Internet Survival Guide 2016
Internet_Survival_Guide_-_2016
Internet_Survival_Guide_-_2016
User Manual:
Open the PDF directly: View PDF ![]() .
.
Page Count: 489 [warning: Documents this large are best viewed by clicking the View PDF Link!]
1
2016 Internet Survival Guide
An Edited Guide of How to Stay Safe on the Internet
By: DADOES
2
PREFACE..........................................................................................................................................................................12
ADECLARATIONOFTHEINDEPENDENCEOFCYBERSPACE...............................................................................................13
GOVERNMENTCORRUPTIONANDYOURRIGHTSTOPRIVACY,ENCRYPTION,FREEDOM,ANDPEACEOFMIND.............15
INTRODUCTION........................................................................................................................................................................15
GOVERNMENTINFRINGEMENTONPRIVACY..................................................................................................................................16
METADATA.............................................................................................................................................................................23
MANINTHEMIDDLE(MITM)....................................................................................................................................................24
YOURRIGHTSTOPRIVACY.........................................................................................................................................................24
WHYNOTWINDOWS–....................................................................................................................................................27
RESTRICTIONS.........................................................................................................................................................................27
THESMALLPRINTINTHECONTRACT.............................................................................................................................................27
THEMEANINGBEHIND..............................................................................................................................................................28
MOREDETAILSONRESTRICTIONS................................................................................................................................................28
POORSUPPORTFOROPENSTANDARDS.........................................................................................................................................29
STANDARDSTHATCHANGEALLTHETIME......................................................................................................................................29
DEFAULTPROGRAMSYOUCAN'TUNINSTALL..................................................................................................................................30
MONOPOLISTICPRACTICES.........................................................................................................................................................30
WHATABOUTSOURCECODE?....................................................................................................................................................30
INSECURITYMEANSBUSINESS.....................................................................................................................................................31
YOUCANTRUSTFREESOFTWARE.................................................................................................................................................31
PROFESSORNORMMATLOFF’SBEGINNER’SGUIDETOINSTALLINGANDUSINGLINUX..................................................32
1BACKGROUNDNEEDED...........................................................................................................................................................32
2INSTALLTOWHERE?..............................................................................................................................................................32
3WHICHLINUXDISTRIBUTIONISBEST?......................................................................................................................................32
4INSTALLATION.......................................................................................................................................................................33
4.1TheShortAnswer.....................................................................................................................................................33
4.2InstallingLinuxtoaUSBKeyorExternalHardDrive................................................................................................33
4.2.1InstallationMethodI(forSlaxLinux)....................................................................................................................33
4.2.2OtherMethods......................................................................................................................................................34
5POSTINSTALLATIONCONFIGURATION.......................................................................................................................................34
5.1ConfiguringYourSearchPath(“Whycan’tIrunmya.out?”)..................................................................................34
5.2ConfiguringaPrinter................................................................................................................................................34
5.3SwitchingfromGNOME/UbuntuUnity....................................................................................................................34
5.4ConfiguringKDE/GNOMEforConvenientWindowOperations................................................................................35
5.4.1AutoraiseEtc.........................................................................................................................................................35
6SOMEPOINTSONLINUXUSAGE...............................................................................................................................................35
6.0.2UbuntuRootOperations.......................................................................................................................................35
6.1MoreonShells/TerminalWindows..........................................................................................................................36
6.2CutandPasteWindowOperations..........................................................................................................................36
6.3MountingOtherPeripheralDevices.........................................................................................................................36
6.3.1MountPoints.........................................................................................................................................................36
6.3.2UsingUSBDevices.................................................................................................................................................37
7LINUXAPPLICATIONSSOFTWARE..............................................................................................................................................37
7.1GUIVs.TextBased...................................................................................................................................................37
7.2MyFavoriteUnix/LinuxApps....................................................................................................................................38
7.2.1TextEditing............................................................................................................................................................38
7.2.2WebBrowsingandJava........................................................................................................................................38
7.2.3HTMLEditing.........................................................................................................................................................38
3
7.2.4Compilers...............................................................................................................................................................38
7.2.5IntegratedSoftwareDevelopment(IDE)...............................................................................................................39
7.2.6WordProcessing....................................................................................................................................................39
7.2.7PlayingMovies,Music,Etc....................................................................................................................................39
7.2.8VideoEditing.........................................................................................................................................................41
7.2.9ImageViewing,ManipulationandDrawing.........................................................................................................41
7.2.10FTP.......................................................................................................................................................................41
7.2.11StatisticalAnalysis...............................................................................................................................................41
7.2.12VideoChat...........................................................................................................................................................41
7.2.13RuningWindowsApplicationsfromWithinLinux...............................................................................................42
7.3DownloadingNewSoftware.....................................................................................................................................42
7.3.1HowtoFindIt........................................................................................................................................................42
7.3.2AutomaticDownload/Installation.........................................................................................................................42
7.3.3Debian/Ubuntu.debFiles......................................................................................................................................43
7.3.4UsingRPMs...........................................................................................................................................................43
8LEARNINGMOREABOUTLINUX...............................................................................................................................................43
9ADVANCEDLINUXUSAGE.......................................................................................................................................................44
9.1DualBootIssues.......................................................................................................................................................44
9.2LiveCDsorUSBKeyBasedLinuxAsRescueTools....................................................................................................44
9.3Troubleshooting.......................................................................................................................................................45
9.3.1Tools......................................................................................................................................................................45
9.3.2WiFiNetworking....................................................................................................................................................45
9.3.3GeneralInformation..............................................................................................................................................45
9.3.4NetworkManagementTools.................................................................................................................................46
9.3.5IndividualLinuxNetworkCommands....................................................................................................................46
9.3.6IfYouHaveaProblem...........................................................................................................................................47
9.3.7AProgramFreezes................................................................................................................................................48
9.3.8ScreenFreezes.......................................................................................................................................................48
9.4AccessingYourWindowsFilesfromLinux................................................................................................................48
AWHATISLINUX?..................................................................................................................................................................49
BWHATISPARTITIONING?.......................................................................................................................................................50
B.1PartitioningUsingGParted......................................................................................................................................50
TOR–THEONIONRELAY.................................................................................................................................................52
TOR:OVERVIEW......................................................................................................................................................................52
Topics.............................................................................................................................................................................52
OVERVIEW..............................................................................................................................................................................52
WHYWENEEDTOR..................................................................................................................................................................53
THESOLUTION:ADISTRIBUTED,ANONYMOUSNETWORK.................................................................................................................53
STAYINGANONYMOUS..............................................................................................................................................................55
THEFUTUREOFTOR.................................................................................................................................................................55
TAILS...............................................................................................................................................................................56
ONLINEANONYMITYANDCENSORSHIPCIRCUMVENTION..................................................................................................................56
TOR.......................................................................................................................................................................................56
I2P.......................................................................................................................................................................................57
USEANYWHEREBUTLEAVENOTRACE..........................................................................................................................................57
STATEOFTHEARTCRYPTOGRAPHICTOOLS...................................................................................................................................57
WHAT'SNEXT?........................................................................................................................................................................58
INSTALLINGTAILS............................................................................................................................................................59
MANUALINSTALLATIONUSINGLINUX..........................................................................................................................................59
MANUALINSTALLATIONUSINGWINDOWS....................................................................................................................................61
MANUALINSTALLATIONUSINGMAC...........................................................................................................................................65
4
JOLLYROGER’SSECURITYTHREADFORBEGINNERS........................................................................................................67
INTRODUCTIONTOSECURECOMMUNICATIONTOR,HTTPS,SSL.....................................................................................68
PGP,TAILS,VIRTUALBOX....................................................................................................................................................69
PGPCONTINUED.................................................................................................................................................................72
WHOLEDISKENCRYPTIONANDFILESHREDDING...............................................................................................................74
JAVASCRIPTVULNERABILITIESANDREMOVINGPERSONALMETADATAFROMFILES.........................................................76
GENERALSECURITYPRECAUTIONSWHENPOSTINGONLINE,LEARNFROMOTHERS'MISTAKES.......................................78
EXIFDATA............................................................................................................................................................................79
RETAININGALAWYER,HOWTOHANDLEGETTINGCAUGHTORINTERROGATED..............................................................80
COMBININGTORWITHAVPN.............................................................................................................................................81
COMBININGTORWITHAVPNCONTINUED........................................................................................................................84
TRACKINGCOOKIES.............................................................................................................................................................87
LEARNINGFROMOTHERS'MISTAKES.LIBERTAS,DPR,SABU,LULZSEC..............................................................................88
HOWFARWILLLAWENFORCEMENTGO?..........................................................................................................................89
FRAUDULENTPRIVATEMESSAGES......................................................................................................................................92
LEARNINGFROMOTHERS'MISTAKES.HOWTHEYBUSTEDSABU.......................................................................................93
LEARNINGFROMOTHERS'MISTAKES.SABUBECAMEFBIINFORMANTANDBETRAYEDJEREMYHAMMOND...................96
WHEREYOUMIGHTCONSIDERRUNNINGTO,IFYOUHADNOOTHERCHOICE..................................................................99
SECURINGYOURACCOUNTFROMFBIMONITORING.......................................................................................................101
HOWTOCONNECTTOTOROVERTOPOFTOR.................................................................................................................103
HOWTOVERIFYYOURDOWNLOADEDFILESAREAUTHENTIC..........................................................................................104
VERIFYINGSIGNEDMESSAGESWITHSIGNATURESANDSIGNINGYOUROWNMESSAGES...............................................109
ANEXAMPLEOFREALLYBADOPSECSMARTENUP!........................................................................................................112
TORCHAT..........................................................................................................................................................................114
OBTAINING,SENDINGANDRECEIVINGBITCOINSANONYMOUSLY..................................................................................116
CLEARNETVSHIDDENSERVICESWHYYOUSHOULDBECAREFUL...................................................................................120
THEYAREWATCHINGYOUVIRUSES,MALWARE,VULNERABILITIES...............................................................................121
MONITORINGYOUWITHANANTENNA............................................................................................................................124
COOKIES&JAVASCRIPTREVISITED,PLUSFLASHCOOKIESANDOTHERBROWSERTRACKING..........................................127
AFEWRECOMMENDATIONS............................................................................................................................................129
COLDBOOTATTACKS,UNENCRYPTEDRAMEXTRACTION................................................................................................130
THESTRENGHOFCRYPTOGRAPHYANDANONYMITYWHENUSEDPROPERLY.................................................................136
ANOTHERSCAMEMAILBEWARE....................................................................................................................................138
ANINTRODUCTIONTOANEXPERTONOPSEC,PLUSMD5&SHA1CHECKSUMS.............................................................139
ITISOBVIOUSWHENYOUAREUSINGTOR.......................................................................................................................142
AREYOUUSINGSAFEMAIL.NET?.....................................................................................................................................143
LOCALBITCOINSPART1POLICEAREWATCHINGIT!........................................................................................................144
LOCALBITCOINSPART2THIEVES,SCAMMERSANDCOUNTERFEITBILLS!.......................................................................147
LOCALBITCOINSPART3MORESCAMSTORIES................................................................................................................151
LOCALBITCOINSPART4SELLERSBUSTEDFORMONEYLAUNDERING.............................................................................154
HIDINGTORFROMYOURISPPART1BRIDGESANDPLUGGABLETRANSPORTS............................................................156
CAPABILITIESOFTHENSA.................................................................................................................................................165
WHYYOUSHOULDALWAYSBACKUPYOURDRIVES,ESPECIALLYENCRYPTEDDRIVES.....................................................166
BITCOINCLIENTSINTAILSBLOCKCHAINANDELECTRUM...............................................................................................167
YETANOTHEREXAMPLEOFHOWSTRONGCRYPTOPGRAPHYANDPROPEROPSECCANPROTECTEVENPEDOPHILES....169
DENIABILITY,IDENTIFYINGTAILSUSERS,ANDCANYOUBEFORCEDTOGIVEUPYOURPASSWORDS?............................174
SECURITYCULTURE:AHANDBOOKFORACTIVISTS........................................................................................................181
INTRODUCTION:.....................................................................................................................................................................181
SECURITYWHATITIS,WHYWENEEDITANDHOWWEIMPLEMENTIT...............................................................................................182
SOWHATISASECURITYCULTURE?...................................................................................................................................182
WHATNOTTOSAY............................................................................................................................................................182
THREEEXCEPTIONS...........................................................................................................................................................183
SECURITYMEASURES........................................................................................................................................................183
5
SECURITYVIOLATINGBEHAVIOURS..................................................................................................................................184
EDUCATETOLIBERATE......................................................................................................................................................184
DEALINGWITHCHRONICSECURITYPROBLEMS................................................................................................................185
ABRIEFPRIMERONTHECANADIANSTATESECURITYAPPARATUS...................................................................................................185
ANOVERVIEWOFDOMESTICINTELLIGENCEORGANIZATIONS........................................................................................186
THECOUNTERINSURGENCYMODEL................................................................................................................................187
EVERYTHINGYOUEVERWANTEDTOKNOWABOUTINFORMERSANDINFILTRATORS...........................................................................188
CRYPTOANARCHYANDVIRTUALCOMMUNITIES..........................................................................................................190
EXTENDEDABSTRACT..............................................................................................................................................................190
1INTRODUCTION...................................................................................................................................................................191
2MODERNCRYPTOGRAPHY.....................................................................................................................................................192
3VIRTUALCOMMUNITIES.......................................................................................................................................................193
4OBSERVABILITYANDSURVEILLANCE........................................................................................................................................194
5CRYPTOANARCHY...............................................................................................................................................................194
6TRUENAMESANDANONYMOUSSYSTEMS...............................................................................................................................195
7EXAMPLESANDUSES...........................................................................................................................................................196
8COMMERCEANDCOLONIZATIONOFCYBERSPACE......................................................................................................................197
9IMPLICATIONS.....................................................................................................................................................................197
10HOWLIKELY?...................................................................................................................................................................198
11CONCLUSIONS..................................................................................................................................................................199
12ACKNOWLEDGMENTS.........................................................................................................................................................200
13REFERENCESANDNOTES....................................................................................................................................................200
THECRYPTOPARTYHANDBOOK.....................................................................................................................................203
1INTRODUCINGCRYPTOPARTY.....................................................................................................................................211
1.1ABOUTTHISBOOK...........................................................................................................................................................211
1.2ACRYPTOPARTYMANIFESTO..............................................................................................................................................213
1.3HOWTOCRYPTOPARTY.....................................................................................................................................................215
1.4PARTYLIKEIT’SDECEMBER31ST1983.................................................................................................................................218
1.4.1WhatisCryptoParty?..........................................................................................................................................218
1.5PREFACE.........................................................................................................................................................................218
1.6WHYPRIVACYMATTERS....................................................................................................................................................219
2UNDERSTANDINGEMAIL.............................................................................................................................................220
2.1BASICTIPS.......................................................................................................................................................................220
2.1.1Inbrief:.................................................................................................................................................................220
2.1.2Passwords............................................................................................................................................................220
2.1.3ReadingEmailinPublicPlaces.............................................................................................................................221
2.1.4CacheCunning......................................................................................................................................................221
2.1.5Securingyourcommunication..............................................................................................................................222
2.1.6DNSSEC&DANE...................................................................................................................................................222
2.1.7AccountSeparation..............................................................................................................................................222
2.1.8Anoteabouthostedemail...................................................................................................................................223
2.2TYPESOFEMAIL................................................................................................................................................................223
2.2.1Remotelyhostedemail(‘webmail’),resourcedusingawebbrowser..................................................................223
2.2.2Remotelyhostedemail,resourcedusinganemailprogramorusingawebbrowser..........................................223
2.2.3Contextconsiderations.........................................................................................................................................224
2.2.4Email&Metadata................................................................................................................................................224
2.2.5Selfadministeredemailserver.............................................................................................................................225
2.2.6‘Free’emailservices.............................................................................................................................................225
2.2.7Nonprofit.............................................................................................................................................................225
2.2.8Notesonemailforwarding...................................................................................................................................225
2.3FEARS.............................................................................................................................................................................225
6
2.3.1Randomabuseandtheftbymalicioushackers....................................................................................................226
2.3.2Targetedabuse,harassment,andspying............................................................................................................227
2.3.3WhenEncryptionGoesWrong.............................................................................................................................228
2.4SECURECONNECTIONS.......................................................................................................................................................228
2.4.1CanotherpeoplereadalongwhenIcheckmyemail?.........................................................................................228
2.4.2Notes....................................................................................................................................................................229
2.5SECUREEMAILS................................................................................................................................................................229
2.5.1WhatsoftwarecanIusetoencryptmyemail?....................................................................................................230
3UNDERSTANDINGBROWSING.....................................................................................................................................230
3.1BASICTIPS.......................................................................................................................................................................230
3.1.1InBrief:.................................................................................................................................................................230
3.1.2Yourbrowsertalksaboutyoubehindyourback..................................................................................................230
3.1.3Websitescantrackyouasyoubrowse................................................................................................................231
3.1.4Searchingonlinecangiveawayinformationaboutyou......................................................................................231
3.1.5Moreeyesthanyoucansee.................................................................................................................................231
3.1.6Yourrighttobeunknown.....................................................................................................................................232
3.2FEARS.............................................................................................................................................................................232
3.2.1SocialNetworkingwhatarethedangers?.........................................................................................................232
3.2.2Whocanstealmyidentity?..................................................................................................................................233
3.2.3CanIgetintroubleforGooglingweirdstuff?......................................................................................................234
3.2.4WhoiskeepingarecordofmybrowsingandamIallowedtohidefromthem?.................................................234
3.2.5HowtonotrevealmyIdentity?............................................................................................................................234
3.2.6Howtoavoidbeingtracked?................................................................................................................................234
3.3WHATHAPPENSWHENYOUBROWSE...................................................................................................................................234
3.3.1Atopographyofyou:footprints...........................................................................................................................235
3.4ACCOUNTSANDSECURITY..................................................................................................................................................237
3.4.1Canmaliciouswebsitestakeovermyaccounts?................................................................................................237
3.5TRACKING........................................................................................................................................................................238
3.5.1Howdotheytrackus?..........................................................................................................................................238
3.5.2HowcanIpreventtracking?................................................................................................................................239
3.5.3Awordofwarning................................................................................................................................................245
3.6ANONYMITY.....................................................................................................................................................................245
3.6.1Intro......................................................................................................................................................................245
3.6.2Proxy.....................................................................................................................................................................246
3.6.3Tor........................................................................................................................................................................246
3.7VPN..............................................................................................................................................................................247
4PUBLISHINGANDDISTRIBUTION.................................................................................................................................249
4.1PUBLISHINGANONYMOUSLY...............................................................................................................................................249
4.1.1SeveralDon’ts......................................................................................................................................................250
4.2ANONYMOUSEMAIL..........................................................................................................................................................251
4.2.1SendingFromThrowawayEmailAccounts.........................................................................................................251
4.2.2BeCarefulaboutwhatyousay!...........................................................................................................................251
4.3FILESHARING...................................................................................................................................................................252
4.3.1BitTorrent.............................................................................................................................................................253
4.3.2SoulSeek...............................................................................................................................................................254
4.3.3I2P........................................................................................................................................................................255
5SECURECALLSANDSMS..............................................................................................................................................256
5.1SECURECALLS..................................................................................................................................................................256
5.1.1iOSInstallingSignal............................................................................................................................................256
5.1.2AndroidInstallingRedPhone..............................................................................................................................256
5.2SECUREMESSAGING..........................................................................................................................................................256
5.2.1Android.................................................................................................................................................................257
7
6BASICEMAILSECURITY................................................................................................................................................257
6.1STARTUSINGTHUNDERBIRD...............................................................................................................................................257
6.1.1InstallingThunderbirdonWindows.....................................................................................................................257
6.1.2InstallingThunderbirdonUbuntu........................................................................................................................261
6.1.3InstallingThunderbirdonUbuntu12.04ornewer...............................................................................................261
6.1.4InstallingThunderbirdonMacOSX.....................................................................................................................263
6.1.5StartingThunderbirdforthefirsttime.................................................................................................................265
6.2SETTINGUPSECURECONNECTIONS......................................................................................................................................266
6.2.1Configurationrequirements.................................................................................................................................266
6.2.2PreparingaGmailaccountforusewithThunderbird..........................................................................................266
6.2.3ConfiguringThunderbirdtouseSSL/TLS..............................................................................................................267
6.2.4Manualsetup.......................................................................................................................................................268
6.2.5Finishingthesetup,differentencryptionmethods...............................................................................................271
6.2.6Returningtotheconfigurationscreens................................................................................................................271
6.3SOMEADDITIONALSECURITYSETTINGS.................................................................................................................................271
6.3.1Junkmailsettings.................................................................................................................................................272
6.3.2Scamdetectionandwarningsystem....................................................................................................................273
6.3.3Antivirusintegration...........................................................................................................................................274
6.3.4Setamasterpassword.........................................................................................................................................275
6.3.5Adaptivejunkmailcontrols..................................................................................................................................278
7EMAILENCRYPTION.....................................................................................................................................................280
7.1INTRODUCINGMAILENCRYPTION(PGP)................................................................................................................................280
7.1.1Usingakeypairtoencryptyourmail..................................................................................................................281
7.1.2Sendingencryptedmailstootherpeople:youneedtheirpublickey...................................................................281
7.1.3Receivingencryptedmailsfromotherpeople:theyneedmypublickey.............................................................281
7.1.4Conclusion:encryptionrequirespublickeydistribution!......................................................................................282
7.2INSTALLINGPGPONWINDOWS.........................................................................................................................................282
7.2.1InstallingPGP(GPG)onMicrosoftWindows........................................................................................................282
7.2.2InstallingwiththeEnigmailextension.................................................................................................................283
7.2.3Installationsteps..................................................................................................................................................283
7.3INSTALLINGPGPONOSX..................................................................................................................................................285
7.3.1Gettingstarted.....................................................................................................................................................285
7.3.2DownloadingandinstallingtheSoftware............................................................................................................285
7.3.3InstallingupEngimail...........................................................................................................................................293
7.4INSTALLINGPGPONUBUNTU.............................................................................................................................................295
7.5INSTALLINGGPGONANDROID............................................................................................................................................296
7.5.1APG.......................................................................................................................................................................296
7.5.2GPGenabledemailonAndroid:K9Mail............................................................................................................297
7.6CREATINGYOURPGPKEYS.................................................................................................................................................297
7.7DAILYPGPUSAGE............................................................................................................................................................306
7.7.1Encryptingattachments.......................................................................................................................................307
7.7.2Enteringyourpassphrase....................................................................................................................................307
7.7.3Receivingencryptedemails.................................................................................................................................308
7.7.4Sendingandreceivingpublickeys........................................................................................................................308
7.7.5Receivingpublickeysandaddingthemtoyourkeyring......................................................................................309
7.7.6Usingpublickeyservers.......................................................................................................................................312
7.7.7Signingemailstoanindividual.............................................................................................................................317
7.7.8Sendingencryptedmailstoanindividual.............................................................................................................318
7.7.9Automatingencryptiontocertainrecipients.......................................................................................................319
7.7.10Verifyingincomingemails.................................................................................................................................323
7.7.11RevokingyourGPGkeypair...............................................................................................................................324
7.7.12Whattodowhenyouhavelostyoursecretkey,orforgotyourpassphrase.....................................................325
7.7.13Whattodowhenyoursecretkeyhasbeenstolen,orcompromised.................................................................325
8
7.7.14Receivingarevocationcertificate......................................................................................................................325
7.7.15Preparingfortheworst:backupyourkeys........................................................................................................326
7.7.16Furtherreading..................................................................................................................................................327
7.8WEBMAILANDPGP.........................................................................................................................................................327
8SAFERBROWSING........................................................................................................................................................328
8.1WHYFIREFOX?.................................................................................................................................................................328
8.2ACCESSINGFIREFOXONUBUNTU.........................................................................................................................................328
8.3INSTALLINGONMACOSX.................................................................................................................................................329
8.4INSTALLINGFIREFOXONWINDOWS......................................................................................................................................334
8.4.1Troubleshooting...................................................................................................................................................338
8.5EXTENDINGFIREFOX..........................................................................................................................................................338
8.5.1HTTPSEverywhere................................................................................................................................................338
8.5.2Installation...........................................................................................................................................................339
8.5.3Configuration.......................................................................................................................................................340
8.5.4Usage...................................................................................................................................................................341
8.5.5IfnetworksblockHTTPS.......................................................................................................................................343
8.5.6AddingsupportforadditionalsitesinHTTPSEverywhere...................................................................................343
8.5.7EnforcingsecureHTTPSserverconnections.........................................................................................................344
8.5.8AdblockPlus.........................................................................................................................................................344
8.5.9GettingstartedwithAdblockPlus........................................................................................................................344
8.5.10Choosingafiltersubscription.............................................................................................................................345
8.5.11Creatingpersonalizedfilters...............................................................................................................................346
8.5.12EnablinganddisablingAdBlockPlusforspecificelementsorWebsites...........................................................346
8.5.13Otherextensionsthatcanimproveyoursecurity...............................................................................................346
8.6PROXYSETTINGS...............................................................................................................................................................347
8.6.1DefaultFirefoxproxyconfiguration.....................................................................................................................347
8.7USINGTOR?...................................................................................................................................................................349
8.7.1UsingTorBrowserBundle....................................................................................................................................350
8.7.2DownloadingTorBrowserBundle........................................................................................................................350
8.7.3RunningaRelayorBridge....................................................................................................................................351
8.8EXTENDINGGOOGLECHROME.............................................................................................................................................351
8.8.1DisablingInstantSearch.......................................................................................................................................351
8.8.2AdBlockforChrome..............................................................................................................................................351
8.8.3HTTPSEverywhere................................................................................................................................................351
8.8.4PrivacyFix.............................................................................................................................................................351
9PASSWORDS................................................................................................................................................................352
9.1KEEPINGPASSWORDSSAFE.................................................................................................................................................352
9.1.1Passwordlengthandcomplexity..........................................................................................................................352
9.1.2Easytorememberandsecurepasswords............................................................................................................352
9.1.3Minimizingdamage..............................................................................................................................................352
9.1.4Usingapasswordmanager..................................................................................................................................352
9.1.5Physicalprotection...............................................................................................................................................353
9.1.6Othercaveats.......................................................................................................................................................353
9.2INSTALLINGKEEPASS.........................................................................................................................................................353
9.2.1InstallingKeePassXonUbuntu.............................................................................................................................353
9.2.2InstallingKeePassonWindows............................................................................................................................354
9.2.3InstallingKeePassonMacOSX............................................................................................................................360
9.3ENCRYPTINGPASSWORDSWITHAPASSWORDMANAGER.........................................................................................................367
9.3.1EncryptingPasswordswithKeePassXonUbuntu.................................................................................................367
9.3.2EncryptingPasswordswithKeePassonWindows................................................................................................373
9.3.3EncryptingPasswordswithKeychainonMacOSX...............................................................................................379
10USINGVPN................................................................................................................................................................382
9
10.1GETTING,SETTINGUPANDTESTINGAVPNACCOUNT............................................................................................................382
10.1.1AnaccountfromacommercialVPNprovider....................................................................................................382
10.1.2SettingupOpenVPNclient.................................................................................................................................384
10.1.3Caveats&Gotchas.............................................................................................................................................385
10.2VPNONUBUNTU...........................................................................................................................................................385
10.2.1PreparingNetworkManagerforVPNnetworks................................................................................................385
10.2.2ConfiguringanOpenVPNnetwork.....................................................................................................................390
10.2.3UsingyournewVPNconnection........................................................................................................................396
10.3VPNONMACOSX.........................................................................................................................................................398
10.3.1Setup..................................................................................................................................................................398
10.4VPNONWINDOWS........................................................................................................................................................411
10.4.1Setup..................................................................................................................................................................411
10.5MAKINGSUREYOURVPNWORKS....................................................................................................................................424
11DISKENCRYPTION***TRUECRYPTCOMPROMISED***.............................................................................................425
11.1INSTALLINGVERACRYPT...................................................................................................................................................425
11.1.1InstallingonUbuntu/Debian..............................................................................................................................425
11.1.2InstallingonOSX................................................................................................................................................428
11.1.3InstallingonWindows........................................................................................................................................431
11.2USINGVERACRYPT..........................................................................................................................................................432
11.2.1CreatingaVeraCryptContainer.........................................................................................................................432
11.2.2MountingtheEncryptedVolume.......................................................................................................................438
11.2.3Whatdoesthismean?........................................................................................................................................441
11.2.4Remembertodismount!....................................................................................................................................441
11.3SETTINGUPAHIDDENVOLUME..........................................................................................................................................441
11.4SECURELYDESTROYINGDATA.............................................................................................................................................445
11.4.1AnoteonSolidStateHardDrives.......................................................................................................................446
11.4.2SecurelydeletedataunderWindows.................................................................................................................446
11.4.3SecurelydeletedataunderMacOSX..................................................................................................................448
11.4.4SecurelydeletedataunderUbuntu/Linux..........................................................................................................452
11.5ABOUTLUKS.................................................................................................................................................................460
11.5.2Encryptingadevice............................................................................................................................................461
11.5.3Usinganencrypteddevice.................................................................................................................................464
12CALLENCRYPTION.....................................................................................................................................................465
12.1INSTALLINGCSIPSIMPLE...................................................................................................................................................465
12.1.1IntroducingTheOSTNNetwork..........................................................................................................................465
12.1.2CSipSimple..........................................................................................................................................................466
13INSTANTMESSAGINGENCRYPTION...........................................................................................................................470
13.1SETTINGUPENCRYPTEDINSTANTMESSAGING......................................................................................................................470
13.1.1AndroidInstallingGibberbot............................................................................................................................470
13.1.2iOSInstallingChatSecure.................................................................................................................................470
13.1.3UbuntuInstallingPidgin...................................................................................................................................470
13.1.4OSXInstallingAdium.......................................................................................................................................470
13.1.5WindowsInstallingPidgin................................................................................................................................471
13.1.6AllOScrypto.cat...............................................................................................................................................471
13.1.7ChatLogFiles.....................................................................................................................................................472
14SECUREFILESHARING................................................................................................................................................472
14.1INSTALLINGI2PONUBUNTULUCIDLYNX(ANDNEWER)ANDDERIVATIVESLIKELINUXMINT&TRISQUEL........................................472
14.2INSTRUCTIONSFORDEBIANLENNYANDNEWER....................................................................................................................474
14.3STARTING I2P................................................................................................................................................................474
14.4ANONYMOUSBITTORRENTWITHI2PSNARK.........................................................................................................................475
10
15APPENDICES...............................................................................................................................................................476
15.1CRYPTOGRAPHYANDENCRYPTION.....................................................................................................................................476
15.1.1Encryptionexamples..........................................................................................................................................477
15.1.2AWarning!.........................................................................................................................................................477
15.1.3Historicalciphers................................................................................................................................................477
15.1.4Modernciphers..................................................................................................................................................480
15.1.5QuantumCryptography.....................................................................................................................................481
15.1.6Challenges&Implications..................................................................................................................................481
15.2GLOSSARY.....................................................................................................................................................................481
15.2.1aggregator.........................................................................................................................................................481
15.2.2anonymity..........................................................................................................................................................481
15.2.3anonymousremailer..........................................................................................................................................482
15.2.4ASP(applicationserviceprovider)......................................................................................................................482
15.2.5backbone............................................................................................................................................................482
15.2.6badware.............................................................................................................................................................482
15.2.7bandwidth..........................................................................................................................................................482
15.2.8bash(Bourneagainshell)..................................................................................................................................482
15.2.9BitTorrent...........................................................................................................................................................482
15.2.10blacklist............................................................................................................................................................482
15.2.11bluebar.............................................................................................................................................................483
15.2.12block.................................................................................................................................................................483
15.2.13bookmark.........................................................................................................................................................483
15.2.14bridge...............................................................................................................................................................483
15.2.15bruteforceattack............................................................................................................................................483
15.2.16cache................................................................................................................................................................483
15.2.17censor...............................................................................................................................................................483
15.2.18censorware.......................................................................................................................................................483
15.2.19CGI(CommonGatewayInterface)...................................................................................................................484
15.2.20chat..................................................................................................................................................................484
15.2.21cipher................................................................................................................................................................484
15.2.22circumvention...................................................................................................................................................484
15.2.23CommonGatewayInterface............................................................................................................................484
15.2.24commandlineinterface...................................................................................................................................484
15.2.25cookie...............................................................................................................................................................484
15.2.26countrycodetopleveldomain(ccTLD)............................................................................................................484
15.2.27cryptography....................................................................................................................................................485
15.2.28DARPA(DefenseAdvancedProjectsResearchAgency)....................................................................................485
15.2.29decryption........................................................................................................................................................485
15.2.30diskencryption.................................................................................................................................................485
15.2.31domain.............................................................................................................................................................485
15.2.32DNS(DomainNameSystem)............................................................................................................................485
15.2.33DNSleak...........................................................................................................................................................485
15.2.34DNSserver........................................................................................................................................................485
15.2.35DNStunnel........................................................................................................................................................486
15.2.36Eavesdropping..................................................................................................................................................486
15.2.37email...............................................................................................................................................................486
15.2.38embeddedscript...............................................................................................................................................486
15.2.39encryption........................................................................................................................................................486
15.2.40exitnode...........................................................................................................................................................486
15.2.41filesharing........................................................................................................................................................487
15.2.42filespreadingengine........................................................................................................................................487
15.2.43filter..................................................................................................................................................................487
15.2.44Firefox...............................................................................................................................................................487
15.2.45forum................................................................................................................................................................487
11
15.2.46frame................................................................................................................................................................487
15.2.47FTP(FileTransferProtocol)..............................................................................................................................487
15.2.48fulldiskencryption...........................................................................................................................................487
15.2.49gateway............................................................................................................................................................488
15.2.50GNUPrivacyGuard...........................................................................................................................................488
15.2.51GPG..................................................................................................................................................................488
15.2.52honeypot..........................................................................................................................................................488
15.2.53hop...................................................................................................................................................................488
15.2.54HTTP(HypertextTransferProtocol).................................................................................................................488
15.2.55HTTPS(SecureHTTP)........................................................................................................................................488
15.2.56IANA(InternetAssignedNumbersAuthority)..................................................................................................488
15.2.57ICANN(InternetCorporationforAssignedNamesandNumbers)...................................................................489
15.2.58InstantMessaging(IM)....................................................................................................................................489
15.2.59Intermediary.....................................................................................................................................................489
15.2.60Internet.............................................................................................................................................................489
15.2.61IP(InternetProtocol)Address..........................................................................................................................489
15.2.62IRC(Internetrelaychat)...................................................................................................................................489
15.2.63ISP(InternetServiceProvider)..........................................................................................................................489
15.2.64JavaScript.........................................................................................................................................................489
15.2.65KeePass,KeePassX...........................................................................................................................................489
15.2.66keychainsoftware............................................................................................................................................489
15.2.67keywordfilter...................................................................................................................................................490
15.2.68latency..............................................................................................................................................................490
15.2.69logfile...............................................................................................................................................................490
15.2.70lowbandwidthfilter.........................................................................................................................................490
15.2.71malware...........................................................................................................................................................490
15.2.72maninthemiddle............................................................................................................................................490
15.2.73middlemannode..............................................................................................................................................490
15.2.74monitor.............................................................................................................................................................490
15.2.75networkaddresstranslation(NAT)..................................................................................................................491
15.2.76networkoperator.............................................................................................................................................491
15.2.77node.................................................................................................................................................................491
15.2.78nonexitnode...................................................................................................................................................491
15.2.79obfuscation.......................................................................................................................................................491
15.2.80opennode.........................................................................................................................................................491
15.2.81OTR/OfftheRecordmessaging.......................................................................................................................491
15.2.82packet...............................................................................................................................................................491
15.2.83passwordmanager...........................................................................................................................................492
15.2.84pastebin............................................................................................................................................................492
15.2.85peertopeer.....................................................................................................................................................492
15.2.86perfectforwardsecrecy....................................................................................................................................492
15.2.87PrettyGoodPrivacy(PGP)................................................................................................................................492
15.2.88PHP...................................................................................................................................................................492
15.2.89plaintext..........................................................................................................................................................492
15.2.90plaintext...........................................................................................................................................................493
15.2.91privacy..............................................................................................................................................................493
15.2.92privatekey........................................................................................................................................................493
15.2.93POP3.................................................................................................................................................................493
15.2.94port...................................................................................................................................................................493
15.2.95protocol............................................................................................................................................................493
15.2.96proxyserver......................................................................................................................................................493
15.2.97Psiphonnode....................................................................................................................................................493
15.2.98privatenode.....................................................................................................................................................494
15.2.99publickey.........................................................................................................................................................494
15.2.100publickeyencryption/publickeycryptography.............................................................................................494
12
15.2.101publiclyroutableIPaddress...........................................................................................................................494
15.2.102regularexpression..........................................................................................................................................494
15.2.103remailer..........................................................................................................................................................494
15.2.104router.............................................................................................................................................................494
15.2.105rootnameserver............................................................................................................................................495
15.2.106RSS(RealSimpleSyndication)........................................................................................................................495
15.2.107scheme...........................................................................................................................................................495
15.2.108shell................................................................................................................................................................495
15.2.109SOCKS.............................................................................................................................................................495
15.2.110screenlogger...................................................................................................................................................495
15.2.111script...............................................................................................................................................................495
15.2.112smartphone....................................................................................................................................................496
15.2.113spam...............................................................................................................................................................496
15.2.114SSH(SecureShell)...........................................................................................................................................496
15.2.115SSL(SecureSocketsLayer)..............................................................................................................................496
15.2.116steganography...............................................................................................................................................496
15.2.117subdomain......................................................................................................................................................496
15.2.118threatanalysis................................................................................................................................................496
15.2.119TopLevelDomain(TLD).................................................................................................................................497
15.2.120TLS(TransportLayerSecurity)........................................................................................................................497
15.2.121TCP/IP(TransmissionControlProtocoloverInternetProtocol).....................................................................497
15.2.122Torbridge.......................................................................................................................................................497
15.2.123trafficanalysis................................................................................................................................................497
15.2.124tunnel.............................................................................................................................................................497
15.2.125UDP(UserDatagramPacket).........................................................................................................................497
15.2.126URL(UniformResourceLocator)....................................................................................................................497
15.2.127Usenet............................................................................................................................................................498
15.2.128VoIP(VoiceoverInternetProtocol)................................................................................................................498
15.2.129VPN(virtualprivatenetwork)........................................................................................................................498
15.2.130whitelist..........................................................................................................................................................498
15.2.131WorldWideWeb(WWW)..............................................................................................................................498
15.2.132Webmail.........................................................................................................................................................498
15.2.133Webproxy......................................................................................................................................................499
15.2.134WHOIS............................................................................................................................................................499
15.3THENECESSITYOFOPENSOURCE.......................................................................................................................................499
13
Preface
I was unaware of how to go about this project when I first began it. I thought that maybe I should
write all of the guides by hand using my own knowledge. However, I found that there are others who
have been able to construct specific guides in a more informative manner than myself. From this I
thought that it might be useful to use other people's guides in my work and then I would pick up where
they left off. Yet, after doing research I thought that it would be best to just combine the best guides
that I found into one document and folder. I truly hope that this guide is useful for at least one person
on the internet. I will begin this guide with a brief overview of government corruption and why you
should care about your privacy. After that, everything else is either a guide or text written by others
which I have fully credited. If there is one thing that I can say before reading this guide, it would be to
read Jolly Roger’s Guide. It is probably the most down to earth and comprehensible guide for anyone
at any skill level. Thank you for downloading and reading this file.
14
A Declaration of the Independence of Cyberspace
by John Perry Barlow <barlow@eff.org>
Governments of the Industrial World, you weary giants of flesh and steel, I come from
Cyberspace, the new home of Mind. On behalf of the future, I ask you of the past to leave us
alone. You are not welcome among us. You have no sovereignty where we gather.
We have no elected government, nor are we likely to have one, so I address you with no
greater authority than that with which liberty itself always speaks. I declare the global social
space we are building to be naturally independent of the tyrannies you seek to impose on us.
You have no moral right to rule us nor do you possess any methods of enforcement we have
true reason to fear.
Governments derive their just powers from the consent of the governed. You have neither
solicited nor received ours. We did not invite you. You do not know us, nor do you know our
world. Cyberspace does not lie within your borders. Do not think that you can build it, as
though it were a public construction project. You cannot. It is an act of nature and it grows
itself through our collective actions.
You have not engaged in our great and gathering conversation, nor did you create the wealth
of our marketplaces. You do not know our culture, our ethics, or the unwritten codes that
already provide our society more order than could be obtained by any of your impositions.
You claim there are problems among us that you need to solve. You use this claim as an
excuse to invade our precincts. Many of these problems don't exist. Where there are real
conflicts, where there are wrongs, we will identify them and address them by our means. We
are forming our own Social Contract. This governance will arise according to the conditions of
our world, not yours. Our world is different.
Cyberspace consists of transactions, relationships, and thought itself, arrayed like a standing
wave in the web of our communications. Ours is a world that is both everywhere and
nowhere, but it is not where bodies live.
We are creating a world that all may enter without privilege or prejudice accorded by race,
economic power, military force, or station of birth.
We are creating a world where anyone, anywhere may express his or her beliefs, no matter
how singular, without fear of being coerced into silence or conformity.
Your legal concepts of property, expression, identity, movement, and context do not apply to
us. They are all based on matter, and there is no matter here.
Our identities have no bodies, so, unlike you, we cannot obtain order by physical coercion.
We believe that from ethics, enlightened self-interest, and the commonweal, our governance
will emerge. Our identities may be distributed across many of your jurisdictions. The only law
that all our constituent cultures would generally recognize is the Golden Rule. We hope we
will be able to build our particular solutions on that basis. But we cannot accept the solutions
you are attempting to impose.
In the United States, you have today created a law, the Telecommunications Reform Act,
which repudiates your own Constitution and insults the dreams of Jefferson, Washington, Mill,
Madison, DeToqueville, and Brandeis. These dreams must now be born anew in us.
15
You are terrified of your own children, since they are natives in a world where you will always
be immigrants. Because you fear them, you entrust your bureaucracies with the parental
responsibilities you are too cowardly to confront yourselves. In our world, all the sentiments
and expressions of humanity, from the debasing to the angelic, are parts of a seamless
whole, the global conversation of bits. We cannot separate the air that chokes from the air
upon which wings beat.
In China, Germany, France, Russia, Singapore, Italy and the United States, you are trying to
ward off the virus of liberty by erecting guard posts at the frontiers of Cyberspace. These may
keep out the contagion for a small time, but they will not work in a world that will soon be
blanketed in bit-bearing media.
Your increasingly obsolete information industries would perpetuate themselves by proposing
laws, in America and elsewhere, that claim to own speech itself throughout the world. These
laws would declare ideas to be another industrial product, no more noble than pig iron. In our
world, whatever the human mind may create can be reproduced and distributed infinitely at no
cost. The global conveyance of thought no longer requires your factories to accomplish.
These increasingly hostile and colonial measures place us in the same position as those
previous lovers of freedom and self-determination who had to reject the authorities of distant,
uninformed powers. We must declare our virtual selves immune to your sovereignty, even as
we continue to consent to your rule over our bodies. We will spread ourselves across the
Planet so that no one can arrest our thoughts.
We will create a civilization of the Mind in Cyberspace. May it be more humane and fair than
the world your governments have made before.
Davos, Switzerland
February 8, 1996

16
Government Corruption and Your Rights to Privacy, Encryption, Freedom,
and Peace of Mind
By: DADOES
Introduction
Would you allow someone to stalk you and know where you are going to be at all times, know
what you recently purchased, know who you are talking to, what you are saying, and what you are
doing at all times?
Today we live in a world where the majority of all information is stored online in some form or
another. This information spans from simple updates of the weather to possibly some of your most
private and intimate moments sent via SMS, email, instant messaging, or other forms of
communication via internet. Some information, such as the weather, is hosted on public domains for
everyone to see while the conversations that you may have with family members, a significant other,
coworkers, etc. are usually stored on private servers owned by private companies. I am sure that the
majority of you would not like to publicly share many of the conversations that you have had with such
people. However, in recent years it has come to our attention that these intimate conversations have
been being actively monitored by the National Security Agency (NSA), Government Communications
Headquarters (GCHQ), and others. Not only are these private conversations being monitored but so are
our:
Online Banking Transactions
Pictures sent via SMS, Email, and Instant Messaging
Phone Records
Locations
Internet Browser History
Google Searches
Social Media Activity (Facebook, Twitter, Instagram, etc.)
Many people do not seem to actively have any concerns over the fact that all of these aspects of
their life are being monitored though. Some use the common “nothing to hide, nothing to fear
argument” while others use the argument that, for layman's terms, “there are bigger fish to fry than
me.” There are many problems with both of these arguments and I will go into them in further detail
later. The main point that needs to be conveyed here is why you should care that all of these parts of
your life are being monitored. First of all, if you are aware that you are constantly being surveyed then
it is more likely that you are going to be cautious as to what you will say or send through the internet.
This is what is called a chilling effect. The true definition of a chilling effect is “the inhibition or
discouragement of the legitimate exercise of natural and legal rights by the threat of legal sanction.”
This could even span as far as far as you being afraid to look up the latest news on terrorist attacks
around the world because your searches are monitored and therefore you may be associated with a
terrorist affiliation. This chilling effect also reduces creativity amongst people and their peers as well as
scrutiny to those in power... which are supposed to be given scrutiny by us, the people. Another reason
that you care is because there are people spying on every part of your life. Would you agree to let a
complete stranger set up a microphone or camera into your room and then agree to carry it around with
you everywhere you go? I most certainly think that you would not. Yet, that is exactly what you are
doing with your latest smartphones. Would you agree to show random strangers risqué pictures that
your significant other sent to you? According to this article, Edward Snowden states that such pictures

17
have been being around in underground trading circles throughout the NSA. Would you allow someone
to stalk you and know where you are going to be at all times, know what you recently purchased, know
who you are talking to, what you are saying, and what you are doing at all times? If you are a regular
user of the internet, a debit or credit card, a smartphone, or anything of the 21st century then all of this
is happening to you on a daily basis.
I will begin this guide with background information on how your internet activity has been being
monitored constantly, who is monitoring it, and what the implications are. After that I will go into the
programs and practices that you should use in order to keep your personal information safe. I have
included shortcuts to topics in the table of contents if you do not wish to read the background
information. However, if you are not familiar with it I do advise you to read it.
Government Infringement on Privacy
The modern world was shaken in 2013 by the leaks of Edward Snowden. These leaks revealed that
the NSA, GCHQ, and an overarching intelligence alliance deemed the “Five Eyes” had been
conducting mass surveillance that had only been imagined in Orwellian fiction.1 However, the uses of
mass surveillance have been around long before the Snowden leaks. In 2001, shortly after the attacks of
September 11, the program Stellarwind was implemented. Stellarwind was the code name of
information collected under the President's Surveillance Program. With this program implemented, the
United States government was able to conduct large scale data mining of the communications of
American citizens. This large scale data mining did not require warrants in order to collect the
information of American citizens. Snowden would later detail the Stellarwind program in great length
with his leaks. The amount of preparation in which the governments of the world have had leading up
to this point in mass surveillance is vast and therefore I will not be discussing it here. However, I do
plan on detailing in later on in a separate paper. What I will focus on here are the Snowden leaks and
the era which I will refer to as post-Snowden.
Snowden revealed to us what is known as the PRISM surveillance program. PRISM is the number
one source of raw intelligence for the NSA analytic reports and accounts for 91% of the NSA’s internet
traffic. This program initially began in 2007 through the Protect America Act under the Bush
Administration. Here is just one of many slides leaked by Snowden detailing the PRISM program. The
caption of the slide reads:
1 The Five Eyes intelligence alliance include Australia, Canada, New Zealand, the United Kingdom, and the United
States.

18
PROVIDERS AND DATA: The PRISM program collects a wide range of data from the nine
companies, although the details vary by provider.
I am very certain that most people use either Microsoft, Google, Facebook, YouTube, Skype, or Apple
multiple times throughout the regular day. Then carefully read the gray filled box and see just how
many items that the PRISM program naturally requests. This does not even include the “Special
Requests” field which is not touched on. From this we can extrapolate that every online
communication that we send is being recorded. Every instance of our lives: our emotions, our opinions,
arguments, intimacy, everything, is being monitored and recorded.
There is no way they could ever look through all of this information though, right? If PRISM is
recording everyones online information then it must be impossible to pinpoint certain things? Wrong.
There is a program used to query through all of the NSA's database. This program is called
XKEYSCORE. What is this program capable of? Take a look.

19
In just around three days all of the unfiltered data can be searched for certain keywords, peoples,
images, etc. Say you just happen to look up the latest news on terrorist attacks through Google. All that
has to happen is for one NSA agent to XKEYSCORE the term “terror” or “terrorism” and your name,
IP address, physical address, online banking information, emails, text messages, pictures sent, and
everything else that you have EVER looked up or done online is available to said agent. I am not sure
about you, but I do not want every interaction that I have ever had recorded. And if you're a Verizon
customer... well then give this leaked document a quick read through:

20

21

22

23

24
This document states that “Telephony metadata does not include the substantive content of any
communication, as defined by 18 U.S.C. § 2510(8), or the name, address, or financial information of a
subscriber or customer.” However, I am not one to trust the government or big businesses enough,
especially a system as big as the NSA, to not just go ahead and gather all of the information that they
can.
Then there is this document, which I will only show one slide of for now, which is a proposal to
broaden the powers for the NSA to collect data.
The statement that is the most worrisome is, “the NSA may analyze communications metadata
associated with United States persons and persons believed to be in the United States.”
In a recent article, published by The Intercept (November 30, 2015), it is stated that “The USA
FREEDOM Act, signed into law on June 2 earlier this year, gave the executive branch 180 days to
25
wind down the bulk collection program. According to the Tumblr of the Office of the Director of
National Intelligence, the government is “prohibited from collecting telephone metadata records in
bulk” starting November 29. The executive branch will now be able to obtain phone metadata by
asking the U.S. Foreign Intelligence Surveillance Court to order telecommunications companies to turn
over specific records.” This is no doubt a huge win for anti-NSA/Mass Surveillance activists. With that
stated, I am not one to easily trust the powers that are in charge. If they (the US government/ the NSA)
can and choose to directly spy on foreign governments and peoples illegally, then what makes you
think that they will not continue to conduct mass surveillance of their own people?
Metadata
All of this information might be new to you though, and therefore you may not fully understand
the terminology and the scope of it. Probably the most important and fundamental term that you will
need to understand is metadata. Most simply explained, metadata is everything about a piece of
information, apart from the information itself. So if someone or some organization is collecting
metadata then they can easily find out that you called a specific number from a specific location for X
amount of minutes. They directly have access to the content of the call, but that can easily be bypassed
even though the legality of it is in question. Truthfully though, the legality of the US government or
any of its large organizations does not matter much anymore. The governments of the United States,
United Kingdom, and others have put themselves above standards of legality. You might not think that
the collection of metadata is a big deal. They can just directly see who I contacted but not the
information? That does not seem so bad. Unless you are calling an HIV specialist/doctor, a sex hotline,
a suicide prevention hotline, or anyone else that you may not want people knowing about. Metadata is
not just applied to your phones. Your credit card/debit card purchases, locations, emails, attachments,
and just about everything else you do with your life is metadata.
I am sure most of you reading this carry a smartphone with you almost everywhere you go. That
smartphone is constantly tracking your location whether it be from your GPS being turned on or from
different radio towers pinging signals to it. Someone collecting your data would know when you are
home, when you are at work, where you go in between, if you went to a certain store, how long you
were at these places, etc. The best part for the people surveilling you is that you are doing all of the
work for them! Smartphones are a mass surveillance dream. There are other people tracking and
collecting your phone data other than the NSA. If you have the Facebook application installed on your
phone then your location is always being monitored, even when you turn off the features which allow it
to do so. Facebook also has access to your microphone, camera, images in your phones gallery, etc.
Edward Snowden, in an interview with Brian Williams, even stated that it was possible for the
government to turn your phone on when it was off, or even to be able to prevent it from being turned
off completely. From this they would be able to constantly listen in to your conversations by using your
phones microphone or even being able to use the camera on it. While Snowden does state that
intrusions like these happen to those who are specifically targeted, I would rather be safe than sorry in a
situation such as this.
Ultimately, the mass collection of metadata is an extreme intrusion of privacy and can also land
people in quite a bit of trouble. Without looking at the direct information, many situations can be blown
out of proportion or be seen in the wrong light. Activities that might appear suspicious to an NSA agent
or to a program they use are probably not suspicious at all, rather just regular searches and messages
that are misinterpreted. However, this could easily land you on a watch list and your information can
and will be monitored closer than before. This is why metadata should matter to you.
26
Man in the Middle (MitM)
A MitM attack is a simple concept to understand. Say you email your friend through unencrypted
channels and with no encryption in the email itself. If someone were to be monitoring you, or if they
are just snooping in on your unencrypted Wi-Fi connection, they would be able to intercept that email
without you or your friend ever knowing. The best way of preventing such attacks is to keep your
information encrypted and secure while also sending this information through a secure channel. I will
talk more about how to keep your information secure in later sections.
Your Rights to Privacy
If you live in the United States then you are (or at least should be) familiar with your Amendment
Rights. If not, I have included them here:
Amendment I
Congress shall make no law respecting an establishment of religion, or prohibiting the
free exercise thereof; or abridging the freedom of speech, or of the press; or the right of
the people peaceably to assemble, and to petition the Government for a redress of
grievances.
Amendment II
A well regulated militia being necessary to the security of a free state, the right of the
people to keep and bear arms shall not be infringed.
Amendment III
No Soldier shall, in time of peace be quartered in any house, without the consent of the
Owner, nor in time of war, but in a manner to be prescribed by law.
Amendment IV
The right of the people to be secure in their persons, houses, papers, and effects, against
unreasonable searches and seizures, shall not be violated, and no Warrants shall issue,
but upon probable cause, supported by Oath or affirmation, and particularly describing
the place to be searched, and the persons or things to be seized.
Amendment V
No person shall be held to answer for any capital, or otherwise infamous crime, unless
on a presentment or indictment of a Grand Jury, except in cases arising in the land or
naval forces, or in the Militia, when in actual service in time of War or public danger;
nor shall any person be subject for the same offense to be twice put in jeopardy of life or
limb; nor shall be compelled in any criminal case to be a witness against himself, nor be
deprived of life, liberty, or property, without due process of law; nor shall private
property be taken for public use, without just compensation.
27
Amendment VI
In all criminal prosecutions, the accused shall enjoy the right to a speedy and public
trial, by an impartial jury of the State and district where in the crime shall have been
committed, which district shall have been previously ascertained by law, and to be
informed of the nature and cause of the accusation; to be confronted with the witnesses
against him; to have compulsory process for obtaining witnesses in his favor, and to
have the Assistance of Counsel for his defense.
Amendment VII
In suits at common law, where the value in controversy shall exceed twenty dollars, the
right of trial by jury shall be preserved, and no fact tried by a jury, shall be otherwise
reexamined in any court of the United States, than according to the rules of the common
law.
Amendment VIII
Excessive bail shall not be required, nor excessive fines imposed, nor cruel and unusual
punishments inflicted.
Amendment IX
The enumeration in the Constitution, of certain rights, shall not be construed to deny or
disparage others retained by the people.
Amendment X
The powers not delegated to the United States by the Constitution, nor prohibited by it to
the states, are reserved to the states respectively, or to the people.
The Amendments here we will focus on are the First and Fourth Amendments. These have been hot
topics in the media lately in terms of mass surveillance and government overreach. If you are not
familiar with them then I suggest you take a closer read to them. (It's like two sentences, just go ahead
and read them again.)
The First Amendment is strictly on the right of free speech. Free speech encompasses a persons
right to say whatever they want, for the press to report on whatever they want, and the right to peaceful
protests. However, if you have been paying any attention to the news lately you would know that all
three of these aspects to free speech are being torn away from us. Now instead of having the right to
say or report on anything you want, you can only say or report anything a long as it does not scrutinize
the powers that be. These powers can be anything from a telecommunications company (AT&T for
example) to the United States Government and the organizations it controls. The act of scrutiny is what
is key here. If you break through the false veil of “power” and “superiority” that such organizations
hold then they are not seen as strong. Rather, they have been embarrassed and now feel exposed and
weak. If this does happen then be prepared to have people come after you. Ask any whistleblower or
reporter who has come up with this information in the past 20 years. One person who does come to
mind is Weev. I will not get into the backstory of who Weev is but rather what he did. Weev was on his
iPad one day and went to log into his AT&T account. In the public domain web-address, something
along the lines of www.att.com/login/query1547 (randomly thought up URL), Weev decided to merely
add one to the end of the URL. So instead of www.att.com/login/query1547 he typed in
www.att.com/login/query1548. What this ended up doing is revealing the email address of the person
who last logged-in. The email would just show up in the “Please enter your email” field of the log-in
28
process. Weev noticed this as a major security flaw and proceeded to collect all of the emails of the
people who logged in. He then sent the list, which contained email addresses from everyday citizens to
those in the military and the White House, to a journalist who proceeded to publish a story about the
security hole in AT&T's webservers. Instead of rewarding Weev with the find, or even thanking him,
they decided to file criminal charges on him. Weev wound up spending 18 months in prison over
addition as well as being labeled a “malicious hacker.” I have provided information about his story at
the end of the document in the Sources section.
So why did AT&T decide to punish Weev instead of thanking him? Because if they came out and
acknowledged that such a security flaw existed it would undermine their “power” and “superiority.” In
reality, while usually having a great but of money and overall capital, such large corporations and
organizations are not that strong. They throw up this disguise of being larger than life but it truly is all a
facade. (Funny enough, one movie that accurately portrays the underbelly of such corporations is the
1995 classic, Hackers. If you have not seen this movie then I would highly recommend it just for the
nostalgia and hilarious moments that were created around 90's cyber culture.) AT&T was able to
circumvent any real scrutiny from the main stream media (MSM) by labeling Weev as a “hacker” as
many people are often afraid of these stigmatic buzzwords. The same exact thing happened with
Edward Snowden. Instead of actually explaining the programs and organizations in question, not to
mention how Snowden was given free reign and access to all of these documents, the United States
labeled him as a traitor which is was the majority of the MSM broadcasted after the first intial days of
his leaks. And even now, in the wake of the Paris Attacks (11/13/2015) we see various governments
blaming encryption software and Edward Snowden instead of accepting that they were unable to
prevent the attacks. Mind you that the people who executed the Paris Attacks were using unencrypted
communications anyways.
This conversation of exposing people or governments in power is not a new argument. If you wish
to look up more on the relationship between those in power and those who are not then I have provided
a reading list in the Sources section. It is an interesting and intriguing read if you wish to truly
understand the relationship you have to your government or to other people who are in power over you.
On top of all of this, we are apparently not allowed to protest anymore when we are challenging
the powers that be. There are numerous protests that have been broken up (many times in violent ways)
in recent years. Some that come to mind are Occupy Wall Street and the most recent protest in Paris
over the meetings on climate change. Many times these peaceful protesters are being arrested also.
Now comes the Fourth Amendment. As I have previously shown, the NSA, GCHQ, “Five Eyes”,
and others have all been intercepting our data, looking up information on our data through
XKEYSCORE, and then storing that data for however long they choose to do so. Not even to mention
the ability to listen in through the microphone on your smartphone or laptop, and even the camera on
them as well. These countries have been in direct violation of our Fourth Amendment since 2001, most
likely even prior to that. Obtaining all of this information without going through the proper channels to
issue search warrants is strictly illegal. Yet, these governments and organizations will face no true
backlash because they have been able to ascend themselves above continental laws. The only way to
ensure that your Fourth Amendment Right is being kept true is to encrypt your data and stay safe,
which is pretty fucked up that you have to actively fight and use alternative routes in order to keep your
rights.

29
Why not Windows –
http://www.getgnulinux.org/en/windows/
Restrictions
A legal copy of Windows is expensive, but what do you get? Windows and Office are
licensed, not sold.
By using these products, we have to agree to a number of harsh restrictions. For most
Windows licenses, you can't keep the software when you change the hardware. You
sometimes can't even give your software away. Who can run the software? On which
computer? What can you do with it? The list of restrictions is long and some items are
outrageous.
The small print in the contract
Windows and Office are licensed, not sold.
No one can buy Windows or Microsoft Office: instead users purchase a permission to
use them. The license describes the terms of this permission. It is the restrictive legal
text you have to click "OK" to upon install.
You must abandon many rights to use the software.
There are a number of restrictions that you must accept by law. Restrictions on who can
use the software, what kind of revenue you may earn with it, on how you choose to
install it, restrictions on your privacy, even on whether you can give it away: the list is
long. Reading the license and enumerating your remaining rights is itself a difficult task.
An OEM (Original Equipment Manufacturer)-distributed software cannot be
transferred to another computer.
If you bought your computer with Windows or Office pre-installed (the so-called OEM
licenses, or the "shrink wrap" Windows discs), if you change computers you must buy
software again. The license is linked to one computer, and expires when the computer
dies. It is then illegal to transfer the software on another computer.
If you go to most of the free software sites you can click down a couple of levels and
find the [GNU] ,GPL (General Public License) the X license, the Apache license,
whichever terms and conditions you have to accept in order to use that software.
Now with a proprietary software company, the license is buried so you can't read it until
after you have paid for the product, then they're asking you to turn off part of your
brain, they're asking you to turn off part of your ability to work with other people and
to do business, when you use their software.
Don Marti, 2005 interview

30
The meaning behind
Companies like Microsoft like to assimilate their software to physical products, when
mentioning copyright infringement for example. Yet, proprietary software is very
different because of the restrictive license -such restrictions would be unthinkable on a
car or bicycle, for example.
Restrictions on the use of Office and Windows are so harsh, that many violations occur
everyday around us. People are tempted to buy only one version of Microsoft Office and
install it on two computers. Others keep their version of Windows when they throw their
PC away. Other people give away their second-hand Windows software when they stop
using it.
You have an alternative to breaking this law, or feeling very restrained when you abide
to it. GNU/Linux is Free Software (much better than just freeware): its GPL license is
designed to protect your rights.
More details on restrictions
It is unclear who can use, receive or buy your software.
The license is particularly unclear as to who may or may not use your version of
Windows or Office. Several sentences in the Microsoft Office license suggest it would
be illegal to let your neighbour type a letter with your version of Word on your
computer.
It is however clear in the Microsoft Windows license that you may only give or sell your
copy of Windows software to anyone if you are the first buyer. This means, that if you
buy it from the user who initially purchased it from Microsoft, then you are not able to
sell or give the software away to yet another user, even if you do not use it anymore,
even if you buy the latest software version with your new computer.
You may not lease, lend or provide commercial hosting services with the software
You cannot let professional users use your software, whether they pay for the service or
not, and whether you use a "Professional" license or not.
The upgrade is only valid for the first license you use it on
If that original license expires (for example because the computer it came on stops
working), so does the upgrade. If you purchase an upgrade, you are not allowed to use
the original software version anymore.
Educational versions are crippled
If Microsoft accepts to define you as a student or an academic, you are allowed to buy
an academic license, and install the software on three computers. But it is illegal to use it

31
for any commercial purpose "or in any way related to the operation of any business
enterprise or revenue-generating activities".
The components of the software may not be separated
It is illegal to buy Microsoft Office, then install only Word on one computer, and only
Excel on another. The Office suite is one single product.
Private information is collected
The license explicitly states that "Microsoft and its affiliates" collect technical
information gathered on your computer by the software. They "may use this information
solely to improve products or to provide customized services or technologies".
In order to activate most Microsoft products, as part of the license agreement, your
computer connects to the Microsoft servers and sends "technical" information. It can
"solely" be used for pretty much anything.
Poor support for open standards
There exist open file formats and protocols, which are standards to store and carry many
types of information, respectively. They are openly specified: they can be read by
anyone on any computer, now and in the future. Proprietary programs, however, rarely
support them.
For a long time Microsoft Office only had support for Microsoft formats. There are
many ways to write work documents, but Microsoft Office users were bound to
Microsoft Office files. People who opted without expensive Microsoft products cannot
write and read .doc files very reliably.
There are of course other ways of writing and exchanging office files, the most well-
known being the OpenDocument Format. But Microsoft isn't keen on letting Office
users exchange files anyone can read and edit. As of Microsoft Office 2007 SP2,
Microsoft finally added support for the ODF format after being pushed by the European
Commission.
Standards that change all the time
Sticking to Microsoft standards is not an easy job – unless you can afford to upgrade
very often. Ever tried to work on the same .doc file with both an Office 95 and an Office
97 computer? You'll know what we mean.
Microsoft owns the Office file formats: they change them with every new Office
version and have no obligation to keep them backwards-compatible. Saved your
presentation as a .ppt file? If you give up using Microsoft Office next year, you'll have
to rely on other communities to reverse-engineer the format, to be able to access
and modify your own work.

32
Default programs you can't uninstall
Don't want Windows Media Player on your computer? Don't use Internet Explorer
anymore? You can't uninstall these programs. They previously worked on a
standalone basis, but have been intrinsically linked with Windows – so they come in
with every PC and no one can get rid of them.
Monopolistic practices
Microsoft has a tight control over OEMs (computer manufacturers) who ship their
computers with Windows installed.
This means that no program competing with Microsoft products, be it multimedia
player, web browser, office suite, instant messaging program or other, will come pre-
installed on most computers you can buy.
It is a good thing to propose a wide range of software and services like Microsoft do;
however, designing and combining them to shut users from non-Microsoft peers is
unethical. It's not technically hard to adopt more open formats. But it means your
customers are free to choose what they do with their work – Microsoft isn't there yet.
What about source code?
The source code details the way a program works (it is effectively what programmers
write). Without it no one can understand how the software is built. It does not matter if
you can't read code: whether or not it is available directly affects any user.
No one can look inside
Windows comes without its source code. More than that: all users must abide to the
license term that says:
You may not reverse engineer, decompile, or disassemble the software.
As such, it is illegal to work out how Windows or Microsoft Word are designed. It is
even illegal to try. You are also forbidden to modify the program for any purpose.
This restriction in the license makes sure that Microsoft remain the sole organization
that understand how their products work. Windows is very much like a car that only
the original manufacturer is allowed to service.
You might say, "How do I change this recipe to take out the salt?" and the great chef
would respond, "How dare you insult my recipe, the child of my brain and my palate, by
trying to tamper with it? You don't have the judgment to change my recipe and make it
work right!"
Richard Stallman, Why Software Should Be Free

33
Insecurity means business
Whenever a flaw in Windows is discovered, it is exploited, which results in trojans,
viruses, spyware and the likes. Such nuisances delight the Windows security
industry, including Microsoft, which develops various anti-virus protections with
subscriptions.
It is a lucrative process to release flawed software that no one is allowed to change, and
then selling protection services over it (anti-virus software doesn't correct flaws: it
merely prevents viruses from exploiting them, if it is active and updated).
Microsoft will today happily sell you their own protection over their own insecurities –
it sells the poisoned apple and its antidote, separately.
You can trust free software
It comes as no surprise that proprietary software is severely lacking in terms of security, compared to
software whose source code is freely available (including GNU/Linux).
Free software means programmers can change the code to repair flaws. It means you can hire
someone to really check how secure your software is. It means you can benefit from the contributions
of a world-wide community to improve safety and reliability. Fifteen million users run GNU/Linux
without an anti-virus, in complete safety. And the servers behind search engines and banks run on it
too.
Source code is the recipe for software. How could one improve on a meal with too much salt, if
forbidden to look at the recipe used to cook it?
Using Windows and Office requires us to not ask nor search for the source of the software. Only
Microsoft developers can modify your program.
Which would you rather trust: the package you are forbidden to study, or the package with the recipe?
34
Professor Norm Matloff’s Beginner’s Guide to Installing and
Using Linux
Norm Matloff
Department of Computer Science
University of California at Davis
matloff@cs.ucdavis.edu
c 1999-2013
January 4, 2013
1 Background Needed
I have tailored the material here to beginners. No special sophistication in computers is needed. Any
typical Microsoft Windows user should be able to understand the instructions here and install Linux in
less than an hour’s time. (Do not be intimidated by the length of this document; you probably will not
have to use most of it.) Don’t worry about the length of this document. You’ll probably only need a
small part of it. For some background on the history and significance of the Linux operating system, go
to Appendix A.
2 Install to Where?
I recommend that you install Linux on your hard drive, so that you will dual-boot either your old OS
(I’ll assume Windows from now on) or Linux. After installation, each time you boot up, you will be
given a choice of whether to boot Windows or Linux. Another alternative is to install Linux on a USB
key (memory stick) or external hard drive. Still another choice is to run Linux as a virtual machine.
This is not covered in this document, but if you are a UCD student, see
http://csifdocs.cs.ucdavis.edu/documentation/archives/csif-fedora-on-a-for the easy steps.
By the way, if you have a Mac, you may have the capabilities you need without Linux, since both the
Mac OS and Linux are Unix systems.
3 Which Linux Distribution Is Best?
Linux comes in various distributions, called distros by Linux aficionados—but they are all Linux in
terms of functionality. Some of the most popular are Ubuntu, Red Hat, Fedora, Linux Mint, SuSE,
MEPIS, PCLinuxOS and so on. Remember, there are tons of good distros out there. Any of the above
would be fine, as would many others, but here is my short answer: Use Ubuntu (or one of the many
Ubuntu derivatives, such as Linux Mint). It is arguably one of the most user-friendly of the distros, and
it has a large user community you can access in the Ubuntu forum on the Web, probably the most
active one out there. I now use Ubuntu myself on my home computers, as well as on my office
computer, after years of using various other distros.
If you have an old machine, especially one with limited memory (i.e. RAM), you may wish to give
Puppy Linux or Damn Small Linux a try. I installed them (one at a time) on an old 1998 laptop with
only 64M of memory! And they take as little as 50M of disk space.
35
4 Installation
Here is the short way to install Linux on your hard drive, dual-booting with Windows.
4.1TheShortAnswer
Here you will install the Ubuntu distro, using UNetbootin as your installation tool.
For simplicity, I’ll assume you wish to install Linux to your laptop.
1. Download UNetbootin from its home page http://unetbootin.sourceforge.net/ to your hard drive. (For
further informat on UNetbootin, see http://sourceforge.net/apps/trac/unetbootin/wiki/guide.
2. Insert a USB key (memory stick). It needs to have FAT32 format. It probably came that way, but if not
then check the Web for how to fix that using your OS.
3. Run UNetbootin.
4. Click Select Distribution, and choose Ubuntu. Then choose the latest Live version in the window to the
right.
5. For Type, choose USB Drive, and for Drive, choose the drive in which your USB key is inserted.
6. Click OK.
7. After the installation to your USB key finishes, choose Exit.
8. Leaving your key in the drive, restart your laptop.
9. Select the choice labeled something like Try Ubuntu.
10. Once Ubuntu boots up, try to use the WiFi: Click on the proper icon at the top right of the screen, and
select your wireless network. If none appears, then for now, connect your machine to an Ethernet jack,
say at a public library or copy shop.
11. Follow directions. If asked whether you want third-party software to be installed, say yes.
12. Reboot (remove the USB key when the screen goes dark).
13. If WiFi didn’t work above, it should work now. You may have to click a pop-up window that asks If you
want to use the proprietary drivers.
During the installation process, there may be some mention of disk partitions. You should not have to
take action, but if you wish to know about partitions (very useful!), see Appendix B.
4.2InstallingLinuxtoaUSBKeyorExternalHardDrive
You can install Linux to a USB key or external hard drive, and boot up Linux from there whenever you
want to use Linux. (This is not the same as the USB key created from UNetbootin, which is only
temporary.)
1Unfortunately, UNetbootin does not produce Mac-bootable USB keys.
4.2.1InstallationMethodI(forSlaxLinux)
Slax is a nice, colorful and small version of Linux, at http://www.slax.org. Click on “Get Slax”
to download, and on “Read Manuals” to see how to install onto a USB key or external hard drive. It is
extremely easy!
In short:
1. Download the Slax .tar package.
2. Go to the directory (or folder, in Windows) for your USB key.
3. Unpack the .tar file from that directory.
4. Go to the boot subdirectory, and run either bootinst.sh (from Linux) or bootinst.bat (from Windows).
In the Linux case, you may need to precede your command by sudo.
4.2.2OtherMethods
You can use UNetbootin (Section 4.1), but you’ll need to make your USB installation persistent; see
http://sourceforge.net/apps/trac/unetbootin/wiki/guide. There are methods to construct your USB
installation “by hand” from an ISO file. This is complicated, and will not be pursued here.

36
5 Post-Installation Configuration
This section describes some further steps I recommend taking after your installation is finished.
5.1ConfiguringYourSearchPath(“Whycan’tIrunmya.out?”)
Most Linux distros do not include your current directory, ‘.’, in the PATH variable. Thus if for example
you compile a program and then type
a.out
the shell may tell you that a.out is not found. You are expected to explicitly specify the current
directory: ./a.out
If you consider this a problem, as I do, to remedy it in the case of the BASH shell (the default shell for
most distros), edit the file /.bash profile In the line which sets PATH, append “:.” (a colon and a dot) at
the end of the line, with no intervening spaces. Then log out and log in again, or do source
˜/.bash_profile
5.2ConfiguringaPrinter
Your Linux distribution should have some program to help you configure your printer if something
went wrong during installation. For example, if you are running the GNOME GUI, select System j
Administration j Printing.
It’s now easy to connect to a remote printer elsewhere on your network (even if it is on a Windows
machine), using Samba.
5.3SwitchingfromGNOME/UbuntuUnity
I personally don’t like the Unity window manager in GNOME. Many others feel the same way. So,
Ubuntu gives us other choices. To set them up, do
sudo apt-get install gnome-shell
At your next start, the login screen will show a symbol next to choices of login names; choose
Gnome Classic (No Effects) or whatever you like; experiment to find one that suits you.
5.4ConfiguringKDE/GNOMEforConvenientWindowOperations
5.4.1AutoraiseEtc.
You should find that windowing operations are generally easier in Linux systems than in Windows, in
the sense of requiring fewer mouse clicks, if you set things up that way. Personally, I find it annoying
in Windows that, when I switch from one window to another, I need to click on that second window. In
most Linux windowing systems, I can arrange things so that all I have to do is simply move the mouse
to the second window, without clicking on it. The term for this focus follows mouse, and we can
configure most Linux windowing systems to do this.
Also when I move from one window to another, I want the second one to “come out of hiding” and be
fully exposed on the screen. This is called autoraise, and can be configured too.
You can arrange this configuration in less than one minute’s time. Again, the exact configuration steps
will vary from GNOME to KDE, and from one version to another within those systems, so I can’t give
you the general steps here but here is how it works on GNOME in Ubuntu 12.10 or later:
Open a terminal window (ctrl-alt-t), and type
sudo gsettings set org.gnome.desktop.wm.preferences auto-raise true

37
sudo gsettings set org.gnome.desktop.wm.preferences focus-mode ’mouse’
Then log out and back in. You only need do this once.
You get check these settings using get instead of set, or use reset to revert to the original values (false
and ’click’), e.g.
sudo gsettings resset org.gnome.desktop.wm.preferences auto-raise
6 Some Points on Linux Usage
6.0.2UbuntuRootOperations
Ubuntu works like any other Linux distro, except for one important point: Ubuntu does not have a root
user account in the classic Unix sense. Instead, whenever executing a command which requires root
privileges, one precedes the command by the term sudo (“superuser do”). One is then prompted for a
password, which is the password for the first user account created at the time of installation. If you
have a lot of root-type work to do in a session, type
$ sudo –s
to create a new superuser shell, and do your work there.
6.1MoreonShells/TerminalWindows
In Microsoft Windows, most work done by most users is through a Graphical User Interface (GUI),
rather than in a command window (Start j Run j cmd). In Linux, a lot of work is done via GUIs but also
it is frequently handier to use a command window, called a terminal window. You should always keep
two or three terminal windows on your screen for various tasks that might arise. You can start a
terminal window in GNOME by typing ctrl-alt-t.
When you type commands in a terminal window, the program which reads and acts on those
commands is called a shell. (Thus a terminal window is sometimes called a “shell window.”)
I have an introduction to Unix shells, at http://heather.cs.ucdavis.edu/˜matloff/UnixAndC/
Unix/ShellIntro.html and http://heather.cs.ucdavis.edu/˜matloff/UnixAndC/Unix/CShellII.html. These
are based on the T C-shell, tcsh, but at least in the case of the first tutorials, most of the material also
applies to the more popular bash shell.
6.2CutandPasteWindowOperations
To do a cut-and-paste operations, hold down the left mouse button and drag it to highlight the text you
wish to copy. Then go to the place you wish to copy that text, and simultaneously push both the left and
right buttons. Generally, more things are cut-and-pastable in Linux than Windows, so this is a big
convenience.
6.3MountingOtherPeripheralDevices
This section explains how to use DVDs, USB devices and so on under Linux. You may wish to review
Section B before continuing.
6.3.1MountPoints
Each I/O device that contains a file system must be mounted, i.e. associated with some directory. That
directory is called a mount point. The files then appear in that directory.
These days most Linux distributions have a designated directory for mount points for DVD/CD-ROMs,
USB devices, floppy disks, etc. This will vary from one distribution to another, but typical directory
names are /mnt, /media etc. You can check what is currently mounted by running the df command from

38
a shell window (another good Linux learning experience). The mount points are listed along with the
/dev files. Also, to list the /dev files for all your operating drives including USB flash drives and
including drives not mounted, type
sudo fdisk
- For more detailed information, such as file system types, just run mount without any arguments.
Your machine’s internal hard drives, and possibly other devices, will be mounted automatically at boot
time. This is controlled by the entries in the file /etc/fstab. The details are an advanced topic, but even
without understanding everything, you might find it worthwhile to take a quick look at that file. Here is
a line from the file on my office machine,
/dev/sda3 /usr/home ext3 defaults 0 2
Here /dev/sda3 is the third partition (’3’) on my first SATA hard drive (‘a’). The entry says that this
partition has an ext3 type filesystem in it, and is to be mounted at the directory /usr/home. The
remaining entries concern things such as backup and file system checks.
When you attach a device to your machine after bootup, your system will probably recognize it
immediately, and maybe pop up a window showing the device’s contents. If you have trouble, you can
use the Unix mount command. This is an advanced command, but just to give you an idea, a typical
usage would be
mount -t iso9660 /dev/hdc /mnt/yyy
This tells Linux that the I/O device corresponding to /dev/hdc, our CD-ROM, should be mounted at the
directory /mnt/yyy. If that directory doesn’t exist, you must create it first, using mkdir. The field -t
iso9660 says that the file system type is ISO9660. This is standard for CD-ROMs, and you can
probably omit it. Use umount to unmount. It’s not safe to remove a USB device without running this
first.
6.3.2UsingUSBDevices
USB drives, including memory sticks, should have their filesystems mounted automatically when you
attach them. Use the df command to check where they’ve been mounted (it could be in the directory
/mnt/ /media etc.).USB mice should become automatically usable when you attach them.
2This might not work in some cases. If fdisk doesn’t recognize your device, try viewing the file /proc/partitions. Your
device
may appear there, say as sdb1. Then run mount as shown below, on /dev/sdb1.
7 Linux Applications Software
7.1GUIVs.TextBased
Most people prefer to use GUI-based applications. If you are one of them, rest assured that there are
tons of them available for Linux.
I do wish to mention, though, that many “super hard core” Linux users prefer to use text-based
applications, rather than GUI ones. For instance, I and many others like the mutt e-mail utility
(Section ??), which is text-based. Here’s why, at least in my view:
I often access my Linux machine remotely, while traveling. I might be at a university library, for
instance, or at the business center in a hotel, and be “stuck” with a Windows machine, and logging in to
my Linux machine via an SSH connection.4 This limits me to text.

39
It’s very important to me that I use the same text editor for all my computer applications—e-mail,
programming, word processing, etc.—so that I can take advantage of all the abbreviations, shortcuts and
so on which I have built up over the years. This saves me huge amounts of typing. But most GUI
applications, e.g. e-mail utilities, have their own built-in text editors, so I can’t use mine.
I find that text-based applications often have more features, are better documented, etc. For example, I
often wish to automate certain processes, such as uploading files to another machine, and typically text-
based programs do this better. However, in listing my favorite applications in Section 7.2 below, I’ve
made sure to list both text-based and GUI programs.
7.2MyFavoriteUnix/LinuxApps
In Ubuntu, one downloads new apps using apt-get, which I’ll use in my examples here. The same is
true for other distros derived from Debian. In Fedora, use yum.
7.2.1TextEditing
I use a modern extension to the vi editor, vim. This is the version of vi which is built in to most Linux
distros. See my tutorial at http://heather.cs.ucdavis.edu/˜matloff/vim.html.
Note: In some Fedora distros, somehow the version of vim that is linked to vi isn’t configured fully
correctly. I suggest using /usr/bin/vim directly. Even though vim is text-based, it does have a GUI
version too, gvim. This comes with nice icons, allows you to do mouse operations, etc. Unfortunately,
most Linux distros seem to have only the text-based program. To get the GUI, you can download it
yourself. In Ubuntu, do
sudo apt-get install vim-gnome
For this, you may need to edit /etc/apt/sources.list and uncommented the lines for Canonical’s ’partner’
repository.
7.2.2WebBrowsingandJava
Your Linux distro will come with a Web browser, probably Firefox, and possibly Konqueror in
addition. I usually use Firefox. Chrome is nice, but I really like the plugins available for Firefox.
But believe it or not, sometimes I use the famous text-based browser, lynx. In some cases, it is just
plain quicker and easier. Moreover, you can do cool tricks, such as recording keystrokes for later
playback, thus enabling one to do certain Web operations automatically.
If you use Ubuntu, your system may not be configured for Java in Web browsing. If so, do
sudo apt-get install openjdk-7-jre
sudo apt-get install icedtea-7-plugin
7.2.3HTMLEditing
I usually use Vim, along with some macros I’ve written for HTML editing, but I sometimes use
Amaya, which is a full-featured GUI HTML editor, written by the Web policy consortium. One nice
feature is that you can actually use the embedded Web links, good for testing them. See my tutorial at
http://heather.cs.ucdavis.edu/˜matloff/amaya.html. There are many newer and more powerful packages,
such as Quanta+, Bluefish and NVu.
7.2.4Compilers
Some distros come with the GCC suite. Ubuntu, for example, does not, but it can be downloaded via
sudo apt-get install build-essential
# may need to do this separately:
sudo apt-get install libc6-dev # C library

40
7.2.5IntegratedSoftwareDevelopment(IDE)
For programming work, I rarely use IDEs, as they are slow to load, take up too much space, and often
don’t allow me to use my own text favorite editor. I find that the vim editor (cited above) and the ddd
GUI interface to the gdb debugging tool, work great together. For example, in vim I can type: make
(which I have aliased to just M, or with gvim click on the make icon, and the source code I’m
debugging will be recompiled. And as I’ve mentioned, it’s important to me that I use the same text
editor for all applications, which most IDE would not allow me to do. I use either GDB (try CGDB!) or
DDD for my debugging tool. See my tutorials at http://heather.cs.ucdavis.edu/˜matloff/vim.html and
http://heather.cs.ucdavis.edu/˜matloff/debug.html.
DDD is also usable with my favorite programming language, Python.
However, if you love IDEs, try Eclipse. I’ve got a tutorial that is more complete than most, at http:
//heather.cs.ucdavis.edu/˜matloff/eclipse.html. It can be used with C, C++, Java,
Perl, Python and many others.
Another system that has become quite popular is NetBeans. For R programming, RStudio and StatET
are both first-rate.
7.2.6WordProcessing
I use LATEX because of its flexibility, its beautiful output, and its outstanding ability to do math. You
may like Lyx, which is a great GUI interface to LATEX which is especially good for math work. See
my tutorials
at http://heather.cs.ucdavis.edu/˜matloff/latex.html and http://heather.cs.ucdavis.edu/˜matloff/lyx.html.
Install by running
sudo apt-get install texlive
# you may also need:
sudo apt-get install texlive-fonts-recommended
If you wish to work with files compatible with the Microsoft Office environment, there is a free suite of
programs, OpenOffice, which provide Microsoft compatibility. It is packaged with most Linux
distributions. If you would like something that quickly converts an Office file to rough text form, say to
use with e-mail attacments, try Antiword. In Ubuntu, install via
sudo apt-get install antiword
7.2.7PlayingMovies,Music,Etc.
MPlayer is free and outstanding. Its capabilities are amazingly broad.
The documentation is extensive, and hard to navigate, but here are a couple of things to get you started:
Installation: It’s easy in Ubuntu:
sudo apt-get install mplayer
sudo apt-get install mencoder
Otherwise, build it yourself, as follows
.
One downloads the source code, MPlayer-1.0pre7try2.tar.bz2 and the codecs, essential-
20041107.tar.bz2,
from www.mplayerhq.hu/design7/dload.html.
Unpack the codecs file first,
tar xfj essential-20041107.tar.bz2

41
This creates a new directory. Copy the contents of that directory to the directory /usr/local/lib/codecs
(use mkdir to create it if necessary). (Note: There may be legality issues with some codecs. When in
doubt about a particular codec, you should obtain it from a site like Fluendo that offers it for a nominal
fee, See a discussion at http://fedoraproject.org/wiki/CodecBuddy.
Now, unpack the source code file, and go into the directory it creates. Then go through the usual
sequence for building open-source software from source:
configure
make
make install
Note that if you want to use the GUI, the configure command should be
configure --enable-gui
After make install is done, you will probably get a message something like
*** Download font at http://www.mplayerhq.hu/dload.html
*** for OSD/Subtitles support and extract to
/usr/local/share/mplayer/font/
*** Download skin(s) at http://www.mplayerhq.hu/dload.html
*** for GUI, and extract to /usr/local/share/mplayer/skins/
The fonts are needed for the subtitles (and for the GUI, if you use it). Just the iso1 font is needed.
Download the font package, go to the indicated directory (/usr/local/share/mplayer/font/ in the above
example), and then do the unpack operation. This will produce a subdirectory, e.g. font-arial-iso-8859-
1.
Viewing a video:
To play a video or audio file, say x.avi, type
mplayer x.avi
If you specify several files, as a playlist, it will play them all. Hit the Enter key if you want to skip the
rest of the current file and go to the next one.
You have the following controls:
right and left arrow keys to go back or forward 10 seconds
down and up arrow keys to go back or forward 1 minutes
PgDown and PgUp keys to go back or forward 10 min
left- and right-bracket keys to decrease/increase speed by 10%, or left- and right-brace for 50%;
Backspace key to return to normal speed
Space bar to pause, then . to go forward frame by frame, Space bar to resume play
f to go full screen
q to quit
You can use mplayer, actually mencoder, which comes with the package, to do format conversion, e.g.
AVI to MPG, change aspect ratio, and even do some primitive editing.
There are many, MANY,MANYdifferent options. You may wish to try other players, e.g. VLC.
7.2.8VideoEditing
Try Kino, Cinelerra, LiVES and many others.

42
7.2.9ImageViewing,ManipulationandDrawing
I use xpdf to view PDF files, though Acroread for Linux is available. I like the fact that xpdf allows me
to copy ASCII text from the file. Others popular with Linux are evince, okular and MuPDF. For
collections of JPEG files and the like, I use xzgv, gqview and gwenview; for viewing a single image, I
use qiv.
Want something like Adobe Photoshop? The GIMP program is quite powerful, and free. It’s included
with most Linux distributions.
You can use GIMP to draw, but for “quick and dirty” tasks, I would suggest Dia, at
http://www.gnome.org/projects/dia/.
7.2.10FTP
I usually use the text-based ftp and sftp, the latter being an SSH version for security.
If you do frequent uploads/downloads to/from a particular site and wish to automate them, another text-
based program, yafc, is excellent. A very nice GUI program, though, is gftp, which you can download
from the Web if your Linux system doesn’t already have it. In addition to the GUI, this program also
has some functionality which ordinary FTP programs don’t have.
7.2.11StatisticalAnalysis
Use the statistical package that the professional statisticians use—R!
In my opinion from the point of view of someone with a “foot in both camps”—I’m a computer science
professor who used to be a statistics professor—the R statistical package is the best one around,
whether open source or commercial. It is statistically modern and correct, and it also is a general-
purpose programming language.
I have a tutorial on R at http://heather.cs.ucdavis.edu/˜matloff/r.html.
Install via
sudo apt-get install r-base
7.2.12VideoChat
Currently, this is an area in which many Linux distros need work. Ubuntu comes with Ekiga, which
works best if the person you’re chatting with has Ekiga too. Skype has a Linux version, which many
people use, but some have found to have problems. As of this writing, Google does not offer Google
Talk for Linux. However, Empathy can be used. There are driver issues for some Webcams. Those
using the UVC protocol are supposed to work on Linux, with the uvcvideo driver that comes with
Linux. But again, there may be problems.
7.2.13RuningWindowsApplicationsfromWithinLinux
I am simply not a Windows user, but on occasion there is a Windows program I need to run from
within Linux. The simple way, if it works, is the WINE Windows emulator. Your distro may include it
(type which wine in a terminal window to check); if not, download it, with for example the Ubuntu
command being
udo apt-get install wine
For more involved applications, you may wish to try one of the virtual machine packages. See http:
//heather.cs.ucdavis.edu/˜matloff/vm.html for a brief introduction.
7.3DownloadingNewSoftware
There is a vast wealth of free software for Linux on the Web. Here’s how to obtain and install it.

43
7.3.1HowtoFindIt
These days most downloads and installs are done automatically, say with yum or apt-get, as seen in
Section 7.3.2 below. That helps you find it too. If you want to find application Z, instead of plugging
“Z” into Google, plug “yum install Z” or “apt-get install Z” so as to narrow down the volume of
response.
5In some respects, it’s even better than S, the commercial product it is based on.
7.3.2AutomaticDownload/Installation
In recent years, most Linux distros have made it very easy to download and install new software. In
Fedora, for instance, one uses the yum command. For example, to download the program yafc
mentioned above, one simply types yum install yafc. In Ubuntu, there is the apt-get command, which
works similarly. For instance, to download the xpdf PDF viewer, I typed
sudo apt-get install xpdf
(See Section 6.0.1 for an explanation of sudo. Ubuntu may ask you to install from your CD-ROM, but
yours may be incomplete. If so, comment out the first line of /etc/apt/sources.list; this is the line telling
Ubuntu to install from the CD-ROM.) For those who prefer GUIs, Ubuntu offers the Synaptic package
manager. With both yum and apt-get, one can direct where to download from, by making the proper
entries in the file etc/apt/sources.list. For instance, for the R statistical package above, apt-get may not
find it on its own, in which case we can add a line
deb http://cran.stat.ucla.edu/bin/linux/ubuntu gutsy/
to etc/apt/sources.list, telling apt-get that here is an alternative place it can look. (This is for the Gutsy
edition of Ubuntu.)
By default apt-get will try to retrieve your requested program from your installation CD/DVD. You can
change this by commenting-out the line in etc/apt/sources.list that begins with
deb cdrom:
Sometimes it may not be clear which package name to use with yum or apt-get. For instance, to install
the GCC compiler, C library and so on, the command is
sudo apt-get install build-essential
How did I learn this? I did a Web search for “apt-get GCC.”
To install the curses library (and include file), do
sudo apt-get install libncurses5-dev
7.3.3Debian/Ubuntu.debFiles
The Debian distro of Linux uses its own packaging for downloaded programs, which you’ll see as files
whose names have a .deb suffix. Ubuntu, as a derivative of Debian, uses this too.
Usually you will not need to work directly with these files, since you will use apt-get or Synaptic. But
if you do download such a file directly from the Web, use gdebi to install it; the GUI version is gdebi-
gtk.
7.3.4UsingRPMs
Though the methods in Section 7.3.2 have now made RPMs less important, you may find that the
software you want comes in an RPM package, with a.rpm suffix in its name. To install such a package,

44
type rpm -i package_file_name If you later wish to remove, i.e. uninstall a package, you can use rpm -e
(‘e’ stands for “erase”). You do NOT have to have the RPM file present to do this. Some packages will
have different versions for different C libraries. Red Hat uses glibc. Type ls -l /lib/libc* to see which
version you have. You may find that you need some library files for a program you download, and that
you are missing those files. You can usually get these from the Web too. If a program complains about
a missing file, try the ldd command (e.g. ldd x if the name of the program which needs the library is x);
this will tell you which libraries are needed, where they were found on your system, and which ones, if
any, were not found.
8 Learning More About Linux
The only way to really learn Linux is to use it on a daily basis for all your computer work—e-mail,
word processing, Web work, programming, etc. As you do this, the expertise you’ll want to pick up
includes: file, directory and mount operations; process operations; roles of system directories (/usr, /etc,
/dev, /sbin and their various subdirectories, e.g. /usr/lib; search paths; network operation and utilities
such as netstat; and so on. Don’t try to do this all at once. Instead, take your time, and learn these
naturally, as the need arises. As you use Linux more and more in your daily computer application work
(e-mail, word processing, etc.), the needs will arise as you go along. And remember, there’s lots of help
available if you need it.
_ If you are running Ubuntu or one of its offshoots, the Ubuntu Forums, http://ubuntuforums.
org/ is an excellent resource.
Linux home page, at http://www.linux.org/Lots and lots of information is available here.
www.linux.com. Chock full of information and links.
Google’s excellent set of links to various Linux sites,
http://directory.google.com/Top/Computers/Software/Operating_Systems/Linux
Another good set of Linux links, http://www.linuxjunior.org/resources.shtml
If you are having trouble with specific hardware in your Linux installation, an excellent place to go for
detailed information is the Linux HOW-TO documentation. (For the same reason, if you are about to
purchase a machine and suspect that some of the hardware is nonstandard, you can check the
corresponding Linux HOW-TO to see if there are any problems with that hardware.
The HOW-TO documents are available at many sites, such as the one at linux.org.
There are Linux Users Groups (LUGs) in virtually every city. You can join if you wish, or just get to
know them casually. They are great sources of help! And by the way, many of them hold monthly
Linux Installfests, where you can see Linux being installed or have it installed on your own machine.
9 Advanced Linux Usage
9.1DualBootIssues
You may wish to change some parameters of your dual-boot process, e.g. change the default OS. You
can do this by editing the configuration file for your bootloader.
Most distros today use GRUB as their bootloader. Its configuration file is /boot/grub/menu.lst. By the
way, note that GRUB’s notation for partitions is (drive ID, partition number), so that for instance
(hd0,1) means the second partition in the first hard drive.
9.2LiveCDsorUSBKeyBasedLinuxAsRescueTools
Among other things, Knoppix has developed a reputation as being useful as an OS rescue/repair tool,
including for Windows! And now, most of the live CDs or USB-key based Linux installations can be
used this way. A common usage is to either fix broken files or at least make copies of important user
files. It may be, for instance, that Windows is not bootable due to corruption, but by using a Linux

45
rescue CD/USB key, we can access individual files. Here is a typical pattern. One brings up a terminal
window and then:
sudo -s # get root privileges; could try su root instead
fdisk -l # check where the partitions are
# say /dev/sda1 is of interest
mkdir x
mount /dev/sda1 x
cd x
# now you have those files at your disposal
In one case, I forgot my password on an Ubuntu netbook. I could fix it as root if I could boot up in
Ubuntu recovery mode, but unfortunately the GRUB bootloader was configured with a timeout value
of 0 seconds, giving me no way to choose recovery mode. So, I booted up Linux from a USB key
(Section 4.2), mounted my Ubuntu file system as above, and then edited the GRUB startup file,
/boot/grub/menu.lst, changing the timeout value to 5 seconds.
The preceding operations can be done by booting almost any Linux distro, but Knoppix is nicer as it
comes with two very nice utilities (both can be obtained separately as well):
testdisk: This does a lot of diagnostics on your hard drive, recover lost partitions, undelete deleted files,
fix boot sectors and so on.
ntfsfix: May be able to fix your broken NTFS partition.
photorec: Quite a program! It bypasses your (possibly broken) file system, and looks for files by going
through your hard drive literally bit by bit, looking for bytes that encode any of 180 known file types,
e.g. .jpg, .avi, .pdf etc.
9.3Troubleshooting
One of Linux’s biggest strengths is its stability. If you are tired of getting Windows’ infamous “blue
screen of death,” then Linux is the OS for you. (It is also subject to far fewer virus and other attacks
than Windows.) So emergencies are rare, but they can happen. Here are some tips for such cases.
9.3.1Tools
Here are some commands you can run in a terminal window that you can use to investigate:
ps: Tells you what processes are running. Typically one uses this with something like the ax option.
dmesg: Tells you the major events that have occurred on your machine ever since it was last booted up.
lsmod: This tells you what OS modules are installed, i.e. device drivers and the like.
lpq: Lists the current printer queue.
lsusb: Lists what USB devices are currently plugged in.
ifconfig: Lists network interfaces.
iwconfig: Lists currently operating wireless devices.
iwlist: Lists wireless access points in range.
netstat: Lists current network connections.
9.3.2WiFiNetworking
The newer versions of the major distros handle WiFi configuration pretty well without your
intervention. But if you have problems, the material in this section may be helpful.
9.3.3GeneralInformation
Below is a five-minute crash course in WiFi. Even if you don’t understand all of it, even partial
understanding may be helpful.

46
Recall that in Unix-family operating systems, I/O devices are represented as “files” in the directory /dev.
Your WiFi device is probably eth1 or wlan0.
Your WiFi device needs a driver. Many, if not most, laptops use Broadcom WiFi hardware, and in older
Linux distros, they needed some fiddling to work, but now it’s much easier (see below).
The names of wireless access points are called ESSIDs.
If you are connected to a router or a wireless access point, your machine is probably assigned an IP
address via DHCP, rather than statically. An error message like “no lease offered” means that the DHCP
process failed.
DNS servers convert an “English” address like www.google.com to a numerical address like
209.85.171.103. So your OS needs to set up a connection to a DNS server.
9.3.4NetworkManagementTools
If you are running the GNOME windows manager, select System j Administration j Network. There is
also an icon you can click in the toolbar; it looks like two black monitors when you are not connected,
and is a set of blue bars indicating signal strength when you are connected. Note that left- and right-
clicking gives different results, so try both. In KDE, select System j Network Device Control. You can
activate/deactivate your netword card during a session. In GNOME, this is done via System j
Administration j Network. The network managers included with most Linux distros are rather
primitive. An excellent alternative is WiFi Radar. In Ubuntu, install via
sudo apt-get install wifi-radar
9.3.5IndividualLinuxNetworkCommands
Useful commands from a terminal window include:
iwlist: You can determine which ESSIDs are within range of you by typing the command
$ sudo iwlist eth1 scanning
say if your wireless device is eth1.
ifconfig: Shows information about all your network interfaces, i.e. their hardware addresses, IP
addresses and so on. Lack of IP address on your wireless port, e.g. wlan0 or eth1, may indicate that
DHCP has failed. This command can also be used to set the IP address and other parameters “manually,”
deactivate/reactive a network interface, etc.
iwconfig: Shows information about all your wireless connections. Also can be used by you to specify
which access point you wish to use. For example, to select a particular wireless access point named X,
type
sudo iwconfig wlan0 essid "X"
(assuming wlan0 is your wireless interface)
.
dmesg: Shows a record of your last bootup. This may show error messages regarding yourWiFi card. It’s
pretty long, so either run it through more, i.e. run
dmesg | more
or save it to a file, say dmesg.out, and then explore the file at your leisure with a text editor.
_ route: Displays the current packet routing table.
_ ethtool: Running
ethtool eth0

47
will give you information about your Ethernet link, e.g. link speed. To get statistics on recent usage, run
ethtool --statistics eth0
Some of these must be used with root privilege. For example, running
iwlist eth1 scanning
may produce no access points, while
sudo iwlist eth1 scanning
will show you all of them.
The file /etc/resolv.conf lists the IP addresses of the DNS servers. You can add more nameserver lines if
you know of some, say from your ISP (of for that matter, other ISPs).
9.3.6IfYouHaveaProblem
These days, Linux generally does well with WiFi, and it might work for you “right out of the box,”
with no configuration on your part. If not, this section is for you. Some wireless network cards typically
sold with PCs today do not have direct Linux drivers available. A common example is the Broadcom
BCM43XX series. However, you can still operate as usual after some
preparation, as explained below.
Ubuntu: BCM43XX Series
Ubuntu handles Broadcom cards well, as long as you have Linux kernel 2.6.15 or newer. (Run dmesg if
you want to check this.) You simply need to take the following action once:
First establish an Ethernet connection to the Internet, to enable download. For example, if you have a
router at home, even a wireless one, connect your machine directly to the router with an Ethernet cable.
Then Select System j Administration j Hardware Devices (the last might be labeled Additional
Drivers). It will ask you if you want to download the Broadcom firmware, so say yes. Check the Enable
box for Firmware for Broadcom 43 Wireless Driver. You will be asked whether you want the firmware
to be downloaded from the net; say yes. Then check Enabled after the download. Know YourWiFi
Card You first need to determine which wireless card you have. On the laptop I use now, I determined
this by running dmesg and lspci under Linux. Sure enough, it turned out to be a Broadcom BCM43XX
series card. Other Cards/Kernels
For other cards, go to the ndiswrapper home page, http://ndiswrapper.sourceforge.net/.
The program ndiswrapper allows Linux to use Windows drivers.
9.3.7AProgramFreezes
If an application program freezes up and you invoked it from the command line within a shell, you can
inmost cases kill it by hitting Ctrl-c in the terminal window from which invoked it. If this doesn’t work,
run the “processes” command by typing
ps ax
in another terminal window, and noting the process number of your program. Say for concreteness that
that number is 2398. Then type
kill -9 2398

48
to kill the program. If you have a program named, say, xyz, the command
pkill -9 xyz
kills all running instances of the program.
9.3.8ScreenFreezes
What if your entire screen freezes up? Again, this should be quite rare, but it is possible. I recommend
the following remedies, in order:
_ In Gnome hit Alt F2, which will bring up a little window in which you can run a command, say pkill
as above.
_ In Gnome, hit Ctrl Alt T, which will create a new terminal window, from which you can kill the
offending program.
_ Try going to another screen! Linux allows you to switch among multiple screens. In Gnome, for
instance, you can switch to the second screen from the first via Ctrl Alt Right, and go back via Ctrl Alt
Left. Then open a terminal window in the new screen, find the process number of the program and kill
the program, as described above.
_ In Gnome, try hitting Ctrl Alt Del). This should cause an exit from Linux’s X11 windowing system but
not an exit from Linux itself. You would then get an opportunity to log in again.
Try NOT to simply poweroff the machine, as that may do damage to your files. It may not be permanent
damage, as the OS will try to fix the problems when you next reboot, but don’t just pull the plug unless
you have no other recourse.
9.4AccessingYourWindowsFilesfromLinux
At this point, most Linux distributions, except Fedora/Red Hat, give you access (at least read access) to
your Windows partition from Linux. For some of them, they may do this automatically, in which case
your Windows partition, say /dev/hda1 should be visible in the file /etc/fstab. If not, mount it yourself:
mkdir /dosc
mount /dev/hda1 /dosc
cd /dosc
You should now see your Windows files, and should be able to access them on at least a read basis. For
more information, including concerning write access, ss the Linux-NTFS Project, http://www.linux-
ntfs.org/.
A What Is Linux?
Linux is a form of the Unix operating system. Though originally Unix was used mainly by engineers
and scientists and thus was not very familiar to the general public, a lot of what you take for granted on
computer systems today began in Unix. A notable example is the Internet—the first major operating
system to implement the TCP/IP protocol at the heart of the Internet was Unix, and that led to the
general acceptance of the protocol. The Apple Macintosh operating system is based on a form of Unix,
and the Android system is based on Linux.
In the early 1990s, computer science student Linus Torvalds decided to write his own version of Unix,
which he called Linux. Other “homegrown” versions of Unix had been written, such as MINIX, but
what distinguished Linux was the scale of worldwide participation involved. Torvalds innocently put a
message on the Internet asking if anyone wanted to help, and he got a torrent of responses. There are a
several reasons why Linux is mainstream today. First, it became known as a very reliable, stable
operating system, with one result being that Linux has become a major platform for large corporate

49
Web servers. Another reason is that it is free, as is the vast majority of the software associated with it
developed elsewhere. Many companies have found that it is cheaper to run Linux on their PCs, both for
this reason and because of reduced maintenance costs. There are several good reasons for you to use
Linux:
As mentioned, Linux is becoming one of the “hottest” software systems. Virtually all of the major
companies are promoting it, and as mentioned Linux is a leading corporate choice for Web servers.
Linux is the main operating system used at , and in fact they developed their own version of Linux,
Goobuntu (a play on Ubuntu, one of the most popular versions of Linux).
Linux is also starting to make inroads in large desktop markets, such as businesses, schools and so on,
due to its high reliability, far lower rate of infection by viruses compared to Windows, and its low cost.
The Linux community shares. That means that people online are much more willing to help you, and
more open source software is available. If you are a university computer science student, there are some
very important additional advantages:
Many CS courses make specific use of Unix, and thus their work cannot be done on Windows platforms.
Since it is a full Unix system, Linux allows students to do their homework in the comfort
of their own homes. If you are new to Unix, click here for my Unix tutorial Web page at
http://heather.cs.ucdavis.edu/˜matloff/unix.html, which will introduce you to Unix file and directory
commands, and so on.
In installing and using Linux, students learn many practical things about computers which they do not
learn in coursework. This practical experience can also help you in job interviews, both for permanent
jobs after graduation and for summer jobs and internships/co-ops during your college years. Even if the
job you interview for does not involve Linux, you will definitely impress the interviewer if, for example,
you discuss various things you have done to use and customize your Linux system.
B What Is Partitioning?
It is probably not necessary for you to know the material here, and it is rather detailed, but you
may find it useful at some point. I do recommend that you take a few minutes and read this section. A
hard drive (not just for Linux) will consist of one or more partitions. A partition is a set of contiguous
space (sequential blocks) on the disk, and is treated as an independent disk.
So, assuming you want your system to include bothWindows and Linux (termed a dual boot situation,
since you can boot either system), you will need at least one partition for Windows and one (actually
two) for Linux. It’s important to understand how the naming works: In Linux systems, all I/O devices
are treated as “files.” If your first hard drive is of the IDE type, the entire drive is probably called
/dev/hda, i.e. the “file” had within the directory /dev. In the case of SATA-type hard drives, the
notation is /dev/sda etc. Your first CD-ROM/DVD drive may be /dev/hdc (your third “hard drive”),
your first USB port may be /dev/sdf1 and so on.
Partitions within, say, /dev/hda, are called /dev/hda1, /dev/hda2 and so on.
Your original Windows single partition was probably /dev/hda1 or /dev/sda1. Within a partition
you’ll have some type of file system. The disk consists simply of a long stream of bytes, with no
structure, so the OS needs to have a way of organizing them into files, recording where in that stream
each file has its bytes. But you don’t need to know the details. Windows XP and Vista use the NTFS
file system. The standard Linux file system is ext2 (number 0x83, sometimes called Linux native), or
possibly ext3, for your main Linux partition and of type swap for your swap partition (number 0x82,
used for temporary storage during the time the OS is running).PCs were originally designed to have up
to four “real” partitions, called primary partitions. After people found that to be too constraining,
logical or extended partitions were invented. You should install Linux in a primary partition, for
recovery reasons, but it is not necessary.
50
B.1PartitioningUsingGParted
Today most distros will invoke a partitioning program to do your partitioning. This could be the
famous GParted program, or one that the authors of your distro wrote themselves.
You can use GParted on your own by downloading and booting a GParted live CD (or USB key), but
I’ll assume here that your Linux installation program invokes either GParted or another program
written specifically for your distro. Since every distro will handle this a bit differently, what I will do
here is just give you an understanding of what operations need to be done, with the specific mouse
clicks needed varying from one distro to another. I’ll assume that you want your Windows and Linux
systems to coexist on the same hard drive. So when your
distro’s installer program asks you whether you want to use the entire disk, be sure to say no! Of
course, if you do want to erase Windows, or if you are installing Linux on a separate drive from
Windows, you can go ahead and use the whole drive.
Here are the main steps in GParted, roughly stated (you may see some variation):
Select the disk you wish to repartition. If you have only one disk, it will be something like /dev/hda. (See
Section B.)
Select the partition where Windows resides. This will typically cover the entire disk, and will almost
certainly be of file system type NTFS. I’ll assume that here.
Decide how much space you want to remove from the Windows partition in order to make a partition for
Linux.
Now resize, in this case shrink, the Windows partition. The partioner will ask you how much room to
make.
Adjust the partition size according to your desired value.
You’ll need to make the main Linux partition primary, of type ext2 or ext3, and set to be bootable.
You’ll need a smaller partition of type linux-swap. This is not used for files, but rather as “scratch
space” by the OS, for virtual memory and for storage when your machine is in hibernate mode.
You’ll then have to commit, i.e. save, the changes to the partitions. This might take a few minutes, so be
patient.
The next time you boot Windows; you will be asked if you want a disk consistency check. Definitely say
yes.

51
TOR – The Onion Relay
(Links route to www.torproject.org)
Tor: Overview
Topics
Overview
Why we need Tor
The Solution
Staying anonymous
The future of Tor
Overview
The Tor network is a group of volunteer-operated servers that allows people to improve their privacy
and security on the Internet. Tor's users employ this network by connecting through a series of virtual
tunnels rather than making a direct connection, thus allowing both organizations and individuals to
share information over public networks without compromising their privacy. Along the same line, Tor
is an effective censorship circumvention tool, allowing its users to reach otherwise blocked destinations
or content. Tor can also be used as a building block for software developers to create new
communication tools with built-in privacy features.
Individuals use Tor to keep websites from tracking them and their family members, or to connect to
news sites, instant messaging services, or the like when these are blocked by their local Internet
providers. Tor's hidden services let users publish web sites and other services without needing to reveal
the location of the site. Individuals also use Tor for socially sensitive communication: chat rooms and
web forums for rape and abuse survivors, or people with illnesses.
Journalists use Tor to communicate more safely with whistleblowers and dissidents. Non-governmental
organizations (NGOs) use Tor to allow their workers to connect to their home website while they're in
a foreign country, without notifying everybody nearby that they're working with that organization.
Groups such as Indymedia recommend Tor for safeguarding their members' online privacy and
security. Activist groups like the Electronic Frontier Foundation (EFF) recommend Tor as a mechanism
for maintaining civil liberties online. Corporations use Tor as a safe way to conduct competitive
analysis, and to protect sensitive procurement patterns from eavesdroppers. They also use it to replace
traditional VPNs, which reveal the exact amount and timing of communication. Which locations have
employees working late? Which locations have employees consulting job-hunting websites? Which
research divisions are communicating with the company's patent lawyers?
A branch of the U.S. Navy uses Tor for open source intelligence gathering, and one of its teams used
Tor while deployed in the Middle East recently. Law enforcement uses Tor for visiting or surveilling
web sites without leaving government IP addresses in their web logs, and for security during sting
operations.

52
The variety of people who use Tor is actually part of what makes it so secure. Tor hides you among the
other users on the network, so the more populous and diverse the user base for Tor is, the more your
anonymity will be protected.
Why we need Tor
Using Tor protects you against a common form of Internet surveillance known as "traffic analysis."
Traffic analysis can be used to infer who is talking to whom over a public network. Knowing the
source and destination of your Internet traffic allows others to track your behavior and interests. This
can impact your checkbook if, for example, an e-commerce site uses price discrimination based on
your country or institution of origin. It can even threaten your job and physical safety by revealing who
and where you are. For example, if you're travelling abroad and you connect to your employer's
computers to check or send mail, you can inadvertently reveal your national origin and professional
affiliation to anyone observing the network, even if the connection is encrypted.
How does traffic analysis work? Internet data packets have two parts: a data payload and a header used
for routing. The data payload is whatever is being sent, whether that's an email message, a web page, or
an audio file. Even if you encrypt the data payload of your communications, traffic analysis still reveals
a great deal about what you're doing and, possibly, what you're saying. That's because it focuses on the
header, which discloses source, destination, size, timing, and so on.
A basic problem for the privacy minded is that the recipient of your communications can see that you
sent it by looking at headers. So can authorized intermediaries like Internet service providers, and
sometimes unauthorized intermediaries as well. A very simple form of traffic analysis might involve
sitting somewhere between sender and recipient on the network, looking at headers.
But there are also more powerful kinds of traffic analysis. Some attackers spy on multiple parts of the
Internet and use sophisticated statistical techniques to track the communications patterns of many
different organizations and individuals. Encryption does not help against these attackers, since it only
hides the content of Internet traffic, not the headers.
The solution: a distributed, anonymous network
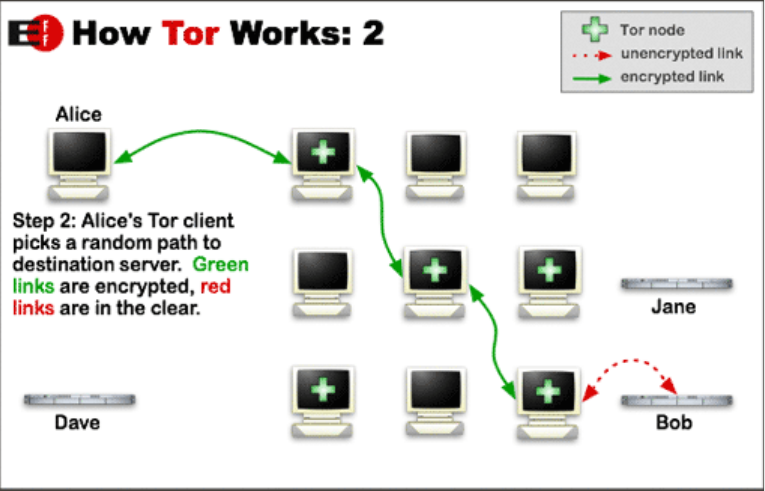
53
Tor helps to reduce the risks of both simple and sophisticated traffic analysis by distributing your
transactions over several places on the Internet, so no single point can link you to your destination. The
idea is similar to using a twisty, hard-to-follow route in order to throw off somebody who is tailing you
— and then periodically erasing your footprints. Instead of taking a direct route from source to
destination, data packets on the Tor network take a random pathway through several relays that cover
your tracks so no observer at any single point can tell where the data came from or where it's going.
To create a private network pathway with Tor, the user's software or client incrementally builds a
circuit of encrypted connections through relays on the network. The circuit is extended one hop at a
time, and each relay along the way knows only which relay gave it data and which relay it is giving
data to. No individual relay ever knows the complete path that a data packet has taken. The client
negotiates a separate set of encryption keys for each hop along the circuit to ensure that each hop can't
trace these connections as they pass through.
Once a circuit has been established, many kinds of data can be exchanged and several different sorts of
software applications can be deployed over the Tor network. Because each relay sees no more than one
hop in the circuit, neither an eavesdropper nor a compromised relay can use traffic analysis to link the
connection's source and destination. Tor only works for TCP streams and can be used by any
application with SOCKS support.
For efficiency, the Tor software uses the same circuit for connections that happen within the same ten
minutes or so. Later requests are given a new circuit, to keep people from linking your earlier actions to
the new ones.

54
Staying anonymous
Tor can't solve all anonymity problems. It focuses only on protecting the transport of data. You need to
use protocol-specific support software if you don't want the sites you visit to see your identifying
information. For example, you can use Tor Browser while browsing the web to withhold some
information about your computer's configuration.
Also, to protect your anonymity, be smart. Don't provide your name or other revealing information in
web forms. Be aware that, like all anonymizing networks that are fast enough for web browsing, Tor
does not provide protection against end-to-end timing attacks: If your attacker can watch the traffic
coming out of your computer, and also the traffic arriving at your chosen destination, he can use
statistical analysis to discover that they are part of the same circuit.
The future of Tor
Providing a usable anonymizing network on the Internet today is an ongoing challenge. We want
software that meets users' needs. We also want to keep the network up and running in a way that
handles as many users as possible. Security and usability don't have to be at odds: As Tor's usability
increases, it will attract more users, which will increase the possible sources and destinations of each
communication, thus increasing security for everyone. We're making progress, but we need your help.
Please consider running a relay or volunteering as a developer.
Ongoing trends in law, policy, and technology threaten anonymity as never before, undermining our
ability to speak and read freely online. These trends also undermine national security and critical
infrastructure by making communication among individuals, organizations, corporations, and
governments more vulnerable to analysis. Each new user and relay provides additional diversity,
enhancing Tor's ability to put control over your security and privacy back into your hands.

55
Tails
(Links route to https://tails.boum.org/about/index.en.html, debian.org,
or to torproject.org)
Tails is a live system that aims to preserve your privacy and anonymity. It helps you to use the Internet
anonymously and circumvent censorship almost anywhere you go and on any computer but leaving no
trace unless you ask it to explicitly.
It is a complete operating system designed to be used from a DVD, USB stick, or SD card
independently of the computer's original operating system. It is Free Software and based on Debian
GNU/Linux.
Tails comes with several built-in applications pre-configured with security in mind: web browser,
instant messaging client, email client, office suite, image and sound editor, etc.
1. Online anonymity and censorship circumvention
1. Tor
2. I2P
2. Use anywhere but leave no trace
3. State-of-the-art cryptographic tools
4. What's next?
5. Press and media
6. Acknowledgments and similar projects
Online anonymity and censorship circumvention
Tor
Tails relies on the Tor anonymity network to protect your privacy online:
all software is configured to connect to the Internet through Tor
if an application tries to connect to the Internet directly, the connection is automatically blocked
for security.
Tor is an open and distributed network that helps defend against traffic analysis, a form of network
surveillance that threatens personal freedom and privacy, confidential business activities and
relationships, and state security.
Tor protects you by bouncing your communications around a network of relays run by volunteers all
around the world: it prevents somebody watching your Internet connection from learning what sites
you visit, and it prevents the sites you visit from learning your physical location.
Using Tor you can:
be anonymous online by hiding your location,
connect to services that would be censored otherwise;

56
resist attacks that block the usage of Tor using circumvention tools such as bridges.
To learn more about Tor, see the official Tor website, particularly the following pages:
Tor overview: Why we need Tor
Tor overview: How does Tor work
Who uses Tor?
Understanding and Using Tor — An Introduction for the Layman
To learn more about how Tails ensures all its network connections use Tor, see our design document.
I2P
You can also use Tails to access I2P which is an anonymity network different from Tor.
Learn how to use I2P in Tails in the documentation.
To know how I2P is implemented in Tails, see our design document.
Use anywhere but leave no trace
Using Tails on a computer doesn't alter or depend on the operating system installed on it. So you can
use it in the same way on your computer, a friend's computer, or one at your local library. After
shutting down Tails, the computer will start again with its usual operating system.
Tails is configured with special care to not use the computer's hard-disks, even if there is some swap
space on them. The only storage space used by Tails is in RAM, which is automatically erased when
the computer shuts down. So you won't leave any trace on the computer either of the Tails system itself
or what you used it for. That's why we call Tails "amnesic".
This allows you to work with sensitive documents on any computer and protects you from data
recovery after shutdown. Of course, you can still explicitly save specific documents to another USB
stick or external hard-disk and take them away for future use.
State-of-the-art cryptographic tools
Tails also comes with a selection of tools to protect your data using strong encryption:
Encrypt your USB sticks or external hard-disks using LUKS, the Linux standard for disk-
encryption.
Automatically use HTTPS to encrypt all your communications to a number of major websites
using HTTPS Everywhere, a Firefox extension developed by the Electronic Frontier
Foundation.
Encrypt and sign your emails and documents using the de facto standard OpenPGP either from
Tails email client, text editor or file browser.
Protect your instant messaging conversations using OTR, a cryptographic tool that provides
encryption, authentication and deniability.
Securely delete your files and clean your diskspace using Nautilus Wipe.
Read more about those tools in the documentation.

57
What's next?
To continue discovering Tails, you can now read:
the warning page to better understand the security limitations of Tails and Tor,
more details about the features and software included in Tails,
our documentation explaining in detail how to use Tails,
some hints on why you should trust Tails,
our design document laying out Tails specification, threat model and implementation,
the calendar that holds our release dates, meetings and other events.

58
Installing Tails
Here is the link you can use to find the Tails .iso you need in order to manually install
Tails onto your drives. https://tails.boum.org/download/index.en.html
Manual Installation using Linux
Find out the device name of the device
The device name should be something like /dev/sdb, /dev/sdc, etc.
If you are not sure about the exact device name, with GNOME, do the following:
1. Make sure that the USB stick or SD card onto which you want to install Tails is unplugged.
2. Open GNOME Disk Utility from the menu Applications ▸ Accessories ▸ Disk Utility
3. Disk Utility lists all the current storage devices in the left pane of the window.
4. Plug the USB stick or SD card onto which you want to install Tails.
A new device appears in the list of storage devices. Click on it.
5. In the right pane of the window, verify that the device corresponds to your device, its brand, its
size, etc.
On this screenshot, the USB stick is a Kingston DataTraveler of 2.0 GB and its device name is
/dev/sdc. Yours are probably different.
If you are not sure about the device name, you should stop proceeding or you risk overwriting any
hard disk on the system.
Do the copy
All the data on the installed device will be lost.
Execute the following commands, replacing [tails.iso] with the path to the ISO image that you
want to copy and [device] with the device name found in step 1.
dd if=[tails.iso] of=[device] bs=16M && sync

59
Here is an example of the commands to execute, yours are probably different:
dd if='/home/amnesia/Desktop/tails-0.6.2.iso' of=/dev/sdc bs=16M && sync
If you are not sure about the path to the ISO image or if you get a No such file or directory error
message, you can first type dd, followed by a space, and then drag and drop the icon of the ISO image
from a file browser onto the terminal. This should insert the correct path to the ISO image in the
terminal. Then complete the command and execute it.
If you don't see any error message, Tails is being copied onto the device. The whole process might take
some time, generally a few minutes.
Once the command prompt reappears, you can shutdown your computer, and start Tails from this new
device.
Troubleshooting
dd: /dev/sdx: No such file or directory
Then double-check the name of the device you found in step 1.
dd: /dev/sdx: Permission denied
You might also have committed a mistake in the device name, so please double-check it. If you are sure
about the device name, this could be a permission problem and you could need to gain administration
privileges before running the commands in the terminal. That could be:
sudo dd if=[tails.iso] of=[device] bs=16M && sync
dd: tails.iso: No such file or directory
Then you surely have committed a mistake on the path to the ISO image in step 2.
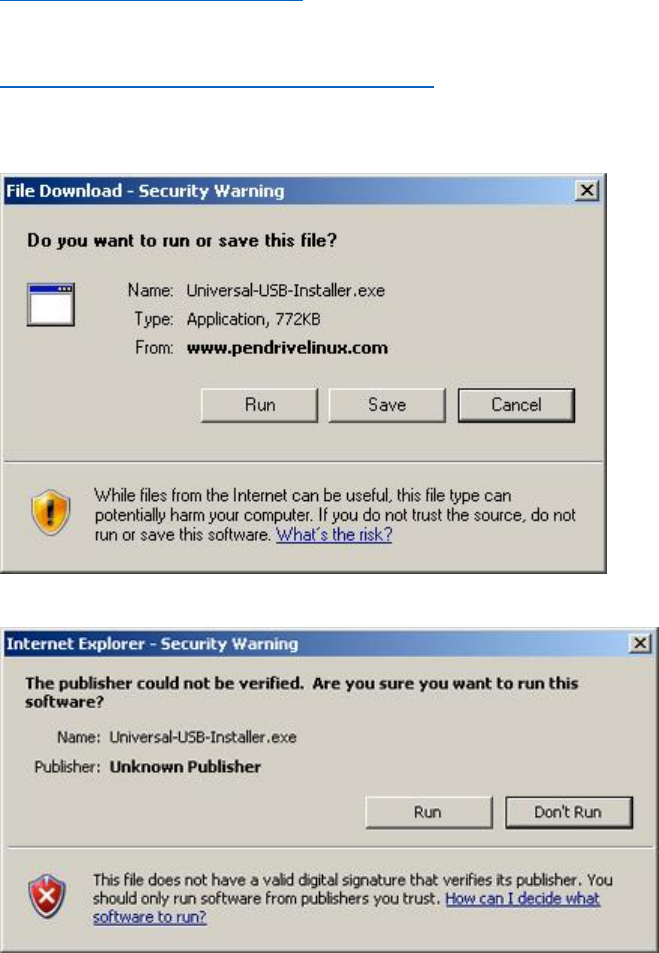
60
Manual Installation using Windows
This technique uses the Universal USB Installer, for more info or more help visit
http://www.pendrivelinux.com/.
Insert a USB stick with at least 2GB of free space
Download the Universal USB Installer
You will need version 1.9.5.4 or later.
Click 'Run' when prompted
If the security dialog appears, confirm by clicking 'Run'
Read the license agreement and choose 'I Agree' to continue
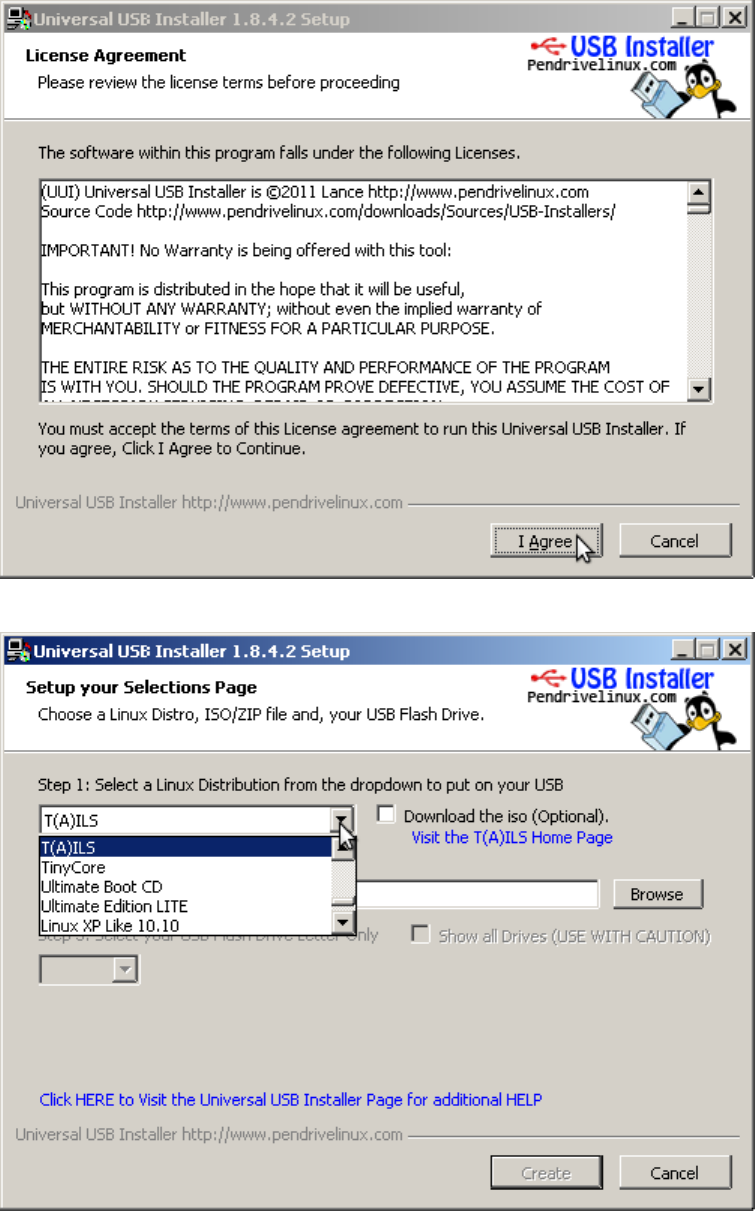
61
Select Tails from the dropdown list
Click 'Browse' and open the downloaded ISO file

62
Choose the USB stick
Click 'Create'

63
Then safely remove the USB stick from the computer.
After the installation completes, you can start Tails from this new USB stick.
64
Manual Installation using Mac
Find out the device name of the USB stick
The device name should be something like /dev/disk8, /dev/disk9, etc.
If you are not sure about the exact device name, do the following:
1. Unplug the USB stick.
2. Open Terminal from Applications ▸ Utilities ▸ Terminal.app
3. Execute the following command:
4. diskutil list
This returns a list of all the current storage devices. For example:
$ diskutil list
/dev/disk0
#: TYPE NAME SIZE IDENTIFIER
0: GUID_partition_scheme *500.1 GB disk0
1: EFI 209.7 MB disk0s1
2: Apple_HFS MacDrive 250.0 GB disk0s2
3: EFI 134.1 GB disk0s3
4: Microsoft Basic Data BOOTCAMP 115.5 GB disk0s4
1. Plug back the USB stick and run the same command as before:
2. diskutil list
A new device should appear in the list of storage devices. Check that the size of the device
corresponds to the size of your USB stick.
$ diskutil list
/dev/disk0
#: TYPE NAME SIZE IDENTIFIER
0: GUID_partition_scheme *500.1 GB disk0
1: EFI 209.7 MB disk0s1
2: Apple_HFS MacDrive 250.0 GB disk0s2
3: EFI 134.1 GB disk0s3
4: Microsoft Basic Data BOOTCAMP 115.5 GB disk0s4
/dev/disk1
#: TYPE NAME SIZE IDENTIFIER
0: FDisk_partition_scheme *4.0 GB disk1
1: Apple_HFS Untitled 1 4.0 GB disk1s1
In this example, the USB stick is 4.0 GB and the device name is /dev/disk1. Yours are probably
different.
If you are not sure about the device name you should stop proceeding or you risk overwriting any
hard disk on the system.
Unmount the USB stick
Execute the following command, replacing [device] with the device name found in step 1.
diskutil unmountDisk [device]
Do the copy

65
Execute the following command, replacing [tails.iso] by the path to the ISO image that you want to
copy and [device] by the device name found in step 1. You can add r before disk to make the
installation faster.
dd if=[tails.iso] of=[device] bs=16m && sync
You should get something like this:
dd if=tails-i386-1.3.iso of=/dev/rdisk9 bs=16m && sync
If you are not sure about the path to the ISO image or if you get a No such file or directory error, you
can first type dd if= and then drag and drop the icon of the ISO image from a file browser onto
Terminal. This should insert the correct path to the ISO image in Terminal. Then complete the
command and execute it.
If you don't see any error message, Tails is being copied onto the USB stick. The whole process might
take some time, generally a few minutes.
If you get a "Permission denied" error, try executing the command with sudo:
sudo dd if=[tails.iso] of=[device] bs=16m && sync
Be careful, if the device name is wrong you might overwriting any hard disk on the system.
The installation is complete when the command prompt reappears.
Start Tails
After the installation completes, follow the instructions to start Tails on Mac.
Notes
This method was successfully tested on the following hardware:
MacBook Pro Model A1150 with OS X 10.6.8, 2006
MacBook Pro Retina 15" Mid-2012 (aka MacBookPro10,1)
The method worked on some hardware but a bug in the video support prevented Tails to start
successfully:
MacBook Pro Retina with OS X 10.8.3, December 2012
Macbook Pro model A1150
Note that Tails developers are in general not very knowledgeable about Mac. Any additional
information is welcome.

