Mobile Revelator 2.2.5 Manual
User Manual:
Open the PDF directly: View PDF ![]() .
.
Page Count: 200 [warning: Documents this large are best viewed by clicking the View PDF Link!]
- Mobile Revelator
- Dump
- Open
- Analysis
- Report
- Utilities
- Cryptanalysis
- Crypto Tools
- Bruteforce
- Decrypt
- Android
- Decrypt Android Application (.asec)
- Decrypt Android Partition / SDCard Files
- Decrypt Whatsapp Databases (.crypt/.crypt5-12)
- Decrypt Threema database
- Decrypt SQLCipher (AES-256) Database
- Decrypt McAfee Suite WSAndroidAppConfig.xml
- Decrypt KeepSafe files
- Convert Android 4.x/5.x Backup File to TAR
- Decrypt Cleanmaster Security Patternlock
- Decrypt SnapChat Received Story Files
- Decrypt Telekom Mail Database
- Decrypt Wickr Database
- Blackberry
- MTK
- Android
- Binary Search Tool
- Settings
- Templates Documentation
- Python API Documentation

Mobile Revelator 2.2.5

Mobile Revelator 2.2.5
2 / 200
Inhaltsverzeichnis
Mobile Revelator .......................................................................................................................... 6
Dump ....................................................................................................................................... 7
Android Dumper ..................................................................................................................... 8
Physical ............................................................................................................................... 9
Filesystem .......................................................................................................................... 11
Packageinfo ....................................................................................................................... 12
Physical Dumper ................................................................................................................... 13
iTunes Browser .................................................................................................................... 14
Dump via Bootloader ............................................................................................................ 15
QC Firehose ....................................................................................................................... 16
MTK ................................................................................................................................... 17
LG ...................................................................................................................................... 18
Port Utils ............................................................................................................................... 19
AT Command Terminal ...................................................................................................... 20
Commands ...................................................................................................................... 21
Port Config ...................................................................................................................... 22
Tools ............................................................................................................................... 23
QC / Bootloader Tool ......................................................................................................... 24
Port Config ...................................................................................................................... 25
Port Switch ...................................................................................................................... 26
Codes .............................................................................................................................. 27
Tools ............................................................................................................................... 28
USB Tool ............................................................................................................................ 29
Send Commands ............................................................................................................. 30
Send SCSI Command ...................................................................................................... 31
Tools ............................................................................................................................... 32
M-Obex Tool ...................................................................................................................... 33
TCP/IP Tool ........................................................................................................................ 34
Command ........................................................................................................................ 35
Tools ............................................................................................................................... 36
Open ....................................................................................................................................... 37
Open raw flash ..................................................................................................................... 38
Partitions .............................................................................................................................. 39
EMMC Partition (MBR/GPT/BCT/WMPART) ......................................................................... 40
QC Partition ....................................................................................................................... 41
Filesystems .......................................................................................................................... 42
Generic .............................................................................................................................. 43
Specific .............................................................................................................................. 44
EXT2/3/4 ......................................................................................................................... 45
Locosto FFS ..................................................................................................................... 46
FAT12/FAT16/FAT32/RFS/TxFat/xFat/NTFS .................................................................... 47
F2FS ................................................................................................................................ 48
Yaffs2 .............................................................................................................................. 49
CRAMFS .......................................................................................................................... 50
Infineon FS (GB102/A100/...) .......................................................................................... 51
QC EFS / SuperEFS ......................................................................................................... 52
HFS+/HFSX ..................................................................................................................... 53
TargetFFS / TFS4 (Samsung E1080i / Philips Dual Band) ................................................ 54

Mobile Revelator 2.2.5
3 / 200
TFFS (AVM FritzBox) ....................................................................................................... 55
Backup Files ......................................................................................................................... 55
Apple Backup ..................................................................................................................... 57
Android Backup / Tar ......................................................................................................... 58
Huawei Backup .................................................................................................................. 58
Reconstruct .......................................................................................................................... 59
Spare Repair ...................................................................................................................... 60
Nokia ................................................................................................................................. 61
Nokia Rap3G NOR Image to FAT ..................................................................................... 62
Nokia Asha 200/201 NOR Image to FAT .......................................................................... 63
Nokia 108 NAND Image to FAT ....................................................................................... 64
Samsung ........................................................................................................................... 65
FSR Partition .................................................................................................................... 66
STL to Raw ................................................................................................................... 68
BML to STL ................................................................................................................... 70
XSR Partition ................................................................................................................... 71
Infineon/LG ....................................................................................................................... 72
LG GS290N NOR .............................................................................................................. 72
MTK ................................................................................................................................... 73
MTK NOR Image to FAT .................................................................................................. 74
Apple ................................................................................................................................. 75
iPhone 3G Nand .............................................................................................................. 76
Sony Ericsson .................................................................................................................... 77
A1/DB2020 Reconstruct ................................................................................................... 78
Alcatel ................................................................................................................................ 79
Spreadtrum (SFR118/OT2060) ........................................................................................ 80
Analysis .................................................................................................................................. 81
Database Utils ...................................................................................................................... 82
SQLite Database Tool ......................................................................................................... 83
View ................................................................................................................................ 84
Right-Click-Menu ........................................................................................................... 86
Python-Plugins ............................................................................................................ 87
Timestamps ................................................................................................................ 88
Blob ............................................................................................................................ 89
Decoder ...................................................................................................................... 90
Text ............................................................................................................................ 91
Combine ..................................................................................................................... 92
Export ............................................................................................................................. 93
Combine .......................................................................................................................... 94
Bada DB2 Database Tool ................................................................................................... 95
View ................................................................................................................................ 96
Right-Click-Menu ........................................................................................................... 98
Timestamps ................................................................................................................ 99
Text .......................................................................................................................... 100
Export ............................................................................................................................ 101
WP7 EDB Database Tool .................................................................................................. 101
View .............................................................................................................................. 102
Export ............................................................................................................................ 103
IPD/BBB Database Tool ................................................................................................... 104
View .............................................................................................................................. 105

Mobile Revelator 2.2.5
4 / 200
Export ............................................................................................................................ 106
Apple Binary PList ............................................................................................................... 107
Android Binary XML ............................................................................................................ 108
HTTP/S data carver ............................................................................................................ 109
Samsung RIL carver ........................................................................................................... 110
Android Password carver .................................................................................................... 111
File Ripper .......................................................................................................................... 112
Apple iThmb Extract ........................................................................................................... 114
Report ................................................................................................................................... 115
Timeline report ................................................................................................................... 116
Location/GPS data report .................................................................................................... 119
Carve 7-Bit SMS ................................................................................................................. 120
Android ............................................................................................................................... 121
Cache.cell/.wifi to GPX ..................................................................................................... 122
Nokia .................................................................................................................................. 123
Nokia PM .......................................................................................................................... 124
Motorola ............................................................................................................................. 125
ODM Inbox SMS ............................................................................................................... 126
ODM Outbox SMS ............................................................................................................ 127
Utilities .................................................................................................................................. 128
Firmware Utils .................................................................................................................... 129
Samsung .......................................................................................................................... 130
Convert .img to .tar.md5 ............................................................................................... 131
HTC ................................................................................................................................. 132
Decrypt HTC RUU .......................................................................................................... 133
LG .................................................................................................................................... 134
Decrypt KDZ .................................................................................................................. 135
Unpack DZ ..................................................................................................................... 136
Android ............................................................................................................................ 137
Android 4.x : Convert .img to raw .bin ........................................................................... 138
Android 5.x : Convert .new.dat to raw .bin .................................................................... 139
Number Decoder ................................................................................................................ 140
Number To Country ......................................................................................................... 141
IMSI Decode .................................................................................................................... 142
ICCID Decode .................................................................................................................. 143
MAC Lookup ..................................................................................................................... 144
SDCard CID Decoder ........................................................................................................ 145
Time Stamp Decoder .......................................................................................................... 146
Compression Util ................................................................................................................. 147
Hex Editor .......................................................................................................................... 148
Cryptanalysis ......................................................................................................................... 149
Crypto Tools ....................................................................................................................... 150
RSA .................................................................................................................................. 151
DES .................................................................................................................................. 152
AES .................................................................................................................................. 153
Twofish ............................................................................................................................ 154
ARC4/RC4 ........................................................................................................................ 155
Blowfish ........................................................................................................................... 156
TEA .................................................................................................................................. 157
SEED ................................................................................................................................ 158

Mobile Revelator 2.2.5
5 / 200
XOR ................................................................................................................................. 159
Base64 ............................................................................................................................. 160
Padding ............................................................................................................................ 161
Bruteforce .......................................................................................................................... 162
Android Encryption GPU Bruteforcer ................................................................................. 163
Android Password / PIN GPU Bruteforcer ......................................................................... 164
WP7.x/WP8.x PIN GPU Bruteforcer ................................................................................... 165
SQLCipher Bruteforcer ..................................................................................................... 166
BB Keystore Bruteforcer ................................................................................................... 167
Android Patternlock CPU Bruteforcer ................................................................................ 168
Bleichenbacher RSA Attack (Exponent 3) ......................................................................... 169
Decrypt ............................................................................................................................... 170
Android ............................................................................................................................ 171
Decrypt Android Application (.asec) ............................................................................... 172
Decrypt Android Partition / SDCard Files ........................................................................ 173
Decrypt Whatsapp Databases (.crypt/.crypt5-12) .......................................................... 174
Decrypt Threema database ........................................................................................... 175
Decrypt SQLCipher (AES-256) Database ........................................................................ 176
Decrypt McAfee Suite WSAndroidAppConfig.xml ............................................................ 177
Decrypt KeepSafe files ................................................................................................... 178
Convert Android 4.x/5.x Backup File to TAR ................................................................... 179
Decrypt Cleanmaster Security Patternlock ..................................................................... 180
Decrypt SnapChat Received Story Files .......................................................................... 181
Decrypt Telekom Mail Database .................................................................................... 182
Decrypt Wickr Database ................................................................................................ 183
Blackberry ........................................................................................................................ 184
Decrypt Blackberry REMF SQLite Database .................................................................... 185
Retrieve Blackberry PGP Private Key .............................................................................. 186
MTK ................................................................................................................................. 187
MTK Decrypt Files .......................................................................................................... 188
Binary Search Tool ............................................................................................................. 189
Settings ................................................................................................................................. 190
Configure ............................................................................................................................ 191
Templates Documentation ....................................................................................................... 193
Timeline XML Documentation ................................................................................................ 194
Template XML Documentation .............................................................................................. 196
Python API Documentation ...................................................................................................... 197

Mobile Revelator 2.2.5
6 / 200
Mobile Revelator
Version 2.2.5
Mobile Revelator is a tool mainly developed by Bjoern Kerler. Its main aim
is to support forensic mobile researchers in conducting better forensic examinations
and in verification of existing commercial forensic solutions.
Mobile Revelator 2.2.5
7 / 200
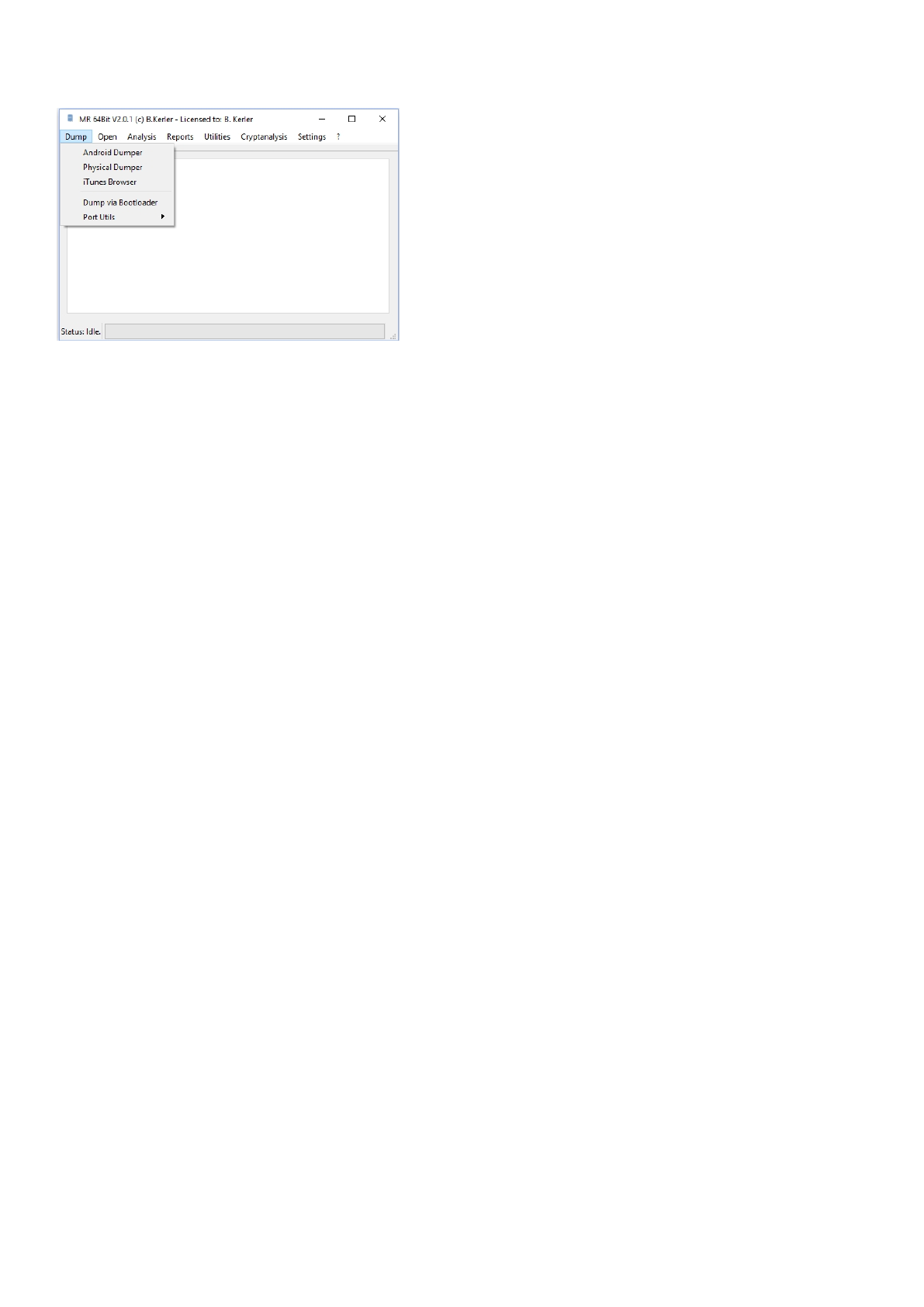
Dump
The "Dump" Menu offers several tools to Dump Android, Physical and iTunes compatible devices.
Mobile Revelator 2.2.5
8 / 200
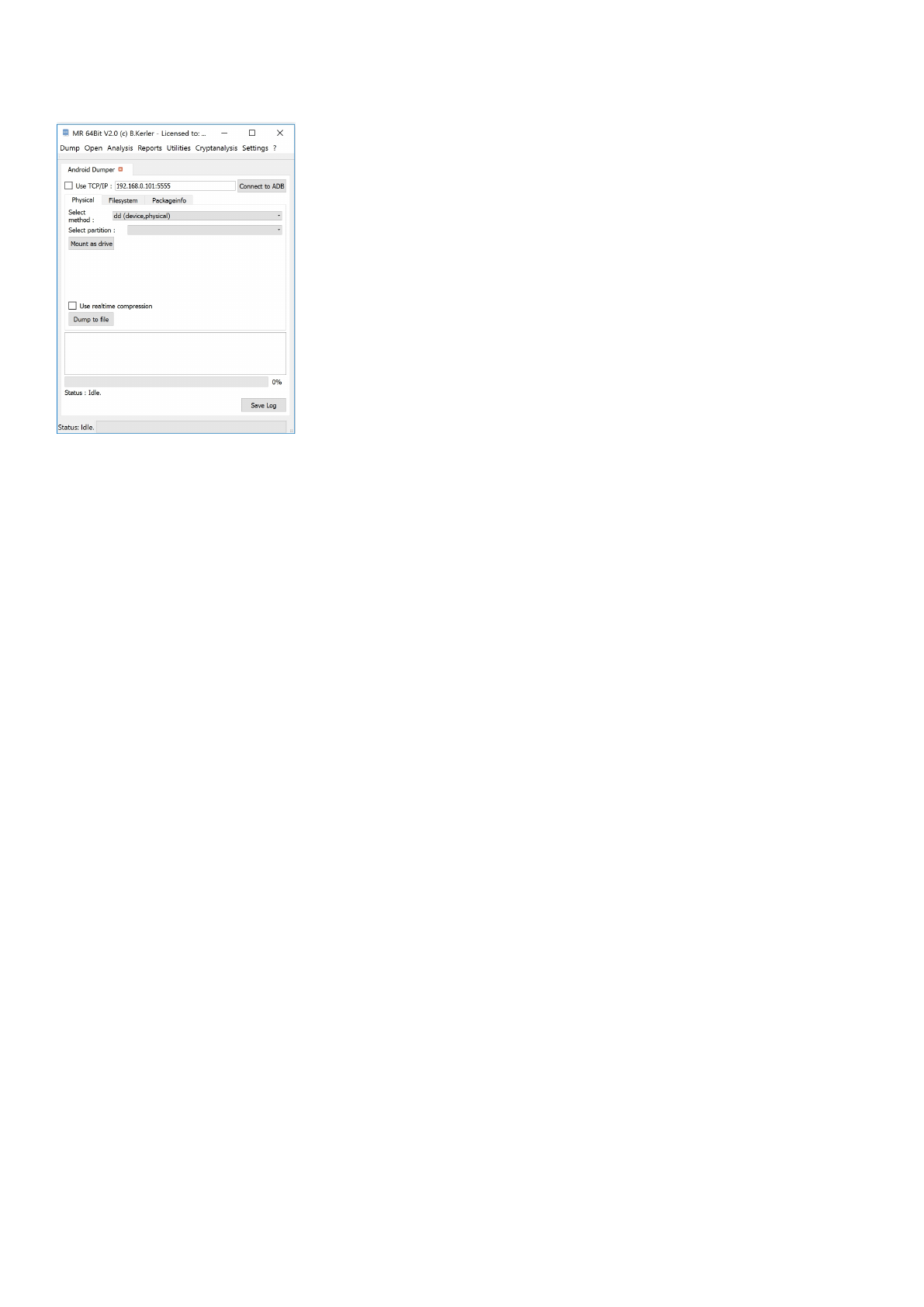
Android Dumper
The android dumper tool enables you to raw dump partitions and whole flash chips using adb connection if the
device has been rooted or if it is being used with a custom recovery such as TWRP or CWM. For some devices
lower android 4.4, it is also able to temproot the device.
Furthermore it enables you to do a logical backup using android backup functionality as well.
Mobile Revelator 2.2.5
9 / 200
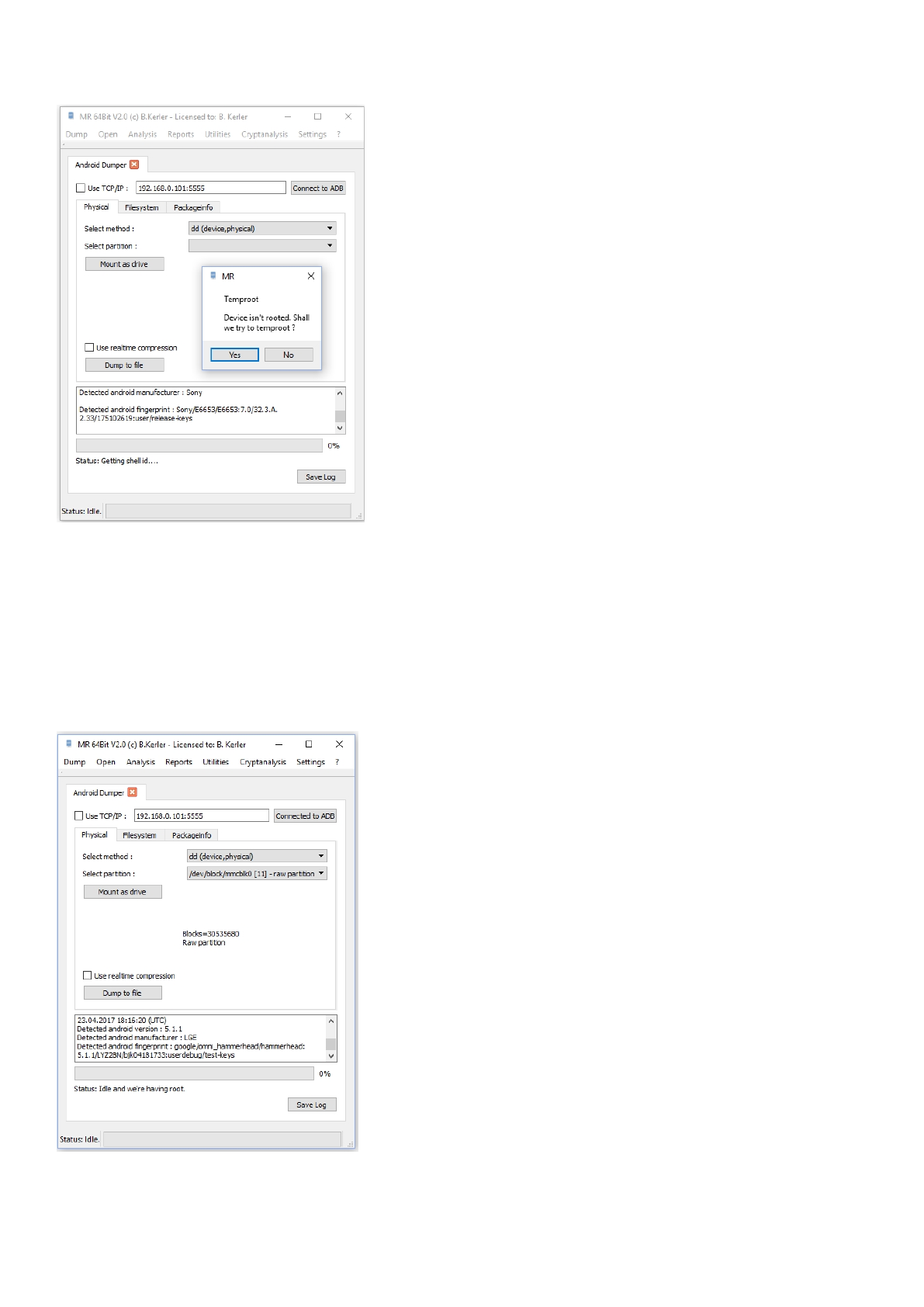
Physical
The Android Dumper provides physical dumping capabilities for unrooted Android < 6.0 stock devices and unlocked
devices with custom recovery.
In order to physically dump, press "Connect to ADB" and make sure that USB Debugging is enabled on the device. If
everything works fine, you will see that it's going to print which android version and manufacturer has been detected.
If the device isn't already rooted, it's going to ask if you want to temproot the device. Temproot does currently only work for
devices with Android < 6.0.
If the device is rooted, you will then be presented the detected partition available for dumping :
MR will automatically select the full flash if available (/dev/block/mmcblk0 or /dev/block/sda).
Mobile Revelator 2.2.5
10 / 200
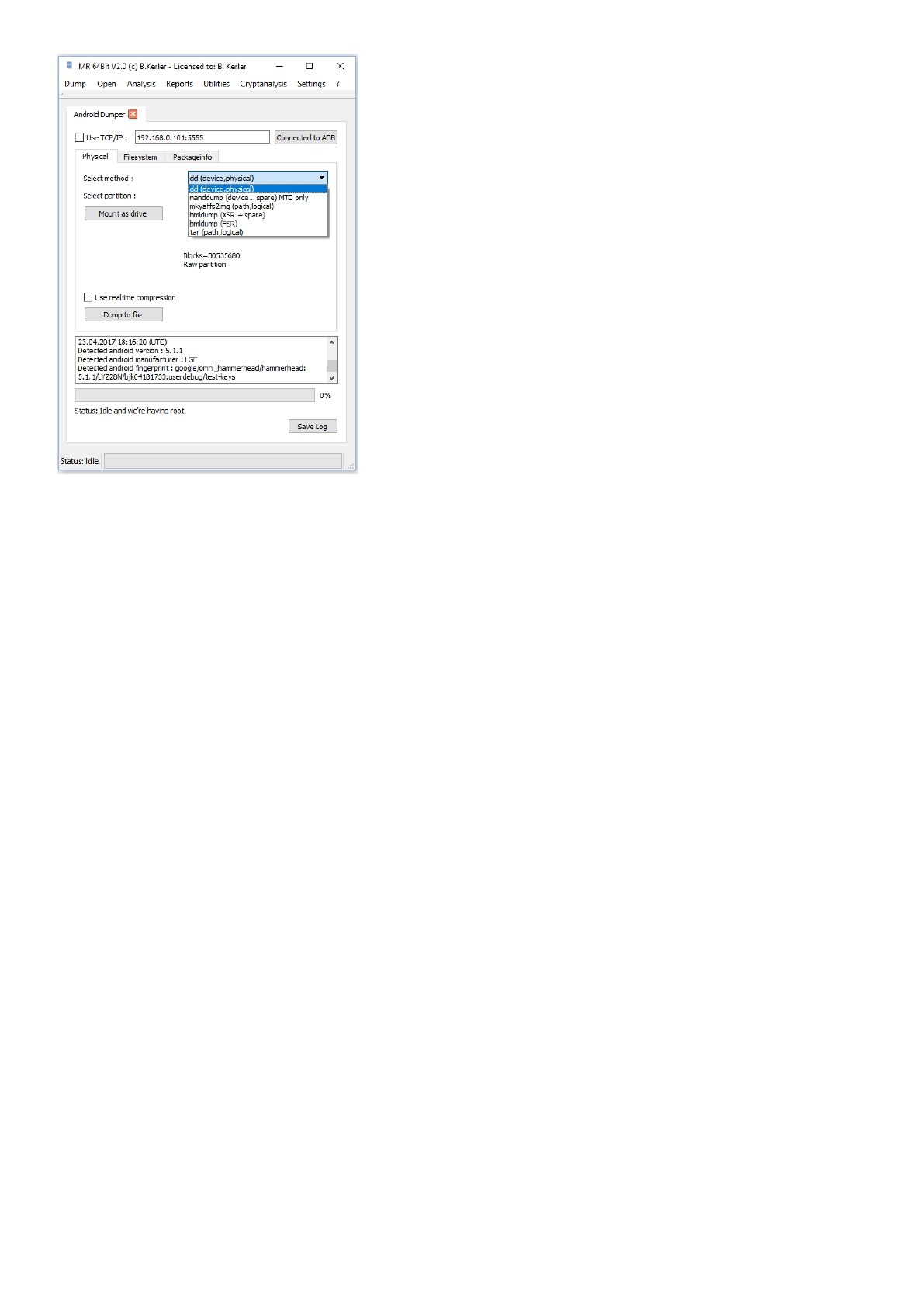
You may then choose several options for dumping. For emmc and sdcards, dd is the most appropriate option
for saving. However if Nand Flash is being used, choose nanddump for MTD or bmldump for samsung devices with
xsr/stl/bml wearleveling or filesystem dump methods such as mkyaffs2img and tar.
"Use realtime compression" does make sense, if you encounter a large flash (128/256 GB) with large areas of empty
space.
Otherwise, selecting this option will slow down the dumping process.
Pressing "Dump to file" will save the flash as raw image. If available, "Mount as drive" will force the usb setting of the
device to enable partition access by usb driver.
Mobile Revelator 2.2.5
11 / 200
Filesystem
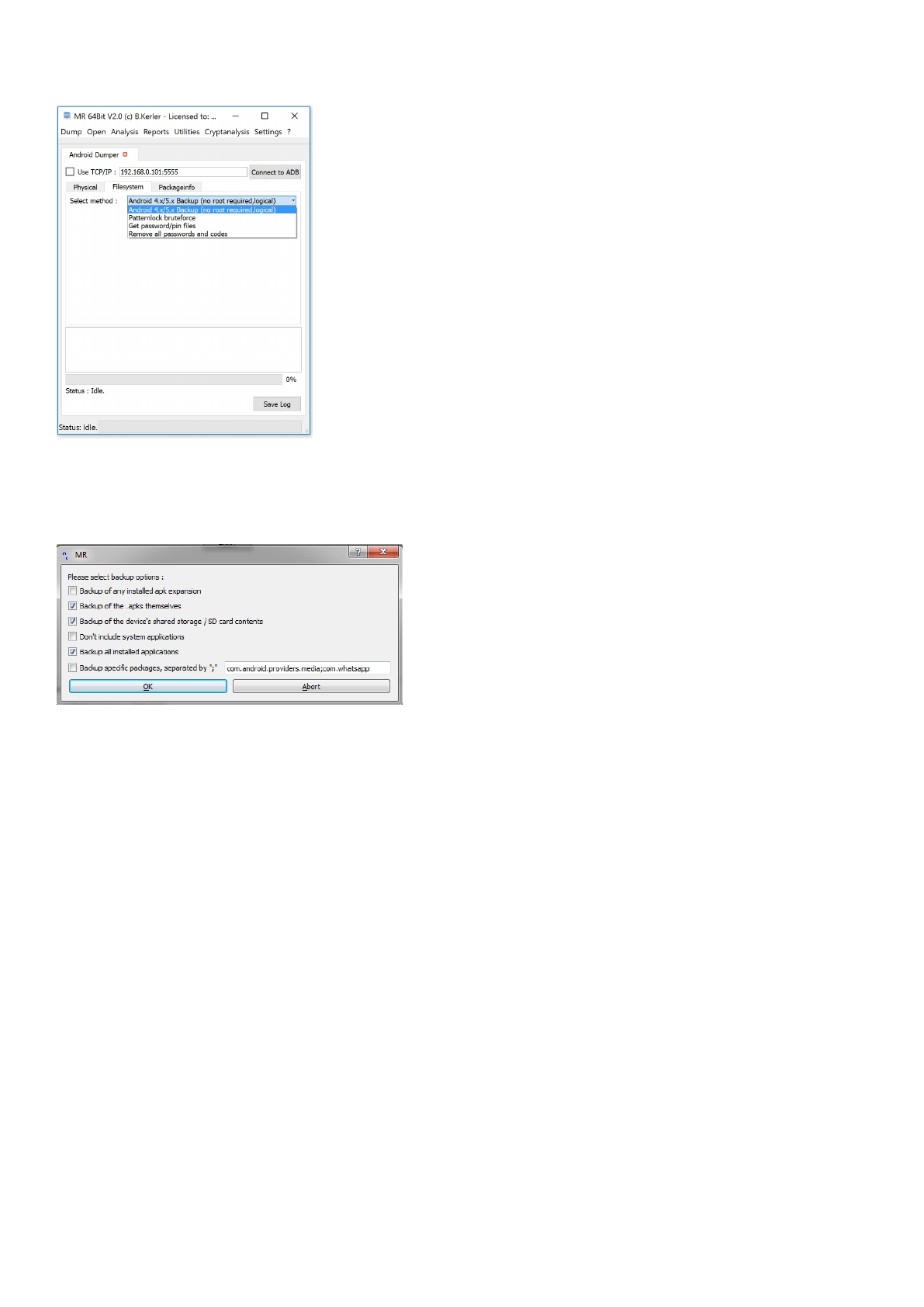
Once you connected to ADB, you may use these Filesystem options :
- Android 4.x/5.x Backup will enable you to dump via the Android internal backup functionality. After you press "Run", you
may choose what to backup :
- Patternlock bruteforce will read the gesture.key file from /data/system, bruteforce the pattern using CPU and then
present the pattern.
- Get password/pin files will extract the most common files used for password/pin/gesture storage from the device
- Remove all passwords and codes will remove passwords and codes from both files and sqlite databases and should thus
be choosen only if it is really needed to be done.
Mobile Revelator 2.2.5
12 / 200
Packageinfo
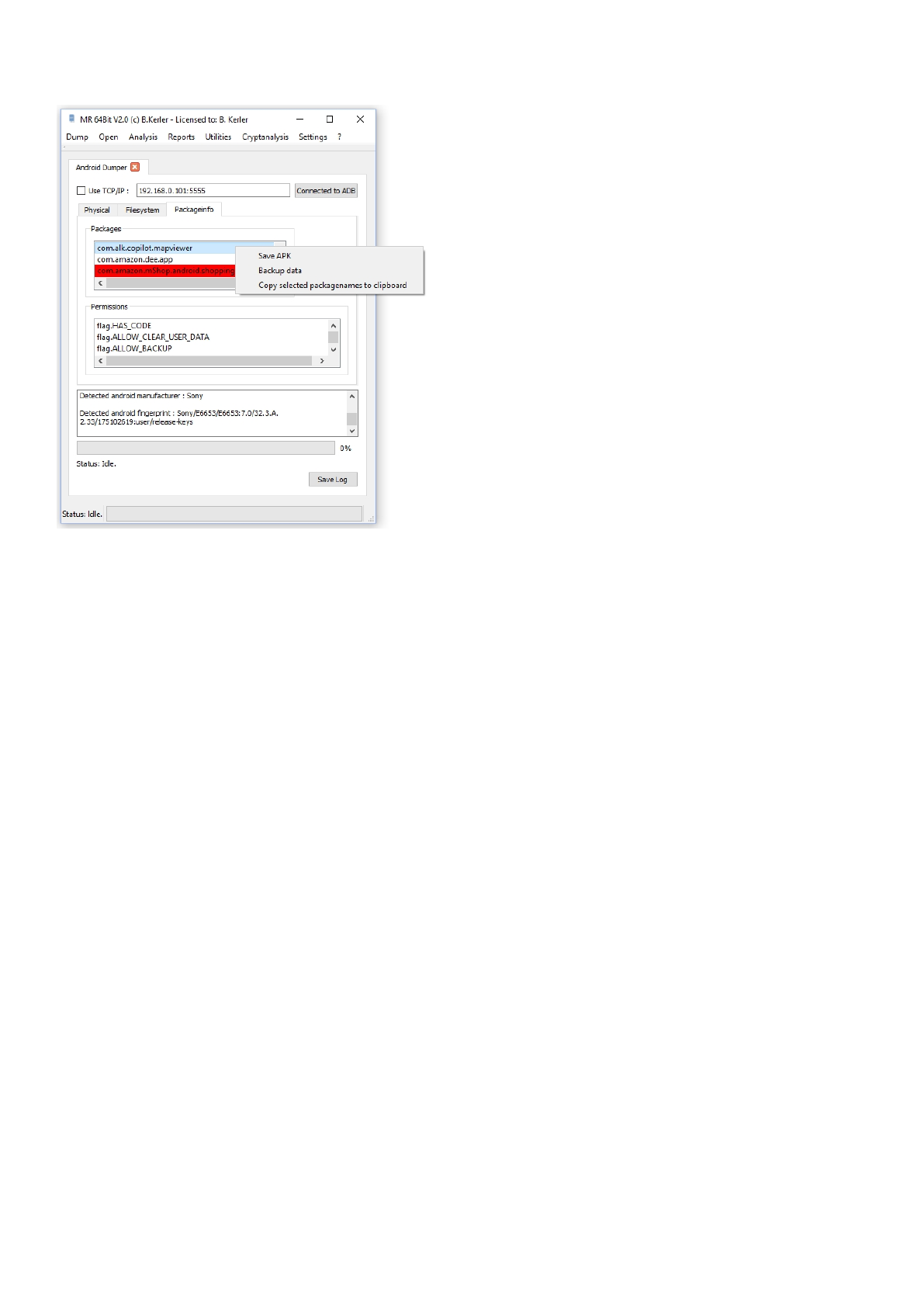
Packageinfo will read all installed and removed packages from the Android Package Manager.
Clicking with the left mouse button on the entries will show specific application rights and properties.
Clicking with the right mouse on the package, it will allow you to save the application apk, backup the
application data and copy the packagename to the clipboard. If the entry is being highlighted in red,
then the package doesn't allow application data to be backed up.
Mobile Revelator 2.2.5
13 / 200
Physical Dumper
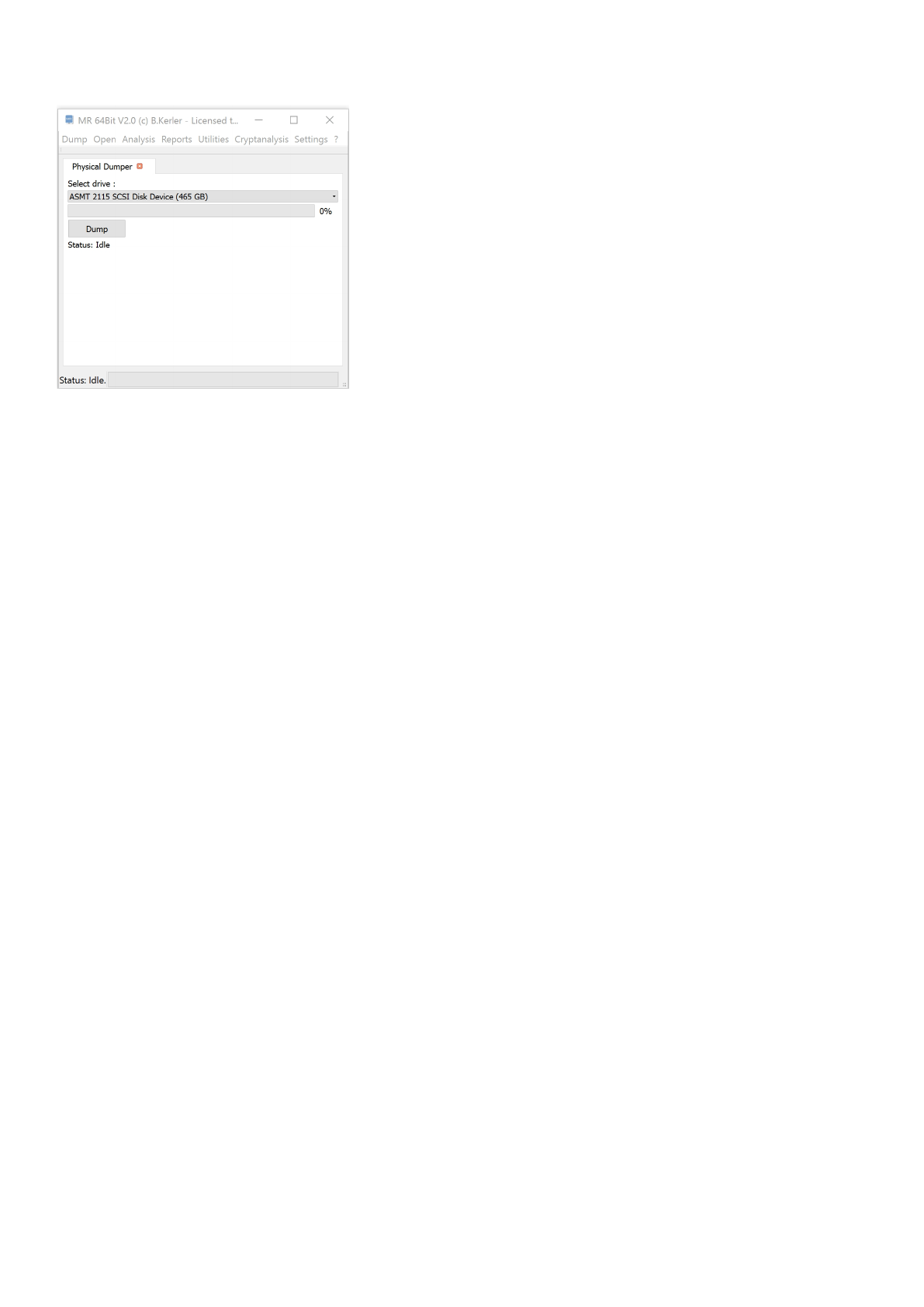
The Physical Dump Tool lets you save full physical devices connected to your PC, like harddrives
or SD-Cards in SD-Cardreaders. Press "Dump" and choose where to save the dump file.
The file will be saved in RAW-Format.
Mobile Revelator 2.2.5
14 / 200
iTunes Browser
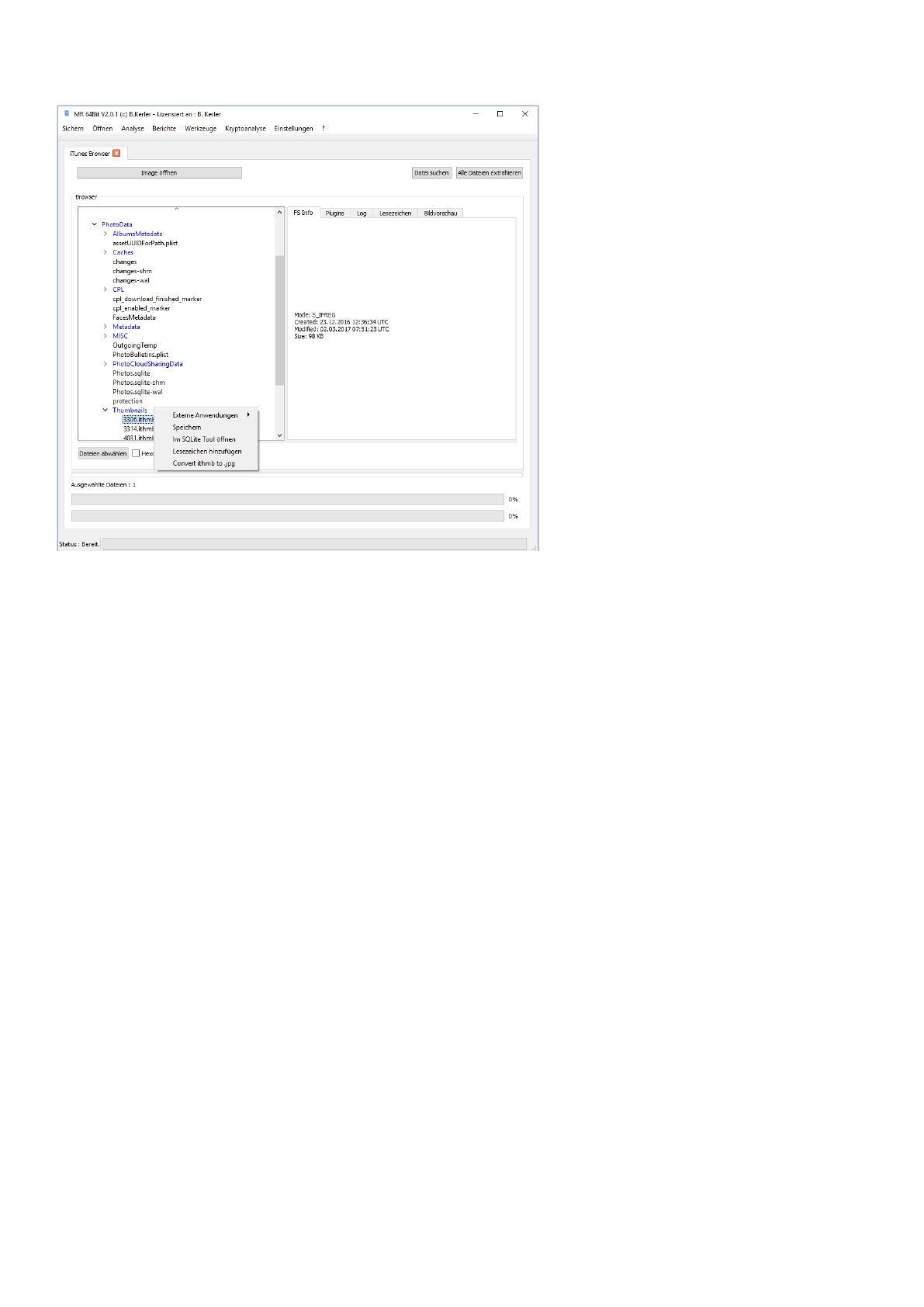
Using this tool, you may connect an iPhone/iPod/iPad. First install iTunes, connect to the device, trust on the device and
trust in iTunes, it will then access the AFC-System of the device and lets you save files but also open them in the internal
sqlite tool or any external viewer you wish. Furthermore, it lets you extract .ithmb databases (from PhotoData/Thumbnails)
to jpg files [see more in Analysis\Apple iThmb Extract chapter in this document].
Mobile Revelator 2.2.5
15 / 200
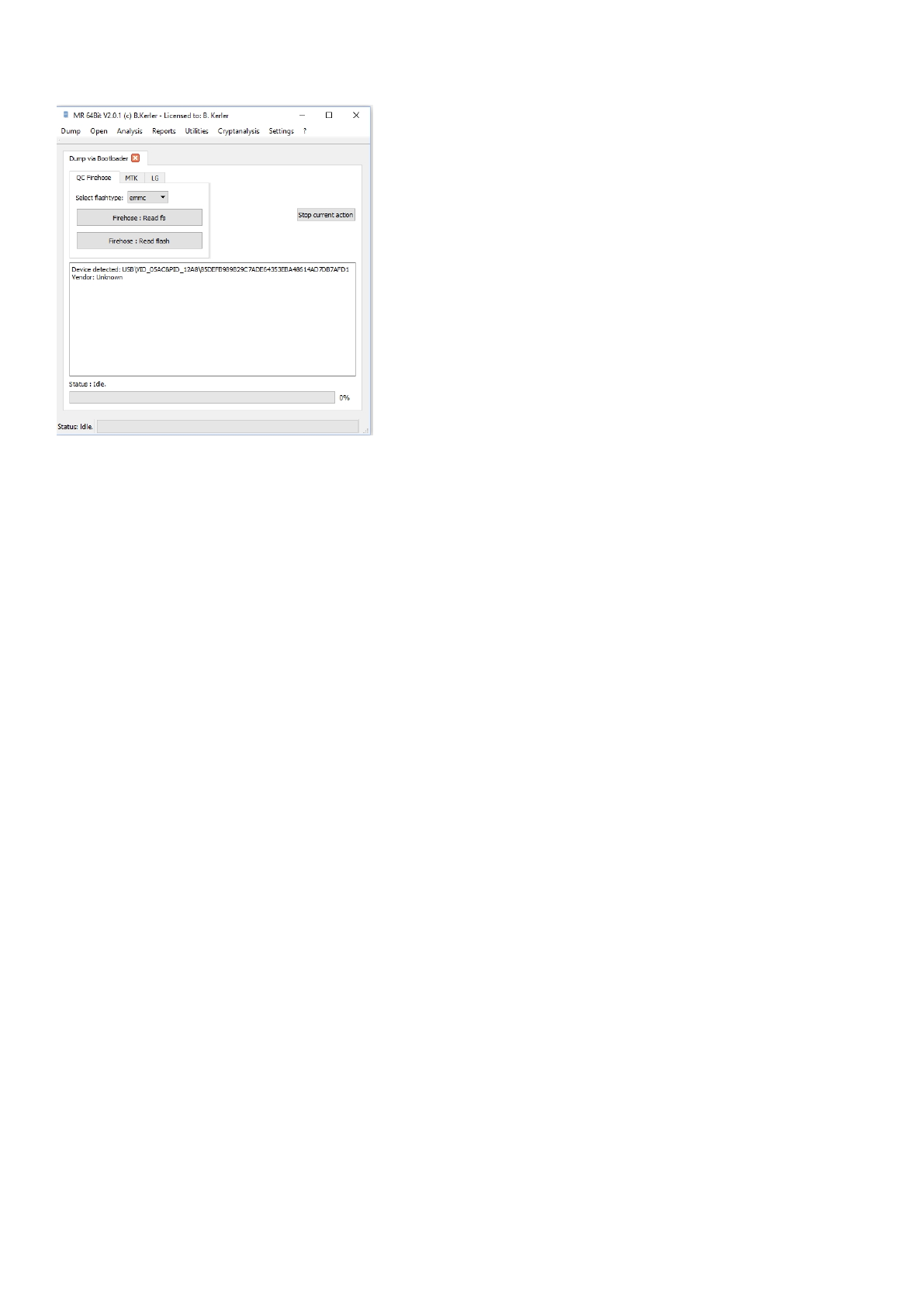
Dump via Bootloader
The "Dump via Bootloader"-Tool allows to dump several devices via bootloader, but does
also show new detected or attached devices.
Mobile Revelator 2.2.5
16 / 200
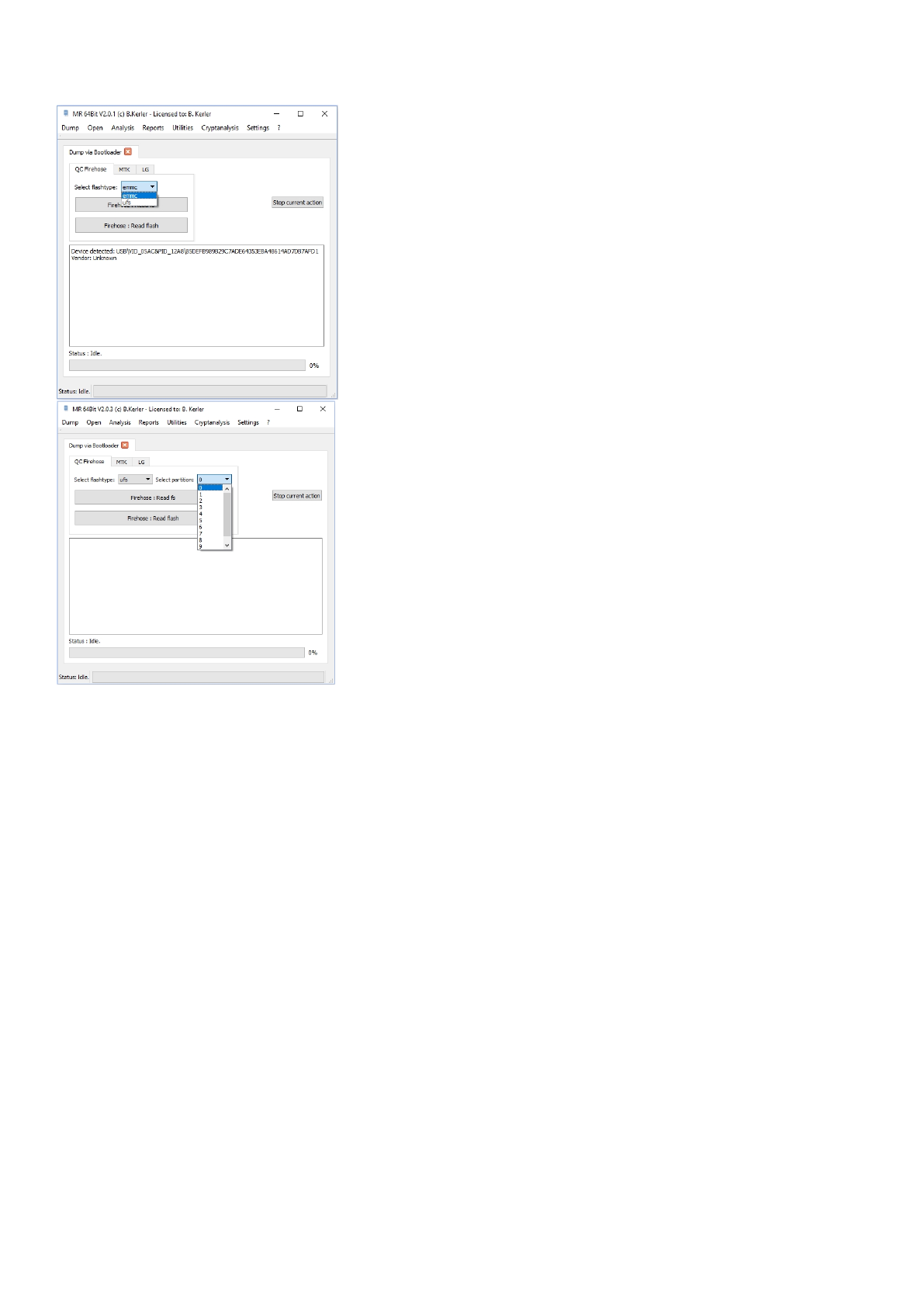
QC Firehose
Some devices like "Oneplus One, X, 3, 3T" and several other devices with Qualcomm CPU
newer than MSM8974 can be dumped or content written using the "QDLoader 9008" Port.
First press "Firehose: Read fs" or "Firehose: Read flash" button, and then connect a device with 9008 Mode via usb to the
host pc.
The 9008 Mode, also called "Sahara" Mode, can be enabled by either using adb and sending "adb reboot edl"
or fastboot by sending "fastboot reboot edl" or by pressing volume up and volume down while connecting the usb cable
to a powered off device. Also this mode can be enabled by shorting CLK Signal of the emmc on the pcb with Ground while
connecting
a powered off device and pressing power for a few seconds or by shortening d+ and gnd on usb while connecting the
mobile and then
releasing the short.
For firehose, you should the right flashtype, either emmc or ufs before connecting. Be aware that a ufs flash can have
multiple
partitions, so you should choose the partition number first. If unsure, let flashtype on ufs and partition number on 0.
"Firehose: Read fs" will allow you to browse and also write partitions, "Firehose: Read flash" will only dump the full flash.
As a reminder, all devices coming with Android 6 out of the box are encrypted, so one option might be to flash a custom
recovery like twrp or cm to the device via firehose in order to dump the unencrypted data.
You may interrupt any action pressing the "Stop current action" button.
Mobile Revelator 2.2.5
17 / 200
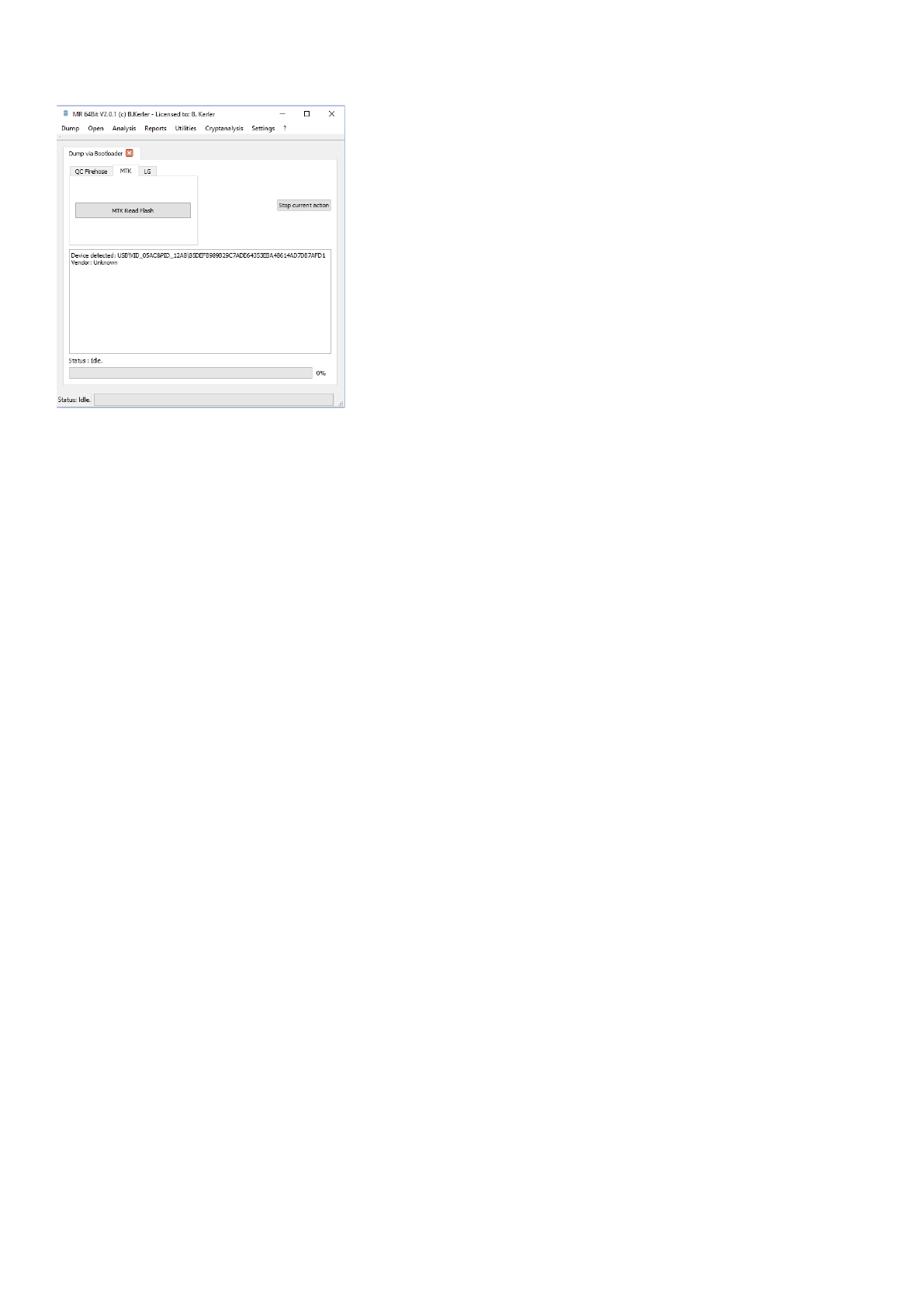
MTK
For devices using MTK chipset, power off the device, install the MTK Preloader Com port driver, press "MTK Read
Flash button" and then just connect the mobile.
You may interrupt any action pressing the "Stop current action" button.
Mobile Revelator 2.2.5
18 / 200
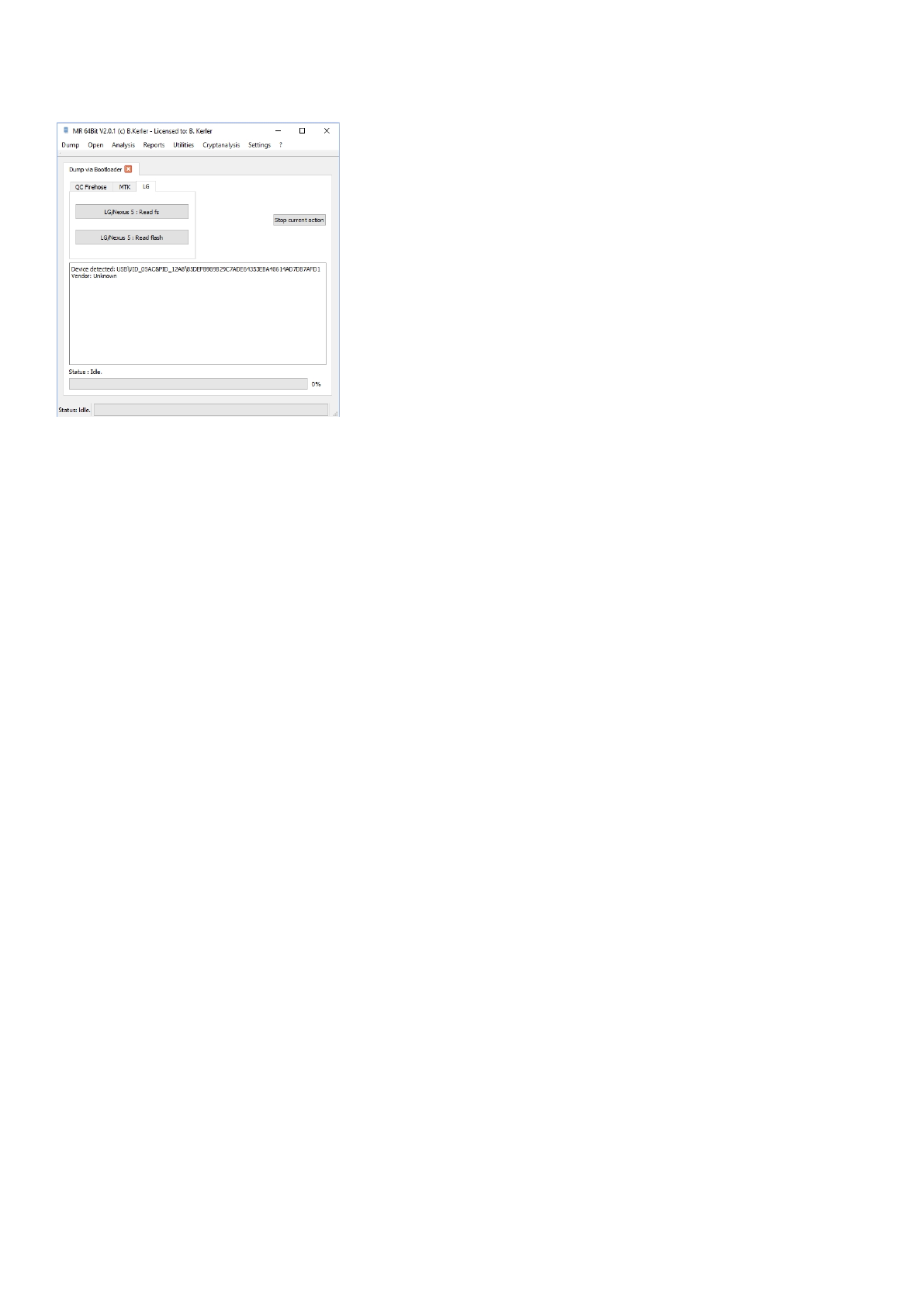
LG
For LG android devices > Android 4.x and < 5.1, you may switch to the download mode by powering the mobile off,
then press and hold volume up button while connecting the usb cable to the mobile. Once you see the download
mode, you may press "LG G2/Nexus 5: Read fs" button to show installed partitions or press "LG G2/Nexus 5: Read
flash" button to get a physical dump of the flash chip.
You may interrupt any action pressing the "Stop current action" button.
Mobile Revelator 2.2.5
19 / 200
Port Utils
The port utilities offer functionality to access mobiles via ports such as usb, tcp/ip and com ports.
Mobile Revelator 2.2.5
20 / 200
AT Command Terminal
The AT Command Terminal is able to send ascii commands to a serial port device such as a modem.
Mobile Revelator 2.2.5
21 / 200
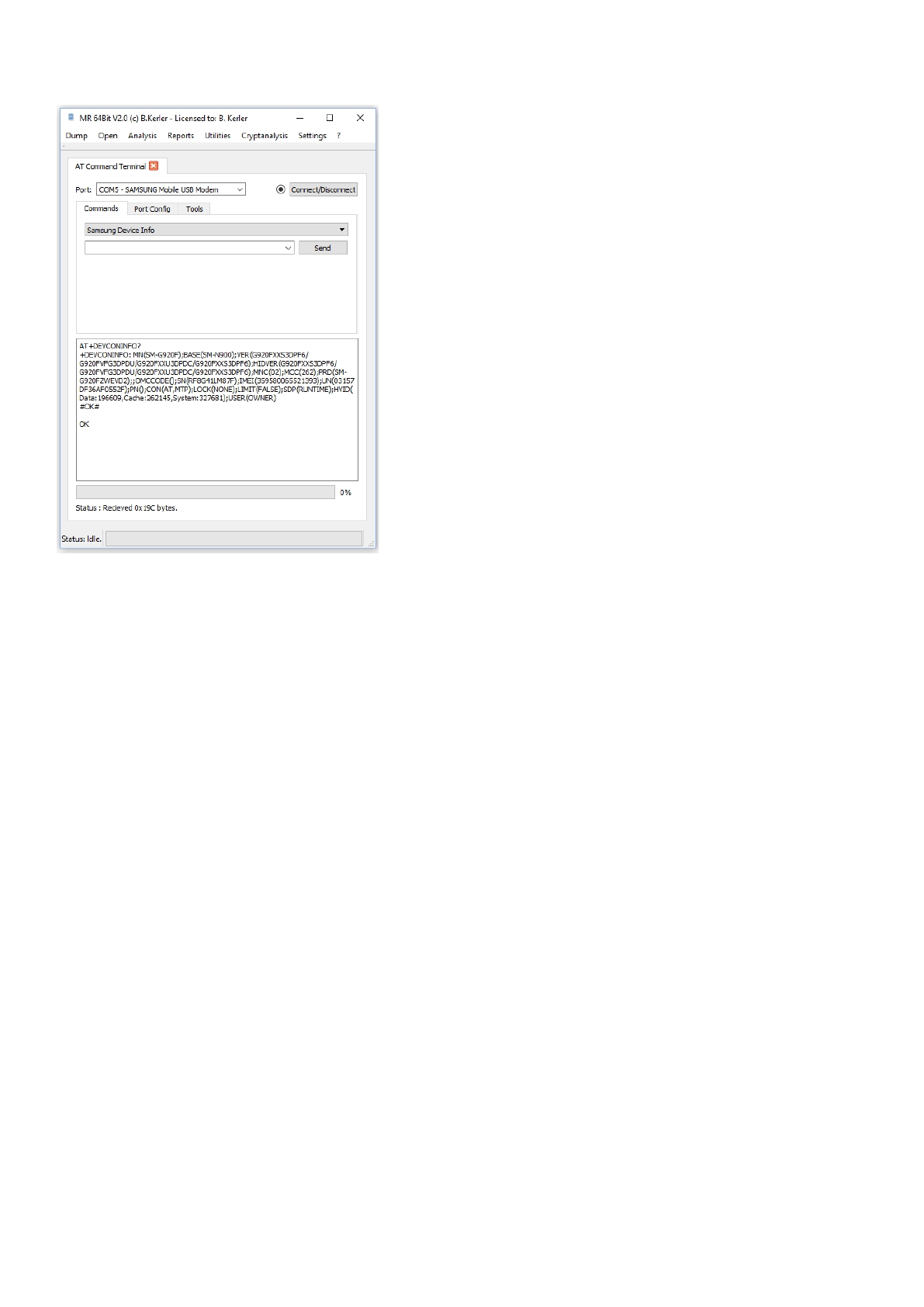
Commands
In order to send any AT commands to modem or serial ports, just select the Port and press "Connect/Disconnect" button.
If the connection has been successfully made, the circle left the the "Connect/Disconnect" button should fill.
After that you may either select a common command from the command list just above the "Send" button or enter any
commands like "ATI" left to the "Send" button and then press "Send". The result will be shown in the text view below.
Mobile Revelator 2.2.5
22 / 200
Port Config
The port config tab allows you to set specific settings, such as baudrate, databits, parity, stopBits and Flow Control.
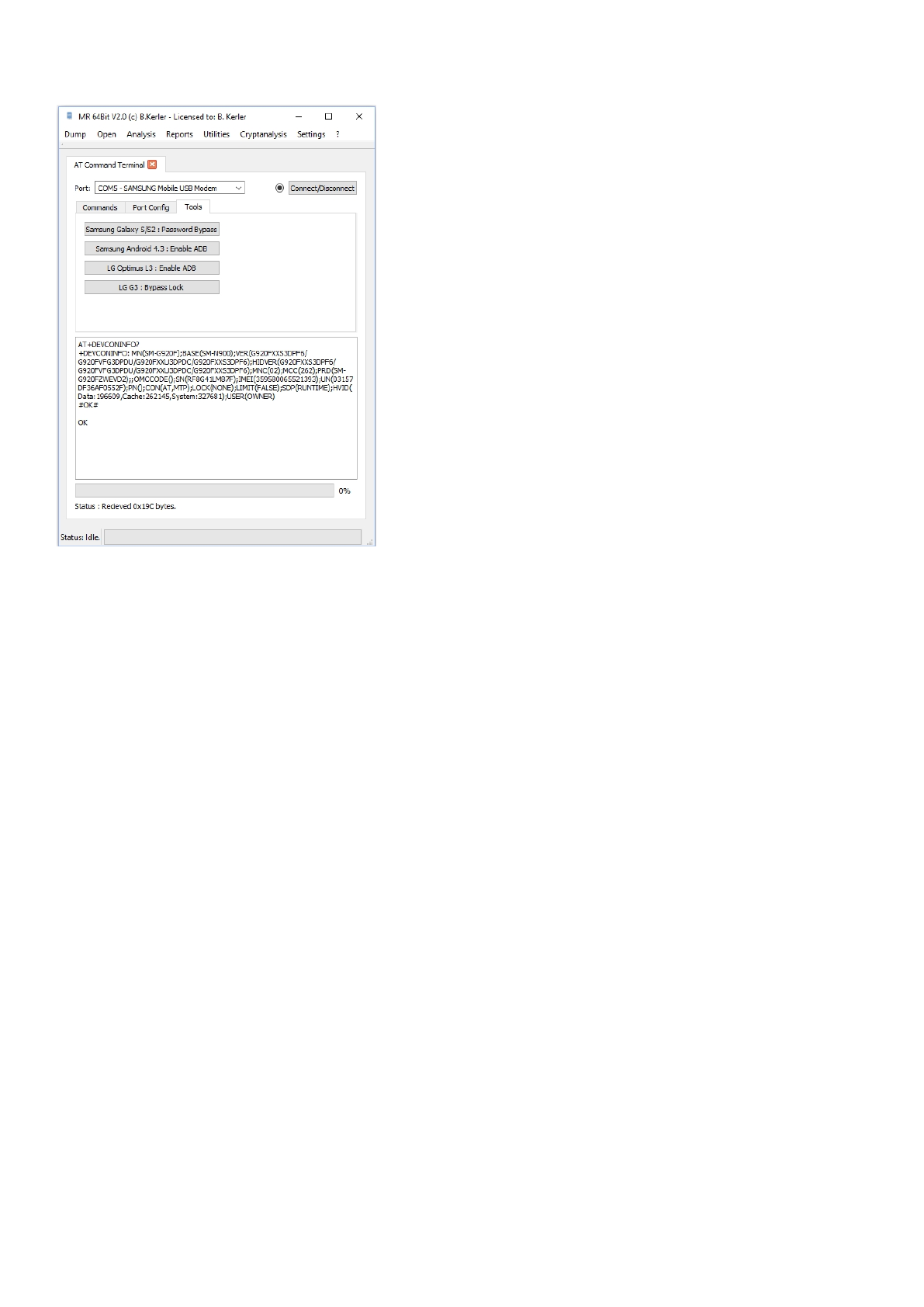
Mobile Revelator 2.2.5
23 / 200
Tools
After a successful connection has been made, some functions may be available on specific devices in order
to enable ADB or to bypass passwords via com port.
Mobile Revelator 2.2.5
24 / 200
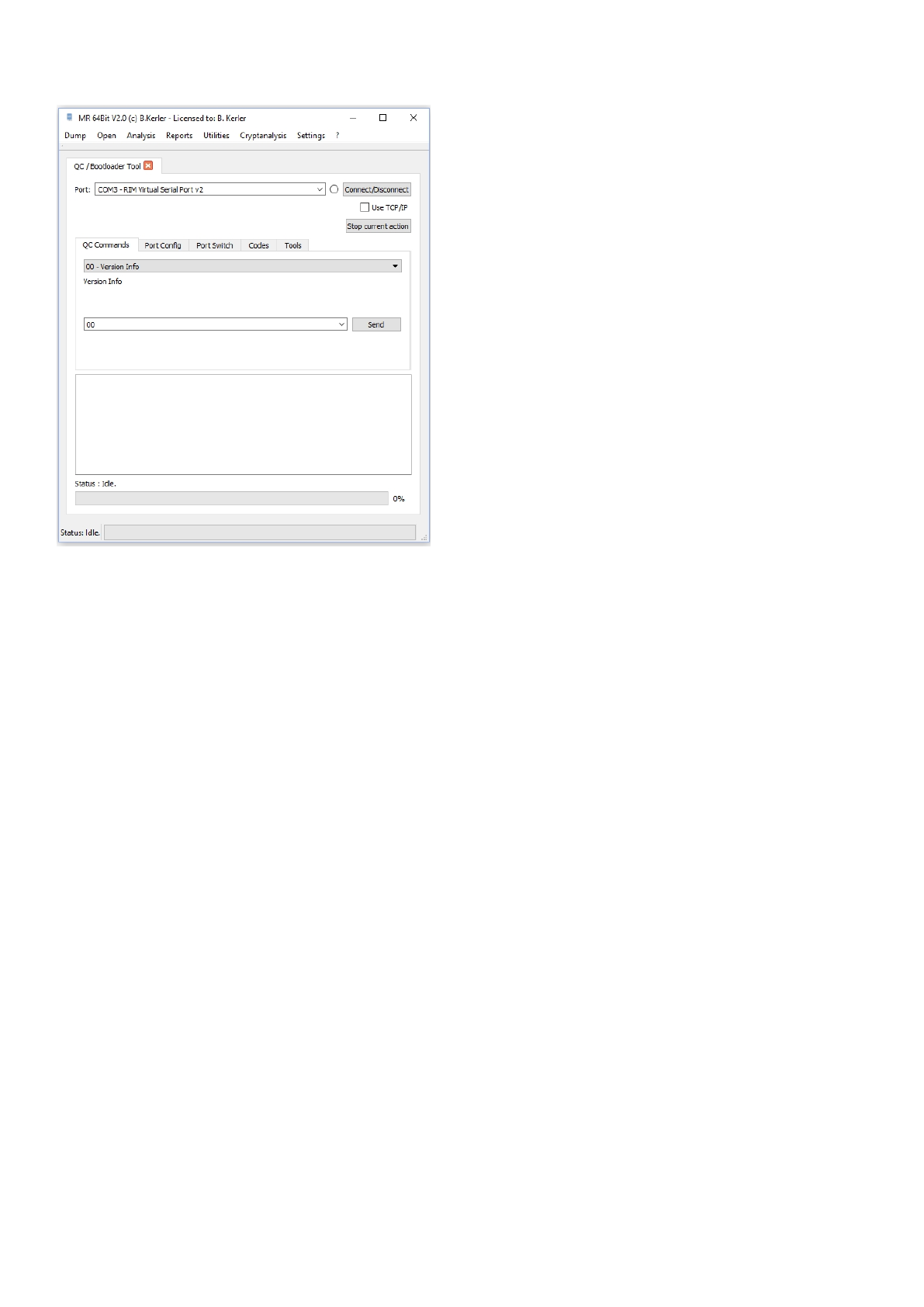
QC / Bootloader Tool
Using the Qualcomm Modem and Bootloader Tool you may send qualcomm specific commands as hex bytes to
ports using qualcomm sahara and diag protocol but also has several tools for bootloaders such as LG and MTK
enabled devices in order to read the flash.
Mobile Revelator 2.2.5
25 / 200
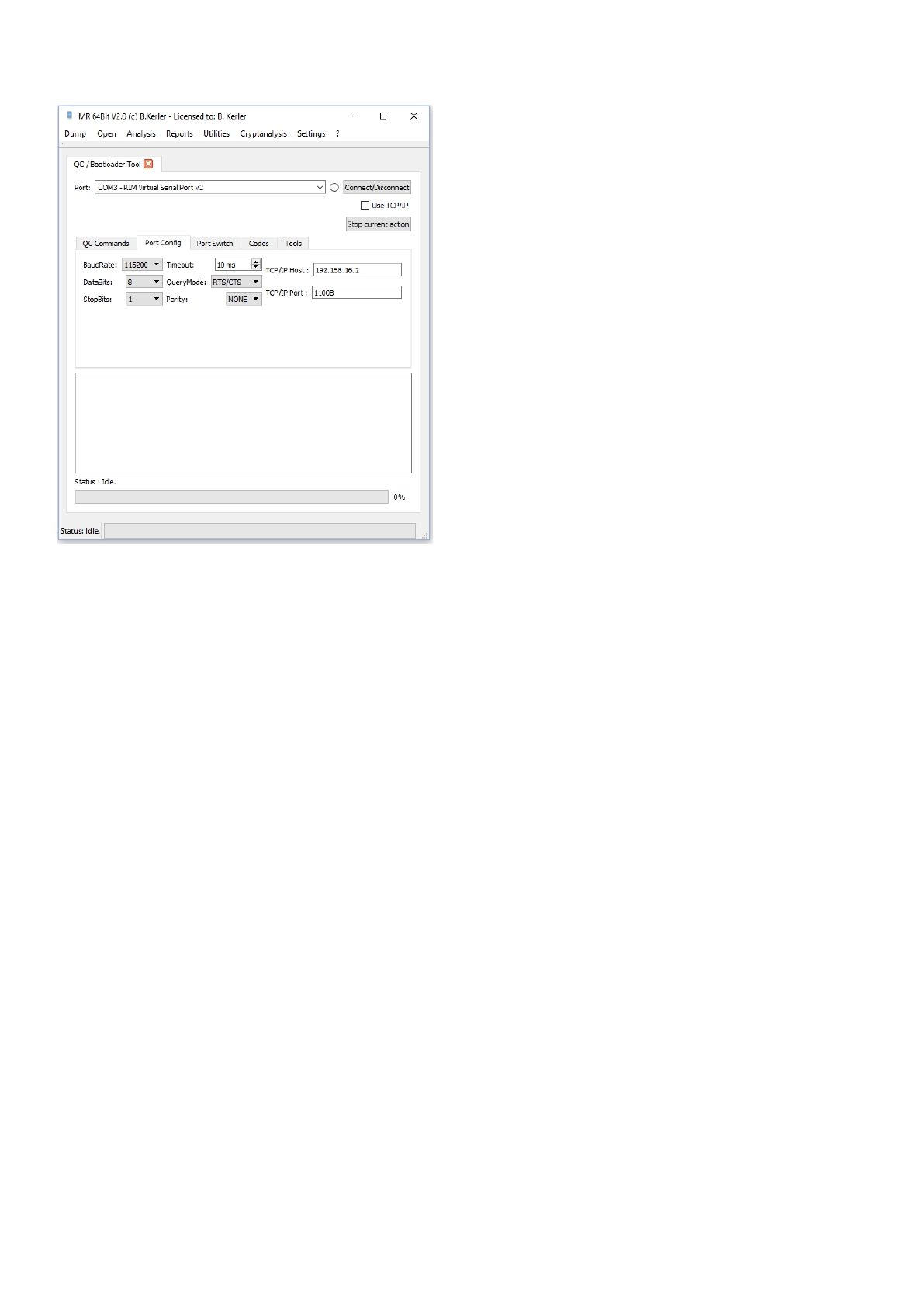
Port Config
The "Port Config" tab shows possible settings for both com ports and tcp/ip connections.

