Progeny 2014
User Manual: Progeny 2014
Open the PDF directly: View PDF ![]() .
.
Page Count: 40

1
www.progeny.co.uk
Products & Solutions

2 www.progeny.co.uk
CONTACT US
Tel: +44 (0) 1254 883348
Fax: +44 (0) 1254 889113
Email: sales@progeny.co.uk
Web: www.progeny.co.uk
BSB Electronics Ltd
Progeny House
Union Court
Heys Lane Industrial Estate
Great Harwood
Lancashire
BB6 7FD
England

3
www.progeny.co.uk
Contents
CONTENTS
Contact Us __________________ 2
Welcome ____________________ 3
What’s New__________________ 4
Website _____________________ 5
Designing a System __________ 6
Compact ____________________ 8
C2 Compact Prox _____________ 10
P1 Stand Alone ______________ 10
P2 Online ___________________ 11
P3 Online ___________________ 14
Crystal Controllers ___________ 19
Interlock ____________________ 24
Readers ____________________ 27
Keyboards __________________ 36
Egress Devices ______________ 37
Training _____________________ 38
Compliance _________________ 38
How to Find Us_______________ 39
V4 November 2014 3

4 www.progeny.co.uk
WHAT’S NEW?
Find out about our NEW additions to our Crystal Range on Page 19

5
www.progeny.co.uk
Website
WWW.PROGENY.CO.UK
WEBSITE
Have you visited our website? At www.progeny.co.uk you will find our software download links, case studies and latest
news. We also have a new Helpesk and eSupport page where you can go if you are experiencing any technical is-
sues. Alternatively, please scan the QR code below with your smart phone to go straight to our site.

6 www.progeny.co.uk
Introduction
Introduction
Electronic Physical Access Control provides 24/7
security. This can be to protect people, valuables or
information. Designing the ideal access control
system involves lots of important choices.
Here are some the main considerations:
Identification method
Reader Technology & Credentials (Crystal, iCLASS,
MIFARE etc.)
Online or Stand Alone / Compact
Communication Method
Which doors will be controlled?
Selecting a computer system
Integration with other systems (Fire, Membership
Software etc.)
Identification
There are three principle methods of electronic
identification:
Secret Knowledge (Access Code or PIN)
Token (Card, Key fob)
Biometric (Fingerprint, Iris Pattern and others)
Each method has its pros and cons. These can be
used individually (“Single Factor Identification”) or in
pairs to get “Two Factor Identification”. Using a Card
and Code, for instance, would be two factor
identification and improves security by cancelling
some of the cons of each factor.
Photo ID
With online access control software it is possible to
manage the printing of PVC cards, personalised with
company name, employee details/photo etc.
Stand Alone / Compact
All programming is done locally for each door via a
keypad provided with the controller. There is no need
for computers of any kind. Ideally suited for small
numbers of doors and users. Compact access
controllers have the reader (usually a keyboard) and
controller built into the same unit. These systems offer
the lowest cost.
See the Compact, P1 & C2 pages for more detail.
Online
With an online networked solution, you can control an
unlimited number of doors and sites from a single
server.
The software allows simple programming and
monitoring of the system. If the connection is lost or
the PC switched off the controllers carry on as
normal. See the P2 & P3 pages for more detail.
Choosing Communication Method
IP addressable Ethernet can make use of an existing
LAN or one can be created for very little cost. The
main advantages are hardwired infrastructure,
freedom of choice for locating server and workstation
PC’s. Also the best choice if you are using any server
based features such as Roll Call or Anti-Pass back.
USB and Serial methods are more suited to small
systems with single PC.
GPRS ideal for those locations were you have power
but it is difficult to get data cable to the controllers.
DESIGNING AN
ACCESS CONTROL
SYSTEM

7
www.progeny.co.uk
Introduction
Emergency Egress
Care needs to be taken, when an access control door
forms part of an emergency egress route. Commonly
used methods with fail open locking devices include:
Fire Relay (Part of the fire alarm system)
Green Call Point
Fire Space Zone (Server based feature only to
be used in conjunction with one of the first two)
Cables
It is important to use the correct cables:
RS 485 Network : Screened twisted pair
(Belden 8132)
Reader : Screened 8 Core
Keyboards : Screened 8 Core
Lock : Rated > Lock Current
RQE : Screened 8 Core
Reporting
Event reporting is one of the main benefits of having
an “Online System”. All events: (Card Transactions,
Releasing, Opening, Closing, failed access, etc) are
time stamped and recorded. This information can then
be filtered and presented in many ways to get at the
management / monitoring information you need. Re-
ports can be exported to TSV, XLS or CSV format.
Reports include History, Attendance, “Roll Call” &
“Time Sheet”.
Read In / Read Out
This is a choice of whether to have a card reader on
one or both sides of the door. If mounted on the out-
side only then a request to exit button / mechanical
egress will be required on the inside. This usually
comes down to whether you need to track the move-
ments of users in and out of that area, e.g. for roll call.
Integration
Integration can happen at three levels:
Credential (Shared use with other systems e.g.
Cashless Vending, T&A, “Follow Me” Printing)
Controller Hardware (Wired connections be-
tween systems e.g. Fire Alarm, CCTV)
Software (Data sharing / exchange between
systems e.g. T&A, Biometric, Membership
Management, E-Booking systems)
Selecting a PC
Selecting the correct PC for an access control system
is very important and can be a challenge. The follow-
ing guidance notes are designed to help you through
the selection process.
Some of the considerations are as follows:
Single PC or Client / Server PC configuration
Dedicated or shared use of the Server PC and / or
Workstation PC
Availability of the server & client PC i.e. 24/7 or only
during working hours etc.
System features being used
Dedicated: refers to a PC that is used entirely for the
access control system. The only other applications
loaded are those needed to maintain the PC.
(Antivirus, backup software etc.). You will need a ded-
icated server if using any of the server based features
such as “Roll Call” or “Zoned APB”.
Shared: refers to a PC that is used for access control,
but also for one or more applications such as Ac-
counts, Contact management Building Management,
DVR, etc. This is generally ok for workstations that
are not required for mission critical tasks such as
“Alarm Handling” and “Roll Call Printing”.
Operating System for the PC / Server
Workstation:
Both “Doors Express” and “Doors Enterprise” are
compatible with Windows 7 and Windows 8. Microsoft
are dropping support for XP in 1st quarter 2014 so not
recommended for new installations.
Server:
Recommended, Server 2008, Server 2012.
Introduction

8 www.progeny.co.uk
Compact &
Standalone
APPLICATIONS -
Small Business
Storage Units
Car Parks
Social Clubs
Recreational Clubs
Remote Sites
COMPACT
These systems comprise of a range
of combined keyboard controllers
(Compact) that can also include a
proximity reader combination (C2).
STAND-ALONE
No PC is required to program these
systems. All programing is done via
the keyboard and is password pro-
tected.
GREAT VALUE
These systems are ideal for small
security applications with a low
number of users, making it cost
effective and easy to manage.
8

9
www.progeny.co.uk
COMPACT
KEYBOARD
CONTROLLERS
Simple and cost effective systems which can be used
in various environments and are ideal for low security
applications. The keyboards have the access control
mechanism built in. To complete the system a low
voltage power supply unit (12V DC), a locking device
(Mag-lock or Electric Strike) and an egress device are
all that is required.
Installation
Any competent installation engineer will be able to
install this equipment without any special training.
Simply connect the power supply unit, locking device
and egress device and you are then ready to program
the control unit.
Simple to Use
Each channel can be operated with up to 50 codes.
The two channels can be combined to give a total of
100 access codes for a single door. The codes can be
4, 5 or 6 digits in length, to operate one of the
channels simply enter the access code for that
channel. A correct code entry will change the LED to
green and the output relay will activate.
Alternatively the second channel may be used as a
secure switch, not just keypad access control. Both
channels have door monitoring to for PDO (prolonged
door open) alarm.
The DF (door forced) alarm is generated when the
door has been opened without a valid code or egress
activation. In order to do this door sensors must be
connected.
2059 Classic
This unit offers the lowest cost of the
compact range. The keyboard is fully
potted and weather proof with a
membrane keyboard and key press
‘beep’.
This particular design features a call
button for visitors and includes a
tamper switch.
2064 VR
Designed for outdoor
environments, this controller is
vandal resistant and weatherproof.
The satin chromed solid zinc keys
and housing are also backlit.
2067 Spy Proof
Traditional ‘Spy Proof’ keyboard allows covert entry of
an access code. The design provides a top quality
product along with architecturally pleasing aesthetics.
High gloss chrome finish. Internal use only.
Keyboard Controllers
2059
Classic
2064
Vandal Resistant
2067
Spy Proof
2131
Flush mount Back Box
2132
Surface mount Back Box
COMPACT FEATURES
Available in three designs
Low Power
2 Channels
50 Codes Per Channel
1 to 99 Seconds and Toggle Mode
Voltage Free Contacts
Tamper Switch
Individual Request to Exit Inputs
Hacker Alarm
“Door Failed to Close” Alarm
Compact

