Lab Manual 1
User Manual:
Open the PDF directly: View PDF ![]() .
.
Page Count: 20

CSE-478 Introduction to Computer Security
Lab 1: Basic Linux Familiarity & Apache Web Server
Objectives:
• To get familiar with Linux and its command systems
Submission:
• Prepare a report with the contents as instructed in different exercised in this manual.
Introduction:
This motivation of this lab is to prepare for you for the subsequent labs in which we will be
using the Ubuntu Linux environment. There are three check-points. Each of these check points
needs to be ticked off by showing to your instructor what you are instructed to do. You will
also need to submit a report at the end of the lab with the required contents. We will start off
the lab with a little bit of history of Unix and Linux. Then, read thorough this lab manual and
complete the instructed tasks.
UNIX:
UNIX is a powerful operating system designed to be a multiuser and multitasking system. The
original UNIX was created by Ken Thompson in 1969 at Bell Labs. Today, the term “UNIX” does
not refer to a single operating system sold by a single company. Instead, it refers to any
operating system that meets certain standards.
Most large-scale computers and some desktop personal computers use an UNIX operating
system, which could be a generic system or one written by the computer manufacturer. Some
of the more popular UNIX operating systems include Linux, Ultrix (DEC), Irix (Silicon Graphics),
and Solaris (Sun Microsystems). Mac OSX is built on BSD Unix.
Since each UNIX operating system must meet the same standards, they function similarly.
Thus, after you are familiar with the use of one UNIX operating system, you will easily adapt
to a different one. The major differences are usually in the administration of the system—
meaning, unless you are the administrator of the system, you never have to worry about that
aspect.
Linux:
The Linux (Lynn-ucks) operating system was created by Linus Torvalds in 1991 while he was a
graduate student at the University of Helsinki (Finland). Torvalds created Linux as an
alternative to Microsoft Windows and to provide a UNIX operating system for use on the PC.
Linux is and has always been an open- source project that allows other programmers to view
and modify the source code. Today, hundreds of programmers work on Linux—mostly in their
spare time—under the direction of Torvalds.
The Linux operating system is very popular today due in part to its availability and open source
status. There are a number of Linux distributions available from different companies and
groups such as Red Hat, Fedora, Ubuntu, Slackware, SuSe, and Corel. All of these use the same
Linux operating system.
The major differences between the distributions are the services provided and the various
applications included with the Linux distribution. Linux is very powerful and is easy to learn

CSE-478 Introduction to Computer Security
and use. All major distributions provide a graphical user interface frontend that will be
familiar to Microsoft and Macintosh users.
In our lab we will be using Ubuntu Linux Distribution.
User Interface:
Users commonly interact with a UNIX system via a text-based command-line interface. In a
terminal, commands are entered at a prompt and results are displayed. Numerous commands
are provided for file and directory manipulation, program execution, and file processing. With
a text-based interface, users can work with the system directly on the physical machine or
connect to a remote system via the Internet. One of the biggest wins with the text-based
interface is how easy it is to automate complicated processes.
In addition to the text-based interface, most UNIX systems also provide a graphical interface
similar to those of the Macintosh and Windows platforms. Unlike those systems, however,
the graphical interface under UNIX consists of several layers, as illustrated below.
The actual graphical environment is provided by a standalone program called X-Windows
(tm). This program is executed on top of the text-based interface. X-Windows is responsible
for managing the monitor, keyboard, and mouse in addition to providing the “windowing
capability”.
The look and feel of the graphical environment is provided by a window manager. The window
manager is a standalone program that works in conjunction with X-Windows to provide
decorations for windows, buttons, and other components in addition to controlling the
behaviour and action of the various components. There are a number of window managers
from which to choose.
Linux systems also provide a desktop manager. The desktop manager is responsible for the
icons on the desktop, the panels that provide menus and application launchers, and virtual
workspaces. The two most popular desktop managers are GNOME (default) and KDE,
however, Unity is the default desktop manager of recent Ubuntu releases.
The Terminal:
Before you can begin working with UNIX commands, you need a terminal window, which runs
a program called a shell. The shell provides an interface between you and the operating
system. The terminal can be launched using the Menu, or typing Terminal into the application
area or using the Ctrl + Alt + T shortcut.
The terminal window on your desktop should contain some characters that look something
like:
2
LAB 01.
WORKING
WITH LINUX
The major differences between the distributions are the services provided and the various applications
included with the Linux distribution.
Linux is very powerful and is easy to learn and use. All major distributions provide a graphical user interface
frontend that will be familiar to Microsoft and Macintosh users.
0.1.4 Interface
Users commonly interact with a UNIX system via a text-based command-line interface. In a terminal,
commands are entered at a prompt and results are displayed. Numerous commands are provided for file and
directory manipulation, program execution, and file processing. With a text-based interface, users can work
with the system directly on the physical machine or connect to a remote system via the Internet. One of the
biggest wins with the text-based interface is how easy it is to automate complicated processes.
In addition to the text-based interface, most UNIX systems also provide a graphical interface similar to
those of the Macintosh and Windows platforms. Unlike those systems, however, the graphical interface
under UNIX consists of several layers, as illustrated below.
The actual graphical environment is provided by a standalone program called X-Windows (tm). This
program is executed on top of the text-based interface. X-Windows is responsible for managing the monitor,
keyboard, and mouse in addition to providing the “windowing capability”.
The look and feel of the graphical environment is provided by a window manager. The window manager is
a standalone program that works in conjunction with X-Windows to provide decorations for windows,
buttons, and other components in addition to controlling the behavior and action of the various com-
ponents. There are a number of window managers from which to choose. The default on our systems is the
Metacity window manager, which is highly configurable and provides a number of “themes” that change
the look and feel.
Linux systems also provide a desktop manager. The desktop manager is responsible for the icons on the
desktop, the panels that provide menus and application launchers, and virtual workspaces. The two most
popular desktop managers are GNOME (default) and KDE, both of which are provided on our system.
4
LAB 01.
WORKING
WITH LINUX
Enter your username in the “Username” text field and press Enter or click the Log In
button.
If you have trouble entering text into the box, you will need to move the mouse over the dialog box. Next,
you will be prompted for your password.
Enter the password provided to you and press Enter or click the Log In button. You
should now be logged in to the system. If not, ask your instructor or lab assistant for help.
0.2.2 Exploring the Desktop
Open the Firefox web browser by clicking on the “Activities” menu in the upper left corner
of your screen and then click the Firefox browser icon (shown below), which should be
the top icon.
Using the browser, navigate to the course Web page. There are lots of different ways to
navigate to the course Web page; you should be able to find one that works. Bookmark
the course Web page. You could even edit your preferences to make it your home page!
There is a link at the top of the Web page labeled “Resources”. Click on the link to open
the Resources page. Then scroll down to the “UNIX” section and select “CS Dept Wiki
Lab Resources”.
The Lab Resources page contains information about the system and various applications, which will be
useful to you throughout the term.
Play with the Linux Desktop yourself to see what you can do! Compare with your neighbors and learn
some helpful tricks. For example, what happens if you click on “Activities” now?
0.3 The Terminal
Before you can begin working with UNIX commands, you need a terminal window, which runs a program
called a shell. The shell provides an interface between you and the operating system.
Open a terminal window from the “Applications” menu, under “Activities” OR by search-
ing for “Terminal” from “Activities”.
Add Terminal to your “Favorites” by clicking on “Activities” and dragging the Terminal
up in the bar to just under Firefox.
The terminal window on your desktop should contain some characters that look something like:
[username@lisp-~]$-

CSE-478 Introduction to Computer Security
This is called the prompt. The prompt gives you information about the account and machine
being used and the current directory you’re in. For example, the prompt above is for someone
whose username is username and who is using the computer named lisp and that the user is
in his home directory, as indicated by the ~, the shortcut for the home directory.
The prompt indicates that UNIX is waiting for (or “prompting”) you to type something.
Whenever you type something after a UNIX prompt, UNIX tries to understand it as a
command. If you type a command that UNIX understands, UNIX carries out the command.
Otherwise UNIX displays a message indicating that the command was not recognizable.
To enter a UNIX command, the terminal window must be the active window. To make a
window active, simply move the mouse so that the mouse pointer is located within the limits
of the window and click on the window. When a window is active, its border changes colour.
• Make the terminal window the active window.
• At the prompt, type in your last name and press Enter.
You should see the error message that UNIX displays when it cannot interpret what you type
as one of its commands (unless your parents happened to name you “ls” or “cp” or some such
thing). Now, answer the following questions in your report:
Q 1. Does the program support multiple sessions (e.g. tabs)? If so, how do you create new
sessions? How do you delete them?
Q 2. What character encoding does the terminal expect (common ones are UTF-8 and
ISO-8859-1, also known as latin-1)?
Linux Manual
Unix documentation is traditionally in the form of a Unix Manual, which is comprised of a set
of manual pages, or simply man pages, organized into nine sections. Section one of the
manual is for user commands, section two for system calls, section three for higher-level API
calls and so on. Sometimes you will see commands (and API functions) written as name(n).
This notation specifies a name and a manual section. For example, tty(1) refers to the user
command t t y, whereas tty(4) refers to the device driver named tty.
You read man pages using the man command. The man command itself has a man page,
which you read by issuing the command man man.
• Type man man in your terminal and try to understand what is written
Before moving on to more advanced tasks, you have to become comfortable reading man
pages, and referring to the man pages must become second nature. Any time you wonder
5
LAB 01.
WORKING
WITH LINUX
This is called the prompt. The prompt gives you information about the account and machine being used and
the current directory you’re in. For example, the prompt above is for someone whose username is username
and who is using the computer named lisp and that the user is in his home directory, as indicated by the ~,
the shortcut for the home directory.
The prompt indicates that UNIX is waiting for (or “prompting”) you to type something. Whenever you type
something after a UNIX prompt, UNIX tries to understand it as a command. If you type a command that
UNIX understands, UNIX carries out the command. Otherwise UNIX displays a message indicating that
the command was not recognizable.
Note: Commands and filenames in UNIX are case sensitive.
Spaces are required between commands, arguments, and options.
The basic template for a UNIX command is
command4name-[options]-[argument1]-[argument2]-...-
To enter a UNIX command, the terminal window must be the active window. To make a window active,
simply move the mouse so that the mouse pointer is located within the limits of the window and click on
the window. When a window is active, its border changes color.
Make the terminal window the active window.
At the prompt, type in your last name and press Enter.
You should see the error message that UNIX displays when it cannot interpret what you type as one of its
commands (unless your parents happened to name you “ls” or “cp” or some such thing).
In the rest of this lab, we’ll focus on commands that UNIX does recognize and on how to use them.
0.4 Running the Help Client
This is a bit early to discuss this, but we created a new program to make it easy to keep track of who needs
assistance during lab.
At the prompt, type in
runHelpClient-&-
We will explain more later about how this command works. For now, you should see the GUI and it
should be pretty intuitive to use.

