Project Report Face&Iris Recognition(Installation Guide And User Manual Exist)
User Manual:
Open the PDF directly: View PDF ![]() .
.
Page Count: 33

ÇANKAYA UNIVERSITY
FACULTY OF ENGINEERING
COMPUTER ENGINEERING DEPARTMENT
Project Report
Version 1
CENG 408
Innovative System Design and Development II
P2017-14
Biometric Based on Face and Iris Recognition
Tolga ÖZALP
201311042
Utku ÖZCAN
201311045
Edanaz PEKDEMİR
201311050
Advisor: Yrd.Doç.Dr Gül TOKDEMİR
Co-Advisor: Doç. Dr. Reza ZARE HASSANPOUR

Contents
Abstract ............................................................................................................................................................... iii
Özet: .................................................................................................................................................................... iii
1. Introduction ................................................................................................................................................... 1
2. Literature Review .......................................................................................................................................... 2
Biometric Recognition ......................................................................................................................................................... 2
Face Recognition Features ................................................................................................................................................... 2
Shortcomings of Face Recognition ....................................................................................................................................... 3
History and Projects which using Face Recognition ............................................................................................................ 3
Iris Recognition Features ...................................................................................................................................................... 4
Shortcomings of Iris Recognition ......................................................................................................................................... 4
History and Projects which using Iris Recognition .............................................................................................................. 4
3. Introduction(SRS) ......................................................................................................................... 5
Purpose ................................................................................................................................................................................. 5
Scope of Project.................................................................................................................................................................... 5
Glossary ................................................................................................................................................................................ 6
References ............................................................................................................................................................................ 6
Overview of Document ........................................................................................................................................................ 6
System Environment ............................................................................................................................................................ 7
Development methodology .................................................................................................................................................. 8
Functional Requirements Specification ................................................................................................................................ 8
User Interface Specification ................................................................................................................................................. 8
Non-Functional Requirements .............................................................................................................................................. 8
Performance The System Requirements ............................................................................................................................... 8
External Interface Requirements .......................................................................................................................................... 9
User Interfaces ...................................................................................................................................................................... 9
Hardware Interfaces ............................................................................................................................................................. 9
Software Interfaces ............................................................................................................................................................... 9
Communication Interfaces.................................................................................................................................................... 9
Employee Use Case ............................................................................................................................................................ 10
Register Use Case ............................................................................................................................................................... 11
Image Acquisition Use Case .............................................................................................................................................. 12
System Login Use Case ...................................................................................................................................................... 12
Get Result Use Case ........................................................................................................................................................... 13
Update Employee Use Case ............................................................................................................................................... 13
Set Configurations Use Case .............................................................................................................................................. 13
Logical Structure of the Data ............................................................................................................................................. 14
Security .............................................................................................................................................................................. 14
Maintainability ................................................................................................................................................................... 14
Portability ........................................................................................................................................................................... 14
4. INTRODUCTION(SDD) .............................................................................................................. 15
ARCHITECTURE DESIGN .............................................................................................................................. 17
Class Diagram .................................................................................................................................................................... 19
Admin Menu ...................................................................................................................................................................... 19
Registration System ............................................................................................................................................................ 20
Recognition System ............................................................................................................................................................ 20
GUI Design ........................................................................................................................................................................ 22
Recognition System Design ............................................................................................................................................... 23
DETECTION - RECOGNITION ....................................................................................................................... 23

Abstract
Today, we are living in the technology age and because of this technology it is
evolving rapidly and grows day by day. Most of the people and companies are
using technological products which include their privacy, so they want to keep
safe their information freely. In the light of that information, some scientists have
tried to produce a new product to which provide people's private information keep
in safely and avoiding the information theft. As a result of these, scientist
developed Face and Iris recognition system which is the products that are the
safest and easiest to use according to other security products, except those
advantages, Face and Iris recognition system still has some shortcomings like
illumination, external factors, so Face and Iris recognition algorithms should
develop for reaching highest matching rate.
Key words:
Face Recognition, Iris Recognition, Biometrics, Identification.
Özet:
Bugün, teknoloji çağında yaşıyoruz ve bu teknoloji nedeniyle dünyamız hızla
gelişiyor ve her geçen gün büyüyor. İnsanın ve şirketlerin çoğu gizliliklerini içeren
teknolojik ürünler kullandığından, bilgilerini özgürce korumak istiyorlar. Bu
bilgiler ışığında, bazı bilim insanları, kişilerin özel bilgilerini güvenli bir şekilde
saklamak ve bilgi hırsızlığından kaçınmak için yeni bir ürün üretmeye çalışıyorlar.
Bunun sonucunda bilim adamları, diğer güvenlik ürünlerine göre en güvenli ve
kullanımı en kolay ürünler olan Yüz ve İris tanıma sistemini geliştirdiler; bu
avantajlar dışında, Yüz ve İris tanıma sisteminin hala aydınlık ve diğer dış etkenler
gibi bazı sorunlarla baş edebilme eksiklikleri var, dolayısıyla en yüksek eşleme
oranına ulaşmak için Yüz ve İris tanıma algoritmaları geliştirilmelidir.
Anahtar Kelimeler:
Yüz Tanıma, İris tanıma, Biyometrik, Kimlik

Page 1
1. Introduction
Problem Statement
There are some issues that still need to be solved like illumination, pose and facial expression
[3]. Firstly, difference of illumination and pose and facial expression affect to face recognition
in a bad way like lighting of ambient can change among indoor and outdoor environments and
because of the 3D of human face shape, illumination angle makes shadow some points on the
face so, nodal points can be affected in a bad way and some information cannot be reached, so
experts still struggle with this problem and they go on improving new image preprocessing
algorithm for illumination variations [3]. In addition, changing the pose and facial expression
can cause loss of nodal points on the face because of changing the measure of existent parts at
a human face like lip, nose so, recognition fail rate can increase than before, so experts need
to robust the algorithms to ensure consistency. There are some problems about Iris
Recognition like Iris Recognition devices can be fooled by an HD image and lighting effect to
an accuracy of scanners in a bad way. Iris Recognition’s cost is more expensive than other
recognition systems. It is a new technology, so it is incompatible with most of the current
technological devices. If the person who does not know about the Iris Recognition system,
s/he may have some trouble because person’s walking speeds need to be maximum up to 1
meter/sec and maximum identifiers distance is the almost 10 meters around [1]. In addition,
researchers can trick Iris scanners with digital codes of stored Irises and also alcohol
consumption affects pupil like dilates/constricts and it leads to deformation in the iris patterns
so, it increases the rate of the false matches [1]. Also, researchers encounter with the rate of
rejection of poor quality images, so they need to reduce delays the enrollment and verification
because it can annoy the users while that all things happen consistently, they need to decrease
failure to enroll rate (FTE) [3].
Solution Statement
We are using Principal component analysis (PCA) which is the reliable algorithm for working
security system process. It is also more accurate than any other descriptors and it is
independent of rotation, luminance, and scale, so its acceptable level is higher than other
algorithms. Also, the acceptable level of Face and Iris recognition can be adjustable according
to company’s request. While the people registration to the system, the main goal of a PCA
analysis is to identify patterns in data; PCA aims to detect the correlation between variables. If
a strong correlation between variables exists, the attempt to reduce the dimensionality only
makes sense. In a nutshell, this is what PCA is all about: Finding the directions of maximum
variance in high-dimensional data and project it onto a smaller dimensional subspace while
retaining most of the information. When the people define their identity on the system, the
PCA gets current user’s features and it searches that features exist in the database or not. If
exist, login can be done correctly, but if not exist in the database, the user cannot access the
document which includes high-level secret information.
Motivation
We are a group of senior students in computer engineering department who are interested in
image processing and security system. As a group, we have taken the course of numerical
computations for a better understanding in image acquisition area. We aimed to combine the

Page 2
fields of education, image acquisition, and security systems technologies in this project. We
have chosen the MATLAB scripting language and C# programming language which all of the
members of the group are already familiar to develop our project.
2. Literature Review
Biometrics
Biometrics means parts of the human body which provide a unique identity for being an
individual in the world, so these parts which are the unique have to be measurable, distinctive
and characteristics for each person. For example, Speech, Face, Iris, Fingerprints, Palm Print
and Hand-Writing are common and popular biometric identifiers which are used in the world
nowadays.
Biometric Recognition
Biometric Recognition provides separate humans’ identification according to their
characteristics and most of the time it uses their physical characteristics because each person
is different from each other according to genetic sequences, so this makes things easier [1].
Also, there is a relation between Biometric Recognition and Computer Science because we
are living in the age of technology and most of the people and companies are using
technological products so that products need to have reliable and consistent security for
protecting their privacy. Verify authenticity, authorization purposes and enforcing security are
examples of some working areas which biometric recognition are using with computer science
[1].
About Face Recognition
Face Recognition is one of the biometric methods for identifying human face which
comparing live capture or digital image data with a stored previous record about that person
and it has a potential to be less invasive according to other recognition methods. “Face and
iris recognition systems are among the top choices; because face recognition is friendly and
non-invasive whereas iris recognition is one of the most accurate biometrics” [6]. It is
generally used for security purposes like mobile payment system, airport security, but
sometimes it is used for gaming area like the Kinect motion gaming systems [2].
Face Recognition Features
One of the biometric identification technique is Multimodal biometric systems. “Multimodal
biometric systems take input from single or multiple sensors measuring two or more different
modalities of biometric characteristics. For example, a system combining face and iris
characteristics for biometric recognition would be considered a “multimodal” system
regardless of whether face and iris images were captured by different or same imaging
devices” [8]. Currently, numeric codes called faceprints are being used on face recognition for
acquiring high yield and providing consistency [2]. There are several existent parts at a human
face like the nose, eye sockets, lip, chin and cheekbones which separate humans’

