Insurgencies And Countering FM 3 Fm3 24
User Manual: FM-3
Open the PDF directly: View PDF ![]() .
.
Page Count: 202 [warning: Documents this large are best viewed by clicking the View PDF Link!]
- Cover
- Contents
- Preface
- Introduction
- PART ONE - Strategic and Operational Context
- PART TWO - Insurgencies
- PART THREE - Counterinsurgencies
- Chapter 6 - Mission Command and Command and Control
- Chapter 7 - Planning and Operational Considerations
- Chapter 8 - Intelligence
- Chapter 9 - Direct Methods for Countering Insurgencies
- Chapter 10 - Indirect Methods for Countering Insurgencies
- Chapter 11 - Working With Host-Nation Forces
- Chapter 12 - Assessments
- Chapter 13 - Legal Considerations
- Source Notes
- Glossary
- References
- Index

FM 3-24
MCWP 3-33.5
INSURGENCIES AND
COUNTERING
INSURGENCIES
MAY 2014
DISTRIBUTION RESTRICTION:
Approved for public release; distribution is unlimited.
HEADQUARTERS, DEPARTMENT OF THE ARMY

FM 3-24/MCWP 3-33.5, C1
Change No. 1 Headquarters
Department of the Army
Washington, DC, 2 June 2014
Insurgencies and Countering Insurgencies
1. Change 1 to FM 3-24/MCWP 3-33.5, 13 May 2014, amends text as necessary.
2. A plus sign (+) marks new material.
3. FM 3-24/MCWP 3-33.5, 13 May 2014, is changed as follows:
Remove Old Pages Insert New Pages
pages 1-13 through 1-14 pages 1-13 through 1-14
pages 2-3 through 2-4 pages 2-3 through 2-4
pages 4-1 through 4-2 pages 4-1 through 4-2
pages 4-5 through 4-6 pages 4-5 through 4-6
pages 4-11 through 4-12 pages 4-11 through 4-12
pages 7-5 through 7-10 pages 7-5 through 7-10
4. File this transmittal sheet in front of the publication for reference purposes.
DISTRUBUTION RESTRICTION: Approved for public release; distribution is unlimited.

FM 3-24/MCWP 3-33.5, C1
2 June 2014
By Order of the Secretary of the Army:
RAYMOND T. ODIERNO
General, United States Army
Chief of Staff
Official:
GERALD B. O’KEEFE
Administrative Assistant to the
Secretary of the Army
1414902
BY DIRECTION OF THE COMMANDANT OF THE MARINE CORPS:
DISTRIBUTION:
Active Army, Army National Guard, and U.S. Army Reserve: To be distributed in accordance with the
initial distribution number 121724, requirements for FM 3-24.
Marine Corps: PCN 143 000124 00
This publication is available at Army Knowledge Online
(https://armypubs.us.army.mil/doctrine/index.html).
To receive publishing updates, please subscribe at
http://www.apd.army.mil/AdminPubs/new_subscribe.asp

*FM 3-24/MCWP 3-33.5
Distribution Restriction: Approved for public release; distribution is unlimited.
*This publication supersedes FM 3-24/MCWP 3-33.5, dated 15 December 2006.
Marine Corps PCN: 143 000124 00
i
Field Manual
No.3-24
Headquarters
Department of the Army
Washington, DC
Marine Corps Warfighting Publication
No. 3-33.5
Headquarters
Marine Corps Combat Development Command
Department of the Navy
Headquarters
United States Marine Corps
Washington, DC
13 May 2014
Insurgencies and Countering Insurgencies
Contents
Page
PREFACE............................................................................................................... v
INTRODUCTION .................................................................................................. vii
PART ONE STRATEGIC AND OPERATIONAL CONTEXT
Chapter 1 UNDERSTANDING THE STRATEGIC CONTEXT............................................ 1-1
United States’ Strategy and Policy to Counter an Insurgency ........................... 1-4
Land Forces and the Range of Military Operations ............................................ 1-6
Legitimacy and Control ....................................................................................... 1-8
Understanding Unified Action ........................................................................... 1-10
Strategic Principles ........................................................................................... 1-19
Chapter 2 UNDERSTANDING AN OPERATIONAL ENVIRONMENT ............................... 2-1
Demographic and Urbanization Trends .............................................................. 2-1
The Operational Variables .................................................................................. 2-2
The Mission Variables and Civil Considerations .............................................. 2-10
Chapter 3 CULTURE........................................................................................................... 3-1
Understanding Culture ........................................................................................ 3-1
Assessing a Cultural Situation ............................................................................ 3-2
Organizing to Understand Culture ...................................................................... 3-4

Contents
ii FM 3-24/MCWP 3-33.5 13 May 2014
PART TWO INSURGENCIES
Chapter 4 INSURGENCY PREREQUISITES AND FUNDAMENTALS .............................. 4-1
Intrastate War ...................................................................................................... 4-1
Insurgency Prerequisites .................................................................................... 4-3
Insurgency Fundamentals ................................................................................... 4-5
Other Analytical Frameworks ............................................................................ 4-22
Chapter 5 INSURGENCY THREAT CHARACTERISTICS ................................................. 5-1
Disposition and Activities .................................................................................... 5-1
Support Activities ................................................................................................ 5-3
Associated Threats ............................................................................................. 5-5
PART THREE COUNTERINSURGENCIES
Chapter 6 MISSION COMMAND AND COMMAND AND CONTROL ................................ 6-1
Command in Counterinsurgency ........................................................................ 6-1
Headquarters Use In Counterinsurgency ........................................................... 6-4
Conventional Forces and Special Operations Forces Synchronization .............. 6-5
Chapter 7 PLANNING FOR COUNTERING INSURGENCIES ........................................... 7-1
Conceptual Planning ........................................................................................... 7-4
Transitions ......................................................................................................... 7-10
Operational Considerations .............................................................................. 7-12
Information Operations ..................................................................................... 7-18
Chapter 8 INTELLIGENCE .................................................................................................. 8-1
Intelligence Fundamentals .................................................................................. 8-2
All-Source Intelligence ........................................................................................ 8-3
Human Intelligence ............................................................................................. 8-4
Chapter 9 DIRECT APPROACHES TO COUNTER AN INSURGENCY ............................ 9-1
Shape-Clear-Hold-Build-Transition Framework .................................................. 9-1
Other Direct Enablers ....................................................................................... 9-11
Chapter 10 INDIRECT METHODS FOR COUNTERING INSURGENCIES........................ 10-1
Nation Assistance and Security Cooperation ................................................... 10-1
Generational Engagement ................................................................................ 10-2
Negotiation and Diplomacy ............................................................................... 10-4
Identify, Separate, Isolate, Influence, and Reintegrate ..................................... 10-6
Other Indirect Enablers ................................................................................... 10-10
Chapter 11 WORKING WITH HOST-NATION FORCES .................................................... 11-1
Assessing and Developing a Host-Nation Force .............................................. 11-2
Relationships ..................................................................................................... 11-6
Security Cooperation Planning ......................................................................... 11-8
Chapter 12 ASSESSMENTS ............................................................................................... 12-1
Assessment Frameworks .................................................................................. 12-1
Assessment Methods ........................................................................................ 12-2
Assessment Considerations ............................................................................. 12-2
Developing Measurement Criteria .................................................................... 12-3

Contents
13 May 2014 FM 3-24/MCWP 3-33.5 iii
Chapter 13 LEGAL CONSIDERATIONS ............................................................................ 13-1
Authority to Assist A Foreign Government ....................................................... 13-1
Rules of Engagement ....................................................................................... 13-2
Law of War ....................................................................................................... 13-2
Non-International Armed Conflict ..................................................................... 13-7
Detention and Interrogation .............................................................................. 13-8
Enforcing Discipline of U.S. Forces ................................................................ 13-10
Training and Equipping Foreign Forces ......................................................... 13-11
Commander’s Emergency Response Program .............................................. 13-12
Claims and Solatia .......................................................................................... 13-13
Establishing the Rule of Law .......................................................................... 13-13
SOURCE NOTES .......................................................................... Source Notes-1
GLOSSARY .......................................................................................... Glossary-1
REFERENCES .................................................................................. References-1
INDEX .......................................................................................................... Index-1
Figures
Figure 1-1. Country team command relationships ............................................................... 1-17
Figure 4-1. Conflict resolution model ................................................................................... 4-15
Figure 4-2. Organizational elements of an insurgency ......................................................... 4-16
Figure 4-3. Networked insurgencies ..................................................................................... 4-18
Figure 4-4. Examples of dyads ............................................................................................. 4-19
Figure 4-5. Examples of dyad networks ............................................................................... 4-21
Figure 4-6. Example of changes to tactics based on density shift ....................................... 4-22
Figure 7-1. Design concept .................................................................................................... 7-5
Figure 7-2. Sample of individual lines of effort ....................................................................... 7-9
Figure 9-1. The capability spectrum of counterinsurgency conflict ........................................ 9-5
Figure 9-2. Example of a possible transition framework ...................................................... 9-11
Figure 10-1. Generational engagement ............................................................................... 10-2
Figure 10-2. Negotiation and diplomacy ............................................................................... 10-5
Figure 11-1. Host-nation security force meter ...................................................................... 11-5
Figure 11-2. Counterinsurgency command relationships ..................................................... 11-6
Figure 11-3. Country planning .............................................................................................. 11-9
Figure 11-4. Phases of building a host-nation security force ............................................. 11-11
Figure 13-1. Provisions binding high contracting parties ..................................................... 13-8
Tables
Table 1-1. Ends, ways, means, and risk in countering an insurgency ................................... 1-5
Table 2-1. Interrelated dimensions of the information environment ....................................... 2-8

Contents
iv FM 3-24/MCWP 3-33.5 13 May 2014
Table 11-1. Developing a host-nation security force ........................................................... 11-1
Table 11-2. Host-nation contributions ................................................................................ 11-13
Table 13-1. Extract of the Detainee Treatment Act of 2005 ................................................ 13-9

13 May 2014 FM 3-24/MCWP 3-33.5 v
Preface
Field Manual (FM) 3-24/ Marine Corps Warfighting Publication (MCWP) 3-33.5 provides doctrine for Army
and Marine units that are countering an insurgency. It provides a doctrinal foundation for counterinsurgency.
FM 3-24/MCWP 3-33.5 is a guide for units fighting or training for counterinsurgency operations.
The principal audience for FM 3-24/MCWP 3-33.5 is battalion, brigade, and regimental commanders and their
staffs. Commanders and staffs of Army and Marine Corps headquarters serving as joint task force or
multinational headquarters should also refer to applicable joint or multinational doctrine concerning the range of
military operations and joint or multinational forces. Trainers and educators throughout the Army and Marine
Corps will also use this publication.
Commanders, staffs, and subordinates ensure their decisions and actions comply with applicable United States
(U.S.), international, and, in some cases, host-nation laws and regulations. Commanders at all levels ensure their
Soldiers operate in accordance with the law of war and the rules of engagement. (See FM 27-10.)
FM 3-24/MCWP 3-33.5 implements standardization agreement (STANAG) 2611.
FM 3-24/MCWP 3-33.5 uses joint terms where applicable. Selected joint, Army, and Marine Corps terms and
definitions appear in both the glossary and the text. For terms and their definitions shown in the text, the term is
italicized and the number of the proponent publication follows the definition.
FM 3-24/MCWP 3-33.5 applies to the United States Marine Corps, the Active Army, Army National
Guard/Army National Guard of the United States, and United States Army Reserve unless otherwise stated.
The proponent of FM 3-24/MCWP 3-33.5 is the United States Army Combined Arms Center. The preparing
agency is the Combined Arms Doctrine Directorate, United States Army Combined Arms Center. Send
comments and recommendations on a DA Form 2028 (Recommended Changes to Publications and Blank
Forms) to Commander, U.S. Army Combined Arms Center and Fort Leavenworth, ATTN: ATZL-MCK-D
(FM 3-24/MCWP 3-33.5), 300 McPherson Avenue, Fort Leavenworth, KS 66027-2337; by e-mail to
usarmy.leavenworth.mccoe.mbx.cadd-org-mailbox@mail.mil; or submit an electronic DA Form 2028.

Preface
vi FM 3-24/MCWP 3-33.5 13 May 2014
ACKNOWLEDGEMENTS
“Al-Sahawa: An Awakening in Al Qaim.” Dr. William Knarr. The Combating Terrorism Exchange Journal.
Copyright © 2013. Institute for Defense Analyses. Reproduced with permission of the Institute for Defense
Analyses, Alexandria, Virginia.
“If a Tactic Works in This Province, it Might Not Work in The Next: The Case of the Dan Aw Patan District,
Afghanistan, 2010.” Combat Studies Institute. Unpublished article. 2013. Reproduced with permission of the
Combat Studies Institute, Fort Leavenworth, Kansas.
“Intelligence and the Shining Path.” Christopher Paul. Unpublished article. 2013. RAND National Defense
Research Institute. Reproduced with permission of the RAND Corporation, Pittsburgh, Pennsylvania.
“Laos, 1959-1975.” Christopher Paul. Paths to Victory: Detailed Insurgency Case Studies. Copyright © 2013.
RAND National Defense Research Institute. Reproduced with permission of the RAND Corporation,
Pittsburgh, Pennsylvania.
“Philippines (Huk Rebellion) 1946-1956.” Molly Dunigan. Paths to Victory: Detailed Insurgency Case Studies.
Copyright © 2013. RAND National Defense Research Institute. Reproduced with permission of the RAND
Corporation, Pittsburgh, Pennsylvania.
“Regimental Command in Counterinsurgency.” Brigadier General W. Blake Crowe, United States Marine
Corps. Counterinsurgency Leadership in Afghanistan, Iraq, and Beyond. 2011. Marine Corps University Press.
Reproduced with permission of the Marine Corps University Press, Quantico, Virginia.
“Security Cooperation in El Salvador.” Christopher Paul. Unpublished article. 2013. RAND National Defense
Research Institute. Reproduced with permission of the RAND Corporation, Pittsburgh, Pennsylvania.
“South Vietnam, 1960-1975” Christopher Paul. Paths to Victory: Detailed Insurgency Case Studies. Copyright
© 2013. RAND National Defense Research Institute. Reproduced with permission of the RAND Corporation,
Pittsburgh, Pennsylvania.
“Sri Lanka, 1976-2009.” Colin P. Clarke. Paths to Victory: Detailed Insurgency Case Studies. Copyright ©
2013. RAND National Defense Research Institute. Reproduced with permission of the RAND Corporation,
Pittsburgh, Pennsylvania.
13 May 2014 FM 3-24/MCWP 3-33.5 vii
Introduction
The 2006 version of FM 3-24/ MCWP 3-33.5, Counterinsurgency, filled an important doctrinal gap at a
time when U.S. forces were engaged in counterinsurgency operations. This version of
FM 3-24/MCWP 3-33.5 builds on that important manual. This field manual provides doctrine that frames
counterinsurgency within the context of the range of military operations and provides a framework for the
different ways land forces could counter an insurgency. Understanding insurgencies and the operational
environment in which they exist, the ways in which the U.S. will attempt to counter insurgencies, and how
commanders synchronize their efforts to achieve end states is at the core of what this manual provides to
both the Army and the Marine Corps.
This version is organized differently than the 2006 version. The new title, Insurgencies and Countering
Insurgencies, provides insight into the thinking behind the organization. Overall, FM 3-24/MCWP 3-33.5 is
divided into three parts. Part one provides strategic and operational context, part two provides the doctrine
for understanding insurgencies, and part three provides doctrine for defeating an insurgency. In short,
FM 3-24/MCWP 3-33.5 is organized to provide the context of a problem, the problem, and possible
solutions.
Part one, the “Strategic and Operational Context,” provides a framework for understanding the environment
where a counterinsurgency exists. Part one consists of chapters one through three.
Part two, “Insurgencies,” provides a doctrinal framework for understanding an insurgency. Part two
consists of chapters four and five.
Part three, “Counterinsurgencies,” describes how to plan and execute operations to enable a host nation to
defeat an insurgency.
Chapter 1, “Understanding the Strategic Context,” answers the questions of how and why U.S. forces might
get involved in a counterinsurgency. Chapter 1 highlights that there are many different ways U.S. forces
could counter an insurgency and that there are a range of various contexts in which an insurgency can
occur. Commanders and staffs must understand the conditions in which an insurgency occurs and the
overall strategy for countering that insurgency so they can effectively support it.
Chapter 2, “Understanding an Operational Environment,” provides context for an operational environment
where an insurgency might be occurring.
Chapter 3, “Culture,” describes the role of culture in counterinsurgency operations. Understanding culture
is essential in any effort to support a counterinsurgency effort. Culture is of unique importance in
understanding an operational environment.
Chapter 4, “Insurgency Prerequisites and Fundamentals,” provides doctrine for understanding the
prerequisites of an insurgency and the root causes that allow an insurgency to keep and gain legitimacy. It
than provides a framework for understanding the strategic decisions an insurgency might make and eight
dynamics for analyzing any particular insurgency.
Chapter 5, “Insurgency Threat Characteristics,” provides doctrine for understanding the threat
characteristics of an insurgency.
Chapter 6, “Command and Control and Mission Command,” provides doctrine for executing command and
control under the philosophy of mission command. In a counterinsurgency effort, many units may perform
many different tasks in decentralized operations. Understanding decentralized operations and ensuring
these units are meeting the overall commander’s intent is essential for successful counterinsurgency
operations.
Chapter 7, “Planning and Operational Considerations,” provides guidance on how commanders and staffs
can work from conceptual planning to detailed planning in counterinsurgency operations. It also provides

Introduction
viii FM 3-24/MCWP 3-33.5 13 May 2014
important operational considerations, such as attack the network, that are essential in counterinsurgency
operations.
Chapter 8, “Intelligence,” provides considerations for intelligence in counterinsurgency. Because
understanding the environment is essential in counterinsurgency, intelligence facilities successful
operations.
Chapter 9, “Direct Approaches to Counter an Insurgency,” provides guidance on how the Army and the
Marine Corps directly counter an insurgency at the operational and tactical level. The operational
philosophy behind the direct approach is shape-clear-hold-build-transition. If tactical units are directly
interfacing with a society, they will perform shape-clear-hold-build-transition. In addition to guiding U.S.
forces’ actions, shape-clear-hold-build-transition also provides a framework for understanding host-nation
actions. If U.S. forces have to be the primary counterinsurgency force until the host nation can deploy its
forces, shape-clear-hold-build-transition provides an effective operational approach.
Chapter 10, “Indirect Methods for Countering Insurgencies,” provides a framework for working with and
through a host nation. While the U.S. may provide the primary counterinsurgent forces, it may also work
indirectly through the host nation. There are also important indirect enablers.
Chapter 11, “Working with Host-Nation Forces,” provides a foundation for understanding how security
cooperation efforts are integrated into a counterinsurgency effort. Whether U.S. forces are, for a time, the
primary counterinsurgent forces or they are working indirectly through a host nation, enabling the host
nation through security cooperation activities is essential.
Chapter 12, “Assessments,” provides doctrine for understanding how a counterinsurgency environment
changes and determining if counterinsurgent actions are having an effect on achieving the desired end state.
Continued assessments are fundamental to understanding how an environment is evolving and reframing
the basic problems commanders and staffs are facing.
Chapter 13, “Legal Considerations” provides some legal considerations that are important for commanders
and staffs to consider in all counterinsurgency operations.
FM 3-24/MCWP 3-33.5 provides doctrine on how to understand a counterinsurgency environment,
determine the counterinsurgency problem, and plan and execute operations in that environment. It provides
guidance to commanders and staffs facing the unique challenges of countering an insurgency. This field
manual is one manual in a larger doctrinal library that commanders and staffs need to understand in order
to be effective in countering an insurgency. Any effort to counter an insurgency must be built on broad
professional competence.
The Army uses the term intelligence preparation of the battlefield while the Marine Corps uses the term
intelligence preparation of the battlespace. Both Services use the same definition for these terms. This
manual uses the term intelligence preparation of the battlefield/battlespace to align with
FM 2-01.3/MCRP 2-3A.

13 May 2014 FM 3-24/MCWP 3-33.5 1-1
PART ONE
Strategic and Operational Context
When the United States (U.S.) conducts or supports counterinsurgency operations, it
does so in a unique strategic and operational environment. While this is true for all
operations, this is of particular importance when the U.S. is countering an
insurgency. Tactical actions often have strategic effects in a counterinsurgency. This
makes it essential to understand both the strategic and operational context when
countering an insurgency. In this manual, part one provides an overview for
commanders and staff to understand the environment and context of an insurgency
and the decision to counter that insurgency. Chapter 1 provides the strategic context
of a counterinsurgency. When the U.S. becomes involved in a counterinsurgency,
policy and strategic decisions affect operations. Chapter 2 provides an overview of
an operational environment and operational variables. In a counterinsurgency, there
are unique considerations that operators and planners consider. Of particular
importance in a counterinsurgency is culture. Chapter 3 provides an in-depth
overview of culture and its relationship to counterinsurgency.
Chapter 1
Understanding the Strategic Context
1-1. Any decision by the President to commit United States (U.S.) forces must be understood within the
larger sphere of U.S. policy. Soldiers and Marines must first understand the strategic context that the U.S.
is acting in to best plan, prepare, conduct, and assess a counterinsurgency operation to protect national
interests. Countering an insurgency should incorporate previous or continuing security cooperation efforts
and other activities, U.S. and host-nation objectives, and U.S. and host-nation whole-of-government efforts
to address the root causes of the conflict. (For more information on root causes, see paragraphs 4-14
through 4-22.) Despite its irregular nature and generally less intense level of combat, counterinsurgency
may be just as critical to U.S. vital interests as conventional warfare.
1-2. Irregular warfare is a violent struggle among state and non-state actors for legitimacy and influence
over the relevant population(s) (JP 1). Irregular warfare favors indirect approaches, though it may employ
the full range of military and other capacities in order to erode an adversary’s power, influence, and will.
Because of its irregular nature, U.S. involvement in a counterinsurgency demands a whole-of-government
approach. Defeating an insurgency requires a blend of both civilian and military efforts that address both
assisting the host-nation government in defeating the insurgents on the battlefield and enabling the host
nation in addressing the root causes of the insurgency. Moreover, after large scale combat or in an
ungoverned space, there may not be a functioning host-nation government. In those cases, U.S. forces must
work with population groups in the area and enable them to build governmental capacity. In either case,
U.S. civilian and military participants in counterinsurgency cannot compensate for lack of will, acceptance
of corruption, or counterproductive behavior on the part of the supported government or the population.
1-3. Insurgency in the most basic form is a struggle for control and influence, generally from a position of
relative weakness, outside existing state institutions. Insurgencies can exist apart from or before, during, or
after a conventional conflict. Elements of a population often grow dissatisfied with the status quo. When a

Chapter 1
1-2 FM 3-24/MCWP 3-33.5 13 May 2014
population or groups in a population are willing to fight to change the conditions to their favor, using both
violent and nonviolent means to affect a change in the prevailing authority, they often initiate an
insurgency. An insurgency is the organized use of subversion and violence to seize, nullify, or challenge
political control of a region. Insurgency can also refer to the group itself (JP 3-24). Counterinsurgency is
comprehensive civilian and military efforts designed to simultaneously defeat and contain insurgency and
address its root causes (JP 3-24). Warfare remains a clash of interests and will between organized groups
characterized by the use of force. In conventional warfare, there are clear determinants of victory.
However, achieving victory for an insurgent may depend less on defeating an armed opponent and more on
a group’s ability to garner support for its political interests (often ideologically based) and to generate
enough violence to achieve political consequences.
1-4. Counterinsurgency is not a substitute for strategy. When counterinsurgents attempt to defeat an
insurgency, they perform a range of diverse methods intended to counter an insurgency. Commanders must
effectively arrange these diverse methods in time and space to accomplish strategic objectives. The U.S.
can use a range of methods to aid a host nation or group in defeating an insurgency. The various
combinations of these methods with different levels of resourcing provide the U.S. with a wide range of
strategic options to defeat an insurgency. The strategy to counter an insurgency is determined by the ends
the U.S. wishes to achieve, the ways it wishes to achieve those ends, and the resources or means it uses to
enable those ways. (See paragraphs 1-10 through 1-13 for more information on strategy.)
1-5. There is a spectrum of involvement in countering an insurgency. The U.S. could enable a host nation
by not providing forces that are directly involved in securing the population or attacking the insurgents. For
example, the U.S. could provide training or intelligence support to a host nation. Moreover, even if the U.S.
is directly involved in defeating the insurgency, its primary role can be only to enable a host nation. A host
nation may be capable of providing civil control and security. The U.S. commander can integrate a force
into the host-nation’s efforts that provides a force to perform direct action or fires provided by airpower or
field artillery. U.S. involvement can range from a modest and supporting commitment to a major ground
force commitment that may, for a time, take the role of primary counterinsurgent force while host-nation
forces become better able to take on that role themselves.
1-6. Ideally, the host nation is the primary actor in defeating an insurgency. Even in an insurgency that
occurs in a country with a nonfunctioning central government or after a major conflict, the host nation must
eventually provide a solution that is culturally acceptable to its society and meets U.S. policy goals. The
conclusion of any counterinsurgency effort is primarily dependent on the host nation and the people who
reside in that nation. Ultimately, every society has to provide solutions to its own problems. As such, one of
the Army and Marine Corps’ primary roles in counterinsurgency is to enable the host nation.
1-7. A counterinsurgency can occur as part of a major combat operation, but it often occurs without a
major conflict. For example, an external threat may sponsor an insurgency, and this could be part of an
effort to attain other strategic objectives. As such, the objectives of a counterinsurgency must be contextual
to that insurgency. Creating objectives that are relevant to a particular insurgency is essential to defeating
that insurgency. Effective counterinsurgency requires clearly defined and obtainable objectives that result
in an end state acceptable to the host-nation government, the populace, and the governments providing
forces. When the U.S. directly involves itself in a counterinsurgency, stability may be essential. Although
all tasks executed to establish the conditions to reach a desired end state are significant, stability operations
may be critical in a counterinsurgency. (The Army understands all operations are made up of offensive,
defensive, and stability tasks. See ADRP 3-07 and FM 3-07 for more information on operations focused on
stability.)
1-8. The military role should be coordinated with the other instruments of national power that include
diplomatic, informational, and economic parts. The Army and Marine Corps are only part of the
instruments of national power that the U.S. can use to counter an insurgency. At times, they may be used in
a supporting role. For example, Soldiers and Marines may be withdrawn from active counterinsurgency
efforts while the U.S. uses other instruments of national power as the primary enablers of a host nation. In
such cases, the Army and Marine Corps may play a supporting role by performing security cooperation
tasks.
1-9. The Laos insurgency highlights the unique nature of an insurgency. This insurgency took place in the
context of Vietnam. Here, internal groups with various interests and outside groups from North Vietnam
Understanding the Strategic Context
13 May 2014 FM 3-24/MCWP 3-33.5 1-3
and the U.S. created a unique context for the Laos insurgency. Moreover, the corrupt and ineffective host
government was not able to wage its own counterinsurgency campaign effectively. To effectively counter
the insurgency in Laos, the U.S. needed an operational approach that would work in that environment, if a
successful operational approach were possible. Unfortunately, U.S. forces failed to create an effective
strategy to counter the insurgency in Laos. Thus, the U.S. government failed to find the needed ways and
means to meet the policy goal.
The Laos Insurgency
Lamented as “the forgotten war,” the insurgency in Laos was heavily
influenced (and often overshadowed) by the conflict in neighboring Vietnam. A victim
of geography, half-hearted fighting between the different factions in Laos may well
have worked itself out in a lasting compromise if not for pressure from North
Vietnamese communists to control areas of Laos for the infiltration of men and
materiel into South Vietnam (along the Ho Chi Min trail) and U.S. efforts to oppose
communist presence and influence.
Beginning in earnest in 1959, fighting pitted variously rightist Royal Lao
forces supported by Hmong guerillas against the leftist Pathet Lao (indigenous
communists) and their North Vietnamese supporters. These participants were at
times joined by other players, including U.S. advisors, Filipino troops, U.S. air power,
Thai commandos and artillery formations, as well as “neutralist” Lao forces. During
the period of conflict, Laos was underdeveloped in every way, including its
government, its economy, and its military. The government and military were corrupt
and ineffective and the economy was wholly dependent on outside support.
As the United States became more invested in Vietnam, it also increased
support to Laos; by the end of 1955, the U.S. provided 100% of the Lao military
budget. North Vietnamese backers of the Pathet Lao sought to grow that force,
supporting a significant recruiting campaign and sending many of the recruits to
North Vietnam for schooling and training. This led to greater investment by the U.S.
in materiel and training for government forces, and included, beginning in 1957,
efforts to arm Hmong guerillas, who would play an important role later in the conflict.
Vietnamese interest in Laos was primarily in securing the so called
“panhandle” region, through which the Ho Chi Min trail allowed the North Vietnamese
to infiltrate men and materiel into South Vietnam. A secondary consideration was the
support of a fellow communist movement (the Pathet Lao). Once fighting began in
1959, the Vietnamese used government chaos to their benefit, increasing attacks on
government forces and expanding the territory under their influence or control. During
this period, many attacks took the form of North Vietnamese Army regulars attacking
and overwhelming a position, and then letting their Pathet Lao allies occupy the area
and claim the victory, thus at least paying lip service to maintaining the neutralization
of Laos.
These North Vietnamese Army-led attacks and several attempted
counterattacks by Royal Laotian Forces against Pathet Lao positions revealed the
gross incompetence of the government’s regular forces. This lack of capability
stemmed from several sources, including a half-hearted martial tradition in general, a
preoccupation with profiteering and political games by the senior leadership, lack of
efforts by the French who were responsible for their training until late 1958, and a
fundamental lack of motivation. Despite the vigorous efforts of U.S. trainers and
millions of dollars in materiel throughout the course of the conflict, Royal Lao Forces
would never become a consequential fighting force. In this phase, the only effective
forces on the government side were the Hmong tribesmen, trained and provisioned
by the Central Intelligence Agency and fighting as guerillas.
International pressure (from the United States as well as from China and
Russia preferring to avoid unnecessarily provoking the United States) and support
(from the United States and other allies) prevented the complete collapse of the
government of Laos in 1962 and pushed for neutralization through a coalition
Chapter 1
1-4 FM 3-24/MCWP 3-33.5 13 May 2014
government. The North Vietnamese were content to allow negotiations to take place,
as they had succeeded in securing what they needed: the Ho Chi Min trail. After
months of wrangling, 1962 finally saw another Geneva agreement, this time for a
neutralized Laos with a coalition government representing the three major factions:
the rightists, the leftists, and the neutralists. Part of the neutralization agreement
included the removal of foreign forces from Laos. While U.S. and allied personnel
who had been fighting on the side of the Royal Lao Government were withdrawn from
the country, very few of the substantial number of North Vietnamese Army forces
withdrew. Nor did the Central Intelligence Agency cease its work with the Hmong.
The new coalition government proved shaky. Turmoil again rocked the Lao
government with continued political maneuvering by greedy generals and a string of
coups. Military region commanders ran their zones like private fiefdoms, rarely
dispatching their troops outside the Mekong River valley. A series of spectacular
failures by the Royal Lao forces all but ensured those forces would never seek to
take the initiative and act in other than a strictly defensive capacity again. Between
1964 and 1968, the conflict was primarily between the U.S.-supported paramilitaries
(backed by U.S. airpower), and the Pathet Lao. The cycle of dry season and wet
season, each favoring one side or the other, saw very modest back and forth
movement between the two primarily irregular forces, with little change from year to
year. That all changed in 1969. The communist dry season offensive of 1968 did not
end with the onset of the rainy season, and gains were substantial. In early 1970, the
communists seized a provincial capital for the first time, and later that year they
seized another.
In the now traditional way, Hmong guerillas counterattacked. However, after
nearly a decade of war, the Central Intelligence Agency’s secret army was nearly
fought out. Fighting against superior numbers of regular troops, the Hmong became
more and more reliant on U.S. airpower and on support from Thai artillery. Bombing
in southern Laos expanded such that by 1971, it was more extensive than bombing
in South Vietnam and Cambodia combined.
The communist dry season offensive that started in December of 1971
brought extraordinary pressure on the government. For the first time, North
Vietnamese Army forces used significant armor, as well as large tube artillery. The
Hmong were battered and quickly thrown back. After another year of significant
communist gains, the Lao government and its international supporters once again
sought a ceasefire.
By the time of the 1973 ceasefire and neutralization, the government of
Laos controlled little more than the capital and the Mekong river valley, and that only
by virtue of the Hmong and U.S. airpower. With the withdrawal of U.S. support (both
airpower and funding) in 1973, the Hmong were demobilized and the Lao
government was left to its fate, which was to fall relatively quickly to the communists.
UNITED STATES’ STRATEGY AND POLICY TO COUNTER AN
INSURGENCY
1-10. When and how the U.S. government provides assistance to other states to counter an insurgency is a
question of policy and strategy. Commanders and staffs should understand that the U.S. can respond with a
range of measures, many of which do not directly involve U.S. forces securing the population or
performing offensive operations, in a counterinsurgency. This manual provides the reader with information
on how counterinsurgents may organize tactical tasks in time and space to reach an end state. It cannot and
should not be the only reference to conduct counterinsurgency operations for someone who wishes to fully
understand the policy tools available to the U.S. to aid a host nation in fighting a counterinsurgency. (See
JP 3-24, Allied Joint Publication 3.4.4, and the U.S. Government Guide to Counterinsurgency for more
information on counterinsurgency policy tools.)

Understanding the Strategic Context
13 May 2014 FM 3-24/MCWP 3-33.5 1-5
1-11. Effective counterinsurgency operations require an understanding of the military profession. The tasks
counterinsurgents perform in countering an insurgency are not unique. It is the organization of these tasks
in time and space that is unique. For example, geographic combatant commanders employ theater strategy
to align and shape efforts, resources, and tasks to support strategic goals and prepare for conflict and
contingencies in their region. In support of this goal, theater strategies normally emphasize security
cooperation activities, building partner capacity and force posture, and preparing for contingencies and
other tasks those are not unique to counterinsurgency operations. For example, a unit can perform security
cooperation tasks in support or not in support of countering an insurgency. (See FM 3-22 for more
information on security cooperation tasks.) Those units that carry out security cooperation tasks to support
a counterinsurgency should understand security cooperation and the tasks they are performing and
teaching. Moreover, they should understand how these tasks are used in defeating an insurgency. Soldiers
and Marines must start from a foundation of professional knowledge and competence to have a framework
for understanding and aiding a host nation in defeating an insurgency. Whether a unit is directly performing
the tasks to defeat an insurgency or indirectly supporting a host nation, this manual provides a doctrinal
framework for counterinsurgency operations. However, to be effective, Soldiers and Marines must be
professionally competent. This is the foundation in understanding another nation’s or group’s actions to
defeat an insurgency and in providing aid to that nation or group. (See ADRP 1 for more information on
professional competence.)
1-12. Political leaders and commanders must have a dialogue to decide the optimal strategy to meet the
security needs of the U.S and states or groups the U.S. supports. Different capabilities provide different
choices that offer different costs and risks. U.S. strategy is defined by how it combines these capabilities
(the ways), resources them (the means), and its willingness to accept risk in attaining its policy goals.
Commanders inform political leaders about the prospects for victory and the different costs and risks of
various options, and political leaders weigh these costs and risks against their importance to U.S. national
interests. Once U.S. policymakers have determined the goals (the ends) of the U.S., the military evaluates
operational approaches to conduct counterinsurgency efforts depending on the ends, ways, means, and
acceptable risk. The joint force provides a range of capabilities that it integrates into the overall strategy.
For example, in a functioning state that is facing an insurgency, the joint force may employ a range of
security cooperation tools. Moreover, other tools fall outside of security cooperation, such as direct action
and counter threat financing, that the U.S. can integrate into the mix of ways that it will use to defeat or
contain an insurgency. The U.S. government integrates the various instruments of national power to create
a range of strategic options, of which military involvement is only one part. (For a further discussion on
strategy, see MCDP 1-1.) (See table 1-1.)
Table 1-1. Ends, ways, means, and risk in countering an insurgency
Ends Ways Means Risk
Defeat or contain an
insurgency.
Support strategic goals
and end state defined by
policy makers.
Direct methods
(See chapter 9.)
Indirect methods
(See chapter 10.)
Unified action
• Military force.
• Other
governmental
capabilities
Determined by a
mismatch in the
ends, ways, and
means.
1-13. An operational approach is a description of the broad actions the force must take to transform
current conditions into those desired at end state (JP 3-0). The commander may use direct or indirect
approaches to counter threats. Commanders may find their operational approach is mainly direct, indirect,
or a mixture of both. The approach is the manner in which a commander contends with a center of gravity.
A direct approach attacks the enemy’s center of gravity or principal strength by applying combat power
directly against it. An indirect approach attacks the enemy’s center of gravity by applying combat power
against a series of decisive points that lead to the defeat of the center of gravity while avoiding the enemy
strength. Commanders may use a single direct or indirect approach or, more likely, may employ a
combination of approaches to counter an insurgency and its influence. Additionally, the emphasis on or
combination of approaches may have to evolve as the security situation and insurgent networks evolve. The
commander’s intent and the approach(es) the commander selects will drive the methods used by
counterinsurgents. These methods may be direct or indirect. Approaches and methods must be nested and

Chapter 1
1-6 FM 3-24/MCWP 3-33.5 13 May 2014
clearly linked, since they often involve support from diplomatic, economic, and informational efforts by
non-military forces. (See chapter 9 for more information on direct methods and chapter 10 for more
information on indirect methods. See JP 5-0 for more information on direct and indirect approaches.)
LAND FORCES AND THE RANGE OF MILITARY OPERATIONS
1-14. The U.S. Army and Marine Corps can prevent or defeat an insurgency across the range of military
operations. This is true if an insurgency starts in the context of a major combat operation or if it starts
during peace. Across the range of military operations and in accordance with U.S. strategy, U.S. land forces
take actions and set priorities to shape an environment to reduce the possibility of insurgencies. In some
instances an operational environment and its related variables are unstable or fragile and hostile actions
against a host-nation government begin. In this environment, the U.S. may make a decision to use some
type of military capability. Commanders must understand the effects that the actions and priorities of the
U.S. force have on an operational environment. When acting in this environment, commanders must have
situational understanding of the environment and the effects of U.S. actions in that environment. This
influences how the commander attempts to shape the environment. An insurgency can also occur in the
context of another conflict. For example, during major combat operations, land forces must take actions to
prevent insurgencies from occurring during operations and once the opposing conventional force is
defeated. While an insurgency is only a possibility in a major combat operation, it could occur during major
operations or afterwards. Commanders and staffs must assess the possibility of an insurgency in any
operational environment and take actions to prevent one from occurring. These actions can include a range
of stability operations and security cooperation activities. (See ADRP 3-07 for more information on
stability operations and FM 3-22 for more information on security cooperation.)
1-15. The circumstances of U.S. involvement in a counterinsurgency are important in understanding the
operational and tactical actions of U.S. forces. The type and scale of involvement, whether the Army and
Marine Corps are involved temporarily as the primary counterinsurgent forces or are providing modest
indirect and direct support to a counterinsurgency effort, will be determined by the circumstances of U.S.
involvement. U.S. forces participate at the direction of the President, based on national security interests.
One example circumstance is the collapse of a fragile state in a geographically strategic area. Even if U.S.
land forces are not in place when the government collapses, the President may deploy land forces to
counter an insurgency and restore stability. The use of indirect capabilities in a failed state is complex
because the commander often has to work with groups outside of the legitimately constituted government.
Building capacity and enabling existing capabilities is difficult when a state lacks functional institutions.
Because these areas lack state institutions to provide various governmental functions to include security
forces, large scale direct involvement is often resource intensive. The U.S. can use smaller direct
capabilities to support groups outside the legitimately constituted government, but this also adds to
uncertainty and strategic risk.
1-16. U.S. forces can participate at the request of a government that seeks to counter an insurgency in its
country with assistance from the U.S. When a requesting government is capable and functioning, the U.S.
can offer a wide range of capabilities. Having a capable government changes the relationship between ends,
ways, and means. A capable government could require fewer resources to intervene, or it could only require
indirect and direct enablers in order to be successful. However, as with any involvement to counter an
insurgency, often unforeseen risks could lead to greater U.S. involvement.
1-17. U.S. involvement can also occur in a country where there are ongoing security cooperation activities.
If the U.S. is performing security cooperation activities in a country and an insurgency develops, continued
security cooperation efforts could result in U.S. involvement in a host nation’s counterinsurgency efforts.
Efforts to train and equip host-nation forces will likely be seen as U.S. involvement by both the insurgents
and the international community. Moreover, U.S. forces could also transition to direct involvement in an
insurgency. Whatever the degree of involvement, a clear policy decision should be made to include the
development of a national strategy.
1-18. Insurgencies could also be part of large scale combat or fueled by a regional or global adversary. In a
protracted large scale operation, an insurgency often develops in controlled areas with populations
sympathetic to the enemy. As such, planning for prevention of an insurgency and integrating stability
operations into a prolonged operation is essential. If an insurgency develops, it will require resources to

Understanding the Strategic Context
13 May 2014 FM 3-24/MCWP 3-33.5 1-7
defeat the insurgents. This will reduce the resources available to defeat the enemy in large-scale combat. In
addition, an adversary can fuel an insurgency in a host nation to undermine U.S. interests. In this case, the
insurgency is part of an adversary’s overall strategy and policy. (See FM 3-05, chapter 2, for more
information on unconventional warfare. It provides a U.S. perspective on enabling an insurgency.)
1-19. An insurgency can also occur at the conclusion of a large scale combat operation when an organized
movement seeks to challenge the authority of the U.S. and its partners. The organized movement may be
remnants of the defeated force or an opportunistic movement that seeks to obtain power using a
political-military challenge to the existing authority. In either case, U.S. land forces, along with other
unified action partners, must be prepared at all stages of conventional warfare to assess the capability of an
insurgency occurring either during the conflict or after hostilities cease. Soldiers and Marines must also
recognize that the presence of U.S. forces in the region can lead to the conditions for an insurgency. U.S.
land forces can help to prevent an insurgency from occurring in the manner in which they conduct
conventional warfare and in the conduct of post-conflict operations. Should prevention fail, U.S. forces will
be exponentially more successful in countering an insurgency if they shape the environment during and
immediately following conventional warfare for an effective transition to counterinsurgency.
1-20. In the military operations, U.S. forces can prevent an insurgency from occurring in large scale
combat operations by integrating stability operations. If an insurgency does begin, U.S. forces can shape its
formation and make it easier to defeat. U.S. land forces can also prevent an insurgency from occurring in
peacetime through security cooperation activities and other capabilities that support the host nation or other
groups. If there is an insurgency, the U.S. can integrate a number of capabilities into an overall operational
approach to defeat that insurgency.
1-21. From the U.S. land forces’ perspective, insurgencies range along a spectrum depending on the scale
of effort and resources the Army and Marine Corps must take to counter them. In a worst-case scenario, an
extremely capable insurgency that has a significant impact on the population exists in a failed state region
in which there is little or no host-nation government capability. The U.S. may have to commit significant
combat power to offset the momentum of the insurgency. While the U.S. can avoid using land forces in
direct combat, the use of other capabilities will often support groups that are not the recognized
government. In such cases, the U.S. would be enabling one group to gain control over the state. For
example, the U.S. could equip groups within a state and empower them to take control over an area. While
the initial cost may be lower, this course of action is fraught with possible unintended consequences. The
group that counterinsurgents enable, which is essentially another insurgency, may act in ways that are
counter to U.S. interests once it gains control of the area. On the other hand, direct involvement could be
extremely costly and provoke a wider conflict. If the U.S. operates in a failed state to defeat an insurgency,
it must create a policy and strategy that matches its goals and the resources that it is willing to spend.
Moreover, it must be willing to accept a large degree of uncertainty and strategic risk.
1-22. The best-case scenario is when the host nation has the capability to defeat an insurgency and the U.S.
plays only a supporting role in enabling the insurgencies’ defeat with equipment, training, or intelligence.
A middle case occurs when a functional state has an insurgency in a remote area where the host-nation
government cannot exert complete control. The existing insurgency is not a challenge to the continued
authority of the host-nation government, but it may seek to gain control of a specific region or area. This
type of scenario can require much fewer resources for U.S. land forces to counter the insurgency than the
worst-case scenario. Since the capacity of the host-nation security forces exists to contain the insurgency to
a specific region or area, the U.S. can integrate a number of capabilities into the host government’s efforts
to increase the effectiveness and capabilities of the host nation. While every insurgency is unique, this basic
framework offers the U.S. the opportunity to achieve policy goals while spending fewer resources and
offering less uncertainty and risk. However, as with any conflict, unintended consequences can change the
insurgency and increase the cost and uncertainty of U.S. involvement.
1-23. In all cases, specific national policies govern U.S. land forces’ actions to counter an insurgency. An
insurgency’s goals and actions are influenced by the conditions the insurgency develops in. An
insurgency’s objectives are not exclusive to the condition of the state, but each can occur anywhere along
the range of state conditions. However, the operational environment an insurgency develops in will affect
how it understands its goals and will affect its actions (See chapter 2 for more information on an

Chapter 1
1-8 FM 3-24/MCWP 3-33.5 13 May 2014
operational environment and section II for more information on understanding the actions of an
insurgency).
1-24. There may be multiple insurgencies in an operational environment. A networked insurgency may
have conflicting goals within its organization and its actions are not controlled by a command structure.
These insurgencies can have links to other insurgencies or criminal organizations. Networked insurgencies
might divide or combine with groups. In such cases it is difficult to analyze an insurgency or insurgencies if
they are treated as monolithic actors. Instead, counterinsurgents must understand the dynamics within the
insurgency or multiple insurgencies. (See paragraphs 4-88 through 4-103 for more information on
networked insurgencies.)
1-25. Victory in a counterinsurgency may not be as clear as winning in a conventional conflict. U.S.
national ends determine the criteria for success, regardless of how the U.S. land force is deployed to
conduct counterinsurgency operations. As it applies to U.S. national objectives, success in an insurgency
often depends on developing host-nation capacity to contain, reduce, and defeat the insurgency without
requiring direct U.S. involvement. In a counterinsurgency, the host nation often determines the criteria for
success. U.S. counterinsurgents should avoid judging host-nation criteria based on their own cultural
expectations. Achieving success may depend less on defeating the armed element of the insurgency and
more on the ability to legitimize host-nation institutions to the populace. Short and mid-term success in
counterinsurgency may be developing a host-nation government that has sufficient capability to secure
itself and address an insurgency on its own. This success allows the U.S. to continue to support the host
nation through a long-term relationship that addresses that nation’s legitimacy. Success includes enabling
the development of resiliency within the host-nation population and host-nation institutions to sustain the
ability to counter the insurgency in the future and prevent the conditions in the area from allowing an
insurgency to gain strength. Achieving the conditions for success may require a mix of application of force,
information operations, cultural acceptance, and building capacity and competency within host-nation
institutions. Counterinsurgents may either persuade the people to support the government or dissuade them
from supporting the insurgents. What capabilities the U.S. uses to counter an insurgency is dependent on
the context of that insurgency and U.S. national interests.
1-26. U.S. forces should expect that the host-nation government will have its own interests that may not
coincide with U.S. national interests. It may not be willing to undertake the political changes necessary to
address the root causes of the insurgency. The commitment of U.S. forces may depend upon the degree to
which U.S. policy makers consider the affected government to be receptive to assistance, advice, and
reform. How Soldiers and Marines are employed will also require a clear determination by national
decisionmakers as to what post-conflict commitments by military and civilian organizations will be
required. Outside counterinsurgents, however, can never fully compensate for lack of will, incapacity, or
counterproductive behavior on the part of the supported government. If a government is unambiguously
committed to the defeat of insurgency, it is more likely to defeat it, regardless of the actions (or
commitment level) of an outside supporter.
LEGITIMACY AND CONTROL
1-27. Legitimacy, the acceptance of an authority by a society, and control are the central issues in
insurgencies and counterinsurgencies. This is true however the U.S. enables a host nation to defeat an
insurgency. The population of a particular society determines who has legitimacy to establish the rules and
the government for that society. A population’s values and cultural norms will determine who that society
perceives as a legitimate authority. Both the insurgency and the host nation attempt to control the
population by some mixture of consent and coercion. Insurgents use all available tools, including political
(diplomatic), informational (including appeals to religious, ethnic, historical, national, class, political, tribal
or ideological beliefs), and social, military, and economic tools to overthrow or undermine an existing
authority. Likewise, the host nation will use all available tools to maintain acceptance of its authority. This
authority may be an established government or an interim governing body. It may be a generally accepted
social order. Control of a population, however, may not be the end state desired by an insurgent. A criminal
enterprise might seek to undermine existing political power in order to enable it to continue its criminal
activities or insurgents could seek political power in order to impose an ideological (or religious) system on
an unwilling population. In counterinsurgencies, if the affected government wants to end the insurgency, it

Understanding the Strategic Context
13 May 2014 FM 3-24/MCWP 3-33.5 1-9
should use all instruments of its national power to prove its legitimacy, to defeat the insurgency, and to
reduce the likelihood of another crisis emerging.
1-28. Legitimacy is essential to understanding the political variable in an insurgency. Who a population
accepts as legitimate is dependent on the norms and values within that particular population. Legitimacy
can change as a society evolves and groups or individuals change their conceptualization of who they are
and what authority they accept. Sometimes large changes, such as the American War of Independence or
the unification of Germany in 1871, create a change in group identity and accepted authority. Sometimes
group identity changes by slow evolution, as is the case with the European Union. However, at the core,
who a group accepts as providing legitimate authority to govern their actions is that group’s legitimate
authority. (See paragraphs 2-16 through 2-19 for information on the political variable.)
1-29. Legitimacy provides willing acceptance of authority and thus requires fewer resources to enforce its
authority than illegitimacy. Most populations are controlled through a combination of consent and coercion.
The host-nation government generally needs some level of legitimacy among the population in order to
retain power. This provides some level of consent. Legitimacy is an indicator of the extent to which
systems of authority, decisions, and conduct are accepted by the local population. Political legitimacy of a
government determines the degree to which the population will voluntarily or passively comply with the
decisions and rules issued by a governing authority. Legitimacy determines the transaction costs of political
and governmental power. Low legitimacy may breed contempt on the part of the population and may
require extensive prodding and incentives by the government to secure compliance of the population; high
legitimacy generally invites compliance by the population and therefore requires less effort by the
government to ensure compliance. An illegitimate government’s only method of controlling its population
is coercion, which can be resource intensive. A legitimate government has to use coercion for policing
power, but its population, in general, sees the rules and directions of its government as intrinsically correct.
A population will follow a legitimate government’s rules and norms passively, and those who break those
rules or norms are disapproved of by the society. Who the population sees as a legitimate authority is a
central issue of a counterinsurgency.
1-30. All population groups are controlled by some combination of consent and coercion. Some
governments may use a range of coercive methods to control the population. Coercive methods can damage
legitimacy if the methods cannot be justified under the values and norms of the population. However,
counterinsurgents should not think of coercion and consent as counter forces to one another. If coercive
acts by the government or insurgency are justifiable under the norms and values of the population, those
acts do not necessarily undermine the legitimacy of the government or host nation. Acts by both the
government and the insurgency must be viewed from the perspective of the population experiencing those
acts and not from an outside perspective that will bring its own bias to viewing actions of the host
government or insurgency.
1-31. The struggle for legitimacy with the population is typically a central issue of an insurgency. The
insurgency will attack the legitimacy of the host-nation government while attempting to develop its own
credibility with the population. The host-nation government should reduce the credibility of the insurgency
while strengthening its own legitimacy. A government that is seen as legitimate magnifies the resources
and capabilities needed to defeat an insurgency and allows the host nation to concentrate finite resources on
targeting the insurgency. However, legitimacy is a condition perceived by the population. Who the
population sees as legitimate will be determined by that population’s norms and values. For example, if a
population does not see outside forces as legitimate, this can undermine the legitimacy of the host-nation
government trying to counter an insurgency.
1-32. The legitimacy of the host-nation government is achieved because the population accepts its
authority and how it governs can be justified in terms of the population’s beliefs. It is not enough for the
host-nation government to be simply seen as effective and credible. The governmental structure must be
justifiable to the population and that justification must be based on the population’s norms and values. In
some situations, providing effective governance may be essential to establish legitimacy among the
population. However, this is not a uniform rule. The key is that legitimacy is ultimately decided in the
minds of the population. Counterinsurgents must understand how the population will perceive a
government. A host nation that is less efficient but perceived as legitimate by the population will be more

Chapter 1
1-10 FM 3-24/MCWP 3-33.5 13 May 2014
effective than an efficient host-nation government that cannot be justified by the values and norms of the
population.
1-33. Even if a population does not see an insurgency or a government as legitimate, control can be
established effectively by coercion. Many states and insurgencies have used domestic intelligence
apparatus or other means to control every aspect of their populations. Illegitimate governments often use
distrust and divisions within a population to effectively control a society. Moreover, a population is not
monolithic. It is made up of many groups and subgroups. In many autocratic regimes, various groups
within a population have a vested interest in continuing the current government, even if it is repressive.
Likewise, an insurgency might receive support from elements within the population, even if it is repressive
and uses coercive methods. Legitimacy must be seen from the different perspectives of the different groups
within a society.
UNDERSTANDING UNIFIED ACTION
1-34. Once the U.S. decides to become involved in a counterinsurgency, all instruments of national power
provide the U.S. important capabilities to defeat an insurgency. Unified action is essential for all types of
involvement in any counterinsurgency. Unified action is the synchronization, coordination, and/or
integration of the activities of governmental and nongovernmental entities with military operations to
achieve unity of effort (JP 1). Paragraphs 1-34 through 1-76 provide commanders and staffs with an
understanding of how civilian agencies and military departments and forces synchronize and integrate their
operations to achieve unity of effort. Paragraphs 1-41 through 1-48 explain both a whole-of-government
and a comprehensive approach to defeat insurgencies and achieve U.S. and host-nation objectives.
Paragraphs 1-59 through 1-76 also explain the roles of intergovernmental, nongovernmental, multinational
forces, private sector organizations, and host-nation government and host-nation forces in
counterinsurgency.
1-35. Unified action must be integrated into the overall host-nation efforts. The focus of U.S. efforts is to
support the host nation’s internal defense and development. Internal defense and development is the full
range of measures taken by a nation to promote its growth and protect itself from subversion, lawlessness,
insurgency, terrorism, and other threats to its security (JP 3-22). Internal defense and development focuses
on building viable institutions that respond to the needs of society. Security cooperation activities must
work with and support a nation’s own internal defense and development programs. Within the context of
counterinsurgency, commanders and staffs must understand and support a host nation’s internal defense
and development strategy. In the long run, the host nation, and not the U.S., will either defeat or be
defeated by the insurgency. Supporting a host nation’s internal defense and development plan is one of the
more effective ways in which the U.S. enables a host nation to defeat an insurgency. (See JP 3-22 for more
information on internal defense and development.)
ETHICAL APPLICATION OF LANDPOWER IN UNIFIED ACTION
1-36. Army and Marine Corps leaders should clearly understand how adherence to a professional ethic
provides the moral basis for unified action and how it becomes a force multiplier in all operations. The
actions of Army and Marine Corps professionals are framed by the disciplined, ethical application of force.
This is the foundation for unified action. Effective, ethical leaders must communicate to their Soldiers and
Marines that American values affect every aspect of how U.S. forces fight and win a counterinsurgency.
This instills in them the concept of honorable service and builds esprit de corps, two essential
characteristics of the military profession, while enhancing resilience and preventing or reducing moral
injuries to Soldiers and Marines. Unified action requires the judicious use of lethal force balanced with
restraint and tempered by professional judgment. Combat in counterinsurgency often obligates leaders,
Soldiers, and Marines to apply force in a precise manner to accomplish the mission without causing
unnecessary loss of life or suffering. To maintain U.S. legitimacy, to ensure international credibility, and to
safeguard the U.S., Soldiers and Marines cannot afford to misuse the lethal power provided to them by the
U.S. government.
1-37. Soldiers and Marines are not permitted to use force disproportionately or indiscriminately. Typically,
more force reduces tactical risk in the short term. But in counterinsurgency, the more force that is used, the
less effective it can be. It is more likely that counterinsurgents will achieve an end state by protecting a

Understanding the Strategic Context
13 May 2014 FM 3-24/MCWP 3-33.5 1-11
population, not the counterinsurgency force. When military forces remain in secure compounds, they lose
touch with the situation, appear to be indifferent to the population, simplify enemy intelligence operations,
or appear afraid to engage the insurgents. In effect, they concede the initiative to the insurgents. To be
successful, counterinsurgency forces must work with and share risks with the host-nation forces and the
population. Soldiers and Marines must accept some risk to minimize harm to noncombatants. Accepting
prudent risk is an essential part of the warrior ethos and an obligation of honorable service.
1-38. Leaders must accept ambiguity and risk, which are inherent to decentralized operations. The
presence of a local population within which insurgents may disappear creates a high degree of ambiguity.
Operationally adaptable leaders observe the rapidly changing situation, identify its key characteristics,
determine what has to be done in consultation with subordinates and host-nation forces, and determine the
best method to accomplish the mission. They must assess and accept prudent risk, and they must adjust
rapidly as conditions change. They must be able to shift operational tasks from capacity building to combat
and back again in days, or even hours. Alert junior leaders recognize the dynamic context of a tactical
situation and can use their professional judgment to apply informed lethal and non-lethal force to achieve
the commander’s intent. Any use of force generates a series of reactions. The general rule for the use of
force for the counterinsurgents is “do not create more enemies than you eliminate with your action.” The
more force is applied, the greater the chance of collateral damage and mistakes. There will be times when
an overwhelming effort is necessary to destroy or intimidate an opponent and reassure the populace.
However, counterinsurgency forces should calculate carefully the type and amount of force to be applied
and who wields it for any operation. Using force precisely and discriminately strengthens the rule of law
that needs to be established in the host nation. Normally, counterinsurgency forces can use escalation of
force procedures to minimize unnecessary loss of life or suffering. These procedures are especially
appropriate during an operation in which the counterinsurgent security force interacts with the local
population. All interactions between security forces and the population directly impact legitimacy. (See
chapter 13 for legal information on the use of force).
1-39. Who wields force is also important. If the police have a reasonable reputation for competence and
impartiality, it may be better for them to execute urban raids than military forces because the population is
more likely to view their application of force as legitimate. This is true even if the police are not as well
armed or as capable as military forces. Local circumstances, however, affect this decision. For example, if
the police are seen as part of an ethnic or sectarian group oppressing the general population, their use may
be counterproductive. (See chapter 10 regarding the development of host-nation security forces and chapter
12 regarding assessing counterinsurgency operations. For further discussions on use of force, see chapter
13.)
1-40. The environments where counterinsurgency operations exist can be much more ethically complex
than those associated with conventional conflicts. Many leadership and ethical imperatives are prominent
and, in some cases, unique to counterinsurgency. The dynamic and ambiguous environment of modern
counterinsurgency places a premium on leadership at every level, from sergeant to general. Application of
decentralized authority and decisionmaking is more prevalent in counterinsurgency than other types of
military operations. Combat in a counterinsurgency is frequently a small-unit leader’s fight; however,
senior leaders set the conditions and the tone for all actions by subordinates. Today’s Soldiers and Marines
must rapidly adapt cognitively and emotionally to the perplexing challenges of counterinsurgency and
master new competencies in dynamic contexts. Those in leadership positions must provide the moral
compass for their subordinates as they navigate this complex environment. Underscoring these imperatives
is the fact that exercising leadership in the midst of ambiguity requires intense, discretionary professional
judgment. Army and Marine Corps leaders are expected to demonstrate their competence, character, and
commitment to their professional ethic. All leaders must continually reconcile mission effectiveness,
ethical standards, and thoughtful stewardship of the nation’s precious resources—human and material—in
the pursuit of national aims. Leaders must link tactical actions to strategic objectives and to the host
nation’s essential political goals. U.S. forces must use the combat multiplier of seeking and maintaining the
moral high ground in a counterinsurgency. Doing so guarantees maintaining trust with the American people
and upholds the ideals of the profession of arms.

Chapter 1
1-12 FM 3-24/MCWP 3-33.5 13 May 2014
A WHOLE-OF-GOVERNMENT EFFORT
1-41. Accomplishing U.S. policy objectives in any conflict requires government expertise and resources
outside of the Department of Defense (DOD). Policy objectives, especially during a conflict, require a
whole-of-government effort. A whole-of-government approach integrates the collaborative efforts of the
departments and agencies of the U.S. government to achieve unity of effort toward a shared goal. A
whole-of-government effort is vital to achieving the balance of resources, capabilities, and activities that
reinforce progress made by one of the instruments of national power while enabling success among the
others. It relies on coordination among the agencies of the U.S. government, including DOD, to ensure that
the full range of available capabilities are used, synchronized, and applied to a given policy objective.
Government agencies usually agree upon relationships and authorities in a memorandum of agreement or
understanding. Military commanders exercise only the authority outlined in these agreements and are often
directed by another agency. The terms in these documents may form the basis for establishing some form
of relationship between commanders and agency chiefs. When unity of command is not possible,
commanders strive to achieve unity of effort. Often, the interpersonal relationships that commanders
establish with their interagency partners are essential.
1-42. A whole-of-government effort incorporates all of the capabilities of the U.S. government to achieve
U.S. national objectives. In many counterinsurgencies, for example, political objectives include assisting
the host nation with managing the nonmilitary aspects of the insurgency. Therefore, these political
objectives include eliminating the root causes of the insurgency. However, counterinsurgency commanders
and planners must understand that, in the end, societies must address their own root causes of insurgency.
Imposing major reforms may result in unintended consequences. Enabling a host nation to address the
insurgency’s root causes increases its chances of defeating it. In dealing with the sorts of complex
socio-cultural problems that counterinsurgents frequently face, “host-nation good enough” is normally
better than what the U.S. would consider perfect, if it meets U.S. objectives.
1-43. A primary challenge for integrating civilian and military efforts into a whole-of-government effort is
the differing capabilities, capacities, cultures, objectives, and approaches in civilian agencies compared to
those of military forces. A successful whole-of-government effort requires that all actors—
- Are represented, integrated, and actively involved in the process.
- Share an understanding of the situation and problem to be resolved.
- Strive for unity of effort toward achieving a common goal.
- Integrate and synchronize capabilities and activities.
- Collectively determine the resources, capabilities, and activities necessary to achieve their goal.
1-44. The importance of the commander’s personal involvement in building interorganizational trust,
understanding, mutual respect, and friendships cannot be overstated. If organizational leaders do not set the
appropriate tone and establish the necessary climate, the best whole-of-government plan will fail.
1-45. A clear understanding of the desired end state and national objectives should infuse all efforts,
regardless of the agencies or individuals charged with their execution. Given the primacy of political
considerations, military forces often support civilian efforts. However, the nature of counterinsurgency
operations means that lead responsibility often shifts among military, civilian, and host-nation authorities.
In other words, as the U.S. shifts its policy and strategy, different agencies take on different roles during an
operation. Different or changing relationships with the host nation may also drive shifts in lead
responsibility between different authorities. Military leaders prepare to assume local leadership for
counterinsurgency efforts if civilian leadership is unavailable or cannot access the area.
1-46. U.S. land forces conducting counterinsurgency operations must recognize the legal authority of the
Department of State, their chief country team, and the chief of mission. The chief of mission, who is
normally the ambassador, is the principal officer in charge of a diplomatic facility of the U.S. The country
team is the senior, in-country, U.S. coordinating and supervising body. Commanders ensure that they gain
an understanding of the purposes, goals, and restrictions under which their interagency partners are
operating. Without such an understanding, the military and nonmilitary efforts may frustrate and interfere
with one another because the military and civilian organizations are functioning under separate statutory
obligations that may lead to conflicting guidance and direction.