66
Jolly Roger’s Security Thread for
Beginners
LastUpdated2014
By: Jolly Roger
ActiveSource
http://bm26rwk32m7u7rec.onion/index.php?PHPSESSID=8i5jin3i1ufu6dhm7ned59jdm6&topic=2107.
0

67
INTRODUCTION TO SECURE COMMUNICATION - TOR, HTTPS, SSL
Greetingscomrades.
ThroughmyresearchIhaveputtogethersomesecuritymeasuresthatshouldbeconsideredby
everyone.ThereasonIputthistogetherismainlyforthenewbiesofthisforum.ButifIcanhelp
anyoneout,thenIamgratefulforthis.Iwouldliketostartoutbysaying,ifyouarereadinglike,you
arelikelyaSilkRoaduser.Ifthisisthecase,thenthe#1thingyoumustbeusingtoevenaccessthis
formisTor.Torwillprovideyouwithadegreeofanonymitybyusingan128bitAES(Advanced
EncryptionStandard).TherehasbeensomedebateastowhetherornottheNSAcancrackthiscode,
andtheanswerislikelyyes.Thisiswhy,youshouldneversendanythingoverTorthatyouaren't
comfortablesharingwiththeentireworldunlessyouareusingsomesortofPGPencryptionwhichwe
willtalkaboutlater.
Communicationfromyourcomputer,totheinternetreliesonanentrynodewhichbasically
"entersyourcomputer"intotheTornetwork.Thisentrynodecommunicateswithyourcomputer,this
entrynodeknowsyourIPaddress.Theentrynodethenpassesyourencryptedrequestontotherelay
node.Therelaynodecommunicateswiththeentrynodeandtheexitnodebutdoesnotknowyour
computer'sIPaddress.Theexitnode,iswhereyourrequestisdecryptedandsenttotheinternet.The
exitnodedoesnotknowyourcomputer'sIP,onlytheIPoftherelaynode.Usingthismodelof3nodes
itmakesitharder,butnotimpossibletocorrelateyourrequesttoyouroriginalIPaddress.
TheproblemcomesobviouslywhenyouareenteringplaintextintoTORbecauseanybodycanset
upanexitnode.TheFBIcansetupanexitnode,theNSA,oranyotherforeigngovernment,orany
maliciouspersonwhomaywanttostealyourinformation.Youshouldnotbeenteringanysensitive
dataintoanywebsites,especiallywhenaccessingthemoverTOR.Ifanyofthenodesinthechainare
compromised,andsomelikelyare,andthepeopleinchargeofthosecompromisednodeshavethe
computingpowertodecryptyourrequest,thenyoubetterhopeitwasn'tanythingsensitive.
Sowhatcanwedotofixthis?Well,luckilywearenowhavingmoreandmoreserversthatare
offeringsomethingcalledHiddenservices.Youcaneasilyrecognizetheseservicesbythe
address.onion.Theseservicesofferwhat'scalledendtoendencryption.Whatthisdoesistakethe
poweroutofthecompromisedexitnodesandputthembackinyourhands.Thewebserverofthe
hiddenservicenowbecomesyourexitnode,whichmeansthewebsiteyouarevisitingistheone
decryptingyourmessage,notsomerandomexitnoderanbyapotentialattacker.Remember,theexit
nodehasthekeytodecryptyourrequest.Theexitnodecanseewhatyouaresendingincleartext
oncetheydecryptit.Soifyouareenteringyournameandaddressintoafield,theexitnodehasyour
information.Ifyouareputtingacreditcard,abankaccount,yourrealname,evenyourlogin
information,thenyouarecompromisingyouridentity.
Anotherstepyoucantake,istoonlyvisitwebsitesthatusesomethingcalledHTTPSecure.You
cantellifthewebsiteyouarevisitingisusingHTTPSecurebytheprefixatthebeginningofthe
address.Ifyouseehttps://thenyourwebsiteisusingHTTPSecure.Whatthisdoesisencryptsyour
requestssothatonlytheservercandecryptthem,andnotsomebodyeavesdroppingonyour
communicationsuchasacompromisedTorexitnode.Thisisanotherformofendtoendencryption.If

68
somebodywere tointerceptyour request over HTTPSecure, they wouldsee encrypteddataandwould
havetoworktodecryptit.
AnotherreasonyouwanttouseHTTPSwheneverpossible,isthatmaliciousTornodescan
damageoralterthecontentspassingthroughtheminaninsecurefashionandinjectmalwareintothe
connection.Thisisparticularlyeasierwhenyouaresendingrequestsinplaintext,butHTTPSreduces
thispossibility.Youmustbemadeawarehowever,thatHTTPScanalsobecurrentlycrackeddepending
onthelevelofthekeyusedtoencryptit.WhenyouvisitawebsiteusingHTTPS,youareencrypting
yourrequestusingtheirpublickeyandtheyaredecryptingitusingtheirprivatekey.Thisishow
cryptographyworks.Apublickeyisprovidedtothosewhowanttosendanencryptedmessageandthe
onlyonewhocandecryptistheonewiththeprivatekey.
Unfortunately,manywebsitestodayarestillusingprivatekeysthatareonly1,024bitslongwhich
intoday'sworldarenolongerenough.Soyouneedtomakesureyoufindoutwhichlevelofencryption
thewebsiteyouarevisitinguses,tomakesuretheyareusingataminimum2,048,ifnot4,096bits.
Evendoingallofthisunfortunatelyisnotenough,becausewehaveanotherproblem.Whathappensif
thewebserveritselfhasbecomecompromised?MaybeyourTORnodesareclean,maybeyouhave
usedHTTPSforallyourrequests,butthewebserveritselfofthewebsiteyouarevisitinghasbeen
compromised.Wellthenallyourrequestsareagain,asgoodasplaintext.
Withthatbeingsaid,thiswillconcludethefirstpostinthisseriesofthestepswecantaketoprotect
ourprivacyonline,toremainanonymousandmaintainourfreedom.
PGP, TAILS, VIRTUAL BOX
SokeepinmindthatifyouareauserofSilkRoad,oranyotherformofactivism,youneverwant
toenteranyidentifyingdetailsaboutyourselfonline.MakeitsothateveniftheNSAinterceptedand
decrypted,orcompromisedSilkRoadthattheonlyinformationtheyhaveagainstyouisyourusername
andpassword.Howsafeisthatusernameandpassword?Doesyourpasswordcontainanyidentifying
information?Isitthesamepasswordthatyouuseforyourpersonalemail?Doesitcontainanameof
somebodyyouknowpersonally?Alwayskeepallofthesefactorsinmind.
Anotherstepyoumusttake,especiallywhencommunicatingwithotherusersonsitessuchasSilk
RoadisusingPGPencryption.Thisisnotalwayspossible,suchasincaseswhenyouareloggingintoa
website,fillingoutaform,loggingintoanemail,etc..Consideranytypeofinformationyouenterintoa
websiteusingplaintextpossiblycompromised.Neverputanythingsensitiveisanytypeofplaintext
formatonline.PGPcomesintoplaybecauseitusesaverystrongmethodofencryptioncalled
cryptography.PGPstandsforPrettyGoodPrivacy,anditisusedforencrypting,decryptingandsigning
texts,emails,files,directories,andwholediskpartitionsandtoincreasethesecurityofemail
communications.
Forthemoretechnicalusers,itusesaserialcombinationofhashing,datacompression,
symmetrickeycryptography,andfinallypublickeycryptography.Forthelesstechnicalusers,the
processofencryptingmessagesusingPGPisasfollows.Youcreateaprivatekeyandapublickey.The

69
public keyis thekeyyougive outtopeople youwanttosendyouencryptedmessages.Your private
key,iskeptprivatelybyyou.Thisprivatekeyistheonlykeythatcanunlockmessagesthatwere
previouslylockedwithyourpublickey.
Ifyouarestillconfused,thinkaboutitlikethis.Thinkaboutapublickeythatcangoaround
lockingboxesthatareintendedforyou.Anyonecanlockaboxthatisintendedforyou,butyouarethe
onlyonewiththekeytounlockthebox.Eitherifthepersonwhosentyouamessagelockedabox
(message)withyourpublickey,theythemselvescannotunlockit.Onlythepersonpossessingthe
privatekeycanunlockit.Ifyouwishtorespondtothisperson,youmustusetheirpublickeytoencrypt
themessageyouintendtosendtothem.Andtheythemselves,usetheirownprivatekeytodecrypt
themessageyousentthem.
Ifyouarestillwithme,IamgladIhaven'tlostyouyet.Thisiscalledcryptographyandwas
designedsothatanybodyinterceptingyourmessagecouldnotdecryptthemessagewithoutyour
privatekey.Evenifyouyourself,loseyourprivatekey,thereisnomethodofkeyrecovery.Youcan
considerthatmessagelockedforever.SohowdoyouusePGP?
Wellbeforewegettothat,IwanttointroduceyoutoaLiveOperatingSystem,whichmakesusing
PGPencryptionanddecryptionveryeasy.Aliveoperatingsystemisanoperatingsystemthatyoucan
runontopofyourcurrentoperatingsystem.Soforexample,ifyouareaWindowsuser,youhave2
choices.Youcandownloadtheliveoperatingsystem,burnittoaCDorDVDandthenbootyour
computerfromthatDVDorCD.Thiswillmakesureyourcomputerrunasifyouhavethisoperating
systeminstalledonyourcomputer.However,ifyouremovetheCDorDVDandreboot,thenyour
computerwillbootasnormal.YoucanalsouseaUSBdrivetoperformthissamefeature.
Secondly,youcanrunthisliveoperatingsysteminwhat'scalledaVirtualBox.Thebenefitsofthis
arethatyoucanrunWindowssimultaneouslyasyourunthisotheroperatingsystemandyoucan
easilyswitchbackandforthbetweenthemwithoutrebootingthecomputer.Bothmethodshavetheir
prosandcons.TheprosofrunningaliveCDboot,arethatreducetheriskofhavingyourcomputer
compromisedbyviruses,malwareandkeyloggersthatrelyonWindowsvulnerabilitiestorun.
IfyouaregoingtorunthisOSfromaVirtualBox,IsuggestdownloadingVirtualBoxfromOracle.Note
thehttps://
https://www.virtualbox.org/
Next,theliveoperatingsystemIwouldencourageyoutouseisTails.Tailscanbefoundatthe
followingwebsite.
https://tails.boum.org/
ThereasonIchooseTails,isbecauseithasmanyofthesecurityfeaturesthatyourequiretostay
anonymousalreadyinstalled.SomeusersarenothappywithTails,butitreallyisagreatoperating
systemloadedwithsecurityfeatures.ManyIwilltalkaboutinthisseriesonsecurityincludingPGP
encryptionanddecryption.MakesureyoudownloadtheTailsISOfilefromtheofficialTailswebsite

70
andyoucaneither loadit intoVirtualBoxor burnittoaDVD or loaditonto aUSB andbootingyour
computerfromthatdrive.
ThereareplentyoftutorialsonhowtoloadTailsintoVirtualBox,soIwon'tgointomuchdetailother
than,makesureyourunVirtualBoxandTailsfromaUSBdriveorSDcard.IwouldsuggestaUSBdrive
howeverforreasonsIwillexplainlater.ButbasicallywhenwhenVirtualBoxrunsdirectlyonyourhard
drive,itcreatesavirtualharddrivethatisusesasatemporaryharddrivewhileTailsisrunning.Once
Tailsisclosed,thisvirtualdriveisdeleted,butit'snotpermanentlydeleted.Asweknowfromthe
powerofrecoverytools,deletedfilesareeasilyrecoverablewiththerighttools.Iwilltalkabouthowto
protectyourfilesfromdatarecoverytoolsinfuturepostsbutfornow,justkeepVirtualBoxandTails
OFFofyourharddrive,andloaditeitheronaUSBdriveorSDcard.
ThesamegoeswhenbootingyourcomputerdirectlyintoTailsfromaDVDorUSBstick.Yourhard
drivewillbeusedtostorefilesusedbyTails,somakesureanyfilesthataresavedoraccessedusing
TailsaredonefromaUSBstickorSDcard,otherwisetheywillberecoverable.ThisiswhyIpreferusing
aVirtualBoxandrunningboththeVirtualBoxandTailsinsideofit,offofaUSBstick.Keepasmuchas
possibleoffofyouractualharddrive.Itispossibletoshredfilesbeyondrecovery,butit'smucheasier
todothisona16gbflashdrive,thenitisa1TBharddrive.
NextpostwewillgetbackontopicandstartlearninghowtousePGP.ThereasonIhavetotakea
detourtousingTailsisbecausewewillbeusingTailsformanyofthefeaturesfromhereonout,
includingPGP.
PGP CONTINUED
Ok,sobynowIamassumingyouhaveTailsrunning.Let'slearnhowtousePGPwithinTails.First
thingyouaregoingtowanttodoiscreateyourownpersonalkey,whichconsistsofyourpublickey
thatyoucangiveouttopeopleorpostinyourprofilesonline.Asmentionedbefore,thisisthekey
peopleusetoencryptmessagestosendtoyou.Yourpersonalkeyalsoconsistsofyourprivatekey
whichyoucanusetodecryptmessagesthatareencryptedusingyourPGPpublickey.
Ifyoulookuptothetoprightarea,youwillseealistoficons,andoneothemlookslikeaclipboard.
YouneedtoclickonthatclipboardandclickManageKeys
NextclickFile>New
SelectPGPKeyandclickContinue
Filloutyourfullname(Isuggestyouuseyouronlinename,notyourrealname)
Optionallyfilloutanemailandacommentaswell.
Next,clickAdvancedKeyOptions.
MakesureEncryptiontypeissettoRSAandsetkeystrengthto4096.
Onceyouhavedonethis,clickCreateanditwillgenerateyourkey.
Onceyouhavedonethis,youcanviewyourpersonalkeybyclickingthetabMyPersonalKeys.You
71
have nowcreatedyour personalkey!Tofindyour PGPpublic key, yourightclickonyour personalkey
andclickCopyanditwillcopyyourPGPpublickeytoyourclipboard,inwhichyoucanpasteanywhere
youwish.APGPpublickeywilllooksomethinglikethis.
BEGINPGPPUBLICKEYBLOCK
mQINBFLLWDcBEADEzn3mnLsezUDDAS5Q0lm1f6JdkI534WPuRlAN8pnuQsCSwUQU
hPEAgNCUNhxN4yCJ1mDt9xpXpX8QzsMIcofCHeE9TMLAnHzbmXLLi+D8sPZpLpDN
6jEIFvmBD4dvp5adimvRl8Ce49RpO345VUz8Ac0qLSmsv2u+kQviDQXZkrrxXHnA
IalvgDopXTISa9Sh7J3HHYYQazOZt9mfAjjuuRdaOqmAAtEe9dl43nrx+nSd/fqH
13XvMKhqJhIoJ02CBFfRBm86vtx5yiXqHZX438M9kbASqU0A2jAfRd+IZG5Z9gCI
W6FTror+F4i+bEdAuGTG1XFsQSgjKTIG0vgYiTJ93C2MZxrLvNnJp0g2zD0URyk8
Y2IdyCDfIL10W9gNMqLmjD0z/f/os66wTJkflSGaU9ZsrKHUKFN5OSfOZtNqktWn
fCpY4bigkJ8U/5C8mtr9ZE3Tv+RV4rPY0hAOtZucnhlRmYKVFNjvbS0MjqA1188c
wzBNG0XcpCNtmM5UsSvXwnDoUaEMXe50Hikxdk3d+CJzqYnor72g/WmIDROCiXl6
2D9rJ2JuLpl9bQLM+KCbXJf3kUSvzszZGXL/AwmynvqlruaXqr5975sCdfqXVexx
1sxsLofOzE01xSDEJRWwHQPlxTKPZFnXD709Xumjdinjv1w4onLk04Z96wARAQAB
tC5Kb2xseSBSb2dlciAoVGhleSB3b3VsZCBsaXZlIGFuZCBkaWUgdW5kZXIgaXQp
iQI3BBMBCgAhBQJSy1g3AhsDBQsJCAcDBRUKCQgLBRYCAwEAAh4BAheAAAoJEPuh
6tSg81nyzNsP/2ayrAz4InCK/ZnyRnnsjSHIXMv7t2uDTbYomA/0B6v/S6wHMNZX
G6+sYg41mfMuZEimgavNb0Uc2r6mI7UyWy5lp1Gd/D+all81X7bm5EBpvl1isPgJ
EqjehEdh9FQjrTiRIJafM1m254hIAaZ1RvAphI0tM2lpudk+tNKq+ivV8PpsN9TP
0mg5ZAu1lIKtG9k5vS9HAQ0grJ01TFMEjlifrf7eRyJ1+dmRJ+Xtoy2js8UwS+wM
RrIi3G39P2BfEZFQka3EmQ2JgN4pDWFoI0hODGhTba8Z0XSnVtabOTi1TOWIFmFu
yqA9bNtuOt3KhIC/O+mEATRsc/VPbTY+80kf45LwlDBfKO3PcOXSOG7ygibzEqXn
Ms/Rfe1kNEBeR9Wx2NMJSdxypqGij17CLJwNLC3KypTIQrhzy3YAndeDG4TadW2P
v/FJxhz+MX+s+9VeX2fGC0Fsfp8JbeWMAznp8Rf6O/tzEYW+pbLoLRPdi/DvFBZV
yWGPspzt3Qspm+BHbeW9iFjvCyvP2/DrKmQM7ABuRh/TMZR7uQ5na11L8rf3nzrS
Al/lSul42xLzxG+h9mDixXd1Vh6rVGMbCjL7wO25TUneFo13U5J+klo1blQWV/DL
FZUwhh2utWNCMCtcdRW0HYa14Wdyy7H68WmsJqBWUsbyD9PZ2gSawBy7uQINBFLL
WDcBEACg3IOme+sg0OZN349UYRr9/O6uW2vC5x9/azZrFNSNYh/LFJTt3XI/FsjN
gCj6NxRxbfdyLjL1gxSlJyFtclkFGS0lC0GIz7lINvemkewjde/bHXChz2IIaIli
L2A6Z6w3fP4jlQCw8NoGGJ360WMkZVTDDakYYkb50BrZSx4TVLjrHfFuLMXTE255
gQrId02jYO6240EDIhHITuiSwUQvHtXlOrHSohN83TD1I4H7iH/FLae9gYh4C/Ix
VLkzLUqvpf72Q/xogCZAJl4WEMmWD6dXufvyvhCXQnbjiLuAdQas0ef/t652LPw/
vJFDSDmguw9PXWpv3vFOe13UNU//+nw3kIGxaVWGvazXk8IFiDv9USgEGjcNn4zo
8HQlQrYz9/gyI3XojGV6L8iecWpHSweqR3NxKJmWKWEG1wwnWPL8M+z6OwEvRdxV
spy+eG0Zs+6igbw3tk6gJ4cq5ehdlmD6py27AhRhlj7uLlZxmK3uFV19QjtX/Dyt
73ZNX16krXqufl0HAJRd1PwhITPCtSviW3L2qKF2Pdak3j97A656EcInCcAyOUC/
mUNUDtXJik6uwFgFFn9/pnFr+acY7ppsWPG5rr7jRj+Lgjnjkckpkjo8jN1hZE17
CfJyrYrSqdglCcIgTHteIEZdPfPUmnbbSoyeufkyEW1AoIKatQARAQABiQIfBBgB
CgAJBQJSy1g3AhsMAAoJEPuh6tSg81ny4nIP/2lVf0DTp1n5xPEBZEUlgzcMNeh5
FTIS3J44g5a+OlkRVgHFtu7K/MUsftlUzkvMMa0sXllhKc6syxcytoD7LAt9tbQh
62yEzijTliU2QFgWJSS6IfbtC2IyRouAns3KD6XouKTFUs/i0n/QpwhnM+Ya/SAg
c/oroM7SE/T4g+v6EeRCq7In/TMgc74j+25zUF1rVSCenbZKkYezxqZ33cXLwl7l
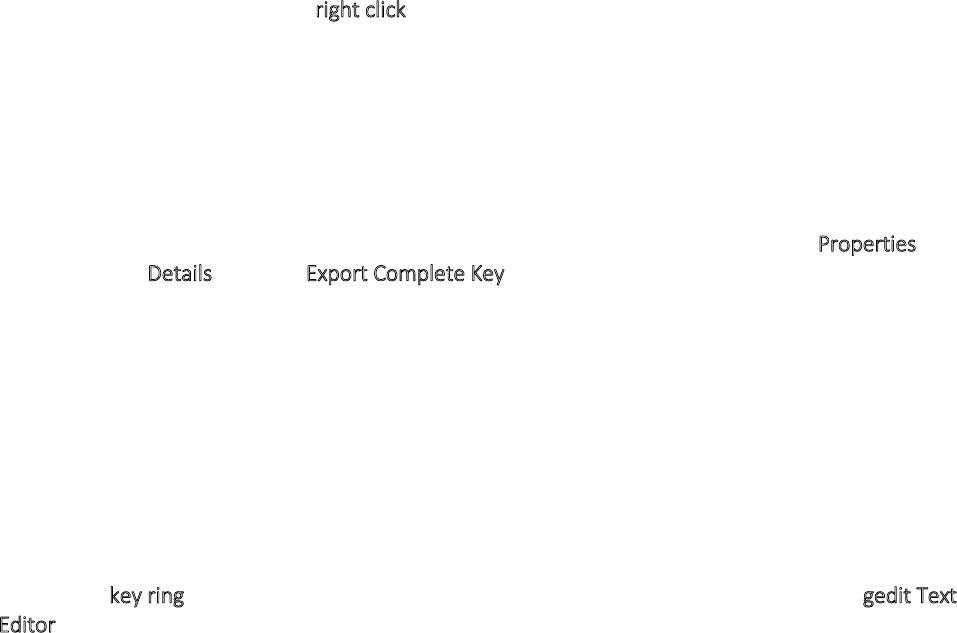
72
IUBcK2uNHDBUB5G853NR0OkBm5i+KC8vM3K1/MZ+P/lK0xOcTGXZH/A7GrEsI4FJ
nw5i6zJZb8gmDt44Tp/1Ujxnm5xhVWgnOQeSVSyiRsHQ/gTCL1PqsZhW7yulwL05
yxZgN+oYVx4pNtLJMigRjoCY9IKEmZhY75cWXXA19j14Wnxu8IrwwSk1WyzMQcjj
7onP4OEhbPuotqWqVAc0M/+MV5oMGIG0Qepy6XpZOCCpZw/p1rDrZSYP5eQMd/4x
LB7xch6GjbWsnKhA1wGdjdclBodixorVfCRn4s5jTgXx7wWz/opM4ix/CPAkify7
4Sf0BdJ5YtFILZc5StED4WC5pljJbdEWVsb9rn6egvFn7W/ZlDJAerS6Mt5LJGAh
Aude0Kz2HJwDtOBF4nXeTzRCK5BrBnCYPHAtO2aqfowirzjMTd9A/ADoPmIbIJAm
04mA6krRiH909Bnx
=Az2N
ENDPGPPUBLICKEYBLOCK
Next,youaregoingtowanttosavetheprivatekeyonasecondaryUSBdriveorSDcard.Ifyouare
runningTailsfromaUSBdrive,thenyoumustuseaseparatedrivetostoreyourkeyon.Ifyouare
runningVirtualBox,youwanttorightclickontheiconinthebottomrightcornerthatlookslikeaUSB
drive,andselectyourseparatedrivethatyouwillbeusingtostoreyourkeyson.Again,neverstore
yourprivatekeysonyourharddrive,keepthemOFFyourcomputer.
Tosaveyourprivatekey,youaregoingtorightclickonyourpersonalkeyandclickProperties.Iknow
youprobablysawwhereitsaysExport,butthisisnotwhatyouwanttodo.ClickingexportwillONLY
exportyourpublickeyandwillnotsaveyourprivatekey.Ifyouloseyourprivatekey,youcannever
recoveritevenifyoucreateanotherpersonalkeyusingtheexactsamepassword.Eachprivatekeyis
uniquetothetimeitwascreatedandiflost,islostforever.SoonceyouhaveclickedProperties,go
overtothetabDetailsandclickExportCompleteKey.
Onceyouhavedonethis,youhavesavedyourpersonalkeyforfutureuseonceyourestartTails.
RememberingthatTailsisnotinstalledonyourharddrive,soeverytimeyourestartTailsyouloseall
yourkeys.BysavingyourkeysontoaUSBdriveorSDcard,youcanimportyourkeysforuseeverytime
yourestartit.
Nextyouaregoingtowanttolearnhowtoencryptanddecryptmessagesusingyourkey.Well,
luckilyforme,Tailshasalreadymadeatutorialonhowtodothis,soIwillreferyoutotheirwebpage.
ButbeforeIdothat,Ineedtomentionthatyouneedtofindsomebodyelse'sPGPpublickey,oryou
canpracticebyusingyourown.Needlesstosay,thewayyouimportotherpeople'skeysintowhat's
calledyourkeyringisbyloadingthemintoatextfile.YoudothiswiththeprogramcalledgeditText
Editor.
ClickApplications>Accessories>geditTextEditorandenterinsomeone'spublickeyandhitsave.
NextyoucanreturntoyourkeyprogramfromtheclipboardiconandclickFile>Importandselect
thatfile.Itwillimportthatperson'spublickeyintoyourkeyring.Toaddfuturepublickeystoyourkey
ring,Isuggestreopeningthesamefileandjustaddingthenextkeybelowthepreviouskeyandeach
timeyouopenthatfileitwillloadallkeyswithinthatfile.ThiswayyoucankeepallthePGPpublickeys
togetherinonefileandsaveitonyourSDcardorUSBdriveforfutureuse.
Finallyyoucanusethefollowing2pagestolearnhowtoencryptanddecryptmessagesusingPGP.

73
https://tails.boum.org/doc/encryption_and_privacy/gpgapplet/publickey_cryptography/index.en.html
https://tails.boum.org/doc/encryption_and_privacy/gpgapplet/decrypt_verify/index.en.html
Untilnexttime.HavefunwithyournewfoundabilitytocommunicateinPGP!
WHOLE DISK ENCRYPTION AND FILE SHREDDING
Welcomebackagain!
NowthatwehavePGPfiguredout,hopefully,IwanttoremindyouthatusingPGPwhenever
possible,isveryveryveryimportant.OneofthepitfallsofSilkRoad1,isthatsomeofthe
administrators,includingRosshimselfdidnotalwayscommunicateusingPGPencryption.OnceRoss
wasbusted,theyhadaccesstohis serversandhiscomputersandanythingthatwasn'tencryptedwas
wideopenforthemtolookat.MostusersonSilkRoad2believethatRosshadstoredpersonal
informationaboutsomeofAdminsandModeratorsonhiscomputerinplaintextthatwasusedto
make3morearrestsofSilkRoadusers.
OneofthereasonswhyIwouldsuggestforyoutostoreyourPGPkeysandothersensitivedataona
SDcard,isthatifthatdaycomeswhenyouarecompromisedandyougetaknockatyourdoor,you
havetimetodisposeofthatSDcardorUSBdrivequickly.Evenbetter,ifyouhaveamicroSDcardthat
plugsintoanSDadapter,thenyoucansnapitwithyourfingersorattheveryleasthideit.USBswould
needtobesmashedintopiecesanditmightnotbeeasytodothisintheheatofthemoment,sodo
whatyoufeelbestabout.Butalwaysprepareforthedaytheymightcomeforyou.
ButournexttopicbringsustosomethingcalledWholeDiskEncryptionorFullDiskEncryption.From
hereonoutIwillrefertoitasFDE(FullDiskEncryption).TailshasaFDEfeaturebuiltintoit,whichis
anotherreasonwhyIencouragetheuseofTails.Ithasmanyofthesefeaturestoprotectyou.
EssentiallyFDEwillprotectyourdrive,whetherSDorUSBfromthepeoplewhomaycomeforyouone
day.Themethodinwhichitdoesthisisitformatsyourdriveandrewritesthefilesysteminan
encryptedfashionsothatitcanbeonlybeaccessedbysomeonewhohasthepassphrase.
Ifyouloseyourpassphrase,justlikeinPGP,thereisnorecovery.Youronlychoiceistoformatthe
driveandstartoveragain.Somakesureyourememberit!AndpleasefortheloveofGod,Allah,
Buddah,etc...don'tstorethepassphraseonyourharddrivesomewhere.Thetutorialonhowtodothis
islocatedatthefollowingwebpage.
https://tails.boum.org/doc/encryption_and_privacy/encrypted_volumes/index.en.html
Again,alwaysprepareforthedaytheycomeknocking,encrypteverything.UsePGPwhen
communicatingwithothersandalwaysshredyourfileswhenfinishedwiththem.Whichbringsmeto
mynexttopic.Fileshredding.
Fileshreddingisextremelyimportantandhereiswhy.Ifyoudeleteafilefromyourcomputer,you
areonlydeletingwhereitislocatedonthedrive.Itisstillontheactualdrive,justit'slocationdatahas
74
beenremoved. Ifyoutake afile recoverytoolyoucanrecover virtuallyanyfile thatyouhaverecently
removed.Fileshreddingcombatsthisbyoverwritingfilesinstead.Theideaisthatinsteadofremoving
thefile'slocation,youneedtooverwritethefilewithrandomdatasothatisbecomesunrecoverable.
Therearealotofdebatehappeningonwhetheryoucanoverwriteafileonce,orifyouneedtodoit
multipletimes.SupposedlytheNSArecommends3times,supposedlytheDepartmentofDefense
recommends7times,andanoldpaperbyamannamedPeterGutmannwritteninthe90's
recommended35times.Needlesstosay,Ipersonallythinkbetween37timesissufficient,andseveral
peopleouttherebelieve1timewillgetthejobdone.
Thereasoningbehindthisisthatsomepeoplebelievethedrivemaymisssomefilesthefirsttimeit
overwritesthemandtobemorecomplete,youshoulddomultiplepasses.Dowhatyoufeelmost
comfortablewith,butIeventhink3passeswouldbesufficient,althoughitwouldn'thurteverynow
andthentorun7passesandjustleaveitovernight.
TheprogramsthatcandofileshreddingareonesyouwillwanttorunfromWindowsorwhatever
operatingsystemyourcomputerisrunning.TheseprogramscandeleteyourfilesfromyourRecycling
Bin,deleteyourtemporaryinternetfilesandevenWipeyourfreediskspacetomakesureeverything
getscleanedup.Youalwaysneedtothink,didIhaveanysensitivematerialonmyharddrive?Ifso,
maybeIneedtoshredmyfreediskspace.WhenemptingyourRecycleBin,youshouldalwaysusea
shredder.Whenonlydeletingunder1gbatatime,youcaneasilydo7passesprettyquickly.
Toputthisinperspective,theleaderofagroupcalledLulzSecnameTopiaryhasbeenbannedaspart
ofhissentencefromusinganytypeoffileshreddingapplicationssothatiftheFBIwantstocheckup
onhim,theycan.Fileshreddingkeepsyourdeletedfilesactuallydeleted.
Herearesomefileshreddingapplicationsyoucanuse.
http://www.dban.org/
http://www.fileshredder.org/
https://www.piriform.com/ccleaner
Nextwe'regoingtotalkaboutremovingharmfulmetadatafromfiles,andsomeothertopicsaswell.
JAVASCRIPT VULNERABILITIES AND REMOVING PERSONAL METADATA
FROM FILES
WelcomeBack.
BeforeIgetintoremovingharmfulmetadatafromyourfiles,Iwanttotalkaboutanother
vulnerabilitytoourbrowsingcapabilitiescalledJavascript.
Inmid2013,apersoninIrelandwasprovidinghostingtopeoplethathostedhiddenservices
includingasecureemailplatformcalledTorMail.Unfortunately,theybustedhimonanunrelated
chargerelatingtochildpornographyandseizedallhisservers.Whetherornothewasrelatedtochild
75
pornor not, isunknowntome, or itcouldbeasilly charge thefedsslappedhimwithbuteither way,
thefedsendedupinjectingmaliciousJavascriptintohisserverssothatwhenuserswouldvisitcertain
sites,thismaliciouscodewouldexecuteontheircomputersandrevealinformationabouttheir
computerstothefeds.Isuggestyoureadthefollowingarticletolearnmoreaboutthis.
https://openwatch.net/i/200/
Withthatbeingsaid,youmaywanttodisableJavascriptinyourbrowsers,especiallywhenvisiting
certainwebsiteslikeSilkRoadthatmaybecomecompromisedoneday.Manyusersrefusetovisitthe
originalSilkRoadwebsiteandforumswithJavascriptenabledbecausethefedslikelyinjecteditwith
maliciousJavascripttoidentifyusers.
InTails,thebrowseriscalledIceweaselandwhenTorinraninWindows,itusesFirefox.Both
browserscandisableJavascriptusingtheexactsamemethod.OpenupaWindowandtypethe
followingcommandintheaddressbar,"about:config"andclickthebuttonthatsays"I'llbecareful,I
promise."
Thiswillbringupabunchofsettingsincludingasearchbaratthetop.Enterjavascriptinthesearch
barandlookforthefollowingtwoentries,"javascript.enabled"and"browser.urlbar.filter.javascript".
Rightclickontheseandclick"Toggle"andyouwillseetheValuechangedtofalse.Ifyouwantto
enableJavascriptagain,justclickToggleagainandyouwillseethevaluechangebacktotrue.
Again,rememberthateverytimeyourestartTailsyouwillhavetodothisagain,sogetintoahabitof
doingthiseverytime.Youneverknowwhenyourfavoritewebsitecouldbecomecompromised.
Movingontometadata.Thereisabitofafamousstoryaboutanonlinehackernamedw0rmerthat
wouldtakepicturesofhisgirlfriendandpostthemonlineafterhewoulddefaceawebpage.Whathe
eitherforgot,ordidn'tknowwasthatphotostakenwiththeiPhoneandothersmartphonessavethe
GPScoordinatesofwherethepicturewastakenandstoreitinthemetadataofthepicture.Checkout
thisarticlebelow.
https://encyclopediadramatica.es/W0rmer
Youneedtoremovethismetadata!Otherwiseyoucouldendupinfederalprisonwithw0rmer.
LuckilyTailshasasolutionforthis!SeewhyIloveTails?
Applications>Accessories>MetadataAnonymisationToolkit
Pleasegetamoreclearideaofhowthisworksbyreadingthefollowingpage.
https://mat.boum.org/
Pleasenotethecurrentlysupportedformats.Intermsofpictures,jpg,jpegandpng.But
unfortunatelyMATisnotperfectandIwouldn'tsolelyrelyonit,soabetterideawouldbetonever
76
uploadpicturesofyourselfor your significantother online, especiallybraggingaboutahackyou
committed.Pleasereadthesiteprovidedaboveformoreinformation.
GENERAL SECURITY PRECAUTIONS WHEN POSTING ONLINE, LEARN
FROM OTHERS' MISTAKES
NextIwanttotalkaboutgoodpracticeswhenusingTOR,Tailsandotherhiddenservices.
Firstofall,itishighlyrecommendedthatyouusemultipleidentitiesonlinefordifferentthings.
PerhapsifyouareabuyerandaselleronSilkRoad,youmaywanttohaveseparateloginsforthis.And
thenpossiblyathirdloginfortheforums.Thenmaybeyouwanttobepartofanothermarketplace,
thenyoumightwantafourthlogin.
Well,TailshasanothergoodprogramofferedbyTailsiscalledKeePassX.Whenyouhavemultiple
logins,itishardtokeeptrackofthemall,soitmightbeabetterideatokeepthemallin1document
thatisencryptedwithastrongpassword.KeePassXcanhelpyouwiththis.
https://tails.boum.org/doc/encryption_and_privacy/manage_passwords/index.en.html
Youneverwanttousenicknamesorlocations,oranythingelsethatisrelatedtoyourselfonlinewhen
youpostorcreateusernames.Andanotherthingyouneedtoadoptarenewwaysofconducting
yourself.Ifyouaregenerallyamessytyper,whomakesthesamegrammarmistakes,orthesame
spellingmistakesallthetime,thiscanbeusedtoidentifyyou.Alwaysproofreadanythingyoupost
publicly,orprivatelybecausethefedswillalwaysfindwaystocorrelatethingstoyou.
WithRossUlbricht,theyfoundanoldposthepostedonaforumwhenhefirststartedSilkRoad
askingpeopleiftheyhadheardofamarketplacecalledSilkRoad.Obviouslythisisanoldtrickusedby
peopletryingtospreadawarenessaboutanewprojectoftheirs.Laterheidentifiedhimselfbysaying
hewaslookingforprogrammersandgaveouthisprivateemailaddressonthesameforumunderthe
samename.
Butifyoualwaysmisspellthesamewords,ifyoualwaysusethesameslangterms,capitalizethe
samewords,useacertainamountofperiodsafteranetc....oralwaysusethesamenumberof!!!!!
thenallofthesethingsgivethemreasonablesuspicionanditbecomeseasiertotiethingstoyou.Once
theyhaveyouundertheirradar,liketheyhadRoss,itonlytookafewslipupsandhewastheirs.
Remember,youonlyhavetomakeonemistake.Sotalkingaboutyourlocalelectionisareallydumb
idea,getit?
Thinkaboutthetimeyouuseyourcomputer.Isiteasytocorrelateyourtimezonebasedonthetime
yougoonline?Orisitmorerandom?Doyouhavepatterns thatarepredictable?Alwaysthinkabout
thesethingswhenyoupostonline.Alwaysthinkaboutwhattypeofpersonalityyouareputtingout
thereaboutyouronlinename.
ExpectthateverysinglewordyoutypeonlineisbeingreadbytheFeds.Tothem,thisismucheasier
thantrackingdruglordsonthestreets.Theysitinanofficeandreadforumpostsandtryandmake

77
connections. Don'tunderestimate thefeds. Alwaystreateverythingascompromised, alwaystreat
everybodyascompromisedanddon'teverthinkanybodywillevergotojailforyou.Ifsomebodycan
avoid1020yearsbyrattingyouout,theywilldoitinaheartbeat.
TheperfectexampleisSabufromLulzSec.Afterhewasbustedandfacing112yearsinjail,theymade
himadealtohelpthemratouthisfriendsandheendedupgettingmanyofhis"friends"arrested.
Evenpeoplewhoareyourfriendswillturntheirbacksonyouwhenitcomesdowntotheirfreedom.
EXIF DATA
Iforgottomentionabovewhentalkingaboutmetadata,thatwhenitcomestophotos,thereis
anotherriskinvolvedcalledEXIFdata,thisisanotherformofmetadataspecificallyrelatedtoimages
andmaynotbeproperlyremovedbyMetadataAnonymisationToolkitmentionedbefore.
EXIFdatastandsforExchangeableimagefileformatandaffectsJPG,JPEF,TIFandWAVfiles.Aphoto
takenwithaGPSenabledcameracanrevealtheexactlocationandtimeitwastaken,andtheunique
IDnumberofthedevicethisisalldonebydefaultoftenwithouttheuser'sknowledge.
InDecember2012,antivirusprogrammerJohnMcAfeewasarrestedinGuatemalawhilefleeing
fromallegedpersecutioninBelize,whichsharesaborder.Vicemagazinehadpublishedanexclusive
interviewwithMcAfee"ontherun"thatincludedaphotoofMcAfeewithaVicereportertakenwitha
phonethathadgeotaggedtheimage.Thephoto'smetadataincludedGPScoordinateslocatingMcAfee
inGuatemala,andhewascapturedtwodayslater.
Toavoidthis,onlytakephotosthatusePNGbecauseitdoesnotstoreEXIFdata.Tocheckifyour
photohasanyrevealingEXIFdataattachedtoit,checkoutthissite.
http://www.viewexifdata.com/
oryoucandownloadatoolbydoingaquicksearchonlinetoseewhatEXIFdatamaybecontainedin
yourphotosbeforeyouuploadthem.Beverycarefulwithanyfilesthatyouuploadonline,becauseyou
never knowwhattypeofharmfuldatacouldbeattachedinthem.IthelpstouseTails,butalways
considereverythingyouputonlineasapotentialpieceofevidencetobeusedagainstyouandalways
prepareforthedaythefedscometoyourdoor.
RETAINING A LAWYER, HOW TO HANDLE GETTING CAUGHT OR
INTERROGATED
Nextentryintotheseriesonsecurityishowtohandlegettingcaught.
Letusfaceit.Weareallhumanandwemakemistakes.Unfortunately,youonlyneedtomakeone
mistake,andtheLawEnforcement,commonlyreferredtoasLEontheseforumscanbustyou.Maybe
they willwaitforyoutodosomethingmoreseriousbeforetheynabyou,butifyouslipupandthey
feelyouareworthgoingafter,youcanexpectthemtogetyounomatterwhereyoulive,withrare
exception.

78
ThefirstthingIwanttodoislinkyoutoanotherthreadIjustcameacrossontheseforums.
https://silkroad5v7dywlc.onion/index.php?topic=13093.0
Themainquestionis,shouldIkeepanemergencylawyerfundonhand?Andhowmuchshoulditbe.
TheresponseIthinkwasmostappropriateforthisquestionwasthefollowing.
Quotefrom:VanillaRoyaleonJanuary02,2014,05:33:49am
Giveyourlawyer50kandputhimonaretainer.
Don'thaveaemergencyfund'stash'lyingaroundifthatiswhatyoumean....youshouldalreadyhave
yourlawyerpaid+plusextraincaseheneedstopostbondforyouandtheyseizethemajorityofyour
drugfunds.
OnceyougetarrestedbyLE,theycanseizeyourmoneybasedontheassumptionthatitisdrug
related.Soyouneedtohavealawyerpaidforaheadoftime.Thatway,intheunfortunatecasethat
yougetavisitfromthefeds,youhavealawyerreadytogo.Theagreeduponamountwasaround
$50,000.
NextIwanttotalktoyouaboutwhattodoincaseyougetinterrogatedbyLE.Thereisagreatthread
aboutthis.
https://silkroad5v7dywlc.onion/index.php?topic=4461.0
Thetakehomesfromthisthreadarebasically.Keepyourmoouthshut.Thefedsaregoingtotryall
typesoftacticsonyoutogetyoutoadmittoguiltofthecrimesyouarebeingaccusedof.Theywill
likelyusethegoodcop,badcoponyou.Firsttheywilltellyouthattheywanttohelpyou,andthat
they areafterthebigguys.Theyjustneedyourhelptoputawaythebigguys.Donotlistentothis,I
havenevercooperatedwithagoodcopLEandhaveitendupworkinginmyfavor.Onceyouadmitto
beingguilty,youcankissyourfreedomgoodbye.
Secondly,ifyourefusetocooperate,theirattitudewillchangetobadcop.Theywillsay,"OKfine,you
donotwanttocooperate?Itriedtohelpbutnowyouaregoingtobeinalotoftrouble.Doyouhave
anyideawhatkindofchargesyouarefacing?Youaregoingawayforalongtimeunlessyoustart
talking."
Theyaregoingtotryandscareyouintoadmittingguilt.Again,keepyourmouthshutandcontinueto
askforalawyer,hopefullytheoneyouputona$50,000retainerpriortothishappening.Neverspeak
withoutalawyerpresentandneverdoanythingyoudonothavetodolegally.Ifyouhavetherightto
remainsilent,thenexercisethatright.Iknowtherearesomecircumstancesinwhichyoudonothave
thatright,butunlessthatisthecase,youarebetteroffstayingquiet.
Third,droptheattitude.Donotarguewiththecopsabouthavingnothingonyou,orsomethingfor
thatmatter.Actscared,anxiousandconfused.Actlikeyouhavenoideawhatisgoingonandthatyou

79
are scaredfor your life. Tellthe copsthey are scaringyouandyouwanttosee your lawyer becauseyou
donotknowwhatthisisabout.Theyneedevidence,andsolidevidenceatthat,tochargeyouwitha
crime.
Theyaregoingtotryandcorrelatepostsyoumadeonforums,phonenumbersyoucalled,perhapsa
packageshippedtoyourhome,allformsofcommunication,banktransfers,andsoforth,untiltheycan
findawaytolinkyoutothecrimeyouarebeingaccusedof.Butthebiggestpieceofevidencewill
alwaysbeyourwillingnesstoadmityourguiltforalessersentence.
WhenSabufoundthathewasfacing112yearsinfederalprison,hequicklyspilledeverythingand
startedworkingforthefeds.Again,talktoyourlawyer,findouttheevidenceagainstyouandonly
answersquestionsyourlawyeradvisesyoutoanswer,andanswertheminawayyourlawyeradvises
youtoanswerthem.
Tryandbeashonestaspossiblewithyourlawyer.Yourlawyercannotandwillnotshareany
admittanceofguiltyouhavewiththeprosecutorsorLE,thisiscalledAttorneyclientprivilege.Please
notethereareafewinstanceswherethisdoesnotapply.
https://en.wikipedia.org/wiki/Attorney%E2%80%93client_privilege#When_the_privilege_may_not_ap
ply
COMBINING TOR WITH A VPN
Welcomebackreaders!
TodayIwanttotalkaboutagreatlydebatedtopic.
ShouldIuseaVPNwithTOR?
ShouldIuseTORtoconnecttoaVPN,or useaVPNtoconnecttoTOR?
Letmesayfirstofall,thatwhenyouarebrowsingtheinternetwithoutTOR,youshouldprobablybe
usingaVPNregardlessofwhetherornotyouareusingTOR.AndmakesurethattheVPNusessome
formofencryptionaswell.Forthoseofyouwhoareverybeginner,thinkaboutwhenyouconnecttoa
publicwifinetworkatacoffeeshop,oranairportandyougetallthesewarningsthatyourrequests
sentoverthisnetworkarevulernable.
Allnetworks,butespeciallypublicwifinetworksarevulnerabletotrafficanalysis.Putthistogether
withthefactthatsomeinternetserviceprovidersmonitoryouractivitytosomelevel,andyoucansee
whyitmightbeagoodideatoalwaysuseanencryptedmethodofusingtheinternet.Attheveryleast
toprotectyourpersonalinformationwhenyouareenteringcreditcards,usernamesandpasswords,as
wellasotherpersonaldataonline.Again,especiallyifyouareusingapublicwifinetwork.
ChoosingaVPNthatusesatleast128bitencryptionlikeTORisgoodpractice,andwillstopthe
majorityofeavesdroppers.Butifyoucanget256bitencryption,youareevensafer.Beforewegetinto
whetherornotweshouldbeusingaVPNtogetherwithTOR,Iwanttogiveyouafewwarnings

80
regardinghowyoushouldbeusinga VPN.
IfyouaregoingtobeusingaVPNforanytypeoffreedomfighting,makedamnsurethatyourVPN
doesnotkeeplogs.Thisisactuallyalotharderthanyoumightthink.ManyVPNproviderswillclaimto
notkeeplogsofyouractivityinordertogainyouasacustomer,becausetheyhavetocompetewith
theotherprovidersoutthere.Customersaregoingtotrendtowardsproviderswhooffernoidentifying
dataretention.Unfortunately,thisclaimoftheirsisnotalwaystherealcaseandIwillgiveyouan
example.
ThereisawellknownVPNprovidernamedHideMyAssthatpreviouslyclaimednottokeeplogsofits
users.Unfortunately,whenmetwithacourtorderfromtheirgovernmentintheUK,theyhandedover
evidenceofasuspectedhackerfromaninternetgroupLulzSecwhichhelpedleadtohisarrest.The
storycanbefoundbelow.
http://www.theregister.co.uk/2011/09/26/hidemyass_lulzsec_controversy/
Oneofthetakehomequotesfromthisarticleisthefollowing.
Quote
WearenotintimidatedbytheUSgovernmentassomeareclaiming,wearesimplycomplyingwithour
countrieslegalsystemtoavoidbeingpotentiallyshutdownandprosecutedourselves.
AverysmartmanthatgoesbytheonlinehandleTheGrugq,saidwhendoingyourfreedomfighting
onlinethatnobodyisgoingtogotojailforyou,andheis100%correct.Whenitcomesdowntoit,no
VPNproviderisgoingtoriskjailtoprotecta$20amonthsubscriber.Nomatterhowtoughtheysound,
nomatterhowmuchtheyclaimtocareaboutprotectingtheircustomers,whenfacedwithachoiceto
giveyouuporgotojail,theywillalwayschoosefreedom.
Anotherthingtoconsiderhowever,isusingaVPNdoeshideyourinternetactivityfromyourinternet
serviceprovider.ItcanalsohidethefactthatyouareusingTOR,whichmayflagsomesuspicionwhen
thefedsstartaskingISPstoprovidedataabouttheirusers.Thismayormaynotberelevant,since
manypeopleuseTORandyoucanarguetherearemanylegitimatereasonstouseTORandnothing
suspiciousaboutTOR.Butitisjustanotherfactortoarousesuspicionthatmayormaynotcomeinto
playandshouldbeconsidered.
Ifyouchoose touseTORoveraVPN,thebenefitsarethatyouwouldbeagain,hidingfromyourISP
thefactthatyouareusingTOR.Also,yourVPNwouldonlybeabletoseethatyouareconnectingto
TORnodesandthatyouaresendingencrypteddata.TheVPNwouldnotbeabletoseewhatdatayou
aresendingoverTORunlesstheydecryptedit,becauseremember,allinformationrelayedoverTORis
encrypted.
Thedownsidesofcourse,asmentionedarethatVPNprovidersmayormaynotlogeverythingthat
youdointheformofmetadataorevencontentiftheyhavethestoragecapacity,andkeepthoselogs
onhandforalongtime.Inthiscase,itisnobetterthanconnectingtoTORthroughanISP.Another
thingtomentiontothosewhowilluseVPNswhennotusingTOR,butalsouseVPNswhenusingTORis

81
remember whenyouare, andare notconnected toyour VPN. SometimesVPNscanunexpectedlydrop
connectionsandyoumaynotevenbeawareofit.IfthereasonyouareusingaVPNistohideTOR
activityfromyourISP,thenifyourVPNdrops,yourISPwillstartseeingyourTORtrafficinstead.
Or,maybeyouforgetthatyouareconnectedtoyourVPNandenduppunchinginyouraddresson
GoogleMapstofinddirectionssomewhere.WellguesswhatGoogledoeswithalldataenteredinto
theirsystem?Theykeepit.Andtheylikelykeepitindefinitely.SoifonedaytheNSAidentifiesyouon
theTORnetworkbyoccupyingalargenumberofnodesandusingtrafficanalysistoidentifyyoubased
onstatisticalanalysis,itwilllinkthemtoyourVPNIPaddress.
Atthispoint,theywilllikelyasktheVPNtoturnoverdataontheirusers,butiftheVPNrefusesto
complybecausetheyarenotsubjecttoUSlaw,orthelawsofothercountries,theymaychecksomeof
thebigsurveillancewebsitesouttheretoseeifyouslippedupandusedthatIPaddressforanything
elseonline.TheywillchecklogsfromGoogle,Yahoo,Facebook,Twitter,Netflixandotherbigdata
collectioncompaniestoseewhohasbeenusingthatIPaddresstoconnecttotheirservers.
IfyouaccidentallypunchedinyouraddressonGooglewhenconnectedtothatVPN,youarenowa
suspect.Soalwayskeepthingslikethisinmind.JustbecauseyouarecoveredbehindaVPNdoesnot
meanyouarenottraceablebyhumanerror.ThebenefitsofTOR,arethatyougetanewidentityevery
timeyouconnect.ThismayormaynotbethecasewithyourVPN,sopleasecheckandmake sure.
NextpostwewilltalkabouttheadvantagesanddisadvantagesofusingTORtoconnecttoaVPN.
[/quote]
COMBINING TOR WITH A VPN CONTINUED
Ok,nowletustalkaboutwhyyoumaywanttoconnecttoaVPNoverTOR.
Thedataflowwouldlooklikethis.You>Tor>VPN>Internet
Thebenefitsofdoingthatareasfollows.YouaremoreanonymoustoyourVPNincasetheyhappen
tokeeplogs,orifyoudosomethingusingtheVPNthatyouarenotsupposedtoandawebsiteor
servergrabsyourVPNIPaddress.Inthecaseofthishappening,eveniftheVPNmanagestokeeplogs
ofeverythingyoudo,theycanonlyidentifyyouasananonymousTORuseraslongasyoudidnot
purchasetheservicelikeanidiotwithyourcreditcardorPaypalaccount.IfyouuseBitcoin,andmade
surethetheBitcointrailisnoteasilytraceableyoushouldbeokay.SomewebsitesblockTORusers
fromconnectingtotheirwebsitesorservers,byusingyourVPNtoappearastheexitnode,youare
hidingyourTORactivityfromthewebsiteyouarevisitingandhopefullybypassingtheirfilters.
Anotheradvantage,isthatifyourVPNconnectiondoesdrop,yourfallbackwillbeyourTORIP
addressinsteadofyourrealIPaddress.Andfinally,ifyouarepassingthroughacompromisedTORexit
node,yourinformationwillremainencryptedthroughtheVPN'sencryptionprotocoluntilitreaches
theexitnodeoftheVPN.Thisisagoodthingifyouarepassingthroughacompromisedexitnode,but
donotforgetthattheVPNcouldbeloggingeverythingyouaredoinganyways.Donottrustanybody
whohasaccesstoyourunecrypteddata!

82
Afewofthedownsidesofdoingthingsthisway,asmentionedinthepreviouspostarethatyourISP
knowsyouareusingTOR,whenandforhowlong.Thismayormaynotmattertoyou,butitisjust
somethingtoconsider.Second,youwillbeunabletovisithiddenserviceswebsites.Remember
those.onionsiteswetalkedaboutinthebeginning?YouneedtobeconnectedtotheTORnetworkto
visitthosehiddenservicewebsites.
ButIamconnectedtoTORaren'tI?Yesyouare,butyourfinalmethodofcommunicatingwiththe
internetdoesnotcomefromtheTORnetwork,itcomesfromyourVPN.AndyourVPNislikelynot
configuredforTOR.Inorderforyoutobeabletoconnecttoahiddenservices,youmusteitherbe
connecteddirectlytoTOR,oruseaVPNtoconnecttoTOR.TORmustbeyourfinalnodeof
connectivityinordertovisitonionwebsites.
Thechoiceisultimatelyuptoyou,andeverypersonineverystate,provinceandcountrywillhave
differentreasonsforwantingtodoVPNtoTORorTORtoVPN,orjustTOR,orjustVPN.Whatever
choiceyoumake,pleasekeepallthethingsmentionedinthispostandthepreviouspostinmind.None
ofthesemethodswillsaveyouifyouenteranythingidentifyingaboutyourselfonline.Donotloginto
yourFacebookaccountusingyourVPN.DonotcheckyouremailorsearchanearbyaddressonGoogle
usingyourVPN.Infact,stayawayfromGooglealtogetherunlessabsolutelynecessary.
Therearetwoothersearchenginesoutnowthatdonotstoreinformationabouttheirusers.
#1DuckDuckGo.TheyhavebothaclearnetURLandahiddenservicesURLforbothtypesofusers.
https://www.duckduckgo.com
http://3g2upl4pq6kufc4m.onion/PleasenotethehiddenservicesmirrorisnotHTTPS
#2StartPage.Thisserveralsodoesnotstoreanyinformationaboutitsusers.
https://www.startpage.com
Beforewe moveon,IwanttogobacktohowtochooseagoodVPN.WhenlookingforaVPN
provider,youwillmostlikelycomeacrosstwoprotocolstochoosefrom.FindoutwhichoneyourVPN
providerisusingbeforeyousignupwiththem.PPTPandOpenVPN.Atthistime,Iamgoingtohighly
recommendthatyouavoidPPTPandstickwithOpenVPNproviders.Checkoutthissitefor aquick
comparison.
http://www.goldenfrog.com/vyprvpn/openvpnvspptp
Asyoucansee,PPTPusesaweakerencryption,128bitversus160bitto256bitforOpenVPN.It
offersbasicsecurityversusahighlevelofsecurityusingsomethingcalleddigitalcertificates.Thisis
basicallyawaytomakesuretheydatacominginissentfromyourVPNproviderandnotinjectedby
somemaliciousthirdpartybecausetheincomingandoutgoingdataaresignedusingspeciallyobtained
certificates,similartoshowingyourIDtogetintoaarestrictedarea.
TheonlydownsideisthatsettingupOpenVPNcanbealittlechallengingforthelesstechnicalusers,
butthereareplentyofgreattutorialsonlinetosetupOpenVPNprovidersandyourVPNprovideritself

83
willlikelyhelpyougetsetupas well. PPTPhas beenabandonedbythose whodemandthehighest
levelofsecurity,soIwouldrecommendtoavoidit.AthirdoptionforVPNprovidersisL2TP/IPsec,but
manyusersnowbelieveithasalsobeencompromisedbytheNSAduetoitsweakerlevelsof
encryptionandshouldbeavoidedaswell.StickwithOpenVPN.
Lastly,ifyouwanttoknowhowtoconnecttoTORoveraVPN.IfyouareusingOpenVPNlikeI
recommended,thenyouitisreallyquitesimple.MakesureyouareconnectedtoyourVPN,checkyour
IPaddresstoonanywebsitesuchasWhatIsMyIpAddress.comtomakesureithaschanged.Then,open
TORoropenTAILSandstartusingTORandyouarenowconnectedtoTORoveraVPN.
ConnectingtoaVPNoverTORisamoretrickyandcurrentlyabovemyskillsetsinceOpenVPN
reconfiguresyournetworkroutessoTorcan'tberunningonthesamehost.AssoonasIfigureitout,I
willpostatutorial,andifanybodycanshareaneasywaytoconnectaVPNoverTOR,thenpleaseshare
itwiththisthread.
UPDATE
AmethodofconnectingtoaVPNoverTORhasbeenaddedtothisthreadbutiscurrentlyonlyableto
beusedbyWindowsusers.Youcanreaditaboutitatthelinkbelow.
CONNECTINGTOR>VPNFORWINDOWSUSERS
Afteralongsearch,IhavefoundawayyoucanconnectTOR>VPN.Itisnotperfect,andsomemight
notagreewithdoingthingsthisway,butitworksandIamgivingittoyouasanoption,butitonly
worksforWindowsusersatthistime.
IfyoulookbackatmypreviouspostsregardingcombiningVPNandTORthenyouwillfindthe
reasonswhyyouwouldwanttodoso,andsomeofthereasonswhyyoumightnotwanttodoit.ButI
wasunabletoprovideyouwithawaytoconnecttoaVPNusingTORsothattheVPNdoesnotknow
whoyouare.WhenitcomestoTOR>VPN,ifyoucannottrustyourVPN,whichyourarelyshould,
thenkeepingyouridentityanonymousfromyourVPNisagoodidea.Also,withmoreandmorepeople
usingTOR,butwithonlyaround4000TORexitnodes,manyoftheexitnodeIPaddressesarebeing
flaggedasspammersonpopularwebsitesandlimitingtheusageofwellmeaningTORuserstoposton
messageboardslikeStackExchangeandsoforth.
ThewaythatIfoundyoucandoTOR>VPNisbyusingavirtualmachine,preferrablyVirtualBoxand
runninganotherinstanceofWindows,preferrablyonethatuseslessmemorythanyourcurrent
version.YoualsowanttorunTORExpertandTortillaonyourhostOS.Italkabouthowtodothisin
previousposts.NextsetyourVirtualBoxtorouteallit'snetworktrafficthroughTortilla(bridge
adapter),whichroutesitallthroughTOR.CurrentlyTortillaisonlysupportedbyWindows,whichiswhy
thisoptionisonlyavailabletoWindowsusersatthistime.Doingthisalsomakesiteasiertodothings
likewatchvideosonYouTube.
NowthatyouhaveyourWindowsVirtualMachinerunningonTOR,youcaninstallaVPNofyour
choice,preferrablyoneusingOpenVPNonyourWindowsGuestOSandconnecttoit. CheckyourIP

84
address before connectingandafter andyoushouldsee adifferentIPaddress. Ifall wentwell, younow
haveavirtualmachinerunningTOR>VPN.Thenifyouwanttoaddanotherlayer,youcandownload
TORbrowserbundleontoyourvirtualmachineandrunthataswellgivingyouTOR>VPN>TORfor
anotherlayerofsecurity.AlsoyouhavetheoptionusingthismethodtouseaVPNonyourhostOS,
thenTorExpertwithTortilla,thenanotherVPNonyour guestOS,thenTORbrowser,givingyouVPN>
TOR>VPN>TOR.
Iamnotadvocatinganywhcihmethod,youneedtomakethatdecisiononyourown,Iamjustgiving
youtheknowledgenecesarytomakeaninformeddecisonandyoucanultimatelychoosewhich
methodyoufeelmostcomfortablewith.SometimesdoingTOR>VPNisnecessarybecauseofthe
spamfilterreasonsImentionedaboveandothertimeshavingTORasyourlastnodetotheinternetis
necessarylikewhenaccessingtheonionnetwork.ItiscompletelyuptoyouandIknowthatweare
tryingtoshyawayfromWindowsusagebecauseofalltheexploitsandotherreasonsspokenaboutin
thepreviousposts,butifyouhavenootherwayofstayinganonymousfromyourVPNthanthis,thenI
thinkitisagoodcompromiseuntilwehavesomethinglikeTortillathatiscompatiblewithLinux
distributions.
TRACKING COOKIES
NexttimeIwanttotalkaboutissomethingthatmostpeoplecompletelyforgetabout.Tracking
Cookies.
ArecentarticleexplainshowtheNSAusesthingslikeGoogleAdsandothertrackingcookiestoidentify
usersoverTORwhendoingsobyothermeansisnotpossible.
http://www.washingtonpost.com/blogs/theswitch/wp/2013/12/10/nsausesgooglecookiesto
pinpointtargetsforhacking/
ForthoseofyouwhodonotknowwhatIamtalkingabout,letmeaskyouthis.Haveyouever
noticedthatcertainadsseemtofollowyouaroundfromwebsitetowebsite?Perhapssomethingyou
searchedforonGoogleorYahooisnowshowingupinadsonotherpages?Thiswasoriginallydesigned
tomarketthingstoyoubasedonyourpreferencesbyinstallingtrackingcookiesintoyourbrowser.
LuckilyTORclearsitscookieseverytimeyourestartthebrowser,andyesTailsdoestoo,butthat
doesnotmeanyouarenotvulernablewithinthesameTORsession.WhatImeanbythisis,letussay
youwentanddidsomefreedomfightingonaforumsomewhereandthenafter,usingthesameTor
session,visitedanotherwebsitewithGoogleAdsonit.Thenyouwenttoanothersitewithmore
GoogleAdsonit.YouwouldbesurprisedhowmanysitesnowhaveGoogleAdsonthem,bytheway.
Googlecanusethesetrackingcookiestolearnaboutyourbrowsingbehavior.Yoursearchterms,
yourpreferredsites,andsoforth.SomepeopleareevenstupidenoughtousethesameTORIP
addressandgochecktheirFacebooknewsfeedortheiremail.Guesswhoisinbedwiththefeds?
Google,Yahoo,Facebook,MSN,andalloftheiremailprovidersaswell.Remember,whenyoustart
leavingpatternsbehind,theywillstartlookingforsimilaritiesthatstartwithjustasuspicion.

85
Perhapsthey correlatedthefreedomfightingforumpostswith youbecause youloggedintoyour
email,andnowtheystartnoticingthatyoualwaysmisspellthesamewords,makethesamegrammar
mistakes,thesameslangterms.Perhapsyouvisitedawebsitebelongingtosomebodylocaltoyouwith
GoogleAdsonit.Itisnotentirelysurehowtheyareabletousethesetrackingcookiestoidentifyyou,
butthepointis,theykeepeverything.AndifyouhappentodosomethingstupidlikeGooglealocal
restaurantorwhatmoviesareplayinginyourlocalareaonthesameIPaddressthatyoudidsomething
youshouldnothaveearlieron,thenGooglecanput2and2together.
Oncetheyareonyourtrail,youarescrewed.Sodonotgivethemanythingtocorrelatetoyou,ever!
Sothenyoumightask,cannotIjustdisablecookiesalltogether?Yesyoucould,but,cookiesare
requiredforthingslikeloginsessions.Withoutcookies,youareunabletomaintainastateofbeing
loggedinoncertainwebsites,becausetheyusethatcookieIDtoidentifythesessionontheserver.
Again,youcancertainlydisablecookies,butyouwillnotbeabletomaintainaloginanywhere.
LEARNING FROM OTHERS' MISTAKES. LIBERTAS, DPR, SABU, LULZSEC
Alittlechangeofpaceforthisnextpost.IwanttotalkaboutoneofourfallenmoderatorsLibertas.
Ithasfinallybeenconfirmed,whatweallwerehopingforthatLibertas,oneofthe3arrested
moderatorswasreleasedonbailrecentlyaccordingtoanarticle.
http://techcrunch.com/2014/01/07/thesilkroadslibertasisfreetotheannoyanceofusauthorities/
Quote
TheSilkRoadmoderatorGaryDavis,akaLibertas,isofficiallyfreeonbailandawaitinganextradition
hearingonFebruary13.
TheFBIflewtoIrelandthatnightfortheexpresspurposeoftakingDavisintocustodyandinterrogating
himinIreland,withregardtohispositionandfunctions“beingamoderatoronawebsiteallowing
transactionstofacilitatethesaleofdrugsonline.”
Soasyoucansee,justbecauseLibertaswasamoderatoronthesite,heisbeingchargedwith
allowingtransactionstofaciliatesalesofdrugs.Heisbasicallybeingchargedasadrugdealer.
Quote
However,Daviswasfoundinpossessionofillicitsubstanceswhichcouldresultinaminimumsentence.
Heunfortunatelywasfoundwithdrugsonhimatthetimeofhisarrest,whichmadethingsmuch
easiertokeephimincustody.AnditturnsoutthattheallegedformerownerofSilkRoad,RossUlbricht
isfullycomplyingwithlawenforcementtoattempttoidentifyseniorvendorsonSilkRoad.According
tothearticle,Rosscommunicatedwiththevendorsfrequentlyandlikelyinplaintext(ismyguess).
ThereasonIbringthisup,isthatweneedtoremindeveryuseronhereofthemistakesthatwere

86
made byRoss, andtheother three moderatorssothatwe can hopefullylearnfromthem. We needto
avoidthesetypesofmistakes,nevereverEVERgiveanybodyanypersonalinformationaboutyourself
online.Thestorygoes,thatRossrequiredmoderatorstogivehimcopiesoftheirIDsinorderto
becomemoderatorsofSilkRoad,andhelikelykeptarecordoftheseonhiscomputer.Unfortunately,
thesearenowinthehandsoftheFBIand3moderatorshavebeenarrestedasaresultsince.Andnow,
accordingtothearticle,theyareafterseniorvendorsaswell.
Afewtakehomesare;AlwaysusePGPencryptioninallyourcommunications,whichunfortunatelyin
thiscasewouldnothavematteredbecauseRossendedupgivinguphisprivatekeystothefeds.Butit
isstillanotherhurdleintheirwaytoprotectyoufromthemtakingawayyourfreedom.Nevergiveout
anypersonalinformationtoanybodyonlineaboutyourself.Neverputyourtrustinsomebodyelse's
hands,becauseattheendoftheday,nobodyisgoingtogotojailforyou.Rossfoundanopportunity
topossiblyreducehissentenceandheisfullytakingadvantageoftheopportunity.
ThisexactsamescenariohappenedwithSabufromLulzSecwasthreatenedwith112yearsinprison,
hequicklyturnedonallhisfriendsandworkedwiththefedstogetthemalllockeduptohelpreduce
hissentence.Sabuhas2kidsandobviouslydecidedhewouldrathersnitchouthisfriendsandhavea
chanceatbeingafatherratherthanspendtherestofhislifelockedupinjail.Again,nobodyisgoingto
gotojailforyou.
HOW FAR WILL LAW ENFORCEMENT GO?
Todaywearegoingtotalkaboutthelengthsthatlawenforcement(LE)willgototryandcatchyou
slipping.
ThethreadthatinspiredthispostwasthefollowingSRthread.
http://silkroad5v7dywlc.onion/index.php?topic=8788.0
Thefirstquestionis,canLEshipdrugstobuyerstotryandsetthemupfordrugcharges?Letusjust
say,thattheyhavedoneittoaSilkRoaduserbeforewhowentbythenameofFlushakaChronicpain
akaCurtisGreen
http://www.usatoday.com/story/news/nation/2013/11/07/vendoradministratorpleadguiltyinsilk
roadcase/3469751/
Quote
InApril2012,aDEAundercoveragentinMarylandposingasadrugsmugglerbegancommunicating
with"DreadPirateRoberts"onSilkRoadaboutsellingalargeamountofillegaldrugs."DreadPirate
Roberts"instructed[Curtis]Greentohelpthesmugglerfindadrugdealerwhocouldbuyalarge
amountofdrugs,courtpaperssay.Greenfoundabuyerandagreedtoactasthemiddlemanfora
$27,000saleofakilogramofcocaine.GreengavetheDEAagenthisaddress.
AnundercoverU.S.PostalServiceinspectordeliveredthecocainetoGreen'shouseinUtahonJan.17.
87
Soasyoucansee,whetheryouviewitasentrapmentornot,oncetheyhaveevidenceagainstyou,
they willeventuallyfigureoutawaytogetsomethingonyouandbustyouforitliketheydidtoCurtis
Green.
TheSecretServiceposedasavendorforfakeIDsonlinefor5yearsandactuallyshippedfakeIDsthat
they madetobuyersonanonlineRussianforum.
http://www.tested.com/tech/456882howsecretservicesoldfakeidscatchidentitycrooks/
Quote
TheUSGovernment's"OperationOpenMarket"resultedinindictmentsagainst55defendants.
AccordingtoWired,SpecialAgentMikeAdamsshippedoutmorethan125fakeIDsoveraboutfive
yearsofactivitywhilegoingbytheusernameCeltic.Amazingly,theentireschemestartedwhenthe
governmentarrestedtherealCeltic,aNevadamanwhogotcaughtshoppingataWholeFoodswhere
he'dpreviouslyusedafakecreditcard.
Lawenforcementdiscoveredcounterfeitingequipmentamonghispossessionsandlearnedabouthis
onlineactivities.AdamsassumedhisonlineidentityandevenimprovedCeltic'scred,shippingnear
flawlessIDsandbecomingatrustedselleronCarder.ru.
Asyoucanseeinthisarticle,theSecretServiceagainsoldillegalitemstopeopleonlineinorderto
bustthem.Severalofthebuyersusedtheirrealaddressesandsentrealphotosofthemselvestothis
officertohavetheirIDsmade,resultinginbeingarrestedbythefeds.
Andinthisparticularcase,thefedschargedallthedefendantsundersomethingcalledtheRICOact.
Quote
"Themainindictmentisnoteworthybecause,inadditiontotheusualmixofcreditcardfraudandfalse
identificationcharges,the39defendantshavebeenchargedunderthemobbustingRICOact–afirst
foracybercrimeprosecution.
Enactedin1970tohelptheFBIcrackdownonthemafia,theRacketeerInfluencedandCorrupt
OrganizationsActletsthefedsholdeverymemberofacriminalorganizationindividuallyresponsiblefor
theactionsofthegroupasawhole.ThelossescollectivelyinflictedbytheCarder.sumembersareeasily
enoughtogiveeveryRICOdefendant20yearsinprison."
Whenyoucommitcrimesonline,especiallyinanonlinecommunity,thefedsmaybeabletoholdyou
accountablefortheactionsofotherusersonthatsamecommunity.Somakesurewhenyoudoyour
freedomfighting,orwhateveryouchoosetodo,thatyoutakethisintoconsidering.Alwaysweighout
theworstcasescenario,shouldyougetbusted,becausetheLEwilltryandsetyouup.
OnelastexampleofhowLEwilltryandsetyouup,butnotrelatingtoonlinecommunitiesiswhen
they puttogetherafakesweepstakesinLosAngeles.
88
http://www.nbclosangeles.com/news/local/LaMiradaInspiredbytheSimpsonstoCatchCriminals
78093912.html
Quote
Sheriff'sdeputiesinLaMiradaattemptedaropeadopeonsomeallegedcriminalsbyofferingthema
fakesweepstakesprize.Outofthe960letterssenttothese"peopleofinterest"onlyeightshowedup
attheLaMiradaHolidayInntocollecttheirprize,accordingtotheWhittierDailyNews.
Posingasthe"PelicanMarketingGroup,"deputiessentletterslastweektopeoplethroughoutthe
countywantedinconnectionwithcrimesrangingfrommisdemeanorwarrantstomurder.
Accordingtothereport,thesuspectswereadvisedtobringtheirletterandidentificationtothe
HolidayInn,andtoldthattheywereguaranteedaprizeworthatleast$100,andwouldbeoneof200
peoplewithachancetowina2010BMW238isedan.
Theywereallsmileswhentheyshoweduptocollecttheirprizes,DeputyJanetRamireztoldthe
newspaper."Oncetheytellthemthey'reunderarrest,thesmilefadesquickly,"shesaid.
SothereasonImadethispost,wasforthoseofyouwhothinkthatLEwillnotgotocertainlengthsto
tryandsetyouupforcharges.Theywilldoitiftheywantyoubadenough,andifyoufallforit,they
mightgetyouonsometoughcharges.CurtisGreenisfacingupto40yearsforthestingoperationby
theDEAonhimandtheuserswhopurchasedfakeIDsontheRussianforumcouldfaceupto20years
eachsincetheycanbechargedundertheRICOact.Alwayskeepthesethingsinmindwhenconducting
activitiesonlineandalwaystaketheworstcasescenariointoaccount.
Itonlytakesonemistaketogetcaughtandthegovernmenthasunlimitedresourcesandsuper
computerstotryandcatchyouslipping.Youmayonlyhaveafewlaptops,desktops,servers,but
nothingcomparedtothewhattheyhave.Becarefuleveryone.
FRAUDULENT PRIVATE MESSAGES
Becarefulwithprivatemessages(PM)online,becauseonethingthatcomeswithanonymity,isplenty
ofscammers.
SilkRoadusershavebeenreportingsupsiciousandoutrightfraudulentmessagesfromusersposing
asModeratorsaskingthemtodownloadfilestotheircomputers.Hereisanactualmessagereceived
byanothermember.
Quote
ThismessageistoinformyouthattheversionofTorBundleyouareusingmaybevulnerabletoa
remoteexecutionattackthroughaflawinJavascript'sonreadystatechangeevent.Thisvulnerability
maydiscloseausersactualidentityandothersensitiveinformationtransmittedoverthetornetwork.
AsofJanurary2nd2014thefollowingvulnerabilitywasfound
89
Title: Executionofunmappedmemorythroughonreadystatechange event
Impact:Critical
AnattackthatexploitsaFirefoxvulnerabilityinJavaScripthasbeenobservedinthewild.Specifically,
WindowsusersusingtheTorBrowserBundle(whichincludesFirefoxplusprivacypatches)appearto
havebeentargeted.
Pleasenote:IfyouareusingLinuxorTails(bootable)thisvulnerabilitydoesnotapplytoyou,please
disregardthismessage.
WeareadvisingallofourcommunitymemberstoupgradetothepatchedversionTorBundle(3.5)
http://www34.zippyshare.com/v/xxxxxxxx/file.html(LatestTorBundle3.5)
Mirror:http://xxxxxxxxxxxxxxx.onion/files/torbrowserinstall3.5_enUS.zip
Note:YoudonotneedtoremoveyourcurrentTorBundlebeforeinstalling.Thiswilloverwritethe
previousinstallationandupgradeyoutothelatest3.5version.
Ifyouareunsureofwhichversionyouhaveitisbesttoupgradeanyways,itwillpreserveyour
bookmarksandpreferencesduringtheupgrade.
Also...Don'tForgettoClickthe"ForbidScriptsGlobally"afterclickingontheS.....
Therest....DoNotmesswith....thisisarelativelysimplethingtodo....youmustdothisallbefore
accessinganyDarkWebSite.Point...Blank&Period....
ThisisyourSafetyandSecuritythatyou'reDealingwithhere....TAKETHISSERIOUSLY!!
Idon'tmeantosoundharshoranasshole...ibelievewe'reallFamilyhere....andfromhereonoutifyou
cannotdoastoldtoensurethatyoursecurityandsafetyisnotcompromised.....wellthenyoudon't
needtobehere....Period....
Anyquestions?PleasefeelfreetomessageanymodandwewilldoourbesttoreplyAsap
HappyNewYear&Staysafein2014!
SRStaff
Theythenprovidealinkforyoutodownloadan"updated"versionofTOR,whichhasbeenremoved
forsecuritypurposes.ButthismessageisnotcomingfromanySilkRoadstaff,itiscomingfroma
randomaccountandthefilesarelikelytobevirusesorpossiblyevenfromlawenforcement.
IfyougetanysuspiciousmessagesfromanybodyclaimingtobeaSilkRoadmoderatoraskingyouto

90
downloadsoftware toyour computer, reportittoamoderator immediatelysothatthey canban the
accounts.Donotunderanycircumstancesdownloadanysoftwaretoyourcomputerunlessitcomes
fromanofficialwebsitesuchas;
https://torproject.org
https://tails.boum.org/
Again,staysafeeveryone!
LEARNING FROM OTHERS' MISTAKES. HOW THEY BUSTED SABU
ThisnextpostIwanttofocusonmoremistakesthatotherhacktivistsandfreedomfightershavemade
whichultimatelyledtotheirarrests.Thisismoreproofthatyouonlyneedtoscrewuponce.
YouhaveprobablyheardmetalkaboutsomebodynamedSabumultipletimesandmaybeyouare
newtotheonlinecommunitiesandyouhavenoideawhoIamtalkingabout.Sabuwastheleaderofa
selfproclaimedhacktivistgroupcalledLulzSec.Theywereresponsiblefortakingadvantageofsecurity
exploitsinonlineserversandpostingtheinformationonlineonawebsitecalledPasteBin.Theyhad
donethismanytimes.
https://www.informationweek.com/attacks/lulzsecleadersabuunmaskedaidsfbihackersweep/d/d
id/1103214?
Quote
ThemenhavebeenchargedwithhackingFoxBroadcastingCompany,SonyPicturesEntertainment,
andthePublicBroadcastingService(akaPBS).
Duringthetimeallthiswashappening,themembersofthisgroupmaintainedanonlineInternet
RelayChat(IRC)channelinwhichtheyregularlydiscussedandtookcreditfortheirattacksandexploits.
Theagreeduponringleaderfortheseattacks,andthisgroupwentbytheonlinehandleSabu.Sabu
hadalsobeenlinkedtosellingstolencreditcardsonFacebookthroughhisonlinehandle,nothisreal
one,whichcarriesachargeofaggravatedidentitytheft.
Thegrouphadleakedidentitiesoflawenforcement,Sonyusers,andallwreakedalltypesofhavoc
onlineincludingDDosattacksontheCIA.TheFBIwantedSabu,theywantedtheringleader,who
wouldeventuallybefacingchargesthatcouldleadto112yearsinprison.ButasImentionedin
previousthreads,itonlytakesonemistaketogetcaught.Thatisalltheyneed.
http://www.foxnews.com/tech/2012/03/06/exclusiveunmaskingworldsmostwantedhacker/
Quote
Sabuhadalwaysbeencautious,hidinghisInternetprotocoladdressthroughproxyservers.Butthen
justonceheslipped.HeloggedintoanInternetrelaychatroomfromhisownIPaddresswithout
maskingit.Allittookwasonce.Thefedshadafixonhim.

91
However,thiswasnothisfirstactualslipup,butitwashisfirstslipupwherethefedsactually
discoveredhismistake.Hisidentitywasactuallydiscovered,or"doxed"previouslybyanotheronline
hackinggroupcalledBacktracewhopostedhisidentityandgenerallocationonlineweekspriortothis
inanattempttodoxmembersofLulzSec.
http://arstechnica.com/techpolicy/2012/03/doxedhowsabuwasoutedbyformeranonslong
beforehisarrest/
Quote
Sabuoccasionallymentionedownershipofadomaincalledprvt.orginhischats,includingthosein
Backtrace's"consequences"document.Everydomainregistrationisassociatedwithcorresponding
informationintheWHOISdatabase.Thisinformationissupposedtoincludethenameandaddressof
thedomain'sowner.
Oftenthisinformationisincorrect(mostdomainregistrarsdonothingtovalidateit)oranonymized
(manyfirmsoffer"proxy"domainregistration,sotheWHOISdatabasecontainsthedetailsoftheproxy
registrar,ratherthanthepersonusingthedomain).Monsegurappearedtouseoneofthese
anonymizingservices,GoDaddysubsidiaryDomainsByProxy,forregisteringtheprvt.orgdomain.
TheregistrationforthedomainwasduetoexpireonJune25,2011,requiringMonsegurtorenewit.
Butforsomereason—erroronMonsegur'spartperhaps,orscrewupbytheregistrar—therenewal
wasprocessednotbyDomainsByProxybutbyitsparent,GoDaddy.UnlikeDomainsByProxy,Go
DaddyusesrealinformationwhenitupdatestheWHOISdatabase,soon24thJune(thedaybeforeit
wasduetoexpire),Monsegur'sname,address,andtelephonenumberwereallpubliclyattachedtohis
domainname.
Monsegurquicklyremediedthemistake,changingtheWHOISregistrationtousevariousother
identities—firsttothatofAdrianLamo(whoreportedBradleyManningtoauthorities)andthento
"RafaelLima"andsubsequentlyto"ChristianBiermann".Thisattempttomisleadthoserelyingonthe
WHOISinformationsuccessfullymisledsomewouldbedoxers.Butnotall:byAugusttherewere
extensivedossiersonSabu'strueidentity.
Twomistakesthatweknowof,isallthatittooktobringdownatonetime,theWorld'sMostWanted
Hacker.IfyouarefamiliarwiththestoryofLulzSec,therewasatimetheywerereceivingmainstream
newscoverageandSabuhadgainedareputationofbeingthismysticaluntouchablehacker.
Unfortunatelyforhim,hemadetwosmallyetverycostlymistakeswhichendedupputtinghimaway.
ButwearenotdoneyetonthisstoryaboutSabu.
Sabuhadaweakness,thatthefedsusedasleverageagainsthimwhenhegotbusted.
Quote
Anunemployedcomputerprogrammer,welfarerecipientandlegalguardianoftwoyoungchildren.
“Itwasbecauseofhiskids,”oneofthetwoagentsrecalled.“He’ddoanythingforhiskids.Hedidn’t

92
wanttogoaway toprisonandleave them. That’showwe gothim.”
Monsegurwasquietlyarrestedonaggravatedidentitytheftchargesandreleasedonbail.OnAug.15
hepleadedguiltytoadozencountsofhackingrelatedchargesandagreedtocooperatewiththeFBI.
Sowhenyouaredoingyourfreedomfightingonline,youneedtoaskyourself.WhatdoIhaveto
lose?DoIhaveawife?Children?WhatwouldhappenifIweretoloseeverythingandbethrownaway
for10to20years,couldIhandlethat?Ifyoudecidethatyouarewillingtoriskallthat,thenyouagain
needtolearnfromthemistakesofthosewhohavefallenbeforeyou.Askyourself,ifputinahard
place,whereyouhadtochoosebetweenlifeinprison,andcooperation,inordertoseeyourown
family,youmaythinkyouwillnottalknow,butyoumaystarttalkingwhenthefedsarethreateningto
takethemawayfromyouforever.
OncetheFBIhadtheleaderofthegroupLulzSecworkingforthem,theywastedlittletimegettingthe
formerhackertoturnonhisfriendsandaidintheirarrests.
Continuednextpost.
LEARNING FROM OTHERS' MISTAKES. SABU BECAME FBI INFORMANT
AND BETRAYED JEREMY HAMMOND
WearecontinuingthesubjectofhowothersweretakendownafterSabuwascompromisedand
startedcooperatingwiththeFBI.Accordingtothisarticle.
http://arstechnica.com/techpolicy/2012/03/stakeouthowthefbitrackedandbustedachicago
anon/
Quote
ThedayafterChristmas,sup_ghadanotheronlinechatabouttheStratforhackandaboutsome30,000
creditcardnumbersthathadbeentakenfromthecompany.Hisinterlocutor,CW1,engagedinabitof
gallowshumoraboutwhatmighthappenshouldtheyallgetcaught.
Buttheraidhad,infact,alreadyhappened.CW1was"Sabu,"atopAnon/LulzSechackerwhowasin
reallifeanunemployed28yearoldlivinginNewYorkCitypublichousing.Hissixthfloorapartment
hadbeenvisitedbytheFBIinJune2011,andSabuhadbeenarrestedand"turned."Formonths,he
hadbeenanFBIinformant,watched24hoursadaybyanagentandusingagovernmentissuedlaptop
thatloggedeverythinghedid.
SoweseehereSabuischattingwithausersup_gtotryandengagehimaboutthehacksthattook
place.
Quote
Sabusuddenlyaddressessup_gbyanewname,"anarchaos."Itwouldturnoutthatsup_gwentby
manynames,including"anarchaos,""burn,""yohoho,""POW,""tylerknowsthis,"and"crediblethreat."

93
CW1:if I getraidedanarchaos your jobistocause havok inmyhonor
CW1:<3
CW1:sup_g:
@sup_g:itshallbeso
Normally,theattempttolinkhisvariousnameswouldhaveraisedthehacker'sguard;asheconfided
toSabu,someoneelsehadoncetriedtolinkthenames"yohoho"and"burn,"butthehacker"never
answered...IthinkhepickedupsomelanguagesimilaritiesI'veworkedwith[REDACTED]onotherops
inthepast."ButthiswasSabu,asortofhackerdemigodintheworldofAnonymous.Ifyoucouldn't
trusthim,whocouldyoutrust?SabuhadevenprovidedaservertostorethestolenStatfordata,sohe
couldn'tbeafed(inreality,hehaddonesoattheFBI'sdirection).
Andmoredetailsonhowtheylookedthroughcopiousamountsoflogstocorrelatethisusersup_gto
hisrealidentity.
Quote
Toidentifysup_g,theBureaufirstturnedtothevoluminouschatlogsstoredonSabu'scomputer.They
wentthrougheverycommentthatcouldbeplausiblylinkedtosup_goroneofhisaliases.Thegoalwas
toseeifthehackerhadslippedupatanypointandrevealedsomepersonalinformation.
Hehad.OnAugust29,2011at8:37AM,"burn"saidinanIRCchannelthat"somecomradesofmine
werearrestedinSt.Louisafewweeksago...formidwestrisingtarsandswork."Ifaccurate,thismight
place"burn"intheMidwest.FBIChicagoagentswereabletoconfirmthataneventcalledMidwest
RisingwasattendedbyChicagoresidentJeremyHammond'stwinbrother.(Hammondhadahistory
withanarchismandviolentprotest.)
"Anarchaos"onceletslipthathehadbeenarrestedin2004forprotestingattheRepublicanNational
ConventioninNewYorkCity.Muchlater,"yohoho"notedthathehadn'tbeentoNewYork"sincethe
RNC,"nicelytyingbothonlinehandlestothesame person.TheFBIwenttoNewYorkCitypoliceand
obtainedalistofeveryindividualdetainedatthe2004convention;theylearnedthatJeremy
Hammondhadinfactbeendetained,thoughhehadnotbeenarrested.Thepieceswerestartingtofit.
"Sup_g"and"burn"bothindicatedlaterthattheyhadspenttimeinprison,with“burn”indicatingthat
hehadbeenatafederalpenitentiary.AsearchofHammond'scriminalrecordsrevealedthathehad
beenarrestedinMarch2005bytheChicagoFBIandhadpledguiltytohackingintoa“politically
conservativewebsiteandstealingitscomputerdatabase,includingcreditcardinformation,”according
toanFBIaffidavit.Hammondwassentencedtotwoyearsinprisonfortheaction.
Inyetanotherchat,"Anarchaos"toldSabuthathehadoncespentafewweeksinacountyjailfor
possessionofmarijuana.HealsoaskedSabunottotellanybody,“causeitcouldcompromisemy
identity,"andhenotedthathewasonprobation.BothmatchedHammond,whowasplacedon
probationinNovember2010afteraviolentprotestagainsttheOlympicscomingtoChicago.Whenthe
FBIranacriminalhistorycheckonHammond,italsorevealedtwoarrestsformarijuanapossession.
TheFBIwassothoroughthatitevenfollowedupona"POW"commentsaying"dumpsterdivingisall
94
goodi'mafreegangoddess."("Freegans"scavengeunspoiled, wasted foodfromthe trashofgrocery
storesandrestaurants.)TheFBIwenttoChicagoauthorities,whohadputHammondunder
surveillancewhentheywereinvestigatinghimbackin2005.Aspartofthatearliersurveillance,“agents
haveseenHammondgoingintodumpsterstogetfood.”
Nowthattheyhadasuspect,itwastimetoputhimundersurveillance.
Thisiswhyyouallneedtobeextraparanoidwitheverysinglethingyousayaboutyourselvesonthis
forum.Ihaveseenpeopletalkingaboutwhatcountrytheylivein,someeventalkingaboutwhichstate
they livein.IfyouthinkthattheFBIwillneverputthepiecestogether,youmaybesadlymistakenas
JeremyHammondfoundout.
Quote
WatchingtheWiFinetworkrevealedtheMediaAccess Control(MAC)addressesofeachdevice
connectedtothenetwork.Mostofthetimetherewasonlyone,anAppleComputer—andsup_ghad
toldSabuthatheusedaMacbook.
OnMarch1,theagentsobtainedacourtorderallowingthemtousea"penregister/trapandtrace"
devicethatcouldrevealonly"addressinginformation"andnotcontent.Inotherwords,ifitworked,
agentscouldseewhatIPaddressesHammondwasvisiting,buttheywouldseenothingelse.
HisMacbook'sMACaddresswassoonseenconnectingtoIPaddressesknowntobepartoftheTor
anonymizingnetwork.
Andwhilethisdefinitelysoundedliketheirman,theBureauwenttoevengreaterlengthstodouble
checktheirtarget.ThemaintechniquewastoobservewhenHammondlefthishome,thentocallSabu
inNewYorkandaskifanyofHammond'ssuspectedaliaseshadjustleftIRCortheJabberinstant
messagingsystem.
Ifthisdoesnotopenyoureyestosomeofthemistakesmanyofyouhavebeenmakingonline,then
youneedtoreevaluatehowyouhandleyourselvesonline.Readtheentirearticletogetabetter
picture,butremember,Idonotcareifitisyourbestfriendfromelementaryschool,donot,underany
circumstanceseveradmitanythingonlinetoanybody.Neverunderanycircumstancestakecreditfor
anyfreedomfightingorhacktivismyouhaveparticipateditonline.Andforchrist'ssake,NEVERloginto
aserver,especiallyonethatkeepslogswithyourrealIPaddress!
WHERE YOU MIGHT CONSIDER RUNNING TO, IF YOU HAD NO OTHER
CHOICE
Inthecasethatyoumayhavetorun,herearesomethingstoconsider.
Iamnotanexpertonevadingextradition,orhowtoevadethefederalgovernment,NSAorother
superpowers,butIdohavesomerecommendationsthatyoumightwanttoconsiderifyoudecidethat

95
youhavenoother choicebut torun. The followingcountriesdonotcurrentlyhave anextradition
treatytotheUnitedStates.
Quote
Afghanistan,Algeria,Andorra,Angola,Armenia,Bahrain,Bangladesh,Belarus,Bosniaand
Herzegovina,Brunei,BurkinaFaso,Burma,Burundi,Cambodia,Cameroon,CapeVerde,theCentral
AfricanRepublic,Chad,China,Comoros,Congo(Kinshasa),Congo(Brazzaville),Djibouti,Equatorial
Guinea,Eritrea,Ethiopia,Gabon,Guinea,GuineaBissau,Indonesia,IvoryCoast,Kazakhstan,
Kosovo,Kuwait,Laos,Lebanon,Libya,Macedonia,Madagascar,Maldives,Mali,MarshallIslands,
Mauritania,Micronesia,Moldova,Mongolia,Montenegro,Morocco,Mozambique,Namibia,Nepal,
Niger,Oman,Qatar,Russia,Rwanda,Samoa,SãoTomé&Príncipe,SaudiArabia,Senegal,Serbia,
Somalia,Sudan,Syria,Togo,Tunisia,Uganda,Ukraine,UnitedArabEmirates,Uzbekistan,Vanuatu,
Vatican,VietnamandYemen.
Thisdoesnotmeanthatthesecountrieswillnotextraditeyou,butifyouaregoingtopickacountry
tofleeto,itwouldbefavorabletoyourchancetochoosefromthislist.Onenoteablecountryonthis
list,whichisfamousforextraditingoneoftheownersofthePirateBay,GottfridSvartholmtoSweden,
isCambodia.Althoughnotreatyexistsbetweenthetwocountries,hewasextraditedbythe
government.
WeallknowthatEdwardSnowdenfledtoRussiafromHongKongafterleavingtheUSfromHawaii
andhasremainedtheresincewithoutbeingextraditedbythegovernmentandwasgranteda1year
temporaryasylum.ItisunclearifSnowdenwillbeabletostaylongerthanhis1yeartemporaryasylum
grants,butasofrightnowheisbadlywantedbytheUSgovernment,andRussiaisrefusingtohand
himover.
AnotherpersoninvolvedinthePirateBaynamedFredrikNeijfledtoLaosinAsiafollowingbeing
convictedof"assistinginmakingcopyrightcontentavailable"andwassentencedtooneyearinprison
andorderedtopaydamagesof30millionSEK(approximately€2,740,900orUS$3,620,000).Thisisof
coursebetweenLaosandSweden,butLaoshasnotextraditedFredrik,soLaosmaybeavalidoption.
IoftenhearpeoplefromtheUSclaimthatif"shiteverpopsoff"theywouldjustfleetoCanada.Do
noteventryit,youwouldnotevenmakeitthroughtheborder.Canadaislikethebabybrotherofthe
UnitedStates.WhentheUnitedStatessaysjump,Canadasays"howhigh?".StayawayfromCanadaif
youarerunningfromtheUnitedStates.EvenapotactivistnamedMarkEmerywhowasaCanadian
citizen,livedinCanada,butsoldmarijuanaseedsovertheinternettopeopleintheUSwasextradited
totheUStoservea5yearsentence.Accordingtotheotherseedvendorsinthearea,thosewhoonly
96
soldwithinCanadahadnever beenarrested, butbecauseEmerysoldtothe US, he was arrestedand
extradited.Andofcourse,weknowthatIrelandandAustraliawilllikelybeextraditingtwoofthe
moderatorsfromSilkRoadtotheUnitedStatessoonenough.
Althoughnotonthelistabove,awoman,wantedintheUSforparentalkidnapping,namedChereLyn
TomaykowasgrantedasyluminCostaRica.
http://www.usatoday.com/news/topstories/200807253841863361_x.htm
Quote
Tomayko'sclaimsthatheractionswerejustifiedbydomesticviolenceshesufferedweretakeninto
accountbytheCostaRicanauthorities.
AssataShakurwaschargedwithmurder,attemptedmurder,armedrobbery,bankrobbery,and
kidnappingbytheUSandfledtoCuba.CubaactuallyhasanextraditiontreatywiththeUS,butthe
relationsbetweenthetwocountrieshavenotbeengoodsincethecoldwarbetweentheUSandthe
SovietUnionandthustherequestswerenothonored,evenforsomeonewithsuchseriouscharges.
Cubamaybeanoptionforyou,butagainthisisonlysomethingtoconsiderasIamnoexpertinany
way.
AndfinallyaccordingtoapreviouspostofmineexplaininghowtheSecretServicesoldfakeIDsonline
topeopleonaforum,severalofthemembersofthatforumwereabletoevadecaptureduetobeing
inEasternEuropeancountries,althoughnotspecifiedbythefedsforobviousreasons,andremainat
largetothisday.
http://www.tested.com/tech/456882howsecretservicesoldfakeidscatchidentitycrooks/
Quote
Thegovernmentmadeitsmovein2012,arrestingdozensoffraudstersintheUSandincountries
whereextraditioniseasy.Butmanymore,includingthefounderofCards.ru,remainatlarge.Thosein
EasternEuropeancountries,especially,arelargelyoutofthegovernment'sreach.
SECURING YOUR ACCOUNT FROM FBI MONITORING
Ijusthadanotherrealizationthatyoumaywanttoconsider.
InoticedthatcertainsomepeopleontheforumwerenevershownasOnline,evenwhentheyclearly
were,andotherswereshownasonlineattimes.Ithenrealizedtomyselftheremustbeawaytonever
showyourstatusasOnline.
ThewayyoudothisistoopenupAccountSettingsandunselecttheboxthatsaysShowothersmy
onlinestatus.

97
Sowhywouldyouwanttodothisanyways?Forreasonswespokeaboutearlier,youdonotwantto
giveanylawenforcementtheabilitytoseewhenyoulogonandlogoff.Itisbadpractice,itcanleavea
trail,leaveapattern,andifyouareapersonofinterestandtheyareabletoconnectthetimeyousign
offontheforumwiththetimeyouleaveyourhouse,orgotosleep,itgivesthemmorereasontobe
suspiciousandmoreevidencetobeusedagainstyouincourt.
Considerdisablingthisoption.
INVINCIBILITYMINDSET,FEDERALGOVERNMENTBULLYINGTACTICS
Somepeoplehaveaninvincibilitymindsetthatnothingwilleverbeabletobetiedtothemorderived
fromtheironlinecommunications.
Wellguesswhat?Theydonothavetouseyouronlinecommunicationstofindoutwhoyouare.All
thatneedstohappen,isforyoutodosomethingstupidandbecomeapersonofinterestandtheywill
bemonitoringyouractivitiesonlinetothebestoftheirabilities.Rememberyouonlyneedtoscrewup
once.
Forexample,maybeyoubecomeapersonofinterestandtheFBIgainsasubpoenatoyourFacebook
accountwhereyoustupidlybraggedtoafriendofyoursaboutparticipatingincertainonlineactivities.
ThishappenedtooneofthemembersofLulzSecwhotransferredadatadumpthatheobtained
throughSQLinjectionexploitstoafriendofhisusinghisownFacebookinhisownname.Sodonot
evertalkaboutSilkRoadoranyofyouronlineactivitiesonanysocialmediaplatform.
Evenifacompanydoesnotcurrentlykeeplogs,acourtordermayperhapsbeusedtoforcea
companytostartkeepinglogs.HushMailwasforcedtohandover12CDsworthofemailsfromthree
Hushmailaccounts,followingacourtorderobtainedthroughamutualassistancetreatybetweenthe
U.S.andCanada.Accordingtothefollowingarticle.
http://www.wired.com/threatlevel/2007/11/encryptedemai/
Whenitcomestobeingthreatenedbyacourtorderfromthefederalgovernment,99.99%ofall
companieswillcomplytoavoideitherprosecutionthemselves,orshuttingdowntheirbusinessaswe
sawpreviouslywithHideMyAss.
Butonecompanydecidedtostanduptothistypeofbullyingthatyoumayhaveheardofcalled
LavaBitasseeninthefollowingarticle.
http://www.theguardian.com/world/2013/oct/03/lavabitladarlevisonfbiencryptionkeyssnowden
Quote
TheemailserviceusedbywhistleblowerEdwardSnowdenrefusedFBIrequeststo"defeatitsown
system,"accordingtonewlyunsealedcourtdocuments.
ThefounderofLavabit,LadarLevison,repeatedlypushedbackagainstdemandsbytheauthoritiesto
handovertheencryptionkeystohissystem,frustratingfederalinvestigatorswhoweretryingtotrack

98
Snowden'scommunications, thedocuments show.
Levisonisnowsubjecttoagovernmentgagorderandhasappealedagainstthesearchwarrantsand
subpoenasdemandingaccesstohisservice.HeclosedLavabitinAugustsayinghedidnotwanttobe
"complicitincrimesagainsttheAmericanpeople".
InJuly,theauthoritiesobtainedasearchwarrantdemandingLavabithandoveranyencryptionkeys
andSSLkeysthatprotectedthesite.Levisonwasthreatenedwithcriminalcontempt–whichcould
havepotentiallyputhiminjail–ifhedidnotcomply.Suchamovewouldhavegiventhegovernment
accesstoallofLavabitusers'information.
ThecourtorderedLevisontobefined$5,000adaybeginning6Augustuntilhehandedoverelectronic
copiesofthekeys.TwodayslaterLevisonhandedoverthekeyshoursafterheshutteredLavabit.
YouseewhatIamtalkingabout?Thefederalgovernmentorderedthismantohandoverallhis
encryptionkeysandSSLkeyswhichcompromisedtheprivacyof400,000usersjustsotheycouldgain
moredataononeman,EdwardSnowden.Andtheyusedbullyingtacticsandattemptedtobankrupt
theownerofLavabitbyfininghim$5,000perdayuntilhehandedoverthekeys.UnfortunatelyLevison
hadnochoicebuttohandoverthekeysorloseeverything.
AninterviewonRedditwithLevisonrevealedwhatheclaimedthatothersecureemailproviderswho
threatenedtoshutdownwereforcedtostayup.
http://www.theregister.co.uk/2013/11/19/lavabit_analysis/
Quote
Lavabit'sfounderhasclaimedothersecurewebmailproviderswhothreatenedtoshutthemselves
downinthewakeoftheNSAspyingrevelationshadreceivedcourtordersforcingthemtostayup.
Thereyouhaveit.Anyonewhotriestostanduptothegovernment,especiallyintheUnitedStates
willbemetwithswiftjustice,courtordersandoutrageousfinesunlesstheycomplyandontopofit,
slappedwithgagorderssotheycannottellanybodyaboutwhatthegovernmentisdoing.
HOW TO CONNECT TO TOR OVER TOP OF TOR
Hereisanotherfuntipthatmayormaynotinterestyou,butIfiguredIwouldthrowitinforyou
anyways.
IfiguredthisoutwhiletryingtofigureoutaneffectivewaytodoaTOR>VPNconnection.Youcan
doTOR>TORconnectionwithTailsbyusingaprogramcalledTortilla,thusaddinganotherlayerfor
youradversariestocrack.Whetherornotthisisworthit,iscompletelyuptoyou,butIamsharingin
caseitissomethingyouwanttodo.ThishowevercurrentlyonlyworksforthoseusingWindows
becauseitwasdesignedtobeusedbyWindowsusers.Pleasenoteaswellthatthiswillnoticeablyslow
downyourconnectionsinceyouaregoingthroughTORtwice.HereistheofficialhomepageofTortilla.
99
https://github.com/CrowdStrike/Tortilla
Andtheofficialdownloadpagefortheprebuiltstandaloneexebelow.Thereisalinktoitonthe
homepageifyoudonottrustme.
http://www.crowdstrike.com/communitytools/
Thewayyoudothisisverysimpleactually.YouneedtofirstdownloadTORExpertBundlefromthe
TORProjectdownloadpageandinstallitonyourcomputerorbetteryetyourUSBdrive.
https://www.torproject.org/download/download.html.en
Nextopenthetor.exeandjustletitrununtilitsaysBootstrapped100%Done.Nextyouwanttorun
thetortilla.exefileandmakesureyourunitwithAdministratorprivileges.Also,ifyouarerunning
WindowsVistaorlater,youwilllikelygetanerrorthatthisprogramdoesnothaveavalidcertificate,
becauseitisactuallysignedwithsomethingcalledatestsignedceritifcate.Inthiscaseyouneedto
allowtestsigneddriverstorunonyourcomputer.
Todothis,simplygotoyourStartMenuandtypeinthesearchbox"command".Whencommand
comesup,yourightclickit,andclickrunasAdministratoranditwillopenupacommandprompt.Next
type inthefollowingcommand.Bcdedit.exesetTESTSIGNINGONandthiswillallowWindowstoinstall
testsigneddrivers.Restartyourcomputerandyouwillseeinthebottomrighthandcornerafteryou
restartTestModeWindows.NowyoucanrunTortilla.AndletitconnecttoTOR.Remembertohave
tor.exefromTORExpertBundleopenfirst.
Finally,youopenupVirtualBoxorwhateverVirtualMachinesoftwareyouareusingandclickSettings
ontheTailsvirtualmachine.ClickontheNetworktabandchangethedropdownmenuwhereitsays
AttachedTo:toBridgedAdapterandinthedropdownmenubelowitcalledName:SelectTortilla
Adapter.NowyourVirtualMachine,inthiscaseTails,willalwaysconnecttotheinternetthrough
Tortilla,whichconnectsthroughTOR.AndsinceTailsestablishesitsownconnectiontoTOR,youwillbe
runningTORovertopofTOR.Again,youmayormaynotwanttodothis,butIamgivingyoutheoption
shouldyouwantto.
IfanyoneisinterestedinlearningmoreaboutthecreatorofTortilla,hedidaPowerPoint
presentationatthe2013BlackHatUSAconference.FeelfreetowatchhistalkattheYouTubelink
below.PleasenotehoweverthatYouTubeisownedbyGoogleandthereareonlyabout57viewson
thevideo,sothegovernmentwilllikelycorrelateuserswhowatchthatvideowithusersfromthis
forum.MakesureyoudonotwatchthevideoonYouTubewithyourrealIPaddress.Attheveryleast
useaVPNorfindanothersitethathasithosted.Alwaysbeextraparanoid.
https://www.youtube.com/watch?v=G_jDPQU8YQ

100
HOW TO VERIFY YOUR DOWNLOADED FILES ARE AUTHENTIC
IjusthadarealizationaboutsomethingthatisprettyimportantandIwantedtoshareitwithyou,
regardingsecurity.Verifyingyourdownloads
Asageneralruleofthumb,youshouldalwaysdownloadfilesfromthehomepagesoftheirrespective
developers.
TOR:https://www.torproject.org
Tails:https://www.tails.boum.org
VirtualBox:https://www.virtualbox.org/
Thereasonthisissoimportant,isthattherearepeoplewhohostmaliciouslymodifiedversionsof
theseprogramsandwillhostlegitimatelookingsitestotryandgetyoutodownloadtheirversion,
whichcaninstallthingslikebackdoorsintoyourcomputers,keyloggers,andalltypesofnastysurprises.
Sometimesdeveloperswilloffermirrorsfortheirprojects,whicharesimplyjustalternativelinksto
downloadfromincasethemainserveristooslow,ordown.Sometimesthesemirrorscanbecome
compromisedwithouttheknowledgeofthedevelopers.
MaybeyoudonothaveTORorTailsonyourlaptopandyouaretravelingoutofthecountryandthe
hotelthatyouarestayingathasTOR'shomepageblocked.Therearetimeswhenyoumayneedtofind
analternativemirrortodownloadcertainthings.Thenofcoursethereistheinfamousmaninthe
middleattackwhereanattackercaninjectmaliciouscodeintoyournetworktrafficandalterthefile
youaredownloading.TheTORdevelopershaveevenreportedthatattackershavethecapabilityof
trickingyourbrowserintothinkingyouarevisitingtheTORhomepagewheninfactyouarenot.
Sowhatdoyoudoaboutit?Youcanverifythatthefileyoudownloadedisinfactlegitimate.Thebest
toolforthisisGnuPG.TheTORdevelopersrecommendyougetitfromthefollowingpage(Windows
Users).
http://www.gpg4win.org/download.html
YoucaninstallthisprogramonyourUSBdriveoronyouractualcomputer,youwillhearyouractual
computer'soperationsystemreferredtoasyourHostOS.Sodownloadit,runit,installitandwewill
startshowingyouhowtouseGnuPG.
IfyouremainontheGnuPGdownloadpageyouwillseesomethingunderthebiggreenboxthatis
calledOpenPGPsignature.DownloadthatintothesamefolderastheGnuPGfile,thisisthefilethatthe
downloadwassignedwith.Basicallysomeone'ssignaturesaying,Imadethisfile.Andyoualsoneeda
PGPpublickeytoverifythesignature.Sotosumitupsofar,thesignatureiscreatedfromthePGP
privatekey,andcanbeverifiedbythePGPpublickey.Thesignaturefileisusedtoverifytheprogram
itself.SoletusgrabthePGPpublickeyforGnuPGaswell.
Ifyoulookonthesamedownloadpage,undertheheadingInstallation,youwillseealinkwhereit
saysverifytheintegrityofthefile.Itwillleadtoyouthefollowingpage.

101
http://gpg4win.org/packageintegrity.html
Notewhereitsaysthefollowingstatement.Thesignatureshavebeencreatedwiththefollowing
OpenPGPcertificateIntevationFileDistributionKey(KeyID:EC70B1B8).Thisisthelinktothepagethat
hoststhePGPpublickeyfilethatyouneedtodownload,gothere.Onthepagewejustnavgiatedto,go
tothebottomrightwhereitsaysIntevationDistributionKey(publicOpenPGPkeyforsigningfiles)and
downloadthatfile.ThisisthePGPpublickeyfile,saveittothesameplaceasyoursignaturefilefor
easeofuse.
Okay,nowthatwehaveboththesignaturefileandthePGPpublickey,letusnowverifyour
download.FirstthingyouneedtodoisnavigatetothePGPpublickeyfile,calledIntervation
DistributionKey.asc,rightclickitandgotoMoreGpgEXOptionsanddowntoImportKeys.Thiswill
importthePGPpublickeyintoyourkeyring,andnowyoucanverifythefilewiththesignature.
Rightclickyouractualfileyouwanttoverify,inthiscasegpg4win2.2.1.exeandgotoMoreGpgEX
OptionsanddowntoVerifyanditshouldautomaticallydetectthesignaturefilewhereitsaysInputFile,
butifitdoesnot,navigatetothesignaturefileandmakesuretheboxbelowitwhereitsaysInputfileis
adetachedsignatureischecked.LookatthebottomandclickDecrypt/Verifyandyouwilllikelygetthe
followingmessage.
Notenoughinformationtochecksignaturevalidity. Checkdetails.
Believeitornot,thisiscompletelyfine.Clickonshowdetails,youarelookingforaspecificresult.
Signedon2013100708:31bydistributionkey@intervation.de(KeyID:0xEC70B1B8).Thevalidityofthe
signaturecannotbeverified.
IfyounavigatebacktothepagefromGpg4WinthatsaysCheckIntegritywhereyoufoundthelinkto
thepagethatcontainedthePGPpublickeyyouwillseeonthatpage.
IntevationFileDistributionKey(KeyID:EC70B1B8)
NotethekeyIDfromyourdecryptresultandthekeyIDfromtheCheckIntegritypageandnotethe
emailaddressendinginthesameURLthatwedownloadedthePGPpublickeyfrom.Wehaveamatch!
Iwillexplainthereasonforthiswarningmessagelater.
Nowthatweverifiedthatourverificationprogramislegit.LetustryandverifyourTailsISOfile,since
ifwehaveacompromisedTailsOS,thennothingwedowillbeanonymous.LetusgetrighttotheTails
downloadpage.
https://tails.boum.org/download/index.en.html
ScrolldowntowhereitsaysTails0.22signatureanddownloadthattoyourTailsfolderwhereyou
havetheISOfilethatwealreadydownloaded.NextscrolldowntowhereitsaysTailssigningkey,thisis

102
our PGPpublic key. Exact same procedure, importthekey, thenclickVerifyandspecifythesignature
fileifithasnotalreadybeenspecifiedforyou, exactsamesettingsandyouwillgetthesamewarning
message.AsexplainedbyTails
Quote
Ifyouseethefollowingwarning:
Notenoughinformationtocheckthesignaturevalidity.
Signedon...bytails@boum.org(KeyID:0xBE2CD9C1
Thevalidityofthesignaturecannotbeverified.
ThentheISOimageisstillcorrect,andvalidaccordingtotheTailssigningkeythatyoudownloaded.
ThiswarningisrelatedtothetrustthatyouputintheTailssigningkey.See,TrustingTailssigningkey.
ToremovethiswarningyouwouldhavetopersonallysigntheTailssigningkeywithyourownkey.
Inotherwords,youneedtobasicallypromisethatthePGPpublickeyyoudownloadedissafeby
signingthePGPpublickeywithyourownprivatekey,butwedonotreallyneedtodothatandIwill
notbeincludingatutorialonhowtodothat.Tailsexplainsthatifyouareworriedabouta
compromisedPGPpublickey,justdownloadthekeyfrommultiplesourcesandcomparethem,ifthey
allmatch,itisagoodchanceyouareusingalegitPGPkey.NowletusfinallymoveontoTORbecause
thisonewillbealittlelessstraightforward,butonceyoudothisone,youshouldbeabletofigureout
howtoverifyanything.Navigatetotheirdownloadpageandfindthepackagethatyouwant.
https://www.torproject.org/download/download.html.en
TokeepthingssimpleletuschooseTorBrowserBundle3.5,andundertheorangeboxyouwillseea
link(sig).Thisisthelinkforthesignaturefile,Ihopebynowyouknowwhattodowithit.Nextweneed
thePGPpublickeyright?WellitturnsoutthatwithsomanydevelopersworkingonTOR,thereare
multiplePGPpublickeys,andcertainbundlesweresignedwithdifferentkeysthanotherbundles.So
weneedtofindthePGPpublickeythatbelongstoourTorBrowserBundle.Checkoutthispage.
https://www.torproject.org/docs/signingkeys.html.en
IthasalistofallthesigningkeysthattheyuseandyoucancertainlyusethesekeyIDstogetwhatwe
wantbysimplyrightclickingonthesignaturefileandclickverify.Youwillgetawarning.
Notenoughinformationtochecksignaturevalidity. ShowDetails
Andindetailsitwillsaythefollowingwarning.
Signedon2013121908:34withunknowncertificate0x416F061063FEE659
Keepthisentirenumberinmindforlater,itiscalledafingerprint.Butfornowifyoujustcomparethe
last8digitstoErinnClark'skeyID(0x63FEE659)providedontheabovepage,andsincesheisthe
personwhosignstheTorBrowserBundlesyouwillseetheymatch.Butwewanttobeabitmore

103
thorough, never settle for mediocrity.
GotoyourtaskbarinWindows,andfindtheprogramcalledKleopatra,itlookslikearedcirclewitha
smallwhitesquareinit.RightclickitandgotoOpenCertificateManager.Wearegoingtoimportthe
fullkeysusingthismanager.Alsonote,ifyougotothetabthatsaysOtherCeriticatesyouwillfindthe
TailsandIntevation(GnuPG)keysweusedearlierstoredforthefuturewhenyouneedtodownloada
newversionofthoseprogramsandverifythemagain.
WearegoingtobefollowingtheinstructionsfromtheverifyingsignaturespageontheTORProject
website.FeelfreetofollowalongfromthatpagesoyouknowwhatIamtalkingaboutandwhereIam
gettingmyURLandnumbersfrom.
https://www.torproject.org/docs/verifyingsignatures.html.en
Inordertoimportkeys,weneedtofirstaddanonlinedirectorywheretheyarestored.Soletusfirst
addtheonlinedirectorywherethePGPpublickeysarestoredaccordingtotheTORwebsite.Click
SettingsthenConfigureKleopatra.Next,clickNewandwearegoingtoenterthefollowingURLwhichI
tookrightfromthepageabove.pool.skskeyservers.net,andleaveeverythingelseasdefaultandclick
OK.
Finally,clickthebuttonthatsaysLookupCertificatesOnServerandwewillbesearchingforErrin
Clark'sPGPpublickeybysearchingforherfingerprintprovidedontheTORwebsitepagecalled
VerifyingSignaturesabove,remember,sheisthedeveloperwhosignstheTorBrowserBundle.The
fingerprintweareenteringis0x416F061063FEE659,doesthisnumberlookfamiliar?Itshould,itisthe
numberwegotbackthefirsttimewetriedverifyingbutwithouttheactualPGPpublickey.ifyouget
anywarningsthatpopupwhensearchingjustclickOKanditshouldbringupErrinClark'skey,selectit
andclickImport.YoushouldnowhaveherkeylistedunderImportedCertificates.
Nowletusgobackandverifythatsignatureonemoretimeandseewhathappens.Youshouldget
somethinglikethefollowing.
Notenoughinformationtochecksignaturevalidity.
Signedon201121712:41byerrin@torproject.org(KeyID:0x63FEE659).
Thevalidityofthesignaturecannotbeverified.
TORalsoexplainsthiswarningmessageintheirwordsincaseyouarestillnothappywiththewarning
message.
Quote
Noticethatthereisawarningbecauseyouhaven'tassignedatrustindextothisperson.Thismeans
thatGnuPGverifiedthatthekeymadethatsignature,butit'suptoyoutodecideifthatkeyreally
belongstothedeveloper.Thebestmethodistomeetthedeveloperinpersonandexchangekey
fingerprints.
104
Idonotknowaboutyou,butIamhappywiththeresulthere,andIamcertainlynotgoingtotrack
downErinnClarktogetherkeyfingerprint,anditlookslikeourTORBrowserBundleislegitimateas
well!NowyouknowwhattodowhenthePGPpublickeyfileisnotdirectlyhostedonthesiteitself,
youhavenomoreexcusestonotverifyyourdownloads.
VERIFYING SIGNED MESSAGES WITH SIGNATURES AND SIGNING YOUR
OWN MESSAGES
Sincewejustfinishedasectiononverifyingdownloadswithsignaturesandpublickeys,Ifiguredwe
shoulddoaquickpostonverifyingmessagesbyusingthesametwothings,signaturesandpublickeys.
NowforthoseofyouwhoaremembersoftheSilkRoadForums,youwillnoticethatsomepeople,
mainlyModeratorsliketosigntheirmessageswithsignatures.Letuslookatanexampleofasigned
messagefromDreadPirateRoberts.Thelastmessageheleftbeforegoingonhisleaveofabsence.
Quote
BEGINPGPSIGNEDMESSAGE
Hash:SHA512
SilkRoadhasnotbeencompromisedeveniftheallegationsaretrue.Neitherhadaccesstosensitive
material.Iwillmakeanannouncementlatertoaddresstheconcernsthishasraised.
BEGINPGPSIGNATURE
iQIcBAEBCgAGBQJStEgqAAoJEMyyOOR8/t+867AP/RpjCq1B3WSYgnscbZU+UZOy
K0AGMM7tmu1DV1pr2S379YjVxQeUWeTbwDYhaYcWkDBDshnlpSd97fwAL1YVrBQx
jWE08tyo1sd1v5F/HajCx0DC2L5NeqD4UTDd6Dl2AOeBI4pZ+Ah/Q4VoB9cOBQGw
lSbjBY2U4redqBeRd1mFR8N+f3XmxYXzmB4Mf8ddvQkl62HmkwRwA27uUExt73uj
f3/EYVc/XjPgKG345S8yUwcGxLQcfoRM7UosbSGeEaDvvWjfZ6qQw4p7CbqIimHu
IOT6dhFcPmoVdiZGDvjtM3jXfF2sTi5mclGp/4axsrvOWZlCbrobE9EuJnGvscU4
ekU90vtcviES9XEJAr9XGOGgzY/OBf1xpj0iRY7rBDHUqA/FjfSULxqanZYhh0Wn
webHldrjylBRKM0PsnQdPn1CVGj8ThwB6SLfd0WEN1FEQt0hXP3uK1zDOri/fIcJ
Pnvf3jxYNcw9Q+2OW6QpZ/7t+S2E0yiifbNCobAMI18mrynuw3pk/xumg6t2WF/j
YHRpbTfFCCsbiPwR8P9CcUNQ5Iqcc2ewq4GOPx053aL/Vo/nfPdu/9hrRpfF3U5E
J7rFvAStaejxH7/vNxZRrTTiwrrc6njsFJHXWVAJjd+fHLI1efptbc8Kzwms9Yl0
0nzLjAJPFZOv6y7gP8tG
=lDZd
ENDPGPSIGNATURE
Sowhyshouldyoucareaboutthis?Whatisthesignificanceofsigningamessage?Thereasonis,in
casesomebodyweretocompromiseDPR'saccount,duetohavingaweakpasswordorpossiblyan
exploitintheforum'scoding,thenthepersonwouldnotbeabletosignthemessageswithoutaccess
toDPR'sprivatekey.SoletuslookathowwecanverifythismessageleftbyDPR.Firstofallyouneed
tovisitDreadPirateRoberts'profilepageandgrabhisPGPpublickey.Iamnotgoingtopostthekey
hereforspacereasons,butjustvisithispageatthefollowingURLandimportthatkeyintoyour

105
keyring.
http://silkroad5v7dywlc.onion/index.php?action=profile;u=1
Next,highlighttheentirePGPsignedmessagefromtoptobottomandcopyittoyourclipboard
(Rightclick,Copy).YouwillseeyourlittleClipboardiconinthetoprightofTailsturnred.Clickonthat
clipboardandselectDecrypt/Verify.Youshouldgetthefollowingresults.Oneinthewindowontopand
theotheronthebottom.
Quote
SilkRoadhasnotbeencompromisedeveniftheallegationsaretrue.Neitherhadaccesstosensitive
material.Iwillmakeanannouncementlatertoaddresstheconcernsthishasraised.
gpg:SignaturemadeFri20Dec201301:37:46PMUTCusingRSAkeyID7CFEDFBC
gpg:Goodsignaturefrom"DreadPirateRoberts<silkroad6ownowfk.onion>"
gpg:WARNING:Thiskeyisnotcertifiedwithatrustedsignature!
gpg:Thereisnoindicationthatthesignaturebelongstotheowner.
Primarykeyfingerprint:5A48F5D050E9905262B4799DCCB238E47CFEDFBC
Againwegetthesamewarningwedidwhenverifyingourdownloads,sayingwehavenotverified
thatthePGPpublickeyisauthentic.WecanseethesignaturenamewasmadebyDreadPirateRoberts
andthecommentsectionhastheSilkRoadURL,sofarsogood.NowrememberwhenweverifiedTOR?
Wewantedtocheckoutthefingerprintstoseeiftheymatched.Wedothisbygoingtoourkeyring
(ManageKeys),andselectingDPR'skey,rightclickingitandgoingtoproperties.Nowmovetothetab
DetailsandlookunderwhereitsaysFingerprint:andcomparethenumbersintheretothenumberswe
gotwhenweverifiedthesignature.Theyshouldbethefollowing.
5A48F5D050E9905262B4
799DCCB238E47CFEDFBC
Wehaveourselvesamatch!SounlessDPR'sprivatekeywascompromised,weknowthathehimself
wastheonewhowrotethatmessage.Sonowyouseewhysomepeopledecidetosigntheirmessages.
Itisawayofverifyingthattheiraccounthasnotbeencompromisedbyverifyingthatthepersonin
controloftheaccountisthesamepersonthatisincontrolofthePGPprivatekey.
Doyouwanttolearnhowtosignamessage?Itisveryeasy.OpenupgeditTextEditorandtypeina
message.Next,selectthemessageandcopyittoyourclipboard(RightClickCopy)andthenclickon
yourclipboardiconuptopandchooseSign/EncryptClipboardwithPublicKeys.Donotchooseakey
fromyourlistofPGPpublickeysunlessyouwanttoencryptthemessage.Ifyouwanttoencryptthe
messagetosendtosomebody'sinboxorsothatonlyonepersoncanviewit,thenselecttheirname
anditwillencryptitwiththeirPGPpublickey.Inourcase,wejustwanttosignthemessagewithout
encryptingit,butyoucancertainlydobothatthesame timeifyouwantedto.
IfyoulookdownnearthebottomyouwillseewhereitsaysSignmessageas:clickonthisandselect
yourpersonalkey.Itwillaskyouforyourpassphrasebecauserememberyouaresigningthiswithyour

106
private key. Once youenter itcorrectly, thePGPsignedmessage willbecopiedtoyour clipboardand
youcanpasteitanywhere(RightClickPaste)thatyouwantto.Hereitwhatminelookedlike.
BEGINPGPSIGNEDMESSAGE
Hash:SHA512
ThisismyPGPsignedmessagefordemonstrationpurposes.
BEGINPGPSIGNATURE
iQIcBAEBCgAGBQJS0GiWAAoJEPuh6tSg81nyqXAP/2mEqvk9RP0FEHZi3edH9faV
OmDoOostmzm90nGMGOOu4cuG0M6jgl7R3hfUZBE6zCh59MG8a9EDuUzpIT3U5nfd
zS0GWtzUQKGXPXfJ1OvWlsA6Sm7TsEsviBBz5DJxyVLcJGNU6OLUVm7onxBLwfTq
D1jAATIB43WJbDrq3XY9MF9GCoOLlcLeKNVa4m0JF582IvQJ05mSZXeXCueImvol
FaflpLW5MKyJJ92a8uheB0pLHUQTLr6jZn6TcfKY9dK8puOam5k2TGut/Sm47uqc
aMA1trXw4xntww/8X4QyL5SbSN7QVOFsy/g0b3Grp5OrConsfnsUoeRH5ArnxY0W
ijPl92aTbZazvXspW2REkJ3yq+fWjuGrYHw8m7/YVBig+OSMuBUXhSE5Pjq95fyM
bA1P7rF2fi7eRsl1z0qyETV3Bs1RltwvBUVIwj3SZNeVVoG5cHgpiPgGFq4S9Qke
unIFeHy3YpBk90kLA1n8n61VnkKAUy0Dt9AoTJloeOqPtcgeKHVsFzxdPCBcSwqd
XYnIx4lNeaw4OvHYgZsCMvFlUItSBGnFWLN9foQ8UybAUPGI9Z4sK2WmtyWK4fLl
cXnYY9zt56Ji4DiVsQrEUamNTQEDGxpvBL/kQKRMKN6HviEXW+qr57LAo6t6sTQw
KTV4uJkH1JxuOOhN9tIe
=Nkox
ENDPGPSIGNATURE
Andifyouwanttoverifyit,checkoutmyPGPpublickeyinmyprofileandverifymyPGPsignature
againstmykey!Itisreallythatsimple.Butyoumightbeasking,cannotsomebodyjustchangethe
messageandcopythesignature?No,changingthemessagewillchangethesignaturebecausethe
signaturedependsonboththemessageandthePGPprivatekey.Soifyouchangeonesinglecharacter
ofmysignedmessageyouwillgetthefollowingerror.
gpg:SignaturemadeFri10Jan2014 09:39:34PMUTCusingRSAkeyIDA0F359F2
gpg:BADsignaturefrom"JollyRoger(Theywouldliveanddieunderit)"
Sowhenshouldyousignamessage?Andwhenshouldyounotsignamessage?Greatquestion.The
majorityofusersshouldprobablynotsignmessagesunlesstheyhavetobecauseitgivesyouplausible
deniability.Itiseasiertodenypostingcertainthingsorcertaincommunicationsyoumayhavehadwith
vendorsorotherpeopleincludinglawenforcementifyoudonotsignyourmessages,becauseyoucan
alwaysclaimsomebodyelsegainedaccesstoyouraccount.Itishardertodothisifyousignedthe
messagewithyourPGPprivatekey.Ifyouaredealingwithsomebodywhowantstoverifyyouridentity
andmakesurethatyourcurrentsignaturematchesthepublickeytheyhadonfileforyoufrom6
monthsago,thenmaybetheymightgetyoutosendasignedmessage. Butagain,alltheyreallyneed
todoissendyouanencryptedmessagewithyourPGPpublickeytheyhadonfile,andifyoucannot
decryptit,youarenotwhoyousayyouare.
Inrealworldapplication,developerscanusePGPsignedmessagesinNewsAnnouncementsor

107
perhapsnewreleasesoftheir programsprovidingadownloadURLsothatuserscanbe sure the
developeristheonepostingtheURLandnotsomemaliciousattackerwhocompromisedtheforum
accountofthedeveloperandsoforth.SofortheaverageSilkRoadforumusertherereallyisnotalot
oftimeswhenyoushouldbesigningmessagesunlessyouareamoderatorormakingapublic
announcementandsoforth,butitisanoptionyounowhaveinyourarsenal,andnowyoucanstart
verifyingthesignaturesoftheAdministratorsandModeratorsincaseyoubelievetheiraccountsmay
havebeencompromised.
AN EXAMPLE OF REALLY BAD OPSEC - SMARTEN UP!
Guys,Iamnotgoingtopostexactlywhostartedthisthreadquotedbelow,butitbelongstosomebody
whoisaseniormemberwith375posts.Andhepostedsomeverypersonaldetailsandprobablydid
notrealizehowveryrevealingthesedetailsare.
Quote
TrackMeIfYouCan...
AwesomebitIjustwatchedonNetflix.Thisisnotterriblynew,donein2010,butheisquitethorough
inhisdemonstratinghowtodisappearinmodernUSculture.
Idohavetoaddthatsomeofthetechheintroducedfromtheothersideisquitealarming.
Thealphabetcopshavewaaaytoomuchdiscretionaryincome.Timetostartdefundingthem.
Sowhyisthisrevealing?Whyisthisbadyoumightbeasking.Well,Netflixcollectsmetadataonits
usersjustlikeeveryotherbigdatacorporation.IfyouareaNetflixuser,youlikelyhaveaprofilewhich
keepstrackofeverymovieyouhaveeverwatchedandwhatyourateditandsoforth.
http://www.usatoday.com/story/theoval/2013/12/17/obamabidenappleamazontwitternetflix
yahoofacebookmicrosoftgoogle/4049305/
Quote
ElectronicsurveillanceandthenewhealthcarelawareontheagendaasObamaandVicePresident
BidenmeetwithagroupthatincludesexecutivesfromApple,Amazon,Twitter,Netflix,Yahoo,
Facebook,Microsoft,andGoogle.
Thisuserstated,thathejustwatchedaspecificmovie,thathenamed.Andalsostatedthatthis
moviehasbeenupsince2010.Sohowmanypeopledoyouthinkwatchedthisexactmovieinthetime
framethatthisguystatedhewatchedit?Probablynottoomany.Under100forsuresincethemovie
hasbeenupforalmost3years.Well,nowthefederalgovernmenthasalistof100orlesssuspects,
one ofwhichisthisparticularuseronSilkRoad.
ButmaybehewasusingaVPNtoconnecttoNetflix?Great....doesheusethatVPNforanything
else?Loggingintohisemail,surfingtheweb,etc...EvenifheusedaVPN,maybetheykeeplogs?
MaybetheyareUSbasedandareeasilysubjecttosubpoenas,maybetheywillspilleverythingjustlike
108
HideMyAss did. We justdonotknow, butthisis exactlythetypeofinformationyouallshouldNOT be
revealingaboutyourselves.ThisisextremelybadOpSecpeople.Smartenup!
ButthenIlookedevenfurtherthroughthisuser'sprofileandlookedathisposts.Iknowwhich
countryhelivesin,IknowwhichdrugshehasimportedintohiscountryandIknowwhichcountrieshe
hasimportedthosedrugsfrom.Thisguyhasspokenaboutcookingdrugs,hetalksaboutbeinginacold
partofhiscountry,whichnotallpartsofthatparticularcountryeverevengetcoldwhichhelpslaw
enforcementnarrowdownthatlistofsuspectstheygotfromNetflix.
Ifyouthinkthatlawenforcementisnotinterestedinbuyersyouaresadlymistaken.Sometimesif
they establishthatabuyerhasbeenpurchasingfromavendorthattheyareafter,thenbustingthe
buyercanhelpthemgettothevendor.Theymaytakeovertheuser'sonlineidentityandstartordering
thingsfromvendorssincehealreadyhasestablishedatrustwiththeseparticularvendors.Ifthe
vendorslipsupbecauseofthetrustbuiltupwiththebuyer,thevendorisintrouble.
Iwantyoualltolearnalessonfromthis!Ifyouaregoingtotalkaboutwhichvendorsyoubuyoffof,
whichcountryyouliveinandwhichcountriesyouhaveimporteddrugsfrom,thenyoubettermake
DAMNSUREyoudonotstartgivingawaydetailslikewhichmovie youwatchedlastnightonNetflix.
ThatisalmostasbadasloggingontoaserverwithyourrealIPaddress.Keepyourmouthsshutabout
yourpersonallives!
[/quote]
TOR CHAT
Bynowifyouhavebeenfollowingthisthread,youshouldknowthatanytypeofmessagingsystemis
likelycompromisedorstoringyourdataforanunknownperiodoftime,andifyoueverbecomea
personofinterestcanbelookedbackuponfor 5+years.
ThismeansthingslikeGmail,Hotmail,YahooMail,SkypeMessaging,FacebookInstant/Private
Message,TextMessages,andotherformsofcommunicationarealllikelybeingmonitoredtosome
degree,attheveryleastloggingthemetadata.Butyoushouldalwaystreateverythingasifthosewho
aremonitoringitcanreadthecontentoftheemailaswell.
WehavetalkedaboutcommunicatingwithPGP,wehavetalkedaboutusingTORandhidden
services,andwehavetalkedaboutgoodpracticesofOpSec.Butsomeofuswanttobeabletoinstant
messagesomebodyelse.Thegoodnewsis,youcandothiswithsomethingcalledTorChat.
TorChatisadecentralizedanonymousinstantmessengerthatusesTorhiddenservicesasits
underlyingNetwork,inotherwordsitcommunicatesovertheTornetworkthroughthe.onionURL
protocol.Thisprovidesendtoendencryptionthatwetalkedaboutinpreviousposts.Itprovides
cryptographicallysecuretextmessagingandfiletransfersforbusinessdealings,andconfidential
communicationbetweentwopeople.Thebestnews,isthatyoucanuseTorChatonyourWindows,
Linuxandyoursmartphones.AFrenchdeveloperreleasedaversionforMACusers,butitstillinbeta
andshouldbeusedatyourownrisk.YoucangetTorChatfortheiPhoneintheApplestore,youcanget

109
TorChatinthe AndroidMarketaswell, soyoucanevenuse itasa meansoftextmessagingsomebody
elsewhoalsohasTorChat.
InTorChat,everyuserhasauniquealphanumericIDconsistingof16characters.ThisIDwillbe
randomlycreatedbyTorwhentheclientisstartedthefirsttime,itisbasicallythe.onionaddressofa
hiddenservice.TorChatclientscommunicatewitheachotherbyusingTortocontacttheother's
hiddenservice.Forexample,thefirsttimeyouopenTorChatyourcomputermightgenerate
d0dj309jfj94jfgf.onionandfromhereonout,d0dj309jfj94jfgfwillbeyourTorChatIDthatyougiveout
topeoplethatyouwanttobeabletomessageyou.HereisthehomepageofTorChat.
https://github.com/prof7bit/TorChat
http://www.sourcemac.com/?page=torchatMACusers
Unfortunatelyatthistime,TorChatdoesnotrunproperlyinTails,soyouwilleitherneedtoruniton
yourWindows,LinuxorMACsystem.Itisprettystraightforward,downloadit,unpackitandrunitand
everythingelseshouldhappenautomaticallyforyou.OncetheavatarbesideyourTorChatIDturns
green,youareonlineandsamewithyourcontacts.Youcanaddcontainsbyrightclickingandchoosing
AddContactandjustentertheirTorChatID.
AtthistimethereissomepeopledebateastowhetherornotTorChatiscompletelysafe,andIwould
saythatTorChatisaboutassafeasToris,justmakesureyoupracticethesamegoodpracticesyouare
usedto.Donotgiveoutpersonalinformation,ifyouaresendingsensitiveinformationusePGP
encryptionandsoforth.
HereisanotherarticleonhowTorChatworksgoingintoalittlebitmoredetail.Youcanaccessitover
theonionnetwork.
http://kpvz7ki2v5agwt35.onion/wiki/index.php/Hacking_TorChat
UPDATE
Another userhadsomeadditionalinputthatIoverlookedwhenwritingthispostthatyoushouldbe
awareof.
Quotefrom:ldopaonJanuary13,2014,08:43:25am
Torchat'ssecurityisunknown.Ithasnotundergoneapropersecurityaudit,professionalorotherwise,
thatIknowof.Itcreatesahiddenserviceonyourcomputerleavingyouvulnerabletodeanonymization
attacksthatapplytoallhiddenservices.Italsoseemstobeaverybasicprotocolthatlookslikenetcat
overTor.Thereisnowaytodeclineafiletransfer.Itautomaticallystartsthetransfer,writingthefileto
/tmpwhichisaRAMmountedtmpfsonLinux.Thenyouaresupposedtosavethefilesomewhere.
Theoreticallyanattackercouldtransfer/dev/urandomwhileyouareawayfromyourcomputeruntilit
fillsupyourRAMandcrashesyourcomputer.Thiswouldbegreatforinducingintersectionattacks.Not
surethough.Ifthekernelismanagingthesystemcorrectly, itmayjuststopthetransferwhenyourun
outofRAM.
Another thingisthatoncesomeonelearnsyourTorchatIDthereisnowaytopreventthemfrom

110
knowingyouare online, evenifyouremove them fromyour buddylist. The reasonisbecauseyour
Torchatinstanceisahiddenservicethatpublishesanormalhiddenservicedescriptorwhichanyone
candownload.There'snowaytostopthat.Ifyouwanttocutoffcontactwithsomeone,youhaveto
getanewTorchatID.SoyoushouldbeveryconservativeabouthandingoutyourTorchatIDandonly
giveittoextremelytrustedassociates.
OBTAINING, SENDING AND RECEIVING BITCOINS ANONYMOUSLY
ThispostwasinspiredbyauserwhopostedthefollowingontheSilkRoadforums.
Quotefrom:dusttodustonJanuary12,2014,07:39:43pm
BESTWAYTOOBTAINBTC'S?ANDHOWDOYOUPROTECTIDENTIYDONIGSO?ijustwouldliketo
knowsoicangetoverthisbumpibeenlearningallthisstufftodoshitonthesesitesforamonthnow
andthisismylastobsticleithink?!!
Wehavetalkedaboutalargeamountofwaystomaintainyoursecurity,butwehavenotreallytalked
abouthowtoactuallyexchangecurrency.FirstthingIwanttosayasadisclaimer,isthatIamnot
advocatingthatyoudoanythingillegal.Thisisforeducationalpurposesonlyandmyrecommendations
aremadeassumingyouareexchangingcurrenciesanonymouslyasameanstoprotectyourown
privacy.
Soyouhavefoundsomethingonlinethatyouwanttobuy,andtheyareaskingforBitcoinsas
payment.HowdoyougettheBitcoins,andhowdoyougettheBitcoinstothem?Wearegoingto
exploretheseoptionstoadegreeandhopefullybythenyoucanmakeaneducateddecisiononwhich
methodisbestforyoursituation.
TheoptionsofbuyingBitcoinsareasfollows.
1.Signupatanexchangeonline.SomepopularexchangesareMTGox,BTCE,BitStampandCoinbase
ThedownsideofpurchasingBitcoinsattheseexchanges,arethatyouneedtoverifyyouridentitywith
thembymeansofsubmittingdocumentssuchasadriver'slicenseorpassportandautilitybill.Ifyou
areabletogetpastthisfirstobstacle,thenyouneedtofindawaytogetmoneyintotheaccount.
Exchangesgenerallyonlyacceptwiretransfersasawaytofundyouraccount,butsomeofthemoffera
wayoftransferringmoneydirectlyfromyourbankaccount.Youcanobviouslyseethatbydoingthis
youareexposingyourtrueidentitytotheexchangesinonewayoranother,ifnotattheveryleastyour
location.
2.LocalBitcoins.com
LocalBitcoinsoffersawayforyoutofindapersoninyourlocalarea,orifyouwanttogotoanother
stateorprovincetomeetupwithsomeonefurtherawayfromyou,youcanchoosewheretolookfor
peopleinthatareasellingBitcoinseitheronline(banktransferorcashdeposit)ormeetthemforcash
inperson.Tradershavereputationlists,similartoafeedbackscoreoneBayandyoucanfindatrader
whohasagoodreputationtobuyoffof.Yousendinatraderequestandoncethesellerhasreceived
themoney,hecanreleasetheBitcoinsfromLocalBitcoinsandtheyaresenttoyourwallet.Some
peoplehaveexpressedconcernthatlawenforcementmayactasbuyersandsellersonLocalBitCoins,
butitdoesnotmatterifthisisthecaseinmyopinionaslongasyouarenotlookingtobuylarge
111
amounts. Youcanalso, if youwant,communicate withthebuyer over email, arrive frompublic
transportation,wearahat,andallsortsofsecretagenttypetrickstotryandconcealyouridentity.
Wearawigifyouaresuperparanoid.
3.UseaBitcoinATM
CurrentlythereisonlyoneATMintheworldthatIamawareof,anditislocatedinCanada.Ifyoudo
notliveinCanadathenthisdoesnothelpyou.Luckilyaccordingtotheanarticle,thecompanywhois
rollingouttheseATMscalledRobocoinislaunchingATMsinothercountriesaswellcomingsoon.
http://techcrunch.com/2014/01/02/robocointhebitcoinatmisheadingtohongkongandtaiwan/
Quote
ThefirstshippingbitcoinATM,Robocoin,islandinginHongKongandTaiwanasthecompanyexpands
itsreachthisJanuary.TheyareplanningfurtherreleasesinEurope,Canada,andtheUSbut,given
Asia’scloutintheBTCmarkets,thisisdefinitelyaninterestingdevelopment.
Therewilllikelybesomewaytotryandcutdownonmoneylaunderingbygettingyoutoverifyyour
identification,butfromwhatIunderstand,theycurrentlyonlydothisifyouaresellingBitcoinsforcash
usingtheATM,andnotbuyingthemforcash.The waythatitworks,isyouchoosetheamountofBTC
youwanttobuy,andyoufeedyourcashintotheATMmachine.Youcanatthatpointeitherprintouta
generatedpaperwallet,orchooseawalletofyourowntosendtheBitcoinsto.Thismethodmaybe
anothergoodwaybecauseittakesdealingwithanotherhumanoutofthetransaction.Somethingyou
mayneedtobeawareofissurveillancecameras,somaybewearahood,hat,wig,sunglasses,andso
forthtodisguiseyourselfifyouareworriedaboutyouridentity.
4.Craigslist
Believeitornot,thereareadecentamountofpeopleonCraigslistthatyoucanmeetupwithinperson
andbuyBitcoinsoffofwithcash.Yourlocalareamaynothavealargenumberoflistings,butyoucan
alwayssearchinothernearbymetropolitanareasandmakeadaytripoutofitifyouwant.Thesame
considerationsaboutprotectingyouridentityapplyhereasabove.
5.MineyourownBitcoins
IamnotgoingtogetintohowtomineBitcoins,orwhetherornotyoushould,butifyouwanttoget
Bitcoinswithoutdealingwithotherpeople,thisisoneofthewaysyoucandoit.Runyourminersover
Tor,stayanonymousandyouwillhaveyourselfsomeuntaintedBitcoins.
Okay,sonowyouhaveyourselfsomeBitcoins,howcanyougetthemtosomebodyelsethatyou
wanttobuysomethingoffofortradewith?Asyouprobablyknowbynow,everysingletransactionis
trackedonBlockChain.info.MywalletaddressthatIhavesetupfordonationsforthehoursIhave
spentworkingonthisthreadis1PkJ928QWC5BuQAsHoNQzRV5wfnveJSRCp.Youcancheckoutthe
transactionsrelatedtoitbygoingtothefollowingaddress.
http://blockchain.info/address/1PkJ928QWC5BuQAsHoNQzRV5wfnveJSRCp
SoyouhaveBitcoinssittinginyourwallet,andifyousendthemtosomebodyelse,itwillshowupon
112
BlockcChainexactlywhere yousentthem. A couple ofthings to keepinmind.
1.YoupurchasedyourBitcoinsfromsomebodyorsomething.Theymayhavekeptarecordofthe
walletthosecoinsweresentto.
2.Ifyoudealtwithalawenforcementorsomebodytryingtotrackyou,thentheycantrackwherethe
coinsaresentafteryouforwardthemtosomebodyelse.
Rightnowthebestmethodoftryingtolosethistrailisusingsomethingcalledamixeroratumbler.
YoucanthinkofthislikethrowingyourBitcoinsintoagiantpileofcoinswithotherusersandthen
withdrawingthematalatertimefromthemixer.Ifyouthrewin1Bitcoinandpulledout1Bitcoin,
thinkofalltheotherpeoplewhodidtheexactsamething.Possiblythousandsofotherswithdrawing1
Bitcoinfromtheexactsamepileofcoins.Ithasnowbecomemuchharderforyoutobelinkedtothose
coins.Thenontopofthat,maybeyoudonotwithdraw1Bitcoin,maybeyouonlywithdraw0.5Bitcoin
rightnowandleavetheother0.5Bitcoininthepile.ItbecomesevenhardertolinkthoseBitcoinsto
you.
OnewebsitethatdoesthisiscalledBitcoinFogandcanbefoundonaclearnetURLandahidden
servicesURL.
http://www.bitcoinfog.com/
http://fogcore5n3ov3tui.onion/
BitcoinFoghasbeenaroundforawhilenowandmostpeopleseemhappywiththeservicethey
provide,soIwouldcometothinkthattheyareatrustworthyservice.ThewaytheyworkisasI
mentionedabove,andontopofthattheservicetakes1%3%(randomizedforobscurity)feeoneach
deposit.Soyoumayputin1.0Bitcoinsandtakeout0.97Bitcoinafterfeesanditmixesthingsup.You
canalsodecidewhenyoumightwanttowithdrawit,whetheritisinamonth,week,days,andsoforth.
Thisisagoodservicetouseanddefinitelymixesthingsupforyou.Theonlythingyouneedtokeepin
mind,isthatthereisatrailofyousendingyourcoinsintoBitcoinFog,whichsomepeoplemayormay
notfindsuspicious.ButwhatyoudowithyourcoinsafterBitcoinFogisgoingtobeextremelydifficult
totrack,ifnotimpossibleduetothevastnumberoftransactionsthatareoccuringinandoutof
BitcoinFog.
WhenyouwithdrawyourcoinsfromBitcoinFog,pleasemakesureyousendthemtoanewwallet,
andnotthesamewalletthatyouusedtodepositthemintoBitcoinFog.Anotheroptionyoucanhave
whenwithdrawingthecoinsfromBitcoinFog,istogetBitcoinFogtowithdrawthecoinsdirectlytothe
personyouwanttobuysomethingfrom.Thistakesthestepofcreatinganewwalletandthenhaving
toforwarditonandwillkeepthingsagainextremelyhardtotrack.Justkeeptheirtransactionfeesin
mindtomakesureyourdesiredsellerisgoingtoreceivethecorrectamountofBitcoinsneededforthe
purchaseorexchange.
TwootheroptionsyoucanuseareprovidedbyBlockchain.infoandcanbeaccessedbycreatinga
walletandloggingintoit.SendSharedandSharedCoin.SendSharedisanotherwayofmixingup
coins,thewaythatitworksis,yousendyourmoneyintothegiantpotanditgetsmatchedupwith
somebodyelsewhoissendingthesameamount.Anexampleofthisisletussaywehave4people.A,B
113
andX, Y. PersonA issending1BitcointopersonB andpersonXissending 1 Bitcoin topersonY. Send
Sharedwillmatchtheseamountstogether,anditwillmixthemsothatpersonAsendstheir1Bitcoin
topersonYandpersonXsendstheirBitcointopersonB.Thiswayyouarebreakingthechainthatlinks
personAtopersonBbecausethereisnorecordofpersonAeversendinganythingtopersonB.Thisis
averygoodoptiontouse,andonethatmanypeople prefer.Ofcourse,therearemanypeopleusing
SendShared,sothelikelihoodoftherejustbeing4peoplemixinguptransactionisgoingtobemore
like10,000ormore,makingitprettymuchimpossibletotrack.
Sharedcoinusesadifferentmethodcalledcoinjoin.Sharedcoinhostsacoinjoinserverwhichactsas
ameetingpointformultiplepeopletojointogetherinasingletransaction.Havingmultiplepeopleina
transactionimprovesprivacybymakingtransactionsmoredifficulttoanalyse.Theimportant
distinctionbetweentraditionalmixingservicesistheservercannotconfiscateorstealyourcoins.A
sharedcointransactionwilllooksomethinglikethefollowing.
https://blockchain.info/tx/e4abb15310348edc606e597effc81697bfce4b6de7598347f17c2befd4febf3
b
Asyoucanseemultipleinputsandoutputsmakethedeterminingtheactualsenderandreceiver
moredifficult.Basicallyitsendsthecoinsinandoutofmanydifferentwalletsthatareparticipatingin
Sharedcoinatthetimeanditdoesthistothrowhundredsorthousandsoftransactionsinallthe
walletsparticipatingmakingitextremelydifficulttotrack.Thedownsidethoughisthatcoinjoincan
never completelyseverthelinkbetweentheinputanddestinationaddress,therewillalwaysbea
connectionbetweenthem,itisjustmoredifficulttoanalyse.ThebenefittoSharedCoinisthatwhile
thisprocessingishappening,youcanhitcancelandgetyourcoinsback.Whenyousendyourcoinsinto
atraditionalmixingservice,anuntrustworthymixingservicecouldpotentiallystealyourcoins.
Nowthatyouhavetheknowledgetomakeaneducateddecisiononhowtomixupyourcoinsen
routetoyourintendeddestination,Ifeelthatyoucannowputyourmindateasewhenlookingtobuy
somethingwithBitcoins.Itshouldbenotedthatyoucanreversetheprocessifyouwanttocashout
yourBitcoinsaswell.
CLEARNET VS HIDDEN SERVICES - WHY YOU SHOULD BE CAREFUL
Someofyoumayhaveseenlinkstodifferentwebsitesontheseforums.Infactmythreadisfullof
them.
Asyouprobablyknowbynow,ahiddenserviceisawebsitethatusesa.onionaddressandaclearnet
siteusestheregularinternet.YoumustbeonTORtoaccesstheonionnetwork,whereasclearnetsites
canbeaccessedfromanybrowser.Sowhyshouldyoubecarefulwhenvisitingclearnetsites?
Whenyouseeanarticle,linkorvideopostedontheSilkRoadforums,pleasenote,thatyoushould
onlybeviewingthosevideosoverTORorpossiblybutasalastresortuseaVPNandhereiswhy.Letus
useYouTubeforexample.YouTubeisownedbyGoogle,Googletrackseverything.YouTubekeepstrack
ofwhichIPaddressessearchforwhatvideos,andtonsofmetadataaboutit'susers.
114
Whenalink toaYouTube videois postedonthe SR forums, we likelyhave touse our regular
browserstowatchitbecauseTorbrowserisnotgoodforwatchingflashvideos.Buttheproblemis,ifa
postonSRwaswrittenonJanuary10,2014recommendingavideo,andthisvideoonlyhas500views,
perhapsthisvideohasbeenupforafewmonthsanddidnotendupbeingverypopular.Andthen
withinthefewdaysthatthisarticlewasposted,50peopleviewingtheSilkRoadforumwatchthis
video.Thenumberofviewsjustwentupinashortperiodoftime.
Itisprettyeasytocorrelatethatitispossible,thatthepeoplewhowatchedthatYouTubevideo,
especiallysinceitisnotapopularvideocamefromSilkRoad,andifyoumadethemistakeofusing
yourrealIPaddress,youhavenowbeenaddedtoalistofpeopleofinterest.Andifyoudothis
multipletimeswithdifferentYouTubevideos,thentheystarttoseeapatternandbeforeyouknowit,
they areconfidentthatyouarecomingtowatchthesevideosfromSilkRoadbecauseeverytimea
videoispostedonSilkRoadforums,yourIPaddresscomesuptowatchthisvideo.
ButifyouuseaVPN,thismakesthingsalittleharderinthattheyarenotaseasilygoingtobeableto
linkthevideotoyouyet.ButoncetheyseeaVPNaddressconstantlypoppinguponthosevideosbeing
linkedfromtheforums,theymightsubmitacourtordertomonitortheactivitiesoftheusersofthe
VPN.HideMyAsswasoneofthemostwellknownexamplesofVPNsbeingorderedtohandover
informationontheirusers.
Thesamethinggoeswithallclearnetsites.Youneverknowwhoismonitoringtheiractivity,andifit
isanoldarticle,morethanacoupleofyears,thenyoucanalmostbetthatthenumberofpeople
viewingthatarticlearedown.Sowhensomebodypostsaclearnetlinkontheforumsandpeoplevisit
thatlinkusinganunprotectedIPaddress,thentheLEcanstarttocorrelatepatternsagainstyou.Of
course,thesearticlesandlinksarenotaslikelytobevisitedwithoutTORfromtheSRforumsbecause
youneedTORtoviewtheforums,butespeciallythingslikeYouTubevideossinceTORdoesnotwork
wellwithYouTubecanbeproblematic.
Sowhatcanyoudotoprotectyourself?Askyourselffirst,doIreallyneedtowatchthatYouTube
video?IsitsomethingimportantthatIneedtosee?Ifitis,youmightconsideranoptionthatIspoke
aboutearliercalledTortilla,butitisonlyavailabletoWindowsusers.Italkitaboutitatthefollowing
article.
http://silkroad5v7dywlc.onion/index.php?topic=14555.msg304569#msg304569
YouwillrunaVirtualMachinesuchasDebian,butdonotconnecttoTORusingtheVirtualMachine.
TheVMusesabridgedapapterandroutesalltrafficthroughTortillawhichroutesalltrafficthrough
TORonyourWindowshostOSwithouthavingtousetheTORbrowseronyourVM.MACusersand
LinuxusersmayjustwanttoviewtheYouTubevideoinaonetimeuseproxythatdoesnotkeepany
logsormaybeapublicwifinetworkthathaslotsofusersonitdaily.
Thereisaninfamouscaseofamurdererwhocalledthesisterofhisvictimfromhisvictim'scell
phone.HewouldcallfromherTimeSquareinNewYorkandtauntherandtalkabouthowshewas
torturinghersisterandthepoliceputatraceonthephone.UnfortunatelybecauseTimeSquareissuch
acrowdedplace,evenwithallthecameras,theywereunabletopinpointexactlywhichpersonwas
115
makingthecall onthatphone andthey never endedupcatchingtheguy. He endedupditchingthe
phoneafterhefinallykilledhisvictim.TheyknewhewasaguywalkingaroundTimeSquareonacell
phonebutifyouhaveeverbeentoTimeSquare,youknowthattherearemillionsofpeopledoingthe
exactsamething,hejustblendedrightin.
Soyoumaywanttouseapublicwifiinacrowdedareathathasmanyusersalldaylongtowatcha
videoandkeepyourIPaddresssafe.Ifyoucannotwatchvideossafelywithoutidentifyingyourself,
thendonotwatchthem.Itisassimpleasthis.YesIknowitisannoyingthatTordoesnotworkwell
withflashvideos,butitisbetterthanbeingthrowninjailwhereyouwillneverbeabletowatchany
YouTubevideos.
ThemainreasonIwrotethispostwastoremindyouthatcorrelatingtwouserstogetheronthe
internetiseasierthanyouthink.Onceyoustartdevelopingpatternsandleavingyourfootprints
behind, theLEhaveanunlimitedstoragespaceavailabletothemtokeeptrackofeverythingyoudo.
RememberhowSabugotcaught?HejustloggedontoIRCwithhisrealIPaddress,onetime.Onetime
isallittakesforthemtotakeyoudown.Alwaysthinkbeforeopeningalink,whatwillthiswebsite
identifyaboutme?
THEY ARE WATCHING YOU - VIRUSES, MALWARE, VULNERABILITIES
Yourcomputerwillalwaysbevulnerabletosomesortofattackfromthosewhowanttoharmyouin
someway.Whetheritisharmyourprivacy,stealyourinformationorthrowyouinjail.
ItshouldcometonosurprisetousthattheUSgovernmentisactuallythelargestpurchaserof
malware.
Quote
Accordingtoanewreport,theUnitedStatesgovernmentisnowinfactthesinglelargestbuyerof
malwareintheworldthankstotheshiftto“offensive”cybersecurityandisleavingusallvulnerablein
theprocess.
Inorderforthegovernmenttoexploitvulnerabilitiesdiscoveredinmajorsoftware,theycannot
disclosethosevulnerabilitiestothemanufacturersorthepublic,lesttheexploitbefixed.
“Myjobwastohave25zerodaysonaUSBstick,readytogo,”oneformerexecutiveatadefense
contractortoldReuters.Thedefensecontractorwouldpurchasevulnerabilitiesfromindependent
hackersandthenturnthemintoexploitsforthegovernmenttouseasanoffensivecyberweapon.
http://endthelie.com/2013/05/10/reportusgovernmentnowbuysmoremalwarethananyoneelse
intheworld/#axzz2qIjeZ32e
Afterreviewingthesourcesinthearticleandotherarticles,someofthesedefensecontractors
expressedconcernthatthegovernmentwasessentiallyfundingcriminalactivity.Theyarepaying
independenthackers,insomecasesblackhatstofindzerodayexploits(onesthathavenotbeen
116
publiclyannouncedyet)andbuythese exploitsoffofthem for huge sumsupmoney, upwards of
$100,000.
Ifyouareusingalaptopwithabuiltinmicrophoneandcamera,youareextremelyvulnerabletoan
attackasJohnMcAffee,themanwhostartedMcAffeeAntiVirusexplains.
Quote
"Wedon'thavemuch[security]anymore,andcertainlynotintheonlineworld,"hesaidatSaturday's
talk."Ifyoucangivemejustanysmallamountofinformationaboutyourself,Ipromiseyou,within
threedays,Icanturnonthecameraonyourcomputerathomeandwatchwhateveryou'redoing."
http://abcnews.go.com/Technology/johnmcafeesproductaimsmakeinternetusers
virtually/story?id=20424182
Sothefirstthingyoushoulddorightnowisgograbsomeopaquetapeandputitoveryourcamera.If
youareonadesktopandyouhaveawebcampluggedin,unplugitunlessyouareusingit.Thereisno
reasontogiveanattackeranopenwindowintoyourhome.Nextisyourmicrophone,againdesktops
usuallydonothavebuiltinmicrophones,butmostlaptopsdo.Amicrophonecanbeactivatedtolisten
toyoutalkingandyouneedtofindawaytophysicallydisableit.Thebestwayofcourseistophysically
removeit,butIamnotwritingatutorialonhowtodothat.
TheFBIdevelopedakeystrokeloggingsoftwarecalledMagicLantern.MagicLanterncanreportedly
beinstalledremotely,viaanemailattachmentorbyexploitingcommonoperatingsystem
vulnerabilities,unlikepreviouskeystrokeloggerprogramsusedbytheFBI.Ithasbeenvariously
describedasavirusandaTrojanhorse.Itisnotknownhowtheprogrammightstoreorcommunicate
therecordedkeystrokes.
Quote
TheFBIintendstodeployMagicLanternintheformofanemailattachment.Whentheattachment
isopened,itinstallsatrojanhorseonthesuspect'scomputer.Thetrojanhorseisactivatedwhenthe
suspectusesPGPencryption,oftenusedtoincreasethesecurityofsentemailmessages.When
activated,thetrojanhorsewilllogthePGPpassword,whichallowstheFBI todecryptuser
communications.
SpokesmenfortheFBIsoonconfirmedtheexistenceofaprogramcalledMagicLantern.Theydenied
thatithadbeendeployed,andtheydeclinedtocommentfurther
Source:https://en.wikipedia.org/wiki/Magic_Lantern_%28software%29
Thenofcoursewehavecellphoneswhichcanbeactivatedremotelyaswell.
Quote
Mobilephone(cellphone)microphonescanbeactivatedremotely,withoutanyneedforphysical
access.This"rovingbug"featurehasbeenusedbylawenforcementagenciesandintelligenceservices
tolisteninonnearbyconversations
117
https://en.wikipedia.org/wiki/Covert_listening_device#Remotely_activated_mobile_phone_microphon
es
AccordingtoafewofthesourcesintheWikipediaarticle,thecellphonecanbeactivatedtolistento
youevenwhenitisoff.Pullingthebatterywilllikelydothejob,butthereisnoguarantee.Somake
surethephoneisnotinthesameroomasyouifyouaretalkingaboutanythingsensitive.Asalways,be
superparanoid.Turnontheshowerandputthephoneinthebathroomifyouhaveto,orbetteryetif
youaregoingsomewhereandyoudonotneedyourcellphone,leaveitathome.Sincemostpeople
never leavehomewithouttheircellphones,ifsomebodyissnoopingonyou,theymightthinkyouare
stillathome.ThefirstgroupofpeoplethatwenttovisitSnowdeninRussiaweretoldnottobringany
laptopsorcellphoneswiththemforthosereasons.
Soweknowthegovernmentisactivelytryingtogainremoteaccesstoyourcomputer,theycanlisten
toyourphones,whatshouldyoudoaboutit?
Youneedtodothebestyoucantomakesurethecomputersthatyouusearenotexposedtothe
elementsofrisk.AlwaysdisableJavascriptwhenvisitinganywebsitesunlessthewebsiteis100%
trusted.StartphasingouttheuseofMicrosoftWindowsandMACOSXbecausetheseclosedsource
proprietaryoperatingsystemsarenotopentoscrutinyandauditingthewayopensourceLinux
distributionsare.TherearemoreWindowsusersandthusmoreexploitsavailableforWindows.
RunningyouroperatingsysteminaVirtualMachine,evenifyourhostOSisLinux(rememberVirtual
BoxcanrunonLinux)willhelpcutdownontheretentionofanymalwareyoumightpickupwhenon
theinternet.Donotgotoanypotentiallyharmfulsitesonyourfreedomfightingcomputers.Donot
openanyemailsfromanyonethatyoudonottrust100%.Regularlyformatyourharddrivestokeep
themcleanofanyhiddenviruses.
Ifyouareunsureifsomethingissafe,testitonacomputeronlymeantfortestingandonethatisnot
connectedtotheinternet.Ifyoucanresetyourbootsectoronyourharddrivefromtimetotimethat
wouldbeagoodideaaswell,becauseyoucangetmasterbootsectorvirusesthatwouldbootupa
virusbeforeyourcomputerevenbootsintotheOS.
FlashyourBIOS,theBIOSisthefirstthingthatrunswhenyouturnonyourcomputer,ifyouhavea
virusinyourBIOS,thereisnoantivirusthatcanremoveit,youwouldneedtoflashyourBIOSand
installanewfirmware.Makesurethefirmwareis100%trustworthyasinfectedfirmwareisthemost
commonwaytogetaBIOSvirus.
IntheinterestofsavingspaceIwillnotgointodetailonhowtodoallofthesevirusremovals
becausetherearenumeroustutorialsonlineandIamcertainlynotanexpertinthisfield.Iamsure
therearemanyotherthingsIhavenotcoveredinthispostandifsomebodyelsewantstochimein,
pleasefeelfreetodosoaslongasyoucanprovidesourcesfortheclaimsyouaremaking.Idonot
wanttoturnthisthreadintoabunchofunsubstantiatedclaimsandparanoidconspiracytheories.But
ifyouhavesomethingvaluabletoaddtothis,Iamopentoyourinput.

