ASDM Book 3 ASA 5515X 71 Vpn Config
User Manual: ASA 5515X
Open the PDF directly: View PDF ![]() .
.
Page Count: 460 [warning: Documents this large are best viewed by clicking the View PDF Link!]
- Contents
- About This Guide
- Configuring Site-to-Site and Client VPN
- VPN Wizards
- Configuring IKE, Load Balancing, and NAC
- Enabling IKE on an Interface
- Setting IKE Parameters for Site-to-Site VPN
- Creating IKE Policies
- Configuring IPsec
- Configuring Load Balancing
- Creating Virtual Clusters
- Geographical Load Balancing
- Comparing Load Balancing to Failover
- Load Balancing Licensing Requirements
- Eligible Clients
- Load Balancing Prerequisites
- Certificate Verification
- Configuring VPN Cluster Load Balancing with the High Availability and Scalability Wizard
- Configuring Load Balancing (Without the Wizard)
- Enable Clientless SSL VPN Load Balancing Using FQDNs
- Setting Global NAC Parameters
- Configuring Network Admission Control Policies
- General VPN Setup
- AnyConnect Customization/Localization
- AnyConnect Customization/Localization > Resources
- AnyConnect Customization/Localization > Binary and Script
- AnyConnect Customization/Localization > GUI Text and Messages
- AnyConnect Customization/Localization > Customized Installer Transforms
- AnyConnect Customization/Localization > Localized Installer Transforms
- Client Software
- Default Tunnel Gateway
- Group Policies
- Configuring External Group Policies
- Configuring Network (Client) Access Internal Group Policies
- Configuring VPN Policy Attributes for a Local User
- Configuring a Browser Proxy for an Internal Group Policy
- Configuring General AnyConnect Client Attributes for an Internal Group Policy
- IPsec (IKEv1) Client
- Configuring IPsec (IKEv1) Client Client Firewall Attributes for an Internal Group Policy
- Configuring IPsec (IKEv1) Client Hardware Client Attributes for an Internal Group Policy
- Configuring Clientless SSL VPN Internal Group Policies
- Configuring Clientless SSL VPN General Attributes for an Internal Group Policy
- Configuring the Clientless SSL VPN Access Portal for an Internal Group Policy
- Configuring Portal Customization for a Clientless SSL VPN Internal Group Policy
- Configuring Login Settings for a Clientless SSL VPN Internal Group Policy
- Configuring Single Signon and Auto Signon Servers for a Clientless SSL VPN Access Internal Group Policy
- Configuring Session Settings for Clientless SSL VPN Access
- Configuring Site-to-Site Internal Group Policies
- Defining Time Ranges
- Access Control List Manager
- Configuring AnyConnect VPN Client Connections
- Configuring AnyConnect VPN Connections
- Specifying a Device Certificate
- Configuring Port Settings
- Setting the Basic Attributes for an AnyConnect VPN Connection
- Setting Advanced Attributes for a Connection Profile
- Setting General Attributes for an AnyConnect SSL VPN Connection
- Setting Client Addressing Attributes for an AnyConnect SSL VPN Connection
- Configuring Authentication Attributes for a Connection Profile
- Configuring Secondary Authentication Attributes for an SSL VPN Connection Profile
- Configuring Authorization Attributes for an SSL VPN Connection Profile
- Adding or Editing Content to a Script for Certificate Pre-Fill-Username
- Configuring AnyConnect Secure Mobility
- Configuring Clientless SSL VPN Connections
- Add or Edit Clientless SSL VPN Connections
- Add or Edit Clientless SSL VPN Connections > Basic
- Add or Edit Clientless SSL VPN Connections > Advanced
- Add or Edit Clientless SSL VPN Connections > Advanced > General
- Add or Edit Clientless or SSL VPN Client Connection Profile or IPsec Connection Profiles> Advanced > Authentication
- Assign Authentication Server Group to Interface
- Add or Edit SSL VPN Connections > Advanced > Authorization
- Assign Authorization Server Group to Interface
- Add or Edit SSL VPN Connections > Advanced > SSL VPN
- Add or Edit Clientless SSL VPN Connections > Advanced > Clientless SSL VPN
- Add or Edit Clientless SSL VPN Connections > Advanced > NetBIOS Servers
- Configure DNS Server Groups
- Add or Edit Clientless SSL VPN Connections > Advanced > Clientless SSL VPN
- IPsec Remote Access Connection Profiles
- Add or Edit an IPsec Remote Access Connection Profile
- Mapping Certificates to IPsec or SSL VPN Connection Profiles
- Configuring Client Addressing
- Add/Edit Connection Profile > General > Authentication
- Add/Edit SSL VPN Connection > General > Authorization
- Add/Edit SSL VPN Connections > Advanced > Accounting
- Add/Edit Tunnel Group > General > Client Address Assignment
- Add/Edit Tunnel Group > General > Advanced
- Add/Edit Tunnel Group > IPsec for Remote Access > IPsec
- Add/Edit Tunnel Group for Site-to-Site VPN
- Add/Edit Tunnel Group > PPP
- Add/Edit Tunnel Group > IPsec for LAN to LAN Access > General > Basic
- Add/Edit Tunnel Group > IPsec for LAN to LAN Access > IPsec
- Clientless SSL VPN Access > Connection Profiles > Add/Edit > General > Basic
- Configuring Internal Group Policy IPsec Client Attributes
- Configuring Client Addressing for SSL VPN Connections
- Assign Address Pools to Interface
- Select Address Pools
- Add or Edit an IP Address Pool
- Authenticating SSL VPN Connections
- System Options
- Zone Labs Integrity Server
- Easy VPN Remote
- Advanced Easy VPN Properties
- AnyConnect Essentials
- DTLS Settings
- AnyConnect VPN Client Images
- Bypass Interface ACL
- Configuring AnyConnect Host Scan
- Configuring Maximum VPN Sessions
- Configuring the Pool of Cryptographic Cores
- AnyConnect Customization/Localization
- Configuring IP Addresses for VPNs
- Configuring Dynamic Access Policies
- Information About Dynamic Access Policies
- Licensing Requirements for Dynamic Access Policies
- Dynamic Access Policies Interface
- Configuring Dynamic Access Policies
- Testing Dynamic Access Policies
- DAP and Authentication, Authorization, and Accounting Services
- Configuring Endpoint Attributes Used in DAPs
- Adding an Anti-Spyware or Anti-Virus Endpoint Attribute to a DAP
- Adding an Application Attribute to a DAP
- Adding Mobile Posture Attributes to a DAP
- Adding a File Endpoint Attribute to a DAP
- Adding a Device Endpoint Attribute to a DAP
- Adding a NAC Endpoint Attribute to a DAP
- Adding an Operating System Endpoint Attribute to a DAP
- Adding a Personal Firewall Endpoint Attribute to a DAP
- Adding a Policy Endpoint Attribute to a DAP
- Adding a Process Endpoint Attribute to a DAP
- Adding a Registry Endpoint Attribute to a DAP
- DAP and AntiVirus, AntiSpyware, and Personal Firewall Programs
- Endpoint Attribute Definitions
- Configuring DAP Access and Authorization Policy Attributes
- Performing a DAP Trace
- Guide to Creating DAP Logical Expressions using LUA
- E-Mail Proxy
- Monitoring VPN
- VPN Connection Graphs
- VPN Statistics
- Sessions Window
- Viewing Active AnyConnect Sessions
- Viewing VPN Sessions Details
- Cluster Loads
- Crypto Statistics
- Compression Statistics
- Encryption Statistics
- Global IKE/IPsec Statistics
- NAC Session Summary
- Protocol Statistics
- VLAN Mapping Sessions
- SSO Statistics for Clientless SSL VPN Session
- VPN Connection Status for the Easy VPN Client
- Configuring SSL Settings
- Configuring an External Server for Authorization and Authentication
- Configuring a Clientless SSL VPN
- Introduction to Clientless SSL VPN
- Basic Clientless SSL VPN Configuration
- Clientless SSL VPN Security Precautions
- Configuring Clientless SSL VPN Access
- Verifying Clientless SSL VPN Server Certificates
- Java Code Signer
- Configuring Browser Access to Plug-ins
- Configuring Port Forwarding
- Configuring File Access
- Ensuring Clock Accuracy for SharePoint Access
- Virtual Desktop Infrastructure (VDI)
- Configuring ACLs
- Configuring Browser Access to Client-Server Plug-ins
- Advanced Clientless SSL VPN Configuration
- Microsoft Kerberos Constrained Delegation Solution
- Understanding How KCD Works
- Configuring the Use of External Proxy Servers
- SSO Servers
- Configuring Application Profile Customization Framework
- Configuring Session Settings
- Encoding
- Content Cache
- Content Rewrite
- Using Email over Clientless SSL VPN
- Configuring Bookmarks
- Configuring Policy Groups
- Configuring Smart Tunnel Access
- Configuring Smart Tunnel Access
- About Smart Tunnels
- Why Smart Tunnels?
- Configuring a Smart Tunnel (Lotus Example)
- Simplifying Configuration of Which Applications to Tunnel
- Adding Applications to Be Eligible for Smart Tunnel Access
- About Smart Tunnel Lists
- Creating a Smart Tunnel Auto Sign-On Server List
- Adding Servers to a Smart Tunnel Auto Sign-On Server List
- Enabling and Switching Off Smart Tunnel Access
- Configuring Smart Tunnel Log Off
- Configuring Smart Tunnel Access
- Configuring Portal Access Rules
- Configuring Smart Tunnel Access
- Clientless SSL VPN Remote Users
- Configuring Clientless SSL VPN Users
- Using Clientless SSL VPN with Mobile Devices
- Customizing Clientless SSL VPN
- Customizing the Clientless SSL VPN User Experience
- Clientless SSL VPN End User Setup
- Defining the End User Interface
- Customizing Clientless SSL VPN Pages
- Information About Customization
- Exporting a Customization Template
- Editing the Customization Template
- Customizing the Portal Page
- Customizing the Logout Page
- Customizing the External Portal Page
- Adding Customization Object
- Importing/Exporting Customization Object
- Creating XML-Based Portal Customization Objects and URL Lists
- Customizing Bookmark Help
- Translating the Language of User Messages
- Clientless SSL VPN Troubleshooting
- Clientless SSL VPN Licensing
- Index

Cisco Systems, Inc.
www.cisco.com
Cisco has more than 200 offices worldwide.
Addresses, phone numbers, and fax numbers
are listed on the Cisco website at
www.cisco.com/go/offices.
Cisco ASA Series VPN ASDM
Configuration Guide
Software Version 7.1
For the ASA 5505, ASA 5510, ASA 5520, ASA 5540, ASA 5550, ASA 5512-X,
ASA 5515-X, ASA 5525-X, ASA 5545-X, ASA 5555-X, ASA 5580, ASA 5585-X,
and the ASA Services Module
Released: December 3, 2012
Updated: March 31, 2014
Text Part Number: N/A, Online only
THE SPECIFICATIONS AND INFORMATION REGARDING THE PRODUCTS IN THIS MANUAL ARE SUBJECT TO CHANGE WITHOUT NOTICE. ALL
STATEMENTS, INFORMATION, AND RECOMMENDATIONS IN THIS MANUAL ARE BELIEVED TO BE ACCURATE BUT ARE PRESENTED WITHOUT
WARRANTY OF ANY KIND, EXPRESS OR IMPLIED. USERS MUST TAKE FULL RESPONSIBILITY FOR THEIR APPLICATION OF ANY PRODUCTS.
THE SOFTWARE LICENSE AND LIMITED WARRANTY FOR THE ACCOMPANYING PRODUCT ARE SET FORTH IN THE INFORMATION PACKET THAT
SHIPPED WITH THE PRODUCT AND ARE INCORPORATED HEREIN BY THIS REFERENCE. IF YOU ARE UNABLE TO LOCATE THE SOFTWARE LICENSE
OR LIMITED WARRANTY, CONTACT YOUR CISCO REPRESENTATIVE FOR A COPY.
The Cisco implementation of TCP header compression is an adaptation of a program developed by the University of California, Berkeley (UCB) as part of UCB’s public
domain version of the UNIX operating system. All rights reserved. Copyright © 1981, Regents of the University of California.
NOTWITHSTANDING ANY OTHER WARRANTY HEREIN, ALL DOCUMENT FILES AND SOFTWARE OF THESE SUPPLIERS ARE PROVIDED “AS IS” WITH
ALL FAULTS. CISCO AND THE ABOVE-NAMED SUPPLIERS DISCLAIM ALL WARRANTIES, EXPRESSED OR IMPLIED, INCLUDING, WITHOUT
LIMITATION, THOSE OF MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT OR ARISING FROM A COURSE OF
DEALING, USAGE, OR TRADE PRACTICE.
IN NO EVENT SHALL CISCO OR ITS SUPPLIERS BE LIABLE FOR ANY INDIRECT, SPECIAL, CONSEQUENTIAL, OR INCIDENTAL DAMAGES, INCLUDING,
WITHOUT LIMITATION, LOST PROFITS OR LOSS OR DAMAGE TO DATA ARISING OUT OF THE USE OR INABILITY TO USE THIS MANUAL, EVEN IF CISCO
OR ITS SUPPLIERS HAVE BEEN ADVISED OF THE POSSIBILITY OF SUCH DAMAGES.
Cisco and the Cisco logo are trademarks or registered trademarks of Cisco and/or its affiliates in the U.S. and other countries. To view a list of Cisco trademarks, go to this
URL: www.cisco.com/go/trademarks. Third-party trademarks mentioned are the property of their respective owners. The use of the word partner does not imply a partnership
relationship between Cisco and any other company. (1110R)
Any Internet Protocol (IP) addresses and phone numbers used in this document are not intended to be actual addresses and phone numbers. Any examples, command display
output, network topology diagrams, and other figures included in the document are shown for illustrative purposes only. Any use of actual IP addresses or phone numbers in
illustrative content is unintentional and coincidental.
Cisco ASA Series VPN ASDM Configuration Guide
Copyright © 2012-2014 Cisco Systems, Inc. All rights reserved.

iii
Cisco ASA Series VPN ASDM Configuration Guide
CONTENTS
About This Guide i
Document Objectives i
Related Documentation i
Conventions ii
Obtaining Documentation and Submitting a Service Request ii
PART
1Configuring Site-to-Site and Client VPN
CHAPTER
2VPN Wizards 2-1
VPN Overview 2-1
IPsec IKEv1 Remote Access Wizard 2-2
Remote Access Client 2-2
VPN Client Authentication Method and Tunnel Group Name 2-3
Client Authentication 2-3
User Accounts 2-4
Address Pool 2-4
Attributes Pushed to Client (Optional) 2-4
IKE Policy 2-5
IPsec Settings (Optional) 2-6
Summary 2-6
IPsec Site-to-Site VPN Wizard 2-7
Peer Device Identification 2-7
Traffic to Protects 2-7
Security 2-7
NAT Excempt 2-8
Summary 2-8
AnyConnect VPN Wizard 2-9
Connection Profile Identification 2-9
VPN Protocols 2-9
Client Images 2-10
Authentication Methods 2-10
Client Address Assignment 2-10
Network Name Resolution Servers 2-11
NAT Exempt 2-11

Contents
iv
Cisco ASA Series VPN ASDM Configuration Guide
AnyConnect Client Deployment 2-11
Summary 2-11
Clientless SSL VPN Wizard 2-11
SSL VPN Interface 2-12
User Authentication 2-12
Group Policy 2-12
Bookmark List 2-13
Summary 2-13
CHAPTER
3Configuring IKE, Load Balancing, and NAC 3-1
Enabling IKE on an Interface 3-1
Setting IKE Parameters for Site-to-Site VPN 3-2
IKE Parmeters 3-2
NAT Transparency 3-2
Identity Sent to Peer 3-3
Session Control 3-3
IKE v2 Specific Settings 3-4
Creating IKE Policies 3-5
About IKE 3-5
Configuring IKE Policies 3-5
Adding an IKEv1 Policy 3-6
Adding an IKEv2 Policy 3-7
Assignment Policy 3-9
Configuring IPsec 3-9
Adding Crypto Maps 3-10
Creating an IPsec Rule/Tunnel Policy (Crypto Map) - Basic Tab 3-12
Creating IPsec Rule/Tunnel Policy (Crypto Map) - Advanced Tab 3-13
Creating IPsec Rule/Traffic Selection Tab 3-15
Pre-Fragmentation 3-17
Edit IPsec Pre-Fragmentation Policy 3-18
IPsec Transform Sets 3-18
Add/Edit IPsec Proposal (Transform Set) 3-19
Add/Edit IPsec Proposal 3-19
Configuring Load Balancing 3-20
Creating Virtual Clusters 3-20
Geographical Load Balancing 3-21
Comparing Load Balancing to Failover 3-22
Load Balancing Licensing Requirements 3-22
Eligible Clients 3-22

Contents
v
Cisco ASA Series VPN ASDM Configuration Guide
Load Balancing Prerequisites 3-23
Certificate Verification 3-23
Configuring VPN Cluster Load Balancing with the High Availability and Scalability Wizard 3-23
Configuring Load Balancing (Without the Wizard) 3-25
Enable Clientless SSL VPN Load Balancing Using FQDNs 3-27
Setting Global NAC Parameters 3-27
Configuring Network Admission Control Policies 3-28
Add/Edit Posture Validation Exception 3-30
CHAPTER
4General VPN Setup 4-1
AnyConnect Customization/Localization 4-1
AnyConnect Customization/Localization > Resources 4-2
AnyConnect Customization/Localization > Binary and Script 4-2
AnyConnect Customization/Localization > GUI Text and Messages 4-3
AnyConnect Customization/Localization > Customized Installer Transforms 4-4
AnyConnect Customization/Localization > Localized Installer Transforms 4-4
Client Software 4-4
Edit Client Update Entry 4-6
Default Tunnel Gateway 4-6
Group Policies 4-7
Configuring External Group Policies 4-8
Adding an LDAP or RADIUS Server to a Network (Client) Access External Group Policy 4-9
Configuring Network (Client) Access Internal Group Policies 4-9
Configuring General Attributes for an Internal Group Policy 4-9
Configuring Server Attributes for an Internal Group Policy 4-12
Configuring Split Tunneling for AnyConnect Traffic 4-13
Configuring VPN Policy Attributes for a Local User 4-16
Configuring a Browser Proxy for an Internal Group Policy 4-18
Configuring General AnyConnect Client Attributes for an Internal Group Policy 4-19
IPsec (IKEv1) Client 4-23
Configuring IPsec (IKEv1) Client Client Firewall Attributes for an Internal Group Policy 4-25
Configuring IPsec (IKEv1) Client Hardware Client Attributes for an Internal Group Policy 4-26
Configuring Clientless SSL VPN Internal Group Policies 4-29
Configuring Clientless SSL VPN General Attributes for an Internal Group Policy 4-29
Configuring the Clientless SSL VPN Access Portal for an Internal Group Policy 4-31
Configuring Portal Customization for a Clientless SSL VPN Internal Group Policy 4-33
Configuring Login Settings for a Clientless SSL VPN Internal Group Policy 4-33
Configuring Single Signon and Auto Signon Servers for a Clientless SSL VPN Access Internal
Group Policy 4-33

Contents
vi
Cisco ASA Series VPN ASDM Configuration Guide
Configuring Session Settings for Clientless SSL VPN Access 4-33
Configuring Site-to-Site Internal Group Policies 4-33
Defining Time Ranges 4-35
Add/Edit Time Range 4-35
Add/Edit Recurring Time Range 4-36
Access Control List Manager 4-36
Standard Access Control List 4-37
Extended Access Control List 4-37
Add/Edit/Paste ACE 4-38
Browse Source/Destination Address 4-40
Browse Source/Destination Port 4-40
Add TCP Service Group 4-40
Browse ICMP 4-41
Add ICMP Group 4-41
Browse Other 4-42
Add Protocol Group 4-42
Client Firewall with Local Printer and Tethered Device Support 4-43
Add/Edit Standard Access List Rule 4-47
Add/Edit Server and URL List 4-47
Add/Edit Server or URL 4-48
Configuring AnyConnect VPN Client Connections 4-48
Using AnyConnect Client Profiles 4-51
Importing an AnyConnect Client Profile 4-52
Exporting an AnyConnect Client Profile 4-52
Exempting AnyConnect Traffic from Network Address Translation 4-52
Configuring AnyConnect VPN Connections 4-57
Specifying a Device Certificate 4-58
Configuring Port Settings 4-59
Setting the Basic Attributes for an AnyConnect VPN Connection 4-59
Setting Advanced Attributes for a Connection Profile 4-61
Setting General Attributes for an AnyConnect SSL VPN Connection 4-61
Setting Client Addressing Attributes for an AnyConnect SSL VPN Connection 4-63
Configuring Authentication Attributes for a Connection Profile 4-63
Configuring Secondary Authentication Attributes for an SSL VPN Connection Profile 4-64
Configuring Authorization Attributes for an SSL VPN Connection Profile 4-66
Adding or Editing Content to a Script for Certificate Pre-Fill-Username 4-67
Configuring AnyConnect Secure Mobility 4-69
Add or Edit MUS Access Control 4-71
Configuring Clientless SSL VPN Connections 4-71

Contents
vii
Cisco ASA Series VPN ASDM Configuration Guide
Add or Edit Clientless SSL VPN Connections 4-72
Add or Edit Clientless SSL VPN Connections > Basic 4-72
Add or Edit Clientless SSL VPN Connections > Advanced 4-73
Add or Edit Clientless SSL VPN Connections > Advanced > General 4-73
Add or Edit Clientless or SSL VPN Client Connection Profile or IPsec Connection Profiles> Advanced
> Authentication 4-74
Assign Authentication Server Group to Interface 4-74
Add or Edit SSL VPN Connections > Advanced > Authorization 4-74
Assign Authorization Server Group to Interface 4-75
Add or Edit SSL VPN Connections > Advanced > SSL VPN 4-75
Add or Edit Clientless SSL VPN Connections > Advanced > Clientless SSL VPN 4-76
Add or Edit Clientless SSL VPN Connections > Advanced > NetBIOS Servers 4-77
Configure DNS Server Groups 4-78
Add or Edit Clientless SSL VPN Connections > Advanced > Clientless SSL VPN 4-78
IPsec Remote Access Connection Profiles 4-78
Add or Edit an IPsec Remote Access Connection Profile 4-79
Add or Edit IPsec Remote Access Connection Profile Basic 4-79
Mapping Certificates to IPsec or SSL VPN Connection Profiles 4-80
Site-to-Site Connection Profiles 4-84
Add/Edit Site-to-Site Connection 4-85
Adding or Editing a Site-to-Site Tunnel Group 4-86
Crypto Map Entry 4-88
Crypto Map Entry for Static Peer Address 4-89
Managing CA Certificates 4-90
Install Certificate 4-90
Configure Options for CA Certificate 4-90
Revocation Check Dialog Box 4-90
Add/Edit Remote Access Connections > Advanced > General 4-91
Configuring Client Addressing 4-92
Add/Edit Connection Profile > General > Authentication 4-95
Add/Edit SSL VPN Connection > General > Authorization 4-95
Add/Edit SSL VPN Connections > Advanced > Accounting 4-96
Add/Edit Tunnel Group > General > Client Address Assignment 4-97
Add/Edit Tunnel Group > General > Advanced 4-97
Add/Edit Tunnel Group > IPsec for Remote Access > IPsec 4-98
Add/Edit Tunnel Group for Site-to-Site VPN 4-99
Add/Edit Tunnel Group > PPP 4-100
Add/Edit Tunnel Group > IPsec for LAN to LAN Access > General > Basic 4-100
Add/Edit Tunnel Group > IPsec for LAN to LAN Access > IPsec 4-102

Contents
viii
Cisco ASA Series VPN ASDM Configuration Guide
Clientless SSL VPN Access > Connection Profiles > Add/Edit > General > Basic 4-103
Configuring Internal Group Policy IPsec Client Attributes 4-104
Configuring Client Addressing for SSL VPN Connections 4-106
Assign Address Pools to Interface 4-106
Select Address Pools 4-106
Add or Edit an IP Address Pool 4-107
Authenticating SSL VPN Connections 4-107
System Options 4-107
Zone Labs Integrity Server 4-108
Easy VPN Remote 4-109
Advanced Easy VPN Properties 4-111
AnyConnect Essentials 4-113
DTLS Settings 4-113
AnyConnect VPN Client Images 4-114
Add/Replace AnyConnect VPN Client Image 4-114
Upload Image 4-115
Bypass Interface ACL 4-115
Configuring AnyConnect Host Scan 4-115
Host Scan Dependencies and System Requirements 4-116
Dependencies 4-116
System Requirements 4-116
Licensing 4-116
Entering an Activation Key to Support Advanced Endpoint Assessment 4-117
Host Scan Packaging 4-117
Installing and Enabling Host Scan on the ASA 4-117
Installing or Upgrading Host Scan 4-118
Enabling or Disabling Host Scan 4-119
Enabling or Disabling CSD on the ASA 4-119
Viewing the Host Scan Version Enabled on the ASA 4-120
Uninstalling Host Scan 4-120
Uninstalling CSD from the ASA 4-120
Assigning AnyConnect Posture Module to a Group Policy 4-121
Other Important Documentation Addressing Host Scan 4-121
Configuring Maximum VPN Sessions 4-122
Configuring the Pool of Cryptographic Cores 4-122
CHAPTER
5Configuring IP Addresses for VPNs 5-1
Configuring an IP Address Assignment Policy 5-1
Contents
ix
Cisco ASA Series VPN ASDM Configuration Guide
Configuring IP Address Assignment Options using ASDM 5-2
Viewing Address Assignment Methods 5-3
Viewing IPv4 and IPv6 Address Assignments using ASDM 5-3
Configuring Local IP Address Pools 5-3
Configuring Local IPv4 Address Pools Using ASDM 5-3
Configuring Local IPv6 Address Pools Using ASDM 5-4
Configuring DHCP Addressing 5-5
Assigning IP addresses using DHCP 5-5
Configure Your DHCP Servers 5-5
Assign the DHCP IP Addressing to a Group Policy 5-5
Assigning IP Addresses to Local Users 5-6
CHAPTER
6Configuring Dynamic Access Policies 6-1
Information About Dynamic Access Policies 6-1
DAP and Endpoint Security 6-2
DAP Support for Remote Access Connection Types 6-2
Remote Access Connection Sequence with DAPs 6-2
Licensing Requirements for Dynamic Access Policies 6-3
Advanced Endpoint Assessment license 6-3
SSL VPN license (client) 6-3
AnyConnect Mobile License 6-3
Dynamic Access Policies Interface 6-4
Configuring Dynamic Access Policies 6-6
Testing Dynamic Access Policies 6-8
DAP and Authentication, Authorization, and Accounting Services 6-9
Configuring AAA Attributes in a DAP 6-9
Retrieving Active Directory Groups 6-11
Configuring Endpoint Attributes Used in DAPs 6-13
Adding an Anti-Spyware or Anti-Virus Endpoint Attribute to a DAP 6-14
Adding an Application Attribute to a DAP 6-15
Adding Mobile Posture Attributes to a DAP 6-16
Adding a File Endpoint Attribute to a DAP 6-17
Adding a Device Endpoint Attribute to a DAP 6-18
Adding a NAC Endpoint Attribute to a DAP 6-19
Adding an Operating System Endpoint Attribute to a DAP 6-20
Adding a Personal Firewall Endpoint Attribute to a DAP 6-20
Adding a Policy Endpoint Attribute to a DAP 6-21
Adding a Process Endpoint Attribute to a DAP 6-22
Contents
x
Cisco ASA Series VPN ASDM Configuration Guide
Adding a Registry Endpoint Attribute to a DAP 6-23
DAP and AntiVirus, AntiSpyware, and Personal Firewall Programs 6-24
Endpoint Attribute Definitions 6-24
Configuring DAP Access and Authorization Policy Attributes 6-27
Performing a DAP Trace 6-31
Guide to Creating DAP Logical Expressions using LUA 6-31
Syntax for Creating Lua EVAL Expressions 6-32
The DAP CheckAndMsg Function 6-33
Additional Lua Functions 6-35
CheckAndMsg with Custom Function Example 6-38
Further Information on Lua 6-38
Operator for Endpoint Category 6-38
DAP Examples 6-38
CHAPTER
7E-Mail Proxy 7-1
Configuring E-Mail Proxy 7-1
AAA 7-2
POP3S Tab 7-2
IMAP4S Tab 7-4
SMTPS Tab 7-5
Access 7-7
Edit E-Mail Proxy Access 7-8
Authentication 7-8
Default Servers 7-10
Delimiters 7-11
CHAPTER
8Monitoring VPN 8-1
VPN Connection Graphs 8-1
IPsec Tunnels 8-1
Sessions 8-2
VPN Statistics 8-2
Sessions Window 8-2
Viewing Active AnyConnect Sessions 8-5
Viewing VPN Sessions Details 8-6
Cluster Loads 8-8
Crypto Statistics 8-9
Compression Statistics 8-9
Encryption Statistics 8-9
Contents
xi
Cisco ASA Series VPN ASDM Configuration Guide
Global IKE/IPsec Statistics 8-10
NAC Session Summary 8-10
Protocol Statistics 8-11
VLAN Mapping Sessions 8-11
SSO Statistics for Clientless SSL VPN Session 8-11
VPN Connection Status for the Easy VPN Client 8-13
CHAPTER
9Configuring SSL Settings 9-1
SSL Settings 9-1
SSL 9-2
CHAPTER
10 Configuring an External Server for Authorization and Authentication 10-1
Understanding Policy Enforcement of Authorization Attributes 10-1
Defining the ASA LDAP Configuration 10-2
Guidelines 10-2
Active Directory/LDAP VPN Remote Access Authorization Examples 10-2
User-Based Attributes Policy Enforcement 10-3
Placing LDAP Users in a Specific Group Policy 10-5
Enforcing Static IP Address Assignment for AnyConnect Tunnels 10-7
Enforcing Dial-in Allow or Deny Access 10-9
Enforcing Logon Hours and Time-of-Day Rules 10-12
Example of Creating a Group Policy for a Local User 10-13
PART
2Configuring a Clientless SSL VPN
CHAPTER
11 Introduction to Clientless SSL VPN 11-1
Introduction to Clientless SSL VPN 11-1
Prerequisites 11-2
Guidelines and Limitations 11-2
CHAPTER
12 Basic Clientless SSL VPN Configuration 12-1
Clientless SSL VPN Security Precautions 12-1
Configuring Clientless SSL VPN Access 12-2
Verifying Clientless SSL VPN Server Certificates 12-3
Java Code Signer 12-6
Configuring Browser Access to Plug-ins 12-7
Preparing the Security Appliance for a Plug-in 12-8
Installing Plug-ins Redistributed by Cisco 12-8
Contents
xii
Cisco ASA Series VPN ASDM Configuration Guide
Providing Access to a Citrix XenApp Server 12-10
Preparing the Citrix XenApp Server for Clientless SSL VPN Access 12-10
Creating and Installing the Citrix Plug-in 12-11
Configuring Port Forwarding 12-11
Information About Port Forwarding 12-12
Configuring DNS for Port Forwarding 12-13
Making Applications Eligible for Port Forwarding 12-16
Adding/Editing a Port Forwarding Entry 12-16
Assigning a Port Forwarding List 12-16
Enabling and Switching off Port Forwarding 12-17
Configuring File Access 12-17
CIFS File Access Requirement and Limitation 12-18
Adding Support for File Access 12-18
Ensuring Clock Accuracy for SharePoint Access 12-18
Virtual Desktop Infrastructure (VDI) 12-19
Citrix Mobile Support 12-19
Supported Mobile Devices 12-19
Limitations 12-19
About Citrix Mobile Receiver User Logon 12-20
Configuring the ASA to Proxy a Citrix Server 12-20
Configuring a VDI Server 12-20
Configuring a VDI Proxy Server 12-21
Assigning a VDI Server to a Group Policy 12-21
Configuring ACLs 12-22
Adding or Editing ACEs 12-23
Configuration Examples for ACLs for Clientless SSL VPN 12-24
Configuring Browser Access to Client-Server Plug-ins 12-24
About Installing Browser Plug-ins 12-24
RDP Plug-in ActiveX Debug Quick Reference 12-26
Preparing the Security Appliance for a Plug-in 12-26
CHAPTER
13 Advanced Clientless SSL VPN Configuration 13-1
Microsoft Kerberos Constrained Delegation Solution 13-1
Requirements 13-1
Understanding How KCD Works 13-2
Authentication Flow with KCD 13-2
Adding a Windows Service Account in Active Directory 13-4
Configuring DNS for KCD 13-4
Configuring the ASA to Join the Active Directory Domain 13-5

Contents
xiii
Cisco ASA Series VPN ASDM Configuration Guide
Configuring the Use of External Proxy Servers 13-7
SSO Servers 13-8
Configuring SiteMinder and SAML Browser Post Profile 13-8
Adding the Cisco Authentication Scheme to SiteMinder 13-10
Adding or Editing SSO Servers 13-10
Configuring Kerberos Server Groups 13-11
Configuring Bookmarks to Access the Kerberos Authenticated Services 13-13
Configuring Application Profile Customization Framework 13-13
Restrictions 13-13
Managing APCF Profiles 13-13
Uploading APCF Packages 13-14
Managing APCF Packets 13-14
APCF Syntax 13-15
Configuring Session Settings 13-18
Encoding 13-19
Content Cache 13-20
Content Rewrite 13-21
Configuration Example for Content Rewrite Rules 13-22
Using Email over Clientless SSL VPN 13-23
Configuring Email Proxies 13-23
Configuring Web email: MS Outlook Web App 13-23
Configuring Bookmarks 13-23
Adding a Bookmark for a URL with a GET or Post Method 13-24
Adding a URL for a Predefined Application Template 13-26
Adding a Bookmark for an Auto Sign-On Application 13-27
Importing and Exporting a Bookmark List 13-28
Importing and Exporting GUI Customization Objects (Web Contents) 13-29
Adding and Editing Post Parameters 13-29
Configuration Example for Setting a Bookmark or URL Entry 13-31
Configuration Example for Configuring File Share (CIFS) URL Substitutions 13-31
Customizing External Ports 13-32
CHAPTER
14 Configuring Policy Groups 14-1
Configuring Smart Tunnel Access 14-1
Configuring Smart Tunnel Access 14-1
About Smart Tunnels 14-1
Why Smart Tunnels? 14-2
Configuring a Smart Tunnel (Lotus Example) 14-3
Simplifying Configuration of Which Applications to Tunnel 14-4
Contents
xiv
Cisco ASA Series VPN ASDM Configuration Guide
Adding Applications to Be Eligible for Smart Tunnel Access 14-5
About Smart Tunnel Lists 14-7
Creating a Smart Tunnel Auto Sign-On Server List 14-8
Adding Servers to a Smart Tunnel Auto Sign-On Server List 14-8
Enabling and Switching Off Smart Tunnel Access 14-9
Configuring Smart Tunnel Log Off 14-10
When Its Parent Process Terminates 14-10
With a Notification Icon 14-10
Using Proxy Bypass 14-11
Configuring Portal Access Rules 14-11
CHAPTER
15 Clientless SSL VPN Remote Users 15-1
Requiring Usernames and Passwords 15-1
Communicating Security Tips 15-2
Configuring Remote Systems to Use Clientless SSL VPN Features 15-2
Capturing Clientless SSL VPN Data 15-7
Creating a Capture File 15-8
Using a Browser to Display Capture Data 15-8
CHAPTER
16 Configuring Clientless SSL VPN Users 16-1
Overview 16-1
Defining the End User Interface 16-1
Viewing the Clientless SSL VPN Home Page 16-2
Viewing the Clientless SSL VPN Application Access Panel 16-2
Viewing the Floating Toolbar 16-3
Managing Passwords 16-4
Adding the Cisco Authentication Scheme to SiteMinder 16-5
Configuring the SAML POST SSO Server 16-5
Configuring SSO with the HTTP Form Protocol 16-6
Gathering HTTP Form Data 16-7
Using Auto Sign-On 16-10
Requiring Usernames and Passwords 16-12
Communicating Security Tips 16-12
Configuring Remote Systems to Use Clientless SSL VPN Features 16-12
Starting Clientless SSL VPN 16-13
Using the Clientless SSL VPN Floating Toolbar 16-13
Browsing the Web 16-14
Browsing the Network (File Management) 16-14
Contents
xv
Cisco ASA Series VPN ASDM Configuration Guide
Using the Remote File Explorer 16-15
Using Port Forwarding 16-16
Using email Via Port Forwarding 16-18
Using email Via Web Access 16-18
Using email Via email Proxy 16-18
Using Smart Tunnel 16-19
CHAPTER
17 Using Clientless SSL VPN with Mobile Devices 17-1
Using Clientless SSL VPN with Mobile Devices 17-1
Restrictions 17-1
CHAPTER
18 Customizing Clientless SSL VPN 18-1
Customizing the Clientless SSL VPN User Experience 18-1
Customizing the Logon Page with the Customization Editor 18-1
Replacing the Logon Page with your own Fully Customized Page 18-3
Creating the Custom Login Screen File 18-4
Importing the File and Images 18-5
Configuring the Security Appliance to use the Custom Login Screen 18-5
Clientless SSL VPN End User Setup 18-6
Defining the End User Interface 18-6
Viewing the Clientless SSL VPN Home Page 18-7
Viewing the Clientless SSL VPN Application Access Panel 18-7
Viewing the Floating Toolbar 18-7
Customizing Clientless SSL VPN Pages 18-8
Information About Customization 18-9
Exporting a Customization Template 18-9
Editing the Customization Template 18-9
Login Screen Advanced Customization 18-15
Modifying Your HTML File 18-17
Customizing the Portal Page 18-18
Configuring Custom Portal Timeout Alerts 18-19
Specifying a Custom Timeout Alert in a Customization Object File 18-19
Customizing the Logout Page 18-20
Customizing the External Portal Page 18-21
Adding Customization Object 18-21
Importing/Exporting Customization Object 18-22
Creating XML-Based Portal Customization Objects and URL Lists 18-22
Understanding the XML Customization File Structure 18-23
Configuration Example for Customization 18-26
Contents
xvi
Cisco ASA Series VPN ASDM Configuration Guide
Using the Customization Template 18-29
The Customization Template 18-29
Help Customization 18-41
Customizing a Help File Provided by Cisco 18-42
Creating Help Files for Languages Not Provided by Cisco 18-43
Import/Export Application Help Content 18-44
Customizing a Help File Provided by Cisco 18-45
Creating Help Files for Languages Not Provided by Cisco 18-46
Customizing Bookmark Help 18-46
Customizing a Help File Provided By Cisco 18-47
Creating Help Files for Languages Not Provided by Cisco 18-48
Translating the Language of User Messages 18-48
Understanding Language Translation 18-48
Editing a Translation Table 18-49
Adding a Translation Table 18-50
Importing/Exporting Language Localization 18-50
CHAPTER
19 Clientless SSL VPN Troubleshooting 19-1
Closing Application Access to Prevent hosts File Errors 19-1
Recovering from Hosts File Errors When Using Application Access 19-1
Understanding the hosts File 19-2
Stopping Application Access Improperly 19-2
Reconfiguring a Host’s File Automatically Using Clientless SSL VPN 19-2
Reconfiguring hosts File Manually 19-3
Sending an Administrator’s Alert to Clientless SSL VPN Users 19-4
CHAPTER
20 Clientless SSL VPN Licensing 20-1
Licensing 20-1
I
NDEX

1
Cisco ASA Series VPN ASDM Configuration Guide
About This Guide
This preface introduces Cisco ASA Series VPN ASDM Configuration Guide and includes the following
sections:
•Document Objectives, page 1
•Related Documentation, page 1
•Conventions, page 2
•Obtaining Documentation and Submitting a Service Request, page 2
Document Objectives
The purpose of this guide is to help you configure VPN on the ASA using ASDM. This guide does not
cover every feature, but describes only the most common configuration scenarios.
This guide applies to the Cisco ASA series. Throughout this guide, the term “ASA” applies generically
to supported models, unless specified otherwise.
Note ASDM supports many ASA versions. The ASDM documentation and online help includes all of the
latest features supported by the ASA. If you are running an older version of ASA software, the
documentation might include features that are not supported in your version. Similarly, if a feature was
added into a maintenance release for an older major or minor version, then the ASDM documentation
includes the new feature even though that feature might not be available in all later ASA releases. Please
refer to the feature history table for each chapter to determine when features were added. For the
minimum supported version of ASDM for each ASA version, see Cisco ASA Series Compatibility.
Related Documentation
For more information, see Navigating the Cisco ASA Series Documentation at
http://www.cisco.com/go/asadocs.

2
Cisco ASA Series VPN ASDM Configuration Guide
Conventions
This document uses the following conventions:
Note Means reader take note.
Tip Means the following information will help you solve a problem.
Caution Means reader be careful. In this situation, you might perform an action that could result in equipment
damage or loss of data.
Obtaining Documentation and Submitting a Service Request
For information on obtaining documentation, using the Cisco Bug Search Tool (BST), submitting a
service request, and gathering additional information, see What’s New in Cisco Product Documentation
at: http://www.cisco.com/c/en/us/td/docs/general/whatsnew/whatsnew.html.
Subscribe to What’s New in Cisco Product Documentation, which lists all new and revised
Cisco technical documentation, as an RSS feed and deliver content directly to your desktop using a
reader application. The RSS feeds are a free service.
Convention Indication
bold font Commands and keywords and user-entered text appear in bold font.
italic font Document titles, new or emphasized terms, and arguments for which you supply
values are in italic font.
[ ] Elements in square brackets are optional.
{x | y | z } Required alternative keywords are grouped in braces and separated by
vertical bars.
[ x | y | z ] Optional alternative keywords are grouped in brackets and separated by
vertical bars.
string A nonquoted set of characters. Do not use quotation marks around the string or
the string will include the quotation marks.
courier font Terminal sessions and information the system displays appear in courier font.
courier bold font Commands and keywords and user-entered text appear in bold courier font.
courier italic font Arguments for which you supply values are in courier italic font.
< > Nonprinting characters such as passwords are in angle brackets.
[ ] Default responses to system prompts are in square brackets.
!, # An exclamation point (!) or a pound sign (#) at the beginning of a line of code
indicates a comment line.

P
ART
1
Configuring Site-to-Site and Client VPN

CHAPTER
2-1
Cisco ASA Series VPN ASDM Configuration Guide
2
VPN Wizards
The ASA provides Secure Socket Layer (SSL) remote access connectivity from almost any
Internet-enabled location using only a Web browser and its native SSL encryption. Clientless,
browser-based VPN lets users establish a secure, remote-access VPN tunnel to the adaptive security
appliance using a web browser. After authentication, users access a portal page and can access specific,
supported internal resources. The network administrator provides access to resources by users on a group
basis. Users have no direct access to resources on the internal network.
The Cisco AnyConnect VPN client provides secure SSL connections to the ASA for remote users with
full VPN tunneling to corporate resources. Without a previously-installed client, remote users enter the
IP address in their browser of an interface configured to accept clientless VPN connections. The ASA
downloads the client that matches the operating system of the remote computer. After downloading, the
client installs and configures itself, establishes a secure connection and either remains or uninstalls itself
(depending on the ASA configuration) when the connection terminates. In the case of a previously
installed client, when the user authenticates, the ASA examines the revision of the client and upgrades
the client as necessary.
With the addition of IKEv2 support in release 8.4, the end user can have the same experience
independent of the tunneling protocol used by the AnyConnect client session. This addition allows other
vendors’ VPN clients to connect to the ASAs. This support enhances security and complies with the
IPsec remote access requirements defined in federal and public sector mandates.
The VPN wizard lets you configure basic LAN-to-LAN and remote access VPN connections and assign
either preshared keys or digital certificates for authentication. Use ASDM to edit and configure advanced
features.
VPN Overview
The ASA creates a Virtual Private Network by creating a secure connection across a TCP/IP network
(such as the Internet) that users see as a private connection. It can create single-user-to-LAN connections
and LAN-to-LAN connections.
For LAN-to-LAN connections using both IPv4 and IPv6 addressing, the security appliance supports
VPN tunnels if both peers are Cisco ASA 5500 series security appliances, and if both inside networks
have matching addressing schemes (both IPv4 or both IPv6). This is also true if both peer inside
networks are IPv6 and the outside network is IPv6.
The secure connection is called a tunnel, and the ASA uses tunneling protocols to negotiate security
parameters, create and manage tunnels, encapsulate packets, transmit or receive them through the tunnel,
and unencapsulate them. The ASA functions as a bidirectional tunnel endpoint: it can receive plain

2-2
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 2 VPN Wizards
IPsec IKEv1 Remote Access Wizard
packets, encapsulate them, and send them to the other end of the tunnel where they are unencapsulated
and sent to their final destination. It can also receive encapsulated packets, unencapsulate them, and send
them to their final destination.
The four VPN wizards described in this section are as follows:
•IPsec IKEv1 Remote Access Wizard
•IPsec Site-to-Site VPN Wizard
•AnyConnect VPN Wizard
•Clientless SSL VPN Wizard
IPsec IKEv1 Remote Access Wizard
Use the IKEv1 Remote Access Wizard to configuresecure remote access for VPN clients, such as mobile
users, and to identify the interface that connects to the remote IPsec peer.
Fields
•VPN Tunnel Interface—Choose the interface that establishes a secure tunnel with the remote IPsec
peer. If the ASA has multiple interfaces, you need to plan the VPN configuration before running this
wizard, identifying the interface to use for each remote IPsec peer with which you plan to establish
a secure connection.
•Enable inbound IPsec sessions to bypass interface access lists—Enable IPsec authenticated inbound
sessions to always be permitted through the security appliance (that is, without a check of the
interface access-list statements). Be aware that the inbound sessions bypass only the interface ACLs.
Configured group-policy, user, and downloaded ACLs still apply.
Remote Access Client
Remote access users of various types can open VPN tunnels to this ASA. Choose the type of VPN client
for this tunnel.
Fields
•VPN Client Type
–
Cisco VPN Client, Release 3.x or higher, or an Easy VPN Remote product.
–
Microsoft Windows client using L2TP over IPsec—Specify the PPP authentication protocol.
The choices are PAP, CHAP, MS-CHAP-V1, MS-CHAP-V2, and EAP-PROXY:
PAP—Passes cleartext username and password during authentication and is not secure.
CHAP—In response to the server challenge, the client returns the encrypted [challenge plus
password] with a cleartext username. This protocol is more secure than the PAP, but it does not
encrypt data.
MS-CHAP, Version 1—Similar to CHAP but more secure in that the server stores and compares
only encrypted passwords rather than cleartext passwords as in CHAP.
MS-CHAP, Version 2—Contains security enhancements over MS-CHAP, Version 1.
EAP-Proxy—Enables EAP which permits the ASA to proxy the PPP authentication process to
an external RADIUS authentication server.
If a protocol is not specified on the remote client, do no specify it.

2-3
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 2 VPN Wizards
IPsec IKEv1 Remote Access Wizard
–
Specify if the client will send tunnel group name as username@tunnelgroup.
VPN Client Authentication Method and Tunnel Group Name
Use the VPN Client Authentication Method and Name pane to configure an authentication method and
create a connection policy (tunnel group).
Fields
•Authentication Method—The remote site peer authenticates either with a preshared key or a
certificate.
–
Pre-shared Key—Click to use a preshared key for authentication between the local ASA and the
remote IPsec peer.
Using a preshared key is a quick and easy way to set up communication with a limited number
of remote peers and a stable network. It may cause scalability problems in a large network
because each IPsec peer requires configuration information for each peer with which it
establishes secure connections.
Each pair of IPsec peers must exchange preshared keys to establish secure tunnels. Use a secure
method to exchange the preshared key with the administrator of the remote site.
–
Pre-shared Key—Type an alphanumeric string between 1 and 128 characters.
–
Certificate—Click to use certificates for authentication between the local ASA and the remote
IPsec peer. To complete this section, you must have previously enrolled with a CA and
downloaded one or more certificates to the ASA.
You can efficiently manage the security keys used to establish an IPsec tunnel with digital
certificates. A digital certificate contains information that identifies a user or device, such as a
name, serial number, company, department or IP address. A digital certificate also contains a
copy of the public key.
To use digital certificates, each peer enrolls with a certification authority (CA), which is
responsible for issuing digital certificates. A CA can be a trusted vendor or a private CA that
you establish within an organization.
When two peers want to communicate, they exchange certificates and digitally sign data to
authenticate each other. When you add a new peer to the network, it enrolls with a CA, and none
of the other peers require additional configuration.
Certificate Signing Algorithm—Displays the algorithm for signing digital certificates, rsa-sig
for RSA.
–
Challenge/response authentication (CRACK)—Provides strong mutual authentication when the
client authenticates using a popular method such as RADIUS and the server uses public key
authentication. The security appliance supports CRACK as an IKE option in order to
authenticate the Nokia VPN Client on Nokia 92xx Communicator Series devices.
• Tunnel Group Name—Type a name to create the record that contains tunnel connection policies for
this IPsec connection. A connection policy can specify authentication, authorization, and accounting
servers, a default group policy, and IKE attributes. A connection policy that you configure with this
VPN wizard specifies an authentication method and uses the ASA Default Group Policy.
Client Authentication
Use the Client Authentication pane to select the method by which the ASA authenticates remote users.

2-4
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 2 VPN Wizards
IPsec IKEv1 Remote Access Wizard
Fields
Select one of the following options:
•Authenticate using the local user database—Click to use authentication internal to the ASA. Use this
method for environments with a small, stable number of users. The next pane lets you create
accounts on the ASA for individual users.
•Authenticate using an AAA server group—Click to use an external server group for remote user
authentication.
–
AAA Server Group Name—Choose a AAA server group configured previously.
–
New...—Click to configure a new AAA server group.
User Accounts
Use the User Accounts pane to add new users to the ASA internal user database for authentication
purposes.
Fields
•Use the fields in this section to add a user.
–
Username—Enter the username.
–
Password—(Optional) Enter a password.
–
Confirm Password—(Optional) Reenter the password.
•Add—Click to add a user to the database after you have entered the username and optional
password.
•Delete—To remove a user from the database, highlight the appropriate username and click Delete.
Address Pool
Use the Address Pool pane to configure a pool of local IP addresses that the ASA assigns to remote VPN
clients.
Fields
• Tunnel Group Name—Displays the name of the connection profile (tunnel group) to which this
address pool applies. You set this name in the VPN Client and Authentication Method pane (step 3).
•Pool Name—Select a descriptive identifier for the address pool.
•New...—Click to configure a new address pool.
•Range Start Address—Type the starting IP address in the address pool.
•Range End Address—Type the ending IP address in the address pool.
•Subnet Mask—(Optional) Choose the subnet mask for these IP addresses.
Attributes Pushed to Client (Optional)
Use the Attributes Pushed to Client (Optional) pane to have the ASA pass information about DNS and
WINS servers and the default domain name to remote access clients.

2-5
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 2 VPN Wizards
IPsec IKEv1 Remote Access Wizard
Fields
•Tunnel Group—Displays the name of the connection policy to which the address pool applies. You
set this name in the VPN Client Name and Authentication Method pane.
•Primary DNS Server—Type the IP address of the primary DNS server.
•Secondary DNS Server—Type the IP address of the secondary DNS server.
•Primary WINS Server—Type the IP address of the primary WINS server.
•Secondary WINS Server— Type the IP address of the secondary WINS server.
•Default Domain Name—Type the default domain name.
IKE Policy
IKE, also called Internet Security Association and Key Management Protocol (ISAKMP), is the
negotiation protocol that lets two hosts agree on how to build an IPsec Security Association. Each IKE
negotiation is divided into two sections called Phase1 and Phase 2.
•Phase 1 creates the first tunnel, which protects later IKE negotiation messages.
•Phase 2 creates the tunnel that protects data.
Use the IKE Policy pane to set the terms of the Phase 1 IKE negotiations, which include the following:
•An encryption method to protect the data and ensure privacy.
•An authentication method to ensure the identity of the peers.
•A Diffie-Hellman group to establish the strength of the of the encryption-key-determination
algorithm. The ASA uses this algorithm to derive the encryption and hash keys.
Fields
•Encryption—Select the symmetric encryption algorithm the ASA uses to establish the Phase 1 SA
that protects Phase 2 negotiations. The ASA supports the following encryption algorithms:
The default, 3DES, is more secure than DES but requires more processing for encryption and
decryption. Similarly, the AES options provide increased security but also require increased
processing.
•Authentication—Choose the hash algorithm used for authentication and ensuring data integrity. The
default is SHA. MD5 has a smaller digest and is considered to be slightly faster than SHA. There
has been a demonstrated successful (but extremely difficult) attack against MD5. However, the
Keyed-Hash Message Authentication Code (HMAC) version used by the ASA prevents this attack.
•Diffie-Hellman Group—Choose the Diffie-Hellman group identifier, which the two IPsec peers use
to derive a shared secret without transmitting it to each other. The default, Group 2 (1024-bit
Diffie-Hellman), requires less CPU time to execute but is less secure than Group 5 (1536-bit).
Algorithm Explanation
DES Data Encryption Standard. Uses a 56-bit key.
3DES Triple DES. Performs encryption three times using a 56-bit key.
AES-128 Advanced Encryption Standard. Uses a 128-bit key.
AES-192 AES using a 192-bit key.
AES-256 AES using a 256-bit key.

2-6
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 2 VPN Wizards
IPsec IKEv1 Remote Access Wizard
Note The default value for the VPN 3000 Series Concentrator is MD5. A connection between the ASA and
the VPN Concentrator requires that the authentication method for Phase I and II IKE negotiations be the
same on both sides of the connection.
IPsec Settings (Optional)
Use the IPsec Settings (Optional) pane to identify local hosts/networks which do not require address
translation. By default, the ASA hides the real IP addresses of internal hosts and networks from outside
hosts by using dynamic or static Network Address Translation (NAT). NAT minimizes risks of attack by
untrusted outside hosts but may be improper for those who have been authenticated and protected by
VPN.
For example, an inside host using dynamic NAT has its IP address translated by matching it to a
randomly selected address from a pool. Only the translated address is visible to the outside. Remote VPN
clients that attempt to reach these hosts by sending data to their real IP addresses cannot connect to these
hosts, unless you configure a NAT exemption rule.
Note If you want all hosts and networks to be exempt from NAT, configure nothing on this pane. If you have
even one entry, all other hosts and networks are subject to NAT.
Fields
•Interface—Choose the name of the interface that connects to the hosts or networks you have
selected.
•Exempt Networks—Select the IP address of the host or network that you want to exempt from the
chosen interface network.
•Enable split tunneling—Select to have traffic from remote access clients destined for the public
Internet sent unencrypted. Split tunneling causes traffic for protected networks to be encrypted,
while traffic to unprotected networks is unencrypted. When you enable split tunneling, the ASA
pushes a list of IP addresses to the remote VPN client after authentication. The remote VPN client
encrypts traffic to the IP addresses that are behind the ASA. All other traffic travels unencrypted
directly to the Internet without involving the ASA.
•Enable Perfect Forwarding Secrecy (PFS)—Specify whether to use Perfect Forward Secrecy, and the
size of the numbers to use, in generating Phase 2 IPsec keys. PFS is a cryptographic concept where each
new key is unrelated to any previous key. In IPsec negotiations, Phase 2 keys are based on Phase 1 keys
unless PFS is enabled. PFS uses Diffie-Hellman techniques to generate the keys.
PFS ensures that a session key derived from a set of long-term public and private keys is not
compromised if one of the private keys is compromised in the future.
PFS must be enabled on both sides of the connection.
–
Diffie-Hellman Group—Select the Diffie-Hellman group identifier, which the two IPsec peers
use to derive a shared secret without transmitting it to each other. The default, Group 2 (1024-bit
Diffie-Hellman), requires less CPU time to execute but is less secure than Group 5 (1536-bit).
Summary
The Summary pane displays all of the attributes of this VPN LAN-to-LAN connection as configured.

2-7
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 2 VPN Wizards
IPsec Site-to-Site VPN Wizard
Fields
Back—To make changes, click Back until you reach the appropriate pane.
Finish—When you are satisfied with the configuration, click Finish. ASDM saves the LAN-to-LAN
configuration. After you click Finish, you can no longer use the VPN wizard to make changes to this
configuration. Use ASDM to edit and configure advanced features.
Cancel—To remove the configuration, click Cancel.
IPsec Site-to-Site VPN Wizard
Use this wizard to set up new site-to-site VPN tunnels. A tunnel between two devices is called a
site-to-site tunnel and is bidirectional. A site-to-site VPN tunnel protects the data using the IPsec
protocol.
Peer Device Identification
Identify the peer VPN device by its IP address and the interface used to access the peer.
Fields
•Peer IP Address—Configure the IP address of the other site (peer device).
•VPN Access Interface—Select the interface to use for the site-to-site tunnel.
•IKEv2
Traffic to Protects
This step lets you identify the local network and remote network These networks protect the traffic using
IPsec encryption.
Fields
•Local Networks—Identify the host used in the IPsec tunnel.
•Remote Networks—Identify the networks used in the IPsec tunnel.
Security
This step lets you configure the methods to authenticate with the peer device. You can either choose the
simple configuration, and supply a pre-shared key. Or you can select Customized Configuration for more
advanced options, which are described below.
Authentication Tab
IKE version 1
•Pre-shared Key—Using a preshared key is a quick and easy way to set up communication with a
limited number of remote peers and a stable network. It may cause scalability problems in a large
network because each IPsec peer requires configuration information for each peer with which it
establishes secure connections.

2-8
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 2 VPN Wizards
IPsec Site-to-Site VPN Wizard
Each pair of IPsec peers must exchange preshared keys to establish secure tunnels. Use a secure
method to exchange the preshared key with the administrator of the remote site.
•Device Certificate—Click to use certificates for authentication between the local ASA and the
remote IPsec peer.
You can efficiently manage the security keys used to establish an IPsec tunnel with digital
certificates. A digital certificate contains information that identifies a user or device, such as a name,
serial number, company, department or IP address. A digital certificate also contains a copy of the
public key.
When two peers want to communicate, they exchange certificates and digitally sign data to
authenticate each other. When you add a new peer to the network, it enrolls with a CA, and none of
the other peers require additional configuration.
IKE version 2
•Local Pre-shared Key—Specify IPsec IKEv2 authentication methods and encryption algorithms.
•Local Device Certificate—Authenticates VPN access through the security appliance.
•Remote Peer Pre-shared Key—Click to use a preshared key for authentication between the local
ASA and the remote IPsec peer.
•Remote Peer Certificate Authentication—When checked, the peer device is allowed to use the
certificate to authenticate itself to this device.
Encryption Algorithm
This tab lets you select the types of encryption algorithms used to protect the data.
IKE version 1
•IKE Policy—Specify IKEv1 authentication methods.
•IPsec Proposal—Specify IPsec encryption algorithms.
IKE version 2
•IKE Policy—Specify IKEv2 authentication methods.
•IPsec Proposal—Specify IPsec encryption algorithms.
NAT Excempt
Fields
•Exempt ASA side host/network from address translation—Use the drop-down to choose a host or
network to be excluded from address translation.
Summary
Provides a summary of your selections from the previous wizard windows. The supported VPN protocols
are included in the summary as well as the IKE version chosen on the VPN Connection Type window.

2-9
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 2 VPN Wizards
AnyConnect VPN Wizard
AnyConnect VPN Wizard
Use this wizard to configure ASA to accept VPN connections from the AnyConnect VPN client. This
wizard configures either IPsec (IKEv2) or SSL VPN protocols for full network access. The ASA
automatically uploads the AnyConnect VPN client to the end user’s device when a VPN connection is
established.
Warn the user that running the wizard does not mean the IKEv2 profile automatically applies in
predeployment scenarios. Either provide a pointer or the steps necessary to successfully predeploy
IKEv2.
Connection Profile Identification
The connection profile identification is used to identify the ASA to the remote acess users.
Fields
•Connection Profile Name—Provide a name that the remote access users will access for VPN
connections.
•VPN Access Interface—Choose an interface that the remote access users will access for VPN
connections.
VPN Protocols
Specify the VPN protocol allowed for this connection profile.
The AnyConnect client defaults to SSL. If you enable IPsec as a VPN tunnel protocol for the connection
profile, you must also create and deploy a client profile with IPsec enabled using the profile editor from
ASDM, and deploy the profile.
If you predeploy instead of weblaunch the AnyConnect client, the first client connection uses SSL, and
receives the client profile from the ASA during the session. For subsequent connections, the client uses
the protocol specified in the profile, either SSL or IPsec. If you predeploy the profile with IPsec specified
with the client, the first client connection uses IPsec. For more information about predeploying a client
profile with IPsec enabled, see the AnyConnect Secure Mobility Client Administrator Guide.
Fields
•SSL
•IPsec (IKE v2)
•Device Certificate—Identifies the ASA to the remote access clients.
Note Some AnyConnect features (such as always on, IPsec/IKEv2) require a valid device
certificate on the ASA.
•Manage—Choosing Manage opens the Manage Identity Certificates window.
–
Add—Choose Add to add an identity certificate and its details.
–
Show Details—If you choose a particular certificate and click Show Details, the Certificate
Details window appears and provides who the certificate was issued to and issued by, as well as
specifics about its serial number, usage, associated trustpoints, valid timeframe, and so on.

2-10
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 2 VPN Wizards
AnyConnect VPN Wizard
–
Delete—Highlight the certificate you want to remove and click Delete.
–
Export—Highlight the certificate and click Export to export the certificate to a file with or
without an encryption passphrase.
–
Enroll ASA SSL VPN with Entrust—Gets your Cisco ASA SSL VPN appliance up and running
quickly with an SSL Advantage digitial certificate from Entrust.
Client Images
ASA can automatically upload the latest AnyConnect package to the client device when it accesses the
enterprise network. You can use a regular expression to match the user agent of a browser to an image.
You can also minimize connection setup time by moving the most commonly encountered operation
system to the top of the list.
Fields
•Add
•Replace
•Delete
Authentication Methods
Specify authentication information on this screen.
Fields
•AAA server group—Enable to let the ASA contact a remote AAA server group to authenticate the
user. Select a AAA server group from the list of pre-configured groups or click New to create a new
group.
•Local User Database Details—Add new users to the local database stored on the ASA.
–
Username—Create a username for the user.
–
Password—Create a password for the user.
–
Confirm Password—Re-type the same password to confirm.
–
Add/Delete—Add or delete the user from the local database.
Client Address Assignment
Provide a range of IP addresses to remote SSL VPN users.
Fields
•IPv4 Address Pools—SSL VPN clients receive new IP addresses when they connect to the ASA.
Clientless connections do not require new IP addresses. Address Pools define a range of addresses
that remote clients can receive. Select an existing IP Address Pool or click New to create a new pool.
If you select New, you will have to provide a starting and ending IP address and subnet mask.
•IPv6 Address Pool—Select an existing IP Address Pool or click New to create a new pool.

2-11
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 2 VPN Wizards
Clientless SSL VPN Wizard
Note IPv6 address pools can not be created for IKEv2 connection profiles.
Network Name Resolution Servers
This step lets you specify which domain names are resolved for the remote user when accessing the
internal network.
Fields
•DNS Servers—Enter the IP address of the DNS server.
•WINS Servers—Enter the IP address of the WINS server.
•Domain Name—Type the default domain name.
NAT Exempt
If network translation is enabled on the ASA, the VPN traffic must be exempt from this translation.
Fields
•Exempt VPN traffic from network address translation
AnyConnect Client Deployment
You can install the AnyConnect client program to a client device with one of the following two methods:
•Web launch—Installs automatically when accessing the ASA using a web browser.
•Pre-deployment—Manually installs the AnyConnect client package.
Fields
•Allow Web Launch—A global setting that affects all connections. If it is unchecked (disallowed),
AnyConnect SSL connections and clientless SSL connections do not work.
For pre-deployment, the disk0:/test2_client_profile.xml profile bundle contains an .msi file, and you
must include this client profile from the ASA in your AnyConnect package to ensure IPsec connection
functions as expected.
Summary
Provides a summary of your selections from the previous wizard windows. The supported VPN protocols
are part of the summary as well as the IKE version chosen.
Clientless SSL VPN Wizard
This wizard enables clientless, browser-based connections for specific, supported internal resources
through a portal page.

2-12
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 2 VPN Wizards
Clientless SSL VPN Wizard
SSL VPN Interface
Provide a connection profile and the interface that SSL VPN users connect to.
Fields
•Connection Profile Name
•SSL VPN Interface—The interface users access for SSL VPN connections.
•Digital Certificate—Specifies what the security appliance sends to the remote web browser to
authenticate the ASA.
–
Certificate—Choose from the drop-down menu.
•Accessing the Connection Profile
–
Connection Group Alias/URL—The group alias is chosen during login from the Group
drop-down list. This URL is entered into the web browser.
–
Display Group Alias list at the login page
User Authentication
Specify authentication information on this screen.
Fields
•Authenticate using a AAA server group—Enable to let the ASA contact a remote AAA server group
to authenticate the user.
–
AAA Server Group Name—Select a AAA server group from the list of pre-configured groups
or click New to create a new group.
•Authenticate using the local user database—Add new users to the local database stored on the ASA.
–
Username—Create a username for the user.
–
Password—Create a password for the user.
–
Confirm Password—Re-type the same password to confirm.
–
Add/Delete—Add or delete the user from the local database.
Group Policy
Group policies configure common attributes for groups of users. Create a new group policy or select an
existing one to modify.
Fields
•Create new group policy—Enables you to create a new group policy. Provide a name for the new
policy.
•Modify existing group policy—Select an existing group policy to modify.

2-13
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 2 VPN Wizards
Clientless SSL VPN Wizard
Bookmark List
Configure a list of group intranet websites that appear in the portal page as links. Some examples include
https://intranet.acme.com, rdp://10.120.1.2, vnc://100.1.1.1 and so on.
Fields
•Bookmark List
•Manage
Summary
Provides a summary of your selections from the previous wizard windows.

2-14
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 2 VPN Wizards
Clientless SSL VPN Wizard

CHAPTER
3-1
Cisco ASA Series VPN ASDM Configuration Guide
3
Configuring IKE, Load Balancing, and NAC
IKE, also called ISAKMP, is the negotiation protocol that lets two hosts agree on how to build an IPsec
security association. To configure the ASA for virtual private networks, you set global IKE parameters
that apply system wide, and you also create IKE policies that the peers negotiate to establish a VPN
connection.
Load balancing distributes VPN traffic among two or more ASAs in a VPN cluster.
Network Access Control (NAC) protects the enterprise network from intrusion and infection from
worms, viruses, and rogue applications by performing endpoint compliance and vulnerability checks as
a condition for production access to the network. We refer to these checks as posture validation.
This chapter describes how to configure IKE, load balancing, and NAC. It includes the following
sections:
•Enabling IKE on an Interface, page 3-1
•Setting IKE Parameters for Site-to-Site VPN, page 3-2
•Creating IKE Policies, page 3-5
•Configuring IPsec, page 3-9
•Configuring Load Balancing, page 3-20
•Setting Global NAC Parameters, page 3-27
•Configuring Network Admission Control Policies, page 3-28
Enabling IKE on an Interface
To use IKE, you must enable it on each interface you plan to use it on.
For VPN connections
Step 1 In ASDM, navigate to Configuration > Remote Access VPN > Network (Client) Access > AnyConnect
Connection Profiles
Step 2 In the Access Interfaces section, check Allow Access under IPsec (IKEv2) Access for the interfaces you
will use IKE on.

3-2
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 3 Configuring IKE, Load Balancing, and NAC
Setting IKE Parameters for Site-to-Site VPN
For Site-to-Site VPN
Step 1 In ASDM, navigate to Configuration > Site-to-Site VPN > Connection Profiles
Step 2 Select the interfaces you want to use IKEv1 and IKEv2 on.
Setting IKE Parameters for Site-to-Site VPN
IKE Parmeters
In ASDM, navigate to Configuration > Site-to-Site VPN > Advanced > IKE Parameters
NAT Transparency
Enable IPsec over NAT-T
IPsec over NAT-T lets IPsec peers establish both remote access and LAN-to-LAN connections through
a NAT device. It does this by encapsulating IPsec traffic in UDP datagrams, using port 4500, thereby
providing NAT devices with port information. NAT-T auto-detects any NAT devices, and only
encapsulates IPsec traffic when necessary. This feature is enabled by default.
•The ASA can simultaneously support standard IPsec, IPsec over TCP, NAT-T, and IPsec over UDP,
depending on the client with which it is exchanging data.
•When both NAT-T and IPsec over UDP are enabled, NAT-T takes precedence.
•When enabled, IPsec over TCP takes precedence over all other connection methods.
The ASA implementation of NAT-T supports IPsec peers behind a single NAT/PAT device as follows:
•One LAN-to-LAN connection.
•Either a LAN-to-LAN connection or multiple remote access clients, but not a mixture of both.
To use NAT-T you must:
•Create an ACL for the interface you will be using to open port 4500 (Configuration > Firewall >
Access Rules).
•Enable IPsec over NAT-T in this pane.
•On the Fragmentation Policy parameter in the Configuration > Site-to-Site VPN > Advanced > IPsec
Prefragmentation Policies pane, edit the interface you will be using to Enable IPsec
pre-fragmentation. When this is configured, it is still alright to let traffic travel across NAT devices
that do not support IP fragmentation; they do not impede the operation of NAT devices that do.
Enable IPsec over TCP
IPsec over TCP enables a VPN client to operate in an environment in which standard ESP or IKE cannot
function, or can function only with modification to existing firewall rules. IPsec over TCP encapsulates
both the IKE and IPsec protocols within a TCP packet, and enables secure tunneling through both NAT
and PAT devices and firewalls. This feature is disabled by default.
3-3
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 3 Configuring IKE, Load Balancing, and NAC
Setting IKE Parameters for Site-to-Site VPN
Note This feature does not work with proxy-based firewalls.
IPsec over TCP works with remote access clients. It works on all physical and VLAN interfaces. It is a
client to ASA feature only. It does not work for LAN-to-LAN connections.
•The ASA can simultaneously support standard IPsec, IPsec over TCP, NAT-Traversal, and IPsec
over UDP, depending on the client with which it is exchanging data.
•The VPN 3002 hardware client, which supports one tunnel at a time, can connect using standard
IPsec, IPsec over TCP, NAT-Traversal, or IPsec over UDP.
•When enabled, IPsec over TCP takes precedence over all other connection methods.
You enable IPsec over TCP on both the ASA and the client to which it connects.
You can enable IPsec over TCP for up to 10 ports that you specify. If you enter a well-known port, for
example port 80 (HTTP) or port 443 (HTTPS), the system displays a warning that the protocol associated
with that port will no longer work. The consequence is that you can no longer use a browser to manage
the ASA through the IKE-enabled interface. To solve this problem, reconfigure the HTTP/HTTPS
management to different ports.
You must configure TCP port(s) on the client as well as on the ASA. The client configuration must
include at least one of the ports you set for the ASA.
Identity Sent to Peer
Choose the Identity that the peers will use to identify themselves during IKE negotiations:
Session Control
Disable Inbound Aggressive Mode Connections
Phase 1 IKE negotiations can use either Main mode or Aggressive mode. Both provide the same services,
but Aggressive mode requires only two exchanges between the peers, rather than three. Aggressive mode
is faster, but does not provide identity protection for the communicating parties. It is therefore necessary
that they exchange identification information prior to establishing a secure SA in which to encrypt in
formation. This feature is disabled by default.
Alert Peers Before Disconnecting
Client or LAN-to-LAN sessions may be dropped for several reasons, such as: a ASA shutdown or reboot,
session idle timeout, maximum connection time exceeded, or administrator cut-off.
Address Uses the IP addresses of the hosts exchanging ISAKMP identity information.
Hostname Uses the fully-qualified domain name of the hosts exchanging ISAKMP identity
information (default). This name comprises the hostname and the domain name.
Key ID Uses the remote peer uses the Key Id String that you specify to look up the preshared
key.
Automatic Determines IKE negotiation by connection type:
•IP address for preshared key
•Cert DN for certificate authentication.

3-4
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 3 Configuring IKE, Load Balancing, and NAC
Setting IKE Parameters for Site-to-Site VPN
The ASA can notify qualified peers (in LAN-to-LAN configurations), VPN Clients and VPN 3002
hardware clients of sessions that are about to be disconnected, and it conveys to them the reason. The
peer or client receiving the alert decodes the reason and displays it in the event log or in a pop-up pane.
This feature is disabled by default.
This pane lets you enable the feature so that the ASA sends these alerts, and conveys the reason for the
disconnect.
Qualified clients and peers include the following:
•Security appliances with Alerts enabled.
•VPN clients running 4.0 or later software (no configuration required).
•VPN 3002 hardware clients running 4.0 or later software, and with Alerts enabled.
•VPN 3000 concentrators running 4.0 or later software, with Alerts enabled.
Wait for All Active Sessions to Voluntarily Terminate Before Rebooting
You can schedule a ASA reboot to occur only when all active sessions have terminated voluntarily. This
feature is disabled by default.
Number of SAs Allowed in Negotiation for IKEv1
Limits the maximum number of SAs that can be in negotiation at any time.
IKE v2 Specific Settings
Additional session controls are available for IKE v2, that limit the number of open SAs. By default, the
ASA does not limit the number of open SAs:
•Cookie Challenge—Enables the ASA to send cookie challenges to peer devices in response to SA
initiate packets.
–
% threshold before incoming SAs are cookie challenged—The percentage of the total allowed
SAs for the ASA that are in-negotiation, which triggers cookie challenges for any future SA
negotiations. The range is zero to 100%. The default is 50%.
•Number of Allowed SAs in Negotiation—Limits the maximum number of SAs that can be in
negotiation at any time. If used in conjunction with Cookie Challenge, configure the cookie
challenge threshold lower than this limit for an effective cross-check.
•Maximum Number of SAs Allowed—Limits the number of allowed IKEv2 connections on the ASA.
By default, the limit is the maximum number of connections specified by the license.
Preventing DoS Attacks with IKE v2 Specific Settings
You can prevent denial-of-service (DoS) attacks for IPsec IKEv2 connections by configuring Cookie
Challenge, which challenges the identify of incoming Security Associations (SAs), or by limiting the
number of open SAs. By default, the ASA does not limit the number of open SAs, and never cookie
challenges SAs. You can also limit the number of SAs allowed, which stops further connections from
negotiating to protect against memory and/or CPU attacks that the cookie-challenge feature may be
unable to thwart and protects the current connections.
With a DoS attack, an attacker initiates the attack when the peer device sends an SA initiate packet and
the ASA sends its response, but the peer device does not respond further. If the peer device does this
continually, all the allowed SA requests on the ASA can be used up until it stops responding.

3-5
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 3 Configuring IKE, Load Balancing, and NAC
Creating IKE Policies
Enabling a threshold percentage for cookie challenging limits the number of open SA negotiations. For
example, with the default setting of 50%, when 50% of the allowed SAs are in-negotiation (open), the
ASA cookie challenges any additional SA initiate packets that arrive. For the Cisco ASA 5580 with
10000 allowed IKEv2 SAs, after 5000 SAs become open, any more incoming SAs are
cookie-challenged.
If used in conjunction with the Number of SAs Allowed in Negotiation, or the Maximum Number of
SAs Allowed, configure the cookie-challenge threshold lower than these settings for an effective
cross-check.
You can also limit the life on all SAs at the IPsec level by choosing Configuration > Site-to-Site VPN >
Advanced > System Options.
Creating IKE Policies
About IKE
Each IKE negotiation is divided into two sections called Phase1 and Phase 2.
Phase 1 creates the first tunnel, which protects later IKE negotiation messages. Phase 2 creates the tunnel
that protects data.
To set the terms of the IKE negotiations, you create one or more IKE policies, which include the
following:
•A unique priority (1 through 65,543, with 1 the highest priority).
•An authentication method, to ensure the identity of the peers.
•An encryption method, to protect the data and ensure privacy.
•An HMAC method to ensure the identity of the sender, and to ensure that the message has not been
modified in transit.
•A Diffie-Hellman group to establish the strength of the of the encryption-key-determination
algorithm. The ASA uses this algorithm to derive the encryption and hash keys.
•A limit for how long the ASA uses an encryption key before replacing it.
For IKEv1, you can only enable one setting for each parameter. For IKEv2, each proposal can have
multiples settings for Encryption, D-H Group, Integrity Hash, and PRF Hash.
If you do not configure any IKE policies, the ASA uses the default policy, which is always set to the
lowest priority, and which contains the default value for each parameter. If you do not specify a value
for a specific parameter, the default value takes effect.
When IKE negotiation begins, the peer that initiates the negotiation sends all of its policies to the remote
peer, and the remote peer searches for a match with its own policies, in priority order.
A match between IKE policies exists if they have the same encryption, hash, authentication, and
Diffie-Hellman values, and an SA lifetime less than or equal to the lifetime in the policy sent. If the
lifetimes are not identical, the shorter lifetime—from the remote peer policy—applies. If no match
exists, IKE refuses negotiation and the IKE SA is not established.
Configuring IKE Policies
Configuration > Remote Access VPN > Network (Client) Access > Advanced > IPsec > IKE Policies

3-6
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 3 Configuring IKE, Load Balancing, and NAC
Creating IKE Policies
Configuration > Site-to-Site VPN > Advanced > IKE Policies
Fields
•IKEv1 Policies—Displays parameter settings for each configured IKE policy.
–
Priority #—Shows the priority of the policy.
–
Encryption—Shows the encryption method.
–
Hash—Shows the hash algorithm.
–
D-H Group—Shows the Diffie-Hellman group.
–
Authentication—Shows the authentication method.
–
Lifetime (secs)—Shows the SA lifetime in seconds.
•Add/Edit/Delete—Click to add, edit, or delete an IKEv1 policy.
•IKEv2 Policies—Displays parameter settings for each configured IKEv2 policy.
–
Priority #—Shows the priority of the policy.
–
Encryption—Shows the encryption method.
–
Integrity Hash—Shows the hash algorithm.
–
PRF Hash—Shows the pseudo random function (PRF) hash algorithm.
–
D-H Group—Shows the Diffie-Hellman group.
–
Lifetime (secs)—Shows the SA lifetime in seconds.
•Add/Edit/Delete—Click to add, edit, or delete an IKEv2 policy.
Adding an IKEv1 Policy
Configuration > VPN > IKE > Policies > Add/Edit IKEv1 Policy
Fields
Priority #—Type a number to set a priority for the IKE policy. The range is 1 to 65535, with 1 the highest
priority.
Encryption—Choose an encryption method. This is a symmetric encryption method that protects data
transmitted between two IPsec peers.The choices follow:
Hash—Choose the hash algorithm that ensures data integrity. It ensures that a packet comes from whom
you think it comes from, and that it has not been modified in transit.
des 56-bit DES-CBC. Less secure but faster than the alternatives. The default.
3des 168-bit Triple DES.
aes 128-bit AES.
aes-192 192-bit AES.
aes-256 256-bit AES.
sha SHA-1 The default is SHA-1. MD5 has a smaller digest and is considered to
be slightly faster than SHA-1. A successful (but extremely difficult)
attack against MD5 has occurred; however, the HMAC variant IKE
uses prevents this attack.
md5 MD5

3-7
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 3 Configuring IKE, Load Balancing, and NAC
Creating IKE Policies
Authentication—Choose the authentication method the ASA uses to establish the identity of each IPsec
peer. Preshared keys do not scale well with a growing network but are easier to set up in a small network.
The choices follow:
D-H Group—Choose the Diffie-Hellman group identifier, which the two IPsec peers use to derive a
shared secret without transmitting it to each other.
Lifetime (secs)—Either check Unlimited or enter an integer for the SA lifetime. The default is 86,400
seconds or 24 hours. With longer lifetimes, the ASA sets up future IPsec security associations less
quickly. Encryption strength is great enough to ensure security without using very fast rekey times, on
the order of every few minutes. We recommend that you accept the default.
Time Measure—Choose a time measure. The ASA accepts the following values:.
Adding an IKEv2 Policy
Configuration > VPN > IKE > Policies > Add/Edit IKEv2 Policy
Fields
Priority #—Type a number to set a priority for the IKEv2 policy. The range is 1 to 65535, with 1 the
highest priority.
Encryption—Choose an encryption method. This is a symmetric encryption method that protects data
transmitted between two IPsec peers.The choices follow:
pre-share Preshared keys.
rsa-sig A digital certificate with keys generated by the RSA signatures algorithm.
crack IKE Challenge/Response for Authenticated Cryptographic Keys protocol for mobile
IPsec-enabled clients which use authentication techniques other than certificates.
1 Group 1 (768-bit) The default, Group 2 (1024-bit Diffie-Hellman) requires less
CPU time to execute but is less secure than Group 1or 5.
2 Group 2 (1024-bit)
5 Group 5 (1536-bit)
120 - 86,400 seconds
2 - 1440 minutes
1 - 24 hours
1 day
des Specifies 56-bit DES-CBC encryption for ESP.
3des (Default) Specifies the triple DES encryption algorithm for ESP.
aes Specifies AES with a 128-bit key encryption for ESP.
aes-192 Specifies AES with a 192-bit key encryption for ESP.
aes-256 Specifies AES with a 256-bit key encryption for ESP.
aes-gcm Specifies AES-GCM/GMAC 128-bit support for symmetric encryption and
integrity.

3-8
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 3 Configuring IKE, Load Balancing, and NAC
Creating IKE Policies
D-H Group—Choose the Diffie-Hellman group identifier, which the two IPsec peers use to derive a
shared secret without transmitting it to each other.
Integrity Hash—Choose the hash algorithm that ensures data integrity for the ESP protocol. It ensures
that a packet comes from whom you think it comes from, and that it has not been modified in transit.
Pseudo-Random Function (PRF)—Specify the PRF used for the construction of keying material for all
of the cryptographic algorithms used in the SA..
aes-gcm-192 Specifies AES-GCM/GMAC 192-bit support for symmetric encryption and
integrity.
aes-gcm-256 Specifies AES-GCM/GMAC 256-bit support for symmetric encryption and
integrity.
NULL Indicates no encryption.
1 Group 1 (768-bit) The default, Group 2 (1024-bit Diffie-Hellman) requires less
CPU time to execute but is less secure than Group 2 or 5.
2 Group 2 (1024-bit)
5 Group 5 (1536-bit)
14 Group 14
19 Group 19
20 Group 20
21 Group 21
24 Group 24
sha SHA 1 The default is SHA 1. MD5 has a smaller digest and is considered to
be slightly faster than SHA 1. A successful (but extremely difficult)
attack against MD5 has occurred; however, the HMAC variant IKE
uses prevents this attack.
md5 MD5
sha256 SHA 2, 256-bit
digest
Specifies the Secure Hash Algorithm SHA 2 with the 256-bit digest.
sha384 SHA 2, 384-bit
digest
Specifies the Secure Hash Algorithm SHA 2 with the 384-bit digest.
sha512 SHA 2, 512-bit
digest
Specifies the Secure Hash Algorithm SHA 2 with the 512-bit digest.
null Indicates that AES-GCM or AES-GMAC is configured as the
encryption algorithm. You must choose the null integrity algorithm if
AES-GCM has been configured as the encryption algorithm.
sha SHA-1 The default is SHA-1. MD5 has a smaller digest and is considered to
be slightly faster than SHA-1. A successful (but extremely difficult)
attack against MD5 has occurred; however, the HMAC variant IKE
uses prevents this attack.
md5 MD5
sha256 SHA 2, 256-bit
digest
Specifies the Secure Hash Algorithm SHA 2 with the 256-bit digest.

3-9
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 3 Configuring IKE, Load Balancing, and NAC
Configuring IPsec
Lifetime (secs)—Either check Unlimited or enter an integer for the SA lifetime. The default is 86,400
seconds or 24 hours. With longer lifetimes, the ASA sets up future IPsec security associations more
quickly. Encryption strength is great enough to ensure security without using very fast rekey times, on
the order of every few minutes. We recommend that you accept the default.
The ASA accepts the following values:.
Assignment Policy
Configuration > Remote Access VPN > Network (Client) Access > Address Assignment > Assignment
Policy
The Assignment Policy configures how IP addresses are assigned to remote access clients.
Fields
•Use authentication server—Choose to assign IP addresses retrieved from an authentication server
on a per-user basis. If you are using an authentication server (external or internal) that has IP
addresses configured, we recommend using this method. Authorization servers are configured in the
Configuration > Remote Access VPN > AAA/Local Users > AAA Server Groups pane.
•Use DHCP— Choose to obtain IP addresses from a DHCP server. If you use DHCP, configure the
server in the Configuration > Remote Access VPN > DHCP Server pane.
•Use internal address pools—Choose to have the ASA assign IP addresses from an internally
configured pool. Internally configured address pools are the easiest method of address pool
assignment to configure. If you use this method, configure the IP address pools in Configuration >
Remote Access VPN > Network (Client) Access > Address Assignment > Address Pools pane.
–
Allow the reuse of an IP address __ minutes after it is released—Delays the reuse of an IP
address after its return to the address pool. Adding a delay helps to prevent problems firewalls
can experience when an IP address is reassigned quickly. By default, this is unchecked, meaning
the ASA does not impose a delay. To add a delay, check the box and enter the number of minutes
in the range 1 - 480 to delay IP address reassignment.
Configuring IPsec
The ASA uses IPsec for LAN-to-LAN VPN connections, and provides the option of using IPsec for
client-to-LAN VPN connections. In IPsec terminology, a “peer” is a remote-access client or another
secure gateway.
sha384 SHA 2, 384-bit
digest
Specifies the Secure Hash Algorithm SHA 2 with the 384-bit digest.
sha512 SHA 2, 512-bit
digest
Specifies the Secure Hash Algorithm SHA 2 with the 512-bit digest.
120 - 86,400 seconds
2 - 1440 minutes
1 - 24 hours
1 day

3-10
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 3 Configuring IKE, Load Balancing, and NAC
Configuring IPsec
Note The ASA supports LAN-to-LAN IPsec connections with Cisco peers (IPv4 or IPv6), and with third-party
peers that comply with all relevant standards.
During tunnel establishment, the two peers negotiate security associations that govern authentication,
encryption, encapsulation, and key management. These negotiations involve two phases: first, to
establish the tunnel (the IKE SA); and second, to govern traffic within the tunnel (the IPsec SA).
A LAN-to-LAN VPN connects networks in different geographic locations. In IPsec LAN-to-LAN
connections, the ASA can function as initiator or responder. In IPsec client-to-LAN connections, the
ASA functions only as responder. Initiators propose SAs; responders accept, reject, or make
counter-proposals—all in accordance with configured SA parameters. To establish a connection, both
entities must agree on the SAs.
The ASA supports these IPsec attributes:
•Main mode for negotiating phase one ISAKMP security associations when using digital certificates
for authentication
•Aggressive mode for negotiating phase one ISAKMP Security Associations (SAs) when using
preshared keys for authentication
•Authentication Algorithms:
–
ESP-MD5-HMAC-128
–
ESP-SHA1-HMAC-160
•Authentication Modes:
–
Preshared Keys
–
X.509 Digital Certificates
•Diffie-Hellman Groups 1, 2, and 5.
•Encryption Algorithms:
–
AES-128, -192, and -256
–
3DES-168
–
DES-56
–
ESP-NULL
•Extended Authentication (XAuth)
•Mode Configuration (also known as ISAKMP Configuration Method)
•Tunnel Encapsulation Mode
•IP compression (IPCOMP) using LZS
Adding Crypto Maps
Configuration > Remote Access VPN > Network (Client) Access > Advanced > IPsec > Crypto
Maps
This pane shows the currently configured crypto maps, which are defined in IPsec rules. Here you can
add, edit, delete and move up, move down, cut, copy, and paste an IPsec rule.

3-11
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 3 Configuring IKE, Load Balancing, and NAC
Configuring IPsec
Fields
Note You cannot edit, delete, or copy an implicit rule. The ASA implicitly accepts the traffic selection
proposal from remote clients when configured with a dynamic tunnel policy. You can override it by
giving a specific traffic selection.
•Add—Click to launch the Create IPsec Rule dialog box, where you can configure basic, advanced,
and traffic selection parameters for a rule.
•Edit—Click to edit an existing rule.
•Delete—Click to delete a rule highlighted in the table.
•Cut—Deletes a highlighted rule in the table and keeps it in the clipboard for copying.
•Copy—Copies a highlighted rule in the table.
•Find—Click to enable the Find toolbar where you can specify the parameters of existing rules that
you want to find:
–
Filter—Filter the find results by selecting Interface, Source, Destination, Destination Service,
or Rule Query, selecting is or contains, and entering the filter parameter. Click ... to launch a
browse dialog box that displays all existing entries that you can choose.
•Diagram—Displays a diagram that illustrates the highlighted IPsec rule.
•Type: Priority—Displays the type of rule (static or dynamic) and its priority.
•Traffic Selection
–
#—Indicates the rule number.
–
Source—Indicates the IP addresses that are subject to this rule when traffic is sent to the IP
addresses listed in the Remote Side Host/Network column. In detail mode (see the Show Detail
button), an address column might contain an interface name with the word any, such as
inside:any. any means that any host on the inside interface is affected by the rule.
–
Destination—Lists the IP addresses that are subject to this rule when traffic is sent from the IP
addresses listed in the Security Appliance Side Host/Network column. In detail mode (see the
Show Detail button), an address column might contain an interface name with the word any,
such as outside:any. any means that any host on the outside interface is affected by the rule. Also
in detail mode, an address column might contain IP addresses in square brackets, for example,
[209.165.201.1-209.165.201.30]. These addresses are translated addresses. When an inside host
makes a connection to an outside host, the ASA maps the inside host's address to an address
from the pool. After a host creates an outbound connection, the ASA maintains this address
mapping. This address mapping structure is called an xlate, and remains in memory for a period
of time.
–
Service—Specifies the service and protocol specified by the rule (TCP, UDP, ICMP, or IP).
–
Action—Specifies the type of IPsec rule (protect or do not protect).
•Transform Set—Displays the transform set for the rule.
•Peer—Identifies the IPsec peer.
•PFS—Displays perfect forward secrecy settings for the rule.
•NAT-T Enabled—Indicates whether NAT Traversal is enabled for the policy.
•Reverse Route Enabled—Indicates whether Reverse Route Injection is enabled for the policy.
•Connection Type—(Meaningful only for static tunnel policies.) Identifies the connection type for
this policy as bidirectional, originate-only, or answer-only).

3-12
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 3 Configuring IKE, Load Balancing, and NAC
Configuring IPsec
•SA Lifetime—Displays the SA lifetime for the rule.
•CA Certificate—Displays the CA certificate for the policy. This applies to static connections only.
•IKE Negotiation Mode—Displays whether IKE negotiations use main or aggressive mode.
•Description—(Optional) Specifies a brief description for this rule. For an existing rule, this is the
description you typed when you added the rule. An implicit rule includes the following description:
“Implicit rule.” To edit the description of any but an implicit rule, right-click this column, and
choose Edit Description or double-click the column.
•Enable Anti-replay window size—Sets the anti-replay window size, between 64 and 1028 in
multiples of 64. One side-effect of priority queueing in a hierarchical QoS policy with traffic
shaping (see the “Rule Actions > QoS Tab”) is packet re-ordering. For IPsec packets, out-of-order
packets that are not within the anti-replay window generate warning syslog messages. These
warnings becomes false alarms in the case of priority queueing. Configuring the anti-replay pane
size helps you avoid possible false alarms.
Creating an IPsec Rule/Tunnel Policy (Crypto Map) - Basic Tab
Configuration > Remote Access VPN > Network (Client) Access > Advanced > IPsec > Crypto
Maps - Edit IPsec Rule - Basic Tab
Use this pane to define a new Tunnel Policy for an IPsec rule. The values you define here appear in the
IPsec Rules table after you click OK. All rules are enabled by default as soon as they appear in the IPsec
Rules table.
The Tunnel Policy pane lets you define a tunnel policy that is used to negotiate an IPsec (Phase 2)
security association (SA). ASDM captures your configuration edits, but does not save them to the
running configuration until you click Apply.
Every tunnel policy must specify a transform set and identify the security appliance interface to which
it applies. The transform set identifies the encryption and hash algorithms that perform IPsec encryption
and decryption operations. Because not every IPsec peer supports the same algorithms, you might want
to specify a number of policies and assign a priority to each. The security appliance then negotiates with
the remote IPsec peer to agree on a transform set that both peers support.
Tunnel policies can be static or dynamic. A static tunnel policy identifies one or more remote IPsec peers
or subnetworks to which your security appliance permits IPsec connections. A static policy can be used
whether your security appliance initiates the connection or receives a connection request from a remote
host. A static policy requires you to enter the information necessary to identify permitted hosts or
networks.
A dynamic tunnel policy is used when you cannot or do not want to provide information about remote
hosts that are permitted to initiate a connection with the security appliance. If you are only using your
security appliance as a VPN client in relation to a remote VPN central-site device, you do not need to
configure any dynamic tunnel policies. Dynamic tunnel policies are most useful for allowing remote
access clients to initiate a connection to your network through a security appliance acting as the VPN
central-site device. A dynamic tunnel policy is useful when the remote access clients have dynamically
assigned IP addresses or when you do not want to configure separate policies for a large number of
remote access clients.
Fields
•Interface—Choose the interface name to which this policy applies.
•Policy Type—Choose the type, static or dynamic, of this tunnel policy.
•Priority—Enter the priority of the policy.

3-13
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 3 Configuring IKE, Load Balancing, and NAC
Configuring IPsec
•IKE Proposals (Transform Sets)--Specifies IKEv1 and IKEv2 IPsec proposals:
–
IKEv1 IPsec Proposal—Choose the proposal (transform set) for the policy and click Add to
move it to the list of active transform sets. Click Move Up or Move Down to rearrange the order
of the proposals in the list box. You can add a maximum of 11 proposals to a crypto map entry
or a dynamic crypto map entry.
–
IKEv2 IPsec Proposal—Choose the proposal (transform set) for the policy and click Add to
move it to the list of active transform sets. Click Move Up or Move Down to rearrange the order
of the proposals in the list box. You can add a maximum of 11 proposals to a crypto map entry
or a dynamic crypto map entry.
•Peer Settings - Optional for Dynamic Crypto Map Entries—Configure the peer settings for the
policy.
–
Connection Type—(Meaningful only for static tunnel policies.) Choose bidirectional,
originate-only, or answer-only to specify the connection type of this policy. For LAN-to-LAN
connections, choose bidirectional or answer-only (not originate-only). Choose answer-only for
LAN-to-LAN redundancy. If you choose Originate Only, you can specify up to 10 redundant
peers. For uni-directional, you can specify originate only or answer only, and neither are
enabled by default.
–
IP Address of Peer to Be Added—Enter the IP address of the IPsec peer you are adding.
•Enable Perfect Forwarding Secrecy—Check to enable perfect forward secrecy for the policy. PFS is
a cryptographic concept where each new key is unrelated to any previous key. In IPsec negotiations,
Phase 2 keys are based on Phase 1 keys unless you specify Perfect Forward Secrecy.
•Diffie-Hellman Group—When you enable PFS you must also choose a Diffie-Hellman group which
the ASA uses to generate session keys. The choices are as follows:
–
Group 1 (768-bits) = Use perfect forward secrecy, and use Diffie-Hellman Group 1 to generate
IPsec session keys, where the prime and generator numbers are 768 bits. This option is more
secure but requires more processing overhead.
–
Group 2 (1024-bits) = Use perfect forward secrecy, and use Diffie-Hellman Group 2 to generate
IPsec session keys, where the prime and generator numbers are 1024 bits. This option is more
secure than Group 1 but requires more processing overhead.
–
Group 5 (1536-bits) = Use perfect forward secrecy, and use Diffie-Hellman Group 5 to generate
IPsec session keys, where the prime and generator numbers are 1536 bits. This option is more
secure than Group 2 but requires more processing overhead.
–
Group 14= Use perfect forward secrecy and use Diffie-Hellman Group 14 for IKEv2.
–
Group 19= Use perfect forward secrecy and use Diffie-Hellman Group 19 for IKEv2 to support
ECDH.
–
Group 20= Use perfect forward secrecy and use Diffie-Hellman Group 20 for IKEv2 to support
ECDH.
–
Group 21= Use perfect forward secrecy and use Diffie-Hellman Group 21 for IKEv2 to support
ECDH.
–
Group 24= Use perfect forward secrecy and use Diffie-Hellman Group 24 for IKEv2.
Creating IPsec Rule/Tunnel Policy (Crypto Map) - Advanced Tab
Configuration > Remote Access VPN > Network (Client) Access > Advanced > IPsec > Crypto
Maps - Edit IPsec Rule - Advanced Tab

3-14
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 3 Configuring IKE, Load Balancing, and NAC
Configuring IPsec
Fields
•Enable NAT-T— Enables NAT Traversal (NAT-T) for this policy.
•Enable Reverse Route Injection—Enables Reverse Route Injection for this policy.
Reverse Route Injection (RRI) is used to populate the routing table of an internal router that runs
dynamic routing protocols such as Open Shortest Path First (OSPF), or Enhanced Interior Gateway
Routing Protocol (EIGRP), if you run ASA, or Routing Information Protocol (RIP) for remote VPN
Clients or LAN to LAN sessions.
•Security Association Lifetime Settings—Configures the duration of a Security Association (SA).
This parameter specifies how to measure the lifetime of the IPsec SA keys, which is how long the
IPsec SA lasts until it expires and must be renegotiated with new keys.
–
Time—Specifies the SA lifetime in terms of hours (hh), minutes (mm) and seconds (ss).
–
Traffic Volume—Defines the SA lifetime in terms of kilobytes of traffic. Enter the number of
kilobytes of payload data after which the IPsec SA expires. Minimum is 100 KB, default is
10000 KB, maximum is 2147483647 KB.
•Static Type Only Settings—Specifies parameters for static tunnel policies.
–
Device Certificate—Choose the certificate to use. If you choose something other than
None (Use Preshared Keys), which is the default. The Send CA certificate chain check box
becomes active when you select something other than None.
–
Send CA certificate chain—Enables transmission of the entire trust point chain.
–
IKE Negotiation Mode—Chooses the IKE negotiation mode, Main or Aggressive. This
parameter sets the mode for exchanging key information and setting up the SAs. It sets the mode
that the initiator of the negotiation uses; the responder auto-negotiates. Aggressive Mode is
faster, using fewer packets and fewer exchanges, but it does not protect the identity of the
communicating parties. Main Mode is slower, using more packets and more exchanges, but it
protects the identities of the communicating parties. This mode is more secure and it is the
default selection. If you choose Aggressive, the Diffie-Hellman Group list becomes active.
–
Diffie-Hellman Group—Choose the Diffie-Hellman group to apply. The choices are as follows:
Group 1 (768-bits), Group 2 (1024-bits), or Group 5 (1536-bits).
•ESP v3—Specify whether incoming ICMP error messages are validated for cryptography and
dynamic cryptography maps, set the per-security association policy, or enable traffic flow packets:
–
Validate incoming ICMP error messages—Choose whether to validate those ICMP error
messages received through an IPsec tunnel and destined for an interior host on the private
network.
–
Enable Do Not Fragment (DF) policy—Define how the IPsec subsystem handles large packets
that have the do-not-fragment (DF) bit set in the IP header. Choose one of the following:
Clear DF bit—Ignores the DF bit.
Copy DF bit—Maintains the DF bit.
Set DF bit—Sets and uses the DF bit.
–
Enable Traffic Flow Confidentiality (TFC) packets—Enable dummy TFC packets that mask the
traffic profile which traverses the tunnel.
Note You must have an IKE v2 IPsec proposal set on the Tunnel Policy (Crypto Map) Basic
tab before enabling TFC.

3-15
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 3 Configuring IKE, Load Balancing, and NAC
Configuring IPsec
Use the Burst, Payload Size, and Timeout parameters to generate random length packets at
random intervals across the specified SA.
Creating IPsec Rule/Traffic Selection Tab
Configuration > VPN > IPSec > IPSec Rules > Add/Edit Rule > Tunnel Policy (Crypto Map) -
Traffic Selection Tab
This pane lets you define what traffic to protect (permit) or not protect (deny).
Fields
•Action—Specify the action for this rule to take. The selections are protect and do not protect.
•Source—Specify the IP address, network object group or interface IP address for the source host or
network. A rule cannot use the same address as both the source and destination. Click ... to launch
the Browse Source dialog box that contains the following fields:
–
Add/Edit—Choose IP Address or Network Object Group to add more source addresses or
groups.
–
Delete—Click to delete an entry.
–
Filter—Enter an IP Address to filter the results displayed.
–
Name—Indicates that the parameters that follow specify the name of the source host or network.
–
IP Address—Indicates that the parameters that follow specify the interface, IP address, and
subnet mask of the source host or network.
–
Netmask—Chooses a standard subnet mask to apply to the IP address. This parameter appears
when you choose the IP Address option button.
–
Description—Enter a description.
–
Selected Source—Click Source to include the selected entry as a source.
•Destination—Specify the IP address, network object group or interface IP address for the
destination host or network. A rule cannot use the same address as both the source and destination.
Click ... to launch the Browse Destination dialog box that contains the following fields:
–
Add/Edit—Choose IP Address or Network Object Group to add more destination addresses or
groups.
–
Delete—Click to delete an entry.
–
Filter—Enter an IP Address to filter the results displayed.
–
Name—Indicates that the parameters that follow specify the name of the destination host or
network.
–
IP Address—Indicates that the parameters that follow specify the interface, IP address, and
subnet mask of the destination host or network.
–
Netmask—Chooses a standard subnet mask to apply to the IP address. This parameter appears
when you choose the IP Address option button.
–
Description—Enter a description.
–
Selected Destination—Click Destination to include the selected entry as a destination.
•Service—Enter a service or click ... to launch the browse service dialog box where you can choose
from a list of services.
•Description—Enter a description for the Traffic Selection entry.

3-16
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 3 Configuring IKE, Load Balancing, and NAC
Configuring IPsec
•More Options
–
Enable Rule—Click to enable this rule.
–
Source Service—Enter a service or click ... to launch the browse service dialog box where you
can choose from a list of services.
–
Time Range—Define a time range for which this rule applies.
–
Group—Indicates that the parameters that follow specify the interface and group name of the
source host or network.
–
Interface—Choose the interface name for the IP address. This parameter appears when you
choose the IP Address option button.
–
IP address—Specifies the IP address of the interface to which this policy applies. This
parameter appears when you choose the IP Address option button.
–
Destination—Specify the IP address, network object group or interface IP address for the source
or destination host or network. A rule cannot use the same address as both the source and
destination. Click ... for either of these fields to launch the Browse dialog box that contain the
following fields:
–
Name—Choose the interface name to use as the source or destination host or network. This
parameter appears when you choose the Name option button. This is the only parameter
associated with this option.
–
Interface—Choose the interface name for the IP address. This parameter appears when you
choose the Group option button.
–
Group—Choose the name of the group on the specified interface for the source or destination
host or network. If the list contains no entries, you can enter the name of an existing group. This
parameter appears when you choose the Group option button.
•Protocol and Service—Specifies protocol and service parameters relevant to this rule.
Note “Any - any” IPsec rules are not allowed. This type of rule would prevent the device and its peer
from supporting multiple LAN -to-LAN tunnels.
–
TCP—Specifies that this rule applies to TCP connections. This selection also displays the
Source Port and Destination Port group boxes.
–
UDP—Specifies that this rule applies to UDP connections. This selection also displays the
Source Port and Destination Port group boxes.
–
ICMP—Specifies that this rule applies to ICMP connections. This selection also displays the
ICMP Type group box.
–
IP—Specifies that this rule applies to IP connections. This selection also displays the IP
Protocol group box.
–
Manage Service Groups—Displays the Manage Service Groups pane, on which you can add,
edit, or delete a group of TCP/UDP services/ports.
–
Source Port and Destination Port —Contains TCP or UDP port parameters, depending on
which option button you chose in the Protocol and Service group box.
–
Service—Indicates that you are specifying parameters for an individual service. Specifies the
name of the service and a boolean operator to use when applying the filter.
–
Boolean operator (unlabeled)—Lists the boolean conditions (equal, not equal, greater than,
less than, or range) to use in matching the service specified in the service box.

3-17
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 3 Configuring IKE, Load Balancing, and NAC
Configuring IPsec
–
Service (unlabeled)—Identifies the service (such as https, kerberos, or any) to be matched. If
you specified the range service operator this parameter becomes two boxes, into which you
enter the start and the end of the range.
–
... —Displays a list of services from which you can choose the service to display in the Service
box.
–
Service Group—Indicates that you are specifying the name of a service group for the source
port.
–
Service (unlabeled)—Choose the service group to use.
–
ICMP Type—Specifies the ICMP type to use. The default is any. Click the ... button to display
a list of available types.
•Options
–
Time Range—Specify the name of an existing time range or create a new range.
–
... —Displays the Add Time Range pane, on which you can define a new time range.
–
Please enter the description below (optional)—Provides space for you to enter a brief
description of the rule.
Pre-Fragmentation
Configuration > VPN > IPSec > Pre-Fragmentation
Use this pane to set the IPsec pre-fragmentation policy and do-not-fragment (DF) bit policy for any
interface.
The IPsec pre-fragmentation policy specifies how to treat packets that exceed the maximum transmission
unit (MTU) setting when tunneling traffic through the public interface. This feature provides a way to
handle cases where a router or NAT device between the ASA and the client rejects or drops IP fragments.
For example, suppose a client wants to FTP get from an FTP server behind a ASA. The FTP server
transmits packets that when encapsulated would exceed the ASA’s MTU size on the public interface.
The selected options determine how the ASA processes these packets. The pre-fragmentation policy
applies to all traffic travelling out the ASA public interface.
The ASA encapsulates all tunneled packets. After encapsulation, the ASA fragments packets that exceed
the MTU setting before transmitting them through the public interface. This is the default policy. This
option works for situations where fragmented packets are allowed through the tunnel without hindrance.
For the FTP example, large packets are encapsulated and then fragmented at the IP layer. Intermediate
devices may drop fragments or just out-of-order fragments. Load-balancing devices can introduce
out-of-order fragments.
When you enable pre-fragmentation, the ASA fragments tunneled packets that exceed the MTU setting
before encapsulating them. If the DF bit on these packets is set, the ASA clears the DF bit, fragments
the packets, and then encapsulates them. This action creates two independent non-fragmented IP packets
leaving the public interface and successfully transmits these packets to the peer site by turning the
fragments into complete packets to be reassembled at the peer site. In our example, the ASA overrides
the MTU and allows fragmentation by clearing the DF bit.
Note Changing the MTU or the pre-fragmentation option on any interface tears down all existing connections.
For example, if 100 active tunnels terminate on the public interface, and you change the MTU or the
pre-fragmentation option on the external interface, all of the active tunnels on the public interface are
dropped.

3-18
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 3 Configuring IKE, Load Balancing, and NAC
Configuring IPsec
Fields
•Pre-Fragmentation—Shows the current pre-fragmentation configuration for every configured
interface.
–
Interface—Shows the name of each configured interface.
–
Pre-Fragmentation Enabled—Shows, for each interface, whether pre-fragmentation is
enabled.
–
DF Bit Policy—Shows the DF Bit Policy for each interface.
•Edit—Displays the Edit IPsec Pre-Fragmentation Policy dialog box.
Edit IPsec Pre-Fragmentation Policy
Configuration > VPN > IPSec > Pre-Fragmentation > Edit IPSec Pre-Fragmentation Policy
Use this pane to modify an existing IPsec pre-fragmentation policy and do-not-fragment (DF) bit policy
for an interface selected on the parent pane, Configuration > VPN > IPsec > Pre-Fragmentation
Fields
•Interface—Identifies the chosen interface. You cannot change this parameter using this dialog box.
•Enable IPsec pre-fragmentation—Enables or disables IPsec pre-fragmentation. The ASA
fragments tunneled packets that exceed the MTU setting before encapsulating them. If the DF bit on
these packets is set, the ASA clears the DF bit, fragments the packets, and then encapsulates them.
This action creates two independent, non-fragmented IP packets leaving the public interface and
successfully transmits these packets to the peer site by turning the fragments into complete packets
to be reassembled at the peer site.
•DF Bit Setting Policy—Choose the do-not-fragment bit policy: Copy, Clear, or Set.
IPsec Transform Sets
Configuration > VPN > IPSec > Transform Sets
Use this pane to view and add or edit transform sets. A transform is a set of operations done on a data
flow to provide data authentication, data confidentiality, and data compression. For example, one
transform is the ESP protocol with 3DES encryption and the HMAC-MD5 authentication algorithm
(ESP-3DES-MD5).
Fields
•IKEv1 IPsec Proposals (Transform Sets)—Shows the configured transform sets.
–
Name—Shows the name of the transform sets.
–
Mode—Shows the mode, Tunnel, of the transform set. This parameter specifies the mode for
applying ESP encryption and authentication; in other words, what part of the original IP packet
has ESP applied. Tunnel mode applies ESP encryption and authentication to the entire original
IP packet (IP header and data), thus hiding the ultimate source and destination addresses.
–
ESP Encryption—Shows the Encapsulating Security Protocol (ESP) encryption algorithms for
the transform sets. ESP provides data privacy services, optional data authentication, and
anti-replay services. ESP encapsulates the data being protected.
–
ESP Authentication—Shows the ESP authentication algorithms for the transform sets.
•Add—Opens the Add Transform Set dialog box, in which you can add a new transform set.

3-19
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 3 Configuring IKE, Load Balancing, and NAC
Configuring IPsec
•Edit—Opens the Edit Transform Set dialog box, in which you can modify an existing transform set.
•Delete—Removes the selected transform set. There is no confirmation or undo.
•IKEv2 IPsec Proposals—Shows the configured transform sets.
–
Name—Shows the name of the IKEv2 IPsec Proposal.
–
Encryption—Shows the Encapsulating Security Protocol (ESP) encryption algorithms for the
IKEv2 IPsec Proposal. ESP provides data privacy services, optional data authentication, and
anti-replay services. ESP encapsulates the data being protected.
–
Integrity Hash—Shows the hash algorithm that ensures data integrity for the ESP protocol. It
ensures that a packet comes from whom you would expect and that no modifications were made
in transit. It ensures that a packet comes from who you would expect and that no modifications
were made in transit. You must choose the null integrity algorithm if AES-GCM/GMAC has
been configured as the encryption algorithm.
•Add—Opens the Add IPsec Proposal dialog box, in which you can add a new proposal.
•Edit—Opens the Edit IPsec Proposal dialog box, in which you can modify an existing proposal.
•Delete—Removes the selected proposal. There is no confirmation or undo.
Add/Edit IPsec Proposal (Transform Set)
(Configuration > VPN > IPSec > Transform Sets > Add/Edit IPsec_Proposal_(Transform Set)
Use this pane to add or modify an IPsec IKEv1 transform set. A transform is a set of operations done on
a data flow to provide data authentication, data confidentiality, and data compression. For example, one
transform is the ESP protocol with 3DES encryption and the HMAC-MD5 authentication algorithm
(ESP-3DES-MD5).
Fields
•Set Name—Specifies a name for this transform set.
•Properties—Configures properties for this transform set. These properties appear in the Transform
Sets table.
–
Mode—Shows the mode, Tunnel, of the transform set. This field shows the mode for applying
ESP encryption and authentication; in other words, what part of the original IP packet has ESP
applied. Tunnel mode applies ESP encryption and authentication to the entire original IP packet
(IP header and data), thus hiding the ultimate source and destination addresses.
–
ESP Encryption—Choose the Encapsulating Security Protocol (ESP) encryption algorithms
for the transform sets. ESP provides data privacy services, optional data authentication, and
anti-replay services. ESP encapsulates the data being protected.
–
ESP Authentication—Choose the ESP authentication algorithms for the transform sets.
Note The IPsec ESP (Encapsulating Security Payload) protocol provides both encryption and
authentication. Packet authentication proves that data comes from whom you think it comes
from; it is often referred to as “data integrity.”
Add/Edit IPsec Proposal
Configuration > VPN > IPSec > Transform Sets > Add/Edit IPsec_Proposal

3-20
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 3 Configuring IKE, Load Balancing, and NAC
Configuring Load Balancing
Use this pane to add or modify an IPsec IKEv2 proposal. A proposal is a set of operations done on a data
flow to provide data authentication, data confidentiality, and data compression. For example, one
proposal is the ESP protocol with 3DES encryption and the HMAC-MD5 authentication algorithm
(ESP-3DES-MD5).
Fields
•Name—Specifies a name for this proposal.
•Encryption—Choose the Encapsulating Security Protocol (ESP) encryption algorithms for the
proposal. ESP provides data privacy services, optional data authentication, and anti-replay services.
ESP encapsulates the data being protected.
•Integrity Hash—Choose the ESP authentication algorithms for the proposal. The hash algorithm
ensures data integrity for the ESP protocol. It ensures that a packet comes from whom you think it
comes from, and that it has not been modified in transit.
Note The IPsec ESP (Encapsulating Security Payload) protocol provides both encryption and
authentication. Packet authentication proves that data comes from whom you think it comes
from; it is often referred to as “data integrity.”
Configuring Load Balancing
If you have a remote-client configuration in which you are using two or more ASAs connected to the
same network to handle remote sessions, you can configure these devices to share their session load. This
feature is called load balancing. Load balancing directs session traffic to the least loaded device, thus
distributing the load among all devices. It makes efficient use of system resources and provides increased
performance anodize availability.
The following sections explain load balancing:
•Creating Virtual Clusters
•Geographical Load Balancing
•Comparing Load Balancing to Failover
•Load Balancing Licensing Requirements
•Load Balancing Prerequisites
•Eligible Clients
•Configuring VPN Cluster Load Balancing with the High Availability and Scalability Wizard
•Configuring Load Balancing (Without the Wizard)
Creating Virtual Clusters
To implement load balancing, you group together logically two or more devices on the same private
LAN-to-LAN network into a virtual cluster.

3-21
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 3 Configuring IKE, Load Balancing, and NAC
Configuring Load Balancing
All devices in the virtual cluster carry session loads. One device in the virtual cluster, the virtual cluster
master, directs incoming connection requests to the other devices, called backup devices. The virtual
cluster master monitors all devices in the cluster, keeps track of how busy each is, and distributes the
session load accordingly. The role of virtual cluster master is not tied to a physical device; it can shift
among devices. For example, if the current virtual cluster master fails, one of the backup devices in the
cluster takes over that role and immediately becomes the new virtual cluster master.
The virtual cluster appears to outside clients as a single virtual cluster IP address. This IP address is not
tied to a specific physical device. It belongs to the current virtual cluster master; hence, it is virtual. A
VPN client attempting to establish a connection connects first to this virtual cluster IP address. The
virtual cluster master then sends back to the client the public IP address of the least-loaded available host
in the cluster. In a second transaction (transparent to the user) the client connects directly to that host.
In this way, the virtual cluster master directs traffic evenly and efficiently across resources.
If a machine in the cluster fails, the terminated sessions can immediately reconnect to the virtual cluster
IP address. The virtual cluster master then directs these connections to another active device in the
cluster. Should the virtual cluster master itself fail, a backup device in the cluster immediately and
automatically takes over as the new virtual session master. Even if several devices in the cluster fail,
users can continue to connect to the cluster as long as any one device in the cluster is up and available.
A load-balancing cluster can consist of ASAs of the same release or of mixed releases subject to the
following restrictions:
•Load-balancing clusters that consist of both same release ASAs can run load balancing for a mixture
of IPsec, AnyConnect, and clientless SSL VPN client and clientless sessions.
•Load-balancing clusters that include mixed release ASAs or same release ASAs can support only
IPsec sessions. In such a configuration, however, the ASAs might not reach their full IPsec capacity.
“Comparing Load Balancing to Failover” on page 22, illustrates this situation.
Since Release 7.1(1), IPsec and SSL VPN sessions count or weigh equally in determining the load that
each device in the cluster carries. This represents a departure from the load balancing calculation for the
ASA Release 7.0(x) software and the VPN 3000 concentrator, in that these platforms both use a
weighting algorithm that, on some hardware platforms, calculates SSL VPN session load differently
from IPsec session load.
The virtual master of the cluster assigns session requests to the members of the cluster. The ASA regards
all sessions, SSL VPN or IPsec, as equal and assigns them accordingly. You can configure the number
of IPsec and SSL VPN sessions to allow, up to the maximum allowed by your configuration and license.
We have tested up to ten nodes in a load-balancing cluster. Larger clusters might work, but we do not
officially support such topologies.
Geographical Load Balancing
In a load balancing environment where the DNS resolutions are being changed at regular intervals, you
must carefully consider how to set the time to live (TTL) value. For the DNS load balance configuration
to work successfully with AnyConnect, the ASA name to address mapping must remain the same from
the time the ASA is selected until the tunnel is fully established. If too much time passes before the
credentials are entered, the lookup restarts and a different IP address may become the resolved address.
If the DNS mapping changes to a different ASA before the credentials are entered, the VPN tunnel fails.
Geographical load balancing for VPN often uses a Cisco Global Site Selector (GSS). The GSS uses DNS
for the load balancing, and the time to live (TTL) value for DNS resolution is defaulted to 20 seconds.
You can significantly decrease the likelihood of connection failures if you increase the TTL value on the
GSS. Increasing to a much higher value allows ample time for the authentication phase when the user is
entering credentials and establishing the tunnel.

3-22
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 3 Configuring IKE, Load Balancing, and NAC
Configuring Load Balancing
To increase the time for entering credentials, you may also consider disabling Connect on Start Up.
Comparing Load Balancing to Failover
Both load balancing and failover are high-availability features, but they function differently and have
different requirements. In some circumstances you can use both load balancing and failover. The
following sections describe the differences between these features.
Load balancing is a mechanism for equitably distributing remote-access VPN traffic among the devices
in a virtual cluster. It is based on simple distribution of traffic without taking into account throughput or
other factors. A load-balancing cluster consists of two or more devices, one of which is the virtual
master, and the others backup. These devices do not need to be of the exact same type, or have identical
software versions or configurations. All active devices in a virtual cluster carry session loads. Load
balancing directs traffic to the least loaded device in the cluster, distributing the load among all devices.
It makes efficient use of system resources and provides increased performance and high availability.
A failover configuration requires two identical ASAs connected to each other through a dedicated
failover link and, optionally, a stateful failover link. The health of the active interfaces and units is
monitored to determine when specific failover conditions are met. If those conditions occur, failover
occurs. Failover supports both VPN and firewall configurations.
The ASA supports two failover configurations, Active/Active failover and Active/Standby failover. VPN
connections run only in Active/Standby, single routed mode. Active/Active failover requires
multi-context mode, so does not support VPN connections.
With Active/Active failover, both units can pass network traffic. This is not true with load balancing,
although it might appear to have the same effect. When failover occurs, the remaining active unit takes
over passing the combined traffic, based on the configured parameters. Therefore, when configuring
Active/Active failover, you must make sure that the combined traffic for both units is within the capacity
of each unit.
With Active/Standby failover, only one unit passes traffic, while the other unit waits in a standby state
and does not pass traffic. Active/Standby failover lets you use a second ASA to take over the functions
of a failed unit. When the active unit fails, it changes to the standby state, while the standby unit changes
to the active state. The unit that becomes active assumes the IP addresses (or, for transparent firewall,
the management IP address) and MAC addresses of the failed unit and begins passing traffic. The unit
that is now in standby state takes over the standby IP addresses of the active unit. If an active unit fails,
the standby takes over without any interruption to the client VPN tunnel.
Load Balancing Licensing Requirements
To use VPN load balancing, you must have an ASA Model 5510 with a Plus license or an ASA Model
5520 or higher. VPN load balancing also requires an active 3DES/AES license. The security appliance
checks for the existence of this crypto license before enabling load balancing. If it does not detect an
active 3DES or AES license, the security appliance prevents the enabling of load balancing and also
prevents internal configuration of 3DES by the load balancing system unless the license permits this
usage.
Eligible Clients
Load balancing is effective only on remote sessions initiated with the following clients:
•Cisco AnyConnect Secure Mobility Client (Release 3.0 and later)

3-23
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 3 Configuring IKE, Load Balancing, and NAC
Configuring Load Balancing
•Cisco ASA 5505 Security Appliance (when acting as an Easy VPN client)
•IOS EZVPN Client devices supporting IKE-redirect (IOS 831/871)
•Clientless SSL VPN (not a client)
Load balancing works with IPsec clients and SSL VPN client and clientless sessions. All other VPN
connection types (L2TP, PPTP, L2TP/IPsec), including LAN-to-LAN, can connect to an ASA on which
load balancing is enabled, but they cannot participate in load balancing.
Load Balancing Prerequisites
•You must have first configured the ASA’s public and private interfaces before configuring load
balancing. To do so select Configuration > Device Setup > Interfaces. See Chapter 11, “Starting
Interface Configuration (ASA 5510 and Higher)” or Chapter 12, “Starting Interface Configuration
(ASA 5505)” in the general operations configuration guide for more information.
•You must have previously configured the interface to which the virtual cluster IP address refers.
•All devices that participate in a cluster must share the same cluster-specific values: IP address,
encryption settings, encryption key, and port. All of the outside and inside network interfaces on the
load-balancing devices in a cluster must be on the same IP network.
Certificate Verification
When performing certificate verification for load balancing with AnyConnect, and the connection is
redirected by an IP address, the client does all of its name checking through this IP address. Make sure
the redirection IP address is listed in the certificates common name or the subject alt name. If the IP
address is not present in these fields, then the certificate will be deemed untrusted.
Following the guidelines defined in RFC 2818, if a subject alt name is included in the certificate, we
only use the subject alt name for name checks, and we ignore the common name. Make sure that the IP
address of the server presenting the certificate is defined in the subject alt name of the certificate.
For a standalone ASA, the IP address is the IP of that ASA. In a clustering situation, it depends on the
certificate configuration. If the cluster uses one certificate, then it would be the IP of the cluster, and the
certificate would contain Subject Alternative Name extensions that have each ASA's IP and FQDN. If
the cluster uses multiple certificates, then it should once again be the IP address of the ASA.
Configuring VPN Cluster Load Balancing with the High Availability and
Scalability Wizard
If you have a remote-client configuration in which you are using two or more ASAs connected to the
same network to handle remote sessions, you can configure these devices to share their session load. This
feature is called load balancing, which directs session traffic to the least loaded device, thereby
distributing the load among all devices. Load balancing makes efficient use of system resources and
provides increased performance and system availability.
Use the VPN Cluster Load Balancing Configuration screen to set required parameters for a device to
participate in a load balancing cluster.
Enabling load balancing involves the following:

3-24
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 3 Configuring IKE, Load Balancing, and NAC
Configuring Load Balancing
•Configuring the load-balancing cluster by establishing a common virtual cluster IP address, UDP
port (if necessary), and IPsec shared secret for the cluster. These values are identical for each device
in the cluster.
•Configuring the participating device by enabling load balancing on the device and defining
device-specific properties. These values vary from device to device.
Prerequisites
If you are using encryption, you must configure the load balancing inside interface. If that interface is
not enabled on the load balancing inside interface, an error message appears when you try to configure
cluster encryption.
Detailed Steps
To implement load balancing, you logically group together two or more devices on the same private
LAN-to-LAN network into a virtual cluster by performing the following steps:
Step 1 Choose Wizards > High Availability and Scalability.
Step 2 In the Configuration Type screen, click Configure VPN Cluster Load Balancing, and click Next.
Step 3 Choose the single IP address that represents the entire virtual cluster. Specify an IP address that is within
the public subnet address range shared by all the ASAs in the virtual cluster.
Step 4 Specify the UDP port for the virtual cluster in which this device is participating. The default value is
9023. If another application is using this port, enter the UDP destination port number that you want to
use for load balancing.
Step 5 To enable IPsec encryption and ensure that all load-balancing information communicated between the
devices is encrypted, check the Enable IPsec Encryption check box. You must also specify and verify
a shared secret. The ASAs in the virtual cluster communicate via LAN-to-LAN tunnels using IPsec. To
disable IPsec encryption, uncheck the Enable IPsec Encryption check box.
Step 6 Specify the shared secret to between IPsec peers when you enable IPsec encryption. The value that you
enter appears as consecutive asterisk characters.
Step 7 Specify the priority assigned to this device within the cluster. The range is from 1 to 10. The priority
indicates the likelihood of this device becoming the virtual cluster master, either at startup or when an
existing master fails. The higher the priority set (for example, 10), the more likely that this device will
become the virtual cluster master.
Note If the devices in the virtual cluster are powered up at different times, the first device to be
powered up assumes the role of virtual cluster master. Because every virtual cluster requires a
master, each device in the virtual cluster checks when it is powered up to ensure that the cluster
has a virtual master. If none exists, that device assumes the role. Devices powered up and added
to the cluster later become secondary devices. If all the devices in the virtual cluster are powered
up simultaneously, the device with the highest priority setting becomes the virtual cluster master.
If two or more devices in the virtual cluster are powered up simultaneously, and both have the
highest priority setting, the one with the lowest IP address becomes the virtual cluster master.
Step 8 Specify the name or IP address of the public interface for this device.
Step 9 Specify the name or IP address of the private interface for this device.
Step 10 Check the Send FQDN to client instead of an IP address when redirecting check box to have the VPN
cluster master send a fully qualified domain name using the host and domain name of the cluster device
instead of the outside IP address when redirecting VPN client connections to that cluster device.

3-25
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 3 Configuring IKE, Load Balancing, and NAC
Configuring Load Balancing
Step 11 Click Next. Review your configuration in the Summary screen.
Step 12 Click Finish.
The VPN cluster load balancing configuration is sent to the ASA.
Configuring Load Balancing (Without the Wizard)
The Load Balancing pane (Configuration > Remote Access VPN > Load Balancing) lets you enable load
balancing on the ASA. Enabling load balancing involves:
•Configuring the load-balancing cluster by establishing a common virtual cluster IP address, UDP
port (if necessary), and IPsec shared secret for the cluster. These values are identical for every device
in the cluster.
•Configuring the participating device by enabling load balancing on the device and defining
device-specific properties. These values vary from device to device.
Prerequisite
•For clients with IPv6 addresses to successfully connect to the ASA’s public-facing IPv4 address, a
device that can perform network address translation from IPv6 to IPv4 needs to be in the network.
•If you are using encryption, you must configure the load balancing inside interface. If that interface
is not enabled on the load balancing inside interface, an error message appears when you try to
configure cluster encryption.
Step 1 Select Configuration > Remote Access VPN > Load Balancing.
Step 2 Check Participate in Load Balancing to indicate that this ASA is a participant in the load-balancing
cluster
You must enable load balancing in this way on every ASA participating in load balancing.
Step 3 Configure the following fields in the VPN Cluster Configuration area. These values must be the same
for the entire virtual cluster. All servers in the cluster must have an identical cluster configuration.
•Cluster IPv4 Address—Specifies the single IPv4 address that represents the entire IPv4 virtual
cluster. Choose an IP address that is within the public subnet address range shared by all the ASAs
in the virtual cluster.
–
UDP Port—Specifies the UDP port for the virtual cluster in which this device is participating.
The default value is 9023. If another application is using this port, enter the UDP destination
port number you want to use for load balancing.
•Cluster IPv6 Address—Specifies the single IPv6 address that represents the entire IPv6 virtual
cluster. Choose an IP address that is within the public subnet address range shared by all the ASAs
in the virtual cluster. Clients with IPv6 addresses can make AnyConnect connections through the
ASA cluster’s public-facing IPv6 address or through a GSS server. Likewise, clients with IPv6
addresses can make AnyConnect VPN connections through the ASA cluster’s public-facing IPv4
address or through a GSS server. Either type of connection can be load-balanced within the ASA
cluster.

3-26
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 3 Configuring IKE, Load Balancing, and NAC
Configuring Load Balancing
Note In the Cluster IPv4 Address and Cluster IPv6 Address fields, you can also specify the fully
qualified domain name of the virtual cluster, provided that you have a DNS server group
configured with at least one DNS server, and DNS lookup is enabled on one of the ASA’s
interfaces.
•Enable IPsec Encryption—Enables or disables IPsec encryption. If you check this box, you must
also specify and verify a shared secret. The ASAs in the virtual cluster communicate via
LAN-to-LAN tunnels using IPsec. To ensure that all load-balancing information communicated
between the devices is encrypted, check this box.
•IPsec Shared Secret—Specifies the shared secret between IPsec peers when you have enabled
IPsec encryption. The value you enter in the box appears as consecutive asterisk characters.
•Verify Secret—Re-enter the shared secret. Confirms the shared secret value entered in the IPsec
Shared Secret box.
Step 4 Configure the fields in the VPN Server Configuration area for a specific ASA:
•Public Interface—Specifies the name or IP address of the public interface for this device.
•Private Interface—Specifies the name or IP address of the private interface for this device.
•Priority—Specifies the priority assigned to this device within the cluster. The range is from 1 to 10.
The priority indicates the likelihood of this device becoming the virtual cluster master, either at
start-up or when an existing master fails. The higher you set the priority (for example, 10), the more
likely this device becomes the virtual cluster master.
Note If the devices in the virtual cluster are powered up at different times, the first device to be
powered up assumes the role of virtual cluster master. Because every virtual cluster requires a
master, each device in the virtual cluster checks when it is powered-up to ensure that the cluster
has a virtual master. If none exists, that device takes on the role. Devices powered up and added
to the cluster later become backup devices. If all the devices in the virtual cluster are powered
up simultaneously, the device with the highest priority setting becomes the virtual cluster master.
If two or more devices in the virtual cluster are powered up simultaneously, and both have the
highest priority setting, the one with the lowest IP address becomes the virtual cluster master.
•NAT Assigned IPv4 Address—Specifies the IP address that this device’s IP address is translated to
by NAT. If NAT is not being used (or if the device is not behind a firewall using NAT), leave the field
blank.
•NAT Assigned IPv6 Address—Specifies the IP address that this device’s IP address is translated to
by NAT. If NAT is not being used (or if the device is not behind a firewall using NAT), leave the field
blank.
•Send FQDN to client—Check this check box to cause the VPN cluster master to send a fully
qualified domain name using the host and domain name of the cluster device instead of the outside
IP address when redirecting VPN client connections to that cluster device.
By default, the ASA sends only IP addresses in load-balancing redirection to a client. If certificates
are in use that are based on DNS names, the certificates will be invalid when redirected to a backup
device.
As a VPN cluster master, this ASA can send a fully qualified domain name (FQDN), using reverse
DNS lookup, of a cluster device (another ASA in the cluster), instead of its outside IP address, when
redirecting VPN client connections to that cluster device.

3-27
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 3 Configuring IKE, Load Balancing, and NAC
Setting Global NAC Parameters
All of the outside and inside network interfaces on the load-balancing devices in a cluster must be
on the same IP network.
Note When using IPv6 and sending FQDNS down to client, those names must be resolvable by
the ASA via DNS.
Enable Clientless SSL VPN Load Balancing Using FQDNs
Step 1 Enable the use of FQDNs for Load Balancing by checking the Send FQDN to client instead of an IP
address when redirecting checkbox.
Step 2 Add an entry for each of your ASA outside interfaces into your DNS server, if such entries are not
already present. Each ASA outside IP address should have a DNS entry associated with it for lookups.
These DNS entries must also be enabled for Reverse Lookup.
Step 3 Enable DNS lookups on your ASA on the dialog box Configuration > Device Management > DNS >
DNS Client for whichever interface has a route to your DNS server.
Step 4 Define your DNS server IP address on the ASA. To do this, click Add on this dialog box. This opens the
Add DNS Server Group dialog box. Enter the IPv4 or IPv6 address of the DNS server you want to add;
for example, 192.168.1.1 or 2001:DB8:2000::1.
Step 5 Click OK and Apply.
Setting Global NAC Parameters
The ASA uses Extensible Authentication Protocol (EAP) over UDP (EAPoUDP) messaging to validate
the posture of remote hosts. Posture validation involves checking a remote host for compliancy with
safety requirements before the assignment of a network access policy. An Access Control Server must
be configured for Network Admission Control before you configure NAC on the ASA.
Fields
The NAC pane lets you set attributes that apply to all NAC communications. The following global
attributes at the top of the pane apply to EAPoUDP messaging between the ASA and remote hosts:
•Port—Port number for EAP over UDP communication with the Cisco Trust Agent (CTA) on the
host. This number must match the port number configured on the CTA. Enter a value in the range
1024 to 65535. The default setting is 21862.
•Retry if no response—Number of times the ASA resends an EAP over UDP message. This attribute
limits the number of consecutive retries sent in response to Rechallenge Interval expirations. The
setting is in seconds. Enter a value in the range 1 to 3. The default setting is 3.
•Rechallenge Interval—The ASA starts this timer when it sends an EAPoUDP message to the host.
A response from the host clears the timer. If the timer expires before the ASA receives a response,
it resends the message. The setting is in seconds. Enter a value in the range 1 to 60. The default
setting is 3.

