Packet Analysis Reference Guide V3.0x V30
User Manual:
Open the PDF directly: View PDF ![]() .
.
Page Count: 46
james@vsnry.com
©2008
Compiled & Written by
Packet Analysis Reference Guide v3.0
Headers, Tables, Tools and Notes
James Summers, CISSP - ISSAP, ISSMP, CISA
GCIA, GCIH, G7799, GAWN-C, GSEC, GFSP, GPCI
CCNA, CCDA, CS-CFWS, CS-CISecS, 4001 Rec, MCSE
This page purposely left blank
Page
1
2
3
4
5
6
7
9
10
11
12
13
14
15
16
17
18
19
21
24
25
26
27
28
29
32
33
35
36
37
41
42
43
Decimal to Hexadecimal to ASCII Chart
Windows TCP / UDP Ports
Address Resolution Protocol - ARP (RFC 826)
Domain Name System - DNS (RFC 1035)
IEEE Framing
Ethernet IEEE 802.3 SNAP Frame Format
Ethernet Novell Netware 802.3 "Raw" Frame Format
OS Fingerprinting
Dynamic Routing Protocols
Generic Routing Encapsulation - GRE (RFC 2784)
Ethernet IEEE 802.2 Frame Format (802.3 with 802.2)
References
Kismet
TCPDUMP / WINDUMP
NGREP
Table of Contents
PING (Echo/Echo Reply) - ICMP Header (792)
IPV6 Header (RFC 2460)
Equations
Internet Control Message Protocol - ICMP Header (RFC 792)
Encapsulating Security Payload - ESP (RFC 2406)
Transmission Control Protocol - TCP Header (RFC 793)
Subnet Breakdown (Binary to decimal)
Subnet Breakdown (Binary to Hexadecimal)
802.11 (IEEE 1999 Reference Specification)
Ethernet II Frame Format (similar to IEEE 802.3)
Ethereal / Wireshark
Header Offset Shortcuts
TCP vs. UDP
OSI vs. TCP/IP
IPv4 Header (RFC 791)
Authentication Header - AH (RFC 2402)
User Datagram Protocol - UDP Header (RFC 768)
OSPF v2 (RFC 1583)
CIDR Octet Mask
128
(1)
/8 1 255
192
(2)
192
(2)
192
(2)
/9 2 128 00000000 0 01000000 64 10000000 128 11000000 192
/10 2 192 00000001 1 01000001 65 10000001 129 11000001 193
/11 2 224 00000010 2 01000010 66 10000010 130 11000010 194
/12 2 240
252
00000011 3 01000011 67 10000011 131 11000011 195
/13 2 248
(6)
00000100 4 01000100 68 10000100 132 11000100 196
/14 2 252 00000101 5 01000101 69 10000101 133 11000101 197
/15 2 254 00000110 6 01000110 70 10000110 134 11000110 198
/16 2 255
248
252
00000111 7 01000111 71 10000111 135 11000111 199
/17 3 128
(5)
(6)
00001000 8 01001000 72 10001000 136 11001000 200
/18 3 192 00001001 9 01001001 73 10001001 137 11001001 201
/19 3 224 00001010 10 01001010 74 10001010 138 11001010 202
/20 3 240
252
00001011 11 01001011 75 10001011 139 11001011 203
/21 3 248
(6)
00001100 12 01001100 76 10001100 140 11001100 204
/22 3 252 00001101 13 01001101 77 10001101 141 11001101 205
/23 3 254 00001110 14 01001110 78 10001110 142 11001110 206
/24 3 255
248
252
00001111
15
01001111
79
10001111
143
11001111
207
/25 4 128
(5)
(6)
00010000 16 01010000 80 10010000 144 11010000 208
/26 4 192 00010001 17 01010001 81 10010001 145 11010001 209
/27 4 224 00010010 18 01010010 82 10010010 146 11010010 210
/28 4 240
252
00010011 19 01010011 83 10010011 147 11010011 211
/29 4 248
(6)
00010100 20 01010100 84 10010100 148 11010100 212
/30 4 252
00010101
21
01010101
85
10010101
149
11010101
213
/32 4 255
00010110
22
01010110
86
10010110
150
11010110
214
248
252
00010111
23
01010111
87
10010111
151
11010111
215
(5)
(6)
00011000
24
01011000
88
10011000
152
11011000
216
A 0 00011001 25 01011001 89 10011001 153 11011001 217
B 10 00011010 26 01011010 90 10011010 154 11011010 218
C 110
252
00011011 27 01011011 91 10011011 155 11011011 219
D 1110
(6)
00011100
28
01011100
92
10011100
156
11011100
220
00011101 29 01011101 93 10011101 157 11011101 221
00011110 30 01011110 94 10011110 158 11011110 222
224
240
248
252
00011111
31
01011111
95
10011111
159
11011111
223
(3) (4) (5) (6) 00100000 32 01100000 96 10100000 160 11100000 224
00100001 33 01100001 97 10100001 161 11100001 225
00100010 34 01100010 98 10100010 162 11100010 226
252
00100011 35 01100011 99 10100011 163 11100011 227
(6)
00100100 36 01100100 100 10100100 164 11100100 228
00100101 37 01100101 101 10100101 165 11100101 229
00100110 38 01100110 102 10100110 166 11100110 230
248
252
00100111 39 01100111 103 10100111 167 11100111 231
(5)
(6)
00101000 40 01101000 104 10101000 168 11101000 232
00101001 41 01101001 105 10101001 169 11101001 233
00101010 42 01101010 106 10101010 170 11101010 234
252
00101011 43 01101011 107 10101011 171 11101011 235
(6)
00101100 44 01101100 108 10101100 172 11101100 236
00101101 45 01101101 109 10101101 173 11101101 237
00101110 46 01101110 110 10101110 174 11101110 238
240
248
252
00101111
47
01101111
111
10101111
175
11101111
239
(4)
(5)
(6)
00110000 48 01110000 112 10110000 176 11110000 240
00110001 49 01110001 113 10110001 177 11110001 241
00110010 50 01110010 114 10110010 178 11110010 242
252
00110011 51 01110011 115 10110011 179 11110011 243
(6)
00110100 52 01110100 116 10110100 180 11110100 244
00110101 53 01110101 117 10110101 181 11110101 245
00110110 54 01110110 118 10110110 182 11110110 246
248
252
00110111 55 01110111 119 10110111 183 11110111 247
(5)
(6)
00111000 56 01111000 120 10111000 184 11111000 248
00111001 57 01111001 121 10111001 185 11111001 249
00111010 58 01111010 122 10111010 186 11111010 250
252
00111011 59 01111011 123 10111011 187 11111011 251
(6)
00111100 60 01111100 124 10111100 188 11111100 252
00111101 61 01111101 125 10111101 189 11111101 253
00111110 62 01111110 126 10111110 190 11111110 254
00111111 63 01111111 127 10111111 191 11111111 255
Subnet Breakdown (Binary to Decimal)
Classes
128
(1)
192
(2)
192
(2)
192
(2)
00000000 00 01000000 40 10000000 80 11000000 C0
00000001 01 01000001 41 10000001 81 11000001 C1
00000010 02 01000010 42 10000010 82 11000010 C2
252
00000011 03 01000011 43 10000011 83 11000011 C3
(6)
00000100 04 01000100 44 10000100 84 11000100 C4
00000101 05 01000101 45 10000101 85 11000101 C5
00000110 06 01000110 46 10000110 86 11000110 C6
248
252
00000111 07 01000111 47 10000111 87 11000111 C7
(5)
(6)
00001000 08 01001000 48 10001000 88 11001000 C8
00001001 09 01001001 49 10001001 89 11001001 C9
00001010 0A 01001010 4A 10001010 8A 11001010 CA
252
00001011 0B 01001011 4B 10001011 8B 11001011 CB
(6)
00001100 0C 01001100 4C 10001100 8C 11001100 CC
00001101 0D 01001101 4D 10001101 8D 11001101 CD
00001110 0E 01001110 4E 10001110 8E 11001110 CE
240
248
252
00001111 0F 01001111 4F 10001111 8F 11001111 CF
(4)
(5)
(6)
00010000 10 01010000 50 10010000 90 11010000 D0
00010001 11 01010001 51 10010001 91 11010001 D1
00010010 12 01010010 52 10010010 92 11010010 D2
252
00010011 13 01010011 53 10010011 93 11010011 D3
(6)
00010100 14 01010100 54 10010100 94 11010100 D4
00010101 15 01010101 55 10010101 95 11010101 D5
00010110 16 01010110 56 10010110 96 11010110 D6
248
252
00010111 17 01010111 57 10010111 97 11010111 D7
(5)
(6)
00011000 18 01011000 58 10011000 98 11011000 D8
00011001 19 01011001 59 10011001 99 11011001 D9
00011010 1A 01011010 5A 10011010 9A 11011010 DA
252
00011011 1B 01011011 5B 10011011 9B 11011011 DB
(6)
00011100 1C 01011100 5C 10011100 9C 11011100 DC
00011101 1D 01011101 5D 10011101 9D 11011101 DD
00011110 1E 01011110 5E 10011110 9E 11011110 DE
224
240
248
252
00011111 1F 01011111 5F 10011111 9F 11011111 DF
(3) (4) (5) (6) 00100000 20 01100000 60 10100000 A0 11100000 E0
00100001 21 01100001 61 10100001 A1 11100001 E1
00100010 22 01100010 62 10100010 A2 11100010 E2
252
00100011 23 01100011 63 10100011 A3 11100011 E3
(6)
00100100 24 01100100 64 10100100 A4 11100100 E4
00100101 25 01100101 65 10100101 A5 11100101 E5
00100110 26 01100110 66 10100110 A6 11100110 E6
248
252
00100111 27 01100111 67 10100111 A7 11100111 E7
(5)
(6)
00101000 28 01101000 68 10101000 A8 11101000 E8
00101001 29 01101001 69 10101001 A9 11101001 E9
00101010 2A 01101010 6A 10101010 AA 11101010 EA
252
00101011 2B 01101011 6B 10101011 AB 11101011 EB
(6)
00101100 2C 01101100 6C 10101100 AC 11101100 EC
00101101 2D 01101101 6D 10101101 AD 11101101 ED
00101110 2E 01101110 6E 10101110 AE 11101110 EE
240
248
252
00101111 2F 01101111 6F 10101111 AF 11101111 EF
(4)
(5)
(6)
00110000 30 01110000 70 10110000 B0 11110000 F0
00110001 31 01110001 71 10110001 B1 11110001 F1
00110010 32 01110010 72 10110010 B2 11110010 F2
252
00110011 33 01110011 73 10110011 B3 11110011 F3
(6)
00110100 34 01110100 74 10110100 B4 11110100 F4
00110101 35 01110101 75 10110101 B5 11110101 F5
00110110 36 01110110 76 10110110 B6 11110110 F6
248
252
00110111 37 01110111 77 10110111 B7 11110111 F7
(5)
(6)
00111000 38 01111000 78 10111000 B8 11111000 F8
00111001 39 01111001 79 10111001 B9 11111001 F9
00111010 3A 01111010 7A 10111010 BA 11111010 FA
252
00111011 3B 01111011 7B 10111011 BB 11111011 FB
(6)
00111100 3C 01111100 7C 10111100 BC 11111100 FC
00111101 3D 01111101 7D 10111101 BD 11111101 FD
00111110 3E 01111110 7E 10111110 BE 11111110 FE
00111111 3F 01111111 7F 10111111 BF 11111111 FF
Subnet Breakdown (Binary to Hexadecimal)
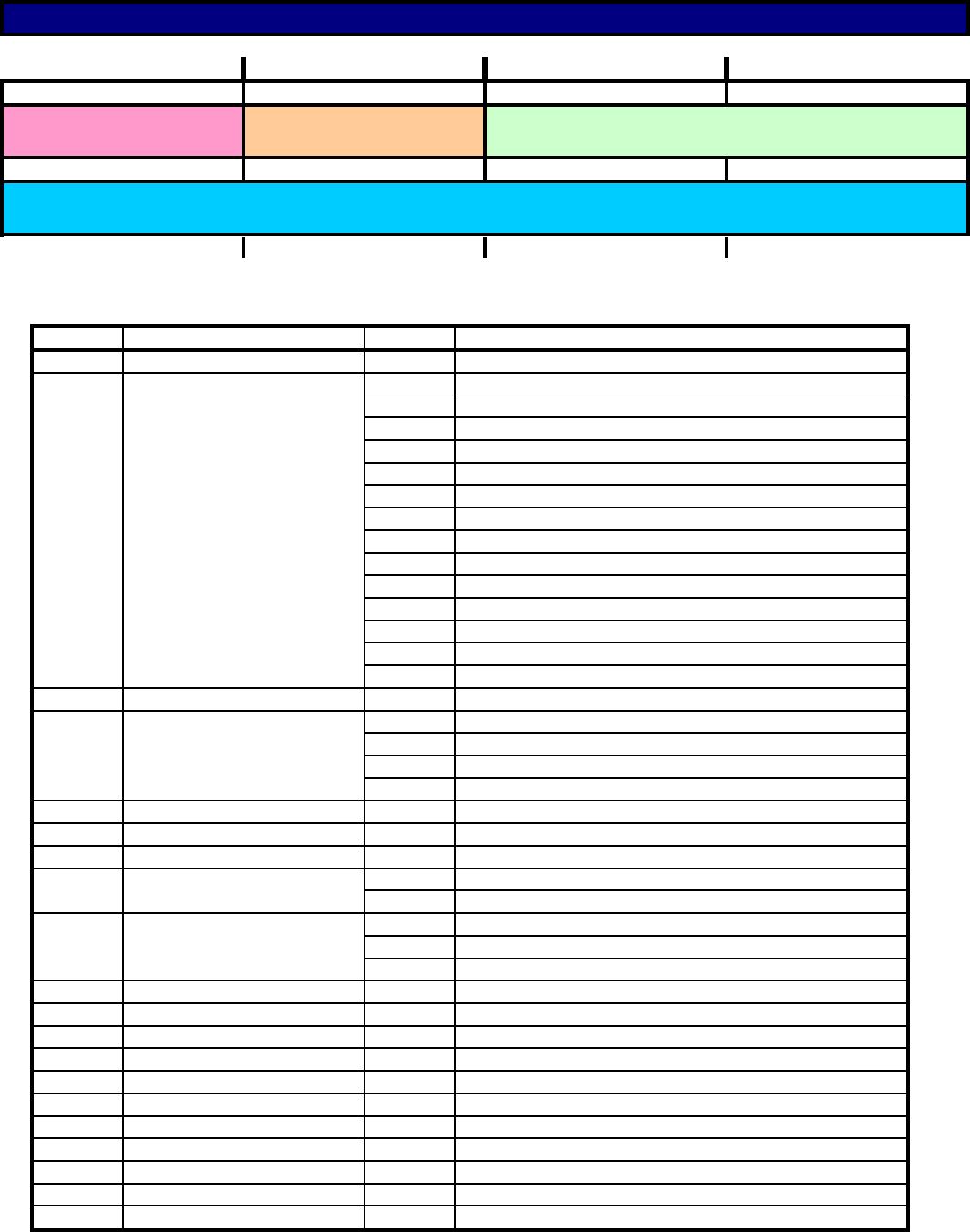
(TCP Header Length * 4 byte multiplier) - (Minimum TCP Header Length * 4 byte multiplier)
(TCP Header Length * 4 byte multiplier) - 20 bytes
IP total Length - ((IP Header Length * 4 byte multiplier) + (TCP Header Length * 4 byte multiplier))
1 AND 1 is 1 1 OR 1 is 1 1 XOR 1 is 0
1 AND 0 is 0 1 OR 0 is 1 1 XOR 0 is 1
0 AND 1 is 0 0 OR 1 is 1 0 XOR 1 is 1
0 AND 0 is 0 0 OR 0 is 0 0 XOR 0 is 0
Number of hosts on a subnet =
2
n
-2 Where n is the number of bits in the ip address / subnet dedicated to the host
Number of subnets that can be created from n subnet bits =
2
n
Where n is the number of bits dedicated to the subnet
Number of host bits needed for X hosts to be on the same subnet =
ln(X+2) Where X is the number of hosts required on the subnet.