Understanding the Strategic Context
2 June 2014 FM 3-24/MCWP 3-33.5, C1 1-13
COMPREHENSIVE EFFORT
1-47. A comprehensive effort, at a minimum, incorporates all the capabilities of U.S and host-nation
governments, and may include intergovernmental and regional organizations, and nongovernmental
organizations (NGOs) to address the root causes of the insurgency, in conjunction with military operations
aimed at the insurgents themselves. This is difficult because many organizations will be operating in the
same area, some conducting combat operations and others using non-lethal methods such as education
programs and humanitarian assistance. Each organization will have different perspectives or interests.
Foreign area officers may be essential in ensuring these various organization work in a comprehensive
effort. Some organizations that may be part of a comprehensive effort are—
- Other governments’ agencies.
- Multinational forces.
- Multinational corporations and contractors.
- Intergovernmental organizations, such as the United Nations.
- NGOs.
- Private sector corporations.
- Other organizations that wield diplomatic, informational, and economic power.
1-48. These various organizations may work with, in parallel to, separately from, or counter to U.S.
government and civilian agencies supporting counterinsurgency efforts. Those organizations whose goals
align at least partially with U.S. government goals frequently have capabilities that, if properly
synchronized and coordinated, can be critical to achieving success in counterinsurgency operations.
Aligning U.S. military, NGO, and intergovernmental organization capabilities requires collaboration and
cooperation focused toward a common goal. This can be more difficult than working with other U.S.
government agencies. Where military operations typically demand unity of command, the challenge for
military and civilian leaders is to forge unity of effort among the diverse array of actors involved in a
counterinsurgency. Often, the legal, cultural, and operational requirements prevent direct collaboration
between U.S. land forces and non-U.S. civilian organizations. U.S. forces may encounter NGOs not aligned
with any insurgent faction who are providing humanitarian assistance. These organizations can be neutral
or hostile to U.S. policy goals. Commanders should handle such groups carefully and professionally.
Commanders work to understand the objectives and priorities of each organization. Unity of effort between
U.S. forces and host-nation forces is particularly critical. Understanding these organizations is essential to
understanding the operational environment and shaping effects on organizations that are hostile or neutral
to U.S. policy goals. (See JP 3-08 for more information on NGOs.)
UNITY OF COMMAND AND EFFORT
1-49. Unity of command is the operation of all forces under a single responsible commander who has the
requisite authority to direct and employ those forces in pursuit of a common purpose (JP 3-0). Where
possible, counterinsurgency leaders achieve unity of command by establishing and maintaining formal
command or support relationships. While designated officers will exercise unity of command of military
forces, such relationships will not usually include nonmilitary U.S. government organizations engaged in a
counterinsurgency mission. (See ADRP 5-0 for more information on unity of command.)
1-50. Unity of command of military forces is operationally desirable and important for the military to
establish. However, unity of command is almost impossible to achieve among all of the various actors in a
counterinsurgency. Differing political objectives, national caveats, the legal limitations on the use of force,
and sensitivities about subordinating national forces to those of other states or intergovernmental
organizations often preclude strong command relationships. While agreements that establish a
multinational force provide a legal foundation for determining the scope and limitations on authorities,
responsibilities, command, support, or other relationships, the reality might be less clear. Unity of
command is one of the most sensitive and difficult to resolve issues in a counterinsurgency.
1-51. When unity of command with part or all of the force, including nonmilitary elements, is not possible,
commanders work to achieve unity of effort. Unity of effort is coordination and cooperation toward
common objectives, even if the participants are not necessarily part of the same command or organization,
which is the product of successful unified action (JP 1). In a counterinsurgency operation, an example of

Chapter 1
1-14 FM 3-24/MCWP 3-33.5, C1 2 June 2014
unity of effort could be a military commander and a civilian leader ensuring that governance and economic
lines of effort are fully coordinated with military operations. Unity of effort among nationally, culturally,
and organizationally distinct partners is difficult to maintain, given their different layers of command. To
achieve unity of effort requires participants to overcome cultural barriers and set aside parochial agendas. It
also requires that each organization understand the capabilities and limitations of the others.
COORDINATION
1-52. In counterinsurgency operations, coordination efforts should include key participants from the outset.
The joint commander, through the strategic concept, works with the engaged civilian organizations to build
an interagency coordination plan during the joint operation planning process. Subordinate joint force
commanders and Army commanders also build civilian organization participation into their operations
plans. This is essential in integrating other government agencies and NGOs. Within an area of
responsibility and a joint operations area, appropriate decisionmaking structures are established at
combatant command, joint task force headquarters, and tactical levels in order to coordinate and resolve
military, political, and humanitarian issues.
1-53. The complex diplomatic, informational, military, and economic context of insurgency and
counterinsurgency precludes military leaders from exercising unity of command over civilian
organizations—and they should not try to do so. Interagency partners, NGOs, and private organizations
have many interests and agendas that military forces cannot control. In addition, the degree of
independence of local institutions affects their legitimacy to the population. However, military leaders
should make every effort to ensure that counterinsurgency actions are as well integrated as possible, taking
into consideration the distinct mission, need for independence, and security requirements of other
organizations. Coordination between the various actors in a counterinsurgency is essential.
1-54. U.S. government agencies should participate in coordination meetings to ensure integration with
military and host-nation plans. At the joint headquarters level, the commander establishes joint interagency
coordination groups. A joint interagency coordination group provides timely, usable information and
advice from an interagency perspective to the commander. Joint interagency coordination groups share and
integrate information and assist with synchronization, training, and exercises. Joint interagency
coordination groups may include representatives from other federal departments and agencies, state and
local authorities, and liaison officers from other commands and DOD components. The interagency
representatives and liaison officers are the subject matter experts for their respective agencies and
commands. They provide the critical bridge between the commander and interagency organizations. (See
JP 3-08 for more information on joint and interagency coordination.)
1-55. Coordination between NGOs may be difficult or impossible. Direct interaction among various
organizations may be impractical or undesirable because of various goals of NGOs and a NGO’s desire to
be seen by the society as autonomous. The differing goals and fundamental independence of NGOs and
local organizations usually prevent formal relationships governed by command authority. In the absence of
such relationships, military leaders seek to cooperate with other participants to contribute to achieving
counterinsurgency objectives. Informal or less authoritative relationships include coordination and liaison.
Basic awareness and general information sharing may be all that is possible. Nevertheless, NGOs and other
organizations may resist or refuse cooperation because of the appearance of cooperating with military
forces. However, government and internal agencies offer links to the various NGOs so coordination can be
accomplished without directly interacting with NGOs and causing potential security issues for them.
1-56. Commanders are responsible for coordinating the activities of military forces and cooperative
nonmilitary organizations in their areas of operations. To carry out this responsibility, military and civilian
leaders may establish a coordinating structure, such as an area coordination center or civil-military
operations center at each subordinate political level of the host-nation government. Area coordination
centers and civil-military operations centers provide forums for sharing information, conducting
coordination and liaison, and ensuring an effective and efficient division of labor. Active commander
involvement ensures coordination, establishes liaison (formal and informal), and shares information.
Influencing and persuading groups outside a commander’s authority requires skill and subtlety. In some
cases, informal meetings with a civilian group at a civil-military operations center will grow to an informal

Understanding the Strategic Context
13 May 2014 FM 3-24/MCWP 3-33.5 1-15
liaison that eventually leads to close cooperation. (See JP 3-22 for more information on coordinating
structures.)
1-57. Leaders ensure the various organizations supporting counterinsurgency operations in each area know
which commander is responsible for the respective areas of operation. Multiple organizations operating
within a land force commander’s area of operations—such as U.S. government, multinational forces, host
nation, interagency organizations, and special operations forces—might increase the risk of fratricide,
insider threats, and civilian casualties and may create tactical and operational gaps that insurgents can
exploit.
1-58. Entities best qualified to accomplish nonmilitary tasks may not always be available. In such cases,
military forces may need to perform those tasks until civilian-led capabilities become available. Within the
Army, civil affairs is the branch ideally organized, trained, and equipped to assist commanders in these
functions. Sometimes forces already have the skills required, and at other times they learn them during
execution. By default, U.S. and multinational military forces often possess the only readily available
capability to meet many of the local population’s fundamental needs. As such, it is important for
commanders to assess the capabilities of their forces and other organizations on the battlefield.
UNIFIED ACTION PARTNERS
1-59. Army and Marine forces conduct counterinsurgency with unified action partners. Unified action
partners are those military forces, governmental and nongovernmental organizations, and elements of the
private sector with whom Army and Marine Corps forces plan, coordinate, synchronize, and integrate
during the conduct of operations. Unified action partners include joint forces and components,
multinational forces, U.S. government agencies and departments, and some intergovernmental and NGOs.
Some important unified action partners in a counterinsurgency are—
- Host-nation government and forces.
- Joint forces.
- Department of State.
- Multinational forces.
- NGOs.
- Other organizations.
Host-Nation Government and Forces
1-60. The essential unified action partner is the host nation and its own forces. The purpose of
counterinsurgency operations, from the viewpoint of the U.S., is to support or enable the host nation to
defeat an insurgency. In the worst case situation, this may require the U.S. becoming the primary
counterinsurgent or working with groups inside a state to build a legitimate government. However, even in
the worse case, the goal is still for the host nation and its forces to defeat an insurgency.
Joint Force
1-61. The maritime component plays a critical role in controlling the seas, which may be vital to isolating
an insurgency, both physically and psychologically. The expeditionary character and versatility of maritime
forces provide an advantage in areas where access is denied or limited. Maritime forces may provide direct
support to a joint task force that does not include combat operations, to include civil-military operations,
logistic support, intelligence, communication sharing, humanitarian relief, maritime civil affairs, and
expeditionary medical aid and training.
1-62. Air forces and capabilities play a vital role in the military contribution to a counterinsurgency. Air
contributions include close air support precision strikes; personnel recovery, air interdiction, intelligence,
surveillance, and reconnaissance, communications, electronic warfare, combat support, and air mobility.

Chapter 1
1-16 FM 3-24/MCWP 3-33.5 13 May 2014
Department of State
1-63. The U.S. Department of State is responsible for implementing U.S. foreign policy and diplomacy
efforts and plays a key role in integrating the capabilities of the U.S. The Department of State leads. It also
oversees U.S. government support to counterinsurgency efforts. Several functional bureaus and offices
have substantive roles in the development and execution of counterinsurgency strategy. These offices
include the Bureau of Political-Military Affairs; the Bureau of Conflict and Stabilization Operations; the
Bureau of International Narcotics and Law Enforcement; the Bureau of Democracy, Human Rights, and
Labor; the Bureau of Population, Refugees, and Migration; the Bureau of Intelligence and Research; and
the Legal Advisor’s Office. The Department of State is responsible for diplomatic programs that assist a
host nation with countering an insurgency. In many U.S. military operations—such as governance capacity
building—the Department of State is the U.S. supported element and the military is the supporting element.
1-64. One important capability that the State Department maintains is the civilian response corps. The
civilian response corps maintains active members who are full time responders whose specific job is to
train for, prepare, and staff overseas conflict prevention and stabilization operations. Active members of the
civilian response corps can deploy on a 48-hour notice. The civilian response corps also maintains standby
members. They are current full-time employees of the U.S. government or retirees of the U.S. Foreign
Service. Members in the standby component must be available to deploy within 30 days, for up to 90 days,
with the possibility to extend their deployment. The civilian response corps’ work focuses on six skill sets:
Planning, operations, and management; security and rule of law; diplomacy and governance; essential
services; and force protection.
Country Team
1-65. The country team is the senior, in-country, United States coordinating and supervising body, headed
by the chief of the United States diplomatic mission, and composed of the senior member of each
represented United States department or agency, as desired by the chief of the United States diplomatic
mission (JP 3-07.4). In a foreign country, the chief of mission is the highest U.S. civil authority. The chief
of mission leads the country team and is responsible for integrating U.S. efforts in support of the host
nation. The defense attaché, usually a foreign area officer, will work directly with a county team. The
defense attaché provides important links to the country team for the commander. As permanently
established interagency organizations, country teams represent a priceless counterinsurgency resource.
They often provide significant local knowledge and interaction with the host-nation government and
population. (See figure 1-1 for an illustration of country team command relationships. See JP 3-07.4 for
more information on the country teams.) Some of the government agencies normally represented on a
country team include—
- The United States Agency for International Development.
- The Department of Justice.
- The Department of Treasury’s Office of Terrorism and Financial Intelligence.
- The Department of Homeland Security.
- The Department of Agriculture.
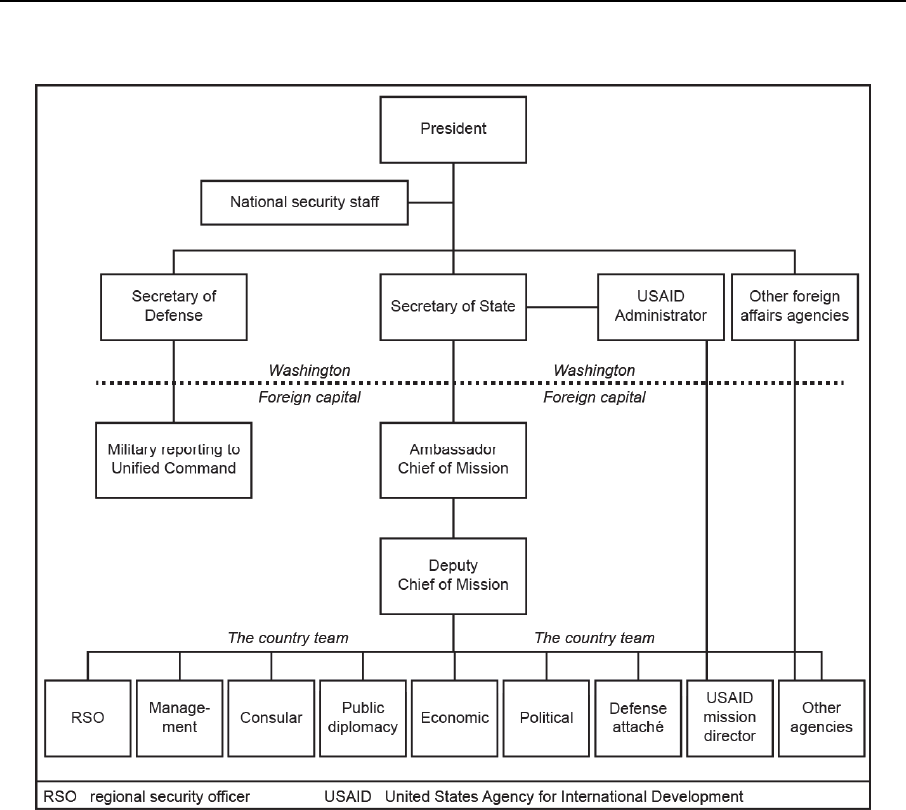
Understanding the Strategic Context
13 May 2014 FM 3-24/MCWP 3-33.5 1-17
Figure 1-1. Country team command relationships
1-66. An important enabler for ensuring unity of effort in countering an insurgency, especially when the
U.S. is enabling a host nation with various capabilities, is foreign area officers. These officers can be an
essential link to an embassy’s country team. By virtue of unique language proficiency and cultural and
regional expertise, foreign area officers can be critical in helping to integrate various capabilities into the
host nation’s ongoing efforts. While foreign area officers are often associated with security cooperation
activities, such as foreign military sales, foreign area officers have historically provided essential strategic
thinking and planning necessary to enable a host nation. As core members of the security cooperation
organization and defense attaché office within the embassy country team, foreign area officers serve as key
advisors to ambassadors and combatant commanders. Foreign area officers routinely operate in a
whole-of-government, joint, intergovernmental, and multinational environment. They can be essential in
integrating resources, capabilities, and activities throughout U.S. and multinational agencies to achieve
unity of effort and accomplish national counterinsurgency objectives.
Multinational Forces
1-67. Soldiers and Marines normally function as part of a multinational force, for example, by supporting
the United Nations or as part of the North Atlantic Treaty Organization. Each multinational participant
provides capabilities and strengths that U.S. forces may not have. Many other countries’ military forces
provide cultural backgrounds, historical experiences, and other capabilities that can be particularly valuable
to counterinsurgency efforts.

Chapter 1
1-18 FM 3-24/MCWP 3-33.5 13 May 2014
1-68. Nations join multinational efforts for various reasons. Although the missions of multinational
partners may appear similar to those of the U.S., rules of engagement, host-nation policies, and sensitivities
may differ among partners. U.S. military leaders require a strong cultural and political awareness of other
multinational military partners. Planners must be aware that multinational forces may also require
significant U.S. enabling capabilities such as medical evaluation and logistic support. (See JP 3-16 and the
American, British, Canadian, Australian, and New Zealand (ABCA) Coalitions Operations Handbook for
more information on multinational partners.)
Nongovernmental Organizations
1-69. A nongovernmental organization is a private, self-governing, not-for-profit organization dedicated to
alleviating human suffering; and/or promoting education, health care, economic development,
environmental protection, human rights, and conflict resolution; and/or encouraging the establishment of
democratic institutions and civil society (JP 3-08). There are several thousand NGOs of many different
types. Organizational charters and their members’ motivations govern their actions. Some NGOs receive at
least part of their funding from national governments or intergovernmental organizations. Some may
become implementing partners according to grants or contracts. For example, the United States Agency for
Internal Development contracts some NGOs to perform certain functions. In these cases, the funding
organization often gains oversight and authority over how to use the funds.
1-70. To ensure their own security and gain access to vulnerable populations in theaters of conflict, most
NGOs maintain neutrality, impartiality, and independence from all sides in a counterinsurgency. These
positions provide NGOs protection against claims of favoritism by the parties to armed conflict and
enhance the credibility and security of these organizations.
1-71. Depending on the degree to which NGOs follow these principles, NGOs may carry out their work
with a very different frame of reference from that of the government. Rather than perceiving their
organization as supporting the overall U.S. or multinational stabilization effort, they may view the situation
from the perspective of the victims of conflict, regardless of their affiliation with belligerent parties. They
may give preference to individuals and communities based on humanitarian need, rather than meeting
operational objectives.
1-72. While NGOs sometimes choose to coordinate their activities with the U.S. government for security,
policy, or funding, often they are reluctant for fear of being associated with the government’s political
goals in conflict. This creates a natural but often unavoidable tension in the relationship. Commander’s ease
this tension through a mutual understanding of respective mandates and a clear delineation of tasks. For
example, some organizations, such as the International Committee of the Red Cross, refuse to take armed
escorts in conflict zones, relying instead on their wide recognition as neutral, independent, and impartial
humanitarian actors. Commanders ensure information is available to NGOs to allow them to deconflict
ground and air routes and provide contact information for them to coordinate safe passage in areas with
active air or ground defense measures. At a minimum, air information should be passed through
International Civil Aviation Organization notices to airmen and host-nation aeronautical information
publications.
1-73. Many NGOs may operate in conflict areas long before external military forces arrive. These NGOs
may remain after forces depart. Depending on their mandate, they can support critical host-nation
government functions, or can contribute to the stabilization effort. To the greatest extent possible,
commanders attempt to complement rather than override their capabilities. Commanders strive to build a
complementary, trust-based relationship based on mutual understanding and a clear delineation of
objectives and tasks.
Other Organizations
1-74. An intergovernmental organization is an organization created by a formal agreement between two or
more governments on a global, regional, or functional basis to protect and promote national interests shared
by member states (JP 3-08). Regional organizations like the Organization of American States and European
Union or global organizations such as the United Nations may be involved in some counterinsurgency

Understanding the Strategic Context
13 May 2014 FM 3-24/MCWP 3-33.5 1-19
operations. The United Nations, in particular, has many subordinate and affiliated agencies active
worldwide.
1-75. In the private sector, multinational corporations and other businesses often operate in a conflict
environment. At a minimum, commanders should know which companies are present in their area of
operations and where those companies are conducting business. Understanding the overall profit motivation
of these business will help commanders understand their actions in the operational environment.
1-76. When the U.S. government pays contractors, the principle of unity of command should apply.
Commanders should influence contractors’ performance through U.S. government contract supervisors.
Commanders should identify contractors operating in their area of operations and determine the nature of
their contract, accountability mechanisms, and appropriate coordination relationships. (See FM 4-92 for
more information on contractors.)
STRATEGIC PRINCIPLES
1-77. Whatever type of strategy and operational approach that a counterinsurgency takes, several strategic
principles are normally relevant. Whether the U.S. is enabling a host nation with certain capabilities or
directly using its land forces, the principles listed in paragraphs 1-78 through 1-92 are relevant to most
counterinsurgency operations. However, these principles are not meant to be exclusive rules for every
conflict. They are provided for the practitioner and planner as a foundation for how they think about
planning and executing counterinsurgency operations.
LEGITIMACY IS THE MAIN OBJECTIVE
1-78. Fostering development of effective governance by a legitimate government that can provide security
and acts in the best interests of its people may be essential to countering an insurgency. Legitimacy can be
seen as the willing acceptance of a government by its population. Counterinsurgency forces may achieve
this objective by the balanced application of both military and nonmilitary means. Governments rule
through a combination of consent and coercion. Governments that are “legitimate” normally rule with the
consent of the governed; those described as “illegitimate” tend to rely mainly or entirely on coercion.
Citizens of the latter tend to obey the state for fear of the consequences of doing otherwise, rather than
because they voluntarily accept its rule. Legitimacy is a perceived condition by the population that can only
be achieved by host-nation government actions that lead to an acceptance of its primacy by the people. (See
paragraphs 1-27 through 1-33 for more information on legitimacy and control.)
COUNTERINSURGENT FORCES MUST UNDERSTAND THE ENVIRONMENT
1-79. Successful conduct of counterinsurgency operations depends on thoroughly understanding the
society and culture within which they are being conducted. In most counterinsurgency operations in which
foreign forces participate, insurgents hold a distinct advantage in their level of local knowledge. They speak
the language, move easily within the society, and are more likely to understand the population’s interests.
Thus, for foreign forces participating in counterinsurgency operations, they require a greater emphasis on
certain skills, such as language and cultural understanding. Understanding the operational environment
allows the counterinsurgent to identify the conditions which impact the prerequisites for the insurgency and
the root causes that are driving the population to accept the insurgency. Only through understanding the
operational environment can the counterinsurgent plan and execute successful operations to counter the
conditions that allow the insurgency to exist in the first place. Nevertheless, U.S. forces must never assume
they will be welcomed by a local population. They may even be viewed as occupiers. (See chapter 2 for a
discussion on developing an understanding of the operational environment.)
INTELLIGENCE DRIVES OPERATIONS
1-80. Effective counterinsurgency operations are shaped by timely, relevant, tailored, predictive, accurate,
and reliable intelligence, gathered and analyzed at the lowest possible level and disseminated throughout
the force. Without accurate and predictive intelligence, it is often better to not act rather than to act.
Gaining situational understanding before action is often essential in avoiding long term damage to mission
objectives. In environments where commanders do not have situational understanding, the first action they

Chapter 1
1-20 FM 3-24/MCWP 3-33.5 13 May 2014
should take is to use forces to gain that understanding while not creating unintended and lasting harm to the
mission. (See chapter 11 for more information on intelligence.)
1-81. Because of the dispersed nature of counterinsurgency operations, the actions of counterinsurgency
forces are key generators of intelligence. In counterinsurgency operations, a cycle often develops where
intelligence drives operations, which produces additional intelligence that facilitates subsequent operations.
Reporting by tactical units and civilian agencies is often of greater importance than reporting by specialized
national intelligence assets. These factors, along with the need to generate a favorable tempo (rate of
military operations) drive the requirement to produce and disseminate intelligence at the lowest practical
level. Commanders are responsible for driving the intelligence process.
1-82. Understanding the operational environment extends beyond insurgent combatants and insurgent
leaders. To truly counter an insurgency, counterinsurgents must gather, analyze, and disseminate civil
information pertaining to the population. If legitimacy is the primary principle of counterinsurgency
operations, then identifying what is preventing legitimacy is as important, if not more so, than intelligence
pertaining to enemy actions. Since Army and Marine Corps forces conduct counterinsurgency with unified
action partners, it is vital to separate intelligence and civil information. Some partners, particularly NGOs,
may not exchange information with Army and Marine Corps forces if that information is overtly tied to
intelligence collection. Achieving a common situational understanding with unified action partners will
require exchanging information outside of the intelligence realm.
SECURITY UNDER THE RULE OF LAW IS ESSENTIAL
1-83. Whenever possible, security forces should be provided by the host nation. To establish legitimacy,
the affected government must strive to transition security activities from military authorities to host-nation
law enforcement authorities as quickly as feasible. When insurgents are seen as criminals, they lose public
support. Prior to any transition to full host-nation responsibility, however, the violence level must be
reduced enough for the host-nation counterinsurgency forces to maintain order; otherwise, the host-nation
counterinsurgency forces will be unable to secure the population and the host nation may lose the
legitimacy gained by the transition. U.S. counterinsurgent forces must also understand how the military and
police are viewed by the population and not assume they are always seen as protectors. The goal of a
change to a host-nation security force is an accountable, self-sustaining, capable, and credible force able to
meet the security challenges faced by the host nation and seen as legitimate by the population.
1-84. Security forces use a legal system that conforms to local culture and practices to deal with insurgents
and criminals and that enhances the affected government’s legitimacy. To succeed in countering an
insurgency, the host-nation government must develop its legal and conflict resolution systems, including
police forces, judicial systems, and penal facilities. The legal use of population control measures, including
curfews, movement restrictions, travel permits, registration cards, and biometric census may assist in
identifying the insurgents and protecting the population.
COUNTERINSURGENT FORCES SHOULD PREPARE FOR A LONG-TERM COMMITMENT
1-85. Counterinsurgency operations can be protracted. Though most insurgencies are quickly defeated by
the host nation and its military forces, U.S. involvement normally comes in insurgencies that are not
quickly defeated. Insurgents can become extremely difficult to identify, track, and interdict if they are
effective in acting clandestinely. Insurgencies may persist for many years after the main threat has been
broken. Thus, counterinsurgency operations may demand considerable expenditures of time and resources.
The population must have confidence in the staying power of both the affected government and any
counterinsurgency forces supporting it. The population may prefer the affected government to the
insurgents; however, people do not actively support a government unless they are convinced that the
government has the means, ability, stamina, and will to win. Stabilizing the security situation and
transforming a failed, failing, or ineffectual government into a functional one is an extremely difficult task
that may take an extended period to complete. (See paragraphs 4-70 through 4-75 for information on the
seventh dynamic, phasing and timing.)

Understanding the Strategic Context
13 May 2014 FM 3-24/MCWP 3-33.5 1-21
MANAGE INFORMATION AND EXPECTATIONS
1-86. Information and expectations are related; skillful counterinsurgency forces manage both. To limit
discontent and build support, the affected government and any counterinsurgency forces assisting it create
and maintain a realistic set of expectations among the population, friendly military forces, and the
international community. The key tools to accomplish this are information operations through the effective
coordination and synchronization of information related capabilities. Effective counterinsurgency
commanders tell the truth; they refuse to give projections; and they do not promise more than can be
provided. Achieving steady progress toward a set of reasonable expectations can increase the population’s
tolerance for the inevitable inconveniences of ongoing counterinsurgency operations. Where a large foreign
force is present to help establish a regime, this progress can extend the period until foreign forces are
perceived by the population as an army of occupation.
1-87. Effective counterinsurgency forces must ensure that their deeds match their words and both are
consistent with the broader narrative. They should also understand that any action has an information
reaction. Counterinsurgency forces should carefully consider that information reaction’s impact on the
many audiences involved in the conflict and on the sidelines. They should work actively to shape responses
that further their ends. In particular, messages to different audiences must be consistent. In the global
information environment, people in the area of operations can access the internet and satellite television to
determine the messages counterinsurgency forces are sending to the international community. Any
perceived inconsistency reduces credibility and undermines counterinsurgency efforts.
USE THE APPROPRIATE LEVEL OF FORCE
1-88. Any use of force generates a series of reactions. There will be times when an overwhelming effort is
necessary to destroy or intimidate an opponent and reassure the population. However, counterinsurgency
forces, whether they are land, maritime, or air, calculate carefully the type and amount of force to be
applied and who wields it for any operation. Normally, counterinsurgency forces can use escalation of force
procedures to minimize unnecessary loss of life or suffering. These procedures are especially appropriate
during any operation in which the counterinsurgent security force interacts with the local population.
1-89. All interactions between security forces and the population directly impact legitimacy, and if the
counterinsurgent security forces show restraint in the eyes of the population, the entire counterinsurgency
effort is further legitimized. The general rule for the use of force for the counterinsurgents is “do not create
more enemies than you eliminate with your action.” Escalation of force does not limit the right of
self-defense, including the use of deadly force when such force is necessary to defend against a hostile act
or demonstrated hostile intent. However, counterinsurgency forces must be properly trained in such
procedures and, more importantly, in methods of shaping situations so that tactical leaders have to make
fewer split-second, life-or-death decisions.
LEARN AND ADAPT
1-90. An effective counterinsurgency force is a learning organization. Insurgents connected with other
organizations constantly exchange information about their enemy’s vulnerabilities—even with insurgents
in distant theaters. However, skillful counterinsurgency forces can adapt at least as fast as insurgents. Every
unit needs to be able to make observations, draw and apply lessons, and assess results. Commanders must
develop an effective system to circulate best practices throughout their command. Commanders might also
need to seek new policies that authorize or resource necessary changes. Insurgents shift their locations
looking for weak links, so widespread competence is required throughout the counterinsurgency force.
EMPOWER THE LOWEST LEVELS
1-91. Local commanders have the best grasp of their situations, but they require access to or control of the
resources needed to produce timely intelligence, conduct effective tactical operations, and manage
intelligence and civil-military operations. Leaders encourage individual initiatives and facilitate the
learning that must occur at every level. Effective counterinsurgency operations are decentralized, and
higher commanders owe it to their subordinates to push as many capabilities as possible down to their
levels. However, this must be balanced with ensuring that tactical leaders have the situational

Chapter 1
1-22 FM 3-24/MCWP 3-33.5 13 May 2014
understanding of the wider operational and strategic consequences of their actions. While tactical missions
are essential, commanders ensure that tactical missions support the overall objectives to defeat the
insurgency.
SUPPORT THE HOST NATION
1-92. In the situation of U.S. and multinational forces committed to assisting a host-nation government
with its counterinsurgency strategy, the long-term goal is to leave a government able to stand by itself. In
the end, the host nation has to win on its own. Achieving this requires development of viable local leaders
and institutions. External assistance can help, but host-nation authorities must accept responsibilities to
achieve real victory. Depending upon the condition of the host-nation government (failed, failing, or
viable), a robust whole-of-government approach is critical to enabling that government to accept those
responsibilities. In a failed or failing state, there may be no functioning government or national economy.
The counterinsurgent, therefore, will be forced to create institutions necessary to provide governance and
support economic development. While it may be easier for U.S. military units to conduct operations
themselves, it is better to work to strengthen local forces and institutions and then assist them. Host-nation
governments have the final responsibility to solve their own problems. Eventually all foreign armies are
seen as interlopers or occupiers. The sooner the decisive effort can transition to host-nation institutions
without unacceptable degradation, the better.
13 May 2014 FM 3-24/MCWP 3-33.5 2-1
Chapter 2
Understanding an Operational Environment
2-1. Regional and strategic conditions affect United States (U.S.) involvement in opposing an insurgency.
How and why the U.S. becomes involved in an insurgency is important. However, some important strategic
trends can also affect the context of an insurgency. These global trends include demographic changes,
globalization, the proliferation of weapons of mass destruction, religious extremism, and failed states
leading to an era of persistent conflict. Persistent conflict is the protracted conflict among state, non-state,
and individual actors who are increasingly willing to use violence to achieve their political and ideological
ends. These trends not only affect the likelihood of conflict, but they also affect the capabilities and action
of friendly, threat, neutral, and nonaligned actors.
2-2. Understanding the conditions that may affect the stability of a nation or region assists commanders as
they focus on a specific operational environment to determine the root causes that led to an insurgency.
Whether operating at the operational or tactical level, commanders must understand and anticipate the
effects of their operations and how they fit into the broader mission. The U.S. may enter situations with
long-standing conflicts and established ways of life that have implications beyond the boundaries of a
specific area of operations. Commanders identify relationships within that area that may exert external
influence on other governments that have their own agendas in the region. Commanders also recognize that
in the modern, interconnected world, actions at any level may have far broader impact than intended. This,
coupled with certain global trends, may provoke more insurgencies in the future.
DEMOGRAPHIC AND URBANIZATION TRENDS
2-3. In the future, the world will become more populated and urbanized. Global population will increase
by approximately 1.2 billion people by 2025 with more than a billion new urban dwellers in that time. Most
population growth will occur in the developing world. Population growth, urbanization, and competition
for limited resources in the Middle East, Africa, and South Central Asia will contribute to increased
resource scarcity and may present governance challenges. Climate change combined with increased
population centers in or near coastal environments may challenge the ability of failing and fragile states to
respond to natural disasters. These conditions enhance the possibility of insurgencies in highly populated
developing countries whose governments lack the capacity to provide effective governance, including
security and the rule of law. These trends could lead to failed states and problems that will affect regional
and global security because of globalization.
2-4. Urbanization is the growth of urban areas due to both a population surge and migration. In 1950,
29 percent of the world’s population lived in urban areas; by 2050, scientists estimate that 60 percent of the
world’s population will live in urban areas. This rapid growth of urban areas, and the accompanying
crowded conditions with the potential for high unemployment, creates a greater potential that future
insurgencies may arise in urban areas.
GLOBALIZATION
2-5. Globalization is a combination of the technological, economic, social, cultural, and political forces
that are bringing nation-states and the people of the world closer together. Globalization affects an
insurgency by providing a freer flow of arms, information, and money to an insurgent group or insurgents
and allows an insurgency to have a wider strategic effect than in the past. It is easy for ethnic groups or
ideological groups to connect internationally because of globalization. Globalization provides a greater
likelihood that insurgents will have access to outside resources, or that they will try to affect objectives
outside of their local area. Through technology, globalization allows an insurgent to gain access to cyber
electromagnetic tools that could be used to attack any country. It also makes ideologically or religiously
motivated insurgencies more prevalent due to closer contact between traditional and modern societies.

Chapter 2
2-2 FM 3-24/MCWP 3-33.5 13 May 2014
PROLIFERATION OF WEAPONS
2-6. The proliferation of weapons of mass destruction and precision weapons will increase the potential
for catastrophic attacks. The threat or use of weapons of mass destruction by terrorist organizations is as
real as it is deadly. Weapons of mass destruction present significant possibilities beyond terrorist actors. If
an insurgent group acquires them, they can allow the insurgent group to pressure the host nation or attack a
target that would have countrywide, regional, or global strategic affects. These weapons can provide an
insurgent group with capabilities unmatched in the history of irregular warfare. The likelihood of an
insurgent group obtaining these weapons has never been higher because of both globalization and the
number of failed states. As ethnic and ideological groups enhance bonds that go beyond state boundaries,
and insurgent groups create vast safe haven areas within failed states, the proliferation of weapons of mass
destruction creates new possibilities for insurgencies. Not only will insurgents strive to obtain weapons of
mass destruction, but the continued availability of more precise, cheaper, and more lethal conventional
weapons will make insurgent actions more deadly than in the past. (See FM 3-11/MCWP 3-37.1 for more
information on chemical, biological, radiological, and nuclear operations.)
FAILING OR FAILED STATES
2-7. Governments of nation-states face increasingly greater challenges in providing effective support to
their growing populations. The problems of both demographic changes and the pressures of globalization,
corruption, lack of government services, and decaying infrastructure can lead to a failed state. A failed state
can provide insurgent groups safe havens to build their organizations, but it may also hinder their ability to
promulgate their message and actions due to a lack of infrastructure. (See FM 3-07 for a detailed discussion
on a failed state framework.)
THE OPERATIONAL VARIABLES
2-8. An operational environment is a composite of the conditions, circumstances, and influences that
affect the employment of capabilities and bear on the decisions of the commander (JP 3-0). Commanders
and staffs analyze and describe an operational environment in terms of eight interrelated operational
variables: political, military, economic, social, information, infrastructure, physical environment, and time.
The operational variables are fundamental to developing a comprehensive understanding of an operational
environment.
2-9. When viewing an operational environment, it is important to identify friendly, neutral, and hostile
actors. However, it is uniquely important in counterinsurgency operations that commanders and staff do not
view these actors as static and unchanging over time. Actors can become more hostile or become less
hostile. It is the interaction between the actors and the changes between their interactions that is important.
The actors have many influences on their actions and those influences help determine if an actor stays the
same, becomes friendlier, or becomes more hostile. (See JP 2-01.3 for more information on an operational
environment.)
2-10. In Iraq's Anbar Province, the eight interrelated operational variables created a unique operational
environment. The al Qaim tribes had different interests, both political and economic, than both the
Americans and al Qaeda. Religion, economic interests, culture, and other variables helped to shape the
actions of everyone in the operational environment. The Marine Corps had to act in this environment and
attempt to shape it. This was a process that required situational understanding and an appreciation for the
unique environment.
The Anbar Province Operational Environment
The Anbar Province’s al Qaim district became increasingly important to Abu
Musab al-Zarqawi’s al Qaeda in Iraq after November 2004 when it lost its sanctuary
to the American forces’ offensive in the second battle of Fallujah. The al Qaim district
is located on Iraq’s border with Syria. Although the district represents only 10% of the
Anbar population, the area holds strategic importance due to its location along the
Iraqi/Syrian border as well as the Euphrates River. Al Qaim is and always has been a
lucrative smuggling route for black market goods and served as al Qaeda in Iraq’s
Understanding an Operational Environment
2 June 2014 FM 3-24/MCWP 3-33.5, C1 2-3
lifeline to infiltrate Baghdad with foreign fighters, money, and other resources that
fueled the insurgency. With the loss of Fallujah, al Qaim became al Qaeda in Iraq’s
newfound sanctuary.
Al Qaeda in Iraq arrived with offers of partnering with al Qaim’s tribes to
defeat and expel the Americans. They promised the indigenous population money
and other resources for their support. As Muslims and Arabs, al Qaeda in Iraq
members exhorted that it was their obligation, their Jihad, to fight the crusaders. After
all, the Americans, supposedly ignorant of tribal customs, religion, and traditions,
allegedly had disrespected and dishonored the people of al Qaim and a patriotic
resistance had already formed in the district. The tribes of al Qaim saw the al Qaeda
movement as the answer to their problem with the Americans. The tribes, together
with al Qaeda in Iraq, felt that the time was ripe to rid the area of the infidel occupiers.
Al Qaim tribes varied in available resources and were incapable of defeating
the American occupiers on their own. For example, the Albu-Mahal tribe, the
strongest tribe in the area, organized and resourced the Hamza Battalion specifically
to fight the Americans. However, it, along with the other tribal militias, lacked the
weaponry, ammunition, and other equipment to win such a fight on their own. Al
Qaeda in Iraq’s offer was tempting and most of the tribes accepted.
As time went on it became apparent that al Qaeda in Iraq’s offer was
deceptive; this partnership was not what it seemed. Al Qaeda in Iraq provided
weaponry and funding, but in return they demanded to lead the Jihad with the intent
of first destroying and then transforming the social fabric of the tribes and al Qaim. Al
Qaeda in Iraq started by taking over the smuggling routes, skimming large profits and
killing those that resisted. They then imposed a radical form of Sharia on the
community with fanatical punishments for transgressors. Religion was used to justify
al Qaeda in Iraq’s actions, which included marriages to the local women, not allowing
cigarettes, the ban of music and films, and the common intimidation tactic of
beheading those that resisted.
3rd Battalion 6th Marines (3/6) executed Operation IRON FIST the first
week of October, attacking from east to west through the town of Sadah and eastern
Karabila, ultimately stopping at the Emerald Wadi in the center of the al Qaim region.
They built four combat outposts, Chosin, Iwo Jima, Belleau Wood, and Khe Sahn,
and left Marines and Iraqis in place, providing a combined, permanent, persistent,
presence.
The next clearing operation was conducted the first week in November by
3/6 and 2/1 commanded by Regimental Combat Team 2. This operation cleared the
Husaybah, Karabilah, Sadah and Ubaydi areas of all insurgents. Immediately upon
clearing the areas, 3/6 began constructing combat outposts in all of the cities.
By late November 3/6 had constructed 14 combat outposts in the areas
from Husaybah to Ubaydi. Each combat outpost consisted of a U. S. Marine platoon
and an Iraqi Army platoon or company. Those positions completed and reflected
combined, permanent, persistent presence, where the Marines and Iraqi Army lived
together and among the people.
The next step was to engage the people. Mission analysis led to assigning
company areas based on the tribal distribution. The idea was to link a company with
a tribe. This was not an exact science because the tribes were intermingled, but they
did locate companies in areas where a majority of a tribe resided. The next step was
a concerted drive to recruit tribesmen into the police force. The Marines solicited help
from the Sheikhs to nominate men from their tribes, and started developing police
stations near the combat outposts. This would allow the Marines and Iraqi Army
forces to partner with the local police forces in those areas and further engender trust
and confidence from the local people.
Moving goods across the Iraqi and Syrian border was closely connected to
the local economy. Undermining this trade would jeopardize a fragile relationship that
U.S. forces worked hard to develop. In fact, U.S. forces had learned from the sheikhs

Chapter 2
2-4 FM 3-24/MCWP 3-33.5, C1 2 June 2014
that disruption of trade was one of the major grievances the locals had against al
Qaeda in Iraq. Local tribes agreed to allow U.S. forces to stop and inspect all
vehicles coming into the country to ensure no foreign fighters, money, or weapons
were entering Iraq. The tribes also agreed to help with the inspection. New local
police largely conducted these inspections with the Iraqi Army (with Marines in
overwatch.) The tribes had picked the Iraqi government’s side in the struggle against
al Qaeda in Iraq and wanted to stop foreign fighters, money, and weapons from
entering Iraq as much as the U.S. forces did.
2-11. Understanding is necessary to begin planning the initial development of measures of effectiveness
and performance. The commander must understand what has happened in an operational environment and
determine the nature, scope, and severity of its problems. A situation is usually more complicated than it
seems when the military force first becomes involved. Understanding an operational environment is a
collaborative effort of the unified action partners. These partners may include U.S. government military and
civilian personnel, international civilian and military personnel, and host-nation civilian and military
personnel. To the maximum extent possible, the military force and unified action partners strive to have a
common situational understanding from the beginning of an operation. If the partnering agencies do not
have the same situational understanding, they can quickly find themselves working at odds with each other.
Commanders will rarely have enough time to fully understand an operational environment. Understanding
an operational environment is a continued and iterative process that will continue throughout an operation.
2-12. An area of operations is an operational area defined by the joint force commander for land and
maritime forces that should be large enough to accomplish their missions and protect their forces (JP 3-0).
For land operations, an area of operations includes subordinate areas of operations as well.
2-13. A commander’s area of operations may be relatively static, but people, weapons, commodities, and
information continuously flow through an area of operations. An area of operations can cross physical
structures, such as roads and rivers, and span diverse population groups. Fabricated borders that divide
natural groupings can create problems in understanding an area of operations. For example, cross-border
ties allow insurgents safe havens outside of a tactical unit’s area of operations. Moreover, international
boundaries often divide population groups. The span of an insurgency may be far larger than the defined
area of operations and areas outside the area of operations may be relevant to a commander. For example,
areas outside a commander’s area of operations may provide a safe haven for an insurgency, or an adjacent
state may support an insurgency. In an insurgency, an area of interest may be large.
2-14. The area of interest is that area of concern to the commander, including the area of influence, areas
adjacent thereto, and extending into enemy territory. This area also includes areas occupied by enemy
forces who could jeopardize the accomplishment of the mission (JP 3-0). It is the area in which events
could have significant impact on areas of operations. An area of interest can be large relative to the area of
operations. When defining an area of interest, commanders should consider the operational variables. (See
JP 3-0 for more information on an area of influence.)
2-15. Commanders analyze operational variables to understand the operational environment in which they
are conducting operations. An operational environment is not static; it continues to evolve. Introducing
units into an operational environment causes shifts and changes. As a result, commanders, their respective
staffs, and all Soldiers and Marines must continuously reassess an operational environment for changing
conditions. Moreover, in addition to understanding U.S. interests and desired end states in an environment,
a commander must understand the environment from three additional perspectives: those of the host nation,
the enemy, and the population.
POLITICAL
2-16. The political variable describes the distribution of responsibility and power at all levels of
governance—formally constituted authorities, as well as informal or covert political powers. The
counterinsurgent seeks to understand not just the formal political system, such as political parties and
elected officials, but also the informal systems of political influence, such as ethnic groups and other
centers of power. There is a connection between the political variable and the social variable. For example,

Understanding an Operational Environment
13 May 2014 FM 3-24/MCWP 3-33.5 2-5
a tribal grouping or a social caste may directly affect whom that group sees as a legitimate authority in an
area. Moreover, these social groupings can affect the formal power structure. For example, in an electoral
system, groups will often vote as blocs, giving them added political power in that formal system. (See
ADRP 5-0 for more information on the political variable.)
2-17. Often, informal groups such as tribes or local councils are the essential actors in the distribution of
political power, especially at the local level. Political power is the ability to influence behavior. The biggest
influence of behavior is often local groupings that can create a norming effect on a population. Most groups
hold power only because the population accepts that power distribution.
2-18. However, the opposite can also be true and the formal political system can change group identity and
influence the actions of any social group. States can create identity in a population through education and
information. For example, an education program that instills nationalist views in an individual from an
early age can be a powerful tool in shaping a person’s identity and in turn whom that person sees as a
legitimate authority. Group and individual identities are not static, nor is whom a population views as
legitimate static. While groups have internal means to view identity, variables outside the group, including
the host nation, also affect them.
2-19. The commitment and motivation of a host nation to defeat an insurgency is an important motivation.
Governments with more than one of the following traits have tended to lose historically, even when
supported by competent and committed external forces:
- Government sponsors or protects unpopular economic and social arrangements or cultural
institutions.
- Government is involved in corrupt and arbitrary personalistic rule.
- Government operates as a kleptocracy.
- Government is controlled by elites with perverse incentives to continue conflict.
- Government is economically dependent on external actors.
The harsh reality for counterinsurgents is that some of these negative characteristics are usually present,
and they are key factors in sparking insurgencies in the first place. As a result, the interests of a host-nation
government are often at odds with what the best practices would be to solve its political problems. (See
paragraphs 1-27 through 1-33 for more information on legitimacy and control.)
MILITARY
2-20. The military variable explores the military and paramilitary capabilities of all relevant actors (enemy,
friendly, and neutral) in a given operational environment. For many countries, the army’s predominant
purpose is to be the military force responsible for maintaining external security. However, this is not a
universal rule, and many militaries become involved in internal security and even governance. In some
cases, there is a degree of military control over the government, which then blends the political and military
variables. This can range from a military dictatorship to a praetorian guard type military that periodically
intervenes in the governance of a society. Even in cases where a host nation appears to have complete
objective control over its military forces, these military forces can be an important bureaucratic and
political actor. The interaction between the military and the political structure is important to understanding
this variable’s relationship with the political distribution of power in a society. (See ADRP 5-0 for more
information on the military variable.)
2-21. A host of institutions including police, paramilitary, intelligence, and other organizations can
maintain internal security. Thus, commanders and staffs need to consider them within the military variable.
In many autocratic societies, intelligence agencies provide an essential means of control over a society.
Many societies maintain civil control and civil security by an accepted rule of law and a police force that
enforces the rule of law. In a counterinsurgency, the host nation may use the military or a paramilitary to
defeat an insurgency.
2-22. The military variable includes all forces involved in both internal and external security. U.S.
counterinsurgents must fully understand how the host nation maintains internal and external security.
Moreover, they must understand both neutral and enemy military forces. Neutral military forces are
common in a counterinsurgency, as some states or multinational corporations will employ or contract for

Chapter 2
2-6 FM 3-24/MCWP 3-33.5 13 May 2014
limited forces to protect personnel, resources, or infrastructure for their own interests. A peacekeeping
force may be maintaining a position of neutrality in the conflict. There can also be informal groupings of
military power. For example, local gangs, armed militias, and private security agents can be a factor in
local areas.
2-23. Commanders and staffs should analyze friendly, neutral, and enemy forces with both qualitative and
quantitative data. Some aspects to consider include—
- Position of forces in national and local governmental structure.
- General organization, training, and doctrine.
- Economic basis (to include the appropriations system).
- Conscription or recruitment systems.
- Police role in the nation’s internal security.
- Rapport with population.
- The impact of other international forces already there or there in the recent past.
These considerations are particularly important with regard to the insurgents. Knowing from what groups
and sources, both within the country of conflict and outside of it, are providing what kinds of support (for
example, financial, personnel, materiel, and provisions) and by what processes or routes is critical.
Insurgencies that continue to meet their tangible support needs are difficult to defeat.
2-24. One enemy force in a counterinsurgency can vary widely from another. Some may be based on
cellular organizations while others may be more hierarchical. Moreover, there may be a wide variance in
enemy capabilities. Some insurgencies may have capabilities to conduct large scale and well coordinated
attacks that may rival the capability of a host nation’s military. Others may have less capability and may
rely on small-unit tactics. (See paragraphs 4-76 through 4-103 for a discussion of the eighth dynamic,
organizational and operational patterns, and see chapter 5 for a further discussion on enemy military
forces.)
ECONOMIC
2-25. The economic variable encompasses individual and group behaviors related to gaining access to,
producing, distributing, and consuming resources. These behaviors determine incentives and disincentives
that encourage or discourage economic decisions. The sum of these individual and group decisions may
determine the production, distribution, and consumption of economic resources. Typically, an economy is
conceptualized as currency, stocks, major commodities, banking, and trade controlled and monitored by the
government. However, informal economies, trade, or economic exchange outside state-controlled or
money-based transactions may be of equal or greater importance than formal economies in understanding
an operational environment. While the world economy continues to grow more interdependent, local
economies remain relatively distinct. These differences significantly influence political choices, including
individuals’ decisions to support or subvert the existing order. When commanders and staffs analyze a local
economy, they consider both governmental policies and the type of local economy.
2-26. Types of economies vary widely. When looking at economic activities, commanders and staffs strive
to understand the relative importance of the various sectors of an economy. Comparing the percentage of
the economy in the public sector versus the private sector provides some understanding of the structure of
the economy. Moreover, the private and public sector can potentially be divided into different sectors based
on type of activities. Agriculture, raw materials, services, and other types of production play an important
role in defining the economy of a local area. It is important to analyze governmental policies. Corruption,
the rule of law, and macroeconomic policy play a role in the structure of a local economy.
2-27. Another important factor in analyzing economic activity is the informal economy. In weak states,
understanding the informal economy is key to providing a full understanding of an operational
environment. The informal economy is those economic interactions and exchanges that are not recognized,
regulated, controlled, or taxed by a state government. In this case, informal does not always equal
illegitimate. For example, a black market is a form of informal economy based on criminal activities such
as racketeering, money laundering, prostitution, drug trafficking, and smuggling. On the other hand,
open-air markets and barter systems are legitimate activities that often contribute to an informal economy.

Understanding an Operational Environment
13 May 2014 FM 3-24/MCWP 3-33.5 2-7
In every country there is a balance between formal and informal economies. In successful states, the
informal economy may be relatively small. However, in failing states the informal economy may form the
majority of all economic activities. The local population may depend on informal markets for their most
basic needs. It is difficult but important for counterinsurgents to develop an understanding of these informal
economies (both legitimate and illegitimate.) Because they are outside host-nation government oversight,
insurgents can exploit even legitimate formal economies as a source of funding. The black market, on the
other hand, will most likely be a direct enabler of an insurgency in terms of both funding and logistics.
2-28. The counterinsurgent must consider other informal economies. Most people work, buy, and sell in
this economy, operating outside legal frameworks but not engaging in illicit or criminal activity (except
perhaps for taxation issues). Sensitivity to the rules of an informal economy is one piece of cultural
sensitivity to the population and the host nation in general. Examples of the rules of an informal economy
include the following:
- People earn income in non-cash payments such as benefits or goods.
- People often use land for decades (or more) through traditional usage rights granted by village
heads and chiefs with no legal title.
- People may work without pay (in arrangements such as the traditional divisions of household
and farm labor).
2-29. Economic variables also tie into other elements of a society. For example, ownership or control of
land and debt indicate something about the power structure within a society. Many developing societies
have highly concentrated ownership of land, which can serve as a driver for social conflict and discontent.
Whoever owns land or controls land has the power to use it for economic profit. Maintaining this
ownership or control during an insurgency indicates a degree of power in a society. The same is true of
debt. The ability to collect a debt indicates a degree of power in a society. Land and debt are examples of
how economic factors link into other social factors.
2-30. If a population views economic conditions as unjust, a lack of economic opportunity can be a root
cause of an insurgency. (See paragraphs 4-14 through 4-22 for more information on motives for an
insurgency.) As part of developing an understanding of an operational environment, counterinsurgents
assess the current economic variables, the economic opportunities available to different segments of the
population, and the effect insurgent and counterinsurgent operations are having on the population’s ability
to meet their most basic economic needs. Economic survival, especially in an area where an insurgency is
occurring, is almost as important and as immediate a challenge for households as physical security. For this
reason, leaders at all levels of the counterinsurgency operation (including platoons and companies) need to
assess the impacts of military operations on the following simple elements of the economic welfare of
households and communities:
- Income (including the capacity to earn streams of income in future).
- Assets and property (used to earn income).
- Work (including traditional patterns of unpaid work).
2-31. Commanders strive to understand the economic impact of the unit’s presence in an area. For better or
worse, the presence of an Army or Marine Corps unit affects normal economic incentives and disincentives
for individual behavior. Introducing foreign wealth can have unintended negative consequences. For this
reason, careful thought and planning are needed for a project intended to have local economic impact.
Commanders anticipate the economic impact of their arrival and their continued presence in the area of
operations. Additionally, commanders and staffs carefully weigh the costs and benefits associated with all
economic activity. Some factors to consider are—
- Prospects of long-term sustainability.
- Possibility of local price inflation.
- Disrupting natural incentives (such as farmers leaving fields to work on trash pickup projects).
SOCIAL
2-32. The social variable describes the cultural, religious, and ethnic makeup within an operational
environment and the beliefs, values, customs, and behaviors of society. Understanding the society is
Chapter 2
2-8 FM 3-24/MCWP 3-33.5 13 May 2014
foundational to understanding the social variable. A society is defined as a population whose members are
subject to the same political authority, occupy a common territory, have a common culture, and share a
sense of identity. However, no society is completely homogeneous. A society usually has a dominant
culture, but it can have secondary cultures. Different societies may share similar cultures, as Canada and
the U.S. do. Societies are not static, but change over time. (For more information on this variable, see
chapter 3 of this publication and ADRP 5-0.)
INFORMATION
2-33. The information variable describes the nature, scope, characteristics, and effects of individuals,
organizations, and systems that collect, process, disseminate, or act on information. The information
environment is the aggregate of individuals, organizations, and systems that collect, process, disseminate,
or act on information (JP 3-13). Understanding the communications systems is important because they
influence international, national, regional, and local audiences. Insurgents often use information and
disinformation to gain credibility and legitimacy with the population, while simultaneously undermining
their opponents. Understanding how people communicate and who influences them on a daily basis is
essential. This is important at all levels. For example, identifying local gathering places is important to
understand or influence the spread of information, rumors, and gossip.
2-34. The information environment is made up of three dimensions: physical, informational, and cognitive.
The cognitive dimension encompasses the mind of the decisionmaker or specific audience and is the
dimension where people think, perceive, visualize, and decide. The informational dimension is the place
where information is collected, processed, stored, disseminated, displayed, and protected with key
components of the content and flow of information. The physical dimension is composed of systems,
human beings (including decisionmakers, leaders, and military forces), and supporting infrastructure that
enable individuals and organizations to create effects conduct operations across air, land, maritime, space
and cyberspace domains across multiple domains. (See table 2-1.)
Table 2-1. Interrelated dimensions of the information environment
Dimension Description
Cognitive
dimension
• Exists in the minds of human beings.
• Consists of individual and collective consciousness.
• Where information is used to develop perceptions and make decisions.
• Significant characteristics include values, beliefs, perceptions, awareness,
and decisionmaking.
Informational
dimension
• Created by the interaction of the physical and cognitive dimensions.
• Where information is collected, processed, and disseminated.
• Significant characteristics are information content and flow.
Physical
dimension
• The tangible, real world.
• Where the information environment overlaps with the physical world.
• Consists of targetable individuals, organizations, information systems, and
the physical networks that connect them.
• Significant characteristics include terrain, weather, civilian information
infrastructure, media, populace, and third party organizations.
2-35. The technological advances in communications offer some unique considerations for insurgencies.
For one, international communication is easier than it used to be. This allows insurgencies to communicate
with organizations outside of their physical control. Connecting to diasporas or sympathetic groups could
be vital to an insurgency. With the ability to communicate comes the ability to move resources and funding.
Moreover, communications can be vital in importing weapons or other supplies to an insurgency. Global
communications can be essential in increasing the military capabilities of an insurgency, significantly
increasing the tempo of insurgent operations and their ability to change tactics.
2-36. At the operational and tactical level, communications allow for effective coordination of attacks.
Organizations can communicate by cell phones, by the internet, or a number of other rapid means. This

Understanding an Operational Environment
13 May 2014 FM 3-24/MCWP 3-33.5 2-9
allows for coordinated large-scale attacks even by dispersed organizations. (For additional information on
the information environment, see FM 3-13.)
INFRASTRUCTURE
2-37. The infrastructure variable is composed of the facilities (buildings and equipment), personnel, and
services needed for the functioning of a community or society. Societies have different infrastructure needs.
For example, the expectation for hours of available electricity vary widely. Counterinsurgents try to access
infrastructure needs to meet the expectation of the user, not their own expectations.
2-38. Infrastructure is also interrelated with other variables. For example, the development of a highway
system will affect the ability of people to move and interact with others. Creating a society in which
humans can easily move based on economic needs or simple desires greatly increases the variety of groups
a person will meet. These interactions and new relationships can change how a person views the world and
change that person’s values. A communications system, such as a cellular network, can have the same
effect. These systems allow for communications outside of one’s areas and allow the transmission of new
ideas and concepts.
2-39. Commanders and staffs conducting counterinsurgency operations must consider the relationship
between infrastructure and the economic variable. An effective infrastructure can allow for the easy
movement of people, goods, and ideas. Many businesses require infrastructure. While it is true that a local
population may not expect 24 hours of electricity a day, a manufacturing plant may require it. Moreover,
infrastructure such as schools can increase the human capital in an area and drive economic growth.
2-40. Infrastructure also has an effect on the military variable. Host-nation forces can use a good
transportation system, but so can an insurgency. A road system provides a means of transportation for
everyone, not simply the population and government. Moreover, infrastructure may be important for the
population and the government’s role in maintaining civil control and security. An attack on the
infrastructure may undermine the government’s legitimacy in an area. However, the opposite is also true.
An attack on infrastructure may also undermine the insurgency if the population places blame on the
insurgency and turns towards to government.
PHYSICAL ENVIRONMENT
2-41. The physical environment includes the geography and man-made structures, as well as the climate
and weather, in an area of operations. The physical environment affects the tactics and operations of both
insurgents and counterinsurgents. Extreme conditions, such as in nations in higher elevations, can make
insurgent movements difficult in the winter. The movement and the tactics of any military force will be
affected by the physical environment of its area of operations. A physical environment will influence
insurgency sanctuaries, the ability of an insurgency to hide resources, and the ability of an insurgency to
mass forces. Understanding a physical environment is essential to understanding an insurgency. (See
chapter 4 for further discussion on how a physical environment relates to an insurgency.)
2-42. A physical environment also relates to the other variables. A mountainous, landlocked country will
have a difficult time building the infrastructure needed for large-scale international trade. Moreover, if the
physical environment precludes the ability to easily produce an excess of food, it is difficult to divert much
labor to other enterprises. This can hamper the development of a highly specialized economy. An increase
in food production will often predate a major increase in industrial production.
TIME
2-43. Time describes the timing and duration of activities, events, or conditions within an operational
environment, as well as how various actors in an operational environment perceive the timing and duration.
Time also has an interrelated relationship with other variables. For example, a multinational coalition may
see its efforts in a counterinsurgency as limited by national objectives or by the public pressure. In other
words, outside parties can always leave a counterinsurgency. On the other hand, for the host nation, the
insurgents and the population in the struggle are less constrained by time than a multinational coalition. An

Chapter 2
2-10 FM 3-24/MCWP 3-33.5 13 May 2014
insurgency may use the time variable to its advantage, while the time variable usually works against an
external counterinsurgent.
2-44. Time can also play a role in the social variable. Ongoing conflicts tax societies. Populations can
become less interested in the nuisance of a conflict and more interested in simple peace. As time passes, a
population may be more interested in who is likely to win an insurgency than the motivation of either side
of the conflict. Counterinsurgents may also see time as working for or against them. (See paragraphs 4-30
through 4-45 for more information on insurgent strategies.)
THE MISSION VARIABLES AND CIVIL CONSIDERATIONS
2-45. Upon receipt of a mission, commanders filter information categorized by the operational variables
into relevant information with respect to the mission. They use the mission variables, in combination with
the operational variables, to refine their understanding of the situation and to visualize, describe, and direct
operations. The mission variables are mission, enemy, terrain and weather, troops and support available,
time available, and civil considerations. (See ADRP 5-0 for more information on the mission variables).
Within the mission variables, civil considerations are of unique importance for counterinsurgency. Civil
considerations are the influence of man-made infrastructure, civilian institutions, and activities of the
civilian leaders, populations, and organizations within an area of operations on the conduct of military
operations. Civil considerations comprise six characteristics, expressed in the memory aid ASCOPE: areas,
structures, capabilities, organizations, people, and events. (See FM 2-01.3/MCRP 2-3A for information on
the use of ASCOPE.)
2-46. The commanders’ refinement of information for their mission and their particular area of operations
is essential. ASCOPE can play an important role in the identification of structures or events that will have
an effect in a unit’s area of operations. As such, ASCOPE is an important tool for the unit in determining
important civil considerations in an insurgency. Units within an insurgency use ASCOPE to identify and
continually refine their understanding of the area of operations over time. Commanders and staffs consider
ASCOPE from the perspective of the population, the insurgent, and the counterinsurgent. This is
particularly important for counterinsurgency operations. (See JP 3-57, FM 3-57, MCWP 3-33.1, and ADRP
2-0 for detailed explanations of ASCOPE.)
13 May 2014 FM 3-24/MCWP 3-33.5 3-1
Chapter 3
Culture
3-1. This chapter addresses culture and its role in a counterinsurgency operational environment. Culture
forms the basis of how people interpret, understand, and respond to events and people around them.
Cultural understanding is critical because who a society considers to be legitimate will often be determined
by culture and norms. Additionally, counterinsurgency operations will likely be conducted as part of a
multinational effort, and understanding the culture of allies and partners is equally critical.
3-2. Insurgents from a local area generally understand local culture, the perspectives of the population,
and the population’s concerns and grievances much better than any foreign military forces understand
them. Therefore, culturally, the insurgent may have an enormous advantage over a foreign military force.
This may not be true if the insurgents are not from the local area. If a military force is to succeed in gaining
support of the population, it must seek to understand the local people and their culture and incorporate the
perspectives and concerns of the population in their plans and operations as well as, if not better than, the
insurgents incorporate them.
3-3. There are many definitions of culture in use by the United States (U.S.) military. As a starting point,
this publication understands culture is a web of meaning shared by members of a particular society or group
within a society.
UNDERSTANDING CULTURE
3-4. To be successful in interacting with the local population to gain information on the enemy, or to
understand their requirements, military members must do more than learn a few basic facts or “do’s and do
nots.” They must understand the way that their actions can change the situation for the local population
(both positively and negatively) and the resulting perceptions of the population towards those actions. To
be successful, commanders and staffs consider four fundamental aspects of culture when planning and
executing military operations:
- Culture influences how people view their world.
- Culture is holistic.
- Culture is learned and shared.
- Culture is created by people and can and does change.
3-5. The way that a culture influences how people view their world is referred to as their worldview.
Many people believe they view their world accurately, in a logical, rational, unbiased way. However,
people filter what they see and experience according to their beliefs and worldview. Information and
experiences that do not match what they believe to be true about the world are frequently rejected or
distorted to fit the way they believe the world should work. More than any other factor, culture informs and
influences that worldview. In other words, culture influences perceptions, understandings, and
interpretations of events. Soldiers and Marines need to know that U.S. interpretations of events are often
quite different from the perceptions of these events by other people in an area of operations. If Soldiers and
Marines assume that the local population will perceive actions the way that they do, they are likely to
misjudge their reactions. The U.S. military refers to this pattern of assuming others see events in the same
way the U.S. does as mirror imaging. Mirror imaging is dangerous because it leads Soldiers and Marines
into thinking that their assumptions about a problem and its solution are shared by the population and
multinational partners, rather than employing perspective taking, and looking at the problem from the
population’s perspective.
3-6. Holism is based on the principle that all socio-cultural aspects of human life are interconnected.
While interacting with people in other cultures, Soldiers and Marines may be tempted to say their problems
“are all about [fill in the blank: tribalism, corruption, lack of work ethic, and so on.].” In truth, very few

Chapter 3
3-2 FM 3-24/MCWP 3-33.5 13 May 2014
counterinsurgency challenges boil down to one simple answer. Politics affects economics. Family structure
affects job choices. Religion affects politics. Every aspect of culture affects every other aspect in some
way, even if indirectly. By acknowledging these interconnections, military members can better assess how
the local population might react to their presence and actions. For instance, when Soldiers and Marines are
not thinking holistically, they may anticipate that closing down a local market will only have an impact on
the local economy. However, after closing the market, it may be that the local reaction seems to be about
religion or tribal concerns instead of economics. Even if Soldiers and Marines do not understand why, they
should be aware that their actions will have unknown second and third order effects. By understanding that
a marketplace is more than a place to exchange goods for money, and that economic conditions may affect
tribal power, the status of religious leaders, and other social conditions, Soldiers and Marines can see a
culture holistically. A holistic perspective helps military members understand the complex
interconnectedness of a culture and avoid being surprised by local reactions to military decisions.
3-7. Culture is learned and shared. Children learn the appropriate way to act in a culture by observing
other people; by being taught accepted values and ways of thinking about the world from their parents,
teachers and others; and by practicing (sharing) what they have learned on a daily basis. This process of
learning a new culture is called socialization. Culture can be learned at any age. Marines and Soldiers, for
example, learn military culture by going through basic training or officer training in their late teens or early
twenties. In fact, these initial training schools recognize their important role in socializing young men and
women into core Marine and Army values. As a result, Marine Corps and Army basic training curriculums
include not only classes on marksmanship, but also classes on ethics and core values. In counterinsurgency
operations, understanding that culture is learned and shared can offer an important operational and tactical
opportunity. Any Marine or Soldier can learn about the culture of the population simply by interacting with
the local people. One of the more successful adaptations of the U.S. military in Iraq and Afghanistan
occurred when service members realized they could learn a lot about the local culture quickly by talking to
and observing their interpreters. Their enhanced understanding of the cultures of their areas of operations
enabled them to better negotiate with leaders, to conduct operations that would be successful, and in a
number of cases (such as the al Anbar Awakening), to gain the support and assistance of the population in
fighting an insurgency.
3-8. One of the keys to success (and failure) in dealing with a population in a counterinsurgency operation
is understanding that cultures are not static; they can and do change, often rapidly. During times of conflict,
the usual methods for getting through the day may stop working for the local population, and they may try
adopting new ideas or start highlighting traditional ways of doing things. Alternatively, they may switch
rapidly among a range of possible behaviors. These changes can occur because of a number of factors were
at play, but probably the greatest cause of this during conflict is a rapid decline in security. As security
declines, the threat of attack, rape, and murder forces many changes in society. The rapid decline in the
status and opportunities for women in these countries, therefore, was not merely due to centuries-old tribal
beliefs, but to very real and pragmatic economic and social changes over time. As the cases of Iraq and
Afghanistan illustrate, cultural practices and attitudes are frequently influenced by changes in very real
physical conditions. Since the arrival of a large military, often accompanied by the destruction of physical
property and the erosion of the local economy and security, is undoubtedly an enormous change for the
local population, counterinsurgency planners need to recognize and plan for the impact that their operations
will have upon the people and cultures in an area of operations.
ASSESSING A CULTURAL SITUATION
3-9. Although it may seem that people around the world are extraordinarily different and have little in
common, in reality all human groups interact with their world and each other in some basic, predictable
patterns. The particular details of these patterns may vary. But the underlying patterns will not. Thus, all
people use, manage, and interact with their environments. All groups have some kind of economy for
exchanging goods and services. Every group has a social structure, with differing roles and status among
members. Political behavior can be found in the smallest community. All people have some kind of belief
system, whether based on religion, tradition, narratives, or history. By identifying these patterns wherever
they deploy, Marines and Soldiers will be in a better position to assess the cultural situation and the
influence of their operations upon the local population.