3-28
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 3 Configuring IKE, Load Balancing, and NAC
Configuring Network Admission Control Policies
•Wait before new PV Session—The ASA starts this timer when it places the NAC session for a remote
host into a hold state. It places a session in a hold state if it does not receive a response after sending
EAPoUDP messages equal to the value of the “Retry if no response” setting. The ASA also starts
this timer after it receives an Access Reject message from the ACS server. When the timer expires,
the ASA tries to initiate a new EAP over UDP association with the remote host. The setting is in
seconds. Enter a value in the range 60 to 86400. The default setting is 180.
The Clientless Authentication area of the NAC pane lets you configure settings for hosts that are not
responsive to the EAPoUDP requests. Hosts for which there is no CTA running do not respond to these
requests.
•Enable clientless authentication—Click to enable clientless authentication. The ASA sends the
configured clientless username and password to the Access Control Server in the form of a user
authentication request. The ACS in turn requests the access policy for clientless hosts. If you leave
this attribute blank, the ASA applies the default ACL for clientless hosts.
•Clientless Username—Username configured for clientless hosts on the ACS. The default setting is
clientless. Enter 1 to 64 ASCII characters, excluding leading and trailing spaces, pound signs (#),
question marks (?), single and double quotation marks (“ ” and "), asterisks (*), and angle brackets
(< and >).
•Password—Password configured for clientless hosts on the ACS. The default setting is clientless.
Enter 4 – 32 ASCII characters.
•Confirm Password—Password configured for clientless hosts on the ACS repeated for validation.
•Enable Audit—Click to pass the IP address of the client to an optional audit server if the client does
not respond to a posture validation request. The audit server, such as a Trend server, uses the host
IP address to challenge the host directly to assess its health. For example, it may challenge the host
to determine whether its virus checking software is active and up-to-date. After the audit server
completes its interaction with the remote host, it passes a token to the posture validation server,
indicating the health of the remote host.
•None—Click to disable clientless authentication and audit services.
Configuring Network Admission Control Policies
The NAC Policies table displays the Network Admission Control (NAC) policies configured on the ASA.
To add, change, or remove a NAC policy, do one of the following:
•To add a NAC policy, choose Add. The Add NAC Framework Policy dialog box opens.
•To change a NAC policy, double-click it, or select it and click Edit. The Edit NAC Framework Policy
dialog box opens.
•To remove a NAC policy, select it and click Delete.
The following sections describe NAC, its requirements, and how to assign values to the policy attributes:
•About NAC
•Uses, Requirements, and Limitations
•Fields
•What to Do Next

3-29
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 3 Configuring IKE, Load Balancing, and NAC
Configuring Network Admission Control Policies
About NAC
NAC protects the enterprise network from intrusion and infection from worms, viruses, and rogue
applications by performing endpoint compliance and vulnerability checks as a condition for production
access to the network. We refer to these checks as posture validation. You can configure posture
validation to ensure that the anti-virus files, personal firewall rules, or intrusion protection software on
a host with an AnyConnect or Clientless SSL VPN session are up-to-date before providing access to
vulnerable hosts on the intranet. Posture validation can include the verification that the applications
running on the remote hosts are updated with the latest patches. NAC occurs only after user
authentication and the setup of the tunnel. NAC is especially useful for protecting the enterprise network
from hosts that are not subject to automatic network policy enforcement, such as home PCs.
The establishment of a tunnel between the endpoint and the ASA triggers posture validation.
You can configure the ASA to pass the IP address of the client to an optional audit server if the client
does not respond to a posture validation request. The audit server, such as a Trend server, uses the host
IP address to challenge the host directly to assess its health. For example, it may challenge the host to
determine whether its virus checking software is active and up-to-date. After the audit server completes
its interaction with the remote host, it passes a token to the posture validation server, indicating the
health of the remote host.
Following successful posture validation or the reception of a token indicating the remote host is healthy,
the posture validation server sends a network access policy to the ASA for application to the traffic on
the tunnel.
In a NAC Framework configuration involving the ASA, only a Cisco Trust Agent running on the client
can fulfill the role of posture agent, and only a Cisco Access Control Server (ACS) can fulfill the role of
posture validation server. The ACS uses dynamic ACLs to determine the access policy for each client.
As a RADIUS server, the ACS can authenticate the login credentials required to establish a tunnel, in
addition to fulfilling its role as posture validation server.
Note Only a NAC Framework policy configured on the ASA supports the use of an audit server.
In its role as posture validation server, the ACS uses access control lists. If posture validation succeeds
and the ACS specifies a redirect URL as part of the access policy it sends to the ASA, the ASA redirects
all HTTP and HTTPS requests from the remote host to the redirect URL. Once the posture validation
server uploads an access policy to the ASA, all of the associated traffic must pass both the Security
Appliance and the ACS (or vice versa) to reach its destination.
The establishment of a tunnel between a remote host and the ASA triggers posture validation if a NAC
Framework policy is assigned to the group policy. The NAC Framework policy can, however, identify
operating systems that are exempt from posture validation and specify an optional ACL to filter such
traffic.
Uses, Requirements, and Limitations
When configured to support NAC, the ASA functions as a client of a Cisco Secure Access Control
Server, requiring that you install a minimum of one Access Control Server on the network to provide
NAC authentication services.
Following the configuration of one or more Access Control Servers on the network, you must register
the Access Control Server group, using the Configuration > Remote Access VPN > Clientless SSL
VPN Access > Group Policies > Add or Edit External menu option. Then add the NAC policy.
ASA support for NAC Framework is limited to remote access IPsec and Clientless SSL VPN sessions.
The NAC Framework configuration supports only single mode.

3-30
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 3 Configuring IKE, Load Balancing, and NAC
Configuring Network Admission Control Policies
NAC on the ASA does not support Layer 3 (non-VPN) and IPv6 traffic.
Fields
•Policy Name—Enter a string of up to 64 characters to name the new NAC policy.
Following the configuration of the NAC policy, the policy name appears next to the NAC Policy
attribute in the Network (Client) Access group policies. Assign a name that will help you to
distinguish its attributes or purpose from others that you may configure.
•Status Query Period—The ASA starts this timer after each successful posture validation and status
query response. The expiration of this timer triggers a query for changes in the host posture, referred
to as a status query. Enter the number of seconds in the range 30 to 1800. The default setting is 300.
•Revalidation Period—The ASA starts this timer after each successful posture validation. The
expiration of this timer triggers the next unconditional posture validation. The ASA maintains
posture validation during revalidation. The default group policy becomes effective if the Access
Control Server is unavailable during posture validation or revalidation. Enter the interval in seconds
between each successful posture validation. The range is 300 to 86400. The default setting is 36000.
•Default ACL— (Optional) The ASA applies the security policy associated with the selected ACL if
posture validation fails. Select None or select an extended ACL in the list. The default setting is
None. If the setting is None and posture validation fails, the ASA applies the default group policy.
Use the Manage button to populate the drop-down list and view the configuration of the ACLs in the
list.
•Manage— Opens the ACL Manager dialog box. Click to view, enable, disable, and delete standard
ACLs and the ACEs in each ACL. The list next to the Default ACL attribute displays the ACLs.
•Authentication Server Group—Specifies the authentication server group to use for posture
validation. The drop-down list next to this attribute displays the names of all server groups of type
RADIUS configured on this ASA that are available for remote access tunnels. Select an ACS group
consisting of at least one server configured to support NAC.
•Posture Validation Exception List—Displays one or more attributes that exempt remote computers
from posture validation. At minimum, each entry lists the operating system and an Enabled setting
of Yes or No. An optional filter identifies an ACL used to match additional attributes of the remote
computer. An entry that consists of an operating system and a filter requires the remote computer to
match both to be exempt from posture validation. The ASA ignores the entry if the Enabled setting
is set to No.
•Add—Adds an entry to the Posture Validation Exception list.
•Edit—Modifies an entry in the Posture Validation Exception list.
•Delete—Removes an entry from the Posture Validation Exception list.
What to Do Next
Following the configuration of the NAC policy, you must assign it to a group policy for it to become
active. To do so, choose Configuration > Remote Access VPN> Network (Client) Access > Group
Policies > Add or Edit > General > More Options and the NAC policy name from the drop-down list
next to the NAC Policy attribute.
Add/Edit Posture Validation Exception
The Add/Edit Posture Validation Exception dialog pane lets you exempt remote computers from posture
validation, based on their operating system and other optional attributes that match a filter.

3-31
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 3 Configuring IKE, Load Balancing, and NAC
Configuring Network Admission Control Policies
•Operating System—Choose the operating system of the remote computer. If the computer is running
this operating system, it is exempt from posture validation. The default setting is blank.
•Enable—The ASA checks the remote computer for the attribute settings displayed in this pane only
if you check Enabled. Otherwise, it ignores the attribute settings. The default setting is unchecked.
•Filter— (Optional) Use to apply an ACL to filter the traffic if the operating system of the computer
matches the value of the Operating System attribute.
•Manage— Opens the ACL Manager dialog box. Click to view, enable, disable, and delete standard
ACLs and the ACEs in each ACL. The list next to the Default ACL attribute displays the ACLs. Use
this button to populate the list next to the Filter attribute.

3-32
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 3 Configuring IKE, Load Balancing, and NAC
Configuring Network Admission Control Policies

CHAPTER
4-1
Cisco ASA Series VPN ASDM Configuration Guide
4
General VPN Setup
A virtual private network is a network of virtual circuits that carry private traffic over a public network
such as the Internet. VPNs can connect two or more LANS, or remote users to a LAN. VPNs provide
privacy and security by requiring all users to authenticate and by encrypting all data traffic.
•AnyConnect Customization/Localization, page 4-1
•Default Tunnel Gateway, page 4-6
•Group Policies, page 4-7
•Access Control List Manager, page 4-36
•Configuring AnyConnect VPN Client Connections, page 4-48
•Configuring AnyConnect VPN Connections, page 4-57
•Configuring AnyConnect Secure Mobility, page 4-69
•IPsec Remote Access Connection Profiles, page 4-78
•Add or Edit an IPsec Remote Access Connection Profile, page 4-79
•Mapping Certificates to IPsec or SSL VPN Connection Profiles, page 4-80
•System Options, page 4-107
•Zone Labs Integrity Server, page 4-108
•Easy VPN Remote, page 4-109
•Advanced Easy VPN Properties, page 4-111
•AnyConnect Essentials, page 4-113
•Configuring AnyConnect Host Scan, page 4-115
•Configuring Maximum VPN Sessions, page 4-122
•Configuring the Pool of Cryptographic Cores, page 4-122
AnyConnect Customization/Localization
You can customize the AnyConnect VPN client to display your own corporate image to remote users,
including clients running on Windows, Linux, and Mac OS X computers. The following ASDM screens
under AnyConnect Customization/Localization allow you to import the following types of customized
files:
•Resources—Modified GUI icons for the AnyConnect client.

4-2
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 4 General VPN Setup
AnyConnect Customization/Localization
•Binary—Executable files to replace the AnyConnect installer. This includes GUI files, plus the
VPN client profile, scripts and other client files.
•Script—Scripts that will run before or after AnyConnect makes a VPN connection.
•GUI Text and Messages—Titles and messages used by the AnyConnect client.
•Customized Installer—Transforms that modify the client installation.
•Localized Installer—Transforms Transforms that change the language used by the client.
Each dialog provides the following actions:
•Import launches the Import AnyConnect Customization Objects dialog, where you can specify a
file to import as an object.
•Export launches the Export AnyConnect Customization Objects dialog, where you can specify a file
to export as an object.
•Delete removes the selected object.
Restrictions
•Customization is not supported for the AnyConnect client running on a Windows Mobile device.
AnyConnect Customization/Localization > Resources
The filenames of the custom components that you import must match the filenames used by the
AnyConnect GUI, which are different for each operating system and are case sensitive for Mac and
Linux. For example, if you want to replace the corporate logo for Windows clients, you must import your
corporate logo as company_logo.png. If you import it as a different filename, the AnyConnect installer
does not change the component. However, if you deploy your own executable to customize the GUI, the
executable can call resource files using any filename.
If you import an image as a resource file (such as company_logo.bmp), the image you import customizes
AnyConnect until you reimport another image using the same filename. For example, if you replace
company_logo.bmp with a custom image, and then delete the image, the client continues to display your
image until you import a new image (or the original Cisco logo image) using the same filename.
AnyConnect Customization/Localization > Binary and Script
The same link is used in ASDM for both Binary and Script, so share this link for now, and submit a defect
against ASDM to have them add another link.
AnyConnect Customization/Localization > Binary
For Windows, Linux, or Mac (PowerPC or Intel-based) computers, you can deploy your own client that
uses the AnyConnect client API. You replace the AnyConnect GUI and the AnyConnect CLI by
replacing the client binary files.
Fields for the Import dialog:
•Name Enter the name of the AnyConnect file that you are replacing.
•Platform Select the OS platform that your file runs on.
•Select a file The filename name does not need to be the same as the name of the imported file.

4-3
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 4 General VPN Setup
AnyConnect Customization/Localization
AnyConnect Customization/Localization > Script
For complete information about deploying scripts, and their limitations and restrictions, see the
AnyConnect VPN Client Administrators Guide.
Fields for the Import dialog:
•Name—Enter a name for the script. Be sure to specify the correct extension with the name. For
example, myscript.bat.
•Script Type—Choose when to run the script.
AnyConnect adds the prefix scripts_ and the prefix OnConnect or OnDisconnect to your filename
to identify the file as a script on the ASA. When the client connects, the ASA downloads the script
to the proper target directory on the remote computer, removing the scripts_ prefix and leaving the
remaining OnConnect or OnDisconnect prefix. For example, if you import the script myscript.bat,
the script appears on the ASA as scripts_OnConnect_myscript.bat. On the remote computer, the
script appears as OnConnect_myscript.bat.
To ensure the scripts run reliably, configure all ASAs to deploy the same scripts. If you want to
modify or replace a script, use the same name as the previous version and assign the replacement
script to all of the ASAs that the users might connect to. When the user connects, the new script
overwrites the one with the same name.
•Platform—Select the OS platform that your file runs on.
•Select a file—The filename name does not need to be the same as the name you provided for the
script.
ASDM imports the file from any source file, creating the new name you specify for Name in Step 3.
AnyConnect Customization/Localization > GUI Text and Messages
You can edit the default translation table, or create new ones, to change the text and messages displayed
on the AnyConnect client GUI . This pane also shares functionality with the Language Localization
pane. For more extensive language translation, go to Configuration > Remote Access VPN > Language
Localization.
In addition to the usual buttons on the top toolbar, this pane also has an Add button, and a Template area
with extra buttons.
Add—The Add button opens a copy of the default translation table, which you can edit directly, or save.
You can select the language of the saved file, and edit the language of the text inside the file later.
When you customize messages in the translation table, do not change msgid, change the text in
msgstr.
Specify a language for the template. The template becomes a translation table in cache memory with
the name you specify. Use an abbreviation that is compatible with the language options for your
browser. For example, if you are creating a table for the Chinese language, and you are using IE, use
the abbreviation zh, that is recognized by IE.
Template Section
•Click Template to expand the template area, which provides access to the default English translation
table.
•Click View to view, and optionally save, the default English translation table
•Click Export to save a copy of the default English translation table without looking at it.

4-4
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 4 General VPN Setup
Client Software
AnyConnect Customization/Localization > Customized Installer Transforms
You can perform more extensive customizing of the AnyConnect client GUI (Windows only) by creating
your own transform that deploys with the client installer program. You import the transform to the ASA,
which deploys it with the installer program.
Windows is the only valid choice for applying a transform. For more information about transforms, see
the AnyConnect Administration Guide.
AnyConnect Customization/Localization > Localized Installer Transforms
You can translate messages displayed by the client installer program with a transform. The transform
alters the installation, but leaves the original security-signed MSI intact. These transforms only translate
the installer screens and do not translate the client GUI screens.
Client Software
Configuration > VPN > General > Client Update
The Client Software pane lets administrators at a central location do the following actions:
•Enable client update; specify the types and revision numbers of clients to which the update applies.
•Provide a URL or IP address from which to get the update.
•In the case of Windows clients, optionally notify users that they should update their VPN client
version.
Note The Client Update function in Configuration > Remote Access VPN > Network (Client) Access >
Advanced > IPsec > Upload Software > Client Software applies only to the IPsec VPN client, (For
Windows, MAC OS X, and Linux), and the VPN 3002 hardware client. It does not apply to the Cisco
AnyConnect VPN clients, which is updated by the ASA automatically when it connects.
For the IPsec VPN client, you can provide a mechanism for users to accomplish that update. For VPN
3002 hardware client users, the update occurs automatically, with no notification. You can apply client
updates only to the IPsec remote-access tunnel-group type.
Note If you try to do a client update to an IPsec Site-to-Site IPsec connection or a Clientless VPN IPsec
connection, you do not receive an error message, but no update notification or client update goes to those
types of IPsec connections.
To enable client update globally for all clients of a particular client type, use this dialog box. You can
also notify all Windows, MAC OS X, and Linux clients that an upgrade is needed and initiate an upgrade
on all VPN 3002 hardware clients from this dialog box. To configure the client revisions to which the
update applies and the URL or IP address from which to download the update, click Edit.
To configure client update revisions and software update sources for a specific tunnel group, choose
Configuration > Remote Access VPN > Network (Client) Access > IPsec > Add/Edit > Advanced >
IPsec > Client Software Update.

4-5
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 4 General VPN Setup
Client Software
Fields
•Enable Client Update—Enables or disables client update, both globally and for specific tunnel
groups. You must enable client update before you can send a client update notification to Windows,
MAC OS X, and Linux VPN clients, or initiate an automatic update to hardware clients.
•Client Type—Lists the clients to upgrade: software or hardware, and for Windows software clients,
all Windows or a subset. If you click All Windows Based, do not specify Windows 95, 98 or ME and
Windows NT, 2000 or XP individually. The hardware client gets updated with a release of the ASA
5505 software or of the VPN 3002 hardware client.
•VPN Client Revisions—Contains a comma-separated list of software image revisions appropriate
for this client. If the user client revision number matches one of the specified revision numbers, there
is no need to update the client, and, for Windows-based clients, the user does not receive an update
notification. The following caveats apply:
–
The revision list must include the software version for this update.
–
Your entries must match exactly those on the URL for the VPN client, or the TFTP server for
the hardware client.
–
The TFTP server for distributing the hardware client image must be a robust TFTP server.
–
A VPN client user must download an appropriate software version from the listed URL.
–
The VPN 3002 hardware client software is automatically updated via TFTP, with no notification
to the user.
•Image URL—Contains the URL or IP address from which to download the software image. This
URL must point to a file appropriate for this client. For Windows, MAC OS X, and Linux-based
clients, the URL must be in the form: http:// or https://. For hardware clients, the URL must be in
the form tftp://.
–
For Windows, MAC OS X, and Linux-based VPN clients: To activate the Launch button on the
VPN Client Notification, the URL must include the protocol HTTP or HTTPS and the server
address of the site that contains the update. The format of the URL is:
http(s)://server_address:port/directory/filename. The server address can be either an IP address
or a hostname if you have configured a DNS server. For example:
http://10.10.99.70/vpnclient-win-4.6.Rel-k9.exe
The directory is optional. You need the port number only if you use ports other than 80 for HTTP
or 443 for HTTPS.
–
For the hardware client: The format of the URL is tftp://server_address/directory/filename. The
server address can be either an IP address or a hostname if you have configured a DNS server.
For example:
tftp://10.1.1.1/vpn3002-4.1.Rel-k9.bin
•Edit—Opens the Edit Client Update Entry dialog box, which lets you configure or change client
update parameters. See Edit Client Update Entry.
•Live Client Update—Sends an upgrade notification message to all currently connected VPN clients
or selected tunnel group(s).
–
Tunnel Group—Selects all or specific tunnel group(s) for updating.
–
Update Now—Immediately sends an upgrade notification containing a URL specifying where
to retrieve the updated software to the currently connected VPN clients in the selected tunnel
group or all connected tunnel groups. The message includes the location from which to
download the new version of software. The administrator for that VPN client can then retrieve
the new software version and update the VPN client software.

4-6
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 4 General VPN Setup
Default Tunnel Gateway
For VPN 3002 hardware clients, the upgrade proceeds automatically, with no notification.
You must check Enable Client Update for the upgrade to work. Clients that are not connected
receive the upgrade notification or automatically upgrade the next time they log on.
Edit Client Update Entry
Configuration > VPN > General > Client Update > Edit Client Update Entry
The Edit Client Update dialog box lets you change information about VPN client revisions and URLs
for the indicated client types. The clients must be running one of the revisions specified for the indicated
client type. If not, the clients are notified that an upgrade is required.
Fields
•Client Type—(Display-only) Displays the client type selected for editing.
•VPN Client Revisions—Lets you type a comma-separated list of software or firmware images
appropriate for this client. If the user client revision number matches one of the specified revision
numbers, there is no need to update the client. If the client is not running a software version on the
list, an update is in order. The user of a Windows, MAC OS X, or Linux-based VPN client must
download an appropriate software version from the listed URL. The VPN 3002 hardware client
software is automatically updated via TFTP.
•Image URL—Lets you type the URL for the software/firmware image. This URL must point to a
file appropriate for this client.
–
For a Windows, MAC OS X, or Linux-based VPN client, the URL must include the protocol
HTTP or HTTPS and the server address of the site that contains the update. The format of the
URL is: http(s)://server_address:port/directory/filename. The server address can be either an IP
address or a hostname if you have configured a DNS server. For example:
http://10.10.99.70/vpnclient-win-4.6.Rel-k9.exe
The directory is optional. You need the port number only if you use ports other than 80 for HTTP
or 443 for HTTPS.
–
For the hardware client: The format of the URL is tftp://server_address/directory/filename. The
server address can be either an IP address or a hostname if you have configured a DNS server.
For example:
tftp://10.1.1.1/vpn3002-4.1.Rel-k9.bin
The directory is optional.
Default Tunnel Gateway
Configuration > VPN > General > Default Tunnel Gateway
To configure the default tunnel gateway, click the Static Route link. The Configuration > Routing >
Routing > Static Route dialog box opens.

4-7
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 4 General VPN Setup
Group Policies
Group Policies
The Group Policies pane lets you manage VPN (AnyConnect or Clientless) group policies. A VPN group
policy is a collection of user-oriented attribute/value pairs stored either internally on the device or
externally on a RADIUS or LDAP server. Configuring the VPN group policy lets users inherit attributes
that you have not configured at the individual group or username level. By default, VPN users have no
group policy association. The group policy information is used by VPN tunnel groups and user accounts.
The “child” panes and dialog boxes let you configure the group parameters, including those for the
default group, DfltGrpPolicy. The default group parameters are those that are most likely to be common
across all groups and users, and they streamline the configuration task. Groups can “inherit” parameters
from this default group, and users can “inherit” parameters from their group or the default group. You
can override these parameters as you configure groups and users.
You can configure either an internal or an external group policy. An internal group policy is stored
locally, and an external group policy is stored externally on a RADIUS or LDAP server. Clicking Edit
opens a similar dialog box on which you can create a new group policy or modify an existing one.
In these dialog boxes, you configure the following kinds of parameters:
•General attributes: Name, banner, address pools, protocols, filtering, and connection settings.
•Servers: DNS and WINS servers, DHCP scope, and default domain name.
•Advanced attributes: Split tunneling, IE browser proxy, AnyConnect client, and IPsec client.
Before configuring these parameters, you should configure:
•Access hours.
•Filters.
•Network lists for filtering and split tunneling
•User authentication servers and the internal authentication server.
You can configure these types of group policies:
•Configuring External Group Policies—An external group policy points the ASA to the RADIUS or
LDAP server to retrieve much of the policy information that would otherwise be configured in an
internal group policy. External group policies are configured the same way for Network (Client)
Access VPN connections, Clientless SSL VPN connections, and Site-to-Site VPN connections.
•Configuring Network (Client) Access Internal Group Policies—These connections are initiated by
a VPN client installed on the endpoint. The AnyConnect Secure Mobility Client and Cisco VPN
IPsec client are examples of VPN clients. After the VPN client is authenticated, remote users can
access corporate networks or applications as if they were on-site. The data traffic between remote
users and the corporate network is secured by being encrypted when going through the Internet.
•Configuring Clientless SSL VPN Internal Group Policies—This is also known as browser-based
VPN access. On successful login to the ASA’s portal page, remote users can access corporate
networks and applications from the links shown in the web pages. The data traffic between remote
users and the corporate network is secured by traveling through SSL tunnel.
•Configuring Site-to-Site Internal Group Policies
Group Policy Pane Fields
Lists the currently configured group policies and Add, Edit, and Delete buttons to help you manage VPN
group policies.

4-8
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 4 General VPN Setup
Group Policies
•Add—Offers a drop-down menu on which you can select whether to add an internal or an external
group policy. If you simply click Add, then by default, you create an internal group policy. Clicking
Add opens the Add Internal Group Policy dialog box or the Add External Group Policy dialog box,
which let you add a new group policy to the list. This dialog box includes three menu sections. Click
each menu item to display its parameters. As you move from item to item, ASDM retains your
settings. When you have finished setting parameters on all menu sections, click Apply or Cancel.
Offers a drop-down menu from which you can select whether to add an internal or an external group
policy. If you simply click Add, then by default, you create an internal group policy.
•Edit—Displays the Edit Group Policy dialog box, which lets you modify an existing group policy.
•Delete—Lets you remove a AAA group policy from the list. There is no confirmation or undo.
•Assign—Lets you assign a group policy to one ore more connection profiles.
•Name—Lists the name of the currently configured group policies.
•Type—Lists the type of each currently configured group policy.
•Tunneling Protocol—Lists the tunneling protocol that each currently configured group policy uses.
•Connection Profiles/Users Assigned to—Lists the connection profiles and users configured directly
on the ASA that are associated with this group policy.
Configuring External Group Policies
An external group policy points the ASA to the RADIUS or LDAP server to retrieve much of the policy
information that would otherwise be configured in an internal group policy. External group policies are
configured the same way for Network (Client) Access VPN connections, Clientless SSL VPN
connections, and Site-to-Site VPN connections.
External group policies take their attribute values from the external server that you specify. For an
external group policy, you must identify the RADIUS or LDAP server group that the ASA can query for
attributes and specify the password to use when retrieving attributes from that external server group. If
you are using an external authentication server, and if your external group-policy attributes exist in the
same RADIUS server as the users that you plan to authenticate, you have to make sure that there is no
name duplication between them.
Note External group names on the ASA refer to user names on the RADIUS server. In other words, if you
configure external group X on the ASA, the RADIUS server sees the query as an authentication request
for user X. So external groups are really just user accounts on the RADIUS server that have special
meaning to the ASA. If your external group attributes exist in the same RADIUS server as the users that
you plan to authenticate, there must be no name duplication between them.
The ASA supports user authorization on an external LDAP or RADIUS server. Before you configure the
ASA to use an external server, you must configure the server with the correct ASA authorization
attributes and, from a subset of these attributes, assign specific permissions to individual users. Follow
the instructions in Appendix 13, “Configuring an External Server for Authorization and Authentication”
to configure your external server.
Fields
•Name—Identifies the group policy to be added or changed. For Edit External Group Policy, this field
is display-only.
•Server Group—Lists the available server groups to which to apply this policy.

4-9
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 4 General VPN Setup
Group Policies
•New—Opens a dialog box that lets you select whether to create a new RADIUS server group or a
new LDAP server group. Either of these options opens the Add AAA Server Group dialog box.
•Password—Specifies the password for this server group policy.
Adding an LDAP or RADIUS Server to a Network (Client) Access External Group Policy
Configuration > Remote Access VPN > Network (Client) Access > Group Policies > Add/Edit >
Add or Edit External Group Policy > New > RADIUS Server Group/New LDAP Server Group >
Add AAA Server Group
The Add AAA Server Group dialog box lets you configure a new AAA server group. The Accounting
Mode attribute applies only to RADIUS and TACACS+ protocols.
Fields
•Server Group—Specifies the name of the server group.
•Protocol—(Display only) Indicates whether this is a RADIUS or an LDAP server group.
•Accounting Mode—Indicates whether to use simultaneous or single accounting mode. In single
mode, the ASA sends accounting data to only one server. In simultaneous mode, the ASA sends
accounting data to all servers in the group. The Accounting Mode attribute applies only to RADIUS
and TACACS+ protocols.
•Reactivation Mode—Specifies the method by which failed servers are reactivated: Depletion or
Timed reactivation mode. In Depletion mode, failed servers are reactivated only after all of the
servers in the group become inactive. In Timed mode, failed servers are reactivated after 30 seconds
of down time.
•Dead Time—Specifies, for depletion mode, the number of minutes (0 through 1440) that must elapse
between the disabling of the last server in the group and the subsequent re-enabling of all servers.
The default value is 10 minutes. This field is not available for timed mode.
•Max Failed Attempts— Specifies the number (an integer in the range 1 through 5) of failed
connection attempts allowed before declaring a nonresponsive server inactive. The default value is
3 attempts.
Configuring Network (Client) Access Internal Group Policies
Configure Network (Client) Access internal group policies for VPN connections made from AnyConnect
Secure Mobility Clients or legacy Cisco IPsec VPN clients installed on an endpoint.
Configuring General Attributes for an Internal Group Policy
The Add or Edit Group Policy dialog box lets you specify tunneling protocols, filters, connection
settings, and servers for the group policy being added or modified. For each of the fields on this dialog
box, checking the Inherit check box lets the corresponding setting take its value from the default group
policy. Inherit is the default value for all of the attributes in this dialog box.
You can configure the general attributes of an internal group policy by starting ASDM and selecting
Configuration > Remote Access VPN > Network (Client) Access > Group Policies > Add or Edit
Internal Group Policy > General.

4-10
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 4 General VPN Setup
Group Policies
Fields
The following attributes appear in the Add Internal Group Policy > General dialog box. They apply to
SSL VPN and IPsec sessions. Thus, some attributes are present for one type of session, but not the other.
•Name—Specifies the name of this group policy up to 64 characters; spaces are allowed. For the Edit
function, this field is read-only.
•Banner—Specifies the banner text to present to users at login. The length can be up to 491
characters. There is no default value.
The IPsec VPN client supports full HTML for the banner. However, the clientless portal and the
AnyConnect client support partial HTML. To ensure the banner displays properly to remote users,
follow these guidelines:
–
For IPsec client users, use the /n tag.
–
For AnyConnect client users, use the <BR> tag.
•SCEP forwarding URL—Address of the CA, required when SCEP Proxy is configured in the client
profile.
•Address Pools—Specifies the name of one or more IPv4 address pools to use for this group policy.
If the Inherit check box is checked, the group policy will use the IPv4 address pool specified in the
Default Group Policy. See Configuring Local IP Address Pools, page 5-3 for information on adding
or editing an IPv4 address pool.
Select—Uncheck the Inherit checkbox to activate the Select command button. Click Select to open
the Address Pools dialog box, which shows the pool name, starting and ending addresses, and subnet
mask of address pools available for client address assignment and lets you select, add, edit, delete,
and assign entries from that list.
•IPv6 Address Pools—Specifies the name of one or more IPv6 address pools to use for this group
policy.
Select—Uncheck the Inherit checkbox to activate the Select command button. Click Select to open
the Select Address Pools dialog box, as previously described. See Configuring Local IP Address
Pools, page 5-3 for information on adding or editing an IPv6 address pool.
Note You can specify both an IPv4 and an IPv6 address pool for an internal group policy.
•More Options—Click the down arrows at the right of the field to display additional configurable
options for this group policy.
•Tunneling Protocols—Specifies the tunneling protocols that this group can use. Users can use only
the selected protocols. The choices are as follows:
–
Clientless SSL VPN—Specifies the use of VPN via SSL/TLS, which uses a web browser to
establish a secure remote-access tunnel to an ASA; requires neither a software nor hardware
client. Clientless SSL VPN can provide easy access to a broad range of enterprise resources,
including corporate websites, web-enabled applications, NT/AD file share (web-enabled),
e-mail, and other TCP-based applications from almost any computer that can reach HTTPS
Internet sites.
–
SSL VPN Client—Specifies the use of the Cisco AnyConnect VPN client or the legacy SSL
VPN client. If you are using the AnyConnect client, you must choose this protocol for Mobile
User Security (MUS) to be supported.
–
IPsec IKEv1—IP Security Protocol. Regarded as the most secure protocol, IPsec provides the
most complete architecture for VPN tunnels. Both Site-to-Site (peer-to-peer) connections and
Cisco VPN client-to-LAN connections can use IPsec IKEv1.

4-11
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 4 General VPN Setup
Group Policies
–
IPsec IKEv2—Supported by the AnyConnect Secure Mobility Client. AnyConnect connections
using IPsec with IKEv2 provide advanced features such as software updates, client profiles,
GUI localization (translation) and customization, Cisco Secure Desktop, and SCEP proxy.
–
L2TP over IPsec—Allows remote users with VPN clients provided with several common PC
and mobile PC operating systems to establish secure connections over the public IP network
to the security appliance and private corporate networks. L2TP uses PPP over UDP (port 1701)
to tunnel the data. The security appliance must be configured for IPsec transport mode.
•Filter—Specifies which unified access control list to use for an IPv4 or an IPv6 connection, or
whether to inherit the value from the group policy. Filters consist of rules that determine whether to
allow or reject tunneled data packets coming through the ASA, based on criteria such as source
address, destination address, and protocol. To configure filters and rules, see the ACL Manager
dialog box.
Manage—Displays the ACL Manager dialog box, with which you can add, edit, and delete Access
Control Lists (ACLs) and Extended Access Control Lists (ACEs). For more information about the
ACL Manager, see the online Help for that dialog box.
•NAC Policy—Selects the name of a Network Admission Control policy to apply to this group policy.
You can assign an optional NAC policy to each group policy. The default value is --None--.
•Manage—Opens the Configure NAC Policy dialog box. After configuring one or more NAC
policies, the NAC policy names appear as options in the drop-down list next to the NAC Policy
attribute.
•Access Hours—Selects the name of an existing access hours policy, if any, applied to this user or
create a new access hours policy. The default value is Inherit, or, if the Inherit check box is not
checked, the default value is --Unrestricted--.
Manage—Opens the Browse Time Range dialog box, in which you can add, edit, or delete a time
range. See Defining Time Ranges, page 4-35 for more information.
•Simultaneous Logins—Specifies the maximum number of simultaneous logins allowed for this user.
The default value is 3. The minimum value is 0, which disables login and prevents user access.
Note While there is no maximum limit, allowing several simultaneous connections might
compromise security and affect performance.
•Restrict Access to VLAN—(Optional) Also called “VLAN mapping,” this parameter specifies the
egress VLAN interface for sessions to which this group policy applies. The ASA forwards all traffic
from this group to the selected VLAN. Use this attribute to assign a VLAN to the group policy to
simplify access control. Assigning a value to this attribute is an alternative to using ACLs to filter
traffic on a session. In addition to the default value (Unrestricted), the drop-down list shows only
the VLANs that are configured on this ASA.
Note This feature works for HTTP connections, but not for FTP and CIFS.
•Connection Profile (Tunnel Group) Lock—This parameter permits remote VPN access only with the
selected connection profile (tunnel group), and prevents access with a different connection profile.
The default inherited value is None.
•Maximum Connect Time—If the Inherit check box is not checked, this parameter specifies the
maximum user connection time in minutes. At the end of this time, the system terminates the
connection. The minimum is 1 minute, and the maximum is 35791394 minutes (over 4000 years,
should we be so lucky). To allow unlimited connection time, check Unlimited (the default).

4-12
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 4 General VPN Setup
Group Policies
•Idle Timeout—If the Inherit check box is not checked, this parameter specifies this user’s idle
timeout period in minutes. If there is no communication activity on the user connection in this
period, the system terminates the connection. The minimum time is 1 minute, and the maximum time
is 10080 minutes. The default is 30 minutes. To allow unlimited connection time, check Unlimited.
This value does not apply to Clientless SSL VPN users.
•On smart card removal—With the default option, Disconnect, the client tears down the connection
if the smart card used for authentication is removed. Click Keep the connection if you do not want
to require users to keep their smart cards in the computer for the duration of the connection.
Smart card removal configuration only works on Microsoft Windows using RSA smart cards.
Configuring Server Attributes for an Internal Group Policy
Configure DNS servers, WINS servers and DHCP Scope in the Group Policy > Servers window. DNS
and WINS servers are applied to full-tunnel clients (IPsec, AnyConnect, SVC, L2TP/IPsec) only and are
used for name resolution. DHCP scope is used when DHCP-address assignment is in place.
Configuring a DNS Server for an Internal Group Policy
Use this procedure to configure a specific DNS server for a group policy.
Note This setting overrides the DNS setting configured on the ASDM in the Configuration > Remote Access
VPN > DNS window.
Step 1 Select Configuration > Remote Access VPN > Network (Client) Access > Group Policies > Add/Edit
> Servers.
Step 2 Unless you are editing the DefaultGroupPolicy, uncheck the DNS Servers Inherit checkbox.
Step 3 In the DNS Servers field, add the IPv4 or IPv6 addresses of the DNS servers you want this group to use.
If you specify more than one DNS server, the remote access client will attempt to use the DNS servers
in the order you specify them in this field.
AnyConnect 3.0.4 and later supports up to 25 DNS server entries in the DNS Servers field, earlier
releases only support up to 10 DNS server entries.
Step 4 Expand the More Options area by clicking the double down arrow in the More Options bar.
Step 5 If there is no default domain specified in the Configuration > Remote Access VPN > DNS window, you
must specify the default domain in the Default Domain field. Use the domain name and top level domain
for example, example.com.
Step 6 Click OK.
Step 7 Click Apply.
Configuring WINS Servers for an Internal Group Policy
Use this procedure to configure primary and secondary WINS servers. WINS servers are applied to
full-tunnel clients (IPsec, AnyConnect, SVC, L2TP/IPsec) only and are used for name resolution. The
default value in each case is none.

4-13
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 4 General VPN Setup
Group Policies
Step 1 Select Configuration > Remote Access VPN > Network (Client) Access > Group Policies > Add/Edit
> Servers.
Step 2 Uncheck the WINS Servers Inherit checkbox.
Step 3 In the WINS Servers field, enter the IP addresses of the primary and secondary WINS servers. The first
IP address you specify is that of the primary WINS server. The second (optional) IP address you specify
is that of the secondary WINS server.
Step 4 Click OK.
Configuring Split Tunneling for AnyConnect Traffic
Split tunneling directs some of the AnyConnect network traffic through the VPN tunnel (encrypted) and
other network traffic outside the VPN tunnel (unencrypted or “in the clear”).
Split tunneling is configured by creating a split tunneling policy, configuring an access control list for
that policy, and adding the split tunnel policy to a group policy. When the group policy is sent to the
client, that client will use the ACLs in the split tunneling policy to decide where to direct network traffic.
For Windows clients, firewall rules from the ASA are evaluated first, then the ones on the client. For Mac
OS X, the firewall and filter rules on the client are not used. For Linux systems, starting with
AnyConnect version 3.1.05149, you can configure AnyConnect to evaluate the client's firewall and filter
rules, by adding a custom attribute named circumvent-host-filtering to a group profile, and setting it to
true.
When you create access lists:
•You can specify both IPv4 and IPv6 addresses in an access control list.
•If you use a standard ACL, only one address or network is used.
•If you use extended ACLs, the source network is the split-tunneling network. The destination
network is ignored.
•Access lists configured with any or with a split include or exclude of 0.0.0.0/0.0.0.0 or ::/0 will not
be sent to the client. To send all traffic over the tunnel, select Tunnel All Networks for the
split-tunnel Policy.
•Address 0.0.0.0/255.255.255.255 or ::/128 will be sent to the client only when the split-tunnel policy
is Exclude Network List Below. This configuration tells the client not to tunnel traffic destined for
any local subnets.
•AnyConnect passes traffic to all sites specified in the split tunneling policy, and to all sites that fall
within the same subnet as the IP address assigned by the ASA. For example, if the IP address
assigned by the ASA is 10.1.1.1 with a mask of 255.0.0.0, the endpoint device passes all traffic
destined to 10.0.0.0/8, regardless of the split tunneling policy. Therefore, use a netmask for the
assigned IP address that properly references the expected local subnet.
Prerequisites
•You must create an access list with ACLs and (optionally) ACEs.
•If you created a split tunnel policy for IPv4 networks and another for IPv6 networks, then the
network list you specify is used for both protocols. So, the network list should contain access control
entries (ACEs) for both IPv4 and IPv6 traffic. If you have not created these ACLs, see the “Adding
ACLs and ACEs” section on page 21-2 in the general operations configuration guide.

4-14
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 4 General VPN Setup
Group Policies
Note Split tunneling is a traffic management feature, not a security feature. For optimum security, we
recommend that you do not enable split tunneling.
In the following procedure, in all cases where there is an Inherit checkbox next to a field, leaving the
Inherit check box checked means that the group policy you are configuring will use the same values for
that field as the default group policy. Unchecking Inherit lets you specify new values specific to your
group policy.
Step 1 Connect to the ASA using ASDM and select Configuration > Remote Access VPN > Network (Client)
Access > Group Policies.
Step 2 Click Add to add a new group policy or select an existing group policy and click Edit.
Step 3 Select Advanced > Split Tunneling.
Step 4 In the DNS Names field, enter the domain names that are to be resolved by AnyConnect via the tunnel.
These names correspond to hosts in the private network. If split-include tunneling is configured, the
network list must include the specified DNS servers. You can enter a full qualified domain name, IPv4
or IPv6 address in the field.
Step 5 To disable split tunneling, select Ye s for Send All DNS Lookups Through Tunnel. This option ensures
that DNS traffic is not leaked to the physical adapter; it disallows traffic in the clear. If DNS resolution
fails, the address remains unresolved and the AnyConnect client does not try to resolve the address
outside the VPN.
To enable split tunneling, choose No (the default). This setting tells the client send DNS queries over the
tunnel according to the split tunnel policy.
Step 6 To configure split-tunneling by unchecking the Inherit check box and choosing a split-tunneling policy.
If you do not uncheck Inherit, your group policy uses the split tunneling settings defined in the default
group policy, DfltGrpPolicy. The default split tunneling policy setting in the default group policy is to
Tunnel All Networks.
To define the split tunneling policy, chose from the drop-downs Policy and IPv6 Policy. The Policy field
defines the split tunneling policy for IPv4 network traffic. The IPv6 Policy field selects the split
tunneling policy for IPv6 network traffic. Other than that difference, these fields have the same purpose.
Unchecking Inherit allows you to choose one of these policy options:
•Exclude Network List Below—Defines a list of networks to which traffic is sent in the clear. This
feature is useful for remote users who want to access devices on their local network, such as printers,
while they are connected to the corporate network through a tunnel.
•Tunnel Network List Below—Tunnels all traffic from or to the networks specified in the Network
List. Traffic to addresses in the include network list are tunneled. Data to all other addresses travels
in the clear and is routed by the remote user’s Internet service provider.
For versions of ASA 9.1.4 and higher, when you specify an include list, you can also specify an
exclude list that is a subnet inside the include range. Those excluded subnets will not be tunneled,
and the rest of the include list networks will be. Networks in the exclusion list that are not a subset
of the include list will be ignored by the client. For Linux, you must add a custom attribute to the
group policy to support excluded subnets.
For example:
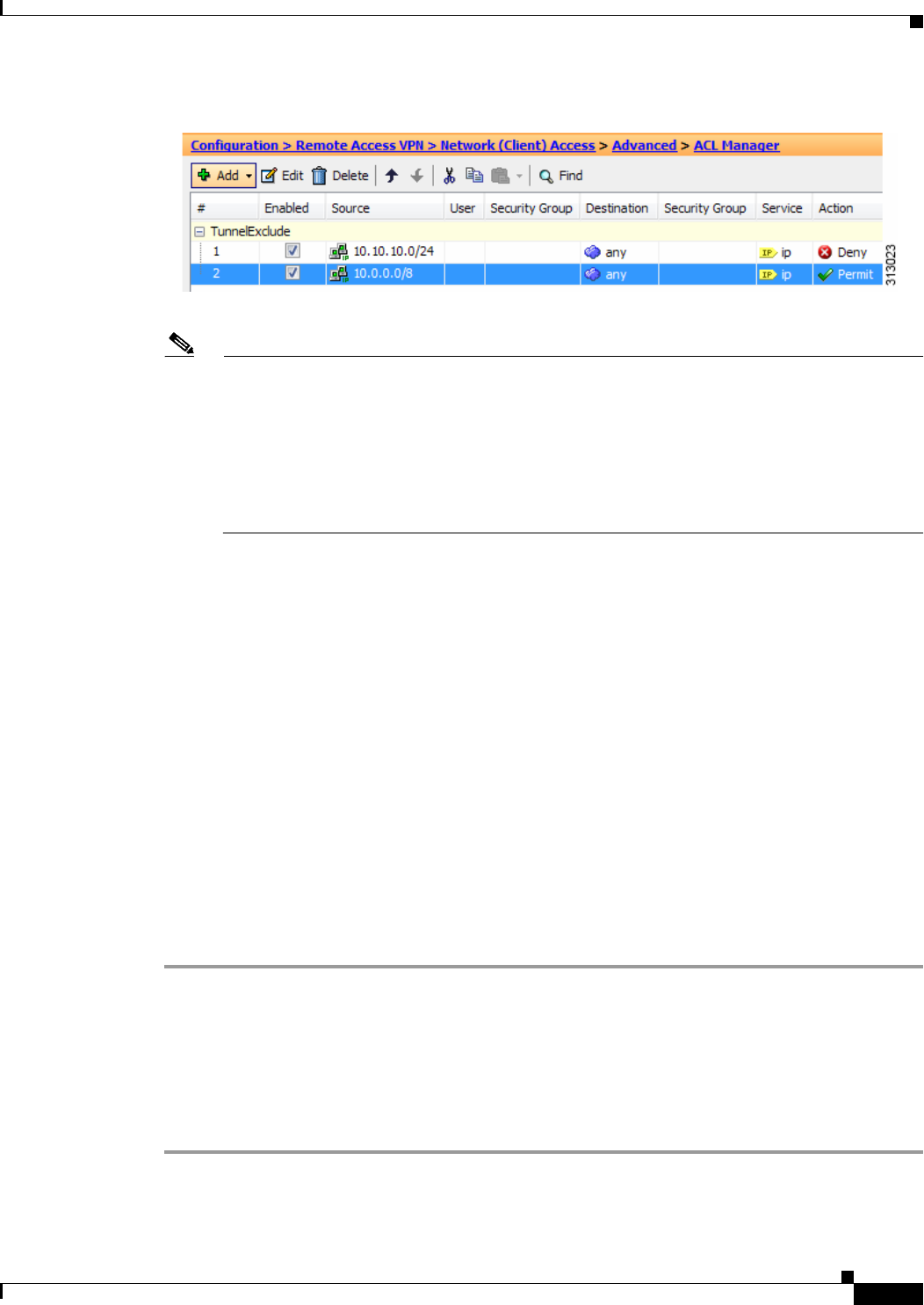
4-15
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 4 General VPN Setup
Group Policies
Note If the split-include network is an exact match of a local subnet (such as 192.168.1.0/24), the
corresponding traffic is tunneled. If the split-include network is a superset of a local subnet (such
as 192.168.0.0/16), the corresponding traffic, except the local subnet traffic, is tunneled. To also
tunnel the local subnet traffic, you must add a matching split-include network(specifying both
192.168.1.0/24 and 192.168.0.0/16 as split-include networks).
If the split-include network is invalid, such as 0.0.0.0/0.0.0.0, then split tunneling is disabled
(everything is tunneled).
•Tunnel All Networks—This policy specifies that all traffic is tunneled. This, in effect, disables split
tunneling. Remote users reach Internet networks through the corporate network and do not have
access to local networks. This is the default option.
Step 7 In the Network List field, select the access control list for the split-tunneling policy. If Inherit is
checked, the group policy uses the network list specified in the default group policy.
Select the Manage command button to open the ACL Manager dialog box, in which you can configure
access control lists to use as network lists. For more information about how to create or edit a network
list, see the “Adding ACLs and ACEs” section on page 21-2 in the general operations configuration
guide.
Extended ACL lists can contain both IPv4 and IPv6 addresses.
Step 8 The Intercept DHCP Configuration Message from Microsoft Clients reveals additional parameters
specific to DHCP Intercept. DHCP Intercept lets Microsoft XP clients use split-tunneling with the ASA.
•Intercept—Specifies whether to allow the DHCP Intercept to occur. If you do not select, Inherit, the
default setting is No.
•Subnet Mask—Selects the subnet mask to use.
Step 9 Click OK.
Configure Linux to Support Excluded Subnets
When Tunnel Network List Below is configured for split tunneling, Linux requires extra configuration
to support exclude subnets. You must create a custom attribute named circumvent-host-filtering, set it to
true, and associate with the group policy that is configured for split tunneling.
The following steps describe how to create the custom attribute.
Step 1 Connect to the ASDM, and select Configuration > Remote Access VPN > Network (Client) Access >
Advanced > AnyConnect Custom Attributes.

4-16
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 4 General VPN Setup
Group Policies
Step 2 Click Add, create a custom attribute named circumvent-host-filtering, and set the value to true.
Step 3 Edit the group policy you plan to use for client firewall, and select Advanced > AnyConnect Client >
Custom Attributes.
Step 4 Add the custom attribute that you created, circumvent-host-filtering, to the group policy you will use
for split tunneling.
Configuring VPN Policy Attributes for a Local User
To configure VPN policy attributes for a user, perform the following steps:
Detailed Steps
Step 1 Start ASDM and choose Configuration > Remote Access VPN > AAA/Local Users > Local Users.
Step 2 Select the user you want to configure and click Edit.
The Edit User Account dialog box appears.
Step 3 In the left-hand pane, click VPN Policy.
Step 4 Specify a group policy for the user. The user policy will inherit the attributes of this group policy. If there
are other fields that are set to inherit the configuration from the Default Group Policy, the attributes
specified in this group policy will take precedence over those set in the Default Group Policy.
Step 5 Specify which tunneling protocols are available for the user, or whether the value is inherited from the
group policy. Check the desired Tunneling Protocols check boxes to choose the VPN tunneling
protocols that you want to make available for use. The choices are as follows:
•Clientless SSL VPN (VPN via SSL/TLS) uses a web browser to establish a secure remote-access
tunnel to a VPN concentrator; this option requires neither a software nor hardware client. Clientless
SSL VPN can provide easy access to a broad range of enterprise resources, including corporate
websites, web-enabled applications, web-enabled NT/AD file shares, e-mail, and other TCP-based
applications from almost any computer that can reach secure Internet sites through HTTPS.
•The SSL VPN Client lets you connect after downloading the Cisco AnyConnect Client application.
You use a clientless SSL VPN connection to download this application the first time. Client updates
then occur automatically as needed whenever you connect.
•IPsec IKEv1—IP Security Protocol. Regarded as the most secure protocol, IPsec provides the most
complete architecture for VPN tunnels. Both site-to-site (peer-to-peer) connections and Cisco VPN
client-to-LAN connections can use IPsec IKEv1.
•IPsec IKEv2—Supported by the AnyConnect Secure Mobility Client. AnyConnect connections
using IPsec with IKEv2 provide advanced features such as software updates, client profiles, GUI
localization (translation) and customization, Cisco Secure Desktop, and SCEP proxy.
•L2TP over IPsec allows remote users with VPN clients provided with several common PC and
mobile PC operating systems to establish secure connections over the public IP network to the ASA
and private corporate networks.
Note If no protocol is selected, an error message appears.

4-17
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 4 General VPN Setup
Group Policies
Step 6 Specify which filter (IPv4 or IPv6) to use, or whether to inherit the value from the group policy. Filters
consist of rules that determine whether to allow or reject tunneled data packets coming through the ASA,
based on criteria such as source address, destination address, and protocol. To configure filters and rules,
choose Configuration > Remote Access VPN > Network (Client) Access > Group Policies >
Add/Edit > General > More Options > Filter.
Click Manage to display the ACL Manager pane, on which you can add, edit, and delete ACLs and
ACEs.
Step 7 Specify whether to inherit the Connection Profile (tunnel group) lock or to use the selected tunnel group
lock, if any. Selecting a specific lock restricts users to remote access through this group only. Tunnel
group lock restricts users by checking to see if the group configured in the VPN client is the same as the
users assigned group. If it is not, the ASA prevents the user from connecting. If the Inherit check box is
not checked, the default value is None.
Step 8 Specify whether to inherit the Store Password on Client System setting from the group. Uncheck the
Inherit check box to activate the Yes and No radio buttons. Click Ye s to store the login password on the
client system (potentially a less-secure option). Click No (the default) to require the user to enter the
password with each connection. For maximum security, we recommend that you not allow password
storage.
Step 9 Specify an Access Hours policy to apply to this user, create a new access hours policy for the user, or
leave the Inherit box checked. The default value is Inherit, or, if the Inherit check box is not checked,
the default value is Unrestricted.
Click Manage to open the Add Time Range dialog box, in which you can specify a new set of access
hours.
Step 10 Specify the number of simultaneous logins by the user. The simultaneous logins setting specifies the
maximum number of simultaneous logins allowed for this user. The default value is 3. The minimum
value is 0, which disables login and prevents user access.
Note While there is no maximum limit, allowing several simultaneous connections could compromise
security and affect performance.
Step 11 Specify the maximum connection time for the user connection time in minutes. At the end of this time,
the system terminates the connection. The minimum is 1 minute, and the maximum is 2147483647
minutes (over 4000 years). To allow unlimited connection time, check the Unlimited check box (the
default).
Step 12 Specify the idle timeout for the user in minutes. If there is no communication activity on the connection
by this user in this period, the system terminates the connection. The minimum time is 1 minute, and the
maximum time is 10080 minutes. This value does not apply to users of clientless SSL VPN connections.
Step 13 Configure the session alert interval. If you uncheck the Inherit check box, the Default check box is
checked automatically and the session alert interval is set to 30 minutes. If you want to specify a new
value, uncheck the Default check box and specify a session alert interval from 1 to 30 minutes in the
minutes box.
Step 14 Configure the idle alert interval. If you uncheck the Inherit check box, the Default check box is checked
automatically. This sets the idle alert interval to 30 minutes. If you want to specify a new value, uncheck
the Default check box and specify a session alert interval from 1 to 30 minutes in the minutes box.
Step 15 To set a dedicated IPv4 address for this user, enter an IPv4 address and subnet mask in the Dedicated
IPv4 Address (Optional) area.
Step 16 To set a dedicated IPv6 address for this user, enter an IPv6 address with an IPv6 prefix in the Dedicated
IPv6 Address (Optional) field. The IPv6 prefix indicates the subnet on which the IPv6 address resides.

4-18
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 4 General VPN Setup
Group Policies
Step 17 Click OK.
The changes are saved to the running configuration.
Configuring a Browser Proxy for an Internal Group Policy
Configuration > Remote Access VPN > Network (Client) Access > Group Policies > Add/Edit >
Advanced > Browser Proxy
This dialog box configures attributes for Microsoft Internet Explorer.
Fields
•Proxy Server Policy—Configures the Microsoft Internet Explorer browser proxy actions
(“methods”) for a client PC.
–
Do not modify client proxy settings—Leaves the HTTP browser proxy server setting in Internet
Explorer unchanged for this client PC.
–
Do not use proxy—Disables the HTTP proxy setting in Internet Explorer for the client PC.
–
Select proxy server settings from the following—Enables the following check boxes for your
selections: Auto detect proxy, Use proxy server settings given below, and Use proxy auto
configuration (PAC) given below.
–
Auto detect proxy—Enables the use of automatic proxy server detection in Internet Explorer for
the client PC.
–
Use proxy server settings specified below—Sets the HTTP proxy server setting in Internet
Explorer to use the value configured in the Proxy Server Name or IP Address field.
–
Use proxy auto configuration (PAC) given below—Specifies the use of the file specified in the
Proxy Auto Configuration (PAC) field as the source for auto configuration attributes.
•Proxy Server Settings—Configures the proxy server parameters for Microsoft clients using
Microsoft Internet Explorer.
–
Server Address and Port—Specifies the IP address or name and the port of an Microsoft Internet
Explorer server that is applied for this client PC.
–
Bypass Proxy Server for Local Addresses—Configures Microsoft Internet Explorer browser
proxy local-bypass settings for a client PC. Click Ye s to enable local bypass or No to disable
local bypass.
–
Exception List—Lists the server names and IP addresses that you want to exclude from proxy
server access. Enter the list of addresses that you do not want to have accessed through a proxy
server. This list corresponds to the Exceptions list in the Proxy Settings dialog box in Internet
Explorer.
•Proxy Auto Configuration Settings—The PAC URL specifies the URL of the auto-configuration file.
This file tells the browser where to look for proxy information. To use the proxy auto-configuration
(PAC) feature, the remote user must use the Cisco AnyConnect VPN client.
Many network environments define HTTP proxies that connect a web browser to a particular
network resource. The HTTP traffic can reach the network resource only if the proxy is specified in
the browser and the client routes the HTTP traffic to the proxy. SSLVPN tunnels complicate the
definition of HTTP proxies because the proxy required when tunneled to an enterprise network can
differ from that required when connected to the Internet via a broadband connection or when on a
third-party network.

4-19
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 4 General VPN Setup
Group Policies
In addition, companies with large networks might need to configure more than one proxy server and
let users choose between them, based on transient conditions. By using .pac files, an administrator
can author a single script file that determines which of numerous proxies to use for all client
computers throughout the enterprise.
The following are some examples of how you might use a PAC file:
–
Choosing a proxy at random from a list for load balancing.
–
Rotating proxies by time of day or day of the week to accommodate a server maintenance
schedule.
–
Specifying a backup proxy server to use in case the primary proxy fails.
–
Specifying the nearest proxy for roaming users, based on the local subnet.
You can use a text editor to create a proxy auto-configuration (.pac) file for your browser. A .pac file
is a JavaScript file that contains logic that specifies one or more proxy servers to be used, depending
on the contents of the URL. Use the PAC URL field to specify the URL from which to retrieve the
.pac file. Then the browser uses the .pac file to determine the proxy settings.
Configuring General AnyConnect Client Attributes for an Internal Group Policy
Clicking the AnyConnect Client icon in the group policy directory tree shows the list of configurable
attributes that follow. Configuring the ASA to distribute and manage AnyConnect client sessions is a
larger procedure than just setting these attribute fields in a group policy. See Configuring AnyConnect
VPN Client Connections, page 4-48, Configuring AnyConnect VPN Connections, page 4-57, and
Configuring AnyConnect Secure Mobility, page 4-69.
Fields
•Keep Installer on Client System—Enable permanent client installation on the remote computer.
Enabling disables the automatic uninstalling feature of the client. The client remains installed on the
remote computer for subsequent connections, reducing the connection time for the remote user.
Note Keep Installer on Client System is not supported after version 2.5 of the AnyConnect client.
•Datagram Transport Layer Security (DTLS)—Avoids latency and bandwidth problems associated
with some SSL connections and improves the performance of real-time applications that are
sensitive to packet delays.
•Ignore Don’t Defrag (DF) Bit—This feature allows the force fragmentation of packets that have the
DF bit set, allowing them to pass through the tunnel. An example use case is for servers in your
network that do not respond correctly to TCP MSS negotiations.
•Client Bypass Protocol—The Client Protocol Bypass feature allows you to configure how the ASA
manages IPv4 traffic when it is expecting only IPv6 traffic or how it manages IPv6 traffic when it is
expecting only IPv4 traffic.
When the AnyConnect client makes a VPN connection to the ASA, the ASA could assign it an IPv4,
IPv6, or both an IPv4 and IPv6 address. If the ASA assigns the AnyConnect connection only an IPv4
address or only an IPv6 address, you can now configure the Client Bypass Protocol to drop network
traffic for which the ASA did not assign an IP address, or allow that traffic to bypass the ASA and
be sent from the client unencrypted or “in the clear”.

4-20
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 4 General VPN Setup
Group Policies
For example, assume that the ASA assigns only an IPv4 address to an AnyConnect connection and
the endpoint is dual stacked. When the endpoint attempts to reach an IPv6 address, if Client Bypass
Protocol is disabled, the IPv6 traffic is dropped; however, if Client Bypass Protocol is enabled, the
IPv6 traffic is sent from the client in the clear.
•FQDN of This Device—This information is used by the client after network roaming in order to
resolve the ASA IP address used for re-establishing the VPN session. This setting is critical to
support roaming between networks of different IP protocols (such as IPv4 to IPv6).
Note You cannot use the ASA FQDN present in the AnyConnect profile to derive the ASA IP
address after roaming. The addresses may not match the correct device (the one the tunnel
was established to) in the load balancing scenario.
If the device FQDN is not pushed to the client, the client will try to reconnect to whatever IP address
the tunnel had previously established. In order to support roaming between networks of different IP
protocols (from IPv4 to IPv6), AnyConnect must perform name resolution of the device FQDN after
roaming, so that it can determine which ASA address to use for re-establishing the tunnel. The client
uses the ASA FQDN present in its profile during the initial connection. During subsequent session
reconnects, it always uses the device FQDN pushed by ASA (and configured by the administrator
in the group policy), when available. If the FQDN is not configured, the ASA derives the device
FQDN (and sends it to the client) from whatever is set under Device Setup > Device Name/Password
and Domain Name.
If the device FQDN is not pushed by the ASA, the client cannot re-establish the VPN session after
roaming between networks of different IP protocols.
•MTU—Adjusts the MTU size for SSL connections. Enter a value in bytes, from 256 to 1410 bytes.
By default, the MTU size is adjusted automatically based on the MTU of the interface that the
connection uses, minus the IP/UDP/DTLS overhead.
•Keepalive Messages—Enter a number, from 15 to 600 seconds, in the Interval field to enable and
adjust the interval of keepalive messages to ensure that an connection through a proxy, firewall, or
NAT device remains open, even if the device limits the time that the connection can be idle.
Adjusting the interval also ensures that the client does not disconnect and reconnect when the remote
user is not actively running a socket-based application, such as Microsoft Outlook or Microsoft
Internet Explorer.
•Optional Client Modules to Download—To minimize download time, the AnyConnect client
requests downloads (from the ASA) only of modules that it needs for each feature that it supports.
You must specify the names of modules that enable other features. The AnyConnect client, version
3.0, includes the following modules (previous versions have fewer modules):
–
AnyConnect DART—The Diagnostic AnyConnect Reporting Tool (DART) captures a snapshot
of system logs and other diagnostic information and creates a .zip file on your desktop so you
can conveniently send troubleshooting information to Cisco TAC.
–
AnyConnect Network Access Manager—Formerly called the Cisco Secure Services Client, this
module provides 802.1X (Layer 2) and device authentication for access to both wired and
wireless network is integrated into AnyConnect 3.0.
–
AnyConnect SBL—Start Before Logon (SBL) forces the user to connect to the enterprise
infrastructure over a VPN connection before logging on to Windows by starting AnyConnect
before the Windows login dialog box appears.
–
AnyConnect Web Security Module—Formerly called ScanSafe Hostscan, this module is
integrated into the AnyConnect 3.0.
4-21
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 4 General VPN Setup
Group Policies
–
AnyConnect Telemetry Module—Sends information about the origin of malicious content to the
web filtering infrastructure of the Cisco IronPort Web Security Appliance (WSA), which uses
this data to provide better URL filtering rules.
–
AnyConnect Posture Module—Formerly called the Cisco Secure Desktop HostScan feature, the
posture module is integrated into AnyConnect 3.0 and provides AnyConnect the ability to
gather credentials for posture assessment prior to creating a remote access connection to the
ASA.
•Always-On VPN—Determine if the always-on VPN flag setting in the AnyConnect service profile
is disabled or if the AnyConnect service profile setting should be used. The always-on VPN feature
lets AnyConnnect automatically establish a VPN session after the user logs onto a computer. The
VPN session remains up until the user logs off the computer. If the physical connection is lost, the
session remains up, and AnyConnect continually attempts to reestablish the physical connection
with the adaptive security appliance to resume the VPN session.
Always-on VPN permits the enforcement of corporate policies to protect the device from security
threats. You can use it to help ensure AnyConnect establishes a VPN session whenever the endpoint
is not in a trusted network. If enabled, a policy is configured to determine how network connectivity
is managed in the absence of a connection.
Note Always-On VPN requires an AnyConnect release that supports AnyConnect Secure
Mobility features. Refer to the Cisco AnyConnect VPN Client Administrator Guide for
additional information.
•Client Profiles to Download—A profile is a group of configuration parameters that the AnyConnect
client uses to configure VPN, Network Access Manager, web security, and telemetry settings. Click
Add to launch the Select Anyconnect Client Profiles window where you can specify
previously-created profiles for this group policy.
Configuring AnyConnect Login Settings for an Internal Group Policy
In this dialog box, you can enable the ASA to prompt remote users to download the AnyConnect client
or go to a Clientless SSL VPN portal page. Figure 4-1 shows the prompt displayed:
Figure 4-1 Prompt Displayed to Remote Users for AnyConnect Client Download
Fields
•Post Login Setting—Choose to prompt the user and set the timeout to perform the default post login
selection.
•Default Post Login Selection—Choose an action to perform after login.

4-22
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 4 General VPN Setup
Group Policies
Configuring AnyConnect Client Client Firewall Attributes for an Internal Group Policy
In ASA 9.0 and later releases, access control lists for client firewalls support both access control entries
for both IPv4 and IPv6 addresses.
See Client Firewall with Local Printer and Tethered Device Support, page 4-43 to configure the group
policy for these situations.
Configuring AnyConnect Client Key Regeneration for an Internal Group Policy
Rekey Negotiation occurs when the security appliance and the client perform a rekey and they
renegotiate the crypto keys and initialization vectors, increasing the security of the connection.
Fields
•Renegotiation Interval—Uncheck the Unlimited check box to specify the number of minutes from
the start of the session until the rekey takes place, from 1 to 10080 (1 week).
•Renegotiation Method—Uncheck the Inherit check box to specify a renegotiation method different
from the default group policy. Select the None radio button to disable rekey, select either the SSL
or New Tunnel radio button to establish a new tunnel during rekey.
Note Configuring the Renegotiation Method as SSL or New Tunnel specifies that the client
establishes a new tunnel during rekey instead of the SSL renegotiation taking place during
the rekey. See the Cisco ASA 5500 Series Command Reference, 8.4 for a history of the
anyconnect ssl rekey command.
Configuring AnyConnect Client Dead Peer Detection for an Internal Group Policy
Dead Peer Detection (DPD) ensures that the security appliance (gateway) or the client can quickly detect
a condition where the peer is not responding, and the connection has failed.
If DPD is enabled on the ASA, you can use the Optimal MTU (OMTU) function to find the largest
endpoint MTU at which the client can successfully pass DTLS packets. Implement OMTU by sending a
padded DPD packet to the maximum MTU. If a correct echo of the payload is received from the head
end, the MTU size is accepted. Otherwise, the MTU is reduced, and the probe is sent again until the
minimum MTU allowed for the protocol is reached.
Note Using OMTU does not interfere with the existing tunnel DPD function.
Limitations
This feature does not work with IPsec, since DPD is based on the standards implementation that does
not allow padding.
Fields
•Gateway Side Detection—Uncheck the Disable check box to specify that DPD is performed by the
security appliance (gateway). Enter the interval, from 30 to 3600 seconds, with which the security
appliance performs DPD.
•Client Side Detection—Uncheck the Disable check box to specify that DPD is performed by the
client. Enter the interval, from 30 to 3600 seconds, with which the client performs DPD.
4-23
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 4 General VPN Setup
Group Policies
Customizing a VPN Access Portal for an Internal Group Policy
To configure customization for a group policy, select a preconfigured portal customization object, or
accept the customization provided in the default group policy. You can also configure a URL to display
Fields
•Portal Customization—Selects the customization to apply to the AnyConnect Client/SSL VPN
portal page. The default is DfltCustomization.
–
Inherit—To inherit a portal customization from the default group policy, check Inherit. To
specify a previously configured customization object, uncheck Inherit and choose the
customization object from the drop-down list.
–
Manage—Opens the Configure GUI Customization objects dialog box, in which you can
specify that you want to add, edit, delete, import, or export a customization object.
•Homepage URL (optional)—To specify a homepage URL for users associated with the group policy,
enter it in this field. The string must begin with either http:// or https://. To inherit a home page from
the default group policy, click Inherit. Clientless users are immediately brought to this page after
successful authentication. AnyConnect launches the default web browser to this URL upon
successful establishment of the VPN connection.
Note AnyConnect does not currently support this field on the Linux platform, Android mobile
devices, and Apple iOS mobile devices. If set, it will be ignored by these AnyConnect clients.
•Access Deny Message—To create a message to users for whom access is denied, enter it in this field.
To accept the message in the default group policy, click Inherit.
The default message, if you deselect Inherit, is: “Login was successful, but because certain criteria
have not been met or due to some specific group policy, you do not have permission to use any of
the VPN features. Contact your IT administrator for more information.”
Configuring AnyConnect Client Custom Attributes for an Internal Group Policy
This dialog box lists the custom attributes that are assigned to this group policy. Custom attributes can
be created in this dialog, or on Configuration > Remote Access VPN > Network (Client) Access >
Advanced > AnyConnect Custom Attributes. In this dialog, you can add custom attributes to this group
policy, and define values for those attributes.
For AnyConnect 3.1, custom attributes are available to support AnyConnect Deferred Upgrade and
Phone Home.
See the Cisco AnyConnect Secure Mobility Client Administrator Guide, Release 3.1, Chapter 2, “User
Control Over Upgrade” for more information about the deferred upgrade custom attributes.
IPsec (IKEv1) Client
Configuring IPsec (IKEv1) Client General Attributes for an Internal Group Policy
Configuration > Remote Access > Network (Client) Access > Group Policies > Advanced > IPsec
(IKEv1) Client
The Add or Edit Group Policy > IPsec dialog box lets you specify tunneling protocols, filters, connection
settings, and servers for the group policy being added or modified.
4-24
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 4 General VPN Setup
Group Policies
Fields
•Re-Authentication on IKE Re-key—Enables or disables reauthentication when IKE re-key occurs,
unless the Inherit check box is checked. The user has 30 seconds to enter credentials, and up to three
attempts before the SA expires at approximately two minutes and the tunnel terminates.
•Allow entry of authentication credentials until SA expires—Allows users the time to reenter
authentication credentials until the maximum lifetime of the configured SA.
•IP Compression—Enables or disables IP Compression, unless the Inherit check box is checked.
•Perfect Forward Secrecy—Enables or disables perfect forward secrecy (PFS), unless the Inherit
check box is selected. PFS ensures that the key for a given IPsec SA was not derived from any other
secret (like some other keys). In other words, if someone were to break a key, PFS ensures that the
attacker would not be able to derive any other key. If PFS were not enabled, someone could
hypothetically break the IKE SA secret key, copy all the IPsec protected data, and then use
knowledge of the IKE SA secret to compromise the IPsec SAs set up by this IKE SA. With PFS,
breaking IKE would not give an attacker immediate access to IPsec. The attacker would have to
break each IPsec SA individually.
•Store Password on Client System—Enables or disables storing the password on the client system.
Note Storing the password on a client system can constitute a potential security risk.
•IPsec over UDP—Enables or disables using IPsec over UDP.
•IPsec over UDP Port—Specifies the UDP port to use for IPsec over UDP.
•Tunnel Group Lock—Enables locking the tunnel group you select from the list, unless the Inherit
check box or the value None is selected.
•IPsec Backup Servers—Activates the Server Configuration and Server IP Addresses fields, so you
can specify the UDP backup servers to use if these values are not inherited.
–
Server Configuration—Lists the server configuration options to use as an IPsec backup server.
The available options are: Keep Client Configuration (the default), Use the Backup Servers
Below, and Clear Client Configuration.
–
Server Addresses (space delimited)—Specifies the IP addresses of the IPsec backup servers.
This field is available only when the value of the Server Configuration selection is Use the
Backup Servers Below.
Configuring IPsec (IKEv1) Client Client Access Rules for an Internal Group Policy
The Client Access Rules table on this dialog box lets you view up to 25 client access rules. If you
uncheck the Inherit check box, the Add, Edit, and Delete buttons become active and the following
column headings appear in the table:
•Priority—Shows the priority for this rule.
•Action—Specifies whether this rule permits or denies access.
•VPN Client Type—Specifies the type of VPN client to which this rule applies, software or hardware,
and for software clients, all Windows clients or a subset.
•VPN Client Version—Specifies the version or versions of the VPN client to which this rule applies.
This column contains a comma-separated list of software or firmware images appropriate for this
client.

4-25
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 4 General VPN Setup
Group Policies
Configuring IPsec (IKEv1) Client Client Firewall Attributes for an Internal Group Policy
Configuration > Remote Access > Network (Client) Access > Group Policies > Advanced > IPsec
(IKEv1) Client > Client Firewall Tab
The Add or Edit Group Policy Client Firewall dialog box lets you configure firewall settings for VPN
clients for the group policy being added or modified.
Note Only VPN clients running Microsoft Windows can use these firewall features. They are currently not
available to hardware clients or other (non-Windows) software clients.
A firewall isolates and protects a computer from the Internet by inspecting each inbound and outbound
individual packet of data to determine whether to allow or drop it. Firewalls provide extra security if
remote users in a group have split tunneling configured. In this case, the firewall protects the user’s PC,
and thereby the corporate network, from intrusions by way of the Internet or the user’s local LAN.
Remote users connecting to the ASA with the VPN client can choose the appropriate firewall option.
In the first scenario, a remote user has a personal firewall installed on the PC. The VPN client enforces
firewall policy defined on the local firewall, and it monitors that firewall to make sure it is running. If
the firewall stops running, the VPN client drops the connection to the ASA. (This firewall enforcement
mechanism is called Are You There (AYT), because the VPN client monitors the firewall by sending it
periodic “are you there?” messages; if no reply comes, the VPN client knows the firewall is down and
terminates its connection to the ASA.) The network administrator might configure these PC firewalls
originally, but with this approach, each user can customize his or her own configuration.
In the second scenario, you might prefer to enforce a centralized firewall policy for personal firewalls
on VPN client PCs. A common example would be to block Internet traffic to remote PCs in a group using
split tunneling. This approach protects the PCs, and therefore the central site, from intrusions from the
Internet while tunnels are established. This firewall scenario is called push policy or Central Protection
Policy (CPP). On the ASA, you create a set of traffic management rules to enforce on the VPN client,
associate those rules with a filter, and designate that filter as the firewall policy. The ASA pushes this
policy down to the VPN client. The VPN client then in turn passes the policy to the local firewall, which
enforces it.
Fields
•Inherit—Determines whether the group policy obtains its client firewall setting from the default
group policy. This option is the default setting. When set, it overrides the remaining attributes in this
dialog boxing dims their names.
•Client Firewall Attributes—Specifies the client firewall attributes, including what type of firewall
(if any) is implemented and the firewall policy for that firewall.
•Firewall Setting—Lists whether a firewall exists, and if so, whether it is required or optional. If you
select No Firewall (the default), none of the remaining fields on this dialog box are active. If you
want users in this group to be firewall-protected, select either the Firewall Required or Firewall
Optional setting.
If you choose Firewall Required, all users in this group must use the designated firewall. The ASA
drops any session that attempts to connect without the designated, supported firewall installed and
running. In this case, the ASA notifies the VPN client that its firewall configuration does not match.
Note If you require a firewall for a group, make sure the group does not include any clients other than
Windows VPN clients. Any other clients in the group (including ASA 5505 in client mode and
VPN 3002 hardware clients) are unable to connect.

4-26
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 4 General VPN Setup
Group Policies
If you have remote users in this group who do not yet have firewall capacity, choose Firewall
Optional. The Firewall Optional setting allows all the users in the group to connect. Those who have
a firewall can use it; users that connect without a firewall receive a warning message. This setting is
useful if you are creating a group in which some users have firewall support and others do not—for
example, you may have a group that is in gradual transition, in which some members have set up
firewall capacity and others have not yet done so.
•Firewall Type—Lists firewalls from several vendors, including Cisco. If you select Custom Firewall,
the fields under Custom Firewall become active. The firewall you designate must correlate with the
firewall policies available. The specific firewall you configure determines which firewall policy
options are supported.
•Custom Firewall—Specifies the vendor ID, Product ID and description for the custom firewall.
–
Vendor ID—Specifies the vendor of the custom firewall for this group policy.
–
Product ID—Specifies the product or model name of the custom firewall being configured for
this group policy.
–
Description—(Optional) Describes the custom firewall.
•Firewall Policy—Specifies the type and source for the custom firewall policy.
–
Policy defined by remote firewall (AYT)—Specifies that the firewall policy is defined by the
remote firewall (Are You There). Policy defined by remote firewall (AYT) means that remote
users in this group have firewalls located on their PCs. The local firewall enforces the firewall
policy on the VPN client. The ASA allows VPN clients in this group to connect only if they
have the designated firewall installed and running. If the designated firewall is not running, the
connection fails. Once the connection is established, the VPN client polls the firewall every 30
seconds to make sure that it is still running. If the firewall stops running, the VPN client ends
the session.
–
Policy pushed (CPP)—Specifies that the policy is pushed from the peer. If you choose this
option, the Inbound Traffic Policy and Outbound Traffic Policy lists and the Manage button
become active. The ASA enforces on the VPN clients in this group the traffic management rules
defined by the filter you choose from the Policy Pushed (CPP) drop-down menu. The choices
available on the menu are filters defined on this ASA, including the default filters. Keep in mind
that the ASA pushes these rules down to the VPN client, so you should create and define these
rules relative to the VPN client, not the ASA. For example, “in” and “out” refer to traffic coming
into the VPN client or going outbound from the VPN client. If the VPN client also has a local
firewall, the policy pushed from the ASA works with the policy of the local firewall. Any packet
that is blocked by the rules of either firewall is dropped.
–
Inbound Traffic Policy—Lists the available push policies for inbound traffic.
–
Outbound Traffic Policy—Lists the available push policies for outbound traffic.
–
Manage—Displays the ACL Manager dialog box, in which you can configure Access Control
Lists (ACLs).
Configuring IPsec (IKEv1) Client Hardware Client Attributes for an Internal Group Policy
Configuration > Remote Access > Network (Client) Access > Group Policies > Advanced > IPsec
(IKEv1) Client > Hardware Client
The Add or Edit Group Policy > Hardware Client dialog box lets you configure settings for the VPN
3002 hardware client for the group policy being added or modified. The Hardware Client dialog box
parameters do not pertain to the ASA 5505 in client mode.

4-27
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 4 General VPN Setup
Group Policies
Fields
•Inherit—(Multiple instances) Indicates that the corresponding setting takes its value from the
default group policy, rather than from the explicit specifications that follow. This is the default
setting for all attributes in this dialog box.
•Require Interactive Client Authentication—Enables or disables the requirement for interactive
client authentication. This parameter is disabled by default. Interactive hardware client
authentication provides additional security by requiring the VPN 3002 to authenticate with a
username and password that you enter manually each time the VPN 3002 initiates a tunnel. With
this feature enabled, the VPN 3002 does not have a saved username and password. When you enter
the username and password, the VPN 3002 sends these credentials to the ASA to which it connects.
The ASA facilitates authentication, on either the internal or an external authentication server. If the
username and password are valid, the tunnel is established.
When you enable interactive hardware client authentication for a group, the ASA pushes that policy
to the VPN 3002s in the group. If you have previously set a username and password on the VPN
3002, the software deletes them from the configuration file. When you try to connect, the software
prompts you for a username and password.
If, on the ASA, you subsequently disable interactive hardware authentication for the group, it is
enabled locally on the VPN 3002s, and the software continues to prompt for a username and
password. This lets the VPN 3002 connect, even though it lacks a saved username and password,
and the ASA has disabled interactive hardware client authentication. If you subsequently configure
a username and password, the feature is disabled, and the prompt no longer appears. The VPN 3002
connects to the ASA using the saved username and password.
•Require Individual User Authentication—Enables or disables the requirement for individual user
authentication for users behind ASA 5505 in client mode or the VPN 3002 hardware client in the
group. To display a banner to hardware clients in a group, individual user authentication must be
enabled. This parameter is disabled by default.
Individual user authentication protects the central site from access by unauthorized persons on the
private network of the hardware client. When you enable individual user authentication, each user
that connects through a hardware client must open a web browser and manually enter a valid
username and password to access the network behind the ASA, even though the tunnel already
exists.
Note You cannot use the command-line interface to log in if user authentication is enabled. You must
use a browser.
If you have a default home page on the remote network behind the ASA, or if you direct the browser
to a website on the remote network behind the ASA, the hardware client directs the browser to the
proper pages for user login. When you successfully log in, the browser displays the page you
originally entered.
If you try to access resources on the network behind the ASA that are not web-based, for example,
e-mail, the connection fails until you authenticate using a browser.
To authenticate, you must enter the IP address for the private interface of the hardware client in the
browser Location or Address field. The browser then displays the login dialog box for the hardware
client. To authenticate, click Connect/Login Status.
One user can log in for a maximum of four sessions simultaneously. Individual users authenticate
according to the order of authentication servers configured for a group.

4-28
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 4 General VPN Setup
Group Policies
•User Authentication Idle Timeout—Configures a user timeout period. The security appliance
terminates the connection if it does not receive user traffic during this period. You can specify that
the timeout period is a specific number of minutes or unlimited.
–
Unlimited—Specifies that the connection never times out. This option prevents inheriting a
value from a default or specified group policy.
–
Minutes—Specifies the timeout period in minutes. Use an integer between 1 and 35791394. The
default value is Unlimited.
Note that the idle timeout indicated in response to the show uauth command is always the idle
timeout value of the user who authenticated the tunnel on the Cisco Easy VPN remote device.
•Cisco IP Phone Bypass—Lets Cisco IP Phones bypass the interactive individual user authentication
processes. If enabled, interactive hardware client authentication remains in effect. Cisco IP Phone
Bypass is disabled by default.
Note You must configure the ASA 5505 in client mode or the VPN 3002 hardware client to use
network extension mode for IP phone connections.
•LEAP Bypass—Lets LEAP packets from Cisco wireless devices bypass the individual user
authentication processes (if enabled). LEAP Bypass lets LEAP packets from devices behind a
hardware client travel across a VPN tunnel prior to individual user authentication. This lets
workstations using Cisco wireless access point devices establish LEAP authentication. Then they
authenticate again per individual user authentication (if enabled). LEAP Bypass is disabled by
default.
Note This feature does not work as intended if you enable interactive hardware client authentication.
IEEE 802.1X is a standard for authentication on wired and wireless networks. It provides wireless
LANs with strong mutual authentication between clients and authentication servers, which can
provide dynamic per-user, per-session wireless encryption privacy (WEP) keys, removing
administrative burdens and security issues that are present with static WEP keys.
Cisco Systems has developed an 802.1X wireless authentication type called Cisco LEAP. LEAP
implements mutual authentication between a wireless client on one side of a connection and a
RADIUS server on the other side. The credentials used for authentication, including a password, are
always encrypted before they are transmitted over the wireless medium.
Note Cisco LEAP authenticates wireless clients to RADIUS servers. It does not include RADIUS
accounting services.
LEAP users behind a hardware client have a circular dilemma: they cannot negotiate LEAP
authentication because they cannot send their credentials to the RADIUS server behind the central
site device over the tunnel. The reason they cannot send their credentials over the tunnel is that they
have not authenticated on the wireless network. To solve this problem, LEAP Bypass lets LEAP
packets, and only LEAP packets, traverse the tunnel to authenticate the wireless connection to a
RADIUS server before individual users authenticate. Then the users proceed with individual user
authentication.
LEAP Bypass works as intended under the following conditions:

4-29
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 4 General VPN Setup
Group Policies
–
The interactive unit authentication feature (intended for wired devices) must be disabled. If
interactive unit authentication is enabled, a non-LEAP (wired) device must authenticate the
hardware client before LEAP devices can connect using that tunnel.
–
Individual user authentication is enabled (if it is not, you do not need LEAP Bypass).
–
Access points in the wireless environment must be Cisco Aironet Access Points. The wireless
NIC cards for PCs can be other brands.
–
The Cisco Aironet Access Point must be running Cisco Discovery Protocol (CDP).
–
The ASA 5505 or VPN 3002 can operate in either client mode or network extension mode.
–
LEAP packets travel over the tunnel to a RADIUS server via ports 1645 or 1812.
Note Allowing any unauthenticated traffic to traverse the tunnel might pose a security risk.
•Allow C—Restricts the use of Network Extension Mode on the hardware client. Choose the option
to let hardware clients use Network Extension Mode. Network Extension Mode is required for the
hardware client to support IP phone connections, because the Call Manager can communicate only
with actual IP addresses.
Note If you disable network extension mode, the default setting, the hardware client can connect to
this ASA in PAT mode only. If you disallow network extension mode here, be careful to
configure all hardware clients in a group for PAT mode. If a hardware client is configured to use
Network Extension Mode and the ASA to which it connects disables Network Extension Mode,
the hardware client attempts to connect every 4 seconds, and every attempt is rejected. In this
situation, the hardware client puts an unnecessary processing load on the ASA to which it
connects; large numbers of hardware clients that are misconfigured in this way reduces the
ability of the security appliance to provide service.
Configuring Clientless SSL VPN Internal Group Policies
Configuring Clientless SSL VPN General Attributes for an Internal Group Policy
Configuration > Remote Access VPN > Clientless SSL VPN Access > Group Policies > Add/Edit >
Add or Edit Internal Group Policy > General
The Add or Edit Group Policy dialog box lets you specify tunneling protocols, filters, connection
settings, and servers for the group policy being added or modified. For each of the fields on this dialog
box, checking the Inherit check box lets the corresponding setting take its value from the default group
policy. Inherit is the default value for all of the attributes in this dialog box.
Fields
The following attributes appear in the Add Internal Group Policy > General dialog box. They apply to
SSL VPN and IPsec sessions, or clientless SSL VPN sessions. Thus, several are present for one type of
session, but not the other.
•Name—Specifies the name of this group policy up to 64 characters; spaces are allowed. For the Edit
function, this field is read-only.
•Banner—Specifies the banner text to present to users at login. The length can be up to 491
characters. There is no default value.

4-30
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 4 General VPN Setup
Group Policies
The IPsec VPN client supports full HTML for the banner. However, the clientless portal and the
AnyConnect client support partial HTML. To ensure the banner displays properly to remote users,
follow these guidelines:
–
For clientless users, use the <BR> tag.
•Tunneling Protocols—Specifies the tunneling protocols that this group can use. Users can use only
the selected protocols. The choices are as follows:
–
Clientless SSL VPN—Specifies the use of VPN via SSL/TLS, which uses a web browser to
establish a secure remote-access tunnel to an ASA; requires neither a software nor hardware
client. Clientless SSL VPN can provide easy access to a broad range of enterprise resources,
including corporate websites, web-enabled applications, NT/AD file share (web-enabled),
e-mail, and other TCP-based applications from almost any computer that can reach HTTPS
Internet sites.
–
SSL VPN Client—Specifies the use of the Cisco AnyConnect VPN client or the legacy SSL
VPN client. If you are using the AnyConnect client, you must choose this protocol for MUS to
be supported.
–
IPsec IKEv1—IP Security Protocol. Regarded as the most secure protocol, IPsec provides the
most complete architecture for VPN tunnels. Both Site-to-Site (peer-to-peer) connections and
Cisco VPN client-to-LAN connections can use IPsec IKEv1.
–
IPsec IKEv2—Supported by the AnyConnect Secure Mobility Client. AnyConnect connections
using IPsec with IKEv2 provide advanced features such as software updates, client profiles,
GUI localization (translation) and customization, Cisco Secure Desktop, and SCEP proxy.
–
L2TP over IPsec—Allows remote users with VPN clients provided with several common PC
and mobile PC operating systems to establish secure connections over the public IP network
to the security appliance and private corporate networks. L2TP uses PPP over UDP (port 1701)
to tunnel the data. The security appliance must be configured for IPsec transport mode.
Note If you do not select a protocol, an error message appears.
•Web ACL—(Clientless SSL VPN only) Choose an access control list (ACL) from the drop-down list
if you want to filter traffic. Click Manage next to the list if you want to view, modify, add, or remove
ACLs before making a selection.
•Manage—Displays the ACL Manager dialog box, with which you can add, edit, and delete Access
Control Lists (ACLs) and Extended Access Control Lists (ACEs). For more information about the
ACL Manager, see the online Help for that dialog box.
•Access Hours—Selects the name of an existing access hours policy, if any, applied to this user or
create a new access hours policy. The default value is Inherit, or, if the Inherit check box is not
checked, the default value is --Unrestricted--.
•Manage—Opens the Browse Time Range dialog box, in which you can add, edit, or delete a time
range. See Defining Time Ranges, page 4-35 for more information.
•Simultaneous Logins—Specifies the maximum number of simultaneous logins allowed for this user.
The default value is 3. The minimum value is 0, which disables login and prevents user access.
Note While there is no maximum limit, allowing several simultaneous connections might
compromise security and affect performance.

4-31
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 4 General VPN Setup
Group Policies
•Restrict Access to VLAN—(Optional) Also called “VLAN mapping,” this parameter specifies the
egress VLAN interface for sessions to which this group policy applies. The ASA forwards all traffic
on this group to the selected VLAN. Use this attribute to assign a VLAN to the group policy to
simplify access control. Assigning a value to this attribute is an alternative to using ACLs to filter
traffic on a session. In addition to the default value (Unrestricted), the drop-down list shows only
the VLANs that are configured on this ASA.
Note This feature works for HTTP connections, but not for FTP and CIFS.
•Connection Profile (Tunnel Group) Lock—This parameter permits remote VPN access only with the
selected connection profile (tunnel group), and prevents access with a different connection profile.
The default inherited value is None.
•Maximum Connect Time—If the Inherit check box is not checked, this parameter specifies the
maximum user connection time in minutes. At the end of this time, the system terminates the
connection. The minimum is 1 minute, and the maximum is 35791394 minutes (over 4000 years).
To allow unlimited connection time, check Unlimited (the default).
•Idle Timeout—If the Inherit check box is not checked, this parameter specifies this user’s idle
timeout period in minutes. If there is no communication activity on the user connection in this
period, the system terminates the connection. The minimum time is 1 minute, and the maximum time
is 10080 minutes. The default is 30 minutes. To allow unlimited connection time, check Unlimited.
This value does not apply to Clientless SSL VPN users.
•Session Alert Interval— If you uncheck the Inherit check box, the Default checkbox is checked
automatically. This sets the session alert interval to 30 minutes. If you want to specify a new value,
uncheck the Default check box and specify a session alert interval from 1 to 30 minutes in the
minutes box.
•Idle Alert Interval—If you uncheck the Inherit check box, the Default checkbox is checked
automatically. This sets the idle alert interval to 30 minutes. If you want to specify a new value,
uncheck the Default check box and specify a session alert interval from 1 to 30 minutes in the
minutes box.
Configuring the Clientless SSL VPN Access Portal for an Internal Group Policy
The Portal attributes determine what appears on the portal page for members of this group policy
establishing Clientless SSL VPN connections. In this pane, you can enable Bookmark lists and URL
Entry, file server access, Port Forwarding and Smart Tunnels, ActiveX Relay, and HTTP settings.
Fields
•Bookmark List—Choose a previously-configured Bookmark list or click Manage to create a new
one. Bookmarks appear as links, from which users can navigate from the portal page.
•URL Entry—Enable to allow remote users to enter URLs directly into the portal URL field.
•File Access Control—Controls the visibility of “hidden shares” for Common Internet File System
(CIFS) files. A hidden share is identified by a dollar sign ($) at the end of the share name. For
example, drive C is shared as C$. With hidden shares, a shared folder is not displayed, and users are
restricted from browsing or accessing these hidden resources.
–
File Server Entry—Enable to allow remote users to enter the name of a file server.
–
File Server Browsing—Enable to allow remote users to browse for available file servers.
–
Hidden Share Access—Enable to hide shared folders.

4-32
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 4 General VPN Setup
Group Policies
•Port Forwarding Control—Provides users access to TCP-based applications over a Clientless SSL
VPN connection through a Java Applet.
–
Port Forwarding List—Choose a previously-configured list TCP applications to associate with
this group policy. Click Manage to create a new list or to edit an existing list.
–
Auto Applet Download—Enables automatic installation and starting of the Applet the first time
the user logs in.
–
Applet Name—Changes the name of the title bar that of the Applet dialog box to the name you
designate. By default, the name is Application Access.
•Smart Tunnel—Specify your smart tunnel options using a clientless (browser-based) SSL VPN
session with the ASA as the pathway and the security appliance as a proxy server:
–
Smart Tunnel Policy—Choose from the network list and specify one of the tunnels options: use
smart tunnel for the specified network, do not use smart tunnel for the specified network, or use
tunnel for all network traffic. Assigning a smart tunnel network to a group policy or username
enables smart tunnel access for all users whose sessions are associated with the group policy or
username but restricts smart tunnel access to the applications specified in the list. To view, add,
modify, or delete a smart tunnel list, click Manage.
–
Smart Tunnel Application—Choose from the drop-down menu to connect a Winsock 2,
TCP-based application installed on the end station to a server on the intranet. To view, add,
modify, or delete a smart tunnel application, click Manage.
–
Smart Tunnel all Applications—Check this check box to tunnel all applications. All
applications are tunneled without choosing from the network list or knowing which executables
an end user may invoke for external applications.
–
Auto Start—Check this check box to start smart tunnel access automatically upon user login.
This option to start smart tunnel access upon user login applies only to Windows. Uncheck the
check box to enable smart tunnel access upon user login but require the user to start it manually,
using the Application Access > Start Smart Tunnels button on the Clientless SSL VPN Portal
Page.
–
Auto Sign-on Server List—Choose the list name from the drop-down menu if you want to
reissue the user credentials when the user establishes a smart tunnel connection to a server. Each
smart tunnel auto sign-on list entry identifies a server with which to automate the submission
of user credentials. To view, add, modify, or delete a smart tunnel auto sign-on list, click
Manage.
–
Windows Domain Name (Optional)—Specify the Windows domain to add it to the username
during auto sign-on, if the universal naming convention (domain\username) is required for
authentication. For example, enter CISCO to specify CISCO\qa_team when authenticating for
the username qu_team. You must also check the “Use Windows domain name with user name”
option when configuring associated entries in the auto sign-on server list.
•ActiveX Relay—Lets Clientless users launch Microsoft Office applications from the browser. The
applications use the session to download and upload Microsoft Office documents. The ActiveX relay
remains in force until the Clientless SSL VPN session closes.
More Options:
•HTTP Proxy—Enables or disables the forwarding of an HTTP applet proxy to the client. The proxy
is useful for technologies that interfere with proper content transformation, such as Java, ActiveX,
and Flash. It bypasses mangling while ensuring the continued use of the security appliance.
The forwarded proxy automatically modifies the old browser proxy configuration and redirects all
HTTP and HTTPS requests to the new proxy configuration. It supports virtually all client side
technologies, including HTML, CSS, JavaScript, VBScript, ActiveX, and Java. The only browser it
supports is Microsoft Internet Explorer.

4-33
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 4 General VPN Setup
Group Policies
•Auto Start (HTTP Proxy)—Check to enable HTTP Proxy automatically upon user login. Uncheck
to enable smart tunnel access upon user login, but require the user to start it manually.
•HTTP Compression—Enables compression of HTTP data over the Clientless SSL VPN session.
Configuring Portal Customization for a Clientless SSL VPN Internal Group Policy
To configure customization for a group policy, select a preconfigured portal customization object, or
accept the customization provided in the default group policy. You can also configure a URL to display.
The procedure for customizing an access portal for a Clientless SSL VPN Access connection is the same
as it is for a Network Client Access connection. See Customizing a VPN Access Portal for an Internal
Group Policy, page 4-23.
Configuring Login Settings for a Clientless SSL VPN Internal Group Policy
In this dialog box, you can enable the ASA to prompt remote users to download the AnyConnect client
or go to a Clientless SSL VPN portal page. See Configuring AnyConnect Login Settings for an Internal
Group Policy, page 4-21.
Configuring Single Signon and Auto Signon Servers for a Clientless SSL VPN Access Internal Group
Policy
To configure single sign-on servers and Auto sign-on servers, see “Auto Signon” in Chapter 71,
“Clientless SSL VPN” in Cisco ASA 5500 Series Configuration Guide using ASDM, 6.4 and 6.6 or
“Using Single Sign-on with Clientless SSL VPN” in Chapter 73 of Cisco ASA 5500 Series Configuration
Guide using the CLI, 8.4 and 8.6.
Configuring Session Settings for Clientless SSL VPN Access
The clientless SSL VPN Add/Edit Internal Group Policy > More Options > Session Settings window lets
you specify personalized user information between clientless SSL VPN sessions. By default, each group
policy inherits the settings from the default group policy. Use this window to specify personalized
clientless SSL VPN user information for the default group policy and any group policies for which you
want to differentiate these values. See “Configuring Session Settings” Chapter 71, “Clientless SSL
VPN” in Cisco ASA 5500 Series Configuration Guide using ASDM, 6.4 and 6.6 or in Chapter 73 of Cisco
ASA 5500 Series Configuration Guide using the CLI, 8.4 and 8.6.
Configuring Site-to-Site Internal Group Policies
Configuration > Remote Access VPN > Network (Client) Access > Group Policies > Add/Edit >
Add or Edit Internal Group Policy > General
The Add or Edit Group Policy dialog box lets you specify tunneling protocols, filters, connection
settings, and servers for the group policy being added or modified. For each of the fields in this dialog
box, checking the Inherit check box lets the corresponding setting take its value from the default group
policy. Inherit is the default value for all of the attributes on this dialog box.

4-34
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 4 General VPN Setup
Group Policies
Fields
The following attributes appear in the Add Internal Group Policy > General dialog box. They apply to
SSL VPN and IPsec sessions, or clientless SSL VPN sessions. Thus, several are present for one type of
session, but not the other.
•Name—Specifies the name of this group policy. For the Edit function, this field is read-only.
•Tunneling Protocols—Specifies the tunneling protocols that this group can use. Users can use only
the selected protocols. The choices are as follows:
–
Clientless SSL VPN—Specifies the use of VPN via SSL/TLS, which uses a web browser to
establish a secure remote-access tunnel to a ASA; requires neither a software nor hardware
client. Clientless SSL VPN can provide easy access to a broad range of enterprise resources,
including corporate websites, web-enabled applications, NT/AD file share (web-enabled),
e-mail, and other TCP-based applications from almost any computer that can reach HTTPS
Internet sites.
–
SSL VPN Client—Specifies the use of the Cisco AnyConnect VPN client or the legacy SSL
VPN client. If you are using the AnyConnect client, you must choose this protocol for MUS to
be supported.
–
IPsec IKEv1—IP Security Protocol. Regarded as the most secure protocol, IPsec provides the
most complete architecture for VPN tunnels. Both Site-to-Site (peer-to-peer) connections and
Cisco VPN client-to-LAN connections can use IPsec IKEv1.
–
IPsec IKEv2—Supported by the AnyConnect Secure Mobility Client. AnyConnect connections
using IPsec with IKEv2 provide advanced features such as software updates, client profiles,
GUI localization (translation) and customization, Cisco Secure Desktop, and SCEP proxy.
–
L2TP over IPsec—Allows remote users with VPN clients provided with several common PC
and mobile PC operating systems to establish secure connections over the public IP network
to the security appliance and private corporate networks. L2TP uses PPP over UDP (port 1701)
to tunnel the data. The security appliance must be configured for IPsec transport mode.
Note If you do not select a protocol, an error message appears.
•Filter—(Network (Client) Access only) Specifies which access control list to use, or whether to
inherit the value from the group policy. Filters consist of rules that determine whether to allow or
reject tunneled data packets coming through the ASA, based on criteria such as source address,
destination address, and protocol. To configure filters and rules, see the Group Policy dialog box.
•Manage—Displays the ACL Manager dialog box, with which you can add, edit, and delete Access
Control Lists (ACLs) and Extended Access Control Lists (ACEs). For more information about the
ACL Manager, see the online Help for that dialog box.
•Idle Timeout—If the Inherit check box is not checked, this parameter specifies this user’s idle
timeout period in minutes. If there is no communication activity on the user connection in this
period, the system terminates the connection. The minimum time is 1 minute, and the maximum time
is 10080 minutes. The default is 30 minutes. To allow unlimited connection time, check Unlimited.
This value does not apply to Clientless SSL VPN users.
•Maximum Connect Time—If the Inherit check box is not checked, this parameter specifies the
maximum user connection time in minutes. At the end of this time, the system terminates the
connection. The minimum is 1 minute, and the maximum is 35791394 minutes (over 4000 years).
To allow unlimited connection time, check Unlimited (the default).

4-35
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 4 General VPN Setup
Group Policies
Defining Time Ranges
You can get to this panel through various paths.
Use the Browse Time Range dialog box to add, edit, or delete a time range. A time range is a reusable
component that defines starting and ending times that can be applied to a group policy. After defining a
time range, you can select the time range and apply it to different options that require scheduling. For
example, you can attach an ACL to a time range to restrict access to the ASA. A time range consists of
a start time, an end time, and optional recurring (that is, periodic) entries. For more information about
time ranges, see the online Help for the Add or Edit Time Range dialog box.
Fields
•Add—Opens the Add Time Range dialog box, in which you can create a new time range.
Note Creating a time range does not restrict access to the device.
•Edit—Opens the Edit Time Range dialog box, in which you can modify an existing time range. This
button is active only when you have selected an existing time range from the Browse Time Range
table.
•Delete—Removes a selected time range from the Browse Time Range table. There is no
confirmation or undo of this action.
•Name—Specifies the name of the time range.
•Start Time—Specifies when the time range begins.
•End Time—Specifies when the time range ends.
•Recurring Entries—Specifies further constraints of active time of the range within the start and stop
time specified.
Add/Edit Time Range
You can get to this panel through various paths.
The Add or Edit Time Range dialog box lets you configure a new time range.
Fields
•Time Range Name—Specifies the name that you want to assign to this time range.
•Start Time—Defines the time when you want the time range to start.
–
Start now—Specifies that the time range starts immediately.
–
Start at—Selects the month, day, year, hour, and minute at which you want the time range to
start.
•End Time—Defines the time when you want the time range to end.
–
Never end—Specifies that the time range has no defined end point.
–
End at (inclusive)—Selects the month, day, year, hour, and minute at which you want the time
range to end.

4-36
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 4 General VPN Setup
Access Control List Manager
•Recurring Time Ranges—Constrains the active time of this time range within the start and end times
when the time range is active. For example, if the start time is start now and the end time is never
end, and you want the time range to be effective every weekday, Monday through Friday, from 8:00
AM to 5:00 PM, you could configure a recurring time range, specifying that it is to be active
weekdays from 08:00 through 17:00, inclusive.
•Add—Opens the Add Recurring Time Range dialog box, in which you can configure a recurring
time range.
•Edit—Opens the Edit Recurring Time Range dialog box, in which you can modify a selected
recurring time range.
•Delete—Removes a selected recurring time range.
Add/Edit Recurring Time Range
You can get to this panel through various paths.
The Add or Edit Recurring Time Range dialog box lets you configure or modify a recurring time range.
Fields
•Specify days of the week and times on which this recurring range will be active—Makes available
the options in the Days of the week area. For example, use this option when you want the time range
to be active only every Monday through Thursday, from 08:00 through 16:59.
–
Days of the week—Specifies the days that you want to include in this recurring time range.
Possible options are: Every day, Weekdays, Weekends, and On these days of the week. For the
last of these, you can check a check box for each day that you want included in the range.
–
Daily Start Time—Specifies the hour and minute, in 24-hour format, when you want the
recurring time range to be active on each selected day.
–
Daily End Time (inclusive)—Specifies the hour and minute, in 24-hour format, when you want
the recurring time range to end on each selected day.
•Specify a weekly interval when this recurring range will be active—Makes available the options in
the Weekly Interval area. The range extends inclusively through the end time. All times in this area
are in 24-hour format. For example, use this option when you want the time range to be active
continuously from Monday at 8:00 AM through Friday at 4:30 PM.
–
From—Selects the day, hour, and minute when you want the weekly time range to start.
–
Through—Selects the day, hour, and minute when you want the weekly time range to end.
Access Control List Manager
You can get to this panel through various paths.
The ACL Manager dialog box lets you define access control lists (ACLs) to control the access of a
specific host or network to another host/network, including the protocol or port that can be used.
You can configure ACLs (access control lists) to apply to user sessions. These are filters that permit or
deny user access to specific networks, subnets, hosts, and web servers.
•If you do not define any filters, all connections are permitted.
•The ASA supports only an inbound ACL on an interface.

4-37
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 4 General VPN Setup
Access Control List Manager
•At the end of each ACL, there is an implicit, unwritten rule that denies all traffic that is not
permitted. If traffic is not explicitly permitted by an access control entry (ACE), the ASA denies it.
ACEs are referred to as rules in this section.
Standard Access Control List
This pane provides summary information about standard ACLs, and lets you add or edit ACLs and ACEs.
Fields
•Add—Lets you add a new ACL. When you highlight an existing ACL, it lets you add a new ACE
for that ACL.
•Edit—Opens the Edit ACE dialog box, in which you can change an existing access control list rule.
•Delete—Removes an ACL or ACE. There is no confirmation or undo.
•Move Up/Move Down—Changes the position of a rule in the ACL Manager table.
•Cut—Removes the selection from the ACL Manager table and places it on the clipboard.
•Copy—Places a copy of the selection on the clipboard.
•Paste—Opens the Paste ACE dialog box, in which you can create a new ACL rule from an existing
rule.
•No—Indicates the order of evaluation for the rule. Implicit rules are not numbered, but are
represented by a hyphen.
•Address—Displays the IP address or URL of the application or service to which the ACE applies.
•Action—Specifies whether this filter permits or denies traffic flow.
•Description—Shows the description you typed when you added the rule. An implicit rule includes
the following description: “Implicit outbound rule.”
Extended Access Control List
This pane provides summary information about extended ACLs, and lets you add or edit ACLs and
ACEs.
Fields
•Add—Lets you add a new ACL. When you highlight an existing ACL, it lets you add a new ACE
for that ACL.
•Edit—Opens the Edit ACE dialog box, in which you can change an existing access control list rule.
•Delete—Removes an ACL or ACE. There is no confirmation or undo.
•Move Up/Move Down—Changes the position of a rule in the ACL Manager table.
•Cut—Removes the selection from the ACL Manager table and places it on the clipboard.
•Copy—Places a copy of the selection on the clipboard.
•Paste—Opens the Paste ACE dialog box, in which you can create a new ACL rule from an existing
rule.
•No—Indicates the order of evaluation for the rule. Implicit rules are not numbered, but are
represented by a hyphen.

4-38
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 4 General VPN Setup
Access Control List Manager
•Enabled—Enables or disables a rule. Implicit rules cannot be disabled.
•Source—Specifies the IP addresses (Host/Network) that are permitted or denied to send traffic to
the IP addresses listed in the Destination column. In detail mode (see the Show Detail radio button),
an address column might contain an interface name with the word any, such as inside: any. This
means that any host on the inside interface is affected by the rule.
•Destination—Specifies the IP addresses (Host/Network) that are permitted or denied to send traffic
to the IP addresses listed in the Source column. An address column might contain an interface name
with the word any, such as outside: any. This means that any host on the outside interface is affected
by the rule. An address column might also contain IP addresses; for example
209.165.201.1-209.165.201.30. These addresses are translated addresses. When an inside host
makes a connection to an outside host, the firewall maps the address of the inside host to an address
from the pool. After a host creates an outbound connection, the firewall maintains this address
mapping. The address mapping structure is called an xlate, and remains in memory for a period of
time. During this time, outside hosts can initiate connections to the inside host using the translated
address from the pool, if allowed by the ACL. Normally, outside-to-inside connections require a
static translation so that the inside host always uses the same IP address.
•Service—Names the service and protocol specified by the rule.
•Action—Specifies whether this filter permits or denies traffic flow.
•Logging—Shows the logging level and the interval in seconds between log messages (if you enable
logging for the ACL). To set logging options, including enabling and disabling logging, right-click
this column, and click Edit Log Option. The Log Options dialog box appears.
•Time—Specifies the name of the time range to be applied in this rule.
•Description—Shows the description you typed when you added the rule. An implicit rule includes
the following description: “Implicit outbound rule.”
Add/Edit/Paste ACE
ACL Manager > Add/Edit/Paste Extended ACE
The Add/Edit/Paste ACE dialog box lets you create a new extended ACE, or modify an existing rule.
The Paste option becomes available only when you cut or copy a rule.
Fields
•Action—Determines the action type of the new rule. Select either permit or deny.
–
Permit—Permits all matching traffic.
–
Deny—Denies all matching traffic.
•Source/Destination—Specifies the source or destination type and, depending on that type, the other
relevant parameters describing the source or destination host/network IP Address. Possible values
are: any, IP address, Network Object Group, and Interface IP. The availability of subsequent fields
depends upon the value of the Type field:
–
any—Specifies that the source or destination host/network can be any type. For this value of the
Type field, there are no additional fields in the Source or Destination area.
–
IP Address—Specifies the source or destination host or network IP address. Both IPv4 and IPv6
addresses are supported. With this selection, the IP Address, ellipsis button, and Netmask fields
become available. Choose an IP address or host name from the drop-down list in the IP Address
field or click the ellipsis (...) button to browse for an IP address or name. Select a network mask
from the drop-down list.

4-39
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 4 General VPN Setup
Access Control List Manager
–
Network Object Group—Specifies the name of the network object group. Choose a name from
the drop-down list or click the ellipsis (...) button to browse for a network object group name.
–
Interface IP—Specifies the interface on which the host or network resides. Select an interface
from the drop-down list. The default values are inside and outside. There is no browse function.
•Protocol and Service—Specifies the protocol and service to which this ACE filter applies. Service
groups let you identify multiple non-contiguous port numbers that you want the ACL to match. For
example, if you want to filter HTTP, FTP, and port numbers 5, 8, and 9, define a service group that
includes all these ports. Without service groups, you would have to create a separate rule for each
port.
You can create service groups for TCP, UDP, TCP-UDP, ICMP, and other protocols. A service group
with the TCP-UDP protocol contains services, ports, and ranges that might use either the TCP or
UDP protocol.
–
Protocol—Selects the protocol to which this rule applies. Possible values are ip, tcp, udp, icmp,
and other. The remaining available fields in the Protocol and Service area depend upon the
protocol you select. The next few bullets describe the consequences of each of these selections:
–
Protocol: TCP and UDP—Selects the TCP/UDP protocol for the rule. The Source Port and
Destination Port areas allow you to specify the ports that the ACL uses to match packets.
–
Source Port/Destination Port—(Available only for TCP and UDP protocols) Specifies an
operator and a port number, a range of ports, or a well-known service name from a list of
services, such as HTTP or FTP. The operator list specifies how the ACL matches the port.
Choose one of the following operators: = (equals the port number), not = (does not equal the
port number), > (greater than the port number), < (less than the port number), range (equal to
one of the port numbers in the range).
–
Group—(Available only for TCP and UDP protocols) Selects a source port service group. The
Browse (...) button opens the Browse Source Port or Browse Destination Port dialog box.
–
Protocol: ICMP—Lets you choose an ICMP type or ICMP group from a preconfigured list or
browse (...) for an ICMP group. The Browse button opens the Browse ICMP dialog box.
–
Protocol: IP—Specifies the IP protocol for the rule in the IP protocol box. No other fields are
available when you make this selection.
–
Protocol: Other—Lets you choose a protocol from a drop-down list, choose a protocol group
from a drop-down list, or browse for a protocol group. The Browse (...) button opens the Browse
Other dialog box.
•Rule Flow Diagram—(Display only) Provides a graphical representation of the configured rule flow.
This same diagram appears on the ACL Manager dialog box unless you explicitly close that display.
•Options—Sets optional features for this rule, including logging parameters, time ranges, and
description.
–
Logging—Enables or disables logging or specifies the use of the default logging settings. If
logging is enabled, the Syslog Level and Log Interval fields become available.
–
Syslog Level—Selects the level of logging activity. The default is Informational.
–
Log Interval—Specifies the interval for permit and deny logging. The default is 300 seconds.
The range is 1 through 6000 seconds.
–
Time Range—Selects the name of the time range to use with this rule. The default is (any). Click
the Browse (...) button to open the Browse Time Range dialog box to select or add a time range.
–
Description—(Optional) Provides a brief description of this rule. A description line can be up
to 100 characters long, but you can break a description into multiple lines.

4-40
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 4 General VPN Setup
Access Control List Manager
Browse Source/Destination Address
ACL Manager > Add/Edit Extended Access List Rule > Source or Destination > Browse button
The Browse Source or Destination Address dialog box lets you select an object to use as a source or
destination for this rule.
Fields
•Type—Determines the type of object to use as the source or destination for this rule. Selections are
IP Address Objects, IP Names, Network Object Groups, and All. The contents of the table following
this field change, depending upon your selection.
•Source/Destination Object Table—Displays the objects from which you can select a source or
destination object. If you choose All in the type field, each category of object appears under its own
heading. The table has the following headings:
–
Name—Displays the network name (which may be an IP address) for each object.
–
IP address—Displays the IP address of each object.
–
Netmask—Displays the network mask to use with each object.
–
Description—Displays the description entered in the Add/Edit/Paste Extended Access List Rule
dialog box.
Browse Source/Destination Port
ACL Manager > Add/Edit Extended Access List Rule > Protocol and Service > Protocol: tcp or
udp >Source or Destination Port > Group option > Browse button
The Browse Source or Destination Port dialog box lets you select a source or destination port for this
protocol in this rule.
Fields
•Add—Opens the Add TCP Service Group dialog box, in which you can configure a new TCP service
group.
•Find—Opens the Filter field.
•Filter/Clear—Specifies a filter criterion that you can use to search for items in the Name list, thus
displaying only those items that match that criterion. When you make an entry in the Filter field, the
Filter button becomes active. Clicking the Filter button performs the search. After you perform the
search, the Filter button is dimmed, and the Clear button becomes active. Clicking the Clear button
clears the filter field and dims the Clear button.
•Type—Determines the type of object to use as the source or destination for this rule. Selections are
IP Address Objects, IP Names, Network Object Groups, and All. The contents of the table following
this field change, depending upon your selection.
•Name—Lists the predefined protocols and service groups for your selection.
Add TCP Service Group
ACL Manager > Add/Edit Extended Access List Rule > Protocol and Service > Protocol: tcp or
udp >Source or Destination Port > Group option > Browse button > Browse Source or Destination
Port > Add button

4-41
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 4 General VPN Setup
Access Control List Manager
The Add TCP Service Group dialog box lets you configure a new a TCP service group or port to add to
the browsable source or destination port list for this protocol in this rule. Selecting a member of either
the Members not in Group or the Members in Group list activates the Add and Remove buttons.
Fields
•Group Name—Specifies the name of the new TCP service group.
•Description—(Optional) Provides a brief description of this group.
•Members not in Group—Presents the option to select either a service/service group or a port number
to add to the Members in Group list.
•Service/Service Group—Selects the option to select the name of a TCP service or service group to
add to the Members in Group list.
•Port #—Selects the option to specify a range of port numbers to add to the Members in Group list.
•Add—Moves a selected item from the Members not in Group list to the Members in Group list.
•Remove—Moves a selected item from the Members in Group list to the Members not in Group list.
•Members in Group—Lists the members already configured in this service group.
Browse ICMP
ACL Manager > Add/Edit Extended Access List Rule > Protocol and Service > Protocol:
icmp >ICMP > Group option > Browse button
The Browse ICMP dialog box lets you select an ICMP group for this rule.
Fields
•Add—Opens the Add ICMP Group dialog box, in which you can configure a new TCP service
group.
•Find—Opens the Filter field.
•Filter/Clear—Specifies a filter criterion that you can use to search for items in the Name list, thus
displaying only those items that match that criterion. When you make an entry in the Filter field, the
Filter button becomes active. Clicking the Filter button performs the search. After you perform the
search, the Filter button is dimmed, and the Clear button becomes active. Clicking the Clear button
clears the filter field and dims the Clear button.
•Type—Determines the type of object to use as the ICMP group for this rule. Selections are IP
Address Objects, IP Names, Network Object Groups, and All. The contents of the table following
this field change, depending upon your selection.
•Name—Lists the predefined ICMP groups for your selection.
Add ICMP Group
ACL Manager > Add/Edit Extended Access List Rule > Protocol and Service > Protocol:
icmp >ICMP > Group option > Browse button > Browse ICMP > Add button
The Add ICMP Group dialog box lets you configure a new a ICMP group by name or by number to add
to the browsable ICMP list for this protocol in this rule. Choosing a member of either the Members not
in Group or the Members in Group list activates the Add and Remove buttons.
Fields
•Group Name—Specifies the name of the new TCP service group.

4-42
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 4 General VPN Setup
Access Control List Manager
•Description—(Optional) Provides a brief description of this group.
•Members not in Group—Presents the option to select either an ICMP type/ICMP group or an ICMP
number to add to the Members in Group list.
•ICMP Type/ICMP Group—Selects the option to select the name of an ICMP group to add to the
Members in Group list.
•ICMP #—Selects the option to specify an ICMP member by number to add to the Members in Group
list.
•Add—Moves a selected item from the Members not in Group list to the Members in Group list.
•Remove—Moves a selected item from the Members in Group list to the Members not in Group list.
•Members in Group—Lists the members already configured in this service group.
Browse Other
ACL Manager > Add/Edit Extended Access List Rule > Protocol and Service > Protocol:
other >Other > Group option > Browse button
The Browse Other dialog box lets you select a protocol group for this rule.
Fields
•Add—Opens the Add Protocol Group dialog box, in which you can configure a new service group.
•Find—Opens the Filter field.
•Filter/Clear—Specifies a filter criterion that you can use to search for items in the Name list, thus
displaying only those items that match that criterion. When you make an entry in the Filter field, the
Filter button becomes active. Clicking the Filter button performs the search. After you perform the
search, the Filter button is dimmed, and the Clear button becomes active. Clicking the Clear button
clears the filter field and dims the Clear button.
•Type—Determines the type of object to use as the protocol group for this rule. Selections are IP
Address Objects, IP Names, Network Object Groups, and All. The contents of the table following
this field change, depending upon your selection.
•Name—Lists the predefined protocol groups for your selection.
Add Protocol Group
ACL Manager > Add/Edit Extended Access List Rule > Protocol and Service > Protocol: other >
Group option > Browse button > Browse Other > Add button
The Add Protocol Group dialog box lets you configure a new a protocol group by name or by number to
add to the browsable protocol list for this rule. Selecting a member of either the Members not in Group
or the Members in Group list activates the Add and Remove buttons.
Fields
•Group Name—Specifies the name of the new TCP service group.
•Description—(Optional) Provides a brief description of this group.
•Members not in Group—Presents the option to select either a protocol/protocol group or a protocol
number to add to the Members in Group list.
•Protocol/Protocol Group—Selects the option to select the name of a protocol or protocol group to
add to the Members in Group list.

4-43
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 4 General VPN Setup
Access Control List Manager
•Protocol #—Selects the option to specify a protocol by number to add to the Members in Group list.
•Add—Moves a selected item from the Members not in Group list to the Members in Group list.
•Remove—Moves a selected item from the Members in Group list to the Members not in Group list.
•Members in Group—Lists the members already configured in this service group.
Client Firewall with Local Printer and Tethered Device Support
When users connect to the ASA, all traffic is tunneled through the connection and users cannot access
resources on their local network. This includes printers, cameras, and Windows Mobile devices (tethered
devices) that synchronize with the local computer. Enabling Local LAN Access in the client profile
resolves this problem, however it can introduce a security or policy concern for some enterprises as a
result of unrestricted access to the local network. You can use the ASA to deploy endpoint OS firewall
capabilities to restrict access to particular types of local resources, such as printers and tethered devices.
To do so, enable client firewall rules for specific ports for printing. The client distinguishes between
inbound and outbound rules. For printing capabilities, the client opens ports required for outbound
connections, but blocks all incoming traffic.
Note Be aware that users logged in as administrators have the ability to modify the firewall rules deployed to
the client by the ASA. Users with limited privileges cannot modify the rules. For either user, the client
reapplies the firewall rules when the connection terminates.
If you configure the client firewall, and the user authenticates to an Active Directory (AD) server, the
client still applies the firewall policies from the ASA. However, the rules defined in the AD group policy
take precedence over the rules of the client firewall.
The following sections describe procedures on how to do this:
•Deploying a Client Firewall for Local Printer Support, page 4-44
•Tethered Devices Support, page 4-45
Usage Notes about Firewall Behavior
The following notes clarify how the AnyConnect client uses the firewall:
•The source IP is not used for firewall rules. The client ignores the source IP information in the
firewall rules sent from the ASA. The client determines the source IP depending on whether the rules
are public or private. Public rules are applied to all interfaces on the client. Private rules are applied
to the Virtual Adapter.
•The ASA supports many protocols for ACL rules. However, the AnyConnect firewall feature
supports only TCP, UDP, ICMP, and IP. If the client receives a rule with a different protocol, it treats
it as an invalid firewall rule, and then disables split tunneling and uses full tunneling for security
reasons.
•Starting in ASA 9.0, the Public Network Rule and Private Network Rule support unified access
control lists. These access control lists can be used to define IPv4 and IPv6 traffic in the same rule.
Be aware of the following differences in behavior for each operating system:
•For Windows computers, deny rules take precedence over allow rules in Windows Firewall. If the
ASA pushes down an allow rule to the AnyConnect client, but the user has created a custom deny
rule, the AnyConnect rule is not enforced.
4-44
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 4 General VPN Setup
Access Control List Manager
•On Windows Vista, when a firewall rule is created, Vista takes the port number range as a
comma-separated string. The port range can be a maximum of 300 ports. For example, from 1-300
or 5000-5300. If you specify a range greater than 300 ports, the firewall rule is applied only to the
first 300 ports.
•Windows users whose firewall service must be started by the AnyConnect client (not started
automatically by the system) may experience a noticeable increase in the time it takes to establish a
VPN connection.
•On Mac computers, the AnyConnect client applies rules sequentially in the same order the ASA
applies them. Global rules should always be last.
•For third-party firewalls, traffic is passed only if both the AnyConnect client firewall and the
third-party firewall allow that traffic type. If the third-party firewall blocks a specific traffic type that
the AnyConnect client allows, the client blocks the traffic.
Deploying a Client Firewall for Local Printer Support
The ASA supports the AnyConnect client firewall feature with ASA version 8.3(1) or later, and ASDM
version 6.3(1) or later. This section describes how to configure the client firewall to allow access to local
printers, and how to configure the client profile to use the firewall when the VPN connection fails.
Limitations and Restrictions of the Client Firewall
The following limitations and restrictions apply to using the client firewall to restrict local LAN access:
•Due to limitations of the OS, the client firewall policy on computers running Windows XP is
enforced for inbound traffic only. Outbound rules and bidirectional rules are ignored. This would
include firewall rules such as 'permit ip any any'.
•Host Scan and some third-party firewalls can interfere with the firewall.
The following table clarifies what direction of traffic is affected by the source and destination port
settings:
Example ACL Rules for Local Printing
The ACL AnyConnect_Client_Local_Print is provided with ASDM to make it easy to configure the
client firewall. When you select that ACL for Public Network Rule in the Client Firewall pane of a group
policy, that list contains the following ACEs:
.
Source Port Destination Port Traffic Direction Affected
Specific port number Specific port number Inbound and outbound
A range or 'All' (value of 0) A range or 'All' (value of 0) Inbound and outbound
Specific port number A range or 'All' (value of 0) Inbound only
A range or 'All' (value of 0) Specific port number Outbound only
Table 4-1 ACL Rules in AnyConnect_Client_Local_Print
Description Permission Interface Protocol
Source
Port
Destination
Address
Destination
Port
Deny all Deny Public Any Default1 Any Default
LPD Allow Public TCP Default Any 515
IPP Allow Public TCP Default Any 631

4-45
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 4 General VPN Setup
Access Control List Manager
Note To enable local printing, you must enable the Local LAN Access feature in the client profile with a
defined ACL rule allow Any Any.
Configuring Local Print Support
Step 1 Enable the AnyConnect client firewall in a group policy. Go to Configuration > Remote Access VPN
> Network (Client) Access > Group Policies.
Step 2 Select a group policy and click Edit. The Edit Internal Group Policy window displays.
Step 3 Select Advanced > AnyConnect Client > Client Firewall. Click Manage for the Private Network Rule.
Step 4 Create an ACL and specify an ACE using the rules in Table 4-1. Add this ACL as a PrivateNetwork Rule.
Step 5 If you enabled the Automatic VPN Policy always-on and specified a closed policy, in the event of a VPN
failure, users have no access to local resources. You can apply the firewall rules in this scenario by going
to Preferences (Cont) in the profile editor and checking Apply last local VPN resource rules.
Tethered Devices Support
To support tethered devices and protect the corporate network, create a standard ACL in the group policy,
specifying destination addresses in the range that the tethered devices use. Then specify the ACL for split
tunneling as a network list to exclude from tunneled VPN traffic. You must also configure the client
profile to use the last VPN local resource rules in case of VPN failure.
Note For Windows Mobile devices that need to sync with the computer running AnyConnect, specify
the IPv4 destination address as 169.254.0.0, or the IPv6 destination address fe80::/64 in the
ACL.
Follow these steps:
Step 1 In ASDM, go to Group Policy > Advanced > Split Tunneling.
Step 2 Uncheck Inherit next to the Network List field and click Manage. The ACL Manager displays.
Step 3 Click the Extended ACL tab.
Step 4 Click Add and then Add ACL. Specify a name for the new ACL.
Printer Allow Public TCP Default Any 9100
mDNS Allow Public UDP Default 224.0.0.251 5353
LLMNR Allow Public UDP Default 224.0.0.252 5355
NetBios Allow Public TCP Default Any 137
NetBios Allow Public UDP Default Any 137
1. The port range is 1 to 65535.
Table 4-1 ACL Rules in AnyConnect_Client_Local_Print (continued)
Description Permission Interface Protocol
Source
Port
Destination
Address
Destination
Port

4-46
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 4 General VPN Setup
Access Control List Manager
Step 5 Choose the new ACL in the table and click Add and then Add ACE. The Edit ACE window displays.
Step 6 For Action, choose the Permit radio button.
Step 7 In the destination criteria area, specify the IPv4 destination address as 169.254.0.0 or the IPv6
destination address fe80::/64.
Step 8 For Service, choose IP.
Step 9 Click OK.
Step 10 Click OK to save the ACL.
Step 11 In the Split Tunneling pane for the internal group policy, uncheck Inherit for the Policy or IPv6 Policy,
depending on the IP address you specified in step 7, and choose Exclude Network List Below. For
Network List, choose the ACL you created.
Step 12 Click OK.
Step 13 Click Apply.
Fields
•Public Network Rule—Use the drop-down list to choose from the existing defined ACLs.
Manage—Displays the ACL Manager dialog box, with which you can add, edit, and delete Access
Control Lists (ACLs) and Extended Access Control Lists (ACEs).
•Private Network Rule—Use the drop-down list to choose from the existing defined ACLs.
Manage—Displays the ACL Manager dialog box, with which you can add, edit, and delete Access
Control Lists (ACLs) and Extended Access Control Lists (ACEs).
Configuring a Web ACLs
Configuration > Remote Access > Clientless SSL VPN Access > Advanced > Web ACLs
Configuration > Remote Access > Clientless SSL VPN Access > Group Policies > General > More
Options > Web ACL
This dialog box lets you configure ACLs for Clientless SSL VPN connections.
Fields
•View (Unlabeled)—Indicates whether the selected entry is expanded (minus sign) or contracted
(plus sign).
•# column—Specifies the ACE ID number.
•Enable—Indicates whether this ACL is enabled or disabled. You can enable or disable the ACL
using this check box.
•Action—Specifies whether this ACL permits or denies access.
•Type—Specifies whether this ACL applies to a URL or a TCP address/port.
•Filter—Specifies the type of filter being applied.
•Syslog Level (Interval)—Specifies the syslog parameters for this ACL.
•Time Range—Specifies the name of the time range, if any, for this ACL. The time range can be a
single interval or a series of periodic ranges.
•Description—Specifies the description, if any, of the ACL.
•Add ACL—Displays the Add Web Type ACL dialog box, in which you can specify an ACL ID.

4-47
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 4 General VPN Setup
Access Control List Manager
•Add ACE—Displays the Add Web Type ACE dialog box, in which you specify parameters for the
named ACL. This button is active only if there are one or more entries in the Web Type ACL table.
•Edit ACE/Delete—Click to edit or delete the highlighted ACL or ACE. When you delete an ACL,
you also delete all of its ACEs. No warning or undelete.
•Move Up/Move Down—Highlight an ACL or ACE and click these buttons to change the order of
ACLs and ACEs. The ASA checks ACLs and their ACEs in priority order according to their position
in the ACLs list box until it finds a match.
Add/Edit Standard Access List Rule
ACL Manager > Add or Edit Standard Access List Rule
The Add/Edit Standard Access List Rule dialog box lets you create a new rule, or modify an existing
rule.
Fields
•Action—Determines the action type of the new rule. Choose either Permit or Deny.
–
Permit—Permits all matching traffic.
–
Deny—Denies all matching traffic.
•Host/Network IP Address—Identifies the networks by IP address.
–
IP address—The IP address of the host or network.
–
Mask—The subnet mask of the host or network
•Description—(Optional) Enter a description of the access rule.
Add/Edit Server and URL List
Configuration > VPN > General > Group Policy > Add/Edit > Internal Group Policy >
Web VPN Tab > Other Tab > Add or Edit Server and URL List
The Add or Edit Server and URL List dialog box lets you add, edit, delete, and order the items in the
designated URL list.
Fields
•List Name—Specifies the name of the list to be added or selects the name of the list to be modified
or deleted.
•URL Display Name—Specifies the URL name displayed to the user.
•URL—Specifies the actual URL associated with the display name.
•Add—Opens the Add Server or URL dialog box, in which you can configure a new server or URL
and display name.
•Edit—Opens the Edit Server or URL dialog box, in which you can configure a new server or URL
and display name.
•Delete—Removes the selected item from the server and URL list. There is no confirmation or undo.
•Move Up/Move Down—Changes the position of the selected item in the server and URL list.

4-48
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 4 General VPN Setup
Configuring AnyConnect VPN Client Connections
Add/Edit Server or URL
Configuration > VPN > General > Group Policy > Add/Edit > Internal Group Policy >
Web VPN Tab > Other Tab > Add or Edit Server and URL
The Add or Edit Server or URL dialog box lets you add or edit, delete, and order the items in the
designated URL list.
Fields
•URL Display Name—Specifies the URL name displayed to the user.
•URL—Specifies the actual URL associated with the display name.
Configuring AnyConnect VPN Client Connections
The Cisco AnyConnect VPN client provides secure SSL or IPsec (IKEv2) connections to the ASA for
remote users. The client gives remote users the benefits of a VPN client without the need for network
administrators to install and configure clients on remote computers.
Without a previously-installed client, remote users enter the IP address in their browser of an interface
configured to accept SSL VPN connections. Unless the ASA is configured to redirect http:// requests to
https://, users must enter the URL in the form https://<address>.
After entering the URL, the browser connects to that interface and displays the login screen. If the user
satisfies the login and authentication, and the ASA identifies the user as requiring the client, it
downloads the client that matches the operating system of the remote computer. After downloading, the
client installs and configures itself, establishes a VPN connection and either remains or uninstalls itself
(depending on the ASA configuration) when the connection terminates.
In the case of a previously installed client, when the user authenticates, the ASA examines the revision
of the client, and upgrades the client as necessary.
The AnyConnect client can be downloaded from the ASA, or it can be installed manually on the remote
PC by the system administrator. For more information about installing the client manually, see the
AnyConnect Administrators Guide.
The ASA downloads the client based on the group policy or username attributes of the user establishing
the connection. You can configure the ASA to automatically download the client, or you can configure
it to prompt the remote user about whether to download the client. In the latter case, if the user does not
respond, you can configure the ASA to either download the client after a timeout period or present the
login page.
Fields
•Keep Installer on Client System—Enable to allow permanent client installation on the remote
computer. Enabling disables the automatic uninstalling feature of the client. The client remains
installed on the remote computer for subsequent connections, reducing the connection time for the
remote user.
Note Keep Installer on Client System is not supported after version 2.5 of the AnyConnect client.
•Compression—Compression increases the communications performance between the security
appliance and the client by reducing the size of the packets being transferred.
4-49
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 4 General VPN Setup
Configuring AnyConnect VPN Client Connections
•Datagram TLS—Datagram Transport Layer Security avoids latency and bandwidth problems
associated with some SSL connections and improves the performance of real-time applications that
are sensitive to packet delays.
•Ignore Don’t Defrag (DF) Bit—This feature allows the force fragmentation of packets that have the
DF bit set, allowing them to pass through the tunnel. An example use case is for servers in your
network that do not respond correctly to TCP MSS negotiations.
•Client Bypass Protocol—The Client Protocol Bypass feature allows you to configure how the ASA
manages IPv4 traffic when it is expecting only IPv6 traffic or how it manages IPv6 traffic when it is
expecting only IPv4 traffic.
When the AnyConnect client makes a VPN connection to the ASA, the ASA could assign it an IPv4,
IPv6, or both an IPv4 and IPv6 address. If the ASA assigns the AnyConnect connection only an IPv4
address or only an IPv6 address, you can now configure the Client Bypass Protocol to drop network
traffic for which the ASA did not assign an IP address, or allow that traffic to bypass the ASA and
be sent from the client unencrypted or “in the clear”.
For example, assume that the ASA assigns only an IPv4 address to an AnyConnect connection and
the endpoint is dual stacked. When the endpoint attempts to reach an IPv6 address, if Client Bypass
Protocol is disabled, the IPv6 traffic is dropped; however, if Client Bypass Protocol is enabled, the
IPv6 traffic is sent from the client in the clear.
•FQDN of This Device—This information is used by the client after network roaming in order to
resolve the ASA IP address used for re-establishing the VPN session. This setting is critical to
support roaming between networks of different IP protocols (such as IPv4 to IPv6).
Note You cannot use the ASA FQDN present in the AnyConnect profile to derive the ASA IP
address after roaming. The addresses may not match the correct device (the one the tunnel
was established to) in the load balancing scenario.
If the device FQDN is not pushed to the client, the client will try to reconnect to whatever IP address
the tunnel had previously established. In order to support roaming between networks of different IP
protocols (from IPv4 to IPv6), AnyConnect must perform name resolution of the device FQDN after
roaming, so that it can determine which ASA address to use for re-establishing the tunnel. The client
uses the ASA FQDN present in its profile during the initial connection. During subsequent session
reconnects, it always uses the device FQDN pushed by ASA (and configured by the administrator
in the group policy), when available. If the FQDN is not configured, the ASA derives the device
FQDN (and sends it to the client) from whatever is set under Device Setup > Device Name/Password
and Domain Name.
If the device FQDN is not pushed by the ASA, the client cannot re-establish the VPN session after
roaming between networks of different IP protocols.
•MTU—Adjusts the MTU size for SSL connections. Enter a value in bytes, from 256 to 1410 bytes.
By default, the MTU size is adjusted automatically based on the MTU of the interface that the
connection uses, minus the IP/UDP/DTLS overhead.
•Keepalive Messages—Enter a number, from 15 to 600 seconds, in the Interval field to enable and
adjust the interval of keepalive messages to ensure that an connection through a proxy, firewall, or
NAT device remains open, even if the device limits the time that the connection can be idle.
Adjusting the interval also ensures that the client does not disconnect and reconnect when the remote
user is not actively running a socket-based application, such as Microsoft Outlook or Microsoft
Internet Explorer.