ln 2 Note:
ln
is the nature log.
Round up to the nearest whole number.
Number of network and subnet bits needed for X hosts to be on the same subnet =
ln(X+2) Where X is the number of hosts required on the subnet.
ln 2 Note:
ln
is the nature log.
Round up to the nearest whole number.
Determining the network address from IP and subnet mask by doing a logical AND on the IP with the subnet mask
00000011 10101010 01010101 11111110
11111111 11111111 11111111 11110000
00000011
10101010
01010101
11110000
The equation: (bp*np) + … + (b1* n1) + (b0* n0)
b is the base (b = 2 for binary and b = 16 for hexadecimal)
p is the position of the number (counting starts from the rightmost character as 0)
n is the number in the p
th
position
Examples:
Convert from binary to decimal
Convert from hexadecimal to decimal
40960 + 3072 + 128 + 9 = 44169
Subneting Equations
AC89
(163* A) + (162* C) + (161* 8) + (160* 9)
This is where you need to know hex A is decimal 10 and hex C is decimal 12
Converting Binary or Hexadecimal to Decimal
(27* 1) + (26* 0) + (25* 1) + (24* 0) + (23* 1) + (22* 1) + (21* 1) + (20* 1)
10.170.85.254 is the IP address
128 + 0 + 32 + 0 + 8 + 4 + 2 + 1 = 175
10101111
(163* 10) + (162* 12) + (161* 8) + (160* 9)
(4096 * 10) + (256 * 12) + (16 * 8) + (1 * 9)
255.255.255.240 is the subnet mask
10.170.85.240 is the network address for the subnet
Equations
32 -
Note: This assume you have something like "ip subnet zero" on your network device.
Otherwise you have to - 2 from your total where all the subnet bits are 0's or 1's
Remember the -2 is because host bits of all 0's is the network address and all 1's is the
broadcast address for that subnet
Length of IP Packet Payload =
TCP & IP Equations
Logic Equations
TCP Options Length =
3 Equations
Length
(bits)
4
16
8
8
Dec Hex Proto Dec Hex Proto Dec Hex Proto
1 0x01 ICMP 9 0x09 IGRP 50 0x32 ESP
2 0x02 IGMP 17 0x11 UDP 51 0x33 AH
6 0x06 TCP 47 0x2F GRE 88 0x58 EIGRP
32
32
flag=3
offset=13
8
8
16
16
4
8
16
16
16
16
IP Protocol ip[9]
ip[12:4]
ip[16:4]
UDP Header Length
IP Address - Src
TCP Src Port
IP Address - Dst
IP Fragmentation
TCP Header Length
TCP Flags
TCP Windows Size
UDP Src Port
UDP Dst Port upd[4:2]
ICMP Type
NotesField
IP Header Length
IP Packet Length
TCPDUMP Filter
ip[0] &0x0F
ip[2:2]
ip[8]IP TTL
ICMP Code
tcp[14:2]
udp[0:2]
udp[2:2]
icmp[0]
icmp[1]
TCP Dst Port
tcp[12] &0x0F
tcp[13]
tcp[0:2]
tcp[2:2]
Header Offset Shortcuts
There is no multipler for this length field
More Fragment bit is set.ip[6] &0x20 = 0x20 Fragment offset in not 0ip[6:2] &0x1fff != 0x0000
Remember to use a 4 byte multiplier to find header
length in bytes
There is no multipler for this length field
Remember to use a 4 byte multiplier to find header
length in bytes
4 Hdr Offset

7
6
5
4
3
2
1
Examples:
Examples:
Examples:
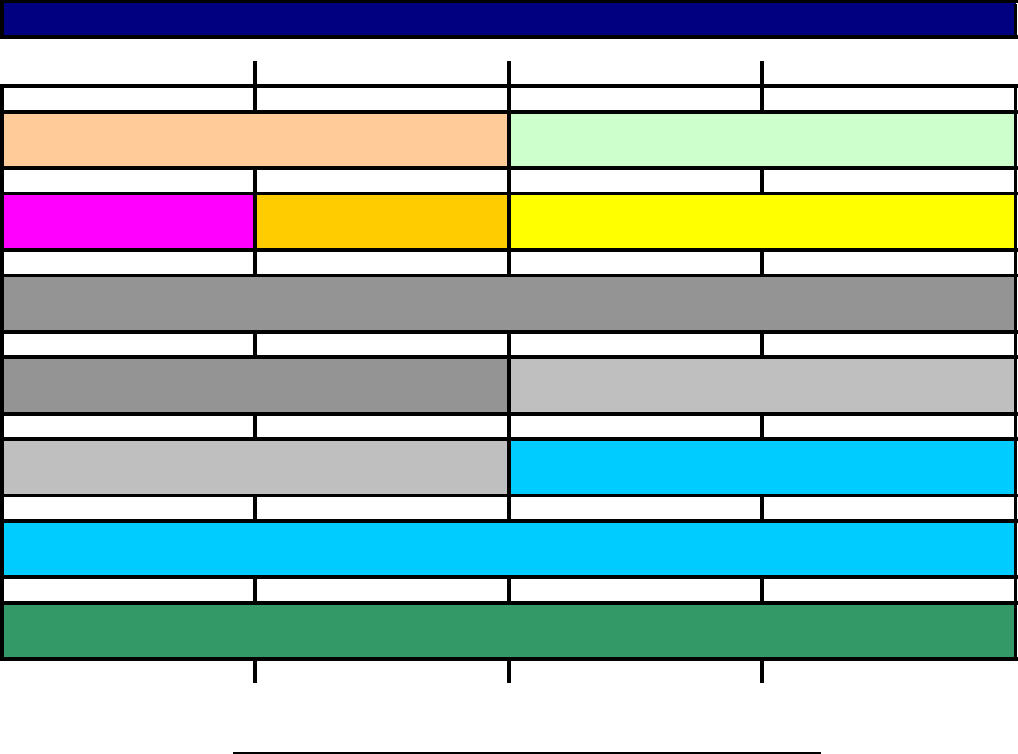
OSI vs. TCP/IP
Determines the network services required.
Application Layer (Layer 7)
Application
Transport (TCP)
Internet (Network) (IP)
Network Access
(Data Link)
Data Link
Physical
OSI TCP/IP
Application
Presentation
Session
Transport
Network
DNS, FTP, LDP, Telent, TFTP, SMTP and WWW
Presents data to the application layer. Essentially functions as a translator from computer to human readable form.
HTTP, TIFF, JPEG, MIDI and MPEG
Presentation Layer (Layer 6)
Defines how to address physical locations, how to make connections between nodes, and how to handle the network
of messages. This layer is responsible for end-to end integrity and control of the session and handles the
sequencing of packets.
Session Layer (Layer 5)
NFS, SQL, RPC
Transport Layer (Layer 4)
Establishes and maintains the connection between systems and formats the data for transfer between nodes.
Examples:
Examples:
Examples:
Examples:
Application Data
Presentation PH Data
Session SH
Transport TH
Network NA
Data Link DH
8 bytes 4 bytes
Preamble
Manchester encoding - Preamble is 62 bits of alternating 1's and 0's. followed by 11.
Data
Data
Data
Data
Incoming Packet
Network Layer (Layer 3)
Defines the protocols that computers use in order to access the network for transmitting and receiving messages.
Has two sub layers: Logical Link Control and Media Access Control .
TCP, UDP, SPX
Defines how packets of data are routed between end systems over interconnected networks. Routing error detection,
and control of node data traffic are managed at this layer.
IP, OSPF, ICMP, RIP
Frame Trailer
14 bytes
Frame Header
46 to 1500 bytes
Data
Ethernet Frame
ARP, SLIP, PPP
For outgoing packets, the data + header from an upper layer is packaged into the data of the layer below it. For
incomming packets, the layer header information is strip off and used to determine where the remaining data is to go.
Layer Header
Physical Layer (Layer 1)
Defines the physical connection (RJ48, BNC, HSSI, etc…) between a host and a network and converts the bits into
voltages or light impulses for transmission.
HSSI, X.21, EIA/TIA-232 and EIA/TIA-449
Outgoing Packet
Data Link Layer (Layer 2)
Encapsulation (In reverse is demultiplexing.)
5 OSI

TCP vs. UDP
6 TCPvsUDP
0
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
R DF MF
0 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31
IP Version Number
Valid values are: 4 for IP version 4 6 for IP version 6
IP Header Length
(4 byte multiplier)
Number of 32-bit words in IP header minimum value 5 (5 x 4 = 20 bytes) maximum value 15 (15 x 4 = 60 bytes)
Type of Service
(Used by gateways as a QoS type field) (Most OS's default to 0)
If the first 3 high order bits are 1's, then possible it came from busy router that had to set tags to get through a backlog
Total Length
(No multiplier)
Number of bytes in packet maximum length = 65,535
IP Identification Number
Uniquely identifies every datagram sent by host, value typically incremented by 1 (AKA Fragment ID)
Flags
R is reserved and must be set to 0
D is Don't Fragment Flag 1=Don't Fragment 0=Can Fragment
MF is More Fragments 1=More Fragments 0=No Fragment or no more Fragments
(frag x:y@z where x is the fragment ID, y is # of bytes (must be divisible by 8) and z is the fragment offset)
(In Ethernet the MTU 1500 should see middle fragments of size 1480 (1480 data + 20 ip header = 1500)
Fragment Offset
(8 byte multiplier) (Measured in units of 64 bits) (Max fragment offset 65528 (8191*8) )
Position of this fragment in the original datagram value is multiplied by 8 to get bytes
Time To Live
IP Protocol
DDDD
1 ICMP 9 IGRP 47 GRE 88 EIGRP
2 IGMP 17 UDP 50 ESP 89 OSPF
6 TCP 47 GRE 51 AH
Header Checksum
Covers IP header only Validated along the path from source to destination
Options
(0-40 bytes; 1st @ 20th byte offset; padded 4-byte boundary) (Processed by each router as packet passes)
D
0 End of Option list Timestamp
1 No operation (pad) Loose source route (security risk)
7 Record Route (security risk) Strict source route (security risk)
20 Bytes
Byte Offset 4 Byte Offset 5 Byte Offset 6 Byte Offset 7
Byte Offset 0 Byte Offset 1 Byte Offset 2 Byte Offset 3
Byte Offset 9
Version
(4-bit)
IP Header
length (4-bit) Type of Service (8-bit) Total Length (16-bit) (in Byte Offsets)
Header Checksum (16-bit)
Byte Offset 15
Fragment Offset (13-bit)
Protocol (8-bit)
Byte Offset 10 Byte Offset 11
Hex
IP Identification Number (16-bit)
Byte Offset 8
Byte Offset 14
Time to Live (8-bit)
Byte Offset 20
0x580x2F
Source IP Address (32-bit)
Destination IP Address (32-bit)
data (variable length…)
Byte Offset 18
Hex
0x01 0x09
Byte Offset 22 Byte Offset 23
Byte Offset 19
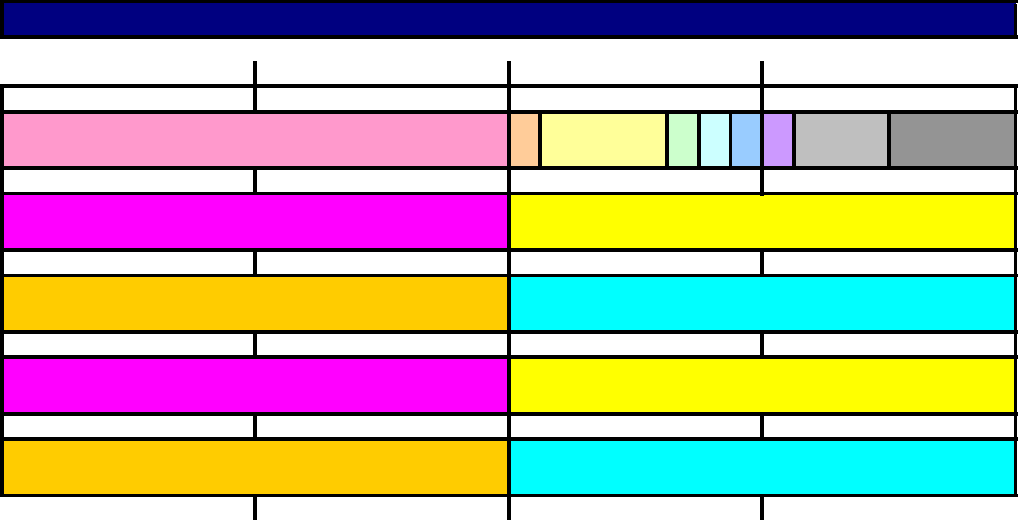
IPv4 Header (RFC 791)
Hex
0x33
0x59
0x2F
0x02
0x06
Hex
0x11
Byte Offset 12 Byte Offset 13
Byte Offset 16 Byte Offset 17
Byte Offset 21
IP Options (variable length…) (if any)
0x32
0x01
0x07
Hex
131 0x83
137 0x89
D Hex
68 0x440x00
7 IPv4 Hdr
Type of Service
(Used by gateways as a QoS type field) (Most OS's default to 0)
D T R 0 0
01234567
Bit 0 - 2 Precedence
Bit 3 0 = Normal Delay 1 = Low Delay
Bit 4 0 = Normal Throughput 1 = High Throughput
Bit 5 0 = Normal Reliability 1 = High Reliability
Bit 6 & 7 Reserved for future use (Always set to 0)
Precedence
1 1 1 Network Control
1 1 0 Internetwork Control
1 0 1 CRITIC / ECP
1 0 0 Flash Override
0 1 1 Flash
0 1 0 Immediate
0 0 1 Priority
0 0 0 Routine
Telnet 0000
1000
0000
0100
0000
0010
0000
0010
0000
Same as request
BOOTP
Protocol
DNS UDP Query
DNS TCP Query
DNE Zone Transfer
NNTP
ICMP - Erros
ICMP - Requests
ICMP - Responces
Any IGP
EGP
SNMP
1000
1000
0100
Telnet
FTP Control
FTP Data
TFTP
SMTP Command
SMTP Data
0100
Precedence
IPv4 Header (cont.)
