Offensive Security's Guide To Alpha Part1
User Manual:
Open the PDF directly: View PDF ![]() .
.
Page Count: 30
09/01/2018 Offensive Security's Complete Guide to Alpha
https://forums.offensive-security.com/showthread.php?t=4689&p=20530#post20530 1/30
Forum PentestingWithKali LabMachines PublicNetwork 10.11.1.71 OffensiveSecurity'sCompleteGuidetoAlpha
Thread:OffensiveSecurity'sCompleteGuidetoAlpha
LogOutSettingsMyProfileNotificationsWelcome, OS26810
What'sNew?
NewPosts PrivateMessages FAQ Calendar Community ForumActions QuickLinks
ReplytoThread Results1to10of125 Page1of13 12 3 11 ... Last
ThreadTools SearchThread
05122016, 03:58PM
JoinDate:
Posts:
Jun2011
538
OffensiveSecurity'sCompleteGuidetoAlpha
WelcometoOffensiveSecurity'scompleteguideto"Alpha".
Warning.Thisthreadcontainsspoilers.
PleasenotethatAlphacannotbeincludedinyourLabReport
TableofContents:
Introduction
Abstract/Overview
Reconnaissance
DNS
LabNotes/ExistingMachines
OffsecNinja/IRCBotHint
InformationGathering
PortScanning
Services(Part1SSH)
Services(Part2HTTP)
WebApplication(Part1Main)
WebApplication(Part2Hidden)
VulnerabilitiesvsExploitsvsCVEs
SearchSploit(Part1)
WebApplication(Part3[SPOILER])
SearchSploit(Part2)
[SPOILER]
WebScanners
LimitedShell
Exploit#1Manually(Part1PoC)
Exploit#1Manually(Part2RemoteShell)
Exploit#1Manually(Part3BashTrick)
Exploit#2ExploitDB
Exploit#3Metasploit
PrivilegeEscalation
InformationGathering(Part1OS)
InformationGathering(Part2RunningProcesses)
InformationGathering(Part3InstalledPackages)
InformationGathering(Part4InstalledPrograms)
InformationGathering(Part5Configfiles)
Method#1[SPOILER](Part1Setup)
Method#1[SPOILER](Part2Exploiting)
Method#2[SPOILER](Part1SSH)
Method#2[SPOILER](Part2SU)
PostExploitation
Lastupdated:2017Sept12
Lasteditedbyg0tmi1k;09122017at12:13PM.
#1
OffsecStaff
g0tmi1k
Forum
09/01/2018 Offensive Security's Complete Guide to Alpha
https://forums.offensive-security.com/showthread.php?t=4689&p=20530#post20530 2/30
PWB/OSCP(2011)|WiFu/OSWP(2013)|CTP/OSCE(2013)|AWAE(2015)|AWE(2016)
Reply ReplyWithQuote
05122016, 04:09PM
JoinDate:
Posts:
Jun2011
538
Abstract/Overview
Introduction
Thisisour(OffensiveSecurity)guidetotargeting,attackingandcompletingthemachine"Alpha".
Itisthefirstpartofaseries,withtheothermachinesof"Beta"&"Gamma"(ComingSoon).
Duringallofthesemachines,wewilldisplayhowwegoabouttacklingthesemachines,showingyouallourfindings&
mistakes.Hopefullythiswillhelpbuildupyourmethodologiesandtechniques.
Pleasenote,thisisacompletewalkthrough.WewillcovereverythingforAlpha.Asaresult,ifyoudonotwantthemachineto
bespoiltforyou,stopreadingnow.
Note,wewillnotacceptanyotherthreadsontheforumwhichcontainspoilers.
Unliketheothertwomachines(Beta&GammaComingSoon),thisisNOTanexOSCPexammachinebutanexedb
machine(10.11.1.219),thatwehavebroughtbackfromthedead!
Normally,wewouldrecommendchoosingatargetbasedontheinformationyouknowaboutamachine,ratherthangoingafter
aspecificone.
e.g.Thelowhangingfruit,ratherthanhuntingforaboxorworkingIPaddressessequentially.
...Butwearegoingtobreakthisruleforthisguide.
Atthisstage,usingtoolssuchasnmap/arpscan/netdiscoverwouldbeusefultoseeallthemachinesinthesubnetwhichwe
wouldhaveaccessto,thenstartportscanningfor"keyservices"(DNS,FTP,HTTP/HTTPS,NetBIOS,SSH/rDesktop/VNC).
Wewillcovermultiplemethodsofgatheringthenecessaryinformationtofindthevulnerability,fromthissingleissueusethree
differentexploitsinordertogetaremoteshellonthemachine.Tofinishtheguideoff,twodifferentvulnerabilitiestogetthe
highestlevelofprivilegeonthesystem,root.
Abstract/Overview
Thismachineisvulnerabletothe"shellshock"exploit,viaApache'sCGImodule.Thewebapplication(BigTreeCMS)isadecoy.
Wecovertwomethodstoescalateprivileges,eitherbytargetingOSSEC(whichismeanttoprotecttheOS)!Orbyretrying
theMySQLcredentialstothenonrootuserontheboxandthensudo'ingtoroot.
Pleasenote:Theremaybeothermethodsofgettinglocalaccessandtechniquestoacquirearootshellwhichmaybe
discoveredatalaterdate(akaundocumentedsolutioninthisguide).
Lasteditedbyg0tmi1k;09272016at10:05AM.
PWB/OSCP(2011)|WiFu/OSWP(2013)|CTP/OSCE(2013)|AWAE(2015)|AWE(2016)
#2
OffsecStaff
g0tmi1k
Reply ReplyWithQuote
05122016, 04:19PM
JoinDate:
Posts:
Jun2011
538
Reconnaissance
DNS
Theveryfirstthingistolocatethismachine(Alpha)inthenetwork.
Theeasierwaytodothisisbycompletingthecoursematerial(*cough*theDNSexercisebecausewediddothat,right?
*cough*).
AsthisisaguidetoAlpha(andnotthecoursematerial),wewillretractcertainbitsofinformationhere.
#3
OffsecStaff
g0tmi1k
09/01/2018 Offensive Security's Complete Guide to Alpha
https://forums.offensive-security.com/showthread.php?t=4689&p=20530#post20530 3/30
Code:
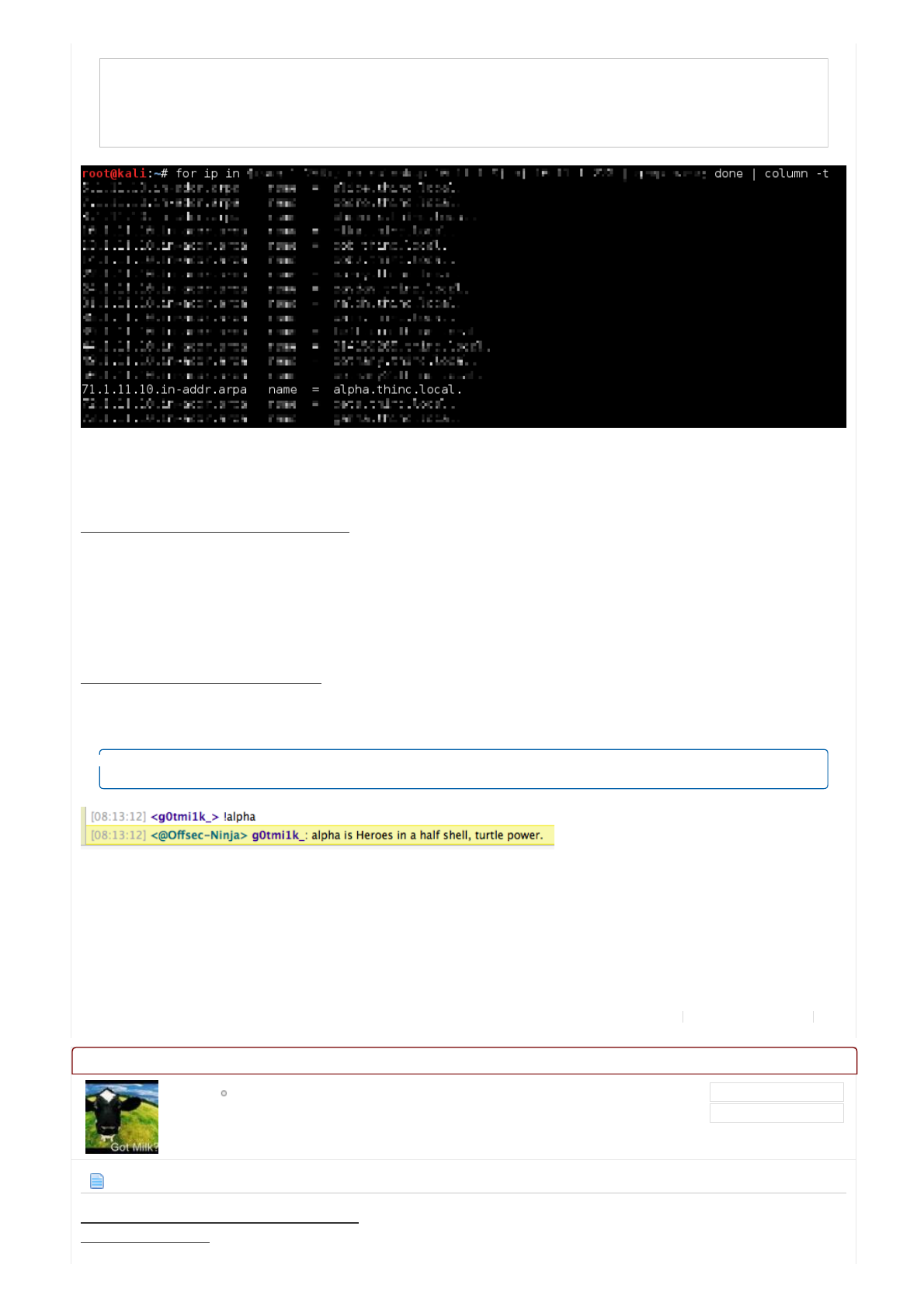
Sowecanseethat10.11.1.71isalpha.thinc.local.
LabNotes/ExistingMachines
SowenowhaveanIPaddress(10.11.1.71)andhostname(alpha.thinc.local).
Atthispoint,itwouldbeagoodtimetocheckourlabnotes(madeupfrominformationgatheredfromalltheothermachines
preandpostexploitation).
e.g.Isthereanymentionofthismachineonanynetworkservicewecanreach?Orarethereanypersonal
files/filenames/contentsthatrelatetoAlpha?
...Asitwouldbespoilinganyothermachine(s)wemadesurethistargetdoesnotrequireanyotherstocompleteit.
OffsecNinja/IRCBotHint
Anotherthingwecandoafterwehavefoundoutthehostnameforamachine,ischeckthe#OffsecIRCbot(OffsecNinja).
Thesecluesherearenotoften"directly"useful.Sometimesitsamusingquotes,othertimesitsreferencestothemachine
whichyoumayonlyunderstandAFTERWARDS.Butsometimes...youmaygetlucky!
Forhowtoconnecttothechannelseeourguidehere.Makesuretoregisteryournicknametoallowyoutotalkinthechannel.
Note#1:Thisisnotreallyusefulatthisstage,butitwillbemadeclearlateron...
Note#2:Somepeopleatthisstagemayalreadyknowofthereferencefromthefranchise"TeenageMutantNinjaTurtles".
Note#3:TheIRChinthasbeenupdatedtopointtothisguide.
Lasteditedbyg0tmi1k;05232017at04:38PM.
PWB/OSCP(2011)|WiFu/OSWP(2013)|CTP/OSCE(2013)|AWAE(2015)|AWE(2016)
root@kali:~# for ip in ...RETRACTED... done | column -t
...SNIP...
71.1.11.10.in-addr.arpa name = alpha.thinc.local.
...SNIP...
root@kali:~#
<g0tmi1k_>!alpha
<@OffsecNinja>g0tmi1k_:alphaisHeroesinahalfshell,turtlepower.
Reply ReplyWithQuote
05122016, 04:43PM
JoinDate:
Posts:
Jun2011
538
InformationGathering
PortScanning
Wearegoingtostartoffby...revertingthemachine!
#4
OffsecStaff
g0tmi1k
09/01/2018 Offensive Security's Complete Guide to Alpha
https://forums.offensive-security.com/showthread.php?t=4689&p=20530#post20530 4/30
Wehaven'tgotacluewhatstatethemachineisincurrentlyandwedonotwanttomissanythingatthisstage.Astudentmay
ofalreadyexploitedacoreservice,andthevulnerabilitykillstheservice,closingtheportandwewouldn'tbeawarewesee
thisdaily.
Oncethemachinehassuccessfullybeenreverted,we'lldoaveryquickportscan,thenperformacompletescanafterwards.
Thisallowsustostarttogetanideaandfeelforthemachinestraightawaywithouthavingtowaitaboutfornmaptocomplete
elsewemayhavetochangeuphowwearescanningthemachine.
#1LightScan
Thequickscan(notusinganyofnmap'sinbuiltscriptingengineorfeatures)willdothe"10mostcommonports"(Thesorting
orderofportsisbasedonnmap'sfindingovertheyears).
Code:
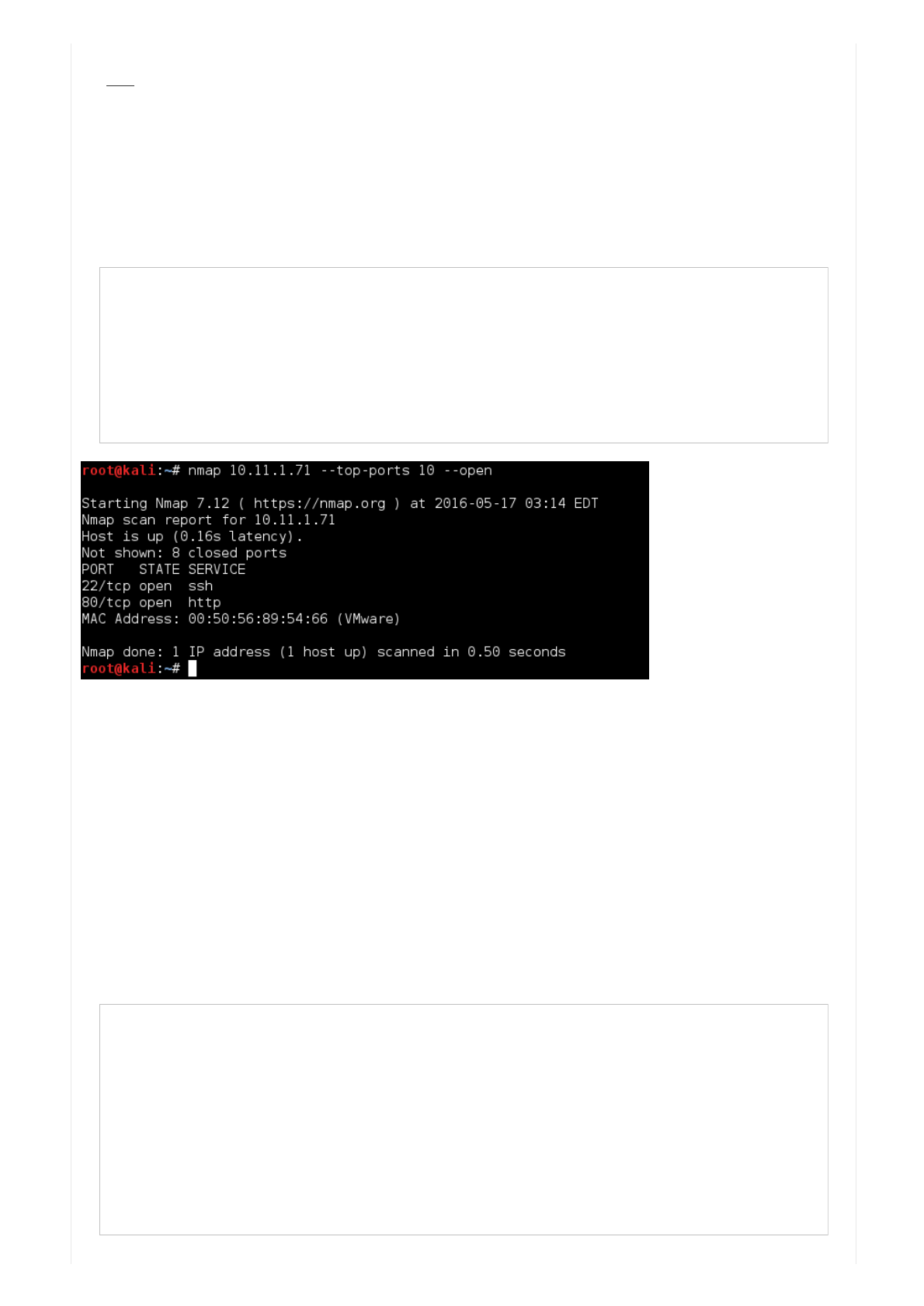
Twoportsopen!TheyarethedefaultportsforSSH(TCP22),andHTTP(TCP80).