10 www.progeny.co.uk
C2 Compact Prox
The new C2 system consists of proximity reader and a
two-channel controller-keyboard. Each channel has its
own relay output. One channel is dedicated to the
proximity reader and cards. The second channel is
used in conjunction with a keyboard to provide code
based secure switch or access control.
The C2 has a 100 card user capacity and 50 access
codes and allows control of 1 or 2 doors.
Installation
Any competent installation engineer will be able to
install this equipment without any special training.
Simply connect the power supply unit, locking device,
proximity reader and egress device and you are then
ready to program the control unit.
Configuration
The proximity reader is normally used for entry. The
keyboard/Control unit can be situated in a number of
locations to serve as an additional role: Second Door,
Secure Switch Etc.
The C2 Range
The C2 system is available in various designs to suit
aesthetic and environment needs and are all suitable
for external use.
Typical applications include: small business
installations and storage rooms.
P1 STAND ALONE
The P1 controller utilises the separate controller/reader
structure, required for higher security applications. It is
designed to work with the Progeny range of readers &
keyboards
The P1 controller is available in one or two door
options and has a built in 12V 5A charger power
supply.
The controller is an ideal solution for “Lobby Entry”
applications, where the product will read any standard
bank card and determine access into semi-secure
areas such as ATM lobbies, high security cash rooms
etc.
The P1 controller has a high security Interlock interface
as standard which allows control of entry to and from
areas that need to be secured against two doors being
opened simultaneously.
C2 Product Codes
3859 C2 Compact Crystal & Keyboard
3859-SP C2 Compact with Switch Plate
Reader
3859-MULL C2 Compact with Mullion Reader
3859-P C2 Compact with Panel Mount
Reader
P1 Product Codes
2163
P1 Controller with 5A PSU (1 Door)
2163D
P1 Controller with 5A PSU (2 Door)
Compact
P1 FEATURES
Available in One or Two Door
Versions
10,000 Card Holders
Built-in 12V 5A Charger PSU
Non-Volatile Memory (40 years)
“Fail Secure” or “Fail Safe” Lock
Drive
Monitored Fire & Intruder Inputs
Second General Purpose Relay
2 x Standard Reader Interface
1 x Dedicated Keyboard Interface
Progeny Touch Switch Compatible
Standard Interlock

11
www.progeny.co.uk
SIMPLY P2
SIMPLE TO SPECIFY
Connectivity is simplified to just two options:
USB and IP Addressable (Ethernet). The P2
network then uses a single twisted pair to daisy
chain controllers up to 1000 metres away. One
controller per door with the option of card in/
card out makes listing the equipment needed
child’s play. Same cost credentials mean card
or fob decisions can be made later.
SIMPLE TO INSTALL
Any competent installation engineer will be able
to install this equipment without any special
training. The wiring has been greatly simplified
reducing the number of both cores and cables.
The 3800 Progeny Crystal reader also mounts
on a standard UK single gang back box, making
first fix possible. Cabling costs can be reduced
by wiring the egress button or switch along with
the door contacts in to the back of the reader
saving running multiple cables to the door con-
troller.
SIMPLE TO USE
The software has been carefully designed to be
easy to use. A setup wizard will help you scan
for any connected door controllers and then
take you through registering the credentials.
The credentials can be entered manually or
simply presented to a reader. The wizard will
then do all the rest of the work to get the cre-
dentials working. Standard Windows interface
techniques have been used so that users will be
able to start using the software with very little
guidance.
APPLICATIONS:
Systems of up to 16 doors
2000 users in size
Small Schools
Nursery Care
Small Offices
Retails shops
Cash & Carry
P2 System

12 www.progeny.co.uk
P2 Hardware
USB Interface
Using a desktop reader can help with card manage-
ment. For convenience, the 3803 USB interface has
been designed to accommodate a reader.
IP Connectivity
Any system that can make use of the existing IP infra-
structure offers cost savings, and reduced disruption
during installation.
Simple Programming
The programming of the ‘IP Address’ into the control-
ler is simply done using the keyboard provided with
the P2.net.
P2 Product Codes
3801
P2 Controller
3802
P2.net Controller
3821
P2 Controller with 5A PSU (1 Door)
3821D
P2 Controller with 5A PSU (2 Door)
3822
P2.net Controller with 5A PSU (1 Door)
3822D
P2.net Controller with 5A PSU (2 Door)
3803
P2 USB Interface
3808
P2 Software: Doors Express
3811
P2 Demo Case (USB)
3812
P2.net Demo Case (IP, Ethernet)
Credentials
3800
Crystal Reader (Switch Plate)
3820
Crystal Reader (Mullion)
3830
Crystal Reader (Panel Mount)
3804
Crystal Card (ISO)
3805
Crystal Fob
3806
Crystal Sticky Dot
P2 Hardware

13
www.progeny.co.uk
P2 SOFTWARE:
DOORS EXPRESS
P2 access controllers require a PC to program the
system. The software used for programming the
system is called Doors Express. The software uses
Microsoft SQL database technology which provides
security and reliability. The software is split into two
main components:
P2 Server
Progeny P2 Server provides the link between the
controllers, database and client.
Doors Express Client
Doors Express Client provides a simple interface for
unlimited end users.
Automatic Setup Wizard
P2 includes a handy setup wizard which will search
for doors wired into the network and add them on to
the system automatically. Cards can also be added
during initial set up meaning that in just a few clicks
the system can be setup and running after loading the
software for the first time.
Hardware Volume Control
The software
allows the end
user to turn
down or mute
the volume of
the general
feedback of
card
transactions
from the reader
and controller.
Hardware Feedback & Fault Monitoring
The P2 system sends the voltage readings from the
controller and readers back to the PC.
Simple Card Management
An easy to use interface allows the user to quickly
add cards on to the system.
Simple Attendance & Absence Reporting
Doors Express allows the user to setup reports that
can show a card holders attendance.
If a more detailed attendance analysis of a card
holder is required then a “Time Sheet” report can be
created.
Floor Plan Alarms
In Doors Express Professional, a CAD or other
suitable drawing of the building can easily be added
into the system.
SOFTWARE FEATURES
Database (SQL Server)
Live Event Reports
History Reports
Attendance/Absence Reports
Roll Call Report
Client Workstations
Photo ID Badge Printing (Fixed
Design)
Text Alarms with Audit Trail
Zoned Door Release on Fire Alarm
Automatic Scheduled Backup
Automatic Scheduled Archive
Setup Wizard
ID Badge Design
Zoned Anti-Pass-Back
Floor Plan Alarms
Card Data Import
P2 Online
Software

14 www.progeny.co.uk
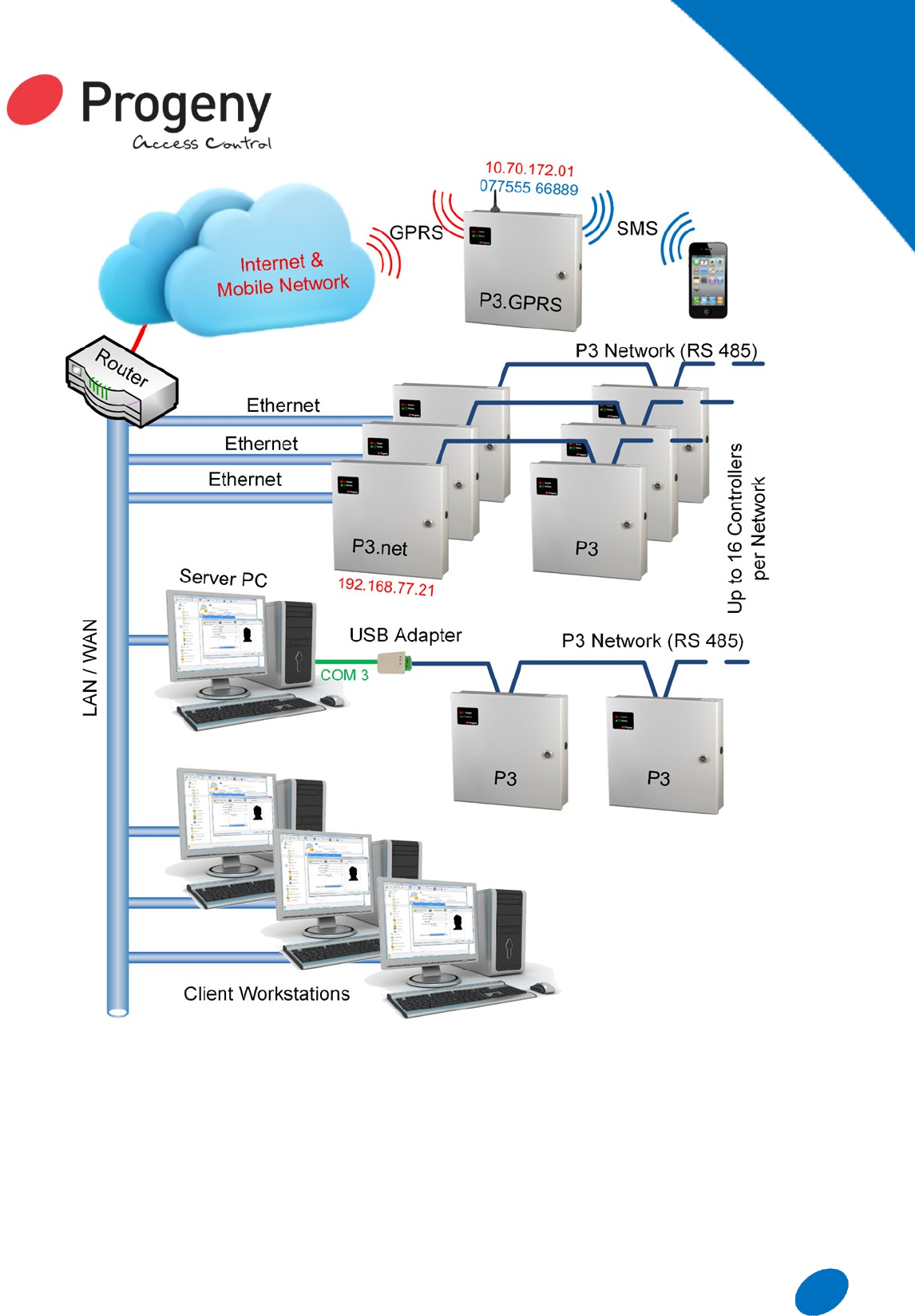
P3 SYSTEM
MULTI-SITE
P3 is an online access control system for single
or multiple sites. IP connectivity gives easy
reach to sites that can be anywhere in the
world.
CONTROL
The PC based software allows live changes to
be made to access profiles; you can enable/
disable users with just a few clicks.
ACCOUNTABILITY
All activity on the system is monitored and rec-
orded. A wide selection of point and click re-
ports are then available to drill down onto that
valuable information.
SCALABLE
P3 systems are scalable from small to large
systems; with capacity for up to 10,000 card-
holders and 65,000 doors.
FLEXIBLE
With a wide range of readers and credentials to
choose from these systems are ideal almost any
application: Health, Leisure, Commercial, Bank-
ing, Building Site and Cash Handling.
INTEGRATION
Credential, Hardware and Software level inte-
gration with other systems including member-
ship management, T & A software, Lift Controls,
Cashless vending etc…
P3
Hardware
15
www.progeny.co.uk
P3
Hardware
P3 SYSTEM
Connectivity Options
To extend the reach of the P3 system three methods
of connectivity are provided:
USB: Using the 3107 P3 USB to 485 adapter, the
server PC can be connected to the P3 network
with 1Km reach.
LAN/WAN (IP addressable): This makes use of
the customer’s existing data network. The P3.net
connects into a standard RJ45, 10/100 Base T
network point and uses UDP/IP to communicate
with the server PC.
GPRS (IP addressable): for mobile and difficult to
reach applications.
Distributed Intelligence
The P3 access controller is designed with the
flexibility to be programmed both stand alone

