Hash Crack: Password Cracking Manual (v2.0) Crack
Hash%20Crack%20Password%20Cracking%20Manual
Hash_Crack_-_Password_Cracking_Manual
Joshua%20Picolet-Hash%20Crack_%20Password%20Cracking%20Manual-CreateSpace%20IPP%20(2017)
Hash%20Crack%20Password%20Cracking%20Manual
User Manual:
Open the PDF directly: View PDF ![]() .
.
Page Count: 179 [warning: Documents this large are best viewed by clicking the View PDF Link!]
- Title Page
- Copyright Page
- TABLE OF CONTENTS
- Intro
- Required Software
- Core Hash Cracking Knowledge
- Cracking Methodology
- Basic Cracking Playbook
- Cheat Sheets
- Extract Hashes
- Password Analysis
- Dictionary / Wordlist
- Rules & Masks
- Foreign Character Sets
- Advanced Attacks
- Cracking Concepts
- Common Hash Examples
- Appendix
- -Terms
- -Online Resources
- -John The Ripper Menu
- -Hashcat Menu
- -Hash Cracking Benchmarks
- -Hash Cracking Speed


HashCrack.Copyright©2017NetmuxLLC
Allrightsreserved.Withoutlimitingtherightsunderthecopyrightreservedabove,nopartofthis
publicationmaybereproduced,storedin,orintroducedintoaretrievalsystem,ortransmittedinanyform
orbyanymeans(electronic,mechanical,photocopying,recording,orotherwise)withoutpriorwritten
permission.
ISBN-10:1975924584
ISBN-13:978-1975924584
NetmuxandtheNetmuxlogoareregisteredtrademarksofNetmux,LLC.Other
productandcompanynamesmentionedhereinmaybethetrademarksoftheir
respectiveowners.Ratherthanuseatrademarksymbolwitheveryoccurrenceof
atrademarkedname,weareusingthenamesonlyinaneditorialfashionandto
thebenefitofthetrademarkowner,withnointentionofinfringementofthe
trademark.
Theinformationinthisbookisdistributedonan“AsIs”basis,withoutwarranty.
Whileeveryprecautionhasbeentakeninthepreparationofthiswork,neither
theauthornorNetmuxLLC,shallhaveanyliabilitytoanypersonorentitywith
respecttoanylossordamagecausedorallegedtobecauseddirectlyor
indirectlybytheinformationcontainedinit.
Whileeveryefforthasbeenmadetoensuretheaccuracyandlegitimacyofthe
references,referrals,andlinks(collectively“Links”)presentedinthis
book/ebook,NetmuxisnotresponsibleorliableforbrokenLinksormissingor
fallaciousinformationattheLinks.AnyLinksinthisbooktoaspecificproduct,
process,website,orservicedonotconstituteorimplyanendorsementby
Netmuxofsame,oritsproducerorprovider.Theviewsandopinionscontained
atanyLinksdonotnecessarilyexpressorreflectthoseofNetmux.

TABLEOFCONTENTS
Intro
RequiredSoftware
CoreHashCrackingKnowledge
CrackingMethodology
BasicCrackingPlaybook
CheatSheets
ExtractHashes
PasswordAnalysis
Dictionary/Wordlist
Rules&Masks
ForeignCharacterSets
AdvancedAttacks
CrackingConcepts
CommonHashExamples
Appendix
-Terms
-OnlineResources
-JohnTheRipperMenu

INTRO
Thismanualismeanttobeareferenceguideforcrackingtoolusageand
supportivetoolsthatassistnetworkdefendersandpentestersinpassword
recovery(cracking).Thismanualwillnotbecoveringtheinstallationofthese
tools,butwillincludereferencestotheirproperinstallation,andifallelsefails,
Google.Updatesandadditionstothismanualareplannedyearlyas
advancementsincrackingevolve.Passwordrecoveryisabattleagainstmath,
time,cost,andhumanbehavior;andmuchlikeanybattle,thetacticsare
constantlyevolving.
ACKNOWLEDGEMENTS
Thiscommunitywouldnotenjoythesuccessanddiversitywithoutthefollowing
communitymembersandcontributors:Alexander‘SolarDesigner’Peslvak,
JohnTheRipperTeam,&CommunityJens‘atom’Steube,HashcatTeam,&
DevotedHashcatForumCommunityJeremi‘epixoip’Gosney
Korelogic&theCrackMeIfYouCanContestRobin‘DigiNinja’Wood(Pipal&
CeWL)CynoSurePrimeTeam
Chris‘Unix-ninja’Aurelio
PerThorsheim(PasswordsCon)
Blandyuk&Rurapenthe(HashKillerContest)Peter‘iphelix’Kacherginsky
(PACK)Royce‘tychotithonus’Williams‘Waffle’
Andmany,many,manymorecontributors.Ifanamewasexcludedfromthe
abovelistpleasereachoutandthenextversionwillgivethemtheirduecredit.
Lastly,thetools,research,andresourcescoveredinthebookaretheresultof
people’shardwork.Assuch,IHIGHLYencourageallreaderstoDONATEto
helpassistintheirefforts.Aportionoftheproceedsfromthisbookwillbe
distributedtothevariousresearchers/projects.
Suggestionsorcomments,sendyourmessagetohashcrack@netmux.com

REQUIREDSOFTWARE
Inordertofollowmanyofthetechniquesinthismanual,youwillwanttoinstall
thefollowingsoftwareonyourWindowsor*NIXhost.Thisbookdoesnot
coverhowtoinstallsaidsoftwareandassumesyouwereabletofollowthe
includedlinksandextensivesupportwebsites.
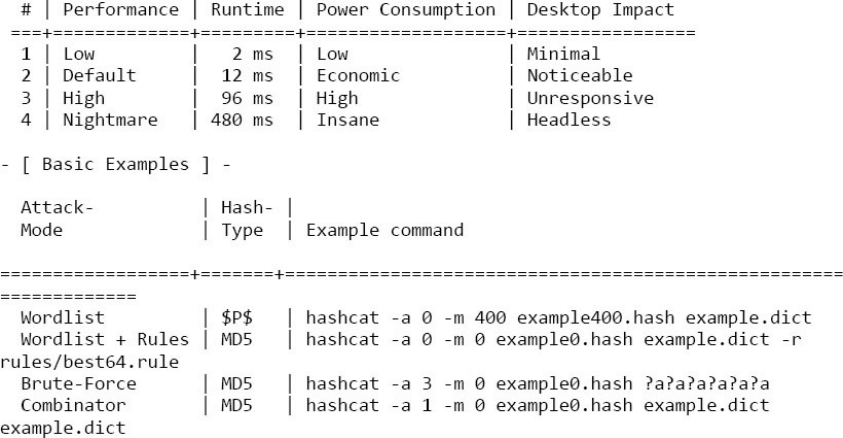
HASHCATv3.6(ornewer)
https://hashcat.net/hashcat/
JOHNTHERIPPER(v1.8.0JUMBO)
http://www.openwall.com/john/
PACKV0.0.4(PasswordAnalysisandCrackingToolkit)
http://thesprawl.org/projects/pack/
Hashcat-utilsv1.7
https://hashcat.net/wiki/doku.php?id=hashcat_utils
Additionallyyouwillneeddictionaries/wordlistsandhighlyrecommendthe
belowsources:WEAKPASSDICTIONARY
https://weakpass.com/wordlist
CRACKSTATIONDICTIONARY
https://crackstation.net/buy-crackstation-wordlist-password-cracking-
dictionary.htm
SKULLSECURITYWORDLISTS
https://wiki.skullsecurity.org/index.php?title=Passwords
Throughoutthemanual,genericnameshavebeengiventothevariousinputs
requiredinacrackingcommandsstructure.Legenddescriptionisbelow:
COMMANDSTRUCTURELEGEND
hashcat=GenericrepresentationofthevariousHashcatbinarynamesjohn=
GenericrepresentationoftheJohntheRipperbinarynames#type=Hashtype;
whichisanabbreviationinJohnoranumberinHashcathash.txt=File
containingtargethashestobecrackeddict.txt=Filecontaining
dictionary/wordlist
rule.txt=Filecontainingpermutationrulestoalterdict.txtinputpasswords.txt
=Filecontainingcrackedpasswordresultsoutfile.txt=Filecontainingresultsof
somefunctionsoutputLastly,asagoodreferencefortestingvarioushashtypes
toplaceintoyour“hash.txt”file,thebelowsitescontainallthevarioushashing
algorithmsandexampleoutputtailoredforeachcrackingtool:HASHCAT
HASHFORMATEXAMPLES
https://hashcat.net/wiki/doku.php?id=example_hashes
JOHNTHERIPPERHASHFORMATEXAMPLES
http://pentestmonkey.net/cheat-sheet/john-the-ripper-hash-formats
http://openwall.info/wiki/john/sample-hashes

COREHASHCRACKINGKNOWLEDGE
ENCODINGvsHASHINGvsENCRYPTING
Encoding=transformsdataintoapubliclyknownschemeforusabilityHashing
=one-waycryptographicfunctionnearlyimpossibletoreverseEncrypting=
mappingofinputdataandoutputdatareversiblewithakeyCPUvsGPU
CPU=2-72coresmainlyoptimizedforsequentialserialprocessingGPU=
1000’sofcoreswith1000’softhreadsforparallelprocessingCRACKING
TIME=KEYSPACE/HASHRATE
Keyspace:charset^length(?a?a?a?a=95^4=81,450,625)
Hashrate:hashingfunction/hardwarepower(bcrypt/GTX1080=13094H/s)
CrackingTime:81,450,625/13094H/s=6,220seconds
*KeyspacedisplayedandHashratevarybytoolandhardwareused
SALT=randomdatathat’susedasadditionalinputtoaone-way
functionITERATIONS=thenumberoftimesanalgorithmisrun
overagivenhashHASHIDENTIFICATION:thereisn’ta
foolproofmethodforidentifyingwhichhashfunctionwasusedby
simplylookingatthehash,buttherearereliableclues(i.e.$6$
sha512crypt).Thebestmethodistoknowfromwherethehashwas
extractedandidentifythehashfunctionforthatsoftware.
DICTIONARY/WORDLISTATTACK=straightattackusesaprecompiled
listofwords,phrases,andcommon/uniquestringstoattempttomatcha
password.
BRUTE-FORCEATTACK=attemptseverypossiblecombinationofagiven
characterset,usuallyuptoacertainlength.
RULEATTACK=generatespermutationsagainstagivenwordlistby
modifying,trimming,extending,expanding,combining,orskippingwords.
MASKATTACK=aformoftargetedbrute-forceattackbyusingplaceholders
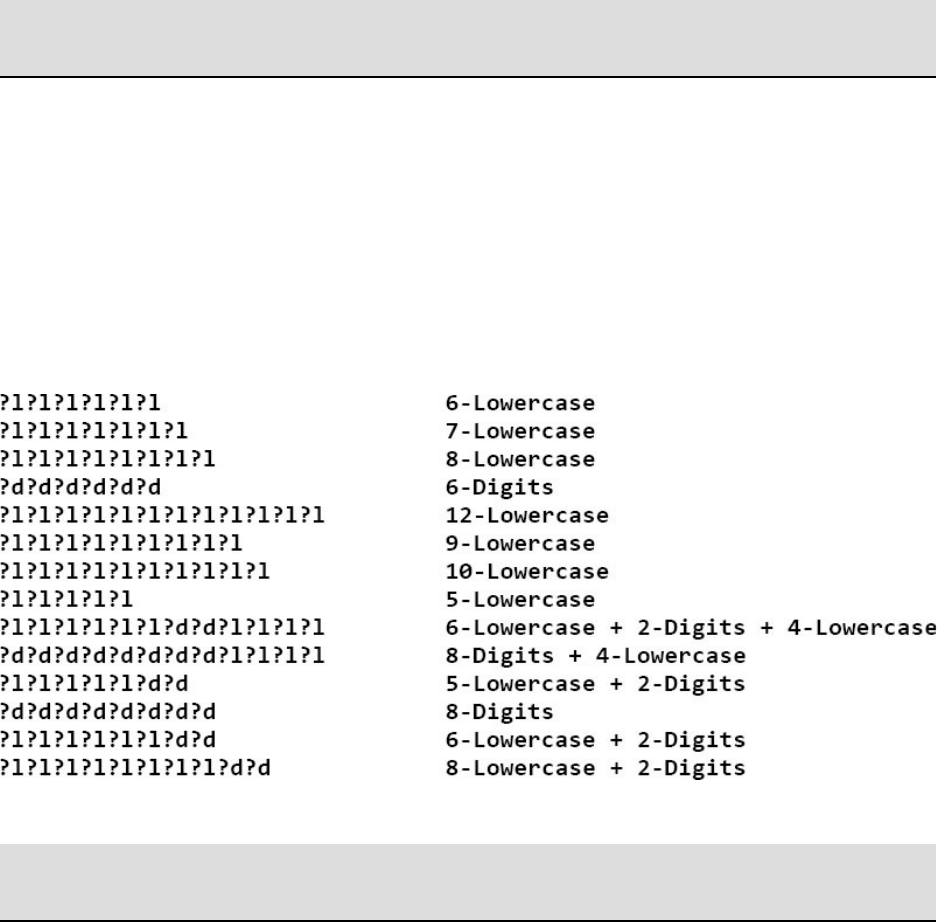
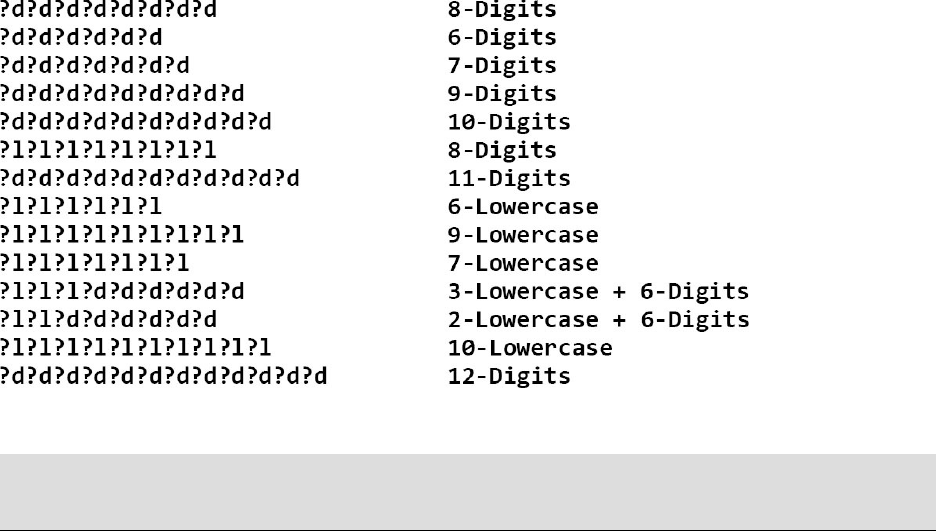
forcharactersincertainpositions(i.e.?a?a?a?l?d?d).
HYBRIDATTACK=combinesaDictionaryandMaskAttackbytakinginput
fromthedictionaryandaddingmaskplaceholders(i.e.dict.txt?d?d?d).
CRACKINGRIG=fromabasiclaptoptoa64GPUcluster,thisisthe
hardware/platformonwhichyouperformyourpasswordhashattacks.
EXPECTEDRESULTS
Knowyourcrackingrig’scapabilitiesbyperformingbenchmarktestingand
don’tassumeyoucanachievethesameresultspostedbyforummembers
withoutusingtheexactsamedictionary,attackplan,orhardwaresetup.
Crackingsuccesslargelydependsonyourabilitytouseresourcesefficientlyand
makecalculatedtrade-offsbasedonthetargethash.
DICTIONARY/WORDLISTvsBRUTE-FORCEvsANALYSIS
Dictionariesandbrute-forcearenottheendallbealltocrackhashes.Theyare
merelythebeginningandendofanattackplan.Truemasteryiseverythinginthe
middle,whereanalysisofpasswords,patterns,behaviors,andpoliciesaffords
theabilitytorecoverthatlast20%.Experimentwithyourattacksandresearch
andcompiletargetedwordlistswithyournewknowledge.Donotrelyheavilyon
dictionariesbecausetheycanonlyhelpyouwithwhatis“known”andnotthe
unknown.

CRACKINGMETHODOLOGY
Followingisbasiccrackingmethodologybrokenintosteps,buttheprocessis
subjecttochangebasedoncurrent/futuretargetinformationuncoveredduring
thecrackingprocess.
1-EXTRACTHASHES
Pullhashesfromtarget,identifyhashingfunction,andproperlyformatoutputfor
yourtoolofchoice.
2-FORMATHASHES
Formatyourhashesbasedonyourtool’spreferredmethod.Seetool
documentationforthisguidance.Hashcat,forexample,oneachlinetakes
<user>:<hash>ORjusttheplain<hash>.
3-EVALUATEHASHSTRENGTH
UsingtheAppendixtable“HashCrackingSpeed(Slow-Fast)”assessyourtarget
hashandit’scrackingspeed.Ifit’saslowhash,youwillneedtobemore
selectiveatwhattypesofdictionariesandattacksyouperform.Ifit’safasthash,
youcanbemoreliberalwithyourattackstrategy.
4-CALCULATECRACKINGRIGCAPABILITIES
Withtheinformationfromevaluatingthehashstrength,baselineyourcracking
rig’scapabilities.PerformbenchmarktestingusingJohnTheRipperand/or
Hashcat’sbuilt-inbenchmarkabilityonyourrig.
john--test
hashcat-b
Basedontheseresultsyouwillbeabletobetterassessyourattackoptionsby
knowingyourrigscapabilitiesagainstaspecifichash.Thiswillbeamore
accurateresultofahash’scrackingspeedbasedonyourrig.Itwillbeusefulto
savetheseresultsforfuturereference.
5-FORMULATEPLAN
Basedonknownorunknownknowledgebegincreatinganattackplan.Included
onthenextpageisa“BasicCrackingPlaybook”togetyoustarted.
6-ANALYZEPASSWORDS
Aftersuccessfullycrackingasufficientamountofhashesanalyzetheresultsfor
anycluesorpatterns.Thisanalysismayaidinyoursuccessonanyremaining
hashes.
7-CUSTOMATTACKS
Basedonyoupasswordanalysiscreatecustomattacksleveragingthoseknown
cluesorpatterns.Exampleswouldbecustommaskattacksorrulestofittarget
users’behaviororpreferences.
8-ADVANCEDATTACKS
ExperimentwithPrinceprocessor,customMarkov-chains,maskprocessor,or
customdictionaryattackstoshakeoutthoseremainingstubbornhashes.Thisis
whereyourexpertiseandcreativityreallycomeintoplay.
9-REPEAT
GobacktoSTEP4andcontinuetheprocessoveragain,tweakingdictionaries,
mask,parameters,andmethods.You’reinthegrindatthispointandneedtorely
onskillandluck.

BASICCRACKINGPLAYBOOK
Thisisonlymeantasabasicguidetoprocessinghashesandeachscenariowill
obviouslybeuniquebasedonexternalcircumstances.Forthisattackplanwe
willassumeweknowthepasswordhashesarerawMD5andassumewehave
alreadycapturedsomeplaintextpasswordsofusers.Ifwehadnoknowledgeof
plaintextpasswordswewouldmostlikelyskiptoDICTIONARY/WORDLIST
attacks.Lastly,sinceMD5isa“Fast”hashwecanbemoreliberalwithour
attackplan.
1-CUSTOMWORDLIST
Firstcompileyourknownplaintextpasswordsintoacustomwordlistfile.Pass
thistoyourtoolofchoiceasastraightdictionaryattack.
hashcat-a0-m0-w4hash.txtcustom_list.txt
2-CUSTOMWORDLIST+RULES
Runyourcustomwordlistwithpermutationrulestocrackslightvariations.
hashcat-a0-m0-w4hash.txtcustom_list.txt-rbest64.rule--loopback
3-DICTIONARY/WORDLIST
Performabroaddictionaryattack,lookingforcommonpasswordsandleaked
passwordsinwellknowndictionaries/wordlists.
hashcat-a0-m0-w4hash.txtdict.txt
4-DICTIONARY/WORDLIST+RULES
Addrulepermutationstothebroaddictionaryattack,lookingforsubtlechanges
tocommonwords/phrasesandleakedpasswords.
hashcat-a0-m0-w4hash.txtdict.txt-rbest64.rule--loopback
5-CUSTOMWORDLIST+RULES
Addanynewlydiscoveredpasswordstoyourcustomwordlistandrunanattack
againwithpermutationrules,lookinganyothersubtlevariations.
awk-F“:”‘{print$2}’hashcat.potfile>>custom_list.txt
hashcat-a0-m0-w4hash.txtcustom_list.txt-rdive.rule--loopback
6-MASK
NowwewillusemaskattacksincludedwithHashcattosearchthekeyspacefor
commonpasswordlengthsandpatterns,basedontheRockYoudataset.
hashcat-a3-m0-w4hash.txtrockyou-1-60.hcmask
7-HYBRIDDICTIONARY+MASK
Usingadictionaryofyourchoice,conducthybridattackslookingforlarger
variationsofcommonwordsorknownpasswordsbyappending/prepending
maskstothosecandidates.
hashcat-a6-m0-w4hash.txtdict.txtrockyou-1-60.hcmask
hashcat-a7-m0-w4hash.txtrockyou-1-60.hcmaskdict.txt
8-CUSTOMWORDLIST+RULES
Addanynewlydiscoveredpasswordsbacktoyourcustomwordlistandrunan
attackagainwithpermutationruleslookinganyothersubtlevariations.
awk-F“:”‘{print$2}’hashcat.potfile>>custom_list.txt
hashcat-a0-m0-w4hash.txtcustom_list.txt-rdive.rule--loopback
9-COMBO
Usingadictionaryofyourchoice,performacomboattackbyindividually
combiningthedictionary’spasswordcandidatestogethertoformnew
candidates.
hashcat-a1-m0-w4hash.txtdict.txtdict.txt
10-CUSTOMHYBRIDATTACK
Addanynewlydiscoveredpasswordsbacktoyourcustomwordlistandperform
ahybridattackagainstthosenewacquiredpasswords.
awk-F“:”‘{print$2}’hashcat.potfile>>custom_list.txt
hashcat-a6-m0-w4hash.txtcustom_list.txtrockyou-1-60.hcmask
hashcat-a7-m0-w4hash.txtrockyou-1-60.hcmaskcustom_list.txt
11-CUSTOMMASKATTACK
Bynowtheeasier,weakerpasswordsmayhavefallentocracking,butstillsome
remain.UsingPACK(onpg.51)createcustommaskattacksbasedonyour
currentlycrackedpasswords.Besuretosortoutmasksthatmatchtheprevious
rockyou-1-60.hcmasklist.
hashcat-a3-m0-w4hash.txtcustom_masks.hcmask
12-BRUTE-FORCE
Whenallelsefailsbeginastandardbrute-forceattack,beingselectiveastohow
largeakeyspaceyourrigcanadequatelybrute-force.Above8charactersthisis
typicallypointlessduetohardwarelimitationsandpasswordentropy/
complexity.
hashcat-a3-m0-w4hash.txt-i?a?a?a?a?a?a?a?a


JOHNTHERIPPERCHEATSHEET
ATTACKMODES
BRUTEFORCEATTACK
john--format=#typehash.txt
DICTIONARYATTACK
john--format=#type--wordlist=dict.txthash.txt
MASKATTACK
john--format=#type--mask=?l?l?l?l?l?lhash.txt-min-len=6
INCREMENTALATTACK
john--incrementalhash.txt
DICTIONARY+RULESATTACK
john--format=#type--wordlist=dict.txt--rules
RULES
--rules=Single
--rules=Wordlist
--rules=Extra
--rules=Jumbo
--rules=KoreLogic
--rules=All
INCREMENT
--incremental=Digits
--incremental=Lower
--incremental=Alpha
--incremental=Alnum
PARALLELCPUorGPU
LISTOpenCLDEVICES
john--list=opencl-devices
LISTOpenCLFORMATS
john--list=formats--format=opencl

MULTI-GPU(example3GPU’s)
john--format=<OpenCLformat>hash.txt--wordlist=dict.txt--rules--dev=
<#>--fork=3
MULTI-CPU(example8cores)
john--wordlist=dict.txthash.txt--rules--dev=<#>--fork=8
MISC
BENCHMARKTEST
john--test
SESSIONNAME
johnhash.txt--session=example_name
SESSIONRESTORE
john--restore=example_name
SHOWCRACKEDRESULTS
johnhash.txt--pot=<johnpotfile>--show
WORDLISTGENERATION
john--wordlist=dict.txt--stdout--external:[filtername]>out.txt
BASICATTACKMETHODOLOGY
1-DEFAULTATTACK
johnhash.txt
2-DICTIONARY+RULESATTACK
john--wordlist=dict.txt--rules
3-MASKATTACK
john--mask=?l?l?l?l?l?lhash.txt-min-len=6
4-BRUTEFORCEINCREMENTALATTACK
john--incrementalhash.txt

HASHCATCHEATSHEET
ATTACKMODES
DICTIONARYATTACK
hashcat-a0-m#typehash.txtdict.txt
DICTIONARY+RULESATTACK
hashcat-a0-m#typehash.txtdict.txt-rrule.txt
COMBINATIONATTACK
hashcat-a1-m#typehash.txtdict1.txtdict2.txt
MASKATTACK
hashcat-a3-m#typehash.txt?a?a?a?a?a?a
HYBRIDDICTIONARY+MASK
hashcat-a6-m#typehash.txtdict.txt?a?a?a?a
HYBRIDMASK+DICTIONARY
hashcat-a7-m#typehash.txt?a?a?a?adict.txt
RULES
RULEFILE-r
hashcat-a0-m#typehash.txtdict.txt-rrule.txt
MANIPULATELEFT-j
hashcat-a1-m#typehash.txtleft_dict.txtright_dict.txt-j<option>
MANIPULATERIGHT-k
hashcat-a1-m#typehash.txtleft_dict.txtright_dict.txt-k<option>
INCREMENT
DEFAULTINCREMENT
hashcat-a3-m#typehash.txt?a?a?a?a?a--increment
INCREMENTMINIMUMLENGTH
hashcat-a3-m#typehash.txt?a?a?a?a?a--increment-min=4
INCREMENTMAXLENGTH
hashcat-a3-m#typehash.txt?a?a?a?a?a?a--increment-max=5
MISC
BENCHMARKTEST(HASHTYPE)

hashcat-b-m#type
SHOWEXAMPLEHASH
hashcat-m#type--example-hashes
DISABLEPASSWORDLENGTHLIMIT(MaxLength256)hashcat-a0-m
#type--length-limit-disablehash.txtdict.txt
SESSIONNAME
hashcat-a0-m#type--session<uniq_name>hash.txtdict.txt
SESSIONRESTORE
hashcat-a0-m#type--restore--session<uniq_name>hash.txtdict.txt
SHOWKEYSPACE
hashcat-a0-m#type--keyspacehash.txtdict.txt-rrule.txt
OUTPUTRESULTSFILE-o
hashcat-a0-m#type-oresults.txthash.txtdict.txt
CUSTOMCHARSET-1-2-3-4
hashcat-a3-m#typehash.txt-1?l?u-2?l?d?s?l?2?a?d?u?l
ADJUSTPERFORMANCE-w
hashcat-a0-m#type-w<1-4>hash.txtdict.txt
BASICATTACKMETHODOLOGY
1-DICTIONARYATTACK
hashcat-a0-m#typehash.txtdict.txt
2-DICTIONARY+RULES
hashcat-a0-m#typehash.txtdict.txt-rrule.txt
3-HYBRIDATTACKS
hashcat-a6-m#typehash.txtdict.txt?a?a?a?a