4-50
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 4 General VPN Setup
Configuring AnyConnect VPN Client Connections
•Optional Client Modules to Download—To minimize download time, the AnyConnect client
requests downloads (from the ASA) only of modules that it needs for each feature that it supports.
You must specify the names of modules that enable other features. The AnyConnect client, version
3.0, includes the following modules (previous versions have fewer modules):
–
AnyConnect DART—The Diagnostic AnyConnect Reporting Tool (DART) captures a snapshot
of system logs and other diagnostic information and creates a .zip file on your desktop so you
can conveniently send troubleshooting information to Cisco TAC.
–
AnyConnect Network Access Manager—Formerly called the Cisco Secure Services Client, this
module provides 802.1X (Layer 2) and device authentication for access to both wired and
wireless network is integrated into AnyConnect 3.0.
–
AnyConnect SBL—Start Before Logon (SBL) forces the user to connect to the enterprise
infrastructure over a VPN connection before logging on to Windows by starting AnyConnect
before the Windows login dialog box appears.
–
AnyConnect Web Security Module—Formerly called ScanSafe Hostscan, this module is
integrated into the AnyConnect 3.0.
–
AnyConnect Telemetry Module—Sends information about the origin of malicious content to the
web filtering infrastructure of the Cisco IronPort Web Security Appliance (WSA), which uses
this data to provide better URL filtering rules.
–
AnyConnect Posture Module—Formerly called the Cisco Secure Desktop HostScan feature, the
posture module is integrated into AnyConnect 3.0 and provides AnyConnect the ability to
gather credentials for posture assessment prior to creating a remote access connection to the
ASA.
•Always-On VPN—Determine if the always-on VPN flag setting in the AnyConnect service profile
is disabled or if the AnyConnect service profile setting should be used. The always-on VPN feature
lets AnyConnnect automatically establish a VPN session after the user logs onto a computer. The
VPN session remains up until the user logs off the computer. If the physical connection is lost, the
session remains up, and AnyConnect continually attempts to reestablish the physical connection
with the adaptive security appliance to resume the VPN session.
Always-on VPN permits the enforcement of corporate policies to protect the device from security
threats. You can use it to help ensure AnyConnect establishes a VPN session whenever the endpoint
is not in a trusted network. If enabled, a policy is configured to determine how network connectivity
is managed in the absence of a connection.
Note Always-On VPN requires an AnyConnect release that supports AnyConnect Secure
Mobility features. Refer to the Cisco AnyConnect VPN Client Administrator Guide for
additional information.
•Client Profiles to Download—A profile is a group of configuration parameters that the AnyConnect
client uses to configure VPN, Network Access Manager, web security, and telemetry settings. Click
Add to launch the Select Anyconnect Client Profiles window where you can specify
previously-created profiles for this group policy.

4-51
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 4 General VPN Setup
Configuring AnyConnect VPN Client Connections
Using AnyConnect Client Profiles
You enable Cisco AnyConnect Secure Mobility client features in the AnyConnect profiles—XML files
that contain configuration settings for the core client with its VPN functionality and for the optional
client modules Network Access Manager, telemetry, and web security. The ASA deploys the profiles
during AnyConnect installation and updates. Users cannot manage or modify profiles.
You can configure a profile using the AnyConnect profile editor, a convenient GUI-based configuration
tool launched from ASDM. The AnyConnect software package, version 2.5 and later (for all OSs),
includes the editor, which activates when you load the AnyConnect package on the ASA as an
AnyConnect client image. Alternatively, you can manually edit the XML file and import the file to the
ASA as a profile.
You can configure the ASA to deploy profiles globally for all AnyConnect users or to users based on
their group policy. Usually, a user has a single profile file for each AnyConnect module installed. In
some cases, you might want to provide more than one profile for a user. Someone who works from
multiple locations might need more than one profile. Be aware that some of the profile settings (such as
SBL) control the connection experience at a global level. Other settings are unique to a particular host
and depend on the host selected.
Some profile settings are stored locally on the user computer in a user preferences file or a global
preferences file. The user file has information the client needs to display user-controllable settings in the
Preferences tab of the client GUI and information about the last connection, such as the user, the group,
and the host. The global file has information about user-controllable settings to be able to apply those
settings before login (since there is no user). For example, the client needs to know if Start Before Logon
and/or AutoConnect On Start are enabled before login. For more information about creating and
deploying AnyConnect client profiles and controlling client features, see the AnyConnect VPN Client
Administrator Guide.
Fields
Add—Displays the Add AnyConnect Client Profiles dialog box, where you can specify a file in flash
memory as a profile, or where you can browse flash memory for a file to specify as a profile. You can
also upload a file from a local computer to the flash memory.
Edit—Displays the Edit SSL VPN Client Profile window, where you can change the settings contained
in the profile for AnyConnect client features.
Delete—Deletes a profile from the table. This does not delete the XML file from flash.
AnyConnect Client Profiles Table—Displays the XML files specified as AnyConnect client profiles:
•Profile Name—The name of the profile specified when the profile was added.
•Profile Usage/Type—Displays the use for this profile, such as VPN, Network Access Manager, or
telemetry.
Specifying an AnyConnect Client Profile
Specify an AnyConnect client profile for this group policy.
For more information about creating and deploying AnyConnect client profiles and controlling client
features, see the AnyConnect VPN Client Administrator Guide.
Fields
Profile Name—Specify an AnyConnect client profile for this group policy.

4-52
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 4 General VPN Setup
Configuring AnyConnect VPN Client Connections
Profile Usage—Displays the usage assigned to the profile when originally created: VPN, Network
Access Manager, web security, or telemetry. If ASDM does not recognize the usage specified in the XML
file, the drop-down list becomes selectable and you can choose a usage type manually.
Profile Location—Specify a path to the profile file in the ASA flash memory. If the file does not exist,
the ASA creates one based on the profile template.
Importing an AnyConnect Client Profile
Import a new AnyConnect client profile in this window. You can import a profile from a local device or
a remote server.
For more information about creating and deploying AnyConnect client profiles and controlling client
features, see the AnyConnect VPN Client Administrator Guide.
Fields
Profile Name—Specify a name for the profile you add.
Profile Usage—Displays the usage assigned to the profile when originally created: VPN, Network
Access Manager, web security, or telemetry. If ASDM does not recognize the usage specified in the XML
file, the drop-down list becomes selectable and you can choose a usage type manually.
Group Policy—Specify a group policy for this profile. The profile downloads to users belonging to the
group policy along with the AnyConnect client.
Profile Location—Specify a path to the profile file in the ASA flash memory. If the file does not exist,
the ASA creates one based on the profile template.
Exporting an AnyConnect Client Profile
Export an AnyConnect VPN client profile from this window. You can export to a local device or a remote
server.
For more information about creating and deploying AnyConnect client profiles and controlling client
features, see the AnyConnect VPN Client Administrator Guide.
Fields
Device Profile Path—Displays the path and filename of the profile file.
Local Path—Specify the path and filename to export the profile file.
Browse Local—Click to launch a window to browse the local device file system.
Exempting AnyConnect Traffic from Network Address Translation
If you have configured your ASA to perform network address translation (NAT), you must exempt your
remote access AnyConnect client traffic from being translated so that the AnyConnect clients, internal
networks, and corporate resources on a DMZ, can originate network connections to each other. Failing
to exempt the AnyConnect client traffic from being translated prevents the AnyConnect clients and other
corporate resources from communicating.
“Identity NAT” (also known as “NAT exemption”) allows an address to be translated to itself, which
effectively bypasses NAT. Identity NAT can be applied between two address pools, an address pool and
a subnetwork, or two subnetworks.
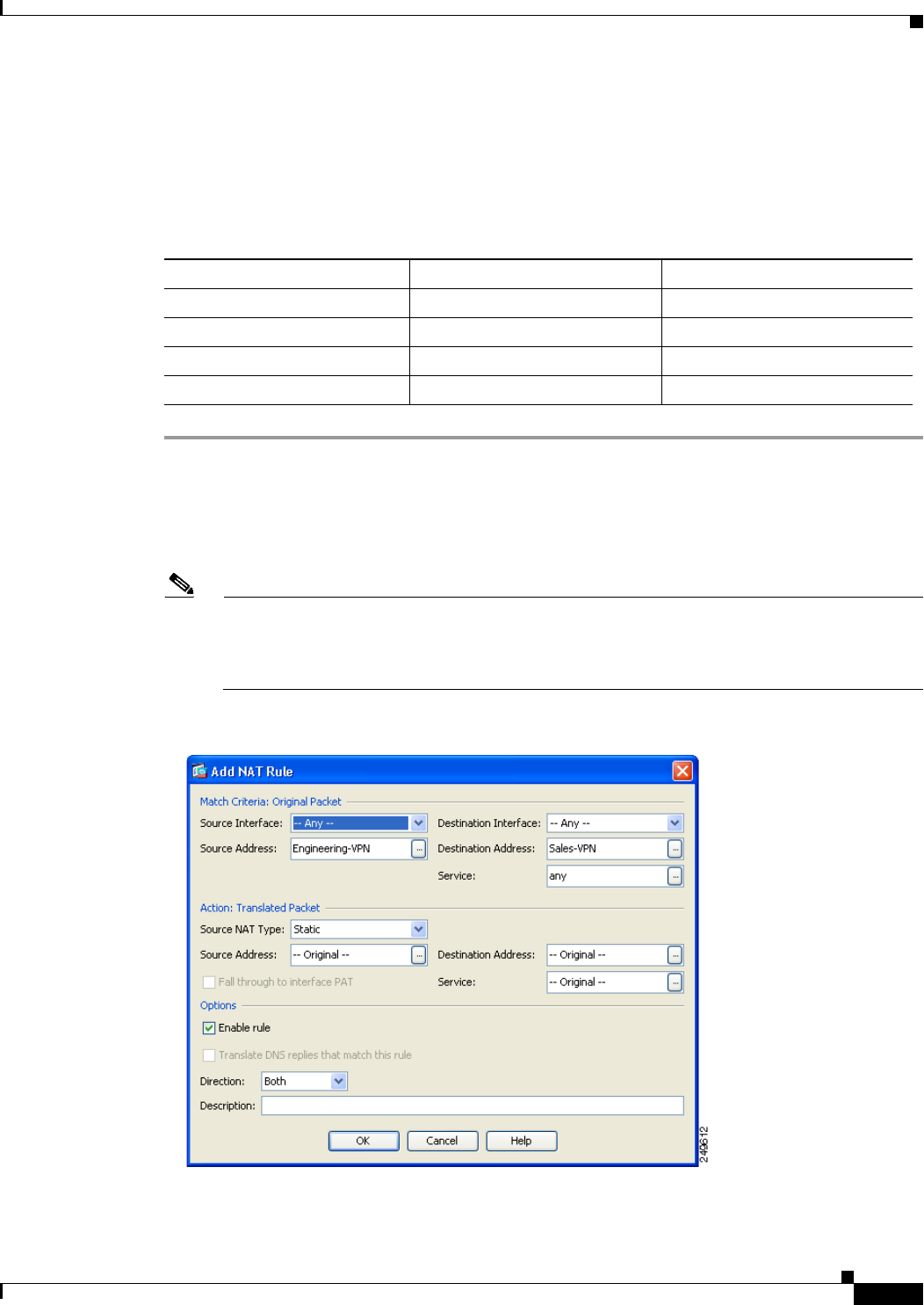
4-53
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 4 General VPN Setup
Configuring AnyConnect VPN Client Connections
This procedure illustrates how you would configure identity NAT between these hypothetical network
objects in our example network topology: Engineering VPN address pool, Sales VPN address pool,
inside network, a DMZ network, and the Internet. Each Identity NAT configuration requires one NAT
rule.
Table 4-2 Network Addressing for Configuring Identity NAT for VPN
Clients
Step 1 Log into the ASDM and select Configuration > Firewall > NAT Rules.
Step 2 Create a NAT rule so that the hosts in the Engineering VPN address pool can reach the hosts in the Sales
VPN address pool. In the NAT Rules pane, select Add > Add NAT Rule Before “Network Object”
NAT rules so that the ASA evaluates this rule before other rules in the Unified NAT table. See Figure 4-2
on page 4-53 for an example of the Add NAT rule dialog box.
Note NAT rule evaluation is applied on a top-down, first match basis. Once the ASA matches a packet
to a particular NAT rule it does not perform any further evaluation. It is important that you place
the most specific NAT rules at the top of the Unified NAT table so that the ASA does not
prematurely match them to broader NAT rules.
Figure 4-2 Add NAT rule dialog box
a. In the Match criteria: Original Packet area, configure these fields:
Network or Address Pool Network or address pool name Range of addresses
Inside network inside-network 10.50.50.0 - 10.50.50.255
Engineering VPN address pool Engineering-VPN 10.60.60.1 - 10.60.60.254
Sales VPN address pool Sales-VPN 10.70.70.1 - 10.70.70.254
DMZ network DMZ-network 192.168.1.0 - 192.168.1.255
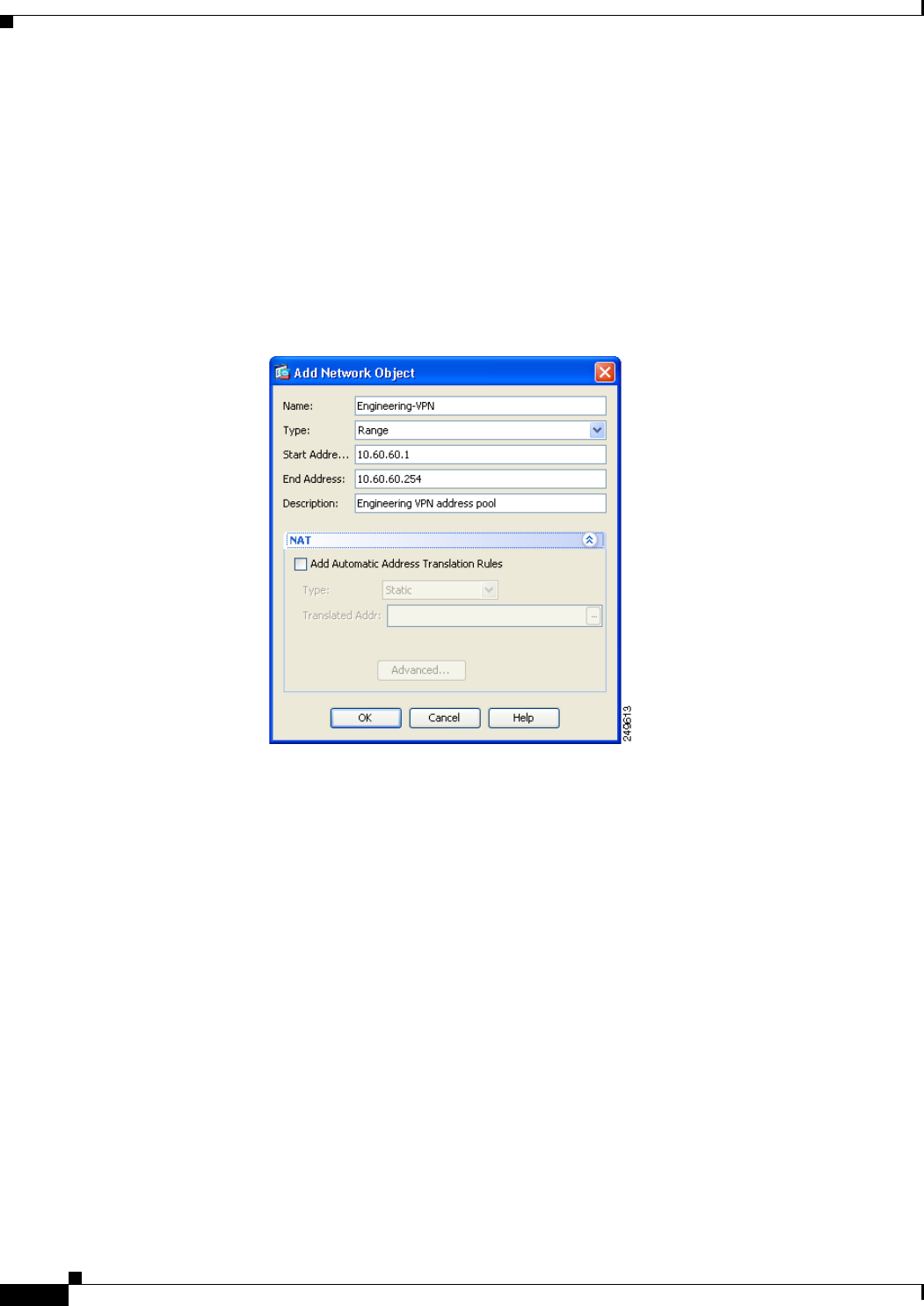
4-54
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 4 General VPN Setup
Configuring AnyConnect VPN Client Connections
–
Source Interface: Any
–
Destination Interface: Any
–
Source Address: Click the Source Address browse button and create the network object that
represents the Engineering VPN address pool. Define the object type as a Range of addresses.
Do not add an automatic address translation rule. See Figure 4-3 for an example.
–
Destination Address: Click the Destination Address browse button and create the network
object that represents the Sales VPN address pool. Define the object type as a Range of
addresses. Do not add an automatic address translation rule.
Figure 4-3 Create Network Object for a VPN address pool
b. In the Action Translated Packet area, configure these fields:
–
Source NAT Type: Static
–
Source Address: Original
–
Destination Address: Original
–
Service: Original
c. In the Options area, configure these fields:
–
Check Enable rule.
–
Uncheck or leave empty the Translate DNS replies that match this rule.
–
Direction: Both
–
Description: Add a Description for this rule.
d. Click OK.
e. Click Apply. Your rule should look like rule 1 in the Unified NAT table in Figure 4-5 on page 4-57.
CLI example:
nat source static Engineering-VPN Engineering-VPN destination static Sales-VPN
Sales-VPN
f. Click Send.
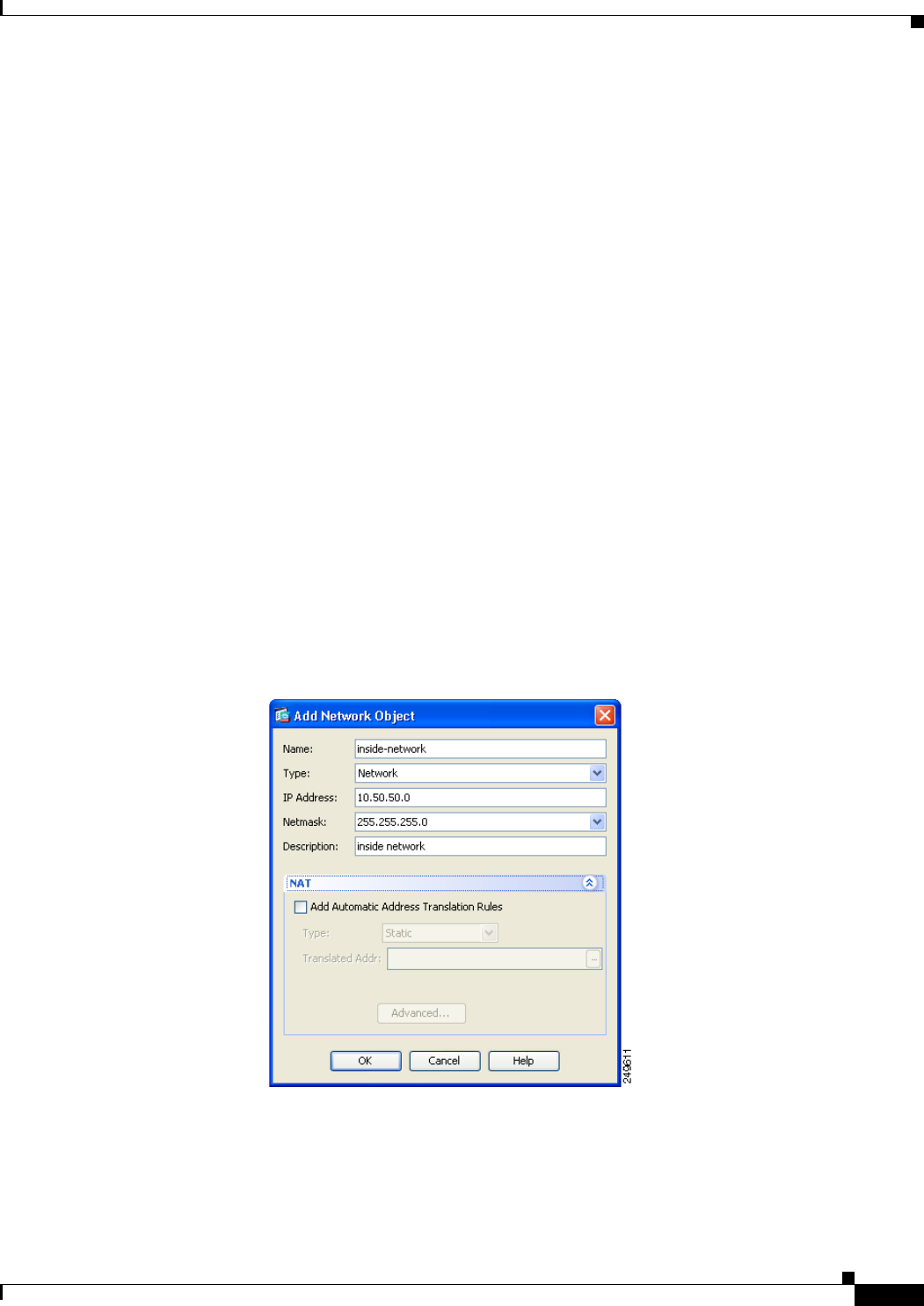
4-55
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 4 General VPN Setup
Configuring AnyConnect VPN Client Connections
Step 3 When ASA is performing NAT, in order for two hosts in the same VPN pool to connect to each other, or
for those hosts to reach the Internet through the VPN tunnel, you must enable the Enable traffic
between two or more hosts connected to the same interface option. To do this, in ASDM, select
Configuration > Device Setup > Interfaces. At the bottom of the Interface panel, check Enable traffic
between two or more hosts connected to the same interface and click Apply.
CLI example:
same-security-traffic permit inter-interface
Step 4 Create a NAT rule so that the hosts in the Engineering VPN address pool can reach other hosts in the
Engineering VPN address pool. Create this rule just as you created the rule in Step 2 except that you
specify the Engineering VPN address pool as both the Source address and the Destination Address in the
Match criteria: Original Packet area.
Step 5 Create a NAT rule so that the Engineering VPN remote access clients can reach the “inside” network. In
the NAT Rules pane, select Add > Add NAT Rule Before “Network Object” NAT rules so that this
rule will be processed before other rules.
a. In the Match criteria: Original Packet area configure these fields:
–
Source Interface: Any
–
Destination Interface: Any
–
Source Address: Click the Source Address browse button and create a network object that
represents the inside network. Define the object type as a Network of addresses. Do not add an
automatic address translation rule.
–
Destination Address: Click the Destination Address browse button and select the network object
that represents the Engineering VPN address pool.
Figure 4-4 Add inside-network object
b. In the Action: Translated Packet area, configure these fields:
–
Source NAT Type: Static
–
Source Address: Original
–
Destination Address: Original

4-56
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 4 General VPN Setup
Configuring AnyConnect VPN Client Connections
–
Service: Original
c. In the Options area, configure these fields:
–
Check Enable rule.
–
Uncheck or leave empty the Translate DNS replies that match this rule.
–
Direction: Both
–
Description: Add a Description for this rule.
d. Click OK.
e. Click Apply. Your rule should look like rule two in the Unified NAT table in Figure 4-5 on
page 4-57.
CLI example
nat source static inside-network inside-network destination static Engineering-VPN
Engineering-VPN
Step 6 Create a new rule, following the method in Step 5, to configure identity NAT for the connection between
the Engineering VPN address pool and the DMZ network. Use the DMZ network as the Source Address
and use the Engineering VPN address pool as the Destination address.
Step 7 Create a new NAT rule to allow the Engineering VPN address pool to access the Internet through the
tunnel. In this case, you do not want to use identity NAT because you want to change the source address
from a private address to an Internet routable address. To create this rule, follow this procedure:
a. In the NAT Rules pane, select Add > Add NAT Rule Before “Network Object” NAT rules so that
this rule will be processed before other rules.
b. In the Match criteria: Original Packet area configure these fields:
–
Source Interface: Any
–
Destination Interface: Any. This field will be automatically populated with “outside” after you
select outside as the Source Address in the Action: Translated Packet area.
–
Source Address: Click the Source Address browse button and select the network object that
represents the Engineering VPN address pool.
–
Destination Address: Any.
c. In the Action: Translated Packet area, configure these fields:
–
Source NAT Type: Dynamic PAT (Hide)
–
Source Address: Click the Source Address browse button and select the outside interface.
–
Destination Address: Original
–
Service: Original
d. In the Options area, configure these fields:
–
Check Enable rule.
–
Uncheck or leave empty the Translate DNS replies that match this rule.
–
Direction: Both
–
Description: Add a Description for this rule.
e. Click OK.
f. Click Apply. Your rule should look like rule five in the Unified NAT table in Figure 4-5 on
page 4-57.
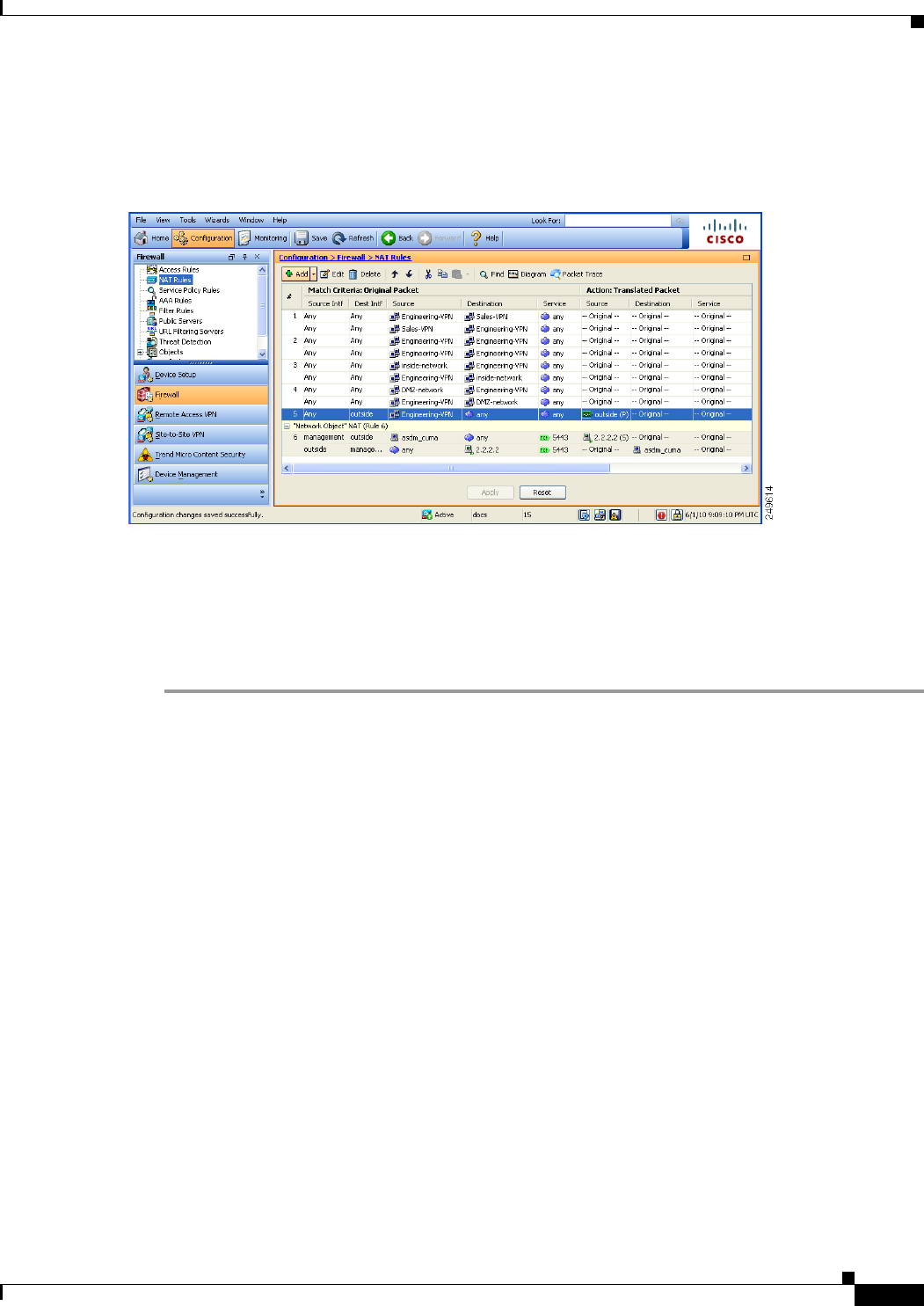
4-57
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 4 General VPN Setup
Configuring AnyConnect VPN Connections
CLI example:
nat (any,outside) source dynamic Engineering-VPN interface
Figure 4-5 Unified NAT table
Step 8 After you have configured the Engineering VPN Address pool to reach itself, the Sales VPN address
pool, the inside network, the DMZ network, and the Internet; you must repeat this process for the Sales
VPN address pool. Use identity NAT to exempt the Sales VPN address pool traffic from undergoing
network address translation between itself, the inside network, the DMZ network, and the Internet.
Step 9 From the File menu on the ASA, select Save Running Configuration to Flash to implement your
identity NAT rules.
Configuring AnyConnect VPN Connections
Use the AnyConnect Connection Profiles pane and its child dialog boxes to specify VPN connection
attributes for client-based connections. These attributes apply to the Cisco AnyConnect VPN client and
to the legacy SSL VPN client.
The initial client deployment requires end-user administrative rights. The Cisco AnyConnect VPN client
supports the HTTPS/TCP (SSL) and Datagram Transport Layer Security (DTLS) tunneling options.
In the main pane, you can enable client access on the interfaces you select and you can select, add, edit,
and delete connections (tunnel groups). You can also specify whether you want to allow a user to select
a particular connection at login.
Fields
•Access Interfaces—Lets you select from a table the interfaces on which to enable access. The fields
in this table include the interface name and check boxes specifying whether to allow access.
–
In the Interface table, in the row for the interface you are configuring for AnyConnect
connections, check the protocols you want to enable on the interface. You can allow SSL
Access, IPsec access, or both.

4-58
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 4 General VPN Setup
Configuring AnyConnect VPN Connections
When checking SSL, DTLS (Datagram Transport Layer Security) is enabled by default. DTLS
avoids latency and bandwidth problems associated with some SSL connections and improves
the performance of real-time applications that are sensitive to packet delays.
When checking IPsec (IKEv2) access, client services are enabled by default. Client services
include enhanced Anyconnect features including software updates, client profiles, GUI
localization (translation) and customization, Cisco Secure Desktop, and SCEP proxy. If you
disable client services, the AnyConnect client still establishes basic IPsec connections with
IKEv2.
–
Device Certificate—Lets you specify a certificate for authentication for either an RSA key or
an ECDSA key. See Specifying a Device Certificate, page 4-58.
–
Port Setting—Configure port numbers for clientless SSL and IPsec (IKEv2) connections. See
Configuring Port Settings, page 4-59.
–
Enable inbound VPN sessions to bypass interface ACLs is checked by default.— The security
appliance allows all VPN traffic to pass through the interface ACLs. For example, even if the
outside interface ACL does not permit the decrypted traffic to pass through, the security
appliance trusts the remote private network and permits the decrypted packets to pass through.
You can change this default behavior. If you want the interface ACL to inspect the VPN
protected traffic, uncheck this box.
•Login Page Setting
–
Allow the user to select a connection profile, identified by its alias, on the login page. If you do
not check this check box, the default connection profile is DefaultWebVPNGroup.
–
Shutdown portal login page.—Shows the web page when the login is disabled.
•Connection Profiles—Configure protocol-specific attributes for connections (tunnel groups).
–
Add/Edit—Click to Add or Edit a Connection Profile (tunnel group).
–
Name—The name of the Connection Profile.
–
Aliases—Other names by which the Connection Profile is known.
–
SSL VPN Client Protocol—Specifies whether SSL VPN client have access.
–
Group Policy—Shows the default group policy for this Connection Profile.
–
Allow user to select connection, identified by alias in the table above, at login page—Check to
enable the display of Connection Profile (tunnel group) aliases on the Login page.
•Let group URL take precedence if group URL and certificate map match different connection
profiles. Otherwise, the connection profile matches the certificate map will be used.—This option
specifies the relative preference of the group URL and certificate values during the connection
profile selection process. If the ASA fails to match the preferred value, it chooses the connection
profile that matches the other value. Check this option only if you want to rely on the preference
used by many older ASA software releases to match the group URL specified by the VPN endpoint
to the connection profile that specifies the same group URL. This option is unchecked by default. If
it is unchecked, the ASA prefers to match the certificate field value specified in the connection
profile to the field value of the certificate used by the endpoint to assign the connection profile.
Specifying a Device Certificate
The Specify Device Certificate screen allows you to specify a certificate that will identify the ASA to
the client when it attempts to create a connection. This screen is for AnyConnect Connection Profiles
and Clientless Connection Profiles.

4-59
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 4 General VPN Setup
Configuring AnyConnect VPN Connections
For VPN connections (not clientless):
•Certain AnyConnect features, such as Always-on IPsec/IKEv2, require that a valid and trusted
device certificate be available on the ASA.
•If your AnyConnect clients are configured to use only SSL, then you only need to specify an RSA
certificate as AnyConnect does not support ECDSA certificates for SSL VPN. If your AnyConnect
clients are configured to use IPsec or SSL, or both IPsec and SSL, you can configure both kinds of
certificates.
•ECDSA certificates are only supported on IPsec connections.
Detailed Steps
Step 1 (For VPN connections only) In the Certificate with RSA Key area, perform one of these tasks:
•Keep the Use the same device certificate for SSL and IPsec IKEv2 box checked if you want to
choose one certificate to authenticate clients using either protocol. You can select the certificate
from those available in the list box or click Manage to create an identity certificate to use.
•Uncheck the Use the same device certificate for SSL and IPsec IKEv2 check box to specify
separate certificates for SSL connections or IPsec connections.
Step 2 Select a certificate from the Device Certficate list box.
If you do not see the certificate you want, click the Manage button to manage the identity
certficiates on the ASA.
Step 3 (For VPN connections only) In the Certificate with ECDSA key field, select the ECDSA certificate from
the list box or click Manage to create an ECDSA identity certificate.
Step 4 Click OK.
Configuring Port Settings
Configure port numbers for SSL and IPsec (IKEv2) connections in this window:
Fields
•SSL Ports:
–
HTTPS Port—The port to enable HTTPS for clientless (browser-based) SSL connections. The
range is 1-65535. The default is port 443.
–
DTLS Port—The port to enable DTLS for SSL connections. The range is 1-65535. The default
is port 443.
•IPsec Client Services Port—The port to enable client services for IKEv2 connections. The range is
1-65535. The default is port 443.
Setting the Basic Attributes for an AnyConnect VPN Connection
To set the basic attributes for an AnyConnect VPN connection, choose Add or Edit in the Anyconnect
Connection Profiles section. The Add (or Edit) Anyconnect Connection Profile > Basic dialog box
opens.

4-60
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 4 General VPN Setup
Configuring AnyConnect VPN Connections
Fields
Set the attributes in the Add AnyConnect Connection Profile > Basic dialog box as follows:
•Name—For Add, specify the name of the connection profile you are adding. For Edit, this field is
not editable.
•Aliases—(Optional) Enter one or more alternative names for the connection. You can spaces or
punctuation to separate the names.
•Authentication—Choose one of the following methods to use to authenticate the connection and
specify a AAA server group to use in authentication.
–
AAA, Certificate, or Both—Select the type of authentication to use: AAA, Certificate, or Both.
If you choose either Certificate or Both, the user must provide a certificate in order to connect.
–
AAA Server Group—Choose a AAA server group from the drop-down list. The default setting
is LOCAL, which specifies that the ASA handles the authentication. Before making a selection,
you can click Manage to open a dialog box over this dialog box to view or make changes to the
ASA configuration of AAA server groups.
–
Choosing something other than LOCAL makes available the Use LOCAL if Server Group Fails
check box.
–
Use LOCAL if Server Group fails—Check to enable the use of the LOCAL database if the group
specified by the Authentication Server Group attribute fails.
•Client Address Assignment—Select the DHCP servers, client address pools, and client IPv6 address
pools to use.
–
DHCP Servers—Enter the name or IP address of a DHCP server to use.
–
Client Address Pools—Enter pool name of an available, configured pool of IPv4 addresses to
use for client address assignment. Before making a selection, you can click Select to open a
dialog box over this dialog box to view or make changes to the address pools. See Configuring
Local IP Address Pools, page 5-3 for more information on adding or editing an IPv4 address
pool.
–
Client IPv6 Address Pools—Enter the pool name of an available, configured pool of IPv6
addresses to use for client address assignment. Before making a selection, you can click Select
to open a dialog box over this dialog box to view or make changes to the address pools. See
Configuring Local IP Address Pools, page 5-3 for more information on adding or editing an
IPv6 address pool.
•Default Group Policy—Select the group policy to use.
–
Group Policy—Select the VPN group policy that you want to assign as the default group policy
for this connection. A VPN group policy is a collection of user-oriented attribute-value pairs
that can be stored internally on the device or externally on a RADIUS server. The default value
is DfltGrpPolicy. You can click Manage to open a dialog box over this one to make changes to
the group policy configuration.
–
Enable SSL VPN client protocol—Check to enable SSL for this VPN connection.
–
Enable IPsec (IKEv2) client protocol—Check to enable IPsec using IKEv2 for this connection.
–
DNS Servers—Enter the IP address(s) of DNS servers for this policy.
–
WINS Servers—Enter the IP address(s) of WINS servers for this policy.
–
Domain Name—Enter a default domain name.
•Find—Enter a GUI label or a CLI command to use as a search string, then click Next or Previous to
begin the search.

4-61
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 4 General VPN Setup
Configuring AnyConnect VPN Connections
Setting Advanced Attributes for a Connection Profile
The Advanced menu items and their dialog boxes let you configure the following characteristics for this
connection:
•General attributes
•Client Addressing attributes
•Authentication attributes
•Authorization attributes
•Accounting attributes
•Name server attributes
•Clientless SSL VPN attributes
Note SSL VPN and secondary authentication attributes apply only to SSL VPN connection profiles.
Setting General Attributes for an AnyConnect SSL VPN Connection
Configure the General attributes to specify the password management parameters.
Fields
Set the Advanced General attributes as follows:
•Enable Simple Certificate Enrollment (SCEP) for this Connection Profile
•Strip the realm from username before passing it on to the AAA server
•Strip the group from username before passing it on to the AAA server
•Group Delimiter—Changing the group delimiter value makes the change globally on all other
remote connection profiles.
•Enable Password Management—Lets you configure parameters relevant to overriding an
account-disabled indication from a AAA server and to notifying users about password expiration.
The ASA supports password management for the RADIUS and LDAP protocols. It supports the
“password-expire-in-days” option only for LDAP. This parameter is valid for AAA servers that
support such notification. The ASA ignores this command if RADIUS or LDAP authentication has
not been configured.
You can configure password management for IPsec remote access and SSL VPN tunnel-groups.
Note Some RADIUS servers that support MS-CHAP currently do not support MS-CHAPv2. This
feature requires MS-CHAPv2, so please check with your vendor.
The ASA, releases 7.1 and later, generally supports password management for the following
connection types when authenticating with LDAP or with any RADIUS configuration that supports
MS-CHAPv2:
–
AnyConnect VPN client
–
IPsec VPN client
–
Clientless SSL VPN

4-62
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 4 General VPN Setup
Configuring AnyConnect VPN Connections
Password management is not supported for any of these connection types for Kerberos/Active
Directory (Windows password) or NT 4.0 Domain. The RADIUS server (for example, Cisco ACS)
could proxy the authentication request to another authentication server. However, from the ASA
perspective, it is talking only to a RADIUS server.
Note For LDAP, the method to change a password is proprietary for the different LDAP servers
on the market. Currently, the ASA implements the proprietary password management logic
only for Microsoft Active Directory and Sun LDAP servers.
Native LDAP requires an SSL connection. You must enable LDAP over SSL before attempting to
do password management for LDAP. By default, LDAP uses port 636.
Note Allowing override account-disabled is a potential security risk.
–
Notify user __ days prior to password expiration—Specifies that ASDM must notify the user at
login a specific number of days before the password expires. The default is to notify the user 14
days prior to password expiration and every day thereafter until the user changes the password.
The range is 1 through 180 days.
–
Notify user on the day password expires—Notifies the user only on the day that the password
expires.
In either case, and, if the password expires without being changed, the ASA offers the user the
opportunity to change the password. If the current password has not expired, the user can still
log in using that password.
Note This does not change the number of days before the password expires, but rather, it enables
the notification. If you select this option, you must also specify the number of days.
–
Override account-disabled indication from AAA server—Overrides an account-disabled
indication from a AAA server.
•Translate Assigned IP Address to Public IP Address—In rare situations, you might want to use a
VPN peer’s real IP address on the inside network instead of an assigned local IP address. Normally
with VPN, the peer is given an assigned local IP address to access the inside network. However, you
might want to translate the local IP address back to the peer’s real public IP address if, for example,
your inside servers and network security is based on the peer’s real IP address. You can enable this
feature on one interface per tunnel group.
–
Enable the address translation on interface—Enables the address translation and allows you to
choose which interface the address appears on. Outside is the interface to which the
AnyConnect client connects, and inside is the interface specific to the new tunnel group.
Note Because of routing issues and other limitations, we do not recommend using this feature
unless you know you need it.
•Find—Enter a GUI label or a CLI command to use as a search string, then click Next or Previous to
begin the search.

4-63
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 4 General VPN Setup
Configuring AnyConnect VPN Connections
Setting Client Addressing Attributes for an AnyConnect SSL VPN Connection
The Client Addressing attributes let you configure interface-specific address pools that your connection
can use. Click Add to add a new address pool or Edit to modify an existing pool. The Select Address
Pools dialog box opens, showing a table listing the pool name, starting and ending address (or number
of addresses), and subnet mask/prefix length of any existing pools. For a complete description of Client
Addressing see Configuring Client Addressing, page 4-92.
Configuring Authentication Attributes for a Connection Profile
•Interface-specific Authentication Server Groups—Manages the assignment of authentication server
groups to specific interfaces.
–
Add or Edit—Opens the Assign Authentication Server Group to Interface dialog box, in which
you can specify the interface and server group, and specify whether to allow fallback to the
LOCAL database if the selected server group fails. The Manage button on this dialog box opens
the Configure AAA Server Groups dialog box. Your selections appear in the Interface/Server
Group table.
–
Delete—Removes the selected server group from the table. There is no confirmation or undo.
•Username Mapping from Certificate—Lets you specify the methods and fields in a digital certificate
from which to extract the username.
–
Pre-fill Username from Certificate—Extracts the username from the specified certificate field
and uses it for username/password authentication and authorization, according to the options
that follow in this panel.
–
Hide username from end user—Specifies to not display the extracted username to the end user.
–
Use script to select username—Specify the name of a script to use to select a username from a
digital certificate. The default is --None--.
–
Add or Edit—Opens the Add or Edit Script Content dialog box, in which you can define a script
to use in mapping the username from the certificate.
–
Delete—Deletes the selected script. There is no confirmation or undo.
–
Use the entire DN as the username—Specifies that you want to use the entire Distinguished
Name field of the certificate as the username.
–
Specify the certificate fields to be used as the username—Specifies one or more fields to
combine into the username.
Possible values for primary and secondary attributes include the following:
Attribute Definition
C Country: the two-letter country abbreviation. These codes conform to ISO
3166 country abbreviations.
CN Common Name: the name of a person, system, or other entity. Not available
a s a secondary attribute.
DNQ Domain Name Qualifier.
EA E-mail address.
GENQ Generational Qualifier.
GN Given Name.

4-64
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 4 General VPN Setup
Configuring AnyConnect VPN Connections
–
Primary Field—Selects the first field to use from the certificate for the username. If this value
is found, the secondary field is ignored.
–
Secondary Field—Selects the field to us if the primary field is not found.
•Find—Enter a GUI label or a CLI command to use as a search string, then click Next or Previous to
begin the search.
Configuring Secondary Authentication Attributes for an SSL VPN Connection
Profile
The Secondary Authentication dialog box lets you configure secondary or “double” authentication for
this connection profile. With double authentication enabled, the end user must present two sets of valid
authentication credentials in order to log on. You can use secondary authentication in conjunction with
pre-filling the username from a certificate. The fields in this dialog box are similar to those you configure
for primary authentication, but these fields relate only to secondary authentication.
When double authentication is enabled, these attributes select one or more fields in a certificate to use
as the username. Configuring the secondary username from certificate attribute forces the security
appliance to use the specified certificate field as the second username for the second username/password
authentication.
Note If you also specify the secondary authentication server group, along with the secondary username from
certificate, only the primary username is used for authentication.
Fields
•Secondary Authorization Server Group—Specifies an authorization server group from which to
extract secondary credentials.
–
Server Group—Select an authorization server group to use as the secondary server AAA group.
The default is none. The secondary server group cannot be an SDI server group.
–
Manage—Opens the Configure AAA Server Groups dialog box.
I Initials.
L Locality: the city or town where the organization is located.
N Name.
O Organization: the name of the company, institution, agency, association or
other entity.
OU Organizational Unit: the subgroup within the organization (O).
SER Serial Number.
SN Surname.
SP State/Province: the state or province where the organization is located
T Title.
UID User Identifier.
UPN User Principal Name.
Attribute Definition

4-65
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 4 General VPN Setup
Configuring AnyConnect VPN Connections
–
Use LOCAL if Server Group fails—Specifies to fall back to the LOCAL database if the
specified server group fails.
–
Use primary username—Specifies that the login dialog must request only one username.
–
Attributes Server—Select whether this is the primary or secondary attributes server.
Note If you also specify an authorization server for this connection profile, the authorization
server settings take precedence—the ASA ignores this secondary authentication server.
–
Session Username Server—Select whether this is the primary or secondary session username
server.
•Interface-Specific Authorization Server Groups—Manages the assignment of authorization server
groups to specific interfaces.
–
Add or Edit—Opens the Assign Authentication Server Group to Interface dialog box, in which
you can specify the interface and server group, and specify whether to allow fallback to the
LOCAL database if the selected server group fails. The Manage button on this dialog box opens
the Configure AAA Server Groups dialog box. Your selections appear in the Interface/Server
Group table.
–
Delete—Removes the selected server group from the table. There is no confirmation or undo.
•Username Mapping from Certificate—Specify the fields in a digital certificate from which to extract
the username.
•Pre-fill Username from Certificate—Check to extract the names to be used for secondary
authentication from the primary and secondary fields specified in this panel. You must configure the
authentication method for both AAA and certificates before checking this attribute. To do so, return
to the Basic panel in the same window and check Both next to Method.
•Hide username from end user—Check to hide the username to be used for secondary authentication
from the VPN user.
•Fallback when a certificate is unavailable —This attribute is configurable only if “Hide username
from end user” is checked. Uses Cisco Secure Desktop Host Scan data to pre-fill the username for
secondary authentication if a certificate is unavailable.
•Password—Choose one of the following methods to retrieve the password to be used for secondary
authentication:
–
Prompt—Prompt the user for the password.
–
Use Primary—Reuse the primary authentication password for all secondary authentications.
–
Use—Enter a common secondary password for all secondary authentications.
•Specify the certificate fields to be used as the username—Specifies one or more fields to match as
the username. To use this username in the pre-fill username from certificate feature for the
secondary username/password authentication or authorization, you must also configure the
pre-fill-username and secondary-pre-fill-username.
–
Primary Field—Selects the first field to use from the certificate for the username. If this value
is found, the secondary field is ignored.
–
Secondary Field—Selects the field to us if the primary field is not found.
The options for primary and secondary field attributes include the following:

4-66
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 4 General VPN Setup
Configuring AnyConnect VPN Connections
•Use the entire DN as the username—Uses the entire subject DN (RFC1779) to derive a name for an
authorization query from a digital certificate.
•Use script to select username—Names the script from which to extract a username from a digital
certificate. The default is --None--.
–
Add or Edit—Opens the Add or Edit Script Content dialog box, in which you can define a script
to use in mapping the username from the certificate.
–
Delete—Deletes the selected script. There is no confirmation or undo.
Configuring Authorization Attributes for an SSL VPN Connection Profile
The Authorization dialog box lets you view, add, edit, or delete interface-specific authorization server
groups. Each row of the table on this dialog box shows the status of one interface-specific server group:
the interface name, its associated server group, and whether fallback to the local database is enabled if
the selected server group fails.
Fields
•Authorization Server Group—Specifies an authorization server group from which to draw
authorization parameters.
–
Server Group—Selects an authorization server group to use. The default is none.
Attribute Definition
C Country: the two-letter country abbreviation. These codes conform to ISO
3166 country abbreviations.
CN Common Name: the name of a person, system, or other entity. Not available
a s a secondary attribute.
DNQ Domain Name Qualifier.
EA E-mail address.
GENQ Generational Qualifier.
GN Given Name.
I Initials.
L Locality: the city or town where the organization is located.
N Name.
O Organization: the name of the company, institution, agency, association or
other entity.
OU Organizational Unit: the subgroup within the organization (O).
SER Serial Number.
SN Surname.
SP State/Province: the state or province where the organization is located
T Title.
UID User Identifier.
UPN User Principal Name.

4-67
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 4 General VPN Setup
Configuring AnyConnect VPN Connections
–
Manage—Opens the Configure AAA Server Groups dialog box.
–
Users must exist in the authorization database to connect—Select this check box to require that
users meet this criterion.
•Interface-specific Authorization Server Groups—Manages the assignment of authorization server
groups to specific interfaces.
–
Add or Edit—Opens the Assign Authentication Server Group to Interface dialog box, in which
you can specify the interface and server group, and specify whether to allow fallback to the
LOCAL database if the selected server group fails. The Manage button on this dialog box opens
the Configure AAA Server Groups dialog box. Your selections appear in the Interface/Server
Group table.
–
Delete—Removes the selected server group from the table. There is no confirmation or undo.
•Username Mapping from Certificate—Specify the fields in a digital certificate from which to extract
the username.
–
Use script to select username—Specifies the name of a script to use to select a username from
a digital certificate. The default is --None--.
–
Add or Edit—Opens the Add or Edit Script Content dialog box, in which you can define a script
to use in mapping the username from the certificate.
–
Delete—Deletes the selected script. There is no confirmation or undo.
–
Use the entire DN as the username—Specifies that you want to use the entire Distinguished
Name field of the certificate as the username.
–
Specify the certificate fields to be used as the username—Specifies one or more fields to
combine into the username.
–
Primary Field—Selects the first field to use in the certificate for the username. If this value is
found, the secondary field is ignored.
–
Secondary Field—Selects the field to use if the primary field is not found.
•Find—Enter a GUI label or a CLI command to use as a search string, then click Next or Previous to
begin the search.
Adding or Editing Content to a Script for Certificate Pre-Fill-Username
The Add or Edit Script Content dialog box lets you create an authentication or authorization script.
Note Both AnyConnect client and clientless WebVPN display “Unknown” in the username field when
pre-fill-username from certificate using a script cannot find the username in the client certificate.
Fields
•Script Name—Specify the name of the script. The script name must be the same in both
authorization and authentication.You define the script here, and CLI uses the same script to perform
this function.
•Select script parameters—Specify the attributes and content of the script.
•Value for Username—Select an attribute from the drop-down list of standard DN attributes to use as
the username (Subject DN).
•No Filtering—Specify that you want to use the entire specified DN name.
4-68
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 4 General VPN Setup
Configuring AnyConnect VPN Connections
•Filter by substring— Specify the Starting Index (the position in the string of the first character to
match) and Ending Index (number of characters to search). If you choose this option, the starting
index cannot be blank. If you leave the ending index blank, it defaults to -1, indicating that the entire
string is searched for a match.
For example, suppose you selected the DN attribute Common Name (CN), which contains a value
of host/user. Table 4-3 shows some possible ways you might filter this value using the substring
option to achieve various return values. The Return Value is what is actually pre-filled as the
username.
Using a negative index, as in the third row of this table, specifies to count from the end of the string
backwards to the end of the substring, in this case, the “r” of “user”.
When using filtering by substrings, you should know the length of the substring that you are seeking.
From the following examples, use either the regular expression matching or the custom script in Lua
format:
•Example 1: Regular Expression Matching—Enter a regular expression to apply to the search in the
Regular Expression field. Standard regular expression operators apply. For example, suppose you
want to use a regular expression to filter everything up to the @ symbol of the “Email Address (EA)”
DN value. The regular expression ^[^@]* would be one way to do this. In this example, if the DN
value contained a value of user1234@example.com, the return value after the regular expression
would be user1234.
•Example 2: Use custom script in Lua format—Specify a custom script written in the Lua
programming language to parse the search fields. Selecting this option makes available a field in
which you can enter your custom Lua script; for example, the script:
return cert.subject.cn..'/'..cert.subject.l
combines two DN fields, username (cn) and locality (l), to use as a single username and inserts the
slash (/) character between the two fields.
Table 4-4 lists the attribute names and descriptions that you can use in a Lua script.
Note Lua is case-sensitive.
Table 4-3 Filtering by Substring
Starting Index Ending Index Return Value
15 host/
610 user
6-1 user
Table 4-4 Attribute Names and Descriptions
Attribute Name Description
cert.subject.c Country
cert.subject.cn Common Name
cert.subject.dnq DN qualifier
cert.subject.ea E-mail Address
cert.subject.genq Generational qualified

4-69
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 4 General VPN Setup
Configuring AnyConnect Secure Mobility
If an error occurs while activating a tunnel group script, causing the script not to activate, the
administrator’s console displays an error message.
Configuring AnyConnect Secure Mobility
AnyConnect Secure Mobility protects corporate interests and assets from Internet threats when
employees are mobile. Use the Mobile User Security dialog box to configure this feature. AnyConnect
Secure Mobility lets Cisco IronPort S-Series Web Security appliances scan Cisco AnyConnect secure
cert.subject.gn Given Name
cert.subject.i Initials
cert.subject.l Locality
cert.subject.n Name
cert.subject.o Organization
cert.subject.ou Organization Unit
cert.subject.ser Subject Serial Number
cert.subject.sn Surname
cert.subject.sp State/Province
cert.subject.t Title
cert.subject.uid User ID
cert.issuer.c Country
cert.issuer.cn Common Name
cert.issuer.dnq DN qualifier
cert.issuer.ea E-mail Address
cert.issuer.genq Generational qualified
cert.issuer.gn Given Name
cert.issuer.i Initials
cert.issuer.l Locality
cert.issuer.n Name
cert.issuer.o Organization
cert.issuer.ou Organization Unit
cert.issuer.ser Issuer Serial Number
cert.issuer.sn Surname
cert.issuer.sp State/Province
cert.issuer.t Title
cert.issuer.uid User ID
cert.serialnumber Certificate Serial Number
cert.subjectaltname.upn User Principal Name
Table 4-4 Attribute Names and Descriptions
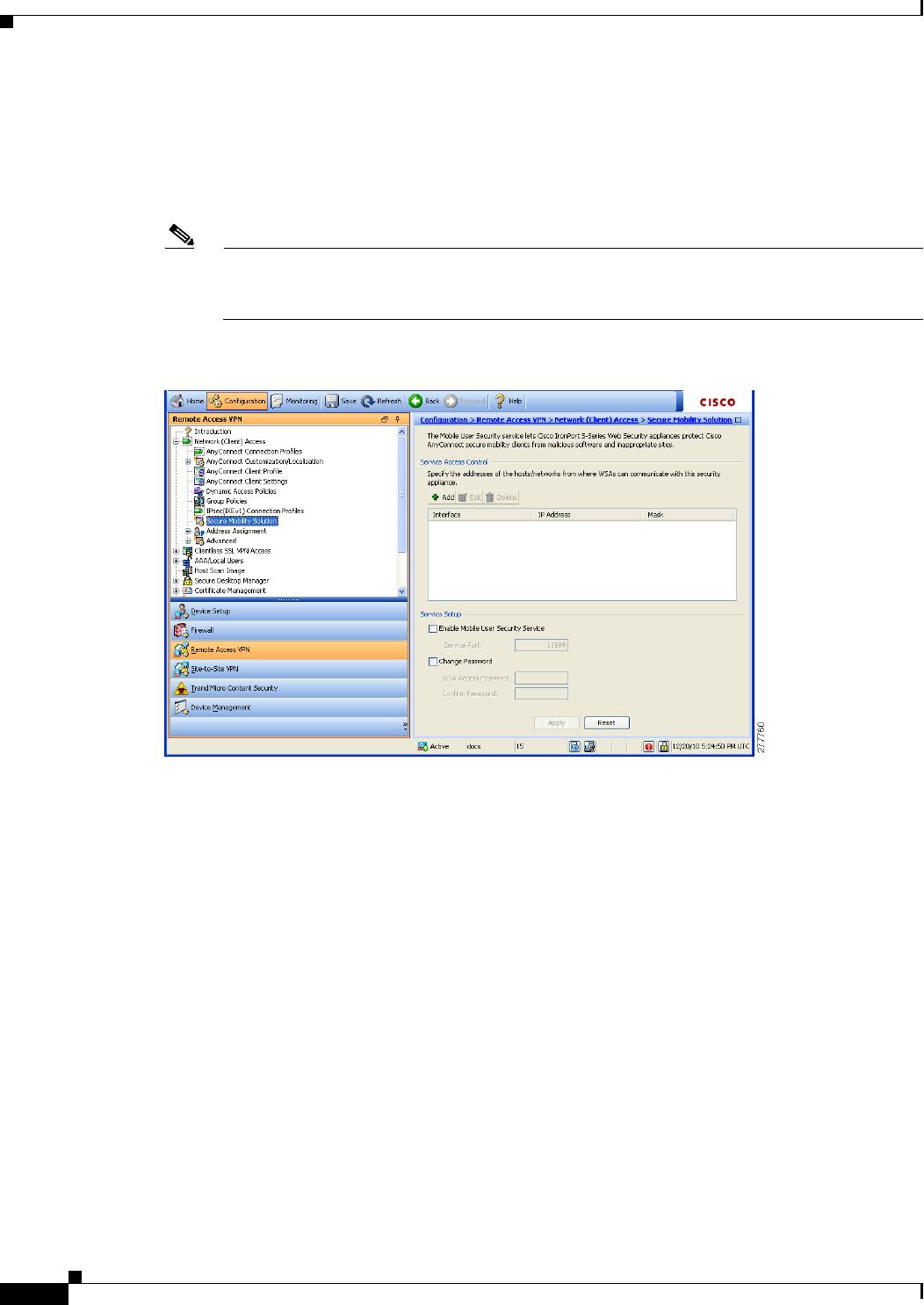
4-70
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 4 General VPN Setup
Configuring AnyConnect Secure Mobility
mobility clients to ensure that clients are protected from malicious software and/or inappropriate sites.
The client periodically checks to ensure that Cisco IronPort S-Series Web Security appliance protection
is enabled.
To configure secure mobility solutions, choose Configuration > Remote Access VPN > Network
(Client) Access > Mobile User Security.
Note This feature requires a release of the Cisco IronPort Web Security appliance that provides
AnyConnect Secure Mobility licensing support for the Cisco AnyConnect secure mobility client.
It also requires an AnyConnect release that supports the AnyConnect Secure Mobility feature.
Figure 4-6 Mobile User Security Window
Fields
•Service Access Control—Specifies from which host or network address the WSAs can
communicate.
–
Add—Opens the Add MUS Access Control Configuration dialog box for the selected
connection.
–
Edit—Opens the Edit MUS Access Control Configuration dialog box for the selected
connection.
–
Delete—Removes the selected connection from the table. There is no confirmation or undo.
•Enable Mobile User Security Service—Starts the connection with the client through the VPN. If
enabled, you are required to enter a password, used by the WSA when contacting the ASA. If no
WSA is present, the status is disabled.
•Service Port—If you choose to enable the service, specify which port number for the service to use.
The port must be between 1 and 65535 and must match the corresponding value provisioned into the
WSA with the management system. The default is 11999.
•Change Password—Enables you to change the WSA access password.

4-71
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 4 General VPN Setup
Configuring Clientless SSL VPN Connections
•WSA Access Password—Specify the shared secret password required for authentication between
the ASA and WSA. This password must match the corresponding password provisioned into the
WSA with the management system.
•Confirm Password—Re-enter the specified password.
•Show WSA Sessions—Allows you to view session information of WSAs connected to the ASA.The
host IP address of the WSA that is connected (or has been connected) and the duration of the
connection is returned in a dialog box.
Add or Edit MUS Access Control
The Add or Edit MUS Access Control dialog box lets you configure MUS access.
Fields
•Interface Name—Use the drop-down menu to choose which interface name you are adding or
editing.
•IP Address—Enter either an IPv4 or IPv6 address.
•Mask—Use the drop-down menu to choose the appropriate mask.
Configuring Clientless SSL VPN Connections
Use the Clientless SSL VPN Access Connections dialog box to configure clientless SSL VPN access
parameters. This dialog box also records the configuration choices you make in its child dialog boxes.
Fields
•Access Interfaces—Lets you select from a table the interfaces on which to enable access. The fields
in this table include the interface name and check boxes specifying whether to allow access.
–
Device Certificate—Lets you specify a certificate for authentication for either an RSA key or
an ECDSA key or trustpoint. You have the option to configure two trustpoints. The client
indicates ECDSA support with a vendor ID payload. The ASA scans the configured trustpoint
list and chooses the first one that the client supports. If ECDSA is preferred, you should
configure that trustpoint before the RSA trustpoint.
–
Manage—Opens the Manage Identity Certificates dialog box, on which you can add, edit,
delete, export, and show details for a selected certificate.
–
Port Setting—Configure port numbers for clientless SSL and IPsec (IKEv2) connections. The
range is 1-65535. The default is port 443.
•Login Page Setting
–
Allow user to select connection profile, identified by its alias, on the login page. Otherwise,
DefaultWebVPN Group will be the connection profile.—Specifies that the user login page
presents the user with a drop-down menu from which the user can select a particular tunnel
group with which to connect.
–
Allow user to enter internal password on the login page.—Adds an option to input a different
password when accessing internal servers.
–
Shutdown portal login page.—Shows the web page when the login is disabled.

4-72
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 4 General VPN Setup
Configuring Clientless SSL VPN Connections
•Connection Profiles—Provides a connection table that shows the records that determine the
connection policy for this connection (tunnel group). Each record identifies a default group policy
for the connection and contains protocol-specific connection parameters.
–
Add—Opens the Add Clientless SSL VPN dialog box for the selected connection.
–
Edit—Opens the Edit Clientless SSL VPN dialog box for the selected connection.
–
Delete—Removes the selected connection from the table. There is no confirmation or undo.
–
Name—The name of the Connection Profile.
–
Enabled—Checkmark when enabled.
–
Aliases—Other names by which the Connection Profile is known.
–
Authentication Method—Specifies which authentication method is used.
–
Group Policy—Shows the default group policy for this Connection Profile.
•Let group URL take precedence if group URL and certificate map match different connection
profiles. Otherwise, the connection profile matches the certificate map will be used.—This option
specifies the relative preference of the group URL and certificate values during the connection
profile selection process. If the ASA fails to match the preferred value specified by the endpoint to
that specified by a connection profile, it chooses the connection profile that matches the other value.
Check this option only if you want to rely on the preference used by many older ASA software
releases to match the group URL specified by the VPN endpoint to the connection profile that
specifies the same group URL. This option is unchecked by default. If it is unchecked, the ASA
prefers to match the certificate field value specified in the connection profile to the field value of the
certificate used by the endpoint to assign the connection profile.
Add or Edit Clientless SSL VPN Connections
The Add or Edit SSL VPN dialog box consists of Basic and Advanced sections, accessible through the
expandable menu on the left of the box.
Add or Edit Clientless SSL VPN Connections > Basic
The Basic dialog box lets you configure essential characteristics for this connection.
Fields
•Name—Specifies the name of the connection. For the edit function, this field is read-only.
•Aliases—(Optional) Specifies one or more alternate names for this connection. The aliases appear
on the login page if you configure that option on the Clientless SSL VPN Access Connections dialog
box.
•Authentication—Specifies the authentication parameters.
–
Method—Specifies whether to use AAA authentication, certificate authentication, or both
methods for this connection. The default is AAA authentication.
–
AAA server Group—Selects the AAA server group to use for authenticating this connection.
The default is LOCAL.
–
Manage—Opens the Configure AAA Server Groups dialog box.
•DNS Server Group—Selects the server to use as the DNS server group for this connection. The
default is DefaultDNS.

4-73
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 4 General VPN Setup
Configuring Clientless SSL VPN Connections
•Default Group Policy—Specifies the default group policy parameters to use for this connection.
–
Group Policy—Selects the default group policy to use for this connection. The default is
DfltGrpPolicy.
–
Clientless SSL VPN Protocol—Enables or disables the Clientless SSL VPN protocol for this
connection.
Add or Edit Clientless SSL VPN Connections > Advanced
The Advanced menu items and their dialog boxes let you configure the following characteristics for this
connection:
•General attributes.
•Authentication attributes.
•Authorization attributes.
•Accounting attributes.
•Name server attributes.
•Clientless SSL VPN attributes.
Add or Edit Clientless SSL VPN Connections > Advanced > General
Use this dialog box to specify whether to strip the realm and group from the username before passing
them to the AAA server, and to specify password management options.
Fields
•Password Management—Lets you configure parameters relevant to overriding an account-disabled
indication from a AAA server and to notifying users about password expiration.
–
Enable notification password management—Checking this check box makes the following two
parameters available. You can select either to notify the user at login a specific number of days
before the password expires or to notify the user only on the day that the password expires. The
default is to notify the user 14 days prior to password expiration and every day thereafter until
the user changes the password. The range is 1 through 180 days.
Note This does not change the number of days before the password expires, but rather, it enables
the notification. If you select this option, you must also specify the number of days.
In either case, and, if the password expires without being changed, the ASA offers the user the
opportunity to change the password. If the current password has not yet expired, the user can
still log in using that password.
This parameter is valid for AAA servers that support such notification; that is, RADIUS,
RADIUS with an NT server, and LDAP servers. The ASA ignores this command if RADIUS or
LDAP authentication has not been configured.
–
Override account-disabled indication from AAA server—Overrides an account-disabled
indication from a AAA server.

4-74
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 4 General VPN Setup
Configuring Clientless SSL VPN Connections
Note Allowing override account-disabled is a potential security risk.
Add or Edit Clientless or SSL VPN Client Connection Profile or IPsec Connection
Profiles> Advanced > Authentication
The Authentication dialog box lets you view, add, edit, or delete interface-specific authentication server
groups. Each row of the table on this dialog box shows the status of one interface-specific server group:
the interface name, its associated server group, and whether fallback to the local database is enabled if
the selected server group fails.
Fields
•Interface-specific Authorization Server Groups—Manages the assignment of authorization server
groups to specific interfaces.
–
Add or Edit—Opens the Assign Authentication Server Group to Interface dialog box, in which
you can specify the interface and server group, and specify whether to allow fallback to the
LOCAL database if the selected server group fails. The Manage button on this dialog box opens
the Configure AAA Server Groups dialog box. Your selections appear in the Interface/Server
Group table.
–
Delete—Removes the selected server group from the table. There is no confirmation or undo.
Assign Authentication Server Group to Interface
This dialog box lets you associate an interface with a AAA server group. The results appear in the table
on the Authentication dialog box.
Fields
•Interface—Selects an interface, DMZ, Outside, or Inside. The default is DMZ.
•Server Group—Selects a server group to assign to the selected interface. The default is LOCAL.
•Manage—Opens the Configure AAA Server Groups dialog box.
•Fallback—Enables or disables fallback to LOCAL if the selected server group fails.
Add or Edit SSL VPN Connections > Advanced > Authorization
This dialog box lets you configure the default authorization server group, interface-specific
authorization server groups, and user name mapping attributes. The attributes are the same for SSL VPN
and Clientless SSL VPN connections.
Fields
•Default Authorization Server Group—Configures default authorization server group attributes.
–
Server Group—Selects the authorization server group to use for this connection. The default is
--None--.
–
Manage—Opens the Configure AAA Server Groups dialog box.
–
Users must exist in the authorization database to connect—Enables or disables this requirement.

4-75
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 4 General VPN Setup
Configuring Clientless SSL VPN Connections
•Interface-specific Authorization Server Groups
–
Table—Lists each configured interface and the server group with which it is associated.
–
Add or Edit—Opens the Assign Authorization Server Group to Interface dialog box.
–
Delete—Removes the selected row from the table.
•User Name Mapping—Specifies user name mapping attributes.
•Username Mapping from Certificate—Lets you specify the fields in a digital certificate from which
to extract the username.
–
Pre-fill Username from Certificate —Enables the use of a username extracted from the specified
certificate field as the username for username/password authentication and authorization, using
the options that follow in this dialog box.
–
Hide username from end user—Specifies not to display the extracted username to the end user.
–
Use script to select username—Specify the name of a script to use to select a username from a
digital certificate. There is no default.
–
Add or Edit—Opens the Add or Edit Script Content dialog box, in which you can define a script
to use in mapping the username from the certificate.
–
Delete—Deletes the selected script. There is no confirmation or undo.
–
Use the entire DN as the username—Enables or disables the requirement to use the entire DN
as the username.
–
Specify individual DN fields as the username. You can select both the primary DN field, for
which the default is CN (Common Name) and the secondary DN field, for which the default is
OU (Organization Unit).
–
Primary Field—Selects the first field to use in the username.
–
Secondary Field—Selects the second field to use in the username.
Assign Authorization Server Group to Interface
This dialog box lets you associate an interface with a AAA server group. The results appear in the table
on the Authorization dialog box.
Fields
•Interface—Selects an interface, DMZ, Outside, or Inside. The default is DMZ.
•Server Group—Selects a server group to assign to the selected interface. The default is LOCAL.
•Manage—Opens the Configure AAA Server Groups dialog box.
Add or Edit SSL VPN Connections > Advanced > SSL VPN
This dialog box lets you configure attributes that affect what the remote user sees upon login.
Fields
•Portal Page Customization—Configures the look and feel of the user login page by specifying which
preconfigured customization attributes to apply. The default is DfltCustomization.
•Enable the display of Radius Reject-Message on the login screen—Select this check box to display
the RADIUS-reject message on the login dialog box when authentication is rejected.

4-76
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 4 General VPN Setup
Configuring Clientless SSL VPN Connections
•Enable the display of SecurId message on the login screen—Select this check box to display
SecurID messages on the login dialog box.
•Manage—Opens the Configure GUI Customization Objects dialog box.
•Connection Aliases—Lists in a table the existing connection aliases and their status and lets you add
or delete items in that table. A connection alias appears on the user login page if the connection is
configured to allow users to select a particular connection (tunnel group) at login. The rows in this
table are editable in place, so there is no Edit button. Clicking the “i” icon above the table opens a
tooltip for the edit function.
–
Add—Opens the Add Connection Alias dialog box, on which you can add and enable a
connection alias.
–
Delete—Removes the selected row from the connection alias table. There is no confirmation or
undo.
–
To edit an alias listed in the table, double-click the line.
•Group URLs—Lists in a table the existing group URLs and their status and lets you add or delete
items in that table. A group URL appears on the user login page if the connection is configured to
allow users to select a particular group at login. The rows in this table are editable in place, so there
is no Edit button. Clicking the “i” icon above the table opens a tooltip for the edit function.
–
Add—Opens the Add Group URL dialog box, on which you can add and enable a group URL.
–
Delete—Removes the selected row from the connection alias table. There is no confirmation or
undo.
–
To edit a URL listed in the table, double-click the line.
•Do not run Cisco Secure Desktop (CSD) on client machine when using group URLs defined above
to access the ASA. (If a client connects using a connection alias, this setting is ignored.)—Check if
you want to exempt users from running CSD who use a URL that matches an entry in the Group
URLs table. Be aware that doing so stops the security appliance from receiving endpoint criteria
from these users, so you might have to change the DAP configuration to provide them with VPN
access.
Add or Edit Clientless SSL VPN Connections > Advanced > Clientless SSL VPN
This dialog box lets you configure attributes that affect what the remote user sees upon login.
Fields
•Portal Page Customization—Configures the look and feel of the user login page by specifying which
preconfigured customization attributes to apply. The default is DfltCustomization.
•Enable the display of Radius Reject-Message on the login screen—Select this check box to display
the RADIUS-reject message on the login dialog box when authentication is rejected.
•Enable the display of SecurId message on the login screen—Select this check box to display
SecurID messages on the login dialog box.
•Manage—Opens the Configure GUI Customization Objects dialog box.
•Connection Aliases—Lists in a table the existing connection aliases and their status and lets you add
or delete items in that table. A connection alias appears on the user login page if the connection is
configured to allow users to select a particular connection (tunnel group) at login.
–
Add—Opens the Add Connection Alias dialog box, on which you can add and enable a
connection alias.

4-77
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 4 General VPN Setup
Configuring Clientless SSL VPN Connections
–
Delete—Removes the selected row from the connection alias table. There is no confirmation or
undo.
•Group URLs—Lists in a table the existing group URLs and their status and lets you add or delete
items in that table. A group URL appears on the user login page if the connection is configured to
allow users to select a particular group at login.
–
Add—Opens the Add Group URL dialog box, on which you can add and enable a group URL.
–
Delete—Removes the selected row from the connection alias table. There is no confirmation or
undo.
•Do not run Cisco Secure Desktop (CSD) on client machine when using group URLs defined above
to access the ASA. (If a client connects using a connection alias, this setting is ignored.)—Check if
you want to exempt users from running CSD who use a URL that matches an entry in the Group
URLs table. Be aware that doing so stops the security appliance from receiving endpoint criteria
from these users, so you might have to change the DAP configuration to provide them with VPN
access.
Add or Edit Clientless SSL VPN Connections > Advanced > NetBIOS Servers
The table on this dialog box shows the attributes of the already-configured NetBIOS servers. The Add
or Edit Tunnel Group dialog box for Clientless SSL VPN access, NetBIOS dialog box, lets you configure
the NetBIOS attributes for the tunnel group. Clientless SSL VPN uses NetBIOS and the Common
Internet File System protocol to access or share files on remote systems. When you attempt a file-sharing
connection to a Windows computer by using its computer name, the file server you specify corresponds
to a specific NetBIOS name that identifies a resource on the network.
The ASA queries NetBIOS name servers to map NetBIOS names to IP addresses. Clientless SSL VPN
requires NetBIOS to access or share files on remote systems.
To make the NBNS function operational, you must configure at least one NetBIOS server (host). You
can configure up to 3 NBNS servers for redundancy. The ASA uses the first server on the list for
NetBIOS/CIFS name resolution. If the query fails, it uses the next server.
Fields
•IP Address—Displays the IP addresses of configured NetBIOS servers.
•Master Browser—Shows whether a server is a WINS server or one that can also be a CIFS server
(that is, a master browser).
•Timeout (seconds)—Displays the initial time in seconds that the server waits for a response to an
NBNS query before sending the query to the next server.
•Retries—Shows the number of times to retry sending an NBNS query to the configured servers, in
order. In other words, this is the number of times to cycle through the list of servers before returning
an error. The minimum number of retries is 0. The default number of retries is 2. The maximum
number of retries is 10.
•Add/Edit—Click to add a NetBIOS server. This opens the Add or Edit NetBIOS Server dialog box.
•Delete—Removes the highlighted NetBIOS row from the list.
•Move Up/Move Down—The ASA sends NBNS queries to the NetBIOS servers in the order in which
they appear in this box. Use this box to change the priority order of the servers by moving them up
or down in the list.

4-78
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 4 General VPN Setup
IPsec Remote Access Connection Profiles
Configure DNS Server Groups
This dialog box displays the configured DNS servers in a table, including the server group name, servers,
timeout in seconds, number of retries allowed, and domain name. You can add, edit, or delete DNS server
groups on this dialog box.
Fields
•Add or Edit—Opens the Add or Edit DNS Server Group dialog box.
•Delete—Removes the selected row from the table. There is no confirmation or undo.
•DNS Server Group—Selects the server to use as the DNS server group for this connection. The
default is DefaultDNS.
•Manage—Opens the Configure DNS Server Groups dialog box.
Add or Edit Clientless SSL VPN Connections > Advanced > Clientless SSL VPN
This dialog box lets you specify portal-related attributes for Clientless SSL VPN connections.
Fields
•Portal Page Customization—Selects the customization to apply to the user interface.
•Manage—Opens the Configure GUI Customization Objects dialog box.
IPsec Remote Access Connection Profiles
Configuration > VPN > General > Tunnel Group
The parameters in the IPsec Connection Profiles dialog box let you configure IPsec remote access
connections. Most of the parameters in this section were formerly configured under tunnel groups. An
IPsec connection represents a connection-specific record for IPsec and Clientless SSL VPN connections.
The IPsec group uses the IPsec connection parameters to create a tunnel. An IPsec connection can be
either remote-access or Site-to-Site. The IPsec group is configured on the internal server or on an
external RADIUS server. For ASA 5505 in client mode or VPN 3002 hardware client parameters, which
enable or disable interactive hardware client authentication and individual user authentication, the IPsec
connection parameters take precedence over parameters set for users and groups.
The Clientless SSL VPN tunnel-group parameters are the parameters of the Clientless SSL VPN group
that you want to apply to this IPsec connection. You configure Clientless SSL VPN access on the
Configuration > Clientless SSL VPN dialog box.
Fields
•Access Interfaces—Selects the interfaces to enable for IPsec access. The default is that no access is
selected.
•Connections—Shows in tabular format the configured parameters for existing IPsec connections.
The Connections table contains records that determine connection policies. A record identifies a
default group policy for the connection and contains protocol-specific connection parameters. The
table contains the following columns:
–
Name—Specifies the name or IP address of the IPsec connection.
–
ID Certificate—Specifies the name of the ID certificate, if available.

4-79
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 4 General VPN Setup
Add or Edit an IPsec Remote Access Connection Profile
–
IPsec Protocol—Indicates whether the IPsec protocol is enabled. You enable this protocol on
the Add or Edit IPsec Remote Access Connection, Basic dialog box.
–
L2TP/IPsec Protocol—Indicates whether the L2TP/IPsec protocol is enabled. You enable this
protocol on the Add or Edit IPsec Remote Access Connection, Basic dialog box.
–
Group Policy—Indicates the name of the group policy for this IPsec connection.
•Add or Edit—Opens the Add or Edit IPsec Remote Access Connection Profile dialog box.
•Delete—Removes the selected server group from the table. There is no confirmation or undo.
Add or Edit an IPsec Remote Access Connection Profile
The Add or Edit IPsec Remote Access Connection Profile dialog box has a navigation pane that lets you
select basic or advanced elements to configure.
Add or Edit IPsec Remote Access Connection Profile Basic
The Add or Edit IPsec Remote Access Connection Profile Basic dialog box lets you configure common
attributes for IPsec connections.
Fields
•Name—Identifies the name of the connection.
•IKE Peer Authentication—Configures IKE peers.
–
Pre-shared key—Specifies the value of the pre-shared key for the connection. The maximum
length of a pre-shared key is 128 characters.
–
Identity Certificate—Selects the name of an identity certificate, if any identity certificates are
configured and enrolled.
–
Manage—Opens the Manage Identity Certificates dialog box, on which you can add, edit,
delete, export, and show details for a selected certificate.
•User Authentication—Specifies information about the servers used for user authentication. You can
configure more authentication information in the Advanced section.
–
Server Group—Selects the server group to use for user authentication. the default is LOCAL.
If you select something other than LOCAL, the Fallback check box becomes available.
–
Manage—Opens the Configure AAA Server Groups dialog box.
–
Fallback—Specifies whether to use LOCAL for user authentication if the specified server group
fails.
•Client Address Assignment—Specifies attributes relevant to assigning client attributes.
–
DHCP Servers—Specifies the IP address of a DHCP server to use. You can add up to 10 servers,
separated by spaces.
–
Client Address Pools—Specifies up to 6 predefined address pools. To define an address pool,
go to Configuration > Remote Access VPN > Network Client Access > Address Assignment >
Address Pools.
–
Select—Opens the Select Address Pools dialog box.
•Default Group Policy—Specifies attributes relevant to the default group policy.

4-80
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 4 General VPN Setup
Mapping Certificates to IPsec or SSL VPN Connection Profiles
–
Group Policy—Selects the default group policy to use for this connection. The default is
DfltGrpPolicy.
–
Manage—Opens the Configure Group Policies dialog box, from which you can add, edit, or
delete group policies.
–
Client Protocols—Selects the protocol or protocols to use for this connection. By default, both
IPsec and L2TP over IPsec are selected.
Mapping Certificates to IPsec or SSL VPN Connection Profiles
When the ASA receives an IPsec connection request with client certificate authentication, it assigns a
connection profile to the connection according to policies you configure. That policy can be to use rules
you configure, use the certificate OU field, use the IKE identity (i.e. hostname, IP address, key ID), the
peer IP address, or a default connection profile. For SSL connections, the ASA only uses the rules you
configure.
For IPsec or SSL connections using rules, the ASA evaluates the attributes of the certificate against the
rules until it finds a match. When it finds a match, it assigns the connection profile associated with the
matched rule to the connection. If it fails to find a match, it assigns the default connection profile
(DefaultRAGroup for IPsec and DefaultWEBVPNGroup for SSL VPN) to the connection and lets the
user choose the connection profile from a drop-down menu displayed on the portal page (if it is enabled).
The outcome of the connection attempt once in this connection profile depends on whether or not the
certificate is valid and the authentication settings of the connection profile.
A certificate group matching policy defines the method to use for identifying the permission groups of
certificate users. You can use any or all of these methods.
First configure the policy for matching a certificate to a connection profile at Configuration > Remote
Access VPN > Network (Client) Access > Advanced > IPsec > Certificate to Connection Profile Maps.
If you choose to use rules you configure, go to Rules to specify the rules. The following procedures
shows how you create the certificate-based criteria for each IPsec and SSL VPN connection profile:
Step 1 Use the table at the top (Certificate to Connection Profile Maps) to do one of the following:
•Create a list name, called a “map,” specify the priority of the list, and assign the list to a connection
profile.
ASDM highlights the list after you add it to the table.
•Confirm that a list is assigned to the connection profile for which you want to add certificate-based
rules.
ASDM highlights the list after you add it to the table and displays any associated list entries in the
table at the bottom of the pane.
Step 2 Use the table at the bottom (Mapping Criteria) to view, add, change or delete entries to the selected list.
Each entry in the list consists of one certificate-based rule. All of the rules in the mapping criteria list
need to match the contents of the certificate for the ASA to choose the associated map index. To assign
a connection if one criterion or another matches, create one list for each matching criterion.
To understand the fields, see the following sections:
•Setting a Certificate Matching Policy
•Add/Edit Certificate Matching Rule

4-81
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 4 General VPN Setup
Mapping Certificates to IPsec or SSL VPN Connection Profiles
•Add/Edit Certificate Matching Rule Criterion
Setting a Certificate Matching Policy
For IPsec connections, a certificate group matching policy defines the method to use for identifying the
permission groups of certificate users. You can use any or all of these methods:
Fields
•Use the configured rules to match a certificate to a group—Lets you use the rules you have defined
under Rules.
•Use the certificate OU field to determine the group—Lets you use the organizational unit field to
determine the group to which to match the certificate. This is selected by default.
•Use the IKE identity to determine the group—Lets you use the identity you previously defined under
Configuration > VPN > IKE > Global Parameters. The IKE identity can be hostname, IP address,
key ID, or automatic.
•Use the peer IP address to determine the group—Lets you use the peer's IP address. This is selected
by default.
•Default to group—Lets you select a default group for certificate users that is used when none of the
preceding methods resulted in a match. This is selected by default. Click the default group in the
Default to group list. The group must already exist in the configuration. If the group does not appear
in the list, you must define it by using Configuration > VPN > General > Tunnel Group.
Add/Edit Certificate Matching Rule
Configuration > VPN > IKE > Certificate Group Matching > Rules >
Add/Edit Certificate Matching Rule
Use the Add/Edit Certificate Matching Rule dialog box to assign the name of a list (map) to a
connection profile.
Fields
•Map—Choose one of the following:
–
Existing—Select the name of the map to include the rule.
–
New—Enter a new map name for a rule.
•Rule Priority—Type a decimal to specify the sequence with which the ASA evaluates the map when
it receives a connection request. For the first rule defined, the default priority is 10. The ASA
evaluates each connection against the map with the lowest priority number first.
•Mapped to Connection Profile—Select the connection profile, formerly called a “tunnel group,”
to map to this rule.
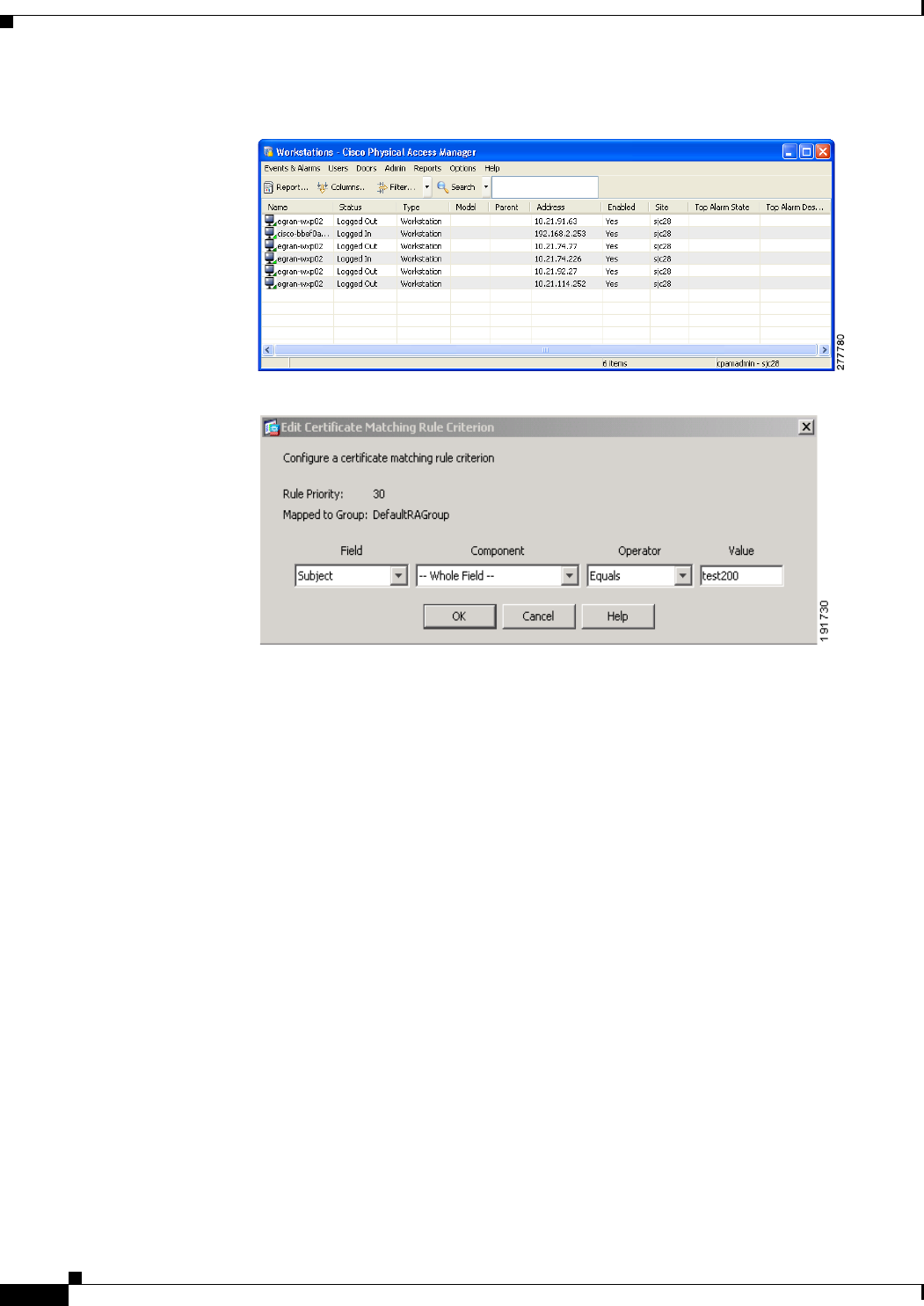
4-82
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 4 General VPN Setup
Mapping Certificates to IPsec or SSL VPN Connection Profiles
If you do not assign a rule criterion to the map, as described in the next section, the ASA ignores the
map entry.
Add/Edit Certificate Matching Rule Criterion
Configuration > VPN > IKE > Certificate Group Matching > Rules >
Add/Edit Certificate Matching Rule Criterion
Use the Add/Edit Certificate Matching Rule Criterion dialog box to configure a certificate matching
rule criterion for the selected connection profile.
Fields
•Rule Priority—(Display only). Sequence with which the ASA evaluates the map when it receives
a connection request. The ASA evaluates each connection against the map with the lowest priority
number first.
•Mapped to Group—(Display only). Connection profile to which the rule is assigned.
•Field—Select the part of the certificate to be evaluated from the drop-down list.
–
Subject—The person or system that uses the certificate. For a CA root certificate, the Subject
and Issuer are the same.
–
Alternative Subject—The subject alternative names extension allows additional identities to
be bound to the subject of the certificate.
–
Issuer—The CA or other entity (jurisdiction) that issued the certificate.
–
Extended Key Usage—An extension of the client certificate that provides further criteria that
you can choose to match.

4-83
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 4 General VPN Setup
Mapping Certificates to IPsec or SSL VPN Connection Profiles
•Component—(Applies only if Subject of Issuer is selected.) Select the distinguished name
component used in the rule:
•Operator—Select the operator used in the rule:
–
Equals—The distinguished name field must exactly match the value.
–
Contains—The distinguished name field must include the value within it.
–
Does Not Equal—The distinguished name field must not match the value
–
Does Not Contain—The distinguished name field must not include the value within it.
•Value —Enter up to 255 characters to specify the object of the operator. For Extended Key Usage,
select one of the pre-defined values in the drop-down list, or you can enter OIDs for other
extensions. The pre-defined values include the following:
DN Field Definition
Whole Field The entire DN.
Country (C) The two-letter country abbreviation. These codes conform to ISO 3166
country abbreviations.
Common Name (CN) The name of a person, system, or other entity. This is the lowest (most
specific) level in the identification hierarchy.
DN Qualifier (DNQ) A specific DN attribute.
E-mail Address (EA) The e-mail address of the person, system or entity that owns the certificate.
Generational Qualifier
(GENQ)
A generational qualifier such as Jr., Sr., or III.
Given Name (GN) The first name of the certificate owner.
Initials (I) The first letters of each part of the certificate owner’s name.
Locality (L) The city or town where the organization is located.
Name (N) The name of the certificate owner.
Organization (O) The name of the company, institution, agency, association, or other entity.
Organizational Unit
(OU)
The subgroup within the organization.
Serial Number (SER) The serial number of the certificate.
Surname (SN) The family name or last name of the certificate owner.
State/Province (S/P) The state or province where the organization is located.
Title (T) The title of the certificate owner, such as Dr.
User ID (UID) The identification number of the certificate owner.
Unstructured Name
(UNAME)
The unstructuredName attribute type specifies the name or names of a
subject as an unstructured ASCII string.
IP Address (IP) IP address field.

4-84
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 4 General VPN Setup
Mapping Certificates to IPsec or SSL VPN Connection Profiles
Site-to-Site Connection Profiles
The Connection Profiles dialog box shows the attributes of the currently configured Site-to-Site
connection profiles (tunnel groups), lets you select the delimiter to use when parsing connection profile
names, and lets you add, modify, or delete connection profiles.
The security appliance supports IPsec LAN-to-LAN VPN connections for IPv4 or IPv6 using IKEv1 or
IKEv2 and supports both inside and outside networks using the inner and outer IP headers.
Fields
•Access Interfaces—Displays a table of device interfaces where you can enable access by a remote
peer device on the interface:
–
Interface—The device interface to enable or disable access.
–
Allow IKEv1 Access—Check to enable IPsec IKEv1 access by a peer device.
–
Allow IKEv2 Access—Check to enable IPsec IKEv2 access by a peer device.
•Connection Profiles—Displays a table of connection profiles where you can add, edit, or delete
profiles:
–
Add—Opens the Add IPsec Site-to-Site connection profile dialog box.
–
Edit—Opens the Edit IPsec Site-to-Site connection profile dialog box.
–
Delete—Removes the selected connection profile. There is no confirmation or undo.
–
Name—The name of the connection profile.
–
Interface—The interface the connection profile is enabled on.
–
Local Network—Specifies the IP address of the local network.
–
Remote Network—Specifies the IP address of the remote network.
–
IKEv1 Enabled—Shows IKEv1 enabled for the connection profile.
–
IKEv2 Enabled—Shows IKEv2 enabled for the connection profile.
–
Group Policy—Shows the default group policy of the connection profile.
Selection Key Usage Purpose OID String
clientauth Client Authentication 1.3.6.1.5.5.7.3.2
codesigning Code Signing 1.3.6.1.5.5.7.3.3
emailprotection Secure Email Protection 1.3.6.1.5.5.7.3.4
ocspsigning OCSP Signing 1.3.6.1.5.5.7.3.9
serverauth Server Authentication 1.3.6.1.5.5.7.3.1
timestamping Time Stamping 1.3.6.1.5.5.7.3.8

4-85
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 4 General VPN Setup
Mapping Certificates to IPsec or SSL VPN Connection Profiles
Add/Edit Site-to-Site Connection
You can get to this panel through various paths.
The Add or Edit IPsec Site-to-Site Connection dialog box lets you create or modify an IPsec Site-to-Site
connection. These dialog boxes let you specify the peer IP address (IPv4 or IPv6), specify a connection
name, select an interface, specify IKEv1 and IKEv2 peer and user authentication parameters, specify
protected networks, and specify encryption algorithms.
The ASA supports LAN-to-LAN VPN connections to Cisco or third-party peers when the two peers have
IPv4 inside and outside networks (IPv4 addresses on the inside and outside interfaces).
For LAN-to-LAN connections using mixed IPv4 and IPv6 addressing, or all IPv6 addressing, the
security appliance supports VPN tunnels if both peers are Cisco ASA 5500 series security appliances,
and if both inside networks have matching addressing schemes (both IPv4 or both IPv6).
Specifically, the following topologies are supported when both peers are Cisco ASA 5500 series ASAs:
•The ASAs have IPv4 inside networks and the outside network is IPv6 (IPv4 addresses on the inside
interfaces and IPv6 addresses on the outside interfaces).
•The ASAs have IPv6 inside networks and the outside network is IPv4 (IPv6 addresses on the inside
interface and IPv4 addresses on the outside interfaces).
•The ASAs have IPv6 inside networks and the outside network is IPv6 (IPv6 addresses on the inside
and outside interfaces).
Fields
•Peer IP Address—Lets you specify an IP address (IPv4 or IPv6) and whether that address is static.
•Connection Name—Specifies the name assigned to this connection profile. For the Edit function,
this field is display-only. You can specify that the connection name is the same as the IP address
specified in the Peer IP Address field.
•Interface—Selects the interface to use for this connection.
•Protected Networks—Selects or specifies the local and remote network protected for this
connection.
–
IP Address Type—Specifies the address is an IPv4 or IPv6 address.
–
Local Network—Specifies the IP address of the local network.
–
...—Opens the Browse Local Network dialog box, in which you can select a local network.
–
Remote Network—Specifies the IP address of the remote network.
•IPsec Enabling—Specifies the group policy for this connection profile and the key exchange
protocol specified in that policy:
–
Group Policy Name—Specifies the group policy associated with this connection profile.
–
Manage—Opens the Browse Remote Network dialog box, in which you can select a remote
network.
–
Enable IKEv1—Enables the key exchange protocol IKEv1 in the specified group policy.
–
Enable IKEv2—Enables the key exchange protocol IKEv2 in the specified group policy.
•IKEv1 Settings tab—Specifies authentication and encryption settings for IKEv1:
–
Pre-shared Key—Specify the value of the pre-shared key for the tunnel group. The maximum
length of the pre-shared key is 128 characters.

4-86
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 4 General VPN Setup
Mapping Certificates to IPsec or SSL VPN Connection Profiles
–
Device Certificate—Specifies the name of the identity certificate, if available, to use for
authentication.
–
Manage—Opens the Manage Identity Certificates dialog box, on which you can see the
certificates that are already configured, add new certificates, show details for a certificate, and
edit or delete a certificate.
–
IKE Policy—Specifies one or more encryption algorithms to use for the IKE proposal.
–
Manage—Opens the Configure IKEv1 Proposals dialog box.
–
IPsec Proposal—Specifies one or more encryption algorithms to use for the IPsec IKEv1
proposal.
•IKEv2 Settings tab—Specifies authentication and encryption settings for IKEv2:
–
Local Pre-shared Key—Specify the value of the pre-shared key for the tunnel group. The
maximum length of the pre-shared key is 128 characters.
–
Local Device Certificate—Specifies the name of the identity certificate, if available, to use for
authentication.
–
Manage—Opens the Manage Identity Certificates dialog box, on which you can see the
certificates that are already configured, add new certificates, show details for a certificate, and
edit or delete a certificate.
–
Remote Peer Pre-shared Key—Specify the value of the remote peer pre-shared key for the
tunnel group. The maximum length of the pre-shared key is 128 characters.
–
Remote Peer Certificate Authentication—Check Allowed to allow certificate authentication for
IKEv2 connections for this connection profile.
–
Manage—Opens the Manage CA Certificates dialog where you can view certificates and add
new ones.
–
IKE Policy—Specifies one or more encryption algorithms to use for the IKE proposal.
–
Manage—Opens the Configure IKEv1 Proposals dialog box.
–
IPsec Proposal—Specifies one or more encryption algorithms to use for the IPsec IKEv1
proposal.
–
Select—Opens the Select IPsec Proposals (Transform Sets) dialog box, where you can assign a
proposal to the connection profile for IKEv2 connections.
Adding or Editing a Site-to-Site Tunnel Group
You can get to this panel through various paths.
The Add or Edit IPsec Site-to-Site Tunnel Group dialog box lets you specify attributes for the IPsec
site-to-site connection that you are adding. In addition, you can select IKE peer and user authentication
parameters, configure IKE keepalive monitoring, and select the default group policy.
Fields
•Name—Specifies the name assigned to this tunnel group. For the Edit function, this field is
display-only.
•IKE Authentication—Specifies the pre-shared key and Identity certificate parameters to use when
authenticating an IKE peer.
–
Pre-shared Key—Specify the value of the pre-shared key for the tunnel group. The maximum
length of the pre-shared key is 128 characters.

4-87
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 4 General VPN Setup
Mapping Certificates to IPsec or SSL VPN Connection Profiles
–
Identity Certificate—Specifies the name of the ID certificate to use for authentication, if
available.
–
Manage—Opens the Manage Identity Certificates dialog box, on which you can see the
certificates that are already configured, add new certificates, show details for a certificate, and
edit or delete a certificate.
–
IKE Peer ID Validation—Specifies whether to check IKE peer ID validation. The default is
Required.
•IPsec Enabling—Specifies the group policy for this connection profile and the key exchange
protocol specified in that policy:
–
Group Policy Name—Specifies the group policy associated with this connection profile.
–
Manage—Opens the Browse Remote Network dialog box, in which you can select a remote
network.
–
Enable IKEv1—Enables the key exchange protocol IKEv1 in the specified group policy.
–
Enable IKEv2—Enables the key exchange protocol IKEv2 in the specified group policy.
•IKEv1 Settings tab—Specifies authentication and encryption settings for IKEv1:
–
Pre-shared Key—Specify the value of the pre-shared key for the tunnel group. The maximum
length of the pre-shared key is 128 characters.
–
Device Certificate—Specifies the name of the identity certificate, if available, to use for
authentication.
–
Manage—Opens the Manage Identity Certificates dialog box, on which you can see the
certificates that are already configured, add new certificates, show details for a certificate, and
edit or delete a certificate.
–
IKE Policy—Specifies one or more encryption algorithms to use for the IKE proposal.
–
Manage—Opens the Configure IKEv1 Proposals dialog box.
–
IPsec Proposal—Specifies one or more encryption algorithms to use for the IPsec IKEv1
proposal.
•IKEv2 Settings tab—Specifies authentication and encryption settings for IKEv2:
–
Local Pre-shared Key—Specify the value of the pre-shared key for the tunnel group. The
maximum length of the pre-shared key is 128 characters.
–
Local Device Certificate—Specifies the name of the identity certificate, if available, to use for
authentication.
–
Manage—Opens the Manage Identity Certificates dialog box, on which you can see the
certificates that are already configured, add new certificates, show details for a certificate, and
edit or delete a certificate.
–
Remote Peer Pre-shared Key—Specify the value of the remote peer pre-shared key for the
tunnel group. The maximum length of the pre-shared key is 128 characters.
–
Remote Peer Certificate Authentication—Check Allowed to allow certificate authentication for
IKEv2 connections for this connection profile.
–
Manage—Opens the Manage CA Certificates dialog where you can view certificates and add
new ones.
–
IKE Policy—Specifies one or more encryption algorithms to use for the IKE proposal.
–
Manage—Opens the Configure IKEv1 Proposals dialog box.

4-88
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 4 General VPN Setup
Mapping Certificates to IPsec or SSL VPN Connection Profiles
–
IPsec Proposal—Specifies one or more encryption algorithms to use for the IPsec IKEv1
proposal.
–
Select—Opens the Select IPsec Proposals (Transform Sets) dialog box, where you can assign a
proposal to the connection profile for IKEv2 connections.
•IKE Keepalive —Enables and configures IKE keepalive monitoring. You can select only one of the
following attributes.
–
Disable Keep Alives—Enables or disables IKE keep alives.
–
Monitor Keep Alives—Enables or disables IKE keep alive monitoring. Selecting this option
makes available the Confidence Interval and Retry Interval fields.
–
Confidence Interval—Specifies the IKE keep alive confidence interval. This is the number of
seconds the ASA should allow a peer to idle before beginning keepalive monitoring. The
minimum is 10 seconds; the maximum is 300 seconds. The default for a remote access group is
10 seconds.
–
Retry Interval—Specifies number of seconds to wait between IKE keep alive retries. The default
is 2 seconds.
–
Head end will never initiate keepalive monitoring—Specifies that the central-site ASA never
initiates keepalive monitoring.
Crypto Map Entry
In this dialog box, specify crypto parameters for the Connection Profile.
Fields
•Priority—A unique priority (1 through 65,543, with 1 the highest priority). When IKE negotiation
begins, the peer that initiates the negotiation sends all of its policies to the remote peer, and the
remote peer searches for a match with its own policies, in priority order.
•Perfect Forward Secrecy—Ensures that the key for a given IPsec SA was not derived from any
other secret (like some other keys). If someone were to break a key, PFS ensures that the attacker
would not be able to derive any other key. If you enable PFS, the Diffie-Hellman Group list becomes
active.
–
Diffie-Hellman Group—An identifier which the two IPsec peers use to derive a shared secret
without transmitting it to each other. The choices are Group 1 (768-bits), Group 2 (1024-bits),
and Group 5 (1536-bits).
•Enable NAT-T— Enables NAT Traversal (NAT-T) for this policy, which lets IPsec peers establish
both remote access and LAN-to-LAN connections through a NAT device.
•Enable Reverse Route Injection—Provides the ability for static routes to be automatically inserted
into the routing process for those networks and hosts that are protected by a remote tunnel endpoint.
•Security Association Lifetime—Configures the duration of a Security Association (SA). This
parameter specifies how to measure the lifetime of the IPsec SA keys, which is how long the IPsec
SA lasts until it expires and must be renegotiated with new keys.
–
Time—Specifies the SA lifetime in terms of hours (hh), minutes (mm) and seconds (ss).
–
Traffic Volume—Defines the SA lifetime in terms of kilobytes of traffic. Enter the number of
kilobytes of payload data after which the IPsec SA expires. Minimum is 100 KB, default is
10000 KB, maximum is 2147483647 KB.

4-89
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 4 General VPN Setup
Mapping Certificates to IPsec or SSL VPN Connection Profiles
Crypto Map Entry for Static Peer Address
In this dialog box, specify crypto parameters for the Connection Profile when the Peer IP Address is a
static address.
Fields
•Priority—A unique priority (1 through 65,543, with 1 the highest priority). When IKE negotiation
begins, the peer that initiates the negotiation sends all of its policies to the remote peer, and the
remote peer searches for a match with its own policies, in priority order.
•Perfect Forward Secrecy—Ensures that the key for a given IPsec SA was not derived from any
other secret (like some other keys). If someone were to break a key, PFS ensures that the attacker
would not be able to derive any other key. If you enable PFS, the Diffie-Hellman Group list becomes
active.
–
Diffie-Hellman Group—An identifier which the two IPsec peers use to derive a shared secret
without transmitting it to each other. The choices are Group 1 (768-bits), Group 2 (1024-bits),
and Group 5 (1536-bits).
•Enable NAT-T— Enables NAT Traversal (NAT-T) for this policy, which lets IPsec peers establish
both remote access and LAN-to-LAN connections through a NAT device.
•Enable Reverse Route Injection—Provides the ability for static routes to be automatically inserted
into the routing process for those networks and hosts that are protected by a remote tunnel endpoint.
•Security Association Lifetime—Configures the duration of a Security Association (SA). This
parameter specifies how to measure the lifetime of the IPsec SA keys, which is how long the IPsec
SA lasts until it expires and must be renegotiated with new keys.
–
Time—Specifies the SA lifetime in terms of hours (hh), minutes (mm) and seconds (ss).
–
Traffic Volume—Defines the SA lifetime in terms of kilobytes of traffic. Enter the number of
kilobytes of payload data after which the IPsec SA expires. Minimum is 100 KB, default is
10000 KB, maximum is 2147483647 KB.
•Static Crypto Map Entry Parameters—Configure these additional parameters when the Peer IP
Address is specified as Static:
–
Connection Type—Specify the allowed negotiation as bidirectional, answer-only, or
originate-only.
–
Send ID Cert. Chain—Enables transmission of the entire certificate chain.
–
IKE Negotiation Mode—Sets the mode for exchanging key information for setting up the SAs,
Main or Aggressive. It also sets the mode that the initiator of the negotiation uses; the responder
auto-negotiates. Aggressive Mode is faster, using fewer packets and fewer exchanges, but it
does not protect the identity of the communicating parties. Main Mode is slower, using more
packets and more exchanges, but it protects the identities of the communicating parties. This
mode is more secure and it is the default selection. If you select Aggressive, the Diffie-Hellman
Group list becomes active.
–
Diffie-Hellman Group—An identifier which the two IPsec peers use to derive a shared secret
without transmitting it to each other. The choices are Group 1 (768-bits), Group 2 (1024-bits),
and Group 5 (1536-bits).

4-90
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 4 General VPN Setup
Mapping Certificates to IPsec or SSL VPN Connection Profiles
Managing CA Certificates
Clicking Manage under IKE Peer Authentication opens the Manage CA Certificates dialog box. Use this
dialog box to view, add, edit, and delete entries on the list of CA certificates available for IKE peer
authentication.
The Manage CA Certificates dialog box lists information about currently configured certificates,
including information about whom the certificate was issued to, who issued the certificate, when the
certificate expires, and usage data.
Fields
•Add or Edit—Opens the Install Certificate dialog box or the Edit Certificate dialog box, which let
you specify information about and install a certificate.
•Show Details—Displays detailed information about a certificate that you select in the table.
•Delete—Removes the selected certificate from the table. There is no confirmation or undo.
Install Certificate
Use this dialog box to install a new CA certificate. You can get the certificate in one of the following
ways:
•Install from a file by browsing to the certificate file.
•Paste the previously acquired certificate text in PEM format into the box on this dialog box.
•Use SCEP—Specifies the use of the Simple Certificate Enrollment Protocol (SCEP) Add-on for
Certificate Services runs on the Windows Server 2003 family. It provides support for the SCEP
protocol, which allows Cisco routers and other intermediate network devices to obtain certificates.
–
SCEP URL: http://—Specifies the URL from which to download SCEP information.
–
Retry Period—Specifies the number of minutes that must elapse between SCEP queries.
–
Retry Count—Specifies the maximum number of retries allowed.
•More Options—Opens the Configure Options for CA Certificate dialog box.
:
Configure Options for CA Certificate
Use this dialog box to specify details about retrieving CA Certificates for this IPsec remote access
connection. The dialog boxes on this dialog box are: Revocation Check, CRL Retrieval Policy, CRL
Retrieval Method, OCSP Rules, and Advanced.
Revocation Check Dialog Box
Use this dialog box to specify information about CA Certificate revocation checking.
Fields
•The radio buttons specify whether to check certificates for revocation. The values of these buttons
are as follows:

4-91
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 4 General VPN Setup
Mapping Certificates to IPsec or SSL VPN Connection Profiles
–
Do not check certificates for revocation
–
Check Certificates for revocation
•Revocation Methods area—Lets you specify the method–CRL or OCSP–to use for revocation
checking, a nd the order in which to use these methods. You can choose either or both methods.
Add/Edit Remote Access Connections > Advanced > General
Use this dialog box to specify whether to strip the realm and group from the username before passing
them to the AAA server, and to specify password management parameters.
Fields
•Strip the realm from username before passing it on to the AAA server—Enables or disables stripping
the realm (administrative domain) from the username before passing the username on to the AAA
server. Check the Strip Realm check box to remove the realm qualifier of the username during
authentication. You can append the realm name to the username for AAA: authorization,
authentication and accounting. The only valid delimiter for a realm is the @ character. The format
is username@realm, for example, JaneDoe@example.com. If you check this Strip Realm check box,
authentication is based on the username alone. Otherwise, authentication is based on the full
username@realm string. You must check this box if your server is unable to parse delimiters.
Note You can append both the realm and the group to a username, in which case the ASA uses
parameters configured for the group and for the realm for AAA functions. The format for this
option is username[@realm]]<#or!>group], for example, JaneDoe@example.com#VPNGroup.
If you choose this option, you must use either the # or ! character for the group delimiter because
the ASA cannot interpret the @ as a group delimiter if it is also present as the realm delimiter.
A Kerberos realm is a special case. The convention in naming a Kerberos realm is to capitalize
the DNS domain name associated with the hosts in the Kerberos realm. For example, if users are
in the example.com domain, you might call your Kerberos realm EXAMPLE.COM.
The ASA does not include support for the user@grouppolicy, as the VPN 3000 Concentrator did.
Only the L2TP/IPsec client supports the tunnel switching via user@tunnelgroup.
•Strip the group from the username before passing it on to the AAA server—Enables or disables
stripping the group name from the username before passing the username on to the AAA server.
Check Strip Group to remove the group name from the username during authentication. This option
is meaningful only when you have also checked the Enable Group Lookup box. When you append
a group name to a username using a delimiter, and enable Group Lookup, the ASA interprets all
characters to the left of the delimiter as the username, and those to the right as the group name. Valid
group delimiters are the @, #, and ! characters, with the @ character as the default for Group
Lookup. You append the group to the username in the format username<delimiter>group, the
possibilities being, for example, JaneDoe@VPNGroup, JaneDoe#VPNGroup, and
JaneDoe!VPNGroup.
•Password Management—Lets you configure parameters relevant to overriding an account-disabled
indication from a AAA server and to notifying users about password expiration.
–
Override account-disabled indication from AAA server—Overrides an account-disabled
indication from a AAA server.

4-92
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 4 General VPN Setup
Configuring Client Addressing
Note Allowing override account-disabled is a potential security risk.
–
Enable notification upon password expiration to allow user to change password—Checking this
check box makes the following two parameters available. You can select either to notify the user
at login a specific number of days before the password expires or to notify the user only on the
day that the password expires. The default is to notify the user 14 days prior to password
expiration and every day thereafter until the user changes the password. The range is 1 through
180 days.
Note This does not change the number of days before the password expires, but rather, it enables
the notification. If you select this option, you must also specify the number of days.
In either case, and, if the password expires without being changed, the ASA offers the user the
opportunity to change the password. If the current password has not yet expired, the user can
still log in using that password.
This parameter is valid for AAA servers that support such notification; that is, RADIUS,
RADIUS with an NT server, and LDAP servers. The ASA ignores this command if RADIUS or
LDAP authentication has not been configured.
This feature requires the use of MS-CHAPv2.
Configuring Client Addressing
To specify the client IP address assignment policy and assign address pools to all IPsec and SSL VPN
connections, open ASDM and select Configuration > Remote Access VPN > Network (Client) Access >
IPsec or SSL VPN Connections > Add or Edit > Advanced > Client Addressing. The Add IPsec Remote
Access Connection or Add SSL VPN Access Connection opens. Use this dialog box to add address pools
and assign them to interfaces, and view, edit, or delete them. The table at the bottom of the dialog box
lists the configured interface-specific address pools.
To understand the fields in this dialog box or its descendent dialog boxes, see the sections that follow
this one. You can view or change the configuration of address pools and their assignment to interfaces,
as follows:
•To view or change the configuration of address pools, click Add or Edit in the Add IPsec Remote
Access Connection or Add SSL VPN Access Connection dialog box. The Assign Address Pools to
Interface dialog box opens. This dialog box lets you assign IP address pools to the interfaces
configured on the ASA. Click Select. The Select Address Pools dialog box opens. Use this dialog
box to view the configuration of address pools. You can change their address pool configuration as
follows:
–
To add an address pool to the ASA, choose Add. The Add IP Pool dialog box opens.
–
To change the configuration of an address pool on the ASA, choose Edit. The Edit IP Pool
dialog box opens if the addresses in the pool are not in use.
Note You cannot modify an address pool if it is already in use. If you click Edit and the
address pool is in use, ASDM displays an error message and lists the connection names
and usernames that are using the addresses in the pool.

4-93
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 4 General VPN Setup
Configuring Client Addressing
–
To remove address pool on the ASA, select the entry in the table and click Delete.
Note You cannot remove an address pool if it is already in use. If you click Delete and the
address pool is in use, ASDM displays an error message and lists the connection names
that are using the addresses in the pool.
•To assign address pools to an interface, click Add in the Add IPsec Remote Access Connection or
Add SSL VPN Access Connection dialog box. The Assign Address Pools to Interface dialog box
opens. Select the interface to be assigned an address pool. Click Select next to the Address Pools
field. The Select Address Pools dialog box opens. Double-click each unassigned pool you want to
assign to the interface or choose each unassigned pool and click Assign. The adjacent field displays
the list of pool assignments. Click OK to populate the Address Pools field with the names of these
address pools, then OK again to complete the configuration of the assignment.
•To change the address pools assigned to an interface, double-click the interface, or choose the
interface in the Add IPsec Remote Access Connection or Add SSL VPN Access Connection dialog
box and click Edit. The Assign Address Pools to Interface dialog box opens. To remove address
pools, double-click each pool name and press the Delete button on the keyboard. Click Select next
to the Address Pools field if you want to assign additional fields to the interface. The Select Address
Pools dialog box opens. Note that the Assign field displays the address pool names that remained
assigned to the interface. Double-click each unassigned pool you want to add to the interface. The
Assign field updates the list of pool assignments. Click OK to revise the Address Pools field with
the names of these address pools, then OK again to complete the configuration of the assignment.
•To remove an entry from the Add IPsec Remote Access Connection or Add SSL VPN Access
Connection dialog box, choose the entry and click Delete.
The Add IPsec Remote Access Connection and Add SSL VPN Access Connection dialog boxes and their
descendent dialog boxes are identical. Use the following sections to understand or assign values to the
fields in these dialog boxes:
•Add IPsec Remote Access Connection and Add SSL VPN Access Connection
•Assign Address Pools to Interface
•Select Address Pools
•Add or Edit IP Pool
Add IPsec Remote Access Connection and Add SSL VPN Access Connection
To access the Add IPsec Remote Access Connection and Add SSL VPN Access Connection dialog
boxes, choose Config > Remote Access VPN > Network (Client) Access > IPsec or SSL VPN
Connections > Add or Edit > Advanced > Client Addressing.
Fields
Use the following descriptions to assign values to the fields in this dialog box:
•Global Client Address Assignment Policy—Configures a policy that affects all IPsec and SSL VPN
Client connections (including AnyConnect client connections). The ASA uses the selected sources
in order, until it finds an address:
–
Use authentication server—Specifies that the ASA should attempt to use the authentication
server as the source for a client address.
–
Use DHCP—Specifies that the ASA should attempt to use DHCP as the source for a client
address.

4-94
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 4 General VPN Setup
Configuring Client Addressing
–
Use address pool—Specifies that the ASA should attempt to use address pools as the source for
a client address.
•Interface-Specific Address Pools—Lists the configured interface-specific address pools.
Assign Address Pools to Interface
Use the Assign Address Pools to Interface dialog box to select an interface and assign one or more
address pools to that interface. To access this dialog box, choose Config > Remote Access VPN >
Network (Client) Access > IPsec or SSL VPN Connections > Add or Edit > Advanced > Client
Addressing > Add or Edit.
Fields
Use the following descriptions to assign values to the fields in this dialog box:
•Interface—Select the interface to which you want to assign an address pool. The default is DMZ.
•Address Pools—Specify an address pool to assign to the specified interface.
•Select—Opens the Select Address Pools dialog box, in which you can select one or more address
pools to assign to this interface. Your selection appears in the Address Pools field of the Assign
Address Pools to Interface dialog box.
Select Address Pools
The Select Address Pools dialog box shows the pool name, starting and ending addresses, and subnet
mask of address pools available for client address assignment and lets you add, edit, or delete entries
from that list. To access this dialog box, choose Config > Remote Access VPN > Network (Client)
Access > IPsec or SSL VPN Connections > Add or Edit > Advanced > Client Addressing > Add or Edit
> Select.
Fields
Use the following descriptions to assign values to the fields in this dialog box:
•Add—Opens the Add IP Pool dialog box, on which you can configure a new IP address pool.
•Edit—Opens the Edit IP Pool dialog box, on which you can modify a selected IP address pool.
•Delete—Removes the selected address pool. There is no confirmation or undo.
•Assign—Displays the address pool names that remained assigned to the interface. Double-click each
unassigned pool you want to add to the interface. The Assign field updates the list of pool
assignments.
Add or Edit IP Pool
The Add or Edit IP Pool dialog box lets you specify or modify a range of IP addresses for client address
assignment. To access this dialog box, choose Config > Remote Access VPN > Network (Client) Access
> IPsec or SSL VPN Connections > Add or Edit > Advanced > Client Addressing > Add or Edit > Select
> Add or Edit.
Fields
Use the following descriptions to assign values to the fields in this dialog box:
•Name—Specifies the name assigned to the IP address pool.
•Starting IP Address—Specifies the first IP address in the pool.
•Ending IP Address—Specifies the last IP address in the pool.

4-95
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 4 General VPN Setup
Configuring Client Addressing
•Subnet Mask—Selects the subnet mask to apply to the addresses in the pool.
Add/Edit Connection Profile > General > Authentication
You can get to this panel through various paths.
This dialog box is available for IPsec on Remote Access and Site-to-Site tunnel groups. The settings on
this dialog box apply to the tunnel group globally across the ASA. To set authentication server group
settings per interface, click Advanced. This dialog box lets you configure the following attributes:
•Authentication Server Group—Lists the available authentication server groups, including the
LOCAL group (the default). You can also select None. Selecting something other than None or
Local makes available the Use LOCAL if Server Group Fails check box. To set the authentication
server group per interface, click Advanced.
•Use LOCAL if Server Group fails—Enables or disables fallback to the LOCAL database if the group
specified by the Authentication Server Group attribute fails.
Add/Edit SSL VPN Connection > General > Authorization
You can get to this panel through various paths.
The settings on this dialog box apply to the connection (tunnel group) globally across the ASA. This
dialog box lets you configure the following attributes:
•Authorization Server Group—Lists the available authorization server groups, including the LOCAL
group. You can also select None (the default). Selecting something other than None makes available
the check box for Users must exist in authorization database to connect.
•Users must exist in the authorization database to connect—Tells the ASA to allow only users in the
authorization database to connect. By default this feature is disabled. You must have a configured
authorization server to use this feature.
•Interface-Specific Authorization Server Groups—(Optional) Lets you configure authorization
server groups on a per-interface basis. Interface-specific authorization server groups take
precedence over the global server group. If you do not explicitly configure interface-specific
authorization, authorization takes place only at the group level.
–
Interface—Select the interface on which to perform authorization. The standard interfaces are
outside (the default), inside, and DMZ. If you have configured other interfaces, they also appear
in the list.
–
Server Group—Select an available, previously configured authorization server group or group
of servers, including the LOCAL group. You can associate a server group with more than one
interface.
–
Add—Click Add to add the interface/server group setting to the table and remove the interface
from the available list.
–
Remove—Click Remove to remove the interface/server group from the table and restore the
interface to the available list.
•Authorization Settings—Lets you set values for usernames that the ASA recognizes for
authorization. This applies to users that authenticate with digital certificates and require LDAP or
RADIUS authorization.
–
Use the entire DN as the username—Allows the use of the entire Distinguished Name (DN) as
the username.

4-96
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 4 General VPN Setup
Configuring Client Addressing
–
Specify individual DN fields as the username—Enables the use of individual DN fields as the
username.
–
Primary DN Field—Lists all of the DN field identifiers for your selection.
–
Secondary DN Field—Lists all of the DN field identifiers (see the foregoing table) for your
selection and adds the option None for no selection.
Add/Edit SSL VPN Connections > Advanced > Accounting
You can get to this panel through various paths.
The settings on this dialog box apply to the connection (tunnel group) globally across the ASA. This
dialog box lets you configure the following attribute:
•Accounting Server Group—Lists the available accounting server groups. You can also select None
(the default). LOCAL is not an option.
•Manage—Opens the Configure AAA Server Groups dialog box.
DN Field Definition
Country (C) Two-letter country abbreviation. These codes conform to ISO 3166 country
abbreviations.
Common Name (CN) Name of a person, system, or other entity. This is the lowest (most specific)
level in the identification hierarchy.
DN Qualifier (DNQ) Specific DN attribute.
E-mail Address (EA) E-mail address of the person, system or entity that owns the certificate.
Generational Qualifier
(GENQ)
Generational qualifier such as Jr., Sr., or III.
Given Name (GN) First name of the certificate owner.
Initials (I) First letters of each part of the certificate owner’s name.
Locality (L) City or town where the organization is located.
Name (N) Name of the certificate owner.
Organization (O) Name of the company, institution, agency, association, or other entity.
Organizational Unit
(OU)
Subgroup within the organization.
Serial Number (SER) Serial number of the certificate.
Surname (SN) Family name or last name of the certificate owner.
State/Province (S/P) State or province where the organization is located.
Title (T) Title of the certificate owner, such as Dr.
User ID (UID) Identification number of the certificate owner.
User Principal Name
(UPN)
Used with Smart Card certificate authentication.
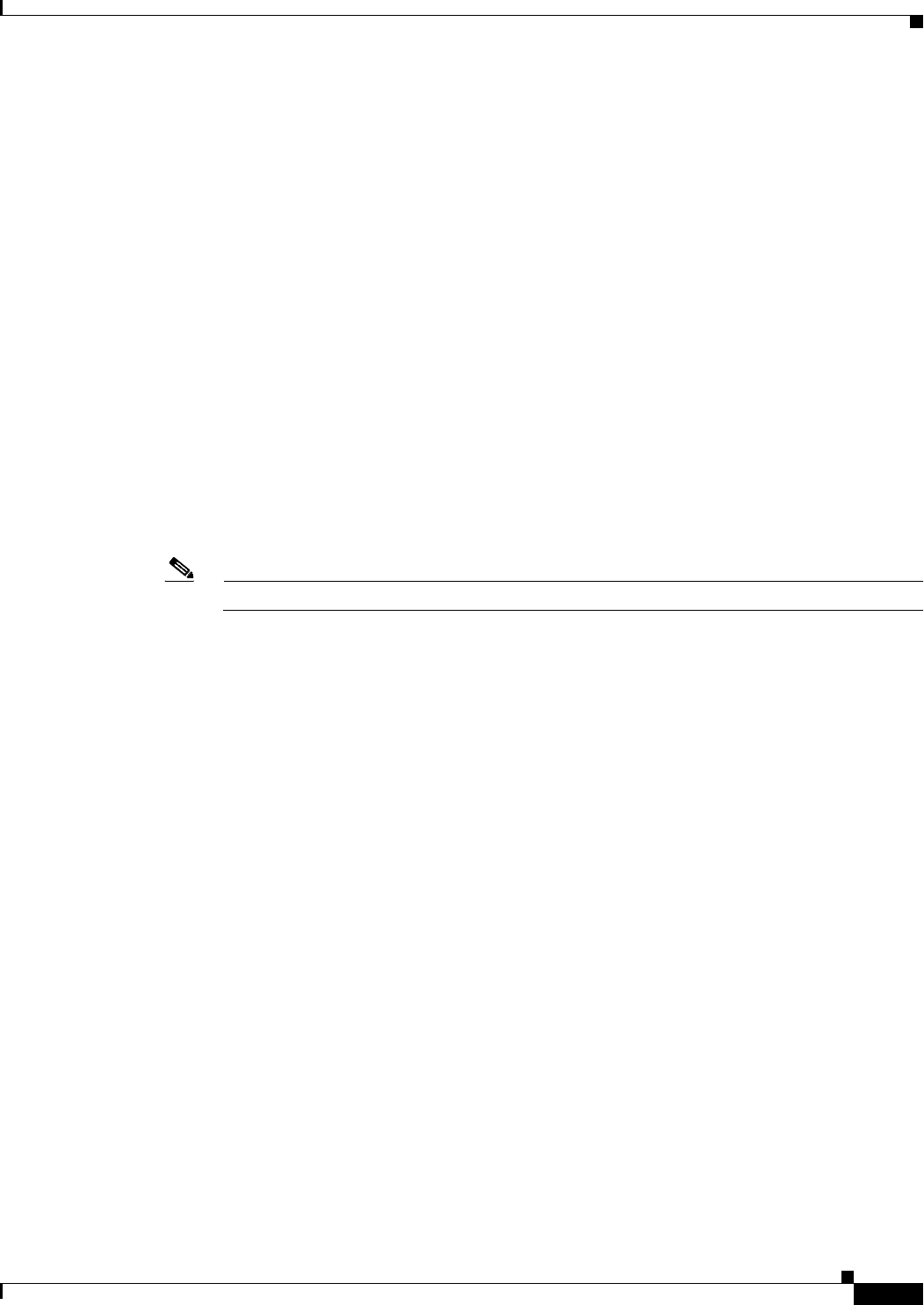
4-97
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 4 General VPN Setup
Configuring Client Addressing
Add/Edit Tunnel Group > General > Client Address Assignment
You can get to this panel through various paths.
To specify whether to use DHCP or address pools for address assignment, go to Configuration > VPN >
I P Address Management > Assignment. The Add or Edit Tunnel Group dialog box > General > Client
Address Assignment dialog box, lets you configure the following Client Address Assignment attributes:
•DHCP Servers—Specifies a DHCP server to use. You can add up to 10 servers, one at a time.
–
IP Address—Specifies the IP address of a DHCP server.
–
Add—Adds the specified DHCP server to the list for client address assignment.
–
Delete—Deletes the specified DHCP server from the list for client address assignment. There
is no confirmation or undo.
•Address Pools—Lets you specify up to 6 address pools, using the following parameters:
–
Available Pools—Lists the available, configured address pools you can choose.
–
Add—Adds the selected address pool to the list for client address assignment.
–
Remove—Moves the selected address pool from the Assigned Pools list to the Available Pools
list.
–
Assigned Pools—Lists the address pools selected for address assignment.
Note To configure interface-specific address pools, click Advanced.
Add/Edit Tunnel Group > General > Advanced
You can get to this panel through various paths.
The Add or Edit Tunnel Group dialog box, General, Advanced dialog box, lets you configure the
following interface-specific attributes:
•Interface-Specific Authentication Server Groups—Lets you configure an interface and server group
for authentication.
–
Interface—Lists available interfaces for selection.
–
Server Group—Lists authentication server groups available for this interface.
–
Use LOCAL if server group fails—Enables or disables fallback to the LOCAL database if the
server group fails.
–
Add—Adds the association between the selected available interface and the authentication
server group to the assigned list.
–
Remove—Moves the selected interface and authentication server group association from the
assigned list to the available list.
–
Interface/Server Group/Use Fallback—Show the selections you have added to the assigned list.
•Interface-Specific Client IP Address Pools—-Lets you specify an interface and Client IP address
pool. You can have up to 6 pools.
–
Interface—Lists the available interfaces to add.
–
Address Pool—Lists address pools available to associate with this interface.
–
Add—Adds the association between the selected available interface and the client IP address
pool to the assigned list.

4-98
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 4 General VPN Setup
Configuring Client Addressing
–
Remove—Moves the selected interface/address pool association from the assigned list to the
available list.
–
Interface/Address Pool—Shows the selections you have added to the assigned list.
Add/Edit Tunnel Group > IPsec for Remote Access > IPsec
Configuration > VPN > General > Tunnel Group > Add/Edit Tunnel Group >
IPSec for Remote Access > IPSec Tab
On the Add or Edit Tunnel Group dialog box for IPsec for Remote Access, the IPsec dialog box lets you
configure or edit IPsec-specific tunnel group parameters.
Fields
•Pre-shared Key—Lets you specify the value of the pre-shared key for the tunnel group. The
maximum length of the pre-shared key is 128 characters.
•Trustpoint Name—Selects a trustpoint name, if any trustpoints are configured. A trustpoint is a
representation of a certificate authority. A trustpoint contains the identity of the CA, CA-specific
configuration parameters, and an association with one enrolled identity certificate.
•Authentication Mode—Specifies the authentication mode: none, xauth, or hybrid.
–
none—Specifies no authentication mode.
–
xauth—Specifies the use of IKE Extended Authentication mode, which provides the capability
of authenticating a user within IKE using TACACS+ or RADIUS.
–
hybrid—Specifies the use of Hybrid mode, which lets you use digital certificates for security
appliance authentication and a different, legacy method—such as RADIUS, TACACS+ or
SecurID—for remote VPN user authentication. This mode breaks phase 1 of the Internet Key
Exchange (IKE) into the following steps, together called hybrid authentication:
1. The security appliance authenticates to the remote VPN user with standard public key
techniques. This establishes an IKE security association that is unidirectionally authenticated.
2. An extended authentication (xauth) exchange then authenticates the remote VPN user. This
extended authentication can use one of the supported legacy authentication methods.
Note Before setting the authentication type to hybrid, you must configure the authentication server
and create a pre-shared key.
•IKE Peer ID Validation—Selects whether IKE peer ID validation is ignored, required, or checked
only if supported by a certificate.
•Enable sending certificate chain—Enables or disables sending the entire certificate chain. This
action includes the root certificate and any subordinate CA certificates in the transmission.
•ISAKMP Keep Alive—Enables and configures ISAKMP keep alive monitoring.
–
Disable Keep Alives—Enables or disables ISAKMP keep alives.
–
Monitor Keep Alives—Enables or disables ISAKMP keep alive monitoring. Selecting this
option makes available the Confidence Interval and Retry Interval fields.
–
Confidence Interval—Specifies the ISAKMP keep alive confidence interval. This is the number
of seconds the ASA should allow a peer to idle before beginning keepalive monitoring. The
minimum is 10 seconds; the maximum is 300 seconds. The default for a remote access group is
300 seconds.