16 www.progeny.co.uk
and from a PC. This means the controller can be
installed and operational even before the network and
PC are available.
Scalable
The system architecture allows for expansion without
any major overhead in equipment.
Distributed Intelligence
The on-board memory of each controller stores all the
access control information for a given door.
Choice of reader Technology
Card reader type can be selected from, “Mag Stripe”,
“Proximity”, and “Biometric”. P3 will interface to 35
standard reader technologies plus the ability to define
custom formats through the advanced engineers
menu.
2000 Event Memory
Each controller has its own real time clock and event
log memory to allow for the system to continue
operation even when isolated from the PC or the
remainder of the network.
Charger Power Supply
The 12V 5A Charger power supply has space for a
standard 12V 6AHr Sealed Lead acid battery (not
supplied).
P3.net IP Addressable (Ethernet) Access
Control
P3.net make use of standard Ethernet local area
network connections to communicate with the central
access control server PC. Each P3.net has an RJ45
socket and uses the UDP/IP protocol with very little
data bandwidth. This can make use of an existing
network, or a separately installed dedicated network.
P3 Lift Controller
The P3 Lift Controllers are available as either 2 floor,
2 shaft controllers (3007-2F) or 4 floor, 2 shaft
controllers (3007-4F). The lift controllers can be
added to an existing P3 system allowing for lift access
to be controlled with a single reader in the lift cab.
P3.SIM (System Integration Module)
SIM stands for Systems Integration Module and is not
to be confused with your mobile phone SIM. The P3
SIM is available in two forms. The P3 SIM has a built
in power supply, 16 inputs and 16 relay outputs.
These are primarily designed to be general purpose
input and output.
Server based features in the Doors Enterprise
Software can then make use of these inputs and
outputs for:
Fire Door Monitoring
CCTV DVR Integration
Alarm Condition Notification
Car Park Full Indications
Many more…
FEATURES
Fully Distributed Intelligence
65,000 Doors
10,000 Card Holders
2000 Event Log Memory
125 Access Levels per site
32 Time Zones per site
CONTROLLER FEATURES:
Stand Alone & Online Operation
12V 5A Charger PSU
Non-Volatile Memory (40 years)
On-board Real-Time Clock
“Fail Secure” or “Fail Safe “Lock
Drive
Second General Purpose Relay
Fire & Intruder Inputs
Connectivity: RS 232, USB,
Ethernet (IP) & GPRS
2 x Standard Reader Interfaces
1 Dedicated Keyboard Interface
Progeny Touch Switch Compatible
P3
Hardware

17
www.progeny.co.uk
P3.SIM (Input Only)
The P3 SIM Inputs have 16 inputs and 1 relay output.
These are primarily designed to be general purpose
input. Most of the functionality comes from server
based features such as triggers and alarms. The P3
SIM provides a good means of monitoring fire doors
that do not have access control connected. The in-
puts can be programmed to be inverted or not, allow-
ing “normally closed” or “normally open” contacts to
be connected
P3 Product Codes
3001
P3 Controller with 5A PSU (1 Door)
3001D
P3 Controller with 5A PSU (2 Door)
3002
P3.net Controller with 5A PSU (1 Door)
3002D
P3.net Controller with 5A PSU (2 Door)
3004
P3.SIM (16 inputs and 16 Outputs)
3004-IN
P3.SIM (16 Inputs and 1 Output)
3006
P3.GPRS Controller (1 Door)
3007-2F
P3 Lift Controller (2 Floor, 2 Shaft)
3007-4F
P3 Lift Controller (4 Floor, 2 Shaft)
3107
P3 USB Interface
3109
P3 Software: Doors Enterprise
Readers & Credentials
Choose from any of the Progeny range of
Keyboards, Readers and Credentials
P3
Hardware
18 www.progeny.co.uk
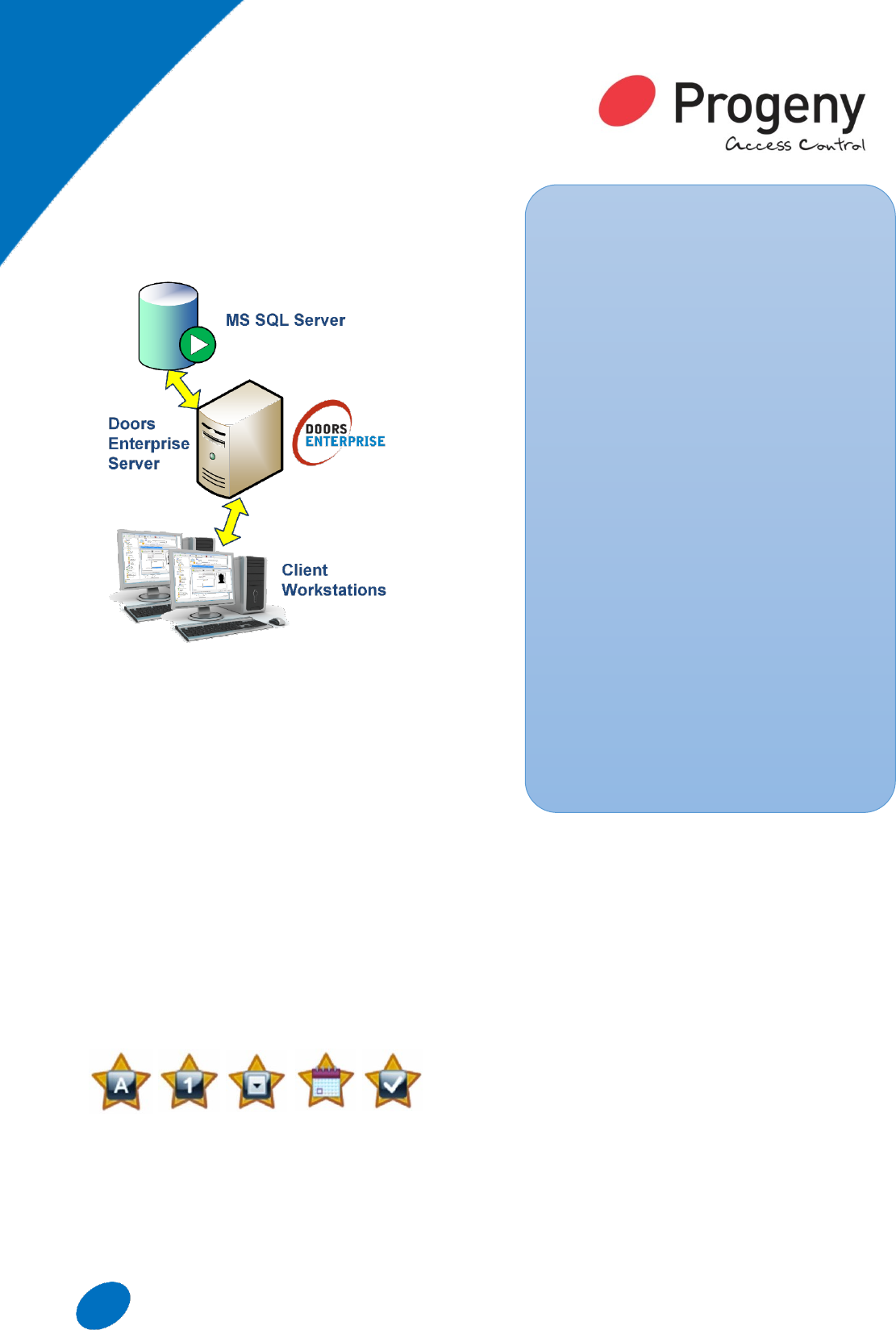
DOORS
ENTERPRISE
MS SQL Server Database
Microsoft SQL Server Database delivers increased
security, scalability and availability to the access
control data.
Doors Enterprise Server
Doors Enterprise Server provides a single point of
communication between clients, the database and the
P3 access controllers.
Doors Enterprise Client
Doors Enterprise allows for an unlimited number of
work stations and software users.
Custom Database Fields
Up to 25 Custom Fields can be created to contain
additional information about cardholders.
Each custom field can be one of 5 types for
example: you might need a drop down box for
department or a calendar date pick for an employee
start date.
Multi-Lingual
Each client workstation can easily select its own
language setting. The client-side translation dictionary
includes English and French with other languages
available on request.
Dormant Card Policy
Doors Enterprise allows you to decide on a maximum
time that a card should legitimately not be used. Once
this time has lapsed the card will be marked as
dormant and disabled from all doors.
Wizards
Wizards make setup and importing of data a very
simple and intuitive process.
Importing data with card data import wizard provides
feedback at every stage.
Space zones keep track of who is currently in that
zone, based on log in and log out use of a card or
token. A roll call report can be run off manually or
automatically.
FEATURES
MS SQL Server database
Each client workstation can easily
select a language setting. The client-
side translation dictionary includes
English and French with other
languages to follow.
Up to 25 Custom Fields can be
created to contain additional
information about cardholders.
Live Event Reports
History Reports
Attendance/Absence Reports
Simple Timesheet Report
Roll Call Report
Client Workstations
Photo ID Badge Design & Printing
Text Alarms with Audit Trail
Zoned Door Release on Fire Alarm
Automatic Scheduled Backup/Archive
Setup Wizard
Zoned Ant-Pass-Back
Floor Plan Alarms
Card Data Import Facility
P3
Software