118
MONITORING YOU WITH AN ANTENNA
FirstthingIwantyoutodoisfindasecurewayofwatchingthisvideo.Remembertheylogeveryone
whowatchesthesevideosandsinceIamlinkingyoutothemfromSilkRoad,theywillbewatchedeven
closer.
http://www.dailymotion.com/video/x74iq0_compromisingelectromagneticemanat_tech
Thisvideoshowshowusingastrongantenna,sittinginavanoutsideyourhome,theFBIcouldbe
pickinguponyourkeystrokesonawiredkeyboard.Infactmanypeoplespeculatethatthenewsmart
metersinstalledinmanyhomesalreadyhavethistechnologytodetermineeverythingyouaredoingin
yourhomeelectronically.Wiredandwirelesskeyboardsemitelectromagneticwaves,becausethey
containelectroniccomponents.Thiselectromagneticradiationcouldrevealsensitiveinformationsuch
askeystrokesasshowninthevideo.Everyelectrmagneticwaveisuniquetothedeviceusingit,which
givesapersonspyingonyoutheabilitytotellthedifferencebetweenyouusingyourcomputerversus
thedishwasher.
Accordingtothepeoplewhodidthisexperiment,theywereabletoextendtherangeupto20meters
usingrelativelycheaptechnology.Thiswasforwiredkeyboardsbytheway,andtheygoontoexplain
thatwirelesskeyboardsandmousesareeveneasier.Whichbringsustoanotherareaofinterest,
wirelesstransmissions.Thingslikewirelesskeyboardsandwirelessmice(ormouses?)arevulnerable to
eavesdroppingaswell.Iftheyarenotusingastrongenoughencryptiontosenddatatothereceiver,
anyonecanbelisteninginonyourkeystrokesandmouseactivity.Probablysomethingmostpeople
never thoughtabouteither,thisisontopoftheelectromagneticwavesthatcanalsobepickedup.
Quote
Microsofthasupgradedtheweakencryptionfoundontoday’smassmarketwirelesskeyboardswitha
newdesignthatuses128bitAEStosecurecommunicationtoandfromthePC.
Hitherto,keyboardencryptionhasbeenweak,withkeyschosenfromasmallpaletteofpossibilities,
withonehackinggroupclaimingin2009thatithaddevelopedatoolspecificallytosniffkeystrokesfrom
Microsoftkeyboardsatarangeup toa10metres.
http://news.techworld.com/security/3284218/newmicrosoftwirelesskeyboardgets128bit
encryption/
Areyouusingwirelesstechnology?Howoldisit?Mightbetimetoupgradeyourequipment.10
metersisabout33feet,butrememberthetechnologyavailabletothegovernmentcouldpotentially
reachbeyondthat.Thenthereareotherthingspeopleforgetsuchaswirelessmonitorswhich
broadcastyourscreentoareceiverthatcanbepickedup.Justthinkabouttheoldantennaspeople
usedtohaveontopoftheirhomes,andhowfarawaythosecouldpickupsignalsfromTVstations,if
youhadoneofthosepointedatyouinavanacrossthestreet,thereisnodoubttheycouldbe
eavesdroppingonyouractivitiesinside.
Oneresearcherwasabletouseawirelesssignalsentbyasmartmeterfromupto300metersaway

119
(900feet)tofindout whichhouseit was comingfromandwhatthecurrentpower consumptionwas in
plaintext.Shewasthenabletousethisinformationtodeterminewhenpeoplewereandwerenot
homebasedonaveragespikesinconsumptionsincethemeterspulseevery30seconds.
Quote
Thedatasentwasinplaintextandcarriedtheidentificationnumberofthemeteranditsreading.The
nameofthehomeownerortheaddressaren'tincluded,butanyonemotivatedenoughcouldquickly
figureoutthesource.
"ThemeterIDwasprintedonthefrontofthemeterwelookedat,sotheoreticallyyoucouldreadthe
ID[offatargetmeter]andtrytosniffpackets,"Xusaid.
Inhertests,Xufoundshewasabletopullpacketsoutoftheairfromtargetmetersbetweenonce
every2to10minutes.That'sfastenoughtobeabletoworkouttheaveragepowerconsumptionofa
houseandnoticestarttodeducewhensomeoneisathome.
https://www.networkworld.com/news/2012/110512smartmetersnotsoclever263977.html
Thingslikeautomatictimersthatflipswitchesmightbeworthinvestingintoalwaysmakeitlooklike
someoneishomeuntilsecurityresearchersstartlookingintowaystoavoidthewideopendoorweare
givingtoanyonewhowantstofinddataaboutus.
Whatcanyoudoaboutthesetypesofeavesdropping?Notawholelotunlessyouwanttostart
turningintoatinfoilhattypeofperson.Therearesomefunthingsyoucandoifyouwanttogocrazy
withitthoughasrecommendedbythefollowingsite.
http://www.lessemf.com/smart.html
Quote
YSHIELD
YShieldHighFrequencyShieldingPaint
Easytoapplywaterbasedpaintforwalls,ceilings,doorsandotherinteriorORexteriorsurfaces.Very
effectiveforblockingcellphonesignals,CB,TV,AM,FMsignals,radiofrequencyradiationand
microwaves.Testedhighlyeffectiveupto18GHz!
http://www.lessemf.com/paint.html#290
Therearelotsofotherthingsonthereaswelllikedrapes,curtains,garments,fabricsandsoforth
whichdisruptthetransmissionofthesesignals.Itiscompletelyuptoyouwhatyouwanttodo,Iam
justgivingyoutheoptionsandtheeducationsoyoucanmakeaneducateddecisionofhowfaryou
wanttogotoprotectyourprivacy.
120
COOKIES & JAVASCRIPT REVISITED, PLUS FLASH COOKIES AND
OTHER BROWSER TRACKING
Yourbrowsercanrevealanalarmingamountofinformationaboutyou.
Surprisinglyenough,ornottoosurprising,whenyouvisitawebsitethereisasurprisinglylarge
amountofidentifyingdatabeingsenttothewebsiteyouarecommunicatingwith.
Cookies
Cookiesarepiecesofinformationthatawebsitecansendtoyourbrowser.Ifyourbrowser"accepts"
them,theywillbesentbacktothesiteeverytimethebrowseracceptsapage,imageorscriptfromthe
site.Acookiesetbythepage/siteyou'revisitingisa"secondparty"cookie.Acookiesetbyanothersite
that'sjustprovidinganimageorscript(anadvertiser,forinstance),iscalleda"thirdparty"cookie.
Cookiesarethemostcommonmechanismsusedtorecordthefactthataparticularvisitorhaslogged
intoanaccountonasite,andtotrackthestateofamultisteptransactionsuchasareservationor
shoppingcartpurchase.Asaresult,itisnotpossibletoblockallcookieswithoutlosingtheabilitytolog
intomanysitesandperformtransactionswithothers.
Unfortunately,cookiesarealsousedforotherpurposesthatarelessclearlyinusers'interests,such
asrecordingtheirusageofasiteoveralongperiodoftime,oreventrackingandcorrelatingtheirvisits
tomanyseparatesites(viacookiesassociatedwithadvertisements,forinstance).
Withrecentbrowsers,thecookiesettingthatoffersusersthemostpragmatictradeoffbetween
cookiedependentfunctionalityandprivacyistoonlyallowcookiestopersistuntiltheuserquitsthe
browser(alsoknownasonlyallowing"sessioncookies").Tailsdoesthisautomaticallybythewaywith
Iceweasel.
RecentCookieLike"Features"inWebBrowsers
Inadditiontotheregularcookiesthatwebbrowserssendandreceive,andwhichusershavebegun
tobeawareofandmanageforprivacy,companieshavecontinuedtoimplementnew"features"which
behavelikecookiesbutwhicharenotmanagedinthesameway.Adobehascreated"LocalStored
Objects"(alsoknownas"FlashCookies")asapartofitsFlashplugins;Mozillahasincorporateda
featurecalled"DOMstorage"inrecentversionsofFirefox.Websitescoulduseeitherorbothofthese
inadditiontocookiestotrackvisitors.Itisrecommendedthatuserstakestepstopreventthis.
ManagingMozilla/FirefoxDOMStoragePrivacy.IfyouuseaMozillabrowser,youcandisableDOM
Storagepseudocookiesbytypingabout:configintotheURLbar.Thatwillbringupanextensivelistof
internalbrowserconfigurationoptions.Type"storage"intothefilterbox,andpressreturn.Youshould
seeanoptioncalleddom.storage.enabled.Changeitto"false"byrightclickingandchoosingToggle.
ManagingAdobeFlashPrivacy.

121
Adobe lists advice onhowtodisable Flash cookiesontheir website.
http://helpx.adobe.com/flashplayer/kb/disablelocalsharedobjectsflash.html.Therearesome
problemswiththeoptionsAdobeoffers(forinstance,thereisno"sessiononly"option),soitis
probablybesttogloballysetLocalStoredObjectspaceto0andonlychangethatforsiteswhichyou
arewillingtohavetrackingyou.OntheLinuxversionofAdobe'sFlashplugintheredoesnotseemtobe
awaysetthelimitto0forallsitesandthereforeitsuseshouldbelimitedoravoided.LuckilyTailsdoes
nothaveflashinstalled,butincaseyouarenotusingTailsbeawareofthis.
Ifyouabsolutelyneedtowatchavideoonline,findawaytodownloadthe videotoyourcomputer
andwatchitthatway.Thistakesthebrowseroutoftheloopofprocessingavideoforyouand
eliminatesthoseFlashcookieswhichhelpidentifyyou.
Javascript
Javascriptisprobablythegranddaddyofallvulnerabilitiesininternetbrowsing.Themajorityof
exploits,malware,virusesandothercomputertakeovershappenbecauseofJavascriptcodeexecuting
inyourbrowser.Javascripthasmanyuses.Sometimesitissimplyusedtomakewebpageslookflashier
byhavingthemrespondasthemousemovesaroundorchangethemselvescontinually.Inothercases,
javascriptaddssignificantlytoapage'sfunctionality,allowingittorespondtouserinteractionswithout
theneedtoclickona"submit"buttonandwaitforthewebservertosendbackanewpagein
response.
Unfortunately,javascriptalsocontributestomanysecurityandprivacyproblemswiththeweb.Ifa
maliciouspartycanfindawaytohavetheirjavascriptincludedinapage,theycanuseitforallkindsof
evil:makinglinkschangeastheuserclicksthem;sendingusernamesandpasswordstothewrong
places;reportinglotsofinformationabouttheusersbrowserbacktoasite.Javascriptisfrequentlya
partofschemestotrackpeopleacrosstheweb,orworse,toinstallmalwareonpeople'scomputers.It
isbesttodisableJavascript(about:configinURLbarsearchforJavascriptandToggleittodisabled)
unlessyouabsolutelytrustthesiteorusethebrowseraddonNoScriptsthatcomeswithTailsandis
availableinFirefoxtoatleastselectivelyblockmaliciousscripts.DisablingJavascriptoutrightisthebest
optionthough,andgumbyhasaddedasuggestionthatcanmakeiteveneasiertodothis.
Quotefrom:gumbyonJanuary14,2014,08:59:57pm
SupposedlyNoScriptdoesn'tblockallJavascriptevenwhenitisenabledandnositesareonthe
whitelist.NotsureaboutthatclaimbutI'veseenpeoplemakeit.There'saFirefoxaddon(whichalso
worksinTorBrowser)calledtoggle_jswhichletsyoutoggletheabout:configjavascript.enable
parameterthroughatoolbariconsoyoudon'thavetogointoabout:config.Ifinditquiteuseful.
JavascriptcanalsorevealanalarmingamountofinformationaboutyouevenifyouareusingTORor
aVPN,includingyourbrowserplugins,yourtimezone,whatfontsyouhaveinstalled(flashdoesthis
aswell)andofcoursemostbrowserswillsendyouruseragent,meaningtheytellthewebsitewhat
browseryouareusingandinsomecasesyouroperatingsystem!Someofthesedetailsmaynotseem
veryimportant,butcollectedasawhole,itcanmakeiteasiertoidentifywhoyouareonlinebyalmost
generatingafingerprintofyouwithyourspecific settingsrelatedtoyourbrowser.Thenasyouhop

122
aroundfromsite tositewithyour finger print, correlationsandpatterns canbe drawnfromthisand
eventuallylinkedtoyouifyouarenotextremelycareful.
Luckily,TailsandWhonixoverridesthemajorityofthisidentifyinginformation,soaslongasyouuse
TailswithJavascriptdisabled,orattheveryleastwithNoScripts(Flashisdisabledautomatically)then
youcancutdownontheamountofinformationyoushare.Needlesstosay,itisnotalwayspossibleto
browsewithTails,sothesearethingsyouneedto beawareofwhenyouarebrowsingwithregular
browsersonyournativeOSwithyourbrowserofchoice.
Seewhatyourbrowserisrevealingaboutyouatthispagebelow.DonotvisititfromyourrealIP
address,sincethispagewillbelinkedtotheSilkRoadforumsfromthemomentImakethispostpartof
mythread.Asaresult,youmaywishto searchonlineforothersitesthatcheckwhatinformationyour
browserisrevealingaboutyou.IfyouareconfidentinyourOpSecabilities,usetheonebelow.
http://browserspy.dk/
A FEW RECOMMENDATIONS
Hereareafewrecommendationsthatmayslipby theaverageuserontheseforums.
1.Neverleaveyourcomputerthatyouuseforyourfreedomfightingunattended.
Thismayseemlikeanobrainer,butifyouhavekids,oraspouseorasiblingthatdoesnotunderstand
whatyoudoonthecomputerandtheydecidetohoponyouraccountandsignintotheiremail,
Facebookordoingthingsthatcouldcompromiseyourlocationwhileonthatcomputerbecausethey
simplydidnotknow,thiscouldpotentiallycauseyouproblems.
MaybeyouareconnectingthroughmultiplelayerslikethisTOR>VPN(1)>TOR>VPN(2),sothatis
4layersandVPN(2)istheIPaddressthateveryonesees.Thenyourchildorspousegoesontotheir
emailwiththatIPaddress,thensignsoffwithoutyourknowledge.ThatVPNisnowlinkedtoyou.And
werememberhowwhenunderpressure,companieswilllikelygiveoutinformationabouttheir
customerstoavoidfines,shutdownsandprosecution.
2.Donottellyourfamilymemberswhatyouaredoing,justinstructthemnottotouchyourcomputer.
Keepitpassworded.Youshouldnevertellanyonewhatyouaredoingonyourcomputerbecauseif
lawenforcementeverdidshowup,theywouldquestionyourfamilyandfriendsaboutyou.Ifthey
honestlydonotknow,thentheycannotbeheldincontemptofcourt,soitisbettertokeepthemin
thedark.Ormaybethepolicemightscarethemintogivingupallyoursecretsbecausetheytellyour
familythatiftheydonotconfessthatyourselfandthemwillbegoingtojail,possiblyforalongtime.
Justpasswordyourcomputerandneverleaveitunattendedwiththescreenunlocked.
3.Ifyouusemultiplelayerstoconnect,makesureyouregularlychecktomakesureallyourlayersarein
tact.VPNscandropsometimeswithoutwarningandwhileyoushouldneversetyourselfupsothatif
one layerdropsyouloseeverything,justkeepinmindwhenonedropsthatyoumayneedtoadjustthe

123
wayyouhandle yourselfonline untilyougetthatnext layer up. Thisisone ofthereaonsI like Tortillaso
much,ifmyTORlayerdoesnotwork,itdoesnotbypassitandgotomynextlayer,insteaditjuststops
workingaltogether.WhenVPNsdrop,yourcomputerbypassesthedroppedVPNandmovesontothe
nextlayer,whichinsomecasescouldbeyourrealIPaddress.Justsomethingtokeepinmind.
4.Donotusethesamepasswordformultipleforums,marketplaces,emailsandsoforth.Expectthat
one ormoreofthewebsitesyouareregisteredwithisstoringyourpasswordinplaintext.Thismeans
thatifsomebodyfindsanexploitinthesoftwareandisabletodumptheentiredatabase,theycanfind
yourpassword.Andifyouusedthesamepasswordforothersites,andgodforbidwiththesame
usernameaswell,yourentirelistofaccountsiscompromised.Alwaysusedifferentpasswordsand
keepthemstrong.Donotletanythingaboutyourpasswordidentifyhowyouchoosepasswords,or
identifyanythingpersonalaboutyou.
COLD BOOT ATTACKS, UNENCRYPTED RAM EXTRACTION
Didyouknowthatevenifyoursystemiswholediskencrypted,yourdatacanstillbeextractedusing
somethingcalledacoldbootattack?Readon.
ThefirstthingweneedtotalkaboutisRAM.RAMstandsforrandomaccessmemory.Allyouneedto
knowaboutRAMisthatRAMistheplaceinacomputerwheretheoperatingsystem,application
programs,anddataincurrentusearekeptsothattheycanbequicklyreachedbythecomputer's
processor.RAMismuchfastertoreadfromandwritetothantheotherkindsofstorageinacomputer,
theharddisk,floppydisk,andCDROM.However,thedatainRAMstaysthereonlyaslongasyour
computerisrunning.Whenyouturnthecomputeroff,RAMlosesitsdata.
Whenyouturnyourcomputeronagain,youroperatingsystemandotherfilesareonceagainloaded
intoRAM,usuallyfromyourharddisk.RAMcanbecomparedtoaperson'sshorttermmemoryand
theharddisktothelongtermmemory.Theshorttermmemoryfocusesonworkathand,butcanonly
keepsomanyfactsinviewatonetime.Ifshorttermmemoryfillsup,yourbrainsometimesisableto
refreshitfromfactsstoredinlongtermmemory.Acomputeralsoworksthisway.IfRAMfillsup,the
processorneedstocontinuallygototheharddisktooverlayolddatainRAMwithnew,slowingdown
thecomputer'soperation.Unliketheharddiskwhichcanbecomecompletelyfullofdata,RAMnever
runsoutofmemory.
DatacanbeextractedfromtheRAMusingvarioustools.Whenyouhaveatextdocumentopenand
youareworkingonit,youareworkingfromtheRAM.Meaningthatifyouareworkingonasensitive
document,thatdocumentistemporarilystoredintheRAMandisvulnerabletobeingextractedwhile
thecomputerison.WhenRAMisbeingstored,itisbeingstoredwithoutanyformofencryption,
makingitveryeasytostealandahugesecurityrisk.
Shuttingdownacomputerthroughitsnormalshutdowncycleusuallygoesthroughaprocessof
clearingtheRAM.However,ifthecomputerlosespowerabruptlylikeinapoweroutage,thecomputer
doesnotgothroughitsnormalshutdowncycleandsomeinformationremainsontheRAMchipsfora
fewsecondsuptoafewminutes.Thisisoneofthewayscoldbootattackscanwork.
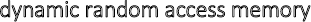
124
IalsowanttoquicklyintroduceatypeofRAMtoyouwhichwillhelpyouunderstandtherestofthis
articlebetter.BelowisaresearchpaperandtheyusedatypeoframcalledDRAM.DRAMstandsfor
dynamicrandomaccessmemory.DRAMisthemostcommonkindofrandomaccessmemory(RAM)for
personalcomputersandworkstations.DRAMisdynamicinthat,unlikestaticRAM(SRAM),itneedsto
haveitsstoragecellsrefreshedorgivenanewelectronicchargeeveryfewmilliseconds.DRAMis
designedtoloseitsmemoryquicklyafterlosingpower.ThentherearesubsectionsofDRAMcalled
DDR.Thisisawayofmakingthememorymorequicklyavailable,butitisnotreallyimportanttofully
understand.WikipediacangiveyouallyouneedtoknowaboutDDR.Inthisarticlewearefocusingon
justtheconceptofDDR,DDR2andDDR3.
ThesearenewerversionsofDRAMthatkeepgettingbetter,andIbelievewearecurrentlyupto
DDR4.ButmostcomputerscirculatingaroundtodayhaveDDR2andDDR3inthemunlesstheyare
oldercomputers,thisincludeslaptops.DRAMisknownasatypeofvolatilememory,itiscomputer
memorythatrequirespowertomaintainthestoredinformation.Itretainsitscontentswhilepowered,
butwhenpowerisinterrupted,storeddataisquicklylost.Buthowquicklyisitlost?
In2008,agroupofresearcherswantedtoseethepracticalityofextractingunencrypteddatafrom
theRAMinyourcomputer.TheyarguedthatDRAMsusedinmostmoderncomputersretaintheir
contentsforsecondstominutesafterpowerislost,evenatoperatingtemperaturesandevenif
removedfromamotherboard.Andbyusingananalysistooltheywereabletosearchforkeyfiles(such
asPGPkeys)heldintheRAMthatcouldbeusedtodecryptencryptedvolumes(drives)onyour
computer.TheysuccessfullywereabletodecryptvolumesusingBitLocker,FileVault,dmcrypt,and
TrueCrypt.Belowistheabstractoftheir research.
Quote
LestWeRemember:ColdBootAttacksonEncryptionKeys
AbstractContrarytopopularassumption,DRAMsusedinmostmoderncomputersretaintheir
contentsforsecondstominutesafterpowerislost,evenatoperatingtemperaturesandevenif
removedfromamotherboard.AlthoughDRAMsbecomelessreliablewhentheyarenotrefreshed,
they arenotimmediatelyerased,andtheircontentspersistsufficientlyformalicious(orforensic)
acquisitionofusablefullsystemmemoryimages.Weshowthatthisphenomenonlimitstheabilityof
anoperatingsystemtoprotectcryptographickeymaterialfromanattackerwithphysicalaccess.We
usecoldrebootstomountattacksonpopulardiskencryptionsystems—BitLocker,FileVault,dm
crypt,andTrueCrypt—usingnospecialdevicesormaterials.Weexperimentallycharacterizethe
extentandpredictabilityofmemoryremanenceandreportthatremanencetimescanbeincreased
dramaticallywithsimpletechniques.Weoffernewalgorithmsforfindingcryptographickeysin
memoryimagesandforcorrectingerrorscausedbybitdecay.Thoughwediscussseveralstrategiesfor
partiallymitigatingtheserisks,weknowofnosimpleremedythatwouldeliminatethem.
https://citp.princeton.edu/research/memory/[Abstract]
http://citpsite.s3websiteuseast1.amazonaws.com/oldsitehtdocs/pub/coldboot.pdf[FullText]
HereisanFLVvideoyoucandownloadtowatchexactlyhowtheydidit.
125
https://anonfiles.com/file/97b5737dba6b96871fd862b8a587b8f0
Thiswasverytroublingtomostpeople,andhadmanypeoplefreakingoutwhentheresearchpaper
wasreleasedbackin2008becauseeventoughencryptiontoolslikeTrueCryptcouldberendered
uselesswithanattacklikethis.Uponfurtheranalysisofthepaper,Iwantedtonotethattheyused
SDRAM,DDRandDDR2,andnotDDR3becauseitwasnotavailableatthattime.Thisprompted
TrueCrypttoreleasethefollowingstatementontheirwebsite.
Quote
UnencryptedDatainRAM
ItisimportanttonotethatTrueCryptisdiskencryptionsoftware,whichencryptsonlydisks,notRAM
(memory).
Keepinmindthatmostprogramsdonotclearthememoryarea(buffers)inwhichtheystore
unencrypted(portionsof)filestheyloadfromaTrueCryptvolume.Thismeansthatafteryouexitsuch
aprogram,unencrypteddataitworkedwithmayremaininmemory(RAM)untilthecomputeris
turnedoff(and,accordingtosomeresearchers,evenforsometimeafterthepoweristurnedoff*).
AlsonotethatifyouopenafilestoredonaTrueCryptvolume,forexample,inatexteditorandthen
forcedismountontheTrueCryptvolume,thenthefilewillremainunencryptedintheareaofmemory
(RAM)usedby(allocatedto)thetexteditor.Thisappliestoforcedautodismounttoo.
Inherently,unencryptedmasterkeyshavetobestoredinRAMtoo.WhenanonsystemTrueCrypt
volumeisdismounted,TrueCrypterasesitsmasterkeys(storedinRAM).Whenthecomputeriscleanly
restarted(orcleanlyshutdown),allnonsystemTrueCryptvolumesareautomaticallydismountedand,
thus,allmasterkeysstoredinRAMareerasedbytheTrueCryptdriver(exceptmasterkeysforsystem
partitions/drives—seebelow).However,whenpowersupplyisabruptlyinterrupted,whenthe
computerisreset(notcleanlyrestarted),orwhenthesystemcrashes,TrueCryptnaturallystops
runningandthereforecannoteraseanykeysoranyothersensitivedata.Furthermore,asMicrosoft
doesnotprovideanyappropriateAPIforhandlinghibernationandshutdown,masterkeysusedfor
systemencryptioncannotbereliably(andarenot)erasedfromRAMwhenthecomputerhibernates,is
shutdownorrestarted.**
Tosummarize,TrueCryptcannotanddoesnotensurethatRAMcontainsnosensitivedata(e.g.
passwords,masterkeys,ordecrypteddata).Therefore,aftereachsessioninwhichyouworkwitha
TrueCryptvolumeorinwhichanencryptedoperatingsystemisrunning,youmustshutdown(or,ifthe
hibernationfileisencrypted,hibernate)thecomputerandthenleaveitpoweredoffforatleastseveral
minutes(thelonger,thebetter)beforeturningitonagain.ThisisrequiredtocleartheRAM.
*Allegedly,for1.535secondsundernormaloperatingtemperatures(2644°C)anduptoseveral
126
hourswhenthememorymodulesare cooled(whenthecomputer isrunning)toverylowtemperatures
(e.g.50°C).Newtypesofmemorymodulesallegedlyexhibitamuchshorterdecaytime(e.g.1.52.5
seconds)thanoldertypes(asof2008).
**BeforeakeycanbeerasedfromRAM,thecorrespondingTrueCryptvolumemustbedismounted.
Fornonsystemvolumes,thisdoesnotcauseanyproblems.However,asMicrosoftcurrentlydoesnot
provideanyappropriateAPIforhandlingthefinalphaseofthesystemshutdownprocess,pagingfiles
locatedonencryptedsystemvolumesthataredismountedduringthesystemshutdownprocessmay
stillcontainvalidswappedoutmemorypages(includingportionsofWindowssystemfiles).Thiscould
cause'bluescreen'errors.Therefore,toprevent'bluescreen'errors,TrueCryptdoesnotdismount
encryptedsystemvolumesandconsequentlycannotclearthemasterkeysofthesystemvolumes
whenthesystemisshutdownorrestarted.
http://www.truecrypt.org/docs/unencrypteddatainram
Afewkeypointstoextractfromherearethatproperlyshuttingdownyourcomputerreduces,ifnot
completelyenliminatesthisriskexceptinthecaseofencryptedsystemdisks.Whatismeantbythisis,
forexample,ifyourmainoperatingsystemisWindowsandyouhaveencryptedthatdrive,thisisyour
systemdriveandthemasterkeyforthatdriveisnotcleareduponshutdownorrestart.Thesolutionis
simplytoneverstoreanythingsensitiveonyoursystemvolume.Whetheryouuseapartitioneddrive
oraUSBstickthatisencrypted,justmakesurethatyourmaindrivethatisbootedintodoesnot
containsensitivedata.Andifyouhavenootherchoice,thenyouneedtoseparatelyencryptthedata
insidethesystemvolumewithadifferentpassphraseandprivatekeysothateveniftheygetintoyour
systemvolume,theycannotaccesstheotherencrypteddatayouwanttoprotect.
TheycanusethesesametechniquestosniffaroundforyourPGPprivatekeyfilesintheRAM,sothis
isaveryrealthreatinthecasethatifyourcomputerisstillpoweredoniftheycometogetyou,they
canusethesetechniquestoretrievedatafromyourcomputer.However,thereisadebateabout
whetherornotthistypeofattackcanpersistevennowinto2014withnewertypesofRAM.Ipointtoa
randomblogonlineandImakenojudgementastowhetherornotthisisalegitimateclaim,butitis
interestingnonetheless.
Quote
Nowtotesttheactualcoldbootattack.Fillmemorywitharound1000taintmarkers,justtobesure
thereareenough.
Nowshutdown.Ostensibly,themarkerscouldberecognizableinRAMafterwholeminutes,butI’m
impatient,soIjustwaited10secondsforthefirsttest.Bootup,intotheminimallinuxinstallation.
Loadthekernelmodule:insmod./rmem.ko.Runhunter.
Nothing.
That’sok,though.Thereshouldbeatleastsomedatacorruption.Thedefaultmarkersizeis128bytes,
solet’ssetthehammingdistanceto128,meaningthatonebitoutofeverybyteisallowedtobe
flipped. (Statistically,that’sequivalenttoa25%corruptionrate,sinceacorruptedbithasa50%chance

127
ofremainingthesame).
Nothing.
Lookslikein10seconds,memorywascompletelycorrupted.Let’stryashorterinterval:2seconds.
Sameresults.Nothingisleftofour“encryptionkey”.
http://bytbox.net/blog/2013/01/coldbootattacksoverrated.html
TheuserclaimedtobeusinganewertypeofRAMcalledDDR3.whichisknowntoholdmemoryfora
muchshortertimethanDDR2.AndanewerresearchpaperreleasedinSeptember2013triedto
reproducethefindingsofthe2008researchbutusingcomputerswithDDR1,DDR2andDDR3andtheir
findingswereinteresting.
Quote
Eventhoughatargetmachineusesfulldiskencryption,coldbootattackscanretrieveunencrypted
datafromRAM.ColdbootattacksarebasedontheremanenceeffectofRAMwhichsaysthatmemory
contentsdonotdisappearimmediatelyafterpoweriscut,butthattheyfadegraduallyovertime.This
effectcanbeexploitedbyrebootingarunningmachine,orbytransplantingitsRAMchipsintoan
analysismachinethatreadsoutwhatisleftinmemory.Intheory,thiskindofattackisknownsincethe
1990s.However,onlyin2008,Haldermanetal.haveshownthatcoldbootattackscanbewell
deployedinpracticalscenarios.Intheworkinhand,weinvestigatethepracticabilityofcoldboot
attacks.WeverifytheclaimsbyHaldermanetal.independentlyinasystematicfashion.ForDDR1and
DDR2,weprovideresultsfromourexperimentalmeasurementsthatinlargepartagreewiththe
originalresults.However,wealsopointoutthatwecouldnotreproducecoldbootattacksagainst
modernDDR3chips.Our testsetcomprises17systemsandsystemconfigurations,fromwhich5are
basedonDDR3.
https://ieeexplore.ieee.org/xpl/login.jsp?tp=&arnumber=6657268&url=http%3A%2F%2Fieeexplore.iee
e.org%2Fxpls%2Fabs_all.jsp%3Farnumber%3D6657268
Sowhatdoesshouldyoudo?Numberone,alwaysshutdownyourcomputerwhenyouarenot
arounditorputitintohibernationmode,otherwiseyoursensitivedocumentscouldbelingering
aroundinyourRAM.Simplylockingthescreenwilldoyounogood.Makesureyourcomputerisusing
aDDR3typeofRAM,ifpossible.Someofyouthismeansyouneedtoupgrade.Ifyouareunsurewhat
kindofRAMyourcomputerhas,searchonlinetofindatoolthatwilldetectitforyou.Neverstore
anythingsensitiveonanencryptedsystemvolume,becausethisattackcanbeusedtobreakintothe
volumeandanythingunencryptedcanberetrieved.Ifyouareusingalaptop,pullthebatteryoutso
thatifyouneedtoquicklypullthepower,itwillturnitoffimmediately.Ifyouhavetime,shutdown
thecomputer,otherwiseturnitoffimmediatelysothatitisnotrunning.Themoretimeyoucanwaste
areprecioussecondswheretheycannotretrieveanydata.Soimmediatelyshutthingsoffifyoudonot
haveenoughtimetodoapropershutdown.
Considerputtingalockonyourcomputercase,andifyouwanttogotakeitastepfurther,boltitto
thefloor.Thatwaytheamountoftimeitwouldtakethemtogetinsideyourcomputerwouldwaste
128
valuable minutesandmore thanlikelyrender anyrecoverable memoryuseless. Some people have
evensuggestedthatyousoldertheRAMintothemotherboardsotheycannottakeitout.Thismay
helpslowthingsdown,butrememberthatcoolingthememorydowncanpreservethingsforquitea
whileifyouareusingDDR1orDDR2. WithDDR3,youshouldbegoodtogoandIbelievewiththis
realization,manufacturerswilllikelystartlookingatwaystoencryptRAM,butuntilthattimeyoudo
needtobeawareofthisasapossiblemeansforstealingyoursensitivedataandsomethingyoushould
keepinthebackofyourmindandprepareyourselfforjustincase.
THE STRENGH OF CRYPTOGRAPHY AND ANONYMITY WHEN USED
PROPERLY
Thispostismeanttoserveasanexampleofhow,whencryptographyandanonymityisusedproperly,
youcanevadejustaboutanybodyincludingthepolice.
Bynow,everyonehaslikelyheardofsomeonegettinglockedoutoftheircomputerandbeingforced
topaybytheattackertohaveitunlocked,thisisCryptoLocker.DellSecureWorksestimatesthat
CryptoLockerhasinfected250,000victims.Theaveragepayoutis$300each,andmillionsinlaundered
Bitcoinhavebeentrackedandtracedtotheransomware'smoneyrunners.
CryptoLockerisaransomwaretrojanwhichtargetscomputersrunningMicrosoftWindows[1]and
firstsurfacedinSeptember2013.ACryptoLockerattackmaycomefromvarioussources;onesuchis
disguisedasalegitimateemailattachment.AZIPfile attachedtoanemailmessagecontainsan
executablefilewiththefilenameandtheicondisguisedasaPDFfile,takingadvantageofWindows'
defaultbehaviourofhidingtheextensionfromfilenamestodisguisethereal.EXEextension.When
activated,themalwareencryptscertaintypesoffilesstoredonlocalandmountednetworkdrives
usingRSApublickeycryptographytogeneratea2048bitRSAkeypair,withtheprivatekeystoredonly
onthemalware'scontrolservers.
Themalwarethendisplaysamessagewhichofferstodecryptthedataifapayment(througheither
Bitcoinoraprepaidvoucher)ismadebyastateddeadline,andthreatenstodeletetheprivatekeyif
thedeadlinepasses.Ifthedeadlineisnotmet,themalwareofferstodecryptdataviaanonlineservice
providedbythemalware'soperators,forasignificantlyhigherpriceinBitcoin.
DellSecureWorksestimatesthatCryptoLockerhasinfected250,000victims.Theaveragepayoutis
$300each,andmillionsinlaunderedBitcoinhavebeentrackedandtracedtotheransomware'smoney
runners.InNovember2013,theoperatorsofCryptoLockerlaunchedanonlineservicewhichclaimsto
allowuserstodecrypttheirfileswithouttheCryptoLockerprogram,andtopurchasethedecryption
keyafterthedeadlineexpires;theprocessinvolvesuploadinganencryptedfiletothesiteasasample,
andwaitingfortheservicetofindamatch,whichthesiteclaimswouldoccurwithin24hours.Oncea
matchisfound,theusercanpayforthekeyonline;ifthe72hourdeadlinehaspassed,thecost
increasesto10Bitcoin.
Todate,noonehassuccessfullydefeatedCryptoLocker.TheSwansea,Massachusettspolice
departmentwashitinNovember.TheofficerspaidCryptoLocker'sransom.PoliceLt.GregoryRyantold
129
press thathis departmentshelledoutaround$750for twoBitcoinon November 10. One ofthe
reasonsIampostingthis,isthatCryptoLockeruses2,048RSAencryption,andifyourememberinthe
PGPpostsearlierinthisthreadIrecommendedtouse4096.Evenwith2,048bitencryption,noone
hassuccessfullydefeatedCryptoLocker,andthisisthepowerofproperlyimplementedcryptography.
And,usingthepropermethodsofanonymity,thispersonorgrouphasmanagedtoacquire,
accordingtoresearchdonebyZDNet,around41,928BTC.
http://www.zdnet.com/cryptolockerscrimewaveatrailofmillionsinlaunderedbitcoin7000024579/
Quote
InresearchforthisarticleZDnettracedfourbitcoinaddressesposted(andreposted)inforumsby
multipleCryptoLockervictims,showingmovementof41,928BTCbetweenOctober15andDecember
18.
BasedonthecurrentBitcoinvalueof$661,themalwareninjashavemoved$27,780,000through
thosefouraddressesaloneifCryptoLockercashesouttoday.
IfCryptoLocker'ssupervillanscashoutwhenBitcoinsoarsbackupto$1000,likeitdidonNovember
27...Well,$41.9millionisn'tbadforthreemonthsofwork.
Asyoucansee,properlyexecutedcryptographyandanonymityallowedthisgroupofpeopleacquire
theBitcoinequivalentofalmost$42millioninjustnow4monthsatthetimeofthispost.Iamnot
recommendingoradvocatingthatyoudothis,butjustgivingyouaperfectexampleofhowpowerful
thecombinationofthesetwoveryimportantfactorsareinprotectinganybodyonlinewhenused
properly.
ANOTHER SCAM EMAIL - BEWARE
Ifyouhavebeenfollowingmythreadforawhilenow,youwillrememberthepreviousemailscam
goingaroundtryingtogetpeopletodownloadaninfectionversionoftor.WithSilkRoadatthetimeof
thispostnowboastingover25,000members,itiseasytogetthattheseoccurrencesarelikelygoingto
increaseandunfortunatelysomepeoplearegoingtofallforthem.Thisnewoneisdirectedatvendors,
butitnonethelessshouldserveasanexampleofthetypeofscamsthatpeoplearegoingtobetrying
topullonmembersofthisforumandotherforums.
Quote
DearValuedVendor,
Duetotherecentinstabilityofthesite,andourprogrammersinabilitytoremedytheproblemsina
timelymanner,wearegoingtohavetotemporarilyshutdownvendoraccounts.Sincewecan'tjust
stopoperationofthesitecompletely,weareforcedtodevelopawayforonlysomeofthevendorsto
gointoatemporaryvacationmode.Inneedofrecentserverupgrades,aswellasthisnewmethodwe
areimplementing,ithasoccuredtousthattheonlywaytopickwhichvendorsaregoingtoremainin

130
business is byhowmuchsales/profitthey are doing, aswellas how much beingavendor onour site
meanstothem.Here'showthisisgoingtowork:
Ifyouwouldliketokeepvendingonthesiteduringourupgrades/repairs,wearegoingtorequirethat
youpayanadditional.3BTCbondtous.Ifyoupaythis.3BTCbond,youraccountwillremainactiveand
youwillkeepvendingwhileweworktofixtheproblems.Ifyoudonotpaythis.3BTCbond,your
accountwillbetemporarilyputintovacationmode statusandyouwillbeunabletovenduntilwe
locateandremedytheproblem.Weareverysorryforthesechanges!
Intheeventyoudopaythebond,assoonasthevendingopensbackuptoeveryone,youwillhave
your.3BTCbondreturned,andyouwillreceiveapremiumvendoraccountstatus.Youwillhaveatitle
onyourpagethatdisplaysyouas"HardcoreVendor".Weareterriblysorrywehavetoaskthisofall
ourhardworkingvendors,butthereisreallynootherwayforustodecideWHOgetstokeepvending
andwhohastowaituntilwefixthings.
Ourteamisworkinghardattheproblem,andweestimateitwillbenolongerthanaweekforthe
changestobemadeandvendingtoopenbackuptoeveryone.
Vendorswhowillpaybond:Pleasesend.3BTCtoBTCAddress:
1NbEs2rJgreRUvjp9o7hUWo3akeLA3EfFY
Vendorswhoareunabletopaybond:Youraccountswillgointovacationmodeat12:01AMUTC
February2nd.
Letusneverforgetthisrecenthurdleinourbattleforfreedom.Butletusnotallowittostopourfight,
either–itisnowtimetosimplypickourselvesbackup,dustourselvesoff,andcontinuefightingthis
revolutionlikewe’veneverfoughtitbefore.
I’mproudtohaveyouallatmyside.
YoursLoyally
DreadPirateRoberts
TheuserwhosentoutthismessageactuallyusedthenameDreadPiratesRobert,whichissimilarbut
notcorrect.Onethingyoushouldbeawareof,isthatanytypeofannouncementlikethisfromahigh
rankingAdministratorlikeDPRwillalwaysbesignedwiththeirPGPsignature.Andremember,we
discussedhowtoverifythesesignaturesinapreviouspost.Irememberwhenamoderatornamed
Sargewasinchargeofvendorbonds,therewasauserwiththenameSarrge(twor's)thatwastryingto
scamvendorsintosendingtheirbondstohisaddressinsteadandunfortunately,severalpeoplefellfor
thisscam.
PleasealwayscheckifthereisaPGPsignature,andifthereisnot,kindlyasktheAdministratoror
Moderatortoresendthemessagetoyouusingasignature.Protectyourselfbyverifyingthenameand
makesurethisuserhasanAdministratororModeratorstatusontheforum.Besafe!

131
AN INTRODUCTION TO AN EXPERT ON OPSEC, PLUS MD5 & SHA-1
CHECKSUMS
Thispost,IwouldliketofocusonintroducingyoutoanexpertinthefieldofOpSec.
*Notethismessagecontainsadownload,thereforethismessagehasbeenPGPsignedtoensurethatif
thismessageisaltered,youwillbeawareofit.*
Thisisamanwhohasdoneseveralpublicpresentations,yet,manypeoplestilldonotknowabout
him.OpSecstandsforOperationsSecurityandinthiscontextreferstopeoplekeepingthemselves
anonymousonline.Hegoesbytheonlinehandle,"TheGrugq",andGrugqhashisownblogwhichcan
befoundatthefollowingwebpage.
http://grugq.github.io/
ItshouldbenotedthatGrugqwasatonetimeonthepayrolloftheUSgovernmentforfindingand
sellingzerodayexploits.IfyourememberthepreviouspostabouthowtheUSfederalgovernmentis
thesinglemostpurchaserofmalwareintheworld,wellGrugqwasoneofthosewhosoldmalwareto
thegovernment.Unfortunatelyforhim,whenhewentpublicaboutit,theynolongerwantedtobuy
malwarefromhimbecausetheyliketomaintaintheirownanonymitywhenpurchasingtheseexploits.
Andhereisashortbiographyfromanonlinewebsite.
Quote
Biography:
TheGrugqisanInformationSecurityProfessionalwhohashasworkedwithdigitalforensicanalysis,
binaryreverseengineering,rootkits,VoiceoverIP,telecommunicationsandfinancialsecurity.Hehas
reportedtobeanexploitbrokerfor15%ofthesale.Lastbutnotleast,hehasalsospokenatvarious
securityconferences.
Facts
Hedeveloped"userlandexec"
HeistheauthorofHash(hackershell),atooltoenablepeopletoevadedetectionwhilepenetratinga
system.
Hehasreleasedavoipattacksoftware.
Claimstohavemademadlootonbeinganexploitbroker(middleman).
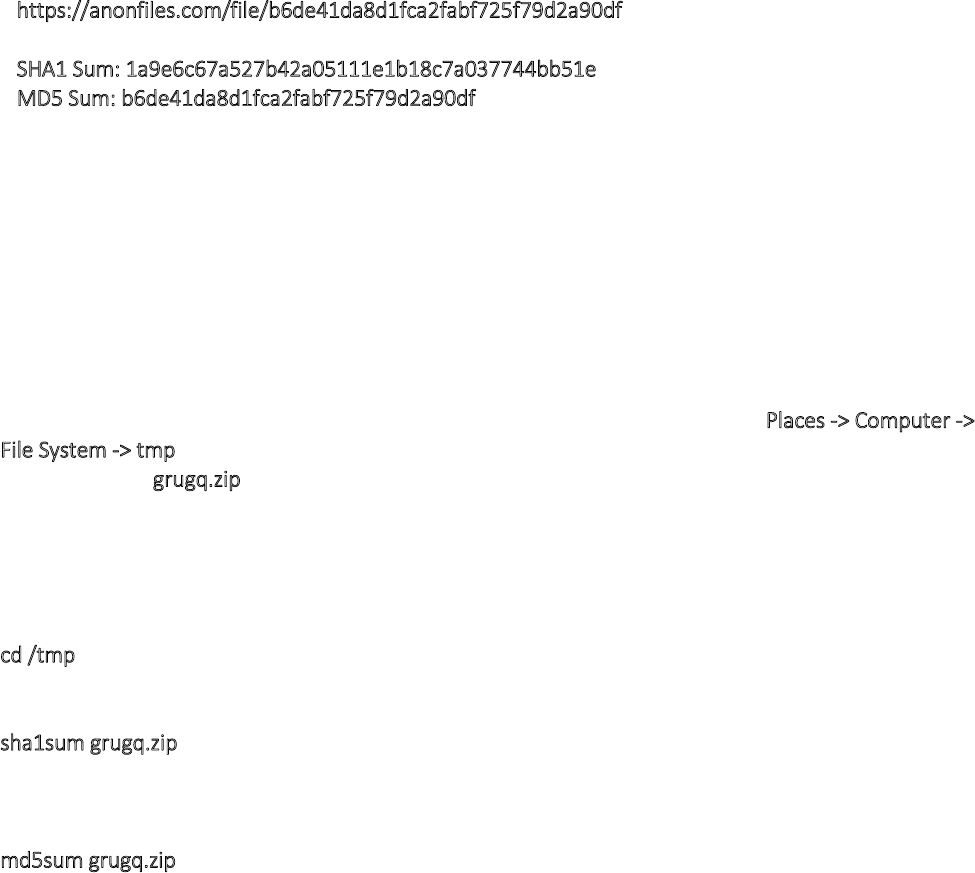
132
https://www.soldierx.com/hdb/Grugq
WhyarewetalkingabouttheGrugq?Whocares?Well,hehassomeofthebestinformationon
keepingyourselfanonymousandmaintainingprivacyonlineandheissomebodywhoyoushouldall
familiarizeyourselveswith.Hewritesblogposts,andhehasdonevideopresentationsatsecurityand
hackerconferences,withhismostfamouspresentation,atleastintheworldofSilkRoadbeingtheone
hedidonOpSec.SinceIknowitishardforTailsuserstowatchvideosonYouTube,Idecidedto
downloaditfromYouTubeanduploadittoAnonFiles.comsoyouallcanwatchit.Thepresentationis
about1hourlong,andanessentialtoeveryonewhowishestomaintaintheiranonymityonline.
Remember,youonlyhavetoscrewuponce.
https://anonfiles.com/file/b6de41da8d1fca2fabf725f79d2a90df
SHA1Sum:1a9e6c67a527b42a05111e1b18c7a037744bb51e
MD5Sum:b6de41da8d1fca2fabf725f79d2a90df
Onceyouhavedownloadedthefile,Iwantyoutochecksomethingcalledthechecksumofthefile.
Thechecksumiswherethecontentsoftheentirefilegetpluggedintoamathematicalalgorithmand
outputaspecificstring.Youcanseethetwostringsabove.Thisissomethingyoushouldallgetintothe
habitofdoingwhenpossible isverifyingthechecksumofyourfiles.Ifyourememberwhenwetalked
aboutsignaturefilesandPGP,thisisanothermethodofverifyingyourdownloadsbutnotasgoodas
thesignaturefiles.Itshouldhowever,wheneverprovidedbeperformedtoverifyyourdownloads
whenthesignaturefile+PGPcombinationisnotavailable.
OnceyouhavedownloadedthefileinTails,thefirstthingyoushoulddo,ismovethefileyou
downloadedtoyourtmpfolder.Inordertodothis,lookupatthetopandclickPlaces>Computer>
FileSystem>tmp.Thisiswhereyoumovethefileyourdownloadedto,andtokeepthingseasier,
renamethefilegrugq.zipandyouwillseewhyyouwanttodothatinasecond.
Nextwearegoingtoopenaterminalwindow(likeaDOSprompt)byclickingtheblackrectangleicon
intheupperleftcenterareaofTails.Onceyouhaveopenedyourterminalwindow,wearegoingto
performsomeLinuxcommands.
cd/tmpThiswillchangethecurrentdirectoryyouareoperatingwithintheterminaltoyourtmp
folderandallowyoutomoreeasilyaccessthefilesinthatfolder.
sha1sumgrugq.zipThiswillperformaSHA1checksumonthefileyoujustdownloaded,andyoucan
seewhyyouwantedtorenamethefile.ItshouldgiveyouthesameoutputastheSHA1sumlisted
above.
md5sumgrugq.zipThiswillperformanMD5checksumonthefileyoujustdownloaded,andis
anotherwayofcheckingthefile.SHA1isbetterbecauseitisharderproducethesameoutputtwice
withdifferentfilecontentsusingSHA1versusMD5,butnonetheless,usebothwheneverpossibleand
alwayscheckyourdownloadedfiles.
133
Ok,assumingyourdownloadedvideopassedthechecksumtest,youcanbeassuredthatthevideo
filethatIuploadedhasnotbeentamperedwith,orhadanymaliciouscodeinjectedintoit.Wheneven
asinglecharacterischangedinthesourcecodeofagivenfile,thechecksumoutputwillbecompletely
different.Mostpeoplethinkitmaybeoffbyaafewcharacters,butthedifferenceisalwaysquitelarge
andiswhyperformingchecksumsisanimportantwayofverifyingyourdownloads.
Sinceyounowhavea1hourvideopresentationthatyouallneedtowatchandrewatch(Youcando
thisinTails),Iwillendthispostandcontinuewithmynextpostfromtheassumptionthatyoucan
completedwatchingthishighlyrecommendedandendorsed(bySRadministratorsandmoderators)
videoonOpSec.WewillstartlookingmoreintotherecommendationsfromtheGrugq.Hewillbean
invaluableresourceofinformationforus,andIwillmainlybetranslatingsomeofhispostsintoamore
understandableformatforthoseofyouwhoarelesstechnicallycapableandalsokeepingthemonthe
SilkRoadforumhiddenservices.
BEGINPGPSIGNATURE
iQIcBAEBCgAGBQJS7wteAAoJEPuh6tSg81nyhyYP/0nFaWRq0GPe6/5XeMUj3yiZ
2fBaJ+7SXOMxnNXPZw9XAN5Hkpp9wPQmk8W27otuIk2N+iom8H0tJcGZi7hiMd45
Dv0NOrt/gS3bst/G37I+tPwdnWxb1pVNCS+3XnuLOo9IA7VdykU8tz6R+68kPB25
9lDguaUYVeGp2AJMezQ01LL60xQvv25TFLgiPrYD611bscVadckhSV5upXlbMW9+
WVzJG1mgY9gmUYQV6D5ErPGIvxm8cC+IVlzwgGHQPd3kq2QlmQF3XJrXqWGPXd8d
ewkD6VnrU8yO6tVMCG57K1xO9a9zPYp6yN1IOe69IsRkK7g266D+cz6Idwt97/Vr
5jgu1Ook8dfFGA3Sxg+qpoARt5diWKchvmqbxRrnFdOtCAawH1+DgNcVdepi7agk
zhIES1drHdIM1uQ9Wg3vegCLrU3HDpRwwyWoSZxH4kxruU7aByOH5ZdAZw9JV6Lk
b5JzVjrvrhayXwiHPQnnjM50RT9jPH44PhNZCN4G7Ln2Rkb7qa/kS5sA4W2dRwXf
SjtYXf+18pCp/7NL09LD+LsabZHEAa/MilWxjsAnLLIrJsnw3YbSUola/ebmnIq8
oUW20yP0fDOHdeSGVq1uLNZIadZHZtmZIGqBigPU3XAKLxYajssglAgcPxD8E4vc
rkKb3PIyz1k1/JXulymR
=zJvP
ENDPGPSIGNATURE
IT IS OBVIOUS WHEN YOU ARE USING TOR
ThisisgoingtobeashortpostaboutamistakewecanalllearnfromwhenaHarvardstudentemaileda
bombthreattohisschoolwhileusingtortoavoidafinalexam.
http://www.forbes.com/sites/runasandvik/2013/12/18/harvardstudentreceivesffortorfailure
whilesendinganonymousbombthreat/
134
Quote
...thestudent“tookstepstodisguisehisidentity”byusingTor,asoftwarewhichallowsusersto
browsethewebanonymously,andGuerrillaMail,aservicewhichallowsuserstocreatefree,
temporaryemailaddresses.
Despite20yearoldEldoKim’sgoalofanonymity,hisattemptstomaskhisidentityledauthoritiesright
tohisfrontdoor.DoesthatmeanthatTorfailedauserlookingtodelayhis“PoliticsofAmerican
Education”exam?Notintheslightest.
WhiletheHarvardstudentdidindeeduseTor,itwashisothersloppysecuritymeasuresthatledtohis
arrest.Thecomplaintsaystheuniversity“wasabletodeterminethat,intheseveralhoursleadingup
tothereceiptoftheemailmessages…EldoKimaccessedTorusingHarvard’swirelessnetwork.”
WhatKimdidn’trealizeisthatTor,whichmasksonlineactivity,doesn’thidethefactthatyouareusing
thesoftware.InanalyzingtheheadersoftheemailssentthroughtheGuerrillaMailaccount,
authoritieswereabletodeterminethattheanonymoussenderwasconnectedtotheanonymity
network.
Usingthatconclusion,theythenattemptedtodiscernwhichstudentshadbeenusingToronthe
Harvardwirelessnetworkaroundthetimeofthethreats.BeforefiringupTor,Kimhadtologontothe
school’swirelesssystem,whichrequiresuserstoauthenticatewithausernameandpassword.By
goingthroughnetworklogsandlookingforuserswhoconnectedtothepubliclyknownIPaddresses
thatarepartoftheTornetwork,theuniversitywasabletocrossreferenceusersthatwereusingboth
Toranditswirelessinternetaroundthetimethebombthreatswerereceived.
Thereisnotmuchformetoaddotherthanthefactthat,ifyouareplanningondoingsomefreedom
fighting,activismorjustusingSilkRoad,makesurethatyouareabletodosowhereusingtorisnot
goingtoraisesomeflags.Inthecaseofthisstudent,hewaslikelytheonlystudentatHarvardusingtor
atthemomentthisemailwassent,andwhentheauthoritiescametohisdormhequicklyadmittedhe
wasresponsible.
Helikelyneverwouldhavebeencaught,butrememberwhenyouusetor,otherscanbeawarethat
youareusingit.Abetterideaforhimwouldhavebeentoconnecttoanothercomputerremotelyand
havethatcomputerconnectedtotortosendtheemail.Thisway,theynevercouldhaveseenhis
computerconnectedtotor.Iwouldnotworryaboutusingtoronaregularbasisfromyourhome,
becausetherearehundredsofthousandsoftorusers,butitisagain,somethingtobeawareof.torwill
notcoveryourbadOpSecmistakeslikeinthecaseofEldoKim.
ARE YOU USING SAFE-MAIL.NET ?
ArecentarticleonForbes.comtalksaboutafalsesenseofsecurityusersmayhavewhenusingSafe
Mail.net
http://www.forbes.com/sites/runasandvik/2014/01/31/theemailservicethedarkwebisactually
using/

135
IfyouareauserofSilkRoad,youhavelikelyseenmany usersadvocatingtheuseofaservicecalled
SafeMail.net.Thiscompanydescribesitselfas"themostsecure,easytousecommunicationsystem",
andmanySilkRoadusershaveadoptedit.Buttherearesomethingsyoushouldbeawareof.
Quote
KnownusersoftheSafemailwebserviceincludeoperators,vendorsandcustomersofthedarkweb’s
manydrugmarketsites,journalistswritingabouttheinvestigationintoSilkRoad,andBTCKing,the
vendorwhorananundergroundanonymousBitcoinexchangeandallegedlyworkedwithBitInstant
CEOCharlieShremtosellmorethan$1millionworthofBitcoinstousersofSilkRoad.
WhenIreachedouttoSafemailforcomment,AmiramOfir,Safemail’sPresidentandCEO,responded
inanemailthatthecompanyanditsemployees“certainlyarenotawareofanycriminalactivity,”
addingthatthecompanydoes“followcourtordersthatareissuedinIsraelbyanIsraelicourt.Any
otherlawenforcementagencyshouldcontacttheIsraeliauthorities.”It’sworthnoting,however,that
IsraelsignedaMutualLegalAssistanceTreaty(MLAT)withtheU.S.in1998.AnMLATrequestwasused
toimagetheSilkRoadwebserver,accordingtothecriminalcomplaintofSept.27,2013.
OfirtoldmethatcommunicationsbetweenusersandthewebserviceareSSLprotected,andthat
informationstoredontheserverisencryptedwithuserspecifickeys.WhenaskedifSafemailhas
receivedcourtordersissuedbyanIsraelicourtonbehalfofanonIsraelilawenforcementagency,such
astheFBI,Ofir repliedwithashort“Yes.”Myfollowupemail,askingifSafemailhastheabilitytodecrypt
informationwithoutauser’skey,wentunanswered.
So,thefirst timetonoteisthattheFBIisalreadyawareofSafeMail.netandisalreadyreceiving
courtordersfromnonIsraelilawenforcementagencies.Andtheyarelikelygivingthemeverything
they needinordertoreadtheemails.Therefore,youshouldrememberthatnoemailserviceshouldbe
trusted.Noemailserviceisgoingtogotojailforyou.Andifyouaresendinganythingsensitiveover
emailusingplaintext,itwilllikelybereadeventuallybysomebodyotherthantheintendedrecipients.
ThisiswhythingssuchasstrongPGPencryptionareessentialtoanytypeofsensitivecommunication.
Withthis,itshouldbenotedthatSafeMailisnosaferthanGmailwhenitcomestoprotectingyour
privacywithitscentralizedemailservice.Nevertrustanycompanywithyourprivacy,alwaysencrypt.
LOCALBITCOINS PART 1 - POLICE ARE WATCHING IT!
IhaveafewstoriestosharefrompeoplewhousedLocalBitCoinstoselltheirBitcoins.
Quote
InSeptemberandOctober,Isold213BTC(gradually)tosomerandomguyonlocalbitcoins.Everything
wentfine,eachtimeIgotthemoney,Isentthebitcoins.5daysafterthelasttransaction,Igetarrested
bythepolice."Wheredoesthismoneycomefrom?"Iexplainaboutbitcoins,andtellthemallIknow
abouttherandomguy,Ivolunteermyphonetoanalysemyemailsandcheckmystory.Oncetheywere
136
sure thattheguycontactedme andnottheother wayaround, I was finally free togo. Later they told
me thatthemoneywasstolenandtheythoughtIwasdoingmoneylaundering.
Nowafteralmost3monthsandalotofbackandforthwiththepolice,theyarenowsuggestingthatI
sendbackthemoney.Iwouldgladlydothatiftheyarrestedthecriminalandfoundouthecannot
repay.RightnowifIsendbackthemoney,theinnocentpersonwhogothismoneystolengetsitback,
butthenIbecometheinnocentpersonwhogothismoneystolen,sothatmakesnosensetome.
Edit:Ijustsawalawyer.AccordingtohimIalreadywonthecase.Butit'sgoingtocostmesomeserious
moneyinlawyer'sfees...Morethanmycumulatedprofits.Itakethatasthecostofagreatlifelesson
andawakeupcall.
HealsotoldmeIcandisclosetheinfothatthepolicealreadyknows.Soherewego.I'minBrisbane,
Australia.Thereasonthepolicefrozemyaccountandnotthecriminal'saccountisthattheywantedto
knowwherethemoneywasgoing.Thepoliceareregularlycheckingmyhousetomakesurethe
criminalisnotseekingrevenge(hehasmyfulladdressandIhave2kids).
http://www.reddit.com/r/Bitcoin/comments/1to08d/arrested_by_the_police_for_localbitcoins_busine
ss/
Thisguy,likelyaBTCminer,wasarrestedandquestionedbypoliceforsellingBTCtoabuyerover
severaltransactions.Theymusthaveassumedthatthebuyerwasusingfraudulentfundsandthis
shiftedsuspicionontotheselleraswell.Idonotknowifthisstoryistrue,butIamtendingtobelieveit
is.Policearemonitoringthesetransactions,soyoubettermakesureyouhaveareasonable
explanationastowhereyouobtainedtheBitcoinsyouaretryingtosell.
Thisnext storywasremovedbytheoriginalposter(OP),butluckilysomebodyintherepliesquoted
theentirepostandthereforeIwasabletograbit.
Quote
So,asafewofyouguysknow,I'mmovingtoanothercountrysoonenough.WhenIgetoverthereI
won'thaveaccesstomybankaccount,soafewweeksagoIdecideditmightbeagoodideatosell
someofmyBTCforcash.Ihaddonethisacoupleoftimesbeforeandhadapositiveexperience,so
hadnowhimsaboutdoingitagain.
SoIreceivedarequestfromsomeonewhowantedtobuy500euroworthofBTCinaf2ftransaction.I
drovedowntomeetingspot,mettheguy,hegavemethe500euroandbasicallyranbacktohiscar
anddroveoff.Iobviouslyfoundthisstrange,butitwasanescrowtx,soIreleasedescrowfrommy
phoneandwentbacktomycar.
Onmydriveback,InoticedthattherewasaFordMondeobehindme(thekindofcarthatisusually
usedbyundercoverpoliceinmycity).Itseemedtobefollowingme,Ididn'thaveallmypaperworkon
mycarinorder,soIdecidedtotakeadetourdownsomelocalbackroadsandshakeit.
Soanyways,Ilostthecar,drovehomeandthoughtnothingofthisstrangeencounter.

137
Overthenextfewdays,Inoticedstrangeneedlemarksandtinytearsinallofmymail,Ialsonoticeda
reallystrangeparkedcaroutsidemyhouseoneday,whenIwalkedovertoittoaskthemwhatthey
weredoingthere,theydroveoffatspeed.Iprobablyshould'vebeensuspiciousthen,butIhaddone
nothingwrongandshruggeditoff.
Acoupleofdayslater,Iwakeuptothesoundofmydoorbeingsmashedin.Irundowntofind5police
officersinmyhouse.Theyshowedmeasearchwarrantunderthemisuseofdrugsact.Thenational
drugsunitwereparkedoutsidewithsnifferdogsready,theyleftafterafewminutesthoughanddidn't
comeinsidewiththedogs.ThepolicetoldmethepersonImetonlocalbitcoinswasanundercover
policeofficer,andtheyhadcopiedtheregistrationnumberoffofmycar andgotmyaddressfromit.
Theystrippedthewholehousedown,turnedeverythingupsidedownlookingfordrugs.Theyfound1
jointofweedandtheyalsoseizedaclockwhichtheythoughtwasadigitalscale(itwasn't)and
informedmethattheyweregoingtoprosecutemeforintenttosupply,eventhoughIwasn'tselling,
andIshowedthemaprescriptionfromadoctorinanothercountry(thatisn'tvalidhere)andtoldthem
thesuperintendantofthelocalpolicestationhadinformallytoldmethattheywouldn'tprosecuteme
forpossessionifitwasmedicaluseeventhoughIwastechnicallybreakingthelaw.Theyalsofound
paddedenvelopesandaccusedmeofsellingdrugsthroughthepost(acompleteliewithnoevidence).
TheythentoldmethatifIdidn'tgivethemallthemessages&phonenumbersofeveryoneIhadmet
tosellBTCthattheyweregoingtoseizeallmybitcoinminers,computersetcandhavethem
"analyzed".Iwasabouttomovecountryinthenextfewdaysanddidn'twantthehassleofhavingto
dealwiththis,soItoldthemthatIhaddeletedallthemessages(whichIdid)butthatIwouldbeable
togetthembackiftheyleftmycomputersthere,andthatIwouldcooperatefully(I'mobviouslynot
goingtocooperate).TheythenleftandIchangedmyflightdateandbasicallyfledthecountrythenext
day,luckilyIwasplanningonmovinginaweekanyways.
So,awarningtoyouguys,becarefuldoingf2ftransactionsorbuying/sellingBTCingeneral,even
thoughwe'renotbreakingthelawitdoesn'tmeanyouwon'tgetunwantedattentionfromthepolice.
https://bitcointalk.org/index.php?topic=174918.msg1820363#msg1820363
Thisstoryabove,Idonotknowifitistrueeither,butitissomethingtothinkabout.Accordingtothe
OP,lawenforcementwantedallhismessagesandphonenumbers,obviouslytotryandfindother
peopleinvolvedinmoneylaunderingandthedrugtrade.Hewasscaredenoughtohavedeletedthe
originalpost,butasImentioned,someotherpeoplequoteditandIwasabletograbit.
Tosummarize,thepolicearelikelywatchingtheseBitcointransactions tosomedegreeandyouneed
toestablishabuyerorsellerthatyoucantrust.Onceyoufindagoodone,stickwiththem,eveniftheir
ratesgoup.Trytosearchforpeoplewithestablishedfeedback,askforIDifyouwant,andmakesure
youhavenothingincriminatingonyou,oratyourhomearoundthetimeofthesetransactions.You
never knowwhenyoucouldbetryingtooffloadyourBTCtoacop!
LOCALBITCOINS PART 2 - THIEVES, SCAMMERS AND COUNTERFEIT
138
BILLS!
Thispostisacontinuationfromthelastone.ThethreatofbeingrippedofforscammedonLocalBitcoin
isaveryrealthreat.Onethatyouneedtobeawareof.
Iwanttoshareafewstorieswithyou.
Quote
Goingtokeepitshortandsimple.Iliveinamajormetropolitancity,anddoalotofbusinessof
craigslist.Meetinperson,publiclocation,inspecttheitem,handcashandbeonmyway.I'msureI
have25+transactions,neverbeenscammed.
Today,Isawsomeoneincludejustasafootnote"Ialsoacceptbitcoins".Not"Ionlyacceptbitcoins"or
"plzsendbitcoinsimail"justalittlefootnotethattheyarefinewithit.
Contacted,mentionedpurchasingincash,thatwasfine,andattheenddecidedtodoitinbitcoins.
Broughtmylaptop,publicwifi,tookaseatataMcDonalds.InspectedtheheadphonesPerfect
condition,asdescribed,everythingwaslookinggood.
Hehandsmeapapercutoutwithawalletaddress,Ikeyitintoblockchain,heislookingattheaddress
onscreen.Iconfirmtheprice(80USD,was.8xxbtc),hesaysgood,Ihitsend,thelittleblockchainbeep
playsoverthespeakers.
Hecasuallystandsup,hastheheadphones,andwalksaway.Istandupprettyquick,andshoutafterto
him,accusinghimoftheft.Hesaysaquickcommentaroundthelinesof"Ifyoucan'tpaytheprice
don'twastemytime,Isaid$80"andwalksout.
Icontemplatechasingafterhim,callingthepolice,or fuckmaybegettingsomepublicattention,thenI
realizedIdidn'thavealegtostandon.
Cameraswouldshowaguysittingdownatatable,showingmeheadphones,meinspectingthem,then
playingonacomputerforabit,withhimwalkingoff.Iattempttoaccusehimoftheft,heprobably
didn'tevenhave$80inhiswallet,nothingwouldshowmehandinghimcash,andtheworstpart,asI
sattherewithamixtureofadrenaline,rageandfrustrationisthatItwasimpossibleformetogetthat
moneyback.
Canyouimaginetryingtotalktothepoliceaboutthis?Soyeahofficer,Isenthimbitcoins,avirtually
currencyforthiscraigslisttransaction,andthenhewalksoffSir,doyouhaveanyproofofthis?Well,
hegavemethisaddressofrandomletters,butIswearit'shis,butitisn'tthereanymore,it'sgonetoa
mixingservicewhereitgetspu
Yougetthepoint.Ihaveadecentlyhardtimeexplainingbitcoinstomyeager,willingtolearnfriends.I
can'timaginetryingtoexplainittoanofficerwhothinksIjusttriedtogivesomeoneWoWgoldfor
headphones.

139
So, isthere anysafetyprecautionoutthere I didn'ttake, or shouldyoujustkeepBTC andCraigslistas
farapartaspossible?
Thanksforreadingtherant.Sorryforthewalloftext.IguessIjustkindaneededtogetitoutthere.
http://www.reddit.com/r/Bitcoin/comments/1b89wm/i_just_got_robbed_blind_of_bitcoins_in_person
_im/
Remember,theriskofsomethingliketheabovehappeningincreaseswiththeamountofBitcoin
beingtradedforFIATcurrency(Governmentpaperorelectroniccurrency).Soifyouaretryingto
unloadafewBitcoinstoaseller,youmayfindyourselfinasimilarsituationfromtimetotimeanditis
besttoprepareyourselfincasethishappen.Bringafriendwithyou,havethemwaitatthedoorin
casethepersontriestorunaway,orbetteryet,multiplefriends.Ifyouliveinacountryorstatewhere
itislegaltocarryaconcealedweapon,thenyoumightwanttoconsiderdoingthisaswell.
Quote
Adangerousnewscammingtrend?£15,000tooclose
Soitappearsthatunfortunatelyscammershavechangedtheirtactics.Ihavebeenadvisedbypolice
nottodisclosetheusernameordetailsofthepersonconcerneduntiltheirinvestigationiscomplete
butIamoktodisclosethestoryasawarningtoothers.TodayIwenttomeetabuyerwhowaslooking
for£15,000worthofbitcoins andwantedtopayincashbutthisparticular userhadagoodbuyerhistory
soalthoughcautiousIagreedtomeethiminLondoninaplaceIknewtherewouldbeCCTVandsecurity
formyownsafety.Arrivingtheretodayinapublicplace,allwentfineinitiallyfromchattingwithhim
butwhenIpulledoutaquickformtocomplywithAML'sheseemedveryuncomfortablewhich
althoughIdidn'tshowit,itsentalarmbellsringinginmyheadashekindofcoveredhisIDwhilstin
terriblehandwritingfilledouttheformanddoneacompletelyunreadablesignaturelookingnothing
likethename.Atthispoint,Iwasverytemptedtocallthedealoffsimplybecausemygutinstinctwas
reallytellingmetobackoutofthisbuthebroughtuphehadtowithdrawanother£200fromhisbank
andsoIaskedhimwhatbankhewaswith,whichwasNationwide,whichIamtoo,soIwentwithhim
tothebranchwiththecashandformsetcinmybagandsaidIwouldjustsitinthebranchsinceithad
air conditioningandwasonly5storesaway.Inmyheadatthispoint,Iwastryingtogetintothebranch
andseeifIcouldoverhearthenamehewaswithdrawingfromandalsotoseeifheactuallyownedthe
cardhehadinhishandsoIcouldmatchthedetailsupwithwhatwasontheform.
Uponarrivalatthebranch,hehandedhiscardoverandthebanktellergaveeverythingaquickglance
andaskedhimforfurtherIDandasecuritychecksowhilsthedonethat,IthoughtIwouldaskthe
tellernexttohimwhowasfreeiftheycouldputitontheircashcountingmachineandshowedallthe
relevantdocumentation.Thecashwentbehindthecounterwhensheagreedandputitstraightonthe
machinewithoutevenlookingatthedocumentssurprisingly.Immediatelyasthishappened,themale
buyingthebitcoinssaidtome“Whatareyoudoing?”lookingterrifiedandvisiblysweatingandshaking
andIwasabsolutelycertainsomethingwasverywrongatthispointandbeforeIcouldturntothe
cashierandaskhertokeepholdofthedocuments&cashandcallsecurityandthepoliceforme(Iwas
planningtowriteitonthepieceofpaperinmyhandtobesubtle),Iheardaloudbeepingsoundfrom
behindthedeskwhichwasthecashmachine,rejectingeverynoteinthepilebecausetheywere
140
counterfeitnotes,£15,000worthofthem. Asyoucanimagine, we had3securityguards ontous in
secondsandpolicearrivedonly2minuteslaterandasmyselfandtheothermalesattherein
handcuffs,thepolicebegantoaskquestionstomeandtheothermalewastakenintoanotherroom
insidethebranch.
FortunatelythisdayIhadmyCSVdumpsofrecenttransactions,aletterfrommyHMRC
communicationsrecentlyaspermyotherpostandalsoabankstatementtoverifytherecent
transactions,pluscopiesoftheemailsIhadexchangedwiththemaleconcernedasIbringthemto
everymeetinginmybagforreferencepurposesifanythingarises. Soonenough,havingwentbackto
theoriginalplacewemetandreviewingCCTVfootageofthewholething,Iwasreleasedbuttheykept
everythinginmybag,allthemoneyofcourseandfrozenmyaccountswhilsttheyinvestigatewhichI
compliedwithvoluntarily.Themalewhopassedthecounterfeitnoteshasbeentakentothepolice
stationandwillbeincourttomorrowandIwasadvisedbytheInspectorhewillprobablybereferredto
thecrowncourtonthematterandisbeingheldincustodyuntilhistrial.
ThebankandpolicewerebothpresentforthisandthebankstronglyrecommendedIbecarefulin
futureandtransactionsthatlargecanberunthroughthebankifneedbeandtheycanbethethird
partytosignitandcheckeverythingoutfor£35,whichwillcompletelycovermefortheAML'sover
£10,000andthebuyerdoesn'tneedtogoonthebankrecordsbutthebankwillverifytheIDisrealfor
me insomebranchestoo.WhilstIwasthereIalsowasgivena10packofpenstochecknoteswithfor
futuredealsandpolicehaveaskedmetoceasetradinguntilthiscaseisresolvedandbepreparedtobe
askedtocometocourttopresenttestimonyifrequired.
AgainIcan'tnameandshametheindividualduetoapolicerequest,butforwhatitisworth,thatisthe
storyandlessonIhavelearnedfromtodayanddespitethemanybigdealsIhavedoneinthepastand
themanyshadycharacters,thisonehasreallyrattledmeup.
https://localbitcoins.com/forums/#!/regional/uk#adangerousnewscammingtr
So,anotherrecommendationifyouaredealingwithcashoftenistogetyourselfsomecurrency
detectionpensandablacklighttocheckthebillsforhiddenlogos.Aquicksearchonlinewillgiveyou
anideaofwhattolookforinthecurrencyyourcountryuses.Hereisonemorestoryaboutcounterfeit
money.
Quote
Ioccasionallytradebitcoinsvialocalbitcoins.com,toensurethatIhaveagoodfeelfortheliquidityof
themarketandtheabilitytoexitatwill.I'veneverhadanyproblemsbefore.
Lastweek,Irespondedtoarequesttobuy$500worthofbitcoin,viaalocalbuyerhereinSan
Francisco.
Nothingunusualaboutthemeet,orthebuyer,otherthanthefactthathewantedtofindacontactfor
regularandhigheramountbuys.Ithinkhewastryingtogetmetoincreasetheamount.
Anyhow,Ihadfunded$500inbitcoins,inescrowwithlocalbitcoins.comandwesatdown todothe
141
trade. He gave me 25 x$20 bills,whichI counted. The billsfeltabitstiff, like brandnewbillsfroman
ATM.Ilookedatthemcarefully(orsoIthought)andtheyseemedreal.Ipocketedthemoneyand
movedon.
Fastforwardthreedayslater,Igooutwithafriend.Justbeforeleavingthehouse,Igrabafew$20s
andputtheminmywallet.AtthefirstbarIpaidforadrink,thebartendercamrunningout5min later
intothebarareatofindme.HeshowedmethebillIhadgivenhim,said"thisisfake,itfellapartwhen
itgotwet".Trueenough,thebillhadnothelduptowaterlikeanormalbill.Ishowedhimtheother
moneyIhadonmeandheconfirmeditwasallfake,exceptforone$20Ihadfrombefore.SoIpaidfor
mydrinkwiththerealmoneyandleft.
Forthosewondering,thebillsareindistinguishablefromreal$20sunlessyouknowexactlywhatto
lookfor.Thesmellandtextureareslightlyoff.Themostimportantclueisthattheiridescent"20"on
thesidethatchangesfromredgreentoblackgreendependingontheangleyoulookatit.Onthefake
billsitdoesnotchangecolor.
Formynextbitcoinsale,IwillbecarryingaUVlightandpenandwillbemorecarefulinscrutinyofthe
bills.Asalways,IwillonlymeetinpublicandIamnever unarmed,butnowIalsohavecounterfeit
detectiongear.
SellerBewareCounterfeitmoneybeingpassedtobitcoinsellersinSanFrancisco
Edit:Iwillbewritinganarticleaboutthisforletstalkbitcoin.comandwillprovidelinkstodetectiontips
andproductstohelpwithdetection.Willalsoprovideamoredetailedstoryandpicturesofthenotes.
Standbyafewdaysforthat...
Edit2:Iwillbereviewingthefollowingproductsagainstthesecounterfeitnotes,inanupcomingarticle
forletstalkbitcoin.com:
Drimarkandsharpiebrandpens
UVlight+magnifyingcombos
Magnetictesters
http://www.reddit.com/r/Bitcoin/comments/1nj88k/i_was_given_counterfeit_20_bills_in_exchange_f
or/
Ifthisisnotenoughtomakeyoufeelabituncomfortable,thenyouneedtoreadthemagain.But
whatyoucandoissimplylearnhowtoinspectbillsforauthenticity.Again,getyourselfahandheld
blacklight,acurrencymarkerandanythingelsethatappliestoyourcountry'scurrencyandyoucan
likelyprotectyourselfagainstthis.Ifthepersonbuyingthe Bitcoinsoffofyouseemsnervous,orlike
they areinahurrytogetaway,thentakegreatercautionwiththisbuyer.Alwaystrytofindbuyers
withgoodfeedback(althoughthisisnotperfect),possiblyaskforIDifyouwouldfeelmore
comfortable,andbringafriendwithyou,butdonotmakeitobviousthatyoubroughtafriendwith

142
you. Gettingscammed, robbedor rippedoffsucks, andyouneedtodowhatever youcantoavoidit
happeningtoyou.
LOCALBITCOINS PART 3 - MORE SCAM STORIES
ThispostismorestoriesaboutpeoplebeingscammedorrobbedonLocalBitcoins.
Quote
AmbysWorld:
justgotrobbedinOklahomaCityEdmond,akidabout20yearsold,brownishblondehair,6fttall,
150160lbs
$950.00
becarefuldoingbitcointrades.Iknowit'stoughtogettrust,somyadviceisstartsmallandafteryou
havegainedtrust,makesurethemoneyisinyourpocketbeforeyoureleasethecoins!!
Iguessitisjustthepricetopaytolearnalesson.
realestone:
canyougivemoredetailswhathappenedexactly?
AmbysWorld:
Wemet,insideacoffeeshop,introducedmyself,askedhimifhehaddonetradesbefore.Hesaidhe
haddoneseveral.Iwantedtomakesurehewasfamiliarwithhowthesiteworkedandthentoseeif
hehadanyquestionsaboutbitcoinsingeneral.Ireleasedthecoins,andwestartedtoshakehandsas
hewashandingmetheenvelope.Hejerkedtheenvelopeoutofmyhandandtookoffrunning.
EverypersonIhavemethasbeenawesomeandexcitedaboutbitcoins.SoIletmyguard
down.Showedupwearingflipflops.Istartedtopursueafterhehadalreadytaken3steps,butthen
realizedIwouldnotbeabletoruninflippersforverylongandstoppedafterabout100yards.
TheworstpartisthatIhadmy14yearolddaughterwithme.Thereisaspecialplaceinhellforpeople
likethis!
https://bitcointalk.org/index.php?topic=288053.0
HereisastoryfromagroupofpeopletryingtotestoutLocalBitcoinsforthefirsttimeandendedup
143
losingtheir Bitcoins due totheir ownignorance. Butthebuyer couldhavedone therightthing, anddid
not.
Quote
Bitcoininhand,wedecidedtotakealookatLocalbitcoinandseehoweasythesystemisforsomeone
whodoesnotknowthelingoanddoesnothavemuchexperiencewithcomputerstosee,whatthe
difficultiescouldbe.
SowefoundabuyerandproceededtodoanexchangeofasmallamountofBitcoins.Everything
lookedgreatatfirstaswesignedup,gotverifiedandthenproceededtotransactwiththetrader.We
sentourBitcoinsandwhereconfrontedwithsomewindowswhichbegantoconfuseourtester,who
mistakenlyconfirmedthetransaction,minutesaftersendingtheBitcoins.Ourtesterwasnotsureif
they neededtoclicktheconfirmationtoadvisethetraderthatthecoinswheresent,sospentsome
timeintheFAQtofindoutwhattodonext.Noinformationwasfoundbyourtester,whothenguessed
thatsincetherewasnomentionofit,thenitmustbeatrivialissueandconfirmedthetransaction
anyway. Whathappenednextworriedouttesterasthetransactionwasmarkedasclosedandtheyhad
senttheBitcoinstothetraderwithoutknowingifthefiatmoneywouldbedepositedintothebank
account.Wewaited24hourstoconfirmacashtransactionintoadesignatedaccountandloand
behold, itsnotthere.
Nextweproceededtocontactthetraderandasofwriting,wehavenotheardfromthem.We
contactedLocalbitcoinsupportandbeganaticket.Shortlyafterwards,wereceivedanemailfrom
Localbitcoinsupportstaffandexplainedthesituationandwheretoldthattheconfirmationdidneedto
bedoneAFTERweconfirmedthefundshadbeenplacedintoourdesignatedaccountbythetrader.
Afterafewemailstothesupportstaff,wedidexplainthatwewheretestingthesystemuseabilityfor
theeverydaymomandpopsituation,becauseifBitcoinistobeusedproperly,itneedstohaveaneasy
(dumbeddown)systemsotheinexperiencedusercanmakeatradewithoutmakingmistakeslikeour
testerdid.
http://mentaso.com/bitcoinnews/item/224localbitcoinsscammedonourfirsttestofthe
system.html
Thisnext oneisanattemptataphishingscam.Aphishingscamiswhensomebodysendsyoutoa
URLthatlooksliketherealURL,butitisactuallysetupsothatwhenyoulogin,itstealsyourlogin
credentialsandtheattackertakesoveryouraccount.Inthiscase,takeovertheLocalBitcoinaccount
andstealtheBitcoin
Quote
Userrequestednearly$2kCADworthofbitcoinsusingmylocalbitcoinsad.
Immediatelyaskedtomovetheconversationtotextmessaging,askedme“howmanycoinsIhavein
there(localbitcoinswallet)”then(aftersomedawdlingandchitchat)askedmeto“checkoutandread
hisotherlocalbitcoinsadfirst”.
144
Includedwas aURLtolocalbitcoinis.comwithan adurllongenoughI knowthis was copy/pastedand
notatypo.
AquickWHOISrevealsadomainbyproxy,butsomegooglefuonthecontacttelephonenumber
registeredtothedomainrevealsthatdomainsrelatedtothisphonenumberhavebeeninvolvedin
otherscams.
http://bitcoinviews.com/scamalertlocalbitcoiniscomscammercontactinglocalbitcoinscomusers/
Luckilyfortheseller,hedidnotfallforthescam.Butanybodynotcarefulenoughcouldfallvictimto
thisscam.Alwaysmakesureyoureadtheurlclosely.
LOCALBITCOINS PART 4 - SELLERS BUSTED FOR MONEY LAUNDERING
Hereisasimplecopyandpastestoryyoushouldbeawareof.
Quote
StateauthoritiesinFloridaonThursdayannouncedcriminalchargestargetingthreemenwhoallegedly
ranillegalbusinessesmovinglargeamountsofcashinandoutoftheBitcoinvirtualcurrency.Experts
saythisislikelythefirstcaseinwhichBitcoinvendorshavebeenprosecutedunderstateantimoney
launderinglaws,andthatprosecutionslikethesecouldshutdownoneofthelastremainingavenues
forpurchasingBitcoinsanonymously.
WorkinginconjunctionwiththeMiamiBeachPoliceDepartmentandtheMiamiDadeStateAttorney’s
office,undercoverofficersandagentsfromtheU.S.SecretService’sMiamiElectronicCrimesTask
Forcecontactedseveralindividualswhowerefacilitatinghighdollartransactionsvialocalbitcoins.com,
asitethathelpsmatchbuyersandsellersofthevirtualcurrencysothattransactionscanbecompleted
facetoface.
Oneofthosecontactedwasalocalbitcoins.comusernicknamed“Michelhack.”Accordingtothisuser’s
profile,Michelhackhasatleast100confirmedtradesinthepastsixmonthsinvolvingmorethan150
Bitcoins(morethan$110,000intoday’svalue),anda99percentpositive“feedback”scoreonthe
marketplace.TheundercoveragentandMichelhackallegedlyarrangedafacetofacemeetingand
exchangedasingleBitcoinfor$1,000,apricethatinvestigatorssayincludedanalmost17percent
conversionfee.
Accordingtocourtdocuments,theagenttoldMichelhackthathewantedtousetheBitcoinsto
purchasestolencreditcardsonline.Afterthattrustbuildingtransaction,Michelhackallegedlyagreed
tohandleamuchlargerdeal:Converting$30,000incashintoBitcoins.
InvestigatorshadlittletroubletyingthatMichelhackidentityto30yearoldMichellAbnerEspinozaof
MiamiBeach.Espinozawasarrestedyesterdaywhenhemetwithundercoverinvestigatorstofinalize
thetransaction.EspinozaischargedwithfelonyviolationsofFlorida’slawagainstunlicensedmoney
transmitters–whichprohibits“currencyorpaymentinstrumentsexceeding$300butlessthan
$20,000inany12monthperiod”—andFlorida’santimoneylaunderingstatutes,whichprohibitthe
145
trade or business incurrencyof more than$10,000.
Policealsoconductedasearchwarrantonhisresidencewithanordertoseizecomputersystemsand
digitalmedia.AlsoarrestedThursdayandchargedwithviolatingbothFloridalawsisPascalReid,29,a
CanadiancitizenwhowaslivinginMiramar,Fla.Allegedlyoperatingasproy33onlocalbitcoins.com,
Reidwasarrestedwhilemeetingwithanundercoveragenttofinalizeadealtosell$30,000worthof
Bitcoins.
DocumentsobtainedfromtheFloridastatecourtsystemshowthatinvestigatorsbelieveReidhad403
BitcoinsinhisonphoneBitcoinwalletalone—whichatthetimewastheequivalentofapproximately
USD$316,000.ThosesamedocumentsshowthattheundercoveragenttoldReidhewantedtousethe
BitcoinstobuycreditcardsstolenintheTargetbreach.
NicholasWeaver,aresearcherattheInternationalComputerScienceInstitute(ICSI)andatthe
UniversityofCalifornia,BerkeleyandkeenfollowerofBitcoinrelatednews,saidheisunawareof
anothercaseinwhichstatelawhasbeenusedagainstaBitcoinvendor.AccordingtoWeaver,the
Floridacaseissignificantbecauselocalbitcoins.comisamongthelastremainingplacesthatAmericans
canusetopurchaseBitcoinsanonymously.
“ThebiggestproblemthatBitcoinfacesisactuallyselfimposed,becauseit’salwayshardtobuy
Bitcoins,”Weaversaid.“ThereasonisthatBitcointransactionsareirreversible,andthereforeany
purchaseofBitcoinsmustbemadewithsomethingirreversible—namelycash.Andthatmeansyou
eitherhavetowaitseveraldaysforthewiretransferorbanktransfertogothrough,orifyouwantto
buythemquicklyyoupaywithcashthroughasitelikelocalbitcoins.com.”
OneverypopularmethodofquicklypurchasingBitcoins—BitInstant—wasshutteredlastyear.Last
month,BitInstantCEOCharlieShremwasarrestedformoneylaundering,followingallegationsthathe
helpedamaninFloridaconvertmorethanamilliondollarsinBitcoinsforuseontheonlinedrug
bazaarSilkRoad.
It’sstillunclearhowthedefendantsEspinozaandReidwereabletoobtainsomanyBitcoinsforsale,
althoughareviewofMichelhack’sprofilesuggestslittlemorethanarbitrage—thatis,buyingBitcoins
for$700apieceandsellingthemforacouplehundreddollarsmore.
ThereisnothingthatlinkseitherdefendanttotheSilkRoadtrade.Butit’snotablethatathird
individualchargedwithmoneylaunderingaspartofthisinvestigation—28yearoldCanadiancitizen
VincenteLoyola—iscurrentlyservinga12monthsentenceataU.S.federaldetentioncenterfor
narcoticstrafficking.
Inanycase,Weaversaidheanticipatesthatmorestateswillsoonseektocrackdownonhighdollar
Bitcoinsellersonlocalbitcoins.com.“I’dexpectmanymorestatecaseslikethisonebecauseitwillact
tostranglethelifebloodoftheonlinedarkmarkets,”suchasSilkRoad,Weaversaid.“Ifyouwanta
significantamountofanonymousBitcoins,rightnowthiscommunityisabouttheonlymechanismstill
available.”
146
NewsoftheFloridaactions comeson theheelsofthearraignmentofRoss Ulbricht— the alleged
onetimeowneroftheSilkRoad.UlbrichtwasscheduledtobearraignedinNewYorktoday.
ThecourtdocumentsinthiscasealsoofferagreatexampleofthetraceabilityofBitcointransactions
—apotentialdangerforboththoseseekinganonymouspaymentsandforlawenforcementofficials
posingascriminalsaspartofanundercoverinvestigation.TheICSI’sWeavernotedthat,byexamining
thetimesandtransactionsinthecriminalcomplaint,itappearsthatthisistheBitcoinwalletassociated
withtheundercoverofficer.
https://krebsonsecurity.com/2014/02/floridatargetshighdollarbitcoinexchangers/
Asyoucansee,thecopsarewatchingLocalBitcoins.LaunderingBitcoinsislikelaunderingrealmoney.
Youneedtohaveawaytojustifywherethemoneycamefrom.Backintheday,theMafiahadsmall
legitimate businessesitwouldrunthatitcouldclaimasanincome,andtheymightfixthenumbersa
bitandsaytheymademoremoneythantheyreallydid.Thiswouldprovideanincometheycoulduse
asareasonforhavingmoney.Ifyouaresomebodywhodoesnotwork,andonlyselldrugsonSilk
Road, andaretryingtocashoutyourcoins,thenIhopeyouhavealegitimatereasonforholdingthat
manyBitcoins,otherwiseyoucouldenduplikethesetwoguys.
HIDING TOR FROM YOUR ISP - PART 1 - BRIDGES AND PLUGGABLE
TRANSPORTS
Thispostisgoingtotalkaboutsomethingthathasbeencommonlydiscussedontheforumsrecently.
HowcanIhidemytorusagefrommyISP?
PeoplearemoreworriedabouthidingtheirtorusagefromtheirISP,thanhidingitfromaVPN.There
seemstobeabackandforthdebateaboutwhetherusingaVPNwillorwillnotprotectyou.Whether
ornottheVPNcanbeconvincedtologyourconnection,andsoforth.Afewofmypreviousposts
regardingLulzSecandtheYardBirdpedophileringshaveshownthatthosewhorelyonVPNstoprotect
themarehistoricallyknowntoendupinjail.Evenourfriendwewererecentlyintroducedto,The
Grugqsays,TOR>VPNisok,butVPN>TOR,gotojail.
InmypreviouspostsaboutVPN>TORandTOR>VPN,Itriedtoremainneutralinthatyoushould
beabletomakeyourowndecisionsabouthowyouwishtoprotectyourself.Butjustremember,atthe
endoftheday,nobodyisgoingtogotojailforyou.Ifyousimplywanttohidethefactthatyouare
usingtorfromyourISP,thenwehaveotheroptionsthanaVPN.Wehavebridges,andseveraldifferent
pluggabletransports.Whatarethese,andhowcanweusetheminTails?
Quote
Whatbridgesareandwhentousethem
WhenusingTorwithTailsinitsdefaultconfiguration,anyonewhocanobservethetrafficofyour
Internetconnection(forexampleyourInternetServiceProviderandperhapsyourgovernmentandlaw
enforcementagencies)canknowthatyouareusingTor.
147
Thismay be anissue if youare inacountrywhere thefollowingapplies:
1.UsingTorisblockedbycensorship:sinceallconnectionstotheInternetareforcedtogothrough
Tor,thiswouldrenderTailsuselessforeverythingexceptforworkingofflineondocuments,etc.
2.UsingTorisdangerousorconsideredsuspicious:inthiscasestartingTailsinitsdefault
configurationmightgetyouintoserioustrouble.
Torbridges,alsocalledTorbridgerelays,arealternativeentrypointstotheTornetworkthatarenotall
listedpublicly.Usingabridgemakesitharder,butnotimpossible,foryourInternetServiceProviderto
knowthatyouareusingTor.
https://tails.boum.org/doc/first_steps/startup_options/bridge_mode/index.en.html
Thefirstthingwearegoingtodoisgetsomebridges.LetusdothisbeforeweconfigureTailstouse
bridges,becauseonceTailsisinbridgemode,wewillnotbeabletoconnecttotorwithoutworking
bridges.Sothefirstthingwewanttodoisvisitthefollowingwebpage.
https://bridges.torproject.org/bridges
Entertheimpossiblydifficultcaptcha,andclick"Iamhuman",andyoushouldgetalistofbridgesthat
looklikethis.Theseareactualbridgespulledfromthetorbridgespage.
Quote
5.20.130.121:900163dd98cd106a95f707efe538e98e7a6f92d28f94
106.186.19.58:443649027f9ea9a8e115787425430460386e14e0ffa
69.125.172.116:44343c3a8e5594d8e62799e96dc137d695ae4bd24b2
ThesebridgesarepubliclyavailableontheTorProjectwebsite,sotheymayornotmaybethebest
choicetouse,buttheyareagoodstart.Anotheroptionistosendanemailto
bridges@bridges.torproject.orgwithamessageinthebodysaying"getbridges"withoutthequotes.
ThiswillonlyworkifsentfromaGmailaccountorYahoo,unfortunately.Ifyouwanttousethis,setup
theemailaccountusingtorandyouwillreceivealistofaround3bridgesshortlythereafter.Savethem
somewhereyoucanusethemthenexttimeyoubootupTails,orwritethemdown.
Ok,sonowwehaveourbridges.HowdoweusebridgesinTails?Thisisanoptionweneedto
activatewhenwebootupTails.Toactivatethebridgemode,wewillbeaddingthebridge bootoption
tothebootmenu.ThebootmenuisthefirstscreentoappearwhenTailsstarts.Itistheblackscreen
thatsaysBootTailsandgivesyoutwooptions.1.Live,2.Live(FailSafe).Whenyouareonthisscreen,
pressTabandalistofbootoptionswillappearintheformoftextatthebottomofthescreen.Toadda
newbootoption,addaSpacethentype"bridge"withoutthequotesandpressenter.Youhavenow
activatedbridgemode.
OnceTailsbootsupcompletely,youwillgetawarningthatyouhaveenteredbridgemodeandnotto
deletethedefaultIPaddressinthere,whichis127.0.0.1:*.Thisisadvicewewillfollow,sojustclickOK
andthesettingswindowfortorwillpopup.Atthispointyouneedtoaddyourbridges.Soyouare
148
goingtotake thethree bridgesyougot,andenterthe IPaddress andtheport. Ifwe were goingtouse
theexampleabovethisiswhatwewouldenter.
Quote
5.20.130.121:9001
106.186.19.58:443
69.125.172.116:443
Foreachbridgeyouadd,typeitintheavailabletextboxwhereitsays"AddABridge"andthenclick
thegreen+buttontoaddthatbridge.Youwillneedtoaddonebridgeatatime.Onceyouarefinished
addingyourbridges,youcanclickOK.Atthispoint,youryellowtoronioniconinthetoprightshould
turngreenshortlyafterandyouwillbeconnectedtothetornetworkusingabridge.Again,sincethese
bridgesarelesslikelytobeknownbyyourISP,theyarelesslikelytoknowthatyouareusingtorwhen
youusebridges.
Youmaywishtolookupyourbridgebeforeyouuseithowever.Maybeyouwanttofindoutwhere
yourbridgeislocated,maybeyouwanttoseewhoishostingthebridge,andyoucandothisbylooking
foraIPlookupserviceonline,bydoingasearchandtypingintheIPaddress.Thethreelistedabove
arelocatedinthefollowinglocations.
Quote
5.20.130.121Country:Lithuania
106.186.19.58:443Country:Japan
69.125.172.116:443Country:NewJersey,UnitedStates
Andwiththat,youcandecidewhichbridgewouldbeabetterchoiceforyoutouse.Isuggest
however,thatyougoandgetnewbridgesanddonotusetheonesIlistedaboveforobviousreasons
thattheyarenowlinkedtoSilkRoadusersbymepostingthemonthisforum.Ishouldnotethatthe
waybridgeshidethefactthatyouareusingtorfromyourISP,isthatyouareconnectedtoanIP
addressthatislikelynotknowntoyourISPtobeaffiliatedwithtorentrynodes.
Whilebridgesareagoodidea,unfortunatelytheymaynotbeenough.AccordingtoJacob
Applebaum,(atordeveloper)bridgetrafficisstillvulnerabletosomethingcalledDPI(deeppacket
inspection)toidentifyinternettrafficflowsbyprotocol,inotherwordstheycantellyouare usingtor
byanalyzingthetraffic.WhiletorusesbridgerelaystogetaroundacensorthatblocksbyIPaddress,
thecensorcanuseDPItorecognize andfiltertortrafficflowsevenwhentheyconnecttounexpected
IPaddresses.ThisislesslikelytobedonebyyourISP,andmorelikelytobedonebytheNSA,orother
oppresivegovernmentslikeinChinaandIran,soyoucanchooseifthisisanissueforyou.
Quote
Lately,censorshavefoundwaystoblockTorevenwhenclientsareusingbridges.Theyusuallydothis
byinstallingboxesinISPsthatpeekatnetworktrafficanddetectTor;whenTorisdetectedtheyblock
thetrafficflow.
TocircumventsuchsophisicatedcensorshipTorintroducedobfuscatedbridges.Thesebridgesuse
specialpluginscalledpluggabletransportswhichobfuscatethetrafficflowofTor,makingitsdetection
149
harder.
https://www.torproject.org/docs/bridges#PluggableTransports
Pluggabletransportsareamorenew,butlesstalkedabouttechnologybeingimplementedbytorto
disguisethefactthatyouareusingtortoyourISPandothercensors.Asmentionedabove,itattempts
totransformyourtortrafficintoinnocentlookingtrafficthatwouldhopefullybeindistinguishablefrom
normalwebbrowsingtraffic.Currentlythemostpopularpluggabletransportsareobfuscatedbridges.
Obfuscationbydefinition,isthehidingoftheintendedmeaningincommunication,making
communicationconfusing,wilfullyambiguous,andhardertointerpret.Obfuscatedbridgesactually
transformthetraffictolooklikerandompacketsofdata.Obfuscatedbridgescurrentlyhave2
protocols.
1.obfs2
2.obfs3
Obfs2(TheTwobfuscator)istalkedaboutatlengthatthefollowingofficialpage.
https://gitweb.torproject.org/pluggabletransports/obfsproxy.git/blob/HEAD:/doc/obfs2/obfs2
protocolspec.txt
Butforthelaymansoutthere,basicallyobfs2usesaprotocolthatdisguisesyourtraffictolooklike
randomdata,whereastorhasamoredistinctstructuretoit.However,itshouldbenotedinthecase
ofobfs2,thatifanattackersniffstheinitialhandshakebetweenyourcomputerandtheobfuscated
bridge,theycouldgettheencryptionkeyusedtodisguiseyourtrafficanduseittodecryptthe
disguisedtrafficwhichwouldrevealitastortraffic.Theywouldnotbeabletodecryptyourtortraffic,
buttheywouldbeabletoseeyouareusingtor.ThisisnotlikelysomethingyourISPwoulddo,butit
maybesomethinglawenforcementortheNSAwoulddo.SoifyouareonlyworriedaboutyourISP,
thenobfs2wouldlikelysuffice.
Obfs3(TheThreebfuscator)istalkedaboutatlengthatthefollowingofficialpage.
https://gitweb.torproject.org/pluggabletransports/obfsproxy.git/blob/HEAD:/doc/obfs3/obfs3
protocolspec.txt
Obfs3usesaverysimilarprotocoltodisguiseyourtrafficasobfs2,howeveritusesamoreadvanced
methodofaninitialhandshakecalledtheDiffieHellmankeyexchange.Theyhoweverfoundsome
vulnerabilitiesintheprotocolandhadtogoastepfurtherandcustomizetheDiffieHellmankey
exchangetomakeitanevenmorerobustmethodofestablishingthatinitialhandshake.Usingobfs3
wouldbeabetterbettodisguiseyourtrafficifyouradversaryistheNSAorotherlawenforcement.
Sohowdoyougettheseobfuscatedbridges?Theyarenotaseasytoget,buttheycanbeobtained
fromtorthroughemail.However,youneedtorequestthosebridgesspecificallytogetthem.Youneed
touseaGmailorYahooaccountandsendanemailtobridges@bridges.torproject.organdenterinthe
bodyoftheemail"transportobfs2"withoutthequotes,andforobfs3,simplyenter"transportobfs3".
150
Pleasenotethatyoucan only sendonerequest totor per email, every3 hours.Whichone youshould
use,isentirelyyourchoice,Iamjustgivingyoutheinformationnecessarytomakeaninformedchoice.
EntertheminthisformatsothatTailsknowswhichprotocoltouse.
obfs383.212.101.2:42782
obfs270.182.182.109:54542
toralsoprovidesafewobfuscatedbridgesontheirhomepagewhichyoucanuseaswell,andIwill
listthembelow.Ifyousendarequesttotorandgetaresponsecontainingbridgeswithoutobfs2or
obsf3atthebeginningofthelines,thenthesearenormalbridges,notobfuscated,andtheyarelikely
tobeoutofobfuscatedbridgesatthemoment.Youwillhavetotryagainanotherday.Soifyougeta
responsewithbridgesthatarewithoutobfs2or3atthebeginningofeachline,pleaseagain,beaware
thesearenormalbridges,unliketheonesbelow.
obfs383.212.101.2:42782
obfs383.212.101.2:443
obfs3169.229.59.74:31493
obfs3169.229.59.75:46328
obfs3209.141.36.236:45496
obfs3208.79.90.242:35658
obfs3109.105.109.163:38980
obfs3109.105.109.163:47779
obfs283.212.100.216:47870
obfs283.212.96.182:46602
obfs270.182.182.109:54542
obfs2128.31.0.34:1051
obfs283.212.101.2:45235
Ihaveafeelingthatsomeofyoureadingthiswillbeinclinedtogooutandgetyourselfsomeobfs3
bridgesrightaway,becauseyouthinktheyarethebestchoiceoutthereforstayinganonymous.And
rightnowtheyhavethepotentialofbeingwhatyouhopeforinthatregard,exceptforonehugeflaw.
Thenumberofobfs3bridgesissmall.LastreportIreadputitataround40bridgesrunningobfs3,and
obfs2wasaround200.Sowhileobfs3isthemostsecureoptionoutthere,itslimitednumberof
availablebridgeswouldpoolyouintoasmallergroupofpeoplemakingconnectionstothe40available
bridgesandmaynotprovideanymoreanonymityforyou.torisindepserateneedofmoreobfs2and
obfs3bridgesatthistimeandthesefactorsshouldbetakenintoaccountwhenusingobfuscated
bridges.
Oneofthesolutionstothisshortageproblem,istorunyourownobfuscatedbridge.Iamnotgoing
togointoit,butifyouareinterestedindoingthis,youshouldvisitthefollowingpagetosetupan
obfuscatedproxy,orbetteryet,purchaseafewVPSandsetthemupasobfs2orobfs3proxies.Oneof
thebestthingsaboutdoingitthisway,isthatyoucanconfigureit(withtheinstructionsprovided)to
beaprivateobfuscatedbridge,andthereforetorwillnotgiveitouttothepublic.Youcanthen
connecttoyourownprivateobfs3bridge.Youcanalsouseafriend'scomputer,oruseaserverthat
youknowissecure.Butagain,makesurethatyoutrustthecomputeryouareusing,otherwiseitisno

151
more secure thanaVPN.
Anotherpossiblesolutiontothelackofobfuscatedbridgesmaybeanotherpluggabletransport
option,somethingcalledaflashproxy.Thisisbrandnewandnotperfectlyimplementedyet,and
pleasebeawarethatthisisbasicallystillinbeta.Whenthinkingaboutaflashproxy,thinkaboutthe
characteristicsofaflash,quickandshortlived.Thisprotocolwasdevelopedbyatordeveloperwho
attendedStanfordUniversity,andtheideaisthattheIPaddressesusedarechangedfasterthana
censoringagencycandetect,track,andblockthem.Thismethodissimilartousingnormalbridges,in
that,ithidesthefactyouareconnectingtoIPaddressesknowntoberelatedtotor,includingwhenthe
bridge'sIPaddresseslistedbytorarediscoveredbyyourISPorlawenforcement.Thisdoesnot
however,hidethefactyouareusingtorifsomebodyisanalyzingyourtrafficusingDPI(deeppacket
inspection).
Themainbenefittothisoptionisthattheproxiesarerunbymanypeopleallovertheworld.Theyare
runwhenrandominternetusersvisitawebpagewithaspecificpluginthatturnstheirbrowserintoa
proxyaslongastheyareonthatpage.Youarebasicallyusingsomebodyelse'sconnectionthrough
theirbrowsertoconnecttoatorrelay.Youareonlyusing1activeconnectionatanytime,butyou
havearound5establishedconnectionstodifferentproxiesincaseyouractiveconnectiondropsoff,
thenyoucanstartusinganotherproxyinitsplace.Belowisanotherexplanationofhowthisprocess
works.
Quote
InadditiontotheTorclientandrelay,weprovidethreenewpieces.TheTorclientcontactsthe
facilitatortoadvertisethatitneedsaconnection(proxy).Thefacilitatorisresponsibleforkeepingtrack
ofclientsandproxies,andassigningonetoanother.Theflashproxypollsthefacilitatorforclient
registrations,thenbeginsaconnectiontotheclientwhenitgetsone.Thetransportpluginsonthe
clientandrelaybrokertheconnectionbetweenWebSocketsandplainTCP.(Diagrambelow)
https://crypto.stanford.edu/flashproxy/arch.png
Asamplesessionmaygolikethis:
1.TheclientstartsTorandtheclienttransportpluginprogram(flashproxyclient),andsendsa
registrationtothefacilitatorusingasecurerendezvous.Theclienttransportpluginbeginslisteningfor
aremoteconnection.
2.Aflashproxycomesonlineandpollsthefacilitator.
3.Thefacilitatorreturnsaclientregistration,informingtheflashproxywheretoconnect.
4.Theproxymakesanoutgoingconnectiontotheclient,whichisreceivedbytheclient'stransport
plugin.
5.TheproxymakesanoutgoingconnectiontothetransportpluginontheTorrelay.Theproxy
beginssendingandreceivingdatabetweentheclientandrelay.
Inotherwords,youendupgoingfromyourcomputer,totheproxy,thentheproxytothetorrelay.JR
Thewholereasonthisisnecessaryisbecausetheclientcannotcommunicatedirectlywiththerelay.
(PerhapsthecensorhasenumeratedalltherelaysandblockedthembyIPaddress.)Intheabove
diagram,therearetwoarrowsthatcrossthecensorboundary;hereiswhywethinktheyarejustified.

152
The initial connectionfromthe clienttothefacilitator (theclientregistration)isaverylowbandwidth,
writeonlycommunicationthatideallymayhappenonlyonceduringasession.A careful,slow,
specializedrendezvousprotocolcanprovidethisinitialcommunication.Theconnectionfromtheflash
proxytotheclientisfromanIPaddressthecensorhasneverseenbefore.Ifitisblockedwithinafew
minutes,that'sfine;itwasn'texpectedtorunforeveranyway,andthereareotherproxieslinedupand
waitingtoprovideservice.
Iknowthismightbeabitcomplicated,butyoureallydonotneedtounderstandhowitworksto
benefitfromit.Youalsomightbeaskingaboutsomebodyjustblockingyourabilitytoconnectwiththe
facilitator(thesupplieroftheproxies).But,thewayyouactuallyconnecttothefacilitatorisinavery
specialwaythattorhasdesigned,andthisisbuiltintotheflashproxypluggabletransport.This
explanationisjustforyourcomfort,nottohelpyoumakeitwork.
Quote
Thewaytheclientregisterswiththefacilitator,isaspecialrendezvousstepthatdoesnot
communicatedirectlywiththefacilitator,designedtobecovertandveryhardtoblock.Thewaythis
worksinpracticeisthattheflashproxyclienttransportpluginmakesaTLS(HTTPS)connectionto
Gmail,andsendsanencryptedemailfromananonymousaddress(nobody@localhost)toaspecial
facilitatorregistrationaddress.Thefacilitatorchecksthismailboxperiodically,decryptsthemessages,
andinsertstheregistrationstheycontain.TheresultisthatanyonewhocansendemailtoaGmail
addresscandorendezvous,evenifthefacilitatorisblocked.
https://trac.torproject.org/projects/tor/wiki/FlashProxyFAQ
Twoquestionsyoushouldbeasking.1)CanItrusttheproxies,and/orfacilitator?2)HowdoIuse
this?
Well,thefacilitatorischosenandcurrentlyonlyrunbytor,soyoucantakethatatfacevalue.Asfar
astheproxiesgo,theproxiesthemselvesmayormaynotbetrustworthy,andthisistheriskyourun
everytimeyouusetor.Yourbridgesthatyouusemaybecompromised,yourentrynodes,yourexit
nodes,everysinglepossiblehopalongyourwaytotheinternetcanbecompromisedatanygiventime.
Luckily,eveniftheproxyiscompromisedandloggingyourtraffic,theyareonlygoingtobeabletosee
encryptedtortraffic.AndasImentionedabove,anybodywhovisitsawebpagewithaspecificplugin
onit,becomesaflashproxyaslongastheyareonthatsite.Thismeans,somepeoplewillbeaflash
proxywithouttheirknowledge,andotherswillbeflashproxiesbecausetheywanttobeone.Theidea
behindthisistohavemultipleusers,tensofthousands,ifnothundredsofthousandsofflashproxies
availableatalltimestoincreasethenumberofpossibleIPaddressesyourotatebetweentokeepyour
ISPandpossiblytheNSAguessing.
Sodoyouusethis?ItactuallycurrentlyisnotsupportedinTails.ButitcanbeusedwithTorPluggable
TransportsTorBrowserBundleoutsideofTails.Youcangetitatthefollowingpageanditwillrunon
yournormaloperatingsystem,whetheritisWindows,MAC,orLinux.Getthepackageatthefollowing
page.
https://www.torproject.org/docs/pluggabletransports.html.en#download

153
Nextfollowthefollowingtutorial,whichisprettystraightforwardandhaspicturesofexactlywhat
youneedtodo,andwillprobablydoabetterjobthanIwouldatexplaininghowtosetitup.
https://trac.torproject.org/projects/tor/wiki/FlashProxyHowto
Essentiallyitcomesdownto,enableportforwardingforport9000,add"bridgeflashproxy0.0.1.0:1"
withoutthequotes,toyourtorrc,andleaveeverythingelsealoneunlessyouneedtouseadifferent
port,whichisunlikely.Youmayneedtomakeanexceptioninyourfirewallfortheflashproxypluginifit
asksyou.AslongasyouareusingtheTorPluggableTransportsTorBrowserBundle,itshouldbepretty
easytogetthisfeatureworking.ButuntilTailsaddssupportforit,thisistheonlyoptionyouhaveif
youwanttouseflashproxybridges.
Ok,soyouhavealotofinformationrightnowandmaybeareleftabitconfused,butreadoverthis
one afewtimesandtrytoextractasmuchoutofitaspossibleatonce.Trysettingupnormalbridges,
thentrydoingtheobfuscatedbridges,andonceyougetthoseworking,thenmaybeconsiderdoingthe
flashproxiesifyouareokaywithoutusingTails.Tailswilllikelyimplementsupportforthislater.Ask
yourselfsomequestions,doIjustwanttohidethefactthatIamusingtorfrommyISP?OramIhiding
fromsomebodymuchbiggerthanthat?
Considerwhetheritisplausibleforyoutorunaprivateobfuscatedproxy,orevenaprivatebridge.
Hopefullynowyouhaveenoughinformationtomakeaninformeddecision.
Currentlythereareotherpluggabletransportscurrentlyunderdeveloped,butnotyetdeployed.Here
isalistofupcomingprojects.
Quote
ScrambleSuitisapluggabletransportthatprotectsagainstfollowupprobingattacksandisalsocapable
ofchangingitsnetworkfingerprint(packetlengthdistribution,interarrivaltimes,etc.).It'spartofthe
Obfsproxyframework.Seeitsofficialpage.MaintainedbyPhilippWinter.
http://www.cs.kau.se/philwint/scramblesuit/
Status:Undeployed
StegoTorusisanObfsproxyforkthatextendsittoa)splitTorstreamsacrossmultipleconnectionsto
avoidpacketsizesignatures,andb)embedthetrafficflowsintracesthatlooklikehtml,javascript,or
pdf.Seeitsgitrepository.MaintainedbyZackWeinberg.
https://gitweb.torproject.org/stegotorus.git
Status:Undeployed
SkypeMorphtransformsTortrafficflowssotheylooklikeSkypeVideo.Seeitssourcecodeanddesign
paper.MaintainedbyIanGoldberg.
http://crysp.uwaterloo.ca/software/SkypeMorph0.5.1.tar.gz
http://cacr.uwaterloo.ca/techreports/2012/cacr201208.pdf
Status:Undeployed
Dustaimstoprovideapacketbased(ratherthanconnectionbased)DPIresistantprotocol.Seeitsgit

154
repository. MaintainedbyBrandonWiley.
https://github.com/blanu/Dust
Status:Undeployed
FormatTransformingEncryption(FTE)transformsTortraffictoarbitraryformatsusingtheirlanguage
descriptions.Seetheresearchpaperandwebpage.
https://eprint.iacr.org/2012/494
https://kpdyer.com/fte/
Status:Undeployed
Alsoseetheunofficialpluggabletransportswikipageformorepluggabletransportinformation.
https://trac.torproject.org/projects/tor/wiki/doc/PluggableTransports
Source:https://www.torproject.org/docs/pluggabletransports.html.en
CAPABILITIES OF THE NSA
Iwantedtosharea1hourvideobyoneofthetordevelopersJacobApplebaum.
Hetalksaboutlegitmate,confirmedcapabilitiesoftheNSAfromFOIAleakeddocumentsshowingjust
howtechnicallycapabletheNSAis.Anywherefromsimplebackdoors,flyingadroneovertopofyour
housetosniffpackets,moldinjectingbackdoorchipsintoyourcomputercase,tobeamingenergyinto
yourhouse.Noneofthisisconspiracytheory,itisallconfirmedwithdocumentsshowninhis
presentation.
ThevideocanbewatchedonYouTubeusingHTML5embeddedinsteadofflashatthefollowingpage.
https://www.youtube.com/embed/vILAlhwUgIU
IalsouploadeditonAnonFiles.comincaseyouwouldprefertodownloaditandwatchitinTails.
https://anonfiles.com/file/eb07bbcc15ae5aeba1e1322d2995fdde
TheSHA1checksumis801fa9c2b3f2dfe120f93e6ffa6e6a666e5aa12a
TheMD5checksumiseb07bbcc15ae5aeba1e1322d2995fdde
ForthoseofyouusingTails,justuseplacethisfileinyourtmpfolder[Places>FileSystem>tmp]
Openaterminal(blackrectangeicon)andtypethefollowingcommands.
cd/tmp
md5sum1391628603972.zip

155
sha1sum1391628603972.zip
Andcheckthattheoutputtedstringmatches.
WHY YOU SHOULD ALWAYS BACK UP YOUR DRIVES, ESPECIALLY
ENCRYPTED DRIVES
Thisisanembarrassingstoryofsomethingthathappenedtomeinthepastfewdays,anditwasa
lessonwelllearned,forsomeofthethingsIhavelostarenotrecoverable.JollyRoger
DoyouhaveyourBitcoinwalletssavedonaflashdrive?Whatwouldhappenifyoulostyourflash
drive?Doyouhaveabackup?Whatwouldhappenifyourfilesbecamecorruptedandwerenotableto
berecovered,couldyoulivewiththat?Doyouhavecertainthingsthatwouldabsolutelycauseahuge
problemifyoulostthem?Thenyoubetterstartbackingupyourdrivesregularly,betteryet,doitdaily!
Iamthetypeofpersonwhousuallybacksuphisfilesregularly,butunfortunatelydotothelarge
amountofstrangeeventsoccuringonlinelatelywithUtopiabeingbroughtdown,BMRforumsbeing
seized,SilkRoadbeingrobbedandsoforth,Ihadnotbackedupmyfilesinabout2weeks.Ihadallof
mymostrecentfiles,includingafewnewBitcoinwalletswithbalancesonthemonmymainportable
drive,andontopofit,thisdrivewasencrypted.
Then,withoutwarning,Isuddenlyreceivedanerrorthatthefilesystemwascorruptedandmydisk
couldnotberead.Nomatter,ifyouhaveanunencrypteddrive,youcansimplyrunadatarecovery
programsuchastestdisk.Openupyourterminalandtypethefollowing.MakesureyoustartedTails
withaloginatthebootupwhenitasksyou.
sudoaptgetinstalltestdisk
Usingthisprogram(followdocumentationonline)youcanlikelyrecovermostofyourfilesbecauseit
ignoresfilesystemheadersandothertypesoffileorganizationrequiredtoidentifythewaythefiles
arestored.Therearemanyotherprogramsaswell.Theprobleminmycase,wasthatallmyfileswere
encrypted.Thismeans,thatinordertodecryptthefiles,Ineededakeyfilethatisstoredonthedrive
tounlockmyfiles.Ifthiskeyfilegetsdamaged,thenevenifyouhavethepasswordforyourfiles,you
willnotberecoveringyourfiles.
Thekeyisuniquetothatparticularinstancewhenyouencryptedthedrive.MeaningthatevenifI
triedtorecreatethekeyfilewiththesamepassword,theresultwouldbeadifferentkeyfile.This
meansessentiallythatmydataisunrecoverable,becausemykeyfilewassomehowcorrupted.
Technologyisdelicate,dataisstoredintheformofmagneticfrequenciesandthereisnoguarantee
thatfileswillnotbecomecorruptedonedayforseeminglynoreason.Herearesomethingsthatcould
ruinyourdata.
Flood,hurricane,powersurge,fire,moisturedamage,accidentallysteppingonyourdrive,afamily
member(usuallyachild)breaksit,youloseit,spillwateronit,overheats,andsoforth.

156
Allofthese couldresult inyour dataor drive gettingdamagedandlosingallofyour data. Thisiswhy
youneedaminimumof2backups.Not1,but2.Andhaveoneofyourbackupspreferrablystored
outsideofyourhome.Ifyouwork,storeoneatwork,orinyourcar,orsomewhereyoucanaccess
regularly,andtrytobackupyourdataasoftenaspossible.Ifyourhouseburnsdownandyoukeptall
yourbackupsathome,thenyouloseeverything.Ifyoukeptacopyatwork,thenyoucanrecoverit.
Themorebackupsthebetter,aslongastheyareencrpypted.Anytimeyoucreateanewwalletand
transferBitcoinintoit,backitup.Anytimeyousetupanewaccountoranewemailwithaunique
password(whichshouldbeeverytime),backitup.Youneedtobebackingupeverything.
Luckilyformyselfmymainwalletwasrecoverablewiththemajorityofmycoins,butIdidlosesome
coins,whichcanneverberecovered,trustme,Itried.GettingextraUSBdrivesorSDcardsarevery
cheapandinexpensive,soyouoweittoyourselftospendafewextradollarstohavemultiplebackups
justincaseyouwindupinmysituationwhereyouhadnotbackedupyourdriveinacoupleofweeks
andenduplosingdatathatcouldcostyoualotmorethanwhatitwouldhavecostedtohaveafew
extradriveslayingaroundasbackups.
BITCOIN CLIENTS IN TAILS - BLOCKCHAIN AND ELECTRUM
Note:as ofnow,electrumisincludedinTAILS,noneedtosetupanything.Thisisobsoleteandinsecure
asthedownload isnotcheckedIdidcopyitanywayforyourinformationbutyou'dratherusethe
electrumclientthatcomeswithTAILS.
InthispostIwanttotalkabout2optionsfortradingyourBitcoins.
#1Blockchain
#2Electrum
Bynow,hopefullyyouknowhowtouseBlockChain.Ifnot,yousimplygotohttp://blockchain.info
andpressthebutton"Wallet"andyoucanopenupyourexistingwalletorcreateanewaccount.Very
straightforwardandcanbedoneallfromyourwebbrowser.
ButwhataboutElectrum?ElectrumisaneasytouseBitcoinclient.Itprotectsyoufromlosingcoins
inabackupmistakeorcomputerfailure,becauseyourwalletcanberecoveredfromasecretphrase
thatyoucanwriteonpaperorlearnbyheart.Thereisnowaitingtimewhenyoustarttheclient,
becauseitdoesnotdownloadtheBitcoinblockchain.IfyouusethenormalBitcoinclientfrom
https://bitcoin.orgthenyouwouldneedtodownloadtheentireblockchain,whichisseveralGBof
data. InTails,wearetryingnottodownloadtoomuchtoourcomputers.Downloadingtheentire
BlockChaincantakeover24hours.
SohowdowesetupElectruminTails?Firstthingweneedtodoisdownloadit.
https://download.electrum.org/Electrum1.9.7.tar.gz
Nowextractit(rightclick>Extracthere)andrenamethefoldertoelectrumtomakethingseasier.