4-99
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 4 General VPN Setup
Configuring Client Addressing
–
Retry Interval—Specifies number of seconds to wait between ISAKMP keep alive retries. The
default is 2 seconds.
–
Head end will never initiate keepalive monitoring—Specifies that the central-site ASA never
initiates keepalive monitoring.
•Interface-Specific Authentication Mode—Specifies the authentication mode on a per-interface
basis.
–
Interface—Lets you select the interface name. The default interfaces are inside and outside, but
if you have configured a different interface name, that name also appears in the list.
–
Authentication Mode—Lets you select the authentication mode, none, xauth, or hybrid, as
above.
–
Interface/Authentication Mode table—Shows the interface names and their associated
authentication modes that are selected.
–
Add—Adds an interface/authentication mode pair selection to the Interface/Authentication
Modes table.
–
Remove—Removes an interface/authentication mode pair selection from the
Interface/Authentication Modes table.
•Client VPN Software Update Table—Lists the client type, VPN Client revisions, and image URL
for each client VPN software package installed. For each client type, you can specify the acceptable
client software revisions and the URL or IP address from which to download software upgrades, if
necessary. The client update mechanism (described in detail under the Client Update dialog box)
uses this information to determine whether the software each VPN client is running is at an
appropriate revision level and, if appropriate, to provide a notification message and an update
mechanism to clients that are running outdated software.
–
Client Type—Identifies the VPN client type.
–
VPN Client Revisions—Specifies the acceptable revision level of the VPN client.
–
Image URL—Specifies the URL or IP address from which the correct VPN client software
image can be downloaded. For dialog boxes-based VPN clients, the URL must be of the form
http:// or https://. For ASA 5505 in client mode or VPN 3002 hardware clients, the URL must
be of the form tftp://.
Add/Edit Tunnel Group for Site-to-Site VPN
Configuration > VPN > General > Tunnel Group > Add/Edit Tunnel Group >
IPSec for Remote Access > IPSec Tab
The Add or Edit Tunnel Group dialog box lets you configure or edit tunnel group parameters for this
Site-to-Site connection profile.
Fields
•Certificate Settings—Sets the following certificate chain and IKE peer validation attributes:
–
Send certificate chain—Enables or disables sending the entire certificate chain. This action
includes the root certificate and any subordinate CA certificates in the transmission.
–
IKE Peer ID Validation—Selects whether IKE peer ID validation is ignored, required, or
checked only if supported by a certificate.
•IKE Keep Alive—Enables and configures IKE (ISAKMP) keepalive monitoring.
–
Disable Keepalives—Enables or disables IKE keep alives.

4-100
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 4 General VPN Setup
Configuring Client Addressing
–
Monitor Keepalives—Enables or disables IKE keep alive monitoring. Selecting this option
makes available the Confidence Interval and Retry Interval fields.
–
Confidence Interval—Specifies the IKE keepalive confidence interval. This is the number of
seconds the ASA should allow a peer to idle before beginning keepalive monitoring. The
minimum is 10 seconds; the maximum is 300 seconds. The default for a remote access group is
300 seconds.
–
Retry Interval—Specifies number of seconds to wait between IKE keepalive retries. The default
is 2 seconds.
–
Head end will never initiate keepalive monitoring—Specifies that the central-site ASA never
initiates keepalive monitoring.
•Default Group Policy—Specifies the following group-policy attributes:
–
Group Policy—Selects a group policy to use as the default group policy. The default value is
DfltGrpPolicy.
–
Manage—Opens the Configure Group Policies dialog box.
–
IPsec Protocol—Enables or disables the use of the IPsec protocol for this connection profile.
Add/Edit Tunnel Group > PPP
Configuration > VPN > General > Tunnel Group > Add/Edit Tunnel Group > PPP Tab
On the Add or Edit Tunnel Group dialog box for a IPsec remote access tunnel group, the PPP dialog box
lets you configure or edit the authentication protocols permitted of a PPP connection. This dialog box
applies only to IPsec remote access tunnel groups.
Fields
•CHAP—Enables the use of the CHAP protocol for a PPP connection.
•MS-CHAP-V1—Enables the use of the MS-CHAP-V1 protocol for a PPP connection.
•MS-CHAP-V2—Enables the use of the MS-CHAP-V2 protocol for a PPP connection.
•PAP—Enables the use of the PAP protocol for a PPP connection.
•EAP-PROXY—Enables the use of the EAP-PROXY protocol for a PPP connection. EAP refers to
the Extensible Authentication protocol.
Add/Edit Tunnel Group > IPsec for LAN to LAN Access > General > Basic
Configuration > VPN > General > Tunnel Group > Add/Edit Tunnel Group >
IPSec for LAN to LAN Access > General Tab > Basic Tab
On the Add or Edit Tunnel Group dialog box for Site-to-Site Remote Access, the General, Basic dialog
box you can specify a name for the tunnel group that you are adding (Add function only) and select the
group policy.
On the Edit Tunnel Group dialog box, the General dialog box displays the name and type of the tunnel
group you are modifying.
Fields
•Name—Specifies the name assigned to this tunnel group. For the Edit function, this field is
display-only.

4-101
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 4 General VPN Setup
Configuring Client Addressing
•Type—(Display-only) Displays the type of tunnel group you are adding or editing. The contents of
this field depend on your selection on the previous dialog box.
•Group Policy—Lists the currently configured group policies. The default value is the default group
policy, DfltGrpPolicy.
•Strip the realm (administrative domain) from the username before passing it on to the AAA
server—Enables or disables stripping the realm from the username before passing the username on
to the AAA server. Check the Strip Realm check box to remove the realm qualifier of the username
during authentication. You can append the realm name to the username for AAA: authorization,
authentication and accounting. The only valid delimiter for a realm is the @ character. The format
is username@realm, for example, JaneDoe@example.com. If you check this Strip Realm check box,
authentication is based on the username alone. Otherwise, authentication is based on the full
username@realm string. You must check this box if your server is unable to parse delimiters.
Note You can append both the realm and the group to a username, in which case the ASA uses
parameters configured for the group and for the realm for AAA functions. The format for this
option is username[@realm]]<#or!>group], for example, JaneDoe@example.com#VPNGroup.
If you choose this option, you must use either the # or ! character for the group delimiter because
the ASA cannot interpret the @ as a group delimiter if it is also present as the realm delimiter.
A Kerberos realm is a special case. The convention in naming a Kerberos realm is to capitalize
the DNS domain name associated with the hosts in the Kerberos realm. For example, if users are
in the example.com domain, you might call your Kerberos realm EXAMPLE.COM.
The ASA does not include support for the user@grouppolicy, as the VPN 3000 Concentrator did.
Only the L2TP/IPsec client supports the tunnel switching via user@tunnelgroup.
•Strip the group from the username before passing it on to the AAA server—Enables or disables
stripping the group name from the username before passing the username on to the AAA server.
Check Strip Group to remove the group name from the username during authentication. This option
is meaningful only when you have also checked the Enable Group Lookup box. When you append
a group name to a username using a delimiter, and enable Group Lookup, the ASA interprets all
characters to the left of the delimiter as the username, and those to the right as the group name. Valid
group delimiters are the @, #, and ! characters, with the @ character as the default for Group
Lookup. You append the group to the username in the format username<delimiter>group, the
possibilities being, for example, JaneDoe@VPNGroup, JaneDoe#VPNGroup, and
JaneDoe!VPNGroup.
•Password Management—Lets you configure parameters relevant to overriding an account-disabled
indication from a AAA server and to notifying users about password expiration.
–
Override account-disabled indication from AAA server—Overrides an account-disabled
indication from a AAA server.
Note Allowing override account-disabled is a potential security risk.
–
Enable notification upon password expiration to allow user to change password—Checking this
check box makes the following two parameters available. If you do not also check the Enable
notification prior to expiration check box, the user receives notification only after the password
has expired.

4-102
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 4 General VPN Setup
Configuring Client Addressing
–
Enable notification prior to expiration—When you check this option, the ASA notifies the
remote user at login that the current password is about to expire or has expired, then offers the
user the opportunity to change the password. If the current password has not yet expired, the
user can still log in using that password. This parameter is valid for AAA servers that support
such notification; that is, RADIUS, RADIUS with an NT server, and LDAP servers. The ASA
ignores this command if RADIUS or LDAP authentication has not been configured.
Note that this does not change the number of days before the password expires, but rather, it
enables the notification. If you check this check box, you must also specify the number of days.
–
Notify...days prior to expiration—Specifies the number of days before the current password
expires to notify the user of the pending expiration. The range is 1 through 180 days.
Add/Edit Tunnel Group > IPsec for LAN to LAN Access > IPsec
Configuration > VPN > General > Tunnel Group > Add/Edit Tunnel Group >
IPSec for LAN to LAN Access > IPSec Tab
The Add or Edit Tunnel Group dialog box for IPsec for Site-to-Site access, IPsec dialog box, lets you
configure or edit IPsec Site-to-Site-specific tunnel group parameters.
Fields
•Name—Specifies the name assigned to this tunnel group. For the Edit function, this field is
display-only.
•Type—(Display-only) Displays the type of tunnel group you are adding or editing. The contents of
this field depend on your selection on the previous dialog box.
•Pre-shared Key—Lets you specify the value of the pre-shared key for the tunnel group. The
maximum length of the pre-shared key is 128 characters.
•Trustpoint Name—Selects a trustpoint name, if any trustpoints are configured. A trustpoint is a
representation of a certificate authority. A trustpoint contains the identity of the CA, CA-specific
configuration parameters, and an association with one enrolled identity certificate.
•Authentication Mode—Specifies the authentication mode: none, xauth, or hybrid.
–
none—Specifies no authentication mode.
–
xauth—Specifies the use of IKE Extended Authentication mode, which provides the capability
of authenticating a user within IKE using TACACS+ or RADIUS.
–
hybrid—Specifies the use of Hybrid mode, which lets you use digital certificates for security
appliance authentication and a different, legacy method—such as RADIUS, TACACS+ or
SecurID—for remote VPN user authentication. This mode breaks phase 1 of the Internet Key
Exchange (IKE) into the following steps, together called hybrid authentication:
1. The security appliance authenticates to the remote VPN user with standard public key
techniques. This establishes an IKE security association that is unidirectionally authenticated.
2. An extended authentication (xauth) exchange then authenticates the remote VPN user. This
extended authentication can use one of the supported legacy authentication methods.
Note Before setting the authentication type to hybrid, you must configure the authentication server
and create a pre-shared key.
•IKE Peer ID Validation—Selects whether IKE peer ID validation is ignored, required, or checked
only if supported by a certificate.

4-103
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 4 General VPN Setup
Configuring Client Addressing
•Enable sending certificate chain—Enables or disables sending the entire certificate chain. This
action includes the root certificate and any subordinate CA certificates in the transmission.
•ISAKMP Keep Alive—Enables and configures ISAKMP keep alive monitoring.
–
Disable Keep Alives—Enables or disables ISAKMP keep alives.
–
Monitor Keep Alives—Enables or disables ISAKMP keep alive monitoring. Selecting this
option makes available the Confidence Interval and Retry Interval fields.
–
Confidence Interval—Specifies the ISAKMP keep alive confidence interval. This is the number
of seconds the ASA should allow a peer to idle before beginning keepalive monitoring. The
minimum is 10 seconds; the maximum is 300 seconds. The default for a remote access group is
300 seconds.
–
Retry Interval—Specifies number of seconds to wait between ISAKMP keep alive retries. The
default is 2 seconds.
–
Head end will never initiate keepalive monitoring—Specifies that the central-site ASA never
initiates keepalive monitoring.
•Interface-Specific Authentication Mode—Specifies the authentication mode on a per-interface
basis.
–
Interface—Lets you select the interface name. The default interfaces are inside and outside, but
if you have configured a different interface name, that name also appears in the list.
–
Authentication Mode—Lets you select the authentication mode, none, xauth, or hybrid, as
above.
–
Interface/Authentication Mode table—Shows the interface names and their associated
authentication modes that are selected.
–
Add—Adds an interface/authentication mode pair selection to the Interface/Authentication
Modes table.
–
Remove—Removes an interface/authentication mode pair selection from the
Interface/Authentication Modes table.
•Client VPN Software Update Table—Lists the client type, VPN Client revisions, and image URL
for each client VPN software package installed. For each client type, you can specify the acceptable
client software revisions and the URL or IP address from which to download software upgrades, if
necessary. The client update mechanism (described in detail under the Client Update dialog box)
uses this information to determine whether the software each VPN client is running is at an
appropriate revision level and, if appropriate, to provide a notification message and an update
mechanism to clients that are running outdated software.
–
Client Type—Identifies the VPN client type.
–
VPN Client Revisions—Specifies the acceptable revision level of the VPN client.
–
Image URL—Specifies the URL or IP address from which the correct VPN client software
image can be downloaded. For Windows-based VPN clients, the URL must be of the form http://
or https://. For ASA 5505 in client mode or VPN 3002 hardware clients, the URL must be of the
form tftp://.
Clientless SSL VPN Access > Connection Profiles > Add/Edit > General > Basic
Configuration > VPN > General > Tunnel Group > Add/Edit> WebVPN Access > General Tab >
Basic Tab
4-104
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 4 General VPN Setup
Configuring Client Addressing
The Add or Edit pane, General, Basic dialog box lets you specify a name for the tunnel group that you
are adding, lets you select the group policy, and lets you configure password management.
On the Edit Tunnel Group dialog box, the General dialog box displays the name and type of the selected
tunnel group. All other functions are the same as for the Add Tunnel Group dialog box.
Fields
•Name—Specifies the name assigned to this tunnel group. For the Edit function, this field is
display-only.
•Type—Displays the type of tunnel group you are adding or editing. For Edit, this is a display-only
field whose contents depend on your selection in the Add dialog box.
•Group Policy—Lists the currently configured group policies. The default value is the default group
policy, DfltGrpPolicy.
•Strip the realm —Not available for Clientless SSL VPN.
•Strip the group —Not available or Clientless SSL VPN.
•Password Management—Lets you configure parameters relevant to overriding an account-disabled
indication from a AAA server and to notifying users about password expiration.
–
Override account-disabled indication from AAA server—Overrides an account-disabled
indication from a AAA server.
Note Allowing override account-disabled is a potential security risk.
–
Enable notification upon password expiration to allow user to change password—Checking this
check box makes the following two parameters available. If you do not also check the Enable
notification prior to expiration check box, the user receives notification only after the password
has expired.
–
Enable notification prior to expiration—When you check this option, the ASA notifies the
remote user at login that the current password is about to expire or has expired, then offers the
user the opportunity to change the password. If the current password has not yet expired, the
user can still log in using that password. This parameter is valid for AAA servers that support
such notification; that is, RADIUS, RADIUS with an NT server, and LDAP servers. The ASA
ignores this command if RADIUS or LDAP authentication has not been configured.
Note that this does not change the number of days before the password expires, but rather, it
enables the notification. If you check this check box, you must also specify the number of days.
–
Notify...days prior to expiration—Specifies the number of days before the current password
expires to notify the user of the pending expiration. The range is 1 through 180 days.
Configuring Internal Group Policy IPsec Client Attributes
Use this dialog box to specify whether to strip the realm and group from the username before passing
them to the AAA server, and to specify password management options.
Fields
•Strip the realm from username before passing it on to the AAA server—Enables or disables stripping
the realm (administrative domain) from the username before passing the username on to the AAA
server. Check the Strip Realm check box to remove the realm qualifier of the username during
authentication. You can append the realm name to the username for AAA: authorization,

4-105
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 4 General VPN Setup
Configuring Client Addressing
authentication and accounting. The only valid delimiter for a realm is the @ character. The format
is username@realm, for example, JaneDoe@example.com. If you check this Strip Realm check box,
authentication is based on the username alone. Otherwise, authentication is based on the full
username@realm string. You must check this box if your server is unable to parse delimiters.
Note You can append both the realm and the group to a username, in which case the ASA uses
parameters configured for the group and for the realm for AAA functions. The format for this
option is username[@realm]]<#or!>group], for example, JaneDoe@example.com#VPNGroup.
If you choose this option, you must use either the # or ! character for the group delimiter because
the ASA cannot interpret the @ as a group delimiter if it is also present as the realm delimiter.
A Kerberos realm is a special case. The convention in naming a Kerberos realm is to capitalize
the DNS domain name associated with the hosts in the Kerberos realm. For example, if users are
in the example.com domain, you might call your Kerberos realm EXAMPLE.COM.
The ASA does not include support for the user@grouppolicy, as the VPN 3000 Concentrator did.
Only the L2TP/IPsec client supports the tunnel switching via user@tunnelgroup.
•Strip the group from the username before passing it on to the AAA server—Enables or disables
stripping the group name from the username before passing the username on to the AAA server.
Check Strip Group to remove the group name from the username during authentication. This option
is meaningful only when you have also checked the Enable Group Lookup box. When you append
a group name to a username using a delimiter, and enable Group Lookup, the ASA interprets all
characters to the left of the delimiter as the username, and those to the right as the group name. Valid
group delimiters are the @, #, and ! characters, with the @ character as the default for Group
Lookup. You append the group to the username in the format username<delimiter>group, the
possibilities being, for example, JaneDoe@VPNGroup, JaneDoe#VPNGroup, and
JaneDoe!VPNGroup.
•Password Management—Lets you configure parameters relevant to overriding an account-disabled
indication from a AAA server and to notifying users about password expiration.
–
Override account-disabled indication from AAA server—Overrides an account-disabled
indication from a AAA server.
Note Allowing override account-disabled is a potential security risk.
–
Enable notification upon password expiration to allow user to change password—Checking this
check box makes the following two parameters available. You can select either to notify the user
at login a specific number of days before the password expires or to notify the user only on the
day that the password expires. The default is to notify the user 14 days prior to password
expiration and every day thereafter until the user changes the password. The range is 1 through
180 days.
Note This does not change the number of days before the password expires, but rather, it enables
the notification. If you select this option, you must also specify the number of days.
In either case, and, if the password expires without being changed, the ASA offers the user the
opportunity to change the password. If the current password has not yet expired, the user can
still log in using that password.

4-106
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 4 General VPN Setup
Configuring Client Addressing
This parameter is valid for AAA servers that support such notification; that is, RADIUS,
RADIUS with an NT server, and LDAP servers. The ASA ignores this command if RADIUS or
LDAP authentication has not been configured.
Configuring Client Addressing for SSL VPN Connections
Use this dialog box to specify the global client address assignment policy and to configure
interface-specific address pools. You can also add, edit, or delete interface-specific address pools using
this dialog box. The table at the bottom of the dialog box lists the configured interface-specific address
pools.
Fields
•Interface-Specific IPv4 Address Pools—Lists the configured interface-specific address pools.
•Interface-Specific IPv6 Address Pools—Lists the configured interface-specific address pools.
•Add—Opens the Assign Address Pools to Interface dialog box, on which you can select an interface
and select an address pool to assign.
•Edit—Opens the Assign Address Pools to Interface dialog box with the interface and address pool
fields filled in.
•Delete—Deletes the selected interface-specific address pool. There is no confirmation or undo.
Assign Address Pools to Interface
Use this dialog box to select an interface and assign one or more address pools to that interface.
Fields
•Interface—Select the interface to which you want to assign an address pool. The default is DMZ.
•Address Pools—Specify an address pool to assign to the specified interface.
•Select—Opens the Select Address Pools dialog box, in which you can select one or more address
pools to assign to this interface. Your selection appears in the Address Pools field of the Assign
Address Pools to Interface dialog box.
Select Address Pools
The Select Address Pools dialog box shows the pool name, starting and ending addresses, and subnet
mask of address pools available for client address assignment and lets you add, edit, or delete entries
from that list.
Fields
•Add—Opens the Add IP Pool dialog box, on which you can configure a new IP address pool.
•Edit—Opens the Edit IP Pool dialog box, on which you can modify a selected IP address pool.
•Delete—Removes the selected address pool. There is no confirmation or undo.
•Assign—Displays the address pool names that remained assigned to the interface. Double-click each
unassigned pool you want to add to the interface. The Assign field updates the list of pool
assignments.

4-107
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 4 General VPN Setup
System Options
Add or Edit an IP Address Pool
Configures or modifies an IP address pool.
Fields
•Name—Specifies the name assigned to the IP address pool.
•Starting IP Address—Specifies the first IP address in the pool.
•Ending IP Address—Specifies the last IP address in the pool.
•Subnet Mask—Selects the subnet mask to apply to the addresses in the pool.
Authenticating SSL VPN Connections
The SSL VPN Connections > Advanced > Authentication dialog box lets you configure authentication
attributes for SSL VPN connections.
System Options
This panel can be reached by navigating these paths:
•Configuration > Site-to-Site VPN > Advanced > System Options
•Configuration > Remote Access VPN > Network (Client) Access > Advanced > IPsec > System
Options
The System Options pane lets you configure features specific to VPN sessions on the ASA.
Fields
•Limit the maximum number of active IPsec VPN sessions—Enables or disables limiting the
maximum number of active IPsec VPN sessions. The range depends on the hardware platform and
the software license.
–
Maximum IPsec Sessions—Specifies the maximum number of active IPsec VPN sessions
allowed. This field is active only when you select the preceding check box to limit the maximum
number of active IPsec VPN sessions.
•L2TP Tunnel Keep-alive Timeout—Specifies the frequency, in seconds, of keepalive messages. The
range is 10 through 300 seconds. The default is 60 seconds. This is an advanced system option for
Network (Client) Access only.
•Reclassify existing flows when VPN tunnels establish
•Preserve stateful VPN flows when the tunnel drops—Enables or disables preserving IPsec tunneled
flows in Network-Extension Mode (NEM). With the persistent IPsec tunneled flows feature enabled,
as long as the tunnel is recreated within the timeout dialog box, data continues flowing successfully
because the security appliance still has access to the state information. This option is disabled by
default.
Note Tunneled TCP flows are not dropped, so they rely on the TCP timeout for cleanup. However,
if the timeout is disabled for a particular tunneled flow, that flow remains in the system until
being cleared manually or by other means (for example, by a TCP RST from the peer).
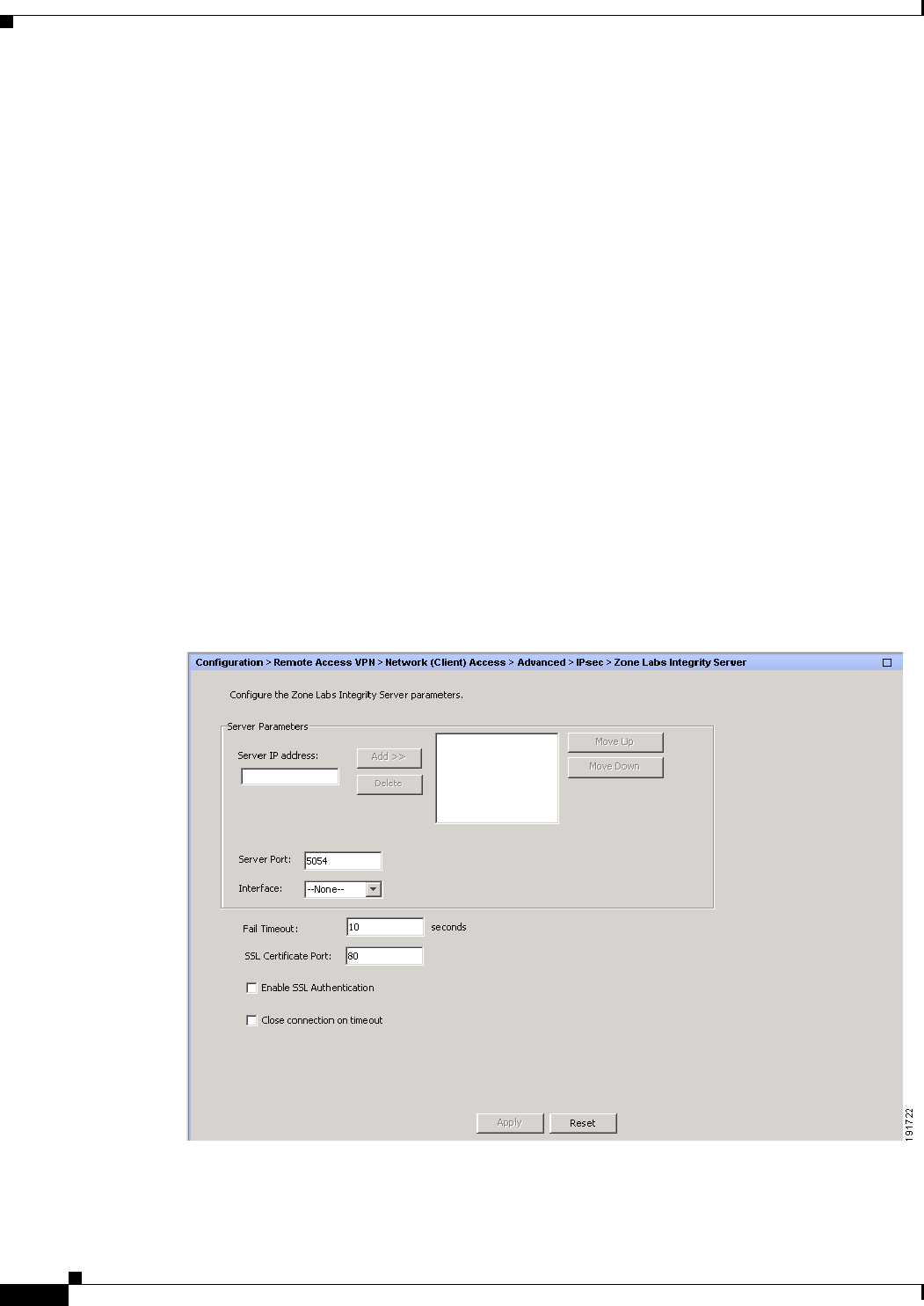
4-108
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 4 General VPN Setup
Zone Labs Integrity Server
•IPsec Security Association Lifetime—Configures the duration of a Security Association (SA). This
parameter specifies how to measure the lifetime of the IPsec SA keys, which is how long the IPsec
SA lasts until it expires and must be renegotiated with new keys.
–
Time—Specifies the SA lifetime in terms of hours (hh), minutes (mm) and seconds (ss).
–
Traffic Volume—Defines the SA lifetime in terms of kilobytes of traffic. Enter the number of
kilobytes of payload data after which the IPsec SA expires, or check unlimited. Minimum is 100
KB, default is 10000 KB, maximum is 2147483647 KB.
•Enable PMTU (Path Maximum Transmission Unit) Aging—Allows an administrator to enable
PMTU aging.
–
Interval to Reset PMTU of an SA (Security Association)—Enter the number of seconds at
which the PMTU value is reset to its original value.
Zone Labs Integrity Server
Configuration > Remote Access VPN > Network (Client) Access > Advanced > IPsec > Zone Labs
Integrity Server
The Zone Labs Integrity Server panel lets you configure the ASA to support a Zone Labs Integrity
Server. This server is part of the Integrity System, a system designed to enforce security policies on
remote clients entering the private network. In essence, the ASA acts as a proxy for the client PC to the
Firewall Server and relays all necessary Integrity information between the Integrity client and the
Integrity server.

4-109
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 4 General VPN Setup
Easy VPN Remote
Note The current release of the security appliance supports one Integrity Server at a time even though the user
interfaces support the configuration of up to five Integrity Servers. If the active Server fails, configure
another Integrity Server on the ASA and then reestablish the client VPN session.
Fields
•Server IP address—Type the IP address of the Integrity Server. Use dotted decimal notation.
•Add—Adds a new server IP address to the list of Integrity Servers. This button is active when an
address is entered in the Server IP address field.
•Delete—Deletes the selected server from the list of Integrity Servers.
•Move Up—Moves the selected server up in the list of Integrity Servers. This button is available only
when there is more than one server in the list.
•Move Down—Moves the selected server down in the list of Integrity Servers. This button is
available only when there is more than one server in the list.
•Server Port—Type the ASA port number on which it listens to the active Integrity server. This field
is available only if there is at least one server in the list of Integrity Servers. The default port number
is 5054, and it can range from 10 to 10000. This field is only available when there is a server in the
Integrity Server list.
•Interface—Choose the interface ASA interface on which it communicates with the active Integrity
Server. This interface name menu is only available when there is a server in the Integrity Server list.
•Fail Timeout—Type the number of seconds that the ASA should wait before it declares the active
Integrity Server to be unreachable. The default is 10 and the range is from 5 to 20.
•SSL Certificate Port: Specify the ASA port to be used for SSL Authorization. The default is port 80.
•Enable SSL Authentication—Check to enable authentication of the remote client SSL certificate by
the ASA. By default, client SSL authentication is disabled.
•Close connection on timeout—Check to close the connection between the ASA and the Integrity
Server on a timeout. By default, the connection remains open.
•Apply—Click to apply the Integrity Server setting to the ASA running configuration.
•Reset—Click to remove Integrity Server configuration changes that have not yet been applied.
Easy VPN Remote
Configuration > VPN > Easy VPN Remote
Easy VPN Remote lets the ASA 5505 act as an Easy VPN client device. The ASA 5505 can then initiate
a VPN tunnel to an Easy VPN server, which can be an ASA, a Cisco VPN 3000 Concentrator, a Cisco
IOS-based router, or a firewall acting as an Easy VPN server.
The Easy VPN client supports one of two modes of operation: Client Mode or Network Extension Mode
(NEM). The mode of operation determines whether the Easy VPN Client inside hosts are accessible from
the Enterprise network over the tunnel. Specifying a mode of operation is mandatory before making a
connection because Easy VPN Client does not have a default mode.
Client mode, also called Port Address Translation (PAT) mode, isolates all devices on the Easy VPN
Client private network from those on the enterprise network. The Easy VPN Client performs Port
Address Translation (PAT) for all VPN traffic for its inside hosts. IP address management is neither
required for the Easy VPN Client inside interface or the inside hosts.
4-110
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 4 General VPN Setup
Easy VPN Remote
NEM makes the inside interface and all inside hosts routable across the enterprise network over the
tunnel. Hosts on the inside network obtain their IP addresses from an accessible subnet (statically or via
DHCP) pre-configured with static IP addresses. PAT does not apply to VPN traffic in NEM. This mode
does not require a VPN configuration for each client. The Cisco ASA 5505 configured for NEM mode
supports automatic tunnel initiation. The configuration must store the group name, user name, and
password. Automatic tunnel initiation is disabled if secure unit authentication is enabled.
The network and addresses on the private side of the Easy VPN Client are hidden, and cannot be accessed
directly.
Fields
•Enable Easy VPN Remote—Enables the Easy VPN Remote feature and makes available the rest of
the fields on this dialog box for configuration.
•Mode—Selects either Client mode or Network extension mode.
–
Client mode—Uses Port Address Translation (PAT) mode to isolate the addresses of the inside
hosts, relative to the client, from the enterprise network.
–
Network extension mode—Makes those addresses accessible from the enterprise network.
Note If the Easy VPN Remote is using NEM and has connections to secondary servers,
establish an ASDM connection to each headend and check Enable Reverse Route
Injection on the Configuration > VPN > IPsec > IPsec Rules > Tunnel Policy (Crypto
Map) - Advanced dialog box to configure dynamic announcements of the remote
network using RRI.
–
Auto connect—The Easy VPN Remote establishes automatic IPsec data tunnels unless both of
the following are true: Network extension mode is configured locally, and split-tunneling is
configured on the group policy pushed to the Easy VPN Remote. If both are true, checking this
attribute automates the establishment of IPsec data tunnels. Otherwise, this attribute has no
effect.
•Group Settings—Specifies whether to use a pre-shared key or an X.509 certificate for user
authentication.
–
Pre-shared key—Enables the use of a pre-shared key for authentication and makes available the
subsequent Group Name, Group Password, and Confirm Password fields for specifying the
group policy name and password containing that key.
–
Group Name—Specifies the name of the group policy to use for authentication.
–
Group Password—Specifies the password to use with the specified group policy.
–
Confirm Password—Requires you to confirm the group password just entered.
–
X.509 Certificate—Specifies the use of an X.509 digital certificate, supplied by a Certificate
Authority, for authentication.
–
Select Trustpoint—Lets you select a trustpoint, which can be an IP address or a hostname, from
the drop-down list. To define a trustpoint, click the link to Trustpoint(s) configuration at the
bottom of this area.
–
Send certificate chain—Enables sending a certificate chain, not just the certificate itself. This
action includes the root certificate and any subordinate CA certificates in the transmission.
•User Settings—Configures user login information.

4-111
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 4 General VPN Setup
Advanced Easy VPN Properties
–
User Name—Configures the VPN username for the Easy VPN Remote connection. Xauth
provides the capability of authenticating a user within IKE using TACACS+ or RADIUS. Xauth
authenticates a user (in this case, the Easy VPN hardware client) using RADIUS or any of the
other supported user authentication protocols. The Xauth username and password parameters
are used when secure unit authentication is disabled and the server requests Xauth credentials.
If secure unit authentication is enabled, these parameters are ignored, and the ASA prompts the
user for a username and password.
–
User Password—Configures the VPN user password for the Easy VPN Remote connection.
–
Confirm Password—Requires you to confirm the user password just entered.
•Easy VPN Server To Be Added—Adds or removes an Easy VPN server. Any ASA or VPN 3000
Concentrator Series can act as a Easy VPN server. A server must be configured before a connection
can be established. The ASA supports IPv4 addresses, the names database, or DNS names and
resolves addresses in that order. The first server in the Easy VPN Server(s) list is the primary server.
You can specify a maximum of ten backup servers in addition to the primary server.
–
Name or IP Address—The name or IP address of an Easy VPN server to add to the list.
–
Add—Moves the specified server to the Easy VPN Server(s) list.
–
Remove—Moves the selected server from the Easy VPN Server(s) list to the Name or IP
Address file. Once you do this, however, you cannot re-add the same address unless you re-enter
the address in the Name or IP Address field.
–
Easy VPN Server(s)—Lists the configured Easy VPN servers in priority order.
–
Move Up/Move Down—Changes the position of a server in the Easy VPN Server(s) list. These
buttons are available only when there is more than one server in the list.
Advanced Easy VPN Properties
Configuration > VPN > Easy VPN Remote > Advanced
Device Pass-Through
Certain devices like Cisco IP phones, printers, and the like are incapable of performing authentication,
and therefore of participating in individual unit authentication. To accommodate these devices, the
device pass-through feature, enabled by the MAC Exemption attributes, exempts devices with the
specified MAC addresses from authentication when Individual User Authentication is enabled.
The first 24 bits of the MAC address indicate the manufacturer of the piece of equipment. The last 24
bits are the unit’s serial number in hexadecimal format.
Tunneled Management
When operating an ASA model 5505 device behind a NAT device, use the Tunneled Management
attributes to specify how to configure device management— in the clear or through the tunnel—and
specify the network or networks allowed to manage the Easy VPN Remote connection through the
tunnel. The public address of the ASA 5505 is not accessible when behind the NAT device unless you
add static NAT mappings on the NAT device.
When operating a Cisco ASA 5505 behind a NAT device, use the vpnclient management command to
specify how to configure device management— with additional encryption or without it—and specify
the hosts or networks to be granted administrative access. The public address of the ASA 5505 is not
accessible when behind the NAT device unless you add static NAT mappings on the NAT device.

4-112
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 4 General VPN Setup
Advanced Easy VPN Properties
Fields
•MAC Exemption—Configures a set of MAC addresses and masks used for device pass-through for
the Easy VPN Remote connection
–
MAC Address—Exempts the device with the specified MAC address from authentication. The
format for specifying the MAC address this field uses three hex digits, separated by periods; for
example, 45ab.ff36.9999.
–
MAC Mask—The format for specifying the MAC mask in this field uses three hex digits,
separated by periods; for example, the MAC mask ffff.ffff.ffff matches just the specified MAC
address. A MAC mask of all zeroes matches no MAC address, and a MAC mask of
ffff.ff00.0000 matches all devices made by the same manufacturer.
–
Add—Adds the specified MAC address and mask pair to the MAC Address/Mask list.
–
Remove—Moves the selected MAC address and mask pair from the MAC Address/MAC list to
the individual MAC Address and MAC Mask fields.
•Tunneled Management—Configures IPsec encryption for device management and specifies the
network or networks allowed to manage the Easy VPN hardware client connection through the
tunnel. Selecting Clear Tunneled Management merely removes that IPsec encryption level and does
not affect any other encryption, such as SSH or https, that exists on the connection.
–
Enable Tunneled Management—Adds a layer of IPsec encryption to the SSH or HTTPS
encryption already present in the management tunnel.
–
Clear Tunneled Management—Uses the encryption already present in the management tunnel,
without additional encryption.
–
IP Address— Specifies the IP address of the host or network to which you want to grant
administrative access to the Easy VPN hardware client through the VPN tunnel. You can
individually add one or more IP addresses and their respective network masks.
–
Mask—Specifies the network mask for the corresponding IP address.
–
Add—Moves the specified IP address and mask to the IP Address/Mask list.
–
Remove—Moves the selected IP address and mask pair from the IP Address/Mask list to the
individual IP Address and Mask fields in this area.
–
IP Address/Mask—Lists the configured IP address and mask pairs to be operated on by the
Enable or Clear functions in this area.
•IPsec Over TCP—Configure the Easy VPN Remote connection to use TCP-encapsulated IPsec.
–
Enable—Enables IPsec over TCP.
Note Choose Configuration > VPN > IPsec > Pre-Fragmentation, double-click the outside
interface, and set the DF Bit Setting Policy to Clear if you configure the Easy VPN Remote
connection to use TCP-encapsulated IPsec. The Clear setting lets the ASA send large
packets.
–
Enter Port Number—Specifies the port number to use for the IPsec over TCP connection.
•Server Certificate—Configures the Easy VPN Remote connection to accept only connections to
Easy VPN servers with the specific certificates specified by the certificate map. Use this parameter
to enable Easy VPN server certificate filtering. To define a certificate map, go to Configuration >
VPN > IKE > Certificate Group Matching > Rules.

4-113
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 4 General VPN Setup
AnyConnect Essentials
AnyConnect Custom Attributes
Custom attributes are added here to support special features that are not defined in the ASDM. Deferred
upgrade is the feature in AnyConnect 3.1 that uses custom attributes. See Configuring AnyConnect
Client Custom Attributes for an Internal Group Policy, page 4-23
AnyConnect Essentials
AnyConnect Essentials is a separately licensed SSL VPN client, entirely configured on the ASA, that
provides the full AnyConnect capability, with the following exceptions:
•No CSD (including HostScan/Vault/Cache Cleaner)
•No clientless SSL VPN
•Optional Windows Mobile Support (requires AnyConnect for Windows Mobile license)
The AnyConnect Essentials client provides remote end users running Microsoft Windows Vista,
Windows Mobile, Windows XP or Windows 2000, Linux, or Macintosh OS X, with the benefits of a
Cisco SSL VPN client.
To enable AnyConnect Essentials, check the Enable AnyConnect Essentials check box on the
AnyConnect Essentials pane, which appears only if the AnyConnect Essentials license is installed on the
ASA.
When AnyConnect Essentials is enabled, AnyConnect clients use Essentials mode, and clientless SSL
VPN access is disabled. When AnyConnect Essentials is disabled, AnyConnect clients use the full
AnyConnect SSL VPN Client.
Note The status information about the AnyConnect Essentials license on the Configuration > Device
Management > Licensing > Activation Key pane simply reflects whether the AnyConnect Essentials
license is installed. This status is not affected by the setting of the Enable AnyConnect Essentials
License check box.
AnyConnect Essentials mode cannot be enabled when active clientless sessions exist to the device. To
view SSL VPN session details click the Monitoring > VPN > VPN Sessions link in the SSL VPN
Sessions section. This opens the Monitoring > VPN > VPN > VPN Statistics > Sessions pane. To see
session details, choose Filter By: Clientless SSL VPN and click Filter. This displays session details.
To see how many clientless SSL VPN sessions are currently active, without showing session details,
click Check Number of Clientless SSL Sessions. If the SSL VPN session count is zero, you can enable
AnyConnect Essentials.
Note Secure Desktop does not work when AnyConnect Essentials is enabled. You can, however, disable
AnyConnect Essentials when you enable Secure Desktop.
DTLS Settings
Enabling Datagram Transport Layer Security (DTLS) allows the AnyConnect VPN client establishing
an SSL VPN connection to use two simultaneous tunnels—an SSL tunnel and a DTLS tunnel. Using
DTLS avoids latency and bandwidth problems associated with some SSL connections and improves the
performance of real-time applications that are sensitive to packet delays.

4-114
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 4 General VPN Setup
AnyConnect VPN Client Images
If you do not enable DTLS, AnyConnect client users establishing SSL VPN connections connect with
an SSL VPN tunnel only.
Fields
•Interface—Displays a list of interfaces on the ASA.
•DTLS Enabled—Click to enable DTLS connections with the AnyConnect client on the interfaces.
•UDP Port (default 443)—(Optional) Specify a separate UDP port for DTLS connections.
AnyConnect VPN Client Images
This pane lists the AnyConnect client images that are configured in ASDM.
Fields
•AnyConnect Client Images table—Displays the package files configured in ASDM, and allows you
to establish the order that the ASA downloads the images to the remote PC.
–
Add—Displays the Add AnyConnect Client Image dialog box, where you can specify a file in
flash memory as a client image file, or you can browse flash memory for a file to specify as a
client image. You can also upload a file from a local computer to the flash memory.
–
Replace—Displays the Replace AnyConnect Client Image dialog box, where you can specify a
file in flash memory as an client image to replace an image highlighted in the SSL VPN Client
Images table. You can also upload a file from a local computer to the flash memory.
–
Delete—Deletes an image from the table. This does not delete the package file from flash.
–
Move Up and Move Down—The up and down arrows change the order in which the ASA
downloads the client images to the remote PC. It downloads the image at the top of the table
first. Therefore, you should move the image used by the most commonly-encountered operating
system to the top.
Add/Replace AnyConnect VPN Client Image
In this pane, you can specify a filename for a file on the ASA flash memory that you want to add as an
AnyConnect client image, or to replace an image already listed in the table. You can also browse the
flash memory for a file to identify, or you can upload a file from a local computer.
Fields
•Flash SVC Image—Specify the file in flash memory that you want to identify as an SSL VPN client
image.
•Browse Flash—Displays the Browse Flash dialog box where you can view all the files on flash
memory.
•Upload—Displays the Upload Image dialog box where you can upload a file from a local PC that
you want to identify as an client image.
•Regular expression to match user-agent—Specifies a string that the ASA uses to match against the
User-Agent string passed by the browser. For mobile users, you can decrease the connection time of
the mobile device by using the feature. When the browser connects to the ASA, it includes the
User-Agent string in the HTTP header. When the ASA receives the string, if the string matches an
expression configured for an image, it immediately downloads that image without testing the other

4-115
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 4 General VPN Setup
Bypass Interface ACL
client images.
Upload Image
In this pane, you can specify the path of a file on the local computer or in flash memory of the security
appliance that you want to identify as an AnyConnect client image. You can also browse the local
computer or the flash memory of the security appliance for a file to identify.
Fields
•Local File Path—Identifies the filename of the file in on the local computer that you want to identify
as an SSL VPN client image.
•Browse Local Files—Displays the Select File Path dialog box where you can view all the files on
local computer and where you can select a file to identify as a client image.
•Flash File System Path—Identifies the filename of the file in the flash memory of the security
appliance that you want to identify as an SSL VPN client image.
•Browse Flash—Displays the Browse Flash Dialog dialog box where you can view all the files on
flash memory of the security appliance and where you can choose a file to identify as a client image.
•Upload File—Initiates the file upload.
Bypass Interface ACL
You can require an access rule to apply to the local IP addresses by unchecking this check box. The
access rule applies to the local IP address, and not to the original client IP address used before the VPN
packet was decrypted.
•Enable inbound IPsec sessions to bypass interface access-lists. Group policy and per-user
authorization ACLs still apply to the traffic—By default, the ASA allows VPN traffic to terminate
on an ASA interface; you do not need to allow IKE or ESP (or other types of VPN packets) in an
access rule. When this check box is checked, you also do not need an access rule for local IP
addresses of decrypted VPN packets. Because the VPN tunnel was terminated successfully using
VPN security mechanisms, this feature simplifies configuration and maximizes the ASA
performance without any security risks. (Group policy and per-user authorization ACLs still apply
to the traffic.)
Configuring AnyConnect Host Scan
Configuration > Remote Access VPN > Host Scan Image
The AnyConnect Posture Module provides the AnyConnect Secure Mobility Client the ability to identify
the operating system, anti-virus, anti-spyware, and firewall software installed on the host. The Host Scan
application gathers this information.
Using the secure desktop manager tool in the Adaptive Security Device Manager (ASDM), you can
create a prelogin policy which evaluates the operating system, anti-virus, anti-spyware, and firewall
software Host Scan identifies. Based on the result of the prelogin policy’s evaluation, you can control
which hosts are allowed to create a remote access connection to the security appliance.

4-116
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 4 General VPN Setup
Configuring AnyConnect Host Scan
The Host Scan support chart contains the product name and version information for the anti-virus,
anti-spyware, and firewall applications you use in your prelogin policies. We deliver Host Scan and the
Host Scan support chart, as well as other components, in the Host Scan package.
Starting with AnyConnect Secure Mobility Client, release 3.0, Host Scan is available separately from
CSD. This means you can deploy Host Scan functionality without having to install CSD and you will be
able to update your Host Scan support charts by upgrading the latest Host Scan package.
Posture assessment and the AnyConnect telemetry module require Host Scan to be installed on the host.
This chapter contains the following sections:
•Host Scan Dependencies and System Requirements, page 4-116
•Host Scan Packaging, page 4-117
•Installing and Enabling Host Scan on the ASA, page 4-117
•Other Important Documentation Addressing Host Scan, page 4-121
Host Scan Dependencies and System Requirements
Dependencies
The AnyConnect Secure Mobility Client with the posture module requires these minimum ASA
components:
•ASA 8.4
•ASDM 6.4
These AnyConnect features require that you install the posture module.
•SCEP authentication
•AnyConnect Telemetry Module
System Requirements
The posture module can be installed on any of these platforms:
•Windows XP (x86 and x86 running on x64)
•Windows Vista (x86 and x86 running on x64)
•Windows 7 (x86 and x86 running on x64)
•Mac OS X 10.5,10.6 (32-bit and 32-bit running on 64-bit)
•Linux (32-bit and 32-bit running on 64-bit)
•Windows Mobile
Licensing
These are the AnyConnect licensing requirements for the posture module:
•AnyConnect Premium for basic Host Scan.
•Advanced Endpoint Assessment license is required for
–
Remediation
4-117
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 4 General VPN Setup
Configuring AnyConnect Host Scan
–
Mobile Device Management
Entering an Activation Key to Support Advanced Endpoint Assessment
Advanced Endpoint Assessment includes all of the Endpoint Assessment features and lets you configure
an attempt to update noncompliant computers to meet version requirements. You can use ASDM to
activate a key to support Advanced Endpoint Assessment after acquiring it from Cisco, as follows:
Step 1 Choose Configuration > Device Management > Licensing > Activation Key.
Step 2 Enter the key in the New Activation Key field.
Step 3 Click Update Activation Key.
Step 4 Choose File > Save Running Configuration to Flash.
An Advanced Endpoint Assessment entry appears and the Configure button becomes active in the Host
Scan Extensions area of the Configuration > Remote Access VPN > Secure Desktop Manager > Host
Scan pane, which is accessible only if CSD is enabled.
Host Scan Packaging
You can load the Host Scan package on to the ASA in one of these ways:
•You can upload it as a standalone package: hostscan-version.pkg
•You can upload it by uploading an AnyConnect Secure Mobility package:
anyconnect-NGC-win-version-k9.pkg
•You can upload it by uploading a Cisco Secure Desktop package: csd_version-k9.pkg
Installing and Enabling Host Scan on the ASA
These tasks describe installing and enabling Host Scan on the ASA:
•Installing or Upgrading Host Scan
•Enabling or Disabling Host Scan
File Description
hostscan-version.pkg This file contains the Host Scan software as well as the Host
Scan library and support charts.
anyconnect-NGC-win-version-k9.pkg This package contains all the Cisco AnyConnect Secure
Mobility Client features including the hostscan-version.pkg
file.
csd_version-k9.pkg This file contains all Cisco Secure Desktop features
including Host Scan software as well as the Host Scan
library and support charts.
This method requires a separate license for Cisco Secure
Desktop.
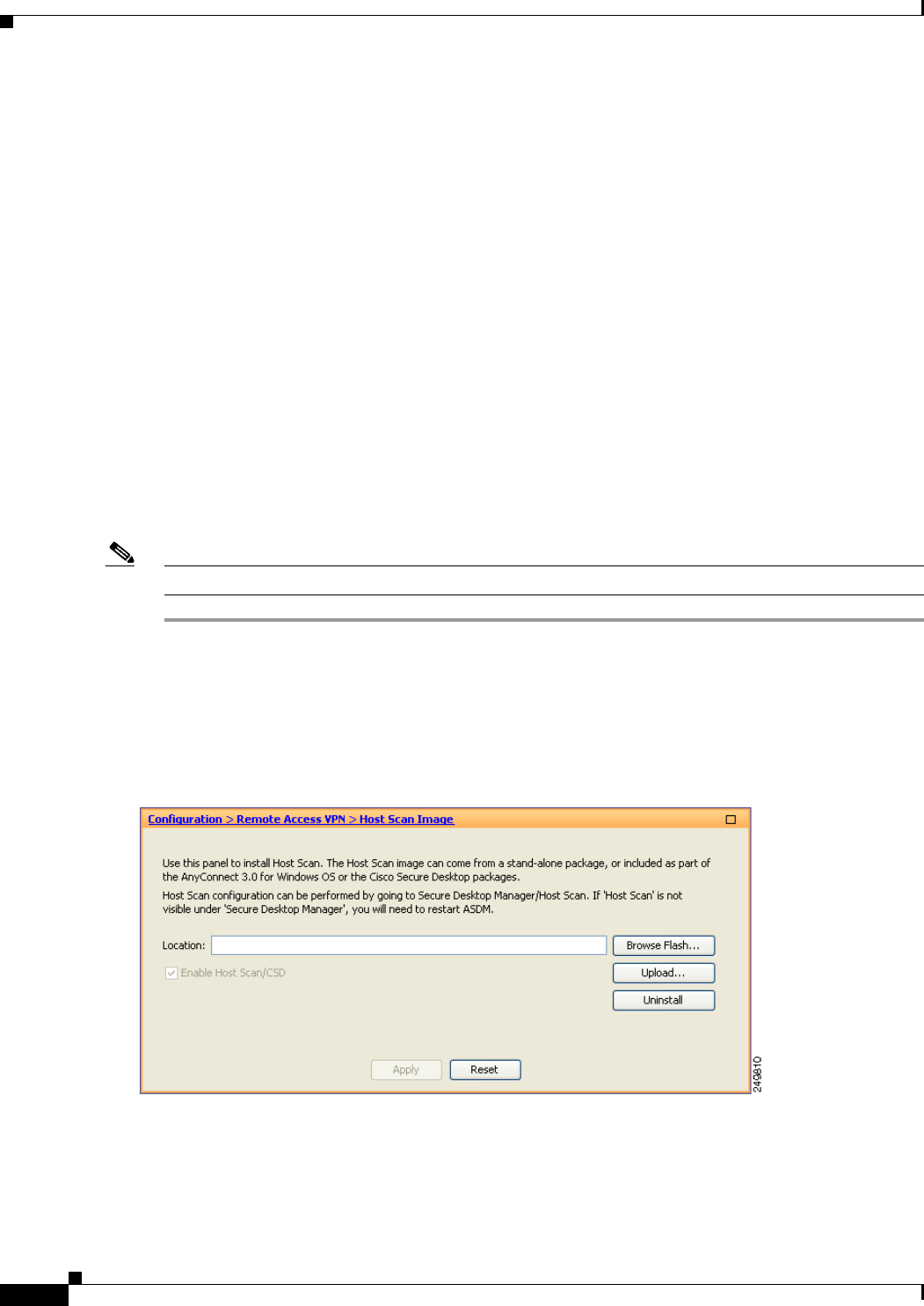
4-118
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 4 General VPN Setup
Configuring AnyConnect Host Scan
•Enabling or Disabling CSD on the ASA
•Viewing the Host Scan Version Enabled on the ASA
•Uninstalling Host Scan
•Uninstalling CSD from the ASA
•Assigning AnyConnect Posture Module to a Group Policy
Installing or Upgrading Host Scan
Use this procedure to upload, or upgrade, and enable a new Host Scan image on the ASA. This image
can enable the host scan functionality for AnyConnect, or you can use it to upgrade the host scan support
chart for an existing deployment of Cisco Secure Desktop (CSD).
You can specify a standalone Host Scan package or an AnyConnect Secure Mobility Client version 3.0
or later package in the field.
If you previously uploaded a CSD image to the ASA, the Host Scan image you specify will upgrade or
downgrade the existing Host Scan files that were delivered with that CSD package.
You do not need to restart the security appliance after you install or upgrade Host Scan; however, you
must exit and restart Adaptive Security Device Manager (ASDM) to access Secure Desktop Manager.
Note Host scan requires an AnyConnect Secure Mobility Client premium license.
Step 1 Use your Internet browser to download the hostscan_version-k9.pkg file or
anyconnect-NGC-win-version-k9.pkg file to your computer. You cannot use a csd_version-k9.pkg with
this procedure.
Step 2 Open ASDM and choose Configuration > Remote Access VPN > Host Scan Image. ASDM opens the
Host Scan Image panel (Figure 4-7).
Figure 4-7 Host Scan Image Panel
Step 3 Click Upload to prepare to transfer a copy of the Host Scan package from your computer to a drive on
the ASA.
Step 4 In the Upload Image dialog box, click Browse Local Files to search for the Host Scan package on your
local computer.

4-119
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 4 General VPN Setup
Configuring AnyConnect Host Scan
Step 5 Select the hostscan_version.pkg file or anyconnect-NGC-win-version-k9.pkg file you downloaded in
Step 1 and click Select. The path to the file you selected is in the Local File Path field and the Flash File
System Path field reflects the destination path of the Host Scan package. If your ASA has more than one
flash drive, you can edit the Flash File System Path to indicate another flash drive.
Step 6 Click Upload File. ASDM transfers a copy of the file to the flash card. An Information dialog box
displays the following message:
File has been uploaded to flash successfully.
Step 7 Click OK.
Step 8 In the Use Uploaded Image dialog, click OK to use the Host Scan package file you just uploaded as the
current image.
Step 9 Check Enable Host Scan/CSD if it is not already checked.
Step 10 Click Apply.
Note If AnyConnect Essentials is enabled on the ASA, you receive a message that CSD will not work
with it. You have the choice to Disable or Keep AnyConnect Essentials.
Step 11 From the File menu, select Save Running Configuration To Flash.
Enabling or Disabling Host Scan
When you first install or upgrade a Host Scan image using ASDM, you enable the image as part of that
procedure. See “Installing and Enabling Host Scan on the ASA” section on page 4-117.
Otherwise, to enable or disable a Host Scan image using ASDM, follow this procedure:
Step 1 Open ASDM and choose Configuration > Remote Access VPN > Host Scan Image. ASDM opens the
Host Scan Image panel (Figure 4-7).
Step 2 Check Enable Host Scan/CSD to enable Host Scan or uncheck Enable Host Scan/CSD to disable Host
Scan.
Step 3 Click Apply.
Enabling or Disabling CSD on the ASA
Enabling CSD loads the CSD configuration file, data.xml, from the flash device to the running
configuration.
Disabling CSD does not alter the CSD configuration.
Use ASDM to enable or disable CSD as follows:
Step 1 Choose Configuration > Clientless SSL VPN > Secure Desktop > Setup.
ASDM opens the Setup pane (Figure 4-7).

4-120
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 4 General VPN Setup
Configuring AnyConnect Host Scan
Note The Secure Desktop Image field displays the image (and version) that is currently installed. The
Enable Secure Desktop check box indicates whether CSD is enabled.
Step 2 Check or uncheck Enable Secure Desktop and click Apply.
ASDM enables or disables CSD.
Step 3 Click the X in the upper right corner of the ASDM window to exit.
A window displays the following message:
The configuration has been modified. Do you want to save the running configuration to
flash memory?
Step 4 Click Save. ASDM saves the configuration and closes.
Viewing the Host Scan Version Enabled on the ASA
Open ASDM and select Configuration > Remote Access VPN > Host Scan Image.
If there is a Host Scan image designated in the Host Scan Image location field, and the Enable
HostScan/CSD box is checked, the version of that image is the Host Scan version being used by the ASA.
If the Host Scan Image filed is empty, and the Enable HostScan/CSD box is checked, select
Configuration > Remote Access VPN > Secure Desktop Manager. The version of CSD in the Secure
Desktop Image Location field is the Host Scan version being used by the ASA.
Uninstalling Host Scan
Uninstalling Host Scan package removes it from view on the ASDM interface and prevents the ASA
from deploying it even if Host Scan or CSD is enabled. Uninstalling Host Scan does not delete the Host
Scan package from the flash drive.
Uninstall Host Scan on the security appliance as follows:
Step 1 Open ASDM and select Configuration > Remote Access VPN > Host Scan Image.
Step 2 In the Host Scan Image pane, click Uninstall. ASDM removes the text from the Location text box.
Step 3 From the File menu select Save Running Configuration to Flash.
Uninstalling CSD from the ASA
Uninstalling CSD removes the CSD configuration file, data.xml, from the desktop directory on the flash
card. If you want to retain the file, copy it using an alternative name or download it to your workstation
before you uninstall CSD.
Uninstall CSD on the security appliance as follows:
Step 1 Open ASDM and choose Configuration > Remote Access VPN > Secure Desktop Manager > Setup.
ASDM opens the Setup pane (Figure 4-7).

4-121
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 4 General VPN Setup
Configuring AnyConnect Host Scan
Step 2 Click Uninstall.
A confirmation window displays the following message:
Do you want to delete disk0:/csd_<n>.<n>.*.pkg and all CSD data files?
Step 3 Click Yes .
ASDM removes the text from the Location text box and removes the Secure Desktop Manager menu
options below Setup.
Step 4 Click the X in the upper right corner of the ASDM window to exit.
A window displays the following message:
The configuration has been modified. Do you want to save the running configuration to
flash memory?
Step 5 Click Save. ASDM saves the configuration and closes.
Assigning AnyConnect Posture Module to a Group Policy
Step 1 Open ASDM and choose Configuration > Remote Access VPN > Network (Client) Access > Group
Policies.
Step 2 In the Group Policies panel, click Add to create a new group policy or select the group policy to which
you want to assign the Host Scan package and click Edit.
Step 3 In the Edit Internal Group Policy panel, expand the Advanced navigation tree on the left side of the panel
and select AnyConnect Client.
Step 4 Uncheck the Optional Client Modules to Download Inherit checkbox.
Step 5 In the Optional Client Modules to Download drop down menu, check the AnyConnect Posture Module
and click OK.
Step 6 Click OK.
Other Important Documentation Addressing Host Scan
Once Host Scan gathers the posture credentials from the endpoint computer, you will need to understand
subjects like, configuring prelogin policies, configuring dynamic access policies, and using Lua
expressions to make use of the information.
These topics are covered in detail in these documents:
•Cisco Secure Desktop Configuration Guides
•Cisco Adaptive Security Device Manager Configuration Guides
See also the Cisco AnyConnect Secure Mobility Client Administrator Guide, Release 3.0 for more
information about how Host Scan works with AnyConnect clients.

4-122
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 4 General VPN Setup
Configuring Maximum VPN Sessions
Configuring Maximum VPN Sessions
To specify the maximum allowed number of VPN sessions or AnyConnect client VPN sessions, perform
the following steps:
Step 1 Choose Configuration > Remote Access VPN > Advanced > Maximum VPN Sessions.
Step 2 In the Maximum AnyConnect Sessions field, enter the maximum number of sessions allowed.
Valid values range from 1 to the maximum number of sessions that are allowed by your license.
Step 3 In the Maximum Other VPN Sessions field, enter the maximum number of VPN sessions allowed, which
includes Cisco VPN client (IPsec IKEv1) LAN-to-LAN VPN, and clientless SSL VPN sessions.
Valid values range from 1 to the maximum number of sessions that are allowed by your license.
Step 4 Click Apply.
Configuring the Pool of Cryptographic Cores
You can change the allocation of cryptographic cores on Symmetric Multi-Processing (SMP) platforms
to give you better throughput performance for AnyConnect TLS/DTLS traffic. These changes can
accelerate the SSL VPN datapath and provide customer-visible performance gains in AnyConnect, smart
tunnels, and port forwarding. To configure the pool of cryptographic cores, perform the following steps.
Limitations
•Cryptographic core rebalancing is available on the following platforms:
–
5585-X
–
5580
–
5545-X
–
5555-X
–
ASASM
•The large modulus operation is only available for 5510, 5520, 5540, and 5550 platforms.
Detailed Steps
Step 1 Choose Configuration > Remote Access VPN > Advanced > Crypto Engine.
Step 2 Check Enable Large Modulus Acceleration if you want to perform large modulus operations in the
hardware.
Step 3 From the Accelerator Bias drop-down menu, choose one of the following:
Note This field only shows up if the feature is available in ASA.
•balanced—Equally distributes cryptography hardware resources (Admin/SSL and IPsec cores).

4-123
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 4 General VPN Setup
Configuring the Pool of Cryptographic Cores
•ipsec—Allocates cryptography hardware resources to favor IPsec (includes SRTP encrypted voice
traffic).
•ssl—Allocates cryptography hardware resources to favor Admin/SSL.
Step 4 Click Apply.

4-124
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 4 General VPN Setup
Configuring the Pool of Cryptographic Cores

CHAPTER
5-1
Cisco ASA Series VPN ASDM Configuration Guide
5
Configuring IP Addresses for VPNs
This chapter describes IP address assignment methods.
IP addresses make internetwork connections possible. They are like telephone numbers: both the sender
and receiver must have an assigned number to connect. But with VPNs, there are actually two sets of
addresses: the first set connects client and server on the public network. Once that connection is made,
the second set connects client and server through the VPN tunnel.
In ASA address management, we are dealing with the second set of IP addresses: those private IP
addresses that connect a client with a resource on the private network, through the tunnel, and let the
client function as if it were directly connected to the private network. Furthermore, we are dealing only
with the private IP addresses that get assigned to clients. The IP addresses assigned to other resources
on your private network are part of your network administration responsibilities, not part of VPN
management. Therefore, when we discuss IP addresses here, we mean those IP addresses available in
your private network addressing scheme that let the client function as a tunnel endpoint.
This chapter includes the following sections:
•Configuring an IP Address Assignment Policy, page 5-1
•Configuring Local IP Address Pools, page 5-3
•Configuring DHCP Addressing, page 5-5
•Configuring DHCP Addressing, page 5-5
Configuring an IP Address Assignment Policy
The ASA can use one or more of the following methods for assigning IP addresses to remote access
clients. If you configure more than one address assignment method, the ASA searches each of the
options until it finds an IP address. By default, all methods are enabled.
•Use authentication server — Retrieves addresses from an external authentication, authorization, and
accounting server on a per-user basis. If you are using an authentication server that has IP addresses
configured, we recommend using this method. You can configure AAA servers in the
Configuration > AAA Setup pane.This method is available for IPv4 and IPv6 assignment policies.
•Use DHCP — Obtains IP addresses from a DHCP server. If you want to use DHCP, you must
configure a DHCP server. You must also define the range of IP addresses that the DHCP server can
use. If you use DHCP, configure the server in the Configuration > Remote Access VPN > DHCP
Server pane. This method is available for IPv4 assignment policies.

5-2
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 5 Configuring IP Addresses for VPNs
Configuring an IP Address Assignment Policy
• Use an internal address pool — Internally configured address pools are the easiest method of
address pool assignment to configure. If you use this method, configure the IP address pools in
Configuration > Remote Access VPN > Network (Client) Access > Address Assignment >
Address Pools pane. This method is available for IPv4 and IPv6 assignment policies.
–
Allow the reuse of an IP address so many minutes after it is released—Delays the reuse of an
IP address after its return to the address pool. Adding a delay helps to prevent problems firewalls
can experience when an IP address is reassigned quickly. By default, this is unchecked, meaning
the ASA does not impose a delay. If you want one, check the box and enter the number of
minutes in the range 1 - 480 to delay IP address reassignment.This configurable element is
available for IPv4 assignment policies.
Use one of these methods to specify a way to assign IP addresses to remote access clients.
•Configuring IP Address Assignment Options using ASDM
Configuring IP Address Assignment Options using ASDM
Step 1 Select Configuration > Remote Access VPN > Network (Client) Access > Address Assignment >
Assignment Policy
Step 2 In the IPv4 Policy area, check the address assignment method to enabled it or uncheck the address
assignment method to disable it. These methods are enabled by default:
•Use Authentication server. Enables the use of a Authentication Authorization and Accounting
(AAA) server you have configured to provide IP addresses.
•Use DHCP. Enables the use of a Dynamic Host Configuration Protocol (DHCP) server you have
configured to provide IP addresses.
•Use internal address pools: Enables the use of a local address pool configured on the ASA.
If you enable Use internal address pools, you can also enable the reuse of an IPv4 address after it has
been released. You can specify a range of minutes from 0-480 after which the IP v4 address can be
reused.
Step 3 In the IPv6 Policy area, check the address assignment method to enable it or uncheck the address
assignment method to disable it. These methods are enabled by default:
•Use Authentication server. Enables the use of a Authentication Authorization and Accounting
(AAA) server you have configured to provide IP addresses.
•Use internal address pools: Enables the use of a local address pool configured on the ASA.
Step 4 Click Apply.
Step 5 Click OK.
Modes
The following table shows the modes in which this feature is available:
5-3
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 5 Configuring IP Addresses for VPNs
Configuring Local IP Address Pools
Viewing Address Assignment Methods
Use one of these methods to view the address assignment method configured on the ASA:
Viewing IPv4 and IPv6 Address Assignments using ASDM
Select Configuration > Remote Access VPN > Network (Client) Access > Address Assignment >
Assignment Policy
Configuring Local IP Address Pools
To configure IPv4 or IPv6 address pools for VPN remote access tunnels, open ASDM and select
Configuration > Remote Access VPN > Network (Client) Access > Address Management >
Address Pools > Add/Edit IP Pool. To delete an address pool, open ASDM and select Configuration >
Remote Access VPN > Network (Client) Access > Address Management > Address Pools. Select the
address pool you want to delete and click Delete.
The ASA uses address pools based on the connection profile or group policy for the connection. The
order in which you specify the pools is important. If you configure more than one address pool for a
connection profile or group policy, the ASA uses them in the order in which you added them to the ASA.
If you assign addresses from a non-local subnet, we suggest that you add pools that fall on subnet
boundaries to make adding routes for these networks easier.
Use one of these methods to configure a local IP address pool:
•Configuring Local IPv4 Address Pools Using ASDM, page 5-3
•Configuring Local IPv6 Address Pools Using ASDM, page 5-4
Configuring Local IPv4 Address Pools Using ASDM
The IP Pool area shows each configured address pool by name with their IP address range, for example:
10.10.147.100 to 10.10.147.177. If no pools exist, the area is empty. The ASA uses these pools in the
order listed: if all addresses in the first pool have been assigned, it uses the next pool, and so on.
If you assign addresses from a non-local subnet, we suggest that you add pools that fall on subnet
boundaries to make adding routes for these networks easier.
Step 1 Select Configuration > Remote Access VPN > Network (Client) Access > Address Assignment >
Address Pools.
Step 2 To add an IPv4 address, click Add > IPv4 Address pool. To edit an existing address pool, select the
address pool in the address pool table and click Edit.
Firewall Mode Security Context
Routed Transparent Single
Multiple
Context System
•—•——

5-4
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 5 Configuring IP Addresses for VPNs
Configuring Local IP Address Pools
Step 3 In the Add/Edit IP Pool dialog box enter this information:
•Pool Name—Enter the name of the address pool. It can be up to 64 characters
•Starting Address—Enter the first IP address available in each configured pool. Use dotted decimal
notation, for example: 10.10.147.100.
•Ending Address—Enter the last IP address available in each configured pool. User dotted decimal
notation, for example: 10.10.147.177.
•Subnet Mask—Identifies the subnet on which this IP address pool resides.
Step 4 Click Apply.
Step 5 Click OK.
Configuring Local IPv6 Address Pools Using ASDM
The IP Pool area shows each configured address pool by name with a starting IP address range, the
address prefix, and the number of addresses configurable in the pool. If no pools exist, the area is empty.
The ASA uses these pools in the order listed: if all addresses in the first pool have been assigned, it uses
the next pool, and so on.
If you assign addresses from a non-local subnet, we suggest that you add pools that fall on subnet
boundaries to make adding routes for these networks easier.
Step 1 Select Configuration > Remote Access VPN > Network (Client) Access > Address Assignment >
Address Pools.
Step 2 To add an IPv6 address, click Add > IPv6 Address pool. To edit an existing address pool, select the
address pool in the address pool table and click Edit.
Step 3 In the Add/Edit IP Pool dialog box enter this information:
•Name—Displays the name of each configured address pool.
•Starting IP Address—Enter the first IP address available in the configured pool. For example:
2001:DB8::1.
•Prefix Length— Enter the IP address prefix length in bits. For example 32 represents /32 in CIDR
notation. The prefix length defines the subnet on which the pool of IP addresses resides.
•Number of Addresses—Identifies the number of IPv6 addresses, starting at the Starting IP Address,
there are in the pool.
Step 4 Click Apply.
Step 5 Click OK.

5-5
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 5 Configuring IP Addresses for VPNs
Configuring DHCP Addressing
Configuring DHCP Addressing
To use DHCP to assign addresses for VPN clients, you must first configure a DHCP server and the range
of IP addresses that the DHCP server can use. Then you define the DHCP server on a connection profile
basis. Optionally, you can also define a DHCP network scope in the group policy associated with a
connection profile or username. This is either an IP network number or IP Address that identifies to the
DHCP server which pool of IP addresses to use.
The following examples define the DHCP server at IP address 172.33.44.19 for the connection profile
named firstgroup. They also define a DHCP network scope of 192.86.0.0 for the group policy called
remotegroup. (The group policy called remotegroup is associated with the connection profile called
firstgroup). If you do not define a network scope, the DHCP server assigns IP addresses in the order of
the address pools configured. It goes through the pools until it identifies an unassigned address.
The following configuration includes more steps than are necessary, in that previously you might have
named and defined the connection profile type as remote access, and named and identified the group
policy as internal or external. These steps appear in the following examples as a reminder that you have
no access to subsequent tunnel-group and group-policy commands until you set these values.
Guidelines and Limitations
You can only use an IPv4 address to identify a DHCP server to assign client addresses.
Assigning IP addresses using DHCP
Configure your DHCP servers, then create group policies that use those servers. When a user selects that
that group policy, the DHCP server will assign an address for the VPN connection.
Configure Your DHCP Servers
DHCP server, configure the IP address Assignment policy to use DHCP follow the instructions below.
You cannot assign IPv6 addresses to AnyConnect clients using a DHCP server.
Step 1 Connect to the ASA using ASDM.
Step 2 Verify that DHCP is enabled on Configuration > Remote Access VPN > Network (Client) Access >
Address Assignment > Assignment Policy.
Step 3 Configure your DHCP servers by selecting Configuration > Remote Access VPN > DHCP Server.
Assign the DHCP IP Addressing to a Group Policy
Step 1 Select Configuration > Remote Access VPN > Network (Client) Access> AnyConnect Connection
Profiles.
Step 2 In the Connection Profiles Area click Add or Edit.
Step 3 Click Basic in the configuration tree for the connection profile.
Step 4 In the Client Address Assignment area, enter the IPv4 address of the DHCP server you want to use to
assign IP addresses to clients. For example, 172.33.44.19.

5-6
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 5 Configuring IP Addresses for VPNs
Assigning IP Addresses to Local Users
Step 5 Edit the group-policy associated with the connection profile to define the DHCP scope. Select
Configuration > Remote Access VPN > Network (Client) Access> Group Policies.
Step 6 Double-click the group policy you want to edit.
Step 7 Click Servers in the configuration tree.
Step 8 Expand the More Options area by clicking the down arrow.
Step 9 Uncheck DHCP Scope Inherit.
Step 10 Enter the IP network number or IP Address that identifies to the DHCP server which pool of IP addresses
to use. For example, 192.86.0.0.
Step 11 Click OK.
Step 12 Click Apply.
Assigning IP Addresses to Local Users
Local user accounts can be configured to use a group policy, and some AnyConnect attributes can also
be configured. These user accounts provide fallback if the other sources of IP address fail, so
administrators will still have access.
This section describes how to configure all the attributes of a local user.
Prerequisites
This procedure describes how to edit an existing user. To add a user select Configuration > Remote
Access VPN > AAA/Local Users > Local Users and click Add. For more information see “Adding a
User Account to the Local Database” in Chapter 42, Configuring AAA Servers and the Local Database
in the Cisco ASA 5500 Configuration Guide Using ASDM.
User Edits
By default, the Inherit check box is checked for each setting on the Edit User Account screen, which
means that the user account inherits the value of that setting from the default group policy,
DfltGrpPolicy.
To override each setting, uncheck the Inherit check box, and enter a new value. The detailed steps that
follow describe each of the settings on the Edit User Account screen.
Detailed Steps
Step 1 Start ASDM and select Configuration > Remote Access VPN > AAA/Local Users > Local Users.
Step 2 Select the user you want to configure and click Edit.
The Edit User Account screen opens.
Step 3 In the left pane, click VPN Policy.
Step 4 Specify a group policy for the user. The user policy will inherit the attributes of this group policy. If there
are other fields on this screen that are set to Inherit the configuration from the Default Group Policy, the
attributes specified in this group policy will take precedence over those in the Default Group Policy.
5-7
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 5 Configuring IP Addresses for VPNs
Assigning IP Addresses to Local Users
Step 5 Specify which tunneling protocols are available for the user, or whether the value is inherited from the
group policy. Check the desired Tunneling Protocols check boxes to choose the VPN tunneling
protocols that are available for use. Only the selected protocols are available for use. The choices are as
follows:
•Clientless SSL VPN (VPN via SSL/TLS) uses a web browser to establish a secure remote-access
tunnel to a VPN Concentrator; requires neither a software nor hardware client. Clientless SSL VPN
can provide easy access to a broad range of enterprise resources, including corporate websites,
web-enabled applications, NT/AD file shares (web-enabled), e-mail, and other TCP-based
applications from almost any computer that can reach HTTPS Internet sites.
•The SSL VPN Client lets users connect after downloading the Cisco AnyConnect Client application.
Users use a clientless SSL VPN connection to download this application the first time. Client
updates then occur automatically as needed whenever the user connects.
•IPsec IKEv1—IP Security Protocol. Regarded as the most secure protocol, IPsec provides the most
complete architecture for VPN tunnels. Both Site-to-Site (peer-to-peer) connections and Cisco VPN
client-to-LAN connections can use IPsec IKEv1.
•IPsec IKEv2—IPsec IKEv2-Supported by the AnyConnect Secure Mobility Client. AnyConnect
connections using IPsec with IKEv2 can make use of the same feature set available to SSL VPN
Connections.
•L2TP over IPsec allows remote users with VPN clients provided with several common PC and
mobile PC operating systems to establish secure connections over the public IP network to the ASA
and private corporate networks.
Note If no protocol is selected, an error message appears.
Step 6 Specify which filter (IPv4 or IPv6) to use, or whether to inherit the value from the group policy. Filters
consist of rules that determine whether to allow or reject tunneled data packets coming through the ASA,
based on criteria such as source address, destination address, and protocol. To configure filters and rules,
choose Configuration > Remote Access VPN > Network (Client) Access > Group Policies >
Add/Edit > General > More Options > Filter.
Click Manage to display the ACL Manager pane, on which you can add, edit, and delete ACLs and
ACEs.
Step 7 Specify whether to inherit the Connection Profile (tunnel group) lock or to use the selected tunnel group
lock, if any. Selecting a specific lock restricts users to remote access through this group only. Tunnel
Group Lock restricts users by checking if the group configured in the VPN client is the same as the users
assigned group. If it is not, the ASA prevents the user from connecting. If the Inherit check box is not
checked, the default value is None.
Step 8 Specify whether to inherit the Store Password on Client System setting from the group. Uncheck the
Inherit check box to activate the Yes and No radio buttons. Click Ye s to store the logon password on the
client system (potentially a less-secure option). Click No (the default) to require the user to enter the
password with each connection. For maximum security, we recommend that you not allow password
storage.
Step 9 Specify an Access Hours policy to apply to this user, create a new access hours policy for the user, or
leave the Inherit box checked. The default value is Inherit, or, if the Inherit check box is not checked,
the default value is Unrestricted.
Click Manage to open the Add Time Range dialog box, in which you can specify a new set of access
hours.

5-8
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 5 Configuring IP Addresses for VPNs
Assigning IP Addresses to Local Users
Step 10 Specify the number of simultaneous logons by the user. The Simultaneous logons parameter specifies
the maximum number of simultaneous logons allowed for this user. The default value is 3. The minimum
value is 0, which disables logon and prevents user access.
Note While there is no maximum limit, allowing several simultaneous connections could compromise
security and affect performance.
Step 11 Specify the maximum connection time for the user connection time in minutes. At the end of this time,
the system terminates the connection. The minimum is 1 minute, and the maximum is 2147483647
minutes (over 4000 years). To allow unlimited connection time, check the Unlimited check box (the
default).
Step 12 Specify the Idle Timeout for the user in minutes. If there is no communication activity on the connection
by this user in this period, the system terminates the connection. The minimum time is 1 minute, and the
maximum time is 10080 minutes. This value does not apply to users of clientless SSL VPN connections.
Step 13 Configure the Session Alert Interval. If you uncheck the Inherit check box, the Default checkbox is
checked automatically. This sets the session alert interval to 30 minutes. If you want to specify a new
value, uncheck the Default check box and specify a session alert interval from 1 to 30 minutes in the
minutes box.
Step 14 Configure the Idle Alert Interval. If you uncheck the Inherit check box, the Default checkbox is checked
automatically. This sets the idle alert interval to 30 minutes. If you want to specify a new value, uncheck
the Default check box and specify a session alert interval from 1 to 30 minutes in the minutes box.
Step 15 To set a dedicated IPv4 address for this user, enter an IPv4 address and subnet mask in the Dedicated
IPv4 Address (Optional) area.
Step 16 To set a dedicated IPv6 address for this user, enter an IPv6 address with an IPv6 prefix in the Dedicated
IPv6 Address (Optional) field. The IPv6 prefix indicates the subnet on which the IPv6 address resides.
Step 17 To configure clientless SSL settings, in the left pane, click Clientless SSL VPN. To override each
setting, uncheck the Inherit check box, and enter a new value.
Step 18 Click Apply.
The changes are saved to the running configuration.

CHAPTER
6-1
Cisco ASA Series VPN ASDM Configuration Guide
6
Configuring Dynamic Access Policies
This chapter describes how to configure dynamic access policies. It includes the following sections.
•Information About Dynamic Access Policies, page 6-1
•Licensing Requirements for Dynamic Access Policies, page 6-3
•Dynamic Access Policies Interface, page 6-4
•Configuring Dynamic Access Policies, page 6-6
•Testing Dynamic Access Policies, page 6-8
•DAP and Authentication, Authorization, and Accounting Services, page 6-9
•Configuring Endpoint Attributes Used in DAPs, page 6-13
•Configuring DAP Access and Authorization Policy Attributes, page 6-27
•Guide to Creating DAP Logical Expressions using LUA, page 6-31
Information About Dynamic Access Policies
VPN gateways operate in dynamic environments. Multiple variables can affect each VPN connection,
for example, intranet configurations that frequently change, the various roles each user may inhabit
within an organization, and logins from remote access sites with different configurations and levels of
security. The task of authorizing users is much more complicated in a VPN environment than it is in a
network with a static configuration.
Dynamic access policies (DAP) on the ASA let you configure authorization that addresses these many
variables. You create a dynamic access policy by setting a collection of access control attributes that you
associate with a specific user tunnel or session. These attributes address issues of multiple group
membership and endpoint security. That is, the ASA grants access to a particular user for a particular
session based on the policies you define. The ASA generates a DAP at the time the user connects by
selecting and/or aggregating attributes from one or more DAP records. It selects these DAP records
based on the endpoint security information of the remote device and the AAA authorization information
for the authenticated user. It then applies the DAP record to the user tunnel or session.
The DAP system includes the following components that require your attention:
•DAP Selection Configuration File—A text file containing criteria that the ASA uses for selecting
and applying DAP records during session establishment. Stored on the ASA. You can use ASDM to
modify it and upload it to the ASA in XML data format. DAP selection configuration files include
all of the attributes that you configure. These can include AAA attributes, endpoint attributes, and
access policies as configured in network and web-type ACL filter, port forwarding and URL lists.
6-2
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 6 Configuring Dynamic Access Policies
Information About Dynamic Access Policies
•DfltAccess Policy—Always the last entry in the DAP summary table, always with a priority of 0.
You can configure Access Policy attributes for the default access policy, but it does not contain—and
you cannot configure—AAA or endpoint attributes. You cannot delete the DfltAccessPolicy, and it
must be the last entry in the summary table.
Refer to the Dynamic Access Deployment Guide (https://supportforums.cisco.com/docs/DOC-1369) for
additional information.
DAP and Endpoint Security
The ASA obtains endpoint security attributes by using posture assessment tools that you configure.
These posture assessment tools include the AnyConnect posture module, the independent Host Scan
package, Cisco Secure Desktop, and NAC.
Table 6-1 identifies each of the remote access protocols DAP supports, the posture assessment tools
available for that method, and the information that tool provides.
DAP Support for Remote Access Connection Types
The DAP system supports the following remote access methods:
•IPsec VPN
•Clientless (browser-based) SSL VPN
•Cisco AnyConnect Secure Mobility Client (SSL VPN)
•PIX cut-through proxy (posture assessment not available)
Remote Access Connection Sequence with DAPs
The following sequence outlines a typical remote access connection establishment.
1. A remote client attempts a VPN connection.
2. The ASA performs posture assessment, using configured NAC and Cisco Secure Desktop Host Scan
values.
Table 6-1 DAP Posture Assessment
Remote Access Protocol
AnyConnect Posture Module
Host Scan package
Cisco Secure Desktop
(without Endpoint Assessment
Host Scan Extension enabled)
AnyConnect Posture Module
Host Scan package
Cisco Secure Desktop
(with Endpoint Assessment
Host Scan Extension enabled)
NAC
Cisco NAC
Appliance
Returns file information,
registry key values, running
processes, operating system
Returns antivirus,
antispyware, and personal
firewall software information
Returns NAC
status
Returns VLAN
Type and
VLAN IDs
IPsec VPN No No Yes Ye s
Cisco AnyConnect VPN Yes Yes Yes Ye s
Clientless VPN Yes Yes No No
PIX Cut-through Proxy No No No No
6-3
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 6 Configuring Dynamic Access Policies
Licensing Requirements for Dynamic Access Policies
3. The ASA authenticates the user via AAA. The AAA server also returns authorization attributes for
the user.
4. The ASA applies AAA authorization attributes to the session, and establishes the VPN tunnel.
5. The ASA selects DAP records based on the user AAA authorization information and the session
posture assessment information.
6. The ASA aggregates DAP attributes from the selected DAP records, and they become the DAP
policy.
7. The ASA applies the DAP policy to the session.
Licensing Requirements for Dynamic Access Policies
The following tables shows the licensing requirements for enforcing Dynamic Access Policies.
Advanced Endpoint Assessment license
Note This feature is not available on No Payload Encryption models.
SSL VPN license (client)
Note This feature is not available on No Payload Encryption models.
AnyConnect Mobile License
Note This feature is not available on No Payload Encryption models.
Model License Requirement
All models Advanced Endpoint Assessment License.
Model License Requirement
All models AnyConnect Premium License
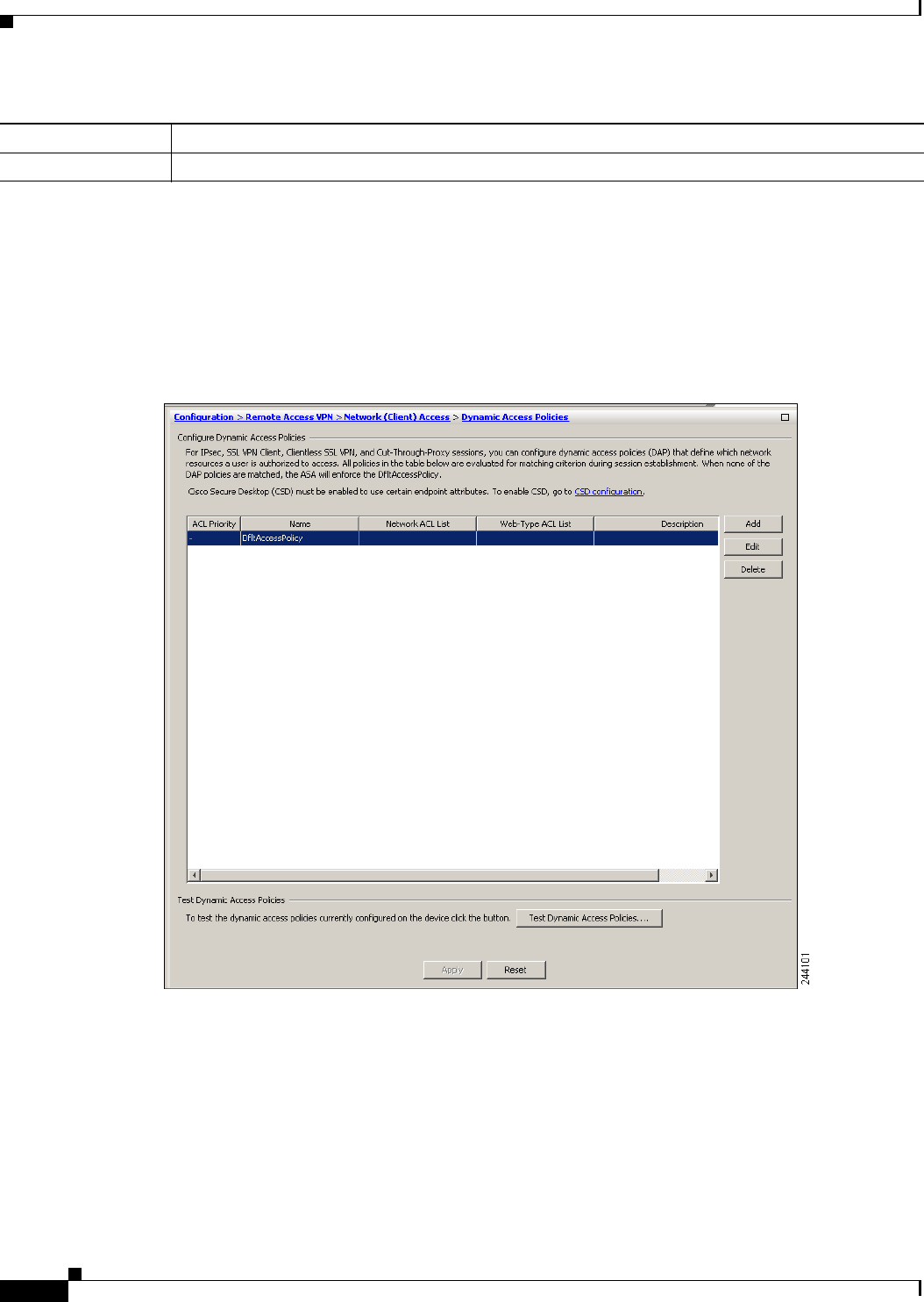
6-4
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 6 Configuring Dynamic Access Policies
Dynamic Access Policies Interface
Dynamic Access Policies Interface
Figure 6-1 shows the Dynamic Access Policies pane.
Figure 6-1 Dynamic Access Policies ASDM pane
Fields
•ACL Priority—Displays the priority of the DAP record. The ASA uses this value to logically
sequence the ACLs when aggregating the network and web-type ACLs from multiple DAP records.
The ASA orders the records from highest to lowest priority number, with lowest at the bottom of the
table. Higher numbers have a higher priority, that is a DAP record with a value of 4 has a higher
priority than a record with a value of 2. You cannot manually sort them.
•Name—Displays the name of the DAP record.
Model License Requirement
All models AnyConnect Mobile license.1
1. This license requires activation of one of the following licenses to specify the total number of SSL VPN sessions permitted: AnyConnect Essentials or
AnyConnect Premium.
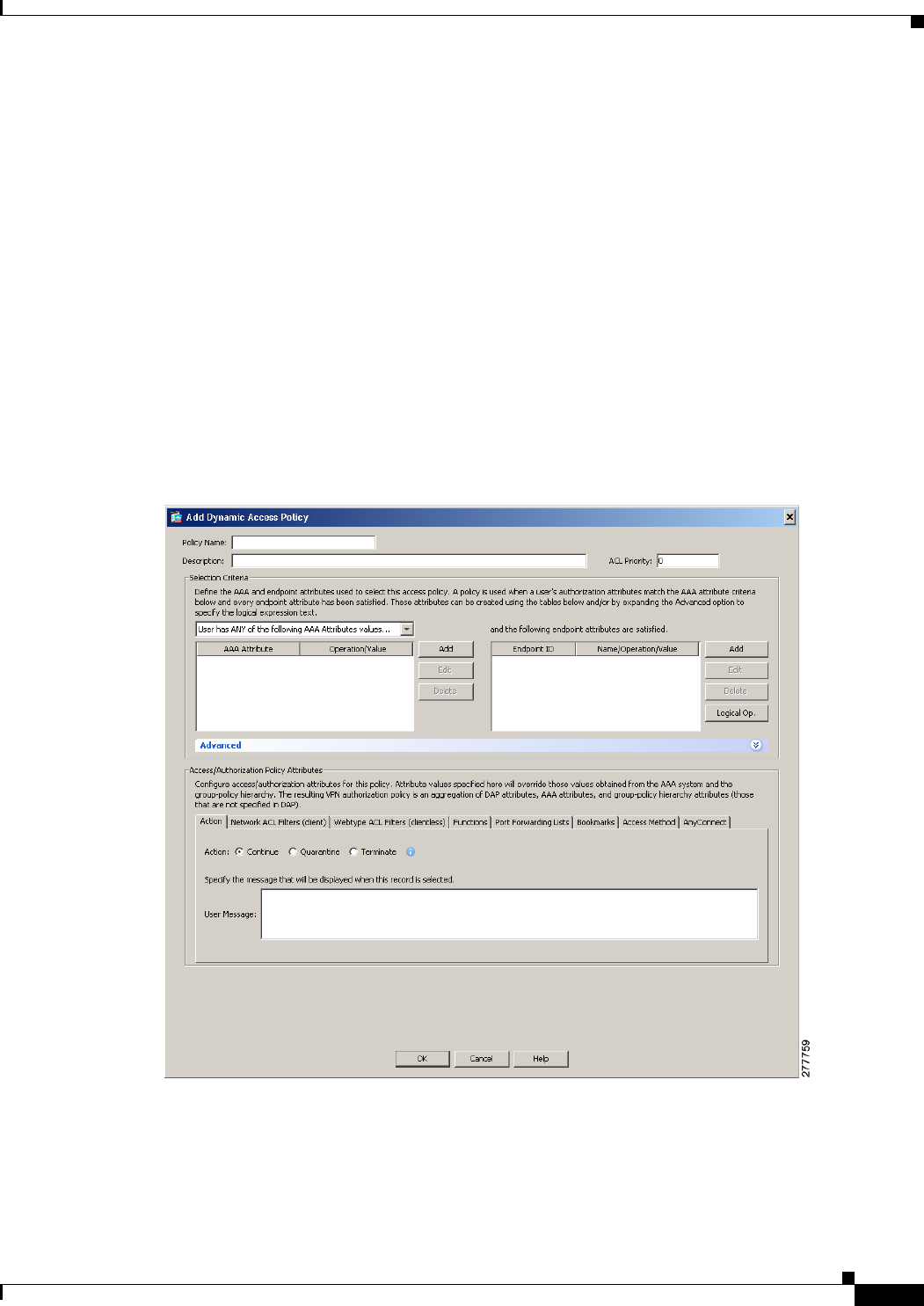
6-5
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 6 Configuring Dynamic Access Policies
Dynamic Access Policies Interface
•Network ACL List—Displays the name of the firewall ACL that applies to the session.
•Web-Type ACL List—Displays the name of the SSL VPN ACL that applies to the session.
•Description—Describes the purpose of the DAP record.
•Test Dynamic Access Policies button—Click to test already configured DAP records.
•Find — You can search for a Dynamic Access Policy (DAP) by using the Find field. Start typing in
the field and the tool will search the beginning characters of every field of the DAP table for a match.
You can use wild cards to expand your search.
For example typing sal in the Find field will match a DAP named Sales but not a DAP named
Wholesalers. If you type *sal in the Find field, the search will find the first instance of either Sales
or Wholesalers in the table.
•Find Arrows — Use the up and down arrows to skip up or down to the next string match.
•Match Case — Checking the Match Case check box will make your search case-sensitive.
Figure 6-2 shows the Add Dynamic Access Policy pane.
Figure 6-2 Add/Edit Dynamic Access Policies Pane

6-6
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 6 Configuring Dynamic Access Policies
Configuring Dynamic Access Policies
Configuring Dynamic Access Policies
Prerequisites
•Other than where noted, you must install Cisco Secure Desktop or Host Scan before configuring
DAP endpoint attributes.
•Before configuring File, Process, and Registry endpoint attributes, configure File, Process, and
Registry Basic Host Scan attributes. For instructions, start ASDM and select Configuration >
Remote Access VPN > Secure Desktop Manager > Host Scan and click Help.
Guidelines and Limitations
DAP supports only ASCII characters.
Mobile Device Guidelines
ASA administrators will use AnyConnect Mobile Posture DAP Attributes differently depending on the
AnyConnect license they have installed. See Adding Mobile Posture Attributes to a DAP, page 6-16 for
more information.
Detailed Steps
Step 1 Start ASDM and select Configuration > Remote Access VPN > Network (Client) Access or Clientless
SSL VPN Access > Dynamic Access Policies.
The Configure Dynamic Access Policies pane opens.
Step 2 To include certain antivirus, antispyware, or personal firewall endpoint attributes, click the CSD
configuration link near the top of the pane. Then enable Cisco Secure Desktop and Host Scan extensions.
This link does not display if you have previously enabled both of these features.
If you enable Cisco Secure Desktop, but do not enable Host Scan extensions, when you apply your
changes ASDM includes a link to enable Host Scan configuration.
Step 3 To create a new dynamic access policy, click Add. To modify an existing policy, click Edit.
The Add/Edit Dynamic Access Policy pane opens.
Step 4 At the top of the Add/Edit Dynamic Access Policy pane, provide a name (required) and a description
(optional) of this dynamic access policy.
•The Policy Name is a string of 4 through 32 characters, no spaces allowed.
•You are allowed a maximum of 80 charaters in the DAP Description field.
Step 5 In the ACL Priority field, set a priority for the dynamic access policy.
The security appliance applies access policies in the order you set here, highest number having the
highest priority. Values of 0 to 2147483647 are valid. The default value is 0.
Step 6 In the Add/Edit AAA Attributes field, use the ANY/ALL/NONE drop-down list (unlabeled) to choose
whether a user must have any, all, or none of the AAA attribute values you configure to use this dynamic
access policy, as well as satisfying every endpoint attribute.
Duplicate entries are not allowed. If you configure a DAP record with no AAA or endpoint attributes,
the ASA always selects it since all selection criteria are satisfied.
Step 7 To Set AAA attributes, click Add or Edit in the AAA Attributes field. Use one or more of these
procedures: See the “Configuring AAA Attributes in a DAP” section on page 6-9 for more information.
6-7
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 6 Configuring Dynamic Access Policies
Configuring Dynamic Access Policies
Step 8 Use one or more of these procedures to add or edit endpoint attributes to the DAP policy:
•Adding an Anti-Spyware or Anti-Virus Endpoint Attribute to a DAP, page 6-14
•Adding an Application Attribute to a DAP, page 6-15
•Adding Mobile Posture Attributes to a DAP, page 6-16
•Adding a File Endpoint Attribute to a DAP, page 6-17
•Adding a Device Endpoint Attribute to a DAP, page 6-18
•Adding a NAC Endpoint Attribute to a DAP, page 6-19
•Adding an Operating System Endpoint Attribute to a DAP, page 6-20
•Adding a Personal Firewall Endpoint Attribute to a DAP, page 6-20
•Adding a Policy Endpoint Attribute to a DAP, page 6-21
•Adding a Process Endpoint Attribute to a DAP, page 6-22
•Adding a Registry Endpoint Attribute to a DAP, page 6-23
You can create multiple instances of each type of endpoint attribute. For each of these types, you need
to decide whether the DAP policy should require that the user have all instances of a type (Match all =
AND) or only one of them (Match Any = OR). To set this value for each of the end point attributes, click
the Logical Op. button.
Step 9 In the Advanced field you can enter one or more logical expressions to set AAA or endpoint attributes
other than what is possible in the AAA and Endpoint areas above. This feature that requires knowledge
of the Lua programming language.
•AND/OR—Click to define the relationship between the basic selection rules and the logical
expressions you enter here, that is, whether the new attributes add to or substitute for the AAA and
endpoint attributes already set. The default is AND.
•Logical Expressions—You can configure multiple instances of each type of endpoint attribute. Enter
free-form Lua text that defines new AAA and/or endpoint selection attributes. ASDM does not
validate text that you enter here; it just copies this text to the DAP XML file, and the ASA processes
it, discarding any expressions it cannot parse.
•Guide—Click to display online help for creating these logical operations or see Guide to Creating
DAP Logical Expressions using LUA, page 6-31.
Step 10 To configure network and webtype ACLs, file browsing, file server entry, HTTP proxy, URL entry, port
forwarding lists and URL lists, set values in the Access Policy Attributes fields. Attribute values that
you configure here override authorization values in the AAA system, including those in existing user,
group, tunnel group, and default group records. See Configuring DAP Access and Authorization Policy
Attributes, page 6-27 for more information.
Step 11 Click OK.
Tip If you want to test your Dynamic Access Policy, in the Configure Dynamic Access Policies dialog box,
click Test Dynamic Access Policies and add the attributes to the test interface. See Testing Dynamic
Access Policies, page 6-8.
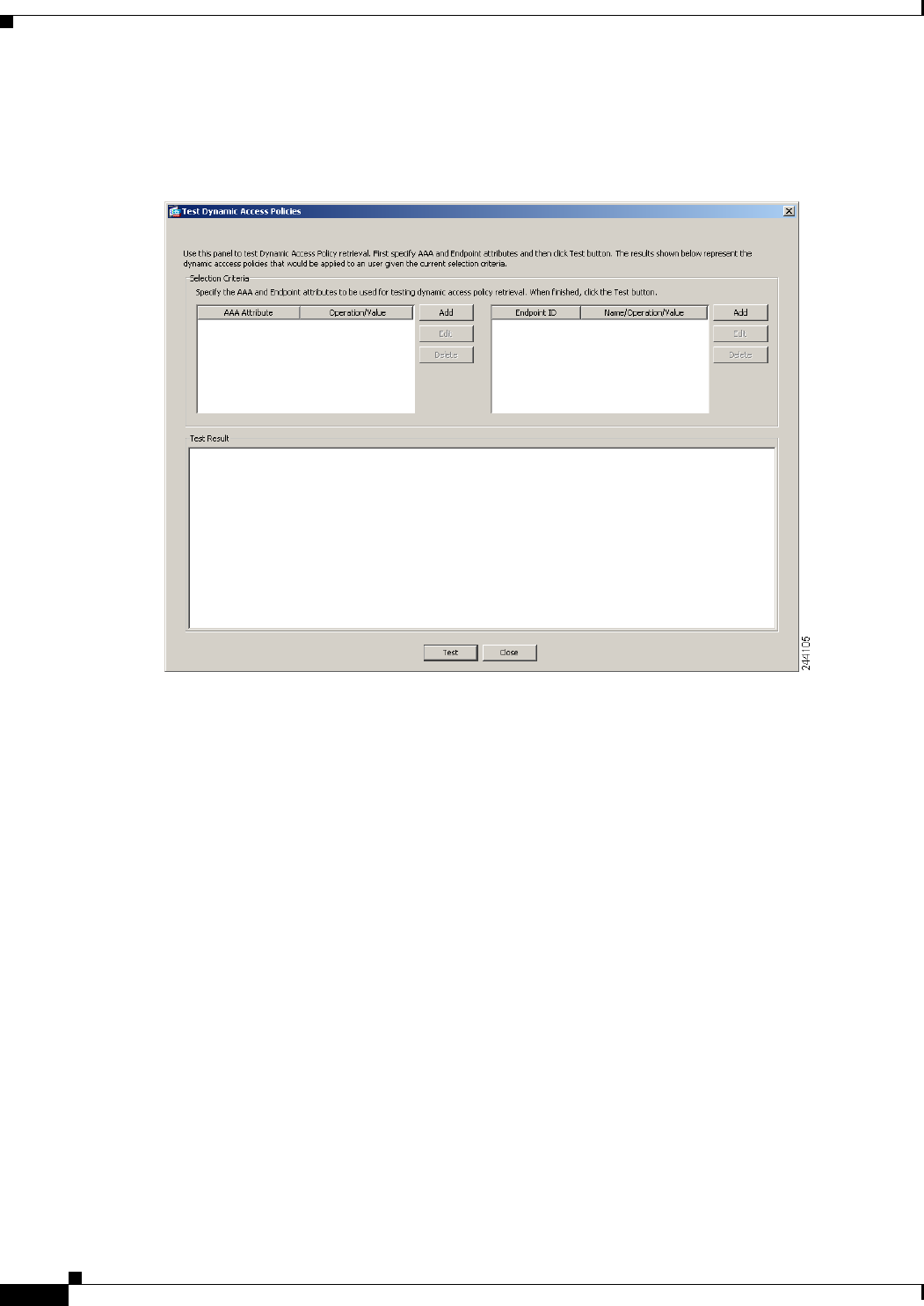
6-8
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 6 Configuring Dynamic Access Policies
Testing Dynamic Access Policies
Testing Dynamic Access Policies
Figure 6-3 Test Dynamic Access Policies Pane
This pane lets you test the retrieval of the set of DAP records configured on the device by specifying
authorization attribute value pairs. To specify these pairs, use the Add/Edit buttons associated with the
AAA Attribute and Endpoint Attribute tables. The dialogs that display when you click these Add/Edit
buttons are similar to those in the Add/Edit AAA Attributes and Add/Edit Endpoint Attributes dialog
boxes.
When you enter attribute value pairs and click the “Test” button, the DAP subsystem on the device
references these values when evaluating the AAA and endpoint selection attributes for each record. The
results display in the “Test Results” text area.
Fields
•Selection Criteria—Determine the AAA and endpoint attributes to test for dynamic access policy
retrieval.
•AAA Attributes
–
AAA Attribute—Identifies the AAA attribute.
–
Operation Value—Identifies the attribute as =/!= to the given value.
–
Add/Edit—Click to add or edit a AAA attribute.
•Endpoint Attributes—Identifies the endpoint attribute.
–
Endpoint ID—Provides the endpoint attribute ID.
–
Name/Operation/Value—
–
Add/Edit/Delete—Click to add, edit or delete and endpoint attribute.
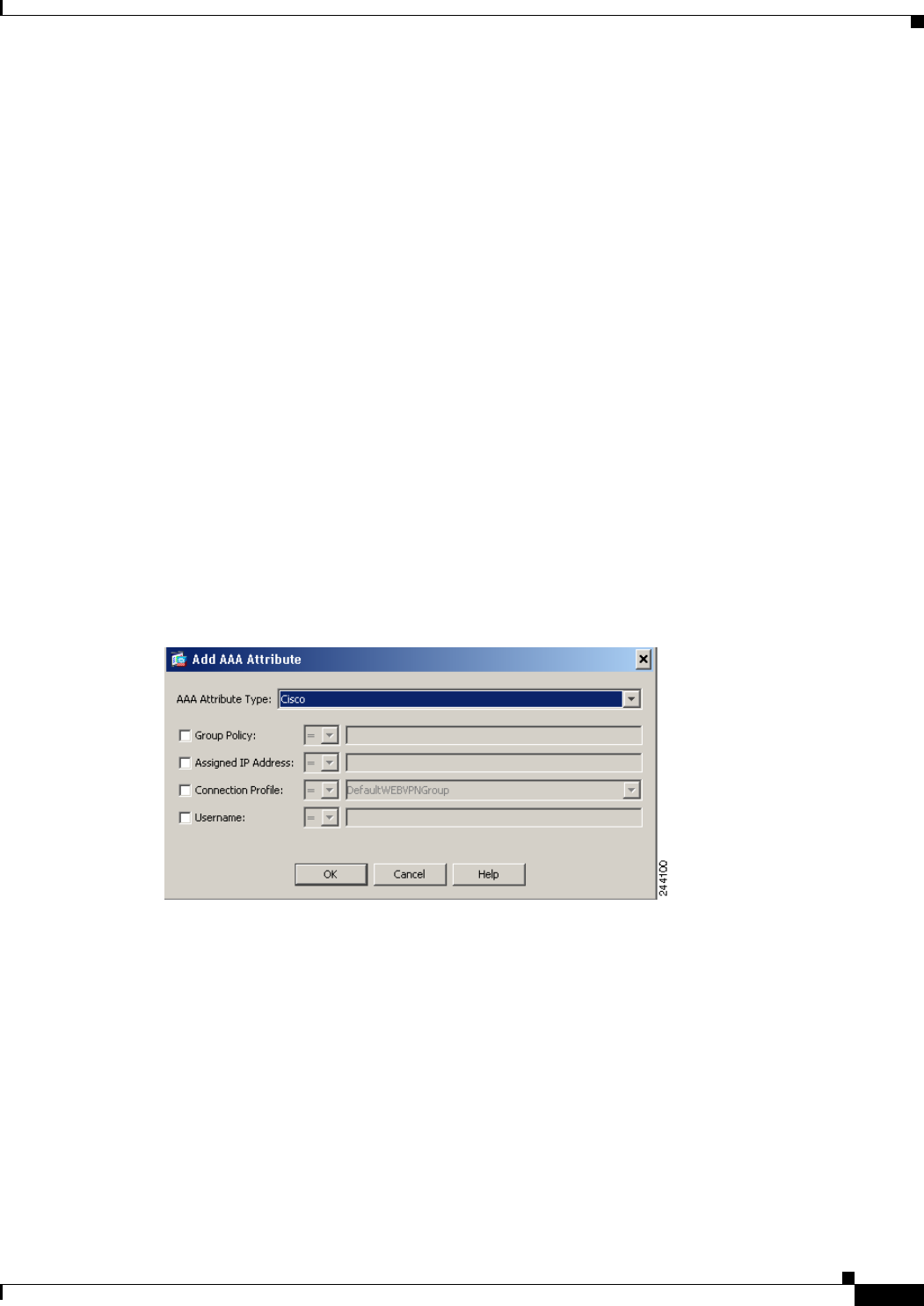
6-9
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 6 Configuring Dynamic Access Policies
DAP and Authentication, Authorization, and Accounting Services
•Test Result—Displays the result of the test.
•Test—Click to test the retrieval of the policies you have set.
•Close—Click to close the pane.
DAP and Authentication, Authorization, and Accounting
Services
DAP complements AAA services. It provides a limited set of authorization attributes that can override
those AAA provides. The ASA selects DAP records based on the AAA authorization information for the
user and posture assessment information for the session. The ASA can select multiple DAP records
depending on this information, which it then aggregates to create DAP authorization attributes.
You can specify AAA attributes from the Cisco AAA attribute hierarchy, or from the full set of response
attributes that the ASA receives from a RADIUS or LDAP server. For more information about DAP and
AAA, see the section, Configuring AAA Attributes in a DAP.
Configuring AAA Attributes in a DAP
Figure 6-4 shows the Add AAA Attribute dialog box.
Figure 6-4 Add AAA Attribute Dialog Box
To configure AAA attributes as selection criteria for DAP records, in the Add/Edit AAA Attributes
dialog box, set the Cisco, LDAP, or RADIUS attributes that you want to use. You can set these attributes
either to = or != the value you enter. There is no limit for the number of AAA attributes for each DAP
record. For detailed information about AAA attributes, see AAA Attribute Definitions.
Fields
AAA Attributes Type—Use the drop-down list to select Cisco, LDAP or RADIUS attributes:
•Cisco—Refers to user authorization attributes that are stored in the AAA hierarchical model. You
can specify a small subset of these attributes for the AAA selection attributes in the DAP
record.These include:
–
Group Policy —The group policy name associated with the VPN user session. Can be set locally
on the security appliance or sent from a RADIUS/LDAP server as the IETF-Class (25) attribute.
Maximum 64 characters.

6-10
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 6 Configuring Dynamic Access Policies
DAP and Authentication, Authorization, and Accounting Services
–
Assigned IP Address—Enter the IPv4 address you want to specify for the policy. The assigned
IP address for full tunnel VPN clients (IPsec, L2TP/IPsec, SSL VPN AnyConnect) does not apply
to Clientless SSL VPN, since there is no address assignment for clientless sessions.
–
Assigned IPv6 Address—Enter the IPv6 address you want to specify for the policy.
–
Connection Profile—The connection or tunnel group name. Maximum 64 characters.
–
Username—The username of the authenticated user. Maximum 64 characters. Applies if you are
using Local, RADIUS, LDAP authentication/authorization or any other authentication type (for
example, RSA/SDI), NT Domain, etc).
–
=/!=—Equal to/Not equal to.
•LDAP—The LDAP client (security appliance) stores all native LDAP response attribute value pairs
in a database associated with the AAA session for the user. The LDAP client writes the response
attributes to the database in the order in which it receives them. It discards all subsequent attributes
with that name. This scenario might occur when a user record and a group record are both read from
the LDAP server. The user record attributes are read first, and always have priority over group record
attributes.
To support Active Directory group membership, the AAA LDAP client provides special handling of
the LDAP memberOf response attribute. The AD memberOf attribute specifies the DN string of a
group record in AD. The name of the group is the first CN value in the DN string. The LDAP client
extracts the group name from the DN string and stores it as the AAA memberOf attribute, and in the
response attribute database as the LDAP memberOf attribute. If there are additional memberOf
attributes in the LDAP response message, then the group name is extracted from those attributes and
is combined with the earlier AAA memberOf attribute to form a comma separated string of group
names, also updated in the response attribute database.
In the case where the VPN remote access session to an LDAP authentication/authorization server
returns the following three Active directory groups (memberOf enumerations):
cn=Engineering,ou=People,dc=company,dc=com
cn=Employees,ou=People,dc=company,dc=com
cn=EastCoastast,ou=People,dc=company,dc=com
the ASA processes three Active Directory groups: Engineering, Employees, and EastCoast which
could be used in any combination as aaa.ldap selection criteria.
LDAP attributes consist of an attribute name and attribute value pair in the DAP record. The LDAP
attribute name is syntax/case sensitive. If for example you specify LDAP attribute Department
instead of what the AD server returns as department, the DAP record will not match based on this
attribute setting.
Note To enter multiple values in the Value field, use the semicolon (;) as the delimiter. For
example:
eng;sale; cn=Audgen VPN,ou=USERS,o=OAG
•RADIUS—The RADIUS client stores all native RADIUS response attribute value pairs in a
database associated with the AAA session for the user. The RADIUS client writes the response
attributes to the database in the order in which it receives them. It discards all subsequent attributes
with that name. This scenario might occur when a user record and a group record are both read from
the RADIUS server. The user record attributes are read first, and always have priority over group
record attributes.

6-11
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 6 Configuring Dynamic Access Policies
DAP and Authentication, Authorization, and Accounting Services
RADIUS attributes consist of an attribute number and attribute value pair in the DAP record. See
Security Appliance Supported RADIUS Attributes and Values for a table that lists RADIUS
attributes that the security appliance supports.
Note For RADIUS attributes, DAP defines the Attribute ID = 4096 + RADIUS ID.
For example:
The RADIUS attribute "Access Hours" has a Radius ID = 1, therefore DAP attribute value =
4096 + 1 = 4097.
The RADIUS attribute "Member Of" has a Radius ID = 146, therefore DAP attribute value =
4096 + 146 = 4242.
•LDAP and RADIUS attributes include:
–
Attribute ID—Names/numbers the attribute. Maximum 64 characters.
–
Value—The attribute name (LDAP) or number (RADIUS).
To enter multiple values in the Value field, use the semicolon (;) as the delimiter. For example:
eng;sale; cn=Audgen VPN,ou=USERS,o=OAG
–
=/!=—Equal to/Not equal to.
•LDAP includes the Get AD Groups button. This button queries the Active Directory LDAP server
for the list of groups the user belong to (memberOf enumerations). It retrieves the AD groups using
the CLI show-ad-groups command in the background
The show ad-groups command applies only to Active Directory servers using LDAP. Use this command
to display AD groups that you can use for dynamic access policy AAA selection criteria.
The default time that the ASA waits for a response from the server is 10 seconds. You can adjust this
time using the group-search-timeout command in aaa-server host configuration mode.
Note If the Active Directory server has a large number of groups, the output of the show ad-groups command
might be truncated based on limitations to the amount of data the server can fit into a response packet.
To avoid this problem, use the filter option to reduce the number of groups reported by the server.
Retrieving Active Directory Groups
Figure 6-5 shows the Retrieve AD Groups from Selected AD Server Group pane.
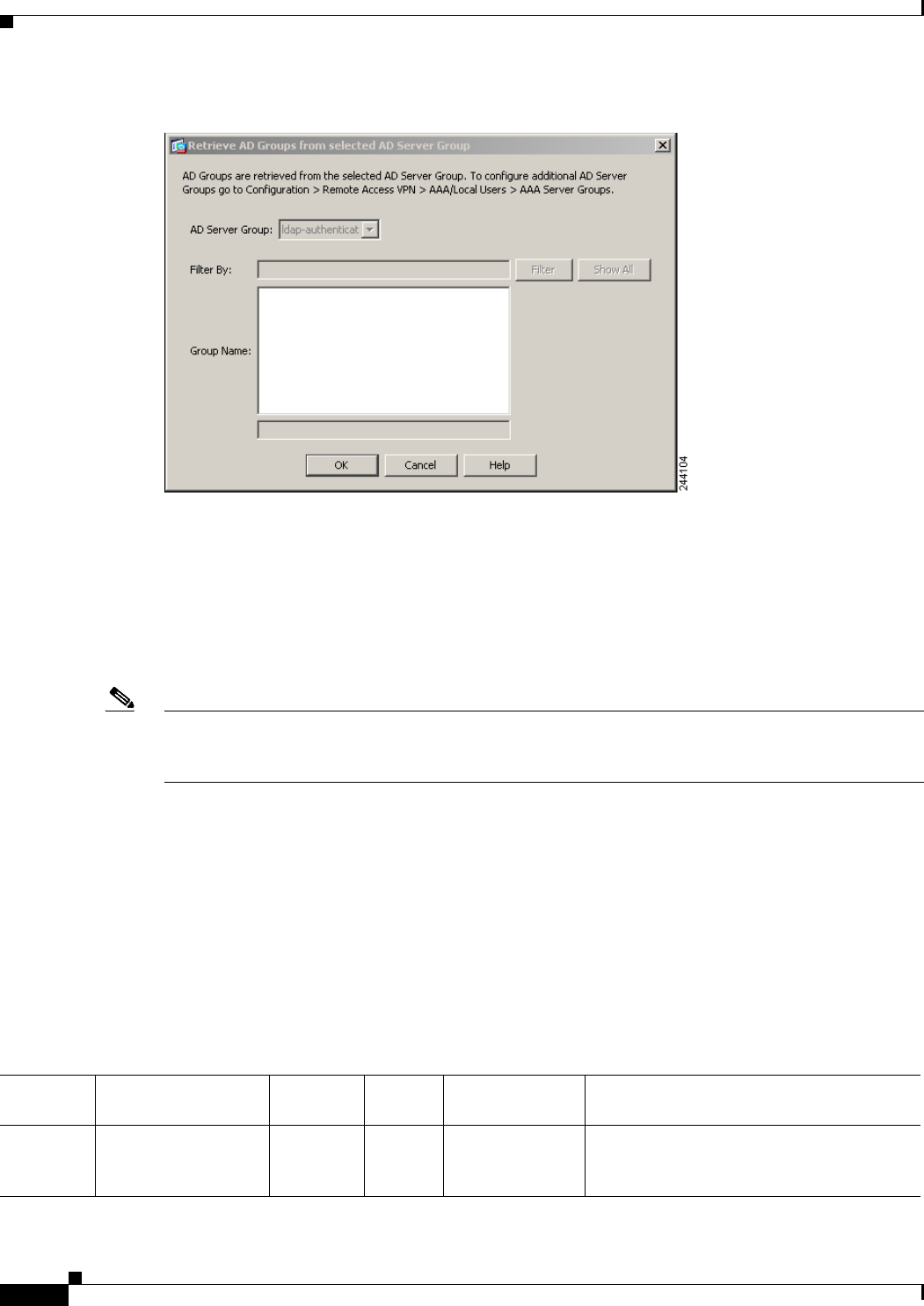
6-12
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 6 Configuring Dynamic Access Policies
DAP and Authentication, Authorization, and Accounting Services
Figure 6-5 Retrieve AD Groups Dialog Box
You can query an Active Directory server for available AD groups in this pane. This feature applies only
to Active Directory servers using LDAP. Use the group information to specify dynamic access policy
AAA selection criteria.
You can change the level in the Active Directory hierarchy where the search begins by changing the
Group Base DN in the Edit AAA Server pane. You can also change the time that the ASA waits for a
response from the server in the window. To configure these features, choose
Configuration > Remote Access VPN > AAA/Local Users > AAA Server Groups > Edit AAA Server.
Note If the Active Directory server has a large number of groups, the list of AD groups retrieved may be
truncated based on limitations of the amount of data the server can fit into a response packet. To avoid
this problem, use the filter feature to reduce the number of groups reported by the server.
Fields
AD Server Group—The name of the AAA server group to retrieve AD groups.
Filter By—Specify a group or the partial name of a group to reduce the groups displayed.
Group Name—A list of AD groups retrieved from the server.
AAA Attribute Definitions
The following table defines the AAA selection attribute names that are available for DAP use. The
Attribute Name field shows you how to enter each attribute name in a Lua logical expression, which you
might do in the Advanced section of the Add/Edit Dynamic Access Policy pane.
Attribute
Type Attribute Name Source Value
Max String
Length Description
Cisco aaa.cisco.grouppolicy AAA string 64 Group policy name on the ASA or sent from
a Radius/LDAP server as the IETF-CLass
(25) attribute
6-13
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 6 Configuring Dynamic Access Policies
Configuring Endpoint Attributes Used in DAPs
Configuring Endpoint Attributes Used in DAPs
Endpoint attributes contain information about the endpoint system environment, posture assessment
results, and applications. The ASA dynamically generates a collection of endpoint attributes during
session establishment and stores these attributes in a database associated with the session. There is no
limit for the number of endpoint attributes for each DAP record.
Each DAP record specifies the endpoint selection attributes that must be satisfied for the ASA to select
it. The ASA selects only DAP records that satisfy every condition configured.
For detailed information about Endpoint attributes, see Endpoint Attribute Definitions.
Configuring endpoint attributes as selection criteria for DAP records is part of the larger process of
Configuring Dynamic Access Policies. Read Configuring Dynamic Access Policies, page 6-6 before you
configuring endpoint attributes in DAPs.
This section includes the following topics:
•Adding an Anti-Spyware or Anti-Virus Endpoint Attribute to a DAP, page 6-14
•Adding an Application Attribute to a DAP, page 6-15
•Adding Mobile Posture Attributes to a DAP, page 6-16
•Adding a File Endpoint Attribute to a DAP, page 6-17
•Adding a Device Endpoint Attribute to a DAP, page 6-18
•Adding a NAC Endpoint Attribute to a DAP, page 6-19
•Adding an Operating System Endpoint Attribute to a DAP, page 6-20
•Adding a Personal Firewall Endpoint Attribute to a DAP, page 6-20
•Adding a Policy Endpoint Attribute to a DAP, page 6-21
•Adding a Process Endpoint Attribute to a DAP, page 6-22
•Adding a Registry Endpoint Attribute to a DAP, page 6-23
Figure 6-6 shows the Add Endpoint Attributes dialog box.
aaa.cisco.ipaddress AAA number - Assigned IP address for full tunnel VPN
clients (IPsec, L2TP/IPsec, SSL VPN
AnyConnect)
aaa.cisco.tunnelgroup AAA string 64 Connection profile (tunnel group) name
aaa.cisco.username AAA string 64 Name of the authenticated user (applies if
using Local authentication/authorization)
LDAP aaa.ldap.<label> LDAP string 128 LDAP attribute value pair
RADIUS aaa.radius.<number> RADIUS string 128 Radius attribute value pair
See Security Appliance Supported RADIUS Attributes and Values for a table that lists RADIUS attributes that the security
appliance supports.
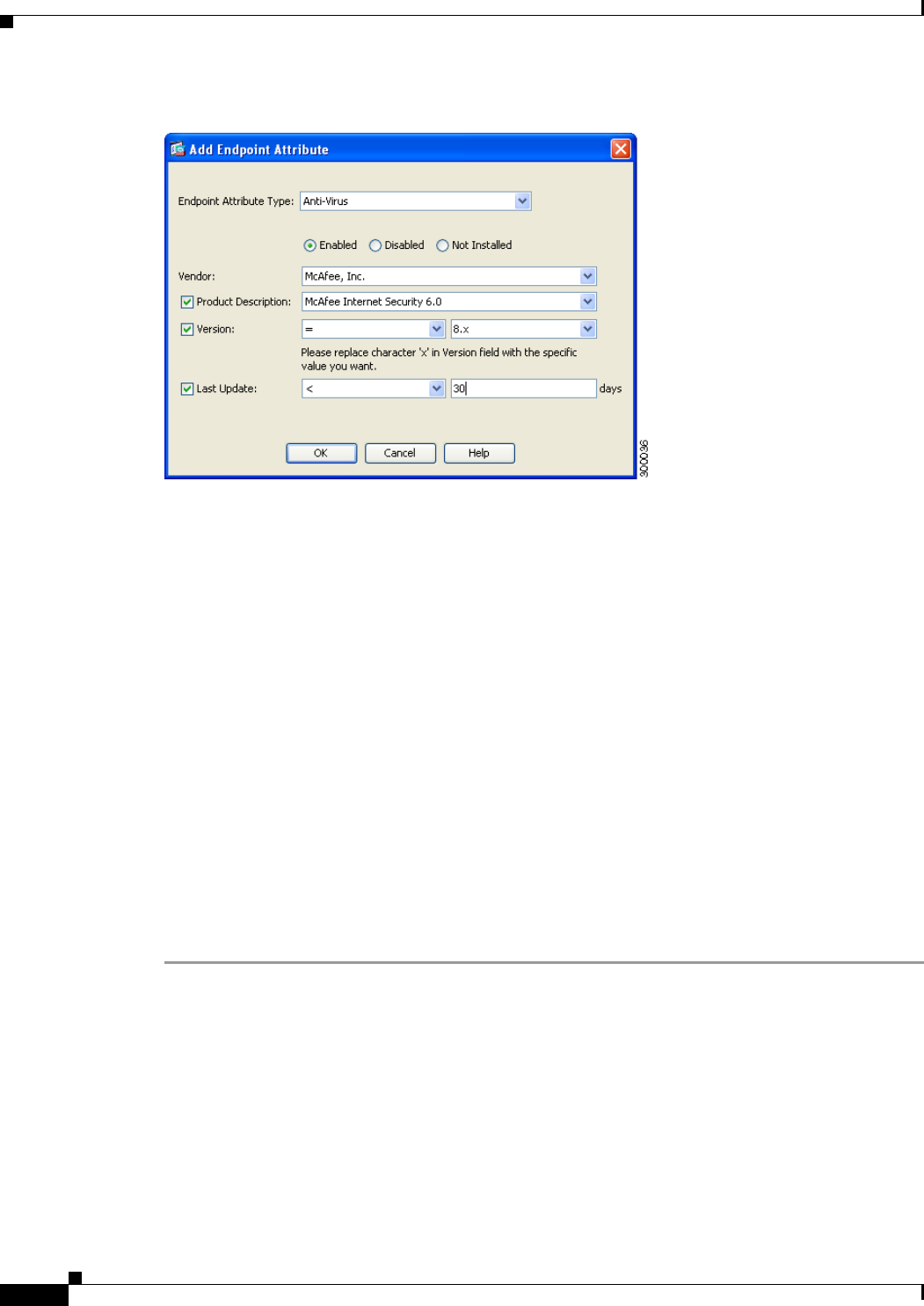
6-14
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 6 Configuring Dynamic Access Policies
Configuring Endpoint Attributes Used in DAPs
Figure 6-6 Add Endpoint Attributes Dialog Box
Adding an Anti-Spyware or Anti-Virus Endpoint Attribute to a DAP
Prerequisites
Configuring Anti-Spyware and Anti-Virus endpoint attributes as selection criteria for DAP records is
part of a larger process. Read Configuring Dynamic Access Policies, page 6-6 before you configure
Anti-Spyware and Anti-Virus endpoint attributes.
Guidelines
You can create multiple instances of each type of endpoint attribute. For each of these types, you need
to decide whether the DAP policy should require that the user have all instances of a type (Match all =
AND) or only one of them (Match Any = OR).
To set this value, after you have defined all instances of the endpoint attribute, click the Logical Op.
button and select the Match Any or Match All button. If you do not specify a Logical Operation, Match
Any is used by default.
Detailed Steps
Step 1 In the Endpoint Attribute Type list box, select Anti-Spyware or Anti-Virus.
Step 2 Click the appropriate Enabled, Disabled, or Not Installed button to indicate whether the selected
endpoint attribute and its accompanying qualifiers (fields below the Enabled/Disabled/Not Installed
buttons) must be enabled, disabled, or are not installed.
Step 3 From the Vendor ID list box, click the name of the anti-spyware or anti-virus vendor you are testing for.
Step 4 Check the Product Description check box and select from the list box the vendor’s product name you
are testing for.
Step 5 Check the Version checkbox and set the operation field to equal to (=), not equal (!=), less than (<),
greater than (>), less that or equal to (<=), or greater than or equal to (>=) the product version number
you select from ther Ver si on list box.

6-15
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 6 Configuring Dynamic Access Policies
Configuring Endpoint Attributes Used in DAPs
If the choice in the version list box has an x, such as 3.x, replace the x with a specific release number,
for example, 3.5.
Step 6 Check the Last Update check box. Specify the number of days since the last update. You might want to
indicate that an update should occur in less than (<) or more than (>) the number of days you enter here.
Step 7 Click OK.
Step 8 Return to Configuring Dynamic Access Policies, page 6-6.
Additional References
•See Endpoint Attribute Definitions, page 6-24 for additional information on the antispyware and
antivirus endpoint attribute requirements.
•See DAP and AntiVirus, AntiSpyware, and Personal Firewall Programs, page 6-24 for information
on how Host Scan checks for antivirus, antispyware, and personal firewall programs that are
memory-resident.
Adding an Application Attribute to a DAP
Prerequisites
Configuring Application endpoint attributes as selection criteria for DAP records is part of a larger
process. Read Configuring Dynamic Access Policies, page 6-6 before you configure Application
endpoint attributes.
Guidelines
You can create multiple instances of each type of endpoint attribute. For each of these types, you need
to decide whether the DAP policy should require that the user have all instances of a type (Match all =
AND) or only one of them (Match Any = OR).
To set this value, after you have defined all instances of the endpoint attribute, click the Logical Op.
button and select the Match Any or Match All button. If you do not specify a Logical Operation, Match
Any is used by default.
Detailed Steps
Step 1 In the Endpoint Attribute Type list box, select Application.
Step 2 In the Client Type operation field, select equals (=) or does not eaqual (!=).
Step 3 In the Client type list box, indicate the type of remote access connection you are testing for.
Step 4 Click OK.
Step 5 Return to Configuring Dynamic Access Policies, page 6-6.
Additional References
See Endpoint Attribute Definitions, page 6-24 for additional information on the Application endpoint
attribute requirements.

6-16
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 6 Configuring Dynamic Access Policies
Configuring Endpoint Attributes Used in DAPs
Adding Mobile Posture Attributes to a DAP
Licensing
Mobile posture requires an AnyConnect Mobile license and an AnyConnect Premium license installed
on the ASA. Enterprises that install these licenses will be able to enforce DAP policies on supported
mobile devices based on DAP attributes and other existing endpoint attributes. This includes allowing or
denying remote access from a mobile device.
Prerequisites
Configuring mobile posture attributes as selection criteria for DAP records is part of a larger process.
Read Configuring Dynamic Access Policies, page 6-6 before you configure Anti-Spyware and
Anti-Virus endpoint attributes.
Guidelines
•These mobile posture attributes can be included in a dynamic access polciy and enforced without
installing Host Scan or Cisco Secure Desktop on the endpoint.
•Some mobile posture attributes are relevant to the AnyConnect client running on mobile devices
only, some mobile posture attributes are relevant to both AnyConnect clients running on mobile
devices and AnyConnect desktop clients.
•When specifying mobile posture attributes and application attributes in a dynamic access policy,
they both should be set to AnyConnect.
Detailed Steps
Step 1 In the Endpoint Attribute Type list box, select AnyConnect.
Step 2 Check the Client Version check box and set the operation field to be equal to (=), not equal to (!=), less
than (<), greater than (>), less than or equal to (<=), or greater than or equal to (>=) the AnyConnect
client version number you then specify in the Client Version field.
You can use this field to evaluate the client version on mobile devices, such as mobile phones and tablets,
or desktop and laptop devices.
Step 3 Check the Platform check box and set the operation field to be equal to (=), or not equal to (!=) the
operating system you then select from the Platform list box.
You can use this field to evaluate the operating system on mobile devices, such as mobile phones and
tablets, as well as the operating system on desktop and laptop devices. Selecting Apple iOS or Android
platforms activates the additional attribute fields for Device Type and Device Unique ID.
Step 4 Check the Platform Version check box and set the operation field to be equal to (=), not equal to (!=),
less than (<), greater than (>), less than or equal to (<=), or greater than or equal to (>=) the operating
system version number you then specify in the Platform Version field.
If you want to create a DAP record that contains this attribute, be sure to also specify a Platform in the
previous step.
Step 5 If you selected the Platform checkbox and selected the Apple iOS or Android platform, you can check
the Device Type checkbox. Set the operation field to be equal to (=) or not equal to (!=) the mobile device
you then select in the Device Type field.

6-17
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 6 Configuring Dynamic Access Policies
Configuring Endpoint Attributes Used in DAPs
When you specify Android in the Platform field, you will be able to pick from a list of supported
Android devices in the Device Type field. When you specify Apple iOS in the Platform field you will
be able to pick from a list of supported Apple devices in the Device Type field. In both cases, the proper
Android or Apple iOS device type information is substituted for the device type you choice from the list
box.
If you have a supported device which is not listed in the Device Type field, you can enter the Android or
Apple iOS device type information in the Device Type field. The most reliable way to obtain the device
type information is to install the AnyConnect client on the endpoint and perform a DAP Trace. In the
DAP trace results, look for the value of endpoint.anyconnect.devicetype. That is the value that you
need to enter in the Device Type field.
Step 6 If you selected the Platform checkbox and selected the Apple iOS or Android platform, you can check
the Device Unique ID checkbox. Set the operation field to be equal to (=) or not equal to (!=) the mobile
device’s unique ID you then specify in the Device Unique ID field.
The Device Unique ID distinguishes individual devices allowing you to set policies for a particular
mobile device. To obtain a device’s unique ID you will need the device to connect to the ASA and
perform a DAP trace. See Performing a DAP Trace, page 6-31 for more information.
Step 7 Click OK.
Step 8 Return to Configuring Dynamic Access Policies, page 6-6.
Additional References
See Endpoint Attribute Definitions, page 6-24 for additional information on the AnyConnect endpoint
attribute requirements.
Adding a File Endpoint Attribute to a DAP
Prerequisites
•Configuring File endpoint attributes as selection criteria for DAP records is part of a larger process.
Read Configuring Dynamic Access Policies, page 6-6 before you configure File endpoint attributes.
•Before configuring a File endpoint attribute, define the file for which you want to scan in the Host
Scan window for Cisco Secure Desktop. In ASDM select Configuration > Remote Access VPN >
Secure Desktop Manager > Host Scan. Click Help on that page for more information.
Guidelines
You can create multiple instances of each type of endpoint attribute. For each of these types, you need
to decide whether the DAP policy should require that the user have all instances of a type (Match all =
AND) or only one of them (Match Any = OR).
To set this value, after you have defined all instances of the endpoint attribute, click the Logical Op.
button and select the Match Any or Match All button. If you do not specify a Logical Operation, Match
All is used by default.
Detailed Steps
You only need to configure one AnyConnect attribute in the Add Endpoint Attribute field except where
noted.

6-18
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 6 Configuring Dynamic Access Policies
Configuring Endpoint Attributes Used in DAPs
Step 1 In the Endpoint Attribute Type list box, select File.
Step 2 Select the appropriate Exists or Does not exist radio button to indicate whether the selected endpoint
attribute and its accompanying qualifiers (fields below the Exists/Does not exist buttons) should be
present or not.
Step 3 In the Endpoint ID list box, choose from the drop-down list the endpoint ID that equates to the file entry
for which you want to scan.
The file information is displayed below the Endpoint ID list box.
Step 4 Check the Last Update check box and set the operation field to be less than (<) or greater than (>) a
certain number of days old. Enter the number of days old in the days field.
Step 5 Check the Checksum checkbox and set the operation field to be equal to (=) or not equal to (!=) the
checksum value of the file you are testing for.
Step 6 Click Compute CRC32 Checksum to determine the checksum value of the file you are testing for.
Step 7 Click OK.
Step 8 Return to Configuring Dynamic Access Policies, page 6-6.
Additional References
See Endpoint Attribute Definitions, page 6-24 for additional information on the File endpoint attribute
requirements.
Adding a Device Endpoint Attribute to a DAP
Prerequisites
Configuring Device endpoint attributes as selection criteria for DAP records is part of a larger process.
Read Configuring Dynamic Access Policies, page 6-6 before you configure Device endpoint attributes.
Guidelines
You can create multiple instances of each type of endpoint attribute. For each of these types, you need
to decide whether the DAP policy should require that the user have all instances of a type (Match all =
AND) or only one of them (Match Any = OR).
To set this value, after you have defined all instances of the endpoint attribute, click the Logical Op.
button and select the Match Any or Match All button. If you do not specify a Logical Operation, Match
Any is used by default.
Detailed Steps
Step 1 In the Endpoint Attribute Type list box, select Device.
Step 2 Check the Host Name checkbox and set the operation field to be equal to (=) or not equal to (!=) the host
name of the device you are testing for. Use the computer’s host name only, not the fully qualified domain
name (FQDN).

