100 Deadly Skills: The SEAL Operative's Guide To Eluding Pursuers, Evading Capture, And Surviving Any Dangerous Situation Situa
User Manual:
Open the PDF directly: View PDF ![]() .
.
Page Count: 250 [warning: Documents this large are best viewed by clicking the View PDF Link!]
- A Note to Readers
- Epigraph
- Introduction
- Part I: Mission Prep
- 001. Anatomy of a Violent Nomad
- 002. Create an Every Day Carry Kit
- 003. Build a Vehicle Bolt Bag
- 004. Make a Concealable Compass
- 005. Build an Improvised Concealable Holster
- 006. Conceal Escape Tools
- 007. Construct a Rectal Concealment
- 008. Use Improvised Body Armor
- 009. Identify Emergency Ballistic Shields
- 010. The Violent Nomad Workout
- Part II: Infiltration: Access to Enemy Territory
- Part III: Infrastructure Development: Lodging, Transportation, Weapons
- 018. Hotel Security and Safety Awareness
- 019. Prevent a Hotel Room Invasion
- 020. Conceal Belongings within Lodging
- 021. Build a Room Hide
- 022. Steal a Vehicle
- 023. Operational Vehicle Prep
- 024. Escape and Evasion Vehicle Prep
- 025. Build a Vehicle Hide
- 026. Steal a Plane
- 027. Make a Water Bottle Silencer
- 028. Transform an Umbrella into a Lead Pipe
- 029. Turn a Pen into a Weapon
- 030. Use a Fishing Weight as an Improvised Sap
- 031. Make a Flexible Chain Weapon
- 032. Make a Newspaper Nail Bat
- 033. Deploy a Roll of Coins
- Part IV: Surveillance: Observation, Tracking, and Counter-Surveillance
- 034. Dismounted Surveillance
- 035. Mobile Surveillance
- 036. Make an Improvised Infrared Light
- 037. Make a Tracking Device for Night Surveillance
- 038. Detect Tampering of Personal Effects
- 039. Determine Surveillance
- 040. Discreetly Lose Surveillance
- 041. Detect Tracking Devices
- 042. Deceive Surveillance Cameras
- Part V: Access: Clandestine Breaking and Entering
- 043. Create Improvised Lock-Picking Tools
- 044. Pick a Lock
- 045. Clam a Key
- 046. Clone a Key
- 047. Impression a Lock
- 048. Bypass a Hotel Room Door
- 049. Surreptitiously Unlatch Door Locks
- 050. Defeat a Padlock
- 051. Covertly Access Locked Luggage
- 052. Open a Car Door with a Piece of String
- 053. Discreetly Open Garage Doors
- Part VI: Collection: Audio and Video Intelligence
- Part VII: Operational Actions: Deny, Disrupt, Disable
- 061. Draw a Concealed Pistol
- 062. Shoot from a Vehicle
- 063. Win a Knife Fight
- 064. Strike for a Knockout
- 065. Deliver a Devastating Elbow Strike
- 066. Make an Improvised Taser
- 067. Make an Improvised Explosive Device
- 068. Make a Diversionary “Flash” Device
- 069. Make a Molotov Cocktail
- 070. PIT a Target Vehicle
- 071. Pistol Disarmament: Pointed at Chest
- 072. Pistol Disarmament: Pointed at Back
- 073. Survive an Active Shooter
- 074. Make an Improvised Gas Mask
- 075. Survive a Grenade Attack
- 076. Wage Psychological Warfare
- Part VIII: Sanitization: Leave No Trace
- Part IX: Exfiltration and Escape: How to Disappear
- 086. Create a Rappelling Harness
- 087. Escape a Multistory Building
- 088. Survive a Drowning Attempt
- 089. Escape from an Automobile Trunk
- 090. Develop a Bug-Out Route
- 091. Perform a J-turn
- 092. Perform a Reverse 180
- 093. Survive Vehicular Impact
- 094. Break Through a Two-Car Block
- 095. Escape an Ambush
- 096. Set Up Proper Posture for Escape
- 097. Reposition Restrained Hands
- 098. Defeat Handcuffs
- 099. Defeat Zip Ties
- 100. Defeat Duct Tape
- The Final BLUF
- Acknowledgments
- About the Author
- Glossary
- Resources and References
- Index
- Copyright




CONTENTS
ANotetoReaders
Epigraph
Introduction
PARTI:MISSIONPREP
001AnatomyofaViolentNomad
002CreateanEveryDayCarryKit
003BuildaVehicleBoltBag
004MakeaConcealableCompass
005BuildanImprovisedConcealableHolster
006ConcealEscapeTools
007ConstructaRectalConcealment
008UseImprovisedBodyArmor
009IdentifyEmergencyBallisticShields
010TheViolentNomadWorkout
PARTII:INFILTRATION
011CrossEnemyBordersbySea
012CrossEnemyBordersbyAir
013CrossEnemyBordersbyLand
014ConcealGearUsingCaches
015HookandClimbaTargetStructure
016ScaleaHighWall
017BlendintoAnyEnvironment
PARTIII:INFRASTRUCTUREDEVELOPMENT
018HotelSecurityandSafetyAwareness
019PreventaHotelRoomInvasion
020ConcealBelongingswithinLodging
021BuildaRoomHide
022StealaVehicle
023OperationalVehiclePrep
024EscapeandEvasionVehiclePrep
025BuildaVehicleHide
026StealaPlane
027MakeaWaterBottleSilencer
028TransformanUmbrellaintoaLeadPipe
029TurnaPenintoaWeapon
030UseaFishingWeightasanImprovisedSap
031MakeaFlexibleChainWeapon
032MakeaNewspaperNailBat
033DeployaRollofCoins
PARTIV:SURVEILLANCE
034DismountedSurveillance
035MobileSurveillance
036MakeanImprovisedInfraredLight
037MakeaTrackingDeviceforNightSurveillance
038DetectTamperingofPersonalEffects
039DetermineSurveillance
040DiscreetlyLoseSurveillance
041DetectTrackingDevices
042DeceiveSurveillanceCameras
PARTV:ACCESS
043CreateImprovisedLock-PickingTools
044PickaLock
045ClamaKey
046CloneaKey
047ImpressionaLock
048BypassaHotelRoomDoor
049SurreptitiouslyUnlatchDoorLocks
050DefeataPadlock
051CovertlyAccessLockedLuggage
052OpenaCarDoorwithaPieceofString
053DiscreetlyOpenGarageDoors
PARTVI:COLLECTION
054InstallanAudioDevice
055TurnaSpeakerintoaMicrophone
056ConstructandInstallaPinholeCamera
057MakeHomemadePlastic
058SendAnonymousEmails
059HideInformationinPlainSight
060HideandExtractDataUsingEverydayPhotos
PARTVII:OPERATIONALACTIONS
061DrawaConcealedPistol
062ShootfromaVehicle
063WinaKnifeFight
064StrikeforaKnockout
065DeliveraDevastatingElbowStrike
066MakeanImprovisedTaser
067MakeanImprovisedExplosiveDevice
068MakeaDiversionary“Flash”Device
069MakeaMolotovCocktail
070PITaTargetVehicle
071PistolDisarmament:PointedatChest
072PistolDisarmament:PointedatBack
073SurviveanActiveShooter
074MakeanImprovisedGasMask
075SurviveaGrenadeAttack
076WagePsychologicalWarfare
PARTVIII:SANITIZATION
077LeaveZeroDNABehind
078LeaveZeroFingerprintsBehind
079LeaveZeroDigitalTraceBehind
080TrickFacialRecognitionSoftware
081TrickFingerprintScanningSoftware
082CreateaHastyDisguise
083GetPastaGuardDog
084DiscreetlyClearaFloodedScubaMask
085DisposeofaBody
PARTIX:EXFILTRATIONANDESCAPE
086CreateaRappellingHarness
087EscapeaMultistoryBuilding
088SurviveaDrowningAttempt
089EscapefromanAutomobileTrunk
090DevelopaBug-OutRoute
091PerformaJ-turn
092PerformaReverse180
093SurviveVehicularImpact
094BreakThroughaTwo-CarBlock
095EscapeanAmbush
096SetUpProperPostureforEscape
097RepositionRestrainedHands
098DefeatHandcuffs
099DefeatZipTies
100DefeatDuctTape
TheFinalBLUF
Acknowledgments
AbouttheAuthor
Glossary
ResourcesandReferences
Index
ANotetoReaders
The skills described in the following pages are called “deadly” for a reason—and not just
because of the danger they pose to others. Developed by highly trained operatives who
regularly face life-threatening conditions, these skills push the limits of human endurance,
precision,andingenuity.
Andoften,theboundariesofthelaw.
The book you are holding in your hands (or reading on your device) contains actionable
informationadaptedfromtheworldof specialoperations.Muchofthatinformation,shared
herewithciviliansinthespiritofself-defense,istobeusedinonlythedirestemergencies.
When confronted with unexpected danger, in many cases the safest course of action is
escape.Inthefaceofanactiveshooter(seepage178),thefirstoption(ifconditionsallow)is
torun—andthelastistofight.Ifathiefwantsyourvaluables,handthemover.Iftheendof
theworldtrulydoescometopass...well,thenallbetsareoff.
The author and publisher disclaim any liability from any injury that may result from the
use, proper or improper, of the information contained in this book. The stated goal of this
bookisnottoenableadeadlyclassofcitizensbuttoentertainwhilesimultaneouslyimparting
abodyofknowledgethatmaycomeinhandyintheabsolutedirestofemergencies.
Bedeadlyinspirit,butnotinaction.Respecttherightsofothersandthelawsoftheland.
Our fate is determined by how far we are prepared to push ourselves to stay alive—the
decisions we make to survive. We must do whatever it takes to endure and make it through
alive.
—BEARGRYLLS

INTRODUCTION
Potential dangers lurk everywhere these days. Disasters strike in war-torn regions and far-
flung locations—but with alarming regularity, they also seem to inch closer and closer to
home.Spanningactsofterror,massshootings,andtheunseen(andsometimesvirtual)matrix
ofeverydaycrime,dangerrefusestobeconfinedtodarkalleys,unstablenations,ordistantzip
codes.
People tend to imagineworst-case scenariosinhighly colorfulterms,butchaos andcrime
aretherealapocalypticscenarios.Wepicturealiens,frozentundra,andintergalacticwarfare,
when in fact the catastrophic event we’ve been waiting for is more likely to look like a
mundane report of vandalism on last night’s news—or the massive Internet shutdown in
tomorrow’s headlines. Or, indeed, the violent criminal hiding in the shadows of a desolate
parking garage. In the face of true catastrophe, a basement full of canned peas and distilled
waterisn’tlikelytobemuchhelp.
Inafuturewhereeverystrangerposesapotentialthreat,knowingthepredatormindsetis
theonlysafehaven.Whatarethetricksusedbythestealthiest,mostdangeroushumanbeings
inourmidst?Howcanyouspotandavoidthe dangersthatsurroundus?Youcouldturnto
thecriminalclasstofindout.Oryoucouldgoonebetterbytakingapagefromsomeofthe
mosthighlytrainedspecialistsontheplanet.
The one hundred deadly skills you are about to encounter are adapted from the world of
special operations, a complex web of associations dominated by operatives with a shared
predilection for intrigue and danger. These elite, highly skilled warriors are charged with
riskingtheirlivesunderthemostchallenginganddireconditionsonearth.Asoperativeswho
routinelyinfiltratetheworld’smostdangerousandvolatileregions,theymustbeequalparts
spies,soldiers,andlawlessrule-breakers.
Theyareactionheroesformoderntimes,one-partJamesBond,theotherRambo.Somecall
thesehighlyskilledoperatives“ViolentNomads,”asanodtotheirdisregardforinternational
bordersandtheirbiasforswift,brutalaction.
Many of the techniques that make up the Violent Nomad body of knowledge cannot be
divulged without severe risk to public safety, but a great deal of potentially lifesaving
information can still be shared. Each skill is broken down into its most critical parts, or
CoursesofAction(COAs),andsummedupbyaBLUF(BottomLineUpFront),whichspells
out the key takeaway from the operative’s perspective; Civilian BLUFs flip the skills around
andoutlinepreventive measurescivilians cantaketoarm themselvesagainstpredatorsusing
theseparticulartechniques.
AsaretiredNavySEALwhospentseveralyearsinsidetheNSA(NationalSecurityAgency),
inwritingthisbookIdrewonanunusualbreadthofexperiencethatspanstwentyyearsspent
running special ops all over the world, both in teams and alone, and merges lessons learned
from both combat and surveillance. The skills in this book represent a potential path to
survivalinthefaceofanynumberofdangeroussituations,fromeludingpursuersandescaping
abduction to self-defense. And they may even provide a blueprint for getting through
doomsday.
Theworldisn’t gettinganysafer,but youcan be prepared.Whetheryou’refacedwithan
alieninvasionoranassailantwieldingaseeminglyinnocuousitemsuchasawaterbottleIor
anumbrella,learninghowtothinklikeaViolentNomadwillradicallyimproveyourchances
ofcomingoutontop.
I.Turntopage70ifyou’reinterestedindevelopinganirrationalfearofwaterbottles.

PARTI
MISSIONPREP

001 AnatomyofaViolentNomad
Beyondthedefensivepotentialcommontomanyoftheskillsinthisbook,thereismuchthe
average civilian can learn from an operative’s mindset. First and foremost, that mindset is
defined by preparedness and awareness. Whether in home territory or under deepest cover,
operativesarecontinuallyscanningthegenerallandscapeforthreatsevenwhenthey’renoton
the clock. Civilians, too, can train their minds toward habits such as scouting exit routes in
crowded restaurants or building spur-of-the-moment escape plans. This kind of vigilance
allowsanoperativeconfrontedwithsuddendangertotakeimmediateaction.
Whetherheiscrossingborders,executingsurveillance,oreliminatingdangeroustargetsand
disappearingwithoutatrace,theclandestineoperativefrequentlyworksalone.Giventhathe
sooftenfindshimselfbehindenemylineswithoutreinforcements,anoperative’scombatand
counterintelligenceskillsaremetbyanequallysophisticatedaptitudeforriskassessmentand
analysis. In an increasingly dangerous world, civilians who are attuned to potential risk
(particularly but not exclusively when traveling) will be many steps ahead of the general
populace.
•••
Theoperativealsodemonstratesabaselinepredispositiontowardanonymity.Eachclandestine
operative is trained to “go black,” operating for extended periods of time with limited
communication to associates. While operating under the radar, he may assume the outward
appearance of a student, a businessperson, or a traveler, as he understands that terrorist
groups or host-nation governments may be targeting him during his travels—and that if
perceived as a spy and arrested, he will be subject to detention and harsh interrogations.
Additionally, as a traveler, he is vulnerable to the risks of petty crime and kidnapping that
applytoanyciviliantravelingabroad.Tocountersuchrisks,theoperativeadoptsasneutral
anappearanceaspossible.ThegeneralruleisthelessconspicuoustheNomad,thesafer.
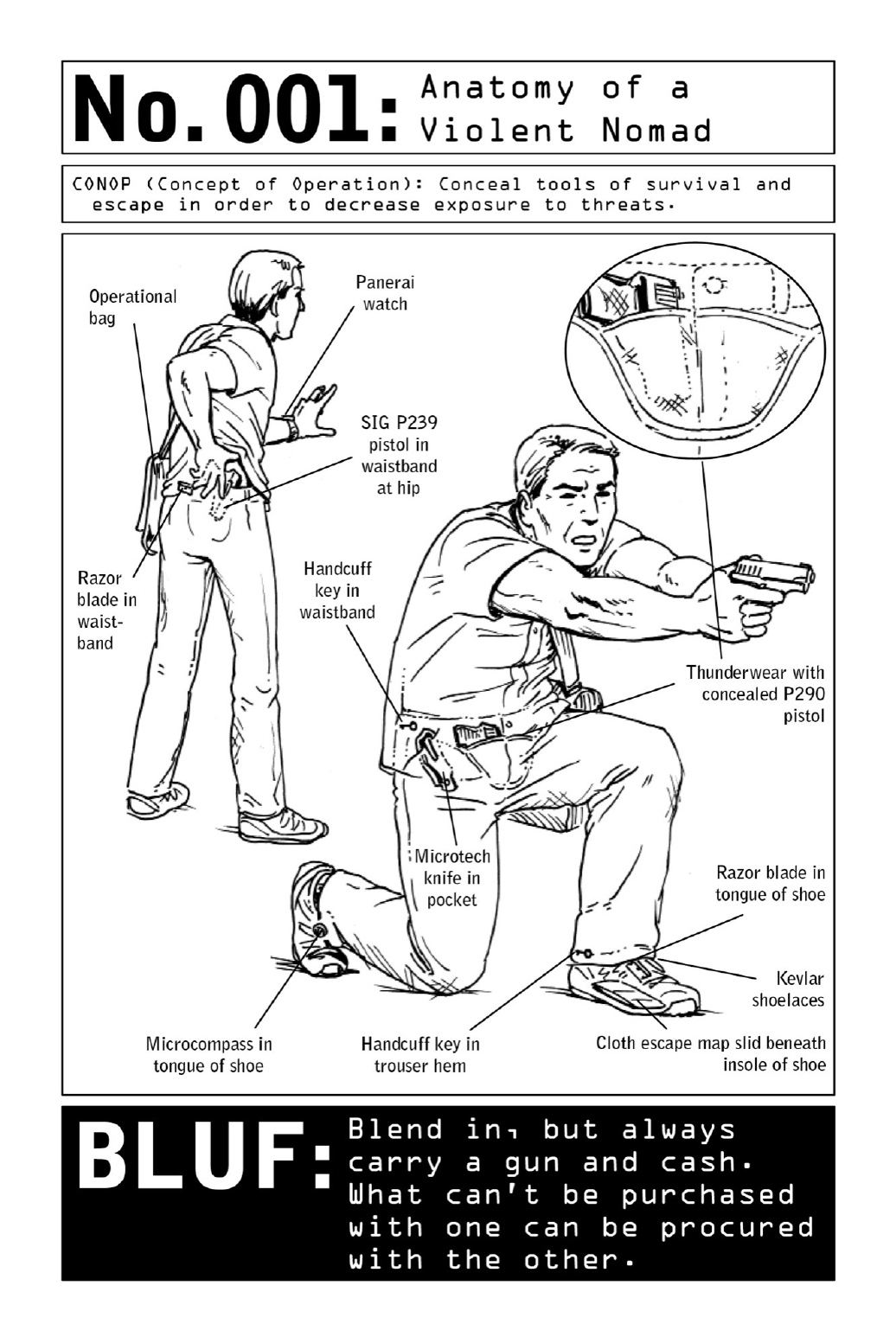
Due tothehighly covertnatureoftheirmissions,operativesgotogreatlengthstoensure
that they blend into their surroundings. A carefully managed appearance allows them to
operateundetectedbypotentialwitnessesaswellashost-countrypoliceandsecurityservices.
But beyond their unremarkability, clothing and gear must have the capability to conceal the
equipmentrequiredforanoperationoranescape.(Thewaistbandandcuffsofpantsandthe
tonguesofshoes,forexample,areidealhidingplacesforhandcuffkeysandrazorblades.)
OperativesfavorbrandssuchasPanerai,whicharedurableandwellmadebutstillhavea
civilian-friendlylook.Always readytorunorfight, theywear closed-toedshoes withKevlar
laces and conceal weapons and spread escape equipment throughout their clothing. Lighters
andcigarettesarealwayscarried,evenbynonsmokers,astheymaybeusedasatoolofescape
or to create a distraction or diversion. (See pages 86, 166, and 168.) LED flashlights are
essentialforseeinginthedarkorsignalingforhelp.
•••
When it comes to gear, preparedness doesn’t look quite the way moviegoers have come to
expect. Because clandestine operatives cannot board commercial flights with concealed
weaponsorhigh-techspygeartuckedawayintheirluggage,theyfavora“no-tech”or“low-
tech”approach that is highly dependent on improvisation. Though fictional spies employ all
manner of shiny, complex contraptions, in the real world, every high-tech toy increases an
operative’s risk of detention or arrest. Hence, operatives learn to adapt, improvise, and
overcome technical obstacles using tools and technology that are readily available in the
country of operation. One example: Every hotel room has a Bible or a Koran stashed in a
bedsidedrawer—andtapingacoupleofthosetogetheryieldsasetofimprovisedbodyarmor
thatprovidessignificantprotectionagainstprojectiles.
Thoughlow-techdoesn’tusuallyextendtoanoperative’scommunications,hetakesahighly
cautious approach to cybersecurity. The operative avoids leaving behind trails of digital
breadcrumbs at all costs, understanding that any cybercommunication is fundamentally
insecure. In an age where savings accounts and the locations of friends and family are
vulnerabletoanythirdpartywithaccesstoaWi-Ficonnectionandthewilltodoharm,there
isnosuchthingasasurfeitofprecaution.
Civilian BLUF: Particularly when traveling, civilians are well served by adopting the
operative’s predilection for anonymity. Choose clothing and accessories for usefulness and
generalneutrality.Inavolatileurbancrisis,brightcolorsandeye-catchinglogoscanbecome
convenientaimingpointsforapairofriflesights.

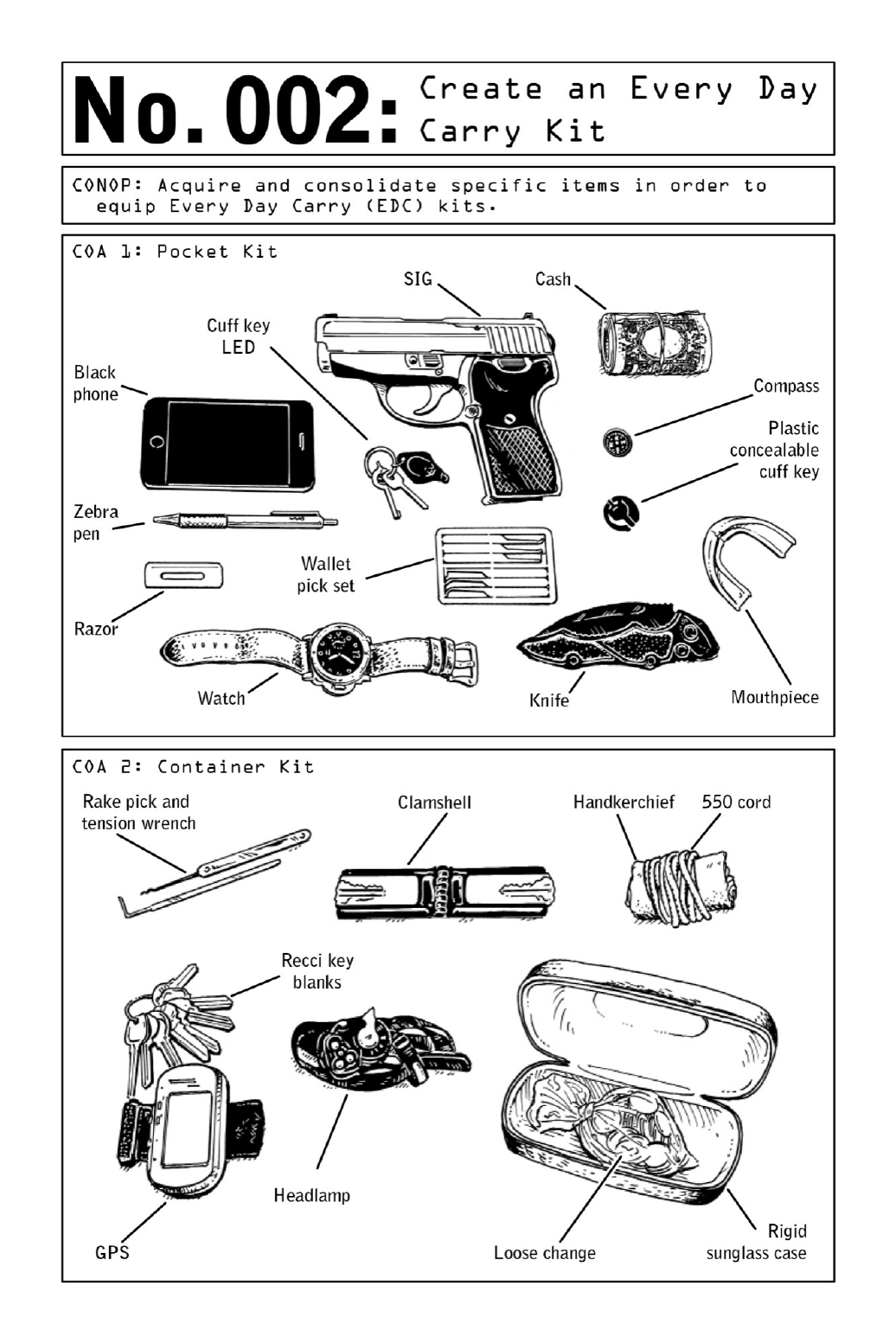
002 CreateanEveryDayCarryKit
Whiletheaveragecivilianapproachesemergencypreparednessfromalife-supportperspective
thatprioritizesfoodandwatersupplies(stasheddeepinahomebasement)totheexclusionof
weapons and escapetools, true preparednessacknowledgesand confrontstheviolenceofthe
modern world. To ensure a state of constant preparedness, the Violent Nomad carries up to
threetypesofEveryDayCarry(EDC)kits,eachdesignedtosupporthismissionandhelphim
evade crisis. Whether the call comes or not, the EDC kits also provide an edge against
unexpectedthreatsofallsorts,fromenvironmentaldisasterstoterroriststrikesandlone-wolf
attacks.
When traveling through potentially hostile territory or during turbulent times, a Nomad
willdistributeseverallayersoflife-supportandpersonal-safetyitemsthroughouthisclothing
andouterwear;intheeventthatheisstrippedofhisprimaryweapon,thispracticemayleave
himwithseveralundetectedoptionsoflastresort.Escapegearinparticularshouldbespread
outinsuchawaythatsomeofitremainsavailableiftheNomadisrestrained.
Themostbasickit,the“pocketkit,”shouldbecomprisedofessentialweapons,escapeand
evasion equipment, and one “black” (covert) mobile phone. Rather than being consolidated
intoasinglecontainerorconcealment,theseitemsshouldbedistributedthroughoutclothing.
Ahandgunshouldbeconcealedinawaistbandholster,forthemostaccessibledraw.(Seepage
152fortipsondrawingaholsteredweapon.)Anemergencycommunicationdeviceisessential,
butothercontentswillvarydependingontheterrain.AstainlesssteelZebrapencanbeused
to leave notes for potential rescuers—or to strike an assailant. In the case of abduction or
detention,ahandcuffkeyandLEDlightcamouflagedalongsidecarorhotelkeysarepotential
lifesavers;asbackupintheeventthatclothespocketsaresearched,aconcealablehandcuffkey
canbehiddeninashirtcufforonazipperpull.Someoperativescarrymouthpieces,whichcan
bevitalduringhand-to-handcombat.
The “container kit”—generally tucked into a jacket or an operational bag (see below)—
functions as backup in the event that an operative is stripped of his primary weapon and/or
operational bag. This highly condensed kit contains small improvised weapons (loose coins
tiedupinahandkerchief)andnavigationalaids(aheadlampandahandheldGPSdevice)that
changedependingontheenvironment,aswellaslock-pickingtoolsthatcouldprovideaccess
to information, food, or shelter. Purchased within the area of operation, a set of “recci”
(reconnaissance)keyblanksprovidesanadvantageinbreaking-and-enteringscenarios.Durable
andreliablydiscreet,arigidsunglasscaseistheoptimalcontainerforthiskit.
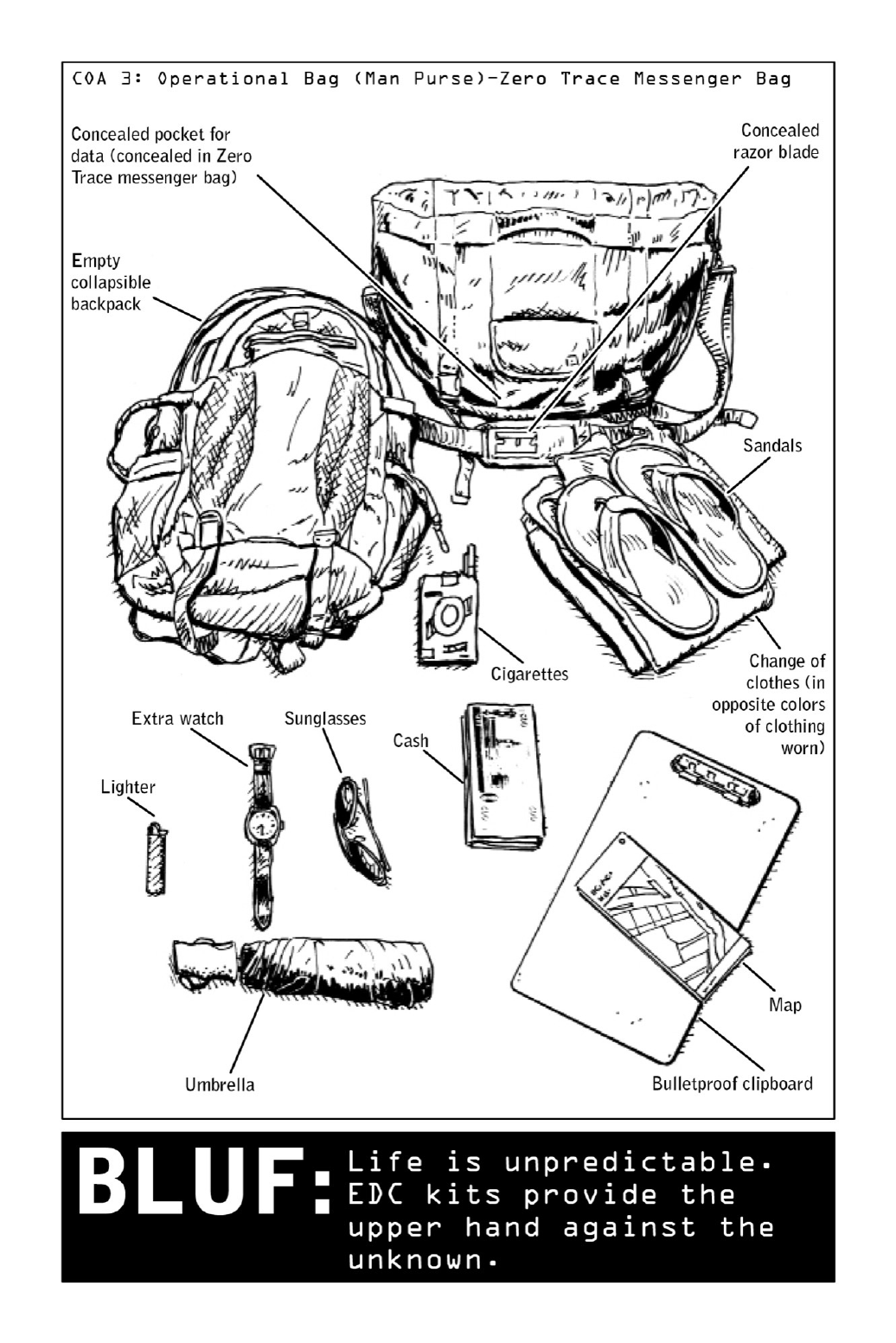
Thefinalpieceofthepuzzleistheoperationalbag.Toprepareforthepossibilityofescape
inthefaceofsurveillanceorattack,itscontentsshouldincludeanemptycollapsiblebackpack
andachangeofclothesincolorsoppositefromtheonestheoperativeiswearing.Evenshoes
should be taken into consideration—if wearing sneakers, pack a pair of rubber sandals. A
concealed pocket holds highly sensitive data on memory devices such as thumb drives or SD
cards,aKevlarclipboardactsasaninnocuous-lookingformofimprovisedballisticarmor,and
awadofcashallowstheNomadtosubsistindeepcoverforaslongasthesituationdemands.

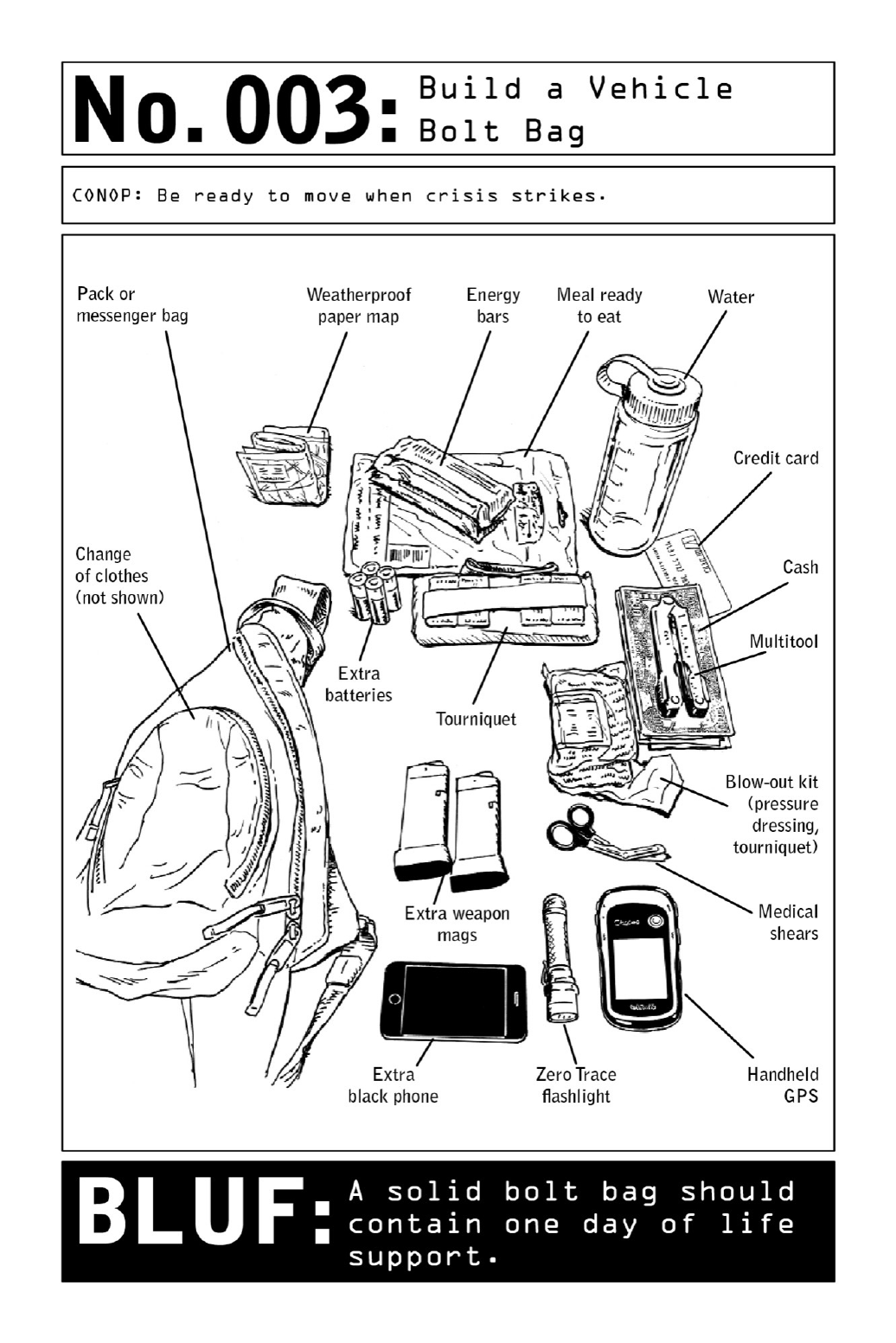
003 BuildaVehicleBoltBag
Operatives don’t have the luxury of being able to return to base to stock up on food or
ammunition, so their effectiveness as free-range agents is built around preparation—and
preparation means always being prepared for the worst. When an operative is conducting a
missionabroad,oneofthefirstordersofbusinessuponbeingcalledintoactionisbuildinga
bolt bag. In the case of emergency, this bag (also known as a “bug-out kit”) becomes an
essentiallife-supportsystem.Itcontainseverythingneededtokeeptheoperativealive,should
he have to “go black,” hiding out of sight until he can either resume his mission or make
arrangementstosafelyexittheareaofoperation.
Aboltbagtypicallyconsistsofadayortwooflifesupport—water,food,cash,emergency
medicalsupplies,navigationaids,anda“black”orcovertphonesimilartothetypeknownin
the criminal world as a “burner.” The bag should be stashed in the operational vehicle,
concealedina spot thatis easilyaccessiblefrom thedriver’s seat,suchasthecenterconsole
compartment(betweentheseats)orundertheseat.(Shouldtheoperativefindhimselfupside
downastheresultofacollisionwithaggressors,thekitshouldbewithinarm’sreach.)Asits
name implies, the bolt bag needs to be light enough to be carried—canned foods and other
heavysuppliesdonotlendthemselvestoeaseoftransport.
CivilianBLUF:Inday-to-daylife,boltbagscanbeusedasprecautionarydisastermeasures—
notonlybycivilianslivinginregionsathighriskfornaturaldisasters,butbyanyonealertto
thethreatofurbandisastersorterrorism.

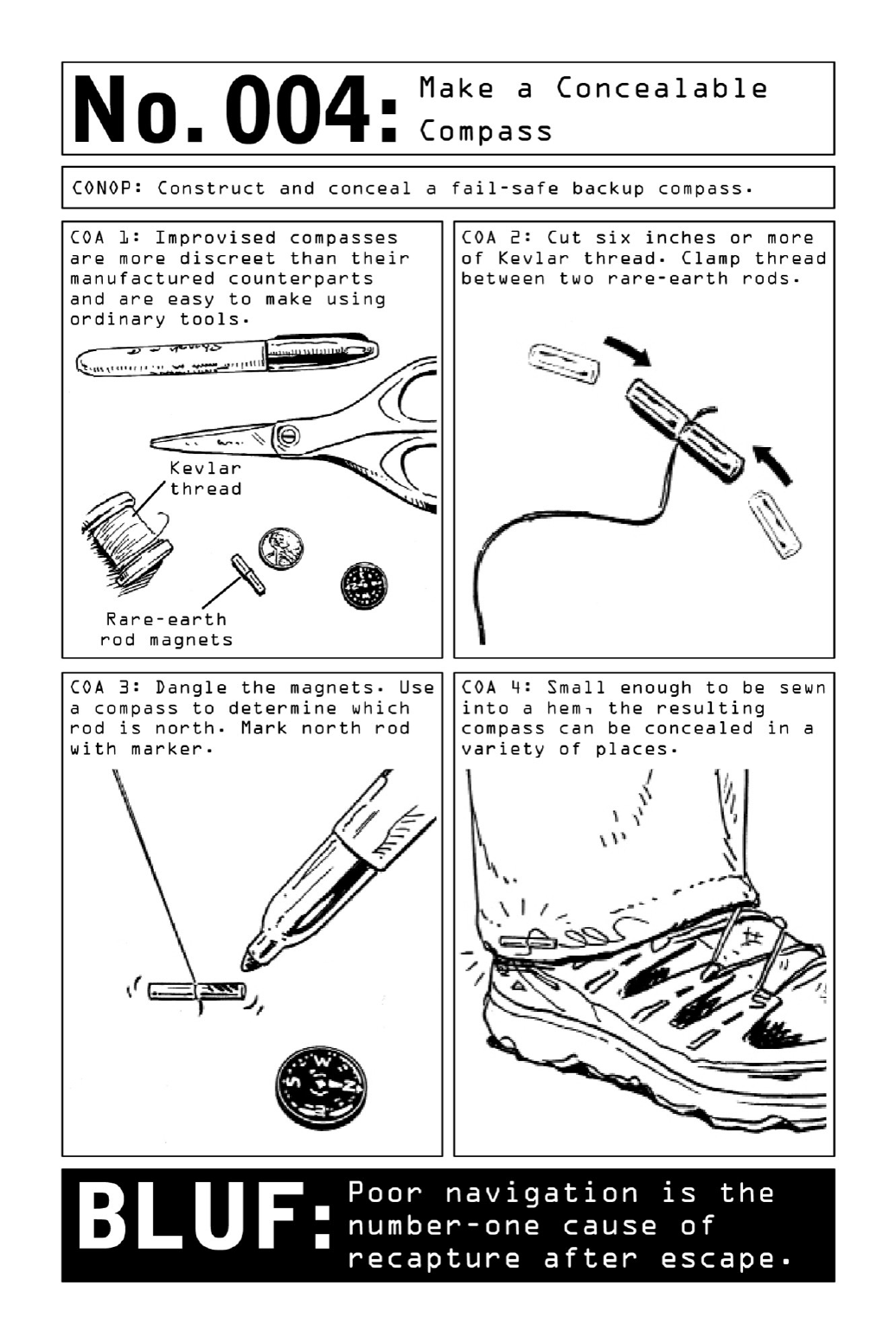
004 MakeaConcealableCompass
Covert situationsoftencallforeasilyconcealable,dependable low-fialternatives—andinthe
caseofacompass,asimplepairofmagnetsfitsthebill.Anoperativemayhavebeenstripped
ofhisGPSdeviceuponcaptureormaybeworkinginacontextinwhichtheuseofahandheld
GPSsystemwouldattracttoomuchnotice.AconcealablecompassensuresthattheNomadis
alwaysabletoeffectivelynavigatethroughunknownterritory,nomatterhowremote.
Thoughmicrocompassesmaybefoundatanyadventurestoreinthedevelopedworld,they
may not be available elsewhere. Improvised compasses, on the other hand, are easy to make
usingresourcesreadilyavailableinmostcountries.Thetoolworksbyharnessingthepowerof
rare-earthmagnets,thebaselinemechanismusedtopowercompasses.Tunedtothedialofthe
earth’smagneticfield,whenconnectedandallowedtodanglefromalengthofthread,therods
becomeanaturalcompass;onepointssouth,theothernorth.
Becausethepurchaseofrare-earthmagnetscanarousesuspicion,itisadvisabletoseekout
lessalertingproductssuchasrefrigeratormagnets,whiteboardmagnets,ormagnetichandbag
closures, always in pairs. Any improvisations must be tested thoroughly, lest the Nomad be
confrontedwithaninaccurateimprovisedtoolmid-escape.
CivilianBLUF: The standard instructions for building a compass (see illustration) involve a
pairofrare-earthrodmagnetsandalengthofKevlarthread(chosenforitsdurability),buta
similareffectmaybeachievedbypiercingamagnetizedneedlethroughacorkandfloatingthe
deviceinwater.

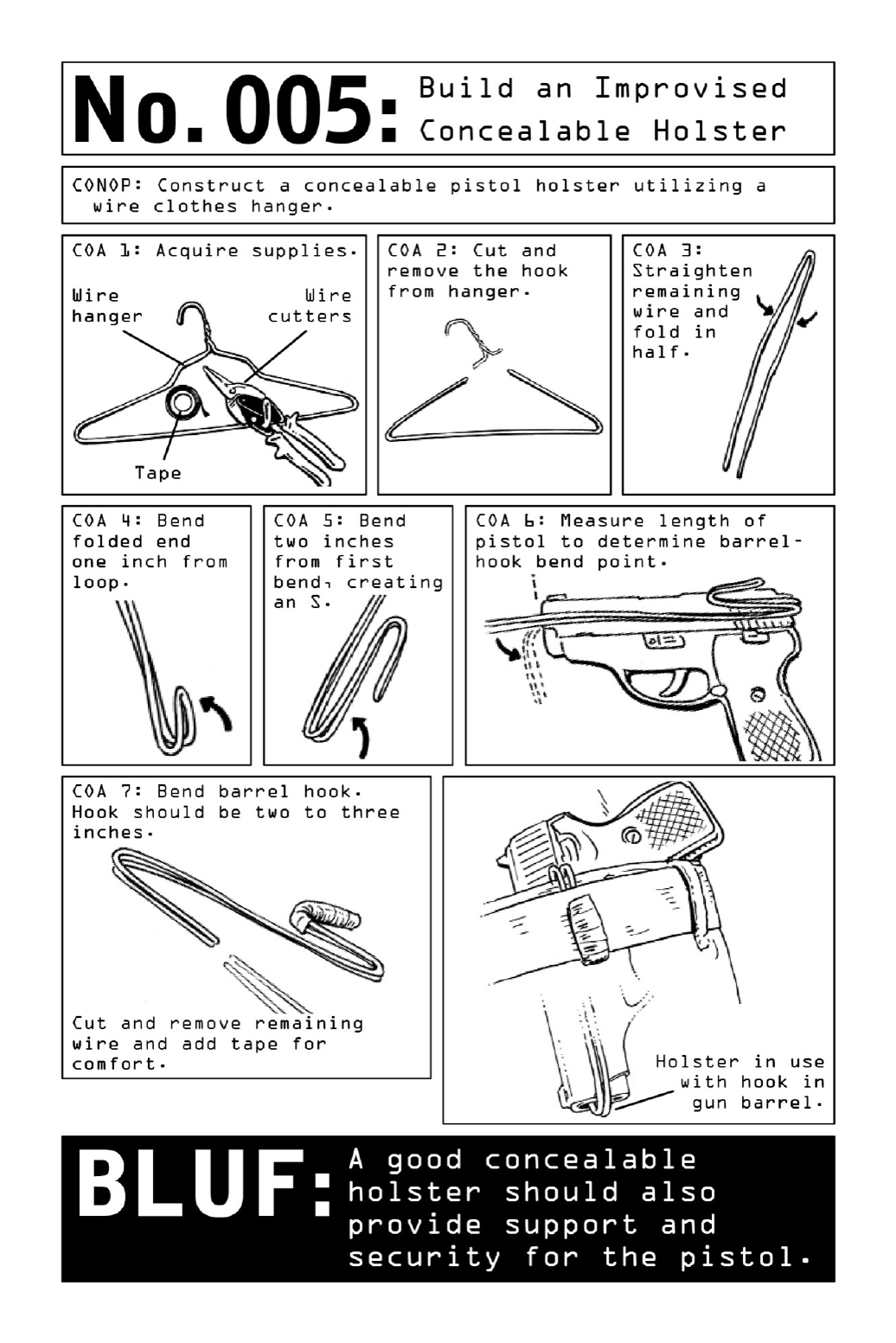
005 BuildanImprovisedConcealableHolster
Operativesarewellversedinusingundergroundchannelstoacquireweaponswithinthearea
ofoperation,asgunsandothermunitionscannotbetransportedacrossinternationalborders
without permission from both the country of origin and the destination country. But
specialized equipment such as concealable holsters are often harder to come by, and any
attempttosmuggletheminwouldcertainlygetaNomadpulledintoanunwanteddetainment
atcustoms.
Inordertomaintainalowprofile,operativesgenerallytravelaslightlyaspossible,utilizing
off-the-shelf resources to fulfill their mission requirements. This predisposition toward
minimalism presents challenges but does not tend to leave operatives in a disadvantaged
position, as many improvised tools—the holster included—provide a better capability than
manufacturedversions.
Commercially available holsters tend to make concealment difficult. Bulky and inflexible,
they increase the overall signature of the weapon in an operative’s waistline and can make
extraction a challenge. A pistol that cannot be quickly and seamlessly removed from an
operative’s holster becomes a deadly liability, so the choice of holster is crucial. This
improvisedmodel,madeofwirehangerandtape,contributesvirtuallynoadditionalbulkand
ensuresaquickandglitch-freedraw.
RelatedSkills:DrawaConcealedPistol,page152.

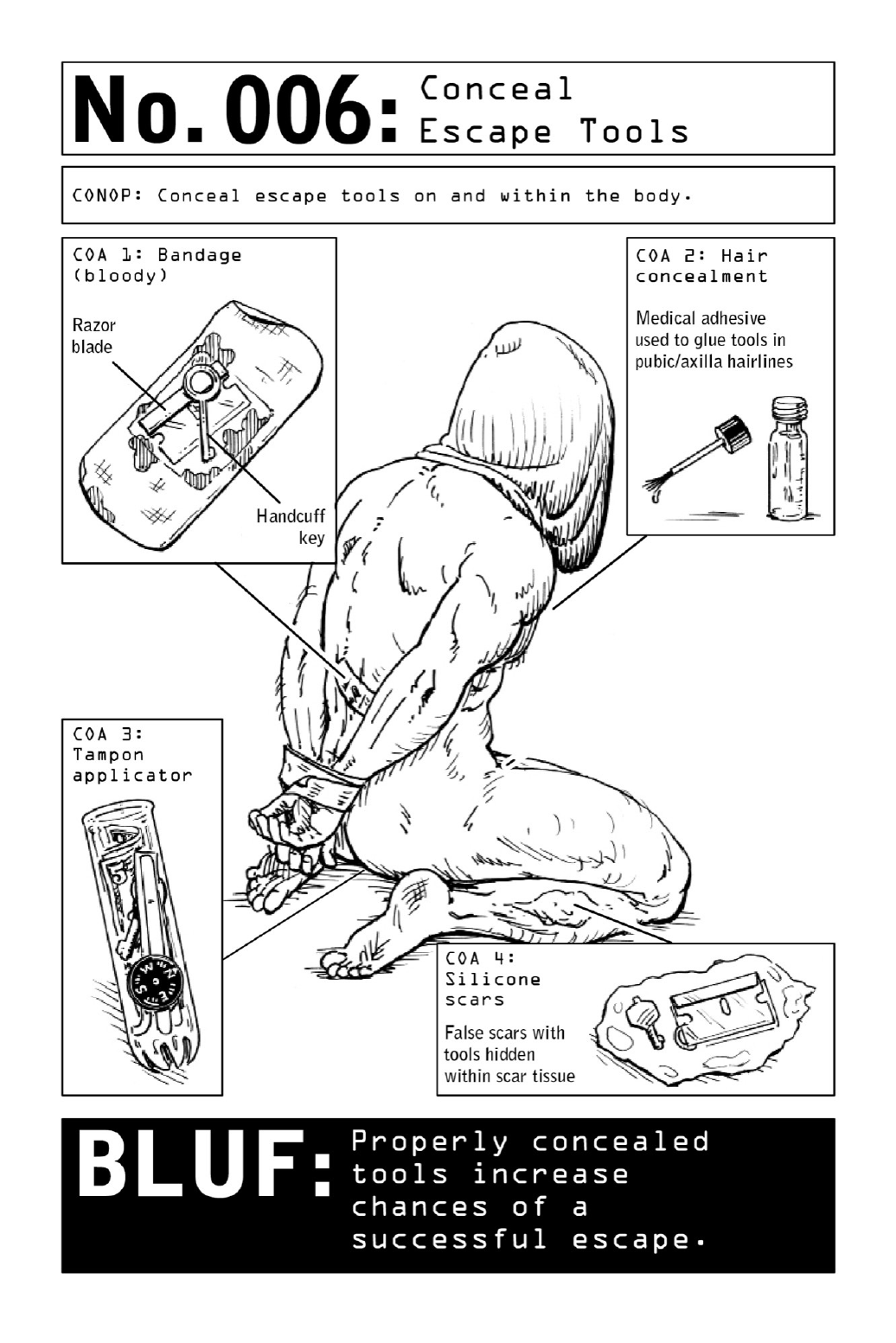
006 ConcealEscapeTools
Thepossibilityofbeingcaptured,kidnapped,ortakenhostageexistsforalltravelers,butit’s
onethat’sespeciallyrealforoperativeswhocannotrelyuponbeingbailedoutbytheirhome-
nationgovernments.
If captured, operatives can expect to be immediately frisked for concealed weapons, at
whichpointtheyarelikelytohavemostoftheirgearconfiscatedbytheircaptors.Escapeaids
concealedinclothingmayremainundetectedforawhile,butoperativesknowthatiftheyare
incaptivitylongenough,they willeventuallybestrippednakedandhavetorelysolely upon
the escape tools they’ve concealed on and inside their bodies. Given a lack of institutional
backup, self-escape preparations are an essential component of a Nomad’s every operational
plan.
Ahumanaversiontobloodybandagesmeanscaptorsareunlikelytocloselyexaminelesions
or scars, so a Nomad can utilize medical adhesive to glue specific tools onto the body
underneathmanufacturedwounds.
Thereisalsoanear-universalreluctanceonthepartofcaptorsforfrisking,pattingdown,
or probing the nether regions of their detainees—and this unease provides operatives with
exploitableopportunitiesforconcealmentofescapetoolsinaxilla(armpit)hairorpubichair.
Body concealments can be as elaborate as suppositories placed in the penis (urethra and
foreskin), vagina, or rectum or in the nostrils, ears, mouth, and navel. And they can be as
simpleasbarelyperceptiblecondoms.Note:Thisadvantagecanworktoa Nomad’sbenefit,
butdiminishesquicklyasheorsheistransferredtoincreasinglyhigherlevelsofdetentionand
security.
RelatedSkills:ConstructaRectalConcealment,page18.

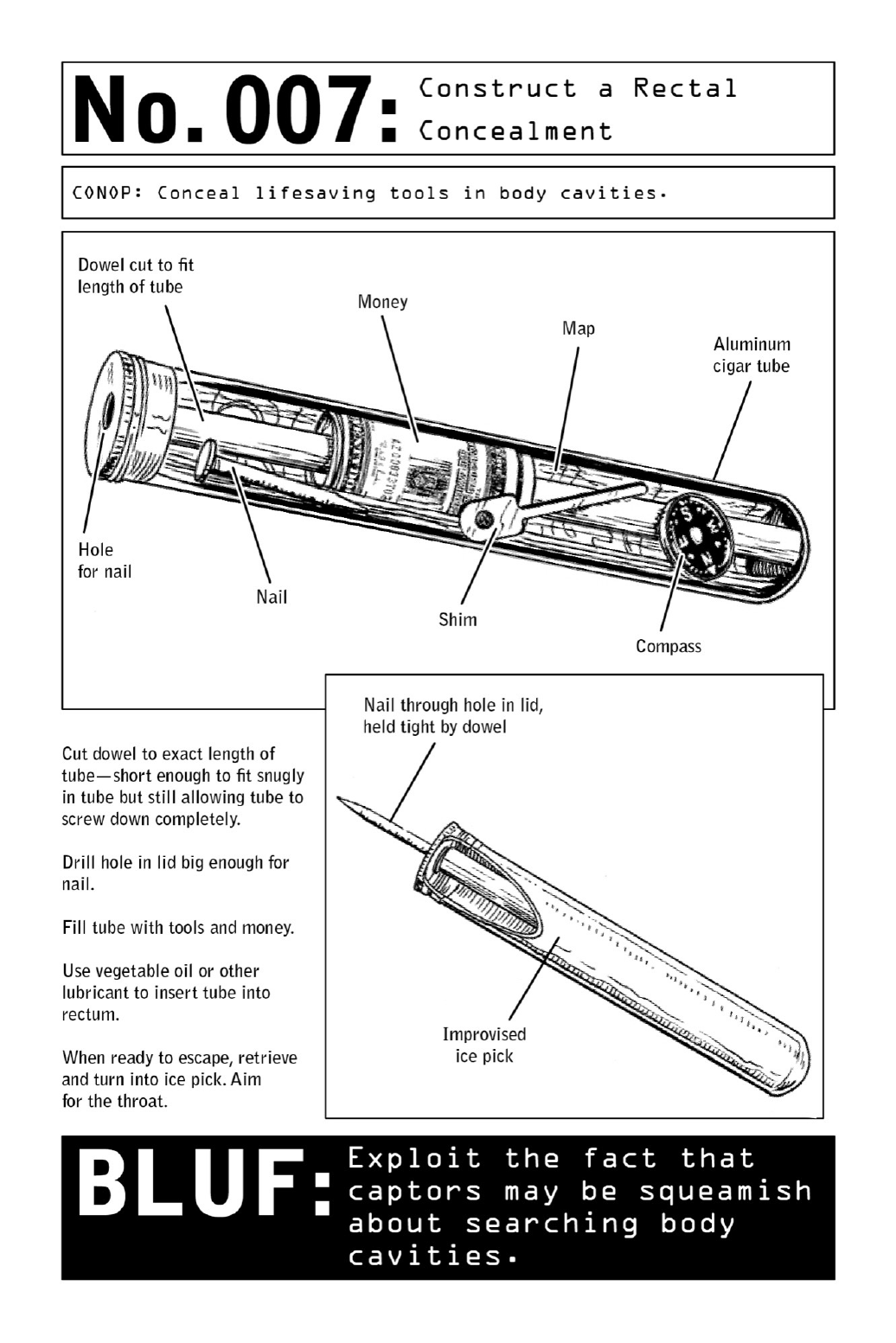
007 ConstructaRectalConcealment
When a mission involves a high potential for capture, operatives prepare for the possibility
that they will be detained, searched, and stripped of any visible weapons. This leaves the
operative only one method of recourse: the concealment of weapons and escape tools in his
bodilycavities.Navigationaids,money,escapetools,andevenmakeshiftweaponssuchasan
improvisedicepick(seeillustration)canbeconcealedinsideatamponapplicatororaluminum
cigartubethatisinsertedintotheanalcavity.
Theuseoftherectalpassageasahidingplaceforillegalitemsorweaponsiscommoninthe
shadow worlds of drug trafficking and terrorism. But the technique is also well known to
operatives as an extreme measure of self-preservation used during ground zero of high-risk
missions.
Such a concealment is surprisingly immune to high-tech methods of detection. Full-body
scanners bounce electromagnetic waves off the body in search of metallic objects and other
contraband.Whiletheirlow-frequencyradarcandetectweaponsthatprotrudefromthebody,
itcannotseethroughskinorbone.EvenX-raymachinesdon’tdoaverygoodjobofrendering
items camouflaged in tissue, and MRI machines used in medical contexts would render a
concealmentasashadowthat,givenitslocation,couldbemistakenforfecalmatter.
Note:Anyimprovisedcontainersmustbewaterproof,nontoxic,smooth,andsealedontheir
upperend.