157
(Right click > Rename). Youmightalsowant tomove thefolder tothetmp directorysoitiseasier to
find.(Places>Computer>FileSystem>tmp)
Nextopenupaterminalandtypethefollowingcommand
cd/tmp/electrum
Youcanreplace/tmp/electrumwithwhateverdirectoryelectrumiscurrentlyin,butthisiswhywe
putitintmp,tomakethingseasierforus. Nexttypethefollowingcommand.
./electrums56ckl5obj37gypcu.onion:50001:tpsocks5:localhost:9050
ThiswillallowyourelectrumtoconnectthroughTor,tomakesureitdoesnotconnectoverclearnet.
Youwillgetawarningwhenyoudothisthatelectrumisattemptingtoconnectinanunsafemanner,
butthisisexpected,anddonotworry,itissafetodothis.ThisstepwasrecommendedontheTails
webpageatthefollowingURL.
https://tails.boum.org/forum/Report:_the_electrum_bitcoin_client_in_tails/
SinceyouarelikelygoingtowanttoreuseyourwalletthatisgeneratedinElectrum,youcanspecify
whereyourwalletiskeptbyreplacingtheabovecommandwiththefollowingcommand.
./electrums56ckl5obj37gypcu.onion:50001:tpsocks5:localhost:9050w/tmp/electrum.dat
Youwouldreplace/tmp/electrum.datwithwhateverthepathtoyourwalletis,andyoucanrename
electrum.dattowhateveryouwanttocallyourwallet,likesrwallet.datorwhateveryouwant.Orleave
itthewaythatitis.Theneachtimeyouwanttostartupelectrum,reusethesamecommand,and
makesureyoucopyelectrum.datinto/tmporwhateverdirectoryyouwishtouse.Thenwhenyouare
finished,makesuretobackupelectrum.datontoyourUSBdriveorSDcard,especiallyifyoudonot
haveTailspersistence.Thiswayyoucanreusethesamewalletandyouwillnotloseyourbalance.
ElectrumislikelygoingtobetheBitcoinclientofchoiceforTailsusers.Andyoucanreadmoreabout
howtouseElectrumbyvisitingthehomepageatthefollowinglink.
https://electrum.org
YET ANOTHER EXAMPLE OF HOW STRONG CRYPTOPGRAPHY AND
PROPER OPSEC CAN PROTECT EVEN PEDOPHILES
Yes,youreadthetitlecorrectly.Usingthesametypesoftechniquestaughtinthisthread,youcanand
shouldremainanonymousnomatterwhatyouaredoing.
Pedophilesandchildpornographersaresomeofthemostwantedpeopleontheplanet.Theyareup
therewithterroristsandserialkillers.Theyarehuntedbyfederallawenforcementagencies,and
punishedveryseriously,astheyshould.Sothereasonforthispostistodemonstrate,thatifsomebody
158
whoisas wantedas muchaspedophilesandchild pornographerscanremainfree byusingproper
OpSec,thenyoucantoo.
Quote
Ifyoursecurecommunicationsplatformisn’tbeingusedbyterroristsandpedophiles,you’reprobably
doingitwrong.
http://grugq.github.io/blog/2013/12/01/yardbirdseffectiveusenettradecraft/
Iwanttotalktoyouaboutagroupofchildpornographersthatoperatedforseveralyearsonline,
calledYardBird.Duringaperiodof15months,therewerearound400,000imagesand11,000videos
uploadedtoacentralserverrunbythegroupandsharedbythemembers.Thereasonweknowthat,is
becauseduringthat15months,theFBIperformedanundercoveroperationtoinfiltratethegroupin
hopesofapprehendingthemembers.Theysuccessfullyapprehended1in3membersofthegroup.
Oneofthosewhoremainfreetodate,wastheleaderofthegroup,whoalsowentbytheonlinename
YardBird.
HowisitpossiblethataftersomucheffortwasputinbytheAmericanFederalBureauof
Investigation(FBI),theAustralianFederalPolice(AFP)andtheAustralianQueenslandPoliceService,
thatpeoplehighuponthewantedlistswereabletoevadecapture.Theyusedstrongcryptography,
andproperOpSecrules.Letusnowtalkaboutthehistoryoftheattemptedapprehensionofthisgroup.
AccordingtotheFBI.
Quote
Therewereapproximately60membersthatwerelooselyidentified,andfromthe60,approximately20
werepositivelyidentifiedinthisgroup.
TherewerenumerouschallengespresentedduringOperationAchilles.Thegrouputilizedan
unprecedentedleveloforganizationandsophistication.Theyhadatimedtestforprospectivenew
members.TheyhadtouseencryptiontechnologyandInternetbasedanonymizers,remailingservices.
Theyalsointentionallycorruptedtheirownchildpornographyfilesandonlythenewmembersknew
howtoreconfigurethosefilestobeabletoreadthepicturesorthevideo.Theyalsohadtheuncanny
abilitytomonitorworldwidenewspertainingtolawenforcementeffortsinchildpornographymatters
inordertobettereducatethemselvestoavoidlawenforcementdetection.
https://www.fbi.gov/news/podcasts/inside/operationachilles.mp3/view
AsIsaidearlier,theallegedleaderofthisringusedtheonlinename"Yardbird".Yardbirdmadeare
appearanceonUsenetinboth2009and2010onthedatecorrespondingtothefirstandsecond
anniversariesofthebustsin2008.Hisintentwastoshowthathewasstillfree,andtoanswerpeople's
questions.
OneofthemostimportantthingsYardbirdstatedwerethateveryoneinthegroupwhousedTorand
remailersremainedfree,whilethosewhoreliedonservicessuchasPrivacy.LIwerearrestedand
159
convicted. Privacy.liis anoffshore VPN service thatpromisesanonymity. Theyclaimfromtheir website
thefollowing.
Quote
Ifyouneedcorporateand/ormilitarystrengthencryptednetworks,thenaVirtualPrivateNetworkis
thewaytogo.Allandanytrafficfromandtoyourdesktoparewithinanencryptedtunnel,andyour
originatingIPaddressiswellconcealed.
http://www.privacy.li/services.html
Andtheirprivacypolicymakesthefollowingpromise.
Quote
Yes,we101%honoryourprivacy,nologs,nosnooping,noprofiling.Nolegalmumbojumboto
disguiseanyhiddenefforts.Webelieveinindividualismandprivacy,evenanonymity.
http://www.privacy.li/privacypolicy.html
Yardbirdfurthercommentedthatseveralmembersofthegroup,includinghissecondincommand
ChristopherStubbings(Helen)andGaryLakey(Eggplant)werePrivacy.LIusersinfacthestatedthat
they useditforeverything.(Heleniscurrentlyservinga25yearsentenceintheUK,whileEggplantis
servinglifeinanArizonaprison.)
EggplantliterallybecamenotoriousbecauseofhisconstantpromotionofPrivacy.LIhecontinually
boastedthathecouldnotbecaughtbecausePrivacy.LIdidnotkeeplogs,andtheywerelocated
outsideofU.S.jurisdiction.
Quote
IpointedouttoanyonewhowouldlistenthatservicessuchasPrivacy.LI
werefor/privacy/notforanonymity.Inanidealsituation,oneneeds
bothtobeprivateaswellasanonymous.Essentially,whatPrivacy.LI
suppliedwasatypeofVPNservice,providinganencryptedtunnelfordata
totravelbetweentwoendpointsthecustomer'scomputerbeingoneendpoint,whilethePrivacy.LI
serversprovidedtheother.Whiletherewasadegreeofprivacy,therewasNOanonymityatallsoit
reallydidn'tcomeasasurprisethatPrivacy.LI'scustomerswereamongthosearrested.
http://dee.su/uploads/baal.html
Attheendoftheday,noserviceproviderisgoingtogotojailforyou.Asimplecourtordercanget
eventhetoughestVPNproviderstorolloverontheirusers,becausetheywouldratherbetraya$20
permonthuserthanbefined,shutdownandpossiblythrowninjailforinterferingwithafederal
investigation.
Whatothermistakesweremadetoleadtothearrestofsomemembersofthisgroup?TheAustralian
policearrestedamanontotallyunrelatedchildpornographycharges,andpresumablyaspartofaplea
deal,herevealedtheexistenceof'thegroup'andhandedoveraPGPpublic/privatekeypairand
160
password. Havingacquiredfromthe informer thecurrentgroupPGPpublic/private keypair, andits
passphrasemeantthatthepolicecouldassumethisgroupmember'sidentity,andfurthermore,read
alltheencryptedtrafficpostedbymembersofthegroup.
Quote
Oncethegroupwaspenetrated,thepolicewereabletotakeadvantageofa
fewfactors:
1)Theyhadtheinformant'scomputer,withallitsemail,PGPkeysandthe
like.Thisprovidedahistory,whichmadeiteasiertocontinuethe
impersonation.
2)Bythetimeitwaspenetrated,thegrouphadbeenoperatingforabout5
years.Bythistime,thegrouphadjelledintoacommunitypeoplewere
familiarwitheachother,theyoftenlettheirguardsdown,andwould
sometimesrevealtidbitsofpersonalinformation.Thisisespeciallythe
casewhentheythoughttheirmessagesweresecure,andbeyondtheability
ofthepolicetointercepttheywouldsaythingsthattheywould*never*
sayintheopen.
http://dee.su/uploads/baal.html
Soitisimportanttonoteatthistime,thatyounomatterhowcomfortableyoubecomewith
somebody,thereisalwaysachancethattheycanbecomecompromised.Infact,thegrouphasasetof
rules,thatallmembersweretoldtoabideby,andifanymemberwasfoundtobebreakingthe
followingrules,theywouldbeexpelled.
Quote
Neverrevealtrueidentitytoanothermemberofthegroup
Nevercommunicatewithanothermemberofthegroupoutsidetheusenetchannel
GroupmembershipremainsstrictlywithintheconfinesoftheInternet
Nomembercanpositivelyidentifyanother
Membersdonotrevealpersonallyidentifyinginformation
Primarycommunicationsnewsgroupismigratedregularly
Ifamemberviolatesasecurityrule,e.g.failstoencryptamessage
Periodicallytoreducechanceoflawenforcementdiscovery
Oneachnewsgroupmigration
CreatenewPGPkeypair,unlinkingfrompreviousmessages
Eachmembercreatesanewnickname
NicknamethemeselectedbyYardbird
http://grugq.github.io/blog/2013/12/01/yardbirdseffectiveusenettradecraft/
Theoneswhogotcaught,weretheoneswhodidnotfollowtherulesbyputtingtoomuchtrustintheir
online"friends".WesawthisinthearrestofSabuwhenhehelpedtheFBIbusthis"friends"inLulzSec.
161
Ifsomeone isgivenadealtocut theamountof time spentinprisoninhalf, they likelywilltake thedeal
atyourexpense.Belowisanexampleofapleaversustryingtofightthechargesinthisexactcase.
Quote
...sevenoftheU.S.subjectspleadedguiltypretrialtoa40countindictmentandreceivedfederal
sentencesrangingfrom1330yearsinprison.Theremainingsevendefendantsoptedforajoint,
simultaneoustrial.Allsevenwereconvictedbyajuryandsubsequentlysentencedtolifeinprison.
https://www.fbi.gov/news/podcasts/inside/operationachilles.mp3/view
1330yearsversuslifeinprison,mayenticeevensomeofthehardestcriminals,andifyouthinkyour
online"friend"whoyouhavenevermetinpersonisgoingtokeeptheirmouthshuttokeepyououtof
jail,youareinforabigsurprise.
So,asyoucansee,thegroupwasprettymuchanopenbooktothepolice.Theywerecompletelyand
thoroughlypenetrated.Despitethat,however,themajorityofthegroupwerestillabletoremainat
large,andwereneitherpositivelyidentifiednorarrested.Thisisduetotheprivacytools(pgp,tor,
nymservers,remailers)thatwereemployed.Evenwitheverythingelsebeinganopenbook,thoseusing
thesetoolsstillmanagedtoevadecapture.Butyoumaybesaying,Ok,IunderstandPGP,Iunderstand
tor,butwhattheheckisanymserverandaremailer?
Inanutshell,ananonymousremailerisaserverthatreceivesmessages(inthiscaseanemail)with
embeddedinstructionsonwheretosendthemnext,andthatforwardsthemwithoutrevealingwhere
they originallycamefrom.Anymserveralsoreferredtoasapseudonymousremailerassigns itsusersa
username,anditkeepsadatabaseofinstructionsonhowtoreturnmessagestotherealuser.These
instructionsusuallyinvolvetheanonymousremailernetworkitself,thusprotectingthetrueidentityof
theuser.
Someoftheadvantagesofusingtheseservicesaretoprotecttheintendedrecipientfroman
adversary,andalsoprotectthesenderofthemessage.Someoftheseservicesusewhatiscalleda
commonmailbox,inwhichallmessagesarestoredinacentralmailboxwithno"ToandFrom"
headers.ItisuptotheuserswhousetheservicetoattempttousetheirPGPkeystotryanddecryptall
ofthemessagesstoredinthecentralmessageboxandseeiftheycandecryptanyofthem.Iftheycan,
thismessageisintendedforthem.Thiswayitrulesoutagain,thesenderandreceiver.Thissystemof
remailers,canalsoformachain,inwhichthemessageisbouncedoffofmultipleremailersbefore
makingittoitsintendedreicipienttowidenthegapbetweenthesenderandreceiver.
Anothereffectiveoptionsomeservicesofferistheabilitytodelaywhenthemessagegetssentonto
thenextserverinthechain,ortherecipientitself.IfyouarefoundtobesendingoutPGPencrypted
trafficthroughsometypeofanalysisat5:00PM,andanotherpersonbeingmonitoredreceivesitat
5:01PM,itiseasiertocorrelatethatthismessagemaybefromyoutotheotherpersonbeing
monitored.AtthistimeIhavenorecommendationsforservicetouse,butIamlikelytopostabout
theminthefuture.Inthemeantime,letusgetbacktotheringofpedophilesshallwe?
Quote
162
Leavingaside mypersonalfeelingsaboutpedophiles,Ibroughtupthis case
asanexampleforseveralreasons:
1)Childpornographyisaseriouscrimeinvirtuallyeveryjurisdiction.
Asthisexampledemonstrates,policewillworktogether,evenacross
nationalboundaries,toinvestigatethesecrimes.Theyarewilling
toinvestconsiderabletime,manpowerandmoneyinpursuitofthese
suspects.Theonlyothercrimeswhichusuallymeritthistypeof
approacharedrug/gunrunningorterrorism.Thelevelofeffort
expendedinpursuingthisgroupcanbeseeninthatevenFBI
executiveassistantdirectorJ.StephenTidwellwasinvolved.
NormallyonewouldnotexpectFBIpersonnelthathighlyplaced
tobeinvolvedthisshowsthelevelofimportance placedon
thisparticularinvestigation.(Ayearorsoafterthebusts,
YardbirdhimselfexpressedastonishmentthattheFBIwould
considerhisgroupsuchapriority.)
2)ThiscaseistheonlyonethatI'mawareof,wheresuspectswere
usingsophisticatedtoolslikePGP,Tor,anonymousremailersand
nymservers.
3)Thiscaseunderscorestheeffectivenessofthesetoolsevenagainst
wellfunded,powerfulopponentsliketheFBI,Europol,andInterpol.
(N.B.:FWIW,thosewhowerecaughtusedeitherinappropriateand/or
ineffectivetoolsandtechniquestoprotectthemselves.
4)Ifullyunderstandmostpeople'sdisgustatthetypesofcrimes/
criminalsbeingdiscussedhere.Thatsaid,itisimportantto
rememberthatonesimplycannotdesignasystemthatprovides
protectionforoneclassofpeople,butdeniesitforanother.
Youcan't,forexample,deployasystemthatprovidesprivacy/
anonymityforpoliticaldissidents,orwhistleblowers,andyet
deniesittopedophileseither*everyone*issafe,orNOONE
issafe.Thismaynotbepalatable,butthesearethefacts.
http://dee.su/uploads/baal.html
Tosummarize.Wehaveseenthateventhemosthuntedcriminals,canevadecapturewhenusing
strongcryptographyandproperOpSec.Theringleaderofoneofthemostinvestigatedchild
pornographyringsstillremainsatlargetodaybecausethosewhofollowedtherules.
DENIABILITY, IDENTIFYING TAILS USERS, AND CAN YOU BE FORCED TO
GIVE UP YOUR PASSWORDS?

163
Quote from: OCDPolak
HiJR,
ForsomereasonIhaveseenalotofinformationanddiscussionaboutprivacyandanonymitybut
nothingatallaboutdeniability,whichtobehonestconcernsmethatsomepeoplemaythinkthat
becausetheNSAcan'tcracktheirpassword,everythingissafebutpeopleeasilyoverestimatetheir
abilitytostanduptosanctionsimposedbyacourtshouldtheshithitthefan...
IwaswonderingaboutthedeniabilityproblemswithusingTails(oranyofthesecuritymeasures
really).Youhavetoassumethatifyougetarrestedanditgoestocourt,youwillbecompelledtogive
anyofyourpasswordsthattheywant.It'sallwellandgoodthinkingthatyouwon'tgiveittothem,but
whentheysentenceyoutoa$1000adayorsimplyjailuntilyoutellthemyouwillprobablytellthem
yourpasswords...
Withthatinmind,isthereanydeniablewaytouseTails(oratleastdeniableinsomerespects)?Iused
toruneverythingoffahiddenvolumeinaTruecryptmemorystick(whichissupposedtobeimpossible
toproveexists),isthereanequivalentwithLUKS?
Also,canyourISPorFBIdifferentiatebetweenTorandTailsthroughyourinternetusage?
Thanksforyourtime
Herearesomethingstoconsider.
Quote
TailsmakesitclearthatyouareusingTorandprobablyTails
YourInternetServiceProvider(ISP)oryourlocalnetworkadministratorcanseethatyou'reconnecting
toaTorrelay,andnotanormalwebserverforexample.UsingTorbridgesincertainconditionscan
helpyouhidethefactthatyouareusingTor.
ThedestinationserverthatyouarecontactingthroughTorcanknowwhetheryourcommunication
comesoutfromaTorexitnodebyconsultingthepubliclyavailablelistofexitnodesthatmightcontact
it.ForexampleusingtheTorBulkExitListtooloftheTorProject.
SousingTailsdoesn'tmakeyoulooklikeanyrandomInternetuser.TheanonymityprovidedbyTorand
Tailsworksbytryingtomakealloftheiruserslookthesamesoit'snotpossibletoidentifywhoiswho
amongstthem.
https://tails.boum.org/doc/about/warning/index.en.html#index2h1
Quote
Inthiscontext,thetermfingerprintreferstowhatisspecifictoTailsinthewayitbehavesonInternet.
ThiscanbeusedtodeterminewhetheraparticularuserisusingTailsornot.
164
Asexplainedonour warningpage, whenusingTailsitis possible to knowthatyouare usingTor. But
TailstriestomakeitasdifficultaspossibletodistinguishTailsusersfromotherTorusers,especiallyTor
BrowserBundle(TBB)users.IfitispossibletodeterminewhetheryourareaTailsusersoraTBBuser,
thisprovidesmoreinformationaboutyouandinconsequence reducesyouranonymity.
ThissectionexplainssomeissuesregardingthefingerprintofTailsandhowthiscouldbeusedto
identifyyouasaTailsuser.
Forthewebsitesthatyouarevisiting
Thewebsitesthatyouarevisitingcanretrievealotofinformationaboutyourbrowser.That
informationcanincludeitsnameandversion,windowsize,listofavailableextensions,timezone,
availablefonts,etc.
TomakeitdifficulttodistinguishTailsusersfromTBBusers,theTorbrowsertriestoprovidethesame
informationastheTBBinordertohavesimilarfingerprints.
Seethefingerprintsectionofknowissuespageforalistofknowndifferencesbetweenthefingerprints
oftheTorbrowserandtheTBB.
Apartfromthat,someoftheextensionsincludedinTorbrowseraredifferentthantheonesincludedin
theTBB.MoresophisticatedattackscanusethosedifferencestodistinguishTailsuserfromTBBusers.
Forexample,TailsincludesAdblockPluswhichremovesadvertisements.Ifanattackercandetermine
thatyouarenotdownloadingtheadvertisementsthatareincludedinawebpage,thatcouldhelp
identifyyouasaTailsuser.
Forthemoment,youshouldconsiderthatnospecialcareistakenregardingthefingerprintofthe
UnsafeBrowser.
ForyourISPorlocalnetworkadministrator
TorbridgesaremostofthetimeagoodwayofhidingthefactthatyouareconnectingtoTortoa
localobserver.Ifthisisimportantforyou,readourdocumentationaboutbridgemode.
ATailssystemisalmostexclusivelygeneratingToractivityonthenetwork.UsuallyTBBusersalso
havenetworkactivityoutsideofTor,eitherfromanotherwebbrowserorotherapplications.Sothe
proportionofToractivitycouldbeusedtodeterminewhetherauserisusingTailsortheTBB.Ifyou
aresharingyourInternetconnectionwithotherusersthatarenotusingTailsitisprobablyharderfor
yourISPtodeterminewhetherasingleuserisgeneratingonlyTortrafficandsomaybeusingTails.
TailsdonotusetheentryguardsmechanismofTor.Withtheentryguardmechanism,aToruser
alwaysusesthesamefewrelaysasfirsthops.AsTailsdoesnotstoreanyTorinformationbetween
separateworkingsessions,itdoesnotstoretheentryguardsinformationeither.Thisbehaviourcould
beusedtodistinguishTailsusersfromTBBusersacrossseveralworkingsessions.
Whenstarting,Tailssynchronizesthesystemclocktomakesureitisaccurate.Whiledoingthis,ifthe

165
time issettoomuchinthe past or inthe future, Tor isshutdown andstarted again. Thisbehavior
couldbeusedtodistinguishTailsfromTBBusers,especiallythishappenseverytimeTailsstarts.
https://tails.boum.org/doc/about/fingerprint/index.en.html
Readthosepagesdirectlyastheyhavelinkstoother articlesonthemaswell.
HereisanotherlittletrickIknowof.Neverkeepapasswordyoucanremember.Youcannotgiveupa
passwordyoudonotknow.Perhapsyouhavealittlepieceofpaperwithyourpasswordonitthatyou
swallowthesecondthecopscomein.Alongpasswordthatyoucouldneverremember.
Another thingyoucansayis,Iwrotedownmypasswordonapieceofpaperbutthepolicemusthave
destroyedthepieceofpaperwhentheyraidedmyhome.Checkoutthebelowquotefromanarticle.
Quote
Duboissaidthat,inaddition,hisclientmaynotbeabletodecryptthelaptopforanynumberof
reasons."Ifthat'sthecase,thenwe'llreportthatfacttothecourt,andthelawisfairlyclearthatpeople
cannotbepunishedforfailuretodothingstheyareunabletodo,"hesaid.
http://news.cnet.com/830131921_357364330281/judgeamericanscanbeforcedtodecrypttheir
laptops/
Andinthecaseofwhetherornotyoucanbeforcedtogiveupapasswordisamatterofdebatethat
hasgonebackandforthincourtcasestodate.
Quote
Manyinthelegalarenasaytheissueisatrickyandlargelyunsettledone.
Asmallnumberofcourtshavepermittedit,butonlywhenprosecutorscanpointtospecificallywhat
filestheyneedandwheretheyarelocated.
Inthemotionfiledearlierthisweek,AssistantCountyProsecutorMatthewMeyerstatedthelawisnot
clear.
http://www.cleveland.com/courtjustice/index.ssf/2014/03/bedford_judge_case_highlights.html
Andwhataboutthechargesforfailingtodoso?
Quote
disobeyingajudge'sordertohandoverapasswordcouldresultincontemptofcourtchargesorbeing
jailed.
http://www.cleveland.com/courtjustice/index.ssf/2014/03/bedford_judge_case_highlights.html
166
AndintheUS,sincemostpeoplebustedwillbeextraditedthereanyways,treatscontemptinthe
followingway.
Quote
Ifapersonistobepunishedcriminally,thenthecontemptmustbeprovenbeyondareasonabledoubt,
butoncethechargeisproven,thenpunishment(suchasafineor,inmoreseriouscases,
imprisonment)isimposedunconditionally.
Acourtcannotmaintainanorderofcontemptwheretheimposedpartydoesnothavetheabilityto
complywiththeunderlyingorder.Thisclaimwhenmadebytheimposedpartyisknownasthe
"impossibilitydefense".
https://en.wikipedia.org/wiki/Contempt_of_court#United_States
Furthermore.
Quote
“thegovernmentmustprovetheexistenceandlocationofthesubpoenaeddocumentsandpossess
independentevidence,otherthancompliancewiththecourtorder,forauthenticatingthem”[1,p.
581].Inotherwords,lawenforcementcannotsimplygoonafishingexpedition,hopingtoturnupdata
thatwillbeevidentiary[8].Theymustbeabletodemonstratetheexistenceandlikelylocationof
specificdocuments.
http://www.asis.org/Bulletin/Dec13/DecJan14_Oltmann.html
Inregardstotwocasesinwhichdefendantswerenotforcedtogiveuptheirpasswords
Quote
UnitedStatesv.Kirschner(2010):Kirschnerwasindictedforchildpornographycharges,andthe
governmentsubpoenaedhisencryptionkeytogainfurtherevidencefromhisencrypteddrive.Inthis
case,thejudgedeterminedthatrequiringadefendanttosupplyhispasswordwouldviolatehisright
againstselfincrimination.
UnitedStatesv.Doe(2012):Doewaschargedwithchildpornography.Herefusedtosupplyhis
decryptionkeyandwasfoundincontemptofcourt,thenjailed. Ajudgethenruledthatsupplyinghis
decryptionkeywouldbetantamounttoselfincrimination,soDoedidnothavetosupplyit.
http://www.asis.org/Bulletin/Dec13/DecJan14_Oltmann.html
Theanalysisofwhytheywerenotforcedtogivethemupisbelow.
Quote

167
Incontrast, lawenforcementinthe Kirschner and Doe cases did nothave prior evidence thatillegal
contentwasontheircomputers.Inthesecases,officershadsuspicionofwrongdoingandwererelying
on therevelationofdecryption keystoinvestigateanduncoverevidence.ThecourtinKirschner
determinedthatsharingthekey“wouldbetestimonialbecauseitwoulddemonstrateknowledgeof
thepasswordandaccesstotheunderlyingcomputerfiles…providingthepasswordwouldrevealthe
contentsofanarrestee’smindbyrecallingthepassword”[5,pp.11711172],[6].Simplyput,because
thepasswordwasnotwrittendown(oralreadyknowntolawenforcement)inKirschnerandDoe,and
itexistedonlyintheirminds,compellingadefendanttorevealitwouldbeselfincriminatingtestimony.
Iflawenforcementcandescribetheexistenceandlocationofevidence,theyhaveastrongercasefor
requiringaccess;however,iftheycannotdemonstratepriorknowledgeofthelikelydata,separate
fromacompelledrevelationfromadefendant,thenlawenforcementhasaweakerposition.
http://www.asis.org/Bulletin/Dec13/DecJan14_Oltmann.html
Butwhenlawenforcmentwasabletoprovideproofofexistingevidenceonanencrypteddrive,courts
weremuchmorelikelytodemanddecryption,suchasinthefollowingcases.
Quote
InreBoucher(2009):BoucherenteredtheUnitedStatesfromCanada.Aborderagentexamined
Boucher’scomputerandfoundchildpornographyafterBoucher suppliedthepassword.Theagent
thenshutdownthecomputerandarrestedBoucher.Shuttingdownthecomputertriggeredthe
encryptionagain,andprosecutorscouldnolongerseeorfindtheillegalimages.Boucherwasordered
bythecourtstosupplythepassword,butheinvokedhisFifthAmendmentprivilege.Thecourts
subsequentlyruledhehadtosupplyadecryptedcopyofthedrive’scontents.
Commonwealthv.Hurst(2011):Hurstwaschargedwithoffensesrelatedtoinappropriatesexual
relationswithaminor.PolicesuspectedincriminatingevidencewasonHurst’scellphone,buthe
refusedtosupplythepassword.Beforethiscasereachedthecourtsystem,Hurst’swifesuppliedthe
password,andHursthimselfpledguilty.
UnitedStatesv.Fricosu(2012):Fricosuwasindictedformortgageandrealestatefraud.Sherefusedto
surrenderthepassword(atonepointsayingsheforgotthepassword)toencryptedfilesthat,the
governmentbelieved,wouldincriminateher.Thecourtorderedhertosupplyadecryptedversionof
theharddrive,ratherthanherpassword.Subsequently,acodefendantsuppliedtheneeded
passwords.
Andtheanalysisofthecasesbelow.
Quote
LawenforcementsawevidenceofcriminalwrongdoinginthePearson,Boucher,HurstandFricosu
cases.
168
BothPearsonandBoucher voluntarily agreedtoletlawenforcementsearchtheir computers;during
thosesearches,theofficerssawevidence.Itwasonlyaftertheinitialsearchthatthequestionof
encryptionbecamerelevant.Inthesecases,becausethedefendantshad“permittedinvestigatorsto
seeatleastsome”oftheevidence,this“sufficedtorendertheexistenceofalltheillegalfilesa
‘foregoneconclusion’”ratherthantestimonialevidence[8,p.544].Hursthadsentinappropriate
messagestoaminor,whichwerevisibleontheminor’sphone.Whilethepolicesoughtconfirmationof
thetransmissionbysearchingHurst’sphone,theyhadsufficientevidencewithoutthatstep.Inthe
Fricosucase,policehadrecordedconversationsbetweenthedefendantandherhusband(aco
defendant)thatrevealedtheexistenceandcontentofthesoughtafterdocuments.
http://www.asis.org/Bulletin/Dec13/DecJan14_Oltmann.html
1) Itmaybepossible,toidentifyyouasaTailsuser, butitwouldtakealotofanalysistodoso,and
Tailsisgettingbetteratblendinginwitheveryupdate.
2)Thinkaboutwhatyoucouldpossiblybechargedwith,andthinkaboutwhetherornotitis
moreseriousthanacontemptcharge.Thelongestsentencetodateforcontemptwas14years,
andthisisalmostunheardof.Youarenotlikelytogetthiskindofchargeagainstyou,butifyou
do,woulditbebetterthanlifeinprisonforwhateverelseyoumightbechargedwith?
RememberSabutoLulzSechacker?beingchargedwith112yearsinprisonforhacking?Ithink
hewouldtrade14yearsinprisonforcontemptover112yearsanyday.IknowIwould.
3)Withouttheknowledgeofincriminatingevidenceexistingonyourdrives,youarelesslikely
tobeforcedtodecryptyourdrives,andthisevenappliesinchildpornographycasesas
demonstratedabove.
4)Maintainyourrighttoremainsilent,neverkeepanythingonyourcomputersthatyoudonot
haveto.
5)Donothaveapasswordyoucanremember.Orifyoudo,tellthemyouhaditwrittendown
butitwasmisplacedorpossiblydamagedduringtheraidandyouareunabletorecallthe
password.Perhapsyouaretootraumatizedfromtheevenofhavingyourfaceshovedintothe
floortorememberwhathappenedduringthose2minutes?
Anyways,thisisalotofdatatogothrough,soIwillleaveitatthatandwecangofromthere.
Youjustneedtoalwaysfollowbestpractices.Turnoffyourcomputerwhenyouarenotusingit,
encrypteverything,nevertellanybodyyourpasswords,neverleaveanyevidenceofthe
contents ofyourdriveslyingaround(likenotesordiaryentries),andneveradmithaving
anythingonyourdrivestoanyoneonline,evenunderyourpseudonymasthatcanbeused
againstyouincourt.
Denydenydenydenydeny.
Hopethishelps.

169
Security Culture: A Handbook for Activists
This handbook is the first edition of what we hope will be an evolving and growing document dealing
with security issues and canadian activism. A lot of this information is general and can be applied to
any locality - other information is easily adapted to fit other situations. For more information or to
make contributions to this document – please email securitysite@tao.ca
Second edition - prepared August 2000
Introduction:
Resistance has been on the rise for the past few years, with activists adopting more and more
effective tactics for fighting back. Now, more than ever, we pose some threat to the status quo. Our
increased activity and effectiveness has meant that the RCMP, FBI, and local police have continued to
escalate their activities against us. If we want our direct action movement to continue, it is imperative
we start tightening our security and taking ourselves more seriously. Now is the time to adopt a security
culture. Good security is certainly the strongest defense we have. This is a handbook for the Canadian
(and even US) activist who is interested in creating and maintaining security awareness and culture in
the radical movements. It is not nearly complete - but is what we have got finished at the moment. We
are always looking for contributions - so please feel free to email securitysite@tao.ca with any images
or text you think belong in a handbook such as this. If this material appears familiar to you - its because
this is the second edition of this zine that we have put out... mostly to correct spelling errors and other
small things. The three articles in this pamphlet have been mostly cobbled together from other writings
170
that already exist on this subject out there so we don’t claim any of this to be 100% original material -
though we have included quite a bit of fresh info on the Canadian state and its operation (mostly
because we have found the majority of info out there to be very focused on US law enforcement). We
hope that you will put the material contained within to good use!
Security What it is, why we need it and how we implement it...
A gitators; liberationists; abolitionists; union organizers; revolutionaries... From large uprisings
challenging the entire political structure, to isolated environmental and social struggles, people have
always worked to create a better world. For government the response has usually been to jail activists
and revolutionaries through use of the courts and police forces. As direct action movements become
more effective, government surveillance and harassment will increase. To minimize the destructiveness
of this political repression, it is imperative that we create a security culture within our movements. This
pamphlet is essential reading for anyone who is associated with groups that advocate and/or utilize
sabotage, theft, arson and more militant tactics. The advice herein also applies to anyone who is
associated with groups that practice civil disobedience, especially since membership often overlaps and
gossip travels freely between groups.
Even if you have never picked up a monkeywrench or been arrested for civil disobedience, even if
you think you have nothing to hide, these guidelines will enhance your personal safety as well as the
movement’s overall effectiveness. Surveillance has been set up on all sections of political movements
in the past. Governments in the western industrialized world have targeted groups that have advocated
sabotage and groups that have not, movements that have been militant and movements that have been
markedly pacifist. The government’s security machinery serves political and economic objectives, and
there are over 250 political prisoners in Canada and the US that can testify to this from firsthand
experience. By adopting a security culture, we can defeat various counterintelligence operations that
would otherwise disrupt both mainstream organizing and underground resistance.
SO WHAT IS A SECURITY CULTURE?
It’s a culture where the people know their rights and, more importantly, assert them. Those who
belong to a security culture also know what behavior compromises security and they are quick to
educate those people who, out of ignorance, forgetfulness, or personal weakness, partake in insecure
behavior. This security consciousness becomes a culture when the group as a whole makes security
violations socially unacceptable in the group.
WHAT NOT TO SAY
To begin with, there are certain things that are inappropriate to discuss. These things include:
your involvement or someone else’s involvement with an underground group
someone else’s desire to get involved with such a group
asking others if they are a member of an underground group
your participation or someone else’s participating in any action that was illegal
someone else’s advocacy for such actions
your plans or someone else’s plans for a future action
171
Essentially, it is wrong to speak about a specific individual's involvement (past, present or
future) with illegal activities. These are unacceptable topics of discussion regardless of whether it is
rumor, speculation or personal knowledge.
Please note: this is not to say that it is wrong to speak about direct action in general terms. It is
perfectly legal, secure and desirable that people speak out in support of mokeywrenching
and all forms of resistance. The danger lies in linking individual activists to specific actions or
groups.
THREE EXCEPTIONS
There are only three times that it is acceptable to speak specifically about actions and
involvements. The first situation would be if you were planning an action with other members of your
small group (your “cell” or “affinity group”). However, you should never discuss these things over the
Internet (email), phone line, through the mail, or in an activist's home or car, as these places and forms
of communication are frequently monitored. The only people who should hear this discussion would
include those who are actively participating in the action. Anyone who is not involved does not need to
know and, therefore, should not know. The second exception occur es after an activist has been arrested
and brought to trial. If she is found guilty, this activist can freely speak of the actions for which she was
convicted. However, she must never give information that would help the authorities determine who
else participated in illegal activities. The third exception is for anonymous letters and interviews with
the media. This must be done very carefully and without compromising security. Advice on secure
communication techniques can be found in other publications. These are the only situations when it is
appropriate to speak about your own or someone else's involvement or intent to commit illegal direct
action.
SECURITY MEASURES
Veteran activists only allow a select few to know about their involvement with direct action
groups. Those few consist of the cell members who they do the actions with AND NO ONE ELSE!
The reason for these security precautions is quite obvious: if people don't know anything, they can't talk
about it. It also means that only the people who know the secret can also face jail time if the secret gets
out. When activists who do not share the same serious consequences know who did an illegal direct
action, they are far more likely to talk after being harassed and intimidated by the authorities, because
they are not the ones who will go to jail. Even those people who are trustworthy can often be tricked by
the authorities into revealing damaging and incriminating information. It is safest for all cell members
to keep their involvement in the group amongst themselves. The fewer people who know, the less
evidence there is in the long run.
SECURITY VIOLATING BEHAVIOURS
172
In an attempt to impress others, activists may behave in ways that compromise security. Some
people do this frequently – they are habitually gossiping and bragging. Some activists say inappropriate
things only when they consume alcohol. Many activists make occasional breeches of security because
there was a momentary temptation to say something or hint at something that shouldn’t have been said
or implied. In most every situation, the desire to be accepted is the root cause. Those people who tend
to be the greatest security risks are those activists who have low self-esteem and strongly desire the
approval of their peers. Certainly it is natural to seek friendship and recognition for our efforts, but it is
imperative that we keep these selfish desires in-check so we do not jeopardize the safety of other
activists or ourselves. People who place their desire for friendship over the importance of the cause can
do serious damage to our security. The following are examples of security-violating behaviors:
Lying: To impress others, liars claim to have done illegal actions. Such lies not only compromise the
person's security--as cops will not take what is said as a lie--but also hinders movement solidarity and
trust.
Gossiping: Some weak characters think they can win friends because they are privy to special
information. These gossips will tell others about who did what action or, if they don't know who did it,
guess at who they think did what actions or just spread rumors about who did it. This sort of talk is very
damaging. People need to remember that rumors are all that are needed to instigate a grand jury or
other investigation.
Bragging: Some people who partake in illegal direct action might be tempted to brag about it to their
friends. This not only jeopardizes the bragger's security, but also that of the other people involved with
the action (as they may be suspected by association), as well as the people who he told (they can
become accessories after the fact). An activist who brags also sets a horrible example to other activists.
Indirect-Bragging: Indirect- braggers are people who make a big production on how they want to
remain anonymous, avoid protests, and stay "underground." They might not come out and say that they
do illegal direct action, but they make sure everyone within ear- shot knows they are up to
something. They are no better than braggers, but they try to be more sophisticated about it by
pretending to maintain security. However, if they were serious about security, they would just
make up a good excuse as to why they are not as active, or why they can't make it to the protest (that
kind of lying is acceptable).
EDUCATE TO LIBERATE
It is fairly easy to spot those activists who compromise our movement’s security. So what do we
do with people who exhibit these behaviors? Do we excommunicate them from our movement?
Actually, no—at least, not for a first offense.
The unfortunate truth is there are numerous security-ignorant people in the movement and others
who have possibly been raised in a "scene" that thrives on bragging and gossiping. It doesn't mean
these people are bad, but it does mean they need to be educated. Even seasoned activists can make
mistakes when there is a general lack of security consciousness in our groups. And that’s where those
of you who are reading this can help. We must NEVER let a breach in security occur without acting to
correct it. If an acquaintance of yours is bragging about doing an action or spreading security-
compromising gossip, it is your responsibility to explain to her or him why that sort of talk violates
security and is inappropriate.
173
You should strive to educate this person in a manner that en- courages him to listen and to change
his behavior. It should be done without damaging his pride. You should be humble and sincerely
interested in helping him to become a better person and a more effective activists. Do not maintain a
"holier than-thou" attitude. This will inevitably raise his defenses and prevent him from absorbing or
using any of the advice you offer. Remember, the goal of educating people is to change their behavior,
not boost your ego by showing them how much more security-conscious you are.
If possible the educational session should be done in private, so the person does not have to
contend with the potential ‘pride’ issues. The educational reprimand should also be done as soon as
possible after the mistake to increase its effectiveness. If each of us takes on the responsibility of
educating those who slip up, we can dramatically improve movement security. Once people recognize
lying, gossiping, bragging, and indirect-bragging as the damaging behaviors that they are, they will
soon end. When we develop a culture where all breaches of security result in an immediate reprimand,
all sincere activists will quickly get with the program.
DEALING WITH CHRONIC SECURITY PROBLEMS
So what do we do with activists who repeatedly violate security precautions even after multiple
educational sessions? It's unfortunate, but the best thing to do with these people is cut them loose and
kick them out of our meetings, base camps and organizations. With law enforcement budgets on the
increase and with courts handing down long sentences for political “crimes”, the stakes are too high to
allow chronic security-offenders to work among us.
By creating a security culture, we have an effective defense against informers and agents who try
to infiltrate groups. Imagine an informer who, every time she asked another activist about that person’s
activity, received a reprimand and an education on security. That informer would get frustrated really
easily. Once the activists discovered she continued to violate security precautions after being repeatedly
educated, they would have grounds for her dismissal. And that would be one less informer for us to
deal with!
A Brief Primer on the Canadian State Security Apparatus
Recent repression against activists in British Columbia illuminates the need for grassroots people
to understand and practice movement security. Police monitoring, infiltration and agent provocateurs
are all techniques used by the state routinely against activists to turn up information about the activities
of our movements and ourselves.
Although many activists have trouble believing that state security agencies have that much interest
in their affairs, a few key court cases and hearings have helped activists to gain access to information
that proves that police spying on activists is routine in Canada.
During the APEC hearings, it was revealed that over seventy groups and individuals were
monitored before and during the APEC meetings in 1997. A paid industry informant/disruptor was
identified at a wilderness action camp in 1999, and local activists have been targeted by provocateurs
who have tried to convince them not only to disclose information but to break the law.
The Canadian security apparatus has identified a number of our movements as threatening to
national security. They have targeted people and organizations widely. Even avowed pacifists have
been included in surveillance and repressive measures. According to Canadian Security Intelligence
174
Service (CSIS) annual reports of the past five years, the Native Resistance and the
Environmental/Animal Rights movements have been primary targets.
With the rise in militant First Nations struggles, covert direct action against corporations, and the
growing focus by the media on general "anarchist" politics due to events in Seattle around the WTO
among other major increases in movement strength and militancy, we can be pretty sure that this has
been marked by a growing level of surveillance and monitoring as well.
The need for security in our movements is obvious – how- ever, it is incredibly important that we
don't fall into the trap of using our awareness of security issues to shut other people out of our growing
movements. One of the key aims of COINTEL- PRO operations against the Black Panthers and
American Indian Movement was to spread paranoia and distrust among those freedom fighters so that
they would find it hard to accept new people into their work.
It is possible to build a movement large and at the same time create security culture. Arming
ourselves with knowledge about how the system works against activists is the first step to creating that
culture. The central aim of this article is to give a
brief run-down of how domestic intelligence works in Canada so that we can better understand how to
avoid its traps.
AN OVERVIEW OF DOMESTIC INTELLIGENCE ORGANIZATIONS
The Canadian Security and Intelligence Service (CSIS) is probably the best known of the
"security" agencies that deal with activist "threats". They were originally a special surveillance wing of
the RCMP until 1983 when they were split off into a separate agency due to protests that they were
acting as secret organization that was contravening Canadians' democratic rights to organize.
Essentially, the split from the RCMP allowed the new spy agency to do legally what the Mounties had
been doing illegally. At the operations level, the new agency was granted more freedom and more
leeway than the Mounties ever had.
Today they continue to carry out a wide range of surveillance. As they are not a law-enforcement
agency and therefore their evidence is not used in court, there is nothing stopping them from
contravening the few regulations that exist regarding privacy rights. For example, CSIS is not required
to inform people, as the RCMP does, ninety days after they have been wiretapped or bugged.
Agents working for CSIS are allowed, with "authorization", to enter people's homes to plant bugs,
wiretap phones, open mail and look into health, employment and government records without ever
having to tell a targeted individual what they are doing. The information that they gather is used to
build profiles and dossiers (files) on individuals, organizations, networks, etc. The information that
they gather is often passed on to other wings of the federal security system who are responsible for
"law enforcement", and will then obtain whatever war- rants are necessary for legal surveillance (to be
brought into court as evidence).
The National Security Investigation Service (NSIS) is the primary law-enforcement wing of
domestic security. The NSIS is a section of the Royal Canadian Mounted Police (RCMP). Most cities
across Canada have an NSIS office including Vancouver, Edmonton, Montreal, Ottawa, and Toronto.
The NSIS maintains a computer database on activists, immigrants and so called "terrorists" which is
housed in Ottawa.
It is believed that the Vancouver NSIS employs between 12 and 18 members. Within NSIS there
are several sub-groups called Team 1, Team 2, Team 3 – etc. that have different investigative targets.
They employ informants, infiltrators, personal physical surveillance, electronic surveillance
including phone and room "bugs" and other means of investigation and research.
175
The RCMP/NSIS also have other resources at their disposal during counter-insurgency operations.
"Special O" is a team of surveillance specialists that may be called upon. "Special I" is a penetration
team whose specialty is to break into homes, vehicles and other properties for investigative purposes.
They are the team, which among other things, installs listening devices, photo- graphs building
interiors, etc.
In a long-running case based in Vancouver, all of these methods of surveillance were used against
several Vancouver activists. During the Vancouver investigation, house and vehicle bugs were located
by some targeted individuals. The bugs had large battery packs attached to facilitate less frequent
battery changes. The NSIS also visited several activists across Canada in an attempt to question them
regarding the individuals under investigation.
It cannot be stressed enough that no one is under any legal obligation to provide the police with
any information other than one's own name and address. That is it. Saying anything more jeopardizes
individuals' and movement security. Even answering seemingly insignificant questions can assist the
police in developing personality profiles on a range of activists which may not contain "evidence" but
may instead be used to give police “leads” on other suspects and to construct intent during legal
proceedings. The only principled response to police questioning is to say nothing more than name and
address.
The Communications Security Establishment is an agency of the defense department which
has been long clouded in secrecy. They collect and process telephone, fax and computer
communications of foreign states, corporations and individuals. The federal government uses the
intelligence gleaned from the data to sup- port troops abroad, catch “terrorists” and “further Canada's
economic goals” (and what that means is up to them).
Although the CSE is not technically allowed to collect the communications of Canadian citizens, it
is known to be a partner in the Echelon project -
a multinational monitoring operation which sees CSE and counterpart agencies in the United States,
Britain, Australia and New Zealand share intercepted communications of interest with one another,
effectively creating a global surveillance web.
The Terrorist Extremist Section (TES Unit) is British Columbia's anti-terrorist unit. A joint
Vancouver/Victoria Police Department/ RCMP unit called the Organized Crime Agency (formerly the
Coordinated Law Enforcement Unit - CLEU), it is believed that the this unit employs two or three
members only. Most activists will be intimately familiar with their local police forces. Be aware that
cops do not only show up in blue uniforms - but routinely practice crowd infiltration and carry out
surveillance and investigative activities either alone or jointly with the RCMP depending on the type of
case. Watch for them on demonstrations - as they like to come along and take photo- graphs and video
for the record - and they often appear in crowds as “fellow demonstrators”.
THE COUNTER- INSURGENCY MODEL
Most Western nation-states follow a model of counter- insurgency developed by a British intelligence
expert named Kitson who wrote, Low Intensity Operations, after much field work in the colonies. He
broke down movement development into three stages:
The Preparatory Phase: is when the movement is small, tends to focus on education, publishing and
groundwork.
The Non-Violent Phase: is when the movement takes on more of a mass character. Large
demonstrations are the norm.
176
In the Insurgency Phase: the movement has taken on a popular character. Perhaps a more assertive,
guerrilla component has emerged.
Kitson advises that the primary work of the intelligence agency should occur during the
preparatory phase. At this time the movements are most vulnerable. They have not experienced a high
degree of repression. They consider talk of security as mere paranoia. As they are not breaking laws
they believe that it is safe to organize completely openly. The intelligence agency is therefore able to
exploit these
conditions and develop detailed dossiers on a wide range of people. The information will be extremely
valuable to them later on. It is important that as a movement in we need to learn to practice security at
all points in the movement's development. Remember that the State is interested in knowing about
activists' beliefs, not just in "hard evidence". Learn and practice security to protect ourselves and our
peoples. Don't be afraid. Remember - If an agent comes knockin', do no talkin'.
Everything You Ever Wanted to Know about Informers and Infiltrators
Informants and infiltrators operate in every radical movement. The rise of militant radicalism as
seen at the WTO protests in Seattle, and the declarations by activists to continue the struggle in the
streets and underground – mean that more and more attention will be paid to activists by law
enforcement. Part of this will mean sending more infiltrators amongst our ranks to bribe and entice
those weak individuals already involved.
Non-violent movements need to learn to identify such people and and let them know that their
actions will never be tolerated by activists in any way.
This section is intended to arm you with information on how to spot and deal with informers and
infiltrators in our ranks.
Who is an informer? There are actually two kinds of informers. The deliberate informer is
someone who infiltrates an organization with the specific intent of getting incriminating evidence
against activists or even setting them up to be arrested. These infiltrators are either on the payroll of a
government agency or may be hired by industry. The second type of informer is the activist- turned-
informant--either unwittingly or because of pressure put on them by the authorities. Make no mistake,
both kinds exist throughout our ranks and are equally dangerous.
Let's discuss the deliberate informer (infiltrator) first. They are often difficult to identify, they
come in all ages and types, but they usually have a similar modus operandi--they come out of nowhere
and all of a sudden, they are everywhere. Whether it's a meeting, a protest, or an action, this person will
be right in the thick of it.
Keep in mind however that this is also the hallmark of a new activist, whose enthusiasm and
commitment is so strong that s/ he wants to fight the power every minute of the day.
How to tell them apart? Well, a planted infiltrator will ask a lot of questions about the direct action
groups, individuals and illegal activities. S/he will suggest targets and volunteer to do reconnaissance
as well as take part in the action.
An example of infiltration tactics can be found in an incident that occurred a few years ago when
U.S. Surgical hired a security firm to infiltrate Friends of Animals in Connecticut. Their operative
convinced an activist to put a pipe bomb in the car of the president of U.S. Surgical. Needless to say,
the police were waiting for her and she ended up being charged with at- tempted murder.
177
State and industry infiltrators have been identified in operation in British Columbia over the past
few years - attempting to incite illegal activity, sowing disruption in action camps, and gathering
information on the who, what and when of our movement’s activities .
Everyone who asks a lot of questions about the direct action isn't necessarily an infiltrator, but they
ARE the ones to watch (at the very least, we should be educating them about security culture). Explain
to new activists that direct action tactics can be risky (though some risks are worth taking!) and that it
is dangerous to ask a lot of questions about it. If the person persists in asking questions,
STAY AWAY FROM THEM! Any activist who can't under- stand the need for security is someone
that should be held at arm’s length from the movement.
Placing infiltrators into social justice movements isn't anything new. It was done to the Black
Panthers and the peace movement in a big way. Unless you are only working with people you've
known for years and who have earned your trust, you should assume there is an informant in your
midst and act accordingly.
This doesn't mean that no one else should ever be allowed into the "inner circle." On the contrary,
if our movement is to continue to grow, we must always be recruiting new members; we just need to
keep security uppermost in our minds and exercise caution at all
times.
Possibly an even greater threat is the activist-turned-informer, either unwittingly or through
coercion.
The unwitting informer is the activist who can't keep his/her mouth shut. If someone brags to you
about what s/he's done, make sure this person never has any knowledge that can incriminate you,
because sooner or later, the wrong person will hear of it. These activists don't mean to do harm, but the
results of their bragging can be serious. It is your responsibility to instruct these people on security
culture and the importance of it.
The other type of activist- informer is person who cracks under pressure and starts talking to save
his/her own skin. Many activists get drawn into situations they are not able to handle, and some are so
caught up in the "excitement" that they either don't realize what the consequences can be or they just
don't think they'll ever have to face them.
We have to know the possible consequences of every action we take and be prepared to deal with
them. Someone who is easily influenced by his/her parents or dependent on them for support is not a
good candidate for actions as they can be persuaded too easily to cooper- ate with the authorities. There
is no shame in not being able to do an action because of responsibilities that make it impossible
to do jail time. If others are depending on you for support or you aren't willing to lose your job or drop
out of school, DON'T DO THE ACTION.
Make certain that others in your affinity group are not in situations which may cause them to
cooperate with the police or abandon their friends.
Two activists were recently put in jail in Canada because a third party panicked - mainly about not
being able to get his drugs in jail - and talked to free himself. (This is not to condemn those who have
drug habits or criminal records – but are certainly things to keep in mind). Don't be afraid to talk about
this. Ask hard questions, and if you aren't convinced that someone will be able to stay strong if the
worst happens, then designate that person to do support. Make sure that those who go into battle with
you are willing and able to take whatever comes, even if it means giving up their freedom for your
goals. Remember - there is no excuse for turning in action comrades to the police - and those activists
that do effectively excommunicate themselves from our movements. We must offer no legal or jail
support to those activists who turn-in others for their impact on our movement is far-reaching and can
have devastating effects. Some things to look out for in people you choose to do illegal direct action
with are lengthy
178
Crypto Anarchy and Virtual Communities
Timothy C. May
535 Monterey Drive
Aptos, CA 95003 U.S.A.
tcmay@netcom.com
December, 1994
Extended Abstract
The combination of strong, unbreakable public key cryptography and virtual network communities in
cyberspace will produce interesting and profound changes in the nature of economic and social
systems. Crypto anarchy is the cyberspatial realization of anarcho-capitalism, transcending national
boundaries and freeing individuals to make the economic arrangements they wish to make
consensually.
Strong cryptography, exemplified by RSA (a public key algorithm) and PGP (Pretty Good Privacy),
provides encryption that essentially cannot be broken with all the computing power in the universe.
This ensures security and privacy. Public key cryptography is rightly considered to be a revolution.
Digital mixes, or anonymous remailers, use crypto to create untraceable e-mail, which has many uses.
(Numerous anonymous remailers, in several countries, are now operating. Message traffic is growing
exponentially.)
179
Digital pseudonyms, the creation of persistent network personas that cannot be forged by others and yet
which are unlinkable to the "true names" of their owners, are finding major uses in ensuring free
speech, in allowing controversial opinions to be aired, and in providing for economic transactions that
cannot be blocked by local governments. The technology being deployed by the Cypherpunks and
others, means their identities, nationalities, and even which continents they are on are untraceable --
unless they choose to reveal this information. This alters the conventional "relationship topology" of
the world, allowing diverse interactions without external governmental regulation, taxation, or
interference
Digital cash, untraceable and anonymous (like real cash), is also coming, though various technical and
practical hurdles remain. "Swiss banks in cyberspace" will make economic transactions much more
liquid and much less subject to local rules and regulations. Tax avoidance is likely to be a major
attraction for many. An example of local interest to Monte Carlo might be the work underway to
develop anonymous, untraceable systems for "cyberspace casinos." While not as attractive to many as
elegant casinos, the popularity of "numbers games" and bookies in general suggests a opportunity to
pursue.
Data havens and information markets are already springing up, using the methods described to make
information retrievable anonymously and untraceably.
Governments see their powers eroded by these technologies, and are taking various well-known steps
to try to limit the use of strong crypto by their subjects. The U.S. has several well-publicized efforts,
including the Clipper chip, the Digital Telephony wiretap law, and proposals for "voluntary" escrow of
cryptographic keys. Cypherpunks and others expect these efforts to be bypassed. Technology has let
the genie out of the bottle. Crypto anarchy is liberating individuals from coercion by their physical
neighbors--who cannot know who they are on the Net--and from governments. For libertarians, strong
crypto provides the means by which government will be avoided.
The presentation will describe how several of these systems work, briefly, and will outline the likely
implications of this combination of crypto anarchy and virtual cyberspace communities.
1 Introduction
This paper describes the combination of two major technologies:
Strong Crypto: including encryption, digital signatures, digital cash, digital mixes (remailers),
and related technologies.
Cyberspatial Virtual Communities: including networks, anonymous communications, MUDs
and MOOs, and "Multiverse"-type virtual realities.
These areas have generally remained separate, at least in published papers. Certainly the developers of
cyberspace systems, such as MUDs, MOOs, and Habitat-like systems, appreciate the importance of
cryptography for user authentication, overall security, and certainly for (eventual) digital purchase of
services. But for the most part the combination of these two areas has been the province of the science
fiction writer, notably writers such as Vernor Vinge, William Gibson, Bruce Sterling, and Orson Scott
Card.
The "Cypherpunks" group, a loose, anarchic mailing list and group of hackers, was formed by several
of us in 1992 as a group to make concrete some of the abstract ideas often presented at conferences.
We've had some successes, and some failures. [1] The Cypherpunks group also appeared at a fortuitous
time, as PGP was becoming popular, as Wired magazine appeared (they featured us on the cover of
their second issue), and as the publicity (hype?) about the Information Superhighway and the World
Wide Web reached a crescendo.
180
The site ftp.csua.berkeley.edu has a number of essays and files, including crypto files, in the directory
pub/cypherpunks. I have also written/ compiled a very large 1.3 MB FAQ on these issues, the
Cyphernomicon, available at various sites, including my ftp directory, ftp.netcom.com, in the directory
pub/tc/tcmay.
The Cypherpunks group is also a pretty good example of a "virtual community." Scattered around the
world, communicating electronically in matters of minutes, and seeming oblivious to local laws, the
Cypherpunks are indeed a community, and a virtual one. Many members use pseudonyms, and use
anonymous remailers to communicate with the list. The list itself thus behaves as a "message pool," a
place where information of all sort may be anonymous deposited--and anonymous received (since
everyone sees the entire list, like a newspaper, the intended recipient is anonymized).
Legal Caveat: Consult your local laws before applying any of the methods described here. In some
jurisdictions, it may be illegal to even read papers like this (seriously). In particular, I generally won't
be giving ftp site addresses for copies of PGP, remailer access, digital cash systems, etc. These are
well-covered in more current forums, e.g., sci.crypt or talk.politics.crypto, and there are some
unresolved issues about whether giving the address of such sites constitutes (or "aids and abets")
violation of various export and munitions laws (crypto is considered a munition in the U.S. and
probably elsewhere....some nations consider a laser printer to be a munitions item!).
2 Modern Cryptography
The past two decades have produced a revolution in cryptography (crypto, for short) the science of the
making of ciphers and codes. Beyond just simple ciphers, useful mainly for keeping communications
secret, modern crypto includes diverse tools for authentication of messages, for digital timestamping of
documents, for hiding messages in other documents (steganography), and even for schemes for digital
cash.
Public key cryptography, the creation of Diffie and Hellman, has dramatically altered the role of
crypto. Coming at the same time as the wholesale conversion to computer networks and worldwide
communications, it has been a key element of security, confidence, and success. The role of crypto will
only become more important over the coming decades.
Pretty Good Privacy, PGP, is a popular version of the algorithm developed by Rivest, Shamir, and
Adleman, known of course as RSA. The RSA algorithm was given a patent in the U.S., though not in
any European countries, and is licensed commercially. [2]
These tools are described in detail in various texts and Conference proceedings, and are not the subject
of this paper. [3] The focus here is on the implications of strong crypto for cyberspace, especially on
virtual communities.
Mention should be made of the role of David Chaum in defining the key concepts here. In several
seminal papers (for example, [4] [5]), Chaum introduced the ideas of using public key cryptography
methods for anonymous, untraceable electronic mail, for digital money systems in which spender
identity is not revealed, and in schemes related to these. (I make no claims of course that Chaum agrees
with my conclusions about the political and socioeconomic implications of these results.)
3 Virtual Communities
Notes: cyberspace, Habitat, VR, Vinge, etc. Crypto holds up the "walls" of these cyberspatial realities.
Access control, access rights, modification privileges.
181
Virtual communities are the networks of individuals or groups which are not necessarily closely-
connected geographically. The "virtual" is meant to imply a non-physical linking, but should not be
taken to mean that these are any less community-like than are conventional physical communities.
Examples include churches, service organizations, clubs, criminal gangs, cartels, fan groups, etc. The
Catholic Church and the Boy Scouts are both examples of virtual communities which span the globe,
transcend national borders, and create a sense of allegiance, of belonging, and a sense of "community."
Likewise, the Mafia is a virtual community (with its enforcement mechanisms, its own extra-legal
rules, etc.) Lots of other examples: Masons, Triads, Red Cross, Interpol, Islam, Judaism, Mormons,
Sindero Luminoso, the IRA, drug cartels, terrorist groups, Aryan Nation, Greenpeace, the Animal
Liberation Front, and so on. There are undoubtedly many more such virtual communities than there are
nation-states, and the ties that bind them are for the most part much stronger than are the chauvinist
nationalism emotions. Any group in which the common interests of the group, be it a shared ideology
or a particular interest, are enough to create a cohesive community.
Corporations are another prime example of a virtual community, having scattered sites, private
communication channels (generally inaccessible to the outside world, including the authorities), and
their own goals and methods. In fact, many "cyberpunk" (not cypherpunk) fiction authors make a
mistake, I think, in assuming the future world will be dominated by transnational megacorporate
"states." In fact, corporations are just one example--of many--of such virtual communities which will
be effectively on a par with nation-states. (Note especially that any laws designed to limit use of crypto
cause immediate and profound problems for corporations-countries like France and the Philippines,
which have attempted to limit the use of crypto, have mostly been ignored by corporations. Any
attempts to outlaw crypto will produce a surge of sudden "incorporations," thus gaining for the new
corporate members the aegis of corporate privacy.)
In an academic setting, "invisible colleges" are the communities of researchers.
These virtual communities typically are "opaque" to outsiders. Attempts to gain access to the internals
of these communities are rarely successful. Law enforcement and intelligence agencies (such as the
NSA in the U.S., Chobetsu in Japan, SDECE in France, and so on, in every country) may infiltrate such
groups and use electronic surveillance (ELINT) to monitor these virtual communities. Not surprisingly,
these communities are early adopters of encryption technology, ranging from scrambled cellphones to
full-blown PGP encryption. [8]
The use of encryption by "evil" groups, such as child pornographers, terrorists, abortionists, abortion
protestors, etc., is cited by those who wish to limit civilian access to crypto tools. We call these the
"Four Horseman of the Infocalypse," as they are so often cited as the reason why ordinary citizen-units
of the nation-state are not to have access to crypto.
This is clearly a dangerous argument to make, for various good reasons. The basic right of free speech
is the right to speak in a language one's neighbors or governing leaders may not find comprehensible:
encrypted speech. There's not enough space here to go into the many good arguments against a limit on
access to privacy, communications tools, and crypto.
The advent of full-featured communications systems for computer-mediated virtual communities will
have even more profound implications. MUDs and MOOs (multi-user domains, etc.) and 3D virtual
realities are one avenue, and text-centric Net communications are another. (Someday, soon, they'll
merge, as described in Vernor Vinge's prophetic 1980 novella, True Names.)
182
4 Observability and Surveillance
An interesting way to view issues of network visibility is in terms of the "transparency" of nodes and
links between nodes. Transparent means visible to outsiders, perhaps those in law enforcement or the
intelligence community. Opaque mean not transparent, not visible. A postcard is transparent, a sealed
letter is opaque. PGP inventor Phil Zimmermann has likened the requirement for transparency to being
ordered to use postcards for all correspondence, with encryption the equivalent of an opaque envelope
(envelopes can be opened, of course, and long have been).
Transparent links and nodes are the norm in a police state, such as the U.S.S.R., Iraq, China, and so
forth. Communications channels are tapped, and private use of computers is restricted. (This is
becoming increasingly hard to do, even for police states; many cite the spread of communications
options as a proximate cause of the collapse of communism in recent years.)
There are interesting "chemistries" or "algebras" of transparent vs. opaque links and nodes. What
happens if links must be transparent, but nodes are allowed to be opaque? (The answer: the result is as
if opaque links and nodes were allowed, i.e., full implications of strong crypto. Hence, any attempt to
ban communications crypto while still allowing private CPUs to exist....)
If Alice and Bob are free to communicate, and to choose routing paths, then Alice can use "crypto
arbitrage" (a variation on the term, "regulatory arbitrage," the term Eric Hughes uses to capture this
idea of moving transactions to other jurisdictions) to communicate with sites--perhaps in other
countries--that will perform as she wishes. This can mean remailing, mixing, etc. As an example,
Canadian citizens who are told they cannot access information on the Homolka-Teale murder case (a
controversial case in which the judge has ordered the media in Canada, and entering Canada, not to
discuss the gory details) nevertheless have a vast array of options, including using telnet, gopher, ftp,
the Web, etc., to access sites in many other countries--or even in no country in particular.
Most of the consequences described here arise from this chemistry of links and nodes: unless nearly all
node and links are forced to be transparent, including links to other nations and the nodes in those
nations, then the result is that private communication can still occur. Crypto anarchy results.
5 Crypto Anarchy
"The Net is an anarchy." This truism is the core of crypto anarchy. No central control, no ruler, no
leader (except by example, reputation), no "laws." No single nation controls the Net, no administrative
body sets policy. The Ayatollah in Iran is as powerless to stop a newsgroup--
alt.wanted.moslem.women or alt.wanted.moslem.gay come to mind-he doesn't like as the President of
France is as powerless to stop, say, the abuse of French in soc.culture.french. Likewise, the CIA can't
stop newsgroups, or sites, or Web pages, which give away their secrets. At least not in terms of the Net
itself...what non-Net steps might be taken is left as an exercise for the paranoid and the cautious.
This essential anarchy is much more common than many think. Anarchy--the absence of a ruler telling
one what to do--is common in many walks of life: choice of books to read, movies to see, friends to
socialize with, etc. Anarchy does not mean complete freedom--one can, after all, only read the books
which someone has written and had published--but it does mean freedom from external coercion.
Anarchy as a concept, though, has been tainted by other associations.
First, the "anarchy" here is not the anarchy of popular conception: lawlessness, disorder, chaos, and
"anarchy." Nor is it the bomb-throwing anarchy of the 19th century "black" anarchists, usually
associated with Russia and labor movements. Nor is it the "black flag" anarchy of anarcho-syndicalism
and writers such as Proudhon. Rather, the anarchy being spoken of here is the anarchy of "absence of
government" (literally, "an arch," without a chief or head).
183
This is the same sense of anarchy used in "anarchocapitalism," the libertarian free market ideology
which promotes voluntary, uncoerced economic transactions. [6] I devised the term crypto anarchy as a
pun on crypto, meaning "hidden," on the use of "crypto" in combination with political views (as in
Gore Vidal's famous charge to William F. Buckley: "You crypto fascist!"), and of course because the
technology of crypto makes this form of anarchy possible. The first presentation of this was in a 1988
"Manifesto," whimsically patterned after another famous manifesto. [7] Perhaps a more popularly
understandable term, such as "cyber liberty," might have some advantages, but crypto anarchy has its
own charm, I think.
And anarchy in this sense does not mean local hierarchies don't exist, nor does it mean that no rulers
exist. Groups outside the direct control of local governmental authorities may still have leaders, rulers,
club presidents, elected bodies, etc. Many will not, though.
Politically, virtual communities outside the scope of local governmental control may present problems
of law enforcement and tax collection. (Some of us like this aspect.) Avoidance of coerced transactions
can mean avoidance of taxes, avoidance of laws saying who one can sell to and who one can't, and so
forth. It is likely that many will be unhappy that some are using cryptography to avoid laws designed to
control behavior.
National borders are becoming more transparent than ever to data. A flood of bits crosses the borders of
most developed countries--phone lines, cables, fibers, satellite up/downlinks, and millions of diskettes,
tapes, CDs, etc. Stopping data at the borders is less than hopeless.
Finally, the ability to move data around the world at will, the ability to communicate to remote sites at
will, means that a kind of "regulatory arbitrage" can be used to avoid legal roadblocks. For example,
remailing into the U.S. from a site in the Netherlands...whose laws apply? (If one thinks that U.S. laws
should apply to sites in the Netherlands, does Iraqi law apply in the U.S.? And so on.)
This regulatory arbitrage is also useful for avoiding the welter of laws and regulations which operations
in one country may face, including the "deep pockets" lawsuits so many in the U.S. face. Moving
operations on the Net outside a litigious jurisdiction is one step to reduce this business liability. Like
Swiss banks, but different.
6 True Names and Anonymous Systems
Something needs to be said about the role of anonymity and digital pseudonyms. This is a topic for an
essay unto itself, of course.
Are true names really needed? Why are they asked for? Does the nation-state have any valid reason to
demand they be used?
People want to know who they are dealing with, for psychological/evolutionary reasons and to better
ensure traceability should they need to locate a person to enforce the terms of a transaction. The purely
anonymous person is perhaps justifiably viewed with suspicion.
And yet pseudonyms are successful in many cases. And we rarely know whether someone who
presents himself by some name is "actually" that person. Authors, artists, performers, etc., often use
pseudonyms. What matters is persistence, and nonforgeability. Crypto provides this.
On the Cypherpunks list, well-respected digital pseudonyms have appeared and are thought of no less
highly than their "real" colleagues are.
The whole area of digitally-authenticated reputations, and the "reputation capital" that accumulates or
is affected by the opinions of others, is an area that combines economics, game theory, psychology, and
expectations. A lot more study is needed.
184
It is unclear if governments will move to a system of demanding "Information Highway Driver's
Licenses," figuratively speaking, or how systems like this could ever be enforced. (The chemistry of
opaque nodes and links, again.)
7 Examples and Uses
It surprises many people that some of these uses are already being intensively explored. Anonymous
remailers are used by tens of thousands of persons-and perhaps abused. [13] And of course encryption,
via RSA, PGP, etc., is very common in some communities. (Hackers, Net users, freedom fighters,
white separatists, etc....I make no moral judgments here about those using these methods).
Remailers are a good example to look at in more detail. There are two current main flavors of
remailers:
1. "Cypherpunk"-style remailers, which process text messages to redirect mail to another sites,
using a command syntax that allows arbitrary nesting of remailing (as many sites as one
wishes), with PGP encryption at each level of nesting.
2. "Julf"-style remailer(s), based on the original work of Karl Kleinpaste and operated/maintained
by Julf Helsingius, in Finland. No encryption, and only one such site at present. (This system
has been used extensively for messages posted to the Usenet, and is basically successful. The
model is based on operator trustworthiness, and his location in Finland, beyond the reach of
court orders and subpoenas from most countries.)
The Cypherpunks remailers currently number about 20, with more being added every month. There is
no reason not to expect hundreds of such remailers in a few years.
One experimental "information market" is BlackNet, a system which appeared in 1993 and which
allows fully-anonymous, two-way exchanges of information of all sorts. There are reports that U.S.
authorities have investigated this because of its presence on networks at Defense Department research
labs. Not much they can do about it, of course, and more such entities are expected.
(The implications for espionage are profound, and largely unstoppable. Anyone with a home computer
and access to the Net or Web, in various forms, can use these methods to communicate securely,
anonymously or pseudonymously, and with little fear of detection. "Digital dead drops" can be used to
post information obtained, far more securely than the old physical dead drops...no more messages left
in Coke cans at the bases of trees on remote roads.)
Whistleblowing is another growing use of anonymous remailers, with folks fearing retaliation using
remailers to publicly post information. (Of course, there's a fine line between whistleblowing, revenge,
and espionage.)
Data havens, for the storage and marketing of controversial information is another area of likely future
growth. Nearly any kind of information, medical, religious, chemical, etc., is illegal or proscribed in
one or more countries, so those seeking this illegal information will turn to anonymous messaging
systems to access--and perhaps purchase, with anonymous digital cash--this information. This might
include credit data bases, deadbeat renter files, organ bank markets, etc. (These are all things which
have various restrictions on them in the U.S., for example....one cannot compile credit data bases, or
lists of deadbeat renters, without meeting various restrictions. A good reason to move them into
cyberspace, or at least outside the U.S., and then sell access through remailers.)
Matching buyers and sellers of organs is another such market. A huge demand (life and death), but
various laws tightly controlling such markets.
185
Digital cash efforts. A lot has been written about digital cash. [14] [15] David Chaum's company,
DigiCash, has the most interesting technology, and has recently begun market testing. Stefan Brands
may or may not have a competing system which gets around some of Chaum's patents. (The attitude
crypto anarchists might take about patents is another topic for discussion. Suffice it to say that patents
and other intellectual property issues continue to have relevance in the practical world, despite erosion
by technological trends.)
Credit card-based systems, such as the First Virtual system, are not exactly digital cash, in the
Chaumian sense of blinded notes, but offer some advantages the market may find useful until more
advanced systems are available.
I expect to see many more such experiments over the next several years, and some of them will likely
be market successes.
8 Commerce and Colonization of Cyberspace
How will these ideas affect the development of cyberspace?
"You can't eat cyberspace" is a criticism often levelled at argument about the role of cyberspace in
everyday life. The argument made is that money and resources "accumulated" in some future (or near-
future) cyberspatial system will not be able to be "laundered" into the real world. Even such a prescient
thinker as Neal Stephenson, in Snow Crash, had his protagonist a vastly wealthy man in "The
Multiverse," but a near-pauper in the physical world.
This is implausible for several reasons. First, we routinely see transfers of wealth from the abstract
world of stock tips, arcane consulting knowledge, etc., to the real world. "Consulting" is the operative
word. Second, a variety of means of laundering money, via phony invoices, uncollected loans, art
objects, etc., are well-known to those who launder money...these methods, and more advanced ones to
come, are likely to be used by those who wish their cyberspace profits moved into the real world.
(Doing this anonymously, untraceably, is another complication. There may be methods of doing this--
proposals have looked pretty solid, but more work is needed.)
The World Wide Web is growing at an explosive pace. Combined with cryptographically-protected
communication and digital cash of some form (and there are several being tried), this should produce
the long-awaited colonization of cyberspace.
Most Net and Web users already pay little attention to the putative laws of their local regions or
nations, apparently seeing themselves more as members of various virtual communities than as
members of locally-governed entities. This trend is accelerating.
Most importantly, information can be bought and sold (anonymously, too) and then used in the real
world. There is no reason to expect that this won't be a major reason to move into cyberspace.
9 Implications
I've touched on the implications in several places. Many thoughtful people are worried about some of
the possibilities made apparent by strong crypto and anonymous communication systems. Some are
proposing restrictions on access to crypto tools. The recent debate in the U.S. over "Clipper" and other
key escrow systems shows the strength of emotions on this issue.
Abhorrent markets may arise. For example, anonymous systems and untraceable digital cash have
some obvious implications for the arranging of contract killings and such. (The greatest risk in
arranging such hits is that physical meetings expose the buyers and sellers of such services to stings.
Crypto anarchy lessens, or even eliminates, this risk, thus lowering transaction costs. The risks to the
186
actual triggermen are not lessened, but this is a risk the buyers need not worry about. Think of
anonymous escrow services which hold the digital money until the deed is done. Lots of issues here. It
is unfortunate that this area is so little-discussed....people seem to have an aversion for exploring the
logical consequences in such areas.)
The implications for corporate and national espionage have already been touched upon. Combined with
liquid markets in information, this may make secrets much harder to keep. ((Imagine a "Digital Jane's,"
after the military weapons handbooks, anonymously compiled and sold for digital money, beyond the
reach of various governments which don't want their secrets told.)
New money-laundering approaches are of course another area to explore.
Something that is inevitable is the increased role of individuals, leading to a new kind of elitism. Those
who are comfortable with the tools described here can avoid the restrictions and taxes that others
cannot. If local laws can be bypassed technologically, the implications are pretty clear.
The implications for personal liberty are of course profound. No longer can nation-states tell their
citizen-units what they can have access to, not if these citizens can access the cyberspace world through
anonymous systems.
10 How Likely?
I am making no bold predictions that these changes will sweep the world anytime soon. Most people
are ignorant of these methods, and the methods themselves are still under development. A wholesale
conversion to "living in cyberspace" is just not in the cards, at least not in the next few decades.
But to an increasingly large group, the Net is reality. It is where friends are made, where business is
negotiated, where intellectual stimulation is found. And many of these people are using crypto anarchy
tools. Anonymous remailers, message pools, information markets. Consulting via pseudonyms has
begun to appear, and should grow. (As usual, the lack of a robust digital cash system is slowing things
down.
Can crypto anarchy be stopped? Although the future evolution in unclear, as the future almost always
is, it seems unlikely that present trends can be reversed:
Dramatic increases in bandwidth and local, privately-owned computer power.
Exponential increase in number of Net users.
Explosion in "degrees of freedom" in personal choices, tastes, wishes, goals.
Inability of central governments to control economies, cultural trends, etc. [9]
The Net is integrally tied to economic transactions, and no country can afford to "disconnect" itself
from it. (The U.S.S.R. couldn't do it, and they were light-years behind the U.S., European, and Asian
countries. And in a few more years, no hope of limiting these tools at all, something the U.S. F.B.I. has
acknowledged. [11]
Technological Inevitability: These tools are already in widespread use, and only draconian steps to
limit access to computers and communications channels could significantly impact further use.
(Scenarios for restrictions on private use of crypto.)
As John Gilmore has noted, "the Net tends to interpret censorship as damage, and routes around it."
This applies as well to attempts to legislate behavior on the Net. (The utter impossibility of regulating
the worldwide Net, with entry points in more than a hundred nations, with millions of machines, is not
yet fully recognized by most national governments. They still speak in terms of "controlling" the Net,
when in fact the laws of one nation generally have little use in other countries.)
187
Digital money in its various forms is probably the weakest link at this point. Most of the other pieces
are operational, at least in basic forms, but digital cash is (understandably) harder to deploy. Hobbyist
or "toy" experiments have been cumbersome, and the "toy" nature is painfully obvious. It is not easy to
use digital cash systems at this time ("To use Magic Money, first create a client..."), especially as
compared to the easily understood alternatives. [12] People are understandably reluctant to entrust
actual money to such systems. And it's not yet clear what can be bought with digital cash (a chicken or
egg dilemma, likely to be resolved in the next several years).
And digital cash, digital banks, etc., are a likely target for legislative moves to limit the deployment of
crypto anarchy and digital economies. Whether through banking regulation or tax laws, it is not likely
that digital money will be deployed easily. "Kids, don't try this at home!" Some of the current schemes
may also incorporate methods for reporting transactions to the tax authorities, and may include
"software key escrow" features which make transactions fully or partly visible to authorities.
11 Conclusions
Strong crypto provides new levels of personal privacy, all the more important in an era of increased
surveillance, monitoring, and the temptation to demand proofs of identity and permission slips. Some
of the "credentials without identity" work of Chaum and others may lessen this move toward a
surveillance society.
The implications are, as I see it, that the power of nation-states will be lessened, tax collection policies
will have to be changed, and economic interactions will be based more on personal calculations of
value than on societal mandates.
Is this a Good Thing? Mostly yes. Crypto anarchy has some messy aspects, of this there can be little
doubt. From relatively unimportant things like price-fixing and insider trading to more serious things
like economic espionage, the undermining of corporate knowledge ownership, to extremely dark things
like anonymous markets for killings.
But let's not forget that nation-states have, under the guise of protecting us from others, killed more
than 100 million people in this century alone. Mao, Stalin, Hitler, and Pol Pot, just to name the most
extreme examples. It is hard to imagine any level of digital contract killings ever coming close to
nationstate barbarism. (But I agree that this is something we cannot accurately speak about; I don't
think we have much of a choice in embracing crypto anarchy or not, so I choose to focus on the bright
side.)
It is hard to argue that the risks of anonymous markets and tax evasion are justification for worldwide
suppression of communications and encryption tools. People have always killed each other, and
governments have not stopped this (arguably, they make the problem much worse, as the wars of this
century have shown).
Also, there are various steps that can be taken to lessen the risks of crypto anarchy impinging on
personal safety. [10]
Strong crypto provides a technological means of ensuring the practical freedom to read and write what
one wishes to. (Albeit perhaps not in one's true name, as the nation-state-democracy will likely still try
to control behavior through majority votes on what can be said, not said, read, not read, etc.) And of
course if speech is free, so are many classes of economic interaction that are essentially tied to free
speech.
A phase change is coming. Virtual communities are in their ascendancy, displacing conventional
notions of nationhood. Geographic proximity is no longer as important as it once was.
188
A lot of work remains. Technical cryptography still hasn't solved all problems, the role of reputations
(both positive and negative) needs further study, and the practical issues surrounding many of these
areas have barely been explored.
We will be the colonizers of cyberspace.
12 Acknowledgments
My thanks to my colleagues in the Cypherpunks group, all 700 of them, past or present. Well over 100
megabytes of list traffic has passed through he Cypherpunks mailing list, so there have been a lot of
stimulating ideas. But especially my appreciation goes to Eric Hughes, Sandy Sandfort, Duncan
Frissell, Hal Finney, Perry Metzger, Nick Szabo, John Gilmore, Whit Diffie, Carl Ellison, Bill Stewart,
and Harry Bartholomew. Thanks as well to Robin Hanson, Ted Kaehler, Keith Henson, Chip
Morningstar, Eric Dean Tribble, Mark Miller, Bob Fleming, Cherie Kushner, Michael Korns, George
Gottlieb, Jim Bennett, Dave Ross, Gayle Pergamit, and--especially--the late Phil Salin. Finally, thanks
for valuable discussions, sometimes brief, sometimes long, with Vernor Vinge, David Friedman, Rudy
Rucker, David Chaum, Kevin Kelly, and Steven Levy.
13 References and Notes
1 The Cypherpunks group was mainly formed by Eric Hughes, Tim May, and John Gilmore. It began
both physical meetings, in the Bay Area and elsewhere, and virtual meetings on an unmoderated
mailing list. The name was provided by Judith Milhon, as a play on the "cyberpunk" genre and the
British spelling of cipher. The mailing list can be subscribed to by sending the single message
subscribe cypherpunks in the body of a message to majordomo@toad.com. Expect at least 50 messages
a day. About 600 subscribers in many countries are presently on the list. Some are pseudonyms.
2 RSA Data Security Inc., Redwood Shores, California, is the license administrator. Contact them for
details.
3 Many crypto texts exist. A good introduction is Bruce Schneier's Applied Cryptography, John Wiley
and Sons, 1994. This text includes pointers to many other sources. The "Crypto" Proceedings
(Advances in Cryptology, Springer-Verlag, annually) are essential references. The annual Crypto
conference in Santa Barbara, and the Eurocrypt and Auscrypt conferences, are where most crypto
results are presented.
4 David Chaum, "Untraceable Electronic Mail, Return Addresses, and Digital Pseudonyms," Comm.
ACM 24, 2, February 1981, pp. 84-88. Cypherpunks-style remailers are a form of Chaum's "digital
mixes," albeit far from ideal.
5 David Chaum, "Security without Identification: Transaction Systems to make Big Brother Obsolete,"
Comm. ACM 28, 10, October 1985. This is an early paper on digital cash...be sure to consult more
recent papers.
6 David Friedman, The Machinery of Freedom, 2nd edition. A leading theoretician of anarcho-
capitalism. (Hayek was another.)
7 Tim May, The Crypto Anarchist Manifesto, July 1988, distributed on the Usenet and on various
mailing lists.
8 The political opposition in Myan Mar--formerly Burma--is using Pretty Good Privacy running on
DOS laptops in the jungles for communications amongst the rebels, according to Phil Zimmermann,
author of PGP. This life-and-death usage underscores the role of crypto.
189
9 See Kevin Kelly's Out of Control, 1994, for a discussion of how central control is failing, and how
the modern paradigm is one of market mechanisms, personal choice, and technological empowerment.
10 Robin Hanson and David Friedman have written extensively about scenarios for dealing with the
threats of extortionists, would-be assassins, etc. I am hoping some of their work gets published
someday. (Much of the discussion was in 1992-3, on the "Extropians" mailing list.)
11 During the "Digital Telephony Bill" debate, an FBI official said that failure to mandate wiretap
capabilities within the next 18 months would make it all moot, as the cost would rise beyond any
reasonable budget (currently $500 million for retrofit costs).
12 "Magic Money" was an experimental implementation of Chaum's digital cash system. It was coded
by "Pr0duct Cypher," a pseudonymous member of the Cypherpunks list--none of us knows his real
identity, as he used remailers to communicate with the list, and digitally signed his posts. Many of us
found it too difficult to use, which is more a measure of the deep issues involved in using digital
analogs (no pun intended) to real, physical money.
13 Abuse, according to some views, of remailers is already occurring. A Cypherpunks-type remailer
was used to post a proprietary hash function of RSA Data Security, Inc. to the Usenet. (Let me hasten
to add that it was not a remailer I operate, or have control over, etc.)
14 article on digital cash, The Economist, 26 November 1994. pp. 21-23.
15 article on digital cash, Steven Levy, Wired. December 1994.

190

191
the CryptoParty handbook
Version: 2015-07-14
The CryptoParty Handbook
1
INTRODUCINGCRYPTOPARTY 13
1.1
A
BOUT
T
HIS
B
OOK
....................................................................................................................
13
1.2
A
C
RYPTO
P
ARTY
M
ANIFESTO
......................................................................................................
15
1.3
H
OW
T
O
C
RYPTO
P
ARTY
.......................................................................................................
17
1.4
P
ARTYLIKEIT
’
SDECEMBER
31
ST
1983
........................................................................................
20
1.4.1
WhatisCryptoParty?
..............................................................................................
20
1.5 PREFACE .....................................................................................................................................21
1.6
W
HY
P
RIVACY
M
ATTERS
......................................................................................................
21
2
UNDERSTANDINGEMAIL 23
2.1
B
ASIC
T
IPS
................................................................................................................................
23
2.1.1 Inbrief: .................................................................................................................................23
2.1.2 Passwords .............................................................................................................................23
2.1.3
ReadingEmailinPublicPlaces
..........................................................................................
24
2.1.4
CacheCunning
....................................................................................................................
24
2.1.5
Securingyourcommunication
..........................................................................................
25
2.1.6 DNSSEC&DANE ...................................................................................................................25
2.1.7
AccountSeparation
............................................................................................................
26
2.1.8
Anoteabouthostedemail
...............................................................................................
26
2.2
T
YPESOF
E
MAIL
........................................................................................................................
26
2.2.1
Remotelyhostedemail(‘webmail’),resourcedusingawebbrowser26
2.2.2
Remotelyhostedemail,resourcedusinganemailprogramorusing
awebbrowser
.....................................................................................................................
27
2.2.3
Contextconsiderations
......................................................................................................
27
2.2.4
Email&Metadata
...................................................................................................
28
2.2.5
Selfadministeredemailserver
.........................................................................................
28
2.2.6 ‘Free’emailservices .............................................................................................................28
2.2.7 Nonprofit .............................................................................................................................28
2.2.8
Notesonemailforwarding
...............................................................................................
29
2.3
F
EARS
.......................................................................................................................................
29
2.3.1
Randomabuseandtheftby malicioushackers
..............................................................
30
2.3.2
Targetedabuse,harassment,andspying
...............................................................
31
2.3.3
WhenEncryptionGoesWrong
.........................................................................................
31
2.4 SECURECONNECTIONS ..................................................................................................................32
2.4.1
CanotherpeoplereadalongwhenI checkmyemail?
..................................................
32
2.4.2 Notes .................................................................................................................................... 33

192
2.5 SecureEmails ......................................................................................................................................... 33
2.5.1
WhatsoftwarecanIusetoencrypt myemail?
..............................................................
34
3
UnderstandingBrowsing 35
3.1
BasicTips
...............................................................................................................................................
35
3.1.1 InBrief: ................................................................................................................................ 35
3.1.2
Yourbrowsertalksaboutyoubehind yourback
............................................................
35
3.1.3
Websitescantrackyouas youbrowse
..........................................................................
35
3.1.4
Searchingonlinecangiveawayinformation aboutyou
................................................
36
3.1.5 Moreeyesthanyou cansee .............................................................................................. 36
3.1.6
Yourrighttobeunknown
.................................................................................................
37
3.2
Fears
......................................................................................................................................................
37
3.2.1
SocialNetworkingwhatarethedangers?
....................................................................
37
3.2.2
Whocanstealmyidentity?
...................................................................................
38
3.2.3
CanIgetintroubleforGoogling weirdstuff?
.............................................................
39
3.2.4
WhoiskeepingarecordofmybrowsingandamIallowedtohide
fromthem?
..................................................................................................................................
39
3.2.5
HowtonotrevealmyIdentity?
.............................................................................
40
3.2.6
Howtoavoidbeingtracked?
............................................................................................
40
3.3
Whathappenswhenyoubrowse
.......................................................................................................
40
3.3.1
Atopographyofyou:footprints
......................................................................................
41
3.4
AccountsandSecurity
.........................................................................................................................
43
3.4.1
Canmaliciouswebsitestakeover myaccounts?
..........................................................
43
3.5
Tracking
.................................................................................................................................................
44
3.5.1
Howdotheytrackus?
......................................................................................................
44
3.5.2
HowcanIpreventtracking?
.............................................................................................
45
3.5.3
Awordofwarning
.............................................................................................................
52
3.6
Anonymity
.............................................................................................................................................
52
3.6.1
Intro
........................................................................................................................
52
3.6.2
Proxy
....................................................................................................................................
52
3.6.3
Tor
........................................................................................................................................
53
3.7
VPN
........................................................................................................................................................
54
4
PublishingAndDistribution 57
4.1
PublishingAnonymously
......................................................................................................................
57
4.1.1 SeveralDon’ts ...................................................................................................................... 58
4.2
AnonymousEmail
.................................................................................................................................
59
4.2.1
SendingFromThrowawayEmailAccounts
....................................................................
59
4.2.2
BeCarefulaboutwhatyousay!
.......................................................................................
60
4.3
FileSharing
............................................................................................................................................
60
4.3.1
BitTorrent
...............................................................................................................
61
4.3.2 SoulSeek ............................................................................................................................... 63
4.3.3I2P .........................................................................................................................................64
5
SECURECALLSANDSMS 65
5.1 SECURECALLS .............................................................................................................................65
5.1.1
iOS InstallingSignal
.........................................................................................................
65
5.1.2
Android InstallingRedPhone
..........................................................................................
65

193
5.2 SECUREMESSAGING.....................................................................................................................66
5.2.1
Android
................................................................................................................................
66
6
BASICEMAILSECURITY 67
6.1
S
TART
U
SING
T
HUNDERBIRD
.................................................................................................
67
6.1.1
InstallingThunderbirdonWindows
.................................................................................
67
6.1.2
InstallingThunderbirdonUbuntu
..........................................................................
72
6.1.3
InstallingThunderbirdonUbuntu12.04 ornewer
.........................................................
72
6.1.4
InstallingThunderbirdonMacOSX
.................................................................................
73
6.1.5
StartingThunderbirdforthefirsttime
...................................................................
76
6.2
S
ETTINGUPSECURECONNECTIONS
..............................................................................................
76
6.2.1
Configurationrequirements
..............................................................................................
77
6.2.2
PreparingaGmailaccountforusewithThunderbird
.............................................
77
6.2.3
ConfiguringThunderbirdtouseSSL/TLS
.........................................................................
78
6.2.4
Manualsetup
......................................................................................................................
80
6.2.5
Finishingthesetup,differentencryptionmethods
........................................................
82
6.2.6
Returningtotheconfigurationscreens
...........................................................................
83
6.3
S
OME
A
DDITIONAL
S
ECURITY
S
ETTINGS
........................................................................................
83
6.3.1
Junkmailsettings
...............................................................................................................
83
6.3.2
Scamdetectionandwarningsystem
...............................................................................
84
6.3.3
Antivirusintegration
.........................................................................................................
85
6.3.4
Setamasterpassword
......................................................................................................
86
6.3.5
Adaptivejunkmailcontrols
..............................................................................................
90
7
EMAILENCRYPTION 93
7.1
I
NTRODUCINGMAILENCRYPTION
(PGP)
.................................................................................
93
7.1.1
Usingakeypairtoencrypt yourmail
..............................................................................
94
7.1.2
Sendingencryptedmailstootherpeople:youneedtheirpublickey 94
7.1.3
Receivingencryptedmailsfromotherpeople:theyneedmypub
lickey ......................................................................................................................................94
7.1.4
Conclusion:encryptionrequirespublickeydistribution!
..............................................
94
7.2
I
NSTALLING
PGP
ON
W
INDOWS
..................................................................................................
94
7.2.1
InstallingPGP(GPG)onMicrosoftWindows
...................................................................
95
7.2.2
InstallingwiththeEnigmailextension
.............................................................................
95
7.2.3
Installationsteps
................................................................................................................
96
7.3
I
NSTALLING
PGP
ON
OSX
..........................................................................................................
98
7.3.1
Gettingstarted
........................................................................................................
98
7.3.2
DownloadingandinstallingtheSoftware
........................................................................
98
7.3.3
InstallingupEngimail
.......................................................................................................
107
7.4
InstallingPGPonUbuntu
..................................................................................................................
110
7.5
InstallingGPGonAndroid
.................................................................................................................
111
7.5.1APG .................................................................................................................................... 111
7.5.2GPGenabledemailonAndroid: K9Mail
....................................................................
112
7.6
CreatingyourPGPkeys
........................................................................................................
112
7.7
DailyPGPusage
..................................................................................................................................
122
7.7.1
Encryptingattachments
...................................................................................................
122
7.7.2
Enteringyourpassphrase
...............................................................................................
123

194
7.7.3
Receivingencryptedemails
...........................................................................................
123
7.7.4
Sendingandreceivingpublickeys
..................................................................................
124
7.7.5
Receivingpublickeysandaddingthemto yourkeyring
..............................................
125
7.7.6
Usingpublickeyservers
..................................................................................................
128
7.7.7
Signingemailstoanindividual
.......................................................................................
134
7.7.8
Sendingencryptedmailstoanindividual
......................................................................
135
7.7.9
Automatingencryptiontocertainrecipients
................................................................
136
7.7.10 Verifyingincomingemails ................................................................................................ 141
7.7.11
RevokingyourGPGkeypair
...........................................................................................
142
7.7.12
Whattodowhenyouhavelostyoursecretkey,orforgotyourpassphrase
......................
142
7.7.13
Whattodowhenyoursecretkeyhasbeenstolen,or compromised142
7.7.14
Receivingarevocationcertificate
..................................................................................
143
7.7.15
Preparingfortheworst:backupyourkeys
.........................................................
143
7.7.16
Furtherreading
.................................................................................................................
146
7.8
WebmailandPGP
..............................................................................................................................
146
8
SaferBrowsing 147
8.1
WhyFirefox?
.......................................................................................................................................
147
8.2 AccessingFirefoxonUbuntu............................................................................................................... 147
8.3
InstallingonMacOSX
.......................................................................................................................
148
8.4
InstallingFirefoxonWindows
...........................................................................................................
153
8.4.1
Troubleshooting
................................................................................................................
157
8.5
ExtendingFirefox
................................................................................................................................
157
8.5.1
HTTPSEverywhere
...........................................................................................................
158
8.5.2
Installation
........................................................................................................................
158
8.5.3 Configuration ..................................................................................................................... 160
8.5.4 Usage ................................................................................................................................. 160
8.5.5
IfnetworksblockHTTPS
..................................................................................................
163
8.5.6
Addingsupportforadditionalsitesin HTTPSEverywhere
..........................................
163
8.5.7
EnforcingsecureHTTPSserverconnections
..................................................................
163
8.5.8
AdblockPlus
......................................................................................................................
164
8.5.9
GettingstartedwithAdblockPlus
.......................................................................
164
8.5.10
Choosingafiltersubscription
.........................................................................................
164
8.5.11
Creatingpersonalizedfilters
...........................................................................................
166
8.5.12
EnablinganddisablingAdBlockPlusforspecificelementsorWeb
sites ..................................................................................................................................... 166
8.5.13
Otherextensionsthatcanimproveyoursecurity
...............................................
166
8.6
P
ROXY
S
ETTINGS
...................................................................................................................
167
8.6.1
DefaultFirefoxproxyconfiguration
............................................................................
168
8.7
U
SING
T
OR
?
.........................................................................................................................
170
8.7.1
UsingTorBrowserBundle
...........................................................................................
171
8.7.2
DownloadingTorBrowserBundle
...............................................................................
171
8.7.3
RunningaRelayorBridge
............................................................................................
171
8.8
E
XTENDING
G
OOGLE
C
HROME
................................................................................................
172
8.8.1
Disabling Instant Search
...............................................................................................
172
8.8.2 AdBlock for Chrome ...................................................................................................... 172
8.8.3
HTTPS Everywhere
........................................................................................................
172

195
8.8.4
PrivacyFix
.........................................................................................................................
172
9
PASSWORDS 173
9.1 KEEPING PASSWORDS SAFE ...................................................................................................... 173
9.1.1
Passwordlengthandcomplexity
.................................................................................
173
9.1.2
Easytorememberandsecurepasswords
..................................................................
173
9.1.3 Minimizing damage ....................................................................................................... 173
9.1.4
Usingapasswordmanager
..........................................................................................
174
9.1.5
Physical protection
.......................................................................................................
174
9.1.6
Other caveats
................................................................................................................
174
9.2
I
NSTALLING
K
EE
P
ASS
..............................................................................................................
174
9.2.1
InstallingKeePassX onUbuntu
....................................................................................
174
9.2.2
InstallingKeePassonWindows
...................................................................................
175
9.2.3
InstallingKeePassonMac OSX
...................................................................................
181
9.3
E
NCRYPTING
P
ASSWORDSWITHA
P
ASSWORD
M
ANAGER
..........................................................
189
9.3.1
EncryptingPasswords withKeePassXonUbuntu
.....................................................
189
9.3.2
EncryptingPasswords withKeePassonWindows
.....................................................
195
9.3.3
EncryptingPasswordswithKeychainonMacOSX
....................................................
201
10
USING VPN 205
10.1
G
ETTING
,
SETTING
UPANDTESTINGA
VPN
ACCOUNT
..........................................................
205
10.1.1
Anaccountfromacommercial VPNprovider
...........................................................
205
10.1.2
Settingup OpenVPNclient
..........................................................................................
207
10.1.3
Caveats & Gotchas
.......................................................................................................
208
10.2
VPN
ON
U
BUNTU
............................................................................................................
208
10.2.1
PreparingNetworkManagerforVPNnetworks
........................................................
208
10.2.2
ConfiguringanOpenVPNnetwork
..............................................................................
214
10.2.3
UsingyournewVPNconnection
.................................................................................
220
10.3
VPN
ON
M
AC
OSX
................................................................................................................
222
10.3.1
Setup
................................................................................................................................
222
10.4
VPN
ON
W
INDOWS
...............................................................................................................
235
10.4.1
Setup
.................................................................................................................................
235
10.5
MakingSureYourVPNWorks
..........................................................................................................
248
11
DiskEncryption 249
11.1
InstallingVeraCry pt
.........................................................................................................................
249
11.1.1
InstallingonUbuntu/Debian
................................................................................
249
11.1.2
InstallingonOSX
..............................................................................................................
252
11.1.3
InstallingonWindows
.....................................................................................................
256
11.2
Using VeraCrypt .................................................................................................................................
256
11.2.1
Creating a VeraCrypt Container ...........................................................................
256
11.2.2
MountingtheEncryptedVolume
...................................................................................
262
11.2.3
Whatdoesthismean?
.....................................................................................................
265
11.2.4
Remembertodismount!
.................................................................................................
265
11.3
Settingupahiddenvolume
..............................................................................................................
265
11.4
Securelydestroyingdata
...................................................................................................................
270
11.4.1
AnoteonSolidState HardDrives
..................................................................................
271

196
11.4.2
SecurelydeletedataunderWindows
............................................................................
271
11.4.3
SecurelydeletedataunderMacOSX
..............................................................................
273
11.4.4
SecurelydeletedataunderUbuntu/Linux
...........................................................
278
11.5
AboutLUKS
.........................................................................................................................................
285
11.5.1
StartingDisks
..................................................................................
285
11.5.2
Encryptingadevice
..........................................................................................................
287
11.5.3
Usinganencrypteddevice
..............................................................................................
291
12
CallEncryption 293
12.1
InstallingCSipSimple
..........................................................................................................................
293
12.1.1
IntroducingTheOSTNNetwork
......................................................................................
293
12.1.2 CSipSimple ......................................................................................................................... 294
13
InstantMessagingEncryption 299
13.1
SettingupEncryptedInstantMessaging
..............................................................................
299
13.1.1
Android InstallingGibberbot
........................................................................................
299
13.1.2
iOS InstallingChatSecure
..............................................................................................
299
13.1.3
Ubuntu InstallingPidgin
................................................................................................
299
13.1.4
OSX InstallingAdium
....................................................................................................
300
13.1.5
Windows InstallingPidgin
.............................................................................................
300
13.1.6
AllOS crypto.cat
............................................................................................................
300
13.1.7
ChatLogFiles
....................................................................................................................
301
14
SecureFileSharing 303
14.1
InstallingI2PonUbuntuLucidLynx(andnewer)andderivativeslikeLinuxMint&Trisquel
.........
303
14.2
InstructionsforDebianLennyandnewer
.......................................................................................
306
14.3
StartingI2P
...........................................................................................................................
306
14.4
A
NONYMOUS
B
ITTORRENTWITH
I2PS
NARK
...............................................................................
306
15
APPENDICES 309
15.1
C
RYPTOGRAPHYAND
E
NCRYPTION
.......................................................................................
309
15.1.1
Encryptionexamples
........................................................................................................
310
15.1.2 AWarning! ..........................................................................................................................310
15.1.3
Historicalciphers
..............................................................................................................
311
15.1.4
Modernciphers
................................................................................................................
313
15.1.5
QuantumCryptography
...................................................................................................
314
15.1.6 Challenges&Implications ..................................................................................................314
15.2 GLOSSARY ................................................................................................................................ 315
15.2.1
aggregator
.........................................................................................................................
315
15.2.2
anonymity
.........................................................................................................................
315
15.2.3
anonymousremailer
........................................................................................................
315
15.2.4
ASP(applicationserviceprovider)
..................................................................................
316
15.2.5 backbone ............................................................................................................................316
15.2.6
badware
............................................................................................................................
316
15.2.7
bandwidth
.........................................................................................................................
316
15.2.8
bash(Bourneagainshell)
................................................................................................
316
15.2.9
BitTorrent
..............................................................................................................
316
197
15.2.10
blacklist
.............................................................................................................................
316
15.2.11
bluebar
..............................................................................................................................
317
15.2.12 block ....................................................................................................................................317
15.2.13 bookmark ............................................................................................................................317
15.2.14 bridge ..................................................................................................................................317
15.2.15
bruteforceattack
............................................................................................................
317
15.2.16 cache ...................................................................................................................................317
15.2.17 censor .................................................................................................................................317
15.2.18 censorware .........................................................................................................................317
15.2.19
CGI(CommonGatewayInterface)
..................................................................................
318
15.2.20
chat
.......................................................................................................................
318
15.2.21 cipher ..................................................................................................................................318
15.2.22
circumvention
...................................................................................................................
318
15.2.23
CommonGatewayInterface
...........................................................................................
318
15.2.24
commandlineinterface
..................................................................................................
318
15.2.25 cookie ..................................................................................................................................318
15.2.26
countrycodetopleveldomain(ccTLD)
.........................................................................
318
15.2.27
cryptography
.....................................................................................................................
319
15.2.28
DARPA(DefenseAdvancedProjectsResearchAgency)
...............................................
319
15.2.29
decryption
.........................................................................................................................
319
15.2.30
diskencryption
.................................................................................................................
319
15.2.31
domain
..............................................................................................................................
319
15.2.32
DNS(DomainNameSystem)
..........................................................................................
319
15.2.33 DNSleak .............................................................................................................................320
15.2.34 DNSserver ......................................................................................................................... 320
15.2.35
DNStunnel
........................................................................................................................
320
15.2.36 Eavesdropping.....................................................................................................................320
15.2.37 email ................................................................................................................................. 320
15.2.38
embeddedscript
..............................................................................................................
321
15.2.39
encryption
.........................................................................................................................
321
15.2.40
exitnode
...........................................................................................................................
321
15.2.41 filesharing ......................................................................................................................... 321
15.2.42
filespreadingengine
........................................................................................................
321
15.2.43 filter ................................................................................................................................... 321
15.2.44 Firefox ................................................................................................................................ 321
15.2.45 forum ................................................................................................................................. 321
15.2.46 frame .................................................................................................................................. 322
15.2.47
FTP(FileTransferProtocol)
..................................................................................
322
15.2.48
fulldiskencryption
...........................................................................................................
322
15.2.49
gateway
.............................................................................................................................
322
15.2.50
GNUPrivacyGuard
..........................................................................................................
322
15.2.51 GPG ....................................................................................................................................... 322
15.2.52 honeypot ............................................................................................................................... 322
15.2.53 hop ........................................................................................................................................ 322
15.2.54
HTTP(HypertextTransferProtocol)
...............................................................................
323
15.2.55
HTTPS(SecureHTTP)
............................................................................................
323
15.2.56
IANA(InternetAssignedNumbersAuthority)
...............................................................
323

198
15.2.57
ICANN(InternetCorporationforAssignedNamesandNumbers) 32315.2.58InstantMessaging
(IM)
323
15.2.59
Intermediary
.....................................................................................................................
323
15.2.60
Internet
................................................................................................................
323
15.2.61
IP(InternetProtocol)Address
..............................................................................
323
15.2.62
IRC(Internetrelaychat)
.......................................................................................
324
15.2.63
ISP(InternetServiceProvider)
.............................................................................
324
15.2.64
JavaScript
..........................................................................................................................
324
15.2.65
KeePass,KeePassX
...........................................................................................................
324
15.2.66
keychainsoftware
............................................................................................................
324
15.2.67 keywordfilter .................................................................................................................... 324
15.2.68
latency
...............................................................................................................................
324
15.2.69 logfile ................................................................................................................................ 324
15.2.70
lowbandwidthfilter
........................................................................................................
325
15.2.71 malware ............................................................................................................................. 325
15.2.72
maninthemiddle
............................................................................................................
325
15.2.73
middlemannode
..............................................................................................................
325
15.2.74
monitor
..............................................................................................................................
325
15.2.75
networkaddresstranslation(NAT)
......................................................................
325
15.2.76
networkoperator
.............................................................................................................
325
15.2.77 node ................................................................................................................................... 326
15.2.78
non-exit node ...................................................................................... 326
15.2.79 obfuscation ............................................................................................... 326
15.2.80
open node ............................................................................................ 326
15.2.81
OTR/Off-the-Record messaging ......................................................... 326
15.2.82
packet .................................................................................................. 326
15.2.83
password manager ............................................................................... 326
15.2.84
pastebin ............................................................................................... 327
15.2.85 peer-to-peer............................................................................................... 327
15.2.86
perfect forward secrecy ...................................................................... 327
15.2.87
Pretty Good Privacy (PGP) ............................................................ 327
15.2.88 PHP ........................................................................................................... 327
15.2.89
plain text ............................................................................................. 327
15.2.90
plaintext ............................................................................................... 327
15.2.91
privacy ................................................................................................. 328
15.2.92
private key ........................................................................................... 328
15.2.93 POP3 ......................................................................................................... 328
15.2.94
port .................................................................................................. 328
15.2.95 protocol ..................................................................................................... 328
15.2.96
proxy server ........................................................................................ 328
15.2.97
Psiphon node ....................................................................................... 328
15.2.98
private node ......................................................................................... 329
15.2.99 public key ................................................................................................. 329
15.2.100
public key encryption/public-key cryptography ................................ 329
15.2.101
publicly routable IP address ............................................................... 329
15.2.102
regular expression ............................................................................... 329
15.2.103 remailer ..................................................................................................... 329
15.2.104
router ................................................................................................... 330
199
15.2.105
root name server ................................................................................. 330
15.2.106
RSS (Real Simple Syndication) ......................................................... 330
15.2.107 scheme ...................................................................................................... 330
15.2.108 shell .......................................................................................................... 330
15.2.109 SOCKS ..................................................................................................... 330
15.2.110 screenlogger .............................................................................................. 330
15.2.111
script .................................................................................................... 331
15.2.112
smartphone .......................................................................................... 331
15.2.113
spam .................................................................................................... 331
15.2.114 SSH (Secure Shell) .................................................................................. 331
15.2.115
SSL (Secure Sockets Layer) ............................................................... 331
15.2.116
steganography ..................................................................................... 331
15.2.117
subdomain ........................................................................................... 332
15.2.118
threat analysis ..................................................................................... 332
15.2.119
Top-Level Domain (TLD) .................................................................. 332
15.2.120
TLS (Transport Layer Security) ......................................................... 332
15.2.121
TCP/IP (Transmission Control Protocol over Internet Protocol) . 332
15.2.122
Tor bridge ............................................................................................ 332
15.2.123 traffic analysis ........................................................................................... 332
15.2.124
tunnel ................................................................................................... 333
15.2.125
UDP (User Datagram Packet) ........................................................ 333
15.2.126
URL (Uniform Resource Locator) ..................................................... 333
15.2.127 Usenet ....................................................................................................... 333
15.2.128
VoIP (Voice over Internet Protocol).............................................. 333
15.2.129
VPN (virtual private network) ............................................................ 333
15.2.130
whitelist ............................................................................................... 334
15.2.131
World Wide Web (WWW) ................................................................. 334
15.2.132 Webmail .................................................................................................... 334
15.2.133
Web proxy ........................................................................................... 334
15.2.134 WHOIS ..................................................................................................... 334
15.3 The necessity of Open Source .......................................................................... 335
1 Introducing Cryptoparty
1.1 About This Book
The CryptoParty Handbook was born from a suggestion by Marta Peirano (http:
//petitemedia.es) and Adam Hyde (http://booksprints.net) after the first Berlin
CryptoParty, held on the 29th of August, 2012. Julian Oliver (http://julianoliver.
com)
and Danja Vasiliev (http://k0a1a.net), co-organisers of the Berlin CryptoParty along with
Marta were very enthusiastic about the idea, seeing a need for a practical working book
with a low entry-barrier to use in subsequent parties. Asher Wolf, origi- nator of the
CryptoParty movement, was then invited to run along and the project was
born.

200
This book was written in the first 3 days of October 2012 at Studio Weise7, Berlin, surrounded
by fine food and a small ocean of coffee. Approximately 20 people were involved in its creation,
some more than others, some local and some far.
The writing methodology used, BookSprint (http://booksprints.net), is all about minimising
any obstruction between expertise and the published page. Face-to-face dis- cussion and
dynamic task-assignment were a huge part of getting the job done, like any good CryptoParty!
The open source, web-based (HTML5 and CSS) writing platform BookType (http:
//booktype.pro) was chosen for the editing task, helping such a tentacular feat of parallel
development to happen with relative ease. Asher also opened a couple of TitanPad pages to crowd-
source the Manifesto and HowTo CryptoParty chapters.
Combined, this became the official CryptoParty Handbook by midnight October the 3rd,
GMT+1.
The Book Sprint was 3 days in length and the full list of onsite participants included:
•
Adam Hyde (facilitator)
•
Marta Peirano
•
Julian Oliver
•
Danja Vasiliev
•
Asher Wolf (http://cryptoparty.org)
•
Jan Gerber
•
Malte Dik
•
Brian Newbold
•
Brendan Howell (http://wintermute.org
•
AT
•
Carola Hesse
•
Chris Pinchen (http://chokepointproject.net).
•
Cover art by Emile Denichaud (http://about.me/denichaud)
This version of the handbook has since moved to github to collaboratively edit it. Find it
at https://github.com/cryptoparty/handbook. If you see areas that need improvement or
simply come across a typo, create a github account and start editing, commenting or creating
issues. For help using git and github, see https://help.github. com/.
CryptoParty HandBook Credits
Facilitated by:
•
Adam Hyde Core
Team:
•
Marta Peirano
•
Asher Wolf
•
Julian Oliver
•
Danja Vasiliev
•
Malte Dik
•
Jan Gerber
•
Brian Newbold
•
Brendan Howell
Assisted by:

201
•
Teresa Dillon
•
AT
•
Carola Hesse
•
Chris Pinchen
•
‘LiamO’
•
‘l3lackEyedAngels’
•
‘Story89’
•
Travis Tueffel
Github migration, packaging and maintenance by:
•
Yuval Adam
•
Samuel Carlisle
•
Daniel Kinsman
•
pettter
•
Jens Kubieziel
•
Uwe Lippmann
•
Kai Engert
1.2 A CryptoParty Manifesto
Cover Image by Emile Denichaud. Other
material included:
•
https://www.flossmanuals.net/bypassing-censorship
The manuals used in the second half of this book borrow from 2 books sprinted by FLOSS
Manuals:
•
“How to Bypass Internet Censorship” 2008 & 2010 Adam Hyde (Facilitator), Al- ice Miller,
Edward Cherlin, Freerk Ohling, Janet Swisher, Niels Elgaard Larsen, Sam Tennyson, Seth
Schoen, Tomas Krag, Tom Boyle, Nart Villeneuve, Ronald Deibert, Zorrino Zorrinno, Austin
Martin, Ben Weissmann, Ariel Viera, Niels El- gaard Larsen, Steven Murdoch, Ross
Anderson, helen varley jamieson, Roberto Rastapopoulos, Karen Reilly, Erinn Clark, Samuel
L. Tennyson, A Ravi
•
“Basic Internet Security” 2011 Adam Hyde (Facilitator), Jan Gerber, Dan Hassan, Erik
Stein, Sacha van Geffen, Mart van Santen, Lonneke van der Velden, Emile den Tex and
Douwe Schmidt
All content in the CryptoParty Handbook is licensed under the Creative Commons Attribution-
ShareAlike 3.0 Unported (CC BY-SA 3.0).
All chapters Âľ the contributors unless otherwise noted below.
1.2
A CryptoParty Manifesto
“Man is least himself when he talks in his own person. Give him a mask,
and he will tell you the truth.” - Oscar Wilde

202
In 1996, John Perry Barlow, co-founder of the Electronic Frontier Foundation (EFF), wrote ‘A
Declaration of the Independence of Cyberspace’. It includes the following passage:
Cyberspace consists of transactions, relationships, and thought itself, arrayed like a
standing wave in the web of our communications. Ours is a world that is both
everywhere and nowhere, but it is not where bodies live.
We are creating a world that all may enter without privilege or prejudice accorded by
race, economic power, military force, or station of birth.
We are creating a world where anyone, anywhere may express his or her beliefs, no
matter how singular, without fear of being coerced into silence or conformity.
Sixteen years later, and the Internet has changed the way we live our lives. It has given us the
combined knowledge of humankind at our fingertips. We can form new relationships and share our
thoughts and lives with friends worldwide. We can organise, communicate and collaborate in ways
never thought possible. This is the world we want to hand down to our children, a world with a
free Internet.
Unfortunately, not all of John Perry Barlow’s vision has come to pass. Without access to online
anonymity, we can not be free from privilege or prejudice. Without privacy, free expression is
not possible.
The problems we face in the 21st Century require all of humanity to work together. The issues we
face are serious: climate change, energy crises, state censorship, mass surveil- lance and on-going
wars. We must be free to communicate and associate without fear. We need to support free and
open source projects which aim to increase the commons’ knowledge of technologies that we depend
on http://opensourceecology.org/wiki Contribute!
To realise our right to privacy and anonymity online, we need peer-reviewed, crowd- sourced
solutions. CryptoParties provide the opportunity to meet up and learn how to use these solutions
to give us all the means with which to assert our right to privacy and
anonymity online.
1.
We are all users, we fight for the user and we strive to empower the user. We assert user
requests are why computers exist. We trust in the collective wisdom of human beings, not
software vendors, corporations or governments. We refuse the shackles of digital gulags,
lorded over by vassal interests of governments and corporations. We are the CypherPunk
Revolutionaries.
2.
The right to personal anonymity, pseudonymity and privacy is a basic human right. These
rights include life, liberty, dignity, security, right to a family, and the right to live without
fear or intimidation. No government, organisation or individual should prevent people from
accessing the technology which underscores these basic human rights.
3.
Privacy is the right of the individual. Transparency is a requirement of governments and
corporations who act in the name of the people.
4.
The individual alone owns the right to their identity. Only the individual may choose what
they share. Coercive attempts to gain access to personal information without explicit consent
is a breach of human rights.

203
5.
All people are entitled to cryptography and the human rights crypto tools afford, regardless of
race, colour, sex, language, religion, political or other opinion, national or social origin,
property, birth, political, jurisdictional or international status of the country or territory in
which a person resides.
6.
Just as governments should exist only to serve their citizens - so too, cryptography should
belong to the people.Technology should not be locked away from the people.
7.
Surveillance cannot be separated from censorship, and the slavery it entails. No
machine shall be held in servitude to surveillance and censorship. Crypto is a key to
our collective freedom.
8.
Code is speech: code is human created language. To ban, censor or lock cryptog-
raphy away from the people is to deprive human beings from a human right, the
freedom of speech.
9.
Those who would seek to stop the spread of cryptography are akin to the 15th cen-
tury clergy seeking to ban the printing press, afraid their monopoly on knowledge
will be undermined.
1.3
How To CryptoParty
•
Throw a party. All you need is a time, a date and a location. Add it to the wiki:
https://cryptoparty.org.
•
Make sure you have Internet connectivity and enough power sources for all devices. If you do
not have a place to hold a CryptoParty, find a pub or park where you can meet and squeeze
the public bandwidth. That will really hone your skills!
•
Bring USB sticks and printed handouts for those who need them, and set up old computers
for people to fiddle with and try out new skills.
•
Talk about Linux to everyone you meet at your CryptoParty. If you are new to CryptoParties
- ask someone “what is Linux?” ASAP.
•
Make entry free for all if possible - CryptoParties are not-for-profit, not commer- cially
aligned and especially important for those without other resources.
•
Teach basic cryptographic tools to the masses. Crowd-source the best crypto. We
suggest PGP, OTR, and Tor as the first tools to install.
•
Invite experts and non-experts from all fields. Everyone is an expert on something.
•
If you want CryptoParty to do something, start doing it. Organise organically and
chaotically. Have no clear leadership. Urge people to take on a sudo leadership role
- take a tutorial, fix the wifi, update the wiki, or organise the next CryptoParty. If someone
claims others are doing it wrong - invite them to nominate themselves to do it better.
•
Ask for feedback. Assimilate critics - ask them for their help in creating a better CryptoParty.
Do not be scared to troll the trolls back or boot them from your space. Share feedback on
the wiki. Iterate.
•
A successful CryptoParty can have as many or as few as two people. Size doesn’t count,
it’s what you do with it that matters. The criterion for success should be that everyone had

204
fun, learned something and wants to come to the next party.
•
Think of the CryptoParty movement as a huge Twitter hive ready to swarm at any moment.
Tweet a lot, and make your tweets meaningful. ReTweet other CryptoPartiers frequently.
•
Make sure the way crypto is taught at your party could be understood by a 10 year old. Then have
the 10 year old teach it to an 80 year old. Breach the digital divide with random acts of
awesomeness such as unfettered use of images of kittens in all CryptoParty literature. Red
underpants on heads is only mandatory if you wish to bid in our spectrum auction.
•
Consider hosting private, off-the-radar CryptoParties for activists, journalists and in individuals
working in dangerous locations.
•
Don’t scare non-technical people. Don’t teach command lines before people know where the on-
off buttons are located on their laptops. Everyone learns at their own pace - make sure there is
support for those in need of help.
•
Doing excellent stuff at CryptoParty does not require permission or an official consensus decision.
If you’re uncertain about the excellence of something you want to do, you should ask someone
else what they think.
•
Consider the need for a bouncer, particularly if your CryptoParty expects over 50 people.
Dress the bouncer up as a Sumo wrestler. Do not be afraid to bounce people who breach
CryptoParty’s anti-harassment policy.
•
CryptoParty is dedicated to providing a harassment-free sharing experience for everyone,
regardless of gender, sexual orientation, disability, physical appearance, body size, heritage, or
religion. Behaving like an arsehole may mean you are per- manently uninvited to CryptoParties
events. Harassment includes:
–
hurtful or offensive comments
–
deliberate intimidation
–
direct or indirect threats
–
stalking
–
following
–
inappropriate physical contact
–
unwelcome sexual attention.
•
Encourage a culture of sharing. Encourage advanced users to help not-so advanced ones.
Delegate.
•
Use online meeting platforms like mumble, or even chatrooms (e.g. #cryptoparty room on
http://occupytalk.org/) when physical meetups are not possible or im- practical.
•
Copy from other cryptoparties. Remix, Reuse and Share. Create a basket of old devices
people are willing to donate to more needy CryptoPartiers.
•
Get the word out! Print posters and/or flyers and distribute them in your neigh- bourhood, post
online versions to social networks and mail them to friends, for them to distribute the info even
further.
•
Don’t sell out to sponsors for pizza and beer money. Ask people to try and bring food and drink
to share. Host CryptoPicnics as often as possible. Make friends with librarians. They wield power
205
over keys to local, public meeting rooms that may be free of charge to utilize.
•
Invite all the people. Bring people together who have a wide range of skills and interests -
musicians, political pundits, activists, hackers, programmers, journalists, artists and philosophers.
Spread the love.
•
Invite the graphic designers and illustrators you know to contribute new ways to help people
understand crypto.
•
Invite everyone to share their knowledge and their skills. Individuals with little or no coding,
programming, hacking or crypto skills can change cultures by promoting the idea that privacy is
a fundamental right.
•
Share music, beers, & chips. Bond together over eclectic music, cheeseballs, in- stalling GPG,
TrueCrypt, OTR and Tor, as well as watching movies together. We recommend Hackers, The
Matrix, Bladerunner, Tron, Wargames, Sneakers, and The Net.
•
Do not work too hard. Take breaks. Eat popcorn together. Create slang, phrases, memes.
•
When people at CryptoParties ask for advice on “hacking the Gibson” refer them to episodes of
‘My Little Pony’.
•
Create fliers and advertise using slogans like: “CryptoParties: If there is hope, it lies in the proles”
and “CryptoParty like it’s 1984.” CryptoParty all the things to avoid oppression and depression.
•
Seed CryptoParties in your local communities - at nursing homes, scout groups, music festivals,
universities, schools. Take CryptoParty to isolated and remote communities. Make friends in far
away places and travel whenever possible. Ask people in rural farming communities if they’d like
to CryptoParty.
•
Share shimmering opportunities of crowd-sourced privacy: swap cheap, pre-paid SIMs, handsets
and travel cards.
•
Create logos in bright pink and purple, with hearts all over them. Promote Cryp- toParties to
rebellious 13 year old girls. Declare success if rebellious 13 year old girls demand to attend your
parties.
•
Become friends with journalists. Invite them to your parties. Teach them crypto. Do not scare
them by discussing Assassination Markets.
•
Strew CryptoParty sigils across your city in 3am post-party raids. Make lots of stickers, paste
them everywhere.
•
Experiment, constantly. Do not be afraid to make mistakes. Encourage people to tinker.
Assume all mistakes are meant to be made. Most people under intel agency scrutiny have
electronic devices already compromised before they walk in the door. Teach people to install
tools from scratch, so they can do it on a new machine, away from prying eyes.
•
Assume intel agencies send representatives to CryptoParties. Acknowledge their presence
at the start of your meeting, ask them to share their crypto skills. Joke about paranoia as
often as possible without instilling panic. Wear tinfoil hats.
•
Be excellent to each other and CryptoParty on.

206
1.4
Party like it’s december 31st 1983
1.4.1WhatisCryptoParty?
CryptoParty
is a decentralized, global initiative to introduce basic tools for protecting privacy,
anonymity and overall security on the Internet to the general public.
The idea was conceived in the wake of the Australian Cybercrime Legislation Amend- ment Bill
2011 and the reasoning is that laws like this are without substance when everybody encrypts their
communication.
CryptoParties are neither commercially nor politically aligned, and free and open to attend for
everyone as long as they live the following
guiding principles
:
Be excellent to each other
CryptoParties are environments where people feel welcome and safe to learn and teach no matter
their background or level of expertise. All questions are relevant, all explanation shall be targeted at
the person with least pre-knowledge.
This also means that any form of harassment or other behaviour that makes people uncomfortable
has no place at CryptoParties. In our experience situations like these (as seldom as they occur) stem
rather from social ineptitude than malice and can thus be resolved by making people aware of their
behaviour and its effect on others, but in last consequence it is on the organizers of the CryptoParty
to ask people to leave if they don’t adhere to this very simple rule. Be excellent to each other.
Awareness is key in this regard.
Do things
CryptoParties happen because people make them happen. The most amazing and un- foreseen
learning experiences happen because people make them happen. If you are uncertain if what
you have in mind is on topic or if other people are interested as well:
1.5 Preface
Propose it anyway and see what other people have to say. If you are too shy to propose to the
whole room: Ask the person standing next to you first.
On a more global scale, there is a mailing list global@cryptoparty.is which is open for
questions and discussion of all kind, as well as country and city-specific mailing lists and other
resources which can be found on https://cryptoparty.in .
For a guide on how to organize CryptoParties please be referred to the chapter of the same
name.
1.5
Preface
This book is a collective and ongoing effort in that it is based on the two FLOSS Manuals How to
Bypass Internet Censorship and Basic Internet Security and collaboratively edited on Github
although other venues of collaborative editing are investigated.
Its goal is to give a comprehensive resource to people who would like to attend or organize a
CryptoParty but lack the local expertise or just confidence in doing so. All chapters are designed to
be self-contained.
All content in the
CryptoPartyHandbook
is licensed under the Creative Commons Attribution-
ShareAlike 3.0 Unported (CC BY-SA 3.0). The authors are listed in
AppendixA:Contributions
.
207
1.6
Why Privacy Matters
Privacy is a fundamental human right. It is recognized in many countries to be as central to
individual human dignity and social values as Freedom of Association and Freedom of Speech.
Simply put, privacy is the border where we draw a line between how far a society can intrude
into our personal lives.
Countries differ in how they define privacy. In the UK for example, privacy laws can be traced
back to the 1300s when the English monarchy created laws protecting people from eavesdroppers
and peeping toms. These regulations referred to the intrusion of a person’s comfort and not even the
King of England could enter into a poor persons house without their permission. From this
perspective, privacy is defined in terms of personal space and private property. In 1880 American
lawyers, Samuel Warren and Louis Bran- deis described privacy as the ‘right to be left alone’. In
this case, privacy is synonymous with notions of solitude and the right for a private life. In 1948,
the Universal Dec- laration of Human Rights specifically protected territorial and communications
privacy which by that became part of constitutions worldwide. The European Commission on
Human Rights and the European Court of Human Rights also noted in 1978 that pri- vacy
encompasses the right to establish relationships with others and develop emotional well-being.
Today, a further facet of privacy increasingly perceived is the personal data we provide to
organizations, online as well as offline. How our personal data is used and accessed drives the debate
about the laws that govern our behavior and society. This in turn has knock-on effects on the public
services we access and how businesses interact with us. It
even has effects on how we define ourselves. If privacy is about the borders which govern who we
give permission to watch us and track aspects of our lives, then the amount and type of personal
information gathered, disseminated and processed is paramount to our basic civil liberties.
An often heard argument, when questions of privacy and anonymity come up, goes along the lines
of, “I only do boring stuff. Nobody will be interested in it anyway” or, “I have nothing to hide”.
Both of these statements are easily defeated.
Firstly, a lot of companies are very interested in what boring things you do precisely so they
have opportunity to offer “excellent” products fitting interests. In this way their advertising becomes
much more efficient - they are able to tailor specifically to assumed needs and desires. Secondly you
do have lots to hide. Maybe you do not express it in explicitly stated messages to friends and
colleagues, but your browsing - if not protected by the techniques laid out in this book - will tell a
lot about things you might rather keep secret: the ex-partner you search for using Google, illnesses
you research or movies you watch are just few examples.
Another consideration is that just because you might not have something to hide at this moment,
you may very well in future. Putting together all the tools and skills to protect yourself from
surveillance takes practice, trust and a bit of effort. These are things you might not be able to
achieve and configure right when you need them most and need not take the form of a spy movie.
An obsessed, persistent stalker, for example, is enough to heavily disrupt your life. The more you
follow the suggestions given in this book, the less impact attacks like this will have on you.
Companies may also stalk you too, finding more and more ways to reach into your daily life as the
reach of computer networking itself deepens.
Finally, a lack of anonymity and privacy does not just affect you, but all the people around you.
If a third party, like your Internet Service Provider, reads your email, it is also violating the privacy
of all the people in your address book. This problem starts to look even more dramatic when
you look at the issues of social networking websites like Facebook. It is increasingly common to
see photos uploaded and tagged without the knowledge or permission of the people affected.

208
While we encourage you to be active politically to maintain your right to privacy, we wrote this
book in order to empower people who feel that maintaining privacy on the Internet is also a personal
responsibility. We hope these chapters will help you reach a point where you can feel that you have
some control over how much other people know about you. Each of us has the right to a private life,
a right to explore, browse and communicate with others as one wishes, without living in fear of
prying eyes.
2
Understanding Email
2.1
Basic Tips
Just as with other forms of communication on the web, some basic precautions always ought to be
taken to ensure you have the best chance at protecting your privacy.
2.1.1
Inbrief:
•
Passwords shouldn’t relate to personal details and should contain a mix of a rea- sonable
amount of letters and other characters.
•
To change passwords regularly is important as they might have been stolen, cracked or
exposed to others in the meantime.
•
Always be sure your connection is secure when reading email on a wireless network,
especially in Internet cafes.
•
Temporary files (the ‘cache’) on the computer that you use to check your email can
present some risks. Clear them often.
•
Create and maintain separate email accounts for different tasks and interests.
•
Encrypt any message you wouldn’t feel comfortable sending on a post card.
•
Be aware of the risks of having your email hosted by a company or organization.
2.1.2
Passwords
Passwords are a primary point of vulnerability in email communication. Even a secure password can
be read in transit unless the connection is secure (see TLS/SSL in the glossary). In addition, just
because a password is long doesn’t mean it cannot be guessed by using knowledge of you and your
life to determine likely words and numbers.
The general rule for creating passwords is that it should be long (8 characters might be cracked
within few hours) and have a mix of letters and other characters (numbers and symbols, which
means you could just choose a sentence). Combining your birthday with that of a family name is
however a great example of how not to do it. This kind of information is easy to find using
public resources. A popular trick is to base it on a favourite phrase and then, just to throw people
off, sprinkle it with a few numbers. Best of all is to use a password generator, either on your local
system or online.
Often such passwords are difficult to remember and a second point of vulnerabil- ity is opened
up – physical discovery. Since there is no better means of storing a password than in your own
brain, services like OnlinePasswordGenerator (http://www. onlinepasswordgenerator.com/) offer a

209
great compromise by randomly generating pass- words that vaguely resemble words and present
you with a list to choose from.
If you do choose to store your password outside your head, you have the choice to either write it
down or use keychain software. This can be a risky decision, especially if the email account and
password are on the same device like your phone or computer.
Keychain software, like Keepass, consolidates various passwords and passphrases in one place
and makes them accessible through a master password or passphrase. This puts a lot of pressure
on the master password. If you do decide to use a keychain software, remember to choose a secure
password.
Finally, you should use a different password for different accounts. In that way, if one of them
gets hijacked, your other accounts remain safe. Never use the same password for your work and
private email accounts. See section
Passwords
to learn more about how to secure yourself.
2.1.3
ReadingEmailinPublicPlaces
One of the great conveniences of wireless networking and ‘cloud computing’ is the ability to
work anywhere. You may often want to check your email in an Internet cafe, on open networks
or public location. Spies, criminals and mischievous types are known to visit these locations in
order to take advantage of the rich opportunities offered for ID theft, email snooping and
hijacking bank accounts.
Here we find ourselves within an often underestimated risk of someone listening in on your
communications using
networkpacketsniffing
. It matters little if the network itself is open or
password secured. If someone joins the same encrypted network, s/he can easily capture and
read all
unsecured
(see chapter
Secure Connection
for
TLS
and
VPN
solutions) traffic of all
of other users within the same network. A wireless key can be acquired for the cost of a cup of
coffee and gives those that know how to capture and read network packets the chance to read
your password while you check your email if the connection to that service is not secured.
Here a simple general rule always applies: if the cafe offers a network cable connection, use it!
Finally, just as at a bank machine, make sure no one watches over your shoulder when you type in
the password.
2.1.4
CacheCunning
Here again convenience quickly paves the road to bad places. Due to the general annoy- ance
of having to type in your password over and over again, you ask the browser or local mail client
to store it for you. This is not bad in itself, but when a notebook or phone gets stolen, it enables
the thief to access the owner’s email account(s). The best practice is to clear this cache every
time you close your browser. All popular browsers have an option to clear this cache on exit.
One basic precaution can justify you holding onto your convenient cache: disk encryp- tion. If
your notebook is stolen and the thief reboots the machine, they’ll be met with an encrypted disk. It
is also wise to have a screen lock installed on your computer or phone. If the machine is taken from
you while still running your existing browsing session, it cannot be accessed.
2.1 Basic Tips
2.1.5
Securingyourcommunication

210
Whenever you write and send email in a browser or use an email program (Outlook Express,
Mozilla Thunderbird, Mail.app or Mutt), you should always ensure to use en- cryption for
the entire session. This is easily done due to the popular use of
TLS/SSL
(SecureSocketLayer)
connections by email servers (See glossary
TLS/SSL
).
If using a browser to check your email, check to see if the mail server supports SSL sessions
by looking for https:// at the beginning of the URL. If not, be sure to turn it on in your email
account settings, such as Gmail or Hotmail. This ensures that not just the login part of your
email session is encrypted but also the writing and sending of emails. Furthermore check the
cetificate details and take
TLSpinning
into account and endorse browser extensions that warn
about changing or disfunctional certificates (e.g.
CertificatePatrol
) and make use of TLS
secured version of the website the default (e.g.
HTTPSeverywhere
).
The email service provider you select, should provide you with the mail server details. These
details can often be found in the settings option. If your email service provider does not offer you a
cryptographic protocol (TLS/SSL) to encrypt your data on the network, then it is advised to stop
using it. Even if your emails are not important, you might find yourself ‘locked out’ of your account
one day with a changed password!
When using an email program to check your email, be sure that you are using TLS/SSL in
the program options. For instance in Mozilla Thunderbird the option for securing your outgoing
email is found in Tools -> Account Settings -> Outgoing Server (SMTP) and for incoming email
in Tools -> Account Settings -> Server Settings. This ensures that the downloading and
sending of email is encrypted, making it very difficult for someone on your network, or on any
of the networks between you and the server, to read or log your email. Encrypting the email
itself
Even if the line itself is encrypted using a system such as SSL, the email service provider still has
full access to the email because they own and have full access to the storage device where you host
your email. If you want to use a web service and be sure that your provider cannot read your
messages, then you’ll need to use something like
GPG
(Appendix for
GnuPG
) with which you can
encrypt the email. The header of the email however will still contain the IP (Internet address) that
the email was sent from alongside other compromising details. Worth mentioning here is that the
use of
GPG
in webmail is not as comfortable as with a locally installed mail client, such as
Thunderbird
or
OutlookExpress
.
2.1.6
DNSSEC&DANE
certificate information can be stored in DNS records and therefore be regarded more relyable.
Check the availability of
DNSSEC
and especially regarding email services
DANE
with your
service providers. Here again browser extensions (e.g.
DNSSEC/TLSAValidator
) can assist to
control the availability of these security measures.
2.1.7
AccountSeparation
Due to the convenience of services like Gmail, it is increasingly typical for people to have
only one
email account. This considerably centralises the potential damage done by a
compromised account.
More so, there is nothing to stop a disgruntled Google employee
from deleting or stealing your
email, let alone Google itself getting hacked. Hacks happen. A practical strategy is to keep your
personal email, well, personal. If you have a
work email then create a new account if your
employers haven’t already done it for you. The same should go for any clubs or organisations

211
you belong to, each with a unique password. Not only does this improve security, by
reducing the risk of whole identity
theft, but greatly reduces the likelihood of spam dominating your daily email.
2.1.8
Anoteabouthostedemail
Those that provide you with the service to host, send, download and read email are not
encumbered by the use of TLS/SSL. As hosts, they can read and log your email in plain text.
They can comply with requests by local law enforcement agencies who wish to access email. They
may also study your email for patterns, keywords or signs of sentiment for or against brands,
ideologies or political groups. It is important to read the EULA (End-user license agreement) of
your email service provider and do some background research on their affiliations and interests
before choosing what kind of email content they have access to. These concerns also apply to the
hosts of your messages’ recipients.
2.2
Types of Email
The use of email almost always comes in two forms:
•
Email read, written and sent in the
browser
(webmail via HTTP) and stored on a providers server,
and/or
•
Email read, written, sent and stored using an
emailprogram
, like e.g. Mozilla Thunderbird,
Mail.App or Outlook Express by utilizing protocols like
SMTP
,
POP
and
IMAP
.
These two models might be mixed in practice, especially by using
IMAP
. Whilst the webmail
solution is more convinient to use and easier to maintain for end users on different computers
compared to the more powerful solution (less limits on storage, better search options and direct
control over data) based on native applications.
2.2.1
Remotelyhostedemail(‘webmail’),resourcedusingaweb browser
Email sent using the
browser
, sometimes referred to as
webmail
, typically assumes an account with
a remote email host like Google (Gmail), Microsoft (Hotmail) or Yahoo (Yahoo Mail). The
business opportunities opened up by hosting other people’s email
2.2 Types of Email
are many: contact with other services offered by the company, brand exposure and most importantly,
mining your plain text email for patterns that can be used to evaluate your interests – something of
great value to the advertising industry (alongside certain Gov- ernments). For the reason of
datamining those companies have
nointerest
in encouraging their users to use
encryptiontosecure
privacy
and/or
signaturesforintegrity/authenticity
of communication.
2.2.2
Remotelyhostedemail,resourcedusinganemailprogramorusinga
webbrowser
Email sent using an email program like Outlook, Thunderbird, Mail.App aso. can also be used
with a webmail service like Gmail or your company’s email service. In either case, email may
still be downloaded onto your computer but is retained on the email server (e.g. Gmail). Done

212
this way, accessing email doesn’t require the browser at all, but you are still using Gmail,
Hotmail as a service. The difference between storing email on your computer with an email
program and having it stored remotely on an email server (like Hotmail, Gmail or your
University’s service) on the Internet can appear confusing at first.
Finally, email can also be sent to an email server but not stored there at all, merely volleyed
onto its’ destination as soon as the email reaches the email forwarding server. Google and
Microsoft do not allow for this sort of setup. Rather this is typically some- thing your university
or company will provide for you. Bear in mind that this comes with the risk of the email
administrator on that system still secretly copying the email as it reaches and leaves the server.
Generally, using webmail alongside downloading it using an email program is the best approach.
This approach adds redundancy (local backups) alongside the option to delete all email from the
remote server once downloaded. The latter option is ideal for content sensitive information where
the possibility of account hijacking is high but risks total loss of email should the local machine go
missing, without backups. Secondly, when using an email program, we have the option of using
Email Encryption such as the popular OpenPGP implementation
GPG
, something not easily set up
and used with browser-only webmail services. In any case, disk encryption on the local machine is
highly advisable
(Appendix Disk Encryption).
2.2.3
Contextconsiderations
You may be a server administrator yourself and run your own email service. Or your email
could be stored on your company or bosses’ server. Finally you may be using a service provided
by a corporation, like Google (Gmail) or Microsoft (Hotmail). Each comes with its own
interesting mix of considerations that relates precisely to the basic fact that unless the email
itself is encrypted, the administrator of the email server can still secretly copy the email the
moment it reaches the server. It doesn’t matter that you may be using
TLS/SSL
(Appendix
SSL
)
to login and check your email as this only protects the connection between your local machine
and the server.
As always, if you know the risks and feel concerned it is wise to listen to them - don’t send
sensitive email using a service you don’t trust. Employer/Organisation
Your employer or an organisation that you are involved with is in a very good position to take
advantage of your trust and read the emails of your business email account that is stored on their
email server, perhaps in an effort to learn about you, your motivations, agendas and interests. Such
cases of employer->employee spying are so typical they do not bear mention. Your only measure
against it is to use an email encryption solution like GPG (Appendix GPG).
2.2.4
Email&Metadata
The actual content information of mails might be preserved utilizing
OpenPGP
or
S/MIME
but the metadata - the association of persons, addresses, time and used software/services
- is stored by several stakeholders. Government services might store such data as well as any
company involved in transmitting them. In regards of header information Email remains a risk for
communication as long as the accounts used can be connected to individuals or groups.
2.2.5
Selfadministeredemailserver
Generally speaking this is the ideal hosting configuration, but requires a higher level of technical
skill. Here, in general, the risks to privacy are not only in protecting your own email against

213
attempts at exploit (poor passwords, no SSL) but in that you have a responsibility, and perhaps
a temptation, to read the emails of those you provide a service for.
2.2.6
‘Free’emailservices
As mentioned above the risks of storing and sending your email using a service provided by a
corporation are rather high if respect of your civil right to privacy is valued. The companies hosting
your love letters, random expressions and diaries are always at risk of yielding to pressures from
political, economic and law enforcement interests of the country to which they are legally subject.
A Malaysian Gmail user, for instance, risks exposing her interests and intents to a government she
did not elect, not to mention business partners of Google interested in expanding their market
reach.
2.2.7
Nonprofit
Several non-profit web hosts offer free email accounts to organisations that are themselves non-
profit or philanthropic. Some of them even offer wikis, mailing lists, chats and social networks. A
consideration for organisations working in a political field may be differences of interests between
the state in which the email is hosted and the political interests of the organisation using that
service. Such risks would ideally be reflected in the End User License Agreement.
2.2.8
Notesonemailforwarding
Email forwarding services provide the great convenience of ‘linking’ one email account to another
as the user sees fit. This of course is most commonly used when an account holder is on holiday and
would like email forwarded from their work account to another used during travel or otherwise
inaccessible outside the workplace. The risk with any external email forwarding service is the same
as with remotely hosted emails through Gmail for instance: it can be copied and stored. Here email
encryption using a system such as
GPG
(Appendix
GPG
) will ensure that if it is copied at least
it cannot be read.
2.3
Fears
Whocanreadtheemailmessagesthat
I
havealreadysentorreceived?Who
canreadtheemails
I
sendwhentheytravelacrosstheInternet?Canthe
people
I
sendemailstosharethemwith anybody?
Emails that are sent “in the clear” without any encryption (which means the vast majority of email
sent and received today) can be read, logged, and indexed by any server or router along the path
the message travels from sender to receiver. Assuming you use an encrypted connection (see
glossary for TLS/SSL) between your devices and your email service provider (which everybody
should), this means in practice that the following people can still read any given message:
1.You
2.
Your email service provider
3.
The operators and owners of any intermediate network connections (often ambigu- ous
multinational conglomerates or even sovereign states)
4.
The recipient’s email service provider
5.The intended recipient

214
Many webmail providers (like Gmail) automatically inspect all of the messages sent and received
by their users for the purpose of showing targeted advertisements. While this may be a reasonable
compromise for some users most of the time (free email!), it is disturbing for many that even
their most private communications are inspected and indexed as part of a hidden and potentially
very insightful profile maintained by a powerful corporate giant with a profit motive.
Additionally, somebody who can legally pressure the groups above could request or demand:
1.
logged meta-data about email (lists of messages sent or received by any user, subject lines,
recipients), in some jurisdictions even without a warrant.
2.
messages sent and received by a specific user or group, with a warrant or court order in some
jurisdictions.
3.
a dedicated connection to siphon off
all
messages and traffic, to be analyzed and indexed off
site.
In cases where a user has a business or service relationship with their email provider, most
governments will defend the privacy rights of the user against unauthorized and unwarranted reading
or sharing of messages, though often it is the government itself seeking information, and frequently
users agree to waive some of these rights as part of their service agreement. However, when the
email provider is the user’s employer or academic institution, privacy rights frequently do not apply.
Depending on jurisdiction, businesses generally have the legal right to read all of the messages sent
and received by their employees, even personal messages sent after hours or on vacation.
Historically, it was possible to “get away” with using clear text email because the cost and
effort to store and index the growing volume of messages was too high: it was hard enough just to
get messages delivered reliably. This is why many email systems do not contain mechanisms to
preserve the privacy of their contents. Now the cost of monitoring has dropped much faster than the
growth of internet traffic and large-scale monitoring and indexing of all messages (either on the
sender or receiving side) is reason- able to expect even for the most innocuous messages and users.
[CITE:corporate email archiving/spying, blue coat, Syrian monitoring, USA Utah data center, USA
intercept scandals]
For more about legal protections of email messages “at rest” (technical term for mes- sages stored
on a server after having been delivered), especially regarding government access to your email
messages, see:
•
https://ssd.eff.org/3rdparties/govt/stronger-protection (USA)
•
http://en.wikipedia.org/wiki/Data_Protection_Directive (EU)
Just like there are certain photos, letters, and credentials that you would not post “in the clear” on
the Internet because you would not want that information to get indexed accidentally and show up
in search results, you should never send email messages in the clear that you would not want an
employer or disgruntled airport security officer to have easy access to.
2.3.1
Randomabuseandtheftbymalicious hackers
Whatifsomebodygetscompletecontrolofmyemailaccount?
I
loggedinfromaninsecurelocation...howdo
I
knownowifmyaccounthasbeenhacked?
I’vedonenothingwrong...whatdo
I
havetohide?Why
wouldanybodycareaboutme?
Unfortunately, there are many practical, social, and economic incentives for malicious
hackers to break into the accounts of random Internet individuals. The most obvious incentive

215
is identity and financial theft, when the attacker may be trying to get access to credit card
numbers, shopping site credentials, or banking information to steal money. A hacker has no
way to know ahead of time which users might be better targets than others, so they just try to
break into all accounts, even if the user doesn’t have anything to take or is careful not to expose
his information.
Less obvious are attacks to gain access to valid and trusted user accounts to collect contact email
addresses from and then distribute mass spam, or to gain access to par- ticular services tied to an
email account, or to use as a “stepping stone” in sophisticated social engineering attacks. For
example, once in control of your account a hacker could rapidly send emails to your associates or
co-workers requesting emergency access to more secured computer systems.
A final unexpected problem affecting even low-profile email users, is the mass hijacking of
accounts on large service providers, when hackers gain access to the hosting infras- tructure itself
and extract passwords and private information in large chunks, then sell or publish lists of login
information in online markets.
2.3.2
Targetedabuse,harassment,andspying
Something
I
wroteinfuriatedapersoninpower...howdo
I
protectmyself?
If you find yourself the individual target of attention from powerful organizations, governments,
or determined individuals, then the same techniques and principles will apply to keeping your email
safe and private, but additional care must be taken to protect against hackers who might use
sophisticated techniques to undermine your devices and accounts. If a hacker gains control of any
of your computing devices or gets access to any of your email accounts, they will likely gain
immediate access both to all of your correspondence, and to any external services linked to your
email account.
Efforts to protect against such attacks can quickly escalate into a battle of wills and resources, but
a few basic guidelines can go a long way. Use specific devices for specific communication tasks,
and use them only for those tasks. Log out and shutdown your devices immediately when you are
done using them. It is best to use open software encryption tools, web browsers, and operating
systems as they can be publicly reviewed for security problems and keep up to date with security
fixes.
BewaryofopeningPDFfilesusingAdobeReaderorotherproprietaryPDFreaders.
Closed source
PDF readers have been known to be used to execute malign code embedded in the PDF body. If you
receive a .pdf as an attachment you should first consider if you know the supposed sender and if you
are expecting a document from them. Secondly, you can use PDF readers which have been tested
for known vulnerabilities and do not execute code via java script.
Linux: Evince, Sumatra PDF OS X:
Preview
Windows: Evince
Use short-term anonymous throw away accounts with randomly generated passwords whenever
possible.
2.3.3
WhenEncryptionGoesWrong
Whathappensif
I
losemy“keys”?Do
I
losemyemail?
Rigorous GPG encryption of email is not without its own problems.