19
www.progeny.co.uk
CONTROLLERS
New Controller Range
Backward compatible with the P1, P2 and
P3 systems. Works with the latest version
of Doors Enterprise.
Models
There are 4 different controllers in the range;
the Module, the 2A Single Door and the 5A
One and Two Door.
Memory
New high speed non volatile memory with
long data retention has been increased as
standard to 32,000 with option for 128,000.
Solid State Lock Drive
The new controllers have an additional switch
that allows for some new lock driving modes
that reduce relay contact wear.
Connectivity
A new expansion interface allows immediate
connection of the new GPRS module as a
‘piggyback’ to the PCB.
New Features
Crystal Controller launches with all the fea-
tures of P3 and more.

20 www.progeny.co.uk
TYPICAL WIRING DIAGRAM
21
www.progeny.co.uk
Access Levels
Up to 4 access levels per site can be
assigned to card holders
250 access levels to choose from per site
LOCK RELAY
The Crystal Controllers have the traditional relay
to switch the +ve leg of the lock supply.
However, it also has a new Electronic Switch in
the negative wire. This allows for some new lock
driving modes that will reduce if not eliminate
relay contact ware. The modes are:
Standard (relay only)
Protected (Relay and Electronic Switch)
Electronic (Electronic Switch only) VA
Electronic (Electronic Switch only)
IP Addressable
The new Ethernet electronics no longer need any
option links. Also, the configuration parameters
has been simplified, faster and more secure.
EXPANSION INTERFACE
A new expansion interface allows immediate
connection of the new P3 GRPS module as a
piggyback to the PCB. Other expansion modules
are in the design pipeline including:
Simplified lift controller
New Input / Output
COMPATIBILITY
The overall terminal block foot print remains
unchanged from the P3 controller. However, an
individual reader buzzer signal is now provided to
simplify wiring
The reader interface now include native support for
the Crystal Readers. Taking advantage of the
simplified 4 wire two way interface.
MEMORY
Card Memory
32,000 as standard
128,000 as an option
200 year data retention
No card packs
No more site code restrictions
Card memory has been upgraded both in capacity
and size. The Crystal Controller will not use card
packs internally and will treat all cards as flexi
cards, increasing flexi card capacity to 128,000.
Event Logging
This is increased to 8,000 events per controller.
Random Search
A new feature that allows for randomised impartial
searches to be carried out. Adjustable search rate
from ‘1 in 1 to 1 in 99. Randomly flags users to be
security searched as they pass through the door or
turnstile.
P1 P2 P3 Crystal Standard Crystal Large Memory
Card Memory 10,000 2000 10,000 32,000 128,000
Event Memory - 2000 2000 8000 8000
Network - 115KBs 19.2KBs 19.2KBs 115KBs
Access Levels 1 of 1 2 of 127 2 of 125 2 of 125 4 of 250
Interlock Yes No Yes Yes Yes
Lock Drive Relay Relay Relay Electronic or Relay Electronic or Relay

22 www.progeny.co.uk
Product
Code Product Description
Controllers
4001M Crystal 1 Door Controller Module
4002M Crystal.net 1 Door Controller Module with Ethernet
4001-2A Crystal 1 Door Controller with 2A Charger PSU
4002-2A Crystal.net 1 Door Controller with 2A Charger PSU
4001-5A Crystal 1 Door Controller with 5A charger PSU
4002-5A Crystal.net 1 Door Controller with 5A charger PSU with Ethernet
4001D-5A Crystal 2 Door Controller with 5A charger PSU
4002D-5A Crystal.net 2 Door Controller with 5A charger PSU with Ethernet
4003 Crystal.POE 1 Door Controller with Power Over Ethernet
4006 1 Door Crystal Controller with 5A Charger PSU & GRPS Interface
4006D 2 Door Crystal Controller with 5A Charger PSU & GRPS Interface
Readers and Touch Switches
3800 Crystal Reader (Switch Plate)
3810 Crystal Reader Touch Switch
38410-MULL Crystal Reader Touch Switch (Mullion)
3820 Crystal Reader (Mullion)
3824 Crystal Reader Surface Spacer (SP)
3824-MULL Crystal Reader Surface Spacer (Mull)
3830 Crystal Reader (Panel Mount)
4803 Crystal USB Desktop Reader
4124 Low cost keyboard with Wiegand or BCD interface
4121 VR Keyboard with Crystal Interface
4124-RF Crystal combined Keyboard & Reader
Credentials
3804-10 Crystal ISO Card Pack
3805-10 Crystal Fob Pack
Miscellaneous
3107 USB Adaptor (RS485)

23
www.progeny.co.uk
Car Park Monitoring
Zoned roll call can also be used to monitor shared car
park usage. A simple roll call report can be set up for
each group of users and the display will show total
quantity and who is using the car park.
Photo ID
The software also includes an ID badge designer.
Photos can be easily captured and saved for each
card holder and printed using a suitable card printer
from within Doors Enterprise.
Time Sheet
The time sheet report will collect all the in and out
transactions for each user. These are tabulated with
totals for each in and out and totals for each user at
the bottom.
Time Zones
Having granted access to a card holder with an
access level, time zones allow you to control when
they have access. This control is further extended by
linking to calendars.
Calendars
Calendars allow exception dates to be planned in,
bank holidays etc.
INTEGRATION
An equally important feature of any contemporary
access control system is its ability to integrate with
other systems. The Progeny range of access control
systems integrate at 3 defined levels:
Credential Level
Credential level of integration a card or
fob is used for access control plus one
or more other systems.
Hardware Level
Integrate with Fire, Intruder, Lifts,
CCTV, Turnstiles, telephone/video
entry; the list goes on.
Software Level
Automated Data Import allows very useful yet simple
integration with third party applications such as
“Membership Management” or “Booking Systems”.
Time and Attendance software is a prime example of
software level integration with an Access Control
System where the SQL server database is shared.
P3
Software