Page 3
unique identification. For example, nose’s and lip’s length and width, eye sockets’ depth and
shape of the cheekbones can be different person to person, so generally, face recognition
systems make comparison according to 80 nodal points on a human face and information of
these nodal points change according to people’s face because of the differences mentioned
above. “Automatic recognition of human faces by computer has been approached in two
ways: holistic and analytic. The holistic approach treats a face as a 2D pattern of intensity
variation. The analytic approach recognizes a face using the geometrical measurements taken
among facial features, such as eyes and mouth” [7].
Shortcomings of Face Recognition
There are some issues that still need to be solved like illumination, pose and facial expression
[3]. Firstly, difference of illumination and pose and facial expression affect to face recognition
in a bad way like lighting of ambient can change among indoor and outdoor environments and
because of the 3D of human face shape, illumination angle makes shadow some points on the
face so, nodal points can be affected in a bad way and some information cannot be reached, so
experts still struggle with this problem and they go on improving new image preprocessing
algorithm for illumination variations [3]. In addition, changing the pose and facial expression
can cause loss of nodal points on the face because of changing the measure of existent parts at
a human face like lip, nose so, recognition fail rate can increase than before, so experts need
to robust the algorithms to ensure consistency.
History and Projects which using Face Recognition
Face Recognition system has been started at the 1960s due to the rise of crimes, so Woodrow
Wilson Bledsoe who is the father of Facial Recognition started the first step of Facial
Recognition systems and when the years show 2011, the government of Panama did first
major installation of Face Recognition in an airport with U.S and also, Osama Bin Laden was
identified by the face recognition system and he was killed in U.S. raid [4].
About Iris Recognition
Iris Recognition is a least invasive biometric method within other known methods and it
separates people from each other according to eye’s colored circle with using mathematical
pattern-recognition techniques on video images for each individual’s eyes [5]. Iris
Recognition generally used for military surveillance, security systems, counter-terrorism
initiatives and recently on smartphones like Samsung’s Galaxy Note8, Lumia 950/950XL, and
iPhone X. Iris is a thin circular structure in the eye and it manages pupils’ diameter and size
according to light. If the pupil is a larger than before, the more light can enter. It can be
different kind colors like blue, green and tons of brown. Iris recognition is a little bit
complicated according to other methods because even the right and left iris of a single person,
seems like very distinctive but from the good side, a structure of the iris does not change with
age just if we can compare iris pattern according to past childhood, it can seem a very little
[1]. Moment-to-moment dynamics is a very significant issue for iris because of the
complicated interaction of the iris’ muscles, small oscillation can happen with a constant state
on the diameter of the pupil [1].
Page 4
Iris Recognition Features
Iris is an internal organ, so it makes it valuable because it can be protected against damage
according to other recognition systems. Iris’s shape is generally like flat, so its shape more
predictable than face [1]. In addition, Iris determined randomly since embryonic gestation and
that makes it unique, so it decreases the rate of the false matches. Iris scan can be performed
between 10cm to a few meters. In addition, there is no need to physically touch between any
equipment and Iris. Currently, John Daugman’s IrisCode is applying as an Iris Recognition
algorithm and It has a rare false match rate like better than 10-11 and if we assume Hamming
distance threshold of 0.26 is used, and it is meaning 26% of bits in two IrisCodes accept
imaging noise and reflections [1].
Shortcomings of Iris Recognition
There are some shortcomings about Iris Recognition like Iris Recognition devices can be
fooled by an HD image and lighting effect to an accuracy of scanners in a bad way. Iris
Recognition’s cost is more expensive than other recognition systems. It is a new technology,
so it is incompatible with most of the current technological devices. If the person who does
not know about the Iris Recognition system, s/he may have some trouble because person’s
walking speeds need to be maximum up to 1 meter/sec and maximum identifiers distance is
the almost 10 meters around [1]. In addition, researchers can trick Iris scanners with digital
codes of stored Irises and also alcohol consumption affects pupil like dilates/constricts and it
leads to deformation in the iris patterns so, it increases the rate of the false matches [1]. Also,
researchers encounter with the rate of rejection of poor quality images, so they need to reduce
delays the enrollment and verification because it can annoy the users while that all things
happen consistently, they need to decrease failure to enroll rate (FTE) [3].
History and Projects which using Iris Recognition
Leonard Flom and Aran Safir who are the Ophthalmology Professors took a broad patent with
named as “Iris Recognition Technology” and they hired John Daugman who has the Ph.D. at
Harvard Computer Science faculty to the company and after that time, Daugman improved
the algorithm for Iris Recognition then, Professors and Daugman founded a company named
as “IridianTechologies, Inc.” [1]. In addition, Daugman algorithm is protected by Flom/Safir
patent list. Winthrop University has a key role in Iris Recognition because they are using it on
EagleEye attendance tracking system nowadays. In addition, Iris recognition is being used at
the Otay Mesa US-Mexico land border for biometric border control pilot project underway.
Lastly, Iris Recognition is used for project CERN which scientific facility in Geneva,
Switzerland for providing a security at Large Hadron Collider [5].
Conclusion
To sum up, technology grows day by day and biometric identification based on Face and Iris
Recognition are using at several different areas in a good way and it makes the world better
and safer place. For example, Biometric Recognition is encouraged as a way to aid detect
terrorists, provide better control of reach to physical simplicities and financial accounts, and
increase the efficiency of access to services and their utilization. Also, Biometric Recognition
has been applied to recognition of offenders, patient following up in medical informatics, and

Page 5
the customization of sociable services, among other fields. In the light of all of them, our
research concentrate on biometric based on Face and Iris Recognition to carry out the team
purpose or demanded results.
3. Introduction(SRS)
Purpose
The purpose of this System Requirement Specification document is describing the security
system which is called Biometric identification based on Face and Iris Recognition. This
system aims to provide a security system which holds a personal information keep in safe and
decrease the rate of information theft against who want to steal your private information. This
document includes detailed information about requirements of the project. It also identifies the
function and non-functional requirements with a use case diagram. Overall, this document is
used for how users interact with the system and understand how the mechanism works at
backend without any problems and explains how concerns of the stakeholders are met.
Scope of Project
Most of the people use a private computer to do their jobs in the company and they may need
to hide information in documents which relevant to work. Some information can be public,
and this files that are not important, if they are seized by someone else, but some files need a
special protection system which is in the high-level secret status because people are wasting
their time for hours on end and some hacker can steal their information from victim’s
computer easily without any protection system and worst of all, people are unprepared for this
situation. The application to be improved is Recognition of Human Iris and Face Patterns for
Biometric Identification. This project involves developing an iris detection system in order to
verify the uniqueness of the human iris and face by detecting the iris pattern from the image.
We offer a high-level security system which is the Biometric based on Face and Iris
Recognition for a company who want to save their information from a hacker or information
theft. The company should identify chosen workers to the security system according to
document while using their iris and face pattern on the camera. After registration done, only
chosen workers can access the high-level secret documents, if iris and face recognition can be
done correctly. We are using Scale-invariant feature transform (SIFT) which is the fastest and
reliable algorithm for working security system process. It is also more accurate than any other
descriptors and it is independent of rotation, luminance, and scale, so its acceptable level is
higher than other algorithms. Also, the acceptable level of Face and Iris recognition can be
adjustable according to company’s request. While the people registration to the system, SIFT
algorithm gets their image as a grayscale and create a matrix according to a pattern of iris and
face, then it makes features personally from a created matrix and transfers the features to the
database. When the people define their identity on the system, the SIFT algorithm gets current
user’s features and it searches that features exist in the database or not. If exist, login can be
done correctly, but if not exist in the database, the user cannot access the document which
includes high-level secret information.
There are actors in the security system which are the worker and admin. Admin should
register worker to the system without any problem and the worker should adjust position
Page 6
during interacting with the iris and face recognition on the camera for capturing best features.
In addition, admin should update worker information on the database because some worker
can wear a lens or worker can be injured in the face, so the admin should intervene to a
situation with manually.
Glossary
Term
Definition
Worker
A person whose Iris and Face is to be recognized
Admin
A person who handles the application and enrolls a person image in the database
Database
Collection of all the information about the image of eye and data of a person
PCA
Principal Component Analysis
Face and Iris
Recognition
Control system for using human iris and face for login to the system
Stakeholders
Any person who has contributed to the project
Features
Result of information of the matrix which derives from grayscale image
Grayscale
A range of grey shades from white to black, as used in a monochrome display or
printout[1]
References
[1] Rouse, M. (2010, May). What is grayscale? – Definition from WhatIs.com. Retrieved
December 03, 2017, from http://whatis.techtarget.com/definition/grayscale
Overview of Document
This will be the content and organization of the rest of this document
•
· Chapter 2 will provide the overall description of the application.
•
· Chapter 2.1 will contain the System Environment for the application
•
· Chapter 2.2 will contain the Functional Requirements Specification for the application
•
· Chapter 2.3 will contain the User Interface Specification for the application
•
· Chapter 2.4 will contain the Non-Functional Requirements for the application
Page 7
•
· Chapter 3 will contain the Requirement Specification for the application
•
· Chapter 3.1 will contain the External Interface Requirements for the application
•
· Chapter 3.1.1 will contain User Interfaces
•
· Chapter 3.1.2 will contain Hardware Interfaces
•
· Chapter 3.1.3 will contain Software Interfaces
•
· Chapter 3.1.4 will contain Communication Interfaces
•
· Chapter 3.2 will contain the Functional Requirements for the application
•
· Chapter 3.2.1 will contain Employee Use Case
•
· Chapter 3.2.2 will contain Register Use Case
•
· Chapter 3.2.3 will contain Image Acquisition Use Case
•
· Chapter 3.2.4 will contain System Login Use Case
•
· Chapter 3.2.5 will contain Get Result Use Case
•
· Chapter 3.2.6 will contain Update Employee Use Case
•
· Chapter 3.2.7 will contain Set Configurations Use Case
•
· Chapter 3.3 will contain the Detailed Non-Functional Requirements for the application
•
· Chapter 3.4 will contain the System Evolution for the application
•
· Chapter 3.5 will contain the Performance Requirements
•
· Chapter 4.0 will contain References
Overall Description
System Environment
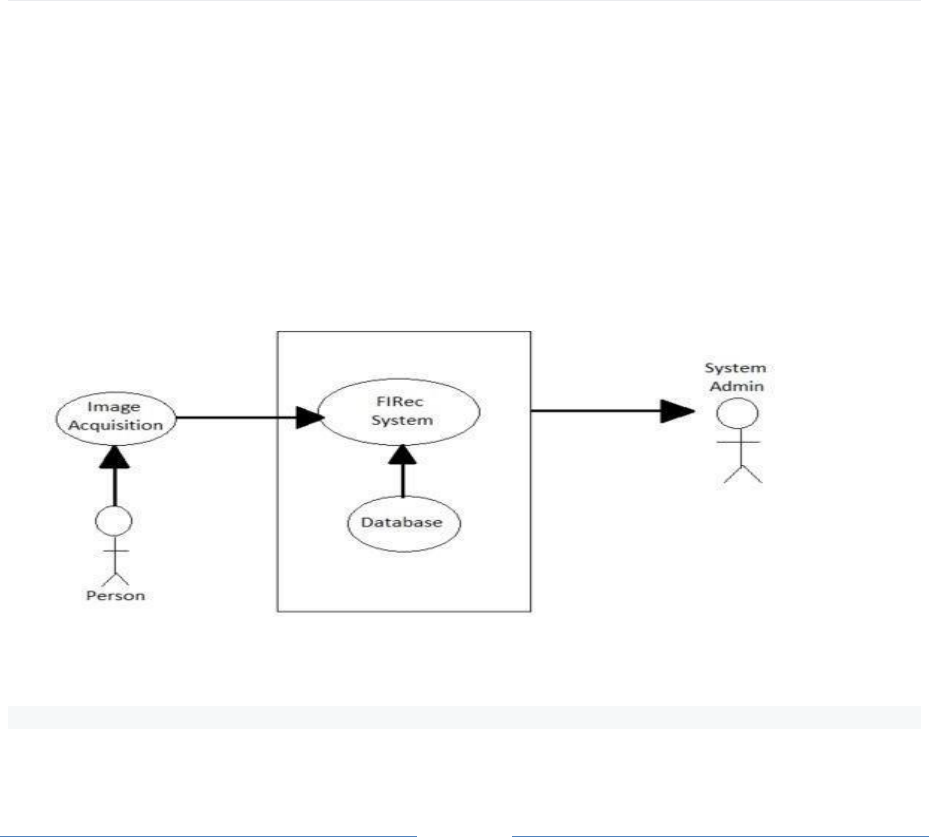
This application is Iris and Face Recognition System as seems as Figure 1. Firstly, A person’s
image should be provided using the camera. Then, camera transfers it to the Iris and Face
Recognition System. Next, an image is preprocessed for features of face and iris. After that,
they are compared with an image in the system database and matched. The System Admin can
do add and delete operations in the database, can set appropriate match rate of accepting user
and handle whole application.
Figure 1 System Environment Use Case