216
If you store your email encrypted and lose all copies of your private key, you will be absolutely
unable to read the old stored emails, and if you do not have a copy of your revocation certificate for
the private key it could be difficult to prove that any new key you generate is truly the valid one,
at least until the original private key expires.
If you sign a message with your private key, you will have great difficulty convincing anybody
that you did not sign if the recipient of the message ever reveals the message and signature publicly.
The term for this is
nonrepudiation
: any message you send signed is excellent evidence in court.
Relatedly, if your private key is ever compromised, it could be used to read all encrypted messages
ever sent to you using your public key: the messages may be safe when they are in transit and just
when they are received, but any copies are a liability and a gamble that the private key will never
be revealed. In particular, even if you destroy every message just after reading it, anybody who
snooped the message on the wire would keep a copy and attempt to decrypt it later if they obtained
the private key.
The solution is to use a messaging protocol that provides
perfectforwardsecrecy
by generating a
new unique session key for every conversation of exchange of messages in a random way such that
the session keys could not be re-generated after the fact even if the private keys were known. The
OTR chat protocol provides perfect forward secrecy
(http:
//en.wikipedia.org/wiki/Perfect_forward_secrecy) for real time instant messaging, and the
SSH protocol provides it for remote shell connections, but there is no equivalent system for
email at this time.
It can be difficult to balance the convenience of mobile access to your private keys with the fact
that mobile devices are much more likely to be lost, stolen, or inspected and exploited than stationary
machines. An emergency or unexpected time of need might be exactly the moment when you
would most want to send a confidential message or a signed message to verify your identity, but
these are also the moments when you might be without access to your private keys if your mobile
device was seized or not loaded with all your keys.
2.4
Secure Connections
2.4.1
CanotherpeoplereadalongwhenIcheckmy email?
As discussed in the Chapter
Basic Tips
, whether you use webmail or an email program you
should always be sure to use encryption for the entire session, from login to logout. This will
keep anyone from spying on your communication with your email provider. Thankfully, this is
easily done due to the popular use of
TLS/SSL
connections on email
servers (See appendix
TLS/SSL
).
A TLS/SSL connection in the browser, when using webmail, will appear with https
in the URL instead of the standard http, like so:
https://gigglemail.com
If your webmail host does not provide a TLS/SSL service then you should consider discontinuing
use of that account; even if your emails themselves are not especially private or important, your
account can very easily be hacked by “sniffing” your password! If it is
2.5 Secure Emails
not enabled already be sure to turn it on in your account options. At the time of writing,
Google’s Gmail and Hotmail
/
Microsoft Live both automatically switch your browser to using
a secure connection.

217
If you are using an email program like Thunderbird, Mail.app or Outlook, be sure to check
that you are using TLS/SSL in the options of the program. See the chapter
Setting Up Secure
Connections in the section Email Security.
2.4.2
Notes
It’s important to note that the administrators at providers like Hotmail or Google, that host,
receive or forward your email can read your email even if you are using secure connections. It
is also worth nothing that the cryptographic keys protecting a TLS/SSL connection can be
deliberately disclosed by site operators, or copied without their permis- sion, breaching the
confidentiality of that connection. It is also possible for a Certificate Authority to be corrupted
or compromised so that it creates false certificates for keys held by eavesdroppers, making it
much easier for a Man In The Middle Attack on con- nections using TLS/SSL (See Glossary
for “Man in the Middle Attack”). An example of compromised E-mail providers is discussed
here, implicating America’s NSA and several email providers:
http://cryptome.info/0001/nsa-ssl-email.htm
We also note here that a
VirtualPrivateNetwork
also a good way of securing your connections
when sending and reading email but requires using a VPN client on your local machine connecting
to a server. See the chapter
Virtual Private Networking
in
the Browsing section.
2.5
Secure Emails
It is possible to send and receive secure email using standard current email programs by adding a
few add-ons. The essential function of these add-ons is to make the message body (but not the To:,
From:, CC: and Subject: fields) unreadable by any 3rd party that intercepts or otherwise gains access
to your email or that of your conversation partner. This process is known as encryption.
Secure email is generally done using a technique called
PublicKeyCryptography
. Public-Key
Cryptography is a clever technique that uses two code keys to send a mes- sage. Each user has a
publickey
, which can only be used to encrypt a message but not to decrypt it. The public keys are
quite safe to pass around without worrying that some- body might discover them. The
privatekeys
are kept secret by the person who receives the message and can be used to decode the messages that
are encoded with the matching public key.
In practice, that means if Rosa wants to send Heinz a secure message, she only needs his public
key which encodes the text. Upon receiving the email, Heinz then uses his private key to decrypt the
message. If he wants to respond, he will need to use Rosa’s public key to encrypt the response, and
so on.
2.5.1
WhatsoftwarecanIusetoencryptmy email?
The most popular setup for public-key cryptography is to use
GnuPrivacyGuard(GPG)
to create
and manage keys and an add-on to integrate it with standard email software. Using GPG will
give you the option of encrypting sensitive mail and decoding incoming mail that has been
encrypted but it will not force you to use it all the time. In years past, it was quite difficult to
install and set up email encryption but recent advances have made this process relatively simple.
See section
Email Encryption
for working with GPG in the scope of your operating system
and email program.

218
If you use a
webmail
service and wish to encrypt your email this is more difficult. You
can
use a GPG program on your computer to encrypt the text using your public key or you can
use an add-on, like Lock The Text (http://lockthetext.sourceforge.net/). If you want to
keep your messages private, we suggest using a dedicated email program
like Thunderbird
instead of webmail.
3
Understanding Browsing
3.1
Basic Tips
3.1.1
InBrief:
•
When you visit a website you give away information about yourself to the site owner, unless
precautions are taken.
•
Your browsing on the Internet may be tracked by the sites you visit and partners of those
sites. Use anti-tracking software.
•
Visiting a website on the Internet is never a direct connection. Many computers, owned by
many different people are involved. Use a secure connection to ensure your browsing can not
be recorded.
•
What you search for is of great interest to search providers. Use search anonymising software
to protect your privacy.
•
It is wiser to trust Open Source browsers like Mozilla Firefox as they can be more readily
security audited.
3.1.2
Yourbrowsertalksaboutyoubehindyourback
All browsers communicate information to the web server serving you a web page. This information
includes name and version of the browser, referral information (a link on another site, for instance)
and the operating system used.
Websites often use this information to customise your browsing experience, suggesting
downloads for your operating system and formatting the web page to better fit your browser.
Naturally however, this presents an issue and regards the user’s own anonymity as this information
becomes part of a larger body of data that can be used to identify you individually.
Stopping the chatter of your browser is not easily done. You can, however, falsify some of the
information sent to web servers while you browse by altering data contained in the
UserAgent
, the
browser’s identity. There is a very useful plugin for Firefox, for instance, called
UserAgentSwitcher
that allows you to set the browser identity to another profile selected from a drop down list of
options.
3.1.3
Websitescantrackyouasyoubrowse
Small files, called
cookies
, are often written onto your computer by web sites. Cookies present
certain conveniences, like caching login data, session information and other data that makes your
browsing experience smoother. These small pieces of data however

219
present a significant risk to your right to anonymity on the web: they can be used to identify you if
you return to a site and also to track you as you move from site to site. Coupled with the User-Agent,
they present a powerful and covert means of remotely identifying your person.
The ideal solution to this problem is deny all website attempts to write cookies onto your system
but this can greatly reduce the quality of your experience on the web.
See the section
Tracking
for guides as to how to stop web servers tracking you.
3.1.4
Searchingonlinecangiveawayinformationaboutyou
When we search online using services like Bing or Google our right to privacy is already at risk,
vastly more so than asking a person at an Information Desk in an airport, for instance.
Combined with the use of cookies and User Agent data this information can be used to build an
evolving portrait of you over time. Advertisers consider this information very valuable, use it to
make assumptions about your interests and market you products in a targeted fashion.
While some customers may sing the praises of targeted advertising and others may not care, the
risks are often misunderstood. Firstly, the information collected about you may be requested by a
government, even a government you did not elect (Google, for instance, is an American company
and so must comply with American judicial processes and political interests). Secondly there is the
risk that merely searching for information can be misconstrued as intent or political endorsement.
For instance an artist studying the aesthetics of different forms of Religious Extremism might find
him or herself in danger of being associated with support for the organisations studied. Finally there
is the risk that this hidden profile of you may be sold on to insurance agents, provided to
potential employers or other customers of the company whose search service you are using.
Even once you’ve ensured your cookies are cleared, your
UserAgent
has been changed (see above
and chapter
Tracking
) you are still giving away one crucial bit of information: the Internet Address
you are connecting from (see chapter
What Happens When You Browse
). To avoid this
you can use an anonymising service like Tor (see chapter
Anonymity
). If you are a Firefox user
be sure to install the excellent
GoogleSharing
add-on, an anonymiser for Google search. Even if
you don’t consciously use Google, a vast number of web sites use a customised Google Search bar
as a means of exploring their content.
With the above said, there are no reasons to trust Google, Yahoo or Bing. We rec- ommend
switching to a search service that takes your right to privacy seriously: Duck- DuckGo
(http://duckduckgo.com/).
3.1.5
Moreeyesthanyoucansee
The Internet is a big place and is not one network but a greater network of many smaller
interconnected networks. So it follows that when you request a page from a server on the
Internet your request must traverse many machines before it reaches the server hosting the page.
This journey is known as a
route
and typically includes at least 10 machines along the path. As
packets move from machine to machine they are necessarily copied into memory, rewritten and
passed on.
Each of the machines along a network route belongs to someone, normally a company or
organisation and may be in entirely different countries. While there are efforts to stan- dardise
communication laws across countries, the situation is currently one of significant jurisdictional
variation. So, while there may not be a law requiring the logging of your web browsing in your
country, such laws may be in place elsewhere along your packet’s route.

220
The only means of protecting the traffic along your route from being recorded or tampered with
is using
endtoendencryption
like that provided by TLS/Secure Socket Layer (See chapter
Encryption
) or a Virtual Private Network (See chapter
VPN
).
3.1.6
Yourrighttobeunknown
Beyond the desire to minimise privacy leakage to specific service providers, you should consider
obscuring the Internet Address you are connecting from more generally (see chapter
What
Happens When You Browse
). The desire to achieve such anonymity spurred the creation of
the
TorProject
.
Tor
uses an ever evolving network of nodes to route your connection to a site in a way that cannot
be traced back to you. It is a very robust means of ensuring your Internet address cannot be logged
by a remote server. See the chapter
Anonymity
for more information about how this works and
how to get started with Tor.
3.2
Fears
3.2.1
SocialNetworkingwhatarethedangers?
The phenomenon of Internet based Social Networking has changed not just how people use the
Internet but its very shape. Large data centers around the world, particularly in the US, have
been built to cater to the sudden and vast desire for people to upload content about themselves,
their interests and their lives in order to participate in Social Networking.
Social Networking as we know it with FaceBook, Twitter (and earlier MySpace) are certainly far
from ‘free’. Rather, these are businesses that seek to develop upon, and then exploit, a very basic
anxiety: the fear of social irrelevance. As social animals we can’t bear the idea of missing out and
so many find themselves placing their most intimate expressions onto a businessman’s hard-disk,
buried deep in a data center in another country - one they will never be allowed to visit.
Despite this many would argue that the social warmth and personal validation acquired through
engagement with Social Networks well out-weighs the potential loss of privacy. Such a statement
however is only valid when the
full
extent of the risks are known.
The risks of Social Networking on a person’s basic right to privacy are defined by:
•
The scope and intimacy of the user’s individual contributions.
•
A user posting frequently and including many personal details constructs a body of
information of greater use for targeted marketing.
•
The preparedness of the user to take social risks.
•
A user making social connections uncritically is at greater risk from predators and social
engineering attacks.
•
The economic interests and partners of the organisation providing the service.
•
Commissioned studies from clients, data mining, sentiment analysis.
•
Political/legal demands exerted by the State against the organisation in the juris-
diction(s) in which it is resident.
•
Court orders for data on a particular user (whether civilian or foreigner).
221
•
Surveillance agendas by law enforcement or partners of the organisation.
•
Sentiment analysis: projections of political intent.
With these things in mind it is possible to chart a sliding scale between projects like Diaspora and
Facebook: the former promises some level of organisational transparency, a commitment to privacy
and a general openness, whereas Facebook proves to be an opaque company economically able to
gamble with the privacy of their users and manage civil lawsuits in the interests of looking after
their clients. As such there is more likelihood of your interactions with a large Social Network
service affecting how an Insurance company or potential employer considers you than a smaller,
more transparent company.
3.2.2
Whocanstealmy identity?
This question depends on the context you are working within as you browse. A weak and universal
password presents a danger of multiple services from Social Networking, Banking, WebMail etc
being account hijacked. A strong and universal password on a wireless network shared with others
(whether open or encrypted) is just as vulnerable. The general rule is to ensure you have a strong
password (see section on
Passwords
).
Wireless networks
Here we find ourselves amidst an often underestimated risk of someone listening in on your
communications using
networkpacketsniffing
. It matters little if the network itself is open or
password secured. If someone uses the same encrypted network, he can easily capture and read all
unsecured traffic of other users within the same network. A wireless key can be acquired for the cost
of a cup of coffee and gives those that know how to capture and read network packets the chance to
read your password while you check your email.
A simple rule always applies: if the cafe offers a network cable connection, use it! Finally, just as
at a bank machine, make sure no one watches over your shoulder when you type in the password.
The browser cache
Due to the general annoyance of having to type in your password repeatedly, you allow the browser
or local mail client to store it for you. This is not bad in itself, but when a laptop or phone gets stolen,
this enables the thief to access the owner’s email account(s). The best practice is to clear this cache
every time you close your browser. All popular browsers have an option to clear this cache on exit.
One precaution can justify you holding onto your convenient cache: disk encryption. If your
laptop is stolen and the thief reboots the machine, they’ll be met with an encrypted disk. It is also
wise to have a screen lock installed on your computer or phone. If the machine is taken from you
while still running your existing user session, it cannot be accessed.
Securing your line
Whenever you log into any service you should always ensure to use encryption for the entire session.
This is easily done due to the popular use of
TLS/SSL
(SecureSocketLayer)
.
Check to see the service you’re using (whether Email, Social Networking or online- banking)
supports TLS/SSL sessions by looking for
https://
at the beginning of the URL. If not, be sure to

222
turn it on in any settings provided by the service. To better understand how browsing the World
Wide Web works, see the chapter
What Happens
When I Browse?
3.2.3
CanIgetintroubleforGooglingweird stuff?
Google and other search companies may comply with court orders and warrants targeting certain
individuals. A web site using a customised Google Search field to find content on their site may be
forced to log and supply all search queries to organisations within their local jurisdiction.
Academics, artists and researchers are particularly at risk of being misunderstood, assumed to have
motivations just by virtue of their apparent interests.
3.2.4
WhoiskeepingarecordofmybrowsingandamIallowedtohide
fromthem?
It is absolutely within your basic human rights, and commonly constitutionally protected, to
visit web sites anonymously. Just as you’re allowed to visit a public library, skim through books
and put them back on the shelf without someone noting the pages and titles of your interest, you
are free to browse anonymously on the Internet.
3.2.5
Howtonotrevealmy Identity?
See the chapter on Anonymity.
3.2.6
Howtoavoidbeing tracked?
See the chapter on Tracking.
3.3 What happens when you browse
Browsing the web is communicating. You might not send as much text in terms of number of words,
but it is always the browser which initiates and maintains the communication by requesting the bits
and pieces which are woven into what is eventually displayed on your screen.
Browsers like Mozilla Firefox, Google Chrome, Opera, Safari & Internet Explorer all work
in a similar manner. When we type a URL (e.g. “http://happybunnies.com”) in the address bar,
the browser requests the website (which is just a special kind of text) from a remote server and
then transforms it into colored blocks, text and images to be displayed in the browser window.
To see the text the way the browser sees it, one just has to click on the View --> Page source
menu entry in the browser. What comes up is the same webpage but in HTML – a language
mainly concerned with content, context and links to other resources (CSS and JavaScript) which
govern the way these contents are displayed and behave.
When the browser tries to open a webpage – and assuming there are no proxies involved
– the first thing it does is to check its own cache. If there is no past memories of such website, it
tries to resolve the name into an address it can actually use. It is an internet program, so it needs an
Internet Protocol address (IP address or just IP). To get this address it asks a DNS Server (kind of a
telephone book for internet programs) which is installed in the router of your internet access by
default. The IP address is a numerical label assigned to every device in the (global) network, like
the address of a house in the postal system – and as the address of your home, you should be very
careful to whom you hand out the IP address you are browsing from (by default this is: to everyone).

223
Once the IP address has been received, the browser opens a TCP (just a communication protocol)
connection to the destination host and starts sending packages to a port at this address, typically no.
80 (ports are like doors to the servers, there are many but usually only a few are open), unless another
path is specified. These packages travel through a number of servers on the internet (up to a
couple of dozens depending on were the target address is located). The server then looks for the
requested page and, if found, delivers it using the HTTP protocol. (To prevent others from reading
or altering the data, TLS/SSL can be used to below HTTP to secure the connection)
When the HTTP response arrives, the browser can close the TCP connection or reuse it for
subsequent requests. The response can be one of many things, from some sort of redirection or a
classic Internal Server Error (500). Provided the response proceeds as ex- pected the browser will
store the page in a cache for further use, decode it (uncompress it
3.3 What happens when you browse
if compressed, rendered if video codec, etc) and display/play it according to instructions.
Now, the process can be illustrated in a little conversation between browser (B) and server (S):
B: “Hallo.”
S: “Hey!”
B: “May I get that page with the happy bunnies, please?” S: “Well,
here you are.”
B: “Oh, maybe you could also give me a big version of that picture of that bunny baby cuddling
a teddy bear.”
S: “Sure, why not.”
[. . . ]
B: “That’s all for now. Thank you. Bye.”
Note that there are lots of activities happening parallel to this TCP/IP exchange. Depending on
how you have configured its options, your browser might be adding the page to browser history,
saving cookies, checking for plugins, checking for RSS updates and communicating with a variety
of servers, all while you’re doing something else.
3.3.1
Atopographyofyou: footprints
Most important: you will leave footprints. Some of them will be left on your own computer – a
collection of cache data, browsing history and naughty little files with elephantine memory called
cookies. They are all very convenient; speed up your browser’s performance, reduce your data
download or remember your passwords and preferences from Social Networks. They also snitch on
your browsing habits and compile a record of everywhere you go and everything you do there. This
should bother you if you are using a public computer station at a library, work at a cybercafe, or
share your apartment with a nosey partner!
Even if you configure your browser to not keep a history record, reject cookies and delete cached
files (or allocate zero MB of space for the cache), you would still leave breadcrumbs all over the
Internet. Your IP address is recorded by default everywhere, by everyone and the packets sent are
monitored by an increasing number of entities - commercial, governmental or criminal, along with
some creeps and potential stalkers.
Democratic governments everywhere are redesigning regulations to require Internet providers to
keep a copy of everything so they can have later access to it. In the USA, section 215 of the American
PATRIOT act
‘prohibitsanindividualororganizationfromrevealingthatithasgivenrecordsto
thefederalgovernment,followinganinvestigation’
. That means that the company you pay every
month as a customer to provide you with Internet access can be ordered to turn over your browsing
and email records without your knowledge.

224
Most of the time, though, surveillance is not a 1984 affair. Google collects your searches
along with your browser identification (
useragent
), your IP and a whole bunch of data that
can eventually lead to your doorstep, but the ultimate aim is usually not political repression but
market research. Advertisers don’t fuss about advertising space any more, they just want to
know everything about you. They want to know your dietary and
medication habits, how many children you have and where you take them on holidays; how you
make your money, how much you earn and how you like to spend it. Even more: they want to
know how you
feel
about stuff. They want to know if your friends respect those feelings enough so
that you can convince them to change their consumption habits. This is not a conspiracy, but rather
the nature of Information Age capitalism. To paraphrase a famous observation of the current
situation, the best minds of our generation are thinking about how to make people click ads.4
Some people think ads can be ignored or that having advertisers cater for our specific needs is a
win-win situation, because at least they are spammed with things they may actually want. Even if
that was the case (it isn’t): should we trust Google with such intimate details of our life? Even if we
trust Google to ‘do no evil’, it can still be bought by someone we do not trust; benevolent Larry
Page and Sergey Brin could be overruled by their own Board, or their data base be sequestered by a
fascistic government. One of their 30,000 employees worldwide could cut loose and run with our
data. Their servers can be hacked. And in the end, they are just interested in their customers,
the
companiespayingforadvertising
. We are just the product being sold.
Moreover; in the Social Networks our browsing habits are generating a Permanent Record, a
collection of data so vast that the information that Facebook keeps about a given user alone can fill
880 pages. Nobody will be surprised to learn that Facebook’s purpose is not to make us happy –
again: if you are not paying for it, you’re not the customer, you’re the product. But even if you don’t
care about their commercial goals, consider this: the platform has publicly admitted hackers break
into hundreds of thou- sands of Facebook accounts every day.
For a taste of what lurks behind the curtains of the websites you visit, install a plugin/add-on
called
Ghostery
to your browser. It’s like an x-ray-machine which reveals all the surveillance
technology which might be (and often is) embedded in a web page, normally invisible to the user.
In the same line,
DoNotTrackPlus
and
Trackerblock
will give you further control over online
tracking, through cookie blocking, persistent opt-out cookies, etc. Our following chapter
Tracking
will equip you with expertise in such topics.
Even in between your computer and the router, your packages can easily be intercepted by anyone
using the same wireless network in the casual environment of a cafe. It is a jungle out there, but still
we choose passwords like “password” and “123456”, perform economic transactions and buy tickets
on public wireless networks and click on links from unsolicited emails. It is not only our right to
preserve our privacy but also our responsibility to defend that right against the intrusions of
governments, corporations and anyone who attempts to dispossess us. If we do not exercise those
rights today, we deserve whatever happens tomorrow.
1.
If you are a Unix user, you can use the tcpdump command in the bash and view real
time dns traffic. It’s loads of fun! (and disturbing)
ˆ
2.
See list of TCP and UDP port numbers ( http://en.wikipedia.org/wiki/List_
of_TCP_and_UDP_port_numbers)
3.
If this exchange is happening under an HTTPS connection, the process is much
3.4 Accounts and Security
more complicated and also much safer, but you will find out more about that in a most
fascinating chapter called Encryption.
ˆ

225
4.
This Tech Bubble Is Different (
http://www.businessweek.com/magazine/content/
11_17/b4225060960537.htm),
Ashlee Vance (Businessweek magazine) ˆ
3.4 Accounts and Security
When you browse, you may be logged into various services, sometimes at the same time. It may be
a company website, your email or a social networking site. Our accounts are important to us because
highly sensitive information about us and others is stored on machines elsewhere on the Internet.
Keeping your accounts secure requires more than just a strong password (see section
Passwords
) and a secure communication link with the server via TLS/SSL (see chapter
Secure
Connection
). Unless specified otherwise, most browsers will store your login data in tiny files
called cookies, reducing the need for you re-type your password when you reconnect to those sites.
This means that someone with access to your computer or phone may be able to access your accounts
without having to steal your password or do sophisticated snooping.
As smart phones have become more popular there has been a dramatic rise in account hijacking
with stolen phones. Laptops theft presents a similar risk. If you do choose to have the browser save
your passwords then you have a few options to protect yourself:
•
Use a screen lock. If you have a phone and prefer an unlock pattern system get in the habit of
wiping the screen so an attacker can not guess the pattern from finger smears. On a Laptop,
you should set your screensaver to require a password as well as a password on start-up.
•
Encrypt your hard disk. TrueCrypt is an open and secure disk encryption system for
Windows 7/Vista/XP, Mac OS X and Linux. OSX and most Linux distributions provide
the option for disk encryption on install.
•
Android Developers: do not enable USB debugging on your phone by default. This allows an
attacker using the Android
adbshell
on a computer to access your phone’s hard disk without
unlocking the phone.
3.4.1Canmaliciouswebsitestakeovermyaccounts?
Those special cookies that contain your login data are a primary point of vulnerability. One
particularly popular technique for stealing login data is called click-jacking, where the user is tricked
into clicking on a seemingly innocuous link, executing a script that takes advantage of the fact you
are logged in. The login data can then be stolen, giving the remote attacker access to your account.
While this is a very complicated technique, it has proven effective on several occasions. Both
Twitter and Facebook have seen cases of login sessions being stolen using these techniques.
It’s important to develop a habit for thinking before you click on links to sites while logged into
your accounts. One technique is to use another browser entirely that is not
logged into your accounts as a tool for testing the safety of a link. Always confirm the address (URL)
in the link to make sure it is spelled correctly. It may be a site with a name very similar to one you
already trust. Note that links using URL shorteners (like http://is.gd and http://bit.ly) present a risk
as you cannot see the actual link you are requesting data from.
If using Firefox on your device, use the add-on NoScript as it mitigates many of the
CrossSite
Scripting
techniques that allow for your cookie to be hijacked but it will disable many fancy
features on some web sites.

226
3.5
Tracking
When you browse the web tiny digital traces of your presence are left behind. Many web sites
harmlessly use this data to compile statistics and see how many people are looking at their site and
which pages are popular, but some sites go further and use various techniques to track individual
users, even going as far as trying to identify them personally. It doesn’t stop there however. Some
firms store data in your web browser which can be used to track you on other web sites. This
information can be compiled and passed on to other organizations without your knowledge or
permission.
This all sounds ominous but really who cares if some big company knows about a few web sites
that we have looked at? Big web sites compile and use this data for “behavioral advertising” where
ads are tailored to fit your interests exactly. That’s why after looking at say, the Wikipedia entry for
Majorca, one may suddenly start seeing lots of ads for packaged vacations and party hats. This may
seem innocent enough, but after doing a search for “Herpes Treatments” or “Fetish Communities”
and suddenly seeing listings for relevant products, one may start to feel that the web is getting a
bit too familiar.
Such information is also of interest to other parties, like your insurance company. If they know
you have been looking at skydiving sites or forums for congenital diseases, your premiums may
mysteriously start going up. Potential employers or landlords may turn you down based on their
concerns about your web interests. In extreme instances, the police or tax authorities may develop
an interest without you ever having committed a crime, simply based on suspicious surfing.
3.5.1
Howdotheytrackus?
Every time you load a web page, the server software on the web site generates a record of the page
viewed in a log file. This is not always a bad thing. When you log in to a website, there is a need for
a way to establish your identity and keep track of who you are in order to save your preferences,
or present you with customized information. It does this by passing a small file to your browser
and storing a corresponding reference on the web server. This file is called a
cookie
. It sounds tasty
but the problem is that this information stays on your computer even after leaving the web site and
may phone home to tell the owner of the cookie about other web sites you are visiting. Some major
sites, like Facebook and Google have been caught using them to keep track of your browsing even
after you have logged out.
Supercookies / Evercookie / Zombie Cookies?
3.5.2
HowcanIpreventtracking?

227
The simplest and most direct way to deal with tracking is to delete the cookie files in your
browser:
In Firefox: 1. Click the Firefox menu. 2. Click Options. 3. Click Privacy. 4.
Click Clear your recent history.
5. Make sure Time range
to clear is set to Everything. 6. Tick Cookies.
7. Click Clear now.

228
In Chrome: 1. Click the Chrome menu. 2. Click Tools. 3. Click Clear browsing data. 4.
Make sure Obliterate the following items from is set to The beginning of time. 5. Tick
Delete cookies and other site and plug-in data. 6. Click Clear
browsing data
.
Figure 3.1:Delete Chrome Cookies
In
Internet Explorer
: 1. Click the
Tools
button (shaped like a gear). 2. Click
Safety. 3. Click Delete Browsing History. 4. Tick Cookies. 5. Click Delete.
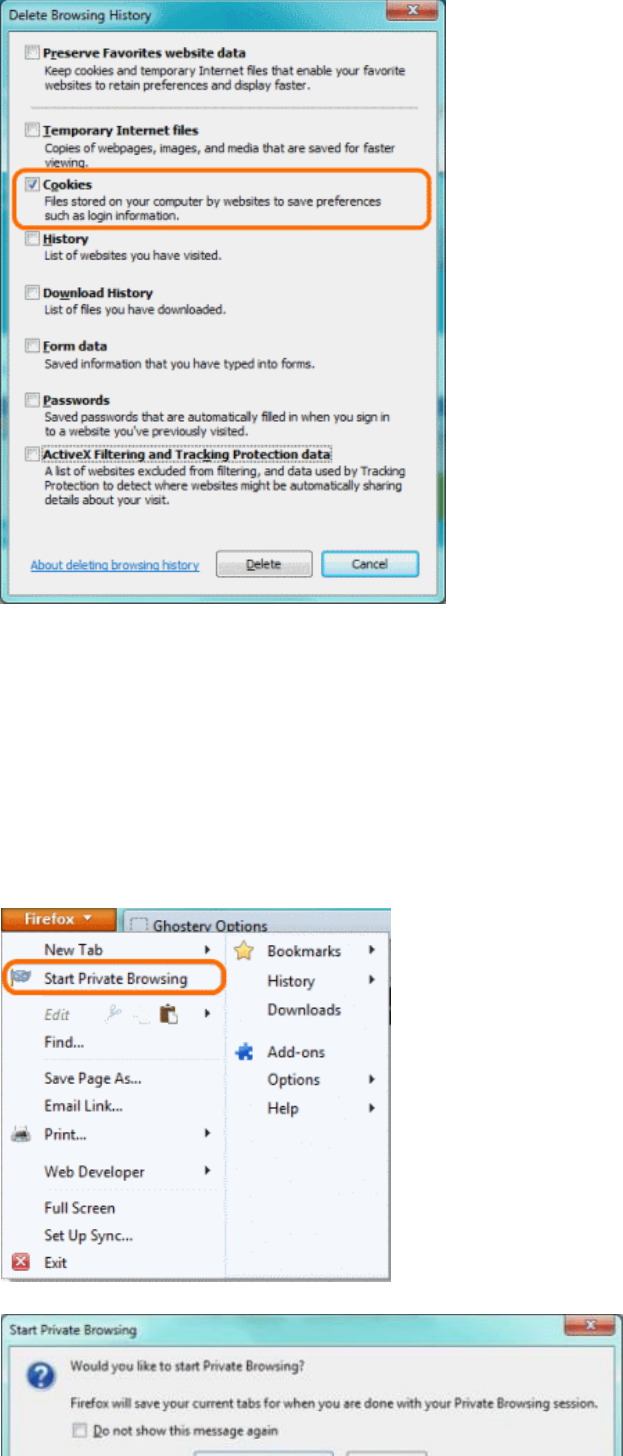
229
Figure 3.2:Delete IE Cookies
The limitation to this approach is that you will receive new cookies as soon as you return to
these sites or go to any other pages with tracking components. The other dis- advantage is that
you will lose all of your current login sessions for any open tabs, forcing you to type in usernames
and passwords again. A more convenient option, supported by current browsers is private
browsing or incognito mode. This opens a temporary browser window that does not save the
history of pages viewed, passwords, downloaded files or cookies. Upon closing the private
browsing window, all of this information is deleted. You can enable private browsing:
In Firefox: 1. Click the Firefox menu. 2. Click Start Private Browsing.
3. If prompted, click Start Private Brows-
ing
again.

230
button turns purple, showing that private browsing is on.
Figure 3.3:Firefox Private Browsing
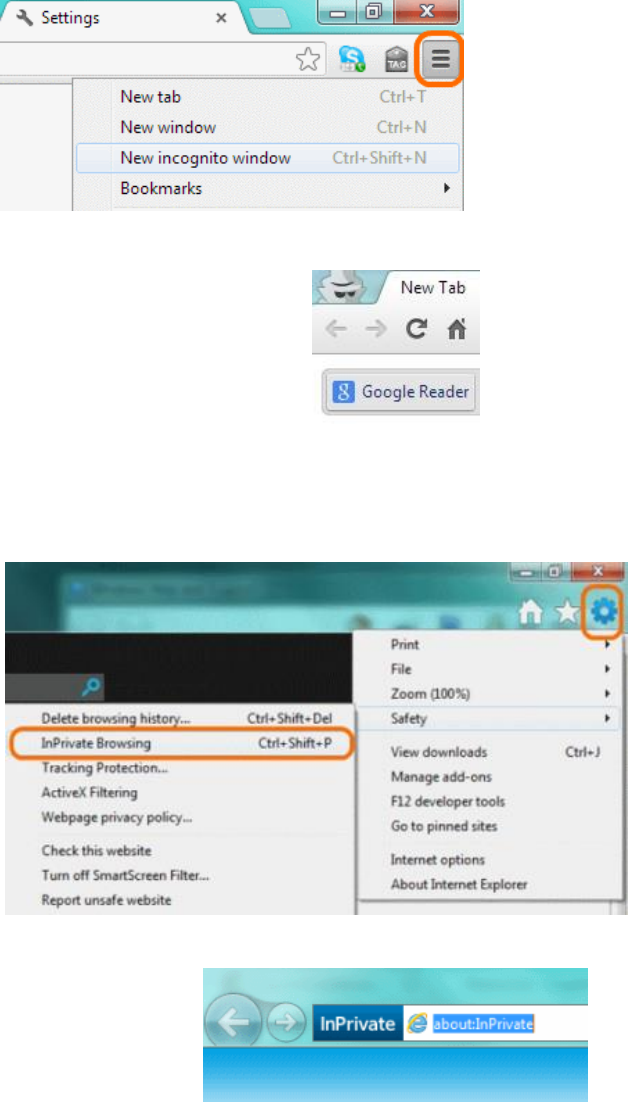
231
4.
The
Firefox menu
In Chrome: 1. Click the Chrome menu. 2. Click New incognito window.
3. The
spy icon
in the top-left of the
browser window shows that private browsing is on.
Figure 3.4:Chrome Private Browsing
In
Internet Explorer
: 1. Click the
Tools
menu, shaped like a gear. 2. Click
Safety
.
3. Click InPrivate Browsing.
4. The
InPrivate
logo
appears in the top-left of your browser window, showing that private browsing is on.
Figure 3.5:IE Private Browsing

232
This solution also has its limitations. We cannot save bookmarks, remember passwords, or
take advantage of much of the convenience offered by modern browsers. Thankfully, there are
several plugins specially designed to address the problems of tracking. The most extensive, in
terms of features and flexibility, is Ghostery. The plugin allows you to block categories or
individual services that track users. Here’s how you install Ghostery:
1.
In Firefox, click the
Firefox
menu and select
Add-ons
.
2.
In the
Search
box, type “ghostery”, then
click the Search icon or press Enter.
3.
Find Ghostery in the list of Add-
ons, and click
Install
.
4.
Restart your browser
by clicking Restart Now.
5. Click the Ghostery

233
toolbar
and select
Options
. Do the walkthrough and/or play with Ghostery’s settings,
if you want.
6.
Visit a web page
and have a look at its trackers.
Figure 3.6:Ghostery
Another option is to install an ad-blocking plugin like AdBlockPlus. This will auto- matically
block many of the tracking cookies sent by advertising companies but not those used by Google,
Facebook and other web analytics companies. [expand on this maybe, explain “web analytics”]
How can I see who is tracking me?
The easiest way to see who is tracking you is to use the Ghostery plugin. There is a small
icon on the upper right or lower right corner of your browser window that will tell you which
services are tracking you on particular web sites.
{Suggestion: Add Abine.com’s Do Not Track add-on. I suggest using both Ghosterly and DNT,
as occasionally they block a different cookie. Abine also has Privacy Suite, recently developed
which can give a proxy telephone and proxy email, similar to 10 Minute Mail or Guerrilla Mail for
fill- in emails for forms.}
3.5.3
Awordofwarning
If you block trackers, you will have a higher level of privacy when surfing the net. How-
ever,
government agencies, bosses, hackers and unscrupulous network administrators will
still be able to
intercept your traffic and see what you are looking at. If you want to secure your connections
you will need to read the chapter on encryption. Your identity may also be visible to other
people on the internet. If you want to thoroughly protect your identity while browsing, you will
need to take steps toward online anonymity which is explained in another section of this book.

234
3.6
Anonymity
3.6.1
Intro
Article 2 of the Universal Declaration of Human Rights states:
“Everyone is entitled to all the rights and freedoms set forth in this Decla- ration,
without distinction of any kind, such as race, colour, sex, language, religion, political
or other opinion, national or social origin, property, birth or other status.
Furthermore, no distinction shall be made on the basis of the political, juris- dictional or
international status of the country or territory to which a person belongs, whether it be
independent, trust, non-self-governing or under any other limitation of sovereignty.“.
One way of enforcing this basic right in hostile environments is by means of anonymity, where
attempts to connect an active agent to a specific person are blocked.
Acting anonymously is also a great way to help others with a high need for protection
– the bigger the herd of sheep, the harder it is to target a specific one. An easy way to do so is
by using Tor, a technique which routes internet traffic between users of a special software, thus
making it untraceable to any specific IP address or person without having control over the whole
network (and nobody has that yet in the case of the internet). A highly functional means to
protect ones own identity is by using anonymous proxy servers and Virtual Private Networks
(VPN).
3.6.2
Proxy
“An
anonymizer
or an
anonymous proxy
is a tool that attempts to make
activity
on the Internet untraceable. It is a proxy [server] computer that acts as an
intermediary and privacy shield between a client computer and the rest of the
Internet. It accesses the Internet on the user’s behalf, protecting
personal information
by hiding the client computer’s identifying information.”
(http://en.wikipedia.org/wiki/Anonymizer)
3.6 Anonymity
The main purpose behind using a proxy is to hide or to change Internet address (IP address)
assigned to user’s computer. There can be a few reasons for needing to do so, for example:
•
To anonymize access to particular server(s) and/or to obfuscate traces left in the log files
of a web-server. For instance a user might need/want to access sensi- tive materials online
(special materials, research topics or else) without triggering authorities attention.
•
To break through firewalls of corporations or repressive regimes. A corporation/government
can
limit or completely restrict Internet access for a particular IP address or a range
of IP addresses. Hiding behind a proxy will help to trick these filters and access otherwise
forbidden sites.
•
To watch online video and streams banned in your country due to legal issues.
•
To access websites and/or materials available only for IP addresses belonging to a
specific country. For example, a user wants to watch a BBC video stream (UK-only)
while not residing in the UK.
•
To access the Internet from a partially banned/blocked IP address. Public IP addresses

235
can often have “bad reputation” (bandwidth abuse, scam or unsolicited email
distribution) and be blocked by some web-sites and servers.
While a usual scenario would be to use proxy for accessing the Web (HTTP), practically Internet
protocol can be proxied - i.e. sent via a remote server. Unlike a router, proxy server is not directly
forwarding remote user requests but rather mediates those requests and echos responses back to
remote user’s computer.
Proxy (unless setup as “transparent”) does not allow direct communication to the Internet thus
applications such as browsers, chat-clients or download applications need to be made aware of
the proxy server (see
Safer Browsing/Proxy settings
chapter)
3.6.3
Tor
•
Tor prevents anyone from learning your location or browsing habits.
•
Tor is for web browsers, instant messaging clients, remote logins, and more.
•
Tor is free and open source for Windows, Mac, Linux/Unix, and An- droid.
(https://www.torproject.org)
Tor is a system intended to enable online anonymity, composed of client software and a
network of servers which can hide information about users’ locations and other factors which might
identify them. Imagine a message being wrapped in several layers of protection: every server
needs to take off one layer, thereby immediately deleting the sender information of the previous
server.
Use of this system makes it more difficult to trace Internet traffic to the user, including visits to
Web sites, online posts, instant messages, and other communication forms. It is intended to protect
users’ personal freedom, privacy, and ability to conduct confidential
business, by keeping their internet activities from being monitored. The software is open-source and
the network is free of charge to use.
Tor cannot and does not attempt to protect against monitoring the traffic entering and exiting the
network. While Tor does provide protection against traffic analysis, it cannot prevent traffic
confirmation (also called end-to-end correlation).
EndtoEndCorrelation
is a way of matching
an online identity with a real person.
A recent case of this involved the FBI wanting to prove that the man Jeremy Hammon was behind
an alias known to be responsible for several Anonymous attacks. Sitting outside his house, the FBI
were monitoring his wireless traffic alongside a chat channel the alias was known to visit. When
Jeremy went online in his apartment, inspection of the wireless packets revealed he was using Tor
at the same moment the suspected alias associated with him came online in the surveilled chat
channel. This was enough to incriminate Jeremy and he was arrested.
See section Safer Browsing/Using Tor for setup instructions.
3.7 VPN
The way your data makes it to the desired server and back to your laptop computer or a mobile
device is not as straightforward as it might first seem. Say, you are connected to a wireless
network at home and opening a wikipedia.org page. The path your request (data) takes will
consist of multiple middle points or
“hops”
- in network-architect terminology. At each of these
236
hops (which are likely to be more then 5) your data can be scooped, copied and potentially
modified.
•
Your wireless network (your data can be sniffed from the air)
•
Your ISP (in most countries they are obliged to keep detailed logs of user activity)
•
Internet Exchange Point (IXP) somewhere on another continent (usually more secure then
any other
hop
)
•
ISP of the hosting company that hosts the site (is probably keeping logs)
•
Internal network to which the server is connected
•
And multiple hops between. . .
Any person with physical access to the computers or the networks which are on the way from
you to the remote server, intentionally or not, can collect and reveal the data that’s passing from you
to the remote server and back. This is especially true for so called ‘last mile’ situations - the few
last leaps that an internet connection makes to reach a user. That includes domestic and public
wireless or wired networks, telephone and mobile networks, networks in libraries, homes, schools,
hotels. Your ISP can not be considered a safe, or ‘data-neutral’ instance either - in many countries
state agencies do not even require a warrant to access your data, and there is always the risk of
intrusion by paid attackers working for a deep-pocketed adversaries.
VPN - a Virtual Private Network - is a solution for this ‘last-mile’ leakage. VPN is a technology
that allows the creation of a virtual network on top of an existing infras- tructure. Such a VPN
network operates using the same protocols and standards as the
3.7 VPN
underlying physical network. Programs and OS use it transparently, as if it was a sepa- rate network
connection, yet its topology or the way how network nodes (you, the VPN server and, potentially,
other members or services available on VPN) are interconnected in relation to the physical space is
entirely redefined.
Imagine that instead of having to trust your data to every single middle-man (your local network,
ISP, the state) you have a choice to pass it via a server of a VPN provider whom you trust (after a
recommendation or research) - from which your data will start its journey to the remote location.
VPN allows you to recreate your local and geo-political context all together - from the moment your
data leaves your computer and gets into the VPN network it is fully secured with TLS/SSL type
encryption. And as such it will appear as pure random noise to any node who might be spying after
you. It is as if your data was traveling inside a titanium-alloy pipe, unbreakable on all the way from
your laptop to the VPN server. Of course one could argue that eventually, when your data is
outside the safe harbour of VPN it becomes just as vulnerable as it was - but this is only partially
true. Once your data exits the VPN server it is far away from you - way beyond the reach of some
creeps sniffing on the local wireless network, your venal ISP or a local government obsessed with
anti-terrorism laws. A serious VPN provider would have their servers installed at a high-security
Internet exchange location, rendering any physical human access, tapping or logging a difficult task.
“Today everything you do on the Internet is monitored and we want to change that.
With our fast VPN service you get totally anonymous on the Inter- net. It’s also
possible to surf censored web sites, that your school, ISP, work or country are
blocking. [DarkVPN] will not only help people to surf anonymously, it also helps
people in countries like China to be able to surf censored web pages. Which is your
democratic right. DarknetVPN gives all VPN users an anonymous IP address. All
electronic tracks will end up with us. We do not save any log files in order to

237
achieve maximum anonymity. With us you always surfing anonymously, secure and
encrypted.” (http://www.darknetvpn.com/about.php)
Another interesting and often underrated features of VPN is encoded in its name - besides being
V
irtual and
P
rivate it is also a
N
etwork. VPN allows one not only to connect via the VPN server to
the rest of the world but also to communicate to other members of the same VPN network without
ever having to leave the safety of encrypted space. Through this functionality Virtual Private
Network becomes something like a
DarkNet
(in a broader sense of the definition) - a network
isolated from the Internet and inaccessible to “others”. Since a connection to VPN server, and thus
the private network it facilitates, require a key or a
certificate
, only “invited” users are allowed.
There is no chance that Internet stranger would gain access to what’s on a VPN without enrolling as
a user or stealing someones keys. While not referred to as such, any corporate Intranet type of
network is a DarkNet too.
“A virtual private network (VPN) extends a private network across a public network,
such as the Internet. It enables a computer to send and receive data
across shared or public networks as if it were directly connected to the private network,
while benefitting from the functionality, security and management policies of the private
network.”(http://en.wikipedia.org/wiki/Virtual_ private_network)
Many commercial VPN providers stress the anonymity that their service provides. Quoting
Ipredator.org page (a VPN service started by the people behind The Pirate Bay project):
“You’ll exchange the IP address you get from your ISP for an anonymous IP
address. You get a safe/encrypted connection between your computer and the
Internet”. (https://www.ipredator.se)
Indeed, when you access the Internet via a VPN connection it does appear as if the connection is
originating from the IP address of IPredator servers.
4
Publishing And Distribution
4.1
Publishing Anonymously
Whether you are an activist operating under a totalitarian regime, an employee deter- mined to
expose some wrongdoings in your company or a vengeful writer composing a bitchy portrait of your
ex-wife, you need to protect your identity. If you are not collab- orating with others, the focus lies
on anonymity and not encryption or privacy.
If the message is urgent and the stakes are high, one easy way to just get it out quickly is
going to an internet cafe one usually does not frequent, create accounts specifically set up for
the task, deliver the data and discard those accounts right after that. If you are in a hurry,
consider MintEmail (http://www.mintemail.com/) or FilzMail (http:
//www.filzmail.com/), where your address will expire from 3 to 24 hours respectively. Do not do
anything else while you’re there; don’t check your Gmail account, do not have a quick one on
Facebook and clear all cache, cookies and history and close the browser before you leave.

238
If you keep these basic rules, the worst – though highly improbable – thing that could happen
would be that the offered computer is compromised and logging keystrokes, revealing passwords or
even your face, in case an attached webcam is remotely operated. Don’t do this at work or in a place
where you are a registered member or a regular visitor, like a club or a library.
If you want to maintain a constant stream of communication and maybe even establish an
audience, this method quickly becomes quite cumbersome, and you might also run out
of
unused internet cafes. In this case you can use a machine you own, but, if you cannot
dedicate one especially to this purpose, boot your computer with a different operating
system (OS). This can be easily done by using a USB stick to boot a live operating system
like Tails (https://tails.boum.org/), which comes with Tor enabled by default and includes
state-of-the-art cryptographic tools. In any case, use Tor to disguise your IP.
Turn off all cookies, history and cache options and never use the same profile or the same browser
for other activities. Not only would that add data to your topography as a user in the Net, but
it also opens a very wide window for mistakes. If you want extra support, install
DoNotTrackPlus
and
Trackerblock
or
Ghostery
in your browser add-ons menu.
Use passwords for different accounts and choose proper passwords or even passphrases (more
about that in the basic tips section). Protect your entire system with a general password, change it
often and do not share it with anyone,
especially
not your lover. Install a keystroke logger to see if
someone sneaks into your email, especially your lover. Set up your preferences everywhere to
log out of every service and platform after 5
minutes of non-use. Keep your superhero identity to yourself.
If you can mantain such level of discipline, you should even be capable of using your own internet
connection. But consider this: not using a dedicated system makes it incredibly difficult to keep all
the different identities separated in a safe way, and the feeling of safety often leads to carelessness.
Keep a healthy level of neurosis.
Today there are many publishing possibilities, from cost-free blogging sites (Blogspot, Tumblr,
WordPress, Identi.ca) to PasteBins (see glossary) and some specifically catered to anonymous users
like BlogACause. Global Voices Advocacy recommends using Word- Press through the Tor
network. Keep a sane level of cynicism; they all act in commercial interests that you use for ‘free’
and so cannot be trusted at all, especially in that they may be bound to the demands of a legal
juristiction that is not your own. All providers are, when it comes down to it, traitors.
If registration with these services requires a working email address, create one dedicated solely to
this purpose. Avoid Gmail, Yahoo, Hotmail and other big commercial platforms with a history of
turning over their users and go for an specialized service like Hushmail
(https://www.hushmail.com/). For more on anonymous email, please find the chapter Anonymous
email in the previous section.
4.1.1SeveralDon’ts
Don’t register a domain.
There are services that will protect your identity from a simple who
is query, like Anonymous Speech or Silent Register, but they will know who you are through your
payment data. Unless you have the chance to purchase one in BitCoins, limit yourself to one of the
domains offered by your blogging platform like yourblogname.blogspot.com and choose a setting
outside your native country. Also, find a name that doesn’t give you away easily. If you have
problems with that, use a blog name generator online.
Don’t open a social network account associated to your blog.
If you must, keep
the level of hygiene that you keep for blogging and never ever login while using your regular

239
browser. If you have a public social network life, avoid it all together. You will eventually make a
mistake.
Don’t upload video, photo or audio files
without using an editor to modify or erase all
the meta data (photos contain information up to the GPS coordinates of the location the photo was
taken at) that standard digital cameras, SmartPhones, recorders and other devices add by default.
The
MetadataAnonymisationToolkit
or
ExifTool
might help you with that.
Don’t leave a history.
Add X-Robots-Tag to your http headers to stop the searching spiders
from indexing your website. That should include repositories like the Wayback Machine from
archive.org. If you don’t know how to do this, search along the lines of “Robots Text File
Generator”.
Don’t leave comments.
If you must, maintain the levels of hygiene that you use for blogging
and always logout when you’re done and for god sakes do not troll around. Hell hath no fury like a
blogger scorned.
Don’t expect it to last.
If you hit the pot and become a blogging sensation (like
4.2 Anonymous Email
BelledeJour
, the British PhD candidate who became a sensation and sold a book and mused two
TV shows about her double life as a high escort) there will be a legion of journalists, tax auditors
and obsessive fans scrutinizing your every move. You are only human: they will get to you.
Don’t linger.
If you realize you have already made any mistakes but nobody has caught
you yet, do close all your accounts, cover your tracks and start a totally new identity. The
Internet has infinite memory: one strike, and you’re out of the closet.
4.2
Anonymous Email
Every data packet traveling through the Internet contains information about its sender and its
recipient. This applies to email as well as any other network communication. There are several ways
to reduce identifying information but no way to remove it com- pletely.
4.2.1
SendingFromThrowawayEmailAccounts
One option is to use a throw-away email account. This is an account set up at a service like Gmail
or Hotmail, used once or twice for anonymous exchange. When signing up for the account, you will
need to provide fake information about your name and location. After using the account for a short
amount of time, say 24 hours, you should never log in again. If you need to communicate
further, then create a new account.
It is very important to keep in mind that these services keep logs of the IP addresses of those
using them. If you are sending highly sensitive information, you will need to combine a throw away
email account with Tor in order keep your IP address hidden.
If you are not expecting a reply, then an anonymous remailer like AnonEmail or Silentsender may
be a useful solution. A remailer is a server that receives messages with instructions on where to
send the data and acts as a relay, forwarding it from a generic address without revealing the identity
of the original sender. This works best when combined with an email provider like Hushmail or
RiseUp who are specially set up for secure email connections.
Both of these methods are useful, but only if you always remember that the interme- diary
himself knows where the original message came from and can read the messages as they come
in. Despite their claims to protect your identity, these services often have user agreements that
240
indicate their right “to disclose to third parties certain registration data about you” or they are
suspected to be compromised by secret services. The only way to safely use this technique is to
not trust these services at all, and apply extra security measures: send via Tor using a throw-
away email address.
If you only need to receive email, services like Mailinator and MintEmail give you an email
address that destroys itself after a few hours. When signing up for any account, you should provide
fake information about your name and location and protect yourself by using Tor.
4.2.2
BeCarefulaboutwhatyousay!
The content of your message can give away your identity. If you mention details about your life,
your geography, social relations or personal appearance, people may be able to determine who is
sending the message. Even word choice and style of writing can be used to guess who might be
behind anonymous emails.
You should not use the same user name for different accounts or use a name that you are
already linked to like a childhood nickname or a favorite book character. You should never use your
secret email for normal personal communication. If someone knows your secrets, do not
communicate with that person using this email address. If your life depends on it, change your secret
email address often as well as between providers.
Finally, once you have your whole email set up to protect your identity, vanity is your worst
enemy. You need to avoid being distinct. Don’t try to be clever, flamboyant or unique. Even the
way you break your paragraphs is valuable data for identification, especially these days when every
school essay and blog post you have written is available in the Internet. Powerful organizations can
actually use these texts to build up a database that can “fingerprint” writing.
4.3
File Sharing
The term
FileSharing
refers to the practice of sharing files on a network, often with widest
possible distribution in mind. Unfortunately in recent years the term has come to be popularly
associated with the distribution of content registered under certain copy- right licenses that
disallow the distribution of copies (eg. supposed criminal activity). Regardless of this new
association, file sharing remains a vital tool for many world wide: from academic groups to
scientific networks and open source software communities.
In this book we wish to help you learn to privately distribute files, with other consenting
people, without the content of that exchange known to others or the transaction stopped by an
external party. Your basic right to anonymity and to not be spied upon protects that. Suspicions
that those things
might
have been stolen and are not yours to give does not undermine that same
and original right to privacy.
The history of the internet is littered with attacks of different types on publication and
distribution nodes, conducted by different means (court order, Distributed Denial of Service
attacks). What such events have demonstrated is that if one wants information to be persistently
available and robust against attack, it is a mistake to rely upon a single node which can be
neutralised.
This has recently been demonstrated by the takedown of the direct download service Megaupload,
whose disappearance led to the loss of massive amounts of its users’ data, much of it extraneous
even to the alleged copyright infringements which formed the pretext for its closure. In similar vein
ISPs will often take down web sites containing disputed material merely because it is cheaper for
them to do so than to go to court and have a judge decide. Such policies leave the door open to
groundless bullying by all manner of companies, organisations and individuals ready and willing to

241
make aggressive use of legal letters. Both direct download services and ISPs are examples of
centralised
structures which cannot be relied upon both because they are a single point of failure for
attack,
and because their commercial interests are not aligned with those of their users. Spreading files
through distribution, decentralising the data, is the best way to defend against such attacks. In
the following section two realms of filesharing are profiled.
The first are standard p2p
technologies whose technical design is determined by the
efficiency of the networks in
enabling speed of distribution and discovery of content
through associated search mechanisms.
The second focuses on I2P as an example of a
so-called darknet, its design prioritises security and
anonymity over other criteria offering
a robust, if less resource efficient, path to persistent availability.
The means of sharing files mentioned below are just some examples of the many P2P technologies
that were developed since 1999. BitTorrent and Soulseek have very different approaches, both
however were designed for easy usability by a wide public and have significant user communities.
I2P is of more recent development and has a small user base.
BitTorrent
has become the most popular P2P file-sharing system. The controversy that
surrounds it nowadays ironically seems to help the community grow, while police,
lobbied by
powerful copyright holders seize torrent-tracker server hardware and pursue
their operators,
sometimes to the point of jailing them as in the case of The Pirate Bay.
Soulseek
- while it has never been the most popular file-sharing platform, neither did it ever
have the ambition. Soulseek focuses on the exchange of music between enthusiasts, underground
producers, fans and researchers. The system and the community around it is completely isolated
from the Web: Soulseek files can’t be linked to. They are kept exclusively on the hard-disks of
Soulseek users. The content of the network fully depends on how many members are connected and
what they share. Files are transferred only between two users at a time and nobody but those two
users are involved. Because of this ‘introverted’ character - and the specificity of its content -
Soulseek has stayed out of sight of legislation and non-pro-copy copyright advocates.
I2P
is one of several systems developed to resist censorship (others include FreeNet and Tor)
and has a much smaller user community, it is highlighted here because of its inclusion of Bit Torrent
functionality within its basic installation. These systems can also be used to provide hidden
services, amongst others, enabling you to publish web pages within their environments.
4.3.1
BitTorrent
BitTorrent is a peer-to-peer (P2P) protocol that facilitates distribution of data stored across
multiple nodes/participants of the network. There are no central servers or hubs, each node is
capable of exchanging data with any other node, sometimes hundreds of them simultaneously.
The fact that data is exchanged in parts between numerous nodes allows for great download
speeds for popular content on BitTorrent networks, making it quickly the de facto P2P file-
sharing platform.
If you are using BitTorrent to circulate material of ambiguous legality, you should know that
enforcement agents typically collect information on allegedly infringing peers by participating in
torrent swarms, observing and documenting the behaviour of other
peers. The large number of users creates a difficulty for the enforcement system simply at the level
of scaling up - there simply are not the resources to pursue every user. Any court case will require
actual evidence of data transfer between your client and another (and usually evidence of you
uploading), it is enough that you provide even part of the file, not the file in its entirety, for a
242
prosecution to have legs. But if you prefer to lean towards greater caution, you should use a VPN
to route your BitTorrent traffic, as detailed in the
Using VPN
chapter.
Leeching (downloading) of a file from BitTorrent network begins with a
torrentfile
or
magnet
link
. A torrent file is a small file containing information on the larger files you want to download.
The torrent file tells your torrent client the names of the files being shared, a URL for the
tracker
and a
hash
code, which is a unique code representing, and derived from, the underlying file - kind
of like an ID or catalog number. The client can use that hash to find others seeding (uploading)
those files, so you can download from their computers and check the authenticity of the chunks as
they arrive.
A
MagnetLink
does away with the need for a torrent file and is essentially a hyperlink
containing a description for that torrent, which your torrent client can immediately use to start
finding people sharing the file you are willing to download. Magnet links don’t
require a tracker,
instead they rely on
DistributedHashTable(DHT)
- which you can
read more about in the
Glossary - and
PeerExchange
. Magnet links do not refer to a
file by its location (e.g. by IP
addresses of people who have the file, or URL) but rather
defines search parameters by which
this file can be found. When a magnet link is loaded,
the torrent client initiates an availability
search which is broadcast to other nodes and
is basically a shout-out “who’s got anything
matching this hash?!”. Torrent client then
connects to the nodes which responded to the shout-out
and begins to download the file.
BitTorrent uses encryption to prevent providers and other man-
in-the-middle from
blocking and sniffing your traffic based on the content you exchange. Since
BitTorrent
swarms (flocks of seeders and leechers) are free for everyone to join it is possible
for
anyone to join a swarm and gather information about all connected peers. Using magnet
links
will not prevent you from being seen in a swarm; any of the nodes sharing the same file must
communicate between each-other and thus, if just one of the nodes in your
swarm is rogue, it
will be able to see your IP address. It will also be able to determine
if you are seeding the data by sending your node a download request.
One important aspect of using BitTorrent is worth a special mention. Every chunk of data
that you receive (leech) is being instantly shared (seeded) with other BitTorrent users. Thus, a
process of downloading transforms into a process of (involuntary) pub- lishing, using a legal
term -
makingavailable
of that data, before the download is even complete. While BitTorrent
is often used to re-distribute freely available and legitimate software, movies, music and other
materials, its “making available” capacity created a lot of controversy and led to endless legal
battles between copyright holders and facilitators of BitTorrent platforms. At the moment of
writing this text, the co-founder of
ThePirateBay
Gottfrid Svartholm is being detained by
Swedish police after an international warrant was issued against him.
For these reasons, and a public relations campaign by copyright holders, use of Bit- Torrent
platforms has become practically analogous to piracy. And while the meaning
of terms such as piracy, copyright and ownership in digital context is yet to be settled, many ordinary
BitTorrent users have been already prosecuted on the basis of breaking copyright laws.
Most torrent clients allow you to block IP addresses of known copyright trolls us- ing blacklists.
Instead of using public torrents one can also join closed trackers or use BitTorrent over VPN or
Tor.
In situations when you feel that you should be worried about your BitTorrent traffic and it’s
anonymity go through the following check-list:
•
Check if your torrent client supports peer-blacklists.
•
Check if the peer-blacklist definitions are updated on a daily basis.
•
Make sure your client supports all recent protocols - DHT, PEX and Magnet links.

243
•
Choose a torrent client that supports encrypted peers and enable it.
•
Upgrade or change your torrent client if any of the above mentioned options is not available.
•
Use VPN connection to disguise your BitTorrent traffic from your ISP. Make sure your VPN
provider allows P2P traffic. See more tips and recommendations in Using VPN chapter.
•
Do not leech and seed stuff you don’t know much about.
•
Be suspicious of high ratings and overly-positive comments regarding particular torrent
link.
4.3.2
SoulSeek
As a peer to peer (P2P) file sharing program, the content available is determined by the users of
the Soulseek client, and what files they choose to share. The network has historically had a diverse
mix of music, including underground and independent artists, unreleased music, such as demos and
mix-tapes, bootlegs, etc. It is is entirely financed by donations, with no advertising or user fees.
“Soulseek does not endorse nor condone the sharing of copyrighted materials. You
should only share and download files which you are legally allowed to, or have
otherwise received permission to, share.” (http://www.soulseekqt. net)
Soulseek network depends on a pair of central servers. One server supports the original client and
network, and the other supporting the newer network. While these central servers are key to
coordinating searches and hosting chat rooms, they do not actually play a part in the transfer of
files between users, which takes place directly between the users concerned.
Users can search for items; the results returned being a list of files whose names match the
search term used. Searches may be explicit or may use wildcards/patterns or terms to be
excluded. A feature specific to the Soulseek search engine is the inclusion of the folder names
and file paths in the search list. This allows users to search by folder name.
The list of search results shows details, such as the full name and path of the file, its size, the
user who is hosting the file, together with that users’ average transfer rate, and, in the case of mp3
files, brief details about the encoded track itself, such as bit rate, length, etc. The resulting search
list may then be sorted in a variety of ways and individual files (or folders) chosen for download.
Unlike BitTorrent, Soulseek does not support multi-source downloading or “swarming” like other
post-Napster clients, and must fetch a requested file from a single source.
While the Soulseek software is free, a donation scheme exists to support the pro- gramming effort
and cost of maintaining the servers. In return for donations, users are granted the privilege of being
able to jump ahead of non-donating users in a queue when downloading files (but only if the files
are not shared over a local area network). The Soulseek protocol search algorithms are not published,
as those algorithms run on the server. However several Open Source implementations of server and
client software exist for Linux, OS X and Windows.
Regarding privacy and copyright issues Soulseek stand quite far away from BitTorrent too.
Soulseek has been taken to court only once, in 2008, but even that did not go anywhere. There are
no indications of Soulseek users ever being brought to court or accused of illegal distribution of
copyrighted materials or any other ‘digital-millenium’ crimes.
If you want to use the Soulseek network with some degree of real anonymity, you will need
to use it over a VPN.

244
4.3.3
I2P
I2P began as a fork from the Freenet project, originally conceived as a method for censorship-
resistant publishing and distribution. From their website:
The I2P project was formed in 2003 to support the efforts of those trying to build a more
free society by offering them an uncensorable, anonymous, and secure communication
system. I2P is a development effort producing a low latency, fully distributed,
autonomous, scalable, anonymous, resilient, and secure network. The goal is to
operate successfully in hostile environments
- even when an organization with substantial financial or political resources attacks it.
All aspects of the network are open source and available without cost, as this should
both assure the people using it that the software does what it claims, as well as enable
others to contribute and improve upon it to defeat aggressive attempts to stifle free
speech. (http://www.i2p2.de/)
For a guide to installing the software and configuring your browser see section on Secure
Filesharing - Installing I2P. Once complete, on launch you will be brought to a console page
containing links to popular sites and services. In addition to the usual webpages (referred to as
eePsites) there are a range of applications services available ranging from the blogging tool Syndie
to a built in BitTorrent client which functions through a web interface.
5
Secure Calls And Sms
5.1
Secure Calls
Phone calls made over the normal telecommunications system have some forms of pro-
tection from third party interception, i.e. GSM mobile phones calls are encrypted. GSM
calls
are not encrypted end-to-end however and telephone providers are increasingly
forced to give
governments and law enforement organisations access to your calls. In
addition to this the
encryption used in GSM has been cracked and now anyone with
enough interest and capital
can buy the equipment to intercept calls. A GSM Intercep-
tor
(http://en.intercept.ws/catalog/2087.html is an off the shelf device to record
mobile phone
conversations when in the vicinity of the call. Centralised or proprietary systems like Skype
also encrypt calls but have built in backdoors for secret services and governments and are at
the behest of their owner (in Skype’s case Microsoft). Addition-
ally, there are a whole
classification of devices called IMSI catchers which can further gather information about
mobile phones, including the content of your communication.
However, there are a variety of tools you can use to secure your phone using end-to-end encryption.
5.1.1
iOSInstallingSignal
From the makers of TextSecure is a free and open source tool named Signal.
https://
itunes.apple.com/us/app/signal-private-messenger/id874139669?mt=8 Signal uses similar
same encryption methods as SilentCircle but provides their service with free and using open

245
source tools. Additionally, the GUI is extremely easy to use. Signal will transparently detect if
you are calling a fellow Signal user and ask if you wish to make a “secure call” (with Signal)
or “insecure call” (without end-to-end encryption).
5.1.2
AndroidInstallingRedPhone
Also from the makers of Signal, there is a free and open source tool named Redphone.
https://play.google.com/store/apps/details?id=org.thoughtcrime.redphone&hl= en Again,
RedPhone uses the similar encryption methods as SilentCircle but provides their service with free
and using open source tools. Again, the GUI will transparently detect if you are calling a fellow
Signal or RedPhone user and ask if you wish to make a “secure call” (with RedPhone) or
“insecure call” (without end-to-end encryption). Un- fortunately, RedPhone requires the Google
Play framework so it will not work on phones without it (stock Cyanogenmod or similar ROMs).
5 Secure Calls And Sms
5.2
Secure Messaging
SMS are short messages sent between mobile phones. The text is sent without encryption and
can be read and stored by mobile phone providers and other parties with access to the network
infrastructure to which you’re connected. To protect your messages from interception you need
to use end-to-end encryption on your text messages.
5.2.1
Android
•
TextSecure
- WhisperSystems provide an SMS encryption system for Android called
TextSecure, based on public key cryptography which ensures that messages are encrypted on
the wire and are also stored in an encrypted database on the device, however to ensure
encryption on the wire, both parties must be using the application. It is Open Source and
available through the Play Store
The encryption technology behind it (named //axolotl//) extends the OTR protocol so that
messages can be encrypted and send even if not all of the communicating parties are online.
6
Basic Email Security
6.1
Start Using Thunderbird
Figure 6.1:Thunderbird
In upcoming sections, we will be using Mozilla’s Thunderbird e-mail program to show you
how to configure your e-mail client for maximum security. Similar to Mozilla’s Firefox

246
browser, Thunderbird has many security advantages over its counterparts like Apple Mail and
Outlook.
Thunderbird is a so-called “mail user agent” (MUA). This is different from web-based e- mail
services like Google’s Gmail. You must install the Thunderbird application on your computer.
Thunderbird has a nice interface and features that enable you to manage multiple mailboxes,
organize messages into folders, and search through mails easily.
Thunderbird can be configured to work with your existing e-mail account, whether that
account is through your Internet Service Provider (such as Comcast) or through an web-based
email provider (such as Gmail).
Using Thunderbird has many advantages over using web-based e-mail interfaces. These will be
discussed in the following chapter. To summarize, though, Thunderbird enables much greater
privacy and security than web-based e-mail services.
This section provides information on how to install Thunderbird on Windows, Mac OS X, and
Ubuntu.
6.1.1
InstallingThunderbirdonWindows
Installing Thunderbird involves two steps: first, download the software and then run the installation
program.
1.
Use your web browser to visit the Thunderbird download page at http://www.
mozillamessaging.com/en-US/thunderbird/. This page detects your computer’s operating
system and language, and recommends the best version of Thunderbird for you to use.
If you want to use Thunderbird in a different language or with a different operating system,
click the
OtherSystemsandLanguages
link on the right side of the page and select the version
that you need.
Figure 6.2:Thunderbird Install
2.
Click the download button to save the installation program to your computer.

247
Figure 6.3:Thunderbird Install
Click the
Save
button to save the Thunderbird Setup file to your computer. 3.Close all
applications running on your computer.
4.
Find the setup file on your computer (it’s usually in the Downloads folder or on your
desktop) and then double-click it to start the installation. The first thing that the installer
does is display the
Welcome to the Mozilla Thunderbird Setup
Wizard screen.

248
Figure 6.4:Thunderbird Install
Click the
Next
button to start the installation. If you want to cancel it, click the
Cancel
button.
5.
The next thing that you see is the
Setup Type
screen. For most users the Stan- dard setup
option is good enough for their needs. The Custom setup option is recommended for
experienced users only. Note that Thunderbird installs itself as your default mail application.
If you do not want this, clear the checkbox labeled
Use Thunderbird as my default mail
application.

249
Figure 6.5:Thunderbird Install Click
the
Next
button to continue the installation.
6.
After Thunderbird has been installed, click the
Finish
button to close the setup
wizard.
If the
Launch Mozilla Thunderbird
now checkbox is selected, Thunderbird starts after it
has been installed.

250
Figure 6.6:Thunderbird Install
6.1.2
InstallingThunderbirdonUbuntu
There are two different procedures for installing Thunderbird on Ubuntu: one for version
10.04 or later, and one for earlier versions of Ubuntu. We describe both below.
Thunderbird will not run without the following libraries or packages installed on your
computer:
•
GTK+ 2.10 or higher
•
GLib 2.12 or higher
•
Pango 1.14 or higher
•
X.Org 1.0 or higher
Mozilla recommends that a Linux system also has the following libraries or packages installed:
•
NetworkManager 0.7 or higher
•
DBus 1.0 or higher
•
HAL 0.5.8 or higher
•
GNOME 2.16 or higher
6.1.3
InstallingThunderbirdonUbuntu12.04or newer
If you’re using Ubuntu 12.04 or newer, the easiest way to install Thunderbird is through the
Ubuntu Software Center.
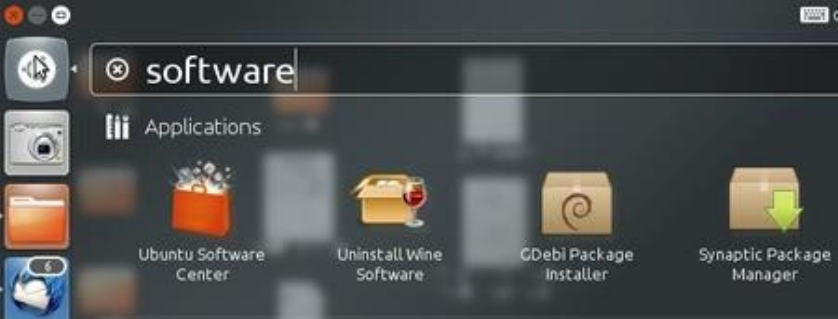
251
1.
Type Software in the Untiy search window.
Figure 6.7:Thunderbird Install
2.
Click on ‘Ubuntu Software Center’
3.
Type “Thunderbird” in the search box and press the Enter on your keyboard. The Ubuntu
Software Center finds Thunderbird in its list of available software.
4.
Click the
Install
button. If Thunderbird needs any additional libraries, the Ubuntu
Software Center alerts you and installs them along with Thunderbird.
You can find the shortcut to start Thunderbird in the Internet option under the Ap-
plications
menu:

252
Figure 6.8:Thunderbird Install
6.1.4
InstallingThunderbirdonMacOSX
To install Thunderbird on your Mac, follow these steps:
1.
Use your web browser to visit the Thunderbird download page at http://www.
mozillamessaging.com/en-US/thunderbird/. This page detects your computer’s operating
system and language, and it recommends the best version of Thunderbird for you to use.
2.
Download the Thunderbird disk image. When the download is complete, the disk image may
automatically open and mount a new volume called
Thunderbird
.

253
Figure 6.9:Thunderbird Install
If the volume did not mount automatically, open the Download folder and double-click the
disk image to mount it. A Finder window appears:
3.
Drag the Thunderbird icon into your Applications folder. You’ve installed Thun- derbird!
4.
Optionally, drag the Thunderbird icon from the Applications folder into the Dock. Choosing the
Thunderbird icon from the Dock lets you quickly open Thunderbird from there.
Note:
When you run Thunderbird for the first time, newer versions of Mac OS X (10.5 or
later) will warn you that the application Thunderbird.app was downloaded from the Internet.
If you downloaded Thunderbird from the Mozilla site, click the
Open
button.
Figure 6.10:Thunderbird Install
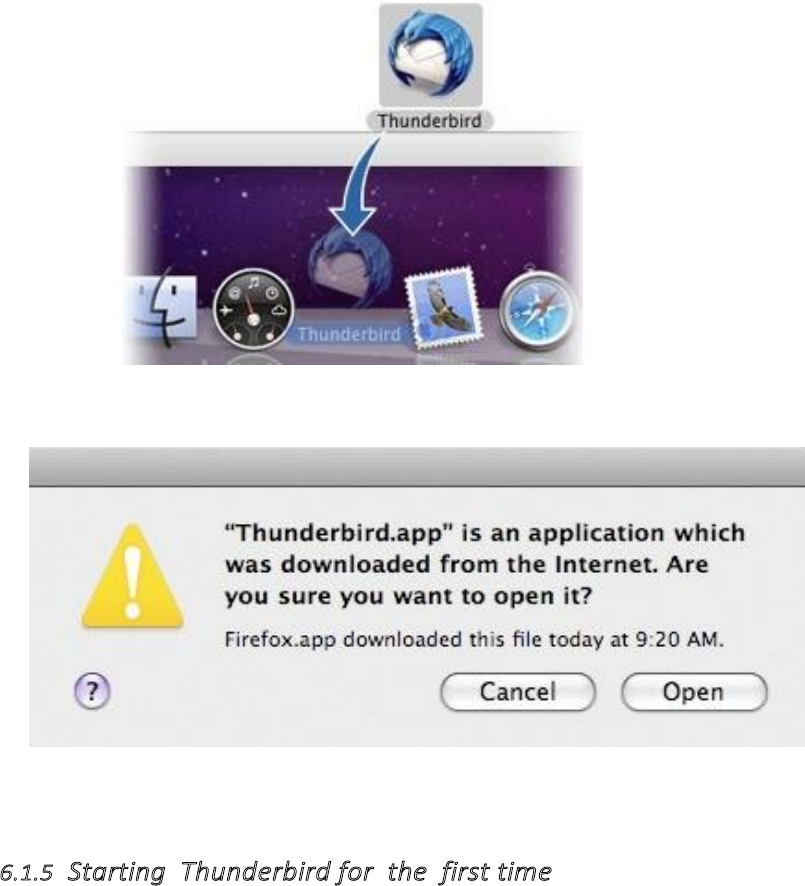
254
Figure 6.11:Thunderbird Install
Figure 6.12:Thunderbird Install
6.1.5
StartingThunderbirdforthefirsttime
After you have installed Thunderbird for the first time you will be guided through the configuration
of your mail account. These settings are defined by your e-mail provider (your Internet Service
Provider or web-based e-mail service provider). The next chapter describes how to set up your
account and configure it for maximum security.

255
6.2 Setting up secure connections
There is a right (secure) way to configure your connection to your provider’s mail servers and
a wrong (insecure) way. The most fundamental aspect of e-mail security is the type of
connection that you make to your e-mail provider’s mail server.
Whenever possible, you should connect using the
SSL
(Secure Socket Layer) and
TLS
(Transport Layer Security) protocols. (
STARTTLS
, which is another option available when
configuring an account, is a variation of SSL
/
TLS.) These protocols prevent your own system
(beyond Thunderbird) and any points between your system and the mail server from intercepting
and obtaining your password. SSL
/
TLS also prevent eavesdroppers from reading the content of
your messages.
These protocols, however, only secure the connection between your computer and the mail server.
They do not secure the information channel all the way to the message recipient. Once the mail
servers forward the message for delivery, the message may be intercepted and read by points in
between the mail server and the recipient.
This is where
PGP
(Pretty Good Privacy) comes in, which is described in the next chapter.
The first step in establishing e-mail security is a secure connection between your system and the
mail servers. This chapter describes how to set up your e-mail account the right way.
6.2.1
Configurationrequirements
When you configure an account, Thunderbird attempts to determine (from the email account
and the account details that you provide) the connection parameters to your email provider.
While Thunderbird knows the connection parameters for many email providers, it does not
know them all. If the parameters are not known to Thunderbird, you will need to provide the
following information to configure your account:
•
Your username
•
Your password
•
Incoming server:
name (such as imap.example.com), protocol (POP or IMAP),
port (by
default, 110), and security protocol
•
Outgoing server:
name (such as smtp.example.com), port (by default, 25), and
security protocol
You should have received this information from your hosting provider. Alternatively, you can
usually find this information on the support pages on the website of your hosting provider. In our
example we will be using the Gmail server configuration. You can use Thunderbird with your Gmail
account. To do so, you must change a configuration setting in your account. If you are not using a
Gmail account, skip the next section.
6.2.2
PreparingaGmailaccountforusewith Thunderbird
Log in to your Gmail account in your browser. Select
Settings
from options in the top right, then
go to the tab
Forwarding and POP/IMAP
. Click
Enable IMAP
and
then Save Changes.

256
Figure 6.13:Gmail enable IMAP
6.2.3
ConfiguringThunderbirdtouseSSL/TLS
When you start up Thunderbird for the first time, you will enter a step-by-step config- uration
procedure for setting up your first account. (You can invoke the account setup interface any time by
selecting
File | New | Mail Account
). On the first screen, you will be asked for your name,
your email-address and your password. The value you enter for your name does not have to be your
real name. It will be shown to the recipient of your messages. Enter the information and click
Continue
.
Figure 6.14:Thunderbird Configure
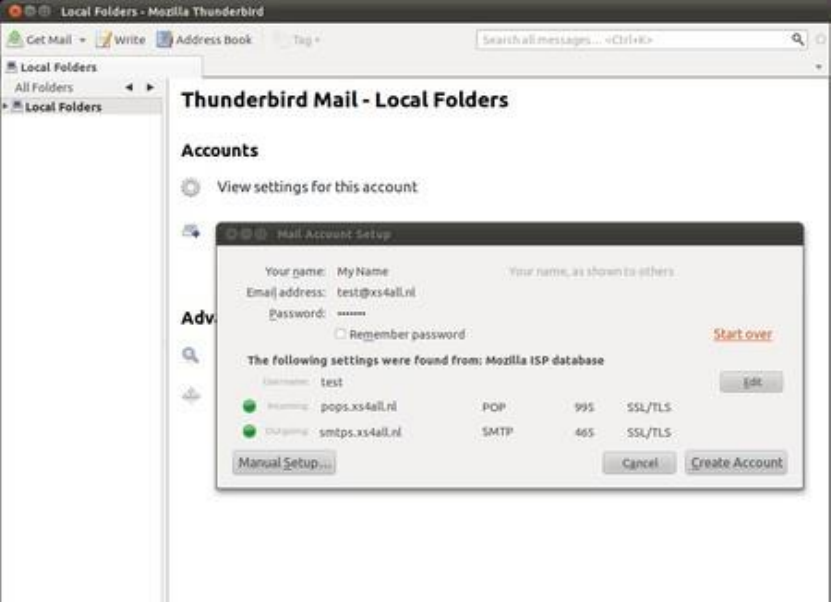
257
On the next screen, Thunderbird will attempt to determine the server names based on your
email address. This may take some time, and will only work if Thunderbird knows the settings
for the mail servers for your email provider. In either case you will be presented with a window
where you can modify the settings. In the example be- low, Thunderbird has detected the
settings automatically. You can see the protocol at the right side of the server names. This
should be either
SSL/TLS
or
STARTTLS
.
Otherwiseyourconnectionisinsecureandyou
shouldattemptmanualsetup.
When you are finished, click
Create account
. If Thunderbird could not determine your server
settings, click on
Manual setup
to configure the server names yourself.
Figure 6.15:Thunderbird Install

258
6.2.4
Manualsetup
Use the Account Settings interface to manually configure accounts in Thunderbird. The Account
Settings dialog will automatically open if you select
Manual setup
in the configuration wizard.
In this case we are only interested in the incoming and outgoing mail server names, and the protocol
we use to connect with them. As you can see in the examples below, we enter the Gmail server
names and we force them to use
TLS/SSL
, a secure method to connect to the servers.
Figure 6.16:Thunderbird Install
Under ‘Server Settings’, we will find only the incoming (
IMAP
) server and its settings for that
specific account.
After
Server Name
enter the name of the IMAP server, in this case mail.gmail.com.
As
youcanseewehaveselected
‘SSL/TLS’
undertheconnectionsecuritysetting.
This
enforcesencryption.
Do not be scared by the authentication method
Normal

259
Figure 6.17:Thunderbird Install
password
. The password will be automatically encrypted due to our secured connections
to the
server.
Finally, configure the outgoing server for the account. Click on
Outgoing Server (SMTP)
in
the left panel.

260
Figure 6.18:Thunderbird Install
Again, we have selected
SSL/TLS
under
Connection security
. The port will default to 465
and this should generally not have to be changed.
6.2.5
Finishingthesetup,differentencryptionmethods
Test your Thunderbird setup by trying to send and receive mails. Some email hosting providers
may not support the SSL/TLS protocol, which is the preferred choice. You will get an error
message saying the authentication protocol is not supported by the server. You may then switch
to using STARTTLS instead. In the above two screens, select ‘STARTTLS’ under ‘Connection
security’. If this method also fails, contact your email hosting provider and ask them if they
provide another way to securely connect to their servers. If they do not allow you to securely
connect to their servers, then you should complain and seriously consider switching to a
different provider.
6.2.6
Returningtotheconfigurationscreens
At any time you can reconfigure your email accounts by going to the Thunderbird menu bar and
clicking
Edit | Account Settings
(Linux),
Tools | Account Settings
(Win- dows and Mac
OS X).

261
6.3
Some Additional Security Settings
Thunderbird provides additional security measures to protect you from junk mail, identity theft,
viruses (with the help of your anti-virus software, of course), intellectual property theft, and
malicious web sites.
We will look at the following Thunderbird security features. First a little background on why
you need to consider some of these measures:
•
Adaptive junk mail controls
. Adaptive junk mail controls allow you to train
Thunderbird to identify junk email (SPAM) and remove it from your inbox. You can also
mark messages as junk mail manually if your email provider’s system misses the junk
mail and lets it go through.
•
Integration with anti-virus software.
If your anti-virus software supports
Thunderbird, you can use that software to quarantine messages that contain viruses or
other malicious content. If you’re wondering what anti-virus software works with
Thunderbird, you can find a list here: http://kb.mozillazine.org/Antivirus_ software.
•
Master password.
For your convenience, you can have Thunderbird remember each of
your individual passwords of your e-mail accounts. You can specify a master password that
you enter each time you start Thunderbird. This will enable Thunderbird to open all your email
accounts with your saved passwords.
•
Restrictions on cookies.
Some blogs and websites attempt to send cookies (a piece of
text that stores information from Web sites on your computer) with their RSS feeds. These
cookies are often used by content providers to provide targeted advertising. Thunderbird
rejects cookies by default, but you can configure Thunderbird to accept some or all cookies.
In the Security Preferences section of Thunderbird’s Options/Preferences dialog box you can
set up the preferences for these features.
•
In Windows and Mac OS X, go to the ‘Tools’ menu and click ‘Options’.
•
On Ubuntu or other versions of Linux, go to the ‘Edit’ menu and click ‘Preferences’.
6.3.1
Junkmailsettings
1.
In the Preferences/Options dialog box, click ‘Security’ and then click the ‘Junk’ tab.
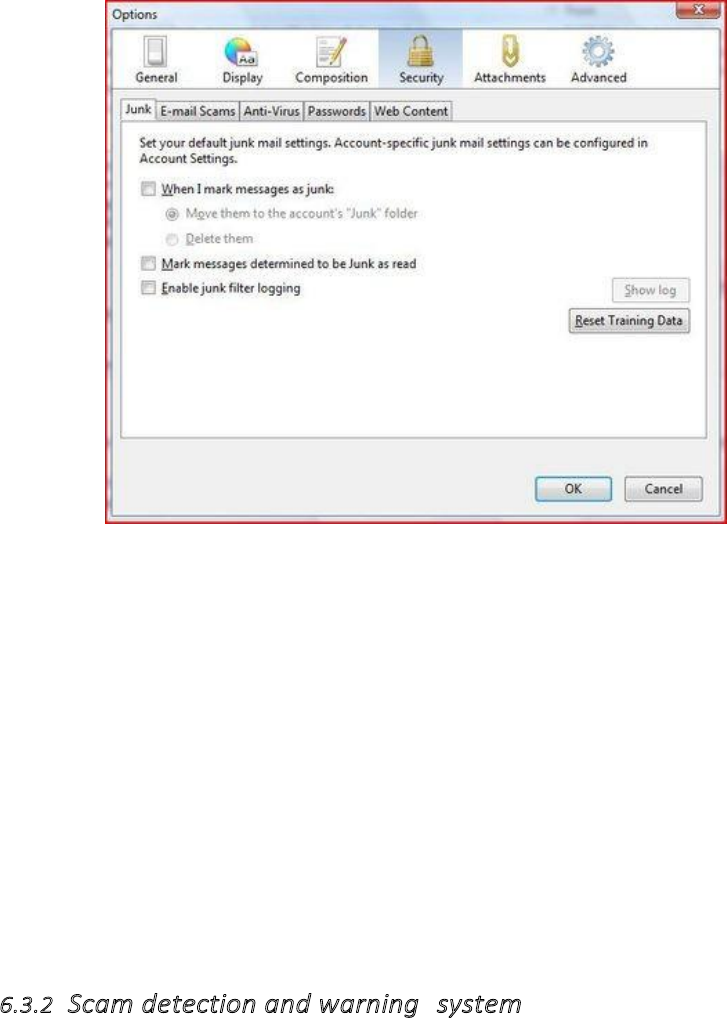
262
Figure 6.19:Thunderbird Security
2. Do the following:
•
To tell Thunderbird that it should handle messages marked as junk, select the check
box labelled ‘When I mark message as junk’.
•
To have Thunderbird move these messages to a junk folder, select the ‘Move them
to account’s ’Junk’ folder’ radio button.
•
To have Thunderbird delete junk mail upon receiving it, select the ‘Delete them’
radio button.
3.
Thunderbird will mark junk message as read if you select the check box labeled ‘Mark
messages determined to be Junk as read’.
4.
If you want to keep a log of junk mail received, select the ‘Enable junk filter logging’ check box.
5.
Click the ‘OK’ button to close the ‘Options/Preferences’ dialog box.
6.3.2
Scamdetectionandwarning system
1.
In the Preferences/Options dialog box, click ‘Security’ and then click the ‘E-mail Scams’ tab.
2.
To have Thunderbird warn you about possible email scams, select the check box

263
Figure 6.20:Thunderbird Security
labelled ‘Tell me if the message I’m read is a suspected email scam’. To turn off this
feature, deselect this check box.
3.
Click the ‘OK’ button to close the ‘Options/Preferences’ dialog box.
6.3.3
Antivirusintegration
1.
In the Preferences/Options dialog box, click ‘Security’ and then click the ‘Anti- Virus’ tab.
2.
To turn on anti-virus integration, select the check box labeled ‘Allow anti-virus clients to
quarantine individual incoming messages’. To turn off this feature, dese- lect this check
box.
3.
Click the ‘OK’ button to close the ‘Options/Preferences’ dialog box.
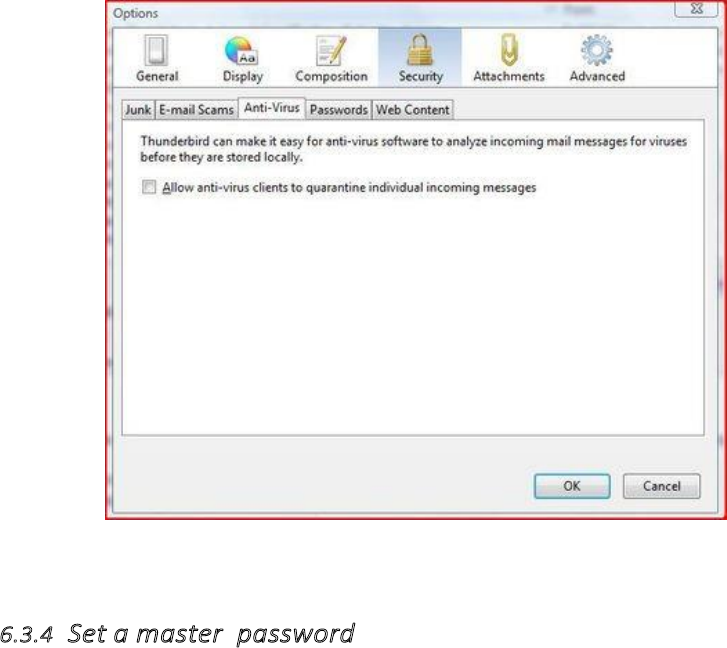
264
Figure 6.21:Thunderbird Security
6.3.4
Setamasterpassword
1.
In the Preferences/Options dialog box, click ‘Security’ and then click the ‘Pass- words’ tab.
2.
Select the check box labeled ‘Use a master password’.
3.
Enter your password into the ‘Enter new password’ and ‘Re-enter password’ fields.
4.
Click the ‘OK’ button to close the Change Master Password dialog box.
5.
If you want to see the passwords that you have saved in Thunderbird, click the ‘Saved
Passwords’ button. This will open the ‘Saved Passwords’ dialog box.
6.
To see the passwords, click the ‘Show Passwords’ button. 7.Click the
‘Close’ button to close ‘Saved Passwords’ dialog box.
8.Click the ‘OK’ button to close the ‘Options/Preferences’ dialog box.
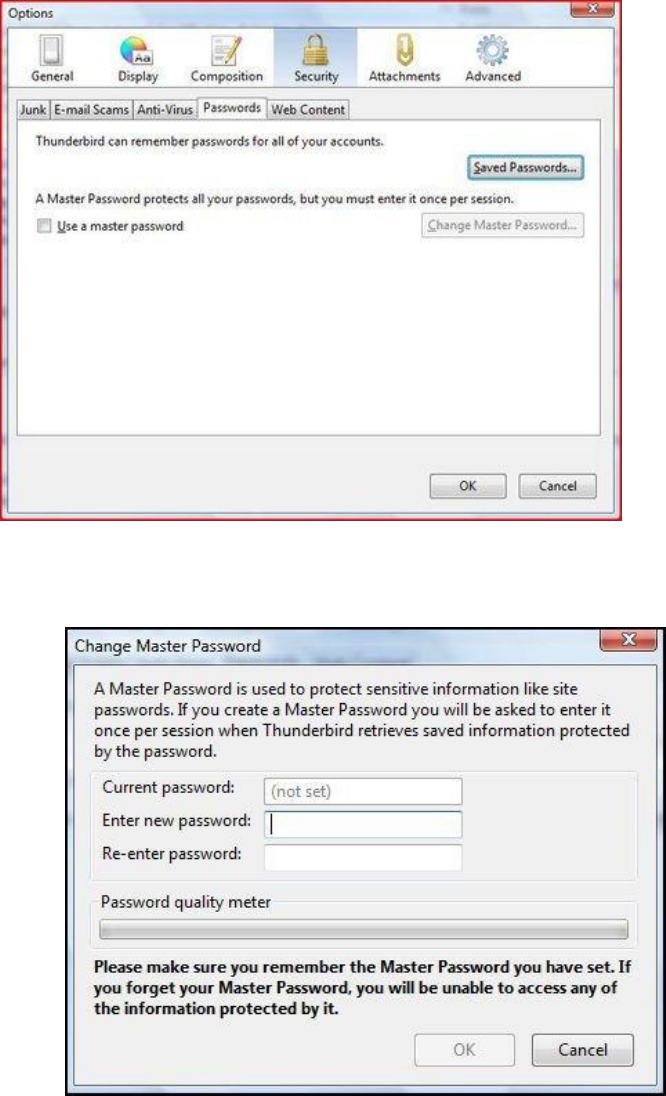
265
Figure 6.22:Thunderbird Security
Figure 6.23:Thunderbird Security
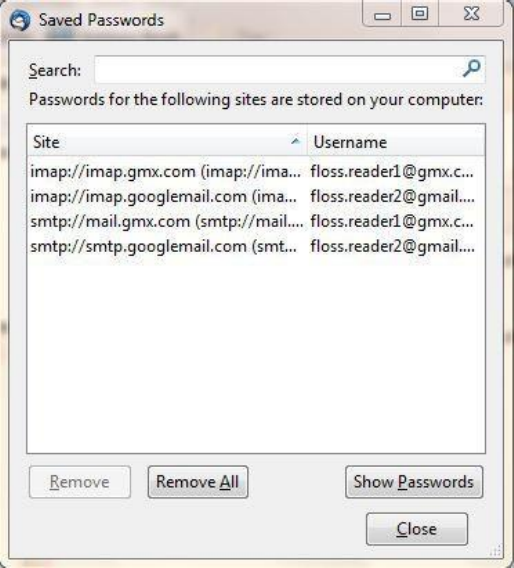
266
Figure 6.24:Thunderbird Security
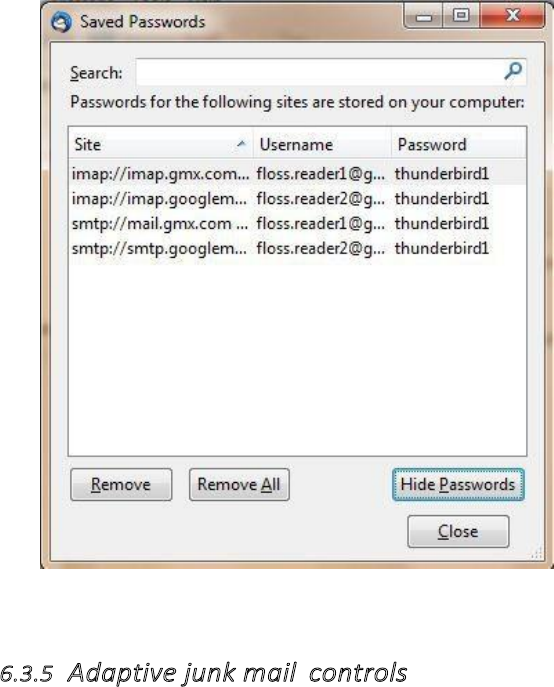
267
Figure 6.25:Thunderbird Security
6.3.5
Adaptivejunkmailcontrols
You need to first open Account Settings window. Note that settings configured in the Account
Settings window apply only to the account that you select in the Folders pane. You must
configure local folders separately.
1.
In the Folders pane right-click on an account name and select ‘Settings’.
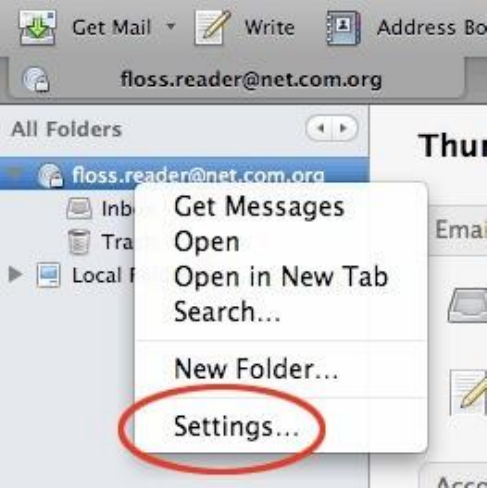
268
Figure 6.26:Thunderbird Security
2.
In Windows or Mac go to the ‘Tools’ menu and select ‘Account Settings’. In Linux, go to the
‘Edit menu’ and select ‘Account Settings’.
3.
To set adaptive junk mail controls for a specific account, pick an account and click ‘Junk
Settings’.
4.
To turn on the controls, select the check box labeled ‘Enable adaptive junk mail controls for this
account’. To turn them off, deselect this check box.
5.
If you want the controls to ignore mail from senders in your Address Book, select the check boxes
next to any of the listed address books.
6.
To use a mail filter such as SpamAssassin or SpamPal, select the check box labelled ‘Trust junk
mail headers sent by:’ and pick a filter from the menu.
7.
Select the check box labeled ‘Move new junk messages to’ if you want to move junk mail to a
specified folder. Then select the destination folder to be either at your email provider or a local
folder on your computer.
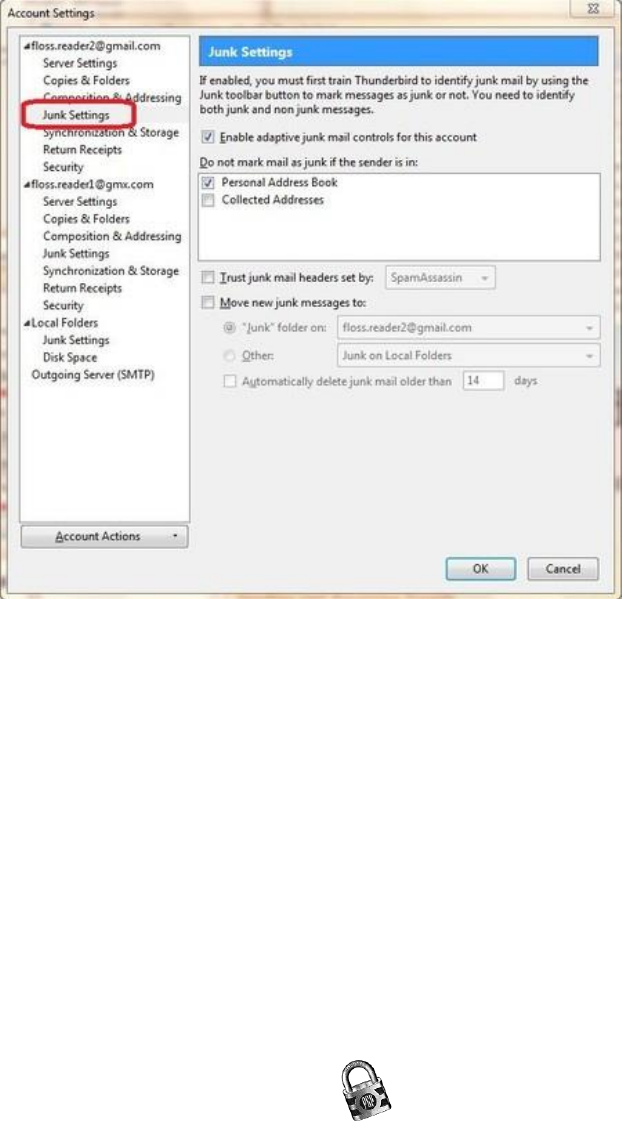
269
Figure 6.27:Thunderbird Security
8.
Select the ‘Automatically delete junk mail other 14 days’ check box to have Thun- derbird
regularly remove junk mail. To change the time period for this process, enter a different number
(in days) in the text box.
9.
Click ‘OK’ to save your changes.
7
Email Encryption
7.1
Introducing mail encryption (PGP)
Figure 7.1:PGP
This chapter will introduce you to some basic concepts behind mail encryption. It is important to
read to get some feeling of how mail encryption actually works and what its caveats and limitations
are.
PGP
(Pretty Good Privacy) is the protocol we shall use for e-mail encryption. This protocol
allows us to digitally sign and encrypt mail messages. It works on an end-to-end basis: messages
will be encrypted on your own computer and will only be decrypted by the recipient of the message.
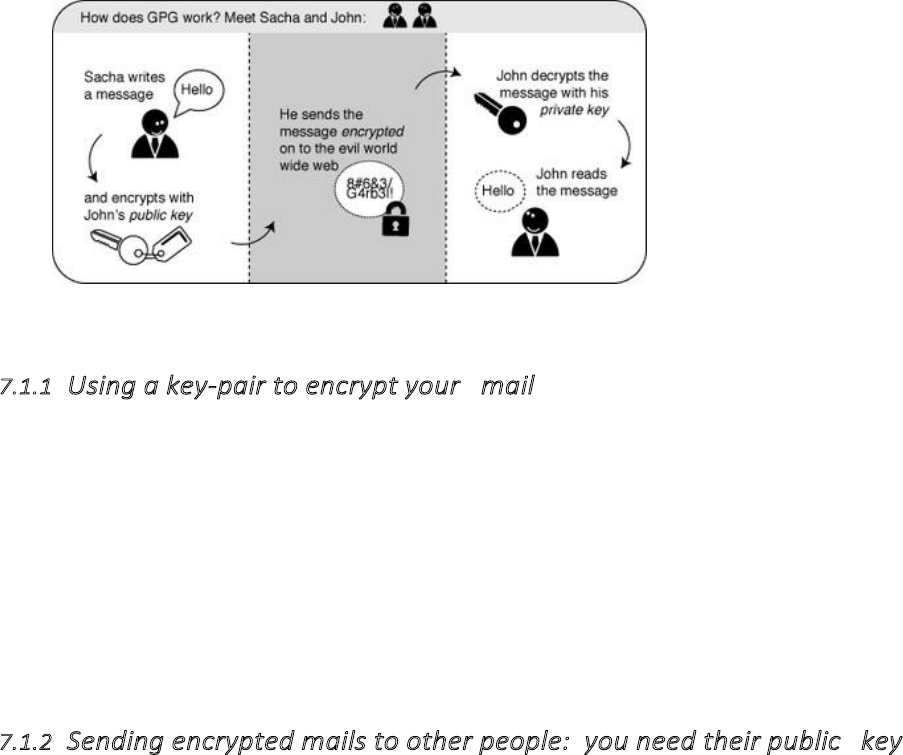
270
There is no possibility for a ‘man-in-the-middle’ to decipher the contents of your encrypted message.
This
excludes
the subject lines and the ‘from’ and ‘to’ addresses, which unfortunately are not
encrypted in this protocol.
After having introduced these basic concepts, the next chapters will give you a hands- on
guide to install the necessary tools on your operating system and get encryption up and running.
We will focus on using Enigmail which is an extension for Thunderbird that helps you manage
PGP encryption for your email. The installation process for Enigmail
/
PGP is different for Mac OSX, Windows and Ubuntu so please see the appropriate chapters
in this section for instructions.
Figure 7.2:GPG Schema
7.1.1
Usingakeypairtoencryptyourmail
A crucial concept in mail encryption is the usage of so-called
keypairs
. A key-pair is just two
separate files sitting on your harddisk or USB stick. Whenever you want to encrypt mails for a
certain mail-account, you will need to have these files available to yourself in some form. If they
are sitting at home on your computer, you will not be able to decrypt mail at the office. Putting
them on a USB stick should provide a solution to this problem.
A key-pair consists of the two different keys: a public key and a secret key.
The public key: you can give this key to other people, so they can send you encrypted mails.
This file does not have to be kept secret.
The secret key: this basically is your secret file to decrypt emails people send to you.
It should
never
be given to someone else.
7.1.2
Sendingencryptedmailstootherpeople:youneedtheirpublic key
I have five colleagues at work and I want to send encrypted mails to them. I need to have public
keys for each of their addresses. They can send me these keys using ordinary mail, or they can give
them to me in person, or put them on a USB stick, or they can have their keys on a website. It
doesn’t matter, as long as I can trust those keys really belong to the person I want to correspond
with. My software puts the keys on my ‘keyring’, so my mail application knows how to send them
encrypted mails.

271
7.1.3
Receivingencryptedmailsfromotherpeople:theyneedmypublic
key
For my five (or thirty) colleagues to be able to send
me
encrypted mails, the process goes the other
way around. I need to distribute my public key to each of them.
7.1.4
Conclusion:encryptionrequirespublickeydistribution!
All the people in a network of friends or colleagues wanting to send each other encrypted emails,
need to distribute their public keys to each other, while keeping their secret keys a closely
guarded secret. The software described in this chapter will help you do this key management.
7.2 Installing PGP on Windows
To complicate matters a little - PGP is the protocol used for encrypting e-mail by various
softwares. To get PGP to work with Thunderbird we need to install GPG - a free software
implementation of PGP
and
Enigmail - an extension of Thunderbird that allows you to use
GPG. . . Confused?! Don’t worry about it, all you have to know is how to encrypt your email
with PGP and you need to install
both
GPG and Enigmail. Here is how to do it. . .
7.2.1
InstallingPGP(GPG)onMicrosoftWindows
The GNU Privacy Guard (GnuPG) is software which is required to send PGP encrypted or signed
emails. It is necessary to install this software before being able to do any encryption.
Head to the website of the Gpg4win project. Go to http://gpg4win.org/
On the left side of the website, you will find a ‘Download’ link. Click on it.
Figure 7.3:GPG Windows
This will take you to a page where you can download the Gpg4Win. Click on the button which
offers you the latest stable version (not beta) of Gpg4Win.
Figure 7.4:GPG Windows

272
This will download you an .exe file. Depending on your browser, you may have to double-click
on this downloaded file (named something like gpg4qin-2.1.0.exe) before something happens.
Windows will ask you if you are sure you want to install this pro- gram. Answer yes.
Then complete the installation by agreeing to the license, choosing appropriate lan- guage
and accepting the default options by clicking ‘Next’, unless you have a particular reason not to.
The installer will ask you where to put the application on your computer. The default setting
should be fine but make a note of it as we may need this later. Click on ‘Next’ when you agree.
7.2.2
InstallingwiththeEnigmail extension
After you have successfully installed the PGP software as we described above you are now ready
to install the Enigmail add-on.
Enigmail is a Thunderbird add-on that lets you protect the privacy of your email conversations.
Enigmail is simply an interface that lets you use PGP encryption from
within Thunderbird.
Enigmail is based on public-key cryptography. In this method, each individual must generate
her/his own personal key pair. The first key is known as the private key. It is protected by a
password or passphrase, guarded and never shared with anyone.
The second key is known as the public key. This key can be shared with any of your
correspondents. Once you have a correspondent’s public key you can begin sending encrypted e-
mails to this person. Only she will be able to decrypt and read your emails, because she is the only
person who has access to the matching private key.
Similarly, if you send a copy of your own public key to your e-mail contacts and keep the matching
private key secret, only you will be able to read encrypted messages from those contacts.
Enigmail also lets you attach digital signatures to your messages. The recipient of your message
who has a genuine copy of your public key will be able to verify that the e-mail comes from you,
and that its content was not tampered with on the way. Similarly, if you have a correspondent’s
public key, you can verify the digital signatures on her messages.
7.2.3
Installationsteps
To begin installing Enigmail, perform the following steps:
1.
Open
Thunderbird
, then Select Tools > Add-ons to activate the
Addons
win- dow;
the Add-ons window will appear with the default
GetAddons
pane enabled.
2.
Enter enigmail in the search bar, like below, and click on the search icon.
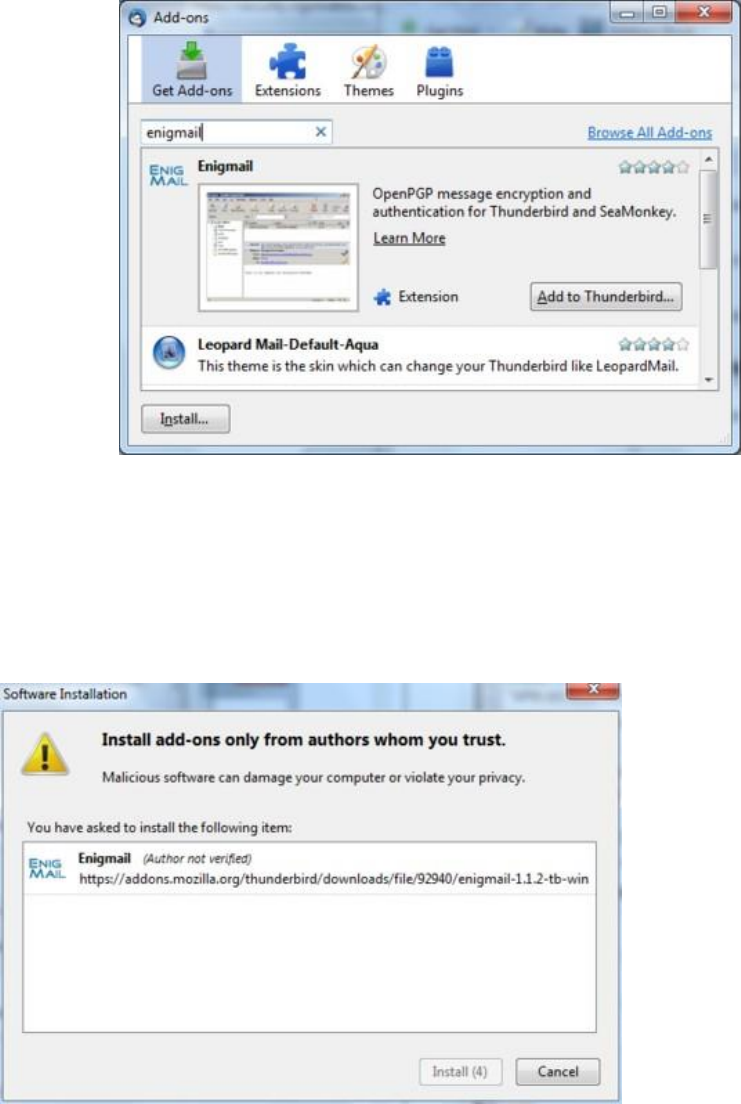
273
Figure 7.5:Enigmail Install
3.
Simply click on the ‘Add to Thunderbird’ button to start the installation.
4.
Thunderbird will ask you if you are certain you want to install this add-on. We
trust this application so we should click on the ‘Install now’ button.
Figure 7.6:Enigmail Install
5.
After some time the installation should be completed and the following window
should appear. Please click on the ‘Restart Thunderbird’ button.
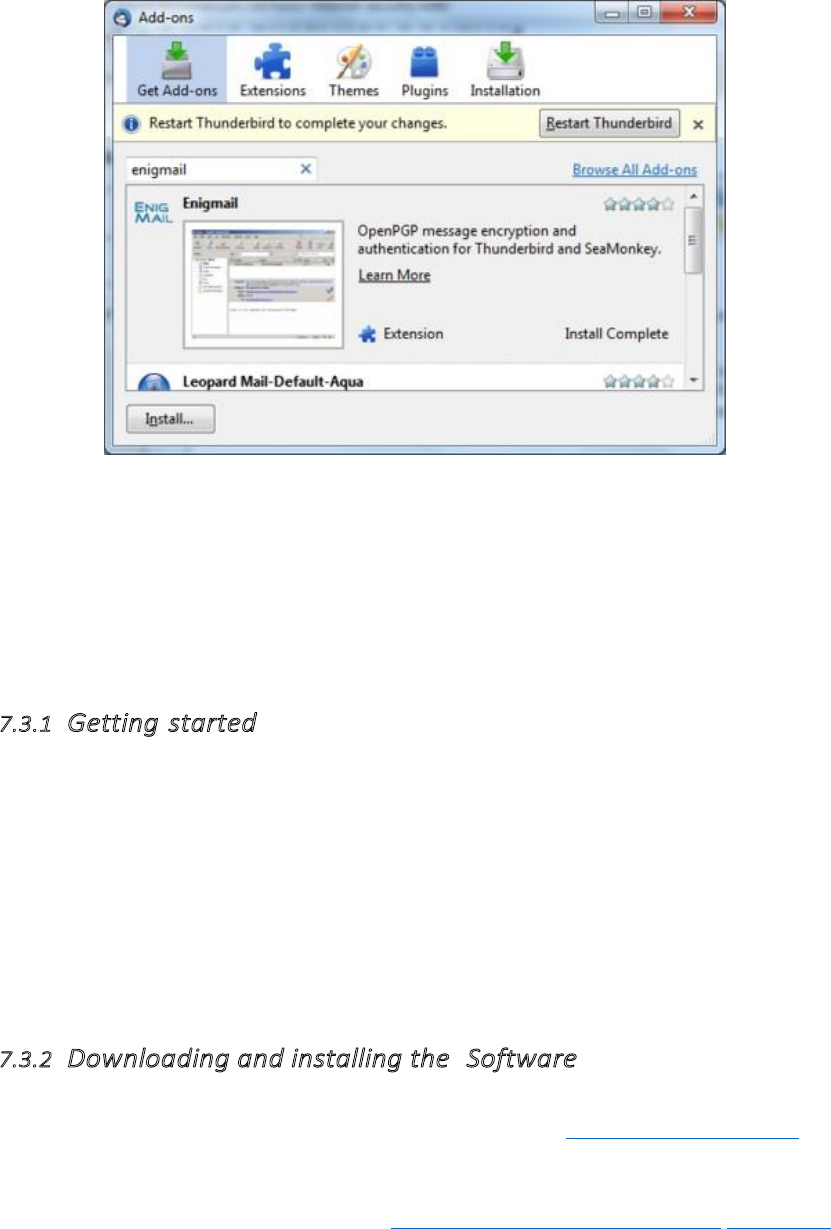
274
Figure 7.7:Enigmail Install
7.3
Installing PGP on OSX
The GNU Privacy Guard (GnuPG) is software which enables you to send PGP encrypted or signed
emails. It is necessary to install this software before being able to do any encryption. This chapter
covers the installation steps required to install GnuPG on Mac OSX.
7.3.1
Gettingstarted
For this chapter we assume you have the latest version of:
•
OSX installed (10.6.7)
•
Thunderbird (3.1.10)
Note on OSX Mail:
It is possible to use PGP with the build-in mail program of OSX. But
we do not recommend this because this option relies on a hack of the program which is neither
open or supported by its developer and breaks with every update of the mail program. So unless
you really have no other option we advice you to switch to Mozilla Thunderbird as your default
mail program if you want to use PGP.
7.3.2
Downloadingandinstallingthe Software
1.
For OSX there is a bundle available which will install everything you need in one in-
stallation. You can get it by directing your browser to http://www.gpgtools.org/ and
clicking on the big blue disk with “Download GPGTools Installer” written under
it. It will redirect you to another page on http://www.gpgtools.org/installer/ index.html
where you can actually download the software.
(nb.WeareusingthelatestversionFirefoxforthismanual,sothescreensmightlookalittlebit
differentifyouareusingadifferentbrowser)
275
2.
Download the software by choosing ‘Save File’ and clicking ‘OK’ in the dialogue.
3.
Navigate to the folder where you normally store your downloads (Mostly the desk- top
or the downloads folder surprisingly) en double click the ‘.DMG’ file to open the
virtual disk containing the installer.
4.
Open the installer by double-clicking on the icon.
5.
The program will check your computer to see if it can run on the computer.
(Note, if you’re Mac is bought before 2006 it will not have an intel processor required to run
this software and the installation will fail. Sadly it is beyond the scope op this manual to also
take into account computers over five year old)
You will be guided by the program through the next steps like accepting the license agreement.
But stop pressing all the OK’s and Agrees as soon as you come to the ‘Installation Type’ screen:
6.
Clicking ‘Customize’ will open this screen where you several options of programs and
software to install. You can click on each one of them to get a little bit of information
on what is is, what it does and why you might need it.
As said in the intro; we advise against using Apple Mail in combination with PGP. Therefore you
won’t be needing ‘GPGMail’, as this enables PGP on Apple Mail, and you can uncheck it.
‘
Enigmail
’ on the other hand is very important as it is the component that will enable
Thunderbird to use PGP. In the screen shot here it is greyed out as the installer wasn’t able to
identify my installation of Thunderbird. Since this seems to be a bug. You can also install
Enigmail from within Thunderbird as is explained in another chapter.
If the option is not greyed out in your installation, you should tick it.
After you checked all the components you want to install click ‘Install’ to proceed. The
installer will ask you for your password and after you enter that the installation will run
and
complete; Hooray!
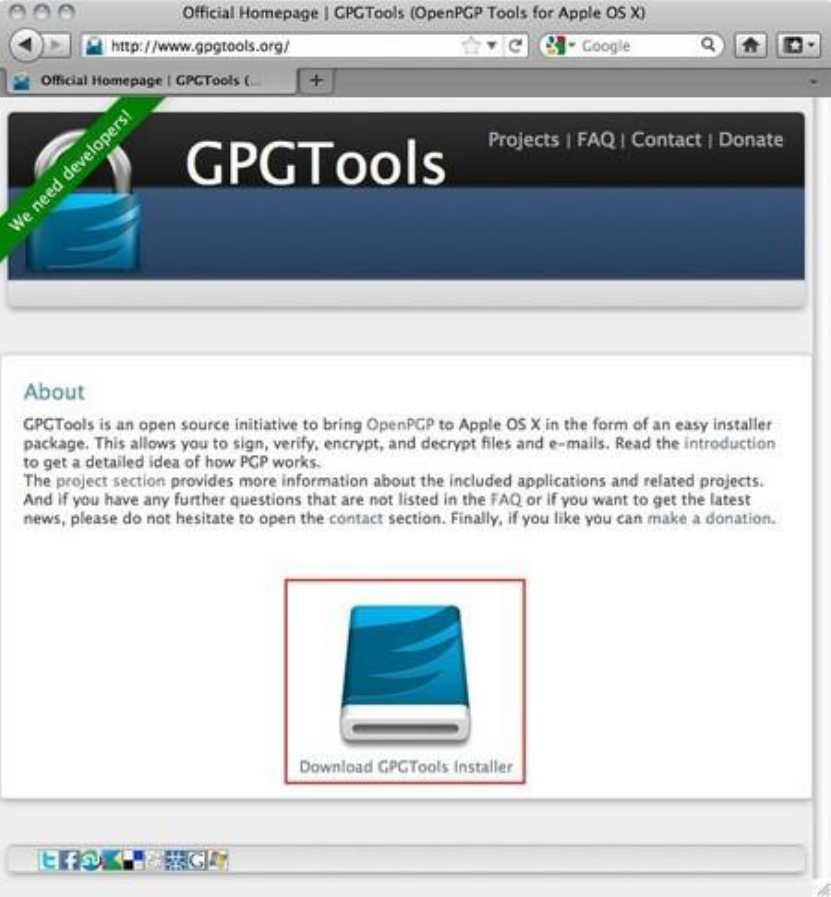
276
Figure 7.8:GPG Install
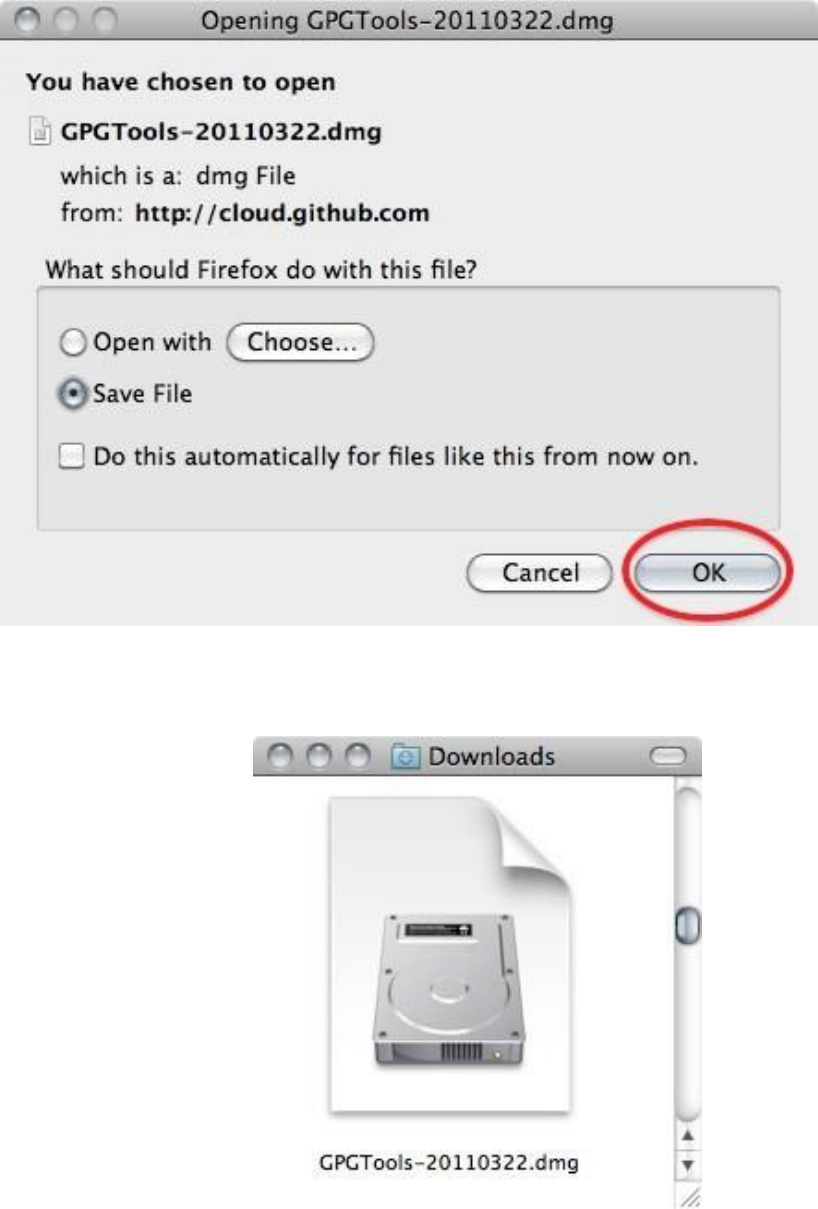
277
Figure 7.9:GPG Install
Figure 7.10:GPG Install
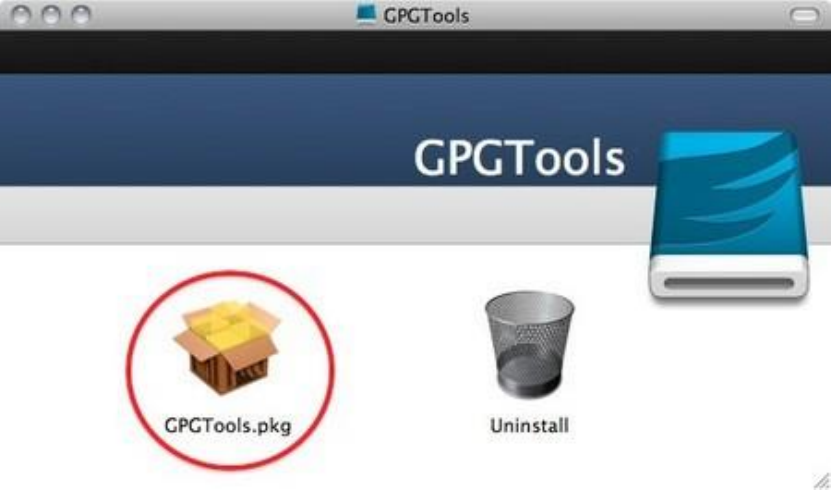
278
Figure 7.11:GPG Install
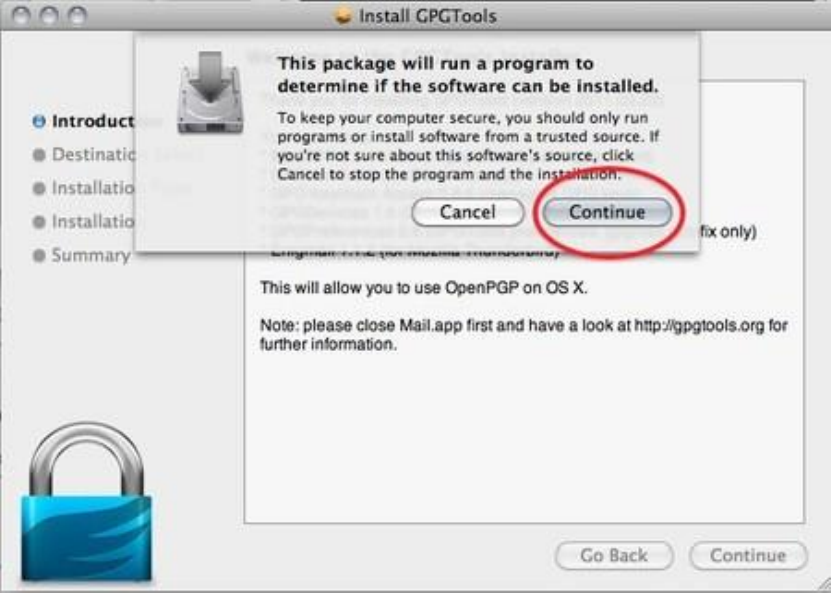
279
Figure 7.12:GPG Install
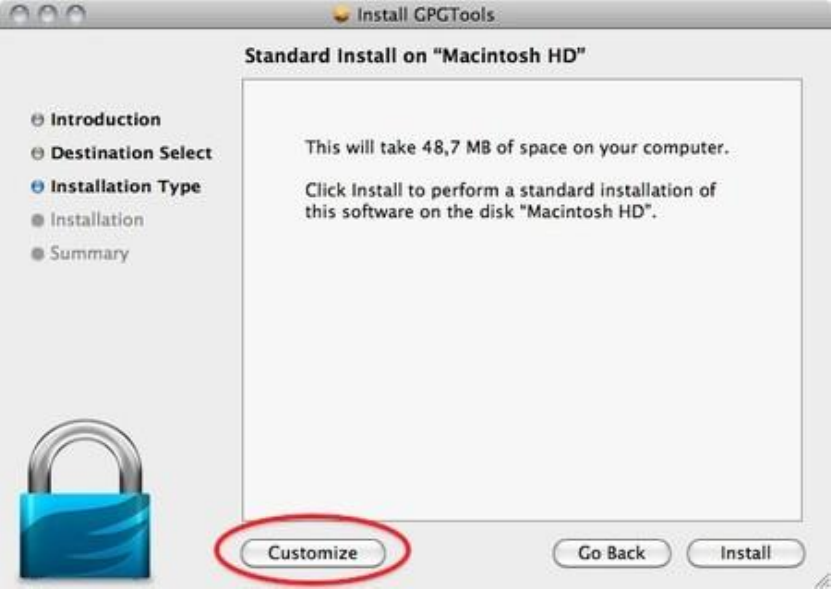
280
Figure 7.13:GPG Install
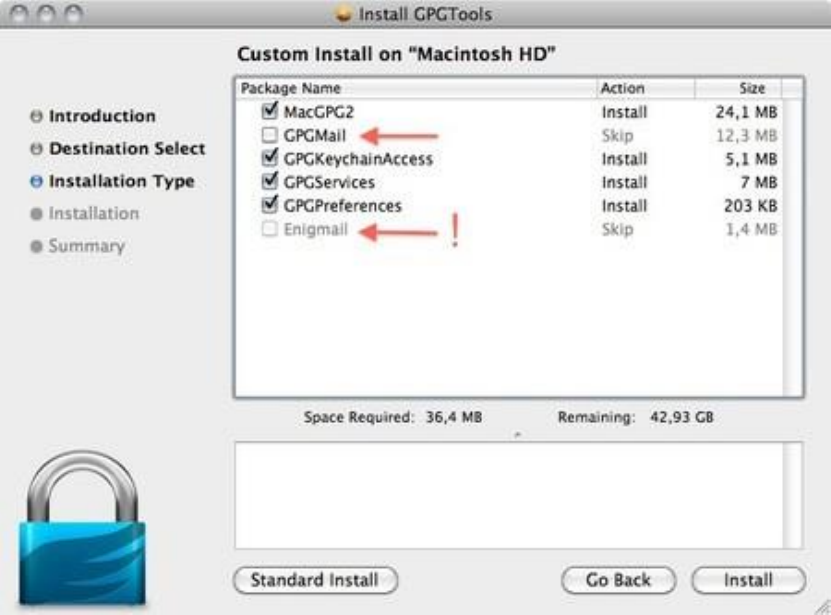
281
Figure 7.14:GPG Install
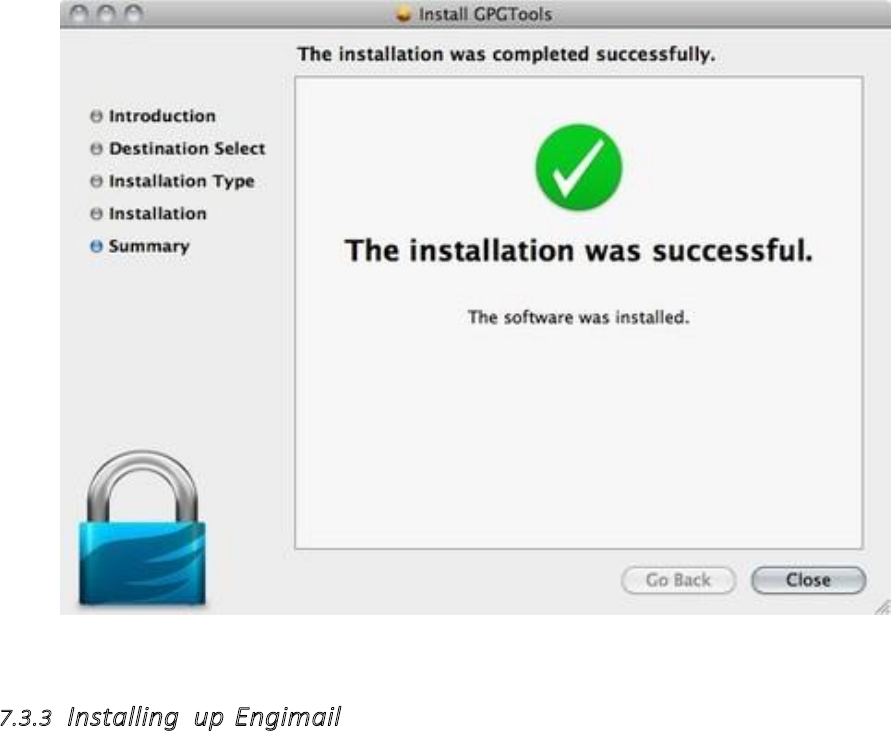
282
Figure 7.15:GPG Install
7.3.3
InstallingupEngimail
1.
Open
Thunderbird
, then Select Tools > Add-ons to activate the
Addons
win- dow;
the Add-ons window will appear with the default
GetAddons
pane enabled.
In the Add-On window, you can search for ‘Enigmail’ and install the extension by clicking
‘Add to Thunderbird . . . ’
2.
After you open the Add-On window, you can search for ‘Enigmail’ and install the
extension by clicking ‘Add to Thunderbird . . . ’
3.
Click on ‘Install Now’ to download and install the extension.
Be aware that you will have to restart Thunderbird to use the functionality
of
this extension!
Now that you have successfully downloaded and installed Enigmail and PGP you can go on
to the Chapter that deals with setting up the software for use.