Mobile Revelator 2.2.5
26 / 200
Port Switch
For some modem devices, you first need to switch the modem to a qualcomm interface port. Just select
the type and then press "Send port switch command" button in order to switch the port.
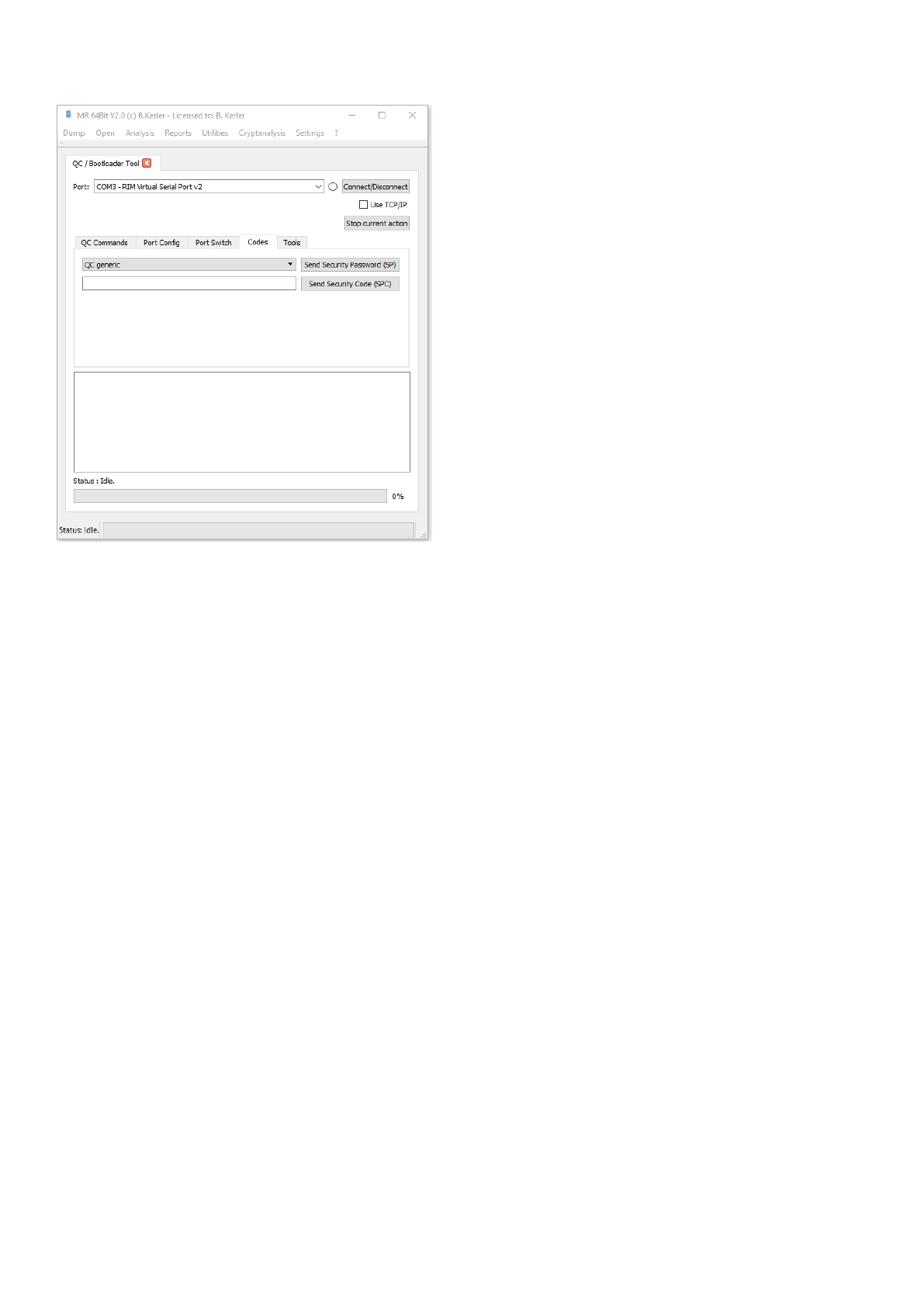
Mobile Revelator 2.2.5
27 / 200
Codes
For some qualcomm devices, reading efs and nvitems is only possible after sending the right security password (SP)
or Security Code (SPC).

Mobile Revelator 2.2.5
28 / 200
Tools
The "Tools" tab has the following functionality :
Once connected to a device with qualcomm chipset, you may read the raw efs or read the nvitems.
You may interrupt any action pressing the "Stop current action" button.
Mobile Revelator 2.2.5
29 / 200
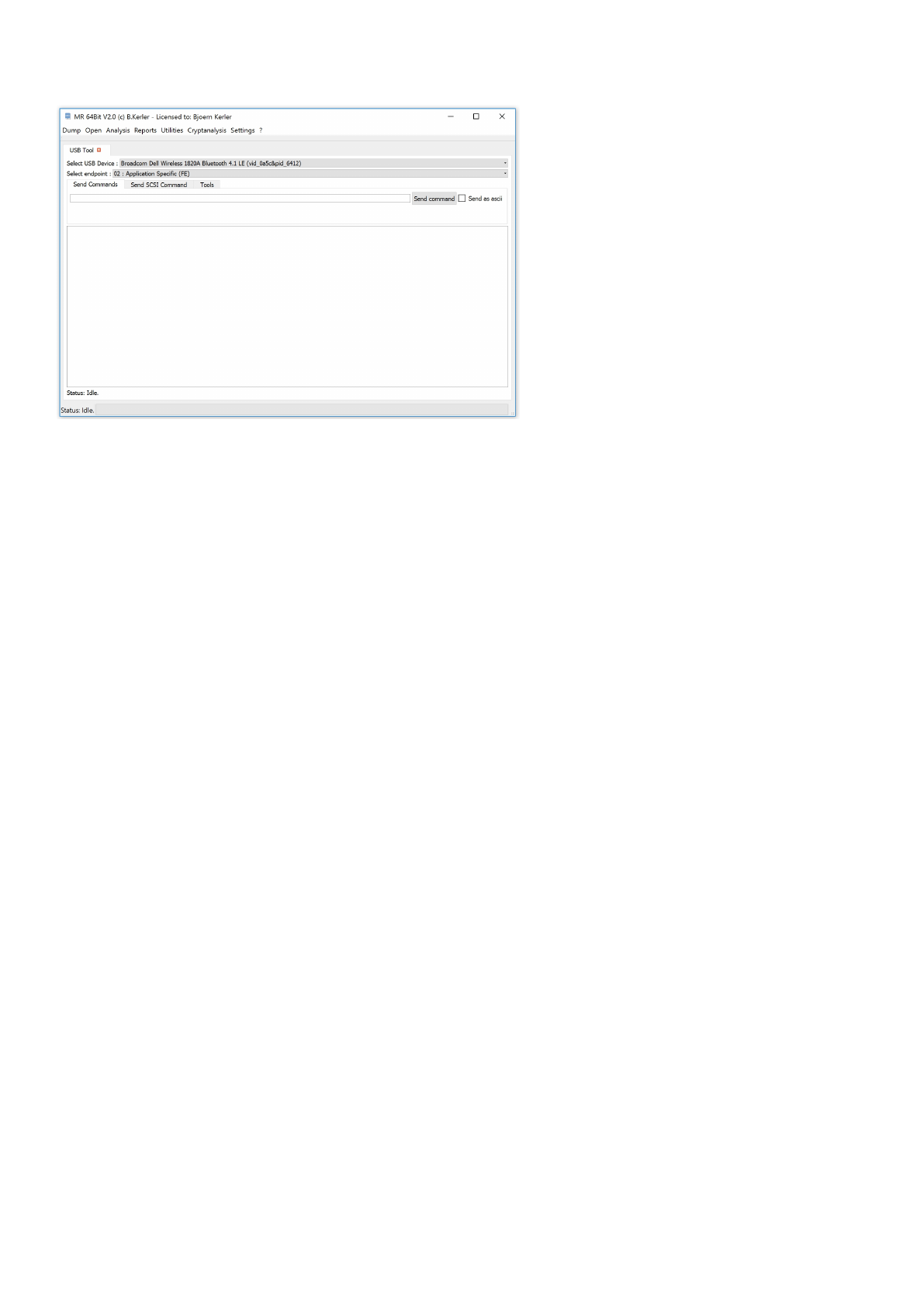
USB Tool
The USB tool enables you to send raw data to connected USB devices.
Mobile Revelator 2.2.5
30 / 200
Send Commands
This tool is able to send raw hex bytes or ascii packets to usb devices.
Mobile Revelator 2.2.5
31 / 200
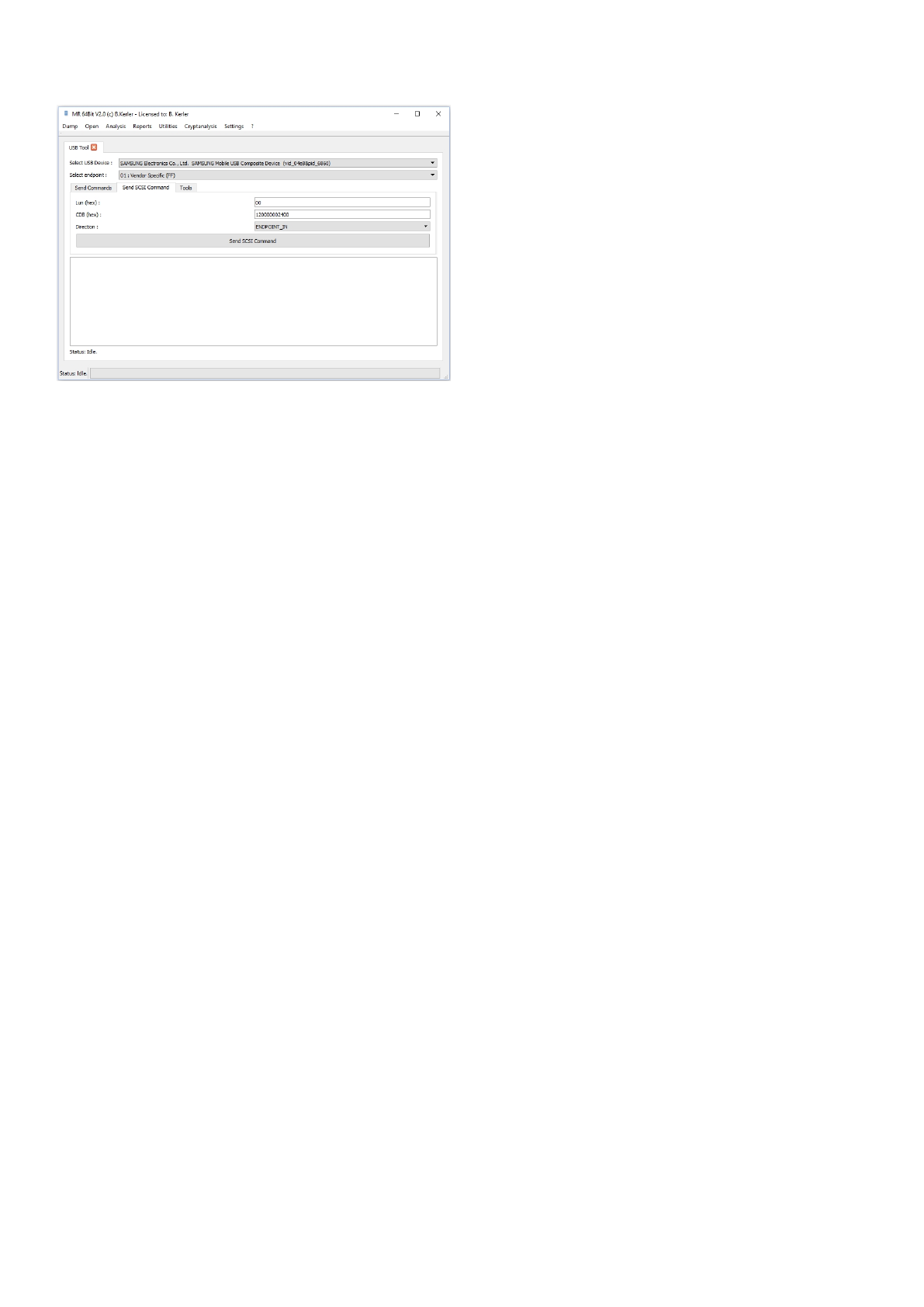
Send SCSI Command
This tool is able to send SCSI commands to USB devices.
Mobile Revelator 2.2.5
32 / 200
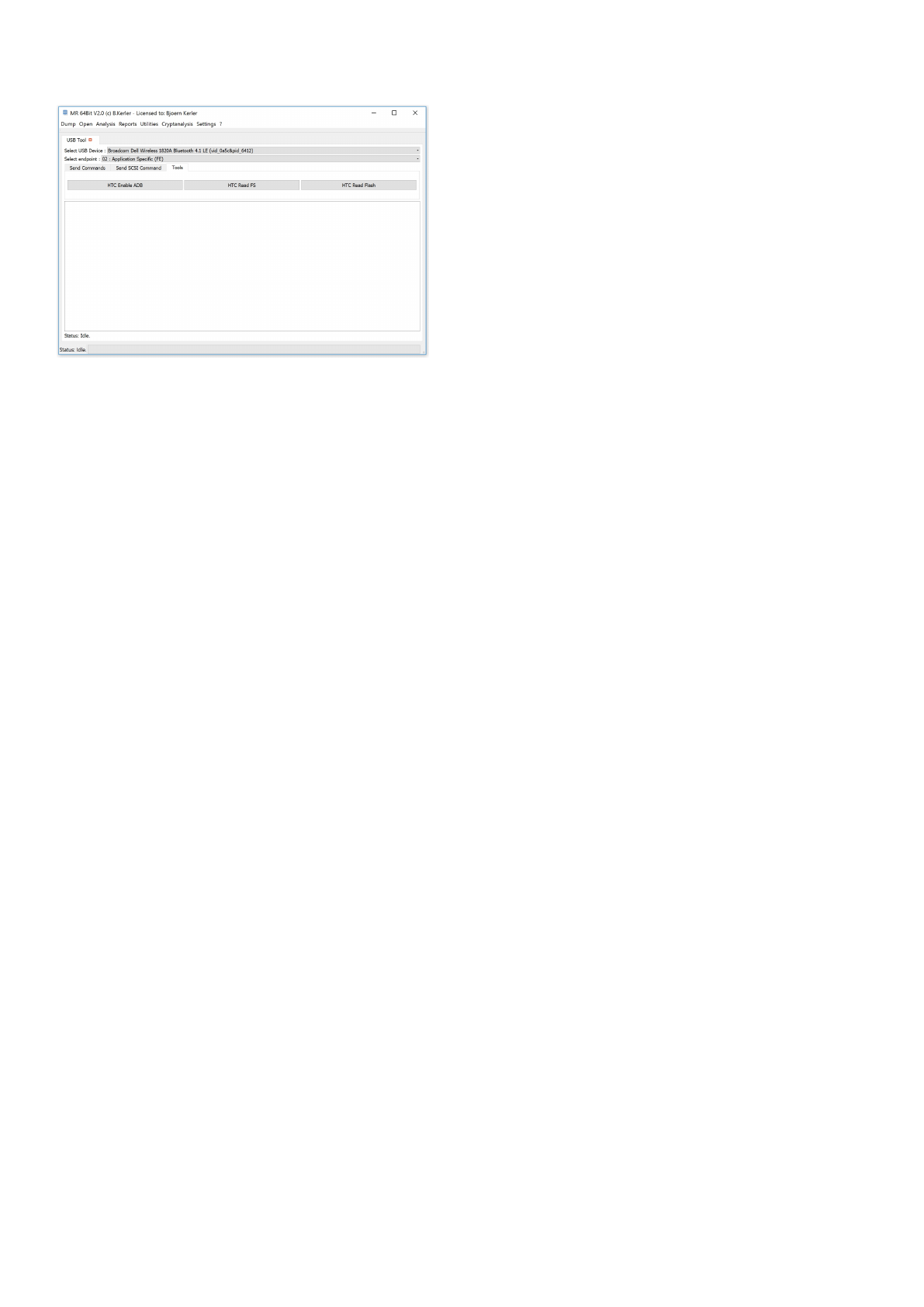
Tools
For enabling ADB for some HTC devices such as "Wildfire", select the HTC device as USB device and Mass Storage
(08) as endpoint and then press "HTC enable ADB" to enable ADB. For older HTC android devices, you may as well boot
the device into bootloader mode, select the HTC devices as USB device and then click "HTC Read FS" to open up the
Partition Tool in order to show/read/save partition contents.
Mobile Revelator 2.2.5
33 / 200
M-Obex Tool
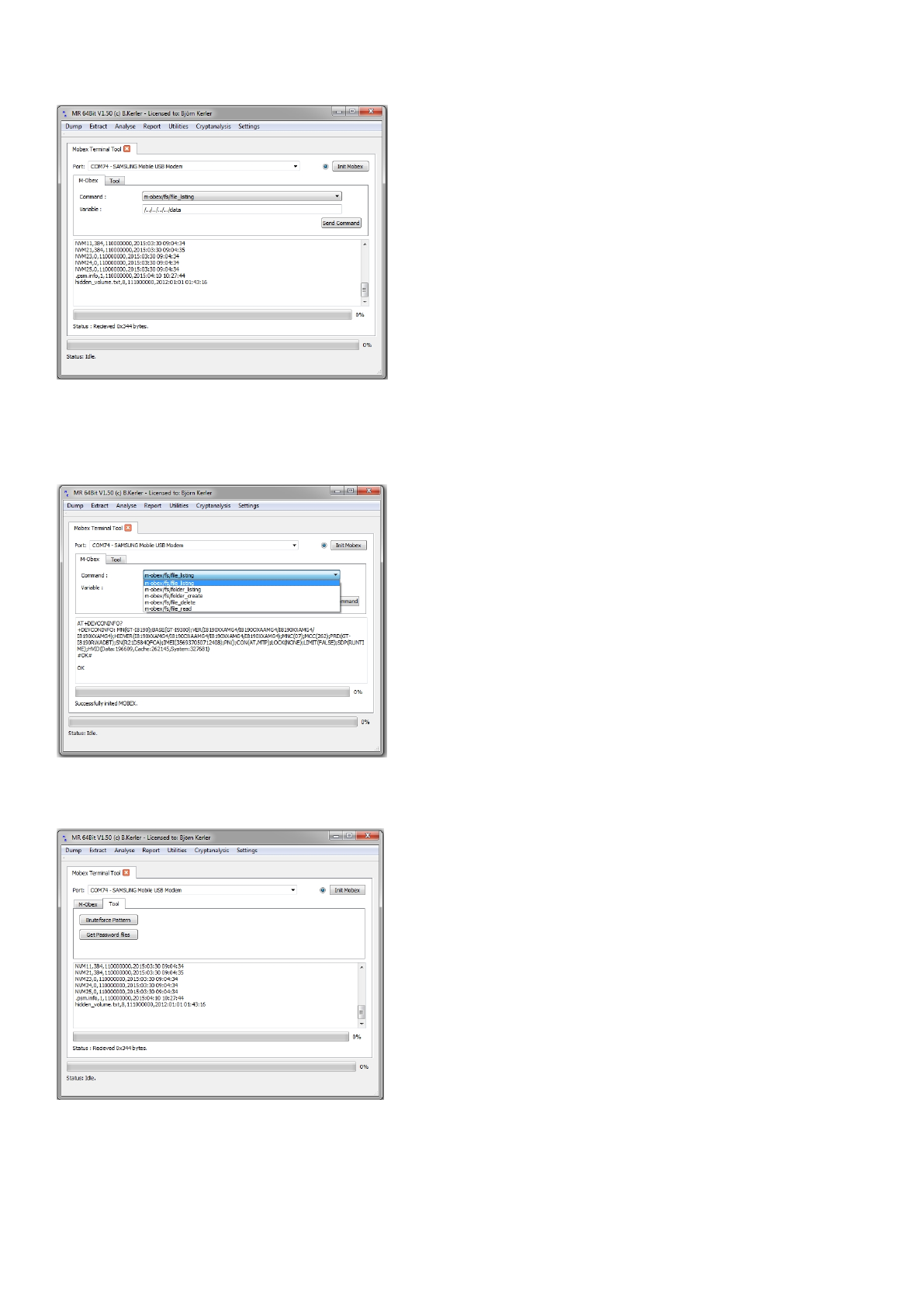
The M-Obex tool offers functionality to access the Samsung Modem Obex interface. Just select the Samsung
Mobile Port and press "Init Mobex". Once it's successfully connected, the circle left of the "Init Mobex" button
will be filled. You may then send any file command by entering into the text field such as "../../../../../data"
and pressing the "Send command" button.
Once Mobex has been successfully connected, you may bruteforce the pattern lock or get password files for Samsung
android mobiles if the firmware version is higher 4.0 and lower than 4.2.2.
Mobile Revelator 2.2.5
34 / 200
TCP/IP Tool
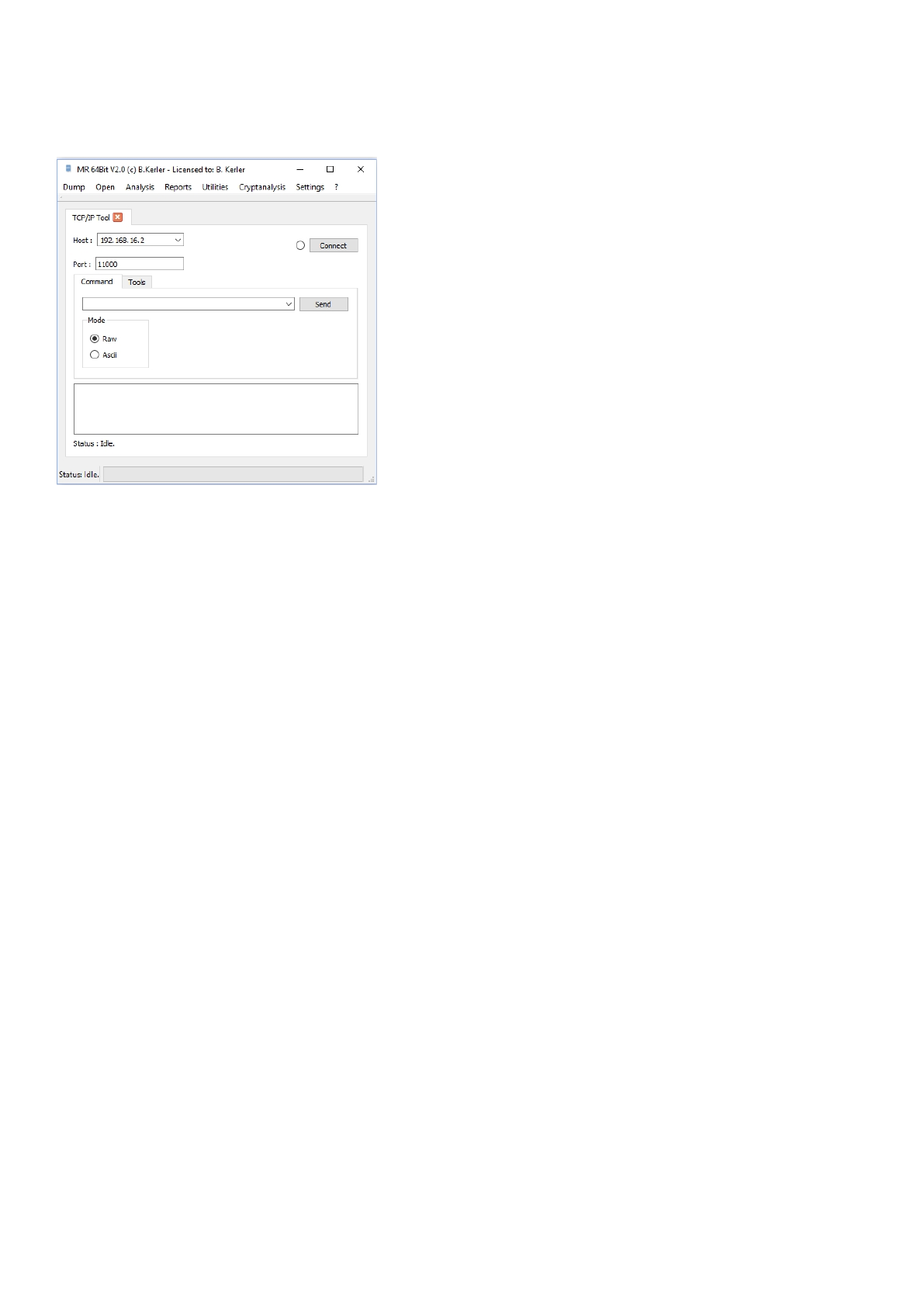
The tcp/ip tools tab offers functions for sending Hex or Ascii messages via tcp/ip such as motorola android mobiles.
Mobile Revelator 2.2.5
35 / 200
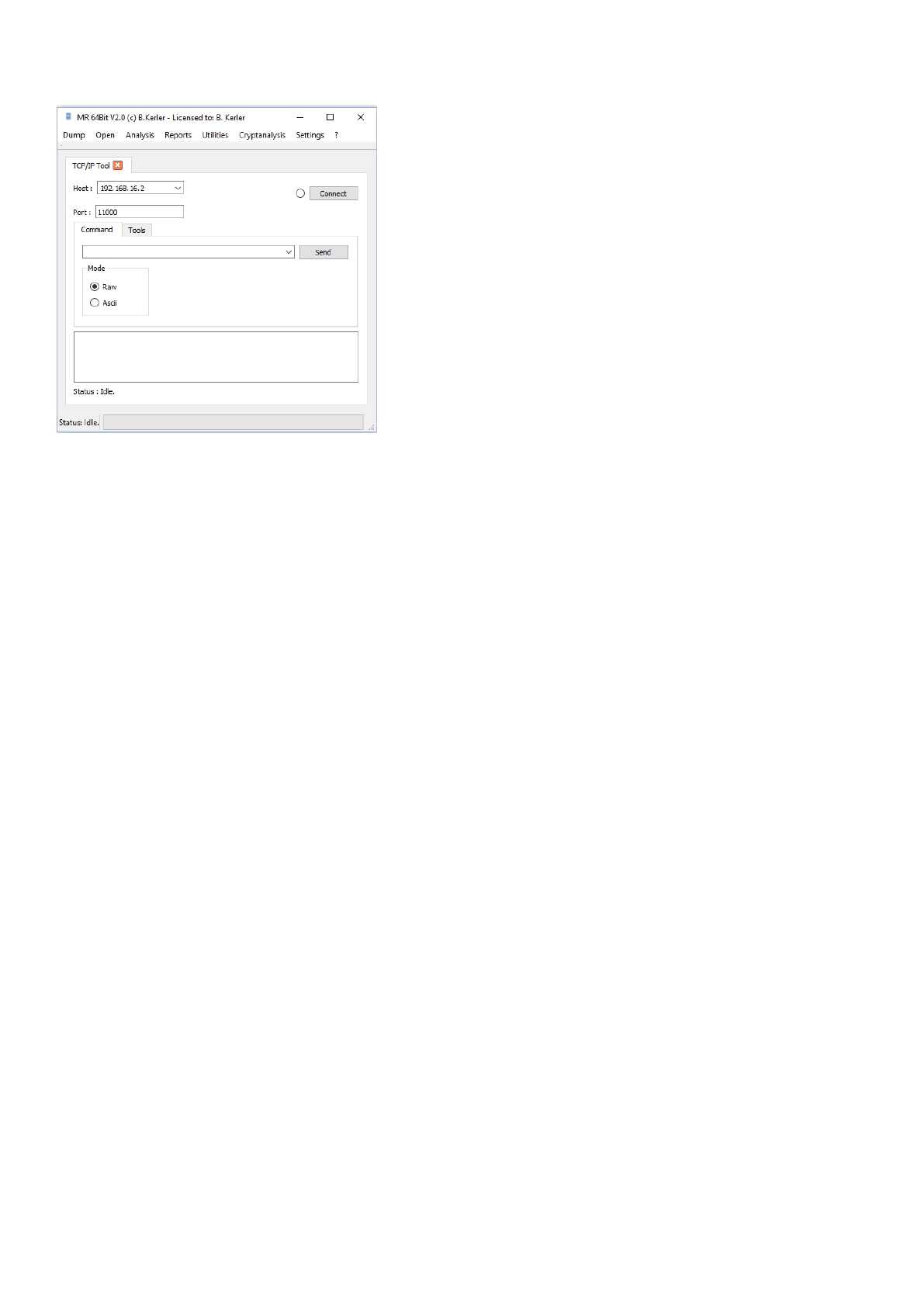
Command
Select the right host and then press connect. Once successfully connected, the left circle at the "Connect" button will be
filled. Then you are able to send either raw bytes as hex values or ascii chars being entered at the left side of the "Send"
button by pressing the "Send" button.
Mobile Revelator 2.2.5
36 / 200
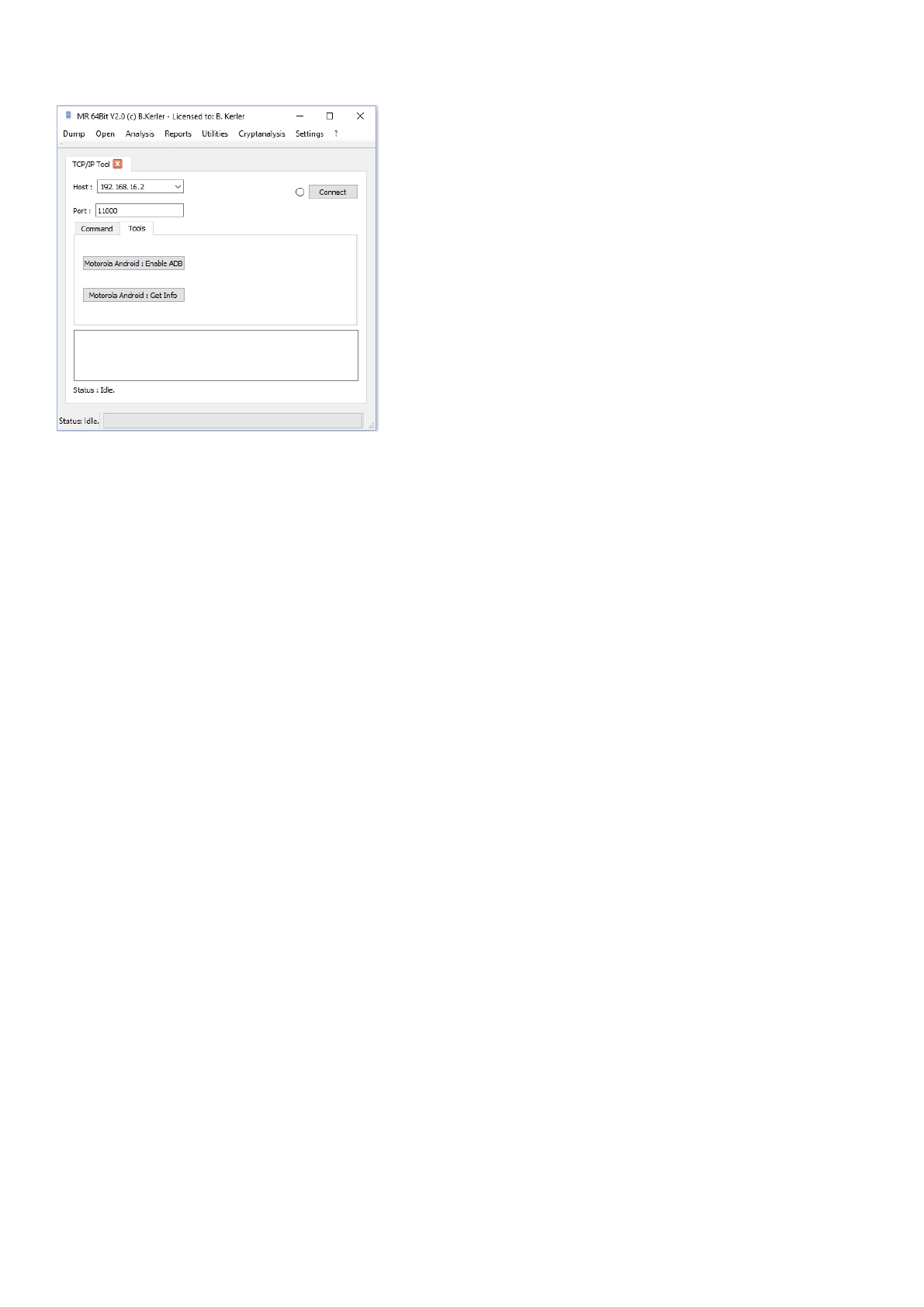
Tools
The tcp/ip tools tab offers functions for motorola android mobiles. Select the right host and then press connect.
Once successfully connected, the left circle at the "Connect" button will be filled.
Mobile Revelator 2.2.5
37 / 200
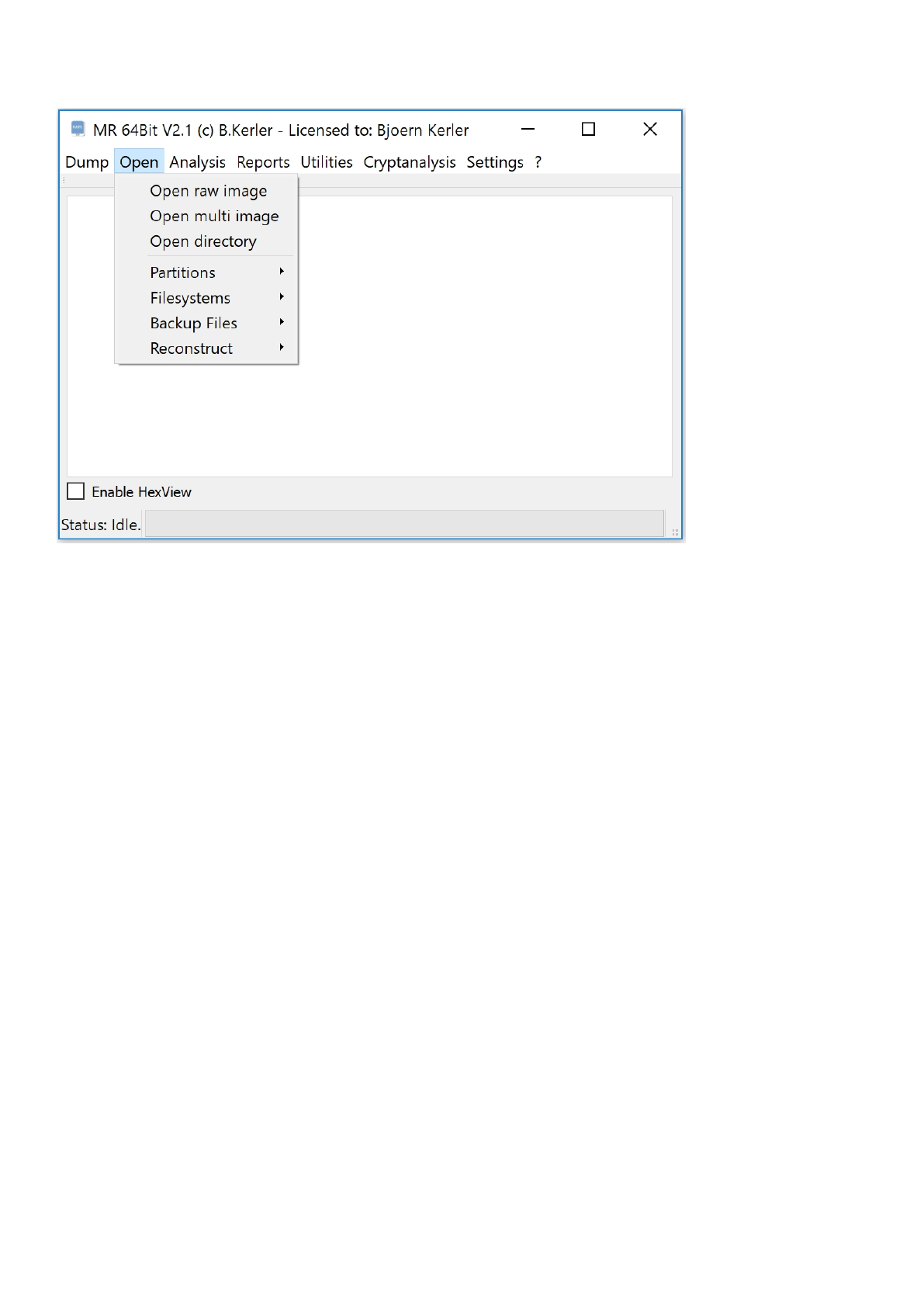
Open
The Open menu offers options to work with partition systems, filesystems, backup files,
flash wearleveling (reconstruct) and options to extract and carve files, including Apple thumbnail databases.
"Open raw image" allows to open full raw dumps of flashchips or jtag images such as emmc dumps.
"Open multi image" combines several dumps or folders into one single filesystem view.
"Open directory" uses a local directory as a filesystem view.
Mobile Revelator 2.2.5
38 / 200
Open raw flash
Using "Open File" you may open any raw flash binary file. If a known Partitiontype is detected, which may be MBR,
GPT, BCT and WM7 it will show all including partitions.
Clicking with the left mouse button on a partition entry will reveal its attributes.
Doubleclicking with the left mouse button will open the partition.
Clicking with the right mouse button on a partition will offer to extract or to open the partition.
The menu button "Extract all partitions" will extract all partitions by their name into separate files.
If no known Partitiontypes have been found, MR will offer an option to carve for FAT and/or EXT partitions.
Mobile Revelator 2.2.5
39 / 200
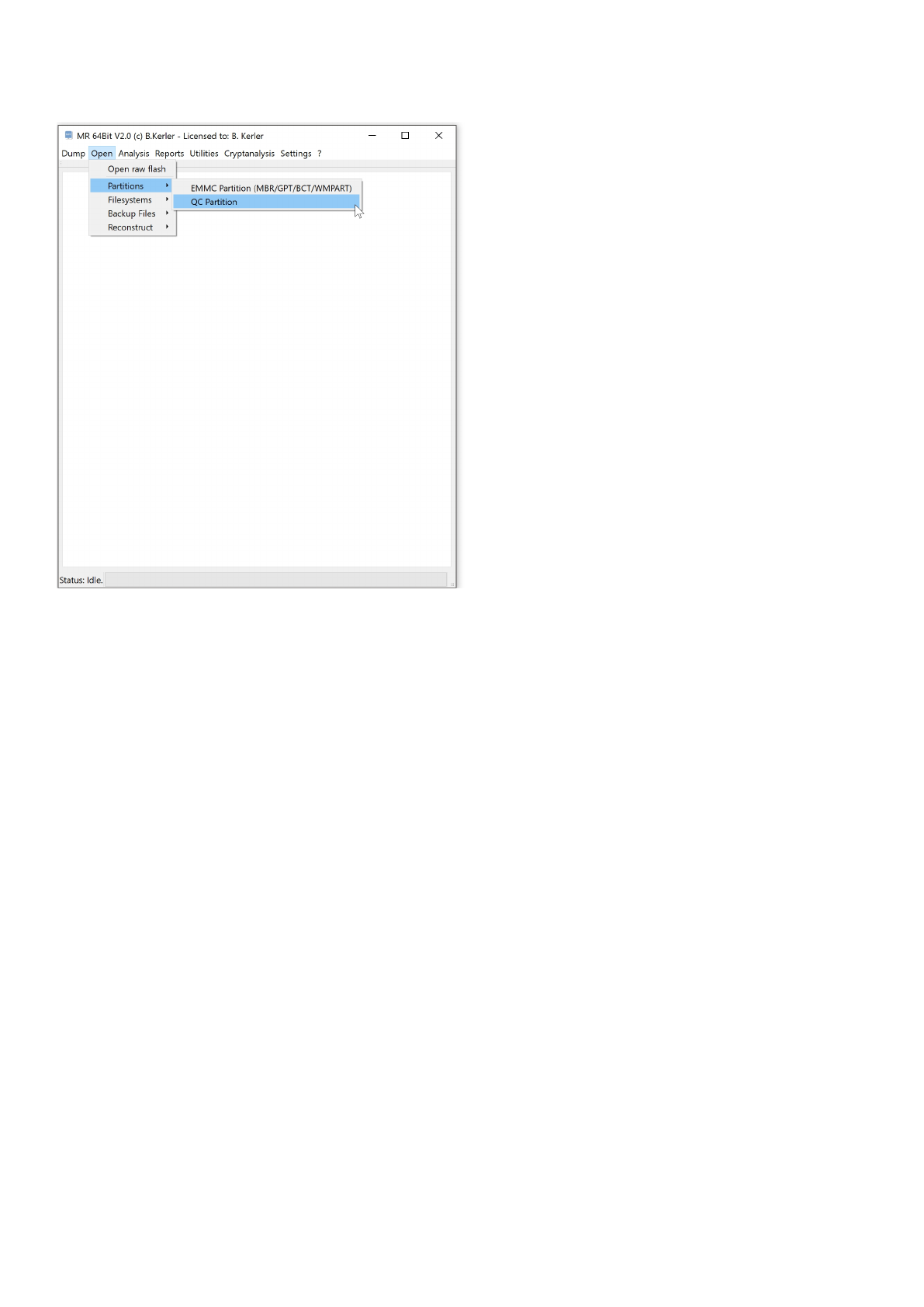
Partitions
The partitions menu helps you extracting and viewing several flash dumps from modern devices using EMMC
flash chips.
Mobile Revelator 2.2.5
40 / 200
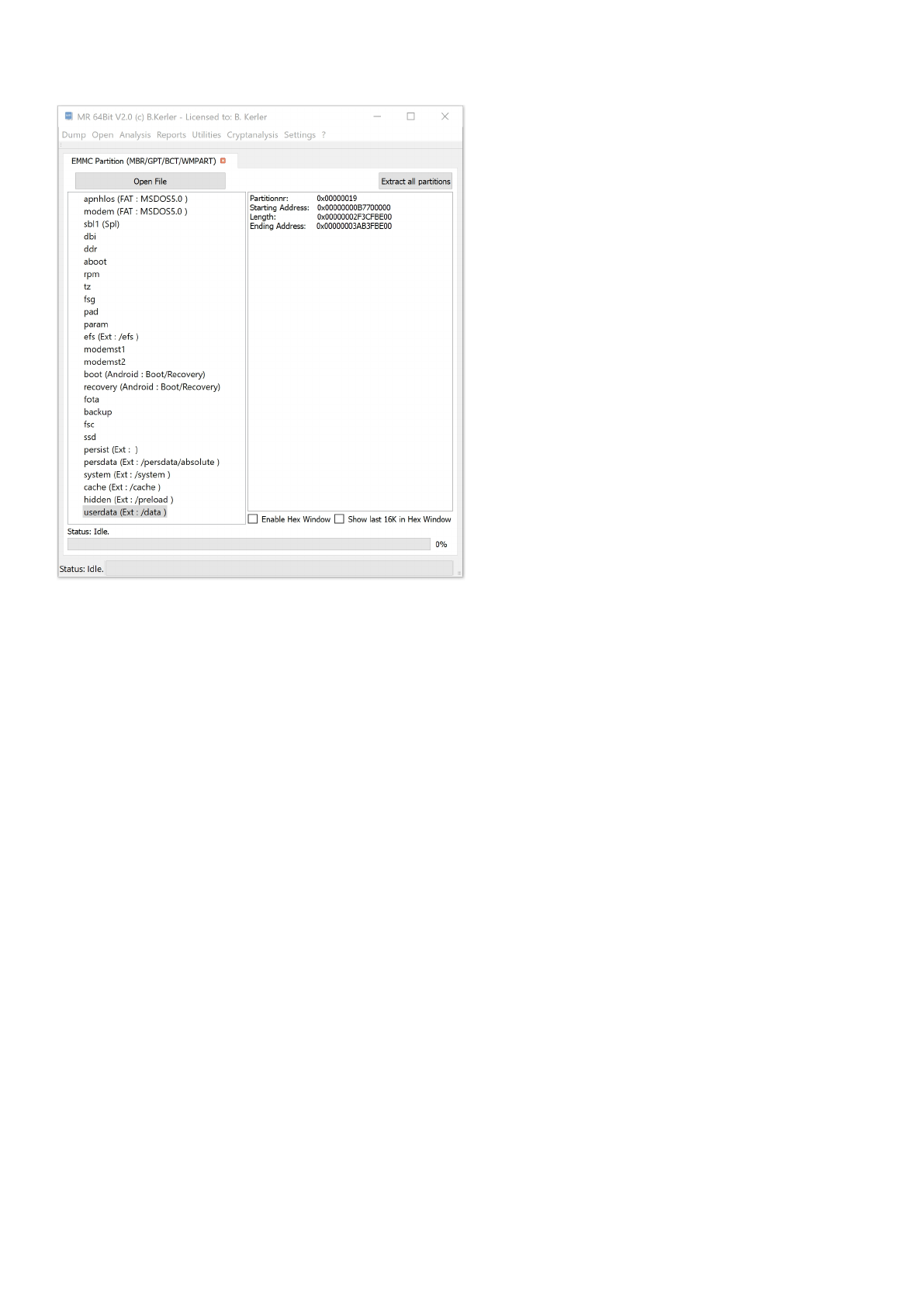
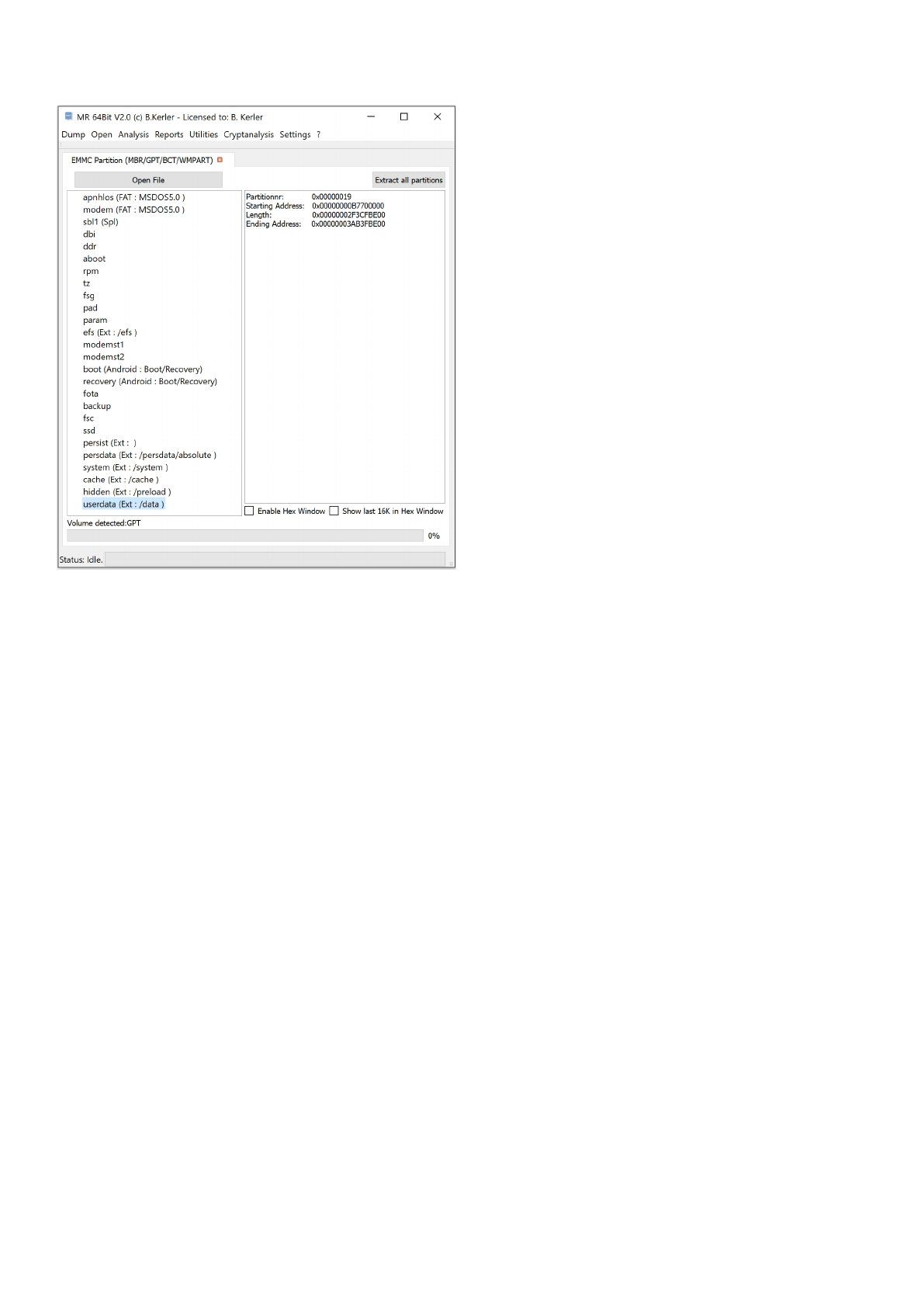
EMMC Partition (MBR/GPT/BCT/WMPART)
Using "Open File" you may open any raw flash binary file. If a known Partitiontype is detected, which may be MBR,
GPT, BCT and WM7 it will show all including partitions.
Clicking with the left mouse button on a partition entry will reveal its attributes.
Doubleclicking with the left mouse button will open the partition.
Clicking with the right mouse button on a partition will offer to extract or to open the partition.
The menu button "Extract all partitions" will extract all partitions by their name into separate files.
If no known Partitiontypes have been found, MR will offer an option to carve for FAT and/or EXT partitions.
Mobile Revelator 2.2.5
41 / 200
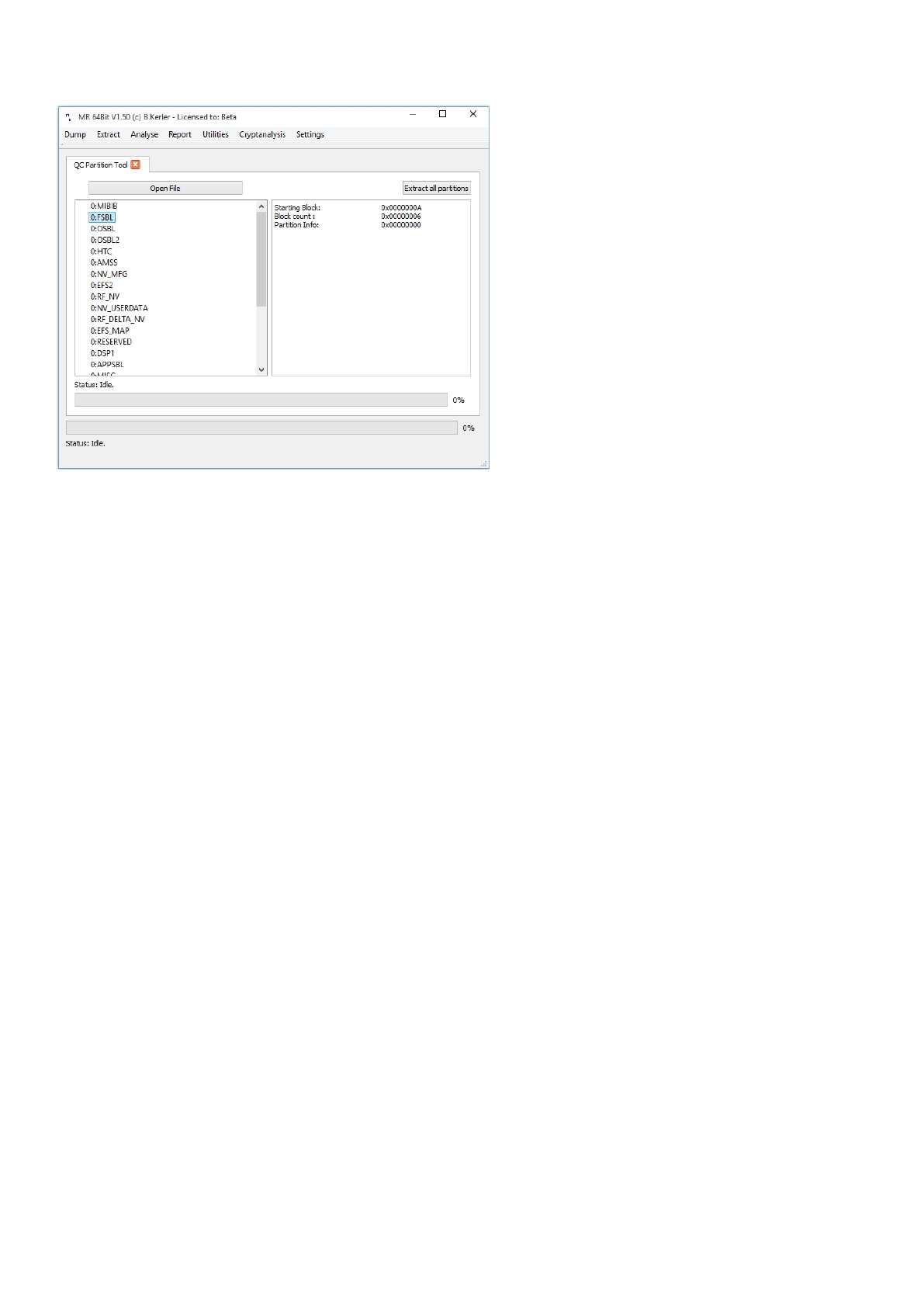
QC Partition
Using "Open File" you may open any raw flash binary file or qualcomm mbn file.
Clicking with the left mouse button on a partition entry will reveal its attributes.
The menu button "Extract all partitions" will try to extract all partitions by their name into separate files.
Mobile Revelator 2.2.5
42 / 200
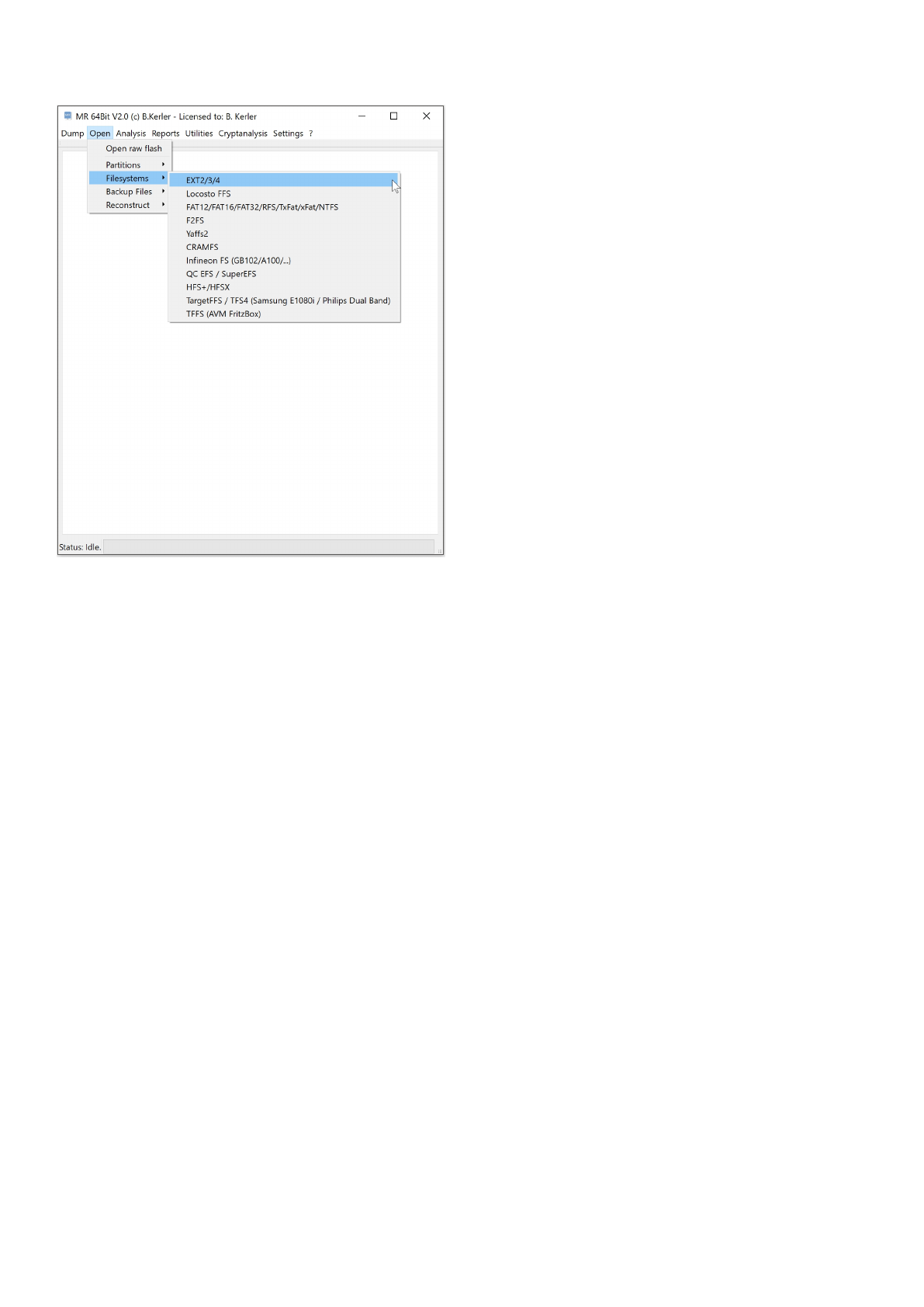
Filesystems
The filesystems menu offers several interpreters for many partition types.
Mobile Revelator 2.2.5
43 / 200
Generic
All filesystem modules have three different tabs :
1. FS Info : Shows the current filesystem information
2. Plugins : Allows to run custom python scripts
3. Log : Logs all user actions within the filesystem tab
4. Bookmark : Press Ctrl-B with selected files to bookmark or select any entry in the bookmark list and press del key to
remove the entry.
5. Image Preview: On enabling Image Preview when clicking any file, pictures will be displayed and can be rotated (alt-r, alt-
l), scaled (ctrl-,ctrl+), etc. using the right-click button on the picture.
You can enable the Hex Viewer by clicking "Enable HexView" and separate/combine the Hex Viewer from main window
by double-clicking the Hex Viewer Titlebar.
Doubleclicking on a file-entry will try to open up the file using associated programs.
Plugins : you may select the main plugin to run all plugins and single plugins as well
to just run one plugin.
Log : you may save the log at any time by pressing the "Save Log" button.