Note,Wehaven'tconfirmedtheservicesbehindtheportsjustthedefaultportsvalueareopen(*cough*Itwouldbesneaky
thingforasystemadministrator/Offsectomixuptheservices*cough*).
Becauseport22isopen,defaultingtotheSSHservice,thishintsthetargetcouldbe*nixbased(itispossibleSSHisinstalled
onWindows,howeverit'snot"common"atthetimeofwritingasitcouldchangewithWindows10inafewyears'time...)
andaddonthefactwedidn'tseeTCP3389beingopen(WindowsRDP),*nixveryoftenusesVNCinsteadwhichisona
differentport.
#2HeavyScan
Now,wecanstartdoingacompletescan(TCP165,535),byusing"p",whichisalotmorenetwork'heavy'(soit'sgoingto
takelonger).
Wearealsogoingtostartgrabbingtheservicebanners,basedonthedefaultserviceport,bydoing"sV".
Itispossibletogetnmaptoshowitsjustificationforitsresultsbydoing"reason".
...andwehaven'talteredourDNSvalue(/etc/resolv.conf)tousethePWKlabnetwork,soletsmanuallyuseadifferentvalue
(removedtonotspoilthecoursematerial,asitisanexercisetofindit!)
Note,wedidn'tuse"A"(whichdoesn'tstandfor"all")option,asitmakestheoutputtoocomplexforthetimebeing(aswell
asmakethescantakelongertocomplete).
Code:
root@kali:~# nmap 10.11.1.71 --top-ports 10 --open
Starting Nmap 7.12 ( https://nmap.org ) at 2016-05-17 03:14 EDT
Nmap scan report for 10.11.1.71
Host is up (0.16s latency).
Not shown: 8 closed ports
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
MAC Address: 00:50:56:89:54:66 (VMware)
Nmap done: 1 IP address (1 host up) scanned in 0.50 seconds
root@kali:~#
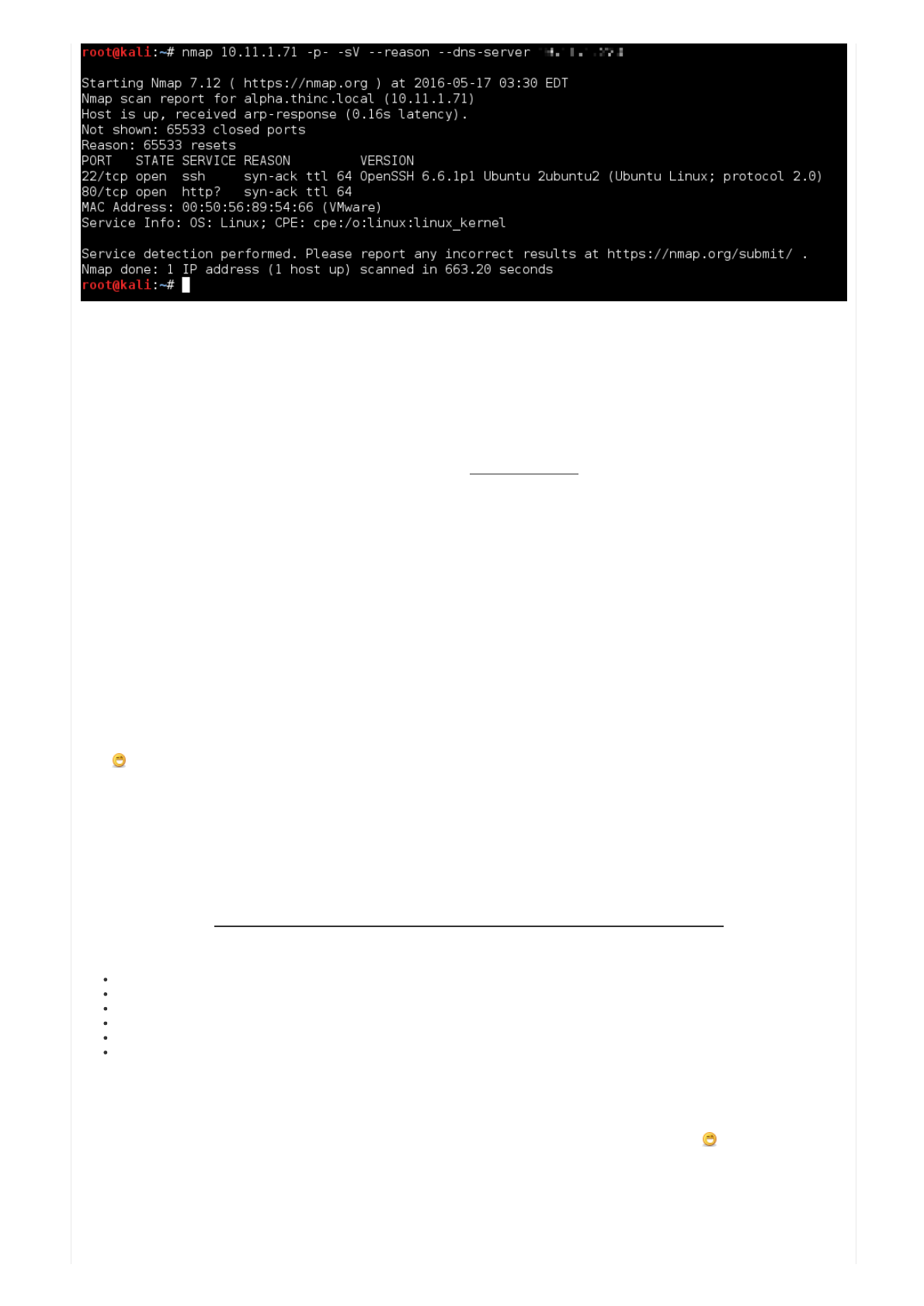
root@kali:~# nmap 10.11.1.71 -p- -sV --reason --dns-server [RETRACTED]
Starting Nmap 7.12 ( https://nmap.org ) at 2016-05-17 03:30 EDT
Nmap scan report for alpha.thinc.local (10.11.1.71)
Host is up, received arp-response (0.16s latency).
Not shown: 65533 closed ports
Reason: 65533 resets
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack ttl 64 OpenSSH 6.6.1p1 Ubuntu 2ubuntu2 (Ubuntu Linux; protocol 2.0)
80/tcp open http? syn-ack ttl 64
MAC Address: 00:50:56:89:54:66 (VMware)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 663.20 seconds
root@kali:~#
09/01/2018 Offensive Security's Complete Guide to Alpha
https://forums.offensive-security.com/showthread.php?t=4689&p=20530#post20530 5/30
Asthisisgoingtotake"awhiletocomplete"(Youcanseethescantookover10minutestocompletethelightscan,less
thanasecond),wecouldriskstartingtolightlyuse/pokeatthetargetatthesametime(orwecanusethistimetolookat
anothermachine,tweak/updateournotes,makeadrink,orgetonwithanyotherworketc.).
Wedon'treallywanttoaddtoomuchtothenetworktrafficorthetarget'ssystemload,asitmaymaketheportscanresult
inaccurate.
...andiftheportscanareincorrect,it'sgoingtoupseteverythingthatfollows(Wehaveseenstudentsspenddaysfailing
becauseofincorrectinformation).
Thisisbecauseportscanningisthefirstthingwedodirectlytothetargeteverythingafteralldependsonitsresults(aka
portscanningisTHEessentialcorestagethatwecannotaffordtobeincorrectwhichlinksnicelybacktorevertinga
machinebeforescanning!).
Somakingafewrequeststoserviceswouldbeacceptable(asanormalenduserwould).Wedon'twanttostartbrute
forcingservices(likeahackerwould),orcauseanyissues/errors(likeahackermaydo)asthatmaytriggersometypeof
protectionandblockourIPaddress...
Sotheportscanfinishes,andweonlyseethetwoportsthatwealreadyknewabout.Thereisn'tanythinghidingonasneaky
higherport(*cough*thatwouldbemeanofus,right?*cough*).Wecannowstartthinkingaboutlookingattheservices
behindtheports...
#3OtherPortScanTypes
SofarwehaveonlytouchedonTCPports.Don'tforgetaboutUDP(*cough*becausewehaven't*cough*).
NmapisabletoscanforUDPservices,howeverifyouthoughtTCPwasslow...
Thereareothertoolsouttherewhichareabletoperformaportscan(thatisn'tpoweredbynmap).Oneofthembeing
"unicornscan".
Ipersonallyfindthistobemuchquickerthannmap(ingeneral),butitdoesn'thavenmap'spowerfulscriptingengine.Oneof
theadvantagesofitistheoptions,controlandpoweryouhaveusingit,butthedownsidetothis,unicornscanisslightlymore
"confusing"touse.
Astudentofours,superkojiman,hasmadeawrapper(onetwopunchhttps://github.com/superkojiman/onetwopunch)which
mergestheadvantagesofunicornscan'sspeedandnmap'sscripts.However,thiscanbesomethingyouresearchinyourown
time .
SideNote:ScanningMultipleTargetsAtOnce&PostExploiting
Wedonotrecommendscanninga"largeamount"oftargetsatonceforvariousreasons.
Whilstitis"doable",dependingonyournetworkconnection(speedandhowstableitisnotetheVPNusesUDPandnot
TCP),youwillbewaiting"awhile"(dependingonwhatscanningoptionsyouuse).
Whenscanningoverarangeoftargets,nmapwillbehavebytreatingallthemachinesequally.Ifamachinehasafirewall
enabledthatslowsnmapdown(oranotherstudentattacking/reverting),nmapwillthenslowdownalltheothermachinesto
matchthesamespeedastheslowestmachine,thustakinglongertocomplete.
Haveyoueverseen:"Increasingsenddelayfor[IP]from0to5duetomax_successful_trynoincreaseto4"before?
Nmapoffersawidevarietyofscanningoptions,soit'shighlyrecommendtocheckthemanpagetogetadeeperunderstanding
ofthetool.Afewoptionstolookintoare:
maxretries
maxscandelay
defeatrstratelimit
reducetheamountofportsyou'rescanningatonce(topports100,ratherthanthedefault1000oreveryport).
don'tuseanyscripts(orreallylimittheamountused).
...ORbashscriptaforloop(*cough*likeinthecoursematerials*cough*).
Alternativelyfindingamachinewithnmappreinstalledonitthereforeyoucanscaninsidethenetwork,removingapossible
bottleneck(yourISP).Therearevariousmachinesovermultiplesubnetswithnmaponthemlazysystemadministrators
forgettingtoremovetoolsorusingtoolsagainstthemselves.
...butatthisstage,youwillhavenoideawhatmachinesthesearebutit'ssomethingtokeepinmind .
Note,it'sisNOTrecommendtoinstallnmap(oranyothertools)ontargetmachines.Areasonforthisisbecauseifanyother
studentrevertsthemachineyouwouldloseit.Plus,itnota"stealthy"optionandina"reallifepentest"thismaybeoutof
scope(dependsonhowyou'reapproachingthePWKlabsasthereisn'tarightorwrongway).
Lasteditedbyg0tmi1k;07222016at04:39PM.
PWB/OSCP(2011)|WiFu/OSWP(2013)|CTP/OSCE(2013)|AWAE(2015)|AWE(2016)
09/01/2018 Offensive Security's Complete Guide to Alpha
https://forums.offensive-security.com/showthread.php?t=4689&p=20530#post20530 6/30
Reply ReplyWithQuote
05132016, 03:43PM
JoinDate:
Posts:
Jun2011
538
InformationGathering
Services
Basedonthenmapreport,wecanonlysee2xTCPportsopen,22(DefaultstoSSH)&80(DefaultstoHTTP).
Bycheckingeachport,wecanstopourselvesfromgetting"tunnelvision",byspendingalongtimegoingdownarabbit
holeonlytofindit'sa"deadendservice".
TCP22(DefaultportforSSH)
TheSSHprotocolitselfis"triedandtested"servicesasithasbeenaroundsince1995(SSH2wasin2006).Themostcommon
servicefor*nixis"OpenSSH"(startedin1999).Itdoesn'tmeanit'swithoutany(publiclyknown)issues.Youcanseefor
yourselfontheCVEDetails.compage(*cough*bookmarkthissite*cough*)
Asaresult,it'snotseenasa'lowhangingfruit'attackvector,asunlesssomethingisseriouslymisconfiguredinthe
SSHDconfiguration(orifthereisasshbackdoor/rootkit!)thechanceofgettingashelloutoftheboxisunlikely.
Theservicesoftengetsbruteforced(*cough*it'sbesttohavealreadygatheredalistofusernamesbeforehandaswellas
usingafewdefaultusernames*cough*),howeverdependingonhowtheserviceisconfiguredyoumayneedtousea"private
key"(ratherthanpasswordbased)toaccessthebox.Youmayormaynotgetapasswordprompt(dependsonhowTHAT
machineissetup),evenifitonlyacceptskeys.
However,wemaystillbeabletouseittogetsomeinformationaboutthetarget:
SSHpackageversionMightbeabletofindtheOSandversion.
SSHkeyfingerprintHasthekeybeenreusedsomewhere(Anothermachine?Samemachine,justanother
port/service?)