6-19
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 6 Configuring Dynamic Access Policies
Configuring Endpoint Attributes Used in DAPs
Step 3 Check the MAC address checkbox and set the operation field to be equal to (=) or not equal to (!=) the
MAC address of the network interface card you are testing for. Only one MAC address per entry. The
address must be in the format xxxx.xxxx.xxxx where x is a hexadecimal character.
Step 4 Check the BIOS Serial Number checkbox and set the operation field to be equal to (=) or not equal to
(!=) the BIOS serial number value of the device you are testing for. The number format is
manufacturer-specific. There is no format requirement.
Step 5 Check the TCP/UDP Port Number checkbox and set the operation field to be equal to (=) or not equal
to (!=) the TCP or UDP port in listening state that you are testing for.
In the TCP/UDP combo box, select the kind of port you are testing for: TCP (IPv4), UDP(IPv4), TCP
(IPv6), or UDP (IPv6). If you are testing for more than one port, make several individual endpoint
attribute rules in the DAP and specify one port in each.
Step 6 Check the Privacy Protection checkbox and set the operation field to be equal to (=) or not equal to (!=)
the component CSD uses to execute the PreLogin Policy.
Step 7 Check the Version of Secure Desktop (CSD) checkbox and set the operation field to be equal to (=) or
not equal to (!=) the version of the Host Scan image running on the endpoint.
Step 8 Check the Version of Endpoint Assessment checkbox and set the operation field to be equal to (=) or
not equal to (!=) the version of endpoint assessment (OPSWAT) you are testing for.
Step 9 Click OK.
Step 10 Return to Configuring Dynamic Access Policies, page 6-6.
Additional References
See Endpoint Attribute Definitions, page 6-24 for additional information on the Device endpoint
attribute requirements.
Adding a NAC Endpoint Attribute to a DAP
Prerequisites
Configuring NAC endpoint attributes as selection criteria for DAP records is part of a larger process.
Read Configuring Dynamic Access Policies, page 6-6 before you configure NAC endpoint attributes.
Guidelines
You can create multiple instances of each type of endpoint attribute. For each of these types, you need
to decide whether the DAP policy should require that the user have all instances of a type (Match all =
AND) or only one of them (Match Any = OR).
To set this value, after you have defined all instances of the endpoint attribute, click the Logical Op.
button and select the Match Any or Match All button. If you do not specify a Logical Operation, Match
Any is used by default.
Detailed Steps
Step 1 In the Endpoint Attribute Type list box, select NAC.

6-20
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 6 Configuring Dynamic Access Policies
Configuring Endpoint Attributes Used in DAPs
Step 2 Check the Posture Status checkbox and set the operation field to be equal to (=) or not equal to (!=) the
posture token string received by ACS. Enter the posture token string in the Posture Status text box.
Step 3 Click OK.
Step 4 Return to Configuring Dynamic Access Policies, page 6-6.
Additional References
See Endpoint Attribute Definitions, page 6-24 for additional information on the NAC endpoint attribute
requirements.
Adding an Operating System Endpoint Attribute to a DAP
Prerequisites
Configuring Operating System endpoint attributes as selection criteria for DAP records is part of a
larger process. Read Configuring Dynamic Access Policies, page 6-6 before you configure Operating
System endpoint attributes.
Detailed Steps
Step 1 In the Endpoint Attribute Type list box, select Operating System.
Step 2 Check the OS Version checkbox and set the operation field to be equal to (=) or not equal to (!=) the
Windows, Mac, or Linux operating system you set in the OS Version list box.
Step 3 Check the OS Update checkbox and set the operation field to be equal to (=) or not equal to (!=) the
Windows, Mac, or Linux service pack for the operating system you enter in the OS Update text box.
Step 4 Click OK.
Step 5 Return to Configuring Dynamic Access Policies, page 6-6.
Additional References
See Endpoint Attribute Definitions, page 6-24 for additional information on the Operating System
endpoint attribute requirements.
Adding a Personal Firewall Endpoint Attribute to a DAP
Prerequisites
Configuring Personal Firewall endpoint attributes as selection criteria for DAP records is part of a
larger process. Read Configuring Dynamic Access Policies, page 6-6 before you configure Personal
Firewall endpoint attributes.

6-21
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 6 Configuring Dynamic Access Policies
Configuring Endpoint Attributes Used in DAPs
Detailed Steps
Step 1 In the Endpoint Attribute Type list box, select Operating System.
Step 2 Click the appropriate Enabled, Disabled, or Not Installed button to indicate whether the selected
endpoint attribute and its accompanying qualifiers (fields below the Enabled/Disabled/Not Installed
buttons) must be enabled, disabled, or are not installed.
Step 3 From the Vendor ID list box, click the name of the personal firewall vendor you are testing for.
Step 4 Check the Product Description check box and select from the list box the vendor’s product name you
are testing for.
Step 5 Check the Version checkbox and set the operation field to equal to (=), not equal (!=), less than (<),
greater than (>), less that or equal to (<=), or greater than or equal to (>=) the product version number
you select from ther Ver si on list box.
If the choice in the Ve rs i on list box has an x, such as 3.x, replace the x with a specific release number,
for example, 3.5.
Step 6 Click OK.
Step 7 Return to Configuring Dynamic Access Policies, page 6-6.
Additional References
•See Endpoint Attribute Definitions, page 6-24 for additional information on the Personal Firewall
endpoint attribute requirements.
•See DAP and AntiVirus, AntiSpyware, and Personal Firewall Programs, page 6-24 for information
on how Host Scan checks for antivirus, antispyware, and personal firewall programs that are
memory-resident.
Adding a Policy Endpoint Attribute to a DAP
Prerequisites
Configuring Policy endpoint attributes as selection criteria for DAP records is part of a larger process.
Read Configuring Dynamic Access Policies, page 6-6 before you configure Policy endpoint attributes.
Guidelines
You can create multiple instances of each type of endpoint attribute. For each of these types, you need
to decide whether the DAP policy should require that the user have all instances of a type (Match all =
AND) or only one of them (Match Any = OR).
To set this value, after you have defined all instances of the endpoint attribute, click the Logical Op.
button and select the Match Any or Match All button. If you do not specify a Logical Operation, Match
Any is used by default.
Detailed Steps
Step 1 In the Endpoint Attribute Type list box, select Policy.

6-22
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 6 Configuring Dynamic Access Policies
Configuring Endpoint Attributes Used in DAPs
Step 2 Check the Location checkbox and set the operation field to be equal to (=) or not equal to (!=) the Cisco
Secure Desktop Microsoft Windows location profile. Enter the Cisco Secure Desktop Microsoft
Windows location profile string in the Location text box.
Step 3 Click OK.
Step 4 Return to Configuring Dynamic Access Policies, page 6-6.
Additional References
See Endpoint Attribute Definitions, page 6-24 for additional information on the Policy endpoint attribute
requirements.
Adding a Process Endpoint Attribute to a DAP
Prerequisites
•Configuring Process endpoint attributes as selection criteria for DAP records is part of a larger
process. Read Configuring Dynamic Access Policies, page 6-6 before you configure Personal
Firewall endpoint attributes.
•Before configuring a Process endpoint attribute, define the process for which you want to scan in
the Host Scan window for Cisco Secure Desktop. In ASDM select Configuration > Remote Access
VPN > Secure Desktop Manager > Host Scan. Click Help on that page for more information.
Guidelines
You can create multiple instances of each type of endpoint attribute. For each of these types, you need
to decide whether the DAP policy should require that the user have all instances of a type (Match all =
AND) or only one of them (Match Any = OR).
To set this value, after you have defined all instances of the endpoint attribute, click the Logical Op.
button and select the Match Any or Match All button. If you do not specify a Logical Operation, Match
All is used by default.
Detailed Steps
Step 1 In the Endpoint Attribute Type list box, select Process.
Step 2 Click the appropriate Exists or Does not exist button to indicate whether the selected endpoint attribute
and its accompanying qualifiers (fields below the Exists and Does not exist buttons) should be present
or not.
Step 3 In the Endpoint ID list box, choose from the drop-down list the endpoint ID for which you want to scan.
The endpoint ID process information is displayed below the list box.
Step 4 Click OK.
Step 5 Return to Configuring Dynamic Access Policies, page 6-6.

6-23
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 6 Configuring Dynamic Access Policies
Configuring Endpoint Attributes Used in DAPs
Additional References
See Endpoint Attribute Definitions, page 6-24 for additional information on the Process endpoint
attribute requirements.
Adding a Registry Endpoint Attribute to a DAP
Prerequisites
•Configuring Process endpoint attributes as selection criteria for DAP records is part of a larger
process. Read Configuring Dynamic Access Policies, page 6-6 before you configure Personal
Firewall endpoint attributes.
•Before configuring a Registry endpoint attribute, define the registry key for which you want to scan
in the Host Scan window for Cisco Secure Desktop. In ASDM select Configuration > Remote
Access VPN > Secure Desktop Manager > Host Scan. Click Help on that page for more
information.
Guidelines
•You can only scan for registry endpoint attributes on Windows operating systems.
•You can create multiple instances of each type of endpoint attribute. For each of these types, you
need to decide whether the DAP policy should require that the user have all instances of a type
(Match all = AND) or only one of them (Match Any = OR).
To set this value, after you have defined all instances of the endpoint attribute, click the Logical Op.
button and select the Match Any or Match All button. If you do not specify a Logical Operation,
Match All is used by default.
Detailed Steps
Step 1 In the Endpoint Attribute Type list box, select Registry.
Step 2 Click the appropriate Exists or Does not exist button to indicate whether the Registry endpoint attribute
and its accompanying qualifiers (fields below the Exists and Does not exist buttons) should be present
or not.
Step 3 In the Endpoint ID list box, choose from the drop-down list the endpoint ID that equates to the registry
entry for which you want to scan.
The registry information is displayed below the Endpoint ID list box.
Step 4 Check the Value checkbox and set the operation field to be equal to (=) or not equal to (!=).
Step 5 In the first Value list box, identify the registry key as a dword or a string.
Step 6 In the second Value operation list box, enter the value of the resgistry key you are scanning for.
Step 7 If you want to disregard the case of the registry entry when scanning, click the Caseless checkbox. If
you want the search to be case-sensitive, do not ccheck the Caseless check box.
Step 8 Click OK.
Step 9 Return to Configuring Dynamic Access Policies, page 6-6.
6-24
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 6 Configuring Dynamic Access Policies
Configuring Endpoint Attributes Used in DAPs
Additional References
See Endpoint Attribute Definitions, page 6-24 for additional information on the Registry endpoint
attribute requirements.
DAP and AntiVirus, AntiSpyware, and Personal Firewall Programs
The security appliance uses a DAP policy when the user attributes matches the configured AAA and
endpoint attributes. The Prelogin Assessment and Host Scan modules of Cisco Secure Desktop return
information to the security appliance about the configured endpoint attributes, and the DAP subsystem
uses that information to select a DAP record that matches the values of those attributes.
Most, but not all, antivirus, antispyware, and personal firewall programs support active scan, which
means that the programs are memory-resident, and therefore always running. Host Scan checks to see if
an endpoint has a program installed, and if it is memory-resident as follows:
•If the installed program does not support active scan, Host Scan reports the presence of the software.
The DAP system selects DAP records that specify the program.
•If the installed program does support active scan, and active scan is enabled for the program, Host
Scan reports the presence of the software. Again the security appliance selects DAP records that
specify the program.
•If the installed program does support active scan and active scan is disabled for the program, Host
Scan ignores the presence of the software. The security appliance does not select DAP records that
specify the program. Further, the output of the debug trace command, which includes a lot of
information about DAP, does not indicate the program presence, even though it is installed.
Endpoint Attribute Definitions
Table 6-2 defines the endpoint selection attribute names that are available for DAP use.The Attribute
Name field shows you how to enter each attribute name in a Lua logical expression, which you might do
in the Advanced area in the Add/Edit Dynamic Access Policy pane. The label variable identifies the
application, filename, process, or registry entry.
Table 6-2 Endpoint Attribute Definitions
Attribute Type Attribute Name Source Value
Max String
Length Description
Antispyware
(Requires
Cisco Secure
Desktop)
endpoint.as["label"].exists Host Scan true — Antispyware program
exists
endpoint.as["label"].version string 32 Version
endpoint.as["label"].description string 128 Antispyware
description
endpoint.as["label"].lastupdate integer — Seconds since update
of antispyware
definitions
6-25
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 6 Configuring Dynamic Access Policies
Configuring Endpoint Attributes Used in DAPs
Antivirus
(Requires
Cisco Secure
Desktop)
endpoint.av["label"].exists Host Scan true — Antivirus program
exists
endpoint.av["label"].version string 32 Version
endpoint.av["label"].description string 128 Antivirus description
endpoint.av["label"].lastupdate integer — Seconds since update
of antivirus definitions
AnyConnect
(Does not
require Cisco
Secure
Desktop or
Host Scan.)
endpoint.anyconnect.clientversion Endpoint version — AnyConnect client
version.
endpoint.anyconnect.platform string — Operating system on
which AnyConnect
client is installed.
endpoint.anyconnect.platformversion version 64 Version of operating
system on which
AnyConnect client is
installed.
endpoint.anyconnect.devicetype string 64 Mobile device type on
which AnyConnect
client is installed.
endpoint.anyconnect.deviceuniqueid caseless 64 Unique ID of mobile
device on which
AnyConnect client is
installed.
Application endpoint.application.clienttype Application string — Client type:
CLIENTLESS
ANYCONNECT
IPSEC
L2TP
Table 6-2 Endpoint Attribute Definitions (continued)
Attribute Type Attribute Name Source Value
Max String
Length Description

6-26
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 6 Configuring Dynamic Access Policies
Configuring Endpoint Attributes Used in DAPs
Device endpoint.device.hostname Endpoint string 64 Host Name only. Not
FQDN.
endpoint.device.MAC string Must be in the
format
xxxx.xxxx.xxxx
where x is a
hexadecimal
character.
Mac Address for a
network interface card.
Only one Mac address
per entry.
endpoint.device.id string 64 BIOS Serial Number.
The number format is
manufacturer-specific.
There is no format
requirement.
endpoint.device.port string An integer
between 1 and
65535.
TCP port in listening
state. You can define a
single port per line.
endpoint.device.protection None
(Host
Scan)
Scure
Desktop
(either
Cache
Cleaner or
Vau lt)
64 Defines which
component of CSD will
execute for the
particular PreLogin
Policy.
endpoint.device.protection_version string 64 Version of Host Scan
image they are running.
endpoint.device.protection_extension string 64 Versionof Endpoint
Assessment
(OPSWAT)
File endpoint.file["label"].exists Secure
Desktop
true — The files exists
endpoint.file[“label”].endpointid
endpoint.file["label"].lastmodified integer — Seconds since file was
last modified
endpoint.file["label"].crc.32 integer — CRC32 hash of the file
NAC endpoint.nac.status NAC string — User defined status
string
Operating
System
endpoint.os.version Secure
Desktop
string 32 Operating system
endpoint.os.servicepack integer — Service pack for
Windows
6-27
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 6 Configuring Dynamic Access Policies
Configuring DAP Access and Authorization Policy Attributes
Configuring DAP Access and Authorization Policy Attributes
To Configure Access and Authorization Policy Attributes for a DAP, click each tab and configure the
fields.
•Action Tab—Specifies special processing to apply to a specific connection or session.
–
Continue—(Default) Click to apply access policy attributes to the session.
–
Quarantine—Through the use of quarantine, you can restrict a particular client who already has
an established tunnel through a VPN. ASA applies restricted ACLs to a session to form a
restricted group, based on the selected DAP record. When an endpoint is not compliant with an
administratively defined policy, the user can still access services for remediation (such as
updating the antivirus and so on), but restrictions are placed upon the user. After the remediation
occurs, the user can reconnect, which invokes a new posture assessment. If this assessment
passes, the user connects.
Note This parameter requires an AnyConnect release that supports AnyConnect Secure
Mobility features.
–
Terminate—Click to terminate the session.
Personal
firewall
(Requires
Secure
Desktop)
endpoint.fw["label"].exists Host Scan true — The personal firewall
exists
endpoint.fw["label"].version string 32 Version
endpoint.fw["label"].description string 128 Personal firewall
description
Policy endpoint.policy.location Secure
Desktop
string 64 Location value from
Cisco Secure Desktop
Process endpoint.process["label"].exists Secure
Desktop
true — The process exists
endpoint.process["label"].path string 255 Full path of the process
Registry endpoint.registry["label"].type Secure
Desktop
dword
string
—dword
endpoint.registry["label"].value string 255 Value of the registry
entry
VLAN endoint.vlan.type CNA string — VLAN type:
ACCESS
AUTH
ERROR
GUEST
QUARANTINE
ERROR
STATIC
TIMEOUT
Table 6-2 Endpoint Attribute Definitions (continued)
Attribute Type Attribute Name Source Value
Max String
Length Description

6-28
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 6 Configuring Dynamic Access Policies
Configuring DAP Access and Authorization Policy Attributes
–
User Message—Enter a text message to display on the portal page when this DAP record is
selected. Maximum 490 characters. A user message displays as a yellow orb. When a user logs
on it blinks three times to attract attention, and then it is still. If several DAP records are
selected, and each of them has a user message, all of the user messages display.
Note You can include in such messages URLs or other embedded text, which require that you use the
correct HTML tags.
For example: All contractors please read <a href='http://wwwin.example.com/procedure.html'>
Instructions</a> for the procedure to upgrade your antivirus software.
•Network ACL Filters Tab—Lets you select and configure network ACLs to apply to this DAP
record. An ACL for DAP can contain permit or deny rules, but not both. If an ACL contains both
permit and deny rules, the ASA rejects it.
–
Network ACL drop-down list—Select already configured network ACLs to add to this DAP
record. Only ACLs having all permit or all deny rules are eligible, and these are the only ACLs
that display here. This field supports unified ACLs which can define access rules for IPv4 and
IPv6 network traffic.
–
Manage...—Click to add, edit, and delete network ACLs.
–
Network ACL list—Displays the network ACLs for this DAP record.
–
Add>>— Click to add the selected network ACL from the drop-down list to the Network ACLs
list on the right.
–
Delete—Click to delete a highlighted network ACL from the Network ACLs list. You cannot
delete an ACL from the ASA unless you first delete it from DAP records.
•Web-Type ACL Filters (clientless) Tab—Lets you select and configure web-type ACLs to apply
to this DAP record. An ACL for DAP can contain only permit or deny rules. If an ACL contains both
permit and deny rules, the ASA rejects it.
–
Web-Type ACL drop-down list—Select already configured web-type ACLs to add to this DAP
record. Only ACLs having all permit or all deny rules are eligible, and these are the only ACLs
that display here.
–
Manage...—Click to add, edit, and delete web-type ACLs.
–
Web-Type ACL list—Displays the web-type ACLs for this DAP record.
–
Add>>—Click to add the selected web-type ACL from the drop-down list to the Web-Type
ACLs list on the right.
–
Delete—Click to delete a web-type ACL from the Web-Type ACLs list. You cannot delete an
ACL from the ASA unless you first delete it from DAP records.
•Functions Tab—Lets you configure file server entry and browsing, HTTP proxy, and URL entry for
the DAP record.
–
File Server Browsing—Enables or disables CIFS browsing for file servers or shared features.
Note Browsing requires NBNS (Master Browser or WINS). If that fails or is not configured,
we use DNS.
The CIFS browse feature does not support internationalization.

6-29
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 6 Configuring Dynamic Access Policies
Configuring DAP Access and Authorization Policy Attributes
–
File Server Entry—Lets or prohibits a user from entering file server paths and names on the
portal page. When enabled, places the file server entry drawer on the portal page. Users can
enter pathnames to Windows files directly. They can download, edit, delete, rename, and move
files. They can also add files and folders. Shares must also be configured for user access on the
applicable Windows servers. Users might have to be authenticated before accessing files,
depending on network requirements.
–
HTTP Proxy—Affects the forwarding of an HTTP applet proxy to the client. The proxy is
useful for technologies that interfere with proper content transformation, such as Java, ActiveX,
and Flash. It bypasses mangling while ensuring the continued use of the security appliance. The
forwarded proxy modifies the browser’s old proxy configuration automatically and redirects all
HTTP and HTTPS requests to the new proxy configuration. It supports virtually all client side
technologies, including HTML, CSS, JavaScript, VBScript, ActiveX, and Java. The only
browser it supports is Microsoft Internet Explorer.
–
URL Entry—Allows or prevents a user from entering HTTP/HTTPS URLs on the portal page.
If this feature is enabled, users can enter web addresses in the URL entry box, and use clientless
SSL VPN to access those websites.
Using SSL VPN does not ensure that communication with every site is secure. SSL VPN ensures
the security of data transmission between the remote user PC or workstation and the ASA on the
corporate network. If a user then accesses a non-HTTPS web resource (located on the Internet or on
the internal network), the communication from the corporate ASA to the destination web server is
not secured.
In a clientless VPN connection, the ASA acts as a proxy between the end user web browser and
target web servers. When a user connects to an SSL-enabled web server, the ASA establishes a
secure connection and validates the server SSL certificate. The end user browser never receives the
presented certificate, so therefore cannot examine and validate the certificate. The current
implementation of SSL VPN does not permit communication with sites that present expired
certificates. Neither does the ASA perform trusted CA certificate validation. Therefore, users cannot
analyze the certificate an SSL-enabled web-server presents before communicating with it.
To limit Internet access for users, choose Disable for the URL Entry field. This prevents SSL VPN
users from surfing the web during a clientless VPN connection.
–
Unchanged—(default) Click to use values from the group policy that applies to this session.
–
Enable/Disable—Click to enable or disable the feature.
–
Auto-start—Click to enable HTTP proxy and to have the DAP record automatically start the
applets associated with these features.
•Port Forwarding Lists Tab—Lets you select and configure port forwarding lists for user sessions.
Port Forwarding provides access for remote users in the group to client/server applications that
communicate over known, fixed TCP/IP ports. Remote users can use client applications that are
installed on their local PC and securely access a remote server that supports that application. Cisco
has tested the following applications: Windows Terminal Services, Telnet, Secure FTP (FTP over
SSH), Perforce, Outlook Express, and Lotus Notes. Other TCP-based applications may also work,
but Cisco has not tested them.
Note Port Forwarding does not work with some SSL/TLS versions.
Caution Make sure Sun Microsystems Java Runtime Environment (JRE) 1.4+ is installed on the remote
computers to support port forwarding (application access) and digital certificates.

6-30
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 6 Configuring Dynamic Access Policies
Configuring DAP Access and Authorization Policy Attributes
–
Port Forwarding—Select an option for the port forwarding lists that apply to this DAP record.
The other attributes in this field are enabled only when you set Port Forwarding to Enable or
Auto-start.
–
Unchanged—Click to remove the attributes from the running configuration.
–
Enable/Disable—Click to enable or disable port forwarding.
–
Auto-start—Click to enable port forwarding, and to have the DAP record automatically start
the port forwarding applets associated with its port forwarding lists.
–
Port Forwarding List drop-down list—Select already configured port forwarding lists to add
to the DAP record.
–
New...—Click to configure new port forwarding lists.
–
Port Forwarding Lists (unlabeled)—Displays the port forwarding lists for the DAP record.
–
Add—Click to add the selected port forwarding list from the drop-down list to the Port
Forwarding list on the right.
–
Delete—Click to delete selected port forwarding list from the Port Forwarding list. You cannot
delete a port forwarding list from the ASA unless you first delete it from DAP records.
•Bookmarks Tab—Lets you select and configure bookmarks for certain user session URLs.
–
Enable bookmarks—Click to enable. When unchecked, no bookmarks display in the portal
page for the connection.
–
Bookmark drop-down list—select already configured bookmarks to add to the DAP record.
–
Manage...—Click to add, import, export, and delete bookmarks.
–
Bookmarks (unlabeled)—Displays the URL lists for the DAP record.
–
Add>>—Click to add the selected bookmark from the drop-down list to the URL area on the
right.
–
Delete—Click to delete the selected bookmark from the URL list area. You cannot delete a
bookmark from the ASA unless you first delete it from DAP records.
•Access Method Tab—Lets you configure the type of remote access permitted.
–
Unchanged—Continue with the current remote access method.
–
AnyConnect Client—Connect using the Cisco AnyConnect VPN Client.
–
Web-Portal—Connect with clientless VPN.
–
Both-default-Web-Portal—Connect via either clientless or the AnyConnect client, with a
default of clientless.
–
Both-default-AnyConnect Client—Connect via either clientless or the AnyConnect client,
with a default of AnyConnect.
•AnyConnect Tab—Lets you choose the status of the Always-on VPN flag.
–
Always-On VPN for AnyConnect client—Determine if the always-on VPN flag setting in the
AnyConnect service profile is unchanged, disabled, or if the AnyConnect profile setting should
be used.
6-31
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 6 Configuring Dynamic Access Policies
Performing a DAP Trace
Note This parameter requires a release of the Cisco IronPort Web Security appliance that
provides Secure Mobility Solution licensing support for the Cisco AnyConnect VPN
client. It also requires an AnyConnect release that supports “Secure Mobility Solution”
features. Refer to the Cisco AnyConnect VPN Client Administrator Guide for additional
information.
Performing a DAP Trace
By performing a DAP trace you can display the DAP endpoint attributes for all connected devices.
Prerequisites
Log on to the ASA from an SSH terminal and enter Privileged Exec mode. In Privileged Exec mode, the
ASA displays this prompt: hostname#
Detailed Steps
Additional References
In order to search the output of the DAP trace, send the output of the command to a sytem log. To learn
more about logging on the ASA see Configuring Logging in the Cisco ASA 5500 Series Configuration
Guide using the CLI, 8.4.
Guide to Creating DAP Logical Expressions using LUA
This section provides information about constructing logical expressions for AAA or Endpoint
attributes. Be aware that doing so requires sophisticated knowledge of Lua (www.lua.org).
Command Purpose
Step 1 debug dap trace
Example
hostname# debug dap trace
Enables DAP debugs to display all DAP attributes for the session in the
terminal window.
Example output:
This is a small fragment of the output one receives from running the
debug dap trace command
endpoint.anyconnect.clientversion="0.16.0021";
endpoint.anyconnect.platform="apple-ios";
endpoint.anyconnect.platformversion="4.1";
endpoint.anyconnect.devicetype="iPhone1,2";
endpoint.anyconnect.deviceuniqueid="dd13ce3547f2fa1b2c3d4e5f
6g7h8i9j0fa03f75";

6-32
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 6 Configuring Dynamic Access Policies
Guide to Creating DAP Logical Expressions using LUA
In the Advanced field you enter free-form Lua text that represents AAA and/or endpoint selection logical
operations. ASDM does not validate text that you enter here; it just copies this text to the DAP policy
file, and the ASA processes it, discarding any expressions it cannot parse.
This option is useful for adding selection criteria other than what is possible in the AAA and endpoint
attribute areas above. For example, while you can configure the ASA to use AAA attributes that satisfy
any, all, or none of the specified criteria, endpoint attributes are cumulative, and must all be satisfied. To
let the security appliance employ one endpoint attribute or another, you need to create appropriate logical
expressions in Lua and enter them here.
For a list of endpoint selection attributes, including proper name syntax for creating logical expressions,
see Table 6-2.
The following sections provide detailed explanations of creating Lua EVAL expressions, as well as
examples.
•Syntax for Creating Lua EVAL Expressions
–
Constructing DAP EVAL Expressions
•The DAP CheckAndMsg Function
–
Checking for a Single Antivirus Program
–
Checking for Antivirus Definitions Within the Last 10 Days
–
Checking for a Hotfix on the User PC
–
Checking for Antivirus Programs
–
Checking for Antivirus Programs and Definitions Older than 1 1/2 Days
•Additional Lua Functions
–
OU-Based Match Example
–
Group Membership Example
–
Antivirus Example
–
Antispyware Example
–
Firewall Example
–
Antivirus, Antispyware, or any Firewall Example
•CheckAndMsg with Custom Function Example
•Further Information on Lua
Syntax for Creating Lua EVAL Expressions
This section provides information about the syntax for creating Lua EVAL expressions.
Note If you must use Advanced mode, we recommend that you use EVAL expressions whenever possible for
reasons of clarity, which makes verifying the program straightforward.
EVAL(<attribute> , <comparison>, {<value> | <attribute>}, [<type>])

6-33
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 6 Configuring Dynamic Access Policies
Guide to Creating DAP Logical Expressions using LUA
Example:
EVAL(endpoint.os.version, “EQ”, “Windows XP”, “string”)
Constructing DAP EVAL Expressions
Study these examples for help in creating logical expressions in Lua.
•This endpoint expression tests for a match on CLIENTLESS OR CVC client types:
(EVAL(endpoint.application.clienttype,”EQ”,"CLIENTLESS") or
EVAL(endpoint.application.clienttype, “EQ”,"CVC"))
•This endpoint expression tests for Norton Antivirus versions 10.x but excludes 10.5.x:
(EVAL(endpoint.av[“NortonAV”].version, “GE”, "10",”version”) and
(EVAL(endpoint.av[“NortonAV”].version,”LT”, "10.5", “version”) or
EVAL(endpoint.av[“NortonAV”].version, “GE”, "10.6", “version”)))
The DAP CheckAndMsg Function
CheckAndMsg is a Lua function that you can configure DAP to call. It generates a user message based
on a condition.
You use ASDM to configure CheckAndMsg through the Advanced field in DAP. The ASA displays the
message to the user only when the DAP record containing the LUA CheckAndMsg function is selected
and results in a clientless SSL VPN or AnyConnect termination.
The syntax of the CheckAndMsg function follows:
<attribute> AAA attribute or an attribute returned from Cisco Secure Desktop, see
Table 6-2 for attribute definitions
<comparison> One of the following strings (quotation marks required)
“EQ” equal
“NE” not equal
“LT” less than
“GT” greater than
“LE” less than or equal
“GE” greater than or equal
<value> A string in quotation marks that contains the value to compare the attribute
against
<type> One of the following strings (quotation marks required)
“string” case-sensitive string comparison
“caseless” case-insensitive string comparison
“integer” number comparison, converts string values to numbers
“hex” number comparison using hexadecimal values, converts hex
string to hex numbers
“version” compares versions of the form X.Y.Z. where X, Y, and Z are
numbers

6-34
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 6 Configuring Dynamic Access Policies
Guide to Creating DAP Logical Expressions using LUA
CheckAndMsg(value, “<message string if value is true>”, “<message string if value if
false>”)
Be aware of the following when creating CheckAndMsg functions:
•CheckAndMsg returns the value passed in as its first argument.
•Use the EVAL function as the first argument if you do not want to use string comparison. For
example:
(CheckAndMsg((EVAL(...)) , "true msg", "false msg"))
CheckandMsg returns the result of the EVAL function and the security appliances uses it to
determine whether to select the DAP record. If the record is selected and results in termination, the
security appliance displays the appropriate message.
Checking for a Single Antivirus Program
This example checks if a single antivirus program, in this case McAfee, is installed on the user PC, and
displays a message if it is not.
(CheckAndMsg(EVAL(endpoint.av[“McAfeeAV”].exists,"NE","true"),"McAfee AV was not
found on your computer", nil))
Checking for Antivirus Definitions Within the Last 10 Days
This example checks antivirus definitions within the last 10 days (864000 sec), in particular the last
update of the McAfee AV dat file, and displays a message to a user lacking the appropriate update that
they need an antivirus update:
((CheckAndMsg(EVAL(endpoint.av[“McAfeeAV”].lastupdate,"GT","864000","integer"),"AV
Update needed! Please wait for the McAfee AV till it loads the latest dat file.",nil) ))
Checking for a Hotfix on the User PC
This example checks for a specific hotfix. If a user does not have the hotfix on their PC, a message that
it is not installed displays.
(not CheckAndMsg(EVAL(endpoint.os.windows.hotfix["KB923414"],"EQ","true"),nil,"The
required hotfix is not installed on your PC."))
or you could define it this way (which makes more sense):
(CheckAndMsg(EVAL(endpoint.os.windows.hotfix["KB923414"],"NE","true"),"The required hotfix
is not installed on your PC.",nil))
You can build the expression in this example because the debug dap trace returns:
endpoint.os.windows.hotfix["KB923414"] = "true";
Checking for Antivirus Programs
You can configure messages so that the end user is aware of and able to fix problems with missing or not
running AVs. As a result, if access is denied, the ASA collects all messages for the DAP that caused the
"terminate" condition and displays them in the browser on the logon page. If access is allowed, the ASA
displays all messages generated in the process of DAP evaluation on the portal page.
The following example shows how to use this feature to check on the Norton Antivirus program.

6-35
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 6 Configuring Dynamic Access Policies
Guide to Creating DAP Logical Expressions using LUA
Step 1 Copy and paste the following Lua expression into the Advanced field of the Add/Edit Dynamic Access
Policy pane (click the double arrow on the far right to expand the field).
(CheckAndMsg(EVAL(endpoint.av[“NortonAV”].exists, "EQ", "false"),"Your Norton AV was found
but the active component of it was not enabled", nil) or
CheckAndMsg(EVAL(endpoint.av[“NortonAV”].exists, "NE", "true"),"Norton AV was not found on
your computer", nil) )
Step 2 In that same Advanced field, click the OR button.
Step 3 In the Access Attributes section below, in the leftmost tab, Action, click Terminate.
Step 4 Connect from a PC that does not have or has disabled Norton Antivirus.
The expected result is that the connection is not allowed and the message appears as a blinking ! point.
Step 5 Click the blinking ! to see the message.
Checking for Antivirus Programs and Definitions Older than 1 1/2 Days
This example checks for the presence of the Norton and McAfee antivirus programs, and whether the
virus definitions are older than 1 1/2 days (10,000 seconds). If the definitions are older than 1 1/2 days,
the ASA terminates the session with a message and links for remediation. To accomplish this task,
perform the following steps.
Step 1 Copy and paste the following Lua expression into the Advanced field of the Add/Edit Dynamic Access
Policy pane (click the double arrow on the far right to expand the field):
((EVAL(endpoint.av[“NortonAV”].exists,”EQ”,”true”,”string”) and
CheckAndMsg(EVAL(endpoint.av[“NortonAV”].lastupdate,”GT”,”10000”,integer”),To
remediate <a href=’http://www.symantec.com’>Click this link </a>”,nil)) or
(EVAL(endpoint.av[“McAfeeAV”].exists,”EQ”,”true”,”string”) and
CheckAndMsg(EVAL(endpoint.av[“McAfeeAV”].lastupdate,”GT”,”10000”,integer”),To
remediate <a href=’http://www.mcafee.com’>Click this link</a>”,nil))
Step 2 In that same Advanced field, click AND.
Step 3 In the Access Attributes section below, in leftmost tab, Action, click Term inate .
Step 4 Connect from a PC that has Norton and McAfee antivirus programs with versions that are older than
1 1/2 days.
The expected result is that the connection is not allowed and the message appears as a blinking ! point.
Step 5 Click the blinking ! to see the message and links for remediation.
Additional Lua Functions
When working with dynamic access policies for clientless SSL VPN, you might need additional
flexibility of match criteria. For example, you might want to apply a different DAP based on the
following:

6-36
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 6 Configuring Dynamic Access Policies
Guide to Creating DAP Logical Expressions using LUA
•Organizational Unit (OU) or other level of the hierarchy for the user object
•Group Name that follows a naming convention but has many possible matches—you might require
the ability to use a wildcard on group names.
You can accomplish this flexibility by creating a Lua logical expression in the Advanced section of the
DAP pane in ASDM.
OU-Based Match Example
DAP can use many attributes returned from an LDAP server in a logical expression. See the DAP trace
section for example output of this, or run a debug dap trace.
The LDAP server returns the user Distinguished Name (DN). This implicitly identifies where in the
directory the user object is located. For example, if the user DN is CN=Example
User,OU=Admins,dc=cisco,dc=com this user is located in OU=Admins,dc=cisco,dc=com. If all
administrators are in this OU (or any container below this level) you can use a logical expression to
match on this criteria as follows:
assert(function()
if ( (type(aaa.ldap.distinguishedName) == "string") and
(string.find(aaa.ldap.distinguishedName, "OU=Admins,dc=cisco,dc=com$") ~= nil) )
then
return true
end
return false
end)()
In this example, the string.find function allows for a regular expression. Use the $ at the end of the string
to anchor this string to the end of the distinguishedName field.
Group Membership Example
You can create a basic logical expression for pattern matching of AD group membership. Because users
can be members of multiple groups, DAP parses the response from the LDAP server into separate entries
in a table. You need an advanced function to accomplish the following:
•Compare the memberOf field as a string (in the event the user belongs to only one group).
•Iterate through each returned memberOf field if the returned data is of type "table".
The function we have written and tested for this purpose is shown below. In this example, if a user is a
member of any group ending with "-stu" they match this DAP.
assert(function()
local pattern = "-stu$"
local attribute = aaa.ldap.memberOf
if ((type(attribute) == "string") and
(string.find(attribute, pattern) ~= nil)) then
return true
elseif (type(attribute) == "table") then
local k, v
for k, v in pairs(attribute) do
if (string.find(v, pattern) ~= nil) then
return true
end
end
end
return false
end)()

6-37
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 6 Configuring Dynamic Access Policies
Guide to Creating DAP Logical Expressions using LUA
Antivirus Example
The following example uses a custom function to check if CSD detects any antivirus software.
assert(function()
for k,v in pairs(endpoint.av) do
if (EVAL(v.exists, "EQ", "true", "string")) then
return true
end
end
return false
end)()
Antispyware Example
The following example uses a custom function to check if CSD detects any antispyware.
assert(function()
for k,v in pairs(endpoint.as) do
if (EVAL(v.exists, "EQ", "true", "string")) then
return true
end
end
return false
end)()
Firewall Example
The following example uses a custom function to check if CSD detects a firewall.
assert(function()
for k,v in pairs(endpoint.fw) do
if (EVAL(v.exists, "EQ", "true", "string")) then
return true
end
end
return false
end)()
Antivirus, Antispyware, or any Firewall Example
The following example uses a custom function to check if CSD detects any antivirus, antispyware, or
any firewall.
assert(function()
function check(antix)
if (type(antix) == "table") then
for k,v in pairs(antix) do
if (EVAL(v.exists, "EQ", "true", "string")) then
return true
end
end
end
return false
end
return (check(endpoint.av) or check(endpoint.fw) or check(endpoint.as))
end)()

6-38
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 6 Configuring Dynamic Access Policies
Guide to Creating DAP Logical Expressions using LUA
CheckAndMsg with Custom Function Example
You can use the following function to deny access in the absence of an antivirus program. Use it with a
DAP that has Action set to terminate.
assert( function()
for k,v in pairs(endpoint.av) do
if (EVAL(v.exists, "EQ”, "true", "string")) then
return false
end
end
return CheckAndMsg(true, "Please install antivirus software before connecting.", nil)
end)()
If a user lacking an antivirus program attempts to log in, DAP displays the following message:
Please install antivirus software before connecting.
Further Information on Lua
You can find detailed LUA programming information at http://www.lua.org/manual/5.1/manual.html.
Operator for Endpoint Category
You can configure multiple instances of each type of endpoint. In this pane, set each type of endpoint to
require only one instance of a type (Match Any = OR) or to have all instances of a type (Match All =
AND).
•If you configure only one instance of an endpoint category, you do not need to set a value.
•For some endpoint attributes, it makes no sense to configure multiple instances. For example, no
users have more than one running OS.
•You are configuring the Match Any/Match All operation within each endpoint type.
The security appliance evaluates each type of endpoint attribute, and then performs a logical AND
operation on all of the configured endpoints. That is, each user must satisfy the conditions of ALL of the
endpoints you configure, as well as the AAA attributes.
DAP Examples
The following sections provide examples of useful dynamic access policies.
•Using DAP to Define Network Resources
•Using DAP to Apply a WebVPN ACL
•Enforcing CSD Checks and Applying Policies via DAP
Using DAP to Define Network Resources
This example shows how to configure dynamic access policies as a method of defining network
resources for a user or group. The DAP policy named Trusted_VPN_Access permits clientless and
AnyConnect VPN access. The policy named Untrusted_VPN_Access permits only clientless VPN
access. Table 6-3 summarizes the configuration of each of these policies.

6-39
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 6 Configuring Dynamic Access Policies
Guide to Creating DAP Logical Expressions using LUA
The ASDM path is Configuration > Remote Access VPN > Clientless SSL VPN Access > Dynamic
Access Policies > Add/Edit Dynamic Access Policy > Endpoint
Using DAP to Apply a WebVPN ACL
DAP can directly enforce a subset of access policy attributes including Network ACLs (for IPsec and
AnyConnect), clientless SSL VPN Web-Type ACLs, URL lists, and Functions. It cannot directly
enforce, for example, a banner or the split tunnel list, which the group policy enforces. The Access
Policy Attributes tabs in the Add/Edit Dynamic Access Policy pane provide a complete menu of the
attributes DAP directly enforces.
Active Directory/LDAP stores user group policy membership as the “memberOf” attribute in the user
entry. You can define a DAP such that for a user in AD group (memberOf) = Engineering the ASA
applies a configured Web-Type ACL. To accomplish this task, perform the following steps:
Step 1 Navigate to the Add AAA attributes pane (Configuration > Remote Access VPN > Clientless SSL VPN
Access > Dynamic Access Policies > Add/Edit Dynamic Access Policy > AAA Attributes section > Add
AAA Attribute).
Step 2 For the AAA Attribute type, use the drop-down menu to choose LDAP.
Step 3 In the Attribute ID field, enter memberOf, exactly as you see it here. Case is important.
Step 4 In the Value field, use the drop-down menu to choose =, and in the adjacent field enter Engineering.
Step 5 In the Access Policy Attributes area of the pane, click the Web-Type ACL Filters tab.
Step 6 Use the Web-Type ACL drop-down menu to select the ACL you want to apply to users in the AD group
(memberOf) = Engineering.
Enforcing CSD Checks and Applying Policies via DAP
This example creates a DAP that checks that a user belongs to two specific AD/LDAP groups
(Engineering and Employees) and a specific ASA tunnel group. It then applies an ACL to the user.
The ACLs that DAP applies control access to the resources. They override any ACLS defined the group
policy on the ASA. In addition, the ASA applied the regular AAA group policy inheritance rules and
attributes for those that DAP does not define or control, examples being split tunneling lists, banner, and
DNS. To accomplish this task, perform the following steps.
Table 6-3 A Simple DAP Configuration for Network Resources
Attribute Trusted_VPN_Access Untrusted_VPN_Access
Endpoint Attribute Type Policy Trusted Untrusted
Endpoint Attribute Process ieexplore.exe —
Advanced Endpoint Assessment AntiVirus= McAfee Attribute
CSD Location Trusted Untrusted
LDAP memberOf Engineering, Managers Vendors
ACL Web-Type ACL
Access AnyConnect and Web Portal Web Portal

6-40
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 6 Configuring Dynamic Access Policies
Guide to Creating DAP Logical Expressions using LUA
Step 1 Navigate to the Add AAA attributes pane (Configuration > Remote Access VPN > Clientless SSL VPN
Access > Dynamic Access Policies > Add/Edit Dynamic Access Policy > AAA Attributes section > Add
AAA Attribute).
Step 2 For the AAA Attribute type, use the drop-down menu to choose LDAP.
Step 3 In the Attribute ID field, enter memberOf, exactly as you see it here. Case is important.
Step 4 In the Value field, use the drop-down menu to choose =, and in the adjacent field enter Engineering.
Step 5 In the Attribute ID field, enter memberOf, exactly as you see it here. Case is important.
Step 6 In the Value field, use the drop-down menu to select =, and in the adjacent field enter Employees.
Step 7 For the AAA attribute type, use the drop-down menu to choose Cisco.
Step 8 Check the Tunnel group box, use the drop-down menu to choose =, and in the adjacent drop-down list
select the appropriate tunnel group (connection policy).
Step 9 In the Network ACL Filters tab of the Access Policy Attributes area, choose the ACLs to apply to users
who meet the DAP criteria defined in the previous steps.

CHAPTER
7-1
Cisco ASA Series VPN ASDM Configuration Guide
7
E-Mail Proxy
E-mail proxies extend remote e-mail capability to users of Clientless SSL VPN. When users attempt an
e-mail session via e-mail proxy, the e-mail client establishes a tunnel using the SSL protocol.
The e-mail proxy protocols are as follows:
POP3S
POP3S is one of the e-mail proxies Clientless SSL VPN supports. By default the Security Appliance
listens to port 995, and connections are automatically allowed to port 995 or to the configured port. The
POP3 proxy allows only SSL connections on that port. After the SSL tunnel establishes, the POP3
protocol starts, and then authentication occurs. POP3S is for receiving e-mail.
IMAP4S
IMAP4S is one of the e-mail proxies Clientless SSL VPN supports. By default the Security Appliance
listens to port 993, and connections are automatically allowed to port 993 or to the configured port. The
IMAP4 proxy allows only SSL connections on that port. After the SSL tunnel establishes, the IMAP4
protocol starts, and then authentication occurs. IMAP4S is for receiving e-mail.
SMTPS
SMTPS is one of the e-mail proxies Clientless SSL VPN supports. By default, the Security Appliance
listens to port 988, and connections automatically are allowed to port 988 or to the configured port. The
SMTPS proxy allows only SSL connections on that port. After the SSL tunnel establishes, the SMTPS
protocol starts, and then authentication occurs. SMTPS is for sending e-mail.
Configuring E-Mail Proxy
Configuring e-mail proxy on the consists of the following tasks:
•Enabling e-Mail proxy on interfaces.
•Configuring e-mail proxy default servers.
•Setting AAA server groups and a default group policy.
•Configuring delimiters.
Configuring E-mail proxy also has these requirements:
•Users who access e-mail from both local and remote locations via e-mail proxy require separate
e-mail accounts on their e-mail program for local and remote access.
•E-mail proxy sessions require that the user authenticate.
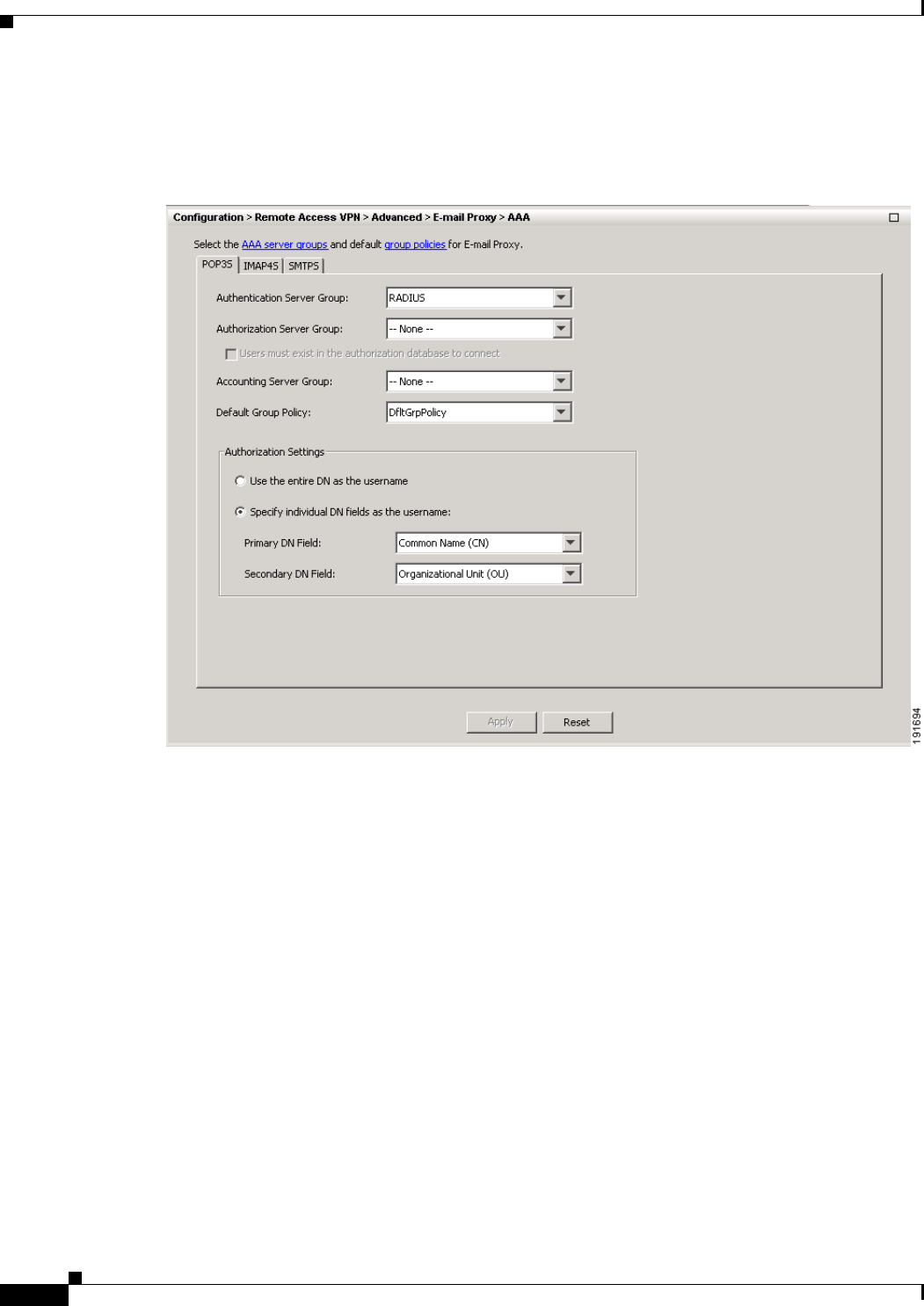
7-2
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 7 E-Mail Proxy
AAA
AAA
Configuration > Features > VPN > E-mail Proxy > AAA
This panel has three tabs:
•POP3S Tab
•IMAP4S Tab
•SMTPS Tab
POP3S Tab
Configuration > Features > VPN > E-mail Proxy > AAA > POP3S Tab
The POP3S AAA panel associates AAA server groups and configures the default group policy for
POP3S sessions.
Fields
•AAA server groups—Click to go to the AAA Server Groups panel (Configuration > Features >
Properties > AAA Setup > AAA Server Groups), where you can add or edit AAA server groups.
•group policies—Click to go to the Group Policy panel (Configuration > Features > VPN >
General > Group Policy), where you can add or edit group policies.

7-3
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 7 E-Mail Proxy
AAA
•Authentication Server Group—Select the authentication server group for POP3S user
authentication. The default is to have no authentication servers configured. If you have set AAA as
the authentication method for POP3S (Configuration > Features AAA > VPN > E-Mail Proxy >
Authentication panel), you must configure an AAA server and select it here, or authentication
always fails.
•Authorization Server Group—Select the authorization server group for POP3S user authorization.
The default is to have no authorization servers configured.
•Accounting Server Group—Select the accounting server group for POP3S user accounting. The
default is to have no accounting servers configured.
•Default Group Policy—Select the group policy to apply to POP3S users when AAA does not return
a CLASSID attribute. The length must be between 4 and 15 alphanumeric characters. If you do not
specify a default group policy, and there is no CLASSID, the ASA can not establish the session.
•Authorization Settings—Lets you set values for usernames that the ASA recognizes for POP3S
authorization. This applies to POP3S users that authenticate with digital certificates and require
LDAP or RADIUS authorization.
–
User the entire DN as the username—Select to use the Distinguished Name for POP3S
authorization.
–
Specify individual DN fields as the username—Select to specify specific DN fields for user
authorization.
You can choose two DN fields, primary and secondary. For example, if you choose EA, users
authenticate according to their e-mail address. Then a user with the Common Name (CN) John
Doe and an e-mail address of johndoe@cisco.com cannot authenticate as John Doe or as
johndoe. He must authenticate as johndoe@cisco.com. If you choose EA and O, John Does must
authenticate as johndoe@cisco.com and Cisco Systems, Inc.
–
Primary DN Field—Select the primary DN field you want to configure for POP3S authorization.
The default is CN. Options include the following:
DN Field Definition
Country (C) The two-letter country abbreviation. These codes conform to ISO 3166
country abbreviations.
Common Name (CN) The name of a person, system, or other entity. This is the lowest (most
specific) level in the identification hierarchy.
DN Qualifier (DNQ) A specific DN attribute.
E-mail Address (EA) The e-mail address of the person, system or entity that owns the certificate.
Generational Qualifier
(GENQ)
A generational qualifier such as Jr., Sr., or III.
Given Name (GN) The first name of the certificate owner.
Initials (I) The first letters of each part of the certificate owner’s name.
Locality (L) The city or town where the organization is located.
Name (N) The name of the certificate owner.
Organization (O) The name of the company, institution, agency, association, or other entity.
Organizational Unit
(OU)
The subgroup within the organization.
Serial Number (SER) The serial number of the certificate.
Surname (SN) The family name or last name of the certificate owner.

7-4
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 7 E-Mail Proxy
AAA
–
Secondary DN Field—(Optional) Select the secondary DN field you want to configure for
POP3S authorization. The default is OU. Options include all of those in the preceding table,
with the addition of None, which you select if you do not want to include a secondary field.
IMAP4S Tab
Configuration > Features > VPN > E-mail Proxy > AAA > IMAP4S Tab
The IMAP4S AAA panel associates AAA server groups and configures the default group policy for
IMAP4S sessions.
Fields
•AAA server groups—Click to go to the AAA Server Groups panel (Configuration > Features >
Properties > AAA Setup > AAA Server Groups), where you can add or edit AAA server groups.
•group policy—Click to go to the Group Policy panel (Configuration > Features > VPN > General
> Group Policy), where you can add or edit group policies.
•Authentication Server Group—Select the authentication server group for IMAP4S user
authentication. The default is to have no authentication servers configured. If you have set AAA as
the authentication method for IMAP4S (Configuration > Features AAA > VPN > E-Mail Proxy
> Authentication panel), you must configure an AAA server and select it here, or authentication
always fails.
•Authorization Server Group—Select the authorization server group for IMAP4S user authorization.
The default is to have no authorization servers configured.
•Accounting Server Group—Select the accounting server group for IMAP4S user accounting. The
default is to have no accounting servers configured.
•Default Group Policy—Select the group policy to apply to IMAP4S users when AAA does not return
a CLASSID attribute. If you do not specify a default group policy, and there is no CLASSID, the
ASA can not establish the session.
•Authorization Settings—Lets you set values for usernames that the ASA recognizes for IMAP4S
authorization. This applies to IMAP4S users that authenticate with digital certificates and require
LDAP or RADIUS authorization.
–
User the entire DN as the username—Select to use the fully qualified domain name for IMAP4S
authorization.
–
Specify individual DN fields as the username—Select to specify specific DN fields for user
authorization.
You can choose two DN fields, primary and secondary. For example, if you choose EA, users
authenticate according to their e-mail address. Then a user with the Common Name (CN) John
Doe and an e-mail address of johndoe@cisco.com cannot authenticate as John Doe or as
johndoe. He must authenticate as johndoe@cisco.com. If you choose EA and O, John Does must
authenticate as johndoe@cisco.com and Cisco. Systems, Inc.
State/Province (S/P) The state or province where the organization is located.
Title (T) The title of the certificate owner, such as Dr.
User ID (UID) The identification number of the certificate owner.
DN Field Definition

7-5
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 7 E-Mail Proxy
AAA
–
Primary DN Field—Select the primary DN field you want to configure for IMAP4S
authorization. The default is CN. Options include the following:
–
Secondary DN Field—(Optional) Select the secondary DN field you want to configure for
IMAP4S authorization. The default is OU. Options include all of those in the preceding table,
with the addition of None, which you select if you do not want to include a secondary field.
SMTPS Tab
Configuration > Features > VPN > E-mail Proxy > AAA > SMTPS Tab
The SMTPS AAA panel associates AAA server groups and configures the default group policy for
SMTPS sessions.
Fields
•AAA server groups—Click to go to the AAA Server Groups panel (Configuration > Features >
Properties > AAA Setup > AAA Server Groups), where you can add or edit AAA server groups.
•group policy—Click to go to the Group Policy panel (Configuration > Features > VPN > General
> Group Policy), where you can add or edit group policies.
DN Field Definition
Country (C) The two-letter country abbreviation. These codes conform to ISO 3166
country abbreviations.
Common Name (CN) The name of a person, system, or other entity. This is the lowest (most
specific) level in the identification hierarchy.
DN Qualifier (DNQ) A specific DN attribute.
E-mail Address (EA) The e-mail address of the person, system or entity that owns the certificate.
Generational Qualifier
(GENQ)
A generational qualifier such as Jr., Sr., or III.
Given Name (GN) The first name of the certificate owner.
Initials (I) The first letters of each part of the certificate owner’s name.
Locality (L) The city or town where the organization is located.
Name (N) The name of the certificate owner.
Organization (O) The name of the company, institution, agency, association, or other entity.
Organizational Unit
(OU)
The subgroup within the organization.
Serial Number (SER) The serial number of the certificate.
Surname (SN) The family name or last name of the certificate owner.
State/Province (S/P) The state or province where the organization is located.
Title (T) The title of the certificate owner, such as Dr.
User ID (UID) The identification number of the certificate owner.

7-6
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 7 E-Mail Proxy
AAA
•Authentication Server Group—Select the authentication server group for SMTPS user
authentication. The default is to have no authentication servers configured. If you have set AAA as
the authentication method for SMTPS (Configuration > Features AAA > VPN > E-Mail Proxy >
Authentication panel), you must configure an AAA server and select it here, or authentication
always fails.
•Authorization Server Group—Select the authorization server group for SMTPS user authorization.
The default is to have no authorization servers configured.
•Accounting Server Group—Select the accounting server group for SMTPS user accounting. The
default is to have no accounting servers configured.
•Default Group Policy—Select the group policy to apply to SMTPS users when AAA does not return
a CLASSID attribute. If you do not specify a default group policy, and there is no CLASSID, the
ASA can not establish the session.
•Authorization Settings—Lets you set values for usernames that the ASA recognizes for SMTPS
authorization. This applies to SMTPS users that authenticate with digital certificates and require
LDAP or RADIUS authorization.
–
User the entire DN as the username—Select to use the fully qualified domain name for SMTPS
authorization.
–
Specify individual DN fields as the username—Select to specify specific DN fields for user
authorization.
You can choose two DN fields, primary and secondary. For example, if you choose EA, users
authenticate according to their e-mail address. Then a user with the Common Name (CN) John
Doe and an e-mail address of johndoe@cisco.com cannot authenticate as John Doe or as
johndoe. He must authenticate as johndoe@cisco.com. If you choose EA and O, John Does must
authenticate as johndoe@cisco.com and Cisco. Systems, Inc.
–
Primary DN Field—Select the primary DN field you want to configure for SMTPS
authorization. The default is CN. Options include the following:
DN Field Definition
Country (C) The two-letter country abbreviation. These codes conform to ISO 3166
country abbreviations.
Common Name (CN) The name of a person, system, or other entity. This is the lowest (most
specific) level in the identification hierarchy.
DN Qualifier (DNQ) A specific DN attribute.
E-mail Address (EA) The e-mail address of the person, system or entity that owns the certificate.
Generational Qualifier
(GENQ)
A generational qualifier such as Jr., Sr., or III.
Given Name (GN) The first name of the certificate owner.
Initials (I) The first letters of each part of the certificate owner’s name.
Locality (L) The city or town where the organization is located.
Name (N) The name of the certificate owner.
Organization (O) The name of the company, institution, agency, association, or other entity.
Organizational Unit
(OU)
The subgroup within the organization.
Serial Number (SER) The serial number of the certificate.
Surname (SN) The family name or last name of the certificate owner.
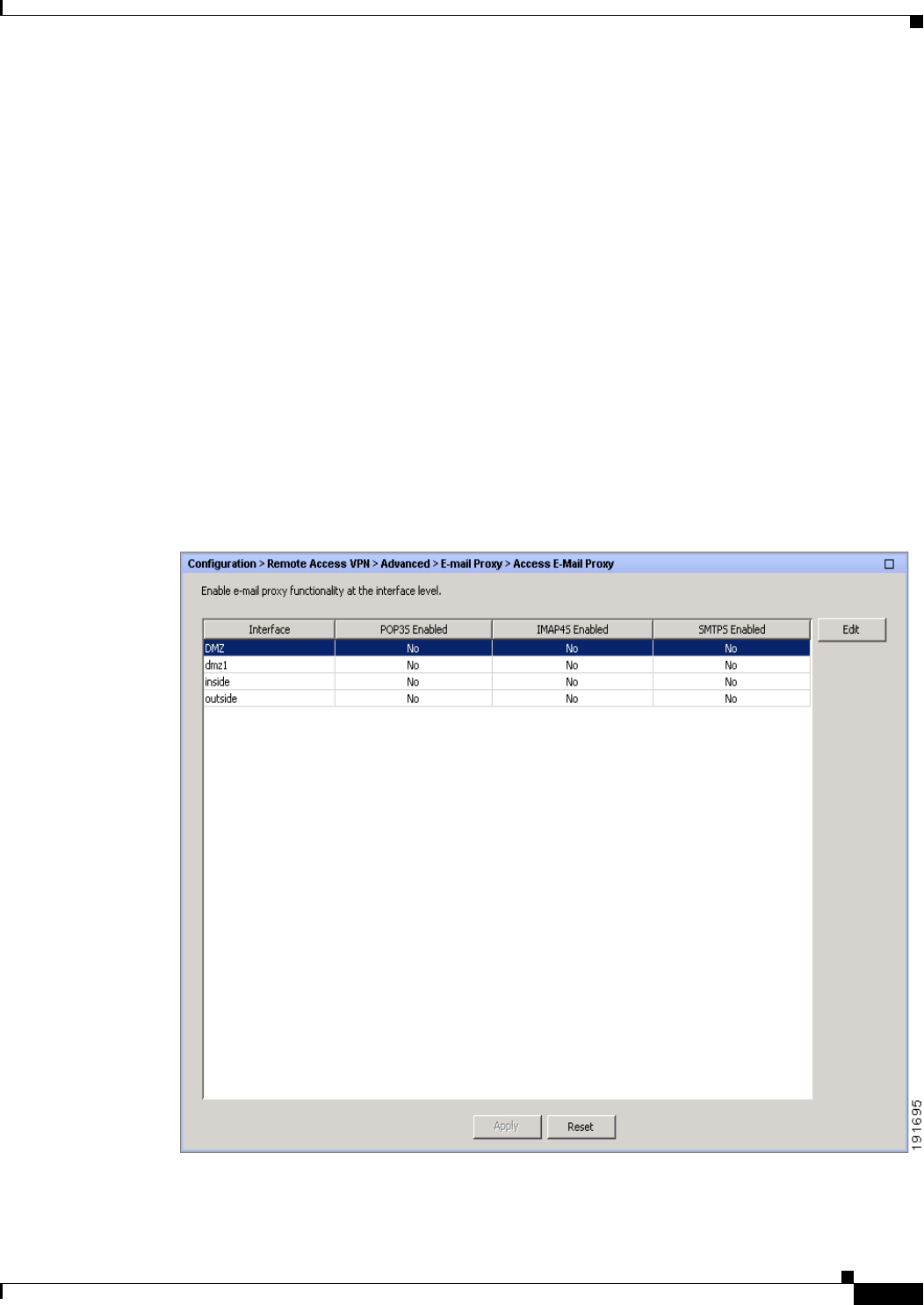
7-7
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 7 E-Mail Proxy
Access
–
Secondary DN Field—(Optional) Select the secondary DN field you want to configure for
SMTPS authorization. The default is OU. Options include all of those in the preceding table,
with the addition of None, which you select if you do not want to include a secondary field.
Access
Configuration > VPN > E-Mail Proxy > Access
The E-mail Proxy Access screen lets you identify interfaces on which to configure e-mail proxy. You
can configure and edit e-mail proxies on individual interfaces, and you can configure and edit e-mail
proxies for one interface and then apply your settings to all interfaces. You cannot configure e-mail
proxies for management-only interfaces, or for subinterfaces.
Fields
•Interface—Displays the names of all configured interfaces.
State/Province (S/P) The state or province where the organization is located.
Title (T) The title of the certificate owner, such as Dr.
User ID (UID) The identification number of the certificate owner.
DN Field Definition
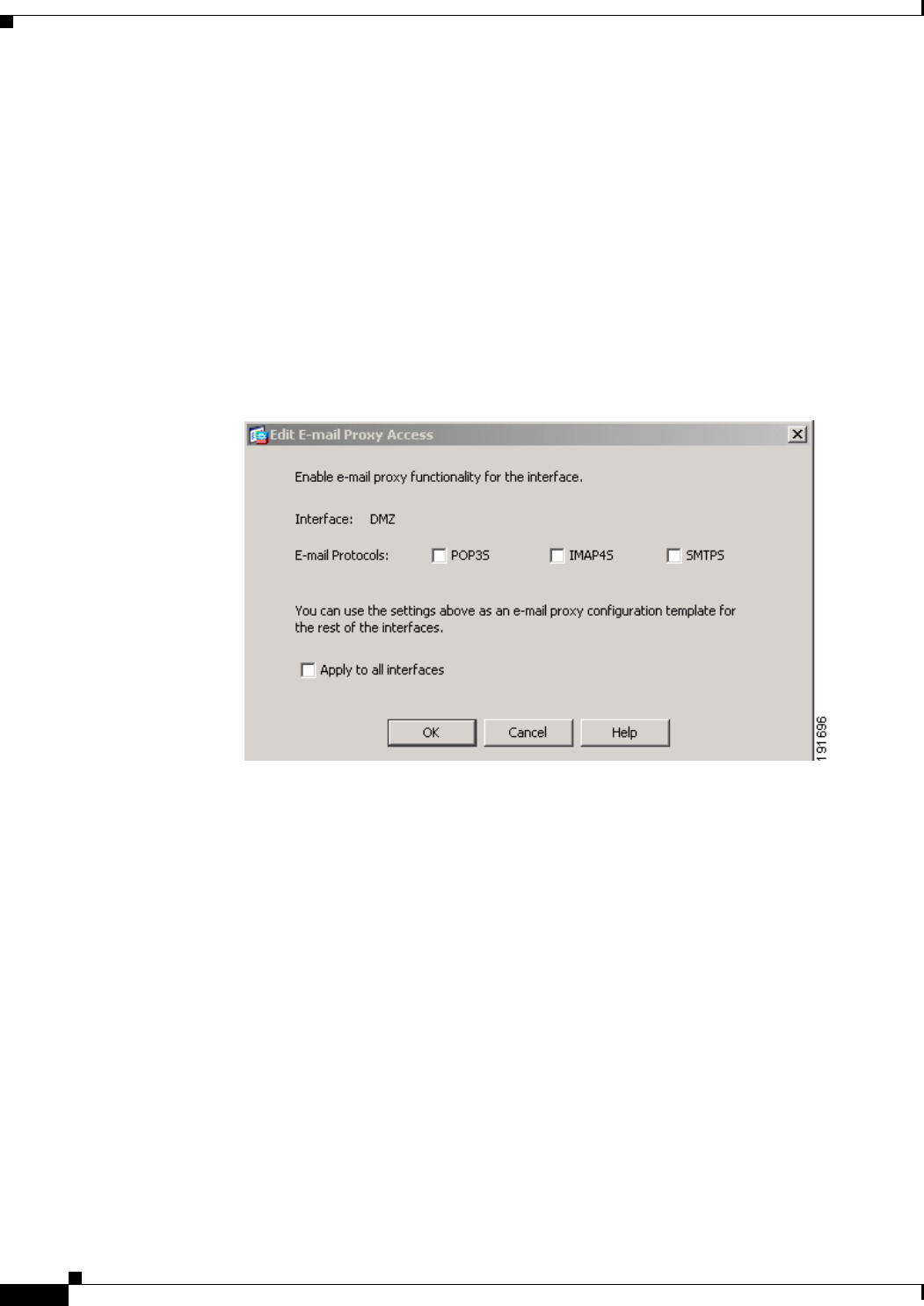
7-8
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 7 E-Mail Proxy
Authentication
•POP3S Enabled—Shows whether POP3S is enabled for the interface.
•IMAP4s Enabled—Shows whether IMAP4S is enabled for the interface.
•SMTPS Enabled—Shows whether SMTPS is enabled for the interface.
•Edit—Click to edit the e-mail proxy settings for the highlighted interface.
Edit E-Mail Proxy Access
Configuration > VPN > E-Mail Proxy > Access > Edit E-Mail Proxy Access
The E-mail Proxy Access screen lets you identify interfaces on which to configure e-mail proxy. You
can configure e-mail proxies on individual interfaces, and you can configure e-mail proxies for one
interface and then apply your settings to all interfaces.
Fields
•Interface—Displays the name of the selected interface.
•POP3S Enabled—Select to enable POP3S for the interface.
•IMAP4S Enabled—elect to enable IMAP4S for the interface.
•SMTPS Enabled—Select to enable SMTPS for the interface.
•Apply to all interface—Select to apply the settings for the current interface to all configured
interfaces.
Authentication
Configuration > Features > VPN >E-mail Proxy > Authentication
This panel lets you configure authentication methods for e-mail proxy sessions.
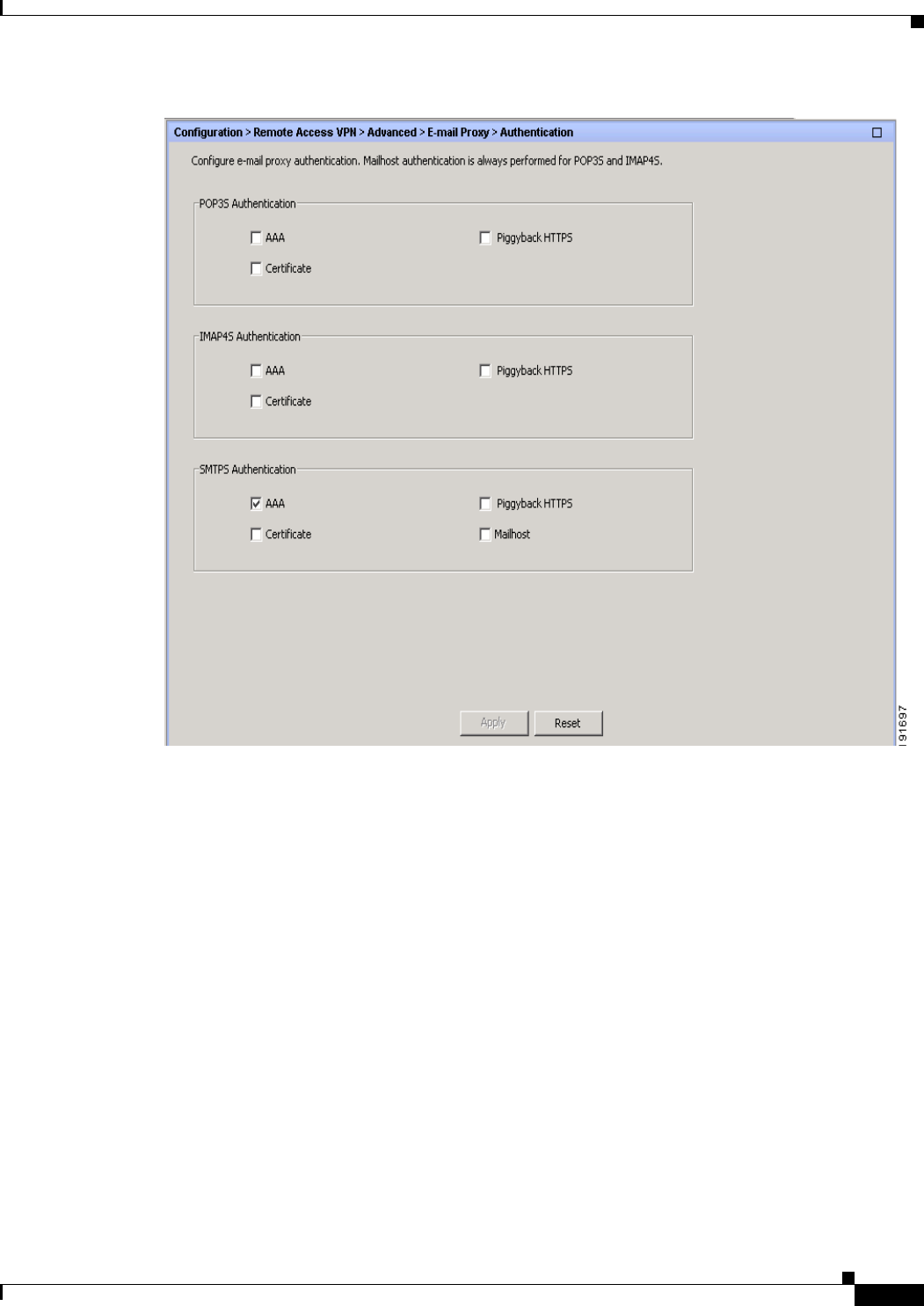
7-9
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 7 E-Mail Proxy
Authentication
Fields
POP3S/IMAP4S/SMTPS Authentication—Let you configure authentication methods for each of the
e-mail proxy types. You can select multiple methods of authentication.
•AAA—Select to require AAA authentication. This option requires a configured AAA server. The
user presents a username, server and password. Users must present both the VPN username and the
e-mail username, separated by the VPN Name Delimiter, only if the usernames are different from
each other.
•Certificate—Certificate authentication does not work for e-mail proxies in the current ASA software
release.
•Piggyback HTTPS—Select to require piggyback authentication.
This authentication scheme requires a user to have already established a Clientless SSL VPN
session. The user presents an e-mail username only. No password is required. Users must present
both the VPN username and the e-mail username, separated by the VPN Name Delimiter, only if the
usernames are different from each other.
SMTPS e-mail most often uses piggyback authentication because most SMTP servers do not allow
users to log in.
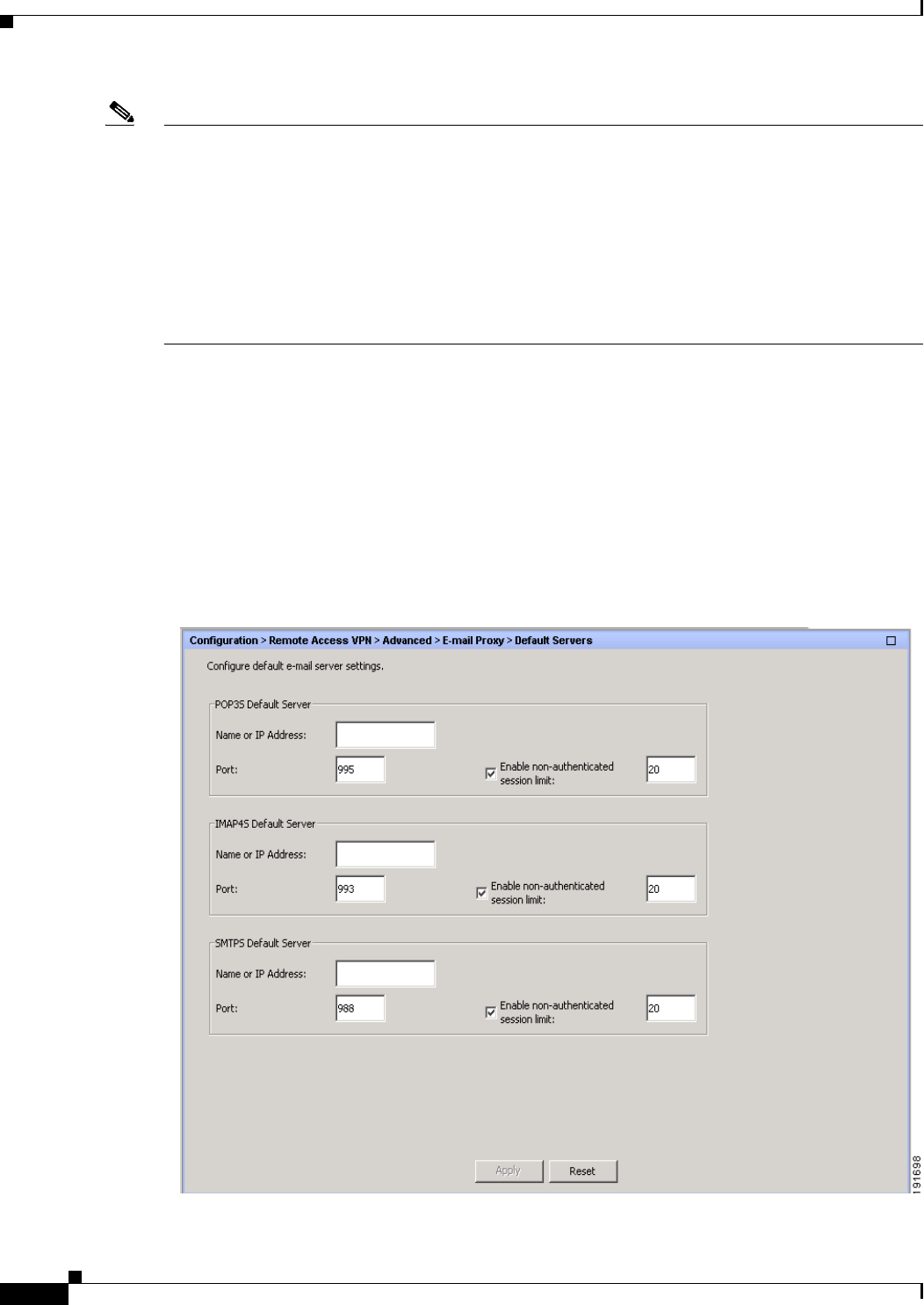
7-10
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 7 E-Mail Proxy
Default Servers
Note IMAP generates a number of sessions that are not limited by the simultaneous user count but do count
against the number of simultaneous logins allowed for a username. If the number of IMAP sessions
exceeds this maximum and the Clientless SSL VPN connection expires, a user cannot subsequently
establish a new connection. There are several solutions:
- The user can close the IMAP application to clear the sessions with the ASA, and then establish a new
Clientless SSL VPN connection.
- The administrator can increase the simultaneous logins for IMAP users (Configuration > Features >
VPN > General > Group Policy > Edit Group Policy > General).
- Disable HTTPS/Piggyback authentication for e-mail proxy.
•Mailhost—(SMTPS only) Select to require mailhost authentication. This option appears for SMTPS
only because POP3S and IMAP4S always perform mailhost authentication. It requires the user’s
e-mail username, server and password.
Default Servers
Configuration > Features > VPN > E-mail Proxy > Default Servers
This panel lets you identify proxy servers to the ASA. Enter the IP address and port of the appropriate
proxy server.

7-11
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 7 E-Mail Proxy
Delimiters
Fields
•POP3S/IMAP4S/SMTPS Default Server—Let you configure a default server, port and
non-authenticated session limit for e-mail proxies.
•Name or IP Address—Type the DNS name or IP address for the default e-mail proxy server.
•Port—Type the port number on which the ASA listens for e-mail proxy traffic. Connections are
automatically allowed to the configured port. The e-mail proxy allows only SSL connections on this
port. After the SSL tunnel establishes, the e-mail proxy starts, and then authentication occurs.
For POP3s the default port is 995, for IMAP4S it is 993, and for SMTPS it is 988.
•Enable non-authenticated session limit—Select to restrict the number of non-authenticated e-mail
proxy sessions.
E-mail proxy connections have three states:
1. A new e-mail connection enters the “unauthenticated” state.
2. When the connection presents a username, it enters the “authenticating” state.
3. When the ASA authenticates the connection, it enters the “authenticated” state.
This feature lets you set a limit for sessions in the process of authenticating, thereby preventing DOS
attacks. When a new session exceeds the set limit, the ASA terminates the oldest non-authenticating
connection. If there are no non-authenticating connections, the oldest authenticating connection is
terminated. The does not terminate authenticated sessions.
Delimiters
Configuration > Features > VPN > E-mail Proxy > Delimiters
This panel lets you configure username/password delimiters and server delimiters for e-mail proxy
authentication.
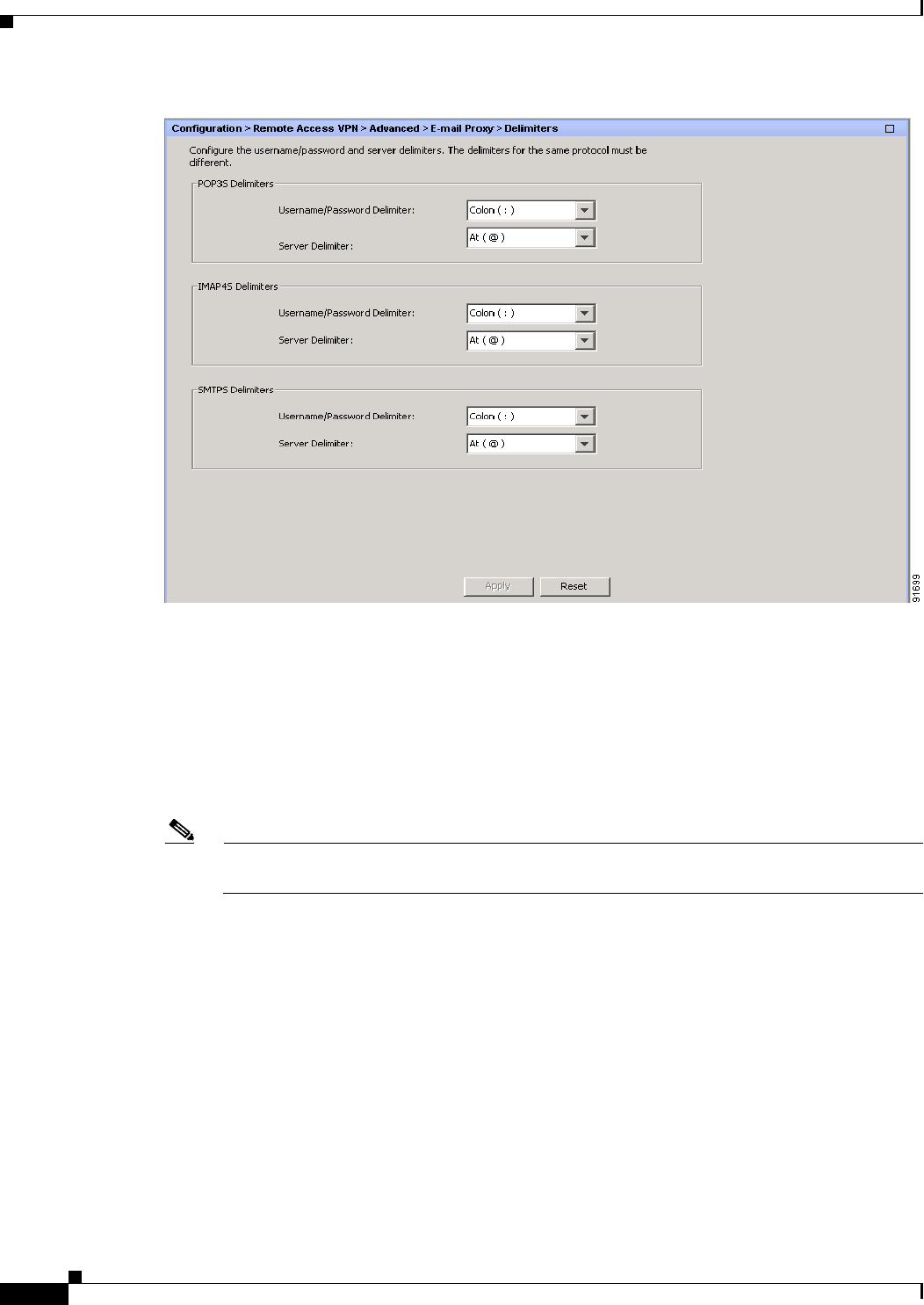
7-12
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 7 E-Mail Proxy
Delimiters
Fields
•POP3S/IMAP4S/SMTPS Delimiters—Let you configure username/password and server delimiters
for each of the e-mail proxies.
–
Username/Password Delimiter—Select a delimiter to separate the VPN username from the
e-mail username. Users need both usernames when using AAA authentication for e-mail proxy
and the VPN username and e-mail username are different. Users enter both usernames,
separated by the delimiter you configure here, and also the e-mail server name, when they log
in to an e-mail proxy session.
Note Passwords for Clientless SSL VPN e-mail proxy users cannot contain characters that are used as
delimiters.
–
Server Delimiter—Select a delimiter to separate the username from the name of the e-mail
server. It must be different from the VPN Name Delimiter. Users enter both their username and
server in the username field when they log in to an e-mail proxy session.
For example, using : as the VPN Name Delimiter and @ as the Server Delimiter, when logging
in to an e-mail program via e-mail proxy, the user would enter their username in the following
format: vpn_username:e-mail_username@server.

CHAPTER
8-1
Cisco ASA Series VPN ASDM Configuration Guide
8
Monitoring VPN
This chapter describes how to use VPN monitoring parameters and statistics for the following:
•VPN statistics for specific Network (Client) Remote Access, Site-to-Site VPN, Clientless SSL VPN,
and E-mail Proxy sessions
•Encryption statistics for tunnel groups
•Protocol statistics for tunnel groups
•Global IPsec and IKE statistics
•Crypto statistics for IPsec, IKE, SSL, and other protocols
•Statistics for cluster VPN server loads
VPN Connection Graphs
Displays VPN connection data in graphical or tabular form for the ASA.
IPsec Tunnels
Monitoring > VPN > VPN Connection Graphs > IPSec Tunnels
Use this pane to specify graphs and tables of the IPsec tunnel types you want to view, or prepare to export
or print.
Fields
•Graph Window Title—Displays the default title that appears in the pane when you click Show
Graphs. This attribute is particularly useful when you want to clarify data in that pane before
printing or exporting it. To change the title, choose an alternative from the drop-down list or type
the title.
•Available Graphs—Shows the types of active tunnels you can view. For each type you want to view
collectively in a single pane, choose the entry and click Add.
•Selected Graphs—Shows the types of tunnels selected.
If you click Show Graphs, ASDM shows the active tunnels types listed in a single pane.
A highlighted entry indicates the type of tunnel to be removed from the list if you click Remove.
•Add—Moves the selected tunnel type from the Available Graphs column to the Selected Graphs
column.

8-2
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 8 Monitoring VPN
VPN Statistics
•Remove—Moves the selected tunnel type from the Selected Graphs column to the Available Graphs
column.
•Show Graphs—Displays a pane consisting of graphs of the tunnel types displayed in the Selected
Graphs column. Each type in the pane displayed has a Graph tab and a Table tab you can click to
alternate the representation of active tunnel data.
Sessions
Monitoring > VPN > VPN Connection Graphs > Sessions
Use this pane to specify graphs and tables of the VPN session types you want to view, or prepare to
export or print.
Fields
•Graph Window Title—Displays the default title that appears in the pane when you click Show
Graphs. This attribute is particularly useful when you want to clarify data in that pane before
printing or exporting it. To change the title, select an alternative from the drop-down list or type the
title.
•Available Graphs—Shows the types of active sessions you can view. For each type you want to view
collectively in a single pane, click the entry in this box and click Add.
•Selected Graphs—Shows the types of active sessions selected.
If you click Show Graphs, ASDM shows all of the active session types listed in this box in a single
pane.
A highlighted entry indicates the type of session to be removed from the list if you click Remove.
•Add—Moves the selected session type from the Available Graphs box to the Selected Graphs box.
•Remove—Moves the selected session type from the Selected Graphs box to the Available Graphs
box.
•Show Graphs—Displays a pane consisting of graphs of the session types displayed in the Selected
Graphs box. Each type in the pane displayed has a Graph tab and a Table tab you can click to
alternate the representation of active session data.
VPN Statistics
These panes show detailed parameters and statistics for a specific remote-access, LAN-to-LAN,
Clientless SSL VPN, or E-mail Proxy session. The parameters and statistics differ depending on the
session protocol. The contents of the statistical tables depend on the type of connection you choose. The
detail tables show all the relevant parameters for each session.
Sessions Window
Monitoring > VPN > VPN Statistics > Sessions
Use this pane to view VPN session statistics for the adaptive security appliance.

8-3
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 8 Monitoring VPN
VPN Statistics
Fields
•Session types (unlabeled)—Lists the number of currently active sessions of each type, the total limit,
and the total cumulative session count.
–
All Remote Access—Shows the number of remote access sessions.
–
Site-to-Site—Shows the number of LAN-to-LAN sessions.
–
Clientless SSL VPN—Shows the number of clientless browser-based VPN sessions.
–
AnyConnect Client—Shows the number of client-based SSL VPN sessions. With ASA version
8.x and above, this represents the AnyConnect SSL VPN client 2.x and above.
–
SSL VPN–Inactive—Shows the number of SSL VPN sessions that are inactive on the remote
computer.
Note An administrator can keep track of the number of users in the inactive state and can look
at the statistics. The sessions that have been inactive for the longest time are marked as
idle (and are automatically logged off) so that license capacity is not reached and new
users can log in. You can also access these statistics using the show vpn-sessiondb CLI
command (refer to the Cisco Security Appliance Command Reference Guide).
–
SSL VPN–Total—Shows the number of client-based and clientless SSL VPN sessions.
–
E-mail Proxy—Shows the number of E-mail proxy sessions.
–
VPN Load Balancing—Shows the number of load-balanced VPN sessions
–
Total—Shows the total number of active concurrent sessions.
–
Total Cumulative—Shows the cumulative number of sessions since the last time the ASA was
rebooted or reset.
•Filter By—Specifies the type of sessions that the statistics in the following table represent.
–
Session type (unlabeled)—Designates the session type that you want to monitor. You can filter
by any of these sessions: IPsec Site-to-Site, All Remote Access, AnyConnect Client, Clientless
SSL VPN, IPsec (IKEv1) Remote Access, OSPFv3 IPsec, or Email Proxy.
The column headings in the results table change depending on the Session type you choose.
–
Filter name (unlabeled)—Specifies the name of the filter to apply. If you specify --All
Sessions-- as the session filter list, this field is not available. For all other session filter
selections, this field cannot be blank.
If you choose a Session type filter of IPsec Site-to-Site, AnyConnect Client, Clientless SSL
VPN, or OSPFv3 IPsec then you would be able to filter by Assigned IP Address Type or Public
IP Address Type.
–
Filter value—Enter the value that corresponds to the filter you are using.
If you are filtering by Assigned IP Address Type or Public IP Address type, specify the IP
address type in this field, either IPv4 or IPv6.
–
Filter—Executes the filtering operation.
The contents of the second table, also unlabeled, in this pane depend on the selection in the Filter By
list. In the following list, the first-level bullets show the Filter By selection, and the second-level bullets
show the column headings for this table.
•All Remote Access—Indicates that the values in this table relate to remote access (IPsec software
and hardware clients) traffic.

8-4
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 8 Monitoring VPN
VPN Statistics
–
Username/Connection Profile—Shows the username or login name and the connection profile
(tunnel group) for the session. If the client is using a digital certificate for authentication, the
field shows the Subject CN or Subject OU from the certificate.
–
Group Policy Connection Profile—Displays the tunnel group policy connection profile for the
session.
–
Assigned IP Address/Public IP Address—Shows the private (“assigned”) IP address assigned to
the remote client for this session. This is also known as the “inner” or “virtual” IP address, and
it lets the client appear to be a host on the private network. Also shows the Public IP address of
the client for this remote-access session. This is also known as the “outer” IP address. It is
typically assigned to the client by the ISP, and it lets the client function as a host on the public
network.
Note The Assigned IP Address field does not apply to Clientless SSL VPN sessions, as the ASA
(proxy) is the source of all traffic. For a hardware client session in Network Extension mode, the
Assigned IP address is the subnet of the hardware client's private/inside network interface.
–
Protocol/Encryption—Shows the protocol and the data encryption algorithm this session is using,
if any.
–
Login Time/Duration—Shows the date and time (MMM DD HH:MM:SS) that the session
logged in. and the length of the session. Time is displayed in 24-hour notation.
–
Client (Peer) Type/Version—Shows the type and software version number (for example, rel.
7.0_int 50) for connected clients, sorted by username.
–
Bytes Tx/Bytes Rx—Shows the total number of bytes transmitted to/received from the remote
peer or client by the ASA.
•IPsec Site-to-Site—Indicates that the values in this table relate to LAN-to-LAN traffic.
–
Connection Profile/IP Address—Shows the name of the tunnel group and the IP address of the
peer.
–
Protocol/Encryption—Shows the protocol and the data encryption algorithm this session is using,
if any.
–
Login Time/Duration—Shows the date and time (MMM DD HH:MM:SS) that the session
logged in. and the length of the session. Time is displayed in 24-hour notation.
–
Bytes Tx/Bytes Rx—Shows the total number of bytes transmitted to/received from the remote
peer or client by the ASA.
•Clientless SSL VPN—Indicates that the values in this table relate to Clientless SSL VPN traffic.
–
Username/IP Address—Shows the username or login name for the session and the IP address of
the client.
–
Group Policy Connection Profile—Displays the connection profile of the tunnel group policy.
–
Protocol/Encryption—Shows the protocol and the data encryption algorithm this session is using,
if any.
–
Login Time/Duration—Shows the date and time (MMM DD HH:MM:SS) that the session
logged in. and the length of the session. Time is displayed in 24-hour notation.
–
Bytes Tx/Bytes Rx—Shows the total number of bytes transmitted to/received from the remote
peer or client by the ASA.
•SSL VPN Client—Indicates that the values in this table relate to traffic for SSL VPN Client sessions.

8-5
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 8 Monitoring VPN
VPN Statistics
–
Username/IP Address—Shows the username or login name for the session and the IP address of
the client.
–
Group Policy Connection Profile—Displays the connection profile of the tunnel group policy.
–
Protocol/Encryption—Shows the protocol and the data encryption algorithm this session is using,
if any.
–
Login Time/Duration—Shows the date and time (MMM DD HH:MM:SS) that the session
logged in. and the length of the session. Time is displayed in 24-hour notation.
–
Bytes Tx/Bytes Rx—Shows the total number of bytes transmitted to/received from the remote
peer or client by the ASA.
•E-Mail Proxy—Indicates that the values in this table relate to traffic for Clientless SSL VPN
sessions.
–
Username/IP Address—Shows the username or login name for the session and the IP address of
the client.
–
Protocol/Encryption—Shows the protocol and the data encryption algorithm this session is using,
if any.
–
Login Time/Duration—Shows the date and time (MMM DD HH:MM:SS) that the session
logged in. and the length of the session. Time is displayed in 24-hour notation.
–
Bytes Tx/Bytes Rx—Shows the total number of bytes transmitted to/received from the remote
peer or client by the ASA.
The remainder of this section describes the buttons and fields beside and below the table.
•Details—Displays the details for the selected session. The parameters and values differ, depending
on the type of session.
•Logout—Ends the selected session.
•Ping—Sends an ICMP ping (Packet Internet Groper) packet to test network connectivity.
Specifically, the ASA sends an ICMP Echo Request message to a selected host. If the host is
reachable, it returns an Echo Reply message, and the ASA displays a Success message with the name
of the tested host, as well as the elapsed time between when the request was sent and the response
received. If the system is unreachable for any reason, (for example: host down, ICMP not running
on host, route not configured, intermediate router down, or network down or congested), the ASA
displays an Error screen with the name of the tested host.
•Logout By—Chooses a criterion to use to filter the sessions to be logged out. If you choose any but
--All Sessions--, the box to the right of the Logout By list becomes active. If you choose the value
Protocol for Logout By, the box becomes a list, from which you can choose a protocol type to use
as the logout filter. The default value of this list is IPsec. For all choices other than Protocol, you
must supply an appropriate value in this column.
•Logout Sessions—Ends all sessions that meet the specified Logout By criteria.
•Refresh—Updates the screen and its data. The date and time indicate when the screen was last
updated.
Viewing Active AnyConnect Sessions
Step 1 Select Monitoring > VPN > VPN Statistics > Sessions.
Step 2 In the Filter By field, select AnyConnect Client.

8-6
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 8 Monitoring VPN
VPN Statistics
Step 3 In the Session Filter field (unlabeled), next to the Filter By field, select the session type you want to use
to further refine your filter. Then, enter a value in the Session Value field (unlabeled) to the right of the
Session Filter field. These are the available session filters and session values:
Step 4 Cick Filter.
Viewing VPN Sessions Details
Monitoring > VPN > VPN Statistics > Sessions >Details
The Session Details pane displays configuration settings, statistics, and state information about the
selected session.
The Remote Detailed table at the top of the Session Details pane displays the following columns:
•Username—Shows the username or login name associated with the session. If the remote peer is
using a digital certificate for authentication, the field shows the Subject CN or Subject OU from the
certificate.
•Group Policy and Tunnel Group—Group policy assigned to the session and the name of the tunnel
group upon which the session is established.
•Assigned IP Address and Public IP Address—Private IP address assigned to the remote peer for this
session. Also called the inner or virtual IP address, the assigned IP address lets the remote peer
appear to be on the private network. The second field shows the public IP address of the remote
computer for this session. Also called the outer IP address, the public IP address is typically
assigned to the remote computer by the ISP. It lets the remote computer function as a host on the
public network.
•Protocol/Encryption—Protocol and the data encryption algorithm this session is using, if any.
•Login Time and Duration—Time and date of the session initialization, and the length of the session.
The session initialization time is in 24-hour notation.
•Client Type and Version—Type and software version number (for example, rel. 7.0_int 50) of the client
on the remote computer.
Session Filter Session Value
Username Then enter the username you want to sort by.
Assigned IP Address The assigned IP address is the IP address assigned by the ASA to
the AnyConnect Client connection.
Enter the IPv4 or IPv6 address you want to sort by.
Assigned IP Address Type Choose IP version 4 or IP version 6.
Public Address The public IP address is the IP address assigned by your
enterprise to the endpoint.
Enter the IPv4 or IPv6 address you want to sort by.
Public Address Type Choose IP version 4 or IP version 6.
Encryption Select the encryption type for the session.
Connection Status Select Active or Inactive.

8-7
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 8 Monitoring VPN
VPN Statistics
•Bytes Tx and Bytes Rx—Shows the total number of bytes transmitted to and received from the
remote peer by the ASA.
•NAC Result and Posture Token—The ASDM displays values in this column only if you configured
Network Admission Control on the ASA.
The NAC Result shows one of the following values:
–
Accepted—The ACS successfully validated the posture of the remote host.
–
Rejected—The ACS could not successfully validate the posture of the remote host.
–
Exempted—The remote host is exempt from posture validation according to the Posture
Validation Exception list configured on the ASA.
–
Non-Responsive—The remote host did not respond to the EAPoUDP Hello message.
–
Hold-off—The ASA lost EAPoUDP communication with the remote host after successful
posture validation.
–
N/A—NAC is disabled for the remote host according to the VPN NAC group policy.
–
Unknown—Posture validation is in progress.
The posture token is an informational text string which is configurable on the Access Control Server.
The ACS downloads the posture token to the ASA for informational purposes to aid in system
monitoring, reporting, debugging, and logging. The typical posture token that follows the NAC
result is as follows: Healthy, Checkup, Quarantine, Infected, or Unknown.
The Details tab in the Session Details pane displays the following columns:
•ID—Unique ID dynamically assigned to the session. The ID serves as the ASA index to the session.
It uses this index to maintain and display information about the session.
•Type—Type of session: IKE, IPsec, or NAC.
•Local Addr., Subnet Mask, Protocol, Port, Remote Addr., Subnet Mask, Protocol, and
Port—Addresses and ports assigned to both the actual (Local) peer and those assigned to this peer
for the purpose of external routing.
•Encryption—Data encryption algorithm this session is using, if any.
•Assigned IP Address and Public IP Address—Shows the private IP address assigned to the remote
peer for this session. Also called the inner or virtual IP address, the assigned IP address lets the
remote peer appear to be on the private network. The second field shows the public IP address of the
remote computer for this session. Also called the outer IP address, the public IP address is typically
assigned to the remote computer by the ISP. It lets the remote computer function as a host on the
public network.
•Other—Miscellaneous attributes associated with the session.
The following attributes apply to an IKE session:
The following attributes apply to an IPsec session:
The following attributes apply to a NAC session:
–
Revalidation Time Interval— Interval in seconds required between each successful posture
validation.
–
Time Until Next Revalidation—0 if the last posture validation attempt was unsuccessful.
Otherwise, the difference between the Revalidation Time Interval and the number of seconds
since the last successful posture validation.

8-8
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 8 Monitoring VPN
VPN Statistics
–
Status Query Time Interval—Time in seconds allowed between each successful posture
validation or status query response and the next status query response. A status query is a
request made by the ASA to the remote host to indicate whether the host has experienced any
changes in posture since the last posture validation.
–
EAPoUDP Session Age—Number of seconds since the last successful posture validation.
–
Hold-Off Time Remaining—0 seconds if the last posture validation was successful. Otherwise,
the number of seconds remaining before the next posture validation attempt.
–
Posture Token—Informational text string configurable on the Access Control Server. The ACS
downloads the posture token to the ASA for informational purposes to aid in system monitoring,
reporting, debugging, and logging. A typical posture token is Healthy, Checkup, Quarantine,
Infected, or Unknown.
–
Redirect URL—Following posture validation or clientless authentication, the ACS downloads
the access policy for the session to the ASA. The Redirect URL is an optional part of the access
policy payload. The ASA redirects all HTTP (port 80) and HTTPS (port 443) requests for the
remote host to the Redirect URL if it is present. If the access policy does not contain a Redirect
URL, the ASA does not redirect HTTP and HTTPS requests from the remote host.
Redirect URLs remain in force until either the IPsec session ends or until posture revalidation,
for which the ACS downloads a new access policy that can contain a different redirect URL or
no redirect URL.
More—Press this button to revalidate or initialize the session or tunnel group.
The ACL tab displays the ACL containing the ACEs that matched the session.
Cluster Loads
Monitoring > VPN > VPN Statistics > Cluster Loads
Use this pane to view the current traffic load distribution among the servers in a VPN load-balancing
cluster. If the server is not part of a cluster, you receive an information message saying that this server
does not participate in a VPN load-balancing cluster.
Fields
•VPN Cluster Loads—Displays the current load distribution in the VPN load-balancing cluster.
Clicking a column heading sorts the table, using the selected column as the sort key.
–
Public IP Address—Displays the externally visible IP address for the server.
–
Role—Indicates whether this server is a master or backup device in the cluster.
–
Priority—Shows the priority assigned to this server in the cluster. The priority must be an
integer in the range of 1 (lowest) to 10 (highest). The priority is used in the master-election
process as one way to determine which of the devices in a VPN load-balancing cluster becomes
the master or primary device for the cluster.
–
Model—Indicates the ASA model name and number for this server.
–
IPsec Load%—Indicates what percentage of a server’s total capacity is in use, based upon the
capacity of that server.
–
SSL Load%—Indicates what percentage of a SSL server’s total capacity is in use, based upon
the capacity of that server.
–
IPsec Sessions—Shows the number of currently active sessions.
–
SSL Sessions—Shows the number of currently active sessions.

8-9
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 8 Monitoring VPN
VPN Statistics
•Refresh—Loads the table with updated statistics.
Crypto Statistics
Monitoring > VPN > VPN Statistics > Crypto Statistics
This pane displays the crypto statistics for currently active user and administrator sessions on the ASA.
Each row in the table represents one crypto statistic.
Fields
•Show Statistics For—Selects a specific protocol, IKE Protocol (the default), IPsec Protocol, SSL
Protocol, or other protocols.
•Statistics—Shows the statistics for all the protocols in use by currently active sessions.
–
Statistic—Lists the name of the statistical variable. The contents of this column vary, depending
upon the value you select for the Show Statistics For parameter.
–
Value—The numerical value for the statistic in this row.
•Refresh—Updates the statistics shown in the Crypto Statistics table.
Compression Statistics
Monitoring > VPN > VPN Statistics > Compression Statistics
This pane displays the compression statistics for currently active user and administrator sessions on the
ASA. Each row in the table represents one compression statistic.
Fields
•Show Statistics For—Lets you select compression statistics for clientless SSL VPN or SSL VPN
Client sessions.
•Statistics—Shows all the statistics for the selected VPN type.
–
Statistic—Lists the name of the statistical variable. The contents of this column vary, depending
upon the value you select for the Show Statistics For parameter.
–
Value—The numerical value for the statistic in this row.
•Refresh—Updates the statistics shown in the Compression Statistics table.
Encryption Statistics
Monitoring > VPN > VPN Statistics > Encryption Statistics
This pane shows the data encryption algorithms used by currently active user and administrator sessions
on the ASA. Each row in the table represents one encryption algorithm type.
Fields
•Show Statistics For—Selects a specific server or group or all tunnel groups.
•Encryption Statistics—Shows the statistics for all the data encryption algorithms in use by currently
active sessions.
–
Encryption Algorithm—Lists the encryption algorithm to which the statistics in this row apply.

8-10
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 8 Monitoring VPN
VPN Statistics
–
Sessions—Lists the number of sessions using this algorithm.
–
Percentage—Indicates the percentage of sessions using this algorithm relative to the total active
sessions, as a number. The sum of this column equals 100 percent (rounded).
•Total Active Sessions—Shows the number of currently active sessions.
•Cumulative Sessions—Shows the total number of sessions since the ASA was last booted or reset.
•Refresh—Updates the statistics shown in the Encryption Statistics table.
Global IKE/IPsec Statistics
Monitoring > VPN > VPN Statistics > Global IKE/IPSec Statistics
This pane displays the global IKE/IPsec statistics for currently active user and administrator sessions on
the ASA. Each row in the table represents one global statistic.
Fields
•Show Statistics For—Selects a specific protocol, IKE Protocol (the default) or IPsec Protocol.
•Statistics—Shows the statistics for all the protocols in use by currently active sessions.
–
Statistic—Lists the name of the statistical variable. The contents of this column vary, depending
upon the value you select for the Show Statistics For parameter.
–
Value—The numerical value for the statistic in this row.
•Refresh—Updates the statistics shown in the Global IKE/IPsec Statistics table.
NAC Session Summary
The NAC Session Summary pane lets you view the active and cumulative Network Admission Control
sessions.
Fields
•Active NAC Sessions—General statistics about remote peers that are subject to posture validation.
•Cumulative NAC Sessions—General statistics about remote peers that are or have been subject to
posture validation.
•Accepted—Number of peers that passed posture validation and have been granted an access policy
by an Access Control Server.
•Rejected—Number of peers that failed posture validation or were not granted an access policy by
an Access Control Server.
•Exempted—Number of peers that are not subject to posture validation because they match an entry
in the Posture Validation Exception list configured on the ASA.
•Non-responsive—Number of peers not responsive to Extensible Authentication Protocol (EAP) over
UDP requests for posture validation. Peers on which no CTA is running do not respond to these
requests. If the ASA configuration supports clientless hosts, the Access Control Server downloads
the access policy associated with clientless hosts to the ASA for these peers. Otherwise, the ASA
assigns the NAC default policy.
•Hold-off—Number of peers for which the ASA lost EAPoUDP communications after a successful
posture validation. The NAC Hold Timer attribute (Configuration > VPN > NAC) determines the
delay between this type of event and the next posture validation attempt.

8-11
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 8 Monitoring VPN
VPN Statistics
•N/A—Number of peers for which NAC is disabled according to the VPN NAC group policy.
•Revalidate All—Click if the posture of the peers or the assigned access policies (that is, the
downloaded ACLs), have changed. Clicking this button initiates new, unconditional posture
validations of all NAC sessions managed by the ASA. The posture validation and assigned access
policy that were in effect for each session before you clicked this button remain in effect until the
new posture validation succeeds or fails. Clicking this button does not affect sessions that are exempt
from posture validation.
•Initialize All—Click if the posture of the peers or the assigned access policies (that is, the
downloaded ACLs) have changed, and you want to clear the resources assigned to the sessions.
Clicking this button purges the EAPoUDP associations and assigned access policies used for posture
validations of all NAC sessions managed by the ASA, and initiates new, unconditional posture
validations. The NAC default ACL is effective during the revalidations, so the session initializations
can disrupt user traffic. Clicking this button does not affect sessions that are exempt from posture
validation.
Protocol Statistics
Monitoring > VPN > VPN Statistics > Protocol Statistics
This pane displays the protocols used by currently active user and administrator sessions on the ASA.
Each row in the table represents one protocol type.
Fields
•Show Statistics For—Selects a specific server or group or all tunnel groups.
•Protocol Statistics—Shows the statistics for all the protocols in use by currently active sessions.
–
Protocol—Lists the protocol to which the statistics in this row apply.
–
Sessions—Lists the number of sessions using this protocol.
–
Percentage—Indicates the percentage of sessions using this protocol relative to the total active
sessions, as a number. The sum of this column equals 100 percent (rounded).
•Total Active Tunnel—Shows the number of currently active sessions.
•Cumulative Tunnels—Shows the total number of sessions since the ASA was last booted or reset.
•Refresh—Updates the statistics shown in the Protocol Statistics table.
VLAN Mapping Sessions
This pane displays the number of sessions assigned to an egress VLAN, as determined by the value of
the Restrict Access to VLAN parameter of each group policy in use. The ASA forwards all traffic to the
specified VLAN.
Field
•Active VLAN Mapping Sessions—Number of VPN sessions assigned to an egress VLAN.
SSO Statistics for Clientless SSL VPN Session
Monitoring > VPN > WebVPN > SSO Statistics
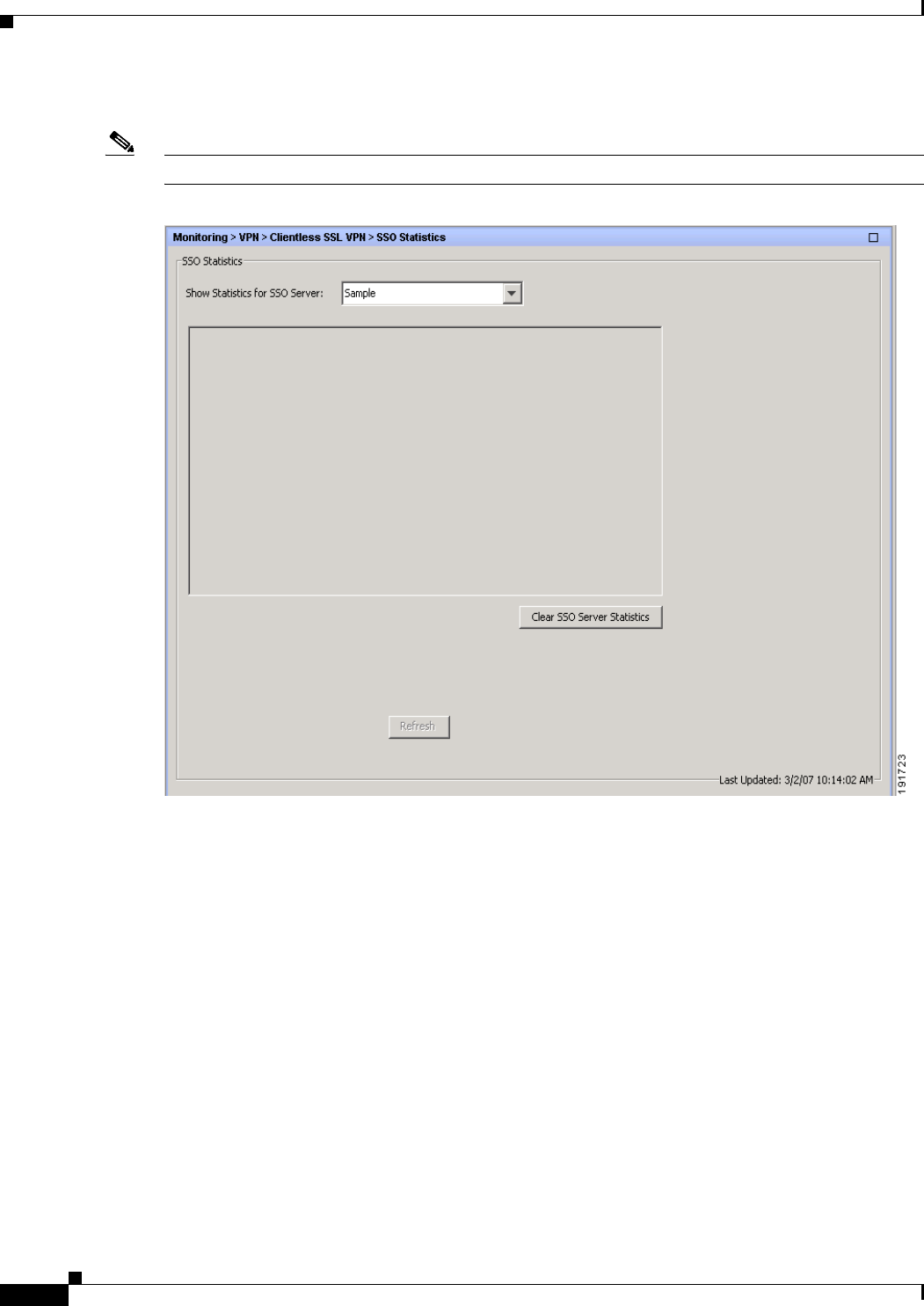
8-12
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 8 Monitoring VPN
VPN Statistics
This pane displays the single sign-on statistics for currently active SSO servers configured for the ASA.
Note These statistics are for SSO with SiteMinder and SAML Browser Post Profile servers only.
Fields
•Show Statistics For SSO Server—Selects an SSO server.
•SSO Statistics—Shows the statistics for all the currently active sessions on the selected SSO server.
SSO statistics that display include:
–
Name of SSO server
–
Type of SSO server
–
Authentication Scheme Version (SiteMinder servers)
–
Web Agent URL (SiteMinder servers)
–
Assertion Consumer URL (SAML POST servers)
–
Issuer (SAML POST servers)
–
Number of pending requests
–
Number of authorization requests
–
Number of retransmissions

8-13
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 8 Monitoring VPN
VPN Statistics
–
Number of accepts
–
Number of rejects
–
Number of timeouts
–
Number of unrecognized responses
•Refresh—Updates the statistics shown in the SSO Statistics table
•Clear SSO Server Statistics—Resets statistics for the displayed server.
VPN Connection Status for the Easy VPN Client
Use this pane to view the status of the ASA configured as an Easy VPN client. This features applies to
the ASA 5505 only.
Fields
VPN Client Detail—Displays configuration information for the ASA5505 configured as an Easy VPN
Client.
Connect—Establishes a client connection
Refresh—Refreshes the information displayed in the VPN Client Detail panel.

8-14
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 8 Monitoring VPN
VPN Statistics

CHAPTER
9-1
Cisco ASA Series VPN ASDM Configuration Guide
9
Configuring SSL Settings
SSL Settings
Configuration > Device Management > Advanced > SSL Settings
Configuration > Remote Access VPN > Advanced > SSL Settings
The ASA uses the Secure Sockets Layer (SSL) protocol and its successor, Transport Layer Security
(TLS) to support secure message transmission for ASDM, Clientless, VPN, and browser-based sessions.
The SSL Settings window lets you configure SSL versions and encryption algorithms for clients and
servers. It also lets you apply previously configured trustpoints to specific interfaces, and to configure a
fallback trustpoint for interfaces that do not have an associated trustpoint.
Fields
•Server SSL Version—Choose to specify the SSL/TLS protocol version the ASA uses to negotiate
as a server. You can make only one selection.
Note To use port forwarding for Clientless SSL VPN, you must select Any or Negotiate SSL V3. The issue is
that JAVA only negotiates SSLv3 in the client Hello packet when you launch the Port Forwarding
application.
•Client SSL Version—Choose to specify the SSL/TLS protocol version the ASA uses to negotiate
as a client. You can make only one selection.
Any The ASA accepts SSL version 2 client hellos, and negotiates either SSL
version 3 or TLS version 1.
Negotiate SSL V3 The ASA accepts SSL version 2 client hellos, and negotiates to SSL version
3.
Negotiate TLS V1 The ASA accepts SSL version 2 client hellos, and negotiates to TLS version
1.
SSL V3 Only The security appliance accepts only SSL version 3 client hellos, and uses
only SSL version 3.
TLS V1 Only The security appliance accepts only TLSv1 client hellos, and uses only TLS
version 1.

9-2
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 9 Configuring SSL Settings
SSL Settings
•Encryption—Add the SSL encryption algorithms you want to support.
–
Available Algorithms—Lists the encryption algorithms the ASA supports that are not in use
for SSL connections. To use, or make active, an available algorithm, highlight the algorithm and
click Add.
–
Active Algorithms—Lists the encryption algorithms the security appliance supports and is
currently using for SSL connections. To discontinue using, or change an active algorithm to
available status, highlight the algorithm and click Remove.
–
Add/Remove—Click to change the status of encryption algorithms in either the Available or
Active Algorithms columns.
–
Move Up/Move Down—Highlight an algorithm and click these buttons to change its priority.
The ASA attempts to use an algorithm
•Certificates—Assign certificates to use for SSL authentication on each interface. Click Edit to
define or modify the Trustpoint for each interface. Trustpoints are configured on Configuration
–
Primary Enrolled Certificate—Select the trustpoint to use for certificates on this interface.
–
Load Balancing Enrolled Certificate—Select a trustpoint to be used for certificates when VPN
load balancing is configured.
•Fallback Certificate—Click to select a certificate to use for interfaces that have no certificate
associated with them. If you select None, the ASA uses the default RSA key-pair and certificate.
•Forced Certification Authentication Timeout- Configure the number of minutes to wait before
timing out certificate authentication.
•Apply—Click to apply your changes.
•Reset—Click to remove changes you have made and reset SSL parameters to the values that they
held when you opened the window.
SSL
any The ASA sends SSL version3 hellos, and negotiates either SSL version 3 or
TLS version 1.
sslv3-only The security appliance sends SSL version 3 hellos, and accepts only SSL
version 3.
tlsv1-only The security appliance sends TLSv1 client hellos, and accepts only TLS
version 1.