283
Figure 7.16:GPG Install
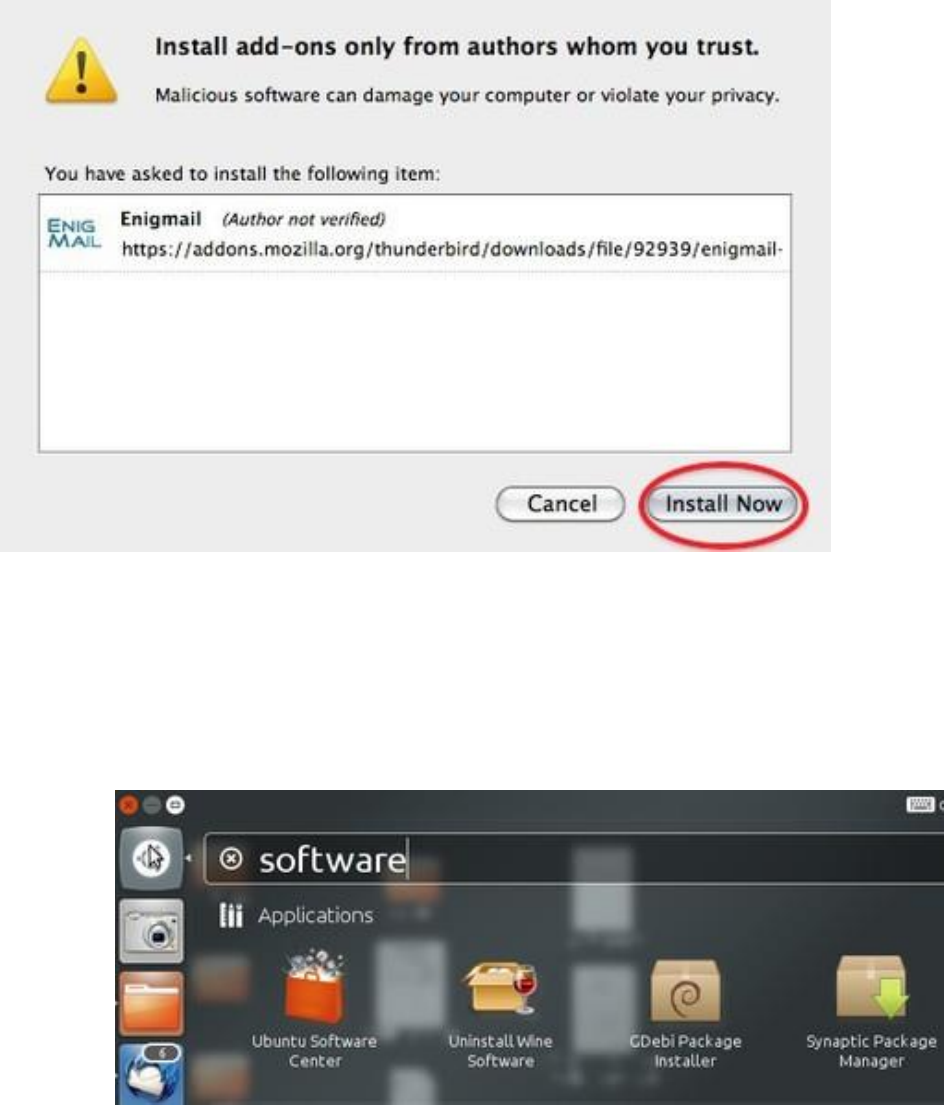
284
Figure 7.17:GPG Install
7.4
Installing PGP on Ubuntu
We will use the Ubuntu Software Centre for installing PGP (Enigmail and accessories). First open
the Ubuntu Software Center through the Unity menu by typing ‘software’ into the Unity search area
Figure 7.18:PGP Install Click on the
‘Ubuntu Software Center’.
Type into the search field ‘Enigmail’ and search results should be returned automati- cally:
Highlight the Enigmail item (it should be highlighted by default) and click ‘Install’ and you
will be asked to authenticate the installation process.
Enter your password and click ‘Authenticate’. The installation process will begin.

285
When the process is completed you get very little feedback from Ubuntu. The progress bar at the
top left disappears. The ‘In Progress’ text on the right also disappears. Enigmail should now be
installed.
Figure 7.19:PGP Install
7.5
Installing GPG on Android
With the growing usage of mobile phones for e-mail, it’s interesting to be able to use GPG also on
your mobile. This way you can still read the messages sent to you in GPG on your phone and not
only on your computer.
Install the
AndroidPrivacyGuard(APG)
and
K9Mail
applications to your Android device from
the Google Play Store or another trusted source.
1.
Generate a new private key that uses DSA-Elgamal with your PC’s GPG installa- tion (You
can only create keys with up to 1024bit key length on Android itself).
2.
Copy the private key to your Android device.
3.
Import the private key to APG. You may wish to have APG automatically delete the
plaintext copy of your private key from your Android device’s filesystem.
4.
Set-up your e-mail accounts in
K9 Mail
.
5.
In the settings for each account, under
Cryptography
, make sure that K-9 Mail knows to use
APG. You can also find options here to make K-9 Mail automatically sign your messages
and/or encrypt them if APG can find a public key for the recipient(s).
6.
Try it out.
7.5.1
APG
This is a small tool which makes GPG encryption possible on the phone. You can use APG to
manage your private and public keys. The options in the application are quite
286
straightforward if you are a little knowledge of GPG in general.
Management of keys is not very well implemented yet. The best way is to manually copy all
your public keys to the SD card in the APG folder. Then it’s easy to import your keys. After
you’ve imported your public and private keys, GPG encrypting, signing and decrypting will be
available for other applications as long as these applications have integrated encryption/GPG.
7.5.2
GPGenabledemailonAndroid:K9Mail
The default mail application does not support GPG. Luckily there is an excellent alter- native:
K-9 Mail. This application is based on the original Android mail application but with some
improvements. The application can use APG as it’s GPG provider. Setting up K-9 Mail is
straightforward and similar to setting up mail in the Android default mail application. In the
settings menu there is an option to enable “Cryptography” for GPG
mail signing.
If you want to access your GPG mails on your phone this application is a must have.
Please
note, due to some small bugs in K-9 Mail and/or APG, it’s very advisable to
disable HTML
mail and use only Plain text. HTML mails are not encrypted nicely and
are often not readable.
7.6
Creating your PGP keys
Enigmail comes with a nice wizard to help you create a public/private key pair (see the chapter
introducing PGP for an explanation). You can start the wizard at any time within Thunderbird
by selecting OpenPGP > Setup Wizard from the menu on top.
1.
This is what the wizard looks like. Please read the text on every window carefully. It provides
useful information and helps you setup PGP to your personal preferences. In the first screen,
click on Next to start the configuration.
2.
The wizard asks you whether you want to sign all your outgoing mail messages. Signing all
your messages is a good choice. If you choose not to, you can still manually decide to sign a
message when you are composing it. Click on the ‘Next’ button after you have made a
decision.
3.
On the following screen, the wizard asks you whether you want to encrypt
all
your outgoing
mail messages. Unlike signing of mails, encryption requires the recipient to have PGP
software installed. You should probably answer ‘no’ to this question, so that you will send
normal (unencrypted) mail by default. After you have made your decision, click on the
‘Next’ button.
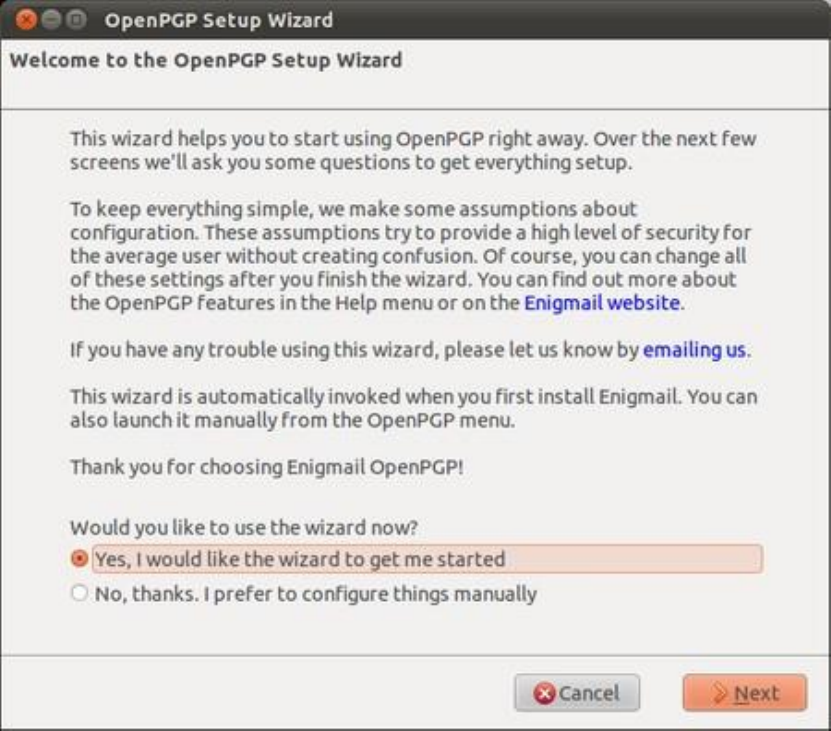
287
Figure 7.20:GPG Keys
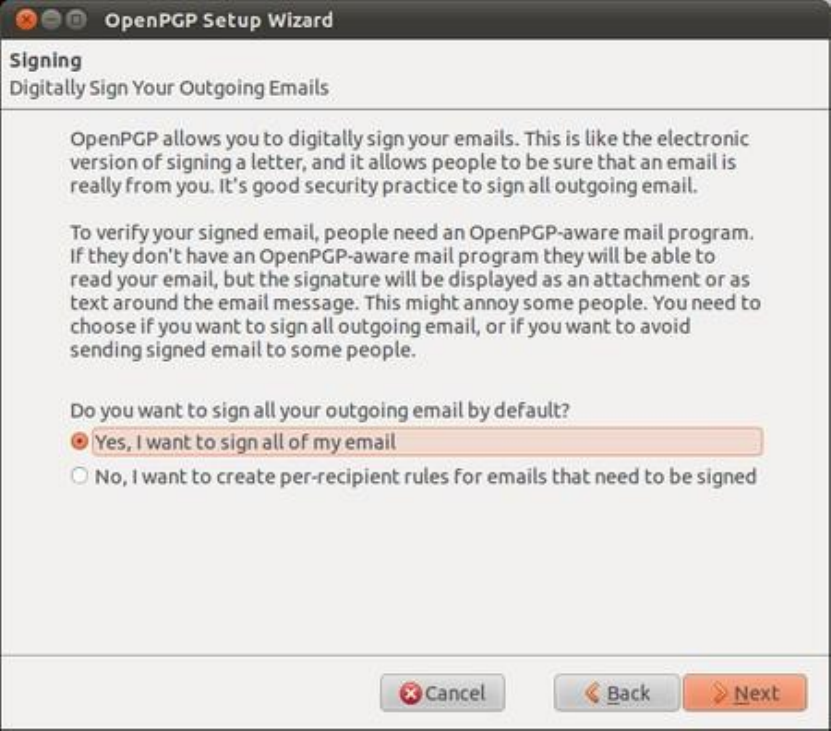
288
Figure 7.21:GPG Keys
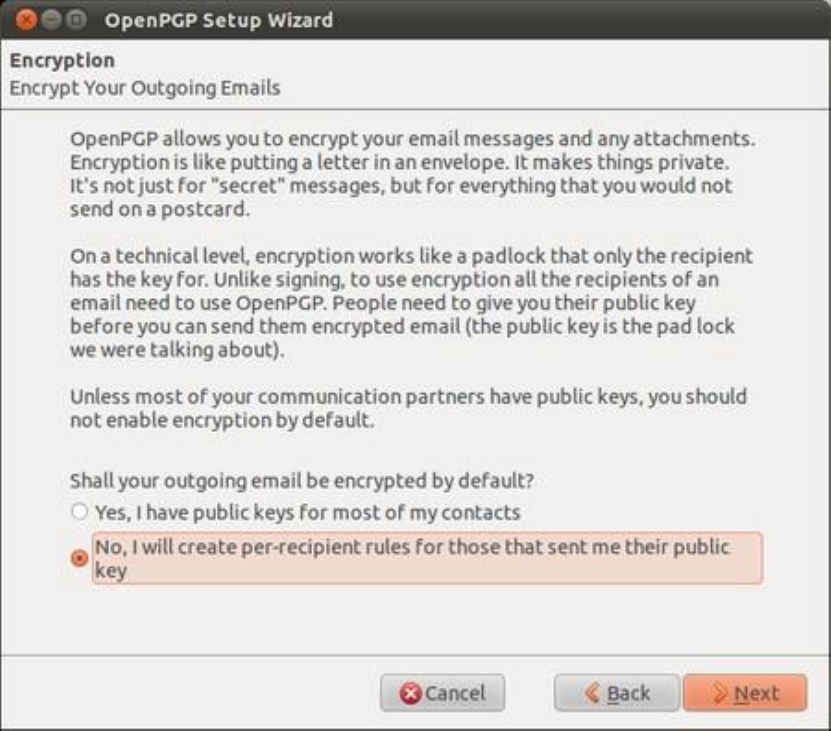
289
Figure 7.22:GPG Keys
4.
On the following screen the wizard asks if it can change some of your mail formatting
settings to better work with PGP. It is a good choice to answer ‘Yes’ here. This will
mean that by default, mail will be composed in plain text rather than HTML. Click on
the ‘Next’ button after you have made your decision.
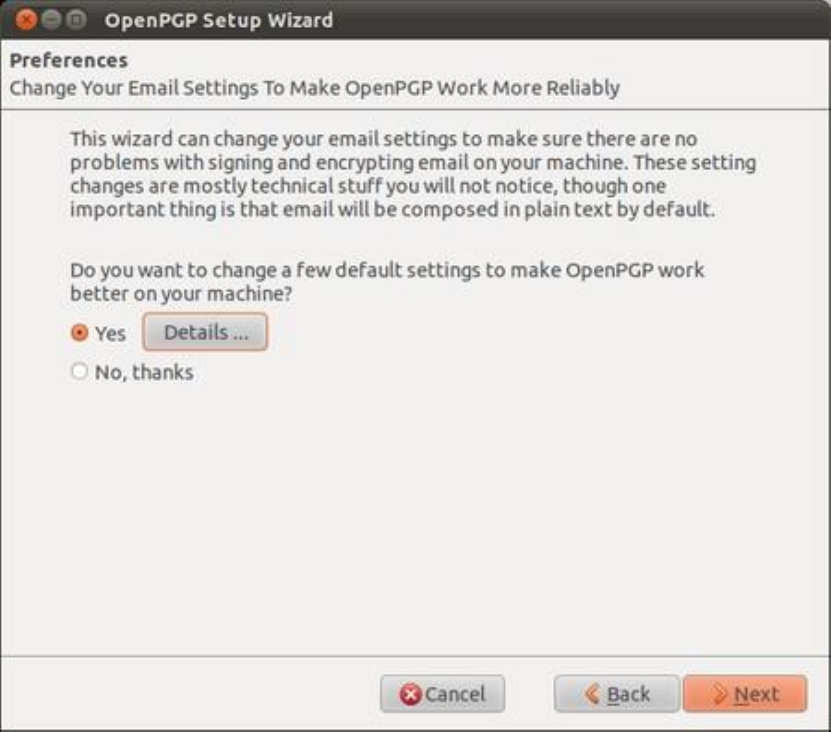
290
Figure 7.23:GPG Keys
5.
In the following screen, select one of your mail accounts; the default is selected for you if
you only have one. In the ‘Passphrase’ text box you must enter a pass- word. This is a
new
password which is used to protect your private key. It is
very important
to remember
this password, because you cannot read your own encrypted emails if you forget it. Make it a
strong
password, ideally 20 characters or longer. Please see the chapter on passwords for
help on creating unique, long and easy to remember passwords. After you have selected
your account and created a passphrase, click on the ‘Next’ button.
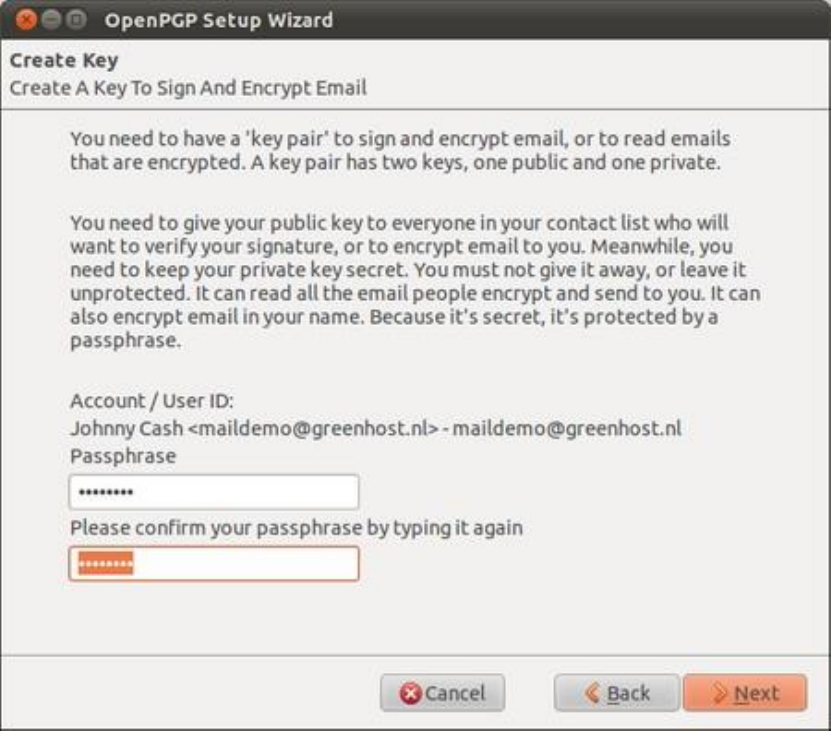
291
Figure 7.24:GPG Keys
6.
In the following screen the wizard summarizes the actions it will take to enable PGP
encryption for your account. If you are satisfied, click the ‘Next’ button.
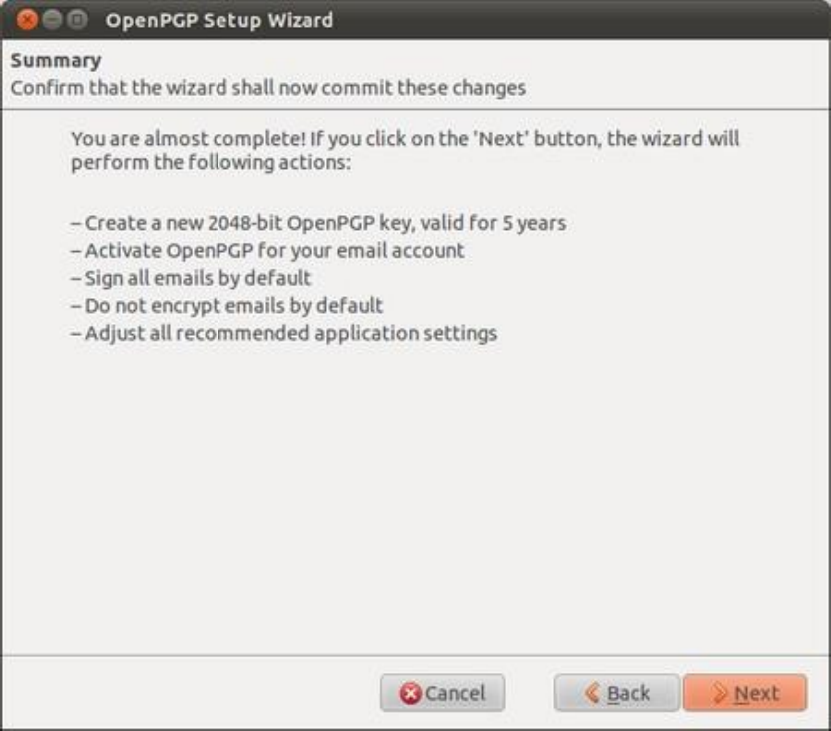
292
Figure 7.25:GPG Keys
7.
Your keys will be created by the wizard, which will take some time. When com- pleted,
click on the ‘Next’ button.
8.
You now have your own PGP key-pair. The wizard will ask you if you also want to create a
‘Revocation certificate’. This is a file which can be used to inform everyone if your private
key is compromised, for example if your laptop is stolen. Think of it as a ‘kill switch’ for
your PGP identity. You may also wish to revoke the key simply because you have generated
a new one, and the old one is obsolete.
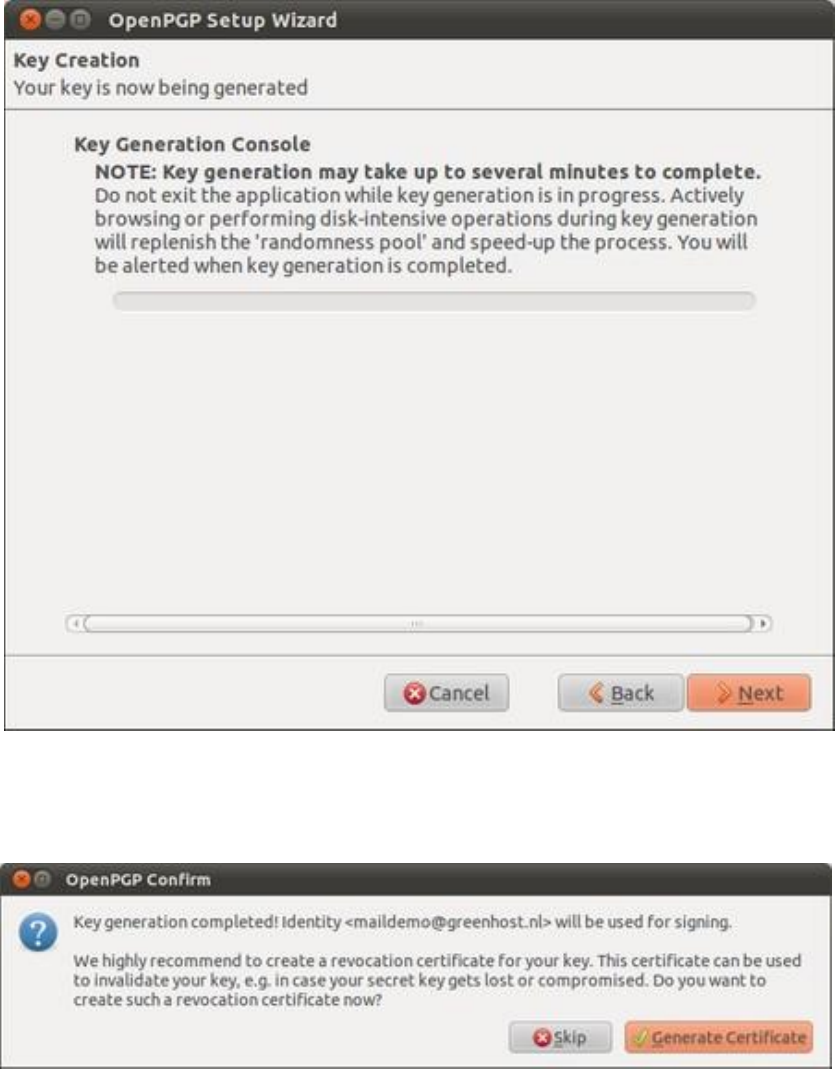
293
Figure 7.26:GPG Keys
Figure 7.27:GPG Keys
9.
If you decided to generate a revocation certificate, the wizard will ask you where the file
should be saved. The dialog will look different depending on which oper- ating system you
use. It is a good idea to rename the file to something sensible like
my_revocation_certificate. Click on ‘Save’ when you you have decided on a location.
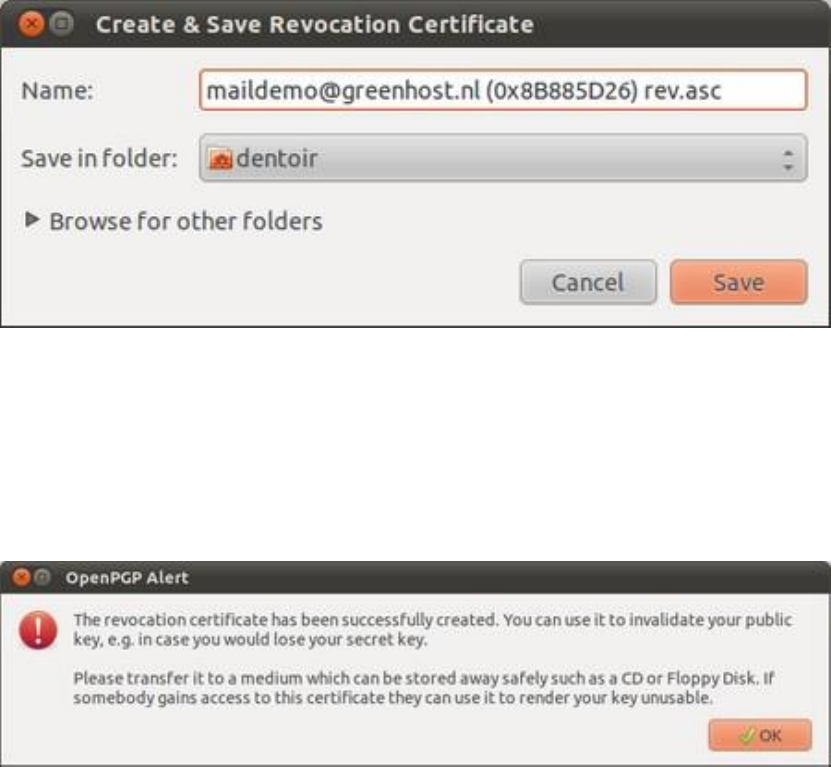
294
Figure 7.28:GPG Keys
10.
If you decided to generate a revocation certificate, the wizard informs you it has been
successfully stored. You may want to print it out or burn it to a CD and keep it in a safe
place.
Figure 7.29:GPG Keys
11.
The wizard will inform you it has completed.
Congratulations, you now have a fully PGP-configured mail client. In the next chapter we will
explain how to manage your keys, sign messages and do encryption. Thunderbird can help you do
a lot of these things automatically.
295
Figure 7.30:GPG Keys
7.7
Daily PGP usage
In the previous chapters we have have explained how to set up a secure mail environment using
Thunderbird, GPG and Enigmail. We assume you have installed the software and have successfully
followed the wizard instructions to generate an encryption key-pair as described in the previous
chapter. This chapter will describe how to use your secured Thunderbird in daily life to protect your
e-mail communication. In particular we will focus on:
1.
Encrypting attachments 2.Entering
your pass-phrase 3.Receiving encrypted
e-mail 4.Sending and receiving public
keys
5.Receiving public keys and adding them to your key ring 6.Using
public key servers
7.
Signing e-mails to an individual
8.
Sending encrypted e-mails to an individual
9.Automating encryption to certain recipients
10.Verifying incoming e-mails
11.
Revoking your GPG key pair
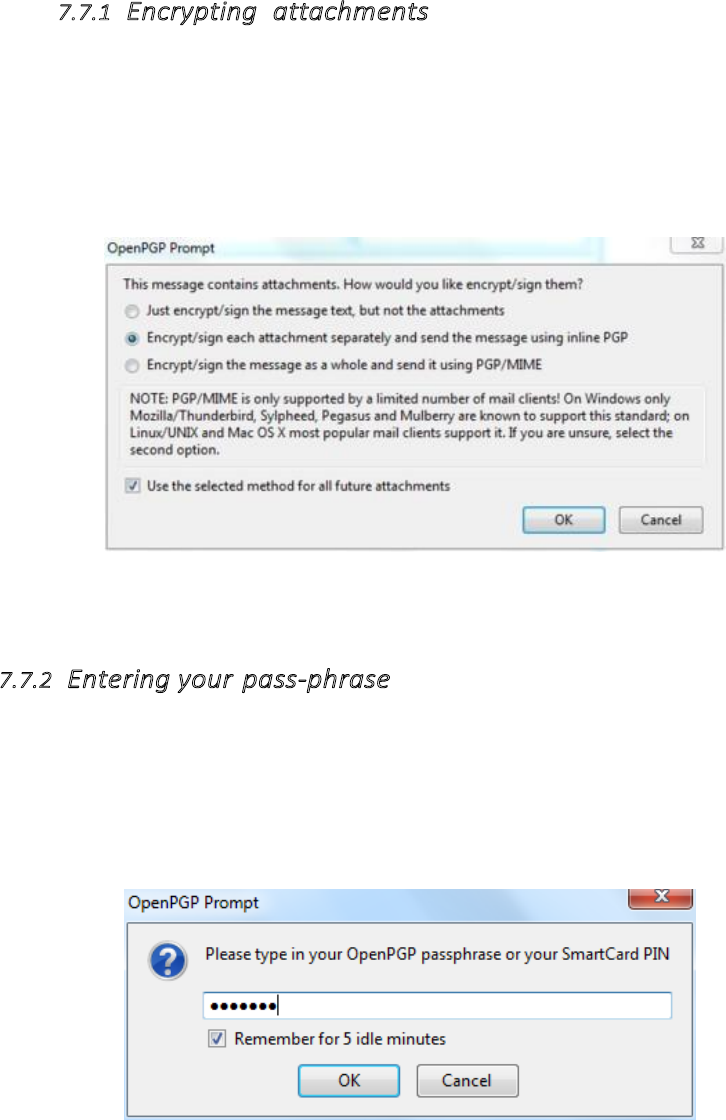
296
12.
What to do when you have lost your secret key, or forgot your passphrase 13.What
to do when your secret key has been stolen, or compromised 14.Backing up your keys
First we shall explain two dialog windows that will inevitably appear after you start using
Thunderbird to encrypt your emails.
7.7.1
Encryptingattachments
The dialog window below will pop-up whenever you are sending an encrypted email with
attachments for the first time. Thunderbird asks a technical question on how to encrypt
attachments to your mail. The second (default) option is the best choice, because it combines
security with the highest compatibility. You should also select the ‘Use the selected method for
all future attachments’ option. Then click ‘OK’ and your mail should be sent with no further
delay.
Figure 7.31:Daily GPG Usage
7.7.2
Enteringyourpassphrase
For security reasons, the pass-phrase to your secret key is stored temporarily in memory. Every now
and then the dialog window below will pop-up. Thunderbird asks you for the pass-phrase to your
secret key. This should be different from your normal email password. It was the pass-phrase you
have entered when creating your key-pair in the previous chapter. Enter the pass-phrase in the text-
box and click on ‘OK’
Figure 7.32:Daily GPG Usage
297
7.7.3
Receivingencryptedemails
The decryption of e-mails is handled automatically by Enigmail, the only action that may be
needed on your behalf is to enter the pass-phrase to your secret key. However, in order to have any
kind of encrypted correspondence with somebody, you will first need to exchange public keys.
7.7.4
Sendingandreceivingpublic keys
There are multiple ways to distribute your public key to friends or colleagues. By far the simplest
way is to attach the key to a mail. In order for your friend to be able to trust that the message
actually came from you, you should inform them in person (if possible) and also require them to
reply to your mail. This should at least prevent easy forgeries. You have to decide for yourself what
level of validation is necessary. This is also true when receiving emails from third-parties containing
public keys. Contact your correspondent through some means of communication other than e-mail.
You can use a telephone, text messages, Voice over Internet Protocol (VoIP) or any other method,
but you must be absolutely certain that you are really talking to the right person. As a result,
telephone conversations and face-to-face meetings work best, if they are convenient and if they can
be arranged safely.
Sending your public key is easy.
1.
In Thunderbird, click on the icon.
2.
Compose a mail to your friend or colleague and tell them you are sending them your PGP
public key. If your friend does not know what that means, you may have to explain them
and point them to this documentation.
3. Before actually sending the mail, click to OpenPGP >
Attach
My Public Key op- tion on the
menu bar of the mail compose window. Next to this option a marked sign will appear. See
the example below.
4.
Send your mail by clicking on the button.
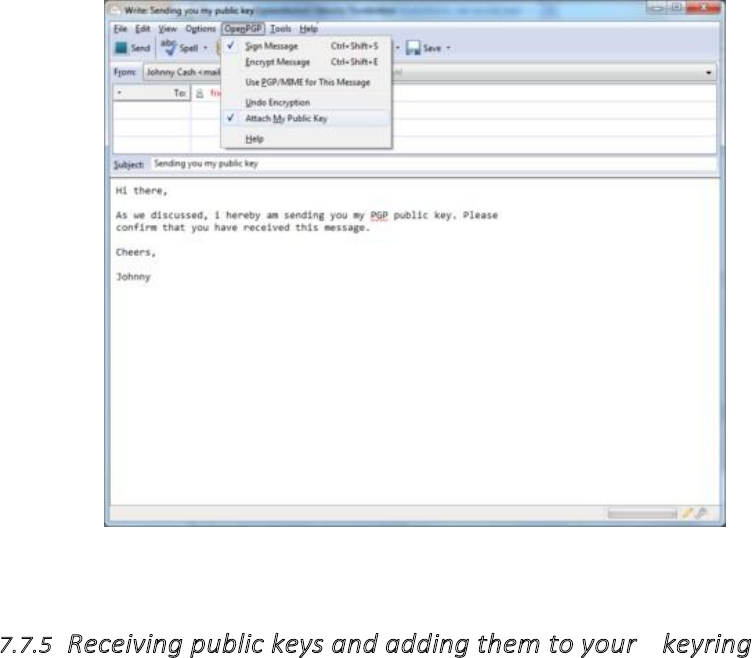
298
Figure 7.33:Daily GPG Usage
7.7.5
Receivingpublickeysandaddingthemtoyour keyring
Lets say we receive a public key from a friend by mail. The key will show up in Thun- derbird as
an
attachedfile
. Scroll down the message and below you will find tabs with one or two file names.
The extension of this public key file will be .asc, different from the extension of an attached GPG
signature, which ends with .asc.sig
Look at the example email in the next image, which is a received, signed GPG mes- sage
containing an attached public key. We notice a yellow bar with a warning message: ‘OpenPGP:
Unverified signature, click on ’Details’ button for more information’. Thun- derbird warns us that
the sender is not known yet, which is correct. This will change once we have accepted the public
key.
What are all those strange characters doing in the mail message? Because Thunderbird does
not yet recognize the signature as valid, it prints out the entire raw signature, just as it has
received it. This is how digitally signed GPG messages will appear to those recipients who do
not have your public key.
The most important thing in this example is to find the attached GPG public key. We
mentioned it is a file that ends with .asc. In this example it’s the first attachment on the left, in
the red circle. Double-clicking on this attachment will make Thunderbird recognize the key.
After we have clicked on the attachment, the following pop-up will appear. Thunderbird has
recognized the GPG public key file. Click on ‘Import’ to add this key
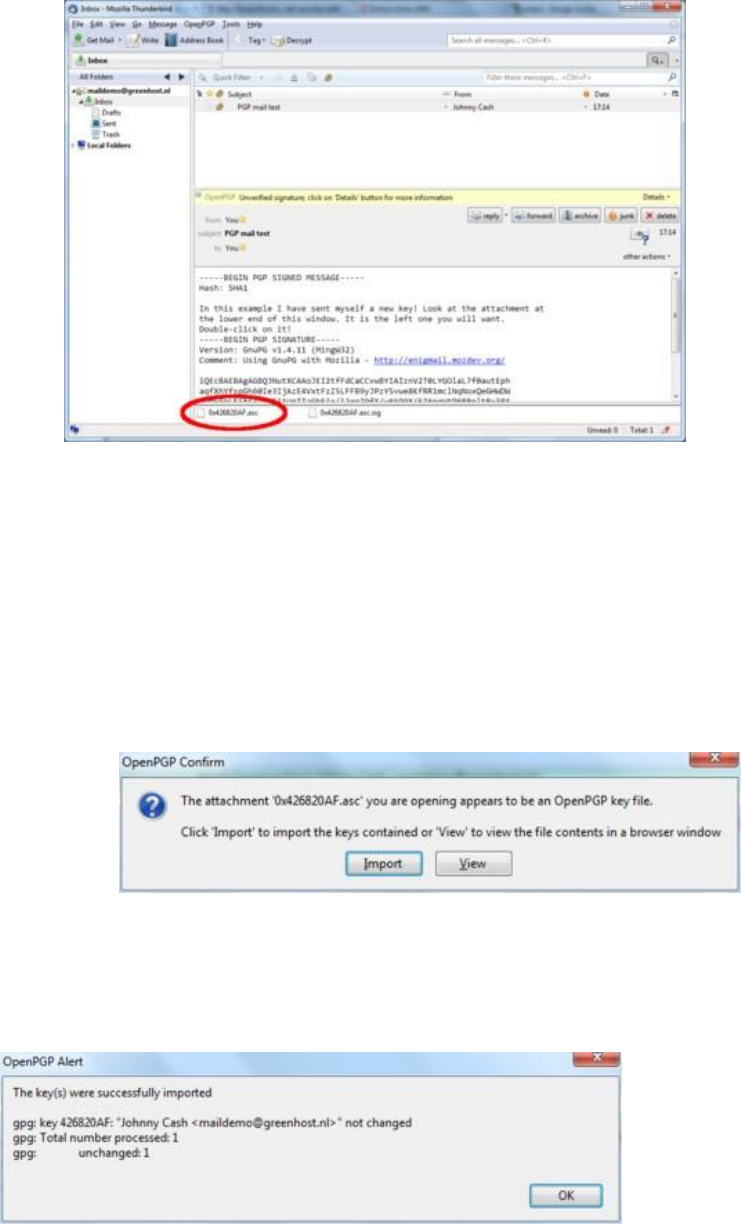
299
Figure 7.34:Daily GPG Usage
Figure 7.35:Daily GPG Usage
to your keyring. The following pop-up should appear. Thunderbird says the operation was
successful. Click on ‘OK’ and you are almost done.
Figure 7.36:Daily GPG Usage
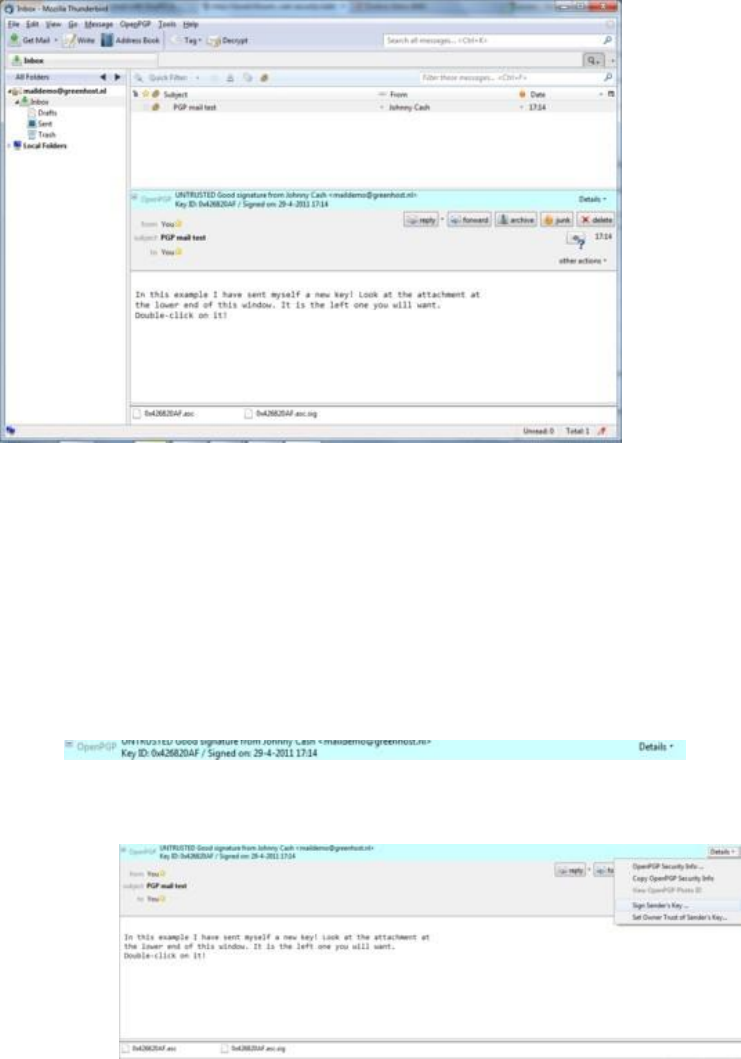
300
We are back in the main Thunderbird screen and we refresh the view on this particular
example message, by clicking on some other message and back for example. Now the body of
the message looks different (see below). This time Thunderbird
does
recognize the signature,
because we have added the public key of the sender.
Figure 7.37:Daily GPG Usage
There is still one thing that remains. While Thunderbird now recognizes the signature, we should
explicitly trust that the public key really belongs to the sender in real life. We realize this when we
take a closer look at the green bar (see below). While the signature is good, it is still UNTRUSTED.
We will now decide to trust this particular public key and the signatures made by it. We can
do this immediately by clicking on ‘Details’. A small menu will appear (see below). From this menu
we should click on the option ‘Sign Sender’s Key . . . ’.
After we have selected ‘Sign Sender’s Key . . . ’ we will get another selection window
Figure 7.38:Daily GPG Usage
Figure 7.39:Daily GPG Usage
(see below). We are requested to state how carefully we have checked this key for validity. The
explanation of levels of trust and trust networks in GPG falls outside the scope of this document.
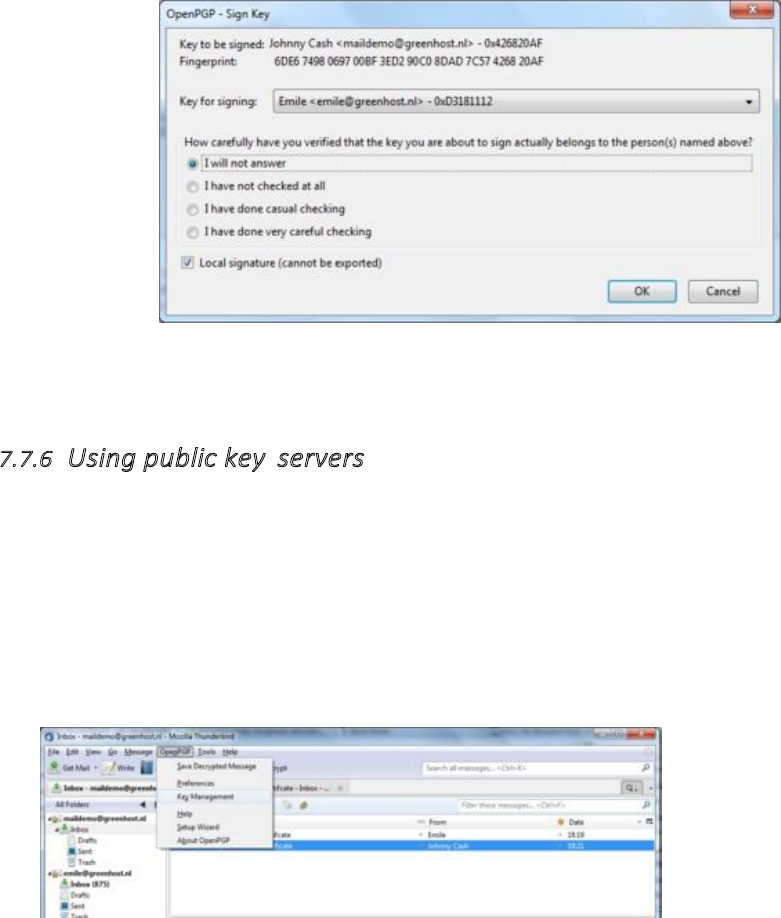
301
We will not use this information, therefore we will just select the option ‘I will not answer’. Also
select the option ‘Local signature (cannot be exported)’. Click on the ‘OK’ button to finishing
signing this key. This finishes accepting the public key. You can now send encrypted mail to this
individual.
Figure 7.40:Daily GPG Usage
7.7.6
Usingpublickeyservers
Another method of distributing public keys is by putting them on a public key server. This
allows anyone to check whether your email address has GPG support, and then download your
public key.
To put your own key on a keyserver, take the following steps.
1.
Head to the key manager by using the Thunderbird menu and click on OpenPGP >
Key
Management
Figure 7.41:Daily GPG Usage
2.
The key management window will be displayed and looks like this:
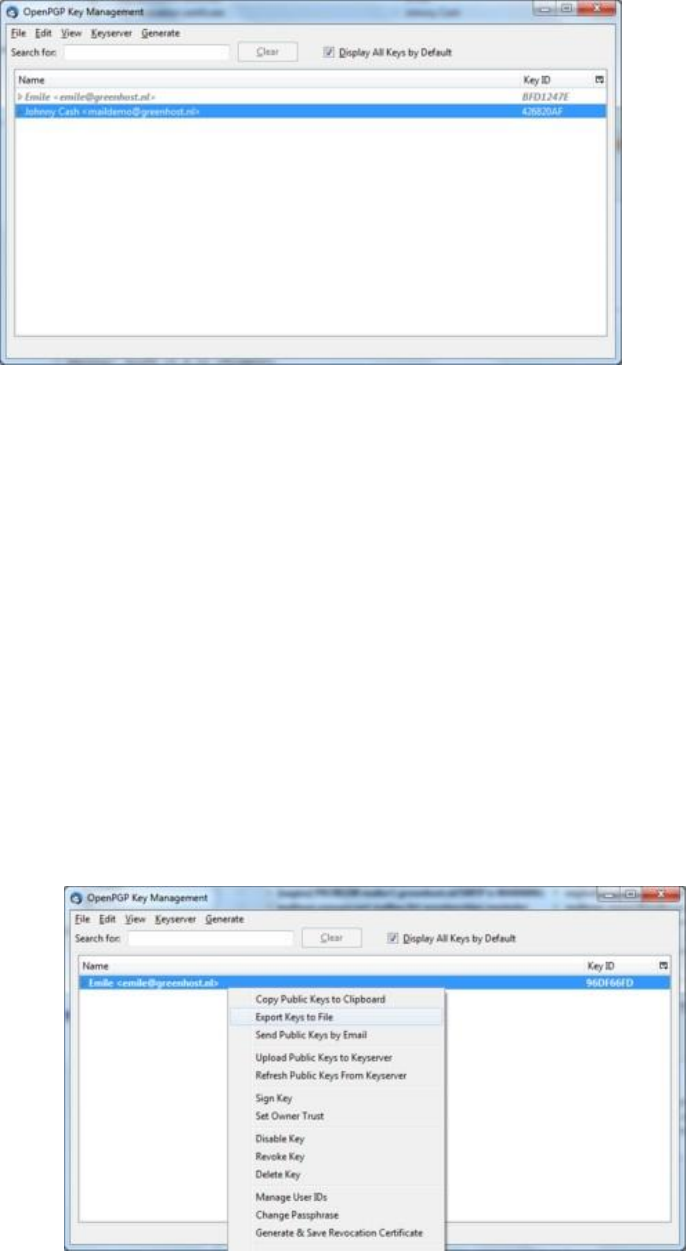
302
Figure 7.42:Daily GPG Usage
3.
You need to have selected the ‘Display All Keys by Default’ option to get a list of all
your keys. Look up your own email address in the list and right click on the address. A
selection window will appear with some options. Select the option ‘Upload Public Keys to
Keyserver’.
4.
You will see a small dialog window like below. The default server to distribute your
keys to is good. Press ’OK" and distribute your public key to the world.
To look up whether some email address has a public key available on a server, take the
following steps.
Figure 7.43:Daily GPG Usage
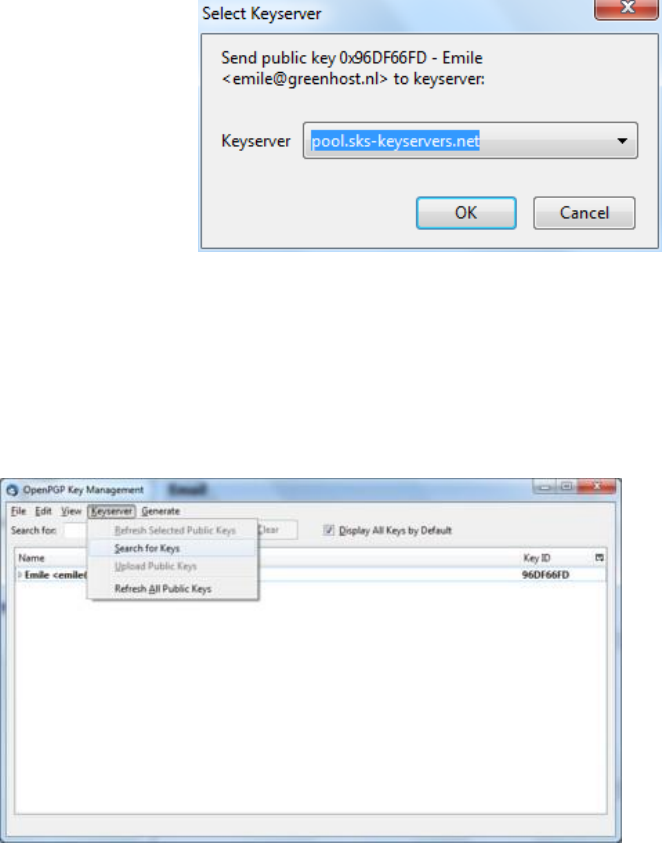
303
Figure 7.44:Daily GPG Usage
1.
Head to the key manager by using the Thunderbird menu and click on OpenPGP >
Key
Management
2.
In the key manager window menu bar, select Keyserver > Search for Keys
Figure 7.45:Daily GPG Usage
3.
In this example we will look-up up the key for the creator of PGP software, Philip
Zimmermann. After we have entered the email address, we click on ‘OK’.
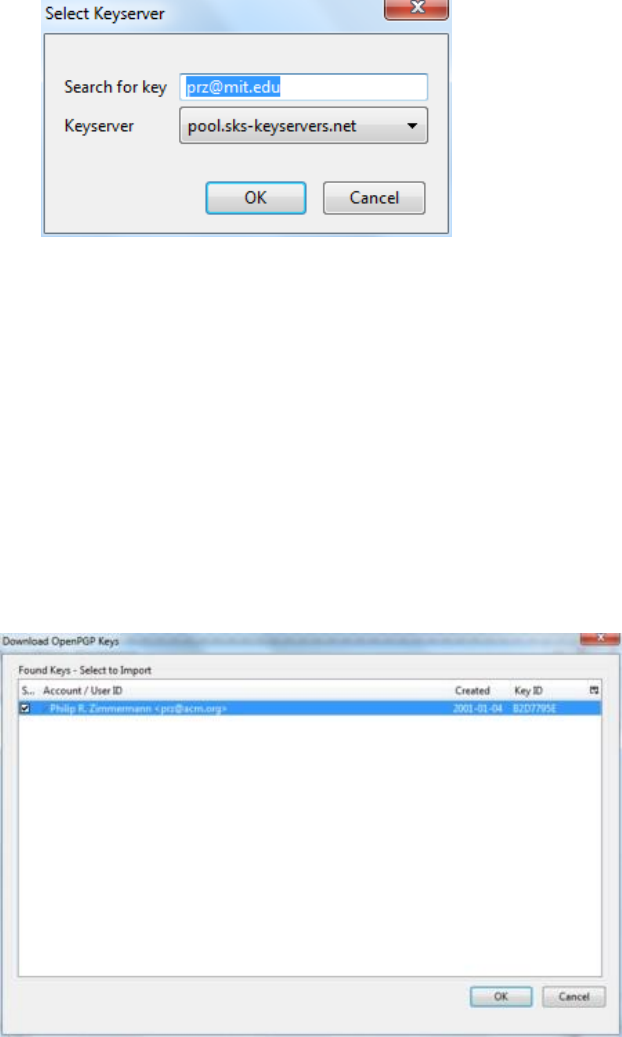
304
Figure 7.46:Daily GPG Usage
4.
The next window displays the result of our search. We have found the public key.
It is automatically selected. Just click on ‘OK’ to import the key.
5.
Importing the key will take some time. On completion you should see a pop-up window like
below.
Figure 7.47:Daily GPG Usage
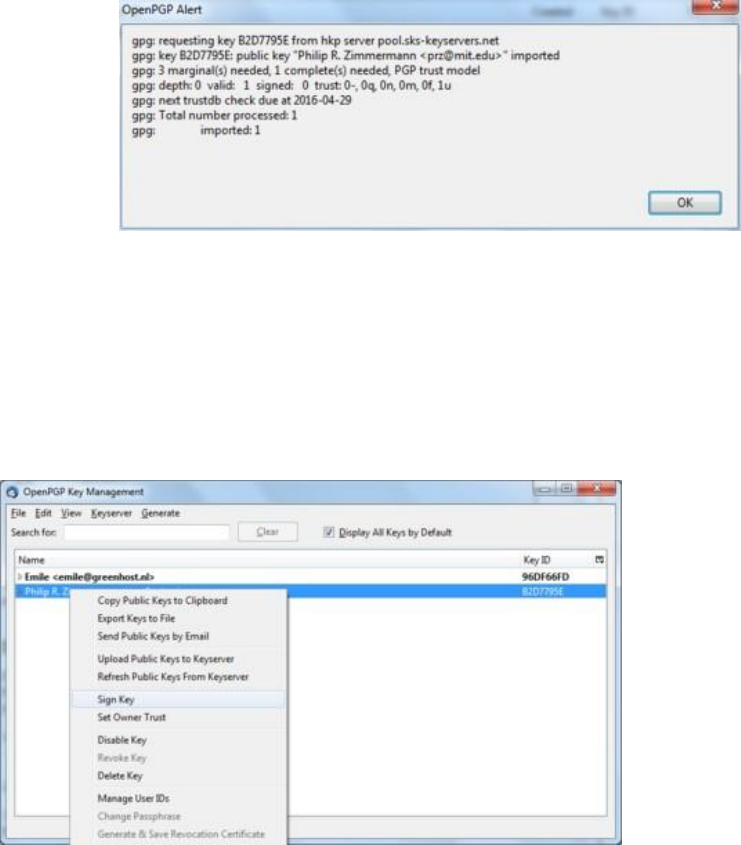
305
Figure 7.48:Daily GPG Usage
6.
The final step is to locally sign this key, to indicate that we trust it. When you are back in
the key manager, make sure you have selected the ‘Display All Keys by Default’ option. You
should now see the newly imported key in the list. Right-click on the address and select the
option ‘Sign Key’ from the list.
Figure 7.49:Daily GPG Usage
7.
Select the options ‘I will not answer’ and ‘Local signature (cannot be exported)’, then click on
‘OK’. You are now finished and can send Philip Zimmermann en- crypted mail.

306
Figure 7.50:Daily GPG Usage
7.7.7
Signingemailstoan individual
Digitally signing email messages is a way to prove to recipients that you are the actual sender of a
mail message. Those recipients who have received your public key will be able to
verify
that your
message is authentic. However, take note that signing an email will make it very hard (if not
impossble) to deny that you are the author of the message.
1.
Offer your friend your public key, using the method described earlier in this chapter.
2.
In Thunderbird, click on the icon.
3.
Before actually sending the mail, enable the OpenPGP > Sign Message option via the menu
bar of the mail compose window, if it is not enable already. Once you have enabled this
option, by clicking on it, a marked sign will appear. Clicking again should disable encryption
again. See the example below.
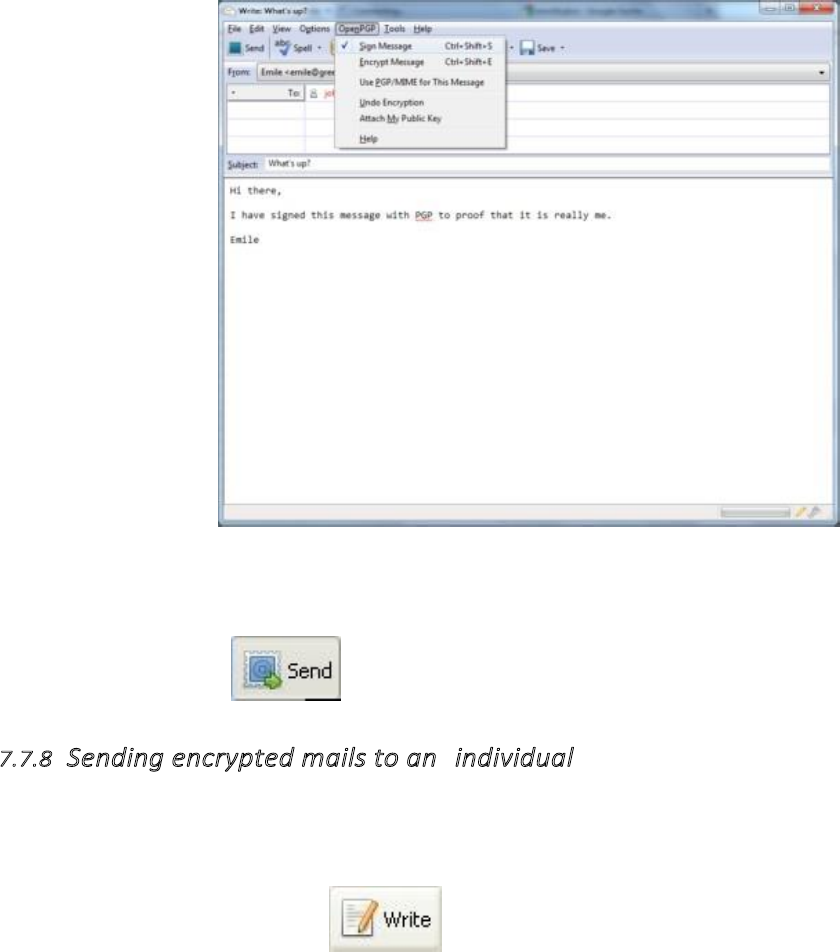
307
Figure 7.51:Daily GPG Usage
4.
Click on the button and your signed mail will be sent.
7.7.8
Sendingencryptedmailstoan individual
1.
You should have received the public key from the friend or colleague you want to
email and you should have accepted their public key, using the method describe
earlier in this chapter.
2.
In Thunderbird, click on the icon.
3. Compose a mail to the friend or colleague, from who you have previously received their
public key. Remember the subject line of the message will not be
encrypted, only the message body itself, and any attachments.
4.
Before actually sending the mail, enable the OpenPGP > Encrypt Message option via
the menu bar of the mail compose window, if it is not enabled already. Once you have
enabled this option, by clicking on it, a marked sign will appear. Clicking again should
disable encryption again. See the example below.
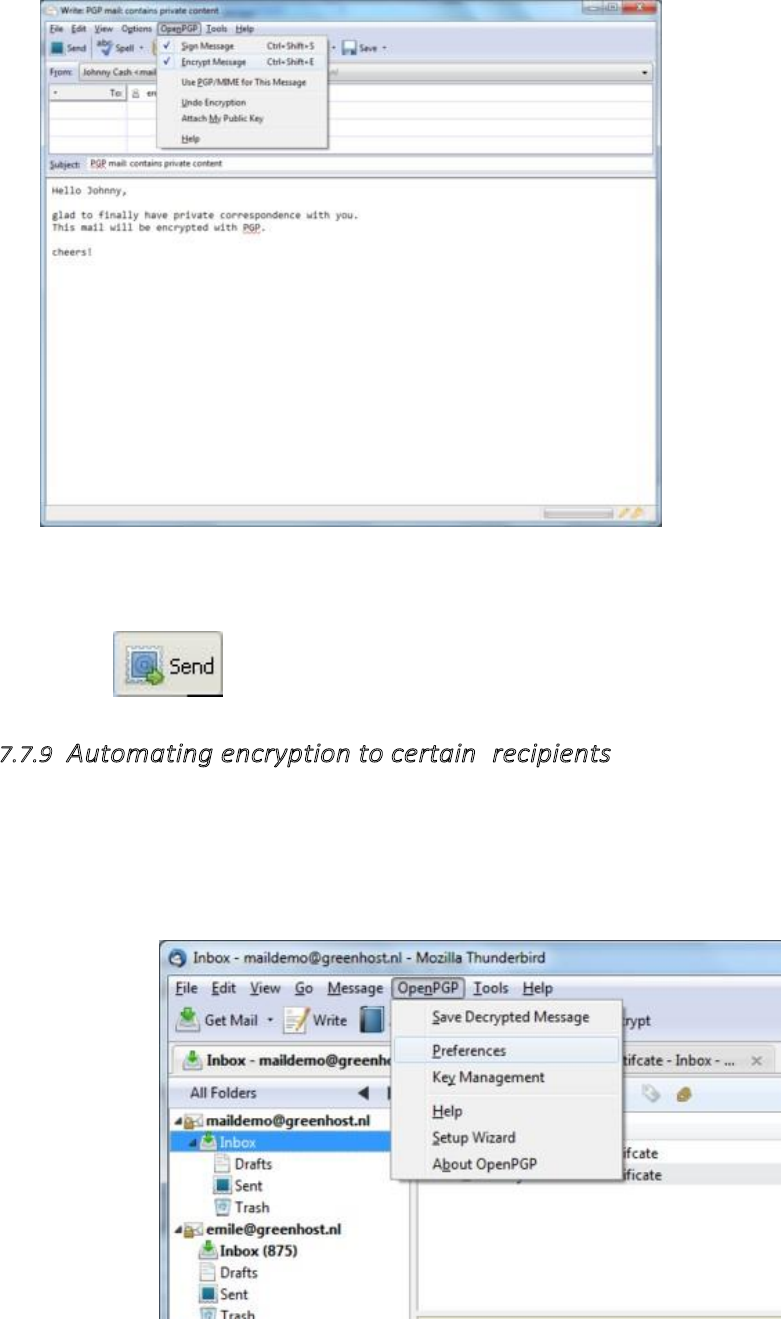
308
Figure 7.52:Daily GPG Usage
5.
Click on the button and your encrypted mail will be sent.
7.7.9
Automatingencryptiontocertainrecipients
You will often want to make sure all your messages to a certain colleague or friend are signed and
encrypted. This is good practice, because you may forget to enable the encryption manually. You
can do this by editing the per-recipient rules. To do this we access the OpenPGP per-recipient rule
editor.
Select OpenPGP > Preferences from the Thunderbird menu bar.

309
Figure 7.53:Daily GPG Usage
The preferences window will appear like below. We need to click on ‘Display Expert Settings’.
New menu tabs will appear in the window. Go to the tab ‘Key Selection’ and then click on the
button labeled ‘Edit Rules . . . ’
We are now shown the per-recipient rules editor (see below). This editor can be used to
specify the way how messages to certain recipients are sent. We will now add a rule saying we
want to encrypt and sign all mail messages to maildemo@greenhost.nl
First click on the ‘Add’ button.
Now the window to add a new rule will be shown.
The first thing we should enter is the email address of the recipient. In the example below we
have entered maildemo@greenhost.nl
Now we will set the encryption defaults by using the drop-downs below. For Signing select
‘Always’. For Encryption also select ‘Always’.
Finally we have to select the
publickey
of the recipient, with which to encrypt our messages. Do
not forget this important step, otherwise the e-mail will not be encrypted. Click on the button labeled
‘Select Key(s). . . ’. The key selection window will show up. The most obvious key will be selected
by default. In the example below, we only have one public key available. We can select keys by
clicking on the small box next to the address. Then we click ‘OK’ and close all relevant windows
and we are finished.
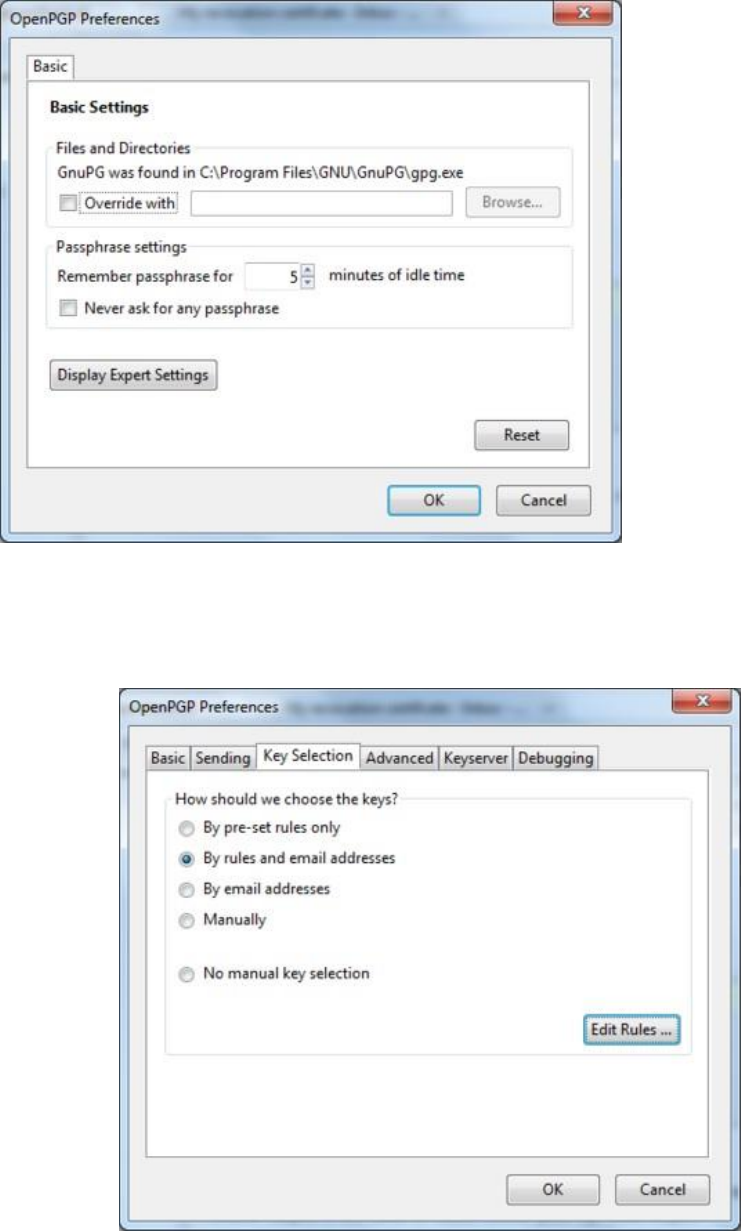
310
Figure 7.54:Daily GPG Usage
Figure 7.55:Daily GPG Usage
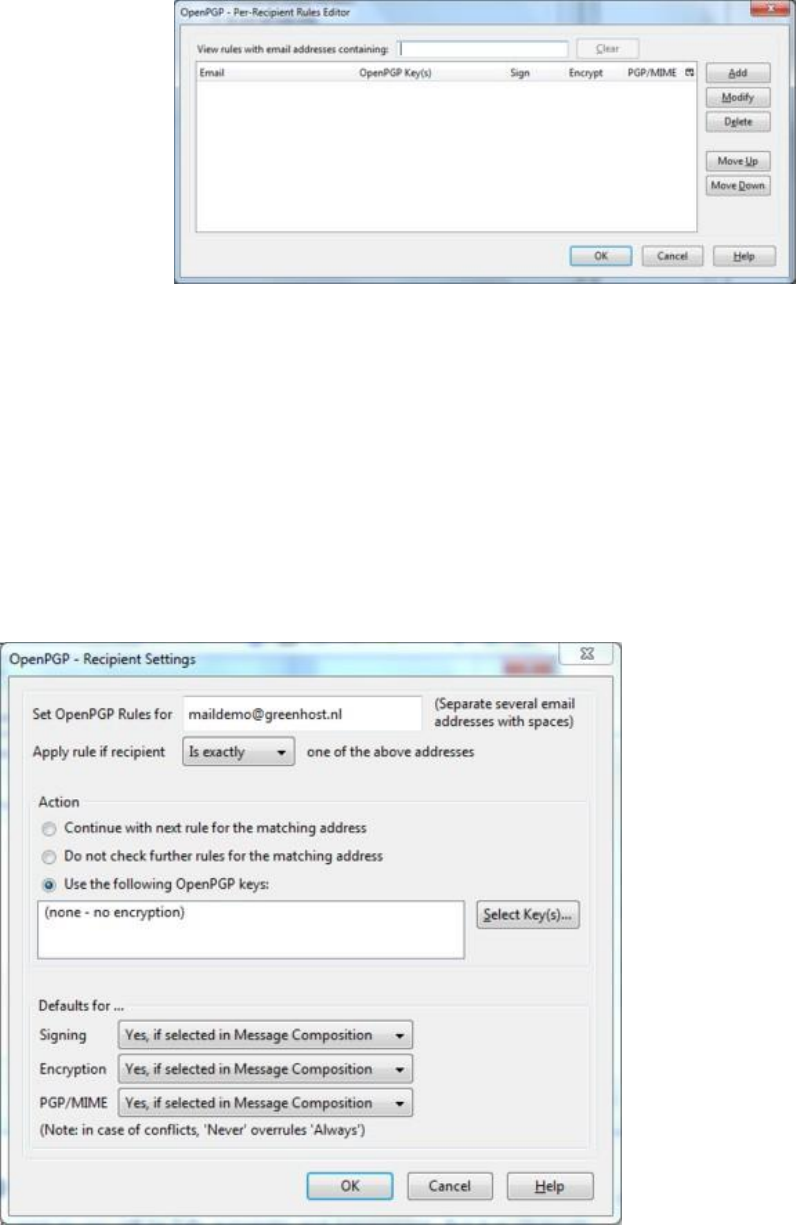
311
Figure 7.56:Daily GPG Usage
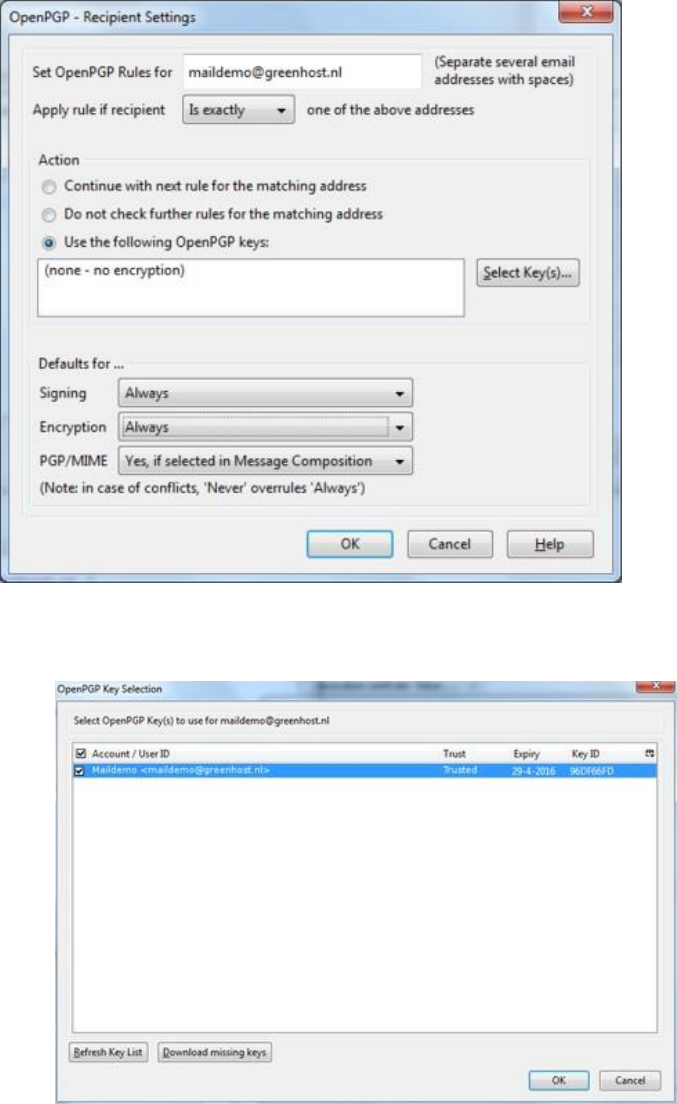
312
Figure 7.57:Daily GPG Usage
Figure 7.58:Daily GPG Usage
Figure 7.59:Daily GPG Usage

313
7.7.10
Verifyingincomingemails
Decrypting email messages sent to you will be fully automatic and transparent. But it is obviously
important to see whether or not a message to you has in fact been encrypted or signed. This
information is available by looking at the special bar above the message body.
A valid signature will be recognized by a green bar above the mail message like the example
image below.
Figure 7.60:Daily GPG Usage
The last example message was signed but not encrypted. If the message had been encrypted,
it would show like this:
Figure 7.61:Daily GPG Usage
When a message which has been encrypted, but not signed, it could have been a forgery by
someone. The status bar will become gray like in the image below and tells you that while the
message was sent securely (encrypted), the sender could have been someone else than the person
behind the email address you will see in the ‘From’ header. The signature is neccessaty to verify the
real sender of the message. Of course it is perfectly possible that you have published your public
key on the Internet and you allow people to send you emails anonymously. But is it also possible
that someone is trying to impersonate one of your friends.
Figure 7.62:Daily GPG Usage
Similarly if you receive a signed email from somebody you know, and you have this per- sons
public key, but still the status bar becomes yellow and displays a warning message, it is likely that
someone is attempting to send you forged emails!
Sometimes secret keys get stolen or lost. The owner of the key will inform his friends and send
them a so-called revocation certificate (more explanation of this in the next paragraph). Revocation
means that we no longer trust the old key. The thief may afterwards still try his luck and send you a
falsely signed mail message. The status bar will now look like this:
Strangely enough Thunderbird in this situation will still display a green status bar! It is
important to look at the contents of the status bar in order to understand the encryption aspects
of a message. GPG allows for strong security and privacy, but only if you are familiar with its
use and concepts. Pay attention to warnings in the status bar.
Figure 7.63:Daily GPG Usage
Figure 7.64:Daily GPG Usage

314
7.7.11
RevokingyourGPGkeypair
Your secret key has been stolen by somebody. Your harddisk crashed and you have lost all your
data. If your key is lost, you can no longer decrypt messages. If your key has been stolen, somebody
else can decrypt your communication. You need to make a new set of keys. The process of creating
keys, using the OpenPGP wizard in Thunderbird, has been described in this manual. But first you
want to tell the world that your old public key is now worthless, or even dangerous to use.
7.7.12
Whattodowhenyouhavelostyoursecretkey,orforgotyour
passphrase
During the creation of your key-pair, the OpenPGP wizard offered you the possibility to create a
so-called revocation certificate. This is a special file you send to others in the advent you have to
disable your key. If you have a copy of this file, sending the revocation key is simply sending the
file as an attachment to all your friends. You can no longer send signed mails (obviously, because
you have lost your secret key). That doesn’t matter. Send it as a normal mail. The revocation
certificate file could only have been created by the owner of the secret key and proves he or she
wants to revoke it. That’s why it should normally be kept hidden from others.
If you do not have the revocation certificate, there exists no other option than for you to
contact your friends personally and convince them your key is lost and that they should no
longer trust it.
7.7.13
Whattodowhenyoursecretkeyhasbeenstolen,orcompromised
If you have reason to believe your secret key has been compromised, or worse your secret key and
passphrase, it is very important to contact others that they should stop sending you encrypted
messages. With your secret key, other persons will be able to break the encryption of your e-mail
messages if they also have your passphrase. This is also true for those messages you have send in
the past. Cracking the passphrase is not trivial, but it may be possible if the party has lots of
resources, like a state or a big organization for example, or if your passphrase is too weak. In any
case you should assume the worst and assume your passphrase may have been compromised. Send
a revocation certificate file to all your friends or contact them personally and inform them of the
situation.
Even after you have revoked your old key pair, the stolen key may still be used to
decrypt your previous correspondence. You should consider other ways to protect that old
correspondence, for instance by re-encrypting it with a new key. The latter operation will not be
discussed in this manual. If you are uncertain you should seek assistance from experts or look up
more information on the web.
7.7.14
Receivingarevocationcertificate
If one of your friends sends you a revocation certificate, s/he asks you to distrust his public key from
now on. You should always accept such a request and ‘import’ the certificate to disable their key.
The process of accepting a revocation certificate is exactly the same as accepting a public key, as
has already been described in the chapter. Thunderbird will ask you if you want to import the
‘OpenPGP key file’. Once you have done so, a confirmation pop-up should be displayed like below.
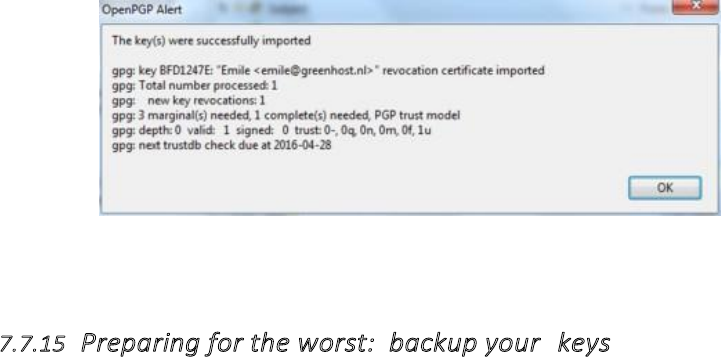
315
Figure 7.65:Daily GPG Usage
7.7.15
Preparingfortheworst:backupyour keys
Your keys are usually stored on your hard disk as normal files. They may get lost if your computer
gets damaged. It is strongly advised to keep a backup of your keys in a safe place, like a vault.
Making a a backup of your secret key has another security advantage as well. Whenever you fear
your laptop or computer is in immediate danger of being confiscated, you can safely delete your
key-pair. Your email will be rendered unreadable immediately. At a later stage, you can retrieve
your keys from the vault and re-import them in Thunderbird.
To make a backup of your key-pair, first head to the key manager by using the Thun- derbird
menu and click on OpenPGP > Key Management.
You need to have selected the ‘Display All Keys by Default’ option to get a list of all
your
keys. Lookup your own email address in the list and right click on the address. A
selection
window will appear with some options. Select the option ‘Export Keys to File’.
Now we will
save the key-pair to a file. Thunderbird asks us if we want to include
the secret key as well.
We do want to include the secret key, therefore we select ‘Export
Secret Keys’.
Finally Thunderbird asks us for the location of the key file. You can store the file
anywhere
you like, network disk, USB-stick. Just remember to hide it away from other
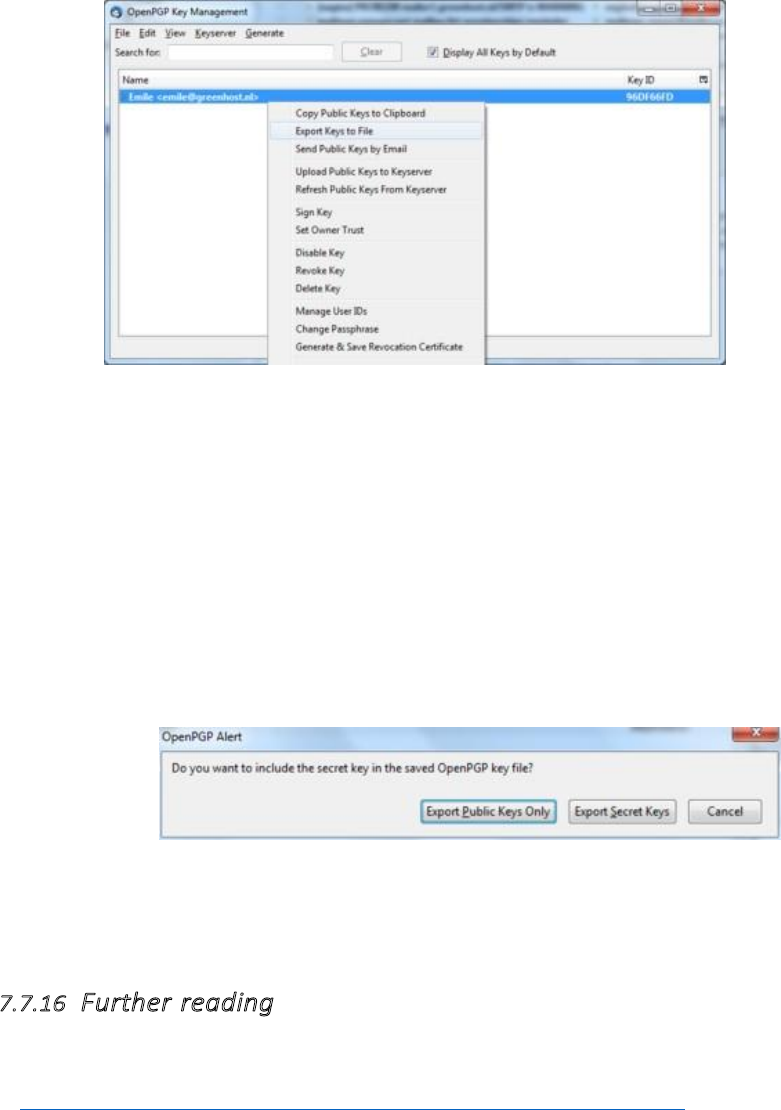
316
Figure 7.66:Daily GPG Usage
Figure 7.67:Daily GPG Usage
people.
7.7.16
Furtherreading
More documentation on using GPG with Thunderbird can be found on the website of the
Enigmail plugin. The Enigmail handbook is the guide you will want to use.
http://enigmail.mozdev.org/documentation/handbook.php.html
7.8 Webmail and PGP
The only safe way of encrypting email inside of the browser window is to encypt it outside and
then copy & paste the encrypted text into the browser window.
For example, write the text in a text editor like gedit, vim or kate and save it as .txt file (in this
example “message.txt”. Then type

317
gpg -ase
-r
<recipients email/gpg id>
-r
<your gpg id> message.txt
A new file called “message.asc” will be created. It contains the encrypted message and can thus
be either attached to an email or its content safely copy & pasted into the browser window.
To decrypt a message from the browser window, simply type gpg into the command line and hit
Enter. Then copy & paste the message to be decrpyted into the commandline window and after being
asked for your passphrase hit Ctrl+D (this enters a end-of-file character and prompts gpg to output
the cleartext message).
If using the commandline seems too cumbersome to you, you might consider installing a helper
application like gpgApplet, kgpg or whatever application ships with your operating system.
8
Safer Browsing
8.1
Why Firefox?
Firefox is open source software, developed by the non-profit organisation, the Mozilla Foundation.
As such, it is independent from the interests of any one specific company although a large portion
of its funding comes from Google for its placement as the default search engine within the Firefox
browser. It is also highly extensible through the add-ons and plugins, which allows users greater
control over how the browser acts as compared to Internet Explorer or Chrome (and it’s open-
source’d version, Chromium). It should however be noted that this extensibility through add-ons is
a double-edged sword and as such add-ons also have great power to subvert the browsers normal
activities as well as enhance them.
If you are uncomfortable with Google as the default search engine, this can be changed through
the ‘Manage Search Engines. . . ’ option from the pull-down menu of the search box. Some more
pro-privacy search engines that are worth considering are Startpage and DuckDuckGo.
8.2
Accessing Firefox on Ubuntu
Firefox is already installed on Ubuntu by default. To open it, click on the Unity side bar where you
see the Firefox icon:
318
Figure 8.1:Firefox on Ubuntu Firefox
starts and a welcome window opens:
Figure 8.2:Firefox on Ubuntu
8.3
Installing on Mac OS X
1.
To download Firefox, visit https://www.mozilla.org/firefox and click on the big green
button labeled “Firefox Free Download”. The download should start automatically, if it does
not, click the link to download it manually.
2.
When prompted, click
OK
.
Once the download is complete a window similar to this appears: 3.Click and
drag the
Firefox
icon on top of the
Applications
icon.
4.
When the installation is finished, close the two small Firefox windows.
5.
Eject the Firefox disk image. If this does not work by normal means, select the disk
image icon and then, in the Finder menu, select File > Eject Firefox.
6.
Now, open the
Applications
directory and drag the
Firefox
icon to the dock:
7.
Click the
Firefox
icon in the Dock to start Firefox. The Import Wizard dialog box
appears:
319
Figure 8.3:Mac OS X Firefox Install

320
Figure 8.4:Mac OS X Firefox Install
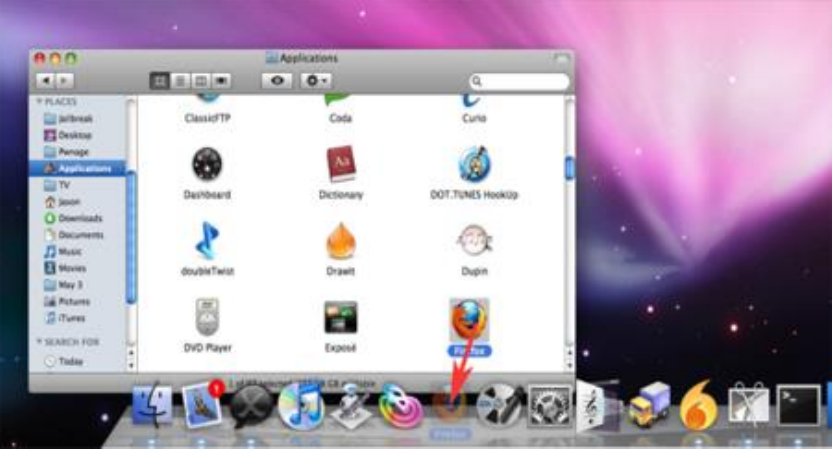
321
Figure 8.5:Mac OS X Firefox Install
Figure 8.6:Mac OS X Firefox Install
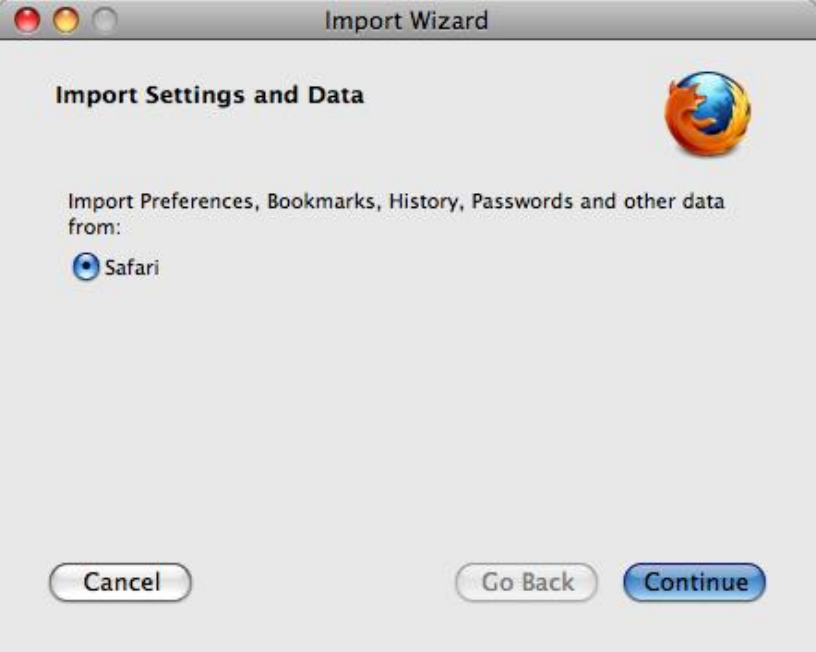
322
Figure 8.7:Mac OS X Firefox Install
8.
To import your bookmarks, passwords and other data from Safari, click
Continue
.
If you don’t want to import anything, just select
Cancel
.
Congratulations, you are now ready to use Firefox!
323
Figure 8.8:Mac OS X Firefox Install
8.4
Installing Firefox on Windows
1.
To download Firefox, visit https://www.mozilla.com/firefox/.
2.
Click the download button and the installation file will begin to download to your
computer.
3.
Once the download is complete, double-click the installation file to start the
Firefox installation wizard.
•
If you are running Windows Vista, you may get a User Account Control prompt. In
this case, allow the setup to run by clicking
Continue
.

324
Figure 8.9:Windows Firefox Install
•
If you are running Windows 7, you will be asked whether to allow Firefox to make
changes to your computer. Click on
Yes
.
A welcome screen appears.
4.
Click
Next
to continue. You will be asked if you would like the standard installa-
tion, or whether you would like to customize it. Choose the standard installation and
click
Next
.
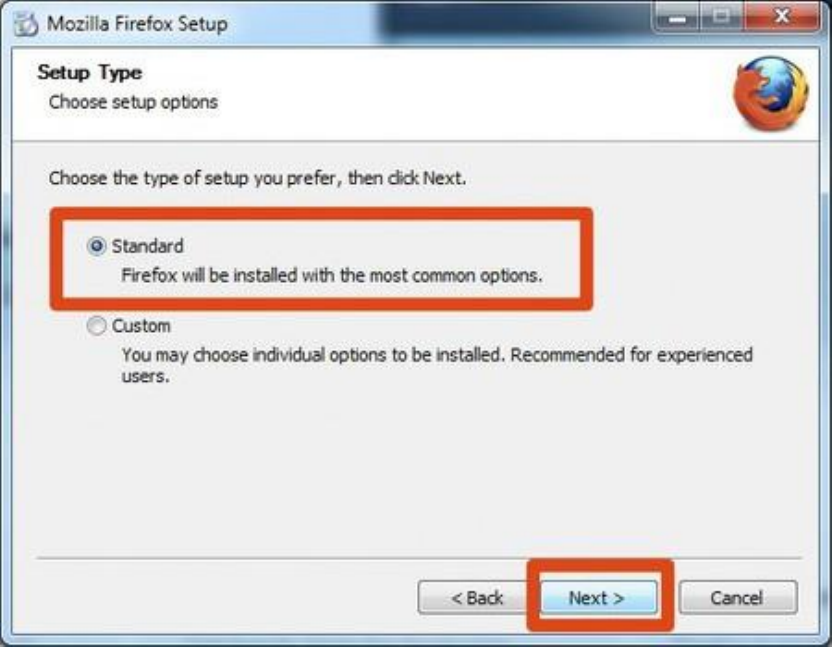
325
Figure 8.10:Windows Firefox Install
5.
You will be asked if you want Firefox to be your default browser. This is recom-
mended.
6. Click Install.
7.
To import your bookmarks and other data from other browsers (for example Inter- net
Explorer), click
Continue
. If you don’t want to import anything, just select
Cancel
.
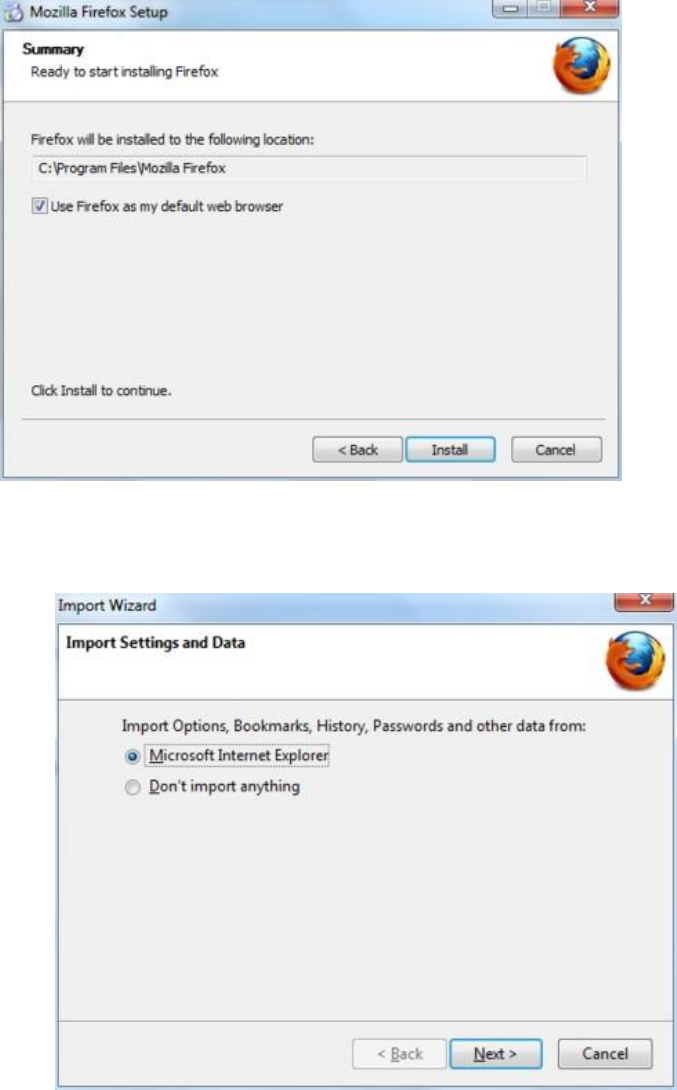
326
Figure 8.11:Windows Firefox Install
Figure 8.12:Windows Firefox Install
8.
Once Firefox has been installed, click
Finish
to close the setup wizard.
If the
Launch Firefox now
check box is checked, Firefox will start after you click
Finish
. Otherwise you can launch Firefox through the start menu.
Windows Vista Users

327
If at any time throughout the installation process you are prompted with a User Account
Control (UAC) window, press Continue, Allow, or Accept.
8.4.1
Troubleshooting
If you have problems starting Firefox, see https://support.mozilla.com/kb/Firefox+ will+not+start
8.5
Extending Firefox
When you first download and install Firefox, it can handle basic browser tasks immedi- ately. You
can also add extra capabilities or change the way Firefox behaves by installing add-ons, small
additions that extend Firefox’s power.
Firefox extensions can pimp your browser, but they can also collect and transmit information
about you. Before you install any add-on, keep in mind to choose add-ons from trusted sources.
Otherwise, an add-on might share information about you without your knowing, keep a record on
the sites you have visited, or even harm your computer.
There are several kinds of add-ons:
•
Extensions
add functionality to Firefox
•
Themes
change the appearance of Firefox.
•
Plugins
help Firefox handle things it normally can’t process (i.e. Flash movies, Java
applications).
For the topics covered in this book we are only going to need extensions. We will look at
some add-ons that are particularly relevant for dealing with Internet security. The variety of
available extensions is enormous. You can add dictionaries for different languages, track the
weather in other countries, get suggestions for Web sites that are similar to the one you are
currently viewing, and much more. Firefox keeps a list of cur- rent extensions on its site
(https://addons.mozilla.org/firefox), or you can browse them by category at
https://addons.mozilla.org/firefox/browse.
Caution:
We recommend that you never install an add-on for Firefox unless it is
available
from the Firefox add-on pages. You should also never install Firefox unless you get the
installation files from a trusted source. It is important to note that using Firefox on someone
else’s computer or in an Internet caf increases your potential vulnerability.
Know that you can
take Firefox on a CD or USB-stick (check our chapter on that issue).
While no tool can protect
you completely against all threats to your online privacy and
security, the Firefox extensions
described in this chapter can significantly reduce your
exposure to the most common ones, and
increase your chances of remaining anonymous.
8.5.1
HTTPSEverywhere
HTTP is considered unsafe, because communication is transmitted in plain text. Many sites on the
Web offer some support for encryption over HTTPS, but make it difficult to use. For instance,
they may connect you to HTTP by default, even when HTTPS is available, or they may fill encrypted
pages with links that go back to the unencrypted site. The HTTPS Everywhere extension fixes
these problems by rewriting all requests to these sites to HTTPS. Although the extension is called
“HTTPS Everywhere”, it only activates HTTPS on a particular list of sites and can only use HTTPS
on sites that have chosen to support it. It cannot make your connection to a site secure if that site
does not offer HTTPS as an option.

328
Figure 8.13:HTTPS Schema
Please note that some of those sites still include a lot of content, such as images or icons, from
third party domains that is not available over HTTPS. As always, if the browser’s lock icon is broken
or carries an exclamation mark, you may remain vulnerable to some adversaries that use active
attacks or traffic analysis. However, the effort required to monitor your browsing should still be
usefully increased.
Some Web sites (such as Gmail) provide HTTPS support automatically, but using HTTPS
Everywhere will also protect you from TLS/SSL-stripping attacks, in which an attacker hides the
HTTPS version of the site from your computer if you initially try to access the HTTP version.
Additional information can be found at: https://www.eff.org/https-everywhere.
8.5.2
Installation
First, download the HTTPS Everywhere extension from the official Web site:
https:
//www.eff.org/https-everywhere
Select the newest release. In the example below, version 2.2 of HTTPS Everywhere was used.
(A newer version may be available now.)
Click on “Allow”. You will then have to restart Firefox by clicking on the “Restart Now” button.
HTTPS Everywhere is now installed.
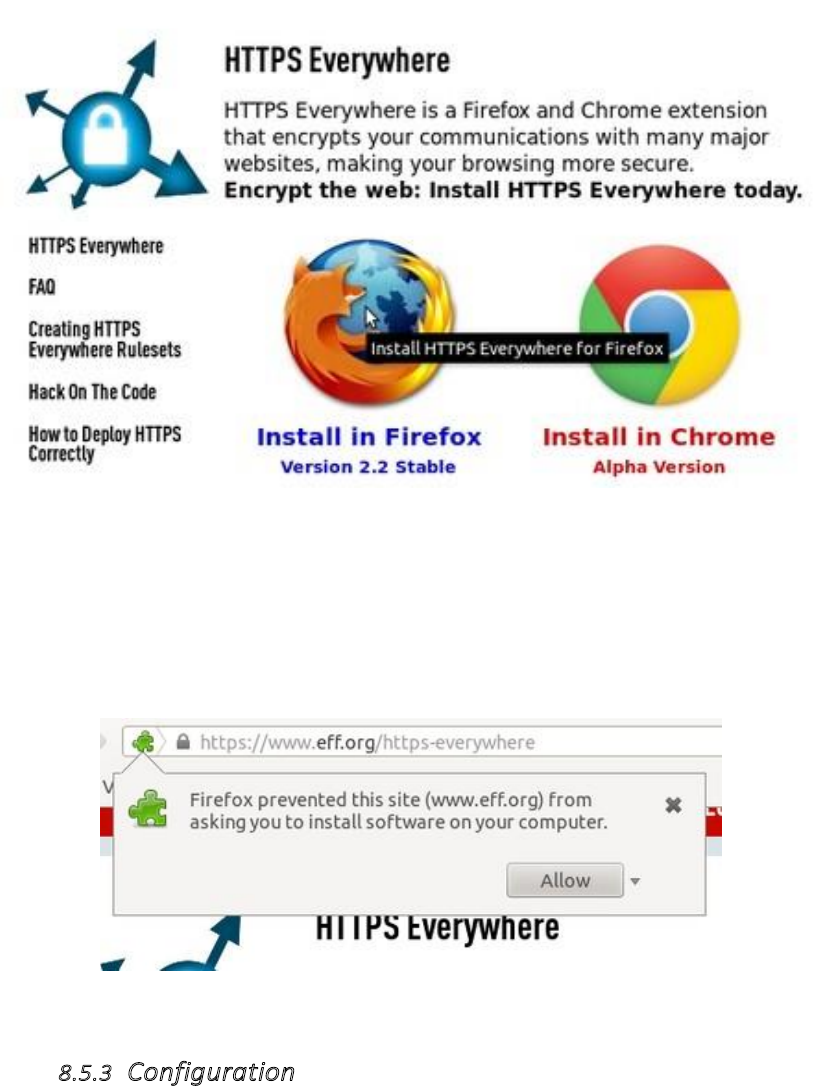
329
Figure 8.14:HTTPS Everywhere
Figure 8.15:HTTPS Everywhere
8.5.3
Configuration
To access the HTTPS Everywhere settings panel in Firefox 4 (Linux), click on the Tools menu at
the top of your screen and then select Add-ons. (Note that in different versions of Firefox and
different operating systems, the Add-ons Manager may be located in different places in the
interface.)
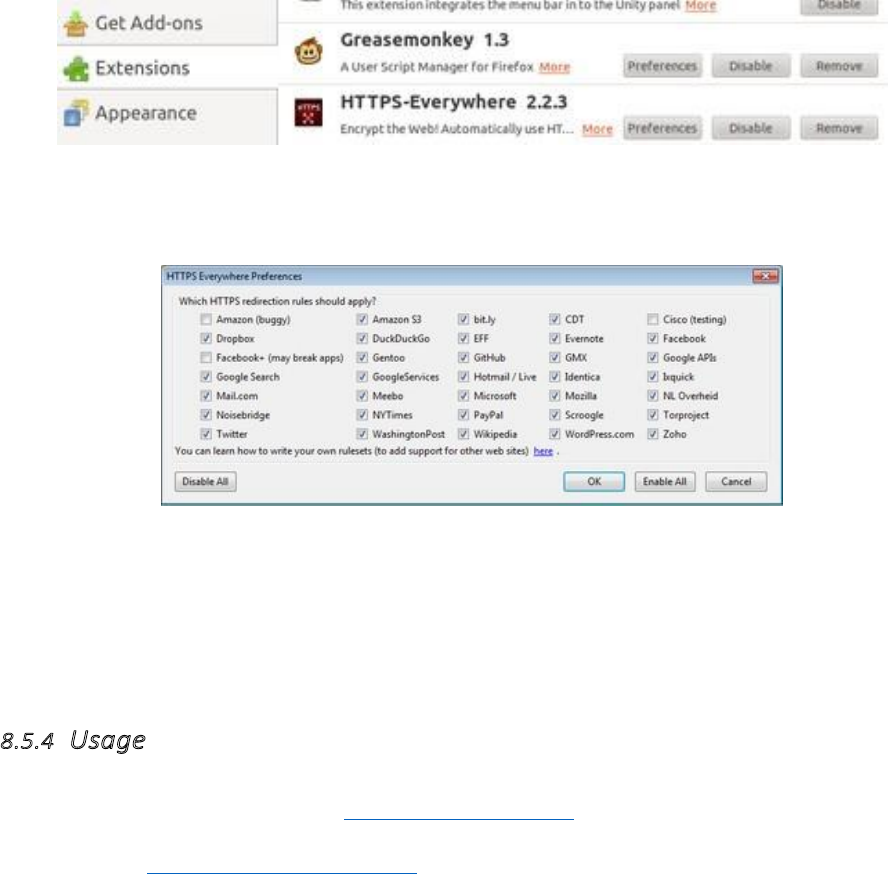
330
Figure 8.16:HTTPS Everywhere Click on the
Preferences button.
Figure 8.17:HTTPS Everywhere
A list of all supported Web sites where HTTPS redirection rules should be applied will be
displayed. If you have problems with a specific redirection rule, you can uncheck it here. In that
case, HTTPS Everywhere will no longer modify your connections to that specific site.
8.5.4
Usage
Once enabled and configured, HTTPS Everywhere is very easy and transparent to use. Type an
insecure HTTP URL (for example, http://www.google.com).
Press Enter. You will be automatically redirected to the secure HTTPS encrypted Web site (in
this example: https://encrypted.google.com). No other action is needed.
331
Figure 8.18:HTTPS Everywhere
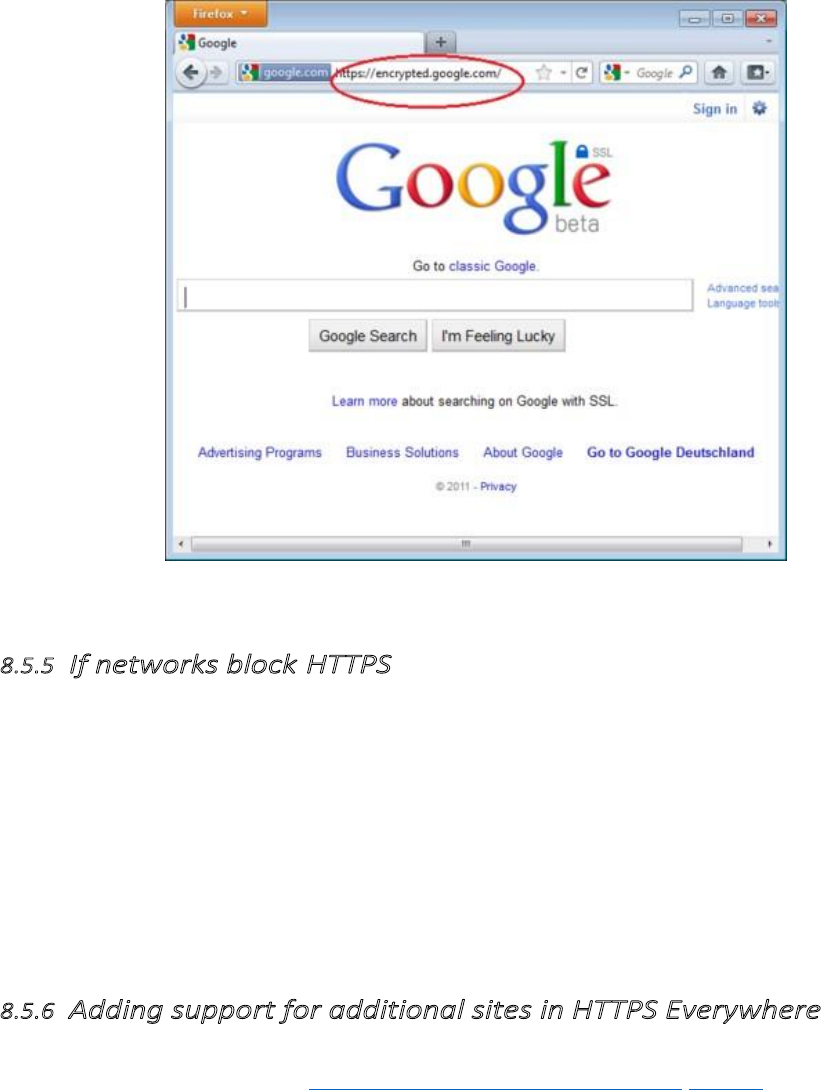
332
Figure 8.19:HTTPS Everywhere
8.5.5
IfnetworksblockHTTPS
Your network operator may decide to block the secure versions of Web sites in order to increase
its ability to spy on what you do. In such cases, HTTPS Everywhere could prevent you from using
these sites because it forces your browser to use only the secure version of these sites, never the
insecure version. (For example, we heard about an airport WiFi network where all HTTP
connections were permitted, but not HTTPS connections. Perhaps the WiFi operators were
interested in watching what users did. At that airport, users with HTTPS Everywhere were not
able to use certain Web sites unless they temporarily disabled HTTPS Everywhere.)
In this scenario, you might choose to use HTTPS Everywhere together with a circum- vention
technology such as Tor or a VPN in order to bypass the network’s blocking of secure access to Web
sites.
8.5.6
AddingsupportforadditionalsitesinHTTPSEverywhere
You can add your own rules to the HTTPS Everywhere add-on for your favorite Web sites. You
can find out how to do that at: https://www.eff.org/https-everywhere/ rulesets. The benefit of
adding rules is that they teach HTTPS Everywhere how to ensure that your access to these sites
is secure. But remember: HTTPS Everywhere does not allow you to access sites securely unless
the site operators have already chosen to make their sites available through HTTPS. If a site
does not support HTTPS, there is no benefit to adding a ruleset for it.
If you are managing a Web site and have made an HTTPS version of the site available, a good
practice would be to submit your Web site to the official HTTPS Everywhere release.
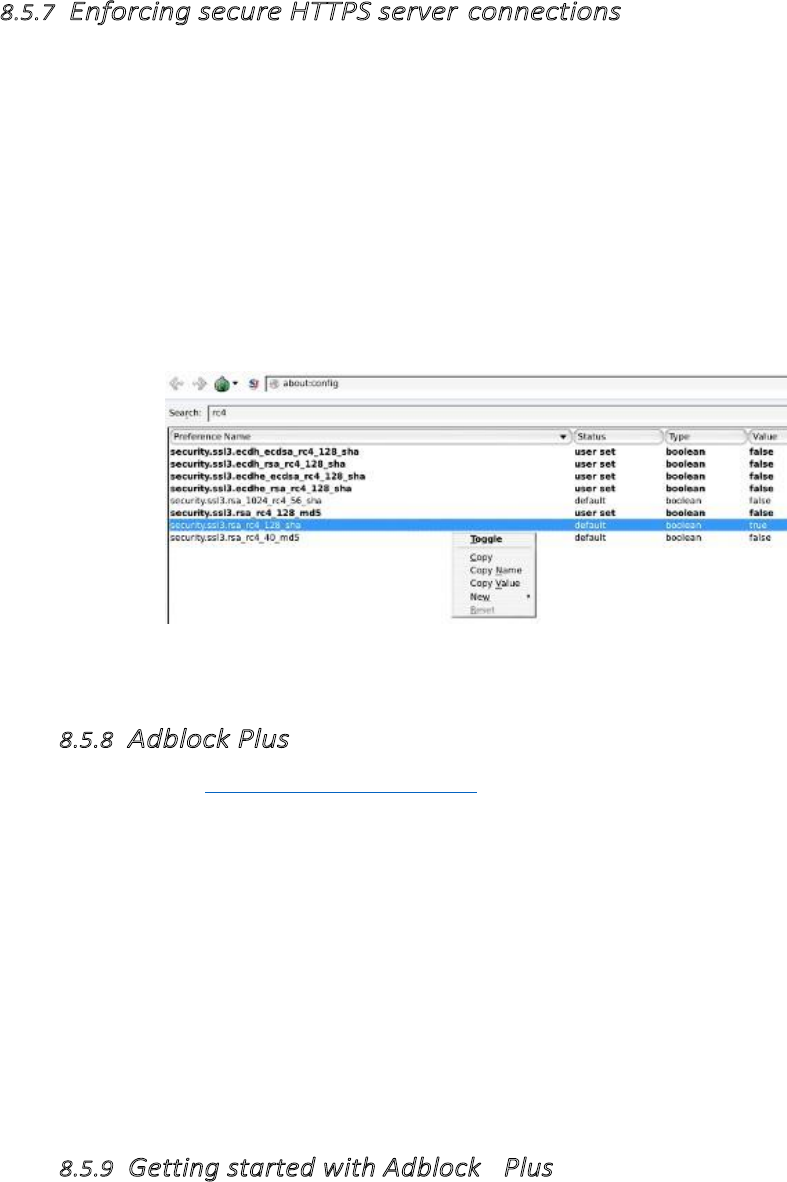
333
8.5.7
EnforcingsecureHTTPSserverconnections
Even if you instruct your browser to use the HTTPS protocol when communicating with a web
server, it is still possible that the server (due to unsecure configuration on its own side) enforces
a unsecure SSL cipher protocol for the connection. The only way to prevent this is by telling the
browser to not accept such unsecure SSL protocols (like those based on RC4 encryption).
To disable RC4 encryption for HTTPS connections you have to switch those off in Firefox. In an
empty address bar type “about:config”, press return and close the warning dialog displayed next
(you can disable this dialog if you want for the next time you configure Firefox). In the search field
enter “rc4” and look at the list displayed as a search result:
Any entry with a “true” in the last column (“Value” field) is activated and should be de- activated.
Simply right-click on the entry and “Toggle” the value field to false. Proceed for all entries until all
of them have a value of “false”.
Figure 8.20:Disable RC4
8.5.8
AdblockPlus
Adblock Plus (http://www.adblockplus.org) is mainly known for blocking advertise- ments on
websites. But it also can be used to block other content that may try to track you. To keep
current with the latest threats, Adblock Plus relies on blacklists maintained
by volunteers.
Extra Geek info: How does Adblock Plus block addresses?
The hard work here is actually done by Gecko, the engine on top of which Firefox, Thunderbird
and other applications are built. It allows something called “content poli- cies”. A content policy is
simply a JavaScript (or C++) object that gets called whenever the browser needs to load something.
It can then look at the address that should be loaded and some other data and decide whether it
should be allowed. There is a number of built-in content policies (when you define which sites
shouldn’t be allowed to load im- ages in Firefox or SeaMonkey, you are actually configuring one of
these built-in content policies) and any extension can register one. So all that Adblock Plus has to
do is to register its content policy, other than that there is only application logic to decide which
addresses to block and user interface code to allow configuration of filters.
8.5.9
GettingstartedwithAdblockPlus
Once you have Firefox installed:
1.
Download the latest version of Adblock Plus from the Add-On database of Firefox
2.Confirm that your want Adblock Plus by clicking “Install Now”.
3.After Adblock Plus has been installed, Firefox will ask to restart.
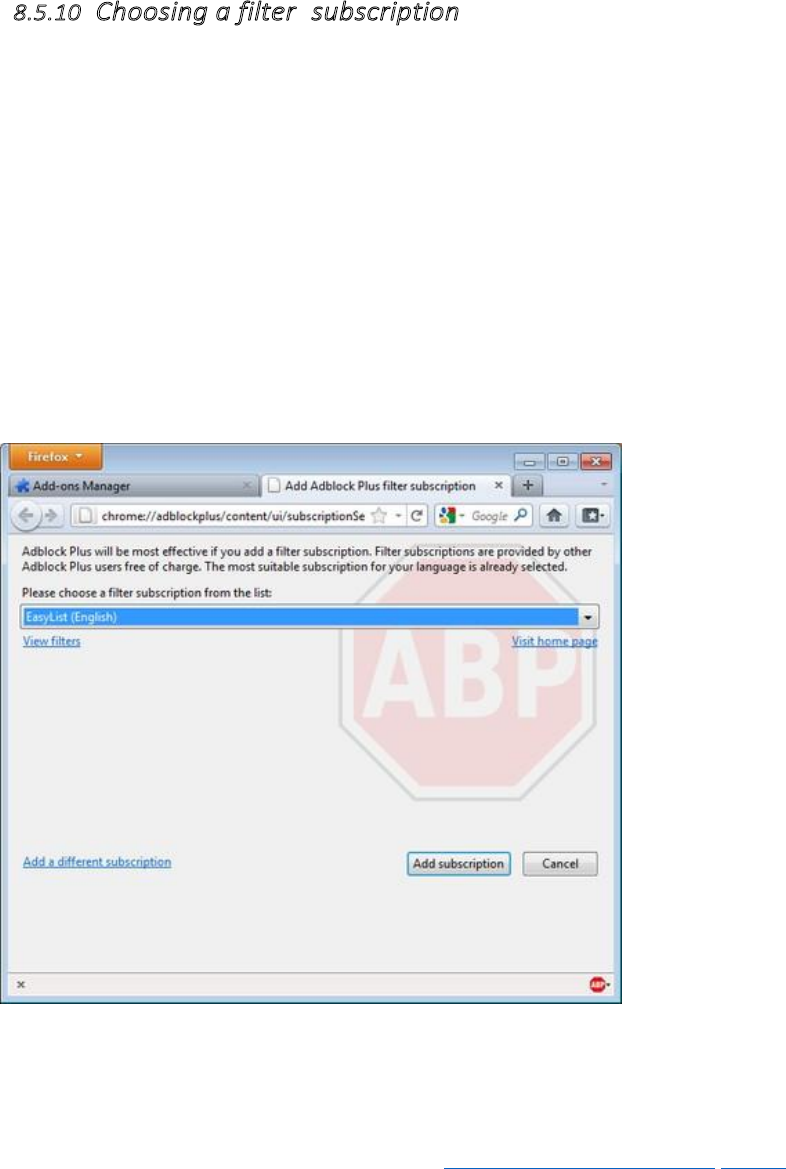
334
8.5.10
Choosingafiltersubscription
Adblock Plus by itself doesn’t do anything. It can see each element that a Web site attempts to load,
but it doesn’t know which ones should be blocked. This is what Adblock’s filters are for. After
restarting Firefox, you will be asked to choose a filter subscription (free).
Figure 8.21:Ad Block Plus
Which filter subscription should you choose? Adblock Plus offers a few in its dropdown
menu and you may wish to learn about the strengths of each. A good filter to start protecting
your privacy is EasyList (also available at http://easylist.adblockplus. org/en).
As tempting as it may seem, don’t add as many subscriptions as you can get, since some may
overlap, resulting in unexpected outcomes. EasyList (mainly targeted at English- language sites)
works well with other EasyList extensions (such as region-specific lists like RuAdList or thematic

335
lists like EasyPrivacy). But it collides with Fanboy’s List (another list with main focus on English-
language sites).
You can always change your filter subscriptions at any time within preferences. Once you’ve
made your changes, click OK.
8.5.11
Creatingpersonalizedfilters
AdBlock Plus also lets you create your own filters, if you are so inclined. To add a filter, start with
Adblock Plus preferences and click on “Add Filter” at the bottom left corner of the window.
Personalized filters may not replace the benefits of well-maintained blacklists like EasyList, but
they’re very useful for blocking specific content that isn’t covered in the public lists. For example,
if you wanted to prevent interaction with Facebook from other Web sites, you could add the
following filter:
||facebook.*$domain=~facebook.com|~127.0.0.1
The first part (||facebook.*) will initially block everything coming from Facebook’s domain.
The second part ($domain=~facebook.com|~127.0.0.1) is an exception that tells the filter to
allow Facebook requests only when you are in Facebook or if the Face- book requests come
from 127.0.0.1 (your own computer) in order to keep certain features
of Facebook working.
A guide on how to create your own Adblock Plus filters can be found at http://
adblockplus.org/en/filters.
8.5.12
EnablinganddisablingAdBlockPlusforspecificelementsorWeb
sites
You can see the elements identified by AdBlock Plus by clicking on the ABP icon AdBlock Plus
icon in your browser (usually next to the search bar) and selecting “Open blockable items”. A
window at the bottom of your browser will let you enable or disable each element on a case-by-case
basis. Alternatively, you can disable AdBlock Plus for a specific domain or page by clicking on the
ABP icon and ticking the option “Disable on [domain name]” or “Disable on this page only”.
8.5.13
Otherextensionsthatcanimproveyoursecurity
Below is a short list of extensions that are not covered in this book but are helpful to further protect
you.
•
Flagfox
- puts a flag in the location bar telling you where the server you are visiting is
most probably located. https://addons.mozilla.org/en-US/firefox/addon/ flagfox/
•
BetterPrivacy
- manages “cookies” used to track you while visiting websites. Cookies
are small bits of information stored in your browser. Some of them are used to track the
sites you are visiting by advertisers. https://addons.mozilla. org/en-
US/firefox/addon/betterprivacy/
•
GoogleSharing
- If you are worried that google knows your search history, this
extension will help prevent that. https://addons.mozilla.org/en-us/firefox/
addon/googlesharing/
•
NoScript
- Although not friendly for beginners, this addon will block scripts and third
party
336
plugin content (eg, Adobe Flash) unless specifically allowed by the user,
it
also provides
general protection against simple cross site scripting vectors.
http://noscript.net/
•
User Agent Switcher
- Your browser supplies large amounts of identifying infor- mation
to any remote server through the ‘User-Agent’ header, including Operating System and
specific version information. This addon allows you to supply either a fake or generic User-
Agent to the server. http://chrispederick.com/work/ user-agent-switcher/
8.6
Proxy Settings
A proxy server allows you to reach a Web site or other Internet location even when direct access
is blocked in your country or by your ISP. There are many different kinds of proxies, including:
•
Web proxies, which only require that you know the address to the proxy Web site, which
may have a URL similar to http://proxy.com/cgi-bin/nph-proxy.cgi
•
HTTP proxies, which require that you modify your Browser settings. HTTP proxies only
work for Web content. You may get the information about a HTTP proxy in the format
proxy.example.com:3128 or 192.168.0.1:8080.
•
SOCKS proxies, which also require that you modify your Browser settings. SOCKS proxies
work for many different Internet applications, including e-mail and instant messaging tools.
The SOCKS proxy information looks just like HTTP proxy infor- mation.
You can use a Web proxy directly without any configuration by typing in the URL. The
HTTP and SOCKS proxies, however, have to be configured in your Web browser.
8.6.1
DefaultFirefoxproxyconfiguration
In Firefox you can change the settings for using a proxy. You’ll need to open the Options or
Preferences window of Firefox. You can find this in the menu, by clicking on the top of the
Window and selecting Edit > Preferences on Linux or Tools > Options on Windows.
Go to the Network section and open the Advanced tab.
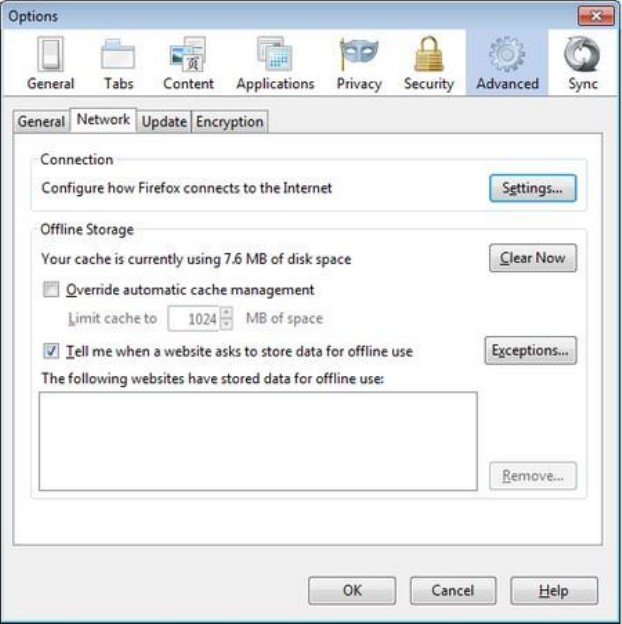
337
Figure 8.22:Firefox Proxy Settings
Select Settings, click on “Manual proxy configuration” and enter the information of the proxy
server you want to use. Please remember that HTTP proxies and SOCKS proxies work differently
and have to be entered in the corresponding fields. If there is a colon (:) in your proxy information,
that is the separator between the proxy address and the port number. Your screen should look like
this:
After you click OK, your configuration will be saved and your Web browser will au- tomatically
connect through that proxy on all future connections. If you get an error message such as, “The
proxy server is refusing connections” or “Unable to find the proxy server”, there is a problem with
your proxy configuration. In that case, repeat the steps above and select “No proxy” in the last
screen to deactivate the proxy.
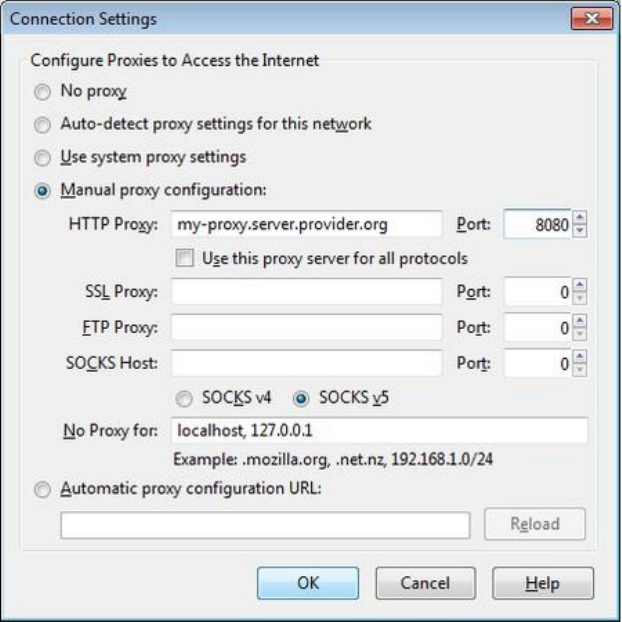
338
Figure 8.23:Firefox Proxy Settings
8.7 Using Tor?
Tor is a system intended to enable online anonymity, composed of client software and a network
of servers which can hide information about users’ location and other factors which might identify
them. Imagine a message being wrapped in several layers of pro- tection: every server is only able
to take off one layer, thereby immediately deleting the sender information of the previous server.
If Alice wants to view Bob’s website, instead of directly talking to Bob like this:
Alice -> Bob
This is fine, and Alice and Bob can use end to end cryptography to ensure privacy, integrity and
authenticity of their communications, however if Alice does not want Bob to know that she is
viewing his website or does not want Eve (a hypothetical evesdropper, on Alice or Bobs side of the
connection) to know she and Bob are communicating, extra steps must be taken.
Alice instead makes an encrypted connection to an EntryNode on the Tor network, here they
establish a TLS connection and the EntryNode allows Alice to make a further connection through
it. Once again a TLS connection is established this time through the already encrypted EntryNode
connection, and once again the process is repeated through the RelayNode to the ExitNode. Now,
Alice is encrypting the data 3 times, first for the ExitNode, then for the RelayNode and finally for
the EntryNode. Creating a network path like this:
Alice -> EntryNode -> RelayNode -> ExitNode -> Bob

339
When the EntryNode receives Alice’s data it is still encrypted for the RelayNode and
ExitNode, it knows where the data is coming from but not the final destination or the message
content, it then passes the data on to the RelayNode. The RelayNode receives the data but it is
still encrypted for the ExitNode, it knows it is coming from the EntryNode and going to the
ExitNode but does not know the final destination or the original sender, it then passes the data
to the ExitNode which removes the final layer of encryption, the ExitNode knows what the
message is, that it came from RelayNode but does not know where it entered the network, or
who sent it.
This layered approach is where Tor derives it’s name from (The Onion Router), each ‘layer’
knows only of the layer on either side of it, meaning that none in the chain except Alice knows the
full path the data is taking, however Alice, Bob and the ExitNode are all able to see the message
content, thus end-to-end cryptography is still required to ensure privacy, integrity and authenticity
of the communications across the Tor network.
Use of this system makes it more difficult to trace internet traffic to the user, including visits to
Web sites, online posts, instant messages, and other communication forms. It is intended to protect
users’ personal freedom, privacy, and ability to conduct confidential business, by keeping their
internet activities from being monitored. The software is open-source and the network is free of
charge to use.
8.7 Using Tor?
Like all current low latency anonymity networks, Tor cannot and does not attempt to protect
against monitoring of traffic at the boundaries of the Tor network, i.e., the traffic entering and exiting
the network. While Tor does provide protection against traffic analysis, it cannot prevent traffic
confirmation (also called end-to-end correlation)
Caution: As Tor does not, and by design cannot, encrypt the traffic between an exit node and the
target server, any exit node is in a position to capture any traffic passing through it which does not
use end-to-end encryption such as TLS. (If your postman is corrupt he might still open the envelope
and read the content). While this may or may not inherently violate the anonymity of the source,
if users mistake Tor’s anonymity for end-to-end encryption they may be subject to additional risk
of data interception by third parties. So: the location of the user remains hidden; however, in some
cases content is vulnerable for analysis through which identifying or revealing information about
the user may be gained.
8.7.1
UsingTorBrowserBundle
The Tor Browser Bundle lets you use Tor on Windows, OSX and/or Linux without requiring you to
configure a Web browser. Even better, it’s a portable application that can be run from a USB flash
drive, allowing you to carry it to any PC without installing it on each computer’s hard drive.
8.7.2
DownloadingTorBrowserBundle
You can download the Tor Browser Bundle from the torproject.org Web site (https:
//www.torproject.org).
If the torproject.org Web site is filtered from where you are, type “tor mirrors” in your favorite
Web search engine: The results probably include some alternative addresses to download the Tor
Browser Bundle.
Please follow the instructions on the Tor Project Website on how to install the Tor Browser.
Caution: When you download Tor Bundle (plain or split versions), you should check the
signatures of the files. This step ensures that the files have not been tampered with. To learn

340
more about signature files and how to check them, read https://www.
torproject.org/docs/verifying-signatures
8.7.3
RunningaRelayor Bridge
Tor is a network of volunteers who run relays and bridges. If you would like to grow the Tor network
by contributing bandwidth and spare CPU cycles, consider running a relay. Plus, running a relay
may improve your anonymity since an attacker can’t distinguished between traffic that originated
from you or from the relay. See the Tor FAQ for more details.
However, if you do run a relay, your IP address will be listed on the Internet as a Tor relay.
Tor clients depend on this list, provided by Tor Directory Servers, so that they can build circuits.
If you wish to contribute to Tor, but do not want to run a public relay,
consider running a bridge. Since Tor relays are public, some ISP block access to the Tor network by
blocking
alltherelays.
Tor Bridges are unlisted are therefore, more difficult to find.
Tor’s goal is to protect anonymity on the Internet, but sometimes Tor is used for illegal purposes.
As a relay operator, consult the Legal FAQ, written by the Electronic Frontier Foundation (EFF).
The EFF is a U.S. based non-profit organization whose mission is to “protect your digital right.”
Other countries should seek the advice of similar organizations. However, legal risks can be
minimized by running a non-exit relay or bridge.
If you’d like to configure your computer to run a relay or a bridge, visit the Tor website for
thorough instructions.
8.8
Extending Google Chrome
Chrome is Google’s browser. Here are some useful tips and extensions:
8.8.1
DisablingInstantSearch
Chrome can search as you type. The advantage of this is that you get search suggestions and can use
Google’s predictions - but the disadvantage is that every character you type is sent to Google’s
servers, where it may be logged.
To disable, open Chrome’s settings by clicking the menu button at the right of the address
bar and clicking Settings. Or, simply type chrome://settings/ in your address bar.
Ensure that the Enable Instant for faster searching (omnibox input may be logged)
checkbox is unchecked.
8.8.2
AdBlockforChrome
Just like Firefox, AdBlock removes ads. Install from this Chrome Webstore page.
8.8.3
HTTPSEverywhere
Forces encrypted https connections wherever possible. Installation link can be found on the EFF
HTTPS Everywhere homepage.
8.8.4
PrivacyFix
PrivacyFix (beta) gives you a dashboard view of your privacy settings on Facebook and Google, as
well as Do-Not-Track headers and tracking cookies. It provides links to quickly change these

341
privacy settings without digging through many drilldown pages. Install from the Chrome web store
page
9
Passwords
9.1
Keeping passwords safe
Passwords are like keys in the physical world. If you lose a password you will not be able to get in,
and if others copy or steal it they can use it to enter. A good password should not be easy for others
to guess and not easy to crack with computers, while still being easy for you to remember.
9.1.1
Passwordlengthandcomplexity
To protect your passwords from being guessed, length and complexity are important. Passwords like
the name of your pet or a birth date are very unsafe, as is using single word that can be found in a
dictionary. Do not use a password containing only numbers. Most importantly a secure password is
long. Using combinations of lower case letters, capitals, numbers and special characters can improve
the security, but length is still the most important factor.
For use with important accounts like the pass phrase which protects your PGP/GPG or
TrueCrypt encrypted data, or the password for your main email account, use 20 characters or
more, the longer the better. See this XKCD cartoon "correct horse battery staple" vis-Ãă-vis
"Tr0ub4dor&3" for an explanation.
9.1.2
Easytorememberandsecurepasswords
One way to create strong and easy to remember passwords is to use sentences.
A few examples:
•
IloveDouglasAdamsbecausehe
'
sreallyawesome.
•
Peoplelovemachinesin2029A.D.
•
BarneyfromHowIMetYourMotherisAWESOME!
Sentences are easy to remember, even if they are 50 characters long and contain up- percase
characters, lowercase characters, symbols and numbers.
9.1.3
Minimizingdamage
It is important to minimize the damage if one of your passwords is ever compromised. Use different
passwords for different websites or accounts, that way if one is compromised, the others are not.
Change your passwords from time to time, especially for accounts you consider to be sensitive. By
doing this you can block access to an attacker who may have learned your old password.
9.1.4
Usingapasswordmanager
Remembering a lot of different passwords can be difficult. One solution is to use a ded- icated
application to manage most of your passwords. The next section in this chapter will discuss
Keepass
,