SSHbannerAnytext(ifatall)beforethepasswordprompt(oftengetlegalwarningsaboutconnectingtoit)
SSHpackageversion
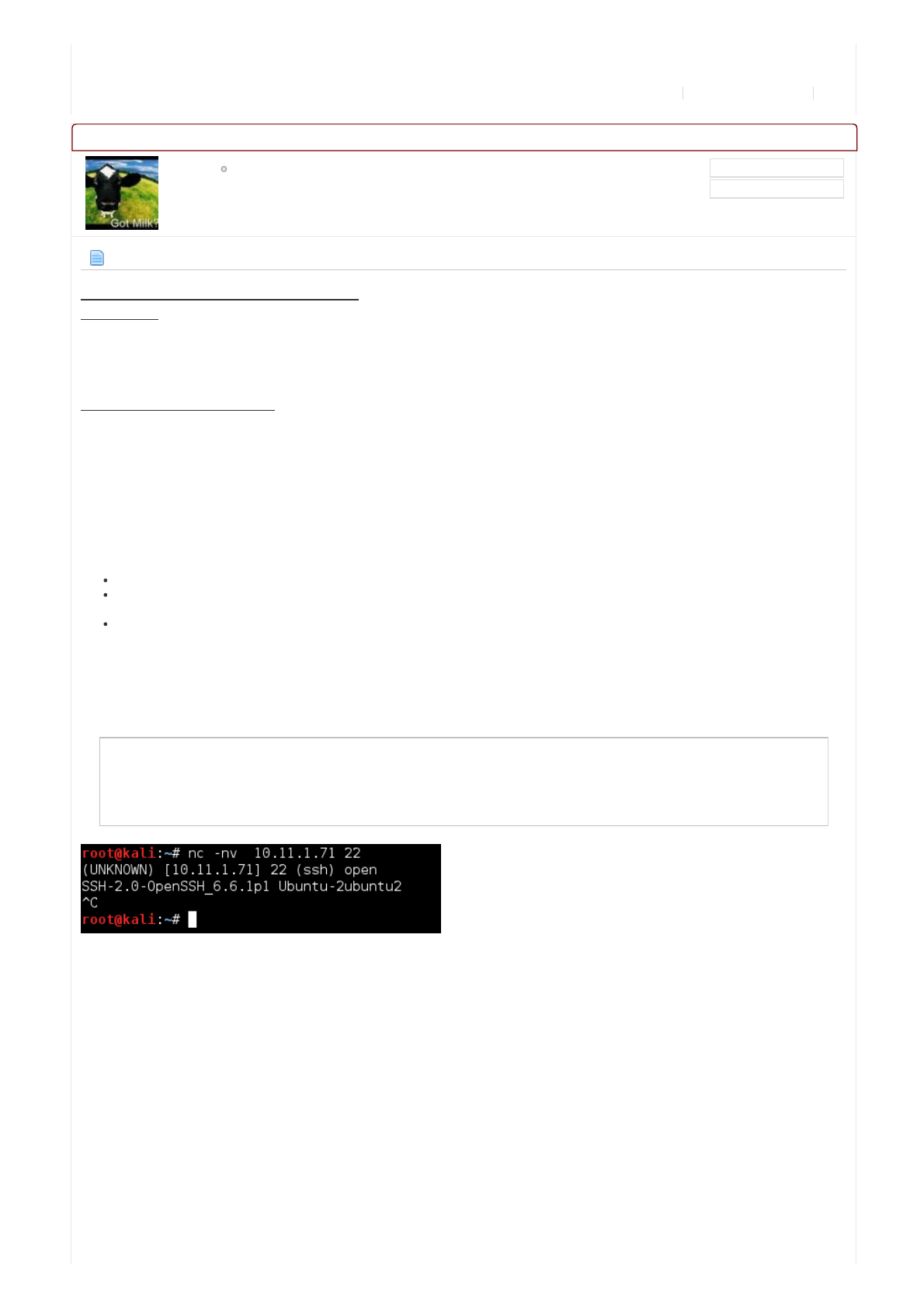
Solet'susenetcattoconnecttotheport(itwillhang,soweneedtokillitoncewehaveourinformation):
Code:
SowecanseethetargetOSis"Ubuntu",using"OpenSSHv6.6"(andpackageis2ubuntu2).Usingthis,wecanlookitupon
Ubuntu'swebsite.Sousingthisinformation,thereisagoodchancethetargetisUbuntu14.04LTS.
root@kali:~# nc -nv 10.11.1.71 22
(UNKNOWN) [10.11.1.71] 22 (ssh) open
SSH-2.0-OpenSSH_6.6.1p1 Ubuntu-2ubuntu2
^C
root@kali:~#
#5
OffsecStaff
g0tmi1k
09/01/2018 Offensive Security's Complete Guide to Alpha
https://forums.offensive-security.com/showthread.php?t=4689&p=20530#post20530 7/30
SSHkeyfingerprint
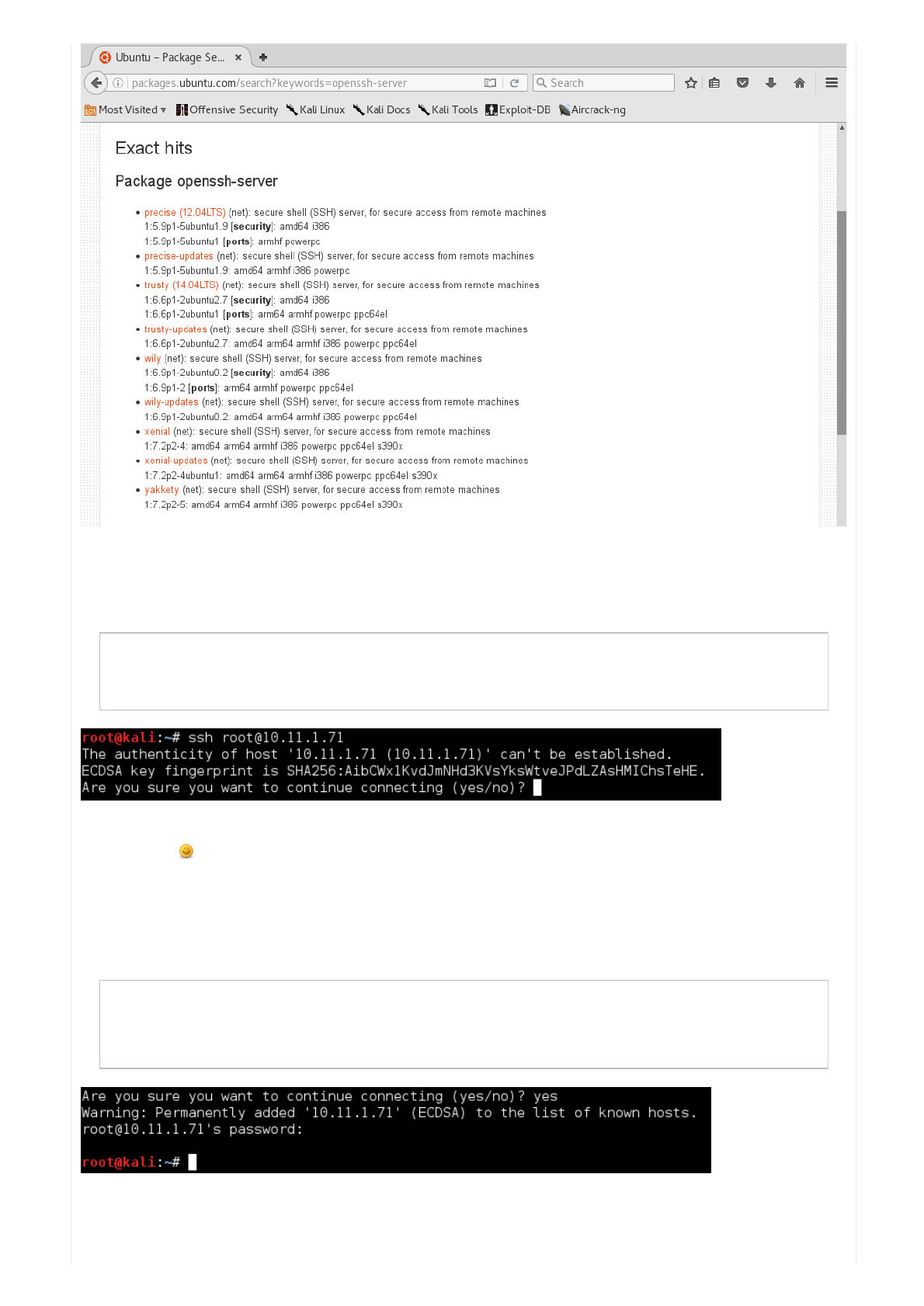
SowhenyouconnecttoaSSHserviceforthefirsttime,SSHwillpromptyou"doyoutrustthiskey"?:
Code:
NowwhathappensifyouseemultipleSSHservicesondifferentportswhichhavethesamekey?Whatcoulditmeaniftheyare
different?Whywouldyouseethesamekeyonanotherbox?Allquestionstothinkabout...Asthisisnotthecasehere,wewill
notanswerthat (*cough*butitisinthelabs*cough*).
Onthissubject:Ausefulresource~https://github.com/rapid7/sshbadkeys
SSHbanner
Let'sgoaheadandcontinueofffromthepreviouscommandandacceptthekey:
Code:
Sotherewasn'tanytextabovethepasswordprompt.
ButweDOgetapasswordprompt,sothemachinemayacceptSOMEuserswithapassword,ratherthankeys(orboth!).
Exampleofabanner(abletogetsomeinformationfromittoodomainname!).
root@kali:~# ssh root@10.11.1.71
The authenticity of host '10.11.1.71 (10.11.1.71)' can't be established.
ECDSA key fingerprint is SHA256:AibCWx1KvdJmNHd3KVsYksWtveJPdLZAsHMIChsTeHE.
Are you sure you want to continue connecting (yes/no)?
Are you sure you want to continue connecting (yes/no)? yes
Warning: Permanently added '10.11.1.71' (ECDSA) to the list of known hosts.
root@10.11.1.71's password:^C
root@kali:~#
09/01/2018 Offensive Security's Complete Guide to Alpha
https://forums.offensive-security.com/showthread.php?t=4689&p=20530#post20530 8/30
NmapScripts
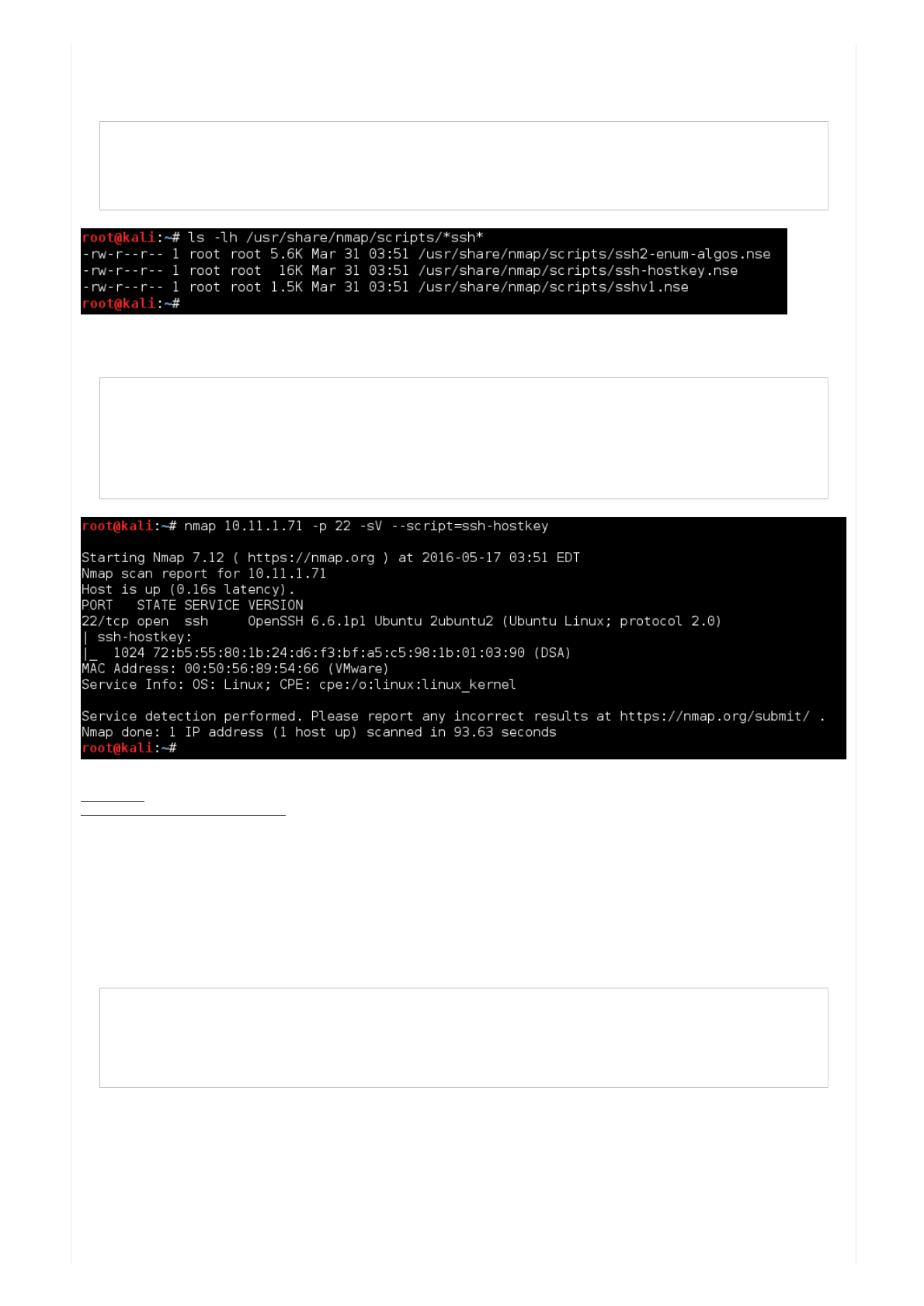
Wecanusenmaptohelpusout.First,let'scheckwhatscriptswehave(basedonournmapversion):
Code:
Sobyusing"sV"and"script=sshhostkey",wecanautomatethebannergrabbingaswellaskeyfingerprints.
Code:
Summary
RecommendSSHbruteforcetools:Acustomwordlistforthetarget(usinganothervulnerabilityorCeWL/wordhound),
Hydra(don'tforgetabout"e[VALUES]"),Patator(Passwordfuzzerratherthanbruteforce),Crowbar(greatforbrute
forcingprivatekeys),Metasploit'sssh_login.
TroubleShooting:MidwayScanning,portclosed?
Duringourpokingabout,wenoticedafterrunningafewcommands,theservicestartedtohaveadelayinresponsetime.Then
SSHcompletelystoppedresponding.
Scanningitagainwithnmap,weseetheporthaschangedstatus(itsnowfiltered):
Code:
root@kali:~# ls -lh /usr/share/nmap/scripts/*ssh*
-rw-r--r-- 1 root root 5.6K Mar 31 08:51 /usr/share/nmap/scripts/ssh2-enum-algos.nse
-rw-r--r-- 1 root root 16K Mar 31 08:51 /usr/share/nmap/scripts/ssh-hostkey.nse
-rw-r--r-- 1 root root 1.5K Mar 31 08:51 /usr/share/nmap/scripts/sshv1.nse
root@kali:~#
root@kali:~# nmap 10.11.1.71 -p 22 -sV --script=ssh-hostkey
...SNIP...
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 6.6.1p1 Ubuntu 2ubuntu2 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
|_ 1024 72:b5:55:80:1b:24:d6:f3:bf:a5:c5:98:1b:01:03:90 (DSA)
...SNIP...
root@kali:~#
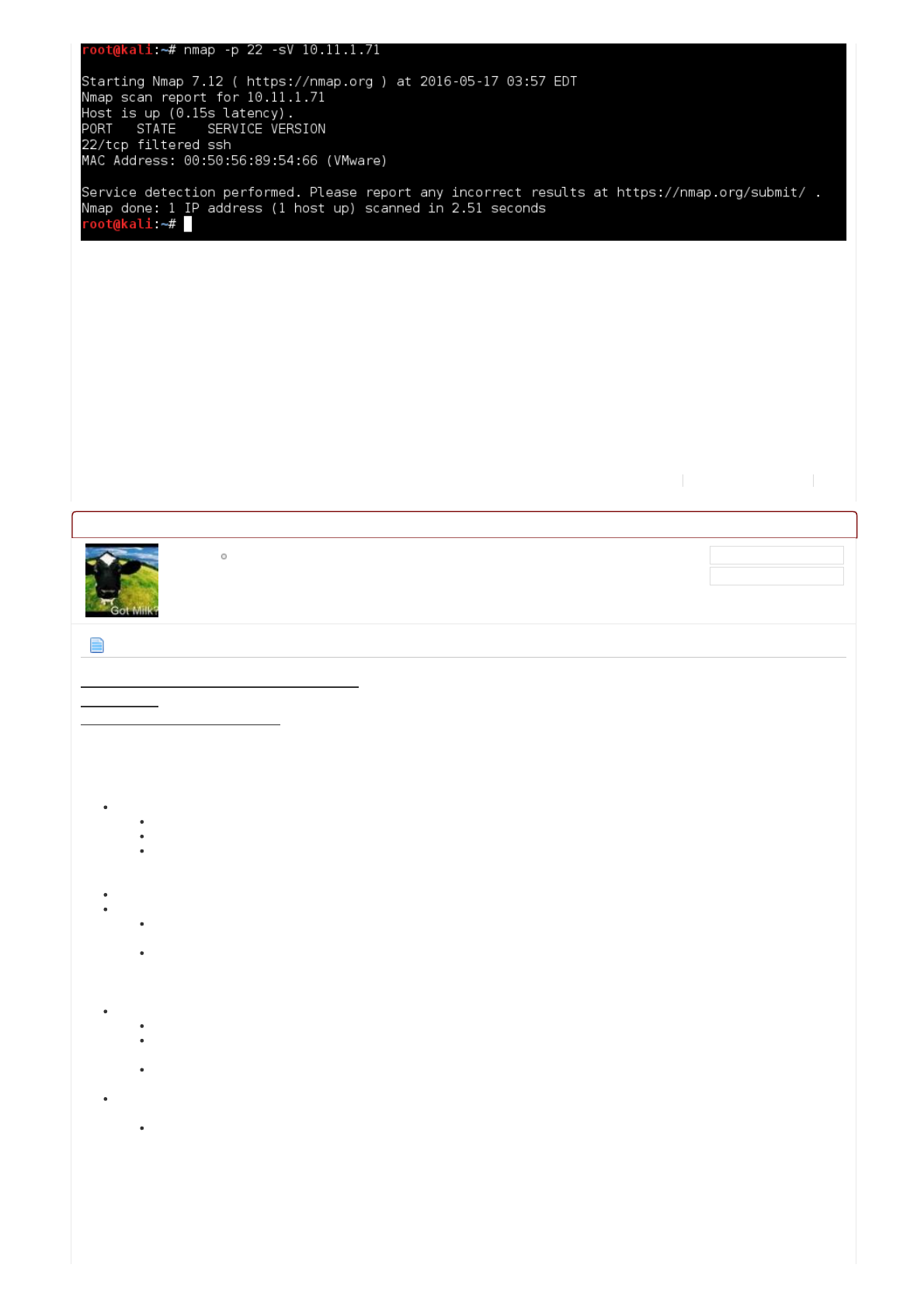
root@kali:~# nmap -p 22 -sV 10.11.1.71
...SNIP...