Mobile Revelator 2.2.5
44 / 200
Specific
This topic takes care about all specific filesystem modules MR has.
Mobile Revelator 2.2.5
45 / 200
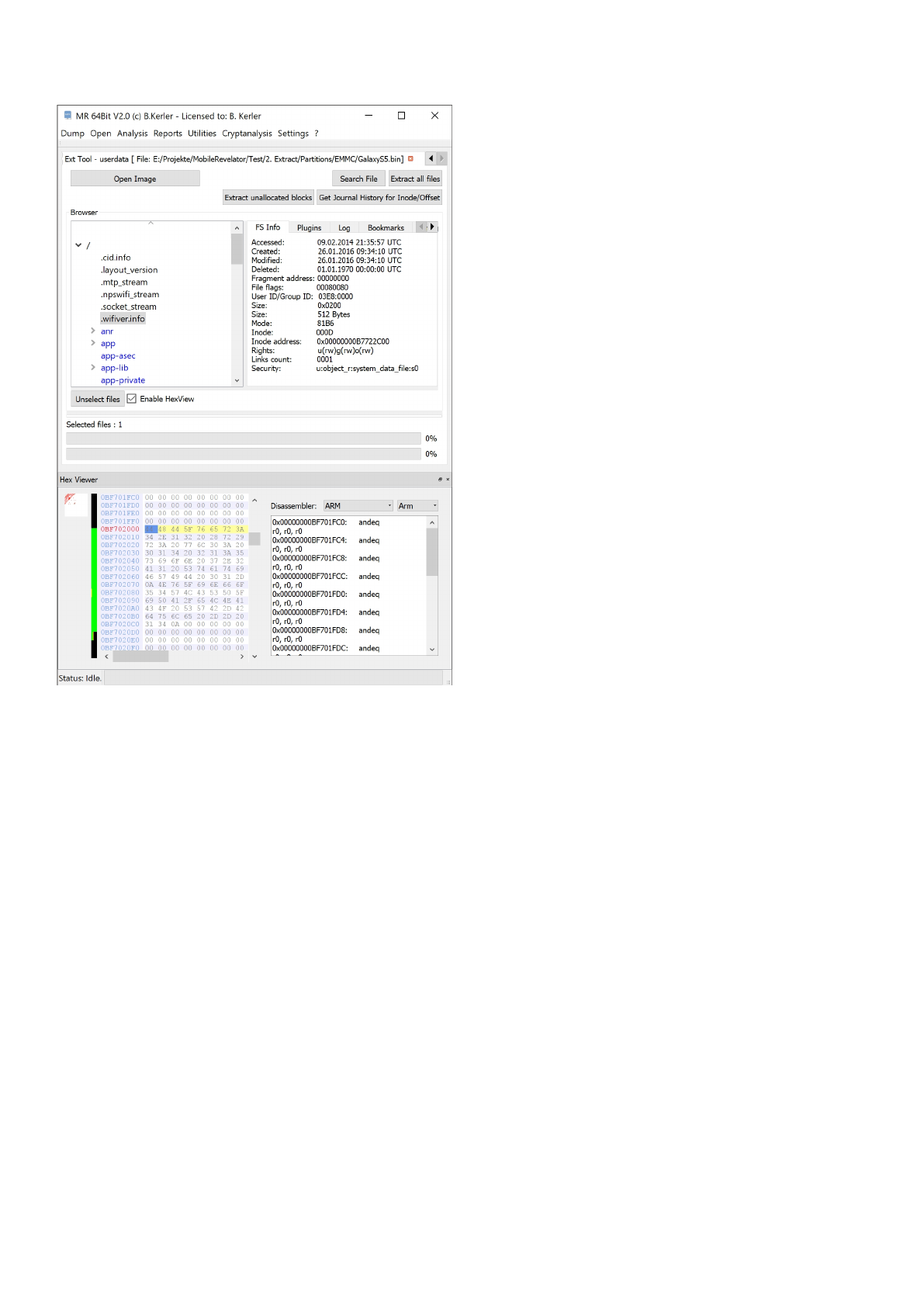
EXT2/3/4
Using "Open Image" you may open any ext2/3/4 partition file/raw file.
Clicking with the left mouse button on a file will reveal its attributes.
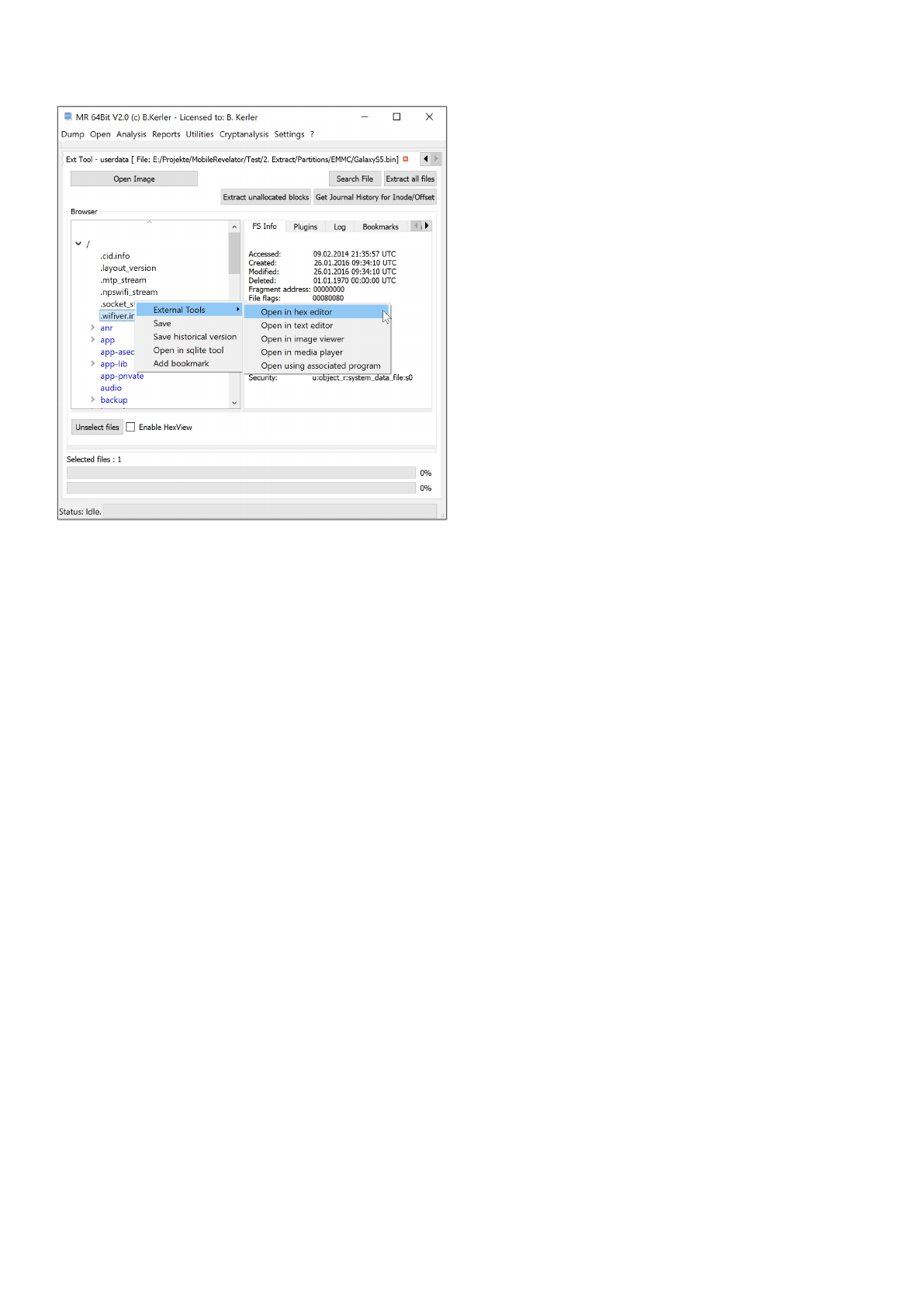
Clicking with the right mouse button on a file will show a menu, which features different options :
- External Tools :
This menu option lets you open you the selected file in a Hex Editor, Text Editor, Image Viewer, Media Player or any
associated
program in the OS. On first run, you must set the application paths in the "Settings"-Main Menu to point to
executables.
- Save :
This menu option will save all selected files. In order to select multiple files, just keep Ctrl-Key on your keyboard
pressed while
selecting files using the left mouse button.
- Save historical version :
This menu option will seek for journal entries for the selected files, and lets you choose to extract a different version
by timestamp.
- Open in sqlite tool :
This menu will open the selected file into the MR internal Sqlite Editor.
The menu button "Extract all files" will extract all files to a given directory, and will also write a log file to its parent directory.
The menu button "Extract unallocated blocks" will extract all blocks that aren't in use of the filesystem.
The menu button "Get Journal History for given Inode/Offset" will show any journal history entry for any inode or physical
data offset.
The menu button "Search" lets you search for any filename and will present a table with all entries found. Clicking using the
left mouse button on the entry will point directly to the entry in the filesystem.
Clicking on "Enable HexView" will show the first data sector of the selected file or directory entry/inode.
Mobile Revelator 2.2.5
46 / 200
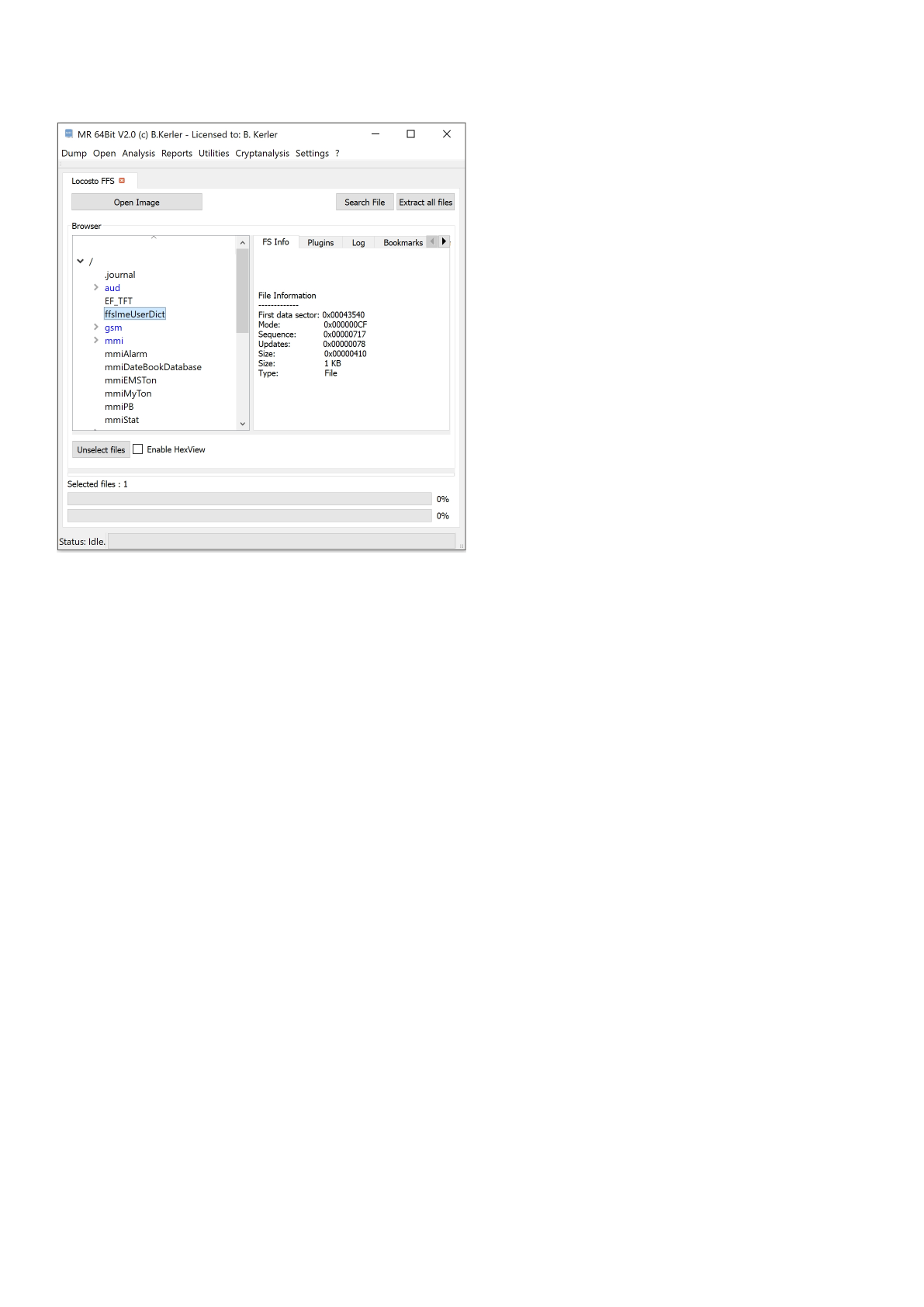
Locosto FFS
Using "Open Image" you may open any TI locosto chipset based FFS flash image.
Clicking with the left mouse button on a file will reveal its attributes.
Clicking with the right mouse button on a file will show a menu, which features different options :
- External Tools :
This menu option lets you open you the selected file in a Hex Editor, Text Editor, Image Viewer, Media Player or any
associated
program in the OS. On first run, you must set the application paths in the "Settings"-Main Menu to point to executables
- Save :
This menu option will save all selected files. In order to select multiple files, just keep Ctrl-Key on your keyboard
pressed while
selecting files using the left mouse button.
- Open in sqlite tool :
This menu will open the selected file into the MR internal Sqlite Editor.
The menu button "Extract all files" will extract all files to a given directory, and will also write a log file to its parent directory.
The menu button "Search" lets you search for any filename and will present a table with all entries found. Clicking using the
left mouse button on the entry will point directly to the entry in the filesystem.
Clicking on "Enable HexView" will show the first data sector of the selected file or directory entry/inode.
Mobile Revelator 2.2.5
47 / 200
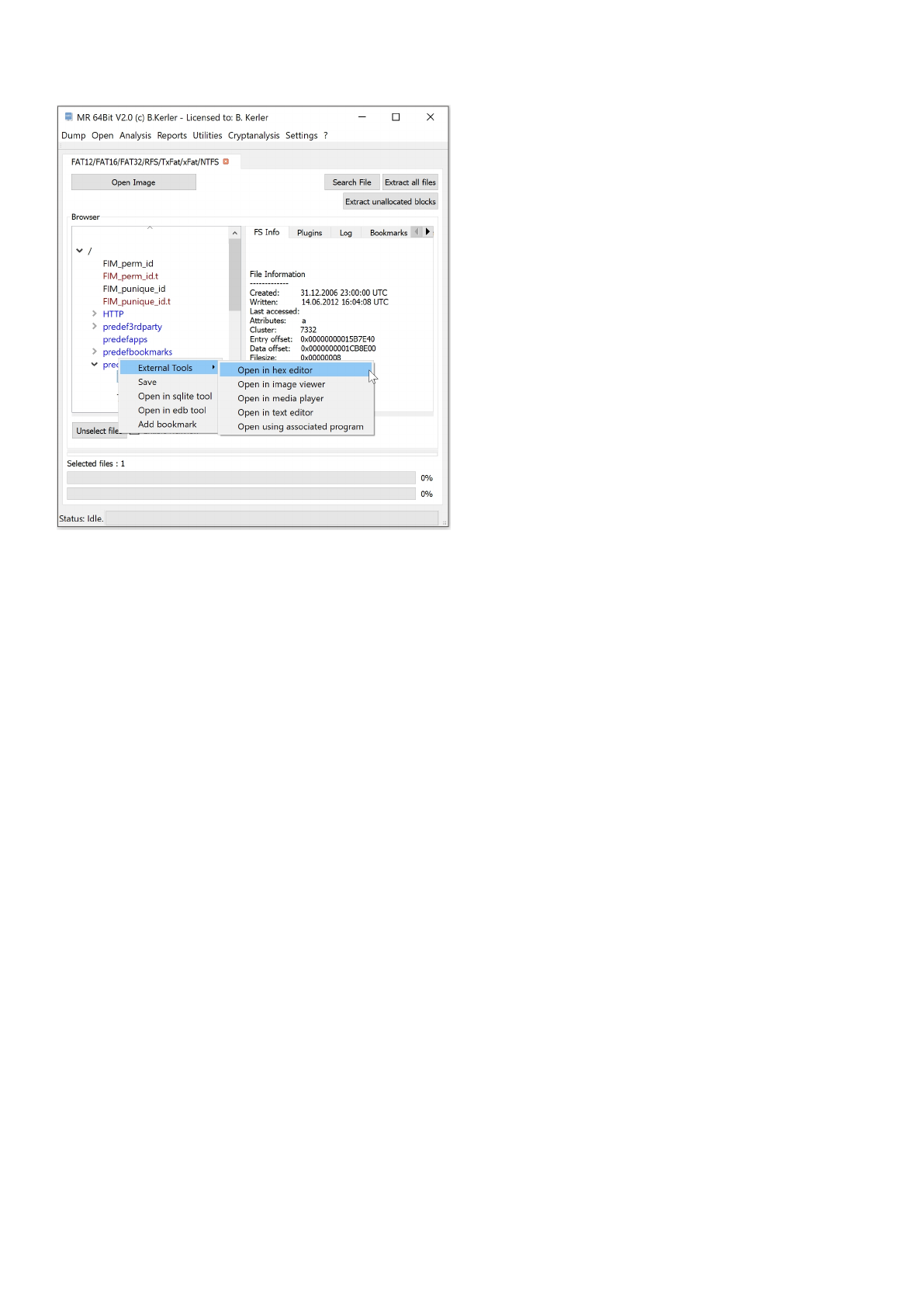
FAT12/FAT16/FAT32/RFS/TxFat/xFat/NTFS
Using "Open Image" you may open any Fat12/Fat16/Fat32/NTFS/RFS/ExFat/Transactioned ExFat partition file/raw file.
Clicking with the left mouse button on a file will reveal its attributes.
Clicking with the right mouse button on a file will show a menu, which features different options :
- External Tools :
This menu option lets you open you the selected file in a Hex Editor, Text Editor, Image Viewer, Media Player or any
associated
program in the OS. On first run, you must set the application paths in the "Settings"-Main Menu to point to executables
- Save :
This menu option will save all selected files. In order to select multiple files, just keep Ctrl-Key on your keyboard
pressed while
selecting files using the left mouse button.
- Open in sqlite tool :
This menu will open the selected file into the MR internal Sqlite Editor.
- Open in edb tool :
This menu will open the selected file into the MR internal WP7 EDB Database Viewer.
The menu button "Extract all files" will extract all files to a given directory, and will also write a log file to its parent directory.
The menu button "Extract unallocated blocks" will extract all blocks that aren't in use of the filesystem.
The menu button "Search" lets you search for any filename and will present a table with all entries found. Clicking using the
left mouse button on the entry will point directly to the entry in the filesystem.
Clicking on "Enable HexView" will show the first data sector of the selected file or directory entry/inode.
Mobile Revelator 2.2.5
48 / 200
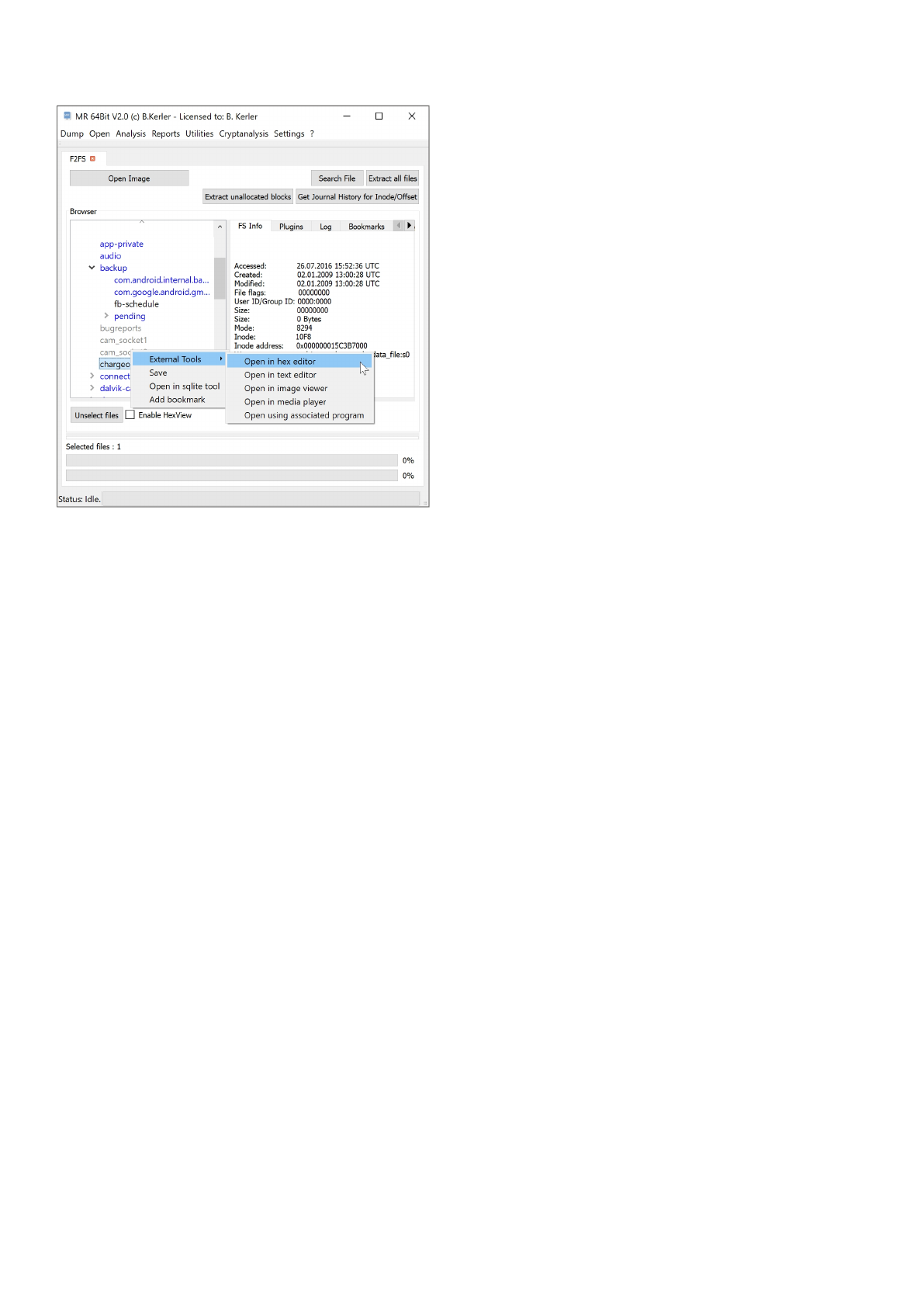
F2FS
Using "Open Image" you may open any f2fs partition file/raw file.
Clicking with the left mouse button on a file will reveal its attributes.
Clicking with the right mouse button on a file will show a menu, which features different options :
- External Tools :
This menu option lets you open you the selected file in a Hex Editor, Text Editor, Image Viewer, Media Player or any
associated
program in the OS. On first run, you must set the application paths in the "Settings"-Main Menu to point to
executables.
- Save :
This menu option will save all selected files. In order to select multiple files, just keep Ctrl-Key on your keyboard
pressed while
selecting files using the left mouse button.
- Open in sqlite tool :
This menu will open the selected file into the MR internal Sqlite Editor.
The menu button "Extract all files" will extract all files to a given directory, and will also write a log file to its parent directory.
The menu button "Extract unallocated blocks" will extract all blocks that aren't in use of the filesystem.
The menu button "Search" lets you search for any filename and will present a table with all entries found. Clicking using the
left mouse button on the entry will point directly to the entry in the filesystem.
Clicking on "Enable HexView" will show the first data sector of the selected file or directory entry/inode.
Mobile Revelator 2.2.5
49 / 200
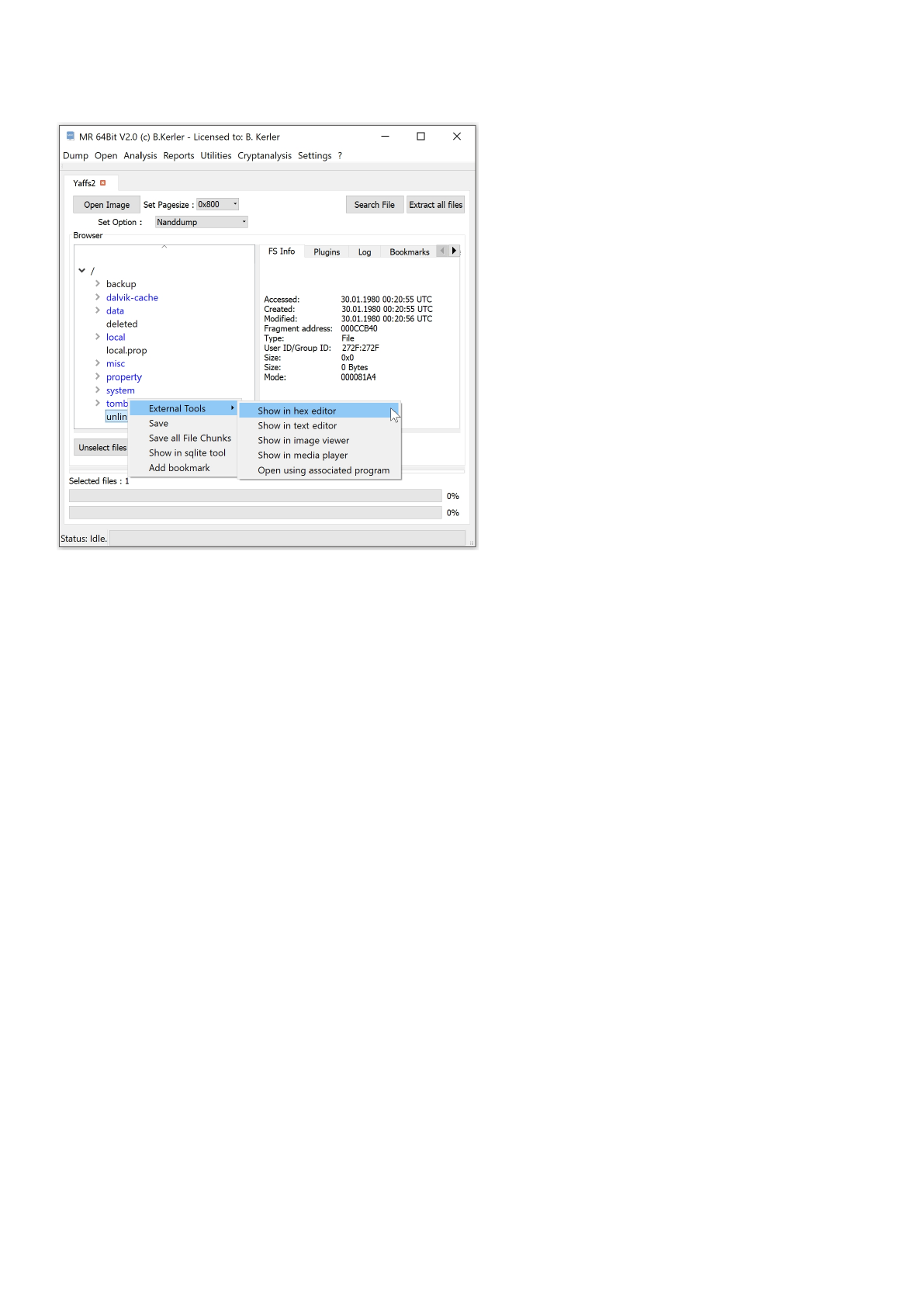
Yaffs2
Using "Open Image" you may open any Yaffs2 partition file/raw file. In order to extract Yaffs2 partitions, you will need the
according spare bytes from the Flash arranged by page/spare/page/spare/... Select the appropriate spare order by
choosing "Generic/Mk2yaffs" or "Nanddump" and its pagesize, which may be 0x200, 0x400, 0x800 (default) and 0x1000.
Clicking with the left mouse button on a file will reveal its attributes.
Clicking with the right mouse button on a file will show a menu, which features different options :
- External Tools :
This menu option lets you open you the selected file in a Hex Editor, Text Editor, Image Viewer, Media Player or
any associated program in the OS. On first run, you must set the application paths in the "Settings"-Main Menu to
point to executables
- Save :
This menu option will save all selected files. In order to select multiple files, just keep Ctrl-Key on your keyboard
pressed while selecting files using the left mouse button.
- Open in sqlite tool :
This menu will open the selected file into the MR internal Sqlite Editor.
The menu button "Extract all files" will extract all files to a given directory, and will also write a log file to its parent directory.
The menu button "Extract unallocated blocks" will extract all blocks that aren't in use of the filesystem.
The menu button "Get Journal History for given Inode/Offset" will show any journal history entry for any inode or physical
data offset.
The menu button "Search" lets you search for any filename and will present a table with all entries found. Clicking using the
left mouse button on the entry will
point directly to the entry in the filesystem.
Clicking on "Enable HexView" will show the first data sector of the selected file or directory entry/inode.
Mobile Revelator 2.2.5
50 / 200
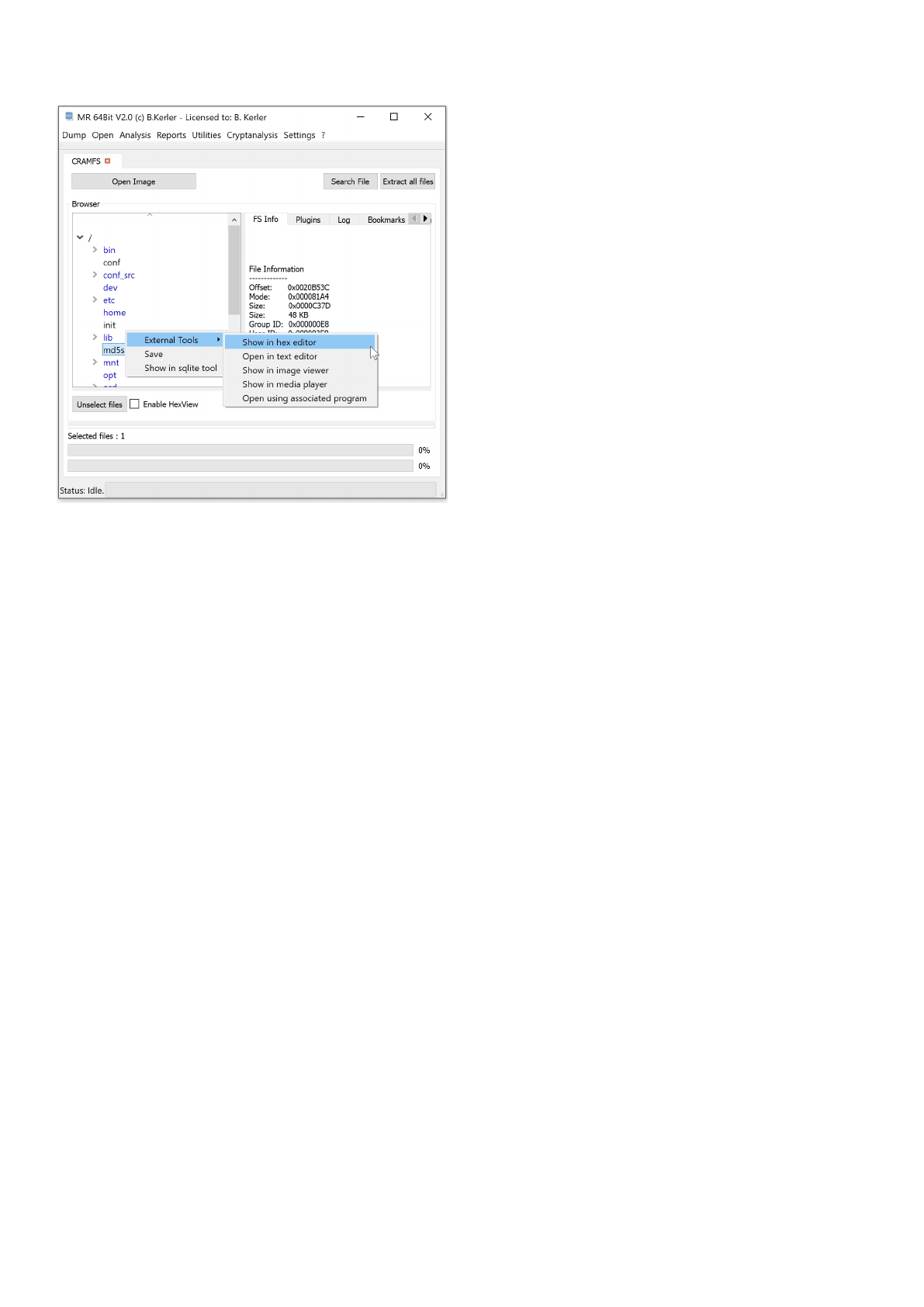
CRAMFS
Using "Open Image" you may open any Compressed ROM flash image, indicated by "Compressed ROMFS" at the start of
the image.
Clicking with the left mouse button on a file will reveal its attributes.
Clicking with the right mouse button on a file will show a menu, which features different options :
- External Tools :
This menu option lets you open you the selected file in a Hex Editor, Text Editor, Image Viewer, Media Player or
any associated program in the OS. On first run, you must set the application paths in the "Settings"-Main Menu to
point to executables
- Save :
This menu option will save all selected files. In order to select multiple files, just keep Ctrl-Key on your keyboard
pressed while selecting files using the left mouse button.
- Open in sqlite tool :
This menu will open the selected file into the MR internal Sqlite Editor.
The menu button "Extract all files" will extract all files to a given directory, and will also write a log file to its parent directory.
The menu button "Search" lets you search for any filename and will present a table with all entries found. Clicking using the
left mouse button on the entry will point directly to the entry in the filesystem.
Clicking on "Enable HexView" will show the first data sector of the selected file or directory entry/inode.
Mobile Revelator 2.2.5
51 / 200
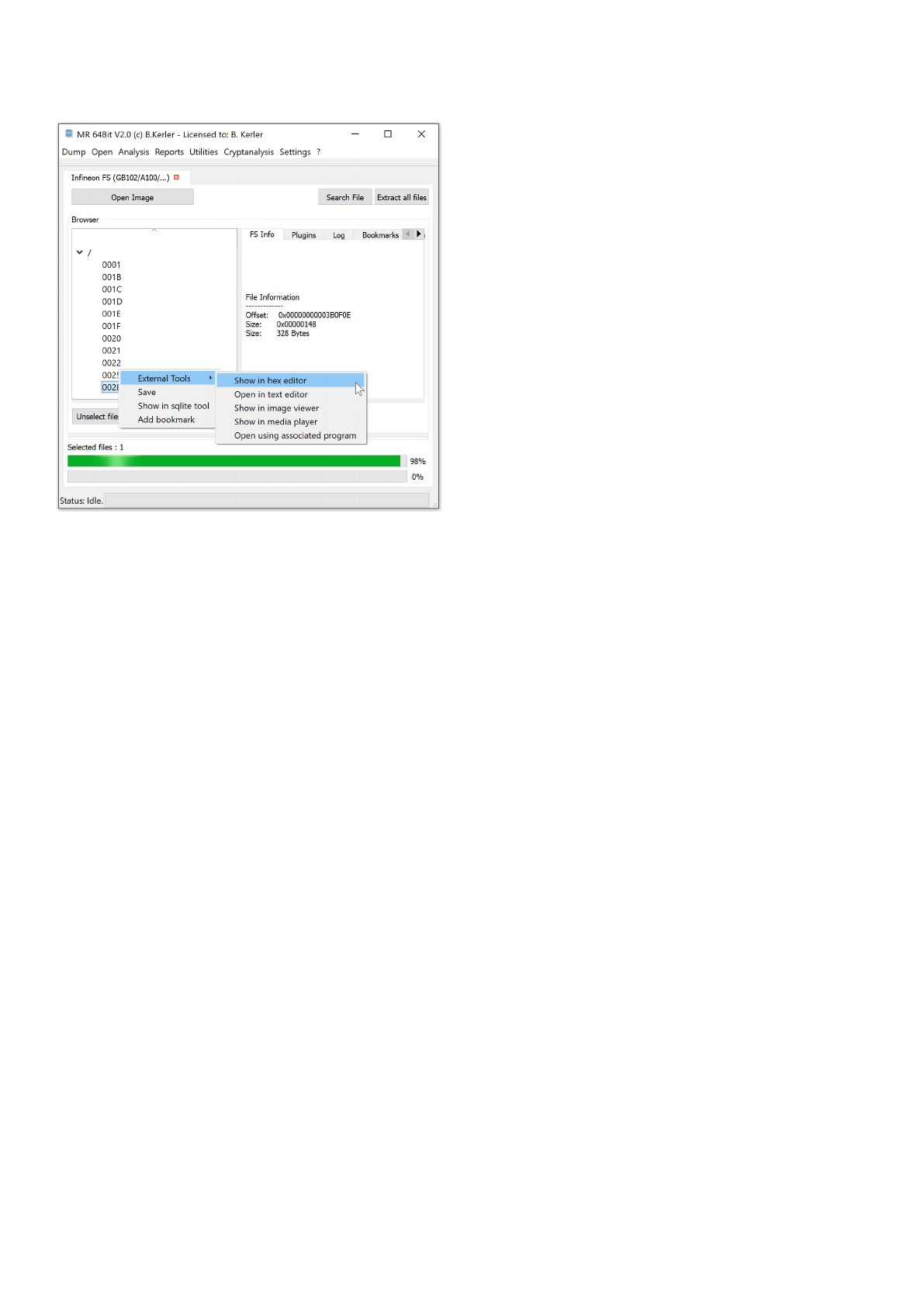
Infineon FS (GB102/A100/...)
Using "Open Image" you may open any Infineon chipset based flash image.
Clicking with the left mouse button on a file will reveal its attributes.
Clicking with the right mouse button on a file will show a menu, which features different options :
- External Tools :
This menu option lets you open you the selected file in a Hex Editor, Text Editor, Image Viewer, Media Player or any
associated
program in the OS. On first run, you must set the application paths in the "Settings"-Main Menu to point to executables
- Save :
This menu option will save all selected files. In order to select multiple files, just keep Ctrl-Key on your keyboard
pressed while selecting files using the left mouse button.
- Open in sqlite tool :
This menu will open the selected file into the MR internal Sqlite Editor.
The menu button "Extract all files" will extract all files to a given directory, and will also write a log file to its parent directory.
The menu button "Search" lets you search for any filename and will present a table with all entries found. Clicking using the
left mouse button on the entry will point directly to the entry in the filesystem.
Clicking on "Enable HexView" will show the first data sector of the selected file or directory entry/inode.
Mobile Revelator 2.2.5
52 / 200
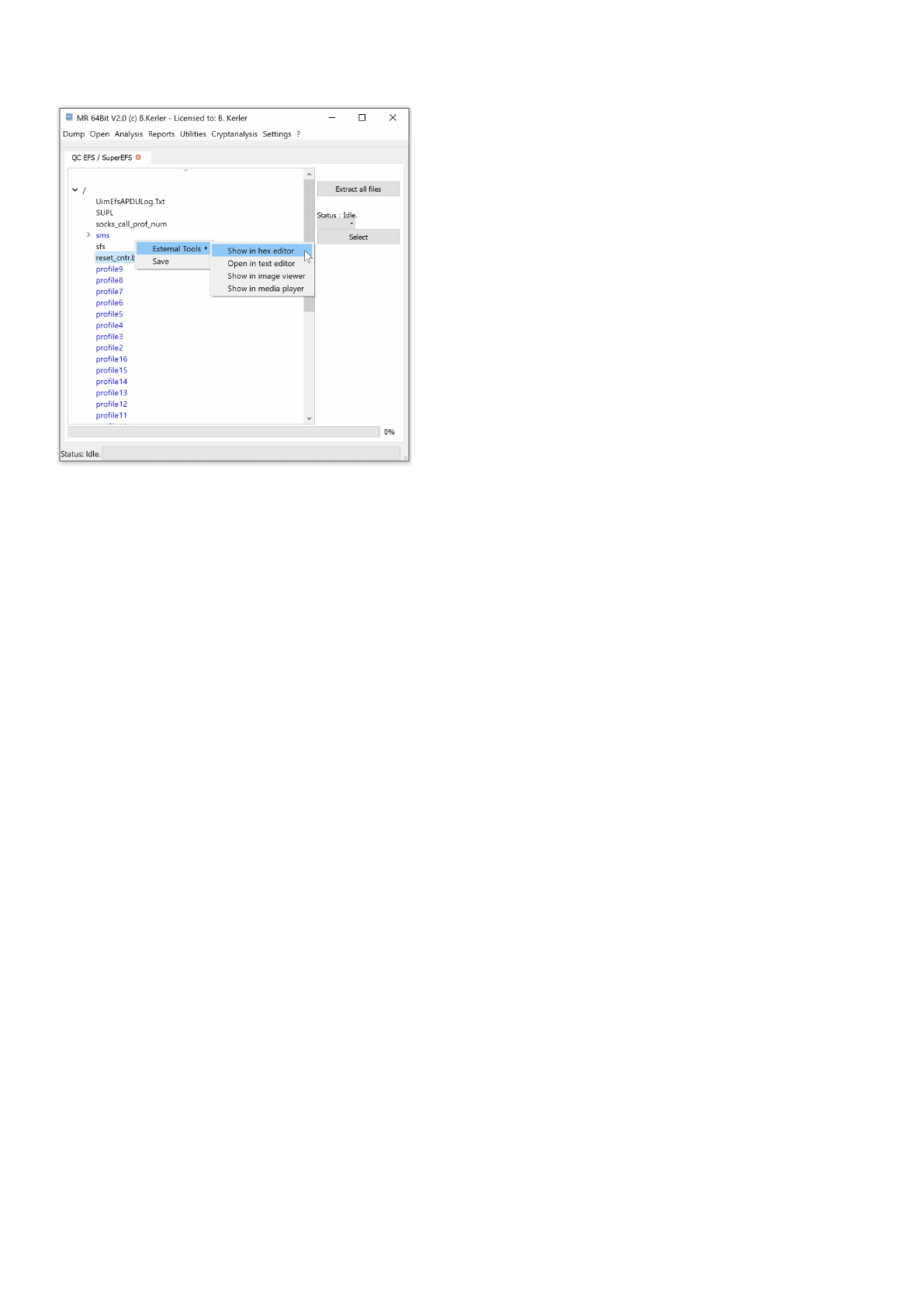
QC EFS / SuperEFS
Using "Open Image" you may open any Qualcomm chipset based Embedded File System (EFS) image.
If the image contains older versions due to journaling, you may select the version just below the "Extract all files" button
.
Clicking with the left mouse button on a file will reveal its attributes.
Clicking with the right mouse button on a file will show a menu, which features different options :
- External Tools :
This menu option lets you open you the selected file in a Hex Editor, Text Editor, Image Viewer, Media Player or any
associated
program in the OS. On first run, you must set the application paths in the "Settings"-Main Menu to point to executables
- Save :
This menu option will save all selected files. In order to select multiple files, just keep Ctrl-Key on your keyboard
pressed while selecting files using the left mouse button.
The menu button "Extract all files" will extract all files to a given directory, and will also write a log file to its parent directory.
Mobile Revelator 2.2.5
53 / 200
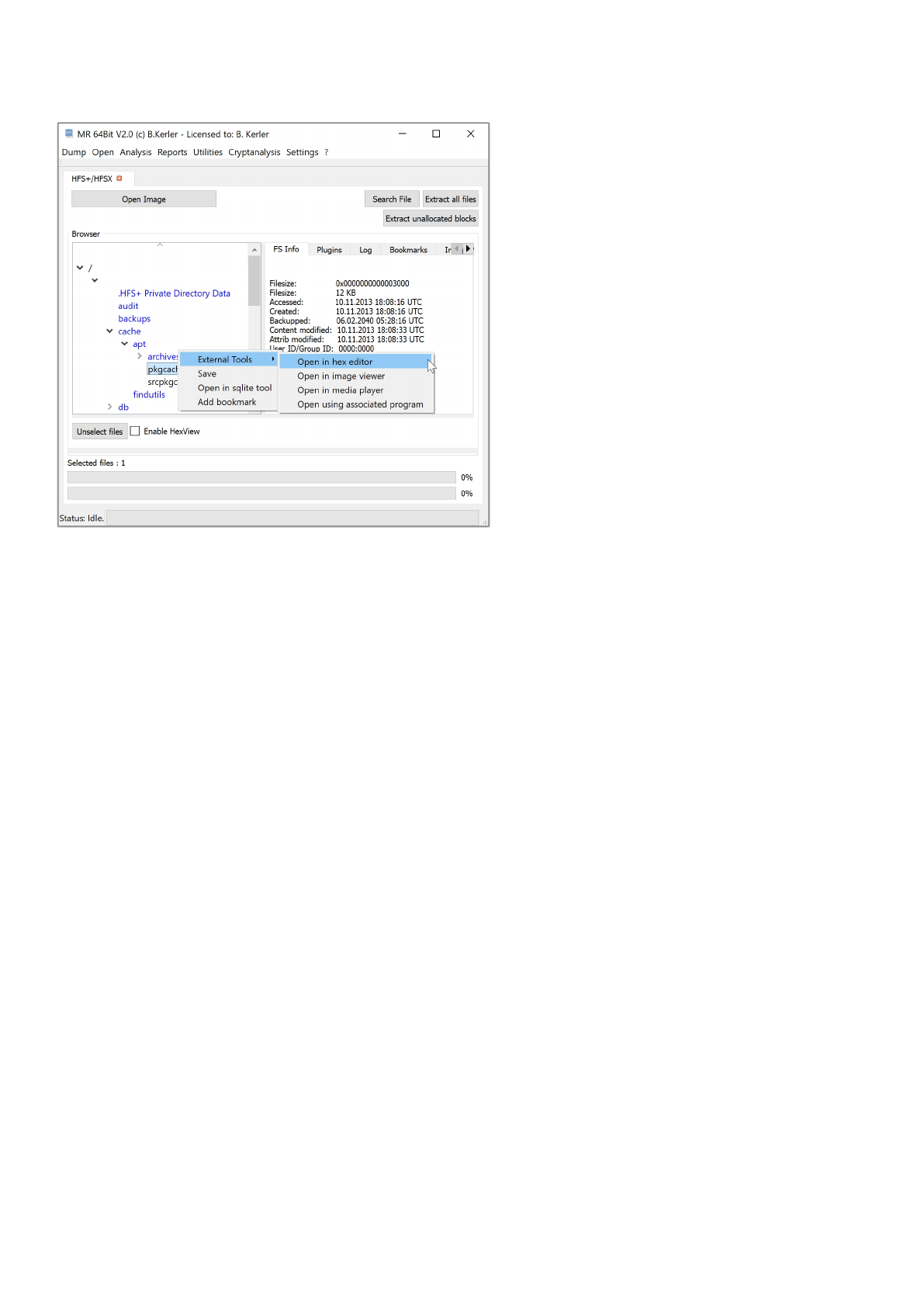
HFS+/HFSX
Using "Open Image" you may open any HFS/HFS+/HFSX image.
Clicking with the left mouse button on a file will reveal its attributes.
Clicking with the right mouse button on a file will show a menu, which features different options :
- External Tools :
This menu option lets you open you the selected file in a Hex Editor, Text Editor, Image Viewer, Media Player or
any associated program in the OS. On first run, you must set the application paths in the "Settings"-Main Menu to
point to executables
- Save :
This menu option will save all selected files. In order to select multiple files, just keep Ctrl-Key on your keyboard
pressed while
selecting files using the left mouse button.
- Open in sqlite tool :
This menu will open the selected file into the MR internal Sqlite Editor.
The menu button "Extract all files" will extract all files to a given directory, and will also write a log file to its parent directory.
The menu button "Search" lets you search for any filename and will present a table with all entries found. Clicking using the
left mouse button on the entry will point directly to the entry in the filesystem.
Clicking on "Enable HexView" will show the first data sector of the selected file or directory entry/inode.
Mobile Revelator 2.2.5
54 / 200
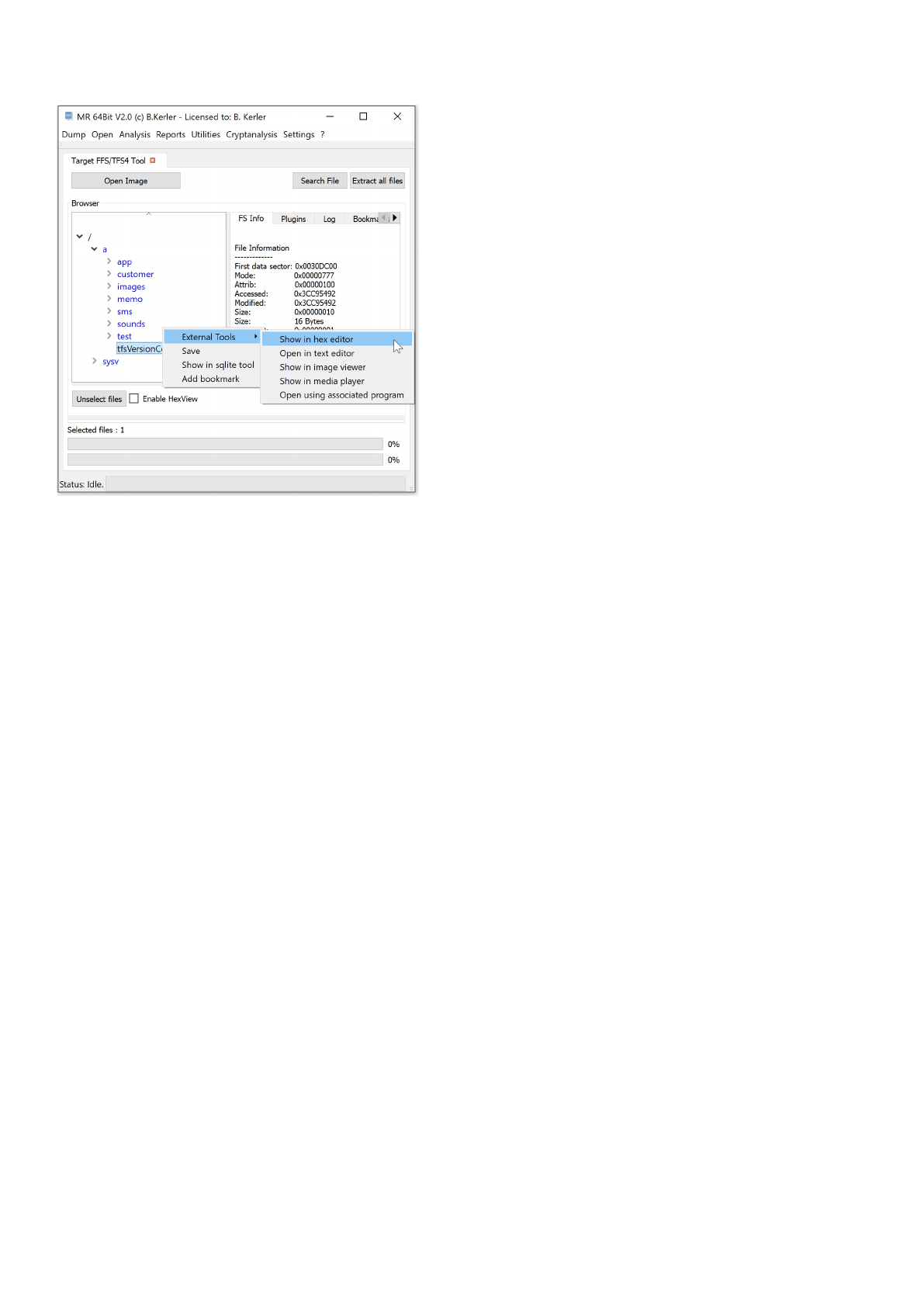
TargetFFS / TFS4 (Samsung E1080i / Philips Dual Band)
Using "Open Image" you may open any TargetFFS/TFS4 image.
Clicking with the left mouse button on a file will reveal its attributes.
Clicking with the right mouse button on a file will show a menu, which features different options :
- External Tools :
This menu option lets you open you the selected file in a Hex Editor, Text Editor, Image Viewer, Media Player or any
associated program in the OS. On first run, you must set the application paths in the "Settings"-Main Menu to point
to executables
- Save :
This menu option will save all selected files. In order to select multiple files, just keep Ctrl-Key on your keyboard
pressed while selecting files using the left mouse button.
- Open in sqlite tool :
This menu will open the selected file into the MR internal Sqlite Editor.
The menu button "Extract all files" will extract all files to a given directory, and will also write a log file to its parent directory.
The menu button "Search" lets you search for any filename and will present a table with all entries found. Clicking using the
left mouse button on the entry will point directly to the entry in the filesystem.
Clicking on "Enable HexView" will show the first data sector of the selected file or directory entry/inode.
Mobile Revelator 2.2.5
55 / 200
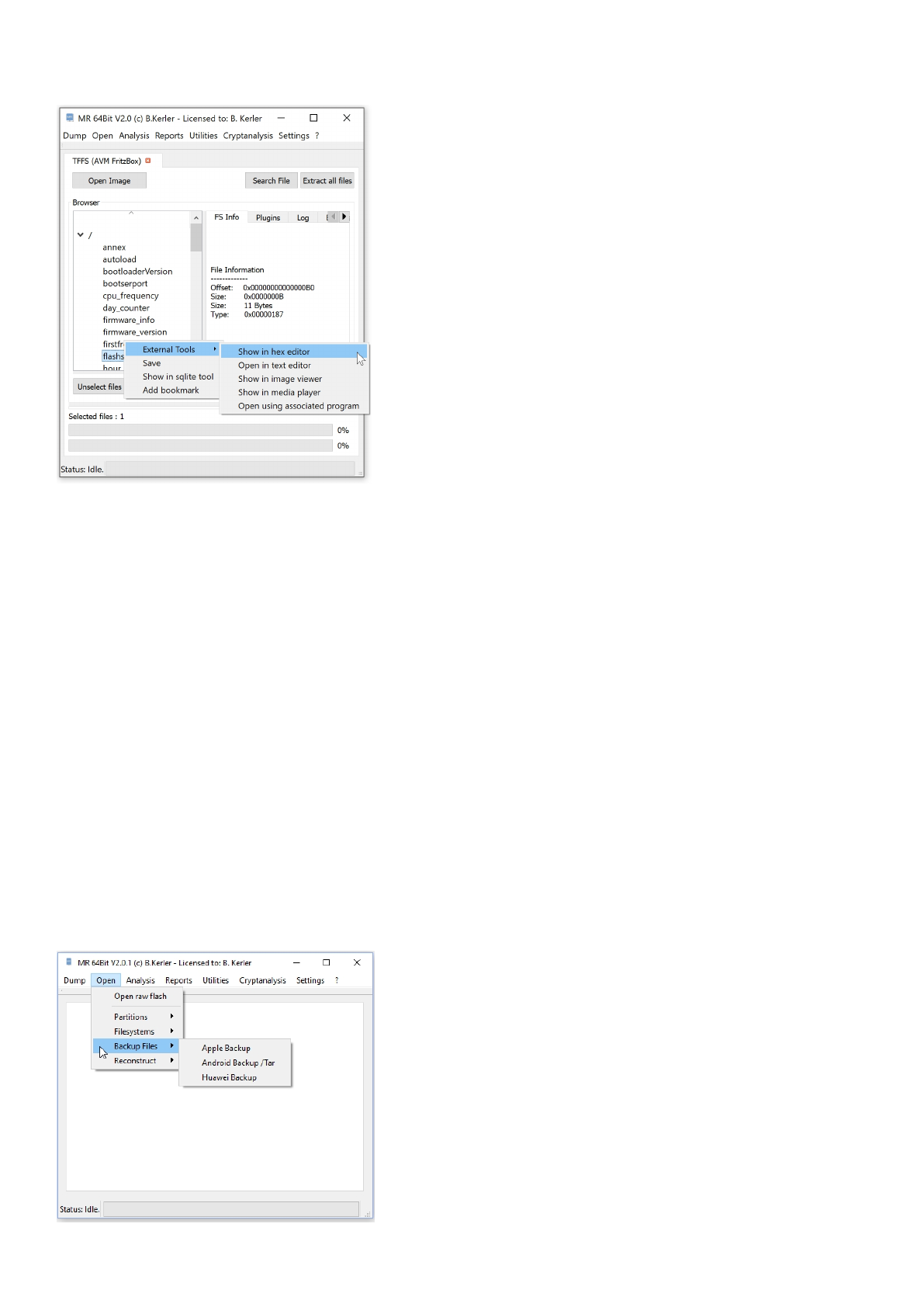
TFFS (AVM FritzBox)
Using "Open Image" you may open any TFFS AVM Fritzbox image. You cannot use RAW flash image, you need to extract
the flash partitions from the RAW flash image first, starting with bytes "01 00 04 00 FF FF FE".
Clicking with the left mouse button on a file will reveal its attributes.
Clicking with the right mouse button on a file will show a menu, which features different options :
- External Tools :
This menu option lets you open you the selected file in a Hex Editor, Text Editor, Image Viewer, Media Player or any
associated program in the OS. On first run, you must set the application paths in the "Settings"-Main Menu to point
to executables
- Save :
This menu option will save all selected files. In order to select multiple files, just keep Ctrl-Key on your keyboard
pressed while selecting files using the left mouse button.
- Open in sqlite tool :
This menu will open the selected file into the MR internal Sqlite Editor.
The menu button "Extract all files" will extract all files to a given directory, and will also write a log file to its parent directory.
The menu button "Search" lets you search for any filename and will present a table with all entries found. Clicking using the
left mouse button on the entry will point directly to the entry in the filesystem.
Clicking on "Enable HexView" will show the first data sector of the selected file or directory entry/inode.
Backup Files