Page 8
Development methodology
While developing the project, we have decided to use Scrum which is an agile software
development methodology. Scrum is part of the Agile movement. Agile is a response to the
failure of the dominant software development project management and borrows many
principles from lean manufacturing. In a scrum, it has a sprint which includes work to do in
the project. It takes a while almost between 2 and 4 weeks. If you add work to the sprint, you
cannot remove that work from the sprint. The team who developed the project should have a
daily meeting every morning which should be maximum 10-15 minutes. Scrum has three
major roles which are a scrum master, project owner, and development team. Scrum master
generally manages the development team, product owner delivers the requirements. A
development team is the team of developers who work on the project together according to
schedule. There are several advantages of Scrum, Firstly, sprint releases end of each sprint.
The team does not have to act according to the product owner, the team identifies their
priority. Delivery happens according to the velocity of the team and development tools work
like cross-functional. The team should use burndown graphics in a project [9]. The scrum
board rebuilds while the beginning of each sprint. In addition, the scrum methodology is
incremental and iterative, so we can change required changes at project according to customer
feedback.
Functional Requirements Specification
In this section, use cases are outlined for every single actor. System admin is the main actor
and just one use case belongs to the user. Functional Requirements of Requirement
Specification and this section are similar to each other.
User Interface Specification
The framework holder is anticipated to be able to utilize button, pull-down menus, and
comparative devices. A window with graphical client interface will be utilized. To begin with,
of all we have chosen to store the highlights of iris of the pictures of an eye of people and
utilize those highlights for acknowledgment. In case the input image's highlights coordinate
up with the already put away highlights in the database, at that point a message will be shown
illuminating an effective acknowledgment along with the subtle elements of the comparing
individual. This is a unique plan. In the planning stage of the Iris Acknowledgment
framework, the layout of the required screen designs, report formats, and menu structures will
be chosen on.
Non-Functional Requirements
In the Face and Iris Recognition system, the input is an image. The system will be
implemented in MATLAB. MSSQL database will be used. Windows operating system will
execute the system.
Performance The System Requirements
The system will accept or reject user in 4 seconds, after scanning.