22/tcp filtered ssh
...SNIP...
Nmap done: 1 IP address (1 host up) scanned in 2.51 seconds
root@kali:~#
09/01/2018 Offensive Security's Complete Guide to Alpha
https://forums.offensive-security.com/showthread.php?t=4689&p=20530#post20530 9/30
Ohdear!There'sachanceanotherstudenthasalteredthebox(thoughslim,asthemachineisstillupandresponding),
howeverwhatismuchmorelikelyiswehavetriggeredsometypeof"defense"onthemachine.There'svarioussolutions
inordertostopbruteforceattempts(multiplefailedloginsoveraperiodoftime),e.g.acommononeis"fail2ban".Wemayof
justlockedourselvesout(couldbejustTHATportorthecompletemachine).
Eitherwecanwaituntilthistimesout(wedon'tknowhowlongthatwouldbe),orrevertthemachine.
Note:TherearevariousmachineswiththisinplacethroughoutourPWK/OSCPlabs.Youwouldnothavetowaitmorethan15
minutesbeforeyouwouldbecomeunbanned.
Lasteditedbyg0tmi1k;07212016at11:09AM.
PWB/OSCP(2011)|WiFu/OSWP(2013)|CTP/OSCE(2013)|AWAE(2015)|AWE(2016)
Reply ReplyWithQuote
05162016, 11:52AM
JoinDate:
Posts:
Jun2011
538
InformationGathering
Services
TCP80(DefaultportforHTTP)
Note:WarningHUGECONTENT!Thiscouldbeawholecourseinjustthissubject.Thereisnowaywecancover*everything*in
thispost!
Beforewestart:
Webservers(e.g.Apache/Nginx/IIS)arenotthesameaswebapplications(e.g.Wordpress/Jooma).
WebapplicationsmaytalktootherservicesontheOS(suchasadatabaseMySQL/MSSQL)
E.g.EndUser<>WebServer<>WebApplication<>Database
Andtheterms:TheInternet(e.g.infrastructure)isnotthesameasWWW(WorldWideWebweb
applications)
Webservers(e.g.Apache/Nginx/IIS)arenotthesameaswebservices(e.g.html/json/xml).
Webservers(e.g.Apache/Nginx/IIS)mayhavemultipletechnologiespoweringthem(e.g.PHP/ASP)viahandlers.
Theseserversidetechnologiesareexecutedonthetargetdirectly,nottheendusersbrowser(like
Javascript).
Theseserversidetechnologiesoftenhavemoreissueswiththem,astheyhavealotmoredifferent
movingparts,astheyneedtorender/process/executecodewrittenbyendusers(andtheendusers
codeisawholeothersetofissues).
Webserversrunontheport(e.g.TCP80).Therecanonlybeasinglewebserver.
However,theremaybemultiplewebapplicationsrunningonthewebserver.
Somemaybe"hidden".E.g.notlinked/clickablefromthelandingpage.Thereforeyouneedtoknow
theURLtogoto.
e.g.AcommonhiddenwebapplicationisPHPMyAdmin.
Webserversmayhavemultiple"modules"(e.g.Apache)loaded,thatexpandtheirfunctionally(andalsobe
misconfigured!)
E.g./servicestatusor"indexof/"aswellasSSL/TLS.
Webserversarefound*everywhere*now(examples:traditionallyGUIdesktopapplicationsmovingtoawebUI,CLItool
developersusingawebUI,ormobileapplicationsjustbeingabrowserpointingtoselectedwebpage,andembeddeddevice
hardwaretocontrolnetworkhardware).
Webserversthemselvesare"dumb",astheyonlyserve/displayoutwhatissenttothem.Theydonotdoanyprocessingor
rendingthemselves.
#6
OffsecStaff
g0tmi1k

09/01/2018 Offensive Security's Complete Guide to Alpha
https://forums.offensive-security.com/showthread.php?t=4689&p=20530#post20530 10/30
ThecommonservicesyouwillseeisApache(bothonWindows&*nix),Ngnix(Easieron*nix,butthereisaWindowsport),
andInternetInformationServices(IISWindowsonly...forthetimebeing!).
Eachofthemhavehad(publiclyknown)issuesovertheyears(Apache,Ngnix,IIS)andtheyhavealsohadtheirshareof"big"
vulnerabilities(whichhavepublicexploitsApache,Nginx,IIS).However,thesethreeservicesaremuchmore"stable"
becausetheyhavebeenaroundforsolong(oldertheversion,themoreissues*cough*soit'salwaysworthacheckingto
seeifthereissomething*cough*).However,thereareotherwebserversotherthanthesethree,whichhaven'tbeenbeaten
upovertheyears(*cough*andyoumayfindafewinthelabs*cough*).
OnthesubjectofApacheonWindows,itiscommontoseeApacheinstalled/usedasa"package"/bundle,suchasXAMPPand
WAMP.Thisthenincludesother"useful"servicesatthesametime.
Sotheseservicesdirectlymaynotgiveyouaniceshellstraightaway,what'sbehindthemMIGHT(serversidetechnologies,
WebApplication,Database).Whattheyaregreatwithisgettinginformationaboutthetargetfrom.Mostwebserversare
"public",allowinganyonetoaccessthem.
However,itisworthnoticingthedifferentinbasic/digest/HTTPauthentication(akawhenyougetapopupwhentryingto
accessaURL)whichhappensonthewebserver,whereastheremaybeauthenticationinthewebapplication(e.g.httpforms).
Sometimestheauthenticationisdoneincorrectly,andonlythe'default/landing'pagehasapasswordprompt,butifyou
knew/guessedaURLyoumaystillbeabletoaccessit...
Becauseoftherange/scaleofwhattheserviceallowsaccessto,it'softenoneofthefirstserviceswestart
probingat.Dependingonthewebapplication(s)wecanaccessitmaybethelowhangingfruit.Untilweaccess
theservice,wedon'tknowwhat'sbehindit.
However,beforejumpingintothewebapplication,let'schecktheheadersfromthewebserveranddefaultlandingpage:
Code:
Sostraightaway:
Ourrequestisbeingredirected(HTTP302)to:"site/index.php/"(Noticehowitistwosubfoldersdeep.Whatis
injust/site/?)
Thewebserverappearstobe"Apache2.4.7"onUbuntu(whichmatcheswhatweknowfromSSH)
GoodchanceoftherebeingPHPontheserver:"v5.5.9"aswellasintheURLredirect:"site/index.php/"
Summary
Sowhatweknowthisfar:
IP:10.11.1.71(DNS:alpha.thinc.local)
Ports:TCP22,TCP80(MighthaveUDP)
OS:Ubuntu(Possibly14.04TrustyTahr)
Services&Applications:
OpenSSH6.6Requiresauthentication.Mightneedtobruteforceit.
Apache2.4.7&PHP5.5.9Nocredentialsrequiredtoaccessit.Bestbetfortheentrypoint(unless
there'sanothermachinedependence).
Optionsleft(inorderofpriority)
Explorethewebapplication.
Searchforvulnerabilitiesintheknownservices&applications.
BruteforceSSHwithcommon&weakcredentials.
Lasteditedbyg0tmi1k;11222016at04:41PM.
PWB/OSCP(2011)|WiFu/OSWP(2013)|CTP/OSCE(2013)|AWAE(2015)|AWE(2016)
root@kali:~# curl -i 10.11.1.71
HTTP/1.1 302 Found
Date: Mon, 16 May 2016 22:39:48 GMT
Server: Apache/2.4.7 (Ubuntu)
X-Powered-By: PHP/5.5.9-1ubuntu4.4
Location: site/index.php/
Content-Length: 0
Content-Type: text/html
root@kali:~#
Reply ReplyWithQuote
09/01/2018 Offensive Security's Complete Guide to Alpha
https://forums.offensive-security.com/showthread.php?t=4689&p=20530#post20530 11/30
05162016, 02:47PM
JoinDate:
Posts:
Jun2011
538
InformationGathering
WebApplication(Main)
WebApplication(HTML)
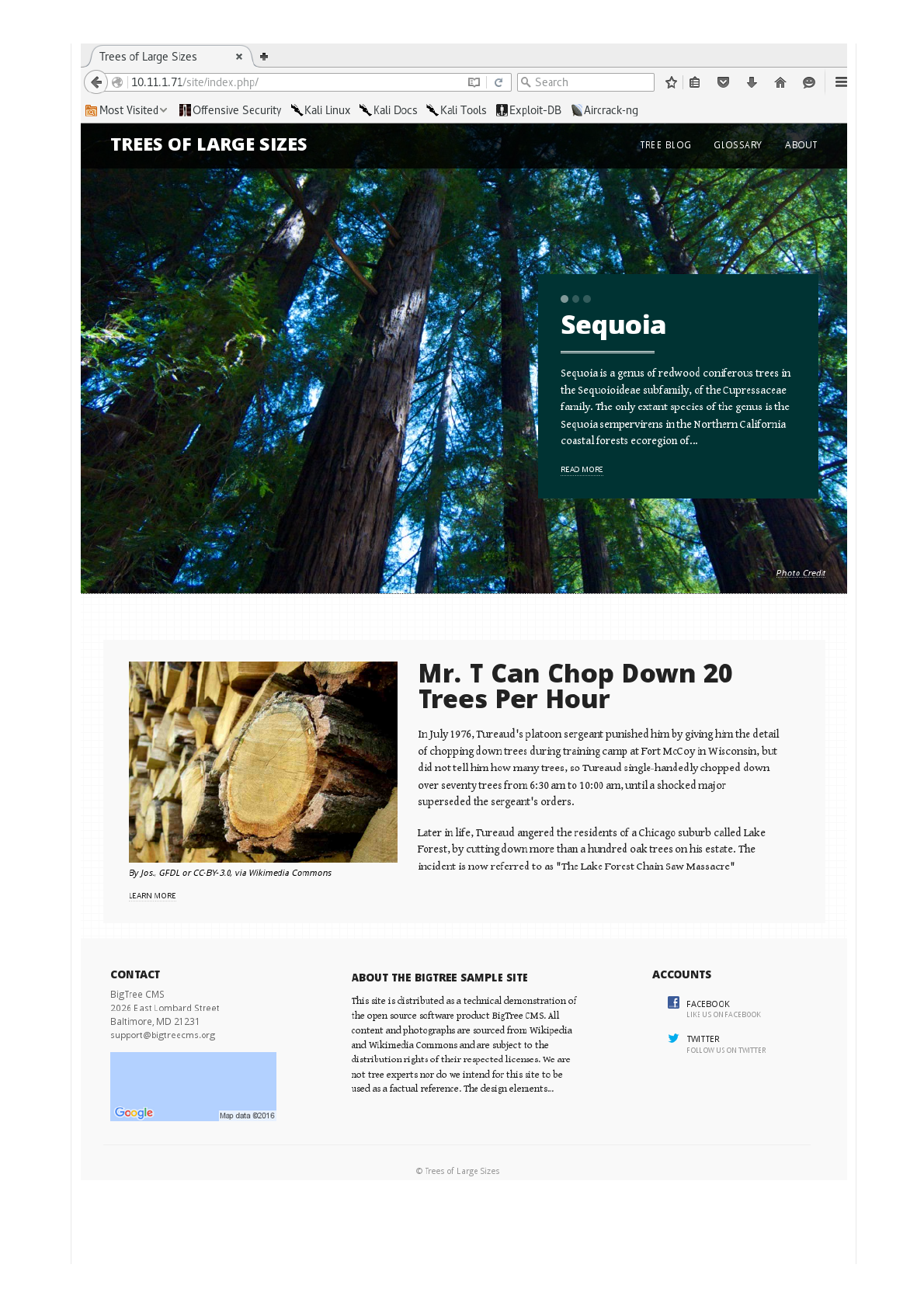
Timetoputour"enduser"hatonagain.Whatwemeanbythisis"usetheapplication,don'ttryandbreakit".
Whatinformationcanyougatherbyjustclickingaboutandreadingwhat'sonscreen.
Firstthing,let'sfollowtheredirect.
Code:
It'savalidwebapplication(ratherthanadefaultwelcomemessage).SowecanseetherawHTMLcode,whichmakesupthe
webpage(becausethisisn'tprocessedontheremoteserverunlikePHPcode).
WebApplication(GUI)
Let'snowstartupaGUIwebbrowsertoseewhatthepagelookslike(asaenduser).
root@kali:~# curl -i -L 10.11.1.71
HTTP/1.1 302 Found
...SNIP...
HTTP/1.1 200 OK
...SNIP...
Set-Cookie: PHPSESSID=f81qqe1crdio83ikmumnpanbe3; path=/
...SNIP...
Content-Length: 6845
Content-Type: text/html
< !DOCTYPE html>
< html lang="en">
< head>
< meta http-equiv="Content-type" content="text/html; charset=utf-8" />
< meta name="viewport" content="width=device-width, initial-scale=1, maximum-scale=1">
< meta name="keywords" content="" />
< meta name="description" content="" />
< title>Trees of Large Sizes< /title>
< link rel="stylesheet" href="http://10.11.1.71/site/index.php/css/site.css" type="text/css" media="al
< link rel="stylesheet" href="http://10.11.1.71/site/css/print.css" type="text/css" media="print" />
...SNIP...
root@kali:~#
#7
OffsecStaff
g0tmi1k
09/01/2018 Offensive Security's Complete Guide to Alpha
https://forums.offensive-security.com/showthread.php?t=4689&p=20530#post20530 12/30
Afewthingsweliketocheckare:comments(asthesewouldn'tbeseenwhenrendered),thewebapplicationname/version,

09/01/2018 Offensive Security's Complete Guide to Alpha
https://forums.offensive-security.com/showthread.php?t=4689&p=20530#post20530 13/30
andlinkstootherpages/domains.
WebApplication(Internal&ExternalLinks)
Wecan'tseeanyHTMLcommentsinthecode,soletsnowquicklycheckthetitletag(asthatcanhavethewebapplication
nameinit)aswellasanylinks:
Code:
WebApplication(HTMLRender)
Sothatsallgreat,butlet'snowseewhatthewebpagerenderslike.
Atthispointwecanstartupiceweasel/firefox/chrometolookatthepage...instead,let'sstickwithcommandlineforthetime
being.Welcome"html2text".
Code:
root@kali:~# curl 10.11.1.71 -s -L | grep "title\|href" | sed -e 's/^[[:space:]]*//'
< title>Trees of Large Sizes< /title>
< link rel="stylesheet" href="http://10.11.1.71/site/index.php/css/site.css" type="text/css" media="all" />
...SNIP...
< a href="http://10.11.1.71/site/index.php/" class="branding">Trees of Large Sizes< /a>
...SNIP...
< a href="http://en.wikipedia.org/wiki/Sequoia_%28genus%29" class="more" target="_blank">Read More< /a>
...SNIP...