Mobile Revelator 2.2.5
56 / 200
The backup files menu offers functionality for viewing and extracting apple and android backup files.
Mobile Revelator 2.2.5
57 / 200
Apple Backup
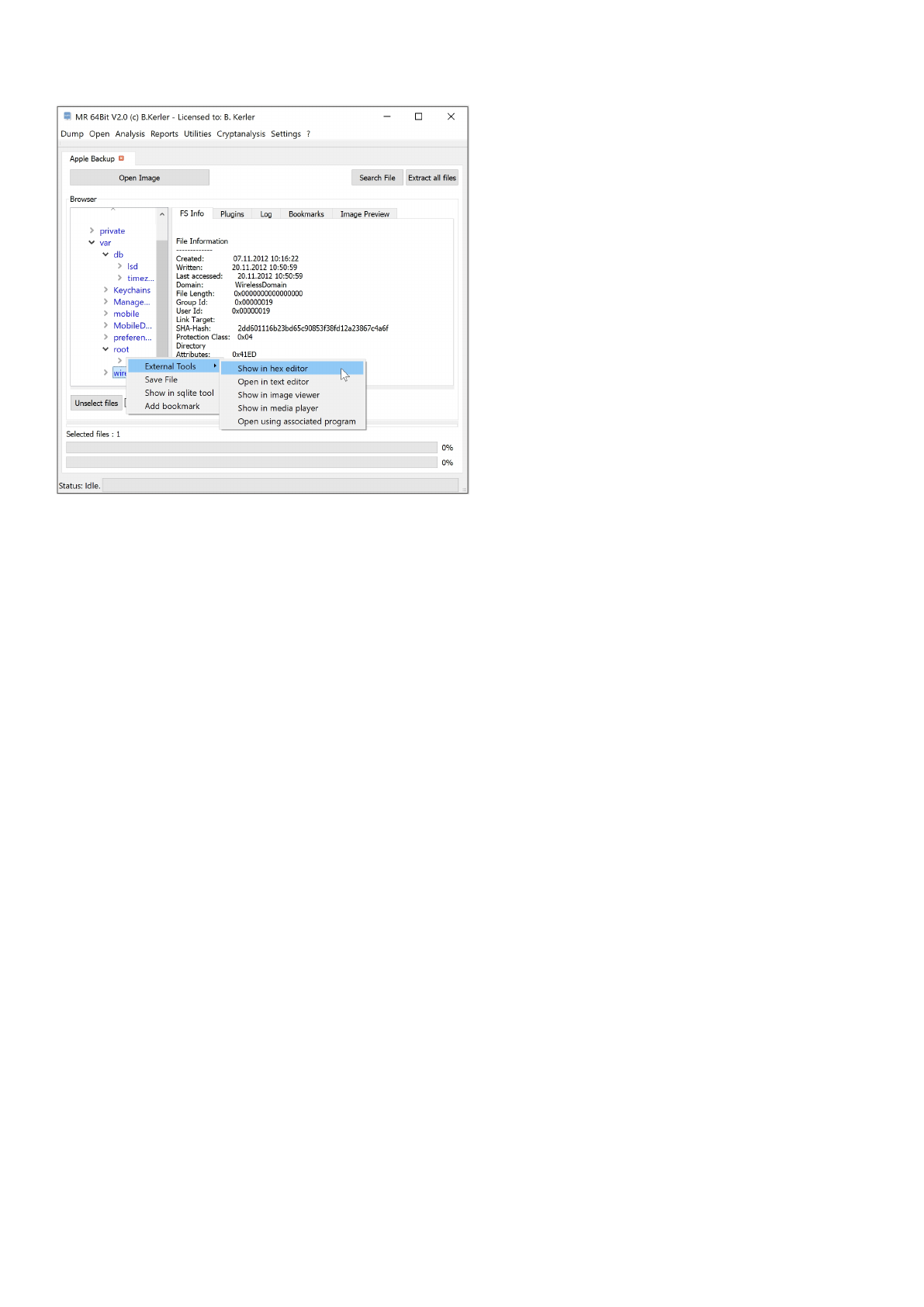
Using "Open Image" you may open any Apple iTunes backup file whether it may be encrypted or not. If the backup is
encrypted,
it will ask for the password for decryption. On "Open Image", choose the appropriate "Manifest.mbdb" file.
Clicking with the left mouse button on a file will reveal its attributes.
Clicking with the right mouse button on a file will show a menu, which features different options :
- External Tools :
This menu option lets you open you the selected file in a Hex Editor, Text Editor, Image Viewer, Media Player or any
associated program in the OS. On first run, you must set the application paths in the "Settings"-Main Menu to point
to executables.
- Save :
This menu option will save all selected files. In order to select multiple files, just keep Ctrl-Key on your keyboard
pressed while selecting files using the left mouse button.
- Open in sqlite tool :
This menu will open the selected file into the MR internal Sqlite Editor.
- Open in plist tool :
This menu will open the selected file into the MR internal Apple PList Editor.
The menu button "Extract all files" will extract all files to a given directory, and will also write a log file to its parent directory.
The menu button "Search" lets you search for any filename and will present a table with all entries found. Clicking using the
left mouse button on the entry will point directly to the entry in the filesystem.
Clicking on "Enable HexView" will show the first data sector of the selected file or directory entry/inode.
Mobile Revelator 2.2.5
58 / 200
Android Backup / Tar
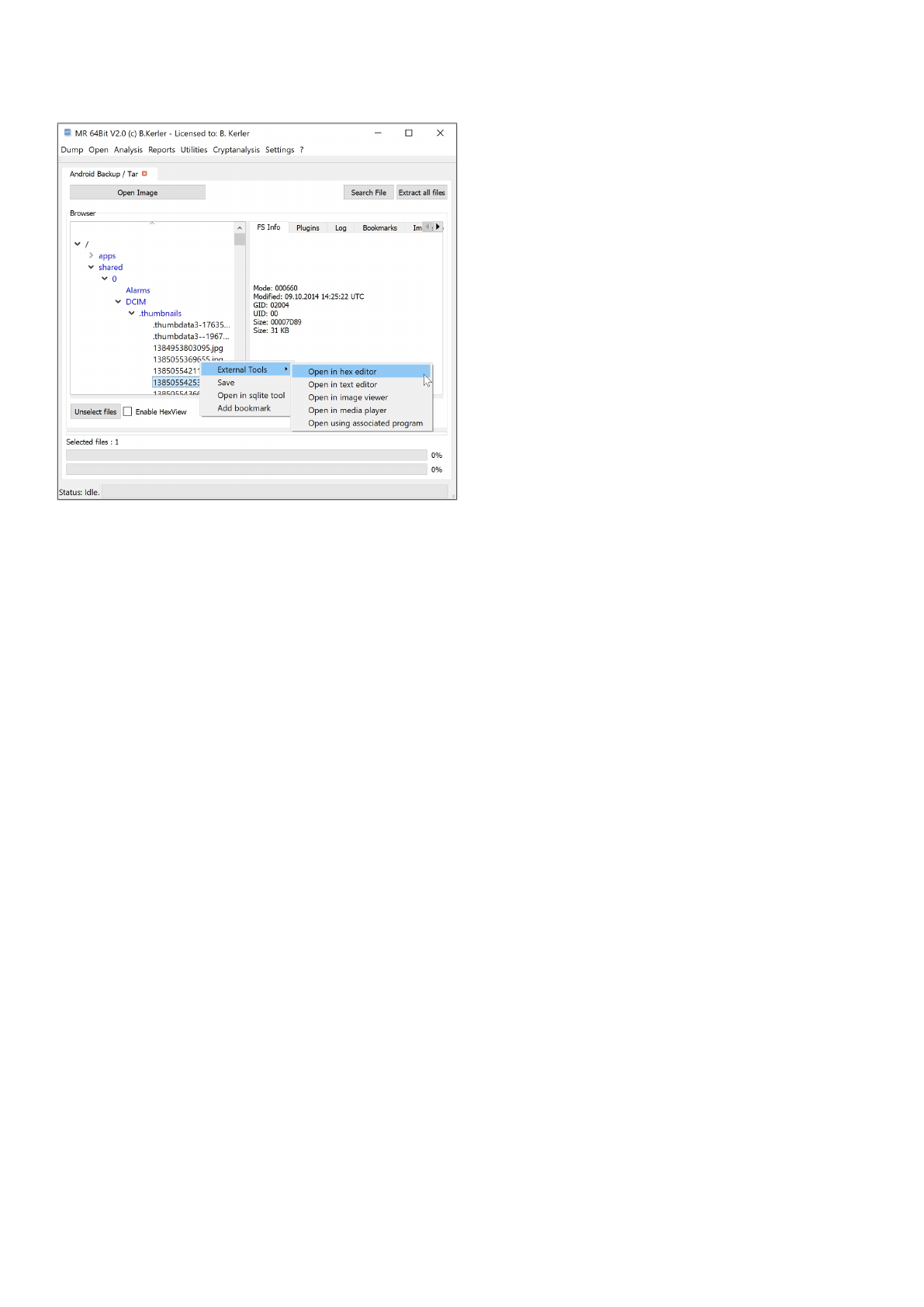
Using "Open Image" you may open any Android Backup "*.ab", Gzipped Tar or Tar file, whether it may be encrypted or not.
If the backup is encrypted, it will ask for the password for decryption.
Clicking with the left mouse button on a file will reveal its attributes.
Clicking with the right mouse button on a file will show a menu, which features different options :
- External Tools :
This menu option lets you open you the selected file in a Hex Editor, Text Editor, Image Viewer, Media Player or any
associated program in the OS. On first run, you must set the application paths in the "Settings"-Main Menu to point
to executables.
- Save :
This menu option will save all selected files. In order to select multiple files, just keep Ctrl-Key on your keyboard
pressed while selecting files using the left mouse button.
- Open in sqlite tool :
This menu will open the selected file into the MR internal Sqlite Editor.
The menu button "Extract all files" will extract all files to a given directory, and will also write a log file to its parent directory.
The menu button "Search" lets you search for any filename and will present a table with all entries found. Clicking using the
left mouse button on the entry will point directly to the entry in the filesystem.
Clicking on "Enable HexView" will show the first data sector of the selected file or directory entry/inode.
Huawei Backup
The Huawei Backup Tool offers a method to convert the sqlite database files and contents to a filesystem.
In order to do a full backup, in the smartphone go to Tools, Huawei Backup and store all data to an external sdcard or
sdcard connected via otg cable.
Mobile Revelator 2.2.5
59 / 200
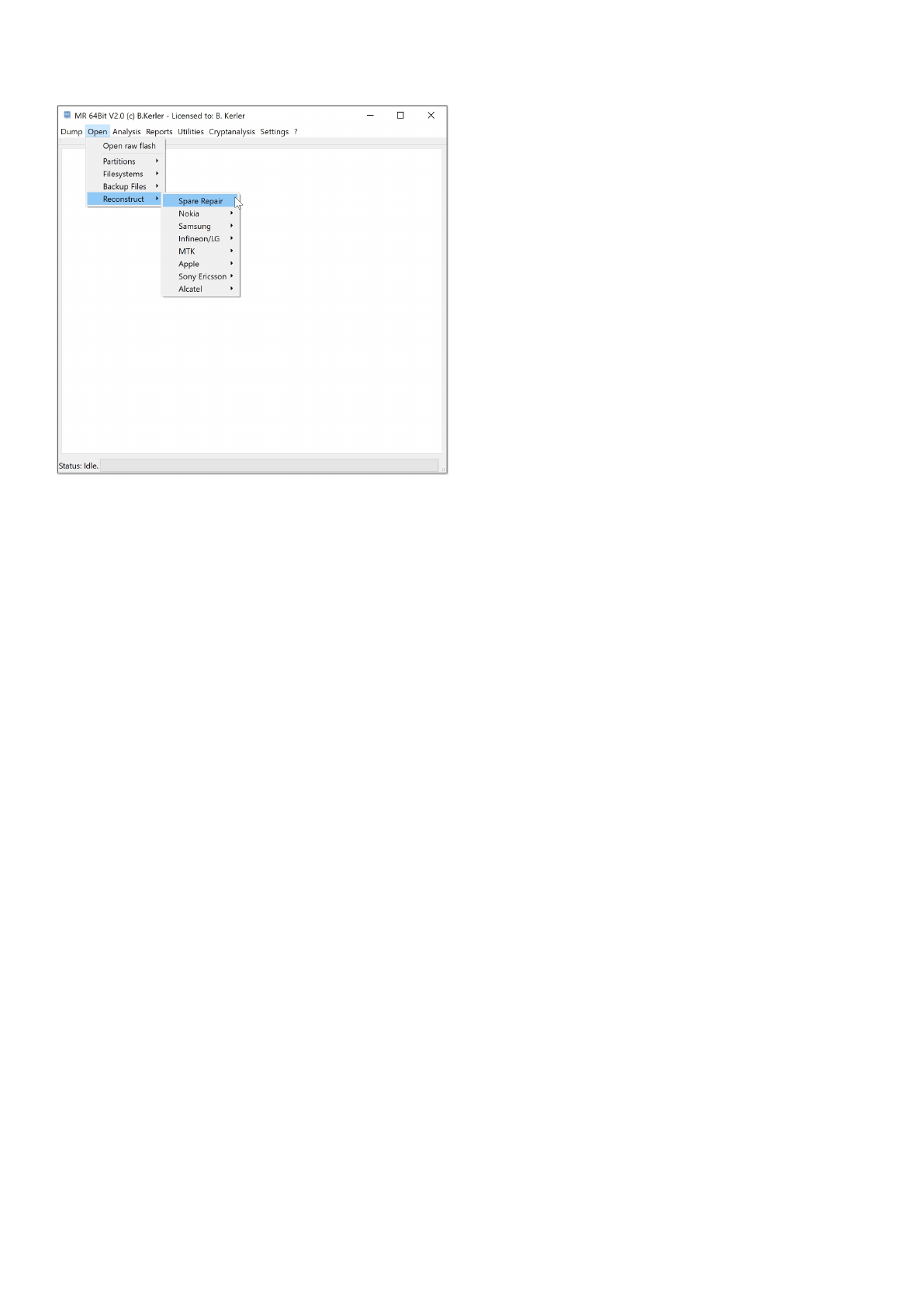
Reconstruct
The Reconstruct menu offers functionality for reconstructing filesystems due to usage of wearleveling or
flash transaction layers.
Mobile Revelator 2.2.5
60 / 200
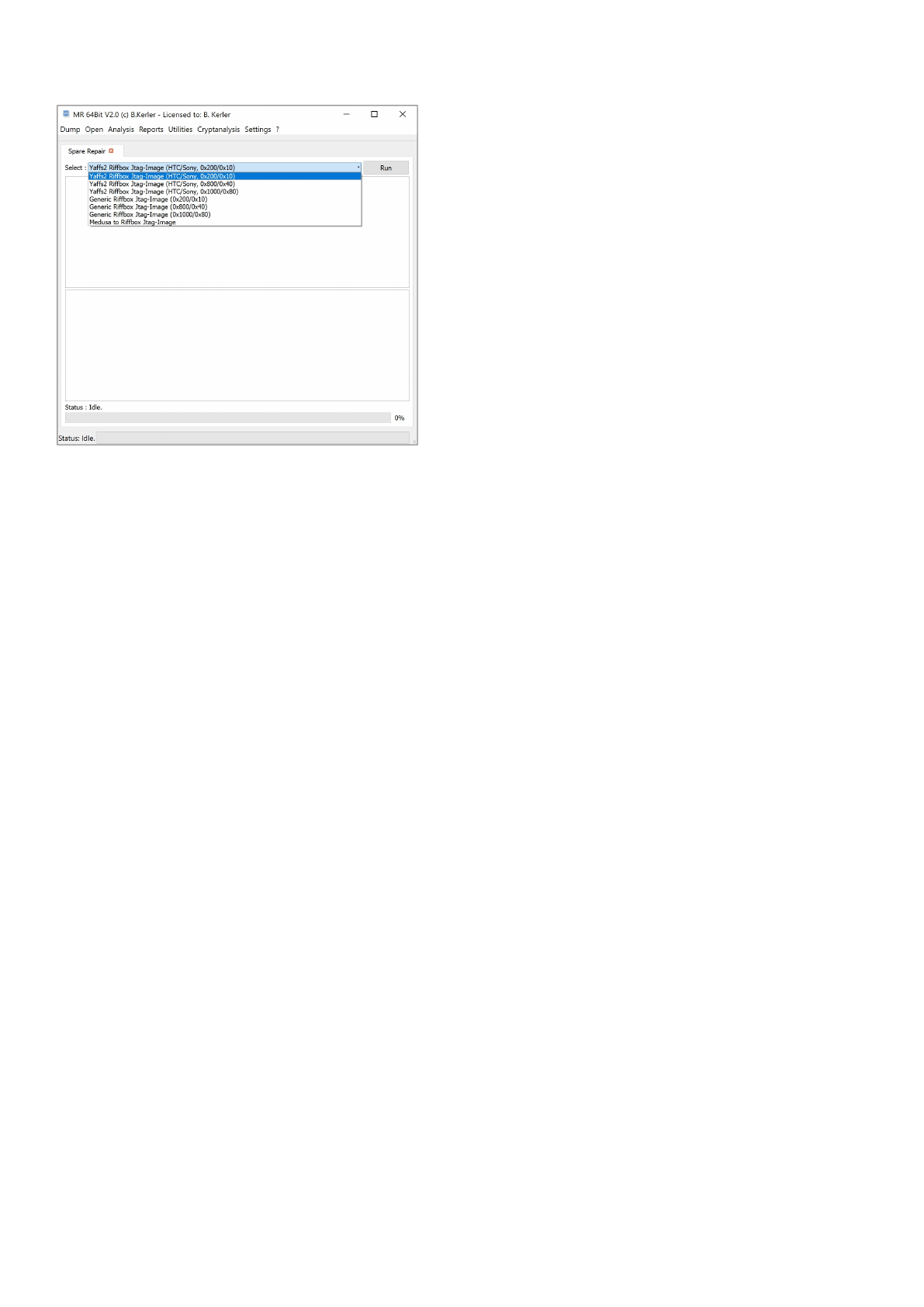
Spare Repair
The Spare Repair Tool will reorder spare areas from other Tools like RiffBox or MedusaBox to make the flash images
being
used by the MR Tool correctly. It will sort the Spares from the end of the flash to the end of each page, where they should
be.
Mobile Revelator 2.2.5
61 / 200
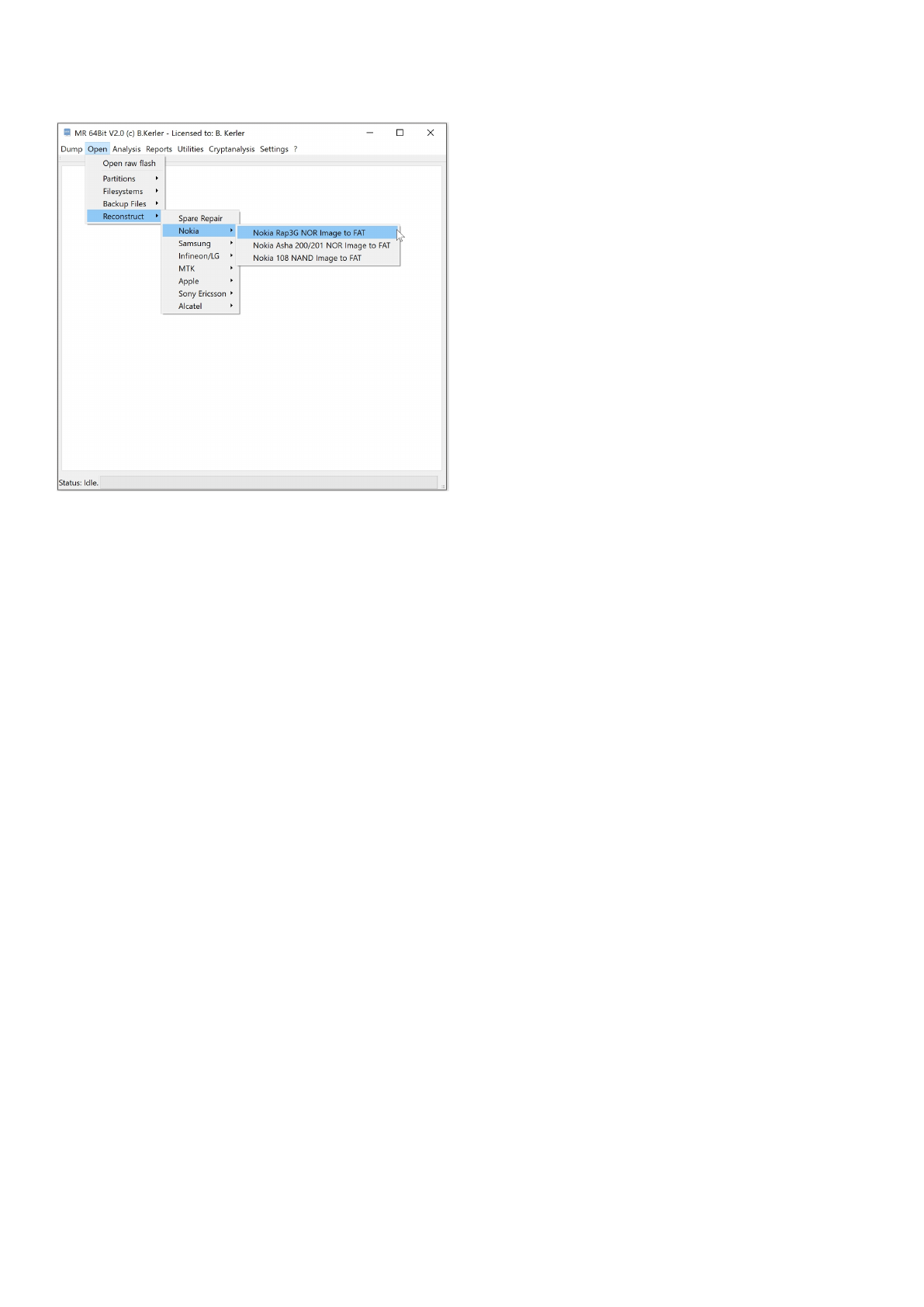
Nokia
The Nokia tools offer specific functions for reconstruction wear-leveling for Nokia devices.

Mobile Revelator 2.2.5
62 / 200
Nokia Rap3G NOR Image to FAT
This tool will extract the FAT partition from any Nokia Rap3G flash image.

Mobile Revelator 2.2.5
63 / 200
Nokia Asha 200/201 NOR Image to FAT
This tool will extract the FAT partition from any Nokia Asha 200/201 flash image.

Mobile Revelator 2.2.5
64 / 200
Nokia 108 NAND Image to FAT
This tool will extract the FAT partition from any Nokia 108 flash image.
Mobile Revelator 2.2.5
65 / 200
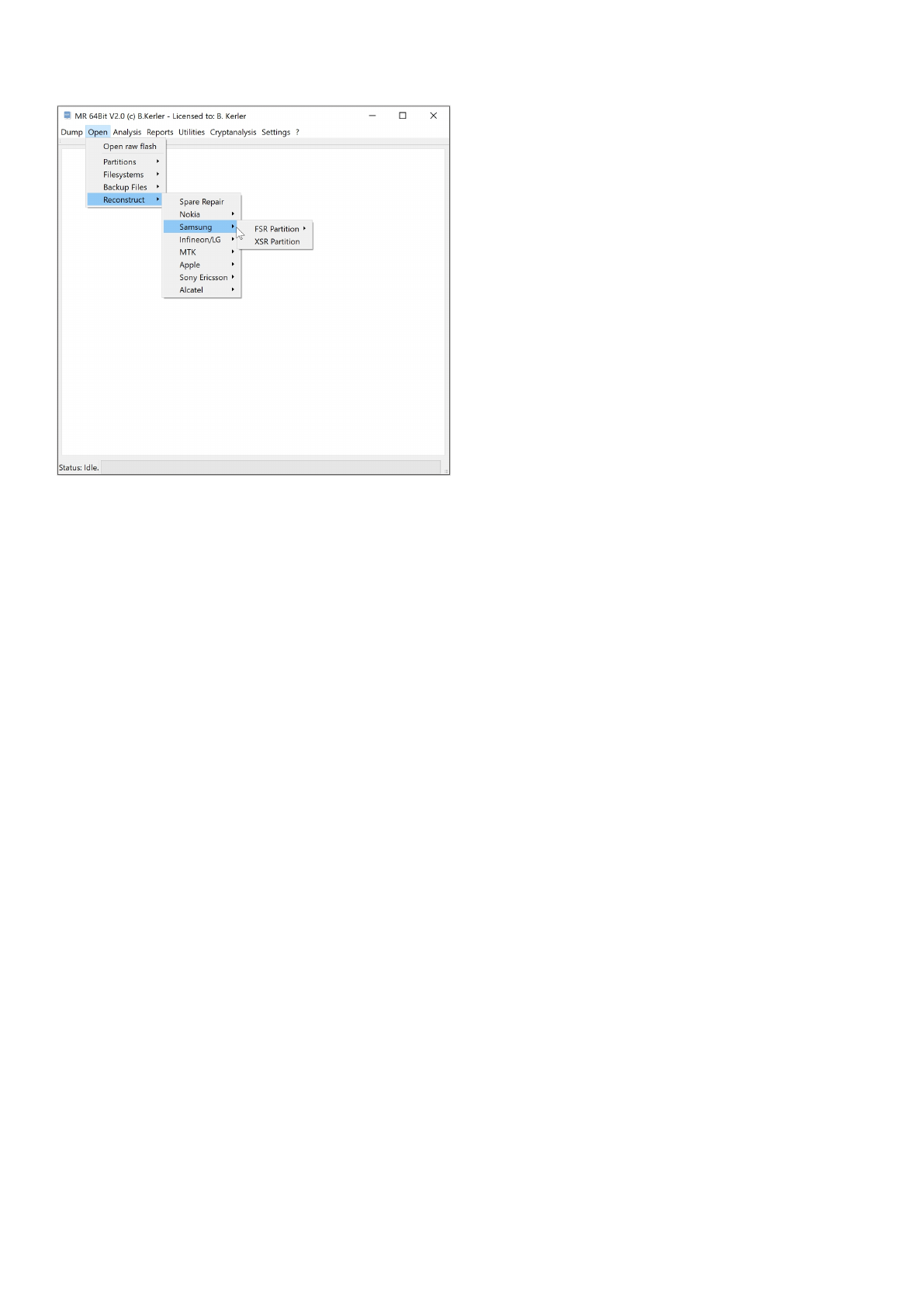
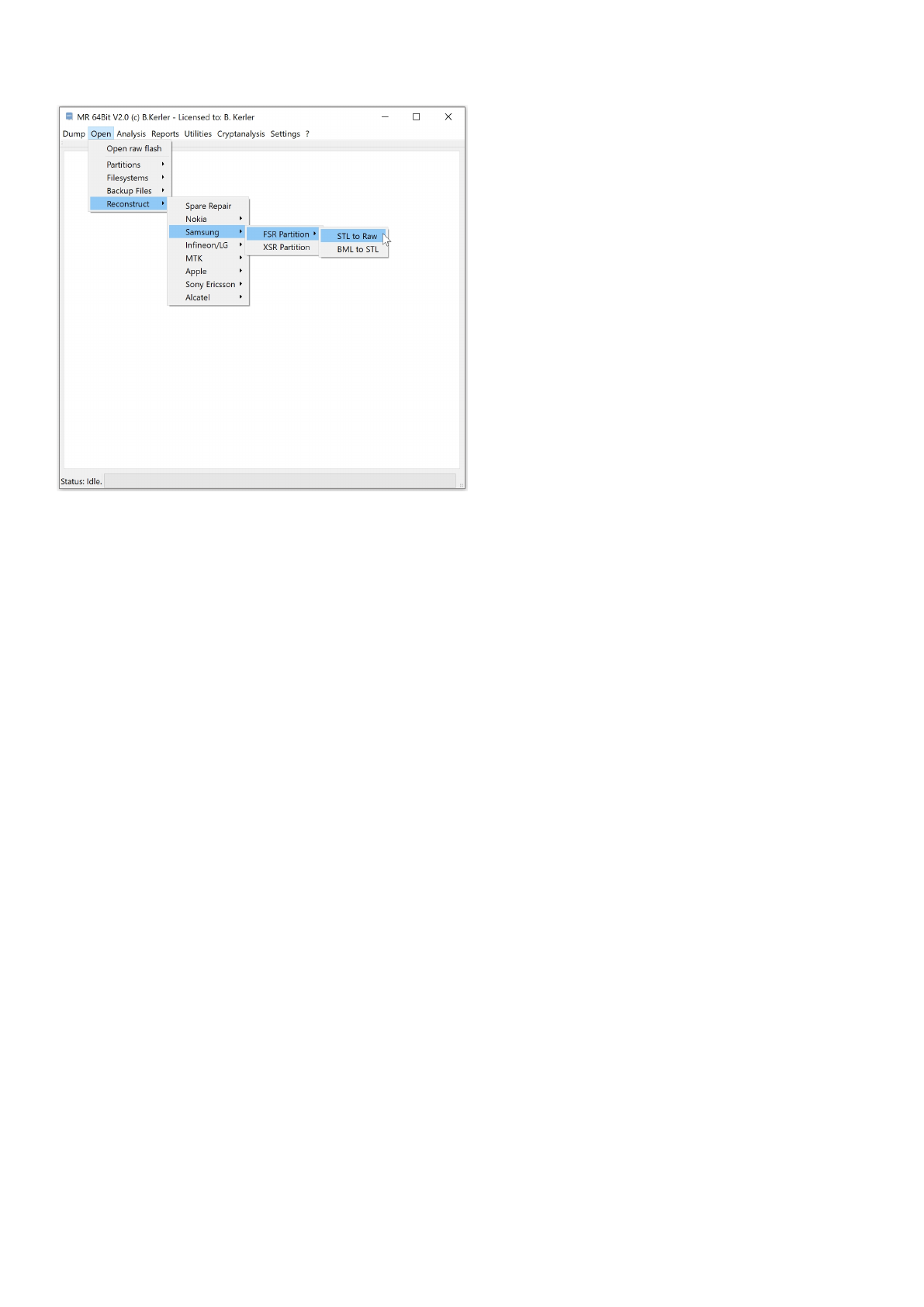
Samsung
The Samsung reconstruction tools will extract RAW Partitions, called BML and filesystems, called STL
from Wear-Leveling as well will reconstruct any partitions from XSR1/2/3.
Mobile Revelator 2.2.5
66 / 200
FSR Partition
The FSR partition is the RAW partition with Flash Transaction Layer by Samsung. BML is the main raw flash image
with flash transaction layers consisting of several STL Partitions.

Mobile Revelator 2.2.5
67 / 200

Mobile Revelator 2.2.5
68 / 200
STL to Raw
This tool will extract any partition from wearleveling STL data flash image.

Mobile Revelator 2.2.5
69 / 200

Mobile Revelator 2.2.5
70 / 200
BML to STL
This tool will extract any STL partition from wearleveling BML data flash image.

Mobile Revelator 2.2.5
71 / 200
XSR Partition
This tool will extract any partition from wearleveling XSR1/2/3 data flash image. It will automatically detect
block and pagesize needed for extraction. In order to extract XSR partition data, spare data has to be at the end
of each page.

Mobile Revelator 2.2.5
72 / 200
Infineon/LG
The Infineon tools offer specific functions for reconstruction wear-leveling for infineon devices.
LG GS290N NOR
This tool will extract any partition from wearleveling LG GS290N NOR data flash image.
Mobile Revelator 2.2.5
73 / 200
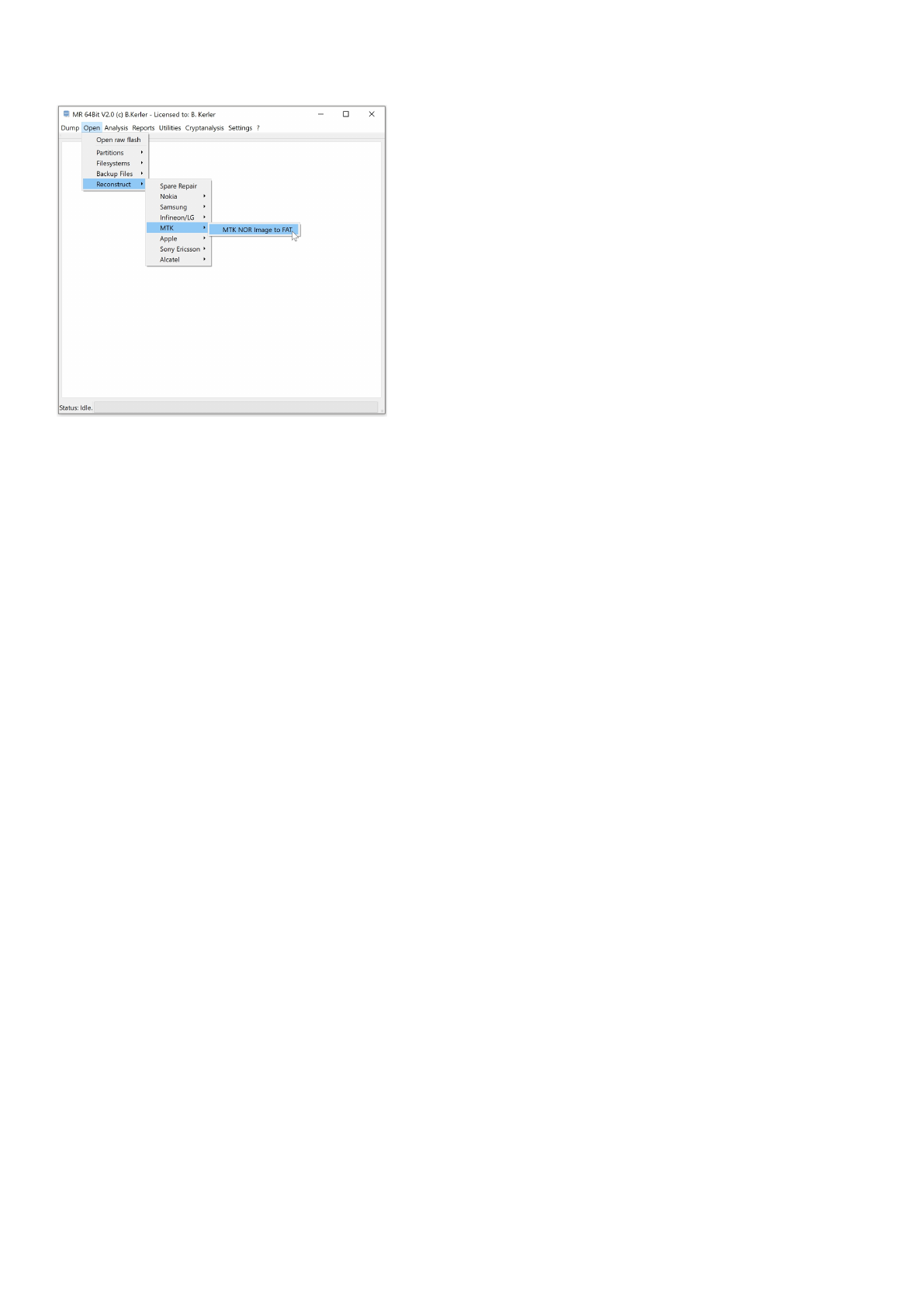
MTK
The MTK tools offer specific functions for reconstruction wear-leveling for MTK devices.

Mobile Revelator 2.2.5
74 / 200
MTK NOR Image to FAT
This tool will extract any partition from wearleveling MTK NOR flash image.
Mobile Revelator 2.2.5
75 / 200
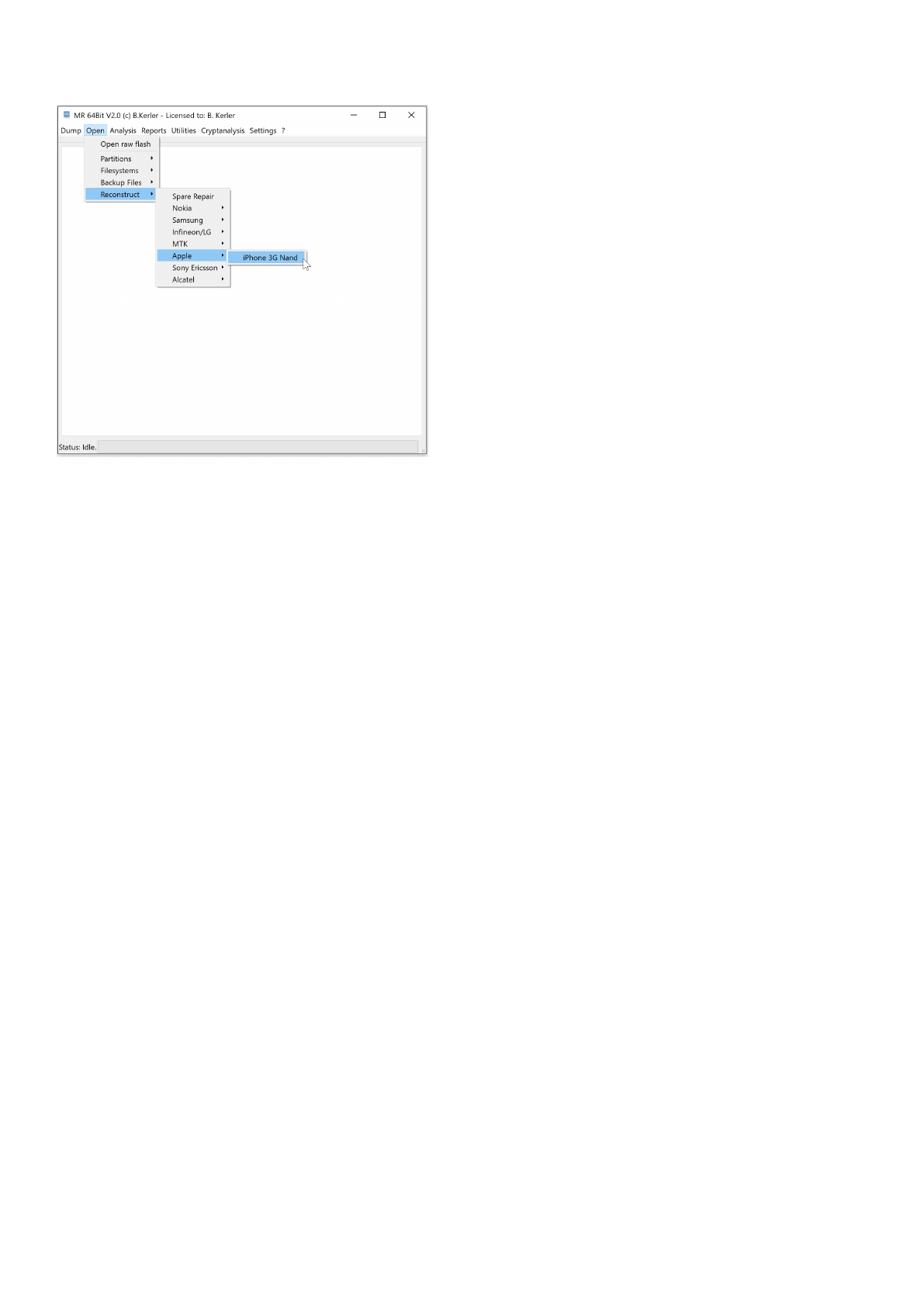
Apple
The Apple tools offer specific functions for reconstruction wear-leveling for Apple devices.