TOS Value
1000
1000
8 IPv4 Hdr (2)
0
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
CWR
ECN
URG
ACK
PSH
RST
SYN
FIN
0 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31
Common Port Numbers
smtp nntp ldap
domain netbios-ns https (ssl)
finger netbios-ssn ms-ds
http imap
ssh pop3 bgp
Sequence Number
32-bit number uniquely identifies initial byte of segment data.
Acknowledgement Number
Represents next byte of data receiving host expects: (last received sequence number + 1)
Header Length
(4 byte multiplier)
Number of 32-bit words in TCP header minimum value 5 (5x4=20bytes) maximum value 15 (5x15=60bytes)
Reserved
4 bits set to 0
Congestion Window Reduced (CWR)
Set to 0 unless ECN is used. (1 = sender cuts congestion window in half)
Explicit Congestion Notification Echo (ECN)
Set to 0 unless ECN is used. (1 = receiver cuts congestion window in half)
Flags
URG = Urgent ACK = Acknowledgment PSH = Push RST = Reset SYN = Syncronize
FIN = Finish (Note: Push means don't buffer data but push it to be processes as soon as it comes in.)
Window Size
Acts as flow control. Window size dynamically changes as data is received. A 0 window size tells src host to wait.
Checksum
Urgent Pointer
Options
0 End of Options List 2 Maximum segment size 4 Selective ACK ok
1 No Operation (pad) 3 Window scale 8 Timestamp
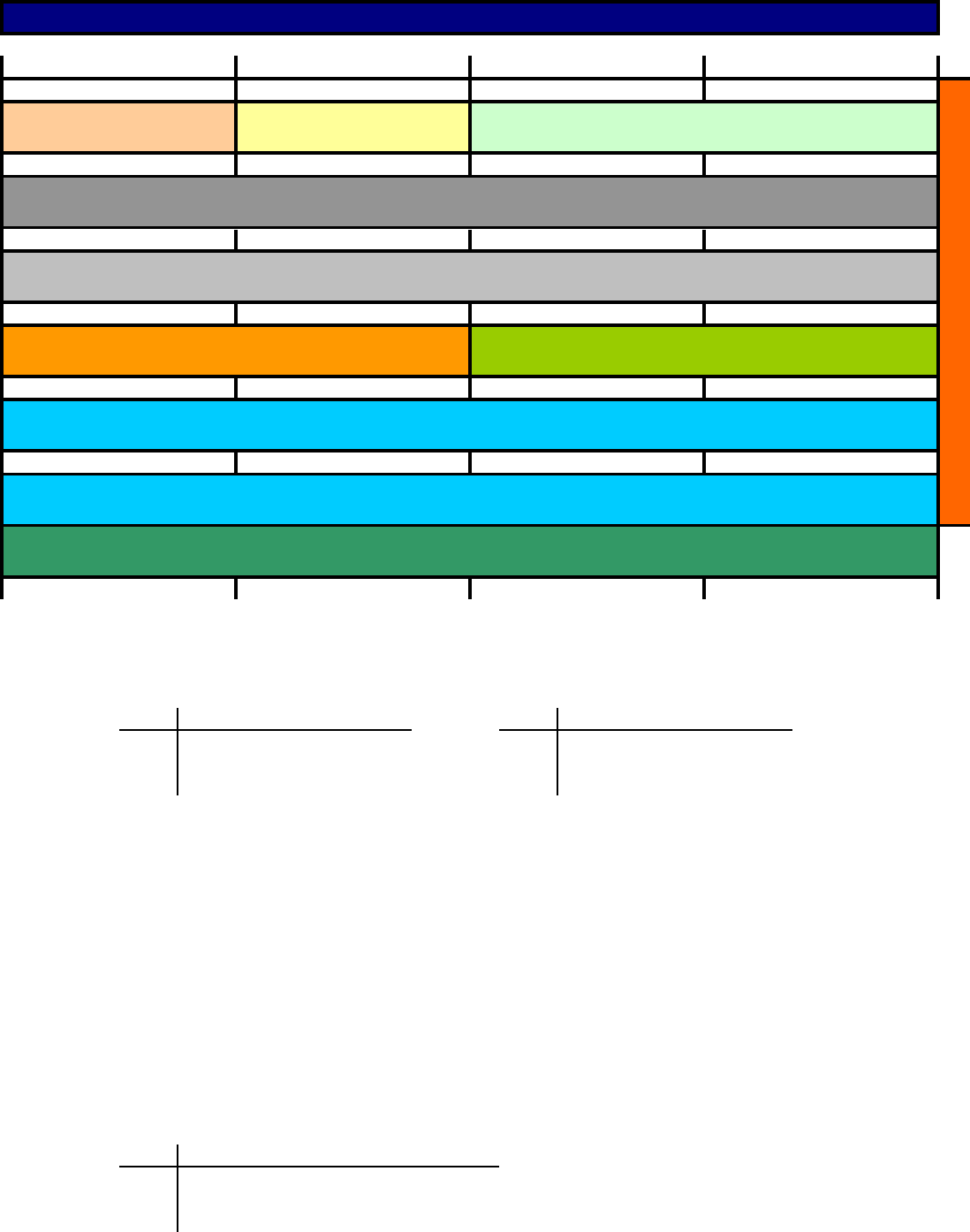
Transmission Control Protocol - TCP Header (RFC 793)
Byte Offset 5 Byte Offset 6
Byte Offset 20
389
Byte Offset 7
Byte Offset 9
Byte Offset 21
Byte Offset 4
Acknowledgement Number (32-bit)
Byte Offset 8
Byte Offset 19
Checksum (16-bit) Urgent Pointer (16-bit)
Hex
Byte Offset 23
20 Bytes
Byte Offset 0 Byte Offset 1 Byte Offset 2 Byte Offset 3
Byte Offset 12 Byte Offset 13 Byte Offset 14 Byte Offset 15
Destination Port Number (16-bit)Source Port Number (16-bit)
Sequence Number (32-bit)
Hdr Length
(4-bit) Window Size (16-bit)
Reserved
(4-bit)
Byte Offset 11
Hex HexDD
TCP Opitions (variable length…) (if any)
TCP Options Length = TCP Header Length in the current packet - 20 bytes (Minimum TCP Header Length)
data (variable length…)
Length of Packet Payload = IP Total Length - (IP Header Length + TCP Header Length)
D DHex
Byte Offset 10
ftp-control
Byte Offset 22
Byte Offset 16 Byte Offset 17
19 0x13
0x8F143
0x89137
139
0x07
Byte Offset 18
7 0x77echo
0x50
53
80
0x35
0x4F79ftp-data
25 0x19
179
119 0x185
445 0x1BD
443
Points to the sequence number of the octet following the urgent data.
Covers psedo header (IP Header source and destinstation addresses, the protocol and the computed TCP length (the
TCP header length the and data length in octets)) and the TCP header
0x1BB
0xB3
chargen
0x1420
21 0x15
0x8B
22 0x16 110 0x6E
9 TCP Hdr
0
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
0 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31
Common Port Numbers
Length
Number of bytes in the entire datagram including header
minimum value 8 bytes
(Which is the length of just the header with no data)
maximum value 65515 bytes (or 65507 bytes of UDP data)
(Max IP is 65535 bytes - 20 byte header = 65515 bytes for UDP packet - 8 bytes of UDP header = 65507)
Checksum
33434 829A traceroute
echo
chargen 514 0x202 syslog
500
ntp
netbios-ns
69 0x45 0x1F4 isakmptftp
68
53
67
37
Byte Offset 0 Byte Offset 1 Byte Offset 2 Byte Offset 3
Byte Offset 4 Byte Offset 7
Destination Port Number (16-bit)Source Port Number (16-bit)
Byte Offset 10 Byte Offset 11Byte Offset 8
User Datagram Protocol - UDP Header (RFC 768)
Byte Offset 5 Byte Offset 6
Length (16-bit) Checksum (16-bit)
Byte Offset 9
D Hex D Protocol
data (variable length…)
HexD ProtocolHex
snmp-trap
123 0x7B
137 0x89
138 0x8A
161
0x35
0x43
7
Protocol
19
0x07
0x13
(Note: By RFC, the crc is not required)
520 rip
162 0xA20x44
domain
bootps
time
0xA1
Covers psedo header (IP Header source and destinstation addresses, the protocol and UDP length) and entire UDP
datagram
netbios-dgm
snmp
0x208
bootpc
0x25
10 UDP Hdr
0
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
0 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31
Common Types & Codes
(Note: Byte offset 4-5: identification #)
(Note: Byte offset 6-7: sequence #)
Byte Offset 0 Byte Offset 1 Byte Offset 2 Byte Offset 3
Byte Offset 4 Byte Offset 7
Checksum (16-bit)
Echo reply
Type Description Message Code DescriptionCode
0
Internet Control Message Protocol - ICMP Header (RFC 792)
Byte Offset 5 Byte Offset 6
Message Type (8-bit) Message Code (8-bit)
0
Type
(contents depends on type and code)
3 Destination Unreachable Net Unreachable
Host Unreachable
Protocol Unreachable
Destination Network Unknown
Port Unreachable
Fragmentation Needed & Don't Fragment Flag Set
Source Route Failed
0
1
4
16
17
Information Request
Information Reply
Source Quench
Redirect
8
9
10
11
18
13
Address Mask Reply
Photuris (RFC 2521)
Timestamp Request
Timestamp Reply
30 Traceroute
31 Datagram Conversion Error
40
Address Mask Request
38 Domain Name Reply
37 Domain Name Request
14
15
12
5
Parameter Problem
Router Advertisement
Router Selection
Time Exceeded
Echo
1
2
0
0
Missing a Required Option
0
0
0
0
0
0
0
Time to Live exceeded in transit
0
0
0
0
0
Fragment Reassembly Time Exceeded1
0
Bad Length
Pointer indicates the error
0
13
0
8
9
12
Redirect Datagram for the TOS & Host
Redirect Datagram for the Network
Redirect Datagram for the Host
Host Unreachable for TOS
10
11
Communication Administratively Prohibited
2
3
Redirect Datagram for the TOS & Network
Destination Host Unknown
2
0
1
3
4
5
6
7
Host Administratively Prohibited
Network Unreachable for TOS
Source Route Isolated
Network Administratively Prohibited
11 ICMP Hdr

0
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
0 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31
PING (Echo/Echo Reply) - ICMP Header (792)
Checksum (16-bit)Message Type (8 or 0)
8 Echo 0
Byte Offset 0 Byte Offset 1 Byte Offset 3Byte Offset 2
Byte Offset 6 Byte Offset 7
data (variable length…)
Message Code (0)
Byte Offset 4
0 Echo reply 0
Byte Offset 5
Type DescriptionType Message Code DescriptionCode
12 Ping
0
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
0 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31
Hardware Address Type
1 Ethernet
6 IEEE 802 Lan
Protocol Address Type
IPv4 (0x0800)
Hardware Address Length
6 for Ethernet/IEEE 802
Protocol Address Length
4 for IPv4
Operation
1 Request
2 Reply
Byte Offset 0 Byte Offset 1 Byte Offset 2 Byte Offset 3
Byte Offset 12 Byte Offset 13 Byte Offset 14 Byte Offset 15
Byte Offset 4
Protocol Address Type (16-bit)Hardware Address Type (16-bit)
Byte Offset 8
Source Hardware Address (48-bit)
Source Hardware Address (cont.) Source Protocol Address (32-bit)
Address Resolution Protocol - ARP (RFC 826)
Byte Offset 5 Byte Offset 6
Byte Offset 9 Byte Offset 10 Byte Offset 11
Byte Offset 7
Hardware Address Length
(8-bit)
Protocol Address Length
(8-bit) Operation (16-bit)
Target Hardware Address (cont.)