24 www.progeny.co.uk
INTERLOCK
SYSTEMS
HIGH SECURITY
Also known as Air Lock & Tiger Traps, Interlock
systems control the locking of two or more
doors, such that if one door is open or unlocked,
the remaining doors refuse access.
ADAPTABLE
Doors can be normally locked (normal action) or
unlocked (reverse action) to suit the application.
Doors may have full access control using card
readers, keyboards etc. They may also be
simply released using push buttons or touch
switches.
SCOPE
Two, three and four way interlocks can be
created as standard. Contact our support team
for systems with more doors involved.
APPLICATIONS:
Clean Rooms
Bank Lobbies
Cash Handling
Laboratories
Jewellery Stores
Interlock
System
20
25
www.progeny.co.uk
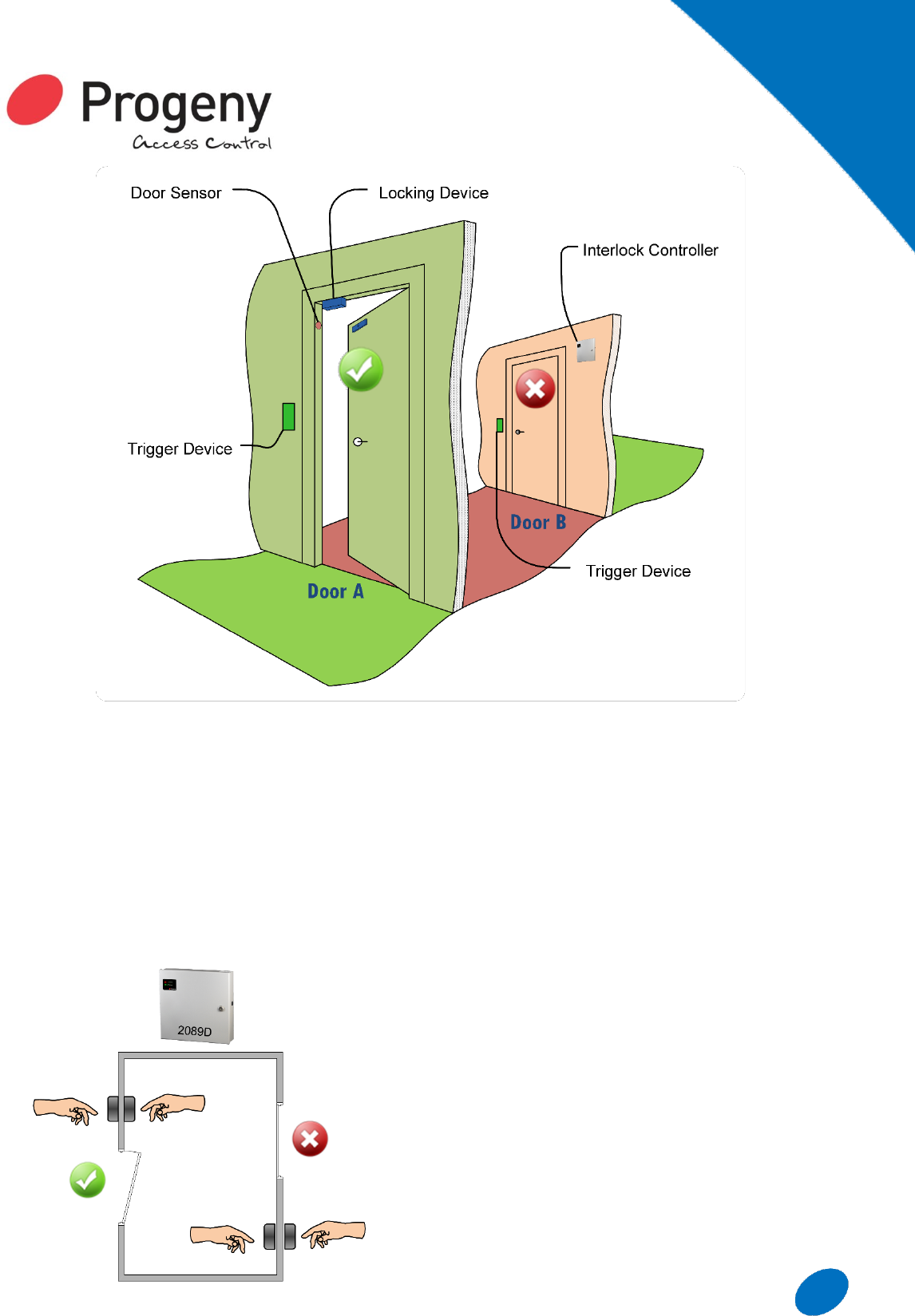
Simple 2 Door Interlock
Each door is electrically locked and monitored. The
control electronics then generates a control signal to
indicate when the door is closed and secure. Each
controller also has a control input that will prevent the
releasing of the locking device. By cross connecting
these control signals, the door controllers
communicate the door status, and only open one door
at any given time. The simplest interlock would have
two doors and standard systems can be made up to
four doors.
Normal Action
With normal action interlocks all the doors are normally
locked and a “Trigger” device of some kind is used to
unlock a door. While a door is unlocked or open, other
doors are prevented from unlocking. This type of
interlock is most commonly used for security, with
typical applications including: Bank Lobbies, Cash
Handling, Photo, Laboratories, Clean Rooms, and
Jewellery Stores.
Reverse Action
With reverse action interlocks all the doors are
normally unlocked but monitored. When any one of the
doors is detected as “open”, all the other doors are
then locked. These are most commonly used for
functional control rather than security. Reverse and
normal action interlocks can also be mixed on the
same system.
Interlock
System
Interlock
System
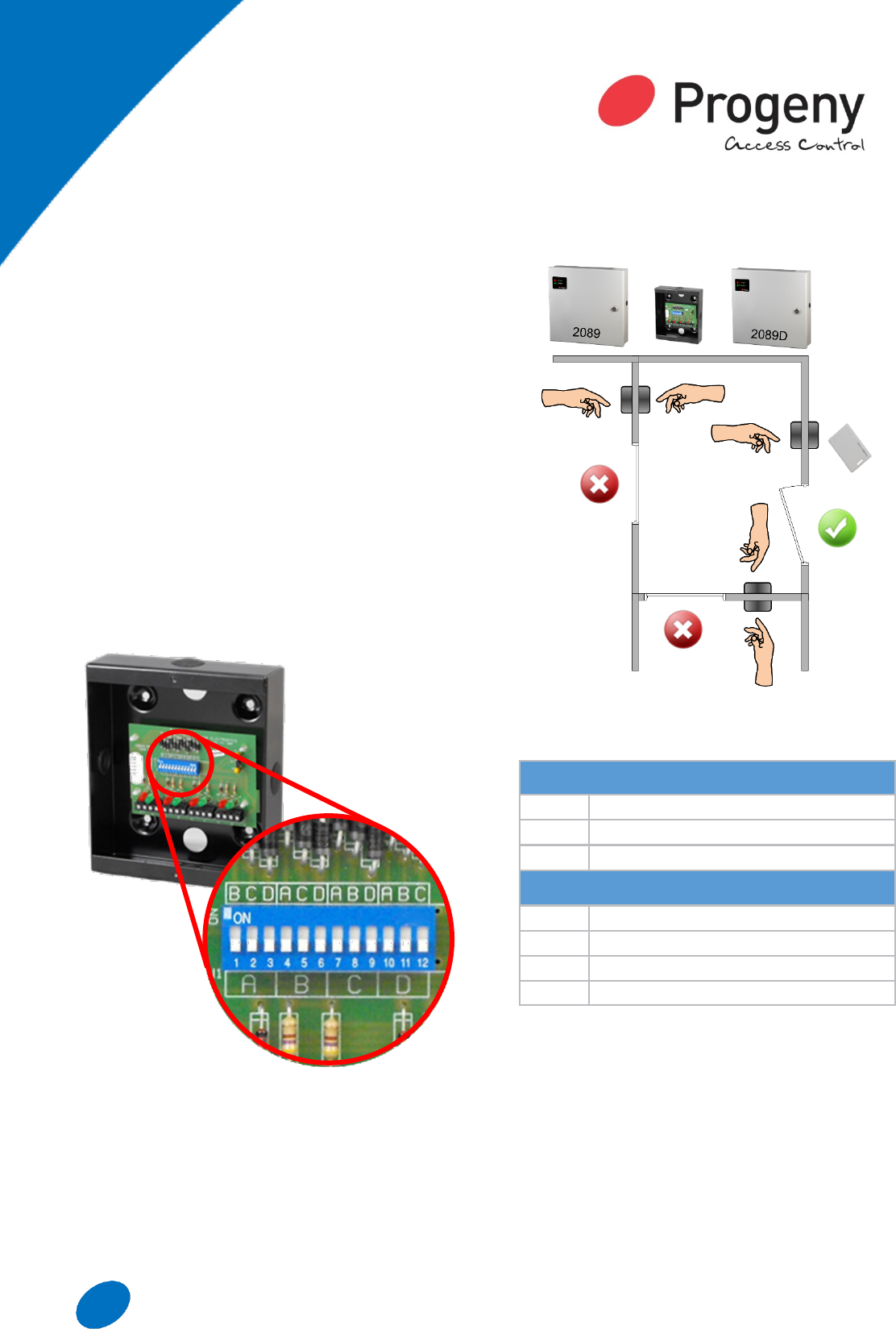
26 www.progeny.co.uk
3 Door Mixed with Access Control
Doors may be controlled by P1, P3 controller and/or
an interlock controller.
The trigger device can be a simple push button or an
access control keyboard or card reader. All the
Progeny P1 and P3 controllers have interlocking
interfaces as standard. This means you can mix
interlock controllers with access controllers on the
same system.
3 Door Mixed with Access Control
An “Interlock Programmer” is used to greatly simplify
connecting the interlock signals. It also allows for
easy and flexible programming of the interlock
system. A 12 way DIP switch allows the interlocking
to be programmed in any combination. On board
indicators show current interlock signal status.
Interlock Product Codes
2089
Interlock Controller with 5A PSU (1 Door)
2089D
Interlock Controller with 5A PSU (2 Door)
2069
Interlock Programmer
Access Controllers with Interlock
2163
P1 Controller with 5A PSU
3001
P3 Controller with 5A PSU
3002
P3.net Controller with 5A PSU
3006
P3.GPRS Controller with 5A PSU
Interlock
System

27
www.progeny.co.uk
READERS &
KEYBOARDS
INTRODUCTION
Identifying a prospective user of a door is one of
the most important tasks of an access control
system.
Keyboards will allow the entry of secret
knowledge in the form of a “PIN” or an
“Access Code”.
Readers will extract a credentials
Identification Number.
Biometric Readers read a physical pattern of
some sort that is unique to person.
For higher security these can be used in
combination to provide two or even three factor
identification.
RFID
“Radio Frequency Identification” (RFID) comes
in many shapes and sizes. All of these can be
interfaced with the Progeny P1 and P3
controller products.
MAGSTRIPE
Still a popular low cost token based means of
identification. These readers extract the
magnetically encoded numbers from the
magnetic strip on the back of a card.
BIOMETRIC
One of the integration success stories has been
that of P3 system with biometric readers. In
particular iRIS ENTRA and the iEVO Fingerprint
readers.
Readers &
Keyboards

28 www.progeny.co.uk
Readers
CRYSTAL RFID
READERS
The Crystal Proximity reader is a universal RFID
reader which can easily be configured by the user to
work with the C2, P1, P2 and P3 systems. The
readers are IP rated and are available in four styles;
Switch Plate, Mullion, Panel Mount and Classic. The
readers are also available with a pigtail flying lead,
further enhancing the IP rating should there be a need
to mount the reader externally. Crystal readers work
with Crystal credentials which ensure compatibility,
reliability and cost savings.
Crystal Switch Plate
This reader mounts directly on to a standard UK
single gang back box making it an ideal solution for
first fix.
Crystal Mullion
This style reader is suitable
for mounting on to door
frames or posts or other
locations that cannot make
use of a single gang back
box. The reader is also
available with a pigtail flying
lead to provide extra flexibility
when mounting on to surfaces
that cannot be easily chased
out or to provide an extra
level of protection for outdoor
environments. The reader is
also supplied with a stainless
steel cover for a more modern
aesthetic.
Crystal Panel Mount
This reader is also supplied with a stainless steel
cover. This IP
rated reader has
standard
mounting holes
and is designed
to fit in to an
intercom or entry
panel.
Spacers
These are
available for
both the switch plate and mullion versions of the
Crystal Proximity readers and are made from the
same durable material as the readers themselves.