Mobile Revelator 2.2.5
76 / 200
iPhone 3G Nand
This tool will extract any partition from wearleveling iPhone 3G nand data flash image. Spare data is needed for
reconstruction
and should be at the end of each page.
Mobile Revelator 2.2.5
77 / 200
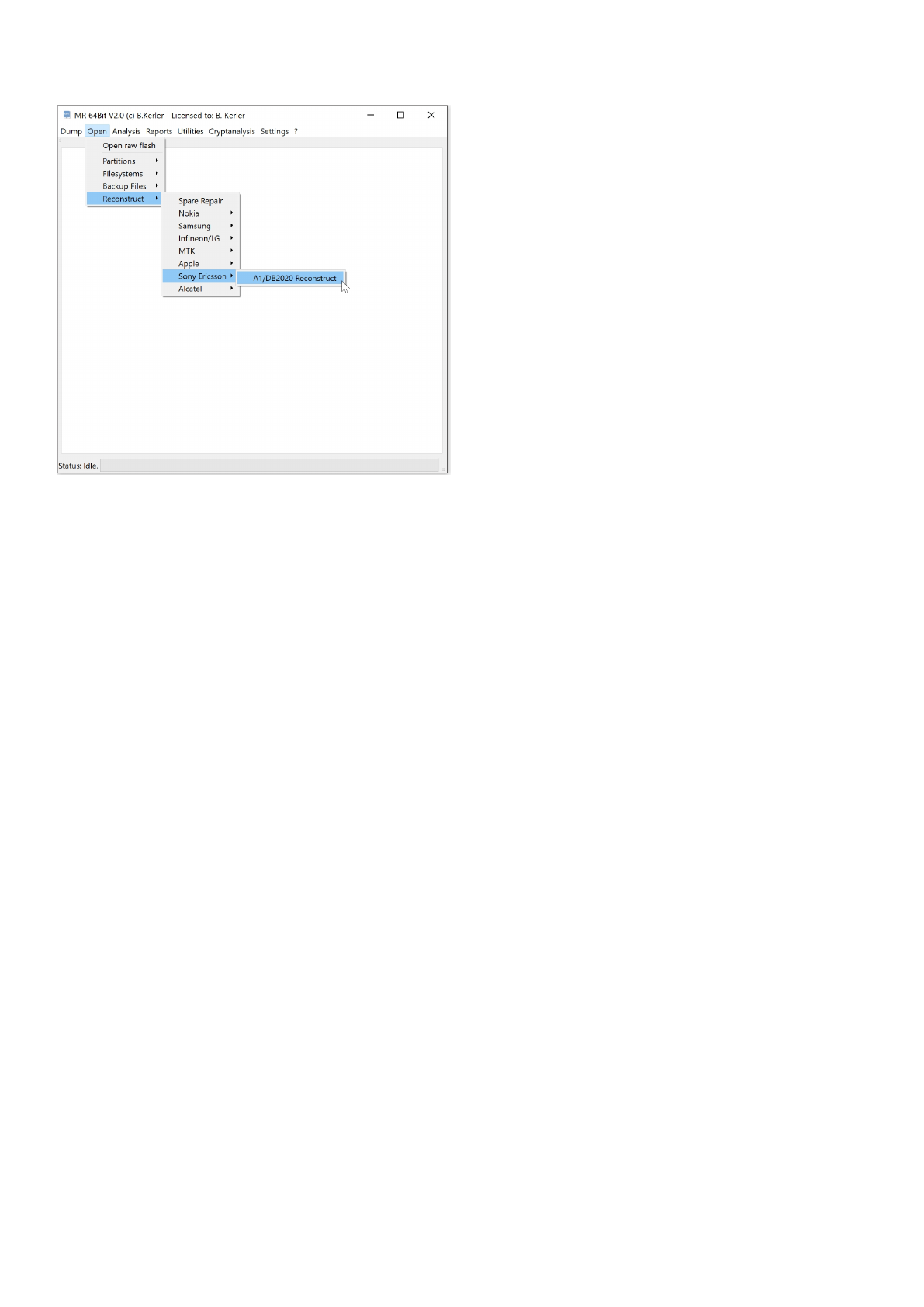
Sony Ericsson
The Sony Ericsson tools offer specific functions for reconstruction wear-leveling for Sony Ericsson devices.

Mobile Revelator 2.2.5
78 / 200
A1/DB2020 Reconstruct
This tool will extract any partition from wearleveling A1/DB2020 nand data flash image. Spare data is needed for
reconstruction
and should be at the end of each page.
Mobile Revelator 2.2.5
79 / 200
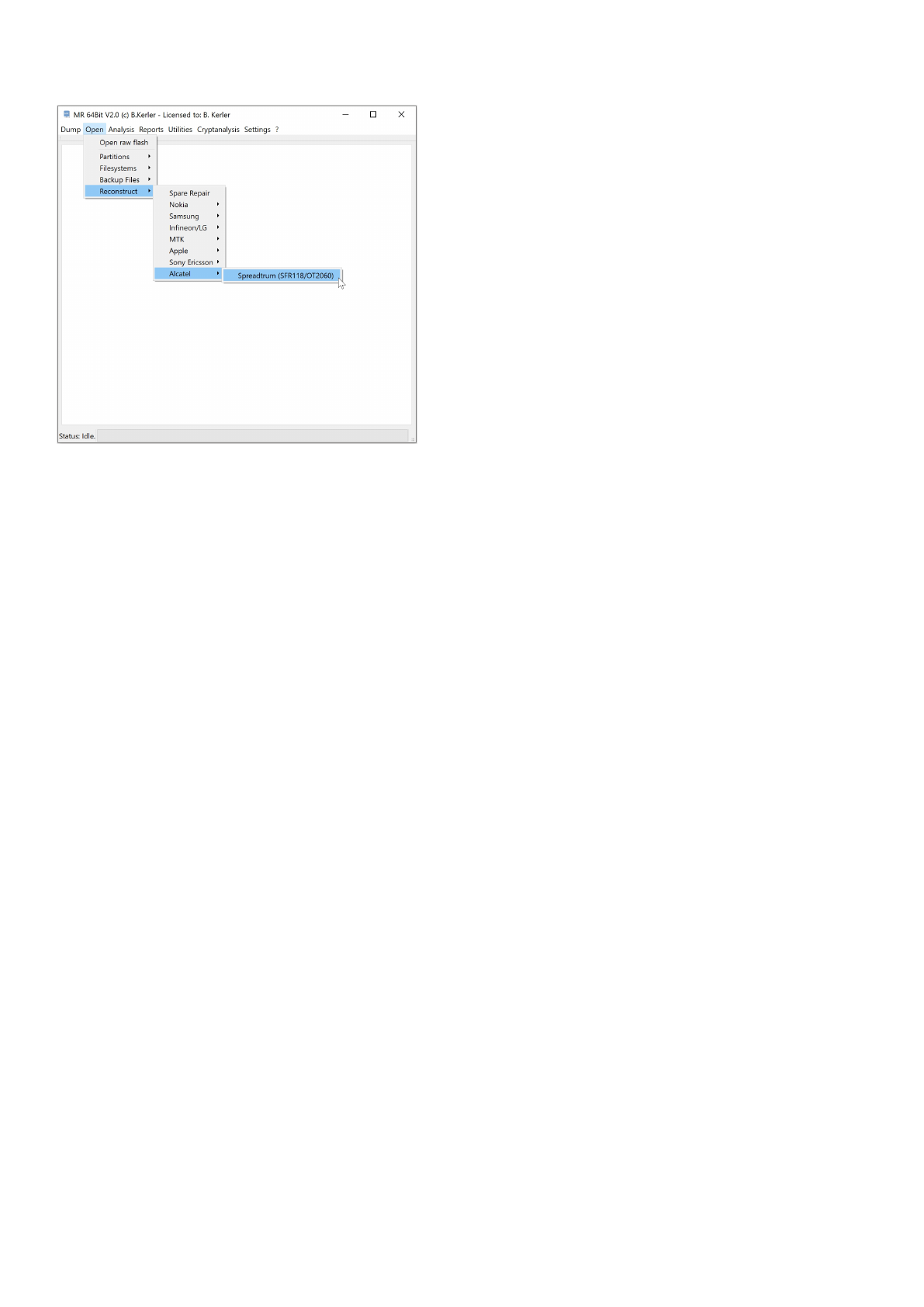
Alcatel
The Alcatel tools offer specific functions for reconstruction wear-leveling for Alcatel devices.

Mobile Revelator 2.2.5
80 / 200
Spreadtrum (SFR118/OT2060)
This tool will extract any partition from wearleveling Alcatel device with Spreadtrum chipset data flash image.

Mobile Revelator 2.2.5
81 / 200
Analysis
The Analyse menu contains several tools for interpretation of various data formats, such as databases, xml files
but also has great tools for carving information from raw images or files.
Mobile Revelator 2.2.5
82 / 200
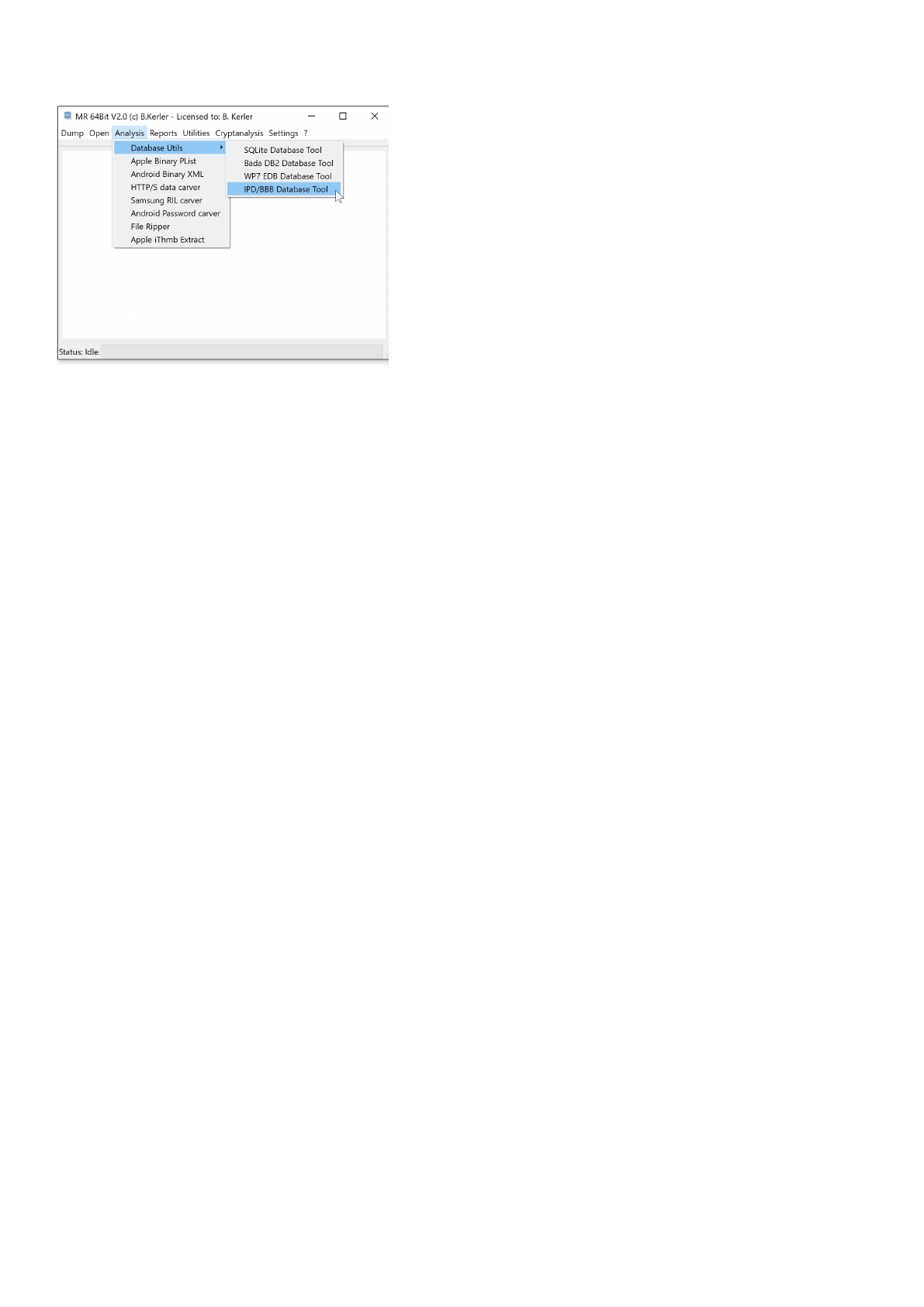
Database Utils
The SQLite Database Tools is able to open generic SQLite3 databases and enables
to reconstruct wal (Write Ahead Logs), Journals and deleted SQLite entries from free pages.
Mobile Revelator 2.2.5
83 / 200
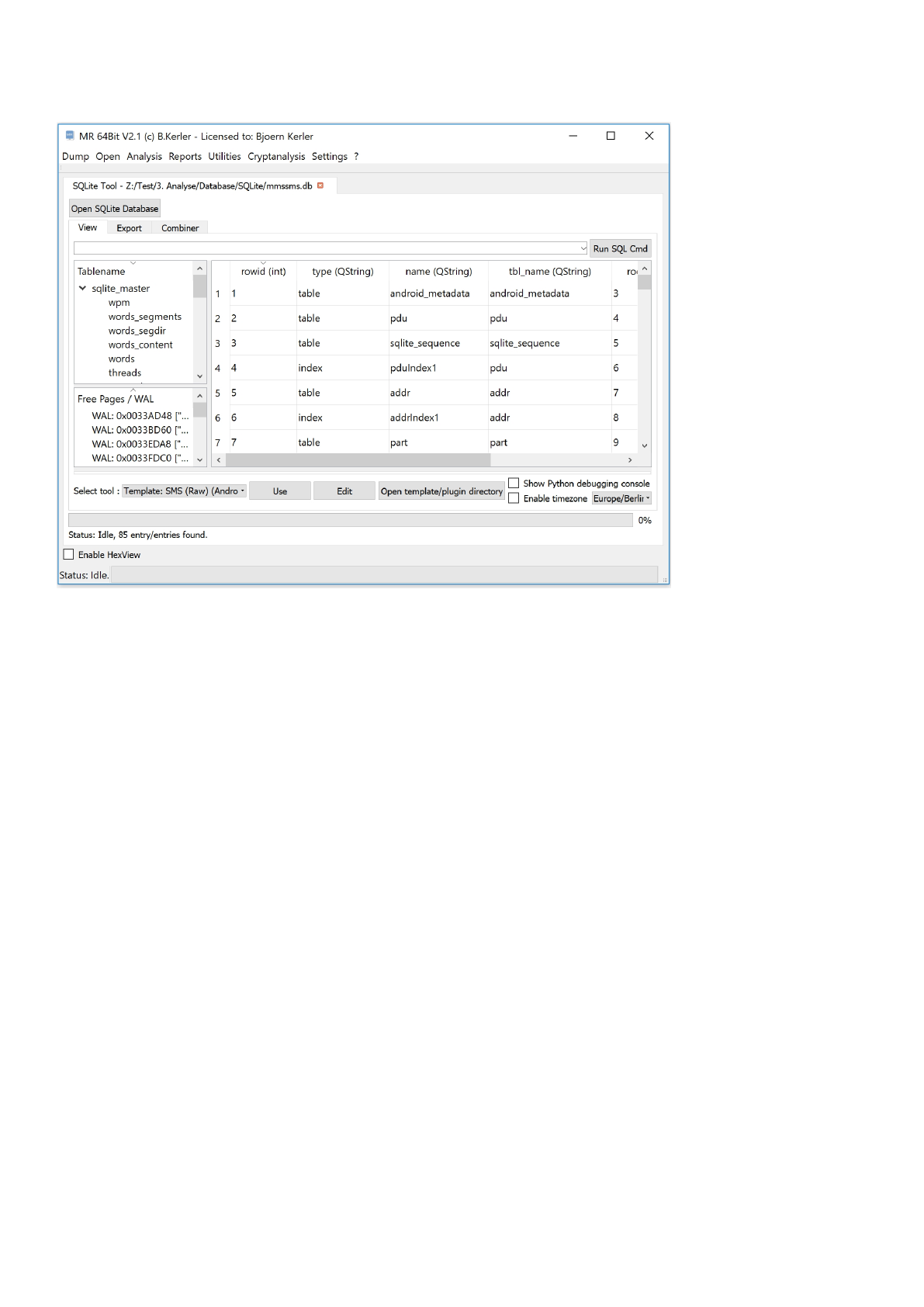
SQLite Database Tool
The sqlite database tool lets you open sqlite database, recover deleted entries from free pages, journal and write-ahead-
logs (WAL) and lets you convert timestamps in a user-friendly way. Moreover, you have the option to export the modified
or current table to a xlsx, csv or xml-file.
Mobile Revelator 2.2.5
84 / 200
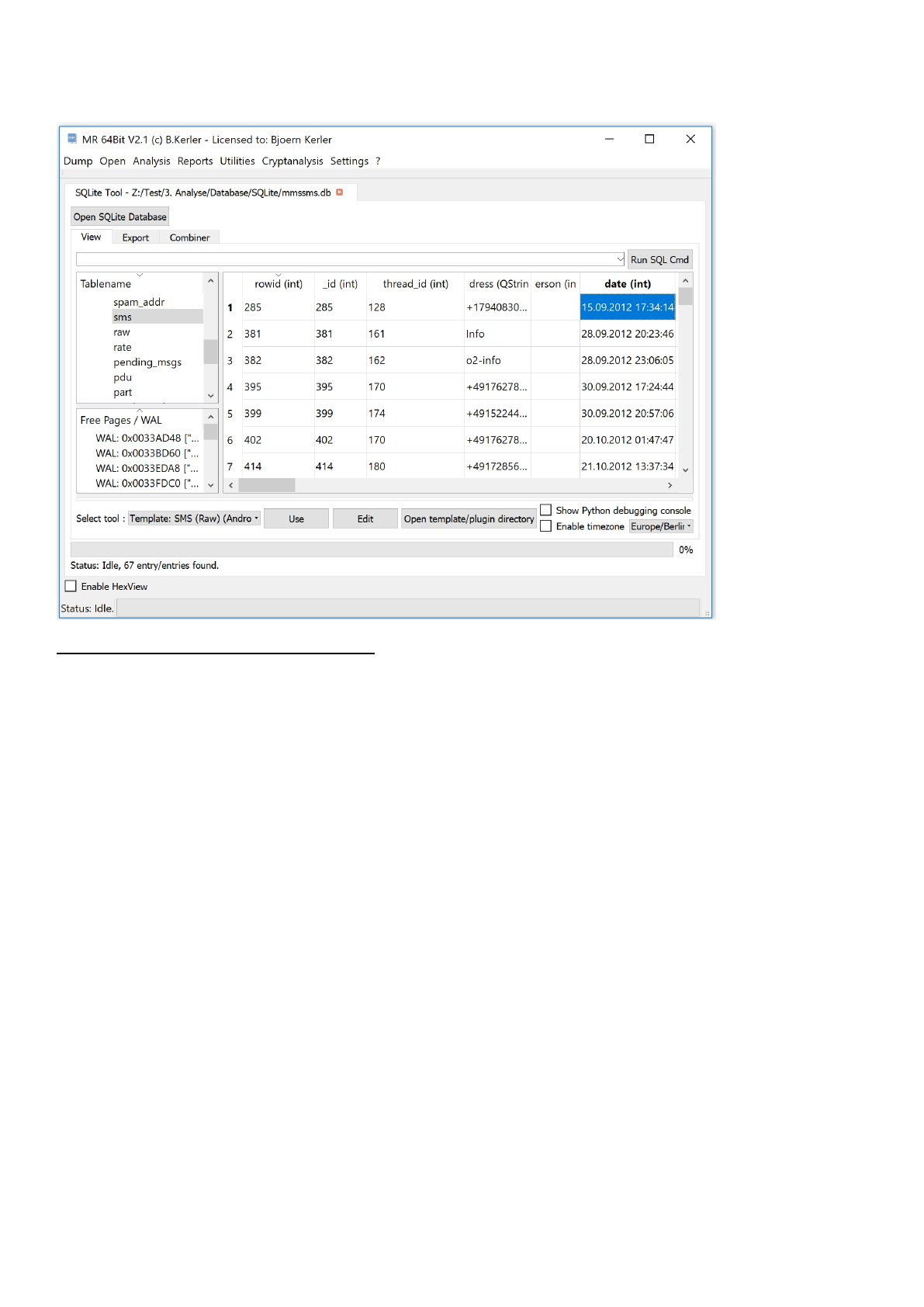
View
The windows is split into three different regions :
On the upper left side, you see the current tables from the database.
The lower left side, you see any deleted or active transactions according to free pages, journals or write-ahead log.
Selecting an entry from either the upper or lower left side, its content is being displayed on the right side.
Using Ctrl-F you can search for any string, clicking on an entry in the result tab will show the selected entry in the table.
Using Ctrl-T if an entry is selected will automatically try to convert the integer value to a readable date / timestamp value
for the
whole column. Converted timestamps via Ctrl-T conversion can also be converted to a local time by choosing the location
and by enabling the
"Enable timezone" checkbox.

Mobile Revelator 2.2.5
85 / 200
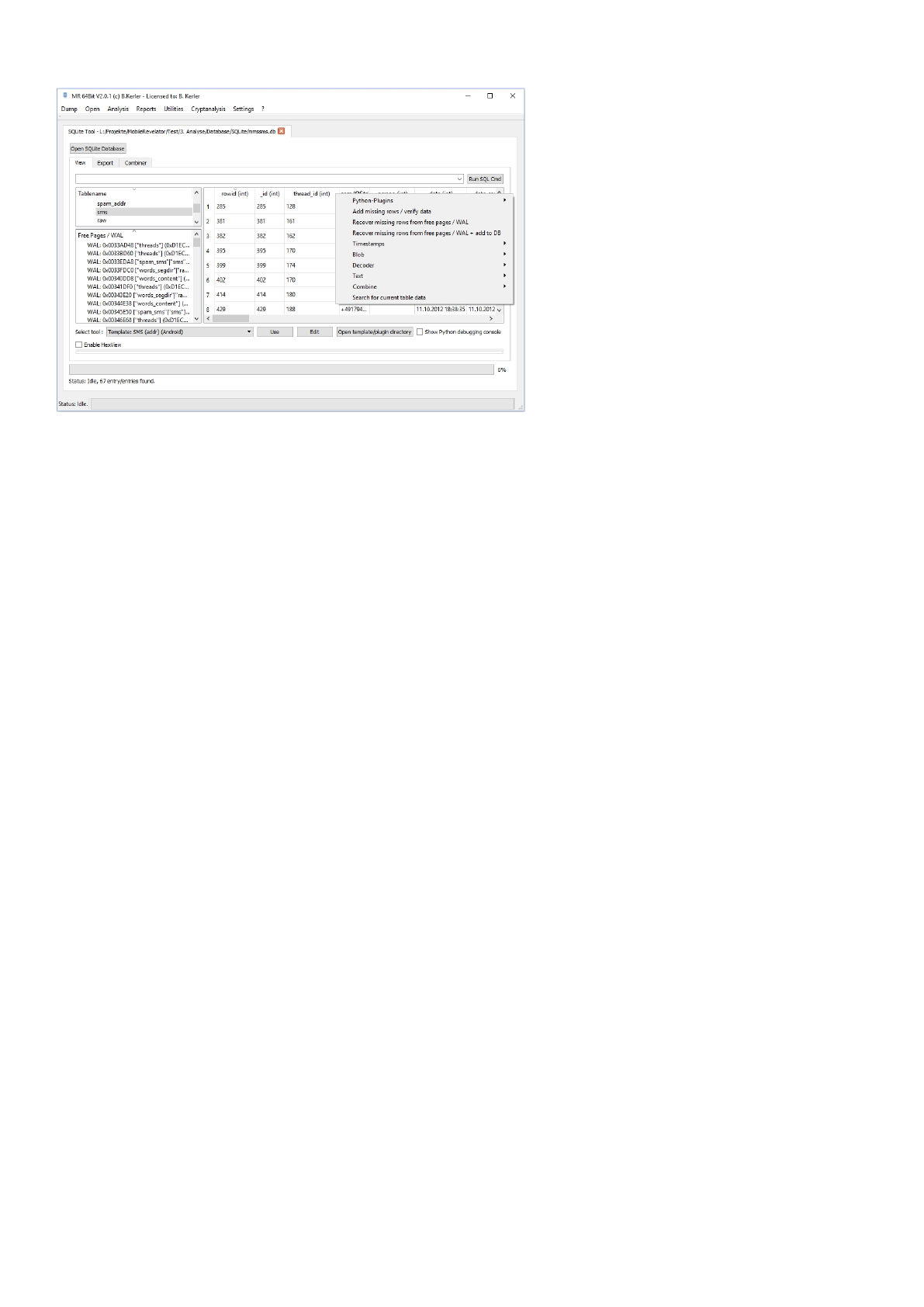
Mobile Revelator 2.2.5
86 / 200
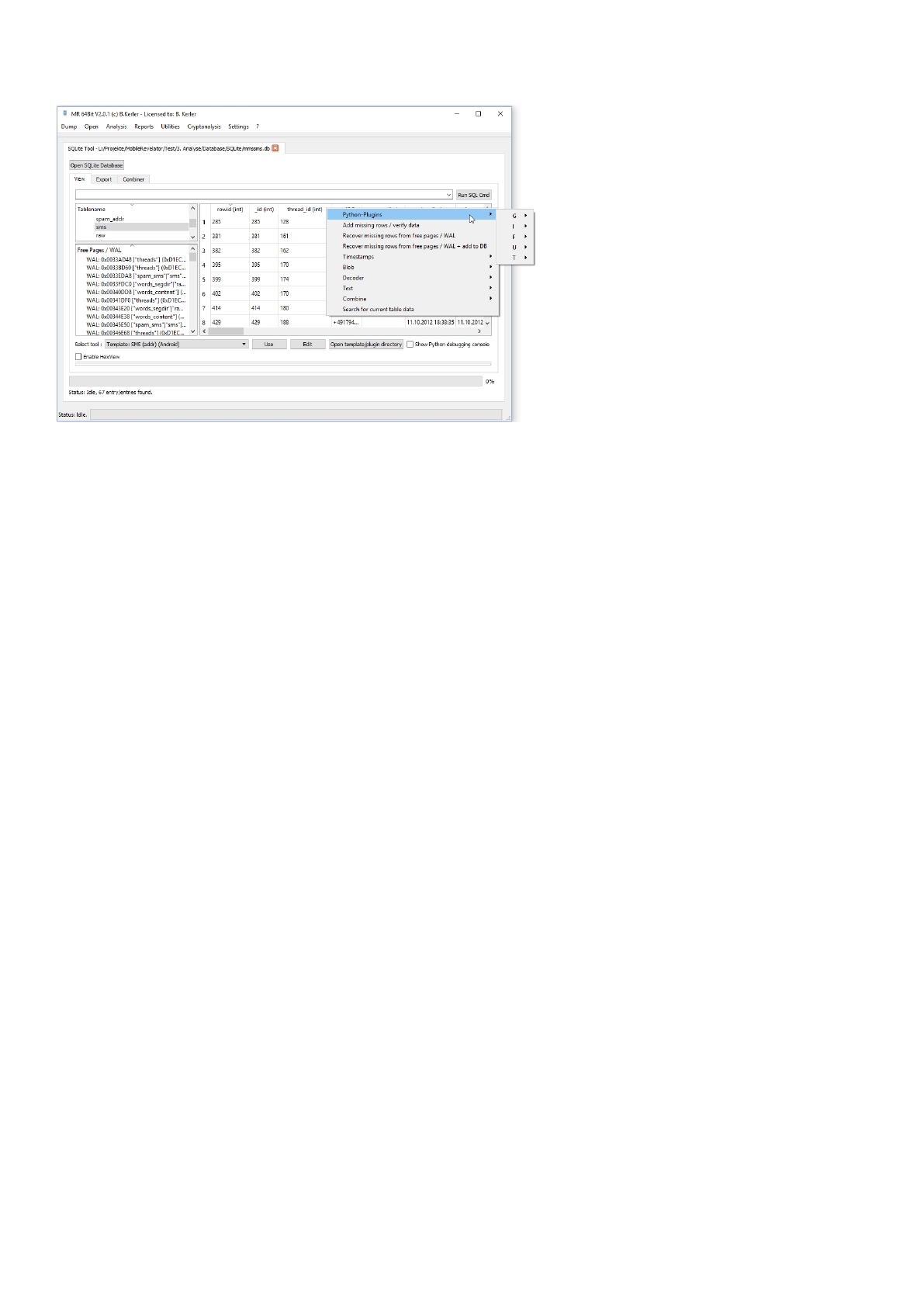
Right-Click-Menu
Mobile Revelator 2.2.5
87 / 200
Python-Plugins
This menu lets you run custom python plugins.
Mobile Revelator 2.2.5
88 / 200
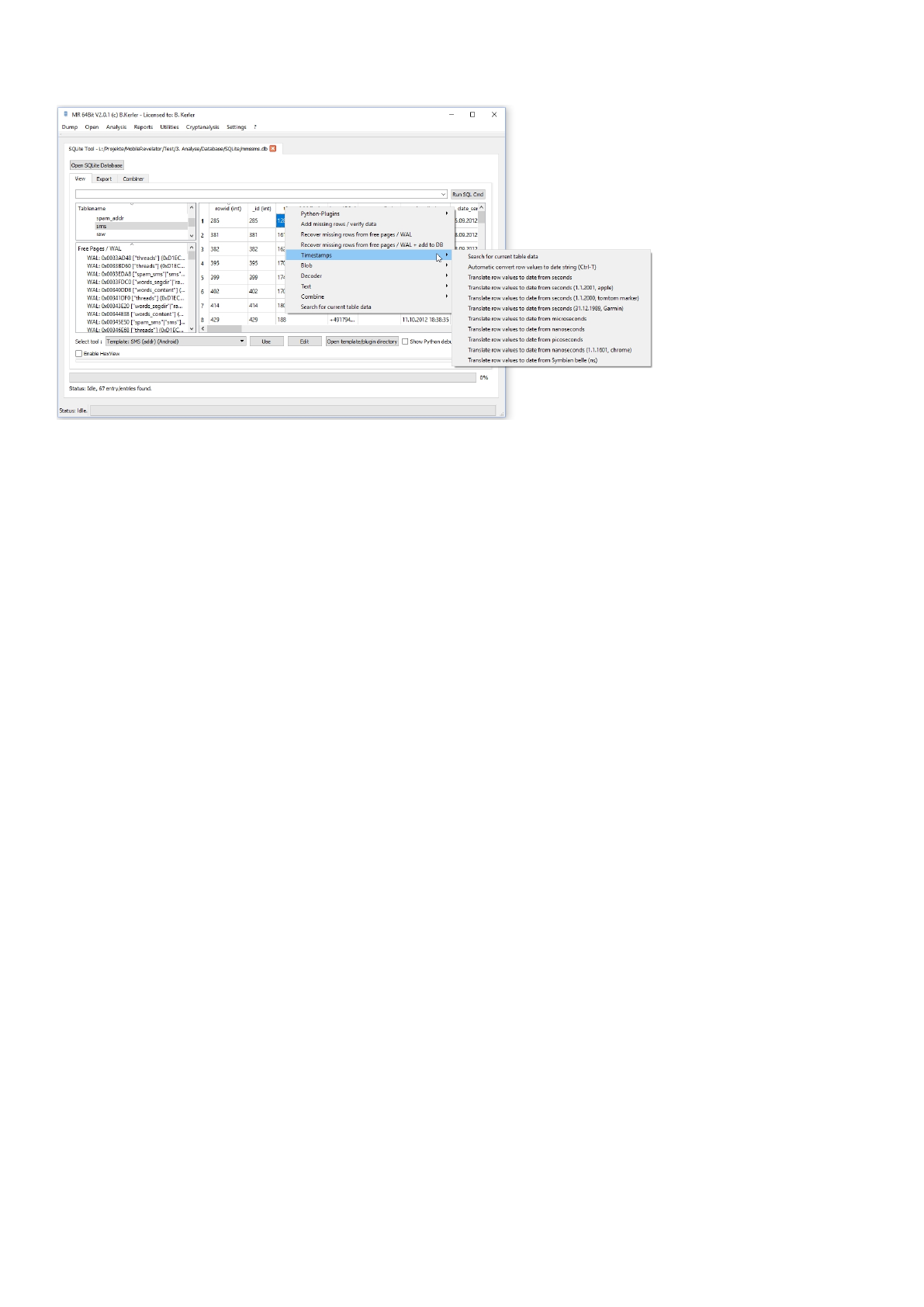
Timestamps
There are two ways to convert current column integer values to a time stamp :
First one, try the automatic algorithm : select any column to be converted and press CTRL-T. If the conversion fails or
seems to be wrong, choose the second one, by right clicking into the field, in the menu select "Timestamps" and the the
appropriate timestamp. If the conversion doesn't seem to be fine, just reselect the table on the left side and the table will be
reset, allowing you to reselect another timestamp method.
Mobile Revelator 2.2.5
89 / 200
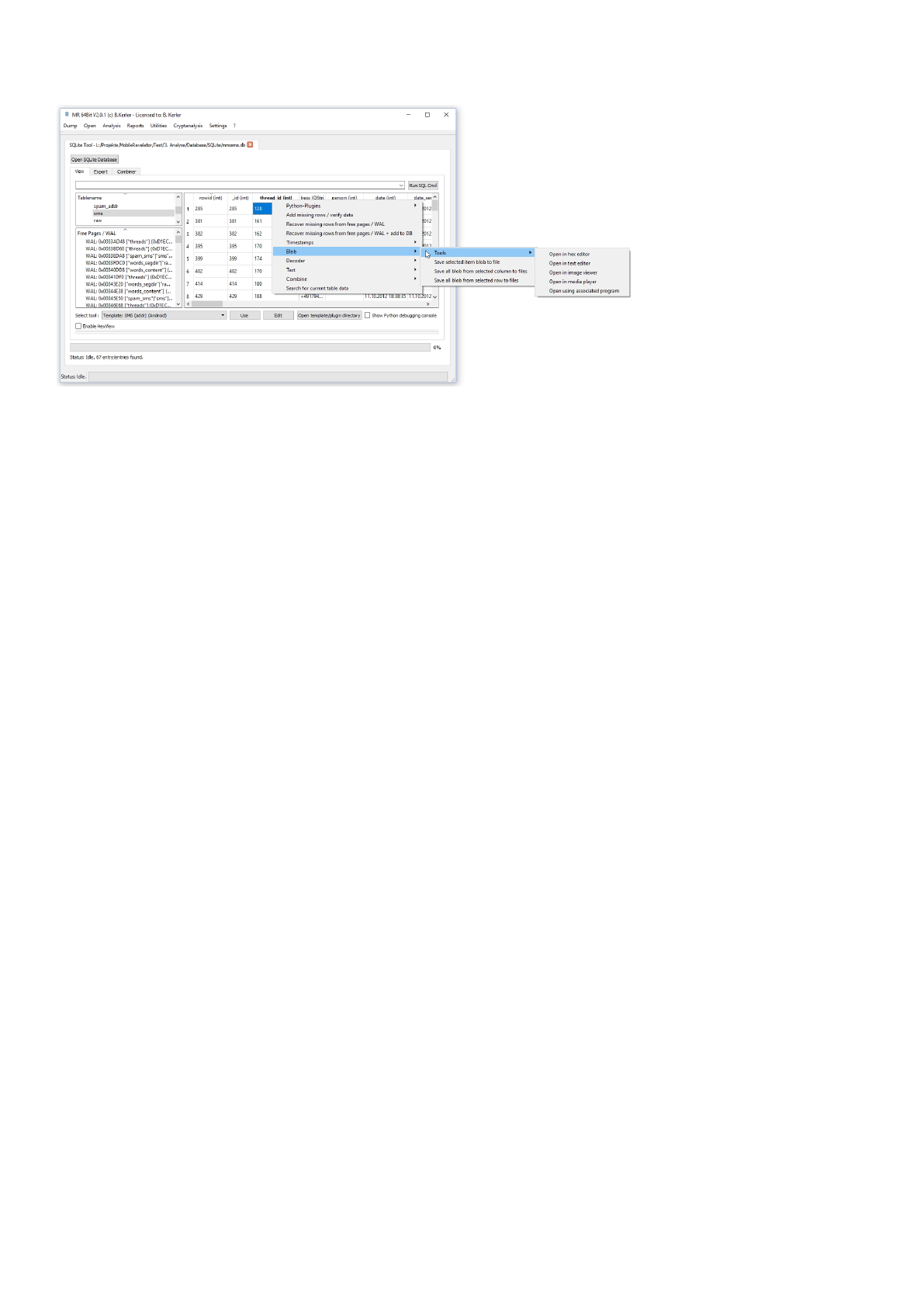
Blob
The blob menu lets you either use your favorite tool for viewing the data or save either the current data field or selected
column or row data field to a file.
Mobile Revelator 2.2.5
90 / 200
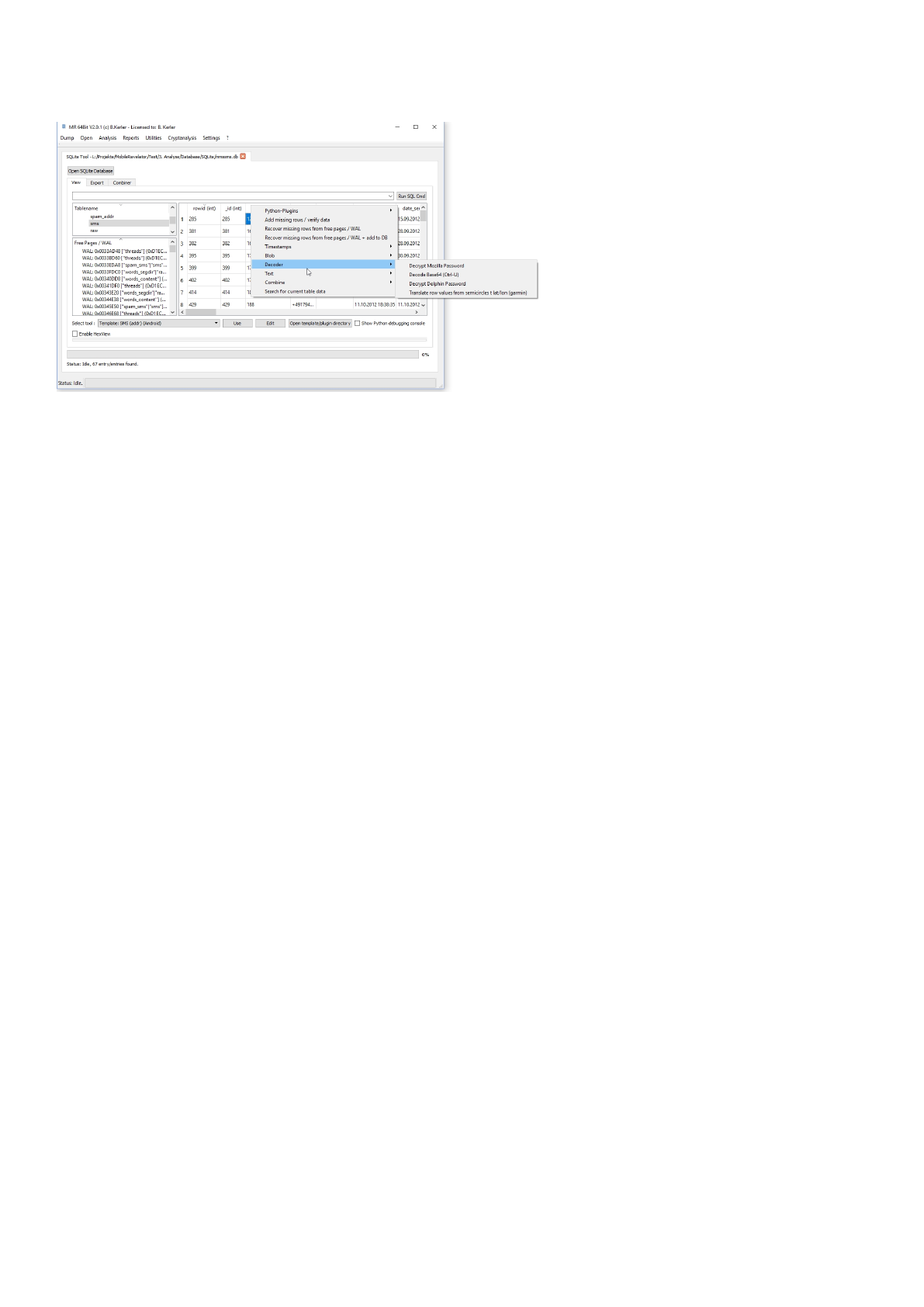
Decoder
The decoder menu has functionality to convert garmin integer values to latitude/longitude, but will also allow to decrypt
saved encrypted key4.db mozilla passwords.
Mobile Revelator 2.2.5
91 / 200
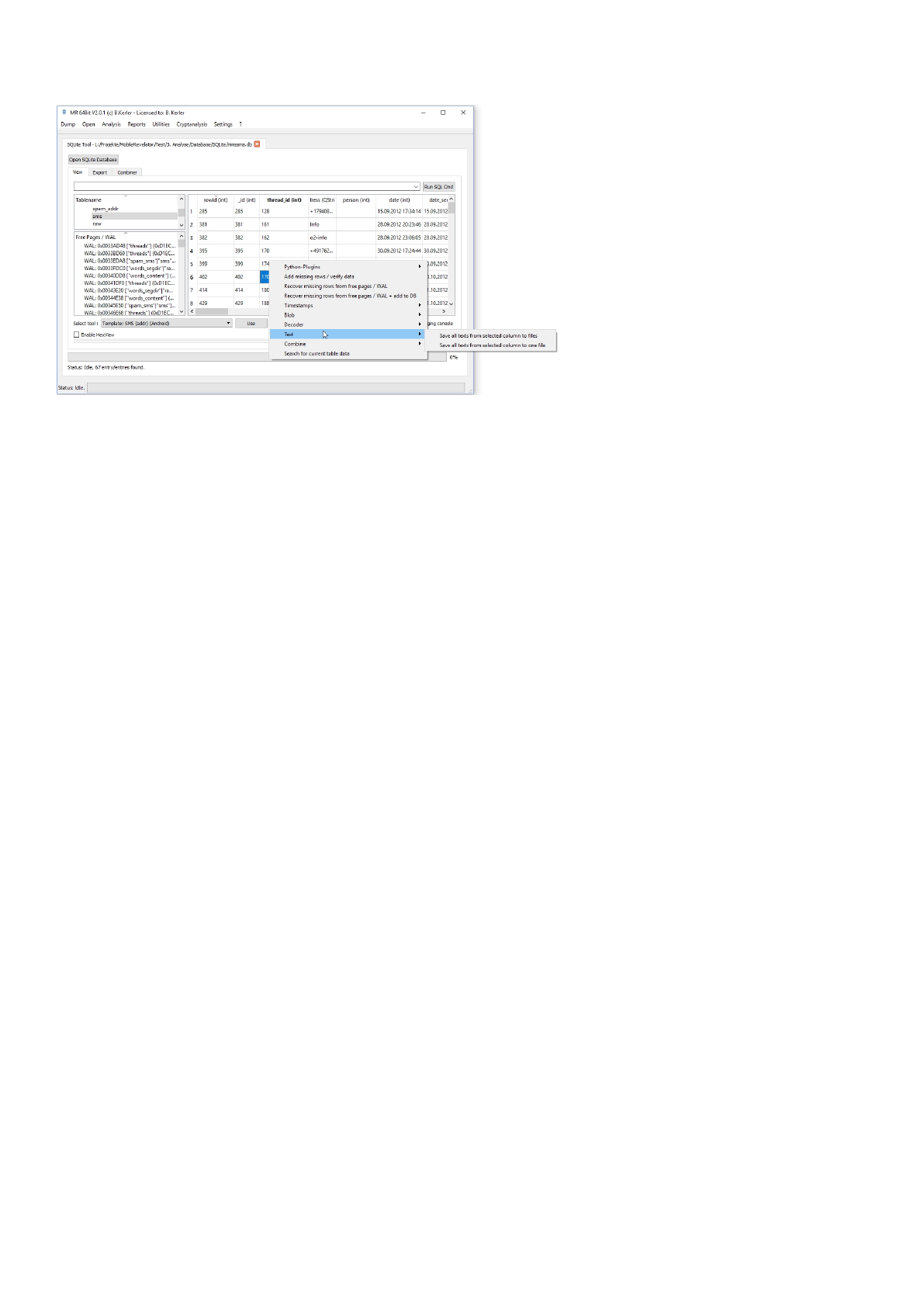
Text
The text menu functions will extract all text within current selected column either as a file for each line or as multiple lines in
one file.

Mobile Revelator 2.2.5
92 / 200
Combine
The combine menu lets you combine database entries. Just click into the column to be combined and then select the
master index first, followed by child indices (columns) you want to combine from different tables.

Mobile Revelator 2.2.5
93 / 200
Export
You may export the current table view either as a xlsx, xml or csv file or even the complete database (without changes
being added). If any data columns may exist, the "Export current table to xls (as text only)" function will just export unicode
text but will filter any data bytes.
Mobile Revelator 2.2.5
94 / 200
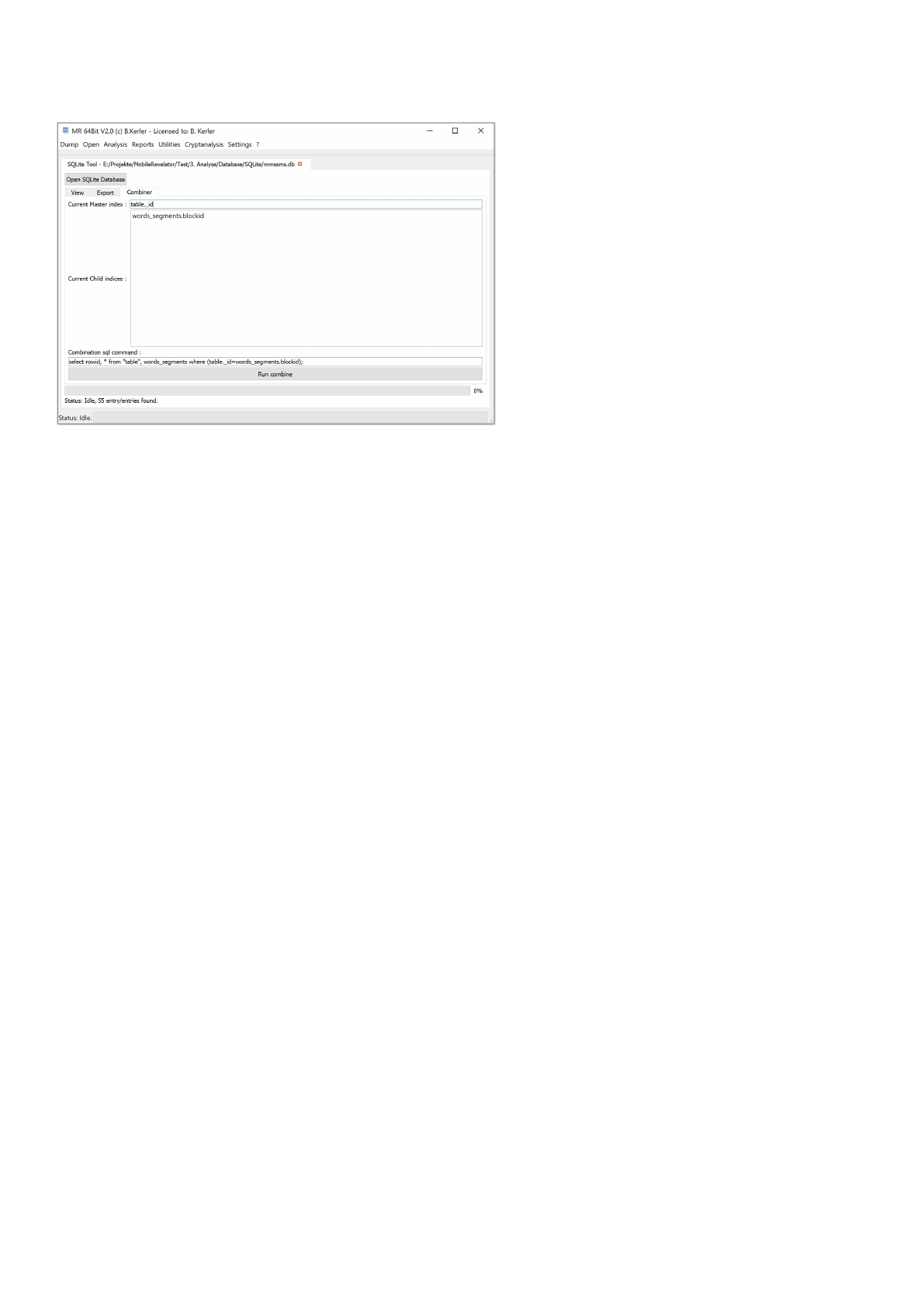
Combine
Once columns have been selected in the table view as main and child indexes, they will be displayed in the combine tab.
You may delete single indices by selecting and pressing the del-key on the keyboard. Pressing the "Run combine" button
will execute the sql query being displayed in the "Combination sql command" field.
Mobile Revelator 2.2.5
95 / 200
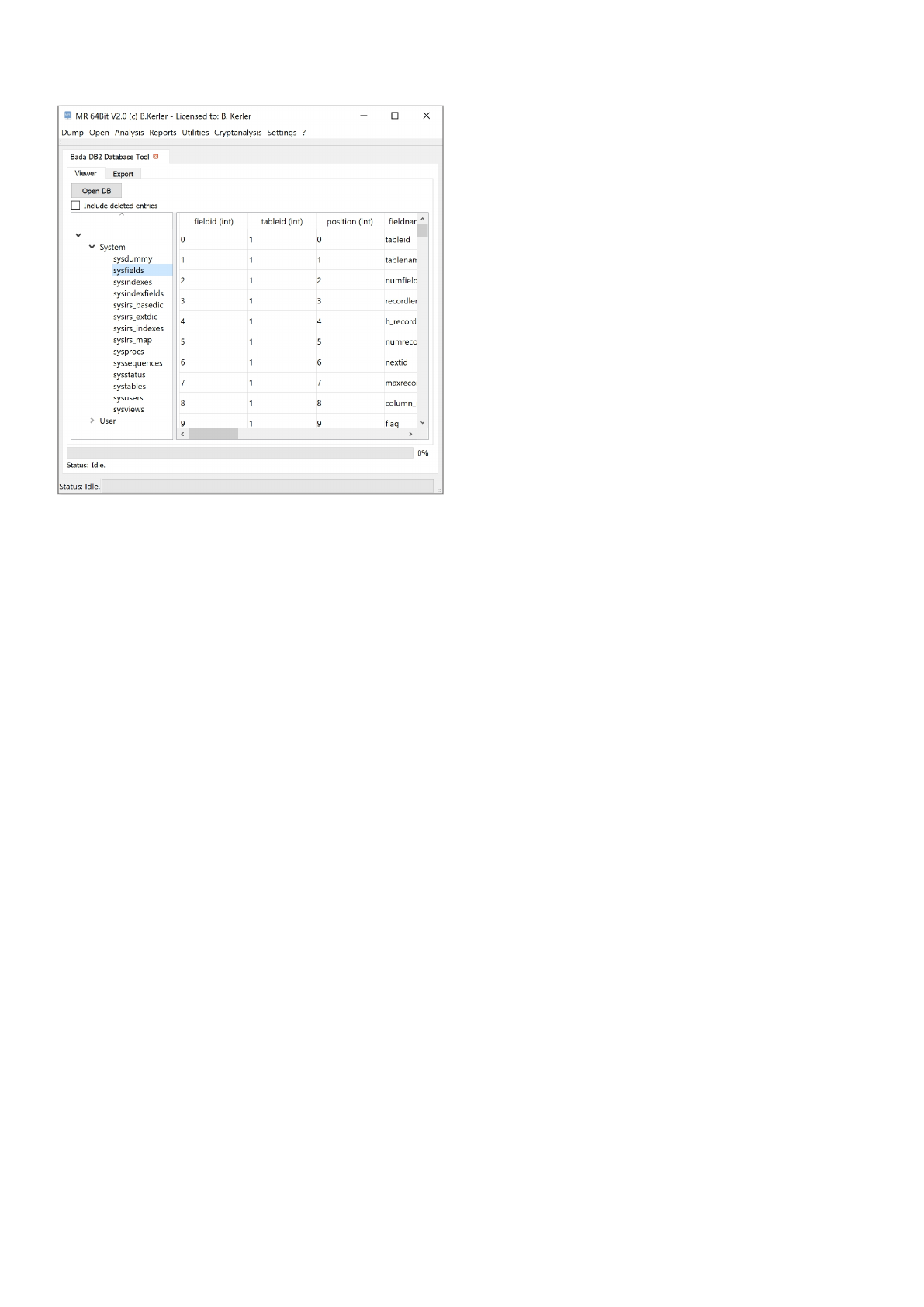
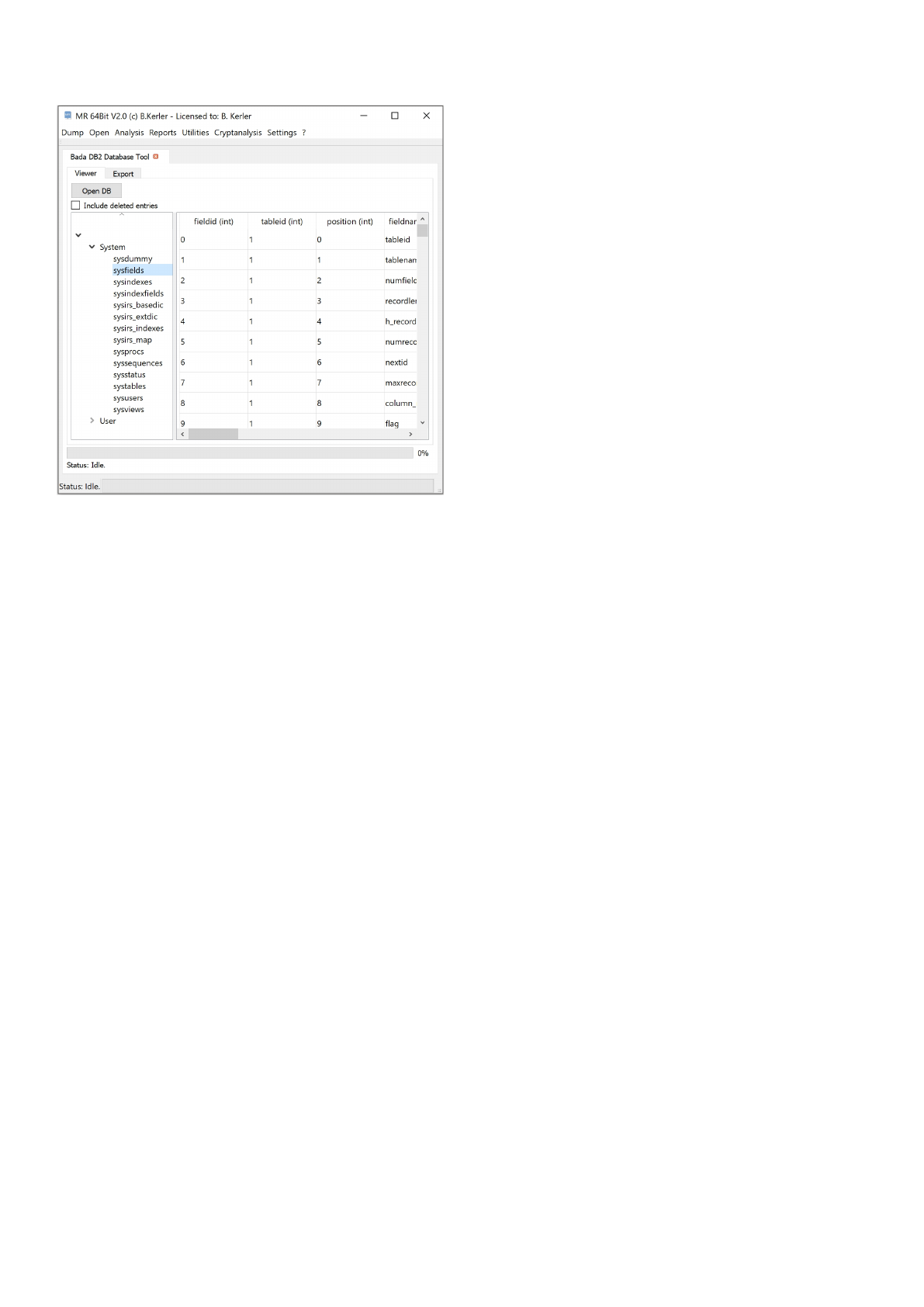
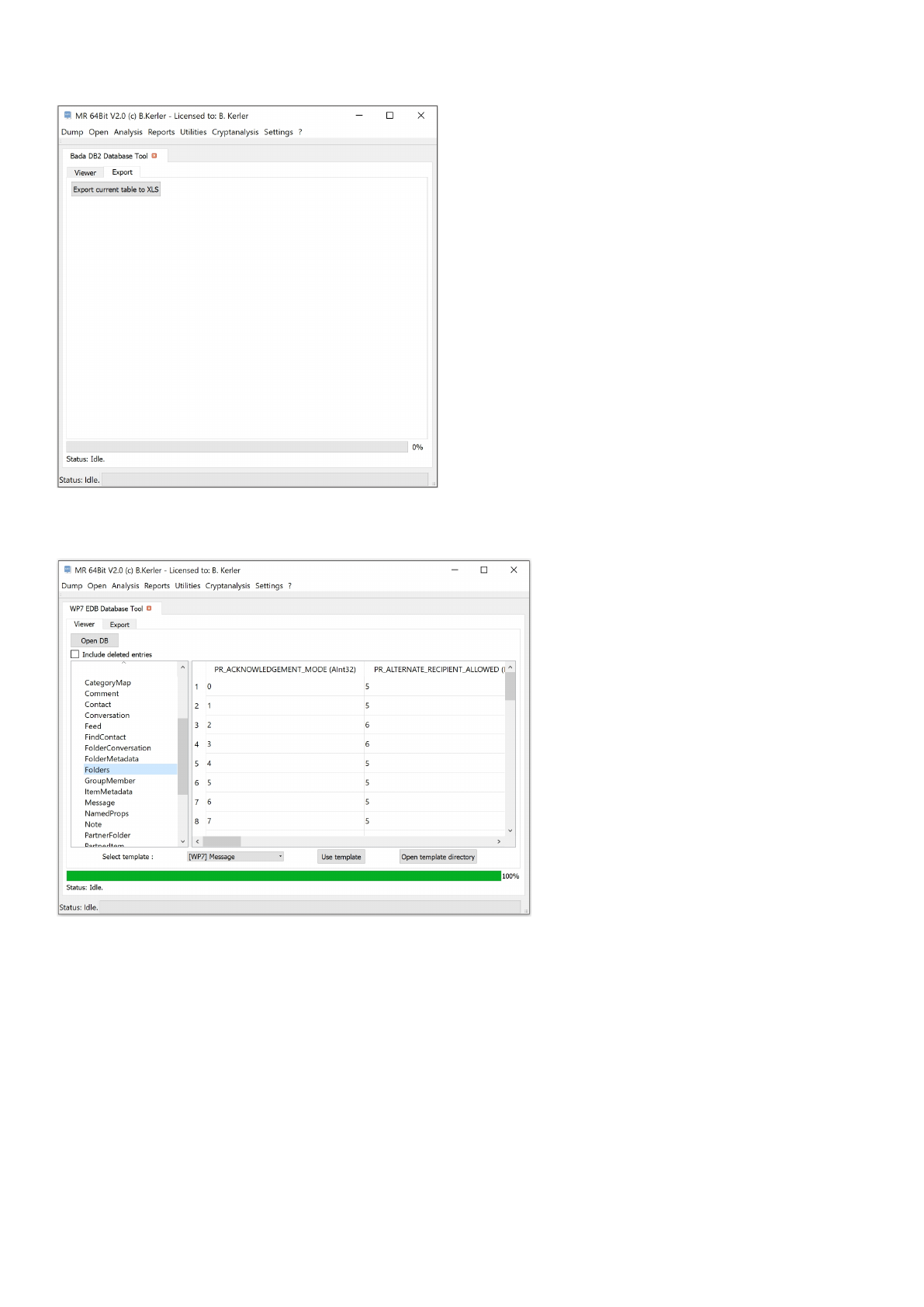
Bada DB2 Database Tool
The bada DB2 database tool is able to open and read Samsung DB2 and EMware databases (mainly to be found on
Samsung Bada based devices at /DB2/phonedb.00).
Mobile Revelator 2.2.5
96 / 200
View
You may select "Include deleted entries" to show deleted entries while clicking at the Index at the left side.