Byte Offset 16 Byte Offset 17 Byte Offset 18 Byte Offset 19
Source Protocol Address (cont.) Target Hardware Address (48-bit)
Byte Offset 20 Byte Offset 21 Byte Offset 22 Byte Offset 23
2048
Byte Offset 24 Byte Offset 25 Byte Offset 26
Target Protocol Address (32-bit)
Byte Offset 27
ARP maps the logical address (IP) to the physical address (MAC)
13 ARP
0
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
QR
AA
TC
RD
RA
0 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31
Query/Response
dig version.bind txt chaos @
server name
0
Query
dig @
server name
txt chaos version.bind
1
Response
Opcode
0 Standard query (QUERY)
1 Inverse query (IQUERY)
2 Server status request (STATUS)
AA
1 Authoritative Answer
TC
1 Truncation
RD
1 Recursion Desired
RA
1 Recursion Available
Z
Reserved; set to 0
Response Code
0 No Error
1 Format Error
2 Server Failure
3 Non-existent Domain (NXDOMAIN)
4 Query Type Not Implemented
5 Query Refused
QDCOUNT
(Number of entries in Question section)
ANCOUNT
(Number of resource records in Answer section)
NSCOUNT
(Number of name server resource records in Authority section)
ARCOUNT
(Number of resource records in Additional Information section)
Domain Name System - DNS (RFC 1035)
Byte Offset 5 Byte Offset 6 Byte Offset 7
Additional Records Count (ADCOUNT) (16-bit)
RCODE
(4-bit)
Byte Offset 8 Byte Offset 9 Byte Offset 10 Byte Offset 11
Answer Count (ANCOUNT) (16-bit)Question Count (QDCOUNT) (16-bit)
Byte Offset 0 Byte Offset 1 Byte Offset 2 Byte Offset 3
Byte Offset 12 Byte Offset 13
Byte Offset 16
Byte Offset 4
Byte Offset 17 Byte Offset 18 Byte Offset 19
DNS ID (16-bit)
Name Server Count (NSCOUNT) (16-bit)
Opcode
(4-bit) Z (3-bit)
Byte Offset 14 Byte Offset 15
Authority Section (16-bit) Additional Information Section (16-bit)
Question Section (16-bit) Answer Section (16-bit)
14 DNS

RIPv1
Ripv2
Distance Vector Distance Vector
Default Administrative Distance 120 Default Administrative Distance 120
Maximum hop count 15 Maximum hop count 15
Classful Classless
Broadcast based (255.255.255.255) Uses multicast (224.0.0.9)
No support for VLSM networks Supports Variable Length Subnet Mask(VLSM) networks
Auto-summarization Auto-summarization
No authentication Allows for MD5 authentication
No support for discontiguous networks Supports discontiguous networks
Broadcast all routes every 30 seconds Broadcast all routes every 30 seconds
Uses lowest hop count for best route (Bellman-Ford) Uses lowest hop count for best route (Bellman-Ford)
Slow convergence Slow convergence
IGRP
(Cisco Proprietary / No longer supported)
EIGRP
(Cisco Proprietary)
Distance Vector Hybrid
Default Administrative Distance 100 Default Administrative Distance 90 (External is 170)
Maximum hop count 255 (default 100) Maximum hop count 255 (default 100)
Classful Classless
Broadcast based (255.255.255.255) Broadcast based (255.255.255.255)
No support for VLSM networks Supports Variable Length Subnet Mask(VLSM) networks
Auto and manual summarization
No authentication Allows for authentication
No support for discontiguous networks Supports discontiguous networks & route summaries
Broadcast all routes every 90 seconds No periodic route updates. Hello messages with neighbors
Uses bandwidth and delay for best route Best Path selection via Diffusing Update Alogorithm (DUAL)
Uses autonomous system numbers Uses autonomous system numbers
Comunication via Reliable Transport Protocol (RTP)
Support for IPv4 and IPv6
OSPF
Link State
Default Administrative Distance 110
Maximum hop count limit - none
Classful
Broadcast based (255.255.255.255)
Supports Variable Length Subnet Mask(VLSM) networks
Manual summarization
Allows for authentication
Supports discontiguous networks & route summaries
Multicast on change
Uses bandwidth and delay for best route (Dijkstra)
Uses autonomous system numbers
Fast convergence
Uses wildcard masks (inverse) in Cisco routers
Dynamic Routing Protocols
15 routing protocols
0
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
0 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31
Version Number
Valid values are: 12 forOSPF version 2
Type
Packet Length
(Used by gateways as a QoS type field) (Most OS's default to 0)
The length of the protocol packet in bytes includinging the standard OSPF header
Router ID
The router ID of the packet's source.
maximum length = 65,535
Area ID
Checksum
Standard IP checksum of the entire contents of the OSPF packet excluding the 64-bit authentication field.
Authentication Type
Identifies the authentication scheme to be used for the packet.
Authentication
Used by the authentication scheme
OSPF v2 (RFC 1583)
Byte Offset 0 Byte Offset 1 Byte Offset 2 Byte Offset 3
Type (8-bit) Packet Length (16-bit)
Byte Offset 4 Byte Offset 5 Byte Offset 6 Byte Offset 7
Byte Offset 10 Byte Offset 11
Hello
Type
1
Type Description
Byte Offset 12 Byte Offset 13 Byte Offset 14 Byte Offset 15
Byte Offset 16 Byte Offset 17
4
Type Description
data (variable length…)
5 Link State Acknowledgment
Identifies the are that this packet belongs to. Packets travelling over a virtual link are labelled with the backbone Area ID
og 0.0.0.0
Description
Link state Update
Databse Description
Link State Update
2
3
0
1
rest
No authentication
Simple password in the clear
Reserved for assignment by the IANA
Router ID (32-bit)
Authentication Type (16-bit)
Area ID (32-bit)
Checksum (16-bit)
24 Bytes
Version Number (8-bit)
Byte Offset 18 Byte Offset 19
Authentication (64-bit)
Byte Offset 20 Byte Offset 21 Byte Offset 22 Byte Offset 23
Authentication (cont...)
Byte Offset 8 Byte Offset 9
16 OSPF

0
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
C
0 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31
Checksum Present Bit
Reserved-0
Version Number
Protocol Type
Checksum
Standard IP checksum of the all the 16 bit words in the GRE header and payload packet.
Reserved - 1
Reserved for future use. Only present if checksum bit is set and if present must be 0.
Authentication
Used by the authentication scheme
IPX
ARP 806 AppleTalk 809B
IP (VINES) 0BAD, 80C4 ARP (Atalk) 80F3
DRP
LAT 6004 IP version 6 86DD
6003
XNS 0600, 0807 LAVC 6007
Contains the protocol type of the payload packet. Values are listed in the "ETHER TYPES" section of RFC 1700
Type Value (Hex) Type
Byte Offset 7
Checksum (16-bit) (optional) Reserved-1 (16-bit) (optional)
Bits 6 through 12 are reserved for future use. The bits must be set to 0 and ignored on receipt.
Value
The version number fields must be 0.
Generic Routing Encapsulation - GRE (RFC 2784)
Byte Offset 0 Byte Offset 1 Byte Offset 2 Byte Offset 3
Protocol Type (16-bit)
Byte Offset 4
DRP 6003 NetWare 8137
data (encapsulated packet) (variable length…)
Version
(3-bit)
Reserved-0 (12-bit)
If the checksum bit is set to 1 then the Checksum and Reserved-1 fields are present.
IP version 4 0800 8037
If bits 1 through 5 are non-zero then the packet should be discarded unless receiver implements RFC 1701.
Byte Offset 5 Byte Offset 6
17 GRE

0
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
0 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31
Next Header
Equivalent to the IP Protocol Identifier field in IPv4
D D Hex D D
1 ICMP 9 IGRP 47 GRE 88 EIGRP
2 IGMP 17 UDP 50 ESP 89 OSPF
6 TCP 47 GRE 51 AH
Payload Length
Specifies the length of the Authentication Header (number of 32-bit words - 2 for IPv6 compatibility)
Reserved
Zero filled field
Security Parameter Index (SPI)
Random 32-bit value used with destination IP address and IP Sec protocol to uniquely identify the SA.
The SPI is generally selected by the destination IP Sec node.
Sequence Number
A 32-bit sequence number starting at zero and incremented by one for each packet.
This monotonically increasing sequence number is the AH anti-replay mechanism.
Authentication Data
A variable-length field that contains the Integrity Check Value (ICV) for the packet.
Original Packet
AH Transport Mode Packet
AH Tunnel Mode Packet
Byte Offset 0 Byte Offset 1 Byte Offset 2 Byte Offset 3
Byte Offset 12 Byte Offset 13
Byte Offset 4
Byte Offset 14 Byte Offset 15
Security Parameter Index (32-bit)
Sequence Number (32-bit)
Authentication Data (variable length…)
Authentication Header - AH (RFC 2402)
Byte Offset 5 Byte Offset 6 Byte Offset 7
Next Header (8-bit) Payload Length (8-bit) Reserved (16-bit)
Hex Hex Hex
Byte Offset 8 Byte Offset 9 Byte Offset 10 Byte Offset 11
0x01 0x09 0x2F 0x58
0x02 0x11 0x32 0x59
0x06 0x2F 0x33
Original IP Header Upper Layer Header Upper Layer Data
The length of the IVC must be an integral multiple of 32 bits (IPv4) or 64 bits (IPv6); will need to be padded or
truncated to meet the requirement.
<--------------------------------------------------------------- Authenticated --------------------------------------------------------------->
<---------------------- Payload ---------------------->
Upper Layer Data
Original IP Header Authentication
Header Upper Layer Header Upper Layer Data
New IP Header Authentication
Header Original IP Header Upper Layer Header
<----------------------------------------------- Authenticated ----------------------------------------------->
<------------------ Encapsulation ------------------>
16 AH
0
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
0 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31
ESP Header
Security Parameter Index (SPI)
Sequence Number
ESP Payload
Payload Data
A variable-length field containing the data to be protected by the ESP protocol; i.e., the original IP packet
ESP Trailer
Padding
Pad Length
8-bit value indicating the number of Pad bytes that were inserted.
Next Header
Equivalent to the IP Protocol Identifier field in IPv4
D
Hex
D Hex D Hex D Hex
1 ICMP 9 IGRP 47 GRE 88 EIGRP
2 IGMP 17 UDP 50 ESP 89 OSPF
6 TCP 47 GRE 51 AH
ESP Authentication
Authentication Data
Authentication Data (variable length…)
0x01
A 0-255 byte field used for variety of purposes. It is primarily used to ensure that the Payload, Pad Length, & Next
Header align on a 32-bit boundary. It can also be used if the ESP encryption algorithm requires a certain minimum
number of bytes. Finally, it may be used to hide the real size of the payload (protect against traffic flow analysis)
A 32-bit sequence number starting at zero and incremented by one for each packet.
Pad Length (8-bit) Next Header (8-bit)
Random 32-bit value used with destination IP address and IP Sec protocol to uniquely identify the SA.
The SPI is generally selected by the destination IP Sec node.
This monotonically increasing sequence number is the AH anti-replay mechanism.
Payload Data (variable length…)
Padding (0-255 bytes)
Payload Data (cont.) Padding (0-255 bytes)
Encapsulating Security Payload - ESP (RFC 2406)
Byte Offset 5 Byte Offset 6 Byte Offset 7
Security Parameter Index (32-bit)
Byte Offset 0 Byte Offset 1 Byte Offset 2 Byte Offset 3
Byte Offset 4
A variable-length field that contains the Integrity Check Value (ICV) for ESP the packet. The length of the this field is
dependent upon the authentication function used. This field is present only if an authentication service is being
employed in the SA.
0x2F
0x32
0x580x09
0x11
0x06 0x2F 0x33
0x590x02
ESP Header ESP
Payload ESP Trailer ESP
Authentication
Sequence Number (32-bit)
19 ESP

Original Packet
ESP Transport Mode Packet
ESP Tunnel Mode Packet
<---------------------------------------------- Authenticated ---------------------------------------------->
<---------------------------------------- Encrypted ---------------------------------------->
New IP Header ESP
Header Upper Layer Header Upper Layer Data ESP AuthOriginal IP Header ESP
Trailer
Original IP Header Upper Layer Header Upper Layer Data
<-------- Encapsulation -------->
<------------------------------------- Authenticated ------------------------------------->
<------------------------------ Encrypted ------------------------------>
Encapsulating Security Payload - ESP (cont.)