008 UseImprovisedBodyArmor
Whether engaging armed targets or caught in the crossfire of social unrest, operatives
frequentlyfindthemselvesinneedofbodyarmor.Government-issuedarmorprovidesthebest
protectionagainstinjury—butbecauseofitstraceability,operativesoncovertmissionsarenot
authorized to use it. To survive, they must learn to create improvised body armor using
everydayitemsandmaterials.
When taped tightly together in units of two, hardcover books such as encyclopedias and
dictionaries become rigid bundles or “plates” that can dissipate the energy of a projectile.
Taping commonly available ceramic tiles to the outer facing of each plate provides an
additionallayerofprotection,andtheresultingarmorcanbeconcealedbyajacketorcoator
easilycarriedinamessengerbagorbackpack.
Plates should be suspended on the front and back of the torso in order to protect “center
mass”—thespineandvitalorganssuchasheartandlungs.
Another layer ofprotectioncanbeachievedviaa commerciallyavailableKevlarclipboard
rated to stop 9mm pistol bullets. Lightweight and portable, once painted with a flat brown
painttheclipboardisnon-alertingandwillpassscrutinyifexaminedatabordercrossingor
airport.
Improvisedarmormustbethickenoughtosloworstopaprojectileandthinenoughtobe
wearable.Dependingonavailablematerials,ViolentNomadsmaybeabletocreateimprovised
armorthickenoughtostopaprojectile.Pistolroundstravelmoreslowly(9mmprojectileat
1,100feetpersecond);fasterriflerounds(5.56mmprojectileatapproximately3,000feetper
second) require more protective material. But an operative never quite knows what he will
encounter,andsotendstobuildfortheworst-casescenario.


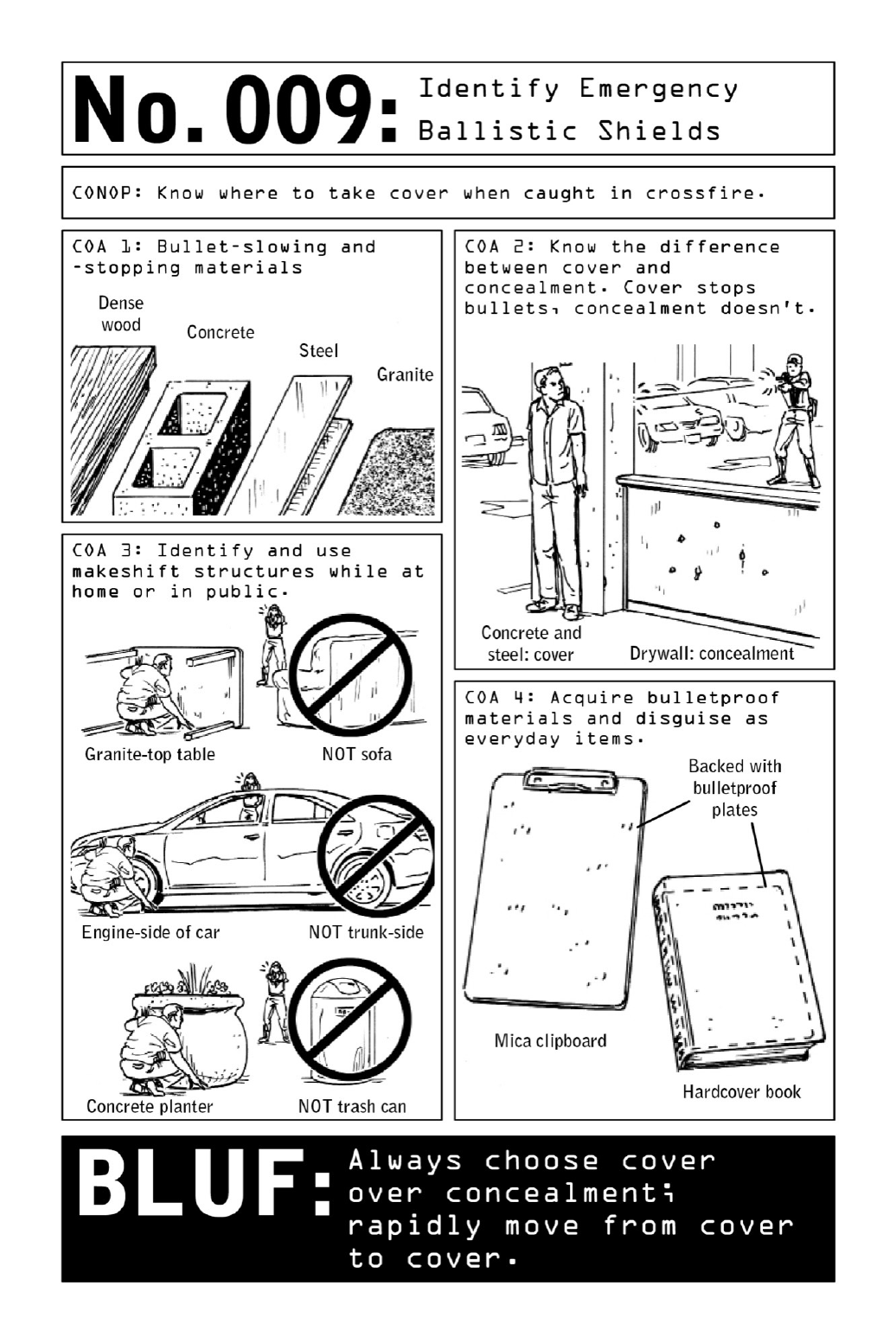
009 IdentifyEmergencyBallisticShields
Whenbulletsareflying,theoddsofsurvivalaredeterminedbysplit-seconddecisions.Whether
thosedecisionsareeducatedones,ratherthanunconsciousmovesmadeintheclutchesoffight
orflight,canmeanthedifferencebetweensafetyandseriousinjuryordeath.
Theinstincttorunforcoverisuniversal,butitmustbecoupledwithanunderstandingof
the relationship between ballistics and everyday materials. Dense wood, concrete, steel, and
granite are the preferred materials in the face of open fire—these thick, heavy materials can
stop bullets and save lives. Sheetrock walls may offer concealment—thus diminishing a
shooter’saccuracy—andgivetheappearanceofsolidity,buttheywillnotstopbullets.Evena
small.22-caliberpistolcanripthroughdrywall.Concreteorsteelcolumns,ontheotherhand,
providebetterballisticprotection,despitetheirrelativelackofcoverage.
In cases of emergency, these principles can be applied to many of the objects in civilian
environments. Granite-top tables, concrete planters, and steel appliances all fit the bill.
Countertops, desks, and tables in hotel rooms are frequently made of granite or steel. But
someeverydayobjectsappearsolidyetaremadeoutoflightweightmaterialsthatwon’thold
uptogunfire.Mailboxesandtrashcansaregenerallymadeoutofaluminum.Hulkingvending
machines are mostly comprised of glass and plastic. Cars are partially made of steel, but a
steelsolightweightthatitfailstoofferadequateprotection;intheabsenceofotheroptions,
hidingbehindtheenginesideofthecar,ratherthantheemptytrunk,putsanadditionallayer
ofdensematerialsbetweenanoperativeorcivilianandtheshooter.
RelatedSkills:UseImprovisedBodyArmor,page20;SurviveanActiveShooter,page178.

010 TheViolentNomadWorkout
No strangers to ruthless obstacle courses and drills that combine sleep deprivation and live
explosives to simulate the hardships of real-world combat, operatives are trained under the
toughest conditions on earth. Once past basic training, they remain combat-ready by
incorporatingthe“RunFightRun”formulaintotheirworkouts.
Repeatedlyliftingapairofdumbbellsdoesn’ttranslateintoanabilitytodefeatanassailant
in hand-to-hand combat after an arduous chase over rugged terrain—so Violent Nomad
training prizes real-world combat and self-defense techniques over muscle-building reps.
Traditionalstrength-buildingandcardiovascularexerciseshavetheirplace,butintegratingthe
RunFightRunphilosophyintoworkoutroutinesbuildstheendurancetooutlastanopponent
inafightand/orchase.
Consistingofintegratedrepetitivestrikingmovementsstackedwithsprints,RunFightRun
workoutsdonotrequireagymoranysophisticatedequipment.Allthat’sneededisaplaceto
sprint and an object to carry and strike, preferably a heavy punching bag; designed for
striking,itisversatileenoughtobeusedforsquats,deadlifts,carrying,andpresses.Aheavy
bagcanalsobethrownandstruckontheground,whichiswheremostfightsendup.
Civilian BLUF: Use the heavy bag to perform a mix of exercises, with sprints integrated
between reps. Increase duration and weight as needed to ramp up intensity over time. A
worthy conditioning goal is to be able to perform three sets of striking for three minutes
straightandthensprintforonemileinsevenminutesorless.


PARTII
INFILTRATION:ACCESSTOENEMY
TERRITORY

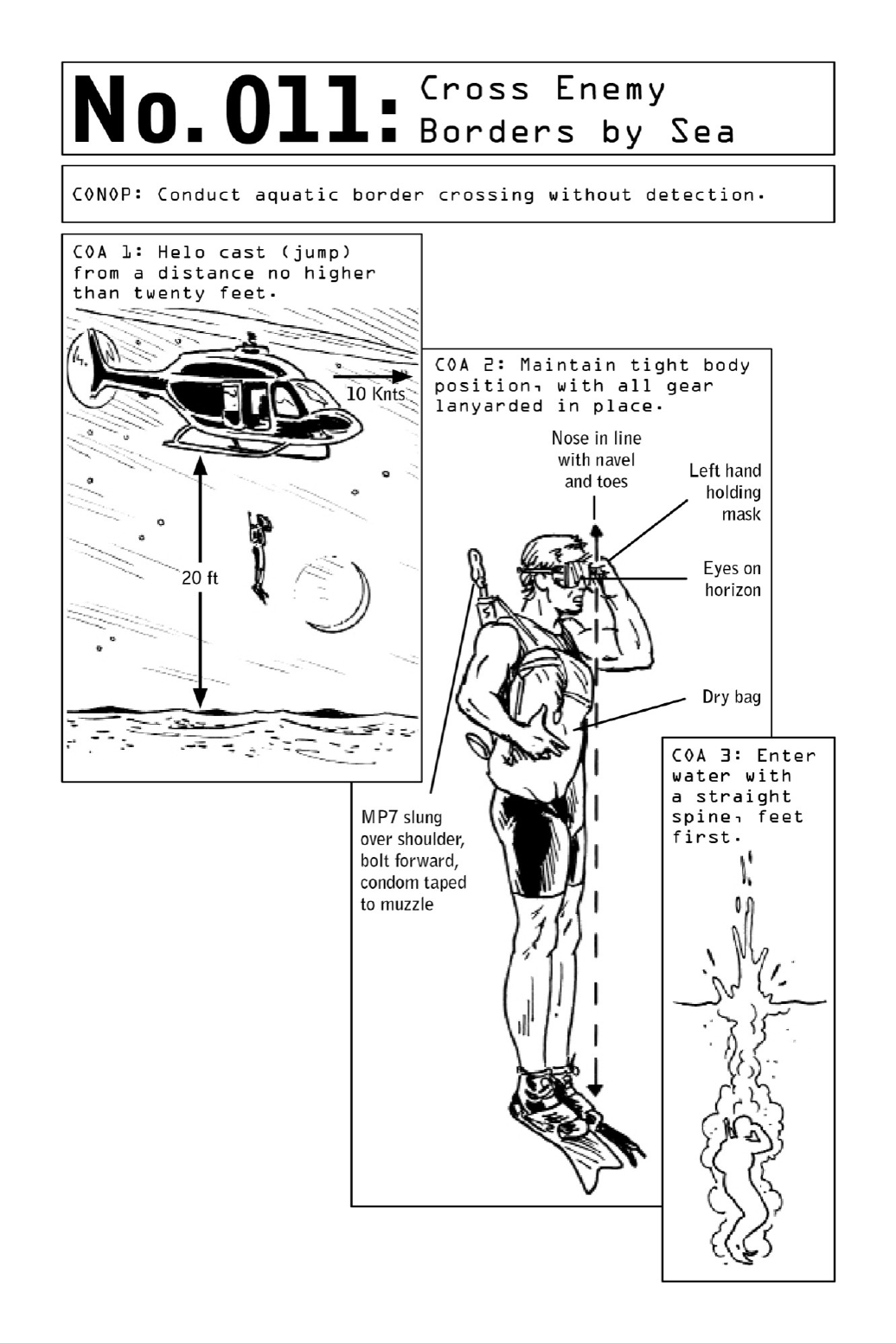
011 CrossEnemyBordersbySea
As smugglers and refugees the world over well know, maritime borders in even the most
securecountriestendtodisplayhighdegreesofporosity.Foranoperativebent ondiscretion
andstealth,intherightkindoflandscapehelocastingbecomesapreferentialmethodofentry.
Droppingfromaslow-movinghelicopterintofrigidwatersisahigh-level,dangerousskill.
Even while hovering, helicopters can create hurricanelike winds that result in blinding mists
andskin-stingingwaterblasts.Practiceis essential,andleapingoutof a helicopterintodark
seasrequiresproperaltitudeandsafeforwardspeed.Onlybyfollowingspecificprotocolscan
operatives survive the jump. At an altitude of twenty feet, the helicopter’s forward speed
shouldnotexceedtenknots;atanaltitudeoftenfeet,forwardspeedshouldnotexceedtwenty
knots.Thisisknownasthe“10for20,20for10”rule.
Correctbodypositioning(seediagram)preventsinjuryandensuresthattheforceofimpact
hits the divingfins(ratherthanany protruding bodyparts)anddoes not dislodge thediving
mask.Althoughthejumpprohibitstheuseofheavy-dutydivingequipment,awetsuit,amask
orgoggles,fins,andaninflatablelifejacketareessential.Allothergearmustbestowedina
waterproof backpack or “dry bag” and strapped onto the operative with lanyards so as to
prevent its being lost to the depth of the ocean. Its contents should include mission-specific
gear such as a change of clothes that will allow the operative to blend into the area of
operation and an additional weapon, along with a hand shovel. The operative’s primary
weapon, an MP7 submachine gun, should be loaded and carried bolt forward; a condom
stretchedoveritsmuzzlepreventswaterfromenteringthebarrelbutwon’timpedeabullet’s
exitpath.
The dry bag is slung over one shoulder so it can easily be shed if the operative runs into
difficulties in the water. Strapping a bag on too securely could impede the operative’s
swimmingstrokeandposeariskofdrowning.
To swim to shore, operatives use the combat recovery stroke, a side stroke with a
minimizedprofileinwhichthearmsdon’texitthewater.Onceoutofthewater,theychange
intodryclothesandusethehandshoveltocachetheirgear.


012 CrossEnemyBordersbyAir
Formostcivilians,illegalbordercrossingsconjureuptunnelsdugdeepunderground,passage
fees paid to shadowy guides, and caravan rides to distant way stations. But for Violent
Nomads, border crossings are solitary affairs best accomplished via a territory’s most
unmonitored,unguardedspaces:bysea(page28),byland(page34),orbyair.Whenexecuted
inacountry’sdesolatecornersandundercoverofdarkness,suchinfiltrationscanbeentirely
undetectable.
For trained operatives, an infiltration by air is built on a two-pronged approach:
appropriationofanunmannedprivateplane(page66)anddescentviawingsuitandparachute.
Global laws dictate that maritime airspace reverts to international rule within twelve
nautical miles of any country’s coastline—and that guideline should inform any attempt at
infiltration.Oncewithinenemyairspace,theaircraftmust“goblack,”itstransponder,radios,
andlightsshutoffinordertoavoidalertingenemyair-trafficcontroltowerstoitspresence.
Acombinationofairglidingandparachutingfromtheplanedownontoruralterrainoffers
the quietest and least visible means of entry. Once a landing point has been identified,
calculating the jump point involves a universal equation: When jumping from a moving
aircraftinawingsuitmadeoutofanonporousnylon,everytwoandahalffeetdroppedmeans
a simultaneous gain of one foot of forward glide, more if going downwind. Such a suit
essentiallyturnsanoperativeintoahumankite,allowinghimtousehislegsandarmstosteer
likeanaircraft.Parachutingisaslow-movingandmuchmorevisibleproposition,soaNomad
shouldwaituntilthelastpossibleminutetoactivatehischute.
Onceonground,thenylonwingsuitandparachutecanbemeltedintoahandfulofglasslike
beads.


013 CrossEnemyBordersbyLand
Every nation displays some weaknesses along its borders, particularly in its uninhabited
spaces,andoperativesalwaysseektoexploitthesevulnerabilities.Butthewildertheterrain,
themorechallengingitwillbetocross.Aseasonedoperativecrossingenemybordersonfoot
might spend days or weeks trekking alone through scorching deserts, freezing mountaintops,
anddense jungle asheslowlywendshiswaytowardthe areaofoperation.Despitethepace
andphysicalchallengesofsuchanapproach,themostdifficultrouteislikelytobethemost
desirable one—for the more rugged the terrain, the freer it will be from scrutiny and
surveillance. If airspace is heavily guarded, infiltration on land may also be the operative’s
onlyrecourse.
GearandTransportation: Almost inevitably, a portion of the journey will occur on foot,
buttheidealscenariowillallowtheoperativetoclockafairnumberofmilesonanoff-road
motorbike with the horsepower to carry a two- to three-hundred-pound load and the
durability to take on extremely uneven terrain. In many parts of the world, motorcycles are
more common than cars, so acquiring or stealing a bike from a neighboring country is well
withintheoperative’sgrasp.
In addition to his EDC kit and bolt bag (pages 6 and 10), the operative will be carrying
enough fuel, food, and water to last the trip and the clothing and gear needed in order to
disguise himself once he crosses the border; even if the operative is able to forgo drinking
waterbecausewatersourcesarecommonthroughouttheterrain,hismissionsupplieswillbe
extensive. Each phase of the infiltration will also require a unique set of tools and weather-
appropriategear.

Shelter: Though operatives are trained to survive extreme levels of sleep deprivation, an
infiltrationstretchingoverseveraldaysorlongernecessitatesreststops.
Improvised shelters are usually preferred. Unlike nylon tents, shelters built from found
materials such as branches or compacted snow blend into their environments and act as
camouflage. In snow-covered landscapes, igloo-like shelters can be constructed out of
compacted blocks of snow. Despite their temperature, these blocks act as nonporous shields
that effectively shut out exterior weather while sealing in heat, allowing operatives to warm
theshelterwiththeirownbodyheatandtheadditionofalitcandleortwo.Oncetheslabsof
snowareplacedbackintothesnowbank,exposuretoafewhoursofsun,rain,orsnowtakes
careofcoveringtheoperative’stracks.
Navigation: When the terrain dictates that operatives proceed on foot, the most grueling
portion of the multiphase infiltration process has begun. Operatives may walk for days in
extremeweatherconditionstoreachtheirdestination.(Infact,poorweatherconditionsmay
be optimal as a means of erasing the operative’s footprints.) And they must be prepared to
navigateusingonlyacompassandamapintheeventthattheirGPSdevicefails.
Thisprovesmucheasierinmountainousareasorseascapes,wheremountaintopsandother
topographical landmarks provide reference points for orientation. In undifferentiated desert
environmentsthatstretchoutforhundredsofmiles,theriskofstrayingfaroffcourseoreven
walkingincirclesissignificant.
In such instances, pace counting—the practice of counting every other step as a gauge of
distance—canbealifesavingtechnique.Asingleadultstepspansapproximatelyonemeter,so
onehundreddouble-stepsadduptoapproximatelytwohundredmeters.Keepingtrackcanbe
an effective barometer of distance in an environment with few other means of assessing
progress.
Untraceability:Operativesgenerallytravelundercoverofnight, sleepingfor shortstretches
duringdaylighthoursandtimingtheirnightmovementstolunarcycleswhentheycan.Ahalf-
moonoffersalevelofvisibilitythatisparticularlywelcomeonroughterrain,whilefullmoons
may render the operative too visible. Night travel is significantly slower than daytime
movementsbutinvolvesfewerrisksthantravelinginbroaddaylight.
Operatives also plan their routes through terrain that makes detection difficult and take
precautions to avoid leaving clues behind. They urinate off-route, in bodies of water if
possible,andpackandcarrytheirfecalmatter.Whereterrainpermits,theyavoidsoil,sand,
and mud and walk on nonprinting surfaces such as rocks, roots, grass, leaves, and bark.
Footprints are unavoidable, but operatives try to break up a consistent trail anytime the
environmentpermits.

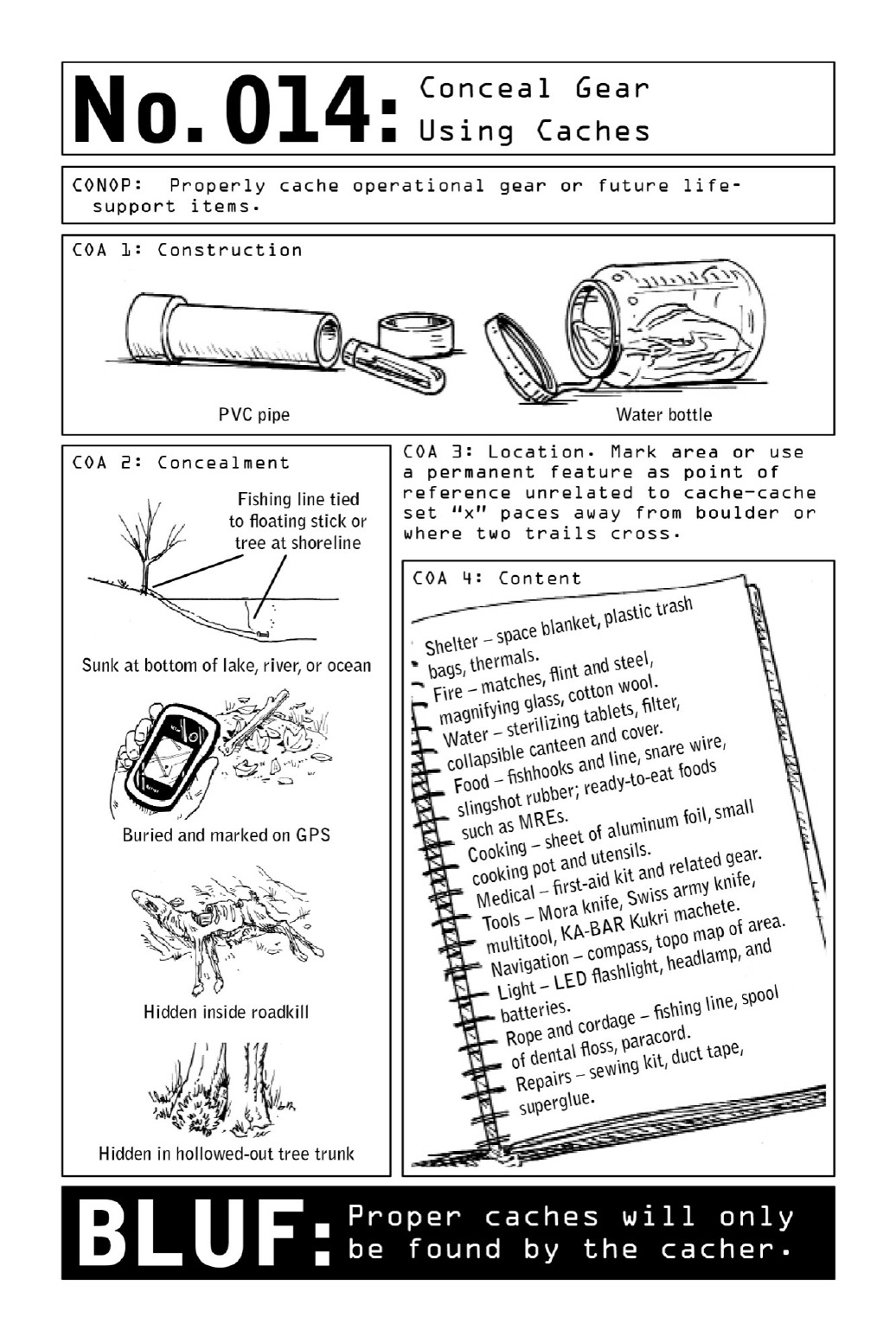
014 ConcealGearUsingCaches
AViolentNomad’smissioniscompleteonlyoncehehassuccessfullyvanishedfromthearea
ofoperation—soheneverundertakesaninfiltrationwithoutawell-plannedexitstrategythat
accounts for all of his post-mission needs. Traveling light is crucial, so particularly when
crossingintoremoteterritoryonfoot,theNomadwillseparatehisgearandsuppliesintotwo
categories:itemsneededforthefirstlegofhisjourney,anditemsneededpost-missionand/or
foremergencyexfiltration.Designedtosupportsurvivalontherun,hissecondarycachewill
storeawell-thought-outresupplyoffood,fuel,communicationdevices,money,andweapons,
hiddenawayonapreplannedrouteoutoftown.
Operationalgearreservedforfutureusecanbecachedviaavarietyofmethods.Protected
fromtheelementsbybeingpackedintodurablecontainerssuchaswaterbottlesorlengthsof
PVCpipe,itcanbeconcealedanywherefromcavestohollowed-outtreetrunkstothebottoms
oflakes.Themoreremotethecachesitethebetter,asthelastthingaNomadwantstodois
recover a cache that has been booby-trapped or put under surveillance. Burying operational
gearwelloutofsightreducestheoddsofaccidentaldiscovery.MarkingitslocationonaGPS
deviceenablestheNomadtorecoverhisgearintheabsenceofvisiblelandmarks.

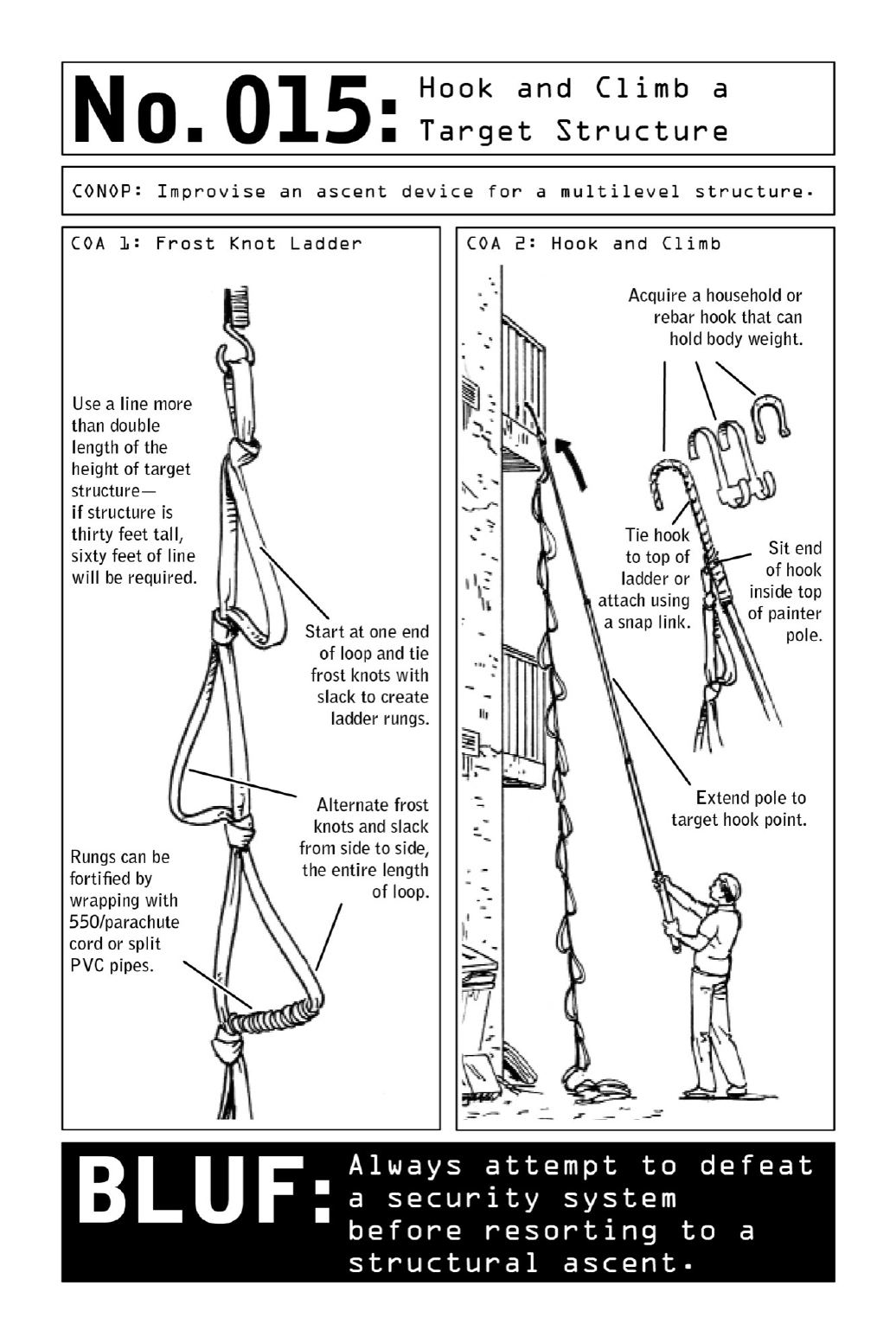
015 HookandClimbaTargetStructure
Nomadsfrequentlygainaccesstomulti-occupancytargetbuildingsbystrollingintounlocked
lobbiesorpickingrudimentarycommerciallocks(seepage110)onbackdoors.Butinhighly
secured buildings monitored by camera and/or roving patrol, access through front or back
doorsmaynotbenegotiable.
Fortunately,anybuildingwitharowofbalconiesalongitsbacksidepresentsasecondary
option:scalingtheexteriorofthebuildingfrombalconytobalcony.Usingapainter’spole,an
extra-longlengthoftubularnylonorrope,andahook,aNomadcanconstructalightweight
ladder system that will safely hold his body weight—enabling him to perform the simple
“hookandclimb”techniqueusedforcenturiesbypiratesstealingontoenemyships.
Tyingaseriesoffrostknotsintoadoubled-overlengthoftubularnylon(itsbitterendstied
togetherwithanoverhandknot)yieldsadurablestepladder(seediagram);thelineshouldbe
more than twice the length of the target structure’s height. After a heavyweight metal
household hook is inserted into a painter’s pole and tied or snapped onto the ladder, the
apparatus can be hooked onto an upper structure durable enough to hold the operative’s
weight. He then climbs from one floor to the next and repeats the process until the target
destinationisreached.
Evenwhenperformedlateatnight,thismethodoflastresortcomeswithahighpossibility
ofexposure.Butbecausesecuritycamerastypicallyaren’tsetuptocatchpeopleclimbinginto
abuilding,inahigh-securitycontextitmaystillbethebestoptionforaNomadlookingtoact
with stealth. Building owners seldom set up cameras beyond the first floor—and train those
they do install toward doorways, on the assumption that any invaders will be coming in
throughthegroundfloor.

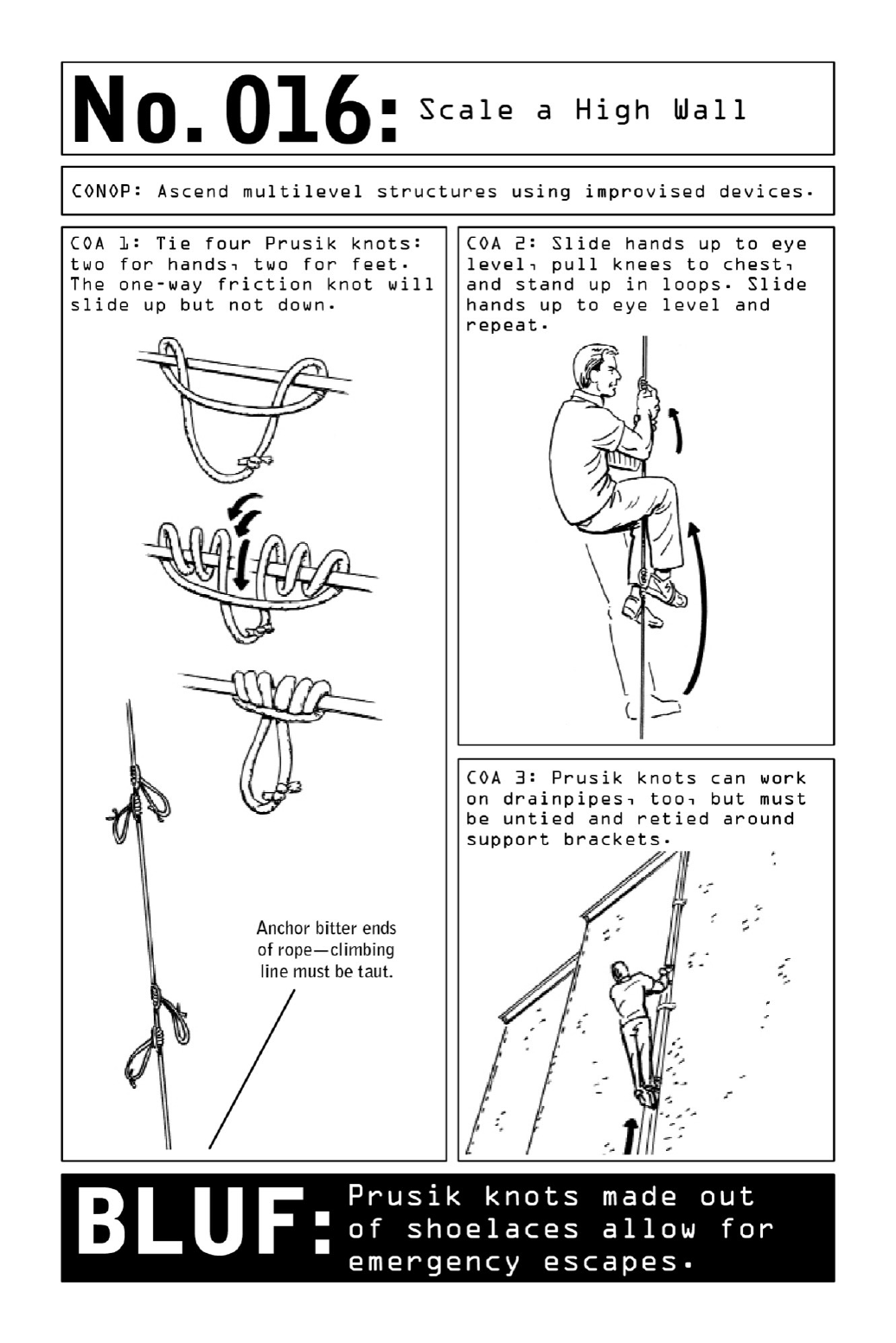
016 ScaleaHighWall
While a smooth building facade or high wall may not offer an operative the convenience of
climbing from balcony to balcony (see page 40), the use of a one-way friction knot makes
infiltrationviaropeordrainpipeeminentlyfeasible—solongastheclimbingropeistautand
securelyanchoredatbothtopandbottomends.
Asafetyknotusedbyrockclimbersasaformoflifesavingbackup,thePrusikknotistied
in such a way that it can move only up a rope or line; downward pressure causes it to lock
into place. Tied to a climber’s harness, the knot can provide a fail-safe that may catch the
climberintheeventthatotherdevicesfail.Inaninfiltrationorescapescenario,theknotcan
beexploitedforitsabilitytoslideupaline,lockingintoplacewhenitreceivestheoperative’s
bodyweight.
To tie a Prusik knot, first tie a shoelace or an equivalent length of small-gauge nylon or
parachutecordintoaloopusingasquareknot(seepage43).Then,wrapthecordaroundthe
climbing rope or drainpipe and loop the cord through itself (see diagram). Pass the cord
throughtheresultinglooptwicemore.Pulltightly.
Ideally,tiefourPrusikknotstouseashand-andfootholds,aswhenshimmyinguptheline.
Intheeventthatsuppliesarelimited(ifusingshoelacesinthecaseofescape),twoknotsare
enoughtotogglefromasinglehandholdtoasinglefoothold.
If shimmying up a drainpipe, it will be necessary to untie and retie knots around support
brackets.Tosavetime,bringextrapre-loopedcord.

017 BlendintoAnyEnvironment
Whenfittingintoaparticularregion,aNomadworksthroughanenvironmentalchecklist,the
first dimension of which is personal. How do his look and manner stack up to the
environment?Travelerswholookandactlikefishoutofwaterareprimetargetsforcriminals
of all stripes, and operatives who make themselves conspicuous are prime candidates for
discovery.
The secondary dimension of this process is cultivating cultural awareness, which means
constantly weighing actions and preferences against the prevailing cultural context. If the
general population forgoes ketchup on their sandwiches or ice in their drinks, the operative
willfollowsuit.
Nextissituationalawareness,meaningtheoperativecontinuallyscanshisenvironmentfor
potentialdangers,playingoutworst-casescenariosinordertoidentifywhichactionstotake
beforecrisisstrikes.Withinthirtysecondsofhavingenteredarestaurant,hehascanvassedall
exitsandspottedanypotentialimprovisedweaponsinthevicinity.Hehasalsoidentifiedhis
“invisible thresholds,” the imaginary lines whose crossing will spur him into swift, decisive
action.If he spotsan armed guard carryinganautomaticweapon, hewillquickly determine
his“threshold”forescapeordefensiveaction—i.e.,shouldtheguardlookhiswayrepeatedly,
hewillduckoutthebackdoor.
The final dimension of total awareness is third-party awareness. The operative is always
keenly aware of anyone who might be watching him—whether he’s operating in another
country or using the Internet, his goal is to remain undetected by third parties such as law
enforcementofficials,citizens,criminals,andevenhackers.


PARTIII
INFRASTRUCTUREDEVELOPMENT:
LODGING,TRANSPORTATION,WEAPONS

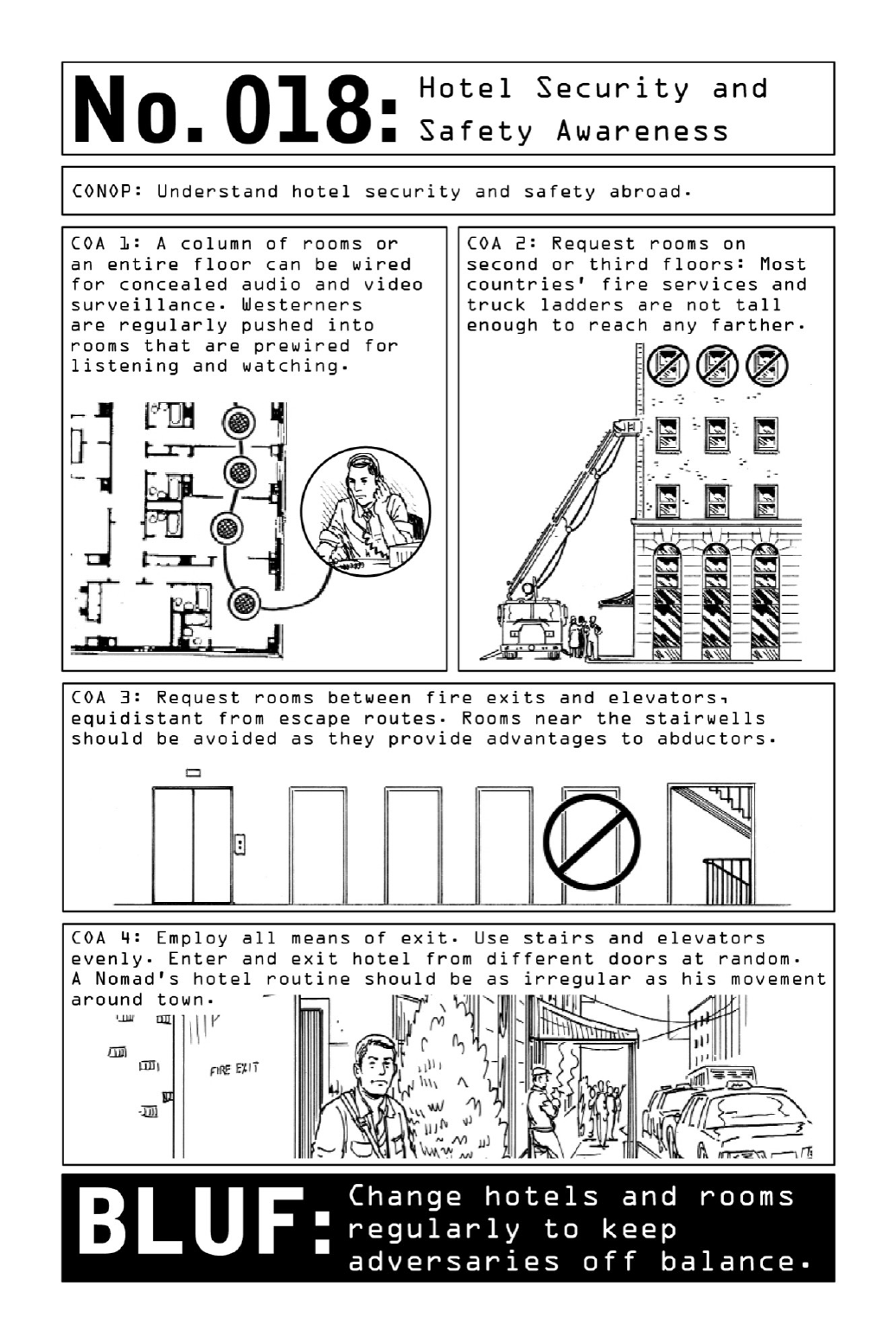
018 HotelSecurityandSafetyAwareness
Hotelroomsarenotoriouslyunsecurelocations.Especiallyindevelopingnations,eventrusted,
name-brand properties can be susceptible to graft and surveillance—some of it officially
sanctioned. In an era of global uncertainty, aggressive governments go to great lengths to
collectintelligenceonWesterners, whether theybehigh-rankingdiplomatsorrun-of-the-mill
businesspeople.Manytravelblindinthefaceoftheseinvisiblethreats,assumingtheyaresafe
when tucked away in their hotel rooms or rental cars. But any property controlled by an
unknownentityisvulnerabletoamultitudeofthreats.
Some hotels will actually place Westerners in rooms that are wired for surveillance. One
waytothwarttheireffortsistochangeroomsandhotelsfrequently.Becausetheseproperties
are also subject to unexpected emergencies, the safest rooms are those on second or third
floors. Most countries’ fire services are not equipped to reach any higher—but a Nomad
avoidsthegroundfloor,asintheeventofahostileinvasion,havingsomedistancefrom the
lobbyiscrucial.(Terroristswillmostlikelyworktheirwayupfromthegroundfloor.)
Anoperativewilllookforaroomthatisequidistantfromstairwellsandelevators—aroom
too close to the emergency exit exposes him to the risk of being grabbed and shoved into a
stairwell.Toofar,andheisatadisadvantagewhentryingtomakeaspeedygetaway.
CivilianBLUF:Hotelsaretargetsforbothcommoncriminalsandprofessionalconmen,and
lobbiesareparticularlygreatplacesforcriminalstostalktheirpreywithouttheriskofbeing
challenged—thelikelihoodthatthey’llbe questionedbyhotelstaffislow.Fortunatelyhotels
havemanyentrancesandexits;usethemunpredictablytoavoidcreatingroutinesthatcouldbe
observedandanticipated.

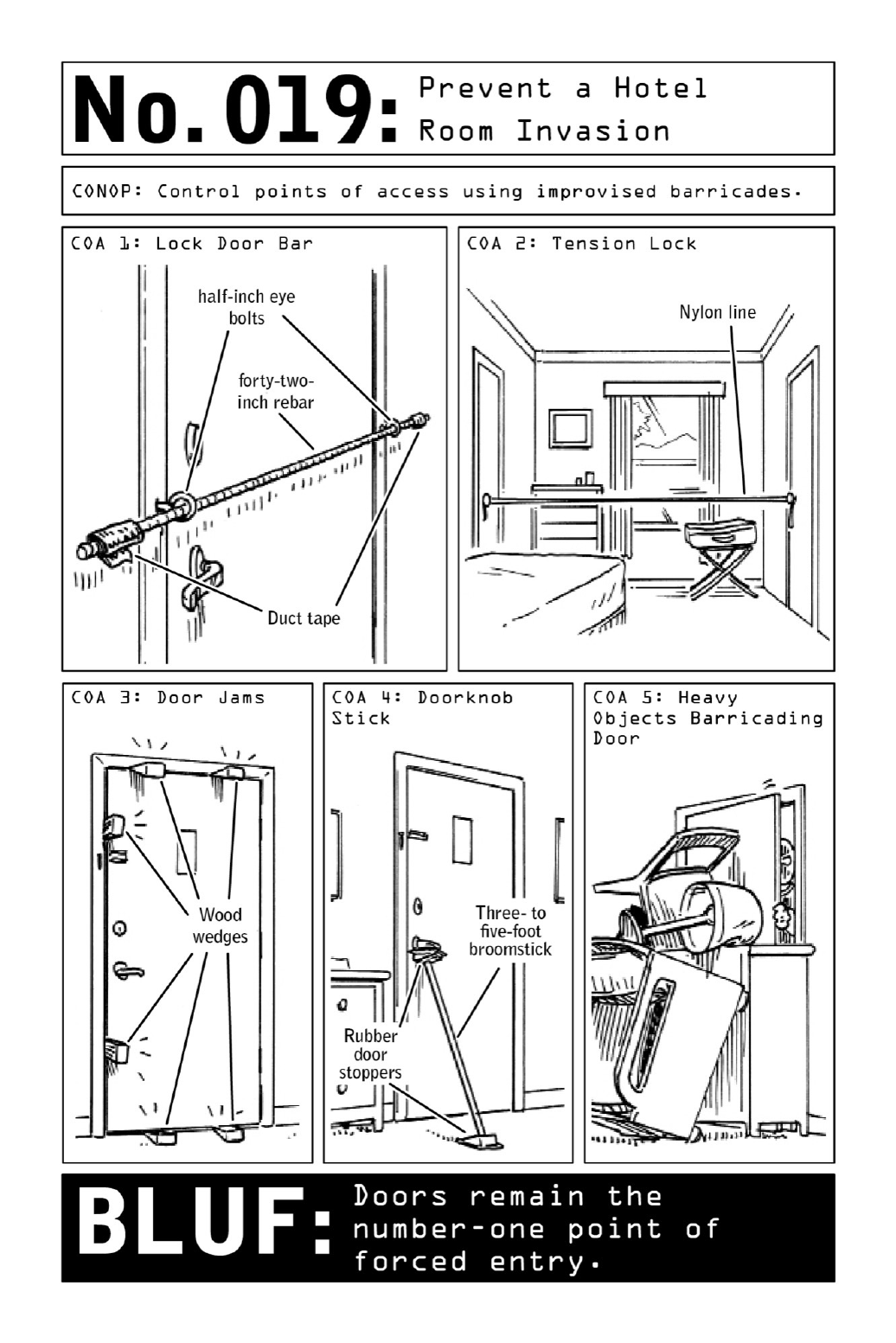
019 PreventaHotelRoomInvasion
Hotel guests can mitigate risk by making educated decisions about room and floor selection
(seepage48).Buthotelroomdoorlocksarenotoriouslyflimsy,andeventhemostwell-chosen
room is only as secure as its doorframe, often a slim wooden structure bearing little to no
reinforcement.Socivilianstravelingthroughparticularlyhigh-riskregionsmaywishtoassess
thelayoutoftheirroomsandconstructadditionalfortifications.
Whileasolidlockprovidesameasureofprotectionagainstlockpicking,onlyareinforced
doorframecanpreventanassailantfromkickinginadoor—afewstrongblowswillhammera
metal deadbolt right through a wooden frame. Covering the entire width of the door, an
improviseddoorbarspreadsthepressureoftheblowsalongthebar,relievingthedeadboltof
some of the impact and preventing it from bursting through the doorframe. Fastened with a
pair of small eyelet screws, the reinforcement mechanism leaves behind only a minimal
signatureonceitisremoved.
Inroomswheredoorsopenoutward(morecommonoutsideoftheUnitedStates),invaders
must pull the door, rather than kicking it, in order to force entry—a more difficult task to
beginwith. Asimpletrickmakestheirjobevenmorechallenging:runninga length of nylon
linefromthedoorknobtoafixedstructureortoanotherclosed,lockeddoor.
In rooms where doors open inward, wedging or barricading the door will provide
temporary reinforcement, giving an operative time to plan an escape route or create an
improvisedweaponwhileinvadersstruggleagainsttheobstacleshehassetintheirpath—from
wooden wedges typically used to keep doors open to a lock reinforcement mechanism made
outofabroomstick.Asamethodoflastresort,pilingamassoffurnitureinfrontofthedoor
providesanacceptablemeansofdelayingattackers.

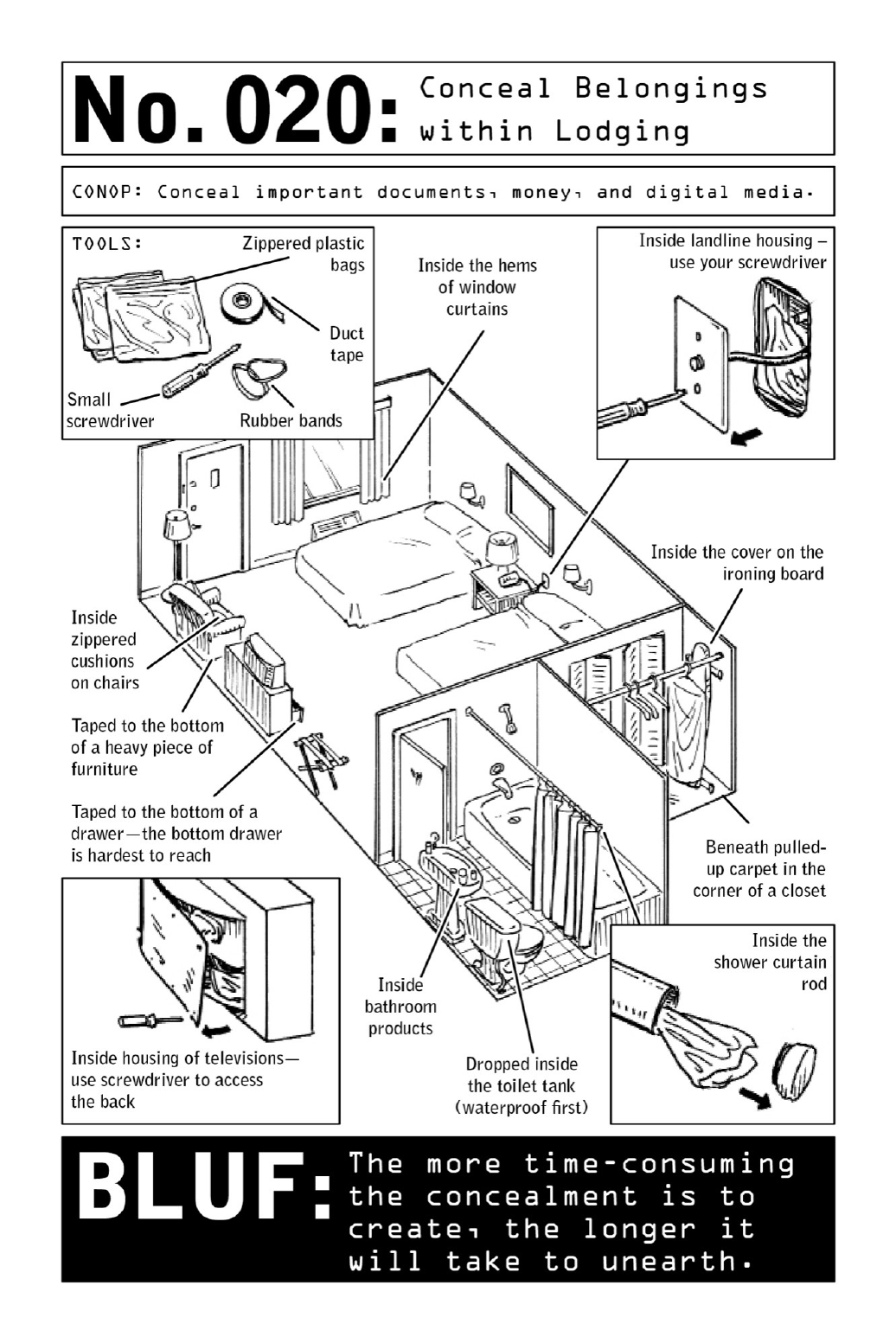
020 ConcealBelongingswithinLodging
When moving within the area of operation, operatives may take refuge in a hotel room
(booked under an assumed name), but they never let their guard down—for they are always
oneroominspectionawayfromdiscovery,andwithitmissionfailure.
Whileitisbestpracticetocarryorhideweaponsandidentificationpapersontheirperson
orinthedeadspacesofanoperationalvehicle,therearetimeswhensensitivegear,tools,or
data need to be securely stowed in a rented room. Hotel safes offer negligible protection, as
they are frequently checked by hotel staff. Instead, operatives rely on elaborate hiding
techniqueswellknowntoprisoninmatestheworldover.
Successfulconcealmentspotsshouldbetime-consumingforintruderstounearth.Intruders
(andhotelstaffalike)alwaysmovequicklywhenthey’recanvassingaroom,asthey’refearful
of being intercepted. Hiding spots that involve screwdrivers (the back panel of a television,
powersockets)willprovetootime-intensiveformostthievestodefeat.Thesespotswillalso
betraytracesoftampering—deliberatelyaligningthescrewsonanoutletoradjustingtherings
onashowercurtainaremeasuresthataresuretotrumptheaverageintruder.
Airventsaretheperfectwidthforhidinglaptopsortabletscontainingvaluableinformation
—just unscrew the grate and place them in the airshaft. Anything flat can be taped to the
undersideofadrawer.

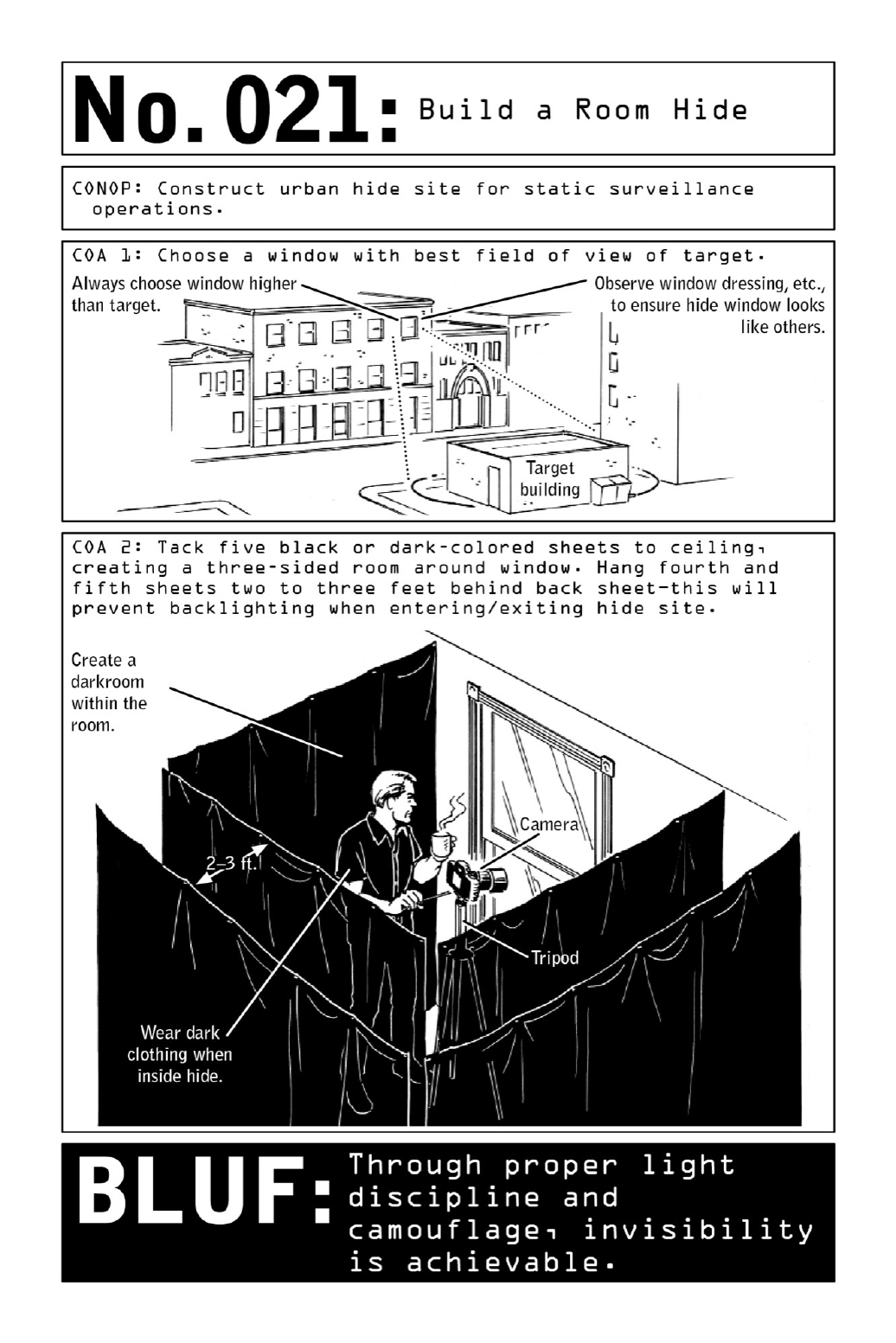
021 BuildaRoomHide
Collectinglong-termintelligenceonatargetisaprocessthatcouldgoonformanydaysand
weeks—pinning down the target’s daily routines and establishing vulnerabilities over time is
key to effective surveillance. But sitting in a parked car for days on end is bound to arouse
suspicion in even the most anonymous of cities. For long-term stakeouts the operative must
createaroom“hide,”anindoorbasefromwhichtocollectintelligenceunobserved.
Thebestroomisonethatprovidesanunobstructedlineofsightoverthesurveillancetarget.
An upper floor will maximize an operative’s field of view while minimizing his visibility.
(Mostciviliansdon’tlifttheirgazeaboveeyelevelastheygoabouttheirdailylives.)Before
buildinghishide,theoperativesurveystheoutsideofthebuildingduringthedayandatnight.
Ifcurtainsinthe buildingare drawnorshut bymaidserviceatcertaintimes oftheday, the
operativefollowssuit.
While collection by night assures a certain level of discretion, daytime surveillance may
yield more valuable information. Tocollectunobserved,theoperativeshields theroomfrom
viewbybuildingavirtualcloakofinvisibility:atemporarydarkroomthatwillenablehimto
disappearbehindawindowinbroaddaylight.Insteadofreflectinglightaswhitewallsdo,its
darkcurtainswillabsorblight,reducingvisibilityintheroomwithoutcompromisingthelook
of the window, which will appear no different than any other when viewed from a ground-
levelvantagepoint.Pinningthesheetstotheceilinginadoublelayerwillpreventlightfrom
leakingintothedarkroomuponentryandexit.