Page 9
Requirements Specification
External Interface Requirements
User Interfaces
The user interface will run on Windows.
Hardware Interfaces
The Face and Iris Recognition system require a camera. The camera requires necessary driver
installed within the operating system. Also, it requires 1 USB port on the PC.
Software Interfaces
There are no external software interface requirements.
Communication Interfaces
There are no external communications interface requirements
Functional Requirements
Use Case Diagram
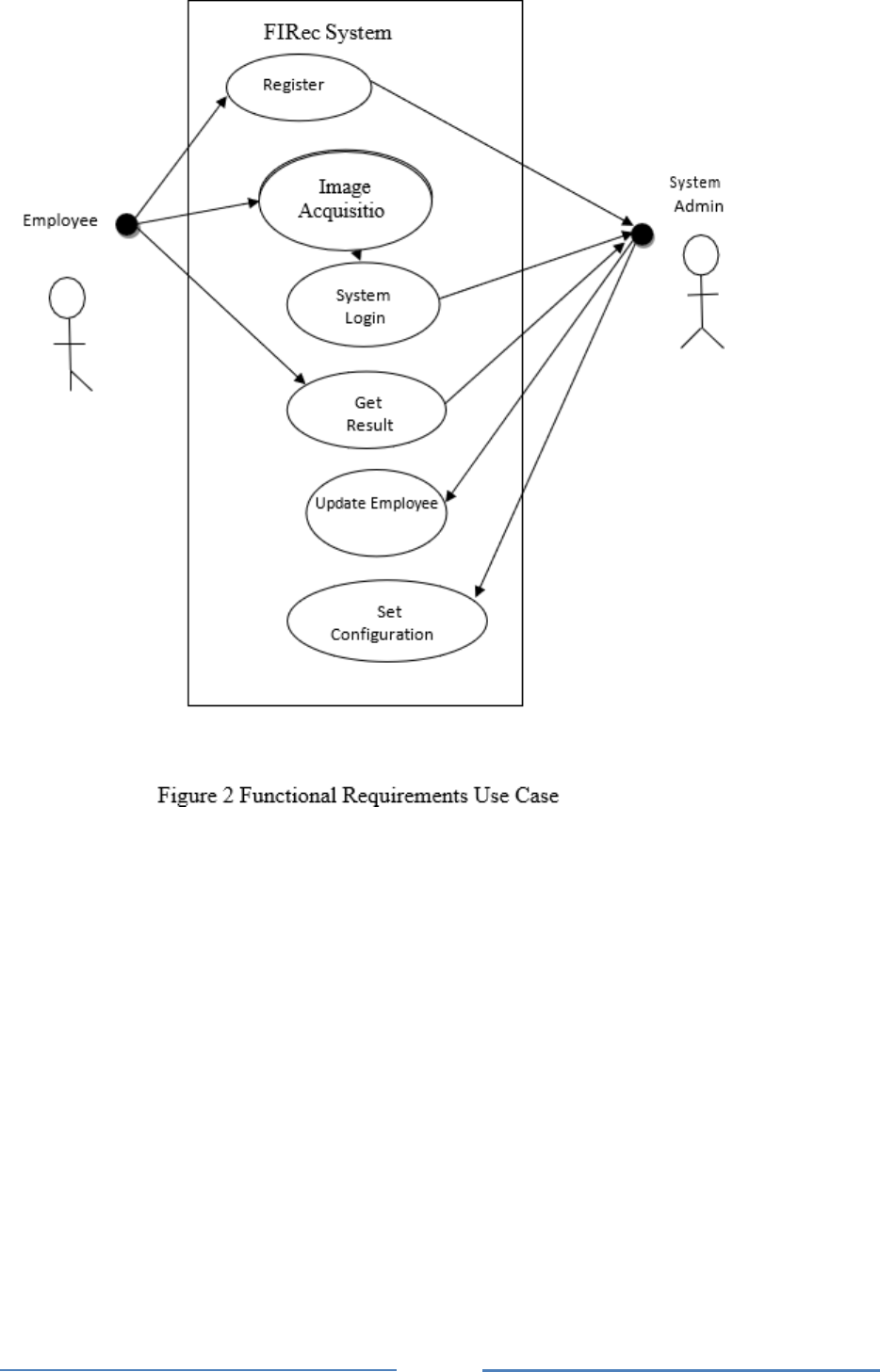
Use Case Diagram (UCD) for this project is shown in Figure 2. After some analysis of the
system development process, The Use Case Diagram is created. This User Case Diagram can
be modified during later parts of the project.
Page
10
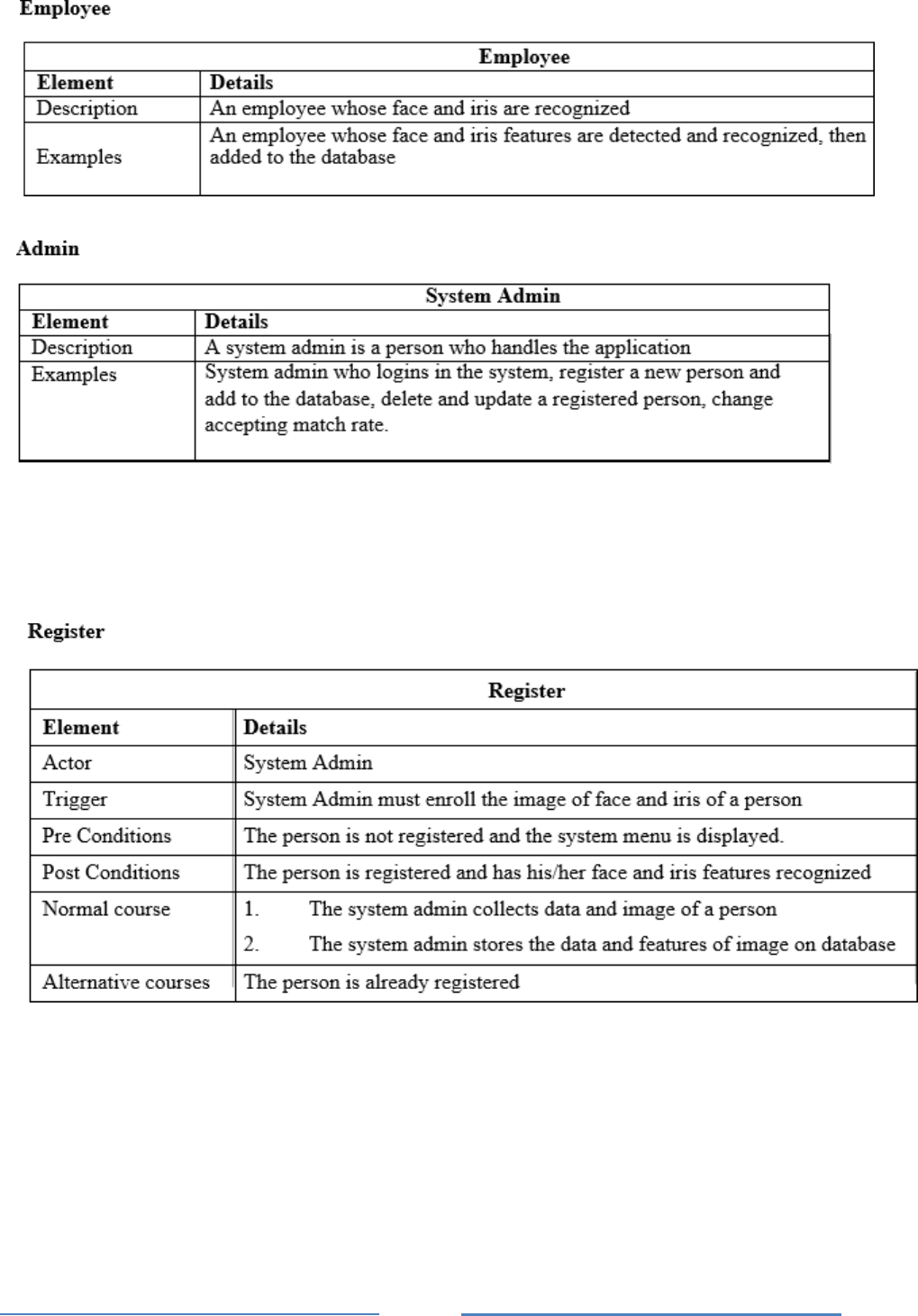
Employee Use Case
Specificaton of Actors
In the analysis stage of the Face and Iris Recognition System development process, actors
below are described so far.
Page
11
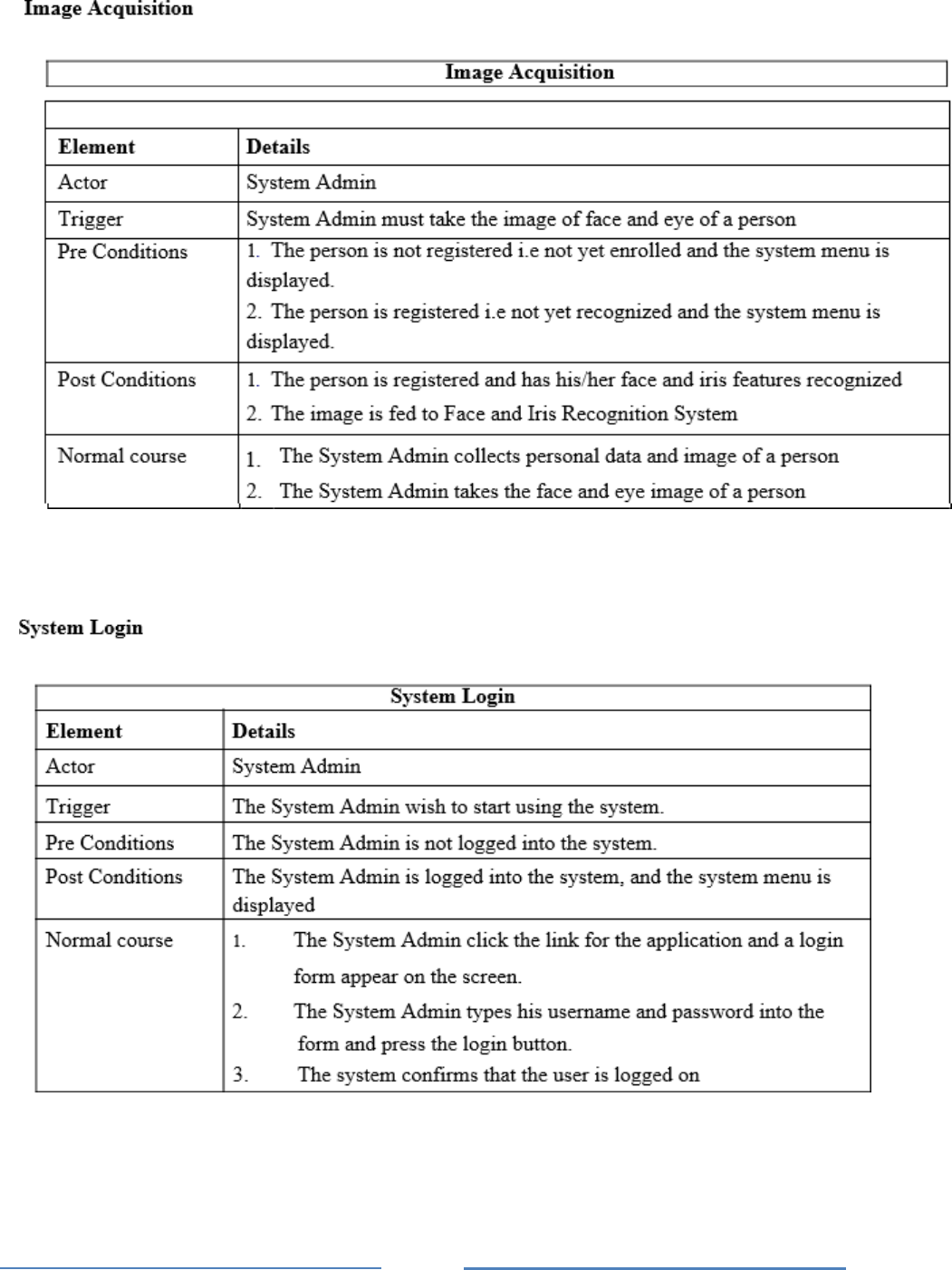
Register Use Case
Specification of Use Cases
Page
12
Image Acquisition Use Case
System Login Use Case
Page
13
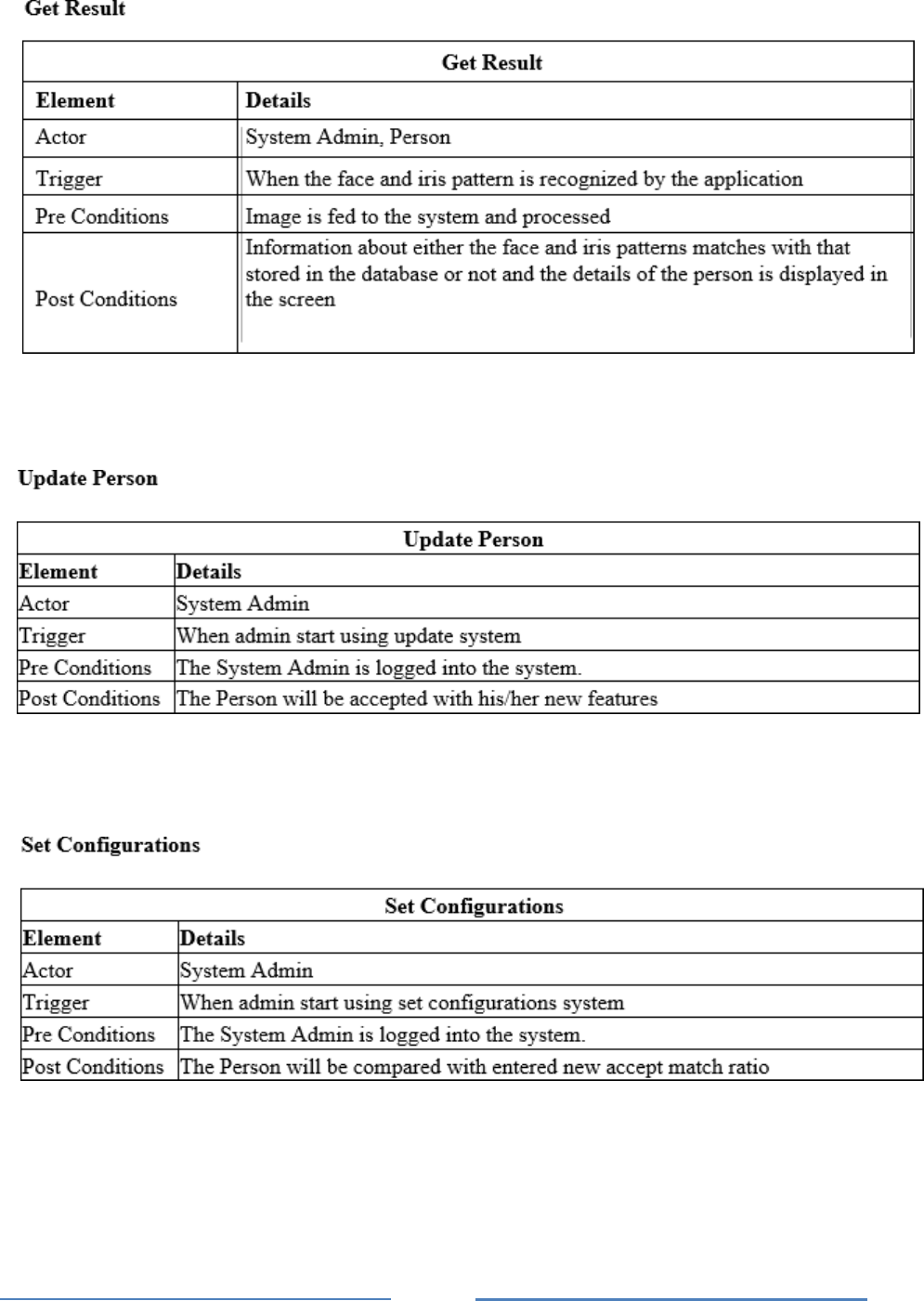
Get Result Use Case
Update Employee Use Case
Set Configurations Use Case
Page
14
Detailed Non-Functional Requirements
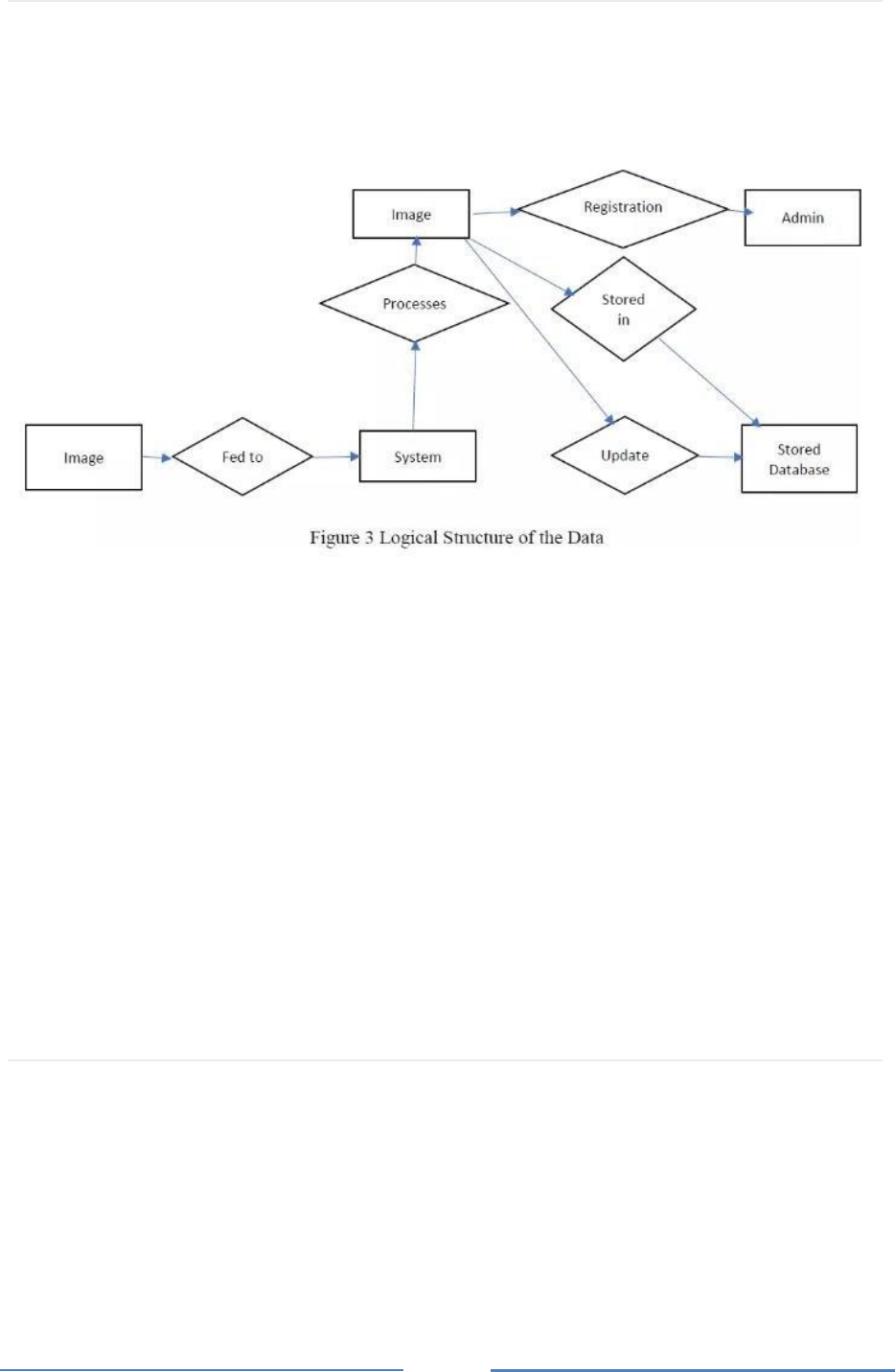
Features of the face and iris of the image will be stored in the database instead of the whole
image because it will use less memory and processing will be fast.
Logical Structure of the Data
Security
The computer that runs the program will have its own security. Only the System Admin will
log in to the system with his/her username and password. The person whose face and the iris
are recognized will access to view the output.
Maintainability
As a tool to obtain the ease of maintainability UML will be used in the development process.
Portability
To ensure portability, the application will be developed in MATLAB language.
System Evolution
The Face and Iris Recognition application are developed in MATLAB. The database we will
use is MSSQL.