29
www.progeny.co.uk
14
Vandal Resistant
Crystal Switch plate reader with protective Stainless
Steel Front Plate
Credentials
Crystal Readers
3800 Crystal Proximity Switch Plate
3820 Crystal Proximity Mullion Reader/
3820P Crystal Proximity Mullion (Pig Tail)
3830 Crystal Proximity Panel Mount
Reader Spacers
3824 Switch Plate Spacer
3824-Mull Mullion Spacer
UID Credentials
3804-10 Crystal ISO Cards pack of 10
3804-100 Crystal ISO Cards pack of 100
3805-10 Crystal Key Fobs pack of 10
3805-100 Crystal Key Fobs pack of 100
Site Coded Credentials
3840 Crystal Site Coded ISO Card
3841 Crystal Site Coded Key Fob
Crystal
Readers

30 www.progeny.co.uk
FEATURES
HI CO Cards
Track 2 or Track 1
Low Cost Credentials
Surface Mount
Weather Proof
Magstripe
MAGSTRIPE
The magnetic stripe, often called a “Magstripe”, is
read by swiping past a reading head. Magnetic stripe
cards are commonly used in credit cards, identity
cards, and transport tickets.
READERS
Progeny Magstripe readers are Track 2 as standard.
Readers for Track 1 are available, please contact our
sales team for more information. Both readers are
compatible with P1 or P3 Controllers.
2075 is a Magstripe reader for indoor or outdoor use.
The reader head provides an extremely reliable
reading capability with over 1 million head passes.
Made from an ultra-tough UV resistant polycarbonate,
this reader is very durable, even in the harshest
conditions.
Magstripe Readers
2075 Magstripe reader (TRK2)
2075-TRK1 Magstripe reader (TRK1)
Cleaning
Reader Spacers
2150 Cleaning Cards (Pack of 10)
Site Coded Credentials
2014 Mono Magstripe Card
2015 Colour Magstripe Card

31
www.progeny.co.uk
Progeny HID Proximity
HID proximity cards and readers are recognized as
the industry standard for physical access control.
Featuring 125 kHz RFID technology, HID proximity
products are robust, affordable and seamlessly
integrate with access control systems.
Progeny iCLASS
Progeny iCLASS offers widely supported card level
integration to third part systems such as:
Cashless Vending
Follow Me Printing
iCLASS SIO-Enabled (SE™) smart card readers
support Secure Identity Object™ (SIO), a new
portable credential methodology from HID, and HID's
Trusted Identity.
Technology-independent - Supports multiple
technologies (iCLASS Seos and iCLASS SE
credential platforms, standard iCLASS, MIFARE, and
MIFARE DESFire EV1).
Progeny HID Prox Readers
2052-HID Prox Point Reader (Mullion Pig Tail)
2050-HID-
KB
Prox Pro Reader with Keyboard
2058-HID Progeny Prox Reader (Mullion Ter-
minal)
2053-HID Vandal Resistant Prox Reader
2060-HID Panel Mount Prox Reader
Site Coded Credentials
2042-HID ISO Prox Card
2043-HID Prox Key Fob
2044-HID Prox Clam Shell Card
2045-HID Prox Sticky Dot
Progeny iCLASS Readers
3231 Progeny iCLASS Reader (Mullion)
3231-M Progeny iCLASS Reader to read
MIFARE CSN
3237 Progeny iCLASS Reader with Key-
board
Site Coded Credentials
3232 ISO iCLASS Card
3233 iCLASS Key Fob
3235 iCLASS Sticky Dot
3238 iCLASS Clam Shell Card
“So you can use the same card for
access to the office and use it to
pay for coffee while you wait for
your print queue to print”
Progeny
HID

32 www.progeny.co.uk
Hands Free & Safety Registration
Basic features:-
“Hands Free” Tags and Readers
Long life active tags
Secure digital data exchanges
Hands free reading range (>3.0m)
Fast (20 tags/sec.) multiple reading
High level noise immunity (digital
transmissions)
Direction sensing firmware
Inert tags until in reader detection zones
Applications
The product is suitable for numerous applications,
they include but are not limited to:
Direction Sensing
Two Door Controller
Personnel & Product Tracking
Time and Attendance
Hands Free Access Control
Car Parking Control
Personnel Identification
Personnel & Article Tracking
Details
The direction sensing reader utilises two external loop
aerials to enable sensing at ranges of up to 3 metres.
Alternatively the same device can monitor two
independent doors which are close together without
providing direction information. The radiofrequency
communications are scrambled to provide high
integrity, and to prevent simulated tokens being used.
Used in the direction sensing mode a tag moving from
one loop to another will have its direction of travel
identified by the reader. The speed of reading tags is
effectively halved compared to a single zone reader.
Hands Free
33
www.progeny.co.uk
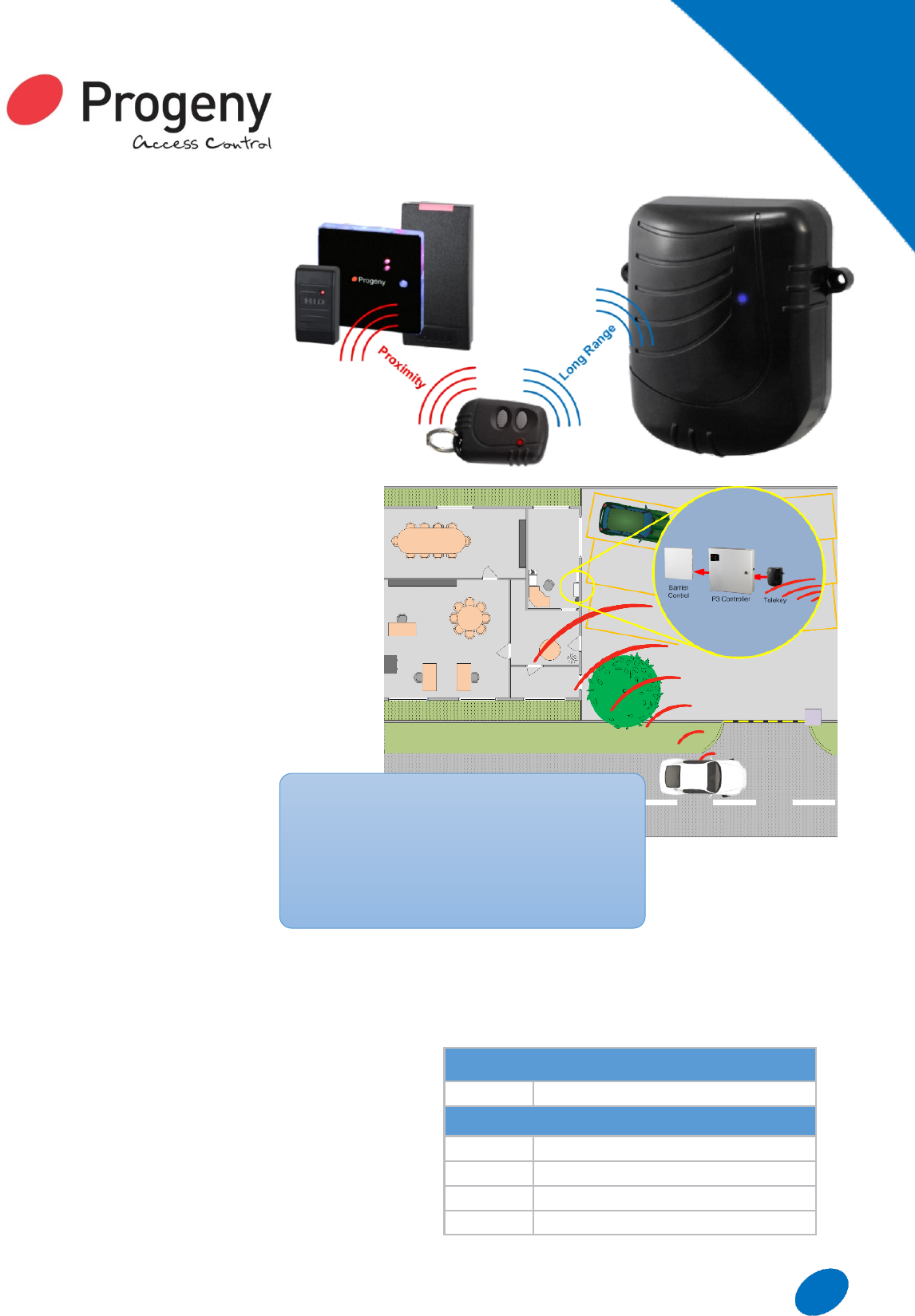
LONG RANGE
RFID
The Progeny Telekey has a read
range up to 25 metres and is an
ideal way to control access through
automated gates, rising barriers etc.
Fobs can be enabled or disabled
from the access control system and
all users will be identified and
logged.
The long read range removes the
need to have the reader on a post by the road
side. Vehicle users do not need to get out of the
cab in order to open a barrier.
The Telekey fob is also available with embedded
Progeny prox, HID prox or iCLASS credentials.
How it works
Each key fob has a unique ID number (site code &
card number), pressing one of the buttons on the
fob transmits this number. When in range, this
number is read by the reader and passed onto a
standard P1 or P3 access controller for decision
making.
Each fob can be treated as any
other credential and allocated:
Access Levels
Time zones
Calendar limits
“Valid from” and “Valid to” dates
The IP 56 enclosure of the reader makes it suitable
for indoor or outdoor mounting. This removes the
possible need to dig up road or car park to run cables
to readers near the gate or barrier. The reader also
has two reader outputs that correspond to the two
buttons on the fob. This can be used to control two
barriers from one reader possibly for in / out
applications.
Telekey can be added to any P1 or P3 access control
system. The reader also works in tandem with
whatever existing reader technology is in
Long Range
Overview
2 channels (2 buttons)
Up to 25 Metre range possible
Available with Crystal, HID or MIFARE
Standard Progeny reader interface
Surface mount
Long Range Readers
3300 Telekey Reader
Site Coded Credentials
3301 Telekey Fob
3806-10 Crystal Sticky Dots pack of 10
2045-HID Prox Sticky Dot
3235 iCLASS Sticky Dot