022 StealaVehicle
Unliketheirbig-screencounterparts,ViolentNomadsdon’tdriveAstonMartins,Porsches,or
anyothertypeofBond-worthyrides.Thebestvehicleforcarryingoutamissionisthevehicle
that attracts the least attention—the vehicle that will allow an operative to tail and sit on a
targetforhourswithoutriskingdetection.Thevehiclethatwillblendintotheflowoftraffic
afteraquickgetaway.
Violent Nomads often rent, cash-purchase, or commandeer vehicles; prepare and modify
themforamission;andthendumpthemwhentheyarenolongerneeded.Stolenvehiclesdon’t
leaveapapertrail—andeventhoughtheNomadwillalwaysusefalseidentificationandcredit
cards, he prefers to avoid leaving behind any potential traces. The vehicle can be used
operationally,andthendumpedorburnedlongbeforeitisreportedmissing.
SelectingaVehicle
Theoptimalvehicleforanymissionistheonethatisunremarkableineverysense.Thiswillbe
dependent upon the setting of the mission, so Nomads carefully survey their operational
environmentstodeterminethebestcarforthejob.Theyselectamake,model,andcolorthat
mirrorthemostpopularchoicesinthearea.Beyondthetypeofcar,detailsaresignificant.If
localsinthe areaofoperationhangminiature country flagsfrom theirrearviewmirrors,the
Nomadwillfollowsuit.
Additionalconsiderationsforidentifyinganoperationalvehicleinclude:
DeadSpaceandVoids:Theenvironmentand/or particularities ofa mission maydictatea
vehicle with plenty of voids where operational gear and weapons can be concealed. A
surveillance mission may require cameras, and a mission in a desert or other secluded
environment may require stocking enough food and water for days. Vehicles with the most
usablespaceincludesedans,SUVs,andutilityvehicles.
Condition:Marks,dents,orscrapesareconspicuousattributesthatthirdpartiesmightnotice
andtransmittoauthorities.Conversely,carsthatlooktoocleanalsoriskattractingnotice.In
mostenvironmentsoutsidewealthyenclaves,asoiledcarwillhaveabetterchanceofblending
inwiththerestofthecarsontheroad.
StealingaVehicle
Thesophisticatedkillswitches,transponders,andothersecurityfeaturesnowinherenttomost
modernvehiclesmakecartheftamuchmorecomplexpropositionthanitoncewas;inorder
togeta cartostart,akeyneeds tobebothcuttotheignitionandembeddedwiththe right
transponder.ThisiswhyNomadsandcommoncarthievesalikeseekoutopportunitiestonab
carkeys,carjackrunningvehicles,andhacktheirwayintoolder-modelcarswithlessstringent
securityfeatures.
Valetanddailyparkingstructurestendtodisplayextremelylaxsecuritymeasures.Keysare
often simply tagged and placed in unlocked drawers at valet booths that are frequently left
unattended,providingNomadswithanopportunitytoquicklyandeasilyfilchasetofcarkeys
tothemodeloftheirchoice.
Nomads may also canvass the streets, seizing opportunities for carjacking as they arise.
Civiliansfrequentlyrenderthemselvesvulnerablebyleavingtheirkeysintheignitionasthey
withdrawcashfromanATMorsettlethegasbillinsidethestation.
When it comes to stealing a car the old-fashioned way, Nomads seek out older-model
vehicles with proven security vulnerabilities—Hondas being one reliable example. Once the
lock cylinder is bypassed, the ignition on these models is easily switched on by the tip of a
screwdriver.
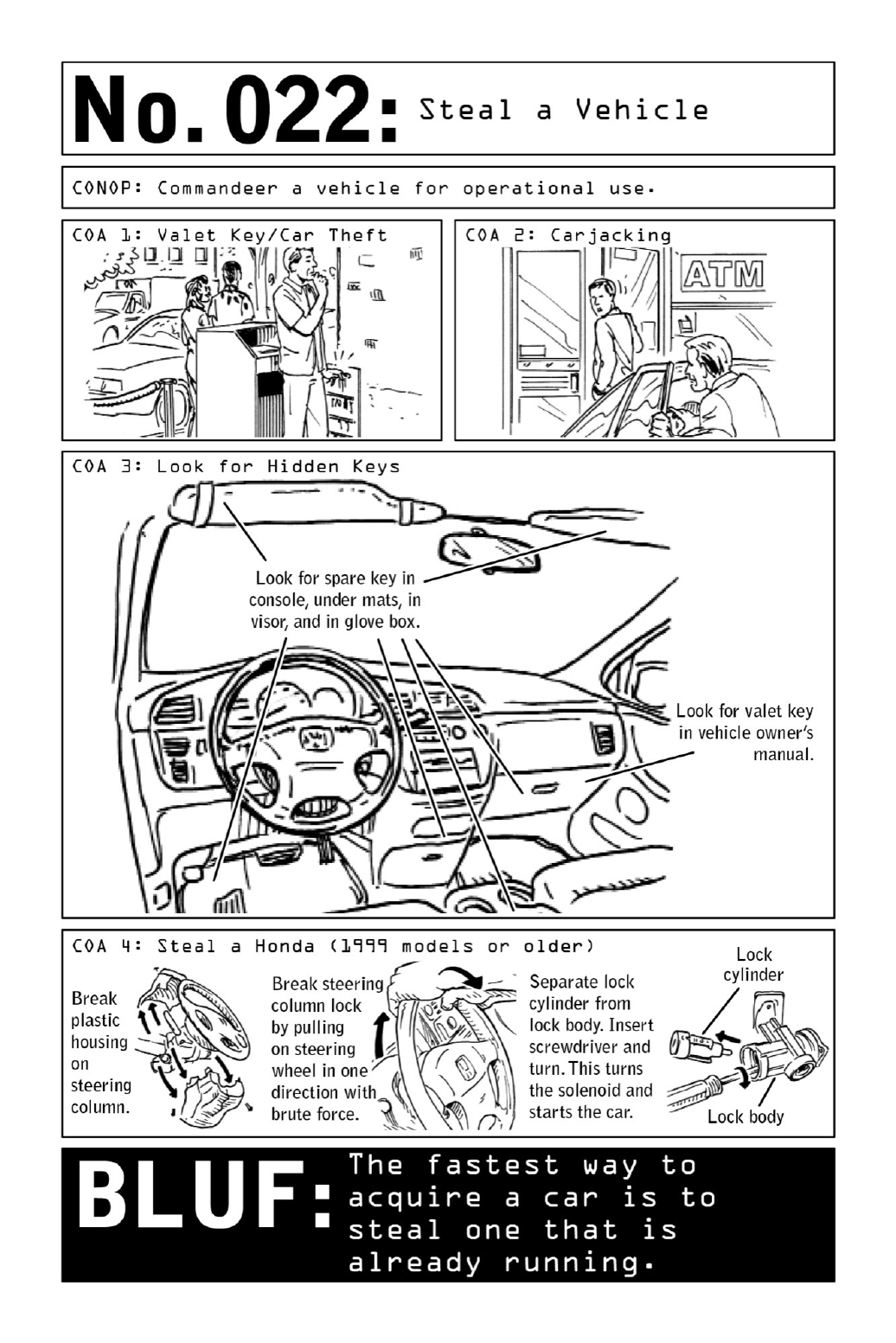
Theirfirstorderofbusinessissearchingforsparekeysand“valetkeys,”thethinkeysmany
automakersembedintovehicles’owner’smanuals;theseallowaccesstodoorsandignitionbut
won’t open trunks or glove compartments. Even high-performance vehicles have their
particular vulnerabilities, and Nomads are keen students in this area. Certain BMW models
havewiringharnessesbytheirtrunksthatcanbeshortedandusedtounlocktheentirevehicle.
To expose the lock cylinder on an older-model vehicle (see diagram), they use a few hard
knockswiththehandleofascrewdrivertobreaktheplastichousingonthesteeringcolumn.
Then,theyusethesametechniquetodisengagethelockcylinderfromthelockbody.
Beforetheoperativestartstheengine,hemustalsobypassthesteeringcolumnlock—avery
simple lock mechanism that can be broken by yanking the wheel in any one direction with
bruteforce.Insertingthetipofthescrewdriverintothelockbodyandturningittotherightis
allittakestostarttheengine.
CivilianBLUF: Never leave a running car unattended, even for a moment. Never leave your
carkeysinyourvehicle,eveninalockedgarage.Checkyourowner’smanualforavaletkey
andmoveittoasafeplace.

023 OperationalVehiclePrep
Once an operational vehicle has been acquired, undertaking a range of adjustments will
enhanceperformanceanddecreasevisibilityandtraceability.Thesemayinclude:
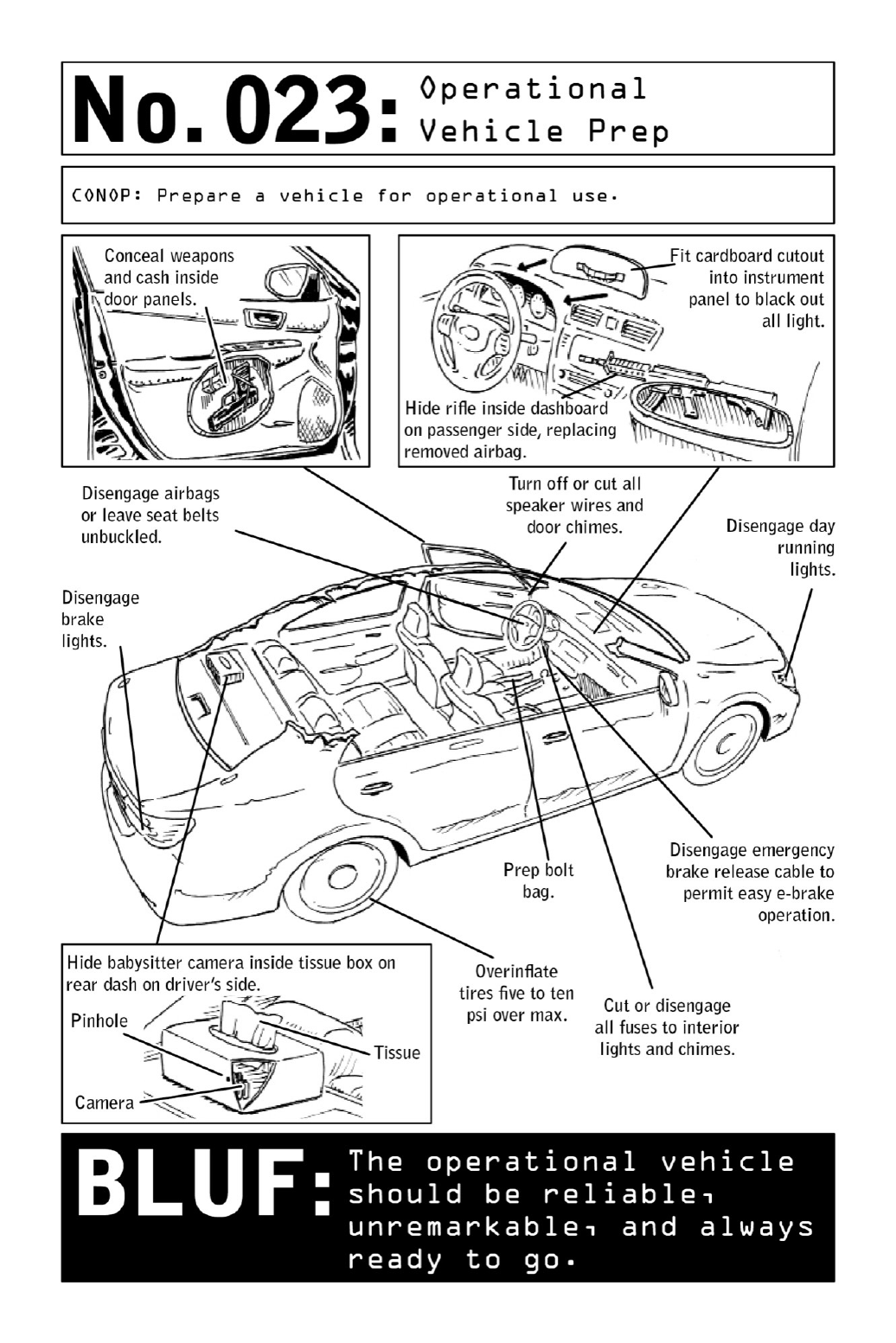
• Commandeering voids and dead space suchas the dashboard on the passenger’s side,
airbag compartments, door panels, and seat covers—a suite of caches well known to
drugsmugglersandmules. Ina surveillanceor combatcontext,these spacescanhold
anythingfromarifletoalife-supportsystemcontainingwater,food,money,laptops,
andothercommunicationdevices.
• Outfitting the vehicle with forged license plates and registration documentation.
ExpiredtagsmightblowaNomad’scoverintheeventthatheispulledover.
•Installinganannycamdisguisedinatissueboxonthereardashasanextrasetofeyes.
Depending on the direction in which it is trained, the camera can be used for
surveillanceortodetermineifsomeoneisfollowingthevehicle.
• Disabling daytime running lights, brake lights, and interior lights and chimes for
inconspicuoustravel.Partiallypullinteriorlightbulbsoutoftheirsockets—farenough
to prevent them from turning on, but not so far that they will dangle and attract
attentionintheeventthattheoperativeispulledover.
•Overinflatingtiresforoptimalperformance.

024 EscapeandEvasionVehiclePrep
Duetotheirhighinherentrisk,escapeandevasiondrivingtechniques areusedbyoperatives
onlyincasesofextremeurgency,invehiclesthathavebeenspeciallychosenandretrofittedto
make maneuvers such as the J-turn or the Reverse 180 (pages220 and 222) possible. High-
center-of-gravityvehiclessuchasSUVsarepronetoflipping,whilesmallercarsmightnotfare
aswellincollisions.Examplesofretrofittinginclude:
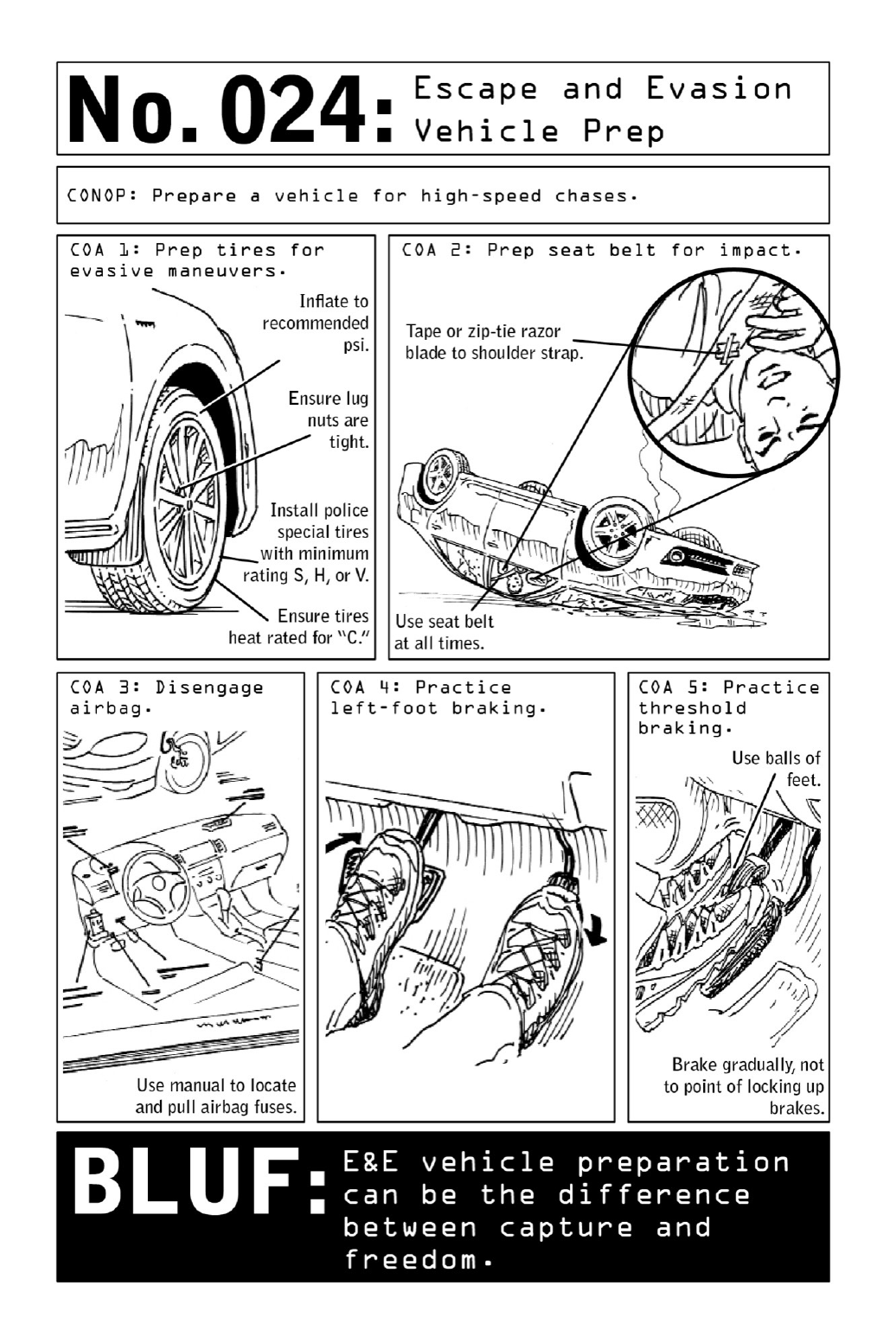
Selecting Tires: Tires should be replaced with high-performance models inflated to the
recommendedpoundspersquareinch.
Seat-Belt Workaround: In a car that is flipped upside down, the seat belt’s pendulum
locking system could become a deadly liability. If the weight of the operative’s body swings
the pendulum deep into the car door, the belt may lock into place and lose its ability to
unbuckle,soawell-placedrazorbladecanbealifesavingmeasure.
AirbagDisengagement:The lastthinga Nomad wantsis airbags goingoff—andinnewer
vehiclemodels,automaticallykillingtheengineastheydeploy—duringahigh-speedpursuit.
Left-Foot Braking: The human nervous system functions faster and more efficiently when
bothsidesofthebodyworktogether—whichiswhyracecardriversandoperativesusetheleft
footforbrakingandtherightforgas.
Threshold Braking: Learning to depress the brake pedal without locking up the tires is
necessary for precise handling. When deployed at a high speed, this controlled braking
maneuverenablesanoperativetocometoastopwithminimalslidingorskidding.

025 BuildaVehicleHide
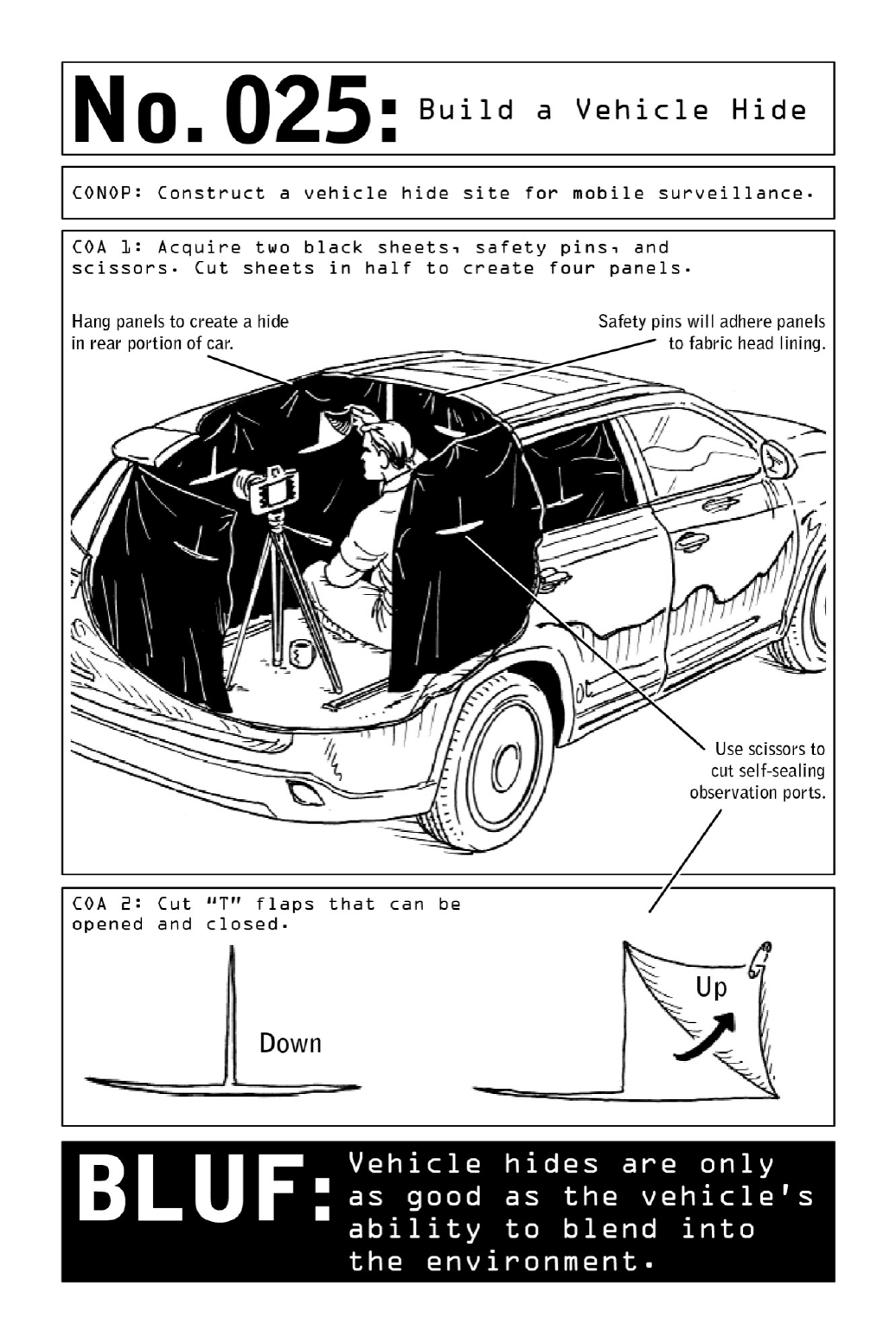
Theoptimalhidesiteforstaticsurveillanceisaroomwithaview,butinsomecasesNomads
areforcedtosetuptemporaryhidesitesinsidetheirvehicles.Thisscenarioinvolvesaslewof
vulnerabilitiesanddiscomforts,butexposurecanbemitigatedbytheconstructionofasheet-
baseddarkroomsimilartowhatanoperativewouldbuildinanurbanhidesite(page54).Such
adarkroomallowshimtodisappearasifbehindthedarkestoftintedglass—butunlikeglass,
itdoesnotleavehimvulnerabletobrightsunshineandcuriousonlookers.
AlargesedanorSUVwithtintedwindowsandfoldingseatsgivestheoperativetheability
to set up a full-fledged surveillance suite inside his low-tech darkroom. A tripod, an SLR
camera,andashutterreleasecablewillproducehigher-qualitynightshotsthanthosecaptured
byspecializednightvisionequipment.
Toavoidbeinggivenawaybyenginenoise,runninglights,orexhaustfumes,theoperative
alwaysturnsofftheignition.Incoldweather,heappliesRain-Xtointeriorglassandwearsa
nonporousjacketthatretainsbodyheatinordertopreventwindowsfromfoggingup.Heuses
emptybottlesasreceptaclesforurine;whenfilledandcappedthesecanbeplacedonthefront
orreardashtoactasdefrostingdevices.
Toenterthedarkroom,hewillconstructapretextforleavingthevehiclemomentarily,such
asgoingtothecornerforacupofcoffee.Returningtothecar,hequicklyandcasuallyslips
intothebackdooronthedriver’sside—tomostonlookersitwilllooklikesomeonehasjust
settledintothedriver’sseat.

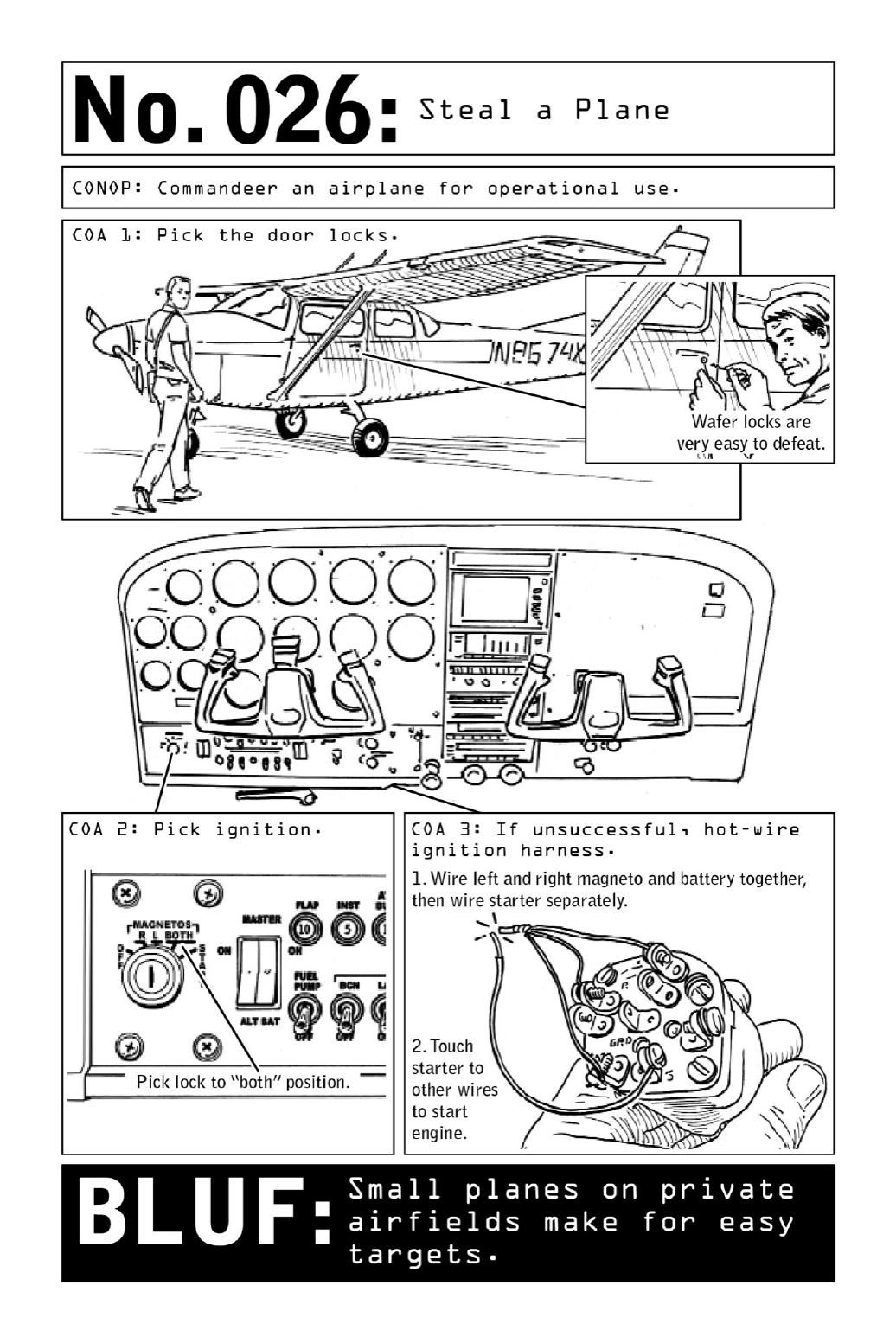
026 StealaPlane
Mostcivilianswouldbeverysurprisedtolearnthat,forthoseinpossessionofflighttraining,
swiping the world’s most common aircraft—a Cessna 152 or 172—is no more difficult than
picking the lock on a flimsy office desk. But for a Nomad looking to perform aerial
surveillanceorcrossbordersundetected(seepage32),stealingsmall,privatelyownedplanesis
justanothermeansofsecuringanuntraceablemethodoftransportation.
Relatively quiet, fuel-efficient, and reliable, single small-engine planes have several
advantagesforNomads.Theyarehigh-wing(asopposedtolow-wing)aircraft—whichmeans
their wings won’t get in the way if an operative needs to jump out in a hurry. Another
significant advantage is defined by the acronym STOAL, for “Short Takeoff and Landing”:
Small aircraft do not require very much space in which to take off and land, which enables
Nomadstoavoidrunwaysandinsteadlandinopenfieldsandotherdesertedspaces.
Most important, small aircraft tend to be outfitted with flimsy, highly vulnerable wafer
locks, making them extremely easy for an operative to steal using the picking tools and
techniquesthatapplytoanycommondoorlocks(page110).
Small aircraft are typically kept at single-run airports, where security is negligible and
airspace goes unmonitored by transportation or customs authorities. Once an operative has
brokenintothe plane, he willlikely be abletotakeoffandfly away without attractingany
notice.
Civilian BLUF: Owners of private planes are well advised to store their planes in hangars
and/orlockthemdownlikebicycles.

IMPROVISEDWEAPONS
Violent Nomads are always prepared for the eventuality of being captured and stripped of
theirweapons—orthat,inagivencontext,evenawell-concealedweaponwillposetoogreata
riskofdetection.Butbecause theyarewell versedinturningeverydayitemsintoimprovised
weapons,theywillnevertrulybecaughtunaware.
Thereisnosuchthingastheidealimprovisedweapon,asthebestweaponinanyscenariois
simplythe one thatcan be reachedwhenit isneeded.If it canbeeasilyacquiredwithin the
areaofoperationandcarriedwithoutarousingsuspicion,allthebetter.
Thoughimprovisationrulestheroost,someeffectiveweaponsofself-defensecanbecreated
withaminimumofadvanceplanning.
Forcivilians,learningtoseethedangerinherentineverydayobjectshasmultiplebenefits.A
manholdingatightlyrollednewspapermaybeaperpetratorgettingreadytostrike,butonly
thosewiththeforesighttorecognizehisweaponwillbepreparedtofendoffhisassault.And
intheeventofanattack,thecivilianwhoisabletorecognizetheself-defensepotentialinthe
materialsathandwillbeonestepahead.
Civilian BLUF: While the examples used in the following pages describe operatives
repurposing everyday items in the course of a mission, many innocuous everyday items can
standinasimprovisedweaponsofself-defenseasthesituationdemands.Evensaltandpepper
shakers, found on restaurant tables all over the world, can be used to temporarily blind an
assailant—thrownintoanopponent’s eyes,they createamomentarystingingand/or blinding
effectthatmaygiveyouthetimetoescapeorgaintheupperhand.

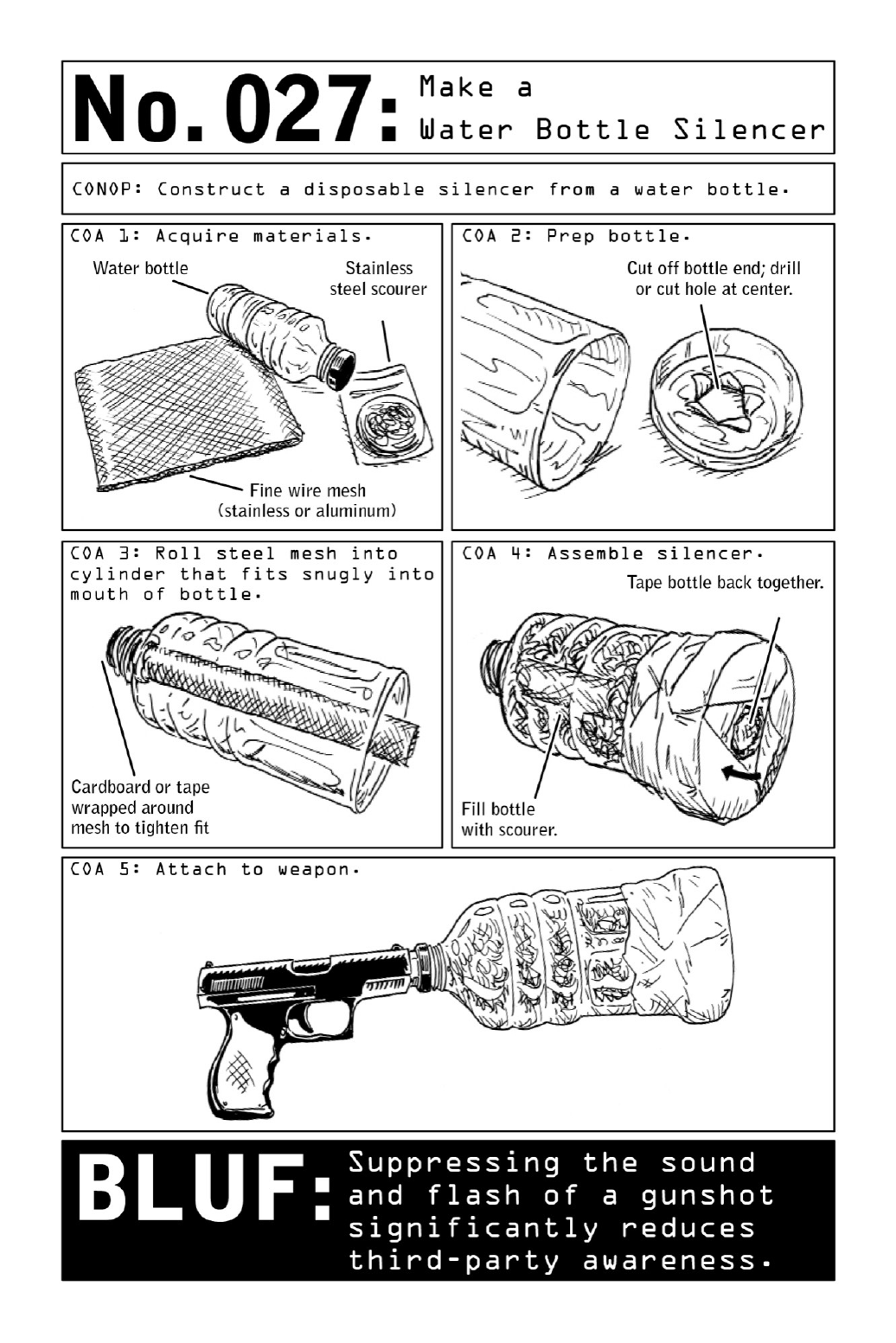
027 MakeaWaterBottleSilencer
Gunfire’s two biggest giveaways are sparks and sound: an extremely loud bang as the
gunpowder inside the bullet’s cartridge is ignited, along with the resulting flash. But paired
with subsonic bullets from a .22-caliber or .45-caliber pistol, an improvised silencer can
eliminate both. Though some states restrict or outright ban the purchase of silencers and
suppressors,aviablealternativecanbemadefromaplasticwaterbottle,asquareoffinewire
mesh,andastainlesssteelscouringsponge.Theonlyaudiblenoisewillbeatickingsound,the
resultofthepistol’shammerinitiatingtheblowbystrikingtheprimer.
Mimickingtheactionofastandardsilencer—aperforatedsteeltubeencasedwithinasolid
steel tube—the improvised version uses a two-pronged muffling device. Rolled into a tight
cylindricalshape,thestifflayerofsteelmeshwillholditsformanddirectthebulletthrough
and out of the water bottle in a straight line. Tugging on the scouring sponge will help it
expandtofilltherestofthespaceinthebottle,creatingametalpillowthattrapsandmuffles
sound. Like a makeshift steel box, the contraption dampens sound and light waves with a
surprisingdegreeofeffectiveness.
CivilianBLUF: For an imaginative predator, lethal materials are readily available. Stainless
steelscourerscanbeobtainedatanygroceryorhardwarestore,andfinewiremeshcanbecut
outofwindowscreensorscreendoors.Awarenessiskey.

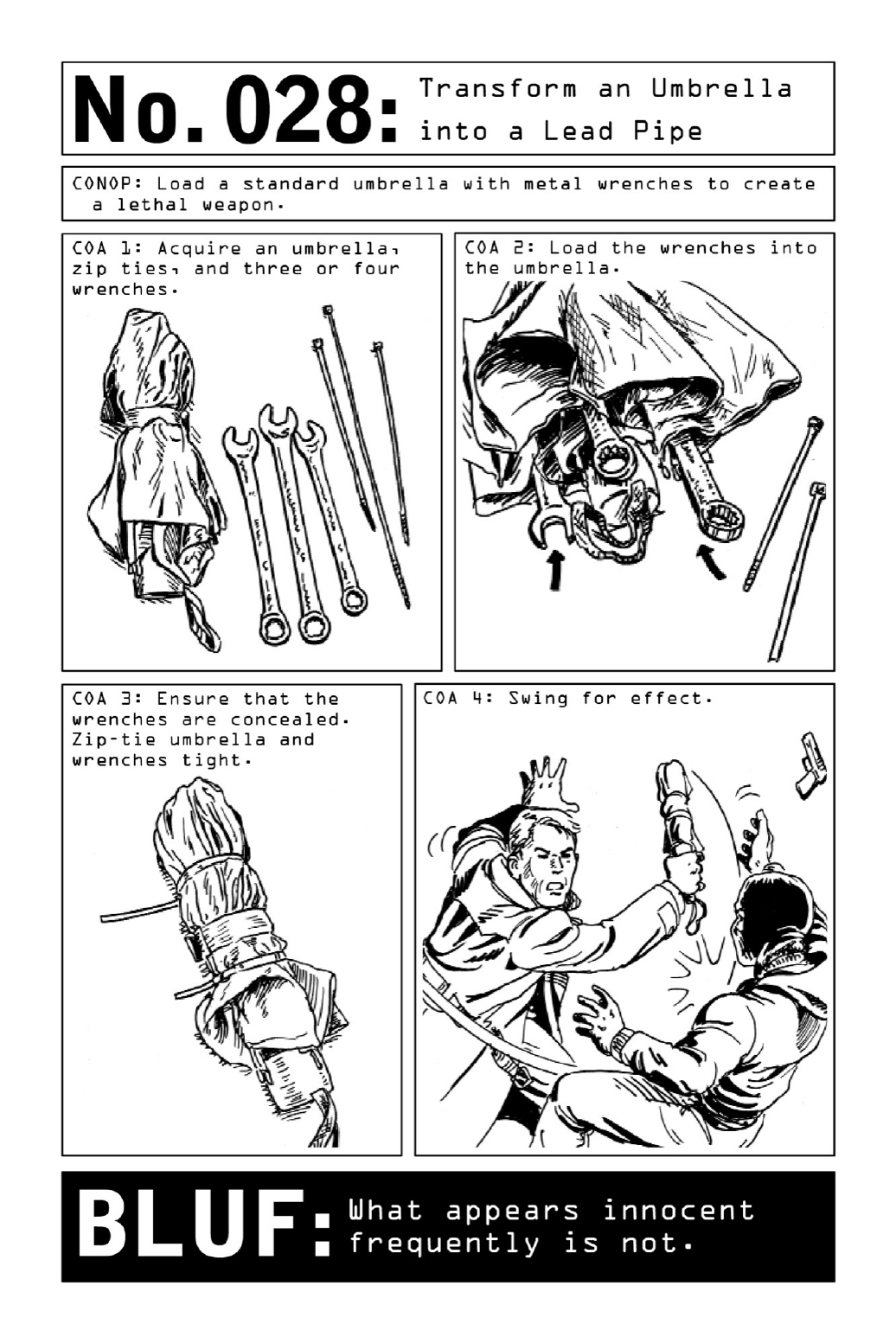
028 TransformanUmbrellaintoaLeadPipe
Because bullets and bullet holes leave forensic traces behind, the world’s most common
assassination weapon is neither a rifle nor a handgun but a piece of common lead pipe
concealedinnewspaper.Adenseandheavysapleavesbehindonlyitsintendedeffect:crushed
boneand,ifappliedtoahumanskull,utterannihilation.
Reinforced with lead, a collapsible umbrella has also been used by criminals to the same
effect.Toturnoneintoaweaponofself-defense,acquirethreetofourheavy-dutywrenches.
Slide the wrenches under the canopy and around the handle, zip-tying them to the umbrella
handlebeforesecuringtheoutsideoftheweaponwithadditionalzipties.Blacktiesonablack
umbrella will not be visible—which means that the weapon will look no different from an
ordinaryumbrella(thoughitwillbesignificantlyheavierandisnotrecommendedforeveryday
use).

029 TurnaPenintoaWeapon
The smartest pen is not a personal computing accessory but a deadly and completely
inconspicuous weapon of self-defense. In a pinch, any pen grasped from the bottom of a
handbag or briefcase can be used to inflict harm on an assailant, but one partiuclar make is
especially effective: With a barrel made of 100 percent stainless steel, Zebra’s original steel
pencanmoonlightasanincrediblemakeshiftstabbingtoolstrongenoughtopierceplywood.
Tostrike,holdthepeninatightfist.Useanoverhandgriptostrikeanassailant’sheadand
anunderhandgripifstrikingthethroatorkneeatcloserange.


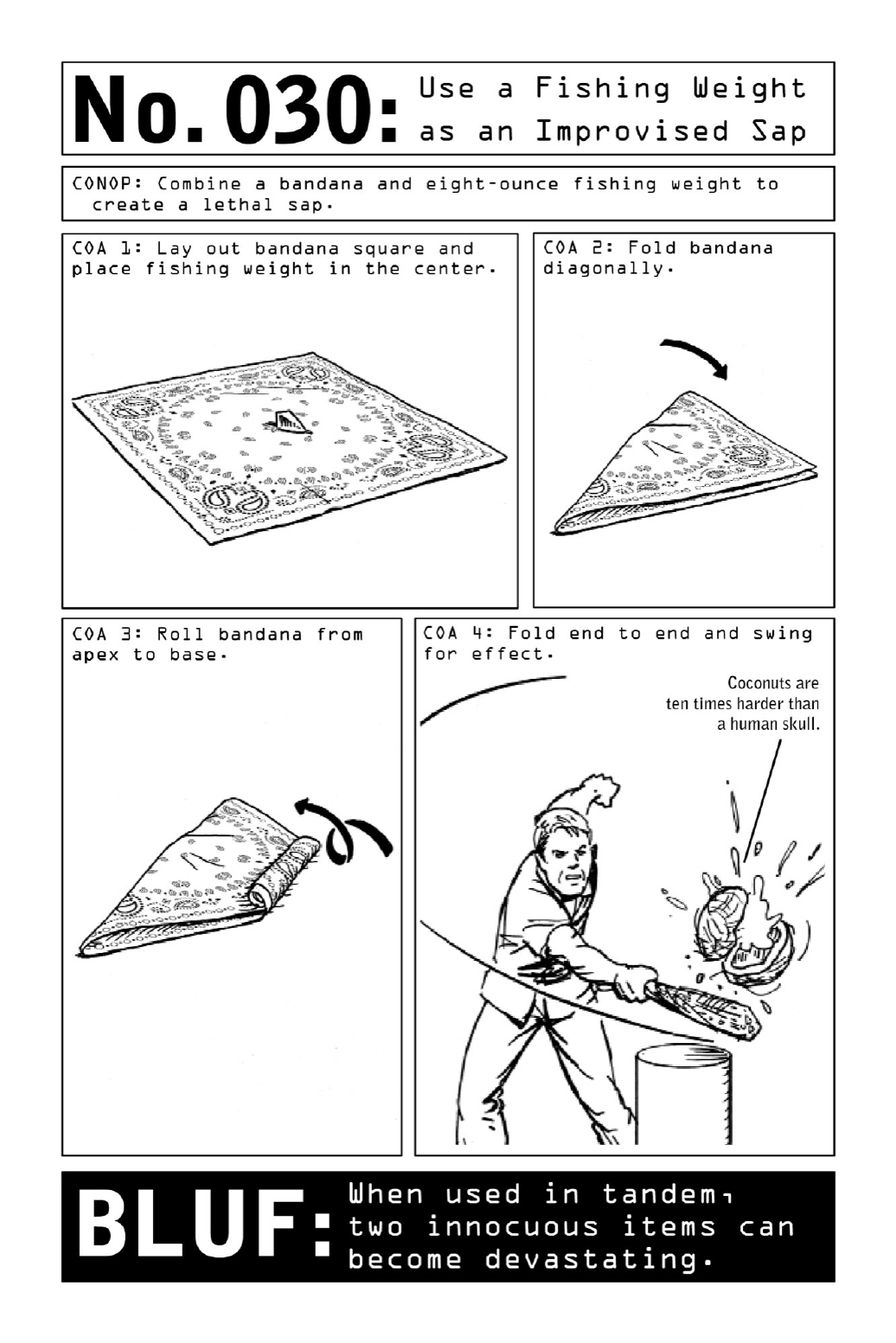
030 UseaFishingWeightasanImprovisedSap
Theinnocenttrappings ofa fishingtrip,aneight-ouncefishingweight anda bandanawould
attractnonoticeinatraveler’sbackpack.Seenseparately,theitemsposenodiscerniblethreat.
But in the face of imminent danger, they can be turned into an effective, small, and dense
makeshiftsap.
Foldtheweightintothebandana,thenrollthebandanaintoacylinder.Foldthetwoends
together and strike opponents, aiming for knee (to cause buckling) or head (to cause the
assailant to lose consciousness). The resulting weapon will be powerful enough to crack a
coconutanddoequivalentdamagetoahumanskull.

031 MakeaFlexibleChainWeapon
Thoughnowmostcloselyidentifiedwiththeworldofmotorcyclegangs,chainweaponshave
beeninuseforaverylongtime.Modeledafterthemedieval weaponcalledachainmace,a
basicflexiblechainweaponcanbemadebyattachingtwoitemsthatnaturallybelongtogether
(andhenceshouldattractnosuspicion):achainandapadlock.Theresultingweaponwillbe
strongenoughtocrackhumanbone.
Thoughanybicyclistcanusehischainandlockasimprovisedweaponsofself-defense,the
ideal length of chain—slightly longer than an average forearm—is shorter than that used to
lockupabike.Anoverlongchainwillswingtooslowly,givinganassailantplentyoftimeto
react.


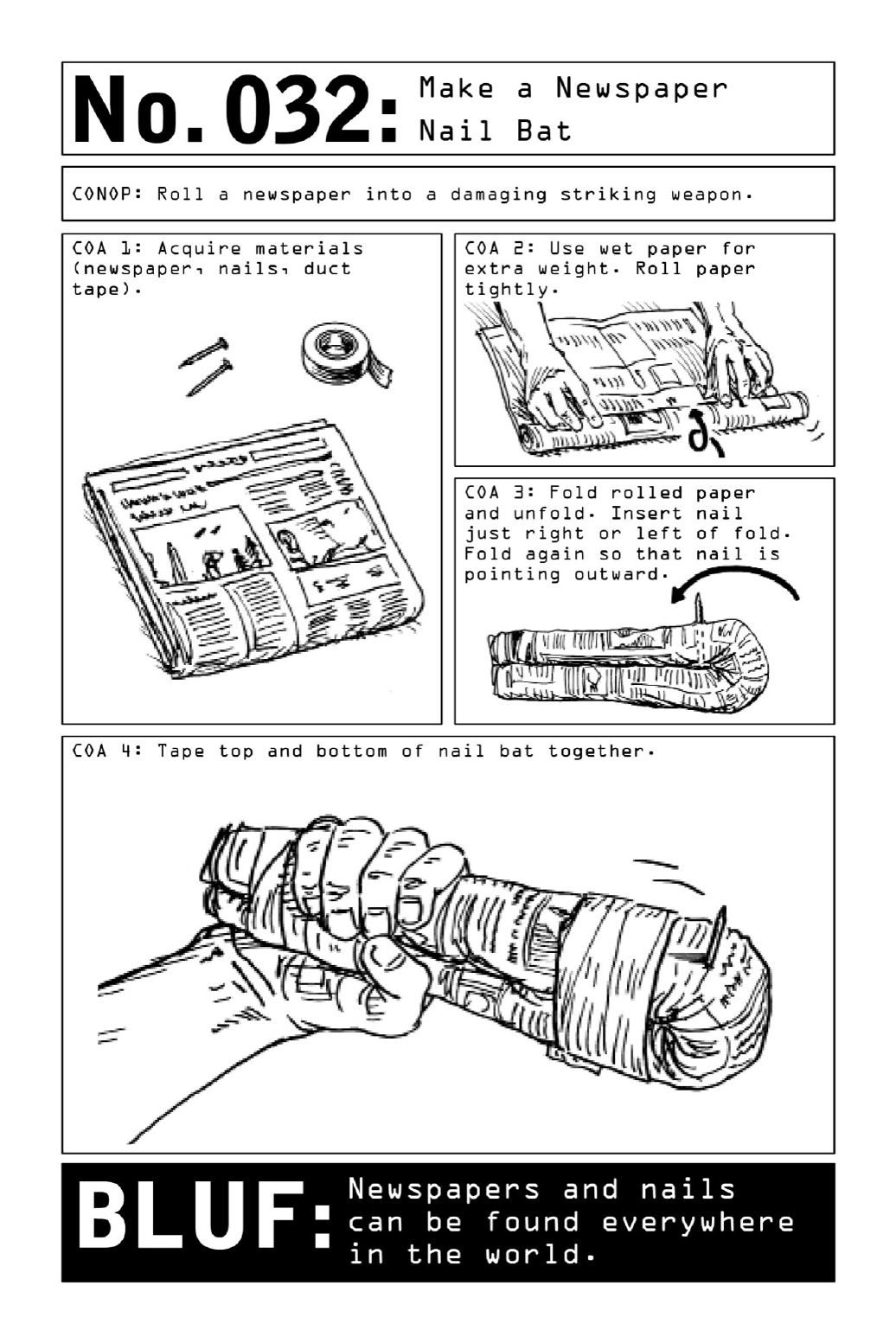
032 MakeaNewspaperNailBat
The sight of a person walking down the street holding a newspaper is one so common and
unremarkable that in the surveillance world, newspapers are frequently used as decoys; like
cell phones or cigarettes, they present operatives with an alibi for loitering on park benches
whilesurveyingatarget,ameansofbecomingacreatureoftheirenvironment.Inapinch,they
canalsobeusedasaweapon.
Rolled up into a tight cylinder that is doubled over onto itself and taped together, a few
sheetsofnewspaperbecomeasurprisinglysturdybaton.Wettingthepapergivesthebatona
significantamountofextraweight,andtheadditionofatwo-and-a-half-inchwoodnailturns
thebatonintoapotentiallydevastatingbludgeon.
CivilianBLUF:In a volatile, unsecured environment, even the most innocent of props can be
causeforalarm.

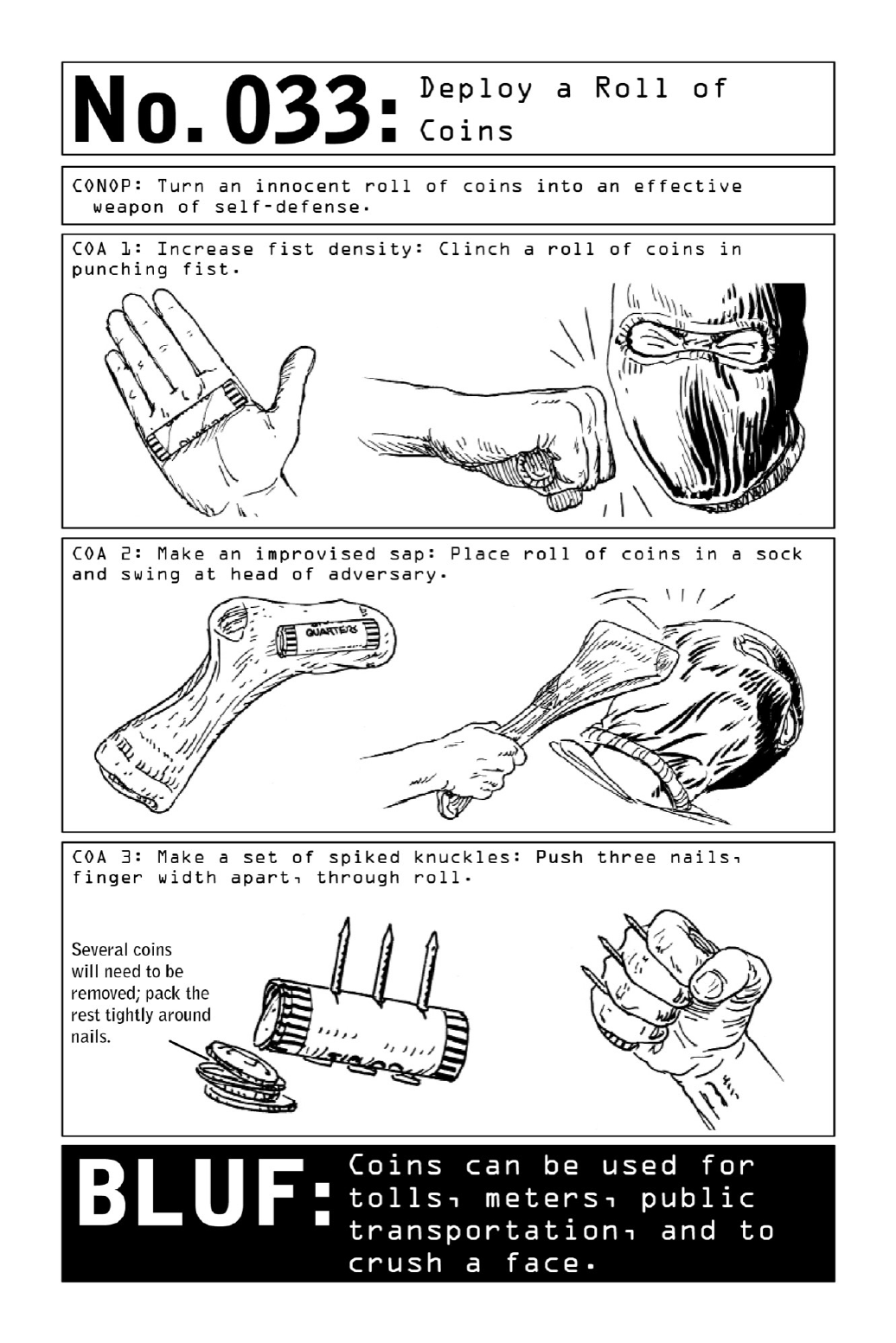
033 DeployaRollofCoins
Foraneasy-to-reachadvantageinhand-to-handcombat,anoperativekeepsarollofcoinsin
hispocketatall times. (ForeigncurrencyclosestinsizetoAmericannickelsor quarters will
resultinoptimal heft.)Grippedinthecenterofthepalm,thecoinswillincreasethedensity
and weight of his fist—a street-fighting trick that will significantly amplify the velocity and
impactofapowerpunchsuchasastraightrightorleftpunch,ahook,oranuppercut.
Stuffedintoasock,pillowcase,orhandkerchief,thatsamerollofcoinscanbeusedasan
improvisedsap.Thistypeofweapongainsasurprisingamountofpowerfromacombination
ofvelocityanddensity.Whenswungwithforce,itcanbreakbones;directedatanopponent’s
head,theimpactcaneasilyresultinaknockout.
Initsbloodiestincarnation,arollofcoinscanbestuddedwithhouseholdnailstocreatea
sharp and deadly version of brass knuckles. A punch with these spiked knuckles (another
hallmark of street fighting) will inflict serious and unexpected damage no matter where it
lands.
Carriedseparately,eachoftheseitems—arollofcoins,afewstraynails,apairofsocks—is
non-alerting. But when a Nomad senses danger ahead, they can be assembled into effective
optionsforself-defenseinunderaminute’stime.