Page
15
Performance Requirements
Camera’s visual must run smoothly without any error and delay more than 4sec to get the
image of the user. This requirement is depended on many aspects of the user pc. Minimum
requirements for running FIRec are:
1. GPU: Intel HD Graphics
2. CPU: Intel Celeron
3. Camera: Minimum 2MP Camera
4. USB port: 1x USB 2.0 or better port
5. Operating system: Windows XP or better
4. INTRODUCTION(SDD)
Purpose
The purpose of this Software Design Document is providing the details of project titled as
“FIRec: Biometric Identification based on Face and Iris Recognition”.
The target audience is especially, technological companies which want to keep in safe their
information against threats. FIRec will provide private security to protect companies’
information with using face and iris pattern which employee authorized at the project. We
goal to provide consistent, perfect security system for the companies which want to protect
their private information.
The purpose of the FIRec project is to design to provide a security system which holds a
personal information keep in safe and decrease the rate of information theft against who want
to steal your private information. This document includes detailed information about
requirements of the project. It also identifies the function and non-functional requirements
with a use case diagram. Overall, this document is used for how users interact with the system
and understand how the mechanism works at backend without any problems and explains
how concerns of the stakeholders are met.
In order to provide a better comprehension, this SDD includes various diagrams such as UML
diagram of the project, activity diagram and block diagram.
Scope
This document contains a complete description of the design of FIRec: Biometric
Identification based on Face and Iris Recognition.
Most of the people use a private computer to do their jobs in the company and they may need
to hide information in documents which relevant to work. Some information can be public
and this files that are not important, if they are seized by someone else, but some files need a
special protection system which is in the high-level secret status because people are wasting
Page
16
their time for hours on end and some hacker can steal their information from victim’s
computer easily without any protection system and worst of all, people are unprepared for this
situation. The application to be improved is Recognition of Human Iris and Face Patterns for
Biometric Identification. This project involves developing an iris detection system in order to
verify the uniqueness of the human iris and face by detecting the iris pattern from the image.
We offer a high-level security system which is the Biometric based on Face and Iris
Recognition for a company who want to save their information from the hacker or
information theft. The company should identify chosen workers to the security system
according to document while using their iris and face pattern on the camera. After registration
done, only chosen workers can access the high- level secret documents, if iris and face
recognition can be done correctly. We are using Scale-invariant feature transform (SIFT)
which is the fastest and reliable algorithm for working security system process. It is also more
accurate than any other descriptors and it is independent of rotation, luminance, and scale, so
its acceptable level is higher than other algorithms. Also, the acceptable level of Face and Iris
recognition system can be adjustable according to company’s request. While the people
registration to the system, SIFT algorithm gets their image as a grayscale and create a matrix
according to a pattern of iris and face, then it makes features personally from a created matrix
and transfers the features to the database. When the people define their identity on the system,
the SIFT algorithm gets current user’s features and it searches that features exist in the
database or not. If exist, login can be done correctly, but if not exist in the database, the user
cannot access the document which includes high- level secret information.
There are actors in the security system which are the worker and admin. Admin should
register worker to the system without any problem and the worker should adjust position
during interacting with the iris and face recognition on the camera for capturing best features.
In addition, admin should update worker information on the database because some worker
can wear a lens or worker can be injured in the face, so the admin should intervene to a
situation with manually.
Glossary
Term
Definition
BLOCK
DIAGRAM
The type of schema which the components in the system are displayed in blocks.
GRAYSCALE
A range of grey shades from white to black, as used in a monochrome display or printout
[9]
PCA
Principal Component Analysis.
FEATURES
Result of information of the matrix which derive from grayscale image
EMPLOYEE
A person whose Iris and Face is to be recognized