< a href="http://commons.wikimedia.org/wiki/File%3ASequoia_sempervirens_BigSur.jpg" target="_blank" class="cre
...SNIP...
< p>Later in life, Tureaud angered the residents of a Chicago suburb called Lake Forest, by cutting down more
< p>< strong>BigTree CMS< /strong>< br /> < span>2026 East Lombard Street < br />Baltimore, MD 21231 < /span><
< a href="http://www.facebook.com/BigTreeCms" class="facebook" target="_blank">Facebook< small>Like us on Face
< a href="http://www.twitter.com/bigtreecms" class="twitter" target="_blank">Twitter< small>Follow us on Twitt
root@kali:~#
root@kali:~# curl 10.11.1.71 -s -L | html2text -width '99' | uniq
...SNIP...
*** Mr. T Can Chop Down 20 Trees Per Hour ***
In July 1976, Tureaud's platoon sergeant punished him by giving him the detail of chopping down
trees during training camp at Fort McCoy in Wisconsin, but did not tell him how many trees, so
Tureaud single-handedly chopped down over seventy trees from 6:30 am to 10:00 am, until a shocked
...SNIP...
* Contact *
BigTree CMS
...SNIP...
support@bigtreecms.org
* Accounts *
FacebookLike_us_on_Facebook TwitterFollow_us_on_Twitter
* About the BigTree Sample Site *
This site is distributed as a technical demonstration of the open source software product BigTree
CMS.
...SNIP...
root@kali:~#
09/01/2018 Offensive Security's Complete Guide to Alpha
https://forums.offensive-security.com/showthread.php?t=4689&p=20530#post20530 14/30
Atthetopofthepage,youwouldseealotofcontent(howeverithasbeensnippedout),whichisallthenavigationmenus,
thenitmovesontocontent.Itdoesn't"fully"makesenseorfitin.ThentheressomenonEnglishtext(removed).Lastly,
there'ssometextatthebottom(inthefooter),whichisexactlywhatwearelookingfor:"AbouttheBigTreeSampleSite
...SNIP...demonstrationoftheopensourcesoftwareproductBigTreeCMS".
Soitsasamplesite(whichexplainstheoddcontextofcontentnow),usingBigTreeCMS.
WebApplication(SocialNetworks)
Thiscanalsobereenforcedbyoneofthesocialnetworklinks,twitter(http://www.twitter.com/bigtreecms):
BigTreeCMSisanopensourcecontentmanagementsystembuiltonPHPandMySQL.Itwascreatedby,andfor,userexperienceand
contentstrategyexperts

09/01/2018 Offensive Security's Complete Guide to Alpha
https://forums.offensive-security.com/showthread.php?t=4689&p=20530#post20530 15/30
WebApplication(AccessingTheSourceCode)
Sofollowingthesocialnetworkhomepagelink(https://www.bigtreecms.org/),wecanclickaboutuntilwegetthesourcecode
(https://github.com/bigtreecms/BigTreeCMS/).
Oneofthekeyfilesweseeiscalled"/README.md".
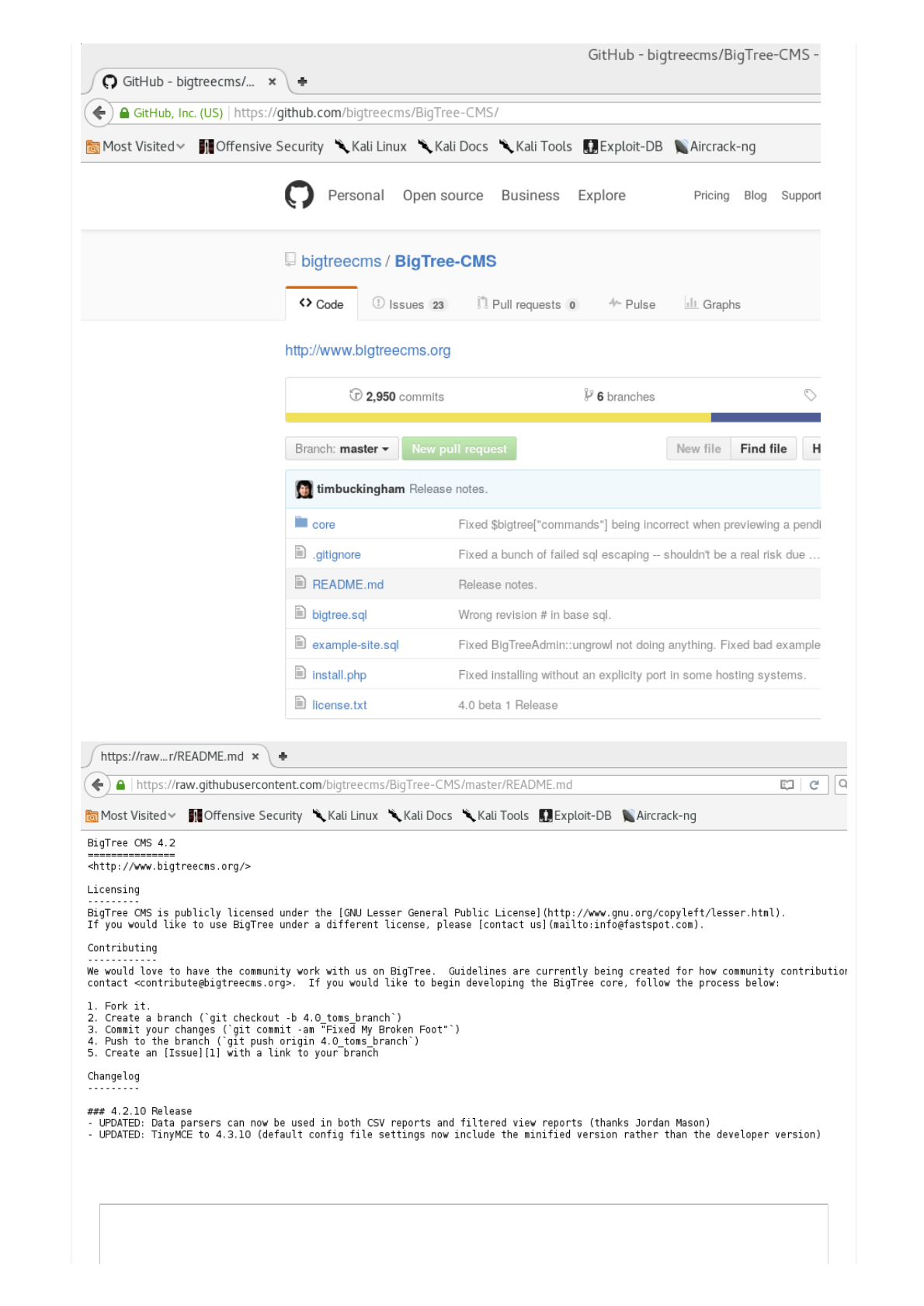
09/01/2018 Offensive Security's Complete Guide to Alpha
https://forums.offensive-security.com/showthread.php?t=4689&p=20530#post20530 16/30
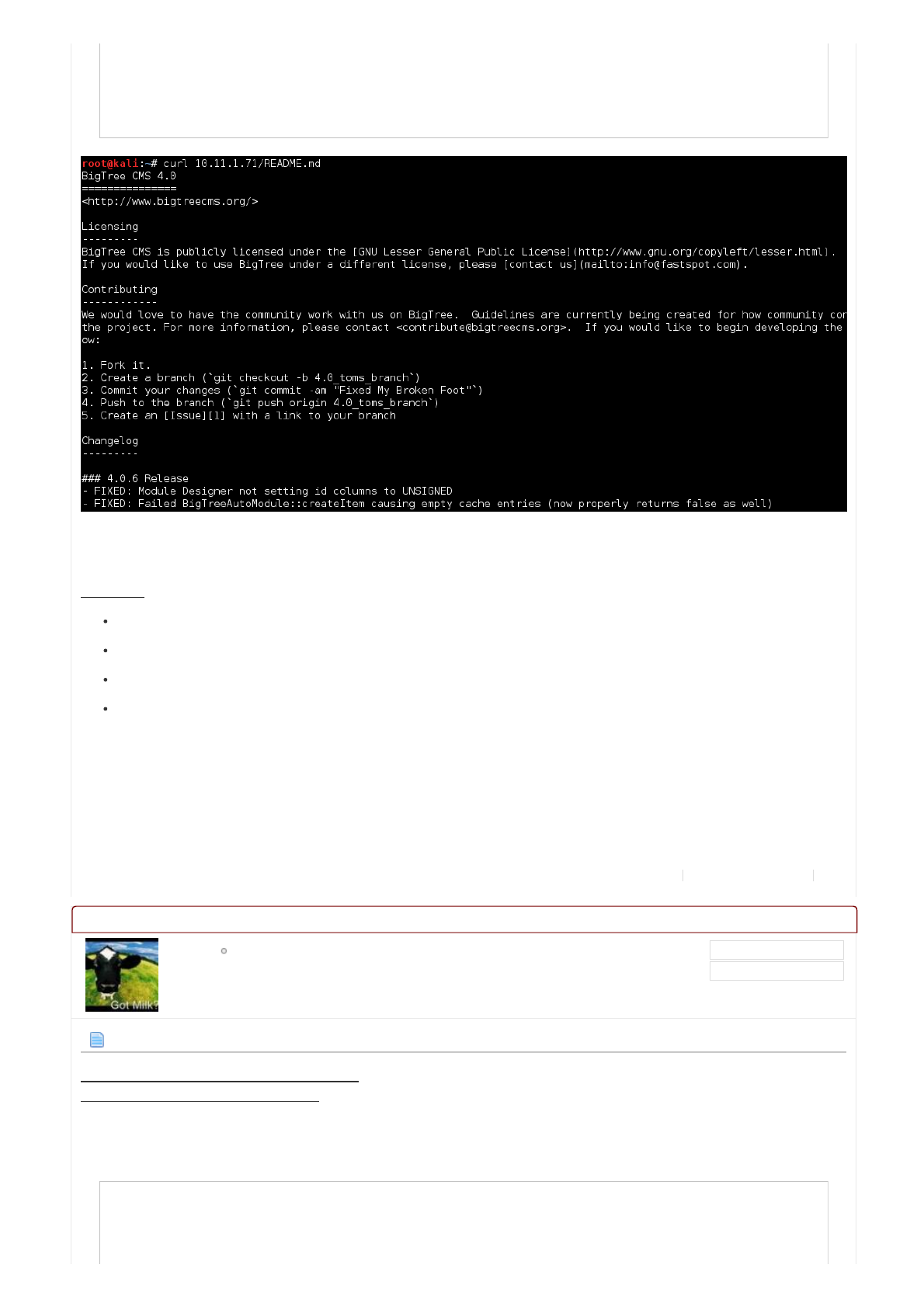
Thisisimportanttousasitcontainsthe"Changelog".Usingthis,weareabletofindouttheversionofthesoftware.
Code:
root@kali:~# curl 10.11.1.71/README.md
BigTree CMS 4.0
===============
< http://www.bigtreecms.org/>
SNIP
09/01/2018 Offensive Security's Complete Guide to Alpha
https://forums.offensive-security.com/showthread.php?t=4689&p=20530#post20530 17/30
Bingo!Sonowweknowthenameandversion,BigTreeCMSv4.0.6.
Summary
Wenowhaveafewoptionswecoulddo:
Pokeaboutabitmore,tryingtoreadany(custom?)contenthowever,asthisisasamplesite,maybenotagood
idea
Tryandfindtheadmincontrolpanelhowever,wedon'thavealistofusernamestotryyet.Couldtrysomewe
havealreadygotteninthelaborlookupthedefaultvalue.
Tryandfindanyotherwebapplicationsonthesite(e.g.checking/robots.txtorbruteforcingURLs)Thiswilltake
sometime,soitsagoodideatokickitoffearly.
Startlookingupiftheresanyvulnerabilityintheservicesandapplicationssofar.
Soourplanofaction,starttocheckifthere'sanymorewebapplicationsontheserver(wearenotworriedaboutbeing
stealthyinthisattack),andthenstartresearchinganyknownissuesandvulnerabilitiesinsoftware.
PWB/OSCP(2011)|WiFu/OSWP(2013)|CTP/OSCE(2013)|AWAE(2015)|AWE(2016)
...SNIP...
Changelog
---------
### 4.0.6 Release
...SNIP...
root@kali:~#
Reply ReplyWithQuote
05172016, 08:59AM
JoinDate:
Posts:
Jun2011
538
InformationGathering
WebApplication(Hidden)
Robots(.txt)vsSpiders
Aquickchecktoseeifthere'sanythingthesystemadministratorwouldn'twantaInternetspidertoindex:
Note:Forcommon/defaultvaluestolook/checkfor:https://github.com/h5bp/html5boilerplate
Code:
root@kali:~# curl 10.11.1.71/robots.txt -s | html2text
****** Not Found ******
The requested URL /robots.txt was not found on this server.
===========================================
Apache/2.4.7 (Ubuntu) Server at 10.11.1.71 Port 80
t@k li #
#8
OffsecStaff
g0tmi1k

09/01/2018 Offensive Security's Complete Guide to Alpha
https://forums.offensive-security.com/showthread.php?t=4689&p=20530#post20530 18/30
Usefultool:parsero
URLBruteForce(General)
Bruteforcingdoesn'talwaysmeanpasswordsattacks.Itstheprocessofguessing,bytryingcertaincombinations(eitherpre
definedfromadictionary/wordlistortryingeverypossiblevalue,increasingitsvalueeachtime).WecanapplythistoURLs
too.
There'svarioustoolstohelpusdothis,suchas:DirB(CLI),DirBuster(GUI),wfuzz(CLI),BurpSuite(GUI),andmy
favouriteGobuster(CLI).
Justlikepasswordbruteforcing,itdoesn'tmatterhow"good"atoolis,thekeyisthewordlist.Ifthe"magic"valueisn'tin
thewordlist,itsnotgoingtobediscovered.Andkeepinmindthelongerthewordlist,thelongertheattackwilltake.
Note:Thelabshavebeendesignedsoyoushouldnotbebruteforcinganythingformorethan30minutes.
Someofthementionedtoolscomewiththeirownwordlistswiththem(suchasDirB&wfuzz)whichhavecommonlyfound
URLsandyoucanmixandmatchthetoolstothewordlists.