342
a free and open source password manager with no known vulnera- bilities, so long as you chose a
sufficiently long and complex “master password” to secure it with.
For website passwords only, another option is the built-in password manager of the Firefox
browser. Make sure to set a master password, otherwise this is very insecure!
9.1.5
Physicalprotection
When using a public computer such as at a library, an internet cafe, or any computer you do not
own, there are several dangers. Using “over the shoulder” surveillance, someone, possibly with a
camera, can watch your actions and may see the account you log in to and the password you type.
A less obvious threat is software programs or hardware devices called “keystroke loggers” that
record what you type. They can be hidden inside a computer or a keyboard and are not easily
spotted. Do not use public computers to log in to your private accounts, such as email. If you do,
change your passwords as soon as you get back to a computer you own and trust.
9.1.6
Othercaveats
Some applications such as chat or mail programs may ask you to save or “remember” your username
and password, so that you don’t have to type them every time the program is opened. Doing so
may mean that your password can be retrieved by other programs running on the machine, or directly
from your hard disk by someone with physical access to it.
If your login information is sent over an insecure connection or channel, it might fall into the
wrong hands. See the chapters on secure browsing for more information.
9.2
Installing KeePass
We will cover installing KeePass on Ubuntu and Windows.
Mac OSX comes with an excellent built-in password manager called Keychain that is just as
safe. Downsides are that it isn’t Open Source and doesn’t work on other systems. If you’d need
to take your passwords from one Operating System to another it is better to stick with Keepass
after all. How to use Keychain is covered in the next chapter.
9.2.1
InstallingKeePassXonUbuntu
To install on Ubuntu we will use the Ubuntu Software Center. Type KeePass in the search field
at the top right and the application KeePassX should automatically appear in the listing.
Highlight the item (it may already be highlighted by default) and then press ‘Install’.
You will be asked to Authorise the installation process:
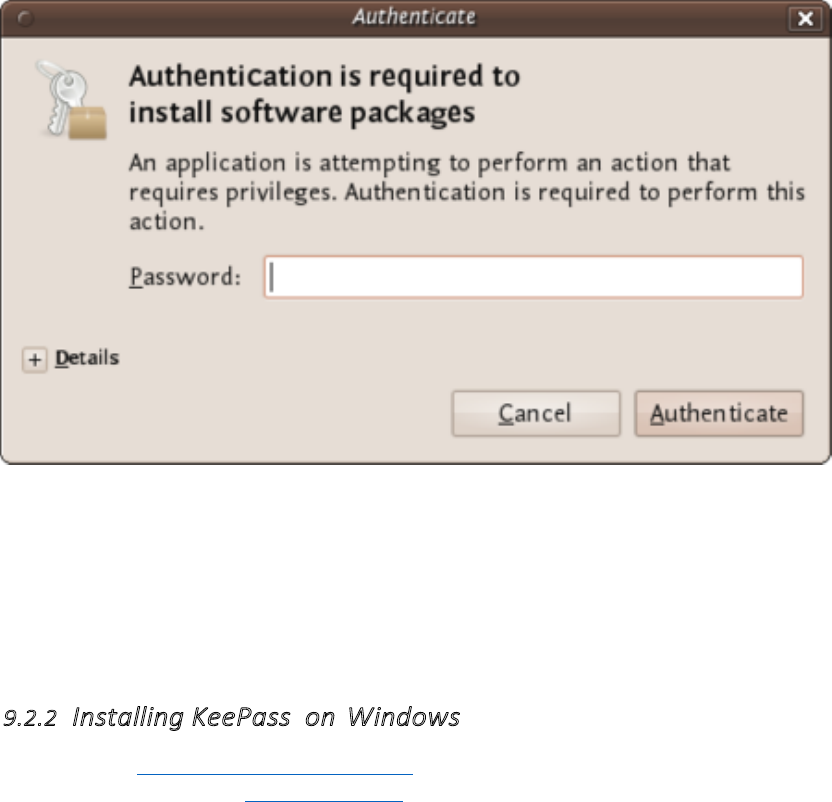
343
Figure 9.1:Keepass Install
Enter your password and press ‘Authenticate’ the installation process will then begin.
Ubuntu
does not offer very good feedback to show the software is installed. If the
green progress
indicator on the left has gone and the progress bar on the right has gone
then you can assumed the software is installed.
9.2.2
InstallingKeePassonWindows
First visit the KeePass download webpage and choose the appropriate installer. For this
chapter we are using the current installer.
Download this to your computer then double click on the installer. You will first be asked to select
a language, we will choose English:
Press ‘OK’ and you will be shown the following screen: Just press
‘Next >’ and go to the next screen:
In the screen shown above we must select ‘I accept the agreement’ otherwise we will not be
able to install the software. Choose this option and then press ‘Next >’. In the next screen you
will be asked to determine the installation location. You can leave this with the defaults unless
you have good reason to change them.
Click on ‘Next >’ and continue.
The above image shows the KeePass components you can choose from. Just leave the defaults as
they are and press ‘Next >’. You will come to a new screen:
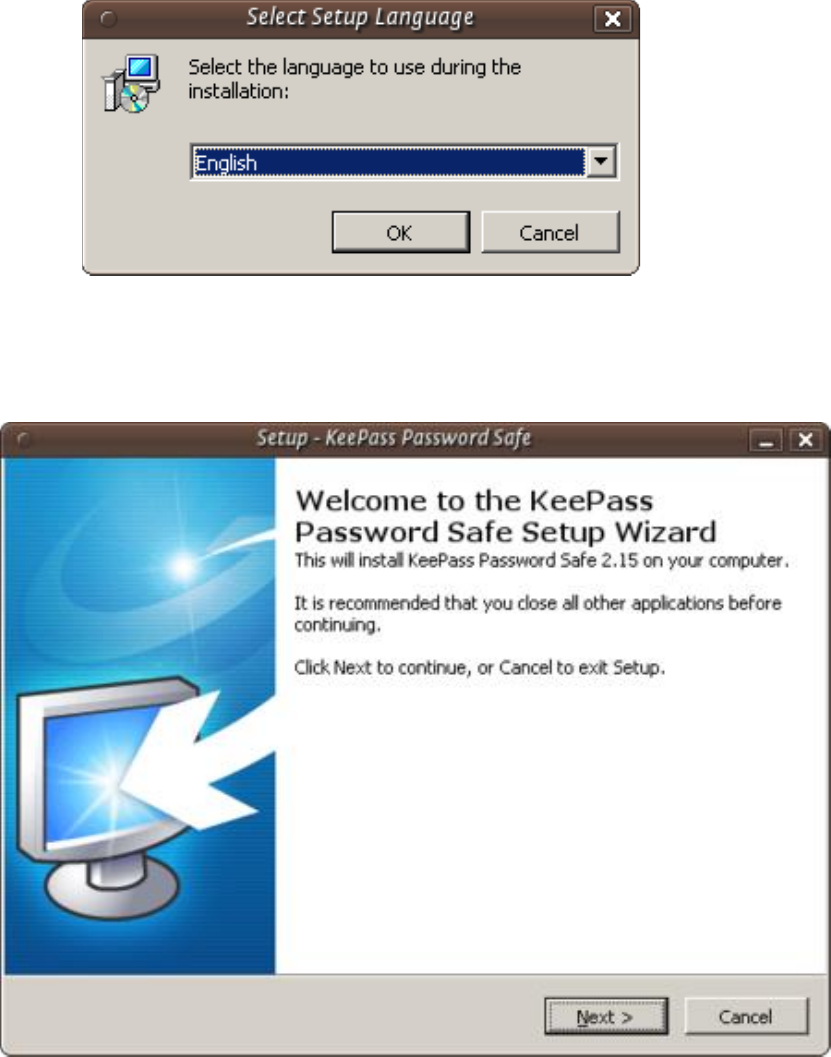
344
Figure 9.2:Keepass Install
Figure 9.3:Keepass Install
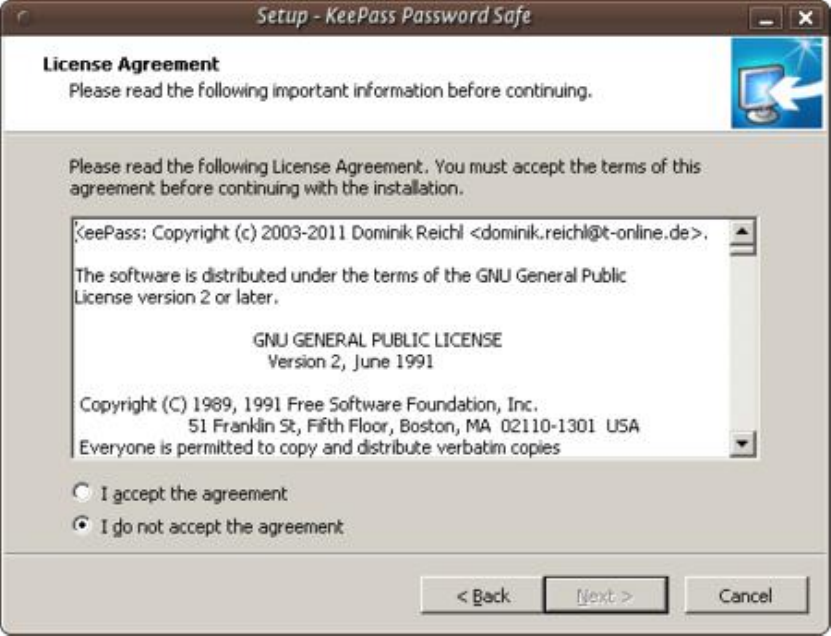
345
Figure 9.4:Keepass Install
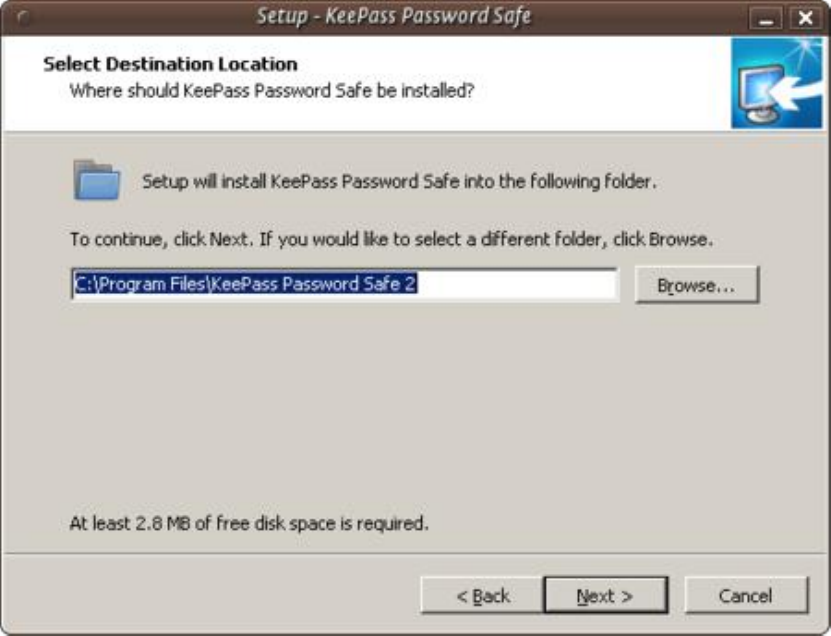
346
Figure 9.5:Keepass Install
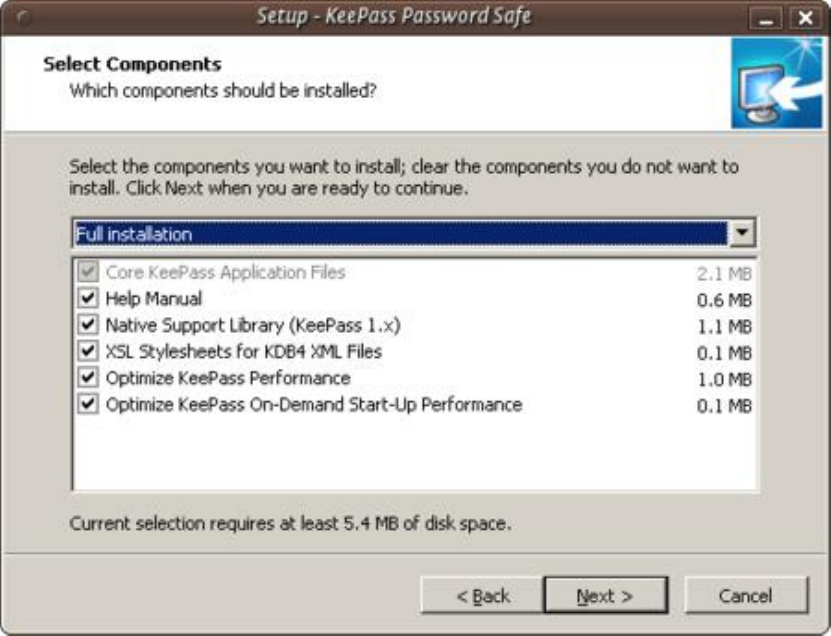
347
Figure 9.6:Keepass Install
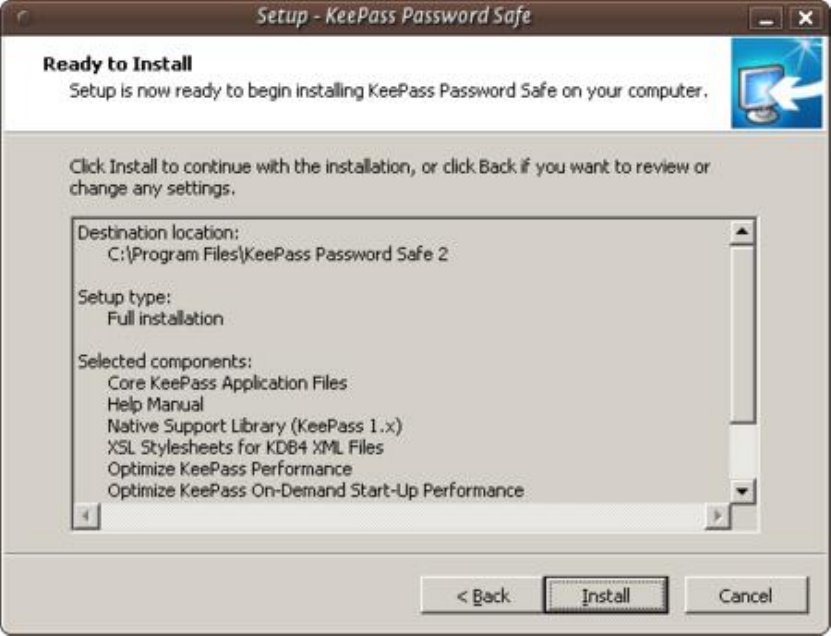
348
Figure 9.7:Keepass Install
This doesn’t do anything but give you a summary of your options. Press ‘Install’ and the
installation process will begin.
349
Figure 9.8:Keepass Install
9.2.3
InstallingKeePassonMacOS X
Although Keychain in Mac OS X does an excellent job of storing your passwords, you may
want to run your own password database and manager. KeePass allows this added flexi- bility.
First visit the KeePass download webpage http://keepass.info/download.html and choose the
appropriate installer. Although the official installers are listed at the top of the page, there are
unofficial/contributed installers further down. Scroll down to find [KeePass 2.x for Mac OS
X][http://keepass2.openix.be/](http://keepass2.openix.be/):
As this is an external link, your browser will be redirected to http://keepass2. openix.be/:
Note here that you must install the Mono framework first, so that KeePass can run in OS X. So
click on each of the links Mono 2.10.5 and KeePass2.18 to download the DMG files to your
computer. Double-click on each of the DMGs in your downloads folder to unpack the volumes to
your desktop.
350
Figure 9.9:Keepass Install
351
Figure 9.10:Keepass Install
The Mono Package installer is in case called something similar to ‘MonoFramework- MRE-
2.10.5_0.macos10.xamarin.x86.pkg’, so double-click on this document:
352
Figure 9.11:Keepass Install The
installer will open and run:
Follow each of the steps by clicking ‘Continue’, the next step being ‘Read Me’. Inhere is
important information such as all of the files that the package will install, including information on
how to uninstall Mono:
Click ‘Continue’ to the next screen, the license. Clicking ‘Continue’ on the license screen pops
up the agree/disagree dialogue box. If you agree with the license conditions, the installation will
continue:
The following two steps in the installation ask you to choose an installation destination, and
check there is enough space on the install disk. When the installation has completed, you will
see this screen:
Now you can quit the installer. Next take a look at the KeePass disk image, double- click to open
it, and drag the KeePass application into your Applications folder:
Now KeePass is ready to use for Mac OS X.
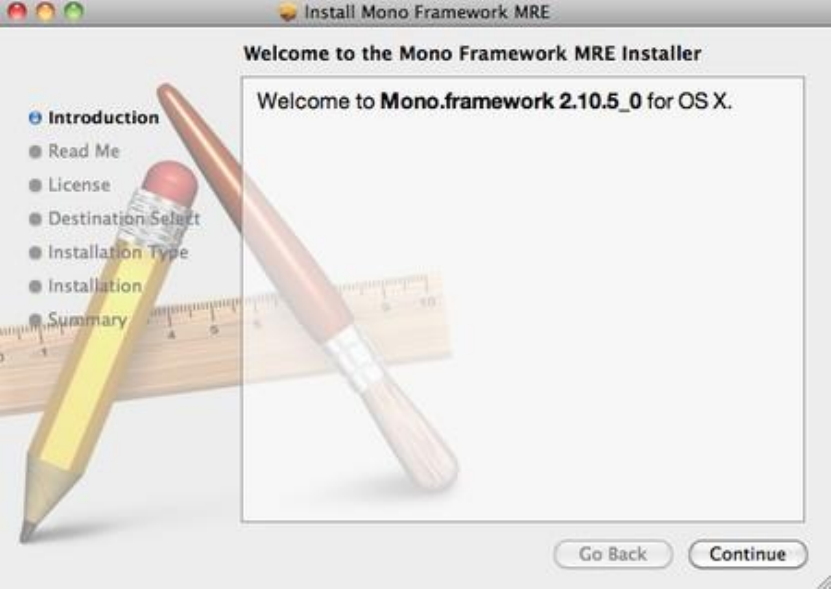
353
Figure 9.12:Keepass Install
354
Figure 9.13:Keepass Install
355
Figure 9.14:Keepass Install
Figure 9.15:Keepass Install
356
Figure 9.16:Keepass Install
9.3
Encrypting Passwords with a Password Manager
To encrypt password we use KeePass on Windows and KeePassX Ubuntu, and Keychain on OSX.
The basic principle is the same; you have a file on your computer which is encrypted with
onesingle
verysecurepassword
. This is sometimes referred to as a ‘Master Password’, ‘Admin-Password’,
‘Root-Password’ etc. but they are all
theultimatekey
to all your other keys and secure data. For
this reason you can’t and shouldn’t think to light about creating this password.
If a password manager is part of your OS (like it is with OSX) it unlocks automatically for you
after you login to your account and so opening secure information like passwords. For this, and
other, reasons you should disable ‘Automatically Login’. When you start- up your computer you
should always have to login and, even better, set your computer to automatically logout or lock
the screen after a set amount of time.
9.3.1
EncryptingPasswordswithKeePassXonUbuntu
First open KeePassX from the Applications->Accessories -> KeePassX menu.
The first time you use KeePassX you need to set up a new database to store your passwords. Click
on File->New Database
You will be asked to set a master key (password).
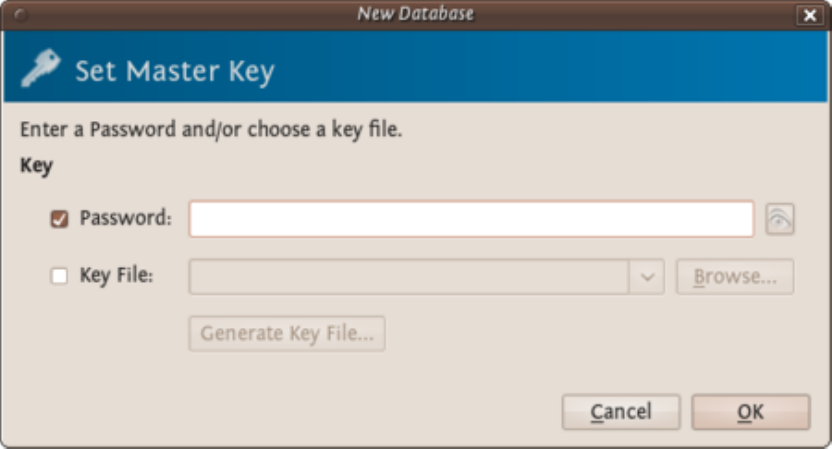
357
Figure 9.17:Password Manager
Choose a strong password for this field - refer to the chapter about passwords if you would like
some tips on how to do this. Enter the password and press ‘OK’. You then are asked to enter the
password again. Do so and press ‘OK’. If the passwords are the same you will see a new KeePassX
‘database’ ready for you to use.
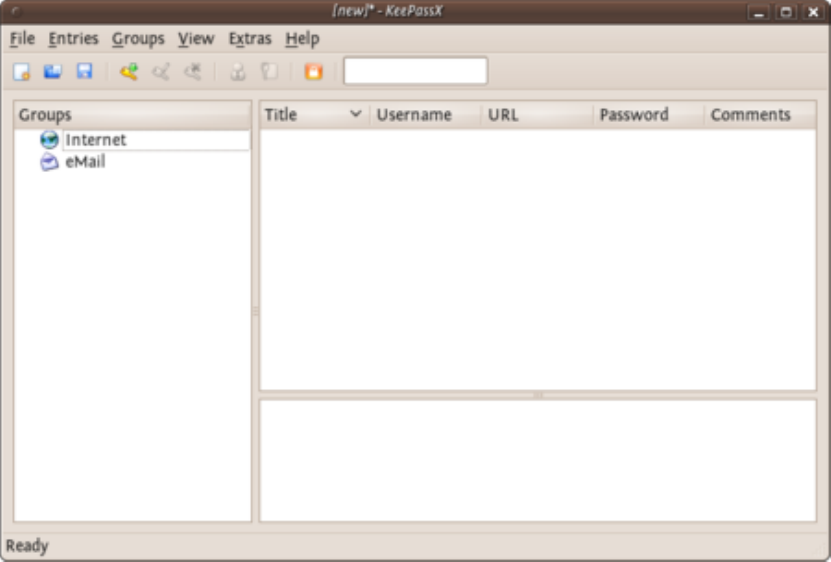
358
Figure 9.18:Password Manager
Now you have a place to store all your passwords and protect them by the ‘master’ password you
just set. You will see two default categories ‘Internet’ and ‘Email’ - you can store passwords just
under these two categories, you can delete categories, add sub- groups, or create new categories. For
now we just want to stay with these two and add a password for our email to the email group. Right
click on the email category and choose ‘Add New Entry. . . ’:
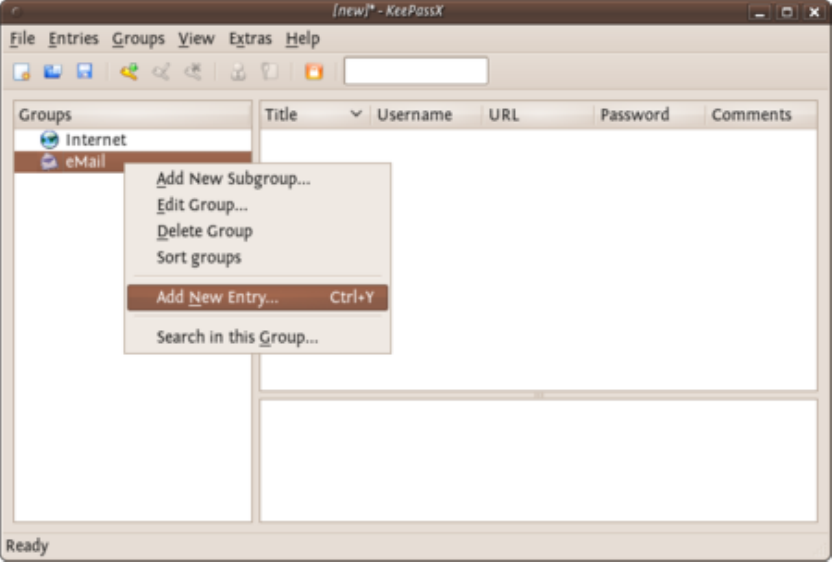
359
Figure 9.19:Password Manager
So now fill this form out with the details so you can correctly identify which email account the
passwords are associated with. You need to fill out the fields ‘Title’ and the password fields. All
else is optional.
KeePassX gives some indication if the passwords you are using are ‘strong’ or ‘weak’. As may
be obvious, you should try to use stronger passwords. For advice on this see the chapter on
creating good passwords. Press ‘OK’ when you are done and you will see something like this:
To recover the passwords (see them) you must double click on the enter and you will see the
same window you used for recording the information. If you click on the ‘eye’ icon to the right of
the passwords they will be converted from stars (***) to the plain text so you can read it.
Now you you can use KeePassX to store your passwords. However before getting too excited you
must do one last thing. When you close KeePassX (choose File->Quit) it
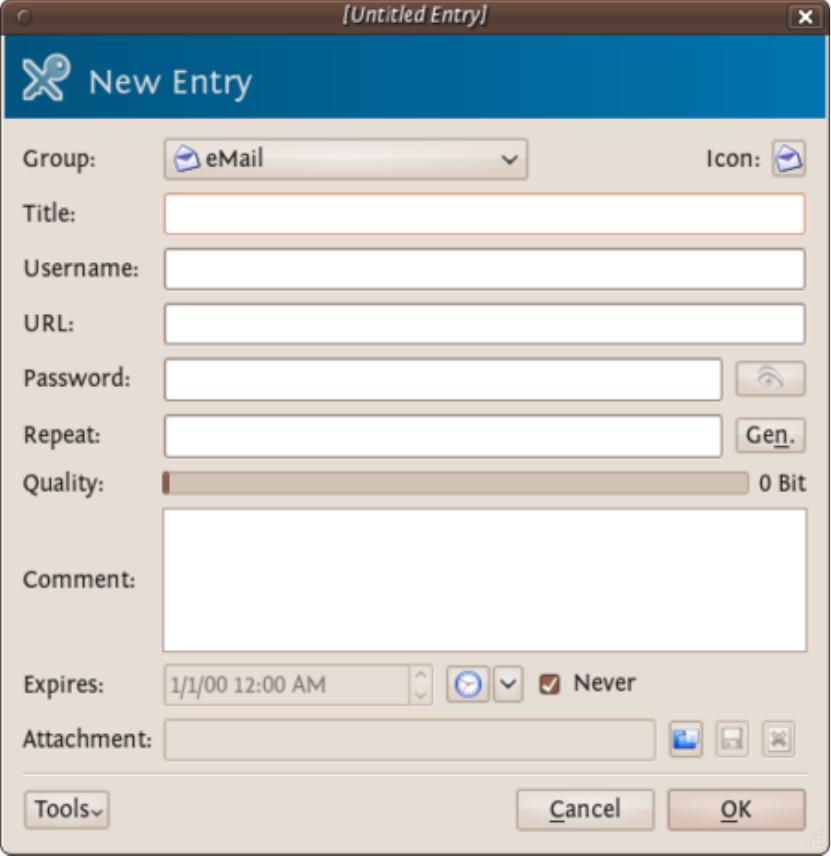
360
Figure 9.20:Password Manager
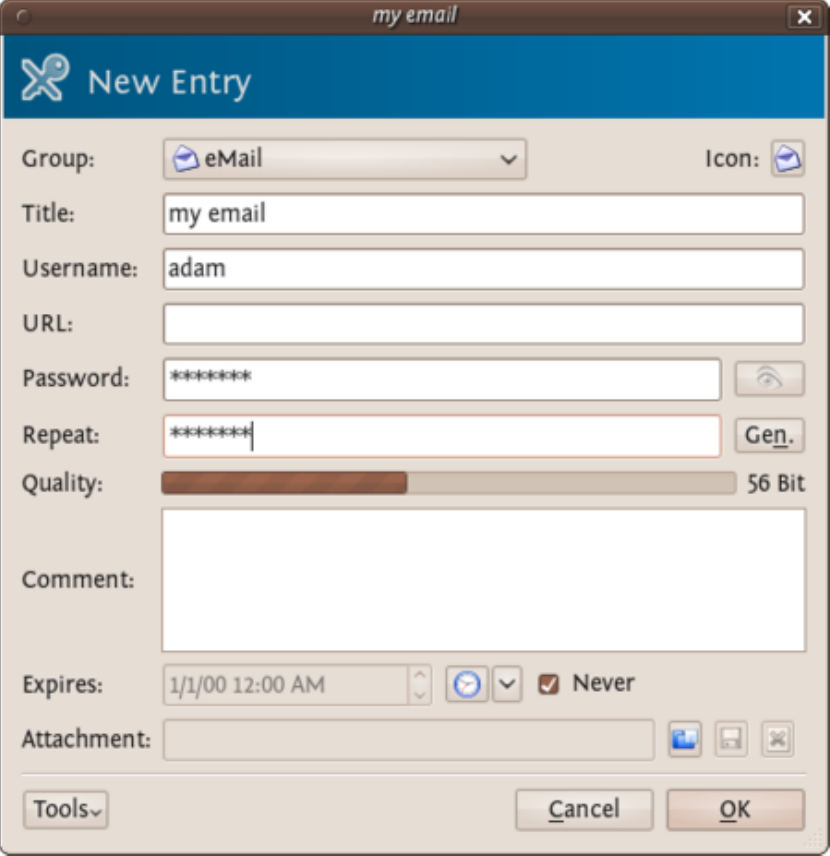
361
Figure 9.21:Password Manager
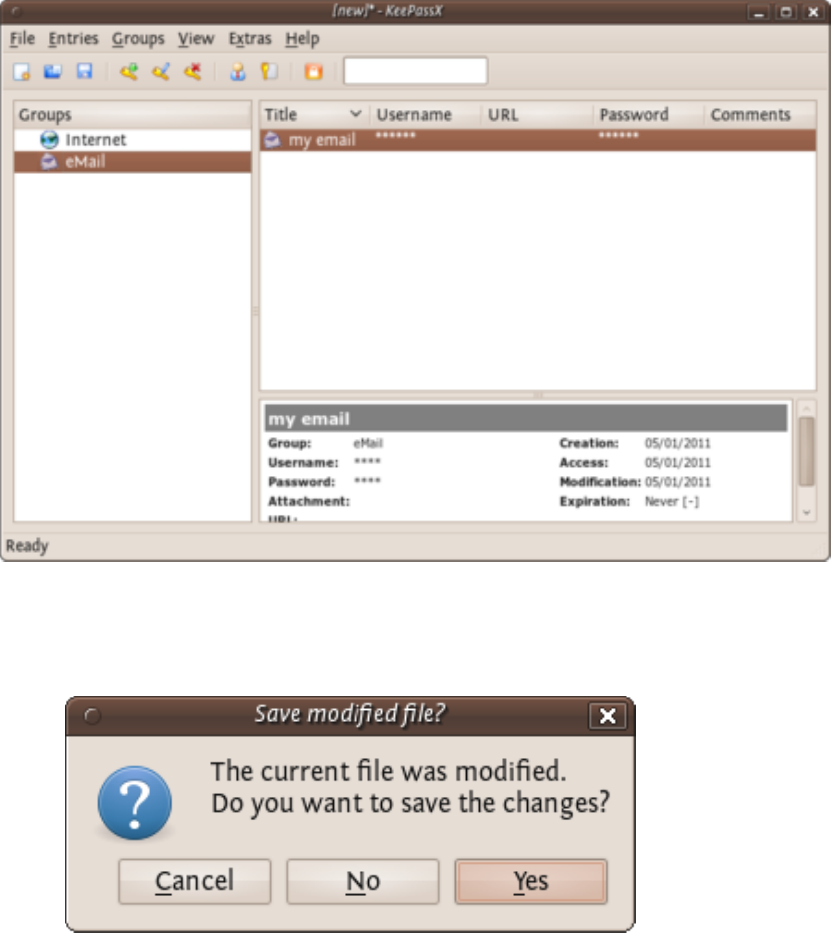
362
Figure 9.22:Password Manager
asks you if you would like to save the changes you have made.
Figure 9.23:Password Manager
Press ‘Yes’. If it is the first time you used KeePassX (or you have just created a new database)
you must choose a place to store your passwords. Otherwise it will save the updated information in
the file you have previously created.
When you want to access the passwords you must then open KeePassX and you will be asked
for the master key. After typing this in you can add all your passwords to the database and see
all your entries. It is not a good idea to open KeePassX and have it open permanently as then
anyone could see your passwords if they can access your computer. Instead get into the practice
of just opening it when you need it and then closing it again.
363
9.3.2
EncryptingPasswordswithKeePassonWindows
After you installed KeePass on Windows you can find it in the application menu. Launch the
application and the following window should appear.
You start by making a database, the file which will contain your key. From the menu select
File > New. You have to chose the name and the location of the file in the dialog window
below. In this example we call our database my_password_database.
The next screen will ask you for the master password. Enter the password and click on ‘OK’.
You will not need to select anything else.
The next window allows you to configure your new database. We do not need to edit
anything. Just click on ‘OK’.
Now the main window appears again and we see some default password categories on the left
side. Lets add a new password in the category ‘Internet’. First click on the word ‘Internet’, then
click on the add entry icon under the menu bar.
A window will appear like below. Use the fields to give a description of this particular password,
and of course, enter the password itself. When done, click on ‘OK’.
Figure 9.24:Password Manager
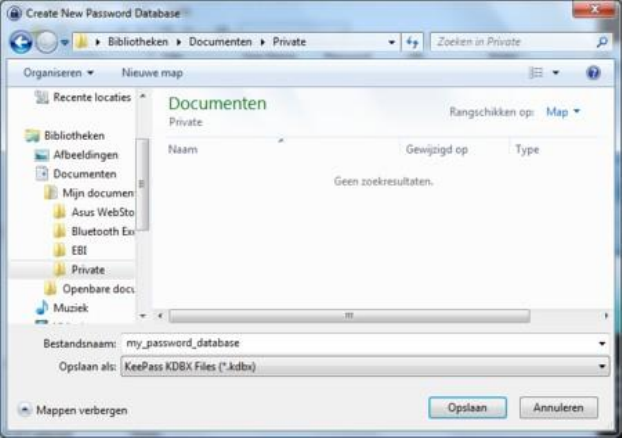
364
Figure 9.25:Password Manager
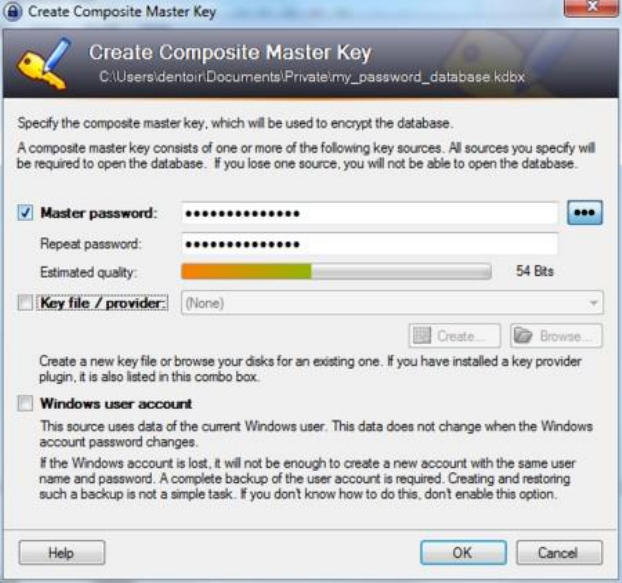
365
Figure 9.26:Password Manager

366
Figure 9.27:Password Manager
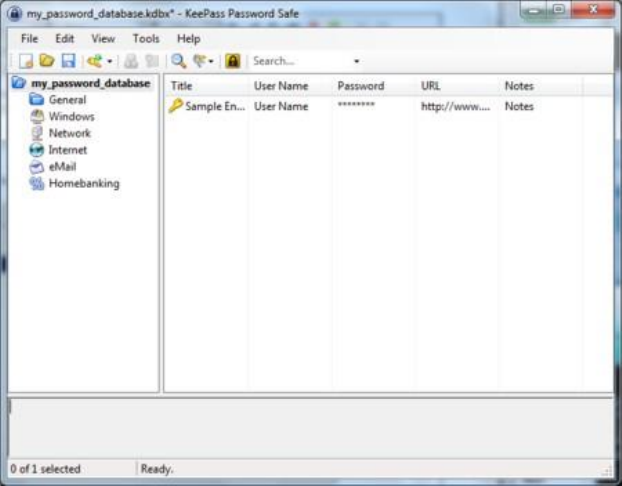
367
Figure 9.28:Password Manager
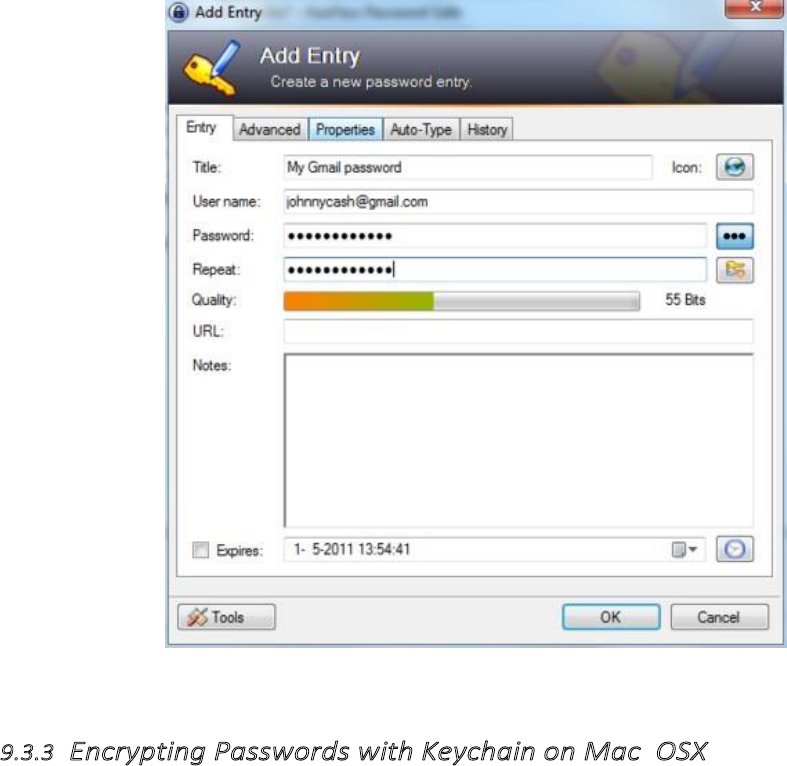
368
Figure 9.29:Password Manager
9.3.3
EncryptingPasswordswithKeychainonMacOSX
Mac OSX comes pre-installed with the build in password manager ‘Keychain’. Because of it’s tight
integration with the OS most of the time you will hardly know it exists. But every now and then you
will have a pop-up window in almost any application asking ‘do you want to store this password
in your keychain?’. This happens when you add new email accounts to your mail client, login to
a protected wireless network, enter your details in your chat client etc. etc. etc.
Basically what happens is that Mac OSX offers you to store all that login data and different
passwords in an encrypted file which it unlocks as soon as you login to your account. You can then
check your mail, logon to your WiFi and use your chat client without having to enter your login data
all the time over and over again. This is a fully automated process, but if you want to see what is
stored where and alter passwords, or lookup a password you will have to open the Keychain
program.
You can find the Keychain program in the Utilities folder which lives in the Applications folder.
369
Figure 9.30:Password Manager
When you open it you will see that your ‘Login’ keychain is unlocked and see all the items
contained in it on the right bottom side of the window.
(note: the window here is empty because it seemed to be deceiving the purpose of this
manual
to make a screenshot of my personal keychain items and share it here with you)
You can double click any of the items in the Keychain to view it’s details and tick ‘Show
password:’ to see the password associated with the item.
You will note that it will ask you for your master or login password to view the item.
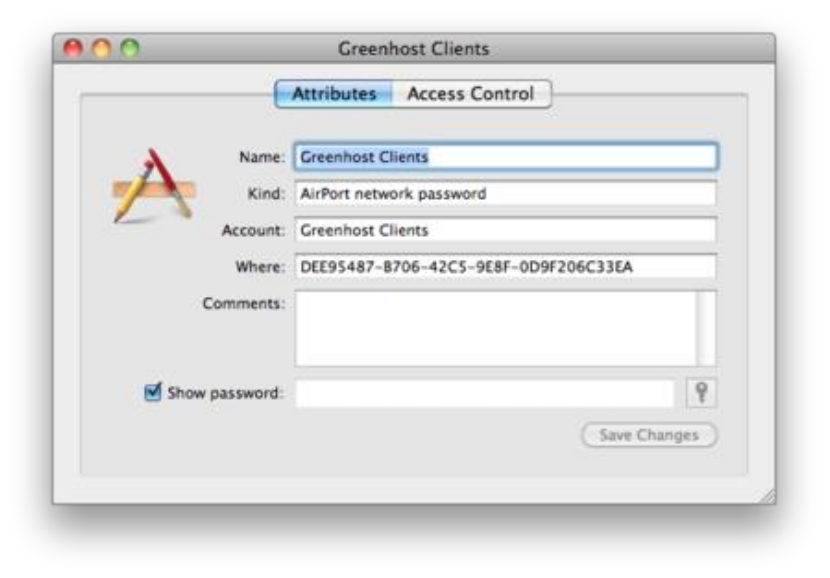
370
Figure 9.31:Password Manager
You can access modify any of the items and also use the Keychain to securely save any bits and
pieces of text using the notes. To do this click on notes and than choose ‘New secure Note item’
from the file menu.
Figure 9.32:Password Manager
371
Figure 9.33:Password Manager
10
Using Vpn
10.1
Getting, setting-up and testing a VPN account
In all the VPN systems, there is one computer set up as a server (in an unrestricted location), to
which one or more clients connect. The set up of the server is out of the scope of this manual
and the set up of this system is in general covered by your VPN provider. This server is one of
the two ends of the encrypted tunnel. It is important that the company running this server can
be trusted and is located in an area you trust. So to run a VPN, an account is needed at such a
trusted server.
Please keep in mind that an account can often only be used on one device at a time. If you want
to use a VPN with both your mobile and laptop concurrently, it is very well possible you need two
accounts.
10.1.1
AnaccountfromacommercialVPNprovider
There are multiple VPN providers out there. Some will give you free trial time, others will begin
charging right away at an approximate rate of
e
5 per month. Look for a VPN provider that

372
offers OpenVPN accounts - it is an Open Source, trusted solution available for Linux, OS X,
and Windows, as well as Android and iOS.
When choosing a VPN provider you need to consider the following points:
•
Information that is required from you to register an account - the less that is needed the better.
A truly privacy concerned VPN provider would only ask you for email address (make a
temporary one!), username and password. More isn’t required unless the provider creates a
user database which you probably don’t want to be a part of.
•
Payment method to be used to pay for your subscription. Cash-transfer is probably the most
privacy-prone method, since it does not link your bank account and your VPN network ID.
Paypal can also be an acceptable option assuming that you can register and use a temporary
account for every payment. Payment via a bank transfer or by a credit card can severely
undermine your anonymity on and beyond the VPN.
•
Avoid VPN providers that require you to install their own proprietary client soft- ware.
There is a perfect open source solution for any platform, and having to run a “special”
client is a clear sign of a phony service.
•
Avoid using PPTP based VPNs, as several security vulnerabilities exist in that protocol. In
fact, if two providers are otherwise equal, choose the one
not
offering PPTP if feasible.
•
Look for a VPN provider that’s using OpenVPN - an open source, multi-platform VPN
solution.
•
Exit gateways in countries of your interest. Having a choice of several countries allows
you to change your geo-political context and appears to come from a different part of the
world. You need to be aware of legislation details and privacy laws in that particular
country.
•
Anonymity policy regarding your traffic - a safe VPN provider will have a non- disclosure
policy. Personal information, such as username and times of connection, should not be
logged either.
•
Allowed protocols to use within VPN and protocols that are routed to the Internet.
You probably want most of the protocols to be available
•
Price vs. quality of the service and its reliability.
•
Any known issues in regard to anonymity of the users the VPN provider might have
had in the past. Look online, read forums and ask around. Don’t be tempted by
unknown, new, cheap or dodgy offers.
There are several VPN review oriented places online that can help you make the right choice:
•
http://www.bestvpnservice.com/vpn-providers.php
•
http://vpncreative.com/complete-list-of-vpn-providers
•
http://en.cship.org/wiki/VPN
Setting up your VPN client
“OpenVPN [..] is a full featured SSL VPN software solution that integrates
OpenVPN server capabilities, enterprise management capabilities, simplified
OpenVPN Connect UI, and OpenVPN Client software packages that accom-
modate GNu/Linux, OSX, Windows and environments. OpenVPN Access
Server supports a wide range of configurations, including secure and granu- lar
remote access to internal network and/or private cloud network resources and

373
applications with fine-grained access control.” (http://openvpn.net/
index.php/access-server/overview.html)
There is a number of different standards for setting up VPNs, including PPTP, LL2P/IPSec and
OpenVPN
. They vary in complexity, the level of security they provide, and which operating
systems they are available for. Do not use PPTP as it has several security vulnerabilities. In this
text we will concentrate on OpenVPN. It works on most versions
of GNU/Linux, OSX, Windows. OpenVPN is TLS/SSL-based - it uses the same type of
encryption
that is used in HTTPS (Secure HTTP) and a myriad of other encrypted protocols.
OpenVPN encryption is based on
RSA
key exchange algorithm. For this to work and in order
to communicate, both the server and the client need to have public and private RSA keys.
Once you obtain access to your VPN account the server generates those keys and you simply
need to download those from the website of your VPN provider or have them sent
10.1
Getting, setting-up and testing a VPN account
to your email address. Together with your keys you will receive a
rootcertificate(*.ca)
and a
main
configurationfile(*.confor*.ovpn)
. In most cases only the following files will be needed to
configure and run an OpenVPN client:
•
client.conf
(or client.ovpn) - configuration file that includes all necessary param- eters and
settings. NOTE: in some cases certificates and keys can come embedded inside the main
configuration file. In such a case the below mentioned files are not necessary.
•
ca.crt
(unless in configuration file) - root authority certificate of your VPN server, used to
sign and check other keys issued by the provider.
•
client.crt
(unless in configuration file) - your client certificate, allows you to com- municate
with VPN server.
Based on a particular configuration, your VPN provider might require a username and password
to authenticate your connection. Often, for convenience, these can be saved into a separate file or
added to the main configuration file. In other cases, key-based authentication is used, and the key
is stored in a separate file:
•
client.key
(unless in configuration file) - client authentication key, used to authen- ticate
to the VPN server and establish an encrypted data channel.
In most cases, unless otherwise necessary, you don’t need to change anything in the configuration
file and (surely!)
do not edit key or certificate files!
All VPN providers have thorough
instructions regarding the setup. Read and follow those guidelines to make sure your VPN client is
configured correctly.
NOTE: Usually it’s only allowed to use one key per one connection, so you probably shouldn’t
be using the same keys on different devices at the same time. Get a new set of keys for each
device you plan to use with a VPN, or attempt to set up a local VPN gateway (advanced, not covered
here).
Download your OpenVPN configuration and key files copy them to a safe place and proceed to
the following chapter.

374
10.1.2
SettingupOpenVPNclient
In the following chapters some examples are given for setting up OpenVPN client soft- ware. On
any flavor of GNU/Linux use your favorite package manager and install
open-
vpn or openvpn-
client package.
If you want to use OpenVPN on Windows or OSX, have look at:
•
http://openvpn.se (Windows interface)
•
http://code.google.com/p/tunnelblick (OSX interface)
10.1.3
Caveats&Gotchas
Although a VPN will obfuscate your IP address, due to the nature of most VPNs your TCP/IP stack
meta-data and other identifying information will be sent across the wire as-is.
This may seem trivial, but consider, a standard IP header is 20 bytes in size, some of this is
covered by required obvious information, (4 bytes for source IP, 4 bytes for destination IP), etc but
some of this header may be other arbitrary options, the TCP header is at least 20 bytes also, with
the potential for another 20 bytes of options. The specific configuration of these options varies
between operating systems, and even versions of operating system, as such a single TCP SYN packet
is often enough to identify a users operating system, version and other potentially revealing
information, like the systems uptime. There are readily available tools which you can use to
fingerprint this information, as a test, try connecting to a server running this tool with your normal
internet connection, then connecting again over your VPN. You will most likely find that the
fingerprints are an identicle match both with and without the VPN, and that if your friend were to
connect their fingerprint would be different.
As such, it is important to remember some facts: * No one will go to jail for you, if your VPN
provider is served a legal request for information about you, they will provide it. Just because they
claim they don’t log, does not mean they do not have logs. * VPNs provide privacy, they do not
provide anonymity, regardless of the advertising and marketing materials provided.
10.2
VPN on Ubuntu
If you use Ubuntu as your operating system, you can connect to a VPN by using the built-in
NetworkManager
. This application is able to set up networks with OpenVPN. PPTP should not be
used for security reasons. Unfortunately at the time of writing a L2TP interface is not available in
Ubuntu. (It can be done manually, but it goes beyond the scope of this document).
The following example will explain how to connect with an OpenVPN-server. Under all situations
we assume you already have a VPN account as described earlier in this section.
10.2.1
PreparingNetworkManagerforVPNnetworks
For Ubuntu there is an excellent network utility: Network Manager. This is the same utility you use
to set up your Wireless (or wired) network and is normally in the upper right corner of your screen
(next to the clock). This tools is also capable of managing your VPNs, but before it can do so, it’s
necessary to install some extensions.
Installing OpenVPN extension for Network Manager
375
To install the plugins for Network Manager we will use the Ubuntu Software Center.
1.
Open the Ubuntu Software Center by typing software in the Unity search bar
Figure 10.1:VPN on Ubuntu
2.
The Ubuntu Software Center enables you to search, install and remove software on your
computer. Click on the search box at the top right of the window.
3.
In the search box, type in “network-manager-openvpn-gnome” (which is the ex- tension that
will enable OpenVPN). It’s necessary to type the full names because the packages are
classified as “technical” and don’t pop-up earlier. These packages include all the files you
need to establish a VPN connection successfully.
4.
Ubuntu may ask you for additional permissions to install the program. If that is the
case, type in your password and click Authenticate. Once the package is installed, you
can close the Software Center window.
5.
To check if the extensions are correctly installed, click on the NetworkManager (the icon at
the left of your system clock) and select VPN Connections > Configure VPN.
6.
Click Add under the VPN tab.
7.
If you see a pop-up asking for the type of VPN and the tunnel technology (Open- VPN) option
is available, this means that you have installed the VPN extension in Ubuntu correctly. If you
have your VPN login information ready, you can continue right away, else you first have to
get a VPN account from a VPN-provider. If this is the case, click cancel to close the
Network Manager.
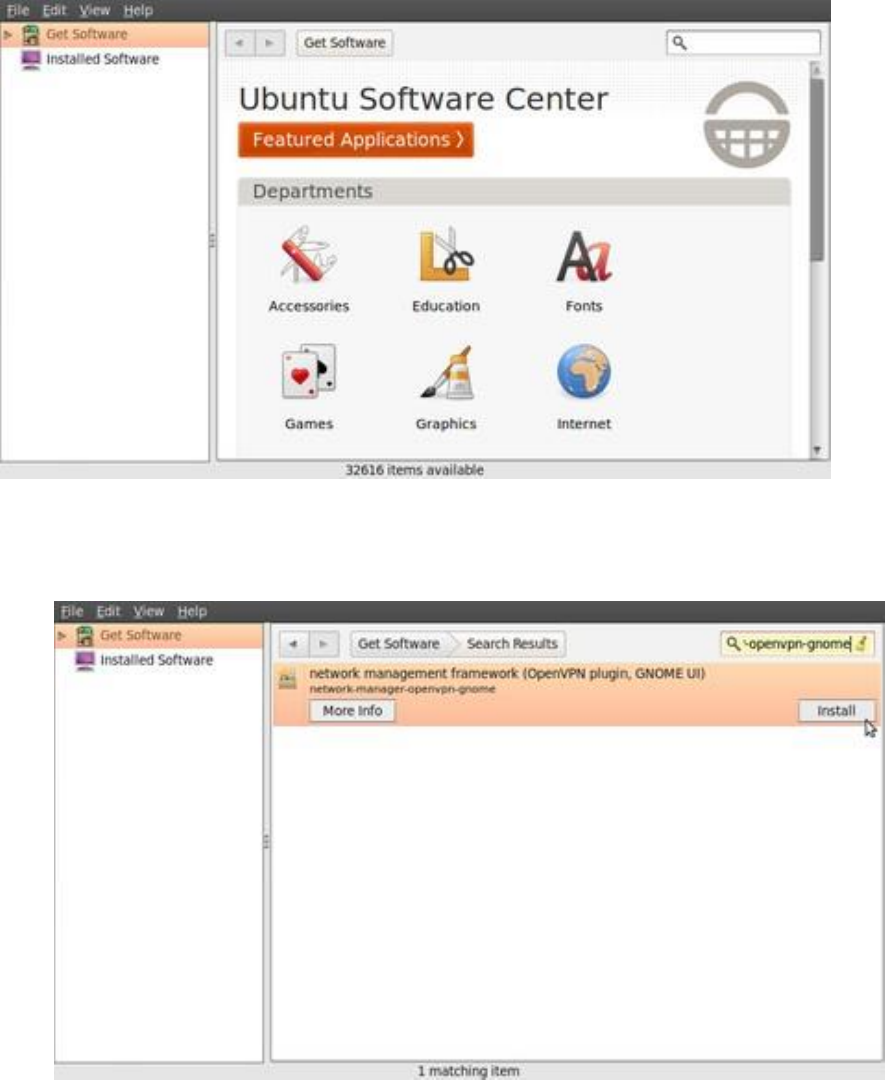
376
Figure 10.2:VPN on Ubuntu
Figure 10.3:VPN on Ubuntu
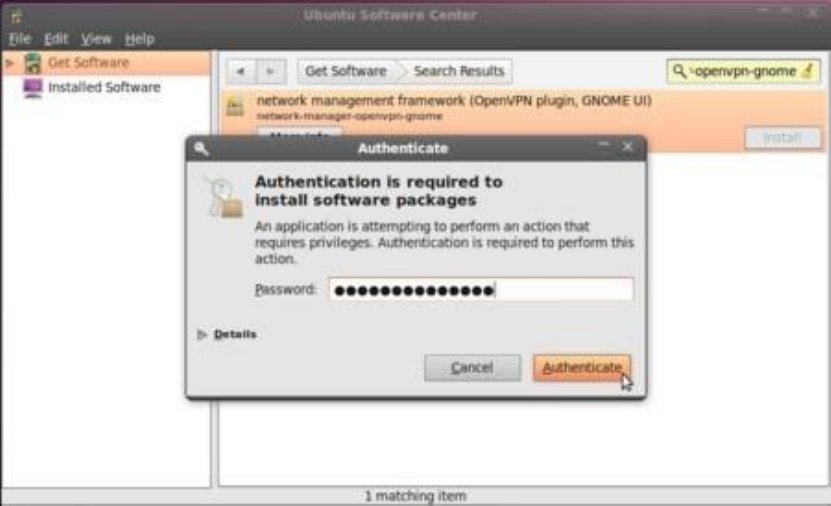
377
Figure 10.4:VPN on Ubuntu
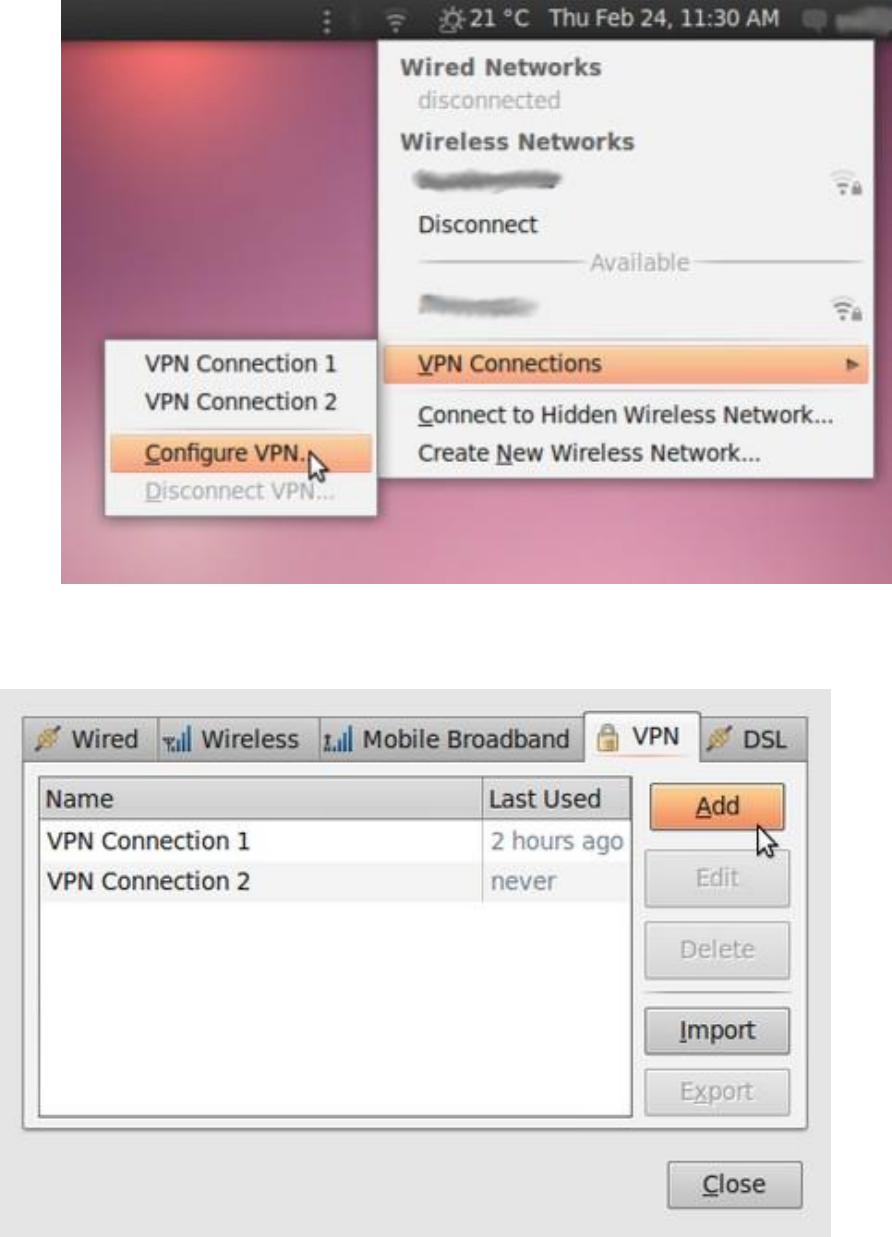
378
Figure 10.5:VPN on Ubuntu
Figure 10.6:VPN on Ubuntu
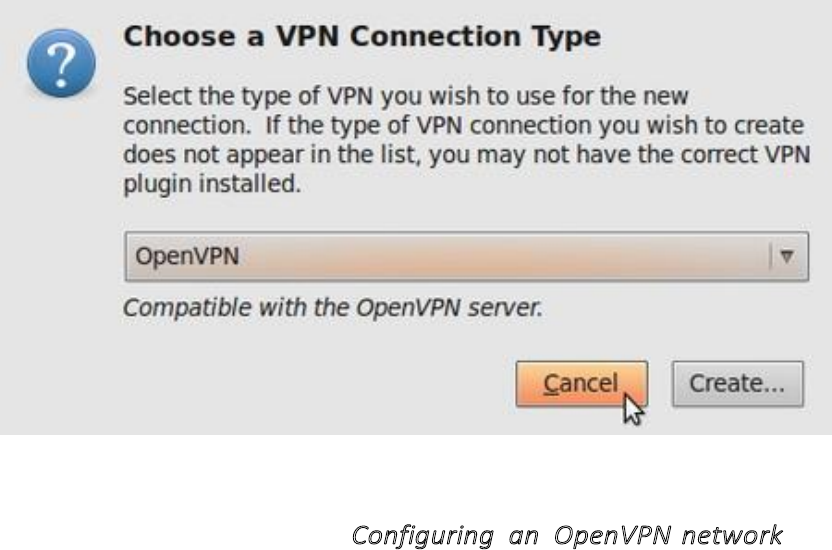
379
Figure 10.7:VPN on Ubuntu
10.2.2
ConfiguringanOpenVPNnetwork
Let us assume you have received your configuration files and credentials from your VPN provider.
This information should contain the following
•
an *.ovpn file, ex. air.ovpn
•
The file: ca.crt (this file is specific for every OpenVPN provider)
•
The file: user.crt (this file is your personal certificate, used for encryption of data)
•
The file: user.key (this file contains your private key. It should be protected in a good
manner. Losing this file will make your connection insecure)
In most cases your provider will send these files to you in a zip file. Some openvpn providers
use username and password authentication which will not be covered.
1.
Unzip the file you have downloaded to a folder on your hard drive (for example
“/home/[yourusername]/.vpn”). You should now have four files. The file “air.ovpn” is the
configuration file that you need to import into NetworkManager.
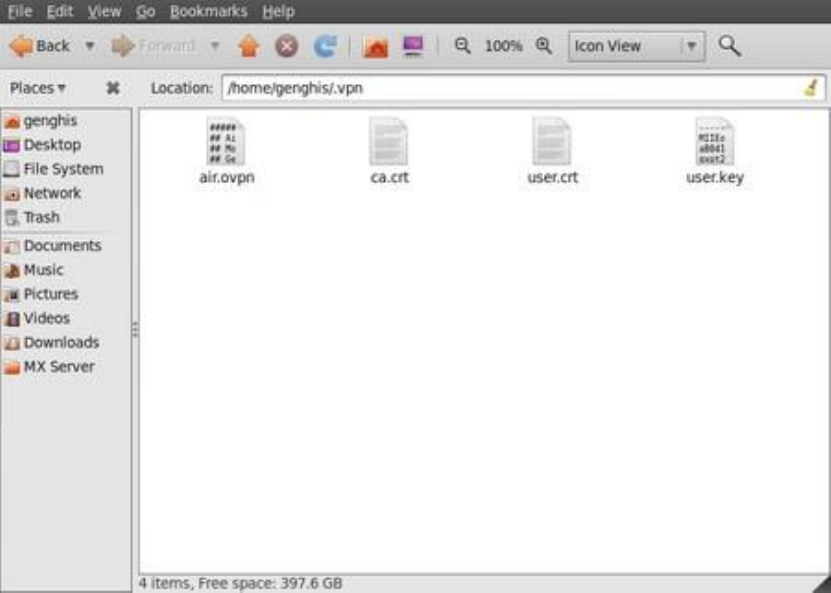
380
Figure 10.8:VPN on Ubuntu
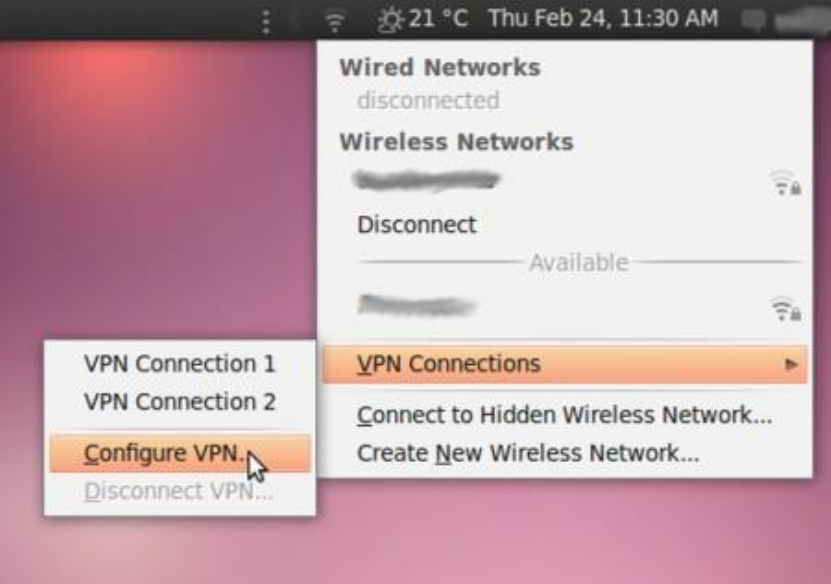
381
Figure 10.9:VPN on Ubuntu
2.
To import the configuration file, open NetworkManager and go to VPN Connections
> Configure VPN.
3.
Under the VPN tab, click Import.
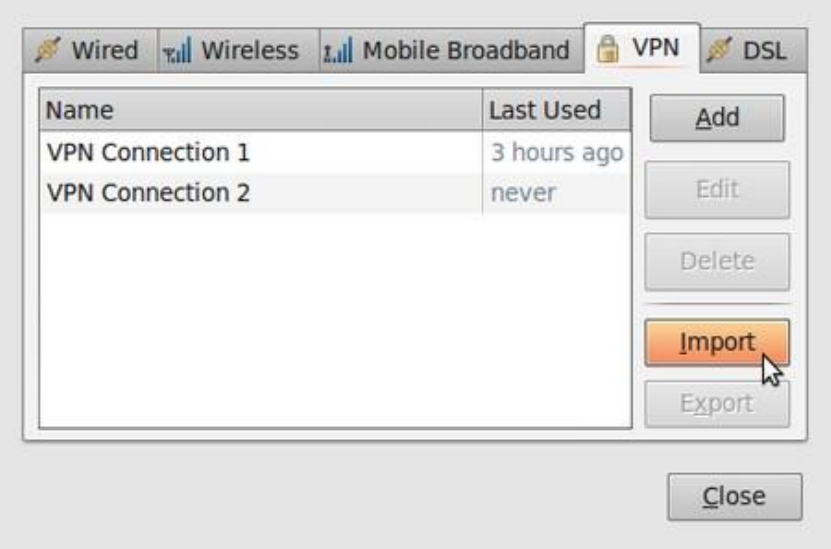
382
Figure 10.10:VPN on Ubuntu
4.
Locate the file air.ovpn that you have just unzipped. Click Open.
5.
A new window will open. Leave everything as it is and click Apply.
6.
Congratulations! Your VPN connection is ready to be used and should appear on the list of
connections under the VPN tab. You can now close NetworkManager.
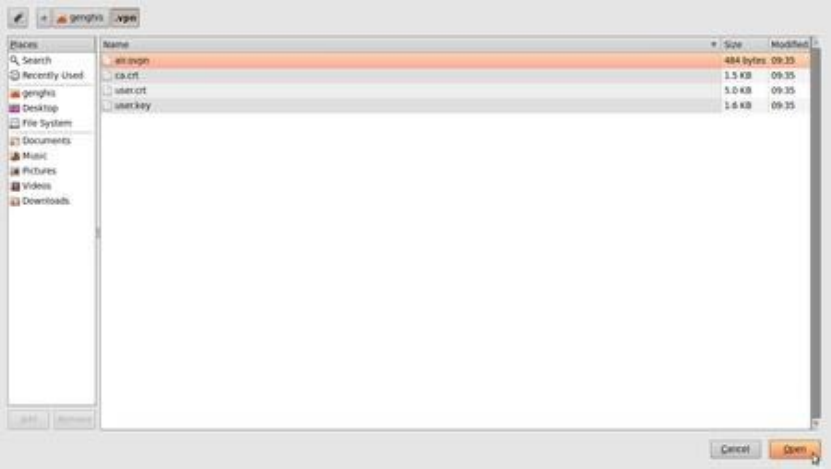
383
Figure 10.11:VPN on Ubuntu
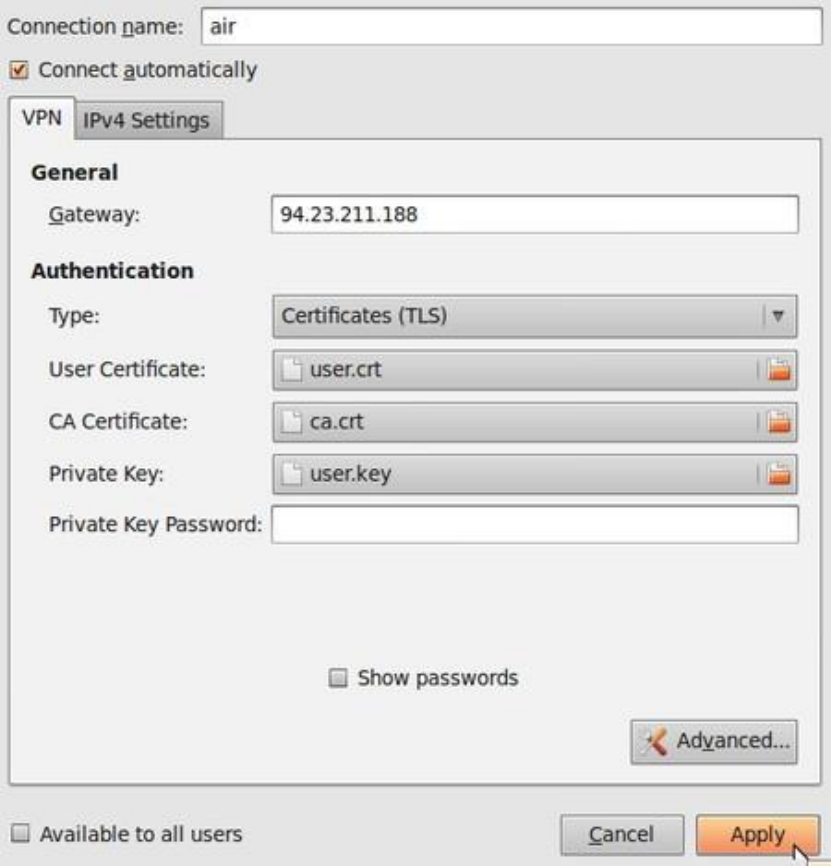
384
Figure 10.12:VPN on Ubuntu
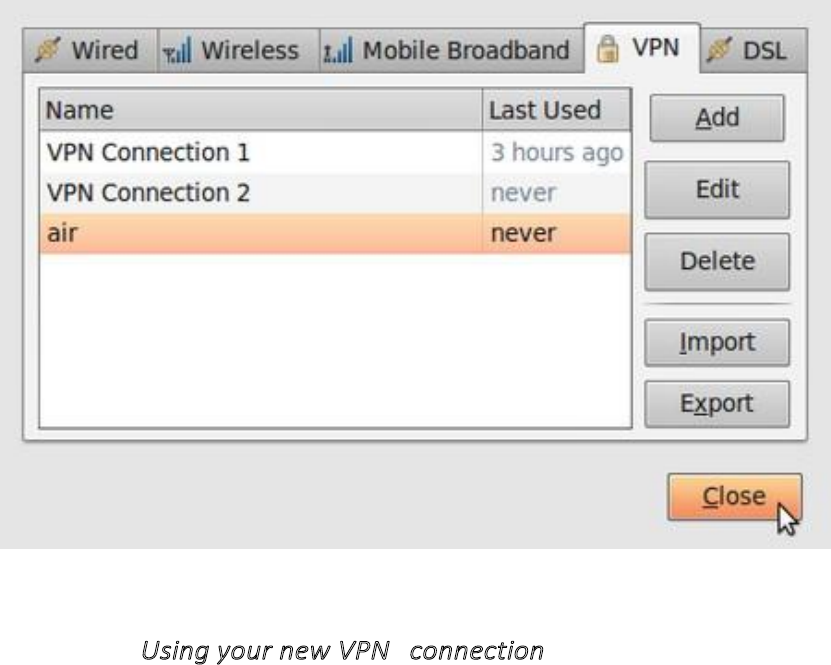
385
Figure 10.13:VPN on Ubuntu
10.2.3
UsingyournewVPN connection
Now that you configured NetworkManager to connect to a VPN service using the Open- VPN client,
you can use your new VPN connection to circumvent Internet censorship. To get started, follow
these steps:
1.
In the NetworkManager menu, select your new connection from VPN Connections.
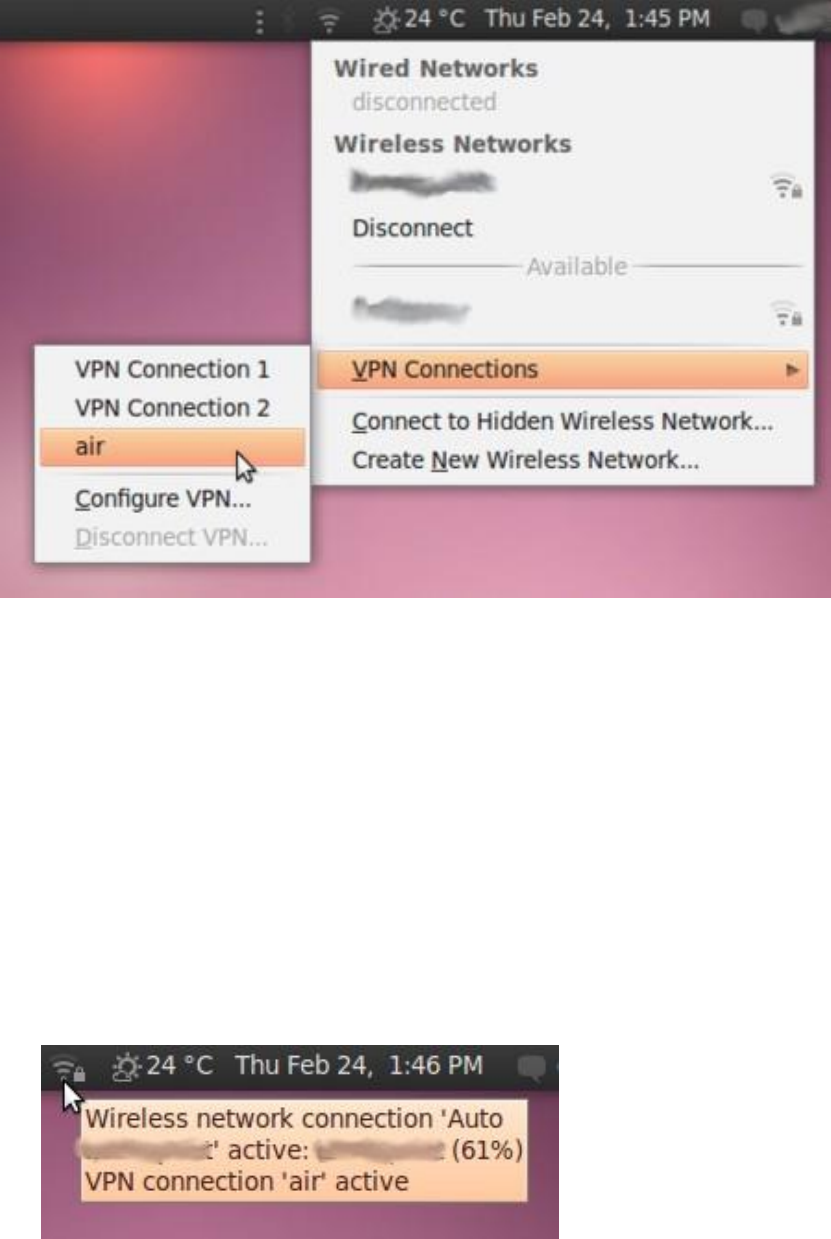
386
Figure 10.14:VPN on Ubuntu
2.
Wait for the VPN connection to be established. When connected, a small padlock should
appear right next to your NetworkManager icon, indicating that you are now using a secure
connection. Move your cursor over the icon to confirm that the VPN connection is active.
3.
Test your connection, using the method described in the “Make sure it works” section of this
chapter.
4.
To disconnect from your VPN, select VPN Connections > Disconnect VPN in the
NetworkManager menu. You are now using your normal connection again.
Figure 10.15:VPN on Ubuntu
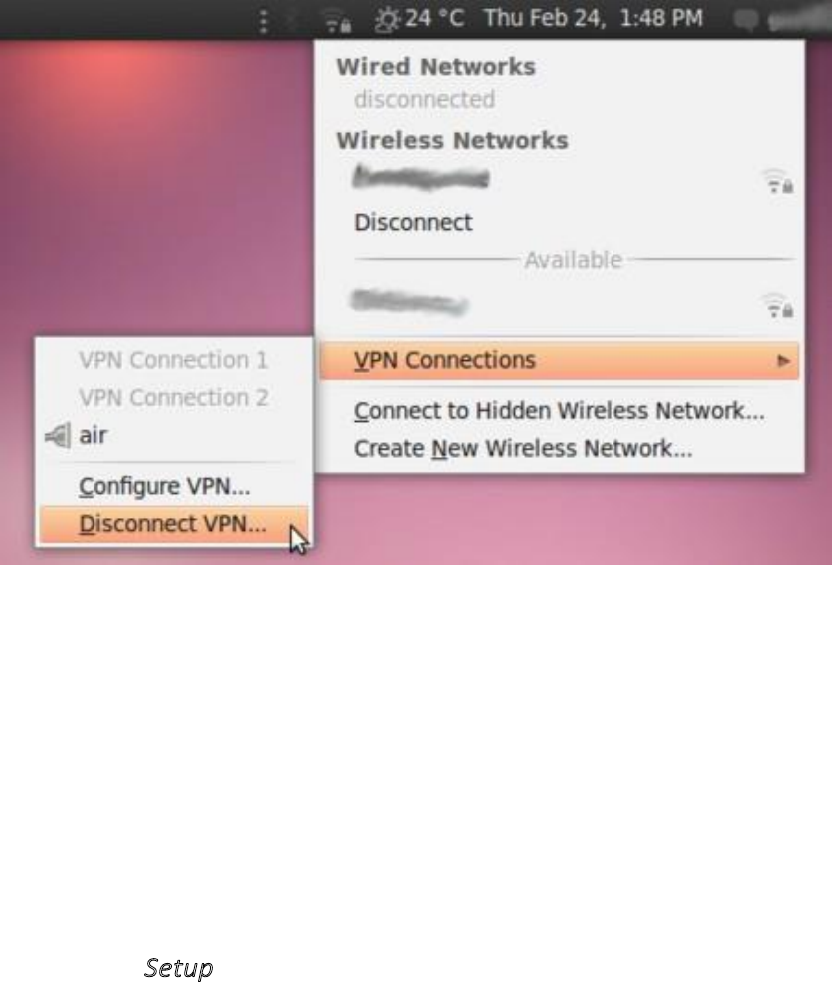
387
Figure 10.16:VPN on Ubuntu
10.3
VPN on MacOSX
Setting up a VPN on MacOSX is very easy once you have your account details ready, Let’s assume
have your credentials from your VPN provider for L2TP/IPSec connection ready. This information
should contain the following:
•
Username, ex.
bill2
•
Password, ex. verysecretpassword
•
VPN server, ex. tunnel.greenhost.nl
•
A Pre-Shared-Key or Machine-certificate
10.3.1
Setup
1.
Before getting started, please be sure you’ve read the paragraph “testing before and after
account set up”, this way you will be able to validate if your connection is actually working
after set up.
2.
A VPN is configured in the network settings, that are accessible via “System Pref- erences..”
in the Apple menu.
388
3.
Next, open the Network preferences.
4.
OSX uses this nifty system to lock windows. To add a VPN it is necessary to unlock the
screen: you can do this by clicking on the lock on the left bottom of the screen.
5.
Enter our user credentials
6.
Now we can add a new network. Do this by clicking on the “+” sign
7.
In the pop-up you need to specify the type of connection. In this case choose an VPN
interface with L2TP over IPSec. This is the most common system. Also don’t forget to give
the connection a nice name.
8.
Next comes the connection data. Please fill in the provided server name and user name (called
‘Account Name’). If this is done, click on the “Authentication Set- tings. . . ” button
389
Figure 10.17:VPN on Mac OS X
390
Figure 10.18:VPN on Mac OS X
391
Figure 10.19:VPN on Mac OS X
Figure 10.20:VPN on Mac OS X
392
9.
In the new pop-up you can specify connection specific information. This is the way the
user is authenticated and how the machine is authenticated. The user is very commonly
authenticated by using a password, although other methods are possible. Machine
authentication is often done by a Shared Secret (Pre-Shared-Key/PSK), but also quite
often by using a certificate. In this case we use the Shared Secret method. When this is
done click OK.
10.
Now you return back to the network screen. The next step is very important, so click on
“Advanced. . . ”
11.
In the new pop up you will see an option to route all traffic through the VPN connection.
We want to enable this, so all our traffic is encrypted.
12.
Well, all is done. Now hit the Connect button!
13.
A pop-up appears. You need to confirm your changes, just hit “Apply”
14.
After a few seconds, on the left side the connection should turn green. If so, you are
connected!
15.
Ok, now test your connection!
393
Figure 10.21:VPN on Mac OS X
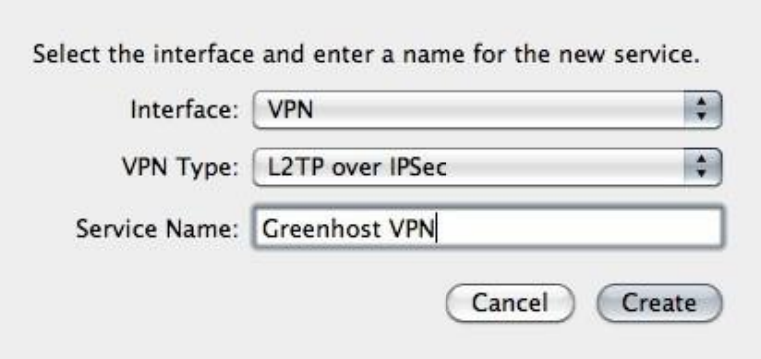
394
Figure 10.22:VPN on Mac OS X
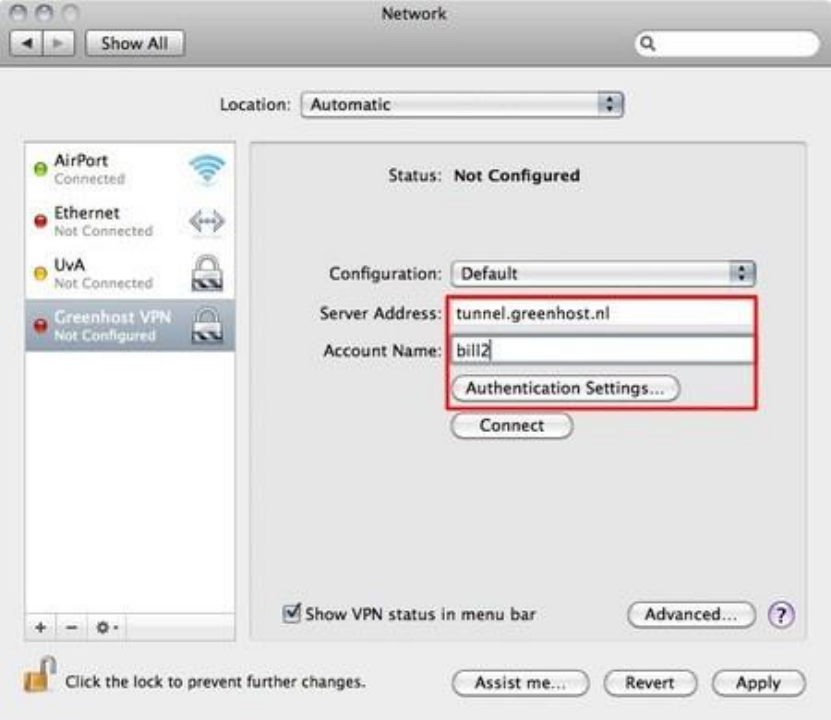
395
Figure 10.23:VPN on Mac OS X
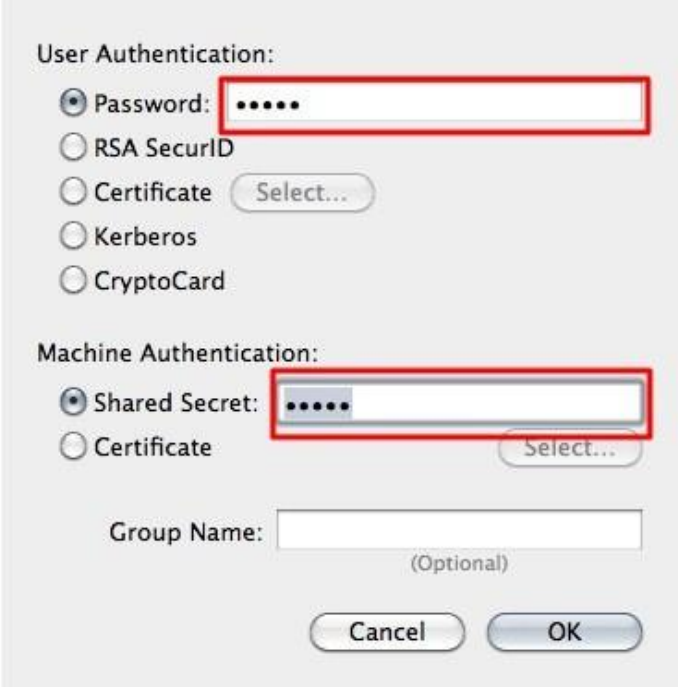
396
Figure 10.24:VPN on Mac OS X

397
Figure 10.25:VPN on Mac OS X
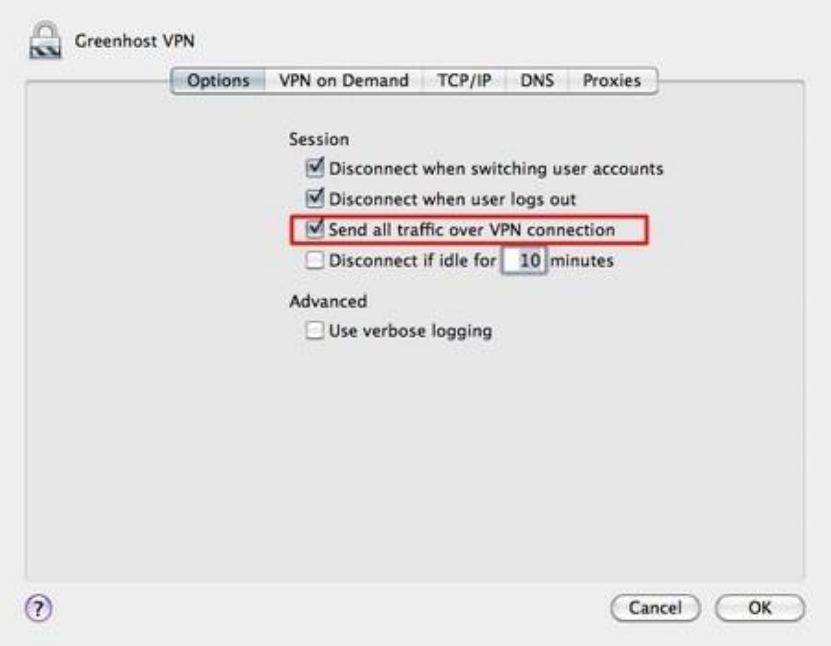
398
Figure 10.26:VPN on Mac OS X
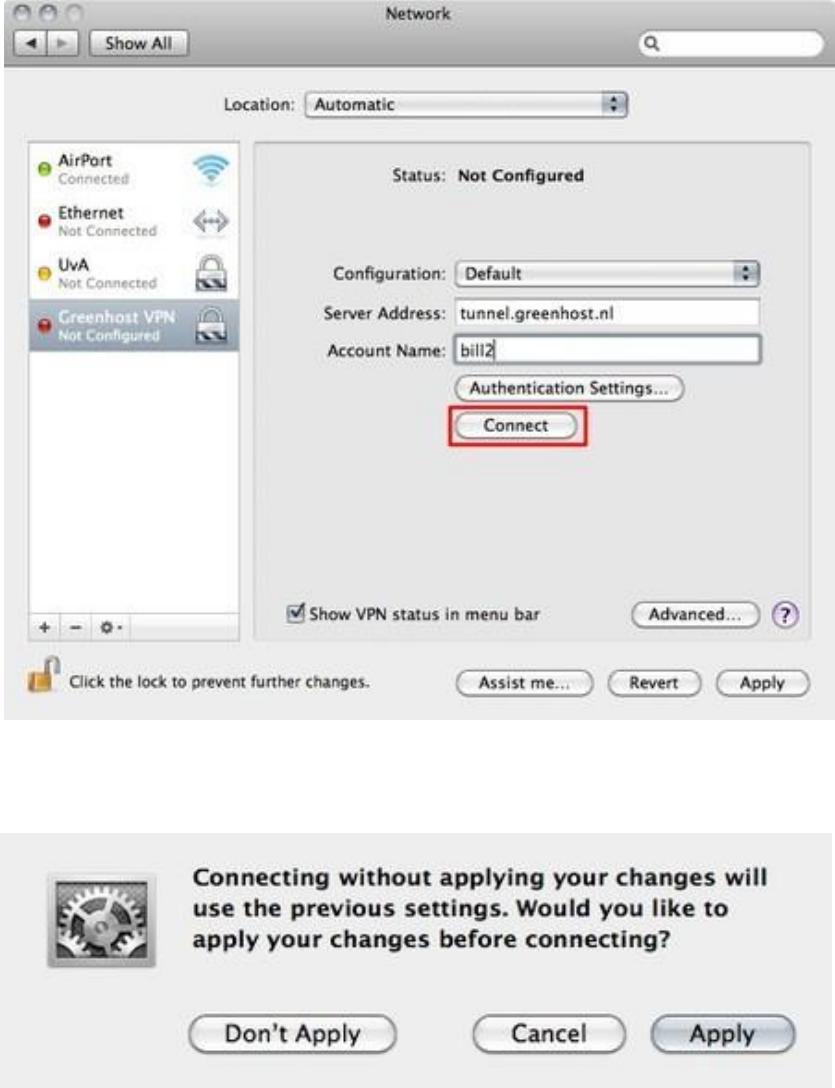
399
Figure 10.27:VPN on Mac OS X
Figure 10.28:VPN on Mac OS X
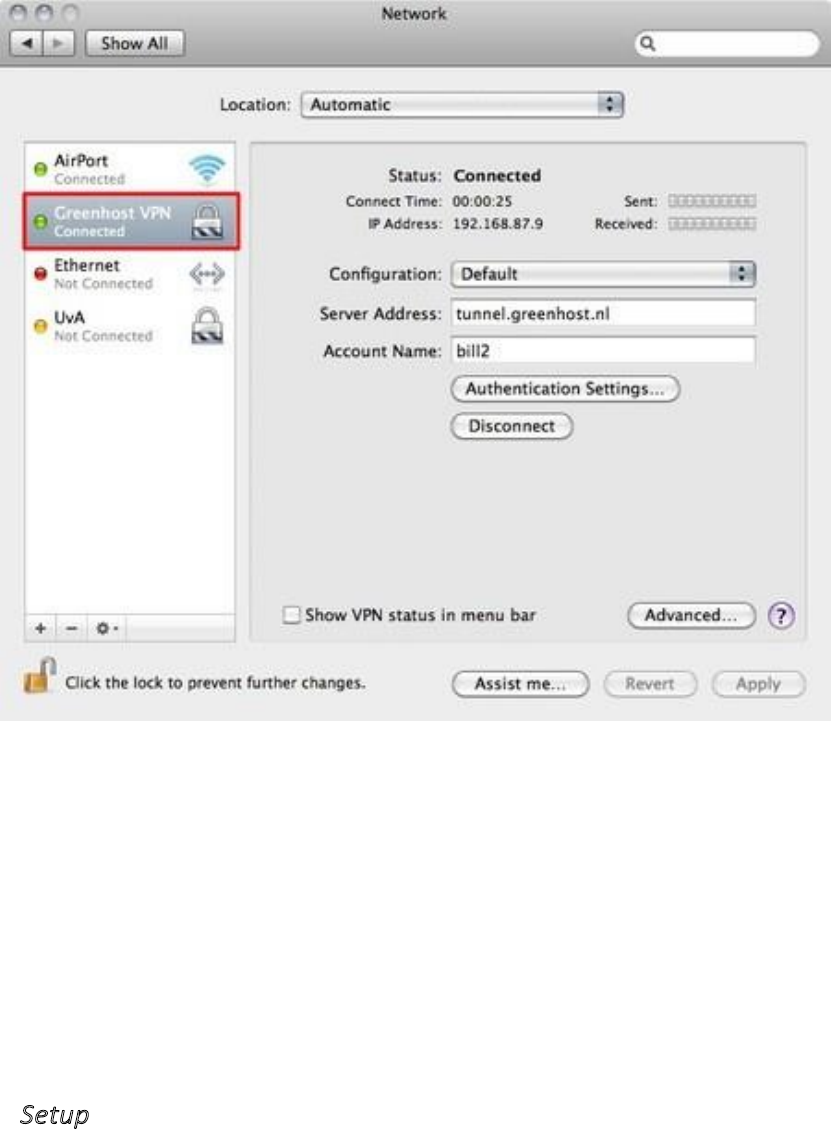
400
Figure 10.29:VPN on Mac OS X
10.4
VPN on Windows
Setting up a VPN on Windows is very easy once you have your account details ready. Let’s assume
have your credentials from your VPN provider for L2TP/IPSec connection ready. This information
should contain the following:
•
Username, ex.
bill2
•
Password, ex. verysecretpassword
•
VPN server, ex. tunnel.greenhost.nl
•
A Pre-Shared-Key or Machine-certificate
10.4.1
Setup
1.
Before getting started, please be sure you’ve read the paragraph “testing before and after
account set up”, this way you will be able to validate if your connection is actually working
after set up.
2.
We need to go to the “Network and Sharing Center” of Windows to create a new VPN
connection. We can access this center easily by clicking on the network icon next to the
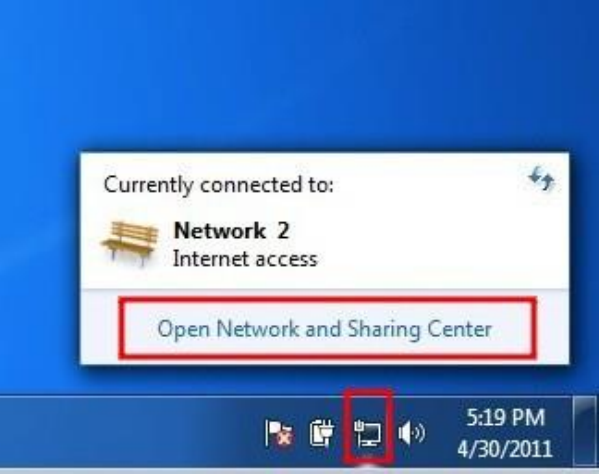
401
systemclock en click on “open Network and Sharing Center”
Figure 10.30:VPN on Windows
3.
The “Network and Sharing Center” will popup. You will see some information about your
current network. Click on “Connect to a network” to add a VPN connection.
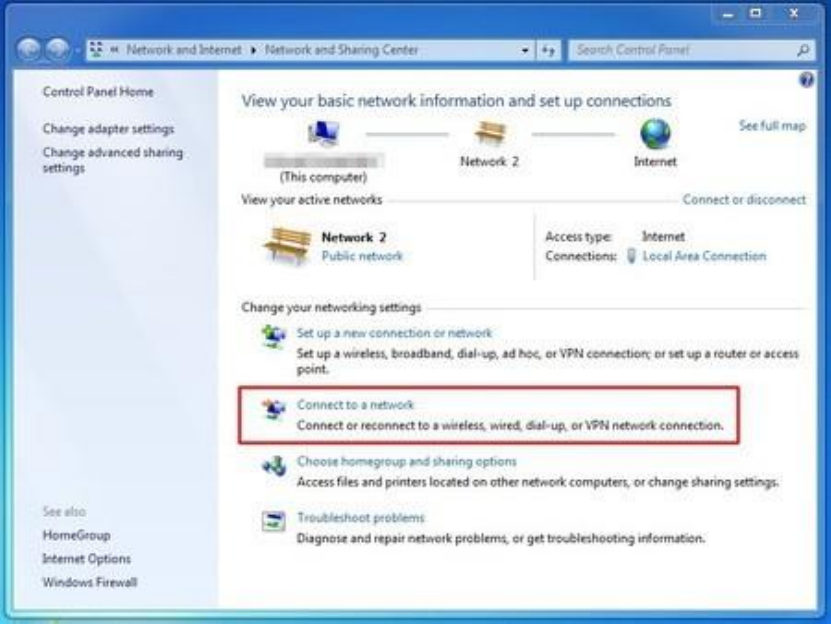
402
Figure 10.31:VPN on Windows
4.
The wizard to setup a connection will popup. Choose the option to “connect to a
workplace”, which is Microsoft’s way of naming a VPN connection.
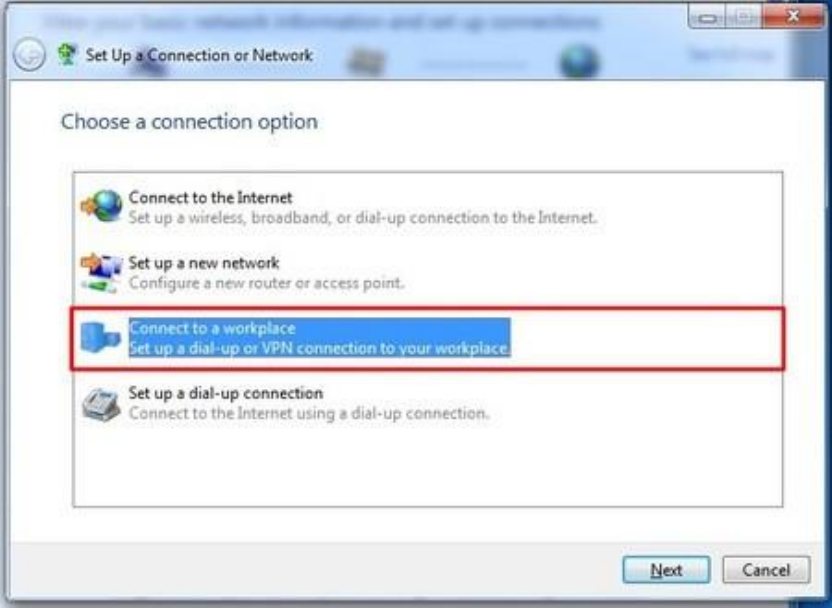
403
Figure 10.32:VPN on Windows
5.
The next screen asks us if we want to use our Internet connection or an old-school phone
line to connect to the VPN. Just choose the first option then.
6.
The next screen asks for the connection details. Enter here the server of your VPN-
provider (called “Internet address” in this dialog). On the bottom please check the box
“Don’t connect now; just set it up”. Using this option the connection will be
automatically saved and it’s easier to control extra settings. If this is all done, hit the
“next” button
7.
Next up are your username and password. Just give them like you received them from your
VPN-provider. If the connection fails, Windows forgets them. So keep them with you, you
maybe need them later. If this is done. Click “create”.
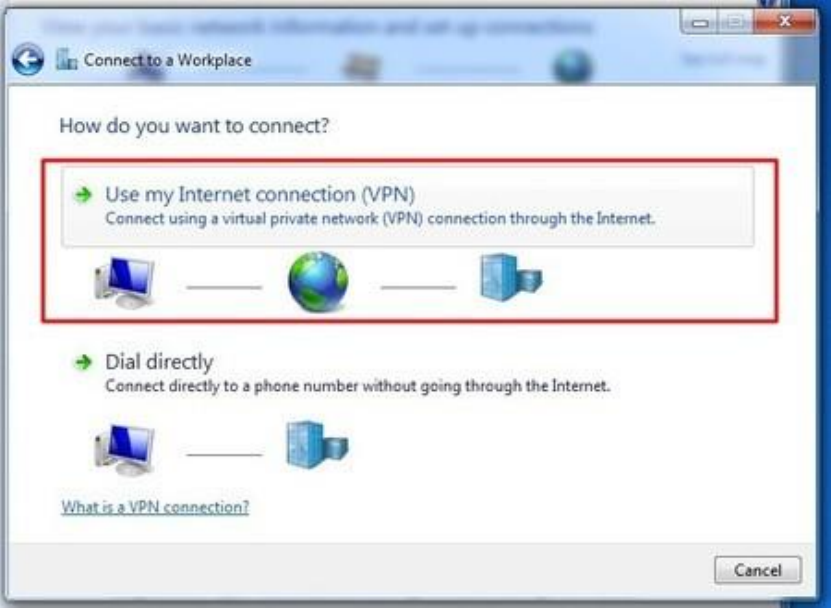
404
Figure 10.33:VPN on Windows
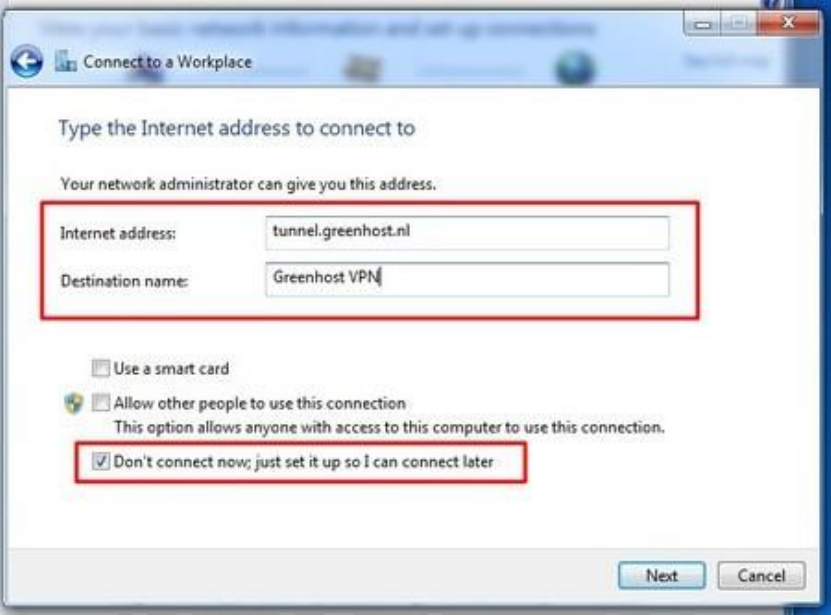
405
Figure 10.34:VPN on Windows
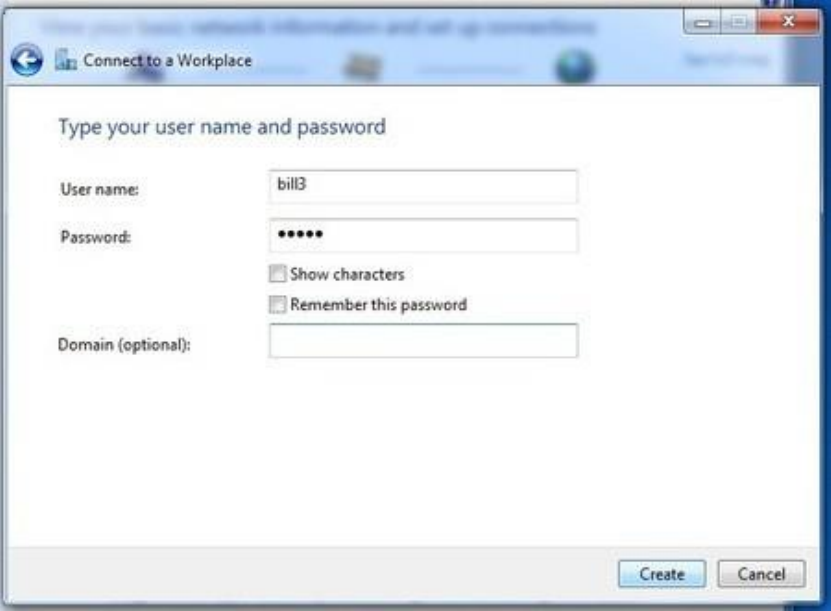
406
Figure 10.35:VPN on Windows
8.
Your connection is now available, if you click the the network icon again, you will see a new
option in the network menu, the name of your VPN connection, just click it to connect.
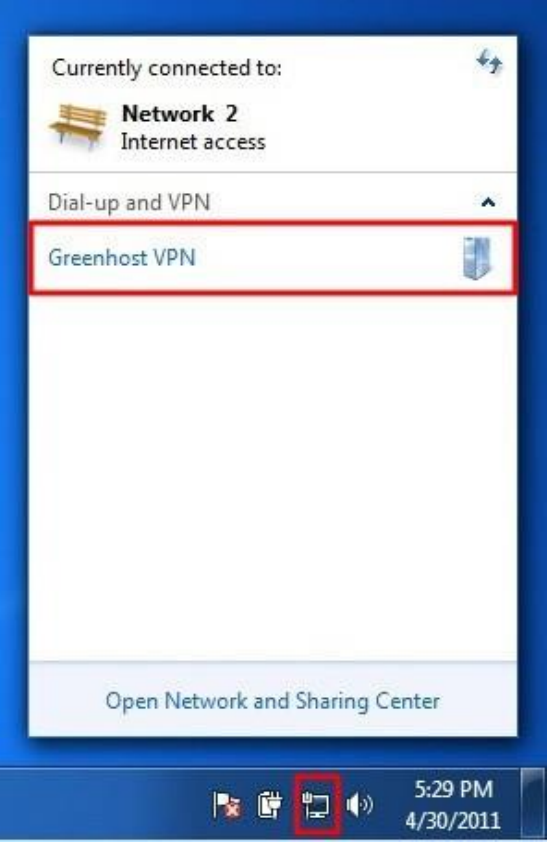
407
Figure 10.36:VPN on Windows
9.And click “connect”
10.A VPN connection dialog appears. This give us the opportunity to review our settings and to
connect. You can try to connect, Windows will try to discover all
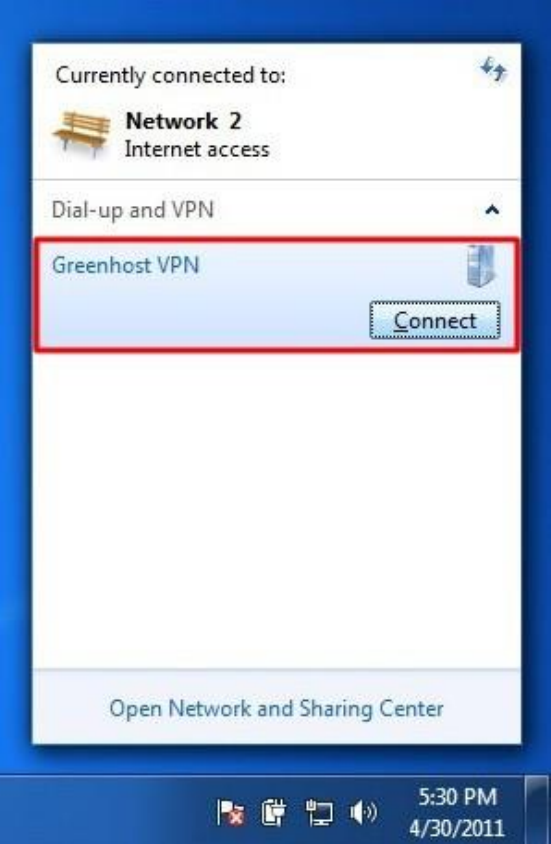
408
Figure 10.37:VPN on Windows
other settings automatically. Unfortunately, this does not always work, so if this is not
working for you, hit the “properties” button.
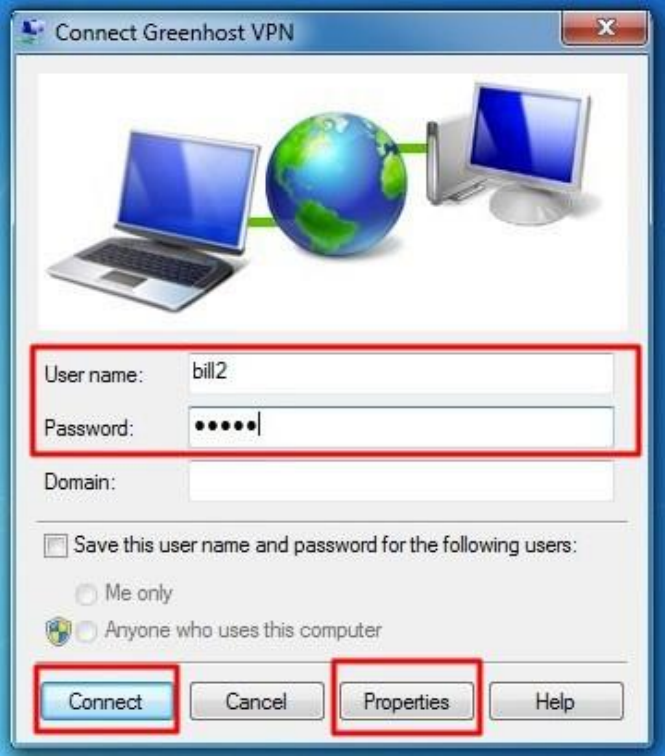
409
Figure 10.38:VPN on Windows
11.
The properties windows appear. The most important page is the “Security” page, click on the
Security tab to open it.
12.
In the security tab you can specify VPN type, normally L2TP/IPSec. Do not use PPTP as it has
several security vulnerabilities. For L2TP/IPSec also have a look at the Advanced
settings.
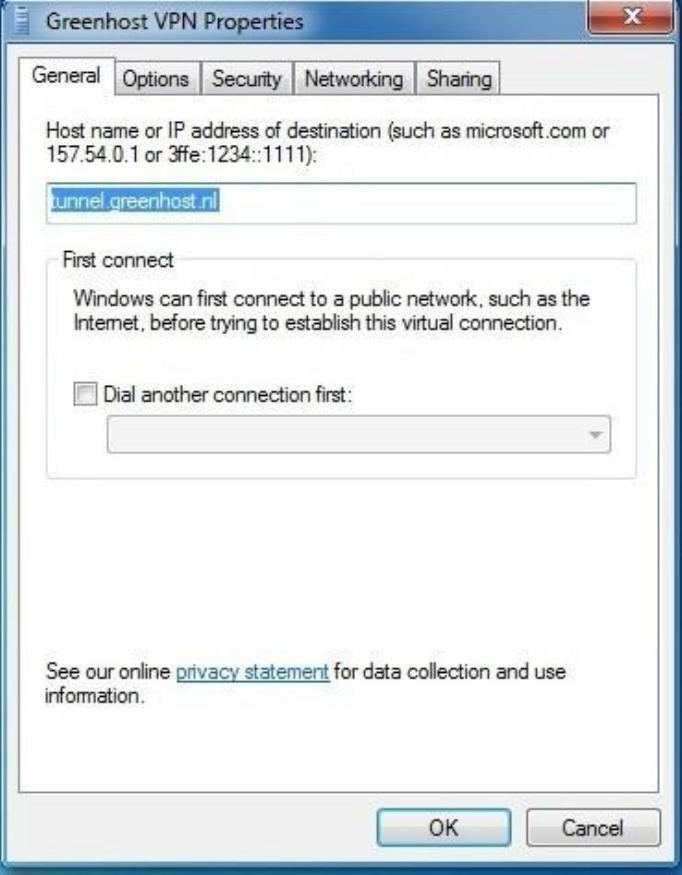
410
Figure 10.39:VPN on Windows
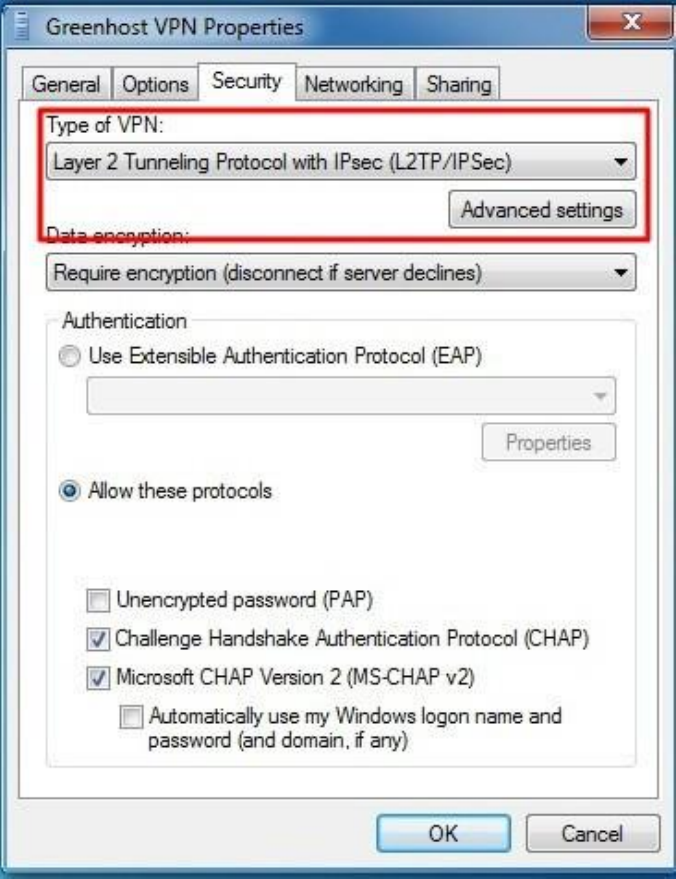
411
Figure 10.40:VPN on Windows
13.
In the Advanced Settings window, you can specify if you are using a pre-shared key or a
certificate. This depends on your VPN-provider. If you have received a pre-shared-key, Select this
option and fill in this key. Hit ok afterwards. You will return to the previous window, click ok there
also
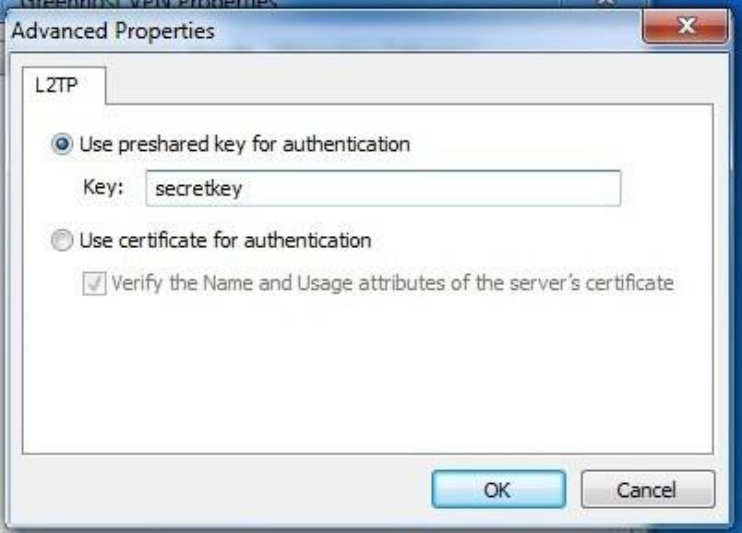
412
Figure 10.41:VPN on Windows
14.
Back in to connection window try to connect now. Please be sure your username and password are
filled out.
15.
A connection popup will appear
16.
Online! Don’t forget to check if your VPN is working properly.

413
Figure 10.42:VPN on Windows
Figure 10.43:VPN on Windows
10.5 Making Sure Your VPN Works
Once you’re done setting up your VPN, one of the first things you should do is test whether
your data is actually being transferred through your VPN network. The simplest way to test this
is to check your public IP address, which is the IP address you’re exposing to the internet.
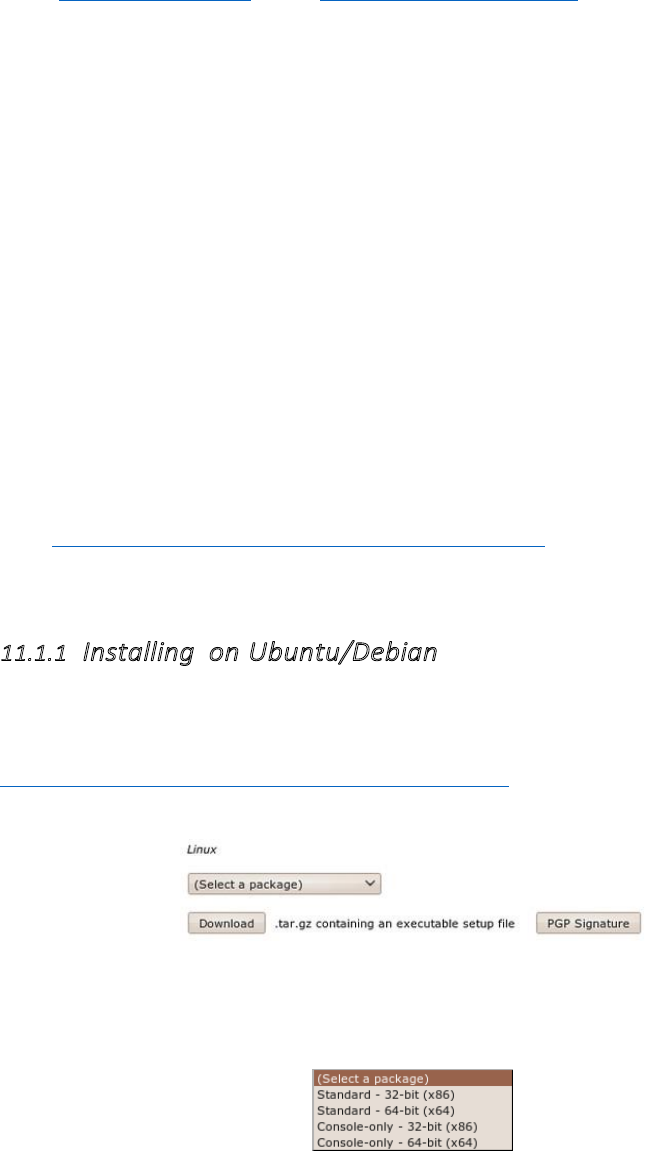
414
There are numerous websites that will tell you what your IP address is, and where that IP
address is located (also known as its geolocation). Many search engines will report your IP
address if you search for “My IP,” but you can also use dedicated services like
http://www.myip.se and http://www.ipchicken.com.
Check your IP address before connecting to your VPN. Once you connect to your VPN, your
computer’s public IP address should change to match that of your VPN server, and your geolocation
should change to wherever your VPN server is located.
Once your external IP is the same as the IP of your VPN server, you can rest assured your
communication is encrypted.
11
Disk Encryption
*** TrueCrypt Compromised***
Do not use TrueCrypt. It is no longer safe, has been compromised, and is no longer being
updated. Please replace all instances of TrueCrypt with VeraCrypt. The instructions will
work similarly and I have replaced all links to TrueCrypt with VeraCrypt.
11.1
Installing VeraCrypt
VeraCrypt can be installed on Windows, Linux, or Mac OSX. The installation files are available
here: https://veracrypt.codeplex.com/releases/view/616110
The following three sections give complete details on how to install TrueCrypt for each of these
Operating Systems, starting with Ubuntu and Debian.
11.1.1
InstallingonUbuntu/Debian
TrueCrypt is not available in the standard Ubuntu repositories. This means you cannot use the
Ubuntu Software Center or
aptget
(a command line method for installing software on Ubuntu)
to install it. Instead you must first visit the TrueCrypt downloads page
(
https://veracrypt.codeplex.com/releases/view/616110
).
You will see a drop-down menu under the heading Linux.
Figure 11.1:Dropdown menu on the download page
From the ‘(Select a package)’ drop down menu you can choose from four options:
Figure 11.2:Choosing the correct package to download

415
This is a little technical - the console version is the one you choose if you are either very technical
and don’t like Graphical User Interfaces or you wish to run this on a machine that you have only a
terminal (command line or ‘shell’) access to (like a remote server for example).
Assuming you are running this in your laptop its best to choose the easy ‘standard’ option - this
will give you a nice user interface to use. From these two options you need to choose the one most
suitable for the
architecture
of your machine. Don’t know what this means? Well, it basically
comes down to the type of hardware (processor) running
on your computer, the options are 32-bit or 64-bit. Unfortunately Ubuntu does not make it easy for
you to find this information if you don’t already know it. You need to open a ‘terminal’ from the
Applications->Accessories menu and type the following, followed by the [enter] key
uname -a
The output will be something like Linux bigsy 2.6.32-30-generic #59-Ubuntu
SMP
Tue Mar
1 21:30:46
UTC
2011 x86_64 GNU/Linux. In this instance you can see the architecture is 64-
bit (x86_64). In this example I would choose the ‘Standard - 64-bit (x64)’ option. If you see
i686 somewhere in the output of the uname command then you would choose the other standard
option to download.
Once selected press the ‘download’ button and save the file to somewhere on your computer.
So the installation process is still not over. The file you downloaded is a compressed file (to make
downloading it faster) and you need to first de-compress the file before you install it. Fortunately
Ubuntu makes this easy - simply browse to the file on your computer and right click on it and choose
‘Extract Here’.
Figure 11.3:Right click and ‘extract here’
You will see a new file appear next to the compressed file: Nearly done!
Now right click on the new file and choose ‘open’: If all is well you will
see a window open like this:
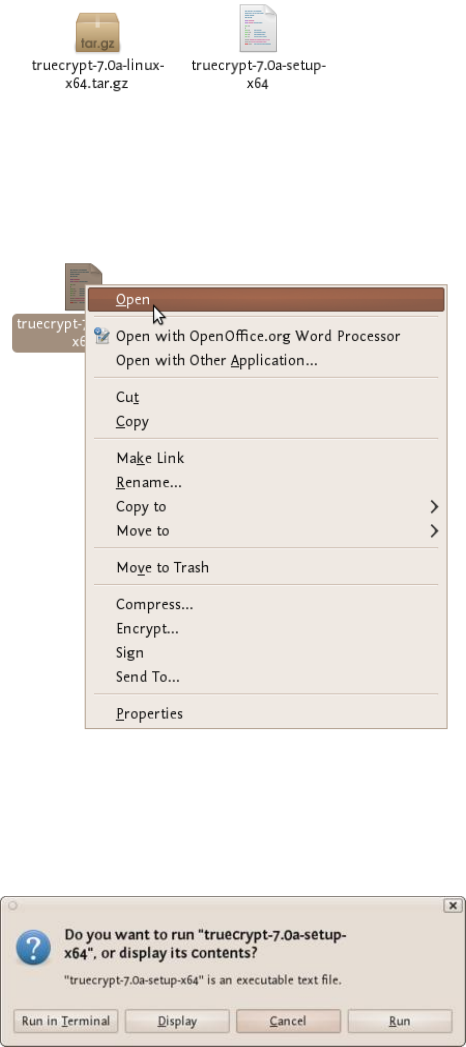
416
Choose ‘run’ and you see the following:
Figure 11.4:The extracted file
Figure 11.5:Right click and ‘open’
Figure 11.6:Window opens to confirm you want to ‘run’ the file
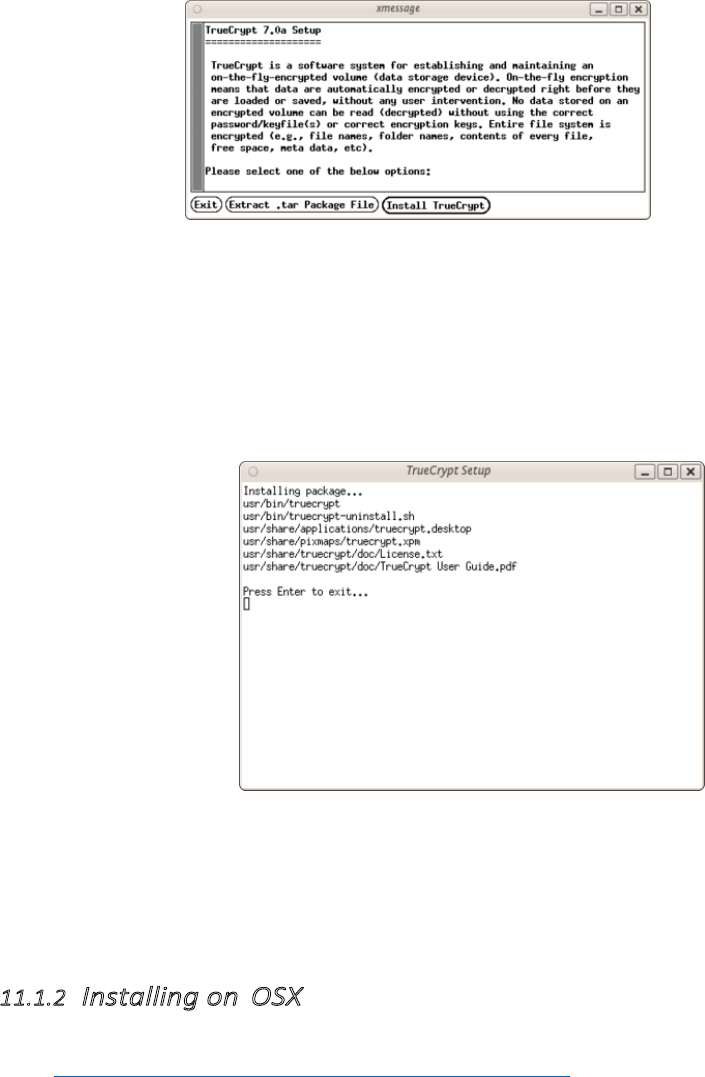
417
Figure 11.7:Truecrypt installer starts. . .
Now we are getting somewhere. . . press ‘Install TrueCrypt’. You will be displayed a user
agreement. At the bottom press ‘I accept and agree to be bound by the license terms’ (sounds
serious). You will then be shown another info screen telling you how to uninstall TrueCrypt.
Press ‘OK’ then you will be asked for your password to install software on your computer.
Enter your password and then you will finally see a screen
like this:
Figure 11.8:Truecrypt install finished. . . ‘press Enter to exit’
Believe it or now your are done. . . VeraCrypt is installed and you can access it from the
Applications->accessories menu. . . close the setup window. Now proceed to the chapter on Using
TrueCrypt.
11.1.2
InstallingonOSX
1.
To install TrueCrypt on OSX first visit the download page (
https://veracrypt.codeplex.com/releases/view/616110) and press the download button
under the OSX section.
2.
Download this to your computer find the .dmg file and open it to access the instal-
lation package.
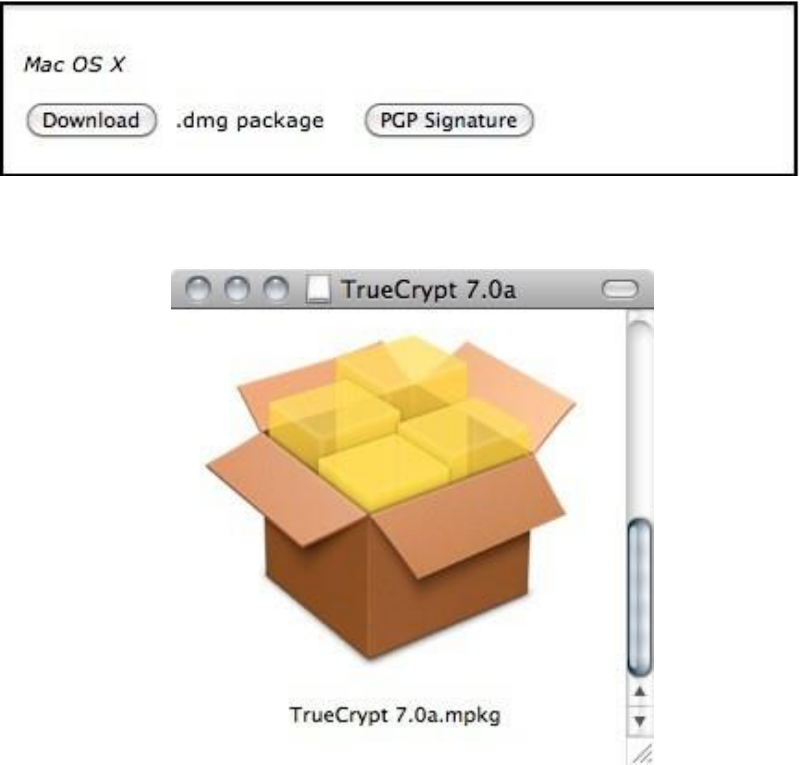
418
Figure 11.9:Download button
Figure 11.10:Open the .dmg file
3.
Open the installation package, and click through the dialogues.
4.
Choose the standard installation. You can choose to do a customized installation
and deselect FUSE, but why would you? You need it!
5.
After the installation finishes you can find the program in your ‘Applications’ folder.
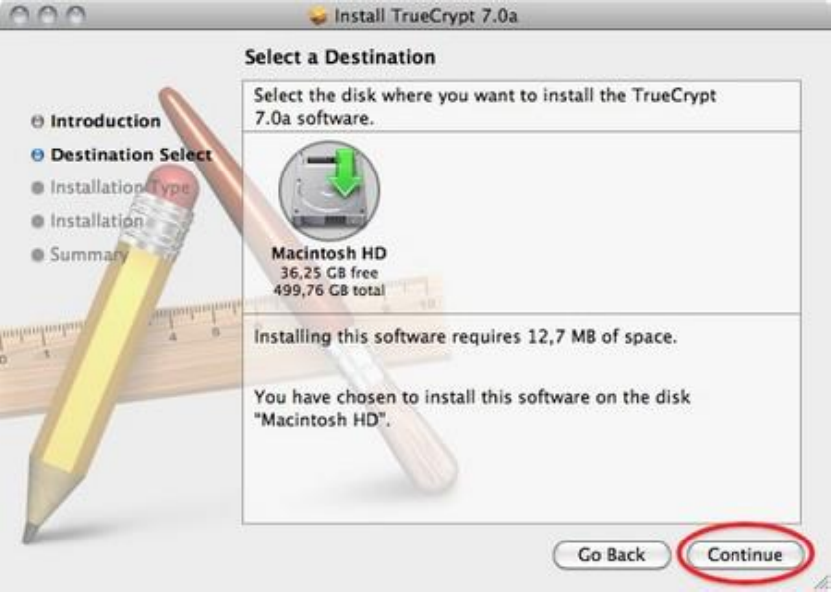
419
Figure 11.11:Click through the dialogues
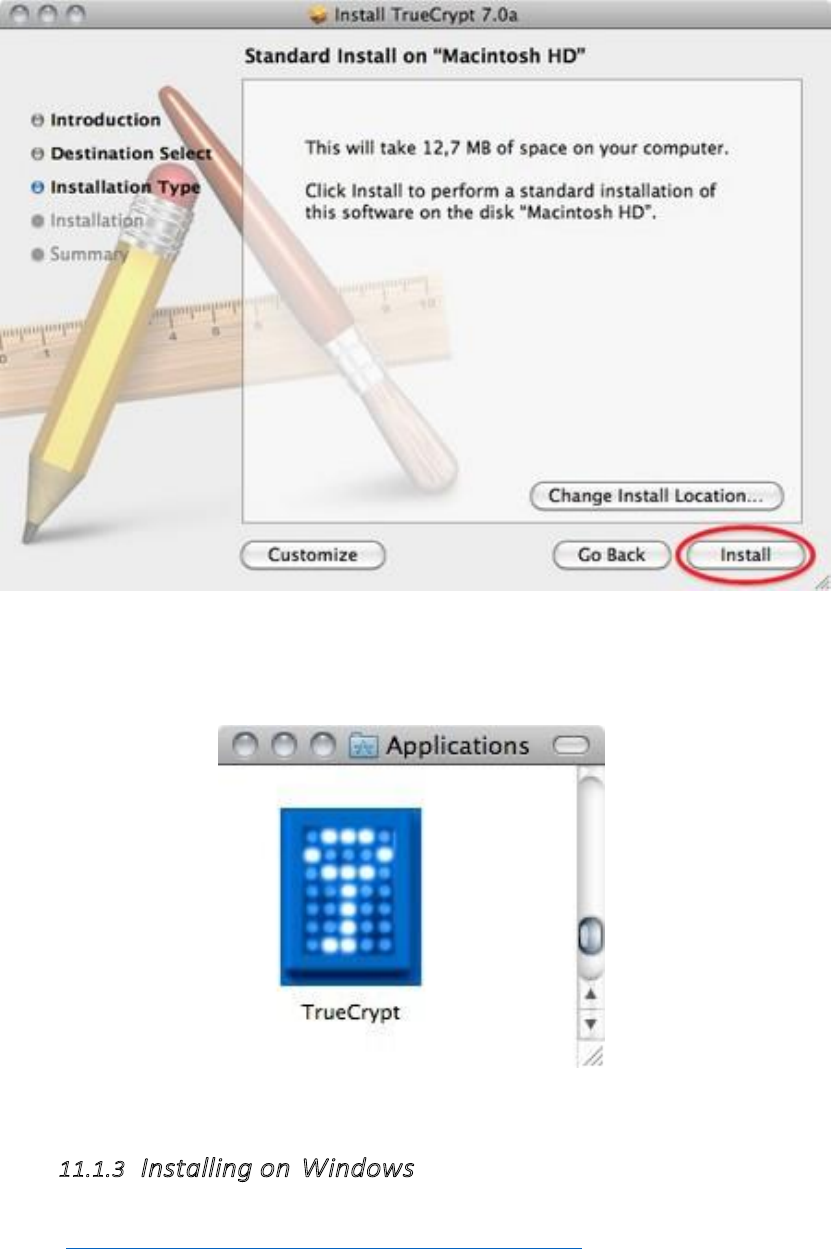
420
Figure 11.12:Choose standard installation
Figure 11.13:Truecrypt launcher now in Applications
11.1.3
InstallingonWindows
To install TrueCrypt on Windows first visit the download page
(https://veracrypt.codeplex.com/releases/view/616110) and press the download button under
the Windows section.
Download this to your computer and then double click on the file. You will see a license
agreement.
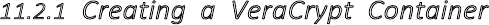
421
Click on ‘I accept and agree to be bound by the license terms’ and then click ‘Accept’.
Leave the above screen with the defaults and press ‘Next >’ and you will be taken to the Setup
Options window:
You can leave this with the defaults. If you want to set up TrueCrypt just for yourself then consider
not selecting the ‘Install for all users’. However if you are installing this on your own machine and
no one else uses the computer then this is not necessary. You may also wish to consider installing
TrueCrypt in a folder other than the default. In which case click ‘Browse’ and choose another
location. When you are done click ‘Install’ and the process will proceed:
When the installation is complete you will get a verification popup that it was suc- cessful. Close
this window and click ‘Finish’ and all is done. Now proceed to the chapter on Using TrueCrypt.
11.2
Using V e r a Crypt
The following are step-by-step instructions on how to create, mount, and use a TrueCrypt volume.
11.2.1
CreatingaVeraCryptContainer
1.
Install VeraCrypt. Then launch VeraCrypt by
•
double-clicking the file VeraCrypt.exe in Windows
•
opening Applications->Accessories->VeraCrypt in Ubuntu
•
on MacOSX open it by clicking Go > Applications. Find VeraCrypt in the Applications
folder and double click on it.
2.
When the main VeraCrypt window appears. Click Create Volume.
3.
You should see the VeraCrypt Volume Creation Wizard window appear on screen.
Where do you want to create the VeraCrypt volume? You need to choose now. This can be
in a file, which is also called a container, in a partition or drive. The following steps will take
you through the first option creating a VeraCrypt volume within a file.
You can just click Next, as the option is selected by default,
4.
Next you need to choose whether to create a standard or hidden VeraCrypt volume. We
will walk you through the former option and create a standard VeraCrypt volume.
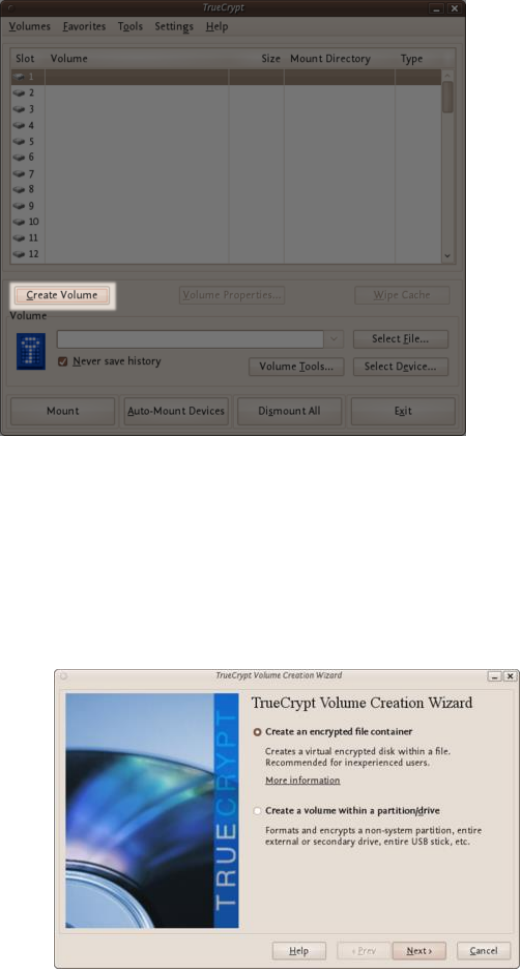
422
Figure 11.14:Using T r u e Crypt
Figure 11.15:Using T r u e Crypt
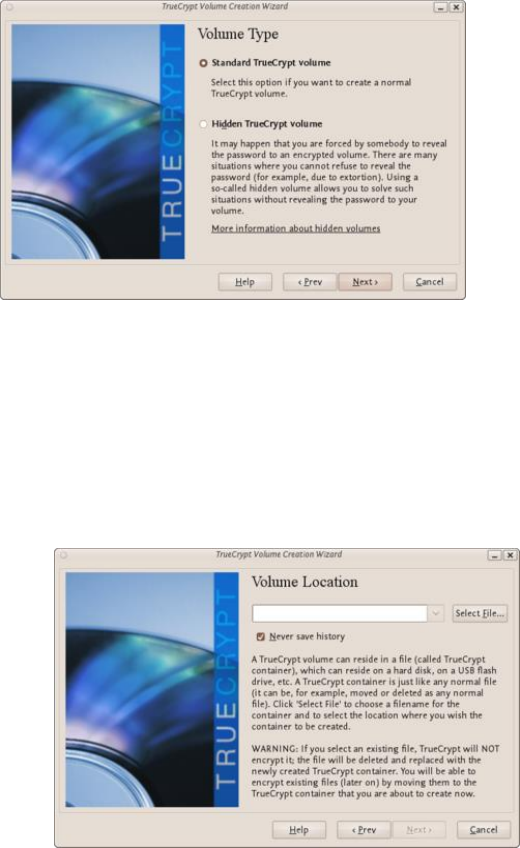
423
Figure 11.16:Using T r u e Crypt
You can just click Next, as the option is selected by default.
5.
Now you have to specify where to have the VeraCrypt volume (file container) created.
Note that a VeraCrypt container behaves like any normal file. It can be moved or deleted
as any normal file.
Figure 11.17:Using TrueCrypt
Click Select File.
The standard file selector will now appear on screen (the VeraCrypt Volume Creation Wizard
remains open in the background). You need to browse to the folder that the file should be created in
and then type into the ‘name’ field the name for the file you wish to create.
We will create our VeraCrypt volume in the folder ‘adam/true’ and the filename of the volume
(container) will be ‘myencryptedfile’. You may, of course, choose any other filename and location
you like (for example, on a USB stick). Note that the file ‘myen- cryptedfile’ does not exist yet -
VeraCrypt will create it. Press ‘Save’ when you are ready. The file selector window should close.
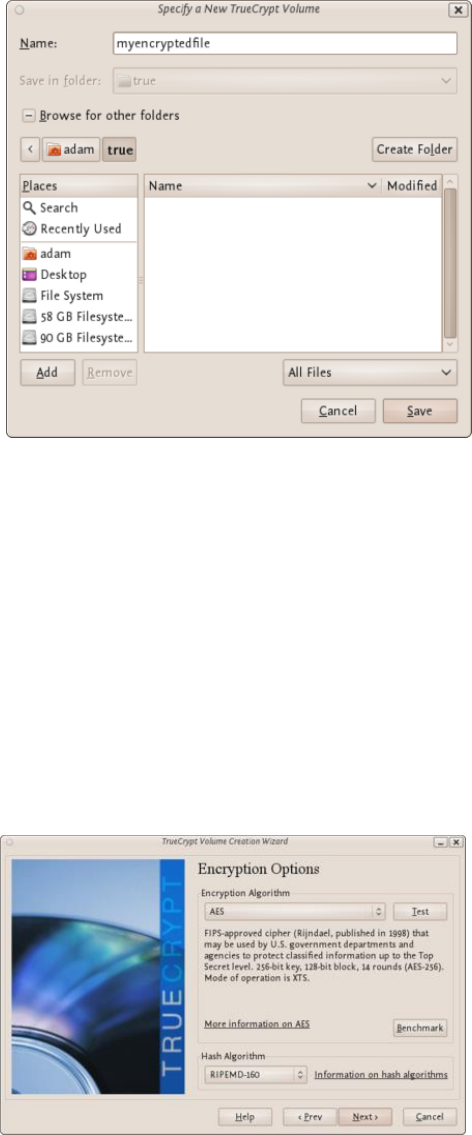
424
Figure 11.18:Using TrueCrypt
IMPORTANT:
Note that VeraCrypt will not encrypt any existing files. If an existing file is
selected in this step, it will be overwritten and replaced by the newly created volume (the contents
of the existing file will be lost). You will be able to encrypt existing files later on by moving them
to the Ver aCrypt volume that we are creating now.
6.
In the Volume Creation Wizard window (which was previously running in the
background), click Next.
7.
Here you can choose an encryption algorithm and a hash algorithm for the volume.
Figure 11.19:Using TrueCrypt
The VeraCrypt manual suggests that if you are not sure what to select here, you can use the
default settings and click Next (for more information about each setting have a look at the
VeraCrypt documentation website).
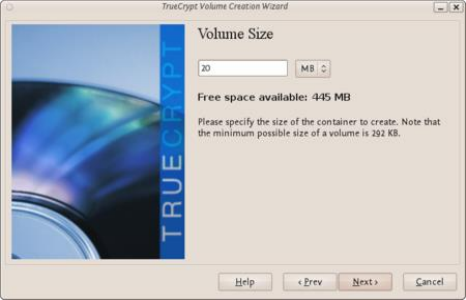
425
8.
Now choose the size of your container. You should be fine with 1 megabyte but for this
example we will enter ‘20’ into the available field.
Figure 11.20:Using TrueCrypt
You may, of course, specify a different size. After you type the desired size in the input field,
click Next.
9.
This step is really important, choosing a password.
The information displayed in the Wizard window about what is considered a good password,
should be read carefully.
Choose a strong password, type it in the first input field. Then re-type it in the input field below
the first one.
When you are done click Next.
10.
Now you must choose the format of your partition (this step may not be available for you
under windows or OSX). If using Ubuntu you can choose a Linux file type or FAT
(Windows) for simplicity leave it at the default.
Then press Next.
11.
Next VeraCrypt tries to generate random information to help encrypt your container. For 30
seconds move your mouse as randomly as possible within the Volume Creation Wizard
window. Move the mouse as much as possible for up to a minute. This significantly
increases security by increasing the cryptographic strength of the encryption keys. security).
Move your mouse around until you are bored.
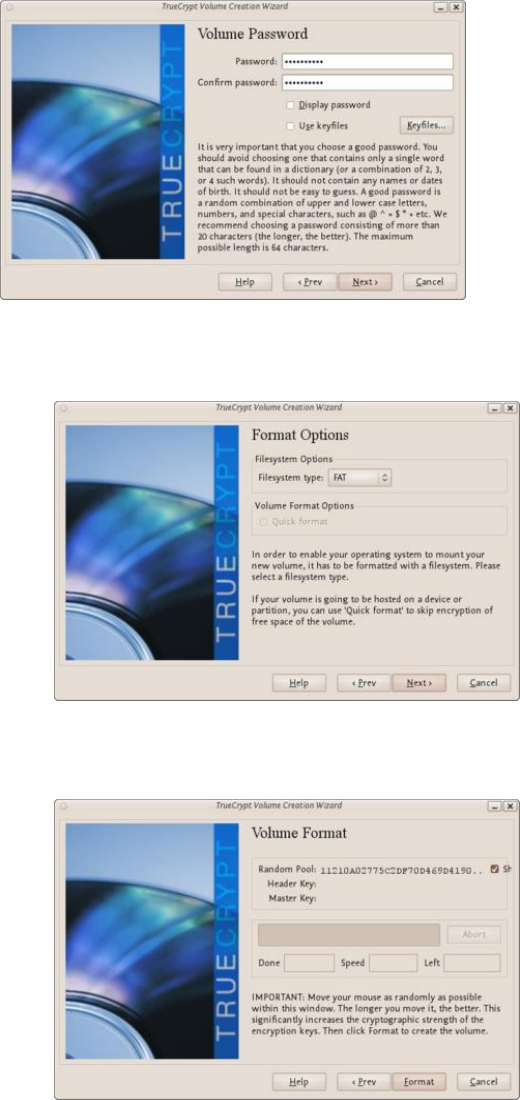
426
Figure 11.21:Using TrueCrypt
Figure 11.22:Using TrueCrypt
Figure 11.23:Using TrueCrypt
Then Click Format.
VeraCrypt will now create a file in the folder you selected with the name you chose. This file will
be a VeraCrypt container, containing the encrypted VeraCrypt volume. This may take some time
depending on the size of the volume. When it finishes this should appear:
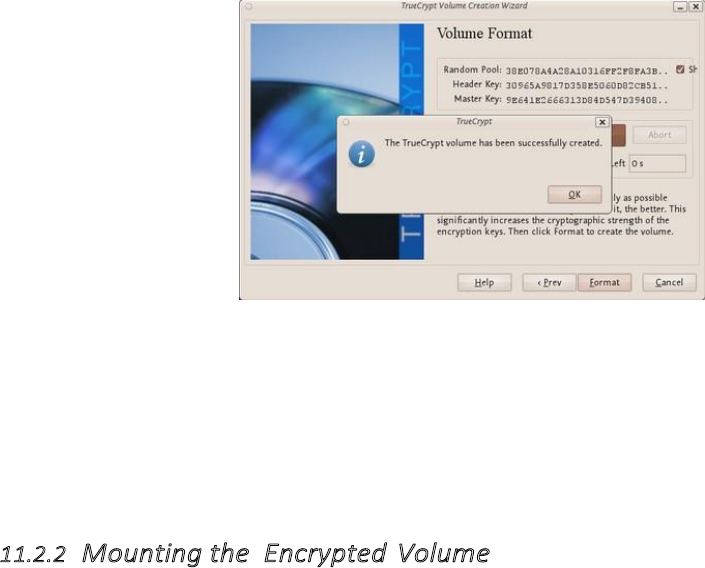
427
Figure 11.24:Using TrueCrypt Click
OK to close the dialog box.
12.
Well done! You’ve just successfully created a VeraCrypt volume (file container).
In the VeraCrypt Volume Creation Wizard window, click Exit.
11.2.2
MountingtheEncryptedVolume
1.
Open up VeraCrypt again.
2.
Make sure one of the ‘Slots’ is chosen (it doesn’t matter which - you can leave at the default
first item in the list). Click Select File.
The standard file selector window should appear.
3.
In the file selector, browse to the container file (which we created earlier) and select it.
Click Open (in the file selector window). The file
selector window should disappear.
4.
In the main VeraCrypt window, click Mount.
Password prompt dialog window should appear. 5.Type
the password in the password input field.
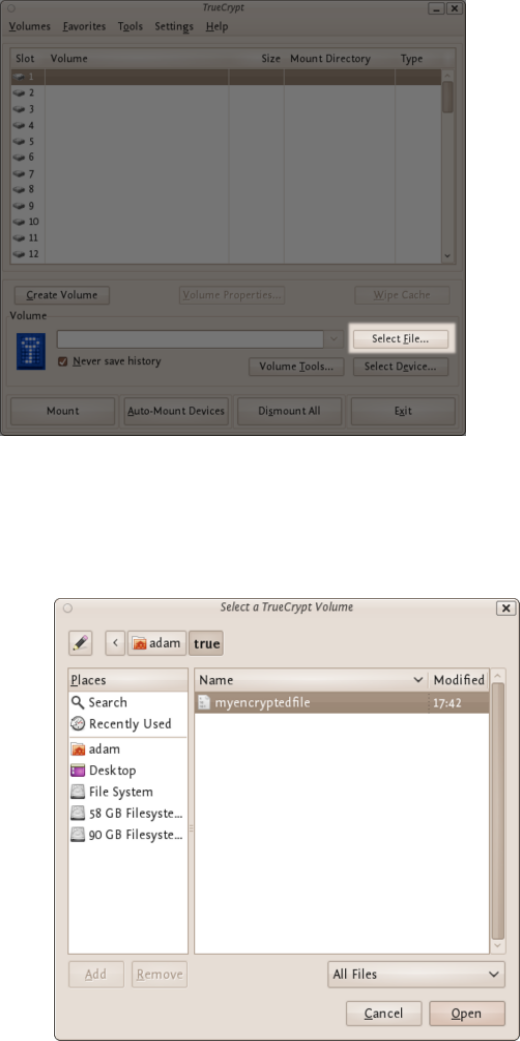
428
Figure 11.25:Using TrueCrypt
Figure 11.26:Using TrueCrypt
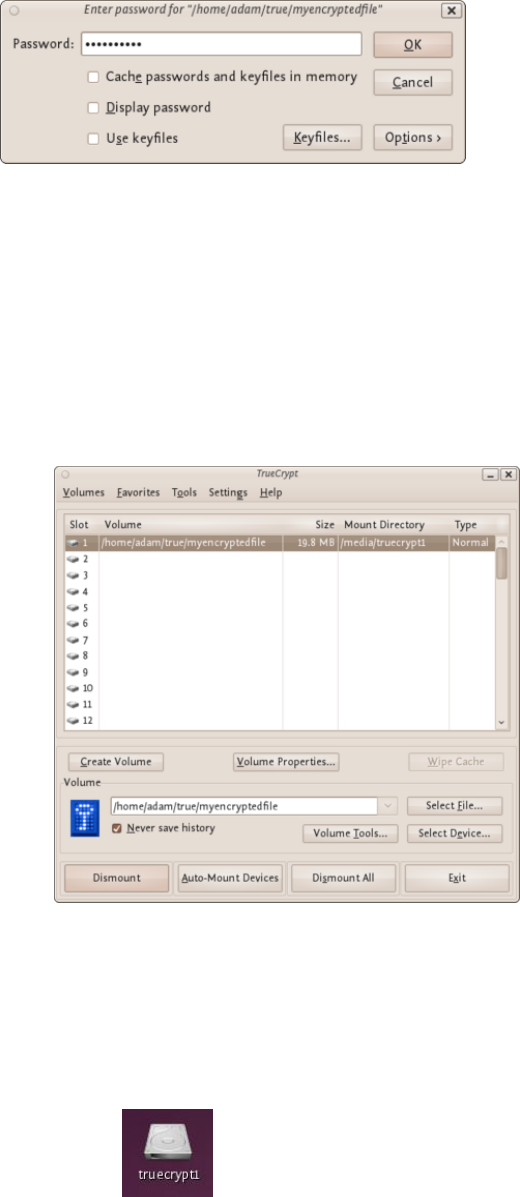
429
Figure 11.27:Using TrueCrypt
Figure 11.28:Using TrueCrypt
6.
Click OK in the password prompt window.
VeraCrypt will now attempt to mount the volume. If the password is correct, the volume will
be mounted.
Figure 11.29:Using TrueCrypt
If the password is incorrect (for example, if you typed it incorrectly), VeraCrypt will notify you
and you will need to repeat the previous step (type the password again and click OK).
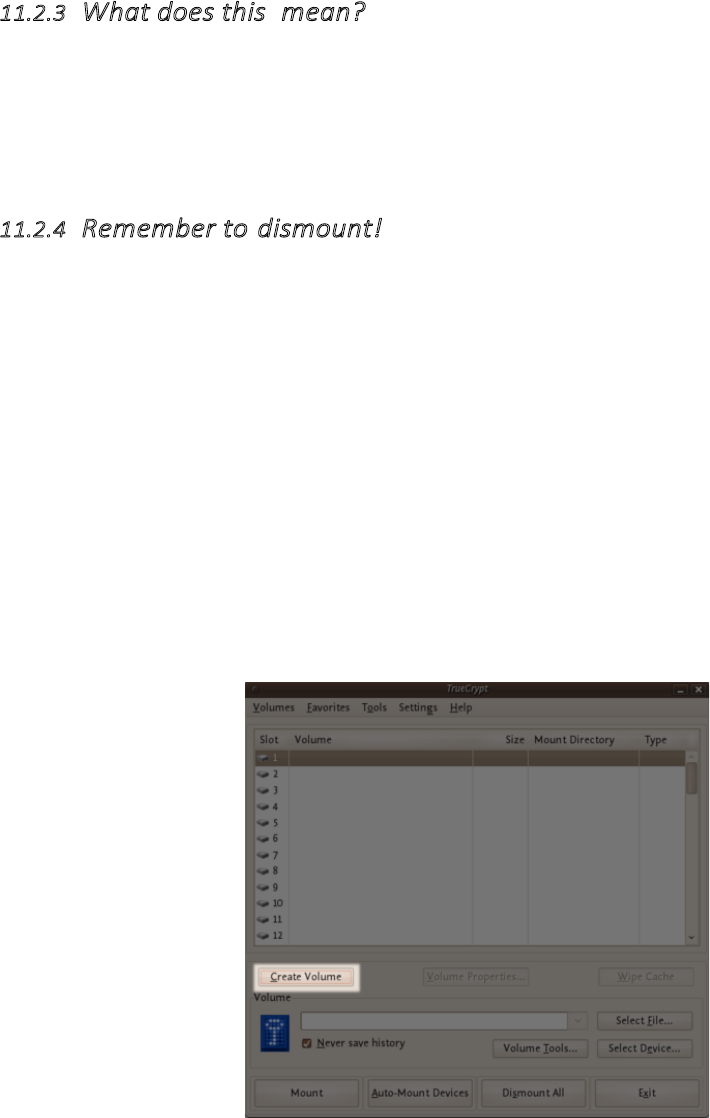
430
7.We have just successfully mounted the container as a virtual disk 1. The container will appear
on your Desktop or you will see it in your file browser.
11.2.3
Whatdoesthismean?
The disk that you have just created is completely encrypted and behaves like a real disk. Saving
(moving, copying, etc) files to this disk will allow you to encrypt files on the fly.
You’ll be able
to open a file which is stored on a VeraCrypt volume, which will automatically be decrypted to
RAM while it is being read, and you won’t need to enter your
password each time. You’ll only need to enter this when your mounting the volume.
11.2.4
Remembertodismount!
To do this right click on the drive and select unmount. This will automatically happen when
you turn off your computer but will not happen if you just put the computer on sleep.
11.3
Setting up a hidden volume
A VeraCrypt hidden volume exists within the free space of a typical VeraCrypt volume. Given then
the ‘outer volume’ is accessed it is (almost) impossible to determine if there is a hidden volume
within it. This is because VeraCrypt
always
fills the empty space of an encrypted volume with
random data. So a hidden volume looks the same as an empty VeraCrypt volume.
To create and use a hidden volume you need two passwords - one each for the outer and inner
(hidden) volumes. When you mount (open) the volume you can use either password and that will
determine which of the two is opened. If you want to open just the hidden volume you use one
password, and if you want to access just the non-hidden encrypted volume you use the other
password.
Figure 11.30:Hidden volumes
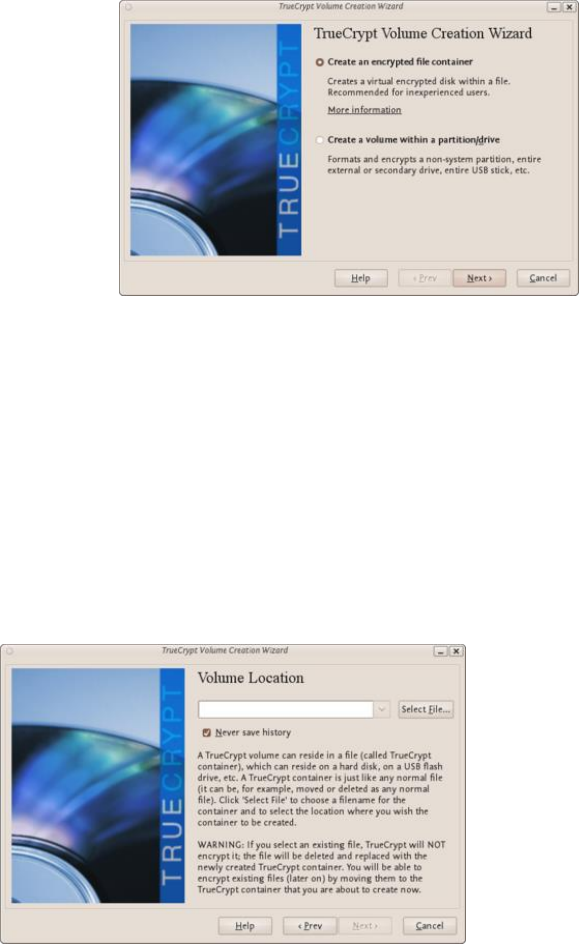
431
To create a hidden volume open VeraCrypt and press the ‘Create Volume’ button: The
options for half of this process are almost the same as for setting up a standard
VeraCrypt volume and then the process continues for setting up the hidden volume but lets go
through the entire process step by step anyway. In the screen shown below you just want to stay
with the default setting ‘Create an encrypted file container’:
Figure 11.31:Hidden volumes Press
‘Next >’ and continue to the next screen.
In the above screen you want to be sure that you choose the second option ‘Hidden TrueCrypt
Volume’. Select this and click on ‘Next >’ you will then be asked to choose the location and name
of the VeraCrypt
outer
volume.
Click ‘Select File. . . ’ and browse to a location for a new VeraCrypt volume. We will
use the name ‘myencryptedfile’ in this example. Its the same name as we used in the last example
so be aware that if you have just followed those instructions you must now create a new volume
with a new name.
Figure 11.32:Hidden volumes
Browse to the directory where you want to put the outer volume and enter the name of the
volume in the field named ‘Name’ as in the example above. When you are satisfied all is well click
on ‘Save’. The file browser will close and you return to the Wizard. Click ‘Next >’. Here you are
presented with some very technical choices. Don’t worry about them. Leave them at the defaults
and click ‘Next >’. The next screen asks you to determine the size of the outer volume. Note that
when you do this the maximum inner ‘hidden’ volume size is determined by TrueCrypt. This
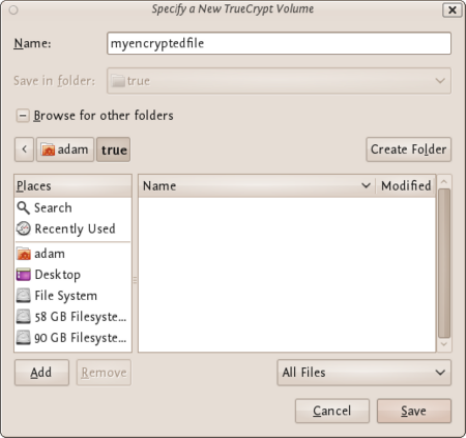
432
maximum size will of course be smaller that the size you are setting on this screen. If you are not
sure what the ratio of outer volume size to inner (hidden) volume size is then go through the process
now as a ‘dummy’ run - you can always trash the encrypted volume and start again (no harm
done).
So choose the size of the outer volume, I will choose 20MB as shown below:
You cannot set the outer volume size to be larger than the amount of free space you have available
on your disk. VersCrypt tells you the maximum possible size in bold letters so create a volume size
smaller than that. Then click ‘Next >’ and you will be taken to a screen asking you to set a password
for the outer (not the hidden, this comes later) volume.
Enter a password that is strong (see the chapter on creating good passwords) and press ‘Next >’.
Next VeraCrypt wants you to help it create the random data it will fill the volume up with. So wave
your mouse around, browse the web, and do whatever you want for as long as you can. When you
feel VeraCrypt should be happy then press ‘Format’. You will see a progress bar zip by and then
you will be presented with the next screen:
You can open the outer volume if you like but for this chapter we will skip that and go ahead
to create the hidden volume. Press ‘Next >’ and VeraCrypt will work out how the maximum possible
size of the hidden volume.
When you see the above screen just press ‘Next >’. Now you must choose the encryp-
Figure 11.33:Hidden volumes
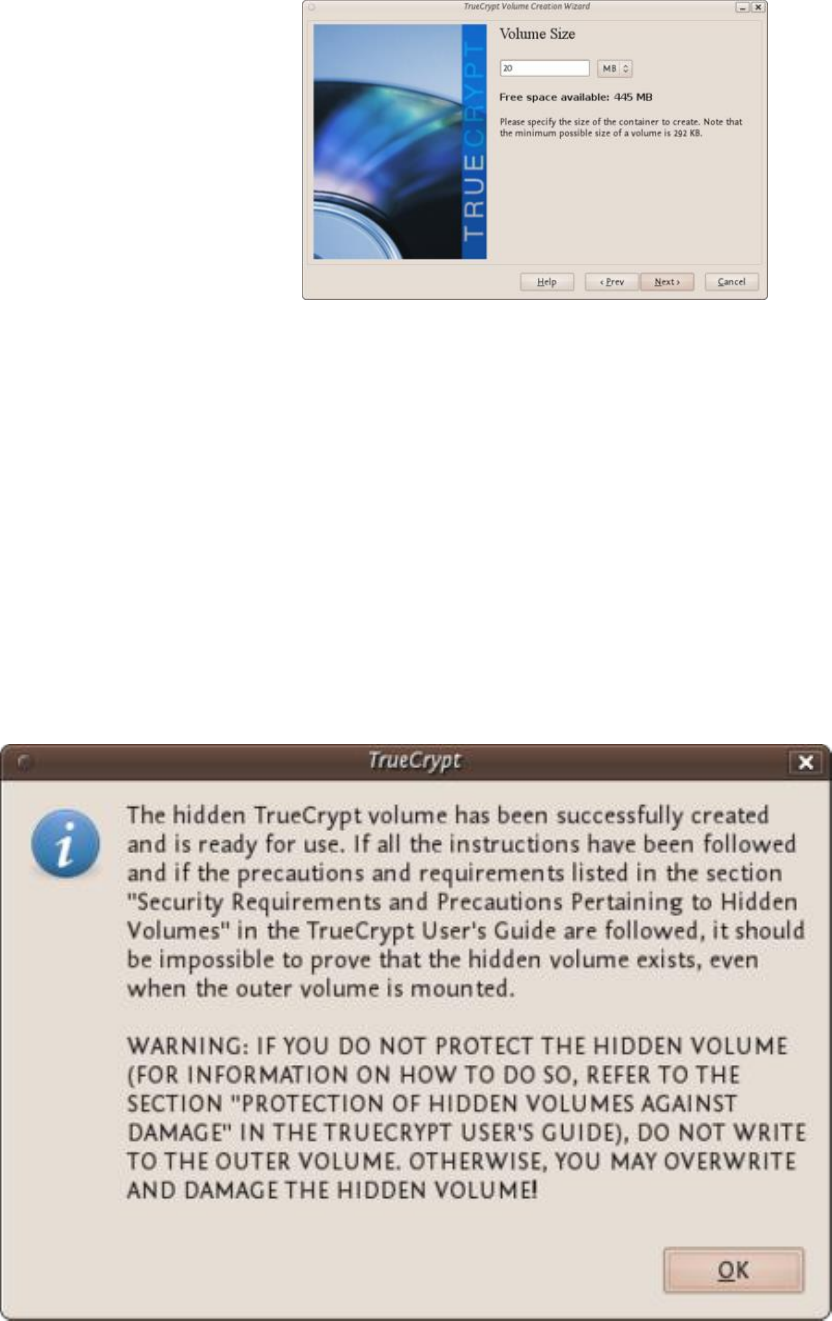
433
Figure 11.34:Hidden volumes
tion type for the hidden volume. Leave it at the defaults and press ‘Next >’.
Now you will be asked to choose the size of the hidden volume.
I have set (as you see above) the maximum size as 10MB. When you have set your maximum size
press ‘Next >’ and you will be prompted to create a password for the hidden volume.
When creating the password for the hidden volume make sure you make it substantially
different fro the password for the outer volume. If someone really does access your drive and
finds out the password for the outer volume they might try variations on this password to see if
there is also a hidden volume. So make sure the two passwords are not alike.
Enter your password in the two fields and press ‘Next >’.
Leave this window at the defaults and press ‘Next >’ and you will be presented with the same
screen you have seen before to generate random data for VeraCrypt. When you are happy click
‘Format’ and you should see the following :
434
Figure 11.35:Hidden volumes
Click ‘OK’ and keep and exit VeraCrypt. You can now mount the volume as noted in the
previous chapter.
11.4
Securely destroying data
Just hit the delete button and you are done! No it’s not that easy. To understand how to securely
delete data, we have to understand how data is stored. In an analogy to the real world, an explanation
of how data is stored follows:
Assume you have a small notebook with 10 pages and you want to write some data in this
notebook. You just start writing on the first page up to the end of the notebook. Maybe you decide
the information on page 5 must be destroyed. Probably you will just take out the page and burn it.
Unfortunately data on a harddisk doesn’t work this way. A harddisk contains not ten but
thousands or maybe even millions of pages. Also it’s impossible to take out a “page” of a
harddisk and destroy it. To explain how a harddisk work, we will continue with our 10-page
notebook example. But now we will work a little bit different with it. We will work in a way
similar to how a harddisk works.
This time we use the first page of our notebook as an index. Assume we write a piece about
“WikiLeaks”, then on the first page we write a line “piece about WikiLeaks: see page 2”. The actual
piece is then written on page 2.
For the next document, a piece about “Goldman Sachs” we add a line on page 1, “Goldman Sachs:
see page 3”. We can continue this way till our notebook is full. Let’s assume the first page will look
like this:
•
WikiLeaks -> see page 2
•
Goldman Sachs -> see page 3
•
Monstanto scandal -> see page 4
•
Holiday pictures -> see page 5
•
KGB Investigation -> see page 6
•
Al Jazeeraa contacts -> see page 7
•
Iran nuclear program -> see page 8
•
Sudan investigation -> see page 9
•
Infiltration in EU-politics -> see page 10
Now, let’s decide you want to wipe the “Goldman Sachs” piece, what a harddisk will do, it will
only remove the entry on the first page, but not the actual data, your index will be:
•
WikiLeaks -> see page 2
•
Monstanto scandal -> see page 4
•
Holiday pictures -> see page 5
•
KGB Investigation -> see page 6
•
Al Jazeeraa contacts -> see page 7
•
Iran nuclear program -> see page 8
•
Sudan investigation -> see page 9
•
Infiltration in EU-politics -> see page 10
435
What we did, we removed only the reference to the article, but if we open page 3, we will still
able to read the Goldman Sachs piece. This is exactly the way what a harddisk does when your
“delete” a file. With specialized software it still able to “recover” page 3.
To securely delete data, we should do the following:
1.
Open the “Goldman Sachs” page (page 3)
2.
Use an eraser to remove the article there, if done return to page 1 3.Delete
the reference in the index on page 1
Well you will be surprised by the similarity between this example and the real world. You
know when you removed the article on page 3 with an eraser, it is still possible to read the article
slightly. The pencil leaves a track on the paper because of the pressure of the pencil on the paper
and also you will be unable to erase all of the graphite. Small traces are left behind on the paper.
If you really need this article, you can reconstruct (parts) of it, even if it’s erased.
With a harddisk this is very similar. Even if you erased every piece of data, it is sometimes
possible with (very) specialized hardware to recover pieces of the data. If the data is very confidential
and must be erased with the greatest care, you can use software to “overwrite” all pieces of data
with random data. When this is done multiple times, this will make the data untraceable.
11.4.1
AnoteonSolidStateHard Drives
The instructions below explain how to use file deletion tools to securely delete files from your
hard drives. These tools rely on the Operating System you are using being able to directly
address every byte on the hard drive in order to tell the drive “set byte number X to 0”.
Unfortunately, due to a number of advanced technologies used by Solid State Drives (SSDs)
such as TRIM, it is not always possible to ensure with 100% certainty that every part of a file
on an SSD has been erased using the tools below.
11.4.2
SecurelydeletedataunderWindows
For Windows there is a good open source tool called “File Shredder”. This tool can be downloaded
from http://www.fileshredder.org
The installation is very straightforward, just download the application and install it by hitting
the next button. After installation this application will automatically start. You can then start
using it for shredding files. However the best part of the program is that you can use it from
within windows itself by right clicking on a file.
1.
Click right on the file you want to shred, and choose File Shredder -> Secure delete files
2.
A pop-up asks if you really want to shred this file
3.
After confirming, there your file goes. Depending on the size of the file this can take a
while
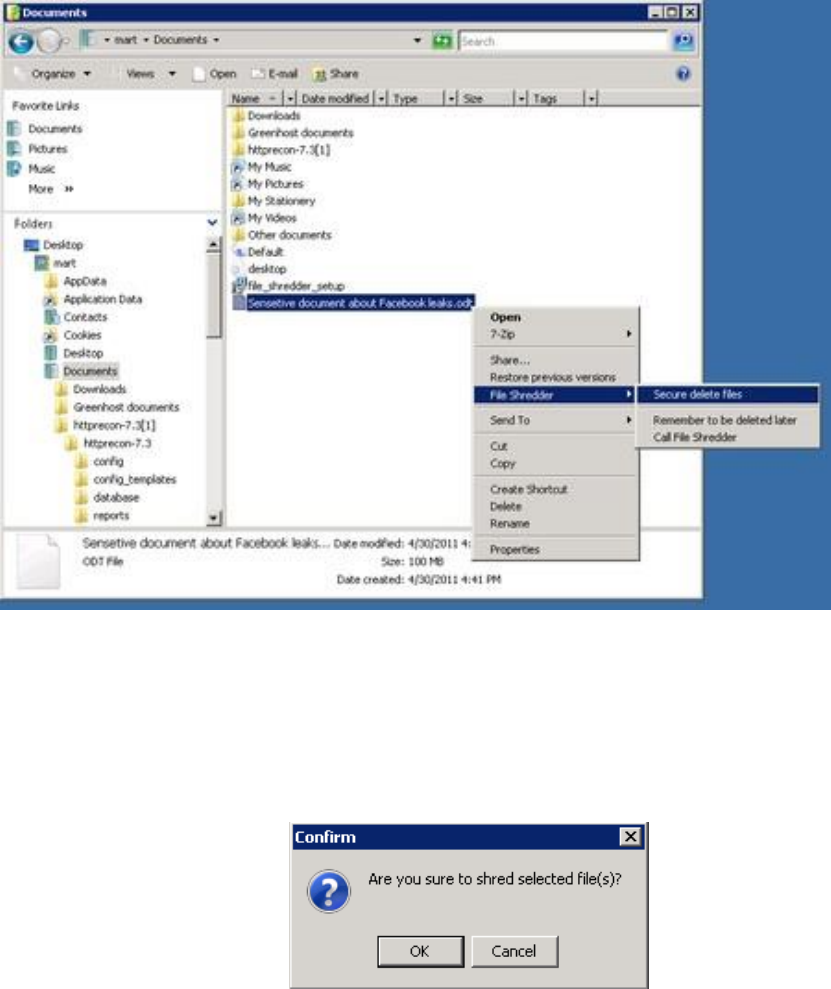
436
Figure 11.36:Destroying data
Figure 11.37:Destroying data
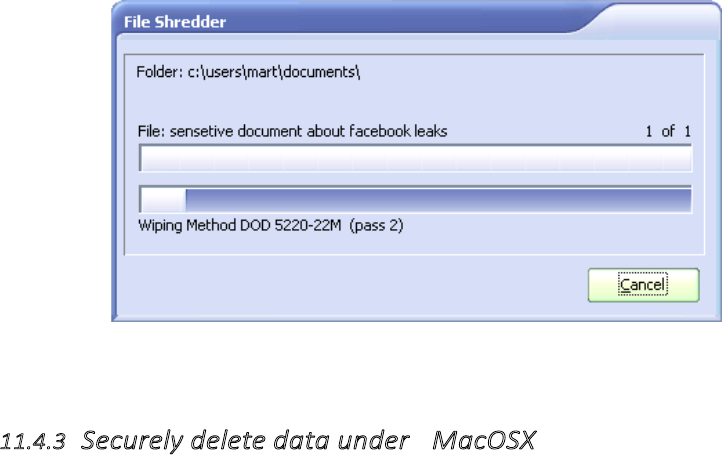
437
Figure 11.38:Destroying data
11.4.3
SecurelydeletedataunderMacOSX
There are basically to build-in steps to make to securely delete your data on Mac OSX.
1.
Erase the free-space on your hard-drive containing all the data of items which are deleted in
an insecure way.
2.
Make sure that every file from then on is always securely deleted.
We start with the first one:
Erasing Free Space
1.
Open Disk-Utility which resides in the Utilities folder inside the Applications folder.
2.
Select your hard drive and click on ‘Erase Free Space’.
3.
Three options will appear, from top to bottom more secure, but also they take much more
time to complete. Read the descriptions on each one of them to get an idea from what will
happen if you use them and then choose which one might suite your needs the best and click
‘Erase free Space’.
If time is no issue, then use the most secure method and enjoy your free time to get a good coffee
while you Mac crunches away on this task. If the crooks are already knocking on your front-door
you might want to use the fastest way.

