããããã¹ãã¼ã¿ã¹
ãã©ããªã£ã¦ããããçµç¹ãç¥ãããä¸è²«æ§ã¨å¹ææ§ã®ãªãé²å¾¡æ
å¢ã«ãª
ãããã¼ãã¦ã¨ã¢/ãã¡ã¼ã ã¦ã¨ã¢/ã½ããã¦ã¨ã¢ã»ææ¸
ã¸ã®å¤æ´ã管çããã
ãã»ã¹ãå®æ½ããã·ã¹ãã å®è£
åã»ä¸ã»å¾ã®ä¸é©åãªæ¹å¤ãã ICS ãä¿è·ã
ããæ§æå¤æ´ç®¡çæé ã®æ¬ å¦ã¯ãã»ãã¥ãªãã£ã®ææãããæé²åã³ãªã¹ã¯
ã«ã¤ãªãããICS ã®ã»ãã¥ãªãã£ããã£ãã確ä¿ããã«ã¯ãã·ã¹ãã è³ç£ã¨
ãã®ç¾è¡æ§æã®æ£ç¢ºãªãªã¹ããæã¤ã¹ãã§ããããã®ãããªæé ãäºæ¥ç¶ç¶
æ§ã¨ç½å®³å¾©æ§è¨ç»ã®å®æ½ã«éè¦ã¨ãªãã

SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
267
Vulnerability
Description
OS and vendor software
patches may not be
developed until significantly
after security vulnerabilities
are found
Because of the tight coupling between ICS software and the underlying ICS, changes must
undergo expensive and time-consuming comprehensive regression testing. The elapsed time
for such testing and subsequent distribution of updated software provides a long window of
vulnerability
OS and application security
patches are not maintained or
vendor declines to patch
vulnerability
Out-of-date OSs and applications may contain newly discovered vulnerabilities that could be
exploited. Documented procedures should be developed for how security patches will be
maintained. Security patch support may not even be available for ICS that use outdated OSs,
so procedures should include contingency plans for mitigating vulnerabilities where patches
may never be available.
Inadequate testing of security
changes
Modifications to hardware, firmware, and software deployed without testing could compromise
normal operation of the ICS. Documented procedures should be developed for testing all
changes for security impact. The live operational systems should never be used for testing.
The testing of system modifications may need to be coordinated with system vendors and
integrators.
Poor remote access controls There are many reasons why an ICS may need to be remotely accessed, including vendors
and system integrators performing system maintenance functions, and also ICS engineers
accessing geographically remote system components. Remote access capabilities must be
adequately controlled to prevent unauthorized individuals from gaining access to the ICS.
Poor configurations are used Improperly configured systems may leave unnecessary ports and protocols open, these
unnecessary functions may contain vulnerabilities that increase the overall risk to the system.
Using default configurations often exposes vulnerabilities and exploitable services. All
settings should be examined.
Critical configurations are not
stored or backed up
Procedures should be available for restoring ICS configuration settings in the event of
accidental or adversary-initiated configuration changes to maintain system availability and
prevent loss of data. Documented procedures should be developed for maintaining ICS
configuration settings.
Data unprotected on portable
device
If sensitive data (e.g., passwords, dial-up numbers) is stored in the clear on portable devices
such as laptops and mobile devices and these devices are lost or stolen, system security
could be compromised. Policy, procedures, and mechanisms are required for protection.
Passwords generation, use,
and protection not in accord
with policy
There is a large body of experience with using passwords in IT that is applicable to ICS.
Password policy and procedure must be followed to be effective. Violations of password
policy and procedures can drastically increase ICS vulnerability.
Inadequate access controls
applied
Access controls must be matched to the way the organization allocates responsibilities and
privilege to its personnel. Poorly specified access controls can result in giving an ICS user too
many or too few privileges. The following exemplify each case:
ã» System configured with default access control settings gives an operator
administrative privileges
ã» System improperly configured results in an operator being unable to take
corrective actions in an emergency situation
Improper data linking ICS data storage systems may be linked with non-ICS data sources. An example of this is
database links, which allow data from one database to be automatically replicated to others.
Data linkage may create a vulnerability if it is not properly configured and may allow
unauthorized data access or manipulation.
Malware protection not
installed or up to date
Installation of malicious software, or malware, is a common attack. Malware protection
software, such as antivirus software, must be kept current in a very dynamic environment.
Outdated malware protection software and definitions leave the system open to new malware
threats.

SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
268
èå¼±æ§
å
容
OS ããã³ãã¼ã®ã½ããã¦ã¨ã¢
ããã
ã¯ãã»ãã¥ãªãã£ã®èå¼±æ§ãæãã
ã«ãªã£ã¦ãã°ããçµã¤ã¾ã§ã¯éçºã
ããªãã
ICS ã½ããã¦ã¨ã¢ã¨åºæ¬ ICS ã®ç·å¯ãªçµã³ã¤ãããããããå¤æ´ãå ããå ´
åã¯ãæéã¨ã³ã¹ãã®ãããå¾¹åºçãªãªã°ã¬ãã·ã§ã³è©¦é¨ãè¡ããªããã°ãª
ããªãããã®ãããªè©¦é¨ã¨ãã®å¾ã®ã½ããã¦ã¨ã¢æ´æ°çã®é
å¸ã¾ã§ã®çµéæ
éã«ãããèå¼±æ§ã®ç©´ã¯å¤§ãããªãã
OS
ãã¢ããªã±ã¼ã·ã§ã³ã®ã»ãã¥ãªã
ã£ããããä¿å®ãããããã³ãã¼ã¯
èå¼±æ§ã顧ã¿ãªã
æ§å¼ OS ãã¢ããªã±ã¼ã·ã§ã³ã«ã¯ãæ°ãã«è¦ã¤ãã£ãæªç¨ãããããèå¼±æ§
ããããã»ãã¥ãªãã£ãããã®ä¿å®è¦é ã«é¢ãã¦ãæ¸é¢ã«ããæé ãä½æã
ã¹ãã§ãããæ§ç OS ã使ã£ã ICS ã§ã¯ãã»ãã¥ãªãã£ããããµãã¼ãã¯ãª
ãå ´åããããããæé ã«ã¯ãã®å ´åã®èå¼±æ§ç·©åç·æ¥æ対å¿è¨ç»ãå«ãã
ã¹ãã§ããã
ã»ãã¥ãªãã£å¤æ´è©¦é¨ã®ä¸å 試é¨ãè¡ããã«å±éãããã¼ãã¦ã¨ã¢/ãã¡ã¼ã ã¦ã¨ã¢/ã½ããã¦ã¨ã¢
å¤æ´ã¯ã
ICS ã®æ£å¸¸éç¨è½åãä½ä¸ãããå¯è½æ§ããããå
¨ã¦ã®å¤æ´å
容ã®ã»ãã¥ãª
ãã£å½±é¿è©¦é¨ã«é¢ãã¦ãæ¸é¢ã«ããæé ãä½æãã¹ãã§ããã稼åä¸ã®ã·ã¹
ãã ã¯æ±ºãã¦è©¦é¨ã«ä½¿ãã¹ãã§ãªããã·ã¹ãã å¤æ´è©¦é¨ã¯ãã·ã¹ãã ãã³ã
ã¼ãã¤ã³ãã°ã¬ã¼ã¿ã¨é£æºãã¦è¡ãå¿
è¦ãããã
ãªã¢ã¼ãã¢ã¯ã»ã¹å¶å¾¡ã®ä¸å ICS ã¸ã®ãªã¢ã¼ãã¢ã¯ã»ã¹ãå¿
è¦ãªçç±ã¯æ§ã
ã§ãä¾ãã°ãã³ãã¼ãã·ã¹ã
ã ã¤ã³ãã°ã¬ã¼ã¿ã®é éä¿å®ãé æ¹ã«ãã ICS ã¨ã³ã¸ãã¢ã«ããã·ã¹ãã ã³
ã³ãã¼ãã³ãã®å©ç¨ãªã©ãããããªã¢ã¼ãã¢ã¯ã»ã¹æ©è½ã¯ãã£ãã管çã
ã¦ã
ICS
ã¸ã®ä¸æ£ã¢ã¯ã»ã¹ãé²æ¢ããªããã°ãªããªãã
è¨å®ã®ä¸å ã·ã¹ãã è¨å®ã«ä¸åããããä¸å¿
è¦ã«ãã¼ãããããã³ã«ãéæ¾ããã¾ã¾ã«
ãã¦ããã¨ãèå¼±æ§ã¨ãªãã·ã¹ãã ã®å
¨ä½çãªã¹ã¯ãé«ã¾ããããã©ã«ãè¨
å®ã使ç¨ããã¨ãèå¼±æ§ãæªç¨å¯è½ãªãµã¼ãã¹ãé²åºãããã¨ã«ãªããå
¨ã¦
ã®è¨å®ãæ¤è¨¼ãã¹ãã§ããã
éè¦ãªè¨å®ã®ä¿åãããã¯ã¢ããã
ãªããã¦ããªã
å¶çºçåã¯æ»æã«ããè¨å®å¤æ´ããã£ãéã«ãã·ã¹ãã ã®å¯ç¨æ§ãç¶æãã
ãã¼ã¿åªå¤±ãé²æ¢ãããããICS è¨å®ã®å復æé ãå©ç¨ã§ããããã«ãã¹ã
ã§ããã
ICS
è¨å®ãç¶æãããããæ¸é¢ã«ããæé ãä½æãã¹ãã§ããã
æºè¡ããã¤ã¹ã®ãã¼ã¿ãä¿è·ããã¦
ããªã
注æãè¦ãããã¼ã¿ï¼ãã¹ã¯ã¼ãããã¤ã¢ã«ã¢ããçªå·çï¼ãå¹³æã®ã¾ã¾ã©
ããããããã¢ãã¤ã«ããã¤ã¹çã®æºè¡ããã¤ã¹ä¸ã«ä¿ç®¡ããã¦ãã¦ããã
ã¤ã¹ãç´å¤±ãããçã¾ãããããå ´åãã·ã¹ãã ã»ãã¥ãªãã£ãå±ãããª
ããä¿è·ããªã·ã¼ãæé åã³ã¡ã«ããºã ãå¿
è¦ã¨ãªãã
ãã¹ã¯ã¼ãã®çæã使ç¨åã³ä¿è·ã
ããªã·ã¼ã«å¾ã£ã¦ããªã
ICS ã«ãé©ç¨å¯è½ãª IT
ã§ã®ãã¹ã¯ã¼ãå©ç¨çµé¨ãèç©ããã¦ããããã¹ã¯ã¼
ãããªã·ã¼åã³æé ã¯å¹æçã§ãªããã°ãªããªãããã¹ã¯ã¼ãããªã·ã¼ã»æ
é éåã¯ã
ICS
ã®èå¼±æ§ãèããé«ããã
ã¢ã¯ã»ã¹å¶å¾¡ã®ä¸å ã¢ã¯ã»ã¹å¶å¾¡ã¨çµç¹ãè·å¡ã«è²¬ä»»åã³ç¹æ¨©ãä¸ããæ¹æ³ã¯ãæ´åãã¦ããªã
ãã°ãªããªããã¢ã¯ã»ã¹å¶å¾¡ããã£ãããã¦ããªãã¨ãICS ã¦ã¼ã¶ã®ç¹æ¨©ã«
éä¸è¶³ãçããã以ä¸ã¯éä¸è¶³ã®ä¾ã§ããã
⢠ããã©ã«ãã¢ã¯ã»ã¹è¨å®ã«ãªã£ãã·ã¹ãã ã¯ãæä½å¡ã«ç®¡çè
ç¹æ¨©ã
ä¸ããã
⢠ã·ã¹ãã è¨å®ã«ä¸åãããã¨ãæä½å¡ãç·æ¥æã«å¯¾çãè¬ãããã¨ã
ã§ããªãã
ãã¼ã¿ãªã³ãã³ã°ã®ä¸å ICS ãã¼ã¿ã¹ãã¬ã¼ã¸ã·ã¹ãã ã¯ãICS 以å¤ã®ãã¼ã¿ã½ã¼ã¹ã«ãªã³ã¯ãã¦ã
ãå ´åããããä¸ä¾ããã¼ã¿ãã¼ã¹ãªã³ã¯ã§ããããã¼ã¿ãã¼ã¹ã®ãã¼ã¿ã
èªåçã«ä»ã®ãã¼ã¿ãã¼ã¹ã«è¤è£½ãããããã¼ã¿ãªã³ã¯ã¯è¨å®ããã£ããã
ã¦ããªãã¨ãèå¼±æ§ãçããç¡è¨±å¯ã®ãã¼ã¿ã¢ã¯ã»ã¹ããã¼ã¿æä½ã許ãã
ã¨ã«ãªãã
ãã«ã¦ã¨ã¢ä¿è·ã½ããã¦ã¨ã¢ãã¤ã³
ã¹ãã¼ã«ããã¦ããªããææ°ã§ãªã
æªæããã½ããã¦ã¨ã¢ï¼ãã«ã¦ã¨ã¢ï¼ã®ã¤ã³ã¹ãã¼ã«ã¯ä¸è¬çãªæ»æã§ã
ããã¢ã³ãã¦ã¤ã«ã¹çã®ãã«ã¦ã¨ã¢ä¿è·ã½ããã¦ã¨ã¢ã¯ãåçç°å¢ã«ããã¦
常ã«ææ°ç¶æ
ã«ä¿ãããªããã°ãªããªããå¤ããªã£ããã«ã¦ã¨ã¢ä¿è·ã½ãã
ã¦ã¨ã¢åã³å®ç¾©ã§ã¯ãã·ã¹ãã ãæ°ãããã«ã¦ã¨ã¢è
å¨ã«ãããããã
SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
269
Vulnerability
Description
Malware protection
implemented without
sufficient testing
Malware protection software deployed without sufficient testing could impact normal
operation of the ICS and block the system from performing necessary control actions.
Denial of service (DoS) ICS software could be vulnerable to DoS attacks, resulting in the prevention of
authorized access to a system resource or delaying system operations and functions.
Intrusion
detection/prevention
software not installed
Incidents can result in loss of system availability and integrity; the capture, modification,
and deletion of data; and incorrect execution of control commands. IDS/IPS software
may stop or prevent various types of attacks, including DoS attacks, and also identify
attacked internal hosts, such as those infected with worms. IDS/IPS software must be
tested prior to deployment to determine that it does not compromise normal operation of
the ICS.
Logs not maintained Without proper and accurate logs, it might be impossible to determine what caused a
security event to occur.
Table C-5. Physical Vulnerabilities and Predisposing Conditions
Vulnerability
Description
Unauthorized personnel
have physical access to
equipment
Physical access to ICS equipment should be restricted to only the necessary personnel,
taking into account safety requirements, such as emergency shutdown or restarts.
Improper access to ICS equipment can lead to any of the following:
ã» Physical theft of data and hardware
ã» Physical damage or destruction of data and hardware
ã» Unauthorized changes to the functional environment (e.g., data connections,
unauthorized use of removable media, adding/removing resources)
ã» Disconnection of physical data links
ã» Undetectable interception of data (keystroke and other input logging)
Radio frequency,
electromagnetic pulse
(EMP), static discharge,
brownouts and voltage
spikes
The hardware used for control systems is vulnerable to radio frequency and electro-
magnetic pulses (EMP), static discharge, brownouts and voltage spikes.. The impact can
range from temporary disruption of command and control to permanent damage to circuit
boards. Proper shielding, grounding, power conditioning, and/or surge suppression is
recommended.
Lack of backup power Without backup power to critical assets, a general loss of power will shut down the ICS
and could create an unsafe situation. Loss of power could also lead to insecure default
settings.
Loss of environmental
control
Loss of environmental control (e.g., temperatures, humidity) could lead to equipment
damage, such as processors overheating. Some processors will shut down to protect
themselves; some may continue to operate but in a minimal capacity and may produce
intermittent errors, continually reboot, or become permanently incapacitated.
Unsecured physical ports Unsecured universal serial bus (USB) and PS/2 ports could allow unauthorized
connection of thumb drives, keystroke loggers, etc.
SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
270
èå¼±æ§
å
容
ãã«ã¦ã¨ã¢ä¿è·ã½ããã¦ã¨ã¢ãåå
試é¨ããã«å®è£
ãã¦ãã
ååãªè©¦é¨ãè¡ããã«ãã«ã¦ã¨ã¢ä¿è·ã½ããã¦ã¨ã¢ãå±éããã¨ãICS ã®æ£
常éç¨ã«å½±é¿ããã·ã¹ãã ã®å¿
è¦ãªå¶å¾¡åä½ã妨害ãããã
ãµã¼ãã¹å¦¨å®³ï¼DoSï¼ ICS ã½ããã¦ã¨ã¢ã¯ DoS æ»æã«èå¼±æ§ãããããããããã·ã¹ãã ãªã½ã¼ã¹
ã¸ã®è¨±å¯ãããã¢ã¯ã»ã¹ã妨ããããã·ã¹ãã ã®åä½ãæ©è½ãé
ããããã
ããã¨ãããã
ä¾µå
¥æ¤ç¥ã»é²æ¢ã½ããã¦ã¨ã¢ãã¤ã³
ã¹ãã¼ã«ããã¦ããªã
ã¤ã³ã·ãã³ãã¯ã·ã¹ãã ã®å¯ç¨æ§åã³å®å
¨æ§ã®åªå¤±ããã¼ã¿ã®ãã£ããã£ã»
æ¹å¤ã»åé¤åã³å¶å¾¡ã³ãã³ãã®ä¸é©åãªå®è¡ã«çµã³ã¤ããã¨ããããIDS/IPS
ã½ããã¦ã¨ã¢ã¯ãDoS æ»æçå¤æ§ãªæ»æãåæ¢åã¯å¦¨å®³ããã¯ã¼ã ã«ææã
ããã®ãªã©ãæ»æãããå
é¨ãã¹ãã®èå¥ãè¡ããIDS/IPS ã½ããã¦ã¨ã¢ã¯å±
éåã«è©¦é¨ãè¡ããICS ã®æ£å¸¸éç¨ã«æªå½±é¿ããªããå¤å®ããªããã°ãªããª
ãã
ãã°ãç¶æããã¦ããªã é©æ£ãã¤æ£ç¢ºãªãã°ããªããã°ãã»ãã¥ãªãã£äºè±¡ã®çºççç±ãå¤å¥ã§ããª
ãã
表C-5.ç©ççèå¼±æ§åã³å¼±ç¹ã¨ãªãç¶æ
èå¼±æ§
å
容
ç¡è¨±å¯ã®äººå¡ãè£
ååã«è¿ã¥ãã¦ã
ã
ICS è£
ååã¸ã®æ¥è¿ã¯ãç·æ¥åæ¢ãåå§åã¨ãã£ãå®å
¨è¦ä»¶ãèæ
®ã«å
¥ã
ã¦ãå¿
è¦ãªè·å¡ã ãã«å¶éãã¹ãã§ãããICS è£
ååã«ä¸ç¨æã«æ¥è¿ã許ã
ã¨ã次ã®ãããªçµæãçããããªãã
⢠ãã¼ã¿åã³ãã¼ãã¦ã¨ã¢ã®çé£
⢠ãã¼ã¿åã³ãã¼ãã¦ã¨ã¢ã®æå·ãç ´æ
â¢
許å¯ããã¦ããªãæ©è½ç°å¢ã®å¤æ´ï¼ãã¼ã¿æ¥ç¶ãåãå¤ãå¯è½ã¡ã
ã£ã¢ã®ç¡æ使ç¨ããªã½ã¼ã¹ã®è¿½å ã»åé¤ï¼
⢠ãã¼ã¿ãªã³ã¯ã®ç©ççåæ
â¢
æ¤ç¥ä¸è½ã®ãã¼ã¿ååï¼ãã¼ã¹ããã¼ã¯ãã®ä»å
¥åè¨é²ï¼
ç¡ç·å¨æ³¢æ°ã»é»ç£æ³¢ï¼EMPï¼ãéé»
æ°ãé»å§ä½ä¸ã»é»å§ãã¤ãº
å¶å¾¡ã·ã¹ãã ã«å©ç¨ãããã¼ãã¦ã¨ã¢ã¯ãç¡ç·å¨æ³¢æ°ã»é»ç£æ³¢ï¼EMPï¼ãé
é»æ°ãé»å§ä½ä¸ã»é»å§ãã¤ãºã«å¼±ããå½±é¿ã¯ãä¸æçãªã³ãã³ãã®ä¸æãã
åè·¯åºæ¿ã®æä¹
çæå·ã¾ã§å¤å²ã«ããããé©åãªã·ã¼ã«ããã¢ã¼ã¹ãé»å§ç®¡
çåã¯ãµã¼ã¸é»å§æå¶ãæ¨å¥¨ãããã
ããã¯ã¢ããé»æºã®æ¬ å¦ åè·¯ã¸ã®ããã¯ã¢ããé»æºããªãã¨ãé»æºã®åªå¤±æãICS
ãåæããã¦ä¸å®
å
¨ãªç¶æ³ã«ãªããããªããã¾ãã»ãã¥ã¢ã§ãªãããã©ã«ãè¨å®ã«æ»ããã¨ã
ããã
ç°å¢å¶å¾¡ã®åªå¤± ç°å¢å¶å¾¡ï¼æ¸©åº¦ã湿度çï¼ã®åªå¤±ã¯ãããã»ããµã®ãªã¼ãã¼ãã¼ããªã©è£
å
åã®æå·ã«ã¤ãªãããããã»ããµã«ãã£ã¦ã¯èªå·±é²è·ã®ããåæãããã®ã
ããããã®ã¾ã¾ç¶è¡ãããã®ãããããæ©è½ã¯æå°éã§ãéæ¬ çã«ã¨ã©ã¼ã¨
ãªãããªãã¼ããç¹°ãè¿ããæä¹
çã«æ
éãããã¨ãããã
ã»ãã¥ã¢ã§ãªãç©çãã¼ã ã»ãã¥ã¢ã§ãªã USB åã³ PS/2 ãã¼ãã¯ããµã ãã©ã¤ãããã¼ã¹ããã¼ã¯ã
ã¬ã¼çã®ç¡ææ¥ç¶ã許ããã¨ã«ãªãã

SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
271
Table C-6. Software Development Vulnerabilities and Predisposing Conditions
Vulnerability
Description
Improper Data Validation ICS software may not properly validate user inputs or received data to ensure validity.
Invalid data may result in numerous vulnerabilities including buffer overflows, command
injections, cross-site scripting, and path traversals.
Installed security
capabilities not enabled by
default
Security capabilities that were installed with the product are useless if they are not
enabled or at least identified as being disabled.
Inadequate authentication,
privileges, and access
control in software
Unauthorized access to configuration and programming software could provide the ability
to corrupt a device.
Table C-7. Communication and Network Configuration Vulnerabilities and Predisposing
Conditions
Vulnerability
Description
Data flow controls not
employed
Data flow controls, based on data characteristics, are needed to restrict which information
is permitted between systems. These controls can prevent exfiltration of information and
illegal operations.
Firewalls nonexistent or
improperly configured
A lack of properly configured firewalls could permit unnecessary data to pass between
networks, such as control and corporate networks, allowing attacks and malware to
spread between networks, making sensitive data susceptible to
monitoring/eavesdropping, and providing individuals with unauthorized access to systems.
Inadequate firewall and
router logs
Without proper and accurate logs, it might be impossible to determine what caused a
security incident to occur.
Standard, well-
documented
communication protocols
are used in plain text
Adversaries that can monitor the ICS network activity can use a protocol analyzer or other
utilities to decode the data transferred by protocols such as telnet, File Transfer Protocol
(FTP), Hypertext Transfer Protocol (HTTP), and Network File System (NFS). The use of
such protocols also makes it easier for adversaries to perform attacks against the ICS and
manipulate ICS network activity.
Authentication of users,
data or devices is
substandard or
nonexistent
Many ICS protocols have no authentication at any level. Without authentication, there is
the potential to replay, modify, or spoof data or to spoof devices such as sensors and user
identities.
Use of unsecure industry-
wide ICS protocols
ICS protocols often have few or no security capabilities, such as authentication and
encryption, to protect data from unauthorized access or tampering. Additionally, incorrect
implementation of the protocols can lead to additional vulnerabilities.
Lack of integrity checking
for communications
There are no integrity checks built into most industrial control protocols; adversaries could
manipulate communications undetected. To ensure integrity, the ICS can use lower-layer
protocols (e.g., IPsec) that offer data integrity protection.
Inadequate authentication
between wireless clients
and access points
Strong mutual authentication between wireless clients and access points is needed to
ensure that clients do not connect to a rogue access point deployed by an adversary, and
also to ensure that adversaries do not connect to any of the ICSâs wireless networks.
Inadequate data protection
between wireless clients
and access points
Sensitive data between wireless clients and access points should be protected using
strong encryption to ensure that adversaries cannot gain unauthorized access to the
unencrypted data.
SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
272
表C-6.ã½ããã¦ã¨ã¢éçºä¸ã®èå¼±æ§åã³å¼±ç¹ã¨ãªãç¶æ
èå¼±æ§
å
容
ãã¼ã¿æ¤è¨¼ã®ä¸å ICS ã½ããã¦ã¨ã¢ã¯ãã¦ã¼ã¶å
¥åãåä¿¡ãã¼ã¿ã®å¦¥å½æ§æ¤è¨¼ãæ£ããè¡ã£ã¦
ããªããã¨ããããç¡å¹ãªãã¼ã¿ã¯ãããã¡ãªã¼ãã¼ããã¼ãã³ãã³ãã¤ã³
ã¸ã§ã¯ã·ã§ã³ãã¯ãã¹ãµã¤ãã¹ã¯ãªããã£ã³ã°ããã¹ãã©ãã¼ãµã«çã種ã
ã®èå¼±æ§ã«ã¤ãªããã
ã¤ã³ã¹ãã¼ã«ããæ¥ç¶ã½ããã¦ã¨ã¢
ãããã©ã«ãã§æ©è½ããªã
製åã®ã¤ã³ã¹ãã¼ã«ã«ããã»ãã¥ãªãã£æ©è½ã¯ãç¡å¹ç¶æ
ã解é¤ãã¦æå¹ã«
ããªãã¨ãã¾ãã¯å°ãªãã¨ããç¡å¹ç¶æ
ã§ãããã¨ãåãããªãã¨å¹æããª
ãã
ã½ããã¦ã¨ã¢ã®èªè¨¼ã»ç¹æ¨©ã»ã¢ã¯ã»
ã¹å¶å¾¡ã®ä¸å
è¨å®åã³ããã°ã©ãã³ã°ã½ããã¦ã¨ã¢ã¸ã®ä¸æ£ã¢ã¯ã»ã¹ã¯ãããã¤ã¹ã®ç ´å£
ã許ããã¨ã«ãªãã
表C-7.éä¿¡åã³ãããã¯ã¼ã¯æ§æä¸ã®èå¼±æ§åã³å¼±ç¹ã¨ãªãç¶æ
èå¼±æ§
å
容
ãã¼ã¿ããã¼ãå¶å¾¡ããã¦ããªã ãã¼ã¿ç¹æ§ã«åºã¥ããã¼ã¿ããã¼å¶å¾¡ã¯ãã·ã¹ãã éã®æ
å ±äº¤æãå¶å¾¡ãã
ãã®ã§ãããå¶éãå ããå¿
è¦ããããå¶å¾¡ã«ããæ
å ±ã®å¼åºããä¸æ³æä½
ãé²æ¢ã§ããã
ãã¡ã¤ã¢ã¦ã©ã¼ã«ã®æ¬ å¦åã¯è¨å®ä¸
å
ãã¡ã¤ã¢ã¦ã©ã¼ã«ãæ£ããè¨å®ããã¦ããªãã¨ãå¶å¾¡ãããã¯ã¼ã¯ã¨ä¼æ¥ã
ããã¯ã¼ã¯çã®ãããã¯ã¼ã¯éã§ããã¼ã¿ãä¸å¿
è¦ã«ééãããæ»æåã³ã
ã«ã¦ã¨ã¢ããããã¯ã¼ã¯éã§æ¡æ£ããè¦æ³¨æãã¼ã¿ãç£è¦ã»ååã«ããã
ããã·ã¹ãã ã¸ã®ä¸æ£ã¢ã¯ã»ã¹ã許ããã¨ã«ãªãã
ãã¡ã¤ã¢ã¦ã©ã¼ã«åã³ã«ã¼ã¿ã®ãã°
ã®ä¸å
é©æ£ãã¤æ£ç¢ºãªãã°ããªããã°ãã»ãã¥ãªãã£ã¤ã³ã·ãã³ãã®çºççç±ãå¤
å¥ã§ããªãã
æ¨æºã®ææ¸åãããéä¿¡ãããã³ã«
ãå¹³æã§ä½¿ç¨ããã¦ãã ICS ã®ãããã¯ã¼ã¯æ´»åãç£è¦ããæ»æå´ã¯ããããã³ã«ã¢ãã©ã¤ã¶ãã®ä»
ã®ã¦ã¼ãã£ãªãã£ãå©ç¨ãã¦ããã«ããããFTPãHTTPãNFS çã®ãããã³
ã«ã転éãããã¼ã¿ããã³ã¼ãããããã®ãããªãããã³ã«ã使ç¨ããã¨ã
æ»æå´ã¯ãICS ã¸ã®æ»æã ICS ãããã¯ã¼ã¯æ´»åã®æä½ã容æã«ã§ãããã
ã«ãªãã
ã¦ã¼ã¶ããã¼ã¿åã¯ããã¤ã¹èªè¨¼ã®
æ¬ å¦åã¯ä¸é©æ ¼ ICS ãããã³ã«ã®å¤ãã¯ãã©ã®ã¬ãã«ã§ãèªè¨¼æ©è½ããªããèªè¨¼ããªãã¨ã
ã¼ã¿ã®ãªãã¬ã¼ãæ¹å¤ããªããã¾ãããã»ã³ãµåã³ã¦ã¼ã¶ ID çã®ããã¤ã¹ã®
ãªããã¾ããçãå¾ãã
æ¥çã§å¤ç¨ãããã»ãã¥ã¢ã§ãªã
ICS ã®ä½¿ç¨
ICS ãããã³ã«ã«ã¯ãèªè¨¼ãæå·åã¨ãã£ããä¸æ£ã¢ã¯ã»ã¹ãæ¹ç«ãé²æ¢ã
ãã»ãã¥ãªãã£æ©è½ãã»ã¨ãã©åã¯å
¨ããªããã®ãå¤ããã¾ããããã³ã«å®
è£
ã®ä¸åã«ãã£ã¦ãä»å çãªèå¼±æ§ãçããã
éä¿¡å®å
¨æ§ç¢ºèªã®æ¬ å¦ ç£æ¥ç¨å¶å¾¡ãããã³ã«ã®ã»ã¨ãã©ã¯å®å
¨æ§ãã§ãã¯æ©è½ããªããæ»æå´ã¯æ¤
ç¥ãããã«éä¿¡ãæä½ã§ãããå®å
¨æ§ã確ä¿ããã«ã¯ããã¼ã¿å®å
¨æ§ä¿è·ã®
ããä¸å±¤ãããã³ã«ï¼
IPsec
çï¼ã使ç¨ãããã¨ã§ããã
ã¯ã¤ã¤ã¬ã¹ã¯ã©ã¤ã¢ã³ãã¨ã¢ã¯ã»ã¹
ãã¤ã³ãéã®èªè¨¼ã®ä¸å
æ»æå´ãå±éãããã¼ã°ã¢ã¯ã»ã¹ãã¤ã³ãã«ã¯ã©ã¤ã¢ã³ããæ¥ç¶ããªããã
ã«ããæ»æå´ã ICS ã¯ã¤ã¤ã¬ã¹ãããã¯ã¼ã¯ã«æ¥ç¶ã§ããªãããã«ããã«
ã¯ãã¯ã¤ã¤ã¬ã¹ã¯ã©ã¤ã¢ã³ãã¨ã¢ã¯ã»ã¹ãã¤ã³ãéã«å¼·åºãªç¸äºèªè¨¼ãå¿
è¦
ã¨ãªãã
ã¯ã¤ã¤ã¬ã¹ã¯ã©ã¤ã¢ã³ãã¨ã¢ã¯ã»ã¹
ãã¤ã³ãéã®ãã¼ã¿ä¿è·ã®ä¸å
ã¯ã¤ã¤ã¬ã¹ã¯ã©ã¤ã¢ã³ãã¨ã¢ã¯ã»ã¹ãã¤ã³ãéã®è¦æ³¨æãã¼ã¿ã¯ãå¼·åºãªæ
å·åã«ãããæ»æå´ãæå·åããã¦ããªããã¼ã¿ã«ä¸æ£ã¢ã¯ã»ã¹ã§ããªãã
ãã«ãã¹ãã§ããã
SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
273
Incidents
A threat event is an event or situations that could potentially cause an undesirable consequence or impact to
the ICS resulting from some threat source. In NIST SP 800-30 Rev. 1, Appendix E identifies a broad set of
threat events that could potentially impact information systems [79]. The properties of an ICS may also
present unique threat events, specifically addressing how the threat events can manipulates the process of
the ICS to cause physical damage. Table C-8 provides an overview of potential ICS threat events.
Table C-8. Example Adversarial Incidents
Threat Event
Description
Denial of Control Action Control systems operation disrupted by delaying or blocking the flow of information,
thereby denying availability of the networks to control system operators or causing
information transfer bottlenecks or denial of service by IT-resident services (such as DNS)
Control Devices
Reprogrammed
Unauthorized changes made to programmed instructions in PLCs, RTUs, DCS, or SCADA
controllers, alarm thresholds changed, or unauthorized commands issued to control
equipment, which could potentially result in damage to equipment (if tolerances are
exceeded), premature shutdown of processes (such as prematurely shutting down
transmission lines), causing an environmental incident, or even disabling control
equipment
Spoofed System Status
Information
False information sent to control system operators either to disguise unauthorized
changes or to initiate inappropriate actions by system operators
Control Logic Manipulation Control system software or configuration settings modified, producing unpredictable
results
Safety Systems Modified Safety systems operation are manipulated such that they either (1) do not operate when
needed or (2) perform incorrect control actions that damage the ICS
Malware on Control
Systems
Malicious software (e.g., virus, worm, Trojan horse) introduced into the system.
In addition, in control systems that cover a wide geographic area, the remote sites are often not staffed and
may not be physically monitored. If such remote systems are physically breached, the adversaries could
establish a connection back to the control network.
Sources of Incidents
An accurate accounting of cyber incidents on control systems is difficult to determine. However,
individuals in the industry who have been focusing on this issue see similar growth trends between
vulnerabilities exposed in traditional IT systems and those being found in control systems. ICS-CERT is a
DHS organization that focuses on reducing the risk across critical infrastructure by identifying threats and
vulnerabilities, while also providing mitigation strategies. ICS-CERT provides a trusted party where system
owners and operators can report information about incidents within their ICS and obtain advice on
mitigating their risk. Information submitted by infrastructure owners and operators is protected under the
Critical Infrastructure Information Act of 2002 as Protected Critical Infrastructure Information (PCII) from
disclosure under the Freedom of Information Act (FOIA), disclosure under state, tribal, and local disclosure
laws, use in regulatory actions, and use in civil litigation. In the event of an incident at critical infrastructure
facilities, ICS-CERT can also perform onsite deployments to respond to and analyze incidents. ICS-CERT
publishes advisories of new security vulnerabilities discovered in common ICS platforms. Figure C-1
demonstrates (1) the number of ICS incidents reported, (2) the number of onsite ICS deployments taken by
ICS-CERT, and (3) number of ICS vulnerabilities reported between years 2010 and 201347.
47 https://ics-cert.us-cert.gov/
SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
274
ã¤ã³ã·ãã³ã
è
å¨äºè±¡ã¨ã¯ããªãããã®è
å¨æºã«èµ·å ãã¦ãICS ã«æã¾ãããªãçµæãå½±é¿ãä¸ããããªãäº
象åã¯ç¶æ³ããããNIST SP 800-30 第1çä»é² Eã«ã¯ãæ
å ±ã·ã¹ãã ã«å½±é¿ãåã¼ãå¤ç¨®å¤æ§ãª
è
å¨äºè±¡ãæããã«ããã¦ãã[79]ãICS ã®ç¹æ§ãåºæã®è
å¨äºè±¡ã¨ãªããã¨ããããç©ççæ
å·ãä¸ãããããè
å¨äºè±¡ãã©ã®ããã« ICS ã®ããã»ã¹ãæä½ããããåãä¸ãããã¦ããã表
C-8 ã«ICS è
å¨äºè±¡ã®æ¦è¦ã示ãã
表C-8. æ»æã¤ã³ã·ãã³ãã®ä¾
è
å¨äºè±¡
å
容
å¶å¾¡å¦¨å®³ æ
å ±ã®æµãã®é
延åã¯å¦¨å®³ã«ããå¶å¾¡ã·ã¹ãã ã®éç¨ãä¸æããã¨ãå¶å¾¡ã·
ã¹ãã æä½å¡ããããã¯ã¼ã¯ã使ç¨ã§ããªããªããæ
å ±è»¢éãããã«ããã¯
ã¨ãªã£ãããIT æµææ§ã®ãããµã¼ãã¹ï¼DNS çï¼ã«ãããµã¼ãã¹ã®å¦¨å®³ãç
ãããããã
å¶å¾¡ããã¤ã¹ã®ããã°ã©ã ãå¤æ´ã
ãã¦ãã
PLCãRTUãDCS è¥ãã㯠SCADA ã³ã³ããã¼ã©ã®ããã°ã©ã åå½ä»¤ã«å¯¾ã
ã許å¯ããã¦ããªãå¤æ´ãã¢ã©ã¼ã é¾ã®å¤æ´åã¯å¶å¾¡è£
ååã«å¯¾ãã許å¯ã
ãã¦ããªãã³ãã³ãçºè¡ã¯ãè£
ååã®æå·ï¼ãã¬ã©ã³ã¹ãè¶
ããå ´åï¼ãã
ãã»ã¹ã®éæ©åæï¼éä¿¡ç·çï¼ããããããç°å¢ã¤ã³ã·ãã³ãã¨ãªãã»ãã
å¶å¾¡è£½åãç¡å¹ã«ããã
ã·ã¹ãã ç¶æ
æ
å ±ã®ãªããã¾ã 許å¯ããã¦ããªãå¤æ´ãé è½ããããä¸é©æ£è¡çºãã·ã¹ãã æä½å¡ã«éå§ã
ãããããå½æ
å ±ãå¶å¾¡ã·ã¹ãã æä½å¡ã«éä¿¡ãããã
å¶å¾¡ãã¸ãã¯ã®æä½ å¶å¾¡ã·ã¹ãã ã½ããã¦ã¨ã¢åã¯æ§æè¨å®ãå¤æ´ãããäºæ³ä¸è½ã®çµæãçã
ãã
å®å
¨ã·ã¹ãã ã®å¤æ´ å®å
¨ã·ã¹ãã ã®åä½ãæä½ãããï¼1ï¼å¿
è¦ãªã¨ãã«ç¨¼åããªããã
(2)ICS
ãæå·ããä¸æ£ç¢ºãªå¶å¾¡ãè¡ãã
å¶å¾¡ã·ã¹ãã ã«ãã«ã¦ã¨ã¢ æªæããã½ããã¦ã¨ã¢ï¼ã¦ã¤ã«ã¹ãã¯ã¼ã ãããã¤ã®æ¨é¦¬çï¼ãã·ã¹ãã ã«
å
¥ãè¾¼ãã§ããã
ã¾ãåºåã網ç¾
ããå¶å¾¡ã·ã¹ãã ã§ãé éãµã¤ãã«è·å¡ãé
ç½®ããã¦ããããç©ççç£è¦ãã§ã
ã¦ããªãããã®ãããªé éã·ã¹ãã ãç©ççã«ä¾µå®³ãããã¨ãæ»æå´ã¯å¶å¾¡ãããã¯ã¼ã¯ã¾ã§æ¥
ç¶ã確ç«ã§ããã
ã¤ã³ã·ãã³ãã®åå
å¶å¾¡ã·ã¹ãã ä¸ã®ãµã¤ãã¼ã¤ã³ã·ãã³ãã®åå ãæ£ç¢ºã«å¤å¥ããã®ã¯é£ãããã¨ã¯è¨ããæ¥çã§
ãã®åé¡ã¨åãçµãã§ãã人ããããå¾æ¥ã® IT ã·ã¹ãã ã§é²åãããèå¼±æ§ã¨å¶å¾¡ã·ã¹ãã ã§
æããã«ãªã£ã¦ããèå¼±æ§ã«ã¯ãå
±éçãªãã¬ã³ãããããã¨ã«æ°ã¥ãã¦ãããICS-CERT ã¯
DHS ã®çµç¹ã§ãè
å¨ãèå¼±æ§ãæããã«ãã¦éè¦ã¤ã³ãã©ã®ãªã¹ã¯ã軽æ¸ããç·©åçãæä¾ã
ã¦ãããICS-CERT ã¯ãã·ã¹ãã ã®ä¿æè
ãæä½å¡ã ICS å
ã®ã¤ã³ã·ãã³ãæ
å ±ãã¬ãã¼ããã
ãªã¹ã¯ç·©åçã«é¢ããå©è¨ãå¾ããã¨ãã§ãããä¿¡é ¼ã®ç½®ããé¢ä¿è
ã«æä¾ãã¦ãããã¤ã³ãã©
ä¿æè
åã³æä½å¡ããæåºãããæ
å ±ã¯ãéè¦ã¤ã³ãã©æ
å ±æ³ï¼2002 å¹´ï¼ã«å¾ããæ
å ±ã®èªç±
æ³ï¼FOIAï¼ã«åºã¥ãé示ãå·ã»é¨æã»å°æ¹é示æ³ã«åºã¥ãé示ãè¦å¶è¡çºã«ããã使ç¨åã³æ°
äºè¨´è¨ã«ããã使ç¨ã«åºã¥ããä¿è·ãããéè¦ã¤ã³ãã©æ
å ±ï¼PCIIï¼ã¨ãã¦ä¿è·ãåãããéè¦
ã¤ã³ãã©ã«ãããã¤ãã³ãã®éã«ã¯ãICS-CERT ã¯ç¾å ´å±éãã¦ãã¤ã³ã·ãã³ãã®å¯¾å¿ã¨åæã«
å½ãããICS-CERT ã¯ãICS ãã©ãããã¼ã ã§å
±éãã¦è¦ã¤ãã£ãæ¥ç¶ä¸ã®èå¼±æ§ã«ã¤ãã¦ãã¢
ããã¤ãµãªã¼ãçºåãã¦ãããå³ C-1 ã«ã(1) ICS ã¤ã³ã·ãã³ãã®å±åºä»¶æ°ã(2) ICS-CERT ã®ICS
ç¾å ´å±é件æ°ã(3) 2010 å¹´ï½2013 å¹´ICS èå¼±æ§å±åºä»¶æ°ã示ã 48ã
48 https://ics-cert.us-cert.gov/
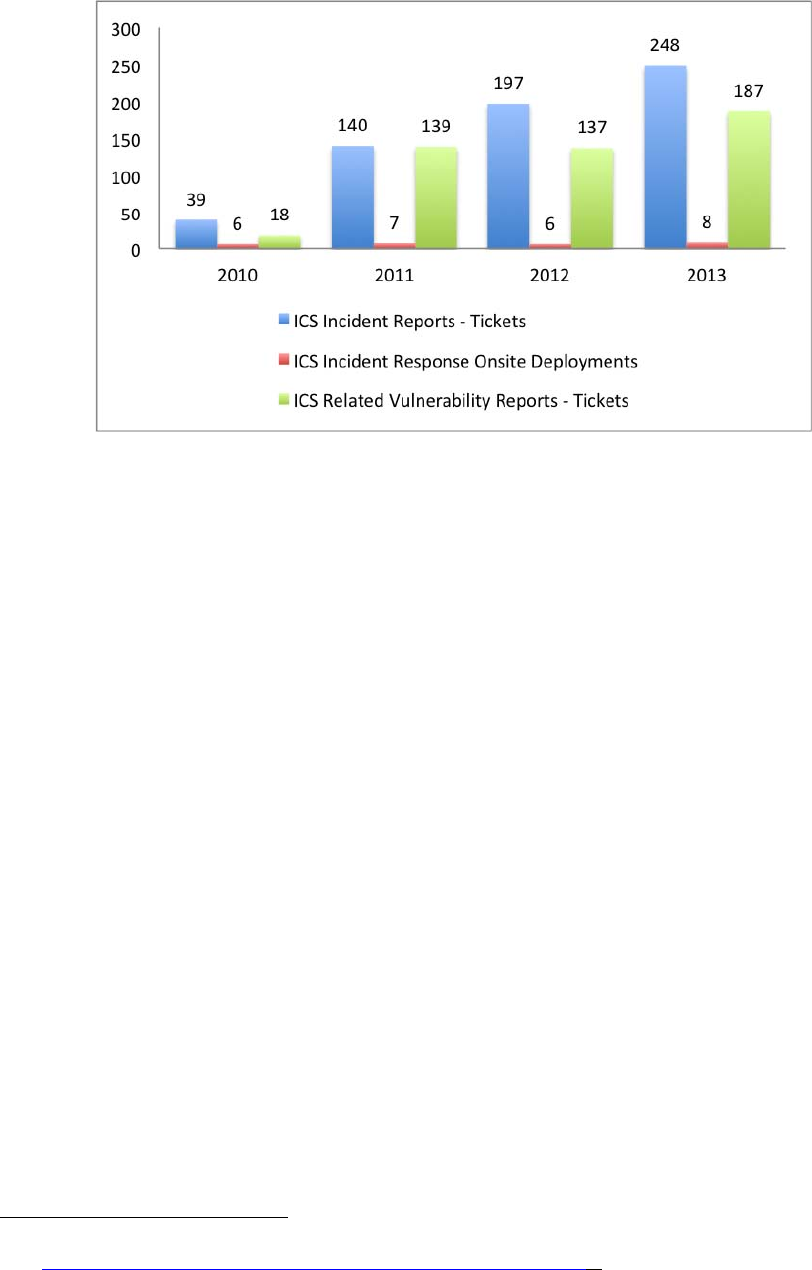
SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
275
Other sources of control system impact information show an increase in control system incidents as well.
This information should not be assumed to contain all ICS related incidents or discovered vulnerabilities as
some information may go unreported.
Figure C-1. ICS-CERT Reported Incidents by Year
Documented Incidents
Numerous ICS incidents have been reported that demonstrate how threat sources can negatively impact an
ICS. These events help demonstrate the severity of the threat sources, vulnerabilities, and impacts within
the ICS domain. As mentioned in Section C.2, the four broad categories of threat sources are adversarial,
accidental, structural, and environmental. Often the incident can be the result of multiple threat sources (e.g.
an environmental event causes a system failure, which is responded to incorrectly by an operator resulting
in an accidental event). Reported incidents from these categories include the following:
Adversarial Events
ï¼ Worcester Air Traffic Communications49. In March 1997, a teenager in Worcester, Massachusetts
disabled part of the public switched telephone network using a dial-up modem connected to the
system. This knocked out phone service at the control tower, airport security, the airport fire
department, the weather service, and carriers that use the airport. Also, the towerâs main radio
transmitter and another transmitter that activates runway lights were shut down, as well as a printer
that controllers use to monitor flight progress. The attack also knocked out phone service to 600
homes and businesses in the nearby town of Rutland.
49 Additional information on the Worcester Air Traffic Communications incident can be found at:
http://www.cnn.com/TECH/computing/9803/18/juvenile.hacker/index.html
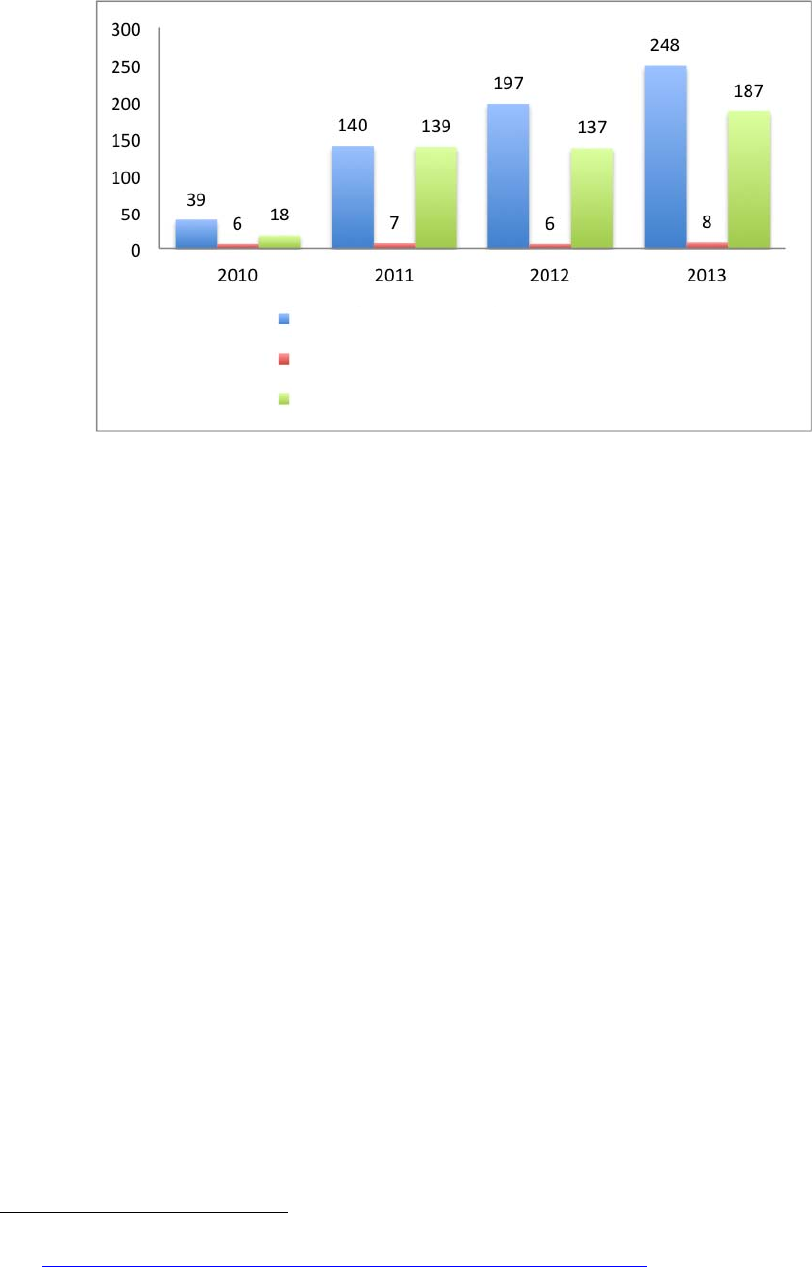
SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
276
å¶å¾¡ã·ã¹ãã ã«å½±é¿ããæ
å ±ã®ä»ã®åå ããå¶å¾¡ã·ã¹ãã ã¤ã³ã·ãã³ãã®å¢å ã示ãã¦ãããæª
å ±åã®æ
å ±ãããããããã®æ
å ±ã ICS é¢é£ã¤ã³ã·ãã³ãåã¯è§£æãããèå¼±æ§ã®å
¨ã¦ã§ããã¨
解ãã¹ãã§ãªãã
å³C-1. ICS-CERT ã«å±åºã®ãã£ã年度å¥ã¤ã³ã·ãã³ã件æ°
ææ¸åãããã¤ã³ã·ãã³ã
ããã¾ã§å¤æ°ã® ICS ã¤ã³ã·ãã³ãã®å±åºããããè
å¨æºã ICS ã«ã©ã®ãããªæªå½±é¿ãä¸ãå¾ãã
ãå®è¨¼ãã¦ããããããã®äºè±¡ã¯ãè
å¨æºãèå¼±æ§åã³ ICS ãã¡ã¤ã³å
ã§ã®å½±é¿ã®é大æ§ãå®è¨¼
ããã®ã«å½¹ç«ã¤ãã»ã¯ã·ã§ã³ C.2 ã§è¨åããããã«ãè
å¨æºã¯æµæ§ãå¶çºæ§ãæ§é çåã³ç°å¢ç
ã®4ã¤ã®åé¡ã«å¤§å¥ã§ãããã¤ã³ã·ãã³ãã¯è¤æ°ã®è
å¨æºã«èµ·å ãããã¨ãå°ãªããªãï¼ç°å¢ç
äºè±¡ãã·ã¹ãã é害ã®åå ã¨ãªããããã«å¯¾ãããªãã¬ã¼ã¿ã®å¯¾å¿ãã¾ããã¨å¶çºçäºè±¡ã¨ãª
ãï¼ãå±åºã®ãã£ãã¤ã³ã·ãã³ãã«ã¯ãåé¡å¥ã«æ¬¡ã®ãããªãã®ãããã
æµæ§äºè±¡
ï¼ ã¦ã¼ã¹ã¿ã¼èªç©ºäº¤ééä¿¡ 501997 å¹´3æãããµãã¥ã¼ã»ããå·ã¦ã¼ã¹ã¿ã¼ã®ãã£ã¼ã³ã¨ã¤ã¸ã£
ã¼ããã¤ã¢ã«ã¢ããã¢ãã ã§ã·ã¹ãã ã«æ¥ç¶ããå
Œ
±äº¤æé»è©±ç¶²ã®ä¸é¨ã使ç¨ä¸è½ã«ããã
ãã®ãã管å¶å¡ã空港è¦åã空港æ¶é²éãæ°è±¡ãµã¼ãã¹åã³ç©ºæ¸¯ãå©ç¨ããèªç©ºä¼ç¤¾ã«å¯¾ã
ãé»è©±ãµã¼ãã¹ã麻çºãããã¾ã管å¶å¡ã®ä¸»ç¡ç·éä¿¡æ©ãæ»èµ°è·¯ç¯ãç¹ç¯ããéä¿¡æ©ãé®æ
ãããã»ããé£è¡ã®é²æãç£è¦ãã管å¶å®ã®ããªã³ã¿ã使ããªããªã£ãããã®æ»æã§ã©ãã©
ã³ãçºè¿åã®ä¸è¬å®¶åº 600 ä¸å¸¯ã¨ä¼æ¥ã®é»è©±ã使ç¨ä¸è½ã«ãªã£ãã
50 ã¦ã¼ã¹ã¿ã¼èªç©ºäº¤ééä¿¡ã¤ã³ã·ãã³ãã®è©³ç´°ã¯æ¬¡ã®ãµã¤ãã«ããã
http://www.cnn.com/TECH/computing/9803/18/juvenile.hacker/index.html
ICS
ã¤ã³ã·ãã³ãã®å±åº
â
è¨å¸³
ICS ã¤ã³ã·ãã³ã対å¿ç¾å ´å±é
ICS é¢é£èå¼±æ§å ±åæ¸ â è¨å¸³
SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
277
ï¼ Maroochy Shire Sewage Spill51. In the spring of 2000, a former employee of an Australian
organization that develops manufacturing software applied for a job with the local government, but
was rejected. Over a two-month period, the disgruntled rejected employee reportedly used a radio
transmitter on as many as 46 occasions to remotely break into the controls of a sewage treatment
system. He altered electronic data for particular sewerage pumping stations and caused malfunctions
in their operations, ultimately releasing about 264 000 gallons of raw sewage into nearby rivers and
parks.
ï¼ Davis-Besse52. In August 2003, the Nuclear Regulatory Commission confirmed that in January 2003,
the Microsoft SQL Server worm known as Slammer infected a private computer network at the i d le d
Davis-Besse nuclear power plant in Oak Harbor, Ohio, disabling a safety monitoring system for nearly
five hours. In addition, the plantâs process computer failed, and it took about six hours for it to become
available again. Slammer reportedly also affected communications on the control networks of at least
five other utilities by propagating so quickly that control system traffic was blocked.
ï¼ Zotob Worm53. In August 2005, a round of Internet worm infections knocked 13 of
DaimlerChryslerâs U.S. automobile manufacturing plants offline for almost an hour, stranding workers
as infected Microsoft Windows systems were patched. Plants in Illinois, Indiana, Wisconsin, Ohio,
Delaware, and Michigan were knocked offline. While the worm affected primarily Windows 2000
systems, it also affected some early versions of Windows XP. Symptoms include the repeated
shutdown and rebooting of a computer. Zotob and its variations caused computer outages at heavy-
equipment maker Caterpillar Inc., aircraft-maker Boeing, and several large U.S. news organizations.
ï¼ Stuxnet Worm54. Stuxnet was a Microsoft Windows computer worm discovered in July 2010 that
specifically targeted industrial software and equipment. The worm initially spread indiscriminately,
but included a highly specialized malware payload that was designed to target only specific SCADA
systems that were configured to control and monitor specific industrial processes
ï¼ Brute Force Attacks on Internet-Facing Control Systems55. On February 22, 2013 ICS-CERT
received a report from a gas compressor station owner about an increase in brute force attempts to
access their process control network. The forensic evidence contained 10 separate IPs and additional
calls of a similar nature from additional natural gas pipeline asset owners, which yielded 39 additional
IPs of concern. Log analysis showed a date range from January 16, 2013 but there have been no
reports since March 8, 2013.
ï¼ Shamoon56. Saudi Aramco, which is the worldâs 8th largest oil refiner, experienced a malware attack
that targeted their refineries and overwrote the attacked systemâs Master Boot Records (MBR),
partition tables and other random data files. This caused the systems to become unusable.
51 Additional information on the Maroochy Shire Sewage Spill incident can be found at:
http://csrc.nist.gov/groups/SMA/fisma/ics/documents/Maroochy-Water-Services-Case-Study_report.pdf and
http://www.theregister.co.uk/2001/10/31/hacker_jailed_for_revenge_sewage/ [each accessed 4/16/15].
52 Additional information on the Davis-Besse incident can be found at:
http://www.securityfocus.com/news/6767 [accessed 4/16/15].
53 Additional information on the Zotob Worm incident can be found at: http://www.eweek.com/c/a/Security/Zotob-
PnP-Worms-Slam-13-DaimlerChrysler-Plants [accessed 4/16/15].
54 Additional information on the Stuxnet worm can be found at: http://en.wikipedia.org/wiki/Stuxnet [accessed
4/16/15].
55 Additional information on ICS-CERT reported incidents can be found at:
https://ics-cert.us-cert.gov/Information-Products [accessed 4/16/15].
56 Additional information on Shamoon can be found at:
http://ics-cert.us-cert.gov/sites/default/files/Monitors/ICS-CERT_Monitor_Sep2012.pdf [accessed 4/16/15].

SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
278
ï¼ ãã«ã¼ãã¼å¸ã®ä¸æ°´æµåº 57 2000 å¹´æ¥ã豪å·ã®å
ã½ããã¦ã¨ã¢éçºä¼ç¤¾ç¤¾å¡ãå°æ¹èªæ²»ä½è·
å¡ã®åéã«å¿åãããä¸æ¡ç¨ã«ãªã£ããä¸æºãæ±ããå½äººã¯ã2ãæéã«ããã 46 åãç¡
ç·éä¿¡æ©ã§ä¸æ°´å¦çè£
ç½®ã«ä¾µå
¥ãããããä¸æ°´ãã³ãã¹ãã¼ã·ã§ã³ã®é»åãã¼ã¿ãæ¹å¤ãã¦ã
é転é害ãçºçãããçµå± 26 ä¸4,000 ã¬ãã³ãã®ä¸æ°´ãè¿é£ã®æ²³å·ãå
¬åã«æ¾åºãããã
ï¼ ãã¤ãã¹ã»ãã¹ 58 2003 å¹´8æãåååè¦å¶å§å¡ä¼ã¯åå¹´ 1æãã¹ã©ãã¼ã¨ãã¦ç¥ãããã
ã¤ã¯ãã½ãã SQLãµã¼ãã®ã¯ã¼ã ãããªãã¤ãªå·ãªã¼ã¯ãã¼ãã¼ã«ããé稼åä¸ã®ãã¤ã
ã¹ã»ãã¹åååçºé»æã®ãã©ã¤ãã¼ãã³ã³ãã¥ã¼ã¿ãããã¯ã¼ã¯ã«ææãã¦ãããã¨ã確èª
ãã5æéç¨åº¦å®å
¨ç£è¦è£
ç½®ã使ç¨ã§ããªãã£ããã¾ããçºé»æã®ããã»ã¹ã³ã³ãã¥ã¼ã¿ã
æ
éãã復æ§ã«ç´ 6æéè¦ãããå ±åã«ããã°ã¹ã©ãã¼ã¯ãå°ãªãã¨ãä»ã® 5ã¤ã®å
Œ
±äºæ¥
å£ä½ã®å¶å¾¡ãããã¯ã¼ã¯ã®éä¿¡ã«ãå½±é¿ãåã¼ãã極ãã¦è¿
éã«ä¼æãã¦å¶å¾¡ã·ã¹ãã ãã©
ãã£ãã¯ãé®æããã
ï¼ Zotob ã¯ã¼ã 59 2005 å¹´8æãã¤ã³ã¿ã¼ãããã¯ã¼ã ã«ææãããã¤ã ã©ã¼ã¯ã©ã¤ã¹ã©ã¼ã®
ç±³å½èªåè»çç£ãã©ã³ã 13 ç®æãç´ 1æéã«ããããªãã©ã¤ã³ã«ãªããWindows ã·ã¹ãã
ã¸ã®ãããä½æ¥ã®éãä½æ¥å¡ãç«ã¡å¾çãããã¤ãªãã¤ãã¤ã³ãã£ã¢ããã¦ã£ã¹ã³ã³ã·ã³ã
ãªãã¤ãªããã©ã¦ã§ã¢ããã·ã¬ã³ã®åå·ã§ã¯ãã©ã³ãããªãã©ã¤ã³ã«ãªã£ããææããã®ã¯
主㫠Windows2000 ã ã£ãããWindows XP ã®åæãã¼ã¸ã§ã³ãææãããææã®å¾´åã¯ãå
æã¨åèµ·åã®ç¹°ãè¿ãã ã£ããZotob åã³ãã®æ´¾çåã¯ã大åè£
ååã¡ã¼ã«ã¼ã® Caterpillar
Inc.ãèªç©ºæ©ã¡ã¼ã«ã¼ã® Boeingããã®ä»å¤§æã®å ±éæ©é¢ã®ã³ã³ãã¥ã¼ã¿ã被害ã«éã£ãã
ï¼ Stuxnet ã¯ã¼ã 60 Stuxnet ã¯2010 å¹´7æã«è¦ã¤ãã£ã Windows ã³ã³ãã¥ã¼ã¿ã®ã¯ã¼ã ã§ã
ç£æ¥ç¨ã½ããã¦ã¨ã¢åã³è£
ååã主ãªæ¨çã¨ãã¦ãããå½åãã®ã¯ã¼ã ã¯å¯¾è±¡ãé¸ã°ãæ¡æ£
ããããç¹æ®ãªãã«ã¦ã¨ã¢ãã¤ãã¼ããçµã¿è¾¼ãã§ãç¹å®ã®ç£æ¥ããã»ã¹ã®å¶å¾¡ã»ç£è¦ã«ç¹
åãã SCADA ã·ã¹ãã ã ããæ¨çã¨ããããã«ãªã£ãã
ï¼ ã¤ã³ã¿ã¼ãããã«å¯¾é¢ããå¶å¾¡ã·ã¹ãã ã¸ã®å¼·åæ»æ 61 2013 å¹´2æ22 æ¥ãICS-CERT ã¯
ã¬ã¹ã³ã³ãã¬ããµã¹ãã¼ã·ã§ã³ã®ä¿æè
ãããå¶å¾¡ç®¡çãããã¯ã¼ã¯ã¸ã®ã¢ã¯ã»ã¹ãããã
ã強大ãªåã®å¢å ãããæ¨å ±åãåããã調æ»ã®çµæãå¥åã® IP ã10 ã¨ãå種ã®è£è¶³çãª
å¼åºããã»ãã®å¤©ç¶ã¬ã¹ãã¤ãã©ã¤ã³ä¿æè
ããããããå
¨é¨ã§ 39 ã®è¿½å IP äºæ¡ã¨ãªã£ãã
ãã°è§£æã®çµæã2013 å¹´1æ16 æ¥ããå§ã¾ã£ã¦ããããåå¹´ 3æ8æ¥ä»¥éã®å±åºã¯ãªãã£
ãã
ï¼ ã·ã£ã ã¼ã³ 62 ä¸ç第 8ä½ã®è£½æ²¹ä¼ç¤¾ Saudi Aramco ã¯ãå社ã®è£½æ²¹æ½è¨ãæ¨çã¨ãããã«ã¦
ã¨ã¢æ»æã«éããã·ã¹ãã ã®ãã¹ã¿ã¼ãã¼ãã¬ã³ã¼ãï¼MBRï¼ããã¼ãã£ã·ã§ã³ãã¼ãã«
ãã®ä»ã©ã³ãã ãã¼ã¿ãã¡ã¤ã«ãæ¸ãæãããããã·ã¹ãã ã¯ä½¿ç¨ä¸è½ã«ãªã£ãã
57 ãã«ã¼ãã¼å¸ã®ä¸æ°´æµåºã¤ã³ã·ãã³ãã®è©³ç´°ã¯æ¬¡ã®ãµã¤ãã«ããã
http://csrc.nist.gov/groups/SMA/fisma/ics/documents/Maroochy-Water-Services-Case-Study_report.pdf
and http://www.theregister.co.uk/2001/10/31/hacker_jailed_for_revenge_sewage/ [each accessed
4/16/15].
58 ãã¤ãã¹ã»ãã¹ã¤ã³ã·ãã³ãã®è©³ç´°ã¯æ¬¡ã®ãµã¤ãã«ãããhttp://www.securityfocus.com/news/6767 [accessed
4/16/15].
59 Zotob ã¯ã¼ã ã¤ã³ã·ãã³ãã®è©³ç´°ã¯æ¬¡ã®ãµã¤ãã«ãããhttp://www.eweek.com/c/a/Security/Zotob-PnP-Worms-
Slam-13-DaimlerChrysler-Plants [accessed 4/16/15].
60 Stuxnet ã¯ã¼ã ã¤ã³ã·ãã³ãã®è©³ç´°ã¯æ¬¡ã®ãµã¤ãã«ãããhttp://en.wikipedia.org/wiki/Stuxnet [accessed
4/16/15].
61 ICS-CERT å±åºã¤ã³ã·ãã³ãã®è©³ç´°ã¯æ¬¡ã®ãµã¤ãã«ãããhttps://ics-cert.us-cert.gov/Information-Products
[accessed 4/16/15].
62 ã·ã£ã ã¼ã³ã®è©³ç´°ã¯æ¬¡ã®ãµã¤ãã«ãããhttp://ics-cert.us-cert.gov/sites/default/files/Monitors/ICS-
CERT_Monitor_Sep2012.pdf [accessed 4/16/15].

SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
279
ï¼ German Steel Mill Attack63. In 2014, hackers manipulated and disrupted control systems to such a
degree that a blast furnace could not be properly shut down, resulting in âmassiveââthough
unspecifiedâdamage.
Structural Events
ï¼ CSX Train Signaling System64. In August 2003, the Sobig computer virus was blamed for shutting
down train signaling systems throughout the east coast of the U.S. The virus infected the computer
system at CSX Corp.âs Jacksonville, Florida headquarters, shutting down signaling, dispatching, and
other systems. According to Amtrak spokesman Dan Stessel, ten Amtrak trains were affected in the
morning. Trains between Pittsburgh and Florence, South Carolina were halted because of dark signals,
and one regional Amtrak train from Richmond, Virginia to Washington and New York was delayed for
more than two hours. Long-distance trains were also delayed between four and six hours.
ï¼ Northeast Power Blackout65. In August 2003, failure of the alarm processor in First Energyâs
SCADA system prevented control room operators from having adequate situational awareness of
critical operational changes to the electrical grid. Additionally, effective reliability oversight was
prevented when the state estimator at the Midwest Independent System Operator failed due to
incomplete information on topology changes, preventing contingency analysis. Several key 345 kV
transmission lines in Northern Ohio tripped due to contact with trees. This eventually initiated
cascading overloads of additional 345 kV and 138 kV lines, leading to an uncontrolled cascading
failure of the grid. A total of 61 800 MW load was lost as 508 generating units at 265 power plants
tripped.
ï¼ Taum Sauk Water Storage Dam Failure66. In December 2005, the Taum Sauk Water Storage Dam
suffered a catastrophic failure releasing a billion gallons of water. The failure of the reservoir occurred
as the reservoir was being filled to capacity or may have possibly been overtopped. The current
working theory is that the reservoir's berm was overtopped when the routine nightly pump-back
operation failed to cease when the reservoir was filled. According to the utility, the gauges at the dam
read differently than the gauges at the Osage plant at the Lake of the Ozarks, which monitors and
operates the Taum Sauk plant remotely. The stations are linked together using a network of microwave
towers, and there are no operators on-site at Taum Sauk.
ï¼ Bellingham, Washington Gasoline Pipeline Failure67. In June 1999, 900 000 liters (237 000
gallons) of gasoline leaked from a 16 in. (40.64 cm) pipeline and ignited 1.5 hours later causing 3
deaths, 8 injuries, and extensive property damage. The pipeline failure was exacerbated by control
systems not able to perform control and monitoring functions. âImmediately prior to and during the
incident, the SCADA system exhibited poor performance that inhibited the pipeline controllers from
seeing and reacting to the development of an abnormal pipeline operation.â A key recommendation
63 Additional information on the German steel mill incident can be found at:
http://www.wired.com/2015/01/german-steel-mill-hack-destruction/ [accessed 4/16/15].
64 Additional information on the CSX Train Signaling System incident can be found at:
http://www.cbsnews.com/stories/2003/08/21/tech/main569418.shtml and
http://www.informationweek.com/story/showArticle.jhtml?articleID=13100807 [each accessed 4/16/15].
65 Additional information on the Northeast Power Blackout incident can be found at:
http://energy.gov/sites/prod/files/oeprod/DocumentsandMedia/BlackoutFinalImplementationReport%282%29.pdf
[accessed 4/16/15].http://www.oe.energy.gov/DocumentsandMedia/BlackoutFinal-Web.pdf
66 Additional information on the Taum Sauk Water Storage Dam Failure incident can be found at:
http://www.ferc.gov/industries/hydropower/safety/projects/taum-sauk/ipoc-rpt/full-rpt.pdf [accessed 4/16/15].
67 Additional information on the Bellingham, Washington Gasoline Pipeline Failure incident can be found at
http://csrc.nist.gov/groups/SMA/fisma/ics/documents/Bellingham_Case_Study_report%2020Sep071.pdf and
http://www.ntsb.gov/investigations/AccidentReports/Reports/PAR0202.pdf [each accessed 4/16/15].
SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
280
ï¼ ãã¤ãéå·¥ææ»æ 68 2014 å¹´ã«ããã«ã¼ã¯å¶å¾¡ã·ã¹ãã ãæä½ãã¦ä¸æããé«çãæ£å¸¸ã«é®
æã§ããªããªããç¹å®ä¸è½ã®ã大è¦æ¨¡ãæ害ã«è³ã£ãã
æ§é çäºè±¡
ï¼ CSX åè»ä¿¡å·ã·ã¹ãã 69 2003 å¹´8æãSobig ã³ã³ãã¥ã¼ã¿ã¦ã¤ã«ã¹ãåå ã¨è¨ããåè»ä¿¡
å·ã·ã¹ãã ã®é®æãç±³å½æ±æµ·å²¸ä¸å¸¯ã襲ã£ããã¦ã¤ã«ã¹ã¯ CSX Corp.ã®ãããªãï¼ã¸ã£ã¯ã½
ã³ãã«ï¼æ¬é¨ã³ã³ãã¥ã¼ã¿ã·ã¹ãã ã«ææããä¿¡å·ããã£ã¹ããããã®ä»ã®ã·ã¹ãã ãé®æ
ãããAmtrak ã®ã¹ãã¼ã¯ã¹ãã³ Dan Stessel ã«ããã°ããã®æåè» 10 両ã«å½±é¿ãåºãããµã¦
ã¹ã«ãã©ã¤ãå·ããããã¼ã°ã¨ããã¼ã¬ã³ã¹éã§ãæä¿¡å·ã®ããåè»ãç«ã¡å¾çãããªãã
ã¢ã³ãããã¼ã¸ãã¢ãã¯ã·ã³ãã³ããã¥ã¼ã¨ã¼ã¯éã§ã 2æé以ä¸ã«ããããã¤ã¤ã«é
ãã
çãããé·è·é¢åè»ã«ã 4ï½6æéã®é
ããåºãã
ï¼ åæ±é¨ã®åé» 70 2003 å¹´8æãFirst Energy ã®SCADA ã·ã¹ãã ã®ã¢ã©ã¼ã ããã»ããµãæ
é
ããé
é»ç¶²ã®é大ãªéç¨å¤æ´ããã£ããã¨ã«ãå¶å¾¡å®¤æä½å¡ãæ°ã¥ããªãã£ããã¾ãã
Midwest Independent System Operator ã®æ»å®å®ãããããã¸ã¼å¤æ´ã«é¢ããæ
å ±ã®ä¸åããè·
åãéè¡ã§ãããä¸æ¸¬äºæ
åæãä¸è½ã§ãä¿¡é ¼æ§ã«å¯¾ããå¹æçãªç£ç£æ¥åãé»å®³ãããã
ãªãã¤ãªå·åé¨ã®ä¸»è¦ãª 345kV éé»ç·ãã樹æ¨ã¨æ¥è§¦ããããã«é®æãããããã®ããé£
éçãªéè² è·ãå¥ã® 345kV åã³ 138kV ã«ããããéé»ç¶²ã®å¶å¾¡ä¸è½ãªé£éé害ã«è³ã£ãã
çµå± 265 ã®çºé»æã®çºé»è£
ç½® 508 åºãé®æãããåè¨ 61,800MW ã失ãããã
ï¼ Taum Sauk 貯水ãã ã®é害 71 2005 å¹´12 æãTaum Sauk 貯水ãã ãå£æ»
çãªè¢«å®³ã«éãã
æ°ååã¬ãã³ã®æ°´ãæ¾åºããããé害ã¯ãè²¯æ°´æ± ãæºæ°´ãããã¯ãããè¶ããããã«çããã
ç¾å¨ã®ä½æ¥çè«ã§ã¯ãè²¯æ°´æ± ã®æºæ°´æã«ãæ¯å¤è¡ããããã³ãããã¯æä½ãåæ¢ããã貯水
æ± ã®é é¨ãã溢ãåºãã¨ããã¦ãããäºæ¥è
ã«ããã°ããã ã®ã²ã¼ã¸ã¨ãTaum Sauk çºé»æ
ãé éç£è¦ã»éç¨ãã Ozarks æ¹ã«ãã Osage çºé»æã®ã²ã¼ã¸ã®å¤è¡¨ç¤ºãéã£ã¦ãããåã¹
ãã¼ã·ã§ã³ã¯ããã¤ã¯ãæ³¢ã¿ã¯ã¼ã®ãããã¯ã¼ã¯ãå©ç¨ãã¦çµã°ãã¦ãããTaum Sauk ã«ã¯
ç¾å ´æä½å¡ãããªãã
ï¼ ã¯ã·ã³ãã³å·ããªã³ã¬ã ã®ã¬ã½ãªã³ãã¤ãã©ã¤ã³é害 72 1999 å¹´6æãã¬ã½ãªã³ 90 ä¸ãªã
ãã«ï¼23 ä¸7,000 ã¬ãã³ï¼ã 16 ã¤ã³ãï¼40.64cmï¼ã®ãã¤ãã©ã¤ã³ããæ¼ãã1æéåå¾ã«
çºç«ããæ»è
3人ãè² å·è
8人ã®ã»ãç大ãªç©æãçãããå¶å¾¡ã·ã¹ãã ã®å¶å¾¡ã»ç£è¦æ©è½
ãåããããã¤ãã©ã¤ã³é害ãæªåããããã¤ã³ã·ãã³ãã®ç´ååã³æä¸ã«ãSCADA ã·ã¹
ãã ã®ããã©ã¼ãã³ã¹ãå£ãããã¤ãã©ã¤ã³æä½å¡ã¯ãç°å¸¸ãªãã¤ãã©ã¤ã³åä½ã«å¯¾ãã¦ã
確èªã対å¦ãã§ããªãã£ãã
68 ãã¤ãã®éå·¥æã¤ã³ã·ãã³ãã®è©³ç´°ã¯æ¬¡ã®ãµã¤ãã«ãããhttp://www.wired.com/2015/01/german-steel-mill-
hack-destruction/ [accessed 4/16/15].
69 CSX åè»ä¿¡å·ã·ã¹ãã ã¤ã³ã·ãã³ãã®è©³ç´°ã¯æ¬¡ã®ãµã¤ãã«ããã
http://www.cbsnews.com/stories/2003/08/21/tech/main569418.shtml and
http://www.informationweek.com/story/showArticle.jhtml?articleID=13100807 [each accessed 4/16/15].
70 åæ±é¨ã®åé»ã¤ã³ã·ãã³ãã®è©³ç´°ã¯æ¬¡ã®ãµã¤ãã«ããã
http://energy.gov/sites/prod/files/oeprod/DocumentsandMedia/BlackoutFinalImplementationReport%282
%29.pdf [accessed 4/16/15].http://www.oe.energy.gov/DocumentsandMedia/BlackoutFinal-Web.pdf
71 Taum Sauk 貯水ãã é害ã¤ã³ã·ãã³ãã®è©³ç´°ã¯æ¬¡ã®ãµã¤ãã«ããã
http://www.ferc.gov/industries/hydropower/safety/projects/taum-sauk/ipoc-rpt/full-rpt.pdf
[accessed 4/16/15].
72 ã¯ã·ã³ãã³å·ããªã³ã¬ã ã®ã¬ã½ãªã³ãã¤ãã©ã¤ã³é害ã¤ã³ã·ãã³ãã®è©³ç´°ã¯æ¬¡ã®ãµã¤ãã«ããã
http://csrc.nist.gov/groups/SMA/fisma/ics/documents/Bellingham_Case_Study_report%2020Sep071.pdf
and http://www.ntsb.gov/investigations/AccidentReports/Reports/PAR0202.pdf [each accessed
4/16/15].

SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
281
from the NTSB report issued October 2002 was to utilize an off-line development and testing system
for implementing and testing changes to the SCADA database.
ï¼ Browns Ferry-3 PLC Failure73. In August 2006, TVA was forced to manually shut down one of their
plant's two reactors after unresponsive PLCs problems caused two water pumps to fail and threatened
the stability of the plant itself. Although there were dual redundant PLCs, they were connected to the
same Ethernet network. Later testing on the failed devices discovered that they would crash when they
encountered excessive network traffic.
Environmental Events
ï¼ Fukushima Daiichi Nuclear Disaster74. The Great East Japan Earthquake on 11 March 2011 struck
off the coast of Japan, sending a massive tsunami inland towards the nuclear plant. The tsunami
compromised the plants seawall, flooding much of the plant including the location housing the
emergency generators. This emergency power was critical to operate the control rooms and also to
provide coolant water for the reactors. The loss of coolant caused the reactor cores to overheat to the
point where the fuel's zirconium cladding reacted with water, releasing hydrogen gas and fueling large
explosions in three of the four reactor buildings. This resulted in large-scale radiation leakage that has
impacted plant employees, nearby citizens, and the local environment. Post event analysis found that
the plantâs emergency response center had insufficient secure communication lines to provide other
areas of the plant with information on key safety related instrumentation.
Accidental Events
ï¼ Vulnerability Scanner Incidents75. While a ping sweep was being performed on an active SCADA
network that controlled 3 meter (9 foot) robotic arms, it was noticed that one arm became active and
swung around 180 degrees. The controller for the arm was in standby mode before the ping sweep was
initiated. In a separate incident, a ping sweep was being performed on an ICS network to identify all
hosts that were attached to the network, for inventory purposes, and it caused a system controlling the
creation of integrated circuits in the fabrication plant to hang. This test resulted in the destruction of
$50,000 worth of wafers.
ï¼ Penetration Testing Incident76. A natural gas utility hired an IT security consulting organization to
conduct penetration testing on its corporate IT network. The consulting organization carelessly
ventured into a part of the network that was directly connected to the SCADA system. The penetration
test locked up the SCADA system and the utility was not able to send gas through its pipelines for four
hours. The outcome was the loss of service to its customer base for those four hours.
73 Additional information on the Browns Ferry -3 PLC Failure incident can be found at:
http://www.nrc.gov/reading-rm/doc-collections/gen-comm/info-notices/2007/in200715.pdf [accessed 4/16/15].
74 Additional information can be found at: http://www-
pub.iaea.org/MTCD/meetings/PDFplus/2011/cn200/documentation/cn200_Final-Fukushima-Mission_Report.pdf and
http://pbadupws.nrc.gov/docs/ML1414/ML14140A185.pdf [each accessed 4/16/15].
75 Additional information on the vulnerability scanner incidents can be found at:
http://energy.sandia.gov/wp/wp-
content/gallery/uploads/sand_2005_2846p.pdfhttp://www.sandia.gov/scada/documents/sand_2005_2846p.pdf
[accessed 4/16/15].
76 Additional information on penetration testing incidents can be found at: http://energy.sandia.gov/wp/wp-
content/gallery/uploads/sand_2005_2846p.pdf [accessed 4/16/15].
SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
282
2002 å¹´10 æçºè¡ã® NTSB å ±åæ¸ã®ä¸»ãªæ¨å¥¨äºé
ã¯ãSCADA ãã¼ã¿ãã¼ã¹ã¸ã®å¤æ´ã®å®è£
åã³è©¦é¨ã¯ããªãã©ã¤ã³éçºè©¦é¨ã·ã¹ãã ã使ç¨ãããã¨ã«ãªã£ã¦ããã
ï¼ Browns Ferry-3 å°ã® PLC é害 77 2006 å¹´8æãPLC ãåå¿ããªããªã 2åºã®æ°´ãã³ããæ¢
ã¾ããçºé»æèªä½ã®å®å®æ§ç¶æãå±ãããªã£ãããã2åºã®ååçã®ãã¡ã® 1åºãæåã§å
æ¢ããã2éåé·æ§ã® PLC ã ã£ãããããããåã Ethernet ãããã¯ã¼ã¯ã«æ¥ç¶ããã¦ããã
æ
éããããã¤ã¹ãå¾æ¥è©¦é¨ããçµæããããã¯ã¼ã¯ãã©ãã£ãã¯ãé大ã«ãªããã¯ã©ãã·
ã¥ãã¦ãããã¨ãåãã£ãã
ç°å¢çäºè±¡
ï¼ ç¦å³¶ç¬¬ 1ååçç½å®³ 78 2011 å¹´3æ11 æ¥ãæ±æ¥æ¬å¤§å°éãæ¥æ¬ã®æ²åã§çºçãã大åã®æ´¥
æ³¢ãçºé»æã襲ã£ãã津波ã¯çºé»æã®é²æ³¢å ¤ãçªç ´ããç·æ¥ç¨çºé»æ©ãå容ããå ´æãå«ãã
çºé»æã®å¤§é¨åã浸水ããããã®ç·æ¥ç¨é»åã¯ãå¶å¾¡å®¤ã®éç¨ã¨ååçç¨å·å´æ°´ã®çµ¦æ°´ã«ä¸
å¯æ¬ ã ã£ããå·å´æ°´ã失ãããããçå¿ãéç±ããçæã®ã¸ã«ã³ãã¦ã 被è¦ãæ°´ã¨åå¿ãã¦
æ°´ç´ ãæ¾åºãã4æ£ãã建å±ã® 3æ£ã§ççºãçããããã®ãã大è¦æ¨¡ã®æ¾å°è½æ¼ããçãã
çºé»æå¾æ¥å¡ãè¿é£ä½äººåã³å°å
ç°å¢ã«å½±é¿ãåãã ãäºå¾è§£æã®çµæãéè¦ãªå®å
¨é¢é£è¨
è£
æ
å ±ãçºé»æã®ä»ã®ã¨ãªã¢ã«ä¼ããããã®ç·æ¥æ対å¿ã»ã³ã¿ã¼ã®éä¿¡ç·ã«ä¸åããã£ãã
å¶çºçäºè±¡
ï¼ èå¼±æ§ã¹ãã£ãã¼ã¤ã³ã·ãã³ã 79 3mï¼9ãã£ã¼ãï¼ã®ããããã¢ã¼ã ãå¶å¾¡ããã¢ã¯ãã£
ãSCADA ã·ã¹ãã ãããã¯ã¼ã¯ã§ããã³ã¹ã¤ã¼ããè¡ã£ã¦ããã¨ããã1æ¬ã®ã¢ã¼ã ãã¢
ã¯ãã£ãã«ãªãã»ã¼ 180°æ¯ããããã³ã¹ã¤ã¼ãã®éå§åãã¢ã¼ã æä½å¡ã¯ã¹ã¿ã³ãã¤ã¢ã¼
ãã ã£ããå¥ã®ã¤ã³ã·ãã³ãã§ã¯ãICS ãããã¯ã¼ã¯ã§ãã³ã¹ã¤ã¼ããè¡ããå¨åº«ç®¡çç®ç
ã§ããããã¯ã¼ã¯ã«æ¥ç¶ãã¦ããå
¨ã¦ã®ãã¹ããèå¥ãã¦ããã¨ãããIC ã®ä½æãå¶å¾¡ã
ã¦ãã製é ãã©ã³ãã®ã·ã¹ãã ããã³ã°ããããçµæã¨ãã¦ã5ä¸ãã«åã®ã¦ã§ãã¼ãç ´æ
ããã
ï¼ ãããã¬ã¼ã·ã§ã³ã»ãã¹ãã»ã¤ã³ã·ãã³ã 80 天ç¶ã¬ã¹äºæ¥ä½ã¯ãèªç¤¾ IT ãããã¯ã¼ã¯ã®
ãããã¬ã¼ã·ã§ã³ã»ãã¹ãå®æ½ã®ãããIT æ¥ç¶ã³ã³ãµã«ãã£ã³ã°çµç¹ãéç¨ãããã³ã³ãµ
ã«ãã£ã³ã°çµç¹ã¯ãä¸æ³¨æã«ã SCADA ã·ã¹ãã ã«ç´æ¥ã¤ãªãã£ããããã¯ã¼ã¯ã®ä¸é¨ã«å
¥
ã£ãããããã¬ã¼ã·ã§ã³ã»ãã¹ãã®ãã㧠SCADA ã·ã¹ãã ãããã¯ããåäºæ¥ä½ã¯ 4æé
ã«ãããã¬ã¹ãé
éã§ããªãã£ããçµæ㯠4æéã«ããã顧客ã¸ã®ãµã¼ãã¹æä¾ã®åªå¤±ã¨ãª
ã£ãã
77 Browns Ferry-3 å°ã® PLC é害ã¤ã³ã·ãã³ãã®è©³ç´°ã¯æ¬¡ã®ãµã¤ãã«ãããhttp://www.nrc.gov/reading-rm/doc-
collections/gen-comm/info-notices/2007/in200715.pdf [accessed 4/16/15].
78 詳細ã¯æ¬¡ã®ãµã¤ãã«ãããhttp://www-
pub.iaea.org/MTCD/meetings/PDFplus/2011/cn200/documentation/cn200_Final-Fukushima-
Mission_Report.pdf and http://pbadupws.nrc.gov/docs/ML1414/ML14140A185.pdf [each accessed
4/16/15].
79 èå¼±æ§ã¹ãã£ãã¼ã¤ã³ã·ãã³ãã®è©³ç´°ã¯æ¬¡ã®ãµã¤ãã«ãããhttp://energy.sandia.gov/wp/wp-
content/gallery/uploads/sand_2005_2846p.pdfhttp://www.sandia.gov/scada/documents/sand_2005_2846p.
pdf [accessed 4/16/15].
80 ãããã¬ã¼ã·ã§ã³ã»ãã¹ãã»ã¤ã³ã·ãã³ãã®è©³ç´°ã¯æ¬¡ã®ãµã¤ãã«ãããhttp://energy.sandia.gov/wp/wp-
content/gallery/uploads/sand_2005_2846p.pdf [accessed 4/16/15].

SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
283
Appendix DâCurrent Activities in Industrial Control System Security
This appendix contains abstracts of some of the many activities that are addressing ICS cybersecurity.
Please be aware that organization descriptions and related information provided in this appendix has been
drawn primarily from the listed organizationsâ Web sites and from other reliable public sources, but has not
been verified. Readers are encouraged to contact the organizations directly for the most up-to-date and
complete information.
American Gas Association (AGA) Standard 12, âCryptographic Protection of SCADA
Communicationsâ
American Gas Association: http://www.aga.org/
The American Gas Association, representing 195 local energy utility organizations that deliver natural gas
to more than 56 million homes, businesses, and industries throughout the United States, advocates the
interests of its energy utility members and their customers, and provides information and services. The
AGA 12 series of documents recommends practices designed to protect SCADA communications against
cyber incidents. The recommended practices focus on ensuring the confidentiality of SCADA
communications.
The purpose of the AGA 12 series is to save SCADA system ownersâ time and effort by recommending a
comprehensive system designed specifically to protect SCADA communications using cryptography. The
AGA 12 series may be applied to water, wastewater, and electric SCADA-based distribution systems
because of their similarities with natural gas systems, however timing requirements may be different.
Recommendations included in the series 12 documents may also apply to other ICS. Additional topics
planned for future addendums in this series include key management, protection of data at rest, and security
policies.
American Petroleum Institute (API) Standard 1164, âPipeline SCADA Securityâ
American Petroleum Institute: http://www.api.org/
The American Petroleum Institute represents more than 400 members involved in all aspects of the oil and
natural gas industry. API 1164 provides guidance to the operators of oil and natural gas pipeline systems
for managing SCADA system integrity and security. The guideline is specifically designed to provide
operators with a description of industry practices in SCADA security, and to provide the framework needed
to develop sound security practices within the operatorâs individual organizations. It stresses the
importance of operators understanding system vulnerability and risks when reviewing the SCADA system
for possible system improvements. API 1164 provides a means to improve the security of SCADA pipeline
operations by:
ï¼ Listing the processes used to identify and analyze the SCADA systemâs susceptibility to incidents.
ï¼ Providing a comprehensive list of practices to harden the core architecture.
ï¼ Providing examples of industry recommended practices.
The guideline targets small to medium pipeline operators with limited IT security resources. The guideline
is applicable to most SCADA systems, not just oil and natural gas SCADA systems. The appendices of the
document include a checklist for assessing a SCADA system and an example of a SCADA control system
security plan.

SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
284
ä»é² D ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ã»ãã¥ãªãã£ã«ãããç¾å¨ã®æ´»å
ãã®ä»é²ã§ã¯ãICS ãµã¤ãã¼ã»ãã¥ãªãã£ã対象ã¨ãã諸活åã®ããã¤ããåãã¾ã¨ãããè¨è¼
ããã¦ããçµç¹ã¨é¢é£æ
å ±ã¯ã主ã«è¨è¼ããã¦ããçµç¹ã®ã¦ã§ããµã¤ããã®ä»ä¿¡é ¼ã§ããå
¬éã®
åºæããåã£ããã®ã§ãæªæ¤è¨¼ã§ãããã¨ã«çæãããããç´æ¥ãããçµç¹ã«åãåãããææ°
æ
å ±ãå
¥æããããã«å¥¨å±ããã
ç±³å½ã¬ã¹åä¼ï¼AGAï¼è¦æ ¼ 12ãSCADA éä¿¡ã®æå·åä¿è·ã
ç±³å½ã¬ã¹åä¼ï¼http://www.aga.org/
195 ã®å°æ¹ã¨ãã«ã®ã¼ä¾çµ¦äºæ¥ä½ã代表ããç±³å½ã¬ã¹åä¼ã¯ãå
¨ç±³ã®ä¸è¬å®¶åº 5,600 ä¸ä¸å¸¯ãä¼
æ¥åã³æ¥çã«å¤©ç¶ã¬ã¹ãä¾çµ¦ããäºæ¥è
ã¨é¡§å®¢åæ¹ã®å©çãæè·ããæ
å ±åã³ãµã¼ãã¹ãæä¾ã
ã¦ãããAGA12 ã·ãªã¼ãºã¯ãSCADA ã·ã¹ãã ããµã¤ãã¼ã¤ã³ã·ãã³ãããå®ãããã®è¦ç¯ãæ¨
奨ãã¦ãããæ¨å¥¨è¦ç¯ã¯ãSCADA éä¿¡ã®æ©å¯æ§ã®ç¢ºä¿ã«éç¹ãç½®ãã¦ããã
åã·ãªã¼ãºã®ç®çã¯ãæå·ãå©ç¨ã㦠SCADA éä¿¡ãä¿è·ããå
æ¬çã·ã¹ãã ã®æ¨å¥¨ã«ããã
SCADA ã·ã¹ãã ä¿æè
ã®æéã¨å´åãç¯ç´ãããã¨ã«ãããåã·ãªã¼ãºã¯ã天ç¶ã¬ã¹ã·ã¹ãã
ã¨ã®å
±éæ§ãå¤ãæ°´éãä¸æ°´åã³ SCADA ãã¼ã¹ã®é
é»ã·ã¹ãã ã«é©ç¨ã§ããããã¿ã¤ãã³ã°ã«
é¢ããè¦ä»¶ã¯ç°ãªããã¨ãããã
æ¨å¥¨äºé
ã¯ä»ã® ICS ã«ãé©ç¨ã§ãããè£éºã¨ãã¦å°æ¥è¨ç»ããã¦ãããã®ã«ã¯ãéè¦ç®¡çäºé
ã
ä¼ç ä¸ã®ãã¼ã¿ä¿è·ãã»ãã¥ãªãã£ããªã·ã¼çãããã
ç±³å½ç³æ²¹åä¼ï¼APIï¼è¦æ ¼ 1164ããã¤ãã©ã¤ã³ SCADA ã»ãã¥ãªãã£ã
ç±³å½ç³æ²¹åä¼ï¼http://www.api.org/
ç±³å½ç³æ²¹åä¼ã¯ãç³æ²¹åã³å¤©ç¶ã¬ã¹æ¥çã®ããããé¢ã«å¾äºãã 400 以ä¸ã®ã¡ã³ãã¼ã代表ãã¦
ãããAPI1164 ã¯ãSCADA ã·ã¹ãã ã®å®å
¨æ§åã³ã»ãã¥ãªãã£ã®ç®¡çã«æºãããç³æ²¹åã³å¤©ç¶
ã¬ã¹ãã¤ãã©ã¤ã³ã·ã¹ãã æä½å¡åãã¬ã¤ãã³ã¹ã¨ãªããç¹ã« SCADA ã»ãã¥ãªãã£ã®æ¥çè¦ç¯
ã«ã¤ãã¦èª¬æããæä½å¡ã®çµç¹ã«ãããå¥å
¨ãªã»ãã¥ãªãã£è¦ç¯ãçå®ããããã®åºæ¬æ§æã示
ãã¦ãããSCADA ã·ã¹ãã ãç²¾æ»ãã¦æ¹åãå³ãéã«ãæä½å¡ãã·ã¹ãã ã®èå¼±æ§ã¨ãªã¹ã¯ã
ç解ãã大åãã強調ãã¦ãããAPI1164 ã¯ãSCADA ãã¤ãã©ã¤ã³éç¨ã®ã»ãã¥ãªãã£ãåä¸
ãããæ段ã¨ãã¦ã以ä¸ãæãã¦ããã
ï¼ SCADA ã·ã¹ãã ã®ã¤ã³ã·ãã³ãæåæ§ãèå¥ã»åæããããã®ããã»ã¹ã®åæ
ï¼ ã³ã¢ã¢ã¼ããã¯ãã£ãå¼·åºã«ããããã®å
æ¬çè¦ç¯ãªã¹ãã®ä½æ
ï¼ æ¥çæ¨å¥¨è¦ç¯ã®ä¾ç¤º
ãã®ã¬ã¤ãã©ã¤ã³ã¯ãIT ã»ãã¥ãªãã£ãªã½ã¼ã¹ãéãããä¸å°è¦æ¨¡ã®ãã¤ãã©ã¤ã³äºæ¥è
ã対象
ã¨ãã¦ãããç³æ²¹åã³å¤©ç¶ã¬ã¹ã®ã¿ãªãããã»ã¨ãã©ã® SCADA ã·ã¹ãã ã«é©ç¨ã§ãããã¬ã¤ã
ã©ã¤ã³ã®ä»é²ã«ã¯ãSCADA ã·ã¹ãã è©ä¾¡ã®ãã§ãã¯ãªã¹ãã SCADA å¶å¾¡ã·ã¹ãã ã»ãã¥ãªã
ã£è¨ç»æ¸ã®ä¾ãããã

SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
285
Electric Power Research Institute (EPRI)
http://www.epri.com/Our-Work/Pages/Cyber-Security.aspx,
http://smartgrid.epri.com/NESCOR.aspx
The Electric Power Research Institute (EPRI) is a nonprofit center for public interest energy and
environmental research. EPRI brings together member organizations, the Institute's scientists and engineers,
and other leading experts to work collaboratively on solutions to the challenges of electric power. These
solutions span nearly every area of power generation, delivery, and use, including health, safety, and
environment. EPRI's members represent over 90% of the electricity generated in the United States.
Industrial Control Systems Cyber Emergency Response Team (ICS-CERT)
https://ics-cert.us-cert.gov/About-Industrial-Control-Systems-Cyber-Emergency-Response-Team
The Industrial Control Systems Cyber Emergency Response Team (ICS-CERT) operates within the
National Cybersecurity and Integration Center (NCCIC), a division of the Department of Homeland
Security's Office of Cybersecurity and Communications (DHS CS&C). NCCIC/ICS-CERT is a key
component of the DHS Strategy for Securing Control Systems. The primary goal of the Strategy is to build
a long-term common vision where effective risk management of control systems security can be realized
through successful coordination efforts. ICS-CERT provides a control system security focus in
collaboration with US-CERT to:
ï¼ Respond to and analyze control systems related incidents.
ï¼ Conduct vulnerability and malware analysis.
ï¼ Provide onsite support for incident response and forensic analysis.
ï¼ Provide situational awareness in the form of actionable intelligence.
ï¼ Coordinate the responsible disclosure of vulnerabilities/mitigations.
ï¼ Share and coordinate vulnerability information and threat analysis through information products and
alerts.
ICS-CERT coordinates control systems-related security incidents and information sharing with Federal,
State, and local agencies and organizations, the intelligence community, and private sector constituents,
including vendors, owners and operators, and international and private sector CERTs. The focus on control
systems cybersecurity provides a direct path for coordination of activities among all members of the critical
infrastructure stakeholder community.
As a functional component of the NCCIC, ICS-CERT provides focused operational capabilities for defense
of control system environments against emerging cyber threats.
ICS-CERT provides efficient coordination of control-systems-related security incidents and information
sharing with federal, state, and local agencies and organizations, the Intelligence Community, private sector
constituents including vendors, owners, and operators, and international and private sector computer
security incident response teams (CSIRTs). The focus on control systems cybersecurity provides a direct
path for coordination of activities for all members of the stakeholder community.

SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
286
ç±³å½é»åç 究æï¼EPRIï¼
http://www.epri.com/Our-Work/Pages/Cyber-Security.aspx,
http://smartgrid.epri.com/NESCOR.aspx
ç±³å½é»åç 究æï¼EPRIï¼ã¯ãå
¬çã¨ãã«ã®ã¼ç°å¢ç 究ã«é¢ããéå¶å©å£ä½ã§ãããå çå£ä½ãç
究æã®ç§å¦è
ã»ã¨ã³ã¸ãã¢ãã®ä»å°é家ãæãã¦ãé»ååé¡ã®è§£æ±ºã«åãçµãã§ããã解決çã¯
çºé»ãé
é»ãå©ç¨ãªã©ããããåéã«ã¾ããããå¥åº·ãå®å
¨ãç°å¢çãå«ã¾ãããå çã¡ã³ãã¼
ã¯ãç±³å½çºé»éã® 90%以ä¸ãçç£ãã¦ããã
ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ãµã¤ãã¼ç·æ¥å¯¾å¿ãã¼ã (ICS-CERT)
https://ics-cert.us-cert.gov/About-Industrial-Control-Systems-Cyber-Emergency-Response-Team
ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ãµã¤ãã¼ç·æ¥å¯¾å¿ãã¼ã (ICS-CERT)ã¯ãå½å®¶ãµã¤ãã¼ã»ãã¥ãªãã£éä¿¡çµ±å
ã»ã³ã¿ã¼(NCCIC)å
ã§ãå½åå®å
¨ä¿éçã®ãµã¤ãã¼ã»ãã¥ãªãã£éä¿¡å±ï¼DHS CS&Cï¼ã®ä¸ã«ã
ããNCCIC/ICS-CERT ã¯ãå¶å¾¡ãµã¼ãã¹ã®ã»ãã¥ãªãã£ã確ä¿ãã DHS æ½çã®ä¸»è¦ãªæ§æè¦ç´
ã§ããããã®æ½çã®ä¸»ãªç®çã¯ãé·æã®å
±éçãã¸ã§ã³ãæã¡ç«ã¦ãç¸äºé£æºãéãã¦å¶å¾¡ã·ã¹
ãã ã»ãã¥ãªãã£ã®å¹æçãªã¹ã¯ç®¡çãå®ç¾ãããã¨ã«ãããICS-CERT ã¯US-CERT ã¨ã®é£æº
ãéãã¦ã以ä¸ãéç¹ã¨ããå¶å¾¡ã·ã¹ãã ã»ãã¥ãªãã£ãæ¨é²ããã
ï¼ å¶å¾¡ã·ã¹ãã é¢é£ã¤ã³ã·ãã³ãã¸ã®å¯¾å¿ã¨åæ
ï¼ èå¼±æ§ã¨ãã«ã¦ã¨ã¢ã®åæ
ï¼ ç¾å ´ã§ã®ã¤ã³ã·ãã³ã対å¿ã¨èª¿æ»åææ¯æ´
ï¼ å®ç¨çãªæ
å ±æä¾ã«ããæèã®é«æ
ï¼ èå¼±æ§ã»ç·©åçã®è²¬ä»»ããé示ã®èª¿æ´
ï¼ æ
å ±éç¥ã»ã¢ã©ã¼ãã«ããèå¼±æ§æ
å ±ã¨è
å¨åæã®å
±æã¨èª¿æ´
ICS-CERT ã¯å¶å¾¡ã·ã¹ãã é¢é£ã»ãã¥ãªãã£ã¤ã³ã·ãã³ãã¨æ
å ±ã調æ´ããå½ã»å·ã»å°æ¹èªæ²»
ä½ã»çµç¹ã»æ
å ±å
±åä½ã»æ°éä¼æ¥ï¼ãã³ãã¼ã»ä¿æè
ã»å½éæ°éä¼æ¥ CERT çï¼ã¨å
±æãããå¶
御ã·ã¹ãã ã®ãµã¤ãã¼ã»ãã¥ãªãã£ã«æ³¨åãããã¨ã§ãå
¨éè¦ã¤ã³ãã©é¢ä¿è
éã®æ´»åãç´æ¥èª¿
æ´ããéçãéããã
NCCIC ã®æ©è½è¦ç´ ã¨ã㦠ICS-CERT ã¯ãå¶å¾¡ã·ã¹ãã ç°å¢ãæ°èãµã¤ãã¼è
å¨ããå®ããããé
ä¸çãªéç¨è½åãä»ä¸ããã
ICS-CERT ã¯å¶å¾¡ã·ã¹ãã é¢é£ã»ãã¥ãªãã£ã¤ã³ã·ãã³ãã¨æ
å ±ã調æ´ããå½ã»å·ã»å°æ¹èªæ²»
ä½ã»çµç¹ã»æ
å ±å
±åä½ã»æ°éä¼æ¥ï¼ãã³ãã¼ã»ä¿æè
ã»æä½å¡ã»å½é/æ°éä¼æ¥ã³ã³ãã¥ã¼ã¿ã»
ãã¥ãªãã£ã¤ã³ã·ãã³ã対å¿ãã¼ã [CSIRT]çï¼ã¨å
±æãããå¶å¾¡ã·ã¹ãã ã®ãµã¤ãã¼ã»ãã¥ãª
ãã£ã«æ³¨åãããã¨ã§ãå
¨é¢ä¿è
ã«æ´»åãç´æ¥èª¿æ´ããéçãéãã

SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
287
ICS-CERT Cyber Security Evaluation Tool (CSET®)
http://ics-cert.us-cert.gov/Assessments
The Cyber Security Evaluation Tool (CSET®) is a DHS product that assists organizations in protecting
their key national cyber assets. It was developed under the direction of the DHS ICS-CERT by
cybersecurity experts and with assistance from NIST. This tool provides users with a systematic and
repeatable approach for assessing the security posture of their cyber systems and networks. It includes both
high-level and detailed questions related to all industrial control and IT systems.
CSET is a desktop software tool that guides users through a step-by-step process to assess their control
system and information technology network security practices against recognized industry standards. The
output from CSET is a prioritized list of recommendations for improving the cybersecurity posture of the
organization's enterprise and industrial control cyber systems. The tool derives the recommendations from a
database of cybersecurity standards, guidelines, and practices. Each recommendation is linked to a set of
actions that can be applied to enhance cybersecurity controls.
CSET has been designed for easy installation and use on a stand-alone laptop or workstation. It
incorporates a variety of available standards from organizations such as NIST, NERC, Transportation
Security Administration (TSA), U.S. Department of Defense (DoD), and others. When the tool user selects
one or more of the standards, CSET will open a set of questions to be answered. The answers to these
questions will be compared against a selected security assurance level, and a detailed report will be
generated to show areas for potential improvement. CSET provides an excellent means to perform a self-
assessment of the security posture of your control system environment.
ICS-CERT Recommended Practices
https://ics-cert.us-cert.gov/Introduction-Recommended-Practices
ICS-CERT works with the control systems community to ensure that recommended practices, which are
made available, have been vetted by subject-matter experts in industry before being made publicly
available in support of this program.
Recommended practices are developed to help users reduce their exposure and susceptibility to cyber
attacks. These recommendations are based on understanding the cyber threats, control systems
vulnerabilities and attack paths, and secure architecture design.
The recommended practices working group selects topics to be implemented in the recommended practices
section. Additional supporting documents detailing a wide variety of control systems topics associated
with cyber vulnerabilities and their mitigation have been developed and vetted by the working group for
accuracy. These documents will be updated and topics added to address additional content and emerging
issues.

SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
288
ICS-CERT ãµã¤ãã¼ã»ãã¥ãªãã£è©ä¾¡ãã¼ã«(CSET®)
http://ics-cert.us-cert.gov/Assessments
ICS-CERT ãµã¤ãã¼ã»ãã¥ãªãã£è©ä¾¡ãã¼ã«(CSET®)ã¯ãçµç¹ãå½ã®éè¦ãµã¤ãã¼è³ç£ãå®ãã®
ãæ¯æ´ãã DHS ã®è£½åã§ãããDHS ICS-CERT ã®æå°ä¸ã§ãNIST ã®æ¯æ´ãå¾ã¦ãµã¤ãã¼ã»ãã¥
ãªãã£å°é家ãéçºããããµã¤ãã¼ã·ã¹ãã åã³ãããã¯ã¼ã¯ã®ã»ãã¥ãªãã£ç¶æ
ãè©ä¾¡ããé
ã®ä½ç³»çãã¤å復çãªåçµãå¯è½ã¨ãªããããããç£æ¥ç¨å¶å¾¡åã³ IT ã·ã¹ãã ã«é¢ä¿ããé«åº¦
ã®è©³ç´°ãªçåã«çãã¦ããã
CSET ã¯ãã¹ã¯ãããã½ããã¦ã¨ã¢ãã¼ã«ã§ãå¶å¾¡ã·ã¹ãã åã³æ
å ±æè¡ãããã¯ã¼ã¯ã»ãã¥ãª
ãã£è¦ç¯ããåºãèªããããæ¥çåºæºã«ç
§ããã¦ã段éçã«è©ä¾¡ãããã¨ãã§ãããCSET ã«ã
ããçµç¹ã®ä¼æ¥ã»ç£æ¥ç¨å¶å¾¡ãµã¤ãã¼ã·ã¹ãã ã®ãµã¤ãã¼ã»ãã¥ãªãã£ç¶æ
ãæ¹åããããã®åª
å
çæ¨å¥¨äºé
ãªã¹ããä½æã§ããããã®ãã¼ã«ã¯ããµã¤ãã¼ã»ãã¥ãªãã£åºæºãã¬ã¤ãã©ã¤ã³å
ã³è¦ç¯ãã¼ã¿ãã¼ã¹ããæ¨å¥¨äºé
ãå°ãåºããããããã®æ¨å¥¨äºé
ã¯ããµã¤ãã¼ã»ãã¥ãªãã£ç®¡
çã®æ¡å¼µã«é©ç¨å¯è½ãªä¸é£ã®è¡åã«çµã³ã¤ãã¦ããã
CSET ã¯ãã¹ã¿ã³ãã¢ãã¼ã³ã©ããããããã¯ã¼ã¯ã¹ãã¼ã·ã§ã³ã«ãç°¡åã«ã¤ã³ã¹ãã¼ã«ãã¦å©
ç¨ã§ããããã«ãªã£ã¦ãããNISTãNERCãé輸ä¿å®å±(TSA)ãå½é²ç·çãã®ä»ã®çµç¹ããå
¥æ
å¯è½ãªç¨®ã
ã®åºæºãåãã¾ã¨ãã¦ããã¦ããããã¼ã«ã®ã¦ã¼ã¶ããããåºæºã®ãããããé¸æã
ãã¨ãä¸é£ã®è³ªåãæ示ãããã質åã¸ã®åçããé¸æãããã»ãã¥ãªãã£ä¿è¨¼ã¬ãã«ã¨ç
§ãã
åãããæ¹åã§ããåéã示ãã詳細ãªã¬ãã¼ããä½æãããããã«ãªã£ã¦ãããCSET ã¯ãå¶
御ã·ã¹ãã ç°å¢ã®ã»ãã¥ãªãã£ç¶æ
ãèªå·±è©ä¾¡ã§ããåªããæ段ã¨ãªãã
ICS-CERT æ¨å¥¨è¦ç¯
https://ics-cert.us-cert.gov/Introduction-Recommended-Practices
ICS-CERT ã¯å¶å¾¡ã·ã¹ãã ã®å
±åä½ã¨é£æºããå
¥æå¯è½ã«ãªã£ãæ¨å¥¨è¦ç¯ãå
¬éããåã«ãæ¥ç
ã®å¯¾è±¡å°é家ã«æ¤è¨¼ãä¾é ¼ããã
æ¨å¥¨è¦ç¯ã¯ããµã¤ãã¼æ»æã«å¯¾ããé²åºãæåæ§ãæ¸ããããã«ä½æãããããµã¤ãã¼è
å¨ãå¶
御ã·ã¹ãã ã®èå¼±æ§ã»æ»æçµè·¯åã³ã»ãã¥ã¢ãªã¢ã¼ããã¯ãã£è¨è¨ã«å¯¾ããç解ãåºã«ãã¦ããã
æ¨å¥¨è¦ç¯ä½æ¥ã°ã«ã¼ãã¯ãæ¨å¥¨è¦ç¯ã»ã¯ã·ã§ã³ã§åãä¸ããã¹ãè«é¡ãé¸å®ããããµã¤ãã¼èå¼±
æ§ã¨ãã®ç·©åçã«é¢ããå¤æ§ãªå¶å¾¡ã·ã¹ãã è«é¡ã«ã¤ãã¦è©³è¿°ããè£è¶³ææ¸ãä½æ¥ã°ã«ã¼ãã«ã
ãä½æãããæ£ç¢ºæ§ãæ¤è¨¼ããã¦ãããææ¸ã¯æ´æ°ãããè£è¶³çãªå
容ãæ°ããåé¡ãåãä¸ã
ãè«é¡ã追å ãããã

SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
289
Institute of Electrical and Electronics Engineers, Inc. (IEEE)
http://www.ieee.org
IEEE 1686-2007 â Standard for Substation IED Cybersecurity Capabilities. The functions and features to
be provided in substation intelligent electronic devices (lEDs) to accommodate critical infrastructure
protection programs are defined in this standard. Security regarding the access, operation, configuration,
firmware revision, and data retrieval from an IED is addressed in this standard. Communications for the
purpose of power system protection (teleprotection) is not addressed. Encryption for the secure
transmission of data both within and external to the substation, including supervisory control and data
acquisition, is not part of this standard as this is addressed in other efforts."
IEEE P1711 - Standard for a Cryptographic Protocol for Cybersecurity of Substation Serial Links. This
standard defines a cryptographic protocol to provide integrity, and optional confidentiality, for
cybersecurity of serial links. It does not address specific applications or hardware implementations, and is
independent of the underlying communications protocol.
IEEE 1815-2012 - Standard for Electric Power System Communications-Distributed Network Protocol
(DNP3). This standard describes the DNP3 SCADA protocol, incorporating version five of the application-
layer authentication procedure called DNP3 Secure Authentication (DNP3-SAv5). DNP3-SAv5 uses a
HMAC process to verify that data and commands are received (without tampering) from authorized
individual users or devices while limiting computational and communications overhead. SAv5 supports
remote update (add/change/revoke) of user credentials using either symmetric or PKI techniques. SAv5
authenticates but does not encrypt messages, hence it does not provide confidentiality. SAv5 can be used
together with encryption techniques such as TLS or IEEE 1711 where confidentiality is required.
Institute for Information Infrastructure Protection (I3P)
http://www.thei3p.org/
The I3P is a consortium of leading national cybersecurity institutions, including academic research centers,
government laboratories, and non-profit organizations. It was founded in September 2001 to help meet a
well-documented need for improved research and development (R&D) to protect the nation's information
infrastructure against catastrophic failures. The institute's main role is to coordinate a national cybersecurity
R&D program and help build bridges between academia, industry, and government. The I3P continues to
work toward identifying and addressing critical research problems in information infrastructure protection
and opening information channels between researchers, policymakers, and infrastructure operators.
Currently, the I3P does the following:
ï¼ Fosters collaboration among academia, industry, and government on pressing cybersecurity problems.
ï¼ Develops, manages, and supports national-scale research projects.
ï¼ Provides research fellowship opportunities to qualified post-doctoral researchers, faculty, and research
scientists.
ï¼ Hosts workshops, meetings, and events on cybersecurity and information infrastructure protection
issues.
ï¼ Builds and supports a knowledge base as an online vehicle for sharing and distributing information to
I3P members and others working on information security challenges.
SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
290
é»æ°é»åæè¡è
åä¼ï¼IEEEï¼
http://www.ieee.org
IEEE 1686-2007 â å¤é»æ IEDãµã¤ãã¼ã»ãã¥ãªãã£è¦æ ¼ãéè¦ã¤ã³ãã©é²è·ããã°ã©ã ã«åã£ã
å¤é»ææ
å ±é»åããã¤ã¹ï¼IEDsï¼ã«è¨è¼ããæ©è½ã»ç¹æ§ã¯ããã®è¦æ ¼ã§å®ç¾©ããããã¢ã¯ã»ã¹ã
éç¨ãæ§æããã¡ã¼ã ã¦ã¨ã¢æ¹æ£åã³ IED ããã®ãã¼ã¿åå¾ã¯ããã®è¦æ ¼ã§åãä¸ãããããé»
åã·ã¹ãã ä¿è·ç¨éä¿¡ï¼éä¿¡ä¿è·ï¼ã¯å¯¾è±¡å¤ã¨ãªããSCADA ãå«ããå¤é»æå
å¤ã§ã®ã»ãã¥ã¢
ãªãã¼ã¿éä¿¡ã®ããã®æå·åã¯ãå¥ã«æ±ãããããããã®è¦æ ¼ã§ã¯åãä¸ããããªãã
IEEE P1711 - å¤é»æã·ãªã¢ã«ãªã³ã¯ã®ãµã¤ãã¼ã»ãã¥ãªãã£ç¨æå·åãããã³ã«è¦æ ¼ããã®è¦æ ¼
ã¯æå·åãããã³ã«ã«ã¤ãã¦å®ããã·ãªã¢ã«ãªã³ã¯ã®å®å
¨æ§åã³ãªãã·ã§ã³ã®æ©å¯æ§ã«ã¤ãã¦è¦
å®ãããç¹å®ã®ã¢ããªã±ã¼ã·ã§ã³ããã¼ãã¦ã¨ã¢å®è£
ã¯åãä¸ãããåºæ¬éä¿¡ãããã³ã«ã«ã¯ä¾
åãã¦ããªãã
IEEE 1815-2012 - é»åã·ã¹ãã éä¿¡ã»é
é»ç¶²ãããã³ã«è¦æ ¼(DNP3)ããã®è¦æ ¼ã¯ãDNP3 ã»ãã¥
ã¢èªè¨¼(DNP3-SAv5)ã¨å¼ã°ããã¢ããªã±ã¼ã·ã§ã³å±¤èªè¨¼æé ã®ãã¼ã¸ã§ã³ 5ãåãå
¥ããã
DNP3 SCADA ã«ã¤ãã¦è¨è¿°ãã¦ãããDNP3-SAv5 ã¯HMAC ããã»ã¹ã使ç¨ãã¦ãæ¼ç®åã³éä¿¡
ãªã¼ãã¼ããããæãã¤ã¤ã権éããã¦ã¼ã¶åã¯ããã¤ã¹ãããã¼ã¿åã³ã³ãã³ããï¼æ¹ç«ãª
ãï¼åä¿¡ãããã©ãããæ¤è¨¼ãããSAv5 ã¯ã対称æè¡å㯠PKI æè¡ãç¨ãã¦ã¦ã¼ã¶èªè¨¼æ
å ±ã®
é éæ´æ°ï¼è¿½å ã»å¤æ´ã»åæ¶ï¼ããµãã¼ããããèªè¨¼ã¯è¡ãããæ©å¯æ§ããªãããã¡ãã»ã¼ã¸ã®
æå·åã¯è¡ããªããæ©å¯æ§ãå¿
è¦ãªå ´åã¯ãTLS ãIEEE 1711 çã®æå·åæè¡ãä½µç¨ããã
æ
å ±ã¤ã³ãã©ä¿è·ç 究æï¼I3Pï¼
http://www.thei3p.org/
I3P ã¯å¤§å¦ã®ç 究æãå½ç«ç 究æãNPO çã®ä¸»è¦ãµã¤ãã¼ã»ãã¥ãªãã£æ©é¢ãããªãã³ã³ã½ã¼ã·
ã¢ã ã§ãããå½ã®æ
å ±ã¤ã³ãã©ãå£æ»
çé害ããå®ãç®çã§ãç 究éçºãæ¹åãã¦ææ¸åããã
ã2001 å¹´9æã«åµè¨ãããã主ãªå½¹å²ã¯ãå½ã®ãµã¤ãã¼ã»ãã¥ãªãã£ç 究éçºããã°ã©ã ã®èª¿
æ´ãè¡ããç£å®å¦ã®é£æºãå³ããã¨ã«ãããI3P ã¯æ
å ±ã¤ã³ãã©ã®ä¿è·ã«ãããéè¦ãªç 究ä¸ã®
åé¡ãæããã«ãã¦åãä¸ããã¨ã¨ãã«ãç 究è
ãæ¿çç«æ¡è
åã³ã¤ã³ãã©éç¨è
éã®æ
å ±çµè·¯
ã®éæãç®æãã¦ãããç¾å¨æ¬¡ã®ãããªåçµãè¡ã£ã¦ããã
ï¼ ãµã¤ãã¼ã»ãã¥ãªãã£åé¡ã¨åãçµãç£å®å¦éã®é£æºå¼·å
ï¼ å½å®¶è¦æ¨¡ã®ç 究ããã¸ã§ã¯ãã®çå®ã»ç®¡çã»æ¯æ´
ï¼ æè³æ ¼å士課ç¨ä¿®äºå¾ç 究è
ã»æå¡ã»ç 究è
ã¸ã®ç 究æ©ä¼ã®æä¾
ï¼ ãµã¤ãã¼ã»ãã¥ãªãã£ã»æ
å ±ã¤ã³ãã©ä¿è·åé¡ã«é¢ããã¯ã¼ã¯ã·ã§ããã»ä¼è°ã»ã¤ãã³ãã®
éå¬
ï¼ I3P ã¡ã³ãã¼ãã®ä»æ
å ±ã»ãã¥ãªãã£åé¡é¢ä¿è
ã¸ã®æ
å ±å
±æã»é
ä¿¡åªä½ã¨ãã¦ã®ç¥èåºç¤
ã®æ§ç¯

SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
291
International Electrotechnical Commission (IEC) Technical Committees 65 and 57
http://www.iec.ch/
IEC is a standards organization that prepares and publishes international standards for all electrical,
electronic, and related technologies. These standards serve as a basis for creating national standards and as
references for drafting international tenders and contracts. IECâs members include manufacturers, providers,
distributors, vendors, consumers, and users, all levels of governmental agencies, professional societies,
trade associations, and standards developers from over 60 countries.
In 2004 the IEC Technical Sub-Committee 65C (Industrial Networks), through its working group WG13
(cybersecurity), started to address security issues - within the IEC 61784 standard â for field buses and
other industrial communication networks. Results of this work are outlined in part 4, entitled âDigital data
communications for measurement and control â Profiles for secure communications in industrial
networks.â
TC65 WG10 is working to extend this field level communication to address security standards across
common automation networking scenarios. The standard being drafted as a result of this work is IEC 62443,
entitled âSecurity for industrial process measurement and control â Network and system security.â It is
based on a modular security architecture consisting of requirement sets. These modules are mapped into
ICS component and network architecture. The resulting requirements can then be formulated for use as the
basis for Requests for Proposals (RFP) for data communication standards, and security audits.
TC 57 is focused on Power Systems Management and Associated Information Exchange and is divided up
into a series of working groups. Each working group is comprised of members of national standards
committees from the countries that participate in the IEC. Each working group is responsible for the
development of standards within its domain. The current working groups are:
ï¼ WG 3: Telecontrol protocols.
ï¼ WG 9: Distribution automation using distribution line carrier systems.
ï¼ WG 10: Power system IED communication and associated data models.
ï¼ WG 13: Energy management system application program interface (EMS-API).
ï¼ WG 14: System interfaces for distribution management (SIDM).
ï¼ WG 15: Data and communication security.
ï¼ WG 16: Deregulated energy market communications.
ï¼ WG 17: Communications Systems for Distributed Energy Resources (DER).
ï¼ WG 18: Hydroelectric power plants â Communication for monitoring and control.
ï¼ WG 19: Interoperability within TC 57 in the long term.
ï¼ WG 20: Planning of (single-sideband) power line carrier systems (IEC 60495) Planning of (single-
sideband) power line carrier systems (IEC 60663).
ï¼ WG 21: Interfaces and protocol profiles relevant to systems connected to the electrical grid.

SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
292
å½éé»æ°æ¨æºä¼è°ï¼IECï¼æè¡å§å¡ä¼ 65 åã³ 57
http://www.iec.ch/
IEC ã¯ããããé»æ°ãé»ååã³é¢é£æè¡ã«é¢ããå½éè¦æ ¼ãä½æããçºè¡¨ããè¦æ ¼çµç¹ã§ããã
è¦æ ¼ã¯ãå½ã®è¦æ ¼ä½æã®æ ¹æ ã¨ãªããå½éå
¥æã»å¥ç´ãèµ·èããéã®åèã¨ãªããIEC ã¡ã³ãã¼
ã¯ã¡ã¼ã«ã¼ããããã¤ããæµéæ¥è
ããã³ãã¼ãæ¶è²»è
ã»ã¦ã¼ã¶ãåç´ã¬ãã«ã®è¡æ¿æ©é¢ãå°é
家åä¼ã貿æåä¼åã³ 60 ãå½ã®è¦æ ¼ä½æå£ä½ã§ããã
IEC æè¡ä¸é¨å§å¡ä¼ 65Cï¼ç£æ¥ç¨ãããã¯ã¼ã¯ï¼ã¯ 2004 å¹´ããã®ä½æ¥ã°ã«ã¼ã WG13ï¼ãµã¤ãã¼
ã»ãã¥ãªãã£ï¼ãéãã¦ãIEC61784 è¦æ ¼ã®ä¸é¨ã¨ãã¦ããã£ã¼ã«ããã¹ãã®ä»ç£æ¥ç¨éä¿¡ãã
ãã¯ã¼ã¯ã®ã»ãã¥ãªãã£åé¡ã®æ¤è¨ã«çæããããã®ä½æ¥ã®çµæã¯ããã¼ã 4ãè¨æ¸¬å¶å¾¡ã®ãã
ã®ãã¸ã¿ã«ãã¼ã¿éä¿¡ï¼ç£æ¥ç¨ãããã¯ã¼ã¯ã«ãããã»ãã¥ã¢ãªéä¿¡ã®ãããã¡ã¤ã«ãã«æ¦èª¬ã
ãã¦ããã
TC65 WG10 ã¯ããã®ãã£ã¼ã«ãã¬ãã«éä¿¡ãæ¡å¼µãã¦ãå
±éãªã¼ãã¡ã¼ã·ã§ã³ãããã¯ã¼ãã³
ã°ã·ããªãªã§ã®ã»ãã¥ãªãã£è¦æ ¼ãåãä¸ããããã®çµæèµ·èãããè¦æ ¼ã IEC 62433 ã§ããç£
æ¥ç¨è¨æ¸¬å¶å¾¡ã®ã»ãã¥ãªã㣠- ãããã¯ã¼ã¯åã³ã·ã¹ãã ã»ãã¥ãªãã£ãã¨é¡ãããããã¤ãã®
è¦ä»¶ãããªãã¢ã¸ã¥ã¼ã«å¼ã®ã»ãã¥ãªãã£ã¢ã¼ããã¯ãã£ãåºæ¬ã¨ãã¦ãããããããã®ã¢ã¸ã¥
ã¼ã«ã¯ãICS ã³ã³ãã¼ãã³ãåã³ãããã¯ã¼ã¯ã¢ã¼ããã¯ãã£ã«ãããã³ã°ããããããããè¦
件ãå®ãããããã¼ã¿éä¿¡è¦æ ¼åã³ã»ãã¥ãªãã£ç£æ»ã«å¯¾ããææ¡è¦æ±ï¼RFPï¼ã®åºç¤ã¨ãã¦å©
ç¨ãããã
TC57 ã¯é»åã·ã¹ãã 管çåã³é¢é£æ
å ±äº¤æã«ç¹åãã¦ãããä¸é£ã®ã°ã«ã¼ãã«ååãã¦ããã
åä½æ¥ã°ã«ã¼ãã¯ãIEC å çåå½ã®è¦æ ¼å§å¡ä¼ã¡ã³ãã¼ã§æ§æããã¦ãããåã°ã«ã¼ãã¯ããã
ããã®ãã¡ã¤ã³å
ã§ã®è¦æ ¼ä½æãæ
å½ãããç¾å¨ã®ä½æ¥ã°ã«ã¼ãã¯ä»¥ä¸ã®ã¨ããã
ï¼ WG 3ï¼é éå¶å¾¡ãããã³ã«
ï¼ WG 9ï¼é
é»ç·æ¬éã·ã¹ãã ãå©ç¨ããé
é»èªåå
ï¼ WG 10ï¼é»åã·ã¹ãã IED éä¿¡åã³é¢é£ãã¼ã¿ã¢ãã«
ï¼ WG 13ï¼ç·æ¥ç®¡çã·ã¹ãã ã¢ããªã±ã¼ã·ã§ã³ããã°ã©ã ã¤ã³ã¿ãã§ã¼ã¹ï¼EMS-APIï¼
ï¼ WG 14ï¼é
é»ç®¡çã·ã¹ãã ã¤ã³ã¿ãã§ã¼ã¹ï¼SIDMï¼
ï¼ WG 15ï¼ãã¼ã¿åã³éä¿¡ã»ãã¥ãªãã£
ï¼ WG 16ï¼ã¨ãã«ã®ã¼å¸å ´éä¿¡ã®è¦å¶ç·©å
ï¼ WG 17ï¼åæ£ã¨ãã«ã®ã¼ãªã½ã¼ã¹éä¿¡ã·ã¹ãã ï¼DERï¼
ï¼ WG 18ï¼æ°´åçºé»æ - ç£è¦å¶å¾¡ç¨éä¿¡
ï¼ WG 19ï¼TC57 å
ã§ã®é·æç¸äºéç¨æ§
ï¼ WG 20ï¼ï¼åå´æ³¢å¸¯ï¼éé»ç·æ¬éã·ã¹ãã ã®ãã©ã³ãã³ã°ï¼IEC 60495ï¼ãï¼åå´æ³¢å¸¯ï¼é
é»ç·æ¬éã·ã¹ãã ã®ãã©ã³ãã³ã°ï¼IEC 60663ï¼
ï¼ WG 21ï¼é
é»ç¶²æ¥ç¶ã·ã¹ãã ã«ä¿ãã¤ã³ã¿ãã§ã¼ã¹åã³ãããã³ã«ãããã¡ã¤ã«

SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
293
ISA99 Industrial Automation and Control Systems Security Standards
http://www.isa.org/isa99
The ISA99 standards development committee brings together industrial cybersecurity experts from across
the globe to develop ISA standards on industrial automation and control system (IACS) security. This
original and ongoing ISA99 work is being standardized by the IEC in producing the multi-standard IEC
62443 series. The committeeâs focus is to improve the confidentiality, integrity, and availability of
components or systems used for automation or control and provides criteria for procuring and
implementing secure control systems. Compliance with the committeeâs guidance will improve industrial
automation and control system electronic security, and will help identify vulnerabilities and address them,
thereby reducing the risk of compromising confidential information or causing industrial automation
control system degradation or failure.
All ISA-62443 standards and technical reports are organized into four general categories called General,
Policies and Procedures, System, and Component.
ï¼ General category includes common or foundational information such as concepts, models and
terminology. Also included are work products that describe security metrics and security life cycles for
IACS.
ï¼ Policies and Procedures category of work products targets the Asset Owner. These address various
aspects of creating and maintaining an effective IACS security program.
ï¼ System category includes work products that describe system design guidance and requirements for
the secure integration of control systems. Core in this is the zone and conduit design model.
ï¼ Component category includes work products that describe the specific product development and
technical requirements of control system products. This is primarily intended for control product
vendors, but can be used by integrator and asset owners for to assist in the procurement of secure
products.
The current status of the ISA-62443 documents is provided on the ISA99 Wiki at
http://isa99.isa.org/ISA99 Wiki/
General
ï¼ ISA-62443-1-1 (IEC/TS 62443-1-1) (formerly referred to as "ISA-99 Part 1") was originally
published as ISA standard ANSI/ISA-99.00.01-2007, as well as an IEC technical specification IEC/TS
62443-1-1. The ISA99 committee is currently revising it to make it align with other documents in the
series, and to clarify normative content.
ï¼ ISA-TR62443-1-2 (IEC 62443-1-2) is a master glossary of terms used by the ISA99 committee. This
document is a working draft.
ï¼ ISA-62443-1-3 (IEC 62443-1-3) identifies a set of compliance metrics for IACS security. This
document is currently under development and the committee will be releasing a draft for comment in
2013.
ï¼ ISA-TR62443-1-4 (IEC/TS 62443-1-4) defines the IACS security life cycle and use case. This work
product has been proposed as part of the series, but as of January 2013 development had not yet
started.

SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
294
ISA99 ç£æ¥ãªã¼ãã¡ã¼ã·ã§ã³åã³å¶å¾¡ã·ã¹ãã ã»ãã¥ãªãã£è¦æ ¼
http://www.isa.org/isa99
ISA99 è¦æ ¼ä½æå§å¡ä¼ã¯ãä¸çã®ç£æ¥ãµã¤ãã¼ã»ãã¥ãªãã£å°é家ãæéãã¦ãç£æ¥ãªã¼ãã¡ã¼
ã·ã§ã³å¶å¾¡ã·ã¹ãã ï¼IACSï¼ã»ãã¥ãªãã£ã® ISA è¦æ ¼ã®ä½æã«åãçµãã§ãããå½ååã³ç¾è¡
ã®ISA99 ä½æ¥ã¯ãIEC ã«ããæ¨æºåãããè¤æ°ã®è¦æ ¼ IEC62443 ã·ãªã¼ãºã®ä½æãç®æãã¦ããã
å§å¡ä¼ã®ç¦ç¹ã¯ãèªååãå¶å¾¡ã«ä½¿ç¨ããã³ã³ãã¼ãã³ããã·ã¹ãã ã®æ©å¯æ§ã»å®å
¨æ§ã»å¯ç¨æ§
ãæ¹åããã»ãã¥ã¢ãªå¶å¾¡ã·ã¹ãã ã®èª¿éã»å®è£
åºæºãå®ãããã¨ã«ãããå§å¡ä¼ã®ã¬ã¤ãã³ã¹
ã«å¾ããã¨ã§ãç£æ¥ãªã¼ãã¡ã¼ã·ã§ã³ãå¶å¾¡ã·ã¹ãã ã®é»åçã»ãã¥ãªãã£ãæ¹åãããèå¼±æ§
ã¨å¯¾å¦æ¹æ³ãæããã«ãªããç§å¯æ
å ±ã®æ¼æ´©ãç£æ¥ãªã¼ãã¡ã¼ã·ã§ã³å¶å¾¡ã·ã¹ãã ã®å£åã»æ
é
ãªã¹ã¯ãæ¸ãã
ISA-62443 è¦æ ¼åã³æè¡å ±åæ¸ã¯ãã©ããå
¨è¬ãããªã·ã¼ã»æé ãã·ã¹ãã åã³ã³ã³ãã¼ãã³ã
ã®ããããã«åé¡ãããã
ï¼ å
¨è¬åºåã«ã¯æ¦å¿µã»ã¢ãã«ã»ç¨èªã¨ãã£ãå
±éçåã¯åºæ¬çæ
å ±ãå«ã¾ãããã¾ããIACS
ã®ã»ãã¥ãªãã£è©ä¾¡åºæºåã³ã»ãã¥ãªãã£ã©ã¤ããµã¤ã¯ã«ã«ã¤ãã¦è¨è¿°ããä½æ¥ææãå«ã¾
ããã
ï¼ ä½æ¥ææã®ããªã·ã¼ã»æé åºåã¯ãè³ç£ä¿æè
ã対象ã«ãããã®ã§ãããå¹æç㪠IACS ã»
ãã¥ãªãã£ããã°ã©ã ã®ä½æåã³ä¿å®ã®æ§ã
ãªé¢ãåãä¸ãã¦ããã
ï¼ ã·ã¹ãã åºåã«ã¯ãå¶å¾¡ã·ã¹ãã ã®ã»ãã¥ã¢ãªçµ±ååã«é¢ããã·ã¹ãã è¨è¨ã¬ã¤ãã³ã¹ã¨è¦
件ã«ã¤ãã¦è¨è¿°ããä½æ¥ææãå«ã¾ãããä¸å¿ã¨ãªãã®ã¯å°ååã³ã³ã³ã¸ããè¨è¨ã¢ãã«ã§
ããã
ï¼ ã³ã³ãã¼ãã³ãåºåã«ã¯ãç¹å®è£½åã®éçºã¨å¶å¾¡ã·ã¹ãã 製åã®æè¡è¦ä»¶ã«ã¤ãã¦è¨è¿°ãã
ä½æ¥ææãå«ã¾ããã主ãªå¯¾è±¡ã¯å¶å¾¡è£½åãã³ãã¼ã§ããããã¤ã³ãã°ã¬ã¼ã¿ãè³ç£ä¿æè
ãã»ãã¥ã¢ãªè£½åã調éããéã®è³ã¨ãããã¨ãã§ããã
ISA-62443 ææ¸ã®ç¾ç¶ã«ã¤ãã¦ã¯ã次㮠ISA99 Wiki ãµã¤ãã§ç¢ºèªã§ããã
http://isa99.isa.org/ISA99 Wiki/
å
¨è¬
ï¼ ISA-62443-1-1 (IEC/TS 62443-1-1)ï¼æ§ç§°ãISA-99 Part 1ãï¼ã¯å½å ISA è¦æ ¼ ANSI/ISA-
99.00.01-2007 åã³ IEC æè¡ä»æ§æ¸ IEC/TS 62443-1-1 ã¨ãã¦çºè¡¨ããããISA99 å§å¡ä¼ã¯ãã·
ãªã¼ãºã®ä»ã®ææ¸ã¨ã®æ´åæ§ã確ä¿ããæ¨æºçãªå
容ãæ確ã«ãããããç¾å¨ããã®è¦ç´ã
ä¸ã§ããã
ï¼ ISA-TR62443-1-2 (IEC 62443-1-2)ã¯ãISA99 ã使ç¨ããç¨èªã®ç·ç¨èªéã§ãããã¾ã èæ¡æ®µ
éã«ããã
ï¼ ISA-62443-1-3 (IEC 62443-1-3)ã¯ãIACS ã»ãã¥ãªãã£ã®ä¸é£ã®ã³ã³ãã©ã¤ã¢ã³ã¹è©ä¾¡åºæºã¨
ãªããç¾å¨ä½æä¸ã§ã2013 å¹´ã«æ¡ãçºè¡¨ããæè¦ãåéããã
ï¼ ISA-TR62443-1-4 (IEC/TS 62443-1-4)ã¯ãIACS ã®ã»ãã¥ãªãã£ã©ã¤ããµã¤ã¯ã«ã¨ä½¿ç¨ä¾ãè¨
è¼ãã¦ããããã®ä½æ¥ææã¯ã·ãªã¼ãºã®ä¸é¨ã¨ãã¦æå±ããããã2013 å¹´1ææç¹ã§ä½æ
ã«æªçæã§ããã

SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
295
Policies and Procedures
ï¼ ISA-62443-2-1 (IEC 62443-2-1) (formerly referred to as "ANSI/ISA 99.02.01-2009 or ISA-99 Part
2") addresses how to establish an IACS security program. This standard is approved and published the
IEC as IEC 62443-2-1. It now being revised to permit closer alignment with the ISO 27000 series of
standards.
ï¼ ISA-TR62443-2-2 (IEC 62443-2-2) addresses how to operate an IACS security program. This
standard is currently under development.
ï¼ ISA-TR62443-2-3 (IEC/TR 62443-2-3) is a technical report on the subject of patch management in
IACS environments. This report is currently under development.
ï¼ ISA-62443-2-4 (IEC 62443-2-4) focuses on the certification of IACS supplier security policies and
practices. This document was adopted from the WIB organization and is now a working product of the
IEC TC65/WG10 committee. The proposed ISA version will be a U.S. national publication of the IEC
standard.
System
ï¼ ISA-TR62443-3-1 (IEC/TR 62443-3-1) is a technical report on the subject of suitable technologies
for IACS security. This report is approved and published as ANSI/ISA-TR99.00.01-2007 and is now
being revised.
ï¼ ISA-62443-3-2 (IEC 62443-3-2) addresses how to define security assurance levels using the zones
and conduits concept. This standard is currently under development.
ï¼ ISA-62443-3-3 (IEC 62443-3-3) defines detailed technical requirements for IACS security. This
standard has been published as ANSI/ISA-62443-3-3 (99.03.03)-2013. It was previously numbered as
ISA-99.03.03.
Component
ï¼ ISA-62443-4-1 (IEC 62443-4-1) addresses the requirements for the development of secure IACS
products and solutions. This standard is currently under development.
ï¼ ISA-62443-4-2 (IEC 62443-4-2) series address detailed technical requirements for IACS components
level. This standard is currently under development.
ISA100 Wireless Systems for Automation
http://www.isa.org/isa100
The ISA100 Committee will establish standards, recommended practices, technical reports, and related
information that will define procedures for implementing wireless systems in the automation and control
environment with a focus on the field level. Guidance is directed towards those responsible for the
complete life cycle including the designing, implementing, on-going maintenance, scalability or managing
industrial automation and control systems, and shall apply to users, system integrators, practitioners, and
control systems manufacturers and vendors.

SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
296
ããªã·ã¼åã³æé
ï¼ ISA-62443-2-1 (IEC 62443-2-1) (æ§ç§°ãANSI/ISA 99.02.01-2009 å㯠ISA-99 Part 2ã)ã¯ãIACS
ã»ãã¥ãªãã£ããã°ã©ã ã®çå®æ¹æ³ãåãä¸ãã¦ããããã®è¦æ ¼ã¯æ¿èªãããIEC 62443-2-
1ã¨ãã¦çºè¡¨ããããç¾å¨ ISO27000 ã·ãªã¼ãºè¦æ ¼ã¨ã®æ´åæ§ã確ä¿ããããæ¹è¨ä¸ã§ããã
ï¼ ISA-TR62443-2-2 (IEC 62443-2-2)ã¯ãIACS ã»ãã¥ãªãã£ããã°ã©ã ã®éç¨æ¹æ³ãåãä¸ããã
ãã®è¦æ ¼ã¯ç¾å¨ä½æä¸ã§ããã
ï¼ ISA-TR62443-2-3 (IEC/TR 62443-2-3)ã¯ãIACS ç°å¢ã«ãããããã管çã«é¢ããæè¡å ±åæ¸
ã§ããããã®å ±åæ¸ã¯ç¾å¨ä½æä¸ã§ããã
ï¼ ISA-62443-2-4 (IEC 62443-2-4)ã¯ãIACS ãµãã©ã¤ã¤ã®ã»ãã¥ãªãã£ããªã·ã¼åã³è¦ç¯ã®èªå®
æ¸ã«ç¹åãã¦ãããæ¬æ¸ã¯ WIB çµç¹ãæ¡ç¨ããIEC TC65/WG10 å§å¡ä¼ã®ä½æ¥ææã¨ãªã£ã¦
ãããISA çã®æ¡ã¯ãIEC è¦æ ¼ã®æ¿åºææ¸ã¨ãªããã
ã·ã¹ãã
ï¼ ISA-TR62443-3-1 (IEC/TR 62443-3-1)ã¯ãIACS ã»ãã¥ãªãã£ã®é©åæè¡ã«é¢ããæè¡å ±åæ¸
ã§ãããæ¬å ±åæ¸ã¯æ¿èªãããANSI/ISA-TR99.00.01-2007 ã¨ãã¦çºè¡¨ãããç¾å¨æ¹è¨ä¸ã§ã
ãã
ï¼ ISA-62443-3-2 (IEC 62443-3-2)ã¯ãå°ååã³ã³ã³ã¸ããè¨è¨æ¦å¿µãå©ç¨ããã»ãã¥ãªãã£ä¿
証ã¬ãã«ã®å®ç¾©æ¹æ³ã«ã¤ãã¦åãä¸ãã¦ããããã®è¦æ ¼ã¯ç¾å¨ä½æä¸ã§ããã
ï¼ ISA-62443-3-3 (IEC 62443-3-3)ã¯ãIACS ã»ãã¥ãªãã£ã®è©³ç´°ãªæè¡è¦ä»¶ã«ã¤ãã¦æããã«ã
ã¦ããããã®è¦æ ¼ã¯ ANSI/ISA-62443-3-3 (99.03.03)-2013 ã¨ãã¦çºè¡¨ããããæ§çªå·ã¯ ISA-
99.03.03 ã ã£ãã
ã³ã³ãã¼ãã³ã
ï¼ ISA-62443-4-1 (IEC 62443-4-1)ã¯ãã»ãã¥ã¢ãª IACS 製ååã³ã½ãªã¥ã¼ã·ã§ã³ã®éçºè¦ä»¶ã«ã¤
ãã¦åãä¸ãã¦ããããã®è¦æ ¼ã¯ç¾å¨ä½æä¸ã§ããã
ï¼ ISA-62443-4-2 (IEC 62443-4-2)ã·ãªã¼ãºã¯ãIACS ã³ã³ãã¼ãã³ãã¬ãã«ã®è©³ç´°ãªæè¡è¦ä»¶ã«
ã¤ãã¦åãä¸ãã¦ããããã®è¦æ ¼ã¯ç¾å¨ä½æä¸ã§ããã
ISA100 ãªã¼ãã¡ã¼ã·ã§ã³ç¨ã¯ã¤ã¤ã¬ã¹ã·ã¹ãã
http://www.isa.org/isa100
ISA100 å§å¡ä¼ã¯ããã£ã¼ã«ãã¬ãã«ã«ç¹åãããªã¼ãã¡ã¼ã·ã§ã³åã³å¶å¾¡ç°å¢ã«ãããã¯ã¤ã¤
ã¬ã¹ã·ã¹ãã ã®æé ãè¦å®ããè¦æ ¼ãæ¨å¥¨è¦ç¯ãå®ããæè¡å ±åæ¸ãé¢é£æ
å ±ãé
ä¿¡ãããã¬ã¤
ãã³ã¹ã¯ç£æ¥ãªã¼ãã¡ã¼ã·ã§ã³åã³å¶å¾¡ã·ã¹ãã ã®è¨è¨ãå®è£
ãæ常çä¿å®ãã¹ã±ã¼ã©ããªãã£ã
管ççã©ã¤ããµã¤ã¯ã«å
¨è¬ã®æ
å½è
ã対象ã¨ããã¦ã¼ã¶ãã·ã¹ãã ã¤ã³ãã°ã¬ã¼ã¿ãå®åå¾äºè
åã³å¶å¾¡ã·ã¹ãã ã¡ã¼ã«ã¼ã»ãã³ãã¼ã«é©ç¨ãããã

SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
297
ISO 27001
http://www.iso.org/, http://www.27000.org
ISO 27001 provides a model for establishing, implementing, operating, monitoring, reviewing, maintaining
and improving an Information Security Management System. The objective of the standard itself is to
"provide requirements for establishing, implementing, maintaining and continuously improving an
Information Security Management System (ISMS).â Regarding its adoption, this should be a strategic
decision. Further, "The design and implementation of an organization's information security management
system is influenced by the organization's needs and objectives, security requirements, the organizational
processes used and the size and structure of the organization.â The content sections of the standard include:
ï¼ Context of the Organization.
ï¼ Information Security Leadership.
ï¼ Planning an ISMS.
ï¼ Support.
ï¼ Operation.
ï¼ Performance Evaluation.
ï¼ Improvement.
ï¼ Annex A â List of controls and their objectives.
The 2005 version of the standard heavily employed the Plan-Do-Check-Act model to structure the
processes, and reflect the principles set out in the OECG guidelines (see oecd.org). However, the latest,
2013 version, places more emphasis on measuring and evaluating how well an organizationâs ISMS is
performing.

SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
298
ISO 27001
http://www.iso.org/, http://www.27000.org
ISO27001 ã¯ãæ
å ±ã»ãã¥ãªãã£ç®¡çã·ã¹ãã ã®ç¢ºç«ãå®è£
ãéç¨ãç£è¦ã調æ»ãä¿å®åã³æ¹å
ã«é¢ããã¢ãã«ã¨ãªãããã®ä¼ç»ã®ç®çã¯ããæ
å ±ã»ãã¥ãªãã£ç®¡çã·ã¹ãã ï¼ISMSï¼ã®ç¢ºç«ã
å®è£
ãä¿å®åã³ç¶ç¶çæ¹åã«é¢ããè¦ä»¶ã示ãããã¨ã«ããããã®æ¡ç¨ã«ã¤ãã¦ã¯ãæ¦ç¥çãªæ±º
å®äºé
ã¨ãªããæ´ã«ãçµç¹ã®æ
å ±ã»ãã¥ãªãã£ç®¡çã·ã¹ãã ã®è¨è¨åã³å®è£
ã¯ãçµç¹ã®å¿
è¦ã»ç®
çãã»ãã¥ãªãã£è¦ä»¶ãçµç¹çããã»ã¹åã³çµç¹ã®è¦æ¨¡ã»æ§é ã«å½±é¿ãããããè¦æ ¼ã®ç®æ¬¡æ§æ
ã¯ä»¥ä¸ã®ã¨ããã
ï¼ çµç¹ã®æ
æ³
ï¼ æ
å ±ã»ãã¥ãªãã£ã®æå°
ï¼ ISMS ã®ãã©ã³ãã³ã°
ï¼ æ¯æ´
ï¼ éç¨
ï¼ æ¥ç¸¾è©ä¾¡
ï¼ æ¹å
ï¼ ä»é² A - å¶å¾¡ã¨ãã®ç®çãªã¹ã
2005 å¹´çè¦æ ¼ã§ã¯ãè¨ç»ã»å®è¡ã»ç¢ºèªã»è¡åã¢ãã«ã大ãã«åãå
¥ããããã»ã¹ãæ§é åãã
OECG ã¬ã¤ãã©ã¤ã³ã«è¨è¼ããã¦ããååãåæ ãã¦ããï¼oecd.org ãåç
§ï¼ããããææ°ã®
2013 å¹´çã§ã¯ãçµç¹ã® ISMS æ¥åéè¡ç¶æ³ã®è¨æ¸¬ã»è©ä¾¡ã«ãã£ããã®éç¹ãç½®ããã¦ããã

SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
299
ISO 27002
http://www.iso.org/, http://www.27000.org
ISO 27002 "established guidelines and general principles for initiating, implementing, maintaining, and
improving information security management within an organization." The actual controls listed in the
standard are intended to address the specific requirements identified via a formal risk assessment. The
standard is also intended to provide a guide for the development of "organizational security standards and
effective security management practices and to help build confidence in inter-organizational activities."81
In 2013 the current version was published. ISO 27002:2013 contains 114 controls, fewer than the 133
documented in the 2005 version. However for additional granularity, these are presented in 14 sections,
rather than the original 11:
ï¼ Security Policy.
ï¼ Organization of Information Security.
ï¼ Human Resource Security.
ï¼ Asset Management.
ï¼ Access Control.
ï¼ Cryptography.
ï¼ Physical and Environmental Security.
ï¼ Operations Security.
ï¼ Communications Security.
ï¼ Information Systems Acquisition, Development, Maintenance.
ï¼ Supplier Relationships.
ï¼ Information Security Incident Management.
ï¼ Information Security Aspects of Business Continuity.
ï¼ Compliance.
81 http://www.27000.org/iso-27002.htm.

SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
300
ISO 27002
http://www.iso.org/, http://www.27000.org
ISO 27002 ã¯ãçµç¹å
ã«ãããæ
å ±ã»ãã¥ãªãã£ç®¡çã®éå§ãå®è£
ãä¿å®åã³æ¹åã«é¢ããã¬
ã¤ãã©ã¤ã³ã¨ä¸è¬ååãå®ããããè¦æ ¼ã®ãªã¹ãã«å«ã¾ãã¦ããå®éã®å¶å¾¡ã¯ãæ£è¦ã®ãªã¹ã¯è©
価ã§å®ããããå
·ä½çè¦ä»¶ãåãä¸ãã¦ãããã¾ããçµç¹ã®ã»ãã¥ãªãã£åºæºåã³å¹æçãªã»ã
ã¥ãªãã£ç®¡çè¦ç¯ï¼ã®çºå±ã«åããã¬ã¤ããä¸ãï¼ãçµç¹éæ´»åã¸ã®ä¿¡é ¼ã®é¸æã«è³ããããã¨
ãç®çã¨ãã¦ããã82
ç¾è¡ç㯠2013 å¹´ã«çºè¡¨ããããISO 27002:2013 ã«ã¯ 114 ã®å¶å¾¡ãç´ãããã¦ããã2005 å¹´çã®
133 ãããæ¸ã£ã¦ããããã ãã»ã¯ã·ã§ã³ã¯ 11 ãã次㮠14 ã«å¢ããããç´°ãããªã£ã¦ããã
ï¼ ã»ã¯ã·ã§ã³ããªã·ã¼
ï¼ æ
å ±ã»ãã¥ãªãã£çµç¹
ï¼ äººçè³ç£ã®ã»ãã¥ãªãã£
ï¼ è³ç£ç®¡ç
ï¼ ã¢ã¯ã»ã¹å¶å¾¡
ï¼ æå·å
ï¼ ç©ççã»ç°å¢çã»ãã¥ãªãã£
ï¼ éç¨ã»ãã¥ãªãã£
ï¼ éä¿¡ã»ãã¥ãªãã£
ï¼ æ
å ±ã·ã¹ãã ã®åå¾ã»éçºã»ä¿å®
ï¼ ãµãã©ã¤ã¤ã¨ã®é¢ä¿
ï¼ æ
å ±ã»ãã¥ãªãã£ã¤ã³ã·ãã³ã管ç
ï¼ æ
å ±ã»ãã¥ãªãã£é¢ããè¦ãäºæ¥ç¶ç¶æ§
ï¼ ã³ã³ãã©ã¤ã¢ã³ã¹
82 http://www.27000.org/iso-27002.htm.

SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
301
International Council on Large Electric Systems (CIGRE)
http://www.cigre.org/
The International Council on Large Electric Systems (CIGRE) is a nonprofit international association based
in France. It has established several study committees to promote and facilitate the international exchange
of knowledge in the electrical industry by identifying recommended practices and developing
recommendations. Three of its study committees focus on control systems:
ï¼ The objectives of the B3 Substations Committee include the adoption of technological advances in
equipment and systems to achieve increased reliability and availability.
ï¼ The C2 System Operation and Control Committee focuses on the technical capabilities needed for the
secure and economical operation of existing power systems including control centers and operators.
ï¼ The D2 Information Systems and Telecommunication for Power Systems Committee monitors
emerging technologies in the industry and evaluates their possible impact. In addition, it focuses on
the security requirements of the information systems and services of control systems.
LOGIIC â Linking the Oil and Gas Industry to Improve Cybersecurity
http://www.dhs.gov/csd-logiic
The LOGIIC (Linking the Oil and Gas Industry to Improve Cybersecurity) program is an ongoing
collaboration of oil and natural gas companies and the DHS Science and Technology Directorate (S&T).
LOGIIC was formed in 2004 to facilitate cooperative research, development, testing, and evaluation
procedures to improve cybersecurity in petroleum industry digital control systems. The program undertakes
collaborative R&D projects to improve the level of cybersecurity in critical systems of interest to the oil
and natural gas sector. The program objective is to promote the interests of the sector while maintaining
impartiality, the independence of the participants, and vendor neutrality. After a successful first project, the
LOGIIC consortium was formally established as a collaboration between DHS, the Automation Federation,
and five of the major oil and gas companies. The LOGIIC program has completed several R&D projects,
and more projects are being planned and started.

SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
302
å½é大é»åã·ã¹ãã ä¼è°ï¼CIGREï¼
http://www.cigre.org/
CIGRE ã¯ãã©ã³ã¹ã«æ ç¹ãç½®ãéå¶å©å½éæ©é¢ã§ãããããã¤ãã®ç 究å§å¡ä¼ããããæ¨å¥¨è¦
ç¯ã®å®ç¾©ã¥ããæ¨å¥¨äºé
ã®çå®ãéãã¦ãé»åæ¥çã«ãããå½éçãªæè¦äº¤æãä¿é²ãã¦ããã
ãã®ãã¡æ¬¡ã® 3å§å¡ä¼ãå¶å¾¡ã·ã¹ãã ã«ç¹åãã¦ããã
ï¼ B3 å¤é»æå§å¡ä¼ã®ç®çã«ã¯ãè£
ååãã·ã¹ãã ã®æè¡çé²æ©ãåãå
¥ãã¦ãä¿¡é ¼æ§ã¨å¯ç¨
æ§ã確ä¿ãããã¨ãå«ã¾ããã
ï¼ C2 ã·ã¹ãã éç¨å¶å¾¡å§å¡ä¼ã¯ãå¶å¾¡ã»ã³ã¿ã¼ãæä½å¡ãå«ããæ¢åé»åã·ã¹ãã ã®éç¨ã
ã»ãã¥ã¢ãã¤çµæ¸çã«ããããã®æè¡åã«éç¹ãç½®ãã¦ããã
ï¼ D2 é»åã·ã¹ãã ç¨æ
å ±ã·ã¹ãã é»æ°éä¿¡å§å¡ä¼ã¯ãæ¥çã®æ°èæè¡ã注è¦ãããã®å½±é¿ã
è©ä¾¡ãããã¾ãå¶å¾¡ã·ã¹ãã ã®æ
å ±ã·ã¹ãã ã»ãµã¼ãã¹ã«é¢ããã»ãã¥ãªãã£è¦ä»¶ããéè¦
ãã¦ããã
LOGIIC â ãµã¤ãã¼ã»ãã¥ãªãã£ãæ¹åããç³æ²¹ã»ã¬ã¹æ¥çã®é£æº
http://www.dhs.gov/csd-logiic
LOGIICï¼ãµã¤ãã¼ã»ãã¥ãªãã£ãæ¹åããç³æ²¹ã»ã¬ã¹æ¥çã®é£æºï¼ããã°ã©ã ã¯ãç³æ²¹ã»ã¬ã¹
ä¼ç¤¾åã³ DHS ç§å¦æè¡å±ï¼S&Tï¼éã§ç¾å¨é²å±ä¸ã®ååæ´»åã§ãããLOGIIC ã¯2004 å¹´ã«å¶å®
ãããå
±åç 究ã»éçºã»è©¦é¨ã»è©ä¾¡æé ãä¿é²ããç³æ²¹æ¥çã®ãã¸ã¿ã«å¶å¾¡ã·ã¹ãã ã®ãµã¤ãã¼
ã»ãã¥ãªãã£åä¸ãç®æãã¦ããã ç³æ²¹ã»å¤©ç¶ã¬ã¹æ¥çã®å©çã«ç´çµããéè¦ã·ã¹ãã ã®ãµã¤
ãã¼ã»ãã¥ãªãã£ã¬ãã«ãä¸ãããããå
±åç 究ã»éçºãæããã¦ãããããã°ã©ã ã®ç®çã¯ã
ã¡ã³ãã¼éã®å
¬å¹³ãç¬ç«æ§åã³ãã³ãã¼ã®ä¸ç«æ§ãä¿ã¡ã¤ã¤ãæ¥çã®å©çãä¿é²ãããã¨ã«ããã
æåã®ããã¸ã§ã¯ããæåããå¾ãLOGIIC ã³ã³ã½ã¼ã·ã¢ã ã DHSããªã¼ãã¡ã¼ã·ã§ã³é£çåã³
ç³æ²¹ã»ã¬ã¹å¤§æ 5社éã§æ£å¼ã«çºè¶³ãããããã¾ã§ããã¤ãã®ç 究éçºããã¸ã§ã¯ããå®äºãã¦
ãããä»å¾æ´ã«æ°è¦è¨ç»ãäºå®ããã¦ããã
SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
303
National SCADA Test Bed (NSTB)
http://energy.sandia.gov/infrastructure-security/cyber/scada-systems/testbeds/national-scada-testbed/
The National Supervisory Control and Data Acquisition (SCADA) Test Bed is a DOE Office of Electricity
Delivery and Energy Reliability (OE) -sponsored resource to help secure our nationâs energy control
systems. It combines state-of-the-art operational system testing facilities with research, development, and
training to discover and address critical security vulnerabilities and threats to the energy sector.
Working in partnership with the energy sector, the National SCADA Test Bed seeks to:
ï¼ Identify and mitigate existing vulnerabilities.
ï¼ Facilitate development of security standards.
ï¼ Serve as an independent entity to test SCADA systems and related control system technologies.
ï¼ Identify and promote best cybersecurity practices.
ï¼ Increase awareness of control systems security within the energy sector.
ï¼ Develop advanced control system architectures and technologies that are more secure and robust.
Partners in the NSTB include Idaho National Laboratory, Sandia National Laboratories, Argonne National
Laboratory, Pacific Northwest National Laboratory, and the National Institute of Standards and Technology.
SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
304
ç±³å½ SCADA ãã¹ããããï¼NSTBï¼
http://energy.sandia.gov/infrastructure-security/cyber/scada-systems/testbeds/national-scada-testbed/
ç±³å½ SCADA ãã¹ããããã¯ãDOE ã®é
é»ã¨ãã«ã®ã¼ä¿¡é ¼æ§å±ï¼OEï¼ã®æ¯æ´ã«ãããªã½ã¼ã¹ã§ã
ç±³å½ã®ã¨ãã«ã®ã¼å¶å¾¡ã·ã¹ãã ã®ã»ãã¥ã¢åãå©æãããææ°ã®éç¨ã·ã¹ãã 試é¨æ½è¨ã¨ç 究ã»
éçºã»è¨ç·´ãä¸ä½åãã¦ãã¨ãã«ã®ã¼æ¥çã«ã¨ã£ã¦ã®é大ãªã»ãã¥ãªãã£èå¼±æ§ã»è
å¨ãè¦ã¤ã
ã¦åãçµãã
ã¨ãã«ã®ã¼æ¥çã¨é£æºããç±³å½ SCADA ãã¹ããããã¯ä»¥ä¸ãç®æ¨ã¨ãã¦ããã
ï¼ æ¢åã®èå¼±æ§ãæããã«ãã¦ç·©åãã
ï¼ ã»ãã¥ãªãã£è¦æ ¼ã®éçºãä¿é²ãã
ï¼ SCADA ã·ã¹ãã æè¡åã³é¢é£å¶å¾¡ã·ã¹ãã æè¡ã®ç¬ç«è©¦é¨æ©é¢ã¨ãã¦æ©è½ãã
ï¼ ãµã¤ãã¼ã»ãã¥ãªãã£ã®æè¯è¦ç¯ãå®ãã¦ä¿é²ãã
ï¼ ã¨ãã«ã®ã¼æ¥çã«ãããå¶å¾¡ã·ã¹ãã ã»ãã¥ãªãã£ã«å¯¾ããæèãé«ãã
ï¼ ããã»ãã¥ã¢ã§å¼·åºãªææ°å¶å¾¡ã·ã¹ãã ã¢ã¼ããã¯ãã£åã³æè¡ãéçºãã
NSTB ã«ã¯ã¢ã¤ããå½ç«ç 究æããµã³ãã£ã¢å½ç«ç 究æãã¢ã¼ã´ã³å½ç«ç 究æã太平æ´å西å½ç«
ç 究æåã³ç±³å½æ¨æºæè¡å±ãå çãã¦ããã
SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
305
NIST Special Publication 800 Series Security Guidelines
http://csrc.nist.gov/publications/nistpubs/index.html
The NIST Special Publication 800 series of documents on information technology reports on the NIST
Information Technology Laboratory (ITL) research, guidance, and outreach efforts in computer security,
and its collaborative activities with industry, government, and academic organizations. Focus areas include
cryptographic technology and applications, advanced authentication, public key infrastructure,
internetworking security, criteria and assurance, and security management and support. In addition to NIST
SP 800-82, the following is a listing of some additional 800 series documents that have significant
relevance to the ICS security community. These as well as many others are available through the URL
listed above.
ï¼ NIST SP 800-18 Revision 1, Guide for Developing Security Plans for Federal Information Systems
[19].
ï¼ NIST SP 800-30 Revision 1, Guide for Conducting Risk Assessments [79].
ï¼ NIST SP 800-37 Revision 1, Guide for Applying the Risk Management Framework to Federal
Information Systems: A Security Life Cycle Approach [21].
ï¼ NIST SP 800-39, Managing Information Security Risk: Organization, Mission, and Information
System View [20].
ï¼ NIST SP 800-40 Revision 3, Guide to Enterprise Patch Management Technologies [40].
ï¼ NIST SP 800-41 Revision 1, Guidelines on Firewalls and Firewall Policy [85].
ï¼ NIST SP 800-48 Revision 1, Guide to Securing Legacy IEEE 802.11 Wireless Networks 0.
ï¼ NIST SP 800-50, Building an Information Technology Security Awareness and Training Program [61].
ï¼ NIST SP 800-53 Revision 4, Security and Privacy Controls for Federal Information Systems and
Organizations [22].
ï¼ NIST SP 800-53A Revision 4, Assessing Security and Privacy Controls in Federal Information
Systems and Organizations: Building Effective Security Assessment Plans [23].
ï¼ NIST SP 800-61 Revision 2, Computer Security Incident Handling Guide [59].
ï¼ NIST SP 800-63-2, Electronic Authentication Guideline [53].
ï¼ NIST SP 800-64 Revision 2, Security Considerations in the Information System Development Life
Cycle [46].
ï¼ NIST SP 800-70 Revision 2, National Checklist Program for IT Products: Guidelines for Checklist
Users and Developers [26].
ï¼ NIST SP 800-77, Guide to IPsec VPNs [74].
ï¼ NIST SP 800-83 Revision 1, Guide to Malware Incident Prevention and Handling for Desktops and
Laptops [60].
ï¼ NIST SP 800-86, Guide to Integrating Forensic Techniques into Incident Response [93].

SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
306
NIST ç¹å¥åºçç© 800 ã·ãªã¼ãºã»ãã¥ãªãã£ã¬ã¤ãã©ã¤ã³
http://csrc.nist.gov/publications/nistpubs/index.html
SP800 ã·ãªã¼ãºã¯ãæ
å ±æè¡ç 究æï¼ITLï¼ã®ç 究ãã¬ã¤ãã³ã¹åã³ã³ã³ãã¥ã¼ã¿ã»ãã¥ãªãã£
ã«ãããåçµä¸¦ã³ã«ç£å®å¦ã¨ã®é£æºã«é¢ããæ
å ±æè¡å ±åæ¸ã§ãããéç¹åéã¨ãã¦æå·æè¡ã¨
ãã®å¿ç¨ãææ°èªè¨¼ãå
¬ééµã¤ã³ãã©ãã¤ã³ã¿ã¼ãããä½æ¥ã®ã»ãã¥ãªãã£ãåºæºã»ä¿è¨¼ãã»ã
ã¥ãªãã£ç®¡çã»æ¯æ´çãå«ã¾ãã¦ãããNIST SP 800-82 ã«å ãã¦ãICS ã»ãã¥ãªãã£é¢ä¿è
ã«å¤§
ãã«é¢ä¿ãããã®ã¨ãã¦ã次㮠800 ã·ãªã¼ãºææ¸ãç¨æããã¦ãããããã以å¤ã«ããä¸è¨ã®
URL ããå©ç¨ã§ãããã®ãããã
ï¼ NIST SP 800-18 第1çãé£é¦æ
å ±ã·ã¹ãã ç¨ã»ãã¥ãªãã£è¨ç»æ¸ã®ä½æã¬ã¤ãã[19]
ï¼ NIST SP 800-30 第1çããªã¹ã¯è©ä¾¡å®æ½ã¬ã¤ãã[79]
ï¼ NIST SP 800-37 第1çãé£é¦æ
å ±ã·ã¹ãã ã¸ã®ãªã¹ã¯ç®¡çä½ç³»é©ç¨ã¬ã¤ãï¼ã»ãã¥ãªãã£ã©
ã¤ããµã¤ã¯ã«ã¢ããã¼ãã[21]
ï¼ NIST SP 800-39ãæ
å ±ã»ãã¥ãªãã£ãªã¹ã¯ã®ç®¡çï¼çµç¹ãä»»ååã³æ
å ±ã·ã¹ãã æ¦èª¬ã[20]
ï¼ NIST SP 800-40 第3çãä¼æ¥ããã管çæè¡ã¬ã¤ãã[40]
ï¼ NIST SP 800-41 第1çããã¡ã¤ã¢ã¦ã©ã¼ã«åã³ãã¡ã¤ã¢ã¦ã©ã¼ã«ããªã·ã¼ã¬ã¤ãã©ã¤ã³ã
[85]
ï¼ NIST SP 800-48 第1çãã¬ã¬ã·ã¼IEEE 802.11 ã¯ã¤ã¤ã¬ã¹ãããã¯ã¼ã¯ã»ãã¥ãªãã£ã¬ã¤
ãã[0]
ï¼ NIST SP 800-50ãæ
å ±æè¡ã»ãã¥ãªãã£æèè¨ç·´ããã°ã©ã ã®æ§ç¯ã[61]
ï¼ NIST SP 800-53 第4çãé£é¦æ
å ±ã·ã¹ãã ã»çµç¹ã®ã»ãã¥ãªãã£ã»ãã©ã¤ãã·ã¼ç®¡çã[22]
ï¼ NIST SP 800-53A 第4çãé£é¦æ
å ±ã·ã¹ãã ã»çµç¹ã®ã»ãã¥ãªãã£ã»ãã©ã¤ãã·ã¼ç®¡çè©
価ï¼å¹æçã»ãã¥ãªãã£è©ä¾¡è¨ç»æ¸ã®ä½æã[23]
ï¼ NIST SP 800-61 第2çãã³ã³ãã¥ã¼ã¿ã»ãã¥ãªãã£ã¤ã³ã·ãã³ãå¦çã¬ã¤ãã[59]
ï¼ NIST SP 800-63-2ãé»åèªè¨¼ã¬ã¤ãã©ã¤ã³ã[53]
ï¼ NIST SP 800-64 第2çãæ
å ±ã·ã¹ãã éçºã©ã¤ããµã¤ã¯ã«ã«ãããã»ãã¥ãªãã£èæ
®äºé
ã
[46]
ï¼ NIST SP 800-70 第2çãIT 製åã®å½å®¶ãã§ãã¯ãªã¹ãããã°ã©ã ï¼ãã§ãã¯ãªã¹ãã¦ã¼ã¶ã»
éçºè
ã¬ã¤ãã©ã¤ã³ã[26]
ï¼ NIST SP 800-77ãIPSsec VPNs ã¬ã¤ãã[74]
ï¼ NIST SP 800-83 第1çããã«ã¦ã¨ã¢ã¤ã³ã·ãã³ãé²æ¢åã³ãã¹ã¯ãããã»ã©ãããããã®å
æ±ã¬ã¤ãã[60]
ï¼ NIST SP 800-86ãã¤ã³ã·ãã³ã対å¿æã®èª¿æ»æè¡ã®é©ç¨ã¬ã¤ãã[93]

SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
307
ï¼ NIST SP 800-88 Revision 1, Guidelines for Media Sanitization [78].
ï¼ NIST SP 800-92, Guide to Computer Security Log Management [68].
ï¼ NIST SP 800-94, Guide to Intrusion Detection and Prevention Systems (IDPS) [55].
ï¼ NIST SP 800-97, Establishing Robust Security Networks: a Guide to IEEE 802.11i [64].
ï¼ NIST SP 800-100, Information Security Handbook: A Guide for Managers [27].
ï¼ NIST SP 800-111, Guide to Storage Encryption Technologies for End User Devices [94].
ï¼ NIST SP 800-115, Technical Guide to Information Security Testing and Assessment [41].
ï¼ NIST SP 800-123, Guide to General Server Security [95].
ï¼ NIST SP 800-127, Guide to Securing WiMAX Wireless Communications [96].
ï¼ NIST SP 800-128, Guide for Security-Focused Configuration Management of Information Systems
[97].
ï¼ NIST SP 800-137, Information Security Continuous Monitoring (ISCM) for Federal Information
Systems and Organizations [81].
NIST Cybersecurity Framework
http://www.nist.gov/cyberframework/index.cfm
Recognizing that the national and economic security of the United States depends on the reliable
functioning of critical infrastructure, the President issued Executive Order 13636, Improving Critical
Infrastructure Cybersecurity, in February 2013 [83]. It directed NIST to work with stakeholders to develop
a voluntary framework â based on existing standards, guidelines, and practices â for reducing cyber risks to
critical infrastructure.
NIST released the first version of the Framework for Improving Critical Infrastructure Cybersecurity
on February 12, 2014 [83]. The Framework, created through collaboration between industry and
government, consists of standards, guidelines, and practices to promote the protection of critical
infrastructure. The prioritized, flexible, repeatable, and cost-effective approach of the Framework helps
owners and operators of critical infrastructure to manage cybersecurity-related risk.
The Department of Homeland Security's Critical Infrastructure Cyber Community C³ Voluntary Program
helps align critical infrastructure owners and operators with existing resources that will assist their efforts
to adopt the Cybersecurity Framework and manage their cyber risks. Learn more about the C³ Voluntary
Program by visiting: www.dhs.gov/ccubedvp.
NIST has also issued a companion Roadmap that discusses NIST's next steps with the Framework and
identifies key areas of cybersecurity development, alignment, and collaboration.

SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
308
ï¼ NIST SP 800-88 第1çãã¡ãã£ã¢ãµãã¿ã¤ãºã¬ã¤ãã©ã¤ã³ã[78]
ï¼ NIST SP 800-92ãã³ã³ãã¥ã¼ã¿ã»ãã¥ãªãã£ãã°ç®¡çã¬ã¤ãã[68]
ï¼ NIST SP 800-94ãä¾µå
¥æ¤ç¥é²æ¢ã·ã¹ãã ï¼IDPSï¼ã¬ã¤ãã[55]
ï¼ NIST SP 800-97ãå¼·åºãªã»ãã¥ãªãã£ãããã¯ã¼ã¯ã®æ§ç¯ï¼IEEE 802.11i ã¬ã¤ãã[64]
ï¼ NIST SP 800-100ãæ
å ±ã»ãã¥ãªãã£ãã³ãããã¯ï¼ç®¡çè
ã¬ã¤ãã[27]
ï¼ NIST SP 800-111ãã¨ã³ãã¦ã¼ã¶ããã¤ã¹ç¨ã¹ãã¬ã¼ã¸æå·åæè¡ã¬ã¤ãã[94]
ï¼ NIST SP 800-115ãæ
å ±ã»ãã¥ãªãã£è©¦é¨è©ä¾¡æè¡ã¬ã¤ãã[41]
ï¼ NIST SP 800-123ãä¸è¬çãµã¼ãã»ãã¥ãªãã£ã¬ã¤ãã[95]
ï¼ NIST SP 800-127ãWiMAX ã¯ã¤ã¤ã¬ã¹éä¿¡ã¬ã¤ãã[96]
ï¼ NIST SP 800-128ãæ
å ±ã·ã¹ãã ã®ã»ãã¥ãªãã£éè¦è¨å®ç®¡çã¬ã¤ãã[97]
ï¼ NIST SP 800-137ãé£é¦æ
å ±ã·ã¹ãã ã»çµç¹ã®æ
å ±ã»ãã¥ãªãã£ç¶ç¶ç£è¦ã[81]
NIST ã®ãµã¤ãã¼ã»ãã¥ãªãã£ä½ç³»
http://www.nist.gov/cyberframework/index.cfm
ç±³å½ã®å½å®¶ã»çµæ¸å®å
¨ä¿éã¯ãä¿¡é ¼æ§ã®é«ãéè¦ã¤ã³ãã©ã®æ©è½ã«ä¾åãã¦ããã¨ãã¦ã大統é
å½ä»¤ 13636 éè¦ã¤ã³ãã©ãµã¤ãã¼ã»ãã¥ãªãã£ã®æ¹åã2013 å¹´2æã«çºä»¤ãã[83]ããã®ä¸ã§
NIST ã¯é¢ä¿è
ã¨é£æºããæ¢åã®è¦æ ¼ãã¬ã¤ãã©ã¤ã³åã³è¦ç¯ãåºã«ãéè¦ã¤ã³ãã©ã¸ã®ãµã¤ã
ã¼ãªã¹ã¯ã®è»½æ¸ã«åãã¦ãèªçºçãªä½ç³»ãæ§ç¯ããããå½ããããã
NIST ã¯2014 å¹´2æ14 æ¥ãéè¦ã¤ã³ãã©ãµã¤ãã¼ã»ãã¥ãªãã£æ¹åä½ç³»ç¬¬1çãçºè¡¨ãã[83]ã
ç£ã»å®éã®é£æºã§æ§ç¯ãããä½ç³»ã¯ãéè¦ã¤ã³ãã©ä¿è·ãä¿é²ããè¦æ ¼ãã¬ã¤ãã©ã¤ã³åã³è¦ç¯
ããæ§æããã¦ãããåªå
é ä½ã¥ãããæè»æ§ããããå復å¯è½ã§è²»ç¨å¹æã®é«ãåçµã«ããã
éè¦ã¤ã³ãã©ã®ææè
åã³éç¨è
ããµã¤ãã¼ã»ãã¥ãªãã£é¢é£ãªã¹ã¯ã管çã§ããããã«æ¯æ´ã
ãã
å½åå®å
¨ä¿éçã®éè¦ã¤ã³ãã©ãµã¤ãã¼ã³ãã¥ãã㣠C³ ä»»æããã°ã©ã ã¯ãéè¦ã¤ã³ãã©ã®ä¿
æè
åã³æä½å¡ãæ¢åãªã½ã¼ã¹ãæ´»ç¨ãã¤ã¤ããµã¤ãã¼ã»ãã¥ãªãã£ä½ç³»ãåãå
¥ãããµã¤ãã¼
ãªã¹ã¯ã管çããè³ã¨ãªããC³ ä»»æããã°ã©ã ã®è©³ç´°ã¯ä»¥ä¸ã® URL ã«ããã
www.dhs.gov/ccubedvp.
NIST ã¯æå¼ãã¨ãªããã¼ãããããçºè¡¨ãããã®ä½ç³»ã®æ¬¡ãªãã¹ãããã«ã¤ãã¦èª¬æãããµã¤
ãã¼ã»ãã¥ãªãã£éçºã»èª¿æ´ã»é£æºã®ä¸»ãªåéãæããã«ãã¦ããã
SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
309
NIST Industrial Control System Security Project
http://csrc.nist.gov/groups/SMA/fisma/ics/
As part of the continuing effort to provide effective security standards and guidance to federal agencies and
their contractors in support of the Federal Information Security Management Act and as part of the effort to
protect the nation's critical infrastructure, NIST continues to work with public and private sector entities on
sector-specific security issues.
Industrial and process control systems are an integral part of the US critical infrastructure and the
protection of those systems is a priority for the federal government. This project intends to build upon the
current FISMA security standards and provide targeted extensions and/or interpretations of those standards
for industrial and process controls systems where needed. Since many industrial and process controls
systems are supporting private sector organizations, NIST will collaborate with ongoing standards efforts
addressing these sector-specific types of systems.
NIST Cybersecurity for Manufacturing Systems Project
http://www.nist.gov/el/isd/cs/csms.cfm
Smart manufacturing systems need to be protected from vulnerabilities that may arise as a result of their
increased connectivity, use of wireless networks and sensors, and use of widespread information
technology. Manufacturers are hesitant to adopt common security technologies, such as encryption and
device authentication, due to concern for potential negative performance impacts in their systems. This is
exacerbated by a threat environment that has changed dramatically with the appearance of advanced
persistent attacks specifically targeting industrial systems, such as Stuxnet. This project will develop a
cybersecurity risk management framework with supporting guidelines, methods, metrics and tools to enable
manufacturers, technology providers, and solution providers to assess and assure cybersecurity for smart
manufacturing systems. The cybersecurity risk management framework and methodology will stimulate
manufacturer adoption and enable effective use of security technologies, leading to smart manufacturing
systems that offer security, reliability, resilience and continuity in the face of disruption and major incidents.
NIST Cybersecurity for Smart Grid Systems Project
http://www.nist.gov/el/smartgrid/cybersg.cfm
Smart grid cybersecurity must address not only deliberate attacks, such as from disgruntled employees,
industrial espionage, and terrorists, but also inadvertent compromises of the information infrastructure due
to user errors, equipment failures, and natural disasters. The Smart Grid Interoperability Panel (SGIP)
Cybersecurity Committee (SGCC), which is led and managed by the NIST Information Technology
Laboratory (ITL), Computer Security Division, is moving forward in fiscal year 2014 to address the critical
cybersecurity needs in the areas of Advanced Metering Infrastructure (AMI) security requirements, cloud
computing, supply chain, and privacy recommendations related to emerging standards. This project will
provide foundational cybersecurity guidance, cybersecurity reviews of standards and requirements,
outreach, and foster collaborations in the cross-cutting issue of cybersecurity in the smart grid.

SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
310
NIST ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ã»ãã¥ãªãã£ããã¸ã§ã¯ã
http://csrc.nist.gov/groups/SMA/fisma/ics/
é£é¦æ¿åºæ©é¢åã³é£é¦æ
å ±ã»ãã¥ãªãã£ç®¡çæ³ãæ¯ããå¥ç´æ¥è
ã«å¹æçãªã»ãã¥ãªãã£è¦æ ¼ã»
ã¬ã¤ãã³ã¹ãæä¾ããç¶ç¶çãªåçµã®ä¸ç°ã¨ãã¦ãã¾ãå½ã®éè¦ã¤ã³ãã©ãä¿è·ããåçµã®ä¸ç°
ã¨ãã¦ãNIST ã¯å®æ°è«¸å£ä½ã¨é£æºãã¦ãæ¥çåºæã®ã»ãã¥ãªãã£åé¡ã¨ç¶ç¶çã«ååãã¦ããã
ç£æ¥ç¨ã·ã¹ãã åã³ããã»ã¹å¶å¾¡ã·ã¹ãã ã¯ãç±³å½ã®éè¦ã¤ã³ãã©ã®ä¸å¯æ¬ ãªä¸é¨ã§ããããã
ãã·ã¹ãã ã«å¯¾ããä¿è·ã¯ãé£é¦æ¿åºã®åªå
ç課é¡ã§ãããæ¬ããã¸ã§ã¯ãã¯ãç¾è¡ FISMA ã»
ãã¥ãªãã£è¦æ ¼ãåºç¤ã¨ãã¦ããããç£æ¥ç¨ã·ã¹ãã åã³ããã»ã¹å¶å¾¡ã·ã¹ãã ã®è¦æ ¼ããå¿
è¦
ã«å¿ãã¦æ¡å¼µã»è§£éãããã¨ã主ç¼ã¨ãã¦ãããå¤ãã®ç£æ¥ç¨ã·ã¹ãã åã³ããã»ã¹å¶å¾¡ã·ã¹ã
ã ã¯ãæ°éæ¥ççµç¹ãæ¯ãã¦ãããããNIST ã¯ããã®ãããªæ¥çåºæã®ã·ã¹ãã ã対象ã¨ãã
ç¾è¡è¦æ ¼ã®åçµã¨é£æºãã¦ããã
çç£ã·ã¹ãã ããã¸ã§ã¯ãç¨ NIST ãµã¤ãã¼ã»ãã¥ãªãã£
http://www.nist.gov/el/isd/cs/csms.cfm
ã¹ãã¼ãçç£ã·ã¹ãã ã¯ãæ¥ç¶æ°ãã¯ã¤ã¤ã¬ã¹ãããã¯ã¼ã¯/ã»ã³ãµã®å©ç¨åã³åºç¯ãªæ
å ±æè¡
ã®å©ç¨ãå¢ããçµæãèå¼±æ§ãçããããä¿è·ãå¿
è¦ã¨ãªããã¡ã¼ã«ã¼ã¯ãã·ã¹ãã ã«ãã¤ãã¹
ã®å½±é¿ãåºããã¨ãæãã¦ãæå·åãããã¤ã¹èªè¨¼ã¨ãã£ããä¸è¬çãªã»ãã¥ãªãã£æè¡ã®æ¡ç¨
ã«æ¶æ¥µçã§ãããStuxnet ã®ãããªç£æ¥ç¨ã·ã¹ãã ã«ç¹åããå·æãªæ»æãåºç¾ããããã«ãè
å¨ç°å¢ãæ¿å¤ãããã¨ã¨ããã¾ã£ã¦ããã£ããäºæ
ã¯æªåãããæ¬ããã¸ã§ã¯ãã§ã¯ãæ ¹æ ã¨ãª
ãã¬ã¤ãã©ã¤ã³ãæ¹æ³ãè©ä¾¡åºæºåã³ãã¼ã«ã®ä¼´ã£ããµã¤ãã¼ã»ãã¥ãªãã£ãªã¹ã¯ç®¡çä½ç³»ãç
å®ããã¡ã¼ã«ã¼ãæè¡æä¾è
åã³ã½ãªã¥ã¼ã·ã§ã³æä¾è
ãã¹ãã¼ãçç£ã·ã¹ãã ç¨ãµã¤ãã¼ã»ã
ã¥ãªãã£ã®è©ä¾¡ã»ä¿è¨¼ãå®æ½ã§ããããã«ããããµã¤ãã¼ã»ãã¥ãªãã£ãªã¹ã¯ç®¡çä½ç³»åã³æ¹æ³
è«ã¯ãã¡ã¼ã«ã¼ãã»ãã¥ãªãã£æè¡ãæ¡ç¨ãã¦æå¹å©ç¨ããå¼¾ã¿ãã¤ããä¸æã大è¦æ¨¡ã¤ã³ã·ã
ã³ãæã®ã»ãã¥ãªãã£ãä¿¡é ¼æ§ãæè»æ§åã³ç¶ç¶æ§ã確ä¿ã§ããã¹ãã¼ãçç£ã·ã¹ãã ã¸å°ãã
ã®ã¨ãªãã
ã¹ãã¼ãã°ãªããã·ã¹ãã ããã¸ã§ã¯ãç¨ NIST ãµã¤ãã¼ã»ãã¥ãªãã£
http://www.nist.gov/el/smartgrid/cybersg.cfm
ã¹ãã¼ãã°ãªãããµã¤ãã¼ã»ãã¥ãªãã£ã§ã¯ãä¸æºãæ±ããå¾æ¥å¡ãç£æ¥ã¹ãã¤ããããªã¹ãç
ã«ããè¨ç»çãªæ»æã ãã§ãªããã¦ã¼ã¶ã®é誤ãè£
ååé害åã³èªç¶ç½å®³ã«èµ·å ããæ
å ±ã¤ã³ã
ã©ã®æ³å®å¤ã®æ©è½ä½ä¸ãæ¤è¨å¯¾è±¡ã«ããªããã°ãªããªããNIST ã®æ
å ±æè¡ç 究æï¼ITLï¼ã³ã³ã
ã¥ã¼ã¿ã»ãã¥ãªãã£é¨ã®ç£ç£ä¸ã«ããã¹ãã¼ãã°ãªããç¸äºéç¨ããã«ï¼SGIPï¼ãµã¤ãã¼ã»ãã¥
ãªãã£å§å¡ä¼ã¯ 2014 ä¼è¨å¹´åº¦ã«ãææ°è¨éã¤ã³ãã©ï¼AMIï¼ã»ãã¥ãªãã£è¦ä»¶ãã¯ã©ã¦ãã³ã³
ãã¥ã¼ãã£ã³ã°ããµãã©ã¤ãã§ã¼ã³åã³æ°èè¦æ ¼é¢é£æ°éæ¨å¥¨äºé
åéã§ã®éè¦ãµã¤ãã¼ã»ãã¥
ãªãã£ã®å¿
è¦æ§ã®æ¤è¨ã«åãã¦æ´»åãéå§ãããæ¬ããã¸ã§ã¯ãã¯åºæ¬çãµã¤ãã¼ã»ãã¥ãªãã£
ã¬ã¤ãã³ã¹ãè¦æ ¼åã³è¦ä»¶ã®ãµã¤ãã¼ã»ãã¥ãªãã£èª¿æ»ã«ã¤ãã¦è¨è¿°ããã¹ãã¼ãã°ãªããã®å
é横æçãªãµã¤ãã¼ã»ãã¥ãªãã£åé¡ã§ã®é£æºãæ§ç¯ããã

SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
311
NIST Smart Grid System Testbed Facility
http://www.nist.gov/el/smartgrid/sgtf.cfm
NIST is charged by the 2007 Energy Independence and Security Act (EISA) with facilitation of
interoperability standards to enable successful implementation of the evolving cyber-physical national
electric grid system known as the smart grid (SG). The Smart Grid Testbed Facility will create a unique set
of interconnected and interacting labs in several key measurement areasâcontiguously located on the
NIST Gaithersburg siteâthat will accelerate the development of SG interoperability standards by
providing a combined testbed platform for system measurements, characterization of smart grid protocols,
and validation of SG standards, with particular emphasis on microgrids. (A microgrid is defined as a subset
of the grid which has the capability of being quickly disconnected from, and functioning independently of,
the larger grid.) Measurements will include eight areas: power conditioning, synchrophasor metrology,
cybersecurity, precision time synchronization, electric power metering, modeling/evaluation of SG
communications, sensor interfaces, and energy storage. The testbed will serve as a core Smart Grid
Program research facility to address measurement needs of the evolving SG industrial community including
the measurement and validation issues.
North American Electric Reliability Corporation (NERC)
http://www.nerc.com/
NERCâs mission is to improve the reliability and security of the bulk power system in North America. To
achieve that, NERC develops and enforces reliability standards; monitors the bulk power system; assesses
future adequacy; audits owners, operators, and users for preparedness; and educates and trains industry
personnel. NERC is a self-regulatory organization that relies on the diverse and collective expertise of
industry participants. As the Electric Reliability Organization, NERC is subject to audit by the U.S. Federal
Energy Regulatory Commission and governmental authorities in Canada
NERC has issued a set of cybersecurity standards to reduce the risk of compromise to electrical generation
resources and high-voltage transmission systems above 100 kV, also referred to as bulk electric systems.
Bulk electric systems include Balancing Authorities, Reliability Coordinators, Interchange Authorities,
Transmission Providers, Transmission Owners, Transmission Operators, Generation Owners, Generation
Operators, and Load Serving Entities. The cybersecurity standards include audit measures and levels of
non-compliance that can be tied to penalties.
The set of NERC cybersecurity Standards includes the following:
ï¼ CIP-002, Cyber Security - Critical Cyber Asset Identification.
ï¼ CIP-003, Cyber Security - Security Management Controls.
ï¼ CIP-004, Cyber Security - Personnel & Training.
ï¼ CIP-005, Cyber Security - Electronic Security Perimeter(s).
ï¼ CIP-006, Cyber Security - Physical Security of Critical Cyber Assets.
ï¼ CIP-007, Cyber Security - Systems Security Management.
ï¼ CIP-008, Cyber Security - Incident Reporting and Response Planning.
ï¼ CIP-009, Cyber Security - Recovery Plans for Critical Cyber Assets.

SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
312
NIST ã¹ãã¼ãã°ãªããã·ã¹ãã ãã¹ããããæ½è¨
http://www.nist.gov/el/smartgrid/sgtf.cfm
NIST ã¯2007 å¹´ãã¨ãã«ã®ã¼ç¬ç«ã»ãã¥ãªãã£æ³ï¼EISAï¼ã«ãããã¹ãã¼ãã°ãªããï¼SGï¼ã¨
ãã¦ç¥ãããå½ã®ãµã¤ãã¼ç©ççé
é»ã·ã¹ãã ãå¹æçã«å®è£
ããããã®ç¸äºéç¨æ§è¦æ ¼ãä½æ
ãããã義åã¥ãããããã¹ãã¼ãã°ãªããã·ã¹ãã ãã¹ããããæ½è¨ã¯ãç¸äºæ¥ç¶ããç¸äºä½
ç¨ããä¸é£ã®ç 究æ群ãããã¤ãã®éè¦è¨æ¸¬ã¨ãªã¢å
ã«æ§ç¯ãï¼NIST ã®ã²ã¤ãµã¼ãºãã¼ã°æ½è¨
ã«é£æ¥ï¼ãã·ã¹ãã è¨æ¸¬ãã¹ãã¼ãã°ãªãããããã³ã«ã®ç¹æ§åæåã³ SG è¦æ ¼æ¤è¨¼ç¨ã®çµåã
ã¹ãããããã©ãããã¼ã ãæä¾ãããã¨ã«ãããç¹ã«ãã¤ã¯ãã°ãªãããéç¹ã¨ãã SG ç¸äº
éç¨æ§è¦æ ¼ã®ä½æãæ¥ãã§ãããï¼ãã¤ã¯ãã°ãªããã¯ã大è¦æ¨¡ã°ãªããããè¿
éã«åé¢ãã¦ã
ç¬ç«ããæ©è½è½åãçºæ®ããã°ãªãããµãã»ããã¨å®ç¾©ããããï¼æ¬¡ã® 8é
ç®ãè¨æ¸¬ãããé»å
ç¶æ
ãã·ã³ã¯ããã§ã¼ã¶è¨æ¸¬ããµã¤ãã¼ã»ãã¥ãªãã£ãç²¾å¯æéåæãé»å測å®ãSG éä¿¡ã®ã¢
ããªã³ã°ã»è©ä¾¡ãã»ã³ãµã¤ã³ã¿ã¼ãã§ã¤ã¹åã³ã¨ãã«ã®ã¼ä¿åããã¹ããããã¯ãä¸æ ¸çãªã¹ã
ã¼ãã°ãªããããã°ã©ã ç 究æ½è¨ã¨ãã¦æ©è½ããè¨æ¸¬ã»æ¤è¨¼åé¡ãå«ãã¦é²å±ä¸ã®ãSG ç£æ¥å
±
åä½ã®è¨æ¸¬ãã¼ãºã«å¯¾å¿ãã¦ããã
åç±³é»åä¿¡é ¼æ§è©è°ä¼ï¼NERCï¼
http://www.nerc.com/
NERC ã®ä»»åã¯ãåç±³ã«ããã大é»åã·ã¹ãã ã®ä¿¡é ¼æ§ã¨ã»ãã¥ãªãã£ãæ¹åãããã¨ã«ããã
ãã®ãã NERC ã¯ãä¿¡é ¼æ§è¦æ ¼ã®ä½æã»æ½è¡ã大é»åã·ã¹ãã ã®ç£è¦ãå°æ¥çãªå¦¥å½æ§ã®è©ä¾¡ã
ä¿æè
ã»æä½å¡ã»ã¦ã¼ã¶ã®å³å¿æ§ç£æ»ãæ¥çè·å¡ã®æè²è¨ç·´ãè¡ã£ã¦ãããNERC ã¯èªä¸»è¦å¶çµ
ç¹ã§ãæ¥çåå è
ã®å¤æ§ãã¤å
æ¬çå°éç¥èã«ä¾åãã¦ãããé»åä¿¡é ¼æ§çµç¹ã¨ãã¦ãç±³å½ã®é£
é¦ã¨ãã«ã®ã¼è¦å¶å§å¡ä¼ã¨ã«ããã®è¡æ¿å½å±ã®ç£æ»ãåãã義åãããã
çºé»ãªã½ã¼ã¹åã³ 100kV è¶
é«é»å§éé»ã·ã¹ãã ï¼å¤§é»åã·ã¹ãã ã¨ãããï¼ã®æ©è½ä½ä¸ãªã¹ã¯ã
軽æ¸ãããããNERC ã¯ä¸é£ã®ãµã¤ãã¼ã»ãã¥ãªãã£è¦æ ¼ãçºè¡¨ãã¦ããã大é»åã·ã¹ãã«ã¯äº
æ¥è
ï¼Balancing Authoritiesï¼ãä¿¡é ¼æ§ã³ã¼ãã£ãã¼ã¿ãéé»ãããã¤ããéé»ä¿æè
ãéé»äºæ¥
è
ãçºé»ä¿æè
ãçºé»äºæ¥è
åã³å°å£²äºæ¥è
ãå«ã¾ããããµã¤ãã¼ã»ãã¥ãªãã£è¦æ ¼ã«ã¯ãç£æ»
æ段åã³ç½°åã«çµã³ã¤ãåç´ãã³ã³ã³ãã©ã¤ã¢ã³ã¹ãå«ã¾ããã
ä¸é£ã® NERC ãµã¤ãã¼ã»ãã¥ãªãã£è¦æ ¼ã«ã¯ä»¥ä¸ã®ãã®ãããã
ï¼ CIP-002ããµã¤ãã¼ã»ãã¥ãªã㣠- éè¦ãµã¤ãã¼è³ç£ã®èå¥ã
ï¼ CIP-003ããµã¤ãã¼ã»ãã¥ãªã㣠- ã»ãã¥ãªãã£ç®¡ç対çã
ï¼ CIP-004ããµã¤ãã¼ã»ãã¥ãªã㣠- è·å¡åã³è¨ç·´ã
ï¼ CIP-005ããµã¤ãã¼ã»ãã¥ãªã㣠- é»åã»ãã¥ãªãã£ã®å¨è¾ºã
ï¼ CIP-006ããµã¤ãã¼ã»ãã¥ãªã㣠- éè¦ãµã¤ãã¼è³ç£ã®ç©ççã»ãã¥ãªãã£ã
ï¼ CIP-007ããµã¤ãã¼ã»ãã¥ãªã㣠- ã·ã¹ãã ã»ãã¥ãªãã£ç®¡çã
ï¼ CIP-008ããµã¤ãã¼ã»ãã¥ãªã㣠- ã¤ã³ã·ãã³ãã®å±åºåã³å¯¾å¿è¨ç»ã®ç«æ¡ã
ï¼ CIP-009ããµã¤ãã¼ã»ãã¥ãªã㣠- éè¦ãµã¤ãã¼è³ç£å¾©æ§è¨ç»ã

SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
313
SANS ICS Security Courses
http://ics.sans.org/
The ICS curriculum provides hands-on training courses focused on Attacking and Defending ICS
environments. These courses equip both security professionals and control system engineers with the
knowledge and skills they need to safeguard our critical infrastructures.
The Global Industrial Cyber Security Professional (GICSP) is the newest certification in the Global
Information Assurance Certification (GIAC) family and focuses on the foundational knowledge of securing
critical infrastructure assets. The GICSP bridges together IT, engineering and cybersecurity to achieve
security for industrial control systems from design through retirement.
Smart Grid Interoperability Panel (SGIP) Cyber Security Working Group (CSWG)
http://collaborate.nist.gov/twiki-sggrid/bin/view/SmartGrid/CyberSecurityCTG
The primary goal of the working group is to develop an overall cybersecurity strategy for the Smart Grid
that includes a risk mitigation strategy to ensure interoperability of solutions across different
domains/components of the infrastructure. The cybersecurity strategy needs to address prevention,
detection, response, and recovery. Implementation of a cybersecurity strategy requires the definition and
implementation of an overall cybersecurity risk assessment process for the Smart Grid.
The working groupâs effort is documented in NIST Interagency Report (NISTIR) 7628 Revision 1,
Guidelines for Smart Grid Cybersecurity [98].

SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
314
SANS ICS ã»ãã¥ãªãã£èª²ç¨
http://ics.sans.org/
ICS ã«ãªãã¥ã©ã ã¯ãICS ç°å¢ã«å¯¾ããæ»æã¨é²å¾¡ã«ç¹åããå®å°è¨ç·´èª²ç¨ã§ãããã»ãã¥ãªã
ã£å°éå¡ã¨å¶å¾¡ã·ã¹ãã ã¨ã³ã¸ãã¢åæ¹ã«ãéè¦ã¤ã³ãã©ãå®ãããã®ç¥èã¨æéãæ示ããã
ä¸çç£æ¥ãµã¤ãã¼ã»ãã¥ãªãã£å°é家ï¼GICSPï¼ã¯ãä¸çæ
å ±ä¿è¨¼èªå®æ¸ï¼GIACï¼ãã¡ããªã®
ä¸ã§ãææ°ã®èªå®æ¸ã§ãéè¦ã¤ã³ãã©è³ç£ã®ã»ãã¥ãªãã£ã«é¢ããåºæ¬ç¥èãéè¦ãã¦ããã
GICSP ã¯ãITãã¨ã³ã¸ãã¢ãªã³ã°åã³ãµã¤ãã¼ã»ãã¥ãªãã£ã®æ¶ãæ©ã¨ãªããè¨è¨ããç¨éå»æ¢
ã¾ã§ãç£æ¥ç¨å¶å¾¡ã·ã¹ãã ã®ã»ãã¥ãªãã£ãå®ç¾ããã
ã¹ãã¼ãã°ãªããç¸äºéç¨æ§ããã«ï¼SGIPï¼ãµã¤ãã¼ã»ãã¥ãªãã£ä½æ¥ã°ã«ã¼ãï¼CSWGï¼
http://collaborate.nist.gov/twiki-sggrid/bin/view/SmartGrid/CyberSecurityCTG
ä½æ¥ã°ã«ã¼ãã®ä¸»ãªç®çã¯ãã¹ãã¼ãã°ãªããã®ãµã¤ãã¼ã»ãã¥ãªãã£æ¦ç¥ãçå®ãããã¨ã«ã
ããããã«ã¯ã¤ã³ãã©ã®ç¨®ã
ã®é åã»ã³ã³ãã¼ãã³ãã«ã¾ãããã½ãªã¥ã¼ã·ã§ã³ã®ç¸äºéç¨æ§ã
確ä¿ããããã®ãªã¹ã¯ç·©åçãå«ã¾ããããµã¤ãã¼ã»ãã¥ãªãã£æ¦ç¥ã¯ãäºé²ã»æ¤ç¥ã»å¯¾å¿ã»å¾©
æ§ãåãä¸ããå¿
è¦ãããããµã¤ãã¼ã»ãã¥ãªãã£æ¦ç¥ãå®æ½ããã«ã¯ãã¹ãã¼ãã°ãªããã®å
¨
è¬çãµã¤ãã¼ã»ãã¥ãªãã£ãªã¹ã¯è©ä¾¡ããã»ã¹ãæããã«ãã¦ãå®æ½ããå¿
è¦ãããã
ä½æ¥ã°ã«ã¼ãã®åçµã¯ãNIST æ¿åºæ©é¢éå ±åæ¸ï¼NISTIRï¼7628 第1çãã¹ãã¼ãã°ãªãããµã¤
ãã¼ã»ãã¥ãªãã£ã¬ã¤ãã©ã¤ã³ãã«è¨è¼ããã¦ãã[98]ã

SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
315
Appendix EâICS Security Capabilities and Tools
This section provides an overview of security capabilities that are available to or being developed in
support of the ICS community. There are several security products that are marketed specifically for ICS,
while others are general IT security products that are being used with ICS. Many of the products available
offer âsingle point solutions,â where a single security product offers multiple levels of protection. In
addition to available products, this section also discusses some research and development work towards
new products and technologies. Each organization should make a risk-based determination whether to
employ the security capabilities and tools mentioned in this appendix.
Data Diode
A data diode (also referred to as a unidirectional gateway, deterministic one-way boundary device or
unidirectional network) is a network appliance or device allowing data to travel only in one direction, used
in guaranteeing information security or protection of critical digital systems, such as industrial control
systems, from inbound cyber attacks. While use of these devices is common in high security environments
such as defense, where they serve as connections between two or more networks of differing security
classifications, the technology is also being used to enforce one-way communications outbound from
critical digital systems to untrusted networks.
Encryption
Encryption protects the confidentiality of data by encoding the data to ensure that only the intended
recipient can decode it. There are some commercially available encryption products designed specifically
for ICS applications, as well as general encryption products that support basic serial and Ethernet-based
communications.
Firewalls
Firewalls are commonly used to segregate networks to protect and isolate ICS. These implementations use
commercially available firewalls that are focused on Internet and corporate application layer protocols and
are not equipped to handle ICS protocols. Research was performed by an IT security vendor in 2003 to
develop a Modbus-based firewall that allows policy decisions to be made on Modbus/TCP header values
just as traditional firewalls filter on TCP/UDP ports and IP addresses [76]. There are currently several
firewalls available for ICS.
Intrusion Detection and Prevention
Intrusion detection systems (IDS) and intrusion prevention systems (IPS) are being deployed on ICS
networks and components to detect well-known cyber attacks. Network IDS products monitor network
traffic and use various detection methods, such as comparing portions of the traffic to signatures of known
attacks. In contrast, host intrusion detection uses software loaded on a host computer, often with attack
signatures, to monitor ongoing events and data on a computer system for possible exploits. IPS products
take intrusion detection a step further by automatically acting on detected exploits to attempt to stop them
[57].
The required task of a security team to constantly monitor, evaluate, and quickly respond to intrusion
detection events is sometimes contracted to a managed security service provider (MSSP). MSSPs have
correlation and analysis engines to process and reduce the vast amounts of events logged per day to a small
subset that needs to be manually evaluated. There are also correlation and analysis engine products
available to large organizations wanting to perform this function in-house. Security information and event

SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
316
ä»é² E ICS ã»ãã¥ãªãã£æ©è½åã³ãã¼ã«
ãã®ã»ã¯ã·ã§ã³ã§ã¯ãICS å
±åä½ãå©ç¨ã§ããã»ãã¥ãªãã£æ©è½ããç¾å¨éçºä¸ã®ãã®ã«ã¤ãã¦
æ¦èª¬ãããå¸å ´ã«ã¯ ICS ã«ç¹åããã»ãã¥ãªãã£è£½åãããã¤ããããICS ã§å©ç¨ããã¦ããä¸
è¬ç㪠IT ã»ãã¥ãªãã£è£½åããããå
¥æå¯è½ãªè£½åã®å¤ãã¯ãåä¸ã½ãªã¥ã¼ã·ã§ã³ãã§ã1ã¤ã®
ã»ãã¥ãªãã£è£½åãå¤æ§ãªã¬ãã«ã®ä¿è·ãä¸ãã¦ãããå
¥æå¯è½ãªè£½åã«å ãã¦ããã®ã»ã¯ã·ã§
ã³ã§ã¯ãæ°è£½åã»æ°æè¡ã«åããç 究éçºã«ã¤ãã¦ãããã¤ãåãä¸ãããåçµç¹ã¯ããã®ä»é²
ã§è¨åããã¦ããã»ãã¥ãªãã£æ©è½åã³ãã¼ã«ã®æ¡ç¨ã®æ¯éã«ã¤ãã¦ããªã¹ã¯ã«ç«èãã¦å¤æã
ã¹ãã§ããã
ãã¼ã¿ãã¤ãªã¼ã
ãã¼ã¿ãã¤ãªã¼ãï¼åæ¹åã²ã¼ãã¦ã§ã¤ã決å®è«çä¸æ¹éè¡å¢çããã¤ã¹åã¯åæ¹åãããã¯ã¼
ã¯ã¨ãå¼ã°ããï¼ã¯ããããã¯ã¼ã¯æ©å¨åã¯ããã¤ã¹ã§ããã¼ã¿ãä¸æ¹åã«ã®ã¿æµãã¦ãæ
å ±ã»
ãã¥ãªãã£ãä¿è¨¼ããç£æ¥ç¨å¶å¾¡ã·ã¹ãã çã®éè¦ãã¸ã¿ã«ã·ã¹ãã ãå¤é¨ãµã¤ãã¼æ»æããä¿
è·ããããã®ãããªããã¤ã¹ã®å©ç¨ã¯ãå½é²çã®ãã¤ã»ãã¥ãªãã£ç°å¢ã§ã¯æ®éã«è¦ãããç°ç¨®
ã»ãã¥ãªãã£åºåãæããã2ã¤ä»¥ä¸ã®ãããã¯ã¼ã¯éã®æ¥ç¶ã確ç«ãããã®æè¡ã¯ãéè¦ãã¸
ã¿ã«ã·ã¹ãã ããå¤é¨ã®ä¿¡é ¼ã§ããªããããã¯ã¼ã¯ã«åããåæ¹åã®éä¿¡ã«ãå©ç¨ãããã
æå·å
æå·åã¯ããã¼ã¿ãã³ã¼ãåãã¦ææã®åä¿¡è
ã ãã復å·ã§ããããã«ãããã¨ã§ããã¼ã¿ã®æ©
å¯æ§ãä¿è·ãããICS ç¨éã«ç¹åããå¸è²©ã®æå·å製åãããã¤ããããåºæ¬çãªã·ãªã¢ã«åã³
Ethernet ãã¼ã¹ã®éä¿¡ã«å¯¾å¿ããæ±ç¨æå·å製åãããã
ãã¡ã¤ã¢ã¦ã©ã¼ã«
ãã¡ã¤ã¢ã¦ã©ã¼ã«ã¯é常ããããã¯ã¼ã¯ãåé¢ã㦠ICS ãä¿è·ã»éé¢ããããã«ä½¿ç¨ãããå®è£
ã¯ãã¤ã³ã¿ã¼ãããåã³ä¼æ¥ã¢ããªã±ã¼ã·ã§ã³å±¤ãããã³ã«ã«ç¹åããICS ãããã³ã«ã¯å¦çã
ãªãå¸è²©ã®ãã¡ã¤ã¢ã¦ã©ã¼ã«ã使ç¨ãã¦è¡ãã2003 å¹´ã« IT ã»ãã¥ãªãã£ãã³ãã¼ã Modbus ã
ã¼ã¹ãã¡ã¤ã¢ã¦ã©ã¼ã«ã®éçºã«åãã¦ç 究ãè¡ã£ããããã¯å¾æ¥ã®ãã¡ã¤ã¢ã¦ã©ã¼ã«ã
TCP/UDP ãã¼ãåã³ IP ã¢ãã¬ã¹ã§ãã£ã«ã¿ãªã³ã°ãè¡ãããã«ãModbus/TCP ãããã¼å¤ã§ã
ãªã·ã¼æ±ºå®ãè¡ããã¨ãã§ãããç¾å¨ ICS ç¨ã«å©ç¨ã§ãããã¡ã¤ã¢ã¦ã©ã¼ã«ãããã¤ãããã
ä¾µå
¥æ¤ç¥åã³é²æ¢
ä¾µå
¥æ¤ç¥ã·ã¹ãã ï¼IDSï¼åã³ä¾µå
¥é²æ¢ã·ã¹ãã ï¼IPSï¼ã¯ãæ¢ç¥ã®ãµã¤ãã¼æ»æãæ¤ç¥ããããã
ICS ãããã¯ã¼ã¯åã³ã³ã³ãã¼ãã³ãã«å±éããã¦ããããããã¯ã¼ã¯ IDS 製åã¯ãããã¯ã¼ã¯
ãã©ãã£ãã¯ãç£è¦ããæ¢ç¥ã®æ»æã®ãã©ãã£ãã¯ã·ã°ããã£ã®ä¸é¨ãæ¯è¼ãããªã©ã種ã
ã®æ¤
ç¥æ¹æ³ãå©ç¨ãã¦ããã対ç
§çã«ãã¹ãä¾µå
¥æ¤ç¥ã§ã¯ããã¹ãã³ã³ãã¥ã¼ã¿ã«ã¤ã³ã¹ãã¼ã«ãã
ã½ããã¦ã¨ã¢ãå©ç¨ããå¤ãã¯æ»æã·ã°ããã£ãåèã«ãã¦ãã³ã³ãã¥ã¼ã¿ã·ã¹ãã ä¸ã§é²è¡ä¸
ã®äºè±¡åã³ãã¼ã¿ãç£è¦ããæªç¨ã®æç¡ãæ¤ç¥ãããIPS 製åã¯ãä¾µå
¥æ¤ç¥ããä¸æ©é²ãã¦ãæ¤
ç¥ããæªç¨ã®ä¸æ¢ã試ã¿ã[57]ã
ã»ãã¥ãªãã£ãã¼ã ã«æ±ããããä¾µå
¥æ¤ç¥ã®å¸¸ç¶ç£è¦ã»è©ä¾¡ã»è¿
é対å¿ã¨ããæ¥åã¯ã管çã»ã
ã¥ãªãã£ãµã¼ãã¹ãããã¤ãï¼MSSPï¼ã«å§è¨ããããã¨ããããMSSP ã®ç¸é¢åæã¨ã³ã¸ã³ã¯ã
æ¯æ¥è¨é²ãããè¨å¤§ãªäºè±¡ãå¦çãã¦å°ããªãµãã»ããã«ããããã¥ã¢ã«æä½ã§è©ä¾¡ã§ãããã
ã«ããããã®æ©è½ã社å
ã§æãããã大ä¼æ¥åãã«ãç¸é¢åæã¨ã³ã¸ã³è£½åãç¨æããã¦ããã
ã»ãã¥ãªãã£æ
å ±ã»äºè±¡ç®¡çï¼SIEMï¼è£½åãå©ç¨ãã¦ãIDS åã³ IPS ãã°ã®äºè±¡ã®ã»ããä»ã®ã³
ã³ãã¥ã¼ã¿ã·ã¹ãã ãã¢ããªã±ã¼ã·ã§ã³ãã¤ã³ãã©è£
ååãã®ä»ãã¼ãã¦ã¨ã¢/ã½ããã¦ã¨ã¢ã®
ç£æ»ãã°ãç£è¦ã»åæã»ç¸é¢ãã¦ãä¾µå
¥ã®ãããã¿ãæ¤åºãã¦ããçµç¹ãããã
SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
317
management (SIEM) products are used in some organizations to monitor, analyze, and correlate events
from IDS and IPS logs, as well as audit logs from other computer systems, applications, infrastructure
equipment, and other hardware and software, to look for intrusion attempts.
IDS and IPS vendors are developing and incorporating attack signatures for various ICS protocols such as
Modbus, DNP3, and ICCP [58]. Snort rules have been developed for Modbus TCP, DNP3, and ICCP.
Snort is an open source network intrusion detection and prevention system using a rule-driven language to
perform signature, protocol, and anomaly-based inspections. Rules for DNP3 and Modbus protocols have
also been added to the Bro IDS platform.
As with any software added to an ICS component, the addition of host IDS or IPS software could affect
system performance. IPSs are commonplace in todayâs information security industry, but can be very
resource intensive. These systems have the ability to automatically reconfigure systems if an intrusion
attempt is identified. This automated and fast reaction is designed to prevent successful exploits; however,
an automated tool such as this could be used by an adversary to adversely affect the operation on an ICS by
shutting down segments of a network or server. False positives can also hinder ICS operation.
Malware/Antivirus Software
Because early malware threats were primarily viruses, the software to detect and remove malware has
historically been called âantivirus software,â even though it can detect many types of malware. Antivirus
software is used to counter the threats of malware by evaluating files on a computerâs storage devices
(some tools also detect malware in real-time at the network perimeter and/or on the userâs workstation)
against an inventory of malware signature files. If one of the files on a computer matches the profile of
known malware, the malware is removed through a disinfection process so it cannot infect other local files
or communicate across a network to infect other files on other computers. There are also techniques
available to identify unknown malware âin-the-wildâ when a signature file is not yet available.
Many end-users and vendors of ICS are recommending the use of COTS antivirus software with their
systems and have even developed installation and configuration guidance based on their own laboratory
testing. Some ICS vendors recommend the use of antivirus software with their products, but offer little to
no guidance. Some end users and vendors are hesitant to use antivirus software due to fears that its use
would cause ICS performance problems or even failure. NIST and Sandia National Laboratories (SNL)
conducted a study and produced a report aimed at helping ICS owners/operators to deploy antivirus
software and to minimize and assess performance impacts of workstation and server-based antivirus
products. This study assembled ICS-based antivirus knowledge and serves as a starting point or a
secondary resource when installing, configuring, running, and maintaining antivirus software on an ICS
[56]. In many cases, performance impacts can be reduced through configuration settings as well as antivirus
scanning and maintenance scheduling outside of the antivirus software practices recommended for typical
IT systems.
In summary, COTS antivirus software can be used successfully on most ICS components. However, special
ICS specific considerations should be taken into account during the selection, installation, configuration,
operational, and maintenance procedures. ICS end-users should consult with the ICS vendors regarding the
use of antivirus software.
SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
318
IDS åã³ IPS ãã³ãã¼ã¯ãModbusãDNP3 åã³ ICCP çã種ã
ã® ICS ãããã³ã«ã®æ»æã·ã°ãã
ã£ãä½æããçµã¿è¾¼ãã§ãã[58]ãModbus TCPãDNP3 åã³ ICCP åãã« Snort ã«ã¼ã«ãä½æãã
ã¦ãããSnort ã¨ã¯ãªã¼ãã³ã½ã¼ã¹ãããã¯ã¼ã¯ä¾µå
¥æ¤ç¥é²æ¢ã·ã¹ãã ã®ãã¨ã§ãã«ã¼ã«ããªã
ã³è¨èªã使ç¨ãã¦ãã·ã°ããã£ããããã³ã«åã³ç°ç¶ã主ä½ã«æ¤æ»ãè¡ããDNP3 åã³ Modbus
ãããã³ã«ã®ã«ã¼ã«ã Bro IDS ãã©ãããã¼ã ã«è¿½å ããã¦ããã
ICS ã³ã³ãã¼ãã³ãã«è¿½å ãããä»ã®ã½ããã¦ã¨ã¢ã¨åæ§ããã¹ã IDS å㯠IPS ã½ããã¦ã¨ã¢ã®
追å ã¯ãã·ã¹ãã ããã©ã¼ãã³ã¹ã«å½±é¿ãããã¨ããããIPSs ã¯æ¨ä»ã®æ
å ±ã»ãã¥ãªãã£æ¥çã§
ã¯æ®éã«è¦ããããã極ãã¦è³æºãæ¶è²»ããããããã®ã·ã¹ãã ã§ã¯ãä¾µå
¥ã®ãããã¿ãæ¤ç¥ã
ããã¨ãã·ã¹ãã è¨å®ãèªåçã«å¤æ´ããè½åãåãã£ã¦ããããã®ãããªèªåè¿
é対å¿ã¯æªç¨
ãé²æ¢ããããã®ãã®ã§ããããæ»æå´ã«éç¨ããããããã¯ã¼ã¯ããµã¼ãã®ã»ã°ã¡ã³ããåæ
ãããã¨ã«ãããICS éç¨ã«æªå½±é¿ãåã¶å ´åããããæ¬é½æ§ã«ãã£ã¦ã ICS éç¨ãé»å®³ãããã
ãã«ã¦ã¨ã¢/ã¢ã³ãã¦ã¤ã«ã¹ã½ããã¦ã¨ã¢
åæã®ãã«ã¦ã¨ã¢è
å¨ã¯ä¸»ã«ã¦ã¤ã«ã¹ã§ãã£ãããããã«ã¦ã¨ã¢æ¤åºã»æé¤ã½ããã¦ã¨ã¢ã¯ã
種ã
ã®ãã«ã¦ã¨ã¢ã«å¯¾ããæ¤åºè½åãæã¤ãã®ã®ãå¾æ¥ãã¢ã³ãã¦ã¤ã«ã¹ã½ããã¦ã¨ã¢ãã¨å¼ã°
ãã¦ãããã¢ã³ãã¦ã¤ã«ã¹ã½ããã¦ã¨ã¢ã¯ããã«ã¦ã¨ã¢ã·ã°ããã£ãã¡ã¤ã«ã®ç®é²ã«ç
§ããã¦ã
ã³ã³ãã¥ã¼ã¿ã®ã¹ãã¬ã¼ã¸ããã¤ã¹ä¸ã®ãã¡ã¤ã«ãè©ä¾¡ãï¼ãã¼ã«ã«ãã£ã¦ã¯ãããã¯ã¼ã¯å¨è¾º
åã¯ã¦ã¼ã¶ã¯ã¼ã¯ã¹ãã¼ã·ã§ã³ä¸ã§ãªã¢ã«ã¿ã¤ã ã«ãã«ã¦ã¨ã¢ãæ¤åºãããã®ãããï¼ããã«ã¦
ã¨ã¢ã®è
å¨ã«å¯¾æãããã³ã³ãã¥ã¼ã¿ä¸ã®ãã¡ã¤ã«ã® 1ã¤ãæ¢ç¥ã®ãã«ã¦ã¨ã¢ã®ãããã¡ã¤ã«ã«
ä¸è´ããã¨ãæ¶æ¯ããã»ã¹ãçµã¦ãã®ãã«ã¦ã¨ã¢ã¯æé¤ãããä»ã®ãã¼ã«ã«ãã¡ã¤ã«ããããã¯
ã¼ã¯ãè¶ããä»ã®ã³ã³ãã¥ã¼ã¿ä¸ã®ãã¡ã¤ã«ã¸ã®ææã¯çããªããªããã¾ãã·ã°ããã£ãã¡ã¤ã«
ããªãå ´åã§ããæªç¥ã®ãéçããã«ã¦ã¨ã¢ãèå¥ããæè¡ãå©ç¨ã§ããã
å¤ãã® ICS ã¨ã³ãã¦ã¼ã¶åã³ãã³ãã¼ã¯ãã·ã¹ãã ã¸ã® COTS ã¢ã³ãã¦ã¤ã«ã¹ã½ããã¦ã¨ã¢ã®å°
å
¥ãæ¨å¥¨ãã¦ãããç¬èªã®ã©ã試é¨ãåºã«ãã¤ã³ã¹ãã¼ã«ã»è¨å®ã¬ã¤ãã³ã¹ãä½æãã¦ããã
ICS ãã³ãã¼ã«ãã£ã¦ã¯ãèªç¤¾è£½åã«ã¢ã³ãã¦ã¤ã«ã¹ã½ããã¦ã¨ã¢ã®ä½¿ç¨ãæ¨å¥¨ãã¦ãããã®ã®ã
ã¬ã¤ãã³ã¹ãå
¨ãåã¯ã»ã¨ãã©ç¨æã§ãã¦ããªãå ´åããããã¢ã³ãã¦ã¤ã«ã¹ã½ããã¦ã¨ã¢ã®å©
ç¨ã«ãããICS ã®ããã©ã¼ãã³ã¹åé¡ãé害ãçºçããã®ãæãã¦ã使ç¨ã«æ¶æ¥µçãªã¦ã¼ã¶ãã
ã³ãã¼ããããNIST ã¨ãµã³ãã£ã¢å½ç«ç 究æï¼SNLï¼ã¯èª¿æ»ãè¡ããICS ä¿æè
ã»æä½å¡åãã¬
ãã¼ããä½æããã¢ã³ãã¦ã¤ã«ã¹ã½ããã¦ã¨ã¢ã®å±éãå©ããã¯ã¼ã¯ã¹ãã¼ã·ã§ã³/ãµã¼ããã¼
ã¹ã¢ã³ãã¦ã¤ã«ã¹è£½åã®ããã©ã¼ãã³ã¹å½±é¿ãæå°åããè©ä¾¡ããè³ã¨ãã¦ãããæ¬ç 究ã«ãã
ICS ãã¼ã¹ã®ã¢ã³ãã¦ã¤ã«ã¹ç¥è¦ãã¾ã¨ã¾ããICS ã¸ã®ã¢ã³ãã¦ã¤ã«ã¹ã½ããã¦ã¨ã¢ã®ã¤ã³ã¹ã
ã¼ã«ã»è¨å®ã»å®è¡ã»ä¿å®ãè¡ãéã®åºçºç¹åã¯äºæ¬¡ãªã½ã¼ã¹ã¨ãªã£ã¦ãã[56]ãå¤ãã®å ´åãè¨
å®ãã¢ã³ãã¦ã¤ã«ã¹ã¹ãã£ãã³ã°ã»ä¿å®ã¹ã±ã¸ã¥ã¼ã«ããä¸è¬ç㪠IT ã·ã¹ãã ã§æ¨å¥¨ããã¦ã
ãã¢ã³ãã¦ã¤ã«ã¹ã½ããã¦ã¨ã¢è¦ç¯ãé¢ãã¦å®æ½ãããã¨ã§ãããã©ã¼ãã³ã¹å½±é¿ãæ¸ãããã¨
ãã§ããã
ã¾ã¨ãã¨ãã¦ãCOTS ã¢ã³ãã¦ã¤ã«ã¹ã½ããã¦ã¨ã¢ã¯ãã»ã¨ãã©ã® ICS ã³ã³ãã¼ãã³ãã§ä½¿ç¨å¯
è½ã§ããããã ããã®é¸å®ã»ã¤ã³ã¹ãã¼ã«ã»è¨å®ã»éç¨ã»ä¿å®æé ã«éãã¦ã¯ãç¹æ®ãª ICS åºæ
ã®èæ
®äºé
ãæ¤è¨ã«å
¥ããã¹ãã§ãããICS ã¨ã³ãã¦ã¼ã¶ã¯ãã¢ã³ãã¦ã¤ã«ã¹ã½ããã¦ã¨ã¢ã®ä½¿
ç¨ã«é¢ãã¦ãICS ãã³ãã¼ã«ç¸è«ãã¹ãã§ããã
SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
319
Vulnerability Assessment Tools
There are many tools available for performing network vulnerability assessments for typical IT networks;
however, the impacts these tools may have on the operation of an ICS should be carefully considered [77].
The additional traffic and exploits used during active vulnerability and penetration testing, combined with
the limited resources of many ICS, have been known to cause ICS to malfunction. As guidance in this area,
SNL developed a preferred list of vulnerability and penetration testing techniques for ICS [77]. These are
less intrusive methods, passive instead of active, to collect the majority of information that is often queried
by automated vulnerability and penetration testing tools. These methods are intended to allow collection of
the necessary vulnerability information without the risk of causing a failure while testing.
Sophia is a patent-pending, passive, real-time diagnostic and security tool designed and built specifically
for control systems professionals. Sophia builds and maintains an ICS network fingerprint and continuously
monitors activity against it, with white, gray and black-listing capabilities, alerting its managers of any
abnormal activity for further investigation, monitoring and/or action. Beta testing conducted by the Battelle
Energy Alliance (BEA) at the Idaho National Laboratories (INL) recently concluded with a group of over
30 participants, including major utilities and control system vendors. Those Beta participants reported
immediate benefits in the fingerprinting process and longer-term benefits in monitoring, securing, and
making on-going modifications to ICS configurations during the Beta testing period. Beta participants, as
well as non-participants, who have been following the development of Sophia by BEA/INL, have long
expressed interest in obtaining commercial grade Sophia software, services and support. Beta testing has
proven that this suite of tools offers unique capabilities, including visualization of activity and tailored
reporting to meet customer needs.
Shodan is a search engine that lets you find specific types of computers (routers, servers, etc.) on the
Internet using a variety of filters. Some have also described it as a search engine of service banners, which
are meta-data the server sends back to the client. This can be information about the server software, what
options the service supports, a welcome message or anything else that the client can find out before
interacting with the server. Shodan users are able to find systems including traffic lights, security cameras,
home heating systems as well as control systems. Users can use Shodan to determine if any of the devices
on their ICS are accessible from the internet.
The Cyber Security Evaluation Tool (CSET) is a Department of Homeland Security (DHS) product that
assists organizations in protecting their key national cyber assets. It was developed under the direction of
the DHS Industrial Control System Cyber Emergency Response Team (ICS-CERT) by cybersecurity
experts and with assistance from NIST. This tool provides users with a systematic and repeatable approach
for assessing the security posture of their cyber systems and networks. It includes both high-level and
detailed questions related to all industrial control and IT systems. CSET is a desktop software tool that
guides users through a step-by-step process to assess their control system and information technology
network security practices against recognized industry standards. The output from CSET is a prioritized list
of recommendations for improving the cybersecurity posture of the organization's enterprise and industrial
control cyber systems. The tool derives the recommendations from a database of cybersecurity standards,
guidelines, and practices. Each recommendation is linked to a set of actions that can be applied to enhance
cybersecurity controls. CSET has been designed for easy installation and use on a stand-alone laptop or
workstation. It incorporates a variety of available standards from organizations such as NIST, NERC, TSA,
DoD, and others. When the tool user selects one or more of the standards, CSET will open a set of
questions to be answered. The answers to these questions will be compared against a selected security
assurance level, and a detailed report will be generated to show areas for potential improvement. CSET
provides an excellent means to perform a self-assessment of the security posture of your control system
environment.
SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
320
èå¼±æ§è©ä¾¡ãã¼ã«
ä¸è¬ç㪠IT ãããã¯ã¼ã¯ã®èå¼±æ§è©ä¾¡ç¨ãã¼ã«ã¯å¤æ°ãããããããã ICS ã®éç¨ã«åã¼ãå½±
é¿ãæ
éã«æ¤è¨ãã¹ãã§ãã[77]ãå¤ãã® ICS ã®ãªã½ã¼ã¹ãå¶éãããã¢ã¯ãã£ãèå¼±æ§ã»ãã
ãã¬ã¼ã·ã§ã³ã»ãã¹ãã«ããã¦ãä»å çãªãã©ãã£ãã¯ãèå¼±æ§ã®æªç¨ãããã¨ãICS ã«é害ã®
åºããã¨ãåãã£ã¦ããããã®åéã§ã®ã¬ã¤ãã³ã¹ã¨ãã¦ãSNL ã¯ICS ã®å¥½ã¾ããèå¼±æ§ã»ãã
ãã¬ã¼ã·ã§ã³ã»ãã¹ãæè¡ãªã¹ããä½æãã[77]ããããã¯ãã侵襲æ§ã®å°ãªãæ¹æ³ã§ãã¢ã¯ã
ã£ãã¨ãããããããã·ãã§ãããèªååèå¼±æ§ã»ãããã¬ã¼ã·ã§ã³ã»ãã¹ããã¼ã«ããç
§ä¼ã
åãããã¨ãå¤ãæ
å ±ã®å¤§åãåéã§ããããã®ãããªæ¹æ³ã¯ã試é¨æã«é害ãçºçããããã¨
ãªããå¿
è¦ãªèå¼±æ§æ
å ±ãåéã§ããããã«ãªã£ã¦ããã
Sophia ã¯ç¹è¨±ç³è«ä¸ã®ããã·ãããªã¢ã«ã¿ã¤ã 診æã»ã»ãã¥ãªãã£ãã¼ã«ã§ãå¶å¾¡ã·ã¹ãã å°é
å¡ç¨ã«è¨è¨ã»æ§ç¯ããã¦ãããICS ãããã¯ã¼ã¯ãã£ã³ã¬ã¼ããªã³ããçæãã¦ç¶æããããã«
対ããæ´»åã常ç¶çã«ç£è¦ããããã¯ã¤ããªã¹ããã°ã¬ã¼ãªã¹ãåã³ãã©ãã¯ãªã¹ãã®ä½æè½å
ãããã詳細ãªèª¿æ»ã»ç£è¦ã»è¡åãè¦ããç°å¸¸æ´»åã«ã¤ãã¦ç®¡çè
ã«è¦å ±ãçºãããã¢ã¤ããå½
ç«ç 究æï¼INLï¼ã«ãã㦠Battelle Energy Allianceï¼BEAï¼ã«ãããã¼ã¿è©¦é¨ãè¡ããã大æå
Œ
±
ä¼æ¥ãå¶å¾¡ã·ã¹ãã ãã³ãã¼ç 30 ãè¶
ããã°ã«ã¼ããåå ãã¦ããã®ã»ã©çµäºããã
åå è
ã¯ããã£ã³ã¬ã¼ããªã³ãå¦çã«ã¯å½é¢ã®å©çãããããã¼ã¿è©¦é¨æéä¸ã® ICS è¨å®ã®ç£
è¦ã»ã»ãã¥ãªãã£ç¢ºä¿ã»è¨å®å¤æ´ã«ã¯é·æçå©çãããã¨å ±åãã¦ãããåå è
ã®ã¿ãªããã
BEA/INL ã«ãã Sophia ã®æãè¡ãã注è¦ãã¦ããéåå è
ããå¸è²©ã¬ãã«ã® Sophia ã½ããã¦ã¨
ã¢ããµã¼ãã¹åã³ãµãã¼ãã«é¢å¿ãå¯ãã¦ããããã¼ã¿è©¦é¨ã«ããããã®ãã¼ã«ã«ã¯æ´»åã®è¦è¦
åã顧客éè¦ã«åãããã«ã¹ã¿ãã¤ãºåå ±åçã®ã¦ãã¼ã¯ãªæ©è½ããããã¨ãå®è¨¼ããã¦ããã
Shodan ã¯æ¤ç´¢ã¨ã³ã¸ã³ã§ã種ã
ã®ãã£ã«ã¿ã使ç¨ãã¦ãã¤ã³ã¿ã¼ãããä¸ã®ç¹æ®ãªã³ã³ãã¥ã¼
ã¿ï¼ã«ã¼ã¿ããµã¼ãçï¼ãæ¢ãåºããã¨ãã§ããããµã¼ããã¯ã©ã¤ã¢ã³ãã«éãè¿ãã¡ã¿ãã¼ã¿
ã§ããããµã¼ãã¹ããã¼ã®æ¤ç´¢ã¨ã³ã¸ã³ã¨è©ããåãããããããã¯ãµã¼ãã½ããã¦ã¨ã¢ããµã¼
ãã¹ã®å¯¾å¿ãªãã·ã§ã³ãã¦ã§ã«ã«ã ã¡ãã»ã¼ã¸ããµã¼ãã¨ã®ç¸äºä½ç¨ãè¡ãåã«ã¯ã©ã¤ã¢ã³ãã
æ¤ç´¢ã§ãããã®ä»ã«ã¤ãã¦ã®æ
å ±ã¨ãªããShodan ã¦ã¼ã¶ã¯ä¿¡å·æ©ãã»ãã¥ãªãã£ã«ã¡ã©ã家åº
ææ¿ã·ã¹ãã ãå¶å¾¡ã·ã¹ãã çã®ã·ã¹ãã ãæ¤ç´¢ã§ããããããå©ç¨ããã°ãã¤ã³ã¿ã¼ãããçµ
ç±ã§ã¢ã¯ã»ã¹å¯è½ãª ICS ä¸ã®ããã¤ã¹ãå¤å¥ã§ããã
ãµã¤ãã¼ã»ãã¥ãªãã£è©ä¾¡ãã¼ã«(CSET)ã¯ãçµç¹ãå½ã®éè¦ãµã¤ãã¼è³ç£ãå®ãã®ãæ¯æ´ããå½
åå®å
¨ä¿éç(DHS)ã®è£½åã§ãããDHS ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ãµã¤ãã¼ç·æ¥å¯¾å¿ãã¼ã (ICS-CERT)
ã®æå°ä¸ã§ãNIST ã®æ¯æ´ãå¾ã¦ãµã¤ãã¼ã»ãã¥ãªãã£å°é家ãéçºããããµã¤ãã¼ã·ã¹ãã å
ã³ãããã¯ã¼ã¯ã®ã»ãã¥ãªãã£ç¶æ
ãè©ä¾¡ããéã®ä½ç³»çãã¤å復çãªåçµãå¯è½ã¨ãªãããã
ããç£æ¥ç¨å¶å¾¡åã³ IT ã·ã¹ãã ã«é¢ä¿ããé«åº¦ã®è©³ç´°ãªçåã«çãã¦ãããCSET ã¯ãã¹ã¯ãã
ãã½ããã¦ã¨ã¢ãã¼ã«ã§ãå¶å¾¡ã·ã¹ãã åã³æ
å ±æè¡ãããã¯ã¼ã¯ã»ãã¥ãªãã£è¦ç¯ããåºãèª
ããããæ¥çåºæºã«ç
§ããã¦ã段éçã«è©ä¾¡ãããã¨ãã§ãããCSET ã«ãããçµç¹ã®ä¼æ¥ã»ç£
æ¥ç¨å¶å¾¡ãµã¤ãã¼ã·ã¹ãã ã®ãµã¤ãã¼ã»ãã¥ãªãã£ç¶æ
ãæ¹åããããã®åªå
çæ¨å¥¨äºé
ãªã¹ã
ãä½æã§ããããã®ãã¼ã«ã¯ããµã¤ãã¼ã»ãã¥ãªãã£åºæºãã¬ã¤ãã©ã¤ã³åã³è¦ç¯ãã¼ã¿ãã¼ã¹
ããæ¨å¥¨äºé
ãå°ãåºããããããã®æ¨å¥¨äºé
ã¯ããµã¤ãã¼ã»ãã¥ãªãã£å¶å¾¡ã®æ¡å¼µã«é©ç¨å¯è½
ãªä¸é£ã®è¡åã«çµã³ã¤ãã¦ãããCSET ã¯ãã¹ã¿ã³ãã¢ãã¼ã³ã©ããããããã¯ã¼ã¯ã¹ãã¼ã·ã§
ã³ã«ãç°¡åã«ã¤ã³ã¹ãã¼ã«ãã¦å©ç¨ã§ããããã«ãªã£ã¦ãããNISTãNERCãTSAãDoD ãã®ä»
ã®çµç¹ããå
¥æå¯è½ãªç¨®ã
ã®åºæºãåãã¾ã¨ãã¦ããã¦ããããã¼ã«ã®ã¦ã¼ã¶ããããåºæºã®ã
ããããé¸æããã¨ãä¸é£ã®è³ªåãæ示ãããã質åã¸ã®åçããé¸æãããã»ãã¥ãªãã£ä¿è¨¼
ã¬ãã«ã¨ç
§ããåãããæ¹åã§ããåéã示ãã詳細ãªã¬ãã¼ããä½æãããããã«ãªã£ã¦ããã
CSET ã¯ãå¶å¾¡ã·ã¹ãã ç°å¢ã®ã»ãã¥ãªãã£ç¶æ
ãèªå·±è©ä¾¡ã§ããåªããæ段ã¨ãªãã
SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
321
SamuraiSTFU is the Samurai Projectâs Security Testing Framework for Utilities and takes best in breed
security tools for traditional network and web penetration testing and adds specialized tools for embedded
and RF testing and mixes in energy sector context, documentation and sample files. It also includes
emulators for SCADA, Smart Meters, and other types of energy sector systems to provide leverage for a
full test lab.
ICS owners must make the individuals using vulnerability assessment tools aware of the criticality of
continuous operation and the risks involved with performing these tests on operational systems. It may be
possible to mitigate these risks by performing tests on ICS components such as redundant servers or
independent test systems in a laboratory setting. Laboratory tests can be used to screen out test procedures
that might harm the operational system. Even with very good configuration management to assure that the
test system is highly representative, tests on the actual system are likely to uncover flaws not represented in
the laboratory.
SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
322
SamuraiSTFU ã¯ãã¦ã¼ãã£ãªãã£ç¨ãµã ã©ã¤ããã¸ã§ã¯ãã®ã»ãã¥ãªãã£è©¦é¨ä½ç³»ã§ãä¼çµ±çãª
ãããã¯ã¼ã¯/ã¦ã§ããããã¬ã¼ã·ã§ã³ã»ãã¹ãç¨ã»ãã¥ãªãã£ãã¼ã«ã®æè¯ã®ãã®ã使ç¨ãã
çµè¾¼ã¿/RF 試é¨ç¨ã®ç¹æ®ãã¼ã«ãå ããã¨ãã«ã®ã¼æ¥çã«ããã¦ææ¸ã¨ãã¡ã¤ã«ãä¸ä½åããã
ã¾ã SCADAãã¹ãã¼ãã¡ã¼ã¿ã¼ãã®ä»ã¨ãã«ã®ã¼æ¥çã®ã·ã¹ãã ç¨ã¨ãã¥ã¬ã¼ã¿ãçµã¿è¾¼ãã§ã
å
¨é¢è©¦é¨ã©ãã«å¼¾ã¿ãä»ãã¦ããã
ICS ä¿æè
ã¯ãèå¼±æ§è©ä¾¡ãã¼ã«ã使ç¨ãã¦ãåã
人ãç¶ç¶éç¨ã®éè¦æ§ã¨ããããã試é¨ãé
ç¨ã·ã¹ãã ã§è¡ãå ´åã®ãªã¹ã¯ãèªèãããªããã°ãªããªããåé·ãµã¼ããã©ãç°å¢ã«ããç¬ç«
試é¨ã·ã¹ãã çã® ICS ã³ã³ãã¼ãã³ãã§è©¦é¨ãè¡ããã¨ã«ããããã®ãããªãªã¹ã¯ãç·©åããã
ã¨ãã§ãããã©ã試é¨ãè¡ãã°ãéç¨ã·ã¹ãã ã«æ害ãªè©¦é¨æé ãæé¤ã§ããã極ãã¦è¯å¥½ãªè¨
å®ç®¡çã§è©¦é¨ã·ã¹ãã ã代表çãªãã®ã«ãªãããã«ãã¦ããå®éã®ã·ã¹ãã ã§è¡ã試é¨ã¯ãã©ã
ã§ã¯åãããªãæ¬ é¥ãæ¤åºã§ãããã¨ãããã

SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
323
Appendix FâReferences
[1] Fraser, Roy E., Process Measurement and Control:Introduction to Sensors, Communication,
Adjustment, and Control, Upper Saddle River, New Jersey:Prentice-Hall, Inc., 2001.
[2] Falco, Joe, et al., IT Security for Industrial Control Systems, NIST Internal Report (NISTIR) 6859,
February 2002, http://www.nist.gov/customcf/get_pdf.cfm?pub_id=821684 [accessed 4/16/15].
[3] Bailey, David, and Edwin Wright, Practical SCADA for Industry, Vancouver: IDC Technologies, 2003.
[4] Boyer, Stuart, SCADA:Supervisory Control and Data Acquisition.4th ed. Research Triangle Park,
North Carolina:International Society of Automation, 2010.
[5] American Gas Association, AGA Report No. 12, Cryptographic Protection of SCADA
Communications, Part 1:Background, Policies and Test Plan, September, March 14, 2006.
[6] Erickson, Kelvin, and John Hedrick, Plantwide Process Control, New York:John Wiley & Sons, Inc.,
1999.
[7] Berge, Jonas, Fieldbuses for Process Control:Engineering, Operation, and Maintenance, Research
Triangle Park, North Carolina:ISA, 2002.
[8] Peerenboom, James, âInfrastructure Interdependencies:Overview of Concepts and Terminology,â
invited paper, NSF/OSTP Workshop on Critical Infrastructure:Needs in Interdisciplinary Research and
Graduate Training, Washington, D.C., June 14-15, 2001.
[9] Rinaldi, Steven, et al., âIdentifying, Understanding, and Analyzing Critical Infrastructure
Interdependencies,â IEEE Control Systems Magazine, (December 2001), pp. 11-25,
http://dx.doi.org/10.1109/37.969131.
[10] GAO-04-354, Critical Infrastructure Protection:Challenges and Efforts to Secure Control Systems,
U.S. GAO, 2004, http://www.gao.gov/new.items/d04354.pdf.
[11] Weiss, Joseph, âCurrent Status of Cybersecurity of Control Systems,â Presentation to Georgia Tech
Protective Relay Conference, May 8, 2003.
[12] Keeney, Michelle et al., Insider Threat Study:Computer System Sabotage in Critical Infrastructure
Sectors, United States Secret Service and Carnegie Mellon Software Institute, 2005,
http://www.cert.org/archive/pdf/insidercross051105.pdf.
[13] Federal Information Security Management Act of 2002, Pub.L. 107-347 (Title III), 116 Stat 2946,
http://www.gpo.gov/fdsys/pkg/PLAW-107publ347/pdf/PLAW-107publ347.pdf [accessed 4/16/15].
[14] Federal Information Security Management Act Implementation Project [Web site],
http://csrc.nist.gov/groups/SMA/fisma/index.html [accessed 4/16/15].
[15] U.S. Department of Commerce, Federal Information Processing Standards (FIPS) Publication 199,
Standards for Security Categorization of Federal Information and Information Systems, February 2004,
http://csrc.nist.gov/publications/fips/fips199/FIPS-PUB-199-final.pdf [accessed 4/16/15].
SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
324

SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
325
[16] U.S. Department of Commerce, Federal Information Processing Standards (FIPS) Publication 200,
Minimum Security Requirements for Federal Information and Information Systems, March 2006,
http://csrc.nist.gov/publications/fips/fips200/FIPS-200-final-march.pdf [accessed 4/16/15].
[17] Knapp, Eric, Industrial Network Security:Securing Critical Infrastructure Networks for Smart Grid,
SCADA, and Other Industrial Control Systems, Waltham, Massachusetts:Syngress, 2011.
[18] U.S. Government Accountability Office (GAO), GAO-15-6, Federal Facility Cybersecurity:DHS and
GSA Should Address Cyber Risk to Building and Access Control Systems, December 12, 2014,
http://www.gao.gov/products/GAO-15-6 [accessed 4/16/15].
[19] Swanson, Marianne, et al., NIST SP 800-18 Revision 1, Guide for Developing Security Plans for
Federal Information Systems, February 2006,
http://csrc.nist.gov/publications/PubsSPs.htmlhttp://csrc.nist.gov/publications/PubsSPs.html#800-18
[accessed 4/16/15].
[20] Joint Task Force Transformation Initiative, NIST SP 800-39, Managing Information Security
Risk:Organization, Mission, and Information System View, March 2011,
http://csrc.nist.gov/publications/PubsSPs.htmlhttp://csrc.nist.gov/publications/PubsSPs.html#800-39
[accessed 4/16/15].
[21] Joint Task Force Transformation Initiative, NIST SP 800-37 Revision 1, Guide for Applying the Risk
Management Framework to Federal Information Systems: a Security Life Cycle Approach, February
2010 (updated June 5, 2014), http://dx.doi.org/10.6028/NIST.SP.800-37r1.
[22] Joint Task Force Transformation Initiative, NIST SP 800-53 Revision 4, Security and Privacy
Controls for Federal Information Systems and Organizations, April 2013 (updated January 22, 2015),
http://dx.doi.org/10.6028/NIST.SP.800-53r4.
[23] Joint Task Force Transformation Initiative, NIST SP 800-53A Revision 4, Assessing Security and
Privacy Controls in Federal Information Systems and Organizations:Building Effective Security
Assessment Plans, December 2014 (updated December 18, 2014),
http://dx.doi.org/10.6028/NIST.SP.800-53Ar4.
[24] Barker, William, NIST SP 800-59, Guideline for Identifying an Information System as a National
Security System, August 2003,
http://csrc.nist.gov/publications/PubsSPs.htmlhttp://csrc.nist.gov/publications/PubsSPs.html#800-59
[accessed 4/16/15].
[25] Stine, Kevin, et al., NIST SP 800-60 Revision 1 (2 vols.), Guide for Mapping Types of Information and
Information systems to Security Categories, August 2008,
http://csrc.nist.gov/publications/PubsSPs.htmlhttp://csrc.nist.gov/publications/PubsSPs.html#800-60
[accessed 4/16/15].
[26] Quinn, Stephen, et al., NIST SP 800-70 Revision 2, National Checklist Program for IT
Products:Guidelines for Checklist Users and Developers, February 2011,
http://csrc.nist.gov/publications/PubsSPs.htmlhttp://csrc.nist.gov/publications/PubsSPs.html#800-70
[accessed 4/16/15].
SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
326

SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
327
[27] Bowen, Pauline, et al., NIST SP 800-100, Information Security Handbook:A Guide for Managers,
October 2006 (updated March 7, 2007),
http://csrc.nist.gov/publications/PubsSPs.htmlhttp://csrc.nist.gov/publications/PubsSPs.html#800-100
[accessed 4/16/15].
[28] NIST Security Configurations Checklists Program for IT Products [Web site],
http://web.nvd.nist.gov/view/ncp/repository [accessed 4/16/15].
[29] Stamp, Jason, et al., Common Vulnerabilities in Critical Infrastructure Control Systems, Sandia
National Laboratories, 2003,
http://citeseerx.ist.psu.edu/viewdoc/download?doi=10.1.1.132.3264&rep=rep1&type=pdf.
[30] SCADA Security - Advice for CEOs, IT Security Expert Advisory Group (ITSEAG)
[31] Franz, Matthew, Vulnerability Testing of Industrial Network Devices, Critical Infrastructure Assurance
Group, Cisco Systems, 2003, http://blogfranz.googlecode.com/files/franz-isa-device-testing-oct03.pdf.
[32] Duggan, David, et al., Penetration Testing of Industrial Control Systems, Sandia National Laboratories,
Report No SAND2005-2846P, 2005.
[33] Presidentâs Critical Infrastructure Protection Board, and U.S. Department of Energy, Office of Energy
Assurance, 21 Steps to Improve Cybersecurity of SCADA Networks, [2002],
http://energy.gov/sites/prod/files/oeprod/DocumentsandMedia/21_Steps_-_SCADA.pdf [accessed
4/16/15].
[34] ISA-62443[multiple parts], Security for Industrial Automation and Control Systems, Research Triangle
Park, North Carolina:International Society of Automation,
http://isa99.isa.org/ISA99%20Wiki/WP_List.aspx [accessed 4/16/15].
[35] Centre for the Protection of National Infrastructure (CPNI), Firewall Deployment for SCADA and
Process Control Networks:Good Practice Guide, February 15, 2005,
http://energy.gov/sites/prod/files/Good%20Practices%20Guide%20for%20Firewall%20Deployment.pd
f [accessed 4/16/15].
[36] U.S. Department of Homeland Security, Recommended Practice:Improving Industrial Control Systems
Cybersecurity with Defense-in-Depth Strategies, October 2009, https://ics-cert.us-
cert.gov/sites/default/files/recommended_practices/Defense_in_Depth_Oct09.pdf [accessed 4/16/15].
[37] Industrial Automation Open Networking Association (IAONA), The IAONA Handbook for Network
Security, Version 1.3, 2005, http://www.iaona.org/pictures/files/1122888138-IAONA_HNS_1_3-
reduced_050725.pdf [accessed 4/16/15].
[38] U.S. Department of Homeland Security, Common Cybersecurity Vulnerabilities in Industrial Control
Systems, May 2011, https://ics-cert.us-
cert.gov/sites/default/files/recommended_practices/DHS_Common_Cybersecurity_Vulnerabilities_I
CS_2010.pdf [accessed 4/16/15].
[39] NIST SP 800-12, An Introduction to Computer Security:The NIST Handbook, 1995,
http://csrc.nist.gov/publications/PubsSPs.html.
SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
328

SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
329
[40] Souppaya, Murugiah, and Karen Scarfone, NIST SP 800-40 Revision 3, Guide to Enterprise Patch
Management Technologies, July 2013, http://dx.doi.org/10.6028/NIST.SP.800-40r3.
[41] Scarfone, Karen, et al., NIST SP 800-115, Technical Guide to Information Security Testing and
Assessment, September 2008,
http://csrc.nist.gov/publications/PubsSPs.htmlhttp://csrc.nist.gov/publications/PubsSPs.html#800-115
[accessed 4/16/15].
[42] Roback, Edward, NIST SP 800-23, Guidelines to Federal Organizations on Security Assurance and
Acquisition/ Use of Tested/Evaluated Products, August 2000,
http://csrc.nist.gov/publications/PubsSPs.htmlhttp://csrc.nist.gov/publications/PubsSPs.html#800-23
[accessed 4/16/15].
[43] Stoneburner, Gary, et al., NIST SP 800-27 Revision A, Engineering Principles for Information
Technology Security (A Baseline for Achieving Security), June 2004,
http://csrc.nist.gov/publications/PubsSPs.htmlhttp://csrc.nist.gov/publications/PubsSPs.html#800-27A
[accessed 4/16/15].
[44] Grance, Tim, et al., NIST SP 800-35, Guide to Information Technology Security Services, October
2003,
http://csrc.nist.gov/publications/PubsSPs.htmlhttp://csrc.nist.gov/publications/PubsSPs.html#800-35
[accessed 4/16/15].
[45] Grance, Tim, et al., NIST SP 800-36, Guide to Selecting Information Technology Security Products,
October 2003,
http://csrc.nist.gov/publications/PubsSPs.htmlhttp://csrc.nist.gov/publications/PubsSPs.html#800-36
[accessed 4/16/15].
[46] Grance, Tim, et al., NIST SP 800-64 Revision 2, Security Considerations in the System Development
Life Cycle, October 2008,
http://csrc.nist.gov/publications/PubsSPs.htmlhttp://csrc.nist.gov/publications/PubsSPs.html#800-64
[accessed 4/16/15].
[47] Hash, Joan, et al., NIST SP 800-65, Integrating IT Security into the Capital Planning and Investment
Control Process, January 2005,
http://csrc.nist.gov/publications/PubsSPs.htmlhttp://csrc.nist.gov/publications/PubsSPs.html#800-65
[accessed 4/16/15].
[48] U.S. Department of Homeland Security, Department of Homeland Security:Cyber Security
Procurement Language for Control Systems, September 2009 https://ics-cert.us-
cert.gov/sites/default/files/documents/Procurement_Language_Rev4_100809.pdf [accessed 4/16/15].
[49] Dray, James, et al., NIST SP 800-73-3, Interfaces for Personal Identity Verification (4 parts), February
2010,
http://csrc.nist.gov/publications/PubsSPs.htmlhttp://csrc.nist.gov/publications/PubsSPs.html#800-73
[accessed 4/16/15].
[50] Grother, Patrick, et al., NIST SP 800-76-2, Biometric Data Specification for Personal Identity
Verification, July 2013, http://dx.doi.org/10.6028/NIST.SP.800-76-2.
SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
330
SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
331
[51] Kuhn, D. Richard, et al., NIST SP 800-46 Revision 1, Guide to Enterprise Telework and Remote
Access Security, June 2009,
http://csrc.nist.gov/publications/PubsSPs.htmlhttp://csrc.nist.gov/publications/PubsSPs.html#800-46
[accessed 4/16/15].
[52] Swanson, Marianne, et al., NIST SP 800-34 Revision 1, Contingency Planning Guide for Federal
Information Systems, May 2010,
http://csrc.nist.gov/publications/PubsSPs.htmlhttp://csrc.nist.gov/publications/PubsSPs.html#800-34
[accessed 4/16/15].
[53] Burr, William, et al., NIST SP 800-63-2, Electronic Authentication Guideline, August 2013,
http://dx.doi.org/10.6028/NIST.SP.800-63-2.
[54] Bace, Rebecca, and Mell, Peter, NIST SP 800-31, Intrusion Detection Systems, 2001,
http://csrc.nist.gov/publications/PubsSPs.html.
[55] Scarfone, Karen, and Peter Mell, NIST SP 800-94, Guide to Intrusion Detection and Prevention
Systems (IDPS), February 2007,
http://csrc.nist.gov/publications/PubsSPs.htmlhttp://csrc.nist.gov/publications/PubsSPs.html#800-94
[accessed 4/16/15].
[56] Falco, Joe, et al., NIST SP 1058, Using Host-based Anti-virus Software on Industrial Control
Systems:Integration Guidance and a Test Methodology for Assessing Performance Impacts, September
18, 2006, http://www.nist.gov/manuscript-publication-search.cfm?pub_id=823596 [accessed 4/16/15].
[57] Peterson, Dale, âIntrusion Detection and Cyber Security Monitoring of SCADA and DCS Networks,â
ISA Automation West (AUTOWEST 2004), Long Beach, California, April 2004,
http://citeseerx.ist.psu.edu/viewdoc/download?doi=10.1.1.121.3420&rep=rep1&type=pdf [accessed
4/16/15].
[58] Symantec Corporation, âSymantec Expands SCADA Protection for Electric Utilities,â [press release],
September 14, 2005, http://www.symantec.com/about/news/release/article.jsp?prid=20050914_01
[accessed 4/16/15].
[59] Grance, Tim, et al., NIST SP 800-61 Revision 2, Computer Security Incident Handling Guide, August
2012, http://dx.doi.org/10.6028/NIST.SP.800-61r2.
[60] Mell, Peter, et al., NIST SP 800-83 Revision 1, Guide to Malware Incident Prevention and Handling
for Desktops and Laptops, July 2013, http://dx.doi.org/10.6028/NIST.SP.800-83r1.
[61] Wilson, Mark, and Joan Hash, NIST SP 800-50, Building an Information Technology Security
Awareness and Training Program, October 2003,
http://csrc.nist.gov/publications/PubsSPs.htmlhttp://csrc.nist.gov/publications/PubsSPs.html#800-50
[accessed 4/16/15].
[62] Mix, S., Supervisory Control and Data Acquisition (SCADA) Systems Security Guide, Electric Power
Research Institute (EPRI), 2003.
SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
332
SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
333
[63] Scarfone, Karen, et al., NIST SP 800-48 Revision 1, Guide to Securing Legacy IEEE 802.11 Wireless
Networks, July 2008,
http://csrc.nist.gov/publications/PubsSPs.htmlhttp://csrc.nist.gov/publications/PubsSPs.html#800-48
[accessed 4/16/15].
[64] Frankel, Sheila, et al, NIST SP 800-97, Establishing Wireless Robust Security Networks: a Guide to
IEEE 802.11i, February 2007,
http://csrc.nist.gov/publications/PubsSPs.htmlhttp://csrc.nist.gov/publications/PubsSPs.html#800-97
[accessed 4/16/15].
[65] U.S. Department of Commerce, Federal Information Processing Standards (FIPS) Publication 201-2,
Personal Identity Verification (PIV) of Federal Employees and Contractors, August 2013,
http://dx.doi.org/10.6028/NIST.FIPS.201-2.
[66] Dray, James, et al, NIST SP 800-96, PIV Card to Reader Interoperability Guidelines, September 2006,
http://csrc.nist.gov/publications/PubsSPs.htmlhttp://csrc.nist.gov/publications/PubsSPs.html#800-96
[accessed 4/16/15].
[67] Polk, W. Timothy, et al, NIST SP 800-78-3, Cryptographic Algorithms and Key Sizes for Personal
Identity Verification, December 2010,
http://csrc.nist.gov/publications/PubsSPs.htmlhttp://csrc.nist.gov/publications/PubsSPs.html#800-78
[accessed 4/16/15].
[68] Kent, Karen, and Murugiah Souppaya, NIST SP 800-92, Guide to Computer Security Log
Management, September 2006,
http://csrc.nist.gov/publications/PubsSPs.htmlhttp://csrc.nist.gov/publications/PubsSPs.html#800-92
[accessed 4/16/15].
[69] Jansen, Wayne, et al., NIST SP 800-28 Version 2, Guidelines on Active Content and Mobile Code,
March 2008,
http://csrc.nist.gov/publications/PubsSPs.htmlhttp://csrc.nist.gov/publications/PubsSPs.html#800-28
[accessed 4/16/15].
[70] Polk, Tim, et al., NIST SP 800-52 Revision 1, Guidelines for the Selection, Configuration, and Use of
Transport Layer Security (TLS) Implementations, April 2014, http://dx.doi.org/10.6028/NIST.SP.800-
52r1.
[71] Barker, Elaine, et al., NIST SP 800-56A Revision 2, Recommendation for Pair-Wise Key
Establishment Schemes Using Discrete Logarithm Cryptography, May 2013,
http://dx.doi.org/10.6028/NIST.SP.800-56Ar2.
[72] Baker, Elaine, et al., NIST SP 800-57 (3 parts), Recommendation for Key Management:Part 1 Revision
3, General, July 2012
http://csrc.nist.gov/publications/PubsSPs.htmlhttp://csrc.nist.gov/publications/PubsSPs.html#800-
57pt1; Part 2, Best Practices for Key Management Organization, August 2005,
http://csrc.nist.gov/publications/PubsSPs.htmlhttp://csrc.nist.gov/publications/PubsSPs.html#800-
57pt2; Part 3 Revision 1, Application-Specific Key Management Guidance, January 2015,
http://dx.doi.org/10.6028/NIST.SP.800-57pt3r1.
SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
334
SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
335
[73] Kuhn, D. Richard, et al., NIST SP 800-58, Security Considerations for Voice Over IP Systems, January
2005,
http://csrc.nist.gov/publications/PubsSPs.htmlhttp://csrc.nist.gov/publications/PubsSPs.html#800-58
[accessed 4/16/15].
[74] Frankel, Sheila, et al., NIST SP 800-77, Guide to IPsec VPNs, December 2005,
http://csrc.nist.gov/publications/PubsSPs.htmlhttp://csrc.nist.gov/publications/PubsSPs.html#800-77
[accessed 4/16/15].
[75] Shirey, R., Internet Security Glossary, Version 2, RFC 4949, August 2007, http://www.rfc-
editor.org/rfc/rfc4949.txt [accessed 4/16/15].
[76] Franz, Matthew, and Venkat Pothamsetty, ModbusFW:Deep Packet Inspection for Industrial Ethernet,
Critical Infrastructure Assurance Group, Cisco Systems, 2004,
http://blogfranz.googlecode.com/files/franz-niscc-modbusfw-may04.pdf [accessed 4/16/15].
[77] Duggan, David, Penetration Testing of Industrial Control Systems, SAND2005-2846P, Sandia
National Laboratories, March 2005, http://energy.sandia.gov/wp/wp-
content/gallery/uploads/sand_2005_2846p.pdf [accessed 4/16/15].
[78] Kissel, Richard, et al., NIST SP 800-88 Revision 1, Guidelines for Media Sanitization, December 2014,
http://dx.doi.org/10.6028/NIST.SP.800-88r1.
[79] Joint Task Force Transformation Initiative, NIST SP 800-30 Revision 1, Guide for Conducting Risk
Assessments, September 2012,
http://csrc.nist.gov/publications/PubsSPs.htmlhttp://csrc.nist.gov/publications/PubsSPs.html#800-30
[accessed 4/16/15].
[80] Johnson, Arnold, et al., NIST SP 800-128, Guide for Security-Focused Configuration Management of
Information Systems, August 2011,
http://csrc.nist.gov/publications/PubsSPs.htmlhttp://csrc.nist.gov/publications/PubsSPs.html#800-128
[accessed 4/16/15].
[81] Dempsey, Kelley, et al., NIST SP 800-137, Information Security Continuous Monitoring (ISCM) for
Federal Information Systems and Organizations, September 2011,
http://csrc.nist.gov/publications/PubsSPs.htmlhttp://csrc.nist.gov/publications/PubsSPs.html#800-137
[accessed 4/16/15].
[82] Waltermire, David, et al., NIST SP 800-126 Revision 2, The Technical Specification for the Security
Content Automation Protocol (SCAP):SCAP Version 1.2, September 2011 (updated March 19, 2012),
http://csrc.nist.gov/publications/PubsSPs.htmlhttp://csrc.nist.gov/publications/PubsSPs.html#800-126-
rev2 [accessed 4/16/15].
[83] Executive Order no. 13636, Improving Critical Infrastructure Cybersecurity, DCPD-201300091,
February 12, 2013, http://www.gpo.gov/fdsys/pkg/FR-2013-02-19/pdf/2013-03915.pdf [accessed
4/16/15].
SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
336
SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
337
[84] National Institute of Standards and Technology, Framework for Improving Critical Infrastructure
Cybersecurity, version 1.0, February 12, 2014,
http://www.nist.gov/cyberframework/upload/cybersecurity-framework-021214.pdf [accessed 4/16/15].
[85] Scarfone, Karen, and Paul Hoffman, NIST SP 800-41 Revision 1, Guidelines on Firewalls and
Firewall Policy, September 2009, http://csrc.nist.gov/publications/PubsSPs.html#800-41 [accessed
4/16/15].
[86] Office of Management and Budget, OMB Memorandum M-07-16, Safeguarding Against and
Responding to the Breach of Personally Identifiable Information, May 22, 2007,
https://www.whitehouse.gov/sites/default/files/omb/memoranda/fy2007/m07-16.pdf [accessed 4/16/15].
[87] Office of Management and Budget, OMB Memorandum M-10-22, Guidance for Online Use of Web
Measurement and Customization Technologies, June 25, 2010,
https://www.whitehouse.gov/sites/default/files/omb/assets/memoranda_2010/m10-22.pdf [accessed
4/16/15].
[88] McCallister, Erika, et al., NIST SP 800-122, Guide to Protecting the Confidentiality of Personally
Identifiable Information (PII), April 2010, http://csrc.nist.gov/publications/PubsSPs.html#800-122
[accessed 4/16/15].
[89] Federal Enterprise Architecture Security and Privacy Profile, Version 3.0, September 2010,
https://cio.gov/wp-content/uploads/downloads/2012/09/FEA-Security-Privacy-Profile-v3-09-30-
2010.pdf [accessed 4/16/15].
[90] U.S. Department of Commerce, Federal Information Processing Standards (FIPS) Publication 140-2,
Security Requirements for Cryptographic Modules, May 25, 2001 (Change Notice 2, 12/3/2002),
http://csrc.nist.gov/publications/PubsFIPS.html#140-2 [accessed 4/16/15].
[91] Tracy, Miles, et al., NIST SP 800-45 Version 2, Guidelines on Electronic Mail Security, February
2007, http://csrc.nist.gov/publications/PubsSPs.html#800-45 [accessed 4/16/15].
[92] Grance, Tim, et al., NIST SP 800-47, Security Guide for Interconnecting Information Technology
Systems, August 2002, http://csrc.nist.gov/publications/PubsSPs.html#800-47 [accessed 4/16/15].
[93] Kent, Karen, et al., NIST SP 800-86, Guide to Integrating Forensic Techniques into Incident Response,
August 2006, http://csrc.nist.gov/publications/PubsSPs.html#800-86 [accessed 4/16/15].
[94] Scarfone, Karen, et al., NIST SP 800-111, Guide to Storage Encryption Technologies for End User
Devices, November 2007, http://csrc.nist.gov/publications/PubsSPs.html#800-111 [accessed 4/16/15].
[95] Scarfone, Karen, et al., NIST SP 800-123, Guide to General Server Security, July 2008,
http://csrc.nist.gov/publications/PubsSPs.html#800-123 [accessed 4/16/15].
[96] Scarfone, Karen, et al., NIST SP 800-127, Guide to Securing WiMAX Wireless Communications,
September 2010, http://csrc.nist.gov/publications/PubsSPs.html#800-127 [accessed 4/16/15].
SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
338

SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
339
[97] Johnson, Arnold, et al., NIST SP 800-128, Guide for Security-Focused Configuration Management of
Information Systems, August 2011, http://csrc.nist.gov/publications/PubsSPs.html#800-128 [accessed
4/16/15].
[98] Smart Grid Interoperability Panel, Smart Grid Cybersecurity Committee, NISTIR 7628 Revision 1,
Guidelines for Smart Grid Cybersecurity, September 2014, http://dx.doi.org/10.6028/NIST.IR.7628r1
[accessed 4/16/15].
[99] Kissel, Richard (ed.), NISTIR 7298 Revision 2, Glossary of Key Information Security Terms, May
2013, http://dx.doi.org/10.6028/NIST.IR.7298r2 [accessed 4/16/15].
SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
340

SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
341
Appendix GâICS Overlay
NOTE TO READERS
The ICS overlay is a partial tailoring of the controls and control baselines in SP 800-53, Revision 4,
and adds supplementary guidance specific to ICS. The concept of overlays is introduced in Appendix I
of SP 800-53, Revision 4. The ICS overlay is intended to be applicable to all ICS systems in all
industrial sectors. Further tailoring can be performed to add specificity to a particular sector (e.g.,
pipeline, energy). Ultimately, an overlay may be produced for a specific system (e.g., the XYZ
company). This ICS overlay constitutes supplemental guidance and tailoring for SP 800-53, Revision
4. Please be sure you are looking at the correct version of SP 800-53. Duplicating Appendix F of SP
800-53 would increase the size of this Appendix by over 65 pages. Therefore, the drafting committee
has decided to not duplicate Appendix F. The reader should have SP 800-53, Revision 4 available. The
authoring team also considered that this ICS overlay may serve as a model for other overlays.
Feedback on this Appendixâs structure would be appreciated, especially in the following areas: the
level of abstraction and whether the examples provided in the supplemental guidance are
sufficient/beneficial for implementation.
Since the ICS overlay exists in the context of SP 800-53, Revision 4, it is important to review that
context. SP 800-53, Revision 4, Security and Privacy Controls for Federal Information Systems and
Organizations, represents the most comprehensive update to the security controls catalog since its
inception in 2005. This update was motivated principally by the expanding threat spaceâ
characterized by the increasing sophistication of cyber attacks and the operations tempo of adversaries
(i.e., the frequency of such attacks, the professionalism of the attackers, and the persistence of
targeting by attackers). State-of-the-practice security controls and control enhancements have been
developed and integrated into the catalog addressing such areas as: mobile and cloud computing;
applications security; trustworthiness, assurance, and resiliency of information systems; insider threat;
supply chain security; and the advanced persistent threat.
To take advantage of the expanded set of security and privacy controls, and to give organizations
greater flexibility and agility in defending their information systems, the concept of overlays was
introduced in this revision. Overlays provide a structured approach to help organizations tailor security
control baselines and develop specialized security plans that can be applied to specific
missions/business functions, environments of operation, and/or technologies. This specialization
approach is important as the number of threat-driven controls and control enhancements in the catalog
increases and organizations develop risk management strategies to address their specific protection
needs within defined risk tolerances.
SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
342
ä»é² G ICS ãªã¼ãã¼ã¬ã¤
èªè
ã¸ã®æ³¨è¨
ICS ãªã¼ãã¼ã¬ã¤ã¯ãSP 800-53 第4çã«ç¤ºãããå¶å¾¡åã³å¶å¾¡ãã¼ã¹ã©ã¤ã³ãé¨åçã«ã«ã¹ã¿ã
ã¤ãºãããã®ã§ãICS ã«ç¹åããè£è¶³ã¬ã¤ãã³ã¹ã¨ãªãããªã¼ãã¼ã¬ã¤ã®æ¦å¿µã¯ SP 800-53 第4
çã®ä»é² Iã«èª¬æããããICS ãªã¼ãã¼ã¬ã¤ã¯ãããããç£æ¥çã®ãããã ICS ã·ã¹ãã ã«é©ç¨
ããããã«ã§ãã¦ãããæ´ã«ã«ã¹ã¿ãã¤ãºãã¦ãç¹å®ã®æ¥çåãã«ãããã¨ãã§ããï¼ãã¤ãã©
ã¤ã³ãã¨ãã«ã®ã¼çï¼ãæçµçã«ã¯ã1ã¤ã®ãªã¼ãã¼ã¬ã¤ã 1ã¤ã®ã·ã¹ãã ç¨ã«ä½æã§ãã
ï¼XYZ 社ç¨çï¼ãICS ãªã¼ãã¼ã¬ã¤ã¯ãSP 800-53 第4çã®è£è¶³ã¬ã¤ãã³ã¹ã«ã¹ã¿ãã¤ãºçã¨ãª
ãã該å½ãã SP 800-53 ã使ç¨ããããçæãããããSP 800-53 ã®ä»é² Fãåé²ããã¨ãç´æ°ã
65 ãã¼ã¸å¢ãããã¨ã«ãªãã®ã§ãèµ·æ¡å§å¡ä¼ã¯è¤åããªããã¨ã«ãããèªè
㯠SP 800-53 第4ç
ãæ許ã«ç½®ãããã«ãã¹ãã§ãããã¾ãå·çãã¼ã ã¯ããã® ICS ãªã¼ãã¼ã¬ã¤ãä»ã®ãªã¼ãã¼ã¬
ã¤ã®ã²ãªå½¢ã¨ãªãããã«ãããä»é²ã®æ§æãç¹ã«æ¦å¿µåã®ã¬ãã«åã³è£è¶³ã¬ã¤ãã³ã¹ã®æ示ä¾
ã¯ãå®è£
ä¸ååã§å½¹ç«ã¤ãã©ããã«ã¤ãã¦ããã£ã¼ãããã¯ãããã ããã°å¹¸ãã§ããã
ICS ãªã¼ãã¼ã¬ã¤ã¯ãSP 800-53 第4çã®æèã«æ²¿ã£ã¦åå¨ãã¦ããããããã®æèãè¦ç´ããã¨
ã¯èè¦ã§ãããSP 800-53 第4çã®é£é¦æ
å ±ã·ã¹ãã ã»çµç¹ã®ã»ãã¥ãªãã£ã»ãã©ã¤ãã·ã¼ç®¡ç
ã«ã¯ã2005 å¹´ã®æ¦å¿µå以æ¥ã®ã»ãã¥ãªãã£å¯¾çã«ã¿ãã°ã«å¯¾ããå
æ¬çãªæ´æ°å
容ã示ããã¦
ãããæ´æ°ã¯ããµã¤ãã¼æ»æãã¾ãã¾ãå·§å¦åããè
å¨ãæ¡å¤§ãã¦ãããã¨ã主ãªçç±ã§ãã
ï¼æ»æã®é »åº¦ãæ»æå´ã®å°éåãæ¨çã«å¯¾ããå·ææ§çï¼ãå®ç¨ã«ä¾ãããã»ãã¥ãªãã£å¯¾çã
管çæ¡å¼µã¯ãé²å±ãéãã次ã®åéã®ã«ã¿ãã°ã«çµã¿è¾¼ã¾ãã¦ãããã¢ãã¤ã«/ã¯ã©ã¦ãã³ã³ã
ã¥ã¼ãã£ã³ã°ãã¢ããªã±ã¼ã·ã§ã³ã»ãã¥ãªãã£ãæ
å ±ã·ã¹ãã ã®ä¿¡é ¼æ§ã»ä¿è¨¼ã»å¼¾åæ§ãã¤ã³ãµ
ã¤ãã¼è
å¨ããµãã©ã¤ãã§ã¼ã³ã»ãã¥ãªãã£ãææ°ã®æç¶çè
å¨ã
æ¡å¼µãããã»ãã¥ãªãã£/ãã©ã¤ãã·ã¼ç®¡çãå©ç¨ããæ
å ±ã·ã¹ãã ãå®ãããã®æè»æ§ã¨æ©æ
æ§ãçµç¹ã«å¢ãå ããããããªã¼ãã¼ã¬ã¤æ¦å¿µããã®çã«å°å
¥ãããããªã¼ãã¼ã¬ã¤ã¯ç³»çµ±ç«ã£
ãåçµã§ãçµç¹ãã»ãã¥ãªãã£å¯¾çã®ãã¼ã¹ã©ã¤ã³ã微調æ´ããåºæã®ä»»åã»äºæ¥æ©è½ãéç¨ç°
å¢åã¯æè¡ã«é©ç¨å¯è½ãªç¬èªã®ã»ãã¥ãªãã£è¨ç»æ¸ãä½æããã®ãæ¯æ´ãããè
å¨ã«å¯¾å¿ããã«
ã¿ãã°ã®ç®¡çåã³ãã®æ¡å¼µä»¶æ°ãå¢ãã¦ãããåçµç¹ã¯ãªã¹ã¯ç®¡çæ¦ç¥ãä½æããåºæã®ä¿è·ã
ã¼ãºãè¦å®ã®ãªã¹ã¯ãã¬ã©ã³ã¹å
ã§åãä¸ãã¦ããããããã®ç¬èªåã«åããåçµã¯èè¦ã§ã
ãã

SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
343
Identification
This overlay may be referenced as the NIST Special Publication 800-82 Revision 2 Industrial Control
System Overlay (âNIST SP 800-82 Rev 2 ICS Overlayâ). It is based on NIST SP 800-53 Revision 4 [22].
NIST developed this overlay in furtherance of its statutory responsibilities under the Federal Information
Security Modernization Act (FISMA) of 2014 (Public Law 113-283), Presidential Policy Directive (PPD)-
21 and Executive Order 13636. NIST is responsible for developing standards and guidelines, including
minimum requirements, for providing adequate information security for all agency operations and assets,
but such standards and guidelines shall not apply to national security systems without the express approval
of appropriate federal officials exercising policy authority over such systems. Comments may be directed to
icsoverlaycomments@nist.gov.
Overlay Characteristics
Industrial Control Systems (ICS) are typically used in industries such as electric, water and wastewater, oil
and natural gas, transportation, chemical, pharmaceutical, pulp and paper, food and beverage, and discrete
manufacturing (e.g., automotive, aerospace, and durable goods). Supervisory control and data acquisition
(SCADA) systems are generally used to control dispersed assets using centralized data acquisition and
supervisory control. Distributed Control Systems (DCS) are generally used to control production systems
within a local area such as a factory using supervisory and regulatory control. Programmable Logic
Controllers (PLCs) are generally used for discrete control for specific applications and generally provide
regulatory control. These control systems are vital to the operation of the U.S. critical infrastructures that
are often highly interconnected and mutually dependent systems. It is important to note that approximately
90 percent of the nation's critical infrastructures are privately owned and operated. Federal agencies also
operate many of the ICS mentioned above; other examples include air traffic control and materials handling
(e.g., Postal Service mail handling.)
Applicability
The purpose of this overlay is to provide guidance for securing ICS, including SCADA and DCS systems,
PLCs, and other systems performing industrial control functions. This overlay has been prepared for use by
federal agencies. It may be used by nongovernmental organizations on a voluntary basis.
Overlay Summary
Table G-1 provides a summary of the security controls and control enhancements from NIST SP 800-53
Appendix F [22, App. F] that have been allocated to the initial security control baselines (i.e., Low,
Moderate, and High) along with indications of ICS Supplemental Guidance and ICS tailoring. Controls and
control enhancements for which there is ICS Supplemental Guidance are bolded. If the control baselines
are supplemented by the addition of a control to the baseline, the control or control enhancement is
underlined. If a control or control enhancement is removed from the baseline, the control or control
enhancement is struck out.
Example:
AU-4
Audit Storage Capacity
AU-4 (1)
AU-4 (1)
AU-4 (1)
In this example, ICS Supplemental Guidance was added to Control Enhancement 1 of AU-4 (bolded). In
addition, Control Enhancement 1 of AU-4 was added to the Low, Moderate (Mod), and High baselines
(underlined).
SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
344
èå¥
ãã®ãªã¼ãã¼ã¬ã¤ã¯ NIST SP 800-82 第2çç£æ¥ç¨å¶å¾¡ã·ã¹ãã ãªã¼ãã¼ã¬ã¤(ãNIST SP 800-82
第2çICS ãªã¼ãã¼ã¬ã¤ã)ã¨å¼ã°ãããã¨ãããããã㯠NIST SP 800-53 第4ç[22]ã«åºã¥ã
ã¦ããã
NIST ã¯ã2014 å¹´é£é¦æ
å ±å¼·åæ³(FISMA)(Public Law 113-283)ã大統é æ¿çæ示(PPD)-21 åã³
大統é å½ä»¤ 13636 ã«å¾ãããã®æ³ç責åãæ¨é²ããããã«ãã®ãªã¼ãã¼ã¬ã¤ãä½æãããNIST
ã¯ããããæ¿åºæ©é¢æ¥åã»è³ç£ã®æ
å ±ã»ãã¥ãªãã£ã確ä¿ãããããæä½è¦ä»¶çãå«ãã è¦æ ¼å
ã³ã¬ã¤ãã©ã¤ã³ã®ä½æãæ
å½ãã¦ãããããã®ãããªè¦æ ¼åã³ã¬ã¤ãã©ã¤ã³ã¯ããã®ãããªã·ã¹
ãã ã«å¯¾ããæ½ç権éãæã£ãé£é¦è¡æ¿å®ã®æ確ãªæ¿èªããªããã°ãå½ã®ã»ãã¥ãªãã£ã·ã¹ãã
ã«ã¯é©ç¨ãããªããæè¦ã¯æ¬¡å®ã«å¯ããããããicsoverlaycomments@nist.gov.
ãªã¼ãã¼ã¬ã¤ã®ç¹å¾´
ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã¯ä¸è¬çã«é»æ°ãä¸ä¸æ°´ãç³æ²¹ã»ã¬ã¹ã輸éãåå¦ãå»è¬åããã«
ãã»è£½ç´ãé£åã»é£²æåã³çµç«è£½é ï¼èªåè»ãèªç©ºå®å®ãèä¹
æ¶è²»è²¡çï¼æ¥çã§å©ç¨ããã¦ããã
SCADA ã¯ãé常ãéä¸ãã¼ã¿åå¾ç£è¦å¶å¾¡ã«ãããåæ£åãããè³ç£ãå¶å¾¡ããããã«ä½¿ç¨ããã
DCS ã¯ãé常ããã¼ã«ã«ã¨ãªã¢å
ã«ããå·¥å ´çã®çç£ã·ã¹ãã ããç£è¦ã»è¦å¶å¶å¾¡ã«ããå¶å¾¡ã
ãããã«ä½¿ç¨ãããããã°ã©ããã«è«çã³ã³ããã¼ã©ï¼PLCï¼ã¯ãé常ãç¹æ®ç¨éã§ã®é¢æ£å¶å¾¡
ã«ä½¿ç¨ããè¦å¶å¶å¾¡ãé常è¡ãããã®ãããªå¶å¾¡ã·ã¹ãã ã¯ãé«åº¦ã«é£æºã»ç¸äºä¾åããã·ã¹ã
ã ã¨ãªããç±³å½ã®éè¦ã¤ã³ãã©ã®éå¶ã«ç·è¦ãªå½¹å²ãæããã¦ãããå½ã®éè¦ã¤ã³ãã©ã®ããã
90%ã¯ãç§ä¼æ¥ãä¿æãéå¶ãã¦ããç¹ãéè¨ããã®ã¯èè¦ã§ãããé£é¦æ¿åºæ©é¢ãåè¿°ã® ICS
ã®å¤ããéå¶ãã¦ãããããã®ã»ãã«ãèªç©ºäº¤é管å¶ãç©æµå¦çï¼æ¸¯æ¹¾æ¥åãéµä¾¿çï¼ãªã©ãã
ãã
é©ç¨æ§
ãã®ãªã¼ãã¼ã¬ã¤ã®ç®çã¯ãSCADA ã·ã¹ãã ãDCS ã·ã¹ãã ãPLC ãã®ä»ç£æ¥ç¨å¶å¾¡æ©è½ãã¤ã
ãã©ãã·ã¹ãã çãICS ã®ã»ãã¥ãªãã£ã確ä¿ããããã®ã¬ã¤ãã³ã¹ã¨ãªããé£é¦æ¿åºæ©é¢åã
ã«æºåããã¦ãããéæ¿åºçµç¹ãèªä¸»çã«å©ç¨ãã¦ããã¾ããªãã
ãªã¼ãã¼ã¬ã¤ã®ã¾ã¨ã
表G-1 ã¯ãNIST SP 800-53 ä»é² F[22, App. F]ã®ã»ãã¥ãªãã£å¯¾çåã³ç®¡çæ¡å¼µãã¾ã¨ãããã®
ã§ããã管çæ¡å¼µã¯ãå½åã®ã»ãã¥ãªãã£å¯¾çãã¼ã¹ã©ã¤ã³ï¼ä½ã»ä¸ã»é«ï¼ã«ãICS è£è¶³ã¬ã¤ã
ã³ã¹åã³ ICS ã®ã«ã¹ã¿ãã¤ãºã¨ã¨ãã«å²ãå½ã¦ããããã®ã§ãããICS è£è¶³ã¬ã¤ãã³ã¹ã®ãã管
çåã³ç®¡çæ¡å¼µã¯å¤ªåã«ãªã£ã¦ããã対çãã¼ã¹ã©ã¤ã³ã«è£è¶³ç®¡çã追å ããã¦ããå ´åã管ç
åã³ç®¡çæ¡å¼µã«ä¸ç·ãä»ãã¦ããã管çåã³ç®¡çæ¡å¼µããã¼ã¹ã©ã¤ã³ããåé¤ããã¦ããå ´åã
ç·ã§æ¶ããã¦ããã
ä¾
AU-4 ç£æ»ã¹ãã¬ã¼ã¸å®¹é AU-4 (1) AU-4 (1) AU-4 (1)
ãã®ä¾ã§ã¯ãICS è£è¶³ã¬ã¤ãã³ã¹ã管çæ¡å¼µ AU-4 ã®1ï¼å¤ªåï¼ã«è¿½å ããã¦ãããã¾ãã管çæ¡
å¼µAU-4 ã®1ãä½ã»ä¸ã»é«ãã¼ã¹ã©ã¤ã³ã«è¿½å ããã¦ããï¼ä¸ç·ï¼ã
SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
345
Table G-1 Security Control Baselines
CNTL
NO.
CONTROL NAME
INITIAL CONTROL BASELINES
LOW
MOD
HIGH
AC-1
Access Control Policy and Procedures
AC-1
AC-1
AC-1
AC-2 Account Management AC-2 AC-2 (1) (2) (3) (4) AC-2 (1) (2) (3) (4)
(5) (11) (12) (13)
AC-3
Access Enforcement
AC-3
AC-3
AC-3
AC-4
Information Flow Enforcement
Not Selected
AC-4
AC-4
AC-5
Separation of Duties
Not Selected
AC-5
AC-5
AC-6 Least Privilege Not Selected AC-6 (1) (2) (5) (9)
(10)
AC-6 (1) (2) (3) (5)
(9) (10)
AC-7
Unsuccessful Logon Attempts
AC-7
AC-7
AC-7
AC-8
System Use Notification
AC-8
AC-8
AC-8
AC-10
Concurrent Session Control
Not Selected
Not Selected
AC-10
AC-11
Session Lock
Not Selected
AC-11 (1)
AC-11 (1)
AC-12
Session Termination
Not Selected
AC-12
AC-12
AC-14 Permitted Actions without Identification or
Authentication
AC-14 AC-14 AC-14
AC-17
Remote Access
AC-17
AC-17 (1) (2) (3) (4)
AC-17 (1) (2) (3) (4)
AC-18
Wireless Access
AC-18
AC-18 (1)
AC-18 (1) (4) (5)
AC-19
Access Control for Mobile Devices
AC-19
AC-19 (5)
AC-19 (5)
AC-20
Use of External Information Systems
AC-20
AC-20 (1) (2)
AC-20 (1) (2)
AC-21
Collaboration and Information Sharing
AC-21
AC-21
AC-21
AC-22
Publicly Accessible Content
AC-22
AC-22
AC-22
AT-1 Security Awareness and Training Policy and
Procedures
AT-1 AT-1 AT-1
AT-2
Security Awareness Training
AT-2
AT-2 (2)
AT-2 (2)
AT-3
Role-Based Security Training
AT-3
AT-3
AT-3
AT-4
Security Training Records
AT-4
AT-4
AT-4
AU-1 Audit and Accountability Policy and
Procedures
AU-1 AU-1 AU-1
AU-2
Audit Events
AU-2
AU-2 (3)
AU-2 (3)
AU-3
Content of Audit Records
AU-3
AU-3 (1)
AU-3 (1) (2)
AU-4
Audit Storage Capacity
AU-4 (1)
AU-4 (1)
AU-4 (1)
AU-5
Response to Audit Processing Failures
AU-5
AU-5
AU-5 (1) (2)
AU-6
Audit Review, Analysis, and Reporting
AU-6
AU-6 (1) (3)
AU-6 (1) (3) (5) (6)
AU-7
Audit Reduction and Report Generation
Not Selected
AU-7 (1)
AU-7 (1)
AU-8
Time Stamps
AU-8
AU-8 (1)
AU-8 (1)
AU-9
Protection of Audit Information
AU-9
AU-9 (4)
AU-9 (2) (3) (4)
AU-10
Non-repudiation
Not Selected
Not Selected
AU-10
AU-11
Audit Record Retention
AU-11
AU-11
AU-11

SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
346
表G-1 ã»ãã¥ãªãã£å¯¾çãã¼ã¹ã©ã¤ã³
管ççªå·
管çå
å½åã®å¯¾çãã¼ã¹ã©ã¤ã³
ä½
ä¸
é«
AC-1
ã¢ã¯ã»ã¹å¶å¾¡
ããªã·ã¼ã»æé
AC-1
AC-1
AC-1
AC-2
ã¢ã«ã¦ã³ã管ç
AC-2 AC-2 (1) (2)
(3) (4)
AC-2 (1) (2)
(3) (4) (5) (11)
(12) (13)
AC-3
ã¢ã¯ã»ã¹æ½è¡
AC-3
AC-3
AC-3
AC-4
æ
å ±ããã¼æ½è¡
æªé¸æ
AC-4
AC-4
AC-5
ä»»åã®åå²
æªé¸æ
AC-5
AC-5
AC-6
æå°æ¨©é
æªé¸æ AC-6 (1) (2)
(5) (9) (10)
AC-6 (1) (2)
(3) (5) (9) (10)
AC-7
ãã°ã¤ã³å¤±æ
AC-7
AC-7
AC-7
AC-8
ã·ã¹ãã å©ç¨éç¥
AC-8
AC-8
AC-8
AC-10
ç¾è¡ã»ãã·ã§ã³ç®¡ç
æªé¸æ
æªé¸æ
AC-10
AC-11
ã»ãã·ã§ã³ããã¯
æªé¸æ
AC-11 (1)
AC-11 (1)
AC-12
ã»ãã·ã§ã³çµäº
æªé¸æ
AC-12
AC-12
AC-14
èå¥ã»èªè¨¼ã®ãªã
許å¯æ¸ã¿è¡çº
AC-14
AC-14
AC-14
AC-17
ãªã¢ã¼ãã¢ã¯ã»ã¹
AC-17 AC-17 (1) (2)
(3) (4)
AC-17 (1) (2)
(3) (4)
AC-18
ã¯ã¤ã¤ã¬ã¹ã¢ã¯ã»ã¹
AC-18 AC-18 (1) AC-18 (1) (4)
(5)
AC-19
ã¢ãã¤ã«ããã¤ã¹ç¨
ã¢ã¯ã»ã¹å¶å¾¡
AC-19
AC-19 (5)
AC-19 (5)
AC-20
å¤é¨æ
å ±ã·ã¹ãã ã®å©ç¨
AC-20
AC-20 (1) (2)
AC-20 (1) (2)
AC-21
é£æºã»æ
å ±
å
±æ
AC-21
AC-21
AC-21
AC-22
å
¬éã³ã³ãã³ã
AC-22
AC-22
AC-22
AT-1
ã»ãã¥ãªãã£æèã»è¨ç·´ããªã·ã¼ã»æé
AT-1
AT-1
AT-1
AT-2
ã»ãã¥ãªãã£æèè¨ç·´
AT-2
AT-2 (2)
AT-2 (2)
AT-3
å½¹å²ãã¼ã¹ã»ãã¥ãªãã£è¨ç·´
AT-3
AT-3
AT-3
AT-4
ã»ãã¥ãªãã£è¨ç·´è¨é²
AT-4
AT-4
AT-4
AU-1
ç£æ»ã»èª¬æ責任ããªã·ã¼ã»æé
AU-1
AU-1
AU-1
AU-2
ç£æ»äºè±¡
AU-2
AU-2 (3)
AU-2 (3)
AU-3
ç£æ»è¨é²å
容
AU-3
AU-3 (1)
AU-3 (1) (2)
AU-4
ç£æ»ã¹ãã¬ã¼ã¸å®¹é
AU-4 (1)
AU-4 (1)
AU-4 (1)
AU-5
ç£æ»å¦çä¸åã¸ã®å¯¾å¿
AU-5
AU-5
AU-5 (1) (2)
AU-6
ç£æ»ã®å¯©æ»ã»åæã»å ±å
AU-6 AU-6 (1) (3) AU-6 (1) (3) (5)
(6)
AU-7
ç£æ»åæ¸ã»å ±åæ¸ä½æ
æªé¸æ
AU-7 (1)
AU-7 (1)
AU-8
ã¿ã¤ã ã¹ã¿ã³ã
AU-8
AU-8 (1)
AU-8 (1)
AU-9
ç£æ»æ
å ±ã®ä¿è·
AU-9
AU-9 (4)
AU-9 (2) (3) (4)
AU-10
å¦èªé²æ¢
æªé¸æ
æªé¸æ
AU-10
AU-11
ç£æ»è¨é²ä¿ç
AU-11
AU-11
AU-11

SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
347
AU-12
Audit Generation
AU-12
AU-12
AU-12 (1) (3)
CA-1 Security Assessment and Authorization
Policies and Procedures
CA-1 CA-1 CA-1
CA-2
Security Assessments
CA-2
CA-2 (1)
CA-2 (1) (2)
CA-3
System Interconnections
CA-3
CA-3 (5)
CA-3 (5)
CA-5
Plan of Action and Milestones
CA-5
CA-5
CA-5
CA-6
Security Authorization
CA-6
CA-6
CA-6
CA-7
Continuous Monitoring
CA-7
CA-7 (1)
CA-7 (1)
CA-8
Penetration Testing
Not Selected
Not Selected
CA-8
CA-9
Internal System Connections
CA-9
CA-9
CA-9
CM-1 Configuration Management Policy and
Procedures
CM-1 CM-1 CM-1
CM-2
Baseline Configuration
CM-2
CM-2 (1) (3) (7)
CM-2 (1) (2) (3) (7)
CM-3
Configuration Change Control
Not Selected
CM-3 (2)
CM-3 (1) (2)
CM-4
Security Impact Analysis
CM-4
CM-4
CM-4 (1)
CM-5
Access Restrictions for Change
Not Selected
CM-5
CM-5 (1) (2) (3)
CM-6
Configuration Settings
CM-6
CM-6
CM-6 (1) (2)
CM-7
Least Functionality
CM-7 (1)
CM-7 (1) (2) (4) (5)
CM-7 (1) (2) (5)
CM-8 Information System Component Inventory CM-8 CM-8 (1) (3) (5) CM-8 (1) (2) (3) (4)
(5)
CM-9
Configuration Management Plan
Not Selected
CM-9
CM-9
CM-10
Software Usage Restrictions
CM-10
CM-10
CM-10
CM-11
User-Installed Software
CM-11
CM-11
CM-11
CP-1
Contingency Planning Policy and Procedures
CP-1
CP-1
CP-1
CP-2 Contingency Plan CP-2 CP-2 (1) (3) (8) CP-2 (1) (2) (3) (4)
(5) (8)
CP-3
Contingency Training
CP-3
CP-3
CP-3 (1)
CP-4
Contingency Plan Testing
CP-4
CP-4 (1)
CP-4 (1) (2)
CP-6
Alternate Storage Site
Not Selected
CP-6 (1) (3)
CP-6 (1) (2) (3)
CP-7
Alternate Processing Site
Not Selected
CP-7 (1) (2) (3)
CP-7 (1) (2) (3) (4)
CP-8
Telecommunications Services
Not Selected
CP-8 (1) (2)
CP-8 (1) (2) (3) (4)
CP-9
Information System Backup
CP-9
CP-9 (1)
CP-9 (1) (2) (3) (5)
CP-10 Information System Recovery and
Reconstitution
CP-10 CP-10 (2) CP-10 (2) (4)
CP-12
Safe Mode
CP-12
CP-12
CP-12
IA-1 Identification and Authentication Policy and
Procedures
IA-1 IA-1 IA-1
IA-2 Identification and Authentication
(Organizational Users)
IA-2 (1) (12) IA-2 (1) (2) (3) (8)
(11) (12)
IA-2 (1) (2) (3) (4)
(8) (9) (11) (12)
IA-3
Device Identification and Authentication
IA-3
IA-3 (1) (4)
IA-3 (1) (4)
IA-4
Identifier Management
IA-4
IA-4
IA-4
IA-5
Authenticator Management
IA-5 (1) (11)
IA-5 (1) (2) (3) (11)
IA-5 (1) (2) (3) (11)

SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
348
AU-12
ç£æ»ä½æ
AU-12
AU-12
AU-12 (1) (3)
CA-1
ã»ãã¥ãªãã£è©ä¾¡ã»æ¨©éä»ä¸ããªã·ã¼ã»
æé
CA-1 CA-1 CA-1
CA-2
ã»ãã¥ãªãã£è©ä¾¡
CA-2
CA-2 (1)
CA-2 (1) (2)
CA-3
ã·ã¹ãã ç¸äºé£æ¥
CA-3
CA-3 (5)
CA-3 (5)
CA-5
è¡åã»
ãã¤ã«ã¹ãã¼ã³è¨ç»æ¸
CA-5
CA-5
CA-5
CA-6
ã»ãã¥ãªãã£æ¨©é
CA-6
CA-6
CA-6
CA-7
ç¶ç¶ç£è¦
CA-7
CA-7 (1)
CA-7 (1)
CA-8
ãããã¬ã¼ã·ã§ã³ã»ãã¹ã
æªé¸æ
æªé¸æ
CA-8
CA-9
å
é¨ã·ã¹ãã æ¥ç¶
CA-9
CA-9
CA-9
CM-1
è¨å®ç®¡çããªã·ã¼ã»æé
CM-1
CM-1
CM-1
CM-2
ãã¼ã¹ã©ã¤ã³è¨å®
CM-2 CM-2 (1) (3) (7) CM-2 (1) (2) (3)
(7)
CM-3
è¨å®å¤æ´ç®¡ç
æªé¸æ
CM-3 (2)
CM-3 (1) (2)
CM-4
æ¥ç¶å½±é¿åæ
CM-4
CM-4
CM-4 (1)
CM-5
å¤æ´ç¨ã¢ã¯ã»ã¹å¶é
æªé¸æ
CM-5
CM-5 (1) (2) (3)
CM-6
æ§æè¨å®
CM-6
CM-6
CM-6 (1) (2)
CM-7
æä½éæ©è½
CM-7 (1) CM-7 (1) (2)
(4) (5)
CM-7 (1) (2) (5)
CM-8
æ
å ±ã·ã¹ãã ã³ã³ãã¼ãã³ãç®é²
CM-8 CM-8 (1) (3) (5) CM-8 (1) (2) (3)
(4) (5)
CM-9
è¨å®ç®¡çè¨ç»æ¸
æªé¸æ
CM-9
CM-9
CM-10
ã½ããã¦ã¨ã¢
使ç¨å¶é
CM-10
CM-10
CM-10
CM-11
ã¦ã¼ã¶ãã¤ã³ã¹ãã¼ã«ãã
ã½ããã¦ã¨ã¢
CM-11
CM-11
CM-11
CP-1
ä¸æ¸¬äºæ
è¨ç»ããªã·ã¼ã»æé
CP-1
CP-1
CP-1
CP-2
ç·æ¥æ対å¿è¨ç»
CP-2 CP-2 (1) (3)
(8)
CP-2 (1) (2) (3)
(4) (5) (8)
CP-3
ä¸æ¸¬äºæ
è¨ç·´
CP-3
CP-3
CP-3 (1)
CP-4
ç·æ¥æ対å¿è¨ç»
è¨ç·´
CP-4
CP-4 (1)
CP-4 (1) (2)
CP-6
代æ¿ã¹ãã¬ã¼ã¸ãµã¤ã
æªé¸æ
CP-6 (1) (3)
CP-6 (1) (2) (3)
CP-7
代æ¿å¦çãµã¤ã
æªé¸æ CP-7 (1) (2) (3) CP-7 (1) (2) (3)
(4)
CP-8
é»æ°éä¿¡ãµã¼
ãã¹ æªé¸æ CP-8 (1) (2) CP-8 (1) (2) (3)
(4)
CP-9
æ
å ±ã·ã¹ãã ããã¯ã¢ãã
CP-9 CP-9 (1) CP-9 (1) (2) (3)
(5)
CP-10
æ
å ±ã·ã¹ãã ã®å¾©æ§ã»åæ§ç¯
CP-10
CP-10 (2)
CP-10 (2) (4)
CP-12
ã»ã¼ãã¢ã¼ã
CP-12
CP-12
CP-12
IA-1
èå¥ã»èªè¨¼ããªã·ã¼ã»æé
IA-1
IA-1
IA-1
IA-2
èå¥ã»èªè¨¼ï¼çµç¹ã¦ã¼ã¶ï¼
IA-2 (1) (12) IA-2 (1) (2)
(3) (8) (11)
(12)
IA-2 (1) (2) (3)
(4) (8) (9) (11)
(12)
IA-3
ããã¤ã¹èå¥ã»èªè¨¼
IA-3
IA-3 (1) (4)
IA-3 (1) (4)
IA-4
èå¥å管ç
IA-4
IA-4
IA-4
IA-5
èªè¨¼ã³ã¼ã管ç
IA-5 (1) (11) IA-5 (1) (2) (3)
(11)
IA-5 (1) (2) (3)
(11)

SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
349
IA-6
Authenticator Feedback
IA-6
IA-6
IA-6
IA-7
Cryptographic Module Authentication
IA-7
IA-7
IA-7
IA-8 Identification and Authentication (Non-
Organizational Users)
IA-8 (1) (2) (3) (4) IA-8 (1) (2) (3) (4) IA-8 (1) (2) (3) (4)
IR-1
Incident Response Policy and Procedures
IR-1
IR-1
IR-1
IR-2
Incident Response Training
IR-2
IR-2
IR-2 (1) (2)
IR-3
Incident Response Testing
Not Selected
IR-3 (2)
IR-3 (2)
IR-4
Incident Handling
IR-4
IR-4 (1)
IR-4 (1) (4)
IR-5
Incident Monitoring
IR-5
IR-5
IR-5 (1)
IR-6
Incident Reporting
IR-6
IR-6 (1)
IR-6 (1)
IR-7
Incident Response Assistance
IR-7
IR-7 (1)
IR-7 (1)
IR-8
Incident Response Plan
IR-8
IR-8
IR-8
MA-1
System Maintenance Policy and Procedures
MA-1
MA-1
MA-1
MA-2
Controlled Maintenance
MA-2
MA-2
MA-2 (2)
MA-3
Maintenance Tools
Not Selected
MA-3 (1) (2)
MA-3 (1) (2) (3)
MA-4
Nonlocal Maintenance
MA-4
MA-4 (2)
MA-4 (2) (3)
MA-5
Maintenance Personnel
MA-5
MA-5
MA-5 (1)
MA-6
Timely Maintenance
Not Selected
MA-6
MA-6
MP-1
Media Protection Policy and Procedures
MP-1
MP-1
MP-1
MP-2
Media Access
MP-2
MP-2
MP-2
MP-3
Media Marking
Not Selected
MP-3
MP-3
MP-4
Media Storage
Not Selected
MP-4
MP-4
MP-5
Media Transport
Not Selected
MP-5 (4)
MP-5 (4)
MP-6
Media Sanitization
MP-6
MP-6
MP-6 (1) (2) (3)
MP-7
Media Use
MP-7
MP-7 (1)
MP-7 (1)
PE-1 Physical and Environmental Protection Policy
and Procedures
PE-1 PE-1 PE-1
PE-2
Physical Access Authorizations
PE-2
PE-2
PE-2
PE-3
Physical Access Control
PE-3
PE-3
PE-3 (1)
PE-4
Access Control for Transmission Medium
Not Selected
PE-4
PE-4
PE-5
Access Control for Output Devices
Not Selected
PE-5
PE-5
PE-6
Monitoring Physical Access
PE-6
PE-6 (1) (4)
PE-6 (1) (4)
PE-8
Visitor Access Records
PE-8
PE-8
PE-8 (1)
PE-9
Power Equipment and Cabling
Not Selected
PE-9 (1)
PE-9 (1)
PE-10
Emergency Shutoff
Not Selected
PE-10
PE-10
PE-11
Emergency Power
PE-11 (1)
PE-11 (1)
PE-11 (1) (2)
PE-12
Emergency Lighting
PE-12
PE-12
PE-12
PE-13
Fire Protection
PE-13
PE-13 (3)
PE-13 (1) (2) (3)
PE-14
Temperature and Humidity Controls
PE-14
PE-14
PE-14
PE-15
Water Damage Protection
PE-15
PE-15
PE-15 (1)
PE-16
Delivery and Removal
PE-16
PE-16
PE-16
PE-17
Alternate Work Site
Not Selected
PE-17
PE-17
PE-18
Location of Information System Components
Not Selected
Not Selected
PE-18
PL-1
Security Planning Policy and Procedures
PL-1
PL-1
PL-1
PL-2
System Security Plan
PL-2 (3)
PL-2 (3)
PL-2 (3)
PL-4
Rules of Behavior
PL-4
PL-4 (1)
PL-4 (1)
PL-7
Security Concept of Operations
PL-7
PL-7

SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
350
IA-6
èªè¨¼ãã£ã¼
ãããã¯
IA-6
IA-6
IA-6
IA-7
æå·åã¢ã¸ã¥ã¼ã«èªè¨¼
IA-7
IA-7
IA-7
IA-8
èå¥ã»èªè¨¼ï¼çµç¹å¤ã¦ã¼ã¶ï¼
IA-8 (1) (2)
(3) (4)
IA-8 (1) (2)
(3) (4)
IA-8 (1) (2) (3)
(4)
IR-1
ã¤ã³ã·ãã³ã対å¿ããªã·ã¼ã»æé
IR-1
IR-1
IR-1
IR-2
ã¤ã³ã·ãã³ã対å¿è¨ç·´
IR-2
IR-2
IR-2 (1) (2)
IR-3
ã¤ã³ã·ãã³ã対å¿è©¦é¨
æªé¸æ
IR-3 (2)
IR-3 (2)
IR-4
ã¤ã³ã·ãã³ãå¦ç
IR-4
IR-4 (1)
IR-4 (1) (4)
IR-5
ã¤ã³ã·ãã³ãç£è¦
IR-5
IR-5
IR-5 (1)
IR-6
ã¤ã³ã·ãã³ãå ±å
IR-6
IR-6 (1)
IR-6 (1)
IR-7
ã¤ã³ã·ãã³ã対å¿æ¯æ´
IR-7
IR-7 (1)
IR-7 (1)
IR-8
ã¤ã³ã·ãã³ã対å¿è¨ç»æ¸
IR-8
IR-8
IR-8
MA-1
ã·ã¹ãã ä¿å®ããªã·ã¼ã»æé
MA-1
MA-1
MA-1
MA-2
管çä¿å®
MA-2
MA-2
MA-2 (2)
MA-3
ä¿å®ã
ã¼ã«
æªé¸æ
MA-3 (1) (2)
MA-3 (1) (2) (3)
MA-4
ãã¼ã«ã«ä»¥å¤ã®ä¿å®
MA-4
MA-4 (2)
MA-4 (2) (3)
MA-5
ä¿å®è¦å¡
MA-5
MA-5
MA-5 (1)
MA-6
é©æçä¿å®
æªé¸æ
MA-6
MA-6
MP-1
ã¡ãã£ã¢ä¿è·ããªã·ã¼ã»æé
MP-1
MP-1
MP-1
MP-2
ã¡ãã£ã¢ã¢ã¯ã»ã¹
MP-2
MP-2
MP-2
MP-3
ã¡ãã£ã¢ãã¼ãã³ã°
æªé¸æ
MP-3
MP-3
MP-4
ã¡ãã£ã¢ã¹ãã¬ã¼ã¸
æªé¸æ
MP-4
MP-4
MP-5
ã¡ãã£ã¢è»¢é
æªé¸æ
MP-5 (4)
MP-5 (4)
MP-6
ã¡ãã£ã¢ãµãã¿ã¤ãº
MP-6
MP-6
MP-6 (1) (2) (3)
MP-7
ã¡ãã£ã¢å©ç¨
MP-7
MP-7 (1)
MP-7 (1)
PE-1
ç©çç°å¢ä¿è·ããªã·ã¼ã»æé
PE-1
PE-1
PE-1
PE-2
ç©ççã¢ã¯ã»ã¹æ¨©é
PE-2
PE-2
PE-2
PE-3
ç©çç
ã¢ã¯ã»ã¹å¶å¾¡
PE-3
PE-3
PE-3 (1)
PE-4
éä¿¡ã¡ãã£ã¢ã®
ã¢ã¯ã»ã¹å¶å¾¡
æªé¸æ
PE-4
PE-4
PE-5
åºåããã¤ã¹ã®
ã¢ã¯ã»ã¹å¶å¾¡
æªé¸æ
PE-5
PE-5
PE-6
ç©ççã¢ã¯ã»ã¹ç£è¦
PE-6
PE-6 (1) (4)
PE-6 (1) (4)
PE-8
æ¥è¨ªè
ç«å
¥è¨é²
PE-8
PE-8
PE-8 (1)
PE-9
é»æ°è£
ç½®åã³é
ç·
æªé¸æ
PE-9 (1)
PE-9 (1)
PE-10
ç·æ¥é®æ
æªé¸æ
PE-10
PE-10
PE-11
ç·æ¥é»æº
PE-11 (1)
PE-11 (1)
PE-11 (1) (2)
PE-12
ç·æ¥ç
§æ
PE-12
PE-12
PE-12
PE-13
é²ç«
PE-13
PE-13 (3)
PE-13 (1) (2) (3)
PE-14
温度ã»æ¹¿åº¦å¶å¾¡
PE-14
PE-14
PE-14
PE-15
水害é²è·
PE-15
PE-15
PE-15 (1)
PE-16
é
éã»æ¤å»
PE-16
PE-16
PE-16
PE-17
代æ¿ä½æ¥å ´
æªé¸æ
PE-17
PE-17
PE-18
æ
å ±ã·ã¹ãã ã³ã³ãã¼ãã³ãã®å ´æ
æªé¸æ
æªé¸æ
PE-18
PL-1
ã»ãã¥ãªãã£è¨ç»ããªã·ã¼ã»æé
PL-1
PL-1
PL-1
PL-2
ã·ã¹ãã ã»ãã¥
ãªãã£è¨ç»æ¸
PL-2 (3)
PL-2 (3)
PL-2 (3)
PL-4
è¡åè¦å
PL-4
PL-4 (1)
PL-4 (1)
PL-7
éç¨ã»ãã¥ãªãã£æ¦å¿µ
PL-7 PL-7

SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
351
PL-8
Information Security Architecture
Not Selected
PL-8
PL-8
PS-1
Personnel Security Policy and Procedures
PS-1
PS-1
PS-1
PS-2
Position Risk Designation
PS-2
PS-2
PS-2
PS-3
Personnel Screening
PS-3
PS-3
PS-3
PS-4
Personnel Termination
PS-4
PS-4
PS-4 (2)
PS-5
Personnel Transfer
PS-5
PS-5
PS-5
PS-6
Access Agreements
PS-6
PS-6
PS-6
PS-7
Third-Party Personnel Security
PS-7
PS-7
PS-7
PS-8
Personnel Sanctions
PS-8
PS-8
PS-8
RA-1
Risk Assessment Policy and Procedures
RA-1
RA-1
RA-1
RA-2
Security Categorization
RA-2
RA-2
RA-2
RA-3
Risk Assessment
RA-3
RA-3
RA-3
RA-5
Vulnerability Scanning
RA-5
RA-5 (1) (2) (5)
RA-5 (1) (2) (4) (5)
SA-1 System and Services Acquisition Policy and
Procedures
SA-1 SA-1 SA-1
SA-2
Allocation of Resources
SA-2
SA-2
SA-2
SA-3
System Development Life Cycle
SA-3
SA-3
SA-3
SA-4
Acquisition Process
SA-4 (10)
SA-4 (1) (2) (9) (10)
SA-4 (1) (2) (9) (10)
SA-5
Information System Documentation
SA-5
SA-5
SA-5
SA-8
Security Engineering Principles
Not Selected
SA-8
SA-8
SA-9
External Information System Services
SA-9
SA-9 (2)
SA-9 (2)
SA-10
Developer Configuration Management
Not Selected
SA-10
SA-10
SA-11
Developer Security Testing and Evaluation
Not Selected
SA-11
SA-11
SA-12
Supply Chain Protection
Not Selected
Not Selected
SA-12
SA-15
Development Process, Standards, and Tools
Not Selected
Not Selected
SA-15
SA-16
Developer-Provided Training
Not Selected
Not Selected
SA-16
SA-17
Developer Security Architecture and Design
Not Selected
Not Selected
SA-17
SC-1 System and Communications Protection Policy
and Procedures
SC-1 SC-1 SC-1
SC-2
Application Partitioning
Not Selected
SC-2
SC-2
SC-3
Security Function Isolation
Not Selected
Not Selected
SC-3
SC-4
Information in Shared Resources
Not Selected
SC-4
SC-4
SC-5
Denial of Service Protection
SC-5
SC-5
SC-5
SC-7 Boundary Protection SC-7 SC-7 (3) (4) (5) (7)
(18)
SC-7 (3) (4) (5) (7)
(8) (18) (21)
SC-8
Transmission Confidentiality and Integrity
Not Selected
SC-8 (1)
SC-8 (1)
SC-10
Network Disconnect
Not Selected
SC-10
SC-10
SC-12 Cryptographic Key Establishment and
Management
SC-12 SC-12 SC-12 (1)
SC-13
Cryptographic Protection
SC-13
SC-13
SC-13
SC-15
Collaborative Computing Devices
SC-15
SC-15
SC-15
SC-17
Public Key Infrastructure Certificates
Not Selected
SC-17
SC-17
SC-18
Mobile Code
Not Selected
SC-18
SC-18
SC-19
Voice Over Internet Protocol
Not Selected
SC-19
SC-19
SC-20 Secure Name /Address Resolution Service
(Authoritative Source)
SC-20 SC-20 SC-20

SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
352
PL-8
æ
å ±ã»ãã¥ãªãã£ã¢ã¼ããã¯ãã£
æªé¸æ
PL-8
PL-8
PS-1
人å¡ã®ã»ãã¥ãªãã£ããªã·ã¼ã»æé
PS-1
PS-1
PS-1
PS-2
é
ç½®ãªã¹ã¯æå®
PS-2
PS-2
PS-2
PS-3
人é¸
PS-3
PS-3
PS-3
PS-4
éè·
PS-4
PS-4
PS-4 (2)
PS-5
転å¤
PS-5
PS-5
PS-5
PS-6
ã¢ã¯ã»ã¹åæ
PS-6
PS-6
PS-6
PS-7
ãµã¼ããã¼ãã£ç¤¾å¡ã»ãã¥ãªãã£
PS-7
PS-7
PS-7
PS-8
æ²æ
PS-8
PS-8
PS-8
RA-1
ãªã¹ã¯è©ä¾¡ããªã·ã¼ã»æé
RA-1
RA-1
RA-1
RA-2
ã»ãã¥ãªãã£åé¡
RA-2
RA-2
RA-2
RA-3
ãªã¹ã¯è©ä¾¡
RA-3
RA-3
RA-3
RA-5
èå¼±æ§æ¤ç´¢
RA-5 RA-5 (1) (2)
(5)
RA-5 (1) (2) (4)
(5)
SA-1
ã·ã¹ãã åã³ãµã¼ãã¹åå¾ããªã·ã¼ã»æé
SA-1
SA-1
SA-1
SA-2
ãªã½ã¼ã¹å²å½
SA-2
SA-2
SA-2
SA-3
ã·ã¹ãã éçºã©ã¤ããµã¤ã¯ã«
SA-3
SA-3
SA-3
SA-4
åå¾ããã»ã¹
SA-4 (10) SA-4 (1) (2)
(9) (10)
SA-4 (1) (2) (9)
(10)
SA-5
æ
å ±ã·ã¹ãã ææ¸å
SA-5
SA-5
SA-5
SA-8
ã»ãã¥ãªãã£ã¨ã³ã¸ãã¢ãªã³
ã°åå
æªé¸æ
SA-8
SA-8
SA-9
å¤é¨æ
å ±ã·ã¹ãã ãµã¼ãã¹
SA-9
SA-9 (2)
SA-9 (2)
SA-10
éçºè
è¨å®ç®¡ç
æªé¸æ
SA-10
SA-10
SA-11
éçºè
ã»ãã¥ãªãã£è©¦é¨è©ä¾¡
æªé¸æ
SA-11
SA-11
SA-12
ãµãã©ã¤ãã§ã¼ã³ä¿è·
æªé¸æ
æªé¸æ
SA-12
SA-15
éçºããã»ã¹ã»è¦æ ¼ã»ãã¼ã«
æªé¸æ
æªé¸æ
SA-15
SA-16
éçºè
ã«ããè¨ç·´
æªé¸æ
æªé¸æ
SA-16
SA-17
éçºè
ã»ãã¥ãªãã£ã¢ã¼ããã¯ãã£ã»è¨è¨
æªé¸æ
æªé¸æ
SA-17
SC-1
ã·
ã¹ãã éä¿¡ä¿è·ããªã·ã¼ã»æé
SC-1
SC-1
SC-1
SC-2
ã¢ããªã±ã¼ã·ã§ã³åå²
æªé¸æ
SC-2
SC-2
SC-3
ã»ãã¥ãªãã£æ©è½é絶
æªé¸æ
æªé¸æ
SC-3
SC-4
å
±æãªã½ã¼ã¹å
æ
å ±
æªé¸æ
SC-4
SC-4
SC-5
ãµã¼ãã¹ä¿è·å¦¨å®³
SC-5
SC-5
SC-5
SC-7
å¢çã®ä¿è·
SC-7 SC-7 (3) (4) (5)
(7) (18)
SC-7 (3) (4) (5)
(7) (8) (18) (21)
SC-8
éä¿¡
æ©å¯æ§ã»å®å
¨æ§
æªé¸æ
SC-8 (1)
SC-8 (1)
SC-10
ãããã¯ã¼ã¯åæ
æªé¸æ
SC-10
SC-10
SC-12
æå·éµ
è¨å®ç®¡ç
SC-12
SC-12
SC-12 (1)
SC-13
æå·ä¿è·
SC-13
SC-13
SC-13
SC-15
å
±åã³ã³ãã¥ã¼ãã£ã³ã°ããã¤ã¹
SC-15
SC-15
SC-15
SC-17
PKI
証ææ¸
æªé¸æ
SC-17
SC-17
SC-18
ã¢ãã¤ã«ã³ã¼ã
æªé¸æ
SC-18
SC-18
SC-19
VoIP
æªé¸æ
SC-19
SC-19
SC-20
ã»ãã¥ã¢ãªåå
/ã¢ãã¬ã¹è§£æ±ºãµã¼ãã¹
ï¼æ¨©éã½ã¼ã¹ï¼
SC-20 SC-20 SC-20

SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
353
SC-21 Secure Name /Address Resolution Service
(Recursive or Caching Resolver)
SC-21 SC-21 SC-21
SC-22 Architecture and Provisioning for
Name/Address Resolution Service
SC-22 SC-22 SC-22
SC-23
Session Authenticity
Not Selected
SC-23
SC-23
SC-24
Fail in Known State
Not Selected
SC-24
SC-24
SC-28
Protection of Information at Rest
Not Selected
SC-28
SC-28
SC-39
Process Isolation
SC-39
SC-39
SC-39
SC-41
Port and I/O Device Access
SC-41
SC-41
SC-41
SI-1 System and Information Integrity Policy and
Procedures
SI-1 SI-1 SI-1
SI-2
Flaw Remediation
SI-2
SI-2 (2)
SI-2 (1) (2)
SI-3
Malicious Code Protection
SI-3
SI-3 (1) (2)
SI-3 (1) (2)
SI-4
Information System Monitoring
SI-4
SI-4 (2) (4) (5)
SI-4 (2) (4) (5)
SI-5
Security Alerts, Advisories, and Directives
SI-5
SI-5
SI-5 (1)
SI-6
Security Function Verification
Not Selected
Not Selected
SI-6
SI-7 Software, Firmware, and Information Integrity Not Selected SI-7 (1) (7) SI-7 (1) (2) (5) (7)
(14)
SI-8
Spam Protection
Not Selected
SI-8 (1) (2)
SI-8 (1) (2)
SI-10
Information Input Validation
Not Selected
SI-10
SI-10
SI-11
Error Handling
Not Selected
SI-11
SI-11
SI-12
Information Handling and Retention
SI-12
SI-12
SI-12
SI-13
Predictable Failure Prevention
Not Selected
Not Selected
SI-13
SI-14
Non-Persistence
Not Selected
Not Selected
Not Selected
SI-15
Information Output Filtering
Not Selected
Not Selected
Not Selected
SI-16
Memory Protection
Not Selected
SI-16
SI-16
SI-17
Fail-Safe Procedures
SI-17
SI-17
SI-17

SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
354
SC-21
ã»ãã¥ã¢ãªåå
/ã¢ãã¬ã¹è§£æ±ºãµã¼ãã¹
ï¼å帰åã¯ãã£ãã·ã³ã°ãªã¾ã«ãï¼
SC-21 SC-21 SC-21
SC-22
åå
/ã¢ãã¬ã¹è§£æ±ºãµã¼ãã¹ç¨ã¢ã¼ããã¯
ãã£ã¼ãããã¸ã§ãã³ã°
SC-22 SC-22 SC-22
SC-23
ã»ãã·ã§ã³ä¿¡é ¼æ§
æªé¸æ
SC-23
SC-23
SC-24
æ¢ç¥ç¶æ
ã®å¤±æ
æªé¸æ
SC-24
SC-24
SC-28
ä¼ç æ
å ±ã®ä¿è·
æªé¸æ
SC-28
SC-28
SC-39
ããã»ã¹éé¢
SC-39
SC-39
SC-39
SC-41
ãã¼ãåã³
I/O ããã¤ã¹ã¢ã¯ã»ã¹
SC-41
SC-41
SC-41
SI-1
ã·ã¹ãã æ
å ±
å®å
¨æ§ããªã·ã¼ã»æé
SI-1
SI-1
SI-1
SI-2
æ¬ é¥ä¿®æ£
SI-2
SI-2 (2)
SI-2 (1) (2)
SI-3
æªæããã³ã¼ãä¿è·
SI-3
SI-3 (1) (2)
SI-3 (1) (2)
SI-4
æ
å ±ã·ã¹ãã ç£è¦
SI-4 SI-4 (2) (4)
(5)
SI-4 (2) (4) (5)
SI-5
ã»ã
ã¥ãªãã£è¦å ±ã»å§åã»æ示
SI-5
SI-5
SI-5 (1)
SI-6
ã»ãã¥ãªãã£æ©è½æ¤è¨¼
æªé¸æ
æªé¸æ
SI-6
SI-7
ã½ããã¦ã¨ã¢
ã»ãã¡ã¼ã ã¦ã¨ã¢ã»æ
å ±ã®å®
å
¨æ§
æªé¸æ SI-7 (1) (7) SI-7 (1) (2) (5)
(7) (14)
SI-8
ã¹ãã ä¿è·
æªé¸æ
SI-8 (1) (2)
SI-8 (1) (2)
SI-10
æ
å ±å
¥åæ¤è¨¼
æªé¸æ
SI-10
SI-10
SI-11
ã¨ã©ã¼å¦ç
æªé¸æ
SI-11
SI-11
SI-12
æ
å ±å¦çä¿ç
SI-12
SI-12
SI-12
SI-13
äºæ³ãããæ
éã®é²æ¢
æªé¸æ
æªé¸æ
SI-13
SI-14
éå·ææ§
æªé¸æ
æªé¸æ
æªé¸æ
SI-15
æ
å ±åºåãã£ã«ã¿ãªã³ã°
æªé¸æ
æªé¸æ
æªé¸æ
SI-16
ã¡ã¢ãªä¿è·
æªé¸æ
SI-16
SI-16
SI-17
ãã§ã¼ã«ã»ã¼ãæé
SI-17 SI-17 SI-17

SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
355
The PM-family is deployed organization-wide, supporting the information security program. It is not
associated with security control baselines and is independent of any system impact level.
PM-1
Information Security Program Plan
PM-1
PM-2
Senior Information Security Officer
PM-2
PM-3
Information Security Resources
PM-3
PM-4
Plan of Action and Milestones Process
PM-4
PM-5
Information System Inventory
PM-5
PM-6
Information Security Measures of Performance
PM-6
PM-7
Enterprise Architecture
PM-7
PM-8
Critical Infrastructure Plan
PM-8
PM-9
Risk Management Strategy
PM-9
PM-10
Security Authorization Process
PM-10
PM-11
Mission/Business Process Definition
PM-11
PM-12
Insider Threat Program
PM-12
PM-13
Information Security Workforce
PM-13
PM-14
Testing, Training, and Monitoring
PM-14
PM-15
Contacts with Security Groups and Associations
PM-15
PM-16
Threat Awareness Program
PM-16

SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
356
PM ãã¡ããªã¯å
¨çµç¹ã«å±éãããæ
å ±ã»ãã¥ãªãã£ããã°ã©ã ãæ¯ãã¦ãããã»ãã¥ãªãã£å¯¾
çãã¼ã¹ã©ã¤ã³ã¯ä»éãã¦ãããããããªãã·ã¹ãã å½±é¿ã¬ãã«ã¨ãç¡é¢ä¿ã§ããã
PM-1
æ
å ±ã»ãã¥ãªãã£ããã°ã©ã è¨ç»æ¸
PM-1
PM-2
ä¸ç´æ
å ±ã»ãã¥ãªãã£æ
å½å®
PM-2
PM-3
æ
å ±ã»ãã¥ãªãã£ãªã½ã¼ã¹
PM-3
PM-4
è¡åã»
ãã¤ã«ã¹ãã¼ã³ããã»ã¹è¨ç»æ¸
PM-4
PM-5
æ
å ±ã·ã¹ãã ç®é²
PM-5
PM-6
æ
å ±ã»ãã¥ãªãã£
ã«é¢ããããã©ã¼ãã³ã¹ã®è¨æ¸¬
PM-6
PM-7
ä¼æ¥ã¢ã¼ããã¯ãã£
PM-7
PM-8
éè¦ã¤ã³ãã©è¨ç»æ¸
PM-8
PM-9
ãªã¹ã¯ç®¡ç
æ¦ç¥
PM-9
PM-10
ã»ãã¥ãªãã£æ¨©éããã»ã¹
PM-10
PM-11
ä»»åã»äºæ¥ããã»ã¹å®ç¾©
PM-11
PM-12
ã¤ã³ãµã¤ãã¼è
å¨ããã°ã©ã
PM-12
PM-13
æ
å ±ã»ãã¥ãªãã£ãªã¯ã¼ã¯ãã©ã¼ã¹
PM-13
PM-14
試é¨ã»è¨ç·´ã»ç£è¦
PM-14
PM-15
ã»ãã¥ãªãã£ã°ã«ã¼ãã»åä¼ã¨ã®å¥ç´
PM-15
PM-16
è
å¨æèããã°ã©ã
PM-16

SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
357
Tailoring Considerations
Due to the unique characteristics of ICS, these systems may require a greater use of compensating security
controls than is the case for general purpose information systems. Compensating controls are not
exceptions or waivers to the baseline controls; rather, they are alternative safeguards and countermeasures
employed within the ICS that accomplish the intent of the original security controls that could not be
effectively employed. See âSelecting Compensating Security Controlsâ in section 3.2 of NIST SP 800-53
Rev. 4 [22].
In situations where the ICS cannot support, or the organization determines it is not advisable to implement,
particular security controls or control enhancements in an ICS (e.g., performance, safety, or reliability are
adversely impacted), the organization provides a complete and convincing rationale for how the selected
compensating controls provide an equivalent security capability or level of protection for the ICS and why
the related baseline security controls could not be employed.
In accordance with the Technology-related Considerations of the Scoping Guidance in NIST SP 800-53
Rev. 4, section 3.2, if automated mechanisms are not readily available, cost-effective, or technically
feasible in the ICS, compensating security controls, implemented through nonautomated mechanisms or
procedures are employed [22].
Compensating controls are alternative security controls employed by organizations in lieu of specific
controls in the baselinesâcontrols that provide equivalent or comparable protection for organizational
information systems and the information processed, stored, or transmitted by those systems.83 This may
occur, for example, when organizations are unable to effectively implement specific security controls in the
baselines or when, due to the specific nature of the ICS or environments of operation, the controls in the
baselines are not a cost-effective means of obtaining the needed risk mitigation. Compensating controls
may include control enhancements that supplement the baseline. Using compensating controls may involve
a trade-off between additional risk and reduced functionality. Every use of compensating controls should
involve a risk-based determination of: (i) how much residual risk to accept, and (ii) how much functionality
should be reduced. Compensating controls may be employed by organizations under the following
conditions:
ï¼ Organizations select compensating controls from NIST SP 800-53 Rev. 4, Appendix F. If appropriate
compensating controls are not available, organizations adopt suitable compensating controls from
other sources 84
ï¼ Organizations provide supporting rationale for how compensating controls provide equivalent security
capabilities for organizational information systems and why the baseline security controls could not be
employed.
ï¼ Organizations assess and accept the risk associated with implementing compensating controls in ICS.
Organizational decisions on the use of compensating controls are documented in the security plan for the
ICS.
83 42 More than one compensating control may be required to provide the equivalent protection for a particular
security control in Appendix F. For example, organizations with significant staff limitations may compensate
for the separation of duty security control by strengthening the audit, accountability, and personnel
security controls.
84 43 Organizations should make every attempt to select compensating controls from the security control catalog
in Appendix F. Organization-defined compensating controls are employed
only
when organizations determine
that the security control catalog does not contain suitable compensating controls.

SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
358
ã«ã¹ã¿ãã¤ãºã®èæ
®äºé
ICS ç¬ç¹ã®ç¹å¾´ããããããã·ã¹ãã ã«å¿
è¦ã¨ãããè£åã»ãã¥ãªãã£ç®¡çã¯ãæ±ç¨ã®æ
å ±ã·ã¹
ãã ãããå¤ãã代æ¿ç®¡çã¯ãã¼ã¹ã©ã¤ã³ç®¡çã®ä¾å¤ãæ¾æ£ã§ã¯ãªãã代æ¿ã®å®å
¨çåã³å¯¾çã¨
ã㦠ICS å
ã§æ¡ç¨ãããæå¹å©ç¨ã§ããªãå
ã®ã»ãã¥ãªãã£å¯¾çã®ç®çãæãããNIST SP 800-
53 第4ç[22]ã®ã»ã¯ã·ã§ã³ 3.2ãè£åã»ãã¥ãªãã£å¯¾çããåç
§ã®ãã¨ã
ICS ãICS ã«ãããã»ãã¥ãªãã£å¯¾çè¥ããã¯ç®¡çæ¡å¼µã«å¯¾å¿ãã¦ããªãå ´ååã¯çµç¹ã ICS ã«
ãããã»ãã¥ãªãã£å¯¾çè¥ããã¯ç®¡çæ¡å¼µã®å®è£
ãä¸é©ã¨å¤æããå ´åï¼ããã©ã¼ãã³ã¹ãå®å
¨
æ§ãä¿¡é ¼æ§ã¸ã®æªå½±é¿çï¼ãé¸å®ããè£åç管ççã«åçã®ã»ãã¥ãªãã£æ©è½åã¯åçã¬ãã«ã®
ICS ä¿è·è½åããããé¢é£ãã¼ã¹ã©ã¤ã³ã»ãã¥ãªãã£å¯¾çãæ¡ç¨ã§ããªãã£ãçç±ã«ã¤ãã¦ãçµ
ç¹ã¯ç´å¾ã®ããçç±ã示ãã
èªååã¡ã«ããºã ãããã«å©ç¨ã§ããªããè²»ç¨å¹æããªãåã¯æè¡çã«ä¸å¯è½ãªå ´åãNIST SP
800-53 第4çã®ã»ã¯ã·ã§ã³ 3.2 ã®ãé©ç¨ç¯å²ã¬ã¤ãã³ã¹ã®æè¡é¢é£èæ
®äºé
ãã«å¾ããè£åã»
ãã¥ãªãã£å¯¾çãéèªååã¡ã«ããºã åã¯æé ã®å®æ½ãéãã¦æ¡ç¨ãã[22]ã
è£åç管ççã¯ãç¹å®ã®ãã¼ã¹ã©ã¤ã³ç®¡çã«ä»£ãã¦çµç¹ãåã代æ¿ã»ãã¥ãªãã£å¯¾çã§ãçµç¹ã®
æ
å ±ã·ã¹ãã ã¨ããã§å¦çãä¿ç®¡åã¯éä¿¡ãããæ
å ±ã«åçã®ä¿è·ãä¸ãããã®ãããã85 ä¾ã
ã°ãç¹å®ã®ãã¼ã¹ã©ã¤ã³ç®¡çãå¹æçã«å®æ½ã§ããªãå ´åããICS åºæã®æ§è³ªè¥ããã¯éç¨ç°å¢
ã«èµ·å ãã¦ããã¼ã¹ã©ã¤ã³ã®ç®¡çããªã¹ã¯ç·©åä¸è²»ç¨å¯¾å¹æã®ãªãå ´åã«ãè£åç管ççãè¬ã
ããããè£åç管ççã«ã¯ããã¼ã¹ã©ã¤ã³ãè£å®ãã管çæ¡å¼µãå«ã¾ãããã¨ããããè£åç管
ççãè¡ãã«ã¯ããªã¹ã¯å¢å ã¨æ©è½ä½ä¸ã®ãã©ã³ã¹ãé¢ä¿ãã¦ãããå¿
ã(1)許容ã§ãããªã¹ã¯
ã®ç¨åº¦ã¨ãï¼2ï¼ã©ã®ç¨åº¦æ©è½ãä½ä¸ããããããªã¹ã¯ã«åºã¥ãã¦å¤æãã¹ãã§ãããçµç¹ã¯ã
次ã®ãããªæ¡ä»¶ã®ä¸ã§è£åç管ççãæ¡ç¨ã§ããã
ï¼ é©å½ãªè£åç管ççã NIST SP 800-53 第4çä»é² Fããé¸ã¶ 86ãé©å½ãªè£åç管ççãåä»
é²ã«ãªãå ´åãä»ã®ã½ã¼ã¹ããé©å½ãªè£åç管ççãæ¡ç¨ããã
ï¼ çµç¹ã¯ãè£åç管ççãæ
å ±ã·ã¹ãã ã«å¯¾ãã¦åçã®ã»ãã¥ãªãã£æ©è½ãæãããã¼ã¹ã©ã¤
ã³ã»ãã¥ãªãã£å¯¾çãæ¡ç¨ã§ããªãã£ãæ ¹æ ã¨ãªãçç±ã示ãã
ï¼ çµç¹ã¯ãICS ã«ãããè£åç管ççã®å®æ½ã«ä»éãããªã¹ã¯ãè©ä¾¡ãåãå
¥ããã
代æ¿ç®¡çãå©ç¨ããçµç¹ã®æ±ºå®ã¯ãICS ã®ã»ãã¥ãªãã£è¨ç»æ¸ã«è¨é²ããã
85 ä»é² Fã®ç¹å®ã®ã»ãã¥ãªãã£å¯¾çã«åçã®ä¿è·ãä¸ããã«ã¯ãè£å管çãè¤æ°å¿
è¦ã¨ãªããã¨ããããä¾ãã°ãè·å¡æ°ã
éããã¦ããçµç¹ã§ã¯ãç£æ»ç®¡çã説æ責任管çåã³è·å¡ã®ã»ãã¥ãªãã£å¯¾çãå¼·åãã¦ãã»ãã¥ãªãã£ç®¡çä»»åãåå²
ãããã¨ã«ãªããã
86 çµç¹ã¯ããããåªåãæã£ã¦ãä»é² Fã®ã»ãã¥ãªãã£å¯¾çã«ã¿ãã°ããè£åç管ççãé¸ã¶ã¹ãã§ãããçµç¹ãèªãå®ç¾©
ããè£åç管ççã¯ãåã«ã¿ãã°ã«é©å½ãªãã®ããªãå ´åã«ã®ã¿æ¡ç¨ããã

SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
359
Controls that contain assignments (e.g., Assignment: organization-defined conditions or trigger events)
may be tailored out of the baseline. This is equivalent to assigning a value of ânone.â The assignment may
take on different values for different impact baselines.
Non-Addressable and Non-Routable Communications
The unique network properties within ICS warrant specific attention when applying certain security
controls. Many of the controls in NIST SP 800-53 Rev. 4 that pertain to communication, devices, and
interfaces implicitly assume the applicability of addressable and routable protocols such as the TCP/IP
Internet protocol suite87 or layers 1, 2, and 3 of the Open Systems Interconnection (OSI) model (ISO/IEC
7498-1). Some devices, or subsystems, used in ICS are exceptions to this assumption. This section
addresses how the controls may be appropriately tailored. Tailoring is primarily required due to the
following situations:
ï¼ Capabilities not present. The intent of certain controls may be more easily achieved through
compensating controls due to certain network properties or capabilities not existing in the ICS
subsystem. For example, physical protections (e.g., locked cabinets) may be used to secure an entire
point-to-point communication channel as a means to compensate for a lack of protocols that support
authentication. Security controls may warrant additional supplemental guidance to help ensure the
implementation of the control or compensating control provides the appropriate level of protection.
ï¼ Non-applicable security controls. Many communication protocols found within an ICS may have
limited functionality (e.g., not addressable or routable). Security controls dealing with addressing and
routing may not be applicable to these protocols.
Security controls for devices that communicate point-to-point using standards and protocols that do not
include addressing generally require tailoring. A modem connected to a computer through an RS-232
interface is an example. RS-232 was commonly employed in ICS equipment that is currently in use, even if
it has been superseded in newer equipment. In telecommunications, RS-232 is the traditional name for a
series of standards for serial binary single-ended data and control signals connecting between DTE (data
terminal equipment) and DCE (data circuit-terminating equipment, originally defined as data
communication equipment). The current version of the standard is Telecommunications Industry
Association (TIA)-232-F, Interface Between Data Terminal Equipment and Data Circuit-Terminating
Equipment Employing Serial Binary Data Interchange, issued in 1997.
An RS-232 serial port was once a standard feature of small computing devices, such as ICS subsystems,
used for connections to peripheral devices. However, the low transmission speed, large voltage swing, and
large standard connectors motivated development of the Universal Serial Bus (USB), which has displaced
RS-232 from most of its peripheral interface roles. RS-232 devices are still found, especially in industrial
machines, networking equipment, and scientific instruments.
Layered Network Models
The layered network models used in both TCP/IP and OSI can provide a basis for understanding the
various properties of network communications and will help identify how security controls can be
appropriately applied to systems and networks. The following table introduces key properties about the
physical, data link, and network layers regarding the application of security controls.
87 44 Currently, the Internet Engineering Task Force, or IETF, manages the TCP/IP protocol suite.

SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
360
å²å½ï¼çµç¹ãå®ç¾©ããæ¡ä»¶ãããªã¬ã¼äºè±¡çï¼ã¯ããã¼ã¹ã©ã¤ã³ãåºã«ã«ã¹ã¿ãã¤ãºã§ãããã
ãã¯ããªããã®å¤ãå²ãå½ã¦ãã®ã¨åããã¨ã§ãããå²å½ã¯ãå½±é¿ãã¼ã¹ã©ã¤ã³ãç°ãªãã¨å¤ã
ç°ãªããã¨ãããã
ã¢ãã¬ã¹æå®åã¯çµè·¯æå®ã®ãªãéä¿¡
ç¹å®ã®ã»ãã¥ãªãã£å¯¾çãé©ç¨ããå ´åãICS å
ã§ã®åºæã®ãããã¯ã¼ã¯ç¹æ§ã«ç¹ã«çæãã¹ã
ã§ãããNIST SP 800-53 第4çã®éä¿¡ãããã¤ã¹åã³ã¤ã³ã¿ãã§ã¼ã¹ã«é¢ãã管çã®å¤ãã¯ã
TCP/IP ã¤ã³ã¿ã¼ãããã¹ã¤ã¼ã 88ããªã¼ãã³ã·ã¹ãã éç¸äºé£æ¥ï¼OSIï¼ã¢ãã«(ISO/IEC 7498-
1)ã®TCP/IP ã¬ã¤ã¤ã¼1ã2ã3çãã¢ãã¬ã¹æå®å¯è½åã¯çµè·¯æå®å¯è½ãããã³ã«ãé©ç¨ããã
ã¨ãæé»ã®åæã«ãã¦ãããICS ã§ä½¿ç¨ãããã種ã®ããã¤ã¹ããµãã·ã¹ãã ã¯ããã®åæã®ä¾
å¤ã¨ãªãããã®ã»ã¯ã·ã§ã³ã§ã¯ã管çã®é©æ£ãªã«ã¹ã¿ãã¤ãºæ¹æ³ã«ã¤ãã¦åãä¸ãããã«ã¹ã¿ã
ã¤ãºã¯ã主ã¨ãã¦æ¬¡ã®ãããªå ´åã«å¿
è¦ã¨ãªãã
ï¼
æ©è½ããªã
ãç¹å®ã®ç®¡çã®ç®çã¯ãç¹å®ã®ãããã¯ã¼ã¯ç¹æ§åã¯æ©è½ã ICS ãµãã·ã¹ãã ã«
ãªããããè£åç管ççã«ãã容æã«éæå¯è½ã§ãããä¾ãã°ç©ççä¿è·ï¼ãã£ããããã®
æ½é çï¼ã¯ãèªè¨¼æ©è½ä»ããããã³ã«ããªãå ´åã®è£åæ段ã¨ãã¦ã2ç¹ééä¿¡ãã£ã³ãã«
ã®ã»ãã¥ã¢åã«å©ç¨ã§ãããã»ãã¥ãªãã£å¯¾çã¯ä»å çãªè£è¶³ã¬ã¤ãã³ã¹ã¨ãã¦ã管çåã¯
è£åç管ççã«ããé©æ§ã¬ãã«ã®ä¿è·ã®ç¢ºä¿ã«å½¹ç«ã¤ã
ï¼
é©ç¨å¯è½ãªã»ãã¥ãªãã£å¯¾çããªã
ãICS ã§ä½¿ç¨ããã¦ãããããã³ã«ã®å¤ãã¯ãæ©è½ãé
ããã¦ããï¼ã¢ãã¬ã¹æå®ãã«ã¼ãæå®ãã§ããªãçï¼ãã¢ãã¬ã¹åã³ã«ã¼ãã«é¢ããã»ã
ã¥ãªãã£å¯¾çã¯ããã®ãããªãããã³ã«ã«ã¯é©ç¨ã§ããªãã
ã¢ãã¬ã¹æå®ã®ãªãè¦æ ¼åã³ãããã³ã«ã使ç¨ãã 2ç¹ééä¿¡ãè¡ãããã¤ã¹ã®ã»ãã¥ãªãã£å¯¾
çã«ã¯ãé常ãã«ã¹ã¿ãã¤ãºãå¿
è¦ã¨ãªããRS-232 ã¤ã³ã¿ãã§ã¼ã¹çµç±ã®ã³ã³ãã¥ã¼ã¿ã«æ¥ç¶
ãããã¢ãã«ããã®ä¸ä¾ã§ãããRS-232 ã¯ãç¾å¨å©ç¨ããã¦ãã ICS è£
ååã§ä¸è¬çã«ä½¿ç¨ã
ãã¦ããï¼ããããè£
ååãæ°ãããã®ã«æè£
ããã¦ããå ´åã§ãã£ã¦ãï¼ãé»æ°éä¿¡ã«ããã¦
RS-232 ã¯ãDTEï¼ãã¼ã¿ç«¯æ«è£
ç½®ï¼ã¨ DCEï¼ãã¼ã¿åç·çµç«¯è£
ç½®ãå
ã¯ãã¼ã¿éä¿¡è£
ç½®ï¼éã®ã·
ãªã¢ã«ãã¤ããªã·ã³ã°ã«ã¨ã³ããã¼ã¿å¶å¾¡ä¿¡å·è¦æ ¼ã®ä¼çµ±çãªå称ã§ãããç¾è¡çè¦æ ¼ã¯ç±³å½é»
æ°éä¿¡å·¥æ¥ä¼ï¼TIAï¼-232-Fãã·ãªã¢ã«ãã¤ããªãã¼ã¿äº¤æã«ãããã¼ã¿ç«¯æ«è£
ç½®ãã¼ã¿åç·ç«¯
æ«è£
ç½®éã¤ã³ã¿ãã§ã¼ã¹ãã¨ãã¦ã1997 å¹´ã«çºè¡¨ãããã
RS-232 ã·ãªã¢ã«ãã¼ãã¯ãICS ãµãã·ã¹ãã çã®å°åã³ã³ãã¥ã¼ãã£ã³ã°ããã¤ã¹ã®è¦æ ¼æ©è½ã¨
ãã¦ãå¨è¾ºããã¤ã¹ã¸ã®æ¥ç¶ã«ä½¿ç¨ãããããããéä¿¡é度ãé
ããé»å§æ¯å¹
ã大ãããè¦æ ¼ã³
ãã¯ã¿ã大ãããã¨ãã USB ãéçºãããRS-232 ã®å¨è¾ºã¤ã³ã¿ãã§ã¼ã¹ã¨ãã¦ã®å½¹å²ã¯çµãã£
ããRS-232 ããã¤ã¹ã¯ãç¹ã«ç£æ¥ç¨ãã·ã³ããããã¯ã¼ãã³ã°è£
ç½®åã³ç§å¦è¨è£
æ©å¨ã§ä»ã§ã
使ç¨ããã¦ããã
é層åãããã¯ã¼ã¯ã¢ãã«
TCP/IP ã¨OSI ã®åæ¹ã§ä½¿ç¨ããã¦ãã é層åãããã¯ã¼ã¯ã¢ãã«ã¯ããããã¯ã¼ã¯éä¿¡ãç解
ããåºæ¬ã§ãã·ã¹ãã åã³ãããã¯ã¼ã¯ã«é©ç¨ãã¹ãã»ãã¥ãªãã£å¯¾çè¦é ã®èå¥ã«å½¹ç«ã¤ã次
ã®è¡¨ã¯ãã»ãã¥ãªãã£å¯¾çã®é©ç¨ã«é¢ããç©ççé層ããã¼ã¿ãªã³ã¯é層åã³ãããã¯ã¼ã¯é層
ã®éè¦ç¹æ§ã示ãã
88 ç¾å¨ã¤ã³ã¿ã¼ãããã¿ã¹ã¯ãã©ã¼ã¹ï¼IETFï¼ã TCP/IP ãããã³ã«ã¹ã¤ã¼ãã®ç®¡çãè¡ã£ã¦ããã

SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
361
Network Layer
Layer properties
Physical
Physical Medium â A networkâs physical medium, specifically whether itâs wired or
wireless can drive the application/tailoring of certain controls. Wireless connections
cannot be physically protected; therefore, compensating controls focusing on physical
security cannot be used.
Topology â The physical topologies may also determine how controls are tailored. For
example point-to-point topologies (e.g., RS-232) generally do not need physically
addressable interfaces, while multipoint topologies (e.g., IEEE 802.3 Ethernet) do
require physically addressable interfaces.
Data link
Physically Addressable â Multipoint protocols require physically addressable
interfaces to allow for multiple systems to communicate. Systems that are not
physically addressable can only be accessed by those systems with which it shared
point-to-point connections.
Network
Network Addressable/Routable â Network addressable/routable systems can be
accessed by any system on an internetwork. That is, communications can be routed
between networks. If a system is not network addressable/routable, it can only be
accessed by systems with which it shares a local network connection.
Definitions
Terms used in this overlay are defined in Appendix Bâ or in NIST Internal Report (NISTIR) 7298
Revision 2, Glossary of Key Information Security Terms [99].
Additional Information or Instructions
None at this time. Organizations may provide any additional information or instructions relevant to the
overlay not covered in the previous sections.

SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
362
ãããã¯ã¼ã¯å±¤
é層ç¹æ§
ç©ç
ç©ççåªä½ -
ãããã¯ã¼ã¯ã®ç©ççåªä½ã§ãç¹ã«æç·
/
ç¡ç·ã®éãã«ãããç¹å®ã®
管çã®é©ç¨ãã«ã¹ã¿ãã¤ãºãã決ã¾ãã
ã¯ã¤ã¤ã¬ã¹æ¥ç¶ã¯ç©ççã«ä¿è·ã§ããªããããç©ççã»ãã¥ãªãã£ã«ç¹åããè£
åç管ççã¯å©ç¨ã§ããªãã
ãããã¸ã¼ - ç©ççãããã¸ã¼ã管çã®ã«ã¹ã¿ãã¤ãºæ¹æ³ã決å®ã¥ãããä¾ãã°
2ç¹éãããã¸ã¼ï¼RS-232 çï¼ã¯ãé常ãç©ççã«ã¢ãã¬ã¹æå®å¯è½ãªã¤ã³ã¿ã
ã§ã¼ã¹ãä¸è¦ã§ãããããã«ããã¤ã³ããããã¸ã¼ï¼IEEE 802.3 Ethernet çï¼ã§
ã¯å¿
è¦ã¨ãªãã
ãã¼ã¿ãªã³ã¯
ç©ççã¢ãã¬ã¹æå®å¯è½ -
ãã«ããã¤ã³ããããã³ã«ã¯ãè¤æ°ã·ã¹ãã éã®éä¿¡
ç¨ã«ãç©ççã«ã¢ãã¬ã¹æå®å¯è½ãªã¤ã³ã¿ãã§ã¼ã¹ãå¿
è¦ã¨ãããç©ççã¢ãã¬
ã¹æå®ä¸è½ã®ã·ã¹ãã ã«ã¯ãå
±æ 2ç¹ééä¿¡ã®ããã·ã¹ãã 以å¤ã«ã¯ã¢ã¯ã»ã¹ã§
ããªãã
ãããã¯ã¼ã¯
ãããã¯ã¼ã¯ã¢ãã¬ã¹æå®å¯è½/ã«ã¼ãæå®å¯è½ -
ã¢ãã¬ã¹
/
ã«ã¼ãæå®å¯è½ã·ã¹
ãã ã«ã¯ããããã¯ã¼ã¯éã®ã©ã®ã·ã¹ãã ãããã¢ã¯ã»ã¹ã§ãããã¤ã¾ãéä¿¡
ã¯ããããã¯ã¼ã¯éã§çµè·¯æå®ããããããã·ã¹ãã ãã¢ãã¬ã¹/ã«ã¼ãæå®ä¸è½
ã®å ´åãã¢ã¯ã»ã¹ã§ããã®ã¯ãã¼ã«ã«ãããã¯ã¼ã¯æ¥ç¶ãå
±æããã·ã¹ãã ã®ã¿
ã¨ãªãã
å®ç¾©
ãã®ãªã¼ãã¼ã¬ã¤ã§ä½¿ç¨ããç¨èªã¯ãä»é² Bå㯠NIST å
é¨å ±åæ¸(NISTIR)7298 第2çè¦æ
å ±ã»
ãã¥ãªãã£ç¨èªé[99]ã«å®ç¾©ãããã
è£è¶³æ
å ±åã¯æ示
ç¾å¨ã®ã¨ãããªããçµç¹ã¯ãåã®ã»ã¯ã·ã§ã³ã«ãªããªã¼ãã¼ã¬ã¤ã«é¢ããè£è¶³æ
å ±åã¯æ示ãä¸
ãããã¨ãã§ããã
SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
363
Detailed Overlay Control Specifications
This Overlay is based on the NIST SP 800-53 Rev. 4, Security and Privacy Controls for Federal
Information Systems and Organizations, which provides a catalog of security and privacy controls for
federal information systems and organizations and a process for selecting controls to protect organizational
operations (including mission, functions, image, and reputation), organizational assets, individuals, other
organizations, and the Nation from a diverse set of threats including hostile cyber attacks, natural disasters,
structural failures, and human errors (both intentional and unintentional). The security and privacy controls
are customizable and implemented as part of an organization-wide process that manages information
security and privacy risk. The controls address a diverse set of security and privacy requirements across the
federal government and critical infrastructure, derived from legislation, Executive Orders, policies,
directives, regulations, standards, and/or mission/business needs. The publication also describes how to
develop specialized sets of controls, or overlays, tailored for specific types of missions/business functions,
technologies, or environments of operation. Finally, the catalog of security controls addresses security from
both a functionality perspective (the strength of security functions and mechanisms provided) and an
assurance perspective (the measures of confidence in the implemented security capability). Addressing both
security functionality and assurance helps to ensure that information technology component products and
the information systems built from those products using sound system and security engineering principles
are sufficiently trustworthy.
In preparation for selecting and specifying the appropriate security controls for organizational information
systems and their respective environments of operation, organizations first determine the criticality and
sensitivity of the information to be processed, stored, or transmitted by those systems. This process is
known as security categorization. FIPS 199 [15] enables federal agencies to establish security categories for
both information and information systems. Other documents, such as those produced by ISA and CNSS,
also provide guidance for defining low, moderate, and high levels of security based on impact. The security
categories are based on the potential impact on an organization or on people (employees and/or the public)
should certain events occur which jeopardize the information and information systems needed by the
organization to accomplish its assigned mission, protect its assets, fulfill its legal responsibilities, maintain
its day-to-day functions, and protect individualsâ safety, health and life. Security categories are to be used
in conjunction with vulnerability and threat information in assessing the risk to an organization.
This overlay provides ICS Supplemental Guidance for the security controls and control enhancements
prescribed for an information system or an organization designed to protect the confidentiality, integrity,
and availability of its information and to meet a set of defined security requirements. This overlay contains
a tailoring of the security control baselines; its specification may be more stringent or less stringent than the
original security control baseline specification and can be applied to multiple information systems. This
overlay is high-level, applicable to all ICS; it may be used as the basis for more specific overlays. Use cases
for specific systems in specific environments may be separately published (e.g., as a NISTIR).
SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
364
詳細ãªã¼ãã¼ã¬ã¤ç®¡çä»æ§æ¸
ãã®ãªã¼ãã¼ã¬ã¤ã¯ NIST SP 800-53 第4çãé£é¦æ
å ±ã·ã¹ãã ã»çµç¹ã®ã»ãã¥ãªãã£ã»ãã©ã¤
ãã·ã¼ç®¡çããåºã«ãã¦ããã第 4çã«ã¯çµç¹éç¨ï¼ä»»åãæ©è½ãã¤ã¡ã¼ã¸ãè©å¤çï¼ãçµç¹è³
ç£ãå人ãä»ã®çµç¹åã³å½ãæµã®ãµã¤ãã¼æ»æãèªç¶ç½å®³ãæ§é çé害åã³äººçé誤ï¼æå³çå
ã¯å¶çºçï¼çã®æ§ã
ãªè
å¨ããä¿è·ããããã®é£é¦æ
å ±ã·ã¹ãã ã»çµç¹åã³ç®¡çé¸å®ããã»ã¹ã®
ã»ãã¥ãªãã£ã»ãã©ã¤ãã·ã¼ç®¡çã«ã¿ãã°ã示ããã¦ãããã»ãã¥ãªãã£ã»ãã©ã¤ãã·ã¼ç®¡çã¯
ã«ã¹ã¿ãã¤ãºãå¯è½ã§ãæ
å ±ã»ãã¥ãªãã£ã»ãã©ã¤ãã·ã¼ã®ãªã¹ã¯ã管çããå
¨çµç¹çããã»ã¹
ã®ä¸ç°ã¨ãã¦å®æ½ãããã管çã¯ãæ³ä»¤ã大統é 令ãæ¿çãæ示ãè¦åãè¦æ ¼åã¯ä»»åã»äºæ¥ã
ã¼ãºããçããé£é¦æ¿åºåã³éè¦ã¤ã³ãã©å
¨ä½ã®æ§ã
ãªã»ãã¥ãªãã£ã»ãã©ã¤ãã·ã¼è¦ä»¶ã対象
ã¨ãã¦ããããã®ææ¸ã«ã¯ãç¹æ®ç®¡çããªã¼ãã¼ã¬ã¤ãåºæã®ä»»åã»äºæ¥æ©è½ãæè¡åã¯éç¨ç°
å¢ã«åããã¦çå®ããæ¹æ³ã説æããã¦ãããæå¾ã«ã»ãã¥ãªãã£å¯¾çã«ã¿ãã°ã¯ãæ©è½çãªé¢
ï¼ã»ãã¥ãªãã£æ©è½ã»ã¡ã«ããºã ã®å¼·åº¦ï¼ã¨ä¿è¨¼é¢ï¼å®æ½ããã»ãã¥ãªãã£è½åã®ä¿¡é ¼æ§ï¼ã®ä¸¡
æ¹ããã»ãã¥ãªãã£ãæ¤è¨ãããæ©è½ã¨ä¿è¨¼ã®ä¸¡é¢ãåãä¸ãããã¨ã§ãæ
å ±æè¡ã³ã³ãã¼ãã³
ã製åã¨ããã®è£½åã使ç¨ãã¦ããã£ããããã·ã¹ãã ååã¨ã»ãã¥ãªãã£ã¨ã³ã¸ãã¢ãªã³ã°å
åãé©ç¨ããæ§ç¯ãããæ
å ±ã·ã¹ãã ãååä¿¡é ¼ã«å¿ãããããã®ã¨ãªãã
çµç¹ã®æ
å ±ã·ã¹ãã ã¨ããããã®éç¨ç°å¢ã«å¯¾ããã»ãã¥ãªãã£å¯¾çãé¸å®ã»æå®ããããã®æº
åã¨ãã¦ãã¾ãçµç¹ã¯ããããã·ã¹ãã ã«ããå¦çãä¿ç®¡åã¯éä¿¡ãããæ
å ±ã®éè¦æ§ã¨è¦æ³¨æ
æ§ãå¤å®ããããã®ããã»ã¹ã¯ã»ãã¥ãªãã£åé¡ã¨ãã¦ç¥ããã¦ãããFIPS 199[15]ã¯ãé£é¦æ¿
åºæ©é¢ãæ
å ±åã³æ
å ±ã·ã¹ãã ç¨ã®ã»ãã¥ãªãã£åé¡ãè¨å®ã§ããããã«ç¤ºãã¦ãããISA ã
CNSS ã«ããä½æãããä»ã®ææ¸ããå½±é¿åº¦ã«å¿ãã¦ä½ã»ä¸ã»é«ã¬ãã«ãå®ããã¬ã¤ãã³ã¹ã示
ãã¦ããã
ã»ãã¥ãªãã£åé¡ã¯ãç¹å®ã®äºè±¡ãèµ·ãã¦ãçµç¹ã®ä»»åéè¡ãè³ç£ä¿è·ãæ³ç責任ã®éè¡ãæ¥å¸¸
æ¥åã®ç¶æåã³å人ã®å®å
¨ã»å¥åº·ã»çå½ä¿è·ã«å¿
è¦ã¨ãããæ
å ±ãæ
å ±ã·ã¹ãã ãå±éºã«é¥ãå ´
åã®ãçµç¹åã¯å人ï¼å¾æ¥å¡åã¯å½æ°ï¼ã«åã¶å½±é¿åº¦ãåºã«ãã¦ãããã»ãã¥ãªãã£åé¡ã¯èå¼±
æ§åã³è
å¨æ
å ±ã¨åããã¦ãçµç¹ã«å¯¾ãããªã¹ã¯è©ä¾¡ã«ä½¿ç¨ãã¹ãã§ããã
ãã®ãªã¼ãã¼ã¬ã¤ã¯ãæ
å ±ã®æ©å¯æ§ãå®å
¨æ§åã³å¯ç¨æ§ãä¿è·ããããã«ãã¾ããå®ããããä¸
é£ã®ã»ãã¥ãªãã£è¦ä»¶ãæºããããã«ãæ
å ±ã·ã¹ãã ãçµç¹åãã«ä½æãããã»ãã¥ãªãã£å¯¾
çã»ç®¡çæ¡å¼µç¨ ICS è£è¶³ã¬ã¤ãã³ã¹ã¨ãªããã»ãã¥ãªãã£ç®¡çãã¼ã¹ã©ã¤ã³ã®ã«ã¹ã¿ãã¤ãºãå«
ã¾ãããã®ä»æ§ã¯å
ã®ã»ãã¥ãªãã£ç®¡çãã¼ã¹ã©ã¤ã³ä»æ§ãããå³ããå ´åãããã°ç·©ãå ´åã
ããã種ã
ã®æ
å ±ã·ã¹ãã ã«é©ç¨å¯è½ã§ããããã®ãªã¼ãã¼ã¬ã¤ã¯é«ã¬ãã«ã§ãå
¨ã¦ã® ICS ã«é©
ç¨å¯è½ã§ãããããå¤ãã®åå¥ãªã¼ãã¼ã¬ã¤ã®åºç¤ã¨ãã¦ä½¿ç¨ã§ãããå
·ä½çãªç°å¢ã«ãããç¹
å®ã·ã¹ãã ã§ã®ä½¿ç¨ä¾ã¯å¥é示ããã¦ããï¼NISTIR çï¼ã
SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
365
Figure G-1 uses the AU-4 control as an example of the format and content of the detailed overlay control
specifications.
ï Control number and title.
ï Column for control and control enhancement number.
ï Column for control and control enhancement name.
ï Columns for baselines. If the baselines have been supplemented, then SUPPLEMENTED appears.
ï A row for each control or control enhancement.
ï Columns for LOW, MODERATE, and HIGH baselines.
ï âSelectedâ indicates the control is selected in NIST SP 800-53 Rev. 4. âAddedâ indicates the
control is added to a baseline in the ICS overlay. A blank cell indicates the control is not selected.
âRemovedâ indicates the control is removed from the baseline.
ï The ICS Supplemental Guidance. If there is none, that is stated.
ï The Control Enhancement ICS Supplemental Guidance. If there is none, that is stated.
ï The rationale for changing the presence of a control or control enhancement in the baseline.
ï AU-4 AUDIT STORAGE CAPACITY
ï ï ï
CNTL NO.
CONTROL NAME
Control Enhancement Name
SUPPLEMENTED
CONTROL BASELINES
LOW
MOD
HIGH
ï
AU-4
Audit Storage Capacity
Selected
Selected
Selected
ï
AU-4 (1)
AUDIT STORAGE CAPACITY | TRANSFER TO ALTERNATE STORAGE
Added
Added
Added
ï No ICS Supplemental Guidance.
ï Control Enhancement: (1) ICS Supplemental Guidance: Legacy ICS typically are typically configured with
remote storage on a separate information system (e.g., the historian in the DMZ accumulates historical operational ICS
data and is backed up for storage at a different site). ICS are currently using online backup services and increasingly
moving to Cloud based and Virtualized services. Retention of some data (e.g., SCADA telemetry) may be required by
regulatory authorities.
ï Rationale for adding control to baseline: Legacy ICS components typically do not have capacity to store or
analyze audit data. The retention periods for some data, particularly compliance data, may require large volumes of
storage.
Figure G-1 Detailed Overlay Control Specifications Illustrated
NIST SP 800-53 Rev. 4, Appendix F, contains Supplemental Guidance for all Controls and Control
Enhancements [22]. ICS Supplemental Guidance in this overlay provides organizations with additional
information on the application of the security controls and control enhancements in NIST SP 800-53 Rev. 4,
Appendix F, to ICS and the environments in which these specialized systems operate. The ICS
Supplemental Guidance also provides information as to why a particular security control or control
enhancement may not be applicable in some ICS environments and may be a candidate for tailoring (i.e.,
the application of scoping guidance and/or compensating controls).
ï
SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
366
å³G-1 ã¯ã詳細ãªãªã¼ãã¼ã¬ã¤ç®¡çä»æ§ã®æ§å¼åã³å
容ã®ä¸ä¾ã¨ãã¦ãAU-4 管çã使ç¨ãã¦ã
ãã
ï 管çã®çªå·ã¨é¡å
ï 管çã»ç®¡çæ¡å¼µçªå·ã示ãã«ã©ã
ï 管çã»ç®¡çæ¡å¼µåã示ãã«ã©ã
ï ãã¼ã¹ã©ã¤ã³ã示ãã«ã©ã ããã¼ã¹ã©ã¤ã³ã®è£è¶³ãããå ´åããè£è¶³ï¼SUPPLEMENTEDï¼ãã¨è¡¨
示ãããã
ï å管çã»ç®¡çæ¡å¼µã示ãè¡ã
ï ä½ã»ä¸ã»é«åã³é«ãã¼ã¹ã©ã¤ã³ã示ãã«ã©ã
ï ãé¸å®ã㯠NIST SP 800-53 第4çã§ç®¡çãé¸å®ããã¦ãããã¨ã示ããã追å ãã¯ç®¡ç
ãICS ãªã¼ãã¼ã¬ã¤ã®ãã¼ã¹ã©ã¤ã³ã«è¿½å ããã¦ãããã¨ã示ãã空ç½ã»ã«ã¯ç®¡çãé¸
å®ããã¦ããªããã¨ã示ãããåé¤ãã¯ç®¡çããã¼ã¹ã©ã¤ã³ããåé¤ããããã¨ã示ãã
ï ICS è£è¶³ã¬ã¤ãã³ã¹ãä½ããªãå ´åããã®æ¨ã®è¨è¿°ãããã
ï 管çæ¡å¼µ ICS è£è¶³ã¬ã¤ãã³ã¹ãä½ããªãå ´åããã®æ¨ã®è¨è¿°ãããã
ï ãã¼ã¹ã©ã¤ã³ã®ç®¡çã»ç®¡çæ¡å¼µã®æç¡ãå¤ãã£ãçç±
ï AU-4 AUDIT STORAGE CAPACITY
ï ï ï
CNTL NO.
CONTROL NAME
Control Enhancement Name
SUPPLEMENTED
CONTROL BASELINES
LOW
MOD
HIGH
ï
AU-4
Audit Storage Capacity
Selected
Selected
Selected
ï
AU-4 (1)
AUDIT STORAGE CAPACITY | TRANSFER TO ALTERNATE STORAGE
Added
Added
Added
ï ICS è£è¶³ã¬ã¤ãã³ã¹ãªã
ï 管çæ¡å¼µï¼(1) ICS è£è¶³ã¬ã¤ãã³ã¹ï¼ã¬ã¬ã·ã¼ICS ã¯ãä¸è¬ã«å¥åã®æ
å ±ã·ã¹ãã ä¸ã®é éã¹ãã¬ã¼ã¸ã§è¨å®ããã¦
ããï¼DMZ ã®ãã¹ããªã¢ã³çã§ãICS ã®éç¨å±¥æ´ãã¼ã¿ãèç©ããå¥ãµã¤ãã®ã¹ãã¬ã¼ã¸ã«ä¿ç®¡ããï¼ãICS ã¯ä»
ã®ã¨ãããªã³ã©ã¤ã³ããã¯ã¢ãããµã¼ãã¹ãå©ç¨ãã¦ããããã¯ã©ã¦ããã¼ã¹ã®ä»®æ³ãµã¼ãã¹ã«æ¬¡ç¬¬ã«ç§»è¡ãã¦ã
ããç¹å®ã®ãã¼ã¿ï¼SCADA ãã¬ã¡ããª-çï¼ã®ä¿æãè¦å¶å½å±ãã義åã¥ããããå ´åãããã
ï ãã¼ã¹ã©ã¤ã³ã«ç®¡çã追å ããçç±ï¼ä¸è¬ã«ã¬ã¬ã·ã¼ICS ã³ã³ãã¼ãã³ãã«ã¯ãç£æ»ãã¼ã¿ã®ä¿ååã¯åæ容éã
ãªããç¹å®ã®ãã¼ã¿ãç¹ã«ã³ã³ãã©ã¤ã¢ã³ã¹ãã¼ã¿ã®ä¿ææéã«ãã£ã¦ãä¿ç®¡éã大ãããªãã
å³G-1 詳細ãªã¼ãã¼ã¬ã¤ç®¡çä»æ§ã®èª¬æ
NIST SP 800-53 第4çä»é² Fã«ãå
¨ã¦ã®ç®¡çã»ç®¡çæ¡å¼µè£è¶³ã¬ã¤ãã³ã¹ããã[22]ããã®ãªã¼
ãã¼ã¬ã¤ã® ICS è£è¶³ã¬ã¤ãã³ã¹ã¯ãNIST SP 800-53 第4çã®ä»é² Fã«è¨è¼ãããã»ãã¥ãªãã£
対çåã³ç®¡çæ¡å¼µããICS åã³ãããå°ç¨ã·ã¹ãã ã®å®è¡ç°å¢ã«é©ç¨ããããã®è£è¶³æ
å ±ã示ãã
ã¾ããICS ç°å¢ã«ãã£ã¦ã¯ç¹å®ã®ã»ãã¥ãªãã£å¯¾çã管çæ¡å¼µãé©ç¨ã§ããã調æ´ãå¿
è¦ã¨ãªã
çç±ã«ã¤ãã¦ã示ãï¼ã¹ã³ã¼ãã³ã°ã¬ã¤ãã³ã¹åã¯è£åå¶å¾¡ï¼ã
ï
SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
367
ACCESS CONTROL â AC
Tailoring Considerations for Access Control Family
Before implementing controls in the AC family, consider the tradeoffs among security, privacy, latency, performance, throughput, and
reliability. For example, the organization considers whether latency induced from the use of confidentiality and integrity mechanisms
employing cryptographic mechanisms would adversely impact the operational performance of the ICS.
In situations where the ICS cannot support the specific Access Control requirements of a control, the organization employs
compensating controls in accordance with the general tailoring guidance. Examples of compensating controls are given with each control, as
appropriate.
Supplemental Guidance
Supplemental Guidance for all Controls and Control Enhancements in NIST SP 800-53 Rev. 4, Appendix F, should be used in
conjunction with the ICS Supplemental Guidance in this overlay, if any.
AC-1 ACCESS CONTROL POLICY AND PROCEDURES
CNTL NO. CONTROL NAME
Control Enhancement Name
CONTROL BASELINES
LOW
MOD
HIGH
AC-1
Access Control Policy and Procedures
Selected
Selected
Selected
ICS Supplemental Guidance: The policy specifically addresses the unique properties and requirements of ICS and the relationship
to non-ICS systems. ICS access by vendors and maintenance staff can occur over a very large facility footprint or geographic area and into
unobserved spaces such as mechanical/electrical rooms, ceilings, floors, field substations, switch and valve vaults, and pump stations.
AC-2 ACCOUNT MANAGEMENT
CNTL NO. CONTROL NAME
Control Enhancement Name
CONTROL BASELINES
LOW
MOD
HIGH
AC-2
Account Management
Selected
Selected
Selected
AC-2 (1) ACCOUNT MANAGEMENT | AUTOMATED SYSTEM ACCOUNT
MANAGEMENT
Selected Selected
AC-2 (2) ACCOUNT MANAGEMENT | REMOVAL OF TEMPORARY /
EMERGENCY ACCOUNTS
Selected Selected
AC-2 (3)
ACCOUNT MANAGEMENT | DISABLE INACTIVE ACCOUNTS
Selected
Selected
AC-2 (4)
ACCOUNT MANAGEMENT | AUTOMATED AUDIT ACTIONS
Selected
Selected
AC-2 (5) ACCOUNT MANAGEMENT | INACTIVITY LOGOUT / TYPICAL
USAGE MONITORING
Selected
AC-2 (11)
ACCOUNT MANAGEMENT | USAGE CONDITIONS
Selected
AC-2 (12) ACCOUNT MANAGEMENT | ACCOUNT MONITORING /
ATYPICAL USAGE
Selected
AC-2 (13)
ACCOUNT MANAGEMENT | ACCOUNT REVIEWS
Selected
ICS Supplemental Guidance: Example compensating controls include providing increased physical security, personnel security,
intrusion detection, auditing measures.
Control Enhancement: (1, 3, 4) ICS Supplemental Guidance: Example compensating controls include employing nonautomated
mechanisms or procedures.
Control Enhancement: (2) ICS Supplemental Guidance: In situations where the ICS (e.g., field devices) cannot support
temporary or emergency accounts, this enhancement does not apply. Example compensating controls include employing nonautomated
mechanisms or procedures.
Control Enhancement: (5) ICS Supplemental Guidance: Example compensating controls include employing nonautomated
mechanisms or procedures.
Control Enhancement: (11, 12, 13) No ICS Supplemental Guidance.
SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
368
ã¢ã¯ã»ã¹å¶å¾¡ - AC
ã¢ã¯ã»ã¹å¶å¾¡ãã¡ããªã®ã«ã¹ã¿ãã¤ãºèæ
®äºé
AC ãã¡ããªã§ç®¡çãå®æ½ããåã«ãã»ãã¥ãªãã£ããã©ã¤ãã·ã¼ãå¾
ã¡æéãããã©ã¼ãã³ã¹ã
ã¹ã«ã¼ããããä¿¡é ¼æ§ãæ¯è¼èéãããä¾ãã°ãæå·ã¡ã«ããºã ãæ¡ç¨ãã¦æ©å¯æ§åã³å®å
¨æ§ã¡
ã«ããºã ãå©ç¨ãããã¨ã«ããçããå¾
ã¡æéããICS ã®éç¨ããã©ã¼ãã³ã¹ãé»å®³ããªããçµ
ç¹ã¯æ¤è¨ããã
ICS ãããå¶å¾¡ã®ç¹å®ã®ã¢ã¯ã»ã¹å¶å¾¡è¦ä»¶ã«å¯¾å¿ãã¦ããªãç¶æ³ã§ã¯ãå
¨ä½çãªã«ã¹ã¿ãã¤ãºã¬
ã¤ãã³ã¹ã«å¾ã£ã¦è£åç管ççãæ¡ç¨ãããè£å管çã®ä¾ãå¿
è¦ã«å¿ãã¦ã管ççãã¨ã«ç¤ºãã
ãã
è£è¶³ã¬ã¤ãã³ã¹
å©ç¨ã§ããå ´åã«ã¯ãNIST SP 800-53 第4çä»é² Fã«ããå
¨ã¦ã®ç®¡çã»ç®¡çæ¡å¼µç¨è£è¶³ã¬ã¤ãã³
ã¹ããICS è£è¶³ã¬ã¤ãã³ã¹ã¨ä½µç¨ãã¹ãã§ããã
AC-1 ã¢ã¯ã»ã¹å¶å¾¡ããªã·ã¼ã»æé
管ççªå·
管çå
管çæ¡å¼µå
管çãã¼ã¹ã©ã¤ã³
ä½
ä¸
é«
AC-1
ã¢ã¯ã»ã¹å¶å¾¡ããªã·ã¼ã»æé
é¸å®
é¸å®
é¸å®
ICS è£è¶³ã¬ã¤ãã³ã¹ï¼ããªã·ã¼ã¯ç¹ã« ICS ã®åºæã®ç¹æ§ã»è¦ä»¶åã³ ICS 以å¤ã®ã·ã¹ãã ã¨ã®é¢ä¿
ãåãä¸ããããã³ãã¼åã³ä¿å®è¦å¡ã«ãã ICS ã¸ã®ã¢ã¯ã»ã¹ã¯ãæ©æ¢°ã»é»æ°å®¤ã天äºãåºãå¤
é»è¨åãã¹ã¤ããã»ãã«ã室ããã³ã室çãåºç¯ãªæ½è¨åã³å°åãç£è¦ä¸ã«ãªã空éã«ã¾ããã£
ã¦ããã
AC-2 ã¢ã«ã¦ã³ã管ç
管ççªå·
管çå
管çæ¡å¼µå
管çãã¼ã¹ã©ã¤ã³
ä½
ä¸
é«
AC-2
ã¢ã«ã¦ã³ã管ç
é¸å®
é¸å®
é¸å®
AC-2 (1)
ã¢ã«ã¦ã³ã管ç
|
åã·ã¹ãã ã¢ã«ã¦ã³ã管ç
é¸å®
é¸å®
AC-2 (2)
ã¢ã«ã¦ã³ã管ç
|
è¨æã»ç·æ¥ç¨ã¢ã«ã¦ã³ãã®åé¤
é¸å®
é¸å®
AC-2 (3)
ã¢ã«ã¦ã³ã管ç
|
ç¡æ´»åã¢ã«ã¦ã³ãã®ç¡å¹å
é¸å®
é¸å®
AC-2 (4)
ã¢ã«ã¦ã³ã管ç
|
èªåç£æ»è¡çº
é¸å®
é¸å®
AC-2 (5)
ã¢ã«ã¦ã³ã管ç
|
ç¡æ´»åãã°ã¢ã¦ãã»ä¸è¬çå©ç¨ç£è¦
é¸å®
AC-2 (11)
ã¢ã«ã¦ã³ã管ç
|
å©ç¨ç¶æ
é¸å®
AC-2 (12)
ã¢ã«ã¦ã³ã管ç
|
ã¢ã«ã¦ã³ãç£è¦ã»é対称å©ç¨
é¸å®
AC-2 (13)
ã¢ã«ã¦ã³ã
管ç
|
ã¢ã«ã¦ã³ã審æ»
é¸å®
ICS è£è¶³ã¬ã¤ãã³ã¹ï¼è£åç管ççã®ä¾ã¨ãã¦ãç©ççã»ãã¥ãªãã£ã人çã»ãã¥ãªãã£ã
ä¾µå
¥æ¤ç¥ãç£æ»æ段ã®å¼·åãããã
管çæ¡å¼µï¼(1, 3, 4) ICS è£è¶³ã¬ã¤ãã³ã¹ï¼è£åç管ççã®ä¾ã¨ãã¦ãéèªåã¡ã«ããºã åã¯æ
é ãããã
管çæ¡å¼µï¼(2) ICS è£è¶³ã¬ã¤ãã³ã¹ï¼ICSï¼ãã£ã¼ã«ãããã¤ã¹çï¼ãè¨æåã¯ç·æ¥ã¢ã«ã¦ã³
ãã«å¯¾å¿ã§ããªãå ´åããã®æ¡å¼µã¯é©ç¨ãããªããè£åç管ççã®ä¾ã¨ãã¦ãéèªåã¡ã«ããºã
åã¯æé ãããã
管çæ¡å¼µï¼(5) ICS è£è¶³ã¬ã¤ãã³ã¹ï¼è£åç管ççã®ä¾ã¨ãã¦ãéèªåã¡ã«ããºã åã¯æé ãã
ãã
管çæ¡å¼µï¼(11, 12, 13) ICS è£è¶³ã¬ã¤ãã³ã¹ãªã

SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
369
AC-3 ACCESS ENFORCEMENT
CNTL NO. CONTROL NAME
Control Enhancement Name
CONTROL BASELINES
LOW
MOD
HIGH
AC-3
Access Enforcement
Selected
Selected
Selected
ICS Supplemental Guidance: The organization ensures that access enforcement mechanisms do not adversely impact the
operational performance of the ICS. Example compensating controls include encapsulation. Policy for logical access control to Non-
Addressable and Non-Routable system resources and the associated information is made explicit. Access control mechanisms include
hardware, firmware, and software that controls or has device access, such as device drivers and communications controllers. Physical access
control may serve as a compensating control for logical access control, however, it may not provide sufficient granularity in situations where
users require access to different functions. Logical access enforcement may be implemented in encapsulating hardware and software.
AC-4 INFORMATION FLOW ENFORCEMENT
CNTL NO. CONTROL NAME
Control Enhancement Name
CONTROL BASELINES
LOW
MOD
HIGH
AC-4
Information Flow Enforcement
Selected
Selected
ICS Supplemental Guidance: Physical addresses (e.g., a serial port) may be implicitly or explicitly associated with labels or
attributes (e.g., hardware I/O address). Manual methods are typically static. Label or attribute policy mechanisms may be implemented in
hardware, firmware, and software that controls or has device access, such as device drivers and communications controllers. Information
flow policy may be supported by labeling or coloring physical connectors as an aid to manual hookup. Inspection of message content may
enforce information flow policy. For example, a message containing a command to an actuator may not be permitted to flow between the
control network and any other network.
AC-5 SEPARATION OF DUTIES
CNTL NO. CONTROL NAME
Control Enhancement Name
CONTROL BASELINES
LOW
MOD
HIGH
AC-5
Separation of Duties
Selected
Selected
ICS Supplemental Guidance: Example compensating controls include providing increased personnel security and auditing. The
organization carefully considers the appropriateness of a single individual performing multiple critical roles.
AC-6 LEAST PRIVILEGE
CNTL NO. CONTROL NAME
Control Enhancement Name
CONTROL BASELINES
LOW
MOD
HIGH
AC-6
Least Privilege
Selected
Selected
AC-6 (1) LEAST PRIVILEGE | AUTHORIZE ACCESS TO SECURITY
FUNCTIONS
Selected Selected
AC-6 (2) LEAST PRIVILEGE | NON-PRIVILEGED ACCESS FOR
NONSECURITY FUNCTIONS
Selected Selected
AC-6 (3) LEAST PRIVILEGE | NETWORK ACCESS TO PRIVILEGED
COMMANDS
Selected
AC-6 (5)
LEAST PRIVILEGE | PRIVILEGED ACCOUNTS
Selected
Selected
AC-6 (9) LEAST PRIVILEGE | AUDITING USE OF PRIVILEGED
FUNCTIONS
Selected Selected
AC-6 (10) LEAST PRIVILEGE | PROHIBIT NON-PRIVILEGED USERS
FROM EXECUTING PRIVILEGED FUNCTIONS
Selected Selected
ICS Supplemental Guidance: Example compensating controls include providing increased personnel security and auditing. The
organization carefully considers the appropriateness of a single individual having multiple critical
SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
370
AC-3 ã¢ã¯ã»ã¹ã®æ½è¡
管ççªå·
管çå
管çæ¡å¼µå
管çãã¼ã¹ã©ã¤ã³
ä½
ä¸
é«
AC-3
ã¢ã¯ã»ã¹æ½è¡
é¸å®
é¸å®
é¸å®
ICS è£è¶³ã¬ã¤ãã³ã¹ï¼çµç¹ã¯ãã¢ã¯ã»ã¹æ½è¡ã¡ã«ããºã ã ICS ã®éç¨ããã©ã¼ãã³ã¹ã«æªå½±
é¿ããªãããã«ãããè£å管çã«ã¯ã«ãã»ã«åããããã¢ãã¬ã¹/ã«ã¼ãæå®ä¸è½ã·ã¹ãã ãªã½
ã¼ã¹åã³é¢é£æ
å ±ã¸ã®è«çã¢ã¯ã»ã¹å¶å¾¡ããªã·ã¼ã¯æ確ã«ãããã¢ã¯ã»ã¹å¶å¾¡ã¡ã«ããºã ã«ã¯ã
ãã¼ãã¦ã¨ã¢ããã¡ã¼ã ã¦ã¨ã¢ã®ã»ããããã¤ã¹ãã©ã¤ããéä¿¡ã³ã³ããã¼ã©çãããã¤ã¹ã®å¶
御åã¯ã¢ã¯ã»ã¹ãè¡ãã½ããã¦ã¨ã¢ããããç©ççã¢ã¯ã»ã¹å¶å¾¡ã¯ãè«çã¢ã¯ã»ã¹å¶å¾¡ã«ä»£ãã
è£åç管ççã¨ãªãããã¦ã¼ã¶ãå¥æ©è½ã¸ã®ã¢ã¯ã»ã¹ãæ±ããå ´åã®ããç´°ããããªããè«çã¢
ã¯ã»ã¹æ½è¡ã¯ããã¼ãã¦ã¨ã¢ã¨ã½ããã¦ã¨ã¢ã®ã«ãã»ã«åã§å®æ½ã§ããã
AC-4 æ
å ±ããã¼ã®æ½è¡
管ççªå·
管çå
管çæ¡å¼µå
管çãã¼ã¹ã©ã¤ã³
ä½
ä¸
é«
AC-4
æ
å ±ããã¼æ½è¡
é¸å®
é¸å®
ICS è£è¶³ã¬ã¤ãã³ã¹ï¼ç©çã¢ãã¬ã¹ï¼ã·ãªã¢ã«ãã¼ãçï¼ã¯ãé»ç¤ºçåã¯æ示çã«ã©ãã«å
ã¯å±æ§ï¼ãã¼ãã¦ã¨ã¢ I/O ã¢ãã¬ã¹çï¼ã«é¢é£ã¥ãããããã¥ã¢ã«æä½ã¯ä¸è¬ã«éçã§ãããã©
ãã«åã¯å±æ§ã¡ã«ããºã ã¯ããã¼ãã¦ã¨ã¢ããã¡ã¼ã ã¦ã¨ã¢ã®ã»ããããã¤ã¹ãã©ã¤ããéä¿¡ã³
ã³ããã¼ã©çãããã¤ã¹ã®å¶å¾¡åã¯ã¢ã¯ã»ã¹ãè¡ãã½ããã¦ã¨ã¢ã«å®è£
ããããæ
å ±ããã¼ããª
ã·ã¼ã¯ãããã¥ã¢ã«æä½ä½æ¥ã®å©ãã¨ãã¦ãç©ççã³ãã¯ã¿ã¸ã®ã©ãã«ä»ããçè²ã«ããæ¯ãã
ãããã¡ãã»ã¼ã¸å
容ã®æ¤æ»ã¯ãæ
å ±ããã¼ããªã·ã¼ãæ½è¡ãããã®ã¨ãªããä¾ãã°ãã¢ã¯ãã¥
ã¨ã¼ã¿ã¸ã®ã³ãã³ããå«ãã ã¡ãã»ã¼ã¸ã¯ãå¶å¾¡ãããã¯ã¼ã¯ã¨ä»ã®ãããã¯ã¼ã¯éã§æµããªã
ããã«ããªããã°ãªããªãã
AC-5 ä»»ååæ
管ççªå·
管çå
管çæ¡å¼µå
管çãã¼ã¹ã©ã¤ã³
ä½
ä¸
é«
AC-5
ä»»ååæ
é¸å®
é¸å®
ICS è£è¶³ã¬ã¤ãã³ã¹ï¼è£åç管ççã®ä¾ã¨ãã¦ã人çã»ãã¥ãªãã£ã¨ç£æ»ã®å¼·åããããçµ
ç¹ã¯ã1人ã§è¤æ°ã®éè¦ãªå½¹å²ãæããã®ãé©åãã©ãããæ
éã«æ¤è¨ããã
AC-6 æå°æ¨©é
管ççªå·
管çå
管çæ¡å¼µå
管çãã¼ã¹ã©ã¤ã³
ä½
ä¸
é«
AC-6
æå°æ¨©é
é¸å®
é¸å®
AC-6 (1)
æå°æ¨©é
|
ã»ãã¥ãªãã£æ©è½ã¸ã®ã¢ã¯ã»ã¹è¨±å¯
é¸å®
é¸å®
AC-6 (2)
æå°æ¨©é
|
éã»ãã¥ãªãã£æ©è½ã¸ã®ç¡æ¨©éã¢ã¯ã»ã¹
é¸å®
é¸å®
AC-6 (3)
æå°æ¨©é
|
ç¹æ¨©ã³ãã³ãã¸ã®ãããã¯ã¼ã¯ã¢ã¯ã»ã¹
é¸å®
AC-6 (5)
æå°æ¨©é
|
ç¹æ¨©ã¢ã«ã¦ã³ã
é¸å®
é¸å®
AC-6 (9)
æå°
権é
|
ç¹æ¨©æ©è½ã®ç£æ»å©ç¨
é¸å®
é¸å®
AC-6 (10)
æå°æ¨©é
|
ç¡æ¨©éã¦ã¼ã¶ã«ããç¹æ¨©æ©è½ã®å®è¡ç¦æ¢
é¸å®
é¸å®
ICS è£è¶³ã¬ã¤ãã³ã¹ï¼è£åç管ççã®ä¾ã¨ãã¦ã人çã»ãã¥ãªãã£ã¨ç£æ»ã®å¼·åããããçµ
ç¹ã¯ã1人ã§è¤æ°ã®éè¦ç¹æ¨©ãæã¤ã®ãé©åãã©ãããæ
éã«æ¤è¨ããã
SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
371
privileges. System privilege models may be tailored to enforce integrity and availability (e.g., lower privileges include read access and higher
privileges include write access).
Control Enhancement: (1) ICS Supplemental Guidance: In situations where the ICS cannot support access control to security
functions, the organization employs nonautomated mechanisms or procedures as compensating controls in accordance with the general
tailoring guidance.
Control Enhancement: (2) ICS Supplemental Guidance: In situations where the ICS cannot support access control to nonsecurity
functions, the organization employs nonautomated mechanisms or procedures as compensating controls in accordance with the general
tailoring guidance.
Control Enhancement: (3) ICS Supplemental Guidance: In situations where the ICS cannot support network access control to
privileged commands, the organization employs nonautomated mechanisms or procedures as compensating controls in accordance with the
general tailoring guidance.
Control Enhancement: (5) ICS Supplemental Guidance: In situations where the ICS cannot support access control to privileged
accounts, the organization employs nonautomated mechanisms or procedures as compensating controls in accordance with the general
tailoring guidance.
Control Enhancement: (9) ICS Supplemental Guidance: In general, audit record processing is not performed on the ICS, but on a
separate information system. Example compensating controls include providing an auditing capability on a separate information system.
Control Enhancement: (10) ICS Supplemental Guidance: Example compensating controls include enhanced auditing.
AC-7 UNSUCCESSFUL LOGIN ATTEMPTS
CNTL NO. CONTROL NAME
Control Enhancement Name
CONTROL BASELINES
LOW
MOD
HIGH
AC-7
Unsuccessful Login Attempts
Selected
Selected
Selected
ICS Supplemental Guidance: Many ICS must remain continuously on and operators remain logged onto the system at all times. A
âlog-overâ capability may be employed. Example compensating controls include logging or recording all unsuccessful login attempts and
alerting ICS security personnel though alarms or other means when the number of organization-defined consecutive invalid access attempts
is exceeded.
AC-8 SYSTEM USE NOTIFICATION
CNTL NO. CONTROL NAME
Control Enhancement Name
CONTROL BASELINES
LOW
MOD
HIGH
AC-8
System Use Notification
Selected
Selected
Selected
ICS Supplemental Guidance: Many ICS must remain continuously on and system use notification may not be supported or
effective. Example compensating controls include posting physical notices in ICS facilities.
AC-10 CONCURRENT SESSION CONTROL
CNTL NO. CONTROL NAME
Control Enhancement Name
CONTROL BASELINES
LOW
MOD
HIGH
AC-10
Concurrent Session Control
Selected
ICS Supplemental Guidance: The number, account type, and privileges of concurrent sessions takes into account the roles and
responsibilities of the affected individuals. Example compensating controls include providing increased auditing measures.
SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
372
ã·ã¹ãã ç¹æ¨©ã¢ãã«ãã«ã¹ã¿ãã¤ãºãã¦ãå®å
¨æ§ã¨å¯ç¨æ§ãæ½è¡ã§ããï¼ããä½ãç¹æ¨©ã«ã¯èªã¿
åãã¢ã¯ã»ã¹ãããé«ãç¹æ¨©ã«ã¯æ¸ãè¾¼ã¿ã¢ã¯ã»ã¹ãããï¼ã
管çæ¡å¼µï¼(1) ICS è£è¶³ã¬ã¤ãã³ã¹ï¼ICS ãã»ãã¥ãªãã£æ©è½ã¸ã®ã¢ã¯ã»ã¹å¶å¾¡ã«å¯¾å¿ãã¦ã
ãªãç¶æ³ã§ã¯ãå
¨ä½çãªã«ã¹ã¿ãã¤ãºã¬ã¤ãã³ã¹ã«å¾ã£ã¦ãçµç¹ã¯éèªåã¡ã«ããºã åã¯æé ã
æ¡ç¨ããã
管çæ¡å¼µï¼(2) ICS è£è¶³ã¬ã¤ãã³ã¹ï¼ICS ãéã»ãã¥ãªãã£æ©è½ã¸ã®ã¢ã¯ã»ã¹å¶å¾¡ã«å¯¾å¿ãã¦
ããªãç¶æ³ã§ã¯ãå
¨ä½çãªã«ã¹ã¿ãã¤ãºã¬ã¤ãã³ã¹ã«å¾ã£ã¦ãçµç¹ã¯éèªåã¡ã«ããºã åã¯æé
ãæ¡ç¨ããã
管çæ¡å¼µï¼(3) ICS è£è¶³ã¬ã¤ãã³ã¹ï¼ICS ãç¹æ¨©ã³ãã³ãã¸ã®ãããã¯ã¼ã¯ã¢ã¯ã»ã¹å¶å¾¡ã«å¯¾
å¿ãã¦ããªãç¶æ³ã§ã¯ãå
¨ä½çãªã«ã¹ã¿ãã¤ãºã¬ã¤ãã³ã¹ã«å¾ã£ã¦ãçµç¹ã¯éèªåã¡ã«ããºã å
ã¯æé ãæ¡ç¨ããã
管çæ¡å¼µï¼(5) ICS è£è¶³ã¬ã¤ãã³ã¹ï¼ICS ãç¹æ¨©ã¢ã«ã¦ã³ãã¸ã®ã¢ã¯ã»ã¹å¶å¾¡ã«å¯¾å¿ãã¦ããª
ãç¶æ³ã§ã¯ãå
¨ä½çãªã«ã¹ã¿ãã¤ãºã¬ã¤ãã³ã¹ã«å¾ã£ã¦ãçµç¹ã¯éèªåã¡ã«ããºã åã¯æé ãæ¡
ç¨ããã
管çæ¡å¼µï¼(9) ICS è£è¶³ã¬ã¤ãã³ã¹ï¼ç·ãã¦ãç£æ»è¨é²å¦ç㯠ICS ã§è¡ããããå¥åã®æ
å ±ã·
ã¹ãã ã§è¡ããããè£åç管ççã®ä¾ã¨ãã¦ãå¥åã®æ
å ±ã·ã¹ãã ã¸ã®ç£æ»è½åã®ä»ä¸ãããã
管çæ¡å¼µï¼(10) ICS è£è¶³ã¬ã¤ãã³ã¹ï¼è£åç管ççã®ä¾ã¨ãã¦ãæ¡å¼µç£æ»ãããã
AC-7 ãã°ã¤ã³å¤±æ
管ççªå·
管çå
管çæ¡å¼µå
管çãã¼ã¹ã©ã¤ã³
ä½
ä¸
é«
AC-7
ãã°ã¤ã³å¤±æ
é¸å®
é¸å®
é¸å®
ICS è£è¶³ã¬ã¤ãã³ã¹ï¼å¤ãã® ICS ã¯é»æºãå
¥ããã¾ã¾ã«ããªããã°ãªãããæä½å¡ã常æã·
ã¹ãã ã«ãã°ãªã³ç¶æ
ãç¶æãã¦ãããããã°ãªã¼ãã¼ãæ©è½ãæ¡ç¨ã§ãããè£åç管ççã®ä¾
ã¨ãã¦ãå
¨ã¦ãã°ã¤ã³å¤±ææã®ãã°åã¯è¨é²ãåããäºã決ããé£ç¶å¤±ææ°ã«éããã¨ãICS ã»
ãã¥ãªãã£æ
å½è
ã«ã¢ã©ã¼ã ãã®ä»ã®æ段ã§è¦å ±ãéãããã«ã§ããã
AC-8 ã·ã¹ãã å©ç¨éç¥
管ççªå·
管çå
管çæ¡å¼µå
管çãã¼ã¹ã©ã¤ã³
ä½
ä¸
é«
AC-8
ã·ã¹ãã å©ç¨éç¥
é¸å®
é¸å®
é¸å®
ICS è£è¶³ã¬ã¤ãã³ã¹ï¼å¤ãã® ICS ã¯é»æºãå
¥ããã¾ã¾ã«ãã¦ãããªããã°ãªãããã·ã¹ãã
å©ç¨éç¥ã¯å¯¾å¿ããªããå¹æçã§ãªããè£åç管ççã®ä¾ã¨ãã¦ãICS æ½è¨å
ã«éç¥ãæ²ç¤ºãã
æ¹æ³ãããã
AC-10 åæã»ãã·ã§ã³ç®¡ç
管ççªå·
管çå
管çæ¡å¼µå
管çãã¼ã¹ã©ã¤ã³
ä½
ä¸
é«
AC-10
åæã»ãã·ã§ã³ç®¡ç
é¸å®
ICS è£è¶³ã¬ã¤ãã³ã¹ï¼åæã»ãã·ã§ã³ã®çªå·ãã¢ã«ã¦ã³ãã¿ã¤ãåã³ç¹æ¨©ã«ã¯ãå½±é¿ãåã
ãå人ã®å½¹å²ã¨è²¬ä»»ãèæ
®ã«å
¥ãããè£åç管ççã®ä¾ã¨ãã¦ãç£æ»æ段ã®å¼·åãããã

SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
373
AC-11 SESSION LOCK
CNTL NO. CONTROL NAME
Control Enhancement Name
CONTROL BASELINES
LOW
MOD
HIGH
AC-11
Session Lock
Selected
Selected
AC-11 (1)
SESSION LOCK | PATTERN-HIDING DISPLAYS
Selected
Selected
ICS Supplemental Guidance: This control assumes a staffed environment where users interact with information system displays.
When this assumption does not apply the organization tailors the control appropriately (e.g., the ICS may be physically protected by
placement in a locked enclosure). The control may also be tailored for ICS that are not configured with displays, but which have the
capability to support displays (e.g., ICS to which a maintenance technician may attach a display). In some cases, session lock for ICS
operator workstations/nodes is not advised (e.g., when immediate operator responses are required in emergency situations). Example
compensating controls include locating the display in an area with physical access controls that limit access to individuals with permission
and need-to-know for the displayed information.
Control Enhancement: (1) ICS Supplemental Guidance: ICS may employ physical protection to prevent access to a display or to
prevent attachment of a display. In situations where the ICS cannot conceal displayed information, the organization employs nonautomated
mechanisms or procedures as compensating controls in accordance with the general tailoring guidance.
AC-12 SESSION TERMINATION
CNTL NO. CONTROL NAME
Control Enhancement Name
CONTROL BASELINES
LOW
MOD
HIGH
AC-12
Session Termination
Selected
Selected
ICS Supplemental Guidance: Example compensating controls include providing increased auditing measures or limiting remote
access privileges to key personnel.
AC-14 PERMITTED ACTIONS WITHOUT IDENTIFICATION OR AUTHENTICATION
CNTL NO. CONTROL NAME
Control Enhancement Name
CONTROL BASELINES
LOW
MOD
HIGH
AC-14
Permitted Actions without Identification or Authentication
Selected
Selected
No ICS Supplemental Guidance.
AC-17 REMOTE ACCESS
CNTL NO. CONTROL NAME
Control Enhancement Name
CONTROL BASELINES
LOW
MOD
HIGH
AC-17
Remote Access
Selected
Selected
Selected
AC-17 (1)
REMOTE ACCESS | AUTOMATED MONITORING / CONTROL
Selected
Selected
AC-17 (2) REMOTE ACCESS | PROTECTION OF CONFIDENTIALITY /
INTEGRITY USING ENCRYPTION
Selected Selected
AC-17 (3)
REMOTE ACCESS | MANAGED ACCESS CONTROL POINTS
Selected
Selected
AC-17 (4)
REMOTE ACCESS | PRIVILEGED COMMANDS / ACCESS
Selected
Selected
ICS Supplemental Guidance: In situations where the ICS cannot implement any or all of the components of this control, the
organization employs other mechanisms or procedures as compensating controls in accordance with the general tailoring guidance.
Control Enhancement: (1) ICS Supplemental Guidance: Example compensating controls include employing nonautomated
mechanisms or procedures as compensating controls (e.g., following manual authentication [see IA-2], dial-in remote access may be enabled
for a specified period of time or a call may be placed from the ICS site to the authenticated remote entity.
SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
374
AC-11 ã»ãã·ã§ã³ããã¯
管ççªå·
管çå
管çæ¡å¼µå
管çãã¼ã¹ã©ã¤ã³
ä½
ä¸
é«
AC-11
ã»ãã·ã§ã³ããã¯
é¸å®
é¸å®
AC-11 (1)
ã»ãã·ã§ã³ããã¯
ãã¿ã¼ã³é表示
é¸å®
é¸å®
ICS è£è¶³ã¬ã¤ãã³ã¹ï¼ãã®ç®¡çã¯ãã¦ã¼ã¶ãæ
å ±ã·ã¹ãã ãã£ã¹ãã¬ã¤ã¨ããåããè¡ãæ
人ç°å¢ãæ³å®ãã¦ãããæ³å®ã¨ç°ãªãç°å¢ã§ã¯ãçµç¹ã¯ç®¡çãé©åã«ã«ã¹ã¿ãã¤ãºããï¼éµã®ã
ãããã£ãããããªã© ICS ã®ç©ççä¿è·çï¼ãè£åç管ççã®ä¾ã¨ãã¦ããã£ã¹ãã¬ã¤ãè¨å®ã
ãã¦ããªããã®ã®ãæ¥ç¶ãããã¨æãã°ã§ãã ICS ã®ã«ã¹ã¿ãã¤ãºãããï¼ä¿å®æè¡è
ã«ããã
ã£ã¹ãã¬ã¤ã®è¨ç½®çï¼ãå ´åã«ãã£ã¦ã¯ãICS æä½å¡ã¯ã¼ã¯ã¹ãã¼ã·ã§ã³/ãã¼ãã®ã»ãã·ã§ã³ã
ãã¯ãæ¨å¥¨ã§ããªããã¨ãããï¼ç·æ¥æã«æä½å¡ã®å³æ対å¿ãå¿
è¦çï¼ãè£åç管ççã®ä¾ã¨ã
ã¦ã権éããã表示æ
å ±ãç¥ãå¿
è¦ã®ãã人å¡ã ããç«å
¥ã§ããå ´æã«ããã£ã¹ãã¬ã¤ãè¨ç½®ã
ããã¨ãããã
管çæ¡å¼µï¼(1) ICS è£è¶³ã¬ã¤ãã³ã¹ï¼ãã£ã¹ãã¬ã¤ã¸ã®ã¢ã¯ã»ã¹ããã£ã¹ãã¬ã¤ã®æ¥ç¶ãé²æ¢
ããç©ççä¿è·ãæ¡ç¨ã§ãããICS ã表示æ
å ±ãé è½ã§ããªãç¶æ³ã§ã¯ãå
¨ä½çãªã«ã¹ã¿ãã¤ãº
ã¬ã¤ãã³ã¹ã«å¾ã£ã¦ãçµç¹ã¯éèªåã¡ã«ããºã åã¯æé ãè£åç管ççã¨ãã¦æ¡ç¨ããã
AC-12 ã»ãã·ã§ã³çµäº
管ççªå·
管çå
管çæ¡å¼µå
管çãã¼ã¹ã©ã¤ã³
ä½
ä¸
é«
AC-12
ã»ãã·ã§ã³çµäº
é¸å®
é¸å®
ICS è£è¶³ã¬ã¤ãã³ã¹ï¼è£åç管ççã®ä¾ã¨ãã¦ãç£æ»æ段ã®å¼·åããªã¢ã¼ãã¢ã¯ã»ã¹ç¹æ¨©ã
éè¦ãªäººå¡ã«å¶éããæ¹æ³ãããã
AC-14 èå¥ã»èªè¨¼ã®ãªã許å¯ãããè¡çº
管ççªå·
管çå
管çæ¡å¼µå
管çãã¼ã¹ã©ã¤ã³
ä½
ä¸
é«
AC-14
èå¥ã»èªè¨¼ã®ãªã許å¯ãããè¡çº
é¸å®
é¸å®
ICS è£è¶³ã¬ã¤ãã³ã¹ãªã
AC-17 ãªã¢ã¼ãã¢ã¯ã»ã¹
管ççªå·
管çå
管çæ¡å¼µå
管çãã¼ã¹ã©ã¤ã³
ä½
ä¸
é«
AC-17
ãªã¢ã¼ãã¢ã¯ã»ã¹
é¸å®
é¸å®
é¸å®
AC-17 (1)
ãªã¢ã¼ãã¢ã¯ã»ã¹
|
èªåç£è¦ã»ç®¡ç
é¸å®
é¸å®
AC-17 (2)
ãªã¢ã¼ãã¢ã¯ã»ã¹
|
æå·åã«ããæ©å¯æ§ã»å®å
¨æ§ã®ä¿è·
é¸å®
é¸å®
AC-17 (3)
ãªã¢ã¼ãã¢
ã¯ã»ã¹
|
管çã¢ã¯ã»ã¹å¶å¾¡ãã¤ã³ã
é¸å®
é¸å®
AC-17 (4)
ãªã¢ã¼ãã¢ã¯ã»ã¹
|
ç¹æ¨©ã³ãã³ãã»ã¢ã¯ã»ã¹
é¸å®
é¸å®
ICS è£è¶³ã¬ã¤ãã³ã¹ï¼ICS ããã®ç®¡çè¦ç´ ã®ä¸é¨åã¯å
¨é¨ãå®è¡ã§ããªãç¶æ³ã§ã¯ãå
¨ä½ç
ãªã«ã¹ã¿ãã¤ãºã¬ã¤ãã³ã¹ã«å¾ã£ã¦ãçµç¹ã¯éèªåã¡ã«ããºã åã¯æé ãè£åç管ççã¨ãã¦æ¡
ç¨ããã
管çæ¡å¼µï¼(1) ICS è£è¶³ã¬ã¤ãã³ã¹ï¼è£åç管ççã®ä¾ã¨ãã¦ãéèªåã¡ã«ããºã åã¯æé ã
è£åç管ççã¨ãã¦æ¡ç¨ã§ããï¼æåèªè¨¼ã«å¾ã[IA-2 åç
§]ããã¤ã¢ã«ã¤ã³ãªã¢ã¼ãã¢ã¯ã»ã¹ã
ä¸å®æéæå¹ã«ããããçºå¼ã ICS ãµã¤ãããèªè¨¼æ¸ã¿é éæ©é¢ã«ç§»è¨ãããªã©ï¼ã
SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
375
Control Enhancement: (2) ICS Supplemental Guidance: ICS security objectives often rank confidentiality below availability and
integrity. The organization explores all possible cryptographic mechanism (e.g., encryption, digital signature, hash function). Each
mechanism has a different delay impact. Example compensating controls include providing increased auditing for remote sessions or limiting
remote access privileges to key personnel).
Control Enhancement: (3) ICS Supplemental Guidance: Example compensating controls include connection-specific manual
authentication of the remote entity.
Control Enhancement: (4) No ICS Supplemental Guidance.
ICS Supplemental Guidance: Example compensating controls include employing nonautomated mechanisms or procedures as
compensating controls in accordance with the general tailoring guidance.
AC-18 WIRELESS ACCESS
CNTL NO. CONTROL NAME
Control Enhancement Name
CONTROL BASELINES
LOW
MOD
HIGH
AC-18
Wireless Access
Selected
Selected
Selected
AC-18 (1)
WIRELESS ACCESS | AUTHENTICATION AND ENCRYPTION
Selected
Selected
AC-18 (4) WIRELESS ACCESS | RESTRICT CONFIGURATIONS BY
USERS
Selected
AC-18 (5) WIRELESS ACCESS | CONFINE WIRELESS
COMMUNICATIONS
Selected
ICS Supplemental Guidance: In situations where the ICS cannot implement any or all of the components of this control, the
organization employs other mechanisms or procedures as compensating controls in accordance with the general tailoring guidance.
Control Enhancement: (1) ICS Supplemental Guidance: See AC-17 Control Enhancement: (1) ICS Supplemental Guidance.
Example compensating controls include providing increased auditing for wireless access or limiting wireless access privileges to key
personnel.
Control Enhancement: (4) (5) No ICS Supplemental Guidance.
AC-19 ACCESS CONTROL FOR MOBILE DEVICES
CNTL NO. CONTROL NAME
Control Enhancement Name
CONTROL BASELINES
LOW
MOD
HIGH
AC-19
Access Control for Mobile Devices
Selected
Selected
Selected
AC-19 (5) ACCESS CONTROL FOR MOBILE DEVICES | FULL DEVICE /
CONTAINER-BASED ENCRYPTION
Selected Selected
No ICS Supplemental Guidance.
AC-20 USE OF EXTERNAL INFORMATION SYSTEMS
CNTL NO. CONTROL NAME
Control Enhancement Name
CONTROL BASELINES
LOW
MOD
HIGH
AC-20
Use of External Information Systems
Selected
Selected
Selected
AC-20 (1) USE OF EXTERNAL INFORMATION SYSTEMS | LIMITS ON
AUTHORIZED USE
Selected Selected
AC-20 (2) USE OF EXTERNAL INFORMATION SYSTEMS | PORTABLE
STORAGE MEDIA
Selected Selected
ICS Supplemental Guidance: Organizations refine the definition of âexternalâ to reflect lines of authority and responsibility;
granularity of organization entity; and their relationships. An organization may consider a system to be external if that system performs
different functions, implements different policies, comes under different managers, or does not provide sufficient visibility into the
implementation of security controls to allow the establishment of a satisfactory trust relationship. For example, a process control system and
a business data processing system would typically be considered external to each other. Access to an ICS for support by a business partner,
such as a vendor or support contractor, is another common example. The definition and trustworthiness of external information systems is
reexamined with respect to ICS functions, purposes, technology, and limitations to
SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
376
管çæ¡å¼µï¼(2) ICS è£è¶³ã¬ã¤ãã³ã¹ï¼ICS ã®ã»ãã¥ãªãã£ç®æ¨ã§ã¯ãæ©å¯æ§ãå¯ç¨æ§åã³å®å
¨
æ§ãããä¸ä½ã«ã©ã³ã¯ããããã¨ãå¤ããçµç¹ã¯ããããæå·ã¡ã«ããºã ãæ´»ç¨ããï¼æå·åã
ãã¸ã¿ã«ç½²åãããã·ã¥é¢æ°çï¼ãåã¡ã«ããºã ã®é
延影é¿ã¯ããããç°ãªããè£åç管ççã®
ä¾ã¨ãã¦ãé éã»ãã·ã§ã³ã«å¯¾ããç£æ»ã®å¼·åããªã¢ã¼ãã¢ã¯ã»ã¹ç¹æ¨©ãéè¦ãªäººå¡ã«å¶éãã
æ¹æ³ãããã
管çæ¡å¼µï¼(3) ICS è£è¶³ã¬ã¤ãã³ã¹ï¼è£åç管ççã®ä¾ã¨ãã¦ãé éæ©é¢ã®æ¥ç¶åºæã®æåèª
証ãããã
管çæ¡å¼µï¼(4) ICS è£è¶³ã¬ã¤ãã³ã¹ãªã
ICS è£è¶³ã¬ã¤ãã³ã¹ï¼è£åç管ççã®ä¾ã¨ãã¦ãå
¨ä½çãªã«ã¹ã¿ãã¤ãºã¬ã¤ãã³ã¹ã«å¾ã£ã¦ã
éèªåã¡ã«ããºã åã¯æé ãè£åç管ççã¨ãã¦æ¡ç¨ã§ããã
AC-18 ã¯ã¤ã¤ã¬ã¹ã¢ã¯ã»ã¹
管ççªå·
管çå
管çæ¡å¼µå
管çãã¼ã¹ã©ã¤ã³
ä½
ä¸
é«
AC-18
ã¯ã¤ã¤ã¬ã¹ã¢ã¯ã»ã¹
é¸å®
é¸å®
é¸å®
AC-18 (1)
ã¯ã¤ã¤ã¬ã¹ã¢ã¯ã»ã¹
|
èªè¨¼ã»æå·å
é¸å®
é¸å®
AC-18 (4)
ã¯ã¤ã¤ã¬ã¹ã¢ã¯ã»ã¹
|
ã¦ã¼ã¶è¨å®ã®å¶é
é¸å®
AC-18 (5)
ã¯ã¤ã¤ã¬ã¹ã¢ã¯ã»ã¹
|
ã¯ã¤ã¤ã¬ã¹éä¿¡ã®å°ãè¾¼ã
é¸å®
ICS è£è¶³ã¬ã¤ãã³ã¹ï¼ICS ããã®ç®¡çè¦ç´ ã®ä¸é¨åã¯å
¨é¨ãå®è¡ã§ããªãç¶æ³ã§ã¯ãå
¨ä½ç
ãªã«ã¹ã¿ãã¤ãºã¬ã¤ãã³ã¹ã«å¾ã£ã¦ãçµç¹ã¯ä»ã®ã¡ã«ããºã åã¯æé ãè£åç管ççã¨ãã¦æ¡ç¨
ããã
管çæ¡å¼µï¼(1) ICS è£è¶³ã¬ã¤ãã³ã¹ï¼AC-17 管çæ¡å¼µãåç
§ï¼(1) ICS è£è¶³ã¬ã¤ãã³ã¹ãè£å
ç管ççã®ä¾ã¨ãã¦ãã¯ã¤ã¤ã¬ã¹ã¢ã¯ã»ã¹ã«å¯¾ããç£æ»ã®å¼·åãã¯ã¤ã¤ã¬ã¹ã¢ã¯ã»ã¹ç¹æ¨©ãéè¦
ãªäººå¡ã«å¶éããæ¹æ³ãããã
管çæ¡å¼µï¼(4) (5) ICS è£è¶³ã¬ã¤ãã³ã¹ãªã
AC-19 ã¢ãã¤ã«ããã¤ã¹ç¨ã¢ã¯ã»ã¹å¶å¾¡
管ççªå·
管çå
管çæ¡å¼µå
管çãã¼ã¹ã©ã¤ã³
ä½
ä¸
é«
AC-19
ã¢ãã¤ã«ããã¤ã¹ç¨ã¢ã¯ã»ã¹å¶å¾¡
é¸å®
é¸å®
é¸å®
AC-19 (5)
ã¢ãã¤ã«ããã¤ã¹ç¨ã¢ã¯ã»ã¹å¶å¾¡
|
ãã«ããã¤ã¹
/
ã³ã³ãããã¼ã¹
æå·å
é¸å® é¸å®
ICS è£è¶³ã¬ã¤ãã³ã¹ãªã
AC-20 å¤é¨æ
å ±ã·ã¹ãã ã®å©ç¨
管ççªå·
管çå
管çæ¡å¼µå
管çãã¼ã¹ã©ã¤ã³
ä½
ä¸
é«
AC-20
å¤é¨æ
å ±ã·ã¹ãã ã®å©ç¨
é¸å®
é¸å®
é¸å®
AC-20 (1)
å¤é¨æ
å ±ã·ã¹ãã ã®å©ç¨
|
許å¯ãããå©ç¨ã®å¶é
é¸å®
é¸å®
AC-20 (2)
å¤é¨æ
å ±ã·ã¹ãã ã®å©ç¨
|
æºè¡ã¹ãã¬ã¼ã¸ã¡ãã£ã¢
é¸å®
é¸å®
ICS è£è¶³ã¬ã¤ãã³ã¹ï¼ãå¤é¨ãã®å®ç¾©ãç²¾æ»ãã¦ã権éã»è²¬ä»»ãçµç¹å®ä½ã®ç²åº¦åã³ããã
ã®é¢ä¿ãåæ ãããããã·ã¹ãã ãéãæ©è½ãå®è¡ããéãããªã·ã¼ãæ¡ç¨ãã管çè
ãéãã
æºè¶³ã§ããä¿¡é ¼é¢ä¿ãç¯ãããã®ã»ãã¥ãªãã£å¯¾çã®å¯è¦åãä¸ååãªå ´åãçµç¹ã¯ãããå¤é¨
ã¨ã¿ãªãããä¾ãã°ãããã»ã¹å¶å¾¡ã·ã¹ãã ã¨äºæ¥ç¨ãã¼ã¿å¦çã·ã¹ãã ã¯ãé常ç¸äºã«å¤é¨ã¨
ã¿ãªãããããã³ãã¼ããµãã¼ãå¥ç´è
çãäºæ¥ææºè
ããã®æ¯æ´ã§ ICS ã«ã¢ã¯ã»ã¹ããå ´åãã
ããããå¤é¨ã®ä¾ã§ãããICS ã®æ©è½ãç®çãæè¡åã³å¶éã«é¢ãã¦ãå¤é¨æ
å ±ã·ã¹ãã ã®å®ç¾©
ã¨ä¿¡é ¼æ§ãåæ¤è¨¼ãã

SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
377
establish a clear documented technical or business case for use and an acceptance of the risk inherent in the use of an external information
system.
Control Enhancement: (1, 2) No ICS Supplemental Guidance.
AC-21 INFORMATION SHARING
CNTL NO. CONTROL NAME
Control Enhancement Name
CONTROL BASELINES
LOW
MOD
HIGH
AC-21
Collaboration and Information Sharing
Added
Selected
Selected
ICS Supplemental Guidance: The organization should collaborate and share information about potential incidents on a timely basis.
The DHS National Cybersecurity & Communications Integration Center (NCCIC), http://www.dhs.gov/about-national-cybersecurity-
communications-integration-center serves as a centralized location where operational elements involved in cybersecurity and
communications reliance are coordinated and integrated. The Industrial Control Systems Cyber Emergency Response Team (ICS-CERT)
http://ics-cert.us-cert.gov/ics-cert/ collaborates with international and private sector Computer Emergency Response Teams (CERTs) to share
control systems-related security incidents and mitigation measures. Organizations should consider having both an unclassified and classified
information sharing capability.
Rationale for adding AC-21 to low baseline: ICS systems provide essential services and control functions and are often connected
to other ICS systems or business systems that can be vectors of attack. It is therefore necessary to provide a uniform defense encompassing
all baselines.
AC-22 PUBLICLY ACCESSIBLE CONTENT
CNTL NO. CONTROL NAME
Control Enhancement Name
CONTROL BASELINES
LOW
MOD
HIGH
AC-22
Publicly Accessible Content
Selected
Selected
Selected
ICS Supplemental Guidance: Generally, public access to ICS systems is not permitted. Selected information may be transferred to a
publicly accessible information system, possibly with added controls (e.g., introduction of fuzziness or delay).

SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
378
å¤é¨æ
å ±ã·ã¹ãã ã®å©ç¨ã¨ãå©ç¨ã«ä¼´ããªã¹ã¯ãåãå
¥ããæ¨ã®æ確ãªæè¡ã»äºæ¥ææ¸ãä½æã
ãã
管çæ¡å¼µï¼(1) (2) ICS è£è¶³ã¬ã¤ãã³ã¹ãªã
AC-21 æ
å ±å
±æ
管ççªå·
管çå
管çæ¡å¼µå
管çãã¼ã¹ã©ã¤ã³
ä½
ä¸
é«
AC-21
é£æºã»æ
å ±å
±æ
追å
é¸å®
é¸å®
ICS è£è¶³ã¬ã¤ãã³ã¹ï¼çµç¹ã¯ãçãå¾ãã¤ã³ã·ãã³ãã«é¢ãã¦ãé£æºãæ
å ±ãé©æã«å
±æã
ã¹ãã§ãããä¸è¨ DHS å½å®¶ãµã¤ãã¼ã»ãã¥ãªãã£éä¿¡çµ±åã»ã³ã¿ã¼(NCCIC)ã¯éä¸æå¨å°ã¨ãã¦
æ©è½ãããµã¤ãã¼ã»ãã¥ãªãã£ã¨éä¿¡ã®ä¿¡é ¼æ§ã«é¢ããéç¨è¦ç´ ã¯ããã§èª¿æ´ãããçµ±ååãã
ã¦ãããhttp://www.dhs.gov/about-national-cybersecurity-communications-integration-center
ä¸è¨ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ãµã¤ãã¼ç·æ¥å¯¾å¿ãã¼ã (ICS-CERT)ã¯ãæµ·å¤åã³æ°éã®ã³ã³ãã¥ã¼
ã¿ç·æ¥å¯¾å¿ãã¼ã (CERT)ã¨é£æºãã¦ãå¶å¾¡ã·ã¹ãã é¢é£ã»ãã¥ãªãã£ã¤ã³ã·ãã³ãæ
å ±ã¨ç·©å
対çãå
±æãã¦ããã
http://ics-cert.us-cert.gov/ics-cert/
çµç¹ã¯ãç§å¯æ
å ±ã¨æ®éæ
å ±ã®å
±æåã«ã¤ãã¦æ¤è¨ãã¹ãã§ããã
AC-21 ãä½ãã¼ã¹ã©ã¤ã³ã«è¿½å ããçç±ï¼ICS ã·ã¹ãã ã¯ãéè¦ãªãµã¼ãã¹ã¨å¶å¾¡æ©è½ãæ
ä¾ãã¦ãããæ»æçµè·¯ã¨ãªãå¾ãä»ã® ICS ã·ã¹ãã ãäºæ¥ã·ã¹ãã ã«æ¥ç¶ãã¦ãããã¨ãå¤ãã
ãããã£ã¦ãå
¨ã¦ã®ãã¼ã¹ã©ã¤ã³ã網ç¾
ããçµ±ä¸çãªé²å¾¡ãå¿
è¦ã¨ãªãã
AC-22 å
¬éã³ã³ãã³ã
管ççªå·
管çå
管çæ¡å¼µå
管çãã¼ã¹ã©ã¤ã³
ä½
ä¸
é«
AC-22
å
¬éã³ã³ãã³ã
é¸å®
é¸å®
é¸å®
ICS è£è¶³ã¬ã¤ãã³ã¹ï¼ä¸è¬çã«ãICS ã·ã¹ãã ã¸ã®å
¬éã¢ã¯ã»ã¹ã¯è¨±å¯ããã¦ããªããé¸å¥
ããæ
å ±ããä»å çãªç®¡çå¶éï¼ææ§ããé
ãçï¼ãå ããä¸ã§ãå
¬éã®æ
å ±ã·ã¹ãã ã«è»¢éã
ãããã¨ãããã
SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
379
AWARENESS AND TRAINING â AT
Supplemental Guidance
Supplemental Guidance for all Controls and Control Enhancements in NIST SP 800-53 Rev. 4, Appendix F, should be used in
conjunction with the ICS Supplemental Guidance in this overlay, if any.
AT-1 SECURITY AWARENESS AND TRAINING POLICY AND PROCEDURES
CNTL NO. CONTROL NAME
Control Enhancement Name
CONTROL BASELINES
LOW
MOD
HIGH
AT-1
Security Awareness and Training Policy and Procedures
Selected
Selected
Selected
ICS Supplemental Guidance: The policy specifically addresses the unique properties and requirements of ICS and the relationship
to non-ICS systems.
AT-2 SECURITY AWARENESS TRAINING
CNTL NO. CONTROL NAME
Control Enhancement Name
CONTROL BASELINES
LOW
MOD
HIGH
AT-2
Security Awareness
Selected
Selected
Selected
ICS Supplemental Guidance: Security awareness training includes initial and periodic review of ICS-specific policies, standard
operating procedures, security trends, and vulnerabilities. The ICS security awareness program is consistent with the requirements of the
security awareness and training policy established by the organization.
Control Enhancement: (2) No ICS Supplemental Guidance.
AT-3 ROLE-BASED SECURITY TRAINING
CNTL NO. CONTROL NAME
Control Enhancement Name
CONTROL BASELINES
LOW
MOD
HIGH
AT-3
Role-Based Security Training
Selected
Selected
Selected
ICS Supplemental Guidance: Security training includes initial and periodic review of ICS-specific policies, standard operating
procedures, security trends, and vulnerabilities. The ICS security training program is consistent with the requirements of the security
awareness and training policy established by the organization.
AT-4 SECURITY TRAINING RECORDS
CNTL NO. CONTROL NAME
Control Enhancement Name
CONTROL BASELINES
LOW
MOD
HIGH
AT-4
Security Training Records
Selected
Selected
Selected
No ICS Supplemental Guidance.
SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
380
æèã»è¨ç·´ â AT
è£è¶³ã¬ã¤ãã³ã¹
å©ç¨ã§ããå ´åã«ã¯ãNIST SP 800-53 第4çä»é² Fã«ããå
¨ã¦ã®ç®¡çã»ç®¡çæ¡å¼µç¨è£è¶³ã¬ã¤ãã³
ã¹ãããã®ãªã¼ãã¼ã¬ã¤ã«ããã¦ãICS è£è¶³ã¬ã¤ãã³ã¹ã¨ä½µç¨ãã¹ãã§ããã
AT-1 ã»ãã¥ãªãã£æèã»è¨ç·´ããªã·ã¼ã»æé
管ççªå·
管çå
管çæ¡å¼µå
管çãã¼ã¹ã©ã¤ã³
ä½
ä¸
é«
AT-1
ã»ãã¥ãªãã£æèã»è¨ç·´ããªã·ã¼ã»æé
é¸å®
é¸å®
é¸å®
ICS è£è¶³ã¬ã¤ãã³ã¹ï¼ããªã·ã¼ã¯ç¹ã« ICS ã®åºæã®ç¹æ§ã»è¦ä»¶åã³ ICS 以å¤ã®ã·ã¹ãã ã¨ã®
é¢ä¿ãåãä¸ããã
AT-2 ã»ãã¥ãªãã£æèè¨ç·´
管ççªå·
管çå
管çæ¡å¼µå
管çãã¼ã¹ã©ã¤ã³
ä½
ä¸
é«
AT-2
ã»ãã¥ãªãã£æè
é¸å®
é¸å®
é¸å®
ICS è£è¶³ã¬ã¤ãã³ã¹ï¼ã»ãã¥ãªãã£æèè¨ç·´ã«ã¯ãICS åºæããªã·ã¼ãæ¨æºéç¨æé ãã»ã
ã¥ãªãã£åååã³èå¼±æ§ã«å¯¾ããå½åã®è¨ç·´ã¨å®æçãªå¾©ç¿ãå«ã¾ãããICS ã»ãã¥ãªãã£æè
ããã°ã©ã ã¯ãçµç¹ãè¨å®ããã»ãã¥ãªãã£æèã»è¨ç·´ããªã·ã¼è¦ä»¶ã¨æ´åãã¦ããã
管çæ¡å¼µï¼(2) ICS è£è¶³ã¬ã¤ãã³ã¹ãªã
AT-3 å½¹å²ãã¼ã¹ã»ãã¥ãªãã£è¨ç·´
管ççªå·
管çå
管çæ¡å¼µå
管çãã¼ã¹ã©ã¤ã³
ä½
ä¸
é«
AT-3
å½¹å²ãã¼ã¹ã»ãã¥ãªãã£è¨ç·´
é¸å®
é¸å®
é¸å®
ICS è£è¶³ã¬ã¤ãã³ã¹ï¼ã»ãã¥ãªãã£è¨ç·´ã«ã¯ãICS åºæããªã·ã¼ãæ¨æºéç¨æé ãã»ãã¥ãª
ãã£åååã³èå¼±æ§ã«å¯¾ããå½åã®è¨ç·´ã¨å®æçãªå¾©ç¿ãå«ã¾ãããICS ã»ãã¥ãªãã£ããã°ã©
ã ã¯ãçµç¹ãè¨å®ããã»ãã¥ãªãã£æèã»è¨ç·´ããªã·ã¼è¦ä»¶ã¨æ´åãã¦ããã
AT-4 ã»ãã¥ãªãã£è¨ç·´è¨é²
管ççªå·
管çå
管çæ¡å¼µå
管çãã¼ã¹ã©ã¤ã³
ä½
ä¸
é«
AT-4
ã»ãã¥ãªãã£è¨ç·´è¨é²
é¸å®
é¸å®
é¸å®
ICS è£è¶³ã¬ã¤ãã³ã¹ãªã
SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
381
AUDITING AND ACCOUNTABILITY â AU
Tailoring Considerations for Audit Family
In general, audit information and audit tools are not present on legacy ICS, but on a separate information system (e.g., the historian).
In situations where the ICS cannot support the specific Audit and Accountability requirements of a control, the organization employs
compensating controls in accordance with the general tailoring guidance. Examples of compensating controls are given with each control, as
appropriate.
Supplemental Guidance
Supplemental Guidance for all Controls and Control Enhancements in NIST SP 800-53 Rev. 4, Appendix F, should be used in
conjunction with the ICS Supplemental Guidance in this overlay, if any.
AU-1 AUDIT AND ACCOUNTABILITY POLICY AND PROCEDURES
CNTL NO. CONTROL NAME
Control Enhancement Name
CONTROL BASELINES
LOW
MOD
HIGH
AU-1
Audit and Accountability Policy and Procedures
Selected
Selected
Selected
ICS Supplemental Guidance: The policy specifically addresses the unique properties and requirements of ICS and the relationship
to non-ICS systems.
AU-2 AUDIT EVENTS
CNTL NO. CONTROL NAME
Control Enhancement Name
CONTROL BASELINES
LOW
MOD
HIGH
AU-2
Auditable Events
Selected
Selected
Selected
AU-2 (3)
AUDITABLE EVENTS | REVIEWS AND UPDATES
Selected
Selected
ICS Supplemental Guidance: The organization may designate ICS events as audit events, requiring that ICS data and/or telemetry
be recorded as audit data.
Control Enhancement: (3) No ICS Supplemental Guidance.
AU-3 CONTENT OF AUDIT RECORDS
CNTL NO. CONTROL NAME
Control Enhancement Name
CONTROL BASELINES
LOW
MOD
HIGH
AU-3
Content of Audit Records
Selected
Selected
Selected
AU-3 (1) CONTENT OF AUDIT RECORDS | ADDITIONAL AUDIT
INFORMATION
Selected Selected
AU-3 (2) CONTENT OF AUDIT RECORDS | CENTRALIZED
MANAGEMENT OF PLANNED AUDIT RECORD CONTENT
Selected
ICS Supplemental Guidance: Example compensating controls include providing an auditing capability on a separate information
system.
Control Enhancement: (1, 2) No ICS Supplemental Guidance.
AU-4 AUDIT STORAGE CAPACITY
CNTL NO. CONTROL NAME
Control Enhancement Name
CONTROL BASELINES
LOW
MOD
HIGH
AU-4
Audit Storage Capacity
Selected
Selected
Selected
AU-4 (1) AUDIT STORAGE CAPACITY | TRANSFER TO ALTERNATE
STORAGE
Added Added Added
No ICS Supplemental Guidance.
Control Enhancement: (1) ICS Supplemental Guidance: Legacy ICS are typically configured with remote storage on a separate
information system (e.g., the historian accumulates historical operational ICS data and is backed up for
SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
382
ç£æ»ã»èª¬æ責任 â AU
ç£æ»ãã¡ããªã®ã«ã¹ã¿ãã¤ãºèæ
®äºé
ä¸è¬ã«ãç£æ»æ
å ±ãç£æ»ãã¼ã«ã¯ãã¬ã¬ã·ã¼ICS ã«ã¯ãªãããå¥åã®æ
å ±ã·ã¹ãã ä¸ã«ããï¼ã
ã¹ããªã¢ã³çï¼ãICS ãããå¶å¾¡ã®ç¹å®ã®ç£æ»ã»èª¬æ責任è¦ä»¶ã«å¯¾å¿ãã¦ããªãç¶æ³ã§ã¯ãå
¨ä½
çãªã«ã¹ã¿ãã¤ãºã¬ã¤ãã³ã¹ã«å¾ã£ã¦è£åç管ççãæ¡ç¨ãããè£åç管ççã®ä¾ãå¿
è¦ã«å¿ã
ã¦ã管ççãã¨ã«ç¤ºãããã
è£è¶³ã¬ã¤ãã³ã¹
å©ç¨ã§ããå ´åã«ã¯ãNIST SP 800-53 第4çä»é² Fã«ããå
¨ã¦ã®ç®¡çã»ç®¡çæ¡å¼µç¨è£è¶³ã¬ã¤ãã³
ã¹ãããã®ãªã¼ãã¼ã¬ã¤ã«ããã¦ãICS è£è¶³ã¬ã¤ãã³ã¹ã¨ä½µç¨ãã¹ãã§ããã
AU-1 ç£æ»ã»èª¬æ責任ããªã·ã¼ã»æé
管ççªå·
管çå
管çæ¡å¼µå
管çãã¼ã¹ã©ã¤ã³
ä½
ä¸
é«
AU-1
ç£æ»ã»èª¬æ責任ããªã·ã¼ã»æé
é¸å®
é¸å®
é¸å®
ICS è£è¶³ã¬ã¤ãã³ã¹ï¼ããªã·ã¼ã¯ç¹ã« ICS ã®åºæã®ç¹æ§ã»è¦ä»¶åã³ ICS 以å¤ã®ã·ã¹ãã ã¨ã®
é¢ä¿ãåãä¸ããã
AU-2 ç£æ»äºè±¡
管ççªå·
管çå
管çæ¡å¼µå
管çãã¼ã¹ã©ã¤ã³
ä½
ä¸
é«
AU-2
ç£æ»äºè±¡
é¸å®
é¸å®
é¸å®
AU-2 (3)
ç£æ»äºè±¡
|
審æ»ã»æ´æ°
é¸å®
é¸å®
ICS è£è¶³ã¬ã¤ãã³ã¹ï¼çµç¹ã¯ ICS äºè±¡ãç£æ»äºè±¡ã¨æå®ããICS ãã¼ã¿ããã¬ã¡ããª-ãç£æ»
ãã¼ã¿ã¨ãã¦ã®è¨é²ã義åã¥ããã
管çæ¡å¼µï¼(3) ICS è£è¶³ã¬ã¤ãã³ã¹ãªã
AU-3 ç£æ»è¨é²å
容
管ççªå·
管çå
管çæ¡å¼µå
管çãã¼ã¹ã©ã¤ã³
ä½
ä¸
é«
AU-3
ç£æ»è¨é²å
容
é¸å®
é¸å®
é¸å®
AU-3 (1)
ç£æ»è¨é²å
容
|
è£è¶³ç£æ»æ
å ±
é¸å®
é¸å®
AU-3 (2)
ç£æ»è¨é²å
容
|
è¨ç»ç£æ»è¨é²å
容ã®éä¸ç®¡ç
é¸å®
ICS è£è¶³ã¬ã¤ãã³ã¹ï¼è£åç管ççã®ä¾ã¨ãã¦ãå¥åã®æ
å ±ã·ã¹ãã ã¸ã®ç£æ»è½åã®ä»ä¸ã
ããã
管çæ¡å¼µï¼(1) (2) ICS è£è¶³ã¬ã¤ãã³ã¹ãªã
AU-4 ç£æ»ã¹ãã¬ã¼ã¸å®¹é
管ççªå·
管çå
管çæ¡å¼µå
管çãã¼ã¹ã©ã¤ã³
ä½
ä¸
é«
AU-4
ç£æ»ã¹ãã¬ã¼ã¸å®¹é
é¸å®
é¸å®
é¸å®
AU-4 (1)
ç£æ»ã¹ãã¬ã¼ã¸å®¹é
|
代æ¿ã¹ãã¬ã¼ã¸ã¸ã®ç§»è¡
追å
追å
追å
ICS è£è¶³ã¬ã¤ãã³ã¹ãªã
管çæ¡å¼µï¼(1) ICS è£è¶³ã¬ã¤ãã³ã¹ï¼é常ã¬ã¬ã·ã¼ICS ã¯ãå¥åã®æ
å ±ã·ã¹ãã ä¸ã®é éã¹ãã¬ã¼ã¸
ã«è¨å®ãããï¼ãã¹ããªã¢ã³ã¯ ICS ã®éç¨å±¥æ´ãã¼ã¿ãèç©ããå¥ãµã¤ãã®ã¹ãã¬ã¼ã¸ã«ä¿ç®¡ããï¼ã
SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
383
storage at a different site). ICS are currently using online backup services and increasingly moving to Cloud based and Virtualized services.
Retention of some data (e.g., SCADA telemetry) may be required by regulatory authorities.
Rationale for adding AU-4 (1) to all baselines: Legacy ICS components typically do not have capacity to store or analyze audit data.
The retention periods for some data, particularly compliance data, may require large volumes of storage.
AU-5 RESPONSE TO AUDIT PROCESSING FAILURES
CNTL NO. CONTROL NAME
Control Enhancement Name
CONTROL BASELINES
LOW
MOD
HIGH
AU-5
Response to Audit Processing Failures
Selected
Selected
Selected
AU-5 (1) RESPONSE TO AUDIT PROCESSING FAILURES | AUDIT STORAGE
CAPACITY
Selected
AU-5 (2)
RESPONSE TO AUDIT PROCESSING FAILURES | REAL-TIME ALERTS
Selected
No ICS Supplemental Guidance.
AU-6 AUDIT REVIEW, ANALYSIS, AND REPORTING
CNTL NO. CONTROL NAME
Control Enhancement Name
CONTROL BASELINES
LOW
MOD
HIGH
AU-6
Audit Review, Analysis, and Reporting
Selected
Selected
Selected
AU-6 (1) AUDIT REVIEW, ANALYSIS, AND REPORTING | PROCESS
INTEGRATION
Selected Selected
AU-6 (3) AUDIT REVIEW, ANALYSIS, AND REPORTING | CORRELATE AUDIT
REPOSITORIES
Selected Selected
AU-6 (5) AUDIT REVIEW, ANALYSIS, AND REPORTING | INTEGRATION /
SCANNING AND MONITORING CAPABILITIES
Selected
AU-6 (6) AUDIT REVIEW, ANALYSIS, AND REPORTING | CORRELATION WITH
PHYSICAL MONITORING
Selected
No ICS Supplemental Guidance.
Control Enhancement: (1) ICS Supplemental Guidance: Example compensating controls include manual mechanisms or
procedures.
Control Enhancement: (3, 5, 6) No ICS Supplemental Guidance.
AU-7 AUDIT REDUCTION AND REPORT GENERATION
CNTL NO. CONTROL NAME
Control Enhancement Name
CONTROL BASELINES
LOW
MOD
HIGH
AU-7
Audit Reduction and Report Generation
Selected
Selected
AU-7 (1) AUDIT REDUCTION AND REPORT GENERATION | AUTOMATIC
PROCESSING
Selected Selected
No ICS Supplemental Guidance.
Control Enhancement: (1) No ICS Supplemental Guidance.
AU-8 TIME STAMPS
CNTL NO. CONTROL NAME
Control Enhancement Name
CONTROL BASELINES
LOW
MOD
HIGH
AU-8
Time Stamps
Selected
Selected
Selected
AU-8 (1) TIME STAMPS | SYNCHRONIZATION WITH AUTHORITATIVE TIME
SOURCE
Selected Selected
ICS Supplemental Guidance: Example compensating controls include using a separate information system designated as an
authoritative time source.
Control Enhancement: (1) ICS Supplemental Guidance: ICS employ suitable mechanisms (e.g., GPS, IEEE 1588) for time
stamps.
SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
384
ICS ã¯ä»ã®ã¨ãããªã³ã©ã¤ã³ããã¯ã¢ãããµã¼ãã¹ãå©ç¨ãã¦ããããã¯ã©ã¦ããã¼ã¹ã®ä»®æ³ãµ
ã¼ãã¹ã«æ¬¡ç¬¬ã«ç§»è¡ãã¦ãããç¹å®ã®ãã¼ã¿ï¼SCADA ãã¬ã¡ããªã¼çï¼ã®ä¿æãè¦å¶å½å±ãã
義åã¥ããããå ´åãããã
AU-4 (1)ãå
¨ã¦ã®ãã¼ã¹ã©ã¤ã³ã«è¿½å ããçç±ï¼ä¸è¬ã«ã¬ã¬ã·ã¼ICS ã³ã³ãã¼ãã³ãã«ã¯ã
ç£æ»ãã¼ã¿ã®ä¿ååã¯åæ容éããªããç¹å®ã®ãã¼ã¿ãç¹ã«ã³ã³ãã©ã¤ã¢ã³ã¹ãã¼ã¿ã®ä¿ææé
ã«ãã£ã¦ä¿ç®¡éã大ãããªãã
AU-5 ç£æ»å¦çä¸åã¸ã®å¯¾å¿
管ççªå·
管çå
管çæ¡å¼µå
管çãã¼ã¹ã©ã¤ã³
ä½
ä¸
é«
AU-5
ç£æ»å¦çä¸åã¸ã®å¯¾å¿
é¸å®
é¸å®
é¸å®
AU-5 (1)
ç£æ»å¦çä¸åã¸ã®å¯¾å¿
|
ç£æ»ã¹ãã¬ã¼ã¸å®¹é
é¸å®
AU-5 (2)
ç£æ»å¦çä¸åã¸ã®å¯¾å¿
|
ãªã¢ã«ã¿ã¤ã è¦å ±
é¸å®
ICS è£è¶³ã¬ã¤ãã³ã¹ãªã
AU-6 ç£æ»ã®å¯©æ»ã»åæã»å ±å
管ççªå·
管çå
管çæ¡å¼µå
管çãã¼ã¹ã©ã¤ã³
ä½
ä¸
é«
AU-6
ç£æ»ã®å¯©æ»ã»åæã»å ±å
é¸å®
é¸å®
é¸å®
AU-6 (1)
ç£æ»ã®å¯©æ»ã»åæã»å ±å
|
ããã»ã¹ã®ä¸ä½å
é¸å®
é¸å®
AU-6 (3)
ç£æ»ã®å¯©æ»ã»åæã»å ±å
|
ç£æ»ã¬ãã¸ããªã®ç¸é¢
é¸å®
é¸å®
AU-6 (5)
ç£æ»ã®å¯©æ»ã»åæã»å ±å
|
ä¸ä½å
ã¹ãã£ã³ã»ç£è¦è½å
é¸å®
AU-6 (6)
ç£æ»ã®å¯©æ»ã»åæã»å ±å
|
ç©ççç£è¦ã¨ã®ç¸é¢
é¸å®
ICS è£è¶³ã¬ã¤ãã³ã¹ãªã
管çæ¡å¼µï¼(1) ICS è£è¶³ã¬ã¤ãã³ã¹ï¼è£åç管ççã®ä¾ã¨ãã¦ãæåã¡ã«ããºã åã¯æé ãã
ãã
管çæ¡å¼µï¼(3, 5, 6) ICS è£è¶³ã¬ã¤ãã³ã¹ãªã
AU-7 ç£æ»åæ¸ã»å ±åæ¸ä½æ
管ççªå·
管çå
管çæ¡å¼µå
管çãã¼ã¹ã©ã¤ã³
ä½
ä¸
é«
AU-7
ç£æ»åæ¸ã»å ±åæ¸ä½æ
é¸å®
é¸å®
AU-7 (1)
ç£æ»åæ¸ã»å ±åæ¸ä½æ
|
èªåå¦ç
é¸å®
é¸å®
ICS è£è¶³ã¬ã¤ãã³ã¹ãªã
管çæ¡å¼µï¼(1) ICS è£è¶³ã¬ã¤ãã³ã¹ãªã
AU-8 ã¿ã¤ã ã¹ã¿ã³ã
管ççªå·
管çå
管çæ¡å¼µå
管çãã¼ã¹ã©ã¤ã³
ä½
ä¸
é«
AU-8
ã¿ã¤ã ã¹ã¿ã³ã
é¸å®
é¸å®
é¸å®
AU-8 (1)
ã¿ã¤ã ã¹ã¿ã³ã
|
å
¬èªæéã½ã¼ã¹ã¨ã®åæ
é¸å®
é¸å®
ICS è£è¶³ã¬ã¤ãã³ã¹ï¼è£åç管ççã®ä¾ã¨ãã¦ãå
¬èªæéã½ã¼ã¹ã«æå®ãããå¥åã®æ
å ±ã·
ã¹ãã ãå©ç¨ããæ¹æ³ãããã
管çæ¡å¼µï¼(1) ICS è£è¶³ã¬ã¤ãã³ã¹ï¼ã¿ã¤ã ã¹ã¿ã³ãã¨ãã¦ãICS ã§ã¯é©æ£ãªã¡ã«ããºã ãæ¡
ç¨ããï¼å
¨å°ç測ä½ã·ã¹ãã [GPS]ãIEEE 1588 çï¼ã
SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
385
AU-9 PROTECTION OF AUDIT INFORMATION
CNTL NO. CONTROL NAME
Control Enhancement Name
CONTROL BASELINES
LOW
MOD
HIGH
AU-9
Protection of Audit Information
Selected Selected Selected
AU-9 (2) PROTECTION OF AUDIT INFORMATION | AUDIT BACKUP ON
SEPARATE PHYSICAL SYSTEMS / COMPONENTS
Selected
AU-9 (3) PROTECTION OF AUDIT INFORMATION | CRYPTOGRAPHIC
PROTECTION
Selected
AU-9 (4) PROTECTION OF AUDIT INFORMATION | ACCESS BY SUBSET OF
PRIVILEGED USERS
Selected Selected
No ICS Supplemental Guidance.
AU-10 NON-REPUDIATION
CNTL NO. CONTROL NAME
Control Enhancement Name
CONTROL BASELINES
LOW
MOD
HIGH
AU-10
Non-repudiation
Selected
ICS Supplemental Guidance: Example compensating controls include providing non-repudiation on a separate information system.
AU-11 AUDIT RECORD RETENTION
CNTL NO. CONTROL NAME
Control Enhancement Name
CONTROL BASELINES
LOW
MOD
HIGH
AU-11
Audit Record Retention
Selected
Selected
Selected
No ICS Supplemental Guidance.
AU-12 AUDIT GENERATION
CNTL NO. CONTROL NAME
Control Enhancement Name
CONTROL BASELINES
LOW
MOD
HIGH
AU-12
Audit Generation
Selected Selected Selected
AU-12 (1) AUDIT GENERATION | SYSTEM-WIDE / TIME-CORRELATED AUDIT
TRAIL
Selected
AU-12 (3)
AUDIT GENERATION | CHANGES BY AUTHORIZED INDIVIDUALS
Selected
No ICS Supplemental Guidance.
Control Enhancement: (1) ICS Supplemental Guidance: Example compensating controls include providing time-correlated audit
records on a separate information system.
Control Enhancement: (3) ICS Supplemental Guidance: Example compensating controls include employing nonautomated
mechanisms or procedures.
SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
386
AU-9 ç£æ»æ
å ±ã®ä¿è·
管ççªå·
管çå
管çæ¡å¼µå
管çãã¼ã¹ã©ã¤ã³
ä½
ä¸
é«
AU-9
ç£æ»æ
å ±ã®ä¿è·
é¸å®
é¸å®
é¸å®
AU-9 (2)
ç£æ»æ
å ±ã®ä¿è·
|
å¥ã®ç©çã·ã¹ãã
/
ã³ã³ãã¼ãã³ãã¸ã®ç£æ»ãã
ã¯ã¢ãã
é¸å®
AU-9 (3)
ç£æ»æ
å ±ã®ä¿è·
|
æå·åä¿è·
é¸å®
AU-9 (4)
ç£æ»æ
å ±ã®ä¿è·
|
ç¹æ¨©ã¦ã¼ã¶ã®ãµãã»ããã«ããã¢ã¯ã»ã¹
é¸å®
é¸å®
ICS è£è¶³ã¬ã¤ãã³ã¹ãªã
AU-10 å¦èªé²æ¢
管ççªå·
管çå
管çæ¡å¼µå
管çãã¼ã¹ã©ã¤ã³
ä½
ä¸
é«
AU-10
å¦èªé²æ¢
é¸å®
ICS è£è¶³ã¬ã¤ãã³ã¹ï¼è£åç管ççã®ä¾ã¨ãã¦ãå¥åã®æ
å ±ã·ã¹ãã ã¸ã®å¦èªé²æ¢æ©è½ã®ä»
ä¸ãããã
AU-11 ç£æ»è¨é²ä¿æ
管ççªå·
管çå
管çæ¡å¼µå
管çãã¼ã¹ã©ã¤ã³
ä½
ä¸
é«
AU-11
ç£æ»è¨é²ä¿ç
é¸å®
é¸å®
é¸å®
ICS è£è¶³ã¬ã¤ãã³ã¹ãªã
AU-12 ç£æ»ä½æ
管ççªå·
管çå
管çæ¡å¼µå
管çãã¼ã¹ã©ã¤ã³
ä½
ä¸
é«
AU-12
ç£æ»ä½æ
é¸å®
é¸å®
é¸å®
AU-12 (1)
ç£æ»ä½æ
|
å
¨ã·ã¹ãã
|
æéç¸é¢ç£æ»è¨¼è·¡
é¸å®
AU-12 (3)
ç£æ»ä½æ
|
権éããå人ã«ããå¤æ´
é¸å®
ICS è£è¶³ã¬ã¤ãã³ã¹ãªã
管çæ¡å¼µï¼(1) ICS è£è¶³ã¬ã¤ãã³ã¹ï¼è£åç管ççã®ä¾ã¨ãã¦ãå¥åã®æ
å ±ã·ã¹ãã ã¸ã®æé
ç¸é¢ç£æ»è¨é²ã®ä»ä¸ãããã
管çæ¡å¼µï¼(3) ICS è£è¶³ã¬ã¤ãã³ã¹ï¼è£åç管ççã®ä¾ã¨ãã¦ãéèªåã¡ã«ããºã åã¯æ
é ãããã
SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
387
SECURITY ASSESSMENT AND AUTHORIZATION â CA
Tailoring Considerations for Security Assessment and Authorization Family
In situations where the ICS cannot support the specific Security Assessment and Authorization requirements of a control, the
organization employs compensating controls in accordance with the general tailoring guidance. Examples of compensating controls are given
with each control, as appropriate.
Supplemental Guidance
Supplemental Guidance for all Controls and Control Enhancements in NIST SP 800-53 Rev. 4, Appendix F, should be used in
conjunction with the ICS Supplemental Guidance in this overlay, if any.
CA-1 SECURITY ASSESSMENT AND AUTHORIZATION POLICY AND PROCEDURES
CNTL NO. CONTROL NAME
Control Enhancement Name
CONTROL BASELINES
LOW
MOD
HIGH
CA-1
Security Assessment and Authorization Policy and Procedures
Selected
Selected
Selected
ICS Supplemental Guidance: The policy specifically addresses the unique properties and requirements of ICS and the relationship
to non-ICS systems.
CA-2 SECURITY ASSESSMENTS
CNTL NO. CONTROL NAME
Control Enhancement Name
CONTROL BASELINES
LOW
MOD
HIGH
CA-2
Security Assessments
Selected
Selected
Selected
CA-2 (1)
SECURITY ASSESSMENTS | INDEPENDENT ASSESSORS
Selected
Selected
CA-2 (2)
SECURITY ASSESSMENTS | TYPES OF ASSESSMENTS
Selected
ICS Supplemental Guidance: Assessments are performed and documented by qualified assessors (i.e., experienced in assessing
ICS) authorized by the organization. The organization ensures that assessments do not interfere with ICS functions. The individual/group
conducting the assessment fully understands the organizational information security policies and procedures, the ICS security policies and
procedures, and the specific health, safety, and environmental risks associated with a particular facility and/or process. The organization
ensures that the assessment does not affect system operation or result in unintentional system modification. If assessment activities must be
performed on the production ICS, it may need to be taken off-line before an assessment can be conducted. If an ICS must be taken off-line to
conduct an assessment, the assessment is scheduled to occur during planned ICS outages whenever possible.
Control Enhancement: (1) No ICS Supplemental Guidance.
Control Enhancement: (2) ICS Supplemental Guidance: The organization conducts risk analysis to support the selection of
assessment target (e.g., the live system, an off-line replica, a simulation).
CA-3 SYSTEM INTERCONNECTIONS
CNTL NO. CONTROL NAME
Control Enhancement Name
CONTROL BASELINES
LOW
MOD
HIGH
CA-3
Information System Connections
Selected
Selected
Selected
CA-3 (5) SYSTEM INTERCONNECTIONS | RESTRICTIONS ON EXTERNAL
SYSTEM CONNECTIONS
Selected
ICS Supplemental Guidance: Organizations perform risk-benefit analysis to support determination whether an ICS should be
connected to other information system(s). The Authorizing Official fully understands the organizational information security policies and
procedures; the ICS security policies and procedures; the risks to organizational operations and assets, individuals, other organizations, and
the Nation associated with the connection to other information system(s); and the specific health, safety, and environmental risks associated
with a particular interconnection. The AO documents risk acceptance in the ICS system security plan.
Control Enhancement: (5) No ICS Supplemental Guidance.
SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
388
ã»ãã¥ãªãã£è©ä¾¡ã»æ¨©éä»ä¸ â CA
ã»ãã¥ãªãã£è©ä¾¡ã»æ¨©éä»ä¸ãã¡ããªã®ã«ã¹ã¿ãã¤ãºèæ
®äºé
ICS ãããå¶å¾¡ã®ç¹å®ã®ã»ãã¥ãªãã£è©ä¾¡ã»æ¨©éä»ä¸è¦ä»¶ã«å¯¾å¿ãã¦ããªãç¶æ³ã§ã¯ãå
¨ä½çãª
ã«ã¹ã¿ãã¤ãºã¬ã¤ãã³ã¹ã«å¾ã£ã¦è£åç管ççãæ¡ç¨ãããè£å管çã®ä¾ãå¿
è¦ã«å¿ãã¦ã管ç
çãã¨ã«ç¤ºãããã
è£è¶³ã¬ã¤ãã³ã¹
å©ç¨ã§ããå ´åã«ã¯ãNIST SP 800-53 第4çä»é² Fã«ããå
¨ã¦ã®ç®¡çã»ç®¡çæ¡å¼µç¨è£è¶³ã¬ã¤ãã³
ã¹ãããã®ãªã¼ãã¼ã¬ã¤ã«ããã¦ãICS è£è¶³ã¬ã¤ãã³ã¹ã¨ä½µç¨ãã¹ãã§ããã
CA-1 ã»ãã¥ãªãã£è©ä¾¡ã»æ¨©éä»ä¸ããªã·ã¼ã»æé
管ççªå·
管çå
管çæ¡å¼µå
管çãã¼ã¹ã©ã¤ã³
ä½
ä¸
é«
CA-1
ã»ãã¥ãªãã£è©ä¾¡ã»æ¨©éä»ä¸ããªã·ã¼ã»æé
é¸å®
é¸å®
é¸å®
ICS è£è¶³ã¬ã¤ãã³ã¹ï¼ããªã·ã¼ã¯ç¹ã« ICS ã®åºæã®ç¹æ§ã»è¦ä»¶åã³ ICS 以å¤ã®ã·ã¹ãã ã¨ã®
é¢ä¿ãåãä¸ããã
CA-2 ã»ãã¥ãªãã£è©ä¾¡
管ççªå·
管çå
管çæ¡å¼µå
管çãã¼ã¹ã©ã¤ã³
ä½
ä¸
é«
CA-2
ã»ãã¥ãªãã£è©ä¾¡
é¸å®
é¸å®
é¸å®
CA-2 (1)
ã»ãã¥ãªãã£è©ä¾¡
|
ç¬ç«è©ä¾¡è
é¸å®
é¸å®
CA-2 (2)
ã»ãã¥ãªãã£è©ä¾¡
|
è©ä¾¡ã®ç¨®é¡
é¸å®
ICS è£è¶³ã¬ã¤ãã³ã¹ï¼æè³æ ¼è
ï¼ICS è©ä¾¡çç·´è
ï¼ã«ããè©ä¾¡ãè¡ãææ¸åããçµç¹ã®æ¿èª
ãå¾ããè©ä¾¡ã ICS æ©è½ã¨å¹²æ¸ããªãããã«ãããè©ä¾¡ãè¡ãå人ãã°ã«ã¼ãã¯ãçµç¹ã®æ
å ±ã»
ãã¥ãªãã£ããªã·ã¼ã»æé ãICS ã®ã»ãã¥ãªãã£ããªã·ã¼ã»æé åã³ç¹å®ã®æ½è¨ãããã»ã¹ã«ä»
éããå
·ä½çãªå¥åº·ã»å®å
¨ã»ç°å¢ãªã¹ã¯ãååç解ãããçµç¹ã¯è©ä¾¡ã«ãã£ã¦ã·ã¹ãã éç¨ãå½±
é¿ãåãããæå³ããªãã·ã¹ãã å¤æ´ã«ãªããªãããã«ãããè©ä¾¡æ´»åãçç£ ICS ã§å®æ½ããªã
ãã°ãªããªãå ´åãè©ä¾¡ã®å®æ½åã«ãªãã©ã¤ã³ã«ããå¿
è¦ãããå ´åãããããªãã©ã¤ã³ã«ããª
ããã°ãªããªãå ´åãå¯è½ã§ããã°ãäºãè¨ç»ããã ICS ã®ææ¥åæ¢æã«è©ä¾¡ãè¡ãããã«äºå®
ãçµãã
管çæ¡å¼µï¼(1) ICS è£è¶³ã¬ã¤ãã³ã¹ãªã
管çæ¡å¼µï¼(2) ICS è£è¶³ã¬ã¤ãã³ã¹ï¼çµç¹ã¯ãªã¹ã¯åæãè¡ããè©ä¾¡å¯¾è±¡ã®é¸å¥ãæ¯æ´ãã
ï¼ã©ã¤ãã·ã¹ãã ããªãã©ã¤ã³ã¬ããªã«ãã·ãã¥ã¬ã¼ã·ã§ã³çï¼ã
CA-3 ã·ã¹ãã é£æ¥
管ççªå·
管çå
管çæ¡å¼µå
管çãã¼ã¹ã©ã¤ã³
ä½
ä¸
é«
CA-3
æ
å ±ã·ã¹ãã ã®æ¥ç¶
é¸å®
é¸å®
é¸å®
CA-3 (5)
ã·ã¹ãã é£æ¥
|
å¤é¨ã·ã¹ãã ã¨ã®æ¥ç¶å¶é
é¸å®
é¸å®
ICS è£è¶³ã¬ã¤ãã³ã¹ï¼çµç¹ã¯ãªã¹ã¯ä¾¿çåæãè¡ããICS ã¨ä»ã®æ
å ±ã·ã¹ãã ã¨ã®æ¥ç¶ã®æ¯
éãå¤æããã許å¯æ¨©è
ã¯ã次ã®äºé
ã«ã¤ãã¦ååç解ãããçµç¹ã®æ
å ±ã»ãã¥ãªãã£ããªã·
ã¼ã»æé ãICS ã®ã»ãã¥ãªãã£ããªã·ã¼ã»æé ãä»ã®æ
å ±ã·ã¹ãã ã¸ã®æ¥ç¶ã«ä»éããçµç¹ã®é
ç¨ãè³ç£ãå人ãä»ã®çµç¹åã³å½ã«å¯¾ãããªã¹ã¯ãç¹å®ã®é£æ¥ã«ä»éããå
·ä½çãªå¥åº·ã»å®å
¨ã»
ç°å¢ãªã¹ã¯ãAO ã¯ãICS ã·ã¹ãã ã»ãã¥ãªãã£è¨ç»æ¸ã«ããããªã¹ã¯å容æ§ã«ã¤ãã¦è¨è¼ãã¦ã
ãã
管çæ¡å¼µï¼(5) ICS è£è¶³ã¬ã¤ãã³ã¹ãªã
SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
389
CA-5 PLAN OF ACTION AND MILESTONES
CNTL NO. CONTROL NAME
Control Enhancement Name
CONTROL BASELINES
LOW
MOD
HIGH
CA-5
Plan of Action and Milestones
Selected
Selected
Selected
No ICS Supplemental Guidance.
CA-6 SECURITY AUTHORIZATION
CNTL NO. CONTROL NAME
Control Enhancement Name
CONTROL BASELINES
LOW
MOD
HIGH
CA-6
Security Authorization
Selected Selected Selected
No ICS Supplemental Guidance.
CA-7 CONTINUOUS MONITORING
CNTL NO. CONTROL NAME
Control Enhancement Name
CONTROL BASELINES
LOW
MOD
HIGH
CA-7
Continuous Monitoring
Selected
Selected
Selected
CA-7 (1)
CONTINUOUS MONITORING | INDEPENDENT ASSESSMENT
Selected Selected
ICS Supplemental Guidance: Continuous monitoring programs for ICS are designed, documented, and implemented by qualified
personnel (i.e., experienced with ICS) selected by the organization. The organization ensures that continuous monitoring does not interfere
with ICS functions. The individual/group designing and conducting the continuous monitoring fully understands the organizational
information security policies and procedures, the ICS security policies and procedures, and the specific health, safety, and environmental
risks associated with a particular facility and/or process. The organization ensures that continuous monitoring does not affect system
operation or result in intentional or unintentional system modification. Example compensating controls include external monitoring.
Control Enhancement: (1) No ICS Supplemental Guidance.
CA-8 PENETRATION TESTING
CNTL NO. CONTROL NAME
Control Enhancement Name
CONTROL BASELINES
LOW
MOD
HIGH
CA-8
Penetration Testing
Selected
ICS Supplemental Guidance: Penetration testing is used with care on ICS networks to ensure that ICS functions are not adversely
impacted by the testing process. In general, ICS are highly sensitive to timing constraints and have limited resources. Example compensating
controls include employing a replicated, virtualized, or simulated system to conduct penetration testing. Production ICS may need to be taken
off-line before testing can be conducted. If ICS are taken off-line for testing, tests are scheduled to occur during planned ICS outages
whenever possible. If penetration testing is performed on non-ICS networks, extra care is taken to ensure that tests do not propagate into the
ICS network.
SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
390
CA-5 è¡åã»ãã¤ã«ã¹ãã¼ã³è¨ç»æ¸
管ççªå·
管çå
管çæ¡å¼µå
管çãã¼ã¹ã©ã¤ã³
ä½
ä¸
é«
CA-5
è¡åã»ãã¤ã«ã¹ãã¼ã³è¨ç»æ¸
é¸å®
é¸å®
é¸å®
ICS è£è¶³ã¬ã¤ãã³ã¹ãªã
CA-6 ã»ãã¥ãªãã£æ¨©é
管ççªå·
管çå
管çæ¡å¼µå
管çãã¼ã¹ã©ã¤ã³
ä½
ä¸
é«
CA-6
ã»ãã¥ãªãã£æ¨©é
é¸å®
é¸å®
é¸å®
ICS è£è¶³ã¬ã¤ãã³ã¹ãªã
CA-7 ç¶ç¶ç£è¦
管ççªå·
管çå
管çæ¡å¼µå
管çãã¼ã¹ã©ã¤ã³
ä½
ä¸
é«
CA-7
ç¶ç¶ç£è¦
é¸å®
é¸å®
é¸å®
CA-7 (1)
ç¶ç¶ç£è¦
|
ç¬ç«è©ä¾¡
é¸å®
é¸å®
ICS è£è¶³ã¬ã¤ãã³ã¹ï¼ICS ã®ç¶ç¶ç£è¦ã¯ãçµç¹ãé¸ä»»ããæè³æ ¼è
ãèæ¡ããææ¸åããå®
æ½ããï¼ICS ã®çç·´è
çï¼ãç¶ç¶ç£è¦ã ICS æ©è½ã¨å¹²æ¸ããªãããã«ãããç¶ç¶ç£è¦ãèæ¡ãã¦
å®æ½ããå人ãã°ã«ã¼ãã¯ãçµç¹ã®æ
å ±ã»ãã¥ãªãã£ããªã·ã¼ã»æé ãICS ã®ã»ãã¥ãªãã£ããª
ã·ã¼ã»æé åã³ç¹å®ã®è¨æ´¥ãããã»ã¹ã«ä»éããå
·ä½çãªå¥åº·ã»å®å
¨ã»ç°å¢ãªã¹ã¯ãååç解ã
ããçµç¹ã¯ç¶ç¶ç£è¦ã«ãã£ã¦ã·ã¹ãã éç¨ãå½±é¿ãåãããæ
æåã¯æå³ããªãã·ã¹ãã å¤æ´ã«
ãªããªãããã«ãããè£åç管ççã®ä¾ã¨ãã¦ãå¤é¨ç£è¦ãããã
管çæ¡å¼µï¼(1) ICS è£è¶³ã¬ã¤ãã³ã¹ãªã
CA-8 ãããã¬ã¼ã·ã§ã³ã»ãã¹ã
管ççªå·
管çå
管çæ¡å¼µå
管çãã¼ã¹ã©ã¤ã³
ä½
ä¸
é«
CA-8
ãããã¬ã¼ã·ã§ã³ã»ãã¹ã
é¸å®
ICS è£è¶³ã¬ã¤ãã³ã¹ï¼ICS ãããã¯ã¼ã¯ã§ã®ãããã¬ã¼ã·ã§ã³ã»ãã¹ãã¯æ
éã«è¡ãã試é¨
ããã»ã¹ã«ãã ICS æ©è½ã«æªå½±é¿ãåã°ãªãããã«ãããç·ã㦠ICS ã¯ãæéçå¶ç´ã«ææã§ã
ãªã½ã¼ã¹ã«éçããããè£åç管ççã®ä¾ã¨ãã¦ãè¤è£½ãä»®æ³åã¯æ¨¡æ¬ã·ã¹ãã ã§ãããã¬ã¼ã·
ã§ã³ã»ãã¹ããè¡ãæ¹æ³ããããçç£ ICS ã¯ã試é¨åã«ãªãã©ã¤ã³ã«ããå¿
è¦ãããããªãã©ã¤
ã³ã«ããå ´åãå¯è½ã§ããã°ãäºãè¨ç»ããã ICS ã®ææ¥åæ¢æã«è©¦é¨ãè¡ãããã«äºå®ãçµãã
ãããã¬ã¼ã·ã§ã³ã»ãã¹ããICS 以å¤ã®ãããã¯ã¼ã¯ã§è¡ãå ´åã試é¨ã ICS ã«æã¡è¾¼ã¾ããªã
ããã«æ³¨æããã

SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
391
CA-9 INTERNAL SYSTEM CONNECTIONS
CNTL NO. CONTROL NAME
Control Enhancement Name
CONTROL BASELINES
LOW
MOD
HIGH
CA-9
Internal System Connections
Selected
Selected
Selected
ICS Supplemental Guidance: Organizations perform risk-benefit analysis to support determination whether an ICS should be
connected to other internal information system(s) and (separate) constituent system components. The Authorizing Official fully understands
the organizational information security policies and procedures; the ICS security policies and procedures; the risks to organizational
operations and assets, individuals, other organizations, and the Nation associated with the connected to other information system(s) and
(separate) constituent system components, whether by authorizing each individual internal connection or authorizing internal connections for
a class of components with common characteristics and/or configurations; and the specific health, safety, and environmental risks associated
with a particular interconnection. The AO documents risk acceptance in the ICS system security plan.

SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
392
CA-9 å
é¨ã·ã¹ãã æ¥ç¶
管ççªå·
管çå
管çæ¡å¼µå
管çãã¼ã¹ã©ã¤ã³
ä½
ä¸
é«
CA-9
å
é¨ã·ã¹ãã æ¥ç¶
é¸å®
é¸å®
é¸å®
ICS è£è¶³ã¬ã¤ãã³ã¹ï¼çµç¹ã¯ãªã¹ã¯ä¾¿çåæãè¡ããICS ã¨ä»ã®å
é¨æ
å ±ã·ã¹ãã ãï¼å¥ï¼
æ§æã·ã¹ãã ã³ã³ãã¼ãã³ãã¨ã®æ¥ç¶ã®æ¯éãå¤æããã許å¯æ¨©è
ã¯ã次ã®äºé
ã«ã¤ãã¦ååç
解ãããçµç¹ã®æ
å ±ã»ãã¥ãªãã£ããªã·ã¼ã»æé ãICS ã®ã»ãã¥ãªãã£ããªã·ã¼ã»æé ãåã
人
ã®å
é¨æ¥ç¶ã許å¯ããããå
±éç¹æ§ã»è¨å®ã®ã³ã³ãã¼ãã³ãã¯ã©ã¹ã¸ã®å
é¨æ¥ç¶ã許å¯ãããã¨
ã«ãããä»ã®æ
å ±ã·ã¹ãã åã³ï¼å¥ï¼æ§æã·ã¹ãã ã³ã³ãã¼ãã³ãã¸ã®æ¥ç¶ã«ä¼´ãçµç¹ã®éç¨ã
è³ç£ãå人ãä»ã®çµç¹åã³å½ã«å¯¾ãããªã¹ã¯ãç¹å®ã®é£æ¥ã«ä»éããå
·ä½çãªå¥åº·ã»å®å
¨ã»ç°å¢
ãªã¹ã¯ãAO ã¯ãICS ã·ã¹ãã ã»ãã¥ãªãã£è¨ç»æ¸ã«ããããªã¹ã¯å容æ§ã«ã¤ãã¦è¨è¼ãã¦ããã
SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
393
CONFIGURATION MANAGEMENT â CM
Tailoring Considerations for Configuration Management Family
In situations where the ICS cannot be configured to restrict the use of unnecessary functions or cannot support the use of automated
mechanisms to implement configuration management functions, the organization employs nonautomated mechanisms or procedures as
compensating controls in accordance with the general tailoring guidance. Examples of compensating controls are given with each control, as
appropriate.
Supplemental Guidance
Supplemental Guidance for all Controls and Control Enhancements in NIST SP 800-53 Rev. 4, Appendix F, should be used in conjunction
with the ICS Supplemental Guidance in this overlay, if any.
CM-1 CONFIGURATION MANAGEMENT POLICY AND PROCEDURES
CNTL NO. CONTROL NAME
Control Enhancement Name
CONTROL BASELINES
LOW
MOD
HIGH
CM-1
Configuration Management Policy and Procedures
Selected
Selected
Selected
ICS Supplemental Guidance: The policy specifically addresses the unique properties and requirements of ICS and the relationship
to non-ICS systems.
CM-2 BASELINE CONFIGURATION
CNTL NO. CONTROL NAME
Control Enhancement Name
CONTROL BASELINES
LOW
MOD
HIGH
CM-2
Baseline Configuration
Selected
Selected
Selected
CM-2 (1)
BASELINE CONFIGURATION | REVIEWS AND UPDATES
Selected
Selected
CM-2 (2) BASELINE CONFIGURATION | AUTOMATION SUPPORT FOR
ACCURACY / CURRENCY
Selected
CM-2 (3) BASELINE CONFIGURATION | RETENTION OF PREVIOUS
CONFIGURATIONS
Selected Selected
CM-2 (7) BASELINE CONFIGURATION | CONFIGURE SYSTEMS,
COMPONENTS, OR DEVICES FOR HIGH-RISK AREAS
Selected Selected
No ICS Supplemental Guidance.
CM-3 CONFIGURATION CHANGE CONTROL
CNTL NO. CONTROL NAME
Control Enhancement Name
CONTROL BASELINES
LOW
MOD
HIGH
CM-3
Configuration Change Control
Selected
Selected
CM-3 (1) CONFIGURATION CHANGE CONTROL | AUTOMATED
DOCUMENT / NOTIFICATION / PROHIBITION OF CHANGES
Selected
CM-3 (2) CONFIGURATION CHANGE CONTROL | TEST / VALIDATE /
DOCUMENT CHANGES
Selected Selected
No ICS Supplemental Guidance.
CM-4 SECURITY IMPACT ANALYSIS
CNTL NO. CONTROL NAME
Control Enhancement Name
CONTROL BASELINES
LOW
MOD
HIGH
CM-4
Security Impact Analysis
Selected
Selected
Selected
CM-4 (1) SECURITY IMPACT ANALYSIS | SEPARATE TEST
ENVIRONMENTS
Selected
ICS Supplemental Guidance: The organization considers ICS safety and security interdependencies.
Control Enhancement: (1) No ICS Supplemental Guidance.
SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
394
è¨å®ç®¡ç â CM
è¨å®ç®¡çãã¡ããªã®ã«ã¹ã¿ãã¤ãºèæ
®äºé
ICS ã§ä¸è¦ãªæ©è½ã®å¶éãè¨å®ç®¡çæ©è½ã®èªåã¡ã«ããºã ã®å©ç¨ãã§ããªãç¶æ³ã§ã¯ãå
¨ä½çãª
ã«ã¹ã¿ãã¤ãºã¬ã¤ãã³ã¹ã«å¾ã£ã¦ãçµç¹ã¯éèªåã¡ã«ããºã åã¯æé ãè£åç管ççã¨ãã¦æ¡ç¨
ãããè£åç管ççã®ä¾ãå¿
è¦ã«å¿ãã¦ã管ççãã¨ã«ç¤ºãããã
è£è¶³ã¬ã¤ãã³ã¹
å©ç¨ã§ããå ´åã«ã¯ãNIST SP 800-53 第4çä»é² Fã«ããå
¨ã¦ã®ç®¡çã»ç®¡çæ¡å¼µç¨è£è¶³ã¬ã¤ãã³
ã¹ãããã®ãªã¼ãã¼ã¬ã¤ã«ããã¦ãICS è£è¶³ã¬ã¤ãã³ã¹ã¨ä½µç¨ãã¹ãã§ããã
CM-1 è¨å®ç®¡çããªã·ã¼ã»æé
管ççªå·
管çå
管çæ¡å¼µå
管çãã¼ã¹ã©ã¤ã³
ä½
ä¸
é«
CM-1
è¨å®ç®¡çããªã·ã¼ã»æé
é¸å®
é¸å®
é¸å®
ICS è£è¶³ã¬ã¤ãã³ã¹ï¼ããªã·ã¼ã¯ç¹ã« ICS ã®åºæã®ç¹æ§ã»è¦ä»¶åã³ ICS 以å¤ã®ã·ã¹ãã ã¨ã®
é¢ä¿ãåãä¸ããã
CM-2 ãã¼ã¹ã©ã¤ã³è¨å®
管ççªå·
管çå
管çæ¡å¼µå
管çãã¼ã¹ã©ã¤ã³
ä½
ä¸
é«
CM-2
ãã¼ã¹ã©ã¤ã³è¨å®
é¸å®
é¸å®
é¸å®
CM-2 (1)
ãã¼ã¹ã©ã¤ã³è¨å®
|
審æ»ã»æ´æ°
é¸å®
é¸å®
CM-2 (2)
ãã¼ã¹ã©ã¤ã³è¨å®
|
æ£ç¢ºæ§ã»ã«ã¬ã³ã·ã¼ã®èªåãµãã¼ã
é¸å®
CM-2 (3)
ãã¼ã¹ã©ã¤ã³è¨å®
|
以åã®è¨å®ä¿æ
é¸å®
é¸å®
CM-2 (7)
ãã¼ã¹ã©ã¤ã³è¨å®
|
é«ãªã¹ã¯ã¨ãªã¢ç¨ã·ã¹ãã ã»ã³ã³ãã¼ãã³
ãã»ããã¤ã¹ã®è¨å®
é¸å® é¸å®
ICS è£è¶³ã¬ã¤ãã³ã¹ãªã
CM-3 è¨å®å¤æ´ç®¡ç
管ççªå·
管çå
管çæ¡å¼µå
管çãã¼ã¹ã©ã¤ã³
ä½
ä¸
é«
CM-3
è¨å®å¤æ´ç®¡ç
é¸å®
é¸å®
CM-3 (1)
è¨å®å¤æ´ç®¡ç
|
èªåææ¸åã»
éç¥
ã»å¤æ´ç¦æ¢
é¸å®
CM-3 (2)
è¨å®å¤æ´ç®¡ç
|
試é¨ã»æ¤è¨¼ã»ææ¸å¤æ´
é¸å®
é¸å®
ICS è£è¶³ã¬ã¤ãã³ã¹ãªã
CM-4 ã»ãã¥ãªãã£å½±é¿åæ
管ççªå·
管çå
管çæ¡å¼µå
管çãã¼ã¹ã©ã¤ã³
ä½
ä¸
é«
CM-4
ã»ãã¥ãªãã£å½±é¿åæ
é¸å®
é¸å®
é¸å®
CM-4 (1)
ã»ãã¥ãªãã£å½±é¿åæ
|
ç¬ç«è©¦é¨ç°å¢
é¸å®
ICS è£è¶³ã¬ã¤ãã³ã¹ï¼çµç¹ã¯ ICS ã®å®å
¨æ§ã¨ã»ãã¥ãªãã£ã®ç¸äºé¢ä¿ãæ¤è¨ããã
管çæ¡å¼µï¼(1) ICS è£è¶³ã¬ã¤ãã³ã¹ãªã
SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
395
CM-5 ACCESS RESTRICTIONS FOR CHANGE
CNTL NO. CONTROL NAME
Control Enhancement Name
CONTROL BASELINES
LOW
MOD
HIGH
CM-5
Access Restrictions for Change
Selected
Selected
CM-5 (1) ACCESS RESTRICTIONS FOR CHANGE | AUTOMATED
ACCESS ENFORCEMENT / AUDITING
Selected
CM-5 (2) ACCESS RESTRICTIONS FOR CHANGE | AUDIT SYSTEM
CHANGES
Selected
CM-5 (3) ACCESS RESTRICTIONS FOR CHANGE | SIGNED
COMPONENTS
Selected
No ICS Supplemental Guidance.
CM-6 CONFIGURATION SETTINGS
CNTL NO. CONTROL NAME
Control Enhancement Name
CONTROL BASELINES
LOW
MOD
HIGH
CM-6
Configuration Settings
Selected
Selected
Selected
CM-6 (1) CONFIGURATION SETTINGS | AUTOMATED CENTRAL
MANAGEMENT / APPLICATION / VERIFICATION
Selected
CM-6 (2) CONFIGURATION SETTINGS | RESPOND TO UNAUTHORIZED
CHANGES
Selected
No ICS Supplemental Guidance.
CM-7 LEAST FUNCTIONALITY
CNTL NO. CONTROL NAME
Control Enhancement Name
CONTROL BASELINES
LOW
MOD
HIGH
CM-7
Least Functionality
Selected
Selected
Selected
CM-7 (1)
LEAST FUNCTIONALITY | PERIODIC REVIEW
Added
Selected
Selected
CM-7 (2)
LEAST FUNCTIONALITY | PREVENT PROGRAM EXECUTION
Removed
Selected
CM-7 (4)
LEAST FUNCTIONALITY | UNAUTHORIZED SOFTWARE
Added
Selected
ICS Supplemental Guidance: Ports, as used in NIST SP 800-53 Rev. 4, are part of the address space in network protocols and are
often associated with specific protocols or functions. As such, ports are not relevant to non-routable protocols and devices. When dealing
with non-routable and non-addressable protocols and devices, prohibiting or restricting the use of specified functions, protocols, and/or
services must be implemented for the (sub)system granularity that is available (e.g., at a low level, interrupts could be disabled; at a high
level, set points could be made read-only except for privileged users). Example compensating controls include employing nonautomated
mechanisms or procedures.
Control Enhancement: (1, 2, 5) No ICS Supplemental Guidance.
Control Baseline Supplement Rationale: (1) Periodic review and removal of unnecessary and/or nonsecure functions,
ports, protocols, and services are added to the LOW baseline because many of the LOW impact ICS components could
adversely affect the systems to which they are connected.
(4, 5) Whitelisting (CE 5) is more effective than blacklisting (CE 4). The set of applications that run in ICS is essentially
static, making whitelisting practical. ICS-CERT recommends deploying application whitelisting on ICS. Reference: http://ics-
cert.us-cert.gov/tips/ICS-TIP-12-146-01B
CM-8 INFORMATION SYSTEM COMPONENT INVENTORY
CNTL NO. CONTROL NAME
Control Enhancement Name
CONTROL BASELINES
LOW
MOD
HIGH
CM-8
Information System Component Inventory
Selected
Selected
Selected
CM-8 (1) INFORMATION SYSTEM COMPONENT INVENTORY |
UPDATES DURING INSTALLATIONS / REMOVALS
Selected Selected
CM-8 (2) INFORMATION SYSTEM COMPONENT INVENTORY |
AUTOMATED MAINTENANCE
Selected
CM-8 (3) INFORMATION SYSTEM COMPONENT INVENTORY |
AUTOMATED UNAUTHORIZED COMPONENT DETECTION
Selected Selected
SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
396
CM-5 å¤æ´ç¨ã¢ã¯ã»ã¹å¶é
管ççªå·
管çå
管çæ¡å¼µå
管çãã¼ã¹ã©ã¤ã³
ä½
ä¸
é«
CM-5
å¤æ´ç¨ã¢ã¯ã»ã¹å¶é
é¸å®
é¸å®
CM-5 (1)
å¤æ´ç¨ã¢ã¯ã»ã¹å¶é
|
èªåã¢ã¯ã»ã¹ã®æ½è¡
/
ç£æ»
é¸å®
CM-5 (2)
å¤æ´
ç¨ã¢ã¯ã»ã¹å¶é
|
ç£æ»ã·ã¹ãã å¤æ´
é¸å®
CM-5 (3)
å¤æ´ç¨ã¢ã¯ã»ã¹å¶é
|
ç½²åã³ã³ãã¼ãã³ã
é¸å®
ICS è£è¶³ã¬ã¤ãã³ã¹ãªã
CM-6 æ§æè¨å®
管ççªå·
管çå
管çæ¡å¼µå
管çãã¼ã¹ã©ã¤ã³
ä½
ä¸
é«
CM-6
æ§æè¨å®
é¸å®
é¸å®
é¸å®
CM-6 (1)
æ§æè¨å®
|
èªåéä¸ç®¡ç
ã¢ããªã±ã¼ã·ã§ã³
/
æ¤è¨¼
é¸å®
CM-6 (2)
æ§æè¨å®
|
ç¡æå¤æ´å¯¾å¿
é¸å®
ICS è£è¶³ã¬ã¤ãã³ã¹ãªã
CM-7 æå°æ¨©é
管ççªå·
管çå
管çæ¡å¼µå
管çãã¼ã¹ã©ã¤ã³
ä½
ä¸
é«
CM-7
æä½éæ©è½
é¸å®
é¸å®
é¸å®
CM-7 (1)
æä½éæ©è½
|
å®æçè¦ç´ã
追å
é¸å®
é¸å®
CM-7 (2)
æä½éæ©è½
|
ããã°ã©ã å®è¡é²æ¢
åé¤
é¸å®
CM-7 (4)
æä½éæ©è½
|
æªè¨±å¯ã½ããã¦ã¨ã¢
追å
é¸å®
ICS è£è¶³ã¬ã¤ãã³ã¹ï¼NIST SP 800-53 第4çã§ä½¿ç¨ããããã¼ãã¯ããããã¯ã¼ã¯ãããã³ã«ã«ãããã¢ã
ã¬ã¹ç©ºéã®ä¸é¨ã§ãç¹å®ã®ãããã³ã«ãæ©è½ã«é¢é£ã¥ãããã¦ãããã¨ãå¤ãããã®ãããªãã¼ãã¯ãçµè·¯æå®
ä¸è½ãããã³ã«åã³ããã¤ã¹ã§ã¯ãªããã¢ãã¬ã¹/ã«ã¼ãæå®ä¸è½ãããã³ã«åã³ããã¤ã¹ã®å ´åãæå®æ©è½ãã
ããã³ã«åã¯ãµã¼ãã¹å©ç¨ã®ç¦æ¢åã¯å¶éã¯ãå©ç¨ã§ããï¼ãµãï¼ã·ã¹ãã ã®ç²åº¦ã«å®è£
ããªããã°ãªããªã
ï¼ä½ã¬ãã«ã§ã¯ä¸æãç¡å¹ã«ããé«ã¬ãã«ã§ã¯è¨å®ç¹ãç¹æ¨©ã¦ã¼ã¶ä»¥å¤ã¯èªã¿åãå°ç¨ã¨ãããªã©ï¼ãè£åç管
ççã®ä¾ã¨ãã¦ãéèªåã¡ã«ããºã åã¯æé ãããã
管çæ¡å¼µï¼(1, 2, 5) ICS è£è¶³ã¬ã¤ãã³ã¹ãªã
管çãã¼ã¹ã©ã¤ã³è£è¶³çç±ï¼(1)ä¸è¦åã¯ã»ãã¥ã¢ã§ãªãæ©è½ããã¼ãããããã³ã«åã³ãµã¼ãã¹ã®å®æçãª
è¦ç´ãã¨åé¤ãä½ãã¼ã¹ã©ã¤ã³ã«è¿½å ãããçç±ã¯å½±é¿åº¦ä½ã® ICS ã³ã³ãã¼ãã³ãã®å¤ãã¯ãæ¥ç¶å
ã·ã¹ãã ã«
æªå½±é¿ãåã¼ãããã
(4, 5) ãã¯ã¤ããªã¹ã(CE 5)ã¯ãã©ãã¯ãªã¹ã(CE 4)ãããå¹æçãICS ã§å®è¡ããã¢ããªã±ã¼ã·ã§ã³ã»ããã¯åºæ¬
çã«éçã§ããããããã¯ã¤ããªã¹ããç¾å®çã§ãããICS-CERT ã¯ããã¯ã¤ããªã¹ãã¢ããªã±ã¼ã·ã§ã³ã® ICS å±
éãæ¨å¥¨ãã¦ãããåèæç®ï¼http://ics-cert.us- cert.gov/tips/ICS-TIP-12-146-01B
CM-8 æ
å ±ã·ã¹ãã ã³ã³ãã¼ãã³ãç®é²
管ççªå·
管çå
管çæ¡å¼µå
管çãã¼ã¹ã©ã¤ã³
ä½
ä¸
é«
CM-8
æ
å ±ã·ã¹ãã ã³ã³ãã¼ãã³ãç®é²
é¸å®
é¸å®
é¸å®
CM-8 (1)
æ
å ±ã·ã¹ãã ã³ã³ãã¼ãã³ãç®é²
|
ã¤ã³ã¹ãã¼ã«ã»åé¤æã®æ´æ°
é¸å®
é¸å®
CM-8 (2)
æ
å ±ã·ã¹ãã ã³ã³ãã¼ãã³ãç®é²
|
èªåä¿å®
é¸å®
CM-8 (3)
æ
å ±ã·ã¹ãã ã³ã³ãã¼ãã³ãç®é²
|
èªåç¡è¨±å¯ã³ã³ãã¼ãã³ãæ¤ç¥
é¸å®
é¸å®
SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
397
CNTL NO. CONTROL NAME
Control Enhancement Name
CONTROL BASELINES
LOW
MOD
HIGH
CM-8 (4) INFORMATION SYSTEM COMPONENT INVENTORY |
PROPERTY ACCOUNTABILITY INFORMATION
Selected
CM-8 (5) INFORMATION SYSTEM COMPONENT INVENTORY | ALL
COMPONENTS WITHIN AUTHORIZATION BOUNDARY
Selected Selected
No ICS Supplemental Guidance.
CM-9 CONFIGURATION MANAGEMENT PLAN
CNTL NO. CONTROL NAME
Control Enhancement Name
CONTROL BASELINES
LOW
MOD
HIGH
CM-9
Configuration Management Plan
Selected
Selected
No ICS Supplemental Guidance.
CM-10 SOFTWARE USAGE RESTRICTIONS
CNTL NO. CONTROL NAME
Control Enhancement Name
CONTROL BASELINES
LOW
MOD
HIGH
CM-10
Software Usage Restrictions
Selected
Selected
Selected
No ICS Supplemental Guidance.
CM-11 USER-INSTALLED SOFTWARE
CNTL NO. CONTROL NAME
Control Enhancement Name
CONTROL BASELINES
LOW
MOD
HIGH
CM-11
User-Installed Software
Selected
Selected
Selected
No ICS Supplemental Guidance.
SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
398
管ççªå·
管çå
管çæ¡å¼µå
管çãã¼ã¹ã©ã¤ã³
ä½
ä¸
é«
CM-8 (4)
æ
å ±ã·ã¹ãã ã³ã³ãã¼ãã³ãç®
é²
|
è³ç£èª¬æ責任æ
å ±
é¸å®
CM-8 (5)
æ
å ±ã·ã¹ãã ã³ã³ãã¼ãã³ãç®é²
|
å
¨ã³ã³ãã¼ãã³ãã権éå
é¸å®
é¸å®
ICS è£è¶³ã¬ã¤ãã³ã¹ãªã
CM-9 è¨å®ç®¡çè¨ç»æ¸
管ççªå·
管çå
管çæ¡å¼µå
管çãã¼ã¹ã©ã¤ã³
ä½
ä¸
é«
CM-9
è¨å®ç®¡çè¨ç»æ¸
é¸å®
é¸å®
ICS è£è¶³ã¬ã¤ãã³ã¹ãªã
CM-10 ã½ããã¦ã¨ã¢ä½¿ç¨å¶é
管ççªå·
管çå
管çæ¡å¼µå
管çãã¼ã¹ã©ã¤ã³
ä½
ä¸
é«
CM-10
ã½ããã¦ã¨ã¢ä½¿ç¨å¶é
é¸å®
é¸å®
é¸å®
ICS è£è¶³ã¬ã¤ãã³ã¹ãªã
CM-11 ã¦ã¼ã¶ãã¤ã³ã¹ãã¼ã«ããã½ããã¦ã¨ã¢
管ççªå·
管çå
管çæ¡å¼µå
管çãã¼ã¹ã©ã¤ã³
ä½
ä¸
é«
CM-11
ã¦ã¼ã¶ãã¤ã³ã¹ãã¼ã«ããã½ããã¦ã¨ã¢
é¸å®
é¸å®
é¸å®
ICS è£è¶³ã¬ã¤ãã³ã¹ãªã

SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
399
CONTINGENCY PLANNING - CP
Tailoring Considerations for Contingency Planning Family
ICS systems often contain a physical component at a fixed location. Such components may not be relocated logically. Some replacement
components may not be readily available. Continuance of essential missions and business functions with little or no loss of operational
continuity may not be possible. In situations where the organization cannot provide necessary essential services, support, or automated
mechanisms during contingency operations, the organization provides nonautomated mechanisms or predetermined procedures as
compensating controls in accordance with the general tailoring guidance. Examples of compensating controls are given with each control, as
appropriate.
Supplemental Guidance
Supplemental Guidance for all Controls and Control Enhancements in NIST SP 800-53 Rev. 4, Appendix F, should be used in
conjunction with the ICS Supplemental Guidance in this overlay, if any.
CP-1 CONTINGENCY PLANNING POLICY AND PROCEDURES
CNTL NO. CONTROL NAME
Control Enhancement Name
CONTROL BASELINES
LOW
MOD
HIGH
CP-1
Contingency Planning Policy and Procedures
Selected
Selected
Selected
ICS Supplemental Guidance: The policy specifically addresses the unique properties and requirements of ICS and the relationship
to non-ICS systems.
CP-2 CONTINGENCY PLAN
CNTL NO. CONTROL NAME
Control Enhancement Name
CONTROL BASELINES
LOW
MOD
HIGH
CP-2
Contingency Plan
Selected
Selected
Selected
CP-2 (1)
CONTINGENCY PLAN | COORDINATE WITH RELATED PLANS
Selected
Selected
CP-2 (2)
CONTINGENCY PLAN | CAPACITY PLANNING
Selected
CP-2 (3) CONTINGENCY PLAN | RESUME ESSENTIAL MISSIONS /
BUSINESS FUNCTIONS
Selected Selected
CP-2 (4) CONTINGENCY PLAN | RESUME ALL MISSIONS / BUSINESS
FUNCTIONS
Selected
CP-2 (5) CONTINGENCY PLAN | CONTINUE ESSENTIAL MISSIONS /
BUSINESS FUNCTIONS
Selected
CP-2 (8)
CONTINGENCY PLAN | IDENTIFY CRITICAL ASSETS
Selected
Selected
ICS Supplemental Guidance: The organization defines contingency plans for categories of disruptions or failures. In the event of a
loss of processing within the ICS or communication with operational facilities, the ICS executes predetermined procedures (e.g., alert the
operator of the failure and then do nothing, alert the operator and then safely shut down the industrial process, alert the operator and then
maintain the last operational setting prior to failure).
Control Enhancement: (1) ICS Supplemental Guidance: Organizational elements responsible for related plans may include
suppliers such as electric power, fuel, fresh water and wastewater.
Control Enhancement: (2) No ICS Supplemental Guidance.
Control Enhancement: (3, 4) ICS Supplemental Guidance: Plans for the resumption of essential missions and business functions,
and for resumption of all missions and business functions take into account the effects of the disruption on the environment of operation.
Restoration and resumption plans should include prioritization of efforts. Disruptions may affect the quality and quantity of resources in the
environment, such as electric power, fuel, fresh water and wastewater, and the ability of these suppliers to also resume provision of essential
mission and business functions. Contingency plans for widespread disruption may involve specialized organizations (e.g., FEMA, emergency
services, regulatory authorities). Reference: NFPA 1600: Standard on Disaster/Emergency Management and Business Continuity Programs.
Control Enhancement: (5, 8) No ICS Supplemental Guidance.
SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
400
ä¸æ¸¬äºæ
è¨ç» - CP
ä¸æ¸¬äºæ
è¨ç»ãã¡ããªã®ã«ã¹ã¿ãã¤ãºèæ
®äºé
ICS ã·ã¹ãã ã«ã¯ãå®ããããå ´æã«ç©çã³ã³ãã¼ãã³ããããå ´åãå¤ãããããã¯è«ççãª
移åãã§ããªãã代ããã®ã³ã³ãã¼ãã³ããããã«å©ç¨ã§ããªããã®ããããä¸æãã»ã¨ãã©å
ã¯å
¨ã許ãããªãéè¦ä»»åãäºæ¥ããããä¸æ¸¬äºæ
éç¨ä¸ã«ãå¿
è¦ãªéè¦ãµã¼ãã¹ããµãã¼ãå
ã¯èªåã¡ã«ããºã ãæä¾ã§ããªãç¶æ³ã§ã¯ãå
¨ä½çãªã«ã¹ã¿ãã¤ãºã¬ã¤ãã³ã¹ã«å¾ã£ã¦ãçµç¹ã¯
éèªåã¡ã«ããºã åã¯äºåè¨å®æé ãè£åç管ççã¨ãã¦æ¡ç¨ãããè£åç管ççã®ä¾ãå¿
è¦ã«
å¿ãã¦ã管ççãã¨ã«ç¤ºãããã
è£è¶³ã¬ã¤ãã³ã¹
å©ç¨ã§ããå ´åã«ã¯ãNIST SP 800-53 第4çä»é² Fã«ããå
¨ã¦ã®ç®¡çã»ç®¡çæ¡å¼µç¨è£è¶³ã¬ã¤ãã³
ã¹ãããã®ãªã¼ãã¼ã¬ã¤ã«ããã¦ãICS è£è¶³ã¬ã¤ãã³ã¹ã¨ä½µç¨ãã¹ãã§ããã
CP-1 ä¸æ¸¬äºæ
è¨ç»ããªã·ã¼ã»æé
管ççªå·
管çå
管çæ¡å¼µå
管çãã¼ã¹ã©ã¤ã³
ä½
ä¸
é«
CP-1
ä¸æ¸¬äºæ
è¨ç»ããªã·ã¼ã»æé
é¸å®
é¸å®
é¸å®
ICS è£è¶³ã¬ã¤ãã³ã¹ï¼ããªã·ã¼ã¯ç¹ã« ICS ã®åºæã®ç¹æ§ã»è¦ä»¶åã³ ICS 以å¤ã®ã·ã¹ãã ã¨ã®
é¢ä¿ãåãä¸ããã
CP-2 ç·æ¥æ対å¿è¨ç»
管ççªå·
管çå
管çæ¡å¼µå
管çãã¼ã¹ã©ã¤ã³
ä½
ä¸
é«
CP-2
ç·æ¥æ対å¿è¨ç»
é¸å®
é¸å®
é¸å®
CP-2 (1)
ç·æ¥æ対å¿è¨ç»
|
é¢é£è¨ç»æ¸ã¨ã®æ´å
é¸å®
é¸å®
CP-2 (2)
ç·æ¥æ対å¿è¨ç»
|
容éè¨ç»
é¸å®
CP-2 (3)
ç·æ¥æ対å¿è¨ç»
|
éè¦ä»»åã»äºæ¥æ©è½ã®åé
é¸å®
é¸å®
CP-2 (4)
ç·æ¥æ対å¿è¨ç»
|
å
¨ä»»åã»äºæ¥æ©è½ã®åé
é¸å®
CP-2 (5)
ç·æ¥æ対å¿è¨ç»
|
éè¦ä»»åã»äºæ¥æ©è½ã®åé
é¸å®
CP-2 (8)
ç·æ¥æ対å¿è¨ç»
|
éè¦è³ç£èå¥
é¸å®
é¸å®
ICS è£è¶³ã¬ã¤ãã³ã¹ï¼çµç¹ã¯ãä¸æãæ
éã®åé¡å¥ã«ç·æ¥æ対å¿è¨ç»ãå®ãããICS å
ã§ã®
å¦çãéç¨æ½è¨ã¨ã®éä¿¡ã失ãããå ´åãICS ã¯äºãå®ããããæé ãå®è¡ããï¼æä½å¡ã«è¦å ±
ãçºä¿¡ãã¦ä½ãããªããæä½å¡ã«è¦å ±ãçºä¿¡ãã¦ç£æ¥ããã»ã¹ãå®å
¨ã«é®æãããæä½å¡ã«è¦å ±
ãçºä¿¡ãã¦æ
éç´åã®åä½ãç¶æãããªã©ï¼ã
管çæ¡å¼µï¼(1) ICS è£è¶³ã¬ã¤ãã³ã¹ï¼é¢é£è¨ç»æ¸ã®æ
å½é¨ç½²ã«ã¯ãé»åãçæãä¸ä¸æ°´éçã®
ãµãã©ã¤ã¤ãå«ã¾ããã
管çæ¡å¼µï¼(2) ICS è£è¶³ã¬ã¤ãã³ã¹ãªã
管çæ¡å¼µï¼(3, 4) ICS è£è¶³ã¬ã¤ãã³ã¹ï¼éè¦ä»»åã»äºæ¥æ©è½ã®åéã«é¢ããè¨ç»æ¸åã³å
¨ã¦ã®
ä»»åã»äºæ¥æ©è½ã®åéã«é¢ããè¨ç»æ¸ã«ã¯ãéç¨ç°å¢ãå´©å£ããå ´åã®å½±é¿ãèæ
®ã«å
¥ããã復
æ§ã»åéè¨ç»æ¸ã«ã¯ãåçµã®åªå
é ä½ãå«ããã¹ãã§ãããä¸æãçããã¨é»åãçæãä¸ä¸æ°´
éçã®ãªã½ã¼ã¹ã®è³ªã»éã®ã¿ãªãããéè¦ä»»åã»äºæ¥ãåéãããµãã©ã¤ã¤ã®è½åã«ãå½±é¿ãåº
ãã大è¦æ¨¡ä¸æã®ç·æ¥æ対å¿è¨ç»ã«ã¯ãç¹å¥çµç¹ãå«ããï¼FEMAãç·æ¥ãµã¼ãã¹ãè¦å¶å½å±
çï¼ãåèæç®ï¼NFPA 1600:ç½å®³ã»æ°çæ管çã»äºæ¥ç¶ç¶ããã°ã©ã ã®åºæº
管çæ¡å¼µï¼(5) (8) ICS è£è¶³ã¬ã¤ãã³ã¹ãªã
SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
401
CP-3 CONTINGENCY TRAINING
CNTL NO. CONTROL NAME
Control Enhancement Name
CONTROL BASELINES
LOW
MOD
HIGH
CP-3
Contingency Training
Selected
Selected
Selected
CP-3 (1)
CONTINGENCY TRAINING | SIMULATED EVENTS
Selected
No ICS Supplemental Guidance.
CP-4 CONTINGENCY PLAN TESTING
CNTL NO. CONTROL NAME
Control Enhancement Name
CONTROL BASELINES
LOW
MOD
HIGH
CP-4
Contingency Plan Testing
Selected
Selected
Selected
CP-4 (1) CONTINGENCY PLAN TESTING | COORDINATE WITH RELATED
PLANS
Selected Selected
P-4 (2)
CONTINGENCY PLAN TESTING | ALTERNATE PROCESSING SITE
Selected
No ICS Supplemental Guidance.
CP-6 ALTERNATE STORAGE SITE
CNTL NO. CONTROL NAME
Control Enhancement Name
CONTROL BASELINES
LOW
MOD
HIGH
CP-6
Alternate Storage Site
Selected
Selected
CP-6 (1) ALTERNATE STORAGE SITE | SEPARATION FROM PRIMARY SITE
Selected Selected
CP-6 (2) ALTERNATE STORAGE SITE | RECOVERY TIME / POINT
OBJECTIVES
Selected
CP-6 (3)
ALTERNATE STORAGE SITE | ACCESSIBILITY
Selected
Selected
No ICS Supplemental Guidance.
CP-7 ALTERNATE PROCESSING SITE
CNTL NO. CONTROL NAME
Control Enhancement Name
CONTROL BASELINES
LOW
MOD
HIGH
CP-7
Alternate Processing Site
Selected
Selected
CP-7 (1) ALTERNATE PROCESSING SITE | SEPARATION FROM PRIMARY
SITE
Selected Selected
CP-7 (2)
ALTERNATE PROCESSING SITE | ACCESSIBILITY
Selected
Selected
CP-7 (3)
ALTERNATE PROCESSING SITE | PRIORITY OF SERVICE
Selected
Selected
CP-7 (4)
ALTERNATE PROCESSING SITE | CONFIGURATION FOR USE
Selected
No ICS Supplemental Guidance.
CP-8 TELECOMMUNICATIONS SERVICES
CNTL NO. CONTROL NAME
Control Enhancement Name
CONTROL BASELINES
LOW
MOD
HIGH
CP-8
Telecommunications Services
Selected
Selected
CP-8 (1) TELECOMMUNICATIONS SERVICES | PRIORITY OF SERVICE
PROVISIONS
Selected Selected
CP-8 (2) TELECOMMUNICATIONS SERVICES | SINGLE POINTS OF
FAILURE
Selected Selected
CP-8 (3) TELECOMMUNICATIONS SERVICES | SEPARATION OF PRIMARY
/ ALTERNATE PROVIDERS
Selected
CP-8 (4) TELECOMMUNICATIONS SERVICES | PROVIDER CONTINGENCY
PLAN
Selected
ICS Supplemental Guidance: Quality of service factors for ICS include latency and throughput.
Control Enhancement: (1, 2, 3, 4) No ICS Supplemental Guidance.
SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
402
CP-3 ä¸æ¸¬äºæ
è¨ç·´
管ççªå·
管çå
管çæ¡å¼µå
管çãã¼ã¹ã©ã¤ã³
ä½
ä¸
é«
CP-3
ä¸æ¸¬äºæ
è¨ç·´
é¸å®
é¸å®
é¸å®
CP-3 (1)
ä¸æ¸¬äºæ
è¨ç·´
|
模æ¬äºè±¡
é¸å®
ICS è£è¶³ã¬ã¤ãã³ã¹ãªã
CP-4 ç·æ¥æ対å¿è¨ç»ã®æ¤è¨¼
管ççªå·
管çå
管çæ¡å¼µå
管çãã¼ã¹ã©ã¤ã³
ä½
ä¸
é«
CP-4
ç·æ¥æ対å¿è¨ç»ã®æ¤è¨¼
é¸å®
é¸å®
é¸å®
CP-4 (1)
ç·æ¥æ対å¿è¨ç»
ã®æ¤è¨¼
|
é¢é£è¨ç»æ¸ã¨ã®æ´å
é¸å®
é¸å®
P-4 (2)
ç·æ¥æ対å¿è¨ç»
ã®æ¤è¨¼
|
代æ¿å¦çãµã¤ã
é¸å®
ICS è£è¶³ã¬ã¤ãã³ã¹ãªã
CP-6 代æ¿ã¹ãã¬ã¼ã¸ãµã¤ã
管ççªå·
管çå
管çæ¡å¼µå
管çãã¼ã¹ã©ã¤ã³
ä½
ä¸
é«
CP-6
代æ¿ã¹ãã¬ã¼ã¸ãµã¤ã
é¸å®
é¸å®
CP-6 (1)
代æ¿ã¹ãã¬ã¼ã¸ãµã¤ã
|
ãã©ã¤ããªãµã¤ãããã®åé¢
é¸å®
é¸å®
CP-6 (2)
代æ¿ã¹ãã¬ã¼ã¸ãµã¤ã
|
復æ§æéã»ãã¤ã³ãç®æ¨
é¸å®
CP-6 (3)
代æ¿ã¹ãã¬ã¼ã¸ãµã¤ã
|
ã¢ã¯ã»ã·ããªãã£
é¸å®
é¸å®
ICS è£è¶³ã¬ã¤ãã³ã¹ãªã
CP-7 代æ¿å¦çãµã¤ã
管ççªå·
管çå
管çæ¡å¼µå
管çãã¼ã¹ã©ã¤ã³
ä½
ä¸
é«
CP-7
代æ¿å¦çãµã¤ã
é¸å®
é¸å®
CP-7 (1)
代æ¿å¦çãµã¤ã
|
ãã©ã¤ããªãµã¤ãããã®åé¢
é¸å®
é¸å®
CP-7 (2)
代æ¿å¦çãµã¤ã
|
ã¢ã¯ã»ã·ããªãã£
é¸å®
é¸å®
CP-7 (3)
代æ¿å¦ç
ãµã¤ã
|
ãµã¼ãã¹ã®åªå
é ä½
é¸å®
é¸å®
CP-7 (4)
代æ¿å¦çãµã¤ã
|
å©ç¨åãè¨å®
é¸å®
ICS è£è¶³ã¬ã¤ãã³ã¹ãªã
CP-8 é»æ°éä¿¡ãµã¼ãã¹
管ççªå·
管çå
管çæ¡å¼µå
管çãã¼ã¹ã©ã¤ã³
ä½
ä¸
é«
CP-8
é»æ°éä¿¡ãµã¼ãã¹
é¸å®
é¸å®
CP-8 (1)
é»æ°éä¿¡ãµã¼ãã¹
|
ãµã¼ãã¹æä¾ã®åªå
é ä½
é¸å®
é¸å®
CP-8 (2)
é»æ°éä¿¡ãµã¼ãã¹
|
é害åç¹
é¸å®
é¸å®
CP-8 (3)
é»æ°éä¿¡ãµã¼ãã¹
|
主ã»å¯ãããã¤ãã®åå²
é¸å®
CP-8 (4)
é»æ°éä¿¡ãµã¼ãã¹
|
ãããã¤ãã®ä¸æ¸¬äºæ
ä½è¨ç»æ¸
é¸å®
ICS è£è¶³ã¬ã¤ãã³ã¹ï¼ICS ã®ãµã¼ãã¹å質ã«ã¯å¾
ã¡æéã¨ã¹ã«ã¼ããããå«ã¾ããã
管çæ¡å¼µï¼(1, 2, 3, 4) ICS è£è¶³ã¬ã¤ãã³ã¹ãªã
SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
403
CP-9 INFORMATION SYSTEM BACKUP
CNTL NO. CONTROL NAME
Control Enhancement Name
CONTROL BASELINES
LOW
MOD
HIGH
CP-9
Information System Backup
Selected
Selected
Selected
CP-9 (1) INFORMATION SYSTEM BACKUP | TESTING FOR RELIABILITY
/ INTEGRITY
Selected Selected
CP-9 (2) INFORMATION SYSTEM BACKUP | TEST RESTORATION
USING SAMPLING
Selected
CP-9 (3) INFORMATION SYSTEM BACKUP | SEPARATE STORAGE FOR
CRITICAL INFORMATION
Selected
CP-9 (5) INFORMATION SYSTEM BACKUP | TRANSFER TO
ALTERNATE SITE
Selected
No ICS Supplemental Guidance.
CP-10 INFORMATION SYSTEM RECOVERY AND RECONSTITUTION
CNTL NO. CONTROL NAME
Control Enhancement Name
CONTROL BASELINES
LOW
MOD
HIGH
CP-10
Information System Recovery and Reconstitution
Selected
Selected
Selected
CP-10 (2) INFORMATION SYSTEM RECOVERY AND RECONSTITUTION |
TRANSACTION RECOVERY
Selected Selected
CP-10 (4) INFORMATION SYSTEM RECOVERY AND RECONSTITUTION |
RESTORE WITHIN TIME PERIOD
Selected
ICS Supplemental Guidance: Reconstitution of the ICS includes consideration whether system state variables should be restored to
initial values or values before disruption (e.g., are valves restored to full open, full closed, or settings prior to disruption). Restoring system
state variables may be disruptive to ongoing physical processes (e.g., valves initially closed may adversely affect system cooling).
Control Enhancement: (2, 4) No ICS Supplemental Guidance.
CP-12 SAFE MODE
CNTL NO. CONTROL NAME
Control Enhancement Name
CONTROL BASELINES
LOW
MOD
HIGH
CP-12
Safe Mode
Added
Added
Added
ICS Supplemental Guidance: The organization-defined conditions and corresponding restrictions of safe mode of operation may
vary among baselines. The same condition(s) may trigger different response depending on the impact level. The conditions may be external
to the ICS (e.g., electricity supply brown-out). Related controls: SI-17.
Rationale for adding CP-12 to all baselines: This control provides a framework for the organization to plan their policy and
procedures for dealing with conditions beyond their control in the environment of operations. Creating a written record of the decision
process for selecting incidents and appropriate response is part of risk management in light of changing environment of operations.
SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
404
CP-9 æ
å ±ã·ã¹ãã ããã¯ã¢ãã
管ççªå·
管çå
管çæ¡å¼µå
管çãã¼ã¹ã©ã¤ã³
ä½
ä¸
é«
CP-9
æ
å ±ã·ã¹ãã ããã¯ã¢ãã
é¸å®
é¸å®
é¸å®
CP-9 (1)
æ
å ±ã·ã¹ãã ããã¯ã¢ãã
|
ä¿¡é ¼æ§ã»å®å
¨æ§ã®æ¤è¨¼
é¸å®
é¸å®
CP-9 (2)
æ
å ±ã·ã¹ãã ããã¯ã¢ãã
|
ãµã³ããªã³ã°ã«ãã復æ§è©¦é¨
é¸å®
CP-9 (3)
æ
å ±ã·ã¹ãã ããã¯ã¢ãã
|
éè¦æ
å ±ã®åé¢ä¿ç®¡
é¸å®
CP-9 (5)
æ
å ±ã·ã¹ãã ããã¯ã¢ãã
|
代æ¿ãµã¤ãã¸ã®ç§»è¡
é¸å®
ICS è£è¶³ã¬ã¤ãã³ã¹ãªã
CP-10 æ
å ±ã·ã¹ãã ã®å¾©æ§ã»åæ§ç¯
管ççªå·
管çå
管çæ¡å¼µå
管çãã¼ã¹ã©ã¤ã³
ä½
ä¸
é«
CP-10
æ
å ±ã·ã¹ãã ã®å¾©æ§ã»åæ§ç¯
é¸å®
é¸å®
é¸å®
CP-10 (2)
æ
å ±ã·ã¹ãã ã®å¾©æ§ã»åæ§ç¯
|
ãã©ã³ã¶ã¯ã·ã§ã³ã®å¾©æ§
é¸å® é¸å®
CP-10 (4)
æ
å ±ã·ã¹ãã ã®å¾©æ§ã»åæ§ç¯
|
æéå
ã®å¾©æ§
é¸å®
ICS è£è¶³ã¬ã¤ãã³ã¹ï¼ICS ã®åæ§ç¯ã«ã¯ãã·ã¹ãã ç¶æ
å¤æ°ãä¸æåã®åæå¤ã«æ»ããã©ã
ãã®æ¤è¨ãå«ã¾ããï¼ãã«ãã¯å
¨éãå
¨éããä¸æåã®è¨å®å¤ããªã©ï¼ãã·ã¹ãã ç¶æ
å¤æ°ãå
ã«æ»ãã¨ãé²è¡ä¸ã®ç©çããã»ã¹ãä¸æããå ´åãããï¼ãã«ããéãã¦ã·ã¹ãã ã®å·å´ã«æªå½±
é¿çï¼ã
管çæ¡å¼µï¼(2) (4) ICS è£è¶³ã¬ã¤ãã³ã¹ãªã
CP-12 ã»ã¼ãã¢ã¼ã
管ççªå·
管çå
管çæ¡å¼µå
管çãã¼ã¹ã©ã¤ã³
ä½
ä¸
é«
CP-12
ã»ã¼ãã¢ã¼ã
追å
追å
追å
ICS è£è¶³ã¬ã¤ãã³ã¹ï¼çµç¹ãå®ç¾©ããæ¡ä»¶åã³å¯¾å¿ããå®å
¨éç¨ã¢ã¼ãã®å¶éã¯ããã¼ã¹ã©
ã¤ã³ã«ãã£ã¦ã¾ã¡ã¾ã¡ã§ãããåãæ¡ä»¶ã§ããå½±é¿åº¦ã«ãã£ã¦å¥ã®å¯¾å¿ã¨ãªããæ¡ä»¶ã¯ ICS ã«ã¨
ã£ã¦ãå¤é¨ã®ãã®ã¨ãªãï¼åé»çï¼ãé¢é£ãã管çï¼SI-17
CP-12 ãå
¨ã¦ã®ãã¼ã¹ã©ã¤ã³ã«è¿½å ããçç±ï¼ãã®ç®¡çã¯ãçµç¹ãéç¨ç°å¢ã§èªãã®å¶å¾¡ã
åã°ãªãæ¡ä»¶ãæ±ãå ´åã«ãããªã·ã¼ã»æé ãè¨ç»ããä½ç³»ã¨ãªããã¤ã³ã·ãã³ãã¨é©åãªå¯¾å¿
ãé¸ã¶éã®æ±ºå®ããã»ã¹ãææ¸ã«ãããã¨ã¯ãéç¨ç°å¢ã®å¤åã¨ãã観ç¹ããããªã¹ã¯ç®¡çã®ä¸
é¨ã¨ãªã
SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
405
IDENTIFICATION AND AUTHENTICATION - IA
Tailoring Considerations for Identification and Authentication Family
Before implementing controls in the IA family, consider the tradeoffs among security, privacy, latency, performance, and throughput.
For example, the organization considers whether latency induced from the use of authentication mechanisms employing cryptographic
mechanisms would adversely impact the operational performance of the ICS.
In situations where the ICS cannot support the specific Identification and Authentication requirements of a control, the organization
employs compensating controls in accordance with the general tailoring guidance. Examples of compensating controls are given with each
control, as appropriate.
Supplemental Guidance
Supplemental Guidance for all Controls and Control Enhancements in NIST SP 800-53 Rev. 4, Appendix F, should be used in
conjunction with the ICS Supplemental Guidance in this overlay, if any.
IA-1 IDENTIFICATION AND AUTHENTICATION POLICY AND PROCEDURES
CNTL NO. CONTROL NAME
Control Enhancement Name
CONTROL BASELINES
LOW
MOD
HIGH
IA-1
Security Identification and Authentication Policy and Procedures
Selected
Selected
Selected
ICS Supplemental Guidance: The policy specifically addresses the unique properties and requirements of ICS and the relationship
to non-ICS systems.
IA-2 USER IDENTIFICATION AND AUTHENTICATION (ORGANIZATIONAL USERS)
CNTL NO. CONTROL NAME
Control Enhancement Name
CONTROL BASELINES
LOW
MOD
HIGH
IA-2
Identification and Authentication (Organizational Users)
Selected
Selected
Selected
IA-2 (1) IDENTIFICATION AND AUTHENTICATION | NETWORK ACCESS TO
PRIVILEGED ACCOUNTS
Selected Selected Selected
IA-2 (2) IDENTIFICATION AND AUTHENTICATION | NETWORK ACCESS TO
NON-PRIVILEGED ACCOUNTS
Selected Selected
IA-2 (3) IDENTIFICATION AND AUTHENTICATION | LOCAL ACCESS TO
PRIVILEGED ACCOUNTS
Selected Selected
IA-2 (4) IDENTIFICATION AND AUTHENTICATION | LOCAL ACCESS TO NON-
PRIVILEGED ACCOUNTS
Selected
IA-2 (8) IDENTIFICATION AND AUTHENTICATION | NETWORK ACCESS TO
PRIVILEGED ACCOUNTS - REPLAY RESISTANT
Selected Selected
IA-2 (9) IDENTIFICATION AND AUTHENTICATION | NETWORK ACCESS TO
NON-PRIVILEGED ACCOUNTS - REPLAY RESISTANT
Selected
IA-2 (11) IDENTIFICATION AND AUTHENTICATION | REMOTE ACCESS -
SEPARATE DEVICE
Selected Selected
IA-2 (12) IDENTIFICATION AND AUTHENTICATION | ACCEPTANCE OF PIV
CREDENTIALS
Selected Selected Selected
ICS Supplemental Guidance: Where users function as a single group (e.g., control room operators), user identification and
authentication may be role-based, group-based, or device-based. For certain ICS, the capability for immediate operator interaction is critical.
Local emergency actions for ICS are not hampered by identification or authentication requirements. Access to these systems may be
restricted by appropriate physical security controls. Example compensating controls include providing increased physical security, personnel
security, and auditing measures. For example, manual voice authentication of remote personnel and local, manual actions may be required in
order to establish a remote access. See AC-17 ICS Supplemental Guidance. Local user access to ICS components is enabled only when
necessary, approved, and authenticated.
SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
406
èå¥åã³èªè¨¼ - IA
èå¥åã³èªè¨¼ãã¡ããªã®ã«ã¹ã¿ãã¤ãºèæ
®äºé
IA ãã¡ããªã§ç®¡çãå®æ½ããåã«ãã»ãã¥ãªãã£ããã©ã¤ãã·ã¼ãå¾
ã¡æéãããã©ã¼ãã³ã¹ã
ã¹ã«ã¼ããããæ¯è¼èéãããä¾ãã°ãæå·ã¡ã«ããºã ãæ¡ç¨ãã¦èªè¨¼ã¡ã«ããºã ãå©ç¨ããã«
ããçããå¾
ã¡æéããICS ã®éç¨ããã©ã¼ãã³ã¹ãé»å®³ããªããçµç¹ã¯æ¤è¨ããã
ICS ãããå¶å¾¡ã®ç¹å®ã®èå¥ã»èªè¨¼è¦ä»¶ã«å¯¾å¿ãã¦ããªãç¶æ³ã§ã¯ãå
¨ä½çãªã«ã¹ã¿ãã¤ãºã¬ã¤
ãã³ã¹ã«å¾ã£ã¦è£åç管ççãæ¡ç¨ããã
è£åç管ççã®ä¾ãå¿
è¦ã«å¿ãã¦ã管ççãã¨ã«ç¤ºãããã
è£è¶³ã¬ã¤ãã³ã¹
å©ç¨ã§ããå ´åã«ã¯ãNIST SP 800-53 第4çä»é² Fã«ããå
¨ã¦ã®ç®¡çã»ç®¡çæ¡å¼µç¨è£è¶³ã¬ã¤ãã³
ã¹ãããã®ãªã¼ãã¼ã¬ã¤ã«ãã㦠ICS è£è¶³ã¬ã¤ãã³ã¹ã¨ä½µç¨ãã¹ãã§ããã
IA-1 èå¥ã»èªè¨¼ããªã·ã¼ã»æé
管ççªå·
管çå
管çæ¡å¼µå
管çãã¼ã¹ã©ã¤ã³
ä½
ä¸
é«
IA-1
ã»ãã¥ãªãã£èå¥ã»èªè¨¼ããªã·ã¼ã»æé
é¸å®
é¸å®
é¸å®
ICS è£è¶³ã¬ã¤ãã³ã¹ï¼ããªã·ã¼ã¯ç¹ã« ICS ã®åºæã®ç¹æ§ã»è¦ä»¶åã³ ICS 以å¤ã®ã·ã¹ãã ã¨ã®
é¢ä¿ãåãä¸ããã
IA-2 ã¦ã¼ã¶èå¥ã»èªè¨¼ï¼çµç¹ã¦ã¼ã¶ï¼
管ççªå·
管çå
管çæ¡å¼µå
管çãã¼ã¹ã©ã¤ã³
ä½
ä¸
é«
IA-2
èå¥ã»èªè¨¼ï¼çµç¹ã¦ã¼ã¶ï¼
é¸å®
é¸å®
é¸å®
IA-2 (1)
èå¥ã»èªè¨¼
|
ç¹æ¨©ã¢ã«ã¦ã³ãã¸ã®ãããã¯ã¼ã¯ã¢ã¯ã»ã¹
é¸å®
é¸å®
é¸å®
IA-2 (2)
èå¥ã»èªè¨¼
|
ç¹æ¨©ã®ãªãã¢ã«ã¦ã³ãã¸ã®ãããã¯ã¼ã¯ã¢ã¯ã»ã¹
é¸å®
é¸å®
IA-2 (3)
èå¥ã»èªè¨¼
|
ç¹æ¨©ã¢ã«ã¦ã³ãã¸ã®ãã¼ã«ã«ã¢ã¯ã»ã¹
é¸å®
é¸å®
IA-2 (4)
èå¥ã»èªè¨¼
|
ç¹æ¨©ã®ãªãã¢ã«ã¦ã³ãã¸ã®ãã¼ã«ã«ã¢ã¯ã»ã¹
é¸å®
IA-2 (8)
èå¥ã»èªè¨¼
|
ç¹æ¨©ã¢ã«ã¦ã³ãã¸ã®ãããã¯ã¼ã¯ã¢ã¯ã»ã¹
-
ãªãã¬ã¼
æµæ
é¸å® é¸å®
IA-2 (9)
èå¥ã»èªè¨¼
|
ç¹æ¨©ã®ãªãã¢ã«ã¦ã³ãã¸ã®ãããã¯ã¼ã¯ã¢ã¯ã»ã¹
-
ãª
ãã¬ã¼æµæ
é¸å®
IA-2 (11)
èå¥ã»èªè¨¼
|
ãªã¢ã¼ãã¢ã¯ã»ã¹
-
å¥ããã¤ã¹
é¸å®
é¸å®
IA-2 (12)
èå¥ã»èªè¨¼
| PIV
èªè¨¼æ
å ±ã®å諾
é¸å®
é¸å®
é¸å®
ICS è£è¶³ã¬ã¤ãã³ã¹ï¼ã¦ã¼ã¶ã 1ã¤ã®ã°ã«ã¼ãã¨ãã¦æ©è½ããå ´åï¼å¶å¾¡å®¤æä½å¡çï¼ãã¦
ã¼ã¶ã®èå¥åã³èªè¨¼ã¯å½¹å²ãã¼ã¹ãã°ã«ã¼ããã¼ã¹åã¯ããã¤ã¹ãã¼ã¹ã¨ãªãããã種㮠ICS ã§
ã¯ãæä½å¡ã®å³æ対å¿ãç·è¦ã§ãããICS ã®ãã¼ã«ã«ç·æ¥å¯¾å¿ã¯ãèå¥ã»èªè¨¼è¦ä»¶ã«é»å®³ãããª
ãããã®ãããªã·ã¹ãã ã¸ã®ã¢ã¯ã»ã¹ã¯ãé©æ£ãªç©ççã»ãã¥ãªãã£å¯¾çã«ããå¶éãããã
è£åç管ççã®ä¾ã¨ãã¦ãç©ççã»ãã¥ãªãã£ã人çã»ãã¥ãªãã£ãç£æ»æ段ã®å¼·åããããä¾
ãã°ããªã¢ã¼ãã¢ã¯ã»ã¹ã確ç«ããããã«ãé éè·å¡ã®æåé³å£°èªè¨¼åã³ãã¼ã«ã«ã®æå対å¿ã
å¿
è¦ã¨ãªããAC-17 è£è¶³ã¬ã¤ãã³ã¹ãåç
§ãICS ã³ã³ãã¼ãã³ãã¸ã®ãã¼ã«ã«ã¦ã¼ã¶ã¢ã¯ã»ã¹ã¯ã
å¿
è¦æã«æ¿èªã¨æ¨©éãããå ´åã®ã¿è¨±å¯ãããã
SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
407
Control Enhancement: (1, 2, 3, 4) ICS Supplemental Guidance: Example compensating controls include implementing physical
security measures.
Control Enhancement: (8, 9) ICS Supplemental Guidance: Example compensating controls include provide replay-resistance in
an external system.
Control Enhancement: (11) No ICS Supplemental Guidance.
Control Enhancement: (12) ICS Supplemental Guidance: Example compensating controls include implementing support for PIV
external to the ICS.
IA-3 DEVICE IDENTIFICATION AND AUTHENTICATION
CNTL NO. CONTROL NAME
Control Enhancement Name
CONTROL BASELINES
LOW
MOD
HIGH
IA-3
Device Identification and Authentication
Added
Selected
Selected
IA-3 (1) DEVICE IDENTIFICATION AND AUTHENTICATION |
CRYPTOGRAPHIC BIDIRECTIONAL AUTHENTICATION
Added Added
IA-3 (4) DEVICE IDENTIFICATION AND AUTHENTICATION | DEVICE
ATTESTATION
Added Added
ICS Supplemental Guidance: The organization may permit connection of devices, also known as non-person entities (NPE),
belonging to and authorized by another organization (e.g., business partners) to their ICS. Especially when these devices are non-local, their
identification and authentication can be vital. Organizations may perform risk and impact analysis to determine the required strength of
authentication mechanisms. Example compensating controls for devices and protocols which do not provide authentication for remote
network connections, include implementing physical security measures.
Control Enhancement: (1, 4) ICS Supplemental Guidance: Configuration management for NPE identification and authentication
customarily involves a human surrogate or representative for the NPE. Devices are provided with their identification and authentication
credentials based on assertions by the human surrogate. The human surrogate also responds to events and anomalies (e.g., credential
expiration). Credentials for software entities (e.g., autonomous processes not associated with a specific person) based on properties of that
software (e.g., digital signatures) may change every time the software is changed or patched. Special purpose hardware (e.g., custom
integrated circuits and printed-circuit boards) may exhibit similar dependencies. Organization definition of parameters may be different
among the impact levels.
Rationale (applies to control and control enhancements): ICS may exchange information with many external systems and
devices. Identifying and authenticating the devices introduces situations that do not exist with humans. These controls include assignments
that enable the organization to categorize devices by types, models, or other group characteristics. Assignments also enable the organizations
to select appropriate controls for local, remote, and network connections.
IA-4 IDENTIFIER MANAGEMENT
CNTL NO. CONTROL NAME
Control Enhancement Name
CONTROL BASELINES
LOW
MOD
HIGH
IA-4
Identifier Management
Selected
Selected
Selected
No ICS Supplemental Guidance.
SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
408
管çæ¡å¼µï¼(1, 2, 3, 4) ICS è£è¶³ã¬ã¤ãã³ã¹ï¼è£åç管ççã®ä¾ã¨ãã¦ãç©ççã»ãã¥ãªãã£å¯¾
çãããã
管çæ¡å¼µï¼(8, 9) ICS è£è¶³ã¬ã¤ãã³ã¹ï¼è£åç管ççã®ä¾ã¨ãã¦ãå¤é¨ã·ã¹ãã ã¸ã®ãªãã¬ã¼
æµææ§ã®ä»ä¸ãããã
管çæ¡å¼µï¼(11) ICS è£è¶³ã¬ã¤ãã³ã¹ãªã
管çæ¡å¼µï¼(12) ICS è£è¶³ã¬ã¤ãã³ã¹ï¼è£åç管ççã®ä¾ã¨ãã¦ãICS å¤é¨ã«å¯¾ãã PIV 対å¿
ã®å®è£
ãããã
IA-3 ããã¤ã¹èå¥ã»èªè¨¼
管ççªå·
管çå
管çæ¡å¼µå
管çãã¼ã¹ã©ã¤ã³
ä½
ä¸
é«
IA-3
ããã¤ã¹èå¥ã»èªè¨¼
追å
é¸å®
é¸å®
IA-3 (1)
ããã¤ã¹èå¥ã»èªè¨¼
|
æå·ååæ¹åèªè¨¼
追å
追å
IA-3 (4)
ããã¤ã¹èå¥ã»èªè¨¼
|
ããã¤ã¹èªè¨¼
追å
追å
ICS è£è¶³ã¬ã¤ãã³ã¹ï¼çµç¹ã¯ãããã®çµç¹ï¼ææºä¼æ¥çï¼ãæ¿èªãã¦ããä¿æããã¤ã¹ï¼äºº
é以å¤ã®å®ä½[NPE]ã¨ãã¦ãç¥ãããï¼ã«ããèªç¤¾ ICS ã¸ã®æ¥ç¶ãèªããå ´åãããããã®ãã
ãªããã¤ã¹ããã¼ã«ã«ä»¥å¤ã®å ´åãèå¥ã¨èªè¨¼ãéè¦ã¨ãªããçµç¹ã¯ãªã¹ã¯ã»å½±é¿åæãè¡ãã
èªè¨¼ã¡ã«ããºã ã®å¿
è¦å¼·åº¦ãå¤å®ãããé éãããã¯ã¼ã¯æ¥ç¶ã®èªè¨¼ããªãããã¤ã¹åã³ããã
ã³ã«ã«å¯¾ããè£åç管ççã®ä¾ã¨ãã¦ãç©ççã»ãã¥ãªãã£å¯¾çãããã
管çæ¡å¼µï¼(1, 4) ICS è£è¶³ã¬ã¤ãã³ã¹ï¼NEP ã®èå¥ã»èªè¨¼ã«å¯¾ããè¨å®ç®¡çã«ã¯ãé常ã人ç©
ãNEP ã«ä»£ããæ¹æ³ãããã人ç©ã®ä»£çèªè¨¼ãåºã«ãããã¤ã¹ã«èå¥ã»èªè¨¼æ
å ±ãä»ä¸ãããã
人ç©ã®ä»£çã«ãããäºè±¡åã³ç°ç¶äºæ
ã«ã対å¿ããï¼èªè¨¼æ
å ±ã®æéåãçï¼ãã½ããã¦ã¨ã¢ã®
ç¹æ§ï¼ãã¸ã¿ã«ç½²åçï¼ã«åºã¥ãã½ããã¦ã¨ã¢å®ä½ã®èªè¨¼æ
å ±ï¼ç¹å®ã®äººç©ã«é¢é£ã¥ãããã¦ã
ãªãèªå¾ããã»ã¹çï¼ã¯ãã½ããã¦ã¨ã¢ãå¤æ´ãããããããå½ã¦ããããã³ã«å¤ãããç¹æ®ç®
çã®ãã¼ãã¦ã¨ã¢ï¼ã«ã¹ã¿ã IC åºæ¿ãããªã³ãåºæ¿çï¼ã¯ãä¼¼ããããªä¾åæ§ãæã¤ãçµç¹ã®
ãã©ã¡ã¼ã¿å®ç¾©ã¯ãå½±é¿åº¦ã«ããç°ãªãã
çç±ï¼ç®¡çã»ç®¡çæ¡å¼µã«é©ç¨ï¼ï¼ICS ã¯ãå¤æ°ã®å¤é¨ã·ã¹ãã ãããã¤ã¹ã¨æ
å ±äº¤æãè¡ãã
ããã¤ã¹ã®èå¥ã»èªè¨¼ã¯ã人éã§ã¯åå¨ããªãç¶æ³ãçããããã®ãããªç®¡çã«ã¯ãçµç¹ããã
ã¤ã¹ãã¿ã¤ããã¢ãã«ãã®ä»ã°ã«ã¼ãç¹æ§ã§åé¡ããããã®å²å½ãå«ã¾ãããã¾ããã®å²å½ã«ã
ãããã¼ã«ã«æ¥ç¶ãé éæ¥ç¶åã³ãããã¯ã¼ã¯æ¥ç¶ãé¸æãããã¨ãã§ããã
IA-4 èå¥å管ç
管ççªå·
管çå
管çæ¡å¼µå
管çãã¼ã¹ã©ã¤ã³
ä½
ä¸
é«
IA-4
èå¥å管ç
é¸å®
é¸å®
é¸å®
ICS è£è¶³ã¬ã¤ãã³ã¹ãªã
SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
409
IA-5 AUTHENTICATOR MANAGEMENT
CNTL NO. CONTROL NAME
Control Enhancement Name
CONTROL BASELINES
LOW
MOD
HIGH
IA-5
Authenticator Management
Selected
Selected
Selected
IA-5 (1) AUTHENTICATOR MANAGEMENT | PASSWORD-BASED
AUTHENTICATION
Selected Selected Selected
IA-5 (2) AUTHENTICATOR MANAGEMENT | PKI-BASED
AUTHENTICATION
Selected Selected
IA-5 (3) AUTHENTICATOR MANAGEMENT | IN PERSON
REGISTRATION
Selected Selected
IA-5 (11) AUTHENTICATOR MANAGEMENT | HARDWARE TOKEN-
BASED AUTHENTICATION
Selected Selected Selected
ICS Supplemental Guidance: Example compensating controls include physical access control, encapsulating the ICS to provide
authentication external to the ICS.
Control Enhancement: (1, 2, 3, 11) No ICS Supplemental Guidance.
IA-6 AUTHENTICATOR FEEDBACK
CNTL NO. CONTROL NAME
Control Enhancement Name
CONTROL BASELINES
LOW
MOD
HIGH
IA-6
Authenticator Feedback
Selected
Selected
Selected
ICS Supplemental Guidance: This control assumes a visual interface that provides feedback of authentication information during
the authentication process. When ICS authentication uses an interface that does not support visual feedback, (e.g., protocol-based
authentication) this control may be tailored out.
IA-7 CRYPTOGRAPHIC MODULE AUTHENTICATION
CNTL NO. CONTROL NAME
Control Enhancement Name
CONTROL BASELINES
LOW
MOD
HIGH
IA-7
Cryptographic Module Authentication
Selected
Selected
Selected
No ICS Supplemental Guidance.
IA-8 IDENTIFICATION AND AUTHENTICATION (NON-ORGANIZATIONAL USERS)
CNTL NO. CONTROL NAME
Control Enhancement Name
CONTROL BASELINES
LOW
MOD
HIGH
IA-8
Identification and Authentication (Non-Organizational Users)
Selected
Selected
Selected
IA-8 (1) IDENTIFICATION AND AUTHENTICATION (NON-ORGANIZATIONAL
USERS) | ACCEPTANCE OF PIV CREDENTIALS FROM OTHER
AGENCIES
Selected Selected Selected
IA-8 (2) IDENTIFICATION AND AUTHENTICATION (NON-ORGANIZATIONAL
USERS) | ACCEPTANCE OF THIRD-PARTY CREDENTIALS
Selected Selected Selected
IA-8 (3) IDENTIFICATION AND AUTHENTICATION (NON-ORGANIZATIONAL
USERS) | USE OF FICAM-APPROVED PRODUCTS
Selected Selected Selected
IA-8 (4) IDENTIFICATION AND AUTHENTICATION (NON-ORGANIZATIONAL
USERS) | USE OF FICAM-ISSUED PROFILES
Selected Selected Selected
ICS Supplemental Guidance: The ICS Supplemental Guidance for IA-2, Identification and Authentication (Organizational Users),
is applicable for Non- Organizational Users.
Control Enhancement: (1, 2, 3, 4) ICS Supplemental Guidance: Example compensating controls include implementing support
external to the ICS and multi-factor authentication.
SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
410
IA-5 èªè¨¼ã³ã¼ã管ç
管ççªå·
管çå
管çæ¡å¼µå
管çãã¼ã¹ã©ã¤ã³
ä½
ä¸
é«
IA-5
èªè¨¼ã³ã¼ã管ç
é¸å®
é¸å®
é¸å®
IA-5 (1)
èªè¨¼ã³ã¼ã管ç
|
ãã¹ã¯ã¼ããã¼ã¹èªè¨¼
é¸å®
é¸å®
é¸å®
IA-5 (2)
èªè¨¼ã³ã¼ã管ç
| PKI
ãã¼ã¹èªè¨¼
é¸å®
é¸å®
IA-5 (3)
èªè¨¼ã³ã¼ã管ç
|
ç´æ¥ç»é²
é¸å®
é¸å®
IA-5 (11)
èªè¨¼ã³ã¼ã管ç
|
ãã¼ãã¦ã¨ã¢ã®ãã¼ã¯ã³ãã¼ã¹èªè¨¼
é¸å®
é¸å®
é¸å®
ICS è£è¶³ã¬ã¤ãã³ã¹ï¼è£åç管ççã®ä¾ã¨ãã¦ãç©ççã¢ã¯ã»ã¹å¶å¾¡ãICS ã®ã«ãã»ã«åã«
ãã ICS å¤é¨èªè¨¼ãããã
管çæ¡å¼µï¼(1, 2, 3, 11) ICS è£è¶³ã¬ã¤ãã³ã¹ãªã
IA-6 èªè¨¼ã³ã¼ããã£ã¼ãããã¯
管ççªå·
管çå
管çæ¡å¼µå
管çãã¼ã¹ã©ã¤ã³
ä½
ä¸
é«
IA-6
èªè¨¼ãã£ã¼ãããã¯
é¸å®
é¸å®
é¸å®
ICS è£è¶³ã¬ã¤ãã³ã¹ï¼ãã®ç®¡çã¯ãèªè¨¼ä¸ã®èªè¨¼æ
å ±ããã£ã¼ãããã¯ããè¦è¦ã¤ã³ã¿ãã§
ã¼ã¹ãæ³å®ãã¦ãããè¦è¦ãã£ã¼ãããã¯ã«å¯¾å¿ãã¦ããªãã¤ã³ã¿ãã§ã¼ã¹ã®ICS èªè¨¼ã®å ´å
ï¼ãããã³ã«ãã¼ã¹èªè¨¼çï¼ãã«ã¹ã¿ãã¤ãºããã
IA-7 æå·åã¢ã¸ã¥ã¼ã«èªè¨¼
管ççªå·
管çå
管çæ¡å¼µå
管çãã¼ã¹ã©ã¤ã³
ä½
ä¸
é«
IA-7
æå·åã¢ã¸ã¥ã¼ã«èªè¨¼
é¸å®
é¸å®
é¸å®
ICS è£è¶³ã¬ã¤ãã³ã¹ãªã
IA-8 èå¥ã»èªè¨¼(çµç¹å¤ã¦ã¼ã¶)
管ççªå·
管çå
管çæ¡å¼µå
管çãã¼ã¹ã©ã¤ã³
ä½
ä¸
é«
IA-8
èå¥ã»èªè¨¼ï¼çµç¹å¤ã¦ã¼ã¶ï¼
é¸å®
é¸å®
é¸å®
IA-8 (1)
èå¥ã»èªè¨¼ï¼çµç¹
å¤ã¦ã¼ã¶ï¼
|
ä»æ©é¢
PIV
èªè¨¼æ
å ±ã®è¨±è«¾
é¸å®
é¸å®
é¸å®
IA-8 (2)
èå¥ã»èªè¨¼ï¼çµç¹å¤ã¦ã¼ã¶ï¼
|
ãµã¼ããã¼ãã£èªè¨¼æ
å ±ã®è¨±è«¾
é¸å®
é¸å®
é¸å®
IA-8 (3)
èå¥ã»èªè¨¼ï¼çµç¹å¤ã¦ã¼ã¶ï¼
| FICAM
èªå®è£½åã®ä½¿ç¨
é¸å®
é¸å®
é¸å®
IA-8 (4)
èå¥ã»èªè¨¼ï¼çµç¹å¤ã¦ã¼ã¶ï¼
| FICAM
çºè¡ãããã¡ã¤ã«ã®ä½¿ç¨
é¸å®
é¸å®
é¸å®
ICS è£è¶³ã¬ã¤ãã³ã¹ï¼IA-2 èå¥ã»èªè¨¼ã«é¢ãã ICS è£è¶³ã¬ã¤ãã³ã¹ï¼çµç¹ã¦ã¼ã¶ï¼ã¯ãçµç¹
å¤ã¦ã¼ã¶ã«é©ç¨ã§ããã
管çæ¡å¼µï¼(1, 2, 3, 4) ICS è£è¶³ã¬ã¤ãã³ã¹ï¼è£åç管ççã®ä¾ã¨ãã¦ãICS ã®å¤é¨åã³å¤è¦ç´
èªè¨¼ã¸ã®å¯¾å¿å®è£
ãããã
SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
411
INCIDENT RESPONSE - IR
Tailoring Considerations for Incident Response Family
The automated mechanisms used to support the tracking of security incidents are typically not part of, or connected to, the ICS.
Supplemental Guidance
Supplemental Guidance for all Controls and Control Enhancements in NIST SP 800-53 Rev. 4, Appendix F, should be used in conjunction
with the ICS Supplemental Guidance in this overlay, if any.
IR-1 INCIDENT RESPONSE POLICY AND PROCEDURES
CNTL NO. CONTROL NAME
Control Enhancement Name
CONTROL BASELINES
LOW
MOD
HIGH
IR-1
Incident Response Policy and Procedures
Selected
Selected
Selected
ICS Supplemental Guidance: The policy specifically addresses the unique properties and requirements of ICS and the relationship
to non-ICS systems.
IR-2 INCIDENT RESPONSE TRAINING
CNTL NO. CONTROL NAME
Control Enhancement Name
CONTROL BASELINES
LOW
MOD
HIGH
IR-2
Incident Response Training
Selected
Selected
Selected
IR-2 (1)
INCIDENT RESPONSE TRAINING | SIMULATED EVENTS
Selected
IR-2 (2) INCIDENT RESPONSE TRAINING | AUTOMATED TRAINING
ENVIRONMENTS
Selected
No ICS Supplemental Guidance.
IR-3 INCIDENT RESPONSE TESTING
CNTL NO. CONTROL NAME
Control Enhancement Name
CONTROL BASELINES
LOW
MOD
HIGH
IR-3
Incident Response Testing
Selected
Selected
IR-3 (2) INCIDENT RESPONSE TESTING | COORDINATION WITH
RELATED PLANS
Selected Selected
No ICS Supplemental Guidance.
IR-4 INCIDENT HANDLING
CNTL NO. CONTROL NAME
Control Enhancement Name
CONTROL BASELINES
LOW
MOD
HIGH
IR-4
Incident Handling
Selected
Selected
Selected
IR-4 (1) INCIDENT HANDLING | AUTOMATED INCIDENT HANDLING
PROCESSES
Selected Selected
IR-4 (4)
INCIDENT HANDLING | INFORMATION CORRELATION
Selected
No ICS Supplemental Guidance.
SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
412
ã¤ã³ã·ãã³ãå¯¾å¿ - IR
ã¤ã³ã·ãã³ã対å¿ãã¡ããªã®ã«ã¹ã¿ãã¤ãºèæ
®äºé
æ¥ç¶ã¤ã³ã·ãã³ã追跡ç¨ã«ä½¿ç¨ããèªåã¡ã«ããºã ã¯ãé常 ICS ã®ä¸é¨ã§ã¯ãªããICS ã«æ¥ç¶ã
ãã¦ãããªãã
è£è¶³ã¬ã¤ãã³ã¹
å©ç¨ã§ããå ´åã«ã¯ãNIST SP 800-53 第4çä»é² Fã«ããå
¨ã¦ã®ç®¡çã»ç®¡çæ¡å¼µç¨è£è¶³ã¬ã¤ãã³
ã¹ãããã®ãªã¼ãã¼ã¬ã¤ã«ããã¦ãICS è£è¶³ã¬ã¤ãã³ã¹ã¨ä½µç¨ãã¹ãã§ããã
IR-1 ã¤ã³ã·ãã³ã対å¿ããªã·ã¼ã»æé
管ççªå·
管çå
管çæ¡å¼µå
管çãã¼ã¹ã©ã¤ã³
ä½
ä¸
é«
IR-1
ã¤ã³ã·ãã³ã対å¿ããªã·ã¼ã»æé
é¸å®
é¸å®
é¸å®
ICS è£è¶³ã¬ã¤ãã³ã¹ï¼ããªã·ã¼ã¯ç¹ã« ICS ã®åºæã®ç¹æ§ã»è¦ä»¶åã³ ICS 以å¤ã®ã·ã¹ãã ã¨ã®
é¢ä¿ãåãä¸ããã
IR-2 ã¤ã³ã·ãã³ã対å¿è¨ç·´
管ççªå·
管çå
管çæ¡å¼µå
管çãã¼ã¹ã©ã¤ã³
ä½
ä¸
é«
IR-2
ã¤ã³ã·ãã³ã対å¿è¨ç·´
é¸å®
é¸å®
é¸å®
IR-2 (1)
ã¤ã³ã·ãã³ã対å¿è¨ç·´
|
模æ¬äºè±¡
é¸å®
IR-2 (2)
ã¤ã³ã·ãã³ã対å¿è¨
ç·´
|
èªåè¨ç·´ç°å¢
é¸å®
ICS è£è¶³ã¬ã¤ãã³ã¹ãªã
IR-3 ã¤ã³ã·ãã³ã対å¿è©¦é¨
管ççªå·
管çå
管çæ¡å¼µå
管çãã¼ã¹ã©ã¤ã³
ä½
ä¸
é«
IR-3
ã¤ã³ã·ãã³ã対å¿è©¦é¨
é¸å®
é¸å®
IR-3 (2)
ã¤ã³ã·ãã³ã対å¿è¨ç·´
|
é¢é£è¨ç»æ¸ã¨ã®æ´å
é¸å®
é¸å®
ICS è£è¶³ã¬ã¤ãã³ã¹ãªã
IR-4 ã¤ã³ã·ãã³ããã³ããªã³ã°
管ççªå·
管çå
管çæ¡å¼µå
管çãã¼ã¹ã©ã¤ã³
ä½
ä¸
é«
IR-4
ã¤ã³ã·ãã³ãå¦ç
é¸å®
é¸å®
é¸å®
IR-4 (1)
ã¤ã³ã·ãã³ãå¦ç
|
èªåã¤ã³ã·ãã³ãå¦çããã»ã¹
é¸å®
é¸å®
IR-4 (4)
ã¤ã³ã·ãã³ãå¦ç
|
æ
å ±ç¸é¢
é¸å®
ICS è£è¶³ã¬ã¤ãã³ã¹ãªã
SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
413
IR-5 INCIDENT MONITORING
CNTL NO. CONTROL NAME
Control Enhancement Name
CONTROL BASELINES
LOW
MOD
HIGH
IR-5
Incident Monitoring
Selected
Selected
Selected
IR-5 (1) INCIDENT MONITORING | AUTOMATED TRACKING / DATA
COLLECTION / ANALYSIS
Selected
No ICS Supplemental Guidance.
IR-6 INCIDENT REPORTING
CNTL NO. CONTROL NAME
Control Enhancement Name
CONTROL BASELINES
LOW
MOD
HIGH
IR-6
Incident Reporting
Selected
Selected
Selected
IR-6 (1)
INCIDENT REPORTING | AUTOMATED REPORTING
Selected
Selected
ICS Supplemental Guidance: The organization should report incidents on a timely basis. The DHS National Cybersecurity &
Communications Integration Center (NCCIC), http://www.dhs.gov/about-national-cybersecurity-communications-integration-center, serves
as a centralized location where operational elements involved in cybersecurity and communications reliance are coordinated and integrated.
The Industrial Control Systems Cyber Emergency Response Team (ICS-CERT) http://ics-cert.us-cert.gov/ics-cert/, collaborates with
international and private sector Computer Emergency Response Teams (CERTs) to share control systems-related security incidents and
mitigation measures.
Control Enhancement: (1) ICS Supplemental Guidance: The automated mechanisms used to support the incident reporting process are
not necessarily part of, or connected to, the ICS.
IR-7 INCIDENT RESPONSE ASSISTANCE
CNTL NO. CONTROL NAME
Control Enhancement Name
CONTROL BASELINES
LOW
MOD
HIGH
IR-7
Incident Response Assistance
Selected
Selected
Selected
IR-7 (1) INCIDENT RESPONSE ASSISTANCE | AUTOMATION SUPPORT FOR
AVAILABILITY OF INFORMATION / SUPPORT
Selected Selected
No ICS Supplemental Guidance.
IR-8 INCIDENT RESPONSE PLAN
CNTL NO. CONTROL NAME
Control Enhancement Name
CONTROL BASELINES
LOW
MOD
HIGH
IR-8
Incident Response Plan
Selected
Selected
Selected
No ICS Supplemental Guidance.
SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
414
IR-5 ã¤ã³ã·ãã³ãç£è¦
管ççªå·
管çå
管çæ¡å¼µå
管çãã¼ã¹ã©ã¤ã³
ä½
ä¸
é«
IR-5
ã¤ã³ã·ãã³ãç£è¦
é¸å®
é¸å®
é¸å®
IR-5 (1)
ã¤ã³ã·ãã³ãç£è¦
|
èªå追跡ã»ãã¼ã¿åéã»åæ
é¸å®
ICS è£è¶³ã¬ã¤ãã³ã¹ãªã
IR-6 ã¤ã³ã·ãã³ãå ±å
管ççªå·
管çå
管çæ¡å¼µå
管çãã¼ã¹ã©ã¤ã³
ä½
ä¸
é«
IR-6
ã¤ã³ã·ãã³ãå ±å
é¸å®
é¸å®
é¸å®
IR-6 (1)
ã¤ã³ã·ãã³ãå ±å
|
èªåå ±å
é¸å®
é¸å®
ICS è£è¶³ã¬ã¤ãã³ã¹ï¼çµç¹ã¯ãã¿ã¤ã ãªã¼ã«ã¤ã³ã·ãã³ãå ±åãè¡ãã¹ãã§ãããä¸è¨ DHS
å½å®¶ãµã¤ãã¼ã»ãã¥ãªãã£éä¿¡çµ±åã»ã³ã¿ã¼(NCCIC)ã¯éä¸æå¨å°ã¨ãã¦æ©è½ãããµã¤ãã¼ã»ã
ã¥ãªãã£ã¨éä¿¡ã®ä¿¡é ¼æ§ã«é¢ããéç¨é¨ç½²ã¯ããã§èª¿æ´ãããçµ±ååããã¦ããã
http://www.dhs.gov/about-national-cybersecurity-communications-integration-center
ä¸è¨ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ãµã¤ãã¼ç·æ¥å¯¾å¿ãã¼ã (ICS-CERT)ã¯ãæµ·å¤åã³æ°éã®ã³ã³ãã¥ã¼ã¿ç·
æ¥å¯¾å¿ãã¼ã (CERT)ã¨é£æºãã¦ãå¶å¾¡ã·ã¹ãã é¢é£ã»ãã¥ãªãã£ã¤ã³ã·ãã³ãæ
å ±ã¨ç·©å対ç
ãå
±æãã¦ãããhttp://ics-cert.us-cert.gov/ics-cert/
管çæ¡å¼µï¼(1) ICS è£è¶³ã¬ã¤ãã³ã¹ï¼ã¤ã³ã·ãã³ãå ±åããã»ã¹ã¸ã®å¯¾å¿ã«ä½¿ç¨ããèªåã¡ã«
ããºã ã¯ãå¿
ããã ICS ã®ä¸é¨ã§ã¯ãªããICS ã«æ¥ç¶ããã¦ããããã§ã¯ãªãã
IR-7 ã¤ã³ã·ãã³ã対å¿æ¯æ´
管ççªå·
管çå
管çæ¡å¼µå
管çãã¼ã¹ã©ã¤ã³
ä½
ä¸
é«
IR-7
ã¤ã³ã·ãã³ã対å¿æ¯æ´
é¸å®
é¸å®
é¸å®
IR-7 (1)
ã¤ã³ã·ãã³ã対å¿æ¯æ´
|
æ
å ±ã»ãµãã¼ãå¯ç¨æ§ã¸ã®èªå対å¿
é¸å®
é¸å®
ICS è£è¶³ã¬ã¤ãã³ã¹ãªã
IR-8 ã¤ã³ã·ãã³ã対å¿è¨ç»
管ççªå·
管çå
管çæ¡å¼µå
管çãã¼ã¹ã©ã¤ã³
ä½
ä¸
é«
IR-8
ã¤ã³ã·ãã³ã対å¿è¨ç»æ¸
é¸å®
é¸å®
é¸å®
ICS è£è¶³ã¬ã¤ãã³ã¹ãªã
SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
415
MAINTENANCE - MA
Tailoring Considerations for Maintenance Family
The automated mechanisms used to schedule, conduct, and document maintenance and repairs are not necessarily part of, or connected to,
the ICS.
In situations where the ICS cannot support the specific Maintenance requirements of a control, the organization employs compensating
controls in accordance with the general tailoring guidance. Examples of compensating controls are given with each control, as appropriate.
Supplemental Guidance
Supplemental Guidance for all Controls and Control Enhancements in NISTSP 800-53 Rev. 4, Appendix F, should be used in conjunction
with the ICS Supplemental Guidance in this overlay, if any.
MA-1 SYSTEM MAINTENANCE POLICY AND PROCEDURES
CNTL NO. CONTROL NAME
Control Enhancement Name
CONTROL BASELINES
LOW
MOD
HIGH
MA-1
Maintenance Policy and Procedures
Selected
Selected
Selected
ICS Supplemental Guidance: The policy specifically addresses the unique properties and requirements of ICS and the relationship
to non-ICS systems.
MA-2 CONTROLLED MAINTENANCE
CNTL NO. CONTROL NAME
Control Enhancement Name
CONTROL BASELINES
LOW
MOD
HIGH
MA-2
Controlled Maintenance
Selected
Selected
Selected
MA-2 (2) CONTROLLED MAINTENANCE | AUTOMATED MAINTENANCE
ACTIVITIES
Selected
No ICS Supplemental Guidance.
MA-3 MAINTENANCE TOOLS
CNTL NO. CONTROL NAME
Control Enhancement Name
CONTROL BASELINES
LOW
MOD
HIGH
MA-3
Maintenance Tools
Selected
Selected
MA-3 (1)
MAINTENANCE TOOLS | INSPECT TOOLS
Selected
Selected
MA-3 (2)
MAINTENANCE TOOLS | INSPECT MEDIA
Selected
Selected
MA-3 (3) MAINTENANCE TOOLS | PREVENT UNAUTHORIZED
REMOVAL
Selected
No ICS Supplemental Guidance.
SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
416
ä¿å® - MA
ä¿å®ãã¡ããªã®ã«ã¹ã¿ãã¤ãºèæ
®äºé
ä¿å®ã»ä¿®çã®äºå®ä½æãå®æ½åã³ææ¸åã«ä½¿ç¨ããèªåã¡ã«ããºã ã¯ãå¿
ããã ICS ã®ä¸é¨ã§ã¯
ãªããICS ã«æ¥ç¶ããã¦ããããã§ã¯ãªãã
ICS ãããå¶å¾¡ã®ç¹å®ã®ä¿å®è¦ä»¶ã«å¯¾å¿ãã¦ããªãç¶æ³ã§ã¯ãå
¨ä½çãªã«ã¹ã¿ãã¤ãºã¬ã¤ãã³ã¹
ã«å¾ã£ã¦è£åç管ççãæ¡ç¨ãããè£åç管ççã®ä¾ãå¿
è¦ã«å¿ãã¦ã管ççãã¨ã«ç¤ºãããã
è£è¶³ã¬ã¤ãã³ã¹
å©ç¨ã§ããå ´åã«ã¯ãNIST SP 800-53 第4çä»é² Fã«ããå
¨ã¦ã®ç®¡çã»ç®¡çæ¡å¼µç¨è£è¶³ã¬ã¤ãã³
ã¹ãããã®ãªã¼ãã¼ã¬ã¤ã«ããã¦ãICS è£è¶³ã¬ã¤ãã³ã¹ã¨ä½µç¨ãã¹ãã§ããã
MA-1 ã·ã¹ãã ä¿å®ããªã·ã¼ã»æé
管ççªå·
管çå
管çæ¡å¼µå
管çãã¼ã¹ã©ã¤ã³
ä½
ä¸
é«
MA-1
ä¿å®ããªã·ã¼ã»æé
é¸å®
é¸å®
é¸å®
ICS è£è¶³ã¬ã¤ãã³ã¹ï¼ããªã·ã¼ã¯ç¹ã« ICS ã®åºæã®ç¹æ§ã»è¦ä»¶åã³ ICS 以å¤ã®ã·ã¹ãã ã¨ã®
é¢ä¿ãåãä¸ããã
MA-2 管çä¿å®
管ççªå·
管çå
管çæ¡å¼µå
管çãã¼ã¹ã©ã¤ã³
ä½
ä¸
é«
MA-2
管çä¿å®
é¸å®
é¸å®
é¸å®
MA-2 (2)
管çä¿å®
|
èªåä¿å®æ´»å
é¸å®
ICS è£è¶³ã¬ã¤ãã³ã¹ãªã
MA-3 ä¿å®ãã¼ã«
管ççªå·
管çå
管çæ¡å¼µå
管çãã¼ã¹ã©ã¤ã³
ä½
ä¸
é«
MA-3
ä¿å®ãã¼ã«
é¸å®
é¸å®
MA-3 (1)
ä¿å®ãã¼ã«
|
æ¤æ»ãã¼ã«
é¸å®
é¸å®
MA-3 (2)
ä¿å®ãã¼ã«
|
æ¤æ»åªä½
é¸å®
é¸å®
MA-3 (3)
ä¿å®ãã¼ã«
|
ç¡æåé¤é²æ¢
é¸å®
ICS è£è¶³ã¬ã¤ãã³ã¹ãªã
SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
417
MA-4 NONLOCAL MAINTENANCE
CNTL NO. CONTROL NAME
Control Enhancement Name
CONTROL BASELINES
LOW
MOD
HIGH
MA-4
Non-Local Maintenance
Selected
Selected
Selected
MA-4 (2) NON-LOCAL MAINTENANCE | DOCUMENT NON-LOCAL
MAINTENANCE
Selected Selected
MA-4 (3) NON-LOCAL MAINTENANCE | COMPARABLE SECURITY /
SANITIZATION
Selected
No ICS Supplemental Guidance.
Control Enhancement: (2) No ICS Supplemental Guidance.
Control Enhancement: (3) ICS Supplemental Guidance: In crisis or emergency situations, the organization may need immediate
access to non-local maintenance and diagnostic services in order to restore essential ICS operations or services. Example compensating
controls include limiting the extent of the maintenance and diagnostic services to the minimum essential activities, carefully monitoring and
auditing the non-local maintenance and diagnostic activities.
MA-5 MAINTENANCE PERSONNEL
CNTL NO. CONTROL NAME
Control Enhancement Name
CONTROL BASELINES
LOW
MOD
HIGH
MA-5
Maintenance Personnel
Selected
Selected
Selected
MA-5 (1) MAINTENANCE PERSONNEL | INDIVIDUALS WITHOUT
APPROPRIATE ACCESS
Selected
No ICS Supplemental Guidance.
MA-6 TIMELY MAINTENANCE
CNTL NO. CONTROL NAME
Control Enhancement Name
CONTROL BASELINES
LOW
MOD
HIGH
MA-6
Timely Maintenance
Selected
Selected
No ICS Supplemental Guidance.
SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
418
MA-4 éãã¼ã«ã«ä¿å®
管ççªå·
管çå
管çæ¡å¼µå
管çãã¼ã¹ã©ã¤ã³
ä½
ä¸
é«
MA-4
éãã¼ã«ã«ä¿å®
é¸å®
é¸å®
é¸å®
MA-4 (2)
éãã¼ã«ã«ä¿å®
| éãã¼ã«ã«ä¿å®
ã®ææ¸å
é¸å®
é¸å®
MA-4 (3)
éãã¼ã«ã«ä¿å®
|
åçã»ãã¥ãªãã£ã»ãµãã¿ã¤ãº
é¸å®
ICS è£è¶³ã¬ã¤ãã³ã¹ãªã
管çæ¡å¼µï¼(2) ICS è£è¶³ã¬ã¤ãã³ã¹ãªã
管çæ¡å¼µï¼(3) ICS è£è¶³ã¬ã¤ãã³ã¹ï¼å±æ©åã¯ç·æ¥äºæ
ã«ã¯ãéè¦ ICS éç¨åã¯ãµã¼ãã¹ã復
æ§ãããããçµç¹ã¯éãã¼ã«ã«ä¿å®åã³è¨ºæãµã¼ãã¹ãç´ã¡ã«å©ç¨ããå¿
è¦ããããè£åç管ç
çã®ä¾ã¨ãã¦ãä¿å®åã³è¨ºæãµã¼ãã¹ãæä½éå¿
è¦ãªç¨åº¦ã«éå®ããéãã¼ã«ã«ä¿å®åã³è¨ºææ´»
åãæ
éã«ç£è¦ã»ç£æ»ããã
MA-5 ä¿å®è¦å¡
管ççªå·
管çå
管çæ¡å¼µå
管çãã¼ã¹ã©ã¤ã³
ä½
ä¸
é«
MA-5
ä¿å®è¦å¡
é¸å®
é¸å®
é¸å®
MA-5 (1)
ä¿å®è¦å¡
|
é©æ§ã¢ã¯ã»ã¹ä»¥å¤ã®å人
é¸å®
ICS è£è¶³ã¬ã¤ãã³ã¹ãªã
MA-6 é©æçä¿å®
管ççªå·
管çå
管çæ¡å¼µå
管çãã¼ã¹ã©ã¤ã³
ä½
ä¸
é«
MA-6
é©æçä¿å®
é¸å®
é¸å®
ICS è£è¶³ã¬ã¤ãã³ã¹ãªã
SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
419
MEDIA PROTECTION âMP
Supplemental Guidance
Supplemental Guidance for all Controls and Control Enhancements in NIST SP 800-53 Rev. 4, Appendix F, should be used in conjunction
with the ICS Supplemental Guidance in this overlay, if any.
MP-1 MEDIA PROTECTION POLICY AND PROCEDURES
CNTL NO. CONTROL NAME
Control Enhancement Name
CONTROL BASELINES
LOW
MOD
HIGH
MP-1
Media Protection Policy and Procedures
Selected
Selected
Selected
ICS Supplemental Guidance: The policy specifically addresses the unique properties and requirements of ICS and the relationship
to non-ICS systems.
MP-2 MEDIA ACCESS
CNTL NO. CONTROL NAME
Control Enhancement Name
CONTROL BASELINES
LOW
MOD
HIGH
MP-2
Media Access
Selected
Selected
Selected
No ICS Supplemental Guidance.
MP-3 MEDIA MARKING
CNTL NO. CONTROL NAME
Control Enhancement Name
CONTROL BASELINES
LOW
MOD
HIGH
MP-3
Media Marking
Selected
Selected
No ICS Supplemental Guidance.
MP-4 MEDIA STORAGE
CNTL NO. CONTROL NAME
Control Enhancement Name
CONTROL BASELINES
LOW
MOD
HIGH
MP-4
Media Storage
Selected
Selected
No ICS Supplemental Guidance.
MP-5 MEDIA TRANSPORT
CNTL NO. CONTROL NAME
Control Enhancement Name
CONTROL BASELINES
LOW
MOD
HIGH
MP-5
Media Transport
Selected
Selected
MP-5 (4)
MEDIA TRANSPORT | CRYPTOGRAPHIC PROTECTION
Selected
Selected
No ICS Supplemental Guidance.
SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
420
ã¡ãã£ã¢ä¿è· âMP
è£è¶³ã¬ã¤ãã³ã¹
å©ç¨ã§ããå ´åã«ã¯ãNIST SP 800-53 第4çä»é² Fã«ããå
¨ã¦ã®ç®¡çã»ç®¡çæ¡å¼µç¨è£è¶³ã¬ã¤ãã³
ã¹ãããã®ãªã¼ãã¼ã¬ã¤ã«ããã¦ãICS è£è¶³ã¬ã¤ãã³ã¹ã¨ä½µç¨ãã¹ãã§ããã
MP-1 ã¡ãã£ã¢ä¿è·ããªã·ã¼ã»æé
管ççªå·
管çå
管çæ¡å¼µå
管çãã¼ã¹ã©ã¤ã³
ä½
ä¸
é«
MP-1
ã¡ãã£ã¢ä¿è·ããªã·ã¼ã»æé
é¸å®
é¸å®
é¸å®
ICS è£è¶³ã¬ã¤ãã³ã¹ï¼ããªã·ã¼ã¯ç¹ã« ICS ã®åºæã®ç¹æ§ã»è¦ä»¶åã³ ICS 以å¤ã®ã·ã¹ãã ã¨ã®
é¢ä¿ãåãä¸ããã
MP-2 ã¡ãã£ã¢ã¢ã¯ã»ã¹
管ççªå·
管çå
管çæ¡å¼µå
管çãã¼ã¹ã©ã¤ã³
ä½
ä¸
é«
MP-2
ã¡ãã£ã¢ã¢ã¯ã»ã¹
é¸å®
é¸å®
é¸å®
ICS è£è¶³ã¬ã¤ãã³ã¹ãªã
MP-3 ã¡ãã£ã¢ãã¼ãã³ã°
管ççªå·
管çå
管çæ¡å¼µå
管çãã¼ã¹ã©ã¤ã³
ä½
ä¸
é«
MP-3
ã¡ãã£ã¢ãã¼ãã³ã°
é¸å®
é¸å®
ICS è£è¶³ã¬ã¤ãã³ã¹ãªã
MP-4 ã¡ãã£ã¢ã¹ãã¬ã¼ã¸
管ççªå·
管çå
管çæ¡å¼µå
管çãã¼ã¹ã©ã¤ã³
ä½
ä¸
é«
MP-4
ã¡ãã£ã¢ã¹ãã¬ã¼ã¸
é¸å®
é¸å®
ICS è£è¶³ã¬ã¤ãã³ã¹ãªã
MP-5 ã¡ãã£ã¢è»¢é
管ççªå·
管çå
管çæ¡å¼µå
管çãã¼ã¹ã©ã¤ã³
ä½
ä¸
é«
MP-5
ã¡ãã£ã¢è»¢é
é¸å®
é¸å®
MP-5 (4)
ã¡ãã£ã¢è»¢é
|
æå·åä¿è·
é¸å®
é¸å®
ICS è£è¶³ã¬ã¤ãã³ã¹ãªã
SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
421
MP-6 MEDIA SANITIZATION
CNTL NO. CONTROL NAME
Control Enhancement Name
CONTROL BASELINES
LOW
MOD
HIGH
MP-6
Media Sanitization
Selected
Selected
Selected
MP-6 (1) MEDIA SANITIZATION | TRACKING / DOCUMENTING /
VERIFYING
Selected
MP-6 (2)
MEDIA SANITIZATION | EQUIPMENT TESTING
Selected
MP-6 (3)
MEDIA SANITIZATION | NON-DESTRUCTIVE TECHNIQUES
Selected
No ICS Supplemental Guidance.
MP-7 MEDIA USE
CNTL NO. CONTROL NAME
Control Enhancement Name
CONTROL BASELINES
LOW
MOD
HIGH
MP-7
Media Use
Selected
Selected
Selected
MP-7 (1)
MEDIA USE | ORGANIZATIONAL RESTRICTIONS
Selected
Selected
No ICS Supplemental Guidance.
SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
422
MP-6 ã¡ãã£ã¢ãµãã¿ã¤ãº
管ççªå·
管çå
管çæ¡å¼µå
管çãã¼ã¹ã©ã¤ã³
ä½
ä¸
é«
MP-6
ã¡ãã£ã¢ãµãã¿ã¤ãº
é¸å®
é¸å®
é¸å®
MP-6 (1)
ã¡ãã£ã¢ãµãã¿ã¤ãº
|
追跡ã»ææ¸åã»æ¤è¨¼
é¸å®
MP-6 (2)
ã¡ãã£ã¢ãµãã¿ã¤ãº
|
è£
åå試é¨
é¸å®
MP-6 (3)
ã¡ãã£ã¢ãµãã¿ã¤ãº
|
éç ´å£æè¡
é¸å®
ICS è£è¶³ã¬ã¤ãã³ã¹ãªã
MP-7 ã¡ãã£ã¢å©ç¨
管ççªå·
管çå
管çæ¡å¼µå
管çãã¼ã¹ã©ã¤ã³
ä½
ä¸
é«
MP-7
ã¡ãã£ã¢å©ç¨
é¸å®
é¸å®
é¸å®
MP-7 (1)
ã¡ãã£ã¢å©ç¨
|
çµç¹ä¸ã®å¶é
é¸å®
é¸å®
ICS è£è¶³ã¬ã¤ãã³ã¹ãªã
SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
423
PHYSICAL AND ENVIRONMENTAL PROTECTION â PE
Supplemental Guidance
Supplemental Guidance for all Controls and Control Enhancements in NIST SP 800-53 Rev. 4, Appendix F, should be used in
conjunction with the ICS Supplemental Guidance in this overlay, if any.
PE-1 PHYSICAL AND ENVIRONMENTAL PROTECTION POLICY AND PROCEDURES
CNTL NO. CONTROL NAME
Control Enhancement Name
CONTROL BASELINES
LOW
MOD
HIGH
PE-1
Physical and Environmental Protection Policy and Procedures
Selected
Selected
Selected
ICS Supplemental Guidance: The policy specifically addresses the unique properties and requirements of ICS and the relationship
to non-ICS systems. The ICS components can be distributed over a large facility footprint or geographic area and can be an entry point into
the entire organizational network ICS. Regulatory controls may also apply.
PE-2 PHYSICAL ACCESS AUTHORIZATIONS
CNTL NO. CONTROL NAME
Control Enhancement Name
CONTROL BASELINES
LOW
MOD
HIGH
PE-2
Physical Access Authorizations
Selected
Selected
Selected
No ICS Supplemental Guidance.
PE-3 PHYSICAL ACCESS CONTROL
CNTL NO. CONTROL NAME
Control Enhancement Name
CONTROL BASELINES
LOW
MOD
HIGH
PE-3
Physical Access Control
Selected
Selected
Selected
PE-3 (1) PHYSICAL ACCESS CONTROL | INFORMATION SYSTEM
ACCESS
Selected
ICS Supplemental Guidance: The organization considers ICS safety and security interdependencies. The organization considers
access requirements in emergency situations. During an emergency-related event, the organization may restrict access to ICS facilities and
assets to authorized individuals only. ICS are often constructed of devices that either do not have or cannot use comprehensive access control
capabilities due to time-restrictive safety constraints. Physical access controls and defense-in-depth measures are used by the organization
when necessary and possible to supplement ICS security when electronic mechanisms are unable to fulfill the security requirements of the
organizationâs security plan. Primary nodes, distribution closets, and mechanical/electrical rooms should be locked and require key or
electronic access control and incorporate intrusion detection sensors.
Control Enhancement: (1) No ICS Supplemental Guidance.
PE-4 ACCESS CONTROL FOR TRANSMISSION MEDIUM
CNTL NO. CONTROL NAME
Control Enhancement Name
CONTROL BASELINES
LOW
MOD
HIGH
PE-4
Access Control for Transmission Medium
Selected
Selected
No ICS Supplemental Guidance.
SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
424
ç©ççç°å¢çä¿è· â PE
è£è¶³ã¬ã¤ãã³ã¹
å©ç¨ã§ããå ´åã«ã¯ãNIST SP 800-53 第4çä»é² Fã«ããå
¨ã¦ã®ç®¡çã»ç®¡çæ¡å¼µç¨è£è¶³ã¬ã¤ãã³
ã¹ãããã®ãªã¼ãã¼ã¬ã¤ã«ããã¦ãICS è£è¶³ã¬ã¤ãã³ã¹ã¨ä½µç¨ãã¹ãã§ããã
PE-1 ç©ççç°å¢çä¿è·ããªã·ã¼ã»æé
管ççªå·
管çå
管çæ¡å¼µå
管çãã¼ã¹ã©ã¤ã³
ä½
ä¸
é«
PE-1
ç©çç°å¢ä¿è·ããªã·ã¼ã»æé
é¸å®
é¸å®
é¸å®
ICS è£è¶³ã¬ã¤ãã³ã¹ï¼ããªã·ã¼ã¯ç¹ã« ICS ã®åºæã®ç¹æ§ã»è¦ä»¶åã³ ICS 以å¤ã®ã·ã¹ãã ã¨ã®
é¢ä¿ãåãä¸ãããICS ã³ã³ãã¼ãã³ãã¯ãåºç¯ãªæ½è¨åã³å°åã«ã¾ããã£ã¦åæ£ãã¦ãããçµ
ç¹ã® ICS ãããã¯ã¼ã¯ã¸ã®å
¥å£ã«ãªã£ã¦ããå ´åããããè¦å¶ç®¡çãé©ç¨ã§ãããã
PE-2 ç©ççã¢ã¯ã»ã¹æ¨©é
管ççªå·
管çå
管çæ¡å¼µå
管çãã¼ã¹ã©ã¤ã³
ä½
ä¸
é«
PE-2
ç©ççã¢ã¯ã»ã¹æ¨©é
é¸å®
é¸å®
é¸å®
ICS è£è¶³ã¬ã¤ãã³ã¹ãªã
PE-3 ç©ççã¢ã¯ã»ã¹å¶å¾¡
管ççªå·
管çå
管çæ¡å¼µå
管çãã¼ã¹ã©ã¤ã³
ä½
ä¸
é«
PE-3
ç©ççã¢ã¯ã»ã¹å¶å¾¡
é¸å®
é¸å®
é¸å®
PE-3 (1)
ç©çç
ã¢ã¯ã»ã¹å¶å¾¡
|
æ
å ±ã·ã¹ãã ã¢ã¯ã»ã¹
é¸å®
ICS è£è¶³ã¬ã¤ãã³ã¹ï¼çµç¹ã¯ ICS ã®å®å
¨æ§ã¨ã»ãã¥ãªãã£ã®ç¸äºé¢ä¿ãæ¤è¨ãããçµç¹ã¯ã
ç·æ¥ç¶æ³ä¸ã§ã®ã¢ã¯ã»ã¹è¦ä»¶ãæ¤è¨ãããç·æ¥é¢é£äºè±¡ãçºçããå ´åãçµç¹ã¯ ICS æ½è¨åã³è³
ç£ã¸ã®ã¢ã¯ã»ã¹ã権éã®ãã人ç©ã ãã«å¶éãããICS ã¯ãæéçãªå¶ç´ããå®å
¨æ§ã«éçãã
ããããå
æ¬çãªã¢ã¯ã»ã¹å¶å¾¡è½åããªããå©ç¨ã§ããªãããã¤ã¹ã§æ§æããã¦ãããã¨ãå¤ãã
é»åçã¡ã«ããºã ã§ã¯çµç¹ã®ã»ãã¥ãªãã£è¨ç»æ¸è¦ä»¶ã«æºããªãå ´åãICS ã»ãã¥ãªãã£ã«ã¨ã£
ã¦å¿
è¦ãã¤è£è¶³å¯è½ã§ããã°ãç©ççã¢ã¯ã»ã¹å¶å¾¡åã³å¤å±¤é²å¾¡å¯¾çãæ¡ç¨ããã主è¦ãã¼ãã
é
é»ã¯ãã¼ã¼ããåã³æ©æ¢°ã»é»æ°å®¤ã¯æ½é ããéµåã¯é»åçæ段ã§ã¢ã¯ã»ã¹å¶å¾¡ããä¾µå
¥æ¤ç¥ã»
ã³ãµãåãä»ããã
管çæ¡å¼µï¼(1) ICS è£è¶³ã¬ã¤ãã³ã¹ãªã
PE-4 éä¿¡ã¡ãã£ã¢ã®ã¢ã¯ã»ã¹å¶å¾¡
管ççªå·
管çå
管çæ¡å¼µå
管çãã¼ã¹ã©ã¤ã³
ä½
ä¸
é«
PE-4
éä¿¡ã¡ãã£ã¢ã®ã¢ã¯ã»ã¹å¶å¾¡
é¸å®
é¸å®
ICS è£è¶³ã¬ã¤ãã³ã¹ãªã
SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
425
PE-5 ACCESS CONTROL FOR OUTPUT DEVICES
CNTL NO. CONTROL NAME
Control Enhancement Name
CONTROL BASELINES
LOW
MOD
HIGH
PE-5
Access Control for Output Devices
Selected
Selected
No ICS Supplemental Guidance.
PE-6 MONITORING PHYSICAL ACCESS
CNTL NO. CONTROL NAME
Control Enhancement Name
CONTROL BASELINES
LOW
MOD
HIGH
PE-6
Monitoring Physical Access
Selected
Selected
Selected
PE-6 (1) MONITORING PHYSICAL ACCESS | INTRUSION ALARMS /
SURVEILLANCE EQUIPMENT
Selected Selected
PE-6 (4) MONITORING PHYSICAL ACCESS | MONITORING PHYSICAL
ACCESS TO INFORMATION SYSTEMS
Added Selected
ICS Supplemental Guidance: Physical access controls and defense-in-depth measures are used as compensating controls by the
organization when necessary and possible to supplement ICS security when electronic mechanisms are unable to monitor, detect and alarm
when an ICS has been accessed. These compensating controls are in addition to the PE-6 controls (e.g., employing PE-3(4) Lockable Casings
and/or PE-3(5) Tamper Protection).
Control Enhancement: (1) No ICS Supplemental Guidance.
Control Enhancement: (4) ICS Supplemental Guidance: The locations of ICS components (e.g., field devices, remote terminal
units) can include various remote locations (e.g., substations, pumping stations).
Rationale (adding CE 4 to MODERATE baseline): Many of the ICS components are in remote geographical and dispersed
locations with little capability to monitor all ICS components. Other components may be in ceilings, floors, or distribution closets with
minimal physical barriers to detect, delay or deny access to the devices and no electronic surveillance or guard forces response capability.
PE-8 VISITOR ACCESS RECORDS
CNTL NO. CONTROL NAME
Control Enhancement Name
CONTROL BASELINES
LOW
MOD
HIGH
PE-8
Visitor Access Records
Selected
Selected
Selected
PE-8 (1) VISITOR ACCESS RECORDS | AUTOMATED RECORDS
MAINTENANCE / REVIEW
Selected
No ICS Supplemental Guidance.
PE-9 POWER EQUIPMENT AND CABLING
CNTL NO. CONTROL NAME
Control Enhancement Name
CONTROL BASELINES
LOW
MOD
HIGH
PE-9
Power Equipment and Cabling
Selected
Selected
PE-9 (1)
POWER EQUIPMENT AND CABLING | REDUNDANT CABLING
Added
Added
No ICS Supplemental Guidance.
Control Enhancement: (1) No ICS Supplemental Guidance.
Rationale (for adding (1): Continuity of ICS control and operation requires redundant power cabling.
SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
426
PE-5 åºåããã¤ã¹ã®ã¢ã¯ã»ã¹å¶å¾¡
管ççªå·
管çå
管çæ¡å¼µå
管çãã¼ã¹ã©ã¤ã³
ä½
ä¸
é«
PE-5
åºåããã¤ã¹ã®ã¢ã¯ã»ã¹å¶å¾¡
é¸å®
é¸å®
ICS è£è¶³ã¬ã¤ãã³ã¹ãªã
PE-6 ç©ççã¢ã¯ã»ã¹ç£è¦
管ççªå·
管çå
管çæ¡å¼µå
管çãã¼ã¹ã©ã¤ã³
ä½
ä¸
é«
PE-6
ç©ççã¢ã¯ã»ã¹ç£è¦
é¸å®
é¸å®
é¸å®
PE-6 (1)
ç©ççã¢ã¯ã»ã¹ç£è¦
|
ä¾µå
¥ã¢ã©ã¼ã ã»ãµã¼ãã¤ã©ã³ã¹è£
ç½®
é¸å®
é¸å®
PE-6 (4)
ç©ççã¢ã¯ã»ã¹ç£è¦
|
æ
å ±ã·ã¹ãã ã¸ã®ç©ççã¢ã¯ã»ã¹ç£è¦
追å
é¸å®
ICS è£è¶³ã¬ã¤ãã³ã¹ï¼é»åçã¡ã«ããºã ã§ã¯ ICS ã¸ã®ã¢ã¯ã»ã¹ãç£è¦ã»æ¤ç¥ã»è¦å ±ã§ããªã
å ´åãICS ã»ãã¥ãªãã£ã«ã¨ã£ã¦å¿
è¦ãã¤è£è¶³å¯è½ã§ããã°ãç©ççã¢ã¯ã»ã¹å¶å¾¡åã³å¤å±¤é²å¾¡
対çãè£åç管ççã¨ãã¦æ¡ç¨ããããã®ãããªè£åç管ççã¯ãPE-6 管çãè£è¶³ãããã®ã¨ãª
ãï¼PE-3(4)æ½é å¯è½é庫å㯠PE-3(5)æ¹ç«é²æ¢ï¼ã
管çæ¡å¼µï¼(1) ICS è£è¶³ã¬ã¤ãã³ã¹ãªã
管çæ¡å¼µï¼(4) ICS è£è¶³ã¬ã¤ãã³ã¹ï¼ICS ã³ã³ãã¼ãã³ãï¼ãã£ã¼ã«ãããã¤ã¹ãé é端æ«è£
ç½®çï¼ã®å ´æã«ã¯ãæ§ã
ãªé éå°ãå«ã¾ããï¼å¤é»æããã³ãã¹ãã¼ã·ã§ã³çï¼ã
çç±ï¼CE 4 ãä¸ãã¼ã¹ã©ã¤ã³ã«è¿½å ï¼ï¼ICS ã³ã³ãã¼ãã³ãã®å¤ãã¯é éå°ã«ç¹å¨ãã¦ãã
ããããã¹ã¦ãç£è¦ãããã¨ã¯ã»ã¼ä¸å¯è½ã§ããã天äºãåºåã³é
é»ã¯ãã¼ã¼ããã«é
ç½®ããã¦
ãããã®ããããã¢ã¯ã»ã¹ãæ¤ç¥ã»é
延ã»é²æ¢ããç©ççéå£ã¯ä¹ãããé»åçãµã¼ãã¤ã©ã³ã¹
ãè¦åå¡çã®åãããªãã
PE-8 æ¥è¨ªè
ç«å
¥è¨é²
管ççªå·
管çå
管çæ¡å¼µå
管çãã¼ã¹ã©ã¤ã³
ä½
ä¸
é«
PE-8
æ¥è¨ªè
ç«å
¥è¨é²
é¸å®
é¸å®
é¸å®
PE-8 (1)
æ¥è¨ªè
ç«å
¥è¨é²
|
èªåè¨é²ä¿å®
è¦ç´ã
é¸å®
ICS è£è¶³ã¬ã¤ãã³ã¹ãªã
PE-9 é»æ°è£
ç½®åã³é
ç·
管ççªå·
管çå
管çæ¡å¼µå
管çãã¼ã¹ã©ã¤ã³
ä½
ä¸
é«
PE-9
é»æ°è£
ç½®åã³é
ç·
é¸å®
é¸å®
PE-9 (1)
é»æ°è£
ç½®åã³é
ç·
|
åé·é
ç·
追å
追å
ICS è£è¶³ã¬ã¤ãã³ã¹ãªã
管çæ¡å¼µï¼(1) ICS è£è¶³ã¬ã¤ãã³ã¹ãªã
çç±ï¼(1)ã®è¿½å ï¼ï¼ICS å¶å¾¡ã»éç¨ãç¶ç¶ããããã«é»æºã±ã¼ãã«ã®åé·åãå¿
è¦ã
SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
427
PE-10 EMERGENCY SHUTOFF
CNTL NO. CONTROL NAME
Control Enhancement Name
CONTROL BASELINES
LOW
MOD
HIGH
PE-10
Emergency Shutoff
Selected
Selected
ICS Supplemental Guidance: It may not be possible or advisable to shutoff power to some ICS. Example compensating controls
include fail in known state and emergency procedures.
PE-11 EMERGENCY POWER
CNTL NO. CONTROL NAME
Control Enhancement Name
CONTROL BASELINES
LOW
MOD
HIGH
PE-11
Emergency Power
Added
Selected
Selected
PE-11 (1) EMERGENCY POWER | LONG-TERM ALTERNATE POWER
SUPPLY - MINIMAL OPERATIONAL CAPABILITY
Added Added Selected
PE-11 (2) EMERGENCY POWER | LONG-TERM ALTERNATE POWER
SUPPLY - SELF-CONTAINED
Added
ICS Supplemental Guidance: Emergency power production, transmission and distribution systems are a type of ICS that are
required to meet extremely high performance specifications. The systems are governed by international, national, state and local building
codes, must be tested on a continual basis, and must be repaired and placed back into operations within a short period of time. Traditionally,
emergency power has been provided by generators for short to mid-term power (typically for fire and life safety systems, some IT load, and
evacuation transport) and UPS battery packs in distribution closets and within work areas to allow some level of business continuity and for
the orderly shutdown of non-essential IT and facility systems. Traditional emergency power systems typically are off-line until a loss of
power occurs and are typically on a separate network and control system specific to the facility they support. New methods of energy
generation and storage (e.g., solar voltaic, geothermal, flywheel, microgrid, distributed energy) that have a real-time demand and storage
connection to local utilities or cross connected to multiple facilities should be carefully analyzed to ensure that the power can meet the load
and signal quality without disruption of mission essential functions.
Control Enhancement: (1) No ICS Supplemental Guidance.
Rationale for adding control to baseline: ICS may support critical activities which will be needed for safety and reliability even in
the absence of reliable power from the public grid.
PE-12 EMERGENCY LIGHTING
CNTL NO. CONTROL NAME
Control Enhancement Name
CONTROL BASELINES
LOW
MOD
HIGH
PE-12
Emergency Lighting
Selected
Selected
Selected
No ICS Supplemental Guidance.
SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
428
PE-10 ç·æ¥é®æ
管ççªå·
管çå
管çæ¡å¼µå
管çãã¼ã¹ã©ã¤ã³
ä½
ä¸
é«
PE-10
ç·æ¥é®æ
é¸å®
é¸å®
ICS è£è¶³ã¬ã¤ãã³ã¹ï¼ç¹å®ã® ICS ã®é»æºé®æã¯ä¸å¯è½åã¯æ¨å¥¨ã§ããªããè£åç管ççã®ä¾
ã¨ãã¦ãæ¢ç¥ç¶æ
ã®å¤±æåã³ç·æ¥æé ãããã
PE-11 ç·æ¥é»æº
管ççªå·
管çå
管çæ¡å¼µå
管çãã¼ã¹ã©ã¤ã³
ä½
ä¸
é«
PE-11
ç·æ¥é»æº
追å
é¸å®
é¸å®
PE-11 (1)
ç·æ¥é»æº
|
é·æ代æ¿é»æº
-
æä½éã®éç¨è½å
追å
追å
é¸å®
PE-11 (2)
ç·æ¥é»æº
|
é·æ代æ¿é»æº
-
å
èµå
追å
ICS è£è¶³ã¬ã¤ãã³ã¹ï¼ç·æ¥çºé»ã»éé
é»ã·ã¹ãã ã¯ä¸ç¨®ã® ICS ã§ã極ãã¦é«åº¦ãªæ§è½ä»æ§è¦
件ã課ããããå½éã»å½å®¶ã»å·ã»èªæ²»ä½ã®å»ºç¯æ³ã«æºæ ããå®æç試é¨ã課ãããçæéã«ä¿®
çã»å¾©æ§ã§ããªããã°ãªããªããå¾æ¥ãç·æ¥é»æºã¨ãã¦çã»ä¸æç¨çºé»æ©ï¼é常ç«ç½ã»å®å
¨è£
ç½®ã
ç¹å®ã® IT ä½æ¥åã³é¿é£è¼¸éï¼ã¨ UPS ããããªã¼ããã¯ãé
é»ã¯ãã¼ã¼ãããä½æ¥ã¨ãªã¢ã«è¨ç½®
ããã¦ãããããç¨åº¦ã®äºæ¥ç¶ç¶ãä¸è¦ IT è£
ç½®ã»æ½è¨è£
ç½®ã®ç§©åºã ã£ãé®æãã§ããããã«ãªã£
ã¦ãããå¾æ¥ç·æ¥é»æºè£
ç½®ã¯ãé»æºã失ãããã¾ã§ãªãã©ã¤ã³ã«ãªã£ã¦ãããã¨ãå¤ãã対å¿ã
ãæ½è¨åºæã®å¥ãããã¯ã¼ã¯åã³å¶å¾¡ã·ã¹ãã ä¸ã«ç½®ããã¦ãããæ°ããªã¨ãã«ã®ã¼çºçã»ä¿å
æ段ï¼å¤ªé½å
ãå°ç±ããã©ã¤ãã¤ã¼ã«ããã¤ã¯ãã°ãªãããåæ£ã¨ãã«ã®ã¼çï¼ã§ãå°æ¹å
Œ
±äº
æ¥è
ãè¤æ°æ½è¨ã«ãªã¢ã«ã¿ã¤ã éè¦ã»èç©æ¥ç¶ãã¦ãã®ã«ã¤ãã¦ã¯ãé大ãªä»»åã»æ©è½ãä¸æã
ããã¨ãªããé»åãè² è·ã»ä¿¡å·å質è¦ä»¶ãæºãããããæ
éã«åæãã¹ãã§ããã
管çæ¡å¼µï¼(1) ICS è£è¶³ã¬ã¤ãã³ã¹ãªã
ãã¼ã¹ã©ã¤ã³ã«ç®¡çã追å ããçç±ï¼å
Œ
±é
é»ç¶²ããã®é»åãå½ã¦ã«ã§ããªãå ´åã§ãã£ã¦
ããICS ã¯ãå®å
¨æ§ãä¿¡é ¼æ§ã®ç¢ºä¿ã«å¿
è¦ãªéè¦æ´»åãæ¯ãã¦ããã
PE-12 ç·æ¥ç
§æ
管ççªå·
管çå
管çæ¡å¼µå
管çãã¼ã¹ã©ã¤ã³
ä½
ä¸
é«
PE-12
ç·æ¥ç
§æ
é¸å®
é¸å®
é¸å®
ICS è£è¶³ã¬ã¤ãã³ã¹ãªã
SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
429
PE-13 FIRE PROTECTION
CNTL NO. CONTROL NAME
Control Enhancement Name
CONTROL BASELINES
LOW
MOD
HIGH
PE-13
Fire Protection
Selected
Selected
Selected
PE-13 (1)
FIRE PROTECTION | DETECTION DEVICES / SYSTEMS
Selected
PE-13 (2)
FIRE PROTECTION | SUPPRESSION DEVICES / SYSTEMS
Selected
PE-13 (3)
FIRE PROTECTION | AUTOMATIC FIRE SUPPRESSION
Selected
Selected
ICS Supplemental Guidance: Fire suppression mechanisms should take the ICS environment into account (e.g., water sprinkler
systems could be hazardous in specific environments).
Control Enhancement: (1, 2, 3) No ICS Supplemental Guidance.
PE-14 TEMPERATURE AND HUMIDITY CONTROLS
CNTL NO. CONTROL NAME
Control Enhancement Name
CONTROL BASELINES
LOW
MOD
HIGH
PE-14
Temperature and Humidity Controls
Selected
Selected
Selected
ICS Supplemental Guidance: Temperature and humidity controls are typically components of other ICS systems such as the HVAC,
process, or lighting systems, or can be a standalone and unique ICS system. ICS can operate in extreme environments and both interior and
exterior locations. For a specific ICS, the temperature and humidity design and operational parameters dictate the performance specifications.
As ICS and IS become interconnected and the network provides connectivity across the hybrid domain, power circuits, distribution closets,
routers and switches that support fire protection and life safety systems must be maintained at the proper temperature and humidity.
PE-15 WATER DAMAGE PROTECTION
CNTL NO. CONTROL NAME
Control Enhancement Name
CONTROL BASELINES
LOW
MOD
HIGH
PE-15
Water Damage Protection
Selected
Selected
Selected
PE-15 (1)
WATER DAMAGE PROTECTION | AUTOMATION SUPPORT
Selected
ICS Supplemental Guidance: Water damage protection and use of shutoff and isolation valves is both a procedural action, and also
a specific type of ICS. ICS that are used in the manufacturing, hydropower, transportation/navigation, water and wastewater industries rely
on the movement of water and are specifically designed to manage the quantity/flow and pressure of water. As ICS and IS become
interconnected and the network provides connectivity across the hybrid domain, power circuits, distribution closets, routers and switches that
support fire protection and life safety systems should ensure that water will not disable the system (e.g. a fire that activates the sprinkler
system does not spray onto the fire control servers, router, switches and short out the alarms, egress systems, emergency lighting, and
suppression systems).
Control Enhancement: (1) No ICS Supplemental Guidance.
PE-16 DELIVERY AND REMOVAL
CNTL NO. CONTROL NAME
Control Enhancement Name
CONTROL BASELINES
LOW
MOD
HIGH
PE-16
Delivery and Removal
Selected
Selected
Selected
No ICS Supplemental Guidance.
SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
430
PE-13 é²ç«
管ççªå·
管çå
管çæ¡å¼µå
管çãã¼ã¹ã©ã¤ã³
ä½
ä¸
é«
PE-13
é²ç«
é¸å®
é¸å®
é¸å®
PE-13 (1)
é²ç«
|
æ¤ç¥ããã¤ã¹ã»ã·ã¹ãã
é¸å®
PE-13 (2)
é²ç«
|
æ¶ç«ããã¤ã¹ã»ã·ã¹ãã
é¸å®
PE-13 (3)
é²ç«
|
èªåæ¶ç«
é¸å®
é¸å®
ICS è£è¶³ã¬ã¤ãã³ã¹ï¼æ¶åæ©æ§ã«ã¯ ICS ç°å¢ãèæ
®ã«å
¥ããï¼ã¹ããªã³ã¯ã©ã¼ã¯ç°å¢ã«ãã
æ害ï¼ã
管çæ¡å¼µï¼(1, 2, 3) ICS è£è¶³ã¬ã¤ãã³ã¹ãªã
PE-14 温度ã»æ¹¿åº¦å¶å¾¡
管ççªå·
管çå
管çæ¡å¼µå
管çãã¼ã¹ã©ã¤ã³
ä½
ä¸
é«
PE-14
温度ã»æ¹¿åº¦å¶å¾¡
é¸å®
é¸å®
é¸å®
ICS è£è¶³ã¬ã¤ãã³ã¹ï¼æ¸©åº¦ã»æ¹¿åº¦å¶å¾¡ã¯ HVACãããã»ã¹ãç
§æè£
ç½®çã® ICS ã·ã¹ãã ã®ã³
ã³ãã¼ãã³ãã§ãããã¹ã¿ã³ãã¢ãã¼ã³åã·ã¹ãã ãããã°ç¹æã® ICS ã·ã¹ãã ããããICS ã¯
å±å
å¤ã®éé
·ãªç°å¢ä¸ã«ç½®ãããå ´åãããããã種㮠ICS ã¯ã温度ã»æ¹¿åº¦è¨è¨ãéç¨ãã©ã¡ã¼
ã¿ã«ãã£ã¦æ§è½ä»æ§ã決ã¾ããICS ã¨IS ã¯é£æ¥ããããããã¯ã¼ã¯ã¯ãã¤ããªããé åã«ã¾ãã
ããããé²ç«è£
ç½®ãçå½å®å
¨è£
ç½®ãæ¯ããé»æ°åè·¯ãé
é»ã¯ãã¼ã¼ãããã«ã¼ã¿åã³ã¹ã¤ããã¯ã
é©æ§æ¸©åº¦ã»æ¹¿åº¦ã«ä¿ãããªããã°ãªããªãã
PE-15 水害é²è·
管ççªå·
管çå
管çæ¡å¼µå
管çãã¼ã¹ã©ã¤ã³
ä½
ä¸
é«
PE-15
水害é²è·
é¸å®
é¸å®
é¸å®
PE-15 (1)
水害é²è·
|
èªå対å¿
é¸å®
ICS è£è¶³ã¬ã¤ãã³ã¹ï¼æ°´å®³é²è·ã¨éæ¢ã»é®æå¼ã®ä½¿ç¨ã¯ãã¨ãã«æé è¡çºã§ãããåæã«ã
ã種㮠ICS ã§ãããã製é ã»æ°´åçºé»ã»è¼¸é/éèªã»ä¸ä¸æ°´éæ¥çã§ä½¿ç¨ããã ICS ã¯ãæ°´ã®éå
ã«ä¾åãã¦ãããç¹ã«æ°´ã®éã»æµéåã³å§åã管çããããã«è¨è¨ããã¦ãããICS ã¨IS ã¯é£æ¥
ããããããã¯ã¼ã¯ã¯ãã¤ããªãããã¡ã¤ã³ã«ã¾ããããããé²ç«è£
ç½®ãçå½å®å
¨è£
ç½®ãæ¯ãã
é»æ°åè·¯ãé
é»ã¯ãã¼ã¼ãããã«ã¼ã¿åã³ã¹ã¤ããã¯ã水害ã§ã·ã¹ãã ãä½åä¸è½ã«ãªããªãã
ãã«ãã¹ãã§ããï¼ç«äºã§ã¹ããªã³ã¯ã©ã¼ãä½åãã¦ããé²ç«ãµã¼ããã«ã¼ã¿ãã¹ã¤ããã«ã¯æ°´
ãããããªãããã«ããã¢ã©ã¼ã ãè±åºã·ã¹ãã ãç·æ¥ç
§æãæ¶ç«ã·ã¹ãã ãã·ã§ã¼ãããªãã
ãã«ããï¼ã
管çæ¡å¼µï¼(1) ICS è£è¶³ã¬ã¤ãã³ã¹ãªã
PE-16 é
éã»æ¤å»
管ççªå·
管çå
管çæ¡å¼µå
管çãã¼ã¹ã©ã¤ã³
ä½
ä¸
é«
PE-16
é
éã»æ¤å»
é¸å®
é¸å®
é¸å®
ICS è£è¶³ã¬ã¤ãã³ã¹ãªã
SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
431
PE-17 ALTERNATE WORK SITE
CNTL NO. CONTROL NAME
Control Enhancement Name
CONTROL BASELINES
LOW
MOD
HIGH
PE-17
Alternate Work Site
Selected
Selected
No ICS Supplemental Guidance.
PE-18 LOCATION OF INFORMATION SYSTEM COMPONENTS
CNTL NO. CONTROL NAME
Control Enhancement Name
CONTROL BASELINES
LOW
MOD
HIGH
PE-18
Location of Information System Components
Selected
Selected
Selected
No ICS Supplemental Guidance.
SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
432
PE-17 代æ¿ä½æ¥å ´
管ççªå·
管çå
管çæ¡å¼µå
管çãã¼ã¹ã©ã¤ã³
ä½
ä¸
é«
PE-17
代æ¿ä½æ¥å ´
é¸å®
é¸å®
ICS è£è¶³ã¬ã¤ãã³ã¹ãªã
PE-18 æ
å ±ã·ã¹ãã ã³ã³ãã¼ãã³ãã®å ´æ
管ççªå·
管çå
管çæ¡å¼µå
管çãã¼ã¹ã©ã¤ã³
ä½
ä¸
é«
PE-18
æ
å ±ã·ã¹ãã ã³ã³ãã¼ãã³ã
é¸å®
é¸å®
é¸å®
ICS è£è¶³ã¬ã¤ãã³ã¹ãªã

SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
433
PLANNING â PL
Supplemental Guidance
Supplemental Guidance for all Controls and Control Enhancements in NIST SP 800-53 Rev. 4, Appendix F, should be used in conjunction
with the ICS Supplemental Guidance in this overlay, if any.
PL-1 SECURITY PLANNING POLICY AND PROCEDURES
CNTL NO. CONTROL NAME
Control Enhancement Name
CONTROL BASELINES
LOW
MOD
HIGH
PL-1
Security Planning Policy and Procedures
Selected
Selected
Selected
ICS Supplemental Guidance: The policy specifically addresses the unique properties and requirements of ICS and the relationship
to non-ICS systems.
PL-2 SYSTEM SECURITY PLAN
CNTL NO. CONTROL NAME
Control Enhancement Name
CONTROL BASELINES
LOW
MOD
HIGH
PL-2
System Security Plan
Selected
Selected
Selected
PL-2 (3) SYSTEM SECURITY PLAN | PLAN / COORDINATE WITH
OTHER ORGANIZATIONAL ENTITIES
Added Selected Selected
No ICS Supplemental Guidance.
Control Enhancement: (3) No ICS Supplemental Guidance.
Rationale for adding PL-2 (3) to low baseline: When systems are highly inter-connected, coordinated planning is essential. A low
impact system could adversely affect a higher impact system.
PL-4 RULES OF BEHAVIOR
CNTL NO. CONTROL NAME
Control Enhancement Name
CONTROL BASELINES
LOW
MOD
HIGH
PL-4
Rules of Behavior
Selected
Selected
Selected
PL-4 (1) RULES OF BEHAVIOR | SOCIAL MEDIA AND NETWORKING
RESTRICTIONS
Selected Selected
No ICS Supplemental Guidance.
PL-7 SECURITY CONCEPT OF OPERATIONS (CONOPS)
CNTL NO. CONTROL NAME
Control Enhancement Name
CONTROL BASELINES
LOW
MOD
HIGH
PL-7
Security Concept of Operations
Added
Added
No ICS Supplemental Guidance.
Rationale for adding PL-7 to moderate and high baselines: ICS are complex systems. Organizations typically employ a
CONOPS to help define a system and share that understanding with personnel involved with that system and other systems with which it
interacts. A CONOPS often helps identify information protection requirements.
SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
434
ãã©ã³ãã³ã° â PL
è£è¶³ã¬ã¤ãã³ã¹
å©ç¨ã§ããå ´åã«ã¯ãNIST SP 800-53 第4çä»é² Fã«ããå
¨ã¦ã®ç®¡çã»ç®¡çæ¡å¼µç¨è£è¶³ã¬ã¤ãã³
ã¹ãããã®ãªã¼ãã¼ã¬ã¤ã«ããã¦ãICS è£è¶³ã¬ã¤ãã³ã¹ã¨ä½µç¨ãã¹ãã§ããã
PL-1 ã»ãã¥ãªãã£è¨ç»ããªã·ã¼ã»æé
管ççªå·
管çå
管çæ¡å¼µå
管çãã¼ã¹ã©ã¤ã³
ä½
ä¸
é«
PL-1
ã»ãã¥ãªãã£è¨ç»ããªã·ã¼ã»æé
é¸å®
é¸å®
é¸å®
ICS è£è¶³ã¬ã¤ãã³ã¹ï¼ããªã·ã¼ã¯ç¹ã« ICS ã®åºæã®ç¹æ§ã»è¦ä»¶åã³ ICS 以å¤ã®ã·ã¹ãã ã¨ã®
é¢ä¿ãåãä¸ããã
PL-2 ã·ã¹ãã ã®ã»ãã¥ãªãã£è¨ç»æ¸
管ççªå·
管çå
管çæ¡å¼µå
管çãã¼ã¹ã©ã¤ã³
ä½
ä¸
é«
PL-2
ã·ã¹ãã ã»ãã¥ãªãã£è¨ç»æ¸
é¸å®
é¸å®
é¸å®
PL-2 (3)
ã·ã¹ãã ã»ãã¥ãªãã£è¨ç»æ¸
|
ä»ã®çµç¹ã¨ã®è¨ç»ã»èª¿æ´
追å
é¸å®
é¸å®
ICS è£è¶³ã¬ã¤ãã³ã¹ãªã
管çæ¡å¼µï¼(3) ICS è£è¶³ã¬ã¤ãã³ã¹ãªã
PL-2 (3)ãä½ãã¼ã¹ã©ã¤ã³ã«è¿½å ããçç±ï¼ã·ã¹ãã å士ãé«åº¦ã«ç¸äºé£æ¥ãã¦ããå ´åã
è¨ç»ã®èª¿æ´ãèè¦ã§ãããå½±é¿åº¦ã®ä½ãã·ã¹ãã ãé«ãã·ã¹ãã ã«æªå½±é¿ãä¸ãããã¨ãããã
PL-4 è¡åè¦å
管ççªå·
管çå
管çæ¡å¼µå
管çãã¼ã¹ã©ã¤ã³
ä½
ä¸
é«
PL-4
è¡åè¦å
é¸å®
é¸å®
é¸å®
PL-4 (1)
è¡åè¦å
|
ã½ã¼ã·ã£ã«ã¡ãã£ã¢
/
ãããã¯ã¼ãã³ã°ã®å¶é
é¸å®
é¸å®
ICS è£è¶³ã¬ã¤ãã³ã¹ãªã
PL-7 éç¨ã»ãã¥ãªãã£æ¦å¿µ (CONOPS)
管ççªå·
管çå
管çæ¡å¼µå
管çãã¼ã¹ã©ã¤ã³
ä½
ä¸
é«
PL-7
éç¨ã»ãã¥ãªãã£æ¦å¿µ
追å
追å
ICS è£è¶³ã¬ã¤ãã³ã¹ãªã
PL-7 ãä¸ã»é«ãã¼ã¹ã©ã¤ã³ã«è¿½å ããçç±ï¼ICS ã·ã¹ãã ãè¤éãªãããé常ãçµç¹ã¯
CONOPS ãæ¡ç¨ãã¦ãã·ã¹ãã ãå®ç¾©ããå½è©²ã·ã¹ãã ãç¸äºä½ç¨ãè¡ãä»ã®ã·ã¹ãã ã®é¢ä¿è
ã¨ç解ãå
±æãããCONOPS ã¯ãæ
å ±ä¿è·è¦ä»¶ãæããã«ããä¸ã§å½¹ç«ã¤ãã¨ãå¤ãã

SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
435
PL-8 INFORMATION SECURITY ARCHITECTURE
CNTL NO. CONTROL NAME
Control Enhancement Name
CONTROL BASELINES
LOW
MOD
HIGH
PL-8
Information Security Architecture
Selected
Selected
No ICS Supplemental Guidance.

SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
436
PL-8 æ
å ±ã»ãã¥ãªãã£ã¢ã¼ããã¯ãã£
管ççªå·
管çå
管çæ¡å¼µå
管çãã¼ã¹ã©ã¤ã³
ä½
ä¸
é«
PL-8
æ
å ±ã»ãã¥ãªãã£ã¢ã¼ããã¯ãã£
é¸å®
é¸å®
ICS è£è¶³ã¬ã¤ãã³ã¹ãªã
SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
437
PERSONNEL SECURITY â PS
Supplemental Guidance
Supplemental Guidance for all Controls and Control Enhancements in NIST SP 800-53 Rev. 4, Appendix F, should be used in conjunction
with the ICS Supplemental Guidance in this overlay, if any.
PS-1 PERSONNEL SECURITY POLICY AND PROCEDURES
CNTL NO. CONTROL NAME
Control Enhancement Name
CONTROL BASELINES
LOW
MOD
HIGH
PS-1
Personnel Security Policy and Procedures
Selected
Selected
Selected
ICS Supplemental Guidance: The policy specifically addresses the unique properties and requirements of ICS and the relationship
to non-ICS systems.
PS-2 POSITION RISK DESIGNATION
CNTL NO. CONTROL NAME
Control Enhancement Name
CONTROL BASELINES
LOW
MOD
HIGH
PS-2
Position Risk Designation
Selected
Selected
Selected
No ICS Supplemental Guidance.
PS-3 PERSONNEL SCREENING
CNTL NO. CONTROL NAME
Control Enhancement Name
CONTROL BASELINES
LOW
MOD
HIGH
PS-3
Personnel Screening
Selected
Selected
Selected
No ICS Supplemental Guidance.
PS-4 PERSONNEL TERMINATION
CNTL NO. CONTROL NAME
Control Enhancement Name
CONTROL BASELINES
LOW
MOD
HIGH
PS-4
Personnel Termination
Selected
Selected
Selected
PS-4 (2)
PERSONNEL TERMINATION | AUTOMATED NOTIFICATION
Selected
No ICS Supplemental Guidance.
PS-5 PERSONNEL TRANSFER
CNTL NO. CONTROL NAME
Control Enhancement Name
CONTROL BASELINES
LOW
MOD
HIGH
PS-5
Personnel Transfer
Selected
Selected
Selected
No ICS Supplemental Guidance.
SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
438
人å¡ã®ã»ãã¥ãªã㣠â PS
è£è¶³ã¬ã¤ãã³ã¹
å©ç¨ã§ããå ´åã«ã¯ãNIST SP 800-53 第4çä»é² Fã«ããå
¨ã¦ã®ç®¡çã»ç®¡çæ¡å¼µç¨è£è¶³ã¬ã¤ãã³
ã¹ãããã®ãªã¼ãã¼ã¬ã¤ã«ããã¦ãICS è£è¶³ã¬ã¤ãã³ã¹ã¨ä½µç¨ãã¹ãã§ããã
PS-1 人å¡ã®ã»ãã¥ãªãã£ããªã·ã¼ã»æé
管ççªå·
管çå
管çæ¡å¼µå
管çãã¼ã¹ã©ã¤ã³
ä½
ä¸
é«
PS-1
人å¡ã®ã»ãã¥ãªãã£ããªã·ã¼ã»æé
é¸å®
é¸å®
é¸å®
ICS è£è¶³ã¬ã¤ãã³ã¹ï¼ããªã·ã¼ã¯ç¹ã« ICS ã®åºæã®ç¹æ§ã»è¦ä»¶åã³ ICS 以å¤ã®ã·ã¹ãã ã¨ã®
é¢ä¿ãåãä¸ããã
PS-2 é
ç½®ãªã¹ã¯æå®
管ççªå·
管çå
管çæ¡å¼µå
管çãã¼ã¹ã©ã¤ã³
ä½
ä¸
é«
PS-2
é
ç½®ãªã¹ã¯æå®
é¸å®
é¸å®
é¸å®
ICS è£è¶³ã¬ã¤ãã³ã¹ãªã
PS-3 人é¸
管ççªå·
管çå
管çæ¡å¼µå
管çãã¼ã¹ã©ã¤ã³
ä½
ä¸
é«
PS-3
人é¸
é¸å®
é¸å®
é¸å®
ICS è£è¶³ã¬ã¤ãã³ã¹ãªã
PS-4 éè·
管ççªå·
管çå
管çæ¡å¼µå
管çãã¼ã¹ã©ã¤ã³
ä½
ä¸
é«
PS-4
éè·
é¸å®
é¸å®
é¸å®
PS-4 (2)
éè·
|
èªåéç¥
é¸å®
ICS è£è¶³ã¬ã¤ãã³ã¹ãªã
PS-5 転å¤
管ççªå·
管çå
管çæ¡å¼µå
管çãã¼ã¹ã©ã¤ã³
ä½
ä¸
é«
PS-5
転å¤
é¸å®
é¸å®
é¸å®
ICS è£è¶³ã¬ã¤ãã³ã¹ãªã
SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
439
PS-6 ACCESS AGREEMENTS
CNTL NO. CONTROL NAME
Control Enhancement Name
CONTROL BASELINES
LOW
MOD
HIGH
PS-6
Access Agreements
Selected
Selected
Selected
No ICS Supplemental Guidance.
PS-7 THIRD-PARTY PERSONNEL SECURITY
CNTL NO. CONTROL NAME
Control Enhancement Name
CONTROL BASELINES
LOW
MOD
HIGH
PS-7
Third-Party Personnel Security
Selected
Selected
Selected
No ICS Supplemental Guidance.
PS-8 PERSONNEL SANCTIONS
CNTL NO. CONTROL NAME
Control Enhancement Name
CONTROL BASELINES
LOW
MOD
HIGH
PS-8
Personnel Sanctions
Selected
Selected
Selected
No ICS Supplemental Guidance.
SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
440
PS-6 ã¢ã¯ã»ã¹åæ
管ççªå·
管çå
管çæ¡å¼µå
管çãã¼ã¹ã©ã¤ã³
ä½
ä¸
é«
PS-6
ã¢ã¯ã»ã¹åæ
é¸å®
é¸å®
é¸å®
ICS è£è¶³ã¬ã¤ãã³ã¹ãªã
PS-7 ãµã¼ããã¼ãã£ç¤¾å¡ã»ãã¥ãªãã£
管ççªå·
管çå
管çæ¡å¼µå
管çãã¼ã¹ã©ã¤ã³
ä½
ä¸
é«
PS-7
ãµã¼ããã¼ãã£ç¤¾å¡ã»ãã¥ãªãã£
é¸å®
é¸å®
é¸å®
ICS è£è¶³ã¬ã¤ãã³ã¹ãªã
PS-8 æ²æ
管ççªå·
管çå
管çæ¡å¼µå
管çãã¼ã¹ã©ã¤ã³
ä½
ä¸
é«
PS-8
æ²æ
é¸å®
é¸å®
é¸å®
ICS è£è¶³ã¬ã¤ãã³ã¹ãªã
SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
441
RISK ASSESSMENT â RA
Supplemental Guidance
Supplemental Guidance for all Controls and Control Enhancements in NIST SP 800-53 Rev. 4, Appendix F, should be used in
conjunction with the ICS Supplemental Guidance in this overlay, if any.
RA-1 RISK ASSESSMENT POLICY AND PROCEDURES
CNTL NO. CONTROL NAME
Control Enhancement Name
CONTROL BASELINES
LOW
MOD
HIGH
RA-1
Risk Assessment Policy and Procedures
Selected
Selected
Selected
ICS Supplemental Guidance: The policy specifically addresses the unique properties and requirements of ICS and the relationship
to non-ICS systems.
RA-2 SECURITY CATEGORIZATION
CNTL NO. CONTROL NAME
Control Enhancement Name
CONTROL BASELINES
LOW
MOD
HIGH
RA-2
Security Categorization
Selected
Selected
Selected
No ICS Supplemental Guidance.
RA-3 RISK ASSESSMENT
CNTL NO. CONTROL NAME
Control Enhancement Name
CONTROL BASELINES
LOW
MOD
HIGH
RA-3
Risk Assessment
Selected
Selected
Selected
No ICS Supplemental Guidance.
RA-5 VULNERABILITY SCANNING
CNTL NO. CONTROL NAME
Control Enhancement Name
CONTROL BASELINES
LOW
MOD
HIGH
RA-5
Vulnerability Scanning
Selected
Selected
Selected
RA-5 (1)
VULNERABILITY SCANNING | UPDATE TOOL CAPABILITY
Selected
Selected
RA-5 (2) VULNERABILITY SCANNING | UPDATE BY FREQUENCY /
PRIOR TO NEW SCAN / WHEN IDENTIFIED
Selected Selected
RA-5 (4)
VULNERABILITY SCANNING | DISCOVERABLE INFORMATION
Selected
RA-5 (5)
VULNERABILITY SCANNING | PRIVILEGED ACCESS
Selected
Selected
ICS Supplemental Guidance: Active vulnerability scanning, which introduces network traffic, is used with care on ICS systems to
ensure that ICS functions are not adversely impacted by the scanning process. The organization makes a risk-based determination whether to
employ active scanning. Passive monitoring /sniffing may be used as part of a compensating control. Example compensating controls include
providing a replicated, virtualized, or simulated system to conduct scanning. Production ICS may need to be taken off-line before scanning
can be conducted. If ICS are taken off-line for scanning, scans are scheduled to occur during planned ICS outages whenever possible. If
vulnerability scanning tools are used on non-ICS networks, extra care is taken to ensure that they do not scan the ICS network. Network
scanning is not applicable to non-addressable communications. Vulnerability examination may be performed using other mechanisms than
scanning to identify the objects being examined. Host-based vulnerability examination is an example compensating control.
Control Enhancement: (1, 2, 4, 5) No ICS Supplemental Guidance.
SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
442
ãªã¹ã¯è©ä¾¡ â RA
è£è¶³ã¬ã¤ãã³ã¹
å©ç¨ã§ããå ´åã«ã¯ãNIST SP 800-53 第4çä»é² Fã«ããå
¨ã¦ã®ç®¡çã»ç®¡çæ¡å¼µç¨è£è¶³ã¬ã¤ãã³
ã¹ãããã®ãªã¼ãã¼ã¬ã¤ã«ããã¦ãICS è£è¶³ã¬ã¤ãã³ã¹ã¨ä½µç¨ãã¹ãã§ããã
RA-1 ãªã¹ã¯è©ä¾¡ããªã·ã¼ã»æé
管ççªå·
管çå
管çæ¡å¼µå
管çãã¼ã¹ã©ã¤ã³
ä½
ä¸
é«
RA-1
ãªã¹ã¯è©ä¾¡ããªã·ã¼ã»æé
é¸å®
é¸å®
é¸å®
ICS è£è¶³ã¬ã¤ãã³ã¹ï¼ããªã·ã¼ã¯ç¹ã« ICS ã®åºæã®ç¹æ§ã»è¦ä»¶åã³ ICS 以å¤ã®ã·ã¹ãã ã¨ã®
é¢ä¿ãåãä¸ããã
RA-2 ã»ãã¥ãªãã£åé¡
管ççªå·
管çå
管çæ¡å¼µå
管çãã¼ã¹ã©ã¤ã³
ä½
ä¸
é«
RA-2
ã»ãã¥ãªãã£åé¡
é¸å®
é¸å®
é¸å®
ICS è£è¶³ã¬ã¤ãã³ã¹ãªã
RA-3 ãªã¹ã¯è©ä¾¡
管ççªå·
管çå
管çæ¡å¼µå
管çãã¼ã¹ã©ã¤ã³
ä½
ä¸
é«
RA-3
ãªã¹ã¯è©ä¾¡
é¸å®
é¸å®
é¸å®
ICS è£è¶³ã¬ã¤ãã³ã¹ãªã
RA-5 èå¼±æ§æ¤ç´¢
管ççªå·
管çå
管çæ¡å¼µå
管çãã¼ã¹ã©ã¤ã³
ä½
ä¸
é«
RA-5
èå¼±æ§æ¤ç´¢
é¸å®
é¸å®
é¸å®
RA-5 (1)
èå¼±æ§æ¤ç´¢
|
æ´æ°ãã¼ã«æ©è½
é¸å®
é¸å®
RA-5 (2)
æ¤èå¼±æ§ç´¢
|
æ°è¦ã¹ãã£ã³åã»èå¥æã®å¨æ³¢æ°ã«ããæ´æ°
é¸å®
é¸å®
RA-5 (4)
èå¼±æ§æ¤ç´¢
|
æ¤åºå¯è½æ
å ±
é¸å®
RA-5 (5)
èå¼±æ§æ¤ç´¢
|
ç¹æ¨©ã¢ã¯ã»ã¹
é¸å®
é¸å®
ICS è£è¶³ã¬ã¤ãã³ã¹ï¼ã¢ã¯ãã£ãèå¼±æ§è¨ç»æ¤ç´¢ã¯ããããã¯ã¼ã¯ãã©ãã£ãã¯ãçããã®
ã§ICS ã·ã¹ãã ä¸ã§æ
éã«è¡ããæ¤ç´¢ããã»ã¹ã«ãã ICS æ©è½ã«æªå½±é¿ãåã°ãªãããã«ããã
çµç¹ã¯ãªã¹ã¯ã«ç«èãã¦ãã¢ã¯ãã£ãæ¤ç´¢å®è¡ã®æ¯éãå¤æãããããã·ãç£è¦ã»ã¹ãããã£ã³
ã°ã¯ãè£åç管ççã®ä¸ç°ã¨ãã¦ä½¿ç¨ã§ãããè£åç管ççã®ä¾ã¨ãã¦ãè¤è£½ãä»®æ³åã¯æ¨¡æ¬ã·
ã¹ãã ã§æ¤ç´¢ããæ¹æ³ããããçç£ ICS ã¯ãæ¤ç´¢åã«ãªãã©ã¤ã³ã«ããå¿
è¦ãããããªãã©ã¤ã³
ã«ããå ´åãå¯è½ã§ããã°ãäºãè¨ç»ããã ICS ã®ææ¥åæ¢æã«æ¤ç´¢ãè¡ãããã«äºå®ãçµãã
èå¼±æ§æ¤ç´¢ãã¼ã«ã ICS 以å¤ã®ãããã¯ã¼ã¯ã§è¡ãå ´åãæ¤ç´¢ã ICS ãããã¯ã¼ã¯ã«åã°ãªãã
ãã«æ³¨æããããããã¯ã¼ã¯æ¤ç´¢ã¯ãã¢ãã¬ã¹æå®ä¸è½ã®éä¿¡ã«ã¯é©ç¨ãããªãã
èå¼±æ§æ¤è¨¼ã¯ãæ¤è¨¼ä¸ã®å¯¾è±¡ãèå¥ããæ¤ç´¢ä»¥å¤ã®ã¡ã«ããºã ã使ç¨ãã¦è¡ãããã¹ããã¼
ã¹ã®èå¼±æ§æ¤è¨¼ã¯ãè£åç管ççã®ä¸ä¾ã§ããã
管çæ¡å¼µï¼(1, 2, 4, 5) ICS è£è¶³ã¬ã¤ãã³ã¹ãªã
SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
443
SYSTEM AND SERVICES ACQUISITION â SA
Tailoring Considerations for System and Services Acquisition Family
In situations where the ICS cannot support the specific System and Services Acquisition requirements of a control, the organization
employs compensating controls in accordance with the general tailoring guidance. Examples of compensating controls are given with each
control, as appropriate.
Supplemental Guidance
Supplemental Guidance for all Controls and Control Enhancements in NIST SP 800-53 Rev. 4, Appendix F, should be used in
conjunction with the ICS Supplemental Guidance in this overlay, if any.
SA-1 SYSTEM AND SERVICES ACQUISITION POLICY AND PROCEDURES
CNTL NO. CONTROL NAME
Control Enhancement Name
CONTROL BASELINES
LOW
MOD
HIGH
SA-1
System and Services Acquisition Policy and Procedures
Selected
Selected
Selected
ICS Supplemental Guidance: The policy specifically addresses the unique properties and requirements of ICS and the relationship
to non-ICS systems.
SA-2 ALLOCATION OF RESOURCES
CNTL NO. CONTROL NAME
Control Enhancement Name
CONTROL BASELINES
LOW
MOD
HIGH
SA-2
Allocation of Resources
Selected
Selected
Selected
No ICS Supplemental Guidance.
SA-3 SYSTEM DEVELOPMENT LIFE CYCLE
CNTL NO. CONTROL NAME
Control Enhancement Name
CONTROL BASELINES
LOW
MOD
HIGH
SA-3
System Development Life Cycle
Selected
Selected
Selected
No ICS Supplemental Guidance.
SA-4 ACQUISITION PROCESS
CNTL NO. CONTROL NAME
Control Enhancement Name
CONTROL BASELINES
LOW
MOD
HIGH
SA-4
Acquisition Process
Selected
Selected
Selected
SA-4 (1) ACQUISITION PROCESS | FUNCTIONAL PROPERTIES OF
SECURITY CONTROLS
Selected Selected
SA-4 (2) ACQUISITION PROCESS | DESIGN / IMPLEMENTATION
INFORMATION FOR SECURITY CONTROLS
Selected Selected
SA-4 (9) ACQUISITION PROCESS | FUNCTIONS / PORTS /
PROTOCOLS / SERVICES IN USE
Selected Selected
SA-4 (10) ACQUISITION PROCESS | USE OF APPROVED PIV
PRODUCTS
Selected Selected Selected
ICS Supplemental Guidance: Since ICS security has historically focused on physical protection and isolation, vendors and
developers may be unfamiliar with cybersecurity. Organizations should anticipate a need to engage with ICS suppliers to raise awareness of
cybersecurity needs. The SCADA/Control Systems Procurement Project provides example cybersecurity procurement language for ICS.
References: Web: https://ics-cert.us-cert.gov/sites/default/files/documents/Procurement_Language_Rev4_100809.pdf
Control Enhancements: (1, 2, 9) ICS Supplemental Guidance: Developers may not have access to required information.
SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
444
ã·ã¹ãã åã³ãµã¼ãã¹åå¾ â SA
ã·ã¹ãã åã³ãµã¼ãã¹åå¾ãã¡ããªã®ã«ã¹ã¿ãã¤ãºèæ
®äºé
ICS ãããå¶å¾¡ã®ç¹å®ã®ã·ã¹ãã åã³ãµã¼ãã¹åå¾è¦ä»¶ã«å¯¾å¿ãã¦ããªãç¶æ³ã§ã¯ãå
¨ä½çãªã«
ã¹ã¿ãã¤ãºã¬ã¤ãã³ã¹ã«å¾ã£ã¦è£åç管ççãæ¡ç¨ããã
è£åç管ççã®ä¾ãå¿
è¦ã«å¿ãã¦ã管ççãã¨ã«ç¤ºãããã
è£è¶³ã¬ã¤ãã³ã¹
å©ç¨ã§ããå ´åã«ã¯ãNIST SP 800-53 第4çä»é² Fã«ããå
¨ã¦ã®ç®¡çã»ç®¡çæ¡å¼µç¨è£è¶³ã¬ã¤ãã³
ã¹ãããã®ãªã¼ãã¼ã¬ã¤ã«ããã¦ãICS è£è¶³ã¬ã¤ãã³ã¹ã¨ä½µç¨ãã¹ãã§ããã
SA-1 ã·ã¹ãã åã³ãµã¼ãã¹åå¾ããªã·ã¼ã»æé
管ççªå·
管çå
管çæ¡å¼µå
管çãã¼ã¹ã©ã¤ã³
ä½
ä¸
é«
SA-1
ã·ã¹ãã åã³ãµã¼ãã¹åå¾ããªã·ã¼ã»æé
é¸å®
é¸å®
é¸å®
ICS è£è¶³ã¬ã¤ãã³ã¹ï¼ããªã·ã¼ã¯ç¹ã« ICS ã®åºæã®ç¹æ§ã»è¦ä»¶åã³ ICS 以å¤ã®ã·ã¹ãã ã¨ã®
é¢ä¿ãåãä¸ããã
SA-2 ãªã½ã¼ã¹å²å½
管ççªå·
管çå
管çæ¡å¼µå
管çãã¼ã¹ã©ã¤ã³
ä½
ä¸
é«
SA-2
ãªã½ã¼ã¹å²å½
é¸å®
é¸å®
é¸å®
ICS è£è¶³ã¬ã¤ãã³ã¹ãªã
SA-3 ã·ã¹ãã éçºã©ã¤ããµã¤ã¯ã«
管ççªå·
管çå
管çæ¡å¼µå
管çãã¼ã¹ã©ã¤ã³
ä½
ä¸
é«
SA-3
ã·ã¹ãã éçºã©ã¤ããµã¤ã¯ã«
é¸å®
é¸å®
é¸å®
ICS è£è¶³ã¬ã¤ãã³ã¹ãªã
SA-4 åå¾ããã»ã¹
管ççªå·
管çå
管çæ¡å¼µå
管çãã¼ã¹ã©ã¤ã³
ä½
ä¸
é«
SA-4
åå¾ããã»ã¹
é¸å®
é¸å®
é¸å®
SA-4 (1)
åå¾ããã»ã¹
|
ã»ãã¥ãªãã£å¯¾çã®æ©è½ç¹æ§
é¸å®
é¸å®
SA-4 (2)
åå¾ããã»ã¹
|
ã»ãã¥ãªãã£å¯¾çã®è¨è¨ã»å®è£
æ
å ±
é¸å®
é¸å®
SA-4 (9)
åå¾ããã»ã¹
|
æ©è½ã»ãã¼ãã»ãããã³ã«
å®ç¨ãµã¼ãã¹
é¸å® é¸å®
SA-4 (10)
åå¾ããã»ã¹
|
èªå¯æ¸ã¿
PIV
製åã®å©ç¨
é¸å®
é¸å®
é¸å®
ICS è£è¶³ã¬ã¤ãã³ã¹ï¼ICS ã®ã»ãã¥ãªãã£ã¯ãæ´å²çã«ç©ççãªä¿è·ã¨éé¢ãéç¹ã ã£ãã
ãããã³ãã¼ãéçºè
ã¯ãµã¤ãã¼ã»ãã¥ãªãã£ã«ãªãã¿ããªããçµç¹ã¯ ICS ãµãã©ã¤ã¤ã¨ã¨ãã«ã
ãµã¤ãã¼ã»ãã¥ãªãã£ã«å¯¾ããæèé«æã®å¿
è¦æ§ãäºæãã¹ãã§ãããSCADA å¶å¾¡ã·ã¹ãã 調
éããã¸ã§ã¯ãã«ã¯ãICS ã®ãµã¤ãã¼ã»ãã¥ãªãã£ç¨èªã示ããã¦ãããåèæç®ï¼ã¦ã§ãï¼
https://ics-cert.us-
cert.gov/sites/default/files/documents/Procurement_Language_Rev4_100809.pdf
管çæ¡å¼µï¼(1, 2, 9) ICS è£è¶³ã¬ã¤ãã³ã¹ï¼éçºè
ã¯å¿
è¦ãªæ
å ±ãå©ç¨ã§ããªãå¯è½æ§ãããã
SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
445
Control Enhancement: (10) ICS Supplemental Guidance: Example compensating controls include employing external products
on the FIPS 201-approved products list for Personal Identity Verification (PIV) capability in conjunction with ICS products.
SA-5 INFORMATION SYSTEM DOCUMENTATION
CNTL NO. CONTROL NAME
Control Enhancement Name
CONTROL BASELINES
LOW
MOD
HIGH
SA-5
Information System Documentation
Selected
Selected
Selected
No ICS Supplemental Guidance.
SA-8 SECURITY ENGINEERING PRINCIPLES
CNTL NO. CONTROL NAME
Control Enhancement Name
CONTROL BASELINES
LOW
MOD
HIGH
SA-8
Security Engineering Principles
Selected
Selected
No ICS Supplemental Guidance.
SA-9 EXTERNAL INFORMATION SYSTEM SERVICES
CNTL NO. CONTROL NAME
Control Enhancement Name
CONTROL BASELINES
LOW
MOD
HIGH
SA-9
External Information System Services
Selected
Selected
Selected
SA-9 (2) EXTERNAL INFORMATION SYSTEMS | IDENTIFICATION OF
FUNCTIONS / PORTS / PROTOCOLS / SERVICES
Selected Selected
No ICS Supplemental Guidance.
SA-10 DEVELOPER CONFIGURATION MANAGEMENT
CNTL NO. CONTROL NAME
Control Enhancement Name
CONTROL BASELINES
LOW
MOD
HIGH
SA-10
Developer Configuration Management
Selected
Selected
No ICS Supplemental Guidance.
SA-11 DEVELOPER SECURITY TESTING AND EVALUATION
CNTL NO. CONTROL NAME
Control Enhancement Name
CONTROL BASELINES
LOW
MOD
HIGH
SA-11
Developer Security Testing and Evaluation
Selected
Selected
No ICS Supplemental Guidance.
SA-12 SUPPLY CHAIN PROTECTION
CNTL NO. CONTROL NAME
Control Enhancement Name
CONTROL BASELINES
LOW
MOD
HIGH
SA-12
Supply Chain Protection
Selected
No ICS Supplemental Guidance.
SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
446
管çæ¡å¼µï¼(10) ICS è£è¶³ã¬ã¤ãã³ã¹ï¼è£åç管ççã®ä¾ã¨ãã¦ãICS 製åã«é¢é£ãã身å証
æï¼PIVï¼æ©è½ã® FIPS 201 æ¿èªè£½åãªã¹ãã®å¤é¨è£½åæ¡ç¨ãããã
SA-5 æ
å ±ã·ã¹ãã ææ¸å
管ççªå·
管çå
管çæ¡å¼µå
管çãã¼ã¹ã©ã¤ã³
ä½
ä¸
é«
SA-5
æ
å ±ã·ã¹ãã ææ¸å
é¸å®
é¸å®
é¸å®
ICS è£è¶³ã¬ã¤ãã³ã¹ãªã
SA-8 ã»ãã¥ãªãã£ã¨ã³ã¸ãã¢ãªã³ã°åå
管ççªå·
管çå
管çæ¡å¼µå
管çãã¼ã¹ã©ã¤ã³
ä½
ä¸
é«
SA-8
ã»ãã¥ãªãã£ã¨ã³ã¸ãã¢ãªã³ã¯åå
é¸å®
é¸å®
ICS è£è¶³ã¬ã¤ãã³ã¹ãªã
SA-9 å¤é¨æ
å ±ã·ã¹ãã ãµã¼ãã¹
管ççªå·
管çå
管çæ¡å¼µå
管çãã¼ã¹ã©ã¤ã³
ä½
ä¸
é«
SA-9
å¤é¨æ
å ±ã·ã¹ãã ãµã¼ãã¹
é¸å®
é¸å®
é¸å®
SA-9 (2)
å¤é¨æ
å ±ã·ã¹ãã
|
æ©è½ã»
ãã¼ãã»ãããã³ã«ã»ãµã¼ãã¹ã®èå¥
é¸å® é¸å®
ICS è£è¶³ã¬ã¤ãã³ã¹ãªã
SA-10 éçºè
è¨å®ç®¡ç
管ççªå·
管çå
管çæ¡å¼µå
管çãã¼ã¹ã©ã¤ã³
ä½
ä¸
é«
SA-10
éçºè
è¨å®ç®¡ç
é¸å®
é¸å®
ICS è£è¶³ã¬ã¤ãã³ã¹ãªã
SA-11 éçºè
ã»ãã¥ãªãã£è©¦é¨è©ä¾¡
管ççªå·
管çå
管çæ¡å¼µå
管çãã¼ã¹ã©ã¤ã³
ä½
ä¸
é«
SA-11
éçºè
ã»ãã¥ãªãã£è©¦é¨è©ä¾¡
é¸å®
é¸å®
ICS è£è¶³ã¬ã¤ãã³ã¹ãªã
SA-12 ãµãã©ã¤ãã§ã¼ã³ä¿è·
管ççªå·
管çå
管çæ¡å¼µå
管çãã¼ã¹ã©ã¤ã³
ä½
ä¸
é«
SA-12
ãµãã©ã¤ãã§ã¼ã³ä¿è·
é¸å®
ICS è£è¶³ã¬ã¤ãã³ã¹ãªã

SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
447
SA-15 DEVELOPMENT PROCESS, STANDARDS, AND TOOLS
CNTL NO. CONTROL NAME
Control Enhancement Name
CONTROL BASELINES
LOW
MOD
HIGH
SA-15
Development Process, Standards, and Tools
Selected
Selected
Selected
No ICS Supplemental Guidance.
SA-16 DEVELOPER-PROVIDED TRAINING
CNTL NO. CONTROL NAME
Control Enhancement Name
CONTROL BASELINES
LOW
MOD
HIGH
SA-16
Developer-Provided Training
Selected
No ICS Supplemental Guidance.
SA-17 DEVELOPER SECURITY ARCHITECTURE AND DESIGN
CNTL NO. CONTROL NAME
Control Enhancement Name
CONTROL BASELINES
LOW
MOD
HIGH
SA-17
Developer Security Architecture and Design
Selected
No ICS Supplemental Guidance.
SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
448
SA-15 éçºããã»ã¹ã»è¦æ ¼ã»ãã¼ã«
管ççªå·
管çå
管çæ¡å¼µå
管çãã¼ã¹ã©ã¤ã³
ä½
ä¸
é«
SA-15
éçºããã»ã¹ã»è¦æ ¼ã»ãã¼ã«
é¸å®
ICS è£è¶³ã¬ã¤ãã³ã¹ãªã
SA-16 éçºè
ã«ããè¨ç·´
管ççªå·
管çå
管çæ¡å¼µå
管çãã¼ã¹ã©ã¤ã³
ä½
ä¸
é«
SA-16
éçºè
ã«ããè¨ç·´
é¸å®
ICS è£è¶³ã¬ã¤ãã³ã¹ãªã
SA-17 éçºè
ã»ãã¥ãªãã£ã¢ã¼ããã¯ãã£ã»è¨è¨
管ççªå·
管çå
管çæ¡å¼µå
管çãã¼ã¹ã©ã¤ã³
ä½
ä¸
é«
SA-17
éçºè
ã»ãã¥ãªãã£ã¢ã¼ããã¯ãã£ã»è¨è¨
é¸å®
ICS è£è¶³ã¬ã¤ãã³ã¹ãªã
SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
449
SYSTEM AND COMMUNICATIONS PROTECTION - SC
Tailoring Considerations for System and Communications Protection Family
The use of cryptography is determined after careful consideration of the security needs and the potential ramifications on system
performance. For example, the organization considers whether latency induced from the use of cryptography would adversely impact the
operational performance of the ICS. While the legacy devices commonly found within ICS often lack direct support of cryptographic
functions, compensating controls (e.g., encapsulations) may be used to meet the intent of the control.
In situations where the ICS cannot support the specific System and Communications Protection requirements of a control, the
organization employs compensating controls in accordance with the general tailoring guidance. Examples of compensating controls are given
with each control, as appropriate.
Supplemental Guidance
Supplemental Guidance for all Controls and Control Enhancements in NIST SP 800-53 Rev. 4, Appendix F, should be used in
conjunction with the ICS Supplemental Guidance in this overlay, if any.
SC-1 SYSTEM AND COMMUNICATIONS PROTECTION POLICY AND PROCEDURES
CNTL NO. CONTROL NAME
Control Enhancement Name
CONTROL BASELINES
LOW
MOD
HIGH
SC-1 System and Communications Protection Policy and
Procedures
Selected Selected Selected
ICS Supplemental Guidance: The policy specifically addresses the unique properties and requirements of ICS and the relationship
to non-ICS systems.
SC-2 APPLICATION PARTITIONING
CNTL NO. CONTROL NAME
Control Enhancement Name
CONTROL BASELINES
LOW
MOD
HIGH
SC-2
Application Partitioning
Selected
Selected
ICS Supplemental Guidance: Systems used to manage the ICS should be separate from the operational ICS components. Example
compensating controls include providing increased auditing measures.
SC-3 SECURITY FUNCTION ISOLATION
CNTL NO. CONTROL NAME
Control Enhancement Name
CONTROL BASELINES
LOW
MOD
HIGH
SC-3
Security Function Isolation
Selected
ICS Supplemental Guidance: Example compensating controls include providing increased auditing measures, limiting network
connectivity, architectural allocation.
SC-4 INFORMATION IN SHARED RESOURCES
CNTL NO. CONTROL NAME
Control Enhancement Name
CONTROL BASELINES
LOW
MOD
HIGH
SC-4
Information in Shared Resources
Selected
Selected
ICS Supplemental Guidance: Example compensating controls include architecting the use of the ICS to prevent sharing system
resources.
SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
450
ã·ã¹ãã åã³éä¿¡ä¿è· - SC
ã·ã¹ãã åã³éä¿¡ä¿è·ãã¡ããªã®ã«ã¹ã¿ãã¤ãºèæ
®äºé
æå·åã®ä½¿ç¨ã¯ãã»ãã¥ãªãã£ä¸ã®å¿
è¦æ§ã¨ã·ã¹ãã ããã©ã¼ãã³ã¹ã¸ã®æªå½±é¿ãæ
éã«èæ
®ã
ã¦å¤æãããä¾ãã°ãæå·ãå©ç¨ããã«ããçããå¾
ã¡æéããICS ã®éç¨ããã©ã¼ãã³ã¹ãé»
害ããªããçµç¹ã¯æ¤è¨ãããé常 ICS ã«è¦ãããã¬ã¬ã·ã¼ããã¤ã¹ã¯ãæå·é¢æ°ã«ç´æ¥å¯¾å¿ãã¦
ããªããã¨ãå¤ããããè£åç管ççï¼ã«ãã»ã«åçï¼ã使ç¨ãã¦ã管çç®çãéæããã
ICS ãããå¶å¾¡ã®ç¹å®ã®ã·ã¹ãã åã³éä¿¡ä¿è·è¦ä»¶ã«å¯¾å¿ãã¦ããªãç¶æ³ã§ã¯ãå
¨ä½çãªã«ã¹ã¿
ãã¤ãºã¬ã¤ãã³ã¹ã«å¾ã£ã¦è£åç管ççãæ¡ç¨ãããè£åç管ççã®ä¾ãå¿
è¦ã«å¿ãã¦ã管çç
ãã¨ã«ç¤ºãããã
è£è¶³ã¬ã¤ãã³ã¹
å©ç¨ã§ããå ´åã«ã¯ãNIST SP 800-53 第4çä»é² Fã«ããå
¨ã¦ã®ç®¡çã»ç®¡çæ¡å¼µç¨è£è¶³ã¬ã¤ãã³
ã¹ãããã®ãªã¼ãã¼ã¬ã¤ã«ããã¦ãICS è£è¶³ã¬ã¤ãã³ã¹ã¨ä½µç¨ãã¹ãã§ããã
SC-1 ã·ã¹ãã åã³éä¿¡ä¿è·ããªã·ã¼ã»æé
管ççªå·
管çå
管çæ¡å¼µå
管çãã¼ã¹ã©ã¤ã³
ä½
ä¸
é«
SC-1
ã·ã¹ãã éä¿¡ä¿è·ããªã·ã¼ã»æé
é¸å®
é¸å®
é¸å®
ICS è£è¶³ã¬ã¤ãã³ã¹ï¼ããªã·ã¼ã¯ç¹ã« ICS ã®åºæã®ç¹æ§ã»è¦ä»¶åã³ ICS 以å¤ã®ã·ã¹ãã ã¨ã®
é¢ä¿ãåãä¸ããã
SC-2 ã¢ããªã±ã¼ã·ã§ã³åå²
管ççªå·
管çå
管çæ¡å¼µå
管çãã¼ã¹ã©ã¤ã³
ä½
ä¸
é«
SC-2
ã¢ããªã±ã¼ã·ã§ã³åå²
é¸å®
é¸å®
ICS è£è¶³ã¬ã¤ãã³ã¹ï¼ICS ã®ç®¡çã«ä½¿ç¨ããã·ã¹ãã ã¯ãå®ç¨ ICS ã³ã³ãã¼ãã³ãã¨å¥ã«ã
ã¹ãã§ãããè£åç管ççã®ä¾ã¨ãã¦ãç£æ»æ段ã®å¼·åãããã
SC-3 ã»ãã¥ãªãã£æ©è½ã®éé¢
管ççªå·
管çå
管çæ¡å¼µå
管çãã¼ã¹ã©ã¤ã³
ä½
ä¸
é«
SC-3
ã»ãã¥ãªãã£æ©è½ã®éé¢
é¸å®
ICS è£è¶³ã¬ã¤ãã³ã¹ï¼è£åç管ççã®ä¾ã¨ãã¦ãç£æ»æ段ã®å¼·åããããã¯ã¼ã¯æ¥ç¶ã®å¶éã
ã¢ã¼ããã¯ãã£å²å½ãããã
SC-4 å
±æãªã½ã¼ã¹å
æ
å ±
管ççªå·
管çå
管çæ¡å¼µå
管çãã¼ã¹ã©ã¤ã³
ä½
ä¸
é«
SC-4
å
±æãªã½ã¼ã¹å
æ
å ±
é¸å®
é¸å®
ICS è£è¶³ã¬ã¤ãã³ã¹ï¼è£åç管ççã®ä¾ã¨ãã¦ãICS ã®ä½¿ç¨è¦é ãè¨å®ãã¦ã·ã¹ãã ãªã½ã¼
ã¹ãå
±æããªãããã«ããæ¹æ³ãããã
SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
451
SC-5 DENIAL OF SERVICE PROTECTION
CNTL NO. CONTROL NAME
Control Enhancement Name
CONTROL BASELINES
LOW
MOD
HIGH
SC-5
Denial of Service Protection
Selected
Selected
Selected
ICS Supplemental Guidance: Example compensating controls include ensuring a loss of communication results in the ICS
operating in nominal or safe mode. Risk-based analysis informs the establishment of policy and procedure.
SC-7 BOUNDARY PROTECTION
CNTL NO. CONTROL NAME
Control Enhancement Name
CONTROL BASELINES
LOW
MOD
HIGH
SC-7
Boundary Protection
Selected
Selected
Selected
SC-7 (3)
BOUNDARY PROTECTION | ACCESS POINTS
Selected
Selected
SC-7 (4) BOUNDARY PROTECTION | EXTERNAL
TELECOMMUNICATIONS SERVICES
Selected Selected
SC-7 (5) BOUNDARY PROTECTION | DENY BY DEFAULT / ALLOW BY
EXCEPTION
Selected Selected
SC-7 (7) BOUNDARY PROTECTION | PREVENT SPLIT TUNNELING FOR
REMOTE DEVICES
Selected Selected
SC-7 (8) BOUNDARY PROTECTION | ROUTE TRAFFIC TO
AUTHENTICATED PROXY SERVERS
Selected
SC-7 (18)
BOUNDARY PROTECTION | FAIL SECURE
Added
Selected
SC-7 (21) BOUNDARY PROTECTION | ISOLATION OF INFORMATION
SYSTEM COMPONENTS
Selected
No ICS Supplemental Guidance.
Control Enhancement: (3, 4, 5, 7, 8, 21) No ICS Supplemental Guidance.
Control Enhancement: (18) ICS Supplemental Guidance: The organization selects an appropriate failure mode (e.g., permit or
block all communications).
Rationale for adding SC-7 (18) to Moderate Baseline: As part of the architecture and design of the ICS, the organization selects
an appropriate failure mode in accordance with the function performed by the ICS and the operational environment. The ability to choose the
failure mode for the physical part of the ICS differentiates the ICS from other IT systems. This choice may be a significant influence in
mitigating the impact of a failure.
SC-8 TRANSMISSION CONFIDENTIALITY AND INTEGRITY
CNTL NO. CONTROL NAME
Control Enhancement Name
CONTROL BASELINES
LOW
MOD
HIGH
SC-8
Transmission Confidentiality and Integrity
Selected
Selected
SC-8 (1) transmission confidentiality and integrity | cryptographic or
alternate physical protection
Selected Selected
No ICS Supplemental Guidance.
Control Enhancement: (1) ICS Supplemental Guidance: The organization explores all possible cryptographic integrity
mechanisms (e.g., digital signature, hash function). Each mechanism has a different delay impact.
SC-10 NETWORK DISCONNECT
CNTL NO. CONTROL NAME
Control Enhancement Name
CONTROL BASELINES
LOW
MOD
HIGH
SC-10
Network Disconnect
Selected
Selected
ICS Supplemental Guidance: Example compensating controls include providing increased auditing measures or limiting remote
access privileges to key personnel.
SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
452
SC-5 ãµã¼ãã¹ä¿è·å¦¨å®³
管ççªå·
管çå
管çæ¡å¼µå
管çãã¼ã¹ã©ã¤ã³
ä½
ä¸
é«
SC-5
ãµã¼ãã¹ä¿è·å¦¨å®³
é¸å®
é¸å®
é¸å®
ICS è£è¶³ã¬ã¤ãã³ã¹ï¼è£åç管ççã®ä¾ã¨ãã¦ãéä¿¡åªå¤±æã« ICS ã®éç¨ãå
¬ç§°ã¢ã¼ãåã¯
ã»ã¼ãã¢ã¼ãã«ãªãããã«ããæ¹æ³ãããããªã¹ã¯ã«ç«èããåæã«ãããããªã·ã¼ã»æé ã®è¨
å®æ
å ±ãå¾ãããã
SC-7 å¢çã®ä¿è·
管ççªå·
管çå
管çæ¡å¼µå
管çãã¼ã¹ã©ã¤ã³
ä½
ä¸
é«
SC-7
å¢çã®ä¿è·
é¸å®
é¸å®
é¸å®
SC-7 (3)
å¢çã®ä¿è·
|
ã¢ã¯ã»ã¹ãã¤ã³ã
é¸å®
é¸å®
SC-7 (4)
å¢çã®ä¿è·
|
å¤é¨é»æ°éä¿¡ãµã¼ãã¹
é¸å®
é¸å®
SC-7 (5)
å¢çã®ä¿è·
|
ããã©ã«ãã§æ絶ã»ä¾å¤ã§è¨±è«¾
é¸å®
é¸å®
SC-7 (7)
å¢çã®ä¿è·
|
é éããã¤ã¹ã®ã¹ããªãããã³ããªã³ã°é²æ¢
é¸å®
é¸å®
SC-7 (8)
å¢çã®ä¿è·
|
èªè¨¼æ¸ã¿ããã¸ã®ãã·ãµã¼ããã©ãã£ãã¯ã®çµè·¯æ
å®
é¸å®
SC-7 (18)
å¢çã®ä¿è·
|
ãã§ã¼ã«ã»ãã¥ã¢
追å
é¸å®
SC-7 (21)
å¢çã®ä¿è·
|
æ
å ±ã·ã¹ãã ã³ã³ãã¼ãã³ãã®éé¢
é¸å®
ICS è£è¶³ã¬ã¤ãã³ã¹ãªã
管çæ¡å¼µï¼(3, 4, 5, 7, 8, 21) ICS è£è¶³ã¬ã¤ãã³ã¹ãªã
管çæ¡å¼µï¼(18) ICS è£è¶³ã¬ã¤ãã³ã¹ï¼çµç¹ã¯é©å½ãªæ
éã¢ã¼ããé¸æããï¼å
¨ã¦ã®éä¿¡ã許
å¯åã¯ãããã¯çï¼ã
SC-7 (18)ãä¸ãã¼ã¹ã©ã¤ã³ã«è¿½å ããçç±ï¼ICS ã¢ã¼ããã¯ãã£åã³è¨è¨ã®ä¸è²«ã¨ãã¦ãçµ
ç¹ã¯ãICS åã³éç¨ç°å¢ãå®æ½ããæ©è½ã«å¾ããé©å½ãªæ
éã¢ã¼ããé¸æãããICS ã®ç©çé¨åã«
æ
éã¢ã¼ããé¸æã§ããè½åã¯ãICS ã¨ä»ã® IT ã·ã¹ãã ã¨ã®éãã§ããããã®é¸æã¯ãæ
éã®å½±
é¿ãç·©åããä¸ã§å¤§ããªå¹æãããã
SC-8 éä¿¡æ©å¯æ§ã»å®å
¨æ§
管ççªå·
管çå
管çæ¡å¼µå
管çãã¼ã¹ã©ã¤ã³
ä½
ä¸
é«
SC-8
éä¿¡æ©å¯æ§ã»å®å
¨æ§
é¸å®
é¸å®
SC-8 (1)
éä¿¡
æ©å¯æ§ã»å®å
¨æ§
|
æå·ååã¯ä»£æ¿ç©ççä¿è·
é¸å®
é¸å®
ICS è£è¶³ã¬ã¤ãã³ã¹ãªã
管çæ¡å¼µï¼(1) ICS è£è¶³ã¬ã¤ãã³ã¹ï¼çµç¹ã¯ããããæå·ä¿å
¨ã¡ã«ããºã ãæ´»ç¨ããï¼ãã¸ã¿
ã«ç½²åãããã·ã¥é¢æ°çï¼ãåã¡ã«ããºã ã®é
延影é¿ã¯ããããç°ãªãã
SC-10 ãããã¯ã¼ã¯åæ
管ççªå·
管çå
管çæ¡å¼µå
管çãã¼ã¹ã©ã¤ã³
ä½
ä¸
é«
SC-10
ãããã¯ã¼ã¯åæ
é¸å®
é¸å®
ICS è£è¶³ã¬ã¤ãã³ã¹ï¼è£åç管ççã®ä¾ã¨ãã¦ãç£æ»æ段ã®å¼·åããªã¢ã¼ãã¢ã¯ã»ã¹ç¹æ¨©ã
éè¦ãªäººå¡ã«å¶éããæ¹æ³ãããã
SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
453
SC-12 CRYPTOGRAPHIC KEY ESTABLISHMENT AND MANAGEMENT
CNTL NO. CONTROL NAME
Control Enhancement Name
CONTROL BASELINES
LOW
MOD
HIGH
SC-12
Cryptographic Key Establishment and Management
Selected
Selected
Selected
SC-12 (1) CRYPTOGRAPHIC KEY ESTABLISHMENT AND MANAGEMENT
| AVAILABILITY
Selected
ICS Supplemental Guidance: The use of cryptographic key management in ICS is intended to support internal nonpublic use.
Control Enhancement: (1) No ICS Supplemental Guidance.
SC-13 CRYPTOGRAPHIC PROTECTION
CNTL NO. CONTROL NAME
Control Enhancement Name
CONTROL BASELINES
LOW
MOD
HIGH
SC-13
Cryptographic Protection
Selected
Selected
Selected
No ICS Supplemental Guidance.
SC-15 COLLABORATIVE COMPUTING DEVICES
CNTL NO. CONTROL NAME
Control Enhancement Name
CONTROL BASELINES
LOW
MOD
HIGH
SC-15
Collaborative Computing Devices
Selected
Selected
Selected
No ICS Supplemental Guidance.
SC-17 PUBLIC KEY INFRASTRUCTURE CERTIFICATES
CNTL NO. CONTROL NAME
Control Enhancement Name
CONTROL BASELINES
LOW
MOD
HIGH
SC-17
Public Key Infrastructure Certificates
Selected
Selected
No ICS Supplemental Guidance.
SC-18 MOBILE CODE
CNTL NO. CONTROL NAME
Control Enhancement Name
CONTROL BASELINES
LOW
MOD
HIGH
SC-18
Mobile Code
Selected
Selected
No ICS Supplemental Guidance.
SC-19 VOICE OVER INTERNET PROTOCOL
CNTL NO. CONTROL NAME
Control Enhancement Name
CONTROL BASELINES
LOW
MOD
HIGH
SC-19
Voice Over Internet Protocol
Selected
Selected
ICS Supplemental Guidance: The use of VoIP technologies is determined after careful consideration and after verification that it
does not adversely impact the operational performance of the ICS.
SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
454
SC-12 æå·éµè¨å®ç®¡ç
管ççªå·
管çå
管çæ¡å¼µå
管çãã¼ã¹ã©ã¤ã³
ä½
ä¸
é«
SC-12
æå·éµè¨å®ç®¡ç
é¸å®
é¸å®
é¸å®
SC-12 (1)
æå·éµ
è¨å®ç®¡ç
|
å¯ç¨æ§
é¸å®
ICS è£è¶³ã¬ã¤ãã³ã¹ï¼æå·éµç®¡çã ICS ã§ä½¿ç¨ããç®çã¯ãå
é¨ã®éå
¬éå©ç¨ã«å¯¾å¿ããã
ãã§ããã
管çæ¡å¼µï¼(1) ICS è£è¶³ã¬ã¤ãã³ã¹ãªã
SC-13 æå·ä¿è·
管ççªå·
管çå
管çæ¡å¼µå
管çãã¼ã¹ã©ã¤ã³
ä½
ä¸
é«
SC-13
æå·ä¿è·
é¸å®
é¸å®
é¸å®
ICS è£è¶³ã¬ã¤ãã³ã¹ãªã
SC-15 å
±åã³ã³ãã¥ã¼ãã£ã³ã°ããã¤ã¹
管ççªå·
管çå
管çæ¡å¼µå
管çãã¼ã¹ã©ã¤ã³
ä½
ä¸
é«
SC-15
å
±åã³ã³ãã¥ã¼ãã£ã³ã°ããã¤ã¹
é¸å®
é¸å®
é¸å®
ICS è£è¶³ã¬ã¤ãã³ã¹ãªã
SC-17 å
¬ééµã¤ã³ãã©è¨¼ææ¸
管ççªå·
管çå
管çæ¡å¼µå
管çãã¼ã¹ã©ã¤ã³
ä½
ä¸
é«
SC-17
å
¬ééµã¤ã³ãã©è¨¼ææ¸
é¸å®
é¸å®
ICS è£è¶³ã¬ã¤ãã³ã¹ãªã
SC-18 ã¢ãã¤ã«ã³ã¼ã
管ççªå·
管çå
管çæ¡å¼µå
管çãã¼ã¹ã©ã¤ã³
ä½
ä¸
é«
SC-18
ã¢ãã¤ã«ã³ã¼ã
é¸å®
é¸å®
ICS è£è¶³ã¬ã¤ãã³ã¹ãªã
SC-19 VoIP
管ççªå·
管çå
管çæ¡å¼µå
管çãã¼ã¹ã©ã¤ã³
ä½
ä¸
é«
SC-19
VoIP
é¸å®
é¸å®
ICS è£è¶³ã¬ã¤ãã³ã¹ï¼VoIP æè¡ã®å©ç¨ã¯ãICS ã®éç¨ã«æªå½±é¿ããªããã¨ãæ¤è¨¼ããæ
éã«
æ¤è¨ãã¦ããå¤æããã
SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
455
SC-20 SECURE NAME / ADDRESS RESOLUTION SERVICE (AUTHORITATIVE SOURCE)
CNTL NO. CONTROL NAME
Control Enhancement Name
CONTROL BASELINES
LOW
MOD
HIGH
SC-20 Secure Name /Address Resolution Service
(Authoritative Source)
Selected Selected Selected
ICS Supplemental Guidance: The use of secure name/address resolution services is determined after careful consideration and after
verification that it does not adversely impact the operation of the ICS.
SC-21 SECURE NAME / ADDRESS RESOLUTION SERVICE (RECURSIVE OR CACHING RESOLVER)
CNTL NO. CONTROL NAME
Control Enhancement Name
CONTROL BASELINES
LOW
MOD
HIGH
SC-21 Secure Name /Address Resolution Service
(Recursive or Caching Resolver)
Selected Selected Selected
ICS Supplemental Guidance: The use of secure name/address resolution services is determined after careful consideration and after
verification that it does not adversely impact the operation of the ICS.
SC-22 ARCHITECTURE AND PROVISIONING FOR NAME / ADDRESS RESOLUTION SERVICE
CNTL NO. CONTROL NAME
Control Enhancement Name
CONTROL BASELINES
LOW
MOD
HIGH
SC-22 Architecture and Provisioning for
Name/Address Resolution Service
Selected Selected Selected
ICS Supplemental Guidance: The use of secure name/address resolution services is determined after careful consideration and after
verification that it does not adversely impact the operational performance of the ICS.
SC-23 SESSION AUTHENTICITY
CNTL NO. CONTROL NAME
Control Enhancement Name
CONTROL BASELINES
LOW
MOD
HIGH
SC-23
Session Authenticity
Selected
Selected
ICS Supplemental Guidance: Example compensating controls include auditing measures.
SC-24 FAIL IN KNOWN STATE
CNTL NO. CONTROL NAME
Control Enhancement Name
CONTROL BASELINES
LOW
MOD
HIGH
SC-24
Fail in Known State
Added
Selected
ICS Supplemental Guidance: The organization selects an appropriate failure state. Preserving ICS state information includes
consistency among ICS state variables and the physical state which the ICS represents (e.g., whether valves are open or closed,
communication permitted or blocked, continue operations).
Rationale for adding SC-24 to moderate baseline: As part of the architecture and design of the ICS, the organization selects an
appropriate failure state of an ICS in accordance with the function performed by the ICS and the operational environment. The ability to
choose the failure mode for the physical part of the ICS differentiates the ICS from other IT systems. This choice may be a significant
influence in mitigating the impact of a failure, since it may be disruptive to ongoing physical processes (e.g., valves failing in closed position
may adversely affect system cooling).
SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
456
SC-20 ã»ãã¥ã¢ãªåå/ã¢ãã¬ã¹è§£æ±ºãµã¼ãã¹ï¼æ¨©éã½ã¼ã¹ï¼
管ççªå·
管çå
管çæ¡å¼µå
管çãã¼ã¹ã©ã¤ã³
ä½
ä¸
é«
SC-20
ã»ãã¥ã¢ãªåå/ã¢ãã¬ã¹è§£æ±ºãµã¼ãã¹ï¼æ¨©éã½ã¼ã¹ï¼
é¸å®
é¸å®
é¸å®
ICS è£è¶³ã¬ã¤ãã³ã¹ï¼ã»ãã¥ã¢ãªåå/ã¢ãã¬ã¹è§£æ±ºãµã¼ãã¹ã®å©ç¨ã¯ãICS ã®éç¨ã«æªå½±é¿
ããªããã¨ãæ¤è¨¼ããæ
éã«æ¤è¨ãã¦ããå¤æããã
SC-21 ã»ãã¥ã¢ãªåå/ã¢ãã¬ã¹è§£æ±ºãµã¼ãã¹ï¼å帰åã¯ãã£ãã·ã³ã°ãªã¾ã«ãï¼
管ççªå·
管çå
管çæ¡å¼µå
管çãã¼ã¹ã©ã¤ã³
ä½
ä¸
é«
SC-21
ã»ãã¥ã¢ãªåå
/
ã¢ãã¬ã¹è§£æ±ºãµã¼ãã¹ï¼å帰åã¯ãã£ãã·ã³ã°ãª
ã¾ã«ãï¼
é¸å® é¸å® é¸å®
ICS è£è¶³ã¬ã¤ãã³ã¹ï¼ã»ãã¥ã¢ãªåå/ã¢ãã¬ã¹è§£æ±ºãµã¼ãã¹ã®å©ç¨ã¯ãICS ã®éç¨ã«æªå½±é¿
ããªããã¨ãæ¤è¨¼ããæ
éã«æ¤è¨ãã¦ããå¤æããã
SC-22 åå/ã¢ãã¬ã¹è§£æ±ºãµã¼ãã¹ç¨ã¢ã¼ããã¯ãã£ã¼ãããã¸ã§ãã³ã°
管ççªå·
管çå
管çæ¡å¼µå
管çãã¼ã¹ã©ã¤ã³
ä½
ä¸
é«
SC-22
åå/ã¢ãã¬ã¹è§£æ±ºãµã¼ãã¹ç¨ã¢ã¼ããã¯ãã£ã¼ãããã¸ã§ãã³ã°
é¸å®
é¸å®
é¸å®
ICS è£è¶³ã¬ã¤ãã³ã¹ï¼ã»ãã¥ã¢ãªåå/ã¢ãã¬ã¹è§£æ±ºãµã¼ãã¹ã®å©ç¨ã¯ãICS ã®éç¨ã«æªå½±é¿
ããªããã¨ãæ¤è¨¼ããæ
éã«æ¤è¨ãã¦ããå¤æããã
SC-23 ã»ãã·ã§ã³èªè¨¼
管ççªå·
管çå
管çæ¡å¼µå
管çãã¼ã¹ã©ã¤ã³
ä½
ä¸
é«
SC-23
ã»ãã·ã§ã³èªè¨¼
é¸å®
é¸å®
ICS è£è¶³ã¬ã¤ãã³ã¹ï¼è£åç管ççã®ä¾ã¨ãã¦ãç£æ»æ段ãããã
SC-24 æ¢ç¥ç¶æ
ã®å¤±æ
管ççªå·
管çå
管çæ¡å¼µå
管çãã¼ã¹ã©ã¤ã³
ä½
ä¸
é«
SC-24
æ¢ç¥ç¶æ
ã®å¤±æ
追å
é¸å®
ICS è£è¶³ã¬ã¤ãã³ã¹ï¼çµç¹ã¯é©å½ãªæ
éç¶æ
ãé¸æãããICS ç¶æ
æ
å ±ã®ä¿åã«ã¯ãICS ç¶
æ
å¤æ°ã¨ ICS ã®ç©ççç¶æ
ã®æ´åæ§ãå«ã¾ããï¼ãã«ãã®éåã¯éãéä¿¡ã®è¨±å¯åã¯ãããã¯
çï¼ã
SC-24 ãä¸ãã¼ã¹ã©ã¤ã³ã«è¿½å ããçç±ï¼ICS ã¢ã¼ããã¯ãã£åã³è¨è¨ã®ä¸è²«ã¨ãã¦ãçµç¹
ã¯ãICS åã³éç¨ç°å¢ãå®æ½ããæ©è½ã«å¾ããé©å½ãª ICS ã®æ
éç¶æ
ãé¸æãããICS ã®ç©çé¨
åã«æ
éã¢ã¼ããé¸æã§ããè½åã¯ãICS ã¨ä»ã® IT ã·ã¹ãã ã¨ã®éãã§ããããã®é¸æã¯ãé²è¡
ä¸ã®ç©çããã»ã¹ãä¸æãããããæ
éã®å½±é¿ãç·©åããä¸ã§å¤§ããªå¹æãããï¼ãã«ããéä½
ç½®ã«ãªãã¨ã·ã¹ãã å·å´ã«æªå½±é¿ãåºããªã©ï¼ã
SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
457
SC-28 PROTECTION OF INFORMATION AT REST
CNTL NO. CONTROL NAME
Control Enhancement Name
CONTROL BASELINES
LOW
MOD
HIGH
SC-28
Protection of Information at Rest
Selected
Selected
ICS Supplemental Guidance: The use of cryptographic mechanisms is determined after careful consideration and after verification
that it does not adversely impact the operational performance of the ICS.
SC-39 PROCESS ISOLATION
CNTL NO. CONTROL NAME
Control Enhancement Name
CONTROL BASELINES
LOW
MOD
HIGH
SC-39
Process Isolation
Selected
Selected
Selected
ICS Supplemental Guidance: Example compensating controls include partition processes to separate platforms.
SC-41 PORT AND I/O DEVICE ACCESS
CNTL NO. CONTROL NAME
Control Enhancement Name
CONTROL BASELINES
LOW
MOD
HIGH
SC-41
Port and I/O Device Access
Added
Added
Added
No ICS Supplemental Guidance.
Rationale for adding SC-24 to all baselines: The function of ICS can be readily determined in advance, making it easier to identify
ports and I/O devices that are unnecessary. Disabling or removing ports reinforces air-gap policy.
SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
458
SC-28 ä¼ç æ
å ±ã®ä¿è·
管ççªå·
管çå
管çæ¡å¼µå
管çãã¼ã¹ã©ã¤ã³
ä½
ä¸
é«
SC-28
ä¼ç æ
å ±ã®ä¿è·
é¸å®
é¸å®
ICS è£è¶³ã¬ã¤ãã³ã¹ï¼æå·ã¡ã«ããºã ã®å©ç¨ã¯ãICS ã®éç¨ã«æªå½±é¿ããªããã¨ãæ¤è¨¼ãã
æ
éã«æ¤è¨ãã¦ããå¤æããã
SC-39 ããã»ã¹éé¢
管ççªå·
管çå
管çæ¡å¼µå
管çãã¼ã¹ã©ã¤ã³
ä½
ä¸
é«
SC-39
ããã»ã¹éé¢
é¸å®
é¸å®
é¸å®
ICS è£è¶³ã¬ã¤ãã³ã¹ï¼è£åç管ççã®ä¾ã¨ãã¦ããã©ãããã¼ã ãåé¢ããããã®ãã¼ãã£
ã·ã§ã³ããã»ã¹ãããã
SC-41 ãã¼ãåã³ I/O ããã¤ã¹ã¢ã¯ã»ã¹
管ççªå·
管çå
管çæ¡å¼µå
管çãã¼ã¹ã©ã¤ã³
ä½
ä¸
é«
SC-41
ãã¼ãåã³ I/O ããã¤ã¹ã¢ã¯ã»ã¹
追å
追å
追å
ICS è£è¶³ã¬ã¤ãã³ã¹ãªã
SC-24 ãå
¨ã¦ã®ãã¼ã¹ã©ã¤ã³ã«è¿½å ããçç±ï¼ICS ã®æ©è½ã¯äºãããã«æ±ºããããããã«ãã
ä¸è¦ãªãã¼ãåã³ I/O ããã¤ã¹ã®èå¥ã容æã«ããããã¼ãã®ç¡å¹åãåé¤ã¯ãã¨ã¢ã®ã£ããã
ãªã·ã¼ãå¼·åããã
SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
459
SYSTEM AND INFORMATION INTEGRITY - SI
Tailoring Considerations for System and Information Integrity Family
In situations where the ICS cannot support the specific System and Information Integrity requirements of a control, the organization employs
compensating controls in accordance with the general tailoring guidance. Examples of compensating controls are given with each control, as
appropriate.
Supplemental Guidance
Supplemental Guidance for all Controls and Control Enhancements in NIST SP 800-53 Rev. 4, Appendix F, should be used in conjunction
with the ICS Supplemental Guidance in this overlay, if any.
SI-1 SYSTEM AND INFORMATION INTEGRITY POLICY AND PROCEDURES
CNTL NO. CONTROL NAME
Control Enhancement Name
CONTROL BASELINES
LOW
MOD
HIGH
SI-1
System and Information Integrity Policy and Procedures
Selected
Selected
Selected
ICS Supplemental Guidance: The policy specifically addresses the unique properties and requirements of ICS and the relationship
to non-ICS systems.
SI-2 FLAW REMEDIATION
CNTL NO. CONTROL NAME
Control Enhancement Name
CONTROL BASELINES
LOW
MOD
HIGH
SI-2
Flaw Remediation
Selected
Selected
Selected
SI-2 (1)
FLAW REMEDIATION | CENTRAL MANAGEMENT
Selected
SI-2 (2) FLAW REMEDIATION | AUTOMATED FLAW REMEDIATION
STATUS
Selected Selected
ICS Supplemental Guidance: Flaw Remediation is complicated since many ICS employ operating systems and other software that
is not current, is no longer being maintained by the vendors, and is not resistant to current threats. ICS operators are often dependent on
product vendors to validate the operability of a patch and also sometimes to perform the installation. Often flaws cannot be remediated based
on circumstances outside of the ICS operator's control (e.g., lack of a vendor patch). Sometime the organization has no choice but to accept
additional risk. In these situations, compensating controls should be implemented (e.g., limit the exposure of the vulnerable system). Other
compensating controls that do not decrease the residual risk but increase the ability to respond may be desirable (e.g., provide a timely
response in case of an incident; devise a plan to ensure the ICS can identify the exploitation of the flaw). Testing flaw remediation in an ICS
may require more resources than the organization can commit.
Control Enhancement: (1) No ICS Supplemental Guidance.
Control Enhancement: (2) ICS Supplemental Guidance: In situations where the ICS cannot support the use of automated
mechanisms to conduct and report on the status of flaw remediation, the organization employs nonautomated mechanisms or procedures
which incorporate methods to apply, track, and verify mitigation efforts as compensating controls in accordance with the general tailoring
guidance.
SI-3 MALICIOUS CODE PROTECTION
CNTL NO. CONTROL NAME
Control Enhancement Name
CONTROL BASELINES
LOW
MOD
HIGH
SI-3
Malicious Code Protection
Selected
Selected
Selected
SI-3 (1)
MALICIOUS CODE PROTECTION | CENTRAL MANAGEMENT
Selected
Selected
SI-3 (2)
MALICIOUS CODE PROTECTION | AUTOMATIC UPDATES
Selected
Selected
ICS Supplemental Guidance: The use and deployment of malicious code protection is determined after careful consideration and
after verification that it does not adversely impact the operation of the ICS. Malicious code
SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
460
ã·ã¹ãã åã³æ
å ±ã®å®å
¨æ§ - SI
ã·ã¹ãã åã³æ
å ±ã®å®å
¨æ§ãã¡ããªã®ã«ã¹ã¿ãã¤ãºèæ
®äºé
ICS ãããå¶å¾¡ã®ç¹å®ã®ã·ã¹ãã åã³æ
å ±å®å
¨æ§è¦ä»¶ã«å¯¾å¿ãã¦ããªãç¶æ³ã§ã¯ãå
¨ä½çãªã«
ã¹ã¿ãã¤ãºã¬ã¤ãã³ã¹ã«å¾ã£ã¦è£åç管ççãæ¡ç¨ããã
è£åç管ççã®ä¾ãå¿
è¦ã«å¿ãã¦ã管ççãã¨ã«ç¤ºãããã
è£è¶³ã¬ã¤ãã³ã¹
å©ç¨ã§ããå ´åã«ã¯ãNIST SP 800-53 第4çä»é² Fã«ããå
¨ã¦ã®ç®¡çã»ç®¡çæ¡å¼µç¨è£è¶³ã¬ã¤ã
ã³ã¹ãããã®ãªã¼ãã¼ã¬ã¤ã«ããã¦ãICS è£è¶³ã¬ã¤ãã³ã¹ã¨ä½µç¨ãã¹ãã§ããã
SI-1 ã·ã¹ãã åã³æ
å ±å®å
¨æ§ããªã·ã¼ã»æé
管ççªå·
管çå
管çæ¡å¼µå
管çãã¼ã¹ã©ã¤ã³
ä½
ä¸
é«
SI-1
ã·ã¹ãã æ
å ±å®å
¨æ§ããªã·ã¼ã»æé
é¸å®
é¸å®
é¸å®
ICS è£è¶³ã¬ã¤ãã³ã¹ï¼ããªã·ã¼ã¯ç¹ã« ICS ã®åºæã®ç¹æ§ã»è¦ä»¶åã³ ICS 以å¤ã®ã·ã¹ãã ã¨ã®
é¢ä¿ãåãä¸ããã
SI-2 æ¬ é¥ä¿®æ£
管ççªå·
管çå
管çæ¡å¼µå
管çãã¼ã¹ã©ã¤ã³
ä½
ä¸
é«
SI-2
æ¬ é¥ä¿®æ£
é¸å®
é¸å®
é¸å®
SI-2 (1)
æ¬ é¥ä¿®æ£
|
éä¸ç®¡ç
é¸å®
SI-2 (2)
æ¬ é¥ä¿®æ£
|
èªåæ¬ é¥ä¿®æ£ç¶æ
é¸å®
é¸å®
ICS è£è¶³ã¬ã¤ãã³ã¹ï¼ICS ã®å¤ãã¯ææ°ç以å¤ã® OS ãã½ããã¦ã¨ã¢ã使ç¨ãããã³ãã¼ã
ä¿å®ãè¡ã£ã¦ããããææ°ã®è
å¨ã«æµææ§ããªããããæ¬ é¥ä¿®æ£ã¯è¤éã¨ãªããICS æä½å¡ã¯ã
ãããã®åä½æ¤è¨¼ããã¨ãã«ã¯ã¤ã³ã¹ãã¼ã«ãè¡ãã ãã§ãã製åãã³ãã¼ã«ä¾åãããã¨ãå¤
ããICS æä½å¡ã®ç®¡çè½åãè¶
ãã¦ããç¶æ³ã§ã¯ãæ¬ é¥ã®ä¿®æ£ãã§ããªããã¨ãå¤ãï¼ãã³ãã¼
ãããã®æ¬ å¦çï¼ãçµç¹ã¯ãä»å çãªãªã¹ã¯ãåãå
¥ããããå¾ãªããã¨ãããããã®ãããªç¶
æ³ã§ã¯ãè£åç管ççãè¡ãï¼èå¼±ãªã·ã¹ãã ã®é²åºå¶éçï¼ããã®ä»ã®è£åç管ççã¨ãã¦ã¯ã
æ®çãªã¹ã¯ã¯æ¸ãããªãã¾ã§ãã対å¿è½åãé«ãããããªãã®ãæã¾ããï¼ã¤ã³ã·ãã³ãæã«ã¿
ã¤ã ãªã¼ãªå¯¾å¿ããæªç¨ããã¦ããæ¬ é¥ãç¹å®ã§ããè¨ç»ã®ä½æçï¼ãICS ã®æ¬ é¥ä¿®æ£æ¤è¨¼ã¯ã
çµç¹ãæå
¥ã§ãã以ä¸ã®ãªã½ã¼ã¹ãè¦ããå ´åãããã
管çæ¡å¼µï¼(1) ICS è£è¶³ã¬ã¤ãã³ã¹ãªã
管çæ¡å¼µï¼(2) ICS è£è¶³ã¬ã¤ãã³ã¹ï¼ICS ãæ¬ é¥ä¿®æ£å®æ½ã»å ±åã®èªåã¡ã«ããºã ã«å¯¾å¿ãã¦
ããªãç¶æ³ã§ã¯ãå
¨ä½çãªã«ã¹ã¿ãã¤ãºã¬ã¤ãã³ã¹ã«å¾ã£ã¦ãçµç¹ã¯éèªåã¡ã«ããºã åã¯æé
ãç·©ååªåã®é©ç¨ã»è¿½è·¡ã»æ¤è¨¼ã®ããã®è£åç管ççã¨ãã¦æ¡ç¨ããã
SI-3 æªæããã³ã¼ãä¿è·
管ççªå·
管çå
管çæ¡å¼µå
管çãã¼ã¹ã©ã¤ã³
ä½
ä¸
é«
SI-3
æªæããã³ã¼ãä¿è·
é¸å®
é¸å®
é¸å®
SI-3 (1)
æªæããã³ã¼ãä¿è·
|
éä¸ç®¡ç
é¸å®
é¸å®
SI-3 (2)
æªæããã³ã¼ãä¿è·
|
èªåæ´æ°
é¸å®
é¸å®
ICS è£è¶³ã¬ã¤ãã³ã¹ï¼æªæããã³ã¼ãä¿è·ã®å©ç¨ã¯ãICS ã®éç¨ã«æªå½±é¿ããªããã¨ãæ¤è¨¼
ããæ
éã«æ¤è¨ãã¦ããå¤æãããæªæããã³ã¼ã
SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
461
protection tools should be configured to minimize their potential impact on the ICS (e.g., employ notification rather than quarantine).
Example compensating controls include increased traffic monitoring and auditing.
Control Enhancement: (1) ICS Supplemental Guidance: The organization implements central management of malicious code
protection with consideration of the impact on operation of the ICS. Example compensating controls include increased auditing.
Control Enhancement: (2) ICS Supplemental Guidance: The organization implements automatic updates of malicious code
protection with consideration of the impact on operation of the ICS. In situations where the ICS cannot support the use of automatic update
of malicious code protection, the organization employs nonautomated procedures as compensating controls in accordance with the general
tailoring guidance.
SI-4 INFORMATION SYSTEM MONITORING
CNTL NO. CONTROL NAME
Control Enhancement Name
CONTROL BASELINES
LOW
MOD
HIGH
SI-4
Information System Monitoring
Selected
Selected
Selected
SI-4 (2) INFORMATION SYSTEM MONITORING | AUTOMATED TOOLS
FOR REAL-TIME ANALYSIS
Selected Selected
SI-4 (4) INFORMATION SYSTEM MONITORING | INBOUND AND
OUTBOUND COMMUNICATIONS TRAFFIC
Selected Selected
SI-4 (5) INFORMATION SYSTEM MONITORING | SYSTEM-GENERATED
ALERTS
Selected Selected
ICS Supplemental Guidance: The organization ensures that the use of monitoring tools and techniques does not adversely impact the
operational performance of the ICS. Example compensating controls include deploying sufficient network monitoring.
Control Enhancement: (2) ICS Supplemental Guidance: In situations where the ICS cannot support the use of automated tools to
support near-real-time analysis of events, the organization employs compensating controls (e.g., providing an auditing capability on a
separate system, nonautomated mechanisms or procedures) in accordance with the general tailoring guidance.
Control Enhancement: (4) ICS Supplemental Guidance: In situations where the ICS cannot monitor inbound and outbound
communications traffic, the organization employs compensating controls include providing a monitoring capability on a separate information
system.
Control Enhancement: (5) ICS Supplemental Guidance: Example compensating controls include manual methods of generating
alerts.
SI-5 SECURITY ALERTS, ADVISORIES, AND DIRECTIVES
CNTL NO. CONTROL NAME
Control Enhancement Name
CONTROL BASELINES
LOW
MOD
HIGH
SI-5
Security Alerts, Advisories, and Directives
Selected
Selected
Selected
SI-5 (1) SECURITY ALERTS, ADVISORIES, AND DIRECTIVES |
AUTOMATED ALERTS AND ADVISORIES
Selected
ICS Supplemental Guidance: The DHS Industrial Control Systems Cyber Emergency Response Team (ICS-CERT) generates
security alerts and advisories relative to ICS http://ics-cert.us-cert.gov/ .
Control Enhancement: (1) No ICS Supplemental Guidance.
SI-6 SECURITY FUNCTIONALITY VERIFICATION
CNTL NO. CONTROL NAME
Control Enhancement Name
CONTROL BASELINES
LOW
MOD
HIGH
SI-6
Security Function Verification
Selected
ICS Supplemental Guidance: The shutting down and restarting of the ICS may not always be feasible upon the identification of an
anomaly; these actions should be scheduled according to ICS operational requirements.
SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
462
ä¿è·ãã¼ã«ã¯ãICS ã¸ã®å½±é¿ãæå°ã«ãªãããã«è¨å®ãã¹ãã§ããï¼æ¤ç«ã§ã¯ãªãéç¥ãæ¡ç¨ã
ããªã©ï¼ãè£åç管ççã®ä¾ã¨ãã¦ããã©ãã£ãã¯ç£è¦ã¨ç£æ»ã®å¼·åãããã
管çæ¡å¼µï¼(1) ICS è£è¶³ã¬ã¤ãã³ã¹ï¼çµç¹ã¯ãICS ã®éç¨ã¸ã®å½±é¿ãèæ
®ã«å
¥ãã¦ãæªæãã
ã³ã¼ãä¿è·ã®éä¸ç®¡çãå®æ½ãããè£åç管ççã®ä¾ã¨ãã¦ãç£æ»ã®å¼·åãããã
管çæ¡å¼µï¼(2) ICS è£è¶³ã¬ã¤ãã³ã¹ï¼çµç¹ã¯ãICS ã®éç¨ã¸ã®å½±é¿ãèæ
®ã«å
¥ãã¦ãæªæãã
ã³ã¼ãä¿è·ã®èªåæ´æ°ãå®æ½ãããICS ãæªæããã³ã¼ãä¿è·ã®èªåæ´æ°å©ç¨ã«å¯¾å¿ãã¦ããªã
ç¶æ³ã§ã¯ãçµç¹ã¯ãå
¨ä½çãªã«ã¹ã¿ãã¤ãºã¬ã¤ãã³ã¹ã«å¾ã£ã¦éèªåã¡ã«ããºã ãè£åç管çç
ã¨ãã¦æ¡ç¨ããã
SI-4 æ
å ±ã·ã¹ãã ç£è¦
管ççªå·
管çå
管çæ¡å¼µå
管çãã¼ã¹ã©ã¤ã³
ä½
ä¸
é«
SI-4
æ
å ±ã·ã¹ãã ç£è¦
é¸å®
é¸å®
é¸å®
SI-4 (2)
æ
å ±ã·ã¹ãã ç£è¦
|
ãªã¢ã«ã¿ã¤ã åæç¨èªåãã¼ã«
é¸å®
é¸å®
SI-4 (4)
æ
å ±ã·ã¹ãã ç£è¦
|
çä¿¡ã»çºä¿¡éä¿¡ãã©ãã£ãã¯
é¸å®
é¸å®
SI-4 (5)
æ
å ±ã·ã¹ãã ç£è¦
|
ã·ã¹ãã çæã¢ã©ã¼ã
é¸å®
é¸å®
ICS è£è¶³ã¬ã¤ãã³ã¹ï¼çµç¹ã¯ãç£è¦ãã¼ã«ã»æè¡ã®å©ç¨ã ICS ã®éç¨ããã©ã¼ãã³ã¹ã«æªå½±
é¿ããªãããã«ãããè£åç管ççã®ä¾ã¨ãã¦ãååãªãããã¯ã¼ã¯ç£è¦ã®å±éãããã
管çæ¡å¼µï¼(2) ICS è£è¶³ã¬ã¤ãã³ã¹ï¼ICS ãã»ã¼ãªã¢ã«ã¿ã¤ã ã§ã®äºè±¡åæ対å¿èªåãã¼ã«ã«
対å¿ãã¦ããªãç¶æ³ã§ã¯ãçµç¹ã¯ãå
¨ä½çãªã«ã¹ã¿ãã¤ãºã¬ã¤ãã³ã¹ã«å¾ã£ã¦è£åç管ççãæ¡
ç¨ããï¼å¥ã·ã¹ãã ã¸ã®ç£æ»æ©è½ä»ä¸ãéèªåã¡ã«ããºã ã»æé çï¼ã
管çæ¡å¼µï¼(4) ICS è£è¶³ã¬ã¤ãã³ã¹ï¼ICS ãçä¿¡ã»çºä¿¡éä¿¡ãã©ãã£ãã¯ãç£è¦ã§ããªãç¶æ³
ã§ã¯ãçµç¹ã¯ãå¥æ
å ±ã·ã¹ãã ã¸ã®ç£è¦æ©è½ä»ä¸çã®è£åç管ççãæ¡ç¨ããã
管çæ¡å¼µï¼(5) ICS è£è¶³ã¬ã¤ãã³ã¹ï¼è£åç管ççã®ä¾ã¨ãã¦ãæåã«ããã¢ã©ã¼ãçæãã
ãã
SI-5 ã»ãã¥ãªãã£è¦å ±ã»å§åã»æ示
管ççªå·
管çå
管çæ¡å¼µå
管çãã¼ã¹ã©ã¤ã³
ä½
ä¸
é«
SI-5
ã»ãã¥ãªãã£è¦å ±ã»å§åã»æ示
é¸å®
é¸å®
é¸å®
SI-5 (1)
ã»ãã¥ãªãã£è¦å ±ã»å§åã»æ示
|
èªåã¢ã©ã¼ãã»å§å
é¸å®
ICS è£è¶³ã¬ã¤ãã³ã¹ï¼DHS ã®ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ãµã¤ãã¼ç·æ¥å¯¾å¿ãã¼ã (ICS-CERT)ã¯ã
ICS ã«é¢é£ããæ¥ç¶ã¢ã©ã¼ãåã³å§åãä½æãã¦ãããhttp://ics-cert.us-cert.gov/
管çæ¡å¼µï¼(1) ICS è£è¶³ã¬ã¤ãã³ã¹ãªã
SI-6 ã»ãã¥ãªãã£æ©è½æ¤è¨¼
管ççªå·
管çå
管çæ¡å¼µå
管çãã¼ã¹ã©ã¤ã³
ä½
ä¸
é«
SI-6
ã»ãã¥ãªãã£æ©è½æ¤è¨¼
é¸å®
ICS è£è¶³ã¬ã¤ãã³ã¹ï¼ICS ã®é®æåã³åèµ·åã¯ãç°ç¶æ¤åºæã«å¿
ãããç´ã¡ã«å¯è½ã§ã¯ãªãã
ICS éç¨è¦ä»¶ã«å¾ã£ã¦ã¹ã±ã¸ã¥ã¼ã«ãç«ã¦ãã¹ãã§ããã
SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
463
SI-7 SOFTWARE AND INFORMATION INTEGRITY
CNTL NO. CONTROL NAME
Control Enhancement Name
CONTROL BASELINES
LOW
MOD
HIGH
SI-7
Software, Firmware, and Information Integrity
Selected
Selected
SI-7 (1) SOFTWARE, FIRMWARE, AND INFORMATION INTEGRITY |
INTEGRITY CHECKS
Selected Selected
SI-7 (2) SOFTWARE, FIRMWARE, AND INFORMATION INTEGRITY |
AUTOMATED NOTIFICATIONS OF INTEGRITY VIOLATIONS
Selected
SI-7 (5) SOFTWARE, FIRMWARE, AND INFORMATION INTEGRITY |
AUTOMATED RESPONSE TO INTEGRITY VIOLATIONS
Selected
SI-7 (7) SOFTWARE, FIRMWARE, AND INFORMATION INTEGRITY |
INTEGRATION OF DETECTION AND RESPONSE
Selected Selected
SI-7 (14) SOFTWARE, FIRMWARE, AND INFORMATION INTEGRITY |
BINARY OR MACHINE EXECUTABLE CODE
Selected
ICS Supplemental Guidance: The organization determines whether the use of integrity verification applications would adversely
impact the operation of the ICS and employs compensating controls (e.g., manual integrity verifications that do not affect performance.
Control Enhancements: (1) ICS Supplemental Guidance: The organization ensures that the use of integrity verification
applications does not adversely impact the operational performance of the ICS.
Control Enhancement: (2) ICS Supplemental Guidance: In situations where the organization cannot employ automated tools that
provide notification of integrity discrepancies, the organization employs nonautomated mechanisms or procedures. Example compensating
controls include performing scheduled manual inspections for integrity violations.
Control Enhancement: (5) ICS Supplemental Guidance: The shutting down and restarting of the ICS may not always be feasible
upon the identification of an anomaly; these actions should be scheduled according to ICS operational requirements.
Control Enhancement: (7) ICS Supplemental Guidance: In situations where the ICS cannot detect unauthorized security-relevant
changes, the organization employs compensating controls (e.g., manual procedures) in accordance with the general tailoring guidance.
Control Enhancement: (14) No ICS Supplemental Guidance.
SI-8 SPAM PROTECTION
CNTL NO. CONTROL NAME
Control Enhancement Name
CONTROL BASELINES
LOW
MOD
HIGH
SI-8
Spam Protection
Selected
Selected
SI-8 (1) SPAM PROTECTION | CENTRAL MANAGEMENT OF
PROTECTION MECHANISMS
Selected Selected
SI-8 (2)
SPAM PROTECTION | AUTOMATIC UPDATES
Selected
Selected
ICS Supplemental Guidance: ICS spam protection may be implemented by removing spam transport mechanisms, functions and
services (e.g., electronic mail, Internet access) from the ICS. If any spam transport mechanisms, functions and services are present in the ICS,
spam protection in ICS takes into account operational characteristics of ICS that differ from general purpose information systems, (e.g.,
unusual traffic flow that may be misinterpreted and detected as spam. Example compensating controls include whitelist mail transfer agents
(MTA), digitally signed messages, acceptable sources, and acceptable message types.
Control Enhancement: (1) ICS Supplemental Guidance: Example compensating controls include employing local mechanisms or
procedures.
Control Enhancement: (2) No ICS Supplemental Guidance.
SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
464
SI-7 ã½ããã¦ã¨ã¢åã³æ
å ±ã®å®å
¨æ§
管ççªå·
管çå
管çæ¡å¼µå
管çãã¼ã¹ã©ã¤ã³
ä½
ä¸
é«
SI-7
ã½ããã¦ã¨ã¢ã»ãã¡ã¼ã ã¦ã¨ã¢ã»æ
å ±ã®å®å
¨æ§
é¸å®
é¸å®
SI-7 (1)
ã½ããã¦ã¨ã¢
ã»ãã¡ã¼ã ã¦ã¨ã¢ã»æ
å ±ã®å®å
¨æ§
|
å®å
¨æ§ãã§ãã¯
é¸å®
é¸å®
SI-7 (2)
ã½ããã¦ã¨ã¢
ã»ãã¡ã¼ã ã¦ã¨ã¢ã»æ
å ±ã®å®å
¨æ§
|
å®å
¨æ§éåã®èª
åéç¥
é¸å®
SI-7 (5)
ã½ããã¦ã¨ã¢
ã»ãã¡ã¼ã ã¦ã¨ã¢ã»æ
å ±ã®å®å
¨æ§
|
å®å
¨æ§éåã®èª
å対å¿
é¸å®
SI-7 (7)
ã½ããã¦ã¨ã¢
ã»ãã¡ã¼ã ã¦ã¨ã¢ã»æ
å ±ã®å®å
¨æ§
|
æ¤åºã»å¯¾å¿ã®ä¸ä½å
é¸å® é¸å®
SI-7 (14)
ã½ããã¦ã¨ã¢
ã»ãã¡ã¼ã ã¦ã¨ã¢ã»æ
å ±ã®å®å
¨æ§
|
ãã¤ããªåã¯ã
ã·ã³å®è¡å¯è½ã³ã¼ã
é¸å®
ICS è£è¶³ã¬ã¤ãã³ã¹ï¼çµç¹ã¯ãå®å
¨æ§æ¤è¨¼ã¢ããªã±ã¼ã·ã§ã³ã®å©ç¨ã«ãããICS ã®éç¨ã«æª
å½±é¿ãåã°ãªããå¤å®ããè£åç管ççãæ¡ç¨ããï¼ããã©ã¼ãã³ã¹ã«å½±é¿ããªãæåæ¤è¨¼çï¼ã
管çæ¡å¼µï¼(1) ICS è£è¶³ã¬ã¤ãã³ã¹ï¼çµç¹ã¯ãå®å
¨æ§æ¤è¨¼ã¢ããªã±ã¼ã·ã§ã³ã®å©ç¨ã ICS ã®é
ç¨ããã©ã¼ãã³ã¹ã«æªå½±é¿ããªãããã«ããã
管çæ¡å¼µï¼(2) ICS è£è¶³ã¬ã¤ãã³ã¹ï¼å®å
¨æ§ã®ä¸åãéç¥ããèªåãã¼ã«ãæ¡ç¨ã§ããªãç¶æ³
ã§ã¯ãçµç¹ã¯ãéèªåã¡ã«ããºã ã»æé ãæ¡ç¨ãããè£åç管ççã®ä¾ã¨ãã¦ãå®å
¨æ§éåã«å¯¾
ããã¹ã±ã¸ã¥ã¼ã«åãããæåç¹æ¤ã®å®æ½ãããã
管çæ¡å¼µï¼(5) ICS è£è¶³ã¬ã¤ãã³ã¹ï¼ICS ã®é®æåã³åèµ·åã¯ãç°ç¶æ¤åºæã«å¿
ãããç´ã¡ã«
å¯è½ã¨ããããã§ã¯ãªããICS éç¨è¦ä»¶ã«å¾ã£ã¦ã¹ã±ã¸ã¥ã¼ã«ãç«ã¦ãã¹ãã§ããã
管çæ¡å¼µï¼(7) ICS è£è¶³ã¬ã¤ãã³ã¹ï¼ICS ãã»ãã¥ãªãã£é¢é£ã®ç¡æå¤æ´ãæ¤åºã§ããªãç¶æ³
ã§ã¯ãçµç¹ã¯ãå
¨ä½çãªã«ã¹ã¿ãã¤ãºã¬ã¤ãã³ã¹ã«å¾ã£ã¦è£åç管ççï¼æåæé çï¼ãæ¡ç¨ã
ãã
管çæ¡å¼µï¼(14) ICS è£è¶³ã¬ã¤ãã³ã¹ãªã
SI-8 ã¹ãã ä¿è·
管ççªå·
管çå
管çæ¡å¼µå
管çãã¼ã¹ã©ã¤ã³
ä½
ä¸
é«
SI-8
ã¹ãã ä¿è·
é¸å®
é¸å®
SI-8 (1)
ã¹ãã ä¿è·
|
ä¿è·ã¡ã«ããºã ã®éä¸ç®¡ç
é¸å®
é¸å®
SI-8 (2)
ã¹ãã ä¿è·
|
èªåæ´æ°
é¸å®
é¸å®
ICS è£è¶³ã¬ã¤ãã³ã¹ï¼ICS ã®ã¹ãã ä¿è·ã¯ãã¹ãã 転éã¡ã«ããºã ãæ©è½åã³ãµã¼ãã¹ï¼é»
åã¡ã¼ã«ãã¤ã³ã¿ã¼ãããã¢ã¯ã»ã¹çï¼ãæé¤ãããã¨ã«ããè¡ããããã¹ãã 転éã¡ã«ããºã ã
æ©è½åã³ãµã¼ãã¹ã ICS ã«åå¨ãã¦ããå ´åãICS ã®ã¹ãã ä¿è·ã¯ãæ±ç¨çãªæ
å ±ã·ã¹ãã ï¼ã¹
ãã ã¨ãã¦èª¤è§£ã»æ¤åºãããé常ã¨éããã©ãã£ãã¯ããã¼çï¼ã¨ã¯ç°ãªã ICS ã®éç¨ç¹æ§ãè
æ
®ã«å
¥ãããè£åç管ççã®ä¾ã¨ãã¦ããã¯ã¤ããªã¹ãã¡ã¼ã«è»¢éã¨ã¼ã¸ã§ã³ãï¼MTAï¼ããã¸
ã¿ã«ç½²åå
¥ãã¡ãã»ã¼ã¸ãåãå
¥ããããã½ã¼ã¹ãåãå
¥ããããã¡ãã»ã¼ã¸ã¿ã¤ããããã
管çæ¡å¼µï¼(1) ICS è£è¶³ã¬ã¤ãã³ã¹ï¼è£åç管ççã®ä¾ã¨ãã¦ããã¼ã«ã«ã¡ã«ããºã åã¯ãã¼
ã«ã«æé ãããã
管çæ¡å¼µï¼(2) ICS è£è¶³ã¬ã¤ãã³ã¹ãªã
SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
465
SI-10 INFORMATION INPUT VALIDATION
CNTL NO. CONTROL NAME
Control Enhancement Name
CONTROL BASELINES
LOW
MOD
HIGH
SI-10
Information Input Validation
Selected
Selected
No ICS Supplemental Guidance.
SI-11 ERROR HANDLING
CNTL NO. CONTROL NAME
Control Enhancement Name
CONTROL BASELINES
LOW
MOD
HIGH
SI-11
Error Handling
Selected
Selected
No ICS Supplemental Guidance.
SI-12 INFORMATION HANDLING AND RETENTION
CNTL NO. CONTROL NAME
Control Enhancement Name
CONTROL BASELINES
LOW
MOD
HIGH
SI-12
Information Handling and Retention
Selected
Selected
Selected
No ICS Supplemental Guidance.
SI-13 PREDICTABLE FAILURE PREVENTION
CNTL NO. CONTROL NAME
Control Enhancement Name
CONTROL BASELINES
LOW
MOD
HIGH
SI-13
Predictable Failure Prevention
Added
ICS Supplemental Guidance: Failures in ICS can be stochastic or deterministic. Stochastic failures can be analyzed using
probability theory, while analysis of deterministic failures is based on non-random properties of the system. Known ICS failure modes and
causes are considered. The calculation and use of statistical descriptors, such as Mean Time To Failure (MTTF), should incorporate
additional analysis to determine how those failures manifest within the cyber and physical domains. Knowledge of these possible
manifestations may be necessary to detect whether a failure has occurred within the ICS, as failures of the information systems may not be
easily identifiable. Emergent properties, which may arise both within the information systems and physical processes, can potentially cause
system failures should be incorporated into the analysis. For example, cumulative effects of resource exhaustion (e.g., memory leakage) or
errors (e.g., rounding and truncation) can occur when ICS processes execute for unexpectedly long periods. Deterministic failures (e.g.,
integer counter overflow), once identified, are preventable.
Often substitute components may not be available or may not be sufficient to protect against faults occurring before predicted failure.
Non-automated mechanisms or physical safeguards should be in place in order to protect against these failures.
In addition to information concerning newly discovered vulnerabilities (i.e., latent flaws) potentially affecting the system/applications that
are discovered by forensic studies, new vulnerabilities may be identified by organizations with responsibility for disseminating vulnerability
information (e.g., ICS-CERT) based upon an analysis of a similar pattern of incidents reported to them or vulnerabilities reported by other
researchers.
Related controls: IR-5, IR-6, RA-5, SI-2, SI-5, SI-11.
Rationale for adding control to baseline: ICS are designed and built with certain boundary conditions, design parameters, and
assumptions about their environment and mode of operation. ICS may run much longer than conventional systems, allowing latent flaws to
become effective that are not manifest in other environments. For example, integer overflow might never occur in systems that are re-
initialized more frequently than the occurrence of the overflow. Experience and forensic studies of anomalies and incidents in ICS can lead
to identification of emergent properties that were previously unknown, unexpected, or unanticipated. Preventative and restorative
SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
466
SI-10 æ
å ±å
¥åæ¤è¨¼
管ççªå·
管çå
管çæ¡å¼µå
管çãã¼ã¹ã©ã¤ã³
ä½
ä¸
é«
SI-10
æ
å ±å
¥åæ¤è¨¼
é¸å®
é¸å®
ICS è£è¶³ã¬ã¤ãã³ã¹ãªã
SI-11 ã¨ã©ã¼å¦ç
管ççªå·
管çå
管çæ¡å¼µå
管çãã¼ã¹ã©ã¤ã³
ä½
ä¸
é«
SI-11
ã¨ã©ã¼å¦ç
é¸å®
é¸å®
ICS è£è¶³ã¬ã¤ãã³ã¹ãªã
SI-12 æ
å ±å¦çä¿ç
管ççªå·
管çå
管çæ¡å¼µå
管çãã¼ã¹ã©ã¤ã³
ä½
ä¸
é«
SI-12
æ
å ±å¦çä¿ç
é¸å®
é¸å®
é¸å®
ICS è£è¶³ã¬ã¤ãã³ã¹ãªã
SI-13 äºæ³ãããæ
éã®é²æ¢
管ççªå·
管çå
管çæ¡å¼µå
管çãã¼ã¹ã©ã¤ã³
ä½
ä¸
é«
SI-13
äºæ³ãããæ
éã®é²æ¢
追å
ICS è£è¶³ã¬ã¤ãã³ã¹ï¼ICS ã«ãããæ
éã¯ã確ççãªãã®ã決å®è«çãªãã®ã®ããããã§ã
ãã確ççæ
éã¯ç¢ºç«çè«ã§åæã§ãã決å®è«çæ
éã®åæã¯ãã·ã¹ãã ã®éã©ã³ãã ç¹æ§ãæ ¹
æ ã«è¡ããæ¢ç¥ã® ICS æ
éã¢ã¼ãåã³åå ã«ã¤ãã¦èæ
®ãããå¹³åæ
éæéï¼MTTFï¼çã®çµ±è¨
è¨è¿°åã®è¨ç®åã³ä½¿ç¨ã¯ããµã¤ãã¼é ååã³ç©çé åã«ããããã®ãããªæ
éã®åºç¾ã®ä»æ¹ãå¤
å¥ããéã®è£è¶³çãªåæåã¨ãªããæ
å ±ã·ã¹ãã ã®æ
éã¯å®¹æã«ã¯ç¹å®ã§ããªãããããããã
åºç¾ã«é¢ããç¥èã¯ãICS ã§ã®æ
éçºçã®æç¡ãå¤æããã®ã«å¿
è¦ã¨ãªããæ
å ±ã·ã¹ãã ã§ãç©
çããã»ã¹ã§ãçããåµçºç¹æ§ã¯ãã·ã¹ãã æ
éã«ãªããããªããããåæã«å«ããã¹ãã§ããã
ä¾ãã°ãICS ããã»ã¹ã®å®è¡ãäºå®ä»¥ä¸ã«é·ã³ãã¨ããªã½ã¼ã¹ã®æ¯æ¸ï¼ã¡ã¢ãªãªã¼ã¯çï¼ã«ãã
ç´¯ç©å½±é¿ãã¨ã©ã¼ï¼æ°å¤ã®åä¸ãã»åä¸ãã»åæ¨ã¦çï¼ãçãããä¸åº¦ç¹å®ããã決å®è«çæ
é
ï¼æ´æ°ã«ã¦ã³ã¿ã®ãªã¼ãã¼ããã¼çï¼ã¯äºé²å¯è½ã§ããã
äºæ³ãããæ
éãããåã«çºçããæ
éã«å¯¾ãã¦ã¯ã代æ¿ã³ã³ãã¼ãã³ãããªããããã£ã¦
ãååã«ã¯é²æ¢ã§ããªãããã®ãããªæ
éã«å¯¾ãã¦ã¯ãéèªåã¡ã«ããºã åã¯ç©çç対çãè¬ã
ãã¹ãã§ããã
調æ»ã§æ°ãã«è¦ã¤ãã£ããã·ã¹ãã ãã¢ããªã±ã¼ã·ã§ã³ã«å½±é¿ãä¸ããããªãèå¼±æ§ï¼æ½å¨
çæ¬ é¥ï¼æ
å ±ã«å ãã¦ãèå¼±æ§æ
å ±ã®é
å¸æ
å½æ©é¢ï¼ICS-CERT çï¼ã«ãã£ã¦ãæ°è¦ã®èå¼±æ§ã
æããã«ããããã¨ããããããããæ
å ±ã¯ãå±åºã®ãã£ãå種ãã¿ã¼ã³ãå¤é¨ç 究è
ãããå¾
ãèå¼±æ§åæã«åºã¥ãã¦ããã
é¢é£ãã管çï¼IR-5, IR-6, RA-5, SI-2, SI-5, SI-11
ãã¼ã¹ã©ã¤ã³ã«ç®¡çã追å ããçç±ï¼ICS ã®è¨è¨åã³æ§ç¯ã«ã¯ãç¹å®ã®å¢çæ¡ä»¶ãè¨è¨ãã©
ã¡ã¼ã¿åã³ç°å¢ã»éç¨ã¢ã¼ãæ³å®ãçãè¾¼ã¾ãã¦ãããICS ã®é転æéã¯ãå¨æ¥ã·ã¹ãã ããã
ã¯ããã«é·ããä»ã®ç°å¢ã§ã¯è¡¨é¢ã«åºã¦ããªãæ½å¨çæ¬ é¥ãç¾ãããä¾ãã°ãæ´æ°ã®ãªã¼ãã¼ã
ãã¼ã¯ããªã¼ãã¼ããã¼é »åº¦ãããå¤ãååæåãããã·ã¹ãã ã§ã¯ãã¾ãçãããã¨ããªãã
ICS ã«ãããç°å¸¸åã³ã¤ã³ã·ãã³ãã®èª¿æ»çµé¨ããããã¾ã§ç¥ããã¦ããããäºæ³ã»äºæããã¦
ããªãã£ãåµçºç¹æ§ã®ç¹å®ã«çµã³ã¤ãã¦ããã
SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
467
actions (e.g., re-starting the system or application) are prudent but may not be acceptable for operational reasons in ICS.
SI-16 MEMORY PROTECTION
CNTL NO. CONTROL NAME
Control Enhancement Name
CONTROL BASELINES
LOW
MOD
HIGH
SI-16
Memory Protection
Selected
Selected
No ICS Supplemental Guidance.
SI-17 FAIL-SAFE PROCEDURES
CNTL NO. CONTROL NAME
Control Enhancement Name
CONTROL BASELINES
LOW
MOD
HIGH
SI-17
Fail-Safe Procedures
Added
Added
Added
ICS Supplemental Guidance: The selected failure conditions and corresponding procedures may vary among baselines. The same
failure event may trigger different response depending on the impact level. Mechanical and analog system can be used to provide
mechanisms to ensure fail-safe procedures. Fail-safe states should incorporate potential impacts to human safety, physical systems, and the
environment. Related controls: CP-6.
Rationale for adding SI-17 to all baselines: This control provides a structure for the organization to identify their policy and
procedures for dealing with failures and other incidents. Creating a written record of the decision process for selecting incidents and
appropriate response is part of risk management in light of changing environment of operations.
SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
468
äºé²ã»å復è¡åï¼ã·ã¹ãã ãã¢ããªã±ã¼ã·ã§ã³ã®åèµ·åçï¼ã¯è¯èçãªæ¹æ³ã§ã¯ããããICS ã®
éç¨ä¸ã®çç±ããåãå
¥ããããªãã
SI-16 ã¡ã¢ãªä¿è·
管ççªå·
管çå
管çæ¡å¼µå
管çãã¼ã¹ã©ã¤ã³
ä½
ä¸
é«
SI-16
ã¡ã¢ãªä¿è·
é¸å®
é¸å®
ICS è£è¶³ã¬ã¤ãã³ã¹ãªã
SI-17 ãã§ã¼ã«ã»ã¼ãæé
管ççªå·
管çå
管çæ¡å¼µå
管çãã¼ã¹ã©ã¤ã³
ä½
ä¸
é«
SI-17
ãã§ã¼ã«ã»ã¼ãæé
追å
追å
追å
ICS è£è¶³ã¬ã¤ãã³ã¹ï¼é¸å®ããæ
éæ¡ä»¶ã¨å¯¾å¿æé ã¯ããã¼ã¹ã©ã¤ã³ã«å¿ãã¦ç°ãªããåã
æ
éäºè±¡ã§ããå½±é¿åº¦ã«ãã£ã¦å¥ã®å¯¾å¿ã¨ãªããæ©æ¢°å¼ã»ã¢ããã°ã·ã¹ãã ã使ç¨ãã¦ããã§ã¼
ã«ã»ã¼ãæé ã¡ã«ããºã ãåãããã¨ãã§ããããã§ã¼ã«ã»ã¼ãç¶æ
ã¯ã人å¡ã®å®å
¨ãç©çã·ã¹
ãã åã³ç°å¢ã«å½±é¿ãåã¼ããããªããé¢é£ãã管çï¼CP-6
SI-17 ãå
¨ã¦ã®ãã¼ã¹ã©ã¤ã³ã«è¿½å ããçç±ï¼çµç¹ã¯ãã®ç®¡çã«ãããæ
éãã®ä»ã®ã¤ã³ã·
ãã³ãå¦çã®ããªã·ã¼ã»æé ãæããã«ã§ãããã¤ã³ã·ãã³ãã¨é©åãªå¯¾å¿ãé¸ã¶éã®æ±ºå®ãã
ã»ã¹ãææ¸ã«ãããã¨ã¯ãéç¨ç°å¢ã®å¤åã¨ãã観ç¹ããããªã¹ã¯ç®¡çã®ä¸é¨ã¨ãªã

SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
469
ORGANIZATION-WIDE INFORMATION SECURITY PROGRAM MANAGEMENT CONTROLS - PM
Characteristics of Organization-Wide Information Security Program Management Control Family
Organization-Wide Information Security Program Management Controls are deployed organization-wide supporting the information
security program. They are not associated with security control baselines and are independent of any system impact level.
Supplemental Guidance
Supplemental Guidance for all Controls and Control Enhancements in NIST SP 800-53 Rev. 4, Appendix F, should be used in
conjunction with the ICS Supplemental Guidance in this overlay, if any.
PM-1 INFORMATION SECURITY PROGRAM PLAN
CNTL NO. CONTROL NAME
Control Enhancement Name
PM-1
Information Security Program Plan Policy and Procedures
ICS Supplemental Guidance: The policy specifically addresses the unique properties and requirements of ICS, the relationship to
non-ICS systems, and the relationship to other programs concerned with operational characteristics of ICS (e.g., safety, efficiency, reliability,
resilience).
PM-2 SENIOR INFORMATION SECURITY OFFICER
CNTL NO. CONTROL NAME
Control Enhancement Name
PM-2
Senior Information Security Officer
No ICS Supplemental Guidance.
PM-3 INFORMATION SECURITY RESOURCES
CNTL NO. CONTROL NAME
Control Enhancement Name
PM-3
Information Security Resources
ICS Supplemental Guidance: Capital planning and investment decisions address all of the relevant technologies and all phases of
the life cycle and needs to be informed by ICS experts as well as other subject matter experts (e.g., information security). Marshaling
interdisciplinary working teams to advise capital planning and investment decisions can help tradeoff and balance among conflicting equities,
objectives, and responsibilities such as capability, adaptability, resilience, safety, security, usability, and efficiency.
PM-4 PLAN OF ACTION AND MILESTONES PROCESS
CNTL NO. CONTROL NAME
Control Enhancement Name
PM-4
Plan of Action and Milestones Process
ICS Supplemental Guidance: The plan of action and milestones includes both computational and physical ICS components.
Records of observed shortcomings and appropriate remedial action may be maintained in a single document or in multiple coordinated
documents (e.g., future engineering plans).
SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
470
å
¨çµç¹çæ
å ±ã»ãã¥ãªãã£ããã°ã©ã 管ç対ç - PM
å
¨çµç¹çæ
å ±ã»ãã¥ãªãã£ããã°ã©ã 管ç対çãã¡ããªã®ç¹å¾´
å
¨çµç¹çæ
å ±ã»ãã¥ãªãã£ããã°ã©ã 管ç対çã¯ãå
¨çµç¹ã«å±éãããæ
å ±ã»ãã¥ãªãã£ããã°
ã©ã ãæ¯ãããã»ãã¥ãªãã£å¯¾çãã¼ã¹ã©ã¤ã³ã¯ä»éãã¦ãããããããªãã·ã¹ãã å½±é¿ã¬ãã«
ã¨ãç¡é¢ä¿ã§ããã
è£è¶³ã¬ã¤ãã³ã¹
å©ç¨ã§ããå ´åã«ã¯ãNIST SP 800-53 第4çä»é² Fã«ããå
¨ã¦ã®ç®¡çã»ç®¡çæ¡å¼µç¨è£è¶³ã¬ã¤ãã³
ã¹ãããã®ãªã¼ãã¼ã¬ã¤ã«ããã¦ãICS è£è¶³ã¬ã¤ãã³ã¹ã¨ä½µç¨ãã¹ãã§ããã
PM-1 æ
å ±ã»ãã¥ãªãã£ããã°ã©ã è¨ç»æ¸
管ççªå·
管çå
管çæ¡å¼µå
PM-1
æ
å ±ã»ãã¥ãªãã£ããã°ã©ã è¨ç»æ¸ããªã·ã¼ã»æé
ICS è£è¶³ã¬ã¤ãã³ã¹ï¼ç¹ã«ããªã·ã¼ã¯ãICS ç¬ç¹ã®ç¹æ§åã³è¦ä»¶ãICS 以å¤ã®ã·ã¹ãã ã¨ã®
é¢ä¿åã³ ICS ã®éç¨ç¹æ§ã«é¢ä¿ããä»ã®ããã°ã©ã ã¨ã®é¢ä¿ï¼å®å
¨æ§ãå¹çãä¿¡é ¼æ§ãå¼¾åæ§
çï¼ãåãä¸ããã
PM-2 ä¸ç´æ
å ±ã»ãã¥ãªãã£æ
å½å®
管ççªå·
管çå
管çæ¡å¼µå
PM-2
ä¸ç´æ
å ±ã»ãã¥ãªãã£æ
å½å®
ICS è£è¶³ã¬ã¤ãã³ã¹ãªã
PL-3 æ
å ±ã»ãã¥ãªãã£ãªã½ã¼ã¹
管ççªå·
管çå
管çæ¡å¼µå
PM-3
æ
å ±ã»ãã¥ãªãã£ãªã½ã¼ã¹
ICS è£è¶³ã¬ã¤ãã³ã¹ï¼ä¸»è¦ãã©ã³ãã³ã°åã³æè³æ±ºå®ã¯ãé¢ä¿ããå
¨æè¡ãå
¨ã©ã¤ããµã¤ã¯
ã«æ®µéåã³ ICS å°é家ãã®ä»ã®å°é家ï¼æ
å ±ã»ãã¥ãªãã£çï¼ããã®æ
å ±ãå¿
è¦ã¨ããåéã«ã¤
ãã¦åãä¸ããã主è¦ãã©ã³ãã³ã°åã³æè³æ±ºå®ã«ã¤ãã¦å©è¨ããåé横æçãªä½æ¥ãã¼ã ãçµ
éããã°ãè½åã»é©å¿æ§ã»å¼¾åæ§ã»å®å
¨æ§ã»ã»ãã¥ãªãã£ã»ã¦ã¼ã¶ããªãã£ã»å¹ççã®å
¬æ£ãç®
çåã³è²¬ä»»ã®ç«¶åã«ã¤ãã¦æ¯è¼èéãããã©ã³ã¹ãåãä¸ã§æ¯æ´ãå·®ã伸ã¹ããã¨ãã§ããã
PM-4 è¡åã»ãã¤ã«ã¹ãã¼ã³ããã»ã¹è¨ç»æ¸
管ççªå·
管çå
管çæ¡å¼µå
PM-4
è¡åã»ãã¤ã«ã¹ãã¼ã³ããã»ã¹è¨ç»æ¸
ICS è£è¶³ã¬ã¤ãã³ã¹ï¼è¡åã»ãã¤ã«ã¹ãã¼ã³è¨ç»æ¸ã«ã¯ãã³ã³ãã¥ã¼ã¿é¢ä¿ã¨ç©ç両é¢ã§ã®
ICS ã³ã³ãã¼ãã³ããå«ã¾ããã観å¯ãããæ¬ ç¹åã³é©åãªä¿®æ£å¦ç½®ã¯ã1åã®ææ¸åã¯è¤æ°ã®
é£æºææ¸ï¼å°æ¥ã®ã¨ã³ã¸ãã¢ãªã³ã°è¨ç»æ¸çï¼ã¨ãã¦ç¶æããã

SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
471
PM-5 INFORMATION SYSTEM INVENTORY
CNTL NO. CONTROL NAME
Control Enhancement Name
PM-5
Information System Inventory
No ICS Supplemental Guidance.
PM-6 INFORMATION SECURITY MEASURES OF PERFORMANCE
CNTL NO. CONTROL NAME
Control Enhancement Name
PM-6
Information Security Measures of Performance
No ICS Supplemental Guidance.
PM-7 ENTERPRISE ARCHITECTURE
CNTL NO. CONTROL NAME
Control Enhancement Name
PM-7
Enterprise Architecture
No ICS Supplemental Guidance.
PM-8 CRITICAL INFRASTRUCTURE PLAN
CNTL NO. CONTROL NAME
Control Enhancement Name
PM-8
Critical Infrastructure Plan
No ICS Supplemental Guidance.
References: Executive Order 13636â Improving Critical Infrastructure Cybersecurity, February 12, 2013
PM-9 RISK MANAGEMENT STRATEGY
CNTL NO. CONTROL NAME
Control Enhancement Name
PM-9
Risk Management Strategy
ICS Supplemental Guidance: Risk management of ICS is considered along with other organizational risks affecting
mission/business success from an organization-wide perspective. Organization-wide risk management strategy includes sector-specific
guidance as appropriate.
PM-10 SECURITY AUTHORIZATION PROCESS
CNTL NO. CONTROL NAME
Control Enhancement Name
PM-10
Security Authorization Process
ICS Supplemental Guidance: The authorization to operate processes for ICS involves multiple disciplines that have existing
approval and risk management process (e.g., physical security, safety). Organization-wide risk management requires harmonization among
these disciplines.

SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
472
PM-5 æ
å ±ã·ã¹ãã ç®é²
管ççªå·
管çå
管çæ¡å¼µå
PM-5
æ
å ±ã·ã¹ãã ç®é²
ICS è£è¶³ã¬ã¤ãã³ã¹ãªã
PM-6 æ
å ±ã»ãã¥ãªãã£ã«é¢ããããã©ã¼ãã³ã¹è¨æ¸¬
管ççªå·
管çå
管çæ¡å¼µå
PM-6
æ
å ±ã»ãã¥ãªãã£ã«é¢ããããã©ã¼ãã³ã¹è¨æ¸¬
ICS è£è¶³ã¬ã¤ãã³ã¹ãªã
PM-7 ä¼æ¥ã¢ã¼ããã¯ãã£
管ççªå·
管çå
管çæ¡å¼µå
PM-7
ä¼æ¥ã¢ã¼ããã¯ãã£
ICS è£è¶³ã¬ã¤ãã³ã¹ãªã
PM-8 éè¦ã¤ã³ãã©è¨ç»æ¸
管ççªå·
管çå
管çæ¡å¼µå
PM-8
éè¦ã¤ã³ãã©è¨ç»æ¸
ICS è£è¶³ã¬ã¤ãã³ã¹ãªã
åèæç®ï¼å¤§çµ±é å½ä»¤ 13636ãéè¦ã¤ã³ãã©ã¹ãã©ã¯ãã£ã®ãµã¤ãã¼ã»ãã¥ãªãã£æ¹åã
ï¼2013 å¹´2æ12 æ¥ï¼
PM-9 ãªã¹ã¯ç®¡çæ¦ç¥
管ççªå·
管çå
管çæ¡å¼µå
PM-9
ãªã¹ã¯ç®¡çæ¦ç¥
ICS è£è¶³ã¬ã¤ãã³ã¹ï¼ICS ã®ãªã¹ã¯ç®¡çã¯ãå
¨çµç¹ç観ç¹ã«ç«ã¡ãä»»åã»äºæ¥ã®æå¦ã«å½±é¿
ããçµç¹ã®ä»ã®ãªã¹ã¯ã¨åããã¦æ¤è¨ãããå
¨çµç¹ç管çæ¦ç¥ã«ã¯ãå¿
è¦ã«å¿ãã¦é¨éåºæã®ã¬
ã¤ãã³ã¹ãå«ã¾ããã
PM-10 ã»ãã¥ãªãã£æ¨©éããã»ã¹
管ççªå·
管çå
管çæ¡å¼µå
PM-10
ã»ãã¥ãªãã£æ¨©éããã»ã¹
ICS è£è¶³ã¬ã¤ãã³ã¹ï¼ICS ã®ããã»ã¹ãæä½ãã権éã«ã¯ãå¤æ°ã®é åãé¢ä¿ãã¦ãããæ¢
åã®æ¿èªã»ãªã¹ã¯ç®¡çããã»ã¹ãããï¼ç©ççã»ãã¥ãªãã£ãå®å
¨æ§çï¼ãå
¨çµç¹çãªã¹ã¯ç®¡ç
ã«ã¯ããããé åéã§ã®è¦å¶ãå¿
è¦ã¨ãªãã

SPECIAL PUBLICATION 800-82 REVISION 2 GUIDE TO INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY
473
PM-11 MISSION/BUSINESS PROCESS DEFINITION
CNTL NO. CONTROL NAME
Control Enhancement Name
PM-11
Mission/Business Process Definition
ICS Supplemental Guidance: Mission/business processes refinement requires protection of physical assets from damage originating
in the cyber domain. These needs are derived from the mission/business needs defined by the organization, the mission/business processes
selected to meet the stated needs, and the organizational risk management strategy.
PM-12 INSIDER THREAT PROGRAM
CNTL NO. CONTROL NAME
Control Enhancement Name
PM-13
Information Security Workforce
No ICS Supplemental Guidance.
PM-13 INFORMATION SECURITY WORKFORCE
ICS Supplemental Guidance: All aspects of information security workforce development and improvement programs include
knowledge and skill levels in both computational and physical ICS components.
PM-14 TESTING, TRAINING, AND MONITORING
CNTL NO. CONTROL NAME
Control Enhancement Name
PM-14
Testing, Training, and Monitoring
No ICS Supplemental Guidance.
PM-15 CONTACTS WITH SECURITY GROUPS AND ASSOCIATIONS
CNTL NO. CONTROL NAME
Control Enhancement Name
PM-15
Contacts with Security Groups and Associations
No ICS Supplemental Guidance.
PM-16 THREAT AWARENESS PROGRAM
CNTL NO. CONTROL NAME
Control Enhancement Name
PM-16
Threat Awareness Program
ICS Supplemental Guidance: The organization should collaborate and share information about potential incidents on a timely basis.
The DHS National Cybersecurity & Communications Integration Center (NCCIC), http://www.dhs.gov/about-national-cybersecurity-
communications-integration-center serves as a centralized location where operational elements involved in cybersecurity and
communications reliance are coordinated and integrated. The Industrial Control Systems Cyber Emergency Response Team (ICS-CERT)
http://ics-cert.us-cert.gov/ics-cert/ collaborates with international and private sector Computer Emergency Response Teams (CERTs) to share
control systems-related security incidents and mitigation measures. Organizations should consider having both an unclassified and classified
information sharing capability.

SP800-82 第2ç ç£æ¥ç¨å¶å¾¡ã·ã¹ãã ï¼ICSï¼ã»ãã¥ãªãã£ã¬ã¤ã
474
PM-11 ä»»åã»äºæ¥ããã»ã¹å®ç¾©
管ççªå·
管çå
管çæ¡å¼µå
PM-11
ä»»åã»äºæ¥ããã»ã¹å®ç¾©
ICS è£è¶³ã¬ã¤ãã³ã¹ï¼ä»»åã»äºæ¥ããã»ã¹ãæ´ç·´ãããã«ã¯ãç©ççè³ç£ããµã¤ãã¼é åã«
èµ·å ããæ害ããä¿è·ããªããã°ãªããªãããã®ãããªéè¦ã¯ãçµç¹ãæããã«ããä»»åã»äºæ¥
ä¸ã®éè¦ãéè¦ãæºããããã«é¸ãã ä»»åã»äºæ¥ããã»ã¹åã³çµç¹ã®ãªã¹ã¯ç®¡çæ¦ç¥ããçããã
PM-12 ã¤ã³ãµã¤ãã¼è
å¨ããã°ã©ã
管ççªå·
管çå
管çæ¡å¼µå
PM-12
ã¤ã³ãµã¤ãã¼è
å¨ããã°ã©ã
ICS è£è¶³ã¬ã¤ãã³ã¹ãªã
PL-3 æ
å ±ã»ãã¥ãªãã£ã¯ã¼ã¯ãã©ã¼ã¹
管ççªå·
管çå
管çæ¡å¼µå
PM-13
æ
å ±ã»ãã¥ãªãã£ã¯ã¼ã¯ãã©ã¼ã¹
ICS è£è¶³ã¬ã¤ãã³ã¹ï¼æ
å ±ã»ãã¥ãªãã£ã¯ã¼ã¯ãã©ã¼ã¹éçºæ¹åããã°ã©ã ã®ããããé¢ã«ã¯ã
ã³ã³ãã¥ã¼ã¿é¢ä¿ã¨ç©ç両é¢ã§ã® ICS ã³ã³ãã¼ãã³ãã«é¢ããç¥èã»æéã¬ãã«ãå«ã¾ããã
PM-14 試é¨ã»è¨ç·´ã»ç£è¦
管ççªå·
管çå
管çæ¡å¼µå
PM-14
試é¨ã»è¨ç·´ã»ç£è¦
ICS è£è¶³ã¬ã¤ãã³ã¹ãªã
PM-15 ã»ãã¥ãªãã£ã°ã«ã¼ãã»åä¼ã¨ã®é£çµ¡
管ççªå·
管çå
管çæ¡å¼µå
PM-15
ã»ãã¥ãªãã£ã°ã«ã¼ãã»åä¼ã¨ã®é£çµ¡
ICS è£è¶³ã¬ã¤ãã³ã¹ãªã
PM-16 è
å¨æèããã°ã©ã
管ççªå·
管çå
管çæ¡å¼µå
PM-16
è
å¨æèããã°ã©ã
ICS è£è¶³ã¬ã¤ãã³ã¹ï¼çµç¹ã¯ãçãå¾ãã¤ã³ã·ãã³ãã«é¢ãã¦é£æºãæ
å ±ãé©æã«å
±æãã¹
ãã§ãããä¸è¨ DHS å½å®¶ãµã¤ãã¼ã»ãã¥ãªãã£éä¿¡çµ±åã»ã³ã¿ã¼(NCCIC)ã¯éä¸æå¨å°ã¨ãã¦æ©
è½ãããµã¤ãã¼ã»ãã¥ãªãã£ã¨éä¿¡ã®ä¿¡é ¼æ§ã«é¢ããéç¨è¦ç´ ã¯ããã§èª¿æ´ãããçµ±ååããã¦
ãããhttp://www.dhs.gov/about-national-cybersecurity-communications-integration-center ä¸è¨ç£æ¥ç¨
å¶å¾¡ã·ã¹ãã ãµã¤ãã¼ç·æ¥å¯¾å¿ãã¼ã (ICS-CERT)ã¯ãæµ·å¤åã³æ°éã®ã³ã³ãã¥ã¼ã¿ç·æ¥å¯¾å¿ãã¼
ã (CERT)ã¨é£æºãã¦ãå¶å¾¡ã·ã¹ãã é¢é£ã»ãã¥ãªãã£ã¤ã³ã·ãã³ãæ
å ±ã¨ç·©å対çãå
±æãã¦
ãããhttp://ics-cert.us-cert.gov/ics-cert/
çµç¹ã¯ãç§å¯æ
å ±ã¨æ®éæ
å ±ã®å
±æåã«ã¤ãã¦æ¤è¨ãã¹ãã§ããã