4-BRUTEFORCE
hashcat-a3-m#typehash.txt?a?a?a?a?a?a?a?a
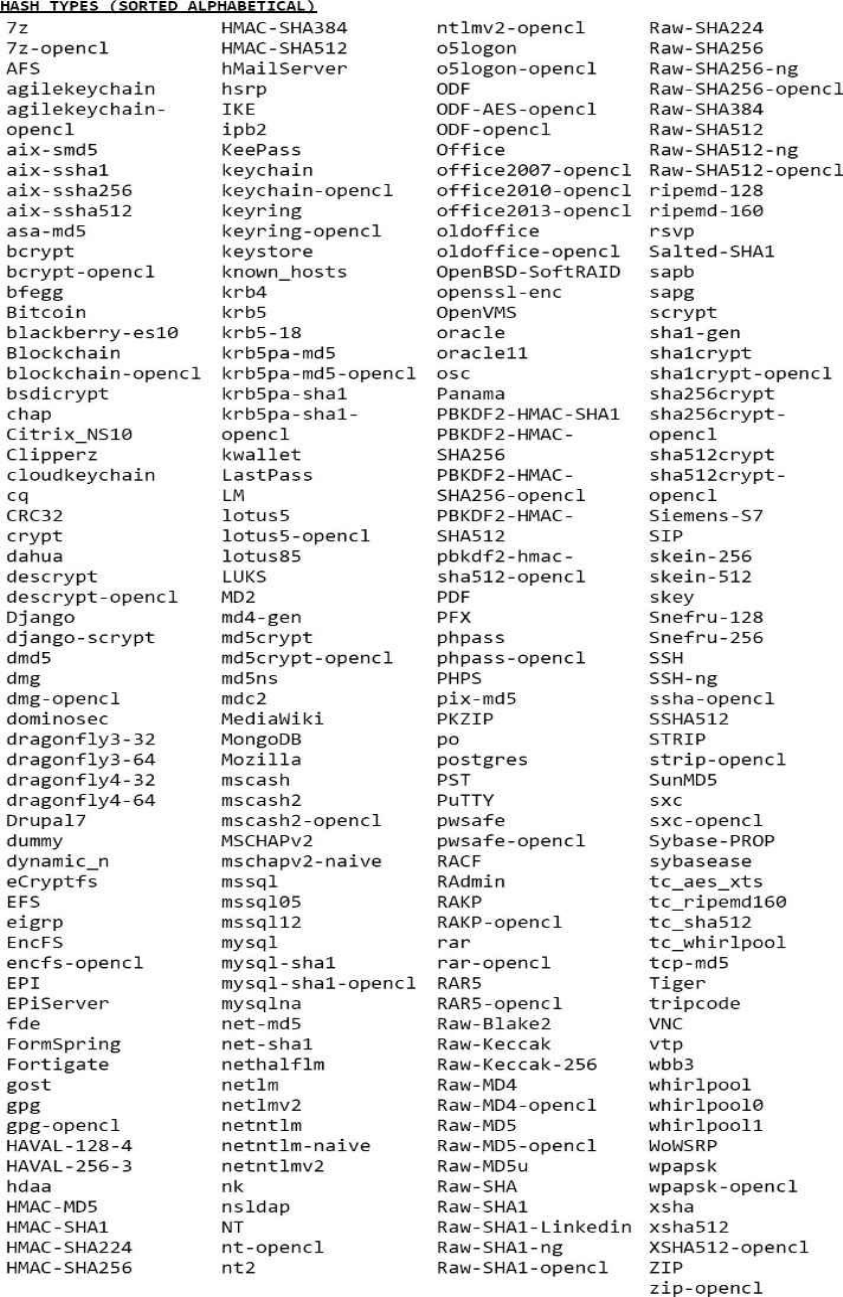
HASHTYPES(SORTEDALPHABETICAL)
6600 1Password,agilekeychain
8200 1Password,cloudkeychain
14100 3DES(PT=$salt,key=$pass)
11600 7-Zip
6300 AIX{smd5}
6400 AIX{ssha256}
6500 AIX{ssha512}
6700 AIX{ssha1}
5800 AndroidPIN
8800 AndroidFDE<v4.3
12900 AndroidFDE(SamsungDEK)
1600 Apache$apr1$
125 ArubaOS
12001 Atlassian(PBKDF2-HMAC-SHA1)
13200 AxCrypt
13300 AxCryptinmemorySHA1
3200 bcrypt$2*$,Blowfish(Unix)
600 BLAKE2-512
12400 BSDiCrypt,ExtendedDES
11300 Bitcoin/Litecoinwallet.dat
12700 Blockchain,MyWallet
15200 Blockchain,MyWallet,V2
15400 ChaCha20
2410 Cisco-ASA
500 Cisco-IOS$1$
5700 Cisco-IOS$4$
9200 Cisco-IOS$8$
9300 Cisco-IOS$9$
2400 Cisco-PIX
8100 CitrixNetscaler
12600 ColdFusion10+
10200 CramMD5
11500 CRC32
14000 DES(PT=$salt,key=$pass)
1500 descrypt,DES(Unix),TraditionalDES
8300 DNSSEC(NSEC3)
124 Django(SHA-1)
10000 Django(PBKDF2-SHA256)
1100 DomainCachedCredentials(DCC),MSCache
2100 DomainCachedCredentials2(DCC2),MSCache2
15300 DPAPImasterkeyfilev1andv2
7900 Drupal7
12200 eCryptfs
141 EPiServer6.x<v4
1441 EPiServer6.x>v4
15600 EthereumWallet,PBKDF2-HMAC-SHA256
15700 EthereumWallet,PBKDF2-SCRYPT
15000 FileZillaServer>=0.9.55
7000 Fortigate(FortiOS)
6900 GOSTR34.11-94
11700 GOSTR34.11-2012(Streebog)256-bit
11800 GOSTR34.11-2012(Streebog)512-bit
7200 GRUB2
50 HMAC-MD5(key=$pass)
60 HMAC-MD5(key=$salt)
150 HMAC-SHA1(key=$pass)
160 HMAC-SHA1(key=$salt)
1450 HMAC-SHA256(key=$pass)
1460 HMAC-SHA256(key=$salt)
1750 HMAC-SHA512(key=$pass)
1760 HMAC-SHA512(key=$salt)
5100 HalfMD5
5300 IKE-PSKMD5
5400 IKE-PSKSHA1
2811 IPB(InvisonPowerBoard)
7300 IPMI2RAKPHMAC-SHA1
14700 iTunesBackup<10.0
14800 iTunesBackup>=10.0
4800 iSCSICHAPauthentication,MD5(Chap)
15500 JKSJavaKeyStorePrivateKeys(SHA1)
11 Joomla<2.5.18
400 Joomla>2.5.18
15100 Juniper/NetBSDsha1crypt
22 JuniperNetscreen/SSG(ScreenOS)
501 JuniperIVE
13400 Keepass1(AES/Twofish)andKeepass2(AES)
7500 Kerberos5AS-REQPre-Authetype23
13100 Kerberos5TGS-REPetype23
6800 Lastpass+Lastpasssniffed
3000 LM
8600 LotusNotes/Domino5
8700 LotusNotes/Domino6
9100 LotusNotes/Domino8
14600 LUKS
900 MD4
0 MD5
10 md5($pass.$salt)
20 md5($salt.$pass)
30 md5(unicode($pass).$salt)
40 md5($salt.unicode($pass))
3710 md5($salt.md5($pass))
3800 md5($salt.$pass.$salt)
3910 md5(md5($pass).md5($salt))
4010 md5($salt.md5($salt.$pass))
4110 md5($salt.md5($pass.$salt))
2600 md5(md5($pass))
4400 md5(sha1($pass))
4300 md5(strtoupper(md5($pass)))
500 md5crypt$1$,MD5(Unix)
9400 MSOffice2007
9500 MSOffice2010
9600 MSOffice2013
9700 MSOffice<=2003$0
9710 MSOffice<=2003$0
9720 MSOffice<=2003$0
9800 MSOffice<=2003$3
9810 MSOffice<=2003$3
9820 MSOffice<=2003$3
12800 MS-AzureSyncPBKDF2-HMAC-SHA256
131 MSSQL(2000)
132 MSSQL(2005)
1731 MSSQL(2012)
1731 MSSQL(2014)
3711 MediawikiBtype
2811 MyBB
11200 MySQLCRAM(SHA1)
200 MySQL323
300 MySQL4.1/MySQL5
1000 NTLM
5500 NetNTLMv1
5500 NetNTLMv1+ESS
5600 NetNTLMv2
101 nsldap,SHA-1(Base64),NetscapeLDAPSHA
111 nsldaps,SSHA-1(Base64),NetscapeLDAPSSHA
13900 OpenCart
21 osCommerce
122 OSXV10.4,OSXV10.5,OSXV10.6
1722 OSXV10.7
7100 OSXV10.8,OSXV10.9,OSXv10.10
112 OracleS:Type(Oracle11+)
3100 OracleH:Type(Oracle7+)
12300 OracleT:Type(Oracle12+)
11900 PBKDF2-HMAC-MD5
12000 PBKDF2-HMAC-SHA1
10900 PBKDF2-HMAC-SHA256
12100 PBKDF2-HMAC-SHA512
10400 PDF1.1-1.3(Acrobat2-4)
10410 PDF1.1-1.3(Acrobat2-4),collider#1
10420 PDF1.1-1.3(Acrobat2-4),collider#2
10500 PDF1.4-1.6(Acrobat5-8)
10600 PDF1.7Level3(Acrobat9)
10700 PDF1.7Level8(Acrobat10-11)
400 phpBB3
400 phpass
2612 PHPS
5200 PasswordSafev3
9000 PasswordSafev2
133 PeopleSoft
13500 PeopleSoftToken
99999 Plaintext
12 PostgreSQL
11100 PostgreSQLCRAM(MD5)
11000 PrestaShop
4522 PunBB
8500 RACF
12500 RAR3-hp
13000 RAR5
9900 Radmin2
7600 Redmine
6000 RipeMD160
7700 SAPCODVNB(BCODE)
7800 SAPCODVNF/G(PASSCODE)
10300 SAPCODVNH(PWDSALTEDHASH)iSSHA-1
8900 scrypt
1300 SHA-224
1400 SHA-256
1411 SSHA-256(Base64),LDAP{SSHA256}
5000 SHA-3(Keccak)
10800 SHA-384
1700 SHA-512
100 SHA1
14400 SHA1(CX)
110 sha1($pass.$salt)
120 sha1($salt.$pass)
130 sha1(unicode($pass).$salt)
140 sha1($salt.unicode($pass))
4500 sha1(sha1($pass))
4520 sha1($salt.sha1($pass))
4700 sha1(md5($pass))
4900 sha1($salt.$pass.$salt)
1410 sha256($pass.$salt)
1420 sha256($salt.$pass)
1440 sha256($salt.unicode($pass))
1430 sha256(unicode($pass).$salt)
7400 sha256crypt$5$,SHA256(Unix)
1710 sha512($pass.$salt)
1720 sha512($salt.$pass)
1740 sha512($salt.unicode($pass))
1730 sha512(unicode($pass).$salt)
1800 sha512crypt$6$,SHA512(Unix)
11400 SIPdigestauthentication(MD5)
121 SMF(SimpleMachinesForum)
1711 SSHA-512(Base64),LDAP{SSHA512}
10100 SipHash
14900 Skip32
23 Skype
8000 SybaseASE
62XY TrueCrypt
X 1=PBKDF2-HMAC-RipeMD160
X 2=PBKDF2-HMAC-SHA512
X 3=PBKDF2-HMAC-Whirlpool
X 4=PBKDF2-HMAC-RipeMD160+boot-mode
Y 1=XTS512bitpureAES
Y 1=XTS512bitpureSerpent
Y 1=XTS512bitpureTwofish
Y 2=XTS1024bitpureAES
Y 2=XTS1024bitpureSerpent
Y 2=XTS1024bitpureTwofish
Y 2=XTS1024bitcascadedAES-Twofish
Y 2=XTS1024bitcascadedSerpent-AES
Y 2=XTS1024bitcascadedTwofish-Serpent
Y 3=XTS1536bitall
2611 vBulletin<V3.8.5
2711 vBulletin>V3.8.5
137XY VeraCrypt
X 1=PBKDF2-HMAC-RipeMD160
X 2=PBKDF2-HMAC-SHA512
X 3=PBKDF2-HMAC-Whirlpool
X 4=PBKDF2-HMAC-RipeMD160+boot-mode
X 5=PBKDF2-HMAC-SHA256
X 6=PBKDF2-HMAC-SHA256+boot-mode
Y 1=XTS512bitpureAES
Y 1=XTS512bitpureSerpent
Y 1=XTS512bitpureTwofish
Y 2=XTS1024bitpureAES
Y 2=XTS1024bitpureSerpent
Y 2=XTS1024bitpureTwofish
Y 2=XTS1024bitcascadedAES-Twofish
Y 2=XTS1024bitcascadedSerpent-AES
Y 2=XTS1024bitcascadedTwofish-Serpent
Y 3=XTS1536bitall
8400 WBB3(WoltlabBurningBoard)
2500 WPA/WPA2
2501 WPA/WPA2PMK
6100 Whirlpool
13600 WinZip
13800 Windows8+phonePIN/Password
400 Wordpress
21 xt:Commerce

TERMINALCOMMANDCHEATSHEET
Ctrl+u
deleteeverythingfromthecursortothebeginningofthelineCtrl+
w
deletethepreviouswordonthecommandlinebeforethecursorCtrl
+l
cleartheterminalwindow
Ctrl+a
jumptothebeginningofthecommandline
Ctrl+e
moveyourcursortotheendofthecommandlineCtrl+r
searchcommandhistoryinreverse,continuepressingkeysequence
tocontinuebackwardssearch.Escwhendoneorcommandfound.
FILEMANIPULATIONCHEATSHEET
Extractalllowercasestringsfromeachlineandoutputtowordlist.
sed’s/[^a-z]*//g’wordlist.txt>outfile.txt
Extractalluppercasestringsfromeachlineandoutputtowordlist.
sed’s/[^A-Z]*//g’wordlist.txt>outfile.txt
Extractalllowercase/uppercasestringsfromeachlineandoutputtowordlist.
sed’s/[^a-Z]*//g’wordlist.txt>outfile.txt
Extractalldigitsfromeachlineinfileandoutputtowordlist.
sed’s/[^0-9]*//g’wordlist.txt>outfile.txt
Watchhashcatpotfileordesignatedoutputfilelive.
watch-n.5tail-50<hashcat.potfileoroutfile.txt>
Pull100randomsamplesfromwordlist/passwordsforvisualanalysis.
shuf-n100file.txt
Printstatisticsonlengthofeachstringandtotalcountsperlength.
awk‘{printlength}’file.txt|sort-n|uniq-c
Removeallduplicatestringsandcounthowmanytimestheyarepresent;then
sortbytheircountindescendingorder.
uniq-cfile.txt|sort-nr
Commandtocreatequick&dirtycustomwordlistwithlength1-15character
wordsfromadesignatedwebsiteintoasortedandcountedlist.
curl-shttp://www.netmux.com|sed-e's/<[^>]*>//g'|tr"""\n"
|tr-dc'[:alnum:]\n\r'|tr‘[:upper:]’‘[:lower:]’|cut-c1-15|sort
|uniq-c|sort-nr
MD5eachlineinafile(MacOSX).
whilereadline;doecho-n$line|md5;done<infile.txt>outfile.txt
MD5eachlineinafile(*Nix).
whilereadline;doecho-n$line|md5sum;done<infile.txt|awk-F““
‘{print$1}’>outfile.txt
Removelinesthatmatchfromeachfileandonlyprintremainingfromfile2.txt.
grep-vwF-ffile1.txtfile2.txt
Taketwoorderedfiles,mergeandremoveduplicatelinesandmaintainordering.
nl-ba-s‘:‘file1.txt>>outfile.txt
nl-ba-s‘:‘file2.txt>>outfile.txt
sort-noutfile.txt|awk-F“:”‘{print$2}’|awk‘!seen[$0]++’>final.txt
Extractstringsofaspecificlengthintoanewfile/wordlist.
awk‘length==8’file.txt>81en-out.txt
Convertalphacharactersoneachlineinfiletolowercasecharacters.
tr[A-Z][a-z]<infile.txt>outfile.txt
Convertalphacharactersoneachlineinfiletouppercasecharacters.
tr[a-z][A-Z]<infile.txt>outfile.txt
SplitafileintoseparatefilesbyXnumberoflinesperoutfile.
split-d-l3000infile.txtoutfile.txt
Reversetheorderofeachcharacterofeachlineinthefile.
revinfile.txt>outfile.txt
Sorteachlineinthefilefromshortesttolongest.
awk‘{printlength,$0}’“”$0;}’infile.txt|sort-n|cut-d‘‘-f2-
Sorteachlineinthefilefromlongesttoshortest.
awk‘{printlength,$0}’“”$0;}’infile.txt|sort-r-n|cut-d‘‘-f2-
SubstringmatchingbyconvertingtoHEXandthenbacktoASCII.
(Examplesearchesfor5characterstringsfromfile1.txtfoundasasubstringin
20characterstringsinfile2.txt)stringsfile1.txt|xxd-u-ps-c5|sort-u>
out1.txt
stringsfile2.txt|xxd-u-ps-c20|sort-u>out2.txt
grep-Ffout1.txtout2.txt|xxd-r-p>results.txt
Cleandictionary/wordlistofnewlinesandtabs.
catdict.txt|tr-cd“[:print:][/n/t]\n”>outfile.txt


SYSTEMHASHEXTRACTION
WINDOWS
METERPRETERHASHDUMP
PostexploitationdumplocalSAMdatabase:
meterpreter>runpost/windows/gather/hashdump
CREDDUMP
https://github.com/Neohapsis/creddump7
Threemodesofattack:cachedump,lsadump,pwdump
DUMPDOMAINCACHEDCREDENTIALS
SaveWindowsXP/Vista/7registryhivetables
C:\WIND0WS\system32>reg.exesaveHKLM\SAMsam_backup.hiv
C:\WIND0WS\system32>reg.exesaveHKLM\SECURITYsec_backup.hiv
C:\WIND0WS\system32>reg.exesaveHKLM\systemsys_backup.hiv
Runcreddumptoolsagainstthesavedhivefiles:cachedump.py<systemhive>
<securityhive><Vista/7>
(Vista/7)
cachedump.pysys_backup.hivsec_backup.hivtrue
(XP)
cachedump.pysys_backup.hivsec_backup.hivfalse
DUMPLSASECRETS
lsadump.pysys_backup.hivsec_backup.hiv
DUMPLOCALPASSWORDHASHES
pwdump.pysys_backup.hivsec_backup.hiv

MIMIKATZ
PostexploitationcommandsmustbeexecutedfromSYSTEMlevelprivileges.
mimikatz#privilege::debug
mimikatz#token::whoami
mimikatz#token::elevate
mimikatz#lsadump::sam
SaveWindowsXP/Vista/7registrytables
C:\WIND0WS\system32>reg.exesaveHKLM\SAMsam_backup.hiv
C:\WIND0WS\system32>reg.exesaveHKLM\SECURITY
C:\WIND0WS\system32>reg.exesaveHKLM\system
mimikatz#lsadump::samSystemBkup.hivSamBkup.hiv*NIX
Requiresrootlevelprivileges.
cat/etc/shadow
Example*NIXsha512crypthash
root:$6$52450745$k5ka2p8bFuSmoVTltz0yyuaREkkKBcCNqoDKzYiDL9RaE8yMnPgh2XzzF0NDrUhgrcLwg78xslw5pJiypEdFX/
MACOSX10.5-10.7
ManualOSXHashExtraction
dscllocalhost-read/Search/Users/<username>|grepGeneratedUID|cut-
c15-cat/var/db/shadow/hash/<GUID>|cut-c169-216>osx_hash.txt
MACOSX10.8-10.12
ManualOSXHashExtraction
sudodefaultsread/var/db/dslocal/nodes/Default/users/<username>.plist
ShadowHashData|tr-dc‘0-9a-f’|xxd-p-r|plutil-convertxml1--o-
ScriptedOSXHashExtraction

JOHN
https://github.com/truongkma/ctf-tools/blob/master/John/run/ml2john.py
sudoml2john.py/var/db/dslocal/nodes/Default/users/<username>.plist
PCAPHASHEXTRACTION
LOCALNETWORKAUTHENTICATION
PCREDZ
Extractsnetworkauthenticationhashesfrompcaps.
Singlepcapfile:
Pcredz-fexample.pcap
Multiplepcapfilesinadirectory:
Pcredz-d/path/to/pcaps
Interfacetolistenonandcollect:
Pcredz-ieth0
WPA/WPA2PSKAUTHENTICATION
Capturethe4-wayWPA/WPA2authenticationhandshake.
AIRMON-NG/AIRODUMP-NG/AIREPLAY-NG
Step1:Createmonitoringinterfacemon0Ex)interfacewlan0
airmon-ngstartwlan0
Step2:CapturepacketstofileontargetAPchannelEx)channel11
airodump-ngmon0--writecapture.cap-c11
Step3:StartdeauthattackagainstBSSIDEx)bb:bb:bb:bb:bb:bbaireplay-ng--
deauth0-abb:bb:bb:bb:bb:bbmon0
Step4:Waitforconfirmationtoappearattopofterminal:CH11][Elapsed:25
s][<DATE/TIME)][WPAhandshake:**
Step5:ExtracthandshakeintoJOHNorHASHCATformat:JOHNFORMAT
EXTRACT
Stepl:cap2hccap.bin-e‘<ESSID>’capture.capcapture_out.hccap

Step2:hccap2johncapture_out.hccap>jtr_captureHASHCAT
FORMATEXTRACT
cap2hccapx.bincapture.capcapture_out.hccapx
MISCWLANTOOLS
HCXTOOLS:captureandconvertpacketsfromwlandevicesforusewith
Hashcat.
https://github.com/ZerBea/hcxtools
DATABASEHASHEXTRACTION
SQLqueriesrequireadministrativeprivileges.
ORACLE10gR2
SELECTusername,passwordFROMdba_usersWHERE
username=‘<username>’;
ORACLE11gR1
SELECTname,password,spare4FROMsys.user$WHERE
name=‘<username>’;MySQL4.1/MySQL5+
SELECTUser,PasswordFROMmysql.userINTOOUTFILE
‘/tmp/hash.txt’;
MSSQL(2012),MSSQL(2014)
SELECTSL.name,SL.password_hashFROMsys.sql_loginsASSL;
POSTGRES
SELECTusername,passwdFROMpg_shadow;
MISCELLANEOUSHASHEXTRACTION
JohnTheRipperJumbocomeswithvariousprogramstoextracthashes:
NAME DESCRIPTION
1password2john.py 1Passwordvaulthashextract
7z2john.py 7zipencryptedarchivehashextract
androidfde2john.py AndroidFDEconvertdisks/imagesintoJTRformat
aix2john.py AIXshadowfile/etc/security/passwd
apex2john.py OracleAPEXhashformating
bitcoin2john.py Bitcoinoldwallethashextraction(check
btcrecover)
blockchain2john.py Blockchainwalletextraction
cisco2john.pl Ciscoconfigfileingestion/extract
cracf2john.py CRACFprogramcrafc.txtfiles
dmg2john.py Appleencrypteddiskimage
ecryptfs2john.py eCryptfsdiskencryptionsoftware
efs2john.py WindowsEncryptingFileSystem(EFS)extract
encfs2john.py EncFSencryptedfilesystemuserspace
gpg2john PGPsymmetricallyencryptedfiles
hccap2john ConvertpcapcaptureWPAfiletoJTRformat
htdigest2john.py HTTPDigestauthentication
ikescan2john.py IKEPSKSHA256authentication
kdcdump2john.py KeyDistributionCenter(KDC)servers
keepass2john Keepassfilehashextract
keychain2john.py ProcessesinputMacOSXkeychainfiles
keyring2john ProcessesinputGNOMEKeyringfiles
keystore2john.py OutputpasswordprotectedJavaKeyStorefiles
known_hosts2john.py SSHKnownHostfile
kwallet2john.py KDEWalletManagertooltomanagethepasswords
ldif2john.pl LDAPDataInterchangeFormat(LDIF)
lion2john.pl
lion2john-alt.pl ConvertsanAppleOSXLionplistfile
lotus2john.py LotusNotesIDfileforDomino
luks2john LinuxUnifiedKeySetup(LUKS)diskencryption
mcafee_epo2john.py McAfeeePolicyOrchestratorpasswordgenerator
ml2john.py ConvertMacOSX10.8andlaterplisthash
mozilla2john.py MozillaFirefox,Thunderbird,SeaMonkeyextract
odf2john.py ProcessesOpenDocumentFormatODFfiles
office2john.py MicrosoftOffice[97-03,2007,2010,2013)hashes
openbsd_softraid2john.py OpenBSDSoftRAIDhash
openssl2john.py OpenSSLencryptedfiles
pcap2john.py PCAPextractionofvariousprotocols
pdf2john.py PDFencrypteddocumenthashextract
pfx2john PKCS12files
putty2john PuTTYprivatekeyformat
pwsafe2john PasswordSafehashextract
racf2john IBMRACFbinarydatabasefiles
radius2john.pl RADIUSprotocolsharedsecret
rar2john RAR3.xfilesinputintoproperformat
sap2john.pl ConvertspasswordhashesfromSAPsystems
sipdump2john.py ProcessessipdumpoutputfilesintoJTRformat
ssh2john SSHprivatekeyfiles
sshng2john.py SSH-ngprivatekeyfiles
strip2john.py ProcessesSTRIPPasswordManagerdatabase
sxc2john.py ProcessesSXCfiles
truecrypt_volume2john TrueCryptencrypteddiskvolume
uaf2john ConvertOpenVMSSYSUAFfiletounix-stylefile
vncpcap2john TightVNC/RealVNCpcapsvsc3.3,3.7and3.8RFB
wpapcap2john ConvertsPCAPorIVS2filestoJtRformat
zip2john ProcessesZIPfilesextractshashintoJTRformat