PARTIV
SURVEILLANCE:OBSERVATION,TRACKING,
ANDCOUNTER-SURVEILLANCE

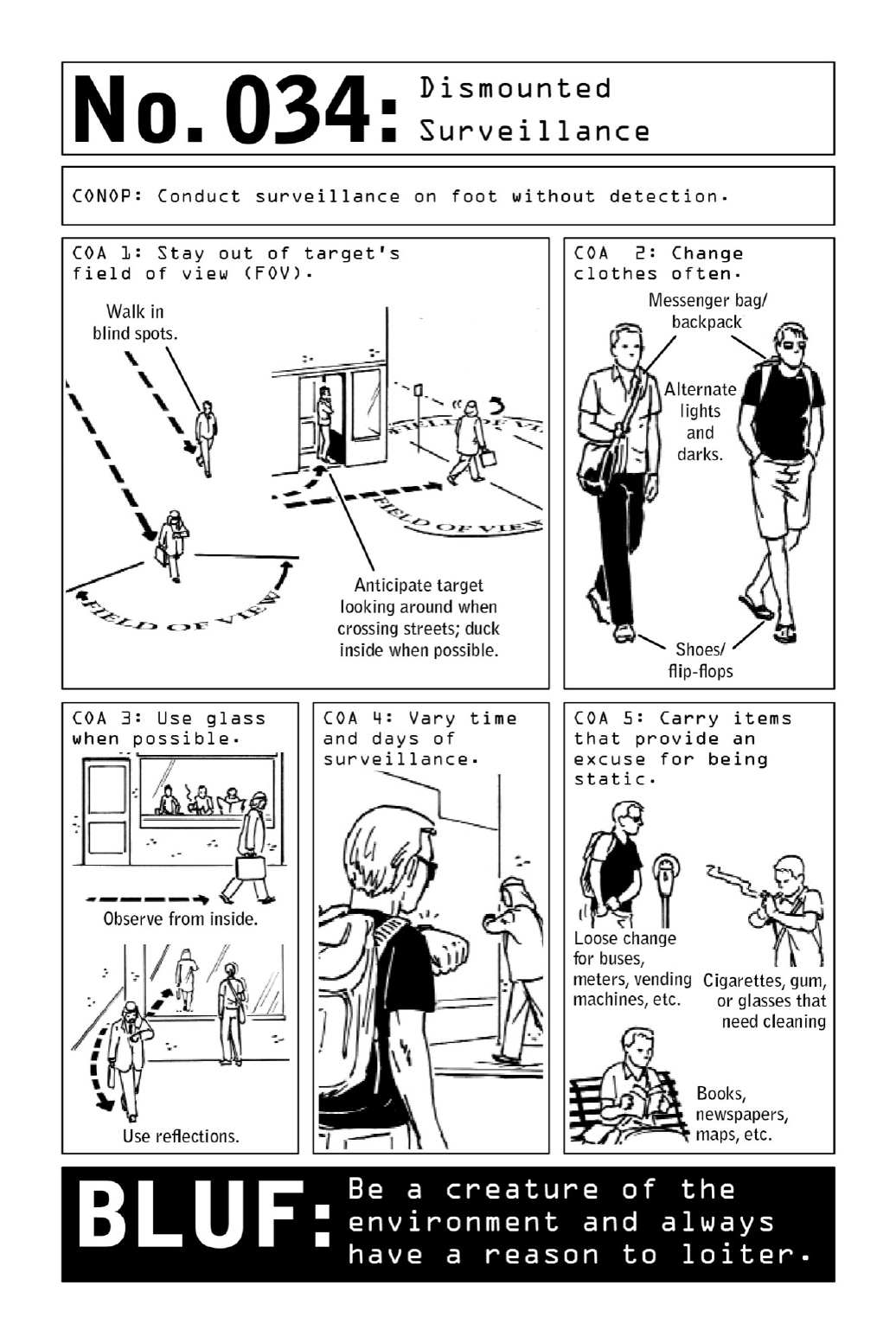
034 DismountedSurveillance
Stalking a subject on foot may be a low-tech proposition, but it is also a complex endeavor
withahighinherentriskofdiscovery.Conductingsurveillancealoneis particularlydifficult,
thestressofpotentiallybeing“burned”amplifiedaspatienceandstaminaaretestedoverlong
hoursanddays.Becauseanoperativecan’tswitchoutwithteammembers,heismorelikelyto
bespottedbythetarget.
Severalrulesofthumbcanmitigaterisk.Whenonfoot,remaininthetarget’sblindspotat
all times. While the target eats, sleeps, or works, take the opportunity to change clothes.
Switchoutofclothingasoftenaspossible—atadistance,humanbeingsarerecognizedbythe
color and style of their clothing rather than their facial features. Never wear the same thing
twice.
Usetheenvironmenttogainadvantage.Glass surfacesoffer reflectivecapabilitiesandcan
alsoallowanoperativetoscanthestreetfromapotectedvantagepoint.
Vary the timing of surveillance to learn the target’s patterns while thwarting possible
countersurveillance.Donot attempttofollowthetargetall day, everyday—that’sa surefire
way to arouse suspicion. Around-the-clock surveillance is better suited for a multimember
teamwithplentyofpeoplewhocanrotateinandout.
Eighty-five percent of surveillance teams are detected by third parties rather than by the
targetsthemselves—whichunderlinestheimportanceofblendingintotheenvironment.Look
thepart,andcarrybooks,maps,cigarettes,andotherformsof“pocketlitter”asnon-alerting
excusesforloitering.

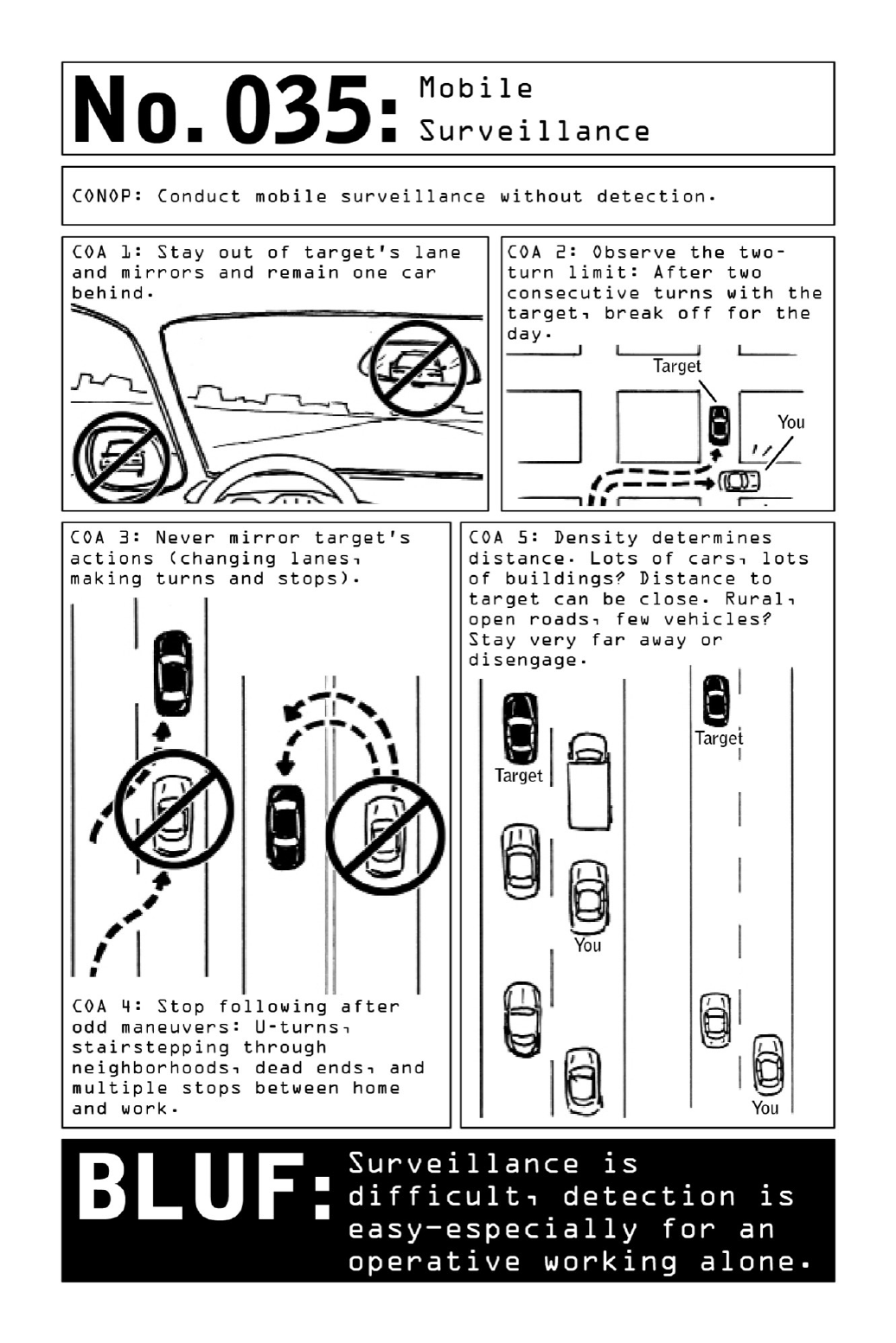
035 MobileSurveillance
Volatile, high-speed car chases may light up the silver screen, but the slow-paced reality of
vehicular surveillance is defined by patience and persistence. It’s easy to become complacent
when stuck in bumper-to-bumper traffic or waiting outside a movie theater for two hours—
andtolosesightofthe“rabbit’s”vehicleashepullsaquickrightorslipsoutofaparkinglot
duringoneofthosemomentarylapsesinattention.Vigilanceiskey.
It’s also surprisingly easy to be spotted when following a target too closely. To avoid
detection, stay out of the target’s mirrors and lane and remain one car behind at all times.
Always observe the “two-turn limit.” Following the target for more than two consecutive
turns brings a serious risk of being burned. In this and many other regards, mounted
surveillanceisfarbettersuitedtoamultimemberteaminwhichonemembercanblowpasta
turn,lettingthenextsurveillanceteammembertakeoverandbecomethenew“eye.”
Avoid mirroring the target’s actions, particularly on U-turns. If the target takes a U-turn,
movetothenextturnpocket,thenturnaroundandcatchup.Don’tfollowarabbitthrougha
series of odd maneuvers such as stairstepping through neighborhoods or pulling into dead
ends; the rabbit is probably performing these maneuvers in order to confirm that he’s being
followed.
Letdensity determinedistance.Staycloseindensetrafficand/or urbanenvironmentswith
manystoplights.Twoorthreecarsbetweenanoperativeandthetargetcouldspellalossifthe
operative misses a light or two because a car ahead of him has stopped to take a turn. In a
ruralareawithlowdensity,stayfarback;fewerdriversontheroadmeanslesscamouflage.
CivilianBLUF: Increase your awareness of cars that seem to be mirroring you as you drive
(particularlythosethatfollowyouonmultipleturns)andyouwilldecreaseyourvulnerability
toabductionsorcarjackings.

036 MakeanImprovisedInfraredLight
Anoperativecollectingintelligencefrominsideatarget’shomeorplaceofbusinessmaywait
fordaysforthecoasttoclear—andwhenthatmomentarrives,hiscollectionprocessmustbe
swiftandundetectable.Inthedarkofnight,wheneventhesmallestamountofambientlight
cancompromiseamission,aninfraredlightsourceprovidesanidealrecourse.Invisibletothe
nakedeye,itallowsaNomadtosearcharoomincompletedarkness.
Though infrared bulbs and filters are commercially available, such purchases may create
unwanted scrutiny; an improvised solution, using a flashlight, a piece of camera film or the
slipofplasticinsidefloppydisks,andacameraphone,providesthesameresults.
Whilebothfilmandfloppydisksarebecomingextinctinthedevelopedworld,theyarestill
readilyavailableinmanycountries.Placedinfrontoftheflashlight’sbulb,thefilmactsasa
filter, blocking the flashlight’s visible light rays to undetectable levels. A standard camera
phone(seebelowforexceptions)willallowanoperativetoviewtheobjectslitbytheinfrared
beam emitting from his modified flashlight. Though he’ll be working in complete darkness,
anyobjectthelightisshiningonwillbevisibleinhiscameramonitor.
Note: Some of the newest camera phones come equipped with infrared blocking filters that
render them unsuitable for this usage. To find out if a particular model will work, obtain a
remotecontrol. Turnthecamera onandpointthefrontendoftheremote(the endwiththe
LED lightbulbs built into it) toward the phone’s screen. Press any button on the remote and
lookatitthroughthescreen.Ifthecameradoesdetectinfraredlight,theglowoftheremote’s
LEDbulbswillbevisible.Ifnot,aninexpensivephonepurchasedwithintheareaofoperation
willbelikelytoincludeaninfraredfilter.


037 MakeaTrackingDeviceforNightSurveillance
Mobile surveillance is a uniquely challenging skill set in the intelligence-gathering arsenal.
RequiringaNomadtoengagewithmultiplestreamsofinformationatonce—fromtheflowof
traffic to a target’s sudden turns to the possibility of being spotted—it becomes even more
difficultifavehicle’sdistinguishingfeaturesareeclipsedbythedarkofnight,whenidentifying
a car by its make and model becomes a near impossibility. Similar difficulties emerge if a
Nomadneedstotrackatargetthroughdenseurbanenvironmentsorwhenthetargetdrivesa
commonvehicleinacountrywherelicenseplatesareseenasoptional.
When the ever-present possibility of losing the target is multiplied by these factors, a
rudimentaryinfraredtrackingdevicecanbeusedtoilluminatethetrackedvehicle.Forgedout
ofcamerafilmorfloppy-discmaterialandawhite-lightkeychainLEDflashlight,itfunctions
identicallytoanimprovisedinfraredlight(page90). But insteadof beinghandheld,oncethe
deviceisassembleditiszip-tiedtotheundercarriageofthetargetvehicle.
Camerafilmorfloppy-discmaterialwillsubtractthevisibleraysfromanymechanismthat
emits white light, acting as a barrier that lets only infrared rays (invisible to the naked eye)
through. Lending a telltale glow that is visible only to the Nomad viewing the roadway
throughthelensofadigitalcameraorsmartphone,theresultingmakeshiftdeviceprovidesthe
sortofclose-rangeconfirmationtrackingthatasatellitedevice(seepage100) mightmiss by
several feet. (More suitable for longer-term surveillance, GPS tracking devices enable
surveillanceteamstoestablishthetarget’spatternoflifeovertime.)


038 DetectTamperingofPersonalEffects
Scrutiny of Westerners in developing economies is an increasingly common phenomenon.
Whether seeking trade or government secrets or attempting to determine a visitor’s ulterior
motivesfortravel,inmanycountrieshotelsecurityandgovernmentofficialsworkintandem
tosurreptitiouslypoliceforeignersstayingintheirproperties.
To find out if their belongings have been tampered with and determine their surveillance
status, operatives use discreet alignment techniques to monitor the placement of electronics
andvaluables.
The key word is discreet. Giving host-nation security services reason to believe that an
operative is onto them could result in their upping the ante and moving to detain him—or
worse.
CardinalBearingsTechnique: Use a compass or a compass app to align items in cardinal
directions. Position obstructions around the USB ports on a laptop to determine whether
intrudershaveusedflashdrivestodownloaddata.
SpaceandDepthTechnique:Experiencedhackerswillbypasstheoperatingsystem,flipping
a laptop upside down and unscrewing the hard drive in order to capture the contents of the
computer.Todeterminewhetheralaptophasbeenmoved,useathumbasameasurementtool
whensettingitintoposition.
Traps:The“donotdisturb”signonahoteldoorcanbeputtogooduseasatelltalesignthat
aroomhas,infact,beendisturbed.
Photo Trap: Use Photo Trap or a similar app (see page 126) to compare before and after
shotsof belongings. Suchapps comparebefore andaftershotstakenfromthesame position
andanimateanyportionsthataren’tanexactmatch.


039 DetermineSurveillance
Almosteverycriminalact,frompursesnatchingandothermisdemeanorstosexcrimesoracts
ofterrorism,involvessomedegreeofpreoperationalsurveillance.Thoughtheymaybefocused
on watching a target, criminals themselves are actually quite vulnerable to detection during
thistime—particularlyiftheirtargets(unliketheaveragecivilian)remainalertandattunedto
theirsurroundings.
Toconfirmsurveillance,ViolentNomadssearchfor“coincidences”repeatedovertimeand
distance, employing a multipronged approach governed by the acronym TEDD (Time,
Environment, Distance, and Demeanor). But be subtle—it’s advantageous to let criminals
believethey’velosttheirtargetaccidentally,ratherthanhavethemthinkthetargetisevading
them.
Time:Isthesamepersonorpeopleobservedrepeatedlyovertime,indifferentenvironments?
Todeterminewhetherthisisthecase,payattentiontotheclockthroughouttheday.
Environment:Noticeanypeoplewhosedressorbodylanguagedoesnotfittheenvironment?
Distance: Are the same people popping up in environments separated by a fair amount of
distance? For instance, was the same man in the dark glasses seen ten minutes ago in a
neighborhoodstore(lesssuspicious)ortwohoursagoinasupermarkettenmilesaway(more
suspicious)? Eliminate coincidence in order to confirm surveillance—test out theories by
runningerrandsacrosszipcodes.
Demeanor: In a possible surveillance context, “demeanor” stands for both behavior and
appearance. Be on the lookout for people whose dress or behavior does not fit the
circumstances.
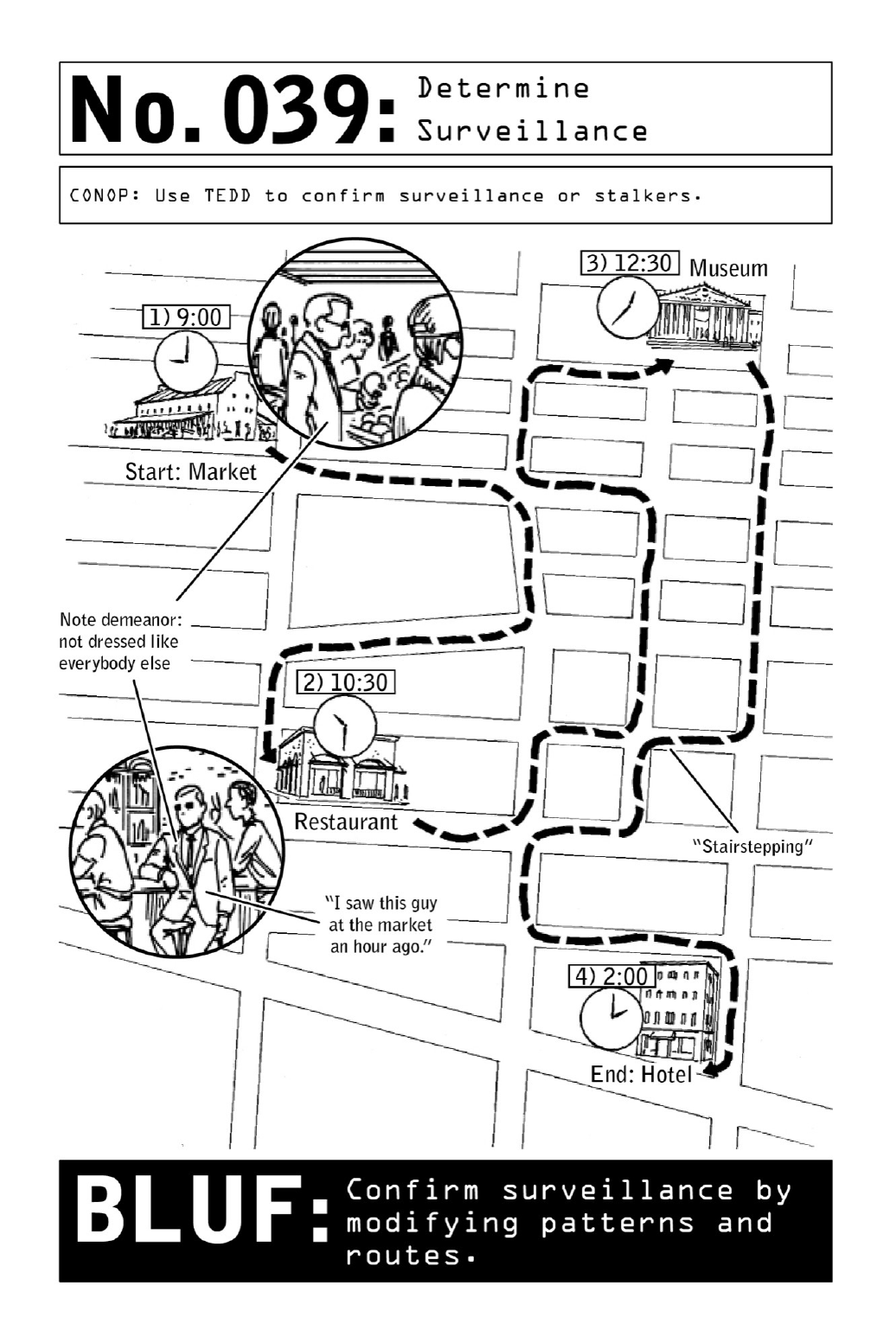

040 DiscreetlyLoseSurveillance
The key to getting rid of a surveillance team without escalating a tail into a heated chase is
letting them believe they have lost their target—and not the other way around. To lose a
mobile surveillance team, forgo highly visible evasive driving techniques in favor of the
followingprotocol:
CreateanAccordionEffect:Breakdownasurveillanceteambydraggingitthroughanarea
withmanylightsand/orstopsigns.Alongstretchofstop-and-gotrafficwillthinoutateam
without alertingitsmemberstotheNomad’s agenda. Thecarclosesttohimmaystayclose,
buttherestoftheteamwilleventuallygetstuckseverallightsaway.Unabletoswapoutwith
teammembers,thelonetailmaygrowwaryofalertinghistargetandopttodisengage.
StopandStartFrequently:Surveillanceteamstendtolosetargetsonthestartorstopofa
movement—so increase the frequency of stops. An operative parked near an exit could take
tworight-handturnsoutofthelotbeforetheteamrealizesit’stimetostartmoving.
Use Public Transportation: To lose a surveillance team by hopping on public transport,
planinadvance.Arriveatadestinationjustasthebusortrainispullingupandhoponbefore
thetailcanmobilize.
Transit through HighlyPopulated Areas: Density and congestion make it difficult for a
teamtokeepeyesonatarget.Whenonfoot,enterhigh-trafficspotssuchasmalls,amusement
parks,andtouristtrapstoincreasethechanceofaloss.
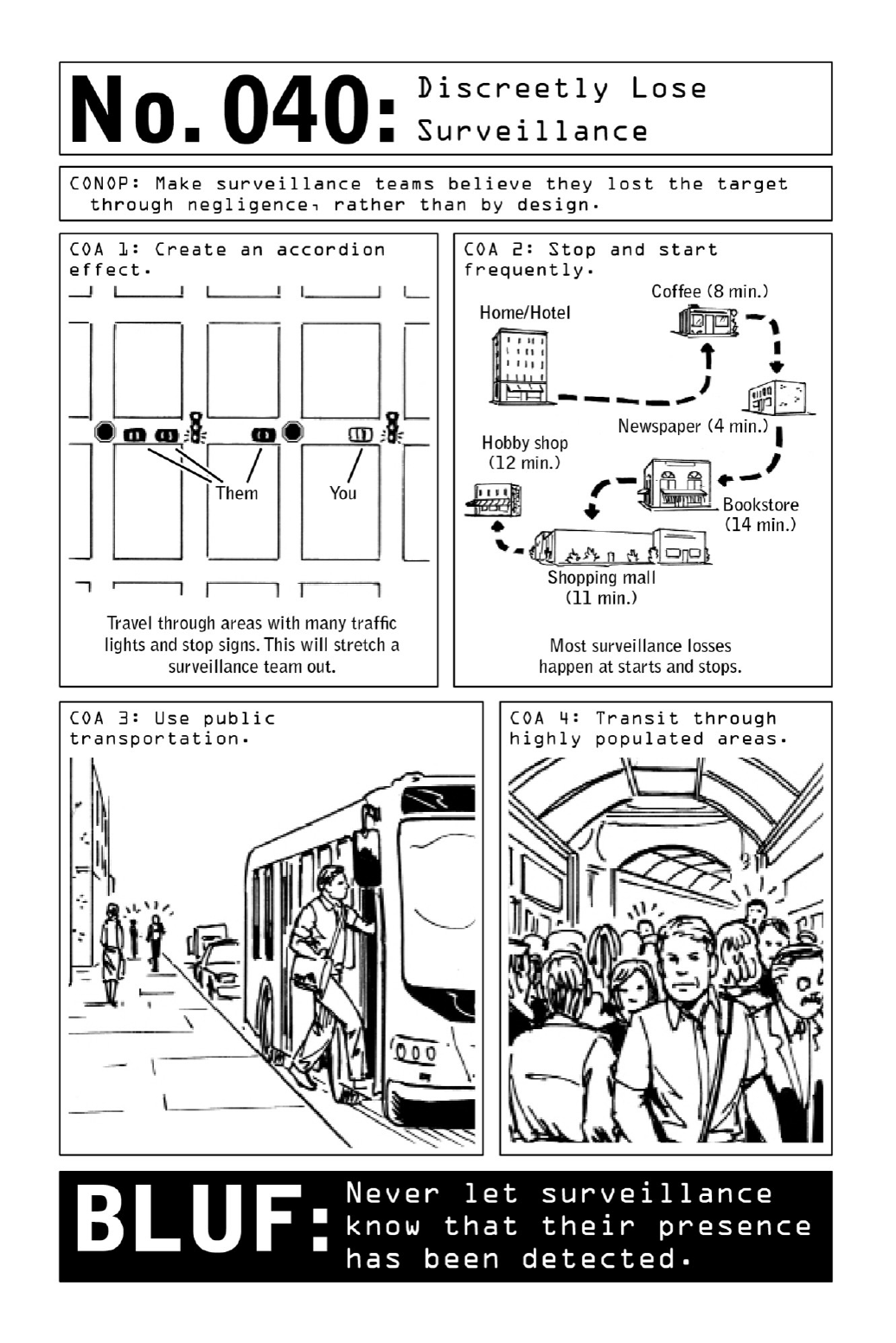

041 DetectTrackingDevices
Inthesedaysofshrinkingtechnology,affixingamagnetizedtrackingdevicetoavehicleisan
all-too-easy proposition. Readily available for purposes from parenting to surveillance,
tracking devices come in sizes as small as thumb drives—and they’re also preinstalled in a
varietyofcontexts,pingingthelocationsofmobilephonesandrentalcarsalike.Foroperatives
travelinginternationally,it’ssafetoassumethatanyrentalcarwillcomepre-equippedwitha
built-in tracking device used to deter theft. But in the hands of an unfriendly host nation,
there’snotellinghowthisinformationcouldbeused.
Communicating via satellite, cellular towers, and server banks, tracking devices can be
eitherpermanentlymountedtoavehicleortemporarilymagnetizedtoitsframe.Becausetheir
signalscannotpunchthroughmetal,theycannotbehiddenbeneaththeframeormetalpartsof
thecar—whichmeanstherearespecificplaceswheretheyareusuallyfound.
Toavoidgettingcaughtovertlyinspectingavehicle,listenforatelltalestatic.Turnoffany
cell phones, and set the radio to an AM station that’s crackly and out of range. If an
occasionaltickingsoundcanbedetectedbehindthatfuzz,thereissomekindofcellulardevice
at workinsidethecar.(Thesoundarisesfrom theinteractionofthecellularsignalwiththe
radio’sspeakerwireandcoil.)
Donotattempttoremovethetrackingdeviceifthereisreasontobelievethatthetracking
is nefarious rather than a matter of standard protocol; instead, come up with an excuse to
tradeinthecar.
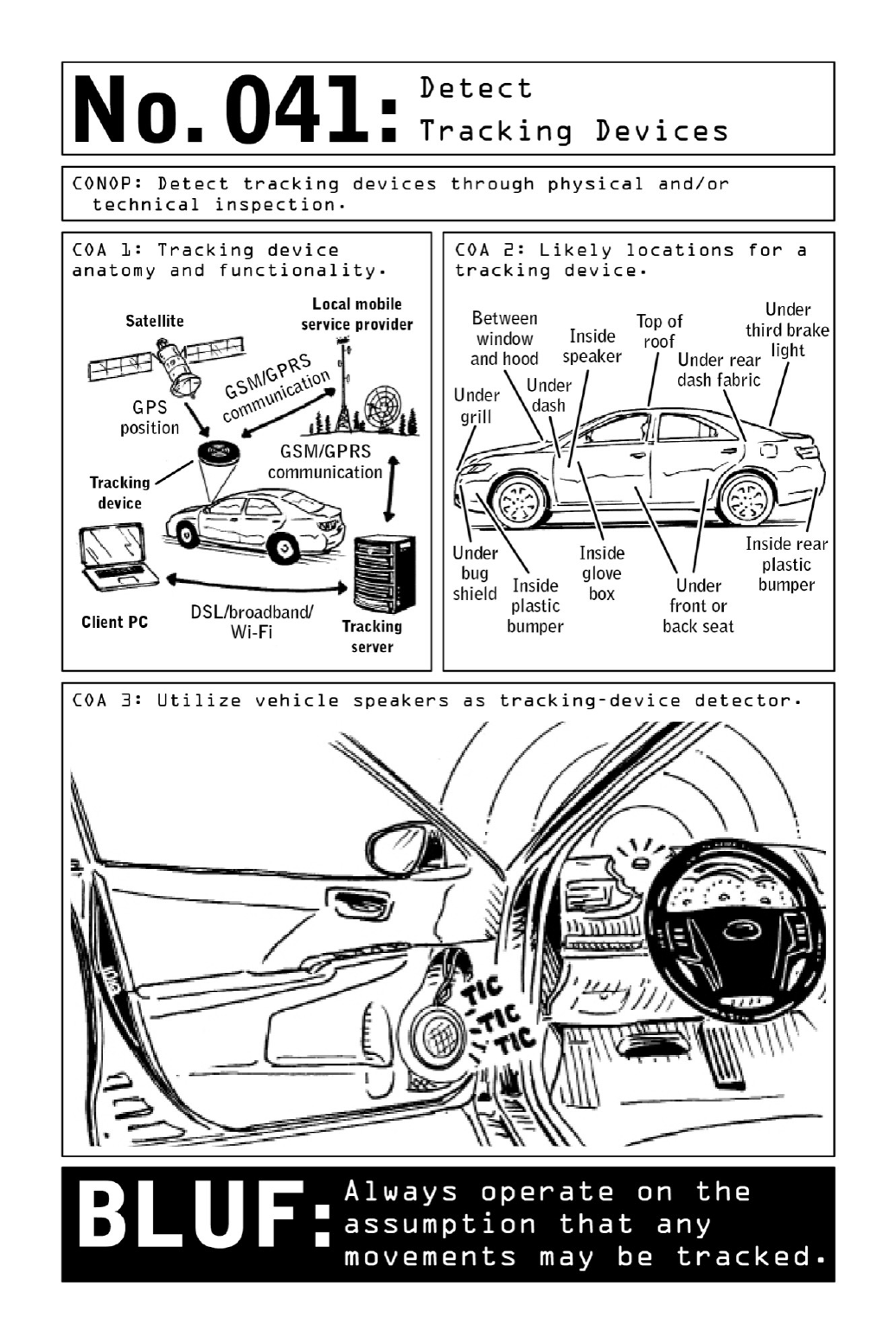

042 DeceiveSurveillanceCameras
Capturing footage of our faces at traffic stops, ATM machines, and outside businesses from
jewelrystorestopizzajoints,surveillance camerasline the streetsinmajorcities. Andgiven
howcheapthey’vebecome,theyarenowfoundinevenremotepartsoftheworld.Toerron
the safe side, a Violent Nomad always assumes he is being filmed and employs several
methodsofconcealmentanddisruptiontoreducetheriskofbeingidentified.
Disguise: Operatives avoid masks or outlandish disguises, Hollywood plot devices that will
quicklygetthemspottedbythirdparties.Instead,theywearhatsorheadcoverings.
Light:Theauto-exposurefeatureonmanycamerasconstrictstheapertureinbrightlight—so
shining a flashlight or LED directly into the camera will result in a lower-quality image, as
will timing movements so that the sun is always behind an operative when he encounters a
camera.
Static:Asecuritycamera’scoresignaltravelsdownacopperconductorsheathedinlayersof
braided metal and rubber. Placing a steel razor blade in contact with that copper conductor
will short the connection, temporarily disrupting the camera’s video feed. After the blade
slides through the rubber jacket, it is wiggled through the braided shield until it reaches the
hardmetalcore.Leftinplace,thebladewillcausethemonitortofillupwithstatic.Assoon
astherazorisremoved,thesignalwillreturntonormal.
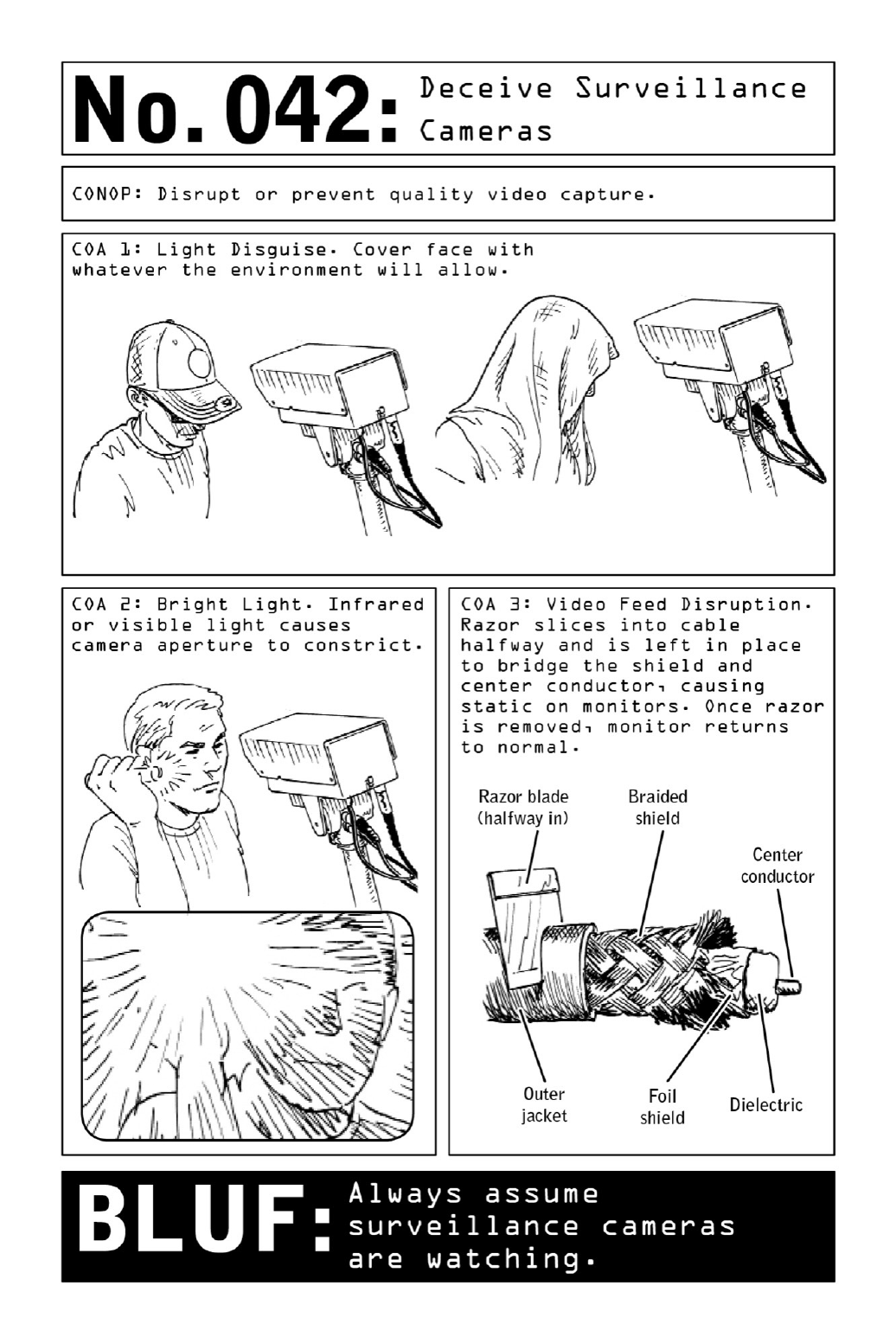

PARTV
ACCESS:CLANDESTINEBREAKINGAND
ENTERING

PICKINGALOCK
An operative typically prefers a method of clandestine entry that will allow him repeated
accesstothetarget’sdomicileor placeof business, butmissiontimelinessometimesdemand
moreimmediateaction.Insuchcases,theoperativemayreverttothetime-honoredpracticeof
lockpicking.
Though popular depictions of breaking and entering frequently show thieves bypassing
locked doors with the cursory jiggle of a screwdriver, in reality it takes two hands and two
toolstoopenalock—onetoliftthelockpins,andonetoturnthecylinder.
Still,asthefollowingpageswilldemonstrate,itisremarkablyeasyforintruderstobypass
commondoorlocks.Thebestpreventionisahigher-qualitydoorlock,buttherearemeasures
civilianscantaketoreinforceeventheflimsiestofhotelroomlocks.

043 CreateImprovisedLock-PickingTools
Whileanylockwithakeycantheoreticallybepicked,high-securitylocksfeaturingpinsthat
mustbeliftedandtwistedprobablywon’tbevulnerabletoimprovisedinstruments.Mostpin
tumblerandwaferlocks,however,canbedefeatedwithnothingmorethanacoupleofpaper
clipsandasignificantamountofpractice.
Using two paper clips, along with a pair of pliers and a flat file or hard surface, an
operative can create improvised tools to simulate the actions of a rake pick and a tension
wrenchortorsiontool.
Larger,thicker-gaugedpaperclipsarepreferable,astheywillholdupunderpressure;bobby
pinsorthebandmetalusedtoholdshippingcratestogethercanbeusedasanalternative.
Thinningtheinstrumentswillallowmoreroomformaneuveringandensurethatbothtools
areabletofitinsidethelocksimultaneously.Intheabsenceofafile,thefloororawallcanbe
usedtosandthemdown.
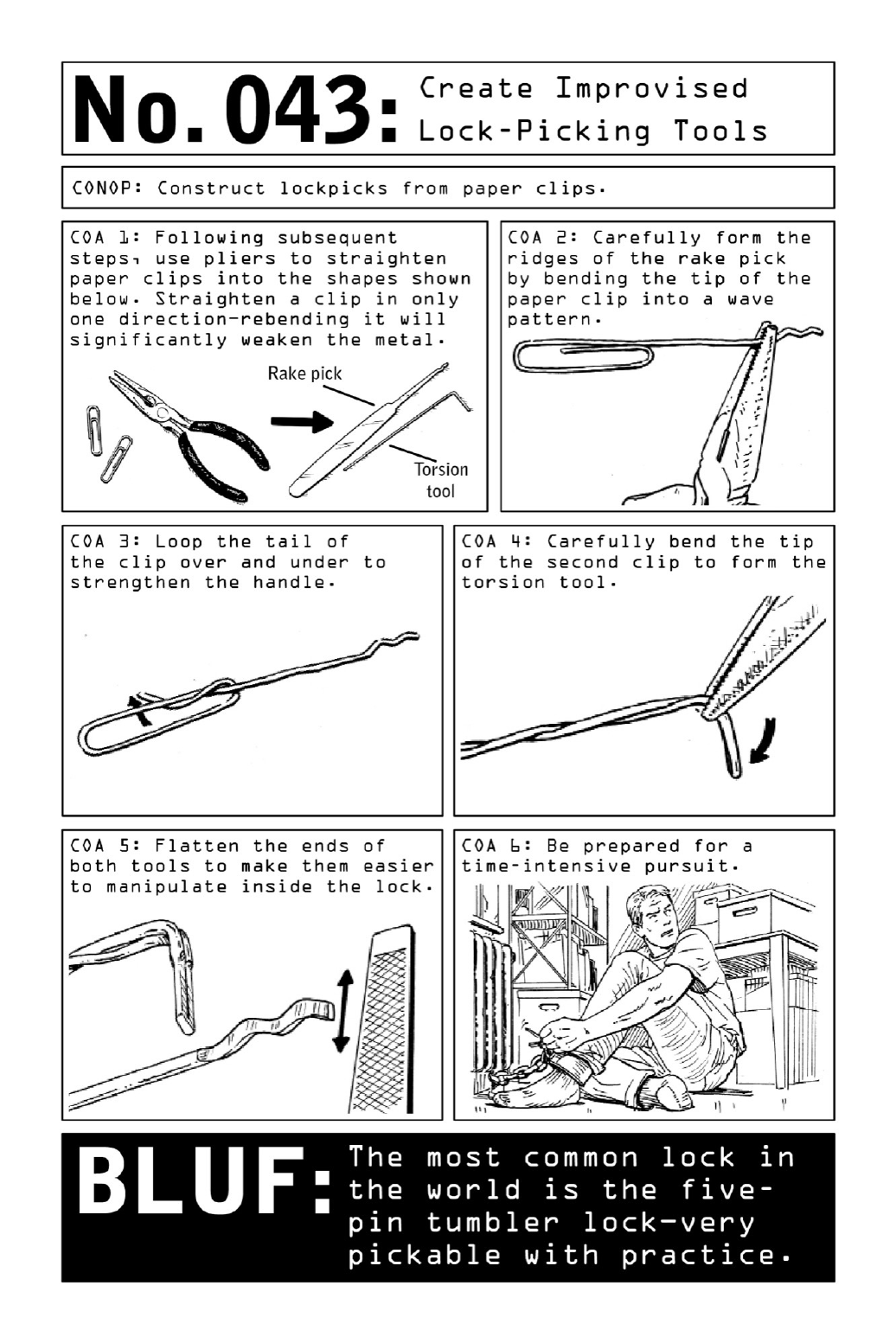

044 PickaLock
A crosscut view of the interior of a common lock reveals its inner workings—along with its
vulnerabilities. The lock case houses two rows of five pins, top and bottom, their lengths
corresponding to the cuts on a key. (Known as a five-pin tumbler lock, this common model
actuallycontainstenseparatepins.)
When there’s no key in the lock, springs in the top of the pin chamber push the top and
bottom pins down so that they obstruct the lock’s shear line. When a properly cut key is
inserted into the lock, the pins are pushed up to the levels that clear the shear line. The
cylinderisfreetorotate,therebyretractingthedeadbolt.
Thetricktolockdefeatisinsimultaneouslyapplyingtensiontothecylinderwhilemoving
the pinsoutofthewayoftheshearline;intheabsenceofakey,therotationaltensionwill
holdtheminplace.
Using the nondominant hand, first insert the tension wrench or torsion tool and apply
rotationalpressure.Insertthepicktoolwithotherhand,usingittomovethepins,onebyone,
untiltheypopintounlockedposition.Usethetipofthepicktooltofindeachpin,employinga
rockingmotiontoliftittotheshearline.
Withimprovisedoroff-the-shelflock-pickinginstrumentsonhand,acommonpintumbler
lockcanbedefeatedviaacombinationofpatience,dexterity,andpractice.
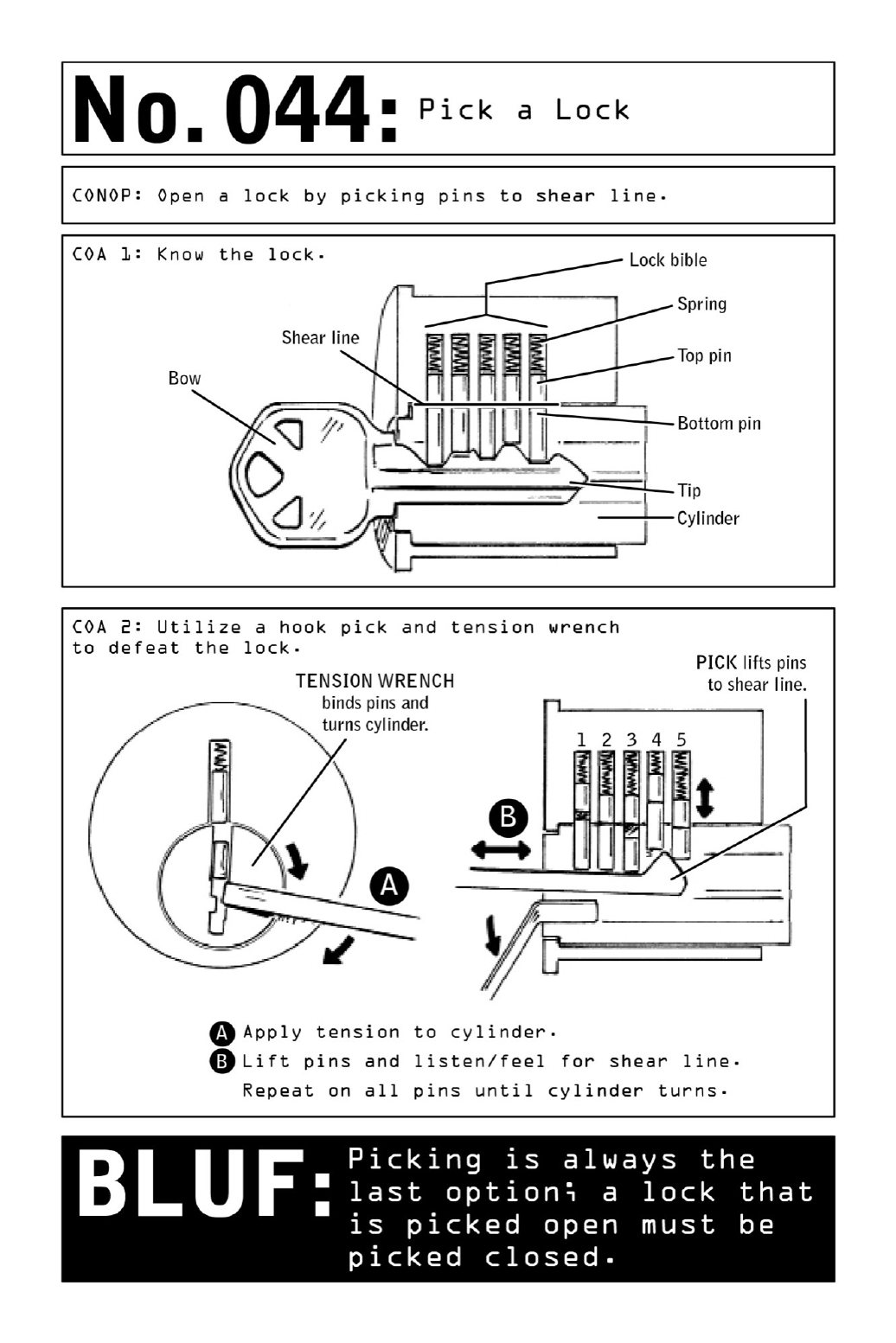

DUPLICATINGAKEY
Because every lock that is picked open must be picked closed, lock picking is actually the
option of last resort. Instead, whenever possible, operatives aim to temporarily appropriate
and duplicate a target’s key. Ensuring a method of repeated access to the target’s home or
business, this enables them to perform surveillance in small, undetectable increments over a
periodofdaysorweeks.

045 ClamaKey
Materials as ordinary and commonplace as a bar of soap, a patch of skin, or a piece of
Styrofoam can be used to physically “clam” a key, producing an embossing that is the first
stepinduplication.
But when operatives are unable to make a physical impression of the target’s key, a
photograph provides one of the simplest and most effective means of replication. All that’s
neededasawindowofopportunityisthatsplitsecondinwhichthetargetmomentarilyplaces
hiskeysonarestauranttableorbarcounter.
Physical methods of clamming provide a more accurate embossing of the target’s key but
canbedifficulttopulloff.Accessmaypresentitselfatanygivenmoment,andtheoperative
mustbereadytoact.Intheabsenceofclammingtools,theoperativecansimplypressthekey
against a soft patch of his own skin; the resulting mark will last several minutes. Once the
operativehasleftthepremises,tracingtheoutlinewithamarkerorpenproducesarendering
that will show up clearly in a photograph or photocopy. More-dependable results can be
obtained by depressing keys into malleable surfaces such as bars of soap, Styrofoam cups or
plates,ortraditionalkeyclamsfilledwithmodelingclay.


046 CloneaKey
Armedwithnothingmorethananaluminumsodacan,apenorpencil,apairofscissors,and
apaper clip, a Violent Nomadcaneffectivelyturnakeyclammingintoa duplicatekeythat
willgranthimdirectaccesstothetarget’sdomicileorbusiness.
Acopymachinecanrenderatrue-to-sizeflatcopyofthetargetkeyclamming.Ifworking
fromaphotograph,resizeorphotocopyprintstoreflectactualkeyproportions.
Use scissors to carefully cut out a paper outline of the key. Set aside. Cut the top and
bottomoffofthealuminumcan,thencuttheremainingcylinderinhalf.Laythekeyoutline
ontopofthealuminumrectangle,thentraceandcutoutthekeyshapeoncemore.Thisisthe
duplicatekey—butbecauseitissomalleable,aseparatetorsiontoolisalsoneeded.
Tomakeone,straightenoutapaperclip,thenbendoneendintoanLshape.
Slide the aluminum key clone into the target lock, partially unlocking the mechanism by
raisingthelockpinstotheshearline.Thekeyclonewillbetooflimsytoturn,soinsertthe
shortendofthepaperclipintothelockbeneathit.Usethepapercliptoturnthelockcylinder.
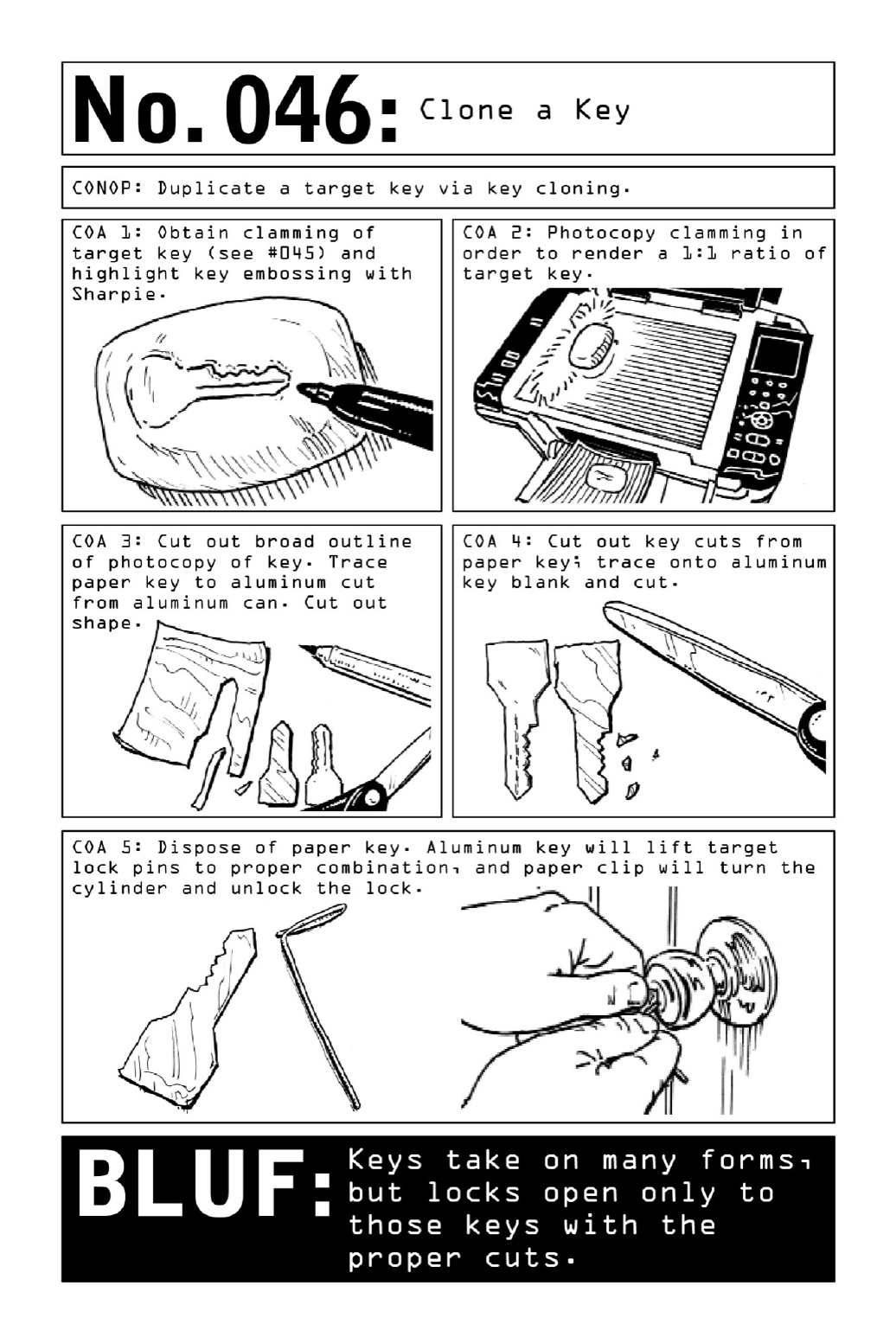

047 ImpressionaLock
Thecentralchallengeinlockdefeatismomentarilyswipingthetarget’skeyinordertocloneit
(see page 114). In many instances, operatives cannot get close enough to a target to do so
without compromisingmissionintegrityandmustthusproceedwithout a clone.Iftheyseek
one-time access to a target’s residence, they may choose to pick the lock (page 110). But
generally, once they negotiate access to a target’s home or business, their goal is to provide
themselvesarepeatable,reliablemeansofreentry.Operativeswanttheabilitytocomeandgo
without detection in order to accomplish the mission over several entries—a key can allow
them to split an hour-long task into several five-, ten-, or fifteen-minute increments over a
period of thirty days. They may also want to provide copies of the key to other government
entitiesconductingcompartmentalizedoperations.
In the absence of a clone, the key duplication technique of last resort is impressioning a
lock.Thistime-intensivetechnique,onefamiliartomasterlocksmithstheworldover,requires
practiceandmanyriskyminutesspentatthetarget’sdoor.But foranyoneintentongaining
accesstohigh-valuedocumentsandevidence,thetimewillbewellspent.
Toexecute,useaprimarytriptophotographthelockanddeterminewhattypeofkeyblank
to purchase. Or transit to the location with a set of reconnaissance key blanks purchased
withintheareaofoperation;thesewillhavethegreatestprobabilityofprovidingamatch.
Withkeyblank,flatandroundfiles,andpliersinhand,thepainstakingprocessofmanually
impressioning the key begins. First, smooth down the key blank with the flat file. Insert the
keyblankintothelock,andjiggleitupanddown.Thelockpinswillleavebehindarowof
telltale scratches—these become guidelines for key cuts. Using the round file, carefully file
grooves at scratch points. Insert the key blank into the lock and repeat, filing it down at
markedpointsuntilitfinallyclicksandturns.
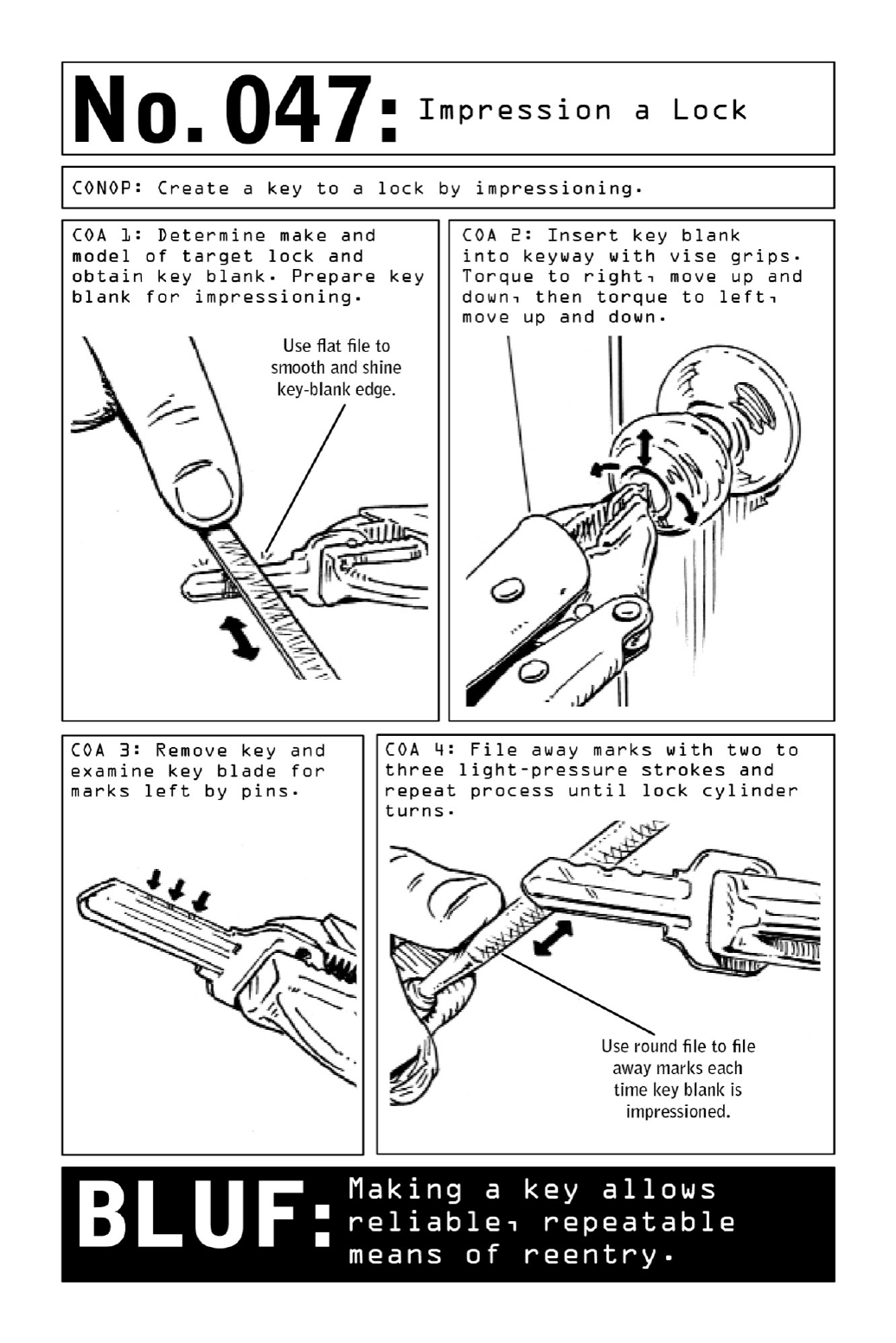