Mobile Revelator 2.2.5
97 / 200
Mobile Revelator 2.2.5
98 / 200
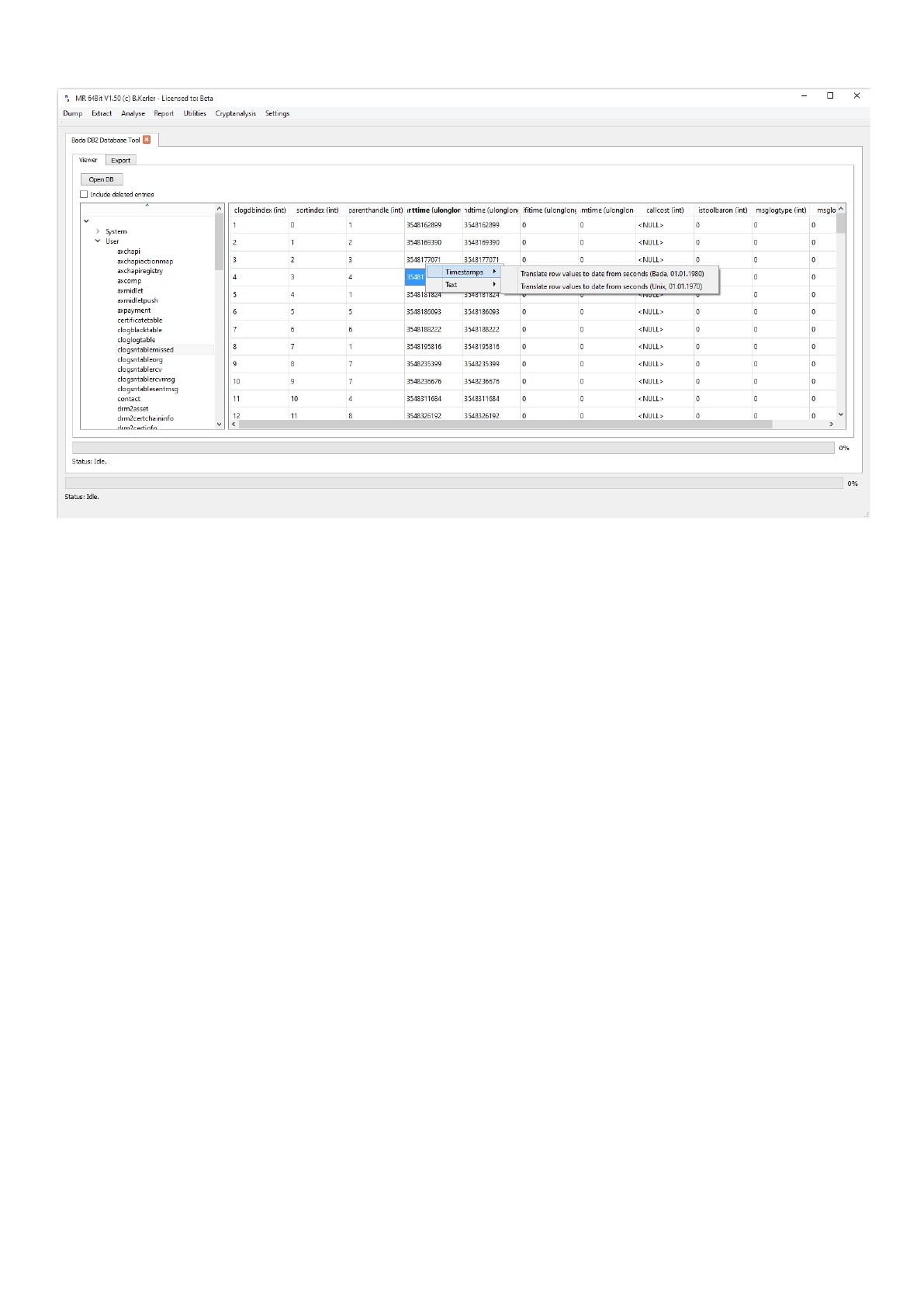
Right-Click-Menu
Mobile Revelator 2.2.5
99 / 200
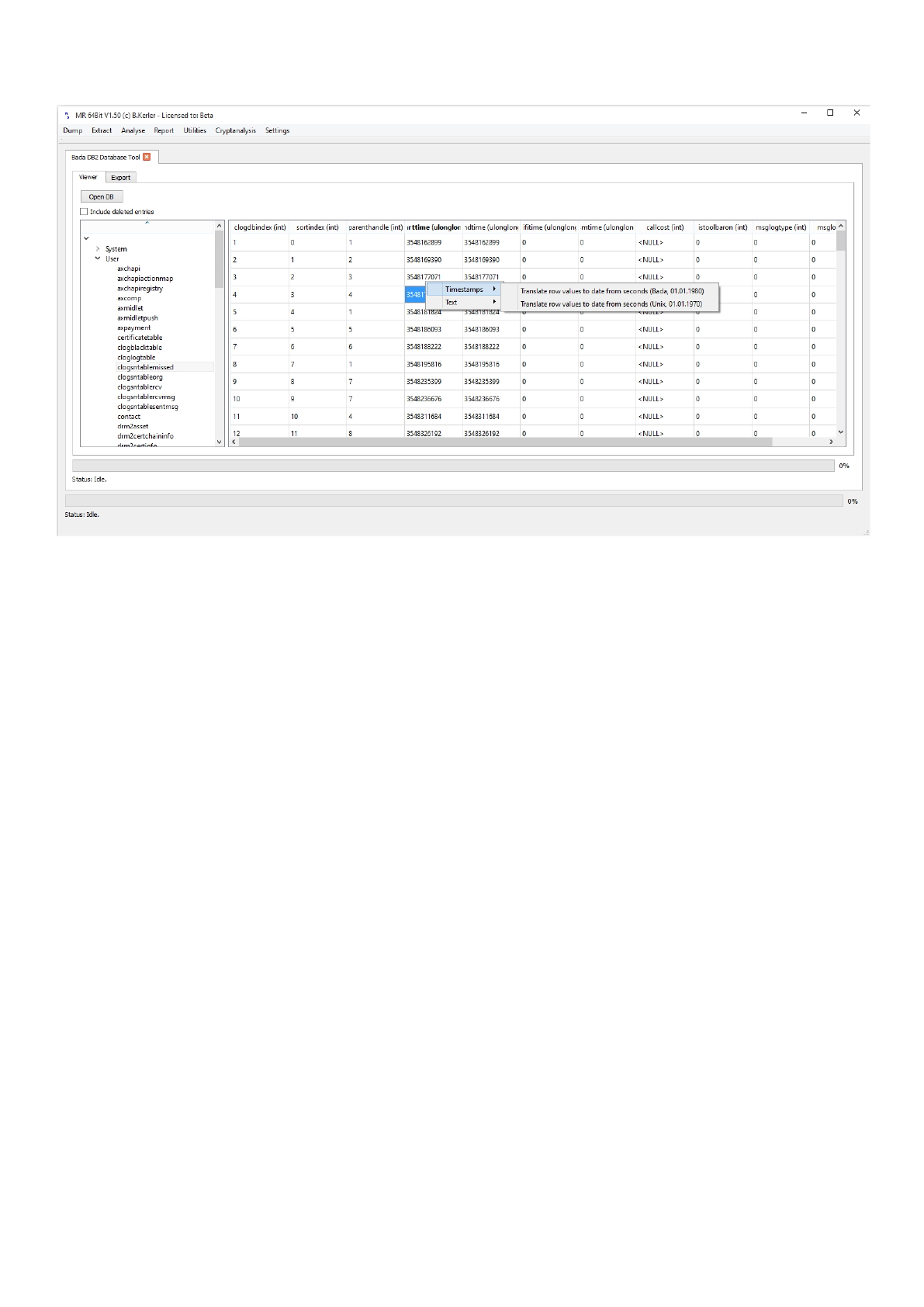
Timestamps
The timestamp submenu allows you to convert integer fields to timestamps.
Mobile Revelator 2.2.5
100 / 200
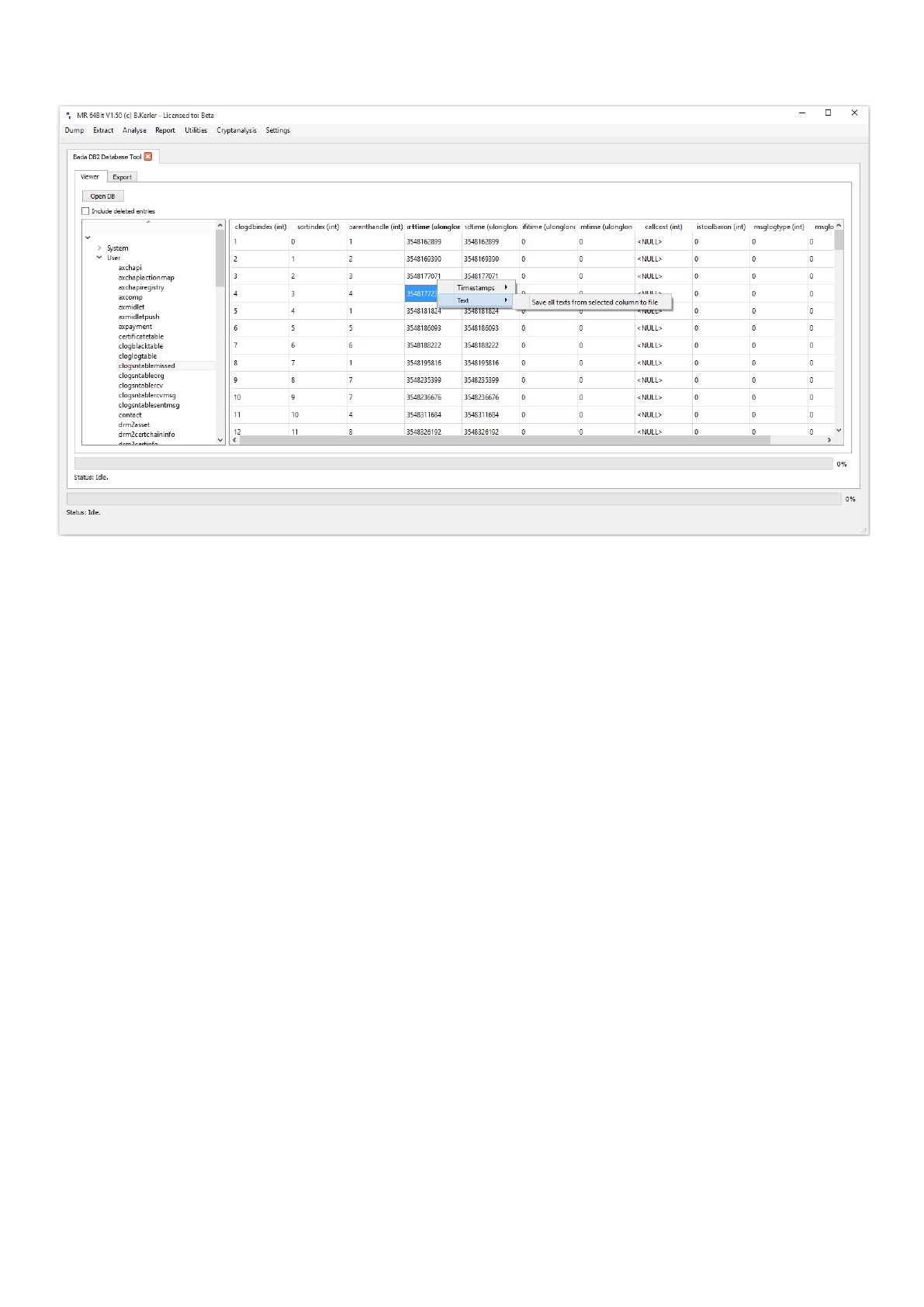
Text
The text submenu allows you to save all texts from selected column in the current table to a file.
Mobile Revelator 2.2.5
101 / 200
Export
The export tab will allow you to save the current table to a xlsx file.
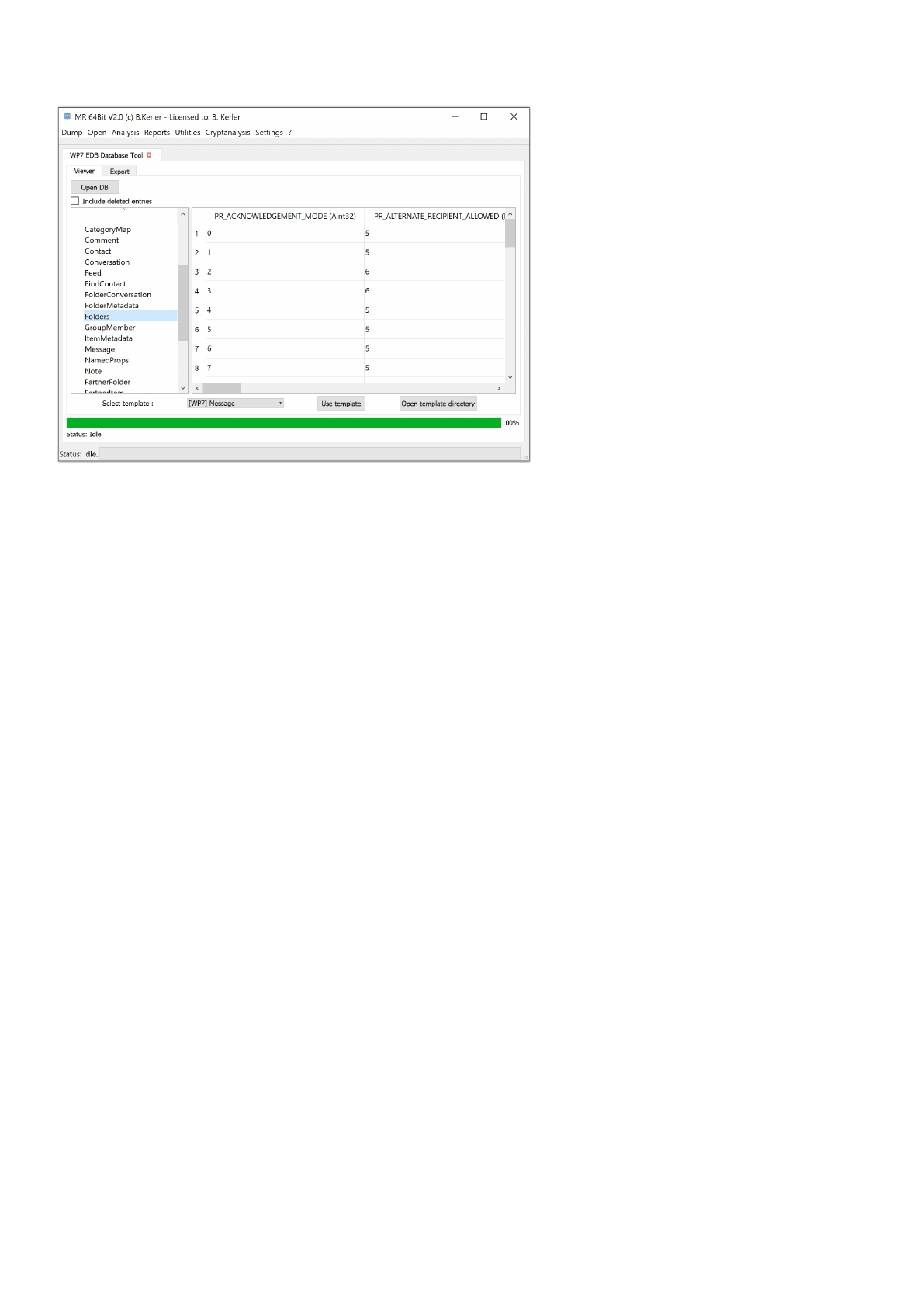
WP7 EDB Database Tool
The WP7 EDB Database Tool lets you open WP7 and WM6 EDB databases like "store.vol".
Mobile Revelator 2.2.5
102 / 200
View
Press "Open DB" to open a database and select "Include deleted entries" to show deleted entries when clicking at the left
index.
Mobile Revelator 2.2.5
103 / 200
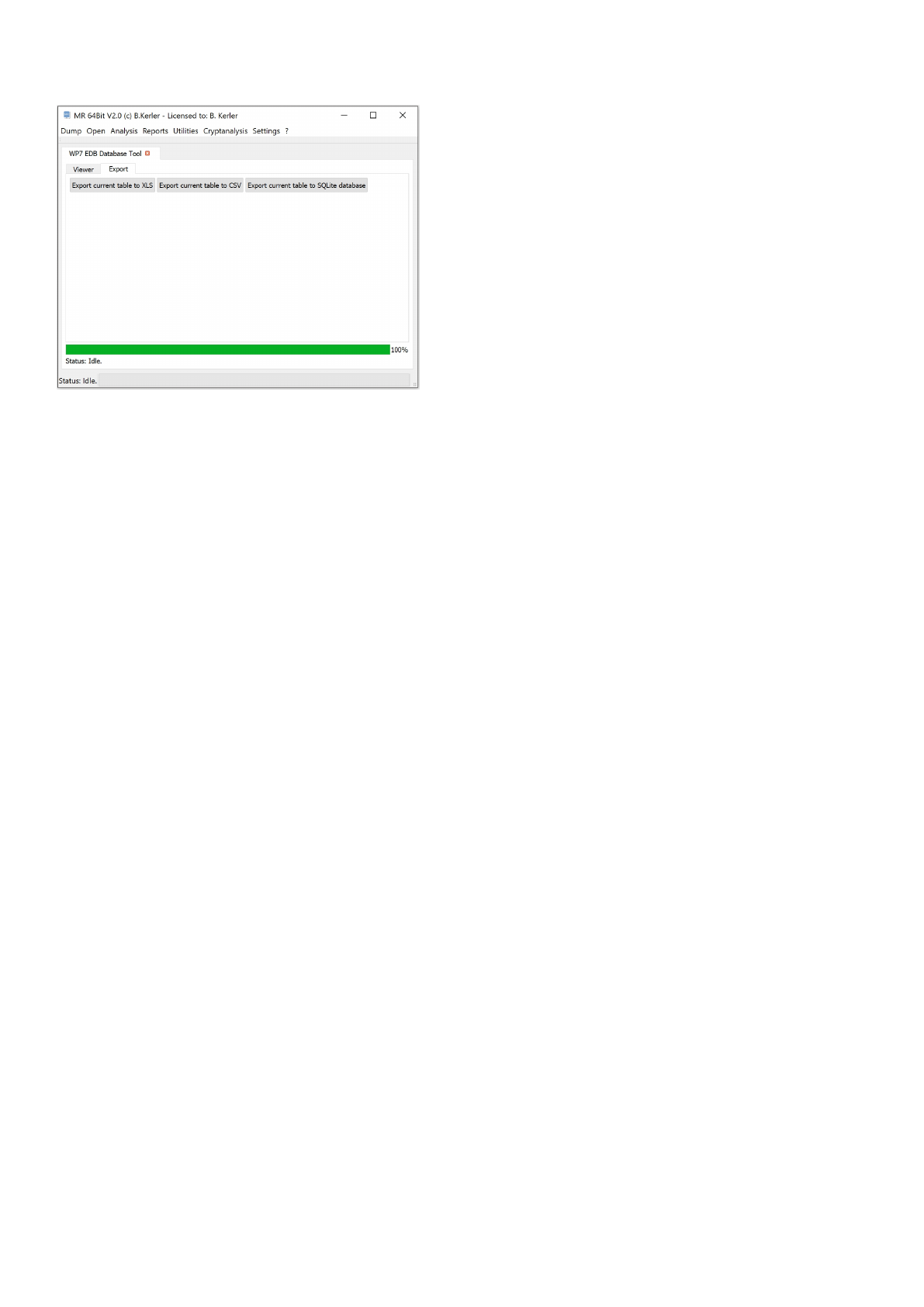
Export
The export tab will allow you to extract the current table to either xls, csv or sqlite database file.

Mobile Revelator 2.2.5
104 / 200
IPD/BBB Database Tool
The Blackberry IPD Database Tool lets you examine .bbb or .ipd database files.

Mobile Revelator 2.2.5
105 / 200
View
Click "Open DB" to open any Blackberry Messenger .bbb or .ipd Backup File. Values not being interpreted are being shown
as Hex Values.

Mobile Revelator 2.2.5
106 / 200
Export
The export function lets you export the current field to a xls or csv file.
Mobile Revelator 2.2.5
107 / 200
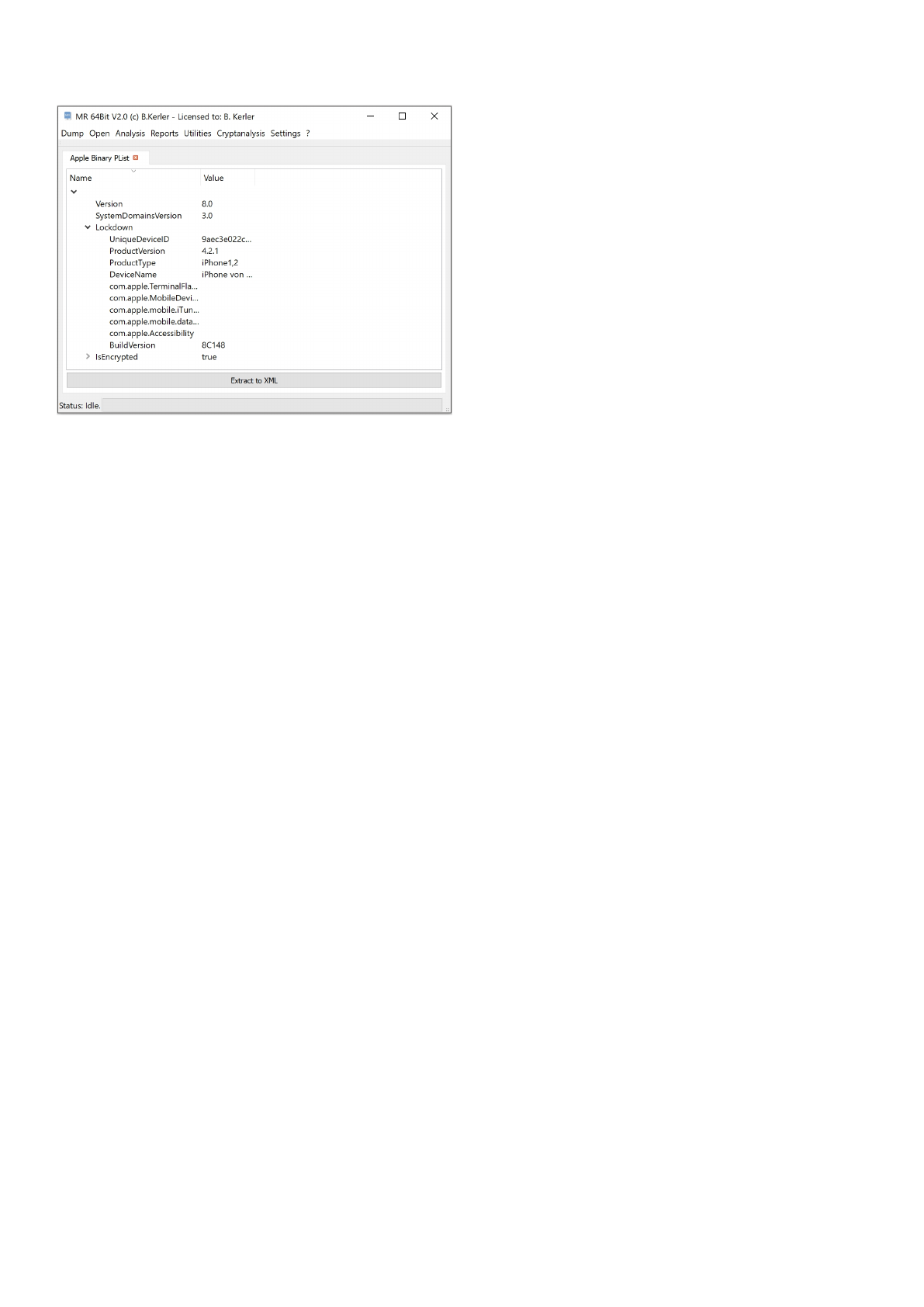
Apple Binary PList
This tool will present all data from both Apple Binary and Raw XML Format and lets you either copy the data to the
clipboard if selected using Ctrl-C or lets you extract all data to a XML-formatted file using the "Extract to XML" button.
Mobile Revelator 2.2.5
108 / 200
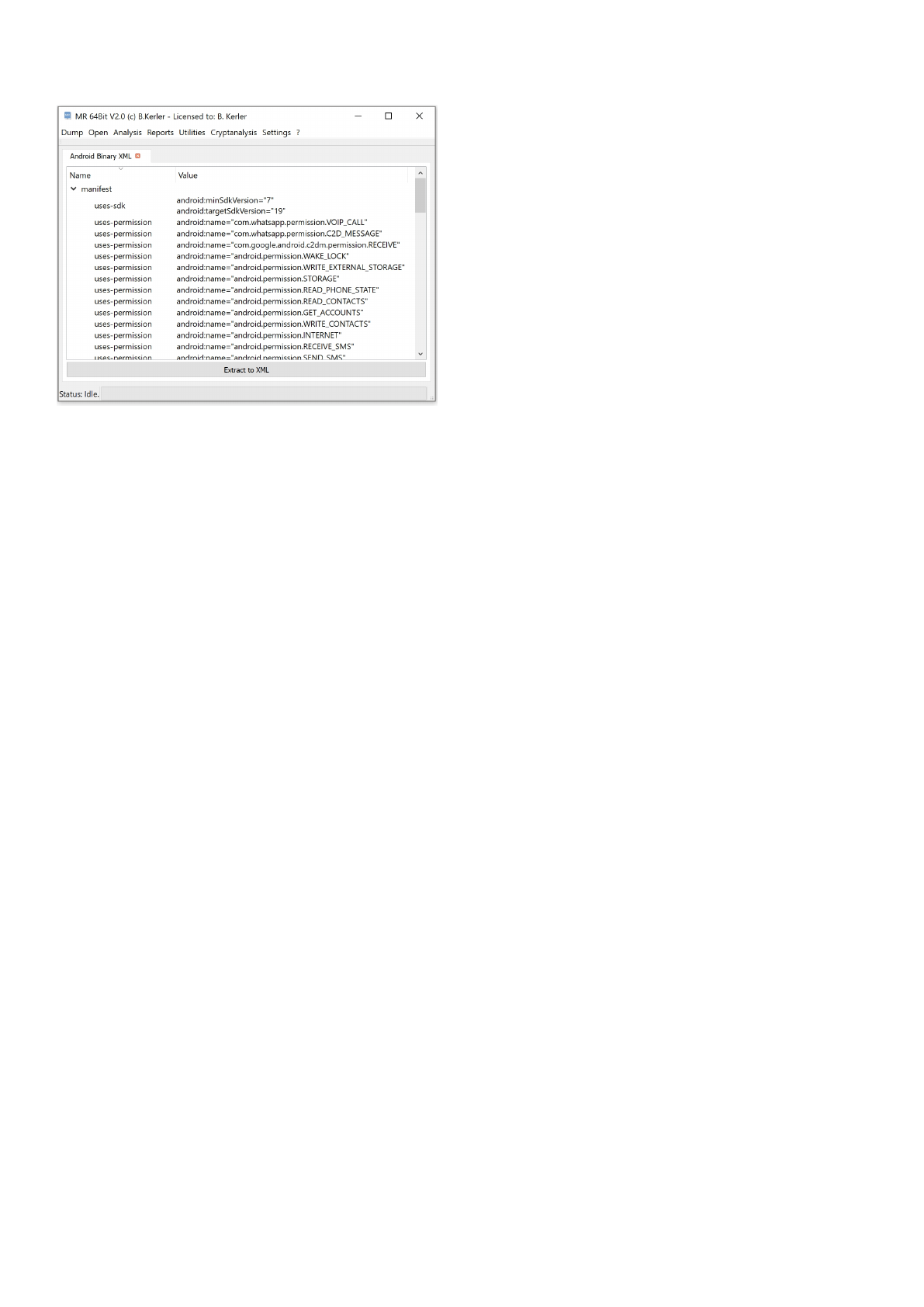
Android Binary XML
This tool will present all data from Android Binary XML Format and lets you either copy the data to the clipboard if selected
using Ctrl-C or lets you extract all data to a XML-formatted file using the "Extract to XML" button.
Mobile Revelator 2.2.5
109 / 200
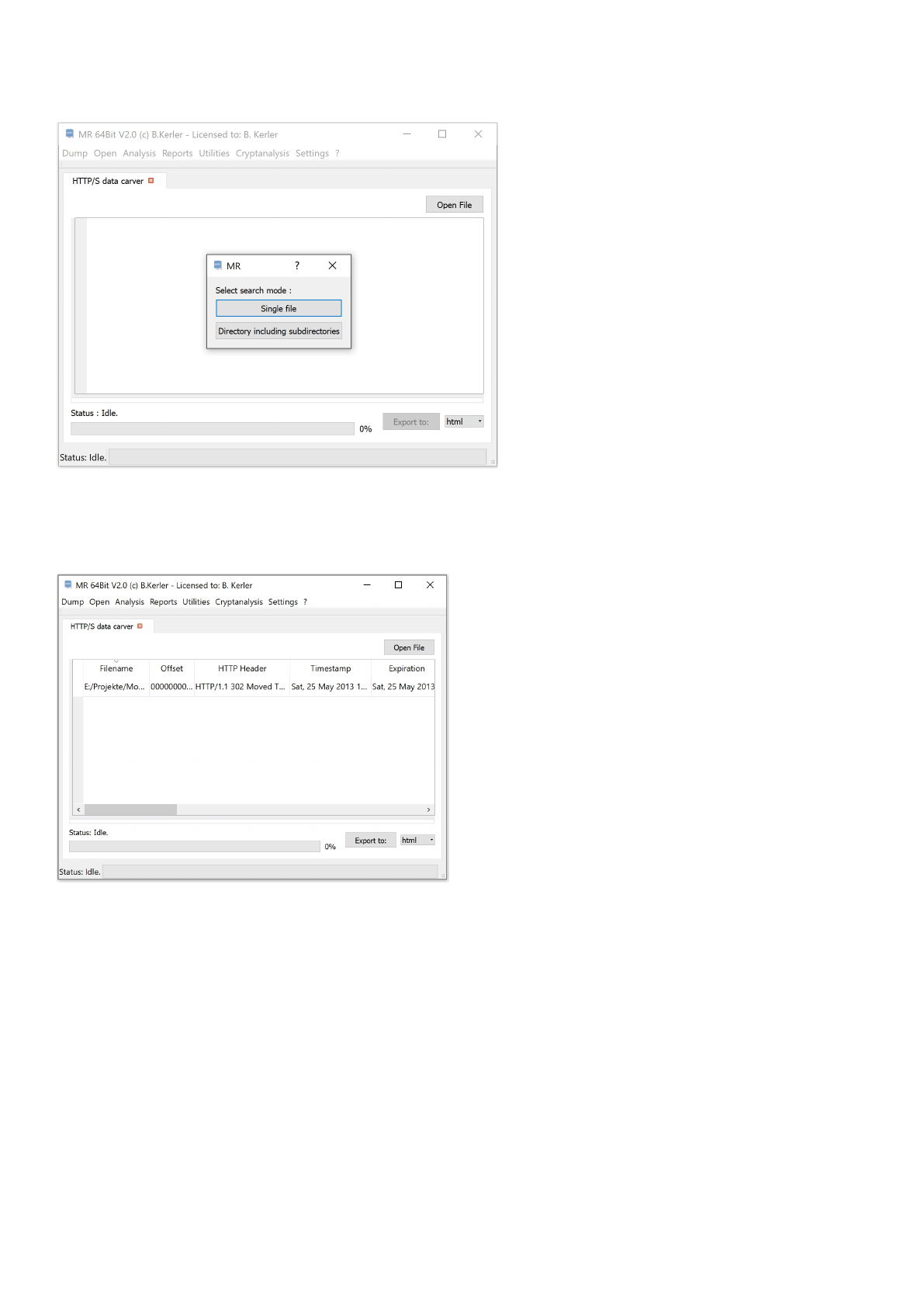
HTTP/S data carver
This tool will search for any HTTP header that might have been cached in the raw flash images or single cache files. Either
choose
"Single file" to search within a single file or "Directory including subdirectories" to search within any folder and its
subfolders being selected.
In order to sort any data, just click on the header. You may export the data to text-formatted CSV-Format, Office XLSX-
Format and SQLite database.
Mobile Revelator 2.2.5
110 / 200
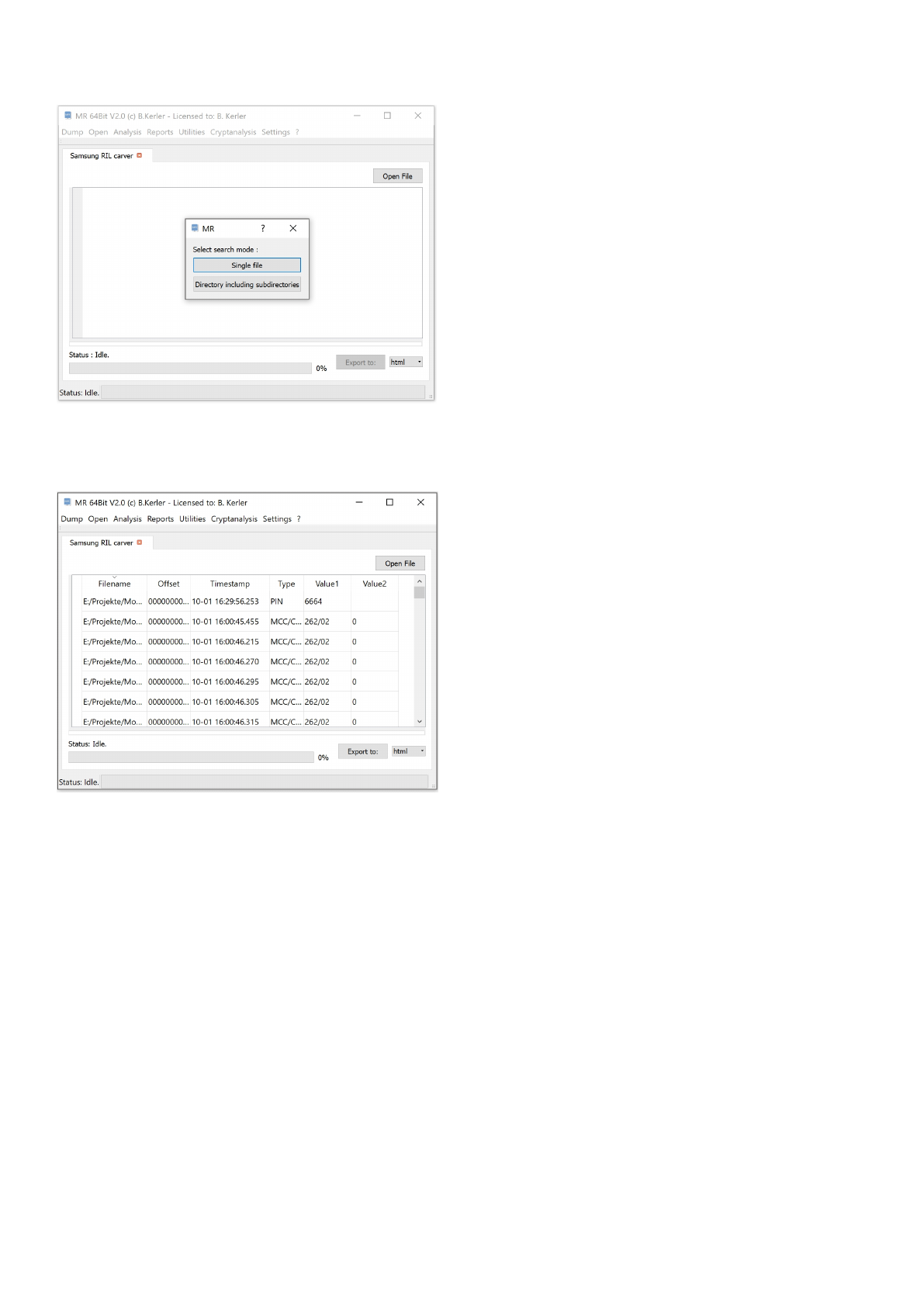
Samsung RIL carver
This tool will extract all Cell-Information, SIM-PIN, SIM-Provider-Information and much more from Samsung
Radio Information Layer (RIL) like on the Samsung Galaxy S3 Mini. Either choose "Single file" to search within a single file
or "Directory including subdirectories" to search within any folder and its subfolders being selected.
In order to sort any data, just click on the header. You may export the data to text-formatted CSV-Format, Office XLSX-
Format and SQLite database.
Mobile Revelator 2.2.5
111 / 200
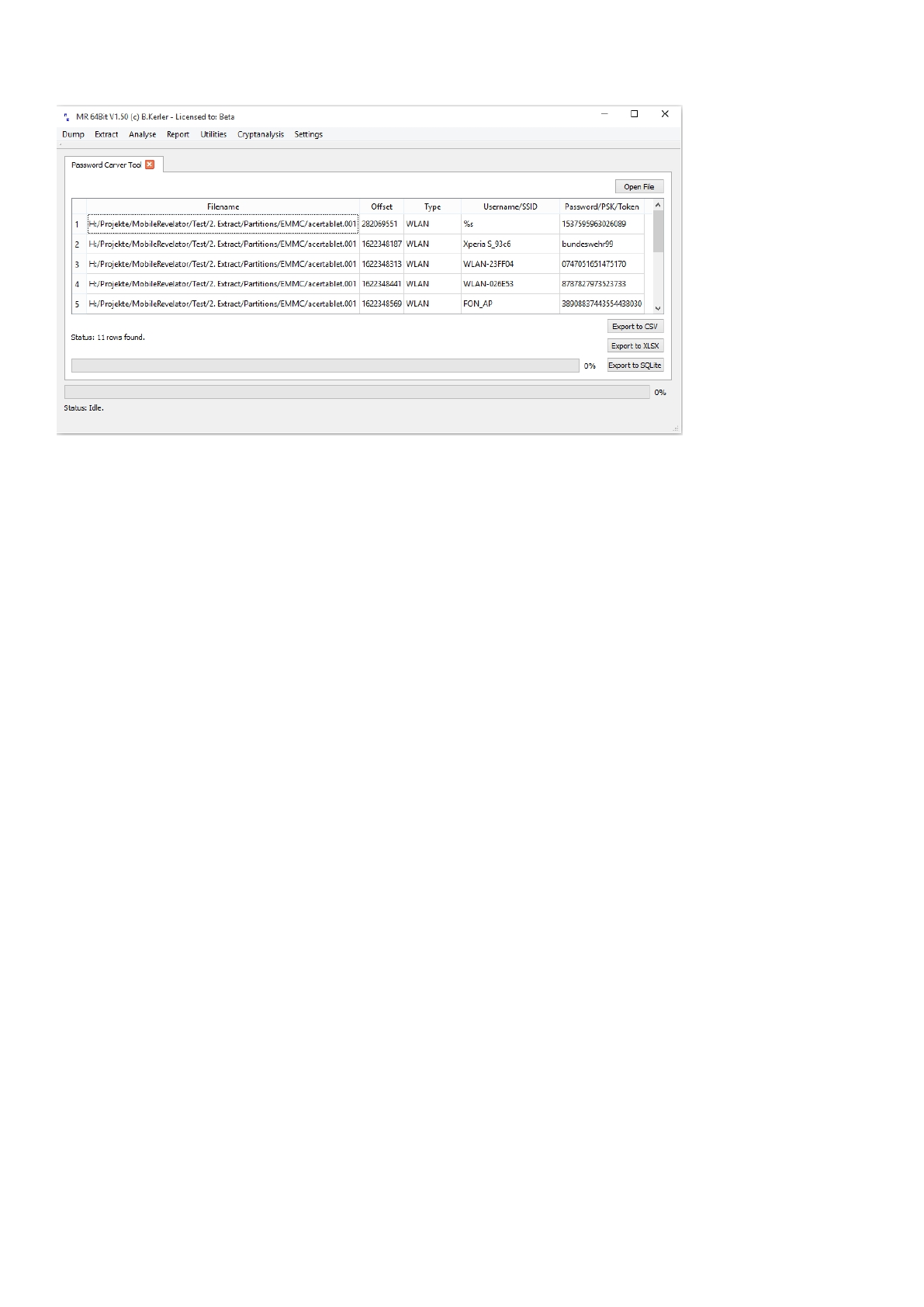
Android Password carver
This tool will extract any WLAN or HTTP Plaintext password. In order to sort any data, just click on the header.
You may export the data to text-formatted CSV-Format, Office XLSX-Format and SQLite database.
Mobile Revelator 2.2.5
112 / 200
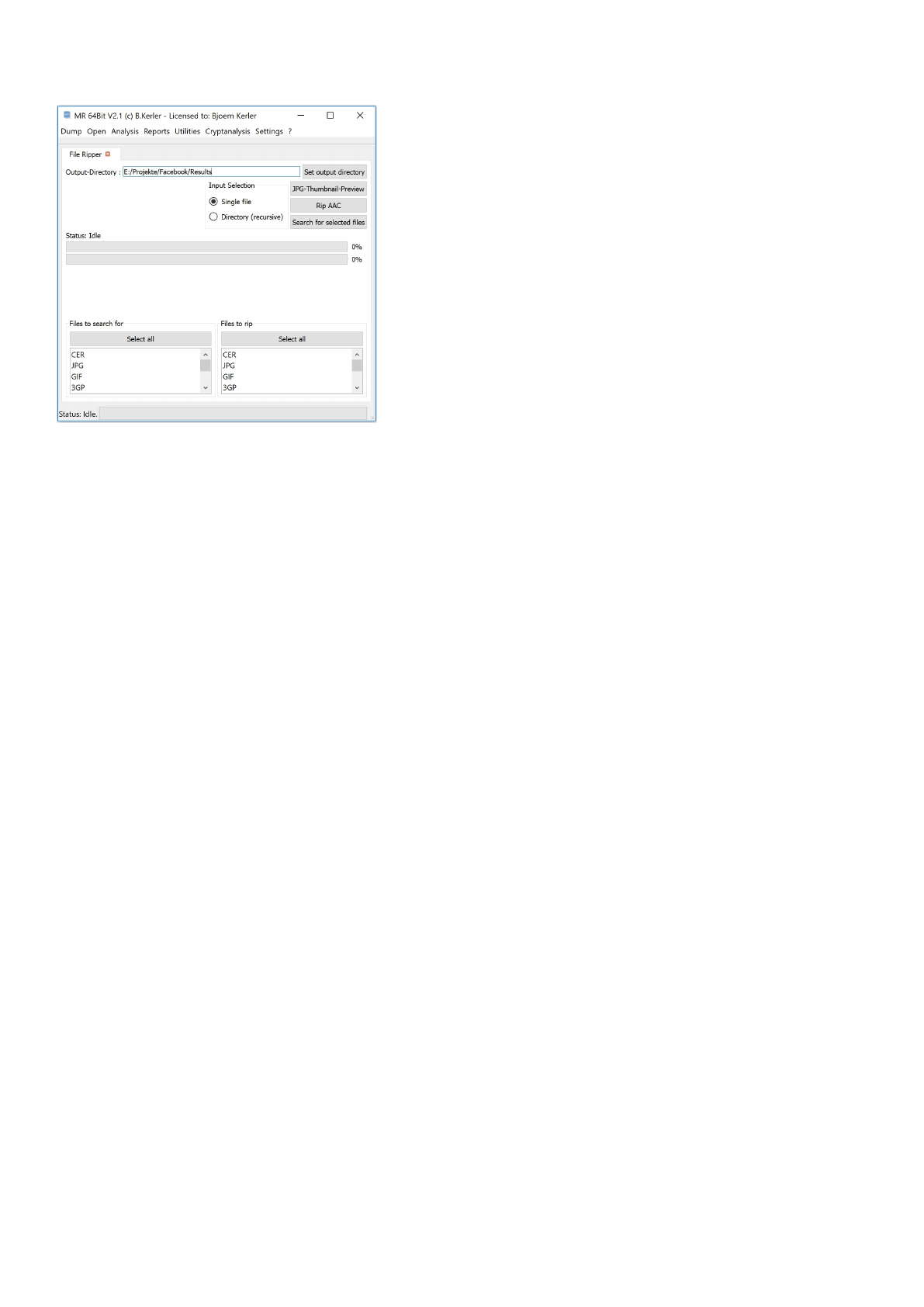
File Ripper
The File Ripper utility lets you search and rip known filetypes. Before running any option, you should select a directory
where the reports and files should be written to using "1. Set Outputdirectory". Then choose if you want to search in one
single file or in a directory using the "Input selection" field.
You may then choose the following functions :
- "Run search" will rip (search full file content) / search (look at file start) any selected file. You may select multiple file
types
using Ctrl-Key as well.
- "Rip AAC" will rip any AAC MP4-Fragments it may find.
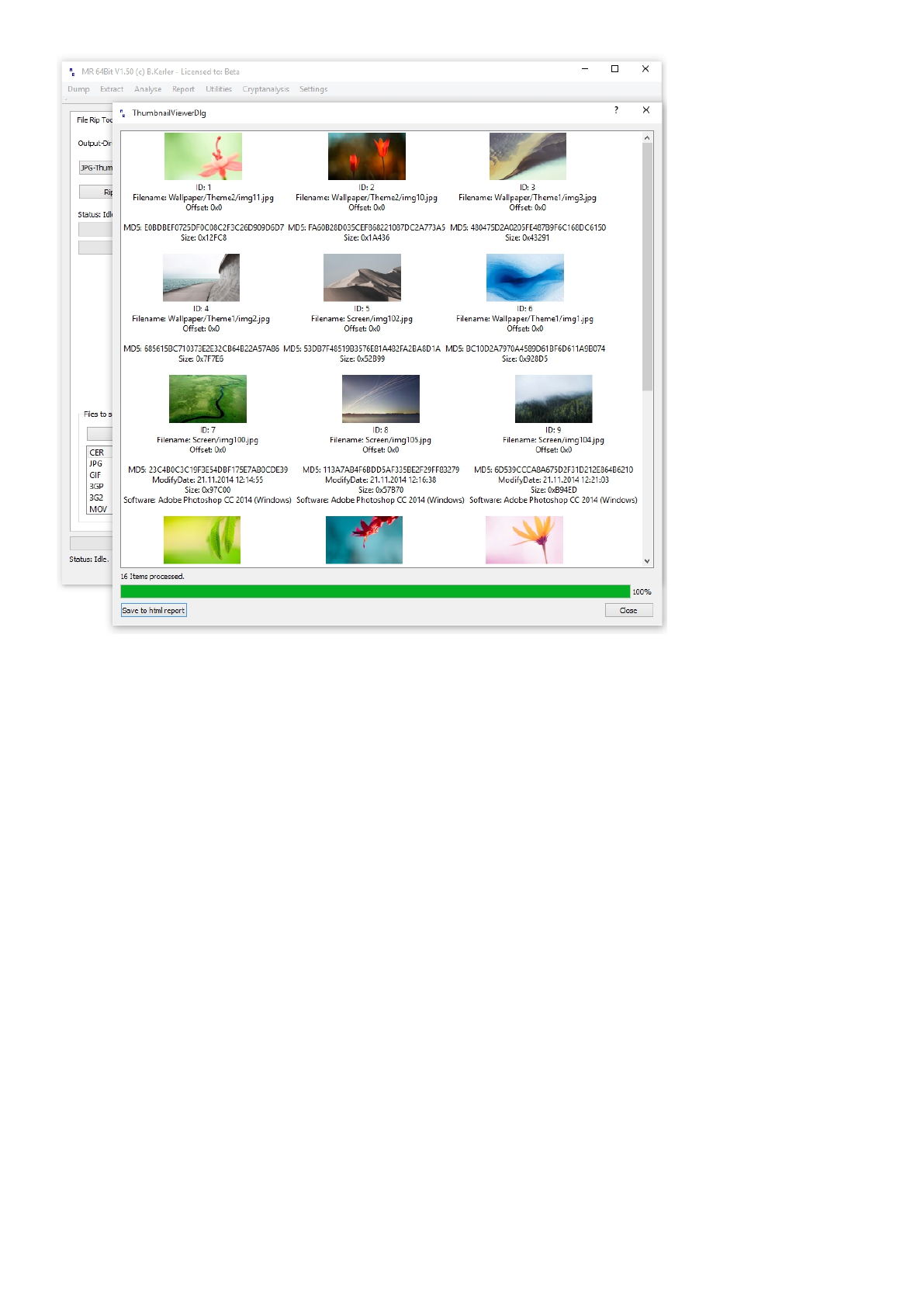
- "JPG-Thumbnail-Preview" extracts and carves jpgs and thumbnails, pressing "Save to html report" will save the found
files
and thumbails to the output-directory. You may doubleclick on the pictures to see the full image size, if available :
Mobile Revelator 2.2.5
113 / 200

Mobile Revelator 2.2.5
114 / 200
Apple iThmb Extract
This tool lets you extract JPG Pictures from .ithmb thumbnail databases being found in Apple devices under
PhotoData/Thumbnails directory. The Filename contains the index which is being used in the /PhotoData/Photos.sqlite
database as well.
For getting information about deleted images, run
"SELECT * FROM ZGENERICASSET as asset, ZADDITIONALASSETATTRIBUTES as attrib WHERE attrib.ZASSET
== asset.Z_PK AND asset.ZTHUMBNAILINDEX == 1234;" as sqlite command
whereas the thumbnail index to be retrieved would be 1234 in this example.