PASSWORDANALYSIS
HISTORICALPASSWORDANALYSISTIPS
-Theaveragepasswordlengthis7-9characters.
-TheaverageEnglishwordis5characterslong.
-Theaveragepersonknows50,000to150,000words.
-50%chanceauser’spasswordwillcontainoneormorevowels.
-Womenpreferpersonalnamesintheirpasswords,andmenpreferhobbies.
-Mostlikelytobeusedsymbols:~,!,@,#,$,%,&,*,and?
-Ifanumber,it’susuallya1or2,sequential,andwilllikelybeattheend.
-Ifmorethanonenumberitwillusuallybesequentialorpersonallyrelevant.
-Ifacapitalletter,it’susuallythebeginning,followedbyavowel.
-66%ofpeopleonlyuse1-3passwordsforallonlineaccounts.
-OneinninepeoplehaveapasswordbasedonthecommonTop500list.
-WesterncountriesuselowercasepasswordsandEasterncountriespreferdigits.
20-60-20RULE
20-60-20ruleisawaytoviewthelevelofdifficultytypicallydemonstratedbya
largepassworddump,havingcharacteristicsthatgenerallyerronthesideofa
GaussianCurve,mirroringthelevelofefforttorecoversaidpassworddump.
20%ofpasswordsareeasilyguesseddictionarywordsorknowncommon
passwords.
60%ofpasswordsaremoderatetoslightvariationsoftheearlier20%.
20%ofpasswordsarehard,lengthy,complex,orofuniquecharacteristics.
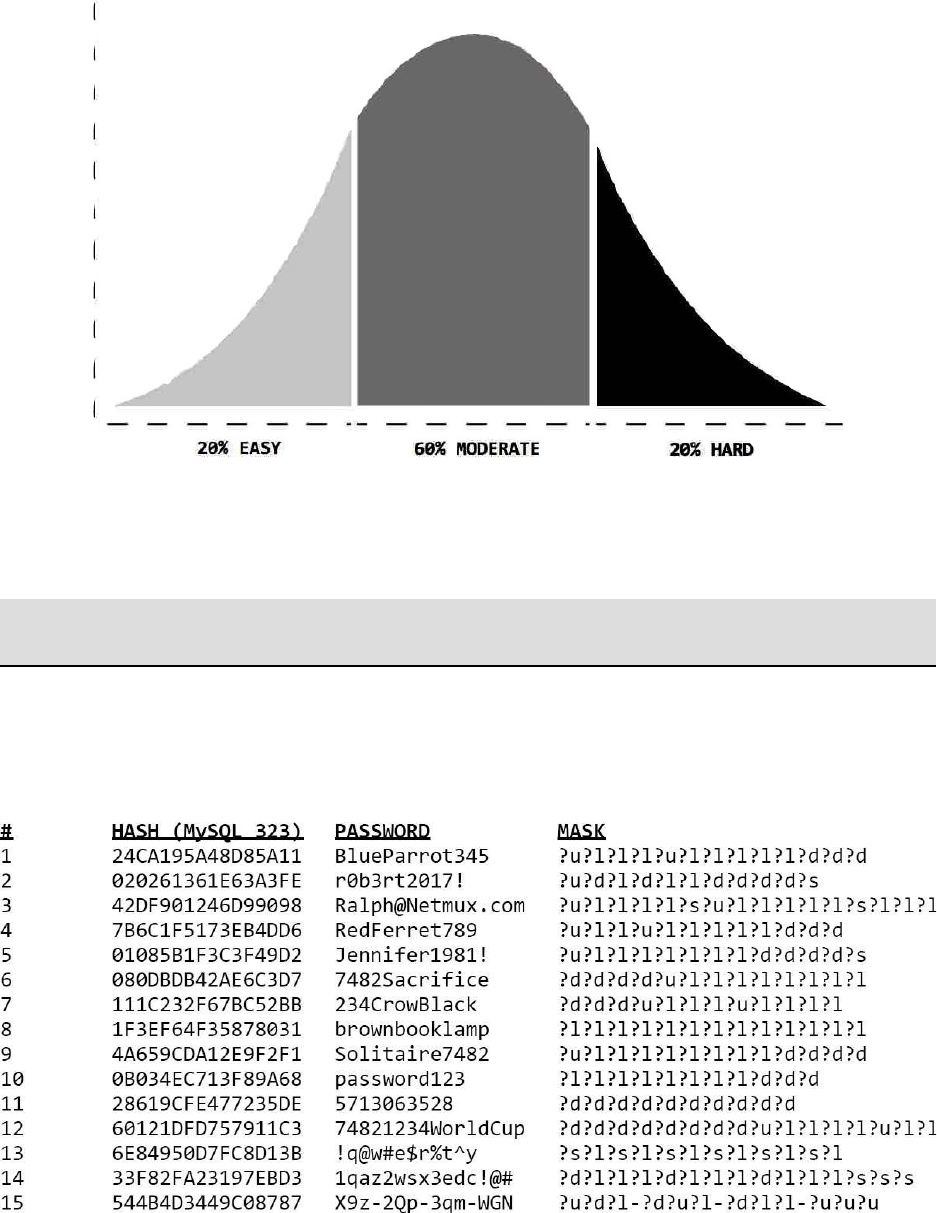
EXAMPLEHASHES&PASSWORDS
Thisisanexamplelistofpasswordstohelpconveythevariationandcommon
complexitiesseenwithtypicalpasswordcreation.Italsoshowsindividualuser
biasestoaidinsegmentingyourattackstobetailoredtowardaspecificuser.

CRACKINGTIPSFOREACHPASSWORD
*ThisListofpasswordswillbereferencedthroughoutthebookandtheListcan
alsobefoundonlineat:https://github.com/netmux/HASH-CRACK
PASSWORDPATTERNANALYSIS
Apasswordcancontainmanyusefulbitsofinformationrelatedtoit’screator
andtheirtendencies/patterns,butyouhavetobreakdownthestructureto
decipherthemeaning.Thisanalysisprocesscouldbeconsideredasub-category
ofTextAnalytics’andsplitintothreepatterncategoriesI’mcalling:Basic
Pattern,Macro-Pattern,&Micro-Pattern.
*RefertoEXAMPLEHASH&PASSWORDSchapter(pg.29)fornumbered
examples.
BasicPattern:visuallyobviouswhencomparedtosimilargroupings(i.e.
languageandbaseword/words&digits).Let’slookatAlice’spasswords(2,5):
R0b3rt2017! Jennifer1981!
-Eachpasswordusesaname:R0b3rt&Jennifer-Endingina4digitdatewith
commonspecialcharacter:2017!&1981!
!TIP!ThistypeofbasicpatternlendsitselftoasimpledictionaryandL33T
speakruleappendingdatesorhybridmaskattackappendingDict+?d?d?d?d?s
Macro-Pattern:statisticsaboutthepasswordsunderlyingstructuresuchas
lengthandcharacterset.Let’slookatCraig’spasswords(6,9):
7482Sacrifice Solitaire7482
-Lengthstructurecanbesummedupas:4Digits+7Alpha&7Alpha+4
Digits
-Usescharsets?l?u?d,sowemaybeabletoignorespecialcharacters.
-BasicPatternpreferenceforthenumbers7482andMicro-Patternfor
capitalizingwordsbeginningin“S”.
!TIP!Youcanassumethisuseris‘unlikely’tohaveapasswordlessthan12
characters(+-1char)andthe4digitconstantlowerstheworkto8chars.These
exampleslendthemselvestoaHybridAttack(Dict+7482)or(7482+Dict).
Micro-Pattern:subtletyandcontextwhichexpressesconsistentcasechanges,
themes,andpersonaldata/interest.Let’slookatBob’spasswords(1,4)
BlueParrot345 RedFerret789
-Eachpasswordbeginswithacolor:Blue&Red-Secondwordisatypeof
animal:Parrot&Ferret
-Consistentcapitalizationofallwords
-Lastly,endingina3digitsequentialpattern:345&789
!TIP!Thispatternlendsitselftoacustomcombodictionaryandruleorhybrid
maskattackappendingsequentialdigits?d?d?dSowhenanalyzingpasswordsbe
suretogrouppasswordsandlookforpatternssuchaslanguage,baseword/digit,
length,charactersets,andsubtlethemeswithpossiblecontextualmeaningor
passwordpolicyrestrictions.
WESTERNCOUNTRYPASSWORDANALYSIS
PasswordLengthDistributionbasedonlargecorpusofEnglishwebsitedumps:
7=15%8=27%9=15%10=12%11=4.8%12=4.9%13=.6%14=.3%
CharacterfrequencyanalysisofalargecorpusofEnglishtexts:
etaoinshrdlcumwfgypbvkjxqz
CharacterfrequencyanalysisofalargecorpusofEnglishpassworddumps:
aeionrlstmcdyhubkgpjvfwzxq
TopWesternpasswordmasksoutofalargecorpusofEnglishwebsitedumps:
EASTERNCOUNTRYPASSWORDANALYSIS
PasswordLengthDistributionbasedonlargecorpusofChinesewebsitedumps:
7=21%8=22%9=12%10=12%11=4.2%12=.9%13=.5%14=.5%
CharacterfrequencyanalysisofalargecorpusofChinesetexts:
aineohglwuyszxqcdjmbtfrkpv
CharacterfrequencyanalysisofalargecorpusofChinesepassworddumps:
inauhegoyszdjmxwqbctlpfrkv
TopEasternpasswordmasksoutofalargecorpusofChinesewebsitedumps:
PASSWORDMANAGERANALYSIS
AppleSafariPasswordGenerator
-defaultpassword15characterswith“-”&fourgroupsofthreerandom
u=ABCDEFGHJKLMNPQRSTUVWXYZl=abcdefghkmnopqrstuvwxyand
d=3456789
Example)X9z-2Qp-3qm-WGN
XXX-XXX-XXX-XXXwhereX=?u?l?d
Dashlane
-defaultpassword12charactersusingjustlettersanddigits.
Example)Up0k9ZAj54Kt
XXXXXXXXXXXXwhereX=?u?l?d
KeePass
-defaultpassword20charactersusinguppercase,lowercase,digits,andspecial.
Example)$Zt={EcgQ.Umf)R,C7XF
XXXXXXXXXXXXXXXXXXXXwhereX=?u?l?d?s
LastPass
-defaultpassword12charactersusingatleastonedigit,uppercaseand
lowercase.
Example)msfNdkG29n38
XXXXXXXXXXXXwhereX=?u?l?d

RoboForm
-defaultpassword15charactersusinguppercase,lowercase,digits,andspecial
withaminimumof5digits.
Example)871v2%%4F0w31zJ
XXXXXXXXXXXXXXXwhereX=?u?l?d?s
SymantecNortonIdentitySafe
-defaultpassword8charactersusinguppercase,lowercase,anddigits.
Example)Ws81f0Zg
XXXXXXXXwhereX=?u?l?d
TrueKey
-defaultpassword16charactersusinguppercase,lowercase,digits,andspecial.
Example)1B1H:9N+@>+sgWs
XXXXXXXXXXXXXXXXwhereX=?u?l?d?s
1Passwordv6
-defaultpassword24charactersusinguppercase,lowercase,digits,andspecial.
Example)cTmM7Tzm6iPhCdpMu.*V],VP
XXXXXXXXXXXXXXXXXXXXXXXXwhereX=?u?l?d?s
PACK(PasswordAnalysisandCrackingKit)
http://thesprawl.org/projects/pack/
STATSGEN
Generatestatisticsaboutthemostcommonlength,percentages,character-setand
othercharacteristicsofpasswordsfromaprovidedlist.
pythonstatsgen.pypasswords.txt

STATSGENOPTIONS
-o<file.txt> outputstatsandmaskstofile
--hiderare hidestatsofpasswordswithlessthan1%of
occurrence
--minlength= minimumpasswordlengthforanalysis
--maxlength= maximumpasswordlengthforanalysis
--charset= passwordcharfilter:loweralpha,upperalpha,
numeric,special
--simplemask= passwordmaskfilter:string,digit,special
STATSGENEXAMPLES
Outputstatsofpasswords.txttofileexample.mask:
pythonstatsgen.pypasswords.txt-oexample.mask
Hidelessthan1%occurrence;onlyanalyzepasswords7charactersand
greater:
pythonstatsgen.pypasswords.txt--hiderare--minlength=7-oexample.mask
Statsonpasswordswithonlynumericcharacters:
pythonstatsgen.pypasswords.txt--charset=numeric
ZXCVBN(LOW-BUDGETPASSWORDSTRENGTH
ESTIMATION)
Arealisticpasswordstrength(entropy)estimatordevelopedbyDropbox.
https://github.com/dropbox/zxcvbn
PIPAL(THEPASSWORDANALYSER)
Passwordanalyzerthatproducesstatsandpatternfrequencyanalysis.
https://digi.ninja/projects/pipal.php
pipal.rb-ooutfile.txtpasswords.txt
PASSPAT(PASSWORDPATTERNIDENTIFIER)
Keyboardpatternanalysistoolforpasswords.
https://digi.ninja/projects/passpat.php
passpat.rb--layoutuspasswords.txt
CHARACTERFREQUENCYANALYSIS
Characterfrequencyanalysisisthestudyofthefrequencyoflettersorgroupsof
lettersinacorpus/text.ThisisthebasicbuildingblockofMarkovchains.
Character-Frequency-CLI-Tool
Tooltoanalyzealargelistofpasswordsandsummarizethecharacterfrequency.
https://github.com/jcchurch/Character-Frequency-CLI-Tool
charfreq.py<options>passwords.txt
Options: -wWindowsizetoanalyze,default=l
-rRollingwindowsize
-sSkipspaces,tabs,newlines
ONLINEPASSWORDANALYSISRESOURCES
WEAKPASS
Analyzespublicpassworddumpsandprovidesefficientdictionariesfor
download.
http://weakpass.com/
PASSWORDRESEARCH
Importantpasswordsecurityandauthenticationresearchpapersinoneplace.
http://www.passwordresearch.com/
THEPASSWORDPROJECT
CompiledanalysisoflargerpassworddumpsusingPIPALandPASSPALtools.


DICTIONARY/WORDLIST
DOWNLOADRESOURCES
WEAKPASS
http://weakpass.com/wordlist
CRACKSTATIONDICTIONARY
https://crackstation.net/buy-crackstation-wordlist-password-cracking-
dictionary.htm
HAVEIBEENPWNED
*You’llhavetocracktheSHA1’s
https://haveibeenpwned.com/passwords
SKULLSECURITYWORDLISTS
https://wiki.skullsecurity.org/index.php?title=Passwords
CAPSOP
https://wordlists.capsop.com/
UNIX-NINJADNADICTIONARY
*Dictionarylinkatbottomofarticle*
https://www.unix-ninja.com/p/Password_DNA
PROBABLE-WORDLIST
https://github.com/berzerk0/Probable-Wordlists
EFF-WORDLIST
Long-list(7,776words)&Short-list(1,296words)
https://www.eff.org/files/2016/07/18/eff_large_wordlist.txt
https://www.eff.org/files/2016/09/08/eff_short_wordlist_1.txt

RAINBOWTABLES
*RainbowTablesareforthemostpartobsoletebutprovidedhereforreference*
http://project-rainbowcrack.com/table.htm
WORDLISTGENERATION
JOHNTHERIPPER
Generatewordlistthatmeetscomplexityspecifiedinthecomplexfilter.
john--wordlist=dict.txt--stdout--external:[filtername]>outfile.txt
STEMMINGPROCESS
Strippingcharactersfromapasswordlisttoreachthe“stem”orbaseword/words
ofthecandidatepassword.Commandsarefrom“FileManipulationCheat
Sheet”.
Extractalllowercasestringsfromeachlineandoutputtowordlist.
sed’s/[^a-z]*//g’passwords.txt>outfile.txt
Extractalluppercasestringsfromeachlineandoutputtowordlist.
sed’s/[^A-Z]*//g’passwords.txt>outfile.txt
Extractalllowercase/uppercasestringsfromeachlineandoutputtowordlist.
sed’s/[^a-Z]*//g’passwords.txt>outfile.txt
Extractalldigitsfromeachlineinfileandoutputtowordlist.
sed’s/[^0-9]*//g’passwords.txt>outfile.txt
HASHCATUTILS
https://hashcat.net/wiki/doku.php?id=hashcat_utils
COMBINATOR
Combinemultiplewordlistswitheachwordappendedtotheother.
combinator.bindict1.txtdict2.txt>combined_dict.txtcombinator3.bindict1.txt
dict2.txtdict3.txt>combined_dict.txtCUTB
CutthespecificlengthofftheexistingwordlistandpassittoSTDOUT.
cutb.binoffset[length]<infile.txt>outfile.txtExampletocutfirst4characters
inawordlistandplaceintoafile:cutb.bin04<dict.txt>outfile.txt
RLI
Comparesafileagainstanotherfileorfilesandremovesallduplicates.
rlidict1.txtoutfile.txtdict2.txt
REQ
Dictionarycandidatesarepassedtostdoutifitmatchesanspecified
passwordgroupcriteria/requirement.Groupscanbeaddedtogether(i.e.1
+2=3)
1=LOWER(abcdefghijklmnoprstuvwxyz)
2=UPPER(ABCDEFGHIJKLMNOPRSTUVWXYZ)
4=DIGIT(0123465789)
8=OTHER(Allothercharactersnotmatching1,2,or4)Thisexamplewould
stdoutallcandidatesmatchingupperandlowercharactersreq.bin3<dict.txt
COMBIPOW
Creates“uniquecombinations”ofacustomdictionary;dictionarycannot
begreaterthan64lines;option-1limitscandidatesto15characters.
combipow.bindict.txt
combipow.bin-1dict.txt
EXPANDER
Dictionaryintostdinisparsedandsplitintoallitssinglechars(upto4)and
senttostdout.
expander.bin<dict.txt
LEN
Eachcandidateinadictionaryischeckedforlengthandsenttostdout.
len.bin<minlen><maxlen><dict.txt
Thisexamplewouldsendtostdoutallcandidates5to10charslong.
len.bin510<dict.txt

MORPH
Autogeneratesinsertionrulesforthemostfrequentchainsofcharacters
morph.bindict.txtdepthwidthpos_minpos_max
PERMUTE
Dictionaryintostdinparsedandrunthrough“TheCountdownQuickPerm
Algorithm”
permute.bin<dict.txt
CRUNCH
Wordlistgeneratorcanspecifyacharactersetandgenerateallpossible
combinationsandpermutations.
https://sourceforge.net/projects/crunch-wordlist/
crunch<minlength><maxlength><characterset>-ooutfile.txtcrunch88
0123456789ABCDEF-ocrunch_wordlist.txt
TARGETEDWORDLISTS
CeWL
Customwordlistgeneratorscrapes&compileskeywordsfromwebsites.
https://digi.ninja/projects/cewl.php
Examplescandepthof2andminimumwordlengthof5outputtowordlist.txt
cewl-d2-m5-wwordlist.txthttp://<targetwebsite>
SMEEGESCRAPE
Textfileandwebsitescraperwhichgeneratescustomwordlistsfromcontent.
http://www.smeegesec.com/2014/01/smeegescrape-text-scraper-and-custom.html
Compileuniquekeywordsfromtextfileandoutputintowordlist.
SmeegeScrape.py-ffile.txt-owordlist.txt
Scrapekeywordsfromtargetwebsiteandoutputintowordlist.
SmeegeScrape.py-uhttp://<targetwebsite>-si-owordlist.txt
GENERATEPASSWORDHASHES
Usethebelowmethodstogeneratehashesforspecificalgorithms.
HASHCAT
https://github.com/hashcat/hashcat/tree/master/tools
test.plpassthrough<#type><#>dict.txt
MDXFIND
https://hashes.org/mdxfind.php
echo|mdxfind-z-h‘<#type>’dict.txt
LYRICPASS(SongLyricsPasswordGenerator)
https://github.com/initstring/lyricpass
Generatorusingsonglyricsfromchosenartisttocreatecustomdictionary.
pythonlyricpass.py“ArtistName”artist-dict.txt
CONVERTWORDLISTENCODING
HASHCAT
ForceinternalwordlistencodingfromX
hashcat-a0-m#typehash.txtdict.txt--encoding-from=utf-8
ForceinternalwordlistencodingtoX
hashcat-a0-m#typehash.txtdict.txt--encoding-to=iso-8859-15
ICONV
Convertwordlistintolanguagespecificencoding
iconv-f<old_encode>-t<new_encode><dict.txt|spongedict.txt.enc

CONVERTHASHCAT$HEXOUTPUT
Exampleofconverting$HEX[]entriesinhashcat.potfiletoASCII
grep‘$HEX’hashcat.pot|awk-F“:”{‘print$2’}|perl-ne‘if($_=~m/\$HEX\
[([A-Fa-f0-9]+)\]/){printpack(“H*”,$1),“\n”}’
EXAMPLECUSTOMDICTIONARYCREATION
1-CreateacustomdictionaryusingCeWLfromwww.netmux.comwebsite:cewl
-d2-m5-wcustom_dict.txthttp://www.netmux.com
2-Combinethenewcustom_dict.txtwiththeGoogle10,000mostcommon
Englishwords:https://github.com/first20hours/google-10000-english
catgoogle-1000.txt>>custom_dict.txt
3-CombinewithTop196passwordsfrom“ProbableWordlists”:
github.com/berzerk0/Probable-Wordlists/blob/master/Real-Passwords
catTopl96-probable.txt>>custom_dict.txt
4-CombotheTopl96-probable.txttogetherusingHashcat-util“combinator.bin”
andaddittoourcustom_dict.txtcombinator.binTopl96-probable.txtTopl96-
probable.txt>>custom_dict.txt
5-Runthebest64.rulefromHashcatonTop196-probable.txtandsendthatoutput
intoourcustomdictionary:hashcat-a0Topl96-probable.txt-rbest64.rule--
stdout>>custom_dict.txt
Canyounowcomeupwithanattackthatcancrackthishash?
e4821dl6a298092638ddb7cadc26d32f
*AnswerintheAppendix