<---------------------- Payload ---------------------->
Upper Layer Header Upper Layer Data ESP Trailer ESP AuthESP HeaderOriginal IP Header
20 ESP (2)
0
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
0 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31
IP Version Number
Traffic Class
8-bit field similar to IPv4 type of service field
Flow Label
To tag packets of a specific flow to differentiate the packets at the network layer. (
QoS
)
Payload Length
The total length of the data portion of the packet
Next Header
Similar to the protocol field of IPv4 packet header
Hop Limit:
Similar to Time to Live field in IPv4 packet header
Source Address
128-bit source address field
Destination Address
128-bit destination address field
6 for IP version 6 4 for IP version 4
Byte Offset 13
data (variable length…)
Byte Offset 40 Byte Offset 41 Byte Offset 42 Byte Offset 43
Next Header (8-bit) Extension Header Information (variable length…)
Destination IP Address (128-bit)
Source IP Address (cont.)
Byte Offset 26 Byte Offset 27
Extension Header Information (variable length…)
Byte Offset 36
Variable Length
Destination IP Address (cont.)
Byte Offset 28 Byte Offset 29 Byte Offset 30 Byte Offset 31
Destination IP Address (cont.)
40 Bytes
Byte Offset 12
Byte Offset 23
Byte Offset 32 Byte Offset 33 Byte Offset 34 Byte Offset 35
Byte Offset 24 Byte Offset 25
Byte Offset 11
Traffic Class (8-bit) Flow Label (20-bit)
Next Header (8-bit) Hop Limit (8-bit)
Byte Offset 7
Payload Length (16-bit)
Version
(4-bit)
Source IP Address (128-bit)
Byte Offset 16
Source IP Address (cont.)
IPv6 Header (RFC 2460)
Byte Offset 5 Byte Offset 6
Byte Offset 14 Byte Offset 15
Byte Offset 4
Byte Offset 0 Byte Offset 1 Byte Offset 2 Byte Offset 3
Byte Offset 8 Byte Offset 9 Byte Offset 10
Destination IP Address (cont.)
Byte Offset 18 Byte Offset 19
Source IP Address (cont.)
Byte Offset 20 Byte Offset 21 Byte Offset 22
Byte Offset 37 Byte Offset 38 Byte Offset 39
Byte Offset 17
21 IPv6 Hdr
Samble IPv6 Address:
A IPv6 Address is 16 bytes (128 bits) this give us 3.4 X 10^38
Reserved for examples and documentation.
Subnet Interface ID
The unique local unicast range. Same Idea as the IPv4 RFC 1918 private addresses.
The link-local unicast range. Same Idea as the IPv4 RFC 1918 private addresses.
But for on a single LAN. Non routeable.
Global Prefix
Special IPv6 Addresses
Address Description
4321
Equal ::. This is the equivalent to IPv4's 0.0.0.0.
Equals ::1. This is equivalent to IPv4's local host of 127.0.0.1.
IPv4 address written in a mixed IPv6 / IPv4 network environment.
The global unicast address range.
abdc: 1234: 0000: 0000: 9865:
IPv6 (cont.)
Used with 6to4, which is the strucuture that allows IPv6 packets to be transmitted
over an IPv4 network without the need to configure explicit tunnels.
2001:0DB8::/32
0:0:0:0:0:0:0:0
0:0:0:0:0:0:0:1
0:0:0:0:0:0:0:192.168.100.1
2000::/3
FC00::/7
FF00::/8
2002::/16
FE80::/10
3FFF:FFF::/32
The multicast range.
Reserved for examples and documentation.
2001: 0db8:
22 IPv6 Hdr (2)
This page purposely left blank
802.1P
802.1Q
802.1X
Flavors of 802.11 (common)
54 Mbit/s using the 5 GHz band with up to 23 non overlapping channels. (~15 users per AP)
11 Mbit/s using the 2.4 GHz band with 3 non-overlapping channels. (~25 users/AP)(Marketed - WiFi)
54 Mbit/s using the 2.4 GHz band with 3 non-overlapping channels. (~20 users/AP)(Marketed - WiFi)
Organizationally Unique Identifier (OUI) This is the first 3 bites of the Media Access Control (MAC) Address)
http://standards.ieee.org/regauth/oui/oui.txt
This framing does have the LLC and SNAP. Used in conjunction with Wireless traffic
on the wired side.
Flavors of 802.1 (common)
Provides a mechanism for implementing Quality of Service (QoS)
VLAN Tagging
Port based network access control
A physical layer standard that defines the CSMA/CD access method on a bus topology. This is the most common
frame type for Ethernet IP traffic.
Ethernet II
IEEE 802.1
IEEE 802.11
IEEE 802.5
IEEE 802.4
Flavors of 802.3
IEEE 802.3
IEEE 802.2
802.3 "RAW"
802.3 with 802.2
802.3 with 802.2 SNAP
This framing does not use 802.2 LLC. Novell used this framing.
This framing does use the 802.2 LLC.
A physical layer standard that defines the CSMA/CD access method on a bus topology.
A data link layer standard used with 802.3, 802.4, and 802.5 & 802.11
802.11a
802.11b
802.11g
802.11n Allows for greater Mbit/s using multiple-input multiple-output (MIMO), channel bonding and frame
aggregation. This standard can be used in the 2.4 with 3 non overlapping channels and 5.0 GHz band
with up to 23 non overlapping channels. (~15 users per AP)
IEEE Framing
802.3 Physical Physical802.11
802.3
Medium
Access
802.4
802.4 802.5
Physical
MediumMedium
802.5
Physical Physical Layer
Wireless LAN Medium Access Control (MAC) and Physical Layer Specifications.
This is Token Passing Bus Access Method and Physical Layer Specifications.
Token Ring Access Method and Physical Layer Specifications.
Layer
802.10 Security
802 Overview & Architecture
802.1 Management
802.1 Bridging
802.2 Logical Link Control (LLC)
Data
Link
Access Access
802.11
Medium
Access
24 IEEE Framing
0
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
0 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31
2 byte (16 bit) field that specifies the upper-layer protocol
46 to 1500 bytes of upper-layer protocol information
The cyclic redundancy check (CRC) or checksum for the Ethernet Frame
LAT
DRP 6003
14 byte frame header + 1500 bytes of encapsulated data + 4byte frame trailer = 1518 bytes
IP version 6 86DD
6003
6004
Max Ethernet Frame:
DRP
Min Ethernet Frame:
14 byte frame header + 46 bytes of encapsulated data + 4byte frame trailer = 64 bytes
Data:
Frame Check Sequence:
8037
ARP (Atalk) 80F3
809B
NetWare 8137
Ethernet II Frame Format (similar to IEEE 802.3)
Byte Offset 5 Byte Offset 6
Byte Offset 18 Byte Offset 19
Byte Offset 8 Byte Offset 9
Byte Offset 14
Byte Offset 11
Destination Address (48-bit)
Byte Offset 12 Byte Offset 13
data (variable length…)
XNS
6 byte (48 bit) destination media access control (MAC) address
Value
Frame Check Sequence (32-bit)
Note: The difference between Ethernet II and IEEE 802.3 is that this field in the IEEE
standard is called the length field.
Most common format of Ethernet packets today.
Type:
6 byte (48 bit) source media access control (MAC) address
Destination Address:
Source Address:
8 bytes (64 bit) At the head of each frame is a preamble used for synchronization
1010…10101011 this is know as Manchester encoding.
Preamble:
6007
Byte Offset 0 Byte Offset 1 Byte Offset 2 Byte Offset 3
Byte Offset 15
Byte Offset 16 Byte Offset 17
Byte Offset 7Byte Offset 4
Source Address (48-bit)
Source Address (cont.)
data (46 to 1500 bytes)
Destination Address (cont...)
Type (16-bit)
Byte Offset 10
IP version 4
0600, 0807
0BAD, 80C4
Value (Hex) Type
0806 AppleTalk
LAVC
IP (VINES)
0800
ARP
Type
IPX
25 Ethernet II Hdr
0
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
0 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31
1 byte is various control information (Connection less)
2 bytes are for connection-oriented LLC
Pads the frame to minimum of 46 bytes of data and LLC (so collisions can be detected)
46 to 1500 bytes of upper-layer protocol information
The cyclic redundancy check (CRC) or checksum for the Ethernet Frame
Ethernet IEEE 802.2 Frame Format (802.3 with 802.2)
Byte Offset 5 Byte Offset 6
Byte Offset 15
Byte Offset 4
Byte Offset 8 Byte Offset 9
Destination Address (48-bit)
Byte Offset 14
Source Address (48-bit)
Source Address (cont.)
Byte Offset 10
Byte Offset 7
Destination Address (cont...)
Byte Offset 2
Length (16-bit)
Byte Offset 16 Byte Offset 19
DSAP (8-bit) SSAP (8-bit)
2 byte (16 bit) field that specifies the number of bytes (3-1500) in the LLC and data fields
(Part of 802.3 Header)
Preamble:
Byte Offset 17 Byte Offset 18
Byte Offset 0 Byte Offset 1
6 byte (48 bit) source media access control (MAC) address (Part of 802.3 Header)
Destination Address:
Source Address:
Length:
Byte Offset 3
Byte Offset 12 Byte Offset 13
6 byte (48 bit) destination media access control (MAC) address (Part of 802.3 Header)
Byte Offset 11
Frame Check Sequence:
The logical link control (LLC) is made up of the DSAP, SSAP and Control fields. This is a
method for telling the 802.3 IEEE and Netware (RAW) formats. The IEEE 802.3 format has
the LLS and the NetWare 802.3 "Raw" format does not. (This is the 802.2 Header)
Logical Link control
SSAP:
Control:
1 byte source service access point; sending process at source
1 byte destination service access point; receiving process at destination
Data:
Pad:
DSAP:
Control (1 or 2 bytes) data + pad (variable length…) (43 to 1497 bytes)
Frame Check Sequence (32-bit)
8 bytes (64 bite) At the head of each frame is a preamble used for synchronization
1010…10101011
data + pad (cont.)
26 Ether 802.3 Hdr
0
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
0 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31
1 byte is various control information (Connection less)
2 bytes are for connection-oriented LLC
3 byte (24 bit) field to identify the vendor
2 byte (16 bit) field that specifies the upper-layer protocol
Pads the frame to minimum of 46 bytes of data and LLC (so collisions can be detected)
46 to 1500 bytes of upper-layer protocol information
The cyclic redundancy check (CRC) or checksum for the Ethernet Frame
0600, 0807
Byte Offset 10 Byte Offset 11
Byte Offset 7
Destination Address (cont...)
Source Address (cont.)
Byte Offset 19
Byte Offset 14
Byte Offset 8 Byte Offset 9
Length (16-bit)
Byte Offset 12 Byte Offset 13
Byte Offset 16 Byte Offset 17
Byte Offset 4
SSAP (8-bit)
Byte Offset 18
Ethernet IEEE 802.2 SNAP Frame Format (802.3 with 802.2 SNAP)
Byte Offset 5 Byte Offset 6
Byte Offset 3
Destination Address (48-bit)
Source Address (48-bit)
Byte Offset 1 Byte Offset 2
DSAP (8-bit)
Type:
Byte Offset 15
SNAP Header The Subnet Access Protocol Header consists of the Vendor Code and Type fields
Frame Check Sequence (32-bit)
1010…10101011
Destination Address: 6 byte (48 bit) destination media access control (MAC) address (Part of 802.3 Header)
1 byte destination service access point; receiving process at destination (Always AA)
Vendor Code:
Control:
Byte Offset 0
Control (8-bit) Vendor code (24-bit)
Type (16-bit) data + pad (variable length…) (43 to 1497 bytes)
2 byte (16 bit) field that specifies the number of bytes (3-1500) in the LLC and data fields
Preamble:
Source Address: 6 byte (48 bit) source media access control (MAC) address (Part of 802.3 Header)
Length:
8 bytes (64 bite) At the head of each frame is a preamble used for synchronization
6007
Type
8137
XNS
This is the Framing formate used on the Ethernet (wired) side with 802.11 with 802.2 SNAP for the wireless.
DRP 6003
Value
Logical Link control The logical link control (LLC) is made up of the DSAP, SSAP and Control fields. This is a
method for telling the 802.3 IEEE and Netware (RAW) formats. The IEEE 802.3 format has
the LLS and the NetWare 802.3 "Raw" format does not. (Part of the 802.2 SNAP Header)
DSAP:
IP (VINES) 0BAD, 80C4
NetWare
IP 800
Frame Check Sequence:
SSAP: 1 byte source service access point; sending process at source (Always AA)
Pad:
ARP 806
Value
RARP 8035
Type
ARP (Atalk) 80F3
LAT 6004
LAVC
Data:
27 Ether 802.3 SNAP Hdr
0
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
0 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31
IP Version Number
Ethernet Novell Netware 802.3 "Raw" Frame Format (802.3 without 802.2)
Byte Offset 5 Byte Offset 6
Byte Offset 17
Byte Offset 14 Byte Offset 15
Byte Offset 4
Byte Offset 10 Byte Offset 11
Byte Offset 7
Destination Address (cont...)
Byte Offset 19
Byte Offset 8 Byte Offset 9
Frame Check Sequence (32-bit)
Byte Offset 0 Byte Offset 1 Byte Offset 2 Byte Offset 3
Byte Offset 12 Byte Offset 13
Byte Offset 16
Type (16-bit)
data (cont.)