CSE-478 Introduction to Computer Security
how a command works, read the man pages. If you need to know what format a file has, read
the man pages. If you don’t have anything else to do, read a man page; you might just learn
something.
Man pages are divided into named sections such as “SYNOPSIS”, “DESCRIPTION”,
“EXAMPLES” and “FILES”. If you are familiar with the more common sections of man pages
you can find information a lot faster than by trying to read the whole thing from beginning to
end. The man page for man itself lists some of the common sections and conventions.
Answer the following questions concerning sections of the Unix Manual into your report.
Most of the information you need can be found in the man page for the man command (you
will need to think a little too):
Q 16. Which are the nine sections of the Unix manual?
Q 17. Which section of the manual contains user commands such as cat and ls?
Q 18. Which section documents file formats, such as configuration files?
Q 19. Display the man page for the l s command.
a) What does the ls command do?
b) What option to ls shows information about file sizes, owner, group,
permissions and so forth?
c) What does the –R option to l s do? (Don’t forget to try it.)
Linux File Systems
Understanding how files and directories are organized and can be manipulated is vital when
using or managing a Linux system. All files and directories in Linux are organized in a single
tree, regardless of what physical devices are involved (unlike Microsoft Windows, where
individual devices typically form separate trees).
The basic unit of storage in UNIX is a file. A file may contain many kinds of information,
including a Python script, an HTML document, a research paper, an image, or an executable
program. Files are organized in a hierarchical system of directories. A directory may contain
files and other directories. The directory at the “top” of the file system, in which all other
directories are located, is called the root directory.
The root of the tree is called /, and is known as the root directory or simply the root. The root
contains a number of directories, most of which are standard on Linux systems. The following
top-level directories are particularly important:

CSE-478 Introduction to Computer Security
The figure below shows part of a Unix system.
File and path names
There are two ways to reference a file in Unix: using a relative path name or using an absolute
path name. An absolute path name always begins with a / and names every directory on the
path from the root to the file in question. For example, in the figure above, the konsole file
has the absolute path name /usr/bin/konsole. A relative path names a path relative the
current working directory. The current working directory is set using the cd command. For
example, if the current working directory is /usr, then the konsole file could be referenced
with the name bin/konsole. Note that there is no leading /. If the current working directory
were /usr/share, then konsole could be referenced with ../bin/konsole. The special name “..”
is used to reference the directory above the current working directory.
Q 20. In the example above name at least one relative path name indicating ssh if
a) The current working directory is /usr/bin.
b) The current working directory is /usr/local/bin.
IDA/ADIT LXB: LINUX BASICS 7
commands have brief man pages, but are fully documented in the info manual. Such commands usually
have a reference to the appropriate info file in the man page. Use the command info to display info
files. Within info, type a question mark to see help on using info.
When reading man pages, you might see something like this (in the SEE ALSO part):
SEE ALSO
The f ul l doc ument at i on f or l s i s mai nt ai ned as a Texi nf o
ma n u a l . I f the info and ls programs are properly inst al l ed at
your si t e, t he comma n d
info ls
shoul d gi ve you access t o t he compl et e manual .
That means that the full documentation is in the info manual, not the man page. You should read the
info manual instead; most of the time, info manuals are more comprehensive and more well written
than man pages.
Package documentation
Every Debian package comes with its own documentation. These files are located in subdirectories of
/usr/share/doc/. For every package that you install, you should look in this directory for README files,
Debian-specific documentation (very important) and examples.
You can save a lot of time by making sure you always check the package documentation when you
want to know something! There can be a lot of information in there, including complete configuration
examples, troubleshooting tips and more.
Most of these files are normal text files, but there are often compressed files and HTML files.
From this point on you will be expected to read documentation to solve most of your problems. In
general, if you have any questions, try to get the answers from the documentation before calling on a
lab assistant. If you haven’t checked, or haven’t checked thoroughly enough, you will be directed to the
documentation by the assistant.
Files and directories
Understanding how files and directories are organized and can be manipulated is vital when using or
managing a Linux system. All files and directories in Linux are organized in a single tree, regardless of
what physical devices are involved (unlike Microsoft Windows, where individual devices typically form
separate trees).
The root of the tree is called /, and is known as the root directory or simply the root. The root contains a
number of directories, most of which are standard on Linux systems. The following top-level directories
are particularly important:
Directory
Purpose
bin
Commands (binaries) needed at startup. Every Unix command is a separate executable
binary file. Commands that are fundamental to operation, and may be needed while the
system is starting, are stored in this directory. Other commands go in the /usr directory.
dev
Interfaces to hardware and logical devices. Hardware and logical devices are represented
by device nodes: special files that are stored in this directory.
etc
Configuration files. The /etc directory holds most of the configuration of a system. In
many Linux systems, /etc has a subdirectory for each installed software package.
home
Home directories. User’s home directories are subdirectories of /home.
sbin
Administrative commands. The commands in /sbin typically require administrative
privileges or are of interest only to system administra
tors. Commands that are needed
when the system is starting go in /sbin. Others go in /usr/sbin.
m
IDA/ADIT LXB: LINUX BASICS 8
tmp
Temporary (non-persistent) files. The /tmp directory is typically implemented in main
memory. Data stored here is lost when the system reboots. Many applications use /tmp
for storing temporary files (others use /var).
usr
The bulk of the system, including commands and data not needed at startup. The usr
subdirectory should only contain files that can be shared between a number of different
computers, so it should contain no configuration data that is unique to a particular
system.
The figure below shows part of a Unix system.
/ bin
dev
etc
home
lib
proc
sbin
tmp
usr
bin
lib
local
sbin
share
rijag112
cosaz039
zbicz922
tomli839
ramsi645
doc
man
bin
man
share
bin
labs
private
man
info
less
konsole
ssh
mplayer
mencoder
File and path names
There are two ways to reference a file in Unix: using a relative path name or using an absolute path
name. An absolute path name always begins with a / and names every directory on the path from the
root to the file in question. For example, in the figure above, the konsole file has the absolute path
name /usr/bin/konsole. A relative path names a path relative the current working directory. The current
working directory is set using the cd command. For example, if the current working directory is /usr,
then the konsole file could be referenced with the name bin/konsole. Note that there is no leading /. If
the current working directory were /usr/share, then konsole could be referenced with ../bin/konsole.
The special name “..” is used to reference the directory above the current working directory.
Exercise 5: Absolute and relative path names
5-1 In the example above name at least one relative path name indicating ssh if
(a) The current working directory is /usr/bin.
(b) The current working directory is /usr/local/bin.
Report: Answers to all questions.
File system permissions
Like most operating systems Linux has permissions on files and directories that grant individual users or
groups of users rights on the files and folders.
In Linux, permissions are divided into three groups: “user”, “group” and “other”. User permissions apply
to the owner of a file or directory; group permissions to the members of the file’s (or directory’s) group;
other permissions apply to everyone else.
Every group contains three main permissions: read, write and execute, and each is represented as one
bit in an integer. The read (r) bit grants permission to read the contents of a file or directory; the write
(w) bit grants permission to write to the file or create files in a directory, and the execute (x) bit grants
permission to execute a file as a program. On directories the execute bit grants permission to traverse
the directory (i.e. set it as the working directory).
/usr/bin/konsole
/home/rijag112/ bin/mplayer
IDA/ADIT LXB: LINUX BASICS 8
tmp Temporary (non-persistent) files. The /tmp directory is typically implemented in main
memory. Data stored here is lost when the system reboots. Many applications use /tmp
for storing temporary files (others use /var).
usr The bulk of the system, including commands and data not needed at startup. The usr
subdirectory should only contain files that can be shared between a number of different
computers, so it should contain no configuration data that is unique to a particular
system.
The figure below shows part of a Unix system.
/ bin
dev
etc
home
lib
proc
sbin
tmp
usr
bin
lib
local
sbin
share
rijag112
cosaz039
zbicz922
tomli839
ramsi645
doc
man
bin
man
share
bin
labs
private
man
info
less
konsole
ssh
mplayer
mencoder
File and path names
There are two ways to reference a file in Unix: using a relative path name or using an absolute path
name. An absolute path name always begins with a / and names every directory on the path from the
root to the file in question. For example, in the figure above, the konsole file has the absolute path
name /usr/bin/konsole. A relative path names a path relative the current working directory. The current
working directory is set using the cd command. For example, if the current working directory is /usr,
then the konsole file could be referenced with the name bin/konsole. Note that there is no leading /. If
the current working directory were /usr/share, then konsole could be referenced with ../bin/konsole.
The special name “..” is used to reference the directory above the current working directory.
Exercise 5: Absolute and relative path names
5-1 In the example above name at least one relative path name indicating ssh if
(a) The current working directory is /usr/bin.
(b) The current working directory is /usr/local/bin.
Report: Answers to all questions.
File system permissions
Like most operating systems Linux has permissions on files and directories that grant individual users or
groups of users rights on the files and folders.
In Linux, permissions are divided into three groups: “user”, “group” and “other”. User permissions apply
to the owner of a file or directory; group permissions to the members of the file’s (or directory’s) group;
other permissions apply to everyone else.
Every group contains three main permissions: read, write and execute, and each is represented as one
bit in an integer. The read (r) bit grants permission to read the contents of a file or directory; the write
(w) bit grants permission to write to the file or create files in a directory, and the execute (x) bit grants
permission to execute a file as a program. On directories the execute bit grants permission to traverse
the directory (i.e. set it as the working directory).
/usr/bin/konsole
/home/rijag112/ bin/mplayer