CHAPTER
13-1
Cisco ASA Series VPN ASDM Configuration Guide
13
Configuring an External Server for Authorization
and Authentication
This chapter describes how to configure an external LDAP, RADIUS, or TACACS+ server to support
AAA for the ASA. Before you configure the ASA to use an external server, you must configure the AAA
server with the correct ASA authorization attributes and, from a subset of these attributes, assign specific
permissions to individual users.
Understanding Policy Enforcement of Authorization Attributes
The ASA supports several methods of applying user authorization attributes (also called user
entitlements or permissions) to VPN connections. You can configure the ASA to obtain user attributes
from any combination of:
•a Dynamic Access Policy (DAP) on the ASA
•an external RADIUS or LDAP authentication and/or authorization server
•a group policy on the ASA
If the ASA receives attributes from all sources, the attributes are evaluated, merged, and applied to the
user policy. If there are conflicts between attributes, the DAP attributes take precedence.
The ASA applies attributes in the following order (see Figure 13-1).
1. DAP attributes on the ASA—Introduced in Version 8.0(2), these attributes take precedence over all
others. If you set a bookmark or URL list in DAP, it overrides a bookmark or URL list set in the
group policy.
2. User attributes on the AAA server—The server returns these attributes after successful user
authentication and/or authorization. Do not confuse these with attributes that are set for individual
users in the local AAA database on the ASA (User Accounts in ASDM).
3. Group policy configured on the ASA—If a RADIUS server returns the value of the RADIUS CLASS
attribute IETF-Class-25 (OU=group-policy) for the user, the ASA places the user in the group policy
of the same name and enforces any attributes in the group policy that are not returned by the server.
For LDAP servers, any attribute name can be used to set the group policy for the session. The LDAP
attribute map that you configure on the ASA maps the LDAP attribute to the Cisco attribute
IETF-Radius-Class.
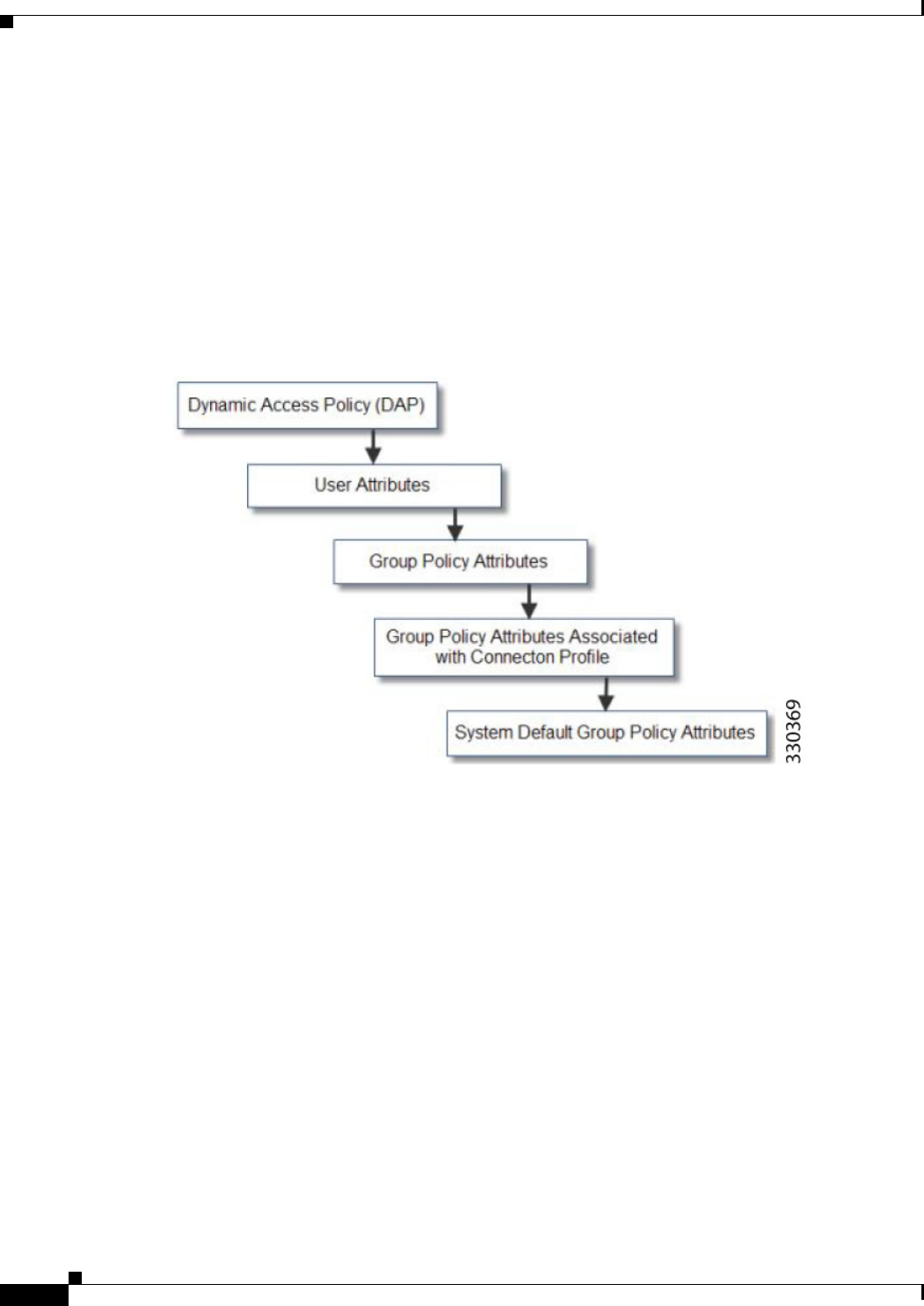
13-2
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 13 Configuring an External Server for Authorization and Authentication
Understanding Policy Enforcement of Authorization Attributes
4. Group policy assigned by the Connection Profile (called tunnel-group in the CLI)—The Connection
Profile has the preliminary settings for the connection, and includes a default group policy applied
to the user before authentication. All users connecting to the ASA initially belong to this group,
which provides any attributes that are missing from the DAP, user attributes returned by the server,
or the group policy assigned to the user.
5. Default group policy assigned by the ASA (DfltGrpPolicy)—System default attributes provide any
values that are missing from the DAP, user attributes, group policy, or connection profile.
Figure 13-1 Policy Enforcement Flow
Defining the ASA LDAP Configuration
Authorization refers to the process of enforcing permissions or attributes. An LDAP server defined as
an authentication or authorization server enforces permissions or attributes if they are configured.
Guidelines
The ASA enforces the LDAP attributes based on attribute name, not numeric ID. RADIUS attributes, are
enforced by numeric ID, not by name.
For ASDM Version 7.0, LDAP attributes include the cVPN3000 prefix. For ASDM Versions 7.1 and
later, this prefix was removed.
LDAP attributes are a subet of the Radius attributes, which are listed in the Radius chapter.
Active Directory/LDAP VPN Remote Access Authorization Examples
This section presents example procedures for configuring authentication and authorization on the ASA
using the Microsoft Active Directory server. It includes the following topics:
•User-Based Attributes Policy Enforcement, page 13-3

13-3
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 13 Configuring an External Server for Authorization and Authentication
Understanding Policy Enforcement of Authorization Attributes
•Placing LDAP Users in a Specific Group Policy, page 13-5
•Enforcing Static IP Address Assignment for AnyConnect Tunnels, page 13-7
•Enforcing Dial-in Allow or Deny Access, page 13-9
•Enforcing Logon Hours and Time-of-Day Rules, page 13-12
Other configuration examples available on Cisco.com include the following TechNotes.
•ASA/PIX: Mapping VPN Clients to VPN Group Policies Through LDAP Configuration Example at
the following URL:
http://www.cisco.com/en/US/products/ps6120/products_configuration_example09186a008089149
d.shtml
•PIX/ASA 8.0: Use LDAP Authentication to Assign a Group Policy at Login at the following URL:
http://www.cisco.com/en/US/products/ps6120/products_configuration_example09186a00808d1a7
c.shtml
User-Based Attributes Policy Enforcement
You can map any standard LDAP attribute to a well-known Vendor-Specific Attribute (VSA), and you
can map one or more LDAP attribute(s) to one or more Cisco LDAP attributes.
The following example shows how to configure the ASA to enforce a simple banner for a user who is
configured on an AD LDAP server. On the server, use the Office field in the General tab to enter the
banner text. This field uses the attribute named physicalDeliveryOfficeName. On the ASA, create an
attribute map that maps physicalDeliveryOfficeName to the Cisco attribute Banner1. During
authentication, the ASA retrieves the value of physicalDeliveryOfficeName from the server, maps the
value to the Cisco attribute Banner1, and displays the banner to the user.
This example applies to any connection type, including the IPsec VPN client, AnyConnect SSL VPN
client, or clientless SSL VPN. In the example, User1 connects through a clientless SSL VPN connection.
To configure the attributes for a user on the AD or LDAP Server, perform the following steps:
Step 1 Right-click a user.
The Properties dialog box appears (see Figure 13-2).
Step 2 Click the General tab and enter banner text in the Office field, which uses the AD/LDAP attribute
physicalDeliveryOfficeName.
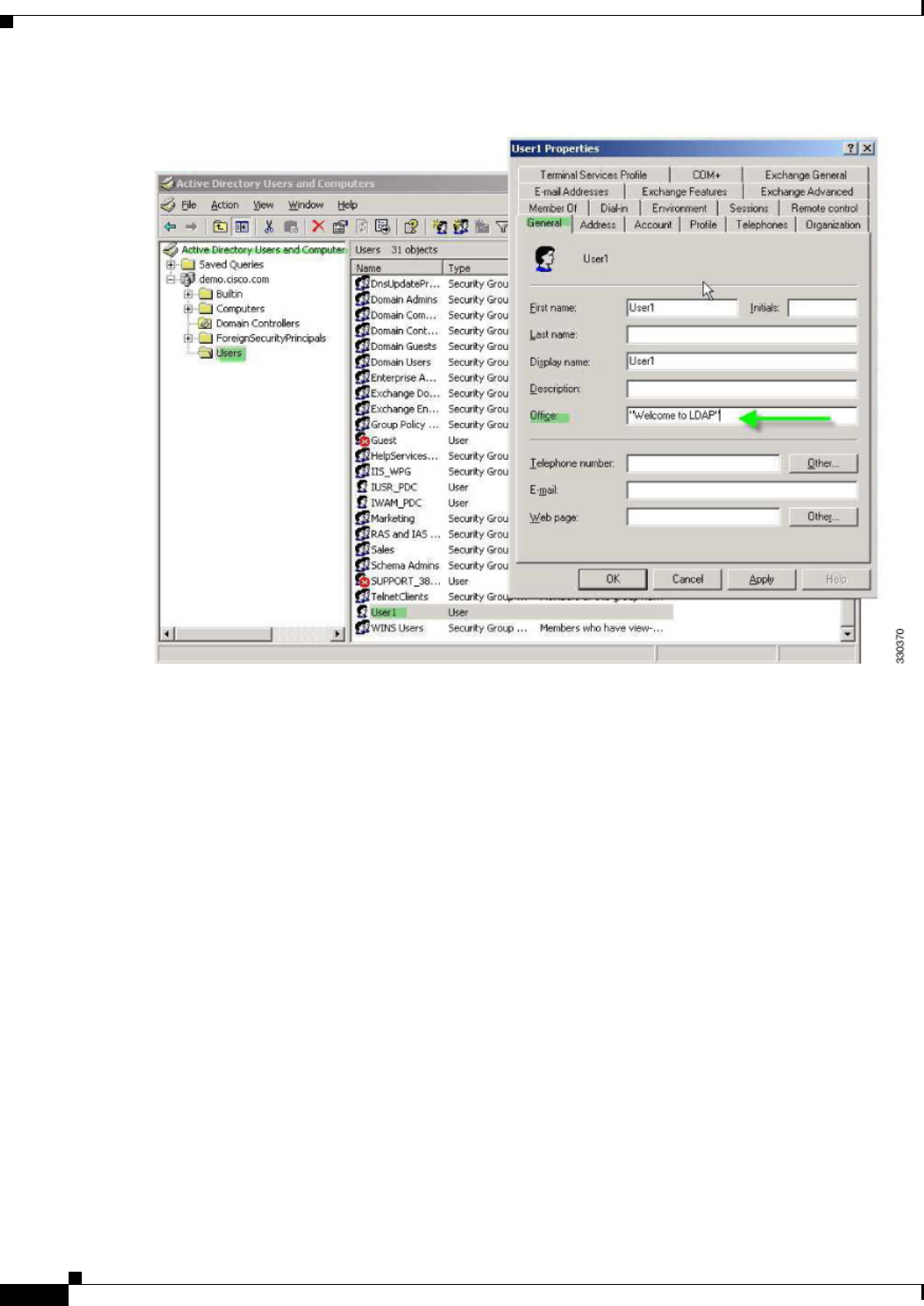
13-4
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 13 Configuring an External Server for Authorization and Authentication
Understanding Policy Enforcement of Authorization Attributes
Figure 13-2 LDAP User Configuration
Step 3 Create an LDAP attribute map on the ASA.
The following example creates the map Banner and maps the AD/LDAP attribute
physicalDeliveryOfficeName to the Cisco attribute Banner1:
ciscoasa(config)# ldap attribute-map Banner
ciscoasa(config-ldap-attribute-map)# map-name physicalDeliveryOfficeName Banner1
Step 4 Associate the LDAP attribute map to the AAA server.
The following example enters the aaa server host configuration mode for the host 10.1.1.2 in the AAA
server group MS_LDAP, and associates the attribute map Banner that you created in Step 3:
ciscoasa(config)# aaa-server MS_LDAP host 10.1.1.2
ciscoasa(config-aaa-server-host)# ldap-attribute-map Banner
Step 5 Test the banner enforcement.
The following example shows a clientless SSL connection and the banner enforced through the attribute
map after the user authenticates (see Figure 13-3).
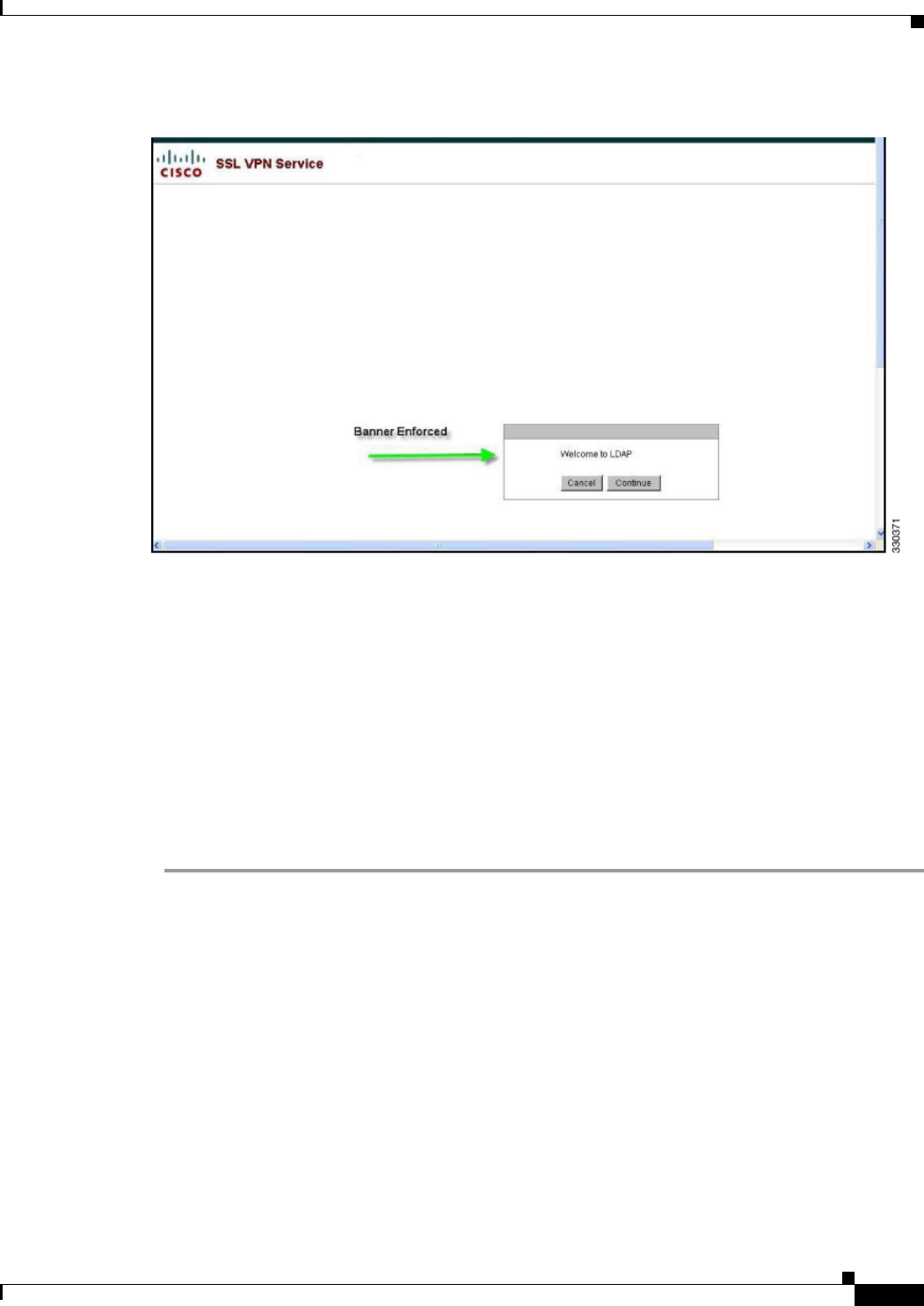
13-5
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 13 Configuring an External Server for Authorization and Authentication
Understanding Policy Enforcement of Authorization Attributes
Figure 13-3 Banner Displayed
Placing LDAP Users in a Specific Group Policy
The following example shows how to authenticate User1 on the AD LDAP server to a specific group
policy on the ASA. On the server, use the Department field of the Organization tab to enter the name of
the group policy. Then create an attribute map, and map Department to the Cisco attribute
IETF-Radius-Class. During authentication, the ASA retrieves the value of Department from the server,
maps the value to the IETF-Radius-Class, and places User1 in the group policy.
This example applies to any connection type, including the IPsec VPN client, AnyConnect SSL VPN
client, or clientless SSL VPN. In this example, User1 is connecting through a clientless SSL VPN
connection.
To configure the attributes for the user on the AD LDAP server, perform the following steps:
Step 1 Right-click the user.
The Properties dialog box appears (see Figure 13-4).
Step 2 Click the Organization tab and enter Group-Policy-1 in the Department field.
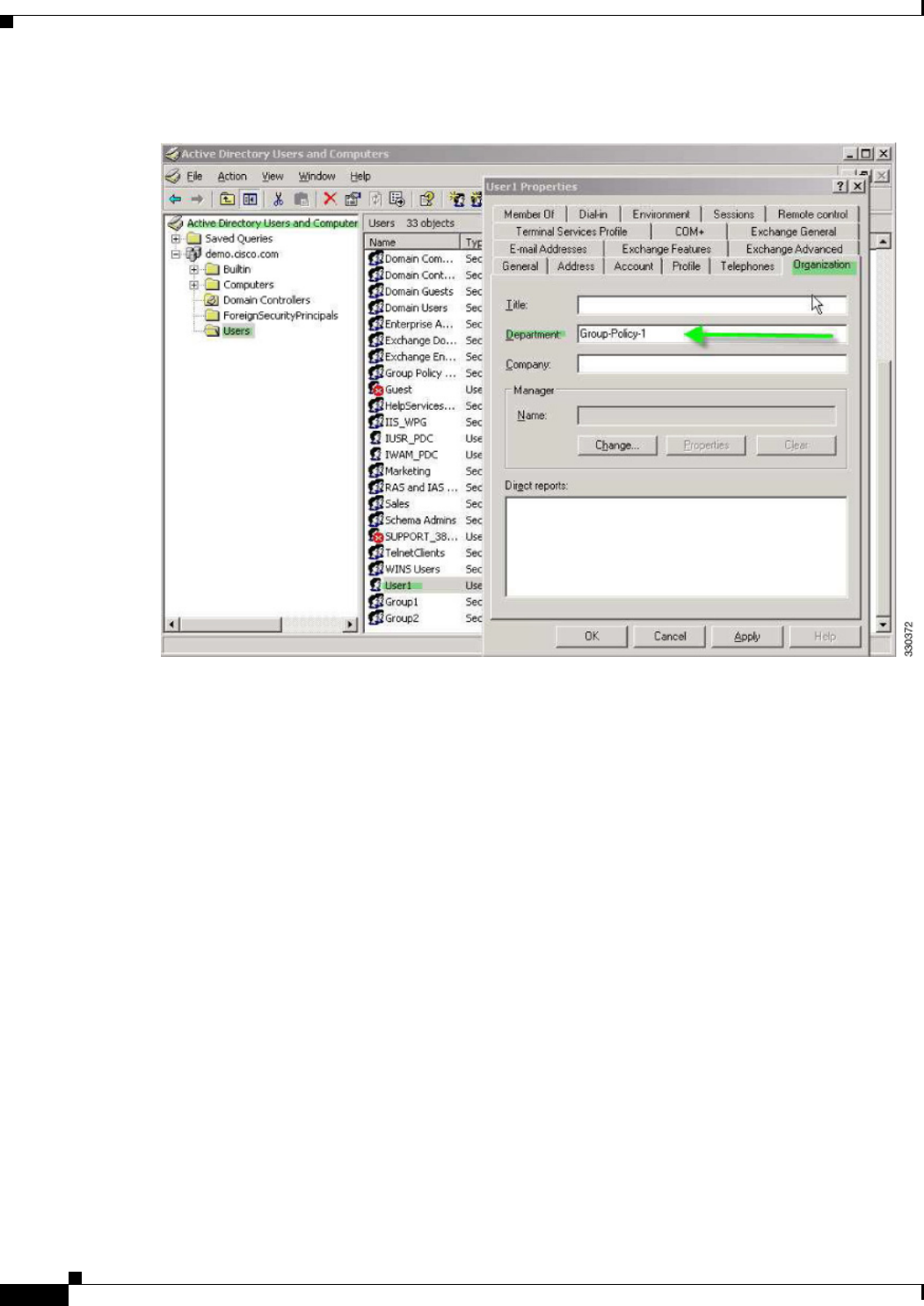
13-6
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 13 Configuring an External Server for Authorization and Authentication
Understanding Policy Enforcement of Authorization Attributes
Figure 13-4 AD/LDAP Department Attribute
Step 3 Define an attribute map for the LDAP configuration shown in Step 1.
The following example shows how to map the AD attribute Department to the Cisco attribute
IETF-Radius-Class.
ciscoasa(config)# ldap attribute-map group_policy
ciscoasa(config-ldap-attribute-map)# map-name Department IETF-Radius-Class
Step 4 Associate the LDAP attribute map to the AAA server.
The following example enters the aaa server host configuration mode for the host 10.1.1.2 in the AAA
server group MS_LDAP, and associates the attribute map group_policy that you created in Step 3:
ciscoasa(config)# aaa-server MS_LDAP host 10.1.1.2
ciscoasa(config-aaa-server-host)# ldap-attribute-map group_policy
Step 5 Add the new group-policy on the ASA and configure the required policy attributes that will be assigned
to the user. The following example creates Group-policy-1, the name entered in the Department field on
the server:
ciscoasa(config)# group-policy Group-policy-1 external server-group LDAP_demo
ciscoasa(config-aaa-server-group)#
Step 6 Establish the VPN connection as the user would, and verify that the session inherits the attributes from
Group-Policy1 (and any other applicable attributes from the default group-policy).
Step 7 Monitor the communication between the ASA and the server by enabling the debug ldap 255 command
from privileged EXEC mode. The following is sample output from this command, which has been edited
to provide the key messages:
[29] Authentication successful for user1 to 10.1.1.2
[29] Retrieving user attributes from server 10.1.1.2
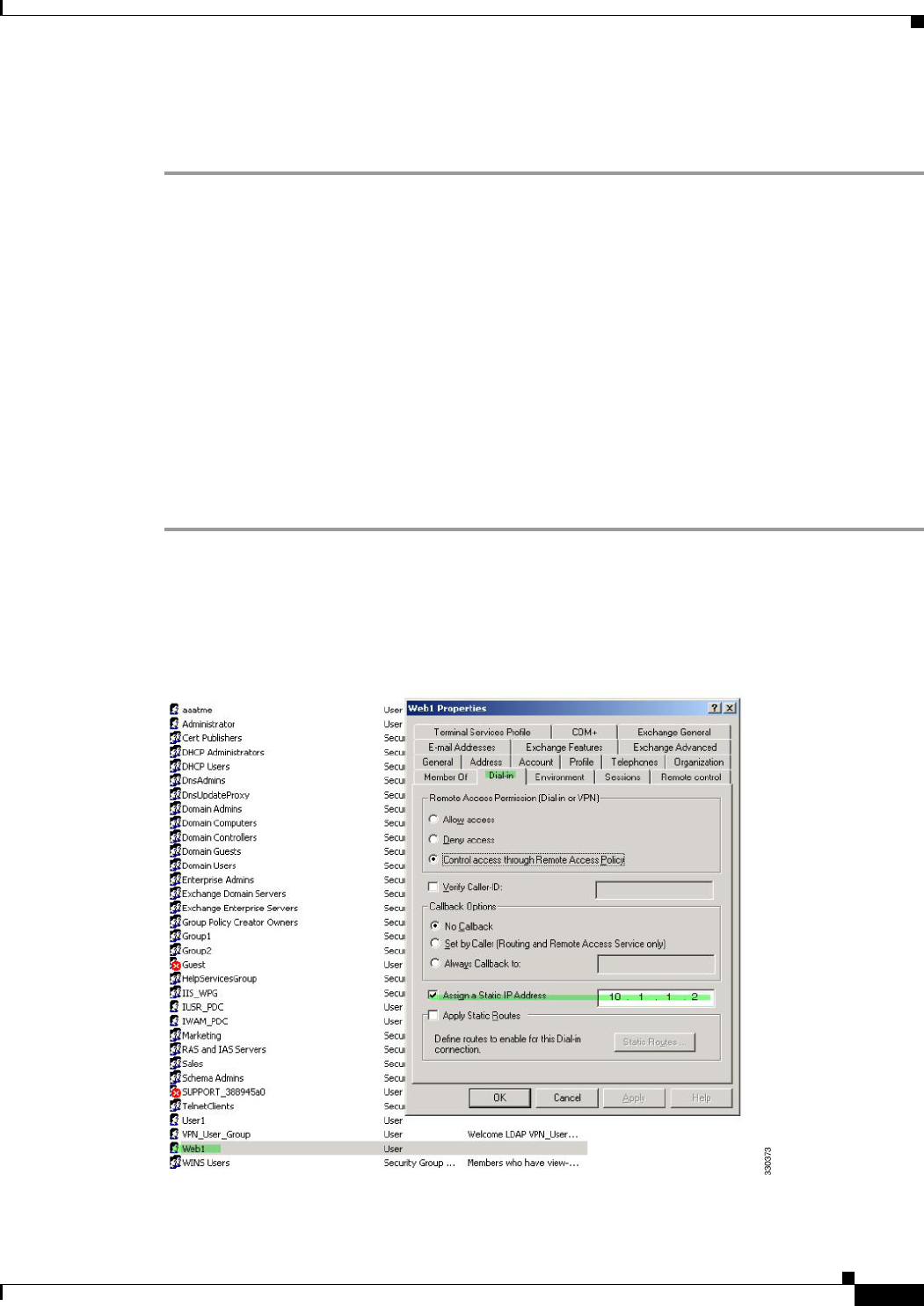
13-7
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 13 Configuring an External Server for Authorization and Authentication
Understanding Policy Enforcement of Authorization Attributes
[29] Retrieved Attributes:
[29] department: value = Group-Policy-1
[29] mapped to IETF-Radius-Class: value = Group-Policy-1
Enforcing Static IP Address Assignment for AnyConnect Tunnels
In this example, configure the AnyConnect client user Web1 to receive a static IP address. then enter the
address in the Assign Static IP Address field of the Dialin tab on the AD LDAP server. This field uses
the msRADIUSFramedIPAddress attribute. Create an attribute map that maps this attribute to the Cisco
attribute IETF-Radius-Framed-IP-Address.
During authentication, the ASA retrieves the value of msRADIUSFramedIPAddress from the server,
maps the value to the Cisco attribute IETF-Radius-Framed-IP-Address, and provides the static address
to User1.
The following example applies to full-tunnel clients, including the IPsec client and the SSL VPN clients
(AnyConnect client 2.x and the SSL VPN client).
To configure the user attributes on the AD /LDAP server, perform the following steps:
Step 1 Right-click the username.
The Properties dialog box appears (see Figure 13-5).
Step 2 Click the Dialin tab, check the Assign Static IP Address check box, and enter an IP address of 10.1.1.2.
Figure 13-5 Assign Static IP Address
Step 3 Create an attribute map for the LDAP configuration shown in Step 1.
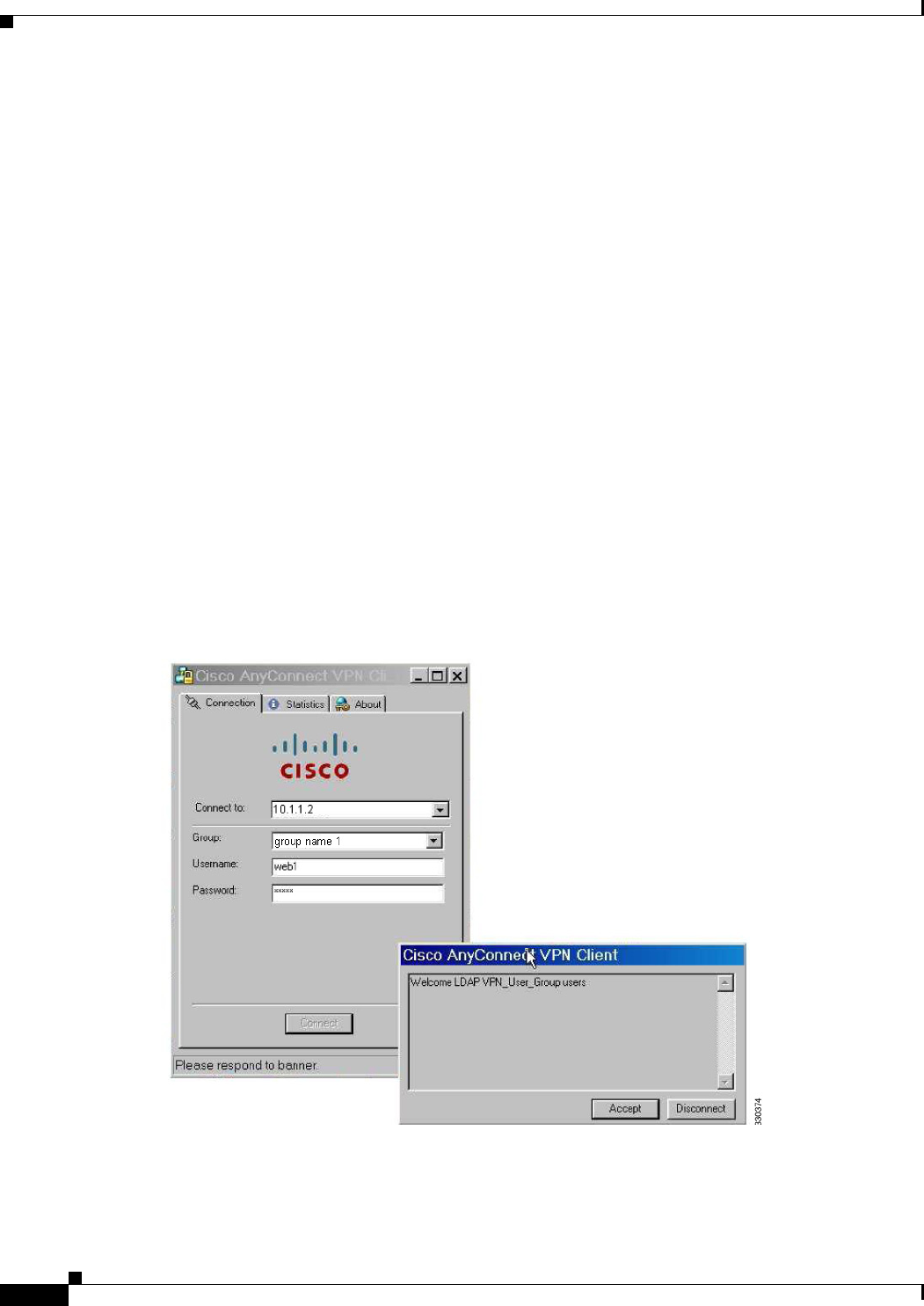
13-8
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 13 Configuring an External Server for Authorization and Authentication
Understanding Policy Enforcement of Authorization Attributes
The following example shows how to map the AD attribute msRADIUSFramedIPAddress used by the
Static Address field to the Cisco attribute IETF-Radius-Framed-IP-Address:
ciscoasa(config)# ldap attribute-map static_address
ciscoasa(config-ldap-attribute-map)# map-name msRADIUSFramedIPAddress
IETF-Radius-Framed-IP-Address
Step 4 Associate the LDAP attribute map to the AAA server.
The following example enters the aaa server host configuration mode for the host 10.1.1.2, in the AAA
server group MS_LDAP, and associates the attribute map static_address that you created in Step 3:
ciscoasa(config)# aaa-server MS_LDAP host 10.1.1.2
ciscoasa(config-aaa-server-host)# ldap-attribute-map static_address
Step 5 Verify that the vpn-address-assignment command is configured to specify AAA by viewing this part
of the configuration with the show run all vpn-addr-assign command:
ciscoasa(config)# show run all vpn-addr-assign
vpn-addr-assign aaa << Make sure this is configured >>
no vpn-addr-assign dhcp
vpn-addr-assign local
ciscoasa(config)#
Step 6 Establish a connection to the ASA with the AnyConnect client. Observe the following:
•The banner is received in the same sequence as a clientless connection (see Figure 13-6).
•The user receives the IP address configured on the server and mapped to the ASA (see Figure 13-7).
Figure 13-6 Verify the Banner for the AnyConnect Session
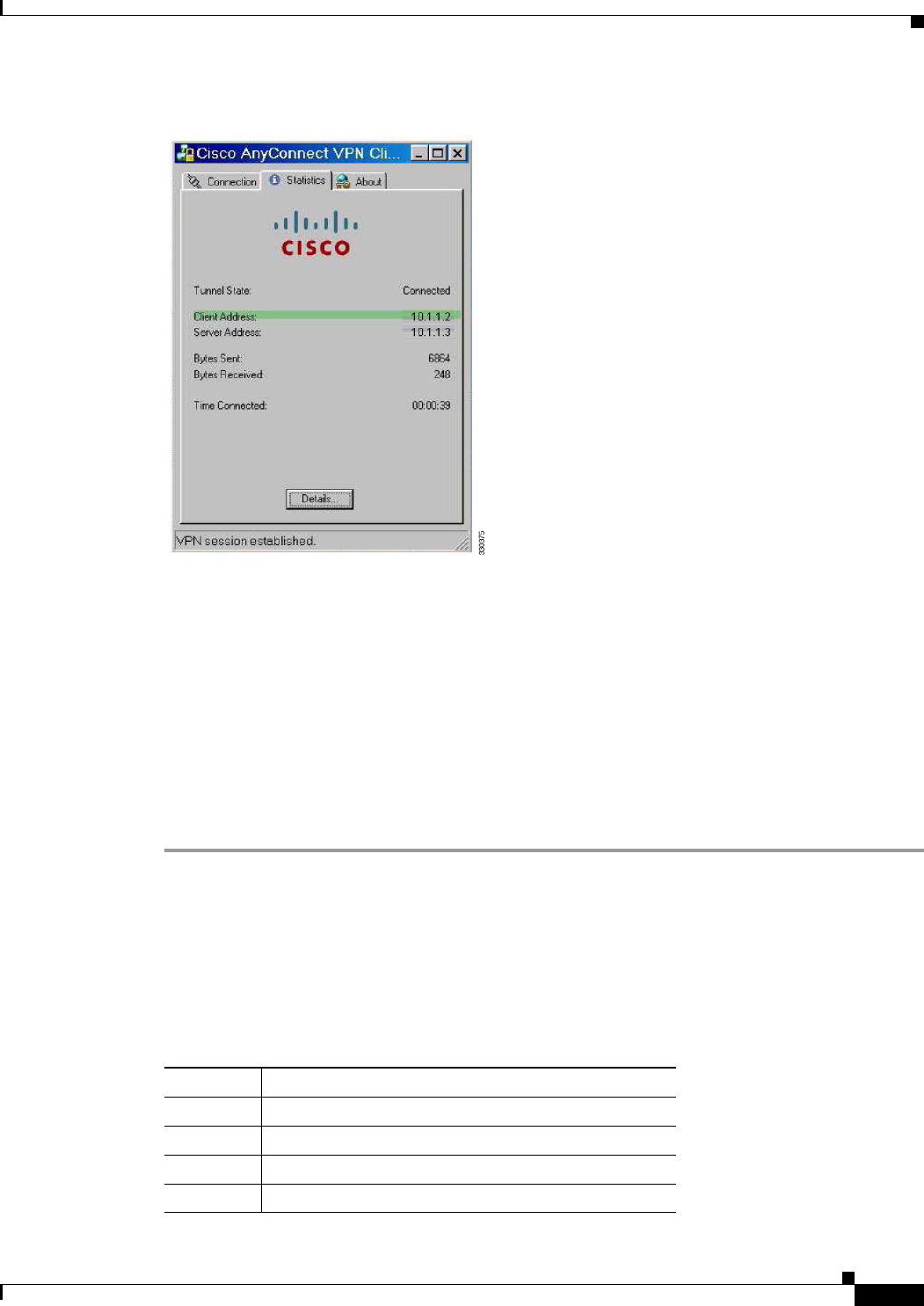
13-9
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 13 Configuring an External Server for Authorization and Authentication
Understanding Policy Enforcement of Authorization Attributes
Figure 13-7 AnyConnect Session Established
Step 7 Use the show vpn-sessiondb svc command to view the session details and verify the address assigned:
ciscoasa# show vpn-sessiondb svc
Session Type: SVC
Username : web1 Index : 31
Assigned IP : 10.1.1.2 Public IP : 10.86.181.70
Protocol : Clientless SSL-Tunnel DTLS-Tunnel
Encryption : RC4 AES128 Hashing : SHA1
Bytes Tx : 304140 Bytes Rx : 470506
Group Policy : VPN_User_Group Tunnel Group : Group1_TunnelGroup
Login Time : 11:13:05 UTC Tue Aug 28 2007
Duration : 0h:01m:48s
NAC Result : Unknown
VLAN Mapping : N/A VLAN : none
Enforcing Dial-in Allow or Deny Access
The following example creates an LDAP attribute map that specifies the tunneling protocols allowed by
the user. You map the allow access and deny access settings on the Dialin tab to the Cisco attribute
Tunneling-Protocol, which supports the bitmap values shown in Table 13-1:
Table 13-1 Bitmap Values for Cisco Tunneling-Protocol Attribute
Value Tunneling Protocol
1 PPTP
2L2TP
41IPsec (IKEv1)
82L2TP/IPsec
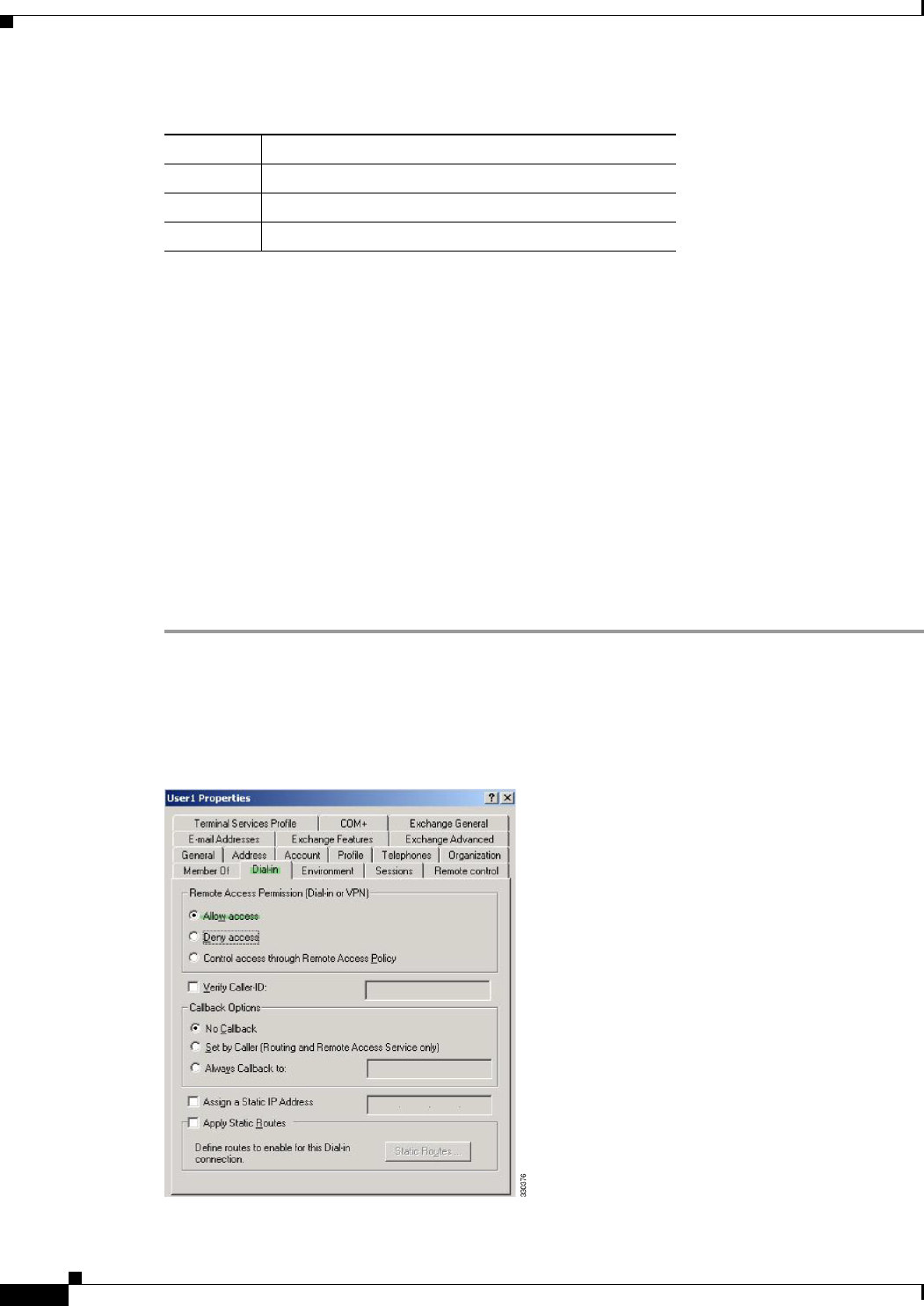
13-10
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 13 Configuring an External Server for Authorization and Authentication
Understanding Policy Enforcement of Authorization Attributes
Use this attribute to create an Allow Access (TRUE) or a Deny Access (FALSE) condition for the
protocols, and enforce the method for which the user is allowed access.
For this simplified example, by mapping the tunnel protocol IPsec/IKEv1 (4), you can create an allow
(true) condition for the Cisco VPN client. You also map WebVPN (16) and SVC/AC (32), which are
mapped as a value of 48 (16+32) and create a deny (false) condition. This allows the user to connect to
the ASA using IPsec, but any attempt to connect using clientless SSL or the AnyConnect client is denied.
Another example of enforcing dial-in allow access or deny access is available in the Tech Note ASA/PIX:
Mapping VPN Clients to VPN Group Policies Through LDAP Configuration Example at the following
URL:
http://www.cisco.com/en/US/products/ps6120/products_configuration_example09186a008089149d.shtml
To configure the user attributes on the AD/LDAP server, perform the following steps:
Step 1 Right-click the user.
The Properties dialog box appears.
Step 2 Click the Dial-in tab, then click the Allow Access radio button (Figure 13-8).
Figure 13-8 AD/LDAP User1 - Allow Access
16 Clientless SSL
32 SSL client—AnyConnect or SSL VPN client
64 IPsec (IKEv2)
1. IPsec and L2TP over IPsec are not supported simultaneously. Therefore, the values
4 and 8 are mutually exclusive.
2. See note 1.
Table 13-1 Bitmap Values for Cisco Tunneling-Protocol Attribute (continued)
Value Tunneling Protocol
13-11
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 13 Configuring an External Server for Authorization and Authentication
Understanding Policy Enforcement of Authorization Attributes
Note If you select the Control access through the Remote Access Policy option, then a value is not
returned from the server, and the permissions that are enforced are based on the internal group
policy settings of the ASA.
Step 3 Create an attribute map to allow both an IPsec and AnyConnect connection, but deny a clientless SSL
connection.
The following example shows how to create the map tunneling_protocols, and map the AD attribute
msNPAllowDialin used by the Allow Access setting to the Cisco attribute Tunneling-Protocols using the
map-name command, and add map values with the map-value command:
ciscoasa(config)# ldap attribute-map tunneling_protocols
ciscoasa(config-ldap-attribute-map)# map-name msNPAllowDialin Tunneling-Protocols
ciscoasa(config-ldap-attribute-map)# map-value msNPAllowDialin FALSE 48
ciscoasa(config-ldap-attribute-map)# map-value msNPAllowDialin TRUE 4
Step 4 Associate the LDAP attribute map to the AAA server.
The following example enters the aaa server host configuration mode for the host 10.1.1.2, in the AAA
server group MS_LDAP, and associates the attribute map tunneling_protocols that you created in Step 2:
ciscoasa(config)# aaa-server MS_LDAP host 10.1.1.2
ciscoasa(config-aaa-server-host)# ldap-attribute-map tunneling_protocols
Step 5 Verify that the attribute map works as configured.
Step 6 Try connections using clientless SSL, the AnyConnect client, and the IPsec client. The clientless and
AnyConnect connections should fail, and the user should be informed that an unauthorized connection
mechanism was the reason for the failed connection. The IPsec client should connect because IPsec is
an allowed tunneling protocol according to the attribute map (see Figure 13-9 and Figure 13-10).
Figure 13-9 Login Denied Message for Clientless User
13-12
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 13 Configuring an External Server for Authorization and Authentication
Understanding Policy Enforcement of Authorization Attributes
Figure 13-10 Login Denied Message for AnyConnect Client User
Enforcing Logon Hours and Time-of-Day Rules
The following example shows how to configure and enforce the hours that a clientless SSL user (such as
a business partner) is allowed to access the network.
On the AD server, use the Office field to enter the name of the partner, which uses the
physicalDeliveryOfficeName attribute. Then we create an attribute map on the ASA to map that attribute
to the Cisco attribute Access-Hours. During authentication, the ASA retrieves the value of
physicalDeliveryOfficeName and maps it to Access-Hours.
To configure the user attributes on the AD /LDAP server, perform the following steps:
Step 1 Select the user, and right-click Properties.
The Properties dialog box appears (see Figure 13-11).
Step 2 Click the General tab.
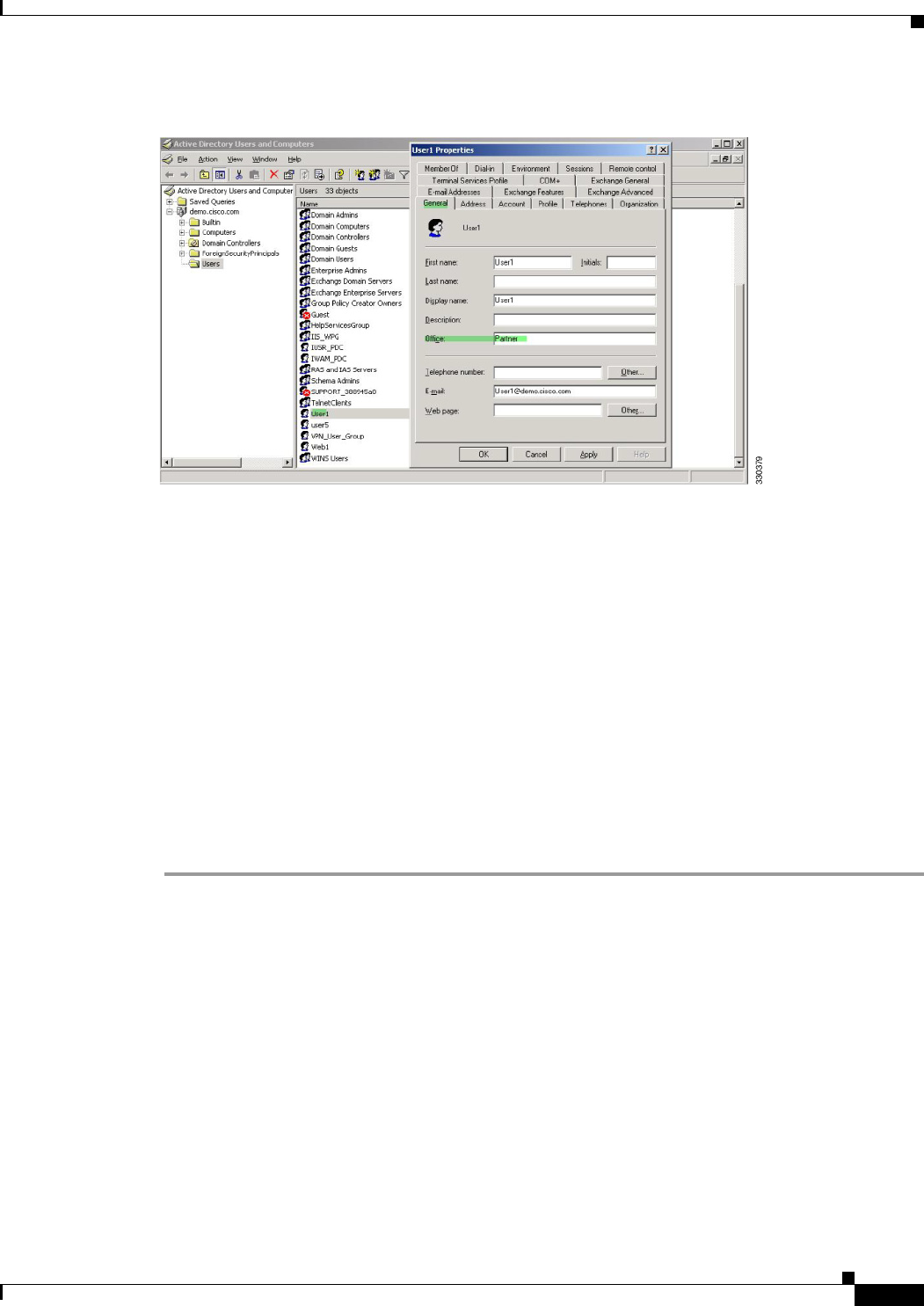
13-13
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 13 Configuring an External Server for Authorization and Authentication
Understanding Policy Enforcement of Authorization Attributes
Figure 13-11 Active Directory Properties Dialog Box
Step 3 Create an attribute map.
The following example shows how to create the attribute map access_hours and map the AD attribute
physicalDeliveryOfficeName used by the Office field to the Cisco attribute Access-Hours.
ciscoasa(config)# ldap attribute-map access_hours
ciscoasa(config-ldap-attribute-map)# map-name physicalDeliveryOfficeName Access-Hours
Step 4 Associate the LDAP attribute map to the AAA server.
The following example enters the aaa server host configuration mode for the host 10.1.1.2, in the AAA
server group MS_LDAP, and associates the attribute map access_hours that you created in Step 3:
ciscoasa(config)# aaa-server MS_LDAP host 10.1.1.2
ciscoasa(config-aaa-server-host)# ldap-attribute-map access_hours
Step 5 Configure time ranges for each value allowed on the server.
The following example configures Partner access hours from 9am to 5pm Monday through Friday:
ciscoasa(config)# time-range Partner
ciscoasa(config-time-range)# periodic weekdays 09:00 to 17:00
Example of Creating a Group Policy for a Local User
Prerequisites
This procedure describes how to edit an existing user. To add a user select Configuration > Remote
Access VPN > AAA/Local Users > Local Users and click Add. For more information see “Adding a
User Account to the Local Database” section on page 33-3.

13-14
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 13 Configuring an External Server for Authorization and Authentication
Understanding Policy Enforcement of Authorization Attributes
Guidelines
By default, the Inherit check box is checked for each setting on the Edit User Account screen, which
means that the user account inherits the value of that setting from the default group policy,
DfltGrpPolicy.
To override each setting, uncheck the Inherit check box, and enter a new value. The detailed steps that
follow describe each of the settings on the Edit User Account screen.
Detailed Steps
Step 1 Start ASDM and select Configuration > Remote Access VPN > AAA/Local Users > Local Users.
Step 2 Select the user you want configure and click Edit.
The Edit User Account screen opens.
Step 3 In the left-hand pane, click VPN Policy.
Step 4 Specify a group policy for the user. The user policy will inherit the attributes of this group policy. If there
are other fields on this screen that are set to Inherit the configuration from the Default Group Policy, the
attributes specified in this group policy will take precedence over those set in the Default Group Policy.
Step 5 Specify which tunneling protocols are available for the user, or whether the value is inherited from the
group policy. Check the desired Tunneling Protocols check boxes to choose one of the following
tunneling protocols:
•Clientless SSL VPN (VPN via SSL/TLS) uses a web browser to establish a secure remote-access
tunnel to a VPN Concentrator; requires neither a software nor hardware client. Clientless SSL VPN
can provide easy access to a broad range of enterprise resources, including corporate websites,
web-enabled applications, NT/AD file shares (web-enabled), e-mail, and other TCP-based
applications from almost any computer that can reach HTTPS Internet sites.
•The SSL VPN Client lets users connect after downloading the Cisco AnyConnect Client application.
Users use a clientless SSL VPN connection to download this application the first time. Client
updates then occur automatically as needed whenever the user connects.
•IPsec IKEv1—IP Security Protocol. Regarded as the most secure protocol, IPsec provides the most
complete architecture for VPN tunnels. Both Site-to-Site (peer-to-peer) connections and Cisco VPN
client-to-LAN connections can use IPsec IKEv1.
•IPsec IKEv2—Supported by the AnyConnect Secure Mobility Client. AnyConnect connections
using IPsec with IKEv2 provide advanced features such as software updates, client profiles, GUI
localization (translation) and customization, Cisco Secure Desktop, and SCEP proxy.
•L2TP over IPsec allows remote users with VPN clients provided with several common PC and
mobile PC operating systems to establish secure connections over the public IP network to the ASA
and private corporate networks.
Note If no protocol is selected, an error message appears.
Step 6 Specify which filter (IPv4 or IPv6) to use, or whether to inherit the value from the group policy. Filters
consist of rules that determine whether to allow or reject tunneled data packets coming through the ASA,
based on criteria such as source address, destination address, and protocol. To configure filters and rules,
choose Configuration > Remote Access VPN > Network (Client) Access > Group Policies >
Add/Edit > General > More Options > Filter.
13-15
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 13 Configuring an External Server for Authorization and Authentication
Understanding Policy Enforcement of Authorization Attributes
Click Manage to display the ACL Manager pane, on which you can add, edit, and delete ACLs and
ACEs.
Step 7 Specify whether to inherit the Connection Profile (tunnel group) lock or to use the selected tunnel group
lock, if any. Selecting a specific lock restricts users to remote access through this group only. Tunnel
Group Lock restricts users by checking if the group configured in the VPN client is the same as the users
assigned group. If it is not, the ASA prevents the user from connecting. If the Inherit check box is not
checked, the default value is None.
Step 8 Specify whether to inherit the Store Password on Client System setting from the group. Uncheck the
Inherit check box to activate the Yes and No radio buttons. Click Ye s to store the login password on the
client system (potentially a less-secure option). Click No (the default) to require the user to enter the
password with each connection. For maximum security, we recommend that you not allow password
storage. This parameter has no effect on interactive hardware client authentication or individual user
authentication for a VPN 3002.
Step 9 Specify an Access Hours policy to apply to this user, create a new access hours policy for the user, or
leave the Inherit box checked. The default value is Inherit, or, if the Inherit check box is not checked,
the default value is Unrestricted.
Click Manage to open the Add Time Range dialog box, in which you can specify a new set of access
hours.
Step 10 Specify the number of simultaneous logins by the user. The Simultaneous Logins parameter specifies the
maximum number of simultaneous logins allowed for this user. The default value is 3. The minimum
value is 0, which disables login and prevents user access.
Note While there is no maximum limit, allowing several simultaneous connections could compromise
security and affect performance.
Step 11 Specify the maximum connection time for the user connection time in minutes. At the end of this time,
the system terminates the connection. The minimum is 1 minute, and the maximum is 2147483647
minutes (over 4000 years, should we all be so lucky). To allow unlimited connection time, check the
Unlimited check box (the default).
Step 12 Specify the Idle Timeout for the user in minutes. If there is no communication activity on the connection
by this user in this period, the system terminates the connection. The minimum time is 1 minute, and the
maximum time is 10080 minutes. This value does not apply to users of clientless SSL VPN connections.
Step 13 Configure the Session Alert Interval. If you uncheck the Inherit check box, the Default check box is
checked automatically. This sets the session alert interval to 30 minutes. If you want to specify a new
value, uncheck the Default check box and specify a session alert interval from 1 to 30 minutes in the
minutes box.
Step 14 Configure the Idle Alert Interval. If you uncheck the Inherit check box, the Default check box is checked
automatically. This sets the idle alert interval to 30 minutes. If you want to specify a new value, uncheck
the Default check box and specify a session alert interval from 1 to 30 minutes in the minutes box.
Step 15 To set a dedicated IPv4 address for this user, enter an IPv4 address and subnet mask in the Dedicated
IPv4 Address (Optional) area.
Step 16 To set a dedicated IPv6 address for this user, enter an IPv6 address with an IPv6 prefix in the Dedicated
IPv6 Address (Optional) field. The IPv6 prefix indicates the subnet on which the IPv6 address resides.
Step 17 To configure clientless SSL settings, in the left-hand pane, click Clientless SSL VPN. To override each
setting, uncheck the Inherit check box, and enter a new value.
Step 18 Click Apply.

13-16
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 13 Configuring an External Server for Authorization and Authentication
Understanding Policy Enforcement of Authorization Attributes
The changes are saved to the running configuration.

13-17
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 13 Configuring an External Server for Authorization and Authentication
Understanding Policy Enforcement of Authorization Attributes

13-18
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 13 Configuring an External Server for Authorization and Authentication
Understanding Policy Enforcement of Authorization Attributes

13-19
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 13 Configuring an External Server for Authorization and Authentication
Understanding Policy Enforcement of Authorization Attributes

13-20
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 13 Configuring an External Server for Authorization and Authentication
Understanding Policy Enforcement of Authorization Attributes

13-21
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 13 Configuring an External Server for Authorization and Authentication
Understanding Policy Enforcement of Authorization Attributes

13-22
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 13 Configuring an External Server for Authorization and Authentication
Understanding Policy Enforcement of Authorization Attributes

P
ART
2
Configuring a Clientless SSL VPN

CHAPTER
11-1
Cisco ASA Series VPN ASDM Configuration Guide
11
Introduction to Clientless SSL VPN
September 13, 2013
Introduction to Clientless SSL VPN
Clientless SSL VPN enables end users to securely access resources on the corporate network from
anywhere using an SSL-enabled Web browser. The user first autehnticates with a Clientless SSL VPN
gateway, which then allows the user to access pre-configured network resources.
Note Security contexts (also called firewall multimode) and Active/Active stateful failover are not supported
when Clientless SSL VPN is enabled.
Clientless SSL VPN creates a secure, remote-access VPN tunnel to an ASA using a Web browser without
requiring a software or hardware client. It provides secure and easy access to a broad range of Web
resources and both web-enabled and legacy applications from almost any device that can connect to the
Internet via HTTP. They include:
•Internal websites.
•Web-enabled applications.
•NT/Active Directory file shares.
•email proxies, including POP3S, IMAP4S, and SMTPS.
•Microsoft Outlook Web Access Exchange Server 2000, 2003, and 2007.
•Microsoft Web App to Exchange Server 2010 in 8.4(2) and later.
•Application Access (smart tunnel or port forwarding access to other TCP-based applications)
Clientless SSL VPN uses Secure Sockets Layer Protocol and its successor, Transport Layer Security
(SSL/TLS1) to provide the secure connection between remote users and specific, supported internal
resources that you configure at an internal server. The ASA recognizes connections that must be proxied,
and the HTTP server interacts with the authentication subsystem to authenticate users.
The network administrator provides access to resources by users of Clientless SSL VPN sessions on a
group basis. Users have no direct access to resources on the internal network.

11-2
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 11 Introduction to Clientless SSL VPN
Introduction to Clientless SSL VPN
Prerequisites
See the Supported VPN Platforms, Cisco ASA 5500 Series for the platforms and browsers supported by
ASA Release 9.0.
Guidelines and Limitations
•ActiveX pages require that you enable ActiveX Relay or enter activex-relay on the associated group
policy. If you do so or assign a smart tunnel list to the policy, and the browser proxy exception list
on the endpoint specifies a proxy, the user must add a “shutdown.webvpn.relay.” entry to that list.
•The ASA does not support clientless access to Windows Shares (CIFS) Web Folders from
Windows 7, Vista, Internet Explorer 8 to 10, Mac OS X, or Linux.
•Certificate authentication, including the DoD Common Access Card and SmartCard, works with the
Safari keychain only.
•The ASA does not support DSA or RSA certificates for Clientless SSL VPN connections.
•Some domain-based security products have requirements beyond those requests that originate from
the ASA.
•Configuration control inspection and other inspection features under the Modular Policy Framework
are not supported.
•Neither NAT or PAT is applicable to the client.
•Some components of Clientless SSL VPN require the Java Runtime Environment (JRE).With Mac
OS X v10.7 and later Java is not installed by default. For details of how to install Java on Mac OS X,
see http://java.com/en/download/faq/java_mac.xml.
When you have several group policies configured for the clientless portal, they are displayed in a
drop-down on the logon page. When the first group policy in the list requires a certificate, then the user
must have a matching certificate. If some of your group policies do not use certificates, you must
configure the list to display a non-certificate policy first. Alternatively, you may want to create a dummy
group policy with the name “0-Select-a-group.”
Tip You can control which policy is displayed first by naming your group polices alphabetically, or prefix
them with numbers. For example, 1-AAA, 2-Certificate.
CHAPTER
12-1
Cisco ASA Series VPN ASDM Configuration Guide
12
Basic Clientless SSL VPN Configuration
September 13, 2013
Clientless SSL VPN Security Precautions
By default, the ASA allows all portal traffic to all Web resources (for example HTTPS, CIFS, RDP, and
plug-ins). Clientless SSL VPN rewrites each URL to one that is meaningful only to the ASA. The user
cannot use this URL to confirm that they are connected to the website they requested. To avoid placing
users at risk from phishing websites, assign a Web ACL to the policies configured for clientless
access—group policies, dynamic access policies, or both—to control traffic flows from the portal. Cisco
recommends switching off URL Entry on these policies to prevent user confusion over what is
accessible.
Figure 12-1 Example URL Entered by User
Figure 12-2 Same URL Rewritten by Security Appliance and Displayed in Browser Window
DETAILED STEPS
Step 1 Configure a group policy for all users who need Clientless SSL VPN access, and enable Clientless SSL
VPN for that group policy only.
Step 2 With the group policy open, choose General > More Options > Web ACL and click Manage.

12-2
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 12 Basic Clientless SSL VPN Configuration
Configuring Clientless SSL VPN Access
Step 3 Create a Web ACL to do one of the following:
•Permit access only to specific targets within the private network.
•Permit access only to the private network, deny Internet access, or permit access only to reputable
sites.
Step 4 Assign the Web ACL to any policies (group policies, dynamic access policies, or both) that you have
configured for Clientless SSL VPN access. To assign a Web ACL to a DAP, edit the DAP record, and
select the Web ACL on the Network ACL Filters tab.
Step 5 Switch off URL Entry on the portal page, the page that opens upon the establishment of a browser-based
connection. Click Disable next to URL Entry on both the group policy Portal frame and the DAP
Functions tab. To switch off URL Entry on a DAP, use ASDM to edit the DAP record, click the
Functions tab, and check Disable next to URL Entry
Step 6 Instruct users to enter external URLs in the native browser address field above the portal page or open a
separate browser window to visit external sites.
Configuring Clientless SSL VPN Access
When configuring Clientless SSL VPN access, you can do the following:
•Enable or switch off ASA interfaces for Clientless SSL VPN sessions.
•Choose a port for Clientless SSL VPN connections.
•Set a maximum number of simultaneous Clientless SSL VPN sessions.
DETAILED STEPS
Step 1 To configure or create a group policy for clientless access, navigate to Configuration > Remote Access
VPN > Clientless SSL VPN Access > Group Policies pane.
Step 2 Navigate to Configuration > Remote Access VPN > Clientless SSL VPN Access > Connection
Profiles.
a. Enable or switch off Allow Access for each ASA interface.
The Interface columns list the configured interfaces. The WebVPN Enabled field displays the status
for Clientless SSL VPN on the interface. A green check next to Yes indicates that Clientless SSL
VPN is enabled. A red circle next to No indicates that Clientless SSL VPN is switched off.
b. Click Port Setting, and enter the port number (1 to 65535) to use for Clientless SSL VPN sessions.
The default is 443. If you change the port number, all current Clientless SSL VPN connections are
terminated, and current users must reconnect. You will also be prompted to reconnect the ASDM
session.
Step 3 Navigate to Configuration > Remote Access VPN > Advanced > Maximum VPN Sessions, and enter
the maximum number of Clientless SSL VPN sessions to allow in the Maximum Other VPN Sessions
field. Different ASA models support Clientless SSL VPN sessions as follows: ASA 5510 supports a
maximum of 250; ASA 5520 maximum is 750; ASA 5540 maximum is 2500; ASA 5550 maximum is
5000.

12-3
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 12 Basic Clientless SSL VPN Configuration
Verifying Clientless SSL VPN Server Certificates
Verifying Clientless SSL VPN Server Certificates
When connecting to a remote SSL-enabled server through Clientless SSL VPN, it is important to know
that you can trust the remote server, and that it is in fact the server you are trying to connect to. ASA 9.0
introduced support for SSL server certificate verification against a list of trusted certificate authority
(CA) certificates for Clientless SSL VPN.
When connecting to a remote server with a Web browser using the HTTPS protocol, the server provides
a digital certificate signed by a certificate authority (CA) to identify itself. Web browsers include a
collection of CA certificates which are used to verify the validity of the server certificate. This is a form
of public key infrastructure (PKI).
The ASA provides trusted pool certificate management facilities in the form of a trustpools. This can be
thought of as a special case of trustpoint representing multiple known CA certificates. The ASA includes
a default bundle of certificates, similar to that provided with Web browsers. It is inactive until activated
by the administrator.
Note ASA trustpools are similar but not identical to Cisco IOS trustpools.
Enabling HTTP Server Verification
Step 1 In the ASDM, navigate to Configuration > Remote Access VPN > Certificate Management > Trusted
Certificate Pool.
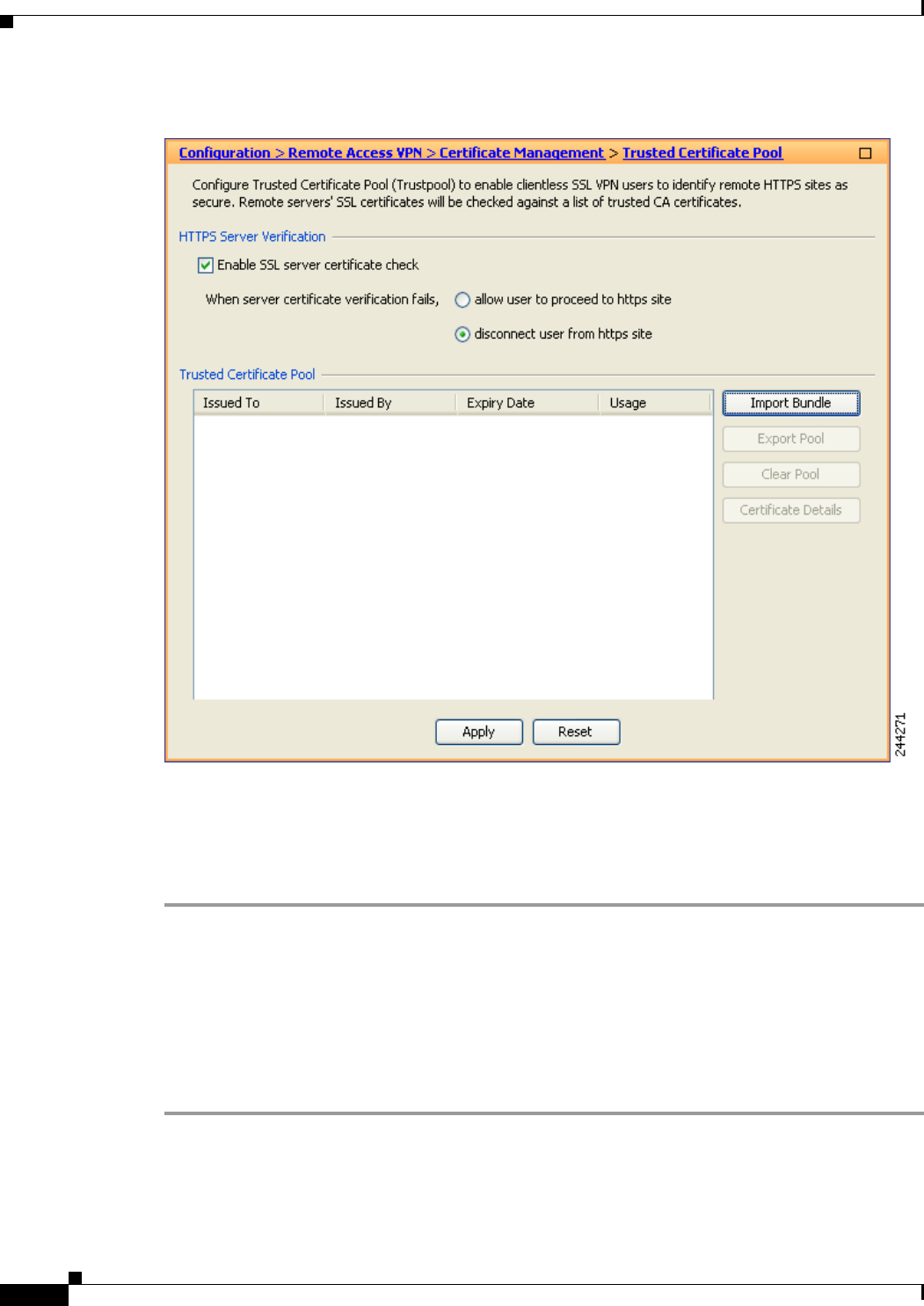
12-4
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 12 Basic Clientless SSL VPN Configuration
Verifying Clientless SSL VPN Server Certificates
Figure 12-3 Enabling HTTPS Server Verification in the ASDM
Step 2 Select the Enable SSL Certificate Check check box.
Step 3 Click Disconnect User From HTTPS Site to disconnect if the server could not be verified.
Alternatively, click Allow User to Proceed to HTTPS Site to allow the user to continue the connection,
even if the check failed.
Step 4 Click Apply to save your changes.
Importing a Certificate Bundle
You can import individual certificates or bundles of certificates from various locations in one of the
following formats:
•x509 certificates in DER format wrapped in a pkcs7 structure.
•A file of concatenated x509 certificates in PEM format (complete with PEM header).
Step 1 In the ASDM, navigate to Configuration > Remote Access VPN > Certificate Management > Trusted
Certificate Pool.
Step 2 Click Import Bundle.
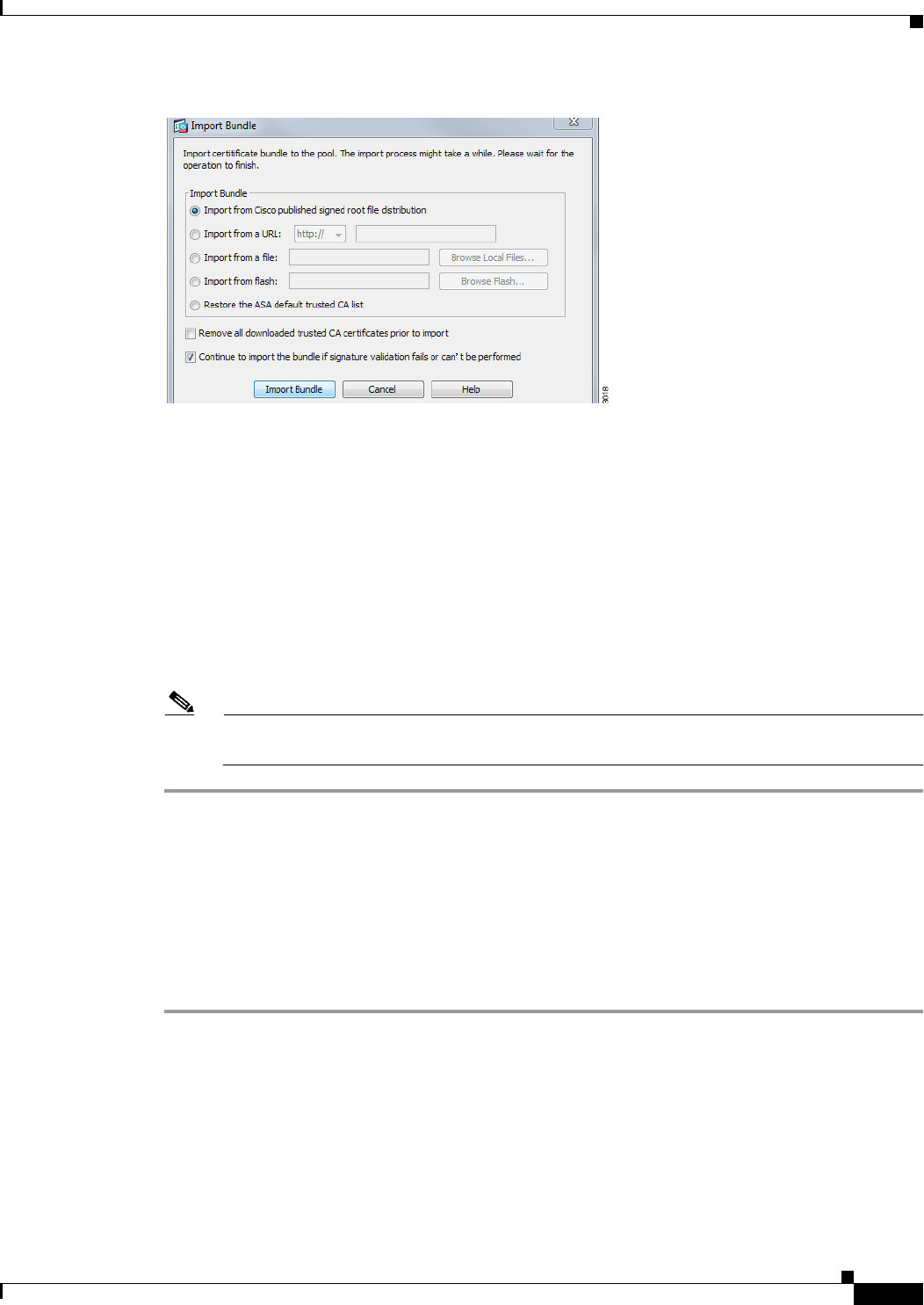
12-5
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 12 Basic Clientless SSL VPN Configuration
Verifying Clientless SSL VPN Server Certificates
Step 3 Select the location of the bundle:
•If the bundle is stored on your computer, click Import From a File, and click Browse Local Files
and navigate to the bundle.
•If the bundle is stored on the ASA flash file system, click Import From Flash, and click Browse
Flash and navigate to the file.
•If the bundle is hosted on a server, click Import From a URL, select the protocol from the list, and
enter the URL in the field.
•Continue to import the bundle if signature validation fails or cannot be performed allows you to
import the bundle, and fix individual certificate errors later. Uncheck this to have the entire bundle
fail if any of the certificates fails.
Step 4 Click Import Bundle. Alternatively, click Cancel to abandon your changes.
Note You can select the Remove All Downloaded Trusted CA Certificates Prior to Import check
box to clear the trustpool before importing a new bundle.
Exporting the Trustpool
When you have correctly configured the trustpool, you should export the pool. This will enable you to
restore the trustpool to this point, for example to remove a certificate that was added to the trustpool after
the export. You can export the pool to the ASA flash file system or your local file system.
In the ASDM, navigate to Configuration > Remote Access VPN > Certificate Management > Trusted
Certificate Pool, and click Export Pool.
Step 1 Click Export to a File.
Step 2 Click Browse Local Files.
Step 3 Navigate to the folder where you want to save the trustpool.
Step 4 Enter a unique memorable name for the trustpool in the File Name box.
Step 5 Click Select.

12-6
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 12 Basic Clientless SSL VPN Configuration
Java Code Signer
Step 6 Click Export Pool to save the file. Alternatively, click Cancel to stop saving.
Removing Certificates
To remove all certificates, in the ASDM, navigate to Configuration > Remote Access VPN >
Certificate Management > Trusted Certificate Pool, then click Clear Pool.
Note Before clearing the trustpool you should export the current trustpool to enable you to restore your current
settings.
Restoring the Default Trusted Certificate Authority List
To restore the default trusted certificate authority (CA) list, in the ASDM, navigate to Configuration >
Remote Access VPN > Certificate Management > Trusted Certificate Pool, then click Restore
Default Trusted CA List and click Import Bundle.
Updating the Trustpool
The trustpool should be updated if either of the following conditions exists:
•Any certificate in the trustpool is due to expire or has been re-issued.
•The published CA certificate bundle contains additional certificates that are required by a specific
application.
A full update will replace all the certificates in the trustpool.
A practical update enables you to add new certificates or replace existing certificates.
Removing a Certificate Bundle
Clearing the trustpool will remove all certificates that are not part of the default bundle.
You cannot remove the default bundle. To clear the trustpool, in the ASDM, navigate to Configuration
> Remote Access VPN > Certificate Management > Trusted Certificate Pool, then click Clear Pool.
Java Code Signer
Code signing appends a digital signature to the executable code itself. This digital signature provides
enough information to authenticate the signer as well as to ensure that the code has not been
subsequently modified since signed.
Code-signer certificates are special certificates whose associated private keys are used to create digital
signatures. The certificates used to sign code are obtained from a CA, with the signed code itself
revealing the certificate origin.
Choose the configured certificate to employ in Java object signing from the drop-down list.
To configure a Java Code Signer, choose Configuration > Remote Access VPN > Clientless SSL VPN
Access > Advanced > Java Code Signer.

12-7
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 12 Basic Clientless SSL VPN Configuration
Configuring Browser Access to Plug-ins
Java objects which have been transformed by Clientless SSL VPN can subsequently be signed using a
PKCS12 digital certificate associated with a trustpoint. In the Java Trustpoint pane, you can configure
the Clientless SSL VPN Java object signing facility to use a PKCS12 certificate and keying material
from a specified trustpoint location.
To import a trustpoint, choose Configuration > Properties > Certificate > Trustpoint > Import.
Configuring Browser Access to Plug-ins
The following sections describe the integration of browser plug-ins for Clientless SSL VPN browser
access:
•Preparing the Security Appliance for a Plug-in, page 12-8
•Installing Plug-ins Redistributed by Cisco, page 12-8
•Providing Access to a Citrix XenApp Server, page 12-10
A browser plug-in is a separate program that a Web browser invokes to perform a dedicated function,
such as connect a client to a server within the browser window. The ASA lets you import plug-ins for
download to remote browsers in Clientless SSL VPN sessions. Of course, Cisco tests the plug-ins it
redistributes, and in some cases, tests the connectivity of plug-ins we cannot redistribute. However, we
do not recommend importing plug-ins that support streaming media at this time.
The ASA does the following when you install a plug-in onto the flash device:
•(Cisco-distributed plug-ins only) Unpacks the jar file specified in the URL.
•Writes the file to the ASA file system.
•Populates the drop-down menu next to the URL attributes in ASDM.
•Enables the plug-in for all future Clientless SSL VPN sessions, and adds a main menu option and
an option to the drop-down menu next to the Address field of the portal page.
Table 12-1 shows the changes to the main menu and Address field of the portal page when you add the
plug-ins described in the following sections.
* Not a recommended plug-in.
When the user in a Clientless SSL VPN session clicks the associated menu option on the portal page, the
portal page displays a window to the interface and displays a help pane. The user can select the protocol
displayed in the drop-down menu and enter the URL in the Address field to establish a connection.The
plug-ins support single sign-on (SSO). Refer to the “Configuring SSO with the HTTP Form Protocol”
section on page 16-6 for implementation details.
Table 12-1 Effects of Plug-ins on the Clientless SSL VPN Portal Page
Plug-in Main Menu Option Added to Portal Page Address Field Option Added to Portal Page
ica Citrix MetaFrame Services ica://
rdp Terminal Servers rdp://
rdp2* Terminal Servers Vista rdp2://
ssh,telnet Secure Shell ssh://
Telnet Services (supporting v1 and v2) telnet://
vnc Virtual Network Computing services vnc://

12-8
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 12 Basic Clientless SSL VPN Configuration
Configuring Browser Access to Plug-ins
Prerequisites
•Clientless SSL VPN must be enabled on the ASA to provide remote access to the plug-ins.
•To configure SSO support for a plug-in, you install the plug-in, add a bookmark entry to display a
link to the server, and specify SSO support when adding the bookmark.
•The minimum access rights required for remote use belong to the guest privilege mode.
•Plug-ins require ActiveX or Oracle Java Runtime Environment (JRE); see the compatibility matrix
for version requirements.
Restrictions
Note The remote desktop protocol plug-in does not support load balancing with a session broker. Because of
the way the protocol handles the redirect from the session broker, the connection fails. If a session broker
is not used, the plug-in works.
•The plug-ins support single sign-on (SSO). They use the same credentials entered to open the
Clientless SSL VPN session. Because the plug-ins do not support macro substitution, you do not
have the options to perform SSO on different fields such as the internal domain password or on an
attribute on a RADIUS or LDAP server.
•A stateful failover does not retain sessions established using plug-ins. Users must reconnect
following a failover.
•If you use stateless failover instead of stateful failover, clientless features such as bookmarks,
customization, and dynamic access-policies are not synchronized between the failover ASA pairs.
In the event of a failover, these features do not work.
Preparing the Security Appliance for a Plug-in
Before installing a plug-in, prepare the ASA as follows:
Prerequisites
Ensure that Clientless SSL VPN is enabled on an ASA interface.
Restrictions
Do not specify an IP address as the common name (CN) for the SSL certificate. The remote user attempts
to use the FQDN to communicate with the ASA. The remote PC must be able to use DNS or an entry in
the System32\drivers\etc\hosts file to resolve the FQDN.
Go to the section that identifies the type of plug-in to provide for Clientless SSL VPN access.
•Installing Plug-ins Redistributed by Cisco, page 12-8
•Providing Access to a Citrix XenApp Server, page 12-10
Installing Plug-ins Redistributed by Cisco
Cisco redistributes the following open-source, Java-based components to be accessed as plug-ins for
Web browsers in Clientless SSL VPN sessions.
12-9
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 12 Basic Clientless SSL VPN Configuration
Configuring Browser Access to Plug-ins
Prerequisites
Ensure Clientless SSL VPN is enabled on an interface on the ASA. To do so, enter the show
running-config command.
* Consult the plug-in documentation for information on deployment configuration and restrictions.
These plug-ins are available on the Cisco Adaptive Security Appliance Software Download site.
DETAILED STEPS
Step 1 Create a temporary directory named plugins on the computer you use to establish ASDM sessions with
the ASA, and download the required plug-ins from the Cisco website to the plugins directory.
Step 2 Choose Configuration > Remote Access VPN > Clientless SSL VPN Access > Portal > Client-Server
Plug-ins.
This pane displays the currently loaded plug-ins that are available to Clientless SSL sessions. The hash
and date of these plug-ins are also provided.
Step 3 Click Import.
The Import Client-Server Plug-in dialog box opens.
Table 12-2 Plug-ins Redistributed by Cisco
Protocol Description Source of Redistributed Plug-in *
RDP Accesses Microsoft Terminal Services hosted by Windows Vista
and Windows 2003 R2.
Supports Remote Desktop ActiveX Control.
We recommend using this plug-in that supports both RDP and
RDP2. Only versions up to 5.1 of the RDP and RDP2 protocols are
supported. Version 5.2 and later are not supported.
http://properjavardp.sourceforge.net/
RDP2 Accesses Microsoft Terminal Services hosted by Windows Vista
and Windows 2003 R2.
Supports Remote Desktop ActiveX Control.
Note This legacy plug-in supports only RDP2. We do not
recommend using this plug-in; instead, use the RDP
plug-in above.
http://properjavardp.sourceforge.net/
SSH The Secure Shell-Telnet plug-in lets the remote user establish a
Secure Shell (v1 or v2) or Telnet connection to a remote computer.
Note Because keyboard-interactive authentication is not
supported by JavaSSH, it cannot be supported with SSH
plugin (used to implement different authentication
mechanisms).
http://javassh.org/
VNC The Virtual Network Computing plug-in lets the remote user use a
monitor, keyboard, and mouse to view and control a computer with
remote desktop sharing (also known as VNC server or service)
turned on. This version changes the default color of the text and
contains updated French and Japanese help files.
http://www.tightvnc.com/

12-10
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 12 Basic Clientless SSL VPN Configuration
Configuring Browser Access to Plug-ins
Step 4 Use the following descriptions to enter the Import Client-Server Plug-in dialog box field values.
•Plug-in Name—Select one of the following values:
–
ica to provide plug-in access to Citrix MetaFrame or Web Interface services.
–
rdp to provide plug-in access to Remote Desktop Protocol services.
–
ssh,telnet to provide plug-in access to both Secure Shell and Telnet services.
–
vnc to provide plug-in access to Virtual Network Computing services.
Note Any undocumented options in this menu are experimental and are not supported.
•Select the location of the plugin file—Select one of the following options and insert a path into its
text field.
–
Local computer—Enter the location and name of the plug-in into the associated Path field, or
click Browse Local Files and navigate to the plug-in, choose it, then click Select.
–
Flash file system—Enter the location and name of the plug-in into the associated Path field, or
click Browse Flash and navigate to the plug-in, choose it, then click OK.
–
Remote Server—Choose ftp, tftp, or HTTP from the drop-down menu next to the associated
Path attribute, depending on which service is running on the remote server. Enter the hostname
or address of the server and the path to the plug-in into the adjacent text field.
Step 5 Click Import Now.
Step 6 Click Apply.
The plug-in is now available for future Clientless SSL VPN sessions.
Providing Access to a Citrix XenApp Server
As an example of how to provide Clientless SSL VPN browser access to third-party plug-ins, this section
describes how to add Clientless SSL VPN support for the Citrix XenApp Server Client.
With a Citrix plug-in installed on the ASA, Clientless SSL VPN users can use a connection to the ASA
to access Citrix XenApp services.
A stateful failover does not retain sessions established using the Citrix plug-in. Citrix users must
reauthenticate after failover.
To provide access to the Citrix plug-in, follow the procedures in the following sections.
•Preparing the Citrix XenApp Server for Clientless SSL VPN Access
•Creating and Installing the Citrix Plug-in
Preparing the Citrix XenApp Server for Clientless SSL VPN Access
You must configure the Citrix Web Interface software to operate in a mode that does not use the (Citrix)
“secure gateway.” Otherwise, the Citrix client cannot connect to the Citrix XenApp Server.
Note If you are not already providing support for a plug-in, you must follow the instructions in the “Preparing
the Security Appliance for a Plug-in” section on page 12-8 before using this section.
12-11
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 12 Basic Clientless SSL VPN Configuration
Configuring Port Forwarding
Creating and Installing the Citrix Plug-in
DETAILED STEPS
Step 1 Download the ica-plugin.zip file from the Cisco Software Download website.
This file contains files that Cisco customized for use with the Citrix plug-in.
Step 2 Download the Citrix Java client from the Citrix site.
In the download area of the Citrix website, select Citrix Receiver, and Receiver for Other Platforms,
and click Find. Click the Receiver for Java hyperlink and download the archive..
Step 3 Extract the following files from the archive, and then add them to the ica-plugin.zip file:
•JICA-configN.jar
•JICAEngN.jar
Step 4 Ensure the EULA included with the Citrix Java client grants you the rights and permissions to deploy
the client on your Web servers.
Step 5 Install the plug-in by using ASDM, or entering the following CLI command in privileged EXEC mode:
import webvpn plug-in protocol ica URL
URL is the hostname or IP address and path to the ica-plugin.zip file.
Note Adding a bookmark is required to provide SSO support for Citrix sessions. We recommend that
you use URL parameters in the bookmark the provide convenient viewing, for example:
ica://10.56.1.114/?DesiredColor=4&DesiredHRes=1024&DesiredVRes=768
Step 6 Establish an SSL VPN clientless session and click the bookmark or enter the URL for the Citrix server.
Use the Client for Java Administrator’s Guide as needed.
Configuring Port Forwarding
The following sections describe port forwarding and how to configure it:
•Information About Port Forwarding, page 12-12
•Configuring DNS for Port Forwarding
•Making Applications Eligible for Port Forwarding
•Adding/Editing a Port Forwarding Entry
•Assigning a Port Forwarding List
•Enabling and Switching off Port Forwarding

12-12
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 12 Basic Clientless SSL VPN Configuration
Configuring Port Forwarding
Information About Port Forwarding
Port forwarding lets users access TCP-based applications over a Clientless SSL VPN connection. Such
applications include the following:
•Lotus Notes
•Microsoft Outlook
•Microsoft Outlook Express
•Perforce
•Sametime
•Secure FTP (FTP over SSH)
•SSH
•Telnet
•Windows Terminal Service
•XDDTS
Other TCP-based applications may also work, but we have not tested them. Protocols that use UDP do
not work.
Port forwarding is the legacy technology for supporting TCP-based applications over a Clientless SSL
VPN connection. You may choose to use port forwarding because you have built earlier configurations
that support this technology.
Consider the following alternatives to port forwarding:
•Smart tunnel access offers the following advantages to users:
–
Smart tunnel offers better performance than plug-ins.
–
Unlike port forwarding, smart tunnel simplifies the user experience by not requiring the user
connection of the local application to the local port.
–
Unlike port forwarding, smart tunnel does not require users to have administrator privileges.
•Unlike port forwarding and smart tunnel access, a plug-in does not require the client application to
be installed on the remote computer.
When configuring port forwarding on the ASA, you specify the port the application uses. When
configuring smart tunnel access, you specify the name of the executable file or its path.
Prerequisites
•The remote host must be running a 32-bit version of one of the following:
–
Microsoft Windows Vista, Windows XP SP2 or SP3; or Windows 2000 SP4.
–
Apple Mac OS X 10.4 or 10.5 with Safari 2.0.4(419.3).
–
Fedora Core 4
•The remote host must also be running Oracle Java Runtime Environment (JRE) 5 or later.
•Browser-based users of Safari on Mac OS X 10.5.3 must identify a client certificate for use with the
URL of the ASA, once with the trailing slash and once without it, because of the way Safari
interprets URLs. For example,
–
https://example.com/
–
https://example.com

12-13
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 12 Basic Clientless SSL VPN Configuration
Configuring Port Forwarding
For details, go to the Safari, Mac OS X 10.5.3: Changes in client certificate authentication.
•Users of Microsoft Windows Vista or later who use port forwarding or smart tunnels must add the
URL of the ASA to the Trusted Site zone. To access the Trusted Site zone, they must start Internet
Explorer and choose the Tools > Internet Options > Security tab. Vista (or later) users can also
switch off Protected Mode to facilitate smart tunnel access; however, we recommend against this
method because it increases the computer’s vulnerability to attack.
•Ensure Oracle Java Runtime Environment (JRE) 1.5.x or later is installed on the remote computers
to support port forwarding (application access) and digital certificates. If JRE 1.4.x is running and
the user authenticates with a digital certificate, the application fails to start because JRE cannot
access the Web browser certificate store.
Restrictions
•Port forwarding supports only TCP applications that use static TCP ports. Applications that use
dynamic ports or multiple TCP ports are not supported. For example, SecureFTP, which uses port
22, works over Clientless SSL VPN port forwarding, but standard FTP, which uses ports 20 and 21,
does not.
•Port forwarding does not support protocols that use UDP.
•Port forwarding does not support Microsoft Outlook Exchange (MAPI) proxy. However, you can
configure smart tunnel support for Microsoft Office Outlook in conjunction with Microsoft Outlook
Exchange Server.
•A stateful failover does not retain sessions established using Application Access (either port
forwarding or smart tunnel access). Users must reconnect following a failover.
•Port forwarding does not support connections to personal digital assistants.
•Because port forwarding requires downloading the Java applet and configuring the local client, and
because doing so requires administrator permissions on the local system, it is unlikely that users will
be able to use applications when they connect from public remote systems.
The Java applet displays in its own window on the end user HTML interface. It shows the contents
of the list of forwarded ports available to the user, as well as which ports are active, and amount of
traffic in bytes sent and received.
•The port forwarding applet displays the local port and the remote port as the same when the local IP
address 127.0.0.1 is being used and cannot be updated by the Clientless SSL VPN connection from
the ASA. As a result, the ASA creates new IP addresses 127.0.0.2, 127.0.0.3, and so on for local
proxy IDs. Because you can modify the hosts file and use different loopbacks, the remote port is
used as the local port in the applet. To connect, you can use Telnet with the hostname, without
specifying the port. The correct local IP addresses are available in the local hosts file.
Configuring DNS for Port Forwarding
Port forwarding forwards the domain name of the remote server or its IP address to the ASA for
resolution and connection. In other words, the port forwarding applet accepts a request from the
application and forwards it to the ASA. The ASA makes the appropriate DNS queries and establishes
the connection on behalf of the port forwarding applet. The port forwarding applet only makes DNS
queries to the ASA. It updates the host file so that when a port forwarding application attempts a DNS
query, the query redirects to a loopback address.
Step 1 Click Configuration > Remote Access VPN > Clientless SSL VPN Access > Connection Profiles.

12-14
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 12 Basic Clientless SSL VPN Configuration
Configuring Port Forwarding
The default Clientless SSL VPN group entry is the default connection profile used for clientless
connections.
Step 2 Highlight the default Clientless SSL VPN group entry, then click Edit if your configuration uses it for
clientless connections. Otherwise, highlight a connection profile used in your configuration for
clientless connections, then click Edit.
The Basic window opens.
Step 3 Scan to the DNS area and select the DNS server from the drop-down list. Note the domain name,
disregard the remaining steps, and go to the next section if ASDM displays the DNS server to use. You
need to enter the same domain name when you specify the remote server while configuring an entry in
the port forwarding list. Continue with the remaining steps if the DNS server is not present in the
configuration.
Step 4 Click Manage in the DNS area.
The Configure DNS Server Groups window opens.
Step 5 Click Configure Multiple DNS Server Groups.
A window displays a table of DNS server entries.
Step 6 Click Add.
The Add DNS Server Group window opens.
Step 7 Enter a new server group name in the Name field, and enter the IP address and domain name (see
Figure 12-4).
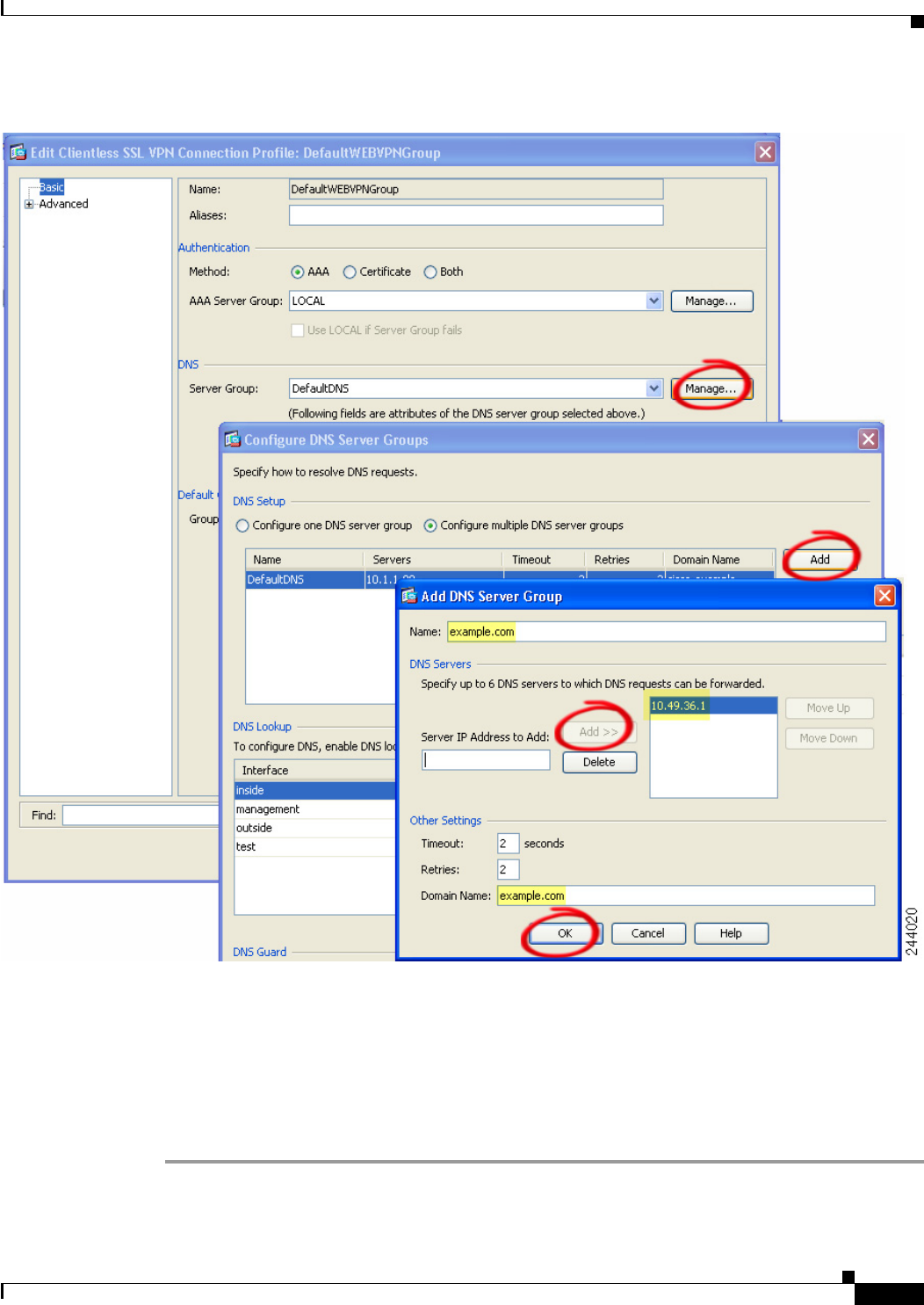
12-15
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 12 Basic Clientless SSL VPN Configuration
Configuring Port Forwarding
Figure 12-4 Example DNS Server Values for Port Forwarding
Note the domain name that you entered. You need it when you specify the remote server later while
configuring a port forwarding entry.
Step 8 Click OK until the Connection Profiles window becomes active again.
Step 9 Repeat Steps 2–8 for each remaining connection profile used in your configuration for clientless
connections.
Step 10 Click Apply.

12-16
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 12 Basic Clientless SSL VPN Configuration
Configuring Port Forwarding
Making Applications Eligible for Port Forwarding
The Clientless SSL VPN configuration of each ASA supports port forwarding lists, each of which
specifies local and remote ports used by the applications for which to provide access. Because each
group policy or username supports only one port forwarding list, you must group each set of ca supported
into a list. To display the port forwarding list entries already present in the ASA configuration, enter the
following commands:
Following the configuration of a port forwarding list, assign the list to group policies or usernames, as
described in the next section.
Adding/Editing a Port Forwarding Entry
The Add/Edit Port Forwarding Entry dialog boxes let you specify TCP applications to associate with
users or group policies for access over Clientless SSL VPN connections. Assign values to the attributes
in these windows as follows:
Prerequisites
The DNS name assigned to the Remote Server parameter must match the Domain Name and Server
Group parameters to establish the tunnel and resolve to an IP address, per the instructions in the
“Assigning a Port Forwarding List” section on page 12-16. The default setting for both the Domain and
Server Group parameters is DefaultDNS.
DETAILED STEPS
Step 1 Click Add.
Step 2 Type a TCP port number for the application to use. You can use a local port number only once for a
listname. To avoid conflicts with local TCP services, use port numbers in the range 1024 to 65535.
Step 3 Enter either the domain name or the IP address of the remote server. We recommend using a domain
name so that you do not have to configure the client applications for the specific IP address.
Step 4 Type the well-known port number for the application.
Step 5 Type a description of the application. The maximum is 64 characters.
Step 6 (Optional) Highlight a port forwarding list and click Assign to assign the selected list to one or more
group policies, dynamic access policies, or user policies.
Assigning a Port Forwarding List
You can add or edit a named list of TCP applications to associate with users or group policies for access
over Clientless SSL VPN connections. For each group policy and username, you can configure Clientless
SSL VPN to do one of the following:
•Start port forwarding access automatically upon user login.
•Enable port forwarding access upon user login, but require the user to start it manually, using
Application Access > Start Applications on the Clientless SSL VPN portal page.

12-17
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 12 Basic Clientless SSL VPN Configuration
Configuring File Access
Note These options are mutually exclusive for each group policy and username. Use only one.
DETAILED STEPS
The Add or Edit Port Forwarding List dialog box lets you add or edit the following:
Step 1 Provide an alphanumeric name for the list. The maximum is 64 characters.
Step 2 Enter which local port listens for traffic for the application. You can use a local port number only once
for a listname. To avoid conflicts with local TCP services, use port numbers in the range 1024 to 65535.
Note Enter the IP address or DNS name of the remote server. We recommend using a domain name
so that you do not have to configure the client applications for the specific IP address.
Step 3 Enter the remote port that listens for traffic for the application.
Step 4 Describe the TCP application. The maximum is 64 characters.
Enabling and Switching off Port Forwarding
By default, port forwarding is switched off.
If you enable port forwarding, the user will have to start it manually, using Application Access > Start
Applications on the Clientless SSL VPN portal page.
Configuring File Access
Clientless SSL VPN serves remote users with HTTPS portal pages that interface with proxy CIFS and/or
FTP clients running on the ASA. Using either CIFS or FTP, Clientless SSL VPN provides users with
network access to the files on the network, to the extent that the users meet user authentication
requirements and the file properties do not restrict access. The CIFS and FTP clients are transparent; the
portal pages delivered by Clientless SSL VPN provide the appearance of direct access to the file systems.
When a user requests a list of files, Clientless SSL VPN queries the server designated as the master
browser for the IP address of the server containing the list. The ASA gets the list and delivers it to the
remote user on a portal page.
Clientless SSL VPN lets the user invoke the following CIFS and FTP functions, depending on user
authentication requirements and file properties:
•Navigate and list domains and workgroups, servers within a domain or workgroup, shares within a
server, and files within a share or directory.
•Create directories.
•Download, upload, rename, move, and delete files.

12-18
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 12 Basic Clientless SSL VPN Configuration
Ensuring Clock Accuracy for SharePoint Access
The ASA uses a master browser, WINS server, or DNS server, typically on the same network as the ASA
or reachable from that network, to query the network for a list of servers when the remote user clicks
Browse Networks in the menu of the portal page or on the toolbar displayed during the Clientless SSL
VPN session.
The master browser or DNS server provides the CIFS/FTP client on the ASA with a list of the resources
on the network, which Clientless SSL VPN serves to the remote user.
Note Before configuring file access, you must configure the shares on the servers for user access.
CIFS File Access Requirement and Limitation
To access \\server\share\subfolder\personal folder, the user must have a minimum of read
permission for all parent folders, including the share itself.
Use Download or Upload to copy and paste files to and from CIFS directories and the local desktop.
The Copy and Paste buttons are intended for remote to remote actions only, not local to remote, or remote
to local.
The CIFS browse server feature does not support double-byte character share names (share names
exceeding 13 characters in length). This only affects the list of folders displayed, and does not affect user
access to the folder. As a workaround, you can pre-configure the bookmark(s) for the CIFS folder(s) that
use double-byte share names, or the user can enter the URL or bookmark of the folder in the format
cifs://server/<long-folder-name>. For example:
cifs://server/Do you remember?
cifs://server/Do%20you%20remember%3F
Adding Support for File Access
Configure file access as follows:
Note The procedure describes how to specify the master browser and WINS servers. As an alternative, you
can use ASDM to configure URL lists and entries that provide access to file shares.
Adding a share in ASDM does not require a master browser or a WINS server. However, it does not
provide support for the Browse Networks link. You can use a hostname or an IP address to refer to
ServerA when entering the nbns-server command. If you use a hostname, the ASA requires a DNS
server to resolve it to an IP address.
For a complete description of these commands, see the Cisco Security Appliance Command Reference.
Ensuring Clock Accuracy for SharePoint Access
The Clientless SSL VPN server on the ASA uses cookies to interact with applications such as Microsoft
Word on the endpoint. The cookie expiration time set by the ASA can cause Word to malfunction when
accessing documents on a SharePoint server if the time on the ASA is incorrect. To prevent this
malfunction, set the ASA clock properly. We recommend configuring the ASA to dynamically
synchronize the time with an NTP server. For instructions, see the section on setting the date and time
in the general operations configuration guide.

12-19
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 12 Basic Clientless SSL VPN Configuration
Virtual Desktop Infrastructure (VDI)
Virtual Desktop Infrastructure (VDI)
The ASA supports connections to Citrix and VMWare VDI servers.
•For Citrix, the ASA allows access through clientless portal to user's running Citrix Receiver.
•VMWare is configured as a (smart tunnel) application.
VDI servers can also be accessed through bookmarks on the Clientless Portal, like other server
applications.
Limitations
•Authentication using certificates or Smart Cards is not supported for auto sign-on, since these forms
of authentication do not allow the ASA in the middle.
•The XML service must be installed and configured on the XenApp and XenDesktop servers.
•Client certificate verifications, double Auth, internal passwords and CSD (all of CSD, not just Vault)
are not supported when standalone mobile clients are used.
Citrix Mobile Support
A mobile user running the Citrix Receiver can connect to the Citrix server by:
•Connecting to the ASA with AnyConnect, and then connecting to the Citrix server.
•Connecting to the Citrix server through the ASA, without using the AnyConnect client. Logon
credentials can include:
–
A connection profile alias (also referred to as a tunnel-group alias) in the Citrix logon screen.
A VDI server can have several group policies, each with different authorization and connection
settings.
–
An RSA SecureID token value, when the RSA server is configured. RSA support includes next
token for an invalid entry, and also for entering a new PIN for an initial or expired PIN.
Supported Mobile Devices
•iPad—Citrix Receiver version 4.x or later
•iPhone/iTouch—Citrix Receiver version 4.x or later
•Android 2.x/3.x/4.0/4.1 phone—Citrix Receiver version 2.x or later
•Android 4.0 phone—Citrix Receiver version 2.x or later
Limitations
Certificate Limitations
•Certificate/Smart Card authentication is not supported as means of auto sign-on.
•Client certificate verifications and CSD are not supported
•Md5 signature in the certificates are not working because of security issue, which is a known
problem on iOS: http://support.citrix.com/article/CTX132798

12-20
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 12 Basic Clientless SSL VPN Configuration
Virtual Desktop Infrastructure (VDI)
•SHA2 signature is not supported except for Windows, as described on the Citrix website:
http://www.citrix.com/
•A key size >1024 is not supported
Other Limitations
•HTTP redirect is not supported; the Citrix Receiver application does not work with redirects.
•XML service must be installed and configured on the XenApp and XenDesktop servers.
About Citrix Mobile Receiver User Logon
The logon for mobile users connecting to the Citrix server depends on whether the ASA has configured
the Citrix server as a VDI server or a VDI proxy server.
When the Citrix server is configured as a VDI server:
1. Using the AnyConnect Secure Mobility Client, connect to ASA with VPN credentials.
2. Using Citrix Mobile Receiver, connect to Citrix server with Citrix server credentials (if
single-signon is configured, the Citrix credentials are not required).
When the ASA is configured as a to a VDI proxy server:
1. Using Citrix Mobile Receiver, connect to the ASA entering credentials for both the VPN and Citrix
server. After the first connection, if properly configured, subsequent connections only require VPN
credentials.
Configuring the ASA to Proxy a Citrix Server
You can configure the ASA to act as a proxy for the Citrix servers, so that connections to the ASA appear
to the user like connections to the Citrix servers. The AnyConnect client is not required when you enable
VDI proxy in ASDM. The following high-level steps show how the end user connects to Citrix.
1. A mobile user opens Citrix Receiver and connects to ASA's URL.
2. The user provides credentials for the XenApp server and the VPN credentials on the Citrix logon
screen.
3. For each subsequent connection to the Citrix server, the user only needs to enter the VPN
credentials.
Using the ASA as a proxy for XenApp and XenDesktop removes the requirement for a Citrix Access
Gateway. XenApp server info is logged on the ASA, and displays in ASDM.
Configure the Citrix server's address and logon credentials, and assign that VDI server to a Group Policy
or username. If both username and group-policy are configured, username settings override group-policy
settings.
Additional Information
http://www.youtube.com/watch?v=JMM2RzppaG8 - This video describes the advantages of using that
ASA as a Citrix proxy.
Configuring a VDI Server
For one server:
1. Navigate to Configuration > Remote Access VPN > Clientless SSL VPN Access > VDI Access

12-21
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 12 Basic Clientless SSL VPN Configuration
Virtual Desktop Infrastructure (VDI)
2. Check Enable VDI Server Proxy, and configure the VDI server.
To assign several group policies to a VDI server:
1. Navigate to Configuration > Remote Access VPN > Clientless SSL VPN Access > VDI Access
2. Check Configure All VDI Servers.
3. Add a VDI Server, and assign one or more group policies.
Configuring a VDI Proxy Server
For one VDI server assigned to one group policy:
1. Navigate to Configuration > Remote Access VPN > Clientless SSL VPN Access > VDI Access
2. Check Enable VDI Server Proxy, and configure the VDI server.
To assign several group policies to a VDI server:
1. Navigate to Configuration > Remote Access VPN > Clientless SSL VPN Access > VDI Access
2. Check Configure All VDI Servers.
3. Add a VDI Server, and assign one or more group policies.
Assigning a VDI Server to a Group Policy
VDI servers are configured and assigned to Group Policies by:
•Adding the VDI server on the VDI Access pane, and assigning a group policy to the server.
•Adding a VDI server to the group policy.
Step 1 Browse to Configuration > Remote Access VPN > Clientless SSL VPN Access > Group Policies.
Step 2 Edit the DfltGrpPolicy and expand the More options menu from the left-side menu.
Step 3 Choose VDI Access. Click Add or Edit to provide VDI server details.
•Server (Host Name or IP Address)—Address of the XenApp or XenDesktop server. This value can
be a clientless macro.
•Port Number (Optional)—Port number for connecting to the Citrix server. This value can be a
clientless macro.
•Active Directory Domain Name—Domain for logging into the virtualization infrastructure server.
This value can be a clientless macro.
•Use SSL Connection—Check the checkbox if you want the server to connect using SSL.
•Username—Username for logging into the virtualization infrastructure server. This value can be a
clientless macro.
•Password—Password for logging into the virtualization infrastructure server. This value can be a
clientless macro.

12-22
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 12 Basic Clientless SSL VPN Configuration
Configuring ACLs
•
Note
Configuring ACLs
ACLs constrain user access to specific networks, subnets, hosts, and Web servers. The Web ACLs table
displays the filters configured on the ASA application to the Clientless SSL VPN traffic. The table shows
the name of each access control list (ACL) and, below and indented to the right of the ACL name, the
ACEs (access control entries) assigned to the ACL.
Each ACL permits or denies access to specific networks, subnets, hosts, and Web servers. Each ACE
specifies one rule that serves the function of the ACL.
Guidelines
If you do not define any filters, all connections are permitted.
Restrictions
•The ASA supports only an inbound ACL on an interface.
•At the end of each ACL, there is an implicit, unwritten rule that denies all traffic that is not
permitted. If traffic is not explicitly permitted by an ACE (access control entry), the ASA denies it.
ACEs are referred to as rules in this topic.
DETAILED STEPS
Web ACLs are configured on the page Configuration > Remote Access VPN > Clientless SSL VPN
Access > Advanced > Web ACLs.
Step 1 Click Add ACL to add an ACL or ACE. To insert a new ACE before or after an existing ACE, click
Insert or Insert After.
Step 2 Click Edit to highlight the ACE to change.
Step 3 Highlight the ACL or ACE to remove and click Delete. When you delete an ACL, you must delete all of
its ACEs. No warning is provided and it is not possible to recover deleted ACL or ACEs.
Step 4 Use the Move Up and Move Down buttons to change the order of ACLs or ACEs. The ASA checks ACLs
to be applied to Clientless SSL VPN sessions and their ACEs in the sequence determined by their
position in the ACLs list until it finds a match.
Step 5 Click + to expand or - to collapse the list of ACEs under each ACL. The priority of the ACEs under each
ACL is displayed. The order in the list determines priority.
Command Purpose
Step 1 webvpn Switches to group policy Clientless SSL VPN
configuration mode.
Step 2 url-entry disable Switches off URL Entry.

12-23
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 12 Basic Clientless SSL VPN Configuration
Configuring ACLs
Step 6 (Optional) Click Find to search for a Web ACL. Start typing in the field, and the tool searches the
beginning characters of every field for a match. You can use wild cards to expand your search. For
example, typing sal in the Find field matches a Web ACL named sales but not a customization object
named wholesalers. If you type *sal in the Find field, the search finds the first instance of either sales or
wholesalers in the table.
Use the up and down arrows to skip up or down to the next string match. Check the Match Case check
box to make your search case sensitive.
Step 7 (Optional) Highlight a Web ACL and click Assign to assign the selected Web ACL to one or more VPN
group policies, dynamic access policies, or user policies.
Step 8 When you create an ACE, by default it is enabled. Clear the check box to switch off an ACE.
The IP address or URL of the application or service to which the ACE applies is displayed. The TCP
service to which the ACE applies is also displayed. The Action field displays whether the ACE permits
or denies Clientless SSL VPN access. The time range associated with the ACE and the logging behavior
(either switched off or with a specified level and time interval) is also displayed.
.
Adding or Editing ACEs
An access control entry (or “access rule”) controls access to specific URLs and services. You can
configure multiple ACEs for an ACL. ACLs apply ACEs in priority order, acting on the first match.
DETAILED STEPS
Step 1 Permit or deny access to specific networks, subnets, hosts, and Web servers specified in the Filter Group
field.
Step 2 Specify a URL or an IP address to which to apply the filter (permit or deny user access):
•URL—Applies the filter to the specified URL.
•Protocols (unlabeled)—Specifies the protocol part of the URL address.
•://x—Specifies the URL of the Web page to which to apply the filter.
•TCP—Applies the filter to the specified IP address, subnet, and port.
•IP Address—Specifies the IP address to which to apply the filter.
•Netmask—Lists the standard subnet mask to apply to the address in the IP Address field.
•Service—Identifies the service (such as https, kerberos, or any) to be matched. Displays a list of
services from which you can select the service to display in the Service field.
•Boolean operator (unlabeled)—Lists the Boolean conditions (equal, not equal, greater than, less
than, or range) to use in matching the service specified in the service field.
Step 3 The Rule Flow Diagram graphically depicts the traffic flow using the filter. This area may be hidden.
Step 4 Specify the logging rules. The default is Default Syslog.
•Logging—Choose to enable a specific logging level.
•Syslog Level—Grayed out until you select Enable for the Logging attribute. Enables you select the
type of syslog messages the ASA displays.
•Log Interval—Lets you select the number of seconds between log messages.
•Time Range—Lets you select the name of a predefined time-range parameter set.

12-24
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 12 Basic Clientless SSL VPN Configuration
Configuring Browser Access to Client-Server Plug-ins
Configuration Examples for ACLs for Clientless SSL VPN
Examples
Here are examples of ACLs for Clientless SSL VPN:
Configuring Browser Access to Client-Server Plug-ins
The Client-Server Plug-in table displays the plug-ins the ASA makes available to browsers in Clientless
SSL VPN sessions.
To add, change, or remove a plug-in, do one of the following:
•To add a plug-in, click Import. The Import Plug-ins dialog box opens.
To remove a plug-in, choose it and click Delete.The following sections describe the integration of
browser plug-ins for Clientless SSL VPN browser access:
•About Installing Browser Plug-ins
•Preparing the Security Appliance for a Plug-in
•Installing Plug-ins Redistributed by Cisco
About Installing Browser Plug-ins
A browser plug-in is a separate program that a Web browser invokes to perform a dedicated function,
such as connect a client to a server within the browser window. The ASA lets you import plug-ins for
download to remote browsers in Clientless SSL VPN sessions. Of course, Cisco tests the plug-ins it
redistributes, and in some cases, tests the connectivity of plug-ins we cannot redistribute. However, we
do not recommend importing plug-ins that support streaming media at this time.
The ASA does the following when you install a plug-in onto the flash device:
•(Cisco-distributed plug-ins only) Unpacks the jar file specified in the URL.
•Writes the file to the csco-config/97/plugin directory on the ASA file system.
•Populates the drop-down menu next to the URL attributes in ASDM.
•Enables the plug-in for all future Clientless SSL VPN sessions, and adds a main menu option and
an option to the drop-down menu next to the Address field of the portal page.
Action Filter Effect
Deny url http://*.yahoo.com/ Denies access to all of Yahoo!
Deny url cifs://fileserver/share/directory Denies access to all files in the specified
location.
Deny url https://www.example.com/ directory/file.html Denies access to the specified file.
Permit url https://www.example.com/directory Permits access to the specified location
Deny url http://*:8080/ Denies HTTPS access to anywhere via
port 8080.
Deny url http://10.10.10.10 Denies HTTP access to 10.10.10.10.
Permit url any Permits access to any URL. Usually used
after an ACL that denies url access.

12-25
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 12 Basic Clientless SSL VPN Configuration
Configuring Browser Access to Client-Server Plug-ins
Table 12-3 shows the changes to the main menu and address field of the portal page when you add
the plug-ins described in the following sections.
Note A secondary ASA obtains the plug-ins from the primary ASA.
When the user in a Clientless SSL VPN session clicks the associated menu option on the portal page, the
portal page displays a window to the interface and displays a help pane. The user can select the protocol
displayed in the drop-down menu and enter the URL in the Address field to establish a connection.
Note Some Java plug-ins may report a status of connected or online even when a session to the destination
service is not set up. The open-source plug-in reports the status, not the ASA.
Before installing the first plug-in, you must follow the instructions in the next section.
Prerequisites
•The plug-ins do not work if the security appliance configures the clientless session to use a proxy
server.
Note The remote desktop protocol plug-in does not support load balancing with a session broker.
Because of the way the protocol handles the redirect from the session broker, the connection
fails. If a session broker is not used, the plug-in works.
•The plug-ins support single sign-on (SSO). They use the same credentials entered to open the
Clientless SSL VPN session. Because the plug-ins do not support macro substitution, you do not
have the options to perform SSO on different fields such as the internal domain password or on an
attribute on a RADIUS or LDAP server.
•To configure SSO support for a plug-in, you install the plug-in, add a bookmark entry to display a
link to the server, and specify SSO support when adding the bookmark.
•The minimum access rights required for remote use belong to the guest privilege mode.
Requirements
•Per the GNU General Public License (GPL), Cisco redistributes plug-ins without having made any
changes to them. Per the GPL, Cisco cannot directly enhance these plug-ins.
Table 12-3 Effects of Plug-ins on the Clientless SSL VPN Portal Page
Plug-in Main Menu Option Added to Portal Page Address Field Option Added to Portal Page
ica Citrix Client citrix://
rdp Terminal Servers rdp://
rdp2 Terminal Servers Vista rdp2://
ssh,telnet SSH ssh://
Telnet telnet://
vnc VNC Client vnc://

12-26
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 12 Basic Clientless SSL VPN Configuration
Configuring Browser Access to Client-Server Plug-ins
•Clientless SSL VPN must be enabled on the ASA to provide remote access to the plug-ins.
•A stateful failover does not retain sessions established using plug-ins. Users must reconnect
following a failover.
•Plug-ins require that ActiveX or Oracle Java Runtime Environment (JRE) 1.4.2 (or later) is enabled
on the browser. There is no ActiveX version of the RDP plug-in for 64-bit browsers.
RDP Plug-in ActiveX Debug Quick Reference
To set up and use an RDP plug-in, you must add a new environment variable.
Step 1 Right-click My Computer to access the System Properties, and choose the Advanced tab.
Step 2 On the Advanced tab, choose the environment variables button.
Step 3 In the new user variable dialog box, enter the RF_DEBUG variable.
Step 4 Verify the new Environment Variable in the user variables section.
Step 5 If you used the client computer with versions of Clientless SSL VPN before version 8.3, you must
remove the old Cisco Portforwarder Control. Go to the C:/WINDOWS/Downloaded Program Files
directory, right-click portforwarder control, and choose Remove.
Step 6 Clear all of the Internet Explorer browser cache.
Step 7 Launch your Clientless SSL VPN session and establish an RDP session with the RDP ActiveX Plug-in.
You can now observe events in the Windows Application Event viewer.
Preparing the Security Appliance for a Plug-in
Step 1 Ensure that Clientless SSL VPN is enabled on an ASA interface.
Step 2 Install an SSL certificate onto the ASA interface to which remote users use a fully-qualified domain
name (FQDN) to connect.
Note Do not specify an IP address as the common name (CN) for the SSL certificate. The remote user
attempts to use the FQDN to communicate with the ASA. The remote PC must be able to use
DNS or an entry in the System32\drivers\etc\hosts file to resolve the FQDN.

CHAPTER
13-1
Cisco ASA Series VPN ASDM Configuration Guide
13
Advanced Clientless SSL VPN Configuration
September 13, 2013
Microsoft Kerberos Constrained Delegation Solution
Many organizations want to authenticate their Clientless VPN users and extend their authentication
credentials seamlessly to web-based resources using authentication methods beyond what the ASA SSO
feature can offer today. With the growing demand to authenticate remote access users with smart cards
and One-time Passwords (OTPs), the SSO feature falls short in meeting that demand, because it forwards
only conventional user credentials, such as static username and password, to clientless web-based
resources when authentication is required.
For example, neither certificate- nor OTP-based authentication methods encompass a conventional
username and password necessary for the ASA to seamlessly perform SSO access to web-based
resources. When authenticating with a certificate, a username and password are not required for the ASA
to extend to web-based resources, making it an unsupported authentication method for SSO. On the other
hand, OTP does include a static username; however, the password is dynamic and will subsequently
change throughout the VPN session. In general, Web-based resources are configured to accept static
usernames and passwords, thus also making OTP an unsupported authentication method for SSO.
Microsoft’s Kerberos Constrained Delegation (KCD), a new feature introduced in software release 8.4
of the ASA, provides access to Kerberos-protected Web applications in the private network. With this
benefit, you can seamlessly extend certificate- and OTP-based authentication methods to Web
applications. Thus, with SSO and KCD working together although independently, many organizations
can now authenticate their clientless VPN users and extend their authentication credentials seamlessly
to Web applications using all authentication methods supported by the ASA.
Requirements
In order for the kcd-server command to function, the ASA must establish a trust relationship between
the source domain (the domain where the ASA resides) and the target or resource domain (the domain
where the Web services reside). The ASA, using its unique format, crosses the certification path from
the source to the destination domain and acquires the necessary tickets on behalf of the remote access
user to access the services.
This crossing of the certificate path is called cross-realm authentication. During each phase of
cross-realm authentication, the ASA relies on the credentials at a particular domain and the trust
relationship with the subsequent domain.

13-2
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 13 Advanced Clientless SSL VPN Configuration
Understanding How KCD Works
Understanding How KCD Works
Kerberos relies on a trusted third party to validate the digital identity of entities in a network. These
entities (such as users, host machines, and services running on hosts) are called principals and must be
present in the same domain. Instead of secret keys, Kerberos uses tickets to authenticate a client to a
server. The ticket is derived from the secret key and consists of the client’s identity, an encrypted session
key, and flags. Each ticket is issued by the key distribution center and has a set lifetime.
The Kerberos security system is a network authentication protocol used to authenticate entities (users,
computers, or applications) and protect network transmissions by scrambling the data so that only the
device that the information was intended for can decrypt it. You can configure KCD to provide Clientless
SSL VPN users with SSO access to any Web services protected by Kerberos. Examples of such Web
services or applications include Outlook Web Access (OWA), Sharepoint, and Internet Information
Server (IIS).
Two extensions to the Kerberos protocol were implemented: protocol transition and constrained
delegation. These extensions allow the Clientless SSL VPN remote access users to access
Kerberos-authenticated applications in the private network.
Protocol transition provides you with increased flexibility and security by supporting different
authentication mechanisms at the user authentication level and by switching to the Kerberos protocol for
security features (such as mutual authentication and constrained delegation) in subsequent application
layers. Constrained delegation provides a way for domain administrators to specify and enforce
application trust boundaries by limiting where application services can act on a user’s behalf. This
flexibility improves application security designs by reducing the chance of compromise by an untrusted
service.
For more information on constrained delegation, see RFC 1510 via the IETF website
(http://www.ietf.org).
Authentication Flow with KCD
Figure 13-1 depicts the packet and process flow a user will experience directly and indirectly when
accessing resources trusted for delegation via the clientless portal. This process assumes that the
following tasks have been completed:
•Configured KCD on ASA
•Joined the Windows Active Directory and ensured services are trusted for delegation
•Delegated ASA as a member of the Windows Active Directory domain
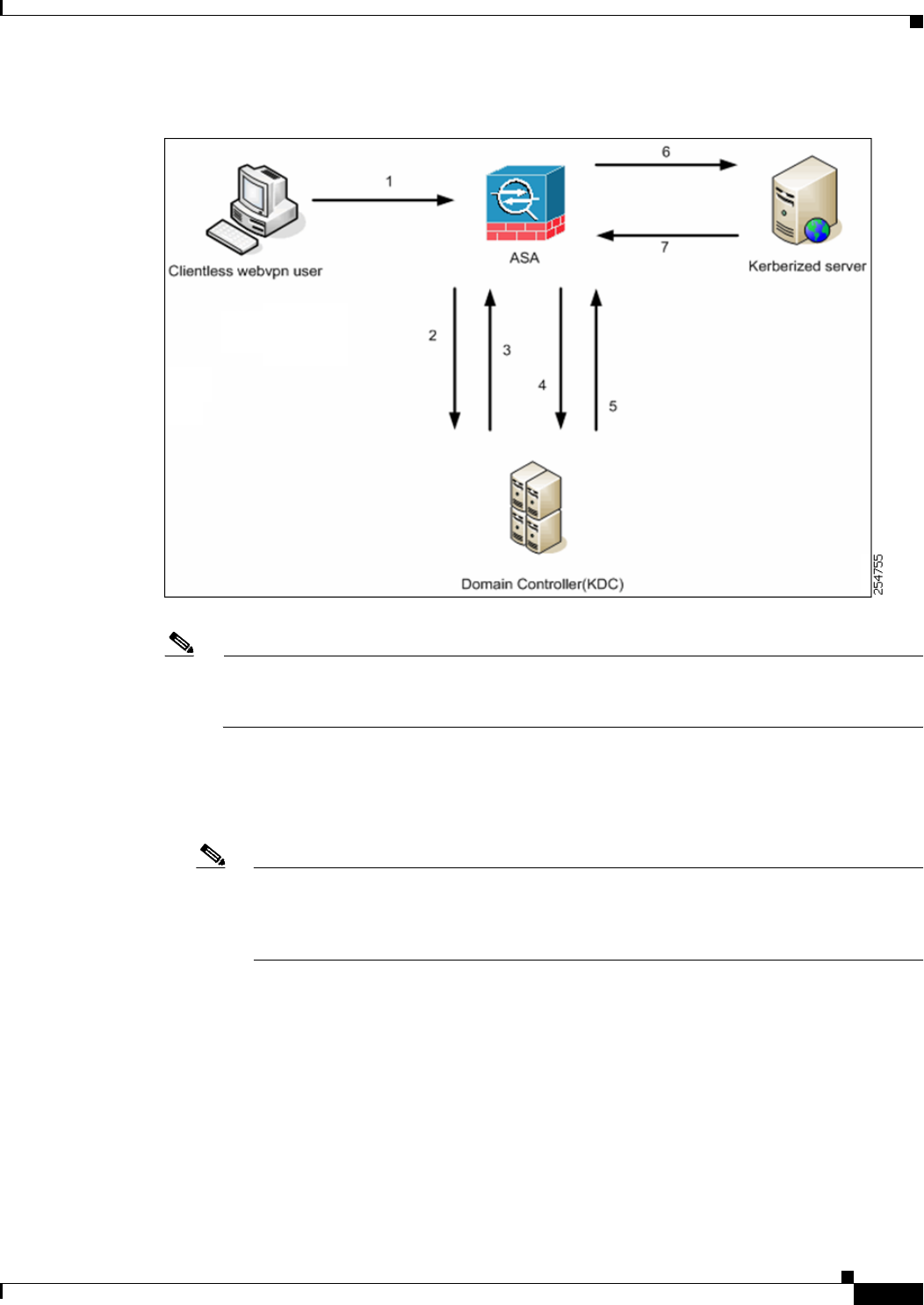
13-3
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 13 Advanced Clientless SSL VPN Configuration
Understanding How KCD Works
Figure 13-1 KCD Process
Note A clientless user session is authenticated by the ASA using the authentication mechanism
configured for the user. (In the case of smartcard credentials, ASA performs LDAP authorization
with the userPrincipalName from the digital certificate against the Windows Active Directory).
1. After successful authentication, the user logs in to the ASA clientless portal page. The user accesses
a Web service by entering a URL in the portal page or by clicking on the bookmark. If the Web
service requires authentication, the server challenges ASA for credentials and sends a list of
authentication methods supported by the server.
Note KCD for Clientless SSL VPN is supported for all authentication methods (RADIUS,
RSA/SDI, LDAP, digital certificates, and so on). Refer to the AAA Support table at
http://www.cisco.com/en/US/docs/security/asa/asa84/configuration/guide/access_aaa.html
#wp1069492.
2. Based on the HTTP headers in the challenge, ASA determines whether the server requires Kerberos
authentication. (This is part of the SPNEGO mechanism.) If connecting to a backend server requires
Kerberos authentication, the ASA requests a service ticket for itself on behalf of the user from the
key distribution center.
3. The key distribution center returns the requested tickets to the ASA. Even though these tickets are
passed to the ASA, they contain the user’s authorization data.ASA requests a service ticket from the
KDC for the specific service that the user wants to access.

13-4
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 13 Advanced Clientless SSL VPN Configuration
Understanding How KCD Works
Note Steps 1 to 3 comprise protocol transition. After these steps, any user who authenticates to
ASA using a non-Kerberos authentication protocol is transparently authenticated to the key
distribution center using Kerberos.
4. ASA requests a service ticket from the key distribution center for the specific service that the user
wants to access.
5. The key distribution center returns a service ticket for the specific service to the ASA.
6. ASA uses the service ticket to request access to the Web service.
7. The Web server authenticates the Kerberos service ticket and grants access to the service. The
appropriate error message is displayed and requires acknowledgement if there is an authentication
failure. If the Kerberos authentication fails, the expected behavior is to fall back to basic
authentication.
Adding a Windows Service Account in Active Directory
The KCD implementation on the ASA requires a service account, or in other words, an Active Directory
user account with privileges necessary to add computers, such as adding the ASA to the domain. For our
example, the Active Directory username JohnDoe depicts a service account with the required privileges.
For more information on how to implement user privileges in Active Directory, contact Microsoft
Support or visit http://microsoft.com.
Configuring DNS for KCD
This section outlines configuration procedures necessary to configure DNS on the ASA. When using
KCD as the authentication delegation method on the ASA, DNS is required to enable hostname
resolution and communication between the ASA, Domain Controller (DC), and services trusted for
delegation.
Step 1 From ASDM, navigate to Configuration > Remote Access VPN > DNS and configure the DNS setup
as shown in Figure 13-2:
•DNS Server Group—Enter the DNS server IP address(es), such as 192.168.0.3.
•Domain Name—Enter the domain name in which the DC is a member.
Step 2 Enable DNS Lookup on the appropriate interface. Clientless VPN deployments require DNS Lookups
via the internal corporate network, typically the inside interface.
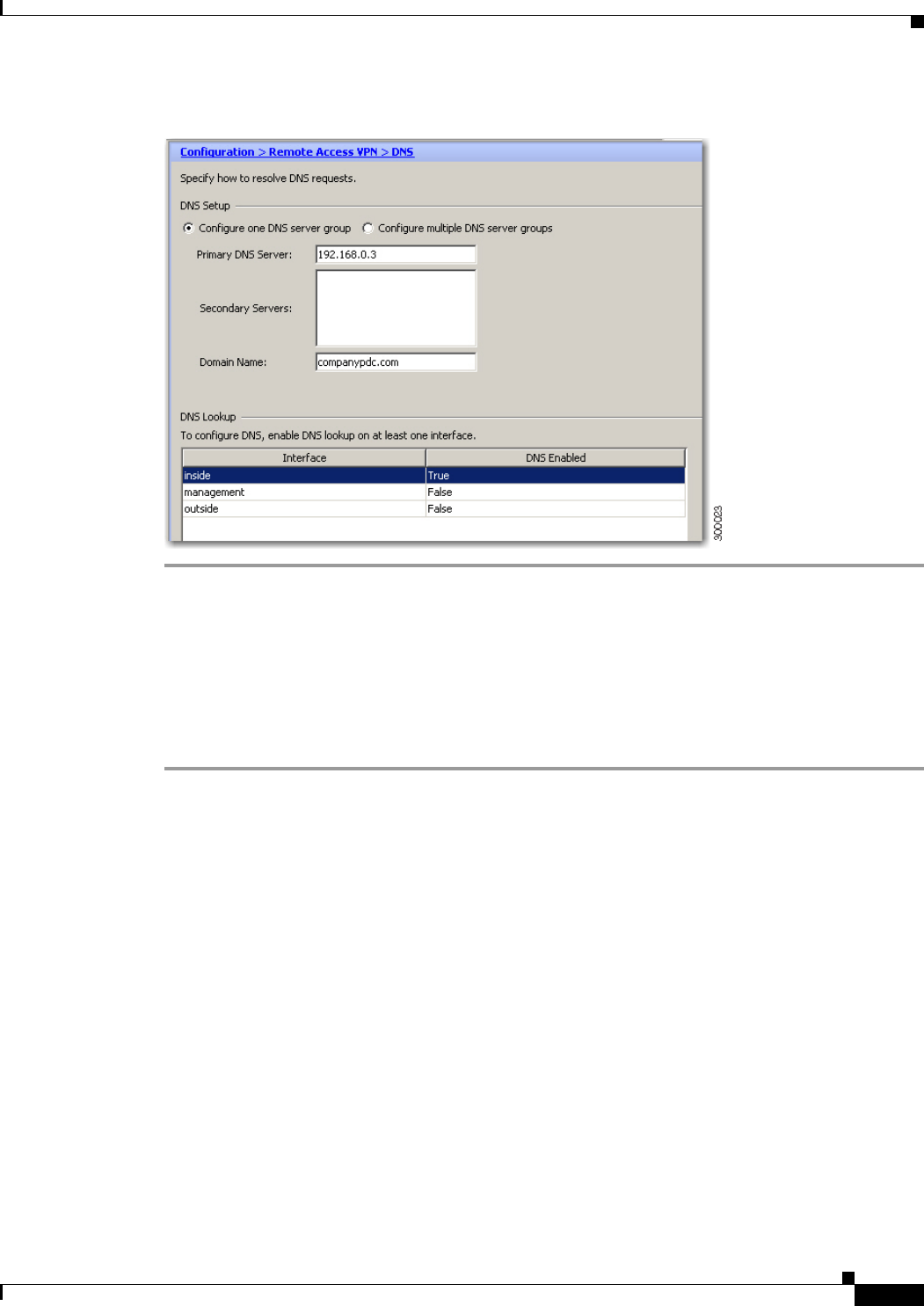
13-5
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 13 Advanced Clientless SSL VPN Configuration
Understanding How KCD Works
Figure 13-2 ASA DNS Configuration Example
Configuring the ASA to Join the Active Directory Domain
This section outlines configuration procedures necessary to enable the ASA to act as part of the Active
Directory domain. KCD requires the ASA to be a member of the Active Directory domain. This
configuration enables the functionality necessary for constrained delegation transactions between the
ASA and the KCD server.
Step 1 From ASDM, navigate to Configuration > Remote Access VPN > Clientless SSL VPN Access >
Advanced > Microsoft KCD Server, as shown in Figure 13-4.
Step 2 Click New to add a Kerberos server group for constrained delegation and configure the following
(see Figure 13-4):
•Server Group Configuration
–
Server Group Name—Define the name of the constrained delegation configuration on the ASA,
such as MSKCD, which is the default value. You can configure multiple server groups for
redundancy; however, you can assign only one server group to the KCD server configuration
used to request service tickets on behalf of VPN users.
–
Reactivation Mode—Click the radio button for the required mode (Depletion or Timed). In
Depletion mode, failed servers are reactivated only after all of the servers in the group are
inactive. In Timed mode, failed servers are reactivated after 30 seconds of downtime. Depletion
is the default configuration.
–
Dead Time—If you choose the Depletion reactivation mode, you must add a dead time interval.
Ten minutes is the default configuration. The interval represents the duration of time, in
minutes, that elapses between the deactivating of the last server in a group and the subsequent
re-enabling of all servers.
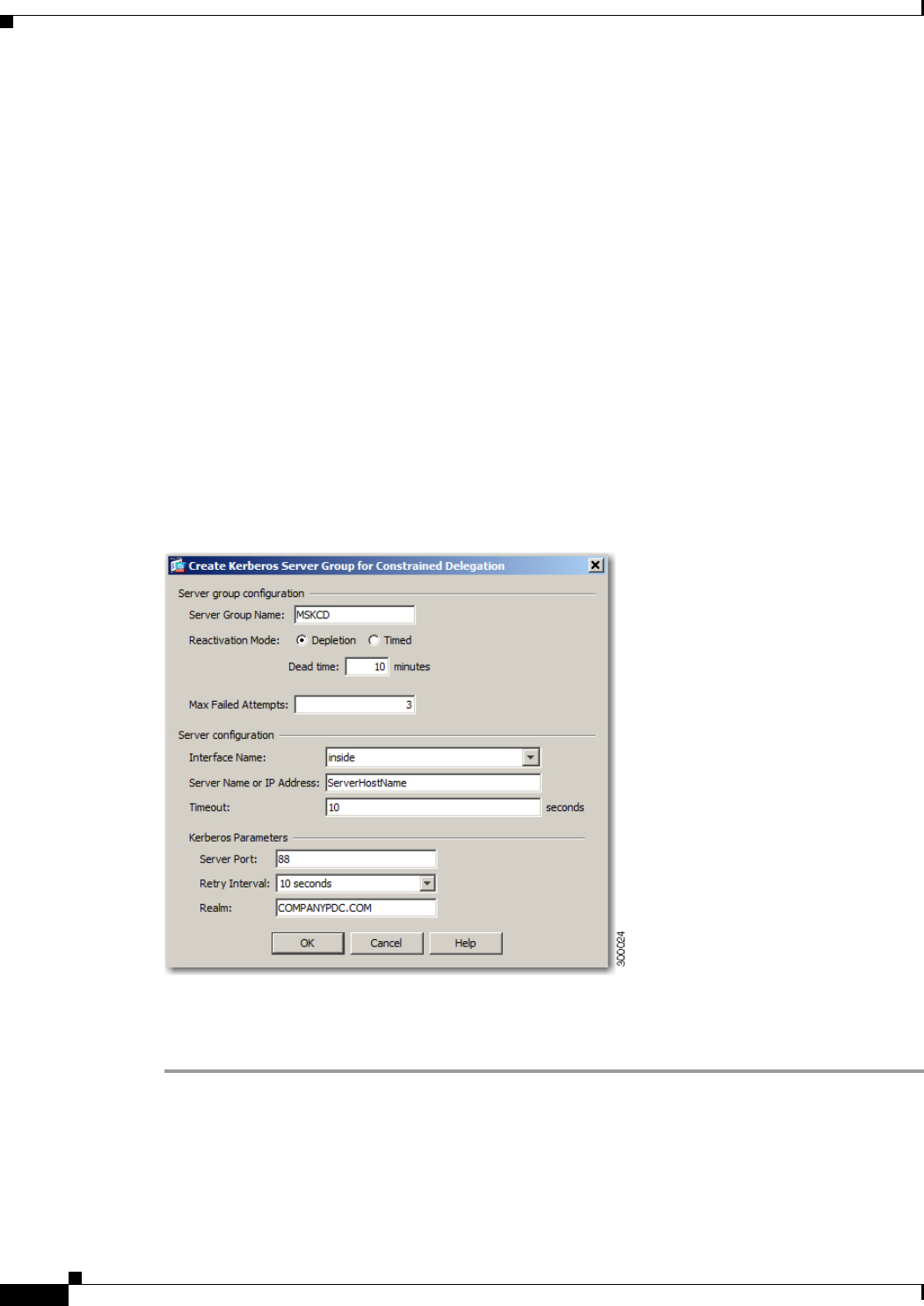
13-6
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 13 Advanced Clientless SSL VPN Configuration
Understanding How KCD Works
–
Max Failed Attempts—Set the number of failed connection attempts allowed before declaring
an unresponsive server to be inactive. Three attempts is the default.
•Server Configuration
–
Interface Name—Choose the interface on which the server resides. In general, authentication
server deployments reside on the internal corporate network, typically via the inside interface.
–
Server Name—Define the hostname of the domain controller, such as ServerHostName.
–
Timeout—Specify the maximum time, in seconds, to wait for a response from the server. Ten
seconds is the default.
•Kerberos Parameter
–
Server Port—88 is the default and the standard port used for KCD.
–
Retry Interval—Choose the desired retry interval. Ten seconds is the default configuration.
–
Realm—Enter the domain name of the DC in all uppercase. The KCD configuration on the ASA
requires the realm value to be in uppercase. A realm is an authentication domain. A service can
accept authentication credentials only from entities in the same realm. The realm must match
the domain name that the ASA joins.
Figure 13-3 KCD Server Group Configuration
Step 3 Click OK to apply your configuration and then configure the Microsoft KCD server to request service
tickets on behalf of the remote access user (see Figure 13-4). The Microsoft KCD Server configuration
window appears upon clicking OK.

13-7
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 13 Advanced Clientless SSL VPN Configuration
Configuring the Use of External Proxy Servers
Configuring the Use of External Proxy Servers
Use the Proxies pane to configure the ASA to use external proxy servers to handle HTTP requests and
HTTPS requests. These servers act as an intermediary between users and the Internet. Requiring all
Internet access via servers you control provides another opportunity for filtering to assure secure Internet
access and administrative control.
Restrictions
HTTP and HTTPS proxy services do not support connections to personal digital assistants.
DETAILED STEPS
Step 1 Click Use an HTTP Proxy Server.
Step 2 Identify the HTTP proxy server by its IP address or hostname.
Step 3 Enter the hostname or IP address of the external HTTP proxy server.
Step 4 Enter the port that listens for HTTP requests. The default port is 80.
Step 5 (Optional) Enter a URL or a comma-delimited list of several URLs to exclude from those that can be
sent to the HTTP proxy server. The string does not have a character limit, but the entire command cannot
exceed 512 characters. You can specify literal URLs or use the following wildcards:
•* to match any string, including slashes (/) and periods (.). You must accompany this wildcard with
an alphanumeric string.
•? to match any single character, including slashes and periods.
•[x-y] to match any single character in the range of x and y, where x represents one character and y
represents another character in the ANSI character set.
•[!x-y] to match any single character that is not in the range.
Step 6 (Optional) Enter this keyword to accompany each HTTP proxy request with a username to provide basic,
proxy authentication.
Step 7 Enter a password to send to the proxy server with each HTTP request.
Step 8 As an alternative to specifying the IP address of the HTTP proxy server, you can choose Specify PAC
File URL to specify a proxy autoconfiguration file to download to the browser. Once downloaded, the
PAC file uses a JavaScript function to identify a proxy for each URL. Enter http:// and type the URL of
the proxy autoconfiguration file into the adjacent field. If you omit the http:// portion, the ASA ignores
it.
Step 9 Choose whether to use an HTTPS proxy server.
Step 10 Click to identify the HTTPS proxy server by its IP address or hostname.
Step 11 Enter the hostname or IP address of the external HTTPS proxy server.
Step 12 Enter the port that listens for HTTPS requests. The default port is 443.
Step 13 (Optional) Enter a URL or a comma-delimited list of several URLs to exclude from those that can be
sent to the HTTPS proxy server. The string does not have a character limit, but the entire command
cannot exceed 512 characters. You can specify literal URLs or use the following wildcards:
•* to match any string, including slashes (/) and periods (.). You must accompany this wildcard with
an alphanumeric string.
•? to match any single character, including slashes and periods.

13-8
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 13 Advanced Clientless SSL VPN Configuration
SSO Servers
•[x-y] to match any single character in the range of x and y, where x represents one character and y
represents another character in the ANSI character set.
•[!x-y] to match any single character that is not in the range.
Step 14 (Optional) Enter a keyword to accompany each HTTPS proxy request with a username to provide basic,
proxy authentication.
Step 15 Enter a password to send to the proxy server with each HTTPS request.
SSO Servers
The SSO Server pane lets you configure or delete single sign-on (SSO) for users of Clientless SSL VPN
connecting to a Computer Associates SiteMinder SSO server or to a Security Assertion Markup
Language (SAML), Version 1.1, Browser Post Profile SSO server. SSO support, available only for
Clientless SSL VPN, lets users access different secure services on different servers without entering a
username and password more than once.
You can choose from four methods when configuring SSO:
•Auto Sign-on using basic HTTP and/or NTLMv1 authentication.
•HTTP Form protocol, or Computer Associates eTrust SiteMinder (formerly Netegrity SiteMinder).
•SAML, Version 1.1 Browser Post Profile.
Restrictions
The SAML Browser Artifact profile method of exchanging assertions is not supported.
The following sections describe the procedures for setting up SSO with both SiteMinder and SAML
Browser Post Profile.
•Configuring SiteMinder and SAML Browser Post Profile, page 13-8—Configures SSO with basic
HTTP or NTLM authentication.
•Configuring Session Settings—Configures SSO with the HTTP Form protocol.
The SSO mechanism starts either as part of the AAA process (HTTP Form) or just after successful user
authentication to either a AAA server (SiteMinder) or a SAML Browser Post Profile server. In these
cases, the Clientless SSL VPN server running on the ASA acts as a proxy for the user to the
authenticating server. When a user logs in, the Clientless SSL VPN server sends an SSO authentication
request, including username and password, to the authenticating server using HTTPS.
If the authenticating server approves the authentication request, it returns an SSO authentication cookie
to the Clientless SSL VPN server. This cookie is kept on the ASA on behalf of the user and used to
authenticate the user to secure websites within the domain protected by the SSO server.
Configuring SiteMinder and SAML Browser Post Profile
SSO authentication with SiteMinder or with SAML Browser Post Profile is separate from AAA and
occurs after the AAA process completes. To set up SiteMinder SSO for a user or group, you must first
configure a AAA server (for example RADIUS, LDAP). After the AAA server authenticates the user,
the Clientless SSL VPN server uses HTTPS to send an authentication request to the SiteMinder SSO
server.