Destination Address (48-bit)
Source Address (48-bit)
Source Address (cont…)
data (variable length…) (46 to 1500 bytes)
Byte Offset 18
Preamble:
Destination Address: 6 byte (48 bit) destination media access control (MAC) address
8 bytes (64 bite) At the head of each frame is a preamble used for synchronization
1010…10101011
Data:
Frame Check Sequence:
2 byte (16 bit) field that specifies the number of bytes (46-1500) in the LLC and data fields
6 byte (48 bit) source media access control (MAC) address
46 to 1500 bytes of upper-layer protocol information. IPX header starting with 2 byte
checksum (usually FFF) followed by NetWare higher layers ('data')
The cyclic redundancy check (CRC) or checksum for the Ethernet Frame
Note the lack of the LLC fields, this is how you tell Netware 802.3 from IEEE 802.3
Source Address:
Length:
28 Ether 802.3 RAW Hdr

0
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
0 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31
Frame Control
Duration / ID
Duration/ID field encoding
15 14
0
1 0
1 0
1 1
1 1
1
1
Address Fields
Sequence Control
Frame Body
Variable length field that contains information specific to individual frame types and subtypes.
FCS
32-bit check sum field calculated over all the fields of the MAC header and Frame body
Consists of the following subfields: Fragment Number (bits 0-3) and Sequence Number (bits 4-
15). Frames that have a payload larger than 2312 bytes will be fragmented.
Consists of the following subfields: Protocol Version (bits 0-1), Type (bits 2-3), Subtype (bits 4-7),
To DS (bit 8), From DS (bit 9), More Fragment (bit 10), Retry (bit 11), Power management (bit
12), More Data (bit 13), WEP (bit 14) and Order (bit 15)
There are 4 address fields in the MAC frame format. These fields are used to indicate the
BSSID, source address (SA), destination address (DA), transmitting station address (TA), and
the receiving station address (RA).
bit 13 - 0 Usage
0 - 32767
0 Fixed value within frames transmitted during the CFP
Duration
1-16383 Reserved
1-2007
Address 4 (cont.)
Sequence Control (16-bit)
0 to 2312 bit Frame Body (variable length)
Address 3 (cont.)
Byte Offset 24 Byte Offset 25 Byte Offset 26 Byte Offset 27
Byte Offset 31Byte Offset 28
Address 4 (48-bit)
802.11 (IEEE 1999 Reference Specification)
Byte Offset 5 Byte Offset 6
Total Duration/ID (16-bit)
Byte Offset 4 Byte Offset 7
Frame Control (16-bit)
Byte Offset 11
Address 1 (48-bit)
Address 2 (cont.)
Byte Offset 15
Address 1 (cont.) Address 2 (48-bit)
Byte Offset 8
Byte Offset 16 Byte Offset 17 Byte Offset 18
Byte Offset 9 Byte Offset 10
Byte Offset 20 Byte Offset 21 Byte Offset 22 Byte Offset 23
30 Byte - MAC Header (Offset 0 to 29)
Byte Offset 0 Byte Offset 1 Byte Offset 2 Byte Offset 3
Byte Offset 12 Byte Offset 13
Byte Offset 29 Byte Offset 30
Byte Offset 14
Byte Offset 19
Address 3 (48-bit)
0 to 2312 bit Frame Body (variable length)
FCS (32-bit)
2008 - 16383 Association Identificatier (AID) in PS-Poll frames (Max association per AP is 2007)
Reserved
0 Reserved
29 802.11

Frame Control
0
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
TDS
FDS
MF
Retry
PM
MD
WEP
Order
Protocol Version
Type / Subtype
b3
b2
b7
b6
b5
b4
00 0000
00 0001
00 0010
00 0011
00 0100
00 0101
0 0
00 1000
00 1001
00 1010
00 1011
00 1100
0 0
0 1
01 1010
01 1011
01 1100
01 1101
01 1110
01 1111
10 0000
10 0001
10 0010
10 0011
10 0100
10 0101
10 0110
10 0111
1 0
1
1
Miscellaneous Info
802.11a 54 Mbit/s using the 5 GHz band
802.11b 11 Mbit/s using the 2.4 GHz band (Marketed under the name WiFi)
802.11g 54 Mbit/s using the 2.4 GHz band (Marketed under the name WiFi)
802.11n
802.11 (cont.)
Reserved 0000-1111
1000-1111
Data
Currently the value should always be 0
The type and subtype field together identify the function of the frame
Data
Data
Data
Data
Data
Data
0000-1001
Data
Data
Control
Control
Reserved
CF-Ack + CF-Poll (no data)
Null function (no data)
CF-Ack (no data)
CF-Poll (no data)
Request To Send (RTS)
Clear To Send (CTS)
Reserved
Control
Control
Control
Data + CF-Ack + CF-Poll
CF-End + CF-Ack
Data + CF-Poll
Acknowledgment (ACK)
Contention-Free (CF)-End
Data
Data + CF-Ack
Management
Management
Reserved
Reserved
Power Save (PS)-Poll
Control
Control
Reassociation Request
Reassociation Response
Association Request
Management
1101-1111
Probe Request
Probe Response
Reserved
Beacon
Announcement traffic indication message (ATIM)
Deauthentication
Management
Management
Management
Management
Management
Byte Offset 0 Byte Offset 1
PV
(2-bit)
Type
(2-bit)
Subtype
(4-bit)
Allows for greater Mbit/s using multiple-input multiple-output (MIMO), channel bonding and frame
aggregation. This standard can be used in the 2.4 and 5.0 GHz band.
Type Type Subtype
802.11 header information was compiled from the 802.11 1999 reference specification available at
http://standards.ieee.org/getieee802/download/802.11-1999.pdf
Management
Disassociation
Authentication
0110-0111
Management
Description Subtype Description
Management
Management
Management
Association Response
30 802.11 (2)
Frame Control
0
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
TDS
FDS
MF
Retry
PM
MD
WEP
Order
Set to 1 in data type frames exiting the DS. It is set to 0 in all other frames.
*
More Fragments
Retry
Power Management
More Data
Order
Sequence Control
0
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
Fragment field
802.11 (cont.)
Byte Offset 22 Byte Offset 23
Note:
To DS Set to 1 in data type frames destined for the DS. This includes all data type frames sent by
wireless stations associated with an AP. The To DS field is set to 0 in all other frames.
From DS
DS TO/From DS Values
Meaning
WEP
Byte Offset 0 Byte Offset 1
PV
(2-bit)
Type
(2-bit)
Subtype
(4-bit)
To From
0
Field value can be 0 to 4096. Normally 0 because packets are not normally fragmented. Each
fragment is assigned a unique fragment number with the entirety of the packet identified with a
single sequence number. Note: Frames that have a payload larger than 2312 bytes will be
fragmented.
Set to 1 in any data or management type frame that is a retransmission of an earlier frame. It is
set to 0 in all other frames. A receiving station uses this indication to aid in the process of
eliminating duplicate frames.
Set to 1 in all data management type frames that have another fragment of the current MSDU or
current MMPDU to follow. It is set to 0 in all other frames.
Set to 1 if any data type frame that contains an MSDU, or fragment thereof, which is being
transferred using the Strictly Ordered service class. Set to 0 in all other frames.
Set to 1 in directed data type frames transmitted by a contention-free (CF)-Pollable STA to the
point coordinator (PC) in response to a CF-Poll to indicate that the STA has at least one
additional buffered MSDU available for transmission in response to a subsequent CF-Poll. Set to
0 in all other directed frames.
Set to 1 indicates that the STA will be in power-save mode. A value of 0 indicates that the STA
will be in active mode. This field is always set to 0 in frames transmitted by an AP.
Set to 1 if the Frame Body field contains information that has been processed by the WEP
algorithm. The WEP field is set to 0 in all other frames. When the WEP bit is set to 1, the Frame
Body field is expanded.
Fragment #
(4-bit) Sequence Number (12-bit)
The BSSID in an IBSS network is a randomly-selected value with the first 2 bits consistenly
set to 01. The value is in the range of 40:00:00:00:00:00 to 7f:ff:ff:ff:ff:ff.
0
1 0
A data frame direct from one wireless station to another wireless within the same IBSS, as well
as all management and control type frames. (AD HOC)
Address 1 is Destination, Address 2 is Source, Address 3 is BSSID*
Data frame exiting the DS (from a wired network) to a wireless station (Infrastructure)
1 1
Wireless distribution system (WDS) frame being distributed from one AP to another AP
Address 1 is Receiver, Address 2 is Transmitter
Address 3 is Destination, Address 4 is Source
0 1 Data frame destined for the DS (to a wired network) from a wireless station (Infrastructure)
Address 1 is Destination, Address 2 is BSSID, Address 3 is Source
Address 1 is BSSID, Address 2 is Source, Address 3 is Destination
31 802.11 (3)
Key
QUICK REFERENCE
e
z
m
t
g
u
c
L
H
+
-
^L
POPUP WINDOWS
h
n
i
s
l (lower case L)
d
r
a
p
f
w
x
Q
Definitions of Symbols
Symbol
Name
Description
P
Probe Request No associated connection yet
A
Access Point Standard wireless network
H
ad-hoc Point-to-point wireless network (IBSS)
T
Turbocell Turbocell (aka Karlnet or Lucent Outdoor Router) network
G
Group Group of wireless networks
D
Data data only network with no control packets
Symbol
Description
F
T#
U#
A#
D
W
Toggle fullscreen zoom of network view
Toggle muting of sound and speech
Tag (or untag) selected network
Kismet
Commands
Description
List Kismet servers
Group tagged networks
Ungroup current group
Show clients in current network
Lock channel hopping to the current network channel
Return to normal channel hopping
Expand groups
Collapse groups
Force a screen redraw
Help
Name current network
detailed information about selected network
Sort network list
Show wireless card power levels
Dump printable strings
Packet rate graph
Statistics
Dump packet type
Follow network center
Cloase popup window
Quit
Track alerts
Information obtained from the Kismet help screen
Network/Group Types:
Vulnerable factory configuration.
Address range of # octets found via TCP traffic
Address range of # octets found via UDP traffic
Address range of # octets found via ARP traffic
Status Flags
Address range found via observed DHCP traffic
WEPed network decrypted with user-supplied key
32 Kismet
windump -i <interface> -nX
windump -i <interface> -nX -s0
windump -r <file> -nXp
host
(host)
ip
vrrp
ether multicast
src host
(host)
ip6
ip broadcast
vlan
(vlan_id)
dst host
(host)
arp
ip proto
(protocol)
atalk
gateway
(host)
icmp
ip protochan
(protocol)
decnet
net
(net/len)
icmp6
ip6 proto
(protocol)
decnet src
src net
(net)
tcp
ip6 protochain
(protocol)
decnet host
dst net
(net)
udp
ip multicast
iso
port
(port)
ah
ip6 multicast
stp
src port
(port)
esp
ether host
(MAC)
ipx
dst port
(port)
igmp
ether src
(MAC)
netbeui
less
(length)
igrp
ether dst
(MAC)
greater
(length)
rarp
ether proto
(protocol)
tcpflags
icmptype
icmp-echoreply
icmp-echo
icmp-paramprob
tcp-fin
icmp-unreachable
icmp-ireq
icmp-tstamp
tcp-syn icmp-sourcequench icmp-tstampreply
tcp-rst icmp-redirect icmp-ireq
tcp-push icmp-routeradvert icmp-ireqreply
tcp-ack icmp-routersolicit icmp-maskreq
tcp-urg
icmp-timxceed
icmp-maskreply
Expressions:
>, <, >=, <=, =, !=, +, -, *, /, &, |
!
or
not
&&
or
and
||
or
or
filter format <protocol header>[offset:length]<relation><value>
host A and B
Connections between host A and host B
ip[9] = 1
icmp
ip[9] = 6
tcp
ip[9] = 17
udp
ip[9] = 0x11
tcp[2:2] < 20
udp[6:2] != 0
tcp[tcpflags]=tcp-syn
Only Syn
tcp[13] &0x02 != 0
tcp[tcpflags]=tcp-ack
Only Ack
tcp[13] &0x10 != 0
tcp[tcpflags]=tcp-fin
or
tcp[13] &0xff=0x01
tcp[13] &0xff = 1
tcp[13] &0xff =16
or
Only the ACK bit is set
Examples
ip[6] &0x20 = 0x20 or ip[6:2]
&0x1fff != 0
Look for more fragment bit set
or
fragment offset greater than 0 (
Look for ALL
fragmented ip packets)
tcpdump [command line options] ['filter']
windump [command line options] ["filter"]
tcp[20:4] = 0x5353482d
icmp[0]=3 and icmp[1]=2
At minimum the SYN bit set
At minimum the ACK bit set
Only the FIN bit is set
(tcp and (tcp[13] &0x0f != 0) and
not port 25 and not port 20)
ip[6] &0x20 = 0 and ip[6:2] &0x1fff
!= 0
Look for more fragment bit
not
set
and
fragment offset greater than 0 (
Last
fragment packets)
The TCP dst port is greater than 20 Non-zero UDP checksum
udp[21:4]=0x56455253 Looks for “VERS” in udp payload for VERSION.BIND
tcp[13] &0xff = 0x10
icmp type 3 is destination unreachable category and a code of 2 specifies that this is
an ICMP protocol unreachable (Good filter for detecting protocol scans)
A tcp packet where any combination of PSH, RST, SYN, FIN are set and the packet
is not port 25 or 20
Looks for “SSH-” in TCP payload
ip[6:2] & 0x3fff != 0 Look for ALL fragmented ip packets
TCPDUMP / WINDUMP
1 AND 0 = 0
1 AND 1 = 1
Bit Masking
And unwanted bits with 0
And wanted bits with 1
0 AND 0 = 0
0 AND 1 = 0
Keywords
capture from interface (-i <interface>) do not convert names(-n) and print out hex
and ascii (-X)
capture from interface (-i <interface>) do not convert names(-n), print out hex and
ascii (-X) and capture all the packet
capture from file (-r <file>), do not convert names (-n), print out hex and ascii (-X),
not in promiscuous mode (-p)
33 TCPDUMP

Options
-a
-A
-B <size>
-c <count>
-C <file size>
-d
-dd
-ddd
-D
-e
-E <algo:secret>
-f
-F <file>
-i <interface>
-l
-L
-m <module>
-n
-nn
-N
-O
-p
-q
-r <file>
-R
-s <snaplen>
-S
-t
-T <type>
-tt
-ttt
-tttt
-u
-U
-v
V
-w <file>
-x
-X
-y <datalinktype>
TCPDUMP / WINDUMP (cont.)