CSE-478 Introduction to Computer Security
File system permissions
Like most operating systems Linux has permissions on files and directories that grant
individual users or groups of users rights on the files and folders.
In Linux, permissions are divided into three groups: “user”, “group” and “other”. User
permissions apply to the owner of a file or directory; group permissions to the members of
the file’s (or directory’s) group; other permissions apply to everyone else.
Every group contains three main permissions: read, write and execute, and each is
represented as one bit in an integer. The read (r) bit grants permission to read the contents
of a file or directory; the write (w) bit grants permission to write to the file or create files in a
directory, and the execute (x) bit grants permission to execute a file as a program. On
directories the execute bit grants permission to traverse the directory (i.e. set it as the
working directory).
There are other permission bits as well. The most important of these are the setuid and setgid
bits (in the user and group permission groups, respectively). When a program with the setuid
bit set is run, it is run as the owner of the file, not the user who started the program. The
setgid bit works the same, but for groups.
To list the permissions of a file or directory, use the ls command with the -l option (to enable
long file listing; see the man page for ls). You can see something like this:
Q 21. Use the ls command to get the file list and then use with the -l option for any
two files and examine what you can see.
Each group of permissions is represented by three characters in the leftmost column of the
listing. The very first character indicates the type of the file, and is not related to permissions.
The next three characters (in this case rwx) represent user permissions. The following three
(in this case r-x) represent group permissions and the final three represent permissions for
others (in this case r--).
The owner and group of the file are given by the third and fourth column, respectively (user
john and group users in this example).
In this example the owner, “john”, is allowed to read, write and execute the file (rwx). Users
belonging to the group “users” are allowed to read and execute the file (r-x), but cannot write
to it. All other users are allowed to read foobar (r--), but not write or execute it.
File types
The first character, the type field, indicates the file type. In the example above the file type is
“-”, which indicates a regular file. Other file types include: d for directory, l (lower case ell) for
symbolic link, s for Unix domain socket, p for named pipe, c for character device file and b for
block device file.
Manipulating access rights
The chmod and chown commands are used to manipulating permissions.
IDA/ADIT LXB: LINUX BASICS 9
There are other permission bits as well. The most important of these are the setuid and setgid bits (in
the user and group permission groups, respectively). When a program with the setuid bit set is run, it is
run as the owner of the file, not the user who started the program. The setgid bit works the same, but
for groups.
To list the permissions of a file or directory, use the ls command with the - l option (to enable long file
listing; see the man page for ls). For example, to see the permissions set for the file “foobar” in the
current directory has, write:
% l s -l foobar
-rwxr-xr -- 1 j ohn user s 64 May 26 09: 55 f oobar
Each group of permissions is represented by three characters in the leftmost column of the listing. The
very first character indicates the type of the file, and is not related to permissions. The next three
characters (in this case rwx) represent user permissions. The following three (in this case r-x) represent
group permissions and the final three represent permissions for others (in this case r--).
The owner and group of the file are given by the third and fourth column, respectively (user john and
group users in this example).
In this example the owner, “john”, is allowed to read, write and execute the file (rwx). Users belonging
to the group “users” are allowed to read and execute the file (r-x), but cannot write to it. All other users
are allowed to read foobar (r--), but not write or execute it.
File types
The first character, the type field, indicates the file type. In the example above the file type is “-”, which
indicates a regular file. Other file types include: d for directory, l (lower case ell) for symbolic link, s for
Unix domain socket, p for named pipe, c for character device file and b for block device file.
Manipulating access rights
The chmod and chown commands are used to manipulating permissions.
chmod is used to manipulate permissions. Permissions can be specified using either “long” format or a
numeric mode (all permission bits together are called the file’s mode). The long format takes a string of
permission values (r, w or x) together with a plus or minus sign. For example, to prevent any user from
changing the file foobar we would do as follows to disable write permission, then verify that the change
has taken place:
% chmod -w f o o b a r
% ls –l f oobar
-r-xr -xr -x 1 j ohn user s 81 May 26 10: 43 f oobar
To enable write access again, replace the minus sign with a plus sign (chmod +w foobar).
Exercise 6: Long format chmod
6-1 It is possible to set individual permissions for user, group and others using chmod. Review the
documentation and answer the following questions:
(a) How can you set the permission string to user read/write, group read, others read
using chmod in long format?
(b) How can you revoke group write permissions on a file without changing any other
permissions?
(c) How can you grant user and group execute permissions without changing any other
permissions?
Report: Answers to the questions above.
In numeric mode, each permission is treated as a single bit value. The read permission has value 4, write
value 2 and execute value 1. The mode is a three character octal string where the first digit contains the
sum of the user permissions, the second the sum of the group permissions and the third the sum of the
others permissions. For example, to set the permission string “-rwxrw-r--” (user may do anything, group

CSE-478 Introduction to Computer Security
chmod is used to manipulate permissions. Permissions can be specified using either “long”
format or a numeric mode (all permission bits together are called the file’s mode). The long
format takes a string of permission values (r, w or x) together with a plus or minus sign. For
example, to prevent any user from changing the file foobar we would do as follows to disable
write permission, then verify that the change has taken place:
Answer the following questions in your report.
Q 22. It is possible to set individual permissions for user, group and others using
chmod. Review the documentation and answer the following questions:
a) How can you set the permission string to user read/write, group read, others
read using chmod in long format?
b) How can you revoke group write permissions on a file without changing any
other permissions?
c) How can you grant user and group execute permissions without changing any
other permissions?
In numeric mode, each permission is treated as a single bit value. The read permission has
value 4, write value 2 and execute value 1. The mode is a three character octal string where
the first digit contains the sum of the user permissions, the second the sum of the group
permissions and the third the sum of the others permissions. For example, to set the
permission string “-rwxrw-r--” (user may do anything, group may read or write, but not
execute and all others may read) for a file, you would calculate the mode as follows:
• User: 4 + 2 + 1 = 7 (rwx)
• Group: 4 + 2 = 6 (rw-)
• Others: 4 = 4 (r--)
Together with chmod the string “764” can then be used to set the file permissions:
Numeric combinations are generally quicker to work with once you learn them, especially
when making more complicated changes to files and directories. Therefore, you are
encouraged to use them. It is useful to learn a few common modes by heart:
IDA/ADIT LXB: LINUX BASICS 9
There are other permission bits as well. The most important of these are the setuid and setgid bits (in
the user and group permission groups, respectively). When a program with the setuid bit set is run, it is
run as the owner of the file, not the user who started the program. The setgid bit works the same, but
for groups.
To list the permissions of a file or directory, use the ls command with the - l option (to enable long file
listing; see the man page for ls). For example, to see the permissions set for the file “foobar” in the
current directory has, write:
% l s -l foobar
-rwxr-xr -- 1 j ohn user s 64 May 26 09: 55 f oobar
Each group of permissions is represented by three characters in the leftmost column of the listing. The
very first character indicates the type of the file, and is not related to permissions. The next three
characters (in this case rwx) represent user permissions. The following three (in this case r-x) represent
group permissions and the final three represent permissions for others (in this case r--).
The owner and group of the file are given by the third and fourth column, respectively (user john and
group users in this example).
In this example the owner, “john”, is allowed to read, write and execute the file (rwx). Users belonging
to the group “users” are allowed to read and execute the file (r-x), but cannot write to it. All other users
are allowed to read foobar (r--), but not write or execute it.
File types
The first character, the type field, indicates the file type. In the example above the file type is “-”, which
indicates a regular file. Other file types include: d for directory, l (lower case ell) for symbolic link, s for
Unix domain socket, p for named pipe, c for character device file and b for block device file.
Manipulating access rights
The chmod and chown commands are used to manipulating permissions.
chmod is used to manipulate permissions. Permissions can be specified using either “long” format or a
numeric mode (all permission bits together are called the file’s mode). The long format takes a string of
permission values (r, w or x) together with a plus or minus sign. For example, to prevent any user from
changing the file foobar we would do as follows to disable write permission, then verify that the change
has taken place:
% chmod -w f o o b a r
% ls –l f oobar
-r-xr -xr -x 1 j ohn user s 81 May 26 10: 43 f oobar
To enable write access again, replace the minus sign with a plus sign (chmod +w foobar).
Exercise 6: Long format chmod
6-1 It is possible to set individual permissions for user, group and others using chmod. Review the
documentation and answer the following questions:
(a) How can you set the permission string to user read/write, group read, others read
using chmod in long format?
(b) How can you revoke group write permissions on a file without changing any other
permissions?
(c) How can you grant user and group execute permissions without changing any other
permissions?
Report: Answers to the questions above.
In numeric mode, each permission is treated as a single bit value. The read permission has value 4, write
value 2 and execute value 1. The mode is a three character octal string where the first digit contains the
sum of the user permissions, the second the sum of the group permissions and the third the sum of the
others permissions. For example, to set the permission string “-rwxrw-r--” (user may do anything, group
IDA/ADIT LXB: LINUX BASICS 10
may read or write, but not execute and all others may read) for a file, you would calculate the mode as
follows:
User: 4+2+1= 7 (rwx)
Group: 4+2 = 6 (rw-)
Others: 4 = 4 (r--)
Together with chmod the string “764” can then be used to set the file permissions:
% c h mo d 764 f oobar
% ls -l foobar
-rwxrw- r -- 1 j ohn user s 81 May 26 10: 43 f oobar
Numeric combinations are generally quicker to work with once you learn them, especially when making
more complicated changes to files and directories. Therefore, you are encouraged to use them. It is
useful to learn a few common modes by heart:
755 Full rights to user, execute and read rights to others. Typically used for executables.
644 Read and write rights to user, read to others. Typically used for regular files.
777 Read, write and execute rights to everybody. Rarely used.
Exercise 7: Numeric file modes
7-1 What do the following numeric file modes represent:
(a) 666
(b) 770
(c) 640
(d) 444
7-2 What command-line argument to chmod allows you to alter the permissions of an entire
directory tree?
7-3 What does execute (x) permission mean on directories?
7-4 A user wants to set the permissions of a directory tree rooted in dir so that the user and
group can list, read and write (but not execute) files, but nobody else has any access. Which
of the following commands is most appropriate? Why?
(a) chmod –R 660 dir
(b) chmod –R 770 dir
(c) chmod –R u+rw,g+rw,o-rwx dir
When answering this question, consider how the execute permission is handled by the
various choices, and what importance the execute permission has on directories.
Report: Answers to the questions above.
chown is used to change the owner and group for a file. To change the user from “john” to “mike” and
the group from “users” to “wheel” issue:
% chown mi ke: wheel f oobar
Note that some Unix systems do not support changing the group with chown. On these systems, use
chgr p to change tile file’s group. Changing owner of a file can only be done by privileged users such as
root. Unprivileged users can change the group of a file to any group they are a member of. Privileged
users can alter the group arbitrarily.
IDA/ADIT LXB: LINUX BASICS 10
may read or write, but not execute and all others may read) for a file, you would calculate the mode as
follows:
User: 4+2+1= 7 (rwx)
Group: 4+2 = 6 (rw-)
Others: 4 = 4 (r--)
Together with chmod the string “764” can then be used to set the file permissions:
% c h mo d 764 f oobar
% ls -l foobar
-rwxrw- r -- 1 j ohn user s 81 May 26 10: 43 f oobar
Numeric combinations are generally quicker to work with once you learn them, especially when making
more complicated changes to files and directories. Therefore, you are encouraged to use them. It is
useful to learn a few common modes by heart:
755 Full rights to user, execute and read rights to others. Typically used for executables.
644 Read and write rights to user, read to others. Typically used for regular files.
777 Read, write and execute rights to everybody. Rarely used.
Exercise 7: Numeric file modes
7-1 What do the following numeric file modes represent:
(a) 666
(b) 770
(c) 640
(d) 444
7-2 What command-line argument to chmod allows you to alter the permissions of an entire
directory tree?
7-3 What does execute (x) permission mean on directories?
7-4 A user wants to set the permissions of a directory tree rooted in dir so that the user and
group can list, read and write (but not execute) files, but nobody else has any access. Which
of the following commands is most appropriate? Why?
(a) chmod –R 660 dir
(b) chmod –R 770 dir
(c) chmod –R u+rw,g+rw,o-rwx dir
When answering this question, consider how the execute permission is handled by the
various choices, and what importance the execute permission has on directories.
Report: Answers to the questions above.
chown is used to change the owner and group for a file. To change the user from “john” to “mike” and
the group from “users” to “wheel” issue:
% chown mi ke: wheel f oobar
Note that some Unix systems do not support changing the group with chown. On these systems, use
chgr p to change tile file’s group. Changing owner of a file can only be done by privileged users such as
root. Unprivileged users can change the group of a file to any group they are a member of. Privileged
users can alter the group arbitrarily.