Page
17
SDD
Software Design Document
UML DIAGRAM
It is a modelling language which is used in Software Engineering
Overview of Document
The remaining chapters and their contents are listed below.
Section 2 is the Architectural Design which describes the project development phase. Also, it
contains class diagram of the system and architecture design of the simulation which
describes actors, exceptions, basic sequences, priorities, pre-conditions and post-conditions.
Additionally, this section includes activity diagram of scenario generator.
Section 3 is Use Case Realization. In this section, a block diagram of the system, which is
designed according to use cases in SRS document, is displayed and explained.
Section 4 is related to Detection. In this section, we have shown the sample images of the
employee for how the recognition system determine while scanning the employee face and
iris.
Motivation
We are a group of senior students in computer engineering department who are interested in
image processing and security system. As a group, we have taken the course of numerical
computations for a better understanding in image acquisition area. We aimed to combine the
fields of education, image acquisition, and security systems technologies in this project. We
have chosen the MATLAB scripting language to develop our project.
ARCHITECTURE DESIGN
FIRec Design Approach
While developing the project, we have decided to use Scrum which is an agile software
development methodology. Scrum is part of the Agile movement. Agile is a response to the
failure of the dominant software development project management and borrows many
principles from lean manufacturing [9]. In the scrum, it has a sprint which includes work to do
in the project. It takes a while almost between 2 and 4 weeks. If you add work to the sprint,
you can not remove that work from the sprint. The team who developed the project should
have a daily meeting every morning which should be maximum 10-15 minutes. Scrum has
three major roles which are scrum master, project owner, and development team. Scrum
master generally manages the development team, product owner delivers the requirements.
The development team is the team of developers who work on the project together according
to schedule [9]. There are several advantages of Scrum, Firstly, sprint releases end of each
sprint. The team does not have to act according to the product owner, the team identifies their
Page
18
priority. Delivery happens according to the velocity of the team and development tools work
like cross-functional. The team should use burndown graphics at the project. The scrum board
rebuilds while the beginning of each sprint. In addition, the scrum methodology is
incremental and iterative, so we can change required changes at project according to customer
feedback.
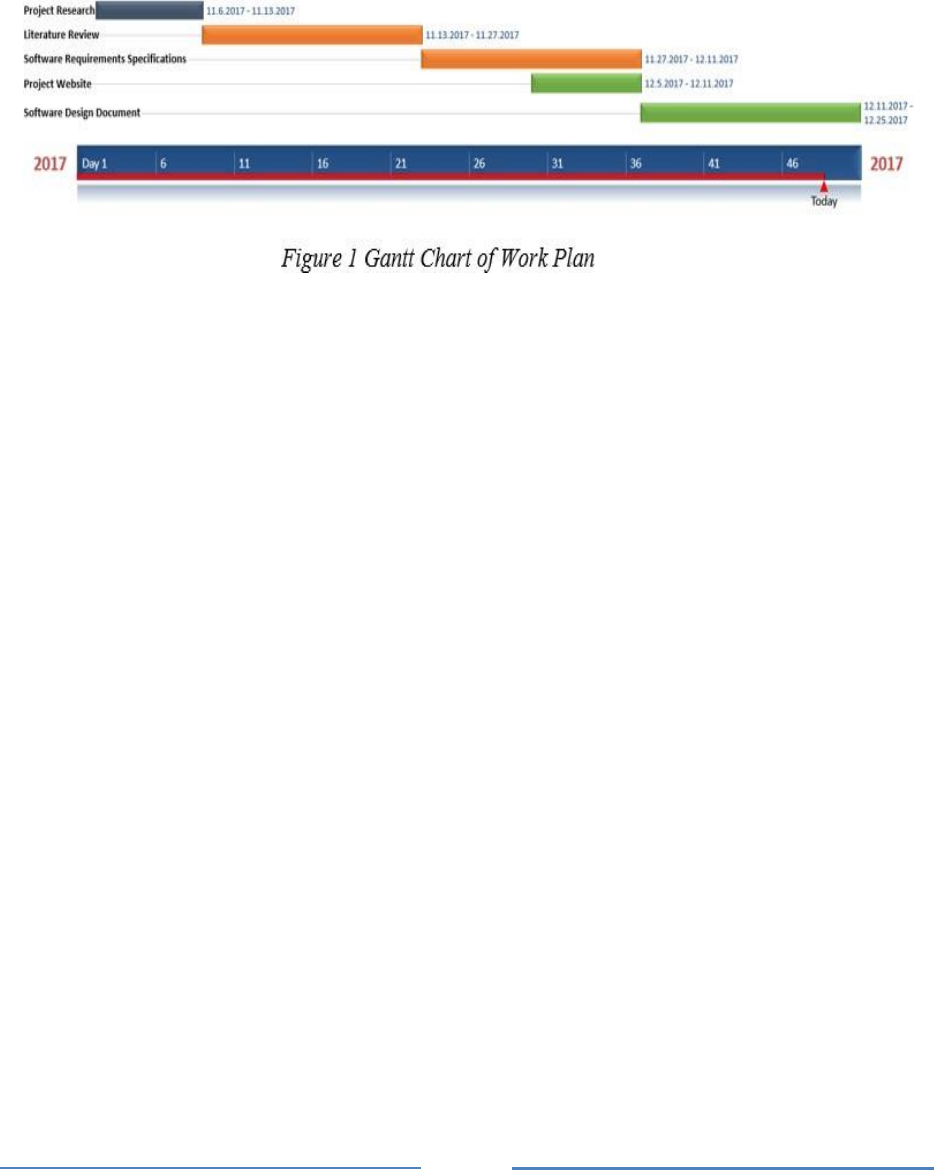
Gantt Chart in Figure 1 includes two parts which are research & documentation part. This
Gantt Chart explains the work to be done with using timeboxes. We approximately 50 days
are spent using waterfall for research and documentation which include information regarding
the project.
Page
19
Class Diagram
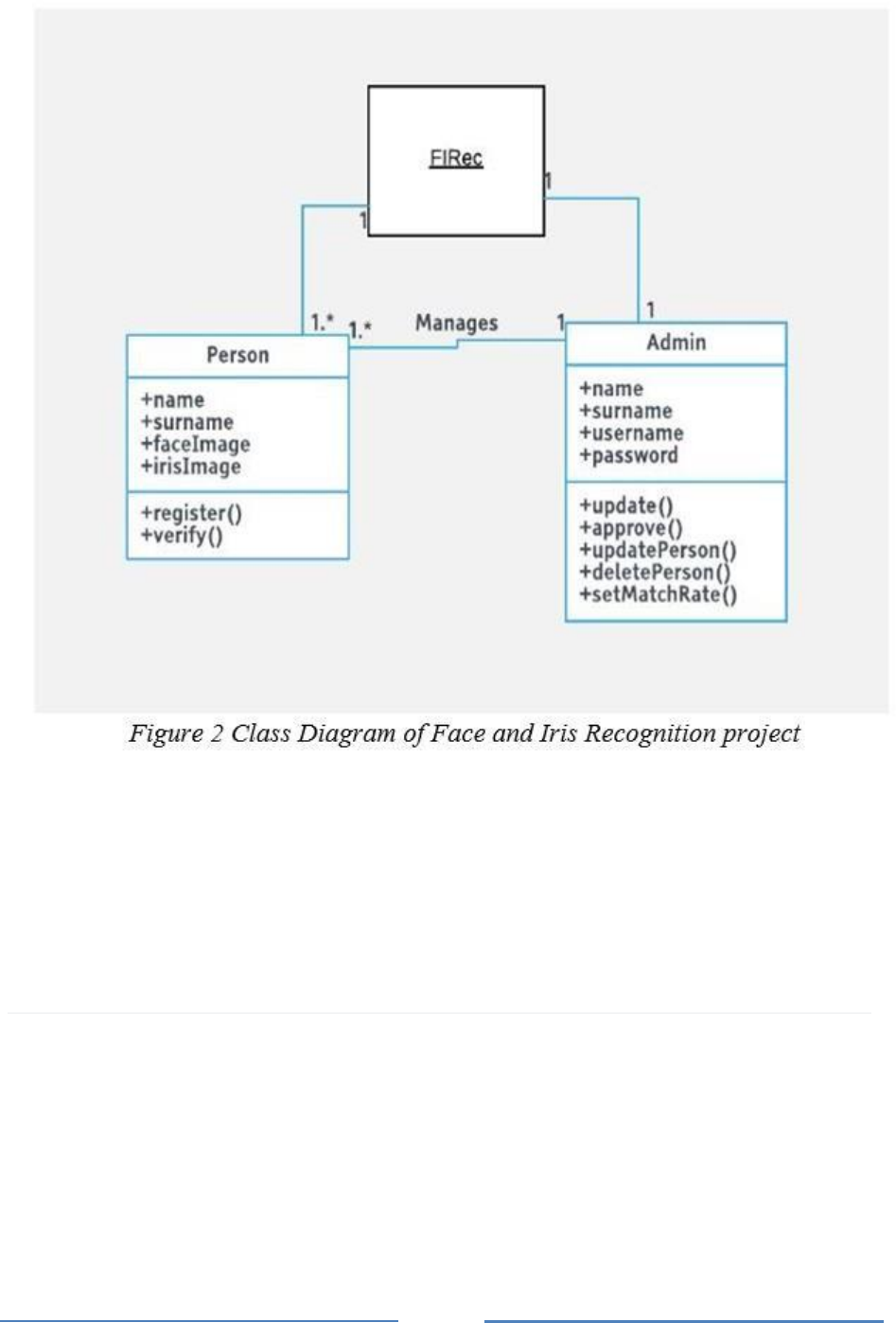
Figure 2 displays information about connections between the systems within the Face and Iris
Recognition System. FIRec is the main system, which contains other systems. It is responsible
for face and iris recognition and connections between other systems such as Admin and
Person. Person class represents all the users who use the system except admin. Admin class is
for users who will use the system to manage employee and set some system configurations.
Admin class is for actor which manages the system.
Architecture Design of FIRec
Admin Menu
Summary: System admin will use this system. System admin can login, update personal
information and exit from the system. Also, System admin can update a person’s information,
delete a person, save a person to the system. In addition, Admin can set matching rate.
Actor: System Admin