Print the link-level header on each dump line
Use algo:secret for decrypting IPsec ESP packets where algorithms may be des-cbc, 3des-cbc,
blowfish-cbc, rc3-cbc, cast128-cbc, or none.
Print ‘foreign’ internet addresses numerically rather than symbolically
Set driver's buffer size to size in KiloBytes. The default buffer size is 1 megabyte (i.e 1000). WINDUMP ONLY
Use file as input for the filter expression
Description
ddd Dump packet-matching code as decimal numbers (preceded with a count)
Print the list of the interface cards available on the system. WINDUMP ONLY
Dump the compiled packet-matching code in a human readable form to standard output and
stop
Dump packet-matching code as a C program fragment
Exit after receiving <count> of packets
Before writing a raw packet to a savefile, check whether the file is currently larger than
file_size and, if so, close the current savefile and open a new one.
Attempt to convert network and broadcast addresses to names
Listen on interface (defaults to lowest numbered interface)
Make stdout line buffered. ``tcpdump -l | tee dat'' or ``tcpdump -l > dat & tail -f dat''
Load SMI MIB module definitions from file module
Don’t convert addresses to names
Don’t print domain name qualification of host names
Do not run the packet-matching code optimizer
Don’t put the interface into promiscuous mode
Quick output – print less protocol information
Read packets from file (created with the –w option)
Print undecoded NFS handles
Assume ESP/AH packets to be based on old specs
Snarf snaplen bytes of data from each packet (default is 68)
Print absolute, rather than relative TCP sequence numbers
Don’t print a timestamp on each dump line
Force packets selected by “expressions” to be interpreted the specified type (cnfp, rpc, rtp,
snmp, wb)
http://www.tcpdump.org/tcpdump_man.html
http://windump.polito.it/docs/manual.htm#Wdump
Command Line Options
Print each packet in hex and ascii
64 Min Ethernet Frame (14 byte Ethernet header + 64 byte IP + 4 byte Ethernet trailer)
1518 Max Ethernet Frame (14 byte Ethernet header + 1500 byte IP + 4 byte Ethernet trailer)
Note: -s0 mean full ethernet packet
Verbose output (TOS, TTL, IP ID, Fragment Offset, IP Flags, length)
Don’t convert addresses or port numbers (port numbers are resolved based on information the
the linux /etc/service file or the windows %windir%\system32\drivers\etc\services file.)
Print an unformatted timestamp on each dump line
Write the raw packet to file rather than parsing and printing to stdout
Print each packet (minus link level header) in hex
Print a delta (in micro-seconds) between current and previous line on each dump line
Print a timestamp in default format proceeded by date on each dump line
34 TCPDUMP (2)
ngrep
<-hXViwqpevxlDtT> <-IO pcap_dump> <-n num> <-d dev> <-A num> <-s snaplen> <-S limitlen>
<match expression>
<bpf filter>
-A
(num)
-D
-d
(device)
-e
-h
-i
-I
(file)
-l
-n
(num)
-O
(file)
-p
-q
-S
(limitlen)
-s
(snaplen)
-t
-T
-V
-v
-w
-X
-x
Examples:
Note:
You can use "frame contains <string>" in ethereal to do similar searches.
http://www.packetfactory.net/projects/ngrep/usage.html
NGREP
Command Line Options
"pinging" host running a Microsoft operating system?
print all packets to or from only TCP port 53
print all UDP packets
print all TCP packets
print all packets to or from TCP or TDP port 53
print all UDP packets
print all packets but those to or from TCP port 53
print all packets to or from TCP port 21 where USER or PASS
ngep -i -I <input file> "Yahoo" read from input file and search for case insensitive "Yahoo"
print all packets to or from TCP port 22 where SSH-
print Microsoft browsing traffic for NT domain LILWORLD
monitor current delivery and print sender and recipients
monitor POP3
ngrep -iq 'rcpt to|mail from' tcp port 25
ngrep 'user' port 110
ngrep -q 'abcd' icmp
ngrep - v '' tcp port 53
ngrep 'USER|PASS' tcp port 21
ngrep 'SSH-' port tcp 22
ngrep 'LILWORD' port 138
ngrep '' tcp
ngrep '' udp
ngrep '' port 53
ngrep '' tcp port 53
is be quiet
is set the limitlen on matched packets
is either an extended regular expression or a hexadecimal string. see the man page for
more information.
is any bpf filter statement.
<bpf filter>
<match expression>
is invert match
is word-regex (expression must match as a word)
is interpret match expression as hexadecimal
is print in alternate hexdump format
is dump num packets after a match
is replay pcap_dumps with their recorded time intervals
is use a device different from the default (pcap)
ngrep '' icmp
is show empty packets
is help/usage
is ignore case
is read packet stream from pcap format file pcap_dump (
Capitol i
)
is make stdout line buffered
is look at only num packets
is set the bpf caplen
is print timestamp every time a packet is matched
is print delta timestamp every time a packet is matched
is version information
is dump matched packets in pcap format to pcap_dump
is don't go into promiscuous mode
35 NGREP

Wireless Filters
wlan.fc.wep = 1
wlan.fc.wep != 1
eapol and eap.type == 17
eap.type == 17 and eap.code == 2
wlan_mgt.tag.number == 221
wlan.bssid == <mac>
wlan.fc.type_subtype eq 32 Displays only data frames
wlan.fc.type_subtype eq 11 or
wlan.fc.type_subtype < 6
wlan.fc.type_subtype != 8
General IP Filters
ip.proto == 0x??
tcp.flags.syn == 0 tcp.flags.ack == 0 tcp.flags.fin == 0
tcp.flags.reset == 0 tcp.flags.push == 0
IPSec Filters
ip.proto == 0x??
isakmp or udp.port eq 500 or
udp.port eq 10000 or udp.port eq
5150 Displays ISAKMP traffic (Note 500/CheckPoint, 10000/Cisco, 5150/agere)
isakmp[18] eq 4
OS Finger Printing
browser.os_major < 5 Display pre-Windows 2000 Clients (Note: eq 5 WK2000 System)
Finds Data In A Packet
data contains "HTTP/1.1 240" Displays a packets with HTTP error code 240 in the header
http.cookie contains "x" Displays data "x" list in the cookie
Organizationally Unique Identifiers
wlan.da[0:1] == 1
1st 24 bits of MAC. OUI to Org. http://standards.ieee.org/regauth/oui/oui.txt
(wlan.fc.wep != 1) and (wlan.fc.type_subtype eq 32) and !(STP or http or nbus or arp or dns or browser or rip)
Display IPSec AH if ??=51 and ESP if ??=50
Display ICMP if ??=01, TCP if ??= 06 and UDP if ??=11
Display IPSec ISAKMP packets using aggressive IKE mode
Displays packets where the 1st byte in the destination MAC address is 0x01, a
multicast address.
http://www.cavebear.com/Cavebear/ethernet/multicast.html
http://www.iana.org/assignments/multicast-addresses
Will exclude all the beacon frames from a wireless packet capture
Displays all the frames that do NOT have the WEP bit (or privacy bit) set
Displays only packets that have the specified BSSID
Ethereal / Wireshark
Displays all the frames that do have the WEP bit (or privacy bit) set
Will display only Cisco Leap packets that are EAP responses
Displays TKIP or AES packets
Will display Cisco Leap packets
Display all probe request and response packets
36 Ethereal
Port
Protocol
Application protocol
System service name
n/a GRE GRE (IP protocol 47) Routing and Remote Access
n/a ESP IPsec ESP (IP protocol 50) Routing and Remote Access
n/a AH IPsec AH (IP protocol 51) Routing and Remote Access
7 TCP Echo Simple TCP/IP Services
7 UDP Echo Simple TCP/IP Services
9 TCP Discard Simple TCP/IP Services
9 UDP Discard Simple TCP/IP Services
13 TCP Daytime Simple TCP/IP Services
13 UDP Daytime Simple TCP/IP Services
17 TCP Quotd Simple TCP/IP Services
17 UDP Quotd Simple TCP/IP Services
19 TCP Chargen Simple TCP/IP Services
19 UDP Chargen Simple TCP/IP Services
20 TCP FTP default data FTP Publishing Service
21 TCP FTP control FTP Publishing Service
21 TCP FTP control Application Layer Gateway Service
23 TCP Telnet Telnet
25 TCP SMTP Simple Mail Transfer Protocol
25 UDP SMTP Simple Mail Transfer Protocol
25 TCP SMTP Exchange Server
25 UDP SMTP Exchange Server
42 TCP WINS Replication Windows Internet Name Service
42 UDP WINS Replication Windows Internet Name Service
53 TCP DNS DNS Server
53 UDP DNS DNS Server
53 TCP DNS Internet Connection Firewall/Internet Connection Sharing
53 UDP DNS Internet Connection Firewall/Internet Connection Sharing
67 UDP DHCP Server DHCP Server
67 UDP DHCP Server Internet Connection Firewall/Internet Connection Sharing
69 UDP TFTP Trivial FTP Daemon Service
80 TCP HTTP Windows Media Services
80 TCP HTTP World Wide Web Publishing Service
80 TCP HTTP SharePoint Portal Server
88 TCP Kerberos Kerberos Key Distribution Center
88 UDP Kerberos Kerberos Key Distribution Center
102 TCP X.400 Microsoft Exchange MTA Stacks
110 TCP POP3 Microsoft POP3 Service
110 TCP POP3 Exchange Server
119 TCP NNTP Network News Transfer Protocol
123 UDP NTP Windows Time
123 UDP SNTP Windows Time
135 TCP RPC Message Queuing
135 TCP RPC Remote Procedure Call
135 TCP RPC Exchange Server
135 TCP RPC Certificate Services
135 TCP RPC Cluster Service
135 TCP RPC Distributed File System
135 TCP RPC Distributed Link Tracking
135 TCP RPC Distributed Transaction Coordinator
135 TCP RPC Event Log
135 TCP RPC Fax Service
135
TCP
RPC
File Replication
The page is from the text provided at http://support.microsoft.com/kb/832017
Windows TCP / UDP Ports
37 MS PORTS
Port
Protocol
Application protocol
System service name
135 TCP RPC Group Policy
135 TCP RPC Local Security Authority
135 TCP RPC Remote Storage Notification
135 TCP RPC Remote Storage Server
135 TCP RPC Systems Management Server 2.0
135 TCP RPC Terminal Services Licensing
135 TCP RPC Terminal Services Session Directory
137 UDP NetBIOS Name Resolution Computer Browser
137 UDP NetBIOS Name Resolution Server
137 UDP NetBIOS Name Resolution Windows Internet Name Service
137 UDP NetBIOS Name Resolution Net Logon
137 UDP NetBIOS Name Resolution Systems Management Server 2.0
138 UDP NetBIOS Datagram Service Computer Browser
138 UDP NetBIOS Datagram Service Messenger
138 UDP NetBIOS Datagram Service Server
138 UDP NetBIOS Datagram Service Net Logon
138 UDP NetBIOS Datagram Service Distributed File System
138 UDP NetBIOS Datagram Service Systems Management Server 2.0
138 UDP NetBIOS Datagram Service License Logging Service
139 TCP NetBIOS Session Service Computer Browser
139 TCP NetBIOS Session Service Fax Service
139 TCP NetBIOS Session Service Performance Logs and Alerts
139 TCP NetBIOS Session Service Print Spooler
139 TCP NetBIOS Session Service Server
139 TCP NetBIOS Session Service Net Logon
139 TCP NetBIOS Session Service Remote Procedure Call Locator
139 TCP NetBIOS Session Service Distributed File System
139 TCP NetBIOS Session Service Systems Management Server 2.0
139 TCP NetBIOS Session Service License Logging Service