CSE-478 Introduction to Computer Security
Answer the following questions in your report.
Q 23. What do the following numeric file modes represent:
a) 666
b) 770
c) 640
d) 444
Q 24. What command-line argument to chmod allows you to alter the permissions of an
entire directory tree?
Q 25. A user wants to set the permissions of a directory tree rooted in dir so that the
user and group can list, read and write (but not execute) files, but nobody else has
any access. Which of the following commands is most appropriate? Why?
a) chmod –R 660 dir
b) chmod –R 770 dir
The chown is used to change the owner and group for a file. To change the user from “john”
to “mike” and the group from “users” to “wheel” issue:
Note that some Unix systems do not support changing the group with chown. On these
systems, use chgrp to change tile file’s group. Changing owner of a file can only be done by
privileged users such as root. Unprivileged users can change the group of a file to any group
they are a member of. Privileged users can alter the group arbitrarily.
Symbolic links
In Unix, it is possible to create a special file called a symbolic link that points to another file,
the target file, allowing the target file to be accessed through the name of the special file.
Similar functions exist in other operating systems, under different names (e.g. “shortcut” or
“alias”).
For example, to make it possible to access /etc/init.d/myservice as /etc/rc2.d/S98myservice,
you would issue the following command:
Symbolic links can point to any type of file or directory, and are mostly transparent to
applications.
File and Directory Manipulation Commands
Many Unix commands are concerned with manipulating files and directories. The following
lists some of the most common commands in their most common forms. The man page for
each command contains full details, and reading the man pages will be necessary to complete
following the exercises.
IDA/ADIT LXB: LINUX BASICS 10
may read or write, but not execute and all others may read) for a file, you would calculate the mode as
follows:
User: 4+2+1= 7 (rwx)
Group: 4+2 = 6 (rw-)
Others: 4 = 4 (r--)
Together with chmod the string “764” can then be used to set the file permissions:
% c h mo d 764 f oobar
% ls -l foobar
-rwxrw- r -- 1 j ohn user s 81 May 26 10: 43 f oobar
Numeric combinations are generally quicker to work with once you learn them, especially when making
more complicated changes to files and directories. Therefore, you are encouraged to use them. It is
useful to learn a few common modes by heart:
755 Full rights to user, execute and read rights to others. Typically used for executables.
644 Read and write rights to user, read to others. Typically used for regular files.
777 Read, write and execute rights to everybody. Rarely used.
Exercise 7: Numeric file modes
7-1 What do the following numeric file modes represent:
(a) 666
(b) 770
(c) 640
(d) 444
7-2 What command-line argument to chmod allows you to alter the permissions of an entire
directory tree?
7-3 What does execute (x) permission mean on directories?
7-4 A user wants to set the permissions of a directory tree rooted in dir so that the user and
group can list, read and write (but not execute) files, but nobody else has any access. Which
of the following commands is most appropriate? Why?
(a) chmod –R 660 dir
(b) chmod –R 770 dir
(c) chmod –R u+rw,g+rw,o-rwx dir
When answering this question, consider how the execute permission is handled by the
various choices, and what importance the execute permission has on directories.
Report: Answers to the questions above.
chown is used to change the owner and group for a file. To change the user from “john” to “mike” and
the group from “users” to “wheel” issue:
% chown mi ke: wheel f oobar
Note that some Unix systems do not support changing the group with chown. On these systems, use
chgr p to change tile file’s group. Changing owner of a file can only be done by privileged users such as
root. Unprivileged users can change the group of a file to any group they are a member of. Privileged
users can alter the group arbitrarily.
IDA/ADIT LXB: LINUX BASICS 11
Exercise 8: Owner and group manipulation
8-1 How can you change the owner and group of an entire directory tree (a directory, its
subdirectories and all the files they contain) with a single command?
Report: Answers to the questions above.
Symbolic links
In Unix, it is possible to create a special file called a symbolic link that points to another file, the target
file, allowing the target file to be accessed through the name of the special file. Similar functions exist in
other operating systems, under different names (e.g. “shortcut” or “alias”).
For example, to make it possible to access /etc/init.d/myservice as /etc/rc2.d/S98myservice, you would
issue the following command:
% l n –s / et c/ i ni t . d/ myser vi ce / et c/ r c2. d/ S98myser vi ce
Symbolic links can point to any type of file or directory, and are mostly transparent to applications.
Unix also supports a concept called “hard linking”, which makes it possible to give a file several different
names (possibly in different directories) that are entirely equal (i.e. there is no concept of “target”, as all
names are equally valid for the file).
File and Directory Manipulation Commands
Many Unix commands are concerned with manipulating files and directories. The following lists some of
the most common commands in their most common forms. The man page for each command contains
full details, and reading the man pages will be necessary to complete the exercise.
Command Purpose
touch filename Change the creation date of filename (creating it if necessary).
pwd Displays the current working directory.
cd di r ect or y Changes the current working directory to directory.
ls Lists the contents of directory. If directory is omitted, lists the contents
of the current working directory. With arguments, can display
information about each file (see the manual page).
cat filename Display the contents of filename
less filename Displays the contents of filename page-by-page (less is a so-called
pager). Press the space bar to advance one page; b to go back one
page; q to quit; and h for help on all commands in less.
rm filename Removes the file filename from the file system.
mv ol dname newname Renames (moves) the file oldname to newname. If newname is an
existing directory, moves oldname into the directory newname.
mk d i r di r name Creates a new directory named dirname.
rmdi r di r name Removes the directory dirname. The directory must be empty for
rmdi r to work.
cp filename newname Creates a copy of filename named newname. If newname is a
directory, creates a copy named filename in the directory newname.
chmod mo d e s f i l e n a me Change permissions on filename according to modes.
chgr p gr oup f i l ename Change the group of filename to group.
chown user f i l ename Change the owner of filename to user.
ln –s ol dname newname Creates a symbolic link, so that oldname can also be accessed as
newname.

CSE-478 Introduction to Computer Security
Q 13. What does cd .. do?
Q 14. What does cd ../.. do?
Q 15. What information about a file is shown by l s - laF?
The Command shell
In Unix, the shell is the program that is responsible for interpreting commands from the user.
The canonical shell is the bourne shell, sh, which has evolved into the POSIX shell. This shell
has limited functionality, but is often used for shell scripts (programs written in the shell
command language). On Linux, the most common shell is bash (bourne again shell). Bash is a
POSIX-compatible shell that adds a number of useful functions. For interactive use, its line
editing and command history are particularly important. There are a number of other shells
available. The Korn shell (ksh), is standard on many systems, as is the C shell (csh) and the TC
shell (t csh).
Each shell uses its own syntax for internal functions (such as setting variables, redirecting I/O
and so forth), but there are two main variants in widespread use. Shells that trace their roots
to the bourne shell use one syntax (which is POSIX-compatible), and shells that are based on
the C shell use another. In addition, there are a number of shells which owe little to either of
IDA/ADIT LXB: LINUX BASICS 11
Exercise 8: Owner and group manipulation
8-1 How can you change the owner and group of an entire directory tree (a directory, its
subdirectories and all the files they contain) with a single command?
Report: Answers to the questions above.
Symbolic links
In Unix, it is possible to create a special file called a symbolic link that points to another file, the target
file, allowing the target file to be accessed through the name of the special file. Similar functions exist in
other operating systems, under different names (e.g. “shortcut” or “alias”).
For example, to make it possible to access /etc/init.d/myservice as /etc/rc2.d/S98myservice, you would
issue the following command:
% l n –s / et c/ i ni t . d/ myser vi ce / et c/ r c2. d/ S98myser vi ce
Symbolic links can point to any type of file or directory, and are mostly transparent to applications.
Unix also supports a concept called “hard linking”, which makes it possible to give a file several different
names (possibly in different directories) that are entirely equal (i.e. there is no concept of “target”, as all
names are equally valid for the file).
File and Directory Manipulation Commands
Many Unix commands are concerned with manipulating files and directories. The following lists some of
the most common commands in their most common forms. The man page for each command contains
full details, and reading the man pages will be necessary to complete the exercise.
Command
Purpose
touch filename
Change the creation date of filename (creating it if necessary).
pwd
Displays the current working directory.
cd di r ect or y
Changes the current working directory to directory.
ls
Lists the contents of directory. If directory is omitted, lists the contents
of the current working directory. With arguments, can display
information about each file (see the manual page).
cat filename
Display the contents of filename
less filename
Displays the contents of filename page-by-page (less is a so-called
pager). Press the space bar to advance one page; b to go back one
page; q to quit; and h for help on all commands in less.
rm filename
Removes the file filename from the file system.
mv ol dname newname
Renames (moves) the file oldname to newname. If newname is an
existing directory, moves oldname into the directory newname.
mk d i r di r name
Creates a new directory named dirname.
rmdi r di r name
Removes the directory dirname. The directory must be empty for
rmdi r to work.
cp filename newname
Creates a copy of filename named newname. If newname is a
directory, creates a copy named filename in the directory newname.
chmod mo d e s f i l e n a me
Change permissions on filename according to modes.
chgr p gr oup f i l ename
Change the group of filename to group.
chown user f i l ename
Change the owner of filename to user.
ln –s ol dname newname
Creates a symbolic link, so that oldname can also be accessed as
newname.

CSE-478 Introduction to Computer Security
these traditions, and they may use a completely different (and occasionally quite bizarre)
syntax.
When the shell starts, it reads one or more files, depending on how it is started. These are
called rc or init files. For example, the bourne shell reads the file .profile in your home
directory, while t csh reads .login and .tcshrc (if started as a login shell). These files may
contain sequences of shell commands to run automatically. Typically, they are used to set up
the shell and environment to suit the user’s preferences.
Using the shell efficiently
Learning to use the shell efficiently is a very worthwhile investment. New users should at the
very least learn how to use the command history (repeating previous commands), command
line editing (editing the current or previous commands) and tab completion (saving time by
letting the computer figure out what you mean).
The following text assumes that you are using bash or zsh with bash-like key bindings. Other
shells will behave differently; the manual for the shell will explain how.
Command history
All (at least many) of the commands you type are kept in the command history. You can
browse the history by using the up and down arrows (or crtl+P and crtl+N). When you find a
command you want to use, you can edit it just as if you had typed it on the command line.
You should also be aware of esc+< and esc+>, which move to the beginning and the end of
the command history, respectively. You can also search the command history by typing crtl+R
and then the word you want to search for.
Tab completion
Completion is one of the most useful features of a good shell. The idea behind completion is
that often the prefix of something (a command, file name or even command-line option)
uniquely identifies it, or at least uniquely identifies part of it. For example, if there are two
files in a directory, READFIRST and READSECOND, when a user types R where the shell expects
a file name, the shell can deduce that the next three characters will be EAD, and when the
user has typed READS, the shell can deduce that the user means READSECOND.
Rather than type out annoyingly long file names, learn to use tab completion.
Environment and shell variables
Unix, and many other operating systems, including Windows NT/2000/XP/2003/Vista have
the concept of environment variables. These are name-to-value mappings that are available
to each running program, and constitute the program’s environment. In Unix, environment
variables are widely used for simple configuration of programs. Unix shells typically support
shell variables in addition to environment variables. These are variables that are available to
the shell, but are not exported to other processes.
Environment and shell variables are altered using shell syntax:

CSE-478 Introduction to Computer Security
All (useful) Unix shells support parameter expansion. This process replaces part of a command
line with the contents of an environment or shell variable. In most shells, the syntax is “${
NAME} ” to expand the environment variable NAME. The echo command can be combined
with variable expansion to output the value of a particular variable. For example, “echo ${
HOME} ”, when HOME is set to “/ home/ user ”, will output “/ home/ user ”. Note that the
shell is responsible for expanding the variable; the echo command will receive the contents
of the variable as its sole argument. The man page for your shell will list various ways of
performing parameter expansion.
Now do the following activities but DO NOT add answers in your report.
• Use the env command to display all environment variables. What is PATH set to (you
might want to use gr ep to find it)? What is this variable used for (the man pages for
your shell might be helpful in answering this question)?
• 11-2 Use echo to display the value of HOME. What does the HOME variable normally
contain?
• 11-3 Prepend/data/kurs/adit/bin:/data/kurs/TDDI09/bintothevariablePATH. The
easiest way to accomplish this is to use variable expansion in the right-hand side of
the assignment.
Redirecting I/O & Pipeline
Unix provides several ways of redirecting the output of commands to files or other commands
and several ways of directing data to the input of commands. The basic mechanisms are
redirections and pipes. The precise mechanisms depend on the shell you are using; these
instructions assume the bash shell (see “The Command shell” above for more information
about shells).
In Unix, I/O is performed from file descriptors. These are simply numbered input or output
streams that point to sources or destinations of data (e.g. files, terminals, network
connections). By convention, file descriptor 0 is called standard input or stdin, and is the
default source for input; file descriptor 1 is called standard out or stdout, and is where output
is sent by default; file descriptor 2 is called standard error or stderr, and is usually used for
printing error messages.
I/O redirection simply is a matter of changing what the file descriptors point to. You can
redirect output from a command to a file using the > or >> operators.
IDA/ADIT LXB: LINUX BASICS 13
Using the shell efficiently
You must run these exercises in the bash shell, or results will not be as expected. You have two simple
options: either run the exercises in a UML instance (this assumes that you know how to start your UML
systems) or start bash manually, by issuing the command bash in a terminal window.
Learning to use the shell efficiently is a very worthwhile investment. New users should at the very least
learn how to use the command history (repeating previous commands), command line editing (editing
the current or previous commands) and tab completion (saving time by letting the computer figure out
what you mean).
The following text assumes that you are using bash or zsh with bash-like key bindings. Other shells will
behave differently; the manual for the shell will explain how.
Command history
All (at least many) of the commands you type are kept in the command history. You can browse the
history by using the up and down arrows (or vP and vN). When you find a command
you want to use, you can edit it just as if you had typed it on the command line. You should also be
aware of s< and s>, which move to the beginning and the end of the command history,
respectively. You can also search the command history by typing vR and then the word you
want to search for.
Command line editing
Edit the command line using emacs-like key bindings: vA moves to the beginning of the line,
vE to the end. Move forward and backwards using vF and vB.
vD deletes the character under the cursor and vK deletes to the end of the line.
Tab completion
Completion is one of the most useful features of a good shell. The idea behind completion is that often
the prefix of something (a command, file name or even command-line option) uniquely identifies it, or
at least uniquely identifies part of it. For example, if there are two files in a directory, READFIRST and
READSECOND, when a user types R where the shell expects a file name, the shell can deduce that the
next three characters will be EAD, and when the user has typed READS, the shell can deduce that the
user means READSECOND.
Rather than type out annoyingly long file names, learn to use tab completion.
Environment and shell variables
You must run these exercises in the bash shell, or results will not be as expected. You have two simple
options: either run the exercises in a UML instance or start bash manually, by issuing the command
bash in a terminal window.
Unix, and many other operating systems, including Windows NT/2000/XP/2003/Vista have the concept
of environment variables. These are name-to-value mappings that are available to each running
program, and constitute the program’s environment. In Unix, environment variables are widely used for
simple configuration of programs. Unix shells typically support shell variables in addition to environment
variables. These are variables that are available to the shell, but are not exported to other processes.
Environment and shell variables are altered using shell syntax:
NAME=VAL UE
POSIX (and bash) syntax. Sets the variable NAME to VALUE. Does not necessarily set the
environment variable (shell dependent).
expor t NAME
POSIX (and bash) syntax. Makes NAME
and its value part of the environment, so its value is
available to any program that is started from the shell after the export command was given
(programs started from other shells are not affected).
m
m
IDA/ADIT LXB: LINUX BASICS 14
set env NAME VAL UE
C shell syntax. Sets the environment variable NAME to VALUE. Use set instead of set env to set
a shell variable.
Exercise 11: Manipulating environment variables
11-1 Use the env command to display all environment variables. What is PATH set to (you might
want to use gr ep to find it)? What is this variable used for (the man pages for your shell
might be helpful in answering this question)?
11-2 Use echo to display the value of HOME. What does the HOME variable normally contain?
11-3 Prepend /data/kur s/adi t /bin:/data/kurs/TDDI09/bin to the variable PATH.
The easiest way to accomplish this is to use variable expansion in the right-hand side of the
assignment.
Report: Answers to 11-1 and 11-2. The commands used in 11-3
All (useful) Unix shells support parameter expansion. This process replaces part of a command line with
the contents of an environment or shell variable. In most shells, the syntax is “${ NAME} ” to expand the
environment variable NAME. The echo command can be combined with variable expansion to output
the value of a particular variable. For example, “echo ${ HOME} ”, when HOME is set to
“/home/user”, will output “/home/user”. Note that the shell is responsible for expanding the
variable; the echo command will receive the contents of the variable as its sole argument. The man
page for your shell will list various ways of performing parameter expansion.
Redirecting I/O
You absolutely must run these exercises in the bash shell, or results will not be as expected. You have
two simple options: either run the exercises in a UML instance (this assumes that you know how to start
your UML systems) or start bash manually, by issuing the command bash in a terminal window.
Unix provides several ways of redirecting the output of commands to files or other commands and
several ways of directing data to the input of commands. The basic mechanisms are redirections and
pipes. The precise mechanisms depend on the shell you are using; these instructions assume the bash
shell (see “The Command shell” above for more information about shells).
In Unix, I/O is performed from file descriptors. These are simply numbered input or output streams that
point to sources or destinations of data (e.g. files, terminals, network connections). By convention, file
descriptor 0 is called standard input or stdin, and is the default source for input; file descriptor 1 is called
standard out or stdout, and is where output is sent by default; file descriptor 2 is called standard error or
stderr, and is usually used for printing error messages.
I/O redirection simply is a matter of changing what the file descriptors point to.
You can redirect output from a command to a file using the > or >> operators.
command > filename
The output of command is written to filename. The file will be created if it doesn’t exist, and any
previous contents will be erased. In some shells there is a noclobber option. If this is set, you may
have to use the >! operator to overwrite an existing file.
In technical terms, this opens filename
for writing, then changes file descriptor 1 (stdout) to point
to the open file.
command >> filename
The output of command is appended to filename. The file will be created if it doesn’t already
exist.
m
CSE-478 Introduction to Computer Security
These basic redirection commands only redirect standard output; they do not redirect
standard error. If you want to redirect all output, you have to redirect file descriptor two as
well. The exact syntax for redirecting errors (and other file descriptors) is very shell-
dependent.
In addition to redirecting output to files, it is possible to redirect output to other commands. The mechanism
that makes this possible is called pipe. The Unix philosophy of command design is that each command should
perform one small function well, and that complex functions are performed by combining simple commands
with pipes and redirection. It actually works quite well.
IDA/ADIT LXB: LINUX BASICS 14
set env NAME VAL UE
C shell syntax. Sets the environment variable NAME to VALUE. Use set instead of set env to set
a shell variable.
Exercise 11: Manipulating environment variables
11-1 Use the env command to display all environment variables. What is PATH set to (you might
want to use gr ep to find it)? What is this variable used for (the man pages for your shell
might be helpful in answering this question)?
11-2 Use echo to display the value of HOME. What does the HOME variable normally contain?
11-3 Prepend /data/kur s/adi t /bin:/data/kurs/TDDI09/bin to the variable PATH.
The easiest way to accomplish this is to use variable expansion in the right-hand side of the
assignment.
Report: Answers to 11-1 and 11-2. The commands used in 11-3
All (useful) Unix shells support parameter expansion. This process replaces part of a command line with
the contents of an environment or shell variable. In most shells, the syntax is “${ NAME} ” to expand the
environment variable NAME. The echo command can be combined with variable expansion to output
the value of a particular variable. For example, “echo ${ HOME} ”, when HOME is set to
“/home/user”, will output “/home/user”. Note that the shell is responsible for expanding the
variable; the echo command will receive the contents of the variable as its sole argument. The man
page for your shell will list various ways of performing parameter expansion.
Redirecting I/O
You absolutely must run these exercises in the bash shell, or results will not be as expected. You have
two simple options: either run the exercises in a UML instance (this assumes that you know how to start
your UML systems) or start bash manually, by issuing the command bash in a terminal window.
Unix provides several ways of redirecting the output of commands to files or other commands and
several ways of directing data to the input of commands. The basic mechanisms are redirections and
pipes. The precise mechanisms depend on the shell you are using; these instructions assume the bash
shell (see “The Command shell” above for more information about shells).
In Unix, I/O is performed from file descriptors. These are simply numbered input or output streams that
point to sources or destinations of data (e.g. files, terminals, network connections). By convention, file
descriptor 0 is called standard input or stdin, and is the default source for input; file descriptor 1 is called
standard out or stdout, and is where output is sent by default; file descriptor 2 is called standard error or
stderr, and is usually used for printing error messages.
I/O redirection simply is a matter of changing what the file descriptors point to.
You can redirect output from a command to a file using the > or >> operators.
command > filename
The output of command is written to filename. The file will be created if it doesn’t exist, and any
previous contents will be erased. In some shells there is a noclobber option. If this is set, you may
have to use the >! operator to overwrite an existing file.
In technical terms, this opens filename
for writing, then changes file descriptor 1 (stdout) to point
to the open file.
command >> filename
The output of command is appended to filename. The file will be created if it doesn’t already
exist.
m
IDA/ADIT LXB: LINUX BASICS 15
In technical terms, this opens filename for writing, seeks to the end of the file, then changes file
descriptor 1 (stdout) to point to the open file.
These basic redirection commands only redirect standard output; they do not redirect standard error. If
you want to redirect all output, you have to redirect file descriptor two as well. The exact syntax for
redirecting errors (and other file descriptors) is very shell-dependent.
command 2> filename
The output of command to standard error (usually error messages) written to filename. The file
will be created if it does not already exist, and any previous contents will be overwritten.
In technical terms, this is the same as >, but it changes file descriptor 2 (stderr) instead of file
descriptor one.
command 2>> filename
The output of command to standard error (usually error messages) is appended to filename. The
file will be created if it does not already exist.
In technical terms, this is the same as >>, but it changes file descriptor 2 (stderr) instead of file
descriptor one.
command 2>&1
Output from command
to standard error is sent to whatever standard out points to at the
moment (it does not link standard error and standard out, so if standard out is redirected later,
that redirection will not affect standard error). The most common use of this is to redirect
standard out and standard error to the same file.
Technically,
file descriptor 2 becomes a copy of file descriptor 1 so that they point to the same
thing. The two file descriptors remain independent of each other. This means that the order in
which you perform redirections matters when using 2>&1.
Exercise 12: Redirecting output
12-1 Where will stdout and stderr be redirected in the following examples? If you want to test your
theories, use /data/kurs/TDDI09/bin/stdio for command. This program outputs a series of E:s
to stderr (file descriptor 2) and a series of O:s to stdout (file descriptor 1).
(a) command >f i l e1
(b) command 2>&1 >f i l e1
(c) command >file1 2>&1
When answering these, remember that the order of redirections matters!
Report: The answers to 12-1.
In addition to redirecting output to files, it is possible to redirect output to other commands. The
mechanism that makes this possible is called pipe. The Unix philosophy of command design is that each
command should perform one small function well, and that complex functions are performed by
combining simple commands with pipes and redirection. It actually works quite well.
command1 | command2
The output (standard out) from command1 is used as the input (standard in) to command2. Note
that this connection is made before any redirection takes place.
From a technical point of view, file descriptor 1 (stdout) of command1 becomes linked to file
descriptor 0 (stdin) of command2.
IDA/ADIT LXB: LINUX BASICS 15
In technical terms, this opens filename for writing, seeks to the end of the file, then changes file
descriptor 1 (stdout) to point to the open file.
These basic redirection commands only redirect standard output; they do not redirect standard error. If
you want to redirect all output, you have to redirect file descriptor two as well. The exact syntax for
redirecting errors (and other file descriptors) is very shell-dependent.
command 2> filename
The output of command to standard error (usually error messages) written to filename. The file
will be created if it does not already exist, and any previous contents will be overwritten.
In technical terms, this is the same as >, but it changes file descriptor 2 (stderr) instead of file
descriptor one.
command 2>> filename
The output of command to standard error (usually error messages) is appended to filename. The
file will be created if it does not already exist.
In technical terms, this is the same as >>, but it changes file descriptor 2 (stderr) instead of file
descriptor one.
command 2>&1
Output from command
to standard error is sent to whatever standard out points to at the
moment (it does not link standard error and standard out, so if standard out is redirected later,
that redirection will not affect standard error). The most common use of this is to redirect
standard out and standard error to the same file.
Technically,
file descriptor 2 becomes a copy of file descriptor 1 so that they point to the same
thing. The two file descriptors remain independent of each other. This means that the order in
which you perform redirections matters when using 2>&1.
Exercise 12: Redirecting output
12-1 Where will stdout and stderr be redirected in the following examples? If you want to test your
theories, use /data/kurs/TDDI09/bin/stdio for command. This program outputs a series of E:s
to stderr (file descriptor 2) and a series of O:s to stdout (file descriptor 1).
(a) command >f i l e1
(b) command 2>&1 >f i l e1
(c) command >file1 2>&1
When answering these, remember that the order of redirections matters!
Report: The answers to 12-1.
In addition to redirecting output to files, it is possible to redirect output to other commands. The
mechanism that makes this possible is called pipe. The Unix philosophy of command design is that each
command should perform one small function well, and that complex functions are performed by
combining simple commands with pipes and redirection. It actually works quite well.
command1 | command2
The output (standard out) from command1 is used as the input (standard in) to command2. Note
that this connection is made before any redirection takes place.
From a technical point of view, file descriptor 1 (stdout) of command1 becomes linked to file
descriptor 0 (stdin) of command2.