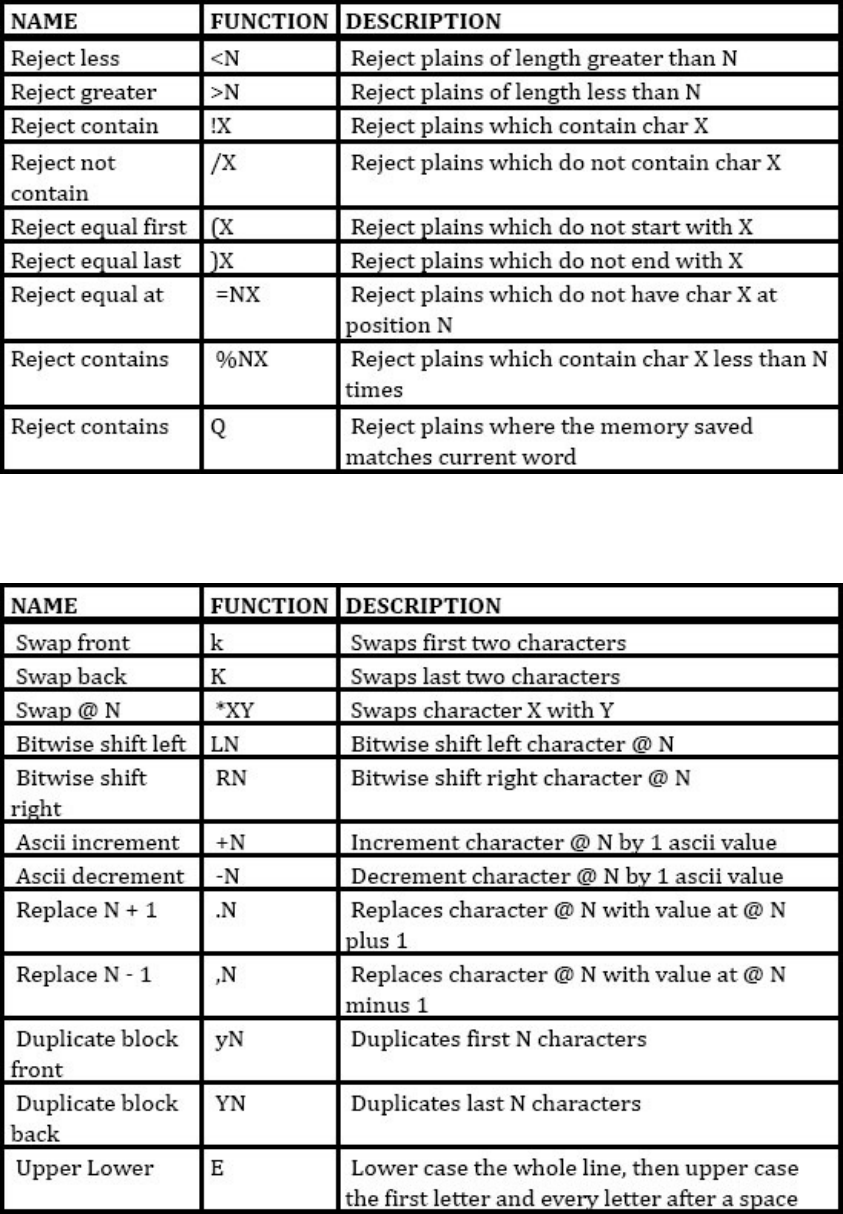
IMPLEMENTEDSPECIFICFUNCTIONS
FollowingfunctionsarenotcompatiblewithJohnTheRipper&PasswordPro
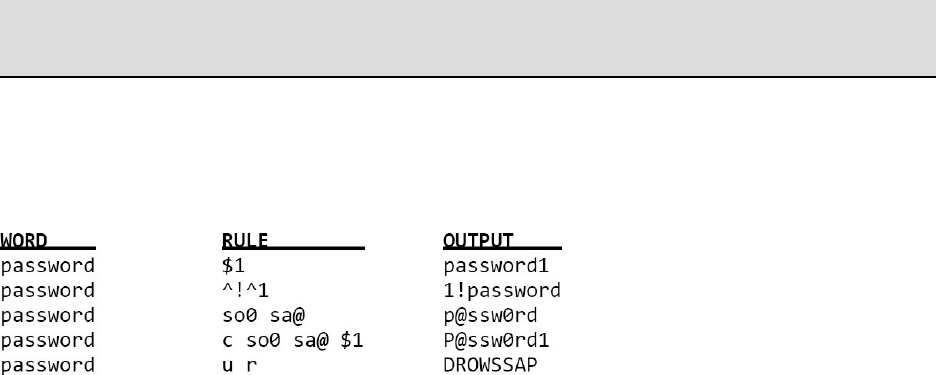
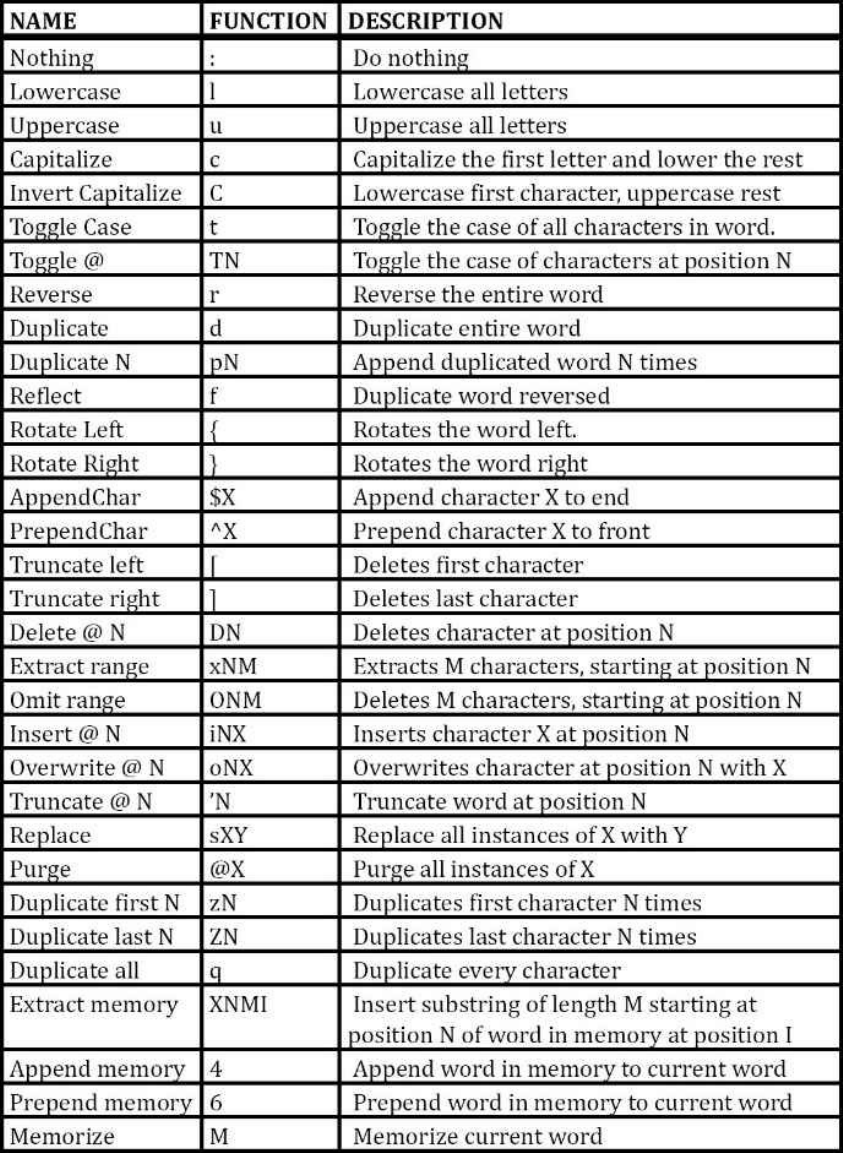
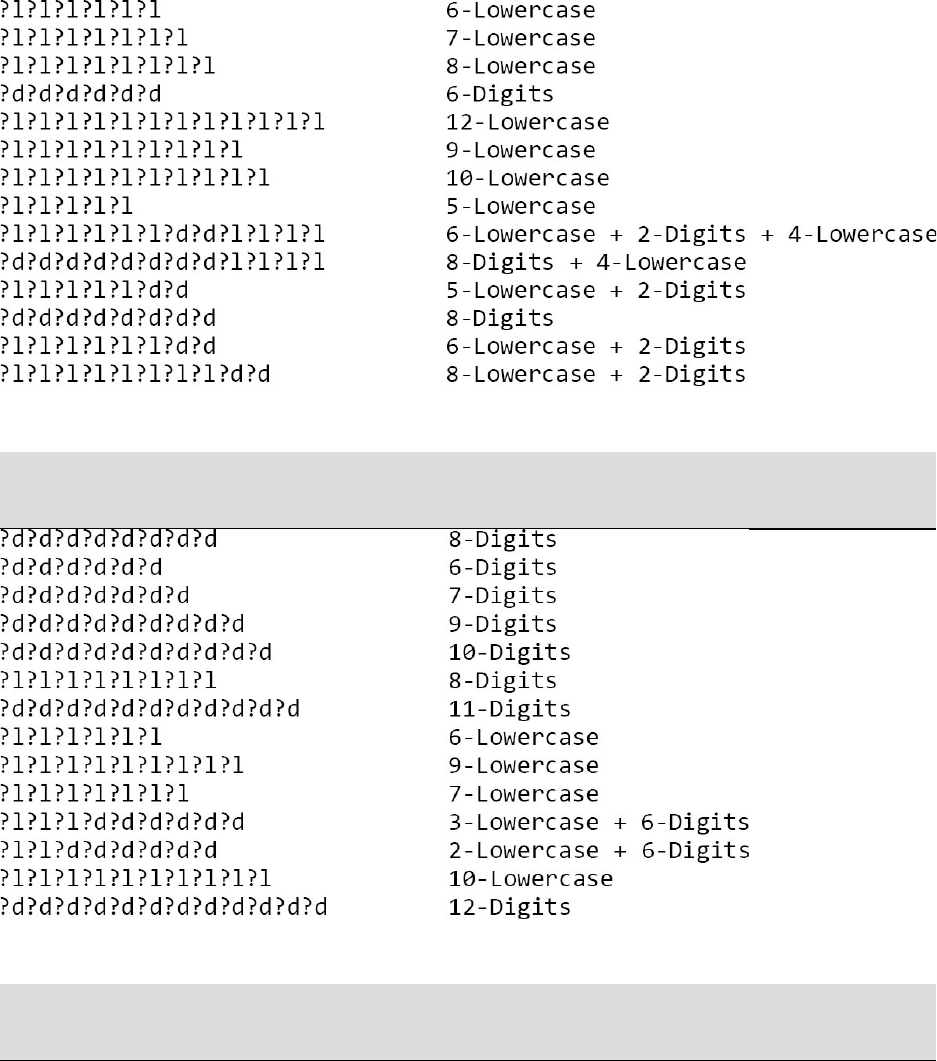
RULEATTACKCREATION
EXAMPLERULECREATION&OUTPUT
Belowweapplybasicrulestohelpexplaintheexpectedoutputwhenusing
rules.
MASKPROCESSORHASHCAT-UTIL
https://github.com/hashcat/maskprocessor
Maskprocessorcanbeusedtogeneratealonglistofrulesveryquickly.
Examplerulecreationofprependdigitandspecialchartodictionarycandidates
(i.e.^l^!,^2^@,...):mp64.bin‘^?d^?s’-orule.txt
Examplecreatingrulewithcustomcharsetappendinglower,uppercasechars
andalldigitstodictionarycandidates(i.e.$a$Q$1,$e$A$2,...):mp64.bin
-1aeiou-2QAZWSX‘$?1$?2$?d’
GENERATERANDOMRULESATTACK(i.e.“Raking”)
hashcat-a0-m#type-g<#rules>hash.txtdict.txtGENERATERANDOM
RULESFILEUSINGHASHCAT-UTIL
generate-rules.bin<#rules><seed>|./cleanup-rules.bin[1=CPU,2=GPU]>
out.txtgenerate-rules.bin100042|./cleanup-rules.bin2>out.txtSAVE
SUCCESSFULRULES/METRICS
hashcat-a0-m#type--debug-mode=l--debug-file=debug.txthash.txt-rrule.txt
SENDRULEOUTPUTTOSTDOUT/VISUALLYVERIFYRULE
OUTPUT
hashcatdict.txt-rrule.txt--stdout
john--wordlist=dict.txt--rules=example--stdout
RULEGEN
Advancedtechniquesforreversingsourcewordsandwordmanglingrulesfrom
alreadycrackedpasswordsbycontinuouslyrecycling/expandinggeneratedrules
andwords.OutputsrulesinHashcatformat.
http://thesprawl.org/research/automatic-password-rule-analysis-generation/
**Ensureyouinstall‘AppleSpell’‘aspell*moduleusingpacketmanager**
pythonrulegen.py--verbose--passwordP@ssw0rdl23
RULEGENOPTIONS
-brockyou
Outputbasename.Thefollowingfileswillbe
generated:basename.words,basename.rulesand
basename.stats
-wwiki.dict Useacustomwordlistforruleanalysis.
-q,--quiet Don’tshowheaders.
--
threads=THREADS Parallelthreadstouseforprocessing.
Finetunesourcewordgeneration::
--maxworddist=10 Maximumwordeditdistance(Levenshtein)
--maxwords=5 Maximumnumberofsourcewordcandidatesto
consider
--morewords Considersuboptimalsourcewordcandidates
--simplewords Generatesimplesourcewordsforgivenpasswords
Finetunerulegeneration::
--maxrulelen=10 Maximumnumberofoperationsinasinglerule
--maxrules=5 Maximumnumberofrulestoconsider
--morerules Generatesuboptimalrules
--simplerules Generatesimplerulesinsert,delete,replace
--bruterules Bruteforcereversalandrotationrules(slow)
Finetunespellcheckerengine::
--providers=aspell,myspell
Comma-separatedlistofproviderengines
Debuggingoptions::
-v,--verbose Showverboseinformation.
-d,--debug Debugrules.
--password Processthelastargumentasapasswordnotafile.
--word=Password Useacustomwordforruleanalysis
--hashcat Testgeneratedruleswithhashcat-cli

RULEGENEXAMPLES
Analysisofasinglepasswordtoautomaticallydetectrulesandpotential
sourcewordusedtogenerateasamplepassword:
pythonrulegen.py--verbose--passwordP@ssw0rdl23
Analyzepasswords.txtandoutputresults:
pythonrulegen.pypasswords.txt-q
analysis.word-unsortedandnon-uniquedsourcewords
analysis-sorted.word-occurrencesortedanduniquesourcewords
analysis.rule-unsortedandnon-uniquedrules
analysis-sorted.rule-occurrencesortedanduniquerules
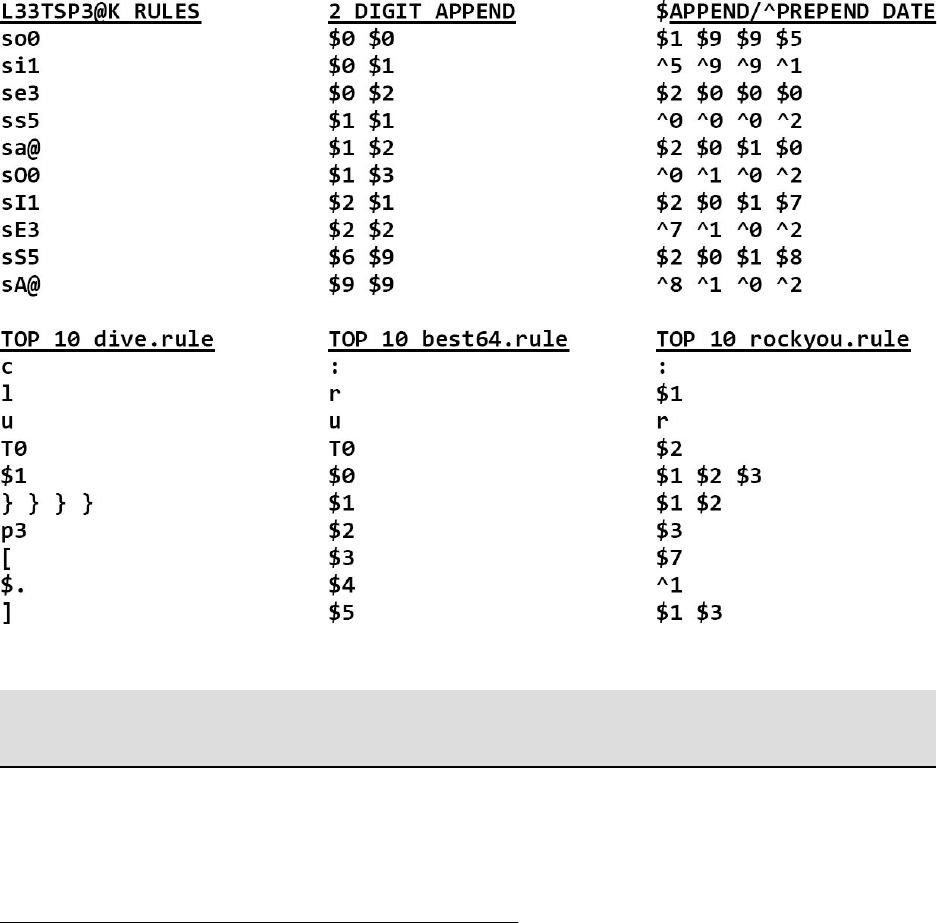
HASHCATINCLUDEDRULES Approx#Rules
Incisive-leetspeak.rule 15,487
InsidePro-HashManager.rule 6,746
InsidePro-PasswordsPro.rule 3,254
T0XlC-insert_00-99_1950-2050_toprules_0_F.rule 4,019
T0XlC-insert_space_and_special_0_F.rule 482
T0XlC-insert_top_100_passwords_l_G.rule 1,603
T0XlC.rule 4,088
T0XlCv1.rule 11,934
best64.rule 77
combinator.rule 59
d3ad0ne.rule 34,101
dive.rule 99,092
generated.rule 14,733
generated2.rule 65,117
leetspeak.rule 29
oscommerce.rule 256
rockyou-30000.rule 30,000
specific.rule 211
toggles1.rule 15
toggles2.rule 120
toggles3.rule 575
toggles4.rule 1,940
toggles5.rule 4,943
unix-ninja-leetspeak.rule 3,073

JOHNINCLUDEDRULES Approx#Rules
All(Jumbo+KoreLogic) 7,074,300
Extra 17
Jumbo(Wordlist+Single+Extra+NT+OldOffice) 226
KoreLogic 7,074,074
Loopback(NT+Split) 15
NT 14
OldOffice 1
Single 169
Single-Extra(Single+Extra+OldOffice) 187
Split 1
Wordlist 25
http://www.openwall.com/john/doc/RULES.shtml
CUSTOMRULEPLANS
MASKATTACKCREATION
DEBUG/VERIFYMASKOUTPUT
hashcat-a3?a?a?a?a--stdout
john--mask=?a?a?a?a--stdout
HASHCATMASKATTACKCREATION
Exampleusage:
hashcat-a3-m#typehash.txt<mask>
Examplebrute-forceallpossiblecombinations7characterslong:
hashcat-a3-m#typehash.txt?a?a?a?a?a?a?a
Examplebrute-forceallpossiblecombinations1-7characterslong:
hashcat-a3-m#typehash.txt-i?a?a?a?a?a?a?a
Examplebrute-forceuppercasefirstletter,3unknownmiddlecharacters,
andendsin2digits(i.e.Passl2):hashcat-a3-m#typehash.txt?u?a?a?a?d?d

Examplebrute-forceknownfirsthalfword“secret”andunknownending:
hashcat-a3-m#typehash.txtsecret?a?a?a?a
Examplehybridmask(leftside)+wordlist(rightside)(i.e.123!Password)
hashcat-a7-m#typehash.txt?a?a?a?adict.txt
Examplewordlist(leftside)+hybridmask(rightside)(i.e.Passwordl23!)
hashcat-a6-m#typehash.txtdict.txt?a?a?a?a
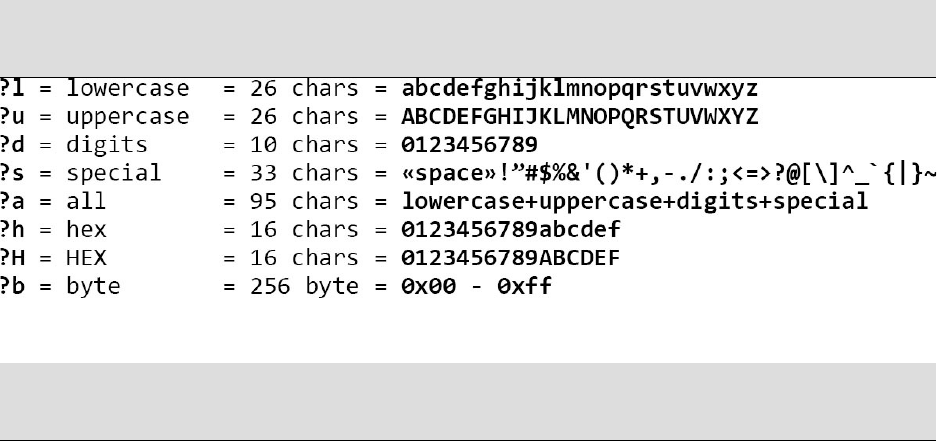
HASHCATCUSTOMCHARSETS
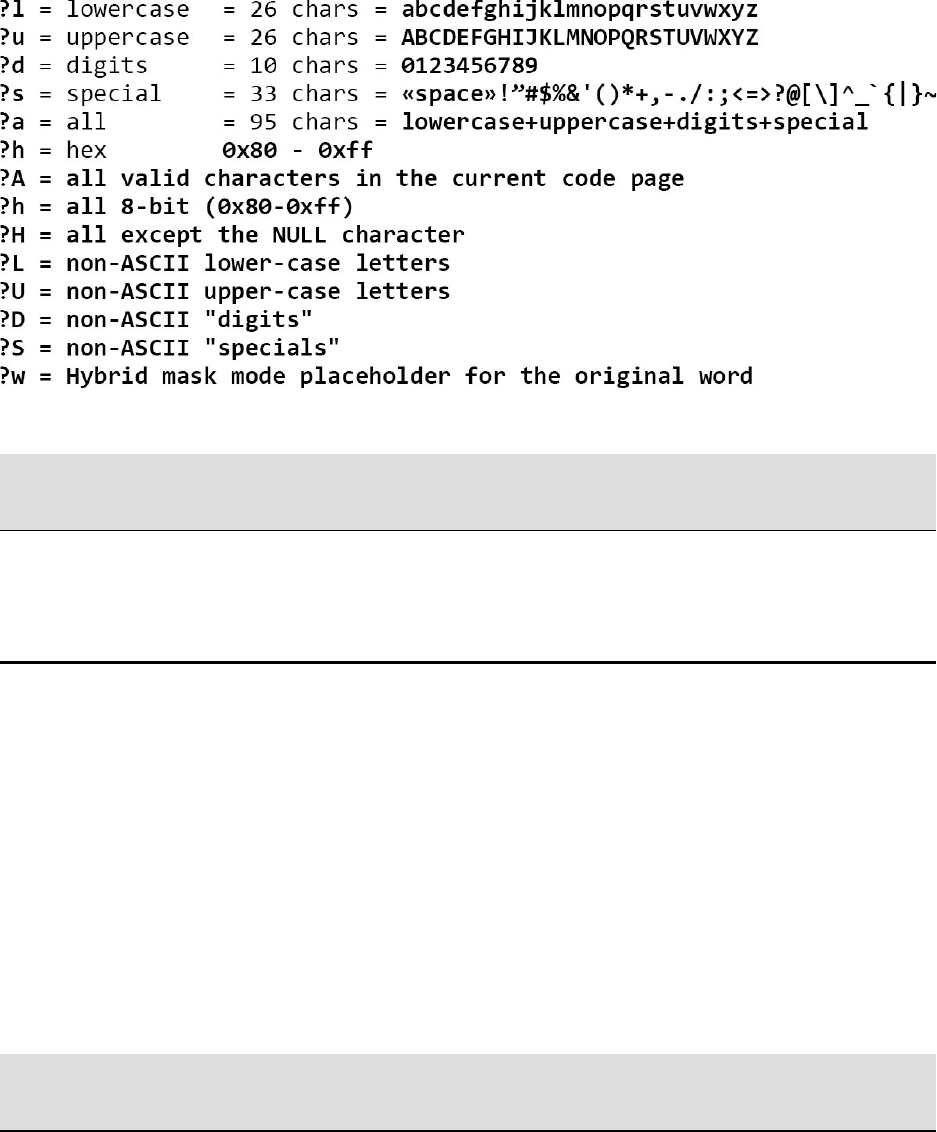
Fourcustombuffercharsetstocreateefficienttargetedmaskattacksdefinedas:
-1-2-3-4
Examplecustomcharsettargetingpasswordsthatonlybeginina,A,b,B,or
c,C,4unknownmiddlecharacters,andendwithadigit(i.e.al7z#q7):
hashcat-a3-m#typehash.txt-1abcABC?l?a?a?a?a?dExamplecustom
charsettargetingpasswordsthatonlybegininuppercaseorlowercase,4
digitsinthemiddle,andendinspecialcharacter!,@,$(i.e.W7462!or
f1234$):hashcat-a3-m#typehash.txt-1?u?l-2!@$?l?d?d?d?d?2
Exampleusingallfourcustomcharsetsatonce(i.e.pow!12er):
hashcat-a3-m#typehash.txt-1qwer-2poiu-3123456-4!@#$%?2?2?1?4?
3?3?1?1
JOHNMASKATTACKCREATION
Exampleusage:
john--format=#typehash.txt--mask=<mask>
Examplebrute-forceallpossiblecombinationsupto7characterslong:
john--format=#typehash.txt--mask=?a?a?a?a?a?a?a
Examplebrute-forceuppercasefirstletter,3unknownmiddlecharacters,
andendsin2digits(i.e.Passl2):
john--format=#typehash.txt--mask=?u?a?a?a?d?d
Examplebrute-forceknownfirsthalfword“secret”andunknownending:
john--format=#typehash.txt--mask=secret?a?a?a?a
Examplemask(leftside)+wordlist(rightside)(i.e.123!Password)
john--format=#typehash.txt--wordlist=dict.txt--mask=?a?a?a?a?wExample
wordlist(leftside)+mask(rightside)(i.e.Password123!)john--format=#type
hash.txt--wordlist=dict.txt--mask=?w?a?a?a?aJOHNCUSTOMCHARSETS
Ninecustombuffercharsetstocreateefficienttargetedmaskattacksdefinedas:
-1-2-3-4-5-6-7-8-9
Examplecustomcharsettargetingpasswordsthatonlybeginina,A,b,B,or
c,C,4unknownmiddlecharacters,andendwithadigit(i.e.a17z#q7):john
--format=#typehash.txt-1=abcABC--mask=?l?a?a?a?a?dExamplecustom
charsettargetingpasswordsthatonlybegininuppercaseorlowercase,4
digitsinthemiddle,andendinspecialcharacter!,@,$(i.e.W7462!or
f1234$):
john--format=#typehash.txt-1=?u?l-2=!@$--mask=?l?d?d?d?d?2
Exampleusingfourcustomcharsetsatonce(i.e.pow!12er):
john--format=#typehash.txt-1=qwer-2=poiu-3=123456-4=!@#$%,--mask=?
2?2?l?4?3?3?1?1
HASHCATMASKCHEATSHEET
JOHNMASKCHEATSHEET
MASKFILES
Hashcatallowsforthecreationofmaskfilesbyplacingcustommasks,oneper
line,inatextfilewith“.hcmask”extension.
HASHCATBUILT-INMASKFILES Approx#Masks
8char-11-1u-1d-1s-compliant.hcmask 40,824
8char-11-1u-1d-1s-noncompliant.hcmask 24,712
rockyou-1-60.hcmask 836
rockyou-2-1800.hcmask 2,968
rockyou-3-3600.hcmask 3,971
rockyou-4-43200.hcmask 7,735
rockyou-5-86400.hcmask 10,613
rockyou-6-864000.hcmask 17,437
rockyou-7-2592000.hcmask 25,043
WESTERNCOUNTRYTOPMASKS
MASKGEN
MaskGenallowsyoutoautomaticallygeneratepattern-basedmaskattacksfrom
knownpasswordsandfilterbylengthanddesiredcrackingtime.
pythonmaskgen.pyexample.mask
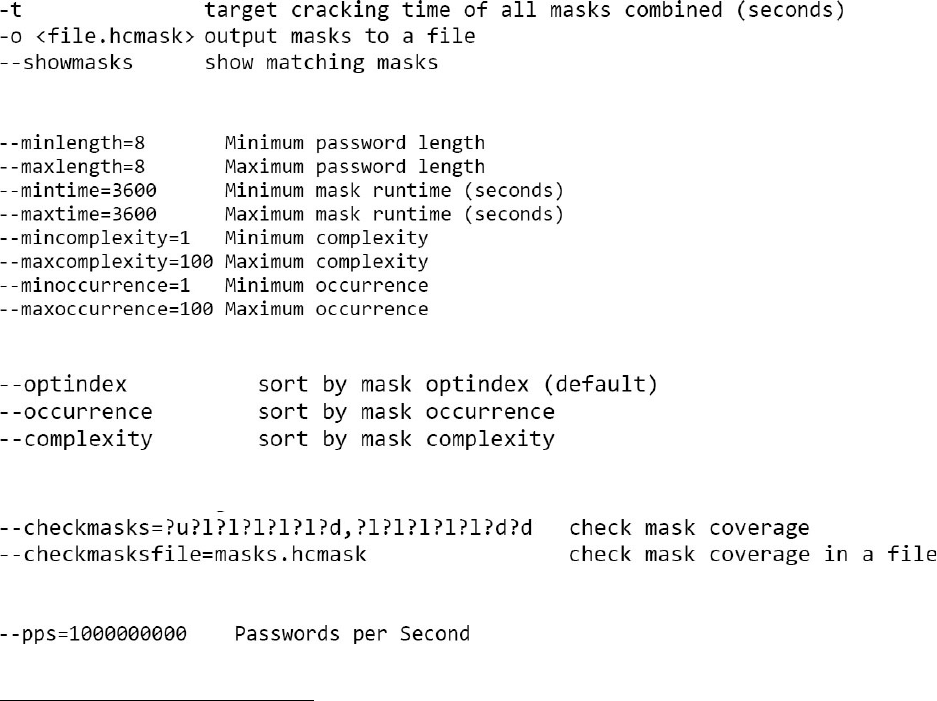
MASKGENOPTIONS
IndividualMaskFilterOptions:
MaskSortingOptions:
Checkmaskcoverage:
Miscellaneousoptions:
MASKGENEXAMPLES
Gatherstatsaboutcrackedpasswords.txtandhidethelessthan1%results:
pythonstatsgen.py--hiderarepasswords.txt
Savemasksstatstoa.maskfileforfurtheranalysis:
pythonstatsgen.py--hiderarepasswords.txt-oexample.maskAnalyze
example.maskresults,numberofmasks,estimatedtimetocrack,etc...
pythonmaskgen.pyexample.mask
Create24hour(86400seconds)maskattackbasedoncrackingspeedofa
singleGTX1080againstMD5hashes24943.1MH/s(basedonappendix
table).
!SubstituteyourGPU’scrackingspeedagainstMD5(c/s)!.
pythonmaskgen.pyexample.mask--targettime=86400--optindex--

pps=24943000000-qOutput24hourmaskattacktoa.hcmaskfileforusein
Hashcat:
pythonmaskgen.pyexample.mask--targettime=86400--optindex--
pps=24943000000-q-oexample.hcmaskUseyournewexample.hcmaskfile
withHashcatinmaskattackmode:
hashcat-a3-m#typehash.txtexample.hcmask
TIMETABLECHEATSHEET
POLICYGEN
Generateacollectionofmasksfollowingthepasswordcomplexityinorderto
significantlyreducethecrackingtime.
pythonpolicygen.py[options]-oexample.hcmask

POLICYGENOPTIONS
PasswordPolicy:
Definetheminimum(ormaximum)passwordstrengthpolicythatyou
wouldliketotest
POLICYGENEXAMPLES
Generatemaskattackforpasswordpolicy8characterlengthrequiringat
least1lowercase,1uppercase,1digit,and1specialcharacter:
pythonpolicygen.py--minlength8--maxlength8--minlower1--minupper1--
mindigit1--minspecial1-oexample.hcmaskGeneratemaskattackand
estimatetimeofcompletionbasedonGTX1080againstMD5hashes
24943.1MH/s(basedonappendixtable)forpasswordpolicy8character
lengthrequiringatleast1lowercase,1uppercase,1digit,and1special
character:
pythonpolicygen.py--minlength8--maxlength8--minlower1--minupper1--
mindigit1--minspecial1-oexample.hcmask--pps=24943000000
CUSTOMMASKPLANS
DATEYYMMDDMASK
hashcat-a3-m#typehash.txt-112-290-301-4123?l?2?3?d?4?dDATE
YYYYMMDDMASK
hashcat-a3-m#typehash.txt-112-290-301-4123?l?2?d?d?3?d?4?d3
SEQUENTIALNUMBERSMASK+SPECIAL
hashcat-a3-m#typehash.txt-1147-2258-3369?l?2?3?s