Culture
13 May 2014 FM 3-24/MCWP 3-33.5 3-3
3-10. All cultures have a unique and interdependent connection with their physical surroundings. The
physical environment (including climate, terrain, and resources) influences the people living in it by
providing a range of possibilities within which they act. People shape their environment by the choices they
make, creating a cultural landscape which reflects their social, cultural, economic, and political attitudes. A
careful reading, or interpretation, of the cultural landscape can provide useful information about the people
who create it, use it, and live in it. A military presence in an area of operations will affect a local population
and its use of the physical environment. For example, Marines and Soldiers may inadvertently divert or
impede access to resources, such as water or food, which in turn may cause real shortages or upset the
balance of power by allowing greater access to these resources by one group and harming another.
Counterinsurgency planners need to anticipate how their operations will impact local populations and their
use of their environment and recognize that since use of the environment is cultural, these impacts may
significantly differ from what might be expected in the U.S.
3-11. All cultures have specific systems for obtaining, producing, and distributing items people need to
survive (for example, food, water, and shelter) or luxuries and material things. This system, which does not
necessarily require money or a banking system, is called the economy of a culture. Frequently, insurgents
use the informal economy to obtain funding and support for their activities. Another aspect of the economic
system that is often overlooked is the concept of reciprocity, which is an exchange between people that
creates a relationship. Although in Western cultures exchange usually involves the exchange of goods and
services of equal monetary value, in other parts of the world exchange may be only partly about what
people expect regarding goods and services and also partly about building working relationships. If
Marines and Soldiers fail to see what the local people expect from the exchange, to include its impact on
interpersonal relationships, it will be hard for them to understand or anticipate people’s behavior.
3-12. In all cultures, people hold differing positions of status and power, often closely related to their roles
in a group. In the military, for example, one’s status and power is based on rank. Depending on a person’s
rank, a person fills different roles in an organization. The way that a group distinguishes among its
members according to their role, status, and power is reflected in its social structure. A person’s position in
the social structure may depend on many factors, including age, gender, class, family name, tribal
membership, ethnicity, religious identity, and even rank. In conflict environments, differing groups (for
example, ethnic, religious, or tribal) may each vie for power, often looking to outside militaries to support
them. In counterinsurgency operations, it is essential that military leaders understand which social groups
have traditionally held power in an area of operations. Otherwise, they are likely to be drawn into power
struggles among competing groups, and possibly even unwittingly end up aiding the insurgents. A concept
central to one’s place in society is that of identity. Identity is a broad term used to describe how people
conceive of themselves and how they are perceived by others. Identity shapes how people view themselves
and the world. Understanding identity is complex because people have multiple identities. In times of
conflict, people may choose to emphasize certain group identities such as nationality or religion, while at
other times different identities, such as one’s profession or gender, may matter more. Social structure and
identity are extremely important concepts for counterinsurgency planners and operators to understand, as
they affect people’s allegiances and influence how groups and individuals will interpret and respond to U.S.
actions.
3-13. In all cultures, people have a system that determines who leads the group and who makes decisions
about its welfare. Although people in the U.S. use an electoral system to select their leaders, this is not the
case in many other countries. In many places around the world, even when the official government is
elected, the local population may not view that government as legitimate or effective. In fact, one of the
primary motivations for people to support an insurgency is their sense that the official or formal
government has failed to provide for their needs. Frequently, insurgents may be providing a “shadow
government” which replaces and competes with the official government in certain parts of the country.
Shadow governments are one example of informal leadership. In most areas of operations, Marines and
Soldiers will find that communities or groups are influenced by a variety of leaders, most of whom are not
part of the government. In some areas, religious leaders may have great influence. In others, people may
look to tribal leaders or respected individuals within their ethnic group. Business leaders and warlords often
have great power and influence too. To be successful in counterinsurgency operations, military members
need to quickly and accurately identify the various community leaders and develop strategies to work with

Chapter 3
3-4 FM 3-24/MCWP 3-33.5 13 May 2014
each of them in order to increase government legitimacy. Without support from the various power brokers
in an area of operations, military action is unlikely to gain support from the local population.
3-14. Cultures are characterized by a shared set of beliefs, values, norms and symbols that unite a group.
These beliefs may come from many sources, such as a person’s background, family, education, religion or
history. Understanding the beliefs and values of a local population is critical for effective information
operations. Failure to respect or understand the beliefs of a local population can result in serious hostility
towards military intervention and attacks upon military personnel. Likewise, information operations that
assume the foreign audience shares the same jokes, history, or values that Soldiers and Marines do
frequently fail to deliver messages effectively. To gain an understanding of belief systems,
counterinsurgents read and monitor information available through media or books, and counterinsurgents
talk to people in the culture. Discussing history with local people can be a window into understanding the
way that people in that area define a problem, who they believe caused it, and who they think the heroes
and villains are. Stories, sayings and even poetry can reveal cultural narratives, the shared explanations of
why the world is a certain way. Frequently, advertising appeals to people by using these narratives, as do
effective information operations. Beliefs, however, are not perfectly shared or understood within a group.
There is usually a range of acceptable thoughts and behaviors. This is called variation. For example, in
reading about Islam, Soldiers and Marines may understand that Muslims are supposed to fast during
Ramadan. However, when deployed they might observe seemingly faithful Muslims drinking and eating
during Ramadan. Within U.S. culture, these internal mismatches and contradictions (variations) are often
accepted without much comment. In a cross-cultural interaction, these contradictions can seem jarring or
confusing. Often, working with others in a foreign culture requires the ability to suspend judgment. People
often act and work in ways that may be difficult to accept or understand. However, by recognizing that all
people share some fundamental patterns and seeking to understand and develop military plans and
operations that build upon these patterns, commanders and staffs can effectively work to counter an
insurgency within an area of operations.
3-15. Religion can be a powerful force in shaping beliefs. In many cultures religion and religious leaders
have significant influence over local populations. Religious ideology can incite conflict, but religion can
also be instrumental in stabilizing a culture by using universal religious concepts of justice, healing, and
transformation. Because religion is often an integral part of the values set of a local culture,
counterinsurgents conducting mission preparation and analysis examine the religion in an area of
operations. Religion can also play an important role in creating peace and stability. Religion can create
cultural instability, but in many cases it can alleviate problems in a society and be a unifying force. Many
religions have messages and themes of pacifism and forgiveness. In many insurgencies, religious leaders
have played an essential role in ending conflicts. The effect of a religion has to be understood within that
religion and within that society. Counterinsurgents conducting a mission analysis may find that insurgents
are using a radical interpretation of a religious text to incite violence. This can be countered by empowering
indigenous religious leaders who promote a different interpretation. For example, radical Muslims may cite
texts from the Quran that justify violence, but they may ignore the passages taught by more moderate
Muslims that advocate compassion, peace, and human dignity.
ORGANIZING TO UNDERSTAND CULTURE
3-16. There are three important methods for trying to understand the cultural element of a
counterinsurgency. First, all counterinsurgents must make every effort to experience and understand the
local culture, including by trying local food and learning local languages and customs. Second,
commanders can organize their staffs in order to concentrate on cultural understanding and inject this
understanding into their unit’s plans and operations. Third, commanders can rely on an outside capability to
allow commanders and staffs to understand the culture. Two techniques that involve organization of staffs
or outside capabilities are—
- Green cell and cultural advisor.
- Human terrain systems.

Culture
13 May 2014 FM 3-24/MCWP 3-33.5 3-5
GREEN CELL AND CULTURAL ADVISOR
3-17. The purpose of a green cell is to consider the population in order to promote a better understanding
of the environment and the problem. At a minimum, the green cell provides for the independent will of the
population. Planning teams must develop an understanding of civilian aspects of the area of operations and
the will of the population. There are many techniques to achieve this capability, and each unit may
approach this differently based on resources and available qualified personnel. Two techniques of note are
the green cell and cultural advisor. (See MCWP 5-1 for more information on green cells.)
3-18. A green cell is an ad hoc working group consisting of individuals with a diversity of education and
experience capable of identifying and considering the perspective of the population, the host-nation
government, and other stakeholders within an operational environment. Ideally, a green cell is composed of
individuals with cultural expertise across all warfighting functions. If a whole-of-government approach is
used, experts from other government agencies such as the Department of State should be included in the
cell. The green cell cooperates closely with the other members of the planning staff so that cultural factors
are considered throughout the range of military operations. The green cell also interfaces and coordinates
with joint and interagency groups, drawing upon the collective knowledge and experience of the
Department of State, nongovernmental organizations (NGOs), and foreign resources, such as provincial
reconstruction teams. (See MCWP 5-1 for more information on green cell activities.)
3-19. The commander forms the green cell during the receipt of mission and problem framing planning
steps to add to the commander’s and the operational planning team’s cultural understanding of an
operational environment. In order to support the operational planning team, the green cell understands the
operational planning team’s mission and tasks and is able to translate cultural information in a way that is
relevant to the mission.
3-20. The cultural advisor is a concept developed and employed in Operation Enduring Freedom in
Afghanistan. Cultural advisors are the principal subject matter experts on culture and planning related to
their designated geographic region of expertise, serving as the cultural and language advisors to the
commander. The cultural advisor is a special staff officer for the commander and a member of the planning
staff. This person not only serves on the planning staff, but also deploys and serves as an ongoing advisor
to senior leaders while they are in theater, if needed. The advantage of having a cultural advisor on staff is
that this advisor can often help explain to the commander what the advisor sees on the ground in the area of
operations. A foreign area officer or a civil affairs Soldier may be a good selection for a cultural advisor.
Both can provide an understanding of the host nation and its specific regional, religious, and ethnic
differences, and they may have foreign language skills. As a result, the commander can adjust operations in
response to a culturally challenging environment.
3-21. Overall, there are many options to task-organize staffs to incorporate culture into planning. While a
green cell creates expertise in one part of the staff, those concerns are also important for other staff
sections. It is important for commanders to create staffs that are well integrated across the warfighting
functions. One danger of creating a cultural cell within the staff is that it will relegate cultural concerns to
one staff element and inhibit cultural concerns being integrated into the planning process. Commanders
ensure that the staff integrates all operational and planning concerns, including cultural concerns.
3-22. Regardless of the particular planning configuration, commanders and planners find and use whatever
cultural resources are available to the unit. Commanders and staffs incorporate culture into planning during
the beginning of mission planning in order to understand an area of operations prior to developing any
course of action. Success is recognized not by stand-alone briefs that describe the culture of an operational
environment, but when all of the operational planning teams’ planning products reflect and have been
informed by the cultural analysis that has been performed by subject matter experts.
HUMAN TERRAIN SYSTEM
3-23. The human terrain system provides tactical to strategic level support to commanders. The human
terrain system conducts field research and analysis of the local population to determine the civil
considerations in order to help commanders better understand the operational environment from the
population’s perspective and assess how actions will potentially impact and be perceived by the local
population.

Chapter 3
3-6 FM 3-24/MCWP 3-33.5 13 May 2014
3-24. A human terrain team typically consists of a team leader, one or two social scientists, and one
research manager. When manning demands permit, human terrain team personnel are recruited and
deployed to promote engagement with elements of the population that typically have restricted access. For
example, in Afghanistan at least one woman is assigned per team to facilitate access to females within the
local population.
3-25. Human terrain teams, part of the human terrain system, represent a capability that traditionally falls
outside of military expertise. These teams are an additional enabler for commanders to gain situational
understanding of their operational environments through the socio-cultural running estimate and are an
important tool in the military decisionmaking process. (See FM 2-01.3/MCRP 2-3A for more information
on human terrain teams.)

2 June 2014 FM 3-24/MCWP 3-33.5, C1 4-1
PART TWO
Insurgencies
Part two provides doctrine to help understand an insurgency. While the first part
provides the context of an insurgency, the second part provides a discussion of an
insurgency within that context. Chapter 4 provides information about insurgency
prerequisites and fundamentals. It helps commanders and staffs understand why an
insurgency may form and how and why it acts. Chapter 5 then provides a description
of an insurgency’s threat characteristics.
Chapter 4
Insurgency Prerequisites and Fundamentals
4-1. Several factors are important in analyzing any particular insurgency. Commanders and staffs must
perform this analysis within an insurgency’s operational environment. Commanders and staffs consider
when an insurgency could start or what the prerequisites are for a particular insurgency. Commanders and
staffs also consider a particular insurgency’s strategy and its eight dynamics. This provides a means to
analyze an insurgency.
INTRASTATE WAR
4-2. One way commanders and staffs view insurgencies is in the context of intrastate conflict. An
intrastate conflict is as war or conflict between a constituted government and its people or representative
factions from the people. It is a war within a state versus a war between two or more nation states.
Intrastate conflict directly relates to insurgencies. Other types of intrastate conflicts are insurgencies that
differ only in the amount of popular support or the amount of governmental capacity. Commanders and
staffs should not only consider an insurgency as an intrastate conflict. Insurgent movements may operate in
multiple countries, as their desired end state may be regional, transnational, or global. The types of
intrastate conflicts include rebellions (also referred to as insurrections), revolutions, civil wars, and coup
d’états.
4-3. A rebellion (also known as an insurrection) may be fomented by a group that challenges state
control. A rebellion is usually manifested by acts of violence when the state is unable or unwilling to
address the group’s concerns. Another insurgency may use a rebellion if it can gain enough popular support
to engage in large scale unrest or open conflict with the governing authority. Rebellions are forms of
insurgency in which an organized group is leading the population, the causes of instability exist, and the
movement enjoys some passive support among the population. Under most international laws it is a crime
to incite, assist, or engage in violent actions against a constituted government. The Geneva Convention
states that “Every government has a right to put down rebellion within its borders and to punish the
insurgents in accordance with its penal laws.” (See the final record of the Diplomatic Conference of
Geneva of 1949 vol. II section B, page 121 for more information on insurrections.)
4-4. A revolution is a popular insurgency with plans to overthrow a government and transform its society
and government from one form of government to another. Revolutions generally evolve from a rebellion,
but in revolutions popular support comes in the form of a fully mobilized population, which differs from
simply passive or active support. A fully mobilized population is a part of a revolution and it is generally

Chapter 4
4-2 FM 3-24/MCWP 3-33.5, C1 2 June 2014
seeking fundamental lasting change in a society’s political, economic, or social order. A significant
distinction between a revolution and a counterinsurgency is a requirement of the host-nation military,
government, and civil authorities to prepare, plan, and conduct counterrevolution, and not simply
counterinsurgency. The main difference is the need to reintegrate the mobilized population and not only
reintegrate members of the insurgency. Although a coup d’état can resemble a revolution in that it can
quickly overthrow a government, this overthrow is generally done rapidly and secretly during a coup d’état
versus a rapid fully mobilization of the population during a revolution.
4-5. Civil wars are condition-based conflicts beginning with an insurgency. Once the insurgency achieves
certain characteristics of organization and resembles an alternate government, the conflict reaches the state
of civil war. This is often characterized by performing tasks associated with a state and having a defined
government. If the insurgency loses the ability to meet these criteria, the status or state of the insurgency is
no longer that of a civil war. The insurgent movement may attempt to gain outside recognition by calling
the conflict a civil war, as a civil war tends to afford international recognition and legal implications as a
competing group and not an illegal movement. According to the Geneva Convention, the criteria of a civil
war is “that the insurgents must have an organization purporting to have the characteristics of a State; that
the insurgent civil authority must exercise de facto authority over persons within a determinate territory;
that the armed forces must act under the direction of the organized civil authority and be prepared to
observe the ordinary laws of war; that the insurgent civil authority must agree to be bound by the
provisions of the Convention.” (See the final record of the Diplomatic Conference of Geneva of 1949 vol.
II section B, page 121 for more information on civil wars.)
4-6. Recognized antigovernment elements in a civil war may be classified as belligerents and not
insurgencies. A belligerent, though generally a sovereign state, can be a non-sovereign state if it is
recognized by the international community (by two or more states or organizations like the United
Nations), organized, and is providing services to the population within its controlled areas. In the case
where antigovernment forces meet the criteria of a state during a civil war, they achieve sufficient
international recognition, and they may achieve belligerent status rather than insurgent status. Although
status may change, counterinsurgency operations, by government forces, generally remain the same at the
theater through lower tactical levels. The difference between a group being classified as an insurgency or a
belligerent can affect the overall status of U.S. involvement, as a belligerent has international recognition.
4-7. +A faction that employs a coup d’état seeks to overthrow the governing authority by a quick decisive
action by an internal faction within the government. Usually, this is the military or part of the security
apparatus. A coup d’état may or may not result in an insurgency, as part of society may reject the change.
Moreover, it is possible for an active insurgency to use a coup d’état to seize control over a government.
With a coup d’état, a small group can kill or remove a leader and the leadership’s supporters and assume
control of a state. The main point of a coup d’état is that it is a means to change a regime by actors who are
part of the government.
4-8. Intrastate conflicts present different challenges than interstate wars, since they often take place
among the population and, therefore, human rights violations and sectarian violence are more likely.
Secondly, intrastate conflicts can spread to adjacent countries that have governments or portions of the
population that share beliefs or goals with one side or the other.
4-9. The nature of an intrastate conflict is a grievance between segments of a state’s population with its
constituted government. There can be a single root cause or a variety of causes perceived as so severe that
they impact the population’s social contract with its government. There are many likely contributors to
intrastate conflicts, including perceived weak, illegitimate, corrupt, or overly oppressive governments,
ethnic or racial tensions, religions conflicts, economic stresses, or a need for land reform. Often an
intrastate conflict causes the formation and growth of insurgencies and other intrastate conflicts.
Commanders and staffs must understand the nature of intrastate conflicts even if they are poorly defined. If
a commander and staff misdiagnosis an intrastate conflict, they can fail to properly identify and address the
root cause of instability and the nature of the threat.

Insurgency Prerequisites and Fundamentals
13 May 2014 FM 3-24/MCWP 3-33.5 4-3
INSURGENCY PREREQUISITES
4-10. The three prerequisites of an insurgency, opportunity, motive, and means, provide a framework for
both planners and executers to plan for and prevent an insurgency. Planners and executers use the
prerequisites for planning and execution of operations in environments where insurgencies are likely, such
as a post-conflict environment. (See JP 3-24 for a further discussion of insurgency prerequisites.)
OPPORTUNITY
4-11. Opportunity refers to the emergence of significant gaps in the ability of the state or its local allies to
control its territory and population. States must have the capacity to detect the early stages of insurgent
organization and mobilization. This requires the cooperation of a significant portion of the population or
the establishment of an extensive program of domestic surveillance and intelligence activities. The state
must also be capable of suppressing the insurgency in a way that deters other potential rebels while
avoiding contributing to the insurgent narrative and provoking wider resistance.
4-12. For a land force, opportunity provides a means to evaluate the likelihood of an insurgency. For
example, after a victory during a major combat operation, if the former government prevented insurgencies
by an intelligence program, the commander and staff need to consider how likely and for how long an
occupying force can prevent an insurgency without gaining the active support of the population or
reestablishing intelligence programs. Understanding the opportunities for an insurgency in an area is
essential for land forces.
4-13. At the tactical and operational level, understanding opportunities for an insurgency provides a means
for commanders and staffs to analyze the local conditions and the likelihood of a successful insurgency
developing. Commanders and staffs actively make assessments on both the support of the population and
the intelligence capability and capacity of the local area. If the population is not supportive of the host
nation and the host nation has no means to prevent an insurgency in a hostile population, there is an
opportunity for an insurgency in that area. (For a further discussion on why a gap in state control might
happen, see JP 3-24.)
MOTIVE
4-14. A population that has grievances does not necessarily cause an insurgency. Grievances are necessary,
but not sufficient, conditions for an insurgency. Poverty, unemployment, economic inequality, inadequate
essential services, political marginalization, and repression are commonplace. These conditions exist in
many places where an insurgency does not. It takes established or emerging leaders to build a compelling
narrative that links grievances to a political agenda and mobilizes the population to support a violent social
movement. The narrative explains who is to blame for grievances, how grievances will be addressed, and
how the population and insurgency should work together to accomplish the goal. Ideology often provides a
coherent set of ideas that provide a compelling framework for a narrative. Where opportunity and motive
(grievances) intersect, individuals emerge to attempt to mobilize the population. When grievances mobilize
a population, they are a root cause of an insurgency. (See JP 3-24 for a further discussion on motive.)
4-15. The root causes of an insurgency are real or perceived grievances that insurgents use to mobilize a
population in support of an insurgency. Insurgents use these grievances to fuel an insurgency. Root causes
are not static and can change over the course of an insurgency. As conditions change, insurgent leaders
create different narratives to mobilize a population. The root causes that led to the insurgency in the first
place may not be the same ones that are sustaining an ongoing insurgency. Commanders and staffs perform
continued assessments and reassessments to determine what an insurgency is using as a root cause.
4-16. A root cause can be summarized as a broad perception of injustice linked to the government that
insurgents use to mobilize a population. If counterinsurgents take actions such as building schools and
roads, or creating jobs, but these actions do not address the perception of injustice, then they will not reduce
support for insurgency. Phrased differently, deprivation that is not considered unjust is much less
destabilizing than relative prosperity which is considered unjust. It is not the thought "I'm poor" that leads
someone to attempt to overthrow or force a change in the government; it is "I'm poor, this is not fair, and

Chapter 4
4-4 FM 3-24/MCWP 3-33.5 13 May 2014
the government is to blame." The solution to the latter thought is more complex than the solution to the
former.
4-17. Identity, based on cultural, religious, or other cultural groupings, can create a strong root cause. In
cases where groups are persecuted and underrepresented, the insurgents can use a narrative that uses this
underrepresentation or persecution as a root cause against the government. In some cases, groups are
concentrated in certain regions where the government exercises biased controls over those groups. This
might be an effective root cause to use for an insurgency based on a nullification of government control.
4-18. Religion can also be an effective root cause. Religious-based movements create a perception that a
certain type of religion should drive politics and groups should convert to that religion. Insurgents attempt
to present their ideology as the true and only correct form of their religion. Insurgents can use religion as
part of an identity based root cause if the government persecutes a certain religious group. However,
insurgents can also use religion to create an ideology that everyone should be a part of, and governed by, a
certain religion. In this case, a religious-based group could seek to overthrow its government and replace it
with a religious based government.
4-19. The presence of a foreign force can be the root cause of an insurgency. The presence of foreign
military forces can also be used as a means to mobilize popular support. The presence can come after a
major combat operation that replaces a government. As such, any major combat operation should include
planning for stability operations to prevent an insurgency. However, this could also be a root cause if there
are Soldiers or Marines stationed in a host nation. Insurgents can use the perception that outsiders exploit
the host nation or that the host-nation government excessively caters to foreigners as a root cause.
4-20. Land disputes concerning ownership, usage, and rights, especially to agrarian, mining, or other land
based livelihoods or identities, can be used as a root cause. Land disputes often manifest themselves as an
issue of income inequality. For example, landowners may have tenant farmers that pay the landowners’
rents. Insurgent groups can often use a narrative that exploits unequal land ownership as a root cause, and
promises redistribution of land and land reform to the tenant farmers as an effective justification for the
farmers to join the insurgency.
4-21. Corruption of the host-nation government can be a root cause. If institutional corruption is systemic,
ongoing, and considered unfair, insurgents can use that as an effective narrative. For example, corruption in
government development programs can cause resentment by the aggrieved group. Corruption can lead to
loss of host-nation legitimacy and can undermine government control of an area.
4-22. Insurgents can use a gap between a population’s expectations and the government’s capability to
meet those expectations as a root cause. The larger the gap, the greater the population’s perceived or real
sense of deprivation. This allows for the development of a narrative in which the insurgents promise to
close the gap.
MEANS
4-23. It takes considerable resources to mount a violent challenge to the incumbent political authorities and
the methods an insurgency uses to secure those means determines a great deal about its behavior. The
leaders of a potential insurgency must assemble and organize personnel, funds, weapons, and systems of
secure communications and logistics. The other prerequisites relate to the means. For example, recruiters
can use existing social networks to find new recruits. (See JP 3-24 for a detailed discussion on means.)
4-24. Commanders’ and staffs’ planning efforts should consider how an insurgent movement resources
itself. An insurgency will often depend on a local population for resourcing and recruitment. In these cases,
insurgents base an insurgency on social relationships to include, but not limited to, villages, clans, tribes,
ethnicities, or other groups. These groups will often freely give resources, but some coercion may be used.
In the cases where resources are freely given, the insurgency may have legitimacy. However, the use of
local resources also restricts an insurgency. For resources to be given freely, the insurgent is constrained by
the social norms of the groups. Moreover, because an insurgency may be seen as aligned to a certain group,
there is a certain amount of difficulty expanding the insurgency beyond its core group.
4-25. A local area’s insurgency and population could connect, through communications, with its diasporas
and attain resources from around the world. If its diasporas relate to the struggle, they may freely give

Insurgency Prerequisites and Fundamentals
2 June 2014 FM 3-24/MCWP 3-33.5, C1 4-5
financial aid to an insurgency. In such cases, commanders and staffs need to determine possible means to
undermine this support. For example, the use of counter threat finance may prevent this funding. On the
other hand, resourcing can be local. Insurgencies can have access to black markets or other resources that
they can use to buy weapons. In these cases, stopping these transactions may be an effective means of
blocking insurgent resources.
4-26. An insurgency with state sponsorship has important advantages and disadvantages. State sponsorship
can offer resources, sanctuary, and training. These are important advantages for any insurgency because
they offer an insurgent group the ability to organize and become tactically and operationally more effective.
On the other hand, state sponsorship can undermine the support of the local population. An insurgency that
depends on outside state support can be perceived as artificial and may not have deep support from the
local population. While recruits may join an insurgency by increased resources, recruits attracted because
of the possibility of wealth may be less effective. However, if an insurgency uses outside support to build a
political base before starting military operations, insurgents mitigate these risks. For the counterinsurgent,
understanding the nature of state support allows the commander and staff to undermine that support before
an insurgency begins.
4-27. A group that already has resourcing could potentially become an insurgency. Groups tied to black
markets, such as those selling drugs, may seek to resist or nullify the government’s ability to stop their
activities. While they may exploit the population and create a root cause, the protection of their resources is
the essential reason for the development of their insurgency. The means for an insurgency can play an
interrelated role with the motive and opportunity.
4-28. When commanders and staffs desire an additional method of analysis other than opportunity, motive,
and means, the prerequisites of an insurgency can be represented as a vulnerable population, leadership for
direction, and a lack of government control. A population is vulnerable if the people have real or perceived
grievances that insurgents can exploit. Moreover, there must be an insurgent leadership element that can
direct the frustrations of a vulnerable population. The insurgency must act on real or perceived lack of
governmental control, which can allow insurgents to operate with little or no interference from security
forces or other agencies. This means that the government is not providing for the people. This may refer to
inadequate services or an overly harsh and repressive government. When all three exist in an area, an
insurgency can operate with increased freedom of movement, gain the support of the people, and become
entrenched over time.
INSURGENCY FUNDAMENTALS
4-29. Few insurgencies fit neatly into a rigid classification. However, insurgencies do have common
characteristics that can provide a basis for building a more accurate picture of an insurgency and help
commanders understand the situation. The fundamentals of insurgencies help commanders and staffs
analyze insurgent strategies, objectives, and tactics. Each fundamental is important independently, but
analyzing the interactions and relationships between the fundamentals as a whole is the key to
understanding an insurgency. The two insurgency fundamentals are—
- Insurgent strategies.
- Dynamics of insurgency.
INSURGENT STRATEGIES
4-30. An insurgency’s strategy is determined by its own ends, ways, and means. There are a range of ends
an insurgency might seek, to include replacing the state, separating from the state, changing the policy of
the state, nullifying state control in an area of a state, and securing a place in a state’s political system.
These basic ends will influence the ways an insurgency uses. However, that influence is not deterministic,
and the way an insurgency fights is also influenced by its resourcing. In addition, the relationships between
an insurgency’s ends, ways, and means is also influenced by numerous important variables. Those variables
include but are not limited to—
- How an insurgency gains legitimacy and controls a population.
- Whether the insurgency is political centric, violence centric, or economic centric.
- The relationship of the insurgency to the economy.

Chapter 4
4-6 FM 3-24/MCWP 3-33.5, C1 2 June 2014
- Organization.
- Sense of time.
- Adaptability.
Insurgent Legitimacy and Control
4-31. How an insurgency gains legitimacy and controls a population within a society helps determine
strategic behavior. Some insurgencies have a clear political message and bring that message to their
society. Others may try to use economic black markets and the wealth that comes from them to make their
population dependent on the insurgency. Others may try to use coercion to control their society. Most will
use a combination of many different methods. However, how an insurgency controls the local population or
tries to gain legitimacy helps determine that insurgency’s strategic behavior.
Political, Economic, and Violence-Centered Insurgencies
4-32. +All insurgencies have a political aim which may be to change their society or simply to protect a
black market. While all insurgencies involve violence, politics, and economics, some insurgencies are
focused on politics, some are focused on violence, and some are focused on economics. This can change
over time. Many insurgencies develop well defined political goals which shape their strategy and an
infrastructure to promote and refine them. In these insurgencies, the role of violence is probably secondary
to the role of building political support. In this case an insurgency’s aims are more likely to be changing
policy, fighting into the state’s political system, or replacing the state. Violence is likely to be more
organized as the political support grows for an insurgency. Other insurgencies are focused on violence,
lacking the ability or incentive to build a political infrastructure and gain wide political support. These
types of +insurgencies are more likely to develop networked organizations with connections to criminal
organizations or other insurgent groups with similar interests. Finally, an insurgency may be focused on
economics. These insurgencies are likely to want simply to stop state interferences with their activities. As
such, these insurgencies may limit the use of violence, unless the state attempts to interfere with their
economic base, whether in the legitimate economy or in black or gray markets.
The Relationship of an Insurgency to the Economy
4-33. Commanders and staffs must understand the relationship of the insurgency to the economy to
understand an insurgency’s strategic behavior. An insurgency could have little dependence on the local
economy and receive all its support from the outside. Insurgents could also gain resources from the formal
economy in which they operate and sustain themselves through kidnapping or theft. An insurgency could
also maintain an economic base on the black market, or it could control a war economy. In all cases, an
insurgency’s relationship with the economy will affect its behavior. For example, if it is dependent on
outside support, the aims of its outside support will influence the insurgency’s behavior. Moreover, outside
support influences tactical and operational behavior. An insurgency that does not depend on the local
population is more likely to use violence against the population. (See paragraphs 2-25 through 2-31 for
more information the economic variable.)
Insurgent Organizational Structure
4-34. The organization of an insurgency is also important. Insurgent organizations can be conceptualized
along a continuum from a formal and hierarchical structure to a networked structure. This structure affects
organization because it affects control over actions and the scale of tactical actions. Without a hierarchical
structure, it is difficult to control individuals or groups within an insurgency. This leads to attacks that can
affect the legitimacy of an insurgency. Moreover, while a networked organization may use terrorist tactics,
it is also difficult for a networked insurgency to mass combat power. It is also difficult to negotiate a
settlement with a networked insurgency because no single person or small group is in charge. A networked
insurgency changes the dynamics of individuals in an insurgency, as no one is likely to be essential to the
continuation of a networked insurgency. A hierarchical insurgency may be easier to penetrate than a
networked insurgency, as a few individuals may be essential to the insurgency and control the actions of
members of the insurgency. (See paragraphs 4-88 through 4-103 for more information on a networked
insurgency.)

Insurgency Prerequisites and Fundamentals
13 May 2014 FM 3-24/MCWP 3-33.5 4-7
Sense of Time
4-35. An insurgents’ sense of time will also affect their actions. If insurgents feel time is on their side, they
are more likely to adopt a lower risk approach and avoid becoming decisively engaged. If they perceive
time as being against them, that will push them towards higher risk activities. Commanders and staffs must
determine an insurgency’s perception of time to determine its behavior. (See paragraphs 2-43 through 2-44
for more information on the time variable.)
Adaptability
4-36. Adaptability is also an essential element to understanding an insurgency’s strategic behavior.
Adaptability determines how well, how often, and how the insurgency adapts tactically, operationally, and
strategically. This can be directly linked to the organization of an insurgency. A networked insurgency may
be highly adaptable at the operational and tactical level, but not at the strategic level. On the other hand, the
reverse may be true for a hierarchal insurgency.
4-37. An insurgency's strategy is not static, and it can shift. Counterinsurgents must recognize and respond
to shifts in strategy. As the operational environment changes, it can affect an insurgency’s resourcing, the
ways an insurgency attempts to achieve its ends, and its calculation of what its ends should be. In a
networked insurgency, different elements of the insurgency may evolve differently than other elements of
the insurgency. An insurgency is not static, and it continues to evolve as conditions evolve.
Insurgent Approaches
4-38. An insurgency might take several approaches to achieve its objectives. In many insurgencies,
different elements of the same insurgency or related insurgencies will have different strategic calculations.
Commanders and staffs must understand an insurgency’s approach to develop effective programs that
attack the root causes of that insurgency. Commanders and staffs combine their understanding of the
insurgent’s ways to accomplish its ends, with the insurgent’s means to pursue those ends, to provide the
most probable and dangerous course of action for all insurgencies operating in an area of operation. This
provides an understanding of the insurgency’s approach.
4-39. Commanders and staffs must understand the insurgent’s ends to understand the insurgent’s
decisionmaking process, capabilities, future actions, current tactics, method of command and control,
recruiting, propaganda, and use of the local population. Examining the ends of an insurgency and the
insurgents’ attempts to achieve those ends through various ways, including combat actions, propaganda,
and subversion, enable counterinsurgents to undermine the enemy’s decisionmaking process. The
insurgents’ strategic ends may be overt and publicly championed or covert. Insurgent operations may have
immediate consequences or delayed effects aligned with long-term objectives. For example, car bombings
among a local population may seem counterproductive because they incite immediate anger against the
bombings and their perpetrators. However, a sustained campaign of massive violence can have two
long-term results, it can—
- Weaken popular support for the government, which has failed to protect the people.
- Make the population susceptible to insurgent intimidation.
Whatever the insurgent’s ends, approaching the problem from the perspectives of the insurgent and the
population can provide counterinsurgents the means to interdict the threat on a number of levels.
4-40. Counterinsurgents are likely to face insurgents who use several different approaches to achieve their
ends. Some common approaches at the tactical level and operational level are the urban (terrorist), military
focused, protracted, and subversive approaches. The urban (terrorist) and military focused are considered
basic approaches and the protracted and subversive are considered advanced approaches. Basic approaches
refer to the insurgent capabilities needed to achieve long-term strategic objectives. Basic approaches do not
mean insurgents are not efficient in tactics or other skills, but overall they lack the means to pursue a more
advanced approach towards achieving their goals. In contrast, advanced approaches probably have political
wings that govern the militant side of the movement and are focused on longer-term political goals.
4-41. Insurgents may use different approaches at different times, applying tactics that take advantage of
circumstances. Insurgents may also combine a number of methods that include tactics drawn from any or

Chapter 4
4-8 FM 3-24/MCWP 3-33.5 13 May 2014
all of the other approaches. In addition, different insurgent forces using different approaches may form
loose coalitions when it serves their interests; however, these same coalitions may fight among themselves,
even while engaging counterinsurgents. A single area of operations may have multiple competing entities,
each seeking to maximize its survivability and influence, and this situation may be duplicated several times
across a joint operations area. This may further complicate understanding both the insurgency and the
counterinsurgent operations necessary for success.
4-42. The urban (terrorist) approach is an approach in which insurgents attack government and symbolic
targets (for example an important religious building) to cause government forces to overreact against the
population. The insurgents want the government’s repressive measures to enrage the people so that they
rise up and overthrow the government. Although this type of method may develop popular support against
a government that is particularly brutal or corrupt, it may only result in shallow support for the insurgency.
The population may only see the insurgency positively because of the brutal response, not because they
identify with the insurgency.
4-43. An insurgency uses the military-focused approach to achieve its policy goals by military success. In
this approach, insurgents’ efforts focus on causing the government to lose legitimacy by military success
and inspiring a population to join the insurgents against the government. The most important idea behind a
military focused method is that it does not require building political support among the population. Instead,
military success and action will gain the support of a population.
4-44. A protracted approach is an advanced approach based on Mao Tse-Tung’s theory of protracted
popular war. It attempts to lengthen the conflict as much as necessary to assemble the resources and forces
necessary for success and to wear down the counterinsurgent forces and their political leadership. The
protracted war method is based upon three distinct phases: latent and incipient, guerrilla warfare, and war
of movement. Each phase builds upon the previous phase and continues activities from all or some of the
previous phases. The protracted method requires both a political wing and a military wing.
4-45. The subversive approach is another advanced approach. A subversive approach attempts to subvert
the government from within by using its political arm to become a legitimate political party and enter the
government. Subversive activities may occur as part of other ways, particularly the protracted war
approach.
DYNAMICS OF INSURGENCY
4-46. Commanders and staffs must understand the nature of an insurgency when conducting a
counterinsurgency. This requires understanding insurgent strategy. However, to understand an insurgent’s
strategy, commanders and staffs must understand insurgency dynamics. The dynamics of insurgency is a
framework for understanding an insurgency.
4-47. An operational environment may have multiple insurgent groups. These groups may be pursuing a
wide variety of goals and interests. As such, these groups may be collaborating, fighting each other, or
acting neutral towards each other. When commanders and staffs analyze an insurgency, they consider each
group and provide a different analysis for each group based on the eight dynamics of insurgency.
4-48. Eight dynamics or some combinations of these dynamics are common to most successful
insurgencies. These dynamics provide a framework for planners to analyze insurgencies. Each of these
dynamics can contribute to the strength of an insurgency, but each can also be used to find fracture points
and weak points in an insurgency. Fracture points are points of internal division within the insurgency. A
weak point is an underlying weakness, such as access to resources, of the insurgency. The eight dynamics
are—
- Leadership.
- Ideology.
- Objectives.
- Environment and geography.
- External support.
- Internal support.

Insurgency Prerequisites and Fundamentals
13 May 2014 FM 3-24/MCWP 3-33.5 4-9
- Phasing and timing.
- Organizational and operational patterns.
First Dynamic—Leadership
4-49. A group committing random violence is not an insurgency. In an insurgency, there is a political
rationale behind the violence. An insurgency requires leadership to provide vision, direction, guidance,
coordination, and organizational coherence. Leadership is required to mobilize the population by using a
root cause. Leadership is needed organize tasks to undermine the legitimacy of the host nation and to
establish legitimacy or acquiescence to their movement. The ability of insurgent leaders to organize and
their willingness to distribute power across their organization is vital to the long-term success of their
movement. Organizations dependent on key charismatic personalities to provide cohesion and motivation
for their movement are vulnerable to disruptions if those leaders are co-opted or killed.
4-50. The political leadership can be the same as its military leadership. However, sometimes this is not the
case and there is well-defined political leadership. When an insurgency has well-defined political
leadership, that leadership is called the political cadre. The political cadre may participate in the political
system or it may be clandestine and illegal. In either case, counterinsurgents define the political cadre of an
insurgency when there are insurgent leaders who are mainly involved in the political struggle and not the
armed struggle.
4-51. The political cadre are the force behind the ideology of an insurgency. They are actively engaged in
the struggle to accomplish insurgent goals. They may also work within a political party to work within the
political system and provide some legitimacy for the insurgency to the population. The cadre is active in
spreading the ideology of the insurgency, if the insurgency has an ideology. Modern noncommunist
insurgencies rarely, if ever, use the term cadre; however, these movements usually include a group that
performs similar functions. In a movement based on religious extremism, religious leaders can play a role
similar to political cadre.
4-52. The leadership of an insurgency is composed of leaders from the political cadre, guerrillas, and
auxiliaries. These may or may not be the same individuals. Moreover, they may work closely together or
operate in a decentralized manner, depending on their need for security or other operational concerns.
Insurgent leaders usually exercise leadership through force of personality, the power of revolutionary ideas,
and personal charisma. In some insurgencies, they may hold their position through religious, clan, or tribal
authority. These leaders may include supporting members, much like command and staff in a regular
military. These supporting members may include advisors, logistics and administration personnel,
spokespersons, and those leading operations. Insurgent leaders may attain positions within the government
and work to undermine the government.
4-53. Poor leadership can undermine an insurgency. Insurgent leaders who undermine their own legitimacy
with the population, for example, will significantly hamper the success of their insurgency. An analysis of
insurgent leadership provides information on how effective its leaders are in mobilizing the population and
effectively using resources to undermine the host nation.
Second Dynamic—Ideology
4-54. The insurgents must have a problem that justifies their actions in relation to the population’s
grievances and explains what is wrong with the status quo. Insurgents use a narrative to connect a
population’s grievances with its actions and demands. When an insurgency uses a narrative to mobilize a
population, these grievances become root causes. An essential part of the ability of an insurgency to
mobilize a population is an insurgency’s ideology. An ideology is the integrated assertions, theories, and
aims that constitute a sociopolitical program. Not all insurgencies are ideological, but an ideology provides
an insurgency with a message of change that is normally coherent and logical, based upon the insurgency’s
underlying assumptions.
4-55. Ideology is a factor that unifies the many divergent interests and goals among the insurgency’s
members and the general population. As a common set of interrelated beliefs, values, and norms, ideology
is used to influence the behavior of individuals within the group. It explains how the world works. Ideology

Chapter 4
4-10 FM 3-24/MCWP 3-33.5 13 May 2014
can serve as a rallying call for all members of the population to join a struggle. Commanders and staffs
answer several questions when analyzing insurgent ideology:
- What is the problem the insurgents will fix, and how will they fix it?
- Are there any ideological divisions within the insurgency or the population?
- Is the ideology supported by outside groups?
- What propaganda are the insurgents using to propagate their ideology?
Third Dynamic—Objectives
4-56. Insurgencies can have strategic, operational, and tactical objectives. Tactical objectives most directly
translate to actions. For example, a tactical goal of destroying a logistics convoy directly translates into an
attack against a logistics convoy. However, these actions are normally performed to achieve an operational
objective. In the example of the attack on the convoy, the operational objective might be to prevent logistic
support of host-nation forces. When insurgents achieve various operational goals, they can achieve the
strategic end state of their insurgency.
4-57. A strategic objective is the movement’s overall political goal or desired end state. An insurgency will
seek to—
- Force significant political, economic, or religious change.
- Overthrow the existing social order and reallocate power.
- Generate resistance to outside occupiers or change within a society.
- Nullify government control in an area.
- Cause a region to secede.
4-58. An insurgency’s strategic objectives will influence the type of insurgency that develops, and its
ideology will influence an insurgency’s end state. For example, an insurgency focused on resistance against
outside occupiers or change in a society may unify many different groups based on that shared end state.
The strategic end state of the insurgency may be as simple as resistance to occupation or a conservative
insurgency’s general resistance to change in a society. Groups that seek to nullify government control may
have an objective of protecting criminal activities and black markets. These groups may be non-ideological,
but they will still need to mobilize the population to nullify governmental control. On the other hand,
groups that wish to force significant change in a society or overthrow an existing social order are likely to
be ideologically driven. There is a connection between an insurgency’s strategic goal and an insurgency’s
ideology.
Fourth Dynamic—Environment and Geography
4-59. The environment and geography affect insurgent actions. Insurgencies may form their base in urban
environments, rural environments, or in a combination of both. Insurgents located in rural areas can enjoy
the relative safety of remote terrain or safe heavens, such as jungles or mountains. These geographical
conditions make it possible for them to form larger units and conduct larger-scale operations. However,
there are some disadvantages to a rural based insurgency. Communications and supply lines are longer and
slower. Insurgents can be isolated from the population, and an insurgency can be destroyed with a decisive
military operation.
4-60. Urban insurgencies tend to operate within ethnic ghettos or enclaves of sympathetic supporters.
Operating in urban settings requires a high degree of compartmentalization, which makes it difficult for
groups to train and organize for larger-scale operations. Urban insurgencies often operate in small cells.
However, an urban setting does allow an insurgency to work within large population groups. The
opportunity for mobilization of the population is therefore higher than in a rural insurgency. Historically,
urban insurgencies have been easier to destroy than rural insurgencies. The lack of isolation is an advantage
for counterinsurgents because they can apply constant pressure on the urban population to undermine the
insurgency.
4-61. Other factors of the area of operations may affect an insurgency. Tribal, religious, and social factors
have relationships with insurgencies. The physical environment also effects insurgent movement and

Insurgency Prerequisites and Fundamentals
2 June 2014 FM 3-24/MCWP 3-33.5, C1 4-11
planning. Commanders and staffs must understand the connections between a physical environment and its
effect on an insurgency. (See chapter 2 for more information on a physical environment.)
Fifth Dynamic—External Support
4-62. Historically, insurgencies are less likely to succeed without some form of external support. This
support can be in the form of—
- Moral support.
- Political support.
- Resources, such as money, weapons, food, advisors, training, and foreign fighters.
- Sanctuary, such as secure training sites, operational bases over a border, or protection from
extradition.
4-63. Governments providing support to an insurgency normally share interests or a common ideology
with the insurgency. Ethnic enclaves or diasporas in third-party countries can provide significant support,
even if a country’s government is not actively supporting an insurgency. For example, global diasporas can
provide significant resources for an insurgency, even if no government is providing active support. (See
FM 3-05, chapter 2, for more information on unconventional warfare.)
4-64. +However, with external support comes a degree of dependency on that support. Limiting access to
external support is a possible means of influencing or changing the actions of an insurgency. Limiting
external support provides one means to affect an insurgency indirectly. External support can help to shape
an insurgency and the outcome of an insurgency. In the case of the insurgency in Sri Lanka, external
support was essential to the success of the Liberation Tigers of Tamil Eelam. Large diasporas provided the
Liberation Tigers of Tamil sanctuary and resources. This allowed them to gain dominance over other
insurgent groups and to wage a long and bloody insurgency against the government of Sri Lanka.
Chapter 4
4-12 FM 3-24/MCWP 3-33.5, C1 2 June 2014
External Support for the Tamil Tigers
Eleven years of discrimination by the Sinhala majority against the Tamil
minority reached a breaking point in Sri Lanka during the Black July riots of 1983.
Soon after, the Liberation Tigers of Tamil Eelam emerged as the most capable Tamil
insurgent group, prepared to wage a campaign of violence and terror against the Sri
Lankan state and non-Tamil civilians. The operational environment was complex,
with insurgents fighting insurgents while also fighting the government, as occurred
with Sunni and Shia groups in Iraq. At various stages of the conflict, the Liberation
Tigers of Tamil Eelam fought against the Sri Lankan state but also against other
antigovernment insurgent groups. The most prominent of these groups was the
Janatha Vimukthi Permuna, a Marxist-Leninist group that blended violence and
left-wing politics before laying down its arms in the mid to late 1990s.
This case illustrates the importance of non-state actors in an operational
environment. While the Liberation Tigers of Tamil Eelam was indeed a non-state
actor in its own right, the group relied on its global diaspora for a range of support
activities. Following the ethnic riots of 1983, thousands of Tamil refugees fled
overseas to India, Australia, Canada, and the United Kingdom. This sowed the seeds
for the Tamil diaspora and the transnational nature of the Liberation Tigers of Tamil
Eelam’s insurgency. The global diaspora was a major part of the organization’s
fundraising and propaganda network. Furthermore, the transnational diaspora
network provided funding and weaponry to sustain the Tigers for most of the group’s
existence.
In addition to enjoying the largesse of a well-organized and entrepreneurial
diaspora, the insurgents relied on co-ethnics in India for sanctuary, which was
essential in the group’s early years. Since the Tamils effectively controlled the Jaffna
peninsula in the northeast of the country, the Liberation Tigers of Tamil Eelam had a
home base from which it could train, plan, and execute attacks against the military.
Furthermore, across the Palk Straits in Tamil Nadu, India, the Liberation Tigers of
Tamil Eelam was able to rely on the support—both active and passive—of thousands
of ethnic Tamils who sympathized with the group.
The Liberation Tigers of Tamil Eelam took advantage of the benefits of
globalization, developing a truly global network of contacts abroad, and soon
engaged in weapons procurement activities throughout East and Southeast Asia, in
Afghanistan, Pakistan, Ukraine, the Balkans, Lebanon, and other well-known arms
markets. At various points throughout the insurgency, the Tigers collaborated with
other terrorists groups as diverse as the Revolutionary Armed Forces Colombia, the
African National Congress in South Africa, Moro Islamic Liberation Front, Hezb-i-
Islami Gulbuddin in Afghanistan, the Japanese Red Army, and the Popular Front for
the Liberation of Palestine. In 1996, the insurgents acquired U.S. Stinger-class
missiles from the Kurdistan Worker’s Party and used these weapons two years later
to shoot down a Sri Lankan civilian Lionair jet.
Over time, the Liberation Tigers of Tamil Eelam distinguished itself as
perhaps the most lethal insurgent force in modern history. By the mid-late 1990s, the
group boasted a navy, an air force, and an elite suicide commando unit used to
assassinate several heads of state and numerous counterinsurgency force
commanders. As a pioneer of suicide techniques, the Tamil Tigers devoted
significant resources to two operational wings that functioned as suicide strike teams,
the Black Tigers and the Sea Tigers. A “no-holds barred” approach to the conflict led
the counterinsurgency force and the insurgents to routinely and systematically
slaughter each other, while also destroying Sri Lanka’s infrastructure and displacing
much of its civilian population.

Insurgency Prerequisites and Fundamentals
13 May 2014 FM 3-24/MCWP 3-33.5 4-13
Sixth Dynamic—Internal Support
4-65. Internal support is any support provided from within the borders of the state where the insurgency is
active. An insurgency must have some internal support, even if it is limited. The level and type of support
varies by insurgency and area. Counterinsurgents must understand the specific nature of the support to
address and counter the relationship between the population and insurgents. This support may be either
willing or based on coercion.
4-66. A large populated area or region where insurgents can operate represents many different
communities that provide varying levels of support for different reasons. There are two types of internal
support: active and passive. Passive support is critical for successful insurgent operations. It provides
freedom of movement for members of the insurgency to reside, train, plan, and conduct operations in an
area without resistance from the local community. Passive supporters do not report insurgents to local
counterinsurgent forces out of sympathy for the cause, antigovernment sentiment, reluctance to get
involved due to peer pressure, threats of violence, or the benefits that the insurgency provides.
4-67. Active supporters provide open sympathy to the insurgency, participate in insurgent operations, and
find new recruits. Active supporters are usually central to the insurgency’s propaganda efforts. They may
provide material, intelligence, or assistance as requested or demanded by insurgents. Active support, like
passive support, may be volunteered or coerced.
4-68. When analyzing the type and amount of support an insurgency has, possible indicators are:
- Reduction in local medical supplies or personnel absent from clinics and hospitals.
- Increased black market activities and extortion for resources.
- Increased theft or purchase of food and gas.
- New presence of bodyguards.
- New areas in which the local police are growing reluctant to patrol or conduct operations.
- New or increased interaction with local civilian leaders by insurgents.
- Intelligence confirming the presence of insurgents in areas where people gather and
communicate.
- Increased assassinations of those opposing insurgents or for symbolic value to frighten locals.
- A drop in the number of walk-ins and tips due to fear of retribution.
- A rise in the reluctance of local civilians to be seen talking with counterinsurgent forces.
- An increase in the absence of local reconstruction crews, police, and military or a decrease in
their willingness to be associated with counterinsurgent forces or to leave their families.
- Suspension of local government or community meeting and events.
4-69. There is a relationship between internal and external support. Insurgents must have significant
strength in at least one of these dynamics (internal or external support) or they will not be able to meet their
tangible support needs. Both of these dynamics must be controlled and reduced in order for the
counterinsurgent to prevail; just eliminating internal support is not enough to defeat an insurgency with
robust external support (and vice versa).
Seventh Dynamic—Phasing and Timing
4-70. Successful insurgencies often progress through three phases (latent and incipient, guerrilla warfare,
and war of movement). Not all insurgencies progress through all three phases, and progression through all
three phases is not a requirement for success. Insurgent success can occur in any phase. In addition,
insurgencies can revert to an earlier phase and resume development when favorable conditions return.
4-71. Movement from one phase to another phase does not end the operational and tactical activities of
earlier phases; it incorporates them. Therefore, it is difficult to determine when an insurgency moves from
one phase to another. In addition, a single insurgency may be in different phases in different parts of the
country. Advanced insurgencies can rapidly shift, split, combine, or reorganize; they are dynamic and
adaptive.

Chapter 4
4-14 FM 3-24/MCWP 3-33.5 13 May 2014
4-72. The first phase is latent and incipient. During this phase, activities include the emergence of
insurgent leadership, creation of initial organizational infrastructure, training, acquisition of resources, and
political actions, such as organizing protests. A group that eventually becomes members of an insurgency
may simply be a legitimate political group at this stage. Governmental actions and changes in society can
transform political groups into insurgencies.
4-73. The second phase is guerrilla warfare. In this phase, successful insurgents use small-unit tactics to
attack security forces while continuing ongoing political efforts. Their goal is to undermine the
government’s legitimacy and replace the government’s legitimacy with the population seeing the
insurgency as legitimate. In this stage, insurgencies may begin performing limited governmental functions
for the population in areas they control.
4-74. The third phase is war of movement. During this phase, an insurgency may be trying to overthrow a
government or trying to force the withdrawal of an occupying power. For success, an insurgency does not
necessarily need to transform into a conventional military, but it must position itself to defeat the
government or occupying power. However, this phase may not be needed. In some cases, all an insurgency
must do is create a continual problem that cannot be solved and wear down the patience of the
counterinsurgents. This is especially true when the counterinsurgents are directed by an outside power. This
phase is characterized by increased military capability, popular support, logistics capacity, and territorial
control.
4-75. Many successful insurgencies go through a process similar to these three phases, but this is not a
uniform rule. Some insurgencies, for example, form rapidly and displace a government quickly. Figure 4-1
provides a model for understanding the possible evolution of insurgencies. This model provides a
simplification of reality in order to understand and analyze a phenomena. A phase-like evolution of an
insurgency tends to create a strong political and military organization with deep roots in a society. Such
organizations are difficult to undermine. However, historically the most likely outcome of an insurgency is
its rapid defeat. These insurgencies demonstrate little phasing beyond the beginning of violence followed
by the quick defeat of the insurgency. (See figure 4-1.)
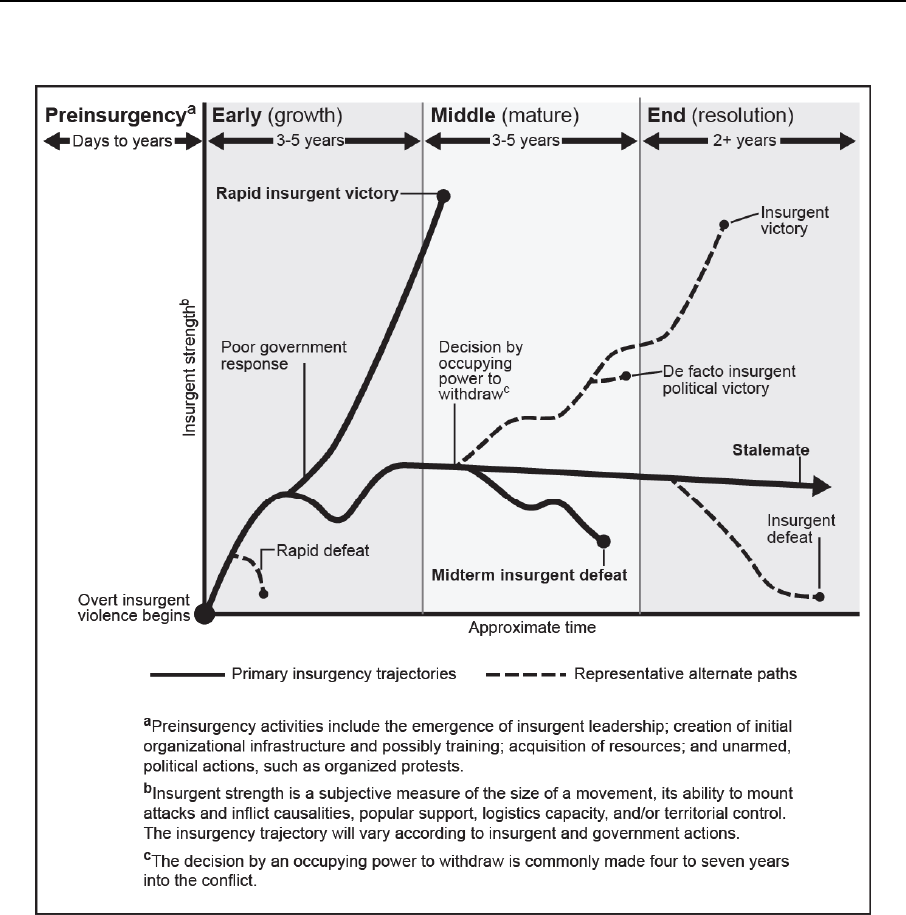
Insurgency Prerequisites and Fundamentals
13 May 2014 FM 3-24/MCWP 3-33.5 4-15
Figure 4-1. Conflict resolution model
Eighth Dynamic—Organizational and Operational Patterns
4-76. Each insurgency’s organization is unique. The specific type and level of organization is an indicator
of the insurgents’ strategy and capabilities. Understanding an insurgency’s organizational and operational
patterns helps counterinsurgents predict the enemy’s tactics, techniques, and procedures, understand their
capabilities, and identify potential targets.
4-77. Insurgents may be organized into networks and require certain elements, characteristics, bonds, and
conditions to operate and survive. A network is a series of direct and indirect ties from one entity to a
collection of entities. There may be a central point of communication or influence (critical node) that
provides a critical vulnerability for targeting against the network. Insurgent networking extends the range
and variety of both insurgent military and political actions. Networks of communications, people, and
activities exist in all populations and have a measureable impact on the organized governance of a
population and, consequently, military operations. These networks tend to heal, adapt, and learn rapidly.
They may be a combination of insurgent, criminal, regular, or irregular forces, and foreign government
sanctioned forces. These networks exist within a population. Existing within a population enhances their
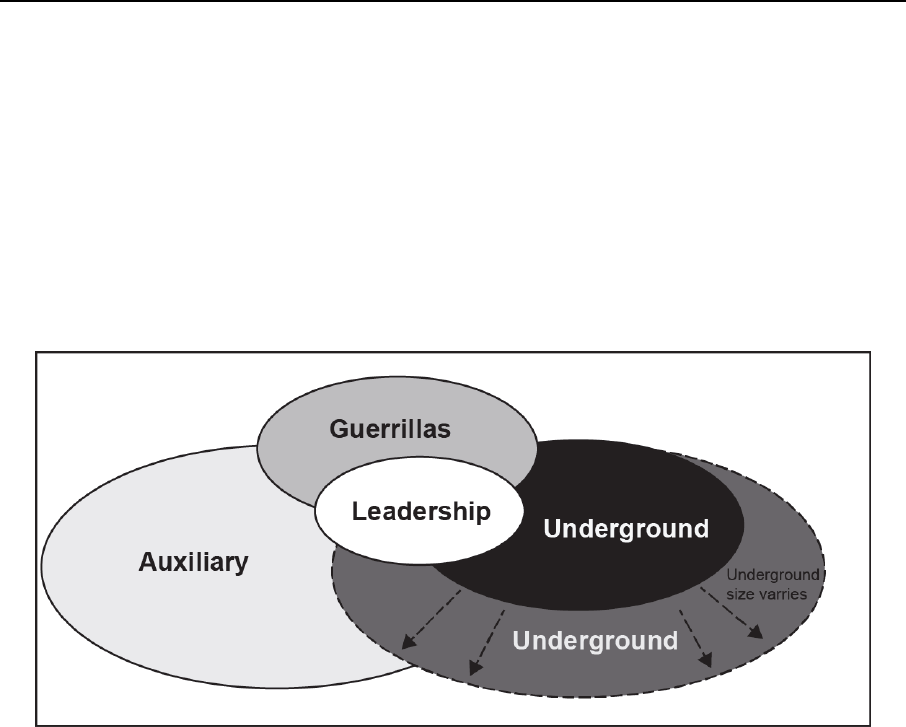
Chapter 4
4-16 FM 3-24/MCWP 3-33.5 13 May 2014
capabilities to sow disorder, survive, and protract the struggle, presenting particularly difficult problems for
counterinsurgency forces. (See paragraphs 4-88 to 4-103 for more information on networked insurgencies.)
Organizational Elements
4-78. The basic organizational elements of an insurgency are the movement’s leadership, guerrillas,
auxiliary forces, and underground elements. While there are almost certainly members of the insurgency
who perform multiple functions, grouping an insurgency into these groups provides a model of
understanding how an insurgency functions. However, commanders and staffs must avoid the trap of mirror
imaging an insurgency against U.S. organizational structure. These groupings help the commander
understand groups that are involved in the various functions of an insurgency, but commanders and staffs
need to realize that insurgencies normally do not have fixed organizational structures. (See figure 4-2.)
Figure 4-2. Organizational elements of an insurgency
Leadership
4-79. An essential element of any insurgency is its leadership and its leadership structure. This can vary
greatly and is dependent on whether the insurgency is a networked insurgency or a hierarchical insurgency.
However, because of its importance, it is covered under the first dynamic.
Guerilla Units
4-80. Guerrillas are used for a wide range military purposes, but their primary purpose is to achieve a
political end. For example, attacks on host-nation forces may undermine host-nation legitimacy among a
population and create insurgent safe heavens. Guerrilla units can conduct small-unit tactical operations and
can mass for larger operations. Ambushes against convoys are examples of small-unit tactics an insurgent
group may use. These tactics have the advantage of preventing an insurgent group from becoming
decisively engaged. As an insurgency gains military power, guerilla units increase their ability to conduct
large scale attacks. During the final insurgency stage, war of movement, guerilla units can perform actions
meant to destroy the host-nation military force. This can be a decisive action for an insurgency. If
successful, a war of movement can overthrow the government or allow the insurgency to reach other
political goals. However, if the insurgency begins a war of movement too soon, the insurgency can deplete
its military power and undermine its political power.
Auxiliary Forces
4-81. Auxiliary forces are the insurgency’s support elements. Anyone involved in an insurgency can
perform logistic functions, and insurgents are probably involved in both logistics and combat. Creating this
division, however, groups certain essential functions of an insurgency in a single category.