CSE-478 Introduction to Computer Security
Now answers the following questions in your report:
Q 16. Where will stdout and stderr be redirected for: command 2>&1 > file1
Q 17. What do the following command do: command 2>&1 | grep –i fail
Processes and jobs
Linux is a multi-tasking, multi-user operating system. Several users can use the computer at
once, and each user can run several programs at the same time. Every program that is
executed results in at least one process. Each process has a process identifier and has its own
memory area not shared with other processes. A job is a processes that is under the control
of a command shell. Since jobs are connected to command shells, they are slightly easier to
manipulate than other processes.
Processes are very important in Unix, so you should be very familiar with the terminology and
commands associated with Unix processes.
Processes and terminals
A terminal is an I/O device, which basically represents a text-based terminal device. Terminals
(or ttys) play a special role in Unix, as they are the main method of interaction between a user
and text-based programs. Traditionally terminals were physical devices; today we tend to use
windowing systems with terminal emulators; in Unix terms, these are implemented using
pseudo-terminals (or ptys), which behave like physical terminals from the program’s point of
view, but are really only implemented in software.
A process in Unix may have a controlling terminal. The controlling terminal is inherited when
a new process is created, so all processes with a common ancestry share the same controlling
terminal. For example, when you log in, a command shell is started with a controlling terminal
representing the terminal or window you logged in on; processes created by the shell inherit
the same controlling terminal. When you log out, all processes with the same controlling
terminal as the process you terminated by logout are sent the HUP signal (see below).
A process with a controlling terminal can be controlled from the keyboard. The default
settings in Unix are that crtl+Z suspends a process, crtl+C terminates it and crtl+\ aborts it
(terminates with extreme prejudice). This is actually implemented by having the terminal
driver intercept the key presses and sending predefined signals to the process.
IDA/ADIT LXB: LINUX BASICS 15
In technical terms, this opens filename for writing, seeks to the end of the file, then changes file
descriptor 1 (stdout) to point to the open file.
These basic redirection commands only redirect standard output; they do not redirect standard error. If
you want to redirect all output, you have to redirect file descriptor two as well. The exact syntax for
redirecting errors (and other file descriptors) is very shell-dependent.
command 2> filename
The output of command to standard error (usually error messages) written to filename. The file
will be created if it does not already exist, and any previous contents will be overwritten.
In technical terms, this is the same as >, but it changes file descriptor 2 (stderr) instead of file
descriptor one.
command 2>> filename
The output of command to standard error (usually error messages) is appended to filename. The
file will be created if it does not already exist.
In technical terms, this is the same as >>, but it changes file descriptor 2 (stderr) instead of file
descriptor one.
command 2>&1
Output from command
to standard error is sent to whatever standard out points to at the
moment (it does not link standard error and standard out, so if standard out is redirected later,
that redirection will not affect standard error). The most common use of this is to redirect
standard out and standard error to the same file.
Technically,
file descriptor 2 becomes a copy of file descriptor 1 so that they point to the same
thing. The two file descriptors remain independent of each other. This means that the order in
which you perform redirections matters when using 2>&1.
Exercise 12: Redirecting output
12-1 Where will stdout and stderr be redirected in the following examples? If you want to test your
theories, use /data/kurs/TDDI09/bin/stdio for command. This program outputs a series of E:s
to stderr (file descriptor 2) and a series of O:s to stdout (file descriptor 1).
(a) command >f i l e1
(b) command 2>&1 >f i l e1
(c) command >file1 2>&1
When answering these, remember that the order of redirections matters!
Report: The answers to 12-1.
In addition to redirecting output to files, it is possible to redirect output to other commands. The
mechanism that makes this possible is called pipe. The Unix philosophy of command design is that each
command should perform one small function well, and that complex functions are performed by
combining simple commands with pipes and redirection. It actually works quite well.
command1 | command2
The output (standard out) from command1 is used as the input (standard in) to command2. Note
that this connection is made before any redirection takes place.
From a technical point of view, file descriptor 1 (stdout) of command1 becomes linked to file
descriptor 0 (stdin) of command2.
IDA/ADIT LXB: LINUX BASICS 16
command1 2>&1 | command2
Both standard out and standard error from command1
will be used as input (standard in) to
command2.
From a technical point of view, both file descriptor 2 (stderr) and file descriptor 1 (stdin) will be
linked to file descriptor 0 (stdin) of command2.This works because pipes are always connected
before redirection.
Exercise 13: Pipelines
13-1 What do the following commands do? If you want to test your theories, use
/data/kurs/TDDI09/bin/stdio for command and grep for “E” rather than “fail”.
(a) ls | gr ep –i doc
(b) command 2>&1 | gr ep –i fail
(c) command 2>&1 >/ dev/ nul l | gr ep –i fail
13-2 Write command lines to perform the following tasks:
(a) Output a recursive listing (using ls) of your home directory, including invisible
files, to the file /tmp/HOMEFILES.
(b) Find any files (using find) on the system that are world-writable (i.e. the write
permission for “others” is set). Error messages should be discarded (redirected to
/dev/null). This command is actually useful for auditing the security of a system
– world-writable files can be security risks.
Report: Answers to 13-1 and the solutions in 13-2.
Processes and jobs
Linux is a multi-tasking, multi-user operating system. Several users can use the computer at once, and
each user can run several programs at the same time. Every program that is executed results in at least
one process. Each process has a process identifier and has its own memory area not shared with other
processes. A job is a processes that is under the control of a command shell. Since jobs are connected to
command shells, they are slightly easier to manipulate than other processes.
Processes are very important in Unix, so you should be very familiar with the terminology and
commands associated with Unix processes.
Processes and terminals
A terminal is an I/O device, which basically represents a text-based terminal device. Terminals (or ttys)
play a special role in Unix, as they are the main method of interaction between a user and text-based
programs. Traditionally terminals were physical devices; today we tend to use windowing systems with
terminal emulators; in Unix terms, these are implemented using pseudo-terminals (or ptys), which
behave like physical terminals from the program’s point of view, but are really only implemented in
software.
A process in Unix may have a controlling terminal. The controlling terminal is inherited when a new
process is created, so all processes with a common ancestry share the same controlling terminal. For
example, when you log in, a command shell is started with a controlling terminal representing the
terminal or window you logged in on; processes created by the shell inherit the same controlling
terminal. When you log out, all processes with the same controlling terminal as the process you
terminated by logout are sent the HUP signal (see below).
A process with a controlling terminal can be controlled from the keyboard. The default settings in Unix
are that vZ suspends a process, vC terminates it and v\ aborts it
(terminates with extreme prejudice). This is actually implemented by having the terminal driver
intercept the key presses and sending predefined signals to the process