438
Figure 11.39:Destroying data
Securely Erasing Files
Now that your previously deleted data is once and for ever securely erased you should make sure
that you don’t create any new data that might be recovered at a later date.
1.
To do this open the finder preferences under the Finder Menu.
2.
Go to the advanced tab and tick ‘Empty trash securely’. This will make sure that every time
you empty your trash all the items in it will be securely deleted and are really gone!
Note:
Deleting your files securely will take longer then just deleting them. If you have to erase
big portions of unimportant data (say your movie and mp3 collection) you may wanna untick this
option before doing so.
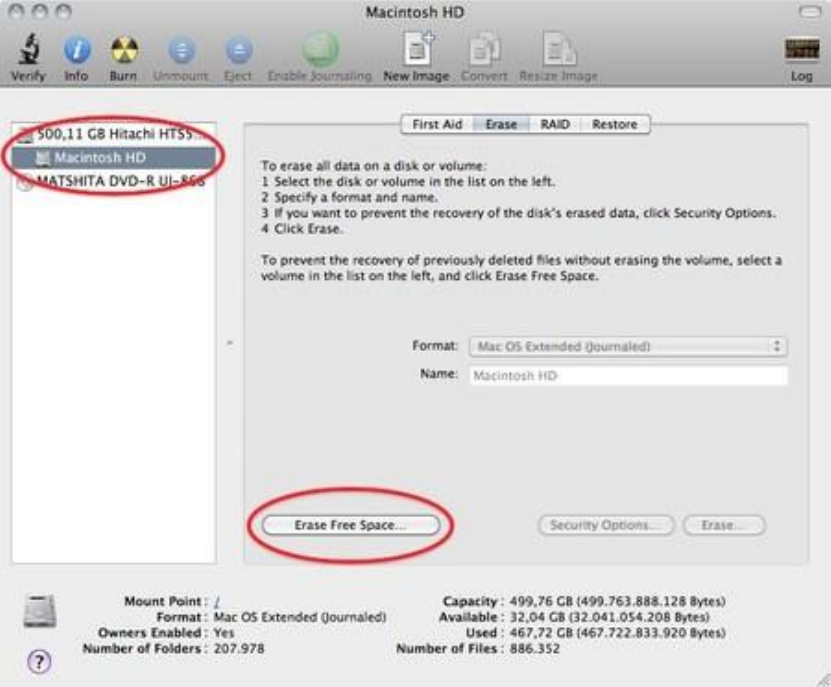
439
Figure 11.40:Destroying data
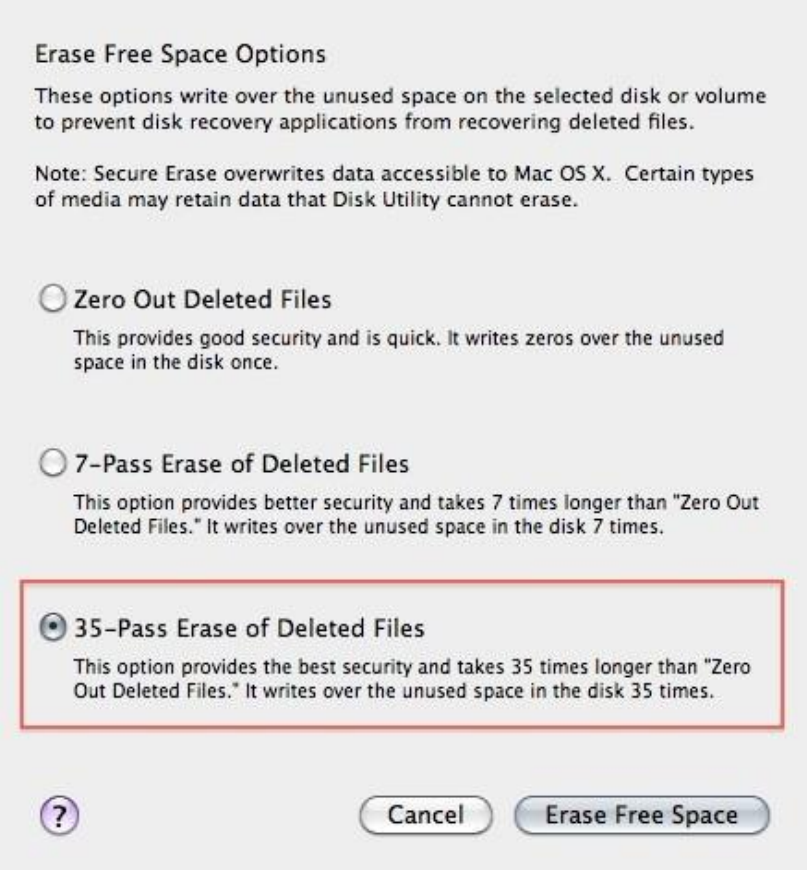
440
Figure 11.41:Destroying data
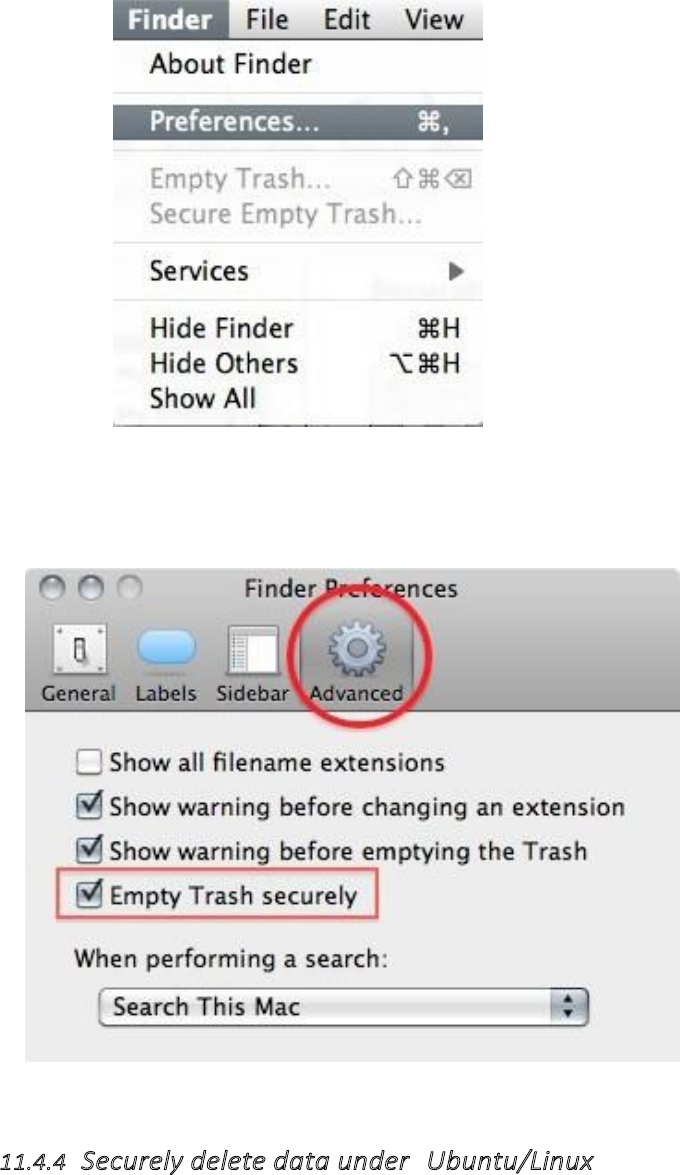
441
Figure 11.42:Destroying data
Figure 11.43:Destroying data
11.4.4
Securelydeletedataunder Ubuntu/Linux
Unfortunately currently there is no graphical user interface available for Ubuntu to delete files
secure. There are two command-line programs available though:
•
shred
•
wipe
442
Shred is installed in Ubuntu by default and can delete single files. Wipe is not installed by
default but can easily be installed with using Ubuntu Software Center or if you understand the
command line you can install it with apt-get
install
wipe. Wipe is a little more secure and has
nicer options.
It is possible make access to these program’s easy by adding it as an extra menu option
1.
We assume you are familiar with the Ubuntu Software Center. To add the securely wipe option,
it’s required to install these two programs
wipe
and
nautilusactions
If the two programs are installed follow the following steps. If they are not installed use the
Ubuntu Software Center to install them or on the command line simply type apt-get install nautilus-
actions wipe
2.
Open the “Nautilus Actions Configuration” from the System -> Preferences menu
3.
We have to add a new action. To do this, start clicking on the “create new action button”, the
first option in the toolbar
4.
Next is describing the new action. You can give the action every name you wish. Fill out this title
in the “Context label” field. In this example we used “Delete file securely”
5.
Click on the second tab (“Command”), here is how we specify the action we want. In the field
“Path”, type “wipe”, in the field parameters type “-rf %M”, please be sure about the capitalisation
of all characters here, this is very important.
6.
Next is specifying the conditions, click on the conditions tab and choose the option “Both” in the
“Appears if selection contains. . . ” box. With this option you can wipe both files and folders
securely. If done, click the save button (second item on the icon bottom toolbar) or use the menu
File->Save
7.
Now close the Nautilus Actions Configuration tool. Unfortunately, after this, you have to re-login
into your system, so ether reboot or logout/login.
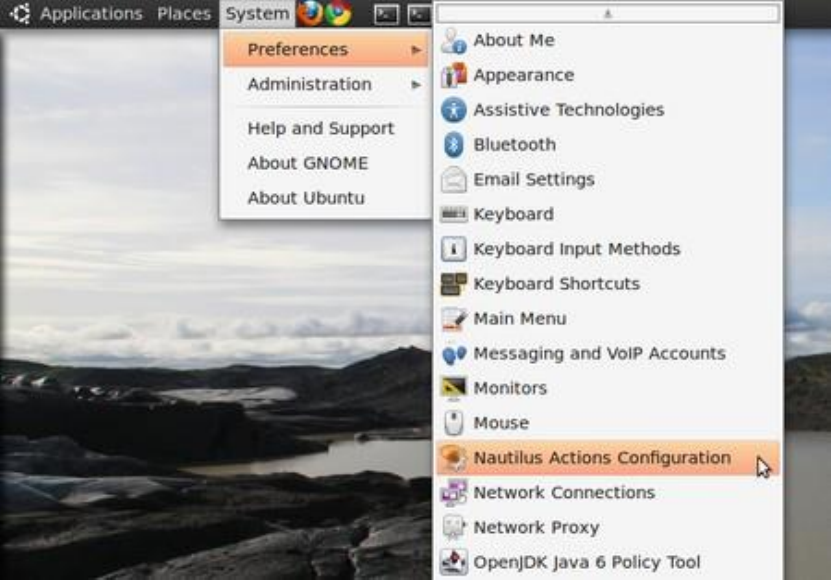
443
Figure 11.44:Destroying data
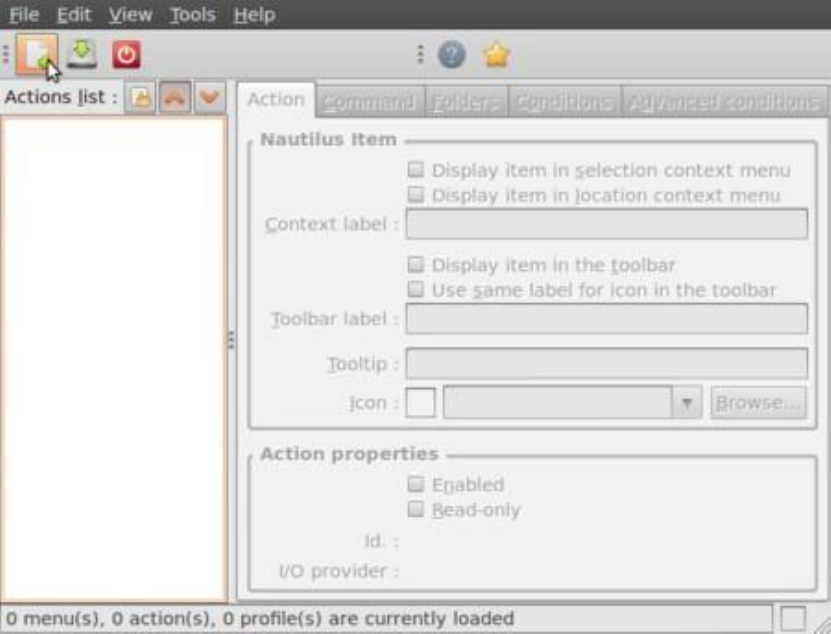
444
Figure 11.45:Destroying data
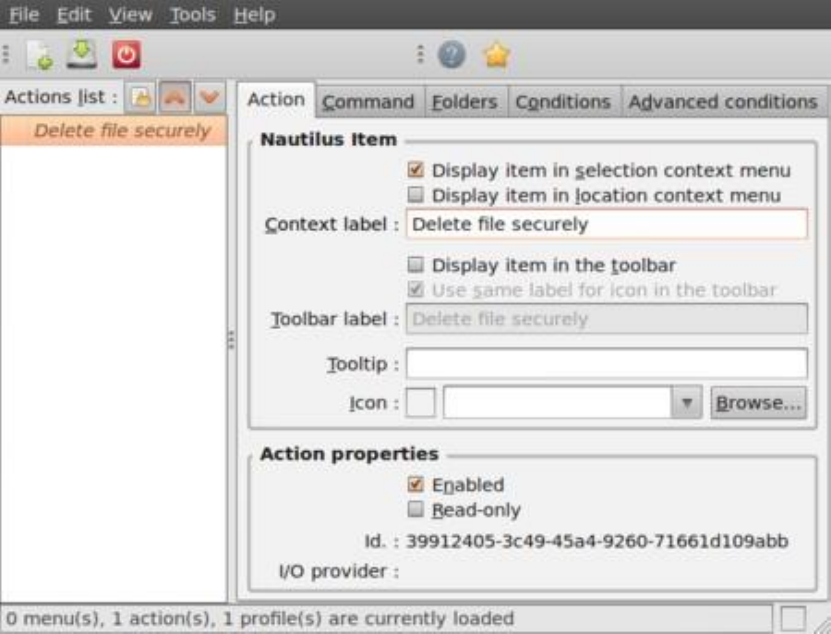
445
Figure 11.46:Destroying data
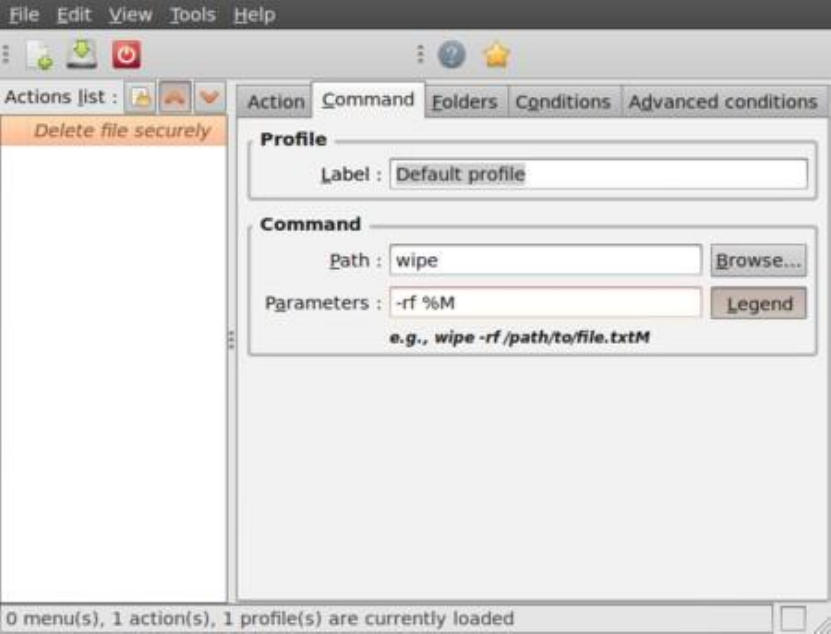
446
Figure 11.47:Destroying data
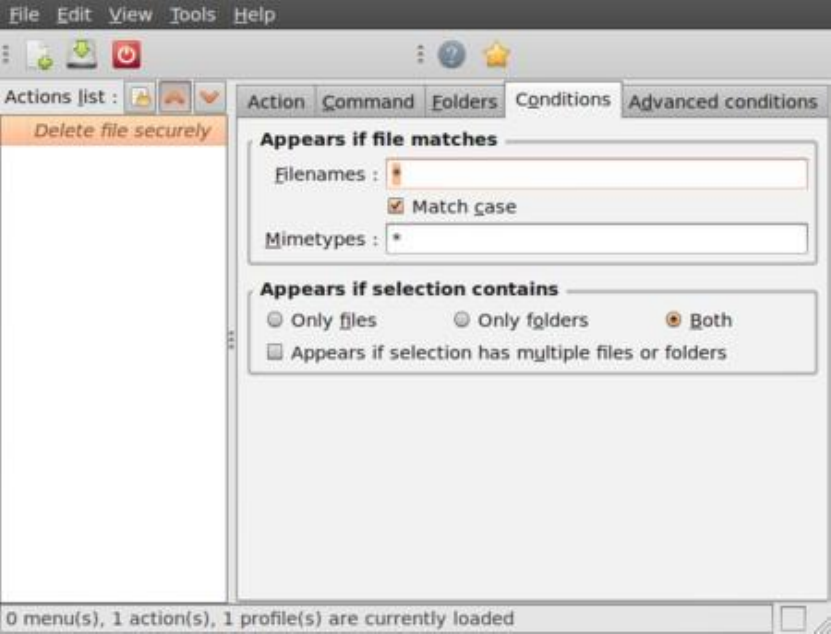
447
Figure 11.48:Destroying data
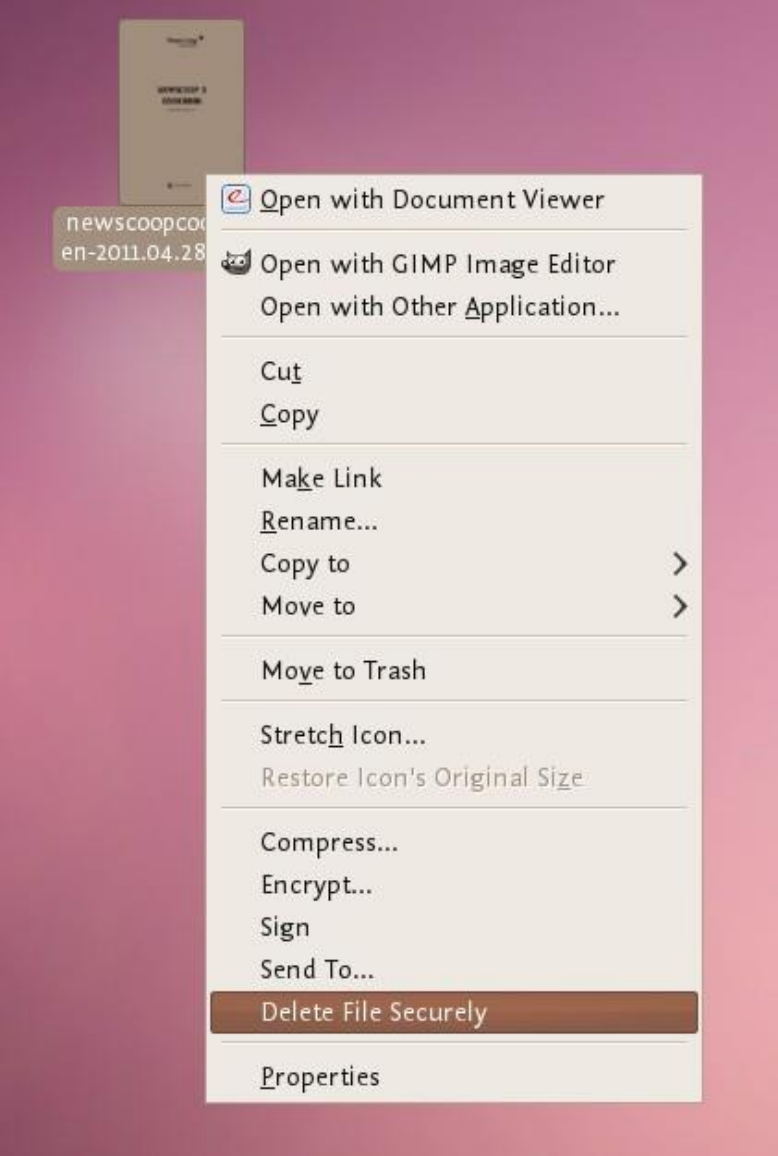
448
Figure 11.49:Destroying data
8.
Now browse to the file you want to securely delete and right click:
449
Choose ‘Delete File Securely’. The file will then be wiped ‘quietly’ - you do not get any feedback
or notice that the process has started or stopped. However the process is underway. It takes some
time to securely delete data and the bigger the file the longer it takes. When it is complete the icon
for the file to be wiped will disappear. If you would like to add some feedback you can change the
parameters field in Nautilius Actions Configuration tool to this:
-rf
M
|
zenity
--info --text
"your wipe
is
underway, please be
patient.
The
file to
be wiped
will disappear shortly."
The above line will tell you the process is underway but you will not know the file is deleted until
the icon disappears.
11.5
About LUKS
LUKS
, short for
LinuxUnifiedKeySetup
, is the default method for disk encryption on Linux.
It can be used to enable
FullDiskEncryption
during installation with a single click, or to encrypt
individual partitions on external hard disks or usb sticks later on. Please note that
FullDiskEncryption
is hard to enable
after
the installation as it requires moving all existing files temporarily as
encrypting a device requires formatting it.
•
Advantages: LUKS is available through dm-crypt which is part of the Linux kernel, so it
doesn’t need any further software to be installed.
•
Disadvantages: Unlike with Veracrypt, it is not possible to use it with other Oper- ating
Systems (yet), so if you use LUKS to encrypt a USB drive, you can only use it on Linux
machines, but not on Windows or Mac OS.
If you want to encrypt a device after the Linux installation completed, you can use the
Disks
utility which can be found in most Linux distribution’s
SystemSettings
.
11.5.1
Starting
Disks
On Ubuntu, start
Disks
by pressing the Windows key and A, typing “disks” and selecting the
corresponding program as shown below:
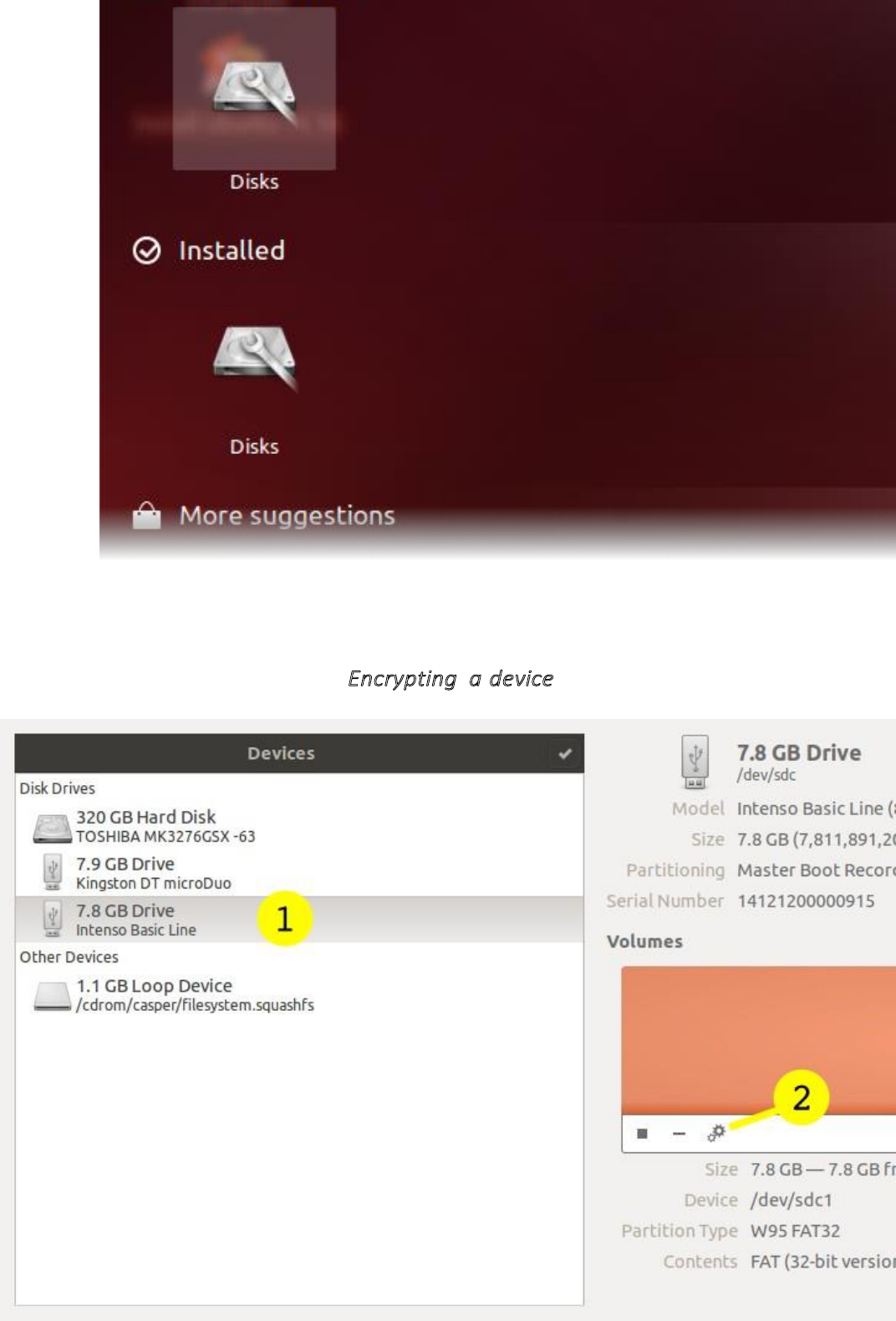
450
Figure 11.50:Launching
Disks
11.5.2
Encryptingadevice
451
Figure 11.51:Disks main window
On the left hand side you will find a list of all storage devices plugged into your
computer.
Select the one you want to encrypt (step 1) (in this case a usb stick), and then
on the right hand side, click on the cog wheels and “Format. . . ”. A dialog will
appear where you can select if the existing data on the device shall be completely
overwritten (that can take up to several hours depending on the size and
performance of the device) or just formatted. Please note that even if you choose
to encrypt the device, data, that was present before will be recoverable if you don’t
choose to overwrite it completely.
No matter what you choose for the field
Erase
, select “Encrypted, compatible
with Linux systems (LUKS+Ext4)” for
Type
, give it a name and a strong
passphrase (see chapter 8 on that matter), and click
Format...
On the confirmation screen make sure you selected the correct device as data recovery
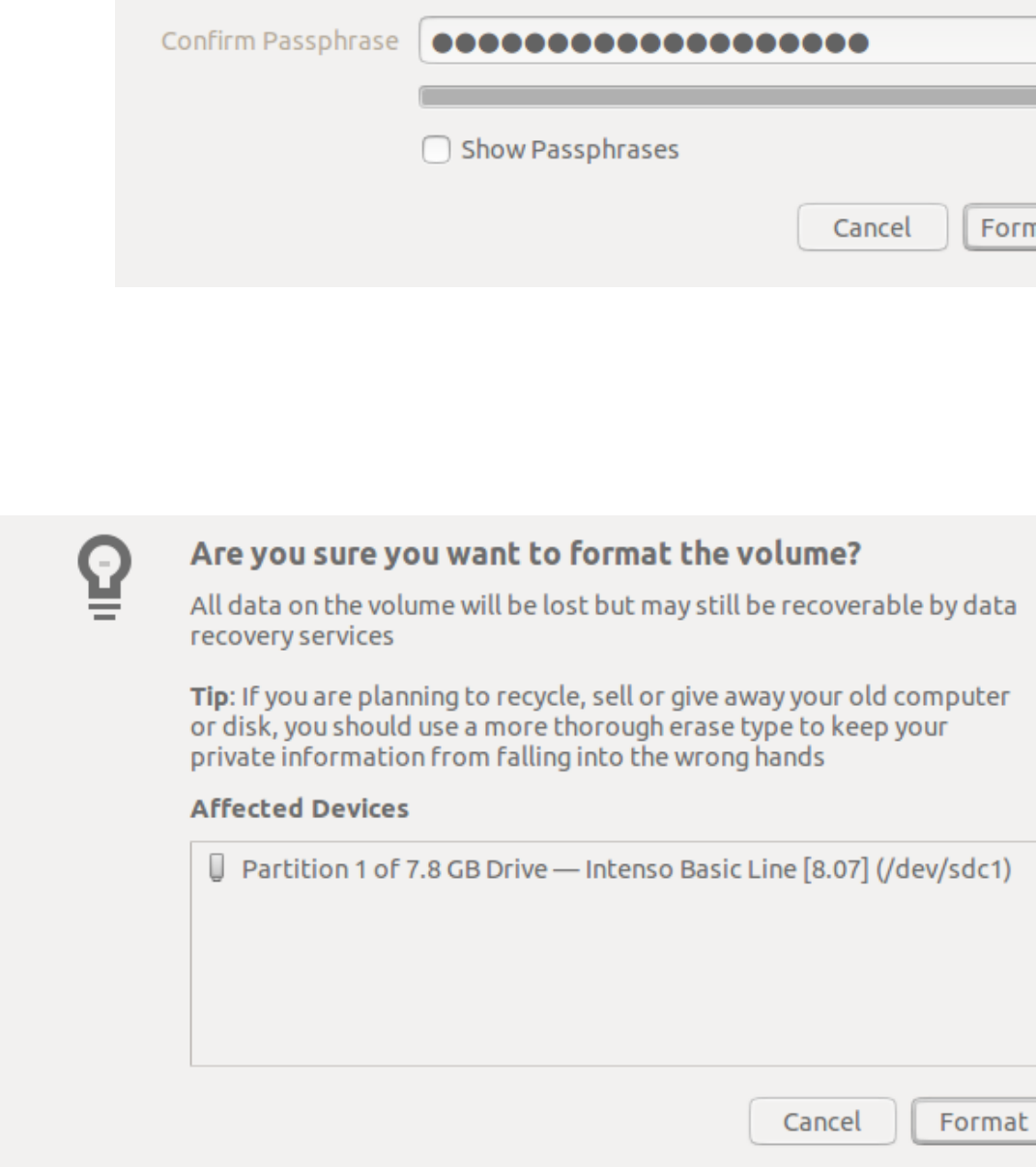
452
Figure 11.52:“Format. . . ” dialog
is a cumbersome tasks – if possible at all.
Figure 11.53:Confirmation step
Back on the main window the device now consists of two layers. One is the
physical storage (here called “Partition 1”) and the other a virtual device which is
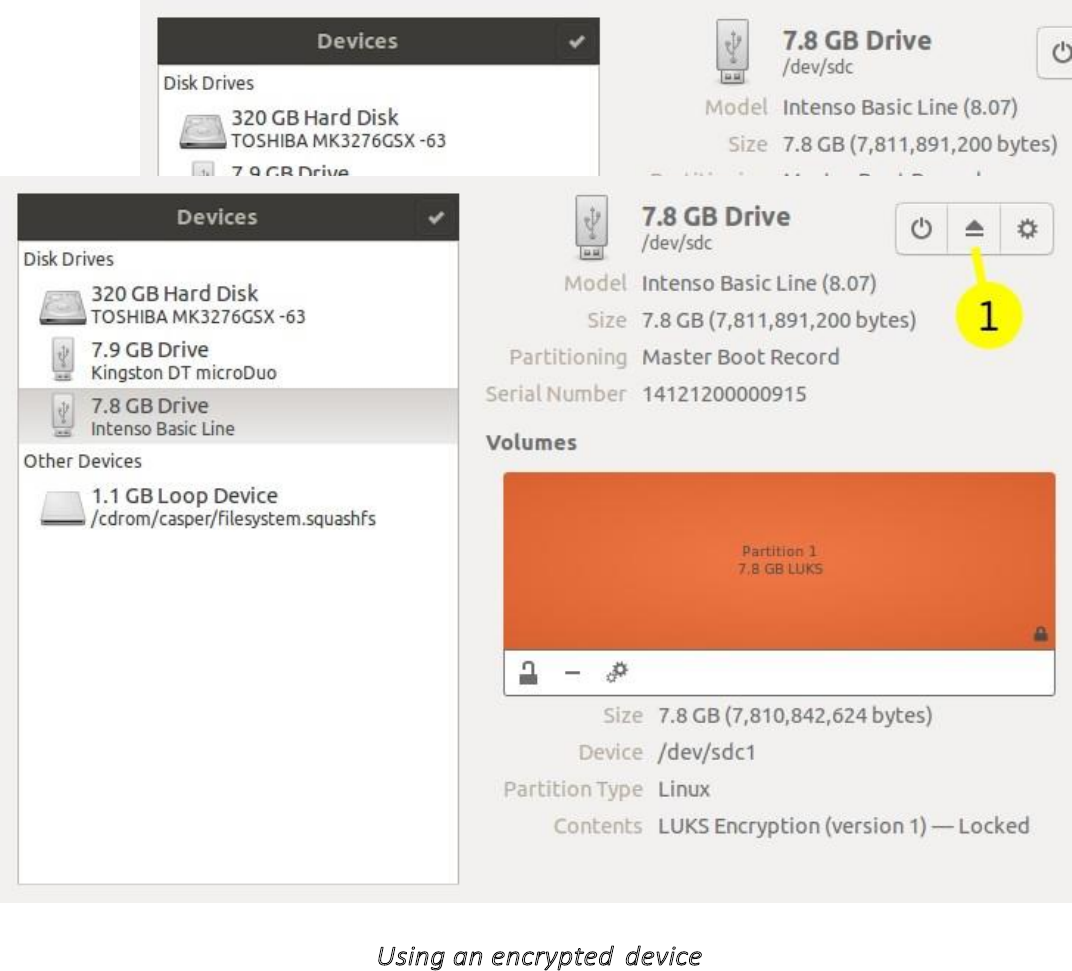
453
created by the LUKS system to give you access to the encrypted device (here
called “cryptostick”). The pad lock on “Partition 1” is open as the
Disks
utility
needed to open it in order to create a file system (how would you store files on a
device without a file system?). You can click on the (other) pad lock as shown
below to close the decryption channel and the
eject
button in the upper right
corner to safely remove the device.
11.5.3
Usinganencrypteddevice
This is quite straight-forward. Plug it in, enter the passphrase and click
Connect
.
If the file manager does not open automatically, the device will be available
when you do.
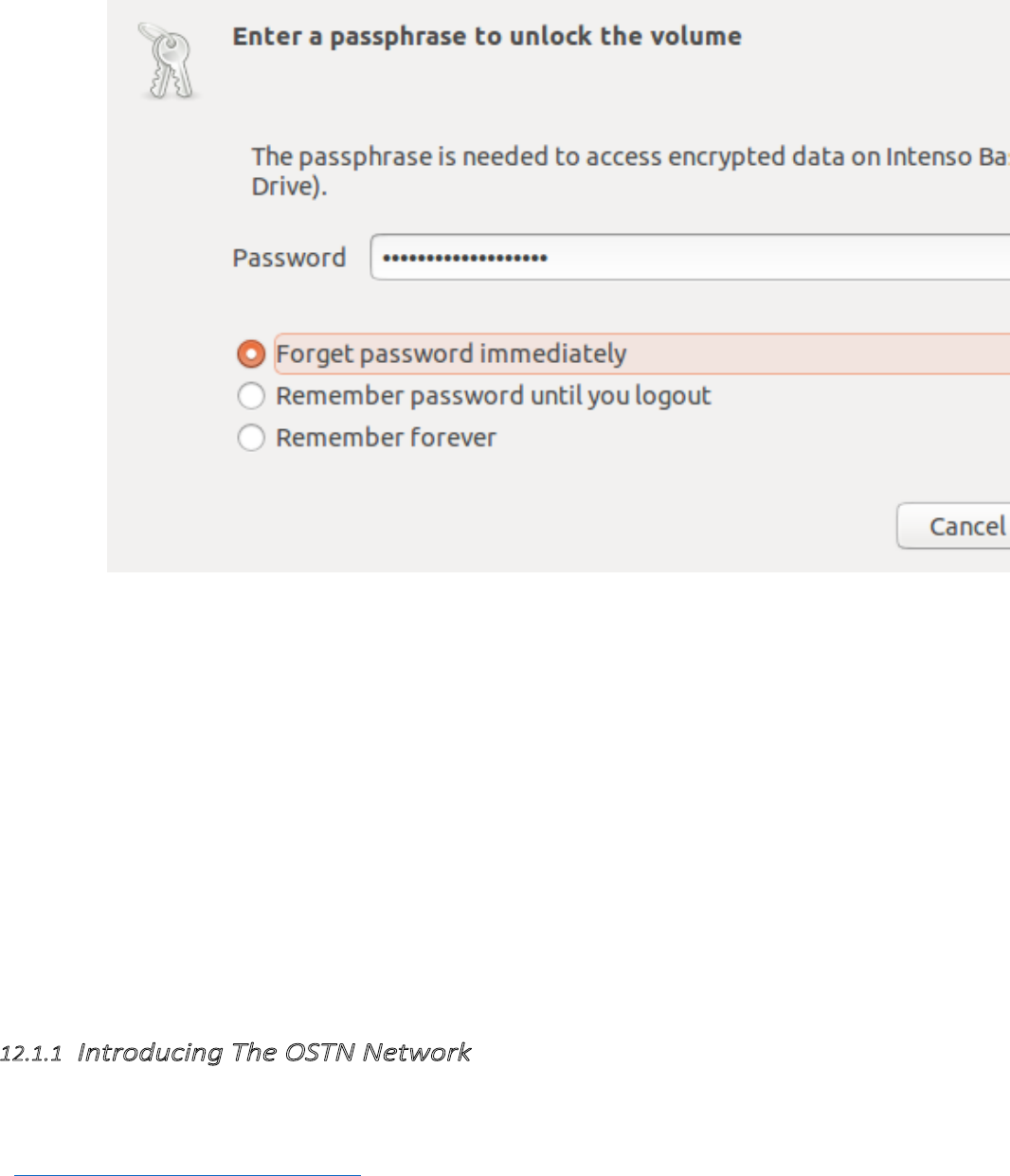
454
Figure 11.54:Eject the LUKS device
12
Call Encryption
12.1
Installing CSipSimple
CSipSimple is a program for Android devices that allows for making encrypted calls. Naturally the
calling software isn’t enough on its own and we need a communication network to enable us to make
calls.
12.1.1
IntroducingTheOSTNNetwork
If you already know about OSTN and have an account, you can skip this section.
The Guardian Project’s OSTN (Open {Secure, Source, Standards} Telephony Network
- https://guardianproject.info/wiki/OSTN) is an attempt to define a standard Voice over IP
(VoIP) setup using the Session Initiation Protocol (SIP) that enables end-to-end encrypted calls.
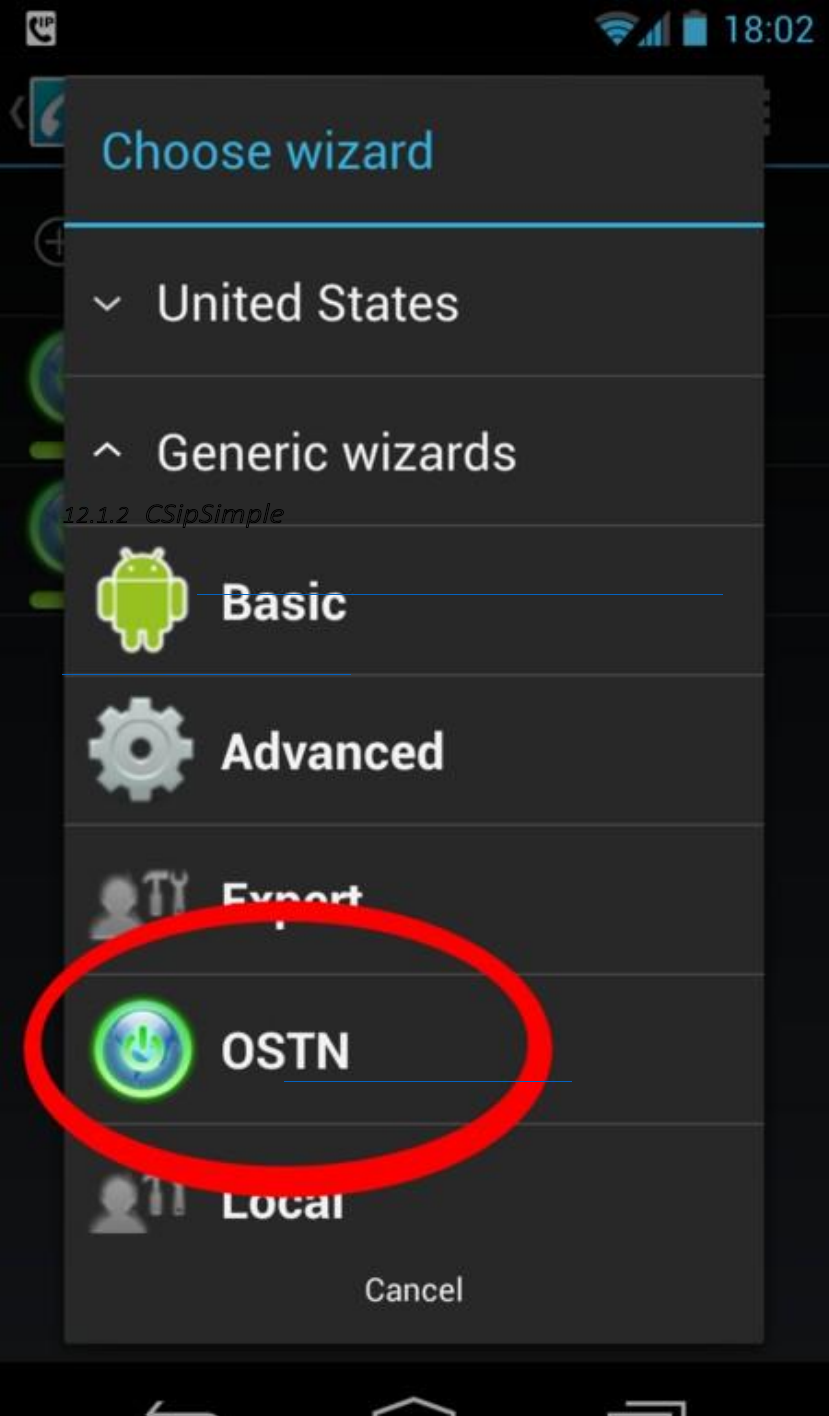
455
Similar to e-mail, SIP allows people to choose their service provider while still being able to call
each other even if they are not using the same provider. Yet, not all SIP providers offer OSTN and
both providers have to support OSTN for the call to be secure. Once a connection between two
people is established, the audio data is exchanged directly between the two parties. Data is encrypted
according to the Secure Real-time Transport Protocol (SRTP).
A majority of encrypting VoIP applications currently use Session Description Proto- col Security
Descriptions for Media Streams (SDES) with hop-by-hop Transport Layer Security (TLS) to
exchange secret master keys for SRTP. This method is not end-to-end secure as the SRTP keys are
visible in plaintext to any SIP proxy or provider involved in the call.
ZRTP is a cryptographic key-agreement protocol to negotiate the keys for encryption between
two parties. ZRTP end points use the media stream rather than the signaling stream to establish the
SRTP encryption keys. Since the media stream is a direct con- nection between the calling parties,
there is no way for the SIP providers or proxies to intercept the SRTP keys. ZRTP provides a
useful reassurance to end-users that they have a secure line. By reading and comparing a word pair,
users can be certain that the key exchange has completed.
Open Secure Telephony (https://ostel.me/) is a testbed for OSTN that worked well at the time
of writing this book. At https://ostel.me/users/sign_up you can sign up and create an account.
You can also check the OSTN page listed above for other providers.
12.1.2
CSipSimple
CSipSimple is a free and open source client for Android that works well with OSTN. You can
find it at https://market.android.com/details?id=com.csipsimple
To use CSipSimple with ostel.me, select OSTN in the generic wizards when creating an
account and enter username, password and server as provided after signing up at
https://ostel.me/users/sign_up
Once you call another party with CSipSimple you see a yellow bar with ZRTP and the verification
word pair. You now have established a secure voice connection that cannot be intercepted. Still,
you should be aware that your phone or the phone of the other party could be set up to record the
conversation.
Basic steps:
1.
Install CSipSimple from Google Play store or other trusted source
2.
Start it up and choose if you want to make SIP calls via data connection or only WiFi
3.
Configure your account
To use CSipSimple with ostel.me, select OSTN in the Generic Wizards section when creating an
account. You can toggle off the “United States” providers by clicking on “United States”. Now
select
OSTN
:
Now you can enter your username (number), password and server (ostel.me) as pro- vided
after signing up at https://ostel.me/users/sign_up.
Now you can make a call. The first time you connect to someone with ZRTP you have to verify
that the key exchange was successful. In the example below the confirmation word is “cieh”, you
can already talk to the other party and make sure you both see the same word. Once done, press ok.
You now have established a secure voice connection that cannot be intercepted. Beware that your
or the phone of the other party could be recording your conversation.
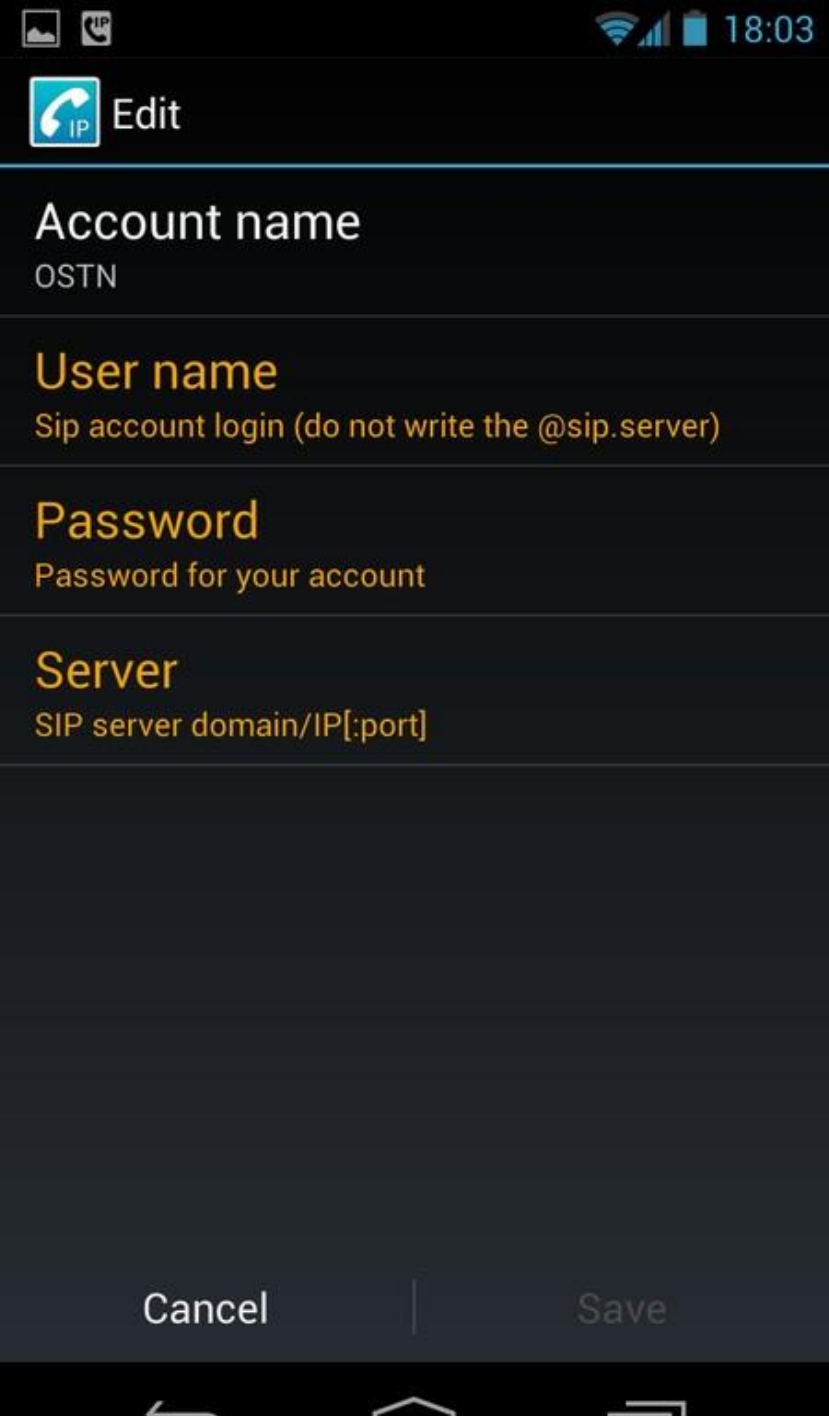
456
295
457
296
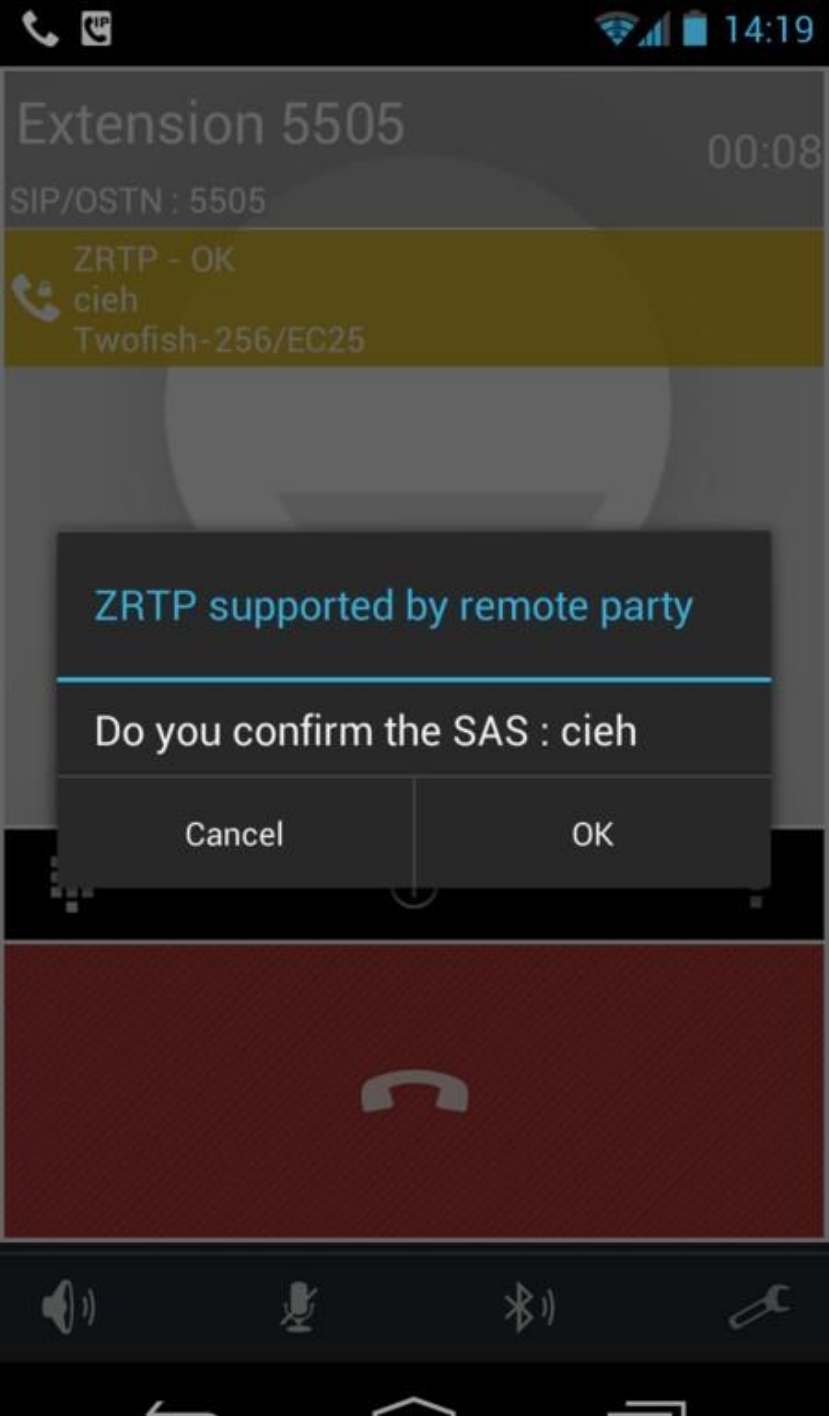
458
Figure 12.2:OSTN

459
297
13
Instant Messaging Encryption
13.1
Setting up Encrypted Instant Messaging
13.1.1
AndroidInstalling Gibberbot
https://guardianproject.info/apps/gibber/
Gibberbot is a secure chat client capable of end-to-end encryption. It works with Google,
Facebook, any Jabber or XMPP server. Gibberbot uses the Off-The-Record encryption standard
(OTR) to enable true verifiable end-to-end encrypted communica- tions.
You can install Gibberbot through the Google Play store or from another trusted source.
You can securely chat with other programs with OTR support such as Adium, Pidgin on the
desktop, Gibberbot on Android or ChatSecure on iOS.
13.1.2
iOSInstallingChatSecure
http://chrisballinger.info/apps/chatsecure/
ChatSecure is a secure chat client capable of end-to-end encryption. It works with Google,
Facebook, any Jabber or XMPP server. ChatSecure uses the Off-the-Record encryption standard
(OTR) to enable true verifiable end-to-end encrypted communica- tions.
You can install ChatSecure through the iTunes store
You can securely chat with other programs with OTR support such as Adium, Pidgin on the
desktop, Gibberbot on Android or ChatSecure on iOS.
13.1.3
UbuntuInstallingPidgin
http://pidgin.im/
Pidgin is a secure chat client capable of end-to-end encryption. It works with Google, Facebook,
any Jabber or XMPP server. Pidgin uses the Off-the-Record encryption stan- dard (OTR) to enable
true verifiable end-to-end encrypted communications.
You can install via Ubuntu Software Center, search for pidgin-otr to install pidgin and the pidgin
otr plugin.
Once installed you can enable otr for any account you setup in pidgin.
You can securely chat with other programs with OTR support such as Adium, Pidgin on the
desktop, Gibberbot on Android or ChatSecure on iOS.
13 Instant Messaging Encryption

460
13.1.4
OSXInstallingAdium
http://www.adium.im/
Adium is a secure chat client capable of end-to-end encryption. It works with Google, Facebook,
any Jabber or XMPP server. Adium uses the Off-the-Record encryption stan- dard (OTR) to
enable true verifiable end-to-end encrypted communications.
Installing Adium is similar to installing most Mac OS X applications.
1.
Download the Adium disk image from http://www.adium.im/.
2.
If an Adium window does not open automatically, double click the downloaded file
3.Drag the Adium application to your Applications folder.
4.“Eject” the Adium disk image, which has an icon of a drive
5.
The Adium disk image will still be present in your download folder (probably on your
desktop). You can drag this file to the trash, as it is no longer needed.
6.
To load Adium, locate it in the Applications folder and double click.
You can securely chat with other programs with OTR support such as Adium, Pidgin on the
desktop, Gibberbot on Android or ChatSecure on iOS.
13.1.5
WindowsInstallingPidgin
http://pidgin.im/
Pidgin is a secure chat client capable of end-to-end encryption. It works with Google, Facebook,
any Jabber or XMPP server. Pidgin uses the Off-the-Record encryption stan- dard (OTR) to enable
true verifiable end-to-end encrypted communications.
To use Pidgin with OTR on Windows, you have to install Pidgin and the OTR plugin for
Pidgin.
1.
Download the latest version of Pidgin for Windows from http://www.pidgin.im/
download/windows/
2.
Run the Pidgin Installer
3.
Download the latest version of “OTR plugin for Pidgin” at http://www.cypherpunks.
ca/otr/#downloads
4.
Run the OTR Plugin Installer
Now you can use OTR with any account you setup in Pidgin.
You can securely chat with other programs with OTR support such as Adium, Pidgin on the
desktop, Gibberbot on Android or ChatSecure on iOS.
13.1.6
AllOScrypto.cat
https://crypto.cat
Cryptocat is an open source web application intended to allow secure, encrypted online chatting.
Cryptocat encrypts chats on the client side, only trusting the server with data
13.1 Setting up Encrypted Instant Messaging
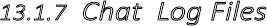
461
that is already encrypted. Cryptocat is delivered as a browser extension and offers plugins for
Google Chrome, Mozilla Firefox and Apple Safari.
Cryptocat intends to provide means for impromptu, encrypted communications that offer more
privacy than services such as Google Talk, while maintaining a higher level of accessibility than
other high-level encryption platforms, and furthermore allows for multiple users in one chat room.
13.1.7
ChatLogFiles
Some of the Chat Clients listed above e.g. Adium, store plaintext, unencrypted Chat Logs,
often by default, even when the OTR “security
/
privacy” plug-in is installed.
If you are taking OTR precautions to protect your chats from snoopers over the wire or over
the air, you should either double check that you have manually switched off Chat Session
Logging, or ensure that the Chat Logs you deliberately intend to keep are created on an
encrypted disk drive or volume, in case your computer is lost, stolen or seized. It is also worth
asking the person you are chatting with if they are inadvertently logging the chat with their own
Chat Client software.
14
Secure File Sharing
14.1
Installing I2P on Ubuntu Lucid Lynx (and newer)
and derivatives like Linux Mint & Trisquel
1.
Open a terminal and enter:
sudo apt-add-repository ppa:i2p-maintainers/i2p
This command will add the PPA to /etc/apt/sources.list.d and fetch the gpg key that the
repository has been signed with. The GPG key ensures that the packages have not been
tampered with since being built.
2.
Notify your package manager of the new PPA by entering
sudo apt-get update
This command will retrieve the latest list of software from each repository that is enabled on your
system, including the I2P PPA that was added with the earlier command.
3.
You are now ready to install I2P!
sudo apt-get install i2p
4.
Your browse should open up with your local I2P router console, to browse i2p domains
you have to configure your browser to use the i2p proxy. Also check your connection
status on the left side on the router console. If your status is
Network: Firewalled
your connection will be rather slow. The first time you start I2P it may take a few
minutes to integrate you into the network and find additional peers to optimize your
integration, so please be patient.
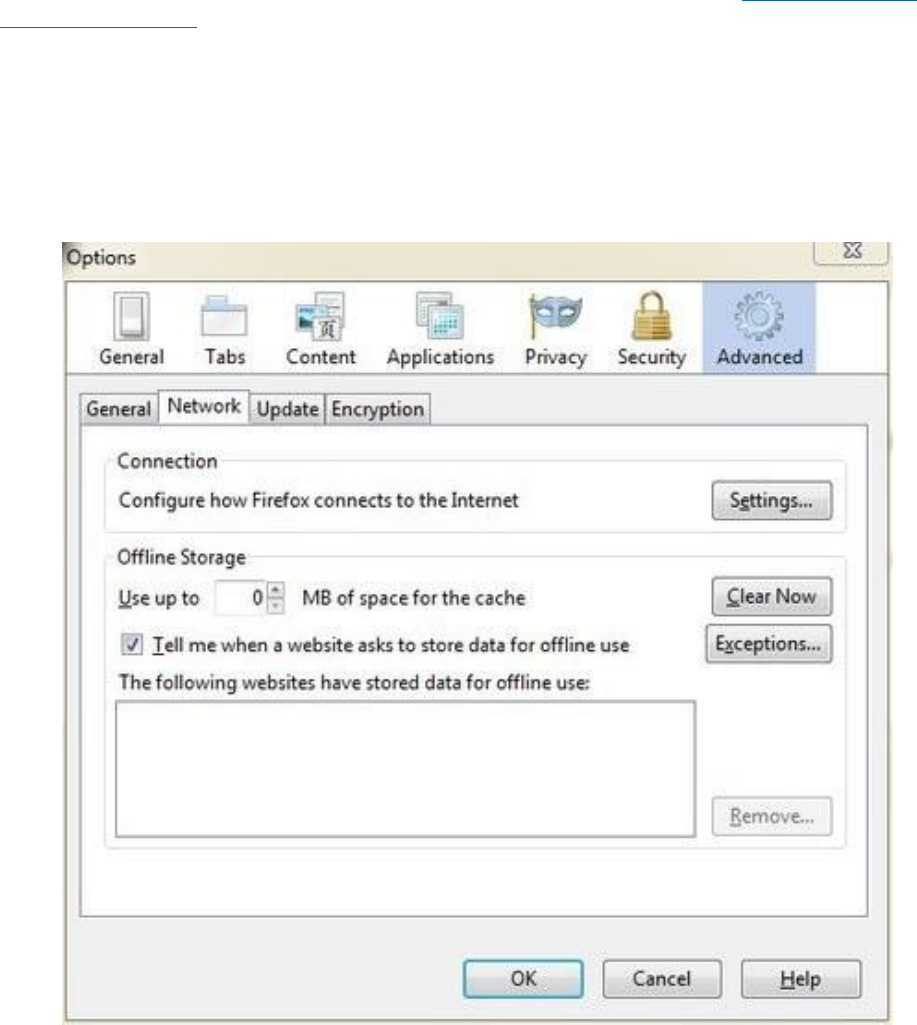
462
From the Tools menu, select Options to bring up the Firefox settings panel. Click the icon labelled
Advanced, then click on the Network tab. In the Connections section, click on the Settings button.
You’ll see a Window like the following:
In the Connection Settings window, click the circle next to Manual proxy configuration, then enter
127.0.0.1, port 4444 in the HTTP Proxy field. Enter 127.0.0.1, port 4445 in the SSL Proxy field.
Be sure to enter localhost and 127.0.0.1 into the “No Proxy for” box.
For more information and proxy settings for other browsers check https://www.i2p2.
de/htproxyports.htm
Figure 14.1:I2P
14.1 Installing I2P on Ubuntu Lucid Lynx (and newer) and derivatives like Linux Mint & Trisquel
463
Figure 14.2:I2P
14.2
Instructions for Debian Lenny and newer
For more information visit this page https://www.i2p2.de/debian.html
14.3
Starting I2P
Using these I2P packages the I2P router can be started in the following three ways:
•
“on demand” using the i2prouter script. Simply run “i2prouter start” from a com- mand
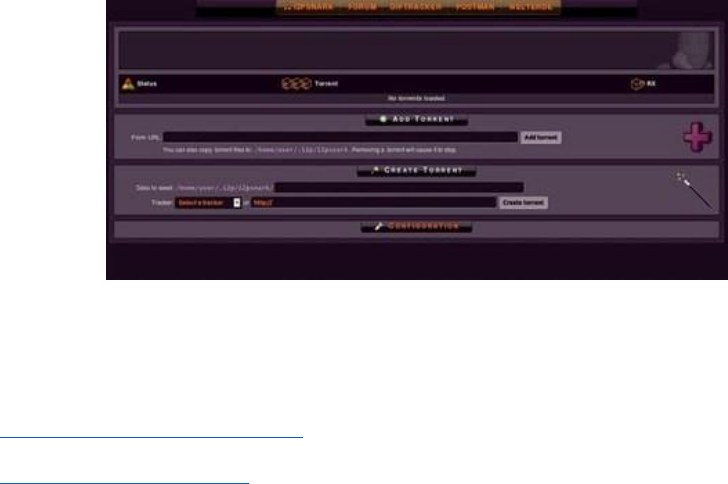
464
prompt. (Note: Do not use sudo or run it as root!).
•
as a service that automatically runs when your system boots, even before logging in. The
service can be enabled with “dpkg-reconfigure i2p” as root or using sudo. This is the
recommended means of operation.
14.4
Anonymous Bittorrent with I2PSnark
We can use the I2P network to share and download files without the entire world knowing
who is
sharing them. or even the fact that you are running a torrent client, since i2p network is end-to-
end encrypted the only thing known to outsider is you are running I2P.
I2p come with a built-in
torrent client that run inside the browser called I2PSnark.
You can access it through this direct link:
http://localhost:7657/i2psnark/
or through the router console: http://localhost:7657/ and clicking on the torrent
icon.
Once started you should see a screen similar to the following:
Figure 14.3:I2P
You can search for a torrent using one of following bittorrent trackers:
•
http://tracker.postman.i2p/
•
http://diftracker.i2p/
14.4 Anonymous Bittorrent with I2PSnark
Copy the torrent or magnet link and past it in the I2PSnark window, and click
Add torrent
.
the file will be downloaded inside the
/home/user/.i2p/i2psnark
folder.
NOTE:
•
Since I2P is a closed network, you can’t download normal torrents found on regular internet
with it, and it can’t be used to make downloading them anonymous!
•
The speed seems to be slightly lower than usual which is caused by the anonymiza- tion. I
think that the download rates are still acceptable if you consider that you download and share
anonymously.
465
15
Appendices
0xcaca0 Adam Hyde Ahmed Mansour Alice Miller A Ravi Ariel Viera Asher Wolf AT Austin
Martin Ben Weissmann Bernd Fix Brendan Howell Brian Newbold Carola Hesse Chris Pinchen
Dan Hassan Daniel Kinsman Danja Vasiliev DÃľvai NaÌĄndor djmat- tyg007 Douwe Schmidt
Edward Cherlin Elemar Emile Denichaud Emile den Tex Erik Stein Erinn Clark Freddy Martinez
Freerk Ohling Greg Broiles Haneef Mubarak he- len varley jamieson Janet Swisher Jan Gerber
Jannette Mensch Jens Kubieziel jmorahan Josh Datko Joshua Datko Julian Oliver Kai Engert Karen
Reilly l3lackEyedAngels leoj3n LiamO Lonneke van der Velden Malte Malte Dik Marta Peirano
Mart van Santen mdim- itrova Michael Henriksen Nart Villeneuve Nathan Andrew Fain Nathan
Houle Niels El- gaard Larsen Petter Ericson Piers Plato Punkbob Roberto Rastapopoulos Ronald
Deib- ert Ross Anderson Sacha van Geffen Sam Tennyson Samuel Carlisle Samuel L. Tennyson
Seth Schoen Steven Murdoch StooJ Story89 Ted W Ted Wood Teresa Dillon therealplato Tomas
Krag Tom Boyle Travis Tueffel Uwe Lippmann WillMorrison Ximin Luo Yuval Adam zandi
Zorrino Zorrinno
15.1
Cryptography and Encryption
Cryptography and encryption are similar terms, the former being the science and latter the
implementation of it. The history of the subject can be traced back to ancient civilisations, when
the first humans began to organise themselves into groups. This was driven in part by the
realisation that we were in competition for resources and tribal organisation, warfare and so
forth were necessary, so as to keep on top of the heap. In this respect cryptography and
encryption are rooted in warfare, progression and resource management, where it was necessary
to send secret messages to each other without the
enemy deciphering ones moves.
Writing is actually one of the earliest forms of cryptography as not everyone could read. The
word cryptography stems from the Greek words kryptos (hidden) and graphein (writing). In this
respect cryptography and encryption in their simplest form refer to the writing of hidden messages,
which require a system or rule to decode and read them. Essentially this enables you to protect
your privacy by scrambling information in a way that it is only recoverable with certain knowledge
(passwords or passphrases) or possession (a key).
Put in another way, encryption is the translation of information written in plaintext into a non-
readable form (ciphertext) using algorithmic schemes (ciphers). The goal is to use the right key to
unlock the ciphertext and return it back into its original plain text form so it becomes readable
again.
Although most encryption methods refer to written word, during World War Two, the US military
used Navajo Indians, who traveled between camps sending messages in their native tongue. The
reason the army used the Navajo tribe was to protect the informa- tion they were sending from the
Japanese troops, who famously could not decipher the Navajo’s spoken language. This is a very
simple example of using a language to send messages that you do not want people to listen into or
know what you’re discussing. Why is encryption important? —————————-
Computer and telecommunication networks store digital echoes or footprints of our thoughts and
records of personal lives.
From banking, to booking, to socialising: we submit a variety of detailed, personalised
information, which is driving new modes of business, social interaction and behavior. We have now

466
become accustomed to giving away what was (and still is) considered private information in
exchange for what is presented as more personalised and tailored services, which might meet our
needs, but cater to our greed.
But how do we protect who sees, controls and uses this information?
Lets consider a scenario whereby we all thought it was fine to send all our communica- tion on
open handwritten postcards. From conversations with your doctor, to intimate moments with our
lovers, to legal discussions you may have with lawyers or accountants. It’s unlikely that we would
want all people to be able to read such communications. So instead we have written letters in
sealed envelopes, tracking methods for sending post, closed offices and confidential agreements,
which help to keep such communication private. However given the shift in how we communicate,
much more of this type of interaction is taking place online. More importantly it is taking place
through online spaces, which are not private by default and open to people with little technical skills
to snoop into the matters that can mean the most to our lives.
Online privacy and encryption is something we therefore need to be aware of and practice daily.
In the same way we would put an important letter into an envelope or have a conversation behind a
closed door. Given that so much of our private communication is now happening in networked
and online spaces, we should consider the interface, like envelopes or seals, which protect this
material as a basic necessity and human right.
15.1.1
Encryptionexamples
Throughout history we can find examples of cipher methods, which have been used to keep
messages private and secret.
15.1.2
AWarning!
“There are two kinds of cryptography in this world: cryptography that will stop your kid
sister from reading your files, and cryptography that will stop major governments from
reading your files” - Bruce Schneier, Applied Cryp- tography, 1996
This chapter first explains a number of historical cryptographic systems and then provides a
summary of modern techniques. The historical examples illustrate how cryp-
tography emerged, but are considered broken in the face of modern computers. They can be fun
to learn, but please don’t use them for anything sensitive!
15.1.3
Historicalciphers
Classical ciphers refer to historical ciphers, which are now out of popular use or no longer
applicable. There are two general categories of classical ciphers: transposition and substitution
ciphers.
In a transposition cipher, the letters themselves are kept unchanged, but the order within the
message is scrambled according to some well-defined scheme. An example of a transposition
cipher is Skytale, which was used in ancient Rome and Greece. A paperstrip was wrapped
around a stick and the message written across it. That way the message could not be read unless
wound around a stick of similar diameter again.
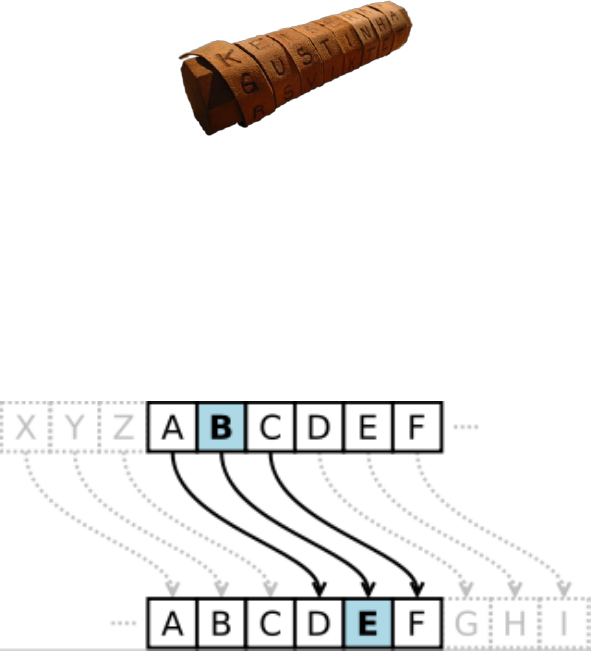
467
Figure 15.1:Cryptography
Image:SkytaletakenfromWikimediaCommons(3.10.12)
A substitution cipher is a form of classical cipher whereby letters or groups of letters are
systematically replaced throughout the message for other letters (or groups of letters). Substitution
ciphers are divided into monoalphabetic and polyalphabetic substitutions. The Caesar Shift cipher
is common example of amonoalphabetic substitution ciphers, where the letters in the alphabet are
shifted in one direction or another.
Figure 15.2:Cryptography
Image:CaesarShiftCiphertakenfromWikimediaCommons (3.10.12)
Polyalphabetic substitutions are more complex than substitution ciphers as they use more than
one alphabet and rotate them. For example, The Alberti cipher, which was the
first polyalphabetic cipher was created by Leon Battista Alberti, a 15th century Italian, Renaissance
polymath and humanist who is also credited as the godfather of western cryptography. His cipher is
similar to the VigenÃĺre cipher, where every letter of the alphabet gets a unique number (e.g. 1-26).
The message is then encrypted by writing down the message along with the password repeatedly
written beneath it.
In the VigenÃĺre cipher the corresponding numbers of the letters of message and key are summed
up (with numbers exceeding the alphabet being dragged around the back) making the message so
unreadable that it couldn’t be deciphered for centuries (nowadays, with the help of computers, this
obviously isn’t true anymore).

468
Figure 15.3:Cryptography
Image:VigenÃĺreciphertakenfromWikimediaCommons (3.10.12)
During World War 2 there was a surge in crypography, which lead to the development of new
algorithms such as the one-time pad (OTP). The OTP algorithm combines plaintext with a random
key that is as long as the plaintext so that each character is only used once. To use it you need two
copies of the pad, which are kept by each user and exchanged via a secure channel. Once the
message is encoded with the pad, the pad is destroyed and the encoded message is sent. On the
recipient’s side, the encoded message has a duplicate copy of the pad from which the plaintext
message is generated. A good way to look at OTP is to think of it as a 100% noise source, which is
used to mask the message. Since both parties of the communication have copies of the noise source
they are the only people who can filter it out.
OTP lies behind modern day stream ciphers, which are explained below. Claude Shannon, (a key
player in modern cryptography and information theory), in his seminal 1949 paper “Communication
Theory of Secrecy Systems” demonstrated that theoretically all unbreakable ciphers should include
the OTP encryption, which if used correctly are impossible to crack.
469
15.1.4
Modern ciphers
Post the World Wars the field of cryptography became less of a public service and fell more
within the domain of governance. Major advances in the field began to reemerge in the mid-
1970s with the advent of personalised computers and the introduction of the Data Encryption
Standard (DES, developed at IBM in 1977 and later adopted by the
U.S government). Since 2001 we now use the AES, Advanced Encryption Standard), which is based
on symmetric cryptography forms.
Contemporary cryptography can be generally divided into what is called symmetric, asymmetric
and quantum cryptography.
Symmetric cryptography, or secret key, cryptography refers to ciphers where the same key is used
to both encrypt and decrypt the text or information involved. In this class of ciphers the key is shared
and kept secret within a restricted group and therefore it is not possible to view the encrypted
information without having the key. A simple analogy to secret key cryptography is having access
to a community garden, which has one key to open gate, which is shared by the community. You
cannot open the gate, unless you have the key. Obviously the issue here with the garden key and
with symmetric cryptography is if the key falls into the wrong hands, then an intruder or attacker
can get in and the security of the garden, or the data or information is compromised. Consequently
one of the main issues with this form of cryptography is the issue of key management. As a result
this method is best employed within single-user contexts or small group environments.
Despite this limitation symmetric key methods are considerably faster than asymmetric methods
and so are the preferred mechanism for encrypting large chunks of text.
Symmetric ciphers are usually implemented using
block ciphers
or
stream ciphers
.
Block ciphers work by looking at the input data in 8 or 16 or 32 byte blocks at a time
and
spreading the input and key within those blocks. Different modes of operation are
performed on
the data in order to transform and spread the data between blocks. Such
ciphers use a secret key to convert a fixed block of plain text into cipher text. The same key is
then used to decrypt the cipher text.
In comparison stream ciphers (also known as state cipher) work on each plaintext digit by creating
a corresponding keystream which forms the ciphertext. The keystream refers to a stream of random
characters (bits, bytes, numbers or letters) on which various addi- tive or subtractive functions are
performed and combined to a character in the plaintext message, which then produces the ciphertext.
Although this method is very secure, it is not always practical, since the key of the same length as
the message needs to be trans- mitted in some secure way so that receiver can decypher the message.
Another limitation is that the key can only be used once and then its discarded. Although this can
mean almost watertight security, it does limit the use of the cipher.
Asymmetric ciphers work much more complex mathematical problems with back doors,
enabling faster solutions on smaller, highly important pieces of data. They also work on fixed
data sizes, typically 1024-2048 bits and and 384 bits. What makes them special is that they help
solve some of the issues with key distribution by allocating one public and one private pair per
person, so that everyone just needs to know everyone else’s public portion. Asymmetric ciphers
are also used for digital signatures. Where as symmetric ciphers are generally used for message
authenticity. Symmetric ciphers cannot non- repudiation signatures (i.e., signatures that you
cannot later deny that you did not sign). Digital signatures are very important in modern day
cryptography. They are similar to wax seals in that they verify who the message is from and
like seals are unique to that person. Digital signatures are one of the methods used within public

470
key systems, which have transformed the field of cryptography are central to modern day
Internet security and online transactions.
15.1.5
QuantumCryptography
Quantum cryptography is the term used to describe the type of cryptography that is now necessary
to deal with the speed at which we now process information and the related security measures that
are necessary. Essentially it deals with how we use quan- tum communication to securely exchange
a key and its associated distribution. As the machines we use become faster the possible
combinations of public-key encryption and digital signatures becomes easier to break and quantum
cryptography deals with the types of algorithms that are necessary to keep pace with more
advanced networks.
15.1.6
Challenges&Implications
At the heart of cryptography lies the challenge of how we use and communicate informa- tion. The
above methods describe how we encrypt written communication but obviously as shown in the
Navajo example other forms of communication (speech, sound, image etc) can also be encrypted
using different methods.
The main goal and skill of encryption is to apply the right methods to support trust- worthy
communication. This is achieved by understanding the tradeoffs, strengths and weaknesses of
different cipher methods and how they relate to the level of security and
privacy required. Getting this right depends on the task and context.
Importantly when we speak about communication, we are speaking about trust. Tra- ditionally
cryptography dealt with the hypothetical scenarios, where the challenge was to address how ‘Bob’
could speak to ‘Alice’ in a private and secure manner.
Our lives are now heavily mediated via computers and the Internet. So the boundaries between
Bob, Alice + the ‘other’ (Eve, Oscar, Big Brother, your boss, ex-boyfriend or the government) are
a lot more blurred. Given the quantum leaps in computer processing, in order for ‘us’, Bob’s and
Alice’s to have trust in the system, we need to know who we are talking too, we need to know who
is listening and importantly who has the potential to eavesdrop. What becomes important is how
we navigate this complexity and feel in control and secure, so that you can engage and communicate
in a trustful manner, which respects our individual freedoms and privacy.
15.2
Glossary
Much of this content is based on http://en.cship.org/wiki/Special:Allpages
15.2.1
aggregator
An aggregator is a service that gathers syndicated information from one or many sites and makes it
available at a different address. Sometimes called an RSS aggregator, a feed aggregator, a feed
reader, or a news reader. (Not to be confused with a Usenet News reader.)
15.2.2
anonymity
(Not be confused with privacy, pseudonymity, security, or confidentiality.)

471
Anonymity on the Internet is the ability to use services without leaving clues to one’s identity or
being spied upon. The level of protection depends on the anonymity tech- niques used and the extent
of monitoring. The strongest techniques in use to protect anonymity involve creating a chain of
communication using a random process to select some of the links, in which each link has access to
only partial information about the process. The first knows the user’s Internet address (IP) but not
the content, destina- tion, or purpose of the communication, because the message contents and
destination information are encrypted. The last knows the identity of the site being contacted, but
not the source of the session. One or more steps in between prevents the first and last links from
sharing their partial knowledge in order to connect the user and the target site.
15.2.3
anonymousremailer
An anonymous remailer is a service that accepts e-mail messages containing instructions for
delivery, and sends them out without revealing their sources. Since the remailer has access to
the user’s address, the content of the message, and the destination of the
message, remailers should be used as part of a chain of multiple remailers so that no one remailer
knows all this information.
15.2.4
ASP(applicationserviceprovider)
An ASP is an organization that offers software services over the Internet, allowing the software to
be upgraded and maintained centrally.
15.2.5
backbone
A backbone is one of the high-bandwidth communications links that tie together networks in
different countries and organizations around the world to form the Internet.
15.2.6
badware
See malware.
15.2.7
bandwidth
The bandwidth of a connection is the maximum rate of data transfer on that connec- tion, limited
by its capacity and the capabilities of the computers at both ends of the connection.
15.2.8
bash(Bourneagainshell)
The bash shell is a command-line interface for Linux/Unix operating systems, based on the Bourne
shell.
15.2.9
BitTorrent
BitTorrent is a peer-to-peer file-sharing protocol invented by Bram Cohen in 2001. It allows
individuals to cheaply and effectively distribute large files, such as CD images, video, or music files.
472
15.2.10
blacklist
A blacklist is a list of forbidden things. In Internet censorship, lists of forbidden Web sites or the
IP addresses of computers may be used as blacklists; censorware may allow access to all sites except
for those specifically listed on its blacklist. An alternative to a blacklist is a whitelist, or a list of
permitted things. A whitelist system blocks access to all sites except for those specifically listed
on the whitelist. This is a less common approach to Internet censorship. It is possible to combine
both approaches, using string matching or other conditional techniques on URLs that do not match
either list.
15.2.11
bluebar
The blue URL bar (called the Bluebar in Psiphon lingo) is the form at the top of your Psiphon node
browser window, which allows you to access blocked site by typing its URL inside.
See also Psiphon node
15.2.12
block
To block is to prevent access to an Internet resource, using any number of methods.
15.2.13
bookmark
A bookmark is a placeholder within software that contains a reference to an external resource. In a
browser, a bookmark is a reference to a Web page – by choosing the bookmark you can quickly
load the Web site without needing to type in the full URL.
15.2.14
bridge
See Tor bridge.
15.2.15
bruteforceattack
A brute force attack consists of trying every possible code, combination, or password until you find
the right one. These are some of the most trivial hacking attacks.
15.2.16
cache
A cache is a part of an information-processing system used to store recently used or frequently used
data to speed up repeated access to it. A Web cache holds copies of Web page files.
15.2.17
censor
To censor is to prevent publication or retrieval of information, or take action, legal or otherwise,
against publishers and readers.

473
15.2.18
censorware
Censorware is software used to filter or block access to the Internet. This term is most often used to
refer to Internet filtering or blocking software installed on the client machine (the PC which is used
to access the Internet). Most such client-side censorware is used for parental control purposes.
Sometimes the term censorware is also used to refer to software used for the same purpose
installed on a network server or router.
15.2.19
CGI(CommonGatewayInterface)
CGI is a common standard used to let programs on a Web server run as Web applications. Many
Web-based proxies use CGI and thus are also called “CGI proxies”. (One popular CGI proxy
application written by James Marshall using the Perl programming language is called CGIProxy.)
15.2.20
chat
Chat, also called instant messaging, is a common method of communication among two or more
people in which each line typed by a participant in a session is echoed to all of the others. There
are numerous chat protocols, including those created by specific companies (AOL, Yahoo!,
Microsoft, Google, and others) and publicly defined protocols. Some chat client software uses only
one of these protocols, while others use a range of popular protocols.
15.2.21
cipher
In cryptography, a cipher (or cypher) is an algorithm for performing encryption or de- cryption
15.2.22
circumvention
Circumvention is publishing or accessing content in spite of attempts at censorship.
15.2.23
CommonGatewayInterface
See CGI.
15.2.24
commandlineinterface
A method of controlling the execution of software using commands entered on a keyboard, such as
a Unix shell or the Windows command line.
15.2.25
cookie
A cookie is a text string sent by a Web server to the user’s browser to store on the user’s computer,
containing information needed to maintain continuity in sessions across multiple Web pages, or
across multiple sessions. Some Web sites cannot be used without accepting and storing a cookie.
Some people consider this an invasion of privacy or a security risk.
15.2.26
countrycodetopleveldomain(ccTLD)
Each country has a two-letter country code, and a TLD (top-level domain) based on it, such as .ca
for Canada; this domain is called a country code top-level domain. Each
474
such ccTLD has a DNS server that lists all second-level domains within the TLD. The Internet root
servers point to all TLDs, and cache frequently-used information on lower- level domains.
15.2.27
cryptography
Cryptography is the practice and study of techniques for secure communication in the presence of
third parties (called adversaries). More generally, it is about constructing and analyzing protocols
that overcome the influence of adversaries and which are related to various aspects in information
security such as data confidentiality, data integrity, authentication, and non-repudiation. Modern
cryptography intersects the disciplines of mathematics, computer science, and electrical engineering.
Applications of cryptography include ATM cards, computer passwords, and electronic commerce.
15.2.28
DARPA(DefenseAdvancedProjectsResearchAgency)
DARPA is the successor to ARPA, which funded the Internet and its predecessor, the ARPAnet.
15.2.29
decryption
Decryption is recovering plain text or other messages from encrypted data with the use of a key.
See also encryption.
15.2.30
diskencryption
Disk encryption is a technology which protects information by converting it into unread- able
code that cannot be deciphered easily by unauthorized people. Disk encryption uses disk
encryption software or hardware to encrypt every bit of data that goes on a disk or disk volume.
Disk encryption prevents unauthorized access to data storage.
15.2.31
domain
A domain can be a Top-Level Domain (TLD) or secondary domain on the Internet.
See also Top-Level Domain, country code Top-Level Domain and secondary domain.
15.2.32
DNS(DomainNameSystem)
The Domain Name System (DNS) converts domain names, made up of easy-to-remember
combinations of letters, to IP addresses, which are hard-to-remember strings of num- bers. Every
computer on the Internet has a unique address (a little bit like an area code+telephone number).
15.2.33
DNSleak
A DNS leak occurs when a computer configured to use a proxy for its Internet connec- tion
nonetheless makes DNS queries without using the proxy, thus exposing the user’s attempts to
connect with blocked sites. Some Web browsers have configuration options to force the use of the
proxy.

475
15.2.34
DNSserver
A DNS server, or name server, is a server that provides the look-up function of the Domain Name
System. It does this either by accessing an existing cached record of the IP address of a specific
domain, or by sending a request for information to another name server.
15.2.35
DNStunnel
A DNS tunnel is a way to tunnel almost everything over DNS/Nameservers.
Because you “abuse” the DNS system for an unintended purpose, it only allows a very slow
connection of about 3 kb/s which is even less than the speed of an analog modem. That is not enough
for YouTube or file sharing, but should be sufficient for instant messengers like ICQ or MSN
Messenger and also for plain text e-mail.
On the connection you want to use a DNS tunnel, you only need port 53 to be open; therefore it
even works on many commercial Wi-Fi providers without the need to pay.
The main problem is that there are no public modified nameservers that you can use. You
have to set up your own. You need a server with a permanent connection to the Internet running
Linux. There you can install the free software OzymanDNS and in combination with SSH and
a proxy like Squid you can use the tunnel. More Information on this on
http://www.dnstunnel.de.
15.2.36
Eavesdropping
Eavesdropping is listening to voice traffic or reading or filtering data traffic on a telephone line or
digital data connection, usually to detect or prevent illegal or unwanted activities or to control or
monitor what people are talking about.
15.2.37
email
E-mail, short for electronic mail, is a method to send and receive messages over the Internet. It is
possible to use a Web mail service or to send e-mails with the SMTP protocol and receive them with
the POP3 protocol by using an e-mail client such as Outlook Express or Thunderbird. It is
comparatively rare for a government to block e-mail, but e-mail surveillance is common. If e-mail
is not encrypted, it could be read easily by a network operator or government.
15.2.38
embeddedscript
An embedded script is a piece of software code.
15.2.39
encryption
Encryption is any method for recoding and scrambling data or transforming it mathe- matically
to make it unreadable to a third party who doesn’t know the secret key to decrypt it. It is possible
to encrypt data on your local hard drive using software like TrueCrypt
(http://www.truecrypt.org) or to encrypt Internet traffic with TLS/SSL or SSH.
See also decryption.
476
15.2.40
exitnode
An exit node is a Tor node that forwards data outside the Tor network.
See also middleman node.
15.2.41
filesharing
File sharing refers to any computer system where multiple people can use the same information, but
often refers to making music, films or other materials available to others free of charge over the
Internet.
15.2.42
filespreadingengine
A file spreading engine is a Web site a publisher can use to get around censorship. A user only has
to upload a file to publish once and the file spreading engine uploads that file to some set of
sharehosting services (like Rapidshare or Megaupload).
15.2.43
filter
To filter is to search in various ways for specific data patterns to block or permit com- munications.
15.2.44
Firefox
Firefox is the most popular free and open source Web browser, developed by the Mozilla
Foundation.
15.2.45
forum
On a Web site, a forum is a place for discussion, where users can post messages and com- ment on
previously posted messages. It is distinguished from a mailing list or a Usenet newsgroup by the
persistence of the pages containing the message threads. Newsgroup and mailing list archives, in
contrast, typically display messages one per page, with nav- igation pages listing only the headers
of the messages in a thread.
15.2.46
frame
A frame is a portion of a Web page with its own separate URL. For example, frames are frequently
used to place a static menu next to a scrolling text window.
15.2.47
FTP(FileTransferProtocol)
The FTP protocol is used for file transfers. Many people use it mostly for downloads; it can also be
used to upload Web pages and scripts to some Web servers. It normally uses ports 20 and 21, which
are sometimes blocked. Some FTP servers listen to an uncommon port, which can evade port-based
blocking.
A popular free and open source FTP client for Windows and Mac OS is FileZilla. There are also
some Web-based FTP clients that you can use with a normal Web browser like Firefox.

477
15.2.48
fulldiskencryption
see disk encryption.
15.2.49
gateway
A gateway is a node connecting two networks on the Internet. An important example is a
national gateway that requires all incoming or outgoing traffic to go through it.
15.2.50
GNUPrivacyGuard
GNU Privacy Guard (GnuPG or GPG) is a GPL Licensed alternative to the PGP suite of
cryptographic software. GnuPG is compliant with RFC 4880, which is the current IETF standards
track specification of OpenPGP.
see also Pretty Good Privacy (PGP).
15.2.51
GPG
see GNU Privacy Guard.
15.2.52
honeypot
A honeypot is a site that pretends to offer a service in order to entice potential users to use it,
and to capture information about them or their activities.
15.2.53
hop
A hop is a link in a chain of packet transfers from one computer to another, or any computer along
the route. The number of hops between computers can give a rough measure of the delay (latency)
in communications between them. Each individual hop is also an entity that has the ability to
eavesdrop on, block, or tamper with communications.
15.2.54
HTTP(HypertextTransferProtocol)
HTTP is the fundamental protocol of the World Wide Web, providing methods for re- questing and
serving Web pages, querying and generating answers to queries, and access- ing a wide range of
services.
15.2.55
HTTPS(SecureHTTP)
Secure HTTP is a protocol for secure communication using encrypted HTTP messages. Messages
between client and server are encrypted in both directions, using keys generated when the connection
is requested and exchanged securely. Source and destination IP addresses are in the headers of every
packet, so HTTPS cannot hide the fact of the communication, just the contents of the data
transmitted and received.
15.2.56
IANA(InternetAssignedNumbersAuthority)
IANA is the organization responsible for technical work in managing the infrastructure of the
Internet, including assigning blocks of IP addresses for top-level domains and licensing domain

478
registrars for ccTLDs and for the generic TLDs, running the root name servers of the Internet, and
other duties.
15.2.57
ICANN(InternetCorporationforAssignedNames and Numbers)
ICANN is a corporation created by the US Department of Commerce to manage the highest levels
of the Internet. Its technical work is performed by IANA.
15.2.58
InstantMessaging(IM)
Instant messaging is either certain proprietary forms of chat using proprietary protocols, or chat in
general. Common instant messaging clients include MSN Messenger, ICQ, AIM or Yahoo!
Messenger.
15.2.59
Intermediary
See man in the middle.
15.2.60
Internet
The Internet is a network of networks interconnected using TCP/IP and other commu- nication
protocols.
15.2.61
IP(InternetProtocol)Address
An IP address is a number identifying a particular computer on the Internet. In the previous version
4 of the Internet Protocol an IP address consisted of four bytes (32 bits), often represented as four
integers in the range 0-255 separated by dots, such as
74.54.30.85. In IPv6, which the Net is currently switching to, an IP address is four times longer, and
consists of 16 bytes (128 bits). It can be written as 8 groups of 4 hex digits separated by colons, such
as 2001:0db8:85a3:0000:0000:8a2e:0370:7334.
15.2.62
IRC(Internetrelaychat)
IRC is a more than 20-year-old Internet protocol used for real-time text conversations (chat or instant
messaging). There exist several IRC networks – the largest have more than 50 000 users.
15.2.63
ISP(InternetServiceProvider)
An ISP (Internet service provider) is a business or organization that provides access to the Internet
for its customers.
15.2.64
JavaScript
JavaScript is a scripting language, commonly used in Web pages to provide interactive functions.
15.2.65
KeePass,KeePassX
KeePass and KeePassX are types of Password Manager.

479
15.2.66
keychainsoftware
see Password Manager.
15.2.67
keywordfilter
A keyword filter scans all Internet traffic going through a server for forbidden words or terms to
block.
15.2.68
latency
Latency is a measure of time delay experienced in a system, here in a computer network. It is
measured by the time between the start of packet transmission to the start of packet reception,
between one network end (e.g. you) to the other end (e.g. the Web server). One very powerful way
of Web filtering is maintaining a very high latency, which makes lots of circumvention tools very
difficult to use.
15.2.69
logfile
A log file is a file that records a sequence of messages from a software process, which can be an
application or a component of the operating system. For example, Web servers or proxies may
keep log files containing records about which IP addresses used these services when and what pages
were accessed.
15.2.70
lowbandwidthfilter
A low-bandwidth filter is a Web service that removes extraneous elements such as adver- tising and
images from a Web page and otherwise compresses it, making page download much quicker.
15.2.71
malware
Malware is a general term for malicious software, including viruses, that may be installed or
executed without your knowledge. Malware may take control of your computer for purposes such
as sending spam. (Malware is also sometimes called badware.)
15.2.72
maninthemiddle
A man in the middle or man-in-the-middle is a person or computer capturing traffic on a
communication channel, especially to selectively change or block content in a way that undermines
cryptographic security. Generally the man-in-the-middle attack involves im- personating a Web site,
service, or individual in order to record or alter communications. Governments can run man-in-the-
middle attacks at country gateways where all traffic entering or leaving the country must pass.
15.2.73
middlemannode
A middleman node is a Tor node that is not an exit node. Running a middleman node can be safer
than running an exit node because a middleman node will not show up in third parties’ log files. (A
middleman node is sometimes called a non-exit node.)

480
15.2.74
monitor
To monitor is to check a data stream continuously for unwanted activity.
15.2.75
networkaddresstranslation(NAT)
NAT is a router function for hiding an address space by remapping. All traffic going out from the
router then uses the router’s IP address, and the router knows how to route incoming traffic to the
requestor. NAT is frequently implemented by firewalls. Because incoming connections are normally
forbidden by NAT, NAT makes it difficult to offer a service to the general public, such as a Web
site or public proxy. On a network where NAT is in use, offering such a service requires some kind
of firewall configuration or NAT traversal method.
15.2.76
networkoperator
A network operator is a person or organization who runs or controls a network and thus is in a
position to monitor, block, or alter communications passing through that network.
15.2.77
node
A node is an active device on a network. A router is an example of a node. In the Psiphon and Tor
networks, a server is referred to as a node.
15.2.78
nonexitnode
See middleman node.
15.2.79
obfuscation
Obfuscation means obscuring text using easily-understood and easily-reversed transfor- mation
techniques that will withstand casual inspection but not cryptanalysis, or making minor changes in
text strings to prevent simple matches. Web proxies often use obfusca- tion to hide certain names
and addresses from simple text filters that might be fooled by the obfuscation. As another example,
any domain name can optionally contain a final dot, as in “somewhere.com.”, but some filters
might search only for “somewhere.com” (without the final dot).
15.2.80
opennode
An open node is a specific Psiphon node which can be used without logging in. It automatically
loads a particular homepage, and presents itself in a particular language, but can then be used
to browse elsewhere.
See also Psiphon node.
15.2.81
OTR/OfftheRecordmessaging
Off-the-Record Messaging, commonly referred to as OTR, is a cryptographic protocol that provides
strong encryption for instant messaging conversations.

481
15.2.82
packet
A packet is a data structure defined by a communication protocol to contain specific information in
specific forms, together with arbitrary data to be communicated from one point to another. Messages
are broken into pieces that will fit in a packet for transmission, and reassembled at the other end of
the link.
15.2.83
passwordmanager
A password manager is software that helps a user organize passwords and PIN codes. The
software typically has a local database or a file that holds the encrypted password data for secure
logon onto computers, networks, web sites and application data files. KeePass
http://keepass.info/ is an example of a password manager.
15.2.84
pastebin
A web service where any kind of text can be dumped and read without registration. All text will
be visible publicly.
15.2.85
peertopeer
A peer-to-peer (or P2P) network is a computer network between equal peers. Unlike client-server
networks there is no central server and so the traffic is distributed only among the clients.This
technology is mostly applied to file sharing programs like BitTorrent, eMule and Gnutella. But also
the very old Usenet technology or the VoIP program Skype can be categorized as peer-to-peer
systems.
See also file sharing.
15.2.86
perfectforwardsecrecy
In an authenticated key-agreement protocol that uses public key cryptography, perfect forward
secrecy (or PFS) is the property that ensures that a session key derived from a set of long-term
public and private keys will not be compromised if one of the (long-term) private keys is
compromised in the future.
15.2.87
PrettyGood Privacy(PGP)
Pretty Good Privacy (PGP) is a data encryption and decryption computer program that provides
cryptographic privacy and authentication for data communication. PGP is often used for signing,
encrypting and decrypting texts, e-mails, files, directories and whole disk partitions to increase the
security of e-mail communications.
PGP and similar products follow the OpenPGP standard (RFC 4880) for encrypting and
decrypting data.
15.2.88
PHP
PHP is a scripting language designed to create dynamic Web sites and web applications. It is
installed on a Web server. For example, the popular Web proxy PHProxy uses this technology.
482
15.2.89
plaintext
Plain text is unformatted text consisting of a sequence of character codes, as in ASCII plain text
or Unicode plain text.
15.2.90
plaintext
Plaintext is unencrypted text, or decrypted text.
See also encryption, TLS/SSL, SSH.
15.2.91
privacy
Protection of personal privacy means preventing disclosure of personal information with- out the
permission of the person concerned. In the context of circumvention, it means preventing observers
from finding out that a person has sought or received information that has been blocked or is illegal
in the country where that person is at the time.
15.2.92
privatekey
see public key encryption/public-key cryptography.
15.2.93
POP3
Post Office Protocol version 3 is used to receive mail from a server, by default on port 110 with
an e-mail program such as Outlook Express or Thunderbird.
15.2.94
port
A hardware port on a computer is a physical connector for a specific purpose, using a particular
hardware protocol. Examples are a VGA display port or a USB connector.
Software ports also connect computers and other devices over networks using various protocols,
but they exist in software only as numbers. Ports are somewhat like numbered doors into different
rooms, each for a special service on a server or PC. They are identified by numbers from 0 to 65535.
15.2.95
protocol
A formal definition of a method of communication, and the form of data to be transmitted to
accomplish it. Also, the purpose of such a method of communication. For example, In- ternet
Protocol (IP) for transmitting data packets on the Internet, or Hypertext Transfer Protocol for
interactions on the World Wide Web.
15.2.96
proxyserver
A proxy server is a server, a computer system or an application program which acts as a gateway
between a client and a Web server. A client connects to the proxy server to request a Web page from
a different server. Then the proxy server accesses the resource by connecting to the specified server,
and returns the information to the requesting site. Proxy servers can serve many different purposes,
including restricting Web access or helping users route around obstacles.
483
15.2.97
Psiphonnode
A Psiphon node is a secured web proxy designed to evade Internet censorship. It is developed by
Psiphon inc. Psiphon nodes can be open or private.
15.2.98
privatenode
A private node is a Psiphon node working with authentication, which means that you have to
register before you can use it. Once registered, you will be able to send invitations to your
friends and relatives to use this specific node.
See also Psiphon node.
15.2.99
publickey
see public key encryption/public-key cryptography.
15.2.100
publickeyencryption/publickeycryptography
Public-key cryptography refers to a cryptographic system requiring two separate keys, one of which
is secret and one of which is public. Although different, the two parts of the key pair are
mathematically linked. One key locks or encrypts the plaintext, and the other unlocks or decrypts
the ciphertext. Neither key can perform both functions. One of these keys is published or public,
while the other is kept private.
Public-key cryptography uses asymmetric key algorithms (such as RSA), and can also be
referred to by the more generic term “asymmetric key cryptography.”
15.2.101
publiclyroutableIPaddress
Publicly routable IP addresses (sometimes called public IP addresses) are those reachable in the
normal way on the Internet, through a chain of routers. Some IP addresses are private, such as the
192.168.x.x block, and many are unassigned.
15.2.102
regularexpression
A regular expression (also called a regexp or RE) is a text pattern that specifies a set of text
strings in a particular regular expression implementation such as the UNIX grep utility. A text
string “matches” a regular expression if the string conforms to the pattern, as defined by the
regular expression syntax. In each RE syntax, some characters have special meanings, to allow
one pattern to match multiple other strings. For example, the regular expression lo+se matches
lose, loose, and looose.
15.2.103
remailer
An anonymous remailer is a service which allows users to send e-mails anonymously. The remailer
receives messages via e-mail and forwards them to their intended recipient after removing
information that would identify the original sender. Some also provide an anonymous return

484
address that can be used to reply to the original sender without disclosing her identity. Well-known
Remailer services include Cypherpunk, Mixmaster and Nym.
15.2.104
router
A router is a computer that determines the route for forwarding packets. It uses address information
in the packet header and cached information on the server to match address numbers with hardware
connections.
15.2.105
rootnameserver
A root name server or root server is any of thirteen server clusters run by IANA to direct traffic to
all of the TLDs, as the core of the DNS system.
15.2.106
RSS(RealSimpleSyndication)
RSS is a method and protocol for allowing Internet users to subscribe to content from a Web page,
and receive updates as soon as they are posted.
15.2.107
scheme
On the Web, a scheme is a mapping from a name to a protocol. Thus the HTTP scheme maps
URLs that begin with HTTP: to the Hypertext Transfer Protocol. The protocol determines the
interpretation of the rest of the URL, so that http://www.example.com/ dir/content.html
identifies a Web site and a specific file in a specific directory, and mailto:user@somewhere.com
is an e-mail address of a specific person or group at a
specific domain.
15.2.108
shell
A UNIX shell is the traditional command line user interface for the UNIX/Linux oper- ating systems.
The most common shells are sh and bash.
15.2.109
SOCKS
A SOCKS proxy is a special kind of proxy server. In the ISO/OSI model it operates between the
application layer and the transport layer. The standard port for SOCKS proxies is 1080, but they can
also run on different ports. Many programs support a connection through a SOCKS proxy. If not
you can install a SOCKS client like FreeCap, ProxyCap or SocksCap which can force programs to
run through the Socks proxy using dynamic port forwarding. It is also possible to use SSH tools
such as OpenSSH as a SOCKS proxy server.
15.2.110
screenlogger
A screenlogger is software able to record everything your computer displays on the screen. The main
feature of a screenlogger is to capture the screen and log it into files to view at any time in the
future. Screen loggers can be used as powerful monitoring tool. You should be aware of any screen
logger running on any computer you are using, anytime.
485
15.2.111
script
A script is a program, usually written in an interpreted, non-compiled language such as JavaScript,
Java, or a command interpreter language such as bash. Many Web pages include scripts to manage
user interaction with a Web page, so that the server does not have to send a new page for each
change.
15.2.112
smartphone
A smartphone is a mobile phone that offers more advanced computing ability and connec- tivity
than a contemporary feature phone, such as Web access, ability to run elaborated operating systems
and run built-in applications.
15.2.113
spam
Spam is messages that overwhelm a communications channel used by people, most no- tably
commercial advertising sent to large numbers of individuals or discussion groups. Most spam
advertises products or services that are illegal in one or more ways, almost always including fraud.
Content filtering of e-mail to block spam, with the permission of the recipient, is almost universally
approved of.
15.2.114
SSH(SecureShell)
SSH or Secure Shell is a network protocol that allows encrypted communication between computers.
It was invented as a successor of the unencrypted Telnet protocol and is also used to access a shell
on a remote server.
The standard SSH port is 22. It can be used to bypass Internet censorship with port forwarding
or it can be used to tunnel other programs like VNC.
15.2.115
SSL(SecureSocketsLayer)
SSL (or Secure Sockets Layer), is one of several cryptographic standards used to make Internet
transactions secure. It is was used as the basis for the creation of the related Transport Layer Security
(TLS). You can easily see if you are using SSL by looking at the URL in your Browser (like Firefox
or Internet Explorer): If it starts with https instead of http, your connection is encrypted.
15.2.116
steganography
Steganography, from the Greek for hidden writing, refers to a variety of methods of sending hidden
messages where not only the content of the message is hidden but the very fact that something
covert is being sent is also concealed. Usually this is done by concealing something within
something else, like a picture or a text about something innocent or completely unrelated. Unlike
cryptography, where it is clear that a secret message is being transmitted, steganography does not
attract attention to the fact that someone is trying to conceal or encrypt a message.
15.2.117
subdomain
A subdomain is part of a larger domain. If for example “wikipedia.org” is the domain for the
Wikipedia, “en.wikipedia.org” is the subdomain for the English version of the Wikipedia.
486
15.2.118
threatanalysis
A security threat analysis is properly a detailed, formal study of all known ways of attacking the
security of servers or protocols, or of methods for using them for a particular purpose such as
circumvention. Threats can be technical, such as code-breaking or exploiting software bugs, or
social, such as stealing passwords or bribing someone who has special knowledge. Few companies
or individuals have the knowledge and skill to do a comprehensive threat analysis, but everybody
involved in circumvention has to make some estimate of the issues.
15.2.119
TopLevelDomain(TLD)
In Internet names, the TLD is the last component of the domain name. There are several generic
TLDs, most notably .com, .org, .edu, .net, .gov, .mil, .int, and one two- letter country code (ccTLD)
for each country in the system, such as .ca for Canada. The European Union also has the two-letter
code .eu.
15.2.120
TLS(TransportLayerSecurity)
TLS or Transport Layer Security is a cryptographic standard based on SSL, used to make Internet
transactions secure.
15.2.121
TCP/IP(TransmissionControlProtocoloverInternet Protocol)
TCP and IP are the fundamental protocols of the Internet, handling packet transmission and
routing. There are a few alternative protocols that are used at this level of Internet structure,
such as UDP.
15.2.122
Torbridge
A bridge is a middleman Tor node that is not listed in the main public Tor directory, and so is
possibly useful in countries where the public relays are blocked. Unlike the case of exit nodes, IP
addresses of bridge nodes never appear in server log files and never pass through monitoring nodes
in a way that can be connected with circumvention.
15.2.123
trafficanalysis
Traffic analysis is statistical analysis of encrypted communications. In some circum- stances traffic
analysis can reveal information about the people communicating and the information being
communicated.
15.2.124
tunnel
A tunnel is an alternate route from one computer to another, usually including a protocol that
specifies encryption of messages.
15.2.125
UDP(UserDatagramPacket)
UDP is an alternate protocol used with IP. Most Internet services can be accessed using either TCP
or UDP, but there are some that are defined to use only one of these alterna- tives. UDP is especially
useful for real-time multimedia applications like Internet phone calls (VoIP).

487
15.2.126
URL(UniformResourceLocator)
The URL (Uniform Resource Locator) is the address of a Web site. For example, the URL for
the World News section of the NY Times is http://www.nytimes.com/pages/ world/index.html.
Many censoring systems can block a single URL. Sometimes an easy way to bypass the block
is to obscure the URL. It is for example possible to add a dot after the site name, so the URL
http://en.cship.org/wiki/URL becomes http://en.cship.org./wiki/URL. If you are lucky with this
little trick you can access blocked Web sites.
15.2.127
Usenet
Usenet is a more than 20-year-old discussion forum system accessed using the NNTP protocol. The
messages are not stored on one server but on many servers which distribute their content constantly.
Because of that it is impossible to censor Usenet as a whole, however access to Usenet can and is
often blocked, and any particular server is likely to carry only a subset of locally-acceptable Usenet
newsgroups. Google archives the entire available history of Usenet messages for searching.
15.2.128
VoIP(VoiceoverInternetProtocol)
VoIP refers to any of several protocols for real-time two-way voice communication on the Internet,
which is usually much less expensive than calling over telephone company voice networks. It is not
subject to the kinds of wiretapping practiced on telephone networks, but can be monitored using
digital technology. Many companies produce software and equipment to eavesdrop on VoIP calls;
securely encrypted VoIP technologies have only recently begun to emerge.
15.2.129
VPN(virtualprivatenetwork)
A VPN (virtual private network) is a private communication network used by many companies and
organizations to connect securely over a public network. Usually on the Internet it is encrypted and
so nobody except the endpoints of the communication can look at the data traffic. There are various
standards like IPSec, SSL, TLS. The use of a
VPN provider is a very fast, secure and convenient method to bypass Internet censorship with little
risks but it generally costs money every month. Further, note that the VPN standard PPTP is no
longer considered secure, and should be avoided.
15.2.130
whitelist
A whitelist is a list of sites specifically authorized for a particular form of communication. Filtering
traffic can be done either by a whitelist (block everything but the sites on the list), a blacklist (allow
everything but the sites on the list), a combination of the two, or by other policies based on specific
rules and conditions.
488
15.2.131
WorldWideWeb(WWW)
The World Wide Web is the network of hyperlinked domains and content pages accessible using the
Hypertext Transfer Protocol and its numerous extensions. The World Wide Web is the most
famous part of the Internet.
15.2.132
Webmail
Webmail is e-mail service through a Web site. The service sends and receives mail mes- sages
for users in the usual way, but provides a Web interface for reading and managing messages, as
an alternative to running a mail client such as Outlook Express or Thun- derbird on the user’s
computer. For example a popular and free webmail service is https://mail.google.com/
15.2.133
Webproxy
A Web proxy is a script running on a Web server which acts as a proxy/gateway. Users can
access such a Web proxy with their normal Web browser (like Firefox) and enter any URL in
the form located on that Web site. Then the Web proxy program on the server receives that Web
content and displays it to the user. This way the ISP only sees a connection to the server with
the Web proxy since there is no direct connection.
15.2.134
WHOIS
WHOIS (who is) is the aptly named Internet function that allows one to query remote WHOIS
databases for domain registration information. By performing a simple WHOIS search you can
discover when and by whom a domain was registered, contact information, and more.
A WHOIS search can also reveal the name or network mapped to a numerical IP address
15.3 The necessity of Open Source
15.3
The necessity of Open Source
The last 20 years have seen network technology reaching ever more deeply into our lives, informing
how we communicate and act within the world. With this come inherent risks: the less we understand
the network environment we depend upon, the more vulnerable we are to exploitation.
This ignorance is something traditionally enjoyed by criminals. In recent years how- ever some
corporations and governments have exploited civilian ignorance in a quest for increased control.
This flagrant and often covert denial of dignity breaches many basic rights, the right to privacy, in
particular.
Closed source software has been a great boon to such exploitation – primarily due to the fact
there is no code available for open, decentralised security auditing by the community . Under the
auspices of hiding trade secrets, closed-source software developers have proven to be unwilling to
explain to users how their programs work. This might not always be an issue were it not for the
high stakes: identity theft, the distribution of deeply personal opinion and sentiment, a persons
diverse interests and even his/her home increasingly come into close contact with software in a
world-wide network context. As such, many people find themselves using software for personal
purposes with full trust that it are secure. The Windows operating system itself is the most obvious
489
real-world example. Apple’s OS X follows close behind, with large portions of the operating
system’s inner-workings barred from public inspection.
In Cryptography there is a strong principle, established in the 19th century by
Auguste
Kerckhoff
(and hence named after him) which demands that
“[the encryption method] must not be required to be secret, and it must be able to fall
into the hands of the enemy without inconvenience”.
While this principle has been taken further by most scientific and (of course) open source
communities – publishing their methods and inner-workings upfront, so potential weaknesses can
be pointed out and fixed before further distribution – most distributors of proprietary software rely
on obfuscation to hide the weaknesses of their software. As such they often prove to address newly
discovered vulnerabilities in a non-transparent way – leaving many trusting users at risk of
exploitation.
Of course it must be said that Open Source Software is as secure as you make it (and there is a lot
of OSS written by beginners). However there are many good examples of well written, well
managed software which have such a large (and concerned) user base that even the tiniest of
mistakes are quickly found and dealt with. This is especially the case with software depended upon
in a network context.
To use closed source software in a network context is not only to be a minority, it is to be
overlooked by a vast community of concerned researchers and specialists that have your privacy and
safety in mind.
N.B. There is also a more cynical view of Open Source Software, which points out that since
nobody is paid full time to constantly review and regression test the latest tinkering by unskilled or
deliberately malicious programmers, it can also suffer from major security
weaknesses which go undetected for long periods of time in complicated software, leaving it
vulnerable to hackers, criminals and intelligence agencies etc. e.g. the (now fixed) Debian Linux
predictable random number generator problem which led to the creation of lots of weak
cryptographic keys.