FOREIGNCHARACTERSETS
UTF8POPULARLANGUAGES
*Incrementalfourcharacterpasswordexamples
Arabic
UTF8(d880-ddbf)
hashcat-a3-m#typehash.txt--hex-charset-1d8d9dadbdcdd-2
80818283848586
8788898a8b8c8d8e8f909192939495969798999a9b9c9d9e9fa0ala2a3a4a5a6a7a8a9aaabacadae
afb0blb2b3b4b5b6b7b8b9babbbcbdbebf-i?1?2?1?2?1?2?1?2
Bengali
UTF8(e0a680-e0adbf)
hashcat-a3-m#typehash.txt--hex-charset-1e0-2a6a7a8a9aaabacad-38081
82838485868788898a8b8c8d8e8f909192939495969798999a9b9c9d9e9fa0ala2a3a4a5a6a7a8a9
aaabacadaeafb0blb2b3b4b5b6b7b8b9babbbcbdbebf-i?1?2?3?1?2?3?1?2?3?1?
2?3
Chinese(CommonCharacters)
UTF8(e4b880-e4bbbf)
hashcat-a3-m#typehash.txt--hex-charset-1e4-2b8b9babb-3808182838485
868788898a8b8c8d8e8f909192939495969798999a9b9c9d9e9fa0ala2a3a4a5a6a7a8a9aaabacad
aeafb0blb2b3b4b5b6b7b8b9babbbcbdbebf-i?1?2?3?1?2?3?1?2?3?1?2?3
Japanese(Katakana&Hiragana)
UTF8(e38180-e3869f)
hashcat-a3-m#typehash.txt--hex-charset-1e3-2818283848586-380818283
8485868788898a8b8c8d8e8f909192939495969798999a9b9c9d9e9fa0ala2a3a4a5a6a7a8a9aaab
acadaeafb0blb2b3b4b5b6b7b8b9babbbcbdbebf-i?1?2?3?1?2?3?1?2?3?1?2?3

Russian
UTF8(d080-d4bf)
hashcat-a3-m#typehash.txt--hex-charset-1d0dld2d3d4-2
8081828384858687
88898a8b8c8d8e8f909192939495969798999a9b9c9d9e9fa0ala2a3a4a5a6a7a8a9aaabacadaeaf
b0blb2b3b4b5b6b7b8b9babbbcbdbebf-i?1?2?1?2?1?2?1?2
HASHCATBUILT-INCHARSETS
German
hashcat-a3-m#typehash.txt-1charsets/German.hcchr-i?1?1?1?1
French
hashcat-a3-m#typehash.txt-1charsets/French.hcchr-i?1?1?1?1
Portuguese
hashcat-a3-m#typehash.txt-1charsets/Portuguese.hcchr-i?1?1?1?1
SUPPORTEDLANGUAGEENCODINGS
hashcat-a3-m#typehash.txt-1charsets/<language>.hcchr-i?1?1?1?1
Bulgarian,Castilian,Catalan,English,French,German,Greek,GreekPolytonic,
Italian,Lithuanian,Polish,Portuguese,Russian,Slovak,Spanish
JOHNUTF8&BUILT-INCHARSETS
OPTIONS:
--encoding=NAME inputencoding(eg.UTF-8,ISO-8859-1).
--input-encoding=NAME inputencoding(aliasfor--encoding)
--internal-encoding=NAME encodingusedinrules/masks(see
doc/ENCODING)
--target-encoding=NAME outputencoding(usedbyformat)
ExampleLMhashesfromWesternEurope,usingaUTF-8wordlist:
john--format=lmhast.txt--encoding=utf8--target:cp850--wo:spanish.txt
ExampleusingUTF-8wordlistwithinternalencodingforrulesprocessing:
john--format=#typehash.txt--encoding=utf8--internal=CP1252--

wordlist=french.1st--rulesExamplemaskmodeprintingallpossible“Latin-
1”wordsoflength4:
john--stdout--encoding=utf8--internal=8859-1--mask:?1?1?1?1
SUPPORTEDLANGUAGEENCODINGS
UTF-8,ISO-8859-1(Latin),ISO-8859-2(Central/EasternEurope),ISO-8859-7
(Latin/Greek),ISO-8859-15(WesternEurope),CP437(Latin),CP737(Greek),
CP850(WesternEurope),CP852(CentralEurope),CP858(WesternEurope),
CP866(Cyrillic),CP1250(CentralEurope),CP1251(Russian),CP1252
(DefaultLatin1),CP1253(Greek)andK0I8-R(Cyrillic).
HASHCAT?bBYTECHARSET
Ifyourunsureastopositionofaforeigncharactersetcontainedwithinyour
targetpassword,youcanattemptthe?bbytecharsetinamaskusingasliding
window.Forexampleifwehaveapassword6characterslong:?b=256byte=
0x00-0xff
hashcat-a3-m#typehash.txt
?b?a?a?a?a?a
?a?b?a?a?a?a
?a?a?b?a?a?a
?a?a?a?b?a?a
?a?a?a?a?b?a
?a?a?a?a?a?b
CONVERTENCODING
HASHCAT
ForceinternalwordlistencodingfromX
hashcat-a0-m#typehash.txtdict.txt--encoding-from=utf-8
ForceinternalwordlistencodingtoX
hashcat-ao-m#typehash.txtdict.txt--encoding-to=iso-8859-15
ICONV
Convertwordlistintolanguagespecificencoding
iconv-f<old_encode>-t<new_encode><dict.txt|spongedict.txt.enc
CONVERTHASHCAT$HEXOUTPUT
Exampleofconverting$HEX[]entriesinhashcat.potfiletoASCII
grep‘$HEX’hashcat.pot|awk-F“:”{‘print$2’}|perl-ne‘if($_=~m/\$HEX\
[([A-Fa-f0-9]+)\]/){printpack(“H*”,$1),“\n”}’


ADVANCEDATTACKS
PRINCEATTACK
PRINCE(PRobabilityINfiniteChainedElements)Attacktakesoneinput
wordlistandbuilds“chains”ofcombinedwordsautomatically.
HASHCATPRINCEPROCESSOR
https://github.com/hashcat/princeprocessor
Attackslowhashes:
pp64.bindict.txt|hashcat-a0-m#typehash.txt
Amplifiedattackforfasthashes:
pp64.bin--case-permutedict.txt|hashcat-a0-m#typehash.txt-rrule.txt
ExamplePRINCEattackproducingminimum8charcandidateswith4
elementspipeddirectlyintoHashcatwithrulesattack.
pp64.bin--pw-min=8--limit=4dict.txt|hashcat-a0-m#hash.txt-rbest64.rule
PRINCECEPTIONATTACK(epixoip)
PipingtheoutputofonePRINCEattackintoanotherPRINCEattack.
pp64.bindict.txt|pp64.bin|hashcat-a0-m#typehash.txtJOHNBUILT-IN
PRINCEATTACK
john--prince=dict.txthash.txt
MASKPROCESSOR

Maskattackgeneratorwithacustomconfigurablecharsetandabilitytolimit
consecutiveandrepeatingcharacterstodecreaseattackkeyspace.
https://github.com/hashcat/maskprocessor
Limit4consecutiveidenticalcharactersinthepasswordstring“-q”option:
mp64.bin-q4?d?d?d?d?d?d?d?d|hashcat-a0-m#typehash.txtLimit4
identicalcharactersinthepasswordstring“-r”option:
mp64.bin-r4?d?d?d?d?d?d?d?d|hashcat-a0-m#typehash.txtLimit2
consecutiveand2identicalcharactersinthepasswordstring:
mp64.bin-r2-q2?d?d?d?d?d?d?d?d|hashcat-a0-m#typehash.txtCustom
charsetlimiting2consecutiveand2identicalcharactersinthepassword
string:
mp64.bin-r2-q2-1aeiuo-2TGBYHN?l?2?l?2?d?d?d?d|hashcat-a0-m
#typehash.txt
CUSTOMMARKOVMODEL/STATSPROCESSOR
Word-generatorbasedontheper-positionmarkov-attack.
https://github.com/hashcat/statsprocessor
HCSTATGEN
CreatecustomMarkovmodelsusinghashcat-utilhcstatgen.binbasedoncracked
targetpasswords.Theutilhcstatgenmakesa32MBfileeachtimenomatterhow
small/largethepasswordlistprovided.Highlyrecommendedyoumakecustom
Markovmodelsfordifferenttargetsets.
hcstatgen.binoutfile.hcstat<passwords.txt
STATSPROCESSOR
Isahigh-performanceword-generatorbasedonausersuppliedper-position
Markovmodel(hcstatfile)usingmaskattacknotation.
Step1:CreateyourcustomMarkovmodel
hcstatgen.binout.hcstat<passwords.txt
Step2.1:SupplyyournewMarkovmodeltoHashcatasmaskorrule
attack.
hashcat-a3-m#typehash.txt--markov-hcstat=out.hcstat?a?a?a?a?a?ahashcat-
a0-m#typehash.txtdict.txt-rrule.txt--markov-hcstat=out.hcstatStep2.2:OR
SupplyyournewMarkovmodelwithsp64andpipeintoHashcat.
sp64.bin--pw-min3--pw-max5out.hcstat?1?1?1?1?1?1|hashcat-a0-m#type
hash.txt
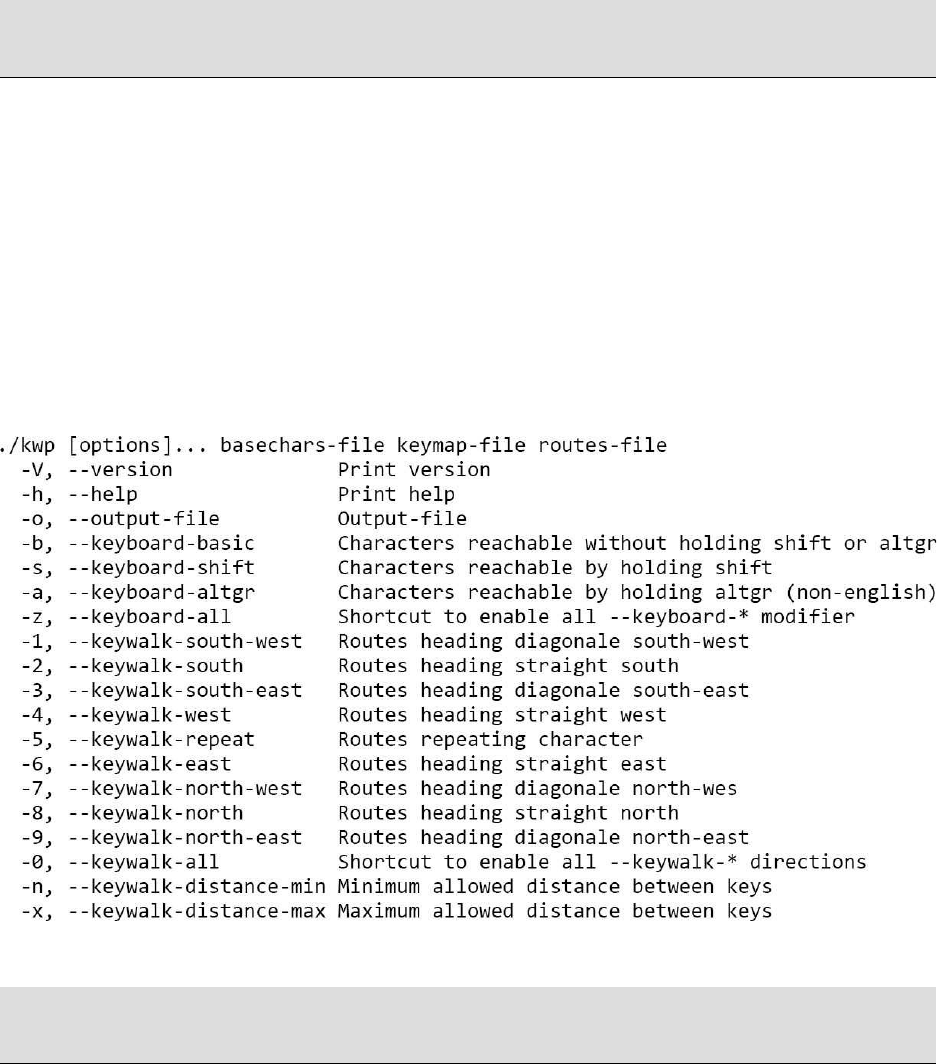
KEYBOARDWALKPROCESSOR
Keyboard-walkgeneratorwithconfigurablebasechars,keymappingsandroutes.
https://github.com/hasheat/kwprocessorExamplekeyboardwalkwithtiny
charsetinenglishmappingandwith2-10adjacentkeyspipingoutresultsintoa
hashcatattack:kwp.binbasechar/tiny.basekeymaps/en.keymaproutes/2-to-
10-max-3-0-z|hashcat-a0-m#typehash.txt
Examplekeyboardwalkwithfullcharsetinenglishmappingandwith3x3
adjacentkeyspipingoutresultsintoahashcatattack:./kwpbasechars/full.base
keymaps/en.keymaproutes/3-to-3-exhaustive.route|hashcat-a0-m#type
hash.txt
[FULLLISTOFOPTIONS]
MDXFIND/MDSPLIT
https://hashes.org/mdxfind.php
(credit‘Waffle’)
MDXFINDisaprogramwhichallowsyoutorunlargenumbersofunsolved
hashesofanytype,usingmanyalgorithmsconcurrently,againstalargenumber

ofplaintextwordsandrules,veryquickly.It’smainpurposewastodealwith
largelists(20million,50million,etc)ofunsolvedhashesandrunthemagainst
newdictionariesasyouacquirethem.
SowhenwouldyouuseMDXFINDonapentest?Ifyoudumpadatabasetiedto
websiteauthenticationandthehashesarenotcrackingbystandardattackplans.
Thehashesmaybegeneratedinauniquenestedhashingseries.Ifyouareableto
viewthesourcecodeofsaidwebsitetoviewthecustomhashingfunctionyou
candirectMDXFINDtoreplicatethathashingseries.Ifnot,youcanstillrun
MDXFINDusingsomeofthebelow‘GenericAttackCommands’.MDXFIND
istailoredtowardintermediatetoexpertlevelpasswordcrackingbutis
extremelypowerfulandflexible.
ExamplewebsiteSHA1customhashingfunctionperformingmultipleiterations:
$hash=sha1($password.$salt);
for($i=1;$i<=65000;++$i)
{
$hash=sha1($hash.$salt);
}
MDXFIND
COMMANDSTRUCTURETHREEMETHODS1-STDOUT2-STDIN3-File
1-Readshashescomingfromcat(orother)commandsstdout.
cathash.txt|mdxfind-h<regex#type>-i<#iterations>dict.txt>out.txt
2-Takesstdinfromoutsideattacksourcesinplaceofdict.txtwhenusingthe
optionsvariable‘-f’tospecifyhash.txtfilelocationandvariable‘stdin’.
mp64.bin?d?d?d?d?d?d|mdxfind-h<regex#type>-i<#iterations>-f
hash.txtstdin>out.txt
3-Specifyfilelocation‘-f’withnoexternalstdout/stdinsources.
mdxfind-h<regex#type>-i<#iterations>-fhash.txtdict.txt>out.txt
[FULLLISTOFOPTIONS]
-a Doemailaddressmunging
-b Expandeachwordintounicode,besteffort
-c Replaceeachspecialchar(<>&,etc)withXMLequivalents
-d De-duplicatewordlists,besteffort...butbesttodoaheadoftime
-e Extendedsearchfortruncatedhashes
-p Printsource(filename)offoundplain-texts
-q
InternaliterationcountsforSHA1MD5X,andothers.Forexample,if
youhaveahashthatisSHA1(MD5(MD5(MD5(MD5($pass)))))),you
wouldset-qto5.
-g Rotatecalculatedhashestoattemptmatchtoinputhash
-s Filetoreadsaltsfrom
-u FiletoreadUserid/Usernamesfrom
-k Filetoreadsuffixesfrom
-n
Numberofdigitstoappendtopasswords.Otheroptions,like:-n6x
wouldappend6digithexvalues,and8iwouldappendallipv4dotted-
quadIP-addresses.
-i Thenumberofiterationsforeachhash
-t Thenumberofthreadstorun
-f filetoreadhashesfrom,elsestdin
-1 AppendCR/LF/CRLFandprintinhex
-r Filetoreadrulesfrom
-v Donotmarksaltsasfound.
-w Numberoflinestoskipfromfirstwordlist
-y Enabledirectoryrecursionforwordlists
-z Enabledebugginginformation/hashresults
-h Thehashtypes:459TOTALHASHESSUPPORTED
GENERICATTACKPLANS
ThisisagoodgeneralpurposeMDXFINDcommandtorunyourhashesagainst
ifyoususpectthemtobe“non-standard”nestedhashingsequences.This
commandsays“Runallhashesagainstdict.txtusing10iterationsexceptones
havingasalt,user,ormd5xvalueinthename.”It’ssmarttoskipsalted/user
hashtypesinMDXFINDunlessyouareconfidentasaltvaluehasbeenused.
cathash.txt|mdxfind-hALL-h‘!salt,!user,!md5x’-i10dict.txt>out.txt

ThedeveloperofMDXFINDalsorecommendsrunningthebelowcommand
optionsasagoodgeneralpurposeattack:cathash.txt|mdxfind-h
<^md5$,^sha1$,^md5md5pass$,^md5sha1$’-i5dict.txt>out.txt
Andyoucouldaddaruleattackaswell:
cathash.txt|mdxfind-h<^md5$,^sha1$,^md5md5pass$,^md5sha1$’-i5
dict.txt-rbest64.rule>out.txt
GENERALNOTESABOUTMDXFIND
-Candomultiplehashtypes/filesallduringasingleattackrun.
catsha1/*.txtsha256/*.txtmd5/*.txtsalted/*.txt|mdxfind-Supports
459differenthashtypes/sequences
-Cantakeinputfromspecial‘stdin’mode
-SupportsVERYlargehashlists(l00mil)and10kbcharacterpasswords-
Supportsusinghashcatrulefilestointegratewithdictionary-Option‘-z’outputs
ALLviablehashingsolutionsandfilecangrowverylarge-Supports
including/excludinghashtypesbyusingsimpleregexparameters-Supports
multipleiterations(upto4billiontimes)bytweaking-iparameterforinstance:
MD5X01isthesameasmd5($Pass)
MD5x02isthesameasmd5(md5($pass))
MD5X03isthesameasmd5(md5(md5($pass)))
...
MD5xl0isthesameas
md5(md5(md5(md5(md5(md5(md5(md5(md5(md5($pass))))))))))-Separateout
-usernames-email-ids-saltstocreatecustomattacks-Ifyouaredoingbrute-
forceattacks,thenhashcatisprobablybetterroute-WhenMDXfindfindsany
solution,itoutputsthekindofsolutionfound,followedbythehash,followedby
thesaltand/orpassword.Forexample:
MD5X01000012273bc5cab48bf3852658b259ef:lEb0TBK3
MD5X05033blll073e5f64ee59f0be9d6b8a561:08061999
MD5X09aadb9dlb23729a3e403d7fc62d507df7:1140
MD5X09326d921d591162eed302ee25a09450ca:1761974
MDSPLIT
Whencrackinglargelistsofhashesfrommultiplefilelocations,MDSPLITwill
helpmatchwhichfilesthecrackedhasheswerefoundin,whilealsooutputing

themintoseparatefilesbasedonhashtype.Additionallyitwillremovethe
foundhashesfromtheoriginalhashfile.
COMMANDSTRUCTURETWOMETHODS1-STDOUT2-STDIN3-File
1-MatchingMDXFINDresultsfileswiththeiroriginalhash_orig.txtfiles.
cathashes_out/out_results.txt|mdsplithashes_orig/hash_orig.txt
ORperformmatchingagainstadirectoryoforiginalhashesandtheirresults.
cathashes_out/*|mdsplithashes_orig/*
2-PipingMDXFINDdirectlyintoMDSPLITtosortinreal-timeresults.
cat*.txt|mdxfind-hALL-h‘!salt,!user,!md5x’-i10dict.txt|mdsplit*.txt
3-SpecifyingafilelocationinMDXFINDtomatchresultsinreal-time.
mdxfind-hALL-fhashes.txt-i10dict.txt|mdsplithashes.txt
GENERALNOTESABOUTMDSPLIT
-MDSPLITwillappendthefinalhashsolutiontotheendofthenewfilename.
Forexample,ifwesubmitteda‘hashes.txt’andthesolutiontothehasheswas
“MD5x01”thentheresultsfilewouldbe‘hashes.MD5x01’.Ifmultiplehash
solutionsarefoundthenMDSPLITknowshowtodealwiththis,andwillthen
removeeachofthesolutionsfromhashes.txt,andplacetheminto
‘hashes.MD5x01’,‘hashes.MD5x02’,‘hashes.SHA1’...andsoon.
-MDSPLITcanhandlesortingmultiplehashfiles,types,andtheirresultsallat
onetime.Anysolutionswillbeautomaticallyremovedfromallofthesource
filesbyMDSPLIT,andtabulatedintothecorrectsolvedfiles.Forexample:cat
dirl/*.txtdir2/*.txtdir3/*.txt|mdxfind-h‘^md5$,^sha1$,^sha256$’-i10dict.txt
|mdsplitdirl/*.txtdir2/*.txtdir3/*.txt
DISTRIBUTED/PARALLELIZATIONCRACKING
HASHCAT
https://hashcat.net/forum/thread-3047.html
Step1:Calculatekeyspaceforattack(ExampleMD5BruteForcex3nodes)
hashcat-a3-m0?a?a?a?a?a?a--keyspace

81450625
Step2:Distributeworkthroughkeyspacedivision(s)kipand(l)imit
81450625/3=27150208.3
Node1#hashcat-a3-m0hash.txt?a?a?a?a?a?a-s0-127150208
Node2#hashcat-a3-m0hash.txt?a?a?a?a?a?a-s27150208-127150208
Node3#hashcat-a3-m0hash.txt?a?a?a?a?a?a-s54300416-127150209
JOHN
http://www.openwall.com/john/doc/OPTIONS.shtml
ManualdistributionusingOptions--node&--forkto3similarCPUnodes
utilizing8cores:
Node#john--format=<#>hash.txt--wordlist=dict.txt--rules=All--fork=8--
node=1-8/24
Node2#john--format=<#>hash.txt--wordlist=dict.txt--rules=All--fork=8--
node=9-16/24
Node3#john--format=<#>hash.txt--wordlist=dict.txt--rules=All--fork=8--
node=17-24/24
OtherJohnOptionsforparallelization:
Option1:EnableOpenMPthroughuncommentinginMakefile
Option2:Createadditionalincrementalmodesinjohn.conf
Option3:Utilizebuilt-inMPIparallelization
PASSWORDGUESSINGFRAMEWORK
https://github.com/RUB-SysSec/Password-Guessing-Framework
https://www.password-guessing.org/
PasswordGuessingFrameworkisanopensourcetooltoprovideanautomated
andreliablewaytocomparepasswordguessers.Itcanhelptoidentifyindividual
strengthsandweaknessesofaguesser,it’smodesofoperation,oreventhe
underlyingguessingstrategies.Therefore,itgathersinformationabouthow
manypasswordsfromaninputfile(passwordleak)havebeencrackedin
relationtotheamountofgeneratedguesses.Subsequenttotheguessingprocess

ananalysisofthecrackedpasswordsisperformed.
OTHERCREATIVEADVANCEDATTACKS
Randomcreativepasswordattacksusingthepowerofstdinandstdout.Not
implyingthey’reusefulbuttodemonstratethepowerofmixingandmatching.
Goforthandcreatesomethinguseful.
PRINCE-MDXFINDATTACK
pp64.bindict.txt|mdxfind-hALL-fhash.txt-i10stdin>out.txtHASHCAT-
UTILCOMBONATORPRINCE
combinator.bindict.txtdict.txt|pp64.bin|hashcat-a0-m#typehash.txt-r
best64.rulecombinator3.bindict.txtdict.txtdict.txt|pp64.bin|hashcat-a0-m
#typehash.txt-rrockyou-30000.ruleHASHCATSTDOUTATTACKS
PRINCE
hashcat-a0dict.txt-rdive.rule--stdout|pp64.bin|hashcat-a0-m#type
hash.txthashcat-a6dict.txt?a?a?a?a--stdout|pp64.bin--pw-min=8|hashcat-a
0-m#typehash.txthashcat-a7?a?a?a?adict.txt--stdout|pp64.bin--pw-min=8
|hashcat-a0-m#typehash.txthashcat-a6dict.txtrockyou-1-60.hcmask--
stdout|pp64.bin--pw-min=8--pw-max=14Ihashcat-a0-m#typehash.txt
hashcat-a7rockyou-1-60.hcmaskdict.txt--stdout|pp64.bin--pw-min=8--pw-
max=14Ihashcat-a0-m#typehash.txt
DISTRIBUTEDCRACKINGSOFTWARE
HASHTOPUSSY
https://bitbucket.org/seinlc/hashtopussy/
HASHSTACK
https://sagitta.pw/software/
DISTHC
https://github.com/unix-ninja/disthc
CRACKLORD

http://jmmcatee.github.io/cracklord/
HASHTOPUS
http://hashtopus.org/Site/
HASHVIEW
http://www.hashview.io/
CLORTHO
https://github.com/ccdes/clortho
ONLINEHASHCRACKINGSERVICES
GPUHASH
https://gpuhash.me/
CRACKSTATION
https://crackstation.net/
ONLINEHASHCRACK
https://www.onlinehashcrack.com/
HASHHUNTERS
http://www.hashhunters.net/

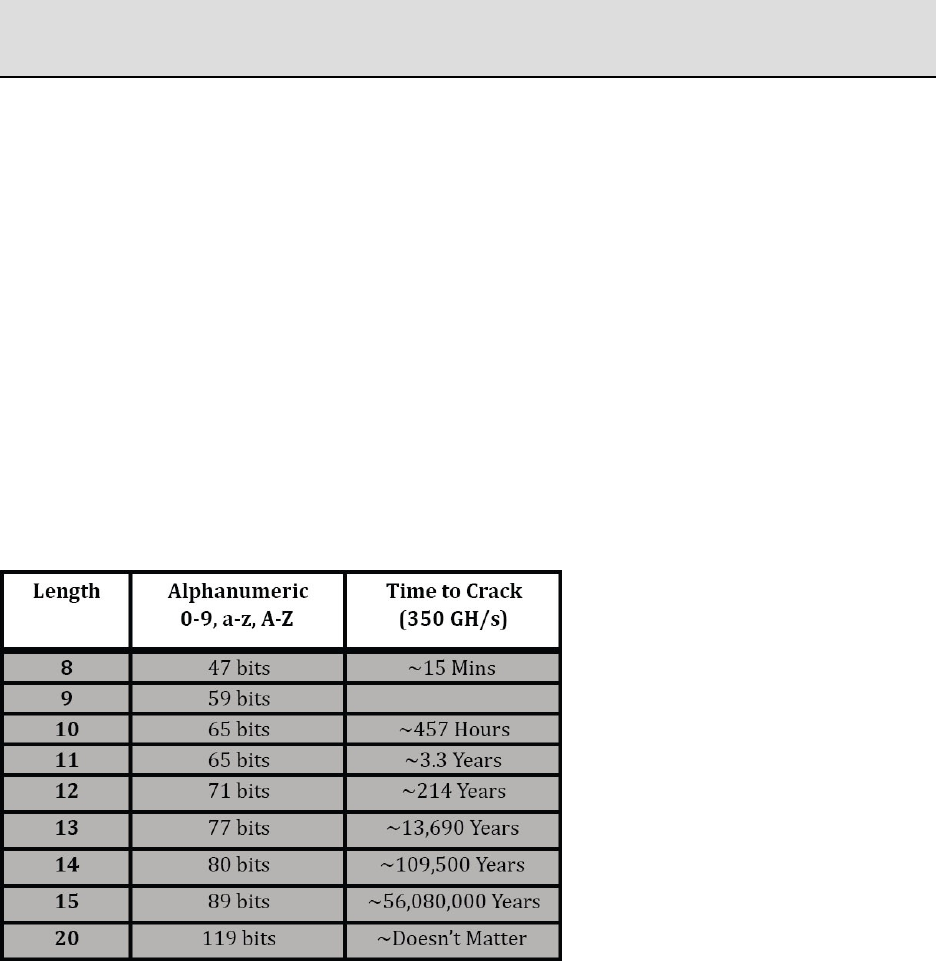
Informationinthischapterisanattempttosummarizeafewofthebasicand
morecomplexconceptsinpasswordcracking.Thisallowsallskilllevelsto
grasptheseconceptswithoutneedingaLinguisticsorMathematicsDegree.It’s
analmostimpossibletasktocondenseintooneparagraph,butthefollowingis
anattempt.Foradeeperunderstanding,Ihighlyencourageyoutoreadthe
Resourcelinksincludedbeloweachsection.
PASSWORDENTROPYvsCRACKTIME
Passwordentropyisameasureofhowrandom/unpredictableapasswordcould
havebeen,soitdoesnotreallyrelatetothepassworditself,buttoaselection
process.Whenjudginghumangeneratedpasswordsforentropy,itfranklyisn’t
anaccuratemeasurement.Thisistruemainlybecausehumansliketouse
memorablewords/sequencesandthusamyriadofattacksaccountforthat
behavior.however,entropyisgoodformeasuringrandomlygenerated
passwordsfrompasswordmanagers,suchas1PasswordorKeepass,inthateach
defaultcharactersetusedcanbecalculated.Passwordentropyismeasuredin
bitsandusesthefollowingformulawhereC=SizeofCharacterset&L=Length
ofpassword:log(C)/log(2)*L
Tocalculatethetimetocrack,justusethebenchmarkingfunctiononyour
favoritecrackingsoftwareagainstyourmodeofhashtoobtaincracksper
second.ThetablebelowestimatespasswordlengthusinganMD4hashing
functionagainstan8GPUxNvidiaGTX1080system:
*Tableonlytrulymattersforrandomlygeneratedpasswords
Resources
PasswordComplexityversusPasswordEntropy
https://blogs.technet.microsoft.com/msftcam/2015/05/19/password-complexity-
versus-password-entropy/
WHATISACRYPTOGRAPHICHASH?
Acryptographichashfunctionisasubclassofthegeneralhashfunctionwhich
possessespropertieslendingitsuseincryptography.Cryptographichash
functionsaremathematicalalgorithmswhichmapdataofanysizetoastring
containingafixedlength,andshouldmakeitinfeasibletoreverse.Forinstance,
thestring“password,”whenmappedusingtheMD5hashfunction,returnsa
fixedlength32characterstring“5f4dcc3b5aa765d61d8327deb882cf99”.The32
characterstringcannottheoreticallybereversedwithanyothermappedinput
dataexcept“password”.Thecurrentmethodofrecreatingthisinputdata
“password”isthroughadictionary/mask/brute-forceattackofallpossibleinputs
matchingthehashedvalue;alsocalledapre-imageattack.Generallyspeaking,
hashfunctionsshouldpossessthebelowcharacteristics:
-Becomputationallyinfeasibletofindtwodifferentsetsofinputdatawiththe
samehashvalue(alsocalledacollision).
-Thehashvalueshouldbe“quick”tocompute(i.e.>~1second).
-ItshouldbedifficulttogeneratetheinputdataJustbylookingatthehashvalue.
-Onesimplechangetotheinputdatashoulddrasticallychangetheresultanthash
value.
Resources
HowHashAlgorithmsWork
http://www.metamorphosite.com/one-way-hash-encryption-sha1-data-software
MARKOVCHAINS
MarkovChainsarecreated,forourpasswordcrackingpurposes,bystatistical
analysisofalargelistofpasswords/words(i.e.theRockYoupassworddataset).