13-9
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 13 Advanced Clientless SSL VPN Configuration
SSO Servers
In addition to configuring the ASA, for SiteMinder SSO, you must also configure your CA SiteMinder
policy server with the Cisco authentication scheme. See Adding the Cisco Authentication Scheme to
SiteMinder
For SAML Browser Post Profile, you must configure a Web agent (protected resource URL) for
authentication.
DETAILED STEPS
Use the SAML server documentation provided by the server software vendor to configure the SAML
server in Relying Party mode. The following fields are displayed:
•Server Name—Display only. Displays the names of configured SSO servers. The minimum number
of characters is 4, and the maximum is 31.
•Authentication Type—Display only. Displays the type of SSO server. The ASA currently supports
the SiteMinder type and the SAML Browser Post Profile type.
•URL—Display only. Displays the SSO server URL to which the ASA makes SSO authentication
requests.
•Secret Key—Display only. Displays the secret key used to encrypt authentication communications
with the SSO server. The key can be comprised of any regular or shifted alphanumeric character.
There is no minimum or maximum number of characters.
•Maximum Retries—Display only. Displays the number of times the ASA retries a failed SSO
authentication attempt. The range is 1 to 5 retries, and the default number of retries is 3.
•Request Timeout (seconds)—Display only. Displays the number of seconds before a failed SSO
authentication attempt times out. The range is 1 to 30 seconds, and the default number of seconds is
5.
•Add/Edit—Opens the Add/Edit SSO Server dialog box.
•Delete—Deletes the selected SSO server.
•Assign—Highlight an SSO server and click this button to assign the selected server to one or more
VPN group policies or user policies.
Step 1 Configure the SAML server parameters to represent the asserting party (the ASA):
•Recipient consumer (Web Agent) URL (same as the assertion consumer URL configured on the
ASA)
•Issuer ID, a string, usually the hostname of the appliance
•Profile type—Browser Post Profile
Step 2 Configure certificates.
Step 3 Specify that asserting party assertions must be signed.
Step 4 Select how the SAML server identifies the user:
•Subject Name type is DN
•Subject Name format is uid=<user>

13-10
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 13 Advanced Clientless SSL VPN Configuration
SSO Servers
Adding the Cisco Authentication Scheme to SiteMinder
Besides configuring the ASA for SSO with SiteMinder, you must also configure your CA SiteMinder
policy server with the Cisco authentication scheme, provided as a Java plug-in. This section presents
general steps, not a complete procedure. Refer to the CA SiteMinder documentation for the complete
procedure for adding a custom authentication scheme. To configure the Cisco authentication scheme on
your SiteMinder policy server, perform the following steps.
Prerequisites
Configuring the SiteMinder policy server requires experience with SiteMinder.
DETAILED STEPS
Step 1 With the SiteMinder Administration utility, create a custom authentication scheme being sure to use the
following specific values:
•In the Library field, enter smjavaapi.
•In the Secret field, enter the same secret configured in the Secret Key field of the Add SSO Server
dialog to follow.
•In the Parameter field, enter CiscoAuthApi.
Step 2 Using your Cisco.com login, download the file cisco_vpn_auth.jar from
http://www.cisco.com/cisco/software/navigator.html and copy it to the default library directory for the
SiteMinder server. This .jar file is also available on the Cisco ASA CD.
Adding or Editing SSO Servers
This SSO method uses CA SiteMinder and SAML Browser Post Profile. You can also set up SSO using
the HTTP Form protocol, or Basic HTML and NTLM authentication. To use the HTTP Form protocol,
see Configuring Session Settings, page 13-18. To set use basic HTML or NTLM authentication, use the
auto sign-on command at the command-line interface.
DETAILED STEPS
Step 1 If adding a server, enter the name of the new SSO server. If editing a server, this field is display only; it
displays the name of the selected SSO server.
Step 2 Enter a secret key used to encrypt authentication requests to the SSO server. Key characters can be any
regular or shifted alphanumeric characters. There is no minimum or maximum number of characters. The
secret key is similar to a password: you create it, save it, and configure it. It is configured on the ASA,
the SSO server, and the SiteMinder policy server using the Cisco Java plug-in authentication scheme.
Step 3 Enter the number of times thatthe ASA retries a failed SSO authentication attempt before the
authentication times out. The range is from 1 to 5 retries inclusive, and the default is 3 retries.
Step 4 Enter the number of seconds before a failed SSO authentication attempt times out. The range is from1
to 30 seconds inclusive, and the default is 5 seconds.
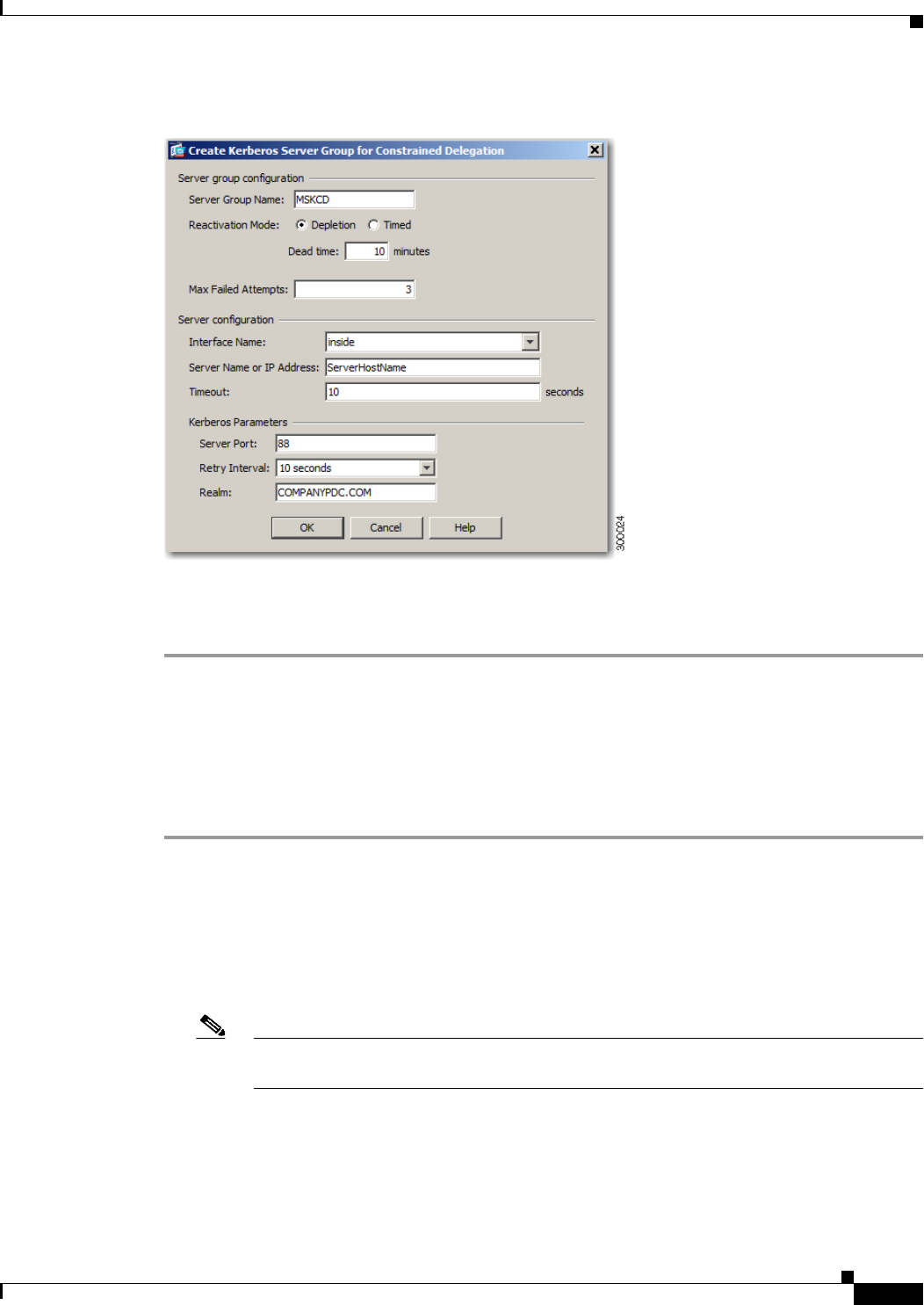
13-11
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 13 Advanced Clientless SSL VPN Configuration
SSO Servers
Figure 13-4 KCD Server Group Configuration
Step 5 Click OK to apply your configuration and then configure the Microsoft KCD Server to request service
tickets on behalf of the remote access user (see Figure 13-4). The Microsoft KCD Server configuration
window appears upon clicking OK.
Configuring Kerberos Server Groups
The Kerberos Server Group for Constrained Delegation, MSKCD, is automatically applied to the KCD
Server Configuration. You can also configure Kerberos Server groups and manage them under
Configuration > Remote Access VPN > AAA/Local User > AAA Server Groups.
Step 1 Under the Server Access Credential section, configure the following:
•Username—Define a Service Account (Active Directory username) such as JohnDoe, which has
been granted privileges necessary to add computer accounts to the Active Directory domain. The
username does not correspond to a specific administrative user but simply to a user with
service-level privileges. This service account is used by the ASA to add a computer account for itself
to the Active Directory domain at every reboot. You must configure the computer account separately
to request Kerberos tickets on behalf of the remote users.
Note Administrative privileges are required for initial join. A user with service-level privileges on
the domain controller will not get access.
•Password—Define the password associated with the username (such as Cisco123). The password
does not correspond to a specific password but simply to a service-level password privilege to add
a device on the Window domain controller.
Step 2 Under the Server Group Configuration section, configure the following:
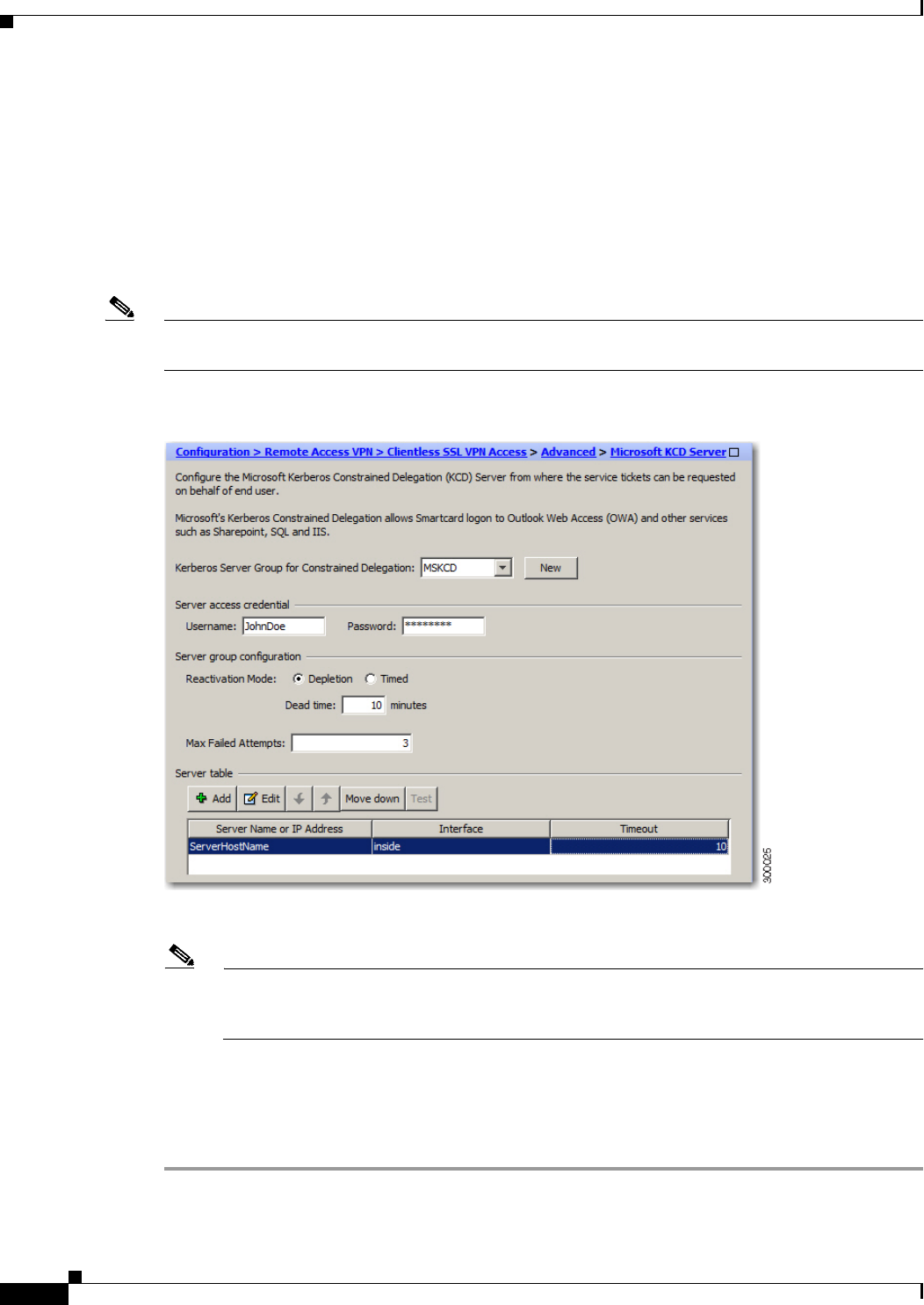
13-12
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 13 Advanced Clientless SSL VPN Configuration
SSO Servers
•Reactivation Mode—Click the mode to use (Depletion or Timed). In Depletion mode, failed servers
are reactivated only after all of the servers in the group are inactive. In Timed mode, failed servers
are reactivated after 30 seconds of down time. Depletion is the default configuration.
•Dead Time—If you choose the Depletion reactivation mode, you must add a dead time interval. The
interval represents the duration of time, in minutes, that elapses between the deactivating of the last
server in a group and the subsequent re-enabling of all servers. Ten minutes is the default.
•Max Failed Attempts—Set the number of failed connection attempts allowed before declaring a
nonresponsive server to be inactive. Three attempts is the default.
Note Under the Server Table section, the previously configured DC hostname, ServerHostName, was
automatically applied to the KCD server configuration (see Figure 13-5).
Figure 13-5 KCD Server Configuration
Step 3 Click Apply.
Note After applying your configuration, the ASA automatically starts the process of joining the
Active Directory domain. The ASA’s hostname appears in the Computers directory in Active
Directory Users and Computers.
To confirm if the ASA has successfully joined the domain, execute the following command from the
ASA prompt.:
host# show webvpn kcd
Kerberos Realm: WEST.LOCAL
Domain Join: Complete

13-13
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 13 Advanced Clientless SSL VPN Configuration
Configuring Application Profile Customization Framework
Configuring Bookmarks to Access the Kerberos Authenticated Services
To access Kerberos authenticated services such as Outlook Web Access using the ASA clientless portal,
you must configure bookmark lists. Bookmark lists are assigned and displayed to remote access users
based on the VPN security policies that they are associated with.
Restrictions
When creating a bookmark to an application that uses Kerberos constrained delegation (KCD), do not
check Enable Smart Tunnel.
DETAILED STEPS
Step 1 Navigate to Configuration > Remote Access VPN > Clientless VPN Access > Portal > Bookmarks
in the ASDM GUI.
Step 2 In Bookmark List, enter the URL to reference for the service location.
Configuring Application Profile Customization Framework
Clientless SSL VPN includes an Application Profile Customization Framework (APCF) option that lets
the ASA handle non-standard applications and Web resources so they display correctly over a Clientless
SSL VPN connection. An APCF profile contains a script that specifies when (pre, post), where (header,
body, request, response), and what (data) to transform for a particular application. The script is in XML
and uses sed (stream editor) syntax to transform strings/text.
You can configure and run multiple APCF profiles in parallel on an ASA. Within an APCF profile script,
multiple APCF rules can apply. The ASA processes the oldest rule first, based on configuration history,
the next oldest rule next.
You can store APCF profiles on the ASA flash memory, or on an HTTP, HTTPS, or TFTP server.
Restrictions
We recommend that you configure an APCF profile only with the assistance of Cisco personnel.
Managing APCF Profiles
You can store APCF profiles on the ASA flash memory or on an HTTP, HTTPS, FTP, or TFTP server.
Use this pane to add, edit, and delete APCF packages, and to put them in priority order.
Step 1 Navigate to Configuration > Remote Access VPN > Clientless SSL VPN Access > Advanced >
Application Helper, where you can perform the following functions.
•Click Add/Edit to create a new APCF profile or change an existing one.
–
Select Flash file to locate an APCF file stored on the ASA flash memory.

13-14
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 13 Advanced Clientless SSL VPN Configuration
Configuring Application Profile Customization Framework
Then click Upload to get an APCF file from a local computer to the ASA flash file system, or
Browse to upload select an APCF file that is already in flash memory.
–
Select URL to retrieve the APCF file from an HTTP, HTTPS, FTP, or TFTP server.
•Click Delete to remove an existing APCF profile. No confirmation or undo exists.
•Click Move Up or Move Down to rearrange APCF profiles within the list. The order determines
which the APCF profile is used.
Step 2 Click Refresh if you do not see the changes you made in the list.
Uploading APCF Packages
DETAILED STEPS
Step 1 The path to the APCF file on your computer is shown. Click Browse Local to automatically insert the
path in this field, or enter the path.
Step 2 Click to locate and choose the APCF file to transfer on your computer. The Select File Path dialog box
displays the contents of the folder you last accessed on your local computer. Navigate to the APCF file,
choose it, and click Open. ASDM inserts the file path into the Local File Path field.
Step 3 The path on the ASA to upload the APCF file is shown in the Flash File System Path. Click Browse
Flash to identify the location on the ASA to upload the APCF file to. The Browse Flash dialog box
displays the contents of flash memory.
Step 4 The file name of the APCF file you selected on your local computer is displayed. We recommend that
you use this name to prevent confusion. Confirm that this file displays the correct filename, and click
OK. The Browse Flash dialog box closes. ASDM inserts the destination file path in the Flash File
System Path field.
Step 5 Click Upload File when you have identified the location of the APCF file on your computer, and the
location to download it to the ASA.
Step 6 A Status window appears and remains open for the duration of the file transfer. Following the transfer,
an Information window displays the message, “File is uploaded to flash successfully.” Click OK. The
Upload Image dialog window removes the contents of the Local File Path and Flash File System Path
fields, indicating you can upload another file. To do so, repeat these instructions. Otherwise, click Close.
Step 7 Close the Upload Image dialog window. Click Close after you upload the APCF file to flash memory or
if you decide not to upload it. If you do upload it, the filename appears in the APCF File Location field
of the APCF window. If you do not upload it, a Close Message dialog box prompts, “Are you sure you
want to close the dialog without uploading the file?” Click OK if you do not want to upload the file. The
Close Message and Upload Image dialog boxes close, revealing the APCF Add/Edit pane. Otherwise,
click Cancel in the Close Message dialog box. The dialog box closes, revealing the Upload Image dialog
box again, with the values in the fields intact. Click Upload File
Managing APCF Packets
Step 1 Use the following commands to add, edit, and delete APCF packets and put them in priority order:

13-15
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 13 Advanced Clientless SSL VPN Configuration
Configuring Application Profile Customization Framework
•APCF File Location—Displays information about the location of the APCF package. This can be in
the ASA flash memory, or on an HTTP, HTTPS, FTP, or TFTP server.
•Add/Edit—Click to add or edit a new or existing APCF profile.
•Delete—Click to remove an existing APCF profile. There is no confirmation or undo.
•Move Up—Click to rearrange APCF profiles within a list. The list determines the order in which the
ASA attempts to use APCF profiles.
Step 2 Click Flash File to locate an APCF file stored in the ASA flash memory.
Step 3 Enter the path to an APCF file stored in flash memory. If you already added a path, it redirects to an
APCF file stored in flash memory after you browse to locate it.
Step 4 Click Browse Flash to browse flash memory to locate the APCF file. A Browse Flash Dialog pane
displays. Use the Folders and Files columns to locate the APCF file. Highlight the APCF file and click
OK. The path to the file then displays in the Path field.
Note If you do not see the name of an APCF file that you recently downloaded, click Refresh.
•Upload—Click to upload an APCF file from a local computer to the ASA flash file system. The
Upload APCF Package pane displays.
•URL—Click to use an APCF file stored on an HTTP, HTTPS, or TFTP server.
•ftp, http, https, and tftp (unlabeled)—Identify the server type.
•URL (unlabeled)—Enter the path to the FTP, HTTP, HTTPS, or TFTP server.
APCF Syntax
APCF profiles use XML format, and sed script syntax, with the XML tags in Table 13-1.
Guidelines
Misuse of an APCF profile can result in reduced performance and undesired rendering of content. In
most cases, Cisco Engineering supplies APCF profiles to solve specific application rendering issues.
Table 13-1 APCF XML Tags
Tag Use
<APCF>...</APCF> The mandatory root element that opens any APCF XML
file.
<version>1.0</version> The mandatory tag that specifies the APCF
implementation version. Currently the only version is
1.0.
<application>...</application> The mandatory tag that wraps the body of the XML
description.
<id> text </id> The mandatory tag that describes this particular APCF
functionality.

13-16
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 13 Advanced Clientless SSL VPN Configuration
Configuring Application Profile Customization Framework
<apcf-entities>...</apcf-entities> The mandatory tag that wraps a single or multiple APCF
entities.
<js-object>…</js-object>
<html-object>…</html-object>
<process-request-header>...</process-request-header>
<process-response-header>...</process-response-header>
<preprocess-response-body>...</preprocess-response-body>
<postprocess-response-body>...</postprocess-response-body>
One of these tags specifies type of content or the stage at
which the APCF processing should take place.
<conditions>… </conditions> A child element of the pre/post-process tags that specifies
criteria for processing such as:
•http-version (such as 1.1, 1.0, 0.9)
•http-method (get, put, post, webdav)
•http-scheme (“http/”, “https/”, other)
•server-regexp regular expression containing ("a".."z"
| "A".."Z" | "0".."9" | ".-_*[]?")
•server-fnmatch (regular expression containing
("a".."z" | "A".."Z" | "0".."9" | ".-_*[]?+()\{},"),
•user-agent-regexp
•user-agent-fnmatch
•request-uri-regexp
•request-uri-fnmatch
•If more than one of condition tags is present, the
ASA performs a logical AND for all tags.
<action> … </action> Wraps one or more actions to perform on the content
under specified conditions; you can use the following
tags to define these actions (shown below):
•<do>
•<sed-script>
•<rewrite-header>
•<add-header>
•<delete-header>
Table 13-1 APCF XML Tags (continued)
Tag Use

13-17
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 13 Advanced Clientless SSL VPN Configuration
Configuring Application Profile Customization Framework
Configuration Examples for APCF
Example:
<APCF>
<version>1.0</version>
<application>
<id>Do not compress content from example.com</id>
<apcf-entities>
<process-request-header>
<conditions>
<server-fnmatch>*.example.com</server-fnmatch>
</conditions>
<action>
<do><no-gzip/></do>
<do>…</do> Child element of the action tag used to define one of the
following actions:
•<no-rewrite/>—Do not mangle the content received
from the remote server.
•<no-toolbar/>—Do not insert the toolbar.
•<no-gzip/>—Do not compress the content.
•<force-cache/>—Preserve the original caching
instructions.
•<force-no-cache/>—Make object non-cacheable.
•< downgrade-http-version-on-backend>—Use
HTTP/1.0 when sending the request to remote server.
<sed-script> TEXT </sed-script> Child element of the action tag used to change the content
of text-based objects. The Text must be a valid Sed script.
The <sed-script> applies to the <conditions> tag defined
before it.
<rewrite-header></rewrite-header> Child element of the action tag. Changes the value of the
HTTP header specified in the child element <header> tag
shown below.
<add-header></add-header> Child element of the action tag used to add a new HTTP
header specified in the child element <header> tag shown
below.
<delete-header></delete-header> Child element of the action tag used to delete the
specified HTTP header specified by the child element
<header> tag shown below.
<header></header> Specifies the name HTTP header to be rewritten, added,
or deleted. For example, the following tag changes the
value of the HTTP header named Connection:
<rewrite-header>
<header>Connection</header>
<value>close</value>
</rewrite-header>
Table 13-1 APCF XML Tags (continued)
Tag Use

13-18
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 13 Advanced Clientless SSL VPN Configuration
Configuring Session Settings
</action>
</process-request-header>
</apcf-entities>
</application>
</APCF>
Example:
<APCF>
<version>1.0</version>
<application>
<id>Change MIME type for all .xyz objects</id>
<apcf-entities>
<process-response-header>
<conditions>
<request-uri-fnmatch>*.xyz</request-uri-fnmatch>
</conditions>
<action>
<rewrite-header>
<header>Content-Type</header>
<value>text/html</value>
</rewrite-header>
</action>
</process-response-header>
</apcf-entities>
</application>
</APCF>
Configuring Session Settings
The Clientless SSL VPN Add/Edit Internal Group Policy > More Options > Session Settings window
lets you specify personalized user information between Clientless SSL VPN sessions. By default, each
group policy inherits the settings from the default group policy. Use this window to specify personalized
Clientless SSL VPN user information for the default group policy and any group policies for which you
want to differentiate these values.
DETAILED STEPS
Step 1 Click none or choose the file server protocol (smb or ftp) from the User Storage Location drop-down
menu. Cisco recommends using CIFS for user storage. You can set up CIFS without using a
username/password or a port number. If you choose CIFS, enter the following syntax:
cifs//cifs-share/user/data. If you choose smb or ftp, use the following syntax to enter the file system
destination into the adjacent text field:
username:password@host:port-number/path
For example
mike:mysecret@ftpserver3:2323/public
Note Although the configuration shows the username, password, and preshared key, the ASA uses
an internal algorithm to store the data in an encrypted form to safeguard it.
Step 2 Type the string, if required, for the security appliance to pass to provide user access to the storage
location.

13-19
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 13 Advanced Clientless SSL VPN Configuration
Encoding
Step 3 Choose one of the following options from the Storage Objects drop-down menu to specify the objects
that the server uses in association with the user. The ASA stores these objects to support Clientless SSL
VPN connections.
•cookies,credentials
•cookies
•credentials
Step 4 Enter the limit in KB transaction size over which to time out the session. This attribute applies only to a
single transaction. Only a transaction larger than this value resets the session expiration clock.
Encoding
With encoding, you can view or specify the character encoding for Clientless SSL VPN portal pages.
Character encoding, also called “character coding” and “a character set,” is the pairing of raw data (such
as 0s and 1s) with characters to represent the data. The language determines the character encoding
method to use. Some languages use a single method, while others do not. Usually, the geographic region
determines the default encoding method used by the browser, but the remote user can change it. The
browser can also detect the encoding specified on the page, and render the document accordingly.
The encoding attribute lets you specify the value of the character-encoding method used on the portal
page to ensure that the browser renders it properly, regardless of the region in which the user is using the
browser, and regardless of any changes made to the browser.
By default, the ASA applies the “Global Encoding Type” to pages from Common Internet File System
servers. The mapping of CIFS servers to their appropriate character encoding, globally with the “Global
Encoding Type” attribute, and individually with the file-encoding exceptions displayed in the table,
provides for the accurate handling and display of CIFS pages when the proper rendering of filenames or
directory paths, as well as pages, is an issue.
DETAILED STEPS
Step 1 Global Encoding Type determines the character encoding that all Clientless SSL VPN portal pages
inherit except for those from the CIFS servers listed in the table. You can type the string or choose one
of the options from the drop-down list, which contains the most common values, as follows:
•big5
•gb2312
•ibm-850
•iso-8859-1
•shift_jis
Note
•unicode
•windows-1252
•none
13-20
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 13 Advanced Clientless SSL VPN Configuration
Content Cache
Note If you click none or specify a value that the browser on the Clientless SSL VPN session does
not support, it uses its own default encoding.
You can type a string consisting of up to 40 characters, and equal to one of the valid character sets
identified in http://www.iana.org/assignments/character-sets. You can use either the name or the alias of
a character set listed on that page. The string is case-insensitive. The command interpreter converts
upper-case to lower-case when you save the ASA configuration.
Step 2 Enter the name or IP address of a CIFS server for which the encoding requirement differs from the
“Global Encoding Type” attribute setting. The ASA retains the case you specify, although it ignores the
case when matching the name to a server.
Step 3 Choose the character encoding that the CIFS server should provide for Clientless SSL VPN portal pages.
You can type the string, or choose one from the drop-down list, which contains only the most common
values, as follows:
•big5
•gb2312
•ibm-850
•iso-8859-1
•shift_jis
Note If you are using Japanese Shift_jis Character encoding, click Do Not Specify in the Font Family
area of the associated Select Page Font pane to remove the font family.
•unicode
•windows-1252
•none
If you click none or specify a value that the browser on the Clientless SSL VPN session does not support,
it uses its own default encoding.
You can type a string consisting of up to 40 characters, and equal to one of the valid character sets
identified in http://www.iana.org/assignments/character-sets. You can use either the name or the alias of
a character set listed on that page. The string is case-insensitive. The command interpreter converts
upper-case to lower-case when you save the ASA configuration.
Content Cache
Caching enhances the performance of Clientless SSL VPN. It stores frequently reused objects in the
system cache, which reduces the need to perform repeated rewriting and compressing of content. The
use of the cache reduces traffic, with the result that many applications run more efficiently.
DETAILED STEPS
Step 1 Select Configuration > Remote Access VPN > Clientless SSL VPN Access > Advanced > Content
Cache.

13-21
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 13 Advanced Clientless SSL VPN Configuration
Content Rewrite
Step 2 If Enable Cache is unchecked, check it.
Step 3 Define the terms for caching.
•Maximum Object Size—Enter the maximum size in KB of a document that the ASA can cache. The
ASA measures the original content length of the object, not rewritten or compressed content. The
range is 0 to 10,000 KB; the default is 1000 KB
•Minimum Object Size—Enter the minimum size in KB of a document that the ASA can cache. The
ASA measures the original content length of the object, not rewritten or compressed content. The
range is 0 to 10,000 KB; the default is 0 KB.
Note The Maximum Object Size must be greater than the Minimum Object Size.
•Expiration Time—Enter an integer between 0 and 900 to set the number of minutes to cache objects
without revalidating them. The default is one minute.
•LM Factor—Enter an integer between 1 and 100; the default is 20.
The LM factor sets the policy for caching objects which have only the last-modified timestamp. This
revalidates objects that have no server-set change values. The ASA estimates the length of time since
the object has changed, also called the expiration time. The estimated expiration time equals the time
elapsed since the last change multiplied by the LM factor. Setting the LM factor to 0 forces
immediate revalidation, while setting it to 100 results in the longest allowable time until
revalidation.
The expiration time sets the amount of time to for the ASA to cache objects that have neither a
last-modified time stamp nor an explicit server-set expiry time.
•Cache static content—Check to cache all content that is not subject to rewrite, for example, PDF
files and images.
•Restore Cache Default—Click to restore default values for all cache parameters.
Content Rewrite
The Content Rewrite pane lists all applications for which content rewrite is enabled or switched off.
Clientless SSL VPN processes application traffic through a content transformation/rewriting engine that
includes advanced elements such as JavaScript, VBScript, Java, and multi-byte characters to proxy
HTTP traffic which may have different semantics and access control rules depending on whether the user
is using an application within or independently of an SSL VPN device.
By default, the security appliance rewrites, or transforms, all clientless traffic. You may not want some
applications and Web resources (for example, public websites) to go through the ASA. The ASA
therefore lets you create rewrite rules that let users browse certain sites and applications without going
through the ASA. This is similar to split-tunneling in a VPN connection.
You can create multiple rewrite rules. The rule number is important because the security appliance
searches rewrite rules by order number, starting with the lowest, and applies the first rule that matches.
“Configuration Example for Content Rewrite Rules” shows example content rewrite rules.
Note These improvements were made to Content Rewriter in ASA 9.0:

13-22
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 13 Advanced Clientless SSL VPN Configuration
Content Rewrite
•Content rewrite added support for HTML5.
•The Clientless SSL VPN rewriter engines were significantly improved to provide better quality and
efficacy. As a result, you can expect a better end-user experience for Clientless SSL VPN users.
DETAILED STEPS
The Content Rewrite table has the following columns:
•Rule Number—Displays an integer that indicates the position of the rule in the list.
•Rule Name—Provides the name of the application for which the rule applies.
•Rewrite Enabled—Displays content rewrite as enabled or switched off.
•Resource Mask—Displays the resource mask.
Step 1 Navigate to Configuration > Remote Access VPN > Clientless SSL VPN Access > Advanced >
Content Rewrite.
Step 2 Click Add or Edit to create or update an content rewriting rule.
Step 3 Enable content rewrite must be checked to enable this rule.
Step 4 Enter a number for this rule. This number specifies the priority of the rule, relative to the others in the
list. Rules without a number are at the end of the list. The range is 1 to 65534.
Step 5 (Optional) Provide an alphanumeric string that describes the rule, maximum 128 characters.
Step 6 Enter a string to match the application or resource to apply the rule to. The string can be up to 300
characters. You can use one of the following wildcards, but you must specify at least one alphanumeric
character.
*—Matches everything. ASDM does not accept a mask that consists of a * or *.*
?—Matches any single character.
[!seq]—Matches any character not in sequence.
[seq]—Matches any character in sequence.
Configuration Example for Content Rewrite Rules
Table 13-2 Content Rewrite Rules
Function
Enable
Content
Rewrite
Rule
Number Rule Name Resource Mask
Switch off rewriter for HTTP
URLs at youtube.com
Unchecked 1 no-rewrite-youtube *.youtube.com/*
Enable rewriter for all HTTP
URLs that do not match above
rules
Check 65,535 rewrite-all *

13-23
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 13 Advanced Clientless SSL VPN Configuration
Using Email over Clientless SSL VPN
Using Email over Clientless SSL VPN
Clientless SSL VPN supports several ways to access email. This section includes the following methods:
•Configuring Email Proxies
•Configuring Web email: MS Outlook Web App
Configuring Email Proxies
Clientless SSL VPN supports IMAP, POP3, and SMTP email proxies. The following attributes apply
globally to email proxy users.
Restrictions
email clients such as MS Outlook, MS Outlook Express, and Eudora lack the ability to access the
certificate store.
Configuring Web email: MS Outlook Web App
The ASA supports Microsoft Outlook Web App to Exchange Server 2010 and Microsoft Outlook Web
Access to Exchange Server 2007, 2003, and 2000.
DETAILED STEPS
Step 1 Enter the URL of the email service into the address field or click an associated bookmark in the
Clientless SSL VPN session.
Step 2 When prompted, enter the email server username in the format domain\username.
Step 3 Enter the email password.
Configuring Bookmarks
The Bookmarks panel lets you add, edit, delete, import, and export bookmark lists.
Use the Bookmarks panel to configure lists of servers and URLs for access over Clientless SSL VPN.
Following the configuration of a bookmark list, you can assign the list to one or more policies – group
policies, dynamic access policies, or both. Each policy can have only one bookmark list. The list names
populate a drop-down list on the URL Lists tab of each DAP.
You can now use bookmarks with macro substitutions for auto sign-on on some Web pages. The former
POST plug-in approach was created so that administrators could specify a POST bookmark with sign-on
macros and receive a kick-off page to load prior to posting the POST request. This POST plug-in
approach eliminated those requests that required the presence of cookies or other header items. Now an
an administrator determines the pre-load page and URL, which specifies where the post login request is
sent. A pre-load page enables an endpoint browser to fetch certain information that is sent along to the
webserver or Web application rather than just using a POST request with credentials.

13-24
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 13 Advanced Clientless SSL VPN Configuration
Configuring Bookmarks
The existing bookmark lists are displayed. You can add, edit, delete, import, or export the bookmark list.
You can configure lists of servers and URLs for access and order the items in the designated URL list.
Guidelines
Configuring bookmarks does not prevent the user from visiting fraudulent sites or sites that violate your
company’s acceptable use policy. In addition to assigning a bookmark list to the group policy, dynamic
access policy, or both, apply a Web ACL to these policies to control access to traffic flows. Switch off
URL Entry on these policies to prevent user confusion over what is accessible. See the “Clientless SSL
VPN Security Precautions” section on page 12-1 for instructions.
DETAILED STEPS
Step 1 Specify the name of the list to be added or select the name of the list to be modified or deleted.
The bookmark title and actual associated URL are displayed.
Step 2 (Optional) Click Add to configure a new server or URL. See these procedures for additional information:
•Adding a Bookmark for a URL with a GET or Post Method, page 13-24
•Adding a URL for a Predefined Application Template, page 13-26
•Adding a Bookmark for an Auto Sign-On Application, page 13-27
Step 3 (Optional) Click Edit to make changes to the server, URL, or display name.
Step 4 (Optional) Click Delete to remove the selected item from the URL list. No confirmation or undo exists.
Step 5 (Optional) Choose the location from which to import or export the file:
•Local computer—Click to import or export a file that resides on the local PC.
•Flash file system—Click to import or export a file that resides on the ASA.
•Remote server—Click to import a file that resides on a remote server accessible from the ASA.
•Path—Identify the method to access the file (ftp, http, or https), and provide the path to the file.
•Browse Local Files/Browse Flash...—Browse to the path for the file.
Step 6 (Optional) Highlight a bookmark and click Assign to assign the selected bookmark to one or more group
policies, dynamic access policies, or LOCAL users.
Step 7 (Optional) Change the position of the selected item in the URL list using the Move Up or Move Down
options.
Step 8 Click OK.
Adding a Bookmark for a URL with a GET or Post Method
The Add Bookmark Entry dialog box lets you create a link or bookmark for a URL list.
Prerequisites
To access a shared folder on your network, use the format \\server\share\subfolder\<personal folder>.
The user must have list permission for all points above <personal folder>.

13-25
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 13 Advanced Clientless SSL VPN Configuration
Configuring Bookmarks
DETAILED STEPS
Step 1 Navigate to Configuration > Remote Access VPN > Clientless SSL VPN Access > Portal >
Bookmarks, and click the Add button.
Step 2 Select URL with GET or POST Method to use for bookmark creation.
Step 3 Enter a name for this bookmark, which will be displayed on the portal.
Step 4 Use the URL drop-down menu to select the URL type: http, https, cifs, or ftp. The URL drop-down
shows standard URL types, plus types for all the plug-ins you installed.
Step 5 Enter the DNS name or IP address for this bookmark (URL). For a plug-in, enter the name of the server.
Enter a forward slash and a question mark (/?) after the server name to specify optional parameters, then
use an ampersand to separate parameter-value pairs, as shown in the following syntax:
server/?Parameter=Va l ue &Parameter=Val u e
For example:
host/?DesiredColor=4&DesiredHRes=1024&DesiredVRes=768
The particular plug-in determines the optional parameter-value pairs that you can enter.
To provide single sign-on support for a plug-in, use the parameter-value pair csco_sso=1. For example:
host/?csco_sso=1&DesiredColor=4&DesiredHRes=1024&DesiredVRes=768
Step 6 (Optional) Enter a preload URL. When you enter a preload URL, you can also enter the wait time, which
is the time you allow for loading of the page until you are forwarded to the actual POST URL.
Step 7 As a subtitle, provide additional user-visible text that describes the bookmark entry.
Step 8 Use the Thumbnail drop-down menu to select an icon to associate with the bookmark on the end-user
portal.
Step 9 Click Manage to import or export images to use as thumbnails.
Step 10 Click to open the bookmark in a new window that uses the smart tunnel feature to pass data through the
ASA to or from the destination server. All browser traffic passes securely over the SSL VPN tunnel. This
option lets you provide smart tunnel support for a browser-based application, whereas the Smart Tunnels
option, also in the Clientless SSL VPN > Portal menu, lets you add nonbrowser-based applications to a
smart tunnel list for assignment to group policies and usernames.
Step 11 Check Allow the Users to Bookmark the Link to let Clientless SSL VPN users use the Bookmarks or
Favorites options on their browsers. Uncheck to prevent access to these options. If you uncheck this
option, the bookmark does not appear in the Home section of the Clientless SSL VPN portal.
Step 12 (Optional) Choose Advanced Options to configure further bookmark characteristics.
•URL Method—Choose Get for simple data retrieval. Choose Post when processing the data may
involve changes to it, for example, storing or updating data, ordering a product, or sending email.
•Post Parameters—Configure the particulars of the Post URL method.
•Add/Edit—Click to add a post parameter.
•Edit—Click to edit the highlighted post parameter.
•Delete—Click to delete the highlighted post parameter.

13-26
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 13 Advanced Clientless SSL VPN Configuration
Configuring Bookmarks
Adding a URL for a Predefined Application Template
This option simplifies bookmark creation with users selecting a predefined ASDM template that contains
the pre-filled necessary values for certain well-defined applications.
Prerequisites
Predefined application templates are currently available for the following applications only:
•Citrix XenApp
•Citrix XenDesktop
•Domino WebAccess
•Microsoft Outlook Web Access 2010
•Microsoft Sharepoint 2007
•Microsoft SharePoint 2010
DETAILED STEPS
Step 1 Enter a name for the bookmark to display for the user.
Step 2 As a subtitle, provide additional user-visible text that describes the bookmark entry.
Step 3 Use the Thumbnail drop-down menu to select an icon to associate with the bookmark on the end-user
portal.
Step 4 Click Manage to import or export images to use as thumbnails.
Step 5 (Optional) Select the Place This Bookmark on the VPN Home Page check box.
Step 6 In the Select Auto Sign-on Application list, click the required application. The available applications
are:
•Citrix XenApp
•Citrix XenDesktop
•Domino WebAccess
•Microsoft Outlook Web Access 2010
•Microsoft Sharepoint 2007
•Microsoft SharePoint 2010
Step 7 Enter the URL of the page which is loaded before the login page. This page will require user interaction
to proceed to the login screen. The URL will allow * to substitute an arbitrary number of symbols, for
example http*://www.example.com/test.
Step 8 Enter the Pre-login Page Control ID. This is the ID of the control / tag that will get a click event on the
pre-login page URL to proceed to the login page.
Step 9 Enter the Application Parameters. Depending on the application these may include the following:
•Protocol. HTTP or HTTPs.
•hostname. For example www.cisco.com.
•Port Number. The port used by the application.
•URL Path Appendix. For example /Citrix/XenApp. This is normally auto-populated.

13-27
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 13 Advanced Clientless SSL VPN Configuration
Configuring Bookmarks
•Domain. The domain to connect to
•User Name. The SSL VPN variable to use as a user name. Click Select Variable to choose a
different variable.
•Password. The SSL VPN variable to use as a password. Click Select Variable to choose a different
variable.
Step 10 (Optional) Click Preview to view the template output. You can click Edit to modify the template.
Step 11 Click OK to make your changes. Alternatively, click Cancel to abandon your changes.
Adding a Bookmark for an Auto Sign-On Application
This option lets you create a bookmark for any complex auto sign-on application.
Prerequisites
Configuring auto sign-on applications requires two steps:
1. Define the bookmark with some basic initial data and without the POST parameters. Save and assign
the bookmark to use in a group or user policy.
2. Edit the bookmark again. Use the capture function to capture the SSL VPN parameters and edit them
in the bookmark.
DETAILED STEPS
Step 1 Enter a name for the bookmark to display for the user.
Step 2 Use the URL drop-down menu to select the URL type: http, https, cifs, or ftp. The URL types of all
imported plug-ins also populate this menu. Select the URL type of a plug-in to display the plug-in as a
link on the portal page.
Step 3 Enter the DNS name or IP address for the bookmark. For a plug-in, enter the name of the server. Enter
a forward slash and a question mark (/?) after the server name to specify optional parameters, then use
an ampersand to separate parameter-value pairs, as shown in the following syntax:
server/?Parameter=Va l ue &Parameter=Val u e
For example:
host/?DesiredColor=4&DesiredHRes=1024&DesiredVRes=768
The particular plug-in determines the optional parameter-value pairs that you can enter.
To provide single sign-on support for a plug-in, use the parameter-value pair csco_sso=1. For example:
host/?csco_sso=1&DesiredColor=4&DesiredHRes=1024&DesiredVRes=768
Step 4 As a subtitle, provide additional user-visible text that describes the bookmark entry.
Step 5 Use the Thumbnail drop-down menu to select an icon to associate with the bookmark on the end-user
portal.
Step 6 Click Manage to import or export images to use as thumbnails.
Step 7 (Optional) Select the Place This Bookmark on the VPN Home Page check box.

13-28
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 13 Advanced Clientless SSL VPN Configuration
Configuring Bookmarks
Step 8 Enter the Login Page URL. Wildcards can be used in the URL you enter. For example, you can enter
http*://www.example.com/myurl*.
Step 9 Enter the Landing Page URL. The ASA requires the Landing Page to be configured to detect a
successful login to the application.
Step 10 (Optional) Enter a Post Script. Some Web applications, such as Microsoft Outlook Web Access, may
execute a JavaScript to change the request parameters before the log-on form is submitted. The Post
Script field enables you to enter JavaScript for such applications.
Step 11 Add the required Form Parameters. For each required SSL VPN Variable, click Add, enter a Name,
and select a variable from the list. You can click Edit to change parameters and Delete to remove them.
Step 12 Enter the URL of the page which is loaded before the login page. This page will require user interaction
to proceed to the login screen. The URL will allow * to substitute an arbitrary number of symbols, for
example http*://www.example.com/test.
Step 13 Enter the Pre-login Page Control ID. This is the ID of the control / tag that will get a click event on the
pre-login page URL to proceed to the login page.
Step 14 Click OK to make your changes. Alternatively, click Cancel to abandon your changes.
When you edit the bookmark you can use the HTML Parameter Capture function to capture the VPN
auto sign-on parameters. The bookmark must have been saved and assigned first to a group policy or
user.
Enter the SSL VPN Username then click Start Capture. Then use a Web browser to start the VPN
session and navigate to the intranet page. To complete the process, click Stop Capture. The parameters
will then be available for editing and inserted in the bookmark.
Importing and Exporting a Bookmark List
You can import or export already configured bookmark lists. Import lists that are ready to use. Export
lists to modify or edit them, and then reimport.
DETAILED STEPS
Step 1 Identify the bookmark list by name. Maximum is 64 characters, no spaces.
Step 2 Choose a method to import or export the list file:
•Local computer—Click to import a file that resides on the local PC.
•Flash file system—Click to export a file that resides on the ASA.
•Remote server—Click to import a url list file that resides on a remote server accessible from the
ASA.
•Path—Identify the method to access the file (ftp, http, or https), and provide the path to the file.
•Browse Local Files/Browse Flash—Browse to the path for the file.
•Import/Export Now—Click to import or export the list file.

13-29
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 13 Advanced Clientless SSL VPN Configuration
Configuring Bookmarks
Importing and Exporting GUI Customization Objects (Web Contents)
This dialog box lets you import and export Web content objects. The names of the Web content objects
and their file types are displayed.
Web contents can range from a wholly configured home page to icons or images to use when you
customize the end user portal. You can import or export already configured Web contents. Import Web
contents that are ready for use. Export Web contents to modify or edit them, and then reimport.
Step 1 Choose the location from which to import or export the file:
•Local computer—Click to import or export a file that resides on the local PC.
•Flash file system—Click to import or export a file that resides on the ASA.
•Remote server—Click to import a file that resides on a remote server accessible from the ASA.
•Path—Identify the method to access the file (ftp, http, or https), and provide the path to the file.
•Browse Local Files.../Browse Flash...—Browse to the path for the file.
Step 2 Determine whether authentication is required to access the content.
The prefix to the path changes depending on whether you require authentication. The ASA uses
/+CSCOE+/ for objects that require authentication, and /+CSCOU+/ for objects that do not. The ASA
displays /+CSCOE+/ objects on the portal page only, while /+CSCOU+/ objects are visible and usable
in either the logon or the portal pages.
Step 3 Click to import or export the file.
Adding and Editing Post Parameters
Use this pane to configure post parameters for bookmark entries and URL lists.
Clientless SSL VPN variables allow for substitutions in URLs and forms-based HTTP post operations.
These variables, also known as macros, let you configure users for access to personalized resources that
contain the user ID and password or other input parameters. Examples of such resources include
bookmark entries, URL lists, and file shares.
DETAILED STEPS
Step 1 Provide the name and value of the parameters exactly as in the corresponding HTML form, for example:
<input name=“param_name” value=“param_value”>.
You can choose one of the supplied variables from the drop-down list, or you can construct a variable.
The variables you can choose from the drop-down list include the following:
Table 13-3 Clientless SSL VPN Variables
No. Variable Substitution Definition
1 CSCO_WEBVPN_USERNAME SSL VPN user login ID.
2 CSCO_WEBVPN_PASSWORD SSL VPN user login password.

13-30
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 13 Advanced Clientless SSL VPN Configuration
Configuring Bookmarks
When the ASA recognizes one of these six variable strings in an end-user request—in a bookmark or a
post form—it replaces it with the user-specific value before passing the request to a remote server.
Note You can obtain the http-post parameters for any application by performing an HTTP Sniffer trace in the
clear (without the security appliance involved). Here is a link to a free browser capture tool, also called
an HTTP analyzer: http://www.ieinspector.com/httpanalyzer/downloadV2/IEHttpAnalyzerV2.exe.
Using Variables 1 to 4
The ASA obtains values for the first four substitutions from the SSL VPN Login page, which includes
fields for username, password, internal password (optional), and group. It recognizes these strings in
user requests and replaces them with the value specific to the user before it passes the request on to a
remote server.
For example, if a URL list contains the link,
http://someserver/homepage/CSCO_WEBVPN_USERNAME.html, the ASA translates it to the
following unique links:
•For USER1, the link becomes http://someserver/homepage/USER1.html
•For USER2, the link is http://someserver/homepage/USER2.html
In the following case, cifs://server/users/CSCO_WEBVPN_USERNAME, lets the ASA map a file drive
to specific users:
•For USER1, the link becomes cifs://server/users/USER1
3 CSCO_WEBVPN_INTERNAL_PASSWORD SSL VPN user internal resource password. This is a cached
credential, and not authenticated by a AAA server. If a user enters
this value, it is used as the password for auto sign-on, instead of the
password value.
4 CSCO_WEBVPN_CONNECTION_PROFILE SSL VPN user login group drop-down, a group alias within the
connection profile
5 CSCO_WEBVPN_MACRO1 Set via the RADIUS/LDAP vendor-specific attribute. If you are
mapping this from LDAP via an ldap-attribute-map, the Cisco
attribute that uses this variable is
WEBVPN-Macro-Substitution-Value1.
Variable substitution via RADIUS is performed by VSA#223.
6 CSCO_WEBVPN_MACRO2 Set via the RADIUS/LDAP vendor-specific attribute. If you are
mapping this from LDAP via an ldap-attribute-map, the Cisco
attribute that uses this variable is
WEBVPN-Macro-Substitution-Value2.
Variable substitution via RADIUS is performed by VSA#224.
7 CSCO_WEBVPN_PRIMARY_USERNAME Primary user login ID for double authentication.
8 CSCO_WEBVPN_PRIMARY_PASSWORD Primary user login password for double authentication.
9 CSCO_WEBVPN_SECONDARY_USERNAME Secondary user login ID for double authentication.
10 CSCO_WEBVPN_SECONDARY_PASSWORD Secondary user login ID for double authentication.
Table 13-3 Clientless SSL VPN Variables
No. Variable Substitution Definition

13-31
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 13 Advanced Clientless SSL VPN Configuration
Configuring Bookmarks
•For USER 2, the link is cifs://server/users/USER2
Using Variables 5 and 6
Values for macros 5 and 6 are RADIUS or LDAP vendor-specific attributes (VSAs). These enable you
to set substitutions configured on either a RADIUS or an LDAP server.
Using Variables 7 to 10
Each time the ASA recognizes one of these four strings in an end-user request (a bookmark or a post
form), it replaces it with the user-specific value before passing the request to a remote server.
Example 1: Setting a Homepage
The following example sets a URL for the homepage:
•WebVPN-Macro-Value1 (ID=223), type string, is returned as wwwin-portal.example.com
•WebVPN-Macro-Value2 (ID=224), type string, is returned as 401k.com
To set a home page value, you would configure the variable substitution as
https://CSCO_WEBVPN_MACRO1, which would translate to https://wwwin-portal.example.com.
The best way to do this is to configure the Homepage URL parameter in ASDM. Without writing a script
or uploading anything, an administrator can specify which homepage in the group policy to connect with
via smart tunnel.
Go to the Add/Edit Group Policy pane, from either the Network Client SSL VPN or Clientless SSL VPN
Access section of ASDM. The paths are as follows:
•Configuration > Remote Access VPN > Network (Client) Access > Group Policies > Add/Edit
Group Policy > Advanced > SSL VPN Client > Customization > Homepage URL attribute.
•Configuration > Remote Access VPN > Clientless SSL VPN Access > Group Policies > Add/Edit
Group Policy > More Options > Customization > Homepage URL attribute.
Configuration Example for Setting a Bookmark or URL Entry
You can use an HTTP Post to log on to an OWA resource using an RSA one-time password (OTP) for
SSL VPN authentication, and then the static, internal password for OWA email access. The best way to
do this is to add or edit a bookmark entry in ASDM.
There are several paths to the Add Bookmark Entry pane, including the following:
•Configuration > Remote Access VPN > Clientless SSL VPN Access > Portal > Bookmarks >
Add/Edit Bookmark Lists > Add/Edit Bookmark Entry > Advanced Options area > Add/Edit Post
Parameters (available after you click Post in the URL Method attribute).
or
(Available after you click Post in the URL Method attribute):
•Network (Client) Access > Dynamic Access Policies > Add/Edit Dynamic Access Policy > URL
Lists tab > Manage button > Configured GUI Customization Objects > Add/Edit button > Add/Edit
Bookmark List > Add/Edit Bookmark Entry > Advanced Options area > Add/Edit Post Parameters.
Configuration Example for Configuring File Share (CIFS) URL Substitutions
You can allow a more flexible bookmark configuration by using variable substitution for CIFS URLs.

13-32
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 13 Advanced Clientless SSL VPN Configuration
Configuring Bookmarks
If you configure the URL cifs://server/CSCO_WEBVPN_USERNAME, the ASA automatically maps it
to the user’s file share home directory. This method also allows for password and internal password
substitution. The following are example URL substitutions:
cifs://CSCO_WEBVPN_USERNAME:CSCO_WEBVPN_PASSWORD@server
cifs://CSCO_WEBVPN_USERNAME:CSCO_WEBVPN_INTERNAL_PASSWORD@server
cifs://domain;CSCO_WEBVPN_USERNAME:CSCO_WEBVPN_PASSWORD@server
cifs://domain;CSCO_WEBVPN_USERNAME:CSCO_WEBVPN_INTERNAL_PASSWORD@server
cifs://domain;CSCO_WEBVPN_USERNAME:CSCO_WEBVPN_PASSWORD@server/CSCO_WEB
VPN_USERNAME
cifs://domain;CSCO_WEBVPN_USERNAME:CSCO_WEBVPN_INTERNAL_PASSWORD@server/
CSCO_WEBVPN_USERNAME
Customizing External Ports
You can use the external portal feature to create your own portal instead of using the pre-configured one.
If you set up your own portal, you can bypass the clientless portal and send a POST request to retrieve
your portal.
DETAILED STEPS
Step 1 Choose Configuration > Remote Access VPN > Clientless SSL VPN Access > Portal >
Customization. Highlight the desired customization and choose Edit.
Step 2 Check the Enable External Portal check box.
Step 3 In the URL field, enter the desired external portal so that POST requests are allowed.

CHAPTER
14-1
Cisco ASA Series VPN ASDM Configuration Guide
14
Configuring Policy Groups
September 13, 2013
Configuring Smart Tunnel Access
The following sections describe how to enable smart tunnel access with Clientless SSL VPN sessions,
specify the applications to be provided with such access, and provide notes on using it.
Configuring Smart Tunnel Access
To configure smart tunnel access, you create a smart tunnel list containing one or more applications
eligible for smart tunnel access, and the endpoint operating system associated with the list. Because each
group policy or local user policy supports one smart tunnel list, you must group the nonbrowser-based
applications to be supported into a smart tunnel list. After creating a list, you assign it to one or more
group policies or local user policies.
The following sections describe smart tunnels and how to configure them:
•About Smart Tunnels
•Why Smart Tunnels?
•Configuring a Smart Tunnel (Lotus Example)
•Simplifying Configuration of Which Applications to Tunnel
•About Smart Tunnel Lists
•Creating a Smart Tunnel Auto Sign-On Server List
•Adding Servers to a Smart Tunnel Auto Sign-On Server List
•Enabling and Switching Off Smart Tunnel Access
About Smart Tunnels
A smart tunnel is a connection between a TCP-based application and a private site, using a clientless
(browser-based) SSL VPN session with the security appliance as the pathway, and the ASA as a proxy
server. You can identify applications for which to grant smart tunnel access, and specify the local path
to each application. For applications running on Microsoft Windows, you can also require a match of the
SHA-1 hash of the checksum as a condition for granting smart tunnel access.

14-2
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 14 Configuring Policy Groups
Configuring Smart Tunnel Access
Lotus SameTime and Microsoft Outlook are examples of applications to which you may want to grant
smart tunnel access.
Configuring smart tunnels requires one of the following procedures, depending on whether the
application is a client or is a web-enabled application:
•Create one or more smart tunnel lists of the client applications, then assign the list to the group
policies or local user policies for whom smart tunnel access is required.
•Create one or more bookmark list entries that specify the URLs of the web-enabled applications
eligible for smart tunnel access, then assign the list to the group policies or local user policies for
whom smart tunnel access is required.
You can also list web-enabled applications for which to automate the submission of login credentials in
smart tunnel connections over Clientless SSL VPN sessions.
Why Smart Tunnels?
Smart tunnel access lets a client TCP-based application use a browser-based VPN connection to access
a service. It offers the following advantages to users, compared to plug-ins and the legacy technology,
port forwarding:
•Smart tunnel offers better performance than plug-ins.
•Unlike port forwarding, smart tunnel simplifies the user experience by not requiring the user
connection of the local application to the local port.
•Unlike port forwarding, smart tunnel does not require users to have administrator privileges.
The advantage of a plug-in is that it does not require the client application to be installed on the remote
computer.
Prerequisites
See the Supported VPN Platforms, Cisco ASA 5500 Series, for the platforms and browsers supported by
ASA Release 9.0 smart tunnels.
The following requirements and limitations apply to smart tunnel access on Windows:
•ActiveX or Oracle Java Runtime Environment (JRE) 4 update 15 or later (JRE 6 or later
recommended) on Windows must be enabled on the browser.
•Only Winsock 2, TCP-based applications are eligible for smart tunnel access.
•For Mac OS X only, Java Web Start must be enabled on the browser.
Restrictions
•Smart tunnel supports only proxies placed between computers running Microsoft Windows and the
security appliance. Smart Tunnel uses the Internet Explorer configuration, which sets system-wide
parameters in Windows. That configuration may include proxy information:
–
If a Windows computer requires a proxy to access the ASA, then there must be a static proxy
entry in the client's browser, and the host to connect to must be in the client's list of proxy
exceptions.
–
If a Windows computer does not require a proxy to access the ASA, but does require a proxy to
access a host application, then the ASA must be in the client's list of proxy exceptions.

14-3
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 14 Configuring Policy Groups
Configuring Smart Tunnel Access
Proxy systems can be defined the client’s configuration of static proxy entry or automatic
configuration, or by a PAC file. Only static proxy configurations are currently supported by Smart
Tunnels.
•Kerberos constrained delegation (KCD) is not supported for smart tunnels.
•With Windows, to add smart tunnel access to an application started from the command prompt, you
must specify “cmd.exe” in the Process Name of one entry in the smart tunnel list, and specify the
path to the application itself in another entry, because “cmd.exe” is the parent of the application.
•With HTTP-based remote access, some subnets may block user access to the VPN gateway. To fix
this, place a proxy in front of the ASA to route traffic between the Web and the end user. That proxy
must support the CONNECT method. For proxies that require authentication, Smart Tunnel supports
only the basic digest authentication type.
•When smart tunnel starts, the ASA by default passes all browser traffic through the VPN session if
the browser process is the same. The ASA only also does this if a tunnel-all policy (the default)
applies. If the user starts another instance of the browser process, it passes all traffic through the
VPN session. If the browser process is the same and the security appliance does not provide access
to a URL, the user cannot open it. As a workaround, assign a tunnel policy that is not tunnel-all.
•A stateful failover does not retain smart tunnel connections. Users must reconnect following a
failover.
•The Mac version of smart tunnel does not support POST bookmarks, form-based auto sign-on, or
POST macro substitution.
•For Mac OS X users, only those applications started from the portal page can establish smart tunnel
connections. This requirement includes smart tunnel support for Firefox. Using Firefox to start
another instance of Firefox during the first use of a smart tunnel requires the user profile named
csco_st. If this user profile is not present, the session prompts the user to create one.
•In Mac OS X, applications using TCP that are dynamically linked to the SSL library can work over
a smart tunnel.
•Smart tunnel does not support the following on Mac OS X:
–
Proxy services.
–
Auto sign-on.
–
Applications that use two-level name spaces.
–
Console-based applications, such as Telnet, SSH, and cURL.
–
Applications using dlopen or dlsym to locate libsocket calls.
–
Statically linked applications to locate libsocket calls.
•Mac OS X requires the full path to the process and is case-sensitive. To avoid specifying a path for
each username, insert a tilde (~) before the partial path (e.g., ~/bin/vnc).
Configuring a Smart Tunnel (Lotus Example)
Note These example instructions provide the minimum instructions required to add smart tunnel support for
an application. See the field descriptions in the sections that follow for more information.
14-4
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 14 Configuring Policy Groups
Configuring Smart Tunnel Access
DETAILED STEPS
Step 1 Choose Configuration > Remote Access VPN > Clientless SSL VPN Access > Portal > Smart
Tunnels.
Step 2 Double-click the smart tunnel list to add an application to; or click Add to create a list of applications,
enter a name for this list in the List Name field, and click Add.
For example, click Add in the Smart Tunnels pane, enter Lotus in the List Name field, and click Add.
Step 3 Click Add in the Add or Edit Smart Tunnel List dialog box.
Step 4 Enter a string in the Application ID field to serve as a unique index to the entry within the smart tunnel
list.
Step 5 Enter the filename and extension of the application into the Process Name dialog box.
Table 14-1 shows example application ID strings and the associated paths required to support Lotus.
Step 6 Select Windows next to OS.
Step 7 Click OK.
Step 8 Repeat Steps 3 to 7 for each application to add to the list.
Step 9 Click OK in the Add or Edit Smart Tunnel List dialog box.
Step 10 Assign the list to the group policies and local user policies to provide smart tunnel access to the
associated applications, as follows:
•To assign the list to a group policy, choose Configuration > Remote Access VPN> Clientless SSL
VPN Access > Group Policies > Add or Edit > Portal and choose the smart tunnel name from the
drop-down list next to the Smart Tunnel List attribute.
•To assign the list to a local user policy, choose Configuration > Remote Access VPN> AAA Setup
> Local Users > Add or Edit > VPN Policy > Clientless SSL VPN and choose the smart tunnel
name from the drop-down list next to the Smart Tunnel List attribute.
Simplifying Configuration of Which Applications to Tunnel
A smart tunnel application list is essentially a filter of what applications are granted access to the tunnel.
The default is to allow access for all processes started by the browser. With a Smart Tunnel enabled
bookmark, the clientless session grants access only to processes initiated by the Web browser. For
non-browser applications, an administrator can choose to tunnel all applications and thus remove the
need to know which applications an end user may invoke. Table 14-2 shows the situations in which
processes are granted access.
Table 14-1 Smart Tunnel Example: Lotus 6.0 Thick Client with Domino Server 6.5.5
Application ID Example Minimum Required Process Name
lotusnotes notes.exe
lotusnlnotes nlnotes.exe
lotusntaskldr ntaskldr.exe
lotusnfileret nfileret.exe

14-5
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 14 Configuring Policy Groups
Configuring Smart Tunnel Access
Restrictions
This configuration is applicable to Windows platforms only.
DETAILED STEPS
Step 1 Choose Configuration > Remote Access VPN > AAA/Local Users > Local Users.
Step 2 In the User Account window, highlight the username to edit.
Step 3 Click Edit. The Edit User Account window appears.
Step 4 In the left sidebar of the Edit User Account window, click VPN Policy > Clientless SSL VPN.
Step 5 Perform one of the following:
•Check the smart tunnel_all_applications check box. All applications will be tunneled without
making a list or knowing which executables an end user may invoke for external applications.
•Or choose from the following tunnel policy options:
–
Uncheck the Inherit check box at the Smart Tunnel Policy parameter.
–
Choose from the network list and specify one of the tunnel options: use smart tunnel for the
specified network, do not use smart tunnel for the specified network, or use tunnel for all
network traffic.
Adding Applications to Be Eligible for Smart Tunnel Access
The Clientless SSL VPN configuration of each ASA supports smart tunnel lists, each of which identifies
one or more applications eligible for smart tunnel access. Because each group policy or username
supports only one smart tunnel list, you must group each set of applications to be supported into a smart
tunnel list.
The Add or Edit Smart Tunnel Entry dialog box lets you specify the attributes of an application in a smart
tunnel list.
Table 14-2 Access for Smart Tunnel Applications and Enabled Bookmarks
Situation Smart Tunnel Enabled Bookmark Smart Tunnel Application Access
Application list specified Any processes that match a
process name in the application
list are granted access.
Only processes that match a
process name in the application
list are granted access.
Smart tunnel is switched off All processes (and their child
processes) are granted access.
No process is granted access.
Smart Tunnel all
Applications check box is
checked.
All processes (and their child
processes) are granted access.
Note This includes processes
initiated by non-Smart
Tunnel Web pages if the
Web page is served by the
same browser process.
All processes owned by the user
who started the browser are
granted access but not child
processes of those original
processes.

14-6
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 14 Configuring Policy Groups
Configuring Smart Tunnel Access
Step 1 Navigate to Configuration > Remote Access VPN > Clientless SSL VPN Access > Portal > Smart
Tunnels, and choose a smart tunnel application list to edit, or add a new one.
Step 2 For a new list, enter a unique name for the list of applications or programs. Do not use spaces.
Following the configuration of the smart tunnel list, the list name appears next to the Smart Tunnel List
attribute in the Clientless SSL VPN group policies and local user policies. Assign a name that will help
you to distinguish its contents or purpose from other lists that you are likely to configure.
Step 3 Click Add and add as many applications as you need to this smart tunnel list. The parameters are
described below:
•Application ID - Enter a string to name the entry in the smart tunnel list. This user-specified name
is saved and then returned onto the GUI. The string is unique for the operating system. It typically
names the application to be granted smart tunnel access. To support multiple versions of an
application for which you choose to specify different paths or hash values, you can use this attribute
to differentiate entries, specifying the operating system, and name and version of the application
supported by each list entry. The string can be up to 64 characters.
•Process Name - Enter the filename or path to the application. The string can be up to 128 characters.
Windows requires an exact match of this value to the right side of the application path on the remote
host to qualify the application for smart tunnel access. If you specify only the filename for Windows,
SSL VPN does not enforce a location restriction on the remote host to qualify the application for
smart tunnel access.
If you specify a path and the user installed the application in another location, that application does
not qualify. The application can reside on any path as long as the right side of the string matches the
value you enter.
To authorize an application for smart tunnel access if it is present on one of several paths on the
remote host, either specify only the name and extension of the application in this field; or create a
unique smart tunnel entry for each path.
Note A sudden problem with smart tunnel access may be an indication that a Process Name value is
not up-to-date with an application upgrade. For example, the default path to an application
sometimes changes following the acquisition of the company that produces the application and
the next application upgrade.
With Windows, to add smart tunnel access to an application started from the command prompt, you
must specify “cmd.exe” in the Process Name of one entry in the smart tunnel list, and specify the
path to the application itself in another entry, because “cmd.exe” is the parent of the application.
•OS—Click Windows or Mac to specify the host operating system of the application.
•Hash (Optional and only applicable to Windows)—To obtain this value, enter the checksum of the
application (that is, the checksum of the executable file) into a utility that calculates a hash using
the SHA-1 algorithm. One example of such a utility is the Microsoft File Checksum Integrity
Verifier (FCIV), which is available at http://support.microsoft.com/kb/841290/. After installing
FCIV, place a temporary copy of the application to be hashed on a path that contains no spaces (for
example, c:/fciv.exe), then enter fciv.exe -sha1 application at the command line (for example,
fciv.exe -sha1 c:\msimn.exe) to display the SHA-1 hash.
The SHA-1 hash is always 40 hexadecimal characters.
Before authorizing an application for smart tunnel access, Clientless SSL VPN calculates the hash
of the application matching the Application ID. It qualifies the application for smart tunnel access
if the result matches the value of Hash.
14-7
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 14 Configuring Policy Groups
Configuring Smart Tunnel Access
Entering a hash provides a reasonable assurance that SSL VPN does not qualify an illegitimate file
that matches the string you specified in the Application ID. Because the checksum varies with each
version or patch of an application, the Hash you enter can only match one version or patch on the
remote host. To specify a hash for more than one version of an application, create a unique smart
tunnel entry for each Hash value.
Note If you enter Hash values and you need to support future versions or patches of an application
with smart tunnel access, you must keep the smart tunnel list updated. A sudden problem with
smart tunnel access may be an indication that the application list containing Hash values is not
up-to-date with an application upgrade. You can avoid this problem by not entering a hash.
Step 4 Click OK to save the application, and create how ever many applications you need for this smart tunnel
list.
Step 5 When you are done creating your smart tunnel list, you must assign it to a group policy or a local user
policy for it to become active, as follows:
•To assign the list to a group policy, choose Config > Remote Access VPN> Clientless SSL VPN
Access > Group Policies > Add or Edit > Portal and choose the smart tunnel name from the
drop-down list next to the Smart Tunnel List attribute.
•To assign the list to a local user policy, choose Config > Remote Access VPN> AAA Setup > Local
Users > Add or Edit > VPN Policy > Clientless SSL VPN and choose the smart tunnel name from
the drop-down list next to the Smart Tunnel List attribute.
About Smart Tunnel Lists
For each group policy and username, you can configure Clientless SSL VPN to do one of the following:
•Start smart tunnel access automatically upon user login.
•Enable smart tunnel access upon user login, but require the user to start it manually, using the
Application Access > Start Smart Tunnels button on the Clientless SSL VPN Portal Page.
Table 14-3 Example Smart Tunnel Entries
Smart Tunnel Support
Application ID
(Any unique string
is OK.) Process Name OS
Mozilla Firefox. firefox firefox.exe Windows
Microsoft Outlook Express. outlook-express msimn.exe Windows
More restrictive alternative—Microsoft
Outlook Express only if the executable file is in
a predefined path.
outlook-express \Program Files\Outlook Express\msimn.exe Windows
Open a new Terminal window on a Mac. (Any
subsequent application launched from within
the same Terminal window fails because of the
one-time-password implementation.)
terminal Terminal Mac
Start smart tunnel for a new window new-terminal Terminal open -a MacTelnet Mac
Start application from a Mac Terminal window. curl Terminal curl www.example.com Mac

14-8
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 14 Configuring Policy Groups
Configuring Smart Tunnel Access
Restrictions
The smart tunnel logon options are mutually exclusive for each group policy and username. Use only
one.
Creating a Smart Tunnel Auto Sign-On Server List
The Smart Tunnel Auto Sign-on Server List dialog box lets you add or edit lists of servers which will
automate the submission of login credentials during smart tunnel setup. Auto sign-on over a smart tunnel
is available for Internet Explorer and Firefox.
Step 1 Navigate to Configuration > Remote Access VPN > Clientless SSL VPN Access > Portal > Smart
Tunnels, and ensure Smart Tunnel Auto Sign-on Server List is expanded to display.
Step 2 Click Add, and enter a unique name for a list of remote servers that will help you to distinguish its
contents or purpose from other lists that you are likely to configure. The string can be up to 64 characters.
Do not use spaces.
After you create a smart tunnel auto sign-on list, that list name appears next to the Auto Sign-on Server
List attribute under Smart Tunnel in the Clientless SSL VPN group policy and local user policy
configurations.
Adding Servers to a Smart Tunnel Auto Sign-On Server List
The following steps describe how to add servers to the list of servers for which to provide auto sign-on
in smart tunnel connections, and assign that list to a group policies or a local user.
Step 1 Navigate to Configuration > Remote Access VPN > Clientless SSL VPN Access > Portal > Smart
Tunnels, select one of the lists, and click Edit.
Step 2 Click the Add button on the Add Smart Tunnel Auto Sign-On Server List dialog to add one more smart
tunnel servers.
Step 3 Enter the hostname or IP address of the server to auto-authenticate to:
•If you select Hostname, enter a hostname or wildcard mask to auto-authenticate to. You can use the
following wildcard characters:
–
* to match any number of characters or zero characters.
–
? to match any single character.
–
[] to match any single character in the range expressed inside the brackets.
–
For example, enter *.example.com. Using this option protects the configuration from dynamic
changes to IP addresses.
•If you select IP Address, enter an IP address.
Note Firefox does not support a host mask with wild cards, a subnet using IP addresses, or a
netmask; you must use an exact hostname or IP address. For example, within Firefox, if you
enter *.cisco.com, auto sign-on to host email.cisco.com will fail.

14-9
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 14 Configuring Policy Groups
Configuring Smart Tunnel Access
Step 4 Windows Domain (Optional)—Click to add the Windows domain to the username, if authentication
requires it. If you do so, ensure you specify the domain name when assigning the smart tunnel list to one
or more group policies or local user policies.
Step 5 HTTP-based Auto Sign-On (Optional)
•Authentication Realm—The realm is associated with the protected area of the website and passed
back to the browser either in the authentication prompt or in the HTTP headers during
authentication. Once auto-sign is configured here, and a realm string is specified, users can
configure the realm string on a Web application (such as Outlook Web Access) and access Web
applications without signing on.
Use the address format used in the source code of the Web pages on the intranet. If you are
configuring smart tunnel auto sign-on for browser access and some Web pages use hostnames and
others use IP addresses, or you do not know, specify both in different smart tunnel auto sign-on
entries. Otherwise, if a link on a Web page uses a different format than the one you specify, it fails
when the user clicks it.
Note If administrators do not know the corresponding realm, they should perform logon once and get
the string from the prompt dialog.
•Port Number—Specify a port number for the corresponding hosts. For Firefox, if no port number is
specified, auto sign-on is performed on HTTP and HTTPS, accessed by default port numbers 80 and
443 respectively.
Step 6 Click OK.
Step 7 Following the configuration of the smart tunnel auto sign-on server list, you must assign it to a group
policy or a local user policy for it to become active, as follows:
•To assign the list to a group policy:
1. Navigate to Configuration > Remote Access VPN > Clientless SSL VPN Access > Group
Policies, and open a group policy,
2. Select the Portal tab, find the Smart Tunnel area, and choose the auto sign-on server list from
the drop-down list next to the Auto Sign-On Server List attribute.
•To assign the list to a local user policy:
1. Choose Configuration > Remote Access VPN > AAA/Local Users > Local Users, and edit
the local user to assign an auto sign-on server list to.
2. Navigate to VPN Policy > Clientless SSL VPN, and find the Auto Sign-on Server setting under
the Smart Tunnel area
3. Uncheck Inherit, and choose a server list from the drop-down list next to the Auto Sign-On
Server List attribute.
Enabling and Switching Off Smart Tunnel Access
By default, smart tunnels are switched off.
If you enable smart tunnel access, the user will have to start it manually, using the Application Access
> Start Smart Tunnels button on the Clientless SSL VPN portal page.

14-10
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 14 Configuring Policy Groups
Configuring Smart Tunnel Access
Configuring Smart Tunnel Log Off
This section describes how to ensure that the smart tunnel is properly logged off. Smart tunnel can be
logged off when all browser windows have been closed, or you can right click the notification icon and
confirm log out.
Note We strongly recommend the use of the logout button on the portal. This method pertains to Clientless
SSL VPNs and logs off regardless of whether smart tunnel is used or not. The notification icon should
be used only when using standalone applications without the browser.
When Its Parent Process Terminates
This practice requires the closing of all browsers to signify log off. The smart tunnel lifetime is now tied
to the starting process lifetime. For example, if you started a smart tunnel from Internet Explorer, the
smart tunnel is turned off when no iexplore.exe is running. Smart tunnel can determine that the VPN
session has ended even if the user closed all browsers without logging out.
Note In some cases, a lingering browser process is unintentional and is strictly a result of an error.
Also, when a Secure Desktop is used, the browser process can run in another desktop even if the
user closed all browsers within the secure desktop. Therefore, smart tunnel declares all browser
instances gone when no more visible windows exist in the current desktop.
With a Notification Icon
You may also choose to switch off logging off when a parent process terminates so that a session survives
if you close a browser. For this practice, you use a notification icon in the system tray to log out. The
icon remains until the user clicks the icon to logout. If the session has expired before the user has logged
out, the icon remains until the next connection is tried. You may have to wait for the session status to
update in the system tray.
Note This icon is an alternative way to log out of SSL VPN. It is not an indicator of VPN session
status.
DETAILED STEPS
Step 1 Choose Configuration > Remote Access VPN > Clientless SSL VPN Access > Portal > Smart
Tunnels.
Step 2 Enable the Click on smart-tunnel logoff icon in the system tray radio button.
Step 3 In the Smart Tunnel Networks portion of the window, check Add and enter both the IP address and
hostname of the network which should include the icon.
Note If you right-click the icon, a single menu item appears that prompts the user to log out of the
SSL VPN.

14-11
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 14 Configuring Policy Groups
Configuring Portal Access Rules
Using Proxy Bypass
You can configure the ASA to use proxy bypass when applications and Web resources work better with
the special content rewriting this feature provides. Proxy bypass is an alternative method of content
rewriting that makes minimal changes to the original content. It is often useful with custom Web
applications.
You can configure multiple proxy bypass entries. The order in which you configure them is unimportant.
The interface and path mask or interface and port uniquely identify a proxy bypass rule.
If you configure proxy bypass using ports rather than path masks, depending on your network
configuration, you may need to change your firewall configuration to allow these ports access to the
ASA. Use path masks to avoid this restriction. Be aware, however, that path masks can change, so you
may need to use multiple pathmask statements to exhaust the possibilities.
A path is everything in a URL after the .com or .org or other types of domain name. For example, in the
URL www.example.com/hrbenefits, hrbenefits is the path. Similarly, for the URL
www.example.com/hrinsurance, hrinsurance is the path. To use proxy bypass for all hr sites, you can
avoid using the command multiple times by using the * wildcard as follows: /hr*.
You can set rules for when the ASA performs little or no content rewriting:
Step 1 Navigate to Configuration > Remote Access VPN > Clientless SSL VPN Access > Advanced > Proxy
Bypass.
Step 2 Select the Interface name for proxy bypass.
Step 3 Specify either a port or a URI for proxy bypass:
•Port—(radio button) Click to use a port for proxy bypass. The valid port numbers are 20000 to
21000.
•Port (field)—Enter a high-numbered port for the ASA to reserve for proxy bypass.
•Path Mask—(radio button) Click to use a URL for proxy bypass.
•Path Mask—(Field) Enter a URL for proxy bypass. It can contain a regular expression.
Step 4 Define target URLs for proxy bypass:
•URL—(drop-down list) Click either http or https as the protocol.
•URL (text field)—Enter a URL for which to apply a proxy bypass.
Step 5 Specify the content to rewrite. The choices are none or a combination of XML, links, and cookies.
•XML—Check to rewrite XML content.
•Hostname—Check to rewrite links.
Configuring Portal Access Rules
This enhancement allows customers to configure a global Clientless SSL VPN access policy to permit
or deny Clientless SSL VPN sessions based on the data present in the HTTP header. If the ASA denies
a Clientless SSL VPN session, it returns an error code to the endpoint immediately.

14-12
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 14 Configuring Policy Groups
Configuring Portal Access Rules
The ASA evaluates this access policy before the endpoint authenticates to the ASA. As a result, in the
case of a denial, fewer ASA processing resources are consumed by additional connection attempts from
the endpoint.
Prerequisites
Log on to the ASA and enter global configuration mode. In global configuration mode, the ASA displays
this prompt:
hostname(config)#
DETAILED STEPS
Step 1 Start ASDM and select Configuration > Remote Access VPN > Clientless SSL VPN Access > Portal
> Portal Access Rule.
The Portal Access Rule window opens.
Step 2 Click Add to create a portal access rule or select an existing rule and click Edit.
The Add (or Edit) Portal Access Rule dialog box opens.
Step 3 Enter a rule number from 1 to 65535 in the Rule Priority field.
Rules are processed in order of priority from 1 to 65535.
Step 4 In the User Agent field, enter the name of the user agent to find in the HTTP header.
•Surround the string with wildcards (*) to generalize the string; for example, *Thunderbird*. We
recommend using wildcards in your search string. Without wildcards, the rule may not match any
strings or it may match many fewer strings than you expect.
•If your string contains a space, ASDM automatically adds quotes to the beginning and end of the
string when it saves the rule. For example, if you enter my agent, ASDM will save the string as “my
agent”. ASA will then search for matches of my agent.
Do not add quotes to a string with spaces unless you require the ASA to match the quotes you added
to the string. For example, if you enter “my agent” ASDM will save the string as "\"my agent\’"
and try to find a match for “my agent” and it will not find my agent.
•To use wildcards with a string that contains a space, start and end the entire string with wildcards,
for example, *my agent* and ASDM will automatically surround that string with quotes when it
saves the rule.
Step 5 In the Action field, select either Deny or Permit.
The ASA will deny or permit a Clientless SSL VPN connection based on this setting.
Step 6 Enter an HTTP message code in the Returned HTTP Code field.
The HTTP message number 403 is pre-populated in the field and is the default value for portal access
rules. The allowed range of message codes is 200 to 599.
Step 7 Click OK.
Step 8 Click Apply.

CHAPTER
15-1
Cisco ASA Series VPN ASDM Configuration Guide
15
Clientless SSL VPN Remote Users
September 13, 2013
This section is for the system administrator who sets up Clientless (browser-based) SSL VPN for end
users. It summarizes configuration requirements and tasks for the user remote system. It also specifies
information to communicate to users to get them started using Clientless SSL VPN. This section includes
the following topics:
•Requiring Usernames and Passwords
•Communicating Security Tips
•Configuring Remote Systems to Use Clientless SSL VPN Features
•Capturing Clientless SSL VPN Data
Note We assume you have already configured the ASA for Clientless SSL VPN.
Requiring Usernames and Passwords
Depending on your network, during a remote session users may have to log on to any or all of the
following: the computer itself, an Internet service provider, Clientless SSL VPN, mail or file servers, or
corporate applications. Users may have to authenticate in many different contexts, requiring different
information, such as a unique username, password, or PIN. Ensure users have the required access.
Table 15-1 lists the type of usernames and passwords that Clientless SSL VPN users may need to know.
Table 15-1 Usernames and Passwords to Give to Clientless SSL VPN Users
Login Username/
Password Type Purpose Entered When
Computer Access the computer Starting the computer
Internet Service Provider Access the Internet Connecting to an Internet service provider
Clientless SSL VPN Access remote network Starting a Clientless SSL VPN session
File Server Access remote file server Using the Clientless SSL VPN file browsing
feature to access a remote file server

15-2
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 15 Clientless SSL VPN Remote Users
Communicating Security Tips
Communicating Security Tips
Advise users always to log out from the session. To log out of Clientless SSL VPN, click the logout icon
on the Clientless SSL VPN toolbar or close the browser.
Advise users that using Clientless SSL VPN does not ensure that communication with every site is
secure. Clientless SSL VPN ensures the security of data transmission between the remote computer or
workstation and the ASA on the corporate network. If a user then accesses a non-HTTPS Web resource
(located on the Internet or on the internal network), the communication from the corporate ASA to the
destination Web server is not secure.
Configuring Remote Systems to Use Clientless SSL VPN
Features
Table 15-2 includes the following information about setting up remote systems to use Clientless SSL
VPN:
•Starting Clientless SSL VPN
•Using the Clientless SSL VPN Floating Toolbar
•Web Browsing
•Network Browsing and File Management
•Using Applications (Port Forwarding)
•Using email via Port Forwarding, Web Access, or Email Proxy
Table 15-2 also provides information about the following:
•Clientless SSL VPN requirements, by feature
•Clientless SSL VPN supported applications
•Client application installation and configuration requirements
•Information you may need to provide end users
•Tips and use suggestions for end users
It is possible that you have configured user accounts differently, and that different features are available
to each Clientless SSL VPN user. Table 15-2 organizes information by user activity, so that you can skip
over the information for unavailable features.
Corporate Application Login Access firewall-protected internal server Using the Clientless SSL VPN Web browsing
feature to access an internal protected website
Mail Server Access remote mail server via Clientless
SSL VPN
Sending or receiving email messages
Table 15-1 Usernames and Passwords to Give to Clientless SSL VPN Users (continued)
Login Username/
Password Type Purpose Entered When
15-3
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 15 Clientless SSL VPN Remote Users
Configuring Remote Systems to Use Clientless SSL VPN Features
Table 15-2 Clientless SSL VPN Remote System Configuration and End User Requirements
Task Remote System or End User Requirements Specifications or Use Suggestions
Starting Clientless SSL
VPN
Connection to the Internet Any Internet connection is supported, including:
•Home DSL, cable, or dial-up
•Public kiosks
•Hotel hook-ups
•Airport wireless nodes
•Internet cafes
Clientless SSL VPN-supported browser We recommend the following browsers for
Clientless SSL VPN. Other browsers may not fully
support Clientless SSL VPN features.
On Microsoft Windows:
•Internet Explorer 8
•Firefox 8
On Linux:
•Firefox 8
On Mac OS X:
•Safari 5
•Firefox 8
Cookies enabled on browser Cookies must be enabled on the browser in order to
access applications via port forwarding.
URL for Clientless SSL VPN An HTTPS address in the following form:
https://address
where address is the IP address or DNS hostname
of an interface of the ASA (or load balancing
cluster) on which Clientless SSL VPN is enabled.
For example: https://10.89.192.163 or
https://cisco.example.com.
Clientless SSL VPN username and password
[Optional] Local printer Clientless SSL VPN does not support printing
from a Web browser to a network printer. Printing
to a local printer is supported.
15-4
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 15 Clientless SSL VPN Remote Users
Configuring Remote Systems to Use Clientless SSL VPN Features
Using the Floating
Toolbar in a Clientless
SSL VPN Connection
A floating toolbar is available to simplify the use
of Clientless SSL VPN. The toolbar lets you enter
URLs, browse file locations, and choose
preconfigured Web connections without
interfering with the main browser window.
If you configure your browser to block popups, the
floating toolbar cannot display.
The floating toolbar represents the current
Clientless SSL VPN session. If you click the Close
button, the ASA prompts you to close the
Clientless SSL VPN session.
Tip To paste text into a text field, use Ctrl-V.
(Right-clicking is not enabled on the
Clientless SSL VPN toolbar.)
Web Browsing Usernames and passwords for protected
websites
Using Clientless SSL VPN does not ensure that
communication with every site is secure. See
“Communicating Security Tips.”
The look and feel of Web browsing with Clientless
SSL VPN may be different from what users are
accustomed to. For example:
•The Clientless SSL VPN title bar appears
above each Web page.
•You access websites by:
–
Entering the URL in the Enter Web
Address field on the Clientless SSL VPN
Home page.
–
Clicking on a preconfigured website link
on the Clientless SSL VPN Home page.
–
Clicking a link on a webpage accessed via
one of the previous two methods.
Also, depending on how you configured a
particular account, it may be that:
•Some websites are blocked.
•Only the websites that appear as links on the
Clientless SSL VPN Home page are available.
Table 15-2 Clientless SSL VPN Remote System Configuration and End User Requirements (continued)
Task Remote System or End User Requirements Specifications or Use Suggestions
15-5
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 15 Clientless SSL VPN Remote Users
Configuring Remote Systems to Use Clientless SSL VPN Features
Network Browsing and
File Management
File permissions configured for shared
remote access
Only shared folders and files are accessible via
Clientless SSL VPN.
Server name and passwords for protected file
servers
—
Domain, workgroup, and server names
where folders and files reside
Users may not be familiar with how to locate their
files through your organization network.
— Do not interrupt the Copy File to Server command
or navigate to a different screen while the copying
is in progress. Interrupting the operation can cause
an incomplete file to be saved on the server.
Table 15-2 Clientless SSL VPN Remote System Configuration and End User Requirements (continued)
Task Remote System or End User Requirements Specifications or Use Suggestions
15-6
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 15 Clientless SSL VPN Remote Users
Configuring Remote Systems to Use Clientless SSL VPN Features
Using Applications
(called Port Forwarding
or Application Access)
Note On Mac OS X, only the Safari browser supports this feature.
Note Because this feature requires installing Oracle Java Runtime Environment (JRE) and
configuring the local clients, and because doing so requires administrator permissions on
the local system, it is unlikely that users will be able to use applications when they connect
from public remote systems.
Caution Users should always close the Application Access window when they finish using
applications by clicking the Close icon. Failure to close the window properly can cause
Application Access or the applications themselves to be inaccessible.
Client applications installed —
Cookies enabled on browser —
Administrator privileges User must have administrator access on the
computer if you use DNS names to specify servers
because modifying the hosts file requires it.
Oracle Java Runtime Environment (JRE)
version 1.4.x and 1.5.x installed.
JavaScript must be enabled on the browser.
By default, it is enabled.
If JRE is not installed, a pop-up window displays,
directing users to a site where it is available.
On rare occasions, the port forwarding applet fails
with Java exception errors. If this happens, do the
following:
1. Clear the browser cache and close the browser.
2. Verify that no Java icons are in the computer
task bar. Close all instances of Java.
3. Establish a Clientless SSL VPN session and
launch the port forwarding Java applet.
Client applications configured, if necessary.
Note The Microsoft Outlook client does
not require this configuration step.
All non-Windows client applications require
configuration.
To see if configuration is necessary for a
Windows application, check the value of the
Remote Server.
•If the Remote Server contains the server
hostname, you do not need to configure
the client application.
•If the Remote Server field contains an IP
address, you must configure the client
application.
To configure the client application, use the server’s
locally mapped IP address and port number. To
find this information:
1. Start Clientless SSL VPN on the remote
system and click the Application Access link
on the Clientless SSL VPN Home page. The
Application Access window appears.
2. In the Name column, find the name of the
server to use, then identify its corresponding
client IP address and port number (in the Local
column).
3. Use this IP address and port number to
configure the client application. Configuration
steps vary for each client application.
Note Clicking a URL (such as one in an -email message) in an application running over
Clientless SSL VPN does not open the site over Clientless SSL VPN. To open a site over
Clientless SSL VPN, cut and paste the URL into the Enter (URL) Address field.
Table 15-2 Clientless SSL VPN Remote System Configuration and End User Requirements (continued)
Task Remote System or End User Requirements Specifications or Use Suggestions
15-7
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 15 Clientless SSL VPN Remote Users
Capturing Clientless SSL VPN Data
Capturing Clientless SSL VPN Data
The CLI capture command lets you log information about websites that do not display properly over a
Clientless SSL VPN connection. This data can help your Cisco customer support engineer troubleshoot
problems. The following sections describe how to use the capture command:
•Creating a Capture File
•Using a Browser to Display Capture Data
Note Enabling Clientless SSL VPN capture affects the performance of the security appliance. Ensure you
switch off the capture after you generate the capture files needed for troubleshooting.
Using email
via Application Access
Fulfill requirements for Application Access
(See Using Applications)
To use mail, start Application Access from the
Clientless SSL VPN Home page. The mail client
is then available for use.
Note If you are using an IMAP client and you lose your mail server connection or are unable to
make a new connection, close the IMAP application and restart Clientless SSL VPN.
Other email clients We have tested Microsoft Outlook Express
versions 5.5 and 6.0.
Clientless SSL VPN should support other SMTPS,
POP3S, or IMAP4S email programs via port
forwarding, such as Lotus Notes, and Eudora, but
we have not verified them.
Using email via
Web Access
Web-based email product installed Supported products include:
•Outlook Web Access
For best results, use OWA on Internet
Explorer 8.x or higher, or Firefox 8.x.
•Lotus Notes
Other web-based email products should also work,
but we have not verified them.
Using email via
email Proxy
SSL-enabled mail application installed
Do not set the ASA SSL version to TLSv1
Only. Outlook and Outlook Express do not
support TLS.
Supported mail applications:
•Microsoft Outlook
•Microsoft Outlook Express versions 5.5 and
6.0
Other SSL-enabled mail clients should also work,
but we have not verified them.
Mail application configured
Table 15-2 Clientless SSL VPN Remote System Configuration and End User Requirements (continued)
Task Remote System or End User Requirements Specifications or Use Suggestions

15-8
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 15 Clientless SSL VPN Remote Users
Capturing Clientless SSL VPN Data
Creating a Capture File
DETAILED STEPS
Step 1 To start the Clientless SSL VPN capture utility, use the capture command from privileged EXEC mode.
capture capture-name type webvpn user csslvpn-username
where:
•capture-name is a name you assign to the capture, which is also prefixed to the name of the capture
files.
•csslvpn-username is the username to match for capture.
The capture utility starts.
Step 2 A user logs in to begin a Clientless SSL VPN session. The capture utility is capturing packets.
Stop the capture by using the no version of the command.
no capture capture-name
The capture utility creates a capture-name.zip file, which is encrypted with the password koleso
Step 3 Send the .zip file to Cisco, or attach it to a Cisco TAC service request.
Step 4 To look at the contents of the .zip file, unzip it using the password koleso.
The following example creates a capture named hr, which captures Clientless SSL VPN traffic for user2
to a file:
hostname# capture hr type webvpn user user2
WebVPN capture started.
capture name hr
user name user2
hostname# no capture hr
Using a Browser to Display Capture Data
DETAILED STEPS.
Step 1 To start the Clientless SSL VPN capture utility, use the capture command from privileged EXEC mode.
capture capture-name type webvpn user csslvpn-username
where:
•capture-name is a name you assign to the capture, which is also prefixed to the name of the capture
files.
•csslvpn-username is the username to match for capture.
The capture utility starts.
Step 2 A user logs in to begin a Clientless SSL VPN session. The capture utility is capturing packets.
Stop the capture by using the no version of the command.
Step 3 Open a browser and in the address box enter:

15-9
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 15 Clientless SSL VPN Remote Users
Capturing Clientless SSL VPN Data
https://IP address or hostname of the ASA/webvpn_capture.html
The captured content displays in a sniffer format.
Step 4 When you finish examining the capture content, stop the capture by using the no version of the
command.

15-10
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 15 Clientless SSL VPN Remote Users
Capturing Clientless SSL VPN Data

CHAPTER
16-1
Cisco ASA Series VPN ASDM Configuration Guide
16
Configuring Clientless SSL VPN Users
September 13, 2013
Overview
This section provides information to communicate to users to get them started using Clientless SSL
VPN. It includes the following topics:
•Managing Passwords, page 16-4
•Using Auto Sign-On, page 16-10
•Communicating Security Tips, page 16-12
•Configuring Remote Systems to Use Clientless SSL VPN Features, page 16-12
Defining the End User Interface
The Clientless SSL VPN end user interface consists of a series of HTML panels. A user logs on to
Clientless SSL VPN by entering the IP address of an ASA interface in the format https://address. The
first panel that displays is the login screen (Figure 16-1).

16-2
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 16 Configuring Clientless SSL VPN Users
Figure 16-1 Clientless SSL VPN Login Screen
Viewing the Clientless SSL VPN Home Page
After the user logs in, the portal page opens.
The home page displays all of the Clientless SSL VPN features you have configured, and its appearance
reflects the logo, text, and colors you have selected. This sample home page includes all available
Clientless SSL VPN features with the exception of identifying specific file shares. It lets users browse
the network, enter URLs, access specific websites, and use Application Access (port forwarding and
smart tunnels) to access TCP applications.
Viewing the Clientless SSL VPN Application Access Panel
To start port forwarding or smart tunnels, a user clicks the Go button in the Application Access box.
The Application Access window opens (Figure 16-2).
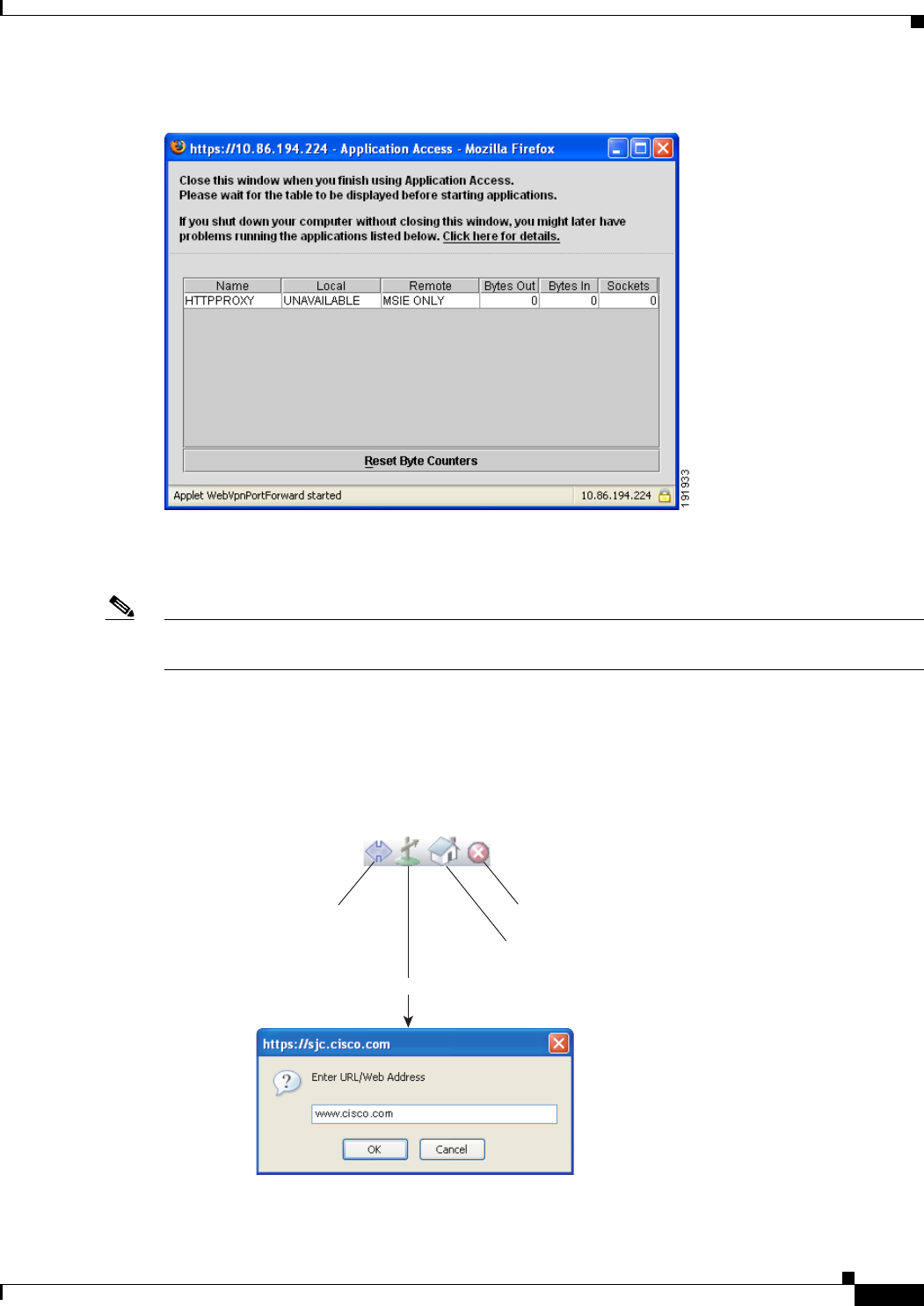
16-3
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 16 Configuring Clientless SSL VPN Users
Figure 16-2 Clientless SSL VPN Application Access Window
This window displays the TCP applications configured for this Clientless SSL VPN connection. To use
an application with this panel open, the user starts the application in the normal way.
Note A stateful failover does not retain sessions established using Application Access. Users must reconnect
following a failover.
Viewing the Floating Toolbar
The floating toolbar shown in Figure 16-3 represents the current Clientless SSL VPN session.
Figure 16-3 Clientless SSL VPN Floating Toolbar
Moves the toolbar to the
other side of the browser
Logs the user out
Displays the portal home page
Launches a dialog box for URL entry
191984

16-4
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 16 Configuring Clientless SSL VPN Users
Managing Passwords
Be aware of the following characteristics of the floating toolbar:
•The toolbar lets you enter URLs, browse file locations, and choose preconfigured Web connections
without interfering with the main browser window.
•If you configure your browser to block popups, the floating toolbar cannot display.
•If you close the toolbar, the ASA prompts you to end the Clientless SSL VPN session.
See Table 16-1 on page 16-12 for detailed information about using Clientless SSL VPN.
Managing Passwords
Optionally, you can configure the ASA to warn end users when their passwords are about to expire.
The ASA supports password management for the RADIUS and LDAP protocols. It supports the
“password-expire-in-days” option for LDAP only.
You can configure password management for IPsec remote access and SSL VPN tunnel-groups.When
you configure password management, the ASA notifies the remote user at login that the user’s current
password is about to expire or has expired. The ASA then offers the user the opportunity to change the
password. If the current password has not yet expired, the user can still log in using that password.
This command is valid for AAA servers that support such notification.
The ASA, releases 7.1 and later, generally supports password management for the following connection
types when authenticating with LDAP or with any RADIUS configuration that supports MS-CHAPv2:
•AnyConnect VPN Client
•IPsec VPN Client
•Clientless SSL VPN
The RADIUS server (for example, Cisco ACS) could proxy the authentication request to another
authentication server. However, from the ASA perspective, it is talking only to a RADIUS server.
Prerequisites
•Native LDAP requires an SSL connection. You must enable LDAP over SSL before attempting to
do password management for LDAP. By default, LDAP uses port 636.
If you are using an LDAP directory server for authentication, password management is supported
with the Sun Java System Directory Server (formerly named the Sun ONE Directory Server) and the
Microsoft Active Directory.
Sun—The DN configured on the ASA to access a Sun directory server must be able to access the
default password policy on that server. We recommend using the directory administrator, or a user
with directory administrator privileges, as the DN. Alternatively, you can place an ACI on the
default password policy.
Microsoft—You must configure LDAP over SSL to enable password management with Microsoft
Active Directory.Restrictions
•Some RADIUS servers that support MSCHAP currently do not support MSCHAPv2. This command
requires MSCHAPv2 so check with your vendor.
•Password management is not supported for any of these connection types for Kerberos/Active
Directory (Windows password) or NT 4.0 Domain.

16-5
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 16 Configuring Clientless SSL VPN Users
Managing Passwords
•For LDAP, the method to change a password is proprietary for the different LDAP servers on the
market. Currently, the ASA implements the proprietary password management logic only for
Microsoft Active Directory and Sun LDAP servers.
•The ASA ignores this command if RADIUS or LDAP authentication has not been configured.
DETAILED STEPS
Step 1 Navigate to Configuration > Remote Access VPN > Clientless SSL VPN Access > Connection
Profiles > Add or Edit > Advanced > General > Password Management.
Step 2 Click the Enable password management option.
Adding the Cisco Authentication Scheme to SiteMinder
In addition to configuring the ASA for SSO with SiteMinder, you must also configure your CA
SiteMinder policy server with the Cisco authentication scheme, a Java plug-in you download from the
Cisco website.
Prerequisites
Configuring the SiteMinder policy server requires experience with SiteMinder.
DETAILED STEPS
This section presents general tasks, not a complete procedure.
Step 1 With the SiteMinder Administration utility, create a custom authentication scheme, being sure to use the
following specific arguments:
•In the Library field, enter smjavaapi.
•In the Secret field, enter the same secret configured on the ASA.
You configure the secret on the ASA using the policy-server-secret command at the command-line
interface.
•In the Parameter field, enter CiscoAuthApi.
Step 2 Using your Cisco.com login, download the file cisco_vpn_auth.jar from
http://www.cisco.com/cisco/software/navigator.html and copy it to the default library directory for the
SiteMinder server. This .jar file is also available on the Cisco ASA CD.
Configuring the SAML POST SSO Server
Use the SAML server documentation provided by the server software vendor to configure the SAML
server in Relying Party mode.
DETAILED STEPS
Step 1 Configure the SAML server parameters to represent the asserting party (the ASA):
•Recipient consumer URL (same as the assertion consumer URL configured on the ASA)

16-6
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 16 Configuring Clientless SSL VPN Users
Managing Passwords
•Issuer ID, a string, usually the hostname of appliance
•Profile type -Browser Post Profile
Step 2 Configure certificates.
Step 3 Specify that asserting party assertions must be signed.
Step 4 Select how the SAML server identifies the user:
•Subject Name Type is DN
•Subject Name format is uid=<user>
Configuring SSO with the HTTP Form Protocol
This section describes using the HTTP Form protocol for SSO. HTTP Form protocol is an approach to
SSO authentication that can also qualify as a AAA method. It provides a secure method for exchanging
authentication information between users of Clientless SSL VPN and authenticating Web servers. You
can use it in conjunction with other AAA servers such as RADIUS or LDAP servers.
Prerequisites
To configure SSO with the HTTP protocol correctly, you must have a thorough working knowledge of
authentication and HTTP protocol exchanges.
Restrictions
As a common protocol, it is applicable only when the following conditions are met for the Web server
application used for authentication:
•The authentication cookie must be set for successful request and not set for unauthorized logons. In
this case, ASA cannot distinguish successful from failed authentication.
DETAILED STEPS
The ASA again serves as a proxy for users of Clientless SSL VPN to an authenticating Web server but,
in this case, it uses HTTP Form protocol and the POST method for requests. You must configure the ASA
to send and receive form data. Figure 16-4 illustrates the following SSO authentication steps:
Step 1 A user of Clientless SSL VPN first enters a username and password to log on to the Clientless SSL VPN
server on the ASA.
Step 2 The Clientless SSL VPN server acts as a proxy for the user and forwards the form data (username and
password) to an authenticating Web server using a POST authentication request.
Step 3 If the authenticating Web server approves the user data, it returns an authentication cookie to the
Clientless SSL VPN server where it is stored on behalf of the user.
Step 4 The Clientless SSL VPN server establishes a tunnel to the user.
Step 5 The user can now access other websites within the protected SSO environment without re-entering a
username and password.
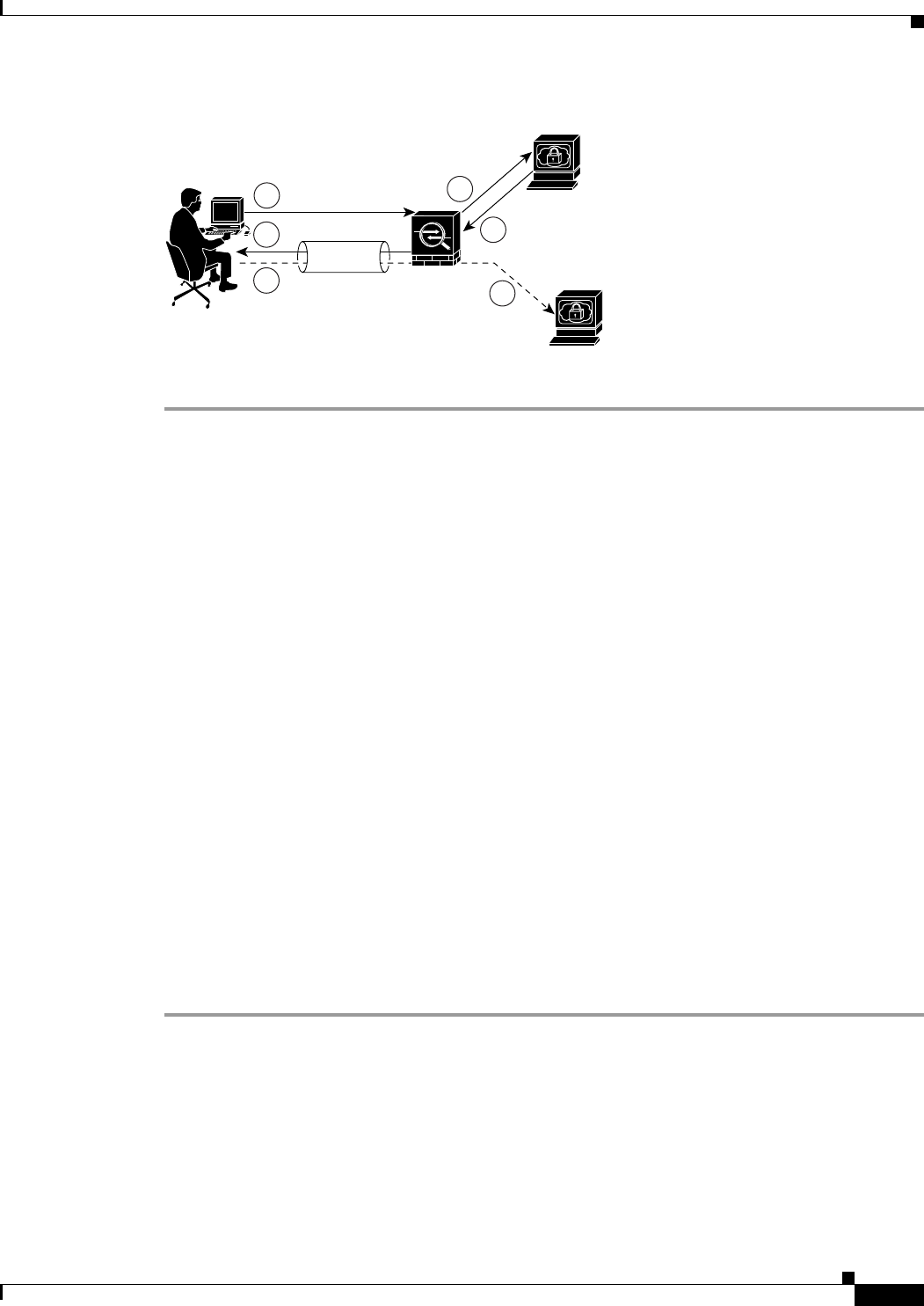
16-7
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 16 Configuring Clientless SSL VPN Users
Managing Passwords
Figure 16-4 SSO Authentication Using HTTP Forms
While you would expect to configure form parameters that let the ASA include POST data such as the
username and password, you initially may not be aware of additional hidden parameters that the Web
server requires. Some authentication applications expect hidden data which is neither visible to nor
entered by the user. You can, however, discover hidden parameters the authenticating Web server expects
by making a direct authentication request to the Web server from your browser without the ASA in the
middle acting as a proxy. Analyzing the Web server response using an HTTP header analyzer reveals
hidden parameters in a format similar to the following:
<param name>=<URL encoded value>&<param name>=<URL encoded>
Some hidden parameters are mandatory and some are optional. If the Web server requires data for a
hidden parameter, it rejects any authentication POST request that omits that data. Because a header
analyzer does not tell you if a hidden parameter is mandatory or not, we recommend that you include all
hidden parameters until you determine which are mandatory.
Gathering HTTP Form Data
This section presents the steps for discovering and gathering necessary HTTP Form data. If you do not
know what parameters the authenticating Web server requires, you can gather parameter data by
analyzing an authentication exchange.
Prerequisites
These steps require a browser and an HTTP header analyzer.
DETAILED STEPS
Step 1 Start your browser and HTTP header analyzer, and connect directly to the Web server login page without
going through the ASA.
Step 2 After the Web server login page has loaded in your browser, examine the login sequence to determine if
a cookie is being set during the exchange. If the Web server has loaded a cookie with the login page,
configure this login page URL as the start-URL.
Step 3 Enter the username and password to log on to the Web server, and press Enter. This action generates the
authentication POST request that you examine using the HTTP header analyzer.
An example POST request—with host HTTP header and body—follows:
148147
Web VPN
server
1
4
5
5
3
2
Auth Web
server
Other protected
web server
Tunnel

16-8
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 16 Configuring Clientless SSL VPN Users
Managing Passwords
POST
/emco/myemco/authc/forms/MCOlogin.fcc?TYPE=33554433&REALMOID=06-000430e1-7443-125c-ac05
-83846dc90034&GUID=&SMAUTHREASON=0&METHOD=GET&SMAGENTNAME=$SM$5FZmjnk3DRNwNjk2KcqVCFbIr
NT9%2bJ0H0KPshFtg6rB1UV2PxkHqLw%3d%3d&TARGET=https%3A%2F%2Fwww.example.com%2Femco%2Fmye
mco%2FHTTP/1.1
Host: www.example.com
(BODY)
SMENC=ISO-8859-1&SMLOCALE=US-EN&USERID=Anyuser&USER_PASSWORD=XXXXXX&target=https%3A%2F%
2Fwww.example.com%2Femco%2Fmyemco%2F&smauthreason=0
Step 4 Examine the POST request and copy the protocol, host, and the complete URL to configure the action-uri
parameter.
Step 5 Examine the POST request body and copy the following:
a. Username parameter. In the preceding example, this parameter is USERID, not the value anyuser.
b. Password parameter. In the preceding example, this parameter is USER_PASSWORD.
c. Hidden parameter. This parameter is everything in the POST body except the username and
password parameters. In the preceding example, the hidden parameter is:
SMENC=ISO-8859-1&SMLOCALE=US-EN&target=https%3A%2F%2Fwww.example.com%2Fe
mco%2Fmyemco%2F&smauthreason=0
Figure 16-5 highlights the action URI, hidden, username and password parameters within sample output
from an HTTP analyzer. This is only an example; output varies widely across different websites.
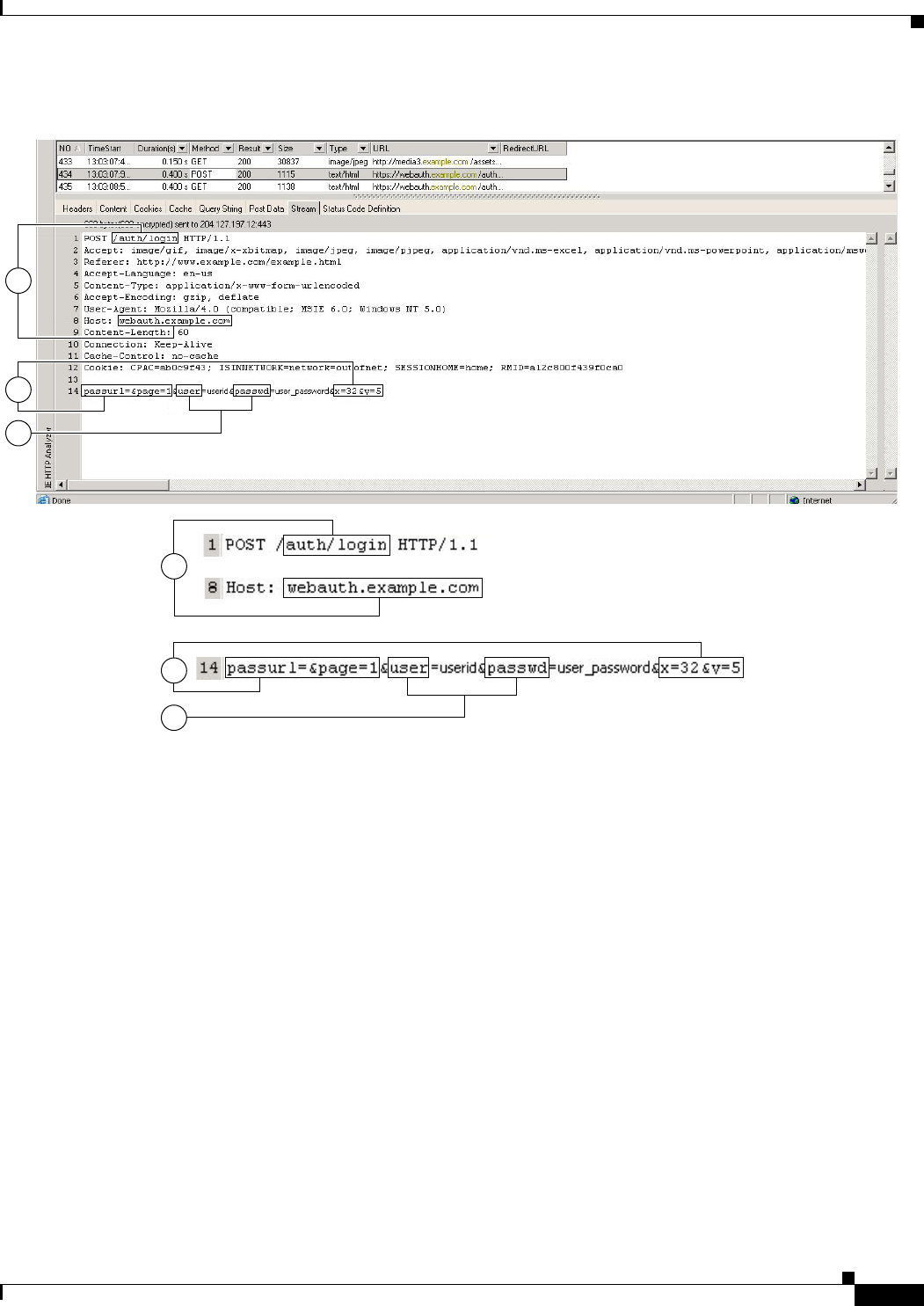
16-9
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 16 Configuring Clientless SSL VPN Users
Managing Passwords
Figure 16-5 Action-uri, hidden, username and password parameters
Step 6 If you successfully log on to the Web server, examine the server response with the HTTP header analyzer
to locate the name of the session cookie set by the server in your browser. This is the auth-cookie-name
parameter.
In the following server response header, the name of the session cookie is SMSESSION. You just need
the name, not the value.Figure 16-6 shows an example of authorization cookies in HTTP analyzer
output. This is only an example; output varies widely across different websites.
249533
1
2
1
2
3
3
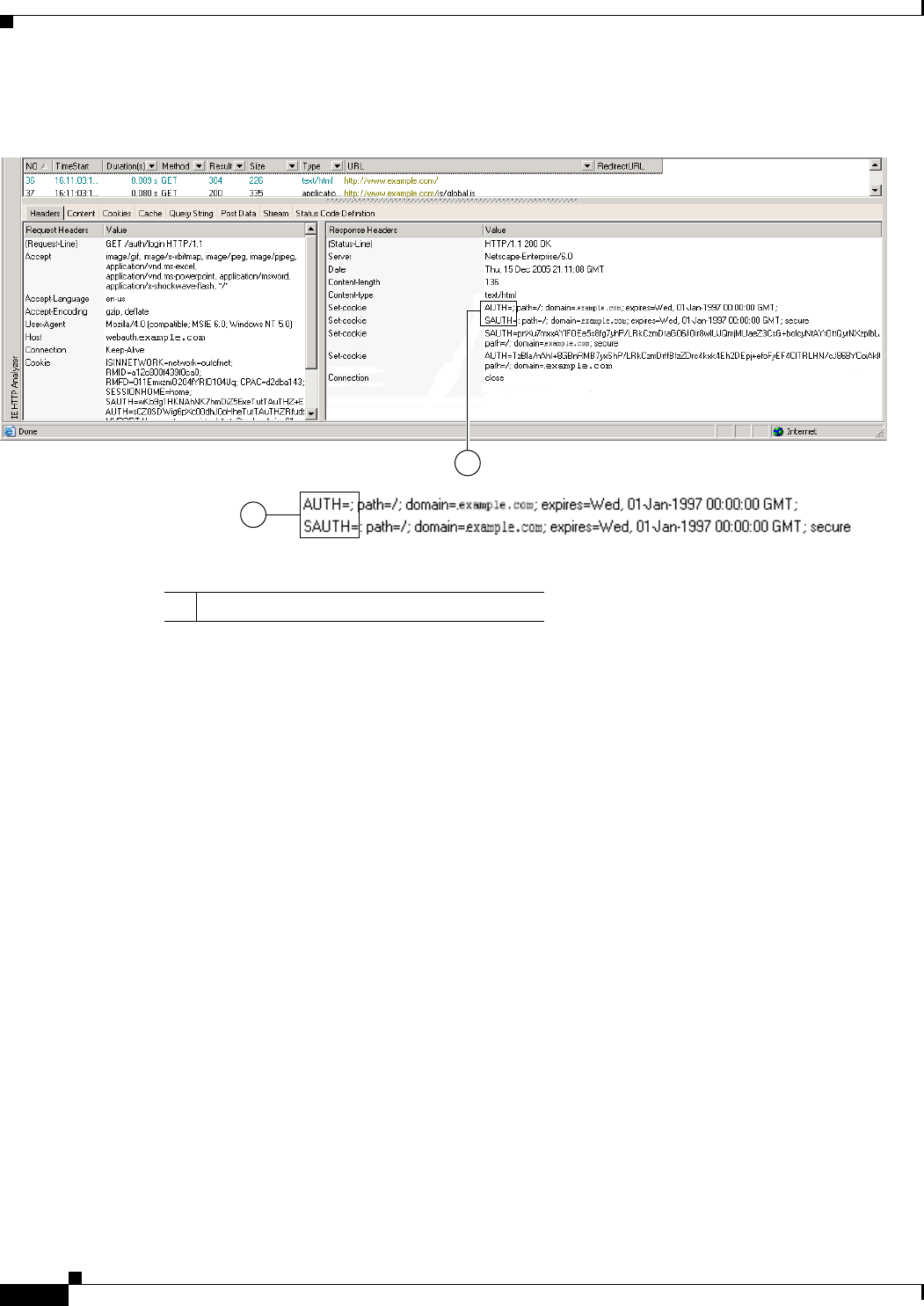
16-10
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 16 Configuring Clientless SSL VPN Users
Using Auto Sign-On
Figure 16-6 Authorization Cookies in Sample HTTP Analyzer Output
Step 7 In some cases, the server may set the same cookie regardless of whether the authentication was
successful or not, and such a cookie is unacceptable for SSO purposes. To confirm that the cookies are
different, repeat Step 1 through Step 6 using invalid login credentials and then compare the “failure”
cookie with the “success” cookie. You now have the necessary parameter data to configure the ASA for
SSO with HTTP Form protocol.
Using Auto Sign-On
The Auto Sign-on window or tab lets you configure or edit auto sign-on for users of Clientless SSL VPN.
Auto sign-on is a simplified single sign-on method that you can use if you do not already have an SSO
method deployed on your internal network. With auto sign-on configured for particular internal servers,
the ASA passes the login credentials that the user of Clientless SSL VPN entered to log on to the ASA
(username and password) to those particular internal servers. You configure the ASA to respond to a
specific authentication method for a particular range of servers. The authentication methods you can
configure the ASA to respond to consists of authentication using Basic (HTTP), NTLM, FTP and CIFS,
or all of these methods.
If the lookup of the username and password fails on the ASA, an empty string is substituted, and the
behavior converts back as if no auto sign-on is available.
Auto sign-on is a straight-forward method for configuring SSO for particular internal servers. This
section describes the procedure for setting up SSO with auto sign-on. If you already have SSO deployed
using Computer Associates SiteMinder SSO server, or if you have Security Assertion Markup Language
(SAML) Browser Post Profile SSO. To configure the ASA to support this solution, see the “SSO Servers”
section on page 13-8.
The following fields are displayed:
1Authorization cookies
1
249532
1

16-11
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 16 Configuring Clientless SSL VPN Users
Using Auto Sign-On
•IP Address—In conjunction with the following Mask, displays the IP address range of the servers
to be authenticated to as configured with the Add/Edit Auto Sign-on dialog box. You can specify a
server using either the server URI or the server IP address and mask.
•Mask—In conjunction with the preceding IP Address, displays the IP address range of the servers
configured to support auto sign-on with the Add/Edit Auto Sign-on dialog box.
•URI—Displays a URI mask that identifies the servers configured with the Add/Edit Auto Sign-on
dialog box.
•Authentication Type—Displays the type of authentication—Basic (HTTP), NTLM, FTP and CIFS,
or all of these methods—as configured with the Add/Edit Auto Sign-on dialog box.
Restrictions
•Do not enable auto sign-on for servers that do not require authentication or that use credentials
different from the ASA. When auto sign-on is enabled, the ASA passes on the login credentials that
the user entered to log on to the ASA regardless of what credentials are in user storage.
•If you configure one method for a range of servers (for example, HTTP Basic) and one of those
servers attempts to authenticate with a different method (for example, NTLM), the ASA does not
pass the user login credentials to that server.
DETAILED STEPS
Step 1 Click to add or edit an auto sign-on instruction. An auto sign-on instruction defines a range of internal
servers using the auto sign-on feature and the particular authentication method.
Step 2 Click to delete an auto sign-on instruction selected in the Auto Sign-on table.
Step 3 Click IP Block to specify a range of internal servers using an IP address and mask.
–
IP Address—Enter the IP address of the first server in the range for which you are configuring
auto sign-on.
–
Mask—From the subnet mask menu, choose the subnet mask that defines the server address
range of the servers supporting auto sign-on.
Step 4 Click URI to specify a server supporting auto sign-on by URI, then enter the URI in the field next to this
button.
Step 5 Determine the authentication method assigned to the servers. For the specified range of servers, the ASA
can be configured to respond to Basic HTTP authentication requests, NTLM authentication requests,
FTP and CIFS authentication requests, or requests using any of these methods.
–
Basic—Click this button if the servers support basic (HTTP) authentication.
–
NTLM—Click this button if the servers support NTLMv1 authentication.
–
FTP/CIFS—Click this button if the servers support FTP and CIFS authentication
–
Basic, NTLM, and FTP/CIFS—Click this button if the servers support all of the above.
16-12
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 16 Configuring Clientless SSL VPN Users
Communicating Security Tips
Requiring Usernames and Passwords
Depending on your network, during a remote session users may have to log on to any or all of the
following: the computer itself, an Internet service provider, Clientless SSL VPN, mail or file servers, or
corporate applications. Users may have to authenticate in many different contexts, requiring different
information, such as a unique username, password, or PIN.
Table 16-1 lists the type of usernames and passwords that Clientless SSL VPN users may need to know.
Communicating Security Tips
Advise users to always click the logout icon on the toolbar to close the Clientless SSL VPN session.
(Closing the browser window does not close the session.)
Clientless SSL VPN ensures the security of data transmission between the remote PC or workstation and
the ASA on the corporate network. Advise users that using Clientless SSL VPN does not ensure that
communication with every site is secure. If a user then accesses a non-HTTPS Web resource (located on
the Internet or on the internal network), the communication from the corporate ASA to the destination
Web server is not private because it is not encrypted.
"Clientless SSL VPN Security Precautions" on page 1 addresses an additional tip to communicate with
users, depending on the steps you follow within that section.
Configuring Remote Systems to Use Clientless SSL VPN
Features
This section describes how to set up remote systems to use Clientless SSL VPN and includes the
following topics:
•Starting Clientless SSL VPN, page 16-13
•Using the Clientless SSL VPN Floating Toolbar, page 16-13
Table 16-1 Usernames and Passwords to Give to Users of Clientless SSL VPN Sessions
Login Username/
Password Type Purpose Entered When
Computer Access the computer Starting the computer
Internet Service Provider Access the Internet Connecting to an Internet service
provider
Clientless SSL VPN Access remote network Starting Clientless SSL VPN
File Server Access remote file server Using the Clientless SSL VPN file
browsing feature to access a
remote file server
Corporate Application Login Access firewall-protected internal
server
Using the Clientless SSL VPN
Web browsing feature to access an
internal protected website
Mail Server Access remote mail server via
Clientless SSL VPN
Sending or receiving email
messages
16-13
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 16 Configuring Clientless SSL VPN Users
Configuring Remote Systems to Use Clientless SSL VPN Features
•Browsing the Web, page 16-14
•Browsing the Network (File Management), page 16-14
•Using Port Forwarding, page 16-16
•Using email Via Port Forwarding, page 16-18
•Using email Via Web Access, page 16-18
•Using email Via email Proxy, page 16-18
•Using Smart Tunnel, page 16-19
You may configure user accounts differently and different Clientless SSL VPN features can be available
to each user.
Starting Clientless SSL VPN
You can connect to the internet using any supported connection including:
•Home DSL, cable, or dial-ups.
•Public kiosks.
•Hotel hotspots.
•Airport wireless nodes.
•Internet cafes.
Note See the Supported VPN Platforms, Cisco ASA 5500 Series for the list of Web browsers supported by
Clientless SSL VPN.
Prerequisites
•Cookies must be enabled on the browser in order to access applications via port forwarding.
•You must have a URL for Clientless SSL VPN. The URL must be an https address in the following
form: https://address, where address is the IP address or DNS hostname of an interface of the ASA
(or load balancing cluster) on which SSL VPN is enabled. For example, https://cisco.example.com.
•You must have a Clientless SSL VPN username and password.
Restrictions
•Clientless SSL VPN supports local printing, but it does not support printing through the VPN to a
printer on the corporate network.
Using the Clientless SSL VPN Floating Toolbar
A floating toolbar is available to simplify the use of Clientless SSL VPN. The toolbar lets you enter
URLs, browse file locations, and choose preconfigured Web connections without interfering with the
main browser window.
The floating toolbar represents the current Clientless SSL VPN session. If you click the Close button,
the ASA prompts you to close the Clientless SSL VPN session.

16-14
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 16 Configuring Clientless SSL VPN Users
Configuring Remote Systems to Use Clientless SSL VPN Features
Tip To paste text into a text field, use Ctrl-V. (Right-clicking is switched off on the toolbar displayed
during the Clientless SSL VPN session.)
Restrictions
If you configure your browser to block popups, the floating toolbar cannot display.
Browsing the Web
Using Clientless SSL VPN does not ensure that communication with every site is secure. See
Communicating Security Tips.
The look and feel of Web browsing with Clientless SSL VPN may be different from what users are
accustomed to. For example:
•The title bar for Clientless SSL VPN appears above each Web page.
•You access websites by:
–
Entering the URL in the Enter Web Address field on the Clientless SSL VPN Home page
–
Clicking on a preconfigured website link on the Clientless SSL VPN Home page
–
Clicking a link on a webpage accessed via one of the previous two methods
Also, depending on how you configured a particular account, it may be that:
•Some websites are blocked
•Only the websites that appear as links on the Clientless SSL VPN Home page are available
Prerequisites
You need the username and password for protected websites.
Restrictions
Also, depending on how you configured a particular account, it may be that:
•Some websites are blocked
•Only the websites that appear as links on the Clientless SSL VPN Home page are available
Browsing the Network (File Management)
Users may not be familiar with how to locate their files through your organization network.
Note Do not interrupt the Copy File to Server command or navigate to a different screen while the copying
is in progress. Interrupting the operation can cause an incomplete file to be saved on the server.
Prerequisites
•You must configure file permissions for shared remote access.
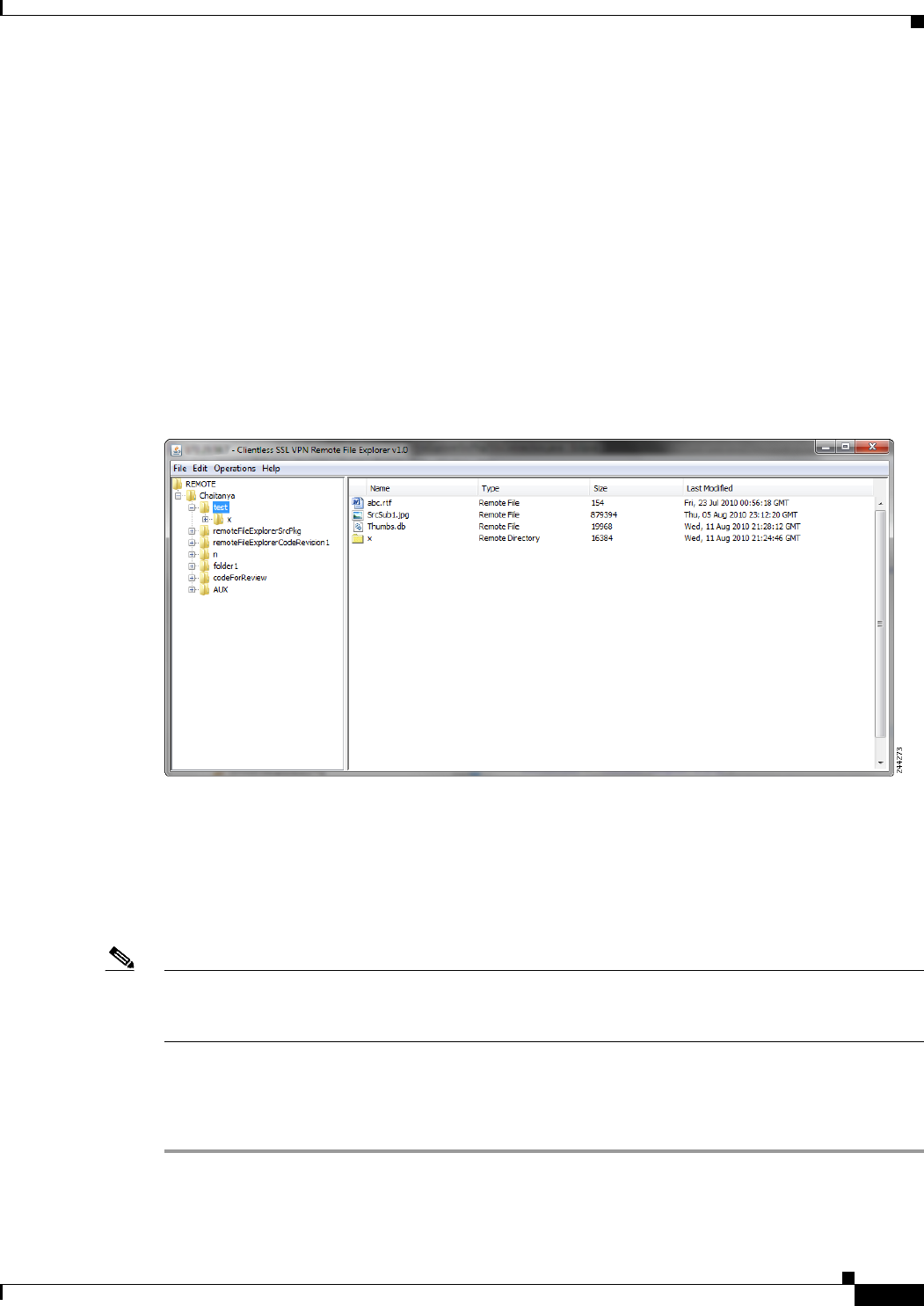
16-15
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 16 Configuring Clientless SSL VPN Users
Configuring Remote Systems to Use Clientless SSL VPN Features
•You must have the server names and passwords for protected file servers.
•You must have the domain, workgroup, and server names where folders and files reside.
Restrictions
Only shared folders and files are accessible via Clientless SSL VPN.
Using the Remote File Explorer
The Remote File Explorer provides the user with a way to browse the corporate network from their Web
browser. When the users clicks the Remote File System icon on the Cisco SSL VPN portal page, an
applet is launched on the user’s system displaying the remote file system in a tree and folder view.
Figure 16-7 Clientless SSL VPN Remote File Explorer
The browser enables the user to:
•Browse the remote file system.
•Rename files.
•Move or copy files within the remote file system and between the remote and local file systems.
•Perform bulk uploads and downloads of files.
Note This functionality requires that the Oracle Java Runtime Environment (JRE) 1.4 or later is installed on
the user’s machine and that Java is enabled in the Web browser. Launching remote files requires JRE 1.6
or later.
Renaming a File or Folder
To rename a file or folder:
Step 1 Click the file or folder to be renamed.
Step 2 Select Edit > Rename.