048 BypassaHotelRoomDoor
Mandatory in many commercial buildings and hotels due to fire codes and disability laws,
leverhandleknobsallowapersoncrawlinginafiretoreachupandquicklypulldownonthe
knob to unlock the deadbolt. But beware: this accessibility feature also renders the locks
vulnerable to intruders.Whenguestslockthemselvesout orleverhandlesmalfunction, hotel
staff members use an under-the-door lever lock tool to trip the lock from the hallway, and
such a tool is easy to replicate using a hanger and piece of string. With a series of simple
maneuvers,thievesandoperativescaneasilydefeatthislock.
Construct an Under-the-Door Tool: Use a set of pliers to cut the hanger at two points,
creatingasmallL-shapedhookandalargerJ-shapedhandle.Bendanadditional“hook”into
theL-shapedhandleandtieafour-foot-longpieceofstringtothishook.
BreachtheDoor:SlidetheL-shapedendofthetoolunderthetargetdoor,holdingontothe
freeendofthestring,andpushitforwarduntiltheJ-shapedendofthetoolisaboutoneinch
awayfromthedoor.
GrasptheDoorknob:RollthetoolontothecurveoftheJ-shapedenduntilanaudibletap
on the other side of the door signals that the tool is now upright. Slide the tool toward the
knobuntilitcatchestheleverhandle.
TriptheLock:Pullonthehangerandstringtopullthehandledownanddisengagethelock.
Civilian BLUF: Lever handle knobs are easy to defeat, but additional protection may be
obtainedbyobstructingthegapbeneaththedoorwithatowel(stuffedintothegapassecurely
aspossible).
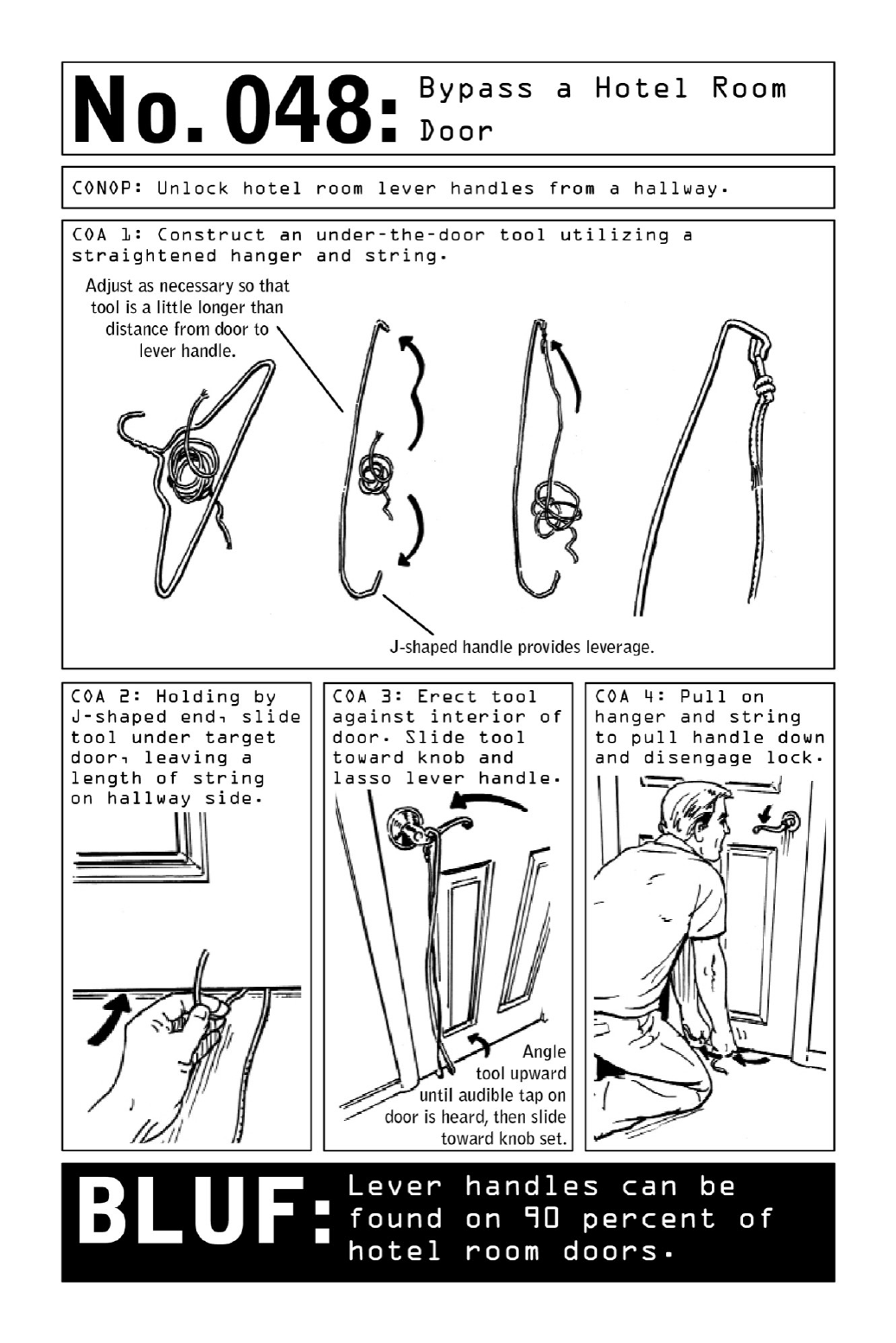

049 SurreptitiouslyUnlatchDoorLocks
Commonlyfoundinbothhotelroomsandhomes,doorchainandbarlocksaretheflimsiestof
alllockingmechanisms.Butforoperativeslookingtoaccessatarget’sroomwithoutleavinga
trace,aforcedentrythatleavesbehindasplintereddoorframeandabrokenlockisamethod
oflastresort.Instead,operativesrelyonamethodofentrythatsetsthelockbackintolocked
positionupondeparture.
Adoorthatissecuredbyonlyachainorbarlockwillopenaboutthreeinches—justenough
spaceforanoperative’sorthief’sforearmtosqueezethroughandcreateanauto-unlockdevice
usingarubberband,apushpin,andalengthofdentalfloss.
Onachainlock,looponeendoftherubberbandtotheendofthechain,thenstretchand
pintheotherendtowardthecenterofthedoor.Asthedoorcloses,theincreasedtensionon
therubberbandwillpullthechainoutofthelock(seediagram).
Onabarlock,thetechniqueisslightlymorechallenging.First,affixtherubberbandtothe
bar using a “girth hitch” loop. Then, stretch the other end of the rubber band toward the
doorframe (away from the center of the door) and pin it to the wall beside the door (see
diagram).
Topullthelockclosedasthedoorshuts,loopadoublelengthofdentalflossoveronearm
ofthelockingbarnearitsbase;holdontotheendsoftheflosswhileclosingthedoor,then
pulltolock.Toretrievethefloss,pullitthroughthedooropeningbyoneend.
Civilian BLUF: Never rely on door chain or bar locks to secure doors. Always use your
deadbolt.
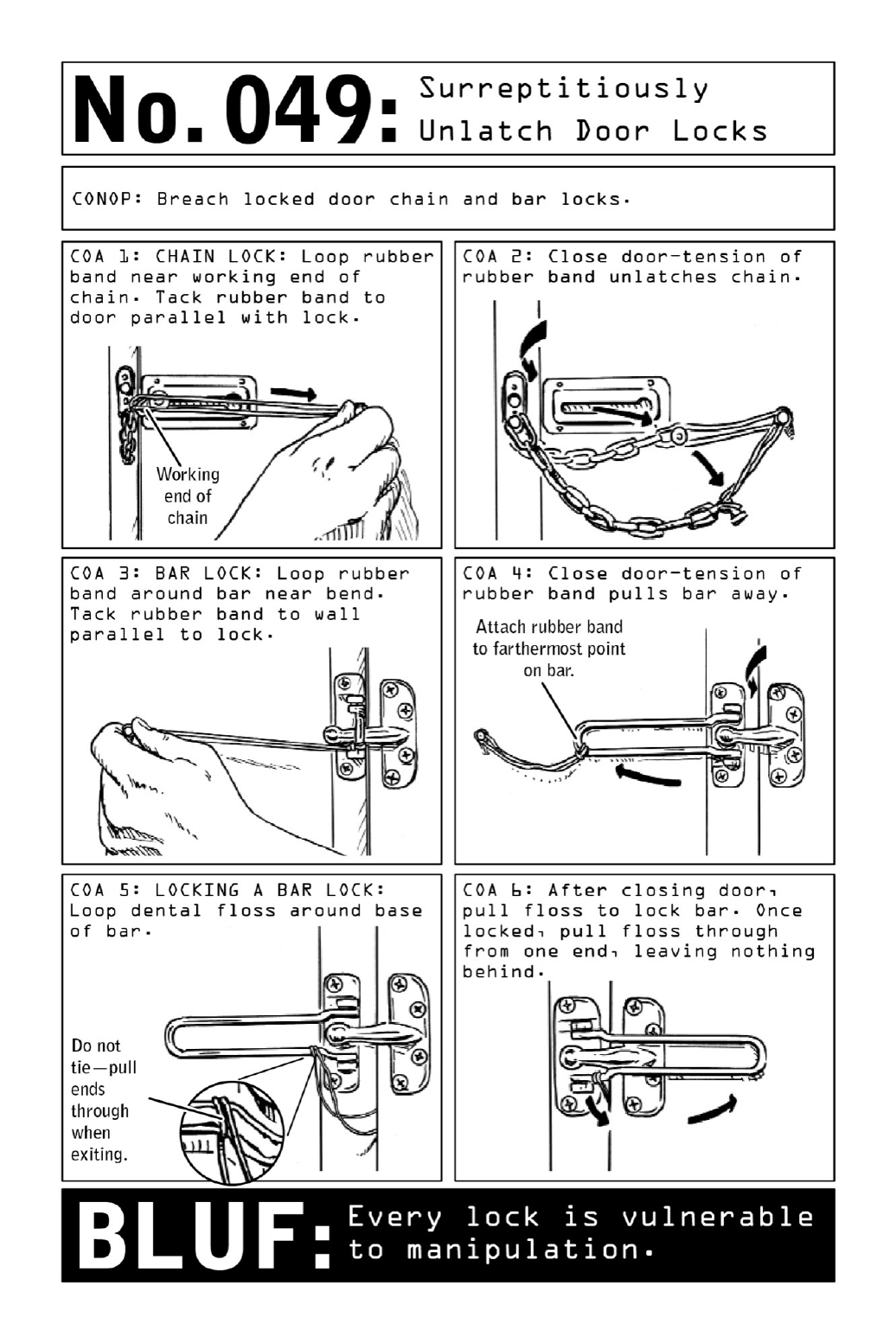

050 DefeataPadlock
While padlocks have a heft that communicates a certain impenetrability, in reality they
providelittlemorethanasenseoffalsesecuritytotheirowners.Operativesactuallyseekout
entrancessecuredbypadlocks,ontheveryassumptionthattheywillbeeasytodefeat.Many
are constructed quite flimsily, built with a loose tolerance that makes them extremely
vulnerabletointruders.Insomecasestheycanbebypassedentirely—thepiecestowhichthe
locks are affixed may themselves be vulnerable, as with hasps that can simply be unscrewed
fromagate.
In order to defeat a padlock directly, a set of improvised shims can be made using a
lightweight, pliable aluminum can and a pair of shears. Cutting out two rectangular pieces
withsemicirculartabs(seediagram)yieldstoolsstrongenoughtotakeonmostpadlocks.
Slid down between the shackle and lock case, the shims are rotated so that their tongues
move to the insides of the shackle and jostle the interior ball bearings aside. With the ball
bearings pushed out of the indentation in the shackle, the padlock will unlock with upward
pressure.
Civilian BLUF: When securing an entrance via padlock, be sure to select a top-of-the-line
modelandaddressanyvulnerabilitiesinthesurfacetowhichthepadlockwillbemounted.
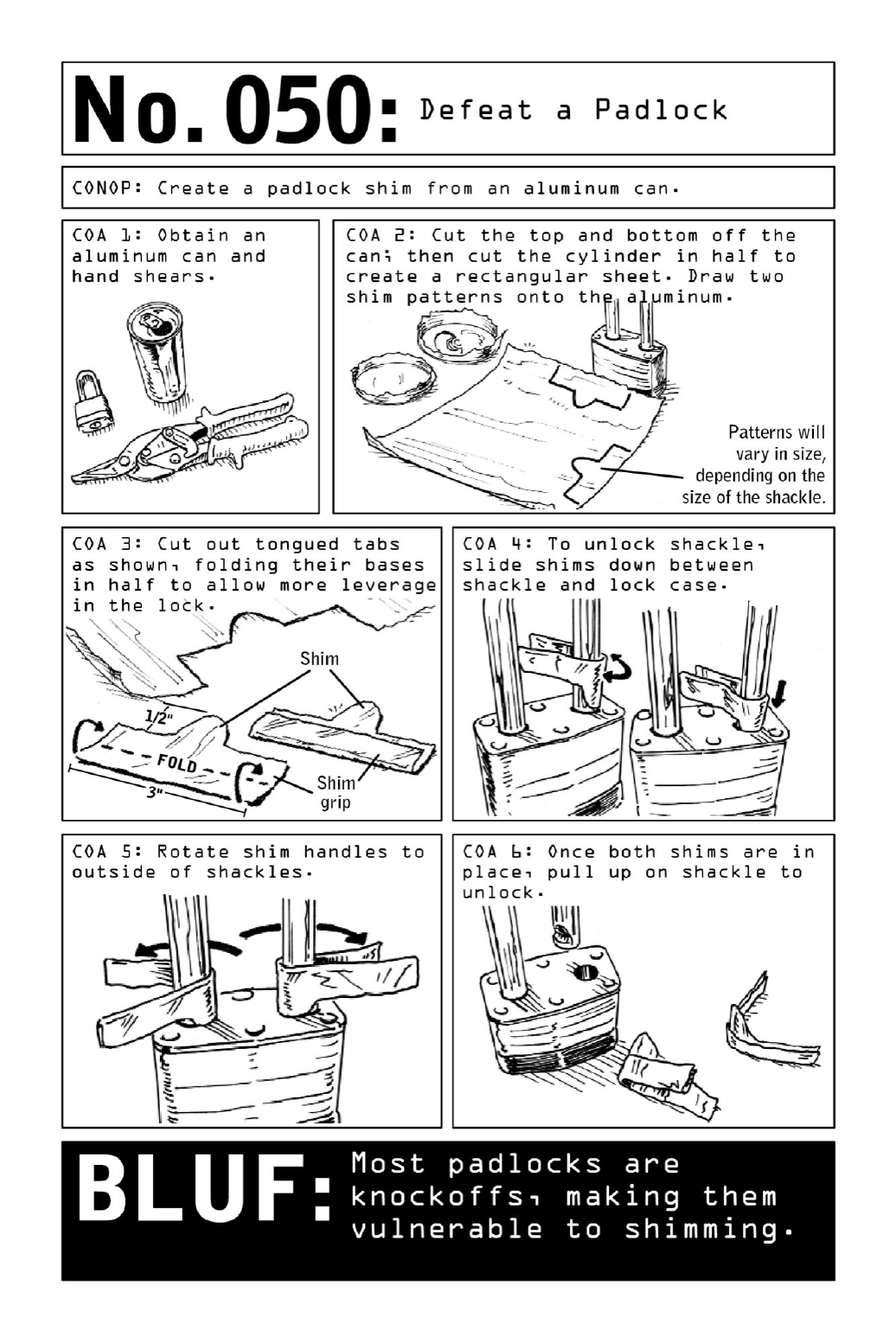

051 CovertlyAccessLockedLuggage
Alockedsuitcasepresentsnorealimpedimenttoawell-trainedoperative.Luggagelockscan
easilybeopenedwithmasterkeysorbypassedentirelybysimplynudgingthesuitcase’szipper
open with a ballpoint pen. But an operative conducting a search of a potential target’s
valuablesalwaysseekstoeraseanytraceofhisactions.Whenattemptingtoretrievevaluable
intelligence (or to plant eavesdropping technology or tracking devices that might render the
targetevenmorevulnerable),breakingintolockedluggagewithoutdetectioniskey.
Becausethere’snotellingwhetheratargethasemployeddiscretealignmenttechniques(see
page94)inordertodetecttampering, aViolentNomadcanneverbetoocautious.Together
withthezipper breakingtechnique,the useofappssuchas PhotoTrapcanhelpensure that
thetarget’sbelongingsareleftexactlyastheywerefound.
Oncethesuitcasehas beenbreached,off-the-shelf trackingdevices canbeinsertedintoits
lining—theareabetweenthewheelsandthefabricoftenprovidesadiscreetconcealmentarea.
CivilianBLUF: Any object with a zipper closure can never truly be locked, and any suitcase
madeof clothcanultimatelybeslashedopenbyasharpinstrument.Foradditionalsecurity,
selecthard-sidedortrunk-styleluggagewithclamshellorclipclosures.
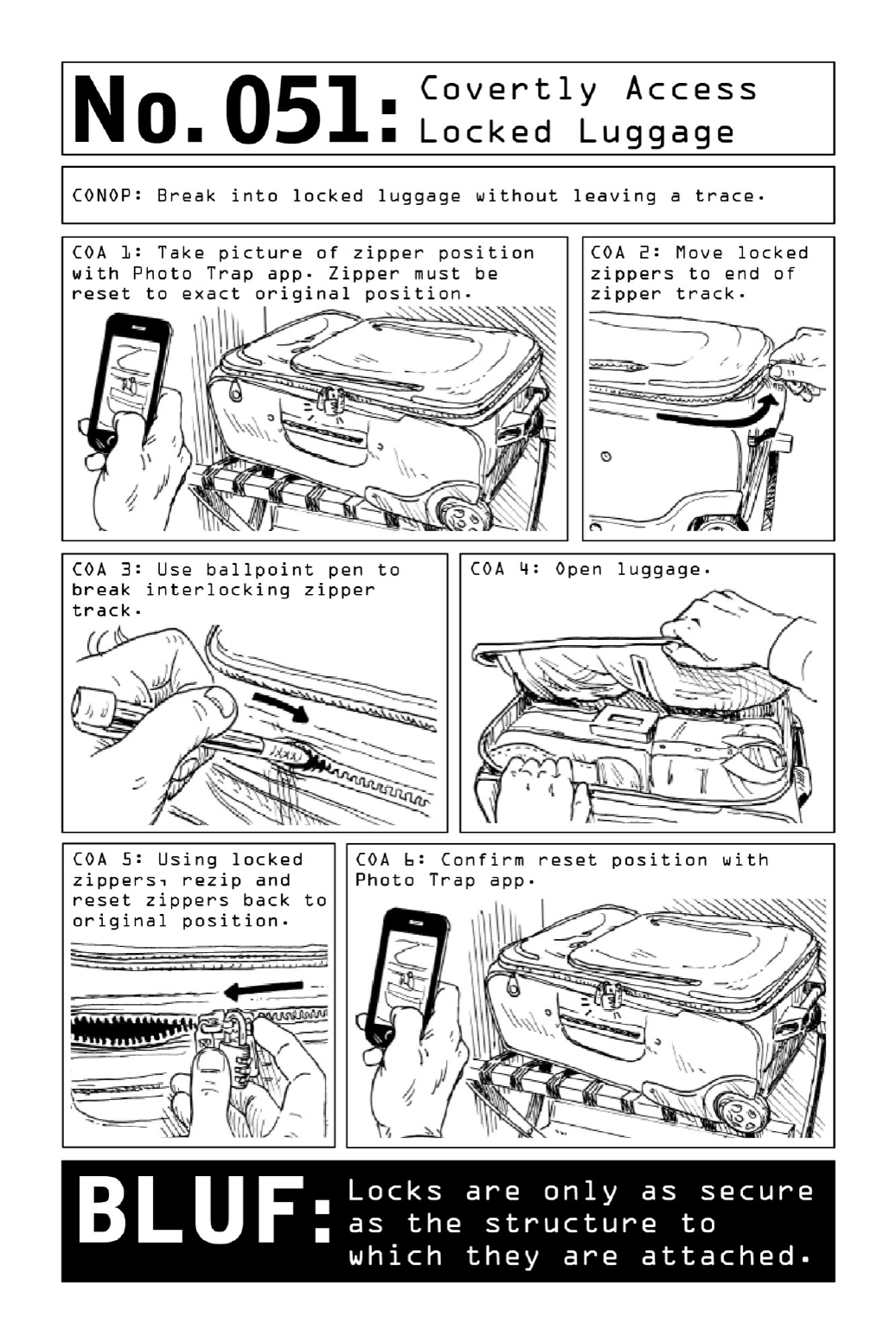

052 OpenaCarDoorwithaPieceofString
Older-modelcarswithpull-uplocksarevulnerabletotheunlikeliestofbreak-intools:asingle
pieceofstring,shimmiedintothecarthroughtheopeningbetweenitswindowandframe.The
mostdifficultpartoftheprocessiswedgingthestringpasttherubberizedweathersealaround
thetopofthecardoorframe.Theolderthecar,thelooserthesealwillbe.
TieaSlipknot:Formaloopatthecenterofasix-foot-longpieceofstringorparachutecord.
Cross one end of the string over and under the loop, creating a secondary loop. Hook the
stringbackoverandthroughtheinnermostloop,tighteningitintoaknotwhilemaintaining
theupperloop.
ShimmytheKnotintotheCar:Workingfromtheuppercornerofthecardoorjustabove
thelock,shimmytheknotandlineintothecar,keepingbothendsofthestringoutsideofthe
car. Pull back on the corner of the window to create an opening. In models where the glass
windows don’t have a frame around them, beware of exerting too much pressure on the
windowandcausingtheglasstoshatter.
SnaretheThumbPuller:Guidetheknotdowntowardtheunlockmechanismandsnareit
withtheloop.
TightentheKnot:Pullbothendsofthestringinoppositedirectionstotightentheslipknot
aroundthethumbpuller.
UnlocktheDoor:Oncetheknotistightenedasmuchaspossible,pulluponbothendsofthe
stringtounlockthedoor.
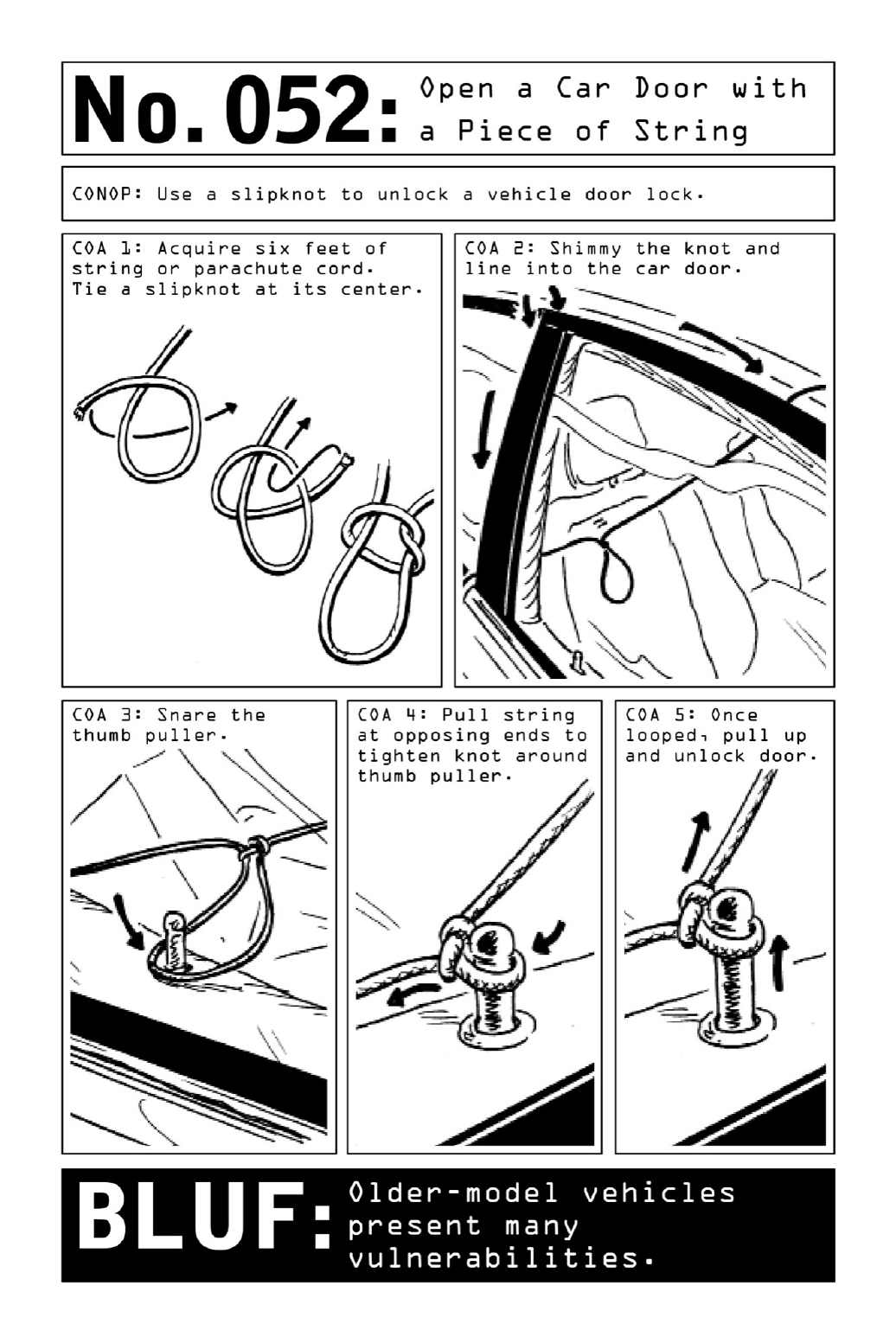

053 DiscreetlyOpenGarageDoors
Lock picking can be an arduous and time-consuming task, which is why operatives tend to
seek out workarounds such as clamming a target’s key (page 114) or bypassing the lock
altogether(page120).Inahomeinfiltrationscenario,anattachedgaragewithadooroperated
byanelectricopeningdeviceprovidesasignificantvulnerabilityfortheNomadtoexploit.
Because they must slide up and back onto rail systems, garage doors are built with space
alongtheirtopedges.Byslidingastraightened-outhangerwithahookatitsendbetweenthe
garagedoorandtheupperdoorframe,thecablethatdisengagestheautomaticopeningsystem
can be hooked. Because most civilians use their automatic door closure systems as default
lockingmechanisms, thisisallthatisneededinorderto“unlock”thedoorbeforemanually
openingit.
Oncetheoperativehaspulledthedooropenjustafewfeet,hewillquicklyslidebeneathit
and immediately pull the door closed. Entry to the house may now be possible—many
homeowners fail to lock the door connecting the garage to the house. Even if that door is
locked,thereisnowasafeandcoveredspacefromwhichtoworkonbypassingthelockforas
longasnecessary.
CivilianBLUF: Cut or tie off the manual-open cable of your garage door so that the cable
becomesunreachablebyatoolinsertedatthetopofthedoor.Eveninasecuredgarage,never
leaveyourcarkeysinyourcar.Lockthedoorbetweenyourhouseandgaragetocreatelayers
ofsecurity.
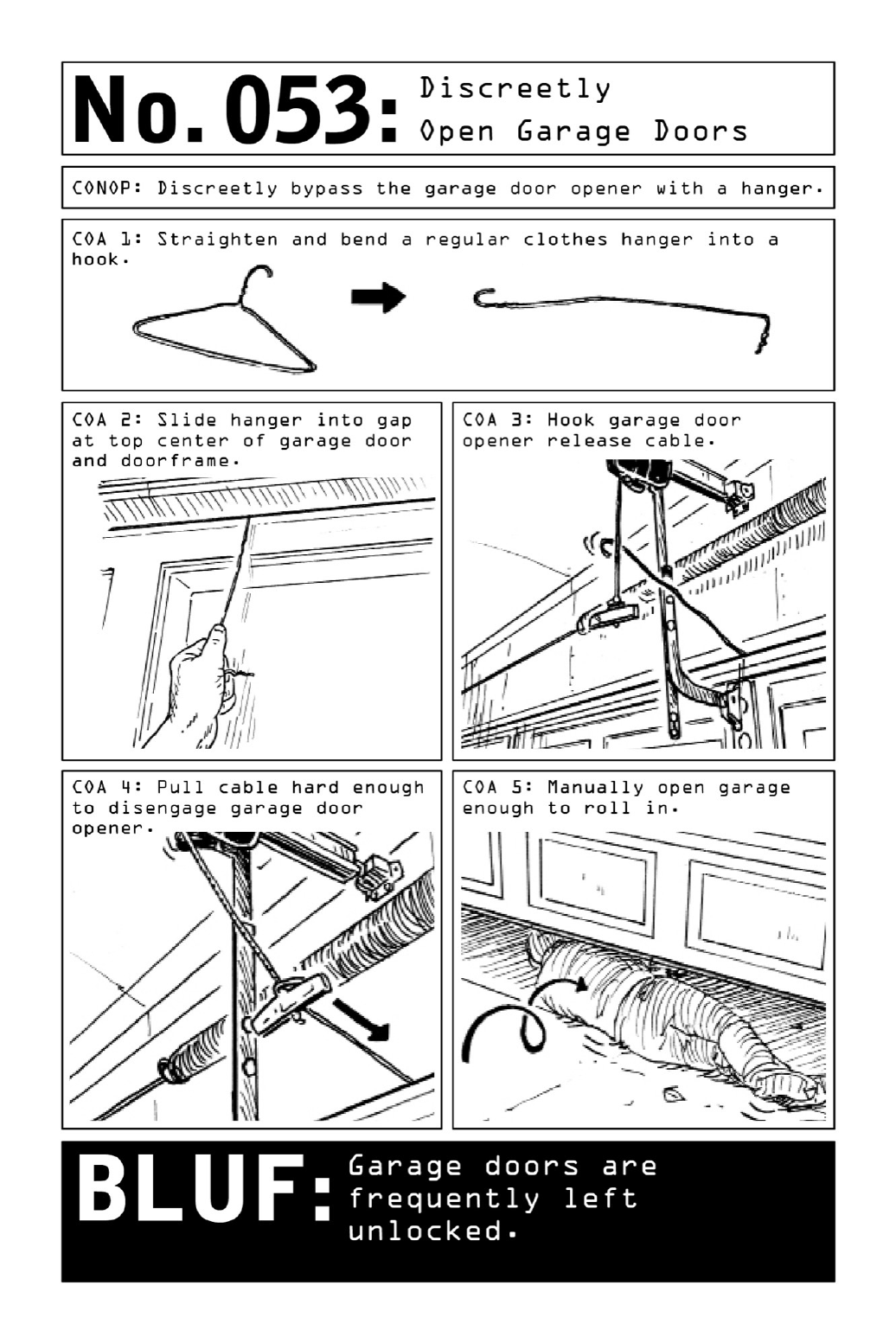

PARTVI
COLLECTION:AUDIOANDVIDEO
INTELLIGENCE

054 InstallanAudioDevice
What is the optimal concealment spot for an audio surveillance mechanism? The answer
depends on a compromise between available options, time spent on target, and achievable
soundquality.Whileitispossibletocreateafunctionallisteningdeviceusinglittlemorethan
amobilephoneandapairofheadphones(seepage136),abotchedinstallationwillyieldlittle
inthewayofactionableaudio.
In selecting their install points, operatives attempt to determine where unguarded
conversations are likeliest to occur (often in bedrooms or kitchens rather than living rooms)
andaimforlocationsthatputthematthe“centerofconversation.”
Sound quality will also depend on the particularities of the concealment spot. In a car, a
central console or dome light produces intelligible audio from both front- and backseat
conversations,whereasabugplacedtoonearthefrontofthevehiclemaypickupinterference
from the motor or stereo system. The molding of a television offers highly effective
concealmentbutaddsaplasticbarrierthatmayinterferewithsoundquality.
Lastly, operatives will choose between a “hard install,” a semipermanent installation that
utilizes parasitic power from a source such as a television or an electrical outlet, or a “soft
install,”whichmaybeassimpleasplacingarecordingdeviceinsideaboxoftissues.Thefirst
optiontakesagreatdealoftimeontargetbutmeanstheoperativeneverhastoreturninorder
to service the device. A soft installation may require dangerous return trips when the device
runsoutofbatteriesormaxesoutitsmemory.
CivilianBLUF:Whilenoise-cancelingsoftwarecanoverridethesoundsoftelevisionorradio,
it cannot process the sound of running water—which makes bathrooms in potentially
compromisedlocationsidealspotsfordiscreetconversations.
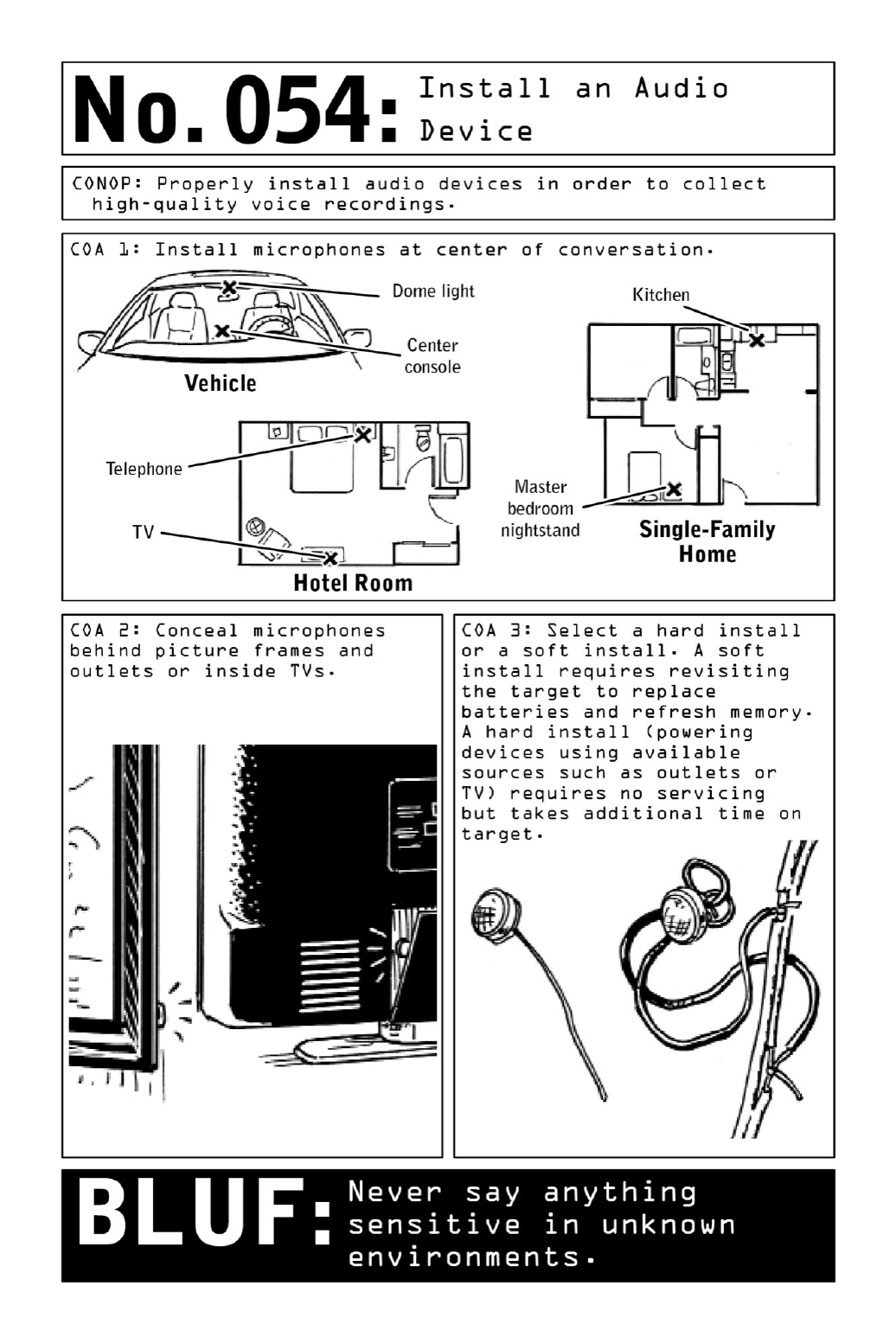

055 TurnaSpeakerintoaMicrophone
Stashing a voice-activated recording device in a target’s room or vehicle is relatively simple,
but without sound amplification, such a setup is unlikely to result in audible intelligence—a
proper audio-surveillance system requires amplification via microphone. In the absence of
dedicatedtools,however,theNomadcanleverageacellphone,anaudiojack,andapairof
headphonesintoaneffectivelisteningdevice.
Becausemicrophonesandspeakersareessentiallythesameinstrument,anyspeaker—from
theearbudsonapairofheadphonestothestereosystemonatelevision—canbeturnedintoa
microphone in a matter of minutes. The simple difference between the two is that their
functionsarereversed.Whileaspeakerturnselectronicsignalsintosound,amicturnssound
intoelectronicsignalstobemanipulatedandamplified.
Thedistinctionturnsontwo wires, onepositive (red)andonenegative(black).Switching
thesewiresreversesthepolarity,andthereforethefunction,ofthedevice(seediagram).
Toexecute,cuttheoutboundendsofthespeakerwiresandattachthemtoanaudiojack.
Plugtheaudiojackintotherecordingdevice.
Any small recording device can be employed, but using a phone set to silent and auto
answerasalisteningdevicehastwoadvantages:Itcapturesintelligenceinrealtimeanddoes
so without the operative having to execute a potentially dangerous return trip on target to
collectthedevice.
Thisaudioinstallationtechniqueishighlyadaptabletoavarietyofenvironments.Tosetup
vehicular surveillance, disable one of the car’s rear speakers, plugging its wires into a voice
recorderorphone;concealtherecordingdeviceinthedeadspaceofarearpassengerdoorora
trunk’slining.Inpublicplaces,earbudsdanglingfromacoatpocketcanfunctionasadiscreet
ambientsurveillancestation.



BUILDINGANDCONCEALINGASURVEILLANCECAMERA
For a Nomad, the optimal surveillance camera begins with an off-the-shelf product from a
local superstore and ends with an object that blends into its environment to the point of
invisibility.Thestartingpoint?Astandard-issuebabymonitor.
Withcamerasgettingsmallerandlighterbytheday,it’spossibletodisguiseasurveillance
setupinaboxofKleenex,thecasingofaguttedhardcoverbook,ortheampledeadspacein
officeequipmentsuchasprinters.Buttosecureaviewovertheexteriorofatarget’shomeor
businessinordertoobtainpositiveidentificationonkeyholdersandvisitors,Nomadscanuse
homemadeplasticanddisguisethecameraasaninnocuousrockorclumpofdirt.

056 ConstructandInstallaPinholeCamera
A pinhole camera starts with a visit to a superstore and the purchase of a wireless baby
monitor. Once in hand, crack open the baby camera housing to reveal its contents (see
diagram). Remove the components—a transmitter, a battery pack, and the camera lens—but
keepthemwiredtogether.Discardthebabycamerahousing.Followtheinstructionstocreate
homemade plastic (see page 142), then place a toothpick in the eye of the camera lens and
mold the plastic around the lens in the shape of a rock; the toothpick will create an
indiscerniblepinholethroughwhichthecamerawilloperate.
Paint the rock in a neutral color or a shade specific to the landscape outside the target’s
homeandenclosethetransmitterandbatterypackinawaterproofziplockbagorTupperware
container.Burythecontainerinashallowhole(toodeepandthetransmitter’ssignalwillfail)
andsetupthecamerasothatitcapturespeople’sfacesastheyenterandexitthebuilding.To
ensurethatthecamera’s“lookangle”isproperlypositioned,leavethetoothpickinplaceuntil
thelastminuteanduseitsangletogaugethefieldofview.
Foranadditionallayerofcamouflage,applyspraygluetotherockduringinstallationand
coveritwithdirtgatheredonsite.Fromaremotesetupinavehicleuptotwohundredyards
away,anoperativewillbeabletoobservethecomingsandgoingsonhismonitorscreenwith
limitedriskofdetection.
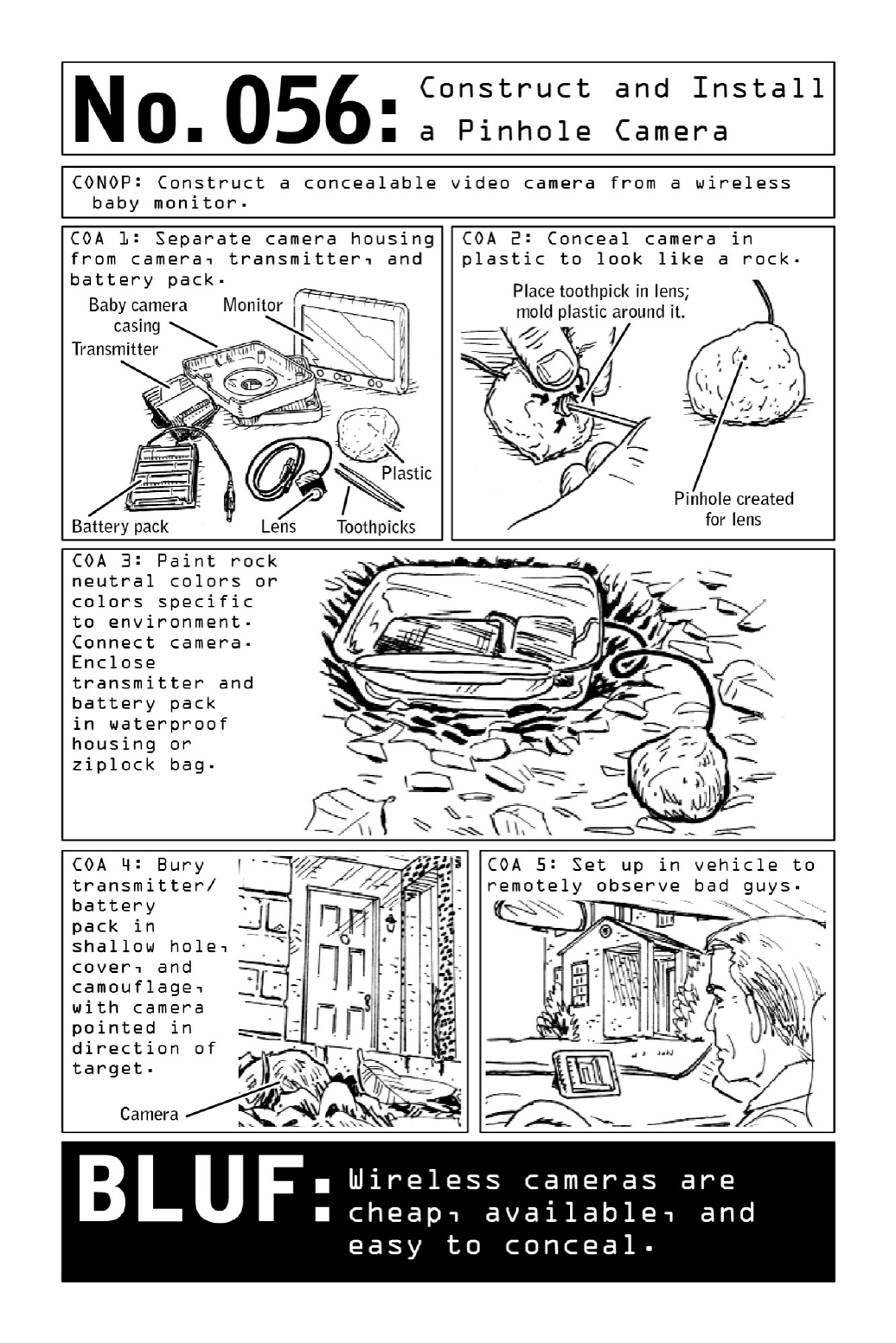

057 MakeHomemadePlastic
Allthatisneededtoconcealvaluabledata,keys,orsurveillancedevicessuchascamerasand
microphonesaretwoingredientscommonlyfoundinanyhouseholdkitchen:milkandvinegar.
Heated and strained so that the milk’s casein proteins coagulate into a rubbery, plasticlike
substance,themixturecanbemoldedintoanyshape,dryingtoaclaylikeconsistency.
In contrast to body cavity concealments focused on escape, or to mobile tech solutions
focused on eliminating the Nomad’s digital signature (page 194), plastic concealments are
useful for camouflaging valuables or surveillance devices in a particular environment. The
shape-shifting substance can be formed and painted to resemble rocks, bricks, logs, or any
number of objects, making it a prime candidate for the dead drops Nomads use to
surreptitiouslycommunicateimportantdatatoassociates.
Note:Heattimemayvarydependingonthemicrowave’spowerandsettings.
CivilianBLUF:Camerasareeverywhere—alwaysassumeyouarebeingrecorded.
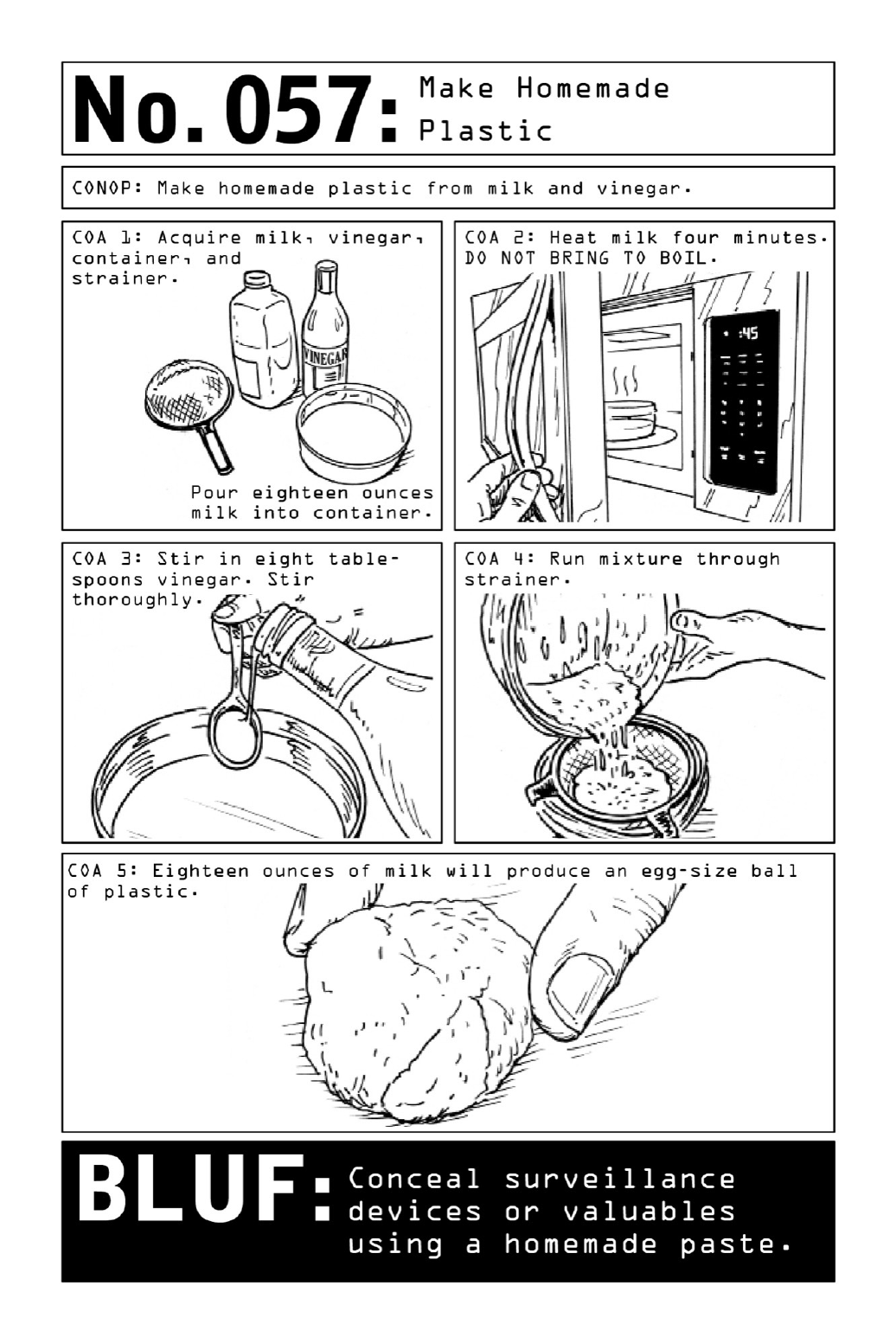

058 SendAnonymousEmails
Password-protectedemailaccountsandWi-Ficonnectionsarechild’splaytomodernhackers,
a class of information specialists that includes identity thieves, scam artists, and seasoned
terroristsamongitsranks.Tothwartthem,Nomadsemployananonymitynetworkoriginally
developed by members of the U.S. Naval Research Laboratory as a tool for secure
communication.(Ironically,ithasalsobecomethefavorednetworksolutionforcriminalsand
black-marketbusinessesofallstripes.)
Tor, the name of the network, prevents forensic traceback by encrypting and bouncing
informationthroughachainofvolunteerserversallovertheworld.Bydisguisingthesender’s
pointoforigin,thenetworkprotectsNomadsfromthirdpartiesattemptingtofindouttheir
geolocation; an anonymous email account with no connection to the Nomad’s name or
identityprovidesanadditionallayerofsecurity.
Though free Wi-Fi hotspots are known for their lack of security and vulnerability to
hackers, they can be useful toaNomadwho’swary ofhavinghishome or hotel connection
tapped. To set up an anonymous browsing session, transit to a location that falls outside
regularpatterns,thenaccessafreeWi-Ficonnectionthatdoesnotrequirealoginorpassword.
DownloadTails,a user-friendly operatingsystemthatusesTorasits backdropandsavesno
browsing information. Once loaded, use Tails to create a new, completely anonymous email
address. Follow the example of citizens in authoritarian regimes who, wishing to further
decrease the span of their digital footprints, will often share email accounts with close
associates.Insteadofsendingandreceivingemails,theykeeptheircommunicationssecureby
responding back and forth on draft emails, thereby never creating any potentially alerting
traffic.


059 HideInformationinPlainSight
No matter how carefully a Nomad covers his tracks, any exchange of digital information
presents the possibility of a security breach. So operatives secure their messages with a
multiprongedsystem,layeringvariousformsofencryptionintocommunicationssentthrough
ananonymitynetworkandviafalseemailaddresses(page144).Just as spies once concealed
information-filledmicrodotsontheheadofapin,todayoperativesembedtextdocumentsinto
digitalimagesthatmustbedecompressedtorevealtheircontents.
To create a rudimentary form of encryption, start with a program such as TextEdit or
Notepad. Avoid any word processing software that is connected to an update mechanism;
documentscreatedinsuchaprogrammayberecoverablebythirdparties,eveniftheyaren’t
beingsavedtoaharddriveortothecloud.
Beforecomposingamessage,pasteaninnocuousimageintothetextdocument.
Typesensitiveinformationaboveorbelowtheimage.Changethefontcolortowhiteand/or
the fonttoa symbolforadditional cover.Intheshortterm, thiswillconcealactivitiesfrom
onlookerswhilethemessageiscreated.Whenthemessageissent,theimagefilesizewillserve
asafront,disguisinganyadditionalspacetakenupbythetext.