Theresultantanalysisofthesewordsandtheirper-positioncharacter
frequency/probabilityarestoredinatable.Thistableisreferencedwhen
performingbrute-force/maskattackstopreventhavingtogeneratepassword
candidatesinasequentialorder,whichisveryinefficient.Instead,themost
commoncharactersareattemptedfirstinorderofprecedingcharacter
probability.Solet’sseesequentialbrute-force?a?a?a?awithoutMarkovChains
applied:
Nowthesamebrute-forceattackwithMarkovChainsapplied:
MarkovChainspredicttheprobabilityofthenextcharacterinapasswordbased
onthepreviouscharacters,orcontextcharacters.It’sthatsimple.
Resources
FastDictionaryAttacksonPasswordsUsingTime-SpaceTradeoff
http://www.cs.utexas.edu/~shmat/shmat_ccs05pwd.pdf
OMEN:FasterPasswordGuessingUsinganOrderedMarkovEnumerator
https://hal.inria.fr/hal-01112124/document
PROBABILISTICCONTEXT-FREEGRAMMARS(PCFG)
AProbabilisticContextFreeGrammar(PCFG)consistsofterminaland
nonterminalvariables.Eachfeaturetobemodeledhasaproductionrulethatis
assignedaprobability,estimatedfromatrainingsetofRNAstructures.
Productionrulesarerecursivelyapplieduntilonlyterminalresiduesareleft.The
notionsupportingPCFGsisthatpasswordsareconstructedwithtemplate
structuresandterminalsthatfitintothosestructures.Forexample,thepassword
candidate‘passwordl23!’is8letters,3digits,1specialandwouldbenotedas
‘L8D3S1’.Apassword’sprobabilityofoccurringistheprobabilityofits
structure,multipliedbythoseofitsunderlyingterminals.
Resources

PasswordCrackingUsingProbabilisticContext-FreeGrammars
https://sites.google.com/site/reusablesec/Home/password-cracking-
tools/probablistic_cracker
NextGenPCFGPasswordCracking
https://github.com/lakiw/pcfg_cracker
NEURALNETWORKS
ArtificialNeuralNetworksorNeuralNetworks(NN)isamachine-learning
techniquecomposedofnodescalledArtificialNeurons,justlikethebrain
possesses.SuchsystemsuseMachineLearningtoapproximatehighly
dimensionalfunctionsandprogressivelylearnthroughexamplesoftrainingset
data,orinourcasealargepassworddump.Theyhaveshowninitialpromiseto
beeffectiveatgeneratingoriginalyetrepresentativepasswordcandidates.
AdvantagestoNN’sforpasswordcrackingarethelowoverheadforstoringthe
finalNNmodel,approximately500kb,andtheabilitytocontinuallylearnover
timethroughretrainingortransferlearning.
Resources
Fast,Lean,andAccurate:ModelingPasswordGuessabilityUsingNeural
Networks(USENIX‘16)
https://www.usenix.org/system/files/conference/usenixsecurity16/sec16_paper_melicher.pdf
https://github.com/cupslab/neural_network_cracking


COMMONHASHEXAMPLES
MD5,NTLM,NTLMv2,LM,MD5crypt,SHA1,SHA256,bcrypt,PDF1.4-
1.6(Acrobat5-8),MicrosoftOFFICE2013,RAR3-HP,Winzip,7zip,
Bitcoin/Litecoin,MACOSXv10.5-v10.6,MySQL4.1-5+,Postgres,
MSSQL(2012)-MSSQL(2014),Oracle11g,CiscoTYPE4589,WPAPSK/
WPA2PSK
MDS
HASHCAT
HASHFORMAT

8743b52063cd84097a65dl633f5c74f5
BRUTEFORCEATTACK
hashcat-m0-a3hash.txt?a?a?a?a?a?a
WORDLISTATTACK
hashcat-m0-a0hash.txtdict.txt
WORDLIST+RULEATTACK
hashcat-m0-a0hash.txtdict.txt-rrule.txtJOHN
HASHFORMAT

8743b52063cd84097a65dl633f5c74f5
BRUTEFORCEATTACK
john--format=raw-md5hash.txt
WORDLISTATTACK
john--format=raw-md5wordlist=dict.txthash.txtWORDLIST+RULE
ATTACK
john--format=raw-md5wordlist=dict.txt--ruleshash.txt
NTLM(PWDUMP)
HASHCAT
HASHFORMAT

b4b9b02e6f09a9bd760f388b67351e2b
BRUTEFORCEATTACK
hashcat-m1000-a3hash.txt?a?a?a?a?a?aWORDLISTATTACK
hashcat-m1000-a0hash.txtdict.txt
WORDLIST+RULEATTACK
hashcat-m1000-a0hash.txtdict.txt-rrule.txtJOHN
HASHFORMAT

b4b9b02e6f09a9bd760f388b67351e2b
BRUTEFORCEATTACK
john--format=nthash.txt
WORDLISTATTACK
john--format=ntwordlist=dict.txthash.txtWORDLIST+RULEATTACK
john--format=ntwordlist=dict.txt--ruleshash.txt
NTLMV2
HASHCAT
HASHFORMAT
username::N46iSNekpT:08ca45b7d7ea58ee:88dcbe4446168966al53a0064958dac6:5c7830315
C7830310000000000000b45c67103d07d7b95acdl2ffall230e0000000052920b85f78d013c31cdb
3b92f5d765c783030
BRUTEFORCEATTACK
hashcat-m5600-a3hash.txt?a?a?a?a?a?aWORDLISTATTACK
hashcat-m5600-a0hash.txtdict.txt
WORDLIST+RULEATTACK
hashcat-m5600-a0hash.txtdict.txt-rrule.txtJOHN
HASHFORMAT
username:$NETNTLMv2$NTLMV2TESTWORKGROUP$1122334455667788$07659A550D5E9D02996DFD9
5C87EC1D5$0101000000000000006CF6385B74CA01B3610B02D99732DD000000000200120057004F
0052004B00470052004F00550050000100200044004100540041002E00420049004E0043002D0053
004500430055005200490000000000
BRUTEFORCEATTACK
john--format=netntlmv2hash.txt
WORDLISTATTACK
john--format=netntlmv2wordlist=dict.txthash.txtWORDLIST+RULE
ATTACK
john--format=netntlmv2wordlist=dict.txt--ruleshash.txt
LM
HASHCAT
HASHFORMAT

299bdl28cll01fd6
BRUTEFORCEATTACK
hashcat-m3000-a3hash.txt?a?a?a?a?a?aWORDLISTATTACK
hashcat-m3000-a0hash.txtdict.txt
WORDLIST+RULEATTACK
hashcat-m3000-a0hash.txtdict.txt-rrule.txtJOHN
HASHFORMAT
$LM$a9c604d244c4e99d
BRUTEFORCEATTACK
john--format=lmhash.txt
WORDLISTATTACK
john--format=lmwordlist=dict.txthash.txtWORDLIST+RULEATTACK
john--format=lmwordlist=dict.txt--ruleshash.txt
MD5CRYPT
HASHCAT
HASHFORMAT
$1$28772684$iEwNOgGugq09.bIz5sk8k/
BRUTEFORCEATTACK
hashcat-m500-a3hash.txt?a?a?a?a?a?aWORDLISTATTACK
hashcat-m500-a0hash.txtdict.txt
WORDLIST+RULEATTACK
hashcat-m500-a0hash.txtdict.txt-rrule.txtJOHN
HASHFORMAT
$l$28772684$iEwNOgGugq09.bIz5sk8k/
BRUTEFORCEATTACK
john--format=md5crypthash.txt
WORDLISTATTACK
john--format=md5cryptwordlist=dict.txthash.txtWORDLIST+RULE
ATTACK
john--format=md5cryptwordlist=dict.txt--ruleshash.txt
SHA1

HASHCAT
HASHFORMAT

b89eaac7e61417341b710b727768294d0e6a277b
BRUTEFORCEATTACK
hashcat-m100-a3hash.txt?a?a?a?a?a?aWORDLISTATTACK
hashcat-m100-a0hash.txtdict.txt
WORDLIST+RULEATTACK
hashcat-m100-a0hash.txtdict.txt-rrule.txtJOHN
HASHFORMAT

b89eaac7e61417341b710b727768294d0e6a277b
BRUTEFORCEATTACK
john--format=raw-sha1hash.txt
WORDLISTATTACK
john--format=raw-sha1wordlist=dict.txthash.txtWORDLIST+RULE
ATTACK
john--format=raw-sha1wordlist=dict.txt--ruleshash.txt
SHA256
HASHCAT
HASHFORMAT

127e6fbfe24a750e72930c220a8el38275656b8e5d8f48a98c3c92df2caba935
BRUTEFORCEATTACK
hashcat-m1400-a3hash.txt?a?a?a?a?a?aWORDLISTATTACK
hashcat-m1400-a0hash.txtdict.txt
WORDLIST+RULEATTACK
hashcat-m1400-a0hash.txtdict.txt-rrule.txtJOHN
HASHFORMAT
127e6fbfe24a750e72930c220a8el38275656b8e5d8f48a98c3c92df2caba935
BRUTEFORCEATTACK
john--format=raw-sha256hash.txt
WORDLISTATTACK
john--format=raw-sha256wordlist=dict.txthash.txtWORDLIST+RULE
ATTACK
john--format=raw-sha256wordlist=dict.txt--ruleshash.txt
BCRYPT
HASHCAT
HASHFORMAT
$2a$05$LhayLxezLhKlLhWvKxCyLOj0jlu.Kj0jZ0pEmml34uzrQlFvQDLF6
BRUTEFORCEATTACK
hashcat-m3200-a3hash.txt?a?a?a?a?a?aWORDLISTATTACK
hashcat-m3200-a0hash.txtdict.txt
WORDLIST+RULEATTACK
hashcat-m3200-a0hash.txtdict.txt-rrule.txtJOHN
HASHFORMAT
$2a$05$LhayLxezLhKlLhWvKxCyLOj0jlu.Kj0jZ0pEmml34uzrQlFvQDLF6
BRUTEFORCEATTACK
john--format=bcrypthash.txt
WORDLISTATTACK
john--format=bcryptwordlist=dict.txthash.txtWORDLIST+RULE
ATTACK
john--format=bcryptwordlist=dict.txt--ruleshash.txt
PDF1.4-1.6(ACROBAT5-8)
HASHCAT
HASHFORMAT
$pdf$2*3*128*-1028*l*16*da42eel5d4b3e08fe5b9ecea0e02ad0f*32*c9b59d72c7c670c42eeb
4fcald2cal5000000000000000000000000000000000*32*c4ff3e868dc87604626c2b8c259297al
4d58c6309c70b00afdfblfbbal0ee571
EXTRACTHASH
pdf2hashcat.pyexample.pdf>hash.txtBRUTEFORCEATTACK
hashcat-m10500-a3hash.txt?a?a?a?a?a?aWORDLISTATTACK
hashcat-m10500-a0hash.txtdict.txt
WORDLIST+RULEATTACK
hashcat-m10500-a0hash.txtdict.txt-rrule.txtJOHN
HASHFORMAT
$pdf$Standard*badadle86442699427116d3e5d5271bc80a27814fc5e80f815efeef839354c5f*2
89ece9b5ce451a5d7064693dab3badfl01112131415161718191alblcldlelf*16*34blb6e593787
af681a9b63fa8bf563b*l*l*0*l*4*128*-4*3*2
EXTRACTHASH
pdf2john.pyexample.pdf>hash.txt
BRUTEFORCEATTACK
john--format=pdfhash.txt
WORDLISTATTACK
john--format=pdfwordlist=dict.txthash.txtWORDLIST+RULEATTACK
john--format=pdfwordlist=dict.txt--ruleshash.txt
MICROSOFTOFFICE2013
HASHCAT
HASHFORMAT
example.docx:$office$*2013*100000*256*16*7dd611d7eb4c899f74816dldec817b3b*948dc0
b2c2c6c32fl4b5995a543ad037*0b7ee0e48e935f937192a59de48a7d561ef2691d5c8a3ba87ec2d
04402a94895
EXTRACTHASH
office2hashcat.pyexample.docx>hash.txtBRUTEFORCEATTACK
hashcat-m9600-a3--usernamehash.txt?a?a?a?a?a?aWORDLISTATTACK
hashcat-m9600-a0--usernamehash.txtdict.txtWORDLIST+RULE
ATTACK
hashcat-m9600-a0--usernamehash.txtdict.txt-rrule.txtJOHN
HASHFORMAT
example.docx:$office$*2013*100000*256*16*7dd611d7eb4c899f74816dldec817b3b*948dc0b2c2c6c32f14b5995a543ad037*0b7ee0e48e935f937192a59de48a7d561ef2691d5c8a3ba87ec2d
04402a94895
EXTRACTHASH
office2john.pyexample.docx>hash.txtBRUTEFORCEATTACK
john--format=office2013hash.txt
WORDLISTATTACK
john--format=office2013wordlist=dict.txthash.txtWORDLIST+RULE
ATTACK
john--format=office2013wordlist=dict.txt--ruleshash.txt
RAR3-HP(ENCRYPTEDHEADER)
HASHCAT
HASHFORMAT
$RAR3$*0*45109af8ab5f297a*adbf6c5385d7a40373e8f77d7b89d317
#!Ensuretoremoveextraneousrar2johnoutputtomatchabovehash!#
EXTRACTHASH
rar2john.pyexample.rar>hash.txt
BRUTEFORCEATTACK
hashcat-m12500-a3hash.txt?a?a?a?a?a?aWORDLISTATTACK
hashcat-m12500-a0hash.txtdict.txt
WORDLIST+RULEATTACK
hashcat-m12500-a0hash.txtdict.txt-rrule.txtJOHN
HASHFORMAT
example.rar:$RAR3$*l*20e041a232b4b7f0*5618c5f0*1472*2907*0*/Path/To/
example.rar*138*33:1::example.txt
EXTRACTHASH
rar2john.pyexample.rar>hash.txt
BRUTEFORCEATTACK
john--format=rarhash.txt
WORDLISTATTACK
john--format=rarwordlist=dict.txthash.txtWORDLIST+RULEATTACK
john--format=rarwordlist=dict.txt--ruleshash.txt
WINZIP
HASHCAT
HASHFORMAT

$zip2$*0*3*0*b5d2b7bf57ad5e86a55c400509c672bd*d218*0**ca3d736d03a34165cfa9*$/
zip2$
#!Ensuretoremoveextraneouszip2johnoutputtomatchabovehash!#
EXTRACTHASH
zip2john.pyexample.zip>hash.txt
BRUTEFORCEATTACK
hashcat-m13600-a3hash.txt?a?a?a?a?a?aWORDLISTATTACK
hashcat-m13600-a0hash.txtdict.txt
WORDLIST+RULEATTACK
hashcat-m13600-a0hash.txtdict.txt-rrule.txtJOHN
HASHFORMAT
example.zip:$zip2$*0*3*0*5b0a8bl53fb94bf719abb81a80e90422*8e91*9*0b76bf50al5
938ce9c*3f37001e241el96195al*$/zip2$:::::example.zipEXTRACTHASH
zip2john.pyexample.zip>hash.txt
BRUTEFORCEATTACK
john--format=ZIPhash.txt
WORDLISTATTACK
john--format=ZIPwordlist=dict.txthash.txtWORDLIST+RULEATTACK
john--format=ZIPwordlist=dict.txt--ruleshash.txt
7-ZIP
HASHCAT
HASHFORMAT
$7z$0$19$0$salt$8$f6196259a7326e3f0000000000000000$185065650$112$98$f3bc2a88062c
419a25acd40c0c2d75421cf23263f69c51bl3f9blaada41a8a09f9adeae45d67c60b56aad338f20c
0dcc5eb811c7a61128ee0746f922cdb9c59096869f341c7a9cblac7bb7d771f546b82cf4e6flla5e
Cd4b61751e4d8de66dd6e2dfb5b7dl022d2211e2d66eal703f96
#!Ensuretoremoveextraneous7zip2johnoutputtomatchabovehash!#
EXTRACTHASH
7z2john.pyexample.7z>hash.txt
BRUTEFORCEATTACK
hashcat-m11600-a3hash.txt?a?a?a?a?a?aWORDLISTATTACK
hashcat-m11600-a0hash.txtdict.txt
WORDLIST+RULEATTACK

hashcat-m11600-a0hash.txtdict.txt-rrule.txtJOHN
HASHFORMAT
example.7z:$7z$0$19$0$salt$8$f6196259a7326e3f0000000000000000$185065650$112$98$f
3bc2a88062c419a25acd40c0c2d75421cf23263f69c51bl3f9blaada41a8a09f9adeae45d67c60b5
6aad338f20c0dcc5eb811c7a61128ee0746f922cdb9c59096869f341c7a9cblac7bb7d771f546b82
Cf4e6flla5ecd4b61751e4d8de66dd6e2dfb5b7dl022d2211e2d66eal703f96
EXTRACTHASH
7z2john.pyexample.7z>hash.txt
BRUTEFORCEATTACK
john--format=7zhash.txt
WORDLISTATTACK
john--format=7zwordlist=dict.txthash.txtWORDLIST+RULEATTACK
john--format=7zwordlist=dict.txt--ruleshash.txt
BITCOIN/LITECOIN
HASHCAT
HASHFORMAT
$bitcoin$96$d011alb6a8d675b7a36d0cd2efaca32a9f8dcld57d6d01a58399ea04e703e8bbb448
99039326f7a00fl71a7bbc854a54$16$1563277210780230$158555$96$628835426818227243334
570448571536352510740823233055715845322741625407685873076027233865346542174$66$6
25882875480513751851333441623702852811440775888122046360561760525
EXTRACTHASH
bitcoin2john.pywallet.dat>hash.txtBRUTEFORCEATTACK
hashcat-m11300-a3hash.txt?a?a?a?a?a?aWORDLISTATTACK
hashcat-m11300-a0hash.txtdict.txt
WORDLIST+RULEATTACK
hashcat-m11300-a0hash.txtdict.txt-rrule.txtJOHN
HASHFORMAT
$bitcoin$96$d011alb6a8d675b7a36d0cd2efaca32a9f8dcld57d6d01a58399ea04e703e8bbb448
99039326f7a00fl71a7bbc854a54$16$1563277210780230$158555$96$628835426818227243334
570448571536352510740823233055715845322741625407685873076027233865346542174$66$6
25882875480513751851333441623702852811440775888122046360561760525
EXTRACTHASH
bitcoin2john.pywallet.dat>hash.txtBRUTEFORCEATTACK
john--format=bitcoinhash.txt

WORDLISTATTACK
john--format=bitcoinwordlist=dict.txthash.txtWORDLIST+RULE
ATTACK
john--format=bitcoinwordlist=dict.txt--ruleshash.txt
MACOSX10.8-10.12
HASHCAT
HASHFORMAT
username:$ml$35714$50973de90d336b5258f01e48ab324aa9ac81ca7959ac470d3d9c4395af624
398$631a0ef84081b37cfe594a5468cf3a63173cd2ec25047b89457ed300f2b41b30a0792a39912f
C5f3f7be8f74b7269ee3713172642de96ee482432a8dl2bf291aEXTRACT
HASH
sudoplist2hashcat.py/var/db/dslocal/nodes/Default/users/<username>.plist
BRUTEFORCEATTACK
hashcat-m122-a3hash.txt?a?a?a?a?a?aWORDLISTATTACK
hashcat-m122-a0hash.txtdict.txt
WORDLIST+RULEATTACK
hashcat-m122-a0hash.txtdict.txt-rrule.txtJOHN
HASHFORMAT
username:$pbkdf2-hmac-
sha512$31724.019739e90d326b5258f01e483bl24aa9ac81ca7959acb
70c3d9c4297af924398.631a0bf84081b37dae594a5468cf3a63183cd2ec25047b89457ed300f2bf
1b40a0793a39512fc5a3f7ae8f74b7269ee3723172642de96eee82432a8dllbf365e:
501:20:HOST
NAME:/bin/bash:/var/db/dslocal/nodes/Default/users/username.plist
EXTRACTHASH
sudoml2john.py/var/db/dslocal/nodes/Default/users/<username>.plistBRUTE
FORCEATTACK
john--format=xshahash.txt
WORDLISTATTACK
john--format=xshawordlist=dict.txthash.txtWORDLIST+RULEATTACK
john--format=xshawordlist=dict.txt--ruleshash.txt
MYSQL4.1/MYSQL5+(DOUBLESHA1)
HASHCAT
HASHFORMAT
FCF7C1B8749CF99D88E5F34271D636178FB5D130
EXTRACTHASH
SELECTuser,passwordFROMmysql.userINTOOUTFILE‘/tmp/hash.txt’;
BRUTEFORCEATTACK
hashcat-m300-a3hash.txt?a?a?a?a?a?aWORDLISTATTACK
hashcat-m300-a0hash.txtdict.txt
WORDLIST+RULEATTACK
hashcat-m300-a0hash.txtdict.txt-rrule.txtJOHN
HASHFORMAT
*FCF7C1B8749CF99D88E5F34271D636178FB5D130
EXTRACTHASH
SELECTuser,passwordFROMmysql.userINTOOUTFILE‘/tmp/hash.txt’;
BRUTEFORCEATTACK
john--format=mysql-sha1hash.txt
WORDLISTATTACK
john--format=mysql-sha1wordlist=dict.txthash.txt
POSTGRESQL
HASHCAT
HASHFORMAT
a6343a68d964ca596d9752250d54bb8a:postgresEXTRACTHASH
SELECTusername,passwdFROMpg_shadow;
BRUTEFORCEATTACK
hashcat-m12-a3hash.txt?a?a?a?a?a?aWORDLISTATTACK
hashcat-m12-a0hash.txtdict.txt
WORDLIST+RULEATTACK
hashcat-m12-a0hash.txtdict.txt-rrule.txtJOHN
HASHFORMAT
a6343a68d964ca596d9752250d54bb8a:postgresEXTRACTHASH
SELECTusername,passwdFROMpg_shadow;
BRUTEFORCEATTACK
john--format=postgreshash.txt
WORDLISTATTACK
john--format=postgreswordlist=dict.txthash.txtWORDLIST+RULE
ATTACK
john--format=postgreswordlist=dict.txt--ruleshash.txt
MSSQL(2012),MSSQL(2014)
HASHCAT
HASHFORMAT

0x02000102030434ealbl7802fd95ea6316bd61d2c94622ca3812793e8fbl672487b5c904a45a31b
2ab4a78890d563d2fcf5663e46fe797d71550494be50cf4915d3f4d55ec375
EXTRACTHASH
SELECTSL.name,SL.password_hashFROMsys.sql_loginsASSL;BRUTE
FORCEATTACK
hashcat-m1731-a3hash.txt?a?a?a?a?a?aWORDLISTATTACK
hashcat-m1731-a0hash.txtdict.txt
WORDLIST+RULEATTACK
hashcat-m1731-a0hash.txtdict.txt-rrule.txtJOHN
HASHFORMAT