However,thereisadedicatedprojectcalled"SecList"whichaimstocoverasmanygeneral/genericwordlistsaspossible(for
everytopic).Itsworthhavingaquickexplore:
DirB/usr/share/dirb/wordlists/
wfuzz/usr/share/wfuzz/wordlist/
SecList/usr/share/seclists/
Note:DependingonyourKaliversion,youmayhavetoinstallthem(aptgetinstally[name])
Code:
root@kali:~#
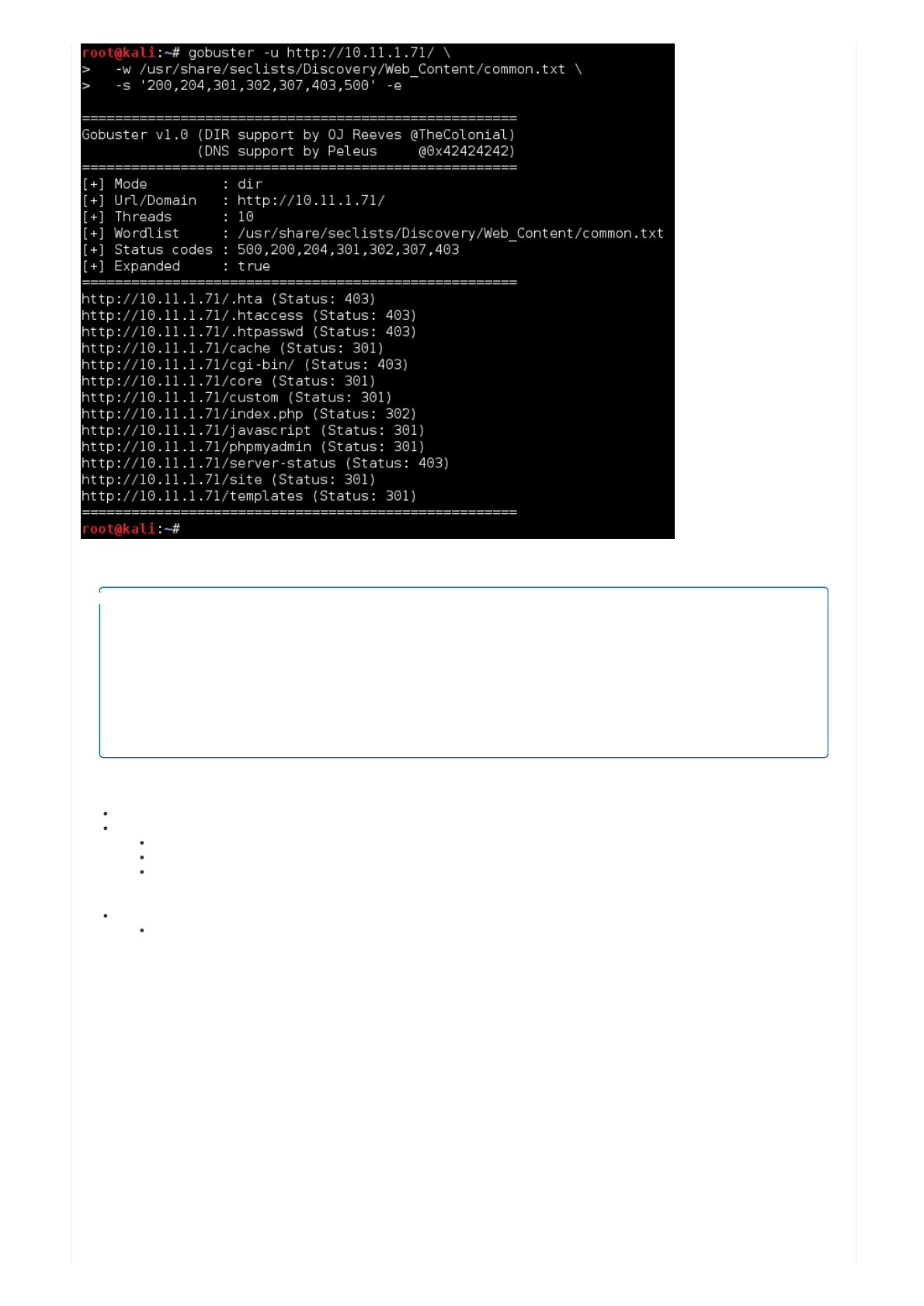
root@kali:~# gobuster -u http://10.11.1.71/ \
-w /usr/share/seclists/Discovery/Web_Content/common.txt \
-s '200,204,301,302,307,403,500' -e
=====================================================
Gobuster v1.0 (DIR support by OJ Reeves @TheColonial)
(DNS support by Peleus @0x42424242)
=====================================================
[+] Mode : dir
[+] Url/Domain : http://10.11.1.71/
[+] Threads : 10
[+] Wordlist : /usr/share/seclists/Discovery/Web_Content/common.txt
[+] Status codes : 500,200,204,301,302,307,403
[+] Expanded : true
=====================================================
http://10.11.1.71/.hta (Status: 403)
http://10.11.1.71/.htaccess (Status: 403)
http://10.11.1.71/.htpasswd (Status: 403)
http://10.11.1.71/cache (Status: 301)
http://10.11.1.71/cgi-bin/ (Status: 403)
http://10.11.1.71/core (Status: 301)
http://10.11.1.71/custom (Status: 301)
http://10.11.1.71/index.php (Status: 302)
http://10.11.1.71/javascript (Status: 301)
http://10.11.1.71/phpmyadmin (Status: 301)
http://10.11.1.71/server-status (Status: 403)
http://10.11.1.71/site (Status: 301)
http://10.11.1.71/templates (Status: 301)
...SNIP...
root@kali:~#
09/01/2018 Offensive Security's Complete Guide to Alpha
https://forums.offensive-security.com/showthread.php?t=4689&p=20530#post20530 19/30
Solet'sbreakthesevaluesdown:
Optionsnow:
PokearoundatphpMyAdmin.
Tryadifferentwordlist.Either/mixture/all:
Anothergeneralone.
Onetargetedtowards:/cgibin/.
...Wedon'thaveenough(custom)informationtogenerateonetowardsourtarget(using
CeWL/wordhound),asitsusingasamplepage.
Startresearchingvulnerabilitiesandissuesinknownsoftware.
Thelaterwedothis,hopefullywewillknowmoreaboutthetargetandhavemoretoresearch,
increasingthepossibleattacksurface.
phpMyAdmin
Sousingiceweasel/firefox/chrome,wecannavigatetohttp://10.11.1.71/phpmyadminandseethefollowing:
/index.php(Status:302)
/cache(Status:301)
/core(Status:301)
/custom(Status:301)
/javascript(Status:301)
/phpmyadmin(Status:301)<Couldbesomething.
/site(Status:301)
/templates(Status:301)
/.hta,/.htaccess,/.htpasswd(Status:403)<Goodchance"dotfiles"arenotallowedtobeaccesseddirectly.
/cgibin/(Status:403)<Couldbesomething.
/serverstatus(Status:403)<Shame.Mightofgotsomeniceinformationaboutthemachine.
09/01/2018 Offensive Security's Complete Guide to Alpha
https://forums.offensive-security.com/showthread.php?t=4689&p=20530#post20530 20/30
Wemanuallytryafewdefaultvaluessuchas:
admin\""(blank),admin\admin,admin\password
root\""(blank),root\root,root\password
However,itwasn'tsuccessful.AGooglesearchshowsthedefaultpasswordsdependsonhowphpMyAdminwasinstalledand
theOSandit'sversionwetriedeveryvalue.
Wecouldstartaonlinepasswordattackonit,howeverthechanceofitbeingsuccessfulisslim.We'llputapinitinnow,
andputitattheendofto"trylist"sowewillrevisititatalatertime(ifrequired).
URLBruteForce(CGI)
Sonextonourlist,anotherwordlisttotry!Aswehavealreadydoneawordlistofcommonvalues,let'susewhatwelearnt
fromitandstarttogetaspecific/specialize,bytargetingCGIURLs.
Allwearegoingtodo,isrerunthesamecommandaslasttime,howeverswitchoutthewordlistwithanotheronefrom
SecList:
Code:
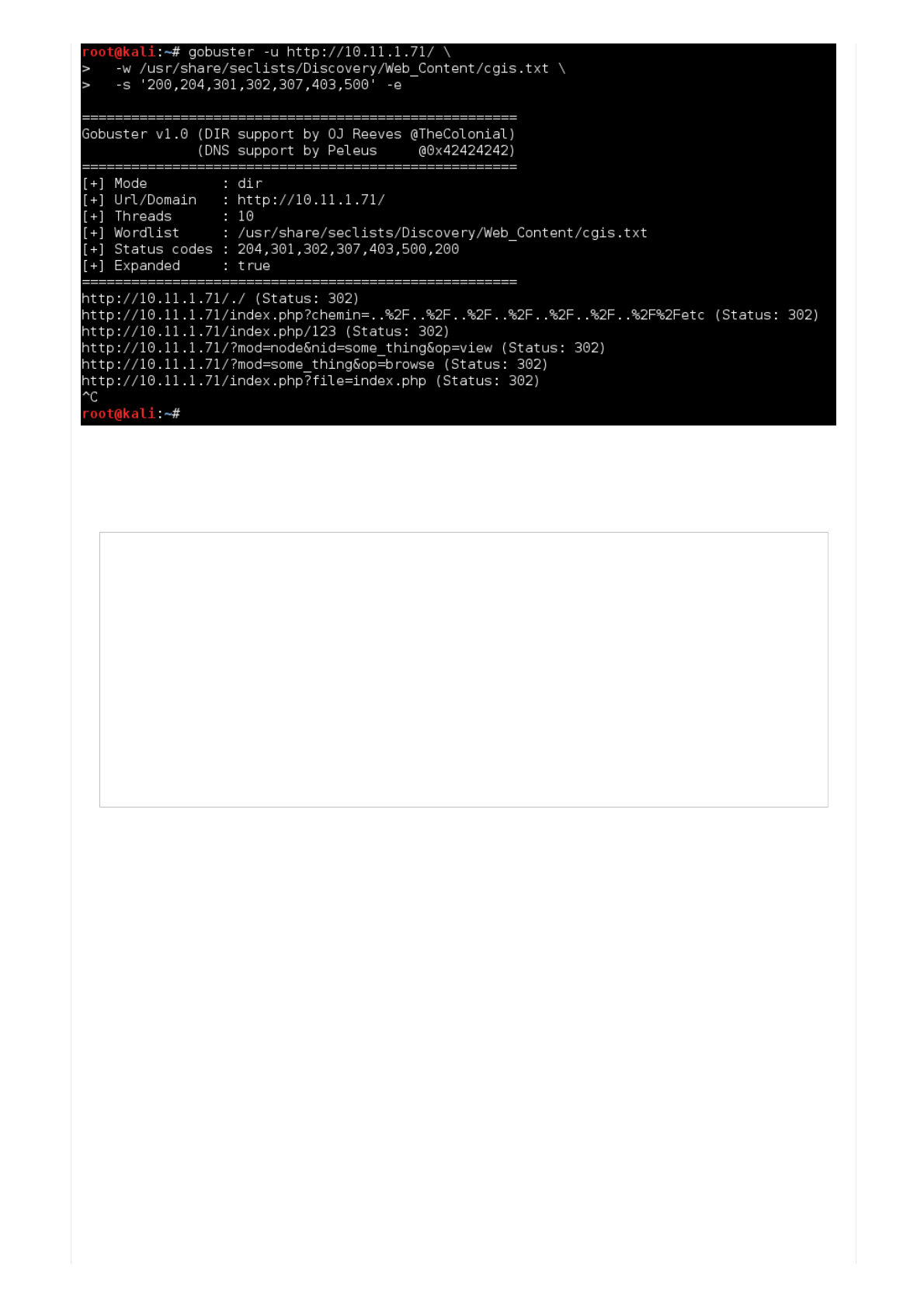
root@kali:~# gobuster -u http://10.11.1.71/ \
-w /usr/share/seclists/Discovery/Web_Content/cgis.txt \
-s '200,204,301,302,307,403,500' -e
=====================================================
Gobuster v1.0 (DIR support by OJ Reeves @TheColonial)
(DNS support by Peleus @0x42424242)
=====================================================
[+] Mode : dir
[+] Url/Domain : http://10.11.1.71/
[+] Threads : 10
[+] Wordlist : /usr/share/seclists/Discovery/Web_Content/cgis.txt
[+] Status codes : 204,301,302,307,403,500,200
[+] Expanded : true
=====================================================
http://10.11.1.71/./ (Status: 302)
http://10.11.1.71/index.php?chemin=..%2F..%2F..%2F..%2F..%2F..%2F..%2F%2Fetc (Status: 302)
http://10.11.1.71/index.php/123 (Status: 302)
http://10.11.1.71/?mod=node&nid=some_thing&op=view (Status: 302)
http://10.11.1.71/?mod=some_thing&op=browse (Status: 302)
http://10.11.1.71/index.php?file=index.php (Status: 302)
^C
root@kali:~#
09/01/2018 Offensive Security's Complete Guide to Alpha
https://forums.offensive-security.com/showthread.php?t=4689&p=20530#post20530 21/30
...Wekilleditbeforeitcouldcomplete.Thisisbecausewearejustbeenfloodedwithdatathatwearenotinterestedinright
now(allthoseredirectsHTTP302).Let'sfilterthemoutforthetimebeing,ifweneedto,rescanagainwiththemenabled
(weputitonouron"totrylater"list).
Useful:ListofHTTPstatuscodes
Code:
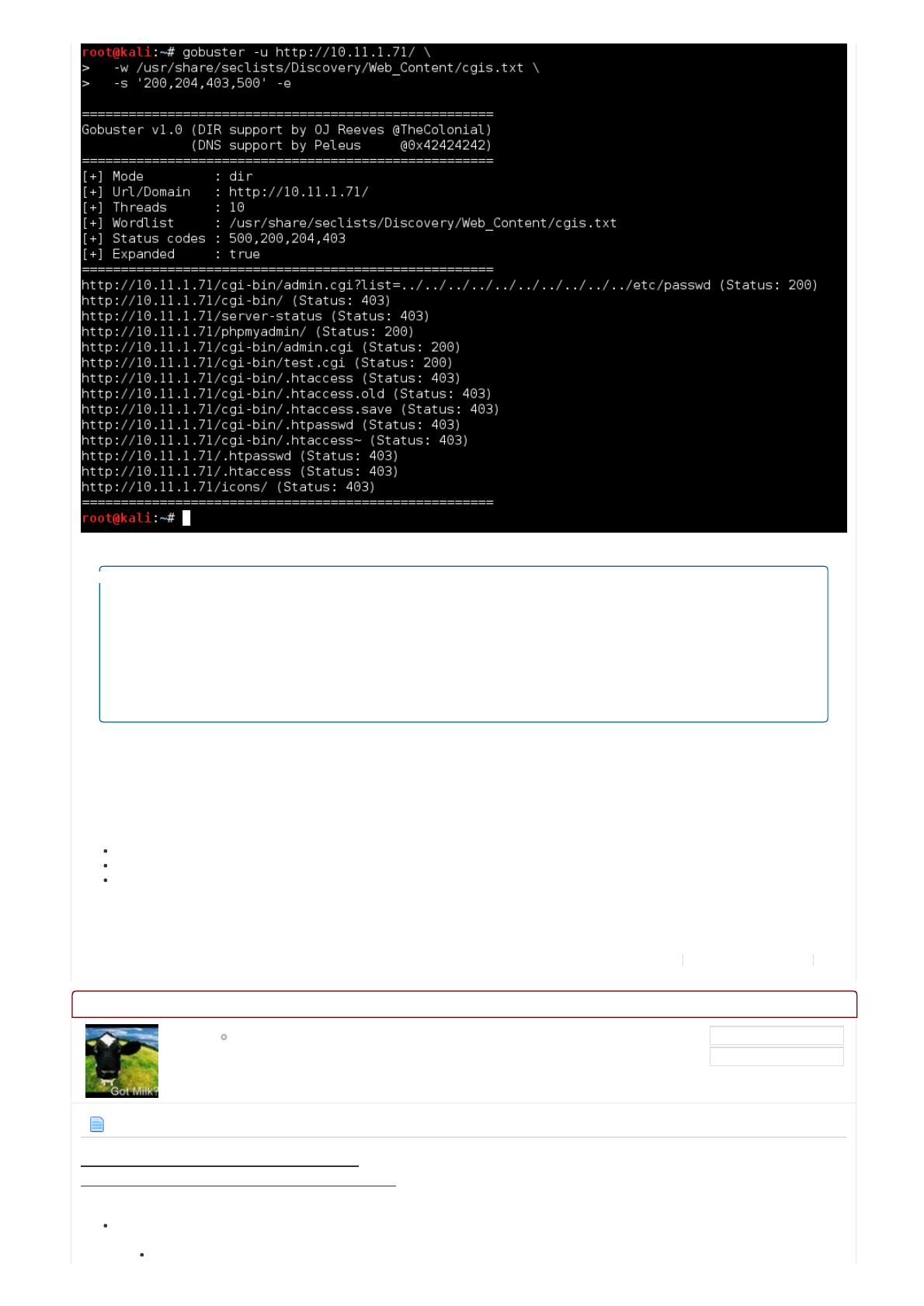
root@kali:~# gobuster -u http://10.11.1.71/ \
-w /usr/share/seclists/Discovery/Web_Content/cgis.txt \
-s '200,204,403,500' -e
...SNIP...