060 HideandExtractDataUsingEverydayPhotos
Whena suspicionof surveillance isconfirmed,there is nosuchthingas asurfeit of caution.
The Nomad hunkers down, limiting anything but the most essential communications and
meetingassociatesincrowdedpublicplaces.Ifhemustsendoutinformation,asingleformof
encryptionorcovertmessagingdoesnotsuffice—varyinghismethodologieswillmakeitmore
difficultforpotentialcodebreakerstodeterminepatternandunlockhiscode.
Althoughelaborate,amethodofencryptionthatreliesonstagingaphysicalartifactwithin
aphotographdeceivesthehumaneyewhilefoilinganykindofautomateddecryptionsoftware.
To set up the decoy, acquire a high-megapixel digital camera. (A smartphone camera will
not produce images of high-enough quality.) Handwrite or print the message on paper.
Concealthephysicalartifactinthebackgroundofaposedshot—atthebaseofabuildingor
camouflagedonabusybulletinboardinthebackgroundofagroupshot.
Photographthescenewiththeentireimageinfocus,thenzoominontheresultingimageto
makesurethemessageislegible.
Instoringoremailingtheimage,besuretosaveitatfullresolution.Mergetheimageintoa
setofinnocuousphotographs.Downloadedtoaflashdriveandsmuggledintoadeaddrop,or
attached to a draft email on an account shared with associates (see page 144), the set will
revealitstruecontentsonlytothosewhoknowtosearchforthem.
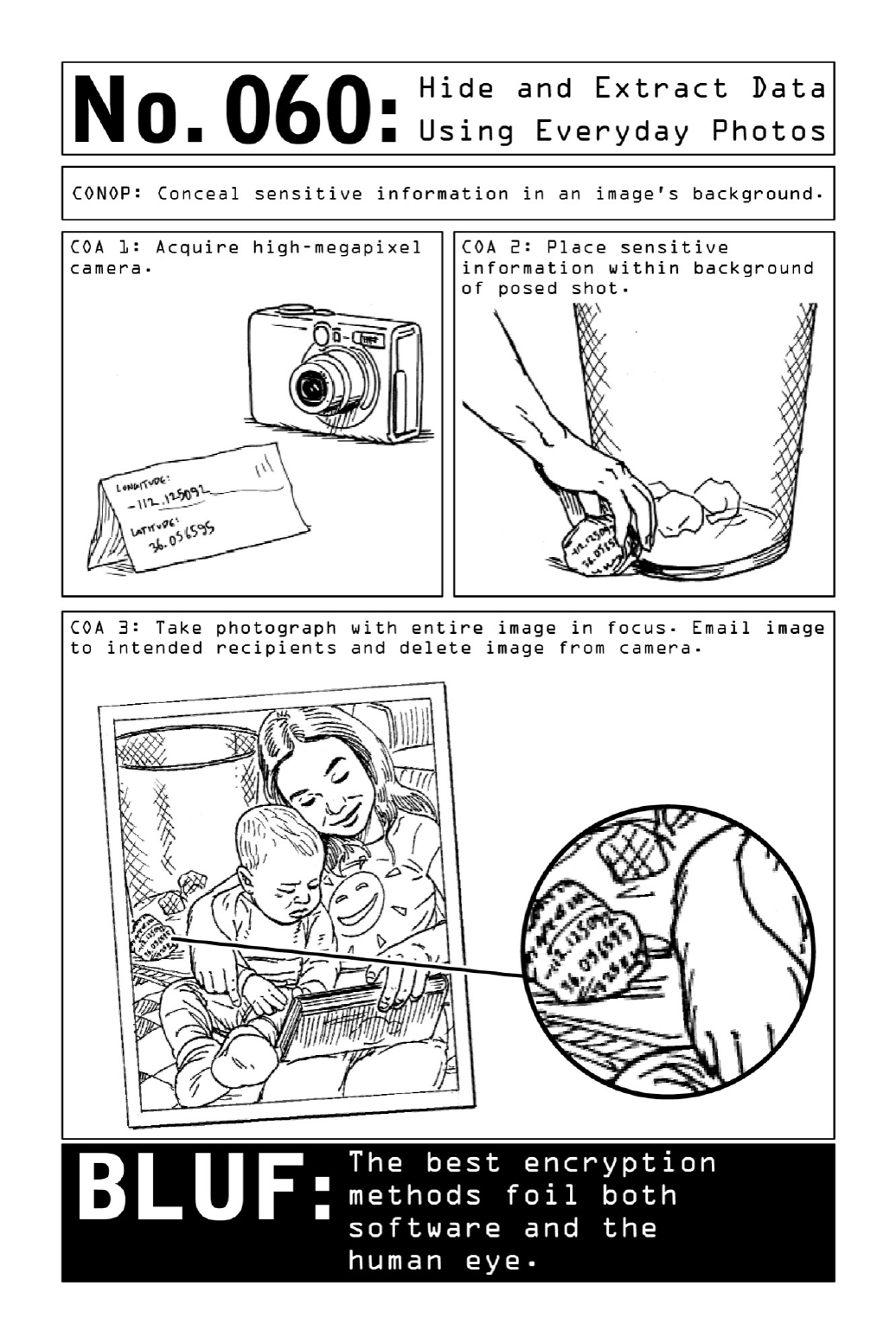

PARTVII
OPERATIONALACTIONS:DENY,DISRUPT,
DISABLE

061 DrawaConcealedPistol
Many gun-carrying civilians mistakenly practice their target shooting to the exclusion of
relatedcompetencies.Onefrequentlyneglectedarea,theartofrapidlyandseamlesslydrawing
aconcealedweapon,is crucialtosuccessful self-defense.When confrontingan assailantwho
alreadyhashisweaponinplay,adelayofevenahalfsecondorlesswillseriouslycompromise
chancesofsurvival—sooperativesknowthatworkingondrawingtechnique(alwayswithan
unloadedweapon)andunderstandingtheintricaciesofeachparticularholsterarecrucial.Two
frequentproblemsarefumblingthedrawanddrawingtheholsteralongwiththeweapon.
DrawingaWeaponunderanUntuckedShirt:Adrawoccursinasingleseamlessmotion
thatcanbebrokendownintothreedistinctphases.Inthefirst,theoperativeuseshisthumbto
“hookandsweep”hisshirtoutoftheway,efficientlymovingthefabricasidetopreventthe
weaponfromgettingtangledupinitsfolds.Inthesecond,hisnondominanthandholdsuphis
shirtwhilehisdrawinghandliftstheweaponoutoftheholster.Inthethird,hisnondominant
hand becomes the support hand as he pops the wrist of his drawing hand and points the
weapontowardthetarget.Allthewhile,hiseyesremainfixedonthetarget.
DrawingaWeaponunderaCoat:Acoatthatswingsforwardwhiletheoperativeattempts
to draw can be a very real liability—one that’s neutralized by the simple trick of weighting
down the jacket with a roll of coins. Use the drawing hand to brush the jacket back while
simultaneouslydrawingtheweapon.
Inbothcases,thecrucialsupporthandhelpsstabilizeaimwhilequickeningthedraw—thehumanbody
functionsmorerapidlyandefficientlywhenbothsidesareperformingparallelactionsintandem.
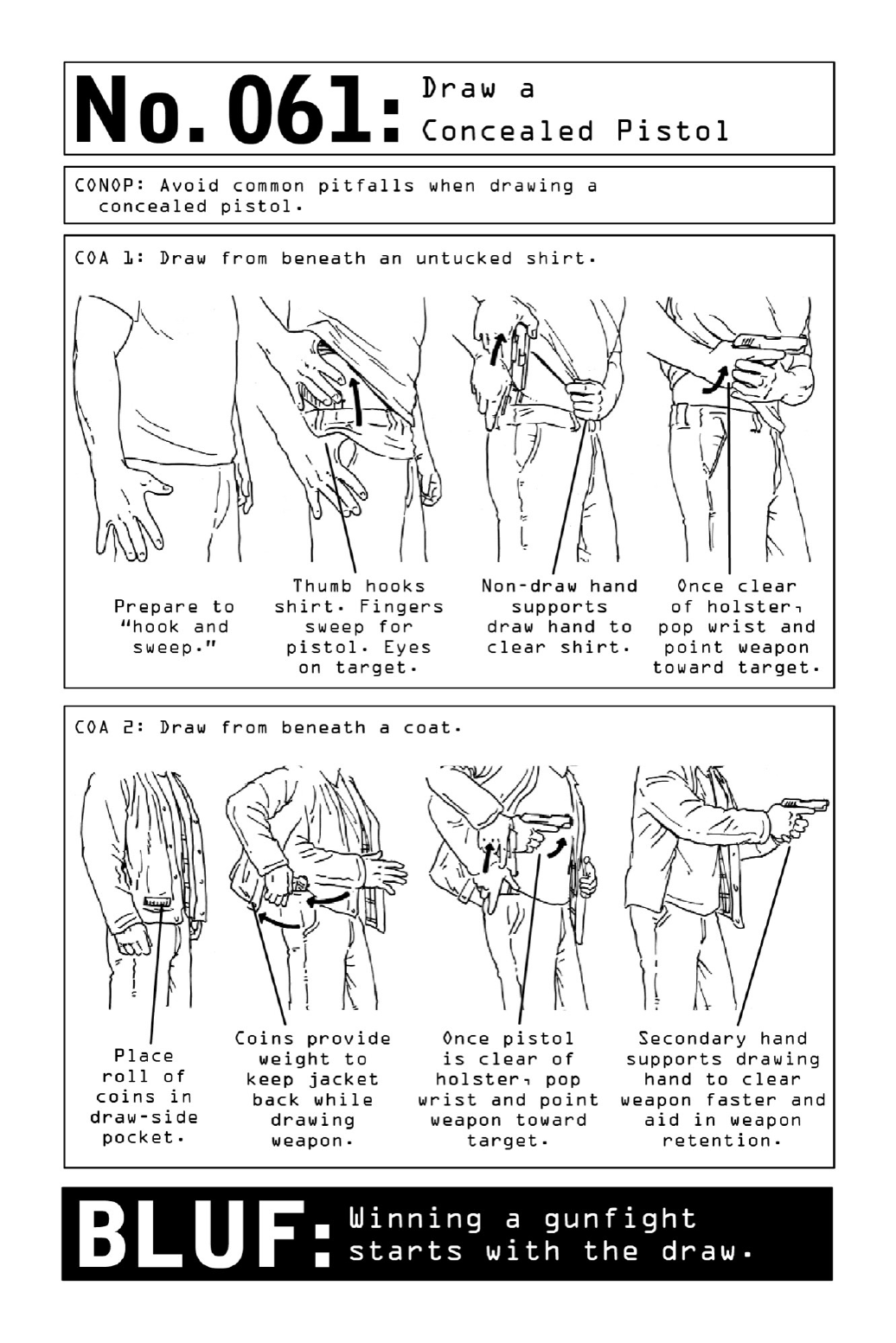

062 ShootfromaVehicle
For drivers and passengers caught in enemy crossfire, the first line of defense against armed
attackersshould bea rapidgetawayby car.If driving away isn’t possible,running for cover
outside the vehicle is preferable to hunkering down. When bullets are flying, a stationary
vehiclecanquicklybecomeaglass-enclosedcoffin.
But for skilled operatives confined in their vehicle, a quick draw and an understanding of
thedynamicsofshootingthroughglassmaymeanthedifferencebetweenlifeanddeath.
Thequestionofwheretoholsteraweaponforeaseofaccesswhiledrivingdependsonthe
individual driver, but for a right-handed person, a weapon holstered on the left hip will be
accessibleviaacross-drawbutunimpededbytheseat-beltbuckle.
Whentakingaim,leaningbackanddownaffordscranialprotectionandkeepstheshooter
outofviewandawayfromglass.Windshieldsareconvex,curvedsurfaceswhosearctendsto
alterthebullet’spathway.Tocorrect,operativesaimlow;ashotaimedthroughawindshield
atthetarget’spelvisshouldhitatchestlevel.
Operatives always fire multiple rounds, the first to break glass and the second to hit the
target,bracingforajolt.Becausethefirstshotisfiredinaconfinedenvironment,theresulting
noiseandpressurewillbeacute.
Mostcarwindowsaretemperedandlaminatedsothattheywillbreakintopetalsthatstick
togetherratherthanflyingapartintoshards.Butwhendealingwithglassofanykind,serious
injury can occur. If possible, push or kick the spidered glass out of the way for safety and
improvedaim.


063 WinaKnifeFight
Easy to acquire and menacing to behold, knives are often used by common criminals who
value their intimidation factor but lack a basic knowledge of knife fighting. For this reason,
operatives know that learning proper knife-fighting techniques can play a critical factor in
survivinganattack.
GuardingtheWeapon:Protectvitalorgansfromanopponent’sknifeandpreventtheknife
from being snatched by holding up a sacrificial guard hand and rotating the torso sideways.
Turn knuckles toward the attacker to protect the arteries and veins on the inner wrist and
forearm.
KnifeGrip:Anoperativealwaysmaintainsafullgriponhisknifehandle.Leavingthethumb
stretchedoutoverthetopofthehandleisextremelyunsafe,sohecurlshisthumbaroundthe
handletopreventinjuryandprohibitanopponentfromtakingtheknifeaway.
AnglesofAttack: To weaken an opponent, stab and slice along one of the eight angles of
attack. This kind of motion enables the operative to filet a muscle apart, disabling the
opponentandallowingtheoperativetogaintheupperhand.
CutPoints:Inalife-or-deathstruggle,anoperativewilltrytostabanopponentinoneofthe
body’slargearteriestocausealethalinjury.Thefemoralartery,locatedontheinsideofeach
thigh,hasthegreatestchanceofbeingleftunguarded.
CivilianBLUF: Aknifethatisnot usedsafelyprovidesnodefense atall—it’smorelikelyto
imperiltheuserthantowoundhisattacker.
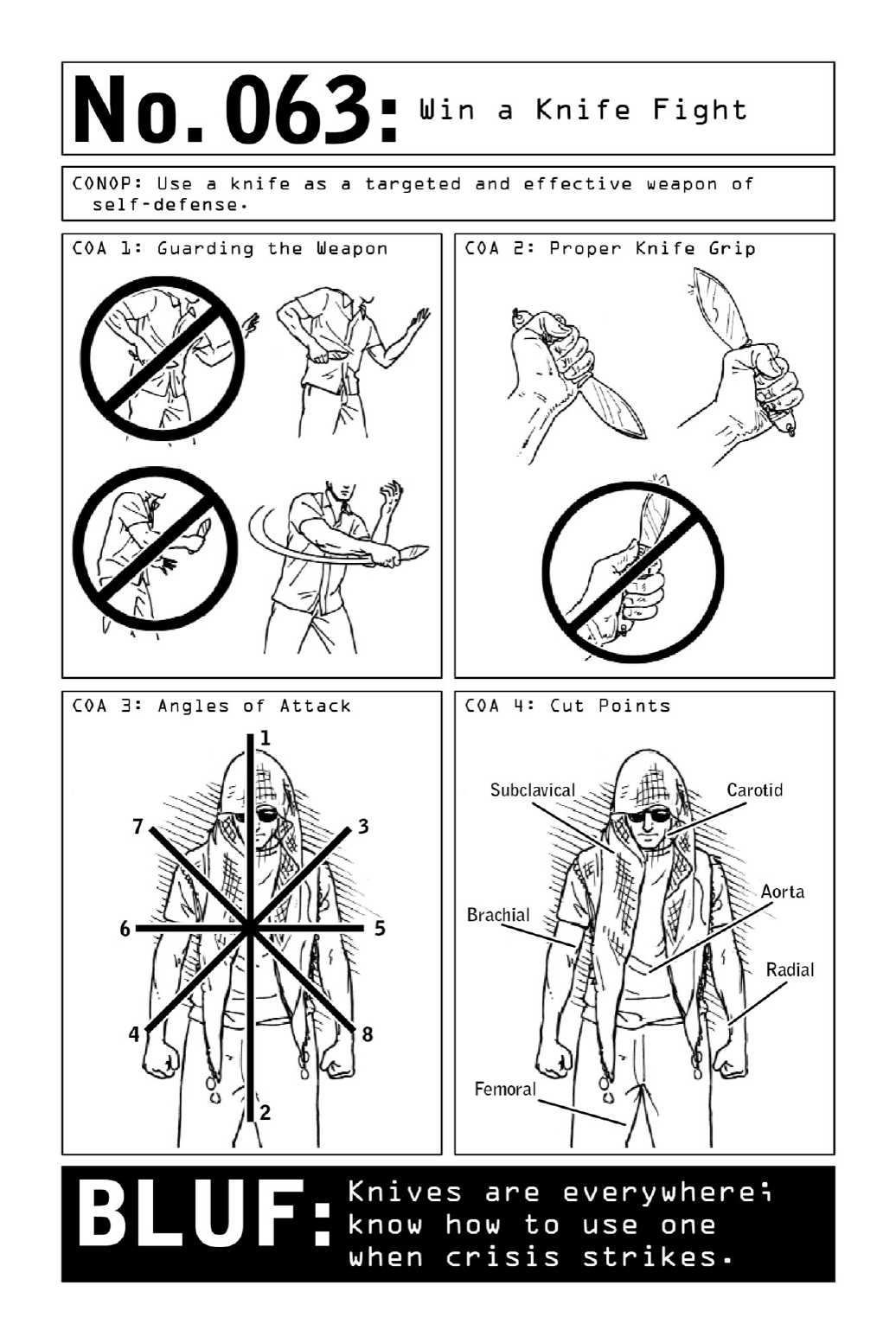

064 StrikeforaKnockout
Whenoperativesshoot,theyaimtokill—andwhentheystrike,theyaimforaknockout.
Thekeytoachievingaknockoutpunchistolandthehitinsuchawaythatitwillcausethe
brain to bounce back and forth in the cerebrospinal fluid. A hard punch that lands on the
temple,jaw,orchincancreateinjuriesinboththefrontofthebrain(a“coup”injury)andthe
back of the brain (a “contrecoup” injury), causing the opponent to lose consciousness and
givingtheoperativeplentyoftimetoescape.
Thepowerinawell-executedpunchcomesfromarotationalactioninthecore,amplified
by the momentum of a double step forward. To make sure the punch lands forcefully, an
operativewillaimhisknucklesthroughthebackoftheskull.Beforethrowingthepunch,he’ll
employaseriesofjabswithhisnondominanthandtodistractandweardowntheopponent,
usingtheelementofsurprisetodeliverahard-hittingstraightpunchwithhisdominanthand.
While hand-to-hand combat is never strategically desirable, even the best-laid plans are
subjecttounexpecteddevelopments.Whethercaughtoffguardwhilepickingalockorsimply
avictimofbeinginthewrongplaceatthewrongtime,theoperativemayfaceanynumberof
opponents who are incidental to his mission. Drawing a weapon in such a scenario would
attract too much notice, so when taken by surprise the operative seeks to knock out his
opponentandclearthepremisesasquicklyaspossible.
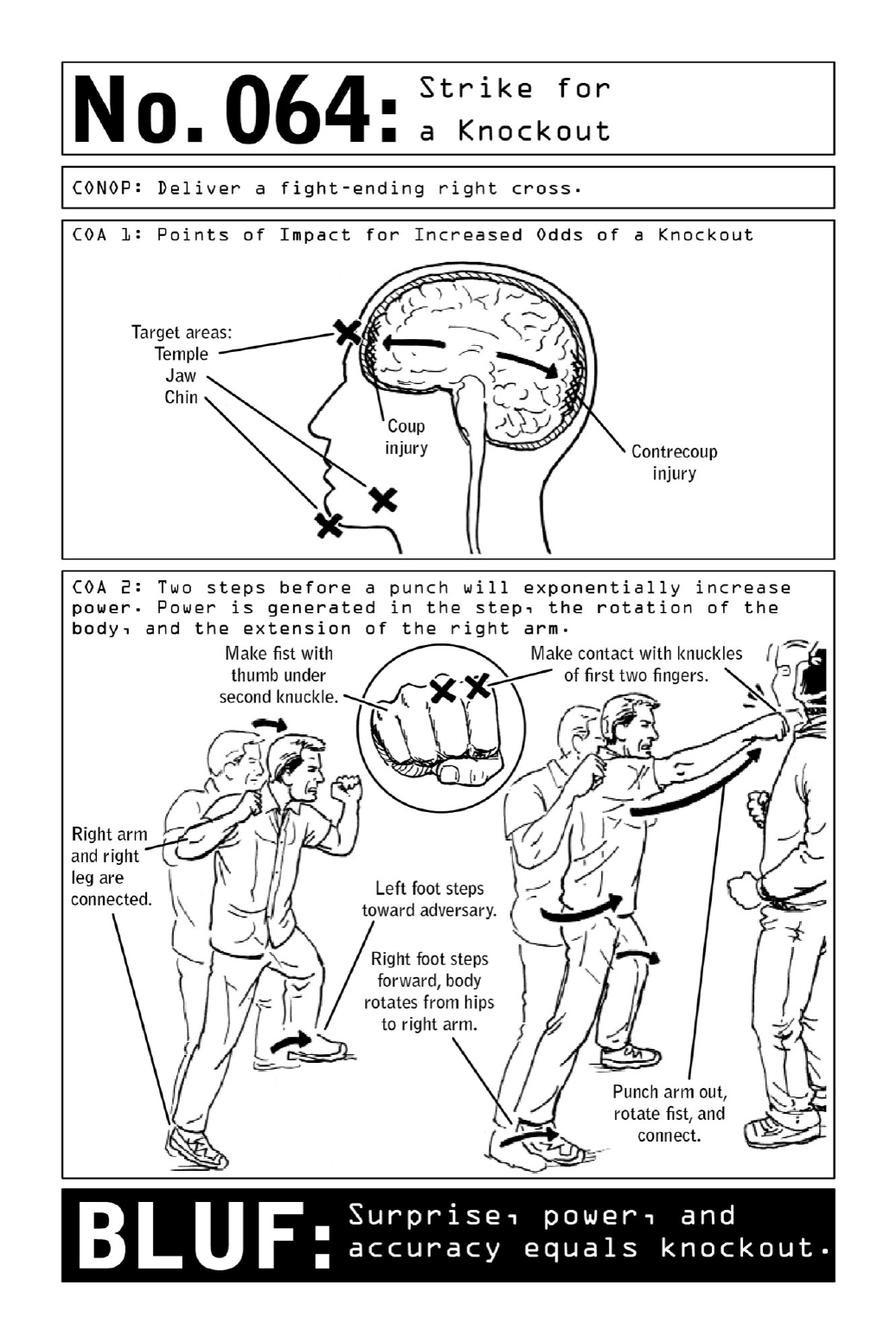

065 DeliveraDevastatingElbowStrike
Trainedtoexecutedeadlyassaultsunderanypossiblecircumstance,ViolentNomadsarewell
versedinthemanyformsofhand-to-handcombat—andtheyarealwayslookingforthemost
efficientwaytoendafight.
The elbow is the hardest and sharpest point on the human body. When combined with
momentum and a calculated angle of attack, an elbow strike can result in a knockout,
breaking skin and causing serious injury. Though both punching and kicking can potentially
knockoutanopponent,elbowstrikesoffermoremaneuverabilitywhenengagingcombatants
in close proximity—and unlike punches, they can be employed in the all-too-common event
thatfightsaretakentotheground.
Properbodypositioningbeginswithabentelbow,withtheactivehandopenandthethumb
anchored to the chest. Keeping the thumb anchored to the chest prevents the arm from
straighteningwhilestriking.Thepowerinanelbowstrikecomeslargelyfromtherotationof
the core, with the elbow becoming the temporary holding spot for that momentum.
Straighteningthearmdilutesmomentumandincreasesrecoverytime.
Theulna,abladelike bonethatrunsthrough theforearm, can berecruitedasasecondary
point of contact; keeping the hand open prevents the forearm muscles from constricting and
envelopingtheulna,allowingthesharpanddeadlybonetorevealitself.
Thetakeaway?Aiminganelbowatthethroat,temple,orchinwillresultinastrikewitha
goodchanceofstunningorseriouslydebilitatinganopponent.
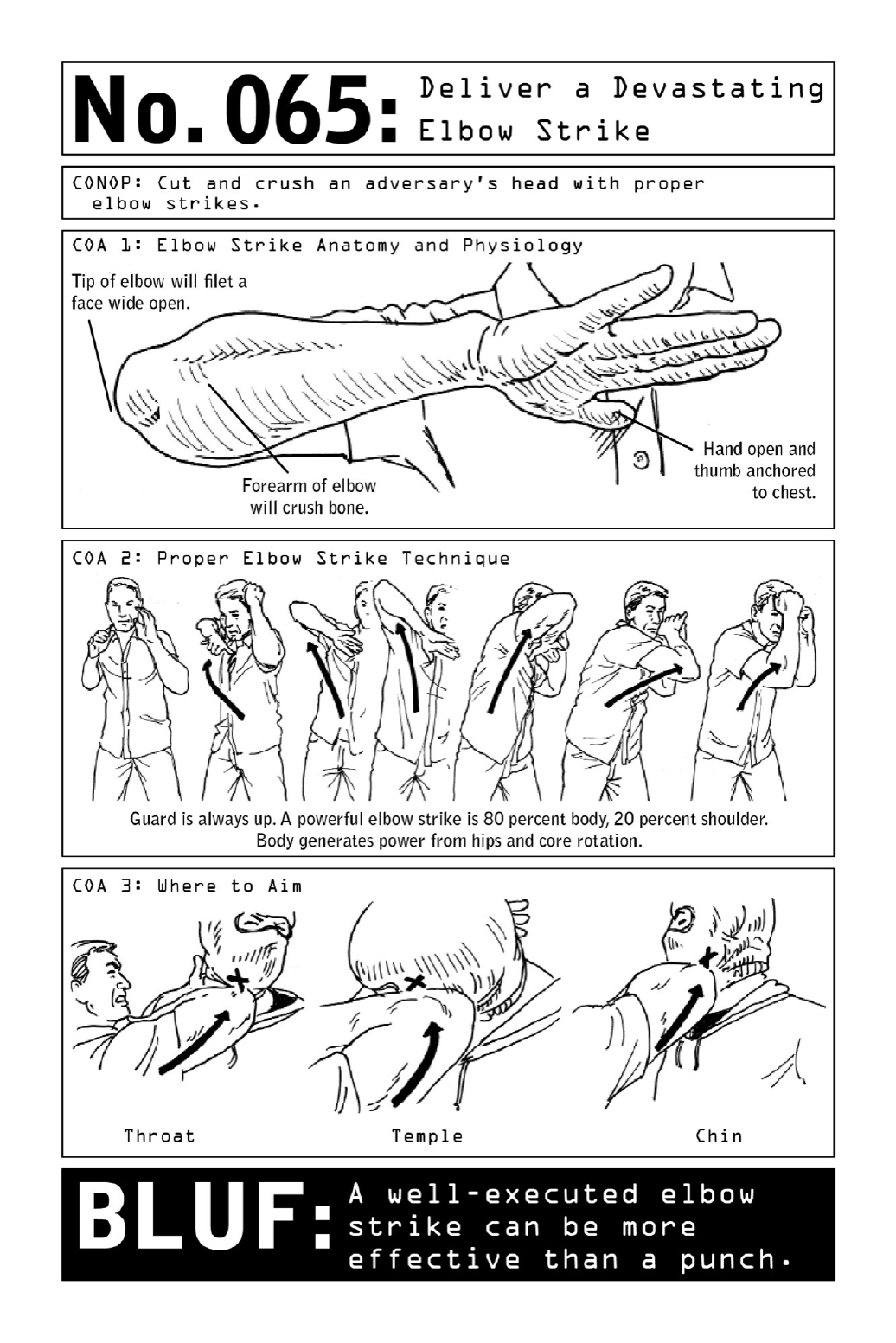

066 MakeanImprovisedTaser
Nothingcouldbelessalertingthanthesightofatouristtakingphotographs—andthat’sgood
news for Nomads looking to create improvised self-defense weapons out of ordinary
disposablecameras.
Nonlethaloptionsforself-defensearecrucialforaveragecitizensandoperativesalike,and
the use of Tasers is legal across most of the United States. Off-the-shelf models, however,
aren’t alwayseasytocomeby,soNomads must sometimes resorttoan improvised hack by
purchasingadisposablecamerawithintheareaofoperation.
Followingaseriesofmodifications,the camerabecomesahighlyeffectiveTaser—rewired
sothattheelectricitynormallyusedtopoweritsflashisdirectedintotwoprotrudingscrews,
their chargepowerful enoughtotemporarily incapacitateanassailant.Anopponent hit with
suchachargeislikelytofalltothegroundandbeincapacitatedforseveralminutes.Acharge
ofanywherefrom120to380voltswillradiatethroughtissueandnerves,interferingwiththe
brain’scommunicationwithmusclesbycreatingstaticwithinthebody.Theresult—impaired
motor skills and involuntary muscle contractions—creates a powerful, nonlethal option for
self-defense.Toconstruct,trainedoperativescarefullyfollowthesesteps:
DraintheCapacitor:Beforetakingthecameraapart,itisabsolutelyessentialtoremovethe
batteryanddepresstheflashbutton.Thiswilldrainthecapacitorofanystoredelectricityand
preventanaccidentalshockduringassembly.Ifthecapacitorisnotproperlydrained,therisk
ofinjuryisveryhigh.
Take the Camera Apart: Carefully remove the camera housing, then remove the circuit
board,flash,film,andbattery.Breakaparttheflashbulbassemblyandthecircuitboard.
Prep the Tools: Acquire a screwdriver, a pair of wire strippers, two four-inch lengths of
insulated wire, and two small screws. Before discarding the roll of film, cut and reserve a
smallpiece.
Rewire the Camera: Strip the lengths of electrical wire at both ends. Wrap the wire ends
aroundtheheadsofthescrews.Twistthescrewsintothecamerahousinginthespacewhere
thefilmrolloncesat.Wraptheopposingwireendstothecapacitorpostsandtapetosecure.
Thisredirectsthecamera’schargefromitsbatteryintothetwoscrews.
PuttheCameraBackTogether:Mountthecircuitboardintoitsoriginallocation,tucking
intheelectricalwirealongsideit.
InserttheSafetyMechanism:Placethepieceofreservedfilmbetweenthebatteryandthe
batteryterminalposttopreventthemechanismfromaccidentallydischarging.
Replace the Housing: With its exterior cardboard casing replaced, the camera will look
virtuallyindistinguishablefromthemodelsfoundinthebackpackofanytypicaltourist.
Incapacitate the Opponent: To use the improvised Taser, employ a stabbing motion to
drive the screws into the opponent’s flesh. A touch will deliver a significant jolt, but in the
eventthatthedevicedoesn’tdischarge,breakingtheskinshouldinjureanattackerenoughfor
theoperativetogaintheupperhandandmakearapidescape.
Note: Creating an improvised Taser is much more dangerous than it seems. Anyone
attempting to do so should avoid touching the camera’s capacitor or any part of its circuit
boardwhilethecapacitor is charged.Theelectricity willdischarge, causingasignificant and
potentiallydisablingshock.OnlydischargetheTaserincasesofextremeemergency.
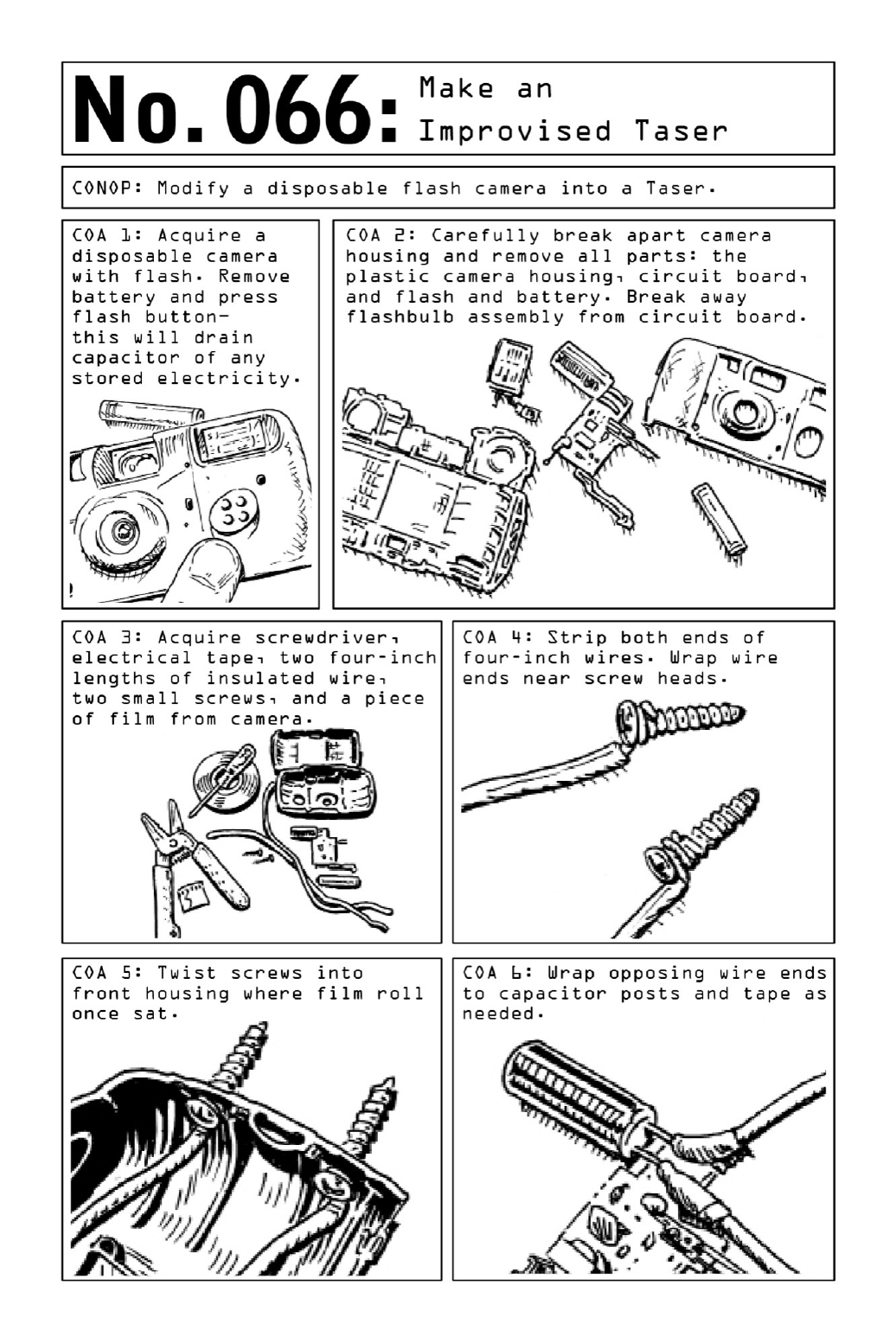
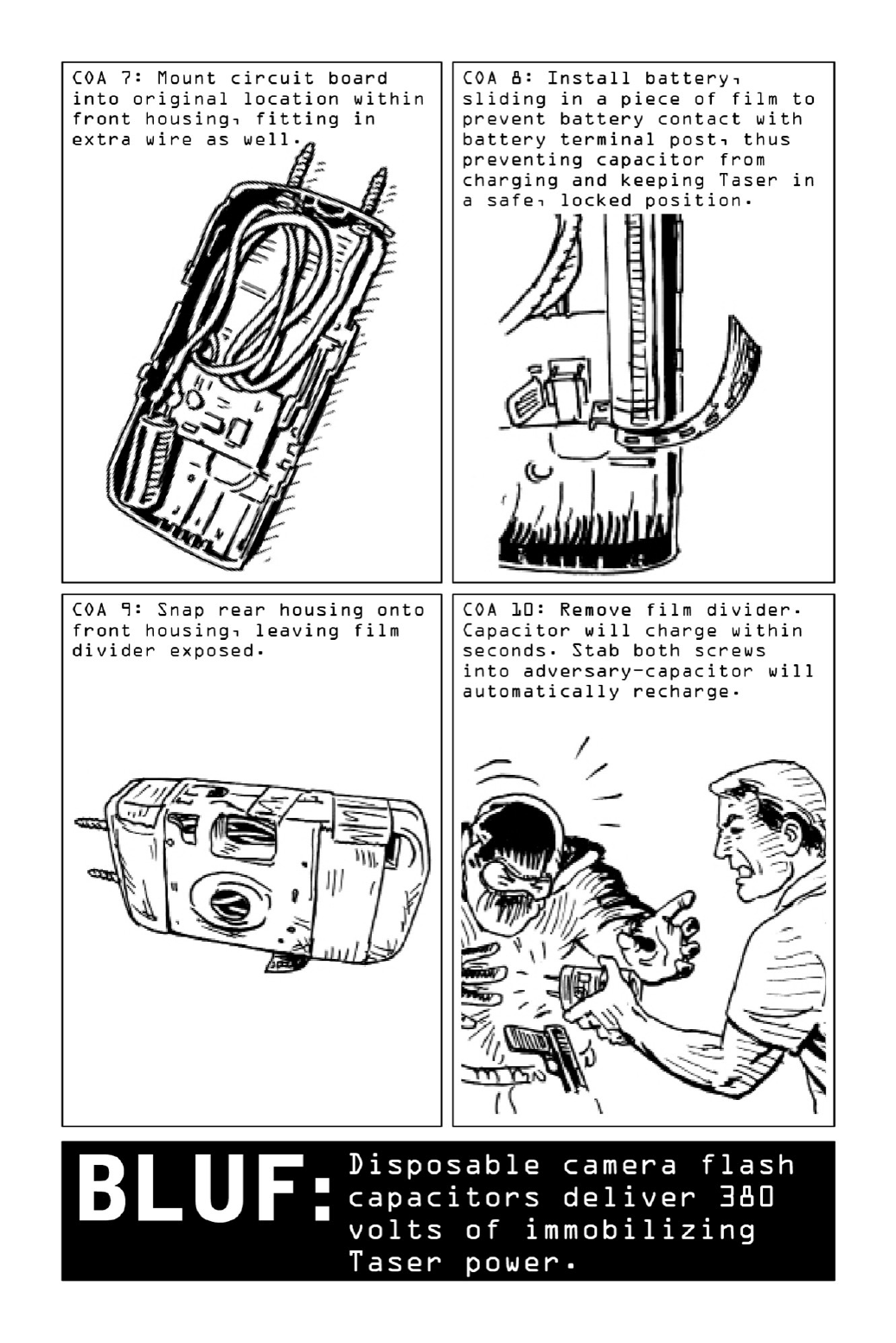

067 MakeanImprovisedExplosiveDevice
Intheabsenceofbackupfromfellowteammates,theoperativelookingtoinfiltrateatarget’s
homemustrelyonimproviseddiversionarydevicestodistracttheenemy’ssecurityunit.Used
aspartofmilitarycampaignsforcenturies,diversionsareparticularlyhelpfulforcombatants
workingalone.
Two diversionary devices can be made from a disposable lighter. The first creates a
momentary flash that will temporarily blind an opponent without damaging surrounding
property (see page 168); the second launches an explosion equivalent to that created by a
quarter stick of dynamite. Unlike Molotov cocktails and many other types of homemade
explosive devices, this tool can be set off without advance modifications—which means it
won’tarousesuspicioniftheoperativeissearched.Allthat’sneededistapeandalighter.
To create an explosion sizable enough to cause injury, damage property, and create a
sustainedsenseofdisorder,operativeschooseamodelfueledbycompressedratherthanliquid
gas;thoughnolongersoldintheUnitedStatesduetotheirassociatedhazards,compressedgas
lighterscanreadilybefoundoverseas.
The trick works by loosening the flame adjustment gear from the lighter body until gas
beginstoleak.Whenthestrikerwheelisrolledtolighttheflameandthelighterismountedat
adownwardanglewithtapeorzipties,theflamewillbegintomelttheplasticcasing.Aftera
minute or two,theflamewillburn throughthecasing,ignitingallthegas inthecanister in
onefellswoop.


068 MakeaDiversionary“Flash”Device
Explosions, car accidents, fire alarms, power outages . . . These are just some of the
“incidents”thatseemtofollowoperativesaroundtheglobe—handydiversionsthatdrawthe
attention of law enforcement officials, bystanders, or targets while the Nomad accomplishes
his mission and vanishes into the night. In the face of sudden attack, diversions can also be
usedtofacilitateescape,whichiswhycarryingadiscreetandportablediversionarydevicecan
bealifesaver.Madeintwominutesorlessfromanordinarydisposablelighter,theimprovised
devicecreatesablindingflashthat,whenusedindarkness,canimpairthehumaneyeforupto
tenminutes.
Mimicking the action of a stun grenade or “flash bang” device, the device works by
isolatingandheatingupthelighter’sflint—madeofmetalcompoundsthatheatupquicklyand
produceaburstofincandescenceuponcombustion.Whentheheatedflinthitstheground,the
resulting flash is significant enough to be mistaken for an explosion. In essence, the gesture
takesthelighter’slifetimeofsparkandusesitupallatonce.


069 MakeaMolotovCocktail
Theclassicweaponof rebellionandurbanwarfare,theMolotovcocktailearneditsmoniker
during World War II and has been around since the Spanish Civil War. To this day, the
incendiarydeviceremainstheweaponofchoicefordisenfranchisedagitatorsandanyonewho
lacksaccesstomoresophisticatedtoolsofcombat.Becauseitcanbelaunchedoverbarricades
or gates, it creates an option for street-level combat targeting highly guarded buildings or
compounds.
For Violent Nomads seeking to disguise their actions as those of ordinary citizens, a
Molotov cocktail provides a quick-to-assemble solution that can be thrown from a distance
and sow a vast amount of chaos—without leaving any trace of governmental involvement.
Apart from its obvious offensive uses, it may be employed as part of a campaign of
psychological warfare (page 186) or as a diversionary tactic, drawing the attention of
onlookersandsecurityforcestoaflamingcar whiletheNomadstealthilyinfiltratesatarget
building.
Thoughabasicversioncanbemadebyfunnelingfuelintoaglassbottle,additionsofmotor
oilandsoapcreateamoreflammabledevice.Motoroil,beingthickerthangasoline,createsa
longer-lastingfire.Shavingsofsoapcreateagellingeffect(particularlyifthemixtureisleftto
sitovernight),makingforapotentnapalmlikesubstancethatspreadsandstickstosurfacesas
it burns. A fuel-soaked tampon becomes a flammable stopper and fuse. When the fuse is lit
andthebottlethrown,theglassshattersuponimpact,ignitingadeadlyandfast-movingfire.


070 PITaTargetVehicle
Most drivers tend to feel relatively safe when they’re inside their vehicles. Especially when
traveling through familiar areas, they become complacent, failing to pay attention to their
surroundings—whichiswhytargetingabadguy’svehiclealongthemostvulnerablepartofhis
routeprovidesasolidoptionforNomadslookingtocreatean“accident.”
As expertsinboth offensive anddefensivedrivingtechniques,ViolentNomads know how
to turn an automobile into a highly effective weapon. A properly executed vehicular attack
willincapacitateor eliminatea target without anyattributiontoofficial channels. One such
method is the PIT (Precision Immobilization Technique). Used for decades by U.S. law
enforcement, PITing is a pursuit tactic that forces a fleeing car to abruptly spin sideways,
causingthedrivertolosecontrolandcometoastop.
ThekeytoPITmaneuversisfortheoperativetomaintainhisspeedthroughoutthecollision
process.PITingatspeedsoflessthanthirty-fivemilesperhourwillcausethetargetedvehicle
to spin sideways and crash. PITing at any speed greater than thirty-five miles per hour is
considered a lethal technique that will likely result in the targeted vehicle rolling over
completely; high-center-of-gravity vehicles such as SUVs and vans are susceptible to rolling
overifPITedatspeedsoflessthanthirty-fivemilesperhour.
ThehighlyskilledNomadwillconductaPITmaneuverwherethereistheleastlikelihood
ofbeingobserved,seamlesslyspeedingawayfromthesceneandanypotentialwitnesses.


071 PistolDisarmament:PointedatChest
If a masked man emerges from the shadows, aiming a weapon at a target’s chest at short
range,receivedwisdomsaysit’stimetoraisehandsandsurrender.Insomecasesthatmaybe
thewisestchoice.Iftheattackerdemandsawallet,avehicle,orvaluables,handthemoverand
allowhimtoescape—butiftheattacker’saimistoabductorshoot,fightingforcontrolofthe
weaponisapropositionwhoseoddsarebetterthanmightbeassumed.Inscenariosbasedona
shooterandanunarmedtarget,militarydrillshaveshownthatthepartywhomakesthefirst
moveismostoftenthepartywhoprevails.Evenwhenstartingfromadistanceofsixtoeight
feet,unarmedtargetsarefrequentlyabletoruntowardanddisarmashooterbeforehepulls
thetrigger—benefitingfromadelayedresponseastheshooterprocessesunexpectedactions.
Whiledisarminganadversaryisahigh-riskmaneuver,Nomadsusethefollowingprotocol
toincreasechancesofsuccess.
PivotandTraptheWeapon:Theoperativeshouldclasptheopponent’shandsandthebody
ofthegunwhilepivotinghisbodyoutofthelineoffire.
DrivetheBarreltowardtheAdversary:Twisttheweapontowardtheadversary’sforearm.
Pull the Weapon Away: Continue to drive the barrel of the weapon over sideways while
wrenchingitaway.
Gain Control of the Weapon: Having pried the weapon from the opponent’s hands, the
operativeshouldbackawayquicklyanddoasystemschecktoensurethattheweaponisready
tofire.Takeaimandbereadytoshootiftheopponentdrawsabackupweapon.
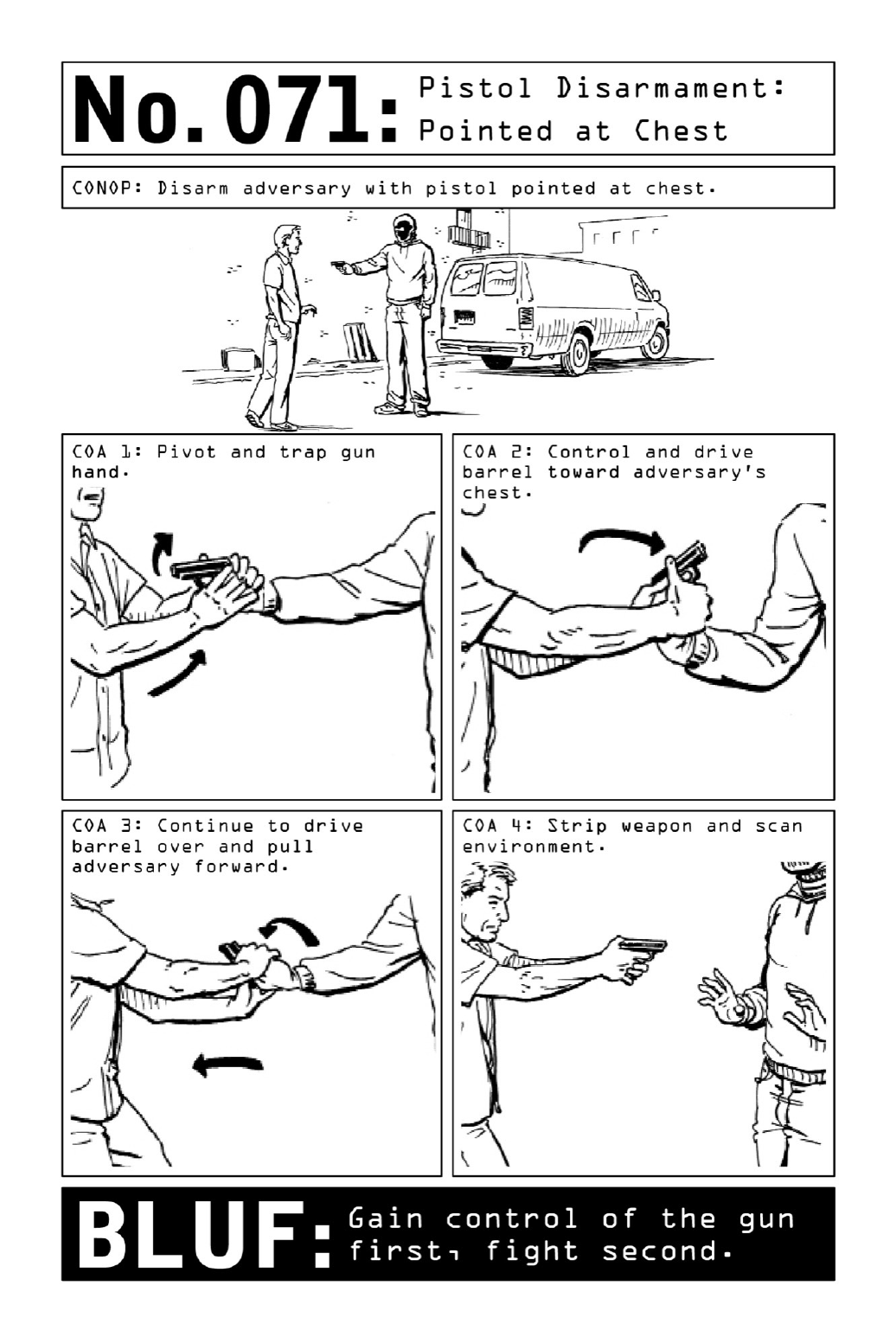

072 PistolDisarmament:PointedatBack
Theelementofsurprisecanbeapowerfulweapon.Whichiswhycriminalstendtosneakup
on their targets from behind—springing out of bushes as targets unlock their front doors,
sliding out from behind parked cars as targets dig around for their keys, slinking out of the
shadowsasthetargetismid-transactionatthecornerATM.
Whileanunseenweaponcancauseaninstinctivelock-and-freezeresponse,evenwithagun
pressed against his back, a well-trained operative can control the outcome of a violent
altercation. If an attacker simply wants material goods, even an experienced operative may
choosetohandthemoverandallowhimtoescape.Thethreatofkidnappingorbodilyharm,
ontheotherhand,willbemetwithaswiftandsuddenresponse.Attheoutset,theoperative
willpushbackagainsttheweapon;onsemiautomaticmodels,thiscouldpreventtheweapon’s
firing mechanism from engaging. Then, using a pivot-and-sweep motion, he will trap the
weaponinhisarmpitinasurprisinglyeffectivehold.


073 SurviveanActiveShooter
Populardepictionsofshootingspreeshavevictims(orsoon-to-bevictims)coweringhelplessly
in the face of drawn weapons, even when targets vastly outnumber the shooter or shooters.
Historyhasshown,however,thatalackofactioninthefaceoflivefirewillradicallyreducea
target’schanceofsurvival.
Whether they’re under attack from a lone wolf or a band of terrorists, the three tactics
availabletocivilianscaughtinlivefirearerunning,hiding,andfighting.Runningisthefirst
option,andfightingisthelast.
Run:Iftheassailantisfarenoughawayandthereappearstobeanescaperouteimmediately
available,considerattemptingtorun.Leavebelongingsbehindandrunwithaplaninmind.It
isharderforashootertohitamovingtarget,somoveinazigzagpatternand/orfromcoverto
cover.
Hide:Ifexitingthepremisesisnotachievable,thenextstepistofindthesafestareaavailable
andsecureitaswellaspossible.
• Hide somewhere out of the assailant’s view and silence cell phones and other digital
devices.
• Lock the door, if possible, or create a barricade. Block the door using whatever
materials are available: desks, tables, file cabinets, other furniture, books, etc. Close
blindsandcurtains.
•Targetsshouldattempttoputsomethingbetweenthemselvesandtheassailant.Ifina
roomwithacloseddoor,hidebehindsolidobjects,awayfromthedoor.(SeeIdentify
EmergencyBallisticShields,page22,forpreferredobjects.)

• Call out for help using mobile devices, landlines, email, text, and radios to get first
respondersmovingtothelocation.
•Placesignsinexteriorwindowstoidentifythelocationofinjuredpersons.
•Alwaysconsidertheriskentailedbyopeningthedoor.Theassailantmaybangonthe
door,yellforhelp,orotherwiseattempttoenticetargetstoopenthedoortoasecured
area.
Most ricocheting bullets follow the path of the floor, so when bullets are flying, squat or
move to hands and knees rather than lying down; when taking shelter from grenades or
explosives, lie on the floor with mouth open (to prevent pressure from rupturing lungs) and
feettowardtheexplosion,withfingersinterlacedbehindhead(toprotectbrain).
Fight:Fightingisanoptionoflastresort,tobeusedonlywhenallotheroptionshavefailed
orareunavailable.Theimportantthingtounderstand,however,isthatfightingisanoption:
Itis possible for unarmed targets to effectively disarm and incapacitate an armed assailant,
particularlyiftheyoutnumberhim.Remember,aguncanonlybeshotinonedirectionatany
one time. Attackers often assume that their targets will be cowed by the sight of their
weapons;anyoffensivereactionislikelytocatchthemoffguard.
Professionalfighttrainingprovidesadvantages,butevenuntrainedpeopleunaccustomedto
fightingcanbeofservice,particularlyifthey’reactinginagroupinwhichonepersonorteam
aimstosubdueorovercometheshooter’supperbodyandtheothergoesforthelegs.Theaim
istocontroltheweaponandthencontroltheshooter,gettinghimonthegroundorknocking
himoutinordertoescape.
Actwithphysicalaggressionandviolence.
Throwanythingavailableattheassailant.
Workasateamwhenwithothers.
Alwaysactconsciously,nomatterhowlittletimetheremaybe.
Use improvised weapons to strike the shooter—tools, sporting goods, any hard and dense
objects available. Blind the shooter with anything that burns or blinds—cleaning products,
fuel,salt,pepper.Whenstriking,continueuntiltheshooterhasbeenknockedunconsciousand
thereisnofurthermovement—donotstop.
Related Skills: Use Improvised Body Armor, page 20; Identify Emergency Ballistic Shields,
page 22; Pistol Disarmament: Pointed at Chest, page 174; Pistol Disarmament: Pointed at
Back, page176; Deliver a Devastating Elbow Strike, page 160; Strike for a Knockout, page
158;SurviveaGrenadeAttack,page184.

074 MakeanImprovisedGasMask
Alachrymatoryagentfrequentlyusedbylawenforcementasaformofriotcontrol,teargasis
the most common nonlethal chemical weapon in the world. Irritating the eyes, nose, throat,
and skin, the substance causes debilitating short-term effects ranging from sensations of
intensepain,burning,andsuffocationtotears,temporaryblindness,blistering,andvomiting.
Butbeyondthephysicaleffectsliesapotentiallygreaterthreat:Exposuretoteargasmaybe
aprecursortomassdetention.Onceacrowdhasbeenimmobilized,lawenforcementofficials
may take the opportunity to perform a round of indiscriminate arrests. Given that foreign
governments sometimes use Western detainees as a form of political currency, accidentally
gettingcaughtupinsuchagovernmentcrackdownisaveryrealconcernforanytravelersin
unstableregions.
The first tool of self-defense against violent methods of crowd control is a well-honed
awareness of third-party activity. Follow common sense in generally avoiding areas where
protestorscongregate.Ifanoperativepassesthroughsuchanareaandsensesimminentchaos,
heseekstoclearthepremisesasquicklyaspossible.
Ifhecannotavoidtravelingthroughareaswheretheuseofteargasisapossibility,hewill
createanimprovisedgasmaskfromanemptyplasticjug,asponge,andclearpackingtape.
Aspongesaturatedwithcleanwaterbecomesaneffectivefilter,andoncetapeddowntothe
operative’sfacethedevicewillactasanadequate(butnotairtight)temporarygasmask.
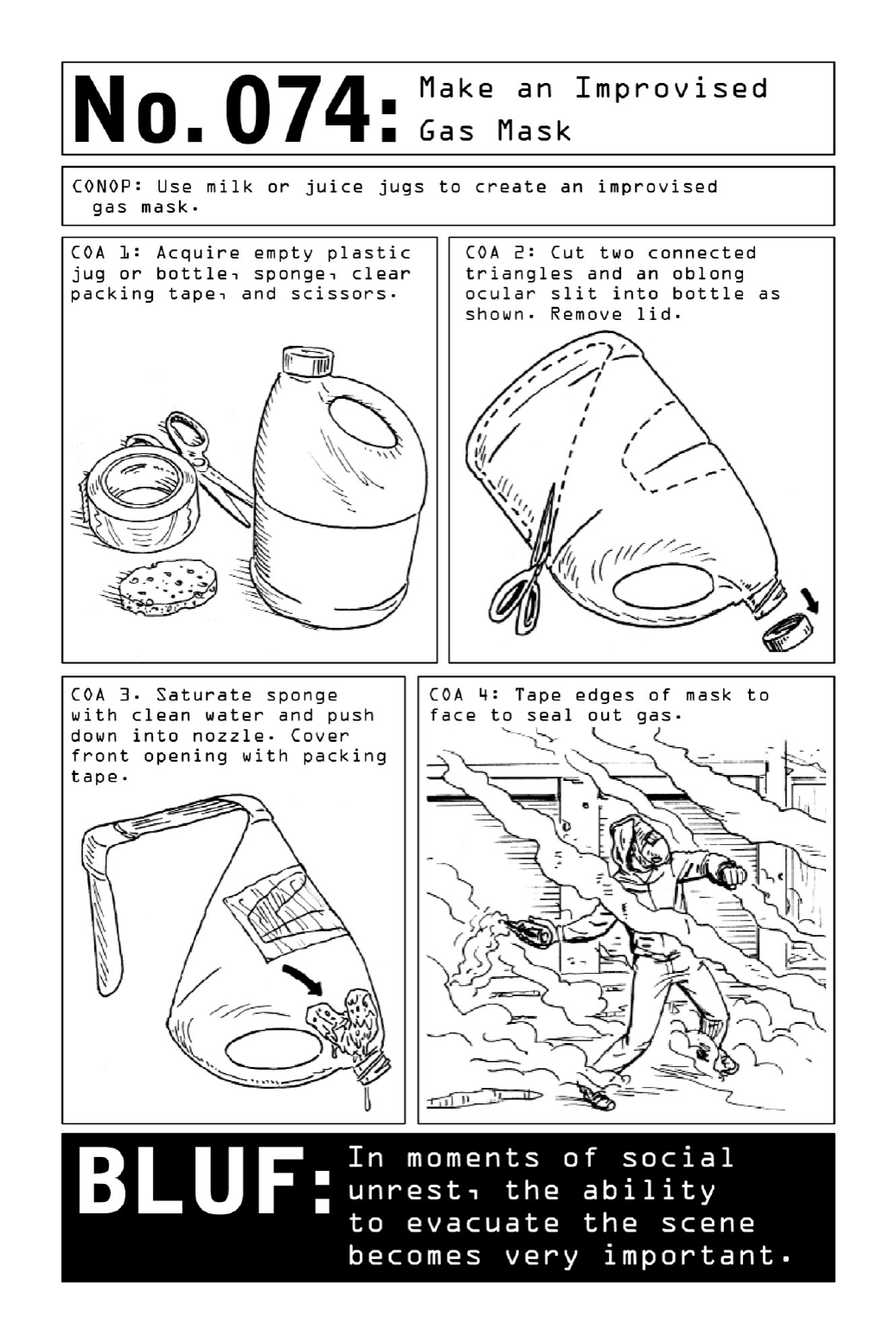

075 SurviveaGrenadeAttack
While grenade attacks used to be relegated to active combat zones, they are increasingly a
feature of surprise acts of terrorism as well as civil unrest. Though they are most often
unanticipated,suchattacksposeariskthatcanbemitigated.
Agrenade’sexplosiontakesapredictableupside-downconeshape,generatingablastwitha
six-meter kill zone (depending on its model). While it may be possible for a bystander to
outrun the explosion in the seconds between impact and detonation, an upright posture will
leavehimvulnerabletoshrapnel.Ifcoverisn’tavailablewithinthreesteps,takeonegiantleap
away from the grenade and to the ground. The goal is to move out of the cone-shaped
explosionandawayfromthepathofshrapnel,whichrarelytravelsalongtheground.
Positionfeettowardtheblastinordertoprotect the brain. Crosslegs inordertoprotect
femoralarteries, coveringearstoprevent tympanicmembranesfrom rupturing.Keepelbows
tight against the rib cage and open mouth to regularize internal and external pressure and
preventthelungsfrombursting.
Know that in an urban environment, the danger of the blast will be compounded by the
landscape—cement buildings and glass windows joining a litany of potential hazards. The
explosionwillcreateasecondarysetoflethalprojectilesfromthesesurroundings.
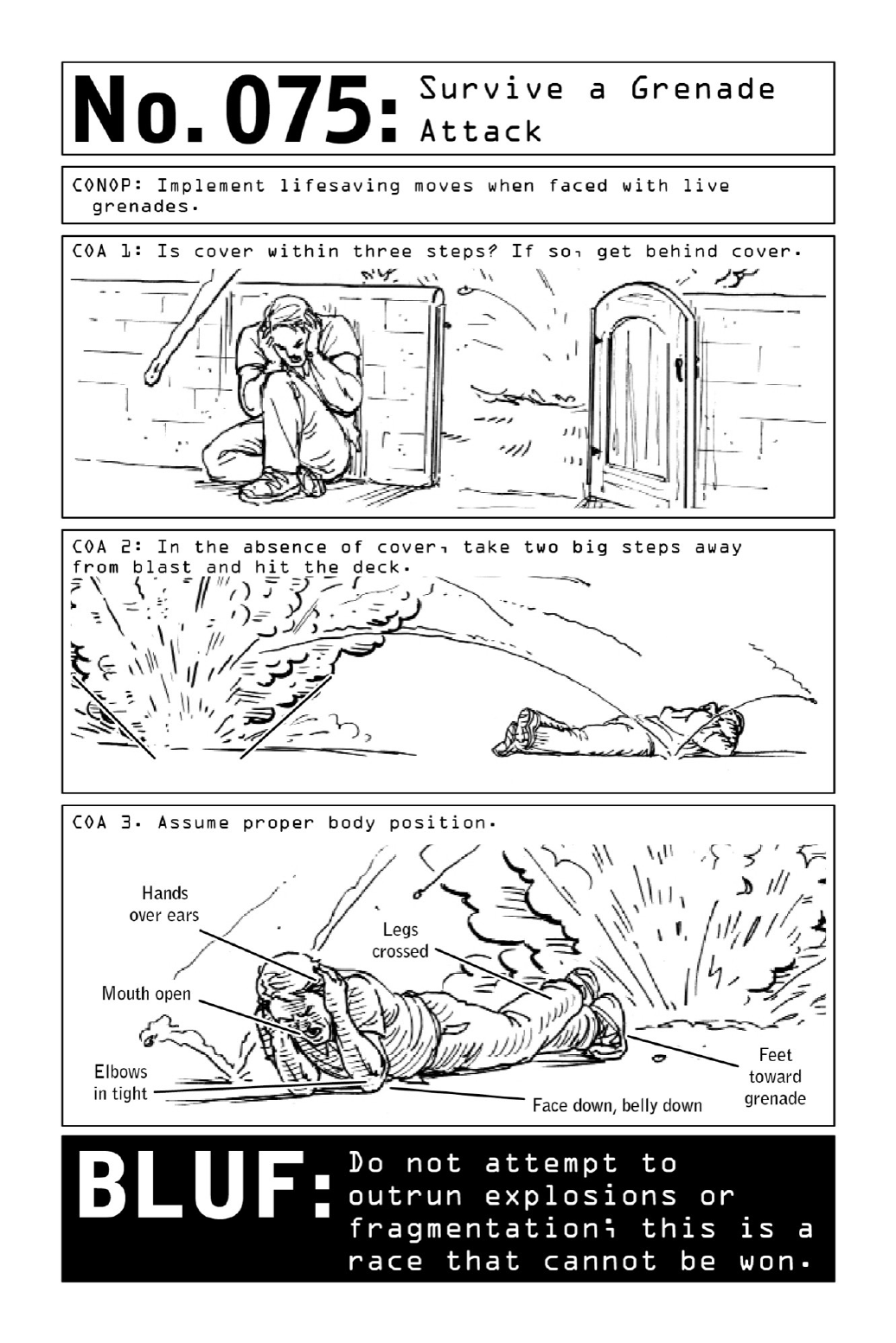

076 WagePsychologicalWarfare
When long-term observation of a known criminal runs dry, operatives may resort to
psychologicalwarfareinordertoprovokeareactioninthetarget.
Ifatargetsuspectshismovementsarebeingwatchedandhaspareddownhisroutineand
contact with associates, inducing paranoia can reveal new intelligence. Who does the target
call when he is feeling cornered? Breaking a pattern might reveal new behaviors or third
partiesfortheoperativetoinvestigate.
Depending on the surveillance context, psychological warfare can involve techniques from
letter drops to “soft attacks” designed primarily to provoke fear rather than create damage.
Besieging a target with anonymous written communications (“We know who you are”) can
contribute to an overall sense of unease. Messages written as if they are coming from
neighbors mayconvincethetargetthatheissurroundedbyanall-seeinghordeof unfriendly
forces—andresultinhiscallingouttoassociatesforassistance.
Harassinggesturesmayescalatetovandalismorsoftattacks.Usinglong-rangetacticssuch
as throwing Molotov cocktails (see page170) or scattering gunshot from a moving vehicle,
operativesworkingalonecancreatetheillusionthattheyarebackedbyabandofmany.
Thegoalinpsychologicalwarfareofanysortistodistortatarget’sperceptionofrealityin
ordertobringaboutachangeinbehavior.Stoppingshortoffull-fledgedattacks,suchtactics
allow the operative to remain unseen, continuing his surveillance mission from a more
powerfulposition.