Mobile Revelator 2.2.5
115 / 200
Report
The report menu offers several tools for generating reports.
Mobile Revelator 2.2.5
116 / 200
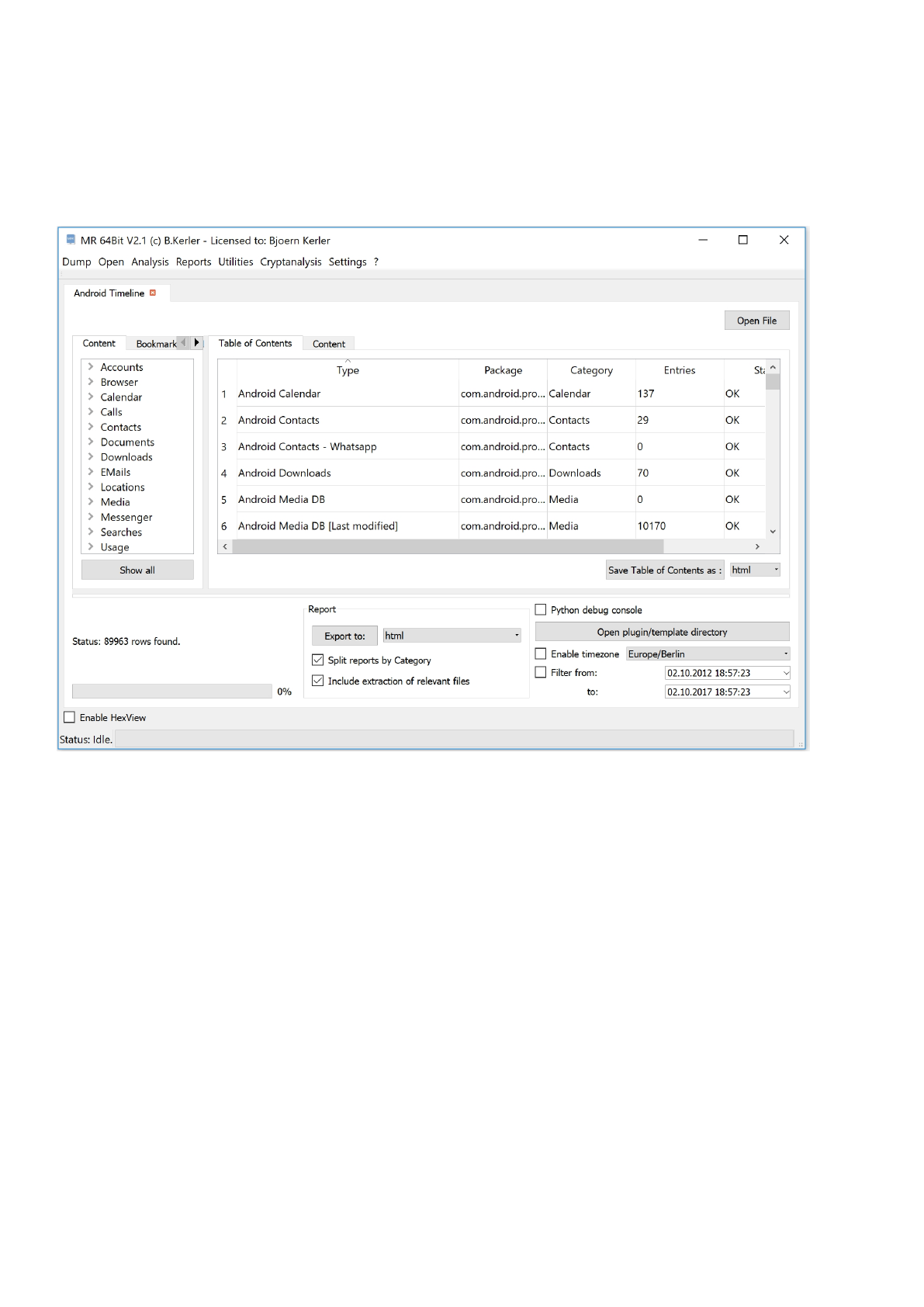
Timeline report
The Android timeline module will search for time relevant information within raw files and/or extracted database files.
Choosing a huawei backup or android backup
as raw file is also possible. You may add custom databases at any time by creating a new xml file in the "C:
\Users\xxx\Documents\Mobile Revelator\Template\[OS]" path. Please see Templates Documentation on how to create and
use Python and Timeline modues. If the additional cell database has been installed, detected cell information from
herrevad databases will be converted to place names automatically.
Mobile Revelator 2.2.5
117 / 200
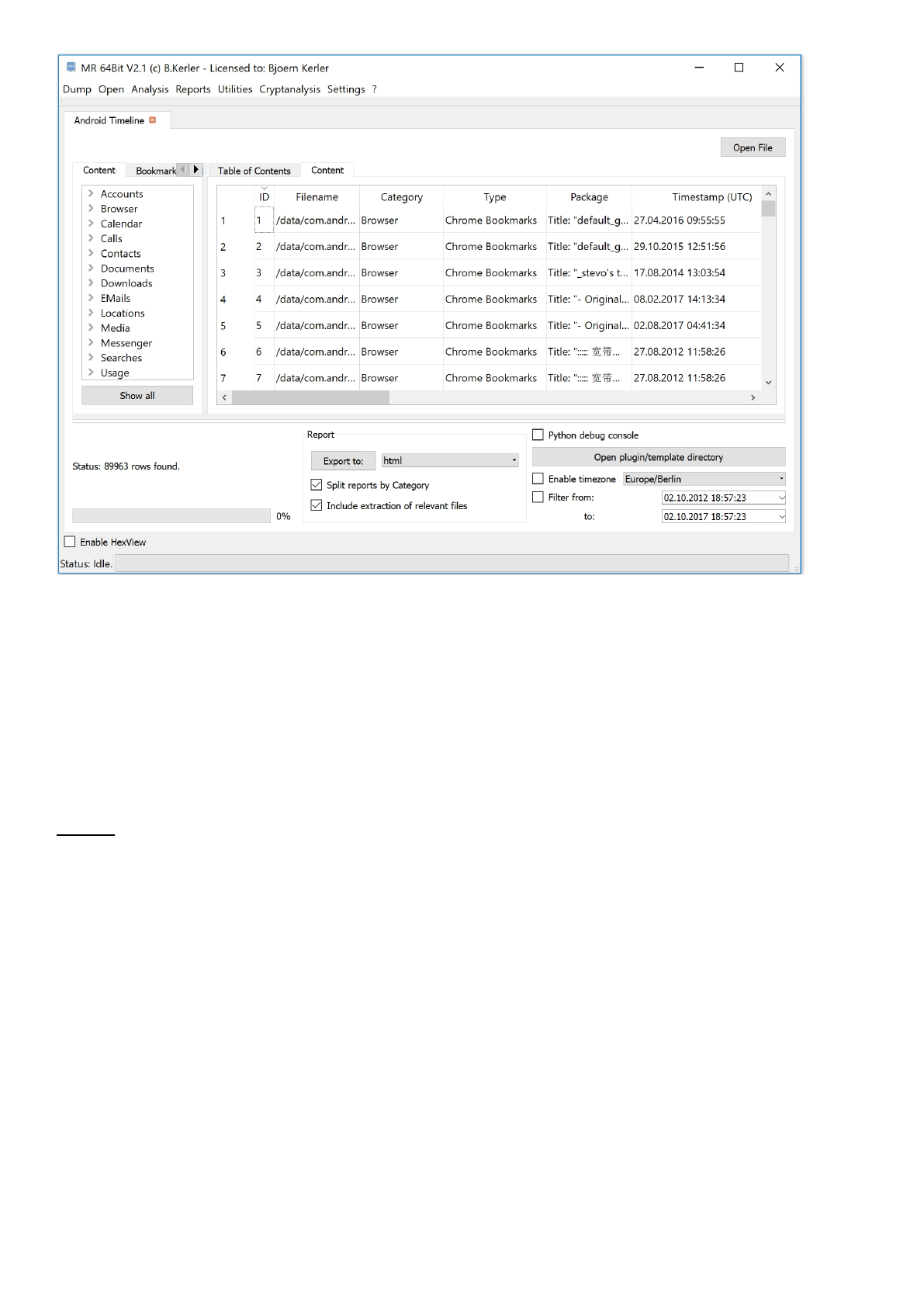
Using Ctrl-F you can search for any string, clicking on an entry in the result tab will show the selected entry in the table.
Double-left-clicking a category with the mouse on the tree will only show the current selected entry. Using CTRL-Key on
the keyboard and left-click with the mouse you can select multiple categories, pressing right-click on the mouse will offer
you a menu to only show selected items or to hide selected items from the current table display.
Using Ctrl-B you can bookmark selected lines. on the bookmarks tab, you can select entries to show which also allows you
to bookmark any results and generate reports based on bookmarked items.
Clicking on the table header, you may sort items as required. Enabling timezones will display the selected timezone in both
view and report.
You can also filter between two dates, which will then show only the entries with timestamps in between.
Reports
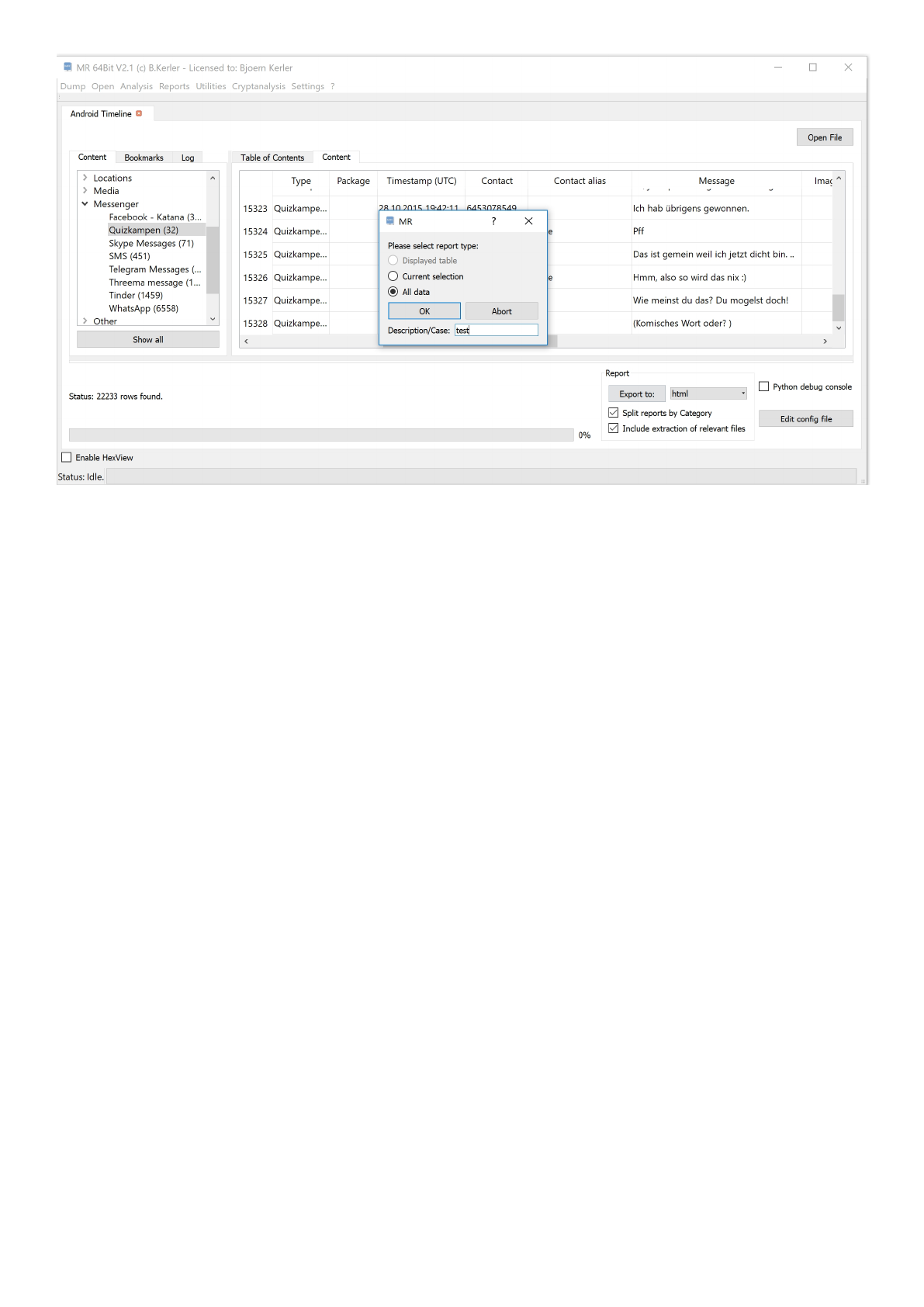
Mobile Revelator 2.2.5
118 / 200
You may select any report type by clicking on the list right hand of the "Export to:" button. Pressing the "Export to: " button,
you may choose whether the currently displayed table, the current selection (in the tree and/or in the content tab) or all
data will
be extracted to reports.
For PDF and HTML reports, you may sort items and report will be sorted as well. Just click on the header of the table to
sort items.
Right clicking on a content filename, you can select "Jump to filename" in order to open up a filesystem view, pointing to
the selected file in the report.
Using "Split reports by Category", you can automatically generate separate report files for each category.
If "Include extraction of relevant files" has been selected, all files including necessary files will be extracted to the "files"
subdirectory in the report folder
and contents will be clickable in both pdf and html reports.
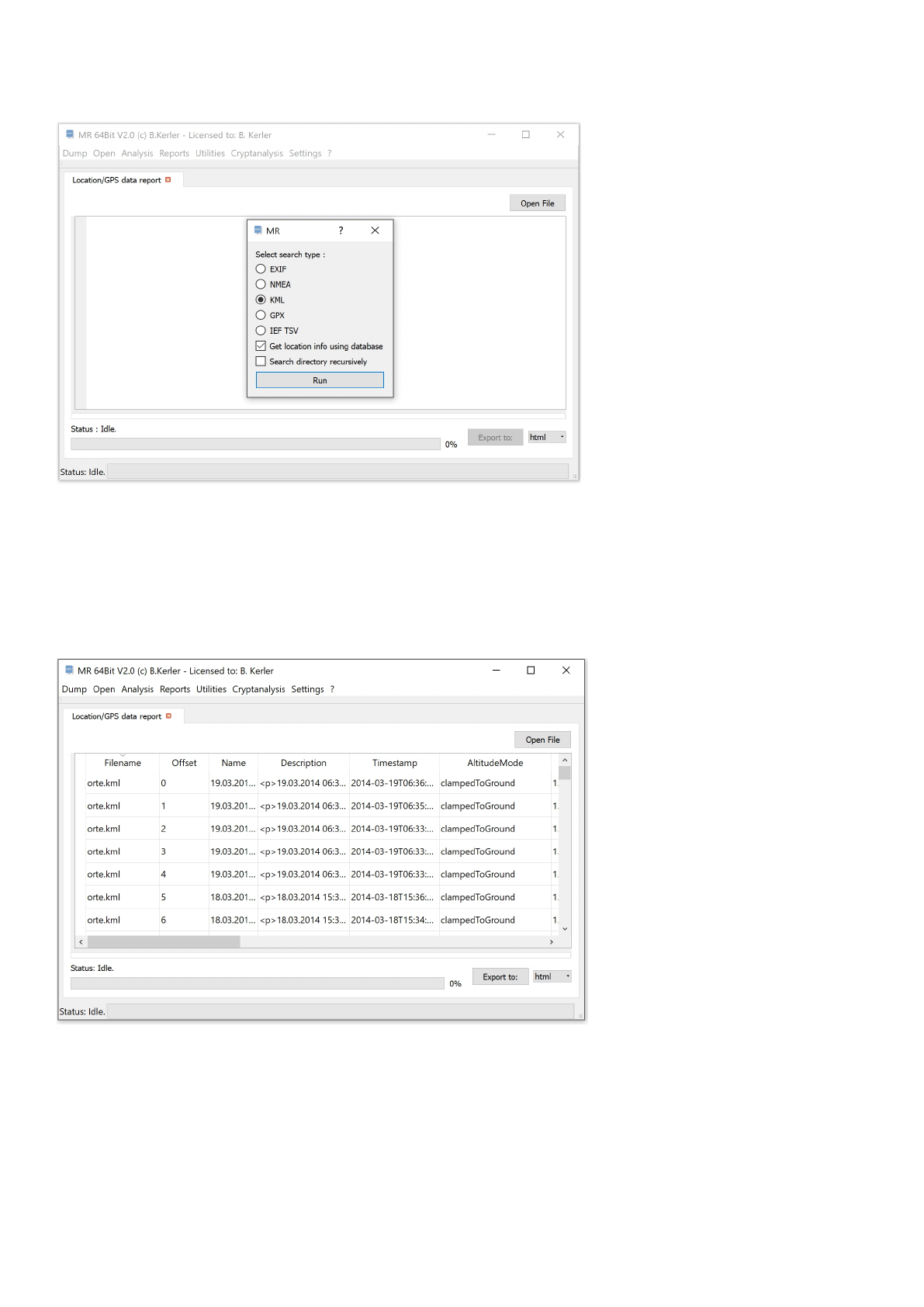
Mobile Revelator 2.2.5
119 / 200
Location/GPS data report
This tool will carve any gps data from either EXIF-information being using in JPG-Files, from GPS-Ascii-Standard NMEA,
from Google KML-based data structures, from any Garming GPX dataset and from Internet Evidence Finder report files
as well.
If you choose to "Get location info using database", MR will retrieve its town and country information without online
connection.
Selecting "Select directory recursively" will seek within any file that has been selected, recursively for each subdirectory.
Pressing "run" you will either be able to select the directory or file to search for.
In order to sort any data, just click on the header. The data fields "Country Code", "Postal Code", "Town" and "Distance to
town" are generated by MR to get a quicker overview about the coordinates. You may export the data to text-formatted
CSV-Format, Office XLSX-Format and SQLite database.
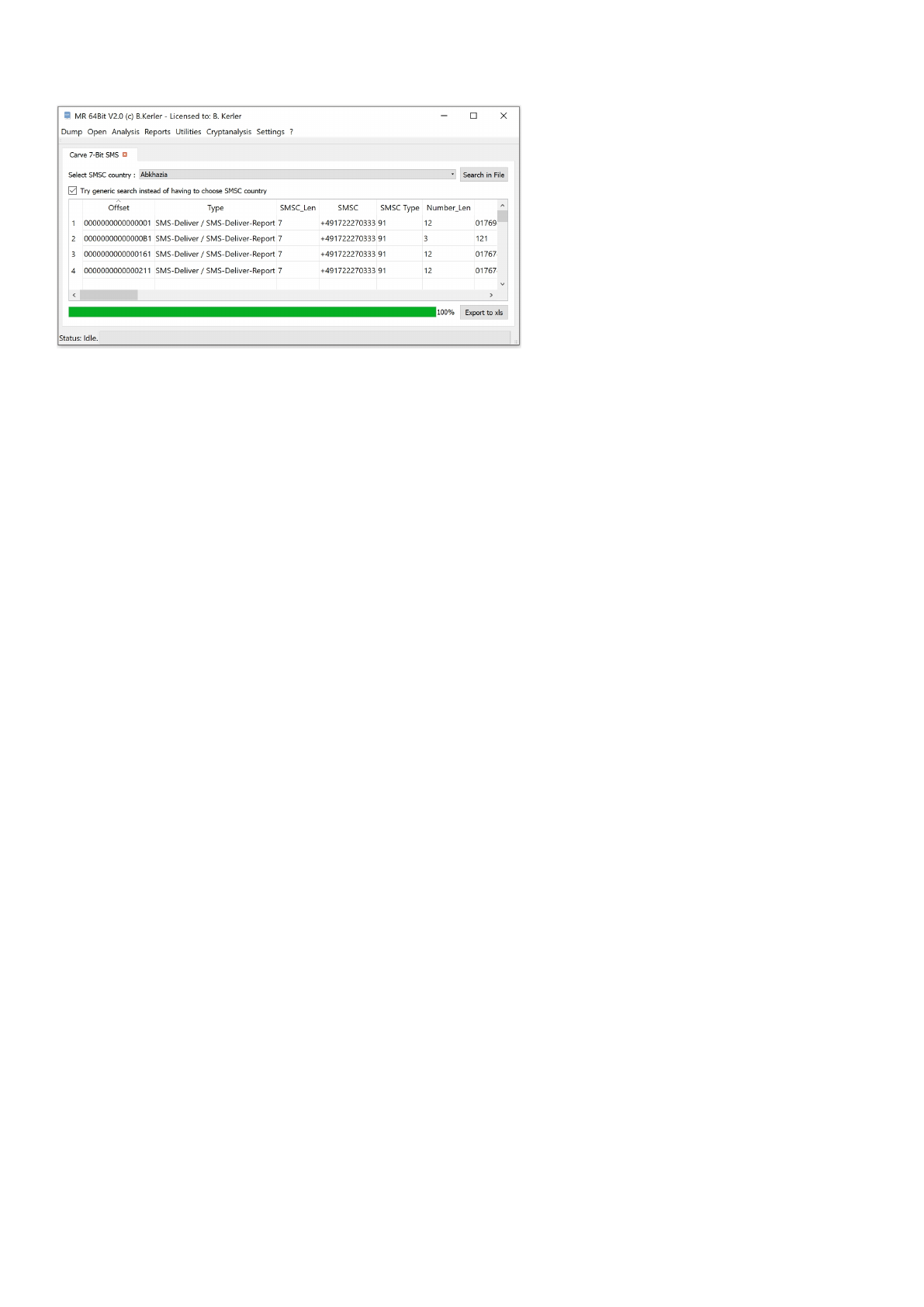
Mobile Revelator 2.2.5
120 / 200
Carve 7-Bit SMS
This tool will extract any 7-Bit formatted sms that matches the 3GPP standard. Either use the generic method by selecting
"Try generic search instead of having to choose SMS country" or, if more precision and less wrongly carved sms data is
needed, uncheck the option and select the appropriate SMSC Country. Export of the data to the Office XLSX-Format
is possible using the button "Export to xls". In order to sort any data, just click on the header.
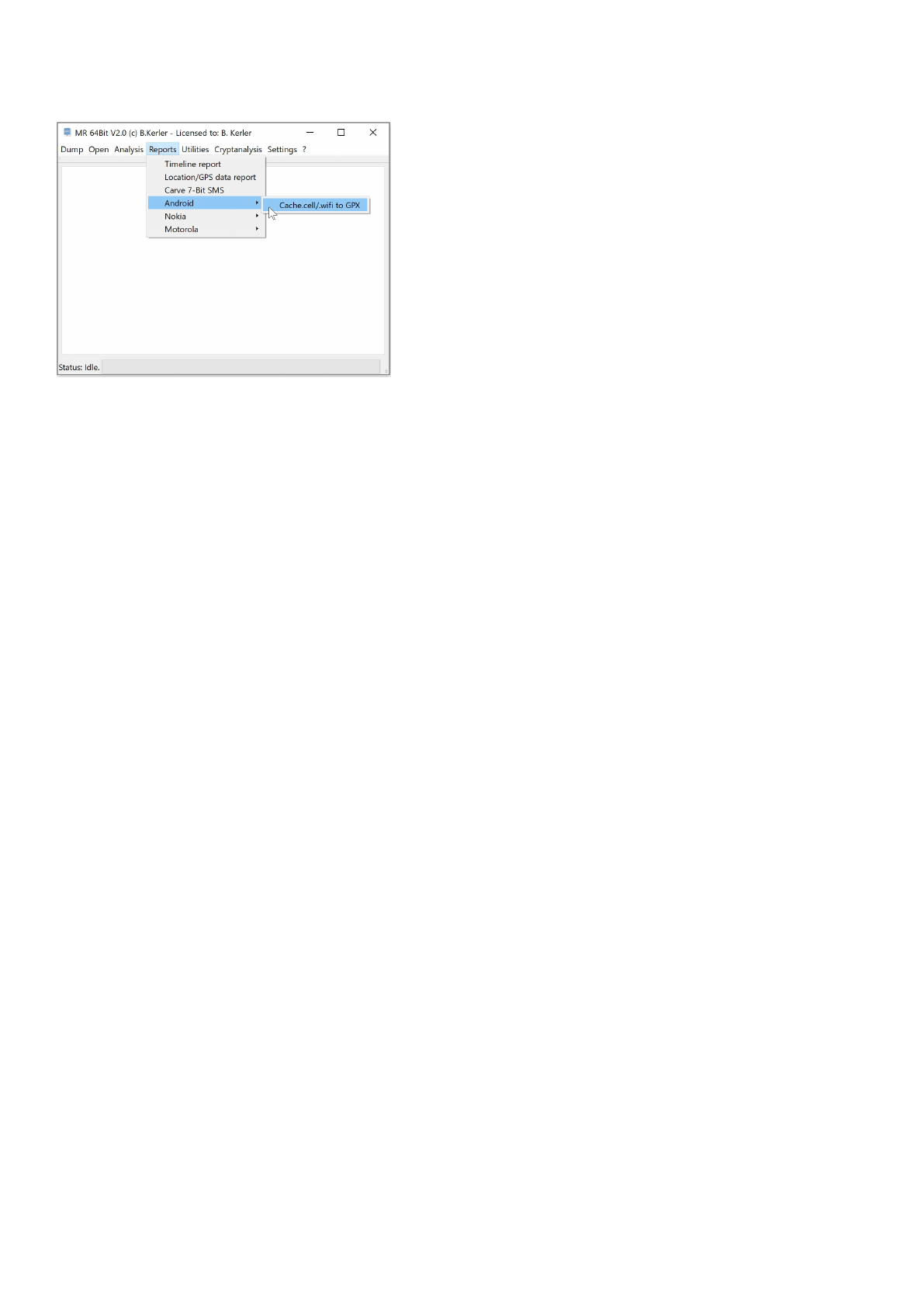
Mobile Revelator 2.2.5
121 / 200
Android
This menu will convert cache.cell and cache.wifi files to Google .gpx Files.

Mobile Revelator 2.2.5
122 / 200
Cache.cell/.wifi to GPX
This function allows to convert cache.cell and cache.wifi files to google gpx files.
Mobile Revelator 2.2.5
123 / 200
Nokia
The Nokia PM report tool is able to extract call logs, sms and much more
from Nokia .pm files.
Mobile Revelator 2.2.5
124 / 200
Nokia PM
The Nokia PM report tool allows you to extract numbers, calllogs, SMS, etc. from PM files. In order to ensure proper
decryption of userlock codes, make sure you enter the right IMEI before. The resulting report will be written as an HTML
file.
Mobile Revelator 2.2.5
125 / 200
Motorola
The Motorola ODM Tool converts raw inbox and outbox sms files to a readable format.

Mobile Revelator 2.2.5
126 / 200
ODM Inbox SMS
The Motorola ODM SMS Inbox tool lets you decode the "smsIBMsg" file. Pressing on "Export to xls", the
decoded data in the table will be written into a XLSX file.

Mobile Revelator 2.2.5
127 / 200
ODM Outbox SMS
The Motorola ODM SMS Inbox tool lets you decode the "smsOBInfo" file. Pressing on "Export to xls", the
decoded data in the table will be written into a XLSX file.

Mobile Revelator 2.2.5
128 / 200
Utilities
The utilities menu contains several tools which are hardware based or offer additional information.
Mobile Revelator 2.2.5
129 / 200
Firmware Utils
The firmware utils offer many tools for conversion between proprietary firmware formats and regular file formats.

Mobile Revelator 2.2.5
130 / 200
Samsung
This util offers functionality to convert Samsung firmware.

Mobile Revelator 2.2.5
131 / 200
Convert .img to .tar.md5
This tool is able to convert Samsung raw image files to .tar.md5 files for usage in Samsung's Odin tool.

Mobile Revelator 2.2.5
132 / 200
HTC
This util offers functionality to convert HTC firmware.

Mobile Revelator 2.2.5
133 / 200
Decrypt HTC RUU
This tool is able to decrypt encrypted HTC RUU .ZIP firmware containers.

Mobile Revelator 2.2.5
134 / 200
LG
This util offers functionality to convert LG firmware.

Mobile Revelator 2.2.5
135 / 200
Decrypt KDZ
This tool is able to convert encrypted LG KDZ containers to LG .DZ containers.

Mobile Revelator 2.2.5
136 / 200
Unpack DZ
This tool is able to convert encrypted LG DZ containers to .cab files.

Mobile Revelator 2.2.5
137 / 200
Android
This util offers functionality to convert Android generic firmware.

Mobile Revelator 2.2.5
138 / 200
Android 4.x : Convert .img to raw .bin
This tool is able to convert android 4.x firmware in ".img" format to raw .bin files.

Mobile Revelator 2.2.5
139 / 200
Android 5.x : Convert .new.dat to raw .bin
This tool is able to convert android 5.x firmware in ".new.dat" format to raw .bin files.

Mobile Revelator 2.2.5
140 / 200
Number Decoder
The number decoder tools offer tools for identification and generating more information about unique serial
numbers and standardized items.
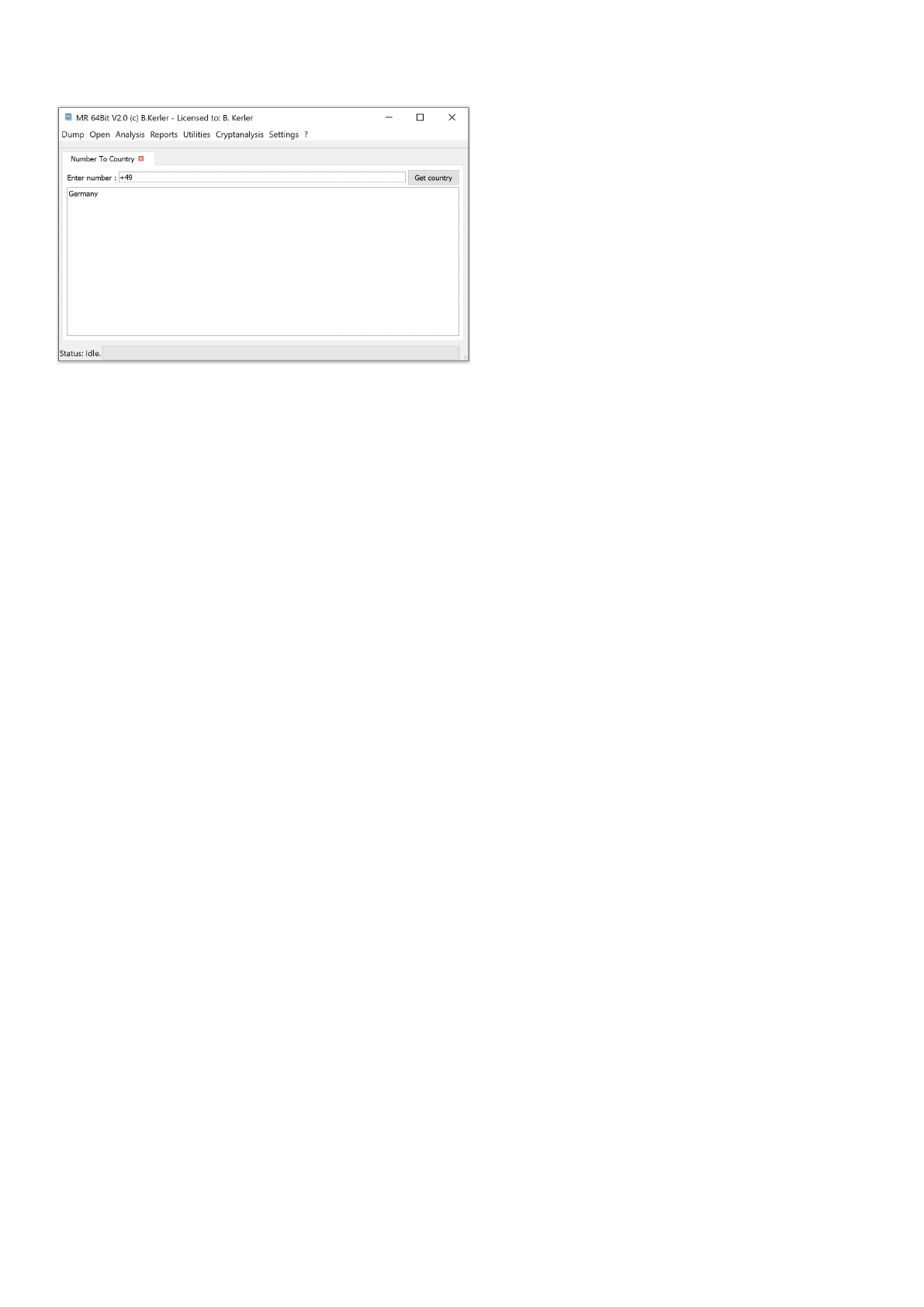
Mobile Revelator 2.2.5
141 / 200
Number To Country
The number decoder will convert international telephony codes into country names.

Mobile Revelator 2.2.5
142 / 200
IMSI Decode
The IMSI decoder is able to decode IMSI data to provider information.

Mobile Revelator 2.2.5
143 / 200
ICCID Decode
This tool converts SIM card ICCID numbers to provider Information according to the ITU E.118 standard.

Mobile Revelator 2.2.5
144 / 200
MAC Lookup
The mac lookup is able to show vendor information for mac addresses.

Mobile Revelator 2.2.5
145 / 200
SDCard CID Decoder
The SDCard CID decoder tool is able to convert hex values into the appropriate JEDEC description.

Mobile Revelator 2.2.5
146 / 200
Time Stamp Decoder
The timestamp converter is able to both convert from dates to values as well from values to dates.
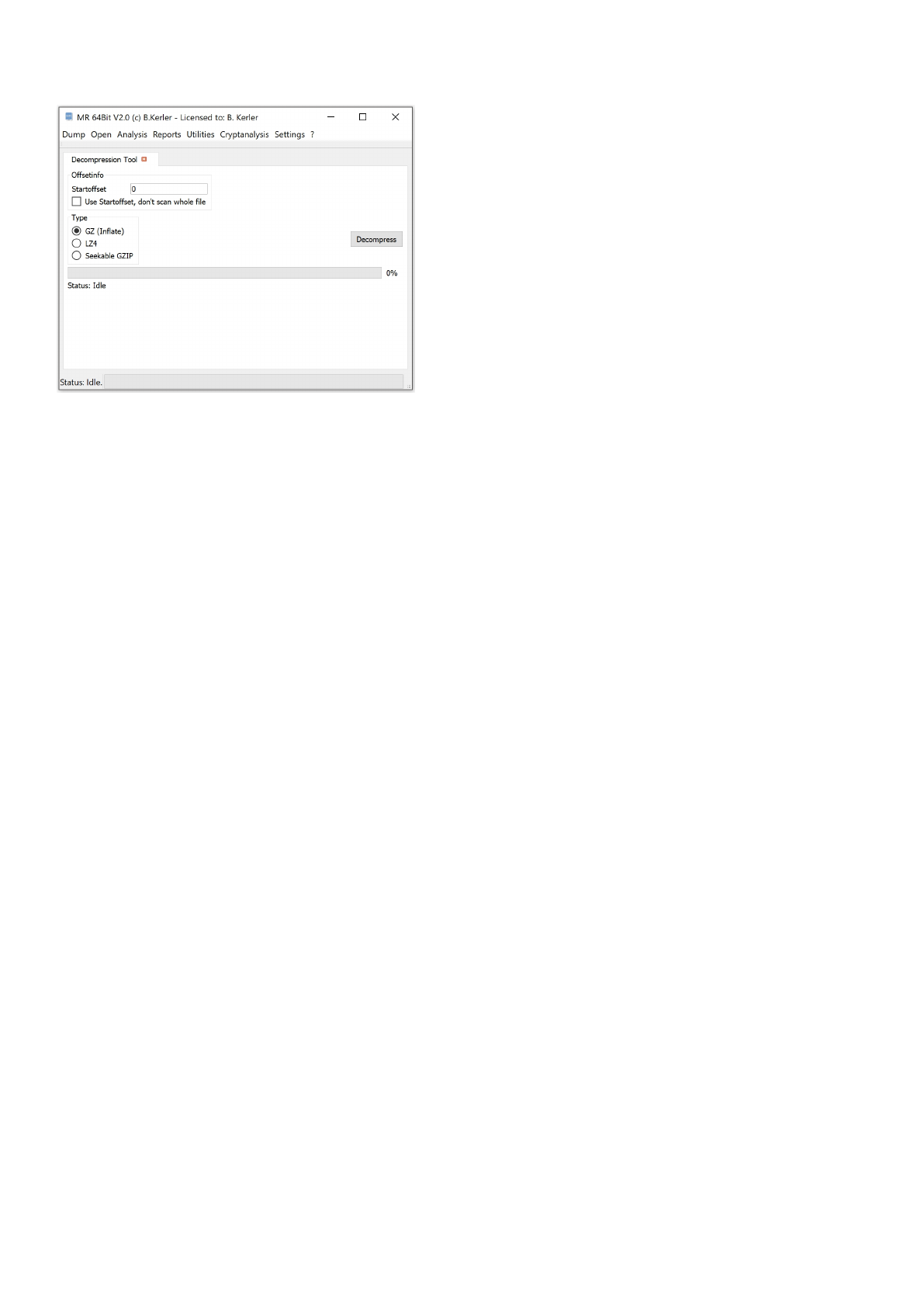
Mobile Revelator 2.2.5
147 / 200
Compression Util
The decompression tool is able to uncompress any gzipped or lz4 zipped data, which is likely common in kernels and
router firmwares.If you leave the settings as they are, the tool will try to find and automatically extract each segment as a
different file. If the autodetection fails you may as well check the "Use startoffset" checkbox, which will allow you to enter a
specific offset as a hex value as the startoffset for decompression.
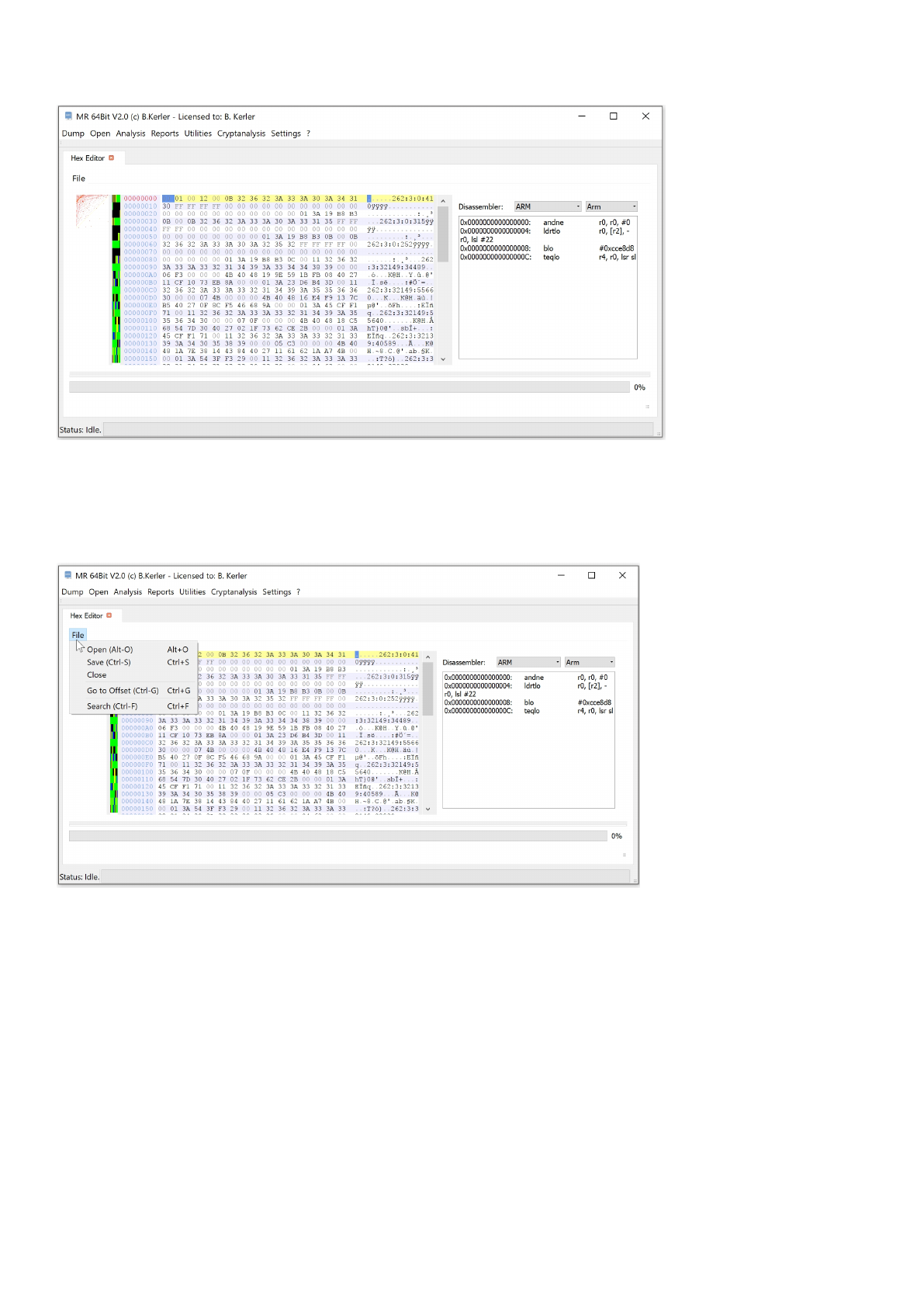
Mobile Revelator 2.2.5
148 / 200
Hex Editor
The hex editor is able to show binary files with different types of interpretation. You may choose a disassembler at the right
for disassembling code patterns in the current hex editor data. On the left side, you may see that ascii bytes are colored
green, 00's and FF's are colored black, and lower bytes in between are colored blue as well as higher bytes in between are
colored yellow. On the left most side, you can see a statistical interpretation of each triple-bytes including entropy, which
may help you identify different file types without having a file header.

Mobile Revelator 2.2.5
149 / 200
Cryptanalysis
The cryptanalysis menu offers several tools for decrypting information from different apps or vendors
and contains "Crypto Tools" for experimentations with several crypto standards and techniques.
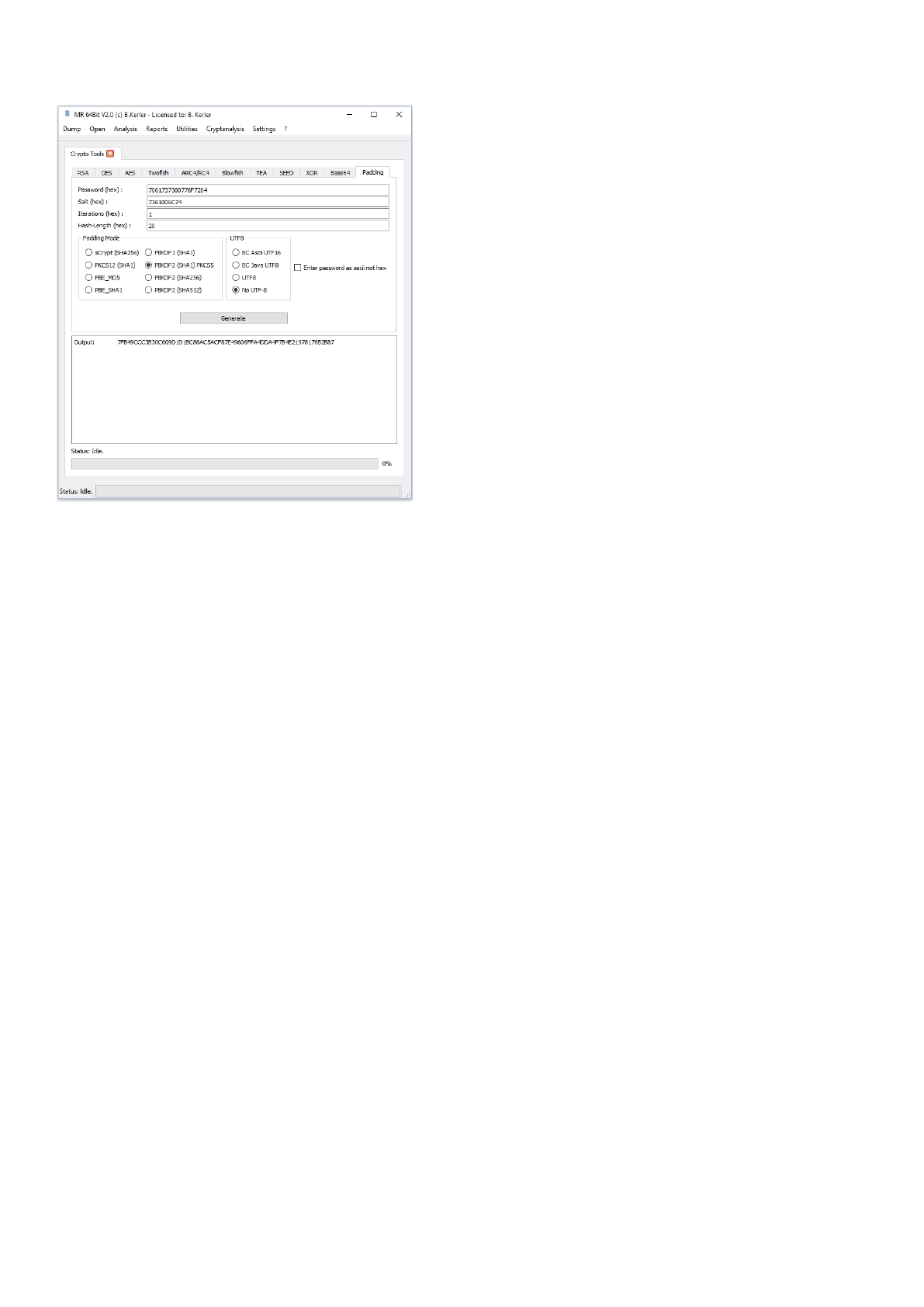
Mobile Revelator 2.2.5
150 / 200
Crypto Tools
The crypto tools allows you to play with several cryptographical functions.

Mobile Revelator 2.2.5
151 / 200
RSA

Mobile Revelator 2.2.5
152 / 200
DES
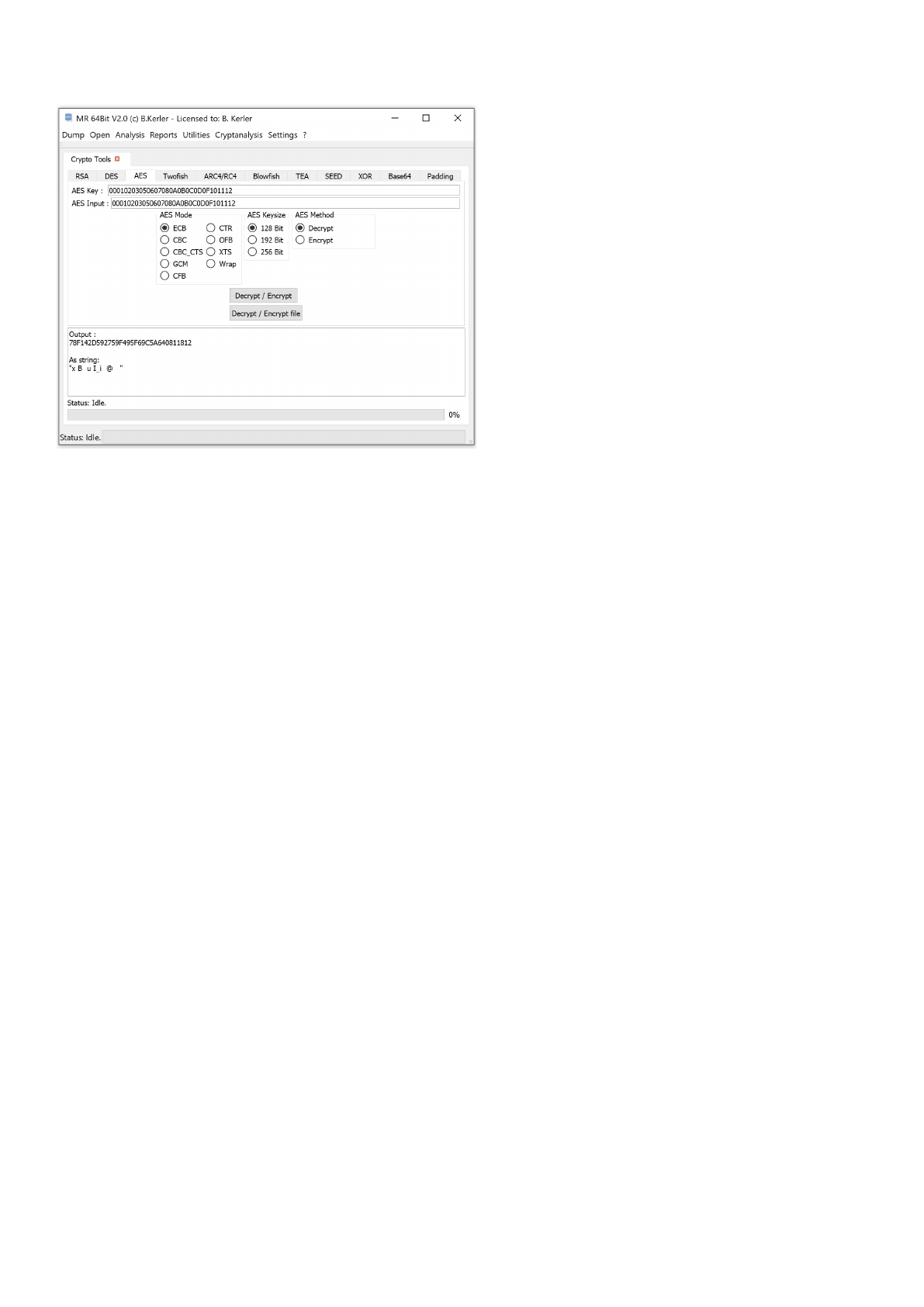
Mobile Revelator 2.2.5
153 / 200
AES

Mobile Revelator 2.2.5
154 / 200
Twofish
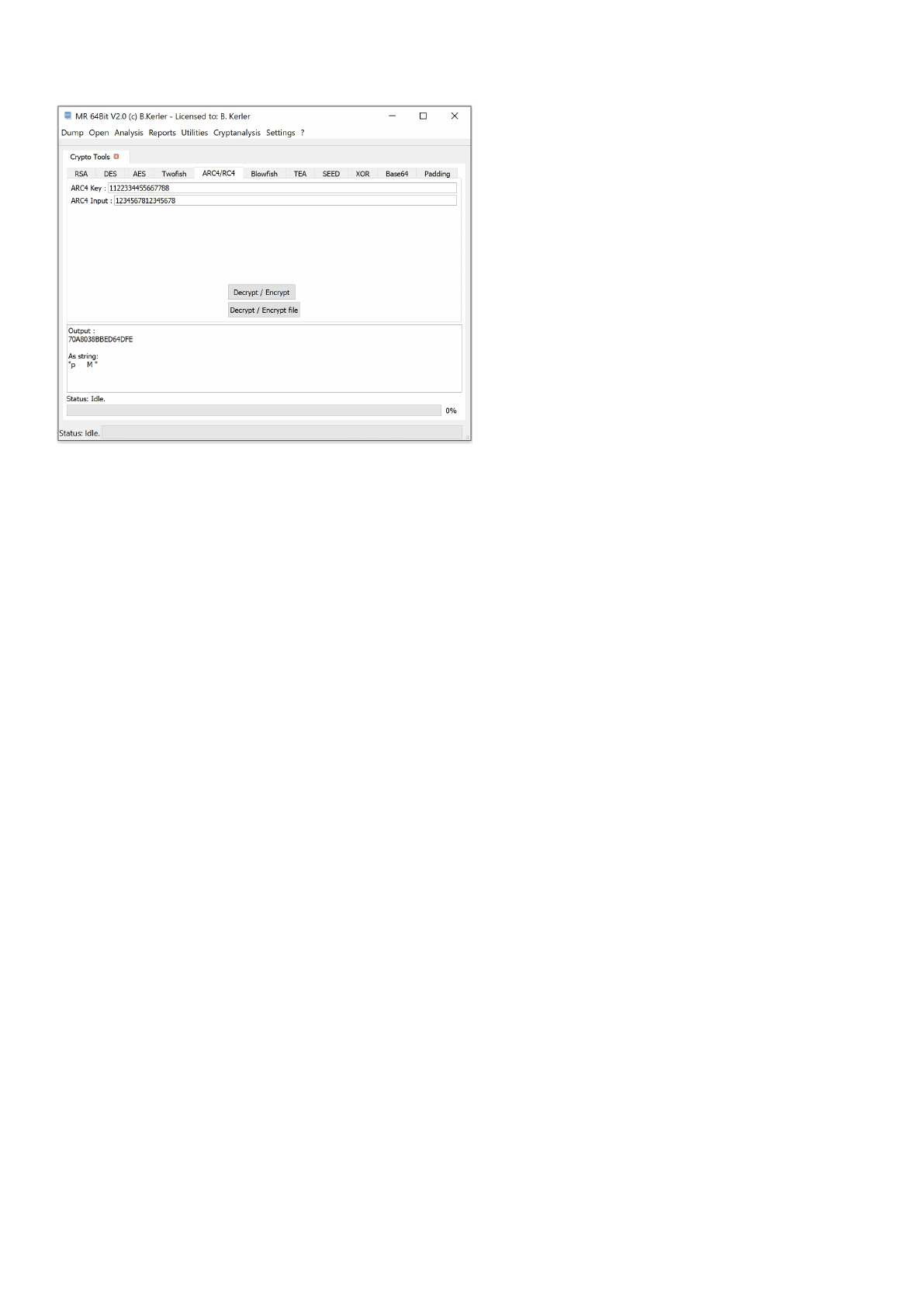
Mobile Revelator 2.2.5
155 / 200
ARC4/RC4
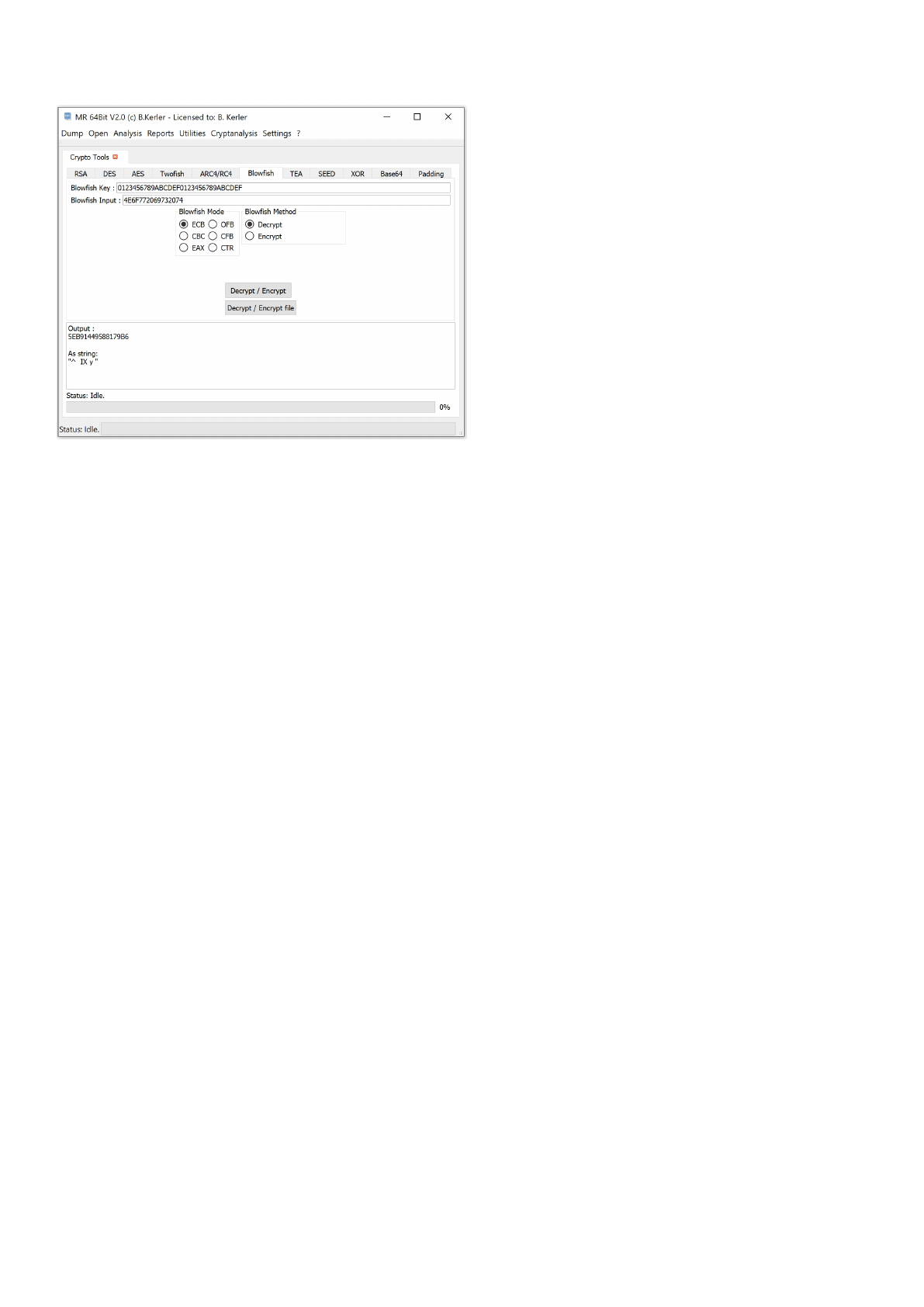
Mobile Revelator 2.2.5
156 / 200
Blowfish
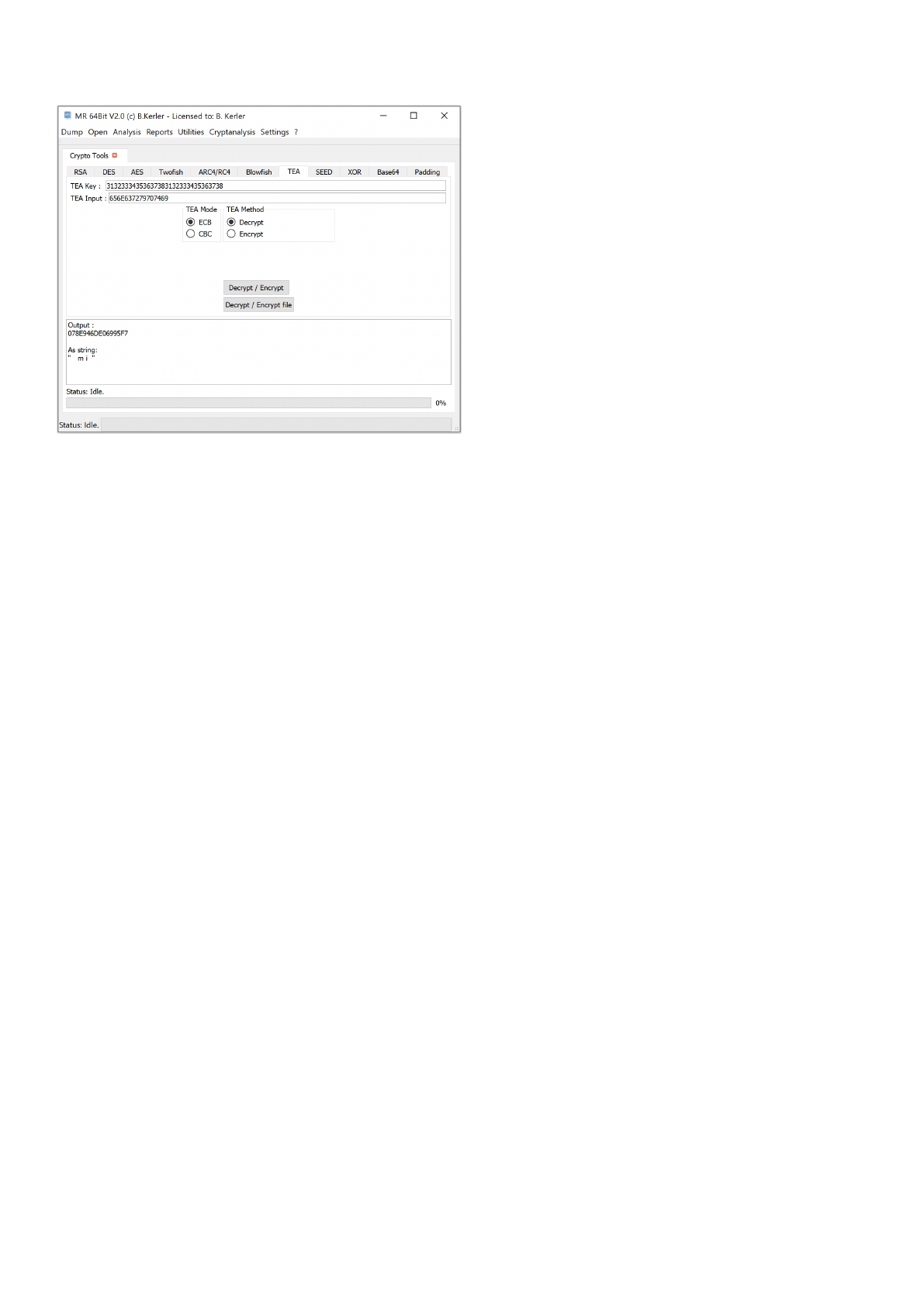
Mobile Revelator 2.2.5
157 / 200
TEA

Mobile Revelator 2.2.5
158 / 200
SEED
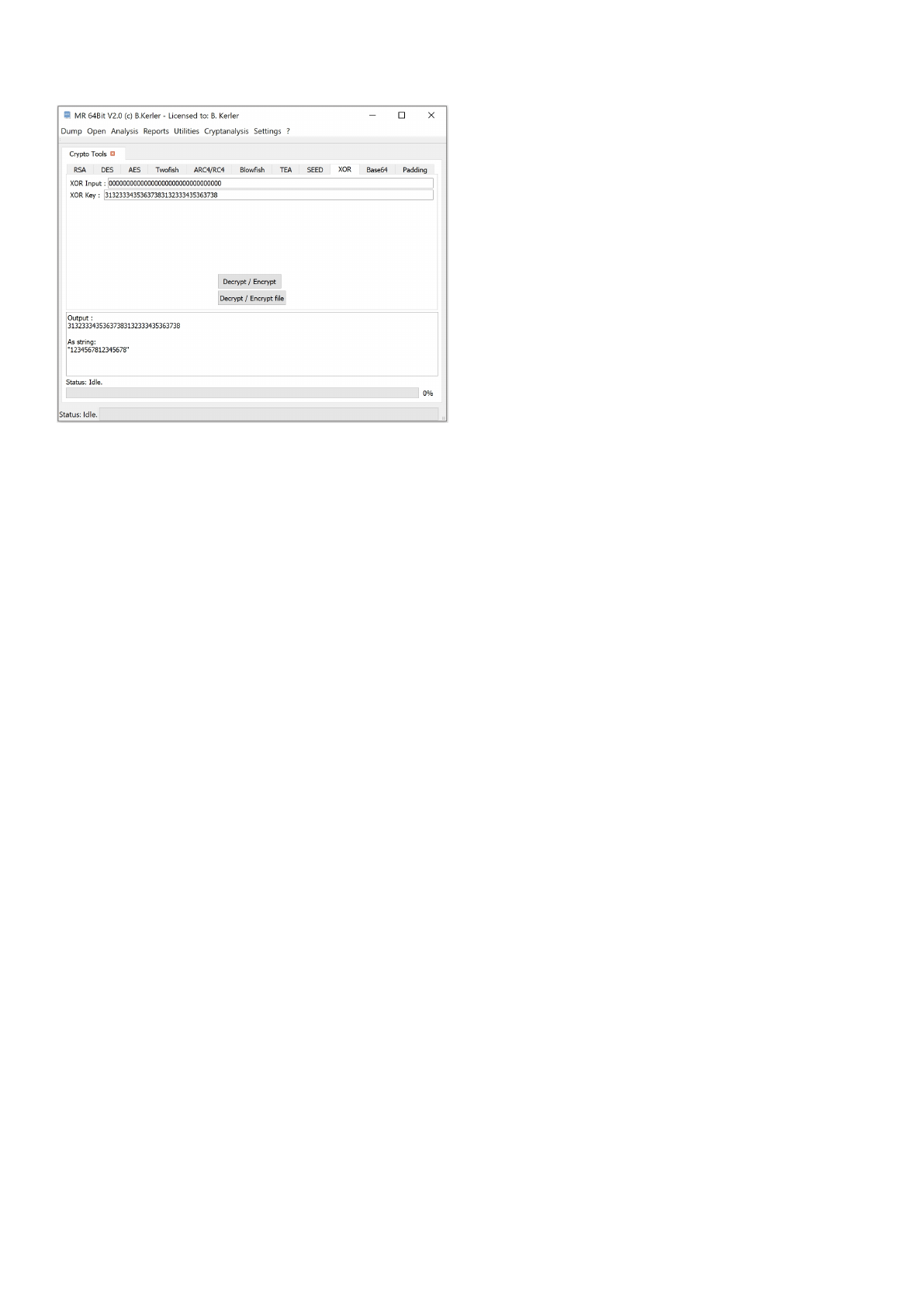
Mobile Revelator 2.2.5
159 / 200
XOR

Mobile Revelator 2.2.5
160 / 200
Base64

Mobile Revelator 2.2.5
161 / 200
Padding

Mobile Revelator 2.2.5
162 / 200
Bruteforce
The bruteforce menu offers several functionality in order to bruteforce passwords and pin codes either via
GPU or CPU. If no GPU has been installed, it is recommended to install the Intel OpenCL SDK, otherwise
the program may crash when trying to use GPU functions. Also we strongly recommend AMD graphic cards,
as NVIDIA cards are comparable slower and error prone.