0x02000102030434ealbl7802fd95ea6316bd61d2c94622ca3812793e8fbl672487b5c904a45a31b
2ab4a78890d563d2fcf5663e46fe797d71550494be50cf4915d3f4d55ec375
EXTRACTHASH
SELECTSL.name,SL.password_hashFROMsys.sql_loginsASSL;BRUTE
FORCEATTACK
john--format=mssql12hash.txt
WORDLISTATTACK
john--format=mssql12wordlist=dict.txthash.txtWORDLIST+RULE
ATTACK
john--format=mssql12wordlist=dict.txt--ruleshash.txt
ORACLE11G
HASHCAT
HASHFORMAT
ac5fle62d21fd0529428b84d42e8955b04966703:38445748184477378130
EXTRACTHASH
SELECTSL.name,SL.password_hashFROMsys.sql_loginsASSL;BRUTE
FORCEATTACK
hashcat-m112-a3hash.txt?a?a?a?a?a?aWORDLISTATTACK
hashcat-m112-a0hash.txtdict.txt
WORDLIST+RULEATTACK
hashcat-m112-a0hash.txtdict.txt-rrule.txtJOHN
HASHFORMAT
ac5fle62d21fd0529428b84d42e8955b04966703:38445748184477378130
EXTRACTHASH
SELECTSL.name,SL.password_hashFROMsys.sql_loginsASSL;BRUTE
FORCEATTACK
john--format=oraclellhash.txt
WORDLISTATTACK
john--format=oraclellwordlist=dict.txthash.txtWORDLIST+RULE
ATTACK
john--format=oraclellwordlist=dict.txt--ruleshash.txt
CISCOTYPE4(SHA256)
HASHCAT
HASHFORMAT
2btjjy78REtmYkkW0csHUbDZOstRXoWdX1mGrmmfeHI
BRUTEFORCEATTACK
hashcat-m5700-a3hash.txt?a?a?a?a?a?aWORDLISTATTACK
hashcat-m5700-a0hash.txtdict.txt
WORDLIST+RULEATTACK
hashcat-m5700-a0hash.txtdict.txt-rrule.txt
CISCOTYPE5(MD5)
HASHCAT
HASHFORMAT
$l$28772684$iEwN0gGugq09.bIz5sk8k/
BRUTEFORCEATTACK
hashcat-m500-a3hash.txt?a?a?a?a?a?aWORDLISTATTACK
hashcat-m500-a0hash.txtdict.txt
WORDLIST+RULEATTACK
hashcat-m500-a0hash.txtdict.txt-rrule.txtJOHN
HASHFORMAT
$1$28772684$iEwN0gGugq09.bIz5sk8k/
BRUTEFORCEATTACK
john--format=md5crypthash.txt
WORDLISTATTACK
john--format=md5cryptwordlist=dict.txthash.txtWORDLIST+RULE
ATTACK
john--format=md5cryptwordlist=dict.txt--ruleshash.txt
CISCOTYPE8(PBKDF2+SHA256)
HASHCAT
HASHFORMAT
$8$TnGX/fE4KGH0VU$pEhnEvxrvaynpi8j4f.EMHr6M.FzU8xnZnBr/tJdFWk
BRUTEFORCEATTACK
hashcat-m9200-a3hash.txt?a?a?a?a?a?aWORDLISTATTACK
hashcat-m9200-a0hash.txtdict.txt
WORDLIST+RULEATTACK

hashcat-m9200-a0hash.txtdict.txt-rrule.txtJOHN
HASHFORMAT
$8$TnGX/fE4KGH0VU$pEhnEvxrvaynpi8j4f.EMHr6M.FzU8xnZnBr/tJdFWk
BRUTEFORCEATTACK
john--format=pbkdf2-hmac-sha256hash.txtWORDLISTATTACK
john--format=pbkdf2-hmac-sha256wordlist=dict.txthash.txtWORDLIST+
RULEATTACK
john--format=pbkdf2-hmac-sha256wordlist=dict.txt--ruleshash.txt
CISCOTYPE9(SCRYPT)
HASHCAT
HASHFORMAT
$9$2MJBozw/9R3UsU$21FhcKvpghcyw8deP25G0fyZaagyU0GBymkryv0dfo6
BRUTEFORCEATTACK
hashcat-m9300-a3hash.txt?a?a?a?a?a?aWORDLISTATTACK
hashcat-m9300-a0hash.txtdict.txt
WORDLIST+RULEATTACK
hashcat-m9300-a0hash.txtdict.txt-rrule.txtJOHN
HASHFORMAT
$9$2MJBozw/9R3UsU$21FhcKvpghcyw8deP25G0fyZaagyU0GBymkryv0dfo6
BRUTEFORCEATTACK
john--format=scrypthash.txt
WORDLISTATTACK
john--format=scryptwordlist=dict.txthash.txtWORDLIST+RULE
ATTACK
john--format=scryptwordlist=dict.txt--ruleshash.txt
WPAPSK/WPA2PSK
HASHCAT
HASHFORMAT
*Capture4-wayauthenticationhandshake>capture.capcap2hccapx.bin
capture.capcapture_out.hccapxBRUTEFORCEATTACK
hashcat-m2500-a3capture_out.hccapx?a?a?a?a?a?aWORDLISTATTACK
hashcat-m2500-a3capture_out.hccapxdict.txtWORDLIST+RULE

ATTACK
hashcat-a0capture_out.hccapxdict.txt-rrule.txtJOHN
HASHFORMAT
*Capture4-wayauthenticationhandshake>capture.capcap2hccap.bin-e
‘<ESSID>’capture.capcapture_out.hccaphccap2johncapture_out.hccap>
jtr_captureBRUTEFORCEATTACK
john--format=wpapskjtr_capture
WORDLISTATTACK
john--format=wpapskwordlist=dict.txtjtr_captureWORDLIST+RULE
ATTACK
john--format=wpapskwordlist=dict.txt--rulesjtr_capture


APPENDIX
TERMS
BRUTE-FORCEATTACK-theactoftryingeverypossiblecombinationof
agivenkeyspaceorcharactersetforagivenlength
DICTIONARY-acollectionofcommonswords,phrases,keyboard
patterns,generatedpasswords,orleakedpasswords,alsoknownasa
wordlist
DICTIONARYATTACK-usingafilecontainingcommonorknown
passwordcombinationsorwordsinanattempttomatchagivenhashing
function’soutputbyrunningsaidwordsthroughthesametargethashing
function
HASH-thefixedbitresultofahashfunction
HASHFUNCTION-mapsdataofarbitrarysizetoabitstringofafixed
size(ahashfunction)whichisdesignedtoalsobeaone-wayfunction,that
is,afunctionwhichisinfeasibletoinvert
ITERATIONS-thenumberoftimesanalgorithmisrunoveragivenhash
KEYSPACE-thenumberofpossiblecombinationsforagivencharacterset
tothepowerofit’slength(i.e.charset^length)
MASKATTACK-usingplaceholderrepresentationstotryallcombinations
ofagivenkeyspace,similartobrute-forcebutmoretargetedandefficient
PASSWORDENTROPY-anestimationofhowdifficultapasswordwillbe
tocrackgivenitscharactersetandlength

PLAINTEXT-unalteredtextthathasn’tbeenobscuredoralgorithmically
alteredthroughahashingfunction
RAKING-generatingrandompasswordrules/candidatesinanattemptto
discoverapreviouslyunknownmatchingpasswordpattern
RAINBOWTABLE-aprecomputedtableofatargetedcryptographichash
functionofacertainminimumandmaximumcharacterlength
RULEATTACK-similartoaprogramminglanguageforgenerating
candidatepasswordsbasedonsomeinputsuchasadictionary
SALT-randomdatathatusedasadditionalinputtoaone-wayfunction
WORDLIST-acollectionofcommonswords,phrases,keyboardpatterns,
generatedpasswords,orleakedpasswords,alsoknownasadictionary
TIMETABLE
60seconds 1minute
3,600seconds 1hour
86,400seconds 1day
604,800seconds 1week
1,209,600seconds 1fortnight
2,419,200seconds 1month(30days)
31,536,000seconds 1year
ONLINERESOURCES
JOHN
http://openwall.info/wiki/john
http://openwall.info/wiki/john/sample-non-hashes
http://pentestmonkey.net/cheat-sheet/john-the-ripper-hash-formats
https://countuponsecurity.com/2015/06/14/jonh-the-ripper-cheat-sheet/
https://xinn.org/blog/JtR-AD-Password-Auditing.html
https://www.owasp.org/images/a/af/2011-Supercharged-Slides-Redman-
OWASP-Feb.pdf
HASHCAT
https://hashcat.net/wiki/
https://hashcat.net/wiki/doku.php?id=hashcat_utils
https://hashcat.net/wiki/doku.php?id=statsprocessor
http://www.netmux.com/blog/ultimate-guide-to-cracking-foreign-character-
passwords-using-has
http://www.netmux.com/blog/cracking-12-character-above-passwords
CRACKINGRIGS
http://www.netmux.com/blog/how-to-build-a-password-cracking-rig
https://www.unix-
ninja.com/p/Building_a_Password_Cracking_Rig_for_Hashcat_-_Part_III
EXAMPLEHASHGENERATION
https://www.onlinehashcrack.com/hash-generator.php
https://www.tobtu.com/tools.php
http://hash.online-convert.com/
https://www.tools4noobs.com/online_tools/hash/
https://quickhash.com/
http://bitcoinvalued.com/tools.php
http://www.sha1-online.com/
http://www.freeformatter.com/hmac-generator.html
http://openwall.info/wiki/john/Generating-test-hashes
OTHER
http://blog.thireus.com/cracking-story-how-i-cracked-over-122-million-sha1-
and-md5-hashed-passwords/
http://www.utf8-chartable.de/
http://thesprawl.org/projects/pack/
https://blog.gotmilk.com/2011/06/dictionaries-wordlists/
http://wpengine.com/unmasked/
https://www.unix-ninja.com/p/A_cheat-sheet_for_password_crackers

https://room362.com/post/2017/05-06-2017-password-magic-numbers/
http://www.netmux.com/blog/how-to-build-a-password-cracking-rig
http://passwordchart.com/
http://www.vigilante.pw
NETMUX
http://www.netmux.com
http://www.hashcrack.io
https://github.com/netmux
https://twitter.com/netmux
https://www.instagram.com/netmux/
***ANSWERTOCUSTOMDICTIONARYCREATIONHASH:
e4821dl6a298092638ddb7cadc26d32f=letmein123456Netmux
10CRACKCOMMANDMENTS
1.Thoushaltknowhashtypesandtheirorigin/function
2.Thoushaltknowcrackingsoftwarestrengths&weaknesses
3.Thoushaltstudy&applypasswordanalysistechniques
4Thoushaltbeproficientathashextractionmethods
5.Thoushaltcreatecustom/targeteddictionaries
6.Thoushaltknowthycrackingrigscapabilities
7.Thoushaltunderstandbasichumanpsychology/behavior
8.Thoushaltcreatecustommasks,rules,andMarkovchains

9.Thoushaltcontinuallyexperimentwithnew
techniques
10.Thoushaltsupportthyfellowcrackingcommunitymembers
JOHNTHERIPPERHELPMENU
JohntheRipperpasswordcracker,version1.8.0-jumbo-1[darwinl5.6.064-bit
AVX2-autoconf]
Copyright (c)1996-2014bySolarDesignerandothers
Homepage: http://www.openwall.com/john/
Usage:john[OPTIONS][PASSWORD-FILES]
--single[=SECTION] “singlecrack”mode
--wordlist[=FILE]--stdin wordlistmode,readwordsfromFILE
orstdin
--pipe like--stdin,butbulkreads,andallows
rules
--loopback[=FILE] like--wordlist,butfetchwordsfroma
.potfile
--dupe-suppression suppressalldupesinwordlist(and
forcepreload)
--encoding=NAME
inputencoding(eg.UTF-8,ISO-8859-
1).Seealsodoc/ENCODINGand--
list=hidden-options.
--rules[=SECTION] enablewordmanglingrulesforwordlist
modes
--incremental[=MODE] “incremental”mode[usingsection
MODE]
--mask=MASK maskmodeusingMASK
--markov[=OPTIONS] “Markov”mode(seedoc/MARKOV)
--external=MODE externalmodeorwordfilter
--stdout[=LENGTH] justoutputcandidatepasswords[cutat
LENGTH]
--restore[=NAME] restoreaninterruptedsession[called
NAME]
--session=NAME giveanewsessiontheNAME
--status[=NAME] printstatusofasession[calledNAME]
--make-charset=FILE makeacharsetfile.Itwillbe
overwritten
--show[=LEFT] showcrackedpasswords[if=LEFT,
thenuncracked]
--test[=TIME] runtestsandbenchmarksforTIME
secondseach
--users=[-]LOGIN|UID[,..] [donot]loadthis(these)user(s)only
--groups=[-]GID[,..] loadusers[not]ofthis(these)group(s)
only
--shells=[-]SHELL[,..] loaduserswith[out]this(these)shell(s)
only
--salts=[-]COUNT[:MAX] loadsaltswith[out]COUNT[toMAX]
hashes
--save-memory=LEVEL enablememorysaving,atLEVEL1..3
--node=MIN[-MAX]/TOTAL thisnode’snumberrangeoutofTOTAL
count
--fork=N forkNprocesses
--pot=NAME potfiletouse
--list=WHAT listcapabilities,see--list=helpor
doc/OPTIONS
--devices=N[,..]devices) setOpenCLdevice(s)(listusing--
list=opencl-
--format=NAME forcehashtypeNAME:
7z7z-openclAFSagilekeychainagilekeychain-openclaix-smd5aix-ssha1aix-
ssha256aix-ssha512asa-md5bcryptbcrypt-openclbfeggBitcoinblackberry-
es10Blockchainblockchain-openclbsdicryptchapCitrix_NS10Clipperz
cloudkeychaincqCRC32cryptdahuadescryptdescrypt-openclDjangodjango-
scryptdmd5dmgdmg-opencldominosecdragonfly3-32dragonfly3-64
dragonfly4-32dragonfly4-64Drupal7dummydynamic_neCryptfsEFSeigrp
EncFSencfs-openclEPIEPiServerfdeFormSpringFortigategostgpggpg-
openclHAVAL-128-4HAVAL-256-3hdaaHMAC-MD5HMAC-SHA1HMAC-
SHA224HMAC-SHA256HMAC-SHA384HMAC-SHA512hMailServerhsrp
IKEipb2KeePasskeychainkeychain-openclkeyringkeyring-openclkeystore
known_hostskrb4krb5krb5-18krb5pa-md5krb5pa-md5-openclkrb5pa-sha1
krb5pa-sha1-openclkwalletLastPassLMlotus5lotus5-opencllotus85LUKS
MD2md4-genmd5cryptmd5crypt-openclmd5nsmdc2MediaWikiMongoDB
Mozillamscashmscash2mscash2-openclMSCHAPv2mschapv2-naivemssql
mssql05mssqll2mysqlmysql-sha1mysql-sha1-openclmysqlnanet-md5net-
sha1nethalflmnetlmnetlmv2netntlmnetntlm-naivenetntlmv2nknsldapNTnt-
openclnt2ntlmv2-openclo51ogono51ogon-openclODFODF-AES-opencl
ODF-openclOfficeoffice2007-opencloffice2010-opencloffice2013-opencl
oldofficeoldoffice-openclOpenBSD-SoftRAIDopenssl-encOpenVMSoracle
oraclelloscPanamaPBKDF2-HMAC-SHA1PBKDF2-HMAC-SHA1-opencl
PBKDF2-HMAC-SHA256PBKDF2-HMAC-SHA256-openclPBKDF2-
HMAC-SHA512pbkdf2-hmac-sha512-openclPDFPFXphpassphpass-opencl
PHPSpix-md5PKZIPpopostgresPSTPuTTYpwsafepwsafe-openclRACF
RAdminRAKPRAKP-openclrarrar-openclRAR5RAR5-openclRaw-Blake2
Raw-KeccakRaw-Keccak-256Raw-MD4Raw-MD4-openclRaw-MD5Raw-
MD5-openclRaw-MD5uRaw-SHARaw-SHA1Raw-SHA1-LinkedinRaw-
SHA1-ngRaw-SHA1-openclRaw-SHA224Raw-SHA256Raw-SHA256-ng
Raw-SHA256-openclRaw-SHA384Raw-SHA512Raw-SHA512-ngRaw-
SHA512-openclripemd-128ripemd-160rsvpSalted-SHA1sapbsapgscrypt
sha1-gensha1cryptsha1crypt-openclsha256cryptsha256crypt-opencl
sha512cryptsha512crypt-openclSiemens-S7SIPskein-256skein-512skey
Snefru-128Snefru-256SSHSSH-ngssha-openclSSHA512STRIPstrip-opencl
SunMD5sxcsxc-openclSybase-PROPsybaseasetc_aes_xtstc_ripemdl60
tc_sha512tc_whirlpooltcp-md5TigertripcodeVNCvtpwbb3whirlpool
whirlpool0whirlpoollWoWSRPwpapskwpapsk-openclxshaxsha512
XSHA512-openclZIPzip-opencl

HASHCATHELPMENU
hashcat3.6-advancedpasswordrecovery
Usage:hashcat[options]...hash|hash-file|hccapxfile[dictionary|mask|
directory]...
-[Options]-

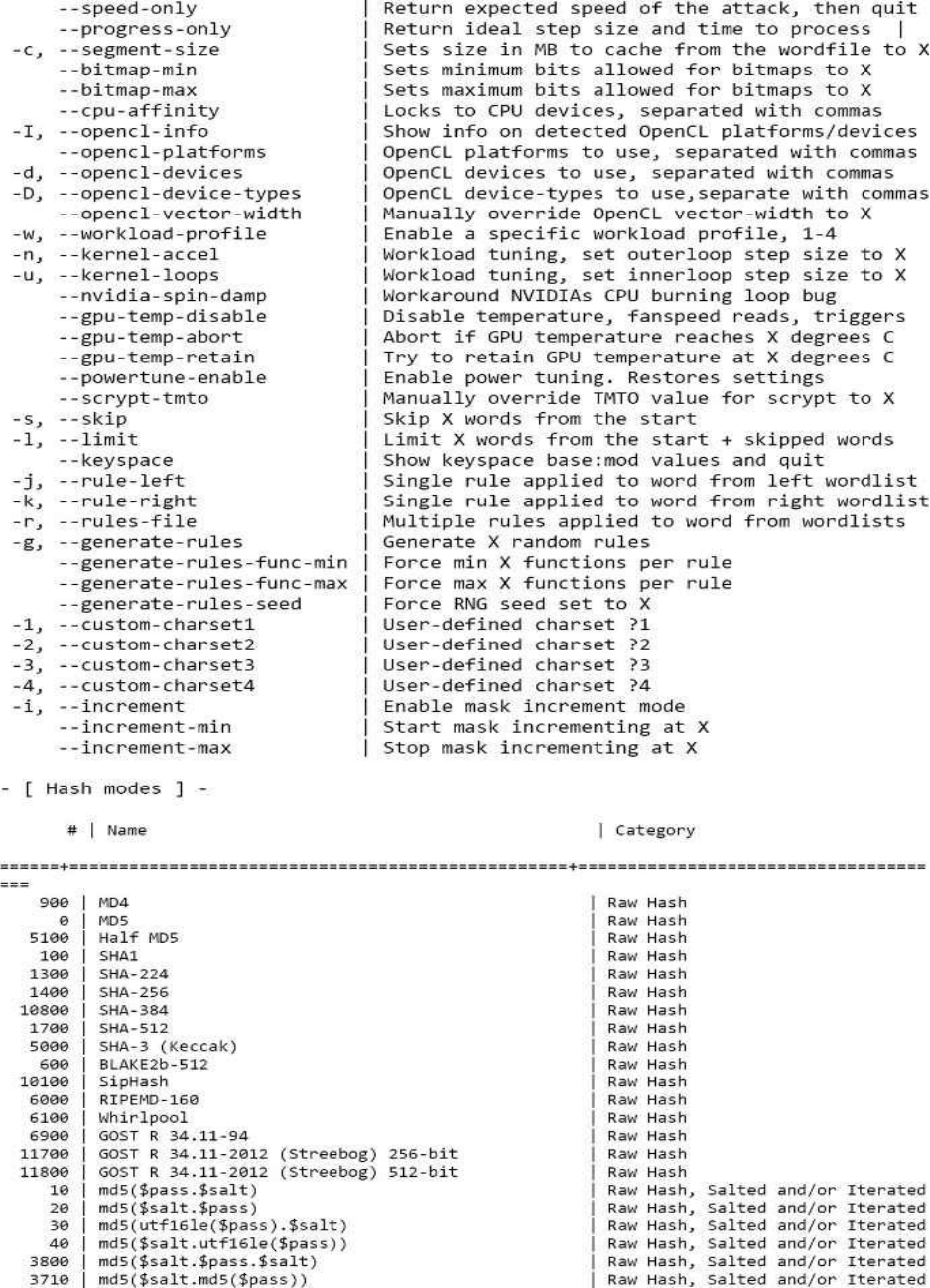
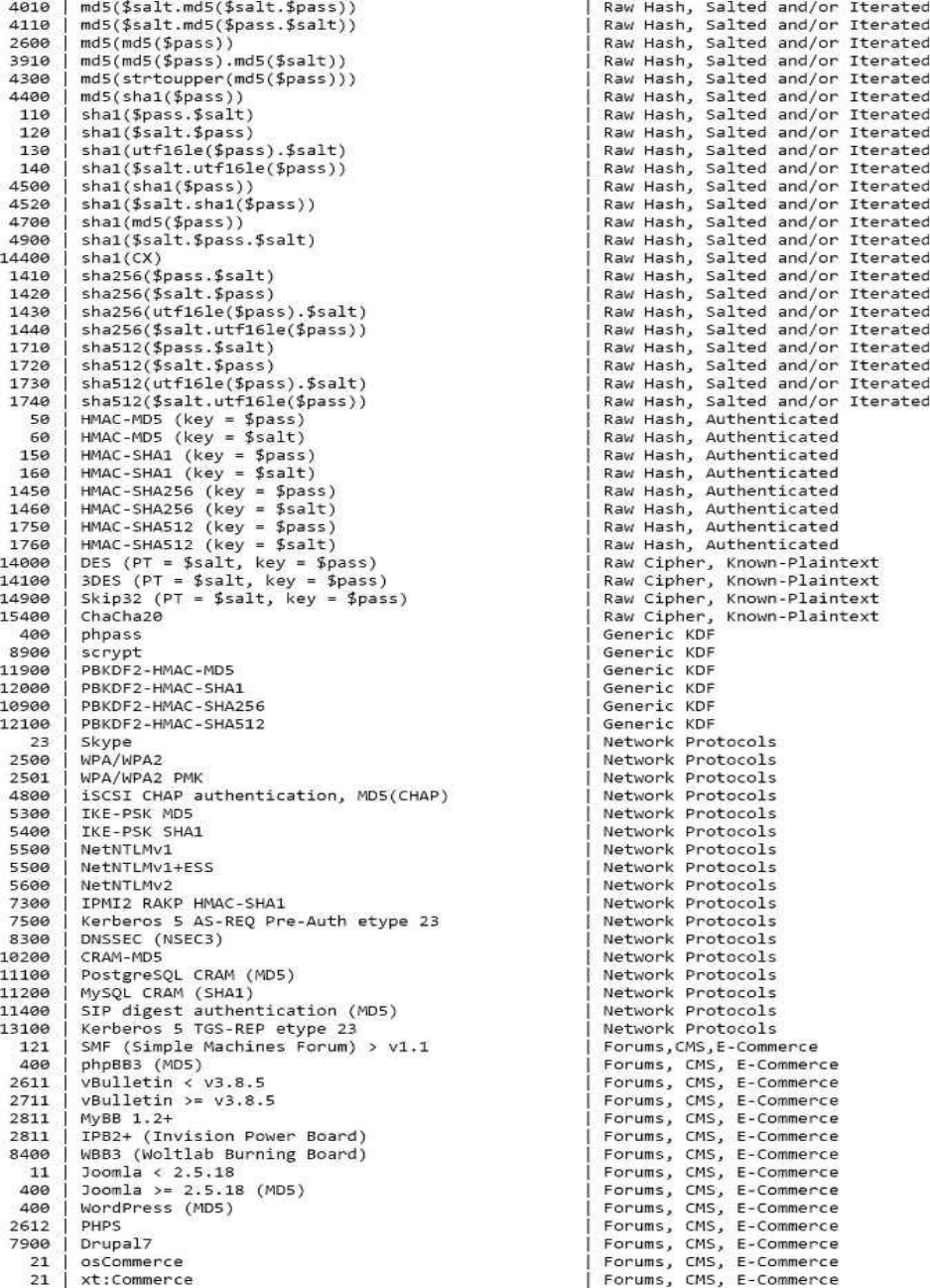
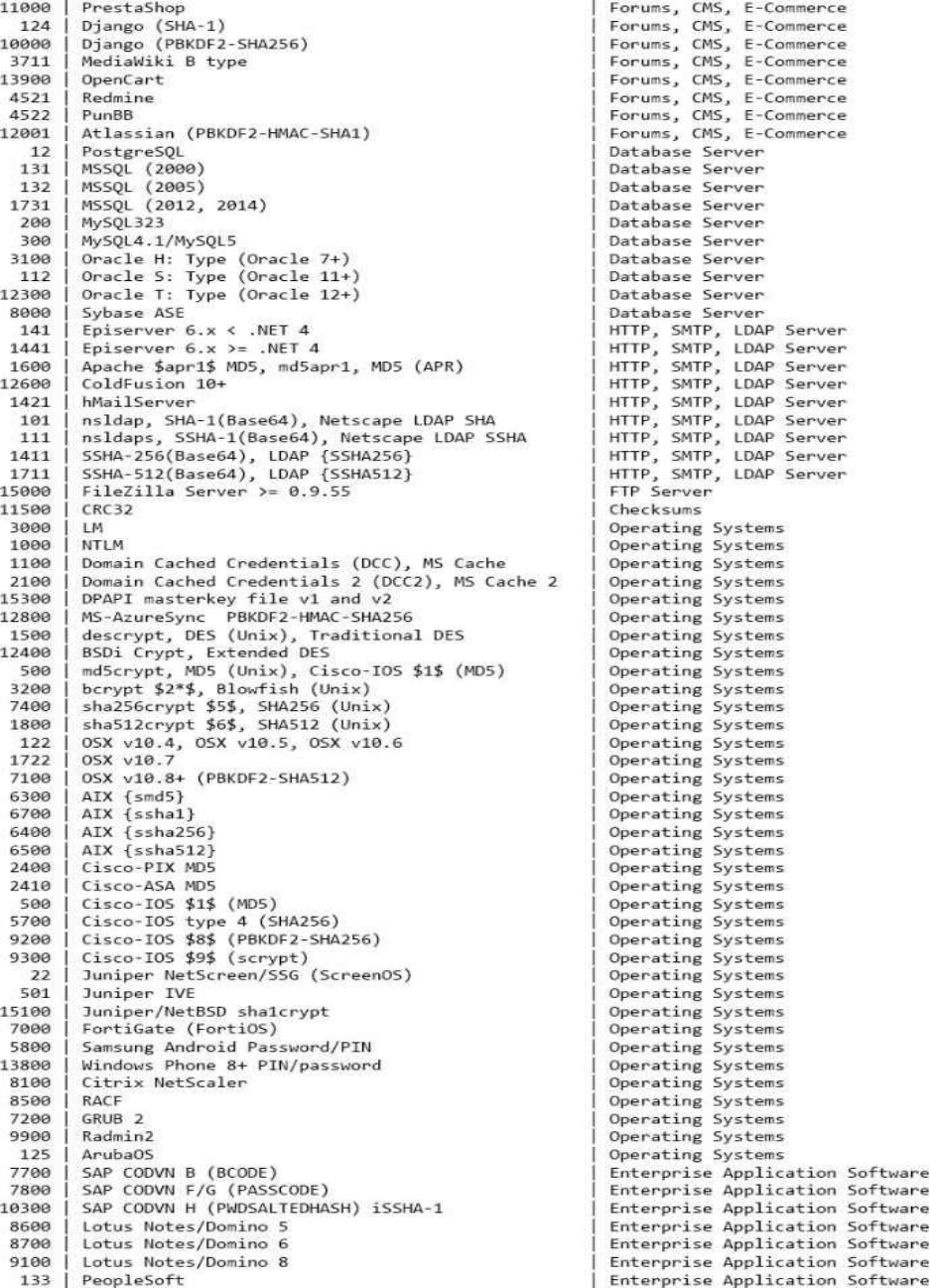
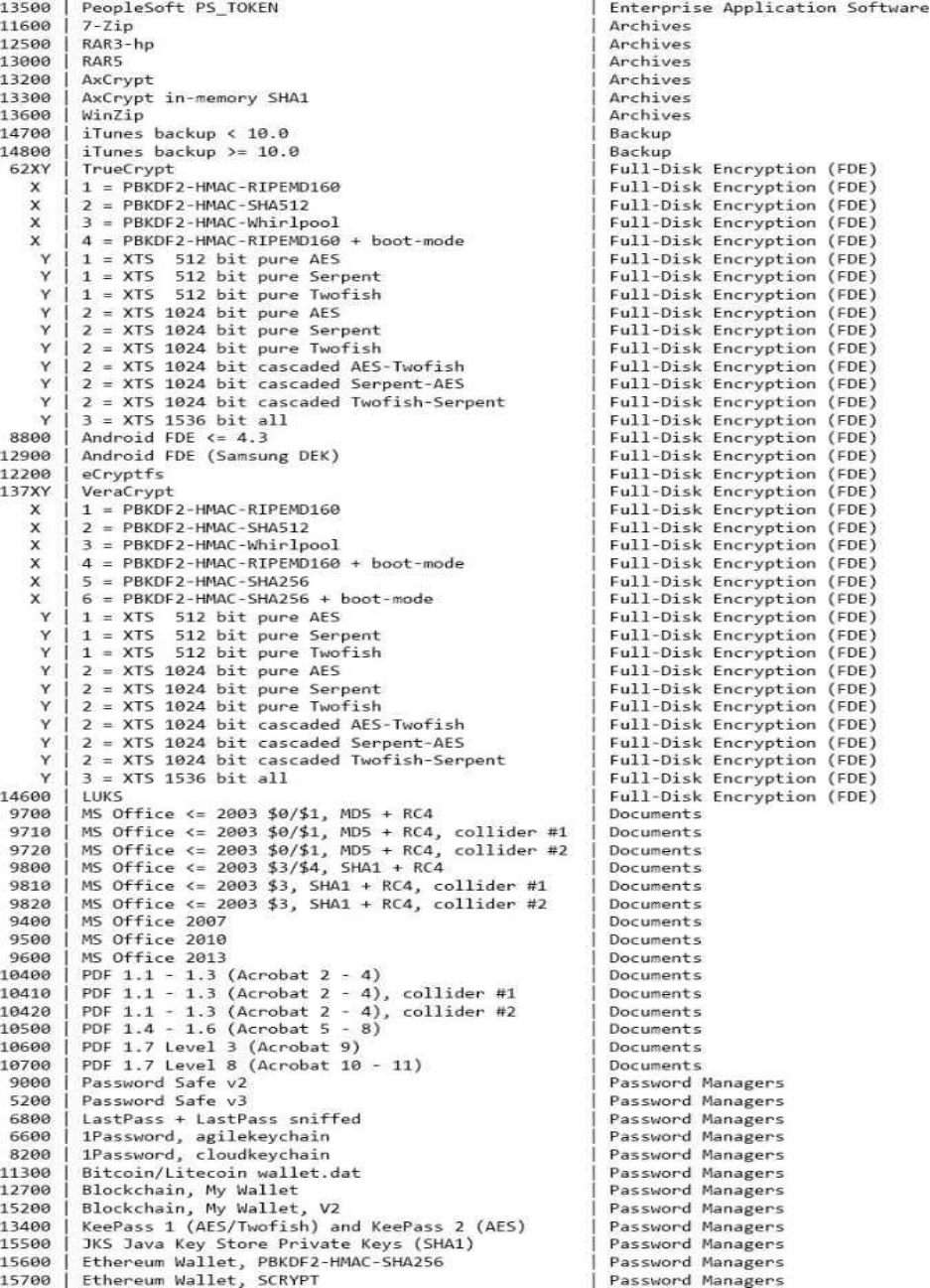
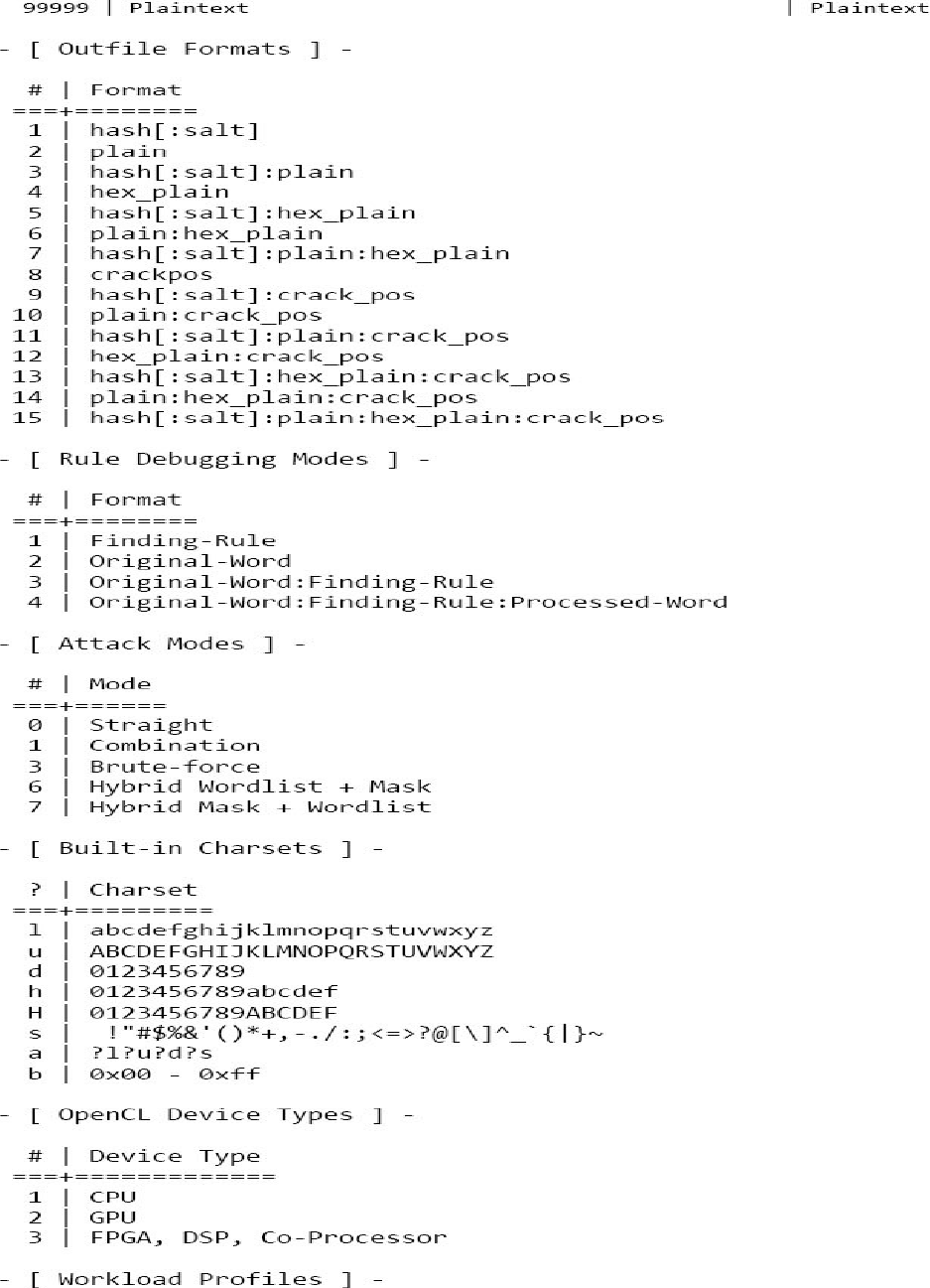