Page
20
Precondition: System admin must run the program and select admin menu.
Basic Sequence:
1. System admin will enter his/her username and password and login to the system.
2. System admin can select update from the menu for updating his/her personal information.
3. System admin can select delete from the menu for deleting a person from the system.
4. System admin can select requests from the menu to accept or reject registration applications of
people.
5. System admin can select a set face and iris matching rate which is used for verifying an
employee.
6. System admin can select exit button to exit the system.
Exception: Database connection can be failed.
Post Conditions: None
Priority: High
Registration System
Summary: Employee will use this system. The employee can show his/her face and eyes to
the camera to create a registration application.
Actor: Employee, system admin
Precondition: Person should not be registered before, and employee should select register
button.
Basic Sequence:
1. An employee can show his/her face and eyes to the camera.
2. After system reads his/her face and eyes, the employee can enter his/her personal information
and then, send the application to the admin by selecting send button.
3. After system reads his/her face and eyes, the employee can cancel the operation by selecting
cancel button.
4. The employee can exit from the system by selecting exit button.
Exception: Database connection can be failed.
Post Conditions: Application will be accepted or rejected by the system admin.
Priority: High
Recognition System
Summary: Person will use this system. The employee will show his/her face and eyes to the
camera and then, the system will verify the user by comparing and matching his/her face and
Page
21
iris features with the features stored in the database. Also, the employee can exit from the
system.
Actor: Employee
Precondition: Program should be run and the employee should select verify button.
Basic Sequence:
1. The employee can show his/her face and eyes to the camera.
2. The employee can exit from the system by selecting exit button.
Exception: Database connection can be failed.
Post Conditions: Accept or reject message will appear on the screen.
Priority: High
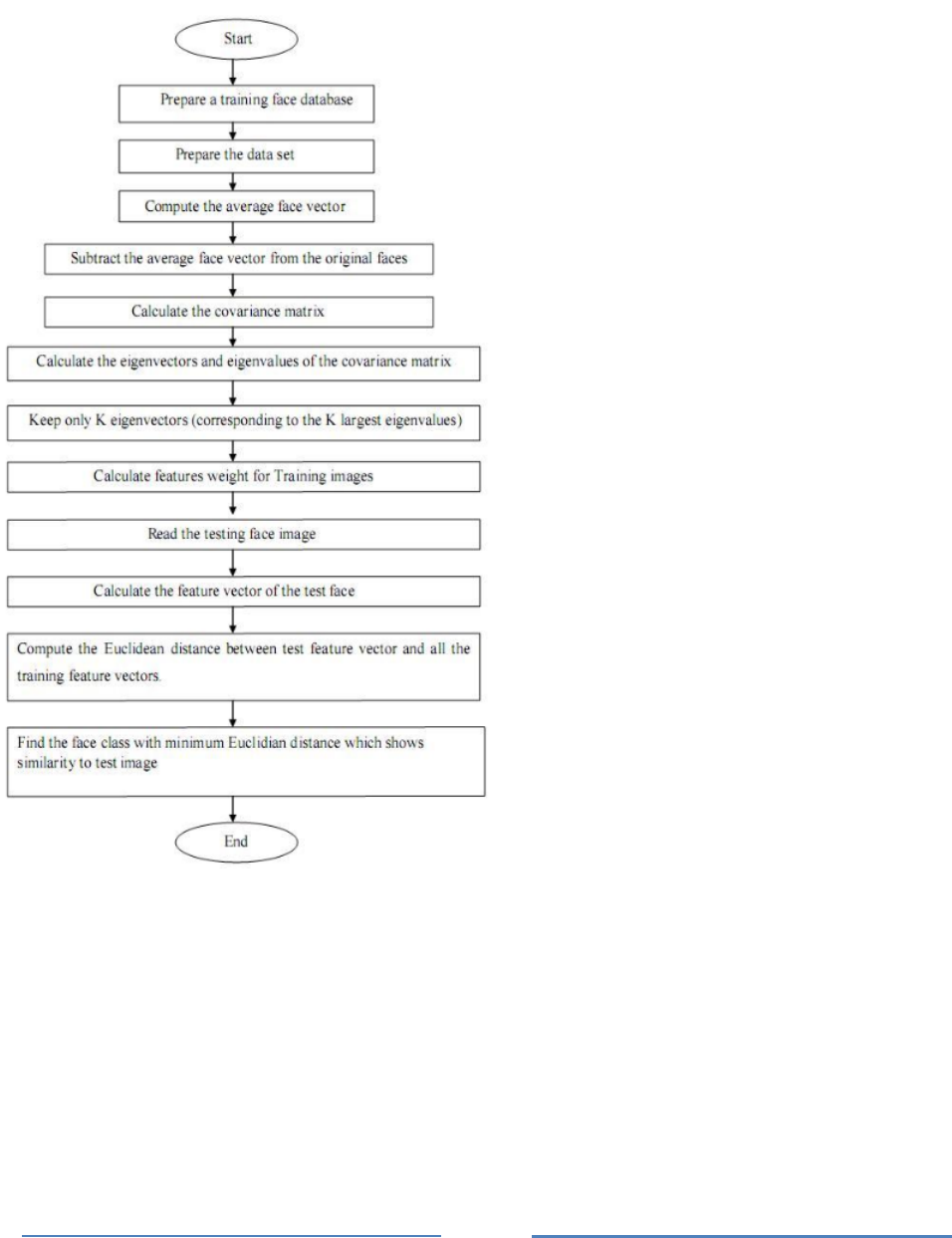
4.2.3 Activity Diagram
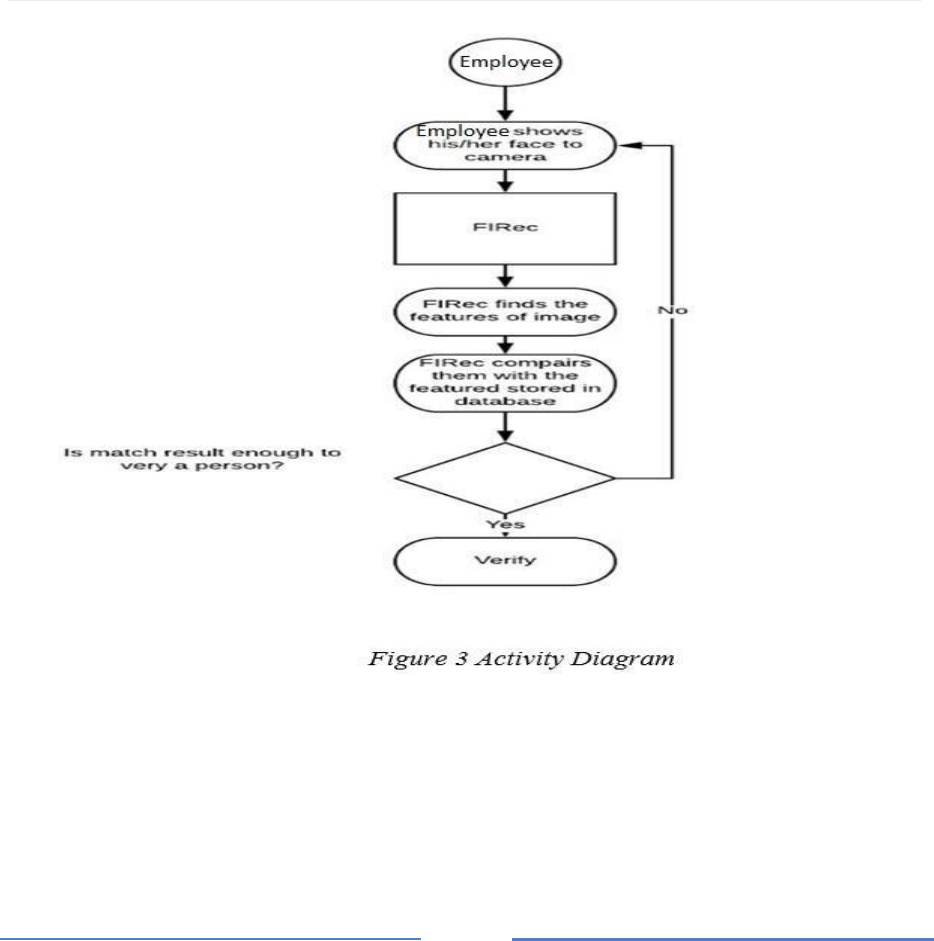
Figure 3 shows how the FIRec works as an activity diagram. When the employee shows
his/her face to the camera, then FIRec system finds the features of image and FIRec compares
them with the features which stored in the database. If matched features are equal or more
than identified correction level of FIRec system, the employee can access to the protected file,
else s/he needs to show his/her face to the camera again.
Page
22
USE CASE REALIZATIONS
FIRec Project
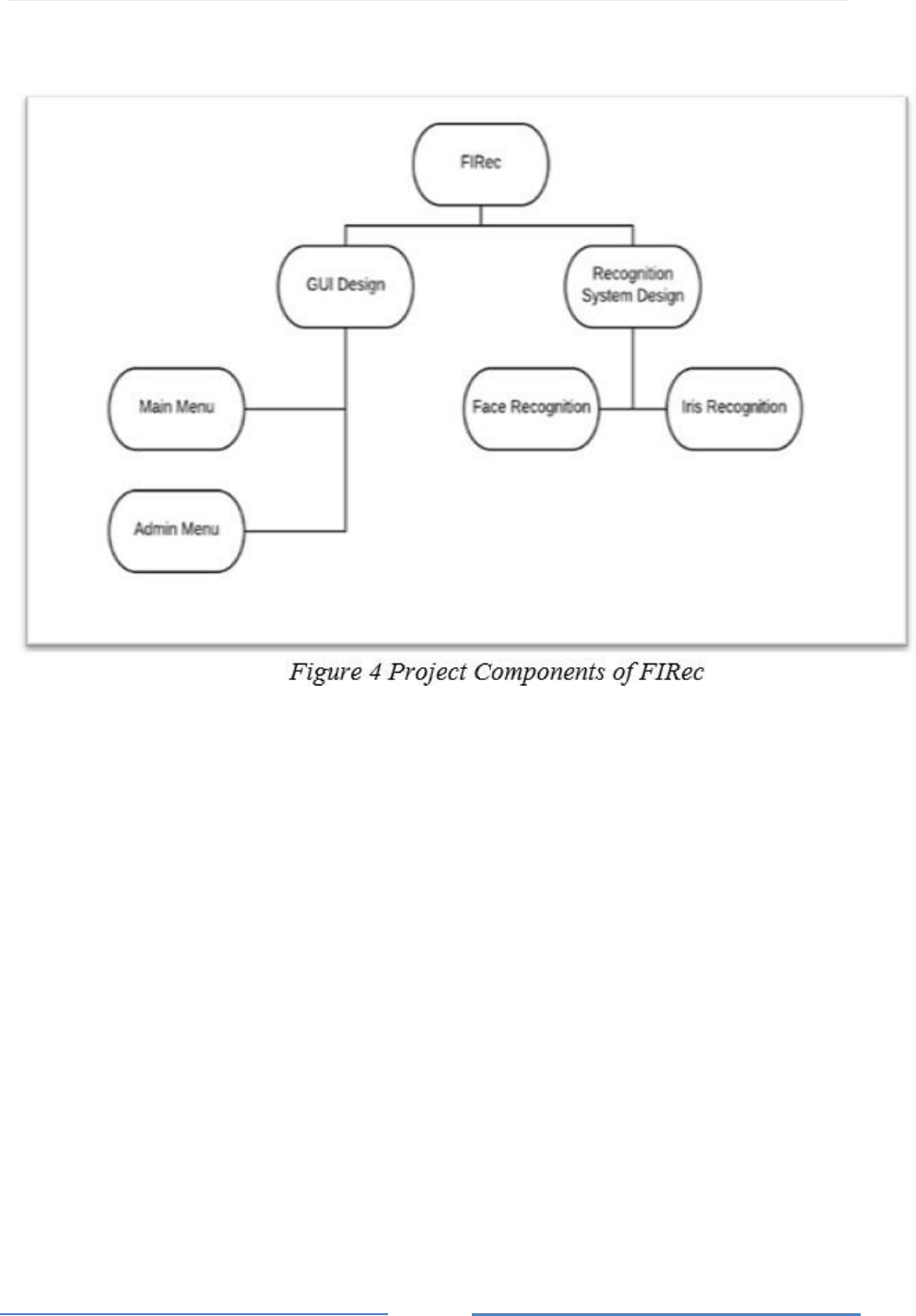
Brief Description of Figure 4
Components of the FIRec Project are shown in Figure 4. Block diagram in the figure shows
all designed systems of the FIRec. FIRec contains two main components which have their
sub-systems.
GUI Design
GUI design takes responsibilities of interactions between actors and the system. GUI design
contains two sub-systems. Sub-systems of GUI design are Main Menu and Admin Menu. The
start page is Main Menu. The employee can register and verify his/her face and iris. Admin
can login the system to the main menu. There is only one way to reach admin menu, after an
admin login the system, admin menu will appear. Admin can update his/her personal
information, approve a person’s register application, update a person’s personal information,
delete a person or set matching rate.