16-16
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 16 Configuring Clientless SSL VPN Users
Configuring Remote Systems to Use Clientless SSL VPN Features
Step 3 When prompted, enter the new name in the dialog.
Step 4 Click OK to rename the file or folder. Alternative, click Cancel to leave the name unchanged.
Moving or Copying Files or Folders on the Remote Server
To move or copy a file or folder on the remote server:
Step 1 Navigate to the source folder containing the file or folder to be moved or copied.
Step 2 Click the file or folder.
Step 3 To copy the file select Edit > Copy. Alternatively, to move the file select Edit > Cut.
Step 4 Navigate to the destination folder.
Step 5 Select Edit > Paste.
Copying Files from the Local System Drive to the Remote Folder
You can copy files between the local file system and the remote file system by dragging and dropping
them between the right pane of the Remote File Browser and your local file manager application.
Uploading and Downloading Files
You can download a file by clicking it in the browser, selecting Operations > Download, and providing
a location and name to save the file in the Save dialog.
You can upload a file by clicking the destination folder, selecting Operations > Upload, and providing
the location and name of the file in the Open dialog,
This functionality has the following restrictions:
•The user cannot view sub-folders for which they are not permitted access.
•Files that the user is not permitted to access cannot be moved or copied, even though they are
displayed in the browser.
•The maximum depth of nested folders is 32.
•The tree view does not support drag and drop copying.
•When moving files between multiple instances of the Remote File Explorer, all instances must be
exploring the same server (root share).
•The Remote File Explorer can display a maximum of 1500 files and folders in a single folder. If a
folder exceeds this limit the folder cannot be displayed.
Using Port Forwarding
Note Users should always close the Application Access window when they finish using applications by
clicking the Close icon. Failure to quit the window properly can cause Application Access or the
applications themselves to be switched off. See the “Recovering from Hosts File Errors When Using
Application Access” section on page 19-1 for details.

16-17
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 16 Configuring Clientless SSL VPN Users
Configuring Remote Systems to Use Clientless SSL VPN Features
Prerequisites
•On Mac OS X, only the Safari browser supports this feature.
•You must have client applications installed.
•You must have Cookies enabled on the browser.
•You must have administrator access on the PC if you use DNS names to specify servers, because
modifying the hosts file requires it.
•You must have Oracle Java Runtime Environment (JRE) version 1.4.x and 1.5.x installed.
If JRE is not installed, a pop-up window displays, directing users to a site where it is available. On
rare occasions, the port forwarding applet fails with Java exception errors. If this happens, do the
following:
a. Clear the browser cache and close the browser.
b. Verify that no Java icons are in the computer task bar.
c. Close all instances of Java.
d. Establish a Clientless SSL VPN session and launch the port forwarding Java applet.
•You must have JavaScript enabled on the browser. By default, it is enabled.
•If necessary, you must configure client applications.
Note The Microsoft Outlook client does not require this configuration step. All non-Windows
client applications require configuration. To determine if configuration is necessary for a
Windows application, check the value of the Remote Server field. If the Remote Server field
contains the server hostname, you do not need to configure the client application. If the
Remote Server field contains an IP address, you must configure the client application.
Restrictions
Because this feature requires installing Oracle Java Runtime Environment (JRE) and configuring the
local clients, and because doing so requires administrator permissions on the local system or full control
of C:\windows\System32\drivers\etc, it is unlikely that users will be able to use applications when they
connect from public remote systems.
DETAILED STEPS
To configure the client application, use the server’s locally mapped IP address and port number. To find
this information:
1. Start a Clientless SSL VPN session and click the Application Access link on the Home page. The
Application Access window appears.
2. In the Name column, find the name of the server to use, then identify its corresponding client IP
address and port number (in the Local column).
3. Use this IP address and port number to configure the client application. Configuration steps vary for
each client application.
Note Clicking a URL (such as one in an -email message) in an application running over a Clientless
SSL VPN session does not open the site over that session. To open a site over the session, paste
the URL into the Enter Clientless SSL VPN (URL) Address field.

16-18
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 16 Configuring Clientless SSL VPN Users
Configuring Remote Systems to Use Clientless SSL VPN Features
Using email Via Port Forwarding
To use email, start Application Access from the Clientless SSL VPN home page. The mail client is then
available for use.
Note If you are using an IMAP client and you lose your mail server connection or are unable to make a new
connection, close the IMAP application and restart Clientless SSL VPN.
Prerequisites
You must fulfill requirements for application access and other mail clients.
Restrictions
We have tested Microsoft Outlook Express versions 5.5 and 6.0.
Clientless SSL VPN should support other SMTPS, POP3S, or IMAP4S email programs via port
forwarding, such as Lotus Notes and Eudora, but we have not verified them.
Using email Via Web Access
The following email applications are supported:
•Microsoft Outlook Web App to Exchange Server 2010.
OWA requires Internet Explorer 7 or later, or Firefox 3.01 or later.
•Microsoft Outlook Web Access to Exchange Server 2007, 2003, and 2000.
For best results, use OWA on Internet Explorer 8.x or later, or Firefox 8.x.
•Lotus iNotes
Prerequisites
You must have the web-based email product installed.
Restrictions
Other web-based email applications should also work, but we have not verified them.
Using email Via email Proxy
The following legacy email applications are supported:
•Microsoft Outlook 2000 and 2002
•Microsoft Outlook Express 5.5 and 6.0
See the instructions and examples for your mail application in “Using Email over Clientless SSL VPN”
section on page 13-23.
Prerequisites
•You must have the SSL-enabled mail application installed.

16-19
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 16 Configuring Clientless SSL VPN Users
Configuring Remote Systems to Use Clientless SSL VPN Features
•Do not set the ASA SSL version to TLSv1 Only. Outlook and Outlook Express do not support TLS.
•You must have your mail application properly configured.
Restrictions
Other SSL-enabled clients should also work, but we have not verified them.
Using Smart Tunnel
Administration privileges are not required to use Smart Tunnel.
Note Java is not automatically downloaded for you as in port forwarder.
Prerequisites
•Smart tunnel requires either ActiveX or JRE (1.4x and 1.5x) on Windows and Java Web Start on Mac
OS X.
•You must ensure cookies enabled on the browser.
•You must ensure JavaScript is enabled on the browser.
Restrictions
•Mac OS X does not support a front-side proxy.
•Supports only the operating systems and browsers specified in “Configuring Smart Tunnel Access”
section on page 14-1.
•Only TCP socket-based applications are supported.

16-20
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 16 Configuring Clientless SSL VPN Users
Configuring Remote Systems to Use Clientless SSL VPN Features

CHAPTER
17-1
Cisco ASA Series VPN ASDM Configuration Guide
17
Using Clientless SSL VPN with Mobile Devices
September 13, 2013
Using Clientless SSL VPN with Mobile Devices
You can access Clientless SSL VPN from your Pocket PC or other certified mobile device. Neither the
ASA administrator nor the Clientless SSL VPN user need do anything special to use Clientless SSL VPN
with a certified mobile device.
Cisco has certified the following mobile device platforms:
HP iPaq H4150
Pocket PC 2003
Windows CE 4.20.0, build 14053
Pocket Internet Explorer (PIE)
ROM version 1.10.03ENG
ROM Date: 7/16/2004
Some differences in the mobile deviceversion of Clientless SSL VPN exist:
•A banner Web page replaces the popup Clientless SSL VPN window.
•An icon bar replaces the standard Clientless SSL VPN floating toolbar. This bar displays the Go,
Home and Logout buttons.
•The Show Toolbar icon is not included on the main Clientless SSL VPN portal page.
•Upon Clientless SSL VPN logout, a warning message provides instructions for closing the PIE
browser properly. If you do not follow these instructions and you close the browser window in the
common way, PIE does not disconnect from Clientless SSL VPN or any secure website that uses
HTTPS.
Restrictions
•Clientless SSL VPN supports OWA 2000 and OWA 2003 Basic Authentication. If Basic
Authentication is not configured on an OWA server and a Clientless SSL VPN user attempts to
access that server, access is denied.
•Unsupported Clientless SSL VPN features:
–
Application Access and other Java-dependent features.

17-2
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 17 Using Clientless SSL VPN with Mobile Devices
Using Clientless SSL VPN with Mobile Devices
–
HTTP proxy.
–
The Citrix Metaframe feature (if the PDA does not have the corresponding Citrix ICA client
software).

CHAPTER
18-1
Cisco ASA Series VPN ASDM Configuration Guide
18
Customizing Clientless SSL VPN
September 13, 2013
Customizing the Clientless SSL VPN User Experience
You can customize the Clientless SSL VPN user experience, including the logon, portal, and logout
pages. There are two methods you can use. You can customize pre-defined page components in the
Add/Edit Customization Object window. This window adds, or makes changes to, an XML file stored on
the ASA (a customization object) that is used to customize the pages. Alternatively, you can export the
XML file to a local computer or server, make changes to the XML tags, and re-import the file to the ASA.
Either method creates a customization object that you apply to a connection profile or group policy.
Rather than customizing the pre-defined components of the logon page, you can create your own page
and import it to the ASA for full customization. To do this see the “Replacing the Logon Page with your
own Fully Customized Page” section on page 18-3.
You can customize pre-defined components of the logon page, including titles, language options, and
messages to users. Alternatively, you can completely replace the page with your own custom page (full
customization). The following sections detail both procedures:
•Customizing the Logon Page with the Customization Editor, page 18-1
•Replacing the Logon Page with your own Fully Customized Page, page 18-3
Customizing the Logon Page with the Customization Editor
Figure 18-1 shows the logon page and the pre-defined components you can customize:
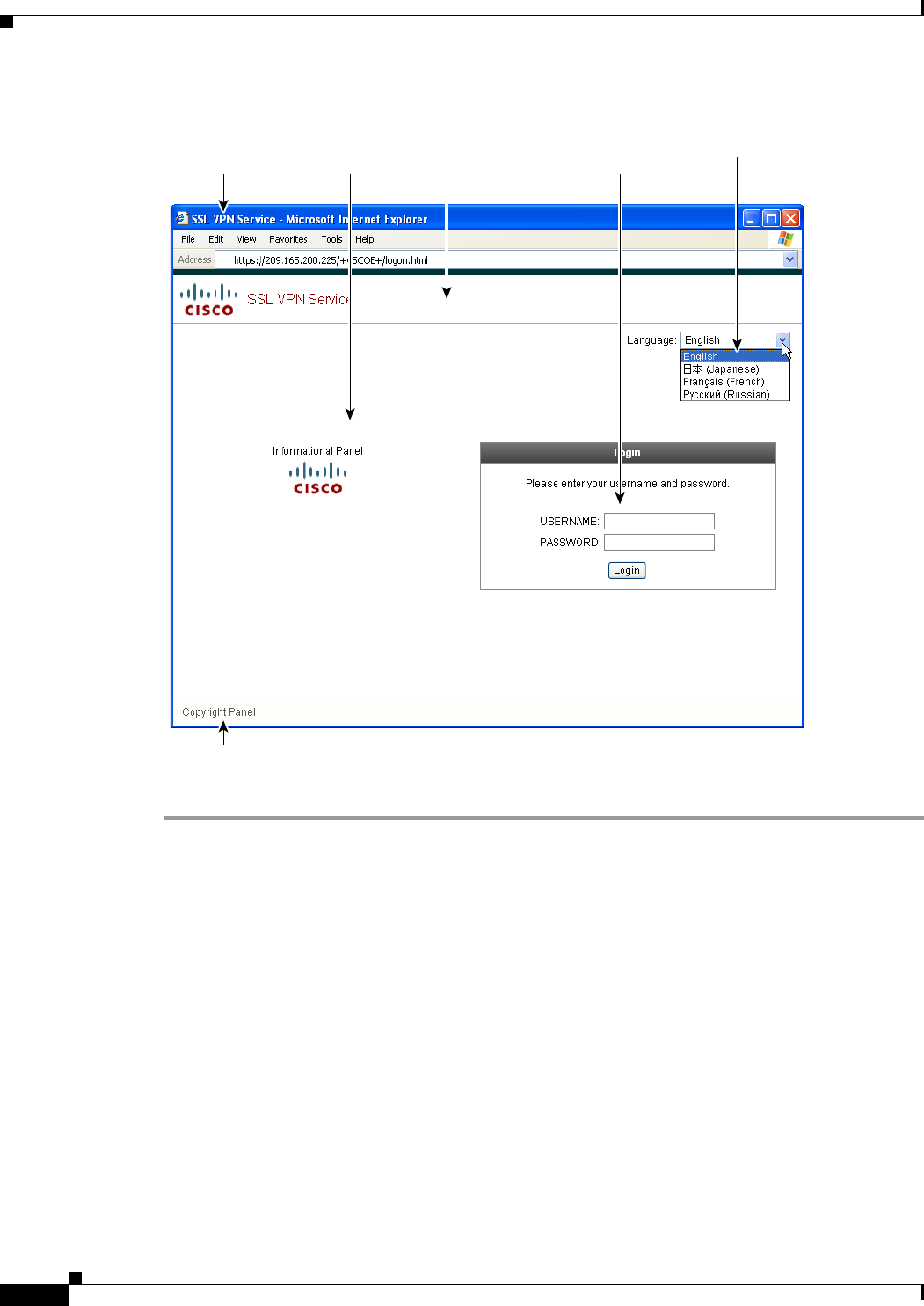
18-2
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 18 Customizing Clientless SSL VPN
Customizing the Clientless SSL VPN User Experience
Figure 18-1 Components of Clientless Logon Page
To customize all the components of the logon page, follow this procedure. You can preview your changes
for each component by clicking the Preview button:
Step 1 Specify pre-defined customization. Go to Logon Page and select Customize pre-defined logon page
components. Specify a title for the browser window.
Step 2 Display and customize the title panel. Go to Logon Page > Title Panel and check Display title panel.
Enter text to display as the title and specify a logo. Specify any font styles.
Step 3 Specify language options to display. Go to Logon Page > Language and check Enable Language
Selector. Add or delete any languages to display to remote users. Languages in the list require translation
tables that you configure in Configuration > Remote Access VPN > Language Localization.
Step 4 Customize the logon form. Go to Logon Page > Logon Form. Customize the text of the form and the font
style in the panel. The secondary password field appears to users only if a secondary authentication
server is configured in the connection profile.
Step 5 Arrange the position of the logon form fields. Go to Logon Page > Form Fields Order. Use the up and
down arrow buttons to change the order that the fields are displayed.
Step 6 Add messages to users. Go to Logon Page > Informational Panel and check Display informational
panel. Add text to display in the panel, change the position of the panel relative to the logon form, and
specify a logo to display in this panel.
247844
Browser Window
Title
Informational
Panel
Title
Panel
LanguageLogon Form
and Fields Order

18-3
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 18 Customizing Clientless SSL VPN
Customizing the Clientless SSL VPN User Experience
Step 7 Display a copyright statement. Go to Logon Page > Copyright Panel and check Display copyright
panel. Add text to display for copyright purposes.
Step 8 Click OK, then apply the changes to the customization object you edited.
Replacing the Logon Page with your own Fully Customized Page
If you prefer to use your own, custom login screen, rather than changing specific components of the
logon page we provide, you can perform this advanced customization using the Full Customization
feature.
With Full Customization, you provide the HTML for your own login screen, and you insert Cisco HTML
code that calls functions on the ASA that create the Login form and the Language Selector drop-down
list.
This document describes the modifications you need to make to your HTML code and the tasks required
to configure the ASA to use your code.
Figure 18-2 shows a simple example of a custom login screen enabled by the Full Customization feature.
Figure 18-2 Example of Full Customization of Logon Page
The following sections describe the tasks to customize the login screen:
•Creating the Custom Login Screen File
•Importing the File and Images
•Configuring the Security Appliance to use the Custom Login Screen

18-4
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 18 Customizing Clientless SSL VPN
Customizing the Clientless SSL VPN User Experience
Creating the Custom Login Screen File
The following HTML code is used as an example and is the code that displays:
<head>
<meta http-equiv="Content-Type" content="text/html; charset=windows-1252">
<title>New Page 3</title>
<base target="_self">
</head>
<p align="center">
<img border="0" src="/+CSCOU+/cisco_logo.jpg" width="188" height="48"><font face="Snap
ITC" size="6" color="#FF00FF">
</font><font face="Snap ITC" color="#FF00FF" size="7"> </font><i><b><font
color="#FF0000" size="7" face="Sylfaen"> SSL VPN Service by the Cisco
ASA5500</font></b></i></p>
<body onload="csco_ShowLoginForm('lform');csco_ShowLanguageSelector('selector')">
<table>
<tr><td colspan=3 height=20 align=right><div id="selector" style="width:
300px"></div></td></tr>
<tr><td></td><td></td><td></td></tr>
<tr>
<td height="379"></td>
<td height="379"></td>
<td align=middle valign=middle>
<div id=lform >
<p> </p>
<p> </p>
<p> </p>
<p>Loading...</p>
</div>
</td>
</tr>
<tr>
<td width="251"></td>
<td width="1"></td>
<td align=right valign=right width="800">
<img border="1" src="/+CSCOU+/asa5500.jpg" width="660" height="220" align="middle">
</td></tr>
</table>
The indented code injects the Login form and the Language Selector on the screen. The function
csco_ShowLoginForm('lform') injects the logon form. csco_ShowLanguageSelector('selector')
injects the Language Selector.
DETAILED STEPS
Step 1 Name your file logon.inc. When you import the file, the ASA recognizes this filename as the logon
screen.
Step 2 Modify the paths of images used by the file to include /+CSCOU+/.
Files that are displayed to remote users before authentication must reside in a specific area of the ASA
cache memory represented by the path /+CSCOU+/. Therefore, the source for each image in the file must
include this path. For example:
src=”/+CSCOU+/asa5520.gif”

18-5
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 18 Customizing Clientless SSL VPN
Customizing the Clientless SSL VPN User Experience
Step 3 Insert the special HTML code below. This code contains the Cisco functions, described earlier, that
inject the login form and language selector onto the screen.
<body onload="csco_ShowLoginForm('lform');csco_ShowLanguageSelector('selector')">
<table>
<tr><td colspan=3 height=20 align=right><div id="selector" style="width:
300px"></div></td></tr>
<tr><td></td><td></td><td></td></tr>
<tr>
<td height="379"></td>
<td height="379"></td>
<td align=middle valign=middle>
<div id=lform >
<p> </p>
<p> </p>
<p> </p>
<p>Loading...</p>
</div>
</td>
</tr>
<tr>
<td width="251"></td>
<td width="1"></td>
<td align=right valign=right width="800">
<img border="1" src="/+CSCOU+/asa5500.jpg" width="660" height="220" align="middle">
</td></tr>
</table>
Importing the File and Images
DETAILED STEPS
Step 1 Go to Clientless SSL VPN Access > Portal > Web Contents.
Step 2 Click Import. The Import Web Content window displays.
a. Select the Source option, and enter the path the Web content files.
b. In the Destination area, select No for Require Authentication to access its content . This ensures the
files are stored in the area of flash memory accessible to users before authentication.
Step 3 Click Import Now, and kee used by the file as Web Content using the same window.
Configuring the Security Appliance to use the Custom Login Screen
DETAILED STEPS
Step 1 Select a customization object. Go to Clientless SSL VPN Access > Portal > Customization. Select a
customization object in the table and click Edit. The Edit Customization Object window displays.
Step 2 In the navigation pane, select Logon Page.
Step 3 Choose Replace pre-defined logon page with a custom page.

18-6
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 18 Customizing Clientless SSL VPN
Clientless SSL VPN End User Setup
Step 4 Click Manage to import your logon page file. The Import Web Content window displays.
Step 5 In the Destination area, select No to ensure your logon page is visible to users before they authenticate.
Step 6 Back in the Edit Customization Object window, click General and enable the customization object for
the connection profile and/or group policies you desire.
Clientless SSL VPN End User Setup
This section is for the system administrator who sets up Clientless SSL VPN for end users. It describes
how to customize the end-user interface.
This section summarizes configuration requirements and tasks for a remote system. It specifies
information to communicate to users to get them started using Clientless SSL VPN. It includes the
following topics:
•Defining the End User Interface
•Customizing Clientless SSL VPN Pages
•Information About Customization
•Exporting a Customization Template
•Editing the Customization Template
Defining the End User Interface
The Clientless SSL VPN end user interface consists of a series of HTML panels. A user logs on to
Clientless SSL VPN by entering the IP address of an ASA interface in the format https://address. The
first panel that displays is the login screen (Figure 18-3).
Figure 18-3 Clientless SSL VPN Login Screen
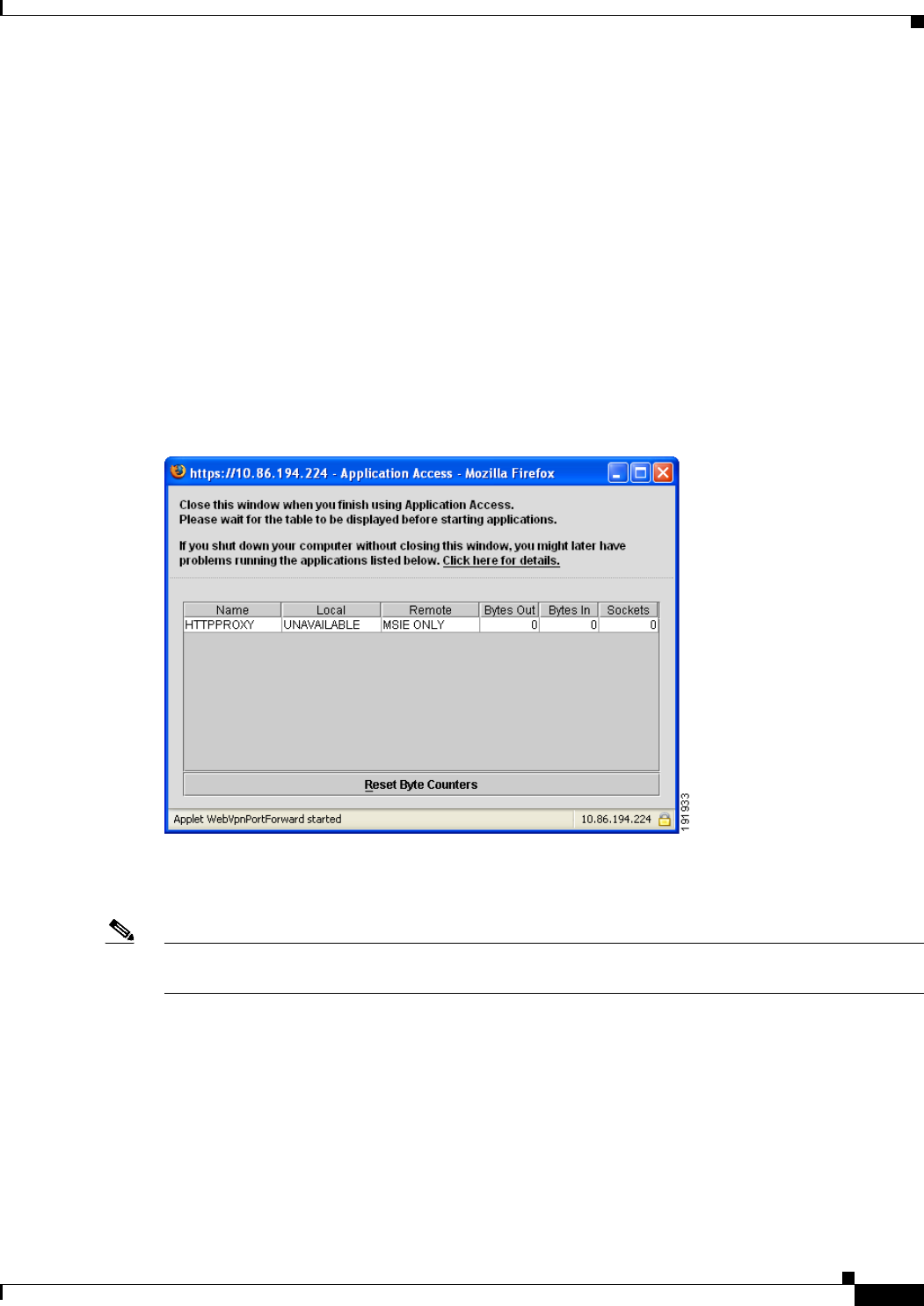
18-7
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 18 Customizing Clientless SSL VPN
Clientless SSL VPN End User Setup
Viewing the Clientless SSL VPN Home Page
After the user logs in, the portal page opens.
The home page displays all of the Clientless SSL VPN features you have configured, and its appearance
reflects the logo, text, and colors you have selected. This sample home page includes all available
Clientless SSL VPN features with the exception of identifying specific file shares. It lets users browse
the network, enter URLs, access specific websites, and use Application Access (port forwarding and
smart tunnels) to access TCP applications.
Viewing the Clientless SSL VPN Application Access Panel
To start port forwarding or smart tunnels, a user clicks the Go button in the Application Access box.
The Application Access window opens (Figure 18-4).
Figure 18-4 Clientless SSL VPN Application Access Window
This window displays the TCP applications configured for this Clientless SSL VPN connection. To use
an application with this panel open, the user starts the application in the normal way.
Note A stateful failover does not retain sessions established using Application Access. Users must reconnect
following a failover.
Viewing the Floating Toolbar
The floating toolbar shown in Figure 18-5 represents the current Clientless SSL VPN session.
18-8
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 18 Customizing Clientless SSL VPN
Clientless SSL VPN End User Setup
Figure 18-5 Clientless SSL VPN Floating Toolbar
Be aware of the following characteristics of the floating toolbar:
•The toolbar lets you enter URLs, browse file locations, and choose preconfigured Web connections
without interfering with the main browser window.
•If you configure your browser to block popups, the floating toolbar cannot display.
•If you close the toolbar, the ASA prompts you to end the Clientless SSL VPN session.
Customizing Clientless SSL VPN Pages
You can change the appearance of the portal pages displayed to Clientless SSL VPN users. This includes
the Login page displayed to users when they connect to the security appliance, the Home page displayed
to users after the security appliance authenticates them, the Application Access window displayed when
users launch an application, and the Logout page displayed when users log out of Clientless SSL VPN
sessions.
After you customize the portal pages, you can save your customization and apply it to a specific
connection profile, group policy, or user. The changes do not take effect until you reload the ASA, or
you switch off and then enable clientless SSL.
You can create and save many customization objects, enabling the security appliance to change the
appearance of portal pages for individual users or groups of users.
This section includes the following topics:
•Information About Customization, page 18-9
•Exporting a Customization Template, page 18-9
•Editing the Customization Template, page 18-9
•Login Screen Advanced Customization, page 18-15
•Login Screen Advanced Customization, page 18-15
Moves the toolbar to the
other side of the browser
Logs the user out
Displays the portal home page
Launches a dialog box for URL entry
191984

18-9
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 18 Customizing Clientless SSL VPN
Clientless SSL VPN End User Setup
Information About Customization
The ASA uses customization objects to define the appearance of user screens. A customization object is
compiled from an XML file which contains XML tags for all the customizable screen items displayed to
remote users. The ASA software contains a customization template that you can export to a remote PC.
You can edit this template and import the template back into the ASA as a new customization object.
When you export a customization object, an XML file containing XML tags is created at the URL you
specify. The XML file created by the customization object named Tem pla te contains empty XML tags,
and provides the basis for creating new customization objects. This object cannot be changed or deleted
from cache memory but can be exported, edited, and imported back into the ASA as a new customization
object.
Customization Objects, Connection Profiles, and Group Policies
Initially, when a user first connects, the default customization object (named DfltCustomization)
identified in the connection profile (tunnel group) determines how the logon screen appears. If the
connection profile list is enabled, and the user selects a different group which has its own customization,
the screen changes to reflect the customization object for that new group.
After the remote user is authenticated, the screen appearance is determined by whether a customization
object that has been assigned to the group policy.
Exporting a Customization Template
When you export a customization object, an XML file is created at the URL you specify. The
customization template (named Template) contains empty XML tags and provides the basis for creating
new customization objects. This object cannot be changed or deleted from cache memory but can be
exported, edited, and imported back into the ASA as a new customization object.
Editing the Customization Template
This section shows the contents of the customization template and has convenient figures to help you
quickly choose the correct XML tag and make changes that affect the screens.
You can use a text editor or an XML editor to edit the XML file. The following example shows the XML
tags of the customization template. Some redundant tags have been removed for easier viewing:
Example:
<custom>
<localization>
<languages>en,ja,zh,ru,ua</languages>
<default-language>en</default-language>
</localization>
<auth-page>
<window>
<title-text l10n="yes"><![CDATA[SSL VPN Service]]></title-text>
</window>
<full-customization>
<mode>disable</mode>
<url></url>
</full-customization>
<language-selector>
<mode>disable</mode>
<title l10n="yes">Language:</title>

18-10
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 18 Customizing Clientless SSL VPN
Clientless SSL VPN End User Setup
<language>
<code>en</code>
<text>English</text>
</language>
<language>
<code>zh</code>
<text>ä¸-国 (Chinese)</text>
</language>
<language>
<code>ja</code>
<text>日本 (Japanese)</text>
</language>
<language>
<code>ru</code>
<text>РуÑÑкий (Russian)</text>
</language>
<language>
<code>ua</code>
<text>УкÑ?аїнÑька (Ukrainian)</text>
</language>
</language-selector>
<logon-form>
<title-text l10n="yes"><![CDATA[Login]]></title-text>
<title-background-color><![CDATA[#666666]]></title-background-color>
<title-font-color><![CDATA[#ffffff]]></title-font-color>
<message-text l10n="yes"><![CDATA[Please enter your username and
password.]]></message-text>
<username-prompt-text l10n="yes"><![CDATA[USERNAME:]]></username-prompt-text>
<password-prompt-text l10n="yes"><![CDATA[PASSWORD:]]></password-prompt-text>
<internal-password-prompt-text l10n="yes">Internal
Password:</internal-password-prompt-text>
<internal-password-first>no</internal-password-first>
<group-prompt-text l10n="yes"><![CDATA[GROUP:]]></group-prompt-text>
<submit-button-text l10n="yes"><![CDATA[Login]]></submit-button-text>
<title-font-color><![CDATA[#ffffff]]></title-font-color>
<title-background-color><![CDATA[#666666]]></title-background-color>
<font-color>#000000</font-color>
<background-color>#ffffff</background-color>
<border-color>#858A91</border-color>
</logon-form>
<logout-form>
<title-text l10n="yes"><![CDATA[Logout]]></title-text>
<message-text l10n="yes"><![CDATA[Goodbye.<br>
For your own security, please:<br>
<li>Clear the browser's cache
<li>Delete any downloaded files
<li>Close the browser's window]]></message-text>
<login-button-text l10n="yes">Logon</login-button-text>
<hide-login-button>no</hide-login-button>
<title-background-color><![CDATA[#666666]]></title-background-color>
<title-font-color><![CDATA[#ffffff]]></title-font-color>
<title-font-color><![CDATA[#ffffff]]></title-font-color>
<title-background-color><![CDATA[#666666]]></title-background-color>
<font-color>#000000</font-color>
<background-color>#ffffff</background-color>
<border-color>#858A91</border-color>
</logout-form>
<title-panel>
<mode>enable</mode>
<text l10n="yes"><![CDATA[SSL VPN Service]]></text>

18-11
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 18 Customizing Clientless SSL VPN
Clientless SSL VPN End User Setup
<logo-url l10n="yes">/+CSCOU+/csco_logo.gif</logo-url>
<gradient>yes</gradient>
<style></style>
<background-color><![CDATA[#ffffff]]></background-color>
<font-size><![CDATA[larger]]></font-size>
<font-color><![CDATA[#800000]]></font-color>
<font-weight><![CDATA[bold]]></font-weight>
</title-panel>
<info-panel>
<mode>disable</mode>
<image-url l10n="yes">/+CSCOU+/clear.gif</image-url>
<image-position>above</image-position>
<text l10n="yes"></text>
</info-panel>
<copyright-panel>
<mode>disable</mode>
<text l10n="yes"></text>
</copyright-panel>
</auth-page>
<portal>
<title-panel>
<mode>enable</mode>
<text l10n="yes"><![CDATA[SSL VPN Service]]></text>
<logo-url l10n="yes">/+CSCOU+/csco_logo.gif</logo-url>
<gradient>yes</gradient>
<style></style>
<background-color><![CDATA[#ffffff]]></background-color>
<font-size><![CDATA[larger]]></font-size>
<font-color><![CDATA[#800000]]></font-color>
<font-weight><![CDATA[bold]]></font-weight>
</title-panel>
<browse-network-title l10n="yes">Browse Entire Network</browse-network-title>
<access-network-title l10n="yes">Start AnyConnect</access-network-title>
<application>
<mode>enable</mode>
<id>home</id>
<tab-title l10n="yes">Home</tab-title>
<order>1</order>
</application>
<application>
<mode>enable</mode>
<id>web-access</id>
<tab-title l10n="yes"><![CDATA[Web Applications]]></tab-title>
<url-list-title l10n="yes"><![CDATA[Web Bookmarks]]></url-list-title>
<order>2</order>
</application>
<application>
<mode>enable</mode>
<id>file-access</id>
<tab-title l10n="yes"><![CDATA[Browse Networks]]></tab-title>
<url-list-title l10n="yes"><![CDATA[File Folder Bookmarks]]></url-list-title>
<order>3</order>
</application>
<application>
<mode>enable</mode>
<id>app-access</id>
<tab-title l10n="yes"><![CDATA[Application Access]]></tab-title>
<order>4</order>
</application>
<application>
<mode>enable</mode>
<id>net-access</id>
<tab-title l10n="yes">AnyConnect</tab-title>
<order>4</order>

18-12
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 18 Customizing Clientless SSL VPN
Clientless SSL VPN End User Setup
</application>
<application>
<mode>enable</mode>
<id>help</id>
<tab-title l10n="yes">Help</tab-title>
<order>1000000</order>
</application>
<toolbar>
<mode>enable</mode>
<logout-prompt-text l10n="yes">Logout</logout-prompt-text>
<prompt-box-title l10n="yes">Address</prompt-box-title>
<browse-button-text l10n="yes">Browse</browse-button-text>
</toolbar>
<column>
<width>100%</width>
<order>1</order>
</column>
<pane>
<type>TEXT</type>
<mode>disable</mode>
<title></title>
<text></text>
<notitle></notitle>
<column></column>
<row></row>
<height></height>
</pane>
<pane>
<type>IMAGE</type>
<mode>disable</mode>
<title></title>
<url l10n="yes"></url>
<notitle></notitle>
<column></column>
<row></row>
<height></height>
</pane>
<pane>
<type>HTML</type>
<mode>disable</mode>
<title></title>
<url l10n="yes"></url>
<notitle></notitle>
<column></column>
<row></row>
<height></height>
</pane>
<pane>
<type>RSS</type>
<mode>disable</mode>
<title></title>
<url l10n="yes"></url>
<notitle></notitle>
<column></column>
<row></row>
<height></height>
</pane>
<url-lists>
<mode>group</mode>
</url-lists>
<home-page>
<mode>standard</mode>
<url></url>
</home-page>
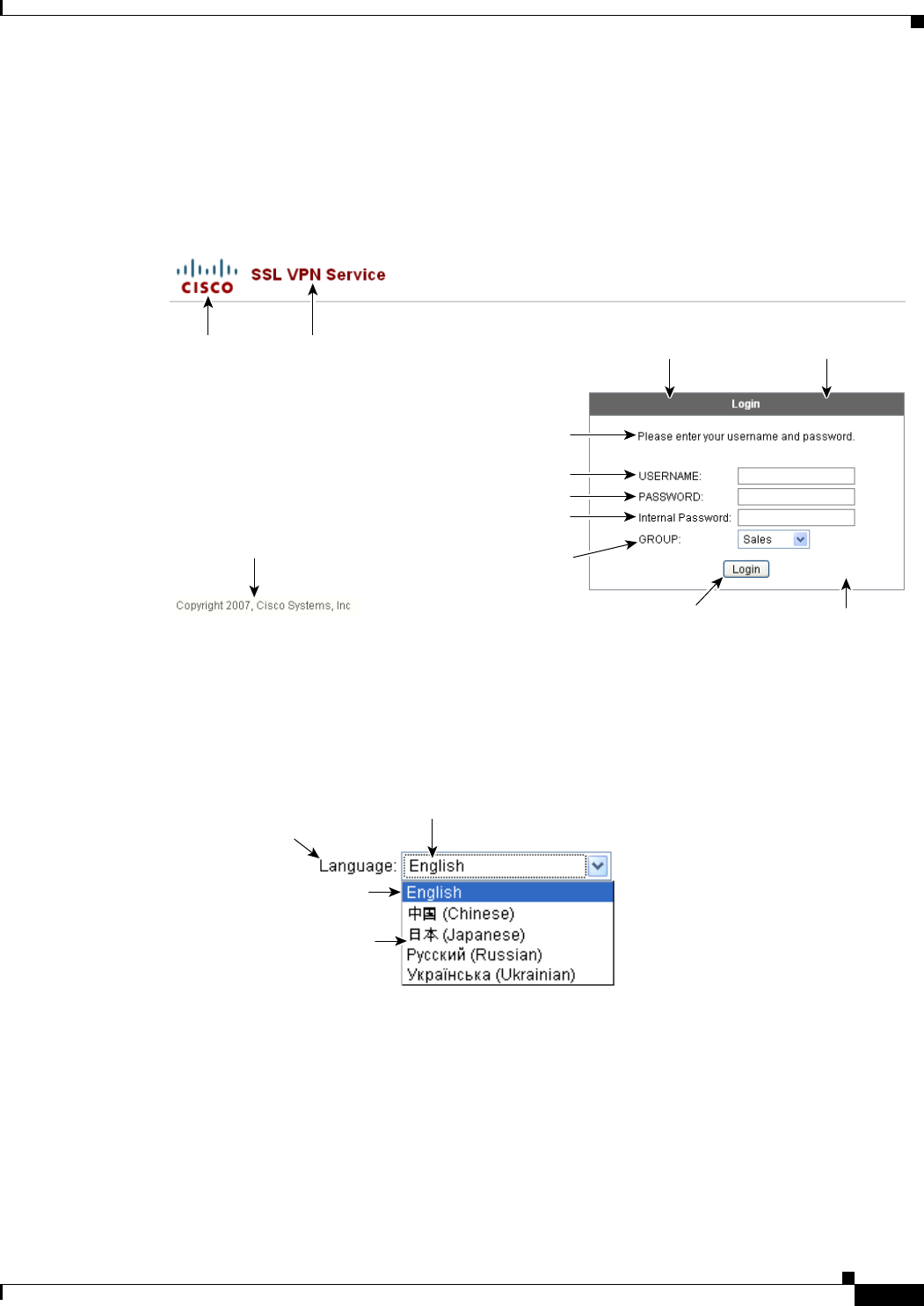
18-13
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 18 Customizing Clientless SSL VPN
Clientless SSL VPN End User Setup
</portal>
</custom>
Figure 18-6 shows the Logon page and its customizing XML tags. All these tags are nested within the
higher-level tag <auth-page>.
Figure 18-6 Logon Page and Associated XML Tags
Figure 18-7 shows the Language Selector drop-down list that is available on the Logon page, and the
XML tags for customizing this feature. All these tags are nested within the higher-level <auth-page> tag.
Figure 18-7 Language Selector on Logon Screen and Associated XML Tags
Figure 18-8 shows the Information Panel that is available on the Logon page, and the XML tags for
customizing this feature. This information can appear to the left or right of the login box. These tags are
nested within the higher-level <auth-page> tag.
191904
<title-panel>
<logo-url>
<title-panel>
<text>
<front-color>
<font-weight>
<font-gradient>
<style>
<title-panel>
<mode>
<title-panel>
<background-colors>
<logon-form>
<title-text>
<title-font-colors>
<logon-form>
<title-background-color>
<logon-form>
<message-text>
<username-prompt-text>
<password-prompt-text>
<internal-password-prompt-text>
<internal-password-first>
<group-prompt-text>
<logon-form>
<submit-button-text>
<logon-form>
<background-color>
<copyright-panel>
<mode>
<text>
<localization>
<default-language>
<language-selector>
<title>
<language-selector>
<mode>
<language-selector>
<language>
<code>
<text>
191903
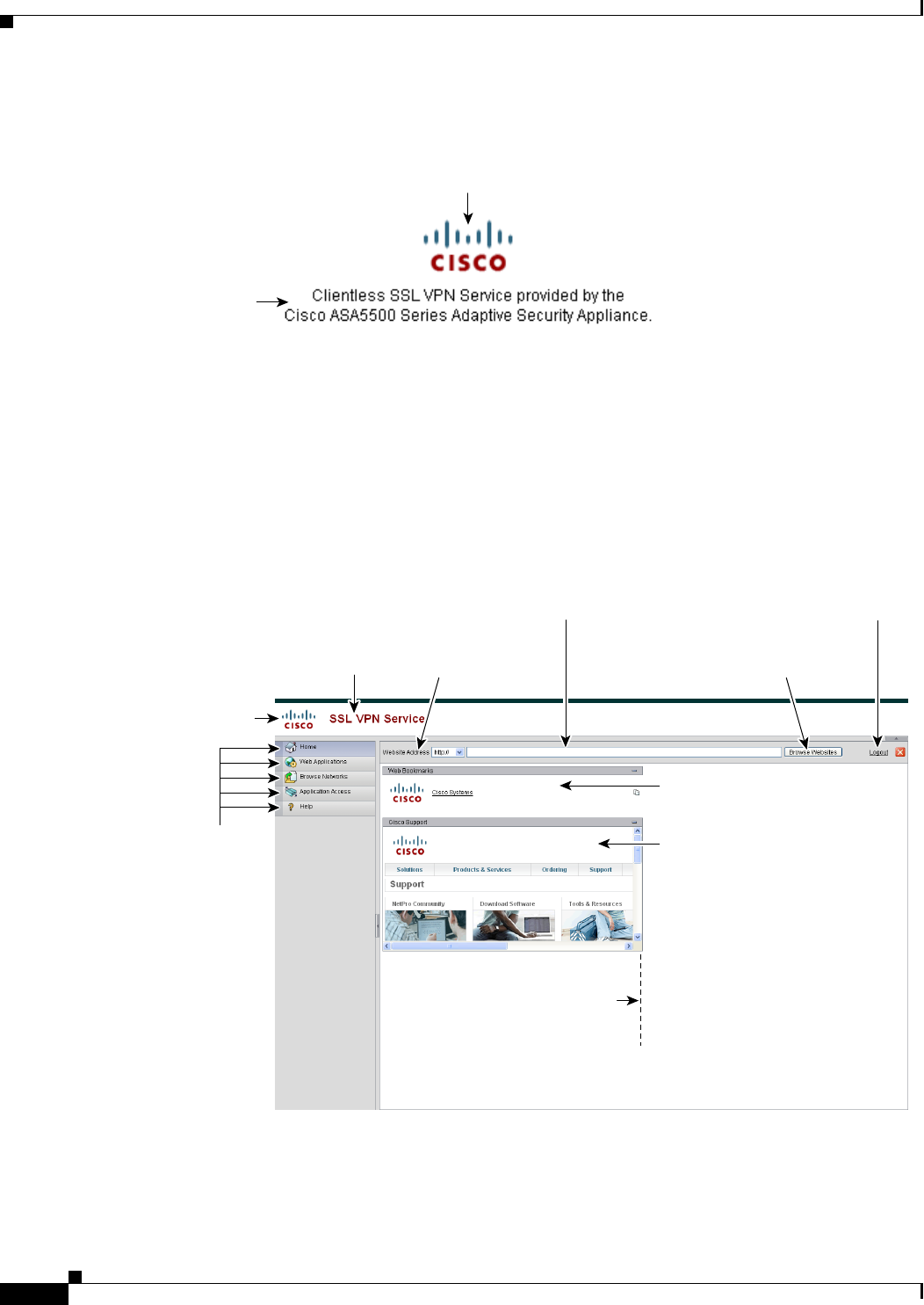
18-14
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 18 Customizing Clientless SSL VPN
Clientless SSL VPN End User Setup
Figure 18-8 Information Panel on Logon Screen and Associated XML Tags
Figure 18-9 shows the Portal page and the XML tags for customizing this feature. These tags are nested
within the higher-level <auth-page> tag.
Figure 18-9 Portal Page and Associated XML Tags
<info-panel>
<image-url>
<image-position>
<info-panel>
<text>
191905
<info-panel>
<mode>
191906
<title-panel>
<logo-url>
<title-panel>
<text>
<gradient>
<font-weight>
<font-size>
<front-color>
<title-panel>
<mode>
<title-panel>
<background-colors>
<toolbar>
<prompt-box-titles>
<toolbar>
<mode>
<toolbar>
<browse-button-text>
<toolbar>
<logout-prompt-te
<url-lists>
<mode>
<pane>
<type>
<mode>
<title>
<text>
<notitle>
<column>
<row>
<height>
<column>
<width>
<order>
<applications>
<tab-Titles>
<order>
<mode>
18-15
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 18 Customizing Clientless SSL VPN
Clientless SSL VPN End User Setup
Login Screen Advanced Customization
If you prefer to use your own, custom login screen, rather than changing specific screen elements of the
login screen we provide, you can perform this advanced customization using the Full Customization
feature.
With Full Customization, you provide the HTML for your own login screen, and you insert Cisco HTML
code that calls functions on the ASA that create the Login form and the Language Selector drop-down
list.
This section describes the modifications you need to make to your HTML code and the tasks required to
configure the ASA to use your code.
Figure 18-10 shows the standard Cisco login screen that displays to Clientless SSL VPN users. The
Login form is displayed by a function called by the HTML code.
Figure 18-10 Standard Cisco Login Page
Figure 18-11 shows the Language Selector drop-down list. This feature is an option for Clientless SSL
VPN users and is also called by a function in the HTML code of the login screen.
Figure 18-11 Language Selector Drop-down List

18-16
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 18 Customizing Clientless SSL VPN
Clientless SSL VPN End User Setup
Figure 18-12 shows a simple example of a custom login screen enabled by the Full Customization
feature.
Figure 18-12 Example of Full Customization of Login Screens
The following HTML code is used as an example and is the code that displays:
Example:
<head>
<meta http-equiv="Content-Type" content="text/html; charset=windows-1252">
<title>New Page 3</title>
<base target="_self">
</head>
<p align="center">
<img border="0" src="/+CSCOU+/cisco_logo.jpg" width="188" height="48"><font face="Snap
ITC" size="6" color="#FF00FF">
</font><font face="Snap ITC" color="#FF00FF" size="7"> </font><i><b><font
color="#FF0000" size="7" face="Sylfaen"> SSL VPN Service by the Cisco
ASA5500</font></b></i></p>
<body onload="csco_ShowLoginForm('lform');csco_ShowLanguageSelector('selector')">
<table>
<tr><td colspan=3 height=20 align=right><div id="selector" style="width:
300px"></div></td></tr>
<tr><td></td><td></td><td></td></tr>
<tr>
<td height="379"></td>
<td height="379"></td>
<td align=middle valign=middle>
<div id=lform >
<p> </p>

18-17
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 18 Customizing Clientless SSL VPN
Clientless SSL VPN End User Setup
<p> </p>
<p> </p>
<p>Loading...</p>
</div>
</td>
</tr>
<tr>
<td width="251"></td>
<td width="1"></td>
<td align=right valign=right width="800">
<img border="1" src="/+CSCOU+/asa5500.jpg" width="660" height="220" align="middle">
</td></tr>
</table>
The indented code injects the Login form and the Language Selector on the screen. The function
csco_ShowLoginForm('lform') injects the logon form. csco_ShowLanguageSelector('selector')
injects the Language Selector.
Modifying Your HTML File
DETAILED STEPS
Step 1 Name your file logon.inc. When you import the file, the ASA recognizes this filename as the logon
screen.
Step 2 Modify the paths of images used by the file to include /+CSCOU+/.
Files that are displayed to remote users before authentication must reside in a specific area of the ASA
cache memory represented by the path /+CSCOU+/. Therefore, the source for each image in the file must
include this path. For example:
src=”/+CSCOU+/asa5520.gif”
Step 3 Insert the special HTML code below. This code contains the Cisco functions, described earlier, that
inject the login form and language selector onto the screen.
<body onload="csco_ShowLoginForm('lform');csco_ShowLanguageSelector('selector')">
<table>
<tr><td colspan=3 height=20 align=right><div id="selector" style="width:
300px"></div></td></tr>
<tr><td></td><td></td><td></td></tr>
<tr>
<td height="379"></td>
<td height="379"></td>
<td align=middle valign=middle>
<div id=lform >
<p> </p>
<p> </p>
<p> </p>
<p>Loading...</p>
</div>
</td>
</tr>
<tr>
<td width="251"></td>
<td width="1"></td>
<td align=right valign=right width="800">
<img border="1" src="/+CSCOU+/asa5500.jpg" width="660" height="220" align="middle">
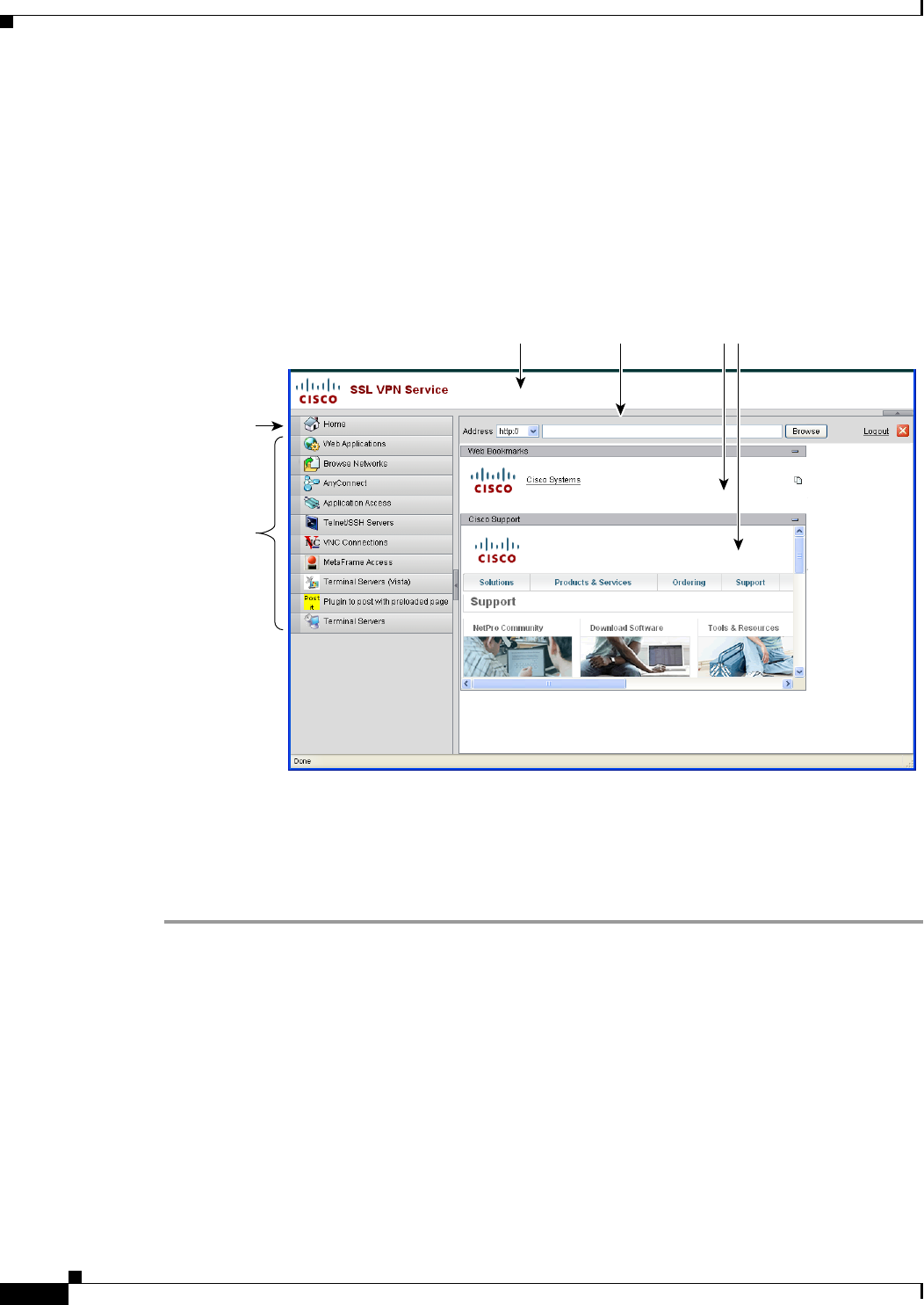
18-18
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 18 Customizing Clientless SSL VPN
Clientless SSL VPN End User Setup
</td></tr>
</table>
Customizing the Portal Page
Figure 18-13 shows the portal page and the pre-defined components you can customize:
Figure 18-13 Customizable Components of the Portal Page
In addition to customizing the components of the page, you can divide the portal page into custom panes
that display text, an image, an RSS feed, or HTML. In Figure 18-13, the portal page is divided into one
column with two rows.
To customize the portal page, follow this procedure. You can preview your changes for each component
by clicking the Preview button:
Step 1 Go to Portal Page and specify a title for the browser window.
Step 2 Display and customize the title panel. Go to Portal Page > Title Panel and check Display title panel.
Enter text to display as the title and specify a logo. Specify any font styles.
Step 3 Enable and customize the toolbar. Go to Portal Page > Toolbar and check Display toolbar. Customize
the Prompt Box, Browse button, and Logout prompt as desired.
Step 4 Customize the Applications list. Go to Portal Page > Applications and check Show navigation panel.
The applications populated in the table are those applications you enabled in the ASA configuration,
including client-server plugins and port forwarding applications.
Step 5 Create custom panes in the portal page space. Go to Portal Page > Custom Panes and divide the window
into rows and columns for text, images, RSS feeds, or HTML pages, as desired.
Title Panel
Home
Page
Applications
Tool Bar Custom Panes

18-19
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 18 Customizing Clientless SSL VPN
Clientless SSL VPN End User Setup
Step 6 Specify a home page URL. Go to Portal Page > Home Page and check Enable custom intranet Web
page. Choose a bookmark mode that defines how bookmarks are organized.
Configure a timeout alert message and a tooltip. Go to Portal Page > Timeout Alerts. See Configuring
Custom Portal Timeout Alerts for full instructions.
Configuring Custom Portal Timeout Alerts
So that users of the Clientless SSL VPN feature can manage their time in the VPN session, the Clientless
SSL VPN portal page displays a countdown timer showing the total time left before the clientless VPN
session expires. Sessions can timeout due to inactivity or because they have reached the end of a
maximum allowed connection time that you have configured.
You can create custom messages to alert users that their session is about to end because of an idle timeout
or a session timeout. Your custom message replaces the default idle timeout message. The default
message is, “Your session will expire in %s .” The %s place holder in your message is replaced by
a ticking countdown timer.
Step 1 Start ASDM and select Configuration > Remote Access VPN > Clientless SSL VPN Access > Portal
> Customization.
Step 2 Click Add to add a new customization object or select an existing customization object and click Edit
to add a custom idle timeout message to an existing customization object.
Step 3 In the Add / Edit Customization Object pane, expand the Portal Page node on the navigation tree and
click Timeout Alerts.
Step 4 Check Enable alert visual tooltip (red background for timer countdown). This displays the
countdown timer as a tool tip on a red background. When users click the Time left area, the time area
expands to display your custom timeout alert message. If you leave this box unchecked, users see the
custom timeout alerts in a pop-up window.
Step 5 Enter a message in the Idle Timeout Message box and in the Session Timeout Message box. An example
of a message could be, Warning: Your session will end in %s. Please complete your work and
prepare to close your applications.
Step 6 Click OK.
Step 7 Click Apply.
Specifying a Custom Timeout Alert in a Customization Object File
If you desire, you can edit an existing customization object file outside of the ASA and import it to the
ASA. For more information about Importing and Exporting Customization objects see
Importing/Exporting Customization Object, page 18-22. See also, Creating XML-Based Portal
Customization Objects and URL Lists, page 18-22.
The timeout messages are configured in the <timeout-alerts> XML element of your XML customization
object file. The <timeout-alerts> element is a child of the <portal> element. The <portal> element is a
child of the <custom> element.
The <timeout-alerts> element is placed after the <home-page> element and before any <application>
elements in the order of the <portal> child elements.

18-20
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 18 Customizing Clientless SSL VPN
Clientless SSL VPN End User Setup
You need to specify these child-elements of <timeout-alerts>:
•<alert-tooltip> – If set to “yes”, users see the countdown timer on a red background as a tool tip.
Clicking the count down timer expands the tooltip to display your custom message. If set to “no” or
if is undefined, users receive your custom messages in pop-up windows.
•<session-timeout-message> – Enter your custom session timeout message in this element. If set and
not empty, users receive your custom message instead of the default message. The %s place holder
in the message will be replaced with a ticking countdown timer.
•<idle-timeout-message> – Enter your custom idle timeout message in this element. If set and not
empty, users receive your custom message instead of the default message. The %s place holder will
be replaced with a ticking countdown timer.
Configuration Example for Timeout-alert Element and Child Elements
This example shows only the <timeout-alerts> elements of the <portal> element.
Note Do not cut and paste this example into an existing customization object.
<portal>
<window></window>
<title-panel></title-panel>
<toolbar></toolbar>
<url-lists></url-lists>
<navigation-panel></navigation-panel>
<home-page>
<timeout-alerts>
<alert-tooltip>yes</alert-tooltip>
<idle-timeout-message>You session expires in %s due to idleness.</idle-timeout-message>
<session-timeout-message>Your session expires in %s.</session-timeout-message>
</timeout-alerts>
<application></application>
<column></column>
<pane></pane>
<external-portal></external-portal>
</portal>
Customizing the Logout Page
Figure 18-14 shows the logout page you can customize:
18-21
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 18 Customizing Clientless SSL VPN
Clientless SSL VPN End User Setup
Figure 18-14 Components of the Logout Page
To customize the logout page, follow this procedure. You can preview your changes for each component
by clicking the Preview button:
Step 1 Go to Logout Page. Customize the title or text as you desire.
Step 2 For the convenience of the user, you can display the Login button on the Logout page. To do this, check
Show logon button. Customize the button text, if desired.
Step 3 Customize the title font or background, as desired.
Step 4 Click OK, then apply the changes to the customization object you edited.
Customizing the External Portal Page
Adding Customization Object
To add a customization object, create a copy of and provide a unique name for the DfltCustomization
object. Then you can modify or edit it to meet your requirements.
DETAILED STEPS
Step 1 Click Add and enter a name for the new customization object. Maximum 64 characters, no spaces.
247845
Title and Text

18-22
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 18 Customizing Clientless SSL VPN
Creating XML-Based Portal Customization Objects and URL Lists
Step 2 (Optional) Click Find to search for a customization object. Start typing in the field, and the tool searches
the beginning characters of every field for a match. You can use wild cards to expand your search. For
example, typing sal in the Find field matches a customization object named sales but not a customization
object named wholesalers. If you type *sal in the Find field, the search finds the first instance of either
sales or wholesalers in the table.
Use the up and down arrows to skip up or down to the next string match. Check the Match Case check
box to make your search case sensitive.
Step 3 Specify when the onscreen keyboard shows on portal pages. The choices are as follows:
•Do not show OnScreen Keyboard
•Show only for the login page
•Show for all portal pages requiring authentication
Step 4 (Optional) Highlight a customization object and click Assign to assign the selected object to one or more
group policies, connection profiles, or LOCAL users.
Importing/Exporting Customization Object
You can import or export already-existing customization objects. Import an object to apply to end users.
Export a customization object already resident on the ASA for editing purposes, after which you can
reimport it.
DETAILED STEPS
Step 1 Identify the customization object by name. Maximum 64 characters, no spaces.
Step 2 Choose the method to import or export the customization file:
•Local computer—Choose this method to import a file that resides on the local PC.
•Path—Provide the path to the file.
•Browse Local Files—Browse to the path for the file.
•Flash file system—Choose this method to export a file that resides on the ASA.
•Path—Provide the path to the file.
•Browse Flash—Browse to the path for the file.
•Remote server—Choose this option to import a customization file that resides on a remote server
accessible from the ASA.
•Path—Identify the method to access the file (ftp, http, or https), and provide the path to the file.
Step 3 Click to import or export the file.
Creating XML-Based Portal Customization Objects and URL Lists
This section includes the following topics:
•Understanding the XML Customization File Structure, page 18-23
18-23
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 18 Customizing Clientless SSL VPN
Creating XML-Based Portal Customization Objects and URL Lists
•Configuration Example for Customization, page 18-26
•Using the Customization Template, page 18-29
•Help Customization, page 18-41
•Import/Export Application Help Content, page 18-44
Understanding the XML Customization File Structure
Table 18-1 presents the file structure for an XML customization object.
Note Absence of a parameter/tag results in a default/inherited value, while presence results in setting the
parameter/tag value even it is an empty string.
Table 18-1 XML-Based Customization File Structure
Tag Type Values Preset value Description
custom node — — Root tag
auth-page node — — Tag-container of
authentication page
configuration
window node — — Browser window
title-text string Arbitrary string empty string —
title-panel node — — The page top pane with
a logo and a text
mode text enable|disable disable —
text text Arbitrary string empty string —
logo-url text Arbitrary URL empty image
URL
—
copyright-panel node — — The page bottom pane
with a copyright
information
mode text enable|disable disable —
text text Arbitrary URL empty string —
info-panel node — — The pane with a custom
text and image
mode string enable|disable disable —
image-position string above|below above The image position,
relative to text
image-url string Arbitrary URL empty image —
text string Arbitrary string empty string —
logon-form node — — The form with
username, password,
group prompt
title-text string Arbitrary string Logon —
18-24
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 18 Customizing Clientless SSL VPN
Creating XML-Based Portal Customization Objects and URL Lists
message-text string Arbitrary string empty string —
username-prompt-text
string Arbitrary string Username —
password-prompt-text
string Arbitrary string Password —
internal-password-prompt
-text
string Arbitrary string Internal
Password
—
group-prompt-text string Arbitrary string Group —
submit-button-text string Arbitrary string Logon
logout-form node — — The form with a logout
message and the
buttons to login or close
the window
title-text string Arbitrary string Logout —
message-text string Arbitrary string Empty string —
login-button-text string Arbitrary string Login
close-button-text string Arbitrary string Close
window
—
language-selector node — — The drop-down list to
select a language
mode string enable|disable disable —
title text — Language The prompt text to
select language
language node
(multiple)
———
code string — — —
text string — — —
portal node — — Tag-container of the
portal page
configuration
window node — — see authentication page
description
title-text string Arbitrary string Empty string —
title-panel node — — see authentication page
description
mode string enable|disable Disable —
text string Arbitrary string Empty string —
logo-url string Arbitrary URL Empty
image URL
—
navigation-panel node — — The pane on the left
with application tabs
mode string enable|disable enable —
Table 18-1 XML-Based Customization File Structure (continued)
18-25
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 18 Customizing Clientless SSL VPN
Creating XML-Based Portal Customization Objects and URL Lists
application node
(multiple)
— N/A The node changes
defaults for the
configured (by id)
application
id string For stock application
web-access
file-access
app-access
net-access
help
For ins:
Unique plug-in
N/A —
tab-title string — N/A —
order number — N/A Value used to sort
elements. The default
element order values
have step 1000, 2000,
3000, etc. For
example, to insert an
element between the
first and second
element, use a value
1001 – 1999.
url-list-title string — N/A If the application has
bookmarks, the title
for the panel with
grouped bookmarks
mode string enable|disable N/A v
toolbar node — — —
mode string enable|disable Enable —
prompt-box-title string Arbitrary string Address Title for URL prompt
list
browse-button-text string Arbitrary string Browse Browse button text
logout-prompt-text string Arbitrary string Logout —
column node
(multiple)
— — One column will be
shown by default
width string — N/A —
order number — N/A Value used to sort
elements.
Table 18-1 XML-Based Customization File Structure (continued)
18-26
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 18 Customizing Clientless SSL VPN
Creating XML-Based Portal Customization Objects and URL Lists
Configuration Example for Customization
The following example illustrates the following customization options:
•Hides tab for the File access application
•Changes title and order of Web Access application
url-lists node — — URL lists are
considered to be default
elements on the portal
home page, if they are
not explicitly switched
off
mode string group | nogroup group Modes:
group – elements
grouped by
application type i.e.
Web Bookmarks, File
Bookmarks)
no-group – url-lists
are shown in separate
panes
disable – do not show
URL lists by default
panel node
(multiple)
— — Allows to configure
extra panes
mode string enable|disable — Used to temporarily
switch off the panel
without removing its
configuration
title string — — —
type string — — Supported types:
RSS
IMAGE
TEXT
HTML
url string — — URL for
RSS,IMAGE or
HTML type paned
url-mode string — — Modes: mangle,
no-mangle
text string — — Text for TEXT type
panes
column number — — —
Table 18-1 XML-Based Customization File Structure (continued)

18-27
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 18 Customizing Clientless SSL VPN
Creating XML-Based Portal Customization Objects and URL Lists
•Defines two columns on the home page
•Adds an RSS pane
•Adds three panes (text, image, and html) at the top of second pane
<custom name="Default">
<auth-page>
<window>
<title-text l10n="yes">title WebVPN Logon</title>
</window>
<title-panel>
<mode>enable</mode>
<text l10n="yes">EXAMPLE WebVPN</text>
<logo-url>http://www.example.com/images/EXAMPLE.gif</logo-url>
</title-panel>
<copyright>
<mode>enable</mode>
<text l10n="yes">(c)Copyright, EXAMPLE Inc., 2006</text>
</copyright>
<info-panel>
<mode>enable</mode>
<image-url>/+CSCOE+/custom/EXAMPLE.jpg</image-url>
<text l10n="yes">
<![CDATA[
<div>
<b>Welcome to WebVPN !.</b>
</div>
]]>
</text>
</info-panel>
<logon-form>
<form>
<title-text l10n="yes">title WebVPN Logon</title>
<message-text l10n="yes">message WebVPN Logon</title>
<username-prompt-text l10n="yes">Username</username-prompt-text>
<password-prompt-text l10n="yes">Password</password-prompt-text>
<internal-password-prompt-text l10n="yes">Domain
password</internal-password-prompt-text>
<group-prompt-text l10n="yes">Group</group-prompt-text>
<submit-button-text l10n="yes">Logon</submit-button-text>
</form>
</logon-form>
<logout-form>
<form>
<title-text l10n="yes">title WebVPN Logon</title>
<message-text l10n="yes">message WebVPN Logon</title>
<login-button-text l10n="yes">Login</login-button-text>
<close-button-text l10n="yes">Logon</close-button-text>
</form>
</logout-form>
<language-slector>
<language>
<code l10n="yes">code1</code>
<text l10n="yes">text1</text>
</language>
<language>
<code l10n="yes">code2</code>
<text l10n="yes">text2</text>

18-28
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 18 Customizing Clientless SSL VPN
Creating XML-Based Portal Customization Objects and URL Lists
</language>
</language-slector>
</auth-page>
<portal>
<window>
<title-text l10n="yes">title WebVPN Logon</title>
</window>
<title-panel>
<mode>enable</mode>
<text l10n="yes">EXAMPLE WebVPN</text>
<logo-url>http://www.example.com/logo.gif</logo-url>
</title-panel>
<navigation-panel>
<mode>enable</mode>
</navigation-panel>
<application>
<id>file-access</id>
<mode>disable</mode>
</application>
<application>
<id>web-access</id>
<tab-title>EXAMPLE Intranet</tab-title>
<order>3001</order>
</application>
<column>
<order>2</order>
<width>40%</width>
<column>
<column>
<order>1</order>
<width>60%</width>
<column>
<url-lists>
<mode>no-group</mode>
</url-lists>
<pane>
<id>rss_pane</id>
<type>RSS</type>
<url>rss.example.com?id=78</url>
</pane>
<pane>
<type>IMAGE</type>
<url>http://www.example.com/logo.gif</url>
<column>1</column>
<row>2</row>
</pane>
<pane>
<type>HTML</type>
<title>EXAMPLE news</title>
<url>http://www.example.com/news.html</url>
<column>1</column>
<row>3</row>
</pane>
</portal>

18-29
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 18 Customizing Clientless SSL VPN
Creating XML-Based Portal Customization Objects and URL Lists
</custom>
Using the Customization Template
A customization template, named Tem plate, contains all currently employed tags with corresponding
comments that describe how to use them. Use the export command to download the customization
template from the ASA, as follows:
hostname# export webvpn customization Template tftp://webserver/default.xml
hostname#
You cannot change or delete the file Template. When you export it, as in this example, you are saving it
to a new name, default.xml. After you make your changes to this file to create a customization object that
meets the needs of your organization, import it to the ASA, either as default.xml or another name of your
choosing. For example:
hostname# import webvpn customization General tftp://webserver/custom.xml
hostname#
where you import an XML object called custom.xml, and name it General on the ASA.
The Customization Template
The customization template, named Template, follows:
<?xml version="1.0" encoding="UTF-8" ?>
- <!--
Copyright (c) 2008,2009 by Cisco Systems, Inc.
All rights reserved.
Note: all white spaces in tag values are significant and preserved.
Tag: custom
Description: Root customization tag
Tag: custom/languages
Description: Contains list of languages, recognized by ASA
Value: string containing comma-separated language codes. Each language code is
a set dash-separated alphanumeric characters, started with
alpha-character (for example: en, en-us, irokese8-language-us)
Default value: en-us
Tag: custom/default-language
Description: Language code that is selected when the client and the server
were not able to negotiate the language automatically.
For example the set of languages configured in the browser
is "en,ja", and the list of languages, specified by
'custom/languages' tag is "cn,fr", the default-language will be
used.
Value: string, containing one of the language coded, specified in
'custom/languages' tag above.
Default value: en-us
*********************************************************

18-30
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 18 Customizing Clientless SSL VPN
Creating XML-Based Portal Customization Objects and URL Lists
Tag: custom/auth-page
Description: Contains authentication page settings
*********************************************************
Tag: custom/auth-page/window
Description: Contains settings of the authentication page browser window
Tag: custom/auth-page/window/title-text
Description: The title of the browser window of the authentication page
Value: arbitrary string
Default value: Browser's default value
*********************************************************
Tag: custom/auth-page/title-panel
Description: Contains settings for the title panel
Tag: custom/auth-page/title-panel/mode
Description: The title panel mode
Value: enable|disable
Default value: disable
Tag: custom/auth-page/title-panel/text
Description: The title panel text.
Value: arbitrary string
Default value: empty string
Tag: custom/auth-page/title-panel/logo-url
Description: The URL of the logo image (imported via "import webvpn webcontent")
Value: URL string
Default value: empty image URL
Tag: custom/auth-page/title-panel/background-color
Description: The background color of the title panel
Value: HTML color format, for example #FFFFFF
Default value: #FFFFFF
Tag: custom/auth-page/title-panel/font-color
Description: The background color of the title panel
Value: HTML color format, for example #FFFFFF
Default value: #000000
Tag: custom/auth-page/title-panel/font-weight
Description: The font weight
Value: CSS font size value, for example bold, bolder,lighter etc.
Default value: empty string
Tag: custom/auth-page/title-panel/font-size
Description: The font size
Value: CSS font size value, for example 10pt, 8px, x-large, smaller etc.
Default value: empty string
Tag: custom/auth-page/title-panel/gradient
Description: Specifies using the background color gradient
Value: yes|no
Default value:no
Tag: custom/auth-page/title-panel/style
Description: CSS style of the title panel
Value: CSS style string
Default value: empty string

18-31
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 18 Customizing Clientless SSL VPN
Creating XML-Based Portal Customization Objects and URL Lists
*********************************************************
Tag: custom/auth-page/copyright-panel
Description: Contains the copyright panel settings
Tag: custom/auth-page/copyright-panel/mode
Description: The copyright panel mode
Value: enable|disable
Default value: disable
Tag: custom/auth-page/copyright-panel/text
Description: The copyright panel text
Value: arbitrary string
Default value: empty string
*********************************************************
Tag: custom/auth-page/info-panel
Description: Contains information panel settings
Tag: custom/auth-page/info-panel/mode
Description: The information panel mode
Value: enable|disable
Default value: disable
Tag: custom/auth-page/info-panel/image-position
Description: Position of the image, above or below the informational panel text
Values: above|below
Default value: above
Tag: custom/auth-page/info-panel/image-url
Description: URL of the information panel image (imported via "import webvpn webcontent")
Value: URL string
Default value: empty image URL
Tag: custom/auth-page/info-panel/text
Description: Text of the information panel
Text: arbitrary string
Default value: empty string
*********************************************************
Tag: custom/auth-page/logon-form
Description: Contains logon form settings
Tag: custom/auth-page/logon-form/title-text
Description: The logon form title text
Value: arbitrary string
Default value: "Logon"
Tag: custom/auth-page/logon-form/message-text
Description: The message inside of the logon form
Value: arbitrary string
Default value: empty string
Tag: custom/auth-page/logon-form/username-prompt-text
Description: The username prompt text
Value: arbitrary string
Default value: "Username"
Tag: custom/auth-page/logon-form/password-prompt-text
Description: The password prompt text
Value: arbitrary string
Default value: "Password"

18-32
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 18 Customizing Clientless SSL VPN
Creating XML-Based Portal Customization Objects and URL Lists
Tag: custom/auth-page/logon-form/internal-password-prompt-text
Description: The internal password prompt text
Value: arbitrary string
Default value: "Internal Password"
Tag: custom/auth-page/logon-form/group-prompt-text
Description: The group selector prompt text
Value: arbitrary string
Default value: "Group"
Tag: custom/auth-page/logon-form/submit-button-text
Description: The submit button text
Value: arbitrary string
Default value: "Logon"
Tag: custom/auth-page/logon-form/internal-password-first
Description: Sets internal password first in the order
Value: yes|no
Default value: no
Tag: custom/auth-page/logon-form/title-font-color
Description: The font color of the logon form title
Value: HTML color format, for example #FFFFFF
Default value: #000000
Tag: custom/auth-page/logon-form/title-background-color
Description: The background color of the logon form title
Value: HTML color format, for example #FFFFFF
Default value: #000000
Tag: custom/auth-page/logon-form/font-color
Description: The font color of the logon form
Value: HTML color format, for example #FFFFFF
Default value: #000000
Tag: custom/auth-page/logon-form/background-color
Description: The background color of the logon form
Value: HTML color format, for example #FFFFFF
Default value: #000000
*********************************************************
Tag: custom/auth-page/logout-form
Description: Contains the logout form settings
Tag: custom/auth-page/logout-form/title-text
Description: The logout form title text
Value: arbitrary string
Default value: "Logout"
Tag: custom/auth-page/logout-form/message-text
Description: The logout form message text
Value: arbitrary string
Default value: Goodbye.
For your own security, please:
Clear the browser's cache
Delete any downloaded files
Close the browser's window
Tag: custom/auth-page/logout-form/login-button-text

18-33
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 18 Customizing Clientless SSL VPN
Creating XML-Based Portal Customization Objects and URL Lists
Description: The text of the button sending the user to the logon page
Value: arbitrary string
Default value: "Logon"
*********************************************************
Tag: custom/auth-page/language-selector
Description: Contains the language selector settings
Tag: custom/auth-page/language-selector/mode
Description: The language selector mode
Value: enable|disable
Default value: disable
Tag: custom/auth-page/language-selector/title
Description: The language selector title
Value: arbitrary string
Default value: empty string
Tag: custom/auth-page/language-selector/language (multiple)
Description: Contains the language settings
Tag: custom/auth-page/language-selector/language/code
Description: The code of the language
Value (required): The language code string
Tag: custom/auth-page/language-selector/language/text
Description: The text of the language in the language selector drop-down box
Value (required): arbitrary string
*********************************************************
Tag: custom/portal
Description: Contains portal page settings
*********************************************************
Tag: custom/portal/window
Description: Contains the portal page browser window settings
Tag: custom/portal/window/title-text
Description: The title of the browser window of the portal page
Value: arbitrary string
Default value: Browser's default value
*********************************************************
Tag: custom/portal/title-panel
Description: Contains settings for the title panel
Tag: custom/portal/title-panel/mode
Description: The title panel mode
Value: enable|disable
Default value: disable
Tag: custom/portal/title-panel/text
Description: The title panel text.
Value: arbitrary string
Default value: empty string
Tag: custom/portal/title-panel/logo-url
Description: The URL of the logo image (imported via "import webvpn webcontent")
Value: URL string
Default value: empty image URL

18-34
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 18 Customizing Clientless SSL VPN
Creating XML-Based Portal Customization Objects and URL Lists
Tag: custom/portal/title-panel/background-color
Description: The background color of the title panel
Value: HTML color format, for example #FFFFFF
Default value: #FFFFFF
Tag: custom/auth-pa/title-panel/font-color
Description: The background color of the title panel
Value: HTML color format, for example #FFFFFF
Default value: #000000
Tag: custom/portal/title-panel/font-weight
Description: The font weight
Value: CSS font size value, for example bold, bolder,lighter etc.
Default value: empty string
Tag: custom/portal/title-panel/font-size
Description: The font size
Value: CSS font size value, for example 10pt, 8px, x-large, smaller etc.
Default value: empty string
Tag: custom/portal/title-panel/gradient
Description: Specifies using the background color gradient
Value: yes|no
Default value:no
Tag: custom/portal/title-panel/style
Description: CSS style for title text
Value: CSS style string
Default value: empty string
*********************************************************
Tag: custom/portal/application (multiple)
Description: Contains the application setting
Tag: custom/portal/application/mode
Description: The application mode
Value: enable|disable
Default value: enable
Tag: custom/portal/application/id
Description: The application ID. Standard application ID's are: home, web-access,
file-access, app-access, network-access, help
Value: The application ID string
Default value: empty string
Tag: custom/portal/application/tab-title
Description: The application tab text in the navigation panel
Value: arbitrary string
Default value: empty string
Tag: custom/portal/application/order
Description: The order of the application's tab in the navigation panel. Applications with
lesser order go first.
Value: arbitrary number
Default value: 1000
Tag: custom/portal/application/url-list-title
Description: The title of the application's URL list pane (in group mode)
Value: arbitrary string
Default value: Tab tite value concatenated with "Bookmarks"
*********************************************************

18-35
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 18 Customizing Clientless SSL VPN
Creating XML-Based Portal Customization Objects and URL Lists
Tag: custom/portal/navigation-panel
Description: Contains the navigation panel settings
Tag: custom/portal/navigation-panel/mode
Description: The navigation panel mode
Value: enable|disable
Default value: enable
*********************************************************
Tag: custom/portal/toolbar
Description: Contains the toolbar settings
Tag: custom/portal/toolbar/mode
Description: The toolbar mode
Value: enable|disable
Default value: enable
Tag: custom/portal/toolbar/prompt-box-title
Description: The universal prompt box title
Value: arbitrary string
Default value: "Address"
Tag: custom/portal/toolbar/browse-button-text
Description: The browse button text
Value: arbitrary string
Default value: "Browse"
Tag: custom/portal/toolbar/logout-prompt-text
Description: The logout prompt text
Value: arbitrary string
Default value: "Logout"
*********************************************************
Tag: custom/portal/column (multiple)
Description: Contains settings of the home page column(s)
Tag: custom/portal/column/order
Description: The order the column from left to right. Columns with lesser order values go
first
Value: arbitrary number
Default value: 0
Tag: custom/portal/column/width
Description: The home page column width
Value: percent
Default value: default value set by browser
Note: The actual width may be increased by browser to accommodate content
*********************************************************
Tag: custom/portal/url-lists
Description: Contains settings for URL lists on the home page
Tag: custom/portal/url-lists/mode
Description: Specifies how to display URL lists on the home page:
group URL lists by application (group) or
show individual URL lists (nogroup).
URL lists fill out cells of the configured columns, which are not taken
by custom panes.
Use the attribute value "nodisplay" to not show URL lists on the home page.

18-36
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 18 Customizing Clientless SSL VPN
Creating XML-Based Portal Customization Objects and URL Lists
Value: group|nogroup|nodisplay
Default value: group
*********************************************************
Tag: custom/portal/pane (multiple)
Description: Contains settings of the custom pane on the home page
Tag: custom/portal/pane/mode
Description: The mode of the pane
Value: enable|disable
Default value: disable
Tag: custom/portal/pane/title
Description: The title of the pane
Value: arbitrary string
Default value: empty string
Tag: custom/portal/pane/notitle
Description: Hides pane's title bar
Value: yes|no
Default value: no
Tag: custom/portal/pane/type
Description: The type of the pane. Supported types:
TEXT - inline arbitrary text, may contain HTML tags;
HTML - HTML content specified by URL shown in the individual iframe;
IMAGE - image specified by URL
RSS - RSS feed specified by URL
Value: TEXT|HTML|IMAGE|RSS
Default value: TEXT
Tag: custom/portal/pane/url
Description: The URL for panes with type HTML,IMAGE or RSS
Value: URL string
Default value: empty string
Tag: custom/portal/pane/text
Description: The text value for panes with type TEXT
Value: arbitrary string
Default value:empty string
Tag: custom/portal/pane/column
Description: The column where the pane located.
Value: arbitrary number
Default value: 1
Tag: custom/portal/pane/row
Description: The row where the pane is located
Value: arbitrary number
Default value: 1
Tag: custom/portal/pane/height
Description: The height of the pane
Value: number of pixels
Default value: default value set by browser
*********************************************************
Tag: custom/portal/browse-network-title
Description: The title of the browse network link
Value: arbitrary string
Default value: Browse Entire Network

18-37
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 18 Customizing Clientless SSL VPN
Creating XML-Based Portal Customization Objects and URL Lists
Tag: custom/portal/access-network-title
Description: The title of the link to start a network access session
Value: arbitrary string
Default value: Start AnyConnect
-->
- <custom>
- <localization>
<languages>en,ja,zh,ru,ua</languages>
<default-language>en</default-language>
</localization>
- <auth-page>
- <window>
- <title-text l10n="yes">
- <![CDATA[
WebVPN Service
]]>
</title-text>
</window>
- <language-selector>
<mode>disable</mode>
<title l10n="yes">Language:</title>
- <language>
<code>en</code>
<text>English</text>
</language>
- <language>
<code>zh</code>
<text>?? (Chinese)</text>
</language>
- <language>
<code>ja</code>
<text>?? (Japanese)</text>
</language>
- <language>
<code>ru</code>
<text>??????? (Russian)</text>
</language>
- <language>
<code>ua</code>
<text>?????????? (Ukrainian)</text>
</language>
</language-selector>
- <logon-form>
- <title-text l10n="yes">
- <![CDATA[
Login
]]>
</title-text>
- <title-background-color>
- <![CDATA[
#666666
]]>
</title-background-color>
- <title-font-color>
- <![CDATA[
#ffffff
]]>
</title-font-color>
- <message-text l10n="yes">
- <![CDATA[
Please enter your username and password.
]]>

18-38
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 18 Customizing Clientless SSL VPN
Creating XML-Based Portal Customization Objects and URL Lists
</message-text>
- <username-prompt-text l10n="yes">
- <![CDATA[
USERNAME:
]]>
</username-prompt-text>
- <password-prompt-text l10n="yes">
- <![CDATA[
PASSWORD:
]]>
</password-prompt-text>
<internal-password-prompt-text l10n="yes" />
<internal-password-first>no</internal-password-first>
- <group-prompt-text l10n="yes">
- <![CDATA[
GROUP:
]]>
</group-prompt-text>
- <submit-button-text l10n="yes">
- <![CDATA[
Login
]]>
</submit-button-text>
- <title-font-color>
- <![CDATA[
#ffffff
]]>
</title-font-color>
- <title-background-color>
- <![CDATA[
#666666
]]>
</title-background-color>
<font-color>#000000</font-color>
<background-color>#ffffff</background-color>
</logon-form>
- <logout-form>
- <title-text l10n="yes">
- <![CDATA[
Logout
]]>
</title-text>
- <message-text l10n="yes">
- <![CDATA[
Goodbye.
]]>
</message-text>
</logout-form>
- <title-panel>
<mode>enable</mode>
- <text l10n="yes">
- <![CDATA[
WebVPN Service
]]>
</text>
<logo-url l10n="yes">/+CSCOU+/csco_logo.gif</logo-url>
<gradient>yes</gradient>
<style />
- <background-color>
- <![CDATA[
#ffffff
]]>
</background-color>
- <font-size>

18-39
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 18 Customizing Clientless SSL VPN
Creating XML-Based Portal Customization Objects and URL Lists
- <![CDATA[
larger
]]>
</font-size>
- <font-color>
- <![CDATA[
#800000
]]>
</font-color>
- <font-weight>
- <![CDATA[
bold
]]>
</font-weight>
</title-panel>
- <info-panel>
<mode>disable</mode>
<image-url l10n="yes">/+CSCOU+/clear.gif</image-url>
<image-position>above</image-position>
<text l10n="yes" />
</info-panel>
- <copyright-panel>
<mode>disable</mode>
<text l10n="yes" />
</copyright-panel>
</auth-page>
- <portal>
- <title-panel>
<mode>enable</mode>
- <text l10n="yes">
- <![CDATA[
WebVPN Service
]]>
</text>
<logo-url l10n="yes">/+CSCOU+/csco_logo.gif</logo-url>
<gradient>yes</gradient>
<style />
- <background-color>
- <![CDATA[
#ffffff
]]>
</background-color>
- <font-size>
- <![CDATA[
larger
]]>
</font-size>
- <font-color>
- <![CDATA[
#800000
]]>
</font-color>
- <font-weight>
- <![CDATA[
bold
]]>
</font-weight>
</title-panel>
<browse-network-title l10n="yes">Browse Entire Network</browse-network-title>
<access-network-title l10n="yes">Start AnyConnect</access-network-title>
- <application>
<mode>enable</mode>
<id>home</id>
<tab-title l10n="yes">Home</tab-title>

18-40
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 18 Customizing Clientless SSL VPN
Creating XML-Based Portal Customization Objects and URL Lists
<order>1</order>
</application>
- <application>
<mode>enable</mode>
<id>web-access</id>
- <tab-title l10n="yes">
- <![CDATA[
Web Applications
]]>
</tab-title>
- <url-list-title l10n="yes">
- <![CDATA[
Web Bookmarks
]]>
</url-list-title>
<order>2</order>
</application>
- <application>
<mode>enable</mode>
<id>file-access</id>
- <tab-title l10n="yes">
- <![CDATA[
Browse Networks
]]>
</tab-title>
- <url-list-title l10n="yes">
- <![CDATA[
File Folder Bookmarks
]]>
</url-list-title>
<order>3</order>
</application>
- <application>
<mode>enable</mode>
<id>app-access</id>
- <tab-title l10n="yes">
- <![CDATA[
Application Access
]]>
</tab-title>
<order>4</order>
</application>
- <application>
<mode>enable</mode>
<id>net-access</id>
<tab-title l10n="yes">AnyConnect</tab-title>
<order>4</order>
</application>
- <application>
<mode>enable</mode>
<id>help</id>
<tab-title l10n="yes">Help</tab-title>
<order>1000000</order>
</application>
- <toolbar>
<mode>enable</mode>
<logout-prompt-text l10n="yes">Logout</logout-prompt-text>
<prompt-box-title l10n="yes">Address</prompt-box-title>
<browse-button-text l10n="yes">Browse</browse-button-text>
</toolbar>
- <column>
<width>100%</width>
<order>1</order>
</column>

18-41
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 18 Customizing Clientless SSL VPN
Creating XML-Based Portal Customization Objects and URL Lists
- <pane>
<type>TEXT</type>
<mode>disable</mode>
<title />
<text />
<notitle />
<column />
<row />
<height />
</pane>
- <pane>
<type>IMAGE</type>
<mode>disable</mode>
<title />
<url l10n="yes" />
<notitle />
<column />
<row />
<height />
</pane>
- <pane>
<type>HTML</type>
<mode>disable</mode>
<title />
<url l10n="yes" />
<notitle />
<column />
<row />
<height />
</pane>
- <pane>
<type>RSS</type>
<mode>disable</mode>
<title />
<url l10n="yes" />
<notitle />
<column />
<row />
<height />
</pane>
- <url-lists>
<mode>group</mode>
</url-lists>
</portal>
</custom>
Help Customization
The ASA displays help content on the application panes during clientless sessions. Each clientless
application pane displays its own help file content using a predetermined filename. For example, the help
content displayed on the Application Access panel is from the file named app-access-hlp.inc. Table 18-2
shows the clientless application panels and predetermined filenames for the help content.
Table 18-2 Clientless Applications
Application Type Panel Filename
Standard Application Access app-access-hlp.inc
Standard Browse Networks file-access-hlp.inc

18-42
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 18 Customizing Clientless SSL VPN
Creating XML-Based Portal Customization Objects and URL Lists
You can customize the help files provided by Cisco or create help files in other languages. Then use the
Import button to copy them to the flash memory of the ASA for display during subsequent clientless
sessions. You can also export previously imported help content files, customize them, and reimport them
to flash memory.
The following sections describe how to customize or create help content visible on clientless sessions:
•Customizing a Help File Provided By Cisco
•Creating Help Files for Languages Not Provided by Cisco
DETAILED STEPS
Step 1 Click Import to launch the Import Application Help Content dialog, where you can import new help
content to flash memory for display during clientless sessions.
Step 2 (Optional) Click Export to retrieve previously imported help content selected from the table.
Step 3 (Optional) Click Delete to delete previously imported help content selected from the table.
Step 4 The abbreviation of the language rendered by the browser is displayed. This field is not used for file
translation; it indicates the language used in the file. To identify the name of a language associated with
an abbreviation in the table, display the list of languages rendered by your browser. For example, a dialog
window displays the languages and associated language codes when you use one of the following
procedures:
•Open Internet Explorer and choose Tools > Internet Options > Languages > Add.
•Open Mozilla Firefox and choose Tools > Options > Advanced > General, click Choose next to
Languages, and click Select a language to add.
The filename that the help content file was imported as is provided.
Customizing a Help File Provided by Cisco
To customize a help file provided by Cisco, you first require a copy of the file from the flash memory
card.
DETAILED STEPS
Step 1 Use your browser to establish a clientless session with the ASA.
Standard AnyConnect Client net-access-hlp.inc
Standard Web Access web-access-hlp.inc
Plug-in MetaFrame Access ica-hlp.inc
Plug-in Terminal Servers rdp-hlp.inc
Plug-in Telnet/SSH Servers1ssh,telnet-hlp.inc
Plug-in VNC Connections vnc-hlp.inc
1. This plug-in is capable of doing both sshv1 and sshv2.
Table 18-2 Clientless Applications
Application Type Panel Filename
18-43
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 18 Customizing Clientless SSL VPN
Creating XML-Based Portal Customization Objects and URL Lists
Step 2 Display the help file by appending the string in “URL of Help File in Flash Memory of the Security
Appliance” in Table 18-3, to the address of the ASA, substituting language as described below, then
press Enter.
language is the abbreviation for the language rendered by the browser. It is not used for file translation;
it indicates the language used in the file. For help files provided by Cisco in English, enter the
abbreviation en.
The following example address displays the English version of the Terminal Servers help:
https://address_of_security_appliance/+CSCOE+/help/en/rdp-hlp.inc
Step 3 Choose File > Save (Page) As.
Note Do not change the contents of the File name box.
Step 4 Change the Save as type option to Web Page, HTML only and click Save.
Step 5 Use your preferred HTML editor to customize the file.
Note You can use most HTML tags, but do not use tags that define the document and its structure (for
example, do not use <html>, <title>, <body>, <head>, <h1>, <h2>, etc. You can use character
tags, such as the <b> tag, and the <p>, <ol>, <ul>, and <li> tags to structure content.
Step 6 Save the file as HTML only, using the original filename and extension.
Step 7 Ensure the filename matches the one in Table 18-4, and that it does not have an extra filename extension.
Return to ASDM and choose Configuration > Remote Access VPN > Clientless SSL VPN Access >
Portal > Help Customization > Import to import the modified help file into flash memory.
Creating Help Files for Languages Not Provided by Cisco
Use standard HTML to create help files in other languages. We recommend creating a separate folder
for each language to support.
Table 18-3 Help Files Provided by Cisco for Clientless Applications
Application
Type Panel
URL of Help File in Flash Memory of the Security
Appliance
Standard Application Access /+CSCOE+/help/language/app-access-hlp.inc
Standard Browse Networks /+CSCOE+/help/language/file-access-hlp.inc
Standard AnyConnect Client /+CSCOE+/help/language/net-access-hlp.inc
Standard Web Access /+CSCOE+/help/language/web-access-hlp.inc
Plug-in Terminal Servers /+CSCOE+/help/language/rdp-hlp.inc
Plug-in Telnet/SSH Servers /+CSCOE+/help/language/ssh,telnet-hlp.inc
Plug-in VNC Connections /+CSCOE+/help/language/vnc-hlp.inc

18-44
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 18 Customizing Clientless SSL VPN
Creating XML-Based Portal Customization Objects and URL Lists
Note You can use most HTML tags, but do not use tags that define the document and its structure (for
example, do not use <html>, <title>, <body>, <head>, <h1>, <h2>, etc. You can use character tags, such
as the <b> tag, and the <p>, <ol>, <ul>, and <li> tags to structure content.
Save the file as HTML only. Use the filename in the Filename column.
Return to ASDM and choose Configuration > Remote Access VPN > Clientless SSL VPN Access >
Portal > Help Customization > Import to import the new help file into flash memory.
Import/Export Application Help Content
Use the Import Application Help Content dialog box to import help files to flash memory for display on
the portal pages during clientless sessions. Use the Export Application Help Content dialog box to
retrieve previously imported help files for subsequent editing.
DETAILED STEPS
Step 1 The Language field specifies the language rendered by the browser but is not used for file translation.
(This field is inactive in the Export Application Help Content dialog box.) Click the dots next to the
Language field and double-click the row containing the language shown in the Browse Language Code
dialog box. Confirm the abbreviation in the Language Code field matches the abbreviation in the row
and click OK.
Step 2 If the language required to provide help content is not present in the Browse Language Code dialog box,
perform the following
1. Display the list of languages and abbreviations rendered by your browser.
2. Enter the abbreviation for the language in the Language Code field and click OK.
OR
You can also enter it into the Language text box to the left of the dots.
A dialog box displays the languages and associated language codes when you use one of the following
procedures:
•Open Internet Explorer and choose Tools > Internet Options > Languages > Add.
•Open Mozilla Firefox and choose Tools > Options > Advanced > General, click Choose next to
Languages, and click Select a language to add.
Step 3 If you are importing, choose the new help content file from the File Name drop-down list. If you are
exporting, this field is unavailable.
Step 4 Configure the parameters for the source file (if importing) or destination file (if exporting):
•Local computer—Indicate if the source or destination file is on a local computer:
–
Path—Identify the path of the source or destination file.
–
Browse Local Files—Click to browse the local computer for the source or destination file.
•Flash file system—Indicate if the source or destination file is located in flash memory on the ASA:
–
Path—Identify the path of the source or destination file in flash memory.
–
Browse Flash—Click to browse the flash memory for the source or destination file.
18-45
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 18 Customizing Clientless SSL VPN
Creating XML-Based Portal Customization Objects and URL Lists
•Remote server—Indicate if the source or destination file is on a remote server:
–
Path—Choose the file transfer (copy) method, either ftp, tftp, or http (for importing only), and
specify the path.
Customizing a Help File Provided by Cisco
To customize a help file provided by Cisco, you first require a copy of the file from the flash memory
card.
DETAILED STEPS
Step 1 Use your browser to establish a clientless session with the ASA.
Step 2 Display the help file by appending the string in “URL of Help File in Flash Memory of the Security
Appliance” in Table 18-4, to the address of the ASA, substituting language as described below, then
press Enter.
language is the abbreviation for the language rendered by the browser. It is not used for file translation;
it indicates the language used in the file. For help files provided by Cisco in English, enter the
abbreviation en.
The following example address displays the English version of the Terminal Servers help:
https://address_of_security_appliance/+CSCOE+/help/en/rdp-hlp.inc
Step 3 Choose File > Save (Page) As.
Note Do not change the contents of the File name box.
Step 4 Change the Save as type option to “Web Page, HTML only” and click Save.
Step 5 Use your preferred HTML editor to customize the file.
Note You can use most HTML tags, but do not use tags that define the document and its structure (for
example, do not use <html>, <title>, <body>, <head>, <h1>, <h2>, etc. You can use character
tags, such as the <b> tag, and the <p>, <ol>, <ul>, and <li> tags to structure content.
Table 18-4 Help Files Provided by Cisco for Clientless Applications
Application
Type Panel
URL of Help File in Flash Memory of the Security
Appliance
Standard Application Access /+CSCOE+/help/language/app-access-hlp.inc
Standard Browse Networks /+CSCOE+/help/language/file-access-hlp.inc
Standard AnyConnect Client /+CSCOE+/help/language/net-access-hlp.inc
Standard Web Access /+CSCOE+/help/language/web-access-hlp.inc
Plug-in Terminal Servers /+CSCOE+/help/language/rdp-hlp.inc
Plug-in Telnet/SSH Servers /+CSCOE+/help/language/ssh,telnet-hlp.inc
Plug-in VNC Connections /+CSCOE+/help/language/vnc-hlp.inc

18-46
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 18 Customizing Clientless SSL VPN
Customizing Bookmark Help
Step 6 Save the file as HTML only, using the original filename and extension.
Step 7 Ensure the filename matches the one in Table 18-4, and that it does not have an extra filename extension.
Return to ASDM and choose Configuration > Remote Access VPN > Clientless SSL VPN Access >
Portal > Help Customization > Import to import the modified help file into flash memory.
Creating Help Files for Languages Not Provided by Cisco
Use standard HTML to create help files in other languages. We recommend creating a separate folder
for each language to support.
Note You can use most HTML tags, but do not use tags that define the document and its structure (for
example, do not use <html>, <title>, <body>, <head>, <h1>, <h2>, etc. You can use character tags, such
as the <b> tag, and the <p>, <ol>, <ul>, and <li> tags to structure content.
Save the file as HTML only. Use the filename in the Filename column of Table 18-5.
Return to ASDM and choose Configuration > Remote Access VPN > Clientless SSL VPN Access >
Portal > Help Customization > Import to import the new help file into flash memory.
Customizing Bookmark Help
The ASA displays help content on the application panels for each selected bookmark. You can customize
those help files or create help files in other languages. You then import them to flash memory for display
during subsequent sessions. You can also retrieve previously imported help content files, modify them,
and reimport them to flash memory.
Each application panel displays its own help file content using a predetermined filename. The
prospective location of each is in the /+CSCOE+/help/language/ URL within flash memory of the ASA.
Table 18-5 shows the details about each of the help files you can maintain for VPN sessions.
Table 18-5 VPN Application Help Files
Application
Type Panel
URL of Help File in Flash Memory of the Security
Appliance
Help File
Provided By
Cisco in English?
Standard Application Access /+CSCOE+/help/language/app-access-hlp.inc Yes
Standard Browse Networks /+CSCOE+/help/language/file-access-hlp.inc Yes
Standard AnyConnect Client /+CSCOE+/help/language/net-access-hlp.inc Yes
Standard Web Access /+CSCOE+/help/language/web-access-hlp.inc Yes
Plug-in MetaFrame Access /+CSCOE+/help/language/ica-hlp.inc No
Plug-in Terminal Servers /+CSCOE+/help/language/rdp-hlp.inc Yes
Plug-in Telnet/SSH Servers /+CSCOE+/help/language/ssh,telnet-hlp.inc Yes
Plug-in VNC Connections /+CSCOE+/help/language/vnc-hlp.inc Yes

18-47
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 18 Customizing Clientless SSL VPN
Customizing Bookmark Help
language is the abbreviation of the language rendered by the browser. This field is not used for file
translation; it indicates the language used in the file. To specify a particular language code, copy the
language abbreviation from the list of languages rendered by your browser. For example, a dialog
window displays the languages and associated language codes when you use one of the following
procedures:
•Open Internet Explorer and choose Tools > Internet Options > Languages > Add.
•Open Mozilla Firefox and choose Tools > Options > Advanced > General, click Choose next to
Languages, and click Select a language to add.
The following sections describe how to customize the help contents:
•Customizing a Help File Provided By Cisco, page 18-47
•Creating Help Files for Languages Not Provided by Cisco, page 18-48
Customizing a Help File Provided By Cisco
To customize a help file provided by Cisco, you need to get a copy of the file from the flash memory
card first. Get the copy and customize it as follows:
DETAILED STEPS
Step 1 Use your browser to establish a Clientless SSL VPN session with the ASA.
Step 2 Display the help file by appending the string in “URL of Help File in Flash Memory of the Security
Appliance” in Table 18-5, to the address of the ASA, then press Enter.
Note Enter en in place of language to get the help file in English.
The following example address displays the English version of the Terminal Servers help:
https://address_of_security_appliance/+CSCOE+/help/en/rdp-hlp.inc
Step 3 Choose File > Save (Page) As.
Note Do not change the contents of the File name box.
Step 4 Change the Save as type option to Web Page, HTML only and click Save.
Step 5 Use your preferred HTML editor to modify the file.
Note You can use most HTML tags, but do not use tags that define the document and its structure
(e.g., do not use <html>, <title>, <body>, <head>, <h1>, <h2>, etc. You can use character tags,
such as the <b> tag, and the <p>, <ol>, <ul>, and <li> tags to structure content.
Step 6 Save the file as HTML only, using the original filename and extension.
Step 7 Ensure the filename matches the one in Table 18-5, and that it does not have an extra filename extension.
Return to ASDM and choose Configuration > Remote Access VPN > Clientless SSL VPN Access >
Portal > Help Customization > Import to import the new help file into flash memory.

18-48
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 18 Customizing Clientless SSL VPN
Translating the Language of User Messages
Creating Help Files for Languages Not Provided by Cisco
Use HTML to create help files in other languages.
We recommend creating a separate folder for each language to support.
Save the file as HTML only. Use the filename following the last slash in “URL of Help File in Flash
Memory of the Security Appliance” in Table 18-5.
See the next section to import the files for display during VPN sessions.
Restrictions
You can use most HTML tags, but do not use tags that define the document and its structure
(e.g., do not use <html>, <title>, <body>, <head>, <h1>, <h2>, etc. You can use character tags, such as
the <b> tag, and the <p>, <ol>, <ul>, and <li> tags to structure content.
Translating the Language of User Messages
The ASA provides language translation for the entire Clientless SSL VPN session. This includes login,
logout banners, and portal pages displayed after authentication such as plugins and AnyConnect.
This section describes how to configure the ASA to translate these user messages and includes the
following sections:
•Understanding Language Translation, page 18-48
•Editing a Translation Table, page 18-49
•Editing a Translation Table, page 18-49
Understanding Language Translation
Functional areas and their messages that are visible to remote users are organized into translation
domains. Table 18-6 shows the translation domains and the functional areas translated.
Table 18-6 Language Translation Domain Options
Translation Domain Functional Areas Translated
AnyConnect Messages displayed on the user interface of the Cisco AnyConnect VPN client.
banners Message displayed when VPN access is denied for a clientless connection.
CSD Messages for the Cisco Secure Desktop (CSD).
customization Messages on the logon and logout pages, portal page, and all the messages
customizable by the user.
plugin-ica Messages for the Citrix plug-in.
plugin-rdp Messages for the Remote Desktop Protocol plug-in.
plugin-rdp2 Messages for the Java Remote Desktop Protocol plug-in.
plugin-telnet,ssh Messages for the Telnet and SSH plug-in.

18-49
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 18 Customizing Clientless SSL VPN
Translating the Language of User Messages
The ASA includes a translation table template for each domain that is part of standard functionality. The
templates for plug-ins are included with the plug-ins and define their own translation domains.
You can export the template for a translation domain, which creates an XML file of the template at the
URL you provide. The message fields in this file are empty. You can edit the messages and import the
template to create a new translation table object that resides in flash memory.
You can also export an existing translation table. The XML file created displays the messages you edited
previously. Reimporting this XML file with the same language name creates a new version of the
translation table object, overwriting previous messages.
Some templates are static, but some change based on the configuration of the ASA. Because you can
customize the logon and logout pages, portal page, and URL bookmarks for clientless users, the ASA
generates the customization and url-list translation domain templates dynamically, and the template
automatically reflects your changes to these functional areas.
After creating translation tables, they are available to customization objects that you create and apply to
group policies or user attributes. With the exception of the AnyConnect translation domain, a translation
table has no affect, and messages are not translated on user screens until you create a customization
object, identify a translation table to use in that object, and specify that customization for the group
policy or user. Changes to the translation table for the AnyConnect domain are immediately visible to
AnyConnect client users.
Editing a Translation Table
Step 1 Navigate to Configuration > Remote Access VPN > Language Localization. The Language
Localization pane displays. Click Add. The Add Language Localization window displays.
Step 2 Choose a Language Localization Template from the drop-down box. The entries in the box correspond
to functional areas that are translated.
Step 3 Specify a language for the template. The template becomes a translation table in cache memory with the
name you specify. Use an abbreviation that is compatible with the language options for your browser.
For example, if you are creating a table for the Chinese language, and you are using IE, use the
abbreviation zh, that is recognized by IE.
Step 4 Edit the translation table. For each message represented by the msgid field to translate, enter the
translated text between the quotes of the associated msgstr field. The example below shows the message
Connected, with the Spanish text in the msgstr field:
msgid "Connected"
msgstr "Conectado"
Step 5 Click OK. The new table appears in the list of translation tables.
plugin-vnc Messages for the VNC plug-in.
PortForwarder Messages displayed to Port Forwarding users.
url-list Text that user specifies for URL bookmarks on the portal page.
webvpn All the layer 7, AAA and portal messages that are not customizable.
Translation Domain Functional Areas Translated

18-50
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 18 Customizing Clientless SSL VPN
Translating the Language of User Messages
Adding a Translation Table
You can add a new translation table, based on a template, or you can modify an already-imported
translation table in this pane.
Step 1 Select a template to modify and use as a basis for a new translation table. The templates are organized
into translation domains and affect certain areas of functionality. Table 18-6 shows the translation
domains and the functional areas affected.
Step 2 Select the translation domain from the drop-down. (This field is greyed out on the GUI Text and
Messages pane).
Step 3 Select a language from the drop-down.
Step 4 Use the editor to change the message translations. The message ID field (msgid) contains the default
translation. The message string field (msgstr) that follows msgid provides the translation. To create a
translation, enter the translated text between the quotes of the msgstr string. For example, to translate
the message “Connected” with a Spanish translation, insert the Spanish text between the msgstr quotes:
msgid "Connected"
msgstr "Conectado"
After making changes, click Apply to import the translation table.
Importing/Exporting Language Localization
This is help for the import button on Configuration > Remote Access VPN > Language Localization.
In the Import Translation Table and Export Translation Table dialog boxes, you can import or export a
translation table to the ASA to provide translation of user messages.
Translation templates are XML files that contain message fields that can be edited with translated
messages. You can export a template, edit the message fields, and import the template as a new
translation table, or you can export an existing translation table, edit the message fields, and re-import
the table to overwrite the previous version.
Detailed Steps
Step 1 Enter a name for the language.
•When exporting, it is automatically filled-in with the name from the entry you selected in the table.
•When importing, you enter the language name in the manner that you want it to be identified. The
imported translation table then appears in the list with the abbreviation you designated. To ensure
that your browser recognizes the language, use language abbreviations that are compatible with the
language options of the browser. For example, if you are using IE, use zh as the abbreviation for the
Chinese language.
Step 2 The name of the XML file containing the message fields includes the following:
•AnyConnect—Messages displayed on the user interface of the Cisco AnyConnect VPN Client.
•banners—Message displayed to Clientless users that VPN access is denied.
•CSD—Messages for the Cisco Secure Desktop (CSD).

18-51
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 18 Customizing Clientless SSL VPN
Translating the Language of User Messages
•customization—Messages on the logon and logout pages, portal page, and all the messages
customizable by the user.
•PortForwarder—Messages displayed to Port Forwarding users.
•url-list—Text that user specifies for URL bookmarks on the portal page.
•webvpn—All the layer 7, AAA and portal messages that are not customizable.
Step 3 Choose the method by which you want to import or export the file:
•Remote server—Select this option to import a customization file that resides on a remote server
accessible from the ASA.
•Path—Identify the method to access the file (ftp, http, or https), and provide the file location.
•Flash file system—Choose this method to export a file that resides on the ASA.
•Path—File location.
•Browse Flash—Browse to the path for the file.
•Local computer—Choose this method to import a file that resides on the local PC.
•Path—Provide the path to the file.
•Browse Local Files—Browse to the path for the file.
Step 4 Click Import/Export Now to import or export the file.

18-52
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 18 Customizing Clientless SSL VPN
Translating the Language of User Messages

CHAPTER
19-1
Cisco ASA Series VPN ASDM Configuration Guide
19
Clientless SSL VPN Troubleshooting
September 13, 2013
Closing Application Access to Prevent hosts File Errors
To prevent hosts file errors that can interfere with Application Access, close the Application Access
window properly when you finish using Application Access. To do so, click the close icon.
Recovering from Hosts File Errors When Using Application
Access
The following errors can occur if you do not close the Application Access window properly:
•The next time you try to start Application Access, it may be switched off; you receive a Backup
HOSTS File Found error message.
•The applications themselves may be switched off or malfunction, even when you are running them
locally.
These errors can result from terminating the Application Access window in any improper way. For
example:
•Your browser crashes while you are using Application Access.
•A power outage or system shutdown occurs while you are using Application Access.
•You minimize the Application Access window while you are working, then shut down your
computer with the window active (but minimized).
This section includes the following topics:
•Understanding the hosts File
•Stopping Application Access Improperly
•Reconfiguring a Host’s File Automatically Using Clientless SSL VPN
•Reconfiguring hosts File Manually
19-2
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 19 Clientless SSL VPN Troubleshooting
Recovering from Hosts File Errors When Using Application Access
Understanding the hosts File
The hosts file on your local system maps IP addresses to hostnames. When you start Application Access,
Clientless SSL VPN modifies the hosts file, adding Clientless SSL VPN-specific entries. Stopping
Application Access by properly closing the Application Access window returns the file to its original
state.
Note Microsoft anti-spyware software blocks changes that the port forwarding Java applet makes to the hosts
file. See www.microsoft.com for information on how to allow hosts file changes when using
anti-spyware software.
Stopping Application Access Improperly
When Application Access terminates abnormally, the hosts file remains in a Clientless SSL
VPN-customized state. Clientless SSL VPN checks the state the next time you start Application Access
by searching for a hosts.webvpn file. If it finds one, a Backup HOSTS File Found error message
(Figure 19-1) appears, and Application Access is temporarily switched off.
Once you shut down Application Access improperly, you leave your remote access client/server
applications in limbo. If you try to start these applications without using Clientless SSL VPN, they may
malfunction. You may find that hosts that you normally connect to are unavailable. This situation could
commonly occur if you run applications remotely from home, fail to quit the Application Access window
before shutting down the computer, then try to run the applications later from the office.
Reconfiguring a Host’s File Automatically Using Clientless SSL VPN
If you are able to connect to your remote access server, follow these steps to reconfigure the host’s file
and re-enable both Application Access and the applications.
DETAILED STEPS
Step 1 Start Clientless SSL VPN and log in. The home page opens.
Step 2 Click the Applications Access link. A Backup HOSTS File Found message appears. (See Figure 19-1.)
Before invoking Application Access... hosts file is in original state.
When Application Access starts.... •Clientless SSL VPN copies the hosts file to
hosts.webvpn, thus creating a backup.
•Clientless SSL VPN then edits the hosts file,
inserting Clientless SSL VPN-specific
information.
When Application Access stops... •Clientless SSL VPN copies the backup file to
the hosts file, thus restoring the hosts file to
its original state.
•Clientless SSL VPN deletes hosts.webvpn.
After finishing Application Access... hosts file is in original state.
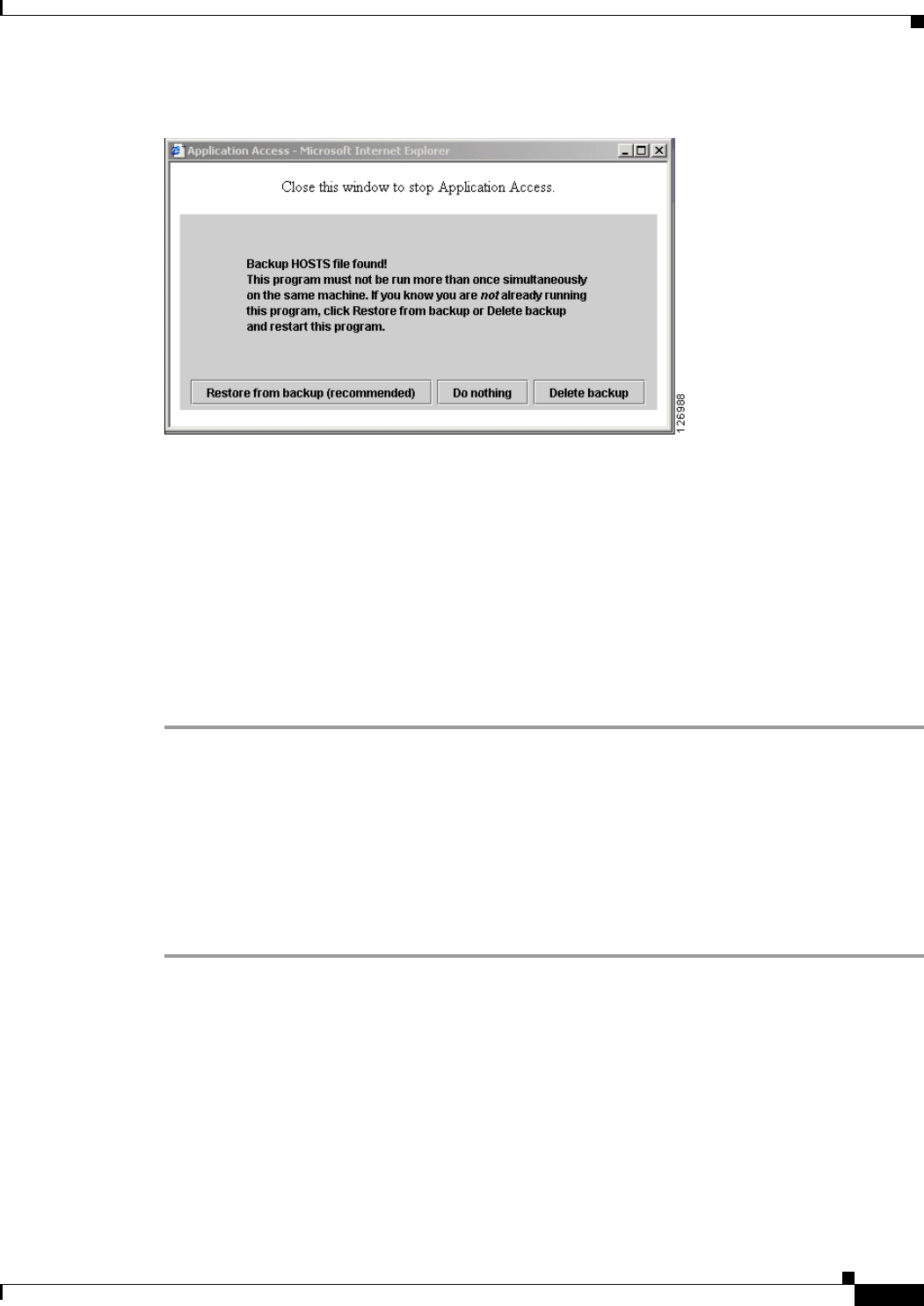
19-3
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 19 Clientless SSL VPN Troubleshooting
Recovering from Hosts File Errors When Using Application Access
Figure 19-1 Backup HOSTS File Found Message
Step 3 Choose one of the following options:
•Restore from backup—Clientless SSL VPN forces a proper shutdown. It copies the hosts.webvpn
backup file to the hosts file, restoring it to its original state, then deletes hosts.webvpn. You then
have to restart Application Access.
•Do nothing—Application Access does not start. The remote access home page reappears.
•Delete backup—Clientless SSL VPN deletes the hosts.webvpn file, leaving the hosts file in its
Clientless SSL VPN-customized state. The original hosts file settings are lost. Application Access
then starts, using the Clientless SSL VPN-customized hosts file as the new original. Choose this
option only if you are unconcerned about losing hosts file settings. If you or a program you use may
have edited the hosts file after Application Access has shut down improperly, choose one of the other
options, or edit the hosts file manually. (See “Reconfiguring hosts File Manually.”)
Reconfiguring hosts File Manually
If you are not able to connect to your remote access server from your current location, or if you have
customized the hosts file and do not want to lose your edits, follow these steps to reconfigure the hosts
file and reenable both Application Access and the applications.
DETAILED STEPS
Step 1 Locate and edit your hosts file. The most common location is c:\windows\sysem32\drivers\etc\hosts.
Step 2 Check to see if any lines contain the string: # added by WebVpnPortForward
If any lines contain this string, your hosts file is Clientless SSL VPN-customized. If your hosts file is
Clientless SSL VPN-customized, it looks similar to the following example:
server1 # added by WebVpnPortForward
server1.example.com invalid.cisco.com # added by WebVpnPortForward
server2 # added by WebVpnPortForward
server2.example.com invalid.cisco.com # added by WebVpnPortForward
server3 # added by WebVpnPortForward
server3.example.com invalid.cisco.com # added by WebVpnPortForward
# Copyright (c) 1993-1999 Microsoft Corp.
#

19-4
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 19 Clientless SSL VPN Troubleshooting
Sending an Administrator’s Alert to Clientless SSL VPN Users
# This is a sample HOSTS file used by Microsoft TCP/IP for Windows.
#
# This file contains the mappings of IP addresses to hostnames. Each
# entry should be kept on an individual line. The IP address should
# be placed in the first column followed by the corresponding hostname.
# The IP address and the hostname should be separated by at least one
# space.
#
# Additionally, comments (such as these) may be inserted on individual
# lines or following the machine name denoted by a '#' symbol.
#
# For example:
#
# 102.54.94.97 cisco.example.com # source server
# 38.25.63.10 x.example.com # x client host
127.0.0.1 localhost
Step 3 Delete the lines that contain the string: # added by WebVpnPortForward
Step 4 Save and close the file.
Step 5 Start Clientless SSL VPN and log in.
The home page appears.
Step 6 Click the Application Access link.
The Application Access window appears. Application Access is now enabled.
Sending an Administrator’s Alert to Clientless SSL VPN Users
Step 1 In the main ASDM application window, choose Tools > Administrator’s Alert Message to Clientless
SSL VPN Users.
The Administrator’s Alert Message to Clientless SSL VPN Users dialog box appears.
Step 2 Enter the new or edited alert content to send, and then click Post Alert.
Step 3 To remove current alert content and enter new alert content, click Cancel Alert.

CHAPTER
20-1
Cisco ASA Series VPN ASDM Configuration Guide
20
Clientless SSL VPN Licensing
September 13, 2013
Licensing
Note This feature is not available on No Payload Encryption models.
Model License Requirement1,2
ASA 5505 AnyConnect Premium license:
•Base License or Security Plus license: 2 sessions.
•Optional permanent or time-based licenses: 10 or 25 sessions.
•Shared licenses are not supported.3
ASA 5510 AnyConnect Premium license:
•Base and Security Plus License: 2 sessions.
•Optional permanent or time-based licenses: 10, 25, 50, 100, or 250 sessions.
•Optional Shared licenses3: Participant or Server. For the Server license, 500-50,000 in increments
of 500 and 50,000-545,000 in increments of 1000.
ASA 5520 AnyConnect Premium license:
•Base License: 2 sessions.
•Optional permanent or time-based licenses: 10, 25, 50, 100, 250, 500, or 750 sessions.
•Optional Shared licenses3: Participant or Server. For the Server license, 500-50,000 in increments
of 500 and 50,000-545,000 in increments of 1000.
ASA 5540 AnyConnect Premium license:
•Base License: 2 sessions.
•Optional permanent or time-based licenses: 10, 25, 50, 100, 250, 500, 750, 1000, or 2500
sessions.
•Optional Shared licenses3: Participant or Server. For the Server license, 500-50,000 in increments
of 500 and 50,000-545,000 in increments of 1000.
20-2
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 20 Clientless SSL VPN Licensing
Licensing
ASA 5550 AnyConnect Premium license:
•Base License: 2 sessions.
•Optional permanent or time-based licenses: 10, 25, 50, 100, 250, 500, 750, 1000, 2500, or 5000
sessions.
•Optional Shared licenses3: Participant or Server. For the Server license, 500-50,000 in increments
of 500 and 50,000-545,000 in increments of 1000.
ASA 5580 AnyConnect Premium license:
•Base License: 2 sessions.
•Optional permanent or time-based licenses: 10, 25, 50, 100, 250, 500, 750, 1000, 2500, 5000, or
10000 sessions.
•Optional Shared licenses3: Participant or Server. For the Server license, 500-50,000 in increments
of 500 and 50,000-545,000 in increments of 1000.
ASA 5512-X AnyConnect Premium license:
•Base License: 2 sessions.
•Optional permanent or time-based licenses: 10, 25, 50, 100, or 250 sessions.
•Optional Shared licenses3: Participant or Server. For the Server license, 500-50,000 in increments
of 500 and 50,000-545,000 in increments of 1000.
ASA 5515-X AnyConnect Premium license:
•Base License: 2 sessions.
•Optional permanent or time-based licenses: 10, 25, 50, 100, or 250 sessions.
•Optional Shared licenses3: Participant or Server. For the Server license, 500-50,000 in increments
of 500 and 50,000-545,000 in increments of 1000.
ASA 5525-X AnyConnect Premium license:
•Base License: 2 sessions.
•Optional permanent or time-based licenses: 10, 25, 50, 100, 250, 500, or 750 sessions.
•Optional Shared licenses3: Participant or Server. For the Server license, 500-50,000 in increments
of 500 and 50,000-545,000 in increments of 1000.
ASA 5545-X AnyConnect Premium license:
•Base License: 2 sessions.
•Optional permanent or time-based licenses: 10, 25, 50, 100, 250, 500, 750, 1000, or 2500
sessions.
•Optional Shared licenses3: Participant or Server. For the Server license, 500-50,000 in increments
of 500 and 50,000-545,000 in increments of 1000.
ASA 5555-X AnyConnect Premium license:
•Base License: 2 sessions.
•Optional permanent or time-based licenses: 10, 25, 50, 100, 250, 500, 750, 1000, 2500, or 5000
sessions.
•Optional Shared licenses3: Participant or Server. For the Server license, 500-50,000 in increments
of 500 and 50,000-545,000 in increments of 1000.
Model License Requirement1,2
20-3
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 20 Clientless SSL VPN Licensing
Licensing
ASA 5585-X with
SSP-10
AnyConnect Premium license:
•Base License: 2 sessions.
•Optional permanent or time-based licenses: 10, 25, 50, 100, 250, 500, 750, 1000, 2500, or 5000
sessions.
•Optional Shared licenses3: Participant or Server. For the Server license, 500-50,000 in increments
of 500 and 50,000-545,000 in increments of 1000.
ASA 5585-X with
SSP-20, -40, and -60
AnyConnect Premium license:
•Base License: 2 sessions.
•Optional permanent or time-based licenses: 10, 25, 50, 100, 250, 500, 750, 1000, 2500, 5000, or
10000 sessions.
•Optional Shared licenses3: Participant or Server. For the Server license, 500-50,000 in increments
of 500 and 50,000-545,000 in increments of 1000.
ASA SM AnyConnect Premium license:
•Base License: 2 sessions.
•Optional permanent or time-based licenses: 10, 25, 50, 100, 250, 500, 750, 1000, 2500, 5000, or
10000 sessions.
•Optional Shared licenses3: Participant or Server. For the Server license, 500-50,000 in increments
of 500 and 50,000-545,000 in increments of 1000.
1. If you start a clientless SSL VPN session and then start an AnyConnect client session from the portal, 1 session is used in total. However, if you start the
AnyConnect client first (from a standalone client, for example) and then log into the clientless SSL VPN portal, then 2 sessions are used.
2. The maximum combined VPN sessions of all types cannot exceed the maximum sessions shown in this table.
3. A shared license lets the security appliance act as a shared license server for multiple client security appliances. The shared license pool is large, but the
maximum number of sessions used by each individual security appliance cannot exceed the maximum number listed for permanent licenses.
Model License Requirement1,2

20-4
Cisco ASA Series VPN ASDM Configuration Guide
Chapter 20 Clientless SSL VPN Licensing
Licensing

IN-1
Cisco ASA Series VPN ASDM Configuration Guide
INDEX
A
AAA server group, add (group-policy) 4-9
Access Control Server 3-29
Accounting tab, tunnel group 4-96
ACE
add/edit/paste 4-38
Extended ACL tab 4-37
ACL
enabling IPSEC authenticated inbound sessions to
bypass ACLs 4-108, 4-115
extended 4-37
for Clientless SSL VPN 4-46
standard 4-37
ACL Manager
Add/Edit/Paste ACE 4-38
dialog box 4-36
Active Directory procedures 10-2 to ??
address assignment, client 4-97
Address Pool panel, VPN wizard 2-4
address pools, tunnel group 4-97
Address Translation Exemption panel, VPN wizard 2-6
Advanced tab, tunnel group 4-97
anti-replay window size 3-12
application access
and e-mail proxy 15-7
and Web Access 15-7
configuring client applications 15-6
enabling cookies on browser 15-6
privileges 15-6
quitting properly 15-6
setting up on client 15-6
using e-mail 15-7
with IMAP client 15-7
Application Access Panel, WebVPN 16-2, 18-7
application access using WebVPN
and hosts file errors 19-1
quitting properly 19-2
Application Profile Customization Framework 13-13
ASA 5505
client
Xauth 4-111
Attributes Pushed to Client panel, VPN wizard 2-4
authentication
WebVPN users with digital certificates 16-10
Authentication tab, tunnel group 4-95
Authorization tab, tunnel group 4-95
B
Basic tab
IPSec LAN-to-LAN, General tab 4-100
bookmarks
configuring to access Kerberos 13-13
Browse ICMP 4-41
Browse Other 4-42
Browse Source or Destination Address 4-40
Browse Source or Destination Port 4-40
Browse Time Range 4-35
C
certificate
authentication, e-mail proxy 13-23
Client Address Assignment 4-97
Client Authentication panel, VPN wizard 2-3

Index
IN-2
Cisco ASA Series VPN ASDM Configuration Guide
Client Firewall tab 4-25
Clientless SSL VPN
client application requirements 15-2
client requirements 15-2
for file management 15-5
for network browsing 15-5
for web browsing 15-4
start-up 15-3
enable cookies for 15-6
printing and 15-3
remote requirements
for port forwarding 15-6
for using applications 15-6
remote system configuration and end-user
requirements 15-3
security tips 15-2
supported applications 15-2
supported browsers 15-3
supported types of Internet connections 15-3
URL 15-3
username and password required 15-3
usernames and passwords 15-1
Client Update, edit , Windows and VPN 3002 clients 4-6
Client Update window, Windows and VPN 3002
clients 4-4
configuring ASA
to join Active Directory domain 13-5
configuring bookmarks
to access Kerberos 13-13
configuring DNS 13-4
configuring mobile user security services 4-69
configuring MUS 4-69
customizing the end-user experience
by the security appliance 4-2
D
dead time 13-5
default tunnel gateway 4-6
destination address, browse 4-40
destination port, browse 4-40
Device Pass-Through 4-111
DHCP
addressing, configuring 5-5
digital certificates
authenticating WebVPN users 16-10
disabling content rewrite 13-21
DNS
configuring 13-4
server, configuring 4-12
E
Easy VPN
client
Xauth 4-111
Easy VPN, advanced properties 4-111
Easy VPN client 4-109
Easy VPN Remote 4-109
e-mail
configuring for WebVPN 13-23
proxies, WebVPN 13-23
proxy, certificate authentication 13-23
WebVPN, configuring 13-23
e-mail proxy
and Clientless SSL VPN 15-7
Enable IPSec authenticated inbound sessions 4-108, 4-115
end-user interface, WebVPN, defining 16-1, 18-6
extended ACL 4-37
external group policy, configuring 4-8
F
firewall, client, configuring settings 4-25
firewall server, Zone Labs 4-108
fragmentation policy, IPsec 3-2

Index
IN-3
Cisco ASA Series VPN ASDM Configuration Guide
G
gateway, default tunnel gateway 4-6
global e-mail proxy attributes 13-23
group policy
external, configuring 4-8
split tunneling attributes 4-13
WINS and DNS servers 4-12
Group Policy window
add or edit, General tab 4-9, 4-29, 4-33
introduction 4-7
IPSec tab, add or edit 4-23
H
Hardware Client tab 4-26
hosts file
errors 19-1
reconfiguring 19-2
WebVPN 19-2
I
ICMP
add group 4-41
browse 4-41
ICMP Group 4-41
IKE Policy panel, VPN wizard 2-5
IP addresses
configuring an assignment method for remote access
clients 5-1
configuring for VPNs 5-1
IPsec
Cisco VPN Client 3-9
fragmentation policy 3-2
IPSec rules
anti-replay window size 3-12
IPSec tab
internal group policy 4-23
IPSec LAN-to-LAN 4-102
tunnel group 4-98
J
join Active Directory domain 13-5
K
KCD 13-1, 13-2
Kerberos parameter 13-6
L
LDAP
example configuration procedures 10-2 to ??
M
maximum sessions, IPSec 4-107
Microsoft KCD 13-1, 13-2
MUS
configuring 4-69
N
NetBIOS server
tab 4-77
Network Admission Control
uses, requirements, and limitations 3-29
O
Outlook Web Access (OWA) and Clientless SSL
VPN 15-7
Index
IN-4
Cisco ASA Series VPN ASDM Configuration Guide
P
password
Clientless SSL VPN 15-1
passwords
WebVPN 16-12
Port Forwarding
configuring client applications 15-6
posture validation
uses, requirements, and limitations 3-29
Posture Validation Exception, add/edit 3-30
PPP tab, tunnel-group 4-100
priority queueing
IPSec anti-replay window size 3-12
Protocol Group, add 4-42
proxy
See e-mail proxy
proxy bypass 14-11
Q
QoS
priority queueing
IPSec anti-replay window size 3-12
R
reactivation mode 13-5
realm 13-6
recurring time range, add or edit 4-36
rewrite, disabling 13-21
S
Server and URL List
add/edit 4-47
server group name 13-5
Server or URL
dialog box 4-48
smart tunnels 14-1
source address, browse 4-40
source port, browse 4-40
split tunneling
group policy 4-13
SSO with WebVPN
configuring HTTP form protocol 16-6
Standard Access List Rule, add/edit 4-47
Standard ACL tab 4-37
Summary panel, VPN wizard 2-6
Sun Microsystems Java™ Runtime Environment (JRE)
and Clientless SSL VPN 15-6
Sun Microsystems Java™ Runtime Environment (JRE)
and WebVPN 12-13
T
TCP Service Group, add 4-41
time range
add or edit 4-35
browse 4-35
recurring 4-36
toolbar, floating, WebVPN 16-3, 18-7
Tunneled Management 4-111
tunnel gateway, default 4-6
U
User Accounts panel, VPN wizard 2-4
username
Clientless SSL VPN 15-1
WebVPN 16-12
Xauth for Easy VPN client 4-111
V
virtual private network
overview 2-1

Index
IN-5
Cisco ASA Series VPN ASDM Configuration Guide
VPN
overview 2-1
system options 4-107
VPN Client, IPsec attributes 3-9
VPN Tunnel Type panel, VPN wizard 2-2
VPN wizard 2-1
Address Pool panel 2-4
Address Translation Exemption panel 2-6
Attributes Pushed to Client panel 2-4
Client Authentication panel 2-3
IKE Policy panel 2-5
Summary panel 2-6
User Accounts panel 2-4
VPN Tunnel Type panel 2-2
W
web browsing with Clientless SSL VPN 15-4
web e-Mail (Outlook Web Access), Outlook Web
Access 13-23
WebVPN
authenticating with digital certificates 16-10
client application requirements 16-12
client requirements 16-12
configuring
e-mail 13-23
defining the end-user interface 16-1, 18-6
definition 11-1
e-mail 13-23
e-mail proxies 13-23
end user set-up 18-6
floating toolbar 16-3, 18-7
hosts file 19-2
hosts files, reconfiguring 19-2
security tips 16-12
supported applications 16-12
troubleshooting 19-1
usernames and passwords 16-12
use suggestions 15-2, 16-12, 18-6
WebVPN, Application Access Panel 16-2, 18-7
Windows Service Account
adding in Active Directory 13-4
WINS server, configuring 4-12
X
Xauth, Easy VPN client 4-111
Z
Zone Labs Integrity Server 4-108

Index
IN-6
Cisco ASA Series VPN ASDM Configuration Guide