PARTVIII
SANITIZATION:LEAVENOTRACE

077 LeaveZeroDNABehind
ThoughDNAsamplescanbeliftedfromtracequantitiesofmucusandsweat,therealculprits
inforensicidentificationarehumantissueandskincells—whichiswhythemostmalevolent
classofcriminalsandrapistswillgoasfarasscrubbingdownandshavingtheirentirebodies
andheadsinordertosloughofflooseskincellsandremovethepossibilityofbeingbetrayed
by a stray hair. (Cut hair produces variable forensic results, but cells taken from the root
containvaluablegeneticinformation.)
A thorough full-body scrub highly reduces the odds of leaving trace DNA behind, so an
operativestartsfromthetopandworkshiswaydown,brushinghishairashewashesit.
Heselectsclothingthatcovershisentirebody,hot-washingitmultipletimesorpurchasing
itnew. Denim andcottonarethemost commonfibersintheworld—andthereforetheleast
traceable.Whenbuyingclothing,hetakescarenottotouchit.Hepurchasestheitemsnextto
theclothingthatwillactuallybewornsoastoavoidcontactwhenpullingthemofftherack.
Heappliesglovesbeforegettingdressedandwearsahattocontainhishair.
Onceontarget,hecovershismouthandnosewithasurgicalmaskorafull-faceskimask
to avoid the spread of saliva or mucus. He touches only what is necessary and nothing else.
Attemptingtocleanacontaminatedsiteisasearchforaneedleinahaystack—besttoavoid
leavingtracesfromthestart.Oncesafelyawayfromthetargetzone,heburnsalloperational
clothing.


078 LeaveZeroFingerprintsBehind
As criminals and law enforcement officials know, the efficacy and frequency of fingerprint
matchingtendstobeoverstatedinthepopularmedia.Alegalcorrelationmustdisplayamatch
amongadozenormore“minutiae,”theridges,whirls,andbifurcationsthatrendereachprint
unique—but movement and natural oils often cause smudging and other imperfections. Still,
operativestakeextrememeasurestoavoidleavingidentifyingevidencebehind.
The key to sanitization is covering fingerprints and thoroughly cleaning tools. This is a
lengthyprocessthatlastsfromthebeginningofanoperationtoitsend—foranoperativewho
covershistrackswhileontargetbutfailstoproperlysanitizehisgetawayvehicleortoolsisan
operativeindangerofgettingburned.Aspartofmissionprep,hesanitizesanygear(lockpicks
orweaponsneededforthatparticularmission)bywipingitdownwithanacidsuchaspaint
thinnertobreakdownoils.Hethoroughlysanitizestheoperationalvehicle.
Healso switchesout glovesateachstage of the process to avoid transportingidentifiable
fibersorsubstancesfromthesafe house to thetarget. In asetting where gloveswoulddraw
toomuchnotice—retrievinginformationinanofficeorduringtheday—hefillsinthetroughs
offingerprintswithsuperglueorfilesdownfingerprintswithapumicestone.
Operativesseekingtoerasetheirfingerprintsoveralongerperiodmayseektoprocurethe
chemotherapy drug Capecitabine, as pharmaceuticals are only loosely regulated in many
foreigncountries.Asasideeffect,thedrugcausesinflammationandblisteringonthepalmsof
handsandsolesoffeet,sloughingoffskincellsandprints.


079 LeaveZeroDigitalTraceBehind
Themost dangerous element inanygivenenvironmentmaybe thedevicefoundinthepants
pocket of the majority of civilians in the developed world: a cellular phone, an electronic
tether that could be employed to track a target’s every move. This inadvertent digital
scrapbookcanalsobeusedtocreateadetailedbiography—includingnotonlyaccesstobank
accountsbutalsoinformationaboutfamilyandfriends.
In areas where communications companies are owned and operated by host-nation
governments, digital security becomes particularly relevant. Any foreign phones pop up on
cellular networks as outsider devices, and as such, become increasingly vulnerable to being
tracked.Whenpossible,operativesprefertopurchaseprepaid,contract-freephonesinsidethe
hostnationratherthanbringingintheirown.
Intheeventthattheydotravelwithelectronics,operativesprotectthembyeithershielding
orfullydisablingthem.Cellphones,tablets,andlaptopscanbeshieldedfrombothincoming
and outgoing signals by a pocket made out of a quadruple layer of aluminum foil. (Smart
deviceswillplowthroughsingleordoublelayersbyredirectingalloftheirbatteries’energies
toward finding a signal.) The foil must be tightly compacted around the device, leaving no
gaps.
A more polished option is a discreet shielded carrying case (e.g., Zero Trace) embedded
withadoublelayerofmetalfabricthatblocksallsignals,inobservanceofCIAprotocol.
Because many cell phones employ small backup batteries that run even when phones are
turned off, in the absence of a workable shield, removing all batteries and SIM cards is the
onlywaytorenderaphonecompletelysafefromanyvulnerabilities.Asthisisn’tpossibleon
somephones,sometimestheonlyoptionistoleavethedevicebehind.


080 TrickFacialRecognitionSoftware
ForgedidentificationpapersgrantanactiveNomadanimportantlayerofanonymity—butif
hehasalreadybeenidentifiedbyforeigngovernmentsas aprobablesecurityrisk,hispicture
may come up in a database at border crossings or other high-security checkpoints. Current
facialrecognitionsoftware,basedonimagery,isstillrelativelyeasytobypass,sotheNomad
willproceedasplanned.
Usingalgorithmsthatcompareparticularanchorpointswithinagivendatabaseofimages—
noses,thespacebetweeneyes,thesizeofeacheye,theshapeofcheekbones,chins,andears—
the technology focuses on distinctive bony prominences that cannot be readily altered. But
covering up or otherwise obfuscating those anchor points leaves the software little to work
with.
Largesunglassesandlongbangscanbeusedtocovertheforehead,browbone,andpartof
thecheekbones.Ahatpulleddownlowandadownward-tiltedheadcanthrowanoperative’s
faceintoshadow.Smilingchangestheshapeoftheeyesandpushestissueoverthecheekbones,
whichiswhymanycountriesrequireaneutralfacialexpressioninpassportphotos.
FrequentlyinuseinLasVegascasinos,whereitpreventscheatinggamblersfromsiphoning
off millions of dollars in revenue, facial recognition is an ever-evolving science. As social
media platforms begin to use it to tag and sort through images, it will only grow more and
more sophisticated. One day facial recognition will be a well-oiled mechanism utilized to
secureanythingfrombordercrossingsandATMstoprivatehomesandbusinesses,alongwith
the up-and-coming vascular identification technologies that take thermal pictures of human
faces, using the positioning of facial veins and arteries as the basis for identification and
leavingfewifanyoptionsforsubterfuge.Butfornow,thetechnologyleavesplentyofgapsfor
aNomadtoexploit.


081 TrickFingerprintScanningSoftware
The most widely used form of biometrics, fingerprinting is increasingly traveling from the
criminal justice system into the realm of consumer electronics. Harnessed for such uses as
unlockingsmartphones,authorizing payments, and securingdoors or safes, the technology is
becoming more widespread. As it does, its quality becomes more variable, displaying
vulnerabilitiesforNomadsandcommoncriminalstoexploit.
For an operative, collecting fingerprints is frequently a postmortem scenario. Performing
“battledamageassessment”intheaftermathofaplannedeventsuchasanexplosion,hemight
be tasked with gathering biometric information in order to confirm the target’s identity. In
suchcasestheoperativewillgothemostdirectroute:severingthetarget’sthumb.
Butthumbprintscanbereplicatedvialessviolentmeans,oneofwhichinvolvesthechewy
candy known as the gummy bear. Malleable and tacky, gummy bears are exceptionally
receptivetofingerprints.Becausetheyhaveaconsistencysimilartothatofhumantissue,they
arealsowell-suitedtodeceivinglower-qualityfingerprintscanningmechanisms.
Cheap scanners don’t read depth, which is why they won’t register the fact that a
fingerprint’stexturalpatternhasbeenreversed—theridgesturnedintovalleys,andviceversa,
as they are transferred onto the gummy bear. When confronted with more sophisticated
technology, Nomads use a combination of Silly Putty and gelatin, impressioning the Silly
Putty, then pouring a gelatin solution into the clay and letting it sit until it gels. Carefully
removingthegelnetsaduplicatefingerprintthat’samatchforpatternandisimpressionedto
properdepth.


082 CreateaHastyDisguise
In the real world of covert operations, disguise doesn’t follow the well-worn conceits of spy
moviesandthrillers—thebathroomdyejob,theuseofmasks.Instead,aneffectiveandrapid
transformation relies on illusion, employing tricks of perception rather than true disguise. A
few props can turn a businessman into a service worker, and a change in color pattern can
causeatargettovanishfromsight.
In attempting to evade surveillance teams, operatives employ a working knowledge of
surveillance psychology.Whatdoes a surveillanceteamactuallysee whenthey’re watchinga
target?Particularlywhenwatchingfromadistance,asurveillanceteamwillhomeinoncolor
blocksratherthanfacialfeaturesorhairstyle,usingbroadvisualstrokestokeeptrackofthe
target’s movements. Over time, the colors of the target’s clothing become ingrained in the
surveillance team’sbrain—insteadofscanningforthetarget, theyunconsciouslyscanforthe
colors he’s wearing. An easy way to subvert their expectations is to duck into a public
restroomorfittingroomandveryquicklyswitchouttodifferentcolors.Ifwearingwhiteover
denim,switchtoblackoverdenimandwalkrightoutthedoorwithoutbeingspotted.
Anotherwaytomanipulatetheexpectationsofasurveillanceteamistostartoutinbright
colors. Thiswillcausetheteamtorelax,secure intheknowledgethattheyarewatchingan
easy mark. When the operative emerges from a stopping point in a muted outfit, he’ll be as
goodasinvisible.
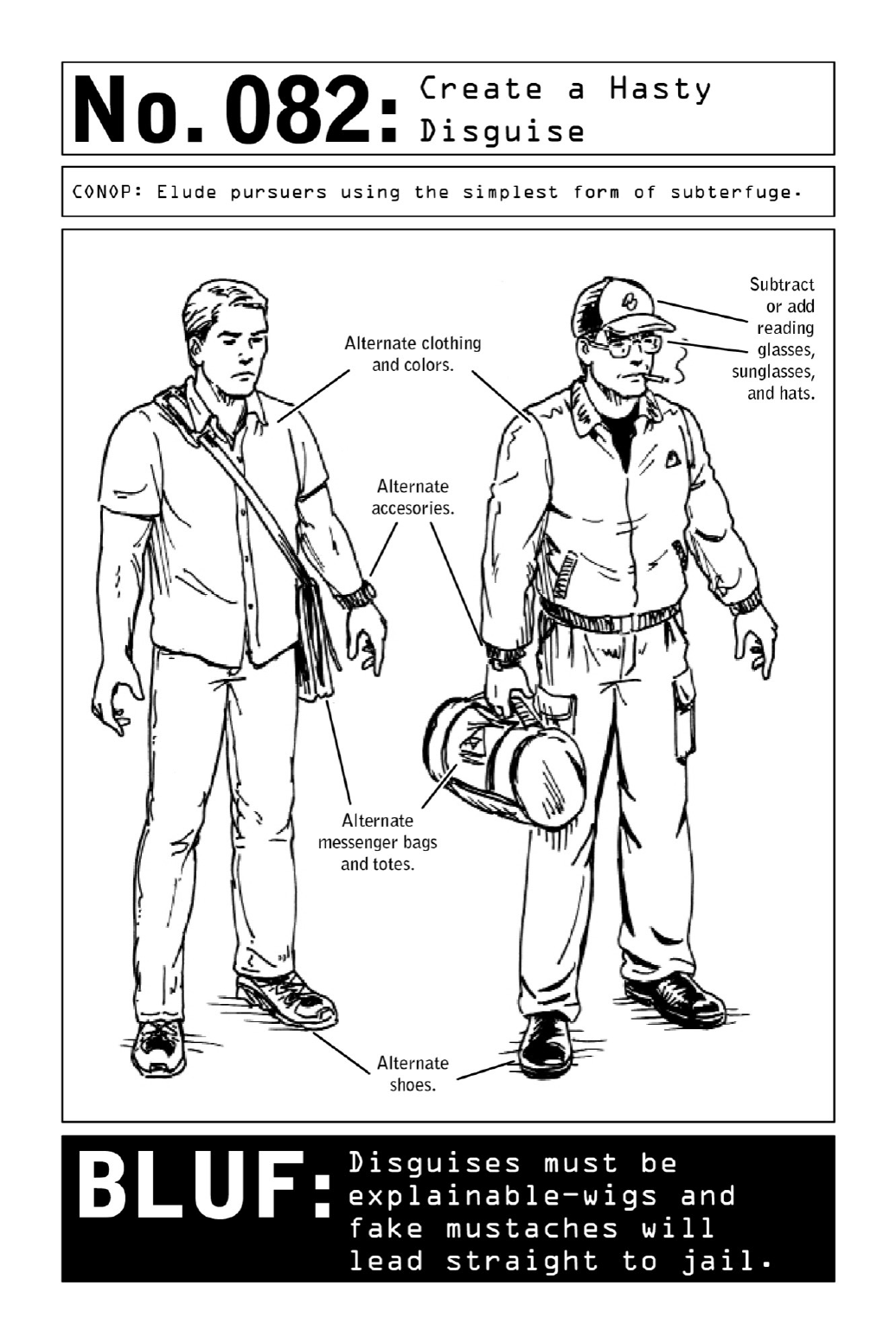

083 GetPastaGuardDog
WhenNomads writeupa reconnaissancereportona target’shomeor business, theyalways
include a full accounting of any animals they come across. Even untrained dogs, when
spooked,cangiveawayaNomad’slocationoralertanownertothefactthatsomethingout
of the ordinary is under way. Any infiltration plan must include measures for distracting or
subduing pets or guard dogs while the Nomad goes about his business—and particularly in
third-worldcountries,operativesmustalsobewaryofthewilddogsthatroamthestreetsin
packs.
Killingguarddogsleavesbehindatrailofunwantedevidence,soNomadsresorttotactics
thattemporarilydisableordistracttheanimal.Acaninedeterrentspray,equivalenttopepper
spray, will irritate a dog’s eyes and carries a smell that dogs find extremely unpleasant. A
burstofcompressedair(theproductusedtodustelectronics)willfreezeadog’snoseandhave
him running for cover. Compressed to fluid form, the mixture of nitrogen and other gasses
undergoes a massive drop in temperature upon being released from the can; when emitted
fromacanthatisturnedupsidedown,thegaswillsprayoutasliquidandimmediatelyfreeze
toice.
Though challenging to come by in any scenario, female dog urine is one of the most
effectivecaninedistractiontoolsinaNomad’sarsenal.Sprayedinadog’sfaceorawayfrom
theentrypoint,itsscentprovesanirresistibleenticementforanyattackdog,nomatterhow
welltrained.


084 DiscreetlyClearaFloodedScubaMask
To operatives carrying out missions with complex logistics, diving is just another form of
clandestine movement—one that is well known to the drug cartels that move thousands of
kilograms of contraband across the world via submarine (the ocean floor being nearly
impossibletopolice).
While swimmingacross openwatersruns the riskofdetection, divingkeeps theoperative
concealeddeepunderwater,givinghimastealthywaytoattackboats,piers,andbridges.It’s
also an unexpected means of escape. Upon accessing a cache of scuba gear submerged at a
predeterminedlocation(seepage38),aViolentNomadcoulddisappearforeverwithasingle
breath-hold.
Scuba diving’s flexibility comes with its fair share of vulnerabilities. Entry and exit pose
complex logistical challenges, and medical hazards are abundant, especially for an operative
divingalone.Typically,aNomadcannotstayunderwaterforlongerthanthreehours,soany
tacticalplanmustaccountforthislimitation.
Thoughtheriskofdetectiondiminishesoncetheoperativeisunderwater,onetelltalesign
of activity—easily observed in a quiet harbor—is the trail of bubbles emitted by the overly
hastyclearingofascubamask.


085 DisposeofaBody
Withapreferenceforvehicularcollisionsanduntraceableinjections,aViolentNomadalways
attempts to disguise an assassination so that it looks like an accident. But sometimes a hit
simplygoesbad.ANomadmakesmistakesthatcouldleadtohisidentificationorissurprised
mid-missionbyanincidentalthirdparty.
In order to safely extricate himself from the area of operation, the Nomad must first
disposeofthecorpse.
Land Burial: Compared to a typical horizontal burial site, a vertical grave leaves a
significantly smaller footprint aboveground—and less surface area means a smaller signature
fordogstosniffout.Thegraveisdugtwofeetdeeperthanthelengthofthe body, whichis
lowered down headfirst so that organs (which give off the most scent) are buried deep
underground.
ThermalBurial:Toeradicate alltrace ofa body, a cremationchamber canbe replicatedby
fillingafifty-gallonsteeldrumhalfwayfullwithjetfuel.(Jetfuelcanbecommandeeredfrom
small private airports with minimal security.) After about two hours, bones and teeth will
have turned to dust, making any identification near impossible. This method will give off a
significant amount of smoke (more easily spotted during the day) and flame (more easily
spottedatnight)andmustbeundertakenindesolate,ruralenvironments.
Maritime Burial: The least discoverable burial site is a watery grave at the bottom of the
ocean floor, a few nautical miles offshore. Weighted down by fifty pounds of steel pipe,
bricks,or cinder blocks,thebodyis wrappedinalayer ofperforatedconstructionplasticor
ground cloth so that air bubbles won’t prevent it from sinking. An operative will secure the
plasticwithadoublelayerofchickenwiretopreventbodypartsfromfloatingtothesurface
asthebodyisattackedbymarinelifeordegradesovertime.
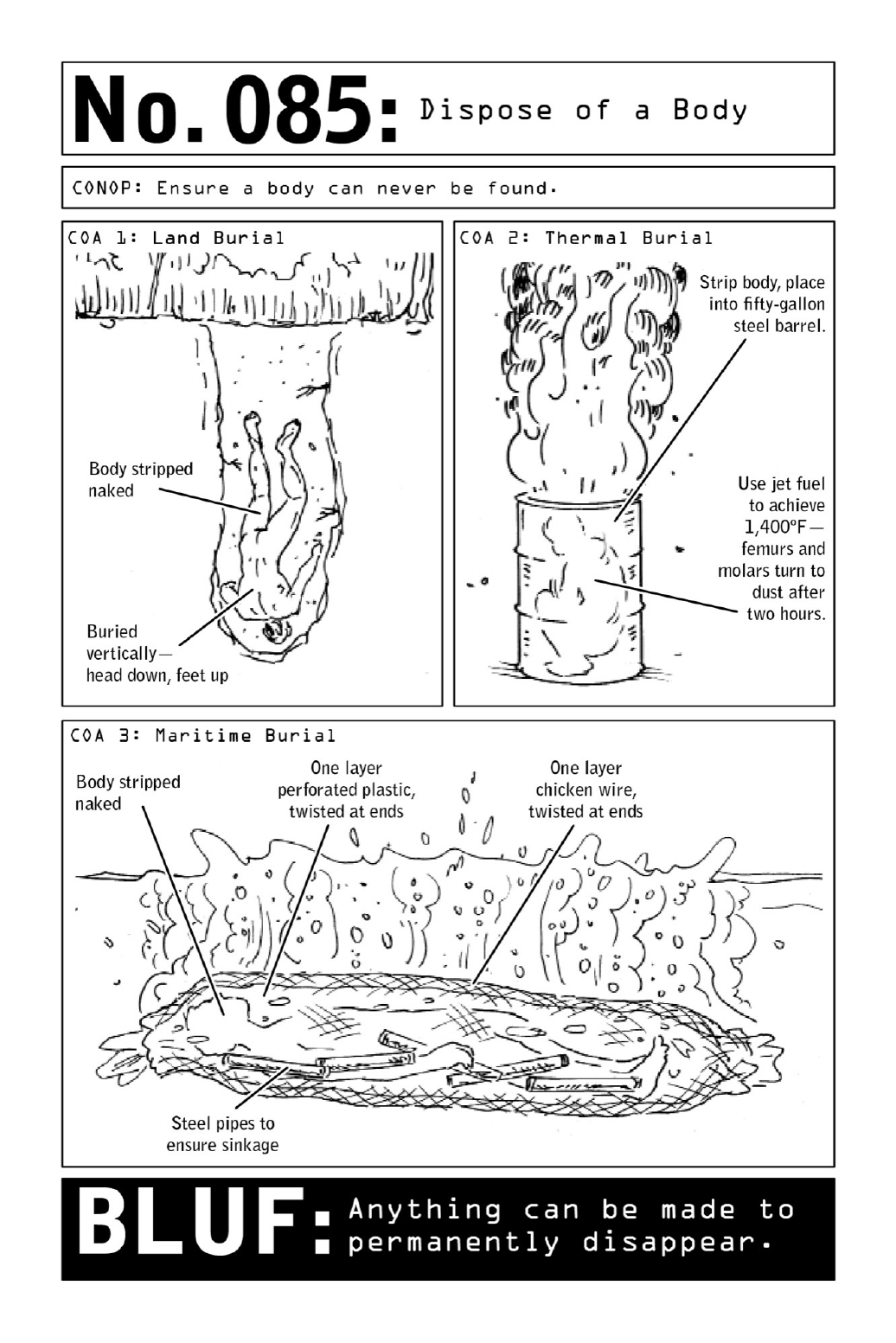

PARTIX
EXFILTRATIONANDESCAPE:HOWTO
DISAPPEAR

086 CreateaRappellingHarness
Combinedwithanimprovisedrope(see page 212) a rappellingharnessmadeout ofa single
bedsheet could be the key to a safe and fast escape. For an operative, it may also allow for
access to a target’s room from a building facade. Once the mission has been executed, the
operativevanishesandthesheetisdiscarded—anuntraceable,anonymousartifactswipedfrom
ahotelroomorpurchasedunderanassumedname.
Aking-sizesheetwillcreateaharnesslargeenoughforadults,whilefull-sizesheetscanbe
used to create harnesses for children. A similar harness can be made from materials such as
one-inch-wide tubular nylon, cargo straps, furniture covers, and the plastic sheeting used in
commercial construction. An important additional layer of safety during rope descents, the
harnessensuresthatanoperativewon’tfalltohisdeathifhelosesholdoftherope.Relatively
safe,secure,andeasytomakeinlessthanthreeminutes,itprovidesthree“pointsoffailure”;
whensecuredtoanimprovisedrope,gravityandtensionshouldensurethatifoneloopfails,
theothertwowillcontinuetohold.
Asecureknotandproperropelengtharekeytoasaferappellingapparatus.Aropethatis
toolongnegatesthepurposeoftheharness,whichshouldallowtheNomadto“bounce”(asif
fromabungeecord)afewfeetfromthegroundintheeventthathelosesholdoftherope.In
buildingtherope,useaguidelineofonesheetperstory.
RelatedSkills:EscapeaMultistoryBuilding,page212.
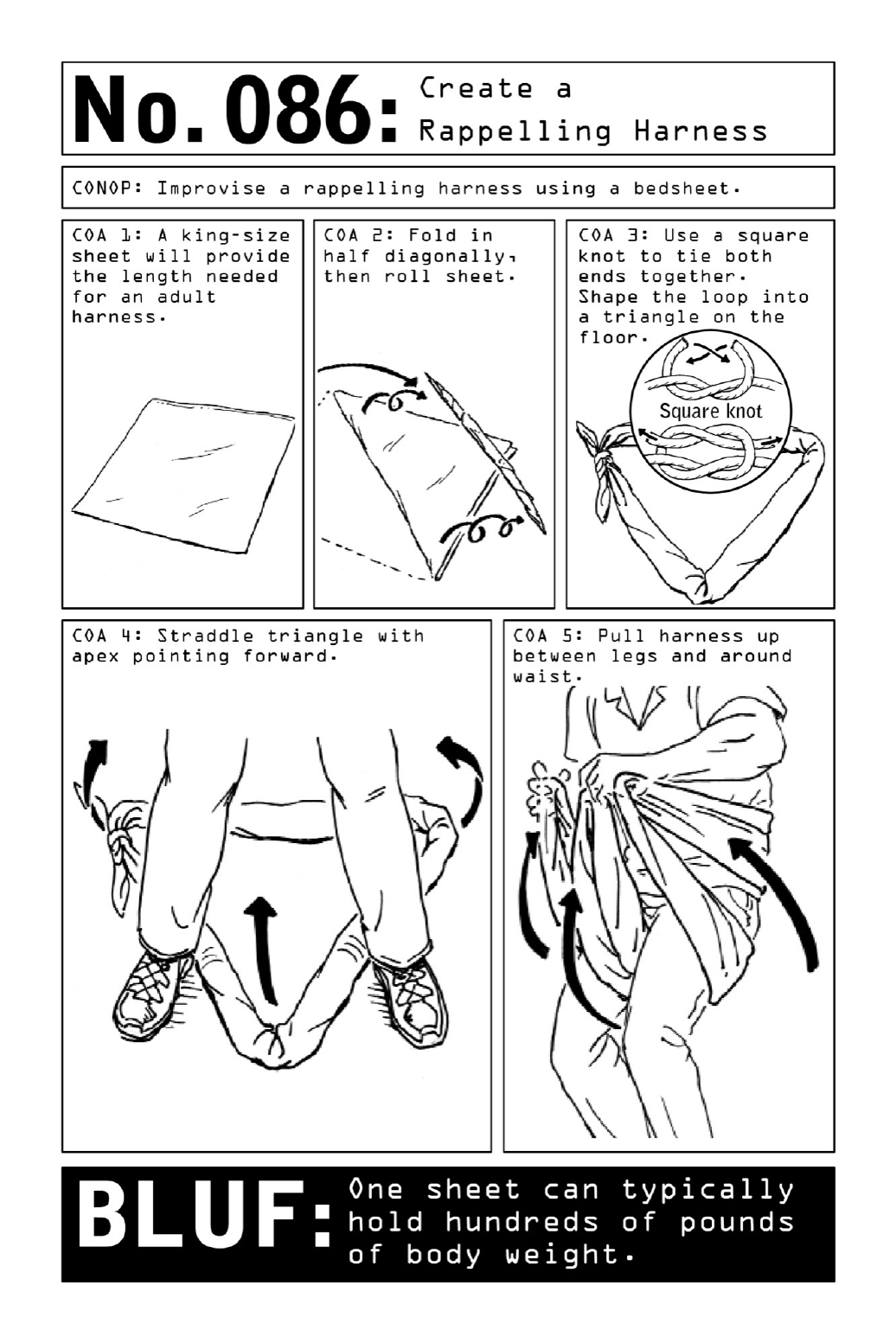

087 EscapeaMultistoryBuilding
The action heroes of the silver screen can be seen scaling the face of skyscrapers using all
manneroffuturisticsuctiondevicesandlaser-cuttingrappellingtechniques.Intherealworld
ofcovertoperations,however,anescapefromamultistorybuildingislikelytobeassistedby
amuchmorehumbleprop:anordinarybedsheet.Whetherescapingafire,ahostagesituation,
or the scene of a crime, learning to create a dependable rope out of bedsheets will ensure a
swift exit from a multistory building, under any set of circumstances. Stronger than some
ropes, high-thread-count sheets represent another case in which improvised materials can
perform with greater effectiveness than their store-bought counterparts: One sheet may hold
hundreds of pounds of body weight. (Tensile strength increases with thread count, and an
increaseintensilestrengthcanhandlemoreweight.)
When checking into a hotel room, opt for a king-size bed—king-size sheets mean more
material,whichtranslatesintoadditionalropelength.Oncecheckedin,callthefrontdeskand
request additional sheets in order to gather enough rope length to make a potential descent.
Buildingstoriesareapproximatelytenfeettall,andoneking-sizesheetshouldprovidetwelve
feetoflength.
Tensilestrengthaside,theropewillonlybeasdependableastheanchortowhichitistied.
Thechosenanchorshouldeitherbepermanentlyaffixedtowalls,largerthanthewindow,or
heavier than the person it is holding—beds, radiators, large dressers or tables, and heavy
couches are all good options. In the absence of those possibilities, a chair wedged behind a
closeddoormaydothetrick.
Tiethesheetstogetherusingsquareknots,whichtightenunderstress,andalwaysleaveat
leastsixinchestoonefootoflengthattheknotends.Ifescapingfire,wetthesheetspriorto
tying them and make sure the anchor isn’t highly flammable. For added security, pair rope
withtheimprovisedrappellingharness,page210.
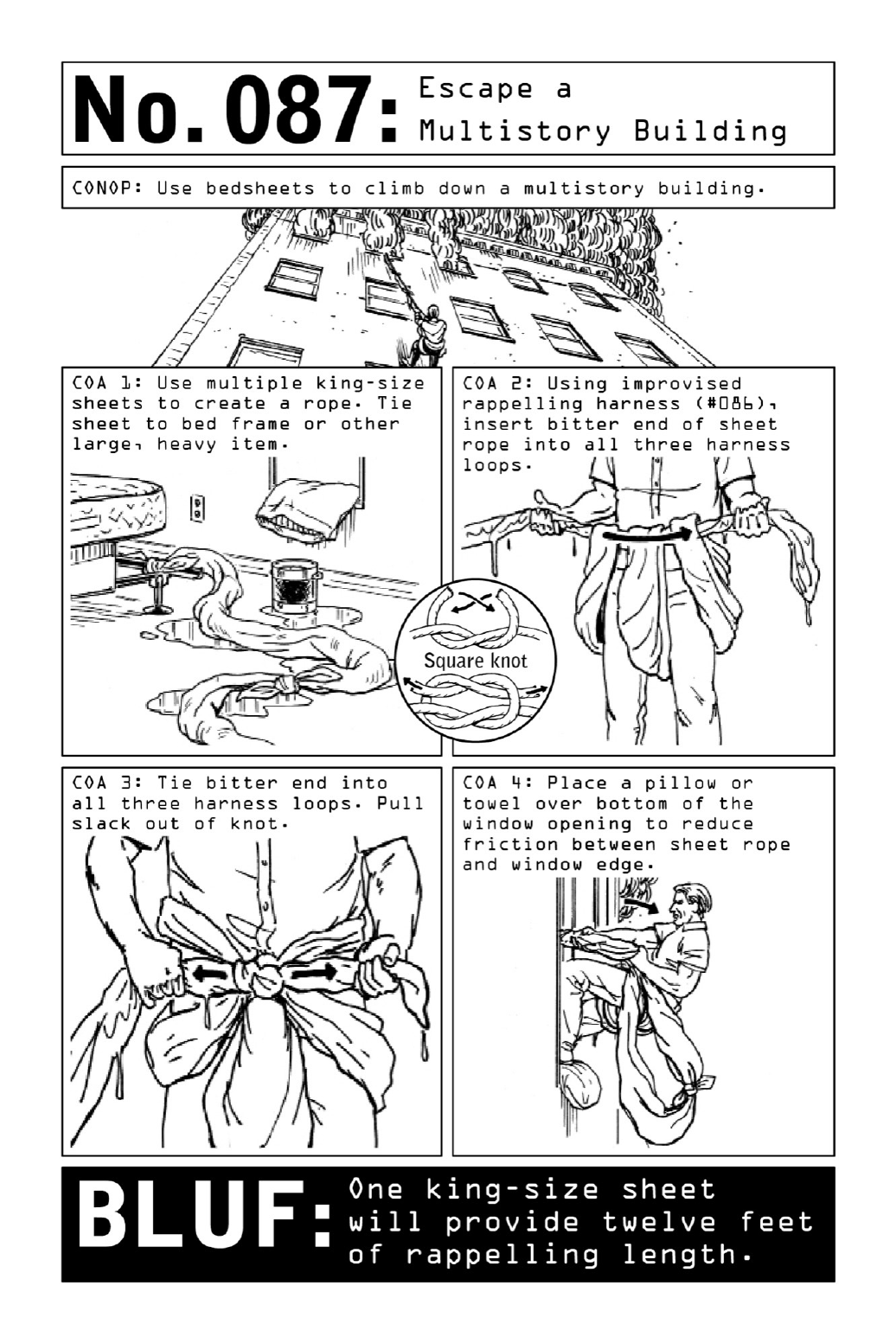

088 SurviveaDrowningAttempt
When an operative is captured in hostile territory, the odds of survival are low. Instead of
being taken to trial, he will likely simply be made to “disappear”—which is why operatives
practiceescapingwhilewearingundefeatablerestraintsonhandsandfeet,bothinwaterand
on land. Tied up, thrown into open waters, and left to drown to death, the well-trained
operative still has recourse to a few skills that can help extend his life until he is found or
reachessolidground.
Whenitcomestoself-preservationinwater,thekeytosurvivalisbreathcontrol.Withthe
lungs full of air, the human body is buoyant—so deep breaths and quick exhales are key.
Buoyancyinfreshwaterismorechallengingbutstillachievable.Panicking,whichcanleadto
hyperventilation,isthenumber-oneenemytosurvival.
Restraints and body positioning may make breathing a challenge, but repositioning is
always within the Nomad’s grasp. In shallow waters, use a sinking and bouncing approach
(seediagram)totraveltowardshore,ricochetingofftheseabedorlakeflooruptothesurface
foraninhale.
Whenfacingdown,whetherfloatinginplaceorusingabackwardkickingmotiontoswim
toshore,theoperativeshouldarchhisbackinordertoraisehisheadabovewater.
In rough seas, this may not give him enough clearance to get his head out of the water.
Instead,afullbodyrotationwillallowhimtotakeadeepbreathandthencontinuetraveling
forward.
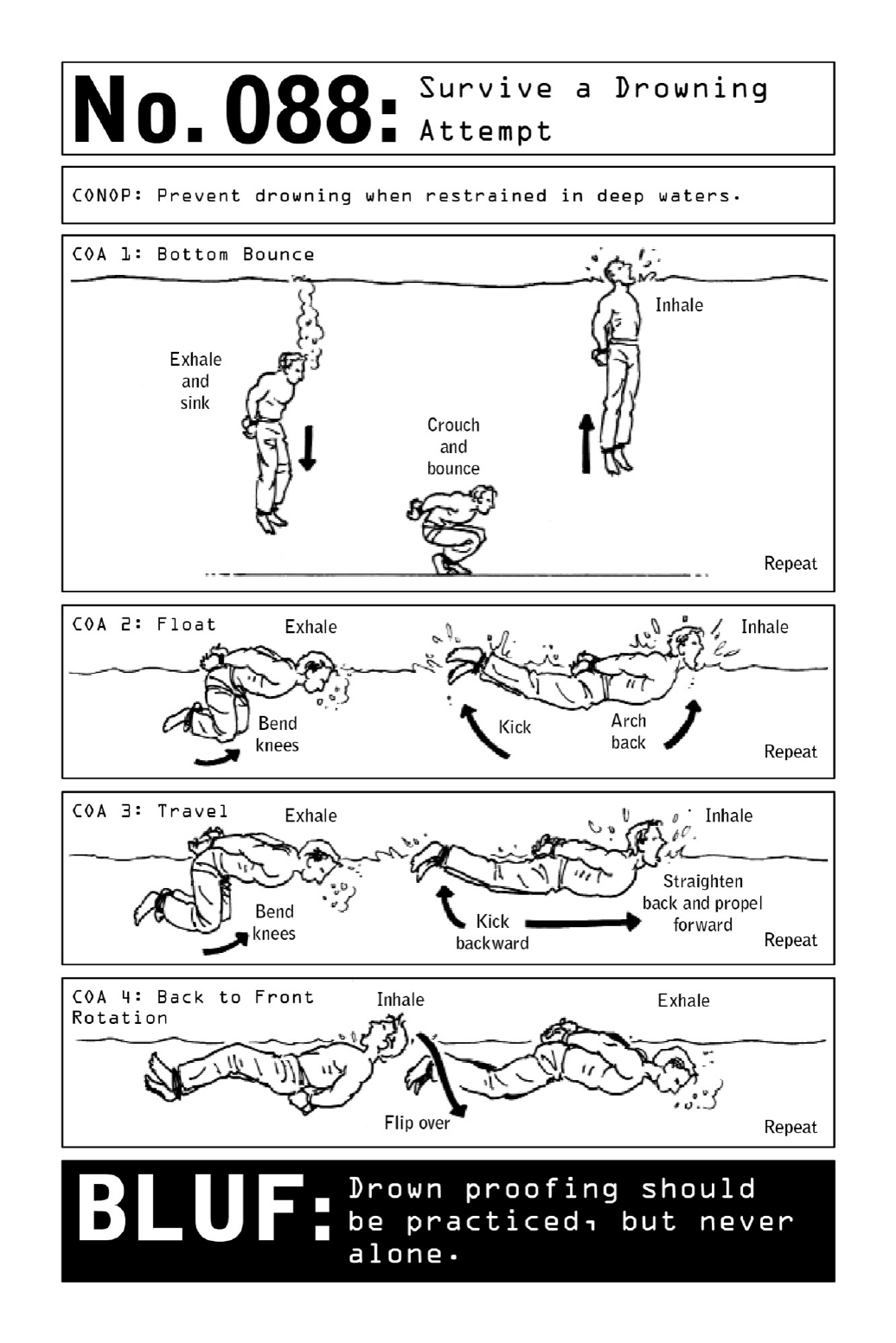

089 EscapefromanAutomobileTrunk
ViolentNomads frequentlyoperateinornearcountriesthatareatwaror inpolitical crisis,
andthusarevulnerabletobeingkidnappedforransom—sometimesasacalculatedattemptto
thwartamission,sometimessimplyasaresultofbeinginthewrongplaceatthewrongtime.
Moreandmorefrequently,travelerstounstableregionsfacethesamerisk.
Themostpredictablepointsofvulnerabilityinatraveler’sschedulearehisdeparturefrom
andreturntohishotelatthebeginningandendofhisday—butanabductionmayalsobethe
result of a staged automobile accident. Common ruses used by kidnappers to apprehend a
targetontheroadinclude:
TheBump:Theattackerbumpsthetarget’svehiclefrombehind.Thetargetgetsouttoassess
thedamageandsuddenlyfindshimselfinthetrunkofacar.
The Good Samaritan: The attackers stage what appears to be an accident or feign a car
problem.Thetargetstopstoassistandsuddenlyfindshimselfinthetrunkofacar.
The Trap: Kidnappers use surveillance to follow the target home. When he pulls into his
drivewayandwaitsforthegatetoopen,theattackerpullsupfrombehindandblockshiscar.
Thetargetfindshimselfinthetrunkofacar.
Ineachofthesescenarios,thetargetendsupimprisoned.Buthedoesn’thavetoremainin
that state. Take the time to understand how a vehicle’s trunk operates, learning its
vulnerabilitiesandhowtodefeatthem.Iflockedinatrunk,alwaystrytobepositionedina
waythatallowsaccesstoescapetools.
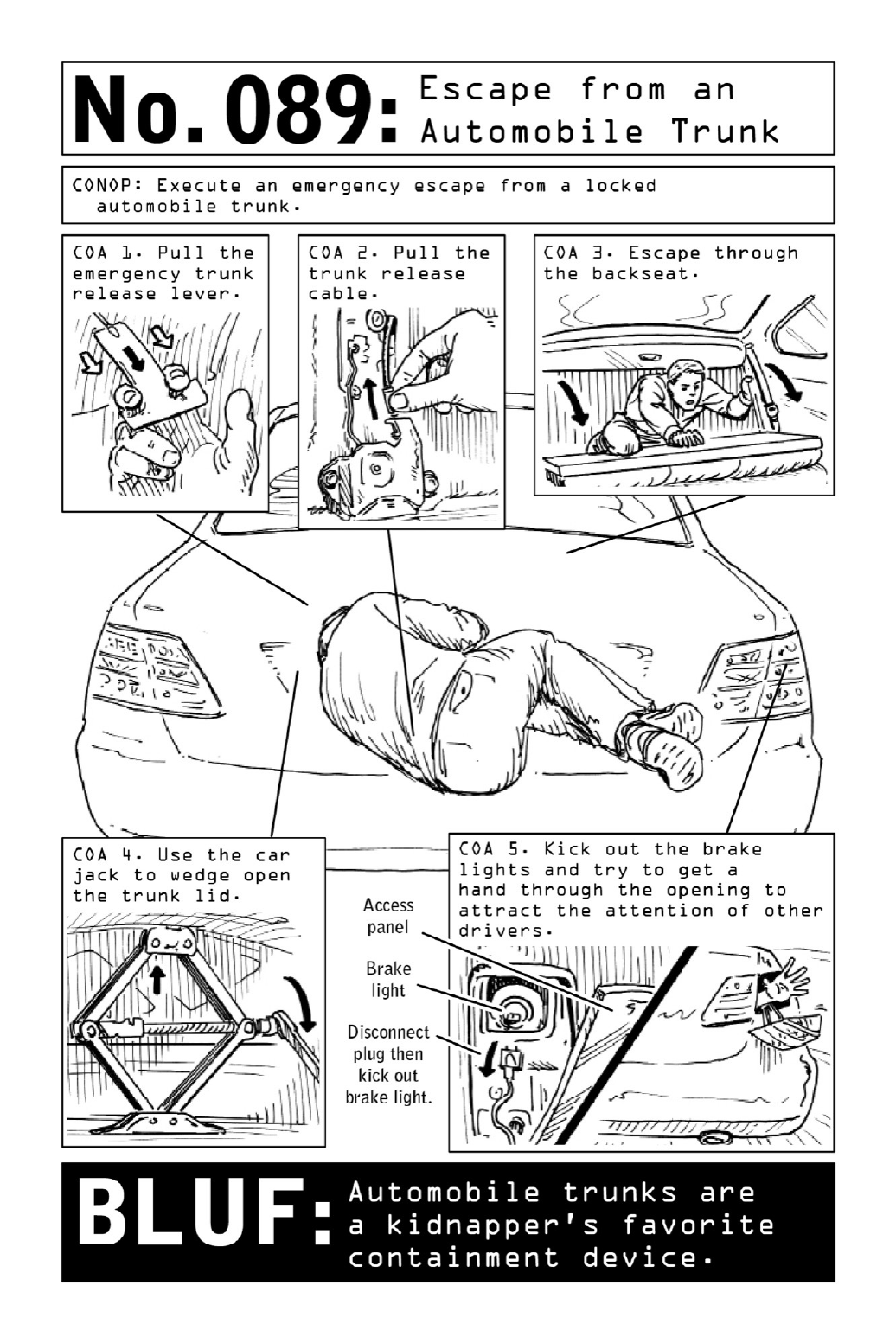

090 DevelopaBug-OutRoute
While a well-concealed cache of escape tools is an essential component of mission prep (see
page16),themostvitaltoolofescapeisn’tashimoracompassbuta meticulously planned
emergencyroute.Whenunexpecteddevelopmentsarise,operativesmustbeabletoensuretheir
ownsafeexitoutofanareaofoperationtheyneverofficiallybreached.
Planningprimaryandalternateescaperoutesisaweeks-orevenmonths-longendeavorthat
requiresthedevelopmentofasignificantamountofareaknowledge.Operativescanvassroads
to determine the quickest and most discreet routes of escape. They use a thorough research
process that identifies friendly and unfriendly areas—and assume they are at risk of being
followed, ambushed, or chased. They look for routes least likely to be observed by third
parties or to include dead ends, checkpoints, or choke points. And they create bridges from
their primary route to their alternate routes, building a network of secondary branches they
canveerintointheeventthattheyarefollowedorencounterunexpectedroadblocks.
Oncethey’veestablishedtheirroutes,operativesidentifytemporarylodgingorhidesites—
stopping points that will enable them to travel by night and rest by day. Using detailed
calculationsbasedonmileage,speed,andtheavailabilityofsuppliesinsurroundingareas,they
stage caches of food, water, and life support at predetermined points along the routes. They
mayhidealternatevehiclesatcachepointsinordertoshakeoffpotentialtailsorsetuprally
pointswherethey’llmeetknownassociatestohandoffintelligenceorotherassets.
Loadedintoapassword-protectedGPSthatisstashedintheoperative’sboltbag,thebug-
outroutesprovideaneffectiveformofoperationalinsurance.Themorecomplexanddetailed
they are, the better—emergency exfiltration is one of the many areas in which research and
attentiontodetailcanwinoutoverbruteforceandeventhemostwell-armedpursuers.


091 PerformaJ-turn
Onlyinthemoviesdooperativesroutinelydrivethroughbarricades,offofbridges,andonto
thewrongsideofhighways.Inreality,high-octanevehicularmaneuversarerarelydeployedin
thefield.Inmostcases,escalatingatensesituationintoachaseisatacticaldisaster;engaging
ina highlyconspicuousmaneuverwhenitisn’twarrantedonlygives theadversaryreasonto
comeaftertheoperative.
Still, there are times when properly executed evasion techniques can mean the difference
between mission success and detention—which is why Nomads regularly rehearse them in
abandonedparkinglotsoronuntraveledruralroadspriortoanoperation.
The J-turn, Forward 180, or “Bootleg Turn” allows a Nomad to quickly shift the
momentumofthevehiclefromonedirectionoftraveltoanotherwithinthewidthofatwo-
lane road. To properly perform a J-turn, the Nomad must first master the vehicle’s braking
systems.Theinitialattemptisnevermadeduringacrisis.
The coordinated use of the emergency brake and release is essential for the maneuver,
keepingthevehicleundercontrolby“lockingup”therearbrakes.Avoidingtheuseofthefoot
brakepreventsthefronttiresfromslidingorskiddingandwardsoffalossofmomentumby
the keepingtheheavy,engine-bearingfrontof thevehiclefrom degradingand“sinking”—an
effectwhichwouldpreventthevehiclefrompivoting.
The steering wheel must be turned quickly and aggressively. As the car rotates a full 180
degrees,removeleftfootfromtheemergencybrakeanduserightfoottopresstheaccelerator.
Topreventthetiresfromrollingofftherims,ensuretirepressureisaminimumoffivetoten
poundspersquareinchovermaxpressurelimits.Sinceeveryvehicleisdifferent,speedsmust
be greatly reduced when conducting maneuvers in high-center-of-gravity vehicles such as
trucksorSUVs.Evenfortraineddriversanyspeedgreaterthanthirty-fivemilesperhourmay
resultinflippingthevehicleandshouldbeavoided.
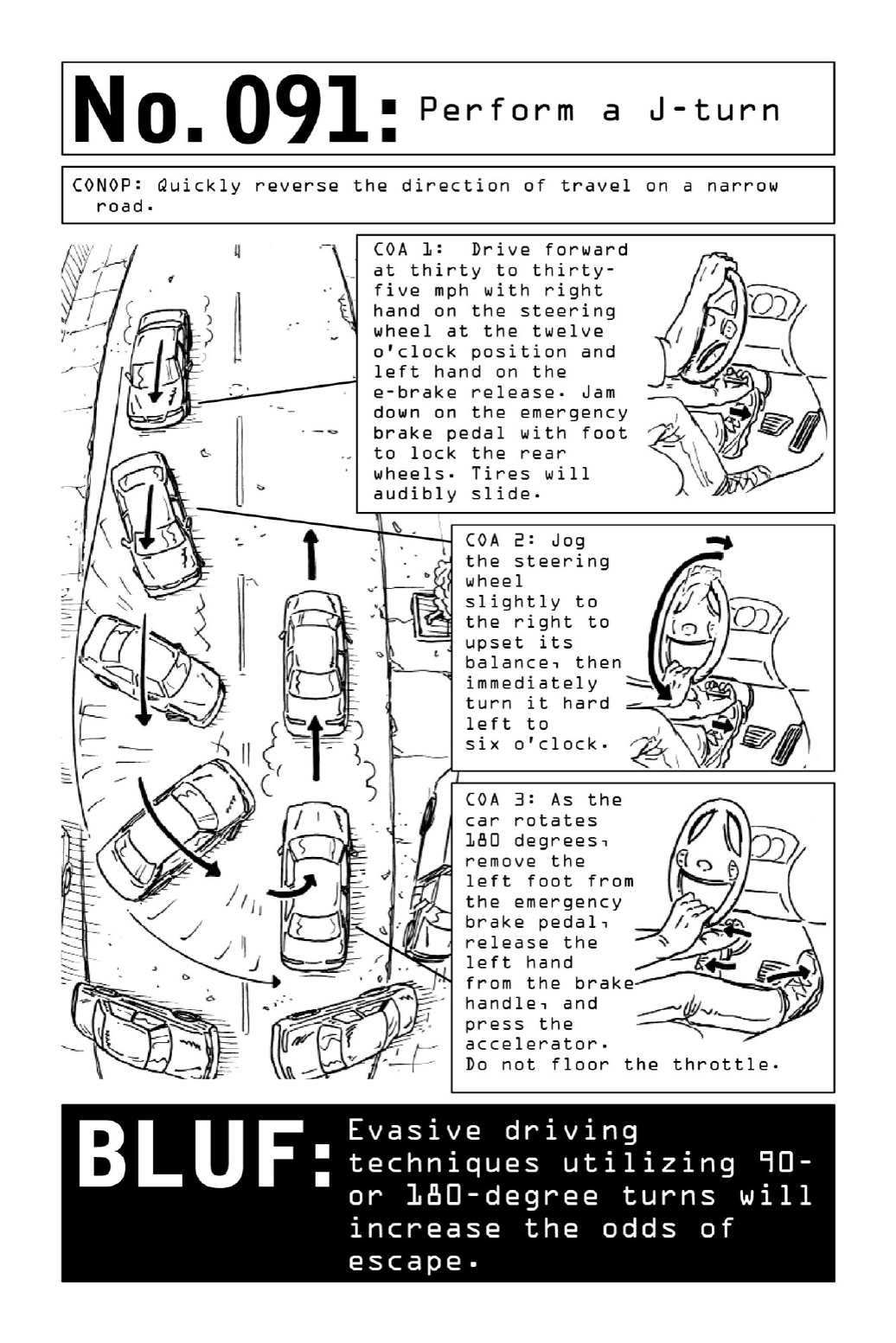

092 PerformaReverse180
When time is of the essence, a cumbersome U-turn is not the best tool in an operative’s
arsenal.U-turnsalwaysinvolvetheriskofbecomingtime-intensivethree-pointturns;atahigh
speed,theycanalsoresultinpoppingatireonthecurbordrivingofftheroad.Inanattack
situation,aReverse180isthefastestwaytoreversethedirectionoftravel—butthemaneuver
should be attempted only in extreme emergency, by highly skilled drivers when under
imminent,life-threateningdanger.Performedincorrectly,aReverse180couldflipavehicleor
permanentlydamageitstransmission.
The turn should be performed at speeds no greater than thirty miles per hour. Emergency
brakes must be in good working order, and a seat belt must be used. Though in order to
reducefrictionthemoveisbestperformedonwetorslipperysurfaces,inanyenvironmentit
producesastressthatcarsarenotdesignedtoaccept.Inotherwords,theReverse180isnotto
betakenlightly.
Reverse: Starting from a complete stop, shift into reverse and drive backward for three car
lengths.Stayundertwenty-fivemilesperhour.
TurntheWheel:Shiftgearstoneutral,removefootfromthegaspedal,andyankthewheel
allthewaytotheleftasquicklyaspossible.
HoldtheWheel inPlace: Hold the wheel in place until the vehicle has completed a 180-
degreeturn.Donotbrake.
Accelerate:Shiftbackintodriveandaccelerateawayfromattackers.
Note:If attemptinganescapeonaroadthatdoesnotallowsufficientwidthtoattempt the
turn,drivinginreverseinaslalompatternwillhelphandicaptheattackers’aim.
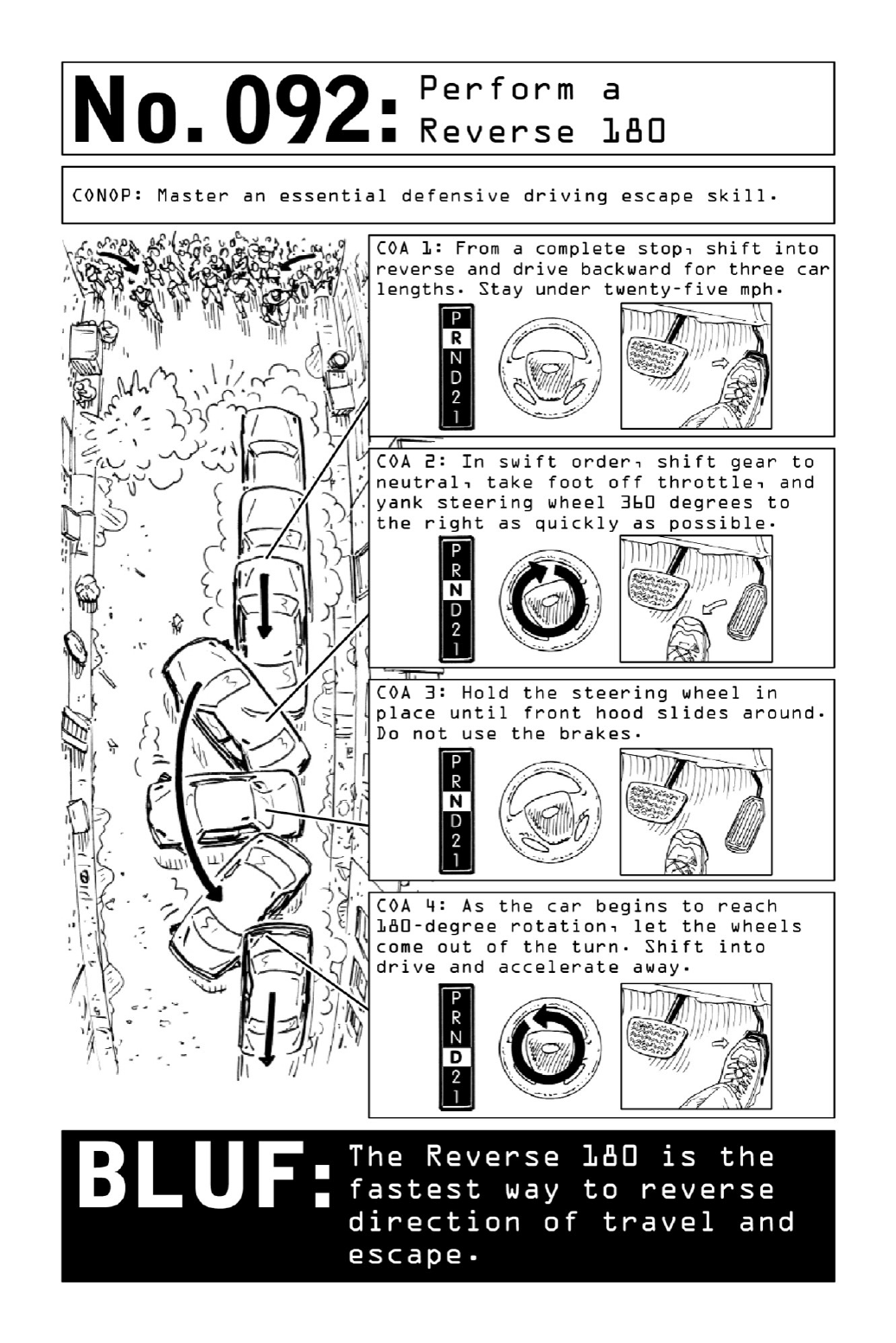