Page
23
Recognition System Design
Responsibilities of recognition part belongs to recognition design for all recognition operations
which are used in FIRec in order to verify an employee for other systems security. This system
contains Face Recognition and Iris Recognition.
DETECTION - RECOGNITION
In this project, image acquisition technique is used to create the face and iris detection in FIRec.
Firstly, as seems at Figure 5, when employee stands his/her face in front of the camera, face
image acquisition actualize thanks to Matlab, then face detection step is happening, then
eventually, employee identity recognized.
In figure 6, when employee stand his/her eye in front of the camera, iris image acquisition
actualizes thanks to MATLAB, then image of localization of the demarcated zones are identified,
then we reached iris phase of the employee using 2-Dimensional Discrete Fourier Transform.
We draw an approach of the face recognition, in this system, among the many possible
approaches, we have decided to use a PCA method and neural network approach for face
recognition part and PCA, Phase based method and neural network approach for iris recognition
part. The main reason for this selection is their smooth applicability and reliability issues [10] and
compare them with each other.
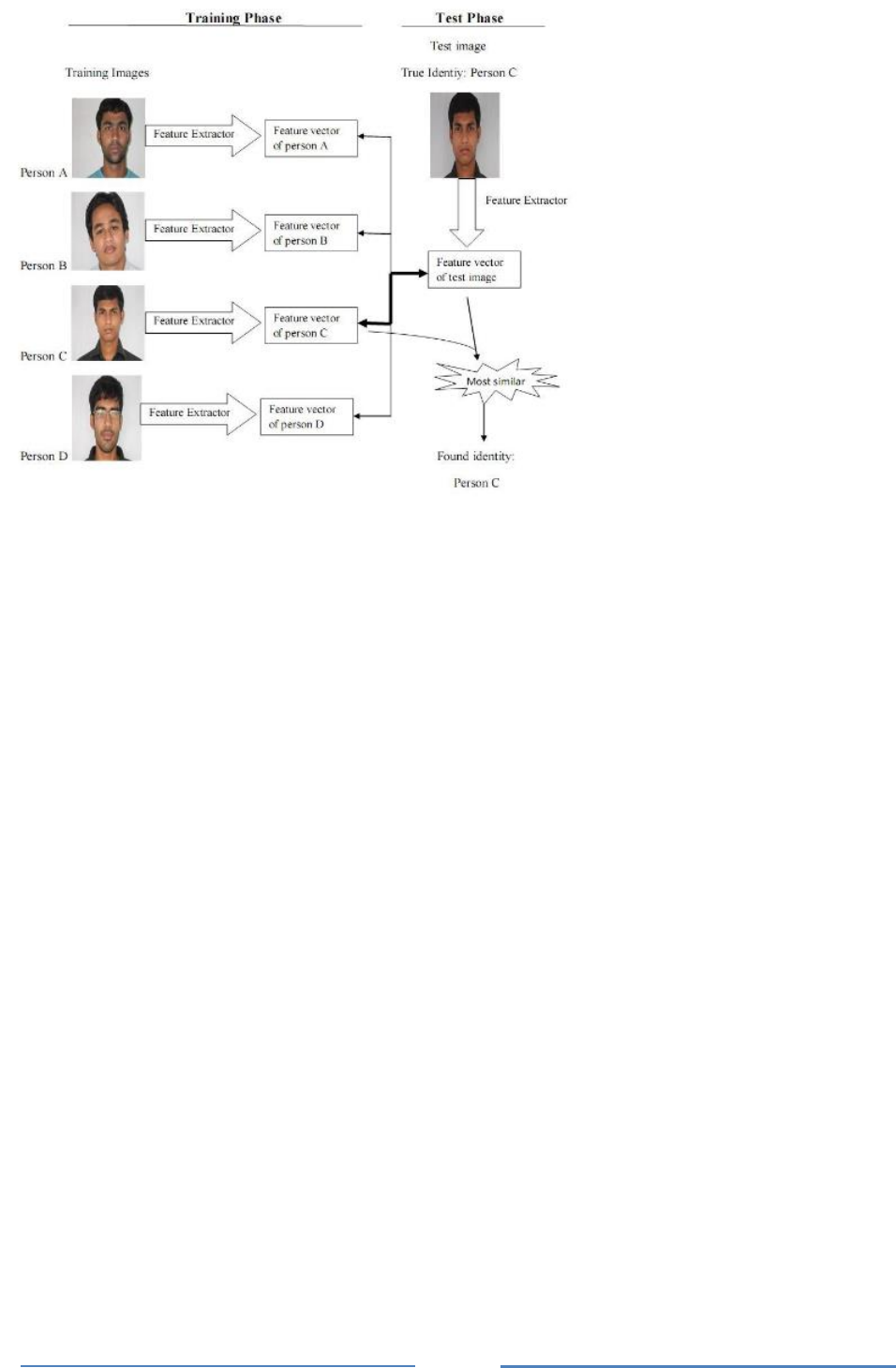
PCA approaches used in face recognition systems is the so-called eigenface approach. This
approach transforms faces into a small set of essential characteristics, eigenfaces, which are the
Page
24
main components of the initial set of learning images (training set). Recognition is done by
projecting a new image in the eigenface subspace, after which the person is classified by
comparing its position in eigenface space with the position of known individuals [3]. The
advantage of this approach over other face recognition systems is in its simplicity, speed and
insensitivity to small or gradual changes on the face. The problem is limited to files that can be
used to recognize the face. Namely, the images must be vertical frontal views of human faces.
Page
25

Page
26
5. Installation Guide/User Manuel
Install MATLAB +2012 with all components.
Install MSSQL +2012.
Download the database file which extention is .bak (includes admin account).
Connect to server with Windows Authentication with your Server name.
Right click to the Databases folder which in the Object Explorer, then click Restore Database...
Select Device for the Source and click ...
Add downloaded .bak file which name is IrisAdmin to the MSSQL.
Open the MATLAB and go to the APPS button which exist top left corner.
Click the Get More Apps, then write Database Toolbox to the search area and download it.
After download it, you can see Database Explorer in the Apps, so open it.
Click Configure Data Source and click the Configure ODBC data source.
Click add, then Select SQL Server Native Client 11.0 and click end button.
Opening screen fill the blank like; Name:MSSQL Description:FIRec , Server: (your MSSQL Server
name which login to the MSSQL with using Windows Authentication, then click next.
Click With Integrated Windows authentication (SPN (Optional) is empty), then click next.
Click next.
Click end.
After click end you can Test Data Source to checking succeed or not, if it is successul, you will see
TESTS COMPLETED SUCCESSFULLY! text at opening screen.
Close every screen except the Database Explorer and again Click Configure Data Source and then
click Configure ODBC data source.
At opening screen, select the MSSQL and click okey., so connection is done between MSSQL and
MATLAB.
Create a folder named "FaceAndIris"
Copy all files to FaceAndIris folder.
Start GuiMain.m

Page
27
Firstly, Admin should add users;
-Click Admin Menu
-Login
In AfterLoginAdmin.m
Scan Database Button
In the begining of the program, If you want to add all users.
Click Scan database button
Choose file path.
->File Path = Path of the folder that contains training files.
Then, Choose Phase path.
->Phase Path = Path of the folder that contains files that are avarage phases of given files.
Basicly, it is the database that program use for recognition.
->Filename will be emnpty.
->Number is number of users.
Register Button
If you want to add a user.
->File Path = Path of the folder that contains a folder that contains training files.
Then, Choose Phase path.
->Phase Path = Path of the folder that contains files that are avarage phases of given files.
->Basicly, it is the database that program use for recognition.
->Filename is the name of the folder that contains images.
->Number is number of images that will be read.
Update Button
If you want to update a user.
->File Path = Path of the folder that contains a folder that contains training files.
Then, Choose Phase path.
->Phase Path = Path of the folder that contains files that are avarage phases of given files.
->Basicly, it is the database that program use for recognition.
->Filename is the name of the folder that contains images.
->Number is number of images that will be read.

Page
28
Set Configuration
Enter treshold and click set conf. button to set treshold.
Recognition Part
In GuiMain.m
Face Recognition(PCA)
Click Face Recognition(PCA) button.
Select Image.
Iris Recognition(Phase)
Click Iris Recognition(Phase) button.
Select Image.
Iris Recognition(DFT)
Click Iris Recognition(DFT) button.
Select Image.
Iris Recognition(PCA)
Click Iris Recognition(PCA) button.
Select Image.
Iris Recognition(Neural)
Click Iris Recognition(Neural) button.
Select Image.
Page
29
References
1.
Academia, 2017 [Online].
Available: https://www.academia.edu/8433912/IRIS_RECOGNITION_DOCUMENT
ATION [Accessed 26 October 2017].
2.
M.Rouse. facial recognition, 2017 [Online].
Available: http://whatis.techtarget.com/definition/facial-recognition [Accessed 28
October 2017].
3.
Wang Y., Tan T., Jain A.K. (2003) Combining Face and Iris Biometrics for Identity
Verification. In: Kittler J., Nixon M.S. (eds) Audio- and Video-Based Biometric
Person Authentication. AVBPA 2003. Lecture Notes in Computer Science, vol 2688.
Springer, Berlin, Heidelberg [Accessed 28 October 2017].
4.
J.D.West.A brief history of face recognition, 2017 [Online].
Available:https://www.facefirst.com/blog/briefhistory-of-face-recognition-
software/ [Accessed 30 October 2017].
5.
Findbiometrics, 2017 [Online]. Available: https://findbiometrics.com/solutions/iris-
scanners-recognition/ [Accessed 29 October 2017].
6.
A. K. Jain, R.M. Bolle, and S. Pankanti. Biometrics: Personal Identification in a
Networked Society. Kluwer, 1999. [Accessed 09 November 2017]
7.
Kawaguchi, T., & Rizon, M. (2003). Iris detection using intensity and edge
information. Pattern Recognition, 36(2), 549-562. doi:10.1016/s0031-3203(02)00066-
3/ [Accessed 09 November 2017].
8.
Ko, T. Multimodal Biometric Identification for Large User Population Using
Fingerprint, Face, and Iris Recognition. 34th Applied Imagery and Pattern
Recognition Workshop (AIPR05). doi:10.1109/aipr.2005.35 [Accessed 09 November
2017].
9.
What is Agile? What is Scrum? (2017, August 01). Retrieved December 10, 2017,
from https://www.cprime.com/resources/what-is-agile-what-is-scrum/
10.
Gürel, C. and Erden, A. (2013). Face Detection. [online] Research Gate. Available
at: https://www.researchgate.net/publication/262875649_Design_of_a_Face_Recognit
ion_System[Accessed 23 Dec. 2017].
11.
P. Peer, J. Kovac, and F. Solina, 2003, “Robust Human Face Detection in Complicated
Color Images”, Proc. 2010 The 2nd IEEE International Conference on Information
Management and Engineering (ICIME), pp. 218 – 221, Chengdu, China.
12.
C. Gürel, 2011, “Development of A Face Recognition System”, M.S. Thesis in
Mechatronics Engineering, Atılım University, Ankara, Turkey.