34 www.progeny.co.uk
Biometric Integration
What are Biometrics?
Biometrics can be taken literally as 'life measurement'
but the term is usually associated with the
measurement and use of unique physiological
characteristics to identify an individual such as
Fingerprints, Face or the Iris.
Advantages of Biometrics
Identification based on biometric techniques removes
the need to remember a password or carry a token
which also eliminates theft of cards or fobs and
therefore constant replacements. Biometric options
are also more cost effective as individuals can be
easily added or removed from the system at no extra
cost.
iEVO Fingerprint Biometric Reader
Fingerprint Recognition
Everyone has a unique, unchanging fingerprint. A
fingerprint is made of a series of ridges and furrows
on the surface of the finger and these are used to
determine the uniqueness of the fingerprint. Once
scanned on the fingerprint sensor, the image of these
patterns is converted into a code through a
mathematical sequence called an algorithm, which
effectively becomes a digital form of you. This is
stored on a database for comparison which identifies
a virtual card number to be sent to the Progeny range
of controllers.
Biometric
Integration
35
www.progeny.co.uk
CRYSTAL BARCODE
READER
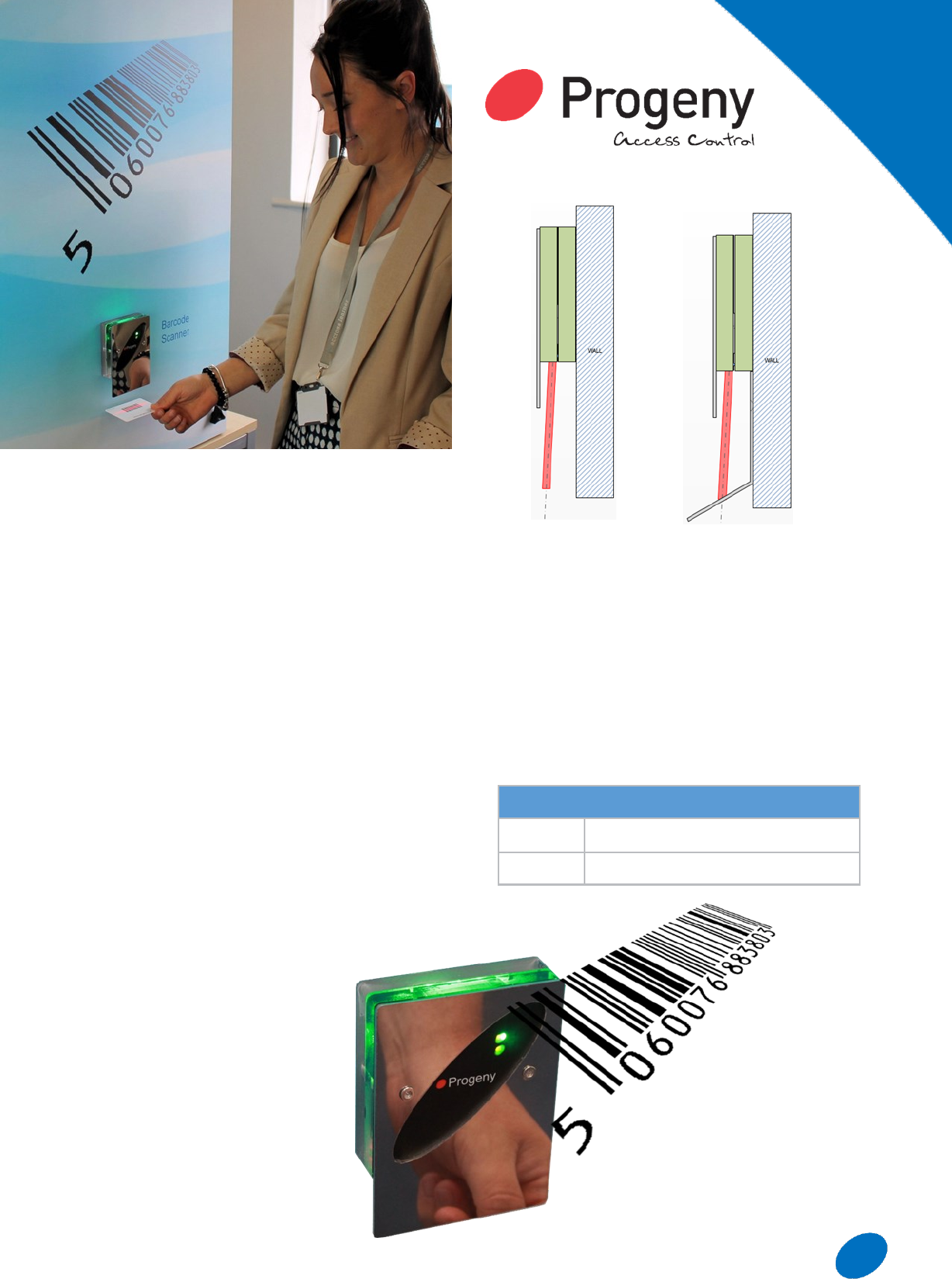
The 2030-SC is a scanning optical barcode reader.
The reader is weather protected and suitable for both
indoor and outdoor use.
Reader
The switch plate style has 60mm spaced mounting
points to fit a standard single gang back box.
The switch plate reader comes with an attractive
stainless steel cover to give protection and a modern
aesthetic.
The switch plate reader can be surface mounted.
Cards are presented below the reader.
Optional Position Target
This optional accessory assists the novice user to
position the card at the correct
distance and location. This is
particularly useful in full sunlight when
the scanning light bar is difficult to
see.
Credentials
The scanning barcode reader will
work with most common coding types:
Code 39
All UPC/EAN/JAN
Code 128
CODABAR/NW7
Interleave 25
And more…
Only numeric data is processed by
the reader.
Specification
Operating Voltage Range 8-14 VDC
Supply Current (Ta > 6 °C) 95mA
Supply Current (Ta < 6 °C) 350mA
Operating Temperature -20 to 65°C
Operating Humidity 0 to 95%
Transmit Frequency 125Khz
Cable Distance 100m
Crystal
Barcode
Reader
P2 Product Codes
2030-SC Crystal Barcode Reader (Scanning)
2030-ST Optional Position Target