Insurgency Prerequisites and Fundamentals
13 May 2014 FM 3-24/MCWP 3-33.5 4-17
4-82. The auxiliary includes cells and external elements. Cells include logistics, intelligence,
counterintelligence, propaganda, population control, and recruiting elements. These are elements that
perform tasks directly connected to an insurgency. External elements provide support for an insurgency,
but they are not directly part of the insurgency. For example, external elements may include drug
smugglers or external support from another state.
4-83. Women can play an essential role in the auxiliary force. Insurgencies generally require a robust
system of financing and supply. In many cases, a woman will have greater freedom of movement in a
society than a man who is actively engaging government forces. For example, a wife, niece, or daughter of
an insurgent might be able to send a message or make financial transitions much easier than the actual
insurgent.
4-84. Auxiliary forces also include economic support systems to fund the insurgency’s military and
political operations. Economic support systems include—
- Fund raising and terrorist finance networks.
- Pillaging, looting, extorting, and enslaving a population.
- Business operations that include both direct control, joint ventures, and taxation of enterprises in
these industries:
Illicit trade in commodities and natural resources (such as oil, timber, and diamonds).
Criminal trafficking in narcotics, humans, and arms.
Sanctions busting.
Legal business enterprises (such as oil, shipping, motor transport, and hotels).
Banking and finance operations.
Underground
4-85. Underground cells conduct clandestine combatant and logistics operations in areas controlled by
government forces. Combat operations can include sabotage, assassinations, and small arms attacks.
Logistic operations can include maintaining safe houses, controlling hostages, moving weapons, and
providing communications. Underground cells include intelligence cells, logistic cells, and combatant cells.
4-86. The underground element includes those elements of the insurgency that conduct covert or
clandestine activities, especially in counterinsurgent occupied areas. Movement leaders may exist within
the underground if they are attempting to keep their affiliation or identity a secret. Insurgencies with
effective undergrounds tend to be more compartmentalized, secretive, vetted, trained, and indoctrinated
than insurgencies without them. For example, the underground can carry out terrorist acts, if desired, while
the insurgency has plausible deniability for these acts. The underground may remain in an area after
counterinsurgency clearing operations to gather information, intimidate civilians, attack members of the
security forces or government, emplace improvised explosive devices, or perform sniper operations. The
underground can be a major part of an insurgency. Its effectiveness (or ineffectiveness) provides
counterinsurgent analysts with indicators of the skill, advancement, and strategy of the insurgency. An
advanced insurgency with an effective underground is capable of operations and tactics that differ from
those of a basic insurgency, with a less capable underground. The underground tends to be the most
difficult element to recruit and train; therefore, its size tends to fluctuate with time and capability.
4-87. Underground cells seek to be self-contained; they often have their own leadership, combatants, and
auxiliary forces. However, the underground can also use members of the auxiliary to provide materials,
intelligence, counterintelligence, and early warning. The auxiliary may also pass messages, propaganda,
and disinformation. This use allows the underground to conduct operations in areas where the regular
auxiliary is present, but the underground does not have a widespread presence.
Networked Insurgencies
4-88. While some insurgencies are hierarchical, it is also likely that an insurgency will be deeply
networked into a society. While auxiliary, guerrillas, leadership, and underground elements are a means of
viewing the basic functions of an insurgency, many insurgencies in the modern era are learning and
adapting networks. An insurgency’s members will often have connections to various resourcing means,
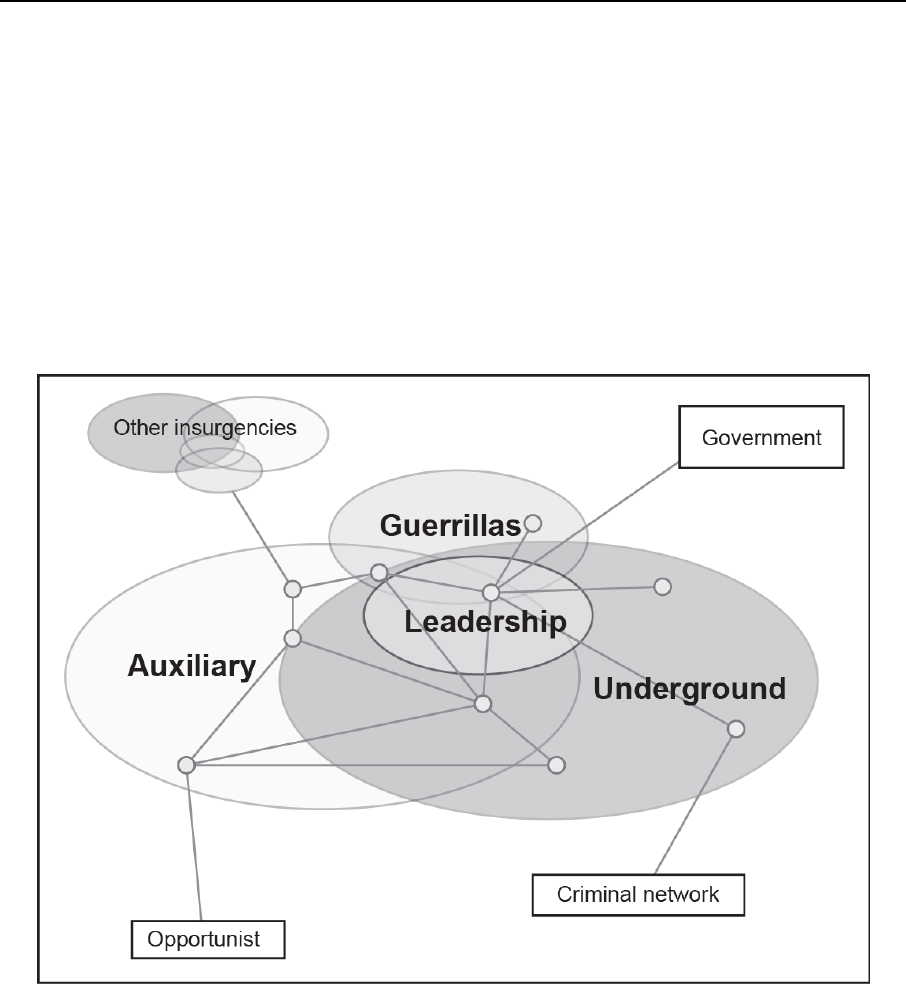
Chapter 4
4-18 FM 3-24/MCWP 3-33.5 13 May 2014
such as the black markets or diasporas. Moreover, there are normally connections to various parts of a
society. Many insurgencies, especially modern insurgencies, have members that perform basic functions
but are also networked organizations that are interwoven with their societies. While it is possible for a
hierarchical style insurgency to exist, a networked structure is more likely today because of modern
communications.
4-89. Networked insurgencies will have many connections to their operational environment. Networked
insurgencies are not monolithic, and decisions are made by different elements within the insurgency. Some
parts of the insurgency may be willing to negotiate, while other parts may decide to keep fighting. In a
networked insurgency, the different elements of an insurgency may have overlapping functions and
connections to other similar insurgencies. A networked insurgency adds to the complexity of an area of
operations because they are not acting as a unified force and because of their complex set of connections to
the rest of society and each other. (See figure 4-3 for an example of a networked insurgency.)
Figure 4-3. Networked insurgencies
4-90. For an insurgency, a network is not just a description of who is in the insurgent organization; it is a
picture of the population, how it is put together and how members interact with one another. For example, a
tribal society already has affiliated social, economic, and military networks easily adapted to warfighting.
The ways in which insurgents works within a tribal network is an expression of inherent cultural and social
customs. In this example, the social dynamic that sustains ongoing fighting is best understood when
considered in tribal terms—in particular, from the perspective of a traditionally networked society. It is the
traditional tribal network that offers insurgents a ready-made social infrastructure from which to draw.
4-91. The full functioning of a network depends on how well, and in what ways, its members are
personally known and connected to one another. Strong personal ties, often ones that rest on friendship and
bonding experiences, ensure high degrees of trust and loyalty. To function well, networks may require
higher degrees of interpersonal trust than do other approaches to organization, like hierarchies. Kinship ties
are often a fundamental aspect of many terrorist, criminal, and gang organizations. Insurgents often form a
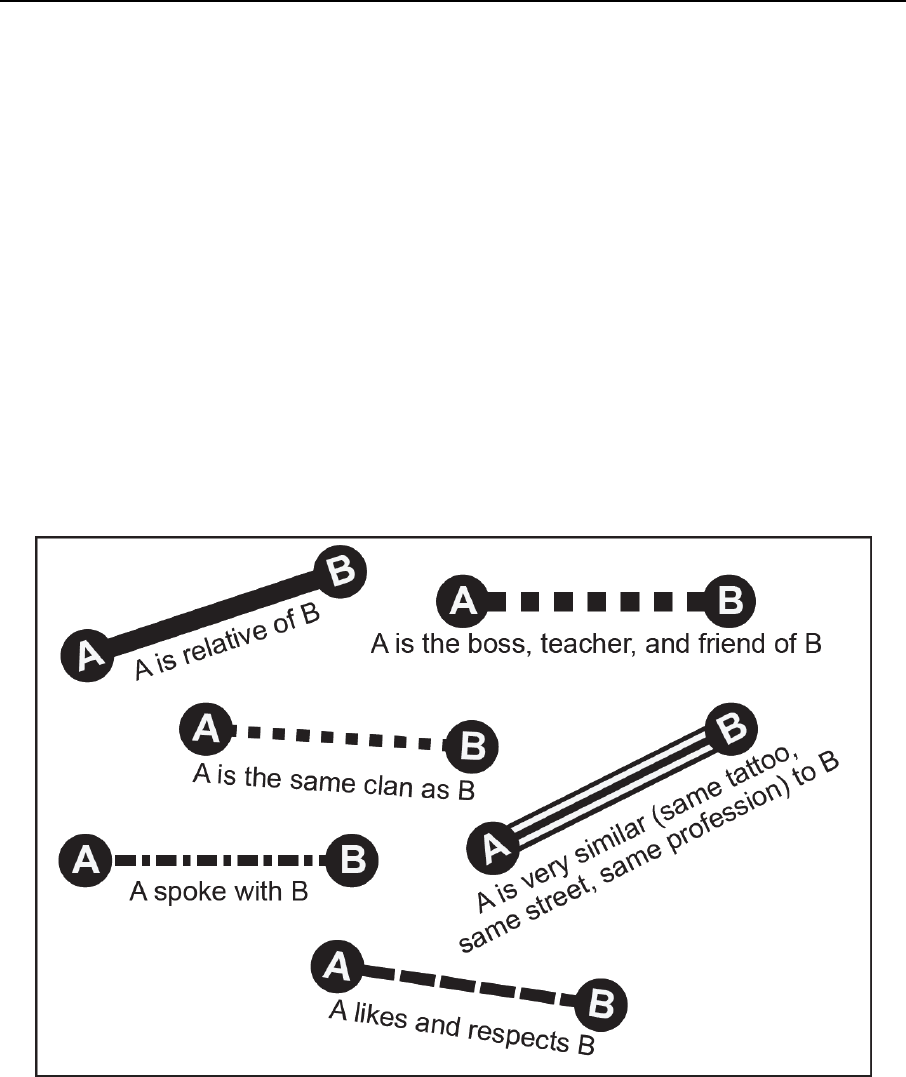
Insurgency Prerequisites and Fundamentals
13 May 2014 FM 3-24/MCWP 3-33.5 4-19
networked organization embedded in a sympathetic population. Differentiating between insurgents,
insurgent supporters, neutrals, and the host-nation government supporters is difficult.
4-92. Insurgencies can be viewed from an overall organizational perspective to the perspective of an
individual. Networked insurgencies often have a great degree of internal complexity and this makes
understanding networked insurgencies difficult. The relationship between two individuals or two groups in
an insurgency may be hierarchal, based on a mutual peer to peer understanding, or a cultural understanding
based upon social norms. Understanding the relationship between groups and individuals within groups is
essential to understanding how an insurgency works and is a part of the overall intelligence preparation of
the area of operations and understanding mission variables. This understanding starts with an individual
level analysis.
4-93. Individual-level analysis characterizes members within an organization, identifies its key members,
describes the types of connections between members, and makes assumptions about unknown members.
Commanders and staffs can describe individuals based on their network position in relation to the network
position of other individuals in the network. A networked insurgency consists of individuals and
connections between them. Commanders and staffs can think of the individuals in an insurgency as actors
or nodes. The connections between nodes are called links. This connection between two people is called a
dyad. Understanding the various types of dyads is essential in understanding the nature of an insurgency.
Person A could be connected to Person B through a number a various types of connections and each type of
relationship represents an important type of dyad. (See figure 4-4 for examples of some of types of dyads.)
Figure 4-4. Examples of dyads
4-94. Individual connections and new connections matter to an insurgency. For example, a marriage
between a combatant and a member of the auxiliary opens new paths in a networked insurgency. Moreover,
the success or lack of success of the couple will now be important. In other words, in this example, both
individuals will be vested in one another, and other insurgents’ perceptions of them will be tied together.
The nature of the bonds between individuals and decisions on who to create new relationships with have a
future impact on both the insurgency and the individuals in the dyad.
4-95. Commanders and staffs must understand the role individuals play in a networked insurgency. One
node or a very few central nodes dominate a very centralized network. If these nodes are removed or
damaged, the network may quickly fragment into unconnected subnetworks. Hubs are nodes with high

Chapter 4
4-20 FM 3-24/MCWP 3-33.5 13 May 2014
degrees of centrality. A network centralized around a well-connected hub can fail abruptly if that hub is
disabled or removed. A less centralized network has no single points of failure, and it has multiple
connections between all members. It is resilient even if some nodes are removed. Many nodes or links can
fail while still allowing the remaining nodes to reach each other over other network paths.
4-96. Commanders and staffs can also understand how an individual fits into a network by looking at that
individual’s degree centrality and betweenness centrality. Degree centrality describes how active an
individual is in the network. Network activity for a node is measured using the concept of degrees—the
number of direct connections a node has. Nodes with the most direct connections are the most active in
their networks. Commanders and staffs determine where those connections lead and how they connect the
otherwise unconnected. If a node has many ties, it is either prominent or influential. Betweenness centrality
indicates the extent to which an individual lies between other individuals in the network, serving as an
intermediary, liaison, or bridge. A node with high betweenness centrality has great influence over what
flows in the network. Depending on position, a person with high betweenness plays a broker role in the
network.
4-97. Nodes on the periphery often receive very low centrality scores. However, peripheral nodes are often
connected to networks that are not currently mapped. The outer nodes may be resource gatherers or
individuals with their own network outside their insurgent group. These characteristics make them very
important resources for fresh information that is not available inside their insurgent group.
4-98. However, understanding a networked insurgency requires more than simply understanding
relationships between individuals. Commanders and staffs must understand an insurgency at the
organizational level. Organizational-level analysis provides insight about the insurgent organization’s form,
efficiency, and cohesion. Commanders and staffs must understand a networked insurgency’s overall
organization to understand the nature of the threat. An insurgency may consist of large numbers of
subinsurgencies. As a result, each group will have a range of capacities as compared to the other groups.
Commanders and staffs can describe organizational capacities using the concept of network density.
4-99. Network density is a general indicator of how connected people are in a network. Network density is
the proportion of links in a network relative to the total number of links possible. Network density within
an insurgency indicates which groups are most capable of conducting a coordinated attack or other type of
coordination. (See figure 4-5.)
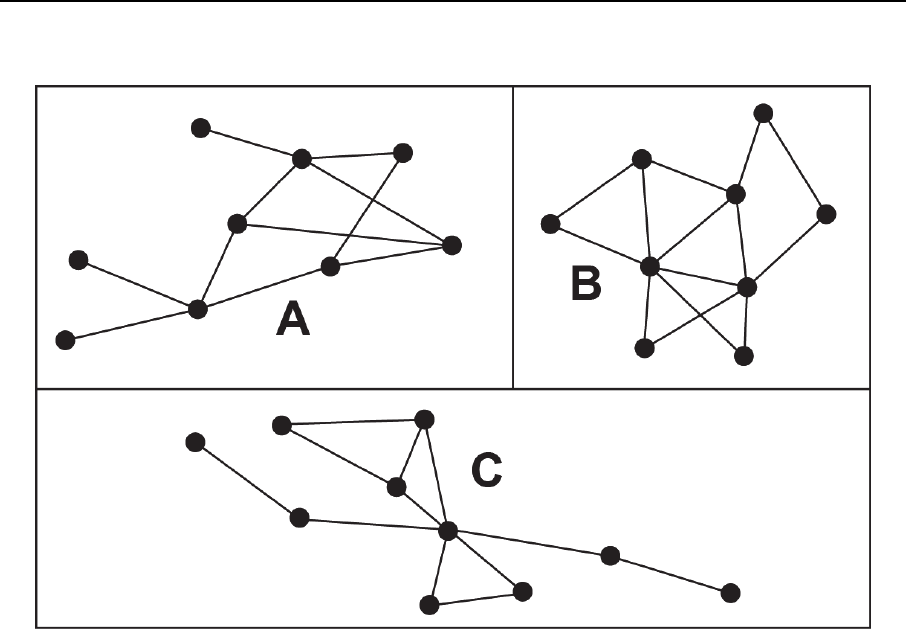
Insurgency Prerequisites and Fundamentals
13 May 2014 FM 3-24/MCWP 3-33.5 4-21
Figure 4-5. Examples of dyad networks
4-100. Changes in network density can also show changes in an insurgency’s capabilities over time. A
decrease in network density means the group is reduced and becoming fragmented. This can be in response
to actions taken by counterinsurgents.
4-101. Most network measures, including network density, can be mapped out to evaluate performance
over time. Based on changes in network density over time, a commander can—
- Monitor enemy capabilities.
- Monitor the effects of recent operations.
- Develop tactics to further fragment the insurgency.
4-102. Changes in network density can also show changes in the capabilities of an insurgency over time.
An increase in network density indicates an increased likelihood that the insurgent group can conduct
coordinated attacks. A decrease in network density means the group is reduced and becoming fragmented.
This can be in response to actions taken by counterinsurgents. An effective counterinsurgency may
eventually face only low-network-density subgroups. This is because high network-density subgroups
require only the capture of one or a few highly connected insurgents to degrade the network. So while
high-network-density groups are the most dangerous, they are also the easiest to disrupt. (See figure 4-6 on
page 4-22 for an example of the possible evolution of a networked insurgency.)
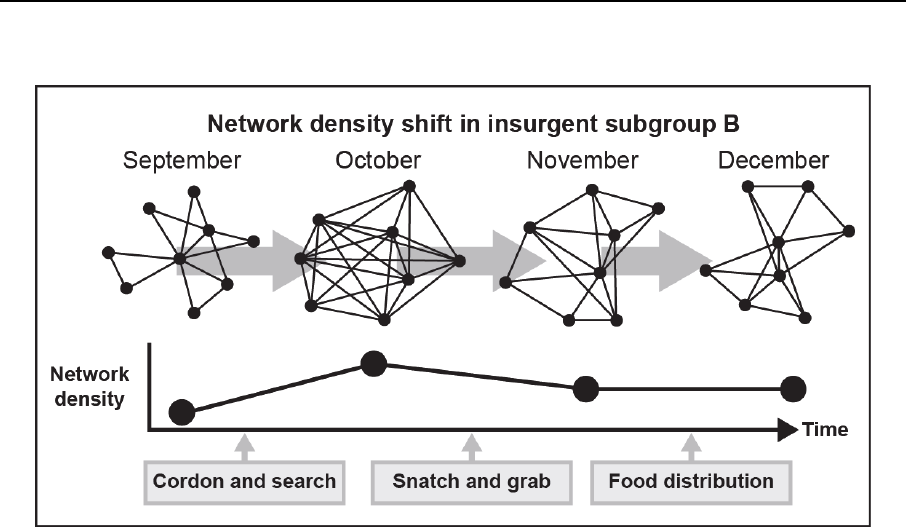
Chapter 4
4-22 FM 3-24/MCWP 3-33.5 13 May 2014
Figure 4-6. Example of changes to tactics based on density shift
4-103. Individuals within a network can also shape an insurgency. If one individual or a small group of
individuals have relationships essential to maintaining an insurgency, counterinsurgents must understand
those relationships. One node or a very few central nodes could dominate a highly centralized network.
These nodes are called hubs and can be essential for an insurgency. A less centralized network may have no
single point of failure.
OTHER ANALYTICAL FRAMEWORKS
4-104. The district stability framework assists planners in identifying and mitigating sources of instability.
Because of the uniqueness of the stability environment in each district within an area of operations, the
district stability framework was designed to identify and mitigate sources of instability. This framework
works as a planning assessment tool and nests into the military decisionmaking process. There are three
steps to the district stability framework: analysis, design, and monitoring and assessment. (See ADRP 3-07
for more details on the district stability framework.)
4-105. The interagency conflict assessment framework is another framework used to understand conflict.
The purpose of the interagency conflict assessment framework is to develop a commonly held
understanding, across relevant U.S. government departments and agencies, of the dynamics driving and
mitigating violent conflict within a country. This common understanding informs U.S. policy and planning
decisions. It may also include steps to establish a strategic baseline against which U.S. government
engagement can be evaluated. It is a both a process and a tool available for use by any U.S. government
agency to supplement interagency planning. (For more information on interagency conflict assessment
framework, see the U.S. government publication Interagency Conflict Assessment Framework.)
13 May 2014 FM 3-24/MCWP 3-33.5 5-1
Chapter 5
Insurgency Threat Characteristics
5-1. Threat characteristics involve the composition, disposition, activities, and tactics of an insurgency.
The composition of an insurgency is covered under the eighth dynamic, organizational and operational
patterns. Tactics for an insurgency include political activities, criminal actions, and military tactics.
Counterinsurgents consider how these threat characteristics create strengths and weaknesses for an
insurgency.
DISPOSITION AND ACTIVITIES
5-2. The disposition is the geographic location of insurgent elements and the way they are deployed,
employed, or located. The dispositions of an insurgency are partially determined by an operational
environment and the operational variables. For example, if an insurgency has connections to a black
market, some of its dispositions will normally be to protect that market. Terrain will also affect the
dispositions of an insurgency. Commanders and staffs must understand an operational environment to
understand an insurgency’s dispositions. (See chapter 2 for more information on an operational
environment.)
5-3. Insurgents who rely solely on violence to achieve their political goals are probably ineffective.
Instead, effective insurgents conduct a wide range of activities to achieve their goals. Many of these
activities are not enemy or terrain oriented, but political. Insurgents use a range of activities supporting
both military and political actions. Insurgent actions can include:
- Political activities.
- Population control.
- Military tactics (including terrorist actions and conventional tactics).
- Support activities.
POLITICAL ACTIVITIES
5-4. Insurgents may use political activities to achieve their goals and enhance their cause’s legitimacy. An
insurgency’s actions can come from inside the government’s political system or can be used to
communicate a message to the population. Political actions that happen within a government normally
happen in a democracy or a semidemocracy. In these systems, an insurgency and related political parties
can have some political power through elections. This gives groups the ability to launch official
investigations and a platform to question government actions. This was a technique used by the Irish
Republican Army and Sinn Fein.
5-5. Insurgent political actions within the government are limited to an autocratic regime, unless those
actions are secretive. An authoritarian regime can have members that are either sympathetic to or actual
members of an insurgency. However, those individuals must remain clandestine if they are to remain inside
the government. In these cases, insurgencies can use these individuals for intelligence and to influence
some governmental decisions.
5-6. The use of political activities to influence a society is another political activity of an insurgency.
Demonstrations, propaganda, strikes, and civil disobedience can be effective means to undermine the
legitimacy of a government and to disrupt a host nation. These actions show the level of support for the
insurgency and transmit the insurgents’ message to the rest of society.
5-7. Propaganda is one of the most important political tools an insurgency has. Propaganda provides the
means for the insurgency to communicate a message, often political, to the population. It allows the

Chapter 5
5-2 FM 3-24/MCWP 3-33.5 13 May 2014
insurgency to create a narrative of why the government’s actions are not legitimate, and how the insurgency
can eliminate the root causes of the conflict.
5-8. In areas of a country where an insurgency is in control, the insurgency can perform governmental
functions. These functions replace the functions of the host-nation government. When an insurgency
provides effective governance of a region or community, it can build local legitimacy.
5-9. At the national level, an insurgency can promote a shadow government. A shadow government offers
a known, tangible alternative to the present government to the population. This can be effective as a
propaganda technique, and a shadow government can be useful in creating a successful transition for an
insurgency. As propaganda, a shadow government allows an insurgency to identify and inform a population
of a known alternative to the current government. In practice, a shadow government allows a governmental
structure to quickly form in insurgent controlled areas. If an insurgency is successful, this allows for a
transition to a coherent national government.
POPULATION CONTROL
5-10. One of the primary goals of a local insurgency is population control. Once the government is
displaced from an area, an insurgency can act as the functioning government. With the use of force to
enforce local rules and norms, an insurgency can become a functioning instrument to control the
population. In such cases, it has displaced the government, at least locally. This control can be used to gain
legitimacy among the population. When an insurgency both controls a local population and is seen as
legitimate by the local population, it becomes more difficult to displace. The host nation must not only
regain control of the area, but maintain control when the population may not view the host nation as a
legitimate authority.
MILITARY TACTICS
5-11. Insurgents use violence to create a wide range of effects. For example, in the early phases of an
insurgency, insurgents plan attacks to achieve the greatest political and informational impact while not
becoming decisively engaged. During the war of movement, insurgents may try to destroy a host nation’s
security forces or its communication channels. Commanders need to understand the wide variety of
insurgent tactics. Insurgents may use both terrorist acts and conventional military tactics.
Terrorist Acts
5-12. Terrorist acts are meant to undermine the legitimacy of the government by demonstrating both the
inability of the government to protect the population and the strength of the insurgency. The perpetrator of
a terrorist act seeks to use the terror that the act produces among the population and the government to gain
some political objective. Insurgents generally select targets based on their strategic, operational, and
tactical importance and propaganda value. A terrorist attack will generally employ some deception and use
techniques outside of accepted norms.
5-13. The possibility of an insurgent group gaining access to weapons of mass destruction changes the
strategic effect of terrorist actions. If an insurgency gains a nuclear capability, which is an increased
possibility in an interconnected world, the threat of using a nuclear weapon would provide that insurgency
leverage for political negotiations. The actual use of a nuclear weapon would have regional and global
effects. The use of biological and chemical weapons would also have a strategic effect, but to a lesser
degree than nuclear weapons. An insurgent’s use of weapons of mass destruction would transform the
nature of a conflict.
Conventional Tactics
5-14. Insurgents use a wide range of tactics to attack counterinsurgents. The tactics insurgents use will be
based on their capabilities. During a war of movement, insurgents may try to destroy host-nation
government forces. However, this may expose insurgents if an attempt to destroy a host nation’s security
force is taken too early. Insurgents must correctly judge their capabilities versus the host nation’s

Insurgency Threat Characteristics
13 May 2014 FM 3-24/MCWP 3-33.5 5-3
capabilities. When the host nation has an advantage in capability, insurgents will probably use small-unit
tactics in order to not become decisively engaged.
5-15. Insurgents may use a wide range of conventional tactics. Insurgents often employ ambushes for
harassment and disruption. Snipers or sharpshooters may be an effective means of engaging government
forces without becoming decisively engaged. Insurgents may use indirect fire, such as mortar and rocket
attacks, to harass counterinsurgents or cause them to commit forces that can then be attacked by other
means. Weapons and munitions are frequently modified to best suit insurgent needs for a specific target or
mission. For example, insurgents may use direct fire rockets or missiles in an indirect manner to avoid
detection. Moreover, insurgents may have to improvise because they lack weapons.
5-16. Improvised explosive devices are effective tools that can be integrated into many different types of
attacks. Improvised explosive devices can be inexpensive to produce and, because of the various detonation
techniques available, may avoid risks to the perpetrator. Also, insurgents may use suicide bombing as an
employment method, and it can be very effective.
5-17. Insurgents may use cyber electromagnetic attacks. Cyber electromagnetic capabilities can give an
insurgency the ability to affect systems both within and outside the host nation. For example, a cyber
electromagnetic attack could undermine the financial system within a state. This may be an effective way to
undermine the legitimacy of a host nation. However, a cyber electromagnetic attack could also affect any
state or region. For example, cyber electromagnetic capabilities provide an insurgent the ability to attack a
country that supports the host nation. If an insurgency attains cyber electromagnetic capabilities, the nature
of the conflict changes.
SUPPORT ACTIVITIES
5-18. Although noticeable, violence may be only a small part of overall insurgent activity. Insurgent
support activities include training, logistics, and communications. These support activities sustain
insurgencies and allow for both military and political actions. They are enabled by an insurgency’s ability
to generate popular support. Insurgent support networks may be large, even when violence levels are low.
These networks can include support from other nations or from population groups outside the country. The
effectiveness of insurgent operations depends heavily on logistics.
5-19. In some parts of the world, a lack of access to weapons may forestall insurgencies. However, there is
widespread availability of weapons in many areas, with especially large surpluses in the most violent
regions of the world. Explosive hazards, such as mines and improvised explosive devices, are likely to be
common weapons in insurgencies. Insurgents can obtain weapons through legal or illegal purchases or from
foreign sources. A common tactic is to capture them from government forces. Counterinsurgency forces
should seek to cut off the flow of arms into an area of operations and eliminate their sources.
5-20. Income is essential, not only for insurgents to purchase weapons, but to pay recruits and bribe
officials. Money and supplies can be obtained through many sources. Foreign support is one possible
source of income. Local supporters or international front organizations may provide financial support.
Sometimes legitimate businesses are established to furnish funding. In areas controlled by insurgents,
confiscation or taxation may be used. Another common source of funding is criminal activity.
5-21. Funding greatly influences an insurgency’s character and vulnerabilities. The insurgents’ approach
determines the movement’s requirements. Protracted popular war strategies that emphasize mobilization of
the masses require considerable resources to build and maintain a counter state. In comparison, the
military-focused approach—which emphasizes armed action—needs only the resources to sustain a
military campaign. Counter threat finance is an important means to interdict an insurgency’s funding. (See
ATP 3-07.20/MCRP 3-33 for more information.)
TRAINING AND INDOCTRINATION
5-22. The quality and quantity of training depends on how advanced the insurgency is and what its specific
strategy is. Indoctrination is a part of training which seeks to maintain allegiance and to focus cells to
conduct continuous operations without frequent communications and direction from insurgent leadership.
The level of indoctrination can help analysts identify the strategy and sophistication of the insurgency and

Chapter 5
5-4 FM 3-24/MCWP 3-33.5 13 May 2014
includes more than just the overall objective of the insurgency. Subordinate leaders within an insurgency
are indoctrinated because they must execute the senior leadership’s intent and vision as well as guide
operations until redirected. With better indoctrination of intent and vision, insurgents may be more
effective in decentralized operations and being self sufficient.
5-23. Training also includes individual and collective training, depending on the role of the insurgent and
the specific skills of the insurgent (such as sniper, information operations, human intelligence, raid or
ambush, communications, logistics and caches, or bomb maker). More advanced training may include how
insurgents conduct themselves if captured, including resistance to interrogation and operations within
detention facilities (recruiting, clandestine communications, and maintaining control of other insurgents).
Other states may play an essential role in training an insurgency. Training can occur at sites in the
supporting country or covertly within the host nation. Many states maintain the ability to conduct
unconventional warfare. (See FM 3-05 for more information on unconventional warfare.)
COMMUNICATIONS
5-24. Communications in an insurgency cannot depend on open and traditional means. Ensuring an
effective network of communications is an essential support activity of an insurgency. Insurgents can
compensate for the lack of regular and reliable communications in numerous ways, including masking their
communications in radio, television, or Internet messages. They may also pass information in cameras,
high frequency, short-wave, and amateur (ham radio) sets, cellular phones, the mail, computers, or memory
storage devices transported by couriers. They may also avoid detection by use of couriers and face-to-face
meetings.
INSURGENT STRENGTHS AND WEAKNESSES
5-25. Insurgents usually have several strengths. They usually have a significant knowledge of an area of
operations. Usually they are operating in their own country and own ethnic group, making it extremely
difficult for friendly forces to identify insurgents in the community or to identify people connected with the
insurgency. Insurgents have intimate knowledge of the area of operations including things like the
characteristics of the local people and their culture, daily schedules, accents, and local slangs that enable
them to blend in with the local population, enhancing their ability to operate with secrecy. They will
probably wear similar clothing, have like postures, mannerisms and hand gestures, body movements,
walking speed, greetings, body motions, and maintain eye contact (or lack of) as the population of the area
of operations. They will also probably observe local social norms of food, drink, and sleeping schedules.
5-26. An insurgent is not usually responsible for maintaining normal governmental obligations to the local
population. While insurgents may conduct some governmental functions and set up a shadow government,
an insurgency does not normally have the same expectations from the population to provide governmental
services. This normally means that insurgencies spend few resources on governmental functions, which
frees more resources to conduct the insurgency.
5-27. Most insurgencies have limited personnel and resources. Long periods without resupply and loss of
key personnel can affect an insurgency’s ability to sustain a conflict. Counterinsurgents can apply pressure
on an insurgency by conducting raids on cell members; recovering enemy caches; interdicting supply
routes; searching or seizing resources from cars, homes, and personnel entering the area of operations;
isolating the insurgents from access to markets, smugglers, and black-market goods; and by conducting
offensive operations that diminish guerrilla numbers. Insurgencies usually fail when their ability to
replenish, either through counterinsurgent action, mismanagement on their own part, or withdrawal of the
support of an external actor, is undermined.
5-28. Insurgent movements are vulnerable to friendly force information operations that show their danger,
futility, privation, and numerical inferiority compared to government forces. In some cases, the fear of
being treated as a criminal if captured, and the fear of violence to an insurgent and the insurgent’s family,
can cause desertions and defections. In some societies, good treatment, pardons, protection, food, shelter,
and participation in the government may be stronger incentives than the fear of criminal punishment to
induce desertions. Other insurgent stress factors include sustained combat and a hostile environment that
weakens insurgent resolve.

Insurgency Threat Characteristics
13 May 2014 FM 3-24/MCWP 3-33.5 5-5
5-29. The decentralized nature of networked insurgencies that provides operations security can also be a
weakness as it is resource intensive, slows responsiveness, and causes information to move slowly. The
difficulty of insurgents receiving encouragement from superiors and members of the political wing, a lack
of direction in the face of counterinsurgent pressures, and an inability to openly call for reinforcements and
logistics due to their operations security plan can make insurgents feel isolated, alone, confused, and
unsupported. Analysts need to identify these points and recommend operations to demoralize and promote
defections among insurgents.
ASSOCIATED THREATS
5-30. Other threats can play interconnected roles in an insurgency. Insurgencies create change in a society
and this can create an opportunity for some organizations. Opportunists are important actors in this type of
operational environment. Two other groups are particularly important, criminal organizations and
nongovernmental militias. These groups can be supportive, neutral, or opposed to an insurgency. Moreover,
these groups can have important connections to an insurgency.
OPPORTUNISTS
5-31. An opportunist is one who takes advantage of any opportunity to achieve an end, often with no
regard for principles or consequences. In the context of counterinsurgency, opportunists often take
advantage of the conditions of instability in the pursuit of their own goals, such as smuggling contraband,
while security forces are distracted from protecting the border due to combating an insurgency.
Commanders and staffs identify opportunists, assess their impact on the mission and force protection,
consider them in planning, and mitigate their impact as needed.
5-32. There are several types of opportunists who, by nature, impede the regular and effective functions of
government and may act contrary to the well-being of the people. Opportunists may be existing local
people or external actors, including civilians, members of the government, or security forces. Opportunists
can be in direct support of the insurgency or outside actors. They can be state sponsored, sponsored by a
non-state actor, or unsponsored, all while taking advantage of unstable conditions. Opportunists understand
and exploit the conditions of instability inherent in counterinsurgency where lawlessness, subversion, and
insurgency are the norm. The extreme conditions of an insurgency may allow activities that are normally
countered with effective law enforcement and governance to proceed with impunity. These conditions
allow opportunists to pursue their political and economic interests.
5-33. Opportunists may tend to exploit populations by conducting kidnapping for ransom; revenge killings;
murder for hire; hijacking; extortion; black marketing; smuggling; and trafficking of drugs, humans, and
weapons. Opportunists use the conditions of instability to conduct activities that are often illegal to further
their interests. They may also work within the political system to further their interests. Insurgencies often
occur in a chaotic political environment. As such, opportunists can take advantage of the chaos to gain
political power.
5-34. Foreign opportunists, such as mercenaries, international criminal groups, and terrorists, may be
sponsored by an external state or non-state actor or act independently. These groups may also work in the
environment of an insurgency. They can act in a similar manner as internal opportunists, but they pursue
the interests of an external actor.
5-35. Opportunists can work for an insurgency, against an insurgency, or both. How they work and who
they work for is determined by an opportunist’s own interests. Opportunists can work both sides of a
conflict to maximize influence and profits while avoiding retribution. An opportunist can provide safe
passage for insurgents, while also providing intelligence to counterinsurgents. An opportunist is not bound
by the objectives of either the counterinsurgent or insurgent.
5-36. Reintegration initiatives, although favorable to resolve many insurgencies, can be exploited by
opportunists due to the inclusive and reconciliatory nature of these programs. Opportunists can infiltrate
local civilian security forces to avoid retribution, influence less secure communities, and provide
opportunities for vigilantism. Reintegration can also offer incentives for opportunists looking for
employment, benefits, or even amnesty from a seditious criminal, social activist, or political past.

Chapter 5
5-6 FM 3-24/MCWP 3-33.5 13 May 2014
5-37. Opportunists can be malign by design or by circumstance. Malign by design refers to the
opportunists whose purpose by character is criminal and counterproductive to effective government and a
population’s well-being. Malign by circumstance refers to opportunists whose purpose is not criminal by
design but which shifts to wholly or partial illicit activities to further their interests based on obstacles to
their original path. Groups like corporations, nongovernmental organizations, or security contractors may
be advocates for a functioning government, but due to conditions which present opportunities for them,
these groups or individuals may act counterproductively to counterinsurgent efforts. These opportunists are
very difficult to identify due to their favorable position and the potentially clandestine activities employed
to sustain their position.
5-38. In the planning process, counterinsurgents analyze the activities of opportunists, even though their
presence may not be apparent. The same conditions that may allow an insurgency to form and enjoy
freedom of movement also allow opportunists to act. Opportunists will probably take advantage of the
vulnerability of the population and exploit the lack of governmental control in pursuit of their goals.
5-39. The presence, actions, and impact of opportunists can affect the success of the mission to defeat the
insurgency and address the root causes of the conflict. This is especially true as opportunists may rely on
the presence of the insurgency and unstable conditions to achieve their ends. Commanders and staffs need
to include opportunists and their activities in understanding an area of operations and address them during
mission planning and in attack the network operations. In the intelligence preparation of the
battlefield/battlespace process, commanders and staffs may address opportunists within civil
considerations, or within the threat, depending on where they are appropriate. The mission analysis must
address identifying opportunists, understanding their impacts, and addressing or mitigating their impacts.
5-40. The commander’s intent may need to include dealing with opportunists, depending on the level of
interference or political nature of opportunists. Opportunists can impact the mission or force protection
operations. This is especially true if the opportunists are from a state sponsor or a border region where an
internal conflict can spread to another country. Overall, counterinsurgents need to understand how
opportunists can aid an insurgency, either directly or indirectly, and how they can undermine the efforts of
a host-nation government or a multinational effort to address the causes of instability.
5-41. Commanders and staffs need to analyze how their units’ actions can provide opportunities for
opportunists. Decisions concerning contracting, for example, can have various effects on giving
opportunities to opportunists. Commanders and staffs must analyze their units’ effects on the battlefield.
Some decisions that might seem to only effect a unit internally may also effect opportunists. Commanders
and staffs must think holistically about how their units interact with the environment in order to minimize
the effects of opportunist.
CRIMINAL ORGANIZATIONS
5-42. Insurgents commonly use criminal organizations to accomplish objectives. Common activities
designed to gain revenue or materials include theft, drug or human trafficking, smuggling of illicit
materials, prostitution, extortion, kidnapping, blackmail, counterfeiting, taxing of civilians, bank robbery,
and bribery. Criminal organizations can appear as street gangs, mafias, or cartels. Criminal organizations
may also assist insurgent groups in achieving objectives other than accumulating resources. Other
objectives may include intimidating government employees or candidates, conducting assassinations,
kidnapping key personnel, initiating sectarian violence, strikes, demonstrations, riots, and smuggling
high-value leaders, advisors, or weapons. Criminal organizations may also conduct operations deemed
unpopular with a civilian population at a distance from an insurgent movement to create deniability.
5-43. Many insurgencies degenerate into criminality. This occurs as the primary movements disintegrate
and the remaining elements become isolated, or the root cause is addressed. Insurgent disintegration is
desirable; it replaces a dangerous, often ideologically inspired body of disaffiliated individuals with a less
dangerous but more diverse body, normally of uneven character. The first is a security threat; the second is
a law-and-order concern. This should not be interpreted as denigrating the armed capacity of a
law-and-order threat. Successful counterinsurgents are prepared to address this disintegration. They
recognize that the ideal approach eliminates both the insurgency and any criminal threats the insurgency’s
elimination produces.

Insurgency Threat Characteristics
13 May 2014 FM 3-24/MCWP 3-33.5 5-7
5-44. However, criminal groups can develop into insurgencies. In the case of localities that depend on
black markets for their general welfare, the local population may depend on criminal activities. This creates
a closely interlocked relationship between the criminal element (running the black market) and the
insurgents (linked to the black market). In some cases, this relationship feeds into the causes of an
insurgency. For example, a local population may support the insurgents because they want to stop
interference with their economic livelihood. An insurgency based on a black market generally has ties to
other black markets and resources through globalization. At its core, a black market requires trade and
contact with others. This can create a well-funded, trained, and equipped commercial insurgency.
5-45. An insurgency can begin with a political aim and then develop into a commercial insurgency because
of connections to a market. For example, the Revolutionary Armed Forces of Colombia started as a
communist insurgent group in 1964. However, through its involvement in the drug trade, it has become the
richest self-sustaining insurgent group in history. In the parts of Columbia that it controls, it is closely
linked to the population because the population depends on the drug trade for its economic well-being.
NONGOVERNMENT MILITIAS
5-46. As the host-nation government weakens and violence increases, people look for ways to protect
themselves. If the government cannot provide protection, people may organize into armed militias to
protect themselves. Moreover, some social structures, such as tribes, may have a militia structure.
Examples of militias include the following:
- Loyalist militias formed in Northern Ireland.
- Right-wing paramilitary organizations formed in Colombia to counter the Revolutionary Armed
Forces of Colombia.
- Militias of various ethnic and political groups formed in Iraq during Operation Iraqi Freedom.
5-47. If militias are outside the host-nation government’s control, they can often be obstacles to ending an
insurgency. Militias may become more powerful than the host-nation government, particularly at the local
level. They may also fuel the insurgency and precipitate a downward spiral into a full-scale civil war.
However, they can also play a constructive role and provide local security. While this can undermine the
host nation’s government, it can also be a building block to help build legitimacy at the local level.
5-48. A militia can also shift into becoming an active insurgency and an insurgency can sometimes shift
into becoming a militia. A militia may not actively oppose the government and may be working within the
system. However, it represents a capability to challenge the host nation. Militias may become insurgencies.
An insurgency may also be integrated by a government and become a militia.
This page intentionally left blank.

13 May 2014 FM 3-24/MCWP 3-33.5 6-1
PART THREE
Counterinsurgencies
Part three provides doctrine for how to counter an insurgency. How commanders and
staffs counter an insurgency is dependent on the strategic and operational context
(part one) and the type of insurgency (part two). Chapter 6 discusses command and
control and mission command. Chapter 7 discusses planning and operational
considerations. Planning is essential in framing the problem and the possible
solutions. Chapter 8 covers intelligence. Intelligence is fundamental in gaining
situational understanding. Chapter 9 discusses direct methods and chapter 10
discusses indirect methods to counter insurgency. These chapters provide a
framework to help commanders and staffs develop an overall operational approach
to counter an insurgency. Chapter 11 discusses working with host-nation forces.
Chapter 12 discusses assessments, which provide information on effectively using
measures of performance and measures of effectiveness in counterinsurgency.
Finally, part three discusses legal considerations in chapter 13.
Chapter 6
Mission Command and Command and Control
6-1. The operations process is the means by which a commander recognizes what needs to be done and
uses the mission command or command and control process to ensure appropriate actions are taken.
Sometimes this recognition takes the form of a conscious command decision, as in deciding on a concept of
operations. Sometimes it takes the form of a rules-based procedure, as in the guiding of an aircraft on final
approach. Other forms may require a degree of judgment and intuition so that they can only be performed
by skilled, experienced people, as in devising tactics, operations, and strategies. (See ADP 6-0, ADRP 6-0,
and MCDP 6 for more information on mission command and command and control.)
COMMAND IN COUNTERINSURGENCY
6-2. Command in counterinsurgency often involves a large geographic area and control over multiple
units performing different types of operations. In Western Iraq, Brigadier General W. Blake Crowe
commanded a large area that began along the Syrian border and extended to the Jordanian border. He
executed command over multiple units, performing multiple tasks in different areas. The vignette
“Command in Counterinsurgency” provides an insight into Brigadier General Crowe’s command during
the Iraqi War in 2006.
Chapter 6
6-2 FM 3-24/MCWP 3-33.5 13 May 2014
Command in Counterinsurgency
Our area of operations began along the Syrian border and extended down
to the Jordanian border. We were also responsible for the Marine expeditionary force
security area, which extended to Saudi Arabia. This was a large area, and it was not
possible to be everywhere. This situation forced us to work with the locals and to
work and play well with other units operating in the region, such as the special
operations forces (SOF). But there in 2006, we were the surrogate government. We
did not have mayors at the time. The provincial governor was in Ramadi, and he
stayed there. Twice we were able to get him out to western al-Anbar in the year I was
there, and it took a regimental-sized operation to get him out to cities such as
Baghdadi, Haditha, and al-Qa’im. We spent nearly thirty days’ worth of planning to
get him out there because for us he was more important than the President of the
United States. I think Marines here would understand that.
Our first mayor came in six months into my deployment in al-Qa’im.
Lieutenant Colonel Dale Alford, commander of the 3d Battalion, 6th Marines, was
involved in setting the conditions for that success. We didn’t have a mayor in Haditha
because we had to arrest him. He was an insurgent. We didn’t have a mayor in Hit
because the previous ones had been killed. So until December 2006, we were the
surrogate local government. We learned very quickly that if we allowed the Iraqis to
fail to build and provision their security forces, then we would have failed as well. So,
we had to step in and fill that surrogate role.
There is a debate concerning these operations and whether or not they are
counterinsurgencies, hybrid operations, or distributed operations. We did them all. In
al-Qa’im, we conducted what I would call a pure counterinsurgency (COIN) operation
because the conditions had been set by the previous regiment. We were still having
major manned gun, tank rounds, and combined arms in downtown Hit with more than
one hundred insurgents surging on twelve- to fifteen-man positions. Phasing,
synchronizing, supporting, and enabling formed what I thought was my primary role
there.
Every battalion commander wants to be the main effort. Every regimental or
brigade commander wants to be the main effort. We weren’t the main effort in Iraq.
And every battalion could not be the main effort, and that’s the hard thing for people
to reconcile. How come I’m not getting all these assets?
When I was in Afghanistan, I received everything. We were one Marine
battalion attached to the Army and we were given everything. In Iraq, I had five
battalions in my command and one reduced force reconnaissance company
commanded by six lieutenant colonels. At least one unit is not going to get what they
want in a timely fashion. The battalions, companies, and platoons had autonomy, but
autonomy doesn’t mean that they operated independently. That’s where
synchronizing comes in. It means going out and working very closely to the battalions
and blurring the borders between zones of responsibility and forcing commanders to
get together and have a cup of coffee. Just as we needed to have tea with the local
nationals, we also needed to do that among ourselves. We did that very well with the
SOF through liaisons. We established an ad-hoc tactical fusion center at the
regimental level.
[W]e raised close to 4,000 police officers. I waited a year and was told the
police stations are coming. They never did. So we created expeditionary forward
operating bases, because that way I could use Marine Corps money. I could put
police in them, although they could not be designated official Iraqi Police stations. If it
was designated as such, you would get reported because it would not be official. So,
there are things that you have to do. It’s not selective disobedience of orders, but
rather a creative way of getting the mission accomplished.
We had two force protection measures: the American standard and what
was acceptable to the Iraqis. Casualties were unacceptable to me as a commander.

Mission Command and Command and Control
13 May 2014 FM 3-24/MCWP 3-33.5 6-3
The first time you go to a scene where you’ve lost a soldier, it does not matter what
uniform he’s wearing. He is one of ours. He was brought in to serve with us, and I
don’t care what nationality he is. We needed to build it to one standard: checkpoints,
force protection, food, weapons, ammunition, all the way down. They fight with us
and we’re going to treat them to our standard. That’s just nonnegotiable.
Note: For Army users, JP 1 defines command as the authority that a commander in the armed
forces lawfully exercises over subordinates by virtue of rank or assignment. Command includes
the authority and responsibility for effectively using available resources and for planning the
employment of, organizing, directing, coordinating, and controlling military forces for the
accomplishment of assigned missions. It also includes responsibility for health, welfare, morale,
and discipline of assigned personnel. ADP 6-0 defines control as the regulation of forces and
warfighting functions to accomplish the mission in accordance with the commander’s intent.
6-3. Many actions contribute to successful mission command, including planning, training, and education.
Moreover, a well understood commander’s intent is essential for mission command. In a
counterinsurgency, the operational environment is changing and real-time guidance or direction will need
to change. Planning, whether hasty or deliberate, provides a foundation of shared understanding. Effective
training and education, which make it more likely that subordinates will take the proper actions in combat,
help ensure the success of mission command. A commander's intent, expressed clearly before an operation
begins, is an essential element of mission command. Likewise, analysis after the operation, which
ascertains the results and lessons of the action and so informs future actions, contributes to mission
command.
Note: For Marine Corps users, mission command does not replace command and control as a
warfighting function. Mission command is a type of command and control that promotes
innovation and requires the strong relationships of trust and mutual understanding necessary for
decentralized decisionmaking necessary to seize the initiative, degrade enemy cohesion, and
strengthen friendly cohesive relationships that are critical elements to any counterinsurgency.
Based on leader character and subordinate initiative, mission command offers no checklist for
success, but instead challenges the services to cultivate a bias for taking appropriate action and
accentuate the senior leadership virtues of trust, moral courage, and restraint. The mission
command philosophy asserts that people are the basis of all military organizations, and military
operations occur as human interactions. Commanders use the philosophy of mission command to
exploit and enhance uniquely human skills. Commanders implement mission command though
leadership, providing direction and guidance as part of command and understanding that
subordinates contribute to control. The other types of command and control are command by
direction and command by planning. For the Army, the philosophy of mission command is the
exercise of authority and direction by the commander using mission orders to enable disciplined
initiative within the commander’s intent to empower agile and adaptive leaders in the conduct of
unified land operations. (For more information, see MCDP 6 and ADP 6-0).
6-4. Due to the nature of counterinsurgency operations, the inculcation of the mission command
philosophy is beneficial in dealing with the local environment. Soldiers and Marines interact with a society
at the platoon, squad, and individual level. Tactical leaders must have the ability, within the commander’s
intent, to have freedom of action to work with a local society. As such, tactical leaders should act with a
conceptual understanding of an operational environment and how their action’s fit into that operational
environment.
6-5. A counterinsurgency involves simultaneous activities at every echelon. Platoons within a company
could be doing different tasks, and companies within a battalion could be doing different tasks, all in
support of a battalion’s method of counterinsurgency. Every task involves potential decisions that can have
an immediate impact on success or failure. Moreover, these tasks are interrelated. This means that junior
leaders will make decisions at the point of effort, relying on mission type orders. This applies to any
operational approach taken to defeat an insurgency. For example, if the commander integrates a direct

Chapter 6
6-4 FM 3-24/MCWP 3-33.5 13 May 2014
action force into a host nation’s counterinsurgency effort, that force will have to understand the operational
environment and the commander’s intent. Any mission can have unintended consequences, and this
includes missions with clear objectives. For example, a direct action mission taken with faulty intelligence
could result in the deaths of civilians. All commanders have to be empowered to make decisions that
positively impact mission accomplishment. Whatever operational approach the commander takes and
however the host nation is supported, mission command is essential.
6-6. When squads, platoons and companies are distributed over wide areas, they must frequently make
decisions, and their understanding of the environment is generally better than that of their higher
headquarters. In an effective counterinsurgency, there is a need for decentralization that puts a premium on
the higher headquarters establishing a clear commander's intent and providing subordinates with vision and
guidance particular to an insurgency and a host nation. In a counterinsurgency, commanders must
effectively execute the art of command, which is the creative and skillful exercise of authority through
timely decisionmaking and leadership. These decisions often have to be made in a time constrained
environment. As such, decentralized decisionmaking is essential, and it provides control over the
operations and activities inherent in a counterinsurgency.
HEADQUARTERS USE IN COUNTERINSURGENCY
6-7. While mission command allows for multiple actions to simultaneously occur at every echelon, every
echelon has an important role in ensuring that the various actions meet the desired end state. Control
requires a shared understanding of an operational environment and operational approach in a
counterinsurgency. A lack of effective control over these activities can create gaps that insurgents can
exploit. For example, if different brigades or different divisions set different prices for weapons buyback
programs or have different policies on wages, this sometimes creates situations that hamper the overall
policy. A lack of understanding of the economic variables within a country can produce policies that
undermine a weapons buyback program or distort the labor market. On the other hand, there might be cases
in counterinsurgents want to allow a local commander more flexibility in setting such policies. The balance
between local control and coordination of overall policy is one of the primary challenges facing the
commanders and staffs of brigades, battalions, and regiments.
6-8. A commander bases the level of flexibility and coordination of activities and policies on an
operational environment and a superior commander’s intent. Moreover, the type and experience level of a
unit may play a role in determining the level of flexibility and coordination. Conditions vary within a
country or region and the cities and towns within it. For example, while different policies on wages could
produce a disjointed overall policy, it is also possible that different wages are justified by the economic
environment in different areas in the country. One city could have low unemployment, while another city
could have high unemployment. The different conditions in the labor market is something commanders
should take into account when designing a policy on economic development and hiring local workers. Also,
an inexperienced unit or a unit that is not performing its traditional mission might have less flexibility than
an experienced unit performing its traditional mission.
6-9. In a counterinsurgency, operations are interrelated, and they must support the overall commander’s
intent. The various activities that different units perform must also work within the operational approach of
the joint commander. The joint commander is responsible for designing the overall operational approach of
the counterinsurgency campaign. The joint commander has to ensure that that various activities being
performed will meet stated United States (U.S.) policy goals. Subordinate commanders ensure that their
operational approaches and activities fit within the overall operational approach. The combination of
tactical actions must produce a strategic result, and every echelon of command shares a responsibility for
ensuring that this occurs. Commanders must understand the end state and the ramifications of their actions
in meeting that end state. The commander drives the operations process. The commander’s staff must
ensure that the commander understands the operational environment and can visualize the
battlefield/battlespace. This is accomplished through staff action during mission analysis. However,
because a counterinsurgency environment is complex, situational understanding is continually developing.
Understanding what counterinsurgents should do is more important than doing tasks that may be
counterproductive. Also, constant engagement of key leaders with the population is essential to enhancing

Mission Command and Command and Control
13 May 2014 FM 3-24/MCWP 3-33.5 6-5
understanding of the population and understanding of the counterinsurgency. Understanding the problem
and having key leaders engage the population may be more important than having a large number of troops.
6-10. Headquarters elements may be essential in coordination with the host nation, other government
agencies, or other unified action partners. Counterinsurgents tailor headquarters units to the requirements to
coordinate and enable subordinate units to be effective. A larger number of headquarters or a more robust
headquarters may provide a further ability to work with interagency and host-nation organizations.
Interagency organizations can integrate their capabilities more effectively if there is a robust headquarters
element to work with. The analysis and intelligence capabilities of a division or corps headquarters may be
essential in integrating interagency organizations’ capabilities. These division and corps capabilities
provide brigades the needed span of control to operate and integrate interagency organizations and their
capabilities. Using multiple headquarters provides a robust capability for working with host-nation
organizations, both military and civilian. Many programs meant to build capacity within a host nation are
national level programs. A robust headquarters element will help to ensure that these programs are
integrated and resourced to maximize the benefit to the counterinsurgency effort. This is needed to ensure
that these programs are effective at the local level.
6-11. A headquarters can also serve as a coordination center. A coordination center can provide a means to
unify multiple governmental, military, police, and civilian partners to gather and share information, provide
support to priority projects, conduct meetings with local leaders, promote a whole of government and
unified effort approach, and lend added credibility to the government. Coordination centers provide needed
flexibility to control and coordinate host nation and multinational actions. Coordination centers can also act
as joint tactical command posts and integrate various joint capabilities, such as air support.
6-12. An operational environment does not normally dramatically change at a unit boundary. It is essential
in a counterinsurgency to understand the actual economic, political, and social boundaries of an operational
environment and not use unit boundaries as the only planning consideration for operations. The
relationships between units that are adjacent is essential. While the conditions in their operational
environment may be different, commanders should understand their adjacent unit’s problem frame and
operational approach. They should also understand how their actions may affect the operational
environment of other units. This is of particular importance when integrating information-related
capabilities. Commanders at every echelon ensure adjacent units have relationships that allow for the
completion of the overall mission.
6-13. The same is true of forces operating in another unit’s area of operations, such as special operations
forces (SOF). While missions to capture an insurgent leader may be essential to the overall mission,
commanders must coordinate with other commanders and units to mitigate negative consequences of these
types of actions with effective information operations. Commanders and staffs at all levels must ensure that
the units under their command have productive relationships with other units. Establishing command and
support relationships helps create channels that streamline information dissemination by ensuring the right
information passes promptly to the right people. The three common channels for information dissemination
are known as command, staff, and technical channels. (See ADRP 6-0 for more information on command
channels.)
6-14. The effective link between planning and assessing the effects of operations in a counterinsurgency is
the foundation for establishing effective mission command. Success in a counterinsurgency is largely
dependent on making lasting changes to an operational environment. This requires that commanders and
staff continue to evolve in their situational understanding. A continuous assessment process is essential for
planning in counterinsurgency operations. (See chapter 12 for more information on assessments.)
CONVENTIONAL FORCES AND SPECIAL OPERATIONS FORCES
SYNCHRONIZATION
6-15. Counterinsurgency requires the integration of all capabilities of the U.S. and often requires this
integration for long periods of time. However, the integration of SOF capabilities into the effort to counter
an insurgency is of particular importance to both Army and Marine commanders. FM 6-05/MCWP 3-36.1
provides a doctrinal foundation for conventional force and special operating force integration. Also,

Chapter 6
6-6 FM 3-24/MCWP 3-33.5 13 May 2014
JP 3-05 provides an overview of special operations. The synchronization of conventional forces and SOF
have special considerations in counterinsurgency.
6-16. Conventional forces and SOF depend on each other. SOF lack long term sustainability without
conventional support. More importantly, if SOF are conducting direct action missions, it becomes vital that
conventional forces and SOF coordinate so that they do not produce negative effects on the operational
environment. However, SOF can provide conventional forces with important cultural and advising
capabilities. They also provide important offensive capabilities. SOF capable of conducting direct action
might be able to conduct raids and gain intelligence that conventional forces cannot.
6-17. Typically, SOF control a joint special operations area either long term or temporarily. A joint special
operations area is simply an area of land, sea, and airspace assigned by a joint force commander to conduct
special operations. This is a means to manage SOF, which tend to operate in small teams, separately from
conventional forces, which are larger in size and capabilities. Creating a joint special operations area is a
means to synchronize actions towards a common goal, prevent conventional forces and SOF from
interfering with one another, and prevent fratricide.
6-18. In some counterinsurgency operations involving a large direct approach and conventional forces that
are likely, at least for a time, to be the primary counterinsurgents, the land forces area of operations will
typically encompass any area where SOF may operate. Unlike other operations, where the joint commander
can separate forces by time and space, a counterinsurgency can involve large scale and long term
involvement by land forces. Joint commanders typically set up joint special operations areas, but joint
special operations areas are normally temporary, and these areas return to the control of the ground
commander once the special operations mission is completed.
6-19. In a long term and large scale counterinsurgency effort, SOF operations, if not coordinated, could
create problems. SOF actions, such as direct action missions, could be highly disruptive to a conventional
unit’s ongoing efforts to build the legitimacy of the host-nation government if not coordinated. For
example, a direct action mission that is not coordinated with information operations can alienate a local
population. In some cases, a direct action mission can undermine a unit’s progress in an area, even if
counterinsurgents attempt to mitigate the negative effects to the conventional unit’s missions. Commanders
and staffs must ensure synchronization of both conventional forces and SOF can to ensure neither force
undermines the overall effort. This synchronization can include decisions on how to perform missions and
decisions on whether or not to perform missions. Both conventional forces and SOF should support the
joint commander’s intent.
6-20. SOF and conventional forces complement each other’s capabilities. When SOF are operating on
short duration missions, if not coordinated, they might not be aware of some of the local knowledge of the
area. Commanders and staffs must share information to ensure progress. Combined operations can enhance
the effectiveness of both SOF and conventional forces. The ground commander will have the daily
experiences in an area and will understand the local population. On the other hand, a successful mission by
the SOF commander could have strategic effects throughout the country. Coordination with SOF by the
ground commander benefits both the SOF and conventional forces, who have to continue the longer term
mission in an area of operation.
6-21. Both the SOF and conventional commanders share responsibility for ensuring an effective
relationship. However, the joint force commander has overall responsibility for effective integration.
FM 6-05/MCWP 3-36.1 offers some important tools, such as the use of liaison officers, to ensure an
effective relationship. Ultimately, the joint force commander has overall responsibility for synchronization.
Both SOF and conventional forces’ commanders and staffs ensure their actions meet the joint forces
commander’s intent. The joint force commander ensures that the mechanisms for effective synchronization
are in place.
13 May 2014 FM 3-24/MCWP 3-33.5 7-1
Chapter 7
Planning and Operational Considerations
7-1. Planning is important for gaining understanding. Military planning processes provide a way to
understand an operational environment and understand the commanders’ intent within that operational
environment. Planning is often conducted simultaneously with other activities, such as execution and
assessment, and both informs, and is informed by, those activities. Planning as understanding, continually
refined and questioned through assessments, helps commanders maintain situational understanding in the
ever changing environment of counterinsurgency. This continued conceptualization of the operational
environment and problem is essential for the use of mission command. However, before commanders and
staffs can conceptualize the problem, they need to understand certain paradoxes of counterinsurgency.
COUNTERINSURGENCY PARADOXES
7-2. A commander planning a counterinsurgency requires a specific mindset before that commander can
plan or execute operations, and that mindset is the foundation for understanding how to counter an
insurgency. When the United States (U.S.) acts, even temporarily, as the primary counterinsurgent,
commanders operate carefully between fighting for a population and being seen as fighting against a
population. When acting indirectly to enable a host nation, these paradoxes provide a framework for
understanding and enabling the host nation. Throughout conceptual and detailed planning, the
counterinsurgency paradoxes described in paragraphs 7-4 through 7-12 provide a set of apparent
contradictions that aid commanders and staffs in developing a counterinsurgency mindset that helps
commanders and staffs operate effectively. These paradoxes are offered to stimulate thinking, not to limit
it. The applicability of the these paradoxes depends on the local situation and, in particular, the state of the
insurgency. For example, the statement that “sometimes, the more force used, the less effective it is”, does
not apply when the enemy is breaching the perimeter; however, that thought is applicable when effective
security has already been achieved in an area. In short, commanders and staffs should not reduce these
paradoxes to a checklist; they should be used with considerable thought.
7-3. The commander must be conscious of the problem of the observer effect, where the act of engaging
the population, itself, makes changes in the operational environment. Any action on the environment
generates a reaction, thereby altering the environment. This means the environment changes with every
interaction with a society. In other words, the very act of interactions with a society changes the operational
environment. Commanders must understand this reality and constantly consider its effects on their
assessment and planning processes. Moreover, this fact is at the heart of many of the paradoxes that follow.
Sometimes, the More You Protect Your Force, the Less Secure You May Be
7-4. Ultimate success in counterinsurgency operations is normally gained by protecting the population,
not the counterinsurgency force. If military forces remain in their compounds, they lose touch with the
people, appear to be running scared, and give the initiative to the insurgents. A possible path to success
could include an increase in outreach programs that focus on protecting the population. Commanders weigh
the effectiveness of establishing patrol bases and operational support bases against the security of using
larger unit bases. Establishing patrol bases ensures access to the intelligence needed to facilitate operations.
Sharing risks with the population reinforces the connections with them that help establish legitimacy.
Sometimes, the More Force is Used, the Less Effective It Is
7-5. Any use of force produces many effects, not all of which can be foreseen. Using substantial force
also increases the opportunity for insurgent propaganda to portray lethal military activities as brutal. In
contrast, using force precisely and discriminately could strengthen the rule of law that needs to be
established. The key to successful counterinsurgency operations is knowing when more force is needed,

Chapter 7
7-2 FM 3-24/MCWP 3-33.5 13 May 2014
and when it might be counterproductive. This judgment involves constant assessment of the security
situation and a sense of timing regarding insurgents’ actions.
The More Successful the Counterinsurgency is, the Less Force Can Be Used and the More Risk
Must Be Accepted
7-6. This paradox is really a corollary to the paradox described in paragraph 7-5. As the level of insurgent
violence drops, expectations of the population may lead to a reduction in direct military actions by
counterinsurgents. More reliance is placed on police work, rules of engagement may be tightened, and
troops may have to exercise increased restraint. Soldiers and Marines may also have to accept more risk to
maintain involvement with the people.
Doing Nothing is Sometimes the Best Action
7-7. Often insurgents carry out a terrorist act or guerrilla raid with the primary purpose of enticing
counterinsurgents to overreact, or at least to react in a way that insurgents can exploit. For example,
counterinsurgents opening fire on a crowd or executing a clearing operation may create more enemies than
it removes from the streets. If an assessment of the effects of a course of action determines that more
negative than positive effects may result, an alternative should be considered, potentially including not
acting.
Some of the Best Weapons for Counterinsurgents Do Not Shoot
7-8. Counterinsurgents often achieve the most meaningful success in garnering public support and
legitimacy for the host-nation government with activities that do not involve killing insurgents (although
killing clearly will often be necessary). Arguably, the decisive effort is to isolate the insurgents by denying
the local population as a base of support. This establishes the need for synchronizing information
operations across the various lines of effort in order to generate operational advantages for the commander
conducting counterinsurgency operations. Every action, including the use of force, must be supported by
adequate information. While security is essential to setting the stage for overall progress, lasting victory
may come from a vibrant economy and political participation that restore hope. Particularly after security
has been achieved, dollars and ballots may have more important effects than bombs and bullets. This is
dependent on the context of a particular insurgency and the strategy to counter that insurgency. As with the
other paradoxes, counterinsurgents cannot treat this as a uniform rule. However, a thriving economy may
be more important than ammunition. Depending on the state of the insurgency, therefore, Soldiers and
Marines should prepare to accomplish many nonmilitary missions to support counterinsurgency efforts. All
unified action partners have a role in supporting efforts to enable governance to counter an insurgency, not
just Department of State and civil affairs personnel.
The Host Nation Doing Something Tolerably is Normally Better Than Us Doing it Well
7-9. It is just as important for counterinsurgents to consider who performs an operation as to assess how
well it is done. Where the U.S. is supporting a host nation, long-term success requires supporting viable
host-nation leaders and institutions that are legitimate and capable. The longer that process takes, the more
U.S. public support will wane and the more the local population will question the legitimacy of their own
forces and government. However, if the host nation cannot perform tolerably, the counterinsurgents
supporting it may have to act. Experience, knowledge of the area of operations, and cultural sensitivity are
essential in deciding when such action is necessary.
If a Tactic Works This Week, It Might Not Work Next Week; If It Works In This Province, It
Might Not Work In The Next
7-10. Competent insurgents are adaptive. They are often part of a widespread network that communicates
constantly and instantly. Insurgents quickly adjust to successful counterinsurgency practices and rapidly
disseminate information throughout an insurgency. Indeed, the more effective a counterinsurgency tactic is,
the faster it may become out of date because insurgents have a greater need to counter it. Effective leaders
Planning and Operational Considerations
13 May 2014 FM 3-24/MCWP 3-33.5 7-3
at all levels avoid complacency and are at least as adaptive as their enemies. There is no single prescribed
set of counterinsurgency procedures. Commanders and staffs must constantly develop new practices.
7-11. The environment of an insurgency is not static and different factors may influence various areas. An
operation or a tactic that works well in one area may not work well in another because of different factors
in the environment. Village stability operations in Afghanistan demonstrate this. Soldiers had success in
one area but did not have success in another. The reason was that the operational environments and the
population’s responses to these environments were vastly different. Commanders and staffs must
understand the local area and not assume that the same methods will work in other areas, even in an
adjacent town.
If a Tactic Works in This Province, it Might Not Work in The Next:
The Case of the Dan Aw Patan District, Afghanistan, 2010
In the fall of 2010, U.S. Army units comprised of special forces teams and
infantry squads from the 1st Battalion, 16th Infantry Regiment introduced village
stability operations in the Dan Aw Patan district of Paktia Province in southeastern
Afghanistan and along the Pakistan border. Village stability operations were an effort
to empower Afghan villagers to defend themselves from insurgents. The primary U.S.
Army mission was to recruit Afghan men in each village to serve in the local police
that would provide physical security for their community and thereby decrease the
power of the Taliban. In the course of the next year Soldiers regularly visited the
villages of the district, meeting with local leaders and equipping and training
members of the local police.
Village stability operations in Dan Aw Patan enjoyed only partial success. In
the north and central areas of the district, U.S. units were able to form and train
squads of local police. The villagers generally supported these efforts, participated in
sustainment training, and provided useful intelligence. More importantly, the Soldiers
never felt they might be in imminent danger while working with the local Afghans. In
the southern part of the district, however, village stability operations failed. U.S.
Soldiers in this region never enjoyed the security their counterparts enjoyed further
north. Moreover, the police units that were established in these villages were far less
interested in conducting patrols than in receiving pay. Despite lengthy negotiations
with village leaders in which the Soldiers offered incentives such as medical
assistance and funds for new schools, bridges, and other infrastructure, these local
police squads never became the means of countering insurgent influence in the
district.
Why did village stability operations work in the northern and central villages
but not in those to the south? The answer was not obvious. The distances between
the central and southern villages were minimal, less than 10 miles in most cases. The
demographics in each region were essentially identical in terms of size, economics,
Pashtun ethnicity, religion, and culture. The U.S. approach was consistent in its
methods and leadership. In fact, the same Soldiers who led the successful efforts in
the north and central regions also worked with the southern villages.
The lack of full success in the southern villages resulted from less visible
factors. The southern area saw much more fighting during the Soviet occupation, and
the local people viewed any foreign troops as “Soviets.” More important was the
existence of insurgent “rat lines” in this part of the district. From the Teri Mangel arms
bazaar, located just across the border in Pakistan, historic smuggling routes crossed
the Afghan border into Paktia Province toward the provincial capital of Gardez.
Because of the routes’ importance to the insurgent campaign, the Taliban exerted
pressure on the southern villages to resist American efforts to deny freedom of
movement to the insurgents and keep the routes open. Village stability operations
were designed to counter exactly this type of influence. Yet because of Taliban
pressure that succeeded despite the U.S. presence, the southern villages never
accepted the program fully. U.S. units were not resourced to collect sufficient
intelligence to discover the extent of Taliban influence, and the newly-hired local