Mobile Revelator 2.2.5
163 / 200
Android Encryption GPU Bruteforcer
The android GPU encryption bruteforcer is able to bruteforce the PIN/passwords for android devices without hardware
encryption using keymaster. Choosing "Markov stats" might speed up password guesses but may not find all
passwords and is slower than the "Charset" attack. If you select "Wordlist", you may use a wordlist for bruteforcing
instead.
The charset may be any of the known hashcat charsets, which are :
?a = all chars
?d = digit
?u = uppercase letters
?l = lowercase letters
?1 = digits, lower and uppercase letters and some special chars
?2 = 0-9 and A-Z
?3 = a-z and A-Z
For bruteforcing password/PINs, you will need the footer which is either at the end of the userdata partition (last 16K, hex
bytes starting with "C5B1B5"
and at least 0xA00 bytes long) or within the metadata partition. The header contains the first 0x1000 bytes from the
encrypted userdata partition.
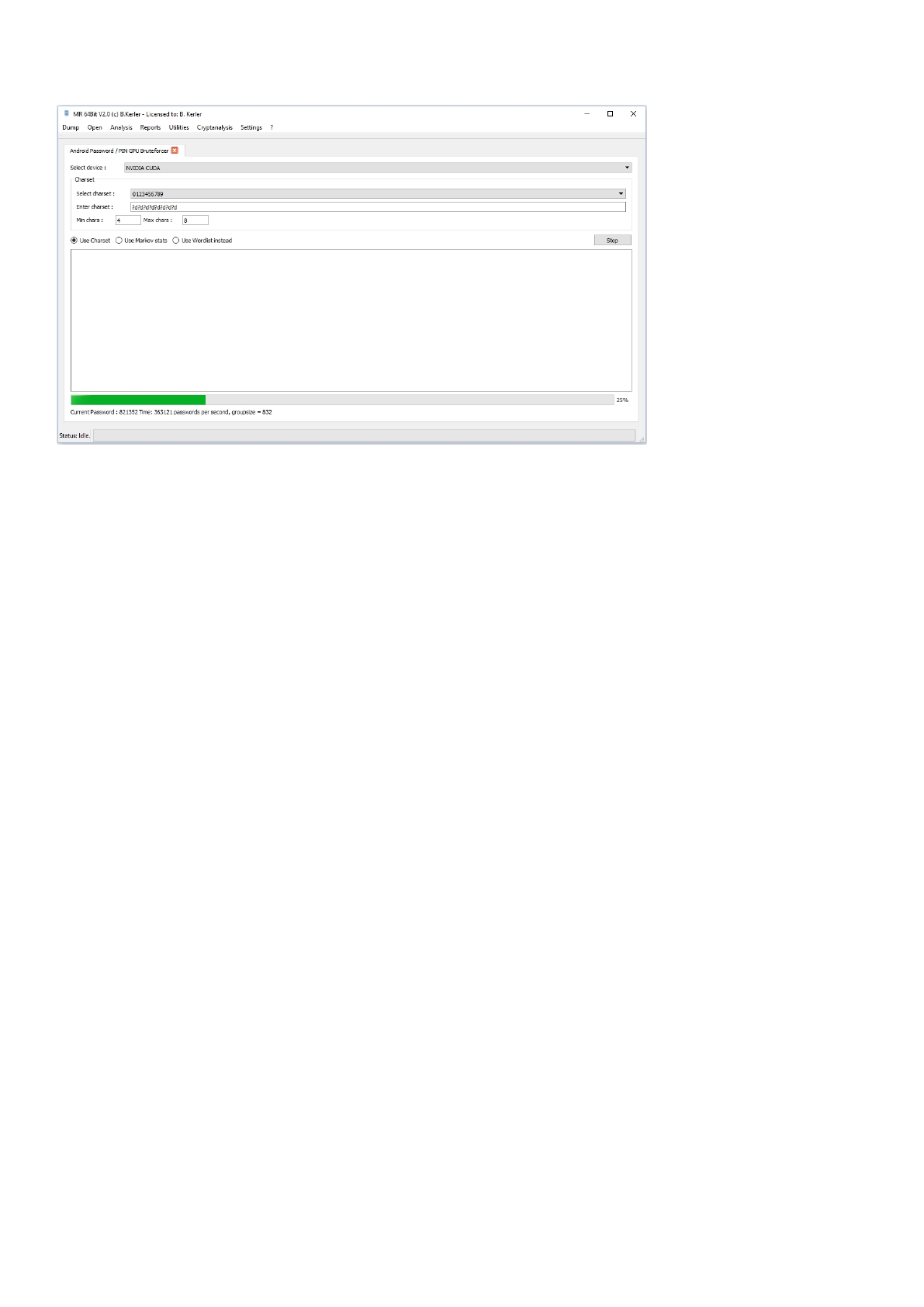
Mobile Revelator 2.2.5
164 / 200
Android Password / PIN GPU Bruteforcer
The android password/PIN GPU bruteforcer is able to bruteforce the PIN/passwords for android devices without hardware
encryption using keymaster. Choosing "Markov stats" might speed up password guesses but may not find all
passwords and is slower than the "Charset" attack. If you select "Wordlist", you may use a wordlist for bruteforcing
instead.
The charset may be any of the known hashcat charsets, which are :
?a = all chars
?d = digit
?u = uppercase letters
?l = lowercase letters
?1 = digits, lower and uppercase letters and some special chars
?2 = 0-9 and A-Z
?3 = a-z and A-Z
For bruteforcing password/PINs, you will need the password.key or sparepassword.key file from /data/system as well
as either /data/com.android.provider.settings/databases/settings.db for android < 4 or /data/system/locksettings.db
including its
-wal and -shm files.
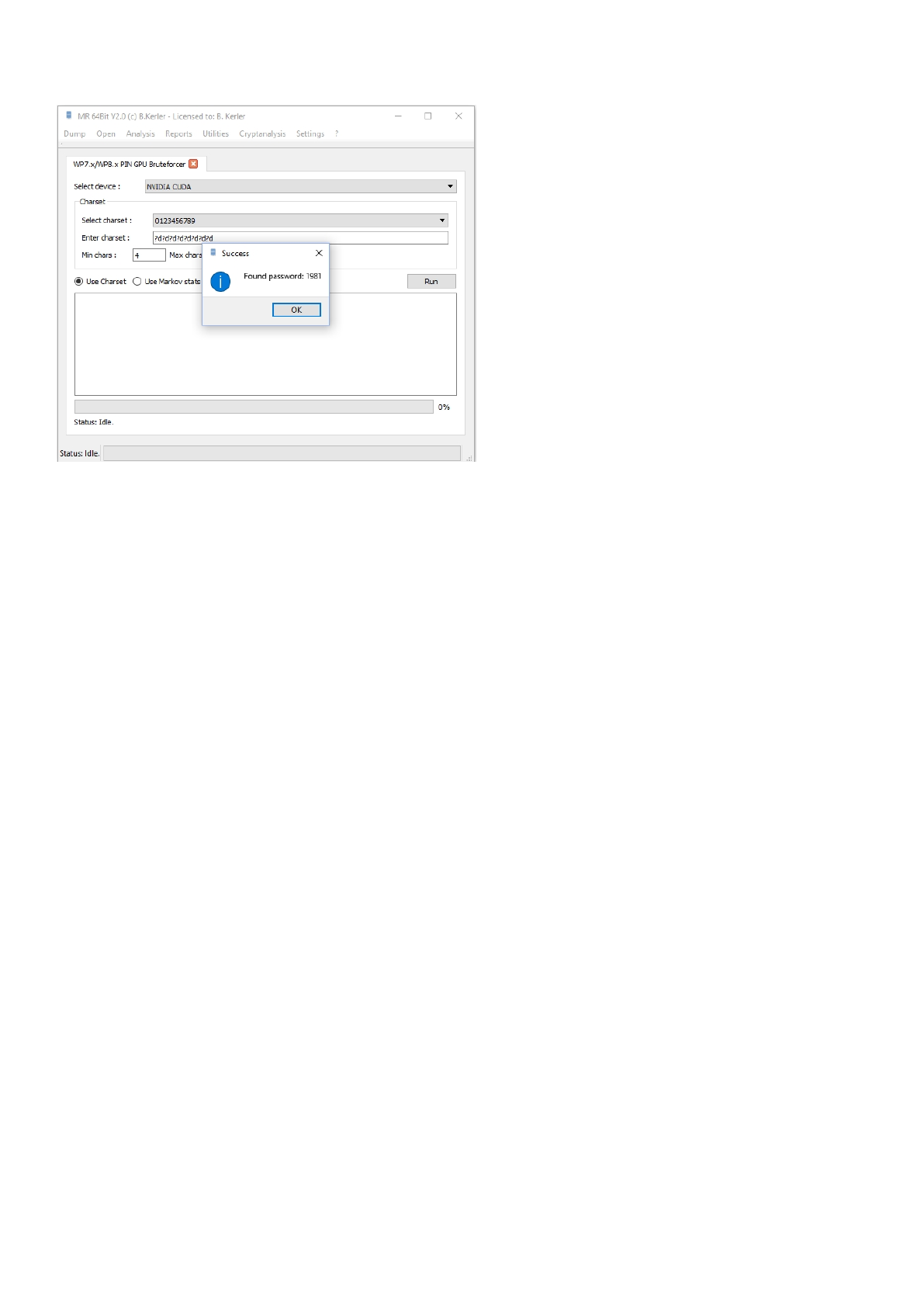
Mobile Revelator 2.2.5
165 / 200
WP7.x/WP8.x PIN GPU Bruteforcer
The WP7.x/WP8.x PIN GPU bruteforcer is able to bruteforce the PIN for Windows Phone 7 and 8 devices. The charset
may be any of the known
hashcat charsets, which are :
?a = all chars
?d = digit
?u = uppercase letters
?l = lowercase letters
?1 = digits, lower and uppercase letters and some special chars
?2 = 0-9 and A-Z
?3 = a-z and A-Z
For bruteforcing WP PINs, you will need the Registry Files, such as "system.hv" or "SOFTWARE" from MainOS/UserFS
partition.
Choosing "Markov stats" might speed up password guesses but may not find all passwords and is slower than the
"Charset" attack.
If you select "Wordlist", you may use a wordlist for bruteforcing instead.

Mobile Revelator 2.2.5
166 / 200
SQLCipher Bruteforcer
The Sqlcipher GPU bruteforcer is able to bruteforce passwords for encrypted sqlite databases using
sqlcipher v2 and v3. The charset may be any of the known hashcat charsets, which are :
?a = all chars
?d = digit
?u = uppercase letters
?l = lowercase letters
?1 = digits, lower and uppercase letters and some special chars
?2 = 0-9 and A-Z
?3 = a-z and A-Z
Choosing "Markov stats" might speed up password guesses but may not find all passwords and is slower than the
"Charset" attack.
If you select "Wordlist", you may use a wordlist for bruteforcing instead.
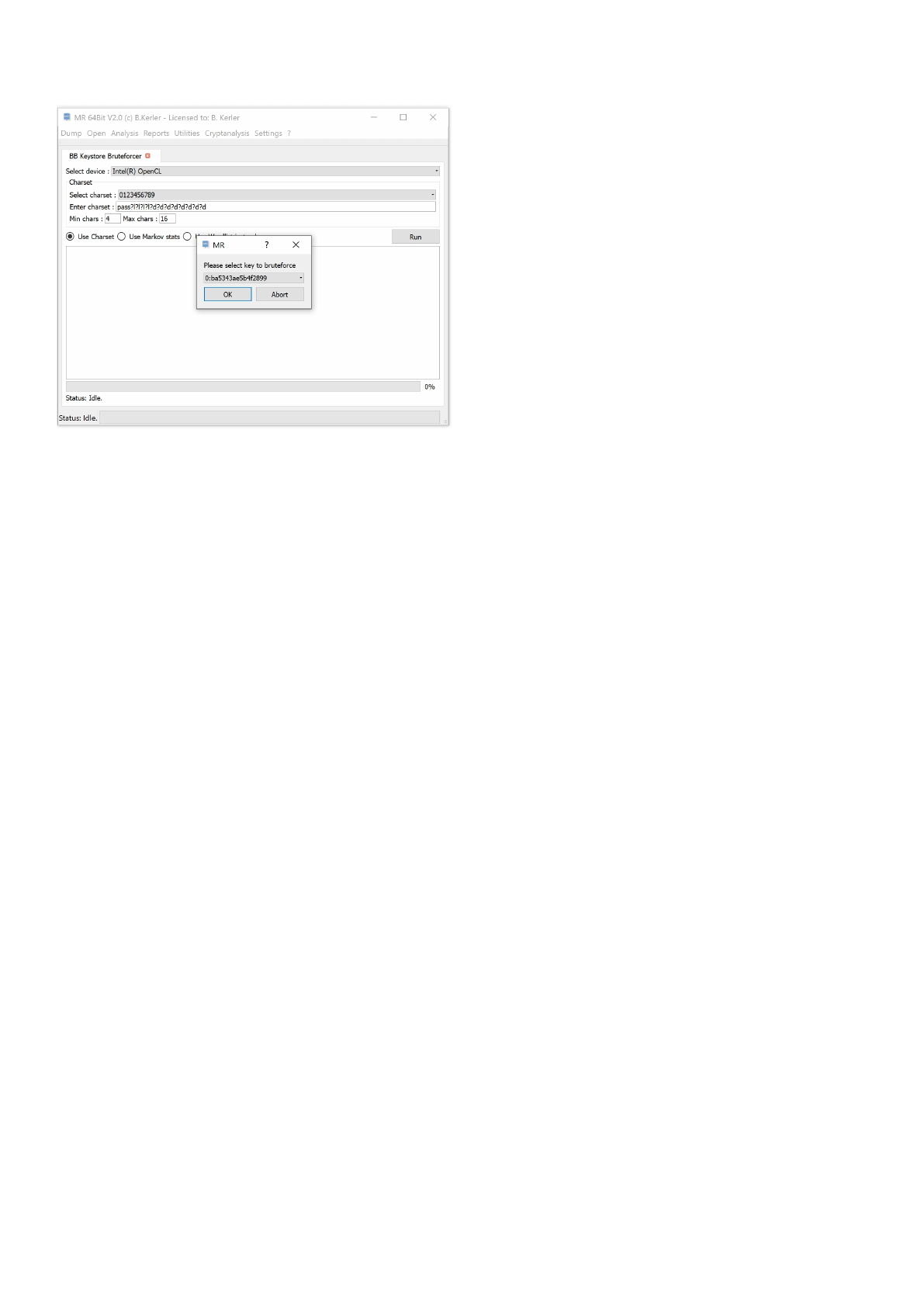
Mobile Revelator 2.2.5
167 / 200
BB Keystore Bruteforcer
The Blackberry Keystore Password GPU bruteforcer is able to bruteforce keystore passwords for either raw images or
.ipd/.bbb backup files. The charset may be any of the known hashcat charsets, which are :
?a = all chars
?d = digit
?u = uppercase letters
?l = lowercase letters
?1 = digits, lower and uppercase letters and some special chars
?2 = 0-9 and A-Z
?3 = a-z and A-Z
Choosing "Markov stats" might speed up password guesses but may not find all passwords and is slower than the
"Charset" attack.
If you select "Wordlist", you may use a wordlist for bruteforcing instead.
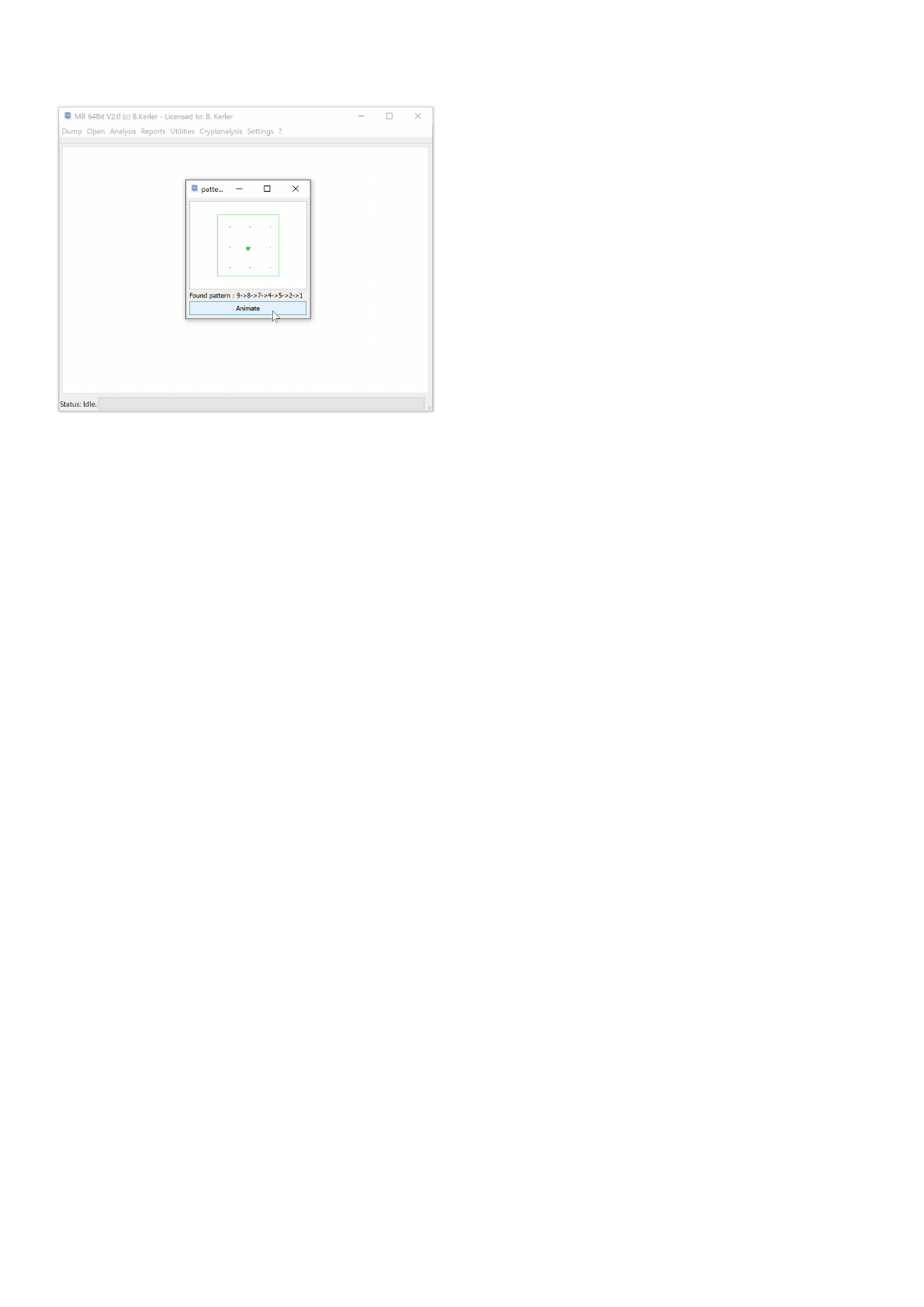
Mobile Revelator 2.2.5
168 / 200
Android Patternlock CPU Bruteforcer
Opening the "gesture.key" file from /data/system directory, this tool will bruteforce and show you the
pattern lock. Just press "Animate" to show an emulation of the pattern.

Mobile Revelator 2.2.5
169 / 200
Bleichenbacher RSA Attack (Exponent 3)
The Bleichenbacher Attack is able to create a fake and valid signature if a rsa certificate with exponent 3 is being used.
Using "Sign image" you are able to sign android images. "Run attack" lets you try fake signatures, just set the correct
modulus (public key) and the hash value to sign for.

Mobile Revelator 2.2.5
170 / 200
Decrypt
The decrypt menu offers several tools to decrypt vendor specific and app specific encryption.
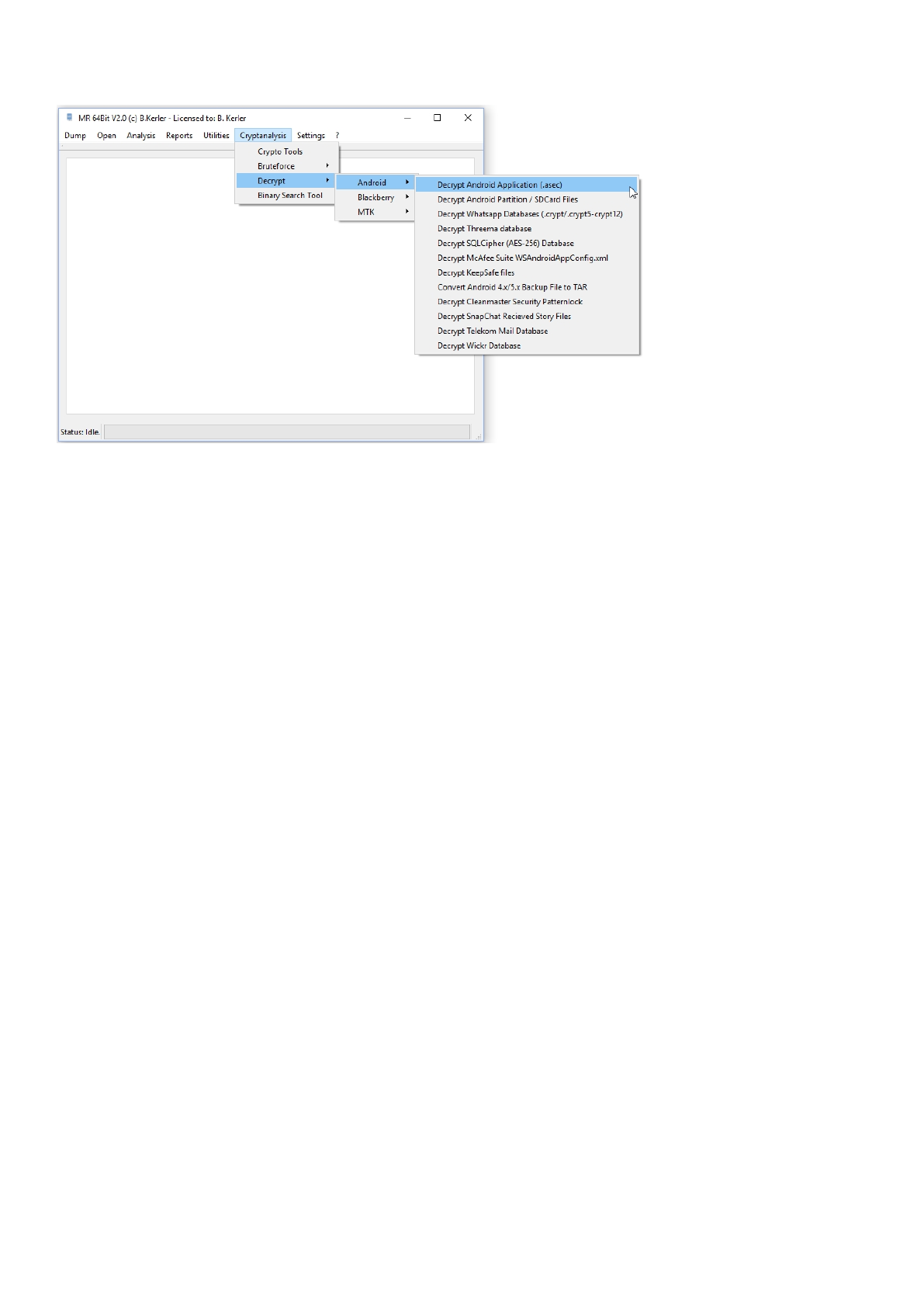
Mobile Revelator 2.2.5
171 / 200
Android

Mobile Revelator 2.2.5
172 / 200
Decrypt Android Application (.asec)
Paid Android Applications may use encrypted Containers with the extension .asec to store the application itself and
application data. Those asec files are normally stored into the directory /data/app-asec. For decryption you will need the
AppsOnSD.sks file from /data/misc/systemkeys.
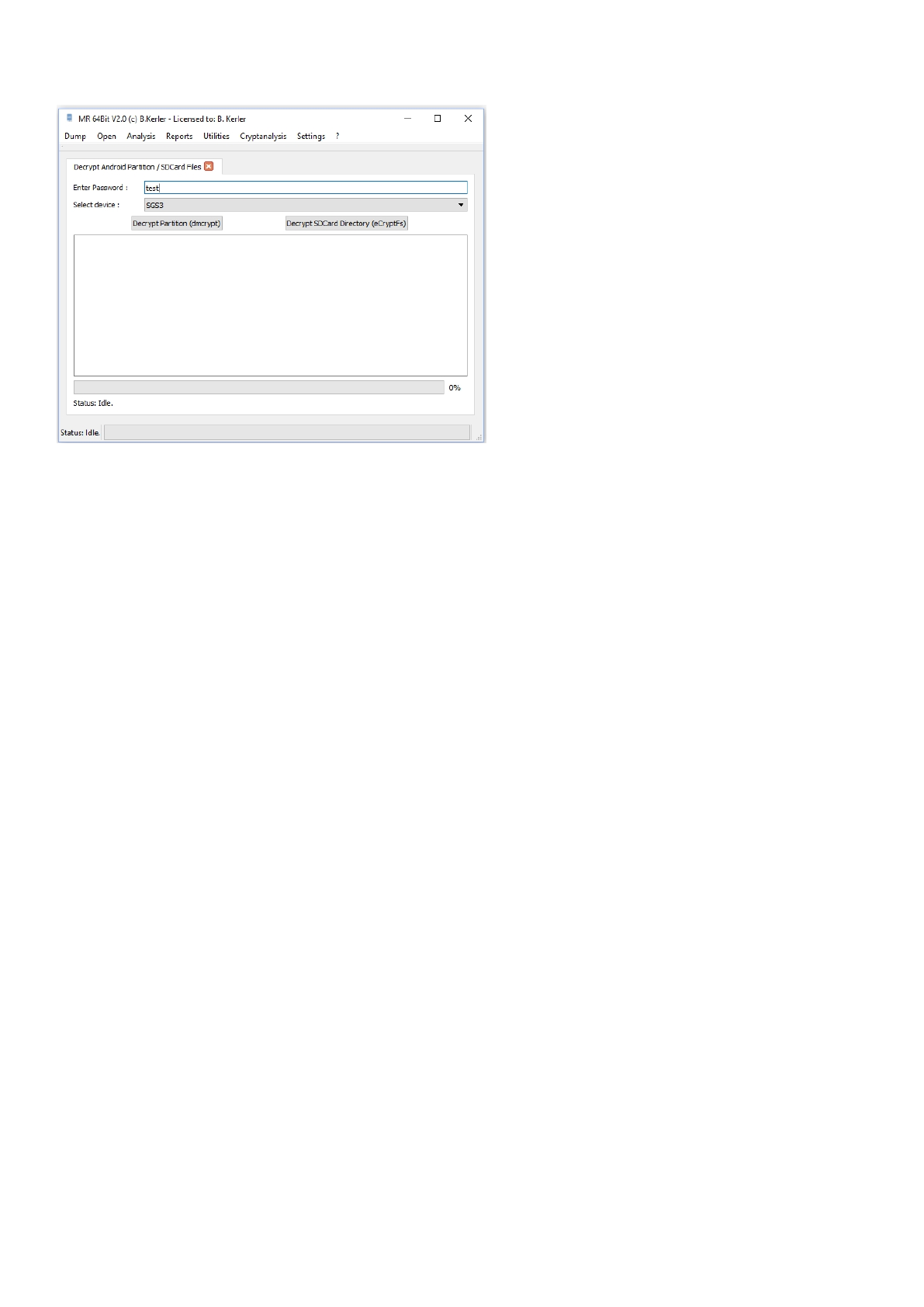
Mobile Revelator 2.2.5
173 / 200
Decrypt Android Partition / SDCard Files
This menu lets you decrypt any Android partition via "Decrypt Partition (dmcrypt)" or sdcard raw image via "Decrypt
SDCard Directory (eCryptFs)" button. Enter the password before pressing any decrypt button. For SDCard decryption you
will need the edk_p_sd file and for partition decryption, you will need the correct footer, starting with hex bytes "C5B1B5"
with a size of at least 0x1000 bytes.

Mobile Revelator 2.2.5
174 / 200
Decrypt Whatsapp Databases (.crypt/.crypt5-12)
This function will decrypt all encrypted whatsapp databases (.crypt/.crypt5/.crypt6/.crypt7/.crypt8/.crypt9/.crypt10/.crypt11/
.crypt12) in one directory using the "key" file from "/data/data/com.whatsapp/files".

Mobile Revelator 2.2.5
175 / 200
Decrypt Threema database
This function will decrypt any Threema application databases.

Mobile Revelator 2.2.5
176 / 200
Decrypt SQLCipher (AES-256) Database
This function will decrypt any sqlcipher version 2 or 3 encrypted application databases.

Mobile Revelator 2.2.5
177 / 200
Decrypt McAfee Suite WSAndroidAppConfig.xml
This function will decrypt McAfee Suite WSAndroidAppConfig.xml file.

Mobile Revelator 2.2.5
178 / 200
Decrypt KeepSafe files
This function will decrypt any keepsafe files without the need of the PIN.

Mobile Revelator 2.2.5
179 / 200
Convert Android 4.x/5.x Backup File to TAR
This function will decrypt android .ab backup files with the given password to a .tar file.

Mobile Revelator 2.2.5
180 / 200
Decrypt Cleanmaster Security Patternlock
This function will deobfuscate the Patternlock stored in the cleanmaster security config xml
"com.cleanmaster.mguard_preferences.xml".

Mobile Revelator 2.2.5
181 / 200
Decrypt SnapChat Received Story Files
This function will try to decrypt all snapchat received story files with known or available aes keys.

Mobile Revelator 2.2.5
182 / 200
Decrypt Telekom Mail Database
This tool is able to decrypt the Telekom Mail App database.

Mobile Revelator 2.2.5
183 / 200
Decrypt Wickr Database
This tool is able to decrypt wickr databases for both PC (using given password and user SID) and Android (using given
password and android_id).
In order to get the user SID for Windows based wickr databases, just run the following command under windows console :
"whoami /user". For android databases, the android_id is stored in the database
"com.android.providers.settings/databases/settings.db" in the table secure.
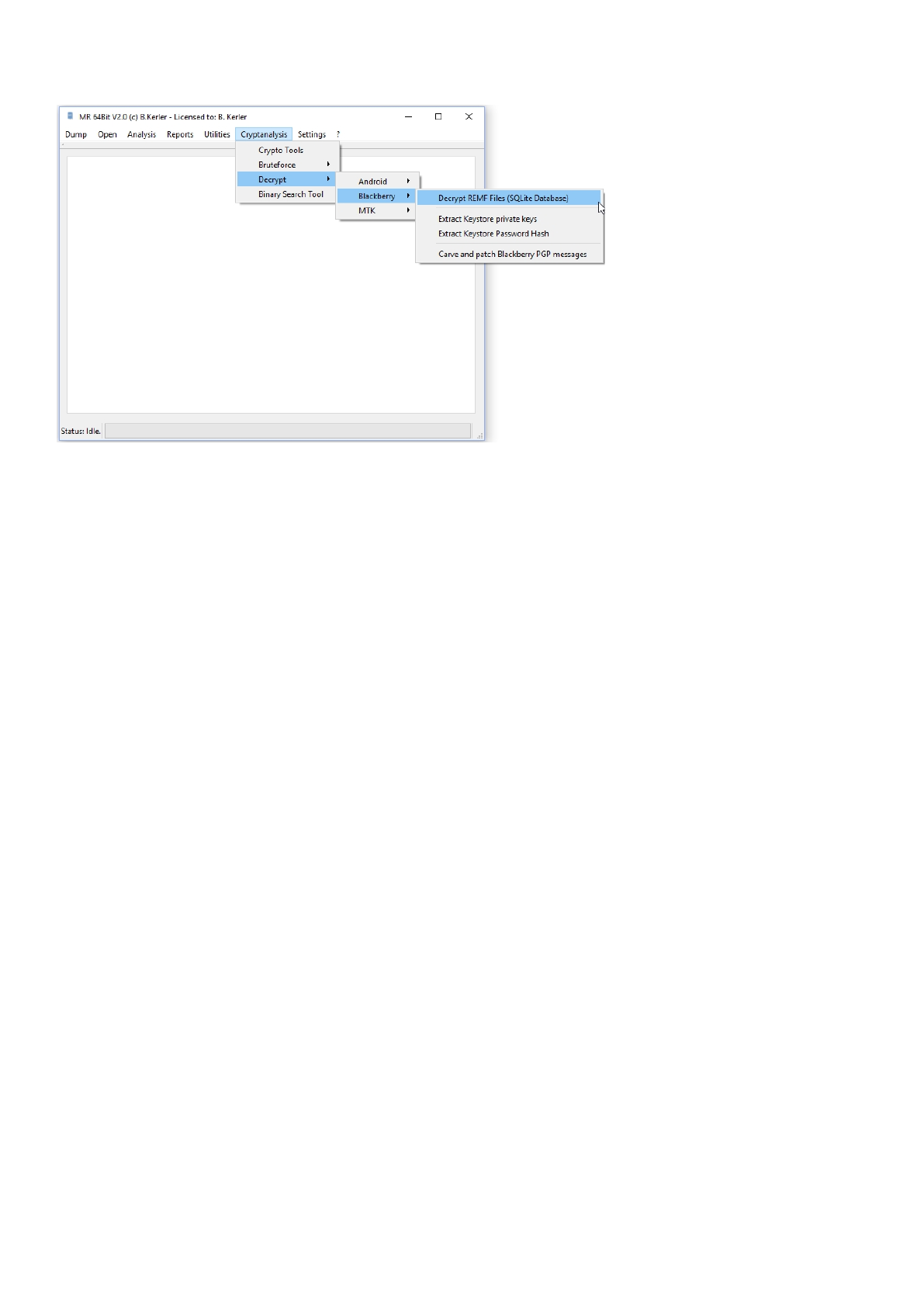
Mobile Revelator 2.2.5
184 / 200
Blackberry
The blackberry menu offers tools to bruteforce/extract passwords, but also extract pgp keys from blackberry backups
(*.bbb / *.ipd) or raw images.

Mobile Revelator 2.2.5
185 / 200
Decrypt Blackberry REMF SQLite Database
This function decrypts any Blackberry SQLite Database encrypted by "REMF" Container using a given Backup .ipd or .bbb
file.

Mobile Revelator 2.2.5
186 / 200
Retrieve Blackberry PGP Private Key
This function will extract any PGP Private key given a password from either Backberry Backup file .ipd/.bbb or any raw
flash image after wear leveling has been reconstructed.
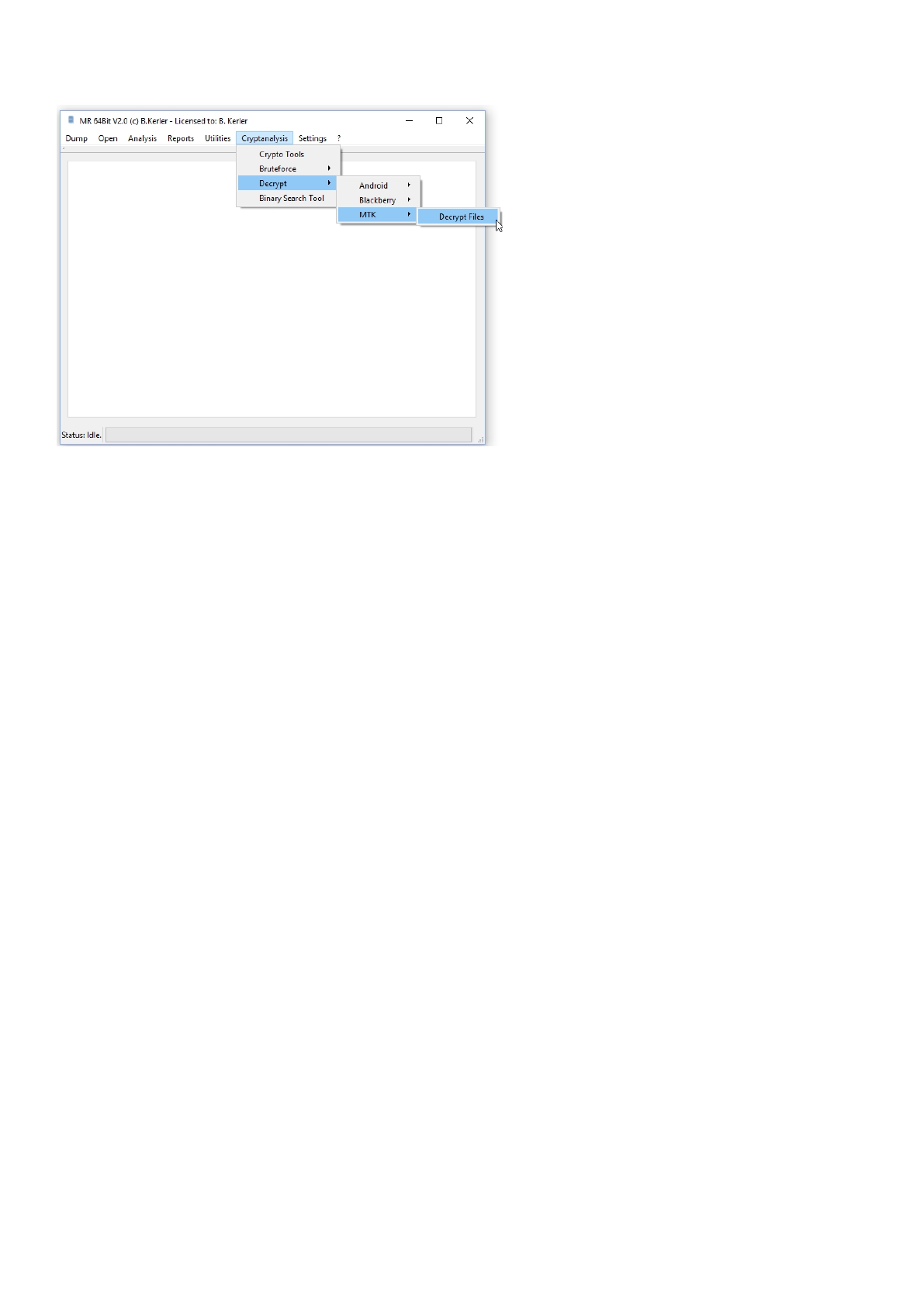
Mobile Revelator 2.2.5
187 / 200
MTK
Mobile Revelator 2.2.5
188 / 200
MTK Decrypt Files
You can decrypt MTK files using this menu. Normally, for correct decryption, segment size has to be modified fitting to the
content. If a non-generic MTK key has been used, enter the customkey as ascii, otherwise leave this field empty.
Depending on the age of the device, you may need to select new or old method for proper decryption.
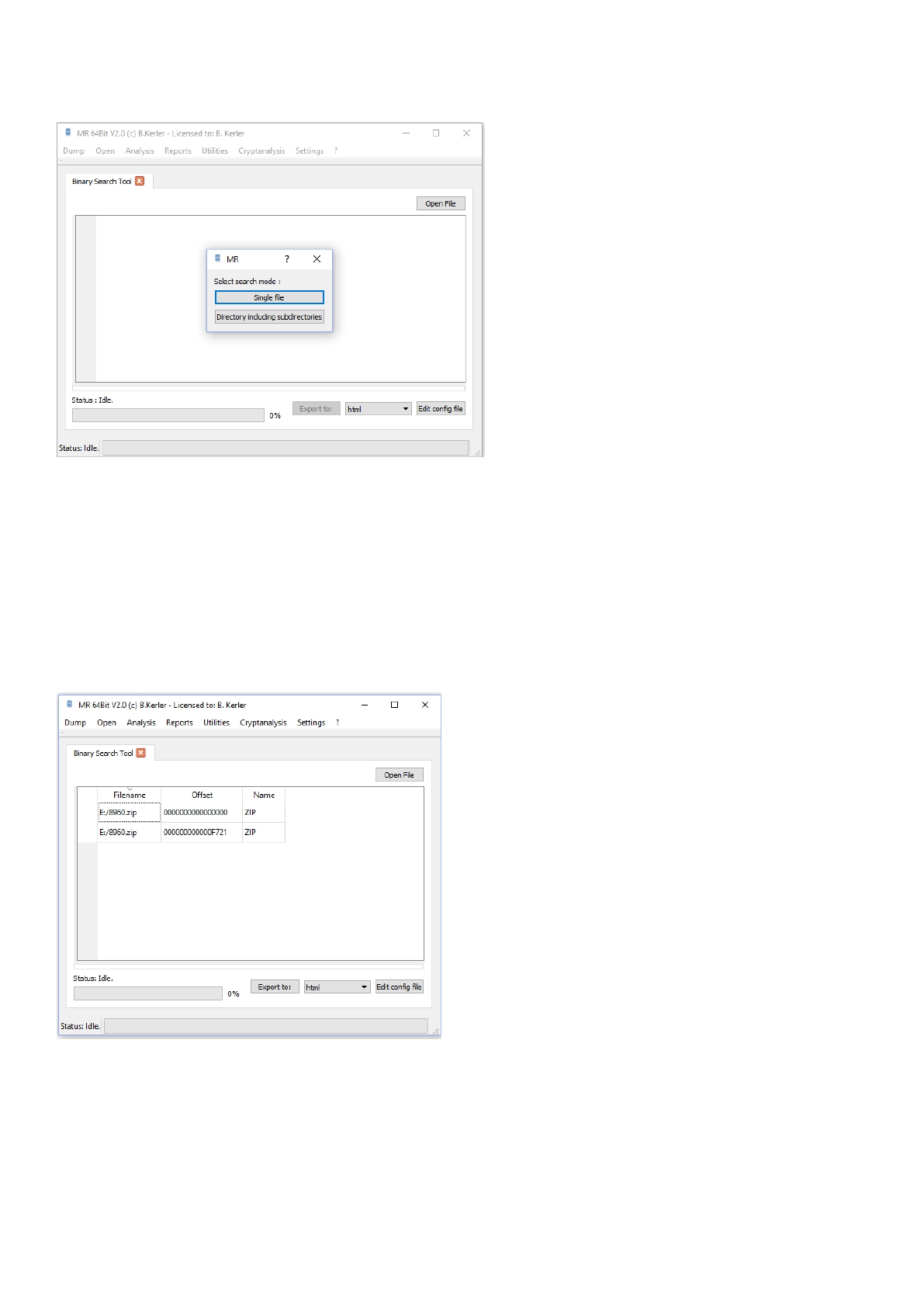
Mobile Revelator 2.2.5
189 / 200
Binary Search Tool
The Binary Search Tool searches for most common file type headers and crypto variables. Using the "Edit config file"
button, you may edit the config file that will be used for searching within files.
The structure within the binarysearch.xml file is :
<crypto signature="EB??904D5357494E" name="FAT MSWIN "/>
- "signature" specifies the signature in hex bytes to search for. "??" is a wildcard for one byte being unknown.
- "name" specifies the displayed name in the report table.
Pressing "Open File", you may specify to search in one single file or in a directory including the subdirectories.
Once it's finished, it's going to show you the corresponding filenames, offsets and the identified name.

Mobile Revelator 2.2.5
190 / 200
Settings
The setting menu uses predefined options for the whole MR program.
Mobile Revelator 2.2.5
191 / 200
Configure
On the Report Settings screen, you can set default settings for reports, including
Examiner and Organisation name and Logo to be displayed on the report.
On the Application Paths screen you can set the application paths for the filesystem tools.
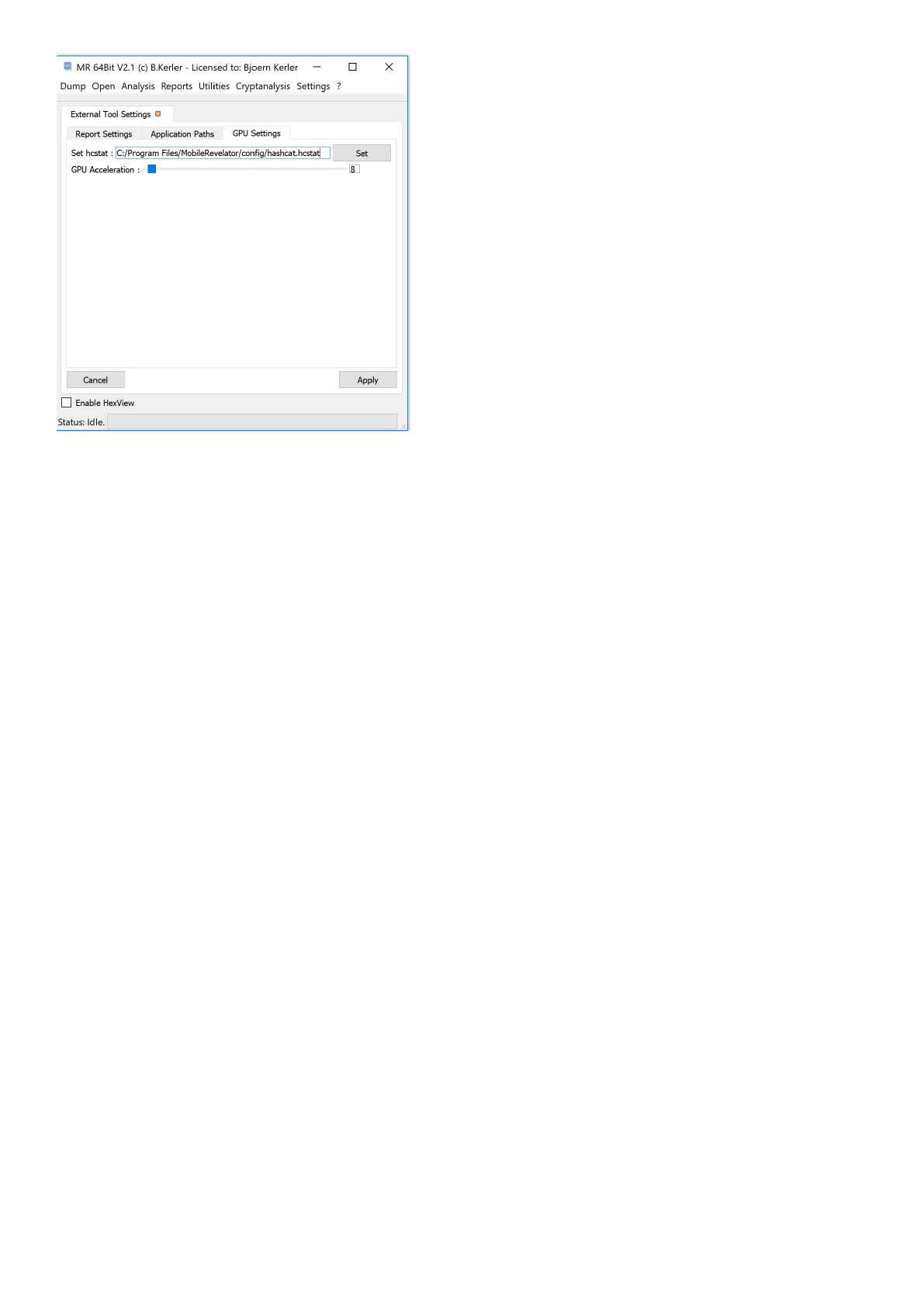
Mobile Revelator 2.2.5
192 / 200
On the GPU Settings tab, you can modify GPU Acceleration and own hcstat files
used for GPU Bruteforcing. Higher GPU Accleration can increase speed, but can also
crash your graphic card driver or slow down your pc to be unusable.
Press "Set" in order to choose the application executable that should be used. Once you're
finished setting up the options, just press "Apply" and the settings will be stored.

Mobile Revelator 2.2.5
193 / 200
Templates Documentation
SQLite Template and Timeline xml Files :
Templates help you to automatically interpret known fields using self-written xml-templates. Pressing "Open template/plugin
directory" will open up the directory containing the template directory. Alternatively, you may open up the path "c:
\Users\[Username]\Documents\MobileRevelator\templates\" on windows. Templates are being written as package name
unter its Operating System Directory name such as "Android" or "iOS".

Mobile Revelator 2.2.5
194 / 200
Timeline XML Documentation
Example :
<?xml version='1.0' encoding='utf-8' standalone='yes' ?>
<Items>
<Template table="messages" name="Tinder tinder.db" path="tinder.db">
<column id="user_id (QString)" type="sqlcmd">
<r cmd="SELECT matches.user_name FROM matches WHERE matches.user_id=='[%1]';"/>
</column>
<column id="match_id (QString)" type="sqlcmd">
<r cmd="SELECT matches.user_name FROM matches WHERE matches.id=='[%1]';"/>
</column>
</Template>
<Timeline path="com.tinder/databases/tinder.db" type="database">
<sql cmd="select messages.rowid, messages.created, matches.user_name, messages.text from messages
INNER JOIN matches ON matches.id = messages.match_id;">
<type text="Tinder" category="Messenger"/>
<package/>
<timestamp field="{%1}" format="yyyy-MM-ddThh:mm:ss.zzzZ"/>
<foregroundtime/>
<desc/>
<contact/>
<contact_alias>
<field addfields="{%2}"/>
</contact_alias>
<message>
<field addfields="{%3}"/>
</message>
</sql>
</Timeline>
</Items>
The timeline module has a fixed amount of table columns and are specified as :
type : Title of the extracted content
package : Package information, such as namespace or application
timestamp : Timestamp
foregroundtime : Total commulated foreground time or total call time
desc : Additional data or description
contact : Raw contact id as used by the application
contact_alias : Alias given for a raw contact id
message: Message or Email content only
image : Images as ByteArray to display
All timeline applications can be defined in separate xml files under the os directory name such as "Android" or "Windows".
Timeline entries always have to start with "<Timeline" entry. Be aware that you may need to replace special chars as
defined at the beginning of the xml file, otherwise the xml file cannot be interpreted correctly.
1. Timeline items
<Timeline path="com.android.providers.media/databases/external.db" type="database">
<Timeline path="databases/analytics_db2" type="database">
<Timeline path="kuaiya.play/databases*emmsg.db" type="database">
Every timeline item is unique for each database being extracted. You can define the path, which points directly to the
application database. You may use * as a wildcard, if filename changes or path is unknown. The type defines whether it is
an sqlite database as "database" or a raw file with type "raw". For raw files, you need to provide python scripts for
decoding.
2. Analysis of Timeline items
<attach database="com.sgiggle.mango/files/profilecache.db" alias="profile"/>
Each item can have different databases being attached using an alias, which can then be used by any sqlite command for

Mobile Revelator 2.2.5
195 / 200
requests. One sqlite request for example with an attached database would be : "select * from profile.table;"
<python run="Zapya (Android)">
<sql cmd="SELECT rowid, name, direction, createtime, url, path, category, totalbytes from transfer;">
You can either run sql commands or run python plugins. Python plugins use the defined plugin name in the python itself. Sql
Commands can be any valid sqlite command.
<python run="Zapya (Android)" arguments="user=False">
Using the arguments field, you can send custom small python scripts to the given python script as initial argument being
run before running the script. Given arguments can then be used within the script.
3. Categories
For each result of the sql or python result table, you can define where the table cell entry should be used for.
Type:
<type text="Tango Messages" category="Messenger">
The Type field has the description text of the module, called "text" and a describing category which will be listed when the
report is done, called "category".
Timestamps and Foregroundtime:
<timestamp field="{%3}" int="/1000"/>
<timestamp field="{%6}" format="yyyy-MM-dd hh:mm:ss"/>
<foregroundtime field="{%5}" int="*1000"/>
In the examples, {%3} and {%6] define the 4th and 7th result entry. The timestamp field additionally contains the function
"int", which can be used for calculations of the returned value and the function "format" in case the result value is a
formatted time string.
Description, Contact, Contact_Alias, Message, Image:
<desc>
<field addfields="Media_Id: {%4};"/>
<field addfields="Del_Status: {%12}" replace="0=False;1=True"/>
<field addfields="Status: "{%5}"" unbase64="0"/>
<field addfields="Memo:"{%3}";" unhtml="1"/>
<field latitude="{%1}" longitude="{%2}"/>
</desc>
The field addfields function can be used to combine Text together with result entries. Each field addfields line only is able to
hold one result entry. Additionally, you can replace result entries using the "replace" function, whereas each value to be
replaced is separated by semicolon. Furthermore result entries with Base64 content can be regulary decoded using the
function "unbase64" and the value 0, and url decoded using the value 1. The function "unhtml" with the value 1 can be used
to unescape html based text. If a field contains latitude and longitude instead of addfields, it will return a location string
based on the given latitude and longitude.

Mobile Revelator 2.2.5
196 / 200
Template XML Documentation
Example :
<?xml version='1.0' encoding='utf-8' standalone='yes' ?>
<Items>
<Template table="messages" name="Tinder tinder.db" path="tinder.db">
<column id="user_id (QString)" type="sqlcmd">
<r cmd="SELECT matches.user_name FROM matches WHERE matches.user_id=='[%1]';"/>
</column>
<column id="match_id (QString)" type="sqlcmd">
<r cmd="SELECT matches.user_name FROM matches WHERE matches.id=='[%1]';"/>
</column>
</Template>
<Timeline path="com.tinder/databases/tinder.db" type="database">
<sql cmd="select messages.rowid, messages.created, matches.user_name, messages.text from messages INNER
JOIN matches ON matches.id = messages.match_id;">
<type text="Tinder" category="Messenger"/>
<package/>
<timestamp field="{%1}" format="yyyy-MM-ddThh:mm:ss.zzzZ"/>
<foregroundtime/>
<desc/>
<contact/>
<contact_alias>
<field addfields="{%2}"/>
</contact_alias>
<message>
<field addfields="{%3}"/>
</message>
</sql>
</Timeline>
</Items>
The name-Field is the name being displayed in the Template List. Path should be the name of the database in order to
autodetect the database when opening up.
Each template for each table starts with either the "table", in this case "btopp" or a sql database query which starts with
"database". If you only want to see
the columns being listed in the template, add the option "deletemissingfields="true". Then, for each column, you may start
the following actions :
1. Replace an integer range with text : r from="xxx" to="xxx" with=text"
2. Replace an integer or text with text : r replace="xxx" with="xxx"
3. Run any sqlcmd with the current value in the column [%1] with : r cmd="sqlquery"
Mobile Revelator 2.2.5
197 / 200
Python API Documentation
1. Generic information :
For SQLite or Timeline plugins :
Each python plugin has to have a first line which indicates the name of the plugin, example :
#Pluginname="Telegram Messages (Android)"
For FS plugins :
Each python plugin has to have two first lines which indicate the name and the category of the plugin, example :
#FSPluginname="Telegram Messages (Android)"
#Category="Reports"
Errors on runs can be shown by using the python console display.
The plugin class is ctx.
2. Python functions :
Main functions which interact with MR GUI:
void gui_setMainMessage (int type, QString text, QString title) Display a messagebox with title and text, type
0 is Information, type 1 is Warning.
void gui_setMainProgressBar (int pos) Set the main progressbar to a position between 0 and
100
void gui_setMainLabel (QString text) Set the main label
QString gui_getpythonpath() Return the path to the installed python executable
QString gui_getpythonscriptpath() Returns the path where the python scripts reside
QString gui_askSaveDir (QString label) Asks for a directory to save to and returns the
directory name, otherwise "" if user aborted.
QString gui_askSaveFile (QString label, QString filename="", QString filter="") Asks for a file name to save and
returns the file name. otherwise "" if user aborted.
QString gui_askFile (QString label, QString filename="", QString filter="") Asks for a file name to read and returns
the file name. otherwise "" if user aborted.
QString gui_askDir (QString label) Asks for a directory and returns the directory name,
otherwise "" if user aborted.
bool gui_askYesNo (QString label) Will display label, asking the user to press yes or no. Result
is true for yes and false for no.
void gui_log_addText (QString text, bool clear=false) Add a text to the log window. Set clear if log window
shall be cleared first
QString gui_getscriptpath() Returns the current script path.
QString gui_getDate (unsigned int query) Convert unix timestamp to time string.
QString gui_add_report_relevant_file (QString filename) Add report relevant file paths for timeline module
to extract.
QVariantList gui_data_size() Return the row and column count from the current table
view as List.
QVariant gui_get_data (int row, int col) Get data from current table view
bool gui_set_data (int row, int col, QVariant entry) Set any data in current table view
bool gui_set_data_bytearray (int row, int col, QVariant entry) Set any data as bytearray in current table view
void gui_update() Refresh gui in order to show table results
void gui_update (int connection) Refresh gui in order to show table results for
a given sqlite connection index.
bool gui_remove_rows (int row, int col, int count) Remove rows from the current table view.
bool gui_remove_columns (int row, int col, int count) Remove columns from the current table view.
bool gui_add_column (QString text) Add Columns to the current table view.
bool gui_set_data_color (int row, int col, int r, int g, int b, int a=0) Set the background color of a specific cell of
the current table view.
QStringList gui_get_headers() Get the headers from the current table view.
bool gui_set_headers (QStringList headers) Set the headers from the current table view.
void gui_clear_data() Clear all table data.
QStringList gui_get_currentcell() Returns current active selected cell (row,column) as an

Mobile Revelator 2.2.5
198 / 200
array.
QStringList pluginfilenames() Returns filenames to be parsed by the timeline module.
FS Browser specific functions:
int fs_file_extract (QString filetoextract, QString outpath) Extract file from file tree, return -1 if it fails.
Example: fs_file_extract("/data/local/tmp/file.db","C:/extracttohere")
void fs_hide (QString filename) Hide a file from file tree
int fs_isDir (QString filename) Returns 1 if given filename is a directory
int fs_isFile (QString filename) Returns 1 if given filename is a file
int fs_dir_extract (QString dirtoextract, QString outdir) Extract directory from file tree, return -1 if it fails.
Example: fstree_dir_extract("/data/local/tmp","C:/extracttohere")
QStringList fs_filelist() Returns a list of all files and directories from the file tree
QStringList fs_getselected() Returns a list of all currently selected files
QStringList fs_getDir (QString filename) Returns a list of all files from a given file tree directory
bool fs_sqlcipher_decrypt (QString inputfile, QString outputfile, QString passwd) Decrypt a sqlciphered database using a
given password.
QStringList fs_gettime (QString filename) Returns created, lastRead and modified timestamp for a
given file as a string list
SQLite functions for accessing databases:
int sqlite_open (QString filename, bool external) Open a file as sqlite database, set external to true
for external files, false for files from file tree. Returns -1 if it fails, otherwise db connection index.
If the filename specific is "gui", the current open database in the program
context is being used.
QString sqlite_last_error (int dbconnection) Return the last Sqlite error using a given connection
index.
bool sqlite_close (int dbconnection) Close the given db connection index.
int sqlite_run_cmd (int dbconnection, QString query) Runs a given query string using a given db
connection index, returns -1 if it fails, otherwise connection index.
Example: "sqlite_run_cmd(dbindex,"SELECT * from table;")",
bool sqlite_cmd_close (int connection) Close the given connection index.
int sqlite_get_deletedrecords (int dbconnection, QString tablename) Returns all reconstructable deleted records
and stores them into the sqlite table using given database
connection index.
Returns -1 if it fails, otherwise connection index.
QStringList sqlite_get_headers (int connection) Returns a list with all field names from given
connection index.
bool sqlite_set_headers (int connection, QStringList headers) Sets all field names from given connection
index and field names as string list.
QVariantList sqlite_get_data_size (int connection) Returns a list with current rows and column count.
QVariant sqlite_get_data (int connection, int row, int col) Return sqlite table entry using given row, column
and connection index.
bool sqlite_set_data (int connection, int row, int col, QVariant entry) Set sqlite table entry using given connection
index. Example: "sqlite_set_data(cmdindex,0,0,"Hello World")".
bool sqlite_set_data_bytearray (int connection, int row, int col, QVariant entry) Set sqlite table entry as bytearray using
given connection index. Example: "sqlite_set_data(cmdindex,0,0,"Hello World")".
bool sqlite_remove_rows (int connection, int row, int count) Remove rows at row index with row count using
given connection index.
bool sqlite_remove_columns (int connection, int col, int count) Remove columns at column index with
column count using given connection index.
bool sqlite_add_column (int connection, QString text) Add column to the sqlite table data with given field
name to given connection index.
bool sqlite_set_data_color (int connection, int row, int col, int r, int g, int b, int a) Set sqlite table entry color using given
row and column, connection index, and color (rgb) as well as
alpha(transparency) value.
void sqlite_clear_data (int connection) Clear the current sqlite table with given connection
index.
bool sqlite_save_as_xlsx (int connection, QString fileName, QString name) Save the current sqlite table as xlsx-file with
given connection index, filename to save to and name.

Mobile Revelator 2.2.5
199 / 200
QString sqlite_get_filename (int connection) Return the current sqlite database filename from a
given connection index.
QString sqlite_get_filename() Return the current sqlite database filename.
Generic functions:
QByteArray base64todata (QString text, int type) Convert Base64 Data to QByteArray.
QString htmltotext (QString html) Convert HTML to plaintext.
QString getlocationcell (QString mcc, QString mnc, QString lac, QString cid) Convert cell data to location string.
QString getlocation (double lat, double lon) Convert latitude and longitude to string.

Mobile Revelator 2.2.5
200 / 200