143 TCP IMAP Exchange Server
161 UDP SNMP SNMP Service
162 UDP SNMP Traps Outbound SNMP Trap Service
389 TCP LDAP Server Local Security Authority
389 UDP LDAP Server Local Security Authority
389 TCP LDAP Server Distributed File System
389 UDP LDAP Server Distributed File System
443 TCP HTTPS HTTP SSL
443 TCP HTTPS World Wide Web Publishing Service
443 TCP HTTPS SharePoint Portal Server
443 TCP RPC over HTTPS Exchange Server 2003
445 TCP SMB Fax Service
445 TCP SMB Print Spooler
445 TCP SMB Server
445 TCP SMB Remote Procedure Call Locator
445 TCP SMB Distributed File System
445 TCP SMB License Logging Service
445 TCP SMB Net Logon
464 TCP Kerberos Password V5 Net Logon
500 UDP IPsec ISAKMP Local Security Authority
515 TCP LPD TCP/IP Print Server
548 TCP File Server for Macintosh File Server for Macintosh
554
TCP
RTSP
Windows Media Services
The page is from the text provided at http://support.microsoft.com/kb/832017
Windows TCP / UDP Ports
38 MS PORTS (2)
Port
Protocol
Application protocol
System service name
563 TCP NNTP over SSL Network News Transfer Protocol
593 TCP RPC over HTTPS endpoint mapper Remote Procedure Call
593 TCP RPC over HTTPS Exchange Server
636 TCP LDAP SSL Local Security Authority
636 UDP LDAP SSL Local Security Authority
993 TCP IMAP over SSL Exchange Server
995 TCP POP3 over SSL Exchange Server
1067 TCP Installation Bootstrap Service Installation Bootstrap protocol server
1068 TCP Installation Bootstrap Service Installation Bootstrap protocol client
1270 TCP MOM-Encrypted Microsoft Operations Manager 2000
1433 TCP SQL over TCP Microsoft SQL Server
1433 TCP SQL over TCP MSSQL$UDDI
1434 UDP SQL Probe Microsoft SQL Server
1434 UDP SQL Probe MSSQL$UDDI
1512 TCP WINS Windows Internet Name Service
1512 UDP WINS Windows Internet Name Service
1645 UDP Legacy RADIUS Internet Authentication Service
1646 UDP Legacy RADIUS Internet Authentication Service
1701 UDP L2TP Routing and Remote Access
1723 TCP PPTP Routing and Remote Access
1755 TCP MMS Windows Media Services
1755 UDP MMS Windows Media Services
1801 TCP MSMQ Message Queuing
1801 UDP MSMQ Message Queuing
1812 UDP RADIUS Authentication Internet Authentication Service
1813 UDP RADIUS Accounting Internet Authentication Service
1863 TCP Microsoft Messenger Protocol MSN Messenger
1863 UDP Microsoft Messenger Protocol MSN Messenger
1900 UDP SSDP SSDP Discovery Service
2101 TCP MSMQ-DCs Message Queuing
2103 TCP MSMQ-RPC Message Queuing
2105 TCP MSMQ-RPC Message Queuing
2107 TCP MSMQ-Mgmt Message Queuing
2383 TCP OLAP Services 9.0 SQL Server: Downlevel OLAP Client Support (SQL 2005)
2393 TCP OLAP Services 7.0 / 8.0 SQL Server: Downlevel OLAP Client Support
2394 TCP OLAP Services 7.0 / 8.0 SQL Server: Downlevel OLAP Client Support
2460 UDP MS Theater Windows Media Services
2535 UDP MADCAP DHCP Server
2701 TCP SMS Remote Control (control) SMS Remote Control Agent
2701 UDP SMS Remote Control (control) SMS Remote Control Agent
2702 TCP SMS Remote Control (data) SMS Remote Control Agent
2702 UDP SMS Remote Control (data) SMS Remote Control Agent
2703 TCP SMS Remote Chat SMS Remote Control Agent
2703 UPD SMS Remote Chat SMS Remote Control Agent
2704 TCP SMS Remote File Transfer SMS Remote Control Agent
2704 UDP SMS Remote File Transfer SMS Remote Control Agent
2725 TCP SQL Analysis Services SQL Analysis Server
2869 TCP UPNP Universal Plug and Play Device Host
2869 TCP SSDP event notification SSDP Discovery Service
3268 TCP Global Catalog Server Local Security Authority
3269 TCP Global Catalog Server over SSL Local Security Authority over SSL
3343
UDP
Cluster Services
Cluster Service
The page is from the text provided at http://support.microsoft.com/kb/832017
Windows TCP / UDP Ports
39 MS PORTS (3)
Port
Protocol
Application protocol
System service name
3389 TCP Terminal Services NetMeeting Remote Desktop Sharing
3389 TCP Terminal Services Terminal Services
3478 UDP STUN OCS A/V Edge Server for STUN Communications
3527 UDP MSMQ-Ping Message Queuing
4011 UDP BINL Remote Installation
4500 UDP NAT-T Local Security Authority
5000 TCP SSDP legacy event notification SSDP Discovery Service
5004 UDP RTP Windows Media Services
5005 UDP RTCP Windows Media Services
5061 TCP SIP/MTLS OCS Access Edge Server Communication
5062 TCP SIP/MTLS OCS Access Edge Server Authentication
6001 TCP Information Store Exchange Server 2003
6002 TCP Directory Referral Exchange Server 2003
6004 TCP DSProxy/NSPI Exchange Server 2003
8057 TCP PSOM/MTLS OCS Web Conferencing Edge Server
42424 TCP ASP.Net Session State ASP.NET State Service
50000-59999 TCP OCS A/V Edge Server Used for inbound and outbound media transfer
51515 TCP MOM-Clear Microsoft Operations Manager 2000
1024-65534
TCP RPC (DCOM) Randomly allocated high TCP ports
Used with RPC endpoint Mapper listening on TCP 135
The page is from the text provided at http://support.microsoft.com/kb/832017
Kerberos
1 Authentication service (AS) Exchange
2 Ticket-Granting Service (TGS) Exchange
3 Client/Server (CS) Excahnge
The AS Excahnge is where the Kerberos key distribution (KDC)
IPC$ Inter-Process Communication
Windows TCP / UDP Ports
40 MS PORTS (4)
OS
Version
Platform
TTL
Window
DF
TOS
TCP Options
DC-Osx
1.1-95 Pyramid/NILE 30 8192 n 0
Windows 9x/NT Intel 32 5000-9000 y 0
NetApp
OnTap 5.1.2-5.2.2 54 8760 y 0
HPJetDirect ? HP_Printer 59 2100-2150 n 0
AIX
4.3.X IBM/RS6000 60 16000-16100 y 0 MSS
AIX 4.2.X IBM/RS6000 60 16000-16100 n 0
Cisco
11.2 7507 60 y 0
DigitalUnix 4 Alpha 60 y 16
IRIX
6.x SGI 60 y 16
OS390
2.6 IBM/S390 60 n 0
Reliant
5.43 Pyramid/RM1000 60 n 0
FreeBSD
3.x Intel 64 y 16
JetDirect
G.07.x J311A 64 n 0
Linux
2.2.x Intel 64 32120 y 0 MSS, SackOK, wscale, Timestamp, one NOP
Linux
2.4 Intel 64
5840
MSS, SackOK, wscale, Timestamp, one NOP
OpenBSD
2.x Intel 64 n 16 MSS, Timestamp, wscale, sacks OK, 5 nops
0s/400
r4.4 AS/400 64 y 0
SCO
R5 Compaq 64 n 0
Solaris
8 Intel/Sparc 64 y 0
FTX(Unix)
3.3 STRATUS 64 32678 n 0
Unisys
x Mainframe 64 32768 n 0
Netware
4.11 Intel 128 32000-32768 y 0
Windows
9x/NT Intel 128 5000-9000 y 0
Windows
2000 Intel 128 17000-18000 y 0 MSS, SackOK, 2 NOPs
Windows
XP Pro Intel 128 ??? ?? 0 MSS, nop, nop, SackOk
Cisco
12 2514 255 3800-5000 n 192
Solaris
2.x Intel/Sparc 255 8760 y 0
## ADDITIONAL NOTES
#
# Cisco IOS 12.0 normally starts all IP sessions with IP ID of 0
# Solaris 8 uses a smaller TTL (64) then Solaris 7 and below (255).
# Windows 2000 uses a much larger Window Size then NT.
The page is from the text provided at http://project.honeynet.org/papers/finger/traces.txt
OS Fingerprinting
41 OS Fingerprinting
Dec
Hex
ASCII
Dec
Hex
ASCII
Dec
Hex
ASCII
Dec
Hex
ASCII
Dec
Hex
ASCII
Dec
Hex
ASCII
Dec
Hex
ASCII
Dec
Hex
ASCII
0 0 NUL 32 20 SP 64 40 @ 96 60 ' 128 80 Ç 160 A0 á 192 C0 └224 E0 α
1 1 SOH 33 21 ! 65 41 A 97 61 a 129 81 ü 161 A1 í 193 C1 ┴225 E1 ß
2 2 STX 34 22 " 66 42 B 98 62 b 130 82 é 162 A2 ó 194 C2 ┬226 E2 Γ
3 3 ETX 35 23 # 67 43 C 99 63 c 131 83 â 163 A3 ú 195 C3 ├227 E3 π
4 4 EOT 36 24 $ 68 44 D 100 64 DEL 132 84 ä 164 A4 ñ 196 C4 ─228 E4 Σ
5 5 ENQ 37 25 % 69 45 E 101 65 e 133 85 à 165 A5 Ñ 197 C5 ┼229 E5 σ
6 6 ACK 38 26 & 70 46 F 102 66 f 134 86 å 166 A6 ª 198 C6 ╞230 E6 µ
7 7 BEL 39 27 ' 71 47 G 103 67 g 135 87 ç 167 A7 º 199 C7 ╟231 E7 τ
8 8 BS 40 28 ( 72 48 H 104 68 h 136 88 ê 168 A8 ¿ 200 C8 ╚232 E8 Φ
9 9 HT 41 29 ) 73 49 I 105 69 i 137 89 ë 169 A9 ⌐201 C9 ╔233 E9 Θ
10 A LF 42 2A * 74 4A J 106 6A j 138 8A è 170 AA ¬ 202 CA ╩234 EA Ω
11 B VT 43 2B + 75 4B K 107 6B k 139 8B ï 171 AB ½ 203 CB ╦235 EB δ
12 C FF 44 2C , 76 4C L 108 6C l 140 8C î 172 AC ¼ 204 CC ╠236 EC ∞
13 D CR 45 2D - 77 4D M 109 6D m 141 8D ì 173 AD ¡ 205 CD ═237 ED φ
14 E SO 46 2E . 78 4E N 110 6E n 142 8E Ä 174 AE « 206 CE ╬238 EE ε
15 F SI 47 2F / 79 4F O 111 6F o 143 8F Å 175 AF » 207 CF ╧239 EF ∩
16 10 DLE 48 30 0 80 50 P 112 70 p 144 90 É 176 B0 ░208 D0 ╨240 F0 ≡
17 11 DC1 49 31 1 81 51 Q 113 71 q 145 91 æ 177 B1 ▒209 D1 ╤241 F1 ±
18 12 DC2 50 32 2 82 52 R 114 72 r 146 92 Æ 178 B2 ▓210 D2 ╥242 F2 ≥
19 13 DC3 51 33 3 83 53 S 115 73 s 147 93 ô 179 B3 │211 D3 ╙243 F3 ≤
20 14 DC4 52 34 4 84 54 T 116 74 t 148 94 ö 180 B4 ┤212 D4 ╘244 F4 ⌠
21 15 NAK 53 35 5 85 55 U 117 75 u 149 95 ò 181 B5 ╡213 D5 ╒245 F5 ⌡
22 16 SYN 54 36 6 86 56 V 118 76 v 150 96 û 182 B6 ╢214 D6 ╓246 F6 ÷
23 17 ETB 55 37 7 87 57 W 119 77 w 151 97 ù 183 B7 ╖215 D7 ╫247 F7 ≈
24 18 CAN 56 38 8 88 58 X 120 78 x 152 98 ÿ 184 B8 ╕216 D8 ╪248 F8 °
25 19 EM 57 39 9 89 59 Y 121 79 y 153 99 Ö 185 B9 ╣217 D9 ┘249 F9 ∙
26 1A SUB 58 3A : 90 5A Z 122 7A z 154 9A Ü 186 BA ║218 DA ┌250 FA ·
27 1B ESC 59 3B ; 91 5B [ 123 7B { 155 9B ¢ 187 BB ╗219 DB █251 FB √
28 1C FS 60 3C < 92 5C \ 124 7C | 156 9C £ 188 BC ╝220 DC ▄252 FC ⁿ
29 1D GS 61 3D = 93 5D ] 125 7D } 157 9D ¥ 189 BD ╜221 DD ▌253 FD ²
30 1E RS 62 3E > 94 5E ^ 126 7E ~ 158 9E ₧190 BE ╛222 DE ▐254 FE ■
31
1F
US
63
3F
?
95
5F
_
127
7F
DEL
159
9F
ƒ
191
BF
┐
223
DF
▀
255
FF
Hardspace
Decimal to Hexadecimal to ASCII Chart
42 ASCII

1.
2. Honeynet Project, "Lists of fingerprints for passive fingerprint monitoring" May 23, 2000
URL: http://project.honeynet.org/papers/finger/traces.txt
3.
4.
5.
6. IEEE, "Get IEEE 802" March, 9 2005
URL: http://standards.ieee.org/getieee802/
7.
8.
9.
10.
11.
12.
13.
14.
15. Todd Lammle, "CCNA: Cisco Certified Network Associate Study Guide"
Wiley Publishing, Inc., Copyright 2007
Kismet, "KISMET PANELS INTERFAC",
URL: http://www.kismetwireless.net/
POLITECNICO DI TORINO, "WinDump: tcpdump for Windows", March 14, 2002
URL: http://windump.polito.it/docs/manual.htm#Wdump.
RFC Editor, "RFC Editor Homepage", August 12, 2002
tcpdump.org, "tcpdump man pages"
URL: http://www.tcpdump.org/tcpdump_man.html
URL: http://www.rfc-editor.org/
SANS Institute's, "TCP/IP and tcpdump Pocket Reference Guide", June 2002
URL: http://www.sans.org/resources/tcpip.pdf
SANS Institute's, "Audit 511: Auditing Wireless Networks, Part 1", 2005
URL: http://standards.ieee.org/getieee802/download/802.11-1999.pdf
URL: http://www.packetfactory.net/projects/ngrep/usage.html
Packetfactory, "ngrep - network grep",
References
IANA, "ICMP TYPE NUMBERS", January 27, 2005
Cisco, "The ABCs of IP Version 6", 2002
URL: http://www.cisco.com/application/pdf/en/us/guest/products/iosswrel/c1127/cdccont_0900aecd8018e369.pdf
IEEE, "Part 11: Wireless LAN Medium Access Control (MAC) and Physical Layer (PHY) Specifications", June 12, 2003
URL: http://www.iana.org/assignments/icmp-parameters
IANA, "IP OPTION NUMBERS", June 06, 2001
URL: http://www.iana.org/assignments/ip-parameters
IANA, "PROTOCOL NUMBERS", October 18, 2004
URL: http://www.iana.org/assignments/protocol-numbers
43 References