***HASHCRACKINGBENCHMARKtablesaremeanttobeareferenceto
enableuserstogaugehowSLOWorFASTahashingalgorithmisbefore
formulatinganattackplan.NvidiaGTX2080waschosenasthedefaultduetoits
prevalenceamongthecrackingcommunityandit’spositionasatopperforming
GPUcard.
HASHCRACKINGBENCHMARKS(ALPHABETICAL)
1Password,agilekeychain 3319.2kH/s
1Password,cloudkeychain 10713H/s
3DES(PT=$salt,key=$pass) 594.3MH/s
7-Zip 7514H/s
AIX 14937.2kH/s
AIX 44926.1kH/s
AIX 6359.3kH/s
AIX 9937.1kH/s
AndroidFDE(SamsungDEK) 291.8kH/s
AndroidFDE<=4.3 803.0kH/s
AndroidPIN 5419.4kH/s
ArubaOS 6894.7MH/s
Atlassian(PBKDF2-HMAC-SHA1) 283.6kH/s
AxCrypt 113.9kH/s
AxCryptinmemorySHA1 7503.3MH/s
bcrypt,Blowfish(OpenBSD) 13094H/s
BSDiCrypt,ExtendedDES 1552.5kH/s
Bitcoin/Litecoinwallet.dat 4508H/s
BLAKE2-512 1488.9MH/s
Blockchain,MyWallet 50052.3kH/s
Blockchain,MyWallet,V2 305.2kH/s
ChaCha20 3962.0MH/s
Cisco$8$ 59950H/s
Cisco$9$ 22465H/s
Cisco-ASAMD5 17727.2MH/s
Cisco-IOSSHA256 2864.3MH/s
Cisco-PIXMD5 16407.2MH/s
CitrixNetScaler 7395.3MH/s
ColdFusion10+ 1733.6MH/s
DES(PT=$salt,key=$pass) 19185.7MH/s
descrypt,DES(Unix),TraditionalDES 906.7MH/s
DNSSEC(NSEC3) 3274.6MH/s
Django(PBKDF2-SHA256) 59428H/s
Django(SHA-1) 6822.6MH/s
DomainCachedCredentials(DCC),MSCache 11195.8MH/s
DomainCachedCredentials2(DCC2),MSCache2 317.5kH/s
DPAPImasterkeyfilev1andv2 73901H/s
Drupal7 56415H/s
eCryptfs 13813H/s
EthereumWallet,PBKDF2-HMAC-SHA256 4518H/s
EthereumWallet,SCRYPT 29H/s
EPiServer6.x<v4 6818.5MH/s
EPiServer6.x>v4 2514.4MH/s
FileZillaServer>=0.9.55 565.2MH/s
FortiGate(FortiOS) 6386.2MH/s
GOSTR34.11-2012(Streebog)256-bit 50018.8kH/s
GOSTR34.11-2012(Streebog)512-bit 49979.4kH/s
GOSTR34.11-94 206.2MH/s
GRUB2 43235H/s
HalfMD5 15255.8MH/s
hMailServer 2509.6MH/s
IKE-PSKMD5 1834.0MH/s
IKE-PSKSHA1 788.2MH/s
IPB2+,MyBB1.2+ 5011.8MH/s
IPMI2RAKPHMAC-SHA1 1607.3MH/s
iTunesbackup<10.0 140.2kH/s
iTunesbackup>=10.0 94H/s
JKSJavaKeyStorePrivateKeys(SHA1) 7989.4MH/s
Joomla<2.5.18 25072.2MH/s
JuniperIVE 9929.1kH/s
Juniper/NetBSDsha1crypt 144.1kH/s
JuniperNetscreen/SSG(ScreenOS) 12946.8MH/s
Keepass1(AES/Twofish)andKeepass2(AES) 139.8kH/s
Kerberos5AS-REQPre-Authetype23 291.5MH/s
Kerberos5TGS-REPetype23 291.1MH/s
LM 18382.7MH/s
Lastpass 2331.2kH/s
LotusNotes/Domino5 205.2MH/s
LotusNotes/Domino6 69673.5kH/s
LotusNotes/Domino8 667.2kH/s
LUKS 8703H/s
MD4 43722.9MH/s
MD5 24943.1MH/s
md5(md5($pass).md5($salt)) 4291.9MH/s
md5($salt.md5($salt.$pass)) 5037.7MH/s
md5($salt.md5($pass.$salt)) 5401.6MH/s
md5apr1,MD5(APR),ApacheMD5 9911.5kH/s
md5crypt,MD5(Unix),FreeBSDMD5,Cisco-IOS
MD5 9918.1kH/s
MSOffice<=2003MD5+RC4,collision-mode#1 339.9MH/s
MSOffice<=2003MD5+RC4,oldoffice$0,oldoffice$l 219.6MH/s
MSOffice<=2003SHA1+RC4,collision-mode#1 330.8MH/s
MSOffice<=2003SHA1+RC4,oldoffice$3,
oldoffice$4 296.7MH/s
MS-AzureSyncPBKDF2-HMAC-SHA256 10087.9kH/s
MSSQL(2000) 8609.7MH/s
MSSQL(2005) 8636.4MH/s
MSSQL(2012) 1071.3MH/s
MediawikiBtype 6515.8MH/s
MySQLChallenge-ResponseAuthentication(SHA1) 2288.0MH/s
MySQL323 51387.0MH/s
MySQL4.1/MySQL5 3831.5MH/s
NTLM 41825.0MH/s
NetNTLMv1-VANILLA/NetNTLMv1+ESS 22308.5MH/s
NetNTLMv2 1634.9MH/s
osCommerce,xt 12883.7MH/s
OSXV10.4,V10.5,V10.6 6831.3MH/s
OSXV10.7 834.1MH/s
OSXV10.8+ 12348H/s
Office2007 134.5kH/s
Office2010 66683H/s
Office2013 8814H/s
OpenCart 2097.0MH/s
OracleH 851.6MH/s
OracleS 8565.0MH/s
OracleT 104.7kH/s
PasswordSafev2 332.0kH/s
PasswordSafev3 1233.4kH/s
PBKDF2-HMAC-MD5 7408.3kH/s
PBKDF2-HMAC-SHA1 3233.9kH/s
PBKDF2-HMAC-SHA256 1173.1kH/s
PBKDF2-HMAC-SHA512 431.4kH/s
PDF1.1-1.3(Acrobat2-4) 345.0MH/s
PDF1.1-1.3(Acrobat2-4)+collider-mode#1 373.4MH/s
PDF1.4-1.6(Acrobat5-8) 16048.0kH/s
PDF1.7Level3(Acrobat9) 2854.1MH/s
PDF1.7Level8(Acrobat10-11) 30974H/s
PeopleSoft 8620.3MH/s
PeopleSoftPS_TOKEN 3226.5MH/s
phpass,MD5(Wordpress),MD5(phpBB3),
MD5(Joomla) 6917.9kH/s
PHPS 6972.6MH/s
Plaintext 37615.5MH/s
PostgreSQL 25068.0MH/s
PostgreSQLChallenge-ResponseAuth(MD5) 6703.0MH/s
PrestaShop 8221.3MH/s
PunBB 2837.7MH/s
RACF 2528.4MH/s
RAR3-hp 29812H/s
RAR5 36473H/s
Radmin2 8408.3MH/s
RedmineProjectManagementWebApp 2121.3MH/s
RipeMD160 4732.0MH/s
SAPCODVNB(BCODE) 1311.2MH/s
SAPCODVNF/G(PASSCODE) 739.3MH/s
SAPCODVNH(PWDSALTEDHASH)iSSHA-1 6096.6kH/s
scrypt 435.1kH/s
SHA-1(Base64),nsldap,NetscapeLDAPSHA 8540.0MH/s
SHA-3(Keccak) 769.8MH/s
SHA1 8538.1MH/s
SHA1(CX) 291.8MH/s
sha1($salt.sha1($pass)) 2457.6MH/s
SHA-224 3076.6MH/s
SHA256 2865.2MH/s
sha256crypt,SHA256(Unix) 388.8kH/s
SHA384 1044.8MH/s
SHA512 1071.1MH/s
sha512crypt,SHA512(Unix) 147.5kH/s
SIPdigestauthentication(MD5) 2004.3MH/s
SKIP32 4940.9MH/s
SMF>v1.1 6817.7MH/s
SSHA-1(Base64),nsldaps,NetscapeLDAPSSHA 8584.5MH/s
SSHA-256(Base64),LDAP{SSHA256} 3216.9MH/s
SSHA-512(Base64),LDAP 1072.2MH/s
SipHash 28675.1MH/s
Skype 12981.9MH/s
SybaseASE 398.1MH/s
TrueCryptPBKDF2-HMAC-
RipeMD160+XTS512bit+boot-mode 512.4kH/s
TrueCryptPBKDF2-HMAC-RipeMD160+XTS512bit 277.0kH/s
TrueCryptPBKDF2-HMAC-SHA512+XTS512bit 376.2kH/s
TrueCryptPBKDF2-HMAC-Whirlpool+XTS512bit 36505H/s
vBulletin<V3.8.5 6947.7MH/s
vBulletin>V3.8.5 4660.5MH/s
VeraCryptPBKDF2-HMAC-RipeMD160+XTS512bit 907H/s
VeraCryptPBKDF2-HMAC-RipeMD160+XTS 1820H/s
512bit+boot-mode
VeraCryptPBKDF2-HMAC-SHA256+XTS512bit 1226H/s
VeraCryptPBKDF2-HMAC-SHA256+XTS
512bit+boot-mode 3012H/s
VeraCryptPBKDF2-HMAC-SHA512+XTS512bit 830H/s
VeraCryptPBKDF2-HMAC-Whirlpool+XTS512bit 74H/s
WBB3,WoltlabBurningBoard3 1293.3MH/s
WPA/WPA2 396.8kH/s
Whirlpool 253.9MH/s
WinZip 1054.4kH/s
*CRACKINGSPEEDBASEDONNVIDIAGTX1080&HASHCATv3.6


HASHCRACKINGSPEED(SLOW-FAST)
EthereumWallet,SCRYPT 29H/s
VeraCryptPBKDF2-HMAC-Whirlpool+XTS512bit 74H/s
iTunesbackup>=10.0 94H/s
VeraCryptPBKDF2-HMAC-SHA512+XTS512bit 830H/s
VeraCryptPBKDF2-HMAC-RipeMD160+XTS512bit 907H/s
VeraCryptPBKDF2-HMAC-SHA256+XTS512bit 1226H/s
VeraCryptPBKDF2-HMAC-RipeMD160+XTS
512bit+boot-mode 1820H/s
VeraCryptPBKDF2-HMAC-SHA256+XTS
512bit+boot-mode 3012H/s
Bitcoin/Litecoinwallet.dat 4508H/s
EthereumWallet,PBKDF2-HMAC-SHA256 4518H/s
7-Zip 7514H/s
LUKS 8703H/s
Office2013 8814H/s
1Password,cloudkeychain 10713H/s
OSXV10.8+ 12348H/s
bcrypt,Blowfish(OpenBSD) 13094H/s
eCryptfs 13813H/s
Cisco$9$ 22465H/s
RAR3-hp 29812H/s
PDF1.7Level8(Acrobat10-11) 30974H/s
RAR5 36473H/s
TrueCryptPBKDF2-HMAC-Whirlpool+XTS512bit 36505H/s
GRUB2 43235H/s
Drupal7 56415H/s
Django(PBKDF2-SHA256) 59428H/s
Cisco$8$ 59950H/s
Office2010 66683H/s
DPAPImasterkeyfilev1andv2 73901H/s
OracleT 104.7kH/s
AxCrypt 113.9kH/s
Office2007 134.5kH/s
Keepass1(AES/Twofish)andKeepass2(AES) 139.8kH/s
iTunesbackup<10.0 140.2kH/s
Juniper/NetBSDsha1crypt 144.1kH/s
sha512crypt,SHA512(Unix) 147.5kH/s
TrueCryptPBKDF2-HMAC-RipeMD160+XTS512bit 277.0kH/s
Atlassian(PBKDF2-HMAC-SHA1) 283.6kH/s
AndroidFDE(SamsungDEK) 291.8kH/s
Blockchain,MyWallet,V2 305.2kH/s
DomainCachedCredentials2(DCC2),MSCache2 317.5kH/s
PasswordSafev2 332.0kH/s
TrueCryptPBKDF2-HMAC-SHA512+XTS512bit 376.2kH/s
sha256crypt,SHA256(Unix) 388.8kH/s
WPA/WPA2 396.8kH/s
PBKDF2-HMAC-SHA512 431.4kH/s
scrypt 435.1kH/s
TrueCryptPBKDF2-HMAC-RipeMD160+XTS
512bit+boot-mode 512.4kH/s
LotusNotes/Domino8 667.2kH/s
AndroidFDE<=4.3 803.0kH/s
WinZip 1054.4kH/s
PBKDF2-HMAC-SHA256 1173.1kH/s
PasswordSafev3 1233.4kH/s
BSDiCrypt,ExtendedDES 1552.5kH/s
Lastpass 2331.2kH/s
PBKDF2-HMAC-SHA1 3233.9kH/s
1Password,agilekeychain 3319.2kH/s
AndroidPIN 5419.4kH/s
SAPCODVNH(PWDSALTEDHASH)iSSHA-1 6096.6kH/s
AIX 6359.3kH/s
phpass,MD5(Wordpress),MD5(phpBB3),
MD5(Joomla) 6917.9kH/s
PBKDF2-HMAC-MD5 7408.3kH/s
md5apr1,MD5(APR),ApacheMD5 9911.5kH/s
md5crypt,MD5(Unix),FreeBSDMD5,Cisco-IOS
MD5 9918.1kH/s
JuniperIVE 9929.1kH/s
AIX 9937.1kH/s
MS-AzureSyncPBKDF2-HMAC-SHA256 10087.9kH/s
AIX 14937.2kH/s
PDF1.4-1.6(Acrobat5-8) 16048.0kH/s
AIX 44926.1kH/s
GOSTR34.11-2012(Streebog)512-bit 49979.4kH/s
GOSTR34.11-2012(Streebog)256-bit 50018.8kH/s
Blockchain,MyWallet 50052.3kH/s
LotusNotes/Domino6 69673.5kH/s
LotusNotes/Domino5 205.2MH/s
GOSTR34.11-94 206.2MH/s
MSOffice<=2003MD5+RC4,oldoffice$0,oldoffice$l 219.6MH/s
Whirlpool 253.9MH/s
Kerberos5TGS-REPetype23 291.1MH/s
Kerberos5AS-REQPre-Authetype23 291.5MH/s
SHA1(CX) 291.8MH/s
MSOffice<=2003SHA1+RC4,oldoffice$3,
oldoffice$4 296.7MH/s
MSOffice<=2003SHA1+RC4,collision-mode#1 330.8MH/s
MSOffice<=2003MD5+RC4,collision-mode#1 339.9MH/s
PDF1.1-1.3(Acrobat2-4) 345.0MH/s
PDF1.1-1.3(Acrobat2-4)+collider-mode#1 373.4MH/s
SybaseASE 398.1MH/s
FileZillaServer>=0.9.55 565.2MH/s
3DES(PT=$salt,key=$pass) 594.3MH/s
SAPCODVNF/G(PASSCODE) 739.3MH/s
SHA-3(Keccak) 769.8MH/s
IKE-PSKSHA1 788.2MH/s
OSXV10.7 834.1MH/s
OracleH 851.6MH/s
descrypt,DES(Unix),TraditionalDES 906.7MH/s
SHA384 1044.8MH/s
SHA512 1071.1MH/s
MSSQL(2012) 1071.3MH/s
SSHA-512(Base64),LDAP 1072.2MH/s
WBB3,WoltlabBurningBoard3 1293.3MH/s
SAPCODVNB(BCODE) 1311.2MH/s
BLAKE2-512 1488.9MH/s
IPMI2RAKPHMAC-SHA1 1607.3MH/s
NetNTLMv2 1634.9MH/s
ColdFusion10+ 1733.6MH/s
IKE-PSKMD5 1834.0MH/s
SIPdigestauthentication(MD5) 2004.3MH/s
OpenCart 2097.0MH/s
RedmineProjectManagementWebApp 2121.3MH/s
MySQLChallenge-ResponseAuthentication(SHA1) 2288.0MH/s
sha1($salt.sha1($pass)) 2457.6MH/s
hMailServer 2509.6MH/s
EPiServer6.x>v4 2514.4MH/s
RACF 2528.4MH/s
PunBB 2837.7MH/s
PDF1.7Level3(Acrobat9) 2854.1MH/s
Cisco-IOSSHA256 2864.3MH/s
SHA256 2865.2MH/s
SHA-224 3076.6MH/s
SSHA-256(Base64),LDAP{SSHA256} 3216.9MH/s
PeopleSoftPS_TOKEN 3226.5MH/s
DNSSEC(NSEC3) 3274.6MH/s
MySQL4.1/MySQL5 3831.5MH/s
ChaCha20 3962.0MH/s
md5(md5($pass).md5($salt)) 4291.9MH/s
vBulletin>V3.8.5 4660.5MH/s
RipeMD160 4732.0MH/s
SKIP32 4940.9MH/s
IPB2+,MyBB1.2+ 5011.8MH/s
md5($salt.md5($salt.$pass)) 5037.7MH/s
md5($salt.md5($pass.$salt)) 5401.6MH/s
FortiGate(FortiOS) 6386.2MH/s
MediawikiBtype 6515.8MH/s
PostgreSQLChallenge-ResponseAuthentication(MD5) 6703.0MH/s
SMF>v1.1 6817.7MH/s
EPiServer6.x<v4 6818.5MH/s
Django(SHA-1) 6822.6MH/s
OSXV10.4,V10.5,V10.6 6831.3MH/s
ArubaOS 6894.7MH/s
vBulletin<V3.8.5 6947.7MH/s
PHPS 6972.6MH/s
CitrixNetScaler 7395.3MH/s
AxCryptinmemorySHA1 7503.3MH/s
JKSJavaKeyStorePrivateKeys(SHA1) 7989.4MH/s
PrestaShop 8221.3MH/s
Radmin2 8408.3MH/s
SHA1 8538.1MH/s
SHA-1(Base64),nsldap,NetscapeLDAPSHA 8540.0MH/s
SSHA-1(Base64),nsldaps,NetscapeLDAPSSHA 8584.5MH/s
MSSQL(2000) 8609.7MH/s
PeopleSoft 8620.3MH/s
MSSQL(2005) 8636.4MH/s
OracleS 8565.0MH/s
DomainCachedCredentials(DCC),MSCache 11195.8MH/s
osCommerce,xt 12883.7MH/s
JuniperNetscreen/SSG(ScreenOS) 12946.8MH/s
Skype 12981.9MH/s
HalfMD5 15255.8MH/s
Cisco-PIXMD5 16407.2MH/s
Cisco-ASAMD5 17727.2MH/s
LM 18382.7MH/s
DES(PT=$salt,key=$pass) 19185.7MH/s
NetNTLMv1-VANILLA/NetNTLMv1+ESS 22308.5MH/s
MD5 24943.1MH/s
PostgreSQL 25068.0MH/s
Joomla<2.5.18 25072.2MH/s
SipHash 28675.1MH/s
Plaintext 37615.5MH/s
MD4 43722.9MH/s
NTLM 41825.0MH/s
MySQL323 51387.0MH/s
*SpeedbasedonNVIDIAGTX1080RunningHashcatv3.6

NOTES