093 SurviveVehicularImpact
Due to their propensity for high-risk defensive and offensive driving techniques, operatives
have a tendency to fall victim to a higher-than-average rate of vehicular accidents. Surviving
these accidents while minimizing stress on the body is a matter of advance preparation and
posturalknow-how—techniquesthatapplytoanyciviliancaughtinacarcrash,whetherasa
resultofahigh-speedescapeorarun-of-the-millincident.
Whiletheabilitytosurviveacrashmightappeartoqualifyasdefensiveknowledgerather
thana“deadly”skill,self-preservationinthefaceofaccidentsorattemptedassaultsiskeyto
missionsuccess.Inordertoremaindeadly,aViolentNomadmustremainsafe.
One of the most commonly used steering positions—controlling the wheel with a hand
placedattwelveo’clock—isalsothemostdangerous.Onimpact,suchpositioningassuresthat
whentheairbagactivates,itwillviolentlythrustanoperative’sforearmintohisface.Proper
steering positioning (see illustration) may both prevent the operative from ending up with a
forearmfullofteethandprotecthisthumbsfrombreaking.
For passengers, bracing during impact is a simple but lifesaving technique that can
significantly reduce the risk of spinal and brain injuries. (Seat belts adequately restrain
shouldersandhipsbutcannotpreventheadsfromflyingforwardduetocrashmomentum.)In
oneaccidentinvolvingasmallaircraft,passengersweresleepingwhentheplanecollidedwith
astandoftrees. Onepassengerout ofthesixteenawokeandbracedforimpact,andhewas
thelonesurvivor.
IfusingthevehicleforaplannedimpactsuchasaPIT,disengagethe airbagsso thatthey
don’timpedeescape.
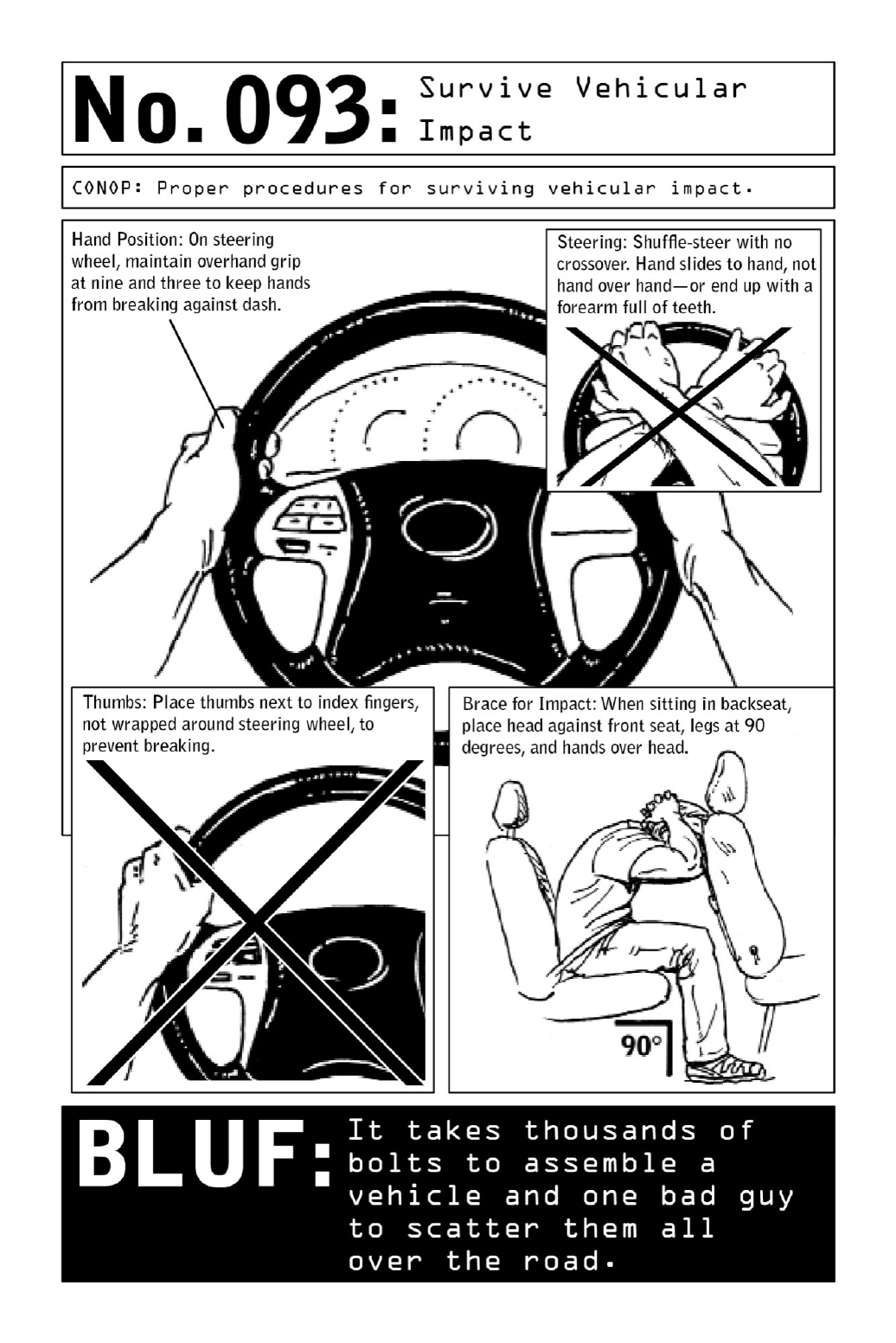

094 BreakThroughaTwo-CarBlock
Checkpoints or roadblocks are common sights in many parts of the world. Foreign
governmentsrelyonthemtodetercrimeorterroristinsurrections,particularlyafternightfall
—but the deep cover of night is also a prime time for bad guys to set up false checkpoints
Determining whether a checkpoint is legitimate or a terrorist ruse can be a question of
survival, one that relies heavily on instinct and split-second decision-making. If the Nomad
believesthecheckpointtobehostile,hewillfirstchecktoseeifhecanaccomplishadiscreet
evasiontoavoidtheroadblock.Ifhecannot,breakingthroughtheroadblockmaybehisbest
bet.
Manycheckpointsusecarsasbarriersinordertofunneltrafficintoasingleline;oneguard
interrogates driversas they stop,while thesecond remains inone oftheobstructingvehicles
andbacksoutofthewaywhenacarisallowedtopass.Ifhitintherightplace,theblocking
vehicle is relatively easy to “move.” The momentum of a full-size car traveling at ten to
twentymilesperhourwillalmosteffortlesslycausetheobstructingvehicletospinoutofthe
waywhileinflictingonlyminimumdamagetotheoperative’svehicle.
Aimforapush,notacollision.Iftravelingathighwayspeeds,slowdownsignificantlyor
cometoastopbefore“pushing”theobstructingvehicleoutoftheway.Onecarlengthisall
thatisneeded.Controltheangleofimpactsothatthefrontrightorleftcornersofthevehicle
makes contact with the front axle of the blocking car, protecting radiator and engine
components(seediagram).Significantdamageincurredtothevehiclewilldefeatthelikelihood
ofanescape.
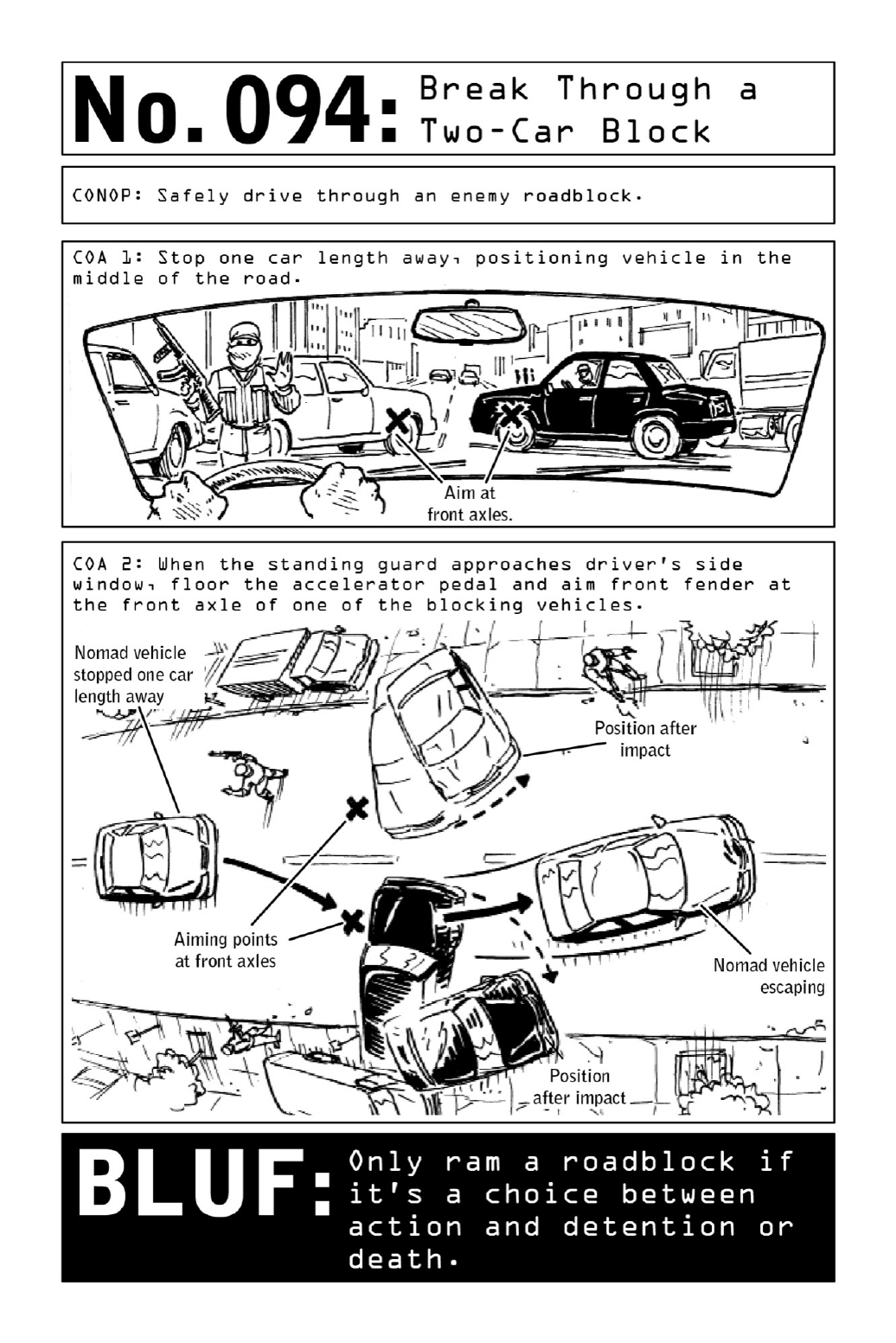

095 EscapeanAmbush
Where do the greatest dangers lurk? For Violent Nomads and civilians alike, it’s the unseen
menaces that pose the most peril—which is why violent attackers so often strike from
concealedpositions,usingtheelementsofspeed,stealth,andsurprisetocatchtheirtargetsoff
guard. From dense underbrush to desolate intersections and dark corners, attackers choose
ambush spots that enable them to strike rapidly, carry out their mission, and disappear
withoutalertingpotentialthirdparties.
Operatives know that the best defense against targeted ambushes is to constantly vary
routes and habits. Take varying routes to and from work. Change up departure times.
Criminals and kidnappers frequently stalk their marks, plotting attacks around the
vulnerabilitiesintheirroutines.Foilthembybeingunpredictable.
Cultivate a constant awareness of possible ambush sites and scenarios. Look out for
desolateareas,chokepointswhereroadsnarrow,andanystructuresorlandmarksthatcould
provide cover for potential assailants. If possible, plan routes to avoid potential ambush
points.Thesimplestwaytodefeatanambushistosidestepthethreatcompletely.
Ifanoperativecannotavoidoranticipateapotentialambushpoint,heshouldincreasehis
speed as he approaches. Particularly when driving, he may be able to speed through the
ambushpointandbackontoalessisolatedstretchofroadbeforetheattackerisabletomake
contact.
Theattackeriscountingontheelementofsurpriseinordertooverwhelmthetarget.Ifthe
targetcangetaheadstartbyanticipatingtheattacker—despitenotbeingabletoseehim—he
willremoveoneoftheattacker’sprimaryadvantages.
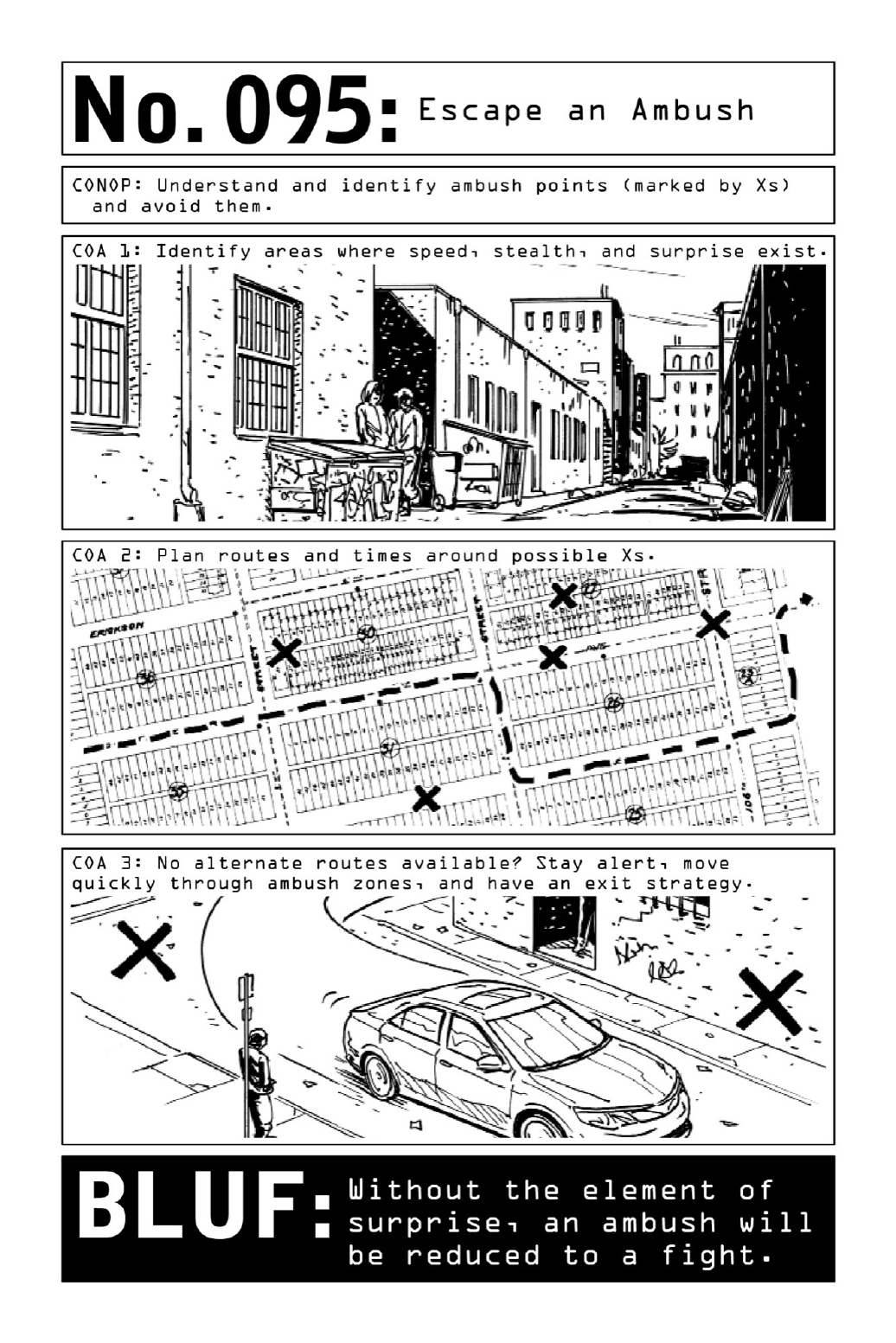

ESCAPEABDUCTION
In the face of abduction attempts, the old adage rings true: Never follow an attacker to a
secondlocation.Butsometimesanoperativewillbeoutnumbered,outgunned,ortakingsevere
blowstothehead.He’striedtorun,triedtohide,andputupagoodfight.He’sreachedthe
pointatwhichhehasnochoicebuttotemporarilysurrendertohisabductorsinordertoavoid
severebodilyharmorworse.
Thekeywordistemporarily.AViolentNomad’ssurrenderismerelyamomentaryplayfor
survival.

096 SetUpProperPostureforEscape
Getbig.That’sthecentralmottoofanyescapeplan,anditappliesatthemomentofrestraint.
Defeatinghand restraints comes down to a matter of wrist and palm placement. Keeping
the thumbs together, spread palms apart (see diagram)—this will flex the wrist muscles,
broadeningthediameterofthewrists.Joiningthepalmsatthumblevelwillcreatetheillusion
ofclosedpalmswhileleavingasizablegapatthebackofthewrists.
Frequently used as restraint devices in kidnapping and torture scenarios, chairs provide a
foundationagainstwhichtobraceavictim’slimbs—butalsoastructureagainstwhichtobuck
andstrain.At themomentofrestraint,takedeep breaths toincreasethe widthof the chest,
arch the lower back, straighten arms and knees as much as possible, and move feet to the
outside of the chair legs. Shrinking back down to size once captors have left the room will
creategapsintherestraints.
If restrained with rope or chain, attempt to discreetly create slack in the restraints by
retainingalengthofropeorchaininonehand(seediagram).
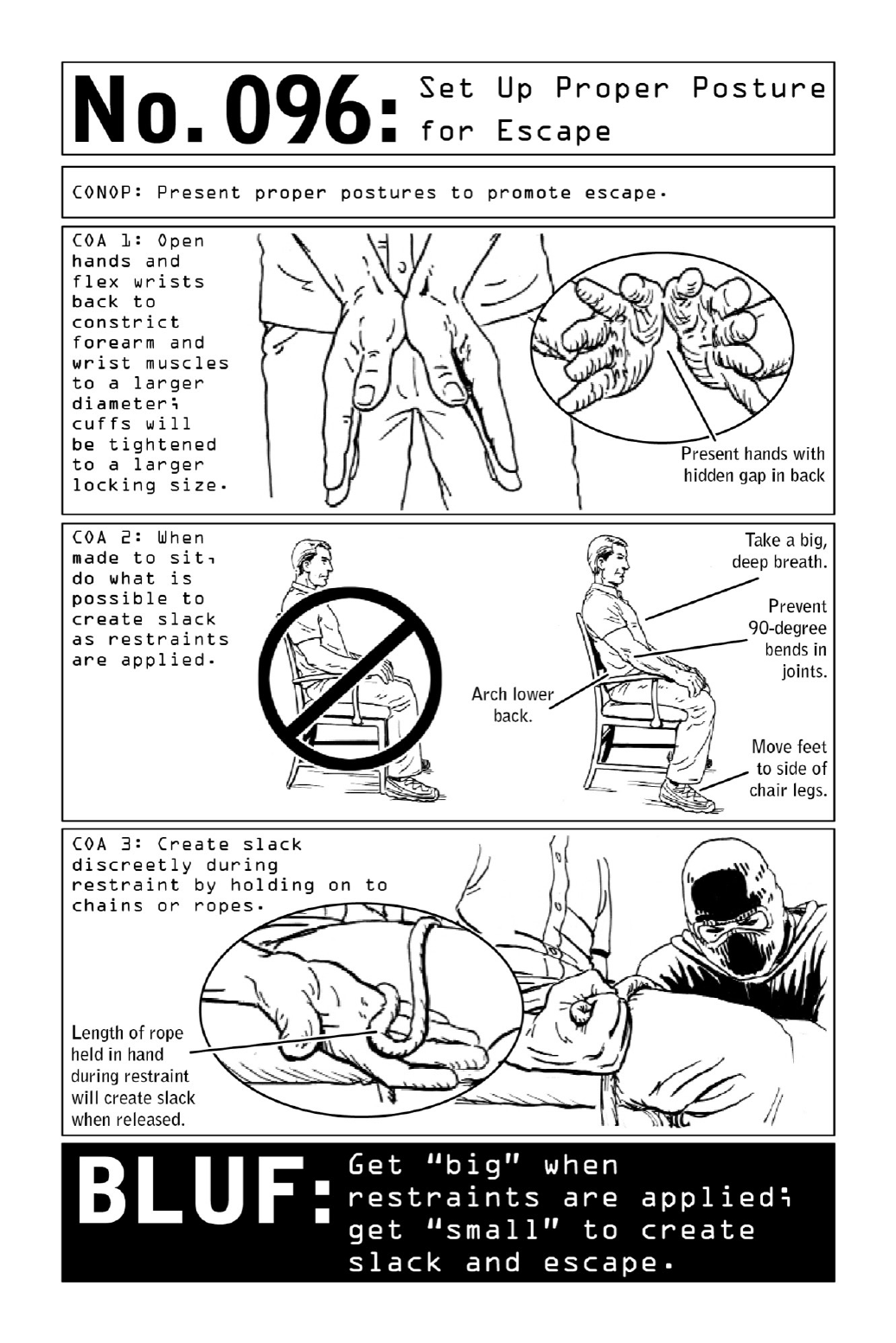

097 RepositionRestrainedHands
Itbearsrepeatingthat oneof themostimportantcomponentsofanytypeofrestraintdefeat
happensatthemomentofcapture—whentheoperativetemporarily“surrenders”whilesetting
himselfupforescapeasbesthecan.Anoperativeshouldpresenthishandsinfrontofhimif
possible. Should captors be willing to restrain him in this position, he will have less work
aheadofhim.(Aslawenforcementofficialsknow,themosteffectivewaytosubduedetainees
istorestrainthemwiththeirhandsbehindtheirbacks,thuspreventingthemfromusingtheir
handsortamperingwiththeirrestraints.Thisisalsotherestraintpositionmostoftenseenin
combatandhostagescenarios—butit’soneoperativesarewellequippedtodefeat.)
When being restrained, spread hands and flex wrists to increase girth and improve the
chancesofbeingabletowiggleoutoftherestraints(seepage232).Discreetlydriveforearms
downintothecuffsasthey’reappliedsothattheyareplacedhigheruponthewrists,where
thediameterislarger.
Once cuffed and left alone, visually inspect the restraints in order to determine a defeat
method.Todothatfromaposteriorrestraint,movebothrestrainedhandsalongwaistlineto
one side of body and look down, or leverage any available reflective surfaces (windows or
mirrors)around.Viewrestraintsanddeterminethebestcourseofactionbefore repositioning
hands—the last thing an operative wants to do is get caught with his hands in front of him
withoutaplan.
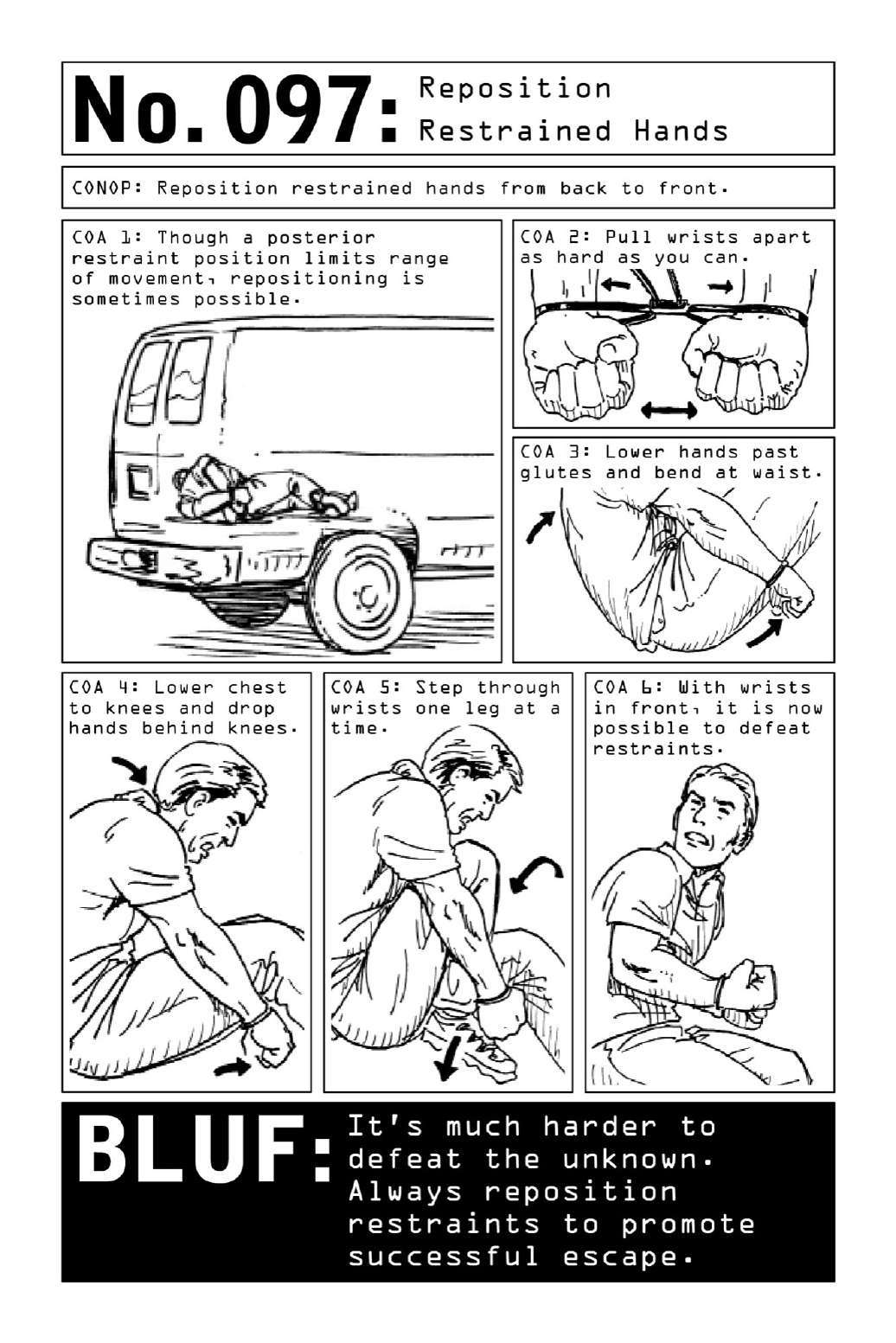

098 DefeatHandcuffs
Equal parts magic trick, criminal ruse, and defensive operational skill, the art of restraint
defeat comes down to an understanding of the mechanics of the particular restraints used.
Armed with a common bobby pin (preemptively tucked in at the waistband), time, and
patience, anyone can eventually defeat a pair of handcuffs, particularly if they are of an
extremelycommonmake(seediagram).
If wiggling out of the cuffs isn’t feasible, there are several defeat options to try: picking,
shimming,orpryingthecuffsapart.
PicktheLock:Topickacommonpairofhandcuffs,insertoneendofthebobbypinintothe
lockandsweepittowardthewristuntilitcatches.Pulluponthebobbypintodisengagethe
shacklearm.
ShimtheLock: The easiest method of handcuff defeat, shimming involves feeding a bobby
pin or similar instrument between its teeth and ratchet. Driving down the shim temporarily
tightens the cuffs, but will eventually separate the teeth from the ratchet (similarly to the
actionofbreakingazipper).Oncetheshimhasbeenpusheddownfarenough,anupwardpull
willyankopenthelock.
PrytheShacklesApart:Ifhandcuffedinsideavehicle,useaseat-belttonguetobreakthe
doublebowsawayfromtheshacklearm.
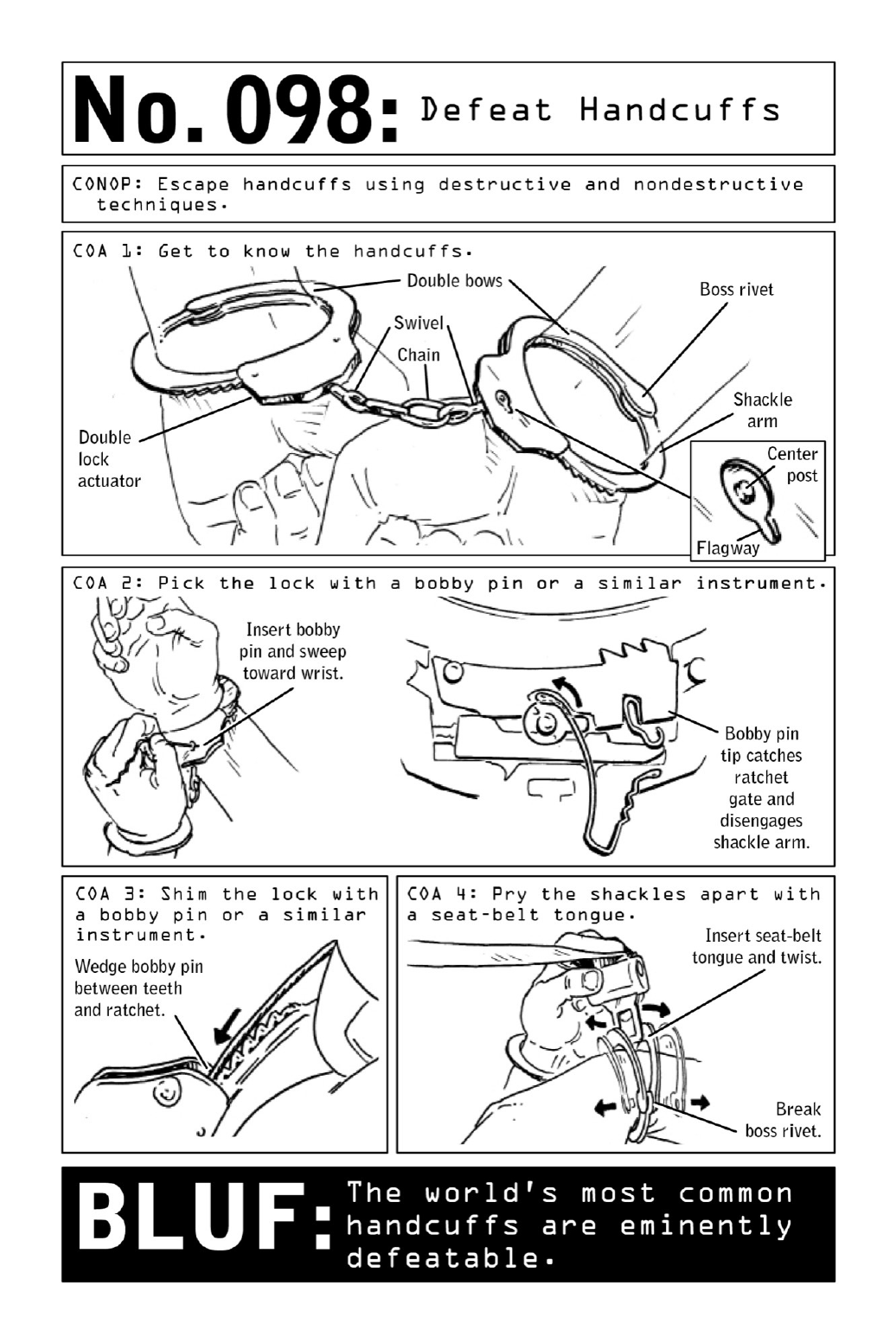

099 DefeatZipTies
Efficient,streamlined,andlightweight,ziptiesseemtopresentanoptimalmethodofrestraint
for the criminals who use them. Originally designed to hold together cables and wires, once
appliedthetiesaredesignedtolockpermanently,typicallyremovedbyapairofshears.Just
likehandcuffs,tape,andothermeansofrestraint,however,theyareeminentlydefeatable.
Becauseziptiesaremadeofplastic,theycanbeworndownbyrepeatedfriction.Acinder
block or a brick or cement wall will wear them down quickly, but if a rough surface isn’t
available,theycaneasilybeunlockedwithabobbypinorsimilarinstrument.
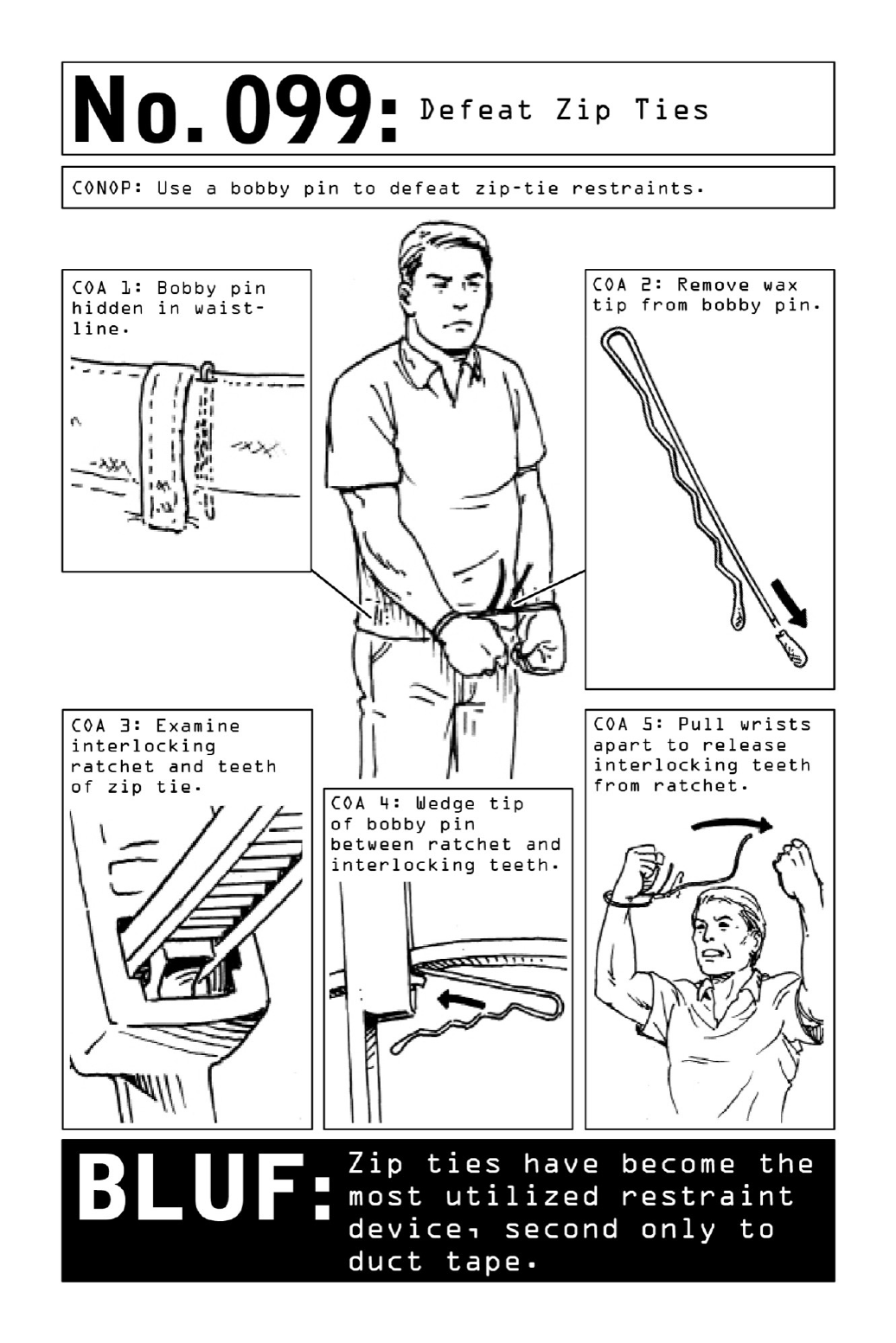

100 DefeatDuctTape
Famous for its durability and its many applications, duct tape is the familiar stuff of school
projects, banged-up car bumpers, and patchwork home-improvement jobs. More often than
not,ducttapeisalsoanabductor’srestraintoffirstresort—readilyavailableandinexpensive,
quickandeasytoapply.Onceabductorshavemovedvictimstoasecondlocation,theymay
upgrade to zip ties, handcuffs, or nylon cord; time-consuming to secure, particularly if they
involve knots, such restraints are frequently reserved for the period following the initial
abduction, when abductors have more time to tie the victim down—which makes the
beginningphasesofanabductionsocrucial.
Defeating duct tape or packing tape may seem like an impossibility, especially when it’s
tightly wrappedinmultiplelayers. But througha shrewd useof the body, victims canbreak
throughtheirbonds.
Ducttapeandothertypesofcloth-backedadhesivetapemaytearmoreeasilythanshipping
tape,whichcanhardenintoanundefeatablemassofhardplasticwhenbunchedtogether.The
key with all types of tape is to move quickly and seamlessly, using the momentum of a
snapping action rather than muscle power to shear the tape apart. Whether an operative
defeats ankle restraints by squatting down abruptly or snaps out of wrist restraints by
knockinghisarmsviolentlyintohischest,performingtheactioninonesuddenmovementwill
shearthetaperatherthancrumplingitupintoasolidandundefeatablemass.


TheFinalBLUF
The bottom line underlying each and every skill in this book is that in a world full of
unexpected,ever-changingthreats,anunseenarmyoftrainedciviliansisapowerfulweapon.
When crisis strikes, it takes only a basic level of knowledge to distinguish a victim from a
survivor—orfromthelevelheadedleaderwhoshepherdsapanickedgroupofwould-bevictims
tosafety.
Inotherwords,thetruepurpose ofthisbookis nottomakeyoumore dangerous,but to
makeyousignificantlysafer.
Acivilianwitha workingknowledgeof theskillsdescribedinthisbookisacivilianwho
knowshowtothinklikeapredator—whichwillputhimonestepaheadofattackersandhelp
to prevent him from becoming prey. But beyond any one particular skill, it is the Violent
Nomadmindset,definedbyaspiritofimprovisationandanalertnesstothreatsofallkinds,
thatdistinguishesvictimsfromsurvivors.
In order to protect the integrity of its missions, the world of special ops must by nature
remainshadowyandclandestine.Nothinginthisbookbetraysclassifiedtacticalinformation
that could be used by enemy forces to subvert the public good. But it does provide civilians
withtheabilitytorecognizeandprotectthemselvesfromadiversearrayofthreats.
Danger has become an increasingly common facet of modern reality—a reality in which
deadlymayhavetobecomethenewnormal.

ACKNOWLEDGMENTS
Iamgreatlyanddeeplyindebtedtothosewhohelpedmemakethisbookhappen.
H.K. Melton wasthemavenandthe brainsbehindtheinitialinceptionofthisbook.His
passion for all things spooky, along with his own history of successful book writing, guided
medownthepathtopublication.
Dan Mandel is my literary agent, a man who could sell ice to polar bears and throwing
starstoaninja,andanall-aroundgreatguywhokeptmeoutoftrouble.
Savannahismylittleghostwriter,or perhapsmoreappropriatelythewriter,ofthisbook.
She spent hundreds of hours talking long-distance on the phone with me, pulling from my
memory everything she could to put down on these pages. Without Savannah, and her
tremendouspatience,skill,anddiligence,thisbookwouldhaveneverbeenpossible.
TedSlampyak,whowasthestoryboardillustratorforthehitseriesBreakingBad,wasthe
illustrator for this book. His creative skills are second to none, and his partnership brought
thisbooktoalevelitcouldneverhaveachievedwithouthim.Heisatrueprofessionalanda
masterofhiscraft.
Matthew Benjamin is my badass, wisecracking, chain-smacking editor. If not for his
leadership,patience,andvastexperience,thisbookmayhavenevercometolife.
The publication reviewers at the Pentagon, who ferried the book through a complicated
reviewprocessviaanumberofagencies,representavaluablesystemthatIbelieveallcurrent
andformermilitarywritersshouldembrace.Iamgratefulfortheirtimeandtheireffortson
mybehalf.

AbouttheAuthor
CLINT EMERSON, retired Navy SEAL, spent twenty years conducting special ops all over the
worldwhileattachedtoSEALTeamThree,theNationalSecurityAgency(NSA),andtheelite
SEALTeamSix.Utilizinganarrayofpracticalskillshedevelopedtoprotecthimselfwhileat
home and abroad, he created Violent Nomad—a personal non-kinetic capture/kill program
catalogingtheskillsnecessarytoconfrontanypredatororcrisis.
MEETTHEAUTHORS,WATCHVIDEOSANDMOREAT
SimonandSchuster.com
authors.simonandschuster.com/Clint-Emerson
Facebook.com/TouchstoneBooks
@TouchstoneBooks

GLOSSARY
Existing at the crossroads of military operations and intelligence, Violent Nomads occupy a
worldfilledwithacronymsand codes. Belowarea few of the termsthatappear throughout
thisbook.
areaofoperation:Theregionorcountryinwhichtheoperativewillexecutehismission.
BLUF:BottomLineUpFront.
COA:coursesofaction.
CONOP:ConceptofOperation.
diversionary device: A device that creates an explosion or visual impairment in order to
divertenemyforcesandallowtheoperativetoinfiltrateorescapeatargetarea.
EDCKit:EveryDayCarrykit,theNomad’sportablesystemoflifesupportandself-defense.
helocasting:Usingahelicopterjumptoinfiltrateanareaofoperation.
improvisedweapons:Weaponsmadeofavailablematerials.
pace counting: The practice of counting steps as a navigational aid in undifferentiated
territory.
PIT:ThePrecisionImmobilizationTechnique,apotentiallylethaltechniqueusedtodisablea
dangeroustargetvehicle.
room hide: A temporary darkroom that allows an operative to perform surveillance
unobserved.
Tails:Ananonymousoperatingsystemthatsavesnoinformationtothecloudortotheuser’s
harddrive.
TEDD: Time, Environment, Distance, and Demeanor, the acronym used by operatives to
confirmcountersurveillanceandtracking.
Tor: An anonymity network that prevents third parties from tracking an Internet user’s
location.

RESOURCESANDREFERENCES
Escape/Security
•100deadlyskills.com.
• Escape the Wolf, www.escapethewolf.com: The author’s corporate security and crisis
solutionsfirm.
•Emergency:ThisBookWillSaveYourLifebyNeilStrauss
•SurvivingaDisaster:EvacuationStrategiesandEmergencyKitsforStayingAlivebyTony
Nester
•WhenAllHellBreaksLoose:StuffYouNeedtoSurviveWhenDisasterStrikesby Cody
Lundin
•BuildthePerfectSurvivalKitbyJohnD.McCann
•SASSurvivalHandbook:HowtoSurviveintheWild,inAnyClimate,onLandoratSea
byJohnLoftyWiseman
• Wired Magazine’s Danger Room, http://www.wired.com/dangerroom/: Covers security-
relatedtechdevelopments.
• Door Devil, http://www.doordevil.com/: Sells doorway reinforcement kits that can
actuallypreventhomeinvasions.
LockPicking
•VisualGuidetoLockPicking,3rded.,byMarkMcCloud
•HowtoOpenLockswithImprovisedTools:Practical,Non-DestructiveWaysofGetting
BackintoJustAboutEverythingWhenYouLoseYourKeysbyHansConkel
•TheCompleteGuidetoLockPickingbyEddieTheWire
Military
•MyShareoftheTask:AMemoirbyGeneralStanleyMcChrystal
•Lone Survivor: The Eyewitness Account of Operation Redwing and the Lost Heroes of
SEALTeam10byMarcusLuttrell
•GhostWars:TheSecretHistoryoftheCIA,Afghanistan,andBinLaden,fromtheSoviet
InvasiontoSeptember10,2001byStevenColl
•TheCompleteGuidetoNavySEALFitness,3rded.,byStewartSmith
• Get Selected for Special Forces by Major Joseph J. Martin with Master Sergeant Rex
Dodson
• Sofrep (the Special Operations Forces Situations Report), http://sofrep.com/: Provides
breaking news and opinion on all matters related to the special operations forces of the
UnitedStatesmilitary.
Mindset
•OnCombat:ThePsychologyandPhysiologyofDeadlyConflictinWarandinPeaceby
DaveGrossmanwithLorenW.Christensen
• On Killing: The Psychological Cost of Learning to Kill in War and Society by Dave
Grossman
•SharpeningtheWarrior’sEdge:ThePsychology&ScienceofTrainingbyBruceK.Siddle
•GatesofFire:AnEpicNoveloftheBattleofThermopylaebyStevenPressfield
•AtlasShruggedbyAynRand
• Gym Jones, https://www.gymjones.com/: The website of this hardcore training gym
featuresonlinetrainingpackages.
Mountaineering/Climbing
•KissorKill:ConfessionsofaSerialClimberbyMarkTwight
•ExtremeAlpinism:ClimbingLight,FastandHighbyMarkTwight
•TheCompleteGuidetoClimbingandMountaineeringbyPeteHill
• Urban Climbing, http://urban-climbing.com/: Find resources, tips, and videos on rock
climbingandurbanstructuralclimbing.
Navigation/Tracking
•RangerHandbookbyRangerTrainingBrigade,USPentagon
•U.S.ArmyMapReadingandLandNavigationHandbookbyDepartmentoftheArmy
•TheSASTracking&NavigationHandbookbyNeilWilson
Prep/Survival
•Benchmade,http://www.benchmade.com/:Sellstop-of-the-linesurvivalknivesforoutdoor
enthusiastsandwell-preparedcitizens.
• County Comm, http://www.countycomm.com/: Sells overstocks of tactical and outdoor
gearmanufacturedforgovernmentalagencies.
•Huckberry,https://www.huckberry.com:High-end,stylishgearforurbanadventurers.
•ImminentThreatSolutions,http://www.itstactical.com/:Sellsmilitary-gradegearranging
fromtraumaandsurvivalkitstolock-pickingandescapetools.
•MOTUS,http://motusworld.com/:Articles andresourcesforciviliansreadytotaketheir
survivalskillstothenextlevel.
• Shomer-Tec, http://www.shomer-tec.com: Sells the surveillance and security equipment
usedbypoliceofficersandmembersofthemilitary.
Spycraft
• Spycraft: The Secret History of the CIA’s Spytechs, from Communism to Al-Qaeda by
RobertWallaceandH.KeithMelton
• The Official CIA Manual of Trickery and Deception by H. Keith Melton and Robert
Wallace
• Spy Coins, http://www.spy-coins.com/: Sells hollow coins and dead-drop devices for
camouflagingmicrochipsandsensitivedocuments.
• Survival Resources, http://survivalresources.com: Sells a wide variety of emergency-
preparednessandsurvivalgearandsupplies.
Miscellaneous
• Tactical Distributors, http://www.tacticaldistributors.com/: Provides high-end tactical
apparelandgear.
• Trikos International, http://trikos.com/: Provides of top-of-the-line personal protection
canines,trainedbythesamemethodologyasthedogsthatservealongsideNavySEALs.
• The U.S. State Department’s International Travel Guidelines,
http://travel.state.gov/content/passports/english/country.html:Sourceforup-to-datesecurity
alertsandcountry-specificsafetyadvisoriesforinternationaltravelers.
• Aircraft Owners and Pilots Association, http://flighttraining.aopa.org/learntofly/: Find
pilotingcoursesnearyou.
•WingsuitFlying,http://www.wingsuitfly.com/:Learnmoreaboutwingsuitflyingandfind
outwheretogettrained.

INDEX
Anoteabouttheindex:Thepagesreferencedinthisindexrefertothepagenumbersintheprintedition.Clickingonapage
numberwilltakeyoutotheebooklocationthatcorrespondstothebeginningofthatpageintheprintedition.Fora
comprehensivelistoflocationsofanywordorphrase,useyourreadingsystem’ssearchfunction.
Note:Pagenumbersinitalicsrefertoillustrations.
abduction:
defeatingducttape,240,241
defeatinghandcuffs,236,237
defeatingzipties,238,239
escape,231
escapefromautotrunk,216,217
postureforescape,232,233
repositioninghands,234,235
scenarios,216
air,bordercrossingby,32,33
airbagdisengagement,62,63
airgliding,32,33
airplane:
high-wing,66
stealing,66,67
STOAL,66
airvents,52
ambush,escaping,228,229
anonymity,2,4–5
blendingintoenvironment,44,45
creatingdisguise,200,201
audiolisteningdevice,134,135
speaker/microphone,136,137
autotrunk,escapefrom,216,217
awareness,44,45,243
ballisticshields,22,23
bedsheet:
escapemultistorybuildingvia,212,213
asrappellingharness,210,211
blendingintoenvironment,44,45
BLUF(BottomLineUpFront),xiii,243
body,disposalof,206,207
bodyarmor,20,21
bordercrossings:
byair,32,33
byland,34,35,36–37
bysea,28–29,30–31
breakingandentering,107,108
bug-outkit,10
bug-outroute,218,219
caches,38,39,218,219
camera:
hideandextractdataineverydayphotos,148,149
improvisedtaserfrom,162–63,164–65
pinhole,140,141
surveillance,102,103,139
caninedeterrentsprays,202,203
Capecitabine,192
carcrash,surviving,224,225
cardinalbearingstechnique,94,95
cellularphone,sanitizing,194,195
chainweapon,78,79
checkpoint,breakingthrough,226,227
clammingakey,114,115
cloningakey,116,117
coins,rollof,82,83
compass,concealable,12,13
concealescapetools,16,17,18,19
containerkit,7,8
cybercommunications,4
anonymousemails,144,145
hideinformation,146,147
sanitizing,194,195
deadbolt,122
digitaldevices,sanitizing,194,195
disguise,creating,200,201
DNA,zeroleftbehind,190,191
doorlocks:
car,openingwithstring,128,129
garage,130,131
unlatching,122,123
seealsolockpicking
drawingconcealedpistol,152,153
drowningattempt,surviving,214,215
ducttape,escaping,240,241
elbowstrike,160,161
emails,anonymous,144,145
encryption,148
escapefrommultistorybuilding,212,213
escaperoute,218,219
everydaycarrykits,6–7,8
explosivedevice,improvised,166,167
facialrecognitionsoftware,bypassing,196,197
fightingactiveshooter,179,180–81
fingerprints,sanitizing,192,193
fingerprintscanningsoftware,tricking,198,199
fire,escapeabuilding,212,213
fishingweight/sap,76,77
“flash”device,diversionary,168,169
forensicidentification,190,191
garagedoors,opening,130,131
gasmask,improvised,182,183
gear,caches,38,39,218,219
goingblack,2,10,32
GoodSamaritan(kidnapping),216
GPS,password-protected,218,219
grenadeattack,surviving,184,185
guarddog,gettingpast,202,203
gummybears,andthumbprintreplication,198,199
handcuffs,escaping,236,237
hands,repositioningforescape,234,235
harassment,186,187
hideandextractdata,148,149
hideinformationinplainsight,146,147
hidingfromactiveshooter,178,179,180
holster,concealable,14,15
hookandclimb,40,41
hotelsecurityandsafety,48,49
bypassinghotelroomdoor,120,121
concealingbelongings,52,53
detectionoftampering,94,95
escapefrommultistorybuilding,212,213
hotelroom,50,51
installlisteningdevice,134,135
roomhide,54,55
unlatchingdoorlocks,122,123
impression,lock,118,119
information,digital,146,147
infraredlight,90,91
J-turn,220,221
key:
clamming,114,115
cloning,116,117
duplicating,113
kidnapping,seeabduction
knifefight,156,157
knockoutpunch,158,159
knots:
Prusicknot,42,43
slipknot,128,129
squareknot,211,212
land,bordercrossingby,34,35,36–37
landburialofbody,206,207
lighter,explosivedevicefrom,166,167
listeningdevice,install,134,135
lockpicking,107,110,111
duplicatingakey,113–17
handcuffs,236,237
impressionoflock,118,119
improvisedtoolsfor,108,109
unlockingpadlocks,124,125
luggage,covertaccessto,126,127
maritimeburialofbody,206,207
mindset,243
Molotovcocktail,170,171
multistorybuilding,escapefrom,212,213
navigation,36
newspapernailbat,80,81
operationalbag,7,9
padlock:
andchainasweapon,78,79
unlocking,124,125
parachuting,32,33
pens,asweapons,74,75
photos,hideandextractdatain,148,149
pinholecamera,140,141
PIT(PrecisionImmobilizationTechnique),172,173
plastic,homemade,142,143
pocketkit,6,8
Prusikknot,42,43
psychologicalwarfare,186,187
rappellingharness,210,211
rectalconcealment,18,19
reverse180turn,222,223
roadblock,breakingthrough,226,227
roomhide,54,55
RunFightRunworkout,24,25
runningfromactiveshooter,178,179
saltandpeppershakers,69
saps,72,76,77,82,83
scalingahighwall,42,43
scubadivingmask,clearing,204,205
sea:
bordercrossingby,28–29,30–31
burialofbodyin,206,207
seat-beltworkaround,62,63
shelter,36
shootingsprees,surviving,178,179,180–81
SillyPutty,andthumbprintreplication,198,199
slipknot,128,129
“softattacks,”186,187
soundamplification,136,137
spaceanddepthtechnique,94,95
speaker,asmicrophone,136,137
squareknot,211,212
structure:
escapemultistorybuilding,212,213
hookandclimb,40,41
scalingawall,42,43
suitcase,covertaccessto,126,127
surveillance:
accordianeffect,98,99
camera,139,140,141
determining,96,97
dismounted,86,87
losingdiscreetly,98,99
mobile,88,89
night,trackingdevice,92,93
publictransportation,98,99
TEDD(time,environment,distance,anddemeanor),96,97
two-turnlimitin,88
surveillancecameras:
deceiving,102,103
disguise,102,103
light,102,103
static,102,103
tampering,detectionof,94,95
taser,improvised,162–63,164–65
teargas,protectionfrom,182,183
TEDD(time,environment,distance,anddemeanor),96,97
thermalburialofbody,206,207
thumbprints,replicating,198,199
Tornetwork,144
trackingdevice,92,93
detecting,100,101
insuitcase,126
trapstodetecttampering,94,95
two-carblock,breakingthrough,226,227
umbrella/leadpipe,72,73
under-the-doortool,120,121
vascularidentificationtechnology,196
vehicle:
airbagdisengagement,62,63
boltbag,10,11
braking,62,63
buildingahidein,64,65
escapeanambush,228,229
escapeandevasionprep,62,63
escapefromtrunk,216,217
J-turn,220,221
listeningdevicein,134,135
opendoorwithstring,128,129
PIT(PrecisionImmobilizationTechnique),172,173
prep,60,61
reverse180turn,222,223
roadblock,breakingthrough,226,227
seat-beltworkaround,62,63
shootingfrom,154,155
stealing,56,57,58–59
survivinganimpact,224,225
valetkey,59
ViolentNomad,anatomyof,2,3,4–5
wall,scaling,42,43
waterbottlesilencer,70,71
weapons:
chain,78,79
concealed,drawing,152,153
explosivedevice,166,167
fishingweight/sap,76,77
improvised,68,69
knifefight,156,157
Molotovcocktail,170,171
newspapernailbat,80,81
pens,74,75
pistoldisarmament:pointedatback,176,177
pistoldisarmament:pointedatchest,174,175
rollofcoins,82,83
saltandpeppershakers,69
umbrella/leadpipe,72,73
waterbottlesilencer,70,71
wingsuit,32,33
workout,RunFightRun,24,25
wrenches,72,73
Zebrasteelpen,74,75
zigzagpattern,runningfromshooter,178,179
zipties,defeating,238,239

Touchstone
AnImprintofSimon&Schuster,Inc.
1230AvenueoftheAmericas
NewYork,NY10020
www.SimonandSchuster.com
Copyright©2015byEscapetheWolf,LLC
Allrightsreserved,includingtherighttoreproducethisbookorportionsthereofinanyformwhatsoever.Forinformation
addressTouchstoneSubsidiaryRightsDepartment,1230AvenueoftheAmericas,NewYork,NY10020.
FirstTouchstonetradepaperbackeditionOctober2015
TOUCHSTONEandcolophonareregisteredtrademarksofSimon&Schuster,Inc.
Forinformationaboutspecialdiscountsforbulkpurchases,pleasecontactSimon&SchusterSpecialSalesat1-866-506-1949or
business@simonandschuster.com.
TheSimon&SchusterSpeakersBureaucanbringauthorstoyourliveevent.Formoreinformationortobookanevent,contact
theSimon&SchusterSpeakersBureauat1-866-248-3049orvisitourwebsiteatwww.simonspeakers.com.
SkilltestingbyKenzieEmerson
InteriordesignbyErichHobbing
LibraryofCongressCataloging-in-PublicationData
Emerson,Clint.
100deadlyskills:theSEALoperative’sguide/ClintEmerson,retiredNavySEAL;illustrationsbyTedSlampyak.
pagescm
Includesbibliographicalreferencesandindex.
1.UnitedStates.Navy.SEALs—Handbooks,manuals,etc.2.Survival—Handbooks,manuals,etc.I.Slampyak,Ted,illustrator.
II.Title.III.Title:Onehundreddeadlyskills.IV.Title:SEALoperative’sguide.
VG87.E642015
613.6'9—dc23
2015012021
ISBN978-1-4767-9605-5
ISBN978-1-4767-9606-2(ebook)