Chapter 7
7-4 FM 3-24/MCWP 3-33.5 13 May 2014
police proved unreliable but in a passive-aggressive manner, demonstrating little
initiative except in the collection of their salaries.
The case of Dan Aw Patan displays the importance of local conditions in the
counterinsurgent’s choice of tactics. In general, village stability operations
represented an innovative approach to the challenge of securing the Afghan
population at the village level. In this case, however, the counterinsurgent learned
that what worked in one village did not work in a neighboring village only a few miles
distant.
Many Important Decisions Are Not Made by Generals
7-12. Successful counterinsurgency operations require competence and judgment by Soldiers and Marines
at all levels. Indeed, young leaders often make decisions at the tactical level that have strategic
consequences. Senior leaders set the proper direction and climate with thorough training and clear
guidance; they then trust their subordinates to do the right thing. Preparation for tactical-level leaders
requires more than just mastering Service doctrine; they must also be trained and educated to adapt to their
local situations, understand the legal and ethical implications of their actions, and exercise initiative and
sound judgment in accordance with their senior commander’s intent.
CONCEPTUAL PLANNING
7-13. The complexity of insurgencies presents problems that have incomplete, contradictory, and changing
requirements. The solutions to these challenging problems are often difficult to recognize because of
interdependencies of the relationships of an operational environment. While attempting to solve these
problems, the solution to one problem may reveal or create another, even more complex, problem.
Operational design employs various elements to develop and refine the commander’s operational approach.
Operational design involves conceptual planning. Conceptual planning establishes aims, objectives, and
intentions, and it also involves developing broad concepts for action. It generally corresponds to the art of
war. The commander’s activities of understanding and visualization are key aspects of conceptual planning.
(See MCDP 5 for more information on the art of war and ADRP 5-0 for more information on
understanding and visualization).
7-14. Design is the conception and articulation of a framework for solving a problem, and it is critical to
conceptual planning. The purpose of design is to achieve a greater understanding of the environment and
the nature of the problem in order to identify an appropriate conceptual solution. While not prescriptive,
design is based on critical thinking, conceptual planning, visualization, emergence of a hypothesis, and
continuous activity. Design is the primary way to develop an operational approach. First, design helps
commanders and staffs create a shared understanding of the current operational environment and visualize
what the environment should look like. Understanding an operational environment is an essential
foundation of counterinsurgency. Second, design enables the collaborative, conceptual planning necessary
to understand a problem and develop broad approaches to solving it. From there, commanders can visualize
their operational approach and describe to staffs and subordinate commanders how to move the
environment from the current state to the desired end state. From an operational approach, the commander
conducts detailed planning. (See figure 7-1.) (See JP 5-0 for more information on design. See ADP 5-0 for
more information on Army design methodology and MCWP 5-1 for more information on Marine Corps
design. See chapter 2 for an understanding of an operational environment.)
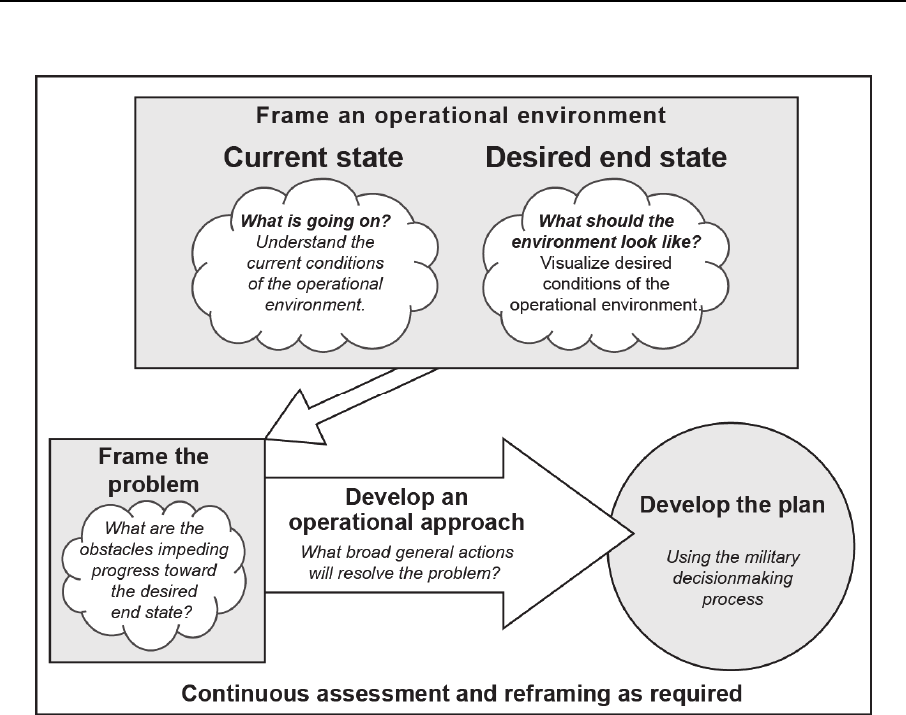
Planning and Operational Considerations
2 June 2014 FM 3-24/MCWP 3-33.5, C1 7-5
Figure 7-1. Design concept
7-15. By definition, design is iterative, and reframing the problem as necessary is essential. Reframing the
problem involves revisiting earlier hypotheses, conclusions, and decisions that underpin the current
operational approach. Reframing can lead to a new problem statement and operational approach, resulting
in an entirely new plan. By their nature, counterinsurgency efforts require repeated assessments from
different perspectives to see the various factors and relationships required for adequate understanding.
Assessment and learning enable incremental improvements to the operational approach. The goal is to
understand the problem, to construct a reasonable explanation of observed events, and to subsequently
construct a framework within which to solve the problem. The essence of this is determining the
mechanism or combination of mechanisms necessary to achieve success. These mechanisms may not be
military activities, or they may involve military actions in support of nonmilitary activities. Once
commanders understand the problem and what needs to be accomplished to succeed, they identify the
means to assess effectiveness and the related information requirements that support assessment. This
feedback becomes the basis for learning, adaptation, and subsequent reframing. (See ADRP 5-0 and
MCWP 5-1 for more information on design and reframing.)
7-16. In an ideal world, a commander engaged in counterinsurgency operations would enjoy clear and
well-defined goals for the campaign from the beginning. However, the reality is that many goals emerge
only as the mission develops and goals can change as a result of interacting with an environment. For these
reasons, counterinsurgents usually seek to achieve a combination of defined and emerging goals. Likewise,
the complex problems encountered during counterinsurgency operations can be so difficult to understand
that a clear operational approach cannot initially be developed and some assumptions must be made during
problem framing. Often, the best choice is to create iterative solutions (also known as discovery learning)
to better understand the problem. The use of design and the planning process allow commanders and staffs
to learn and achieve greater understanding as they interact with the environment. As this interaction with

Chapter 7
7-6 FM 3-24/MCWP 3-33.5, C1 2 June 2014
the population and insurgents occurs, it will reveal the validity of planning assumptions, test the strengths
and weaknesses of designs, inform the operational approach, and provide guidance to further planning and
engagement. Other considerations include:
- Systems thinking.
- Continuous assessment.
- Structured learning.
7-17. Systems thinking involves understanding a problem in terms of systems and how they relate to, and
influence, each other. For counterinsurgents this includes not only how the various systems in an
insurgency interact, but how they interact and affect the various systems in the operational environment.
Additionally, systems thinking should drive commanders and staffs to develop an understanding of how
their lines of operations and lines of effort relate and influence each other. (See paragraphs 4-88 through
4-103 for more information on networked insurgencies.)
7-18. Continuous assessment is essential to learning and adapting within the inherent complexity of
counterinsurgency operations. No design or model completely matches reality, and reasonable and feasible
solutions at one moment can become ineffective at the next moment due to changes in the situation. The
object of continuous assessment is to identify where and how the actions and activities of the
counterinsurgent are working or failing and to consider adjustments to design and the operational approach.
(See chapter 12 for more information on assessments.)
7-19. The objective of structured learning is to develop a reasonable initial design and then learn, adapt,
and iteratively and continuously improve the initial plan as more about the dynamics of the
counterinsurgency problem become evident. The operational approach and framing of the problem can be
thought of as models. In counterinsurgency, these models must always be tested to determine how well
they match reality. In other words, counterinsurgents may believe they have an understanding and general
idea of how to solve a problem, but they review that belief to ensure it is still valid at any given time.
Counterinsurgents must understand the actual problem to ensure that tactical actions have an effect on the
environment.
CENTER OF GRAVITY
7-20. An important element of conceptual planning is center of gravity analysis. The center of gravity is
important in understanding both the environment and the enemy. A center of gravity is the source of power
that provides moral or physical strength, freedom of action, or will to act (JP 5-0). A center of gravity
construct is useful as an analytical tool to help counterinsurgency forces analyze the insurgency’s sources
of strength as well as its weaknesses and vulnerabilities. Centers of gravity may change over time, they
may be different at the operational and strategic level, and they could be different from location to location.
(See JP 2-01.3 for more information on centers of gravity.)
7-21. In an insurgency, the population is not necessarily the center of gravity for an insurgent. A center of
gravity could be external support from another country, it could be a group of core leadership or believers,
or it could be a host of other factors or vital functions. Center of gravity analysis begins with the
understanding that every environment is unique, and a center of gravity analysis must not begin with a
preconceived center of gravity.
7-22. Counterinsurgents must understand their own center of gravity and that of the host nation. In many
cases, political support is the strategic center of gravity for the U.S. Some tactical actions, such as war
crimes, can undermine political support for the counterinsurgency. Host nations may also have a wide
range of centers of gravity. Operational and tactical leaders must plan and execute operations that do not
undermine the host nation’s center of gravity.
LINES OF OPERATION AND EFFORT
7-23. Lines of operation and effort are important planning tools to move conceptual planning into detailed
planning. These planning tools help describe how a military force will turn a commander’s understanding
of the current situation into a desired end state. An end state is the set of required conditions that defines
achievement of the commander’s objectives (JP 3-0). The primary source for any commander’s end state is
Planning and Operational Considerations
2 June 2014 FM 3-24/MCWP 3-33.5, C1 7-7
the mission the commander received. The use of conceptual planning helps commanders visualize how to
generate the conditions that achieve that end state. Conceptual planning also allows commanders to
determine if the dictated end state is achievable, if additional resources are necessary, what level of risk
must be accepted, and if modification of the mission and expectations is required. The end state may
change as the situation changes. Lines of operations and effort help provide the detail necessary to turn the
commander’s visualization and the operational approach (how to move from the current situation to the
desired end state) into a detailed plan.
7-24. A line of operation is a line that defines the interior or exterior orientation of the force in relation to
the enemy or that connects actions on nodes and/or decisive points related in time and space to an
objective(s) (JP 5-0). Lines of operation are normally associated with the spatial aspects of a tactical
problem. Lines of operation are useful, especially when addressing the physical aspects of
counterinsurgency, such as infrastructure protection, control of movement, and locating and engaging
insurgent forces. Lines of operation and lines of effort can be used separately or in combination.
In Service-level doctrine, United States Marine Corps doctrine does not make a distinction
between lines of effort and lines of operation. MCDP 1-0 states that, “A line of operations helps
define the orientation of the force. In conventional operations, lines of operations connect
actions related in time and space to an objective. During counterinsurgency or other irregular
warfare operations, lines of operations, for example, could focus on major stability-related
objectives, such as security, restoration of essential services, and training host-nation military
and police forces. In either case, lines of operations reinforce the idea of the single battle, since
success or failure in any line of operations will have an impact on the other lines of operations.”
7-25. A line of effort is, in the context of joint operation planning, using the purpose (cause and effect) to
focus efforts toward establishing operational and strategic conditions by linking multiple tasks and missions
(JP 5-0). Because counterinsurgencies are often more oriented towards an intended outcome or purpose
than an enemy force, counterinsurgency operations generally use lines of effort. If a line of operation is
spatially oriented, then that line of effort is purpose oriented and is appropriate when positional references
to an enemy or adversary are not the determining factor in friendly action. Because counterinsurgency
operations involve many nonmilitary factors, lines of effort may form a way to link tasks, effects,
conditions, and the desired end state. Lines of effort help commanders visualize how to integrate their
military capabilities into the efforts of the rest of the unified action community. (See JP 5-0 for more
information on lines of effort.)
7-26. +Lines of effort are important tools to link conceptual planning to detailed planning. They are an
essential means that commanders can use to arrange tactical events in time, space, and purpose. The
benefits of using this type of framework include—
- Aiding the commander in visualizing, describing, and directing operations toward a definitive
end state.
- Unifying the efforts of joint, interagency, multinational, host-nation government, and host-nation
security forces toward a common purpose.
- Allowing commanders and staffs to synchronize activities along all lines of operation and effort
to gain unity of effort.
- Ensuring all efforts converge on a well-defined, commonly understood end state.
- Combining the effects of long-term operations with short-, mid-, and long-term goals.
- Helping commanders identify missions, assign tasks, allocate resources, and assess operations.
- Enhancing mutual support between echelons and adjacent organizations.
7-27. Lines of effort depict how the actions of a counterinsurgent, over time, achieve the end state
visualized by the commander. In a counterinsurgency, lines of effort must also be nested into the actions
and activities of the host nation. From the tactical level to the strategic level, the goal of the
counterinsurgent may be to support the host nation, depending on the operational design of the
counterinsurgency. While that may require some tactical actions that do not involve host-nation forces, the
overall effort must be to support the host nation’s efforts at all levels. The counterinsurgent forces support
and integrate their efforts with the efforts of the host nation’s strategic and operational approaches.

Chapter 7
7-8 FM 3-24/MCWP 3-33.5, C1 2 June 2014
7-28. Commanders and staffs must consistently question and evaluate lines of effort as part of the
operations process. As assessment indicates changes to the situation (sudden opportunities to exploit,
failure of certain activities, new actors, and an actual change to the end state) the tasks and objectives of
various lines of operation and effort may no longer be relevant or appropriate. Worse, they can trap the
commander into a preconceived notion that accomplishment of various tasks will result in a successful
completion. Lines of operation and effort are useful means to help plan activities, but they are not measures
of mission success. All leaders must guard against the assumption that their actions are relevant because
they support any particular line of operation or effort. The underlying assumptions behind the tasks and
objectives of any detailed plan must be constantly questioned and evaluated. Just because counterinsurgents
take an action, that does not make that action relevant.
7-29. The effects of actions in one line of effort are not contained to only that line. For example, the
commander could have a line of effort to support the rule of law and a line of effort to support economic
development. However, a working legal system has a direct effect on the economic system. A system in
which contract law is enforced, for example, will have a much wider range of economic activity than a
system where contract law is not enforced. In this example, progress in the support economic development
line of effort may be hindered by struggles within the support rule of law line of effort. The use of systems
thinking allows commanders and staffs to use lines of operation and effort not only for planning and
conceptualization, but also for visualization of how they relate and influence each other.
7-30. Figure 7-2 illustrates one example of lines of effort in a counterinsurgency. However, while this is an
example that may apply well to a counterinsurgency after large-scale combat operations, it may not apply
well to other counterinsurgency operations. The U.S. could be providing only enablers for a
counterinsurgency effort. For example, U.S. forces might be combining capabilities such as counter threat
finance, signals intelligence, and a direct action force to enable the host nation by stopping the insurgency
from attaining the means to fight, providing intelligence on an insurgency’s communications, and providing
a means to neutralize insurgent leadership. The host nation may have the capability to handle basic
functions such as governance. When designing lines of effort for a counterinsurgency, the context the
counterinsurgent is operating in is not important. If commanders and staffs reduce lines of effort to some
standard solution set, they are no longer using the tool, but they are being used by the tool. This illustrates
that complex problems in counterinsurgency require critical thinking and defy solution by checklist and
battle drill methodologies. When commanders and staffs use them properly, and when they are tied to
operational and strategic purposes, lines of operation and effort are means to help commanders and staffs
perform successful counterinsurgency operations. Figure 7-2 provides examples of possible tasks on each
line of effort. However, commanders and staffs must remember that these are sample lines of effort and
sample tasks on the lines of effort. Just as the individual lines of effort must meet the situation commanders
and staffs find themselves in, tasks on a lines of effort must fit an operational environment and its desired
end states. (See figure 7-2.)
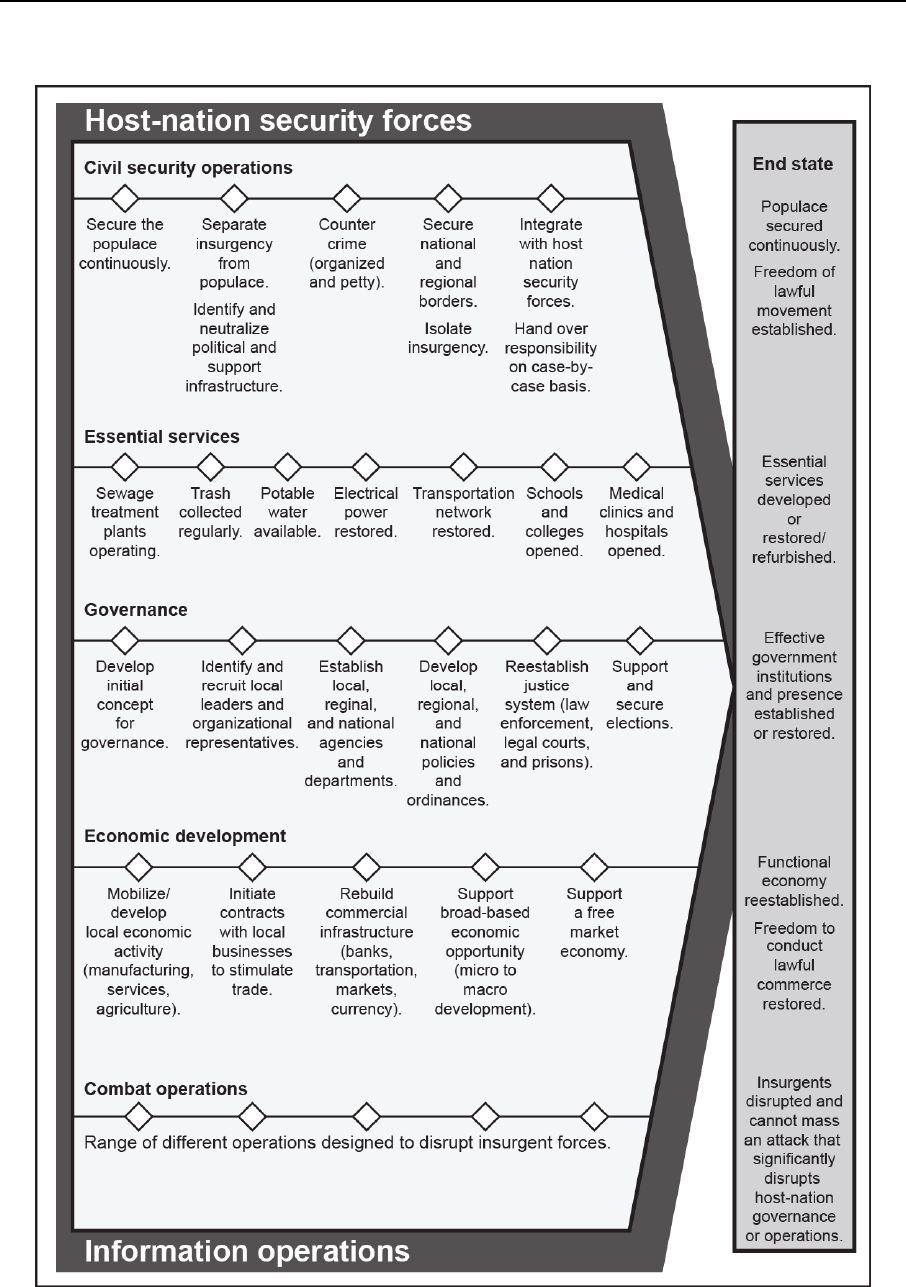
Planning and Operational Considerations
2 June 2014 FM 3-24/MCWP 3-33.5, C1 7-9
Figure 7-2. Sample of individual lines of effort

Chapter 7
7-10 FM 3-24/MCWP 3-33.5, C1 2 June 2014
DEVELOP SIMPLE, FLEXIBLE PLANS THROUGH MISSION ORDERS
7-31. Effective plans and orders are simple and direct. During insurgency and counterinsurgency
operations, not all participates will understand military language and terms. Staffs must be careful to
prepare clear, concise orders that communicate to all organizations involved a clear understanding of the
operation using operational terms and symbols that are understood by all or enabling understanding through
liaisons or other coordination means.
7-32. Flexible plans help participates adapt quickly to changing circumstances. Commanders and planners
build opportunities for initiative into plans by anticipating events. This allows them to operate inside of the
enemy’s decision cycle or to react promptly to deteriorating situations. Identifying decision points and
designing branches ahead of time—combined with a clear commander’s intent—help create flexible plans.
7-33. Commanders stress the importance of using mission orders as a way of building simple, flexible
plans. Mission orders are directives that emphasize to subordinates the results to be attained, not how they
are to achieve them (ADP 6-0). Mission orders clearly convey the unit’s mission and the commander’s
intent. Mission orders provide subordinates information on what to do and the purpose of doing it, without
prescribing exactly how to do it.
7-34. +Commanders must also give guidance concerning risk when they issue mission orders. It is the
responsibility of commanders and staff to assess tactical and operational risk. Moreover, they should ensure
their forces are using techniques that take safety into account. That said, tactical initiative that supports
mission accomplishment should never be sacrificed because of safety. An over focus on safety undermines
the needed aggressive behavior to attack the enemy and take the needed risk to maintain contact with the
population. However, informing decisionmakers of hazards, recommended controls (resources), and
residual risk allows responsible individuals to weigh benefit against risk, direct resources to best mitigate
the risk, and employ forces in the most efficient manner. (See ATP 5-19 for details on the risk management
process and processes for integrating the process in both deliberate planning and under real-time
constraints.)
TRANSITIONS
7-35. Transitions are fundamental to the planning and execution of any line of operation or effort.
Transitions may occur as a result of both success and failure in terms of friendly actions, host-nation
actions, and adversary actions. There are four types of transitions in counterinsurgency operations:
- Transitions between changes in the environment.
- Transitions between phases.
- Transitions between units in an area of operations.
- Transitions of responsibilities to host nation or other agencies.
7-36. Transitions are critical events. They are critical because they represent significant changes to the
situation and because a failure to properly execute them can stall or even negate progress. Whatever their
nature, transitions are milestones that require reassessment. Even if a transition is a result of success, such
as moving forward in phases, it is a cause to assess whether the basic assumptions and plans associated
with the next phase are still appropriate and relevant. In counterinsurgency, in addition to possible
transitions due to enemy actions, the commander and staff base transitions on changes in the population’s
perception of legitimacy.
Because transitions are based on the conditions of an operational environment, they must be a part of both
the planning process and based on assessments of an operational environment. Transitions in
counterinsurgency are essential because they generally measure progress towards the desired end state.
However, the commander must link transitions to an assessment process that allows that commander to
attain situational understanding. A transition to another phase or a transition to the host nation not linked to
the assessment process can undermine the achievement of the end state. For example, a transition to a
host-nation agency before that host-nation agency is ready to assume responsibility may ultimately have the
effect of undermining the legitimacy of the host nation as the host nation fails to meet the basic
expectations of the population.

Planning and Operational Considerations
13 May 2014 FM 3-24/MCWP 3-33.5 7-11
7-38. Transitions and assessments should be planned and executed from the beginning of any
counterinsurgency. Commanders can build legitimacy by ensuring that the host nation takes responsibility
for basic functions when it can. Therefore, building towards and executing that transition to the host nation
is fundamental to the commander’s planning and operations. Transitions to other units or other agencies
maintain a coherent and logical progression towards an ultimate transition to the host nation. The
commander avoids allowing any U.S. element to transition with another U.S. or multinational element in a
way that sets back the mission. This is also true for transitions between phases. A transition to another
phase before the operational environment allows can have disastrous consequences.
7-39. Effective counterinsurgency is about effectively linking tasks to a purpose and achieving that
purpose. This is what makes lines of effort effective planning tools for a counterinsurgency. Whether
commanders and staffs are using direct or indirect methods, they must link those methods to an end state.
However, linking both assessments and transitions into each line of effort is just as essential. The end state
of every line of effort is the creation of the conditions that satisfy the requirements of mission
accomplishment. (See figure 7-2 on page 7-9.) In counterinsurgency, ultimate success comes when a
society maintains its own legitimate government and defeats its insurgency using its own resources, not
through outside enablers. Transitioning to that point requires a well planned effort that evaluates progress
and executes all transitions in a way that does not undermine the objective of the line of effort. (See chapter
12 for a further discussion on assessments.)
7-40. A transition is a sequence of actions required to reorient on a changed situation, change to the next
phase of action, or shift responsibility from one organization to another, not a specific point in time.
Transitions require adequate time to allow for all transitional tasks to be completed. Thinking of a transition
as a general series of actions rather than a point in time better aids commanders and staffs in recognizing
transitions, planning for them, and executing them seamlessly.
7-41. When transitions occur between organizations, whether between military units or from a military unit
to a civilian agency, all involved organizations must clearly understand the tasks and responsibilities being
transferred and the time expected for completion. Commanders and staffs enable coordination between
units, agencies, and organizations to reduce the friction normally associated with a transition. Commanders
identify a collaborative transition planning team early in the process.
7-42. Commanders and staffs identify the criteria and conditions that must be met prior to executing a
transition. For example, transitioning a strongpoint to host-nation control may require the host nation to
allocate specialized personnel to replace the specialized personnel previously provided by other forces.
Additionally, host-nation manning may need to be increased to offset the departure of transitioning forces.
Commanders identify criteria for all parties involved or gaps will develop in execution. One criteria is the
minimum sustainable effort of the host nation prior to transition. Getting the host nation’s minimum
sustainable effort right with the proper balance for sustained effectiveness and long-term maintenance may
reflect a less than optimal solution from the perspective of the counterinsurgent, but any higher level of
effort by the host nation may actually jeopardize the legitimacy of the host nation in the long term by being
too heavy-handed or too costly.
7-43. Counterinsurgents must understand that transitions occur at varying times and locations based on the
situation in a given area. A transition may be linear at the local level, but transitions may occur at multiple
levels in the aggregate. For example, one battalion or brigade may have three village clusters in a build
phase, one that has transitioned, and two that are in a clear phase without any geographic context. One
host-nation security unit may be more advanced in training and equipping than another. As a result,
counterinsurgent forces may have to tailor their approach on a daily basis depending on the area, village, or
unit where they are operating. Success in counterinsurgency operations requires small-unit leaders agile
enough to transition among many types of missions and able to adapt to change. (See chapter 9 for more
information on the shape-clear-hold-build-transition framework.)
7-44. Maintaining unity of effort is particularly important during transitions, especially between
organizations of different capabilities and capacities. Relationships tend to break down during transitions.
A poorly executed transition affects the success of the mission and places the new unit at risk. Ego and
unhealthy competition are often the greatest impediments to achieving an effective transition, and they
increase unnecessary risks to Soldiers, Marines, and the mission. Commanders must set the tone for their
forces to accomplish effective physical and contextual transitions.

Chapter 7
7-12 FM 3-24/MCWP 3-33.5 13 May 2014
7-45. A successful transition is achieved when it is executed properly and in synchronization with all the
relevant organizations, entities, and agencies. Planning for transitions is more than the identification of the
events that govern phases and branches for planning. It requires a holistic framing to develop the full
appreciation of the tasks, time, and resources required to execute effectively and efficiently in a
counterinsurgency environment. Well-planned transitions require proactive analysis and continuous
assessment during execution. Assessment of qualitative and quantitative criteria, supported by expert
opinion, should inform the decision to transition.
OPERATIONAL CONSIDERATIONS
7-46. There are certain operational considerations that have important consequences for planning and
executing counterinsurgency operations. Currently, insurgencies are likely to be networked. This makes
attack the network an essential operational consideration in understanding an insurgency and planning and
executing a counterinsurgency. Other considerations include remote area considerations, border
considerations, and basing. Counterinsurgency operations normally integrate information related
capabilities with other capabilities, and information operations are essential to most operational approaches.
This makes information operations uniquely important to counterinsurgents. (See paragraphs 4-88 through
4-103 for more information on networked insurgencies.)
ATTACK THE NETWORK
7-47. Attack the network operations can be essential in planning and an essential consideration for every
step in the operations process. When an insurgency is deeply networked into a society, it is important that
attack the network operations are integrated into planning, preparing, executing, and assessing operations.
Networked insurgencies must be understood and attacked.
7-48. Attack the network operations provide the primary means to attack an insurgent network or enable a
host-nation force to defeat a networked insurgency. As such, they must be integrated and used when
counterinsurgents are facing a networked insurgency. (See paragraphs 4-88 through 4-103 for more
information on networked insurgencies.)
7-49. Attack the network operations consist of activities that employ lethal and nonlethal means to support
friendly networks, influence neutral networks, and neutralize threat networks. Attack the network
operations are conducted continuously and simultaneously at multiple levels (tactical, operational, and
strategic) throughout the whole of government. Attack the network operations are constructed around six
fundamentals:
- Understand the mission.
- Understand the operational environment.
- Understand the networks. (See paragraphs 4-88 through 4-103 for more information on networked
insurgencies.)
- Organize for the fight.
- Engage the network.
- Assess.
7-50. While listed sequentially, these actions occur continuously and simultaneously and are designed as
an enhancement to planning processes and intelligence preparation of the battlefield/battlespace. Effective
attack the network operations occur when operations and intelligence efforts are synchronized. Failure to
synchronize efforts may hamper a unit’s ability to plan and operate in an efficient manner.
7-51. Attack the network operations predominantly support problem framing and mission analysis within
planning. During the initial stages of planning, intelligence preparation of the battlefield/battlespace must
include an analysis and graphical (geospatial) representation of an operational environment as a series of
interconnected networks (friendly, neutral, and threat) in addition to weather, terrain, and civil
considerations. Threats to mission accomplishment can be presented by any network, not solely threat
networks.

Planning and Operational Considerations
13 May 2014 FM 3-24/MCWP 3-33.5 7-13
7-52. Attack the network operations enable greater understanding of the human networks and those
variables critical to insurgent and threat networks. Network mapping, charting, and social network analysis
are intelligence products that can aid in refined analysis and course of action developments, bridge
conceptual planning and detailed planning by visually depicting time sensitive intelligence and mission
requirements, and provide a shared understanding of the operational environment and design. Additionally,
these network analysis products assist commanders and staffs in recognizing dynamic and static network
relationships for targeting to support mission accomplishment. The evaluation and measurement of
targeting effects continually aid in refined understanding and provide potential follow-on targets to degrade
threat and insurgent networks.
7-53. Attack the network operations require that commanders and staffs understand social networks. A
social network analysis is a tool for understanding the organizational dynamics of an insurgency and how
best to attack or exploit them. A social network analysis allows analysts to identify and portray the details
of a network structure. It shows how an insurgency’s networked organization behaves and how that
connectivity affects its behavior. A social network analysis allows analysts to assess the network’s design,
how its members may or may not act autonomously, where the leadership resides, how leadership is
distributed among members, and how hierarchical dynamics may mix or not mix with network dynamics.
7-54. Attack the network operations provide a construct to identify, define, and engage any network,
regardless of its design. The framework for attack the network operations can be applied against any type
or combination of adaptive networks. It allows leaders to effectively engage neutral and threat networks
with the appropriate lethal or nonlethal targeting, once a network has been defined through information
collection and analysis. It also provides a means to protect friendly networks. Assessments of targeting and
the measurement of the effects on networks (friendly, neutral, and threat) in an operational environment
assist the staff in providing further targeting recommendations in sustainment of lethal or nonlethal
activities.
7-55. Attack the network operations are tactical, operational, and strategic operations that capitalize on or
create vulnerabilities to neutralize the threat network’s ability to function and enable success of the
operation. Adaptive networked threats present an enduring challenge to all military operations. Neutralizing
them may require an attack the network approach that includes the following activities:
- Support friendly networks.
- Influence neutral networks.
- Neutralize threat networks.
Support Friendly Networks
7-56. Friendly network actions are intended to establish, reinforce, or set the conditions necessary for
friendly networks to function effectively and increase capability. These operations also have indirect effects
on threat networks, driving down their capabilities and altering the environmental conditions those
networks require to survive and operate. Actions supporting friendly networks are intended to establish,
reinforce, or set the conditions necessary for the host nation or civil authorities to function effectively, add
capability, and increase capacity.
7-57. Commanders and staffs use all resources available, both Department of Defense (DOD) and
non-DOD, in an area of operations to ensure a comprehensive approach to supporting and enabling friendly
networks. Host-nation networks such as government agencies, local business or religious organizations,
tribal or cultural communities, and educational institutions all have an impact on a population and can alter
its perceptions. Commanders can affect these organizations positively, thus altering public perceptions in
favor of supporting those organizations. This results in increased cooperation, support, and even active
rebuttal of threat networks. (See paragraphs 1-47 and 1-48 for more information on comprehensive effort.)
Influence Neutral Networks
7-58. Influence neutral networks activities include operations intended to alter the opinions and attitudes of
a population segment through information, influence, presence, and conduct. These activities reflect the
ability of friendly forces to operate within the cultural and societal norms of the local population while

Chapter 7
7-14 FM 3-24/MCWP 3-33.5 13 May 2014
accomplishing the mission. They require legitimacy. Developing legitimacy requires time, patience, and
coordinated, cooperative efforts across the operational area. Influencing neutral networks to be more
favorably disposed to U.S. and host-nation objectives has indirect effects on threat networks by making the
operational environment in which threat networks operate less hospitable to their formation, growth, and
sustainment.
Neutralize Threat Networks
7-59. Threat networks are typically the immediate concern for any unit arriving in an area of operations.
These networks must be neutralized in order to protect friendly forces and populations while creating time
and space for other attack the network operations. While local friendly networks are being bolstered, there
is a period when host-nation capabilities are insufficient to address the threat. U.S. forces and multinational
partners must take direct actions against threats, reducing their functionality and impact, in order to set
conditions for supporting friendly networks and influencing neutral networks. The goal is to change the
perceptions and behaviors of neutral audiences to support the achievement of U.S., multinational, and
host-nation objectives.
7-60. A solid understanding of threat networks helps commanders engage those networks to achieve their
desired end state. Knowledge of numerous characteristics of networks can assist in the engagement process.
Conditions for network formation can help commanders and staffs understand the cognitive domain of
networks. Knowing the strengths and types of links can help commanders determine whether or not they
want to target or engage key nodes within networks or all known and potential nodes and actors of a
network.
7-61. Attack the network operations require that commanders understand and integrate specific staffing
requirements. Commanders and staffs integrate organic capabilities with enablers including, but not limited
to, other government agencies, nongovernmental organizations (NGOs), intergovernmental organizations,
law enforcement professionals, and theater-specific joint task force explosive ordnance disposal elements to
conduct attack the network operations.
OTHER OPERATIONAL CONSIDERATIONS
7-62. Operations that occur in three additional types of environments have important considerations for
counterinsurgency. They include—
- Remote area considerations.
- Border considerations.
- Basing.
Remote Area Considerations
7-63. Operations in remote areas may be conducted in rural areas where a decentralized array of forces can
be most effective. Operations in remote areas are generally conducted in insurgent-controlled or contested
areas to establish pockets of popular support for the host-nation government and deny support to
insurgents. These operations may be conducted to establish bases in unpopulated areas where insurgent
forces have established staging areas, training areas, rest areas, logistic facilities, or command posts. Units
operate in remote areas to interdict insurgent activity, destroy insurgent base areas, and demonstrate that the
host-nation government has not ceded control to the insurgents.
7-64. Operations in remote areas are usually conducted in areas that are either under insurgent control or
are contested. In these areas, ground or water modes of entry are often used, but air assault or parachute
operations can be employed. These operations may use offensive tactics such as raids, reconnaissance in
force, cordon and searches, hasty or deliberate attacks, and pursuit (or combinations of these tactics). Their
purpose may be to—
- Harass insurgents to prevent the buildup of personnel and logistic resources.
- Isolate insurgents from their support.
- Demonstrate support for the government and for the populace in the local area.

Planning and Operational Considerations
13 May 2014 FM 3-24/MCWP 3-33.5 7-15
- Expand controlled areas.
- Destroy the insurgent force and its base complexes.
7-65. To the extent possible, the counterinsurgency force should include personnel indigenous to the
operational area. The type of force employed, along with its host-nation counterpart (regular forces or
paramilitary) depends on the objectives, characteristics of the area, attitude of the local population, political
considerations, and the equipment and logistic support available. The size and composition of the
host-nation unit is, in part, determined by the insurgent’s influence over the population and the
government’s ability to recruit and develop an adequate local force. When the unit is recruited from local
inhabitants, local leaders should be used even though their military ability may be limited. By using local
leaders, assisted by advisors, better control and motivation are possible. Training, indoctrinating, and
incorporating the local force into the governmental structure is facilitated by using local leaders.
7-66. Understanding the host nation’s population’s issues from their perspectives enables
counterinsurgents to address the prerequisites of the insurgency and obtain local support for remote area
operations. Success is more likely if—
- A significant segment of the local population supports the program.
- The host nation recruits local personnel for its remote area paramilitary or irregular force.
- Host-nation forces conduct remote area operations to interdict infiltration routes in areas nearly
devoid of people. In this case, U.S. and multinational elements and host-nation forces operate in
a manner similar to that of the insurgents, but with access to superior sustainment resources.
7-67. In a rural environment, insurgents rely on friendly elements within the population to provide supplies
and intelligence. Rural insurgents prefer to operate in regions providing plenty of cover and concealment,
such as heavily forested and mountainous areas that hinder a counterinsurgency force from gaining access
to them. Often operating from their own home or village, rural insurgents often move to camps if security
does not permit them to remain at home. Insurgent camps are chosen with a view toward easy access to the
target population, access to a friendly or neutral border, prepared escape routes, and good observation of a
counterinsurgency force’s approach routes. When counterinsurgency operations force the insurgents from
their preferred base camps, insurgents tend to establish camps in rugged inhospitable areas that are not
easily penetrated. Like counterinsurgency in urban areas, remote counterinsurgency operations must focus
on both locating and eliminating insurgents and on severing the supportive element of the population from
providing supplies and intelligence to them.
7-68. Operations in remote areas typically call for use of combat outposts that are linked to the local
population. Commanders and staffs consider three perspectives (the population, insurgents, and
counterinsurgents) when choosing combat outpost locations. Establishing an outpost close to the local
population does not serve to advance the counterinsurgency’s goals without certain factors. These
include—
- Gaining acceptance of the local civilian leadership.
- Maintaining a constant presence in the community.
- Maintaining constant communications with the local community to provide immediate
emergency assistance.
- Maintaining situational understanding and an awareness of any changes in the population’s
patterns of life. This includes movement of outsiders (such as visitors, merchants, nomads, or
seasonal labor).
7-69. Operations in remote areas may include civil affairs, defense support of civil authorities, intelligence,
population and resources control, and advisory assistance operations. Most remote operations are long term
and continuous. They are initially directed at disrupting the insurgent’s operations and then destroying the
insurgent armed forces. Counterinsurgents destroy the insurgent infrastructure as quickly as possible.
7-70. Initially, strong combat and sustainment forces establish secure operational bases. Counterinsurgents
may conduct remote area operations in areas with little or no population to interdict infiltration routes.
Counterinsurgents make maximum use of special equipment to provide continuous coverage of suspected
areas and routes. Firepower and combat forces, with air assault capabilities, should be prepared to quickly
attack identified targets. Because remote area operations can stress the capability of land forces to make

Chapter 7
7-16 FM 3-24/MCWP 3-33.5 13 May 2014
rapid responses, commanders can mitigate risk by coordinating with joint enablers for close air support,
tactical airdrops, information collection, communications relays, and personnel recovery forces.
Border Considerations
7-71. In a counterinsurgency environment, armed forces may be responsible for border security, and they
may have to help other security forces with immigration, customs, and internal security operations. The
specific threat level, however, may require combat-type border operations, particularly in remote areas. The
threat level may require units or advisor teams to advise and assist host-nation forces assigned to prevent or
interdict the infiltration of insurgent personnel and materiel across international boundaries. This method is
a terrain-centric approach to combating an insurgency. The commander’s intent is to isolate insurgent
forces from their external support and sanctuaries. Secondary purposes include locating and interdicting
insurgent land infiltration routes, destroying insurgent forces and bases in areas adjacent to the border, and
collecting and reporting information on insurgent capabilities and intentions. Border operations normally
require restrictive control measures for populations and resources that are particularly annoying to tribal
and ethnic border groups who do not recognize the international boundary. The host-nation government
must make a continuing effort to physically and psychologically gain and maintain the loyalty of the
affected population.
7-72. Designated border forces may be composed of border police and guards and may include
paramilitary forces and regular armed forces with supporting or direct responsibility for portions of the
national border or key internal routes to access other regions. Border operations are planned, conducted,
and supervised from the national level, to the regional level, and finally through commanders at the local
level. Border task forces are tailored units designed to meet requirements in their assigned areas. They
should contain sufficient sustainment warfighting function and sustainment elements to support civil
authorities’ operations for extended periods.
7-73. Tasks that may be performed in controlling the border include the following:
- Security of populated areas.
- Intelligence and counterintelligence operations.
- Operation of authorized points of entry.
- Refugee and internally displaced person control.
- Enforcement of movement and travel restrictions.
- Military information support operations.
- Reconnaissance, surveillance, and target acquisition.
- Attacks against insurgent forces.
- Destruction of insurgent base areas.
- Barrier and denial operations.
7-74. In a phase I insurgency, operations in border areas are normally a function of police, customs, and
other government organizations. Armed and paramilitary forces may assist these organizations, particularly
in remote areas. In phases II and III, denial of external support for the insurgency may require combat
operations in border areas. These operations require close coordination and cooperation between the armed
forces, paramilitary forces, and all government agencies involved. Attempts by insurgents to infiltrate can
be mitigated through the use of biometrics to identify subversive activities and limit or disrupt insurgent
mobility. (See paragraphs 4-70 through 4-75 for a discussion on the insurgency phases.)
7-75. Physically sealing a border may not be possible, since it could require the commitment of more
government forces and materiel than overall resources permit. Intelligence must be gathered by all means
available to determine the locations and extent of insurgent activities in border areas.
7-76. Commanders determine infiltration and exfiltration routes, support sites, frequency and volume of
traffic, type of transportation, number and type of personnel, amount and type of materiel, terrain and
traffic conditions, and the probable location of base areas and sanctuaries. Units conduct continuous and
detailed surveillance of these areas. Since placing forces and barriers at all possible crossings or entry sites
may be impossible, commanders establish priorities. Counterinsurgents use natural barriers wherever
possible. Using patrols, sensors, and obstacles in selected areas increase the effectiveness of natural

Planning and Operational Considerations
13 May 2014 FM 3-24/MCWP 3-33.5 7-17
barriers. Herbicides, if approved for the area of operations, may be used to enhance visibility in vegetated
areas.
7-77. A restricted zone is a carefully selected area, of varied width, that is contiguous to the border.
Counterinsurgents give public notice that all unauthorized individuals or groups encountered in the
restricted zone will be dealt with as infiltrators or insurgents. A friendly population buffer zone is an area in
which civilians living within the area of operations are limited to those believed to be loyal to the
government. Persons whose loyalty cannot be established are monitored. This concept offers a good
potential for establishing information nets and using loyal citizens in self-defense border units. It denies
insurgents potential civilian contacts and base areas for border-crossing activities. Commanders and staffs
direct a continuing military information support operation effort toward maintaining the morale and loyalty
of the population.
7-78. Counterinsurgents may employ aerial reconnaissance, unattended ground sensors, and ground
reconnaissance patrols to ensure adequate reconnaissance and surveillance of remote areas. Surveillance
and control of extensive coastal areas normally require the use of coordinated ground patrols on the
shoreline, coordinated offshore patrols, aerial surveillance, strategically located observation posts, and an
effective system of licensing and identifying friendly, military, and civilian watercraft.
7-79. Commanders and staffs must consider the population of the host nation’s neighbor country.
Counterinsurgent actions will be viewed and interpreted by local populations in neighboring countries.
Counterinsurgents must consider the impact their actions have on these populations. If the neighboring
local populations sympathize with host-nation insurgents or believe that counterinsurgent programs are
counterproductive to their individual goals, then negative perceptions can lead to increased foreign fighters,
weapons, and resource trafficking to support an insurgency. Counterinsurgents lack the physical means to
influence this population, but they can mitigate risk by performing effective information operations that
explain counterinsurgent programs and their benefits.
Basing
7-80. Counterinsurgency forces operate within a host country and must have a base from which to operate.
A base is a locality from which operations are projected or supported (JP 4-0). All bases must be securable
and defendable. Bases vary according to the size and missions of the units occupying a base. All types of
bases require clear command relationships. In counterinsurgency operations, forward operating bases and
combat outposts are important.
7-81. Normally, when U.S. forces are the primary counterinsurgents, at least one forward operating base
exists in an area of operations. The size of the area, its physical characteristics, and the number and size of
the units operating within the area often require additional operating bases. The forward operating bases
established by a brigade or battalion are often semipermanent and provide deployed units with command,
control, and communications facilities; sustainment; personnel systems support; staging areas; and
intelligence activities. They provide units with relatively secure locations from which to plan and prepare
for operations. During counterinsurgency operations, they aid in limiting insurgent mobility nearby and in
providing some security and contact to the local population.
7-82. There are a few differences between brigade and battalion forward operating bases. Brigade forward
operating bases are larger than battalion forward operating bases and provide a secure location for
nondeployed elements of the deployed battalions, such as battalion forward support companies. A battalion
forward operating base is normally staffed with the minimum personnel needed to operate and provide
security. Other assets are normally positioned in a brigade operational base. A battalion forward operating
base should maintain two methods for sustainment: by road and either air or water.
7-83. A combat outpost is a reinforced observation post capable of conducting limited combat operations
(FM 3-90-2). In counterinsurgency operations, combat outposts are often company and platoon-sized bases
inside of insurgent influenced territory. When U.S. forces are acting as the primary counterinsurgents,
combat outposts represent a cornerstone of counterinsurgency operations. Located in strategically
important areas, a combat outpost provides security in its immediate area and direct contact with the local
population not possible from remote bases. Although this method carries with it potential downsides in

Chapter 7
7-18 FM 3-24/MCWP 3-33.5 13 May 2014
terms of increased proportion of forces used for force protection, thus limiting combat power available,
combat outposts provide an increase in security for the population.
INFORMATION OPERATIONS
7-84. Information operations is the integrated employment, during military operations, of
information-related capabilities in concert with other lines of operations to influence, disrupt, corrupt, or
usurp the decisionmaking of adversaries and potential adversaries while protecting our own (JP 3-13). For
the Army, information operations integrates information related capabilities into the overall operational
approach. The joint and multinational communities continue to use the term information operations. The
joint construct for conducting information operations is the information-influence relational framework.
The framework describes the application, integration, and synchronization of information-related
capabilities to influence, disrupt, corrupt, or usurp the decisionmaking of target audiences to create a
desired effect to support achievement of an objective. An information-related capability is a tool,
technique, or activity employed within a dimension of the information environment that can be used to
create effects and operationally desirable conditions (JP 3-13). (See Army doctrine for more information on
integrating information-related capabilities.)
7-85. A target audience is an individual or group selected for influence (JP 3-13). Information operations
seek to generate effects against the decisionmaking of individuals, a group, or perhaps elements of a
population. In general, the integration of information-related capabilities is most effective when employed
against precisely selected targets to achieve clearly defined objectives.
7-86. Information-related capabilities generate effects that support achievement of the commander’s
objectives. There are many military capabilities that contribute to operations, and commanders and staffs
should consider them during the planning process. Some of these capabilities are:
- Soldier and key leader engagement.
- Civil-military operations.
- Cyberspace operations.
- Military deception.
- Electronic warfare.
- Operations security.
- Military information.
- Physical attack.
- Physical security.
- Counterintelligence.
- Public affairs.
- Combat camera.
- Defense support to public diplomacy.
- Space operations.
- Special technical operations.
- Intelligence.
- Joint electromagnetic spectrum operations.
- Information assurance.
7-87. A commander can use many other capabilities to enhance and reinforce the shaping of the area of
operations and the accomplishment of mission objectives in the information environment. (See JP 3-13 for
additional information on the use of information-related capabilities.)
7-88. Information-related capabilities, whether applied in shaping the operational environment to deter
conflict or in enabling decisive maneuver, must be recognized as an essential enabling activity that
facilitates development of an operational advantage for the commander. In current and future operational
environments, the integrated employment of information-related capabilities into operations is critical to
mission success. (See the Marine Corps operating concept for information operations for more information
on information-related capabilities.)

Planning and Operational Considerations
13 May 2014 FM 3-24/MCWP 3-33.5 7-19
7-89. The actions of Soldiers and Marines in an area of operations are the most powerful influence on
credibility of their commanders’ message. All audiences (including local, regional, and threat) compare the
friendly force’s message with its actions. Consistency contributes to the success of friendly operations by
building trust and credibility. Conversely, if actions and messages are inconsistent, friendly forces lose
credibility. Loss of credibility makes land forces vulnerable to threat counter propaganda and information
warfare and places Army and Marine forces at a disadvantage. (See FM 3-13 for more information on
messaging.)
7-90. Commanders, staffs, and unified action partners construct a narrative to help understand and explain
an operational environment, its problem, and solutions. Narratives are tied to actions in an operational
environment. A narrative is a brief description of a commander’s story used to visualize the effects the
commander wants to achieve in an information environment to support and shape an operational
environment.
7-91. The key to successful information operations during an insurgency is the commander’s intent. The
commander’s intent provides a focus for the coordination and synchronization of information-related
capabilities. Staffs and information operations planners must balance the use of different
information-related capabilities, such as civil affairs operations, physical attack, and cyberspace operations,
in order to communicate the intended message to the target audience with an understanding of possible
second and third order effects on the rest of the global population.
7-92. When commanders and staffs use the various types of information capabilities, there is a tension
between a broad message and engaging the population to achieve a two way understanding. The U.S. is
generally involved in counterinsurgencies to aid host nations. As such, commanders and staffs integrate
information capabilities with the host nation’s message to tell the population the reason for U.S.
involvement. Commanders and staffs have to establish relationships, seek two-way understanding, and
listen to what others think. Effective counterinsurgency normally requires an effective broad message and
engaging the population in a dialogue. Commanders and staffs must find the right balance between using
information capabilities to give a broad message versus creating a dialogue.
7-93. Commanders and staffs balance between controlling the message and allowing for complete freedom
of messaging. Having a perfectly controlled message does not allow for real, timely communication with a
population. Leaders must have some ability to actually engage a population and create a shared
understanding. However, if representatives of a command have total freedom of message, the population is
bombarded with contradictions and inconsistencies. Commanders and staffs must find the right balance to
allow real communication, but also to ensure that the command has a coherent message.
7-94. Public affairs and information operations are separate but related functions. Public affairs are those
public information, command information, and community engagement activities directed toward both the
external and internal publics with interest in the Department of Defense (JP 3-61). External publics include
allies, neutrals, and threats. When addressing external publics, opportunities for information overlap exist
between public affairs and information operations.
7-95. Information operations and public affairs personnel must maintain a common awareness of each
other’s support to operations to preclude the potential for information conflict. The information operations
cell provides an excellent place to coordinate and deconflict information operations and public affairs
activities that could result in information fratricide. Information fratricide is the result of employing
information-related capabilities in a way that causes effects in the information environment that impede the
conduct of friendly operations or adversely affect friendly forces (FM 3-13). Final coordination of public
affairs and information operations must occur within the operations process.
7-96. In a counterinsurgency, the insurgent often targets the U.S. population with themes and messages
concerning the insurgency. There are legal and professional reasons why the armed forces cannot attempt
to influence American public opinion; to do so would undermine civil control over the military. However,
the military has a responsibly to provide information to the U.S. public. Transparency and truthful
information allows policy decisions to be debated between decisionmakers and the public. Although
providing that information during an insurgency is a responsibility of the military, trying to influence the
actual debate is unethical and damages the military’s relationship with the society.
This page intentionally left blank.

13 May 2014 FM 3-24/MCWP 3-33.5 8-1
Chapter 8
Intelligence
8-1. Intelligence must drive operations in a counterinsurgency. Commanders and staffs must understand
the area of operations in a counterinsurgency. The insurgency in Peru demonstrates that intelligence
capabilities can be integrated with information operations and integrated monetary shaping operations to
successfully undermine an insurgency. The Peruvian government was eventually successful in using
economic development and an information campaign to weaken the Shining Path insurgency. With the
gradual development of an effective military, Peru was able to continue its success. Intelligence, resulting
in the capture of the Shining Path’s leader, changed the nature of the insurgency and significantly reduced
the threat of the Shining Path to Peru.
Intelligence and the Shining Path
Peru suffered an unprecedented economic downturn in the 1970s and
1980s. The Peruvian government, though democratic, was characteristically
ineffective and unable to stem the worsening crisis. This opened the door for an
insurgent organization, the Sendero Luminoso (Shining Path), and its establishment
of alternative governance structures in the economically devastated Peruvian
highlands. Sendero Luminoso leaders purged local officials and established their own
authority in the villages, beating back control efforts by the Peruvian police.
In the first few years of the insurgency, the government did not take the
threat seriously. Opposition to the insurgents (such as it was) was organized by local
police, and the government made no effort to improve the desperate socioeconomic
conditions in the highlands or to define a clear mission for regional security forces.
With its superior organization and a lack of effective response by the government,
Sendero Luminoso made significant progress. Its operations and propaganda were
coordinated to create the perception that the group was a “winner” and was meeting
its Maoist strategic goals, in sharp contrast to the largely ineffective government.
Still plagued by a lack of internal unity both in the government and in the
military, the state moved forward with two competing counterinsurgency strategies:
one focused on development and the other focused on ideology and military force.
First proposed in 1984, the developmental approach finally got its turn in 1985. The
state recognized that the highlands were particularly hard hit by the economic crisis
and were the heartland of the insurgency, so its goal was to increase development
and job opportunities in these regions. Public investment in Ayacucho (a region in the
southern highlands) quadrupled between 1985 and 1986. Unfortunately, the
insurgents actively resisted this development, or co-opted it, forcing government
teachers to include Sendero Luminoso materials in their curricula. The government
did not provide the security necessary for development to have any effect.
Subsequent to 1986, development funding fell off, and embezzlement became
common. As a result, this initial push of development and investment fell far short of
meeting the needs of the economically disadvantaged population in the highlands.
The election of Alberto Fujimori in June 1990 raised new hopes of resolving
the conflicts within the government and making greater headway against the
insurgents. Fujimori promised a better human rights record and a new commitment to
development. In addition to renewed government legitimacy, the Fujimori
administration also brought two significant improvements to Peru’s approach to
counterinsurgency: first, the use of the police and the national intelligence service to
track the movements of Sendero Luminoso sympathizers and attempt to infiltrate the
group and, second, the arming of rondas, peasant civil-defense militias. These

Chapter 8
8-2 FM 3-24/MCWP 3-33.5 13 May 2014
rondas were possible only because the insurgents’ treatment of villagers in its areas
of operation had become so harsh that the locals were finally pushed to stand up for
themselves. Improved intelligence and an end to internal divisions within the military
allowed effective engagement of insurgent forces and effective (and rapid) support to
threatened rondas. For the first time in the conflict, the government, police, and
military made effective use of what would now be called strategic communication,
with a greater emphasis on government credibility, consistency between actions and
messages, and significant efforts to woo the population in the highlands away from
the insurgents (efforts of which the rondas were an integral part).
In 1992 good intelligence led to Abimael Guzmán’s (the leader of Sendro
Luminoso) capture. The capture of Guzman changed the ongoing insurgency and
significantly undermined insurgent efforts. At the time of his capture, the police seized
Guzmán's computer, in which they found a very detailed roster of his armed forces
and the weapons each formation had in each region of the country. His authoritarian
management of Sendero Luminoso had proven very effective when he was at large,
but when he was captured, it provided a wealth of information. This information was
used for further operations.
INTELLIGENCE FUNDAMENTALS
8-2. Intelligence is the product resulting from the collection, processing, integration, evaluation, analysis,
and interpretation of available information concerning foreign nations, hostile or potentially hostile forces
or elements, or areas of actual or potential operations (JP 2-0). Intelligence can be broken down into seven
disciplines, and it is an enabler of any counterinsurgency effort. Each discipline provides a means for the
counterinsurgent to gain a higher level of situational understanding. These disciplines include
counterintelligence, human intelligence, geospatial intelligence, measurement and signature intelligence,
open-source intelligence, signals intelligence, and technical intelligence. The intelligence disciplines are
integrated to ensure a multi-disciplined approach to intelligence analysis. Ultimately all-source intelligence
facilitates situational understanding and supports decisionmaking. All intelligence disciplines are important
in counterinsurgency. However, this chapter will focus on elements of intelligence that have unique
considerations in counterinsurgency. (See ADRP 2-0 for more information on intelligence.)
8-3. An essential part of understanding the operational environment is the process of intelligence
preparation of the battlefield/battlespace. Intelligence preparation of the battlefield/battlespace is a
systematic process of analyzing and visualizing the portions of the mission variables of threat/adversary,
terrain, weather, and civil considerations in a specific area of interest and for a specific mission. By
applying intelligence preparation of the battlefield/battlespace, commanders gain the information necessary
to selectively apply and maximize operational effectiveness at critical points in time and space
(FM 2-01.3/MCRP 2-3A). (See FM 2-01.3/MCRP 2-3A for more information on intelligence preparation
of the battlefield/battlespace.) In a counterinsurgency environment, intelligence preparation of the
battlefield/battlespace must take into account operational environment considerations. (See chapter 2 for
considerations about the operational environment and chapter 4 for considerations on analyzing an
insurgency.)
8-4. Culture is an element of the operational environment and, like the physical terrain, creates both
opportunities and challenges for Soldiers and Marines. A nation’s culture is a set of complex,
ever-changing, and interconnected social, historical, political, and environmental factors that shape the
perceptions, motives, and behaviors of its population. Cultural intelligence is the analysis and
understanding of groups of people and the reasons they do certain things. Cultural intelligence includes
gaining an understanding of the mindset of a local population to support the commander’s decisionmaking
and help drive operations. (See chapter 3 for more information on culture.)
8-5. The counterinsurgency force must understand the cultural foundations of the operational
environment in order to transform seemingly random and irrational activity into describable and
semipredictable acts. Commanders and staffs must devote as much effort to understand the local population
being supported as they do to understand the insurgents. Cultural intelligence requires historical perspective
as well as collection and analysis of current information, because cultures and cultural factors are

Intelligence
13 May 2014 FM 3-24/MCWP 3-33.5 8-3
consistently shifting. Periods of warfare, instability, and natural disasters increase the rate of cultural
change within a society.
8-6. Also, cyberspace is an essential domain for the gathering of intelligence in a counterinsurgency.
Cyberspace is a global domain within the information environment consisting of the interdependent
network of information technology infrastructures and resident data, including the Internet,
telecommunications networks, computer systems, and embedded processors and controllers (JP 1-02). The
commander and senior intelligence officer must be highly aware of the intelligence oversight implications
of collecting against United States (U.S.) persons, as the distinction of citizenship is difficult to assess in
cyberspace. The distinction is required because intelligence collection is enabled by and must comply with
all applicable U.S. laws and policy. However, cyberspace is used by insurgents and cannot be ignored by
counterinsurgents. Cyberspace and the technologies that enable it allow people of every nationality, race,
faith, and point of view to communicate, cooperate, and prosper like never before. Some adversaries clearly
understand the power of cyberspace. Terrorists employ the Internet for recruiting, training, motivating, and
synchronizing their followers. Adversaries frequently operate in cyberspace unrestrained, and they exploit
its potential. To be effective in defeating an insurgency, commanders and staffs must gather intelligence on
how an insurgency is using cyberspace.
ALL-SOURCE INTELLIGENCE
8-7. The Army defines all-source intelligence as the integration of intelligence and information from all
relevant sources to analyze situations or conditions that impact operations. (See ADRP 2-0.) The joint force
defines all-source intelligence as intelligence products and/or organizations and activities that incorporate
all sources of information in the production of finished intelligence (JP 2-0). All-source intelligence is used
to develop the intelligence products necessary to aid situational understanding, support the development of
plans and orders, and answer information requirements. Although all-source intelligence normally takes
longer to produce, it is more reliable and less susceptible to deception than single-source intelligence.
Intelligence organizations fuse data and information into all-source intelligence products to support
counterinsurgency operations. Analysis for counterinsurgency operations is challenging, due in part to
the—
- Need to understand perceptions and culture.
- Need to track hundreds or thousands of personalities.
- Local nature of insurgencies.
- Tendency of insurgencies to change over relatively short periods of time.
8-8. Commanders and staffs need data to analyze and synthesize insurgent activities and personalities.
Intelligence staffs should create a common searchable combatant command database of insurgent actions
and personnel, and another database(s) that provides discoverable, accessible, and retrievable data on
insurgent actions and personnel, and provide similar access to all intelligence reporting. This data should be
accessible by analysts both in and out of the theater as well as conventional, special operations forces, and
multinational units.
8-9. Because all echelons collect and use intelligence, all staffs are heavily involved in analysis. Units are
simultaneously intelligence producers and consumers. Intelligence capabilities are normally greater at
higher echelons of command. For example, battalion staffs have fewer personnel than brigade staffs to
collect patrol debriefs, analyze incoming information from multiple sources, produce finished intelligence
products, and disseminate products to appropriate consumers. In many cases, brigade intelligence sections
may be inadequately staffed to handle the vast amounts of information necessary to conduct operations in a
counterinsurgency environment.
8-10. Counterinsurgency requirements may require pushing analysts to battalion and brigade staffs to give
those echelons the required analytical support. Often analysts can be beneficial at the company level. In
these cases, developing company intelligence support teams may be useful. Many maneuver company
commanders organize small intelligence support teams from within their units to provide tailored
intelligence products to the company leadership. They may receive augmentation from the brigade military
intelligence company or other intelligence Soldiers and Marines to form the nucleus of a company
intelligence support team. The company intelligence support team combines information gained from

Chapter 8
8-4 FM 3-24/MCWP 3-33.5 13 May 2014
company operations with intelligence received from adjacent and higher units. The team analyzes and
reports information collected by the company while receiving, parsing, and reporting intelligence collected
by other organizations. The battalion intelligence cell is responsible for integrating the various company
reports into intelligence products. This is particularly useful when a maneuver company must collect large
amounts of information on the local population and insurgents. A company intelligence support team can
help focus collection, process information collected, and develop a common operational picture of an area
of operations. Pushing analysts to brigades and lower echelons places analysts closer to collectors,
improves the common operational picture, and helps higher echelon staffs receive answers to the
commander’s priority intelligence requirements. Commanders may need to be creative in developing
analytical capabilities within their units. Though it is not ideal, commanders can assign non-intelligence
personnel to work in the intelligence section. (See TC 2-19.63 for more information on company
intelligence support teams).
8-11. In a counterinsurgency, a bottom-up flow of intelligence is important. Battalions and brigades
develop intelligence for their area of operations. Higher echelons fuse it into intelligence of the insurgency
throughout the combatant command. Higher echelons can also integrate the human intelligence that
battalions and brigades receive with the other intelligence disciplines. Comprehensive insurgency analysis
focuses on the people in the area of operations. It develops information about relationships among them and
the ideas and beliefs driving their actions. Comprehensive insurgency analysis brings together all other
forms of analysis.
FUSION CENTERS
8-12. A fusion center is an ad hoc collaborative effort between several units, organizations, or agencies that
provides resources, expertise, information, and intelligence to a center with the goal of supporting the rapid
execution of operations by contributing members. Fusion centers are primarily designed to focus collection
and promote information sharing across multiple participants within a specific geographic area or mission
type. These centers are not operations centers. Commanders at various echelons create fusion centers to
manage the flow of information and intelligence, focus information collection to satisfy information
requirements, and to process, exploit, analyze, and disseminate the resulting collection. Fusion centers are
most effective if they have participation from all the key elements in an area of operations and
representatives from all the warfighting functions. When possible, fusion centers include unified action
partners. The intelligence portion of a fusion center typically comprises intelligence representatives from
different tactical echelons, interagency partners, multinational organizations, host-nation organizations, and
nongovernmental organizations (NGOs) operating in the area of operations. (See ADRP 2-0 for more
information on fusion centers.)
8-13. In a counterinsurgency, commanders and staffs must create shared situational understanding. Fusion
cells are important in creating this understanding. The mixture of personnel and expertise allows for the
integration of information and analysis. This is an effective means of understanding the operational
environment from multiple perspectives. Fusion cells aid in understanding intelligence and informing
operations to avoid unintended consequences.
HUMAN INTELLIGENCE
8-14. Human intelligence is the collection by a trained human intelligence collector of foreign information
from people and multimedia to identify elements, intentions, composition, strength, dispositions, tactics,
equipment, and capabilities (FM 2-22.3). For the joint force, human intelligence is defined as a category of
intelligence derived from information collected and provided by human sources (JP 2-0). Because
insurgency and counterinsurgency are struggles for legitimacy, human intelligence plays a vital role in
determining legitimacy. Human intelligence uses human sources for information collection and uses a
variety of collection methods, both passive and active, to collect information to meet intelligence
requirements and inform other intelligence disciplines. Interrogation is one of the human intelligence tasks,
along with screening, debriefing, liaison, and conducting controlled source operations in support of Army
operations. During counterinsurgency operations, a great deal of intelligence is based on information
gathered from people. However, military source intelligence operations are only conducted by human
intelligence collectors. A human intelligence collector is a person who is trained to collect information

Intelligence
13 May 2014 FM 3-24/MCWP 3-33.5 8-5
from individuals for the purpose of answering requirements. (See FM 2-22.3 for more information on
human intelligence.)
8-15. Operational reporting may have information of intelligence value that originates from a local
population. People may approach Soldiers and Marines during the course of their day-to-day operations and
offer information. Soldiers and Marines record information and report it to the intelligence section. This
allows for verification of information and establishes a means for human intelligence collectors to contact
individuals offering information of value.
8-16. People offering information on insurgents are often in danger as insurgents continuously try to defeat
collection operations. Commanders ensure that the appropriate personnel are trained in handling human
sources in accordance with Army, Marine Corps, and Department of Defense (DOD) standards and
policies. Human intelligence collectors are trained in procedures that limit risks to sources and handlers.
Counterinsurgents should not expect people to willingly provide information if insurgents have the ability
to violently intimidate sources. Human intelligence reporting increases if counterinsurgents protect the
population from insurgents and people begin to believe the insurgency is defeated.
8-17. People often provide inaccurate and conflicting information to counterinsurgents. They may spread
rumors or provide inaccurate information for their own reasons. For example, people may give inaccurate
information to settle tribal, ethnic, or business disputes. The accuracy of information obtained by Soldiers
and Marines is verified before using it to support operations. This means that information reported to
patrols should be verified with all-source intelligence. Improved accuracy will come from collecting
intelligence from the whole population. Information must be seen as part of a whole picture and parts or
segments of information cannot override the whole picture. An important part of gaining access from the
whole population is gaining access to restricted populations. These populations often include women, but
they can include any element that the counterinsurgent cannot access because of cultural considerations.
Restricted access teams may be helpful in ensuring that information is attained from the whole population,
including women.
COUNTERINTELLIGENCE
8-18. Counterintelligence also uses human sources to assist in collection of information on foreign
intelligence, international terrorist, or insider threat activities that may threaten the counterinsurgency.
Counterintelligence efforts may be directed toward assisting commanders in detecting and neutralizing the
insider threat by ensuring that counterinsurgency operations are not compromised by adversaries operating
inside a base. Counterintelligence operations, including the use of humans as sources, must be
accomplished by trained counterintelligence special agents.
INFORMATION COLLECTION AND INTELLIGENCE, SURVEILLANCE, AND RECONNAISSANCE
8-19. Information collection is an activity that synchronizes and integrates the planning and employment of
sensors and assets as well as the processing, exploitation, and dissemination of systems in direct support of
current and future operations. The deputy chief of staff, (G-2 [S-2]) and assistant chief of staff, operations
(G-3 [S-3]) staffs collaborate to collect, process, and analyze information the commander requires
concerning threats, terrain and weather, and civil considerations that affect operations. The information
collection tasks are—
- Plan requirements and assess collection.
- Task and direct collection.
- Execute collection.
(See FM 3-55 for more information on information collection and planning requirements and assessing
collection.)
8-20. Intelligence, surveillance, and reconnaissance provides commanders with detailed and timely
intelligence. This intelligence helps commanders gain situational understanding of a threat and an
operational environment. This is accomplished by answering requirements focused in time and space and
identifying any threats to mission accomplishment. The intelligence staff provides commanders with
predictive assessments of threats, terrain and weather, and civil considerations. These assessments also

Chapter 8
8-6 FM 3-24/MCWP 3-33.5 13 May 2014
provide commanders with a running estimate regarding the degree of confidence the staff places in each
analytic assessment. A running estimate is the continuous assessment of the current situation used to
determine if the current operation is proceeding according to the commander’s intent and if planned future
operations are supportable (ADP 5-0).
INTELLIGENCE-RELATED CAPABILITIES
8-21. Commanders and staffs consider several capabilities for intelligence in a counterinsurgency. They
include—
- Biometrics and biometric-enabled intelligence.
- Forensics and forensic-enabled intelligence.
- Site exploitation.
Biometric-Enabled Intelligence
8-22. Understanding biometrics-enabled intelligence requires knowledge of biometrics and its contribution
to Army and Marine Corps missions. The term biometric describes both a characteristic (biometric) and a
process (biometrics):
- A biometric is a measurable physical characteristic or personal behavior trait used to recognize
the identity or verify the claimed identity of an individual.
- Biometrics is the process of recognizing an individual based on measurable anatomical,
physiological, and behavioral characteristics (JP 2-0).
8-23. The Army and Marine Corps employ automated biometric systems to deny threat forces any freedom
of movement within the population and to positively identify known threats, threat forces, friendly
populations, local nationals, and third-country nationals throughout their areas of operation to separate
insurgents and foreign fighters from the general population. Biometric systems collect biometric data, such
as iris images, fingerprints, and facial images, and combine them with contextual and biographic data to
produce an electronic dossier on an individual. Automated biometric systems may support the following
tasks:
- Positively identify high-value targets.
- Screen and badge personnel.
- Manage the population.
- Perform force protection (local access).
- Conduct detention operations.
8-24. Biometrics are important assets in any counterinsurgency operation. These tools allow the
counterinsurgent to gain both civil security and control. Through positive identification, biometrics allow
the counterinsurgent to effectively execute offensive operations against the insurgency while at the same
time protecting the civilian population by not detaining innocent civilians. If used correctly, biometrics
allow the counterinsurgent to effectively execute offensive operations against the insurgency and protect
the population. Moreover, the host nation can be enabled with these capabilities. Biometric abilities can be
essential in building legitimacy among the population. (For more information on biometrics, see
FM 2-22.3, ATTP 2-91.6, TC 2-33.4, and TC 2-22.82.)
Forensic-Enabled Intelligence
8-25. Although not an intelligence discipline, police intelligence operations can support the overall
intelligence effort through the analysis, production, and dissemination of information collected from police
activities. Information gathered from military police operations may contribute to a commander’s critical
information requirement and focusing police forces on maintaining order. Criminal acts such as robberies,
kidnappings, terrorism, and extortion may be linked to insurgent psychological or money-gathering
activities. Police information, police intelligence, and criminal intelligence are subtasks of police
intelligence operations. (See ATTP 3-39.20 for additional information on law enforcement.)