[+] Status codes : 500,200,204,403
...SNIP...
http://10.11.1.71/cgi-bin/admin.cgi?list=../../../../../../../../../../etc/passwd (Status: 200)
http://10.11.1.71/cgi-bin/ (Status: 403)
http://10.11.1.71/server-status (Status: 403)
http://10.11.1.71/phpmyadmin/ (Status: 200)
http://10.11.1.71/cgi-bin/admin.cgi (Status: 200)
http://10.11.1.71/cgi-bin/test.cgi (Status: 200)
http://10.11.1.71/cgi-bin/.htaccess (Status: 403)
http://10.11.1.71/cgi-bin/.htaccess.old (Status: 403)
http://10.11.1.71/cgi-bin/.htaccess.save (Status: 403)
http://10.11.1.71/cgi-bin/.htpasswd (Status: 403)
http://10.11.1.71/cgi-bin/.htaccess~ (Status: 403)
http://10.11.1.71/.htpasswd (Status: 403)
http://10.11.1.71/.htaccess (Status: 403)
http://10.11.1.71/icons/ (Status: 403)
...SNIP...
root@kali:~#
09/01/2018 Offensive Security's Complete Guide to Alpha
https://forums.offensive-security.com/showthread.php?t=4689&p=20530#post20530 22/30
Let'sbreakitdownagain:
Thetakeawayonitthistimearound,anythingstartingwith".hta"isblocked.
ThishasNOTbeenappliedto"./cgibin/"URLs,soifyoucanguess/predictwhat'sonthetarget,wecanaccessthem(justnot
theindexpage!).
Summary
WehavethreehiddenURLstolookat:
http://10.11.1.71/phpmyadmin/
http://10.11.1.71/cgibin/admin.cgi
http://10.11.1.71/cgibin/test.cgi
Lasteditedbyg0tmi1k;07222016at04:34PM.
/cgibin/(Status:403)<Wecan'taccessintheindexpage...but...
/cgibin/admin.cgi(Status:200)<...wecananypage(ifweknow/guesstheaddress!).Couldbesomething.
/cgibin/admin.cgi?list=../../../../../../../../../../etc/passwd(Status:200)<ThismightbeaLFIvulnerability(ifitaccepts/uses'list'asa
input).
/cgibin/test.cgi(Status:200)<Couldbesomething.
/phpmyadmin/(Status:200)<Knewthisalreadyforlasttime.
/cgibin/.htaccess,/cgibin/.htaccess.old,/cgibin/.htaccess.save,/cgibin/.htpasswd,/cgibin/.htaccess~,/.htpasswd,/.htaccess
(Status:403)<Likelasttime,goodchance"dotfiles"arenotallowedtobeaccessed.
/serverstatus(Status:403)<Likelasttime,Can'tuseittogetsomeniceinformationaboutthemachine.
/icons/(Status:403)<Nothelpful.
Reply ReplyWithQuote
05182016, 12:19PM
JoinDate:
Posts:
Jun2011
538
InformationGathering
VulnerabilitiesvsExploitsvsCVEs
Aquickoverviewofafewterms:
AvulnerabilityisflawinasystemwhichCOULDprovideanattackerwithawayintothesoftwareitself,ina
unattendedmanner.
Itisnotanopendoor,butaweakdoor,whichMIGHTallowanattackerawayin.
#9
OffsecStaff
g0tmi1k

09/01/2018 Offensive Security's Complete Guide to Alpha
https://forums.offensive-security.com/showthread.php?t=4689&p=20530#post20530 23/30
AexploitisthewayINTOthesystem.Anattackerturnsthevulnerabilityintoamethodintothesystem.
Anexploitisthetoolusedtobustdownthedoorallowingtheattackertowalkthroughthedoor.
0daymeanstheexploithasbeenknownaboutforlessthanaday.Sothesoftwareauthorsdidn'thaveany
notice/chancetocreateapatch,toprotectfromthevulnerability.
Someonehasfoundawaytobustdownadoorwithoutgivingthechancetoputupanyprotections,
stoppingtheattackfromhappening.
1daymeansthevulnerabilityispubliclyknownabout,allowingforthesoftwareauthorstocreateapatch.
However,thereisn'tyetanypublicexploitcode.
Abletoprotectadoorfrombeingbusteddowneventhoughthereisn'tyetaknownwaytoopenthe
door.
CVEisastandard,formakingalistofvulnerabilities,usingacertainnamingformatandterms.Itmakesiteasier
toidentityandreferencevulnerabilities.
Abletoidentitywhattheissueis.
A"feature"isusingthesoftwarehowitwasdesignedinordertoperformanaction
Suchasallowingfileuploadsonawebsite,tosharepictures,mightalsoallowforwebshellstobe
uploaded.
Pleasenote:
Noteveryvulnerabilitycanbeexploited(forvariousreasons).
Noteveryvulnerabilityhasanexploit(forvariousreasons).
Noteveryvulnerabilityorexploitis"public"(Sometimesarekept"private"sotheyarenotsharedwithanyoneor
requiredtobepurchased.Sometimesthesevulnerabilitiesarenotevenpubliclyknownabout!)
NoteveryvulnerabilityhasaCVE(forvariousreasons).
ThereareothernamingconventionsthanCVEstoidentityissues(suchasMicrosoft'sBulletins).
Theremightbemultipleexploitsforthesamevulnerability(e.g.rewrittenindifferentcodinglanguages).
Oneexploitmightuse/targetmultiplevulnerabilities.
Exploitsmaygetupdatedovertime(justlikeanyothersoftware)!
Exploitsmayaffectarangeofsoftwareversions(dependsonthevulnerability,whichdependsonthecodeusedin
thesoftwareinthefirstplace).
It'spossibletochainvulnerabilitiestocreateaexploit(Allowingtoaccess/reachplacesincodewhichnormally
wouldn'tbeaccessible).
Some"DenialofService(DoS)"exploitsarethebeginningofcreatingaPoCexploit.NoteveryDoSexploitcanbe
converted(goesbacktonoteveryvulnerabilitycanbeexploited).
A"ProofofConcept(PoC)"exploitistodemonstratethevulnerabilityisexploitable.Dependingonthestateofthe
PoC,itmayrequireworkinordertoreachdesiredgoal(E.g.itdisplaysapopupalert,ratherthanexecuting
commandsonthetarget).Thesearenotalwaysstable.
Aweaponizedexploit,meansthepayloadwillworkforeveryone/anyoneeverytime,outoftheboxwithoutany
configurationneeded.Thesearestable.
...Thisisonlyaquickoverview/guide!
AttackSurfacebasedonTarget'sInformation
Uptillnow,wereallyhaven'ttriedto"hack"intothetargetmoreaboutjustbeinganenduserandgatheringinformation
aboutthesystem(mightofjusttriedadefault.Usingwhatweknow,wehavesomeinformationaboutthesoftwareinstalledon
thetarget.Let'sputwhatweknowinorder(basedontheattacksurfacechanceofbeingvulnerable):
1.WebApplicationBigTreeCMS4.0.6
2.WebTechnologiesPHP5.5.9
3.WebServerApache2.4.7
4.SSHServiceOpenSSH6.6
5.DatabaseMySQL(Notsureontheversion)
6.OSUbuntu(14.04?notsureontheversion)
Thejustificationforthis,mainlycomesfromexperience(backgroundknowledgebasedonissuesseeninthepast):
Wedon'thavedirectaccesstoeithertheOSorMySQLdatabase,aswellasknowtheirversionnumberatthis
stagewhichiswhytheyareatthebottom.
SSHisknownbeing'stable'service(whichweknowfromresearchingCVEs).
Thewebserverisrelativelymodern.Theresonlyaveryslimchancetherewillbeanvulnerableissuewithit.
ThePHPcoreitself(notusercreatedcode)hashadvariousissuesinrecentyearssothereisachanceitcouldbe
vulnerableto*something*
howeveroftenrequiresacertainsetting/actions,whichlowersitspossibilitywecanexploitsomething.
Thehighestchanceoftherebeingaexploit,allowingustogetafootholdintothesystem,wouldbeintheweb
application.
Thisisbecauseitisthenewesttechnologysowouldhavehadlesstimetomatureduetoless
developers/pairsofeyeslookingandworkingonthecode.
Italsohasthelargestattacksurfacebasedonitbeingabletoaccessthedatabase(nothingelsewhich
wecaninteractwithcan).
09/01/2018 Offensive Security's Complete Guide to Alpha
https://forums.offensive-security.com/showthread.php?t=4689&p=20530#post20530 24/30
ExploitDatabase&CVEs
ExploitDatabase(sometimescalled,ExploitDBorEDB)isexactlywhatitsays,acollectionofexploits(allofwhicharefreeto
access).
Thiscanbeaccessedeitheronlineviathewebsite(https://www.exploitdb.com/)orofflineusingthecommandlinetool,
searchsploit.
Usingthem,itispossibletosearchforknownexploits(notvulnerabilities!)usingvariousterms/criteria,suchassoftware,
versionsandCVEs.
FormoreinformationaboutExploitDB,seehere,elseseehereforSearchSploit.
Note:Whilstthereareothersourcesforexploits(suchasSecurityFocusandPacketStorm),alltheexploitsyouwillrequirefor
thelabscanbefoundonExploitDB(whichismaintainedbyOffensiveSecurity)!
Usefultools:vFeed(allowssearchingforknownvulnerabilities,notexploits),searchsploit(exploitdatabase)
Somethingtokeepinmind,astheexploitshostedonExploitDBaresubmittedfromtheexploitauthors,theirexploittitle
formatsmaydifferslightly.Thismeansitmaytakemultipledifferentsearchtermstofindtheexploityouarelookingfor(more
aboutthislater).
ThisiswhensearchingforCVEsismoreuseful,howeveritrequiresresearchingandknowingofaCVEvaluebeforehand...
UsefulCVEsites:
CVElookuphttps://www.cvedetails.com/vendor.php(Greattoseeanoverview)
CVEinformationhttps://www.cvedetails.com/cve/[CVE]
CVEinformationhttp://cve.mitre.org/cgibin/cvename.cgi?name=[CVE]
CVEinformationhttps://web.nvd.nist.gov/view/vuln/detail?vulnId=[CVE]
Dependingonthesiteofthesoftware,itmayalsobetrackingCVEsonitsownpage(andoftenhasalotmore
informationabouttheissue)e.g.https://securitytracker.debian.org/tracker/[CVE]
CVEsourceshttps://cve.mitre.org/data/refs/index.html
Lasteditedbyg0tmi1k;11222016at04:29PM.
Reply ReplyWithQuote
05182016, 02:35PM
JoinDate:
Posts:
Jun2011
538
InformationGathering
SearchSploit(Part1)
Forthepurposeofdemonstratingsearching,let'sforgettheattacksurfaceorderingwhichwasdefined/discussearlier.Thiswill
allowustoshowadditionaltipsonsearching,allowingustofindexploitsquicker.
OpenSSH6.6
Let'sseewhatwecanfindoutaboutthisservice.
Code:
Greatstart0results.
Wewerealittlespecificwithwhatwesearchedfor,solet'sloosenitup,byremovingthesubversion.
Example#1:Whatiftheexploittitlewascalled"OpenSSH6.x"(meaningforeverysubversionofv6?)?
Example#2:Whatifthetitleis"OpenSSH<=6.8"(meaningeveryversionof6.8andunder)
SideNote:ThisissomethingtoalwayskeepinmindwhensearchingforLinuxKernelexploits!
Code:
root@kali:~# searchsploit OpenSSH 6.6
...
root@kali:~# searchsploit OpenSSH 6
...
#10
OffsecStaff
g0tmi1k

09/01/2018 Offensive Security's Complete Guide to Alpha
https://forums.offensive-security.com/showthread.php?t=4689&p=20530#post20530 25/30
SearchSploitstartedsearchinginthepathfor"6",however,itsnottoomanyresultstoquicklyeyeball.
Wesoonseethereisn'tanyexploitsthatwould"fit".Weareusingtwoloseterms,andthereisn'tanyotherwaytheycouldbe
calledsowecanruleoutthisoneforthetimebeing(weaddtoour"totry"listaboutlookingupCVEsandthensearchfor
them).
Ontothenext,Apache2.4.7.
Code:
Thismightbeanexactmatchforthesoftwareandversion,howeveritsnot"helpful"forusforafewreasons.
1.ItsaDoSexploit(basedonthepath./linux/dos/34133.txt)notreallygoingtohelpanyonehere(itsnotlabeled
asaPoC,andnotlookingtodevelopaPoC)
2.WeknowfrombruteforcingtheURLthatthepagerespondedwithaHTTP403request.Asthetitleoftheexploit
doesn'tevenhintatbypassingthislimitation,itsnotgoingtowork)
Note:DevelopingaexploitfromaDoSexploitisoutofscopeforOSCP,asitisNOTinthecoursematerialorsyllabus.
Byusingabitof"grepfu",weareabletoremoveanyDoSexploitsinoursearches.Example:
Code:
Note:Wedidn'tuse"grepv'dos'",aswewanttheslashes,hintingitsapath.Elsewemightbefilteringout"dos"fromthe
titles(asgrepisn'tremovingbasedonwholewords!)
Timetorelaxthesearchtermsagain,bytrying:"searchsploitApache2.4"andsearchsploitApache2.x"
Code:
root@kali:~# searchsploit Apache 2.4.7
...
root@kali:~# searchsploit Apache 2.4.7 | grep -v '/dos/'
...
root@kali:~# searchsploit apache 2.4 | grep -v '/dos/'
...
root@kali:~# searchsploit apache 2.x | grep -v '/dos/'
...
09/01/2018 Offensive Security's Complete Guide to Alpha
https://forums.offensive-security.com/showthread.php?t=4689&p=20530#post20530 26/30
Noneoftheseresultsareagoodmatchforus.
Timeforthenextsoftware,PHP5.5.9.
Thisiswerethepowerofbash'scommandlinetoolsreallyhelpout(overusingthewebinterface).
WearewantingtosearchforPHP's"core",ratherthanPHPplatformbasedexploits,orfilenameswith".PHP"init(itscommon
inexploitstitlestoindicatethevulnerablewebpage).Ifweweretosearchlikewehavebeen,wewouldget87possibleexploits
(whichwilltakeashortwhiletolookthroughhoweverwecandobetter!).
Code:
Sowhatwearegoingtodo,islookatONLYtheexploittitles(byusing"t"),soweforgetaboutthetheexploitpath(akathe
platform):
Code:
That'safewunwantedresultsgone,butwecandobetter.Now,let'sremoveallDoSexploits(justlikebefore).
Code:
Now,let'stryandremoveall".php"results(weareonlyafterPHP'score,ratherthanwebpageendingwith.php)..
Code:
root@kali:~# searchsploit php 5.x
...
root@kali:~# searchsploit -t php 5.x
...
root@kali:~# searchsploit -t php 5.x | grep -v '/dos/'
...