CSE-478 Introduction to Computer Security
Foreground, background and suspended processes
The distinction between foreground and background processes is mostly related to how the
process interacts with the terminal driver. There may be at most one foreground process at
a time, and this is the process which receives input and signals from the terminal driver.
Background processes may send output to the terminal, but do not receive input or signals.
If a background process attempts to read from the terminal it is automatically suspended. It
is shown like this in the terminal:
A process that is suspended is not executing. It is essentially frozen in time waiting to be
woken. Processes are suspended by sending them the TSTP or STOP signals. The TSTP signal
can be sent by typing vZ when the process is in the foreground (assuming standard shell and
terminal settings). The STOP signal can be sent using the ki l l command. A process which is
suspended can be resumed by sending it the CONT signal (e.g. using f g, bg or ki l l ).
Sometimes it is desirable to run a process in the background, detached from its parent and
from its controlling terminal. This ensures that the process will not be affected by its parent
terminating or a terminal closing. Processes which run in the background like this are called
daemons, and the logic that detaches them is in the program code itself. Some shells (e.g.
zsh) have a feature that allows the user to turn any process into a daemon.
Signals
The simplest form of inter-process communication in Unix are signals. These are content-free
messages sent between processes, or from the operating system to a process, used to signal
exceptional conditions. For example, if a program attempts to violate memory access rules,
the operating system sends it a SEGV signal (known as a segmentation fault).
There is a wide range of signals available, and each has a predefined meaning (there are two
user- defined signals, USR1 and USR2 as well) and default reaction. By default, some signals
are ignored (e.g. WINCH, which is signaled when a terminal window changes its size), while
others terminate the receiving program (e.g. HUP, which is signaled when the terminal a
process is attached to is closed), and others result in a core dump (dump of the process
memory; e.g. SEGV, which is sent when a program violates memory access rules).
Programs may redefine the response to most, but not all, signals. For example, a program
may ignore HUP signals, but it can never ignore KILL (kill process) ABRT (process aborted) or
STOP (suspend process). A few process related commands are given in the next page.
Do the following activities, but DO NOT include them in the report:
• Create a long running process by typing pi ng 127. 0. 0. 1. Suspend it with vZ and bring
it to the foreground with f g. Terminate it with vC.
• 14-2 Create a long running process in the background by typing pi ng 127. 0. 0. 1 >/
dev/ nul l &. Find out its process id using ps and kill it using ki l l .
• 14-3 What does the command ki l l - 9 pi d do, where pid is the number of a process?
What does ki l l - 9 - 1 do? Read the documentation to figure the last one out as it is a
somewhat dangerous command.
CSE-478 Introduction to Computer Security
Editing and viewing files
There are lots of text editors available for Linux. Regardless of which text editor your prefer,
it is useful to have a working knowledge of vi , since it is shipped with almost every Unix
variant that exists. You should learn vi to the point where you can edit text files, but there is
no point in becoming an expert – you only need to know enough so you can get a system to
the point where you can install emacs.
Inexperienced Unix users tend to load text files into editors to view them. The problem with
opening text files in an editor is that you might accidentally change them. In this course,
please use the appropriate commands to view files rather than opening them in editors.
To display a short file, use the cat command. Simply typing cat filename will display the file
named filename.
Practically all Unix systems come with a so-called pager. A pager is a program that displays
text files one page at a time. The default pager on most Unix systems is named mor e. To
display a text file (named filename) one page at a time, simply type:
You can use more to display the output of any program one page at a time. For example, to
list all files that end in “.h” on the system, one page at a time, type:
IDA/ADIT LXB: LINUX BASICS 17
Foreground, background and suspended processes
The distinction between foreground and background processes is mostly related to how the process
interacts with the terminal driver. There may be at most one foreground process at a time, and this is
the process which receives input and signals from the terminal driver. Background processes may send
output to the terminal, but do not receive input or signals. If a background process attempts to read
from the terminal it is automatically suspended. It is shown like this in the terminal:
[1]+ Stopped(SIGTTIN) command
A process that is suspended is not executing. It is essentially frozen in time waiting to be woken.
Processes are suspended by sending them the TSTP or STOP signals. The TSTP signal can be sent by
typing vZ when the process is in the foreground (assuming standard shell and terminal
settings). The STOP signal can be sent using the ki l l command. A process which is suspended can be
resumed by sending it the CONT signal (e.g. using fg, bg or ki l l ).
Sometimes it is desirable to run a process in the background, detached from its parent and from its
controlling terminal. This ensures that the process will not be affected by its parent terminating or a
terminal closing. Processes which run in the background like this are called daemons, and the logic that
detaches them is in the program code itself. Some shells (e.g. zsh) have a feature that allows the user
to turn any process into a daemon.
Signals
The simplest form of inter-process communication in Unix are signals. These are content-free messages
sent between processes, or from the operating system to a process, used to signal exceptional
conditions. For example, if a program attempts to violate memory access rules, the operating system
sends it a SEGV signal (known as a segmentation fault).
There is a wide range of signals available, and each has a predefined meaning (there are two user-
defined signals, USR1 and USR2 as well) and default reaction. By default, some signals are ignored (e.g.
WINCH, which is signaled when a terminal window changes its size), while others terminate the
receiving program (e.g. HUP, which is signaled when the terminal a process is attached to is closed), and
others result in a core dump (dump of the process memory; e.g. SEGV, which is sent when a program
violates memory access rules).
Programs may redefine the response to most, but not all, signals. For example, a program may ignore
HUP signals, but it can never ignore KILL (kill process) ABRT (process aborted) or STOP (suspend
process).
Process-related commands
Command
Purpose
ps aux
List all running processes.
ki l l - si gnal pi d
Send signal number signal to process with ID pid. Omit signal to just
terminate the process. If pid has the form %n
, then send signal to job
n.
kill -9 pi d
Send signal number 9 (SIGKILL) to process with ID pid. This is a last-
resort method to terminate a process.
pki l l pat t er n
Kill all processes that match pattern. By default, only the command
name is searched for pattern.
jobs
Display running jobs.
vC
Interrupts (terminates) the process currently in the foreground.
vZ
Suspends the process currently running in the foreground.
vS
Stops output in the active terminal (this is not strictly process control,
but output control).
vQ
Resumes output in the active terminal.
IDA/ADIT LXB: LINUX BASICS 18
command &
Runs command in the background.
bg
Resumes a suspended process in the background. If the process needs
to read from the terminal, it will be suspended again.
fg
Brings a process in the background to the foreground. This will resume
the process if it is currently suspended.
Exercise 14: Processes and jobs
14-1 Create a long running process by typing pi ng 127. 0. 0. 1. Suspend it with vZ
and bring it to the foreground with fg. Terminate it with vC.
14-2 Create a long running process in the background by typing pi ng 127. 0. 0. 1
>/ dev/ nul l &. Find out its process id using ps and kill it using ki l l .
14-3 What does the command ki l l - 9 pi d do, where pid is the number of a process? What does
ki l l - 9 - 1 do? Read the documentation to figure the last one out as it is a somewhat
dangerous command.
14-4 Create a long running process in the background by typing pi ng 127. 0. 0. 1
>/ dev/ nul l &. Kill it using pkill. The pkill command is very useful when you need to
kill several processes that share some attribute (such as a command name).
Report: Answers to the questions above and the commands executed.
Part 2: Archives and compressed files
When working with Unix (or Linux) you are bound to encounter archives and compressed files (and
compressed archives). For example, most of the Debian package documentation is compressed to save
space, and source code is typically distributed in archive form.
Compressed files
In the Linux world the two most popular compression standards are gzi p and bzi p2. A gzi p
compressed file usually has a .gz file name extension, while a bzip2 compressed file ends in .bz2. In more
venerable Unix-like systems, you will see the .Z file extension, which indicates a file compressed with the
compr ess command.
Command Purpose
zcat FI LENAME.gz
bzcat FI LENAME.bz2
Output the uncompressed contents of FILENAME.gz or FILENAME.bz2
to stdout.
gzi p –d FI LENAME.gz
bzi p2 –d FI LENAME.bz2
Uncompress FILENAME.gz or FILENAME.bz2, removing the compressed
file and leaving the uncompressed file in its place.
gzi p FI LENAME
bzi p2 FI LENAME
Compress FILENAME using gzi p or bzi p2.
Note that unlike compression utilities that are popular on the Windows platform, gzi p and bzi p2
compress single files. Combining several files into an archive is the job of another program, usually tar,
but sometimes cpi o.
The choice of gzi p or bzi p2 depends on how portable you need to be. At the moment, gzi p has a
far larger installed base than bzi p2. If portability is not a consideration, bzi p2 performs slightly
better than gzi p.
Archives
To combine several files into a single archive, Unix users almost exclusively use the tar utility. tar was
originally designed to create a byte stream that could be written to tape in such a way that individual
IDA/ADIT LXB: LINUX BASICS 20
Looking at files
Inexperienced Unix users tend to load text files into editors to view them. The problem with opening
text files in an editor is that you might accidentally change them. In this course, please use the
appropriate commands to view files rather than opening them in editors.
To display a short file, use the cat command. Simply typing cat filename will display the file
named filename.
A pager: more
Practically all Unix systems come with a so-called pager. A pager is a program that displays text files one
page at a time. The default pager on most Unix systems is named mo r e . To display a text file (named
filename) one page at a time, simply type:
mo r e filename
You can use more to display the output of any program one page at a time. For example, to list all files
that end in “.h” on the system, one page at a time, type:
find / -name ‘ * . h’ –pr i nt | mor e
Or to read a compressed file:
zcat filename.gz | more
If you try this you may notice that you can only move forward in the output – mo r e will not let you
move back and forth. You may also notice that mo r e exits when the last line of output has been
displayed.
A better pager: less
The preferred alternative to mo r e is called less. It is not installed by default, but it is worthwhile
installing it as soon as you can on a new system. less has several advantages over mo r e , chief of
which is that it allows paging forwards and backwards in any file, even if it is piped into less. It also has
better search facilities. Learn about less by reading the man page. Typing ‘h’ in less will display a list
of keyboard commands.
Exercise 16: Using the pager less… eh, using the pager named less
16-1 What keystroke in less moves to the beginning of the file?
16-2 What keystroke in less moves to the end of the file?
16-3 What would you type in less to start searching for “option”?
16-4 What would you type in less to move to the next match for “option”?
16-5 Locate the package documentation for the ssh package and answer the following questions by
reading the README.Debian.gz file (hint: remembering the answers to these questions may
be useful in the project):
(a) What is the default setting for ForwardX11?
(b) If you want X11 forwarding to work, what other package(s) need to be installed on
the server?
Report: Answers to the questions above.
Non-interactive text editors
Sometimes it is convenient to edit a file without using an interactive editor. This is often the case when
editing files from shell scripts, or when making a large number of systematic changes to a file. Unix
includes a number of utilities that can be used to non-interactively edit a file. Read the man pages for
sed, awk, cut and past e for detailed information about some of the more useful commands. Here
are some common examples:
IDA/ADIT LXB: LINUX BASICS 20
Looking at files
Inexperienced Unix users tend to load text files into editors to view them. The problem with opening
text files in an editor is that you might accidentally change them. In this course, please use the
appropriate commands to view files rather than opening them in editors.
To display a short file, use the cat command. Simply typing cat filename will display the file
named filename.
A pager: more
Practically all Unix systems come with a so-called pager. A pager is a program that displays text files one
page at a time. The default pager on most Unix systems is named mo r e . To display a text file (named
filename) one page at a time, simply type:
mo r e filename
You can use more to display the output of any program one page at a time. For example, to list all files
that end in “.h” on the system, one page at a time, type:
find / -name ‘ * . h’ –pr i nt | mor e
Or to read a compressed file:
zcat filename.gz | more
If you try this you may notice that you can only move forward in the output – mo r e will not let you
move back and forth. You may also notice that mo r e exits when the last line of output has been
displayed.
A better pager: less
The preferred alternative to mo r e is called less. It is not installed by default, but it is worthwhile
installing it as soon as you can on a new system. less has several advantages over mo r e , chief of
which is that it allows paging forwards and backwards in any file, even if it is piped into less. It also has
better search facilities. Learn about less by reading the man page. Typing ‘h’ in less will display a list
of keyboard commands.
Exercise 16: Using the pager less… eh, using the pager named less
16-1 What keystroke in less moves to the beginning of the file?
16-2 What keystroke in less moves to the end of the file?
16-3 What would you type in less to start searching for “option”?
16-4 What would you type in less to move to the next match for “option”?
16-5 Locate the package documentation for the ssh package and answer the following questions by
reading the README.Debian.gz file (hint: remembering the answers to these questions may
be useful in the project):
(a) What is the default setting for ForwardX11?
(b) If you want X11 forwarding to work, what other package(s) need to be installed on
the server?
Report: Answers to the questions above.
Non-interactive text editors
Sometimes it is convenient to edit a file without using an interactive editor. This is often the case when
editing files from shell scripts, or when making a large number of systematic changes to a file. Unix
includes a number of utilities that can be used to non-interactively edit a file. Read the man pages for
sed, awk, cut and past e for detailed information about some of the more useful commands. Here
are some common examples:

CSE-478 Introduction to Computer Security
If you try this you may notice that you can only move forward in the output – more will not
let you move back and forth. You may also notice that mor e exits when the last line of output
has been displayed.
The preferred alternative to more is called less. It is not installed by default, but it is
worthwhile installing it as soon as you can on a new system. less has several advantages over
more, chief of which is that it allows paging forwards and backwards in any file, even if it is
piped into less. It also has better search facilities. Learn about less by reading the man page.
Typing ‘h’ in less will display a list of keyboard commands.
Sometimes it is convenient to edit a file without using an interactive editor. This is often the
case when editing files from shell scripts, or when making a large number of systematic
changes to a file. Unix includes a number of utilities that can be used to non-interactively edit
a file. Read the man pages for sed, awk, cut and past e for detailed information about some
of the more useful commands. Here are some common examples:
Do the following activities, but DO NOT include them in the report:
• Create a file called temp in command prompt in your home directory.
• Use the vi editor to open the file and explore the file.
• Add a few lines of text in the file, with at least one occurrence of the text: hello
• Save the file.
• Exit from the file.
• Use the sed command to replace the world hello with world.
Shell scrips
Writing shell scripts is one of the most widely used tasks that might be required for any
security administrator. There are lots of mundane tasks that will required to execute on day
to day basis. These can be automated using shell scripts. In the following we will learn the
basic of writing shell scripts.
The whole purpose of this script is nothing else but print "Hello World" using echo command
to the terminal output. Using any text editor to create a new file named hello.sh containing
the below code:
IDA/ADIT LXB: LINUX BASICS 21
sed –e ‘ s/ REGEX/REPL ACEMENT /g’ < INFILE > OUT F I L E
Replace all occurrences of REGEX in INFILE with REPLACEMENT, and write the output to OUTFILE.
This is probably the most common use of sed.
awk –e ‘ { pr i nt $2 } ’ < INFILE
Print the second column of INFILE to standard output. The column separator can be changed by
setting the FS variable. See the awk manual for details.
cut –d: -f1 < /etc/passwd
Print all user names in /etc/passwd (really, print the first column in /etc/passwd,
assuming that columns are separated by colons).
Exercise 17: Using non-interactive text editors (this exercise is optional)
17-1 Use sed to change all occurrences of “/bin/tcsh” to “/bin/sh” in /etc/passwd (output to a
different file). This exercise is optional.
17-2 Examine the files shadow and passwd in the directory /data/kurs/TDDI09/labs/lxb. Use
past e and awk to output a file where each line consists of column one from passwd and
column two from the corresponding line in shadow. The pr i nt f function in awk is helpful
here. This exercise is optional since it goes beyond the basics.
Report: No report is required.
Part 4: System logging
System logs are some of the most important source of information when troubleshooting a problem, or
when testing a system. Most Unix services print diagnostic information to the system logs. A good habit
to develop is to always look in the log files when you have reconfigured or restarted a service, just to
make sure that there are no obvious problems.
Logging is managed by the sysl ogd process, which is accessed through a standard API. By default, the
sysl ogd process outputs log messages to various log files in /var/log, but it is also possible to send log
messages over the network to another machine. It is also possible to configure exactly which log
messages are sent to which files, and which are simply ignored.
For the purpose of this course, the default configuration is sufficient. It creates a number of log files, the
most important of which are: /var/log/auth.log for log messages related to authentication (e.g. logins
and logouts); /var/log/syslog and /var/log/messages contain most other messages; mail.log contains log
messages from the mail subsystem. For details on what goes where, see /etc/syslog.conf.
Since log files grow all the time, there needs to be a facility to remove old logs. In Debian/Gnu Linux, a
service called logrotate is commonly used. It “rotates” log files regularly, creating a series of
numbered log files, some of which are compressed. For example, you may see the files
/var/log/auth.log, /var/log/auth.log.0, /var/log/auth.log.1.gz and /var/log/auth.log.2.gz on a system.
/var/log/auth.log is the current log file. /var/log/auth.log.0 is the next most recent and so forth.
To test these exercises you may need to use a UML system as you may lack sufficient permissions to see
the log files on the lab server.
Exercise 18: Log files
18-1 What does tail -f /var/log/syslog do?
18-2 If you want to extract the last ten lines in /var/log/syslog that are related to the service cr on,
what command would you use? (Hint: the gr ep command can search for matching lines in a
file).
Report: Answers to the questions above.
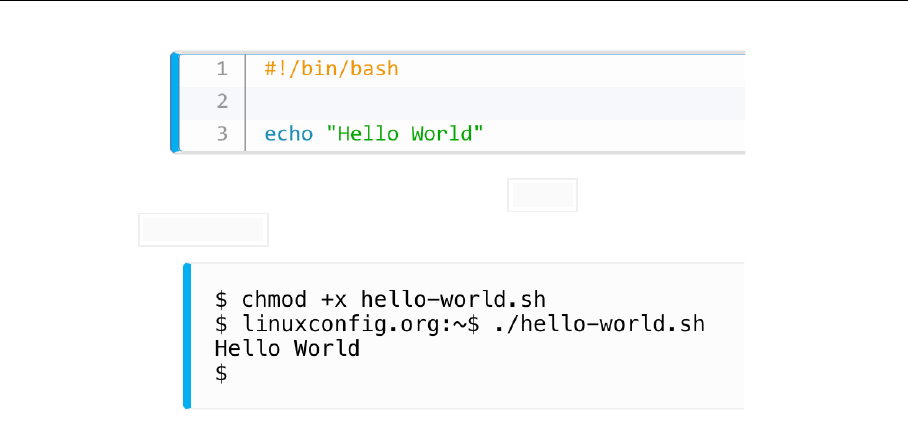
CSE-478 Introduction to Computer Security
Once%ready,%make%your%script%executable%with%the chmod %command%and%execute%it%using%
relative%path% ./hello.sh :%
Examples of Some other programming are given below:
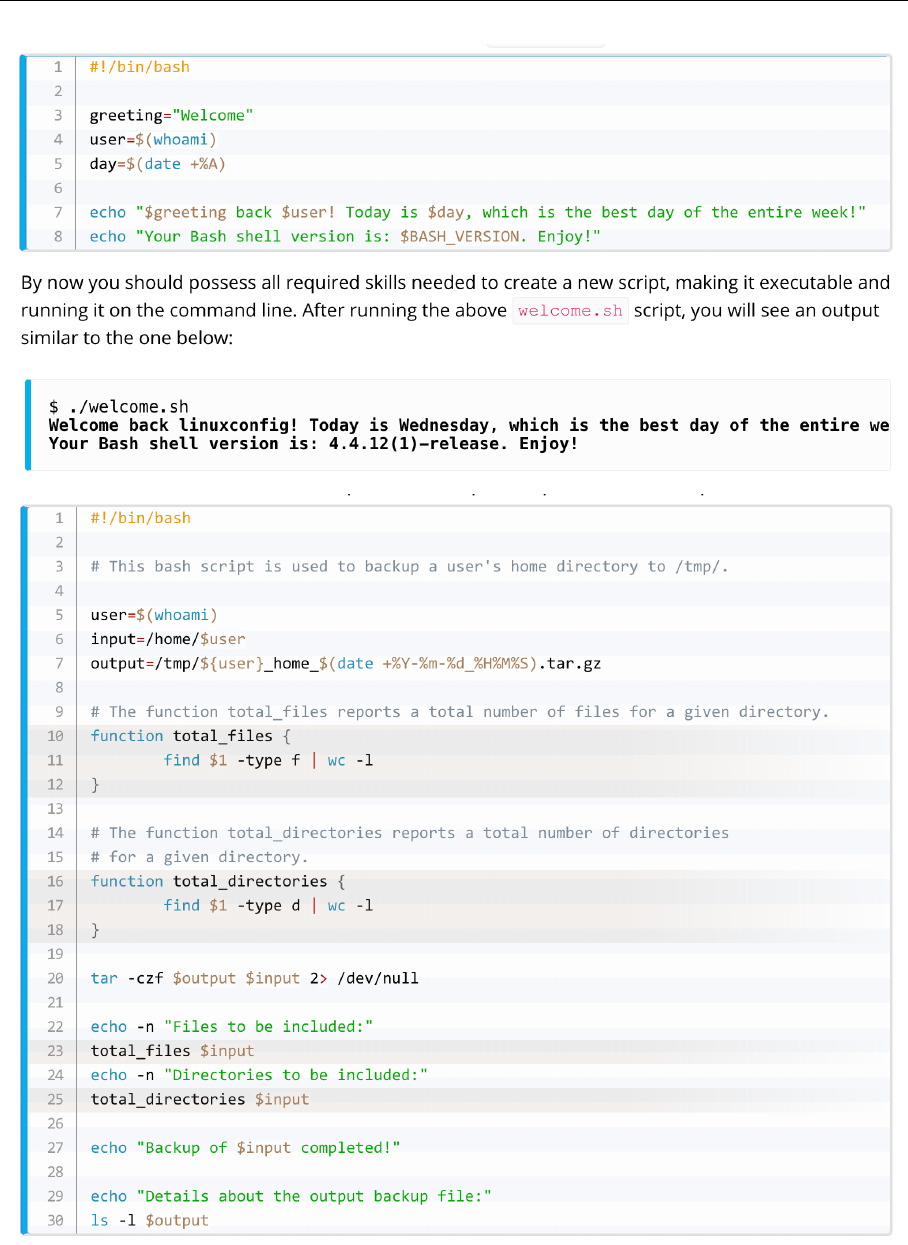
CSE-478 Introduction to Computer Security
CSE-478 Introduction to Computer Security
Now, the final phase of the exercise:

CSE-478 Introduction to Computer Security
Q 18. Write a shell script that will take three inputs of the first name, last name and birth
place and display the result into the console as well as redirect to a file named
input.
Q 19. Write a shell script that will take three numbers and display the result of their
addition, subtraction, multiplication and division into a file called math.
Q 20. Write a shell script that will input three numbers and display the highest and lowest
number in the console.