Intelligence
13 May 2014 FM 3-24/MCWP 3-33.5 8-7
8-26. Forensics involves methodically gathering and analyzing evidence to establish facts that can be
presented in a legal proceeding. It applies multidisciplinary scientific processes to establish facts. Forensics
operations, to include site and document exploitation, further aid the positive identification efforts of a
counterinsurgent and help to separate insurgents from the general population, thus contributing to overall
situational understanding. Commanders and staffs should make every effort to operate within status of
forces agreements and combatant command requirements. (See ATTP 2-91.6 for more information on
forensics.)
8-27. For example, latent fingerprints discovered on pieces of improvised explosive devices provide
critical information that analysts need to link individuals, insurgent organizations, their capabilities, and
their activities. Forensics that includes site exploitation and forensic documents is of great benefit to
substantiating information if detainees are insurgents. The methods of forensics allow the counterinsurgent
to work towards situational understanding.
Site Exploitation
8-28. Site exploitation is a series of activities to recognize, collect, process, preserve, and analyze
information, personnel, and/or materiel found during the conduct of operations (JP 3-31). When countering
an insurgency, site exploitation of an insurgent location is essential. Computers, cell phones, and other
means of communication and storing information are vital to understanding the insurgent structure.
8-29. Site exploitation uses the full range of resources at the commander’s disposal, starting with the
Soldier’s basic cognitive skills to sophisticated analytical processes conducted by joint, interagency, and
intergovernmental organizations. Exploitation operations provide answers to the commander’s information
requirements regardless of whether the information was gained by a squad on patrol or through external
sensor platform outputs.
8-30. Site exploitation may require additional technical expertise not resident within the theater to process
the collected information, material, and personnel to maintain their unique physical or forensic attributes.
Detailed technical exploitation of collected items can divulge actionable information or intelligence that
can be used to positively identify any unique threat characteristics or threat networks for follow-on actions.
8-31. Knowledge management enables the effective dissemination of actionable information and
intelligence to units for their integration into the intelligence, targeting, and operations processes. This
facilitates follow-on operations and enhances commanders’ and staffs’understanding.
This page intentionally left blank.
13 May 2014 FM 3-24/MCWP 3-33.5 9-1
Chapter 9
Direct Methods for Countering Insurgencies
9-1. The direct method of using United States (U.S.) land, maritime, and air forces in a decisive action
role is resource intensive when done on a large scale, but it is often necessary to fully support a
counterinsurgency effort. A direct method may be used, for example, when the success of a host nation’s
counterinsurgency efforts is critical to U.S. interests. The U.S. can use a direct method after or during a
major conflict or when U.S. interests necessitate stability in a failed or failing state. Leaders can also
integrate land forces into a host nation’s ongoing effort. Unfortunately, unintended consequences, such as
increased tensions among segments of society or resistance to U.S. involvement, often accompany a direct
approach. Leaders must carefully plan and execute operations before and during a direct response to avoid
negative consequences. However, using direct capabilities remains a valid option and an important
capability that the Army and Marine Corps provide the joint force.
9-2. The level of direct U.S. involvement can vary. In many cases, a host nation will be fully capable of
providing security for its population. However, integration of fires or a direct action force could enable a
host nation’s counterinsurgency efforts. The Army and Marine Corps bring many capabilities that can be
integrated into a counterinsurgency effort. When counterinsurgents consider direct involvement, they
should consider a wide spectrum of activities that range from a modest force conducting limited missions to
a large force that could be, at least for a time, the primary counterinsurgency force.
9-3. The U.S. has a wide range of capabilities that it can use to create many different operational
approaches to counter an insurgency. Direct involvement by U.S. forces can take place along a spectrum,
from little direct U.S. involvement to U.S. forces acting as the primary counterinsurgents. If U.S. forces are
acting temporarily as the primary counterinsurgents, the shape-clear-hold-build-transition framework forms
a tactical and operational background for battalion and brigade operations. While the shape-clear-hold-
build-transition framework must be enabled with other capabilities, such as security force assistance, the
shape-clear-hold-build-transition framework provides a framework for how Army and Marine forces will
defeat an insurgency at the tactical level. Moreover, this tactical background also creates a frame of
reference for understanding actions by the host nation to defeat an insurgency. This understanding is
essential in integrating U.S. capabilities into a host-nation effort.
9-4. Counterinsurgents should not think that all counterinsurgencies end the same way. The shape-clear-
hold-build-transition framework provides a good framework for a protracted struggle. Counterinsurgencies
are conducted using a wide range of different approaches. For example, the insurgency in Sri Lanka was
fought using conventional tactics and ended in a traditional offensive operation. It ended in something that
looked much more like a conventional offensive operation then an application of the shape-clear-hold-
build-transition framework. In some cases, the government or insurgents can impose their impose their will
and control the population. While counterinsurgents should remember that specific insurgencies are unique,
for many insurgencies, the shape-clear-hold-build-transition framework is a starting point for understanding
host-nation actions and then enabling those actions.
SHAPE-CLEAR-HOLD-BUILD-TRANSITION FRAMEWORK
9-5. For a tactical and operational ground commander acting as the primary counterinsurgent commander,
the shape-clear-hold-build-transition framework provides a foundation for detailed planning. Moreover, the
shape-clear-hold-build-transition framework is well-suited to those commanders and staffs engaged in
training, advising, or integrating capabilities into a host-nation effort. If a host nation is performing
operations, whatever the U.S. role in the counterinsurgency, Soldiers and Marines must have a framework
for understanding that host nation’s actions. Commanders and staffs cannot evaluate, advise, or train
another force unless they have a base of knowledge on the operations being conducted. In many
counterinsurgency efforts, a state will try to defeat insurgencies by performing a general operational
Chapter 9
9-2 FM 3-24/MCWP 3-33.5 13 May 2014
approach that is similar to the shape-clear-hold-build-transition framework at the tactical level. While this
is certainly not a uniform rule, having some framework in understanding another counterinsurgent’s actions
provides a point of reference for understanding. Commanders and staffs must have an understanding of
how to solve a particular problem before they advise or assist another commander solve that problem.
Understanding the shape-clear-hold-build-transition framework is a fundamental framework for
understanding what units are trying to accomplish in a counterinsurgency. This framework applies to all
units involved in the counterinsurgency, including, for example, an infantry battalion directly performing
actions, a member of a special forces team advising a host nation, or a member of a combatant command
integrating and evaluating various security cooperation capabilities.
9-6. Whether U.S. forces are executing the shape-clear-hold-build-transition framework or another state
is executing it, it can be very effective in defeating an insurgency. For example, in the Philippines, the
government was successful in using the shape-clear-hold-build-transition framework, even if it was not
called shape-clear-hold-build-transition by the counterinsurgents at the time. Commanders and staffs must
understand the shape-clear-hold-build-transition framework to understand what a host nation is trying to
achieve in its counterinsurgency efforts. This framework is used by U.S. and foreign forces.
Shape-Clear-Hold-Build-Transition: The Huks
The Hukbalahap, or “Huks,” were one of several guerilla organizations that
appeared in the Philippines during the Japanese occupation of World War II. By the
time of the country’s liberation from the Japanese occupation, the Huks were
well-armed with weapons taken from the Japanese or shipped to them from the U.S.
The Philippines gained independence from the U.S. on July 4, 1946, and
held its first national election in November 1946. The Huks participated in the
elections, and the head of the wartime Huk movement, Luis Taruc, won a seat in the
Philippine Congress. However, the newly elected President, Manuel Roxas, refused
to seat Mr. Taruc or his allies in Congress, leading many Filipino peasants to join the
Huk movement.
By late 1946, there was open fighting between the Huks and the forces of
the newly independent Republic of the Philippines. The insurgency was motivated by
vast economic inequality during the country’s transition to an export-led capitalist
economy, with abject poverty affecting 90 percent of the population.
The Huks’ primary tactics in the beginning of the conflict included bank,
payroll office, and train robberies, as well as small hit-and-run raids and ambushes
that allowed them to avoid contact with large government formations. During these
first few years, the Huks numbered 5,000 active insurgents, 10,000 lightly armed
reserves, and 35,000 other supporters. The Huks also enjoyed incredible levels of
internal support, with an estimated 250,000 peasants actively supporting them during
the early years of the insurgency.
The counterinsurgency force was unable to control the insurgency in the
early years. Shortly after the country was granted independence, the Philippine Army
was reduced from 132,000 to 37,000 men. Approximately 24,000 of these men were
in the Military Police Command, which was tasked with combating the insurgency.
However, the Military Police Command was poorly led and poorly equipped, and
pursued tactics that accomplished little beyond alienating the population between
1946 and 1948. In 1948, President Roxas reorganized the Military Police Command
into the Philippine Constabulary, which remained neither well-trained nor
well-equipped. It mainly practiced encirclement and sweeps, both of which were
easily evaded by the Huks, and systematically committed abuses against civilians:
raiding villages, stealing possessions, and treating the population worse than the
Huks did.
The Huks then began making strategic and operational errors, failing to
reach out to other disaffected groups to form a broad front, and employing many
common criminals in their ranks, causing peasants to fear the group. Probably most
catastrophic to the group’s public image was the assassination of Mrs. Aurora
Quezon, the well-liked and popular wife of the late former President, Manuel Quezon.

Direct Methods for Countering Insurgencies
13 May 2014 FM 3-24/MCWP 3-33.5 9-3
As a result of Mrs. Quezon’s murder, President Quirino appointed then-Congressman
Ramon Magsaysay as Secretary of Defense in 1950.
After this, the Huk Rebellion became a good example of successful
shape-clear-hold operations, with Magsaysay immediately instituting a
shape-clear-hold approach. Shaping operations focused on efforts to win popular
support for the counterinsurgency effort in preparation for future operations to clear
insurgent areas. These operations included putting a stop to the abuses of civilians
by the Constabulary and Army, firing many high-level military officers, placing the
Constabulary under Magsaysay’s personal control, suppressing troop brutality
towards the population, and increasing pay for enlisted troops to remove their
incentives for looting. They also involved the establishment of a civil affairs office
through which troops became involved in civic action projects (including digging wells
and building bridges) and the Army’s provision of medical assistance to villagers.
Additionally, Magsaysay pursued a population engagement strategy, even going so
far as to set up a telegraph system that provided a direct line to the Defense Ministry
for any villager on Luzon to use.
9-7. The shape-clear-hold-build-transition framework describes an operational approach that moves
through each of its phases to destroy insurgent capacity and empower host-nation capacity. The phases of
this method are not mutually exclusive, but the phases represent a general progression of operations. The
shape phase refers to making changes to the environment, through information operations or other methods,
that create the conditions for success of the other phases. The population needs to understand that there will
be an increase in security and initially local leaders should be contacted. The clear phase is an effort to
remove the open insurgent presence in an area. The hold phase is defined by providing security for the
population in an area so an open insurgent presence cannot return. The build phase entails efforts to
increase security and governmental capacity so that government and local forces can control the area and
prevent the return of insurgents. The transition phase is the transition of security to local and government
forces.
9-8. The commitment of resources, to include time, troops, money, development programs, and other
enablers depends entirely on the capacity of the insurgency, the capacity of the host nation’s institutions,
the capacity of the host nation’s security forces, and the capacity of the host nation’s population. The
capacity requirement for the external counterinsurgent is that capacity which overcomes the capacity
differential between the insurgents and the host nation’s systems. As the framework is predicated on the
conditions on the ground, the shape-clear-hold-build-transition framework is based on understanding areas
of operation and understanding the comprehensive threat. To transition between the clear, the hold, and the
build, a unit must be able to measure the conditions on the ground and how those conditions are achieving
the commander’s end state. This ties the shape-clear-hold-build-transition framework to assessments.
9-9. The shape-clear-hold-build-transition framework can be used as a method for constructing specific
tactical operations, planning short-range operations for a specific area, or developing a mid- to long-range
operational framework for a unit’s plan for countering an insurgency. The shape-clear-hold-build-transition
framework can be used as a campaign framework, guiding planning from the introduction of foreign forces
to conflict resolution. It can be used as campaign design to be executed by multiple units on a rotational
basis. The imperatives, structure, considerations, and conditions listed here apply no matter how the
shape-clear-hold-build-transition framework is applied.
9-10. Counterinsurgents must be aware that the shape-clear-hold-build-transition framework is not a phase
by phase linear process. The phase that a unit performs is determined by the environment in an area of
operations and each area must be assessed. Different villages, cities, or regions can be in varying degrees of
insurgent control to host-nation control. Moreover, different areas in one city or different towns in one
region might be along a spectrum of insurgent to host-nation control. Areas can reverse progress during a
counterinsurgency. While the shape-clear-hold-build-transition framework can be a phased operation in
each area, the environment must dictate its progress. The counterinsurgent uses the framework as the way
to synchronize subordinate unit actions, prioritize efforts, allocate resources, and direct specific effects to
achieve end state criteria in an ever-changing environment. The overall objective of using the shape-clear-
hold-build-transition framework is to transition responsibility for countering the insurgency to the host

Chapter 9
9-4 FM 3-24/MCWP 3-33.5 13 May 2014
nation’s institutions. The commander must understand that conditions associated with the clear, the hold,
and the build phases may be present at any time in different areas. U.S. ground forces can expect to carry
out a range of tasks simultaneously in varying combinations and varying intensity throughout the entirety
of shape-clear-hold-build-transition framework.
9-11. The shape-clear-hold-build-transition method has imperatives that help counterinsurgents turn the
method from theory into practical application. The imperatives are—
- The conditions are assessed across several variables and cannot be taken in isolation.
- The phase that the environment is in dictates the decisive operation, priorities, and resourcing.
- In the clear, hold, and build phases, counterinsurgents must simultaneously conduct offensive,
defensive, and stability tasks.
- Each area requires its own assessment and assessments change over time.
- The shape-clear-hold-build-transition framework is not a straightforward path, as the operational
environment can change and cause the counterinsurgent to lose progress. However, the
methodology is meant to be progressive. Improving conditions in the environment allows for
progression from one phase to the next. In essence, the operational framework is determined by
the operational environment. Changes in the capacity of any element in the environment can
change the conditions on the ground and, therefore, change the priorities and actions of the
counterinsurgent, including the host-nation forces.
- The shape-clear-hold-build-transition framework is only reactive if the unit on the ground
responds to conditions. The framework can be proactive if the counterinsurgents dictate the
conditions they want to establish and provide the resources and emphasis necessary to achieve
them.
- Although an area is in a certain phase, this does not preclude operations associated with other
phases. For example, although a unit is in the build phase, that does not preclude that unit from
performing offensive operations against underground cells.
9-12. Executing operations in the shape-clear-hold-build-transition framework requires counterinsurgents
to continually address the root causes of the insurgency. Actions taken in the clear, hold, and build phases
are not executed in isolation. Instead, elements of each phase must be conducted simultaneously. The
shape-clear-hold-build-transition framework does not require phasing or stages of operations, but a
commander may create phases or stages of operations corresponding generally to shape-clear-hold-build-
transition phases in order to synchronize actions and priorities effectively.
9-13. The shape-clear-hold-build-transition framework is driven by the conditions in an area of operations.
To facilitate discussion of these conditions, figure 9-1 depicts the generic spectrum of counterinsurgency
conflict. The graph portrays the relationship of capacity between insurgents, the host-nation government,
the host-nation security forces, the host-nation population, and external counterinsurgents. Capacity
represents the ability to change the conditions in the environment towards insurgents or counterinsurgents.
As counterinsurgents are able to impact these conditions, the capability spectrum changes. The left hand
side of the graph depicts the worst-case scenario in which insurgents possess increased capacity compared
to the host nation. The right hand side of the graph depicts the best-case scenario in which the host-nation
capacity is sufficient to counter the insurgent capability without assistance from external counterinsurgents.
The shape-clear-hold-build-transition framework describes the process counterinsurgents take to progress
from the left of the graph to the right. (See figure 9-1.)
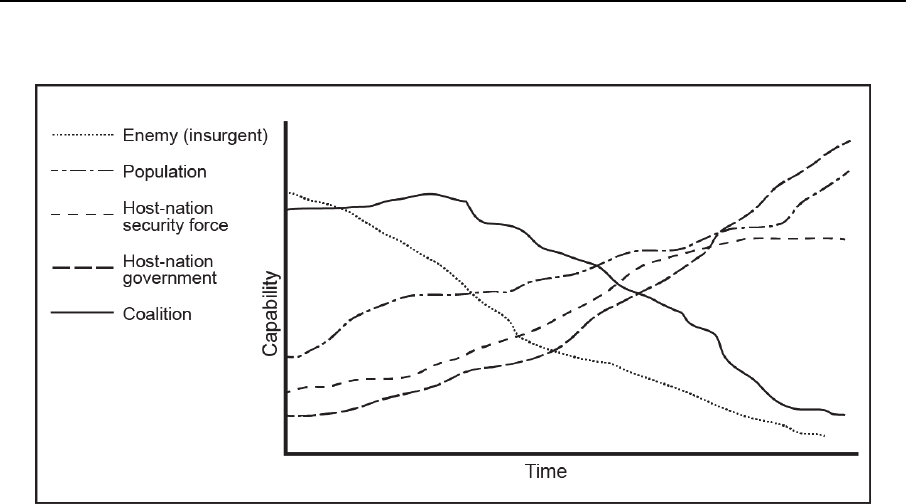
Direct Methods for Countering Insurgencies
13 May 2014 FM 3-24/MCWP 3-33.5 9-5
Figure 9-1. The capability spectrum of counterinsurgency conflict
9-14. As part of developing understanding, counterinsurgents must identify the conditions that exist in
particular regions that lead to instability or allow the insurgency to impact the environment. Commanders
must decide where to focus actions and priorities to impact the conditions in a designated area for tactical
or operational reasons. In many instances, commanders specify a preparation phase or shape phase of the
shape-clear-hold-build-transition framework which clarifies the period of time, series of tasks, and effects
to be achieved before counterinsurgents begin taking deliberate action against insurgents. Whether phasing
is used or not, preparation of the environment is an absolute requirement to achieve conditions to progress
along the shape-clear-hold-build-transition framework.
SHAPE
9-15. Shaping operations involve identifying which areas in an operational environment exhibit conditions
that counterinsurgents can impact to change the capability differential between insurgents and
counterinsurgents. Commanders choose where to execute operations in the shape-clear-hold-build-
transition framework based on a host nation’s ability (and unified action partners’ abilities if the host
nation’s capabilities are still being built) to impact the root causes of the insurgency, alter or eliminate the
conditions which allow the insurgency to exist in that area, or isolate the insurgents from the population.
During preparation, commanders and staffs execute include information collection on the components of an
insurgency. An initial census in towns or cities using biometrics data collection devices is the most
effective tool to establish initial accountability for everyone. Additional information collection includes the
specific root cause or causes in the particular area, the expectations of the host-nation population, and the
capability of host-nation institutions such as government, security, and rule of law. Commanders and staffs
conduct disruption operations to impact an insurgency’s ability to influence an operational environment.
Counterinsurgents may conduct deception operations while preparing for shape-clear-hold-build-transition
framework operations to force the insurgency to alter its course of action. While preparing to execute the
shape-clear-hold-build-transition framework, counterinsurgents (and whenever possible the unified action
and host-nation partners) conduct information operations. Counterinsurgents conduct information
operations aimed at the insurgency, the insurgency’s support mechanisms (both internal and external to the
country), the host-nation population, and host-nation institutions such as governance and security functions.
9-16. U.S. ground forces do not prepare for the shape-clear-hold-build-transition framework in isolation.
Elements of the unified action partners are essential in shaping the area, the population, and the insurgency
for future operations. In some instances, the area indicated for shape-clear-hold-build-transition framework
operations may not be suitable for some partners to directly operate in, but other unified action partners

Chapter 9
9-6 FM 3-24/MCWP 3-33.5 13 May 2014
may have the capability to shape the environment in areas of limited access. U.S. special operations forces
(SOF) can conduct reconnaissance, information collection, and precision targeting. The United States
Agency for International Development has the capability to introduce implementing partners who have
access to initiate governance or development programs. The Department of State has the ability to
influence the diplomatic process to generate initial governmental structures prior to the introduction of U.S.
ground forces. Soldiers and Marines must recognize the potential that unified action partners have in
shaping an operational environment prior to shape-clear-hold-build-transition framework operations.
CLEAR
9-17. Once counterinsurgents have effectively shaped the environment, including host-nation partners and
enablers, and prepared all elements of the unified action partners appropriately, decided on where to focus
the counterinsurgent effort, and has developed the plan to progress through to transition to host-nation
responsibility, the force begins executing tasks associated with clear. Clear is as a tactical mission task that
requires the commander to remove all enemy forces and eliminate organized resistance within an assigned
area (FM 3-90-1). When used in this context, the term clear is considered the desired effect by U.S. ground
forces: to eliminate the insurgency’s combatants to enable the host nation to develop the capability to
address the insurgency’s root cause and eliminate the conditions that allow it to exist. While attempting to
achieve the clear, the insurgency’s underground and auxiliary elements probably remain in the area of
operations. While the counterinsurgent can target them along with the insurgency’s combatants, it is
unlikely that the counterinsurgent will be successful in removing all of the underground or auxiliary
elements.
9-18. During the clear phase, counterinsurgents should be actively securing the population.
Counterinsurgents must displace insurgents and enable basic governmental functions in their area.
Moreover, the population must have the confidence that counterinsurgents will remain and insurgents will
not control the area. During this period, the population may face intimidation, threats, and assassinations
from insurgent forces. To gain legitimacy during this period, counterinsurgents must focus on securing the
population.
9-19. Operations and tasks associated with achieving the clear begin by controlling access to an area and
then by controlling key points within that area. Security and influence can then spread out from this area.
Commanders and staffs should consider the following points for operations in the clear:
- Create a secure physical and psychological environment.
- Provide continuous security for the local populace.
- Eliminate the insurgent combatants.
- Reinforce culturally appropriate political primacy within the context of host-nation systems.
- Enforce the rule of law.
9-20. Security tasks associated with the clear include—
- Implement the provisions of a cease fire and control, capture, and disarm belligerents.
- Provide territorial security until the host-nation national army can defend itself.
- Protect the population—provide immediate law and order and humanitarian assistance.
- Protect key individuals and sites—civilian government agencies, infrastructure, and institutions.
9-21. During the clear, counterinsurgents must execute offensive, defensive, and stability tasks. Offensive
operations are the priority for counterinsurgents. In most cases, the measure of effectiveness (MOE)
associated directly with impacting the insurgency’s combatants (for example, isolate insurgents from the
population) is the decisive operation. Offensive operations conducted during the clear include raid,
deliberate attack, cordon and search, seize key terrain, and movement to contact. Counterinsurgents execute
defensive operations as well, to include block access routes, establish and secure combat outposts, conduct
sniper operations, and secure the population. To set the conditions to progress through the framework,
counterinsurgents must execute stability tasks and operations at this point. Stability tasks include
identifying potential government or security leaders, identifying civic capacity requirements from the
population, establishing a local security force (in the context of host-nation systems) and beginning a
training program (if necessary), and identifying the root causes for that area. Throughout these operations,

Direct Methods for Countering Insurgencies
13 May 2014 FM 3-24/MCWP 3-33.5 9-7
the commander must consider securing the population and building host-nation capability. Actions taken
while achieving the effects necessary for clear should not alienate the population. The messages of
information operations are important while performing clear. Responsible use of force is essential.
9-22. Counterinsurgents conduct information operations to achieve the effects of the clear component. The
focus for information operations during the clear is the insurgency’s combatants, the underground and
auxiliary elements, and the host-nation population. Counterinsurgents’ information operations should
facilitate operations which eliminate the combatants from an area, facilitate effective information collection
on the combatants, and build a sense of security among the population.
HOLD
9-23. Counterinsurgents do not execute tasks associated with the clear component unless they have
developed the capability to execute tasks in the hold. Beginning shape-clear-hold-build-transition
framework operations requires resources in the form of manpower, time, money, and development
programs (but this framework is based on capacity, not resources). For this reason, these type of operations
cannot be conducted everywhere and must be prioritized. To meet the imperatives listed above, the
counterinsurgent must progress along the framework to continue to improve conditions in the environment.
Therefore, units should not clear an area that they cannot hold. Until those conditions exist, the
counterinsurgent may choose to continue to prepare or shape the environment for future
shape-clear-hold-build-transition framework operations.
9-24. As the capability of the insurgency decreases in an area based on counterinsurgency operations, the
capacity of the host-nation government and security force must increase. As the conditions improve to the
point that offensive operations aimed at eliminating the insurgency’s combatants are no longer the priority
and the host-nation population has freedom of movement, counterinsurgents can begin to execute tasks and
operations associated with hold. The hold involves disrupting insurgent activities in an area and providing a
good security environment for the population. The objective of the hold is to set the conditions for the
host-nation security apparatus to provide security for the population. For this reason, the hold lasts as long
as it takes to—
- Develop the capability of the host-nation security forces.
- Reduce the enemy strength in the area to the point that the host-nation security forces can take
lead responsibility for security.
9-25. Lead responsibility means that the host-nation security forces are the decision authority for allocation
of resources, priority of tasks and operations, and tactical decisions during operations. Counterinsurgents
continue to eliminate the insurgency’s leadership and infrastructure. However, perhaps more importantly,
counterinsurgents should focus on securing the population. During this period, proper basing of
counterinsurgent forces is essential. If an area is supportive of an insurgency, then a base of
counterinsurgent forces may sever the relationship between insurgents and the population. If the area is
neutral or has pockets of support for the government, then the base should be established where it can best
help in developing the area.
9-26. Contact with the population should be continuous, predominantly with host-nation entities (security
forces, law and order officials, and government representatives) leading and U.S. counterinsurgents in
support. Information operation activities provide opportunities for contact with the population. From the
start of operations, Soldier and Marine actions in these areas, if culturally astute, can build bonds with the
local population and in many cases change the attitudes of the people. Ultimately, the goal of this contact is
twofold: to gain a better picture of the actual situation and to turn the population’s support toward the
government.
9-27. Counterinsurgents must also secure key physical infrastructure. Because resources are always
limited, parts of the infrastructure vital for stability and vulnerable to attack must receive the priority of
protection, specifically the protection of capable host-nation security forces (if possible). This can be
accomplished by analyzing the risk and likelihood of attack on various sites in the area of operations.
9-28. Much like the clear, achieving the hold requires counterinsurgents execute offense, defense, and
stability tasks. While achieving the hold, defensive tasks and operations are the priority. However, to meet
the objectives of the hold, the line of effort associated with development of the host-nation security forces

Chapter 9
9-8 FM 3-24/MCWP 3-33.5 13 May 2014
is the decisive operation. Examples of stability tasks include manning, equipping, and training the
host-nation security forces, establishing local governance functions, and establishing culturally appropriate
rule of law systems within the host nation’s plan. Examples of some defensive tasks during the hold include
counter cache operations, area denial, combined security at fixed sites, block infiltration routes,
countermobility, and securing the population. Counterinsurgents must execute offensive tasks to attack the
insurgency’s underground and auxiliaries. Examples of offensive operations in the hold include raids
against insurgent leaders, ambushes, and disruption operations to impact support structures and local
sanctuaries. The amount and scope of stability tasks and operations increase during the hold.
9-29. Security operations to achieve the hold are dominated by developing the host-nation security forces
and then transitioning security responsibilities to them. Examples of security focus during the hold
include—
- Reform of local security institutions—reestablish military and police forces which may include
the entire rebuilding of the enduring institution including recruiting, educating, training,
manning, equipping, sustaining and leader development for the Army, police, rule of law,
detention capacity, and court systems.
- Develop the host-nation military to provide security and external defense of the nation; develop
the capacity to become self-sufficient in the development and conduct of their own enduring
training programs at individual and collective levels.
9-30. Counterinsurgents conduct information operations to achieve the hold as well, but the focus and
message changes as conditions improve. The focus for information operations during the hold is on the
remaining underground and auxiliary, the host-nation population, the host-nation security forces, and
host-nation governance institutions. Counterinsurgent information operations should facilitate operations
that improve the perception of security among the population, legitimize the host-nation security forces,
dissuade the underground and auxiliaries from continuing insurgent activities, and promote effective
host-nation governance solutions. During the hold, it is critical that the host nation becomes an integral part
of information operations.
BUILD
9-31. When the conditions in an operational environment allow the host-nation security forces to take lead
responsibility for security, counterinsurgents transition to the build. The build comprises carrying out
programs designed to remove the conditions that allow the insurgency to exist, specifically addressing the
root causes, tying inhabitants to host-nation security institutions, governing and rule of law, and
strengthening the host nation’s ability to provide legitimate and effective governance. Stability tasks
predominately build, with many important activities being conducted by nonmilitary agencies. Progress in
building support for the host-nation government requires protecting the local population. People who do not
believe they are secure from insurgent intimidation, coercion, and reprisals do not risk overtly supporting
host-nation efforts.
9-32. Counterinsurgents execute offense, defense, and stability tasks in the build as well. The priority for
tasks and operations during the build is on the stability tasks. The line of effort that addresses increasing the
host-nation government capacity becomes the decisive operation during the build. Examples of stability
tasks in the build include advising and assisting the host-nation security forces, developing professional
development programs (including professional education) for host-nation security and governance
individuals, facilitating host-nation governance activities, support to local and national demilitarization,
demobilization, and reintegration programs, and development of host-nation rule of law and conflict
resolution mechanisms. However, U.S. forces execute offensive operations during the build. Examples of
offensive operations in the build include providing a quick reaction force for the host-nation security
forces, conducting tactical overwatch for specific host-nation security forces operations, conducting follow
and assume or follow and support for host-nation security forces operations, or conducting precision strike
operations in support of host-nation or U.S. objectives. Counterinsurgents execute defensive operations and
tasks as well, to include protecting the population, combined action with the host-nation security forces to
secure combined positions, and sanctuary denial and disruption operations.
9-33. U.S. counterinsurgents conduct information operations as part of the build in support of host-nation
programs. The focus of information operations during the build is on the host-nation population, the

Direct Methods for Countering Insurgencies
13 May 2014 FM 3-24/MCWP 3-33.5 9-9
host-nation security forces, and host-nation governance institutions. U.S. counterinsurgents conduct
information operations during build operations to facilitate host-nation leaders’ messaging and to
emphasize success in generating the conditions that further the connection between the population and the
host-nation institutions. U.S. ground force information operations reinforce the host nation’s ability to
counter an insurgency without the direct involvement of U.S. ground forces. Host-nation information
operations should focus on increasing the perception of security, increasing the legitimacy of the
host-nation government and security forces, and promoting the host nation’s ability to address root causes.
TRANSITION
9-34. Transition allows the counterinsurgent to delineate tasks associated with development of host-nation
institutions (governance, rule of law, security, and economic) with those tasks associated with transitioning
to host-nation lead of operations. To make transition effective, U.S. commanders incorporate planning and
execution of transition as part of the shape-clear-hold-build-transition framework.
9-35. This transition is not a onetime event. Counterinsurgents transition responsibility to host-nation
agencies when they are capable of taking over a function. This may mean multiple transitions to multiple
host-nation agencies at different times during a counterinsurgency. Transition is a continued process in
which the host nation assumes any responsibility that an external counterinsurgency may temporarily have.
9-36. Security tasks associated with transition represent the U.S. forces’ transition to security cooperation
tasks. During this phase, the U.S. ground force, under the combatant command and in conjunction with the
American embassy, helps generate and then implement theater engagement plans and programs.
9-37. The end goal of shape-clear-hold-build-transition framework is to create the conditions necessary for
the host nation to counter an insurgency independently. However, creating these conditions may not
eliminate the presence of external counterinsurgents. U.S. counterinsurgents may remain in an area during
and beyond transition to help train host-nation security forces or institutions, provide enablers, or begin
security cooperation tasks at the request of the host-nation government. (See FM 3-22 for more information
on security cooperation tasks.)
9-38. To better facilitate the integration of all components of the unified action environment into the
shape-clear-hold-build-transition framework, counterinsurgents may establish an area coordination center.
An area coordination center controls, manages, and coordinates shape-clear-hold-build-transition
framework operations. Commanders and staffs can establish area coordination centers and subordinate area
coordination center civil-military task forces from the tactical to the strategic level. An area coordination
center’s membership includes representatives of all multinational forces and host-nation agencies (military,
police, intelligence, political, and civil administration) operating at the regional and local level. To be truly
effective, Department of State representatives (including United States Agency for International
Development personnel) should lead an area coordination center. As an area coordination center
coordinates all efforts that affect the ability to transition to host-nation control, the area coordination center
is responsible for generating host-nation capability beyond just the security realm. For that reason,
diplomatic and governmental leaders should run an area coordination center with the goal of turning over
decisionmaking and coordination authority to the host nation at the earliest opportunity. In the absence of
Department of State personnel, the military force assigned an area of operations should initiate and manage
an area coordination center until a government representative can take control. An area coordination center
coordinates the allocation of material and personnel resources, methods of policy implementation, and
evaluation of intelligence in the area within which it is organized.
9-39. The area coordination center consists of civilian and military elements necessary to plan the political,
economic, social, psychological, security, intelligence, and tactical operations within that area.
Commanders and staffs base operation plans on an integrated civil-military approach, and unity of effort is
essential. The leadership must have authority to control the allotted resources of all agencies and activities
operating within its respective area of responsibility. In those instances where U.S. or multinational forces
are operating in support of host-nation forces, an exceptionally high degree of cooperation must exist and
advisory efforts are critically important for success. All armed civilian defense forces and civilian
organizations normally remain under operational command of their respective area coordination center task
force chiefs: however, in cases where civilian administration is ineffective, military forces may provide

Chapter 9
9-10 FM 3-24/MCWP 3-33.5 13 May 2014
civil administration until civilian programs have taken effect. A composite view of the shape-clear-hold-
build-transition framework is provided in figure 9-2.
9-40. Transitions can also occur within the shape-clear-hold-build-transition framework. Soldiers and
Marines will have different tasks when an operational environment changes. For example, a unit must
understand when it transitions from eliminating the combatants in an area to creating an environment for
host-nation control. Units will change their mix of offensive, defensive, and stability tasks. More
importantly, they will have to change their mindsets. Figure 9-2 provides the changes of capacity over time,
the changes in the mix of tasks units could perform, and finally when a transition may occur. This graph
provides a snapshot of the shape-clear-hold-build-transition framework. In it, counterinsurgents are moving
from clearing, to holding, and then to building. During this movement, the local population is becoming
more supportive of the counterinsurgency, and the insurgency is losing capabilities and moving from being
in a possible war of movement back to being in phrase I. As insurgent capacity decreases and
counterinsurgent capabilities increase, several transitions take place that involve a different mindset and
performing different tactical tasks. This is in addition to the final transition to the host-nation lead, which is
the end point for the U.S. when it acts as the primary counterinsurgent. (See figure 9-2.) (See chapter 4 for
more information on the phases of an insurgency and chapter 7 for more information on transitions.)
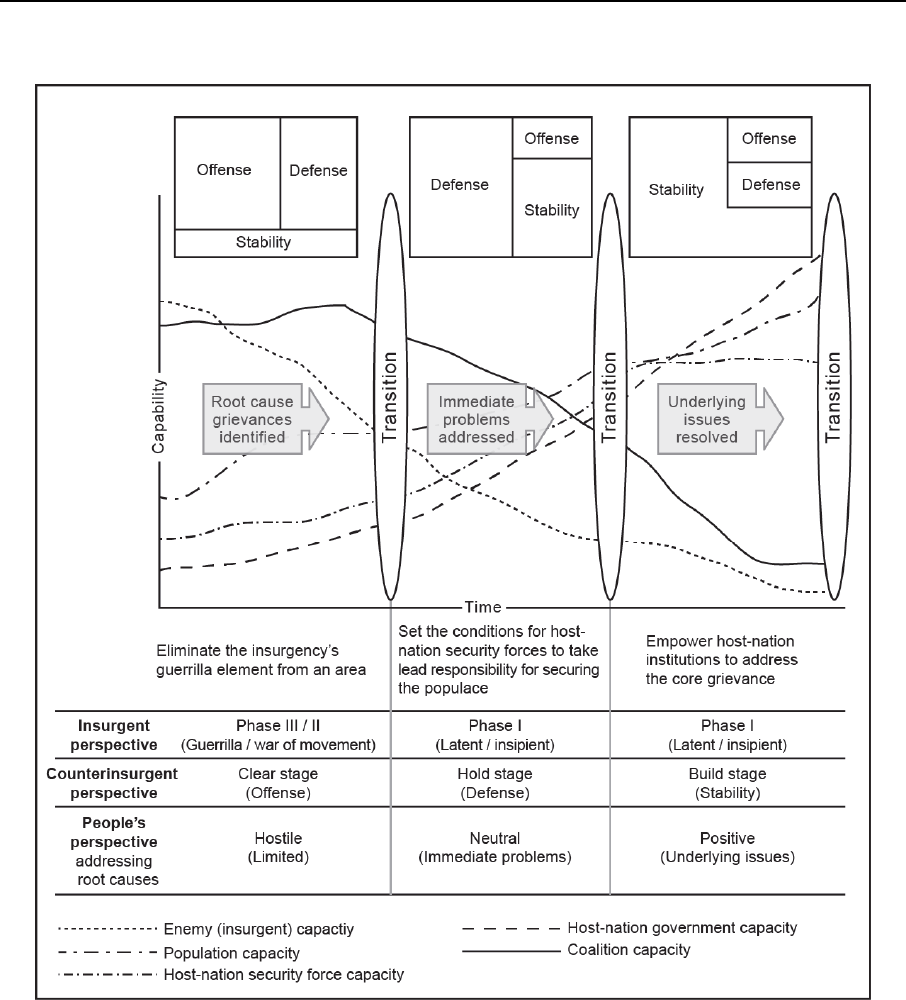
Direct Methods for Countering Insurgencies
13 May 2014 FM 3-24/MCWP 3-33.5 9-11
Figure 9-2. Example of a possible transition framework
OTHER DIRECT ENABLERS
9-41. The Army and Marine Corps can also integrate other direct enablers into a counterinsurgency
operation. For example, indirect fires can be integrated into an ongoing counterinsurgency effort. Special
forces have the capability to perform direct actions. These are short-duration strikes. Special forces can also
conduct other small-scale offensive actions conducted in hostile, denied, or politically sensitive
environments that employ specialized military capabilities to seize, destroy, capture, exploit, recover, or
damage designated targets. As with indirect enablers, the Army and Marine Corps have a wide range of
direct capabilities that can be integrated into an ongoing counterinsurgency effort. Tactical units that can be
successfully integrated into a host nation’s efforts to perform cordon and searches or raids could be an
effective capability for any counterinsurgency operation.

Chapter 9
9-12 FM 3-24/MCWP 3-33.5 13 May 2014
9-42. As part of the joint force, the air component provides Army and Marine Corps units a number of
critical direct enablers. Airpower provides supported ground forces a significant asymmetric advantage
over insurgents as a result of their flexibility, situational understanding, freedom of maneuver, and access
to immediate joint fires. Direct air and space enablers include, but are not limited to, air mobility, casualty
evacuation, intelligence, surveillance and reconnaissance, communications, cyber, global positioning
system, personnel recovery, precision engagement (close air support and air interdiction), and electronic
warfare.
9-43. Two other important enablers are targeted threat infrastructure and strikes. Targeted threat
infrastructure provides a means for a counterinsurgent to attack the resources that an insurgency uses to
continue its effort. However, targeted threat infrastructure must always be conducted in support of other
efforts. Counterinsurgents must weigh the effect of the operations on the legitimacy of the host nation
among the local population. Strikes are conducted to disrupt an insurgency, and they can allow other efforts
to succeed. Targeted threat infrastructure and strikes are not to be conducted in isolation, and
simultaneously some force should be actively securing the population and building legitimacy.
TARGETED THREAT INFRASTRUCTURE
9-44. Targeted threat infrastructure is a method that seeks to destroy an insurgent force’s physical
infrastructure. This is a method that will normally only work if another force is securing the population and
building legitimacy. In other words, it is a method to enable another force. This method seeks to destroy the
necessary requirements of an insurgency to conduct combat operations. Targeted threat infrastructure
proactively targets the physical and societal mechanisms that support and fuel the insurgency. It involves
an aggressive spirit of the offense. When using this method, commanders and staffs must consider the law
of war principle of proportionality. The anticipated injury or damage caused to civilians or civilian property
must not be excessive in relation to the concrete and direct military advantage anticipated by an attack on a
military objective. Commanders and staffs using targeted threat infrastructure must also ensure it is not
contributing to the recruitment of insurgent fighters by using too heavy a hand against elements of society
that are not fully or willingly supporting the insurgency.
9-45. Targeted threat infrastructure must be integrated into an effective host-nation effort that is securing
the population. Targeted threat infrastructure can be an effective tool, if it is well planned and executed to
avoid possible negative consequences of alienating the population and decreasing the legitimacy of the host
nation. If the effect of targeted threat infrastructure is the physical elimination of the basic physical
infrastructure needed by an insurgency, and it avoids the negative effects of alienating the population, it can
be essential in a host nation’s counterinsurgency effort. However, it is a means to enable a host nation, not
a method that should be used without an additional effort to secure the population.
9-46. For targeted threat infrastructure to be effective, commanders and staffs must understand where an
insurgency is attaining its strength and attack those areas and facilities. These efforts must further the
desired overall end state and not undermine a host-nation government’s legitimacy. Commanders and staffs
plan for and limit second and third order effects of attacks. Moreover, attacks are only targeted against the
infrastructure the insurgency relies on. For example, crop eradication aimed at reducing cash flow is
unlikely to effect an insurgency with a large amount of financial resources. It may, however, hurt the
legitimacy of the host nation.
9-47. Illicit crops such as marijuana, coca, or poppy used to fuel and fund an insurgency can be the targets
threatened under the targeted threat infrastructure method. The cash from these crops may help arm, train,
and pay insurgent fighters or pay condolence payments to the families of terrorists who kill themselves in
suicide acts. Attacking such crops may hurt individual farmers. In some cases, farmers may be coerced by
insurgents and have no real choice in the crops they produce. In others, farmers may support the
insurgency. However, the illicit nature of these crops make them valid targets. To avoid creating new
insurgents through crop destruction, counterinsurgents can work with interagency partners and the United
States Agency for International Development to establish crop substitution programs that can help ease
hardships farmers may experience.
9-48. Another key target for the targeted threat infrastructure method is any material or physical item used
to fuel the insurgency. For example, a road network that is the primary means of movement for insurgents

Direct Methods for Countering Insurgencies
13 May 2014 FM 3-24/MCWP 3-33.5 9-13
needs to be interdicted by checkpoints or destroyed. This may inconvenience the local population, but if
consistent with the principle of proportionality this can be a valid course of action. Power systems and
water systems deep in insurgent controlled areas are prime targets for targeted threat infrastructure, but
targeting them requires careful proportionality analysis. As critical components of a society, power and
water are staples that the insurgents need to survive in their own region. By impairing these resources,
counterinsurgents may undermine the insurgency’s resources and its ability to continue the insurgency.
However, any effort to attack these resources must be balanced with the host nation’s legitimacy among the
local population that is affected. Aggressive strikes and raids are central to the targeted threat infrastructure
method to destroy the physical infrastructure that supports an insurgency. This tactic is not a slash-and-burn
technique, but consists of well-planned, pinpointed attacks on those critical enablers that the insurgency
needs to operate.
9-49. Another key target is the illicit funds used to fuel an insurgency. By establishing counter threat
finance fusion centers, commanders and staffs can work with the power of interagency law enforcement
and international legal partners to find, interdict, and seize huge sums of money that the illicit regime must
launder before it can be used again for legal currency. By using unit counter threat finance specialists in
targeted threat infrastructure operations, funds determined to have been gained through illicit means can be
targeted for seizure at the local level. For example, if a man is a small farm owner and lives in a palatial
home with three cars, he should be investigated, and his funds can be targeted if it is determined that his
wealth is from illicit means and those means are being used to fuel an insurgency.
STRIKE
9-50. A strike is an attack to damage or destroy an objective or a capability (JP 3-0). A strike may be
useful in disrupting an insurgency, especially in insurgent controlled areas. Strikes can be made on guerrilla
bases, large, enclosed or isolated compounds, and training camps. Normally these operations are meant to
disrupt an insurgency and allow for the success of other operations. Strike operations can be integrated into
a host nation’s operations to secure a population. The U.S. may contribute a force to perform strikes.
9-51. The purpose of a strike is to destroy insurgent forces and base areas, isolate insurgent forces from
their support, and interdict insurgent infiltration routes and lines of communications. Strikes are primarily
offensive operations. They are characterized by reconnaissance, intelligence gathering, and careful
planning, followed by vigorously executed, coordinated attacks or raids by small, highly mobile combat
forces operating in dispersed formations to locate and fix an insurgent force. Upon locating an insurgent
force, strike force commanders attack, pursue, and destroy that insurgent force. If contact is lost, the strike
forces resume aggressive patrolling to reestablish contact and destroy the insurgent force before it can rest,
reorganize, and resume combat operations.
9-52. Strikes can be conducted in support of shape-clear-hold-build-transition framework operations after
guerrilla forces are initially driven out of an area during the clear phase. Strikes are often employed to
assault objectives outside cleared areas to fix and destroy guerilla forces and prevent counterattacks against
government and reconstruction personnel. Counterinsurgents conduct assaults in areas where guerrillas
attempt to consolidate during the hold and build phases. Precision airpower weapons can be used to support
other units conducting strike operations or to conduct strike operations on their own.
9-53. Reconnaissance to locate and test insurgent dispositions and strengths or to develop additional
intelligence can be followed immediately by a hasty attack or raid. Reconnaissance should emphasize
thorough coverage of an area, and it is characterized by continuous, decentralized, small-unit operations.
Since strike campaigns are conducted in insecure areas, plans must provide for force withdrawal after
mission accomplishment.
9-54. Strike forces are generally task forces composed of military units and may contain intelligence,
police, and paramilitary elements. Civilian elements may be represented. Forces designated to conduct
strikes should be relieved of routine area defense responsibilities well in advance of an operation. Strike
forces can be controlled at the national, regional, or local levels. Strike forces are organized as
self-sufficient task forces capable of operating for extended periods in areas remote from home bases.
9-55. Once insurgent bases have been located, strike forces maneuver to destroy them. An insurgency’s
ability to hide weapons and to assume noncombatant guises in attempting to avoid capture may require a

Chapter 9
9-14 FM 3-24/MCWP 3-33.5 13 May 2014
thorough reconnaissance and search of the area. Suspects must be managed firmly but treated fairly to
avoid turning innocent suspects into insurgency sympathizers. When small units conducting reconnaissance
locate relatively large insurgent operating forces, surveillance should be maintained and reaction forces
quickly deployed to destroy them. In areas suspected of harboring insurgent forces or installations,
reconnaissance and surveillance should be conducted and followed with an immediate raid by reaction
forces when sufficient information has been developed on a target. Good communications and mobility are
essential for success in these combat operations.
9-56. Speed and surprise are important in strikes. The sudden and unexpected delivery of combat forces
into an insurgent held or contested area provides significant advantages to the forces conducting strike
operations. If caught by surprise, guerrillas may be unable to react effectively. Speed and surprise can be
achieved by using air assault tactics to insert the first forces into the area of operations. Subsequent forces
can be delivered on later airlifts or by other modes of transportation. Fires can be used to restrict escape
routes or areas that are not secured by land forces.
9-57. However, strikes do not address the root causes for beginning or sustaining an insurgency, nor do
they necessarily increase the legitimacy of the host-nation government. Strikes are integrated with other
approaches to counterinsurgency as part of the overall operational design. In some cases, the U.S. can
integrate this ability into an ongoing host-nation effort.
13 May 2014 FM 3-24/MCWP 3-33.5 10-1
Chapter 10
Indirect Methods for Countering Insurgencies
10-1. An indirect approach seeks to support existing governments, security forces, and groups through
increasing capacity to counter an insurgency and enabling existing capabilities. This approach indirectly
counters an insurgency by working through host-nation institutions or with groups in the society. The
United States (U.S.) can use nation assistance and security cooperation to aid a host nation in building its
institutions.
10-2. Beyond nation assistance and security cooperation, there are several methods that are indirect
methods for countering an insurgency. Among these are generational engagement, negotiation and
diplomacy, and identify, separate, isolate, influence, and reintegrate. Beyond these methods, there are
several indirect enablers that are important in any counterinsurgency. This includes integrated monetary
shaping operations.
NATION ASSISTANCE AND SECURITY COOPERATION
10-3. Nation assistance is assistance rendered to a nation by foreign forces within that nation’s territory
based on agreements mutually concluded between nations (JP 3-0). This civil or military assistance (other
than foreign humanitarian assistance) is rendered to a nation by U.S. forces within that nation’s territory
during peacetime, crises or emergencies, or war, based on agreements mutually concluded between the U.S.
and that nation. Nation assistance operations support the host nation by promoting sustainable development
and growth of responsive institutions. The goal is to promote long-term regional stability.
10-4. Nation assistance involves other government agencies that provide expertise in building civil
institutions. This is an essential element in counterinsurgency because the military lacks the expertise to
build civil control over the population, perform economic reforms, or aid in other basic functions that a host
nation may need to prevent or prevail against an insurgency. Using a whole-of-government approach is
essential in conducting nation assistance to prevent insurgencies from developing freedom of movement by
exploiting the root causes of conflict within an operational environment.
10-5. Security cooperation is all Department of Defense interactions with foreign defense establishments to
build defense relationships that promote specific US security interests, develop allied and friendly military
capabilities for self-defense and multinational operations, and provide US forces with peacetime and
contingency access to a host nation. (JP 3-22). This includes-
- Military to military exchanges (for example, seminars and symposia).
- Combined exercises.
- Humanitarian assistance.
- Security assistance.
When these activities are used to defeat an insurgency, they are part of a counterinsurgency operation.
While not all security cooperation activities are in support of counterinsurgency, security cooperation can
be an effective counterinsurgency tool. These activities help the U.S. and the host nation gain credibility
and help the host nation build legitimacy. These efforts can help prevent insurgencies or shape the host
nation’s ability to defeat or contain insurgencies.
10-6. When directed, the Army and Marine Corps provide forces to support security cooperation missions.
This requirement can include assistance in training, equipping, and advising the military forces of foreign
nations. Security cooperation includes security assistance, foreign internal defense, and security force
assistance. (See FM 3-22 and chapter 10 for more information on security cooperation activities. See
chapter 10 for more information on working with other forces by using security cooperation.)
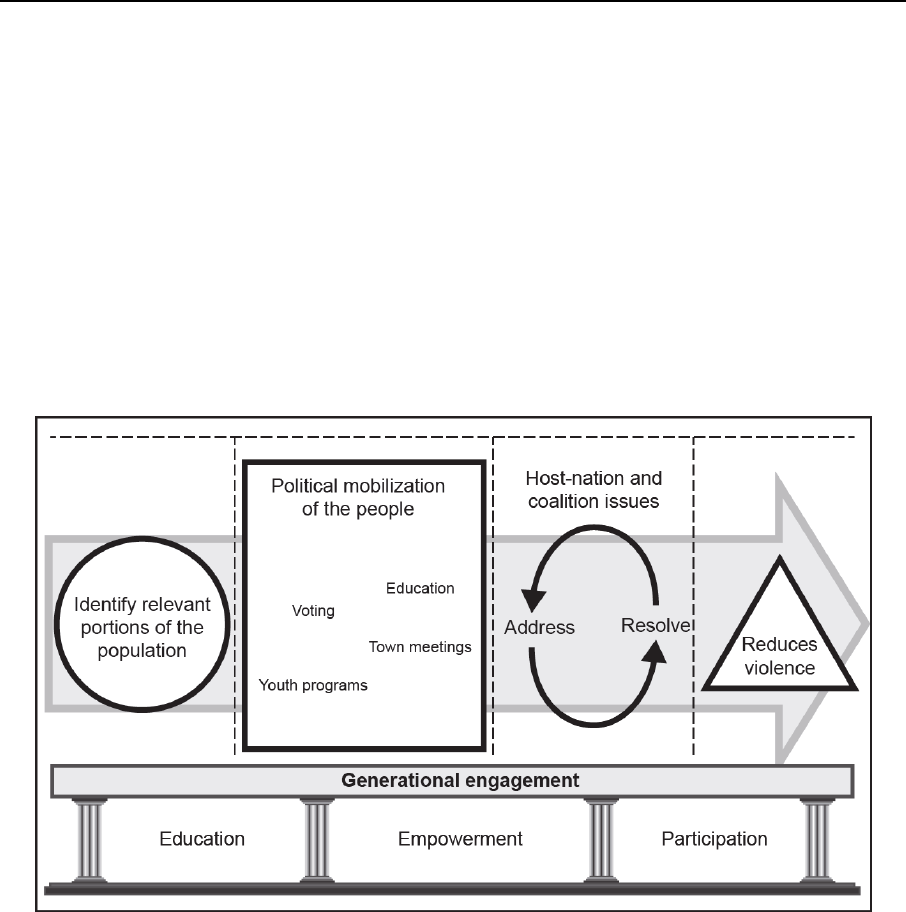
Chapter 10
10-2 FM 3-24/MCWP 3-33.5 13 May 2014
GENERATIONAL ENGAGEMENT
10-7. Generational engagement is a method that can be conducted in conjunction with other approaches
that seeks to get the host nation to educate and empower the population to participate in legal methods of
political discourse and dissent. This can be done in both high threat situations and situations where an
insurgency is at its infancy and combat is less intense. It is best that the host nation undertake this method
as soon as possible to affect the next generation. Generational engagement focuses on the population.
Generational engagement focuses on building new constituents in the host-nation population to counter
insurgent actions. Generational engagement is a method of political mobilization of the people. The
purpose of the method is to get population groups to side with the host nation.
10-8. Figure 10-1 provides a general framework for generational engagement. First, counterinsurgents
identify the population that they wish to engage. This relevant population may politically engage and this
will encourage the host nation to redress any grievances. This may lead to a reduction of violence. This is
all built on a foundation of education, empowerment, and participation. (See figure 10-1.)
Figure 10-1. Generational engagement
10-9. Five principles are fundamental to generational engagement:
- Groups with whom counterinsurgents partner (such as nongovernmental organizations [NGOs])
must be seen as indigenous, not as foreign constructs.
- Independence of funding and resources are important. Support groups can lose credibility the
more they are perceived as solely reliant on foreign funding, possibly due to a shift in priorities
by a sole and influential benefactor. Organizations and their partners should identify alternative
sources of support, including local sponsors, funding from the relevant ministries, or collecting
dues from members.
- In selecting partners, counterinsurgents should not limit themselves to the vocal intellectual elite.
If the insurgency is based on the root causes of a rural population, intellectual elites might not
have legitimacy among the rural poor. Therefore, counterinsurgents should balance support
between the central leadership and local branches in the provinces or townships (where youth
engagement is usually most important).

Indirect Methods for Countering Insurgencies
13 May 2014 FM 3-24/MCWP 3-33.5 10-3
- Expansion and membership numbers should not be used as a key indicator of success. It can be
difficult to accurately track and confirm these numbers with national organizations. A more
accurate measure is the staff, number of offices, actual activity levels, and efficacy. Activity
reports and photos can verify progress.
- A main role for organizations is to make the connections between the local administrations and
the provincial or national level government, as well as other stakeholders and peer organizations.
At some point the NGOs will not be present to facilitate government access, and will be most
effective when they facilitate cooperative and enduring relationships between the population and
the government.
10-10. Generational engagement works with factions from a population to get them to see the benefit of
participating in peaceful means to address their core grievances. Getting youths to understand the legal
means they have to address root causes of conflict is a critical tool for reducing violence. If commanders
and staffs believe that insurgencies may occur over extended periods, then some efforts must be made to
engage this next generation of leaders who can establish a lasting peace. Engagement also has to be made
with the intellectual elites of the country. They may still be residing in the country of conflict or in another
country that has significant influence over the insurgent cause.
10-11. Soldiers and Marines planning to use generational engagement must identify relevant portions of
the population through their planning. Plans and methods for engagements can vary, depending on the
operational environment and the culture. This method is used in conjunction with direct methods as part of
a comprehensive approach to combating insurgent forces. Counterinsurgents can make progress in
defeating insurgent forces, but if they neglect the younger generation of the population they may lose the
war. Continued and prolonged efforts must be made to ensure that counterinsurgents and the host-nation
government are seen as positive influences. The population must identify with and trust their government.
Counterinsurgent efforts are coordinated and tracked through continued assessments to ensure success.
10-12. Counterinsurgents engage with young factions of the population by implementing youth programs.
Counterinsurgents also participate in local council meetings that include representatives from different
generations of the population.
10-13. The idea behind these engagements is that they are initiated by the counterinsurgent forces and
eventually taken over or continued by the host nation. It is not enough for the host nation to just continue to
implement these engagements, rather the host nation must make every effort to ensure that these elements
of the population identify more with the government than with the insurgents. Local leaders who identify
with the government must be protected and supported.
10-14. Some examples of generational engagement can be as simple as ensuring that schools are open and
available to students and ensuring adequate access to medical attention as part of the effort to ensure
essential services. This can address younger portions of the population who, over the long term, will have a
positive view of counterinsurgents and the efforts of their own government to ensure for their care and
protection.
10-15. Some examples of generational engagement along the governance line of effort can include
recruitment of younger influential leaders and including others in the electoral process. This may be
difficult based on the culture in which counterinsurgents are operating because some cultures only allow for
leadership positions for older members of the population. If members of the younger generation cannot
assume roles in the government, they can still be encouraged to participate in the governance process and
feel that they have a place where they can make their views heard by their local government.
10-16. Local participation that builds civil society has proven important in countering an insurgency. This
can be essential in building legitimacy for a host government. For example, in Vietnam, the U.S. military
and Department of State, along with the government of South Vietnam, established several youth groups
that were very successful. One example, the 4-T Youth Club, was modeled after the American 4-H
organization. Over 2000 4-T clubs served as a model of success for organizing youths at the grassroots
level. A host government is essential in building local participation and a civil society. The Republican
Youth Movement, National Revolutionary Movements, and Personnel Labor Revolutionary Parties were all
models of successful youth engagement. These efforts increased the legitimacy of the host nation while
decreasing the ability of the insurgency to recruit. These programs were generators of self-esteem for the

Chapter 10
10-4 FM 3-24/MCWP 3-33.5 13 May 2014
participants and worked out pent-up student energy by deploying them to the provinces. In Vietnam, youth
programs proved beneficial.
10-17. Outside groups can be very effective at generational engagement. For example, the Afghanistan
Youth National and Social Organization is a non-profit, non-governmental organization that enrolls young
Afghani males. It has district chapters, made up of around 45,000 dues-paying members, it enjoys a great
deal of autonomy, and it organizes according to the needs of its local members. Its civic education program
educated Afghans about their political rights and obligations, and it strengthened dialogue between local
leaders and government officials. The importance of engaging local youth in Afghanistan was indicated in
after action reviews and outside groups play an important part in building civic society. In sum, a non-
governmental organization was effective at engaging the population and encouraging dialogue.
10-18. The first step that counterinsurgents can take to ensure that this happens is by leveraging key
leadership at the local and district levels to meet with and discuss significant issues with the population.
Just meeting with the younger elements of the population will not constitute completion of generational
engagement. There must be efforts to follow through on major discussion topics and resolve issues that are
significant to them. Where counterinsurgent forces are able to, they must continue to push local leaders to
not just meet with them but also to address and resolve issues. This can be done initially by
counterinsurgents and eventually by the host-nation government in concert with host-nation security forces.
10-19. Lastly, host-nation security forces must ensure that these actions are taken and that they are
perceived as supportive of all elements of the population. This may done initially with counterinsurgent
forces as the lead elements and later as host-nation forces develop their ability to take the lead on providing
security as a supporting element of government representatives.
NEGOTIATION AND DIPLOMACY
10-20. Negotiation and diplomacy are ways to resolve or defeat an insurgency. Counterinsurgents must
influence the host-nation government and its subordinate elements (for example, the office of land reform)
to remove the root causes that have led to acts of subversion and violence in order to seize, nullify, or
challenge political control of a region. (See figure 10-2 which shows the process of negotiation and
diplomacy.)
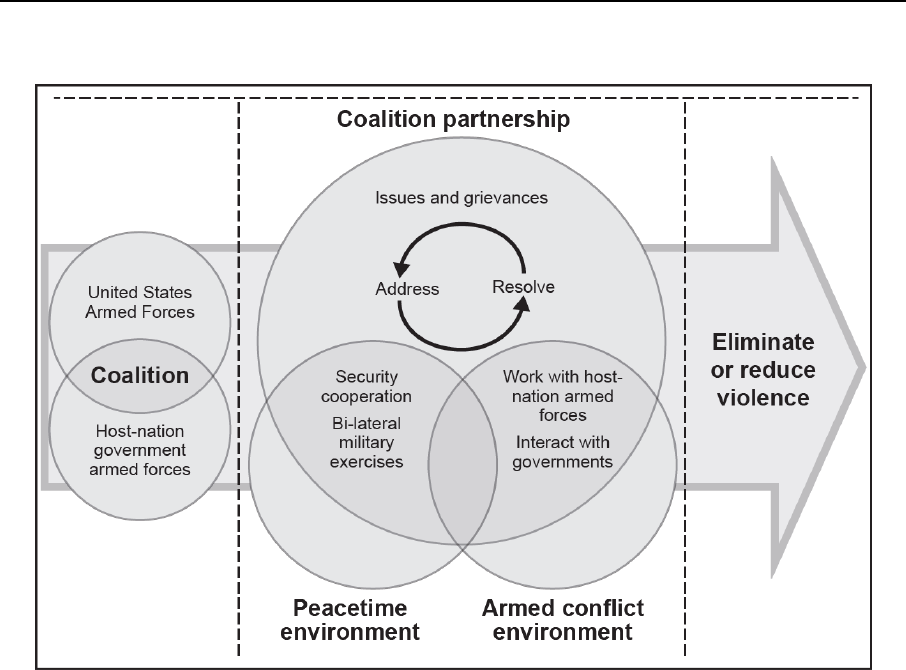
Indirect Methods for Countering Insurgencies
13 May 2014 FM 3-24/MCWP 3-33.5 10-5
Figure 10-2. Negotiation and diplomacy
10-21. The goal of negotiation and diplomacy is to address the insurgent root cause and therefore reduce
the causes for armed conflict. If a host nation can be influenced by U.S. government or military personnel
to peacefully address root causes, then the expected outcome is a reduction in violence and bringing the
insurgents into the political process to have their issues resolved peacefully. If the host-nation government
can do this successfully, the insurgency may not totally go away, but it may only use force of arms in a
limited context that would manifest as limited insurrections compared to a full blown armed insurgency.
10-22. The U.S. has many tools at its disposal to influence a host nation in addressing the root causes of
an insurgency. For example, economic and military aid can be tied to certain actions or standards of
behavior by a host nation. Counterinsurgents must also evaluate how their actions help shape the
environment. Contracting, for example, has direct links to the economy and the society. Using contracts to
encourage a host nation to address root causes is another possible tool. In sum, commanders should make
an assessment of how they are interfacing with a host nation and determine what tools are available to
enable and encourage the host nation to take the needed actions to defeat an insurgency.
10-23. In an armed conflict environment where U.S. forces have been sent in to assist a host nation to
fight its insurgency, U.S. military personnel can work with the host-nation armed forces to reduce causes
for conflict, and U.S. military personnel can also interact with U.S. and host-nation government personnel
to take steps to peacefully address core grievances and root causes of conflict.
10-24. In a peacetime environment where U.S. forces are not committed to help a host nation combat its
insurgency, U.S. military personnel can lessen the causes of a potential crisis or insurgency in the conduct
of security cooperation activities and bi-lateral military exercises. If one of the insurgents’ root causes is
against the host-nation military for human rights abuses or using heavy handed tactics with the local
population, U.S. military personnel can work with the military wing of the government to find alternative
ways of dealing with the population.