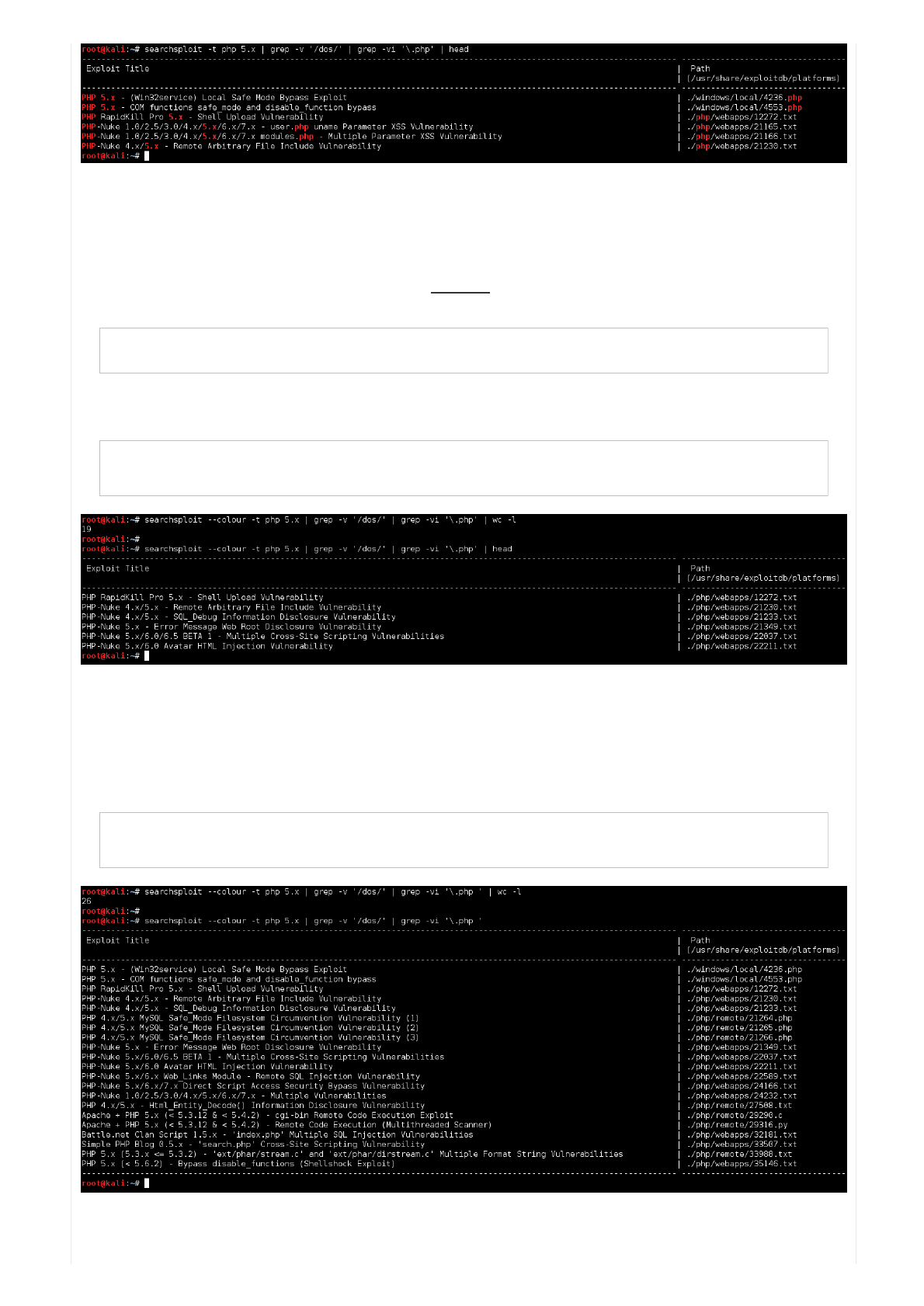
root@kali:~# searchsploit -t php 5.x | grep -v '/dos/' | grep -vi '\.php' | head
...
09/01/2018 Offensive Security's Complete Guide to Alpha
https://forums.offensive-security.com/showthread.php?t=4689&p=20530#post20530 27/30
Wait.Thatdidn'tworkright.Whydidn'tthatremovewhatwewanted?
Theproblemisbecauseofthehighlighting.Seehowwesearchfor'php',andallthevaluesinred?Nowwearewantingto
remove"dotphp".Buttous/endusersthatlooksthesame,butthatsnothowitisonKali.Thisisbecausetheressome
"invisible"stringsused,toperformthehighlighting.
Pickingon"PHPNuke1.0/2.5/3.0/4.x/5.x/6.x/7.xuser.phpunameParameterXSSVulnerability"
Code:
Sowecantellsearchsploitnottoaddcolour("colour"),thusmakinggrepworkaswewantitto!
Code:
Bingo!Muchless!
However,thereisaslightmistakeinthecommand.Ifaexploithasa".PHP"fileextensionforthePHPcore,itwouldbe
removed.Wecanfixthisbyaddingatrailingspace.
Notcompletelyperfect,aswearegoingtosee...
Code:
Soweareremovingpotentialexploits!However,wehaveaddedafewmorefalsepositivevaluesbackin.
Ifwereallywanttogetfancy,wecanstarttouse"regex"(RegularExpressions)tofilterall".php"resultsexceptforwhenthe
user.\[\033[1;31m\]php
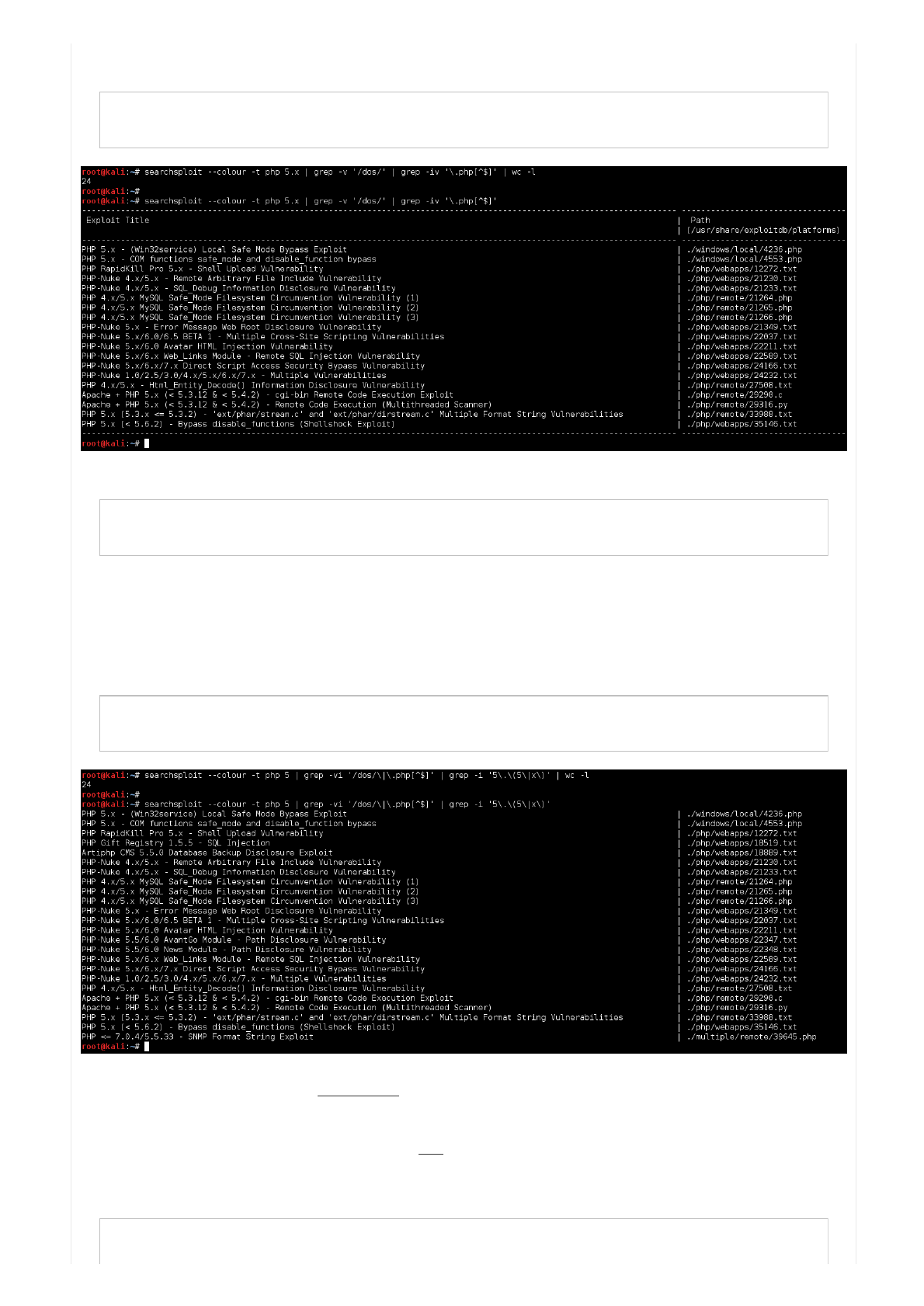
root@kali:~# searchsploit --colour -t php 5.x | grep -v '/dos/' | grep -vi '\.php'
...
root@kali:~# searchsploit --colour -t php 5.x | grep -v '/dos/' | grep -vi '\.php '
...
09/01/2018 Offensive Security's Complete Guide to Alpha
https://forums.offensive-security.com/showthread.php?t=4689&p=20530#post20530 28/30
endoftheline,endswith".php"
Code:
...ifwereallywanttogetflashy,wecancompressthelineslightlybyremovingapipe.
Code:
Butwearenotyetoutofthewoods!
Let'salsoinasinglecommandlookfora"5.x"and"5.5"exploits.Canuseeither"grep'5\.\(5\|x\)'"or"grep
'5\.5\|5\.x'"
Code:
...Ifyouaresayingtoyourselfnow"buttheybothhave24results"correct!However,thelattercommanddoesn'thavethe
"header"and"footer"lines.Sothereismoreexploits!
SoafterallofthatwithSearchSploit,isthereanything?Yes!
Afterremovingthe"Windows"exploits(targetisUbuntu,remember?),aswellasprogramsthatusePHPinthename(suchas
"PHPNuke","RapidKillPro","GiftRegistry"etc),weget...
Code:
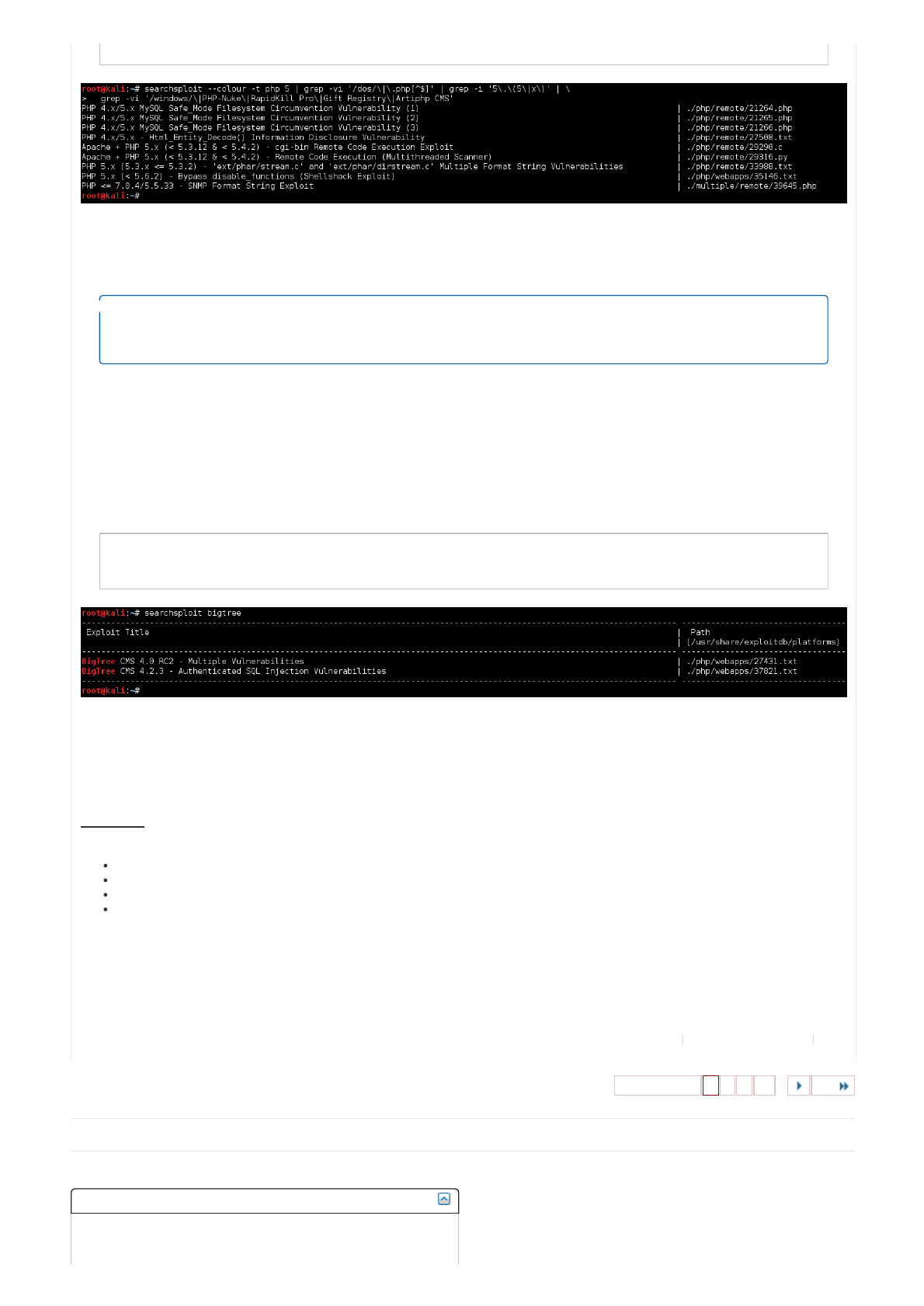
root@kali:~# searchsploit --colour -t php 5.x | grep -v '/dos/' | grep -iv '\.php[^$]'
...
root@kali:~# searchsploit --colour -t php 5.x | grep -vi '/dos/\|\.php[^$]'
...
root@kali:~# searchsploit --colour -t php 5 | grep -vi '/dos/\|\.php[^$]' | grep -i '5\.\(5\|x\)'
...
root@kali:~# searchsploit --colour -t php 5 | grep -vi '/dos/\|\.php[^$]' | grep -i '5\.\(5\|x\)' | \
grep -vi '/windows/\|PHP-Nuke\|RapidKill Pro\|Gift Registry\|Artiphp CMS'
...
09/01/2018 Offensive Security's Complete Guide to Alpha
https://forums.offensive-security.com/showthread.php?t=4689&p=20530#post20530 29/30
«PreviousThread|NextThread»
Nowwecanmanuallyremovethelowerversions(e.g.5.4.x),wehavethefollowingcandidates:
Wewillmakeanoteoftheseandkeepsearchingon.
OurlastoneisBigTree4.0.6.
Wehaveafeelingthere'snotgoingtobemanyresultsforthis,sowearenotgoingtoincludeaversionnumberdirectlyinthe
search.Sometimesthewebapplicationiswrittenas"BigTreeCMS","BigTreeCMS","BigTreeCMS"or"BigTree_CMS".So
let'salsoremovetheCMSpart.
Code:
Thereisn'tanythingwhichwouldbea"perfect"match.
Thereisaslimchancethe4.2.3exploitmightwork,howevertheresbeenvarioussubversionreleasessincethen.Plusit
requiresauthentication(whichatthisstagewedonothavenorevenknowoftheloginURL).
Summary
ThehighestchangeofsuccessrightnowwouldbethePHPexploits:
PHP4.x/5.xMySQLSafe_ModeFilesystemCircumventionVulnerability(1),(2)&(3)
PHP4.x/5.xHtml_Entity_Decode()InformationDisclosureVulnerability
PHP5.x(<5.6.2)Bypassdisable_functions(ShellshockExploit)
PHP<=7.0.4/5.5.33SNMPFormatStringExploit
Lasteditedbyg0tmi1k;09122017at10:48AM.
PWB/OSCP(2011)|WiFu/OSWP(2013)|CTP/OSCE(2013)|AWAE(2015)|AWE(2016)
root@kali:~# searchsploit bigtree
...
PHP4.x/5.xMySQLSafe_ModeFilesystemCircumventionVulnerability(1),(2)&(3)
PHP4.x/5.xHtml_Entity_Decode()InformationDisclosureVulnerability
PHP5.x(<5.6.2)Bypassdisable_functions(ShellshockExploit)
PHP<=7.0.4/5.5.33SNMPFormatStringExploit
Reply ReplyWithQuote
ReplytoThread Page1of13 12 3 11 ... Last
Youmaypostnewthreads
Youmaypostreplies
Youmaypostattachments
PostingPermissions
BBcodeisOn
SmiliesareOn
[IMG]codeisOn

09/01/2018 Offensive Security's Complete Guide to Alpha
https://forums.offensive-security.com/showthread.php?t=4689&p=20530#post20530 30/30
PerfexionRed
| ContactUs | OffensiveSecurityTraining | Archive |
AlltimesareGMT+1.Thetimenowis05:31PM.
PoweredbyvBulletin®Version4.2.4
Copyright©2018vBulletinSolutions,Inc.Allrightsreserved.
OffensiveSecurity
Skindesignedby:SevenSkins
Youmayedityourposts
[VIDEO]codeisOn
HTMLcodeisOff
ForumRules