36 www.progeny.co.uk
KEYBOARDS
Keyboards cater for the “Secret Knowledge” method
of identification. They can be used by themselves or
in conjunction with token based credentials for
additional security. Keyboards can be used to enter a
common code used by more than one user or a true
Personal Identification Number (PIN). P3 systems
also allow for the entry of a “virtual card” via the
keyboard.
The principle advantage of using code or PIN alone is
that the user does not need to carry anything around.
There is no credential to get lost or stolen. Keeping
the “secret knowledge” secret is very important
however. The spy proof and scramble keyboards
have some interesting features to help with this and
are explained below.
“Spy-Proof” Keyboard
Allows covert entry of an access code. The design
provides a top quality product along with
architecturally pleasing aesthetics. The heavy gauge
chrome plated front is 7mm thick and is bright
polished to mirror finish. This provides a top quality
feel and a comfortable edge to rest the hand whilst
entering the code.
Vandal Resistant Keyboard
This keyboard is robust enough for any public facing,
outdoor applications. The back lit keys make access
code entry in the dark easy. Integral sounder gives
key beep and “Prolonged Door Open” alarm function.
FEATURES
Stylish Design
Spy Proof Front
Indoor Use Only
Keyboards
FEATURES
Vandal Resistant
Back Lit Keys
Surface Mount
Weather Proof
37
www.progeny.co.uk
FEATURES
No Moving Parts
Auto Adjust to Environment
Status Indication
Audible Feedback
Keyboards
Keyboards
2040
Spy Proof Keyboard
2121
Vandal Resistant Keyboard
2011S
Scramble Keyboard (Surface Mount)
2011P
Scramble Keyboard (Panel Mount)
Egress Devices
3810 Touch Switch (Switch Plate)
3810-MUL Touch Switch (Mullion)
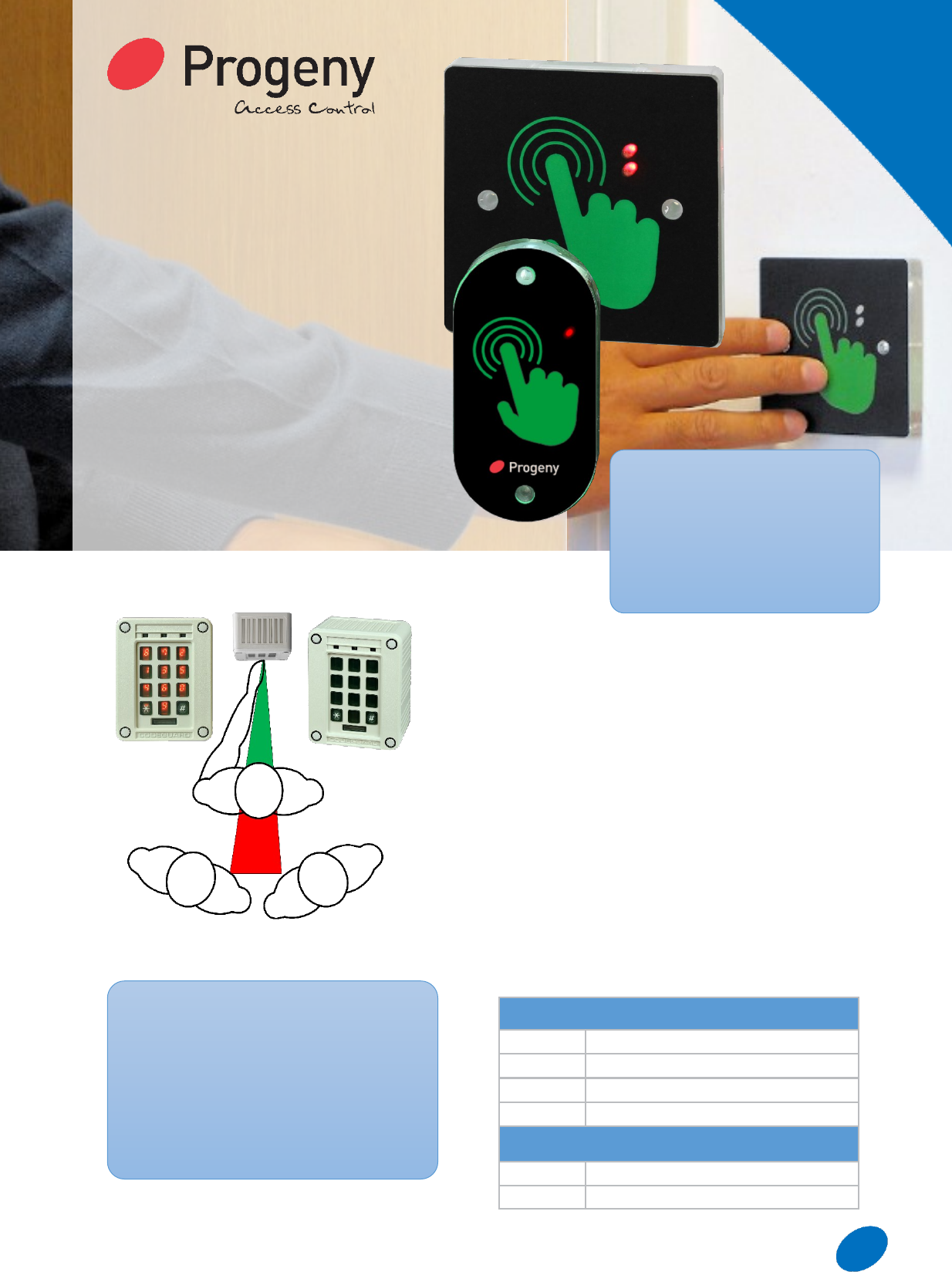
Scramble Keyboard
Interfaces with the P1 & P3 controllers in much the
same way as any other Progeny KB, but provides much
greater security by ensuring that only the person using
the keypad can see which numbers are being entered.
In addition, the numbers behind each key are moved
randomly each time the keyboard is used.
As the digits are scrambled observing which keys are
pressed will not reveal the code or PIN to a potential
intruder.
Each time the Progeny Scramble keyboard is used, the
digits 0 to 9 are allocated at random to the keyboard’s
10 keys. There are over 3.6 million permutations! This
also ensures that the keys wear equally, even if the
same code is always used.
EGRESS DEVICES
The Progeny Touch Switch is a general purpose
switch capable of detecting near-proximity or
touch. It detects tiny changes in the capacitance
at the front surface. The switch uses a patented
spread-spectrum charge-transfer technology.
Every 80 seconds the switches self-calibrate, this
means that the switch can accommodate large
changes in surface capacitance due to; humidity,
nearby objects etc. Designed specifically for
"Request to Exit" or "Request to Enter Call"
applications. The fully sealed IP66 enclosure
makes it suitable for both, internal or external use.
The "Switch Plate" version will mount on any
standard single gang light switch back box.
The "Mullion" version is ideal for those space
restricted locations.
FEATURES
High Security
Covert Code / PIN Entry
3.6 million permutations
Even Key top Wear
Surface Mount or Panel Mount

38 www.progeny.co.uk
TRAINING
BSB Electronics provide training courses at Progeny
House. Our training courses run for a full day.
If you would like to attend then please contact our
customer support team.
On Site Training
BSB Electronics can also provide onsite training. The
course length will be approximately five hours long
and will provide an overview of the product along with
a solid grounding on use and the setup of the system
on Doors Enterprise.
On Site Commissioning and End User
Training
To check that Progeny equipment has been installed
to the correct standard, BSB Electronics can provide
a commissioning day if required or time permitting,
on site end user training. The hardware installation
will be inspected and tested, and the software
installation (if an online system) will also be inspected
and tested for correct setup. A commissioning day
commences at 10:00 and lasts until approximately
16:00
COMPLIANCE
We are committed to working closely with our
suppliers, distributors, installers and customers to
ensure that we are properly prepared and taking the
necessary steps so as to comply with any European
Directive. More detailed information on compliance
can be found on the website.
CE
CE marking is a declaration by the manufacturer that
the product meets all the appropriate provisions of the
relevant legislation implementing certain European
Directives.
WEEE
(Waste Electrical and Electronics Equipment
Directive)
This directive is aimed at the reduction of waste from
Electrical and Electronic Equipment and to improve
the environment. Producers are encouraged to
improve the life cycles of the equipment they
manufacture.
DDA 2005
(Disability Discrimination Act 2005)
This directive builds on and extends earlier disability
discrimination legislation, principally the Disability
Discrimination Act 1995. Under the Act, small to
medium sized businesses have to make reasonable
adjustments so they do not discriminate against
disabled customers or employees.
Touch Switches - Clear labelling & no
moving parts
P2 & P3 - Two stage lock release for
automatic door openers
P3 delay to lock release
P2 & P3 auto relock feature
Doors Express/P2 - Adjust the sound level
of readers
RoHS
(Restricted Use of Certain Hazardous Substances
Directive)
Directive 2002/95/EC on the Restriction of the use of
certain
Hazardous Substances in Electrical and Electronic
Equipment (RoHS)
IP Ratings
(Ingress Protection)
IP Ratings are defined in international standard EN
60529 (British BS EN 60529:1992, European IEC
60509:1989).
Compliance
& Training

39
www.progeny.co.uk
ADDRESS
BSB Electronics
Progeny House
Union Court
Heys Lane Industrial Estate
Great Harwood
Lancashire
BB6 7FD
England
Tel +44 (0)1254 883348
Fax +44 (0)1254 889113
DIRECTIONS FROM THE M6
Exit M6 at Junction 29 - follow the signs for the M65
Burnley. Exit M65 at Junction 7 (A6175) and bear left to
the traffic lights.
At the traffic lights turn right and proceed to the next set
of traffic lights.
Turn left onto the A680 and follow the road until you see
the Hyndburn Bridge pub, on the left.
Take the next left turn at the traffic lights into Hyndburn
Road (sign-posted ‘Great Harwood’) then turn first left
into Heys Lane Industrial Estate onto Alan Ramsbottom
Way.
Continue along Alan Ramsbottom Way for approximately
600m and Progeny House on the right.
DIRECTIONS FROM MANCHESTER AIRPORT
Join the M56 slip road and follow the signs to Manchester.
Join the M60 (Manchester Orbital Motorway).
At Junction 18 leave the M60 and turn onto the M66 (Bury).
Continue to the end of the M66. The road becomes the A56.
At the end of the A56 turn left and join the M65 at Junction 8.
Leave M65 at Junction 7.
Take the third exit off the roundabout up to the traffic lights.
At the traffic lights turn right and proceed to the next set of
traffic lights.
Turn left onto the A680 and follow the road until you see the
Hyndburn Bridge pub on the left.
Take the next left turn at the traffic lights into Hyndburn
Road (signposted ‘Great Harwood’) then turn first left into
Heys Lane Industrial Estate. Progeny House is on the right.
Finding
Us
HOW TO FIND US

40 www.progeny.co.uk
BSB Electronics Ltd
Progeny House
Union Court
Heys Lane Industrial Estate
Great Harwood
Lancashire
England
BB6 7FD
www. progeny.co. uk
Designed and Manufactured in England
T : 0 1 2 5 4 883348 F: 0 1 2 5 4 889113