Chapter 10
10-6 FM 3-24/MCWP 3-33.5 13 May 2014
IDENTIFY, SEPARATE, ISOLATE, INFLUENCE, AND
REINTEGRATE
10-25. Identify, separate, isolate, influence, and reintegrate is a method that combines several activities
that affect relevant population groups. This can be done in both high threat situations and situations where
the insurgency is at its infancy and combat is less intense. This method works by, with, and through the
host nation; however, it may have some elements which Soldiers and Marines are directly interacting with a
local population.
10-26. Identify, separate, isolate, influence, and reintegrate is a proactive method of addressing root
causes before a full blown armed insurgency can develop. Its purpose is to identify and separate the
insurgents from the population. This is a primary requirement for forces conducting counterinsurgency. By
identifying who is an insurgent and who is not, and then applying resources to separate insurgents from the
population, commanders and planners can more effectively focus their efforts on making the insurgency
feel isolated. Insurgents may then believe that their causes for conflict are not supported by the population.
Once the insurgent leaders and members feel isolated from the population, peaceful efforts can be made to
influence insurgents to surrender, return, and be reintegrated into society.
10-27. Commanders conduct a detailed assessment of the insurgent and population networks before
executing the identify, separate, isolate, influence, and reintegrate method. This assessment guides the
application of individual means to disassemble the insurgent network. Joint forces and other actors may
enter the process at many different stages; therefore, assessment is a continuous process used to guide
decisionmaking throughout operations.
IDENTIFY
10-28. The identify, separate, isolate, influence, and reintegrate method is used to divide and conquer the
insurgency, including all elements of the insurgency listed in chapter 4. The U.S. Marine Corps refers to
these as identity operations (See Marine Corps order [MCO] 5530.17), while the Army uses identity
activities. The elements of an insurgency are the leadership (including the political cadre), guerilla units,
auxiliary forces, and the underground elements. Although all elements of the insurgent network should be
identified, the main target of the identify, separate, isolate, influence, and reintegrate effort is to identify the
guerillas and eventually neutralize them, since they are the main source of the violence. Military operations
should support the host nation in any thorough population screening to identify and eliminate insurgents
and to identify any lingering insurgent support structures.
10-29. Operations that support identity activities include—
- Raids and cordon operations.
- Base access, checkpoints, and protection of critical sites.
- Area security operations.
- Border control and ports of entry.
- Site exploitation.
- Population census using biometric data collection devices and mapping the human environment
and patterns of life
- Medical capacity and tracking medical records.
10-30. Tools to support identity activities include—
- Biometrics and biometrically enabled intelligence collection.
- Tip lines.
- Civil records (land documents and registration databases).
- Reward programs (paying civilians to identify insurgents and their networks).
- Forensics and forensics-enabled intelligence collection.
- Document and media exploitation.

Indirect Methods for Countering Insurgencies
13 May 2014 FM 3-24/MCWP 3-33.5 10-7
SEPARATE
10-31. While killing or capturing insurgents in counterinsurgency operations may be necessary, an
alternate and still effective method in the long run is to separate an insurgency from the population, the
second phase of the identify, separate, isolate, influence, and reintegrate method. Counterinsurgents need to
isolate their adversaries from the relevant population, both physically and psychologically. At the same
time, counterinsurgents should also seek to bolster their own legitimacy and credibility to exercise
influence over that same population.
10-32. Establishing security forces in bases among the population furthers the continued separation of the
local insurgents and the population. The success or failure of the effort depends on effectively and
continuously securing the population. In some cases, it may be useful to physically secure an area using
barriers or other means.
10-33. Combined action programs, such as community stability operations, are local level stability
operations designed to augment wider counterinsurgency operations. Village or community stability
operations can work in areas with limited insurgent activity and attempt to establish security and stability
“bubbles” around rural communities. These cordons are created and ideally expanded to make the area
inhospitable to insurgents and enable legitimate local governance, which further separates the insurgents
from the local population. (See JP 3-24, chapter 5, for more information on stability operations.)
Appropriate tasks for units include, but are not limited to, the following:
- Helping host-nation security forces maintain entry control points.
- Providing reaction force capabilities through the parent unit.
- Conducting multinational, coordinated day and night patrols to secure the town and area.
- Facilitating local contacts to gather information in conjunction with local host-nation security
force representatives.
- Training host-nation security forces in leadership and general military subjects, so they can
secure the town or area on their own.
- Conducting operations with other multinational forces and host-nation units, if required.
- Operating as a team with host-nation security forces to instill pride, leadership, and patriotism.
- Assisting host-nation government representatives with civic action programs to establish an
environment where the people have a stake in the future of their town and nation.
- Protecting host-nation judicial and government representatives and helping them establish the
rule of law.
10-34. The lines of operations that support the separation process include—
- Sweeps and cordon and searches.
- Combat outposts.
- Village and community stability operations.
- Border operations and port of entry operations.
- Strikes, raids, and ambushes.
- Interdiction operations.
- Military deception and military information support operations.
- Electronic warfare.
- Information collection.
ISOLATE
10-35. The isolation phase objective is to break the psychological and physical links between insurgents
and the remainder of the insurgent organization and its support base. The first step in this segregation is to
identify vulnerabilities of the insurgents. This requires a deep understanding of the operational environment
and, more specifically, an understanding of all the adversaries (for example, the insurgent network,
transnational terrorists, and external supporters).

Chapter 10
10-8 FM 3-24/MCWP 3-33.5 13 May 2014
10-36. Counterinsurgents ensure efforts strive to physically isolate the insurgency in all domains (air,
land, maritime, and cyberspace) from other nodes of the insurgent network. Ultimately this means
controlling the physical and cognitive domains. However, completely controlling the domains at all times is
not realistic.
10-37. Patrolling and cordon and search operations can physically isolate insurgents through capture or
deterrence. Following these operations, counterinsurgents’ treatment of captured insurgents has immense
potential impact on insurgent morale, retention, and recruitment. Humane and just treatment may afford
counterinsurgents many short-term opportunities as well as potentially damaging insurgent recruitment.
Abuse may foster resentment and hatred, offering the enemy an opportunity for propaganda and assist
potential insurgent recruitment and support. It is important that unless they are entitled to another standard
based on status, all detainees or other persons captured in any conflict, regardless of how it is characterized,
shall be treated, at a minimum, in accordance with Common Article 3 of the Geneva Conventions of 1949.
10-38. Isolation must include operations to counter the insurgency lines of communication to recruit,
obtain funding, weapons, equipment, direct operations, or gain intelligence. Operations such as information
operations, electronic warfare, and cyberspace operations are examples of efforts designed to detect and
respond to enemy insurgent networks. These operations are vital as force multipliers to identify insurgent
activities and create conditions to deny or defeat their operations.
10-39. In addition to physical and psychological isolation, efforts to isolate the insurgency economically
are necessary, but must be narrowly focused on the activities of insurgents. These efforts seek to isolate the
insurgency as much as possible, as complete isolation of the insurgency is not realistic. If implemented too
broadly, efforts to isolate may have a negative effect on the population and strengthen the insurgency. (For
example, eradicating the poppy harvest in Afghanistan may have cut funding to the Taliban, but it also
alienated the farmers who subsisted on the illicit crop.) Economic efforts to isolate an insurgent require
both physical and informational interruption of financial, business, and criminal enterprises. Attempts to
isolate insurgents from the population economically must be narrowly focused on the insurgents and
minimize the effect on the population by offering viable replacement sources of employment and revenue.
A primary means of the financial isolation is through counter threat finance operations.
10-40. The lines of operations that support the isolation process include—
- Border operations and port of entry operations.
- Strikes, raids, and interdiction operations.
- Counter threat finance.
- Military deception and military information support operations.
- Cyber electromagnetic activities.
- Electronic warfare.
- Intelligence operations.
- Information collection.
INFLUENCE
10-41. The intent to influence the insurgent network is for the population to abandon support to the
insurgency’s efforts. Planned influence operations should convey selected information and indicators to
insurgent networks to influence their emotions, motives, objective reasoning, and ultimately the behavior of
insurgent network itself. While it is unlikely counterinsurgents will change insurgents’ beliefs, it is possible
to change their behavior. The counterinsurgency lines of effort (shown in figure 7-2 on page 7-9) support
this behavior modification, but to further mitigate the insurgent threat to the host nation, additional
programs should be offered as enticement solutions. In other words, counterinsurgents must leave a way
out for insurgents who have lost the desire to continue the struggle.
10-42. Effective amnesty and reintegration programs provide insurgents this avenue; amnesty provides
the means to quit the insurgency and reintegration allows former insurgents to become part of greater
society. Rifts between insurgent leaders, if identified, can be exploited in this fashion. Offering amnesty or
a seemingly generous compromise can also cause divisions within an insurgency and present opportunities
to split or weaken it. Counterinsurgents can also act to magnify existing rifts. If insurgent forces are

Indirect Methods for Countering Insurgencies
13 May 2014 FM 3-24/MCWP 3-33.5 10-9
expelled or have broken into smaller groups, they must be prevented from reentering the area or
reestablishing an organizational structure inside the area.
10-43. Amnesty programs provide a means for members of an insurgency to stop fighting. The essential
part of an amnesty program is that insurgents believe they will be treated well and protected from their
former comrades’ potential reprisal. Thus, counterinsurgents must have detailed information operation
plans to inform the insurgents about the program, to turn themselves in, and to support subsequent amnesty
efforts. Pragmatism must be the first consideration of amnesty programs, not ideology or vendetta.
Counterinsurgents also must have methods to protect the former insurgents. Incentives for disaffected
insurgents or their supporters are important, especially modest monetary rewards.
10-44. Turning former insurgents against their previous comrades can prove invaluable to
counterinsurgency efforts. Former insurgents can provide vital information and even become valuable allies
and combatants. However, information provided by a former insurgent must be evaluated and validated to
prevent misinformation and deception. Incentives and a sense of fair treatment by counterinsurgents are
vital to effective defector programs, which are also dependent on effective information operations so
insurgents are aware of their options. Insurgents may be prone to defect when conflict has been prolonged,
the broad population is weary of conflict, or if the insurgents have an uneven sense of purpose or drive.
Defector knowledge of how the insurgents are led, organized, and operate can prove invaluable. This can
include personality profiles of insurgent leaders, current communication procedures, plans, and tactics,
techniques, and procedures. This detailed intelligence is difficult to gain without defector operations.
10-45. The influence lines of operations include—
- Information operations.
- Military information support operations.
- Military deception.
- Cyber electromagnetic activities.
- Engagement.
- Stability operations.
- Defense support to public diplomacy.
- Negotiation and diplomacy.
- Targeted strikes and raids.
- Support to amnesty programs.
REINTEGRATE
10-46. The objective of reintegrating an insurgent is for the former insurgent to become a productive
member of the society. Military forces, governmental organizations, NGOs from the international
community, and the host nation must cooperate to plan and execute reintegration programs. Former
insurgents must develop confidence in reintegration and the organizations charged with implementing it.
To build this confidence, reintegration programs must be holistic and encompass efforts to restore the
society, the government, and the economy at all levels.
10-47. Reintegration programs should help protect and empower moderate insurgents from extremist
influence and encourage them to not rejoin the insurgency. Programs must be tailored for each area and
insurgency. They can include vocational, educational (especially reading and writing), and religious
programs. The employment opportunities extended to former insurgents depend on an effectively governed,
viable economy with an active market sector. If the reintegration process does not provide alternative
economic opportunities to the former combatants, the likelihood of their return to violence substantially
increases.
10-48. Demobilization of insurgents normally involves the controlled discharge of active combatants from
paramilitary groups, militias, and insurgent forces that have stopped fighting. Demobilization under these
circumstances may include identifying and gathering ex-combatants for demobilization efforts.
Demobilization involves deliberately dismantling insurgent organizations and belligerent group loyalties,
replacing those with more appropriate group affiliations, and restoring the identity of former fighters as part

Chapter 10
10-10 FM 3-24/MCWP 3-33.5 13 May 2014
of the national population. The demobilization of insurgents enables the eventual development of value
systems, attitudes, and social practices that help them reintegrate into civil society.
10-49. Reintegration is the process through which former combatants, belligerents, and displaced civilians
receive amnesty, reenter civil society, gain sustainable employment, and become contributing members of
the local population. It encompasses the reinsertion of individual former insurgents into host-nation
communities, villages, and social groups. Reintegration is a social and economic recovery process focused
on the local community. It complements other community-based programs that spur economic recovery,
training, and employment services. It includes programs to support resettlement in civilian communities,
basic and vocational education, and assistance in finding employment in local economies. It accounts for
the specific needs of women and children associated with insurgent and other armed groups.
10-50. Insurgents, when properly protected, reintegrated, and well treated, can become positive members
of their community. Conversely, unprotected, poorly prepared, or poorly treated former insurgents will
become powerful propaganda opportunities for the insurgents. Reintegration processes and programs, such
as host nation-led moderate ideological or religious education and job training, should be started early in
the reintegration process.
10-51. Counterinsurgency operations ultimately support reintegration through the integration of the
stability functions in planning and execution. The stability functions are security, governance and
participation, humanitarian assistance, rule of law, and economic stabilization and infrastructure. Specific
consideration within stability operations to support the reintegration process include—
- Civil-military operations and commander’s emergency response program funds for special
projects.
- Support to civic education projects.
- Support to employment programs.
- Support to relocation to prevent reprisals.
- Support to integration into the political process.
- Support to transitional justice.
10-52. The importance of influencing members of an insurgency to surrender cannot be overstated. The
importance of how a former insurgent is reintegrated into a peaceful society is also critical because the way
a war is won will decide how long the peace will last.
10-53. Counterinsurgents should offer surrendered insurgents generous terms, and counterinsurgents
should follow those terms. By separating an insurgent from the population, commanders and staffs make
that insurgent feel vulnerable and also take from the insurgency a means for recruitment and logistic
support. Planners and commanders should work toward creating liberal and generous surrender terms.
Counterinsurgents must protect surrendered insurgents from reprisals from their former insurgent
colleagues.
OTHER INDIRECT ENABLERS
10-54. The U.S. can integrate enablers into a host nation’s counterinsurgency efforts. These enablers can
provide intelligence or prevent the flow of resources to a counterinsurgency. Various intelligence
capabilities, such as signals intelligence, human intelligence, and geospatial intelligence, may be essential
to a host nation’s counterinsurgency. Sharing of information from these sources may enable a host nation to
defeat an insurgency. Also, other enablers, such as airlift capabilities, might be important for
counterinsurgency. Another capability that can be integrated into a counterinsurgency effort is counter
threat finance. Counter threat finance works to detect, counter, contain, disrupt, deter, or dismantle the
transitional financing of state and non-state enemies threatening the U.S. Counter threat finance can deny
an insurgent access to vital funding streams by identifying the sources and conduits of funding. In
counterinsurgency, this can play an important role because of the connection between insurgencies and
black markets. It provides one means to prevent an insurgency from obtaining resources. (For more
information on counter threat finance, see ATTP 3-07.20/MCRP 3-33 and DODD 5205.14.)

Indirect Methods for Countering Insurgencies
13 May 2014 FM 3-24/MCWP 3-33.5 10-11
10-55. The effective integration and synchronization of many capabilities, organizations, and functions
that support the collection, analysis, exploitation and sharing of identity information leads to the
identification of threat personnel, groups, and networks. These capabilities include biometric data, forensic
data, document and media exploitation, intelligence, and other information exchanges. Identification of
personnel allows multinational partners to prevent or mitigate insurgents or counterinsurgents from
conducting operations among the innocent population. U.S. forces must comply with U.S. Army Forces
Command predeployment training requirements. These requirements (such as training in personnel
recovery, mitigation of insider threats, biometrics, languages, and cultural awareness) will further enable
U.S. forces in a counterinsurgency environment.
INTEGRATED MONETARY SHAPING OPERATIONS
10-56. Integrated monetary shaping operations are the use of monetary resources, provided with various
types of aid (for example, economic, financial, humanitarian, or developmental), involving the voluntary
transfer of resources (for example, money, equipment, knowledge, or training other than military) from
U.S. or unified action partners to a host nation, directly or indirectly, for mutual benefit. (See
ATP 3-07.20/MCRP 3-33.1G for more information on integrated monetary shaping operations.) Integrated
monetary shaping operations are the coordinated use of money, goods, or services to support the
commander’s objectives. They are a means to an end. Integrated monetary shaping operations are used to
attack sources of instability, build partnerships, and provide for economic stabilization and security.
Integrated monetary shaping operations have two major components:
- Supporting operations by funding developmental assistance, infrastructure, and governance
support projects to win the support of an indigenous populace and erode support for the
adversary.
- Denying adversaries sanctuary and operational flexibility by hindering their ability to reliably
fund operations.
10-57. Integrated monetary shaping operations can be an effective tool to stabilize the security
environment. However, they can also undermine both the local and national economies. One essential
consideration of counterinsurgencies is to understand that long-term counterinsurgency efforts have an
economic impact on the host nation. Additionally, the implementation of funding and projects can have
negative secondary and tertiary effects. Commanders should recognize decisions over which contractors,
communities, and individuals are chosen to receive funding could create winners and losers in their area.
These effects can exacerbate tensions in the area. Finally, a counterinsurgency can last many years, and this
effort can distort the pricing of goods and services within the local and national economy.
Counterinsurgents must understand that they can undermine their own efforts by demanding goods in such
quantities that they fundamentally alters market forces, which results in economic dependence on the
counterinsurgency. This can result in economic problems that can undermine the host nation’s stability
when the external counterinsurgent departs.
10-58. Integrated monetary shaping operations can be effective, but they should be linked into an overall
development plan. Without that link, the haphazard use of money can be highly destructive to an economy
because it creates an unsustainable economy once the counterinsurgent leaves. The basic point of integrated
monetary shaping operations is primarily to be a catalyst for long-term and natural development and only
secondarily to meet short-term needs or security concerns. Counterinsurgents must understand that
interactions with the local culture do have far-reaching effects. The host-nation economy is one area where
counterinsurgents can have both positive and negative effects.
10-59. Integrated monetary shaping operations can also inform a commander’s situational understanding.
Property ownership records include census records, deeds, and other means of determining ownership of
land and buildings. They help counterinsurgents to determine who should or should not be living in a
specific area and help them secure the population. In some cases, it may be necessary for Soldiers and
Marines to go door to door and collect census data themselves.
10-60. Financial records can provide information on sources of insurgent funding. Collection of financial
records often requires help from agencies like the Department of the Treasury and financial institutions. It
may require analyzing criminal activities or traditional means of currency transfer.

Chapter 10
10-12 FM 3-24/MCWP 3-33.5 13 May 2014
10-61. Property ownership and financial records can reveal information about the structure of a society.
Who owns and controls land and who controls debt provide some information on who may be a power
broker in a particular society. Finding these individuals or institutions provides greater situational
understanding for counterinsurgents.
10-62. Integrated monetary shaping operations can be used to aid stability efforts. Applicable funding
authorities guide what types of uses of money are authorized. If authorized for the area of operations, some
possible uses of money include—
- Repairing damage resulting from operations.
- Providing condolence payments to civilians for death or injury resulting from operations. This
type of payment must be in accordance with prevailing standards for payments of solatia, a
victim’s bereavement fund, or compensatory statutes provided by donor agencies and the United
Nations. (Counterinsurgents must be aware of the going rates and, as far as possible, ensure that
the right messaging is provided to the village or other district leadership where death or injury
has occurred resulting from operations.) Further, counterinsurgents must guard against payment
for injury or accident becoming a means of extortion or harassment.
- Funding civic clean-up projects and other sanitation projects and equipment to provide those
services.
- Funding small-scale infrastructure improvements to improve the quality of life of citizens.
- Funding agricultural projects to improve farming practices, improve livestock health, or
implement cooperative farming programs. This type of activity should be conducted in
consultation with donor agricultural agencies or the host-nation departments of agriculture to
ensure that land rights and water rights of communities are not infringed and crop management
is according to agriculturally sustainable principles.
- Repairing civic and cultural sites and facilities. Preservation of cultural heritage is a sensitive
issue and due respect to the site or culture and its practices must be adhered to.
Counterinsurgents might be better to maintain a low profile and let the cultural leaders take a
leading role in this initiative.
- Repairing institutions and infrastructure critical to governance and rule of law (such as prisons,
courthouses, and police stations).
- Purchasing education supplies or repairing infrastructure critical to providing education to the
local population.
- Paying rewards, often discreetly, to citizens who provide information on enemy activities and
locations.
- Supporting the creation, training, and operation of host-nation security forces.
- Funding events and activities designed to build relationships with host-nation officials and
citizens.
Money Usage Principles in Counterinsurgency
10-63. Seven principles can help guide the commander and staff in integrated monetary shaping
operations in a counter insurgency. They are—
- Host-nation ownership.
- Capacity building.
- Sustainability.
- Selectivity.
- Partnership.
- Flexibility.
- Accountability.
Host- Nation Ownership
10-64. Units must ensure that there is counterinsurgent and host-nation ownership of any project. The
local population and local government officials should view any project as their own and not one that has

Indirect Methods for Countering Insurgencies
13 May 2014 FM 3-24/MCWP 3-33.5 10-13
been imposed on them by outside agencies. A project that has been conceptualized, funded, and constructed
at the local level legitimizes the local government in the eyes of the population and further contributes to
stability. However, host-nation officials might lack the capacity to implement and manage the project.
Counterinsurgents often consult development agencies to promote adequate ownership and accountability
for projects.
Capacity Building
10-65. Capacity building involves the transfer of knowledge, techniques, and skills to the local people,
institutions, and government. This transfer enables those people to develop the capabilities to deliver
essential services to the population. Ultimately, the local officials and institutions that gain capacity are
better prepared to lead their regions through political, economic, and security-related issues.
Sustainability
10-66. The principle of sustainability states that commanders should design and select projects and
services that have a lasting effect on the local population. In other words, the impact of the projects under
consideration must endure after forces hand over the facility or service to local authorities and the unit (or
contractors) departure from the site. Sustainability implies that the local government has the necessary
resources to staff and maintain the project. There are examples where commanders have failed to conduct
adequate analysis and built new schools or medical clinics only to discover that too few teachers or doctors
were available to staff these facilities. Similarly, some commanders have purchased large generator systems
to address electricity shortfalls for neighborhoods within their areas of operation. However, without
addressing the fuel, maintenance, and service requirements of these systems, the machines eventually failed
and were unable to serve as a sustainable solution for the local electrical deficit.
Selectivity
10-67. The development community defines the principle of selectivity as the allocation of resources
based on need, local commitment, and foreign policy interests. These characteristics, while strategic, are
equally important at the tactical level. Commanders seldom receive all of the financial resources they
would like to have when implementing their essential service, economic, and governance lines of effort.
Therefore, commanders and staffs allocate the available resources into select areas where there is a strong
local commitment to the reconstruction program, where the project can positively impact the most people,
and where the project under consideration can simultaneously best achieve the commander’s intent.
10-68. Commanders and staffs carefully research nominations, adopt best practices, and design for local
conditions in their proposed projects. Commanders assess local conditions before investing financial
resources into any potential relief or reconstruction program. Commanders and staffs do not invest money
in an intelligence vacuum. They consider all available information about local conditions (such as the
population’s requirements, animosities, traditions, capabilities, and economics). A detailed assessment of
local conditions will best inform the commander on the project’s potential to deliver its desired effects.
Each project should have a clearly defined, decisive, and attainable objective. Commanders and staffs must
assess potential unintended results from their integrated monetary shaping operations. Many second or third
order negative effects from a project may potentially outweigh the benefits from the original commander’s
intent.
Partnership
10-69. The principle of partnership involves close collaboration with local governments, communities,
donors, nonprofit organizations, the private sector, international organizations, and universities. Partnership
plays a central role in any relief, reconstruction, or development program, as it supports each of the other
principles of reconstruction and development. In the context of money in integrated monetary shaping
operations, effective partnership ensures the unit’s financial resources are well invested and synchronized
to support the host nation’s internal defense and development programs and support other U.S. government
strategic objectives for the country.

Chapter 10
10-14 FM 3-24/MCWP 3-33.5 13 May 2014
Flexibility
10-70. The principle of flexibility mandates that units adjust to changing conditions, take advantage of
opportunities, and maximize effectiveness as part of their reconstruction and development program. Just as
the conditions for offensive and defensive operations are often changing and uncertain, so are the relief and
reconstruction tasks associated with stability operations. These conditions often require commanders to
change tactics to achieve desired objectives.
Accountability
10-71. Enforcing accountability, building transparency into systems, and emplacing effective checks and
balances to guard against corruption are important components to any relief, reconstruction, or
development program. Accountability in all actions, to include the unit’s integrated monetary shaping
operations, reinforces the legitimacy of the commander and operations, as well as the legitimacy of the
local government, in the eyes of the population. (See ATP 3-07.20/MCRP3-33.1G for more information on
integrated monetary shaping operations.)
13 May 2014 FM 3-24/MCWP 3-33.5 11-1
Chapter 11
Working With Host-Nation Forces
11-1. The use of security cooperation tools to build governmental capability, including building a host
nation’s forces, may be essential. In the eyes of a local population, the credibility of the host-nation
government is vital in counterinsurgency efforts to address the threat and conditions of instability. The host
nation’s military, police, and paramilitary forces are often the most visible elements of a host-nation
government’s power and authority. Therefore, building the capacity of a host nation’s security forces
should work toward improving the security force’s competence, capability, commitment, and confidence.
(See table 11-1.)
Table 11-1. Developing a host-nation security force
Developmental Area Developmental Indicators
Competence Host-nation security forces must possess and demonstrate
individual and collective skills in their respective warfighting or
law enforcement tasks. They must also support institutional
functions.
Capability
Host-nation security force organizations must be appropriately
sized to accomplish their respective missions. A host-nation
security force must be adequately manned and equipped at a
level that is sustainable, given that host nation’s own resources.
A host-nation security forces’ supporting institutions, such as
their national level force generation and logistic agencies, must
be organized and directed in a manner that adds value to the
lower-level, host-nation security forces’ mission requirements.
Commitment
A host-nation security force must be committed to the peaceful
transition of political power. It must also be committed to the
security and survival of the state, the rule of law, the
preservation of human rights, civil liberties for the population,
and to fighting hard (when necessary) to defeat the active
insurgency.
Confidence A host-nation’s population must believe that its host-nation
security forces’ actions are always in the best interests of the
people. A host-nation government must believe that its
host-nation security force supports that government’s legal
authority. Also, the international community must see a host
nation’s security force as a force for good that respects human
rights and the international law of war.
11-2. To enable a host-nation security force to conduct counterinsurgency operations, United States (U.S.)
or multinational forces conduct various security cooperation activities. Commanders often view host-nation
security force development as an essential task and one of their primary lines of effort. The resulting
increase in a host nation’s ability to secure its own population yields significant benefits because
host-nation troops are normally more effective in conducting operations among the local population than
U.S. or multinational forces. Transitioning responsibility for operations to the host-nation security force
reduces the visible presence of U.S. or multinational troops, further enhancing the legitimacy of the
host-nation government.
11-3. Security cooperation can be an effective means to shape and aid a host nation’s counterinsurgency
efforts. In the case of El Salvador, the U.S. had limits on its level of direct involvement. The U.S. mainly

Chapter 11
11-2 FM 3-24/MCWP 3-33.5 13 May 2014
provided the government of El Salvador with security assistance. By following an effective strategy that
linked this aid to governmental and military reform, the U.S. was able to shape the ongoing
counterinsurgency and aid the government of El Salvador in defeating its insurgency.
Security Cooperation in El Salvador
In 1979, a group of disparate insurgent groups formed a coalition that would
become a significant threat to the Salvadoran government. They were opposed by
the Salvadoran armed forces, at that time a barracks-bound, defensively minded
organization with severe deficiencies in command and control, tactical intelligence,
tactical mobility, and logistics. The Salvadoran army did poorly in combat, and its only
significant successes early in the conflict were in intimidating and massacring the
civilian population.
The mid-1980s saw a massive U.S. aid effort, and considerable civilian and
military reform. Congressionally constrained to an initial limit of no more than 55
military advisors and no combat troops, U.S. aid consisted of arms, military trainers,
and reform and civic action programs. Several of these programs made slow
progress because many in the Salvadoran military resented their imposition by an
outside power.
Though resentful of the imposition, many in the Salvadoran military
recognized the incentive structure, where much U.S. aid was contingent on improving
El Salvador’s human rights record. Salvadoran Defense Minister Vides Casanova
said, “We know that improving our image is worth millions of dollars of aid for the
country.” Even if many Salvadoran counterinsurgents were principally motivated by
the flow of foreign aid, they did learn, they did increase their competence, and they
did improve their human rights behavior. The idea of focusing on all aspects of the
struggle, political, social, economic, as well as military, had taken root and continued
to the end of the war.
11-4. One issue with developing security forces in counterinsurgency is the issue of the quality versus the
quantity of host-nation counterinsurgency forces. In the case of counterinsurgency, quality tends to be more
important than quantity. While quantity and quality must be balanced to some degree and “quantity has a
quality all its own” to the extent that too small a force will not be able to accomplish its mission, quantity is
not a substitute for quality.
11-5. U.S. or multinational efforts to develop the capability and capacity of a host-nation security force
must focus on operational and developmental needs of host-nation counterparts. Developing a sound plan
to develop a host nation’s capability to address the root causes of the insurgency requires a deliberate,
comprehensive assessment of that host nation’s security force. The set of metrics that the U.S. or
multinational forces selects to assess a host-nation security force must be appropriate for the type of
security force being assessed. For example, assessment of a host-nation army may require a completely
different set of criteria from those used to assess a host-nation police force. Likewise, a host nation’s border
or customs police, local (city or county) police, and provincial, state, or national police must all be assessed
according to their specific mission requirements, while taking into consideration that host nation’s federal
or local laws, political considerations, culture, and tribal affiliations.
ASSESSING AND DEVELOPING A HOST-NATION FORCE
11-6. Assessment of host-nation army or land forces typically comes more naturally to U.S. or
multinational forces than assessing host-nation police forces. It is easier for a Soldier or Marine to assess
another Army or Marine Corps unit than it is for a Soldier or Marine to accurately assess a police precinct,
fire department, or sanitation department. Developing measures of performance and measures of
effectiveness based on their standards and how effective those standards are is important. (See chapter 12
for more information on assessments.)
11-7. One method to create an assessment framework is to form a working group of subject matter experts.
This working group will review any lines of effort and tasks identified by the host nation and recommend

Working With Host-Nation Forces
13 May 2014 FM 3-24/MCWP 3-33.5 11-3
additions and subtractions based on their expert opinion. They will then identify relevant objective and
subjective metrics that accurately measure the capability and capacity of the security force based on its
doctrine, organization, training, materiel, leadership, personnel, facilities, policies, and operations.
11-8. U.S. or multinational forces working to develop the capability and capacity of host-nation security
forces during the course of counterinsurgency operations must understand the difference between the
assessment of host-nation security forces and the fulfillment of higher headquarters’ reporting
requirements. Assessment requires a steady, persistent cycle of observation. Those observations help
inform plans for subsequent security cooperation activities. They are also generally included in reports that
help higher echelons make assessments of the overall effort. However, the data required for a report may
not be enough to assess a host-nation security force. Historical examples of these kinds of reports include
the operational readiness assessment submitted by advisor teams during operation Iraqi Freedom, and the
commander’s unit assessment tool prepared by advisors or partner units during operation Enduring
Freedom in Afghanistan. Higher headquarters reports rarely constitute a complete assessment of the
host-nation security force at the tactical level.
11-9. Learning from how a host nation fights could benefit U.S. and multinational efforts in countering an
insurgency. When the U.S. decides to become involved in an insurgency, U.S. forces need to learn how the
host nation fights. If possible, the U.S. should send officers and noncommissioned officers to the host
nation’s professional military schools. If the host nation does not have a developed institutional military,
the U.S needs to find ways for leaders to observe how the host nation operates. To the extent possible,
host-nation forces are built following host-nation doctrine or otherwise following the host nation’s
traditional organization and approach.
11-10. Security cooperation is a multi-echelon endeavor that builds the capability and capacity of a
host-nation security force at the executive direction, generating force, and operating force functions. During
counterinsurgency operations, U.S. or multinational forces may take a bottom-up approach to building a
host nation’s capacity to defeat the insurgency and defend its sovereignty by first developing host-nation
security forces at the small-unit level. This approach buys time and space for a host nation to develop
capacity at higher echelons. In time, a host-nation security force establishes the capacity to generate its own
forces through recruiting, vetting, and induction of enlistees as well as officer candidates; initial entry
training for all personnel, to include basic warrior or police skills and advanced technical, tactical, and
leadership training; and processes for promotion, noncommissioned officer training, and senior leader
training. A host-nation security force must also develop processes for acquisition and life-cycle
management of major end items, as well as processes for procurement of all classes of supply, and
contracting of other services or capabilities. At the executive direction levels, a host-nation security force
must establish policies and a system of orders and directives that supports that host nation’s statutory
framework and drives standardization of policies and procedures through a top-down flow of information
and a robust command inspection program. U.S. or multinational personnel charged with conducting
security cooperation activities in a counterinsurgency environment must look beyond the immediate tactical
conditions on the ground and collaborate with multiple agencies to develop the supporting infrastructure
required for a host-nation security force to sustain and regenerate itself over the long term.
11-11. A bottom up approach does not negate the importance of strategic and operational planning in
security cooperation. In fact, decisions made at the strategic level may have strategic value and yet make
little tactical or operational sense to local commanders and staffs. The is especially true with foreign
military sales. For example, the U.S. may sell a major weapon system to a host nation that has inadequate
means to maintain and support that weapon system. However, the sale may accomplish an essential
political goal, or it may ensure a continued relationship between the host nation and the U.S. If a host
nation is dependent on the U.S. for maintaining a major weapon system, this gives the U.S. influence over
that host nation’s decisionmaking process. Tactical leaders must understand how their actions fit into the
overall operational approach.
11-12. Counterinsurgency usually requires an adaptable campaign plan that includes specific objectives
for all lines of effort, to include host-nation security force development. Comprehensive assessments of
host-nation security force units conducted at regular intervals (possibly aligned with reporting
requirements) provide critical information that can shape and inform U.S. or multinational units’ goals and
objectives for host-nation security force development. One proven technique for creating an adaptable

Chapter 11
11-4 FM 3-24/MCWP 3-33.5 13 May 2014
campaign plan is to prepare a draft plan prior to deployment, and then complete the plan once the initial
assessment is complete. Following every subsequent assessment, the U.S. or multinational commander
develops new goals and objectives based upon the developmental needs of the host-nation security force,
and then the commander issues a fragmentary order with specific tasks for the advisor teams or partner
units that support the new goals.
11-13. Host-nation security force developmental goals must include harmonized coordination among the
various branches of the host-nation security force, particularly between the land forces and the police. All
components of a host-nation security force must understand their own constitutional mandates and
limitations. For example, a host-nation army must know if or when it has the authority to detain individuals
suspected of a crime. Host-nation police forces must understand and support the rule of law, and ensure that
their actions harmonize with the nation’s criminal courts, as well as with the prison system. Finally, when
U.S. and multinational forces advise host-nation security force personnel, they must conduct the proper
troop-to-task analysis to ensure that land forces orient their operations according to host-nation army
doctrine, while police forces should be employed in a way that meets the expectations of a host-nation
government and the people they protect.
11-14. Monitoring of host-nation security forces serves multiple functions, including intelligence and
operations security. U.S. or multinational forces must always be aware of a host-nation security forces
leadership’s loyalty to its host nation and be sensitive to any perceived intentions on the part of a
host-nation security force that may run counter to legitimization of its nation’s government.
11-15. Unified action partners advise host-nation security forces to affect changes in the way they operate.
If host-nation security forces are efficient across all functions, no advising is necessary. However, the only
way a host-nation security force will undergo enduring growth and improvement is if the motivation comes
from within. Therefore, advisors must shape host-nation security force actions so that they make their own
processes and their systems work as intended. Prior to and during deployment, advisors must apply a
motivated approach to learning and understanding a host-nation security force’s organizational design. To
build effective working relationships, advisors need to possess a basic understanding of the host nation’s
culture, social mores, and taboos. Language capability (focused on rapport-building words and phrases
instead of just operational jargon) further enhances an advisor’s credibility and status. The ability to
negotiate and communicate diplomatically is essential for effective advising.
11-16. Once the U.S. or multinational forces gain an understanding of their counterparts’ culture and
organizational design and have completed an initial assessment of the host-nation security force unit’s
capabilities and capacity, advising activities can commence. Advisors consider culture, resources available,
and the base line assessment when choosing which advising task to employ when advising the host-nation
security force. There are three tasks that impart knowledge to the host-nation security force: teach, coach
and advise.
- Teaching involves a number of activities designed to impart knowledge or skills to host-nation
security force counterparts, but the advisor or partner unit drives the process.
- Coaching also involves the transfer of knowledge, skills, and abilities, but host-nation security
force units or individuals assume responsibility for applying what they have learned when
executing counterinsurgency tasks.
- Advising simply involves providing advice to commanders and staffs on their actions. There is
no longer a need to actively transfer knowledge. Advising is passive and allows a host nation to
be the primary actor.
In many counterinsurgencies, the U.S. will only provide equipment, training, and advice. The host nation
has a better understanding of the operational environment and is able to better maintain its legitimacy if it
does not employ foreign forces directly. Advisors must keep in mind that they are also students and they
probably have a great deal to learn from their host-nation counterparts. (See figure 11-1.)
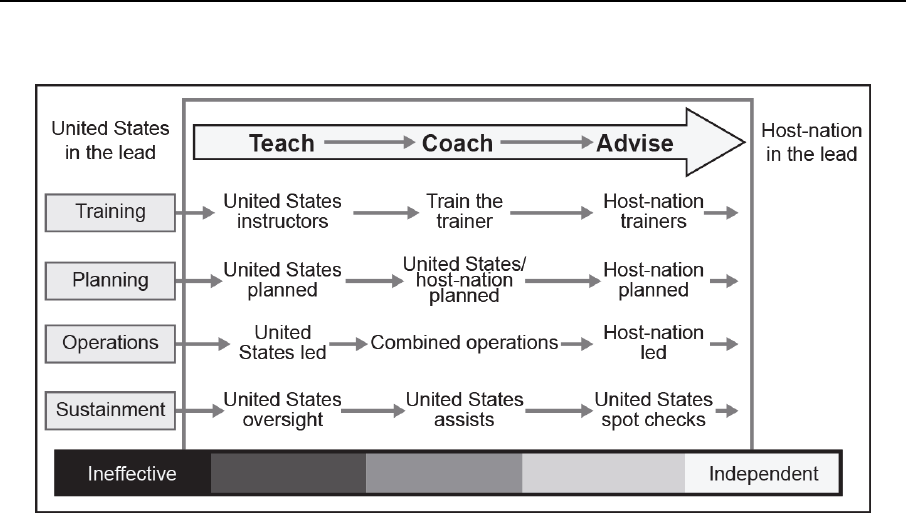
Working With Host-Nation Forces
13 May 2014 FM 3-24/MCWP 3-33.5 11-5
Figure 11-1. Host-nation security force meter
11-17. Regardless of the tasks taken to develop the capabilities of a host-nation security force, a key
interest of security cooperation in counterinsurgency is to legitimize a host-nation security force in the eyes
of its population. This is best accomplished by setting the conditions for a host-nation security force to
conduct security and law enforcement operations independently and professionally.
11-18. Assisting a host-nation security force in counterinsurgency means providing or augmenting a host
nation’s security forces with U.S. or multinational capabilities or resources that they cannot generate on
their own. Forms of assistance may include enablers such information collection assets and capabilities in
support of a host-nation security force’s intelligence collection efforts. U.S. or multinational forces may
provide assistance in the form of certain battlefield effects such as close air support, electronic warfare,
secure long-range communications, or information operations. Assistance to host-nation security forces
often complements their nascent logistics capabilities, such as transportation or mobility, medical
capabilities, or corrective maintenance support. Assistance may also come in the form of materiel support
across one or more classes of supply. For example, the U.S. may provide a host nation with fuel under a
bilateral agreement, even if that host nation could acquire its own fuel for operational efficiency.
Historically, host-nation security force personnel have shown few reservations about asking U.S. forces for
materiel or other forms of assistance. Before providing any of these types of assistance, U.S. forces must
ensure legal authorities permit the assistance. When pressed for assistance of any kind, U.S. or
multinational personnel should ask themselves three questions:
- Do my counterparts really need this materiel or capability to accomplish their mission?
- Is there any way host-nation security forces could procure or acquire this resource or capability
using their own systems, processes, or methods?
- Can host-nation security forces sustain this system or capability over the long term?
11-19. Commanders and staffs should consider the following example. Host-nation security force
counterparts suspect that insurgent forces have established camps on the far side of a ridgeline where they
assemble and conduct final preparations prior to conducting attacks into major towns in the area. These
counterparts ask if the U.S. commander can arrange for unmanned aircraft systems to maintain persistent
surveillance over these suspected campsites to provide early warning of pending attacks. By posing the
three fundamental questions listed in paragraph 11-18, it may be possible to determine other courses of
action whereby a host-nation security force can produce and sustain the same effects. For example, the
commander might offer a host-nation security force instruction on how to build an information collection
plan and techniques for determining named areas of interest. Next, the advisors could coach their
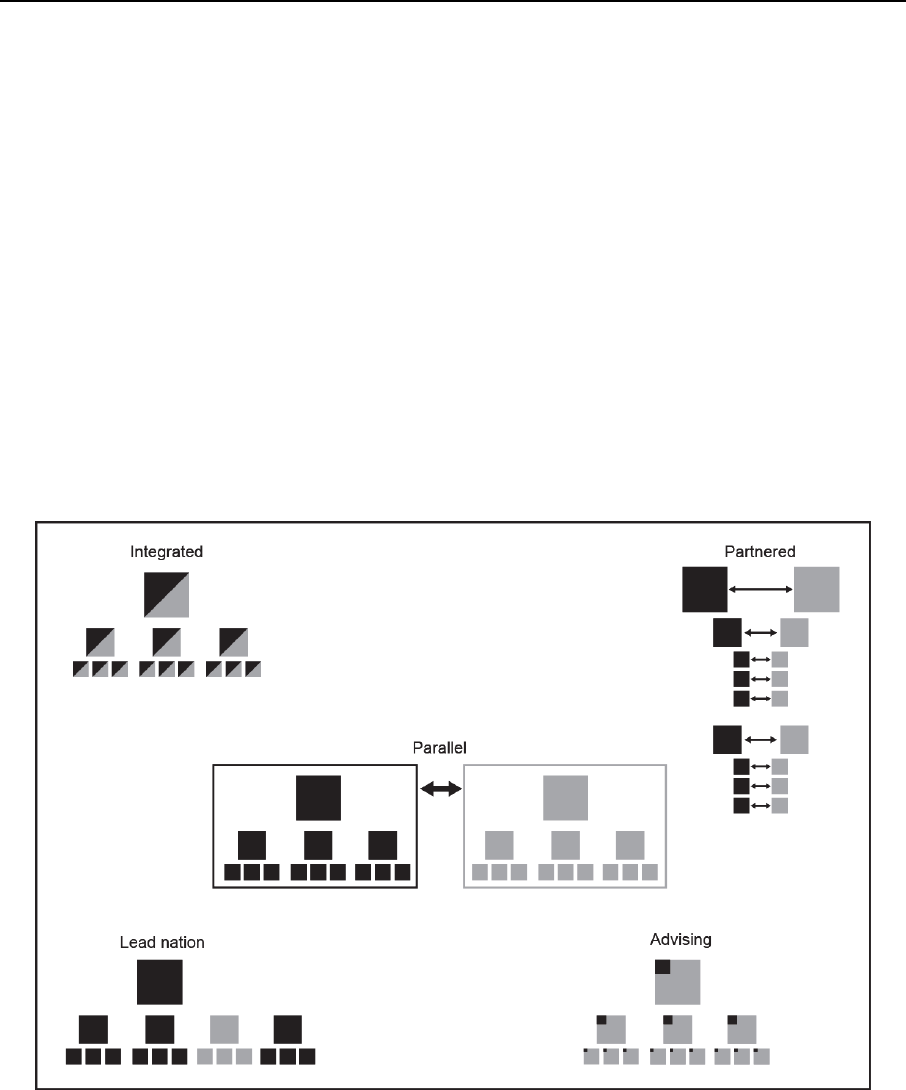
Chapter 11
11-6 FM 3-24/MCWP 3-33.5 13 May 2014
counterparts on determining what capabilities they have at hand to observe those named areas of interest.
Can they establish permanent outposts or temporary observation posts that overlook these named areas of
interest? Can they establish or improve relations with local police forces or tribal networks to establish
hotlines linking the local population and the host-nation security force? Host-nation security force
personnel may often imagine U.S. or multinational technological or logistic capabilities as more powerful
than they truly are, and they may also fail to consider or neglect their own capabilities that can ultimately
create the same effect.
RELATIONSHIPS
11-20. Counterinsurgency operations require well-defined and understood relationships between U.S. and
multinational forces and a host-nation security force. Insurgent forces will quickly identify and exploit gaps
in counterinsurgents’ leadership and cohesion. Clearly defined relationships that evolve as a host-nation
security force’s operational capabilities grow are essential for effective mission command and facilitate a
smooth transition to a host-nation security force lead for security. Broadly stated, five possible command
relationship types are worth considering for each specific counterinsurgency operation. These relationships
are parallel, lead nation, partnered, integrated, and advisory. Each of these relationships requires U.S. or
multinational forces to modify or adapt their organizations for combat to complement combined U.S. or
multinational and host-nation security force counterinsurgency goals. (See figure 11-2.)
Figure 11-2. Counterinsurgency command relationships
11-21. These relationships are useful for tactical and operational forces to understand. However, they are
also somewhat different than the relationships found in JP 3-16. While JP 3-16 outlines a command
structure in which the joint force can integrate multinational partners, paragraphs 11-22 through 11-26
provide information for understanding how to integrate forces at the tactical and operational level.

Working With Host-Nation Forces
13 May 2014 FM 3-24/MCWP 3-33.5 11-7
PARALLEL
11-22. A parallel command is when U.S. or multinational forces maintain their own command structure
with no integration or partnership with a host nation. Under a parallel command structure, no single force
commander is designated. This arrangement is suitable when a host-nation security force has well
established, mature operational and institutional capabilities, and U.S. or multinational forces deploy to
provide additional capabilities. The relationship may be based on U.S. forces being given a specific task.
For example, U.S. forces may only conduct raids or only gather intelligence for the national command
authority. It can also be based on the U.S. forces being given their own area of operations within a host
nation. This can be done for various reasons, including that the area is sensitive to host-nation forces and an
external counterinsurgent may provide a temporary stabilization of the area. This arrangement supports unit
cohesion, and it also supports unity of command.
LEAD NATION
11-23. A lead nation structure exists when all member nations place their forces under the control of one
nation. This relationship works with one nation’s forces in the lead, and the supporting nation provides a
unit or units that are attached to and under operational or tactical control of the lead nation. This
arrangement provides flexibility in that the U.S. or multinational force may initially serve as the lead
nation, and as the operational capacity of the host-nation security force grows, the host nation can
eventually assume the role of lead nation. In also provides a possible means for the U.S. to aid a host nation
in an ongoing insurgency. For example, the U.S. could provide a brigade to a host nation in an ongoing
insurgency. Like parallel command, this arrangement supports unit cohesion, and it also supports unity of
command.
PARTNERED
11-24. This arrangement differs from parallel command in that U.S. or multinational forces and
host-nation security forces are paired down to the small-unit level. Commanders and staffs must consider
how to manage unity of command, logistics challenges, and language and cultural barriers. Partnering has
the advantage of maintaining a degree of unit cohesion (individual units are still homogenous), and the
specific capabilities of each nation’s force can be leveraged down to the small-unit levels.
INTEGRATED
11-25. Integrate means to assemble forces from both the U.S. or multinational and a host-nation security
force, and meld them into a single, inseparable unit. Integration, also referred to as augmenting, poses many
challenges, but it has been used successfully in the past. For example, the Korean augmentation to the U.S.
Army was a very successful program that integrated individual South Korean soldiers into Army units. This
yielded units with enhanced manpower, and cultural and linguistic fluency, down to the squad level. The
drawback is that integration requires significant time to institutionalize and does little to enable a
host-nation security force as a whole to assume lead responsibility for operations. Integration requires a
single shared language for all personnel, so either the U.S. or multinational forces will have to learn the
host nation’s language or host-nation security force personnel will have to learn English. Furthermore,
integration of U.S. and host-nation security forces into a single coherent force requires significant
combined training in individual and collective tasks, which will result in a period at the beginning of the
deployment when the integrated force is not fully combat capable. This could result in extended
deployment periods to compensate for this operational integration and training period. Finally, integration
does little to build the capability and capacity of the host nation’s ministerial-level leadership or the
security forces’ supporting institutions.
ADVISING
11-26. When host-nation security force units achieve a certain degree of organizational maturity at a
specific echelon, U.S. or multinational forces may assign individuals or teams of advisors to perform any
number of advisory tasks. One advantage of this approach is that is imposes the smallest possible U.S. or
multinational force requirement. It also puts the host-nation security force in the most visible role of

Chapter 11
11-8 FM 3-24/MCWP 3-33.5 13 May 2014
providing security to local population. Finally, since the basing and force requirements are relatively small
for U.S. or multinational forces, it is the most flexible and adaptable relationship. Advisor teams can be
quickly reassigned to different host-nation security force units based upon capability gaps across the
host-nation security force. (See FM 3-22 for more information on advisors.)
SECURITY COOPERATION PLANNING
11-27. Security cooperation activities occur across the range of military operations. Two important
activities relevant to counterinsurgency are foreign internal defense and security force assistance. Foreign
internal defense is participation by civilian and military agencies of a government in any of the action
programs taken by another government or other designated organization to free and protect its society from
subversion, lawlessness, insurgency, terrorism, and other threats to its security (JP 3-22). Security force
assistance consists of the Department of Defense activities that contribute to unified action by the US
Government to support the development of the capability and capacity of foreign security forces and their
supporting institutions (JP 3-22). Moreover, security assistance, which includes activities in which the U.S.
provides defense articles, military training, and other defense-related services by grant, loan or credit, could
be important in equipping and resourcing a counterinsurgency force. Both foreign internal defense and
security force assistance represent important defense activities to build the capacity of a host nation to
defeat an insurgency. (For a further discussion on foreign internal defense, security force assistance, and
security assistance, see FM 3-22).
11-28. Security cooperation activities are part of both strategy and policy. In planning security
cooperation activities, combatant commanders start with the National Security Strategy issued by the White
House and expanded upon in overarching Department of Defense (DOD) guidance documents. The
National Defense Strategy influences the Guidance for Employment of the Force, which provides the
parameters for combatant commands to develop their theater and functional campaign plans, which are the
mechanisms to support the synchronization of the comprehensive civilian and military efforts specifically
designed to end insurgent violence and facilitate a return to peaceful political processes. The combatant
commander’s plans are comprehensive, as they consider design, organization, integration, conditions and
objectives for a region during steady state, crisis, and contingency (including counterinsurgency). DOD
develops its plans, taking into consideration all relevant stakeholders (including other partner nations and
international organizations.) These plans should incorporate the full range of capabilities that are required
to meet the desired end state. These plans set conditions for actions that take place throughout all phases of
joint operations. (See figure 11-3 for a graphic representation of this relationship.) (See FM 3-22 for a
detailed explanation on security cooperation activities and planning.)
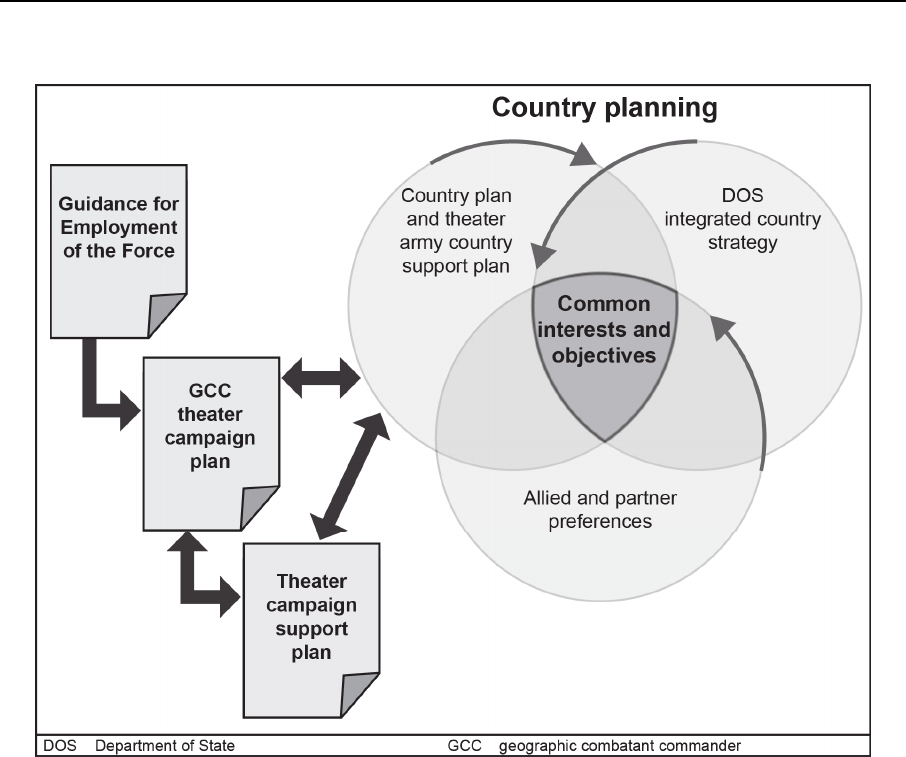
Working With Host-Nation Forces
13 May 2014 FM 3-24/MCWP 3-33.5 11-9
Figure 11-3. Country planning
JOINT PHASING MODE
11-29. Security cooperation takes place during all phases of the joint phasing model. Counterinsurgents
may use security cooperation to prevent an insurgency before a major combat operation, during a combat
operation, and after a major operation. This can also apply to an active insurgency. While the joint phasing
model does not provide a universally prescriptive template for all conceivable joint operations, it does
provide a flexible model to arrange operations. The operation plan consists of six phases:
- Phase 0, shape.
- Phase I, deter.
- Phase II, seize the initiative.
- Phase III, dominate.
- Phase IV, stabilize.
- Phase V, enable civil authority.
11-30. Shape, or phase 0, operations of the joint phasing model are joint and multinational operations that
include normal and routine military activities. During phase 0, both the Army and Marine Corps perform
security cooperation activities as directed in higher plans and orders to indirectly support a host nation in
countering an insurgency. Since security cooperation operations can continue through all phases of the
operation, many of the activities, such as foreign internal defense direct support and foreign internal
defense combat operations, must have the unified application of U.S. forces to achieve the desired effects in
countering insurgent operations. This is critically important as these efforts are important elements in
phases II and III. Foreign internal defense, security force assistance, and other security cooperation

Chapter 11
11-10 FM 3-24/MCWP 3-33.5 13 May 2014
activities are essential throughout the phases of any operation. (See JP 5-0 for more information on the joint
phasing model.)
11-31. If the U.S. commits forces to a counterinsurgency conflict, it will normally deploy a joint task
force or multinational joint task force headquarters to provide planning and command and control. The
multinational joint task force’s desired end state is to terminate the operation plan at the conclusion of
Phase V, stand-down or redeploy the multinational joint task force headquarters, and revert to Phase 0
operations. The geographic combatant command and respective Service component commands, in
coordination with the country team, resume security cooperation activities directed by the country plan.
Counterinsurgency operations typically extend across all phases (0 through V). Therefore, U.S. or
multinational security force assistance and foreign internal defense activities in support of the host-nation
security force’s counterinsurgency conflict may occur under the auspices of the American ambassador to
the host nation and the geographic combatant commander, or under the authority of the multinational joint
task force commander.
DEVELOPING HOST-NATION SECURITY FORCES
11-32. Both foreign internal defense and security force assistance can be used as part of a long term plan
to develop and deploy a host-nation force to defeat an insurgency. While the U.S. may intervene in a
country that only needs enablers to enhance an already effective military force, a host nation may lack an
effective military. If the host nation lacks an effective military, aid in the development of that host-nation
military could follow five phases: planning and resourcing host-nation security force, generation of
host-nation security force, employment of host-nation security force, transition of responsibility for security
to host-nation security force, and sustainment of host-nation security force. These phases are distinct and
independent of those in the joint phasing model. U.S. or multinational forces conduct parallel planning with
their host-nation security force counterparts to achieve strategic, operational, and tactical objectives in
support of the overall counterinsurgency campaign, while at the same time working toward milestones that
lead to a successful transition from U.S. or multinational lead to host-nation security force lead for security.
11-33. Typically, the first phase of building a host-nation security force, planning and resourcing, falls to
the responsibility of geographic combatant command-level planners in coordination with the country team.
Coordination of legal authorities and funding for security force assistance and foreign internal defense
activities is an interagency process because it typically involves resources provided under a number of
different sections of the United States Code (USC). Moreover, other security cooperation programs, such as
foreign military sales, may be essential in equipping another military to perform foreign internal defense
operations.
11-34. Generating the host-nation security force is the second phase in building a host-nation security
force. If the U.S. is deploying conventional forces, this will probably be the initial phase in which
regiments or brigade combat teams will actually have an active role. These forces can partner with
host-nation security forces of varying developmental levels in the conduct of counterinsurgency operations.
For example, while supporting recent counterinsurgency operations in Colombia and the Philippines,
host-nation security force counterparts had already fielded relatively sophisticated, well-developed
operational units supported by robust supporting institutions and well established executive-level or
ministerial leadership. In other U.S. historical counterinsurgency operations such as Afghanistan and Iraq,
the host-nation security force operational units, their supporting institutions, and the most senior-level
executive leadership functions were undeveloped or completely non-existent. In situations such as these,
U.S. and multinational forces must organize, train, and equip host-nation security force units while
assisting in the building or rebuilding of their supporting infrastructure. The organize, train, and equip
security force assistance tasks may be assigned to U.S. or multinational regiment- or brigade-sized units
while they are simultaneously battling the insurgents. At the same time, unified action must be taken to
establish a host-nation security force’s own sustainable force generation capabilities and capacity. U.S. or
multinational personnel, working with their host-nation security force counterparts, are placed in a difficult
predicament in that they must carefully select key host-nation security force leaders to be pulled away from
the immediate counterinsurgency fight to assume critical command and staff positions within the
host-nation security force’s organizations. Counterinsurgents must exercise restraint by not assigning all of
the best host-nation security force leaders to operating force units while neglecting to invest in their own
force generation capacity. (See figure 11-4.)
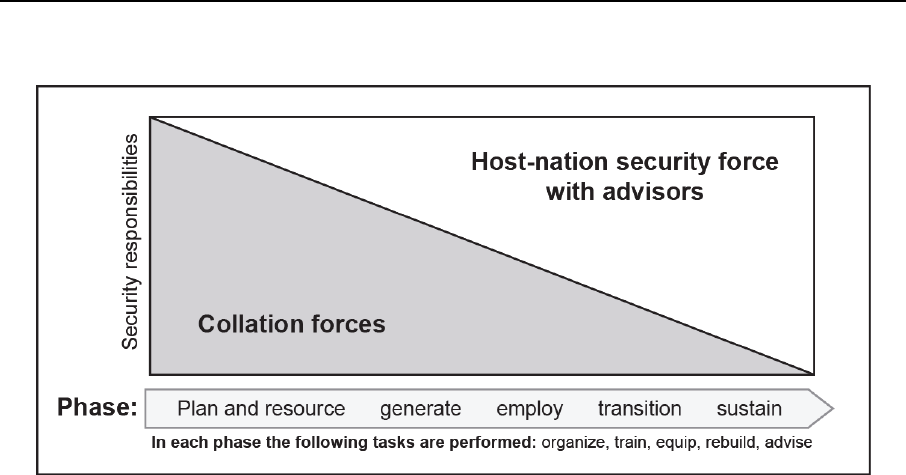
Working With Host-Nation Forces
13 May 2014 FM 3-24/MCWP 3-33.5 11-11
Figure 11-4. Phases of building a host-nation security force
11-35. The third phase of building a host-nation security force is the employment of a host-nation security
force to protect the population and defeat the insurgents. During this phase, the primary focus shifts from
organizing, training, equipping, and rebuilding host-nation security forces to employing host-nation
security forces to perform the security tasks for which they were designed. As one host-nation security
force unit enters the employment phase, other units may have just begun the force generation process.
Meanwhile, there may be more seasoned host-nation security force units that are ready to transition to the
lead for security operations in their assigned area of operations. Additionally, it may be possible to generate
host-nation police forces more quickly than army units, since they can be employed individually or in small
station-level units, they do not need to conduct large-scale collective training exercises, and they typically
have fewer materiel requirements. However, it may take considerably longer for police forces to show their
effectiveness during the employment phase due to the length of time it takes for police forces to gain the
trust of the local population and build productive, enduring relationships with local or tribal leaders.
11-36. The fourth phase of building a host-nation security force in a counterinsurgency is the transition of
responsibility for security operations from the U.S. or multinational forces to a host-nation security force.
In some instances, such as in Colombia or the Philippines, a host-nation security force may already be
mature and highly capable in most or all operational realms (land, air, and maritime). Security force
assistance activities and the resulting transition to a host-nation security force lead may refer only to
specific functions such as intelligence or an even more discreet set of tactical tasks, such as employment of
remote sensors, that supports the host nation’s strategic or operational counterinsurgency goals. In these
instances, the U.S. may provide operational capabilities to meet the immediate threat, while conducting
security force assistance in the form of equipment or training to close the capabilities gap. Once the
capability gap is filled, a host nation’s security force assumes responsibility for that function, and U.S.
forces redeploy, with the country team providing the host nation access to long-term security assistance
programs as appropriate.
11-37. The defense attaché office and foreign area officers play an important role in long-term security
assistance programs. In other cases such as Iraq, U.S. or multinational forces may initially have to assume
responsibility for all security tasks in all operational realms, and across all security force functions (land
forces, police, and border security). In the latter case, transition is a lengthy process with no clearly defined
beginning or end date.
11-38. Transition will likely be conducted in steps or subphases, and the steps or subphases may be
geographic, functional, or a combination of both. For example, the transition to host-nation security force
lead for land force security operations may transpire one province at a time until the entire country has
transitioned. A second example might be for transition to occur for land forces across the entire country by

Chapter 11
11-12 FM 3-24/MCWP 3-33.5 13 May 2014
January 20XX, all police forces by June 20XX, and air and maritime forces by December 20XX. A
transition to a host-nation security force lead should be conditions or assessments-based, although the U.S.
or multinational forces may elect to use a set transition date as a forcing function to compel the host-nation
security forces to assume greater responsibility for securing their own country and their own people.
Transitions will rarely be simple. In cases where U.S. or multinational general-purpose brigade combat
teams deploy for extended tours such as 12-month rotations, units may find that they are supporting the
host-nation security force transition to lead for security when they arrive in-country and still supporting the
same transition when they redeploy one year later.
11-39. The fifth phase of building a host-nation security force in counterinsurgency is sustainment. In this
context, the term sustainment does not refer exclusively to logistic sustainment or sustainment functions.
Rather, sustainment is an ongoing set of security assistance activities (Title 22) and security cooperation
activities (Title 10) designed to enhance the capabilities and capacity of a host nation to provide for its own
security and to participate in regional or global multinational operations. These programs also seek to
develop enduring relationships with key leaders within the host-nation security force and to facilitate
peacetime or contingency access to host-nation facilities such as ports, airfields, and training venues. As the
transition to the host-nation security force lead for security draws to a close, there may be a number of
security force assistance tasks that require an extended period to be completed properly. Examples include
foreign military sales of new equipment such as tanks, artillery, helicopters, or watercraft and subsequent
deployment of mobile training teams to train the host-nation security force on the employment of these new
weapons systems. Enduring geographic combatant command-level security cooperation activities, such as
rotational deployment of U.S. forces to conduct combined exercises with the host-nation security force,
sustain and extend the development of the capability and capacity of a host-nation security force to deal
with residual insurgent threats and potential future external threats to that host nation’s sovereignty.
11-40. In a counterinsurgency, the host-nation security force’s executive and ministerial leadership, its
force generation capacity, and its operating forces’ capabilities must develop and mature quickly, while
U.S. or multinational forces initially provide time in the form of security to allow this process to succeed.
U.S. or multinational forces gradually reduce and eventually relinquish control of the counterinsurgency to
a host-nation security force. Parallel planning with a host-nation security force provides the blueprint for
what must occur from the U.S. or multinational side and a host-nation security force side of an operation.
Both entities plan for transition to host-nation security force lead, but they approach the transition from
different perspectives. Initially, teaching, coaching, and advising host-nation security forces in their
planning efforts is part of the overall process, but it ultimately should result in a host-nation security force
having the capability and capacity to defeat an insurgency on its own.
PARALLEL PLANNING
11-41. When enabling a host nation to develop a security force, parallel planning is essential. Parallel
planning is a time-saving technique that enables leaders at all levels from fire team to division to initiate the
operations process (plan, prepare, execute, and assess) prior to the receipt of a complete operation order.
Parallel planning allows units to generate tempo by conducting a multi-tiered planning process. This
reduces haste and provides all echelons more available time to prepare for future actions. Likewise, parallel
planning with host-nation security forces enables greater efficiency and the ability to conduct simultaneous
actions. It also serves as an essential step in the host-nation security force transition to the lead for security
in a counterinsurgency.
11-42. Parallel planning with the host-nation security force assumes adequate planning capabilities on the
part of at least some of the host-nation security force commanders and staffs. When making this
assumption, U.S. or multinational forces assume operational risks relating to the ability of the host-nation
security force staffs to deliver on their planning requirements. Considerations when conducting parallel
planning with the host-nation security force commanders and staffs may include, but are not limited to,
varying or competing agendas, lower literacy rates, access to computer technology, and use of graphics or
visuals. U.S. commanders and staffs conducting parallel planning consider these points:
Working With Host-Nation Forces
13 May 2014 FM 3-24/MCWP 3-33.5 11-13
- U.S. or multinational forces have their own national security objectives, while host-nation
counterparts may have conflicting objectives from the national to the local level.
- Literacy rates in many of the countries that the U.S. or multinational forces may partner with are
often far below that of the U.S. or other western countries. Lack of formal education, however,
does not preclude the host nation from being capable of understanding the western style of
military planning.
- Access to computer technology in various host nations often does not match that of the U.S. or
western countries. Commanders and staffs may have to use manual methods of data collection,
storage, and dissemination.
- Instructional programs, whether computer based or done on a terrain model, are based on
western preference for the presentation of information through visual modalities. Successful
counterinsurgency operations require U.S. or multinational advisors to imbue their host-nation
security force counterparts with the capability to process raw data into information that provides
knowledge and leads to an understanding of an operational environment.
- Security classification of host-nation counterparts.
- Foreign disclosure restrictions.
11-43. Regardless of the difficulties of parallel planning, U.S. and multinational forces make every effort
to understand host-nation planning capabilities prior to conducting operations. Despite the many challenges
presented by conducting parallel planning with host-nation security forces, U.S. and multinational forces
should be completely integrated into the planning process as early as possible because the host nation can
potentially bring to the counterinsurgency specific and essential abilities. (See table 11-2 for examples of
host-nation contributions.)
Table 11-2. Host-nation contributions
Task Reason for contribution
Understand an operational
environment
An area of operations is a host nation’s home and its
culture; a host-nation force knows the language, the
different groups, the political situation, educational levels,
economic considerations, historical bad actors, and
unofficial community leaders.
Provide human intelligence Host-nation security forces may be able to better gather
information that leads to human intelligence for many
reasons, including speaking the same language and
understanding the important players in the area.
Put the pieces together Host-nation forces can often better integrate the different
fragments of intelligence into the context of an operational
environment.
Determine credibility of
intelligence assets (sources,
walk-ins, call-ins)
Host-nation forces possess a vastly superior sense of
cultural intelligence and may be able to assist in assigning
credibility to sources.
Validate and check
interpreters
Host-nation forces can assist in confirming the locally hired
interpreters’ abilities to interpret.
Identify and root out
infiltrators
Host-nation forces can pick out minute differences between
normal and abnormal behaviors.
Gain information superiority Host-nation forces can help write messages that may
resonate with the local population.
Vet locally hired personnel for
counterintelligence and
security purposes
Host-nation forces have access to resources not
necessarily available to U.S. personnel.
11-44. Tactical-level planners in the U.S. military employ either the military decisionmaking process or
the Marine Corps planning process to gain an understanding of an operational environment, identify the

Chapter 11
11-14 FM 3-24/MCWP 3-33.5 13 May 2014
tactical problem, develop possible courses of action, and evaluate and select the best course of action to
most effectively address the tactical problem. Commanders and staffs first properly frame the problem.
When given a set of inputs, such as an order from higher headquarters or some other initiating directive,
certain intelligence products, and an initial commander’s visualization, commanders and staffs complete
the steps to work toward a specified output, such as a finished operation order. In cases where host-nation
security force leaders have been directly involved in combat operations over many years, those leaders who
survive often owe their lives to their own ability to improvise. As a result, many host-nation security force
leaders apply an intuitive, instead of a process-oriented, method of making decisions. They can
immediately size up a tactical situation, almost instantaneously recognize dangers and opportunities, and
decide upon a course of action. While this capability can serve in critical situations, it cannot be taught to
others, and it is of no use in situations unrelated to the leader’s own experiential learning. Therefore, U.S.
or multinational advisors may have to work patiently with their host-nation security force counterparts for
them to develop a planning and decision support process instead of allowing them to rely solely on the
intuitive approach.
11-45. U.S. and multinational planners ensure that they have conducted basic mission analysis prior to
parallel planning with host-nation partners. This allows advisors to develop and assess assumptions,
identify implied and specified tasks, determine what assets and capabilities are available, and formulate a
tentative timeline to coordinate advisory efforts throughout the planning process.
13 May 2014 FM 3-24/MCWP 3-33.5 12-1
Chapter 12
Assessments
12-1. Assessment is a continuous process that measures the overall effectiveness of employing joint force
capabilities during military operations. It is also a determination of the progress toward accomplishing a
task, creating a condition, or achieving an objective (JP 3-0). The assessment process monitors the effects
of actions on mission accomplishment. Operational assessments have three enduring purposes. First, they
monitor the nature, scope, and severity of a situation. Second, they track a military force’s implementation
of a plan in combination with collaborating agencies. Finally, operational assessments evaluate progress
towards achieving goals or objectives. Commanders and staffs must integrate assessments into the Army
design methodology and conceptual planning. Assessments are crucial for successful adaptation and
innovation by commanders within their respective areas of operation. Assessments are also essential in any
type of transition. They are a key ingredient in adapting and learning. Assessments must be part of initial
design. Commanders and staffs must conceptualize what is actually important and determine how to
question those assumptions from the beginning of understanding a problem. (See ADRP 5-0 and ADRP 6-0
for doctrine on assessments.) Assessment precedes and is integrated into every operations activity and
entails two broad, enduring tasks:
- Continuously monitoring the current situation (including the environment as it affects friendly
forces, enemy forces, and the population) and the progress of the operation.
- Evaluating the operation against established criteria, expected outcomes, and the desired end
state.
12-2. Commanders, assisted by their staffs, continuously evaluate an operation’s progress against the
established commander’s intent, mission, and concept of the operation. Based on their assessments,
commanders may adjust the operation and associated activities to better achieve the end state and adjust
assessment criteria to address the most credible and relevant activities.
12-3. The critical role of assessment necessitates establishing measures of effectiveness and performance
during planning. Commanders choose these measures carefully so that they align with the overall
operational design and the superior commander’s intent. These measures reflect the interrelationship among
the lines of effort. Commanders and staffs revise their assessment and measures of effectiveness and
performance as an operation progresses to most effectively focus limited collection and analytical
resources.
12-4. Sound assessment blends qualitative and quantitative analysis with the judgment and intuition of all
leaders. Commanders must apply assessments carefully, as counterinsurgency operations most often
involve complex societal issues that may not lend themselves to quantifiable measures of effectiveness.
Moreover, bad assumptions and false data can undermine the validity of both assessments and conclusions
drawn from them. Data and metrics can inform a commander’s assessment. However, they must not be
allowed to dominate it in uncertain situations. Subjective and intuitive assessment must not be replaced by
an exclusive focus on data or metrics. Commanders must exercise their professional judgment in
determining the proper balance.
ASSESSMENT FRAMEWORKS
12-5. Several assessment frameworks have been developed over the past decade. Depending on their
specific purpose, they can be used as tools to develop an interagency initial assessment, assess conflicts, or
measure progress. For example, the Interagency Conflict Assessment Framework is a recognized and very
useful initial assessment framework (See United States [U.S.] Government publication Interagency Conflict
Assessment Framework). Alternatively, units may use some form of systems analysis based on the
operational variables.

Chapter 12
12-2 FM 3-24/MCWP 3-33.5 13 May 2014
ASSESSMENT METHODS
12-6. Selecting the appropriate approach to assessment is the commander’s most important assessment
decision. Assessment methodologies may be centralized, decentralized, or both. A centralized methodology
requires units to collect and report information requirements to their higher headquarters for analysis and
situational understanding. This is a common methodology and is often described as pattern and trend
analysis. Pattern and trend analysis uses centralized quantitative analysis to produce a snapshot of the
operation’s momentum over time. Pattern and trend analysts tend to accept that counterinsurgency data will
be inaccurate and incomplete, but when viewed in aggregate this data will be sufficient to produce relevant,
centralized, and quantifiable analysis. Pattern and trend analysis measures progress, but it is not truly an
assessment. The problem with the centralized approach to assessment is that the decentralized nature of
counterinsurgency prevents the development of any centralized model to understand the important nuances
of local context. Decentralized assessments enable subordinate units to develop and measure progress
locally. The interaction between levels of command is critical to informing the higher commander.
Although decentralized assessments are preferred by the lower tactical levels, actual measurement of
progress is limited by the lack of a common starting point. This often gives the best picture of a local
situation, but it lacks the context of how it compares to other locations. Senior commanders must weigh the
results by comparing assessments with dissimilar measurements. This makes the development of an
aggregate analysis very difficult.
12-7. Military forces in counterinsurgencies usually use a combination of these two assessment methods,
choosing common reporting requirements for all subordinates but also requiring a subjective analysis from
each of the subordinate commanders to aid in informing the senior commanders’ situational understanding.
Units report qualitative statistics to enable pattern analysis, and commanders provide quantitative analysis
to fully depict what the statistics mean at the local level. The combined assessment involves a top down
planning, bottom-up refinement approach in which analysis is conducted at the level the data is collected
and reports to higher headquarters include narratives from local commanders. This type of assessment
eschews the establishment of core level metrics at the highest levels and allows commanders to establish
additional metrics in accordance with their situation and their resources. Combined assessment generally
results in more accurate reporting and efficient use of collection and analysis resources.
12-8. In geographically distributed, decentralized counterinsurgency campaigns, only a few activities
produce similar outcomes or are consistently implemented across the theater of operations. What is
important in one area may not be important in another. Similarly, what works in one area may not work in
another area.
ASSESSMENT CONSIDERATIONS
12-9. Assessment begins as soon as a military force receives an alert or warning and does not end until
after that force has ceased operations and left the area of operations. Assessment begins with an initial
assessment that serves as the basis for planning. Planning develops this into an operational assessment that
evaluates plan effectiveness and focus. The assessment is continually reassessed. Often plans are updated
because of the reassessment process.
12-10. The assessment should reflect the achievements of collaborating partners. Military forces cannot
defeat an insurgency alone. Assessors must realize that information about the underlying root causes for
social, cultural, political, and economic turbulence will probably be incomplete. Obtaining reliable
information can be costly and time-consuming. Assessors should be extremely wary of methods that claim
to provide this information quickly. An assessment based on faulty information can result in military force
actions that are counterproductive. It is better for assessors to monitor the situation, track what every
organization is doing, and be clear about what they do not know. The next step is to postulate, hypothesize,
and clearly state what assumptions the evaluation process is making. Assessors seek information to test
assumptions and revise estimates as operations continue.
12-11. At its core, a counterinsurgency environment is a political problem. Understanding and solving the
political problem is the essence of counterinsurgency operations. A counterinsurgency environment is
complex, with many lines of effort covering a variety of political, military, economic, social,
infrastructural, and informational activities. As such, developing a comprehensive assessment is a

Assessments
13 May 2014 FM 3-24/MCWP 3-33.5 12-3
time-consuming process that is difficult to perform properly and effectively. Counterinsurgents must assess
not only their own actions or inactions, but also those of insurgents and the population. In understanding
these actions and inactions, counterinsurgents must have a thorough knowledge of the history and culture
of their areas of operations. These assessments must include, among many other factors, the context for any
given situation, the perceptions of those involved, and the possible outcomes of actions or inactions.
12-12. Commanders are responsible for assessments. The commander’s direct and personal involvement
in the assessment process is critical. Moreover, assessments must contain both subjective and objective
elements. Assessments combine elements of science and art. They are not simply a collection of numbers
or indicators. Commanders and staffs must understand assessments in the context of the overall campaign,
not just from a military perspective.
12-13. Countering an insurgency most often involves an extended campaign. Counterinsurgents must
assess actions or inactions broadly, to include how they are viewed locally, within the multinational force
(if one exists), host nation, and the region. Counterinsurgents also assesses actions against host-nation
strategic goals. Without the backing of each of these levels, counterinsurgents risk loss of legitimacy and
potential failure.
12-14. Eliminating the root causes of an insurgency is the goal of a counterinsurgency. Assessment must
focus on those activities and actions that are most important in addressing these root causes. Assessment
must be focused on gathering the right information needed to understand what to do. The commander must
determine if counterinsurgents are doing things right, if counterinsurgents are doing the right things, and if
change is necessary.
12-15. Balanced assessments include information from all relevant and objective sources, including both
quantitative and qualitative data. This data includes the proper combination of centralized and decentralized
reporting. A balanced assessment includes countering opinions and data that contradict overall findings. A
combination of quantitative and qualitative types of indicators reduces the chance of misconstruing trends.
12-16. No assessment will ever show all the aspects of a counterinsurgency campaign. Efforts to show all
aspects of a counterinsurgency waste resources and place unrealistic demands on subordinate units that
often result in falsified reporting. Assessment should rely principally on information gathered through
ongoing intelligence and operational reporting. Demands for additional reporting should be minimized.
12-17. There is no substitute for seeing a battlefield as a means for understanding a situation. Battlefield
circulation is critical to establishing relationships between commanders at all levels. The view of a
commander who daily walks and lives in a particular area of operations provides a level of insight that no
statistic or report can replace. These first-hand encounters provide commanders a lens with which to review
and compare centralized reports and trend analysis with the intuition and local understanding of
subordinate commands.
12-18. Collecting, assembling, and analyzing information is a time and labor-intensive process.
Commanders balance time and resources for assessment just as they do across the planning, decision, and
execution continuum. To help achieve this balance, commanders and staffs ask the following questions:
- What must be understood to begin planning?
- What will be assessed and to what detail?
- How will a particular task, objective, end state condition, or assumption be assessed?
- What measures of effectiveness and measures of performance will be used?
- What information requirements (indicators) are needed to support a particular assessment?
- Who on the staff has primary responsibility for assessing a particular area?
- What is the collection plan?
- How can the host nation help?
- How can the other agencies of the U.S. government assist?
DEVELOPING MEASUREMENT CRITERIA
12-19. Assessment requires determining why and when progress is being achieved along each line of
effort. Traditionally, commanders use discrete quantitative and qualitative measurements to evaluate

Chapter 12
12-4 FM 3-24/MCWP 3-33.5 13 May 2014
progress. However, the complex nature of counterinsurgency operations makes progress difficult to
measure. Subjective assessment at all levels is essential to understand the diverse and complex nature of
counterinsurgency problems. It is also needed to measure local success or failure against the overall
operation’s end state. Additionally, commanders need to know how actions along different lines of effort
complement each other; therefore, planners evaluate not only progress along each line of effort but also
interactions among lines of efforts.
12-20. The most common types of assessment measures are measures of effectiveness (MOEs) and
measures of performance (MOPs). A measure of effectiveness is a criterion used to assess changes in
system behavior, capability, or operational environment that is tied to measuring the attainment of an end
state, achievement of an objective, or creation of an effect (JP 3-0). MOEs focus on the results or
consequences of actions. MOEs answer the question, “Are we achieving results that move
counterinsurgents towards the desired end state, or are additional or alternative actions required?” A
measure of performance is a criterion used to assess friendly actions that is tied to measuring task
accomplishment (JP 3-0). MOPs answer the question, “Was the task or action performed as the commander
intended?”
12-21. MOEs and MOPs for assessing counterinsurgency operations are designed with the same
characteristics. MOEs and MOPs are measurable, observable, distinctive, relevant, and responsive:
- MOEs and MOPs have quantitative or qualitative standards against which they can be measured.
The most effective measurement is a combination of quantitative and qualitative measures to
guard against an inaccurate view of results.
- Each MOE and MOP measures a separate, distinct aspect of the task, purpose, or condition.
- MOEs and MOPs are relevant to the measured task, outcome, and condition. Host-nation local,
regional, and national leaders, and NGO personnel, may provide practical ideas, professional
ideas, and feedback to craft relevant MOPs and MOEs.
- Assessment tools detect environmental and situational changes.
DESIGNING MEASURES OF EFFECTIVENESS AND PERFORMANCE
12-22. An MOE provides some information about how an operational environment is changing. An MOE
of a number of attacks on counterinsurgents can indicate a successful counterinsurgency, or it can indicate
insurgent control of an area and an unwillingness of counterinsurgents to contest that control. In this
example, commanders and staffs need to understand why the number of attacks are down. What is essential
to any MOE is the development of an effective measure that tells the commander critical information about
how an operational environment is changing.
12-23. Moreover, in developing MOPs, commanders and staffs measure a unit’s performance based on
the conditions of its area of operations. In other words, MOPs should be developed as a means to measure
if a unit is effectively doing the things that the commander and staff view as essential to defeating an
insurgency. MOPs are developed based on a counterinsurgency mission and an area of operations.
12-24. When designing MOEs and MOPs, commanders and staffs consider several points:
- Raw counts of something is usually not as important as how many out of a possible total and
how important each one is.
- Knowledge of the state of insurgent training may provide information about the overall
capability of the insurgency. If an insurgency can produce trained units, it may have a higher
military and sustainment capacity.
- Training in other states could indicate support from another state.
- A high number of un-coerced informant reports could be an important indicator of a breakdown
in insurgent security. Also, the position of the informer in the society might be an important
indicator.
- The number of insurgent attacks is not always as important as the scale of an insurgent attack.
Large-scale attacks require a level of operational sophistication that may imply an increased
insurgent capability.
Assessments
13 May 2014 FM 3-24/MCWP 3-33.5 12-5
- How many insurgents are caught and jailed may be an important MOE. However, the number
convicted and sentenced by government judicial authorities and remaining in jail over time is
also an important MOE of governmental capability and corruption.
- The number of recruits available for an insurgency can be an important indicator of the
government’s and the insurgency’s legitimacy.
- An MOP based on the number of patrols in a given area over a period may not be as effective as
the persistence of patrols in a given area over the same period of time.
- An MOE based on the amount of money seized may not be as important as an MOE based on
denying funding sources. It may simply show an increased flow of funds into an area.
12-25. When developing MOPs and MOEs, commanders and staffs avoid developing MOPs or MOEs
that highlight what a commander and staff are actively doing to defeat an insurgency. For example,
building a number of schools can be used as an MOP, and the number of students in the school can be used
as an MOE. However, these activities may have no effect on an insurgency at all. Commanders and staffs
connect MOEs and MOPs to their operational environment and insurgency. Accepting the assumption that
what one is doing is actually relevant to defeating an insurgency is an easy means to undermine the
effectiveness of MOPs and MOEs. Commanders and staffs avoid the trap of thinking that because they do
something and measure it, it is important.
12-26. Commanders and staffs generally avoid measures that lack context. For example, the number of
enemy killed, without any context, is normally a dangerous MOP. The number of enemy killed can indicate
that the insurgency is increasing its recruitment and capabilities, thus more insurgents are being killed in
more attacks. Commanders and staffs establish some context in any measure that they use.
12-27. Vietnam highlights the importance of creating an assessment framework that is contextual to the
insurgency and is relevant to actually measuring success. In Vietnam, U.S. leadership made assumptions
about what were important measures of success without connecting those measurements to situational
understanding. Many U.S. leaders did not actively question their assumptions. Even worse, their ineffective
assessment framework had an influence on operations.
Measuring Effectiveness and Performance in Vietnam
Historical accounts of the conflict in Vietnam vary widely in the points
emphasized and the explanations offered. Disputes are facilitated by the different
personal experiences of many different direct observers who saw or participated in
sometimes very different slices of the conflict at different times, at different
operational levels, and in different parts of the country. What, if anything, could have
been done to change the outcome of the war and who to blame for that outcome
remains fairly hotly contested. What the outcome was, however, is not contested:
U.S. forces withdrew in 1973, and the Saigon government fell to the combined
pressure of the insurgency and North Vietnamese regular forces in April of 1975,
unequivocally a counterinsurgent loss.
The literature on the U.S. military’s Vietnam-era assessment process is
highly negative; even the most strident defenders of the assessment reports
produced during that period expressed some dissatisfaction with the process.
Assessments of the Vietnam War varied in type, purpose, and intended consumer.
The entire process changed and grew between the early 1960s and the early 1970s;
there was no single “Vietnam War assessment.” There were many assessment
processes, and many were burdened with murky objectives, measures that were
poorly connected to those objectives, and poor data collection. Quantitative data of
questionable veracity were used to make optimistic prognostications, such as the
illusion of a trend toward “a light at the end of the tunnel.” Distrust of Vietnam-era
military briefings became so endemic that members of the press corps referred to the
daily military press briefings as the “five o’clock follies.”
The Military Assistance Command, Vietnam, or MACV, was the theater-
level military command in Saigon, South Vietnam. MACV was the neck of the funnel
for nearly all field reports on operations, intelligence, pacification, and other data
Chapter 12
12-6 FM 3-24/MCWP 3-33.5 13 May 2014
categories. Some of the MACV reports and nearly all of the Secretary of Defense’s
reports relied heavily on aggregated quantitative data and pattern and trend analysis.
In some cases, data collection requirements were developed to meet perceived
operational or strategic needs; in other cases, they were specifically designed to
provide data that would show some kind of progress without context. For example, in
1968, MACV reported the number of cakes of soap it had issued to Vietnamese
villagers in 1967 (572,121), an irrelevant input metric. More famous (or infamous) is
the use of “body counts” as a primary progress metric. Not only were body counts a
poor proxy for progress driven by an untenable assumption about adversary attrition,
but data collected were wildly inaccurate because of the adversary emphasis on
reclaiming bodies, difficult terrain, duplicate reporting, and the temptation to
exaggerate, among other reasons.
Assessment of the Vietnam War was haphazard before MACV became a
theater combat command in the early 1960s. Between the mid-1960s and the early
1970s, MACV and the Office of the Secretary of Defense (with Central Intelligence
Agency assistance) created the single largest and most comprehensive military
counterinsurgency assessment apparatus in the history of warfare. It involved the
efforts of hundreds of thousands of military personnel, civilians, Vietnamese
nationals, intelligence experts, and analysts over the course of several years. These
contributors produced hundreds of millions of data items (in Department of Defense
[DOD] parlance), tens of thousands of tactical and operational analytic reports, and
hundreds of comprehensive assessments that addressed nearly every aspect of the
war. Data flowed up from the hundreds of thousands of troops on the ground,
province advisors, military advisors to Republic of Vietnam units, U.S. civilian
officials, and U.S. intelligence officers, as well as Republic of Vietnam military units,
government agencies, and civilian development teams. These data points were then
fed into catalogs and computer databases, including the Hamlet Evaluation System,
the Terrorist Incident Reporting System, the Territorial Forces Effectiveness System,
the Pacification Attitude Analysis System, the Situation Reports Army File, and many
others. “Data” could mean anything from a simple number (for example, rounds fired
in a single artillery attack) to a more complex set of ostensibly correlated survey data
(for example, hamlet evaluation data).
Assessment in Vietnam was non-trivial: A July 26, 1970, U.S. military
intelligence briefing listed 44 provinces, 257 districts, 2,464 villages, 11,729 hamlets,
and 1,500 miles of coastline from the demilitarized zone with North Vietnam to the
border with Cambodia in the Gulf of Siam. The challenges of assessment in Vietnam
are the same challenges faced in any counterinsurgency: How should policymakers
determine progress and decide strategy if all they have to choose from is inaccurate,
decontextualized, and aggregated numbers or thousands of pages of lengthy
narrative?
While it is not possible to state that poor assessment led to the loss of the
Vietnam War, the war was distinguished by internal confusion, poor decisionmaking,
and, ultimately, strategic defeat. It is apparent from analyzing the way in which
assessments were presented and used that they contributed to many of the poor
decisions that led to this defeat.
BROAD INDICATORS OF PROGRESS
12-28. Numerical and statistical indicators have limits when measuring social environments. For example,
in South Vietnam U.S. forces used the body count to evaluate success or failure of combat operations. Yet,
the body count only communicated a small part of the information commanders needed to assess their
operations. It was therefore misleading. Body counts can be a partial, effective indicator only when
adversaries and their identities can be verified. (Normally, this identification is determined through a
uniform or possession of an insurgent identification card.) Additionally, an accurate appreciation of what
insurgent casualty numbers might indicate regarding enemy strength or capability requires knowing the
exact number of insurgent armed fighters initially present. In addition, this indicator does not measure

Assessments
13 May 2014 FM 3-24/MCWP 3-33.5 12-7
several important factors. For example, it does not measure which side the local population blames for
collateral damage, whether this fighting and resultant casualties damaged the insurgent infrastructure and
affected the insurgency strategy in that area, and where families of dead insurgents reside and how they
might react. Within the essential services lines of effort, the number of schools built or renovated does not
equate to the effective operation of an educational system, nor is it as important as the number of children
in school. Moreover, counterinsurgents should question whether the number of children taught is an
important measure at all.
12-29. Planners start with broad measures of social and economic health or weakness when assessing
environmental conditions. Examples of possible counterinsurgency indicators include—
- Acts of violence (numbers of attacks and friendly or host-nation casualties).
- Dislocated civilians. The number, population, and demographics of dislocated camps or the lack
of lack of camps are indicators of overall security and stability. A drop in the number of people
in camps often indicates a return to normalcy. The numbers of people and families exiled from
or fleeing their homes and property and people returning to them are measurable and revealing.
Human movement and religious attendance. Religious activity can be used as a measure of
religious freedom and of how much confidence the population has in their government’s
security. Possible indicators include the ability or lack of ability of religious pilgrims to move
about the country.
Development and active use of places of worship.
Number of religious structures (for example, temples, churches, mosques, religious schools)
closed by a government.
- Presence and activity of small- and medium-sized businesses. When danger or insecure
conditions exist, these businesses close. Patrols can report on the number of businesses that are
open and how many customers they have. Tax collections may indicate the overall amount of
sales activity.
- Level of agricultural activity:
Is a province, region, or nation self-sustaining, or must life-support type foodstuffs be
imported?
How many acres are under cultivation? Are the fields well maintained and watered?
Are agricultural goods getting to market? Has the annual need increased or decreased?
- Presence or absence of associations. The formation and presence of multiple political parties
indicates more involvement of the people in government. Meetings of independent professional
associations demonstrate the viability of the middle class and professions. Trade union activity
indicates worker involvement in the economy and politics.
- Government services available. Examples include—
Police stations operational and police officers present throughout the area.
Clinics and hospitals in full operation, and whether or not new facilities sponsored by the
private sector are open and operational.
Schools and universities open, functioning, with increasing attendance over time.
- Freedom of movement of people, goods, and communications. This is a classic measure to
determine if an insurgency has denied areas in the physical, electronic, or print domains.
- Tax revenue. If people are paying taxes, this can be an indicator of host-nation government
influence and subsequent civil stability.
- Industry exports.
- Employment or unemployment rate over time. An increasing employment rate over time is
generally a sign of stability.
- Amount of electricity produced. Increasing production of electricity is associated with provisions
for essential services. However, increased stability often results in greater demand so care must
be taken in the use of this indicator.
- Specific attacks on infrastructure.

Chapter 12
12-8 FM 3-24/MCWP 3-33.5 13 May 2014
ASSESSMENT CELL
12-30. An assessment cell normally shadows the planning effort, looking for areas of the plan that may
require assistance in measuring progress toward planned goals and the purpose of the operation. Assessing
progress is the responsibility of all staff sections and not the sole responsibility of any one staff section or
command post cell. Each staff section assesses the operation from its specific area of expertise. However,
staff sections must coordinate and integrate their individual assessments and associated recommendations
across the warfighting functions to produce comprehensive assessments for the commander, particularly in
counterinsurgency operations.
12-31. The function and purpose of an assessment cell or working group must include not only the
assessment of the plan and progress of operations, but also the effects of those operations on operational
environments. To understand the effect, it is important to assess not only what happened or how, but why a
particular result was achieved. This level of understanding aids in informing future decisions and plans.
12-32. In counterinsurgency operations, especially in widely decentralized operations, assessment cells
with analysts are organized down to and including the battalion level. This capability greatly assists in the
development of bottom-up assessment metrics that provide context and balance for other types of
assessment.
DIRECTED TELESCOPE TECHNIQUE
12-33. The directed telescope technique aids commanders with assessments by providing eyes on the
ground. Military commanders often find value in a separate and objective source of information regarding
actions and events “on the ground.”
12-34. When using the directed telescope technique, commanders send trusted subordinates and teams to
the battlefield to swiftly assess and report. This helps commanders get a sense for what is transpiring in the
field. This technique does not take the place of regular after action reviews or reporting, but instead it helps
commanders confirm or deny the visual image they have of how operations are going and the impact their
troops efforts’ are having.
12-35. The duties of a team assigned to a directed telescope mission include a variety of skills and
qualities to be successful. They include—
- Good judgment.
- Unfailing tact.
- Initiative.
- Sympathy, which implies a desire to help rather than to criticize.
- Acute perception, coupled with exactness and accuracy in determining facts.
- Ability to express themselves and deliver impartial reports in the clearest and most concise
terms.
- Good tactical knowledge.
12-36. Instead of spying or informing the commander on personnel or single events, the focus is to
provide advice to units based on their findings, report trends to the commander, and most importantly
provide recommendations that are feasible, acceptable, and suitable.
12-37. The directed telescope technique can work at various echelons and can be included when battalion
and brigade staff and personnel are supporting subordinate units in information analysis, operations,
planning, and training.
13 May 2014 FM 3-24/MCWP 3-33.5 13-1
Chapter 13
Legal Considerations
13-1. Counterinsurgency operations are complex and raise challenging legal issues for Soldiers, Marines,
and their commanders. Counterinsurgency commanders, staffs, and planners should consult their servicing
legal advisors often in their initial planning and as they encounter changing conditions that may change the
application of relevant legal authorities. This chapter is not intended as a complete legal guide or a
substitute for legal advice, but rather serves to alert counterinsurgency leaders of some of the more
common legal issues that may affect United States (U.S.) counterinsurgency operations. This summary
cannot replace a consultation with the unit’s supporting legal advisor.
13-2. All U.S. military operations, including counterinsurgency operations, are governed by U.S. domestic
law, the international law binding on the U.S. (to include the law of war), and U.S. policy and regulations.
A number of areas of the law are critical for counterinsurgency operations, including the authority to
deploy forces and conduct counterinsurgency operations in the first instance, the laws governing the
conduct of operations, and the laws that fund counterinsurgency operations. The law of war, including the
treatment of civilians and detainees, and the application of rules of engagement, in particular, are critical
issues that have a significant impact on the conduct of counterinsurgency operations.
AUTHORITY TO ASSIST A FOREIGN GOVERNMENT
13-3. In addition to the authorities to use military force, through a variety of statutes contained in Title 10,
United States Code (USC) and Title 22, USC, Congress has authorized and directed the Department of
Defense (DOD) and Department of State, respectively, to provide assistance to foreign governments
relevant to counterinsurgency. For example, U.S. forces may be called upon to provide foreign internal
defense or training to foreign security forces (such as military forces and police).
AUTHORITY FOR FOREIGN INTERNAL DEFENSE
13-4. The President or Secretary of Defense may issue a deployment or execution order, which may
authorize U.S. forces to make limited contributions during operations that involve foreign internal defense.
If the Secretary of State requests and the Secretary of Defense approves, U.S. forces can participate in
foreign internal defense. The request and approval may go through the standing statutory authorities in
Title 22, USC. Among other foreign relations programs, Title 22 contains the Foreign Assistance Act and
the Arms Export Control Act. Programs under Title 22 authorize security assistance, developmental
assistance, and other forms of aid. The request and approval might also occur under various provisions of
Title 10, as well. Title 10 authorizes certain types of military-to-military contacts, exchanges, exercises, and
limited forms of humanitarian and civic assistance in coordination with the U.S. ambassador for the host
nation. In such situations, U.S. military personnel ordinarily work as administrative and technical personnel
of the embassy. They are part of the U.S. diplomatic mission, pursuant to a status of forces agreement, or
pursuant to an exchange of notes. This cooperation and assistance is limited to liaison, contacts, training,
equipping, and providing defense articles and services. It does not include direct involvement in operations.
GENERAL PROHIBITION ON ASSISTANCE TO POLICE
13-5. The Foreign Assistance Act specifically prohibits assistance to foreign police forces except within
carefully circumscribed exceptions. The lead role in providing police assistance within those exceptions
normally has been delegated to the Department of State's Bureau of International Narcotics and Law
Enforcement Affairs. U.S. commanders are not able to train foreign law enforcement personnel unless
given specific legal authority. That said, Congress granted DOD the authority to train the police forces of
Iraq and Afghanistan. Moreover, Congress has provided limited authority for U.S. forces to train foreign
law enforcement personnel in counternarcotics and counter narco-terrorism operations

Chapter 13
13-2 FM 3-24/MCWP 3-33.5 13 May 2014
RULES OF ENGAGEMENT
13-6. Rules of engagement are directives issued by competent military authority that delineate the
circumstances and limitations under which United States forces will initiate and/or continue combat
engagement with other forces encountered (JP 1-04). Often these directives are specific to an operation.
Absent operation-specific rules of engagement, U.S. forces apply the standing rules of engagement. When
working with a multinational force, commanders must thoroughly coordinate the rules of engagement.
MISSION-SPECIFIC RULES OF ENGAGEMENT
13-7. The standing rules of engagement provide a mechanism for combatant commanders to develop
mission-specific rules of engagement by implementing supplemental measures within their discretion, or by
submitting a request for supplemental measures to the Secretary of Defense for approval. These
mission-specific rules of engagement are then passed down the chain of command in the form of a rules of
engagement execute order, fragmentary order, or other formal operational tasking. The combatant
commander and subordinate commanders must follow these mission-specific rules of engagement.
Combatant commanders may augment the rules of engagement as necessary by implementing supplemental
measures within their authority to approve. Both combatant commanders and subordinate commanders are
required to notify the Secretary of Defense of any restrictions placed on the Secretary of Defense-approved
mission-specific rules of engagement. Commanders at all levels are required to evaluate the rules of
engagement and request changes if they determine the rules of engagement are inadequate for the mission.
13-8. Taken as a whole, the rules of engagement regulate the conduct of U.S. forces for the application of
force for mission accomplishment and the exercise of self-defense. For instance, for mission
accomplishment, U.S. forces may be authorized to engage enemy forces declared hostile anywhere in the
area of operations at anytime without the need to observe a hostile act or demonstrated hostile intent. With
respect to self-defense, unit commanders always retain the inherent right and obligation to exercise unit
self-defense in response to a hostile act or demonstrated hostile intent. U.S. forces may exercise individual
self-defense in response to a hostile act or demonstrated hostile intent; however, unit commanders may
limit individual self-defense by members of their unit. The rules of engagement in counterinsurgency
operations change from time to time. To meet the ever-changing operational environment, supplemental
measures and the level of force commanders employ from day to day may change often. Commanders must
regularly review the rules of engagement for their effectiveness in a complex counterinsurgency
environment. Counterinsurgency leaders should frequently train their Soldiers and Marines in the
application of the rules of engagement to the situations they may encounter in the area of operations so
their actions become instinctive, effective, and legally sound.
MULTINATIONAL RULES OF ENGAGEMENT
13-9. U.S. forces assigned to the operational or tactical control of a multinational force follow the rules of
engagement of the multinational force for mission accomplishment, if authorized by the Secretary of
Defense. U.S. forces retain the right of self-defense. Apparent inconsistencies between the right of
self-defense contained in U.S. rules of engagement and the rules of engagement of the multinational force
will be submitted through the U.S. chain of command for resolution. While final resolution is pending, U.S.
forces will continue to operate under the U.S. rules of engagement. When U.S. forces, under U.S.
operational or tactical control, operate with a multinational force, reasonable efforts are made to develop
combined or common rules of engagement. If common rules of engagement cannot be developed, U.S.
forces operate under U.S. rules of engagement. The multinational forces will be informed prior to U.S.
participation in the operation that U.S. forces intend to operate under U.S. rules of engagement. U.S. forces
remain bound by international agreements to which the U.S. is a party even though other multinational
force members may not be bound by them. The U.S. does not interpret any international agreements, such
as status-of-forces agreements, to limit U.S. forces’ right of self-defense.
LAW OF WAR
13-10. Counterinsurgency operations may occur in both an international armed conflict (state versus state)
and a non-international armed conflict (state versus armed nonstate actor). Situations can occur, such as

Legal Considerations
13 May 2014 FM 3-24/MCWP 3-33.5 13-3
during occupation, where armed forces are engaged in combat with armed nonstate actors, or other persons
who are not part of a state’s armed forces. Any hostilities between state and non-state actors may rise to the
level of a non-international armed conflict. A non-international armed conflict may exist in the same area
of operations as an ongoing international armed conflict. An armed conflict exists whenever there is a
resort to armed force between states (in an international armed conflict) or protracted armed violence
between governmental authorities and organized armed groups or between such groups within a state (in a
non-international armed conflict). Regardless of the context, U.S. forces obey the law of war. The U.S. is
bound by the law of war treaties to which it is a party, as well as binding norms of customary international
law.
13-11. The law of war is the branch of international law applicable to the conduct of armed conflict and
concerns the rights and relationships among the participants and victims of armed conflicts. It is often
called the law of armed conflict or international humanitarian law. The law of war generally regulates the
use of force to the amount necessary to achieve the aim of the conflict and spares those who do not or no
longer directly participate in hostilities. The purposes of adhering to the law of war include—
- Ensuring good order and discipline.
- Fighting in a disciplined manner consistent with U.S. national values.
- Maintaining domestic, international, and local support.
- Protecting combatants, noncombatants, and civilians from unnecessary suffering.
- Safeguarding persons who fall into the hands of an enemy.
- Facilitating the restoration of peace.
13-12. The primary sources of the law of war include the various Hague Conventions, the four Geneva
Conventions of 1949, the 1980 UN Conventional Weapons Convention and its five protocols, and
customary international law. Many nations that have been recent coalition partners with the U.S. are also
parties to two additional 1977 protocols to the Geneva Conventions, Additional Protocol I and Additional
Protocol II. However, the U.S. is not a party to these two protocols. Without recognizing the authority of
these two protocols, the U.S. recognizes that many of their provisions, some of which are discussed in this
manual, are either an accurate statement of the law or consistent with U.S. practice.
13-13. The law of war is based on the following fundamental principles:
- First, military necessity, that is, that a belligerent is justified in applying those measures not
forbidden by international law which are indispensable for securing the complete submission of
the enemy as soon as possible.
- Second, humanity, which requires military forces to avoid inflicting gratuitous violence on the
enemy.
- Third, discrimination, which posits that military attacks should be directed at combatants and
other military targets, not civilians or civilian property.
- Fourth, proportionality, expressed in the concept that the expected incidental loss of civilian life,
injury to civilians, and damage to civilian objects must not be excessive in relation to the
concrete and direct military advantage anticipated.
MILITARY NECESSITY
13-14. The principle of military necessity is expressed in Article 23(g), of Hague IV Annex., which
forbids a belligerent to destroy or seize the enemy’s property, unless such destruction or seizure be
imperatively demanded by the necessities of war. While no law of war treaty defines military necessity, its
role is recognized in many treaties to which the U.S. is a state party. Moreover, the U.S. has defined
military necessity in its law of war manuals. Military necessity is that principle which justifies those
measures not forbidden by international law which are indispensable for securing the complete submission
of the enemy as soon as possible. (See FM 27-10 for more information on military necessity.)
13-15. Military necessity does not authorize all military action and destruction. Under no circumstances
may military necessity authorize actions specifically prohibited by the law of war, such as the murder of
prisoners of war, ill-treatment of prisoners of war or internees, the taking of hostages, or the execution of a
reprisal against a person or object specifically protected from reprisal. Civilian objects are generally

Chapter 13
13-4 FM 3-24/MCWP 3-33.5 13 May 2014
protected from intentional attack or destruction. However, civilian objects may lose their protections if they
are being used for military purposes, or there is a military necessity for their destruction or seizure. Civilian
objects may, in such circumstances, become military objectives, and if so, the law of war permits their
destruction. In treaties such as Hague IV and its annex and the Geneva Conventions, where an express
prohibition has been stated, neither military necessity nor any other rationale of necessity may override that
prohibition. In short, the principle of military necessity authorizes that use of force that is required to
accomplish the mission, but it does not authorize acts otherwise prohibited by the law of war. This principle
must be applied in conjunction with other law of war principles as well as other, more specific legal
constraints set forth in law of war treaties to which the U.S. is a party.
HUMANITY, UNNECESSARY SUFFERING, OR SUPERFLUOUS INJURY
13-16. The right of belligerents to adopt means of injuring the enemy is not unlimited, as Hague IV
Annex, Article 22, states. Article 23(e) then captures the essence of the Law of War principle of humanity
as it prohibits the employment of arms, projectiles, or material calculated to cause unnecessary suffering.
The principle of humanity is also called the principle of unnecessary suffering or superfluous injury. The
terms unnecessary suffering and superfluous injury are regarded as synonymous. Although neither of the
terms is defined, they are understood to refer to injury to persons, rather than damage to objects. The
prohibition of unnecessary suffering constitutes acknowledgement that the suffering of combatants is
lawful and expected, and may include severe injury or loss of life. As a general proposition, the suffering
inflicted by weapons or munitions would be deemed unnecessary only if—
- Its use was calculated to cause unnecessary suffering.
- The inevitable result of the normal use causes an injury the nature of which is considered by
governments as manifestly disproportionate in relation to the military advantage anticipated
from employment of the weapons or munitions.
13-17. Weapons’ or munitions’ effects must be weighed in light of comparable lawful weapons and
munitions in use on the modern battlefield. A weapon cannot be declared unlawful merely because it may
cause severe suffering or injury. The appropriate determination is whether a weapon’s or munitions’
employment for its normal or expected use would be prohibited under some or all circumstances. The
correct criterion is whether the employment of a weapon for its normal or expected use inevitably would
cause injury or suffering manifestly disproportionate to its military effectiveness. A state is not required to
foresee or anticipate all possible uses or misuses of a weapon or munitions, since almost any weapon or
munition can be misused in ways that might be prohibited.
13-18. Under the law of war, combatants may kill or wound enemy combatants and civilians taking a
direct part in hostilities; such acts are legitimate if accomplished with lawful means and methods. For
example, the prohibition of unnecessary suffering does not limit the bringing of overwhelming firepower
on an opposing military force in order to subdue or destroy it. What the law of war does prohibit is the
design, modification, or employment of a weapon or munitions for the purpose of increasing or causing
suffering beyond that required by military necessity.
DISCRIMINATION
13-19. The principle of discrimination, sometimes referred to as the principle of distinction, is the
international law obligation of parties to a conflict to distinguish between the civilian population (or
individual civilians not taking a direct part in the hostilities) and combatant forces when engaged in
military operations, directing the application of force solely against personnel belonging to the latter.
Similarly, military force may be directed only against military objects or objectives, and not against civilian
objects. A military objective is not limited to military bases, forces, or equipment, but includes other
objects that contribute to an opposing state’s ability to wage war. Additionally, a civilian object is immune
from intentional attack unless and until it loses its protected status through enemy abuse of that status. The
principle of discrimination also provides civilians immunity from direct attack for as long as they take no
part in hostile acts against military forces.
13-20. The principle of discrimination applies to military forces engaged in offensive or defensive
operations, and to governments providing protection for their civilian population and civilian objects. Each

Legal Considerations
13 May 2014 FM 3-24/MCWP 3-33.5 13-5
government and its military forces, as well as armed nonstate parties to a conflict, are obligated to separate
their military or other fighting forces and military objects from the civilian population and civilian objects,
to take steps to protect the civilian population (or civilians within its control) through affirmative steps such
as evacuation from the vicinity of military operations or air raid precautions, and to minimize or avoid
actions that might otherwise place the civilian population at risk from lawful military operations by the
opposing force. The employment of voluntary or involuntary human shields to protect military objectives,
individual military units, or military personnel is a violation of the law of war principle of discrimination.
13-21. Physical damage or destruction of property is an inevitable and lawful aspect of combat. Military
equipment (other than military medical equipment and transportation) is subject to lawful attack and
destruction at all times. Civilian objects, including cultural property, are protected from seizure or
intentional attack unless there is military necessity for their seizure or destruction, that is, they become
military objectives. Destruction of civilian objects that is expressly prohibited, or that is not justified by
military necessity, or that is wanton or excessive, is unnecessary destruction for which a commander may
be culpable.
13-22. The civilian population and individual civilians not taking a direct part in hostilities are protected
from intentional attack. Where civilians are present on the battlefield or in proximity to legitimate military
objectives, or they are being used to shield legitimate targets from an attack that otherwise would be lawful,
they are at risk of injury incidental to the lawful conduct of military operations. A law of war violation
occurs when—
- The civilian population is attacked intentionally.
- Civilian casualties incidental to an otherwise lawful attack become excessive in relation to the
concrete and direct military advantage to be gained and are attributed to the wanton conduct of
an attacking force, for which the defending force or individual civilians or groups of civilians
(such as voluntary human shields) bear no responsibility.
- A defender or attacker employs civilians as voluntary or involuntary human shields. Each of
these acts constitutes a violation of the principle of discrimination.
13-23. The law of war does not expressly prohibit civilians from taking a direct part in hostilities. If they
do, however, they may be targeted for so long as they take a direct part. Civilians do not enjoy the
combatant’s privilege—that is, they do not have combatant immunity—and if captured, they may be
prosecuted for their belligerent acts under the domestic law of the captor. Civilians engaging in belligerent
acts not only forfeit their immunity from direct attack; they also make it more difficult for military
personnel to apply the principle of discrimination and, thereby, put all civilians at risk. There is no
definition of direct part in hostilities in treaty law or customary international law. At a minimum, it
encompasses actions that are belligerent per se, that is, by their very nature and purpose can be expected to
cause actual harm to an enemy. In general, the qualification of an act as direct participation in hostilities is
a fact-dependent analysis that must be made after analyzing all relevant available facts, in the
circumstances prevailing at the time.
13-24. Within an international armed conflict or a non-international armed conflict, the armed forces of a
state may engage in hostilities with armed nonstate actors. This is the classic counterinsurgency
environment. While most international armed conflict involves warfare between the armed forces of two or
more states, situations can occur, such as during occupation, where such armed forces and other armed
security forces of the state (including police forces) are engaged in combat with armed nonstate actors, or
other persons who are not part of a state armed force. These groups can take a variety of forms, including
an organized resistance movement that belongs to a state party but fails to meet the requirements for
prisoner of war status under the Geneva Convention Relative to the Treatment of Prisoners of War Article
4A (2), or a terrorist organization such as al Qaeda that, without regard to compliance with any of the other
requirements of Article 4A(2) (such as being under responsible command, wears fixed distinctive sign
recognizable at a distance, carries arms openly, and conducts operations in compliance with the law of
war), operates without any authorization or affiliation with a state and thereby falls outside of the Geneva
Convention’s protections. An individual who is formally or functionally part of an organized armed group
that is engaged in hostilities may be targeted at any time. In essence, membership in armed forces or armed
groups (such as the status of belonging to such a group) and direct participation in hostilities (such as a
conduct-based standard) are separate bases for targeting under the law of war.

Chapter 13
13-6 FM 3-24/MCWP 3-33.5 13 May 2014
13-25. U.S. practice is that the designation of an armed nonstate group as hostile (as such targetable at all
times) and its members as direct participants in hostilities, should only be made by an official authorized to
do so. Without such a designation, the determination of whether a civilian may be targeted depends on
whether that civilian is committing specific acts that amount to hostile acts or demonstrations of hostile
intent, in accordance with the standing rules of engagement. In addition, individual conflicts may involve
specific rules of engagement that incorporate direct participation in hostilities analysis.
PROPORTIONALITY
13-26. Proportionality requires that the anticipated loss of life and damage to property incidental to
attacks must not be excessive in relation to the concrete and direct military advantage expected to be
gained. Proportionality is process-oriented rather than result-oriented. Decisionmakers are expected to take
all feasible precautions in planning military operations, but they remain dependent on the (often imperfect
and incomplete) information available at the time to weigh the risk these operations may pose to the
civilian population. In this context, proportionality may be viewed as a fulcrum upon which military forces
and commanders must weigh the legitimate destructive effect of an attack (the law of war principle of
military necessity) against the undesirable incidental effects of an attack (such as the risk of death or injury
to civilians not taking a direct part in hostilities). Proportionality may be applied by decisionmakers at the
national, strategic, operational, or tactical level.
13-27. Proportionality does not prohibit destruction for which there is military necessity, or limit the
degree of engagement of enemy military forces in the absence of civilians or civilian objects. In particular,
it does not prohibit bringing overwhelming firepower to bear on an opposing military force to subdue or
destroy it. Nor does it prohibit injury to civilians that is incidental to lawful military operations. As used in
this context, proportionality constitutes an acknowledgment of the unfortunate inevitability—but
lawfulness—of incidental injury to civilians not taking a direct part in hostilities, or of the incidental
damage or destruction of civilian objects, despite precautions, in the execution of legitimate military
operations, particularly when these persons or objects have been intermingled with military forces or
objectives.
13-28. Proportionality is weighed by a commander in determining whether, in engaging in offensive or
defensive operations, that commander’s actions may be expected to cause incidental loss of civilian life,
injury to civilians, damage to civilian objects, or a combination thereof, that would be excessive in relation
to the concrete and direct military advantage anticipated by those actions. The military advantage
anticipated is intended to refer to the advantage anticipated from those actions considered as a whole, and
not only from isolated or particular parts thereof. Generally, military advantage is not restricted to tactical
gains, but is linked to the full context of a war strategy.
HONOR
13-29. Honor has long been a basis of warrior ethos and of the law of war. Honor demands a certain
mutual respect and trust between opposing forces. It denounces and forbids resort to dishonorable means,
expedients, or conduct that would constitute a breach of trust. An example of this form of honor is the use
of a white flag, which in land warfare represents a flag of truce. Its display is predicated upon good faith.
Its misuse is prohibited and constitutes a war crime. Another example of how honor applies comes from
law of war requirements regarding the treatment of persons hors de combat—that is, military personnel
who are no longer able to fight due to sickness, injury, or wounds, or because they are shipwrecked. The
principle of honor (and other humanitarian considerations) requires that an individual who is hors de
combat be treated and protected in the same manner as one would wish to be treated and protected by the
enemy if the roles were reversed. However, this principle is not dependent upon reciprocity.
THE SOLDIER’S AND MARINE’S BASIC RULES
13-30. It is DOD policy that members of DOD components comply with the law of war during all armed
conflicts, however such conflicts are characterized (such as international armed conflict or
non-international armed conflict), and in all other military operations. The law of war principles discussed
in paragraphs 13-13 through 13-29 can be safely applied by Soldiers and Marines by adhering to the
following ten basic rules:

Legal Considerations
13 May 2014 FM 3-24/MCWP 3-33.5 13-7
- Soldiers and Marines fight only enemy combatants.
- Soldiers and Marines do not harm enemies who surrender. They disarm them and turn them over
to their superiors.
- Soldiers and Marines do not kill or torture enemy prisoners of war or detainees.
- Soldiers and Marines collect and care for the wounded, whether friend or foe.
- Soldiers and Marines do not attack medical personnel, facilities, or equipment.
- Soldiers and Marines destroy no more than the mission requires.
- Soldiers and Marines treat all civilians humanely.
- Soldiers and Marines do not steal. They respect private property and possessions.
- Soldiers and Marines do their best to prevent violations of the law of war.
- Soldiers and Marines report all violations of the law of war to their superior.
13-31. When working with host-nation or local friendly forces in a counterinsurgency, it is critical to both
teach and enforce these rules among allies and friendly forces. Following the law of war is a critical
component of counterinsurgency operations that directly supports the accomplishment of the strategic
mission to defeat the insurgency and establish local rule by gaining the trust of the local civilian population,
or at a minimum, enabling a local population to cease active support of an insurgency. Violations of the law
of war have a direct and significant negative impact on the ability to conduct successful counterinsurgency
operations.
13-32. The law of war includes rules governing situations in which the military forces of one state occupy
the territory of another. Occupation is not a transfer of sovereignty. It does, however, grant the occupying
power the authority and responsibility to restore and maintain public order and safety. The occupying
power must enforce, as much as possible, the laws in force in the host nation. One of the four Geneva
Conventions of 1949—the Geneva Convention Relative to the Protection of Civilian Persons in Time of
War—becomes a prominent source of law during occupation, as well as the Hague Convention IV
Regulations of 1907.
NON-INTERNATIONAL ARMED CONFLICT
13-33. The full body of the law of war only applies during international armed conflict. It does not apply
during a non-international armed conflict. This does not mean no rules apply during a non-international
armed conflict. For instance, the law of war principle of distinction still applies. It requires force to be
directed at combatants and not innocent civilians, and a proportionality analysis is required when targeting
combatants and military objectives if civilians or civilian objects may be impacted. Counterinsurgency
operations are almost certain to be a feature of non-international armed conflict, the most common form of
armed conflict today. During counterinsurgency operations, Common Article 3 of the Geneva Conventions
applies. Commanders must be aware of Common Article 3, and the basic protections that must be afforded
to insurgents or others captured by U.S. forces, as well as the status of insurgents under the laws of the host
nation.
GENEVA CONVENTION, COMMON ARTICLE 3
13-34. Although insurgencies can occur within the context of an international armed conflict, they are
classically conflicts between states and non-state actors that are considered to be non-international armed
conflicts.
13-35. It bears emphasis, however, that one article contained in all four of the Geneva Conventions—
Common Article 3—is specifically intended to apply to non-international armed conflicts. Common Article
3 affords significantly fewer protections to combatants fighting in a non-international armed conflict than
does the full body of the law of war in an applicable international armed conflict. However, it does set a
simple baseline of humane protection, along with fundamental rules that reflect the principles captured in
the broader law of war.
13-36. Common Article 3 requires that in the case of armed conflict not of an international character (a
non-international armed conflict) occurring in the territory of one of the high contracting parties to the

Chapter 13
13-8 FM 3-24/MCWP 3-33.5 13 May 2014
Geneva Conventions, each party to the conflict shall be bound to apply, as a minimum, to six provisions of
Common Article 3. (See figure 13-1 for a list of these provisions.)
(1) Persons taking no active part in the hostilities, to include members of armed forces
who have laid down their arms and those placed hors de combat by sickness, wounds,
detention, or any other cause, shall in all circumstances be treated humanely, without any
adverse distinction founded on race, color, religion or faith, sex, birth or wealth, or any other
similar criteria.
(2) To this end, the following acts are and shall remain prohibited at any time and in any
place whatsoever with respect to the above-mentioned persons:
(a) Violence to life and person, in particular murder of all kinds, mutilation, cruel treatment
and torture;
(b) Taking of hostages;
(c) Outrages upon personal dignity, in particular humiliating and degrading treatment;
(d) The passing of sentences and the carrying out of executions without previous
judgment pronounced by a regularly constituted court, affording all the judicial guarantees
which are recognized as indispensable by civilized peoples.
(3) The wounded and sick shall be collected and cared for.
(4) An impartial humanitarian body, such as the International Committee of the Red Cross,
may offer its services to the Parties to the conflict.
(5) The Parties to the conflict should further endeavor to bring into force, by means of
special agreements, all or part of the other provisions of the present Convention.
(6) The application of the preceding provisions shall not affect the legal status of the
Parties to the conflict.
Figure 13-1. Provisions binding high contracting parties
APPLICATION OF CRIMINAL LAWS OF A HOST NATION
13-37. There is no concept of prisoner-of-war status in non-international armed conflict, as reflected in
Common Article 3. Insurgents may be prosecuted by a host nation as criminals for offenses related to
participation in hostilities, such as bearing arms against government forces. Similarly, U.S. forces captured
by insurgents are not prisoners of war, but must be treated in accordance with Common Article 3. U.S.
forces conducting counterinsurgency operations should remember that the insurgents are, as a legal matter,
criminal suspects within the legal system of a host nation. To support criminal prosecution of insurgents,
counterinsurgents must develop and implement procedures to carefully preserve weapons, witness
statements, photographs, and other evidence collected at a scene. This evidence is used to process the
insurgents into a host-nation legal system and hold them accountable for their crimes, thus promoting the
rule of law.
13-38. U.S. personnel may be subject to host-nation law, depending on the terms of any existing status of
forces agreement between a host nation and the U.S. Status of forces agreements establish the legal status
of military personnel in foreign countries and generally provide the U.S. military some level of protection
from host-nation criminal jurisdiction. In the absence of an agreement or some other arrangement with the
host nation, DOD personnel in foreign countries may be subject to the criminal law of that host nation.
DETENTION AND INTERROGATION
13-39. Human intelligence is essential in counterinsurgency operations. Acquiring human intelligence
requires interrogation. The need for intelligence within a counterinsurgency, especially in conjunction with
a third country or host-nation capture and detention scenario, can create great pressure to obtain
time-sensitive information from detained individuals and suspected insurgents. Soldiers and Marines
adhere to only approved detainee handling methods and interrogation techniques. In addition to complying
with the law of war, U.S. forces must comply with domestic legal authorities such as the Detainee
Legal Considerations
13 May 2014 FM 3-24/MCWP 3-33.5 13-9
Treatment Act of 2005, DODD 3115.09, FM 2-22.3, and other specific standards that guide U.S. forces
working with detainees.
DETAINEE TREATMENT ACT OF 2005
13-40. U.S. law prohibits U.S. forces, including officials from other government agencies, from using
certain methods to obtain information. In response to documented instances of detainee abuse, to include
maltreatment involving interrogation, Congress passed, and the President signed into law, the Detainee
Treatment Act of 2005. (See table 13-1 for an extract of the Detainee Treatment Act of 2005.)
Table 13-1. Extract of the Detainee Treatment Act of 2005
Section 1002: Uniform Standards for the Interrogation of Persons Under the Detention of
the Department of Defense
(a) In General.—No person in the custody or under the effective control of the Department of
Defense or under detention in a Department of Defense facility shall be subject to any
treatment or technique of interrogation not authorized by and listed in the United States Army
Field Manuel on Intelligence Interrogation [FM 2-22.3].
(b) Applicability—Subsection (a) shall not apply with respect to any person in the custody or
under the effective control of the Department of Defense pursuant to a criminal law or
immigration law of the United States.
(c) Construction.—Nothing in this section shall be construed to affect the rights under the
United States Constitution of any person in the custody or under the physical jurisdiction of the
United States.
Section 1003: Prohibition on Cruel, Inhuman, or Degrading Treatment or Punishment of
Persons Under Custody or Control of the United States Government
(a) In General—No individual in custody or under the physical control of the United States Government,
regardless of nationality or physical location, shall be subject to cruel, inhuman or degrading treatment
or punishment.
(b) Construction—Nothing in this section shall be construed to impose any geographical limitation on
the applicability of the prohibition against cruel, inhuman, or degrading treatment or punishment under
this section.
(c) Limitation on Supersedure.—The provision of this section shall not be superseded, except by a
provision of law enacted after the date of the enactment of this Act which specifically repeals, modifies,
or supersedes the provisions of this section.
(d) Cruel, Inhuman, or Degrading Treatment or Punishment defined.—In this section, the term “cruel,
inhuman, or degrading treatment or punishment” means the cruel, unusual, and inhumane treatment or
punishment prohibited by the Fifth, Eighth, and Fourteenth Amendments to the Constitution of the
United States, as defined in the United States Reservations, Declarations and Understandings to the
United Nations Convention Against Torture and Other Forms of Cruel, Inhuman, or Degrading
Treatment or Punishment done at New York, December 10, 1984.
INTERROGATION FIELD MANUAL
13-41. The Detainee Treatment Act established FM 2-22.3 as the legal standard for interrogations. U.S.
forces may not use any interrogation technique other than those prescribed by FM 2-22.3. Commanders
ensure that interrogators receive proper training and supervision. Executive Order 13491 extends this
requirement to all U.S. government agencies.
STANDARDS FOR DETENTION AND INTERNMENT
13-42. Regardless of the precise legal status of those persons captured, detained, or otherwise held in
custody by U.S. forces, they must receive humane treatment until properly released to host-nation
authorities, who then assume legal responsibility. They must be provided the minimum protections of
Common Article 3 to the Geneva Conventions. Specially trained, organized, and equipped military police
units in adequately designed and resourced facilities should accomplish prolonged detention. Such

Chapter 13
13-10 FM 3-24/MCWP 3-33.5 13 May 2014
detention must follow the detailed standards contained in Army Regulation 190-8/Marine Corps Order
3461.1. Military police operating such facilities shall not be used to assist in or set the conditions for
interrogation.
TRANSFER OF DETAINEES TO THE HOST NATION
13-43. There are certain conditions under which U.S. forces may not transfer the custody of detainees to
the host nation or any other foreign government. U.S. forces retain custody if they have substantial grounds
to believe that the detainees would be in danger in the custody of others. Such danger could include being
subjected to torture or inhumane treatment. (See DODD 2310.01E for more information on transferring
detainees and consult the legal advisor or staff judge advocate.)
ENFORCING DISCIPLINE OF U.S. FORCES
13-44. Despite rigorous selection and training, some personnel will commit infractions requiring
discipline. The Uniform Code of Military Justice is the criminal code applicable to all U.S. military
members and, in time of declared war or contingency operations, other persons serving with or
accompanying U.S. armed forces in the field. Commanders and general officers are responsible for their
subordinates and their behavior. Commanders must give clear guidance and ensure compliance. All
civilians, including contractors, working in support of operations of the U.S. forces overseas must comply
with the law of war.
UNIFORM CODE OF MILITARY JUSTICE
13-45. Although most well-led and well-trained U.S. military personnel perform their duties honorably
and lawfully, some will commit various crimes, including violations of the law of war. U.S. military
personnel remain subject at all times to the Uniform Code of Military Justice. Suspected criminal behavior
must be investigated and, where appropriate, remedied by corrective action. This includes violations of
orders, maltreatment of detainees, assaults, thefts, sexual offenses, destruction of property, and other
crimes, to include homicides, which may be committed during a counterinsurgency. All reportable
incidents committed by or against U.S. personnel, enemy persons, or any other individual must be reported
promptly, investigated thoroughly, and, where appropriate, remedied by corrective action. A reportable
incident is a possible, suspected, or alleged violation of the law of war, for which there is credible
information, or conduct during any operation in the range of military operations that would constitute a
violation of the law of war if it occurred during an armed conflict.
COMMAND RESPONSIBILITY
13-46. In some cases, military commanders may be deemed responsible for crimes committed by
subordinates or others subject to their control. This situation arises when the criminal acts are committed
pursuant to the commander’s order. A commander is legally responsible for a war crime committed by that
commander’s subordinates if that commander knew, or should have known, that the subordinates were
about to commit the violation and the commander did nothing to prevent it or that the subordinates had
committed the violation and the commander failed to address the violation. Commanders must know that
under international law, commanders are responsible if they know, or should have known, their
subordinates are about to commit or have committed a violation of the law of war. In a counterinsurgency
environment, where compliance with the law of war is critical to the success of the mission, commanders
should expect to be held accountable for failing to report and investigate reportable incidents. Commanders
may not ignore credible information that indicates U.S. forces may have committed, intend to commit, or
are in the process of committing violations of the law of war. In addition, commanders must pay close
attention to the command climate within their units. Commanders must foster a climate through leadership
and training that helps Soldiers and Marines understand the critical need to abide by the law of war, in
particular, to distinguish between civilians and insurgents, to refrain from unnecessarily harming civilians,
and to treat detainees in accordance with all applicable laws, policies, and regulations.

Legal Considerations
13 May 2014 FM 3-24/MCWP 3-33.5 13-11
GENERAL ORDERS
13-47. Orders issued by general officers in command during counterinsurgency will include provisions,
such as a prohibition against drinking alcohol or against entering host-nation places of religious worship,
important to maintaining discipline of the force. These types of orders safeguard the image of U.S. forces
and promote the legitimacy of a host-nation government. These types of orders are readily enforceable
under the Uniform Code of Military Justice.
CIVILIAN PERSONNEL AND CONTRACTORS
13-48. Modern counterinsurgency operations involve many DOD civilians as well as civilian personnel
employed by government contractors. These civilians may be made subject to general orders. They are
subject to U.S. laws and to the laws of the host nation. These civilians may be prosecuted or receive
adverse administrative action by the U.S. or contract employers. Article 2(a)(10) of the Uniform Code of
Military Justice provides court-martial jurisdiction over persons serving with or accompanying an armed
force in the field during a time of declared war or a contingency operation. Under this authority,
commanders have Uniform Code of Military Justice authority to disarm, apprehend, and detain DOD
civilians and contractors suspected of having committed a felony offense in violation of the rules for the
use of force, or outside the scope of their authorized mission, and to conduct the basic Uniform Code of
Military Justice pretrial process and trial procedures currently applicable to courts-martial of military
service members. Before bringing a DOD civilian or contractor to a court-martial, however, the Department
of Justice must have the opportunity to review and determine whether it will pursue the matter pursuant to
the Military Extraterritorial Jurisdiction Act. This act extends federal criminal jurisdiction over felony
offenses committed by DOD civilians, contractor personnel, and others while employed by or accompany
the armed forces overseas. The Military Extraterritorial Jurisdiction Act is implemented within the DOD by
DODI 5525.11. Third country nationals employed by U.S. forces are covered under the Military
Extraterritorial Jurisdiction Act, but host-nation personnel are not.
TRAINING AND EQUIPPING FOREIGN FORCES
13-49. Foreign forces need training and equipment to be effective. U.S. laws require Congress to
authorize such expenditures. U.S. laws require the Department of State to verify that the host nation
receiving the assistance has not engaged in a consistent pattern of gross violations of internationally
recognized human rights. All training and equipping of foreign security forces must be specifically
authorized. Usually, DOD involvement is limited to a precise level of man-hours and materiel requested
from the Department of State under the Foreign Assistance Act or Arms Export Control Act. The President
may authorize deployed U.S. forces to train or advise host-nation security forces as part of an operational
mission. In this case, DOD personnel and operation and maintenance appropriations provide an incidental
benefit to those security forces. All other weapons, training, equipment, logistic support, supplies, and
services provided to foreign forces must be paid for with funds appropriated by Congress for that purpose.
Examples include the Iraq Security Forces Fund and the Afghan Security Forces Fund appropriations.
Moreover, the President must give specific authority to DOD for its role in such training and equipping
efforts.
13-50. In counterinsurgency, like all operations, commands require specific authority to expend funds.
That authority is normally found in the National Defense Authorization Act (NDAA), specifically,
operation and maintenance funds. In recent counterinsurgency operations, Congress appropriated additional
funds to commanders for the specific purpose of dealing with counterinsurgency. Recent examples include
the Commanders’ Emergency Response Program, Global Train and Equip Program, and the Global
Security Contingency Fund.
DOD FUNDS GENERALLY NOT EXPENDABLE BY COMMANDERS FOR THIS PURPOSE
13-51. Congress specifically appropriates funds for foreign assistance. The United States Agency for
International Development expends such funds under the legal authorities in Title 22. Provisions of Title 22
authorize small amounts of money. These funds are appropriated annually for commanders to provide
humanitarian relief, disaster relief, or civic assistance in conjunction with military operations. These

Chapter 13
13-12 FM 3-24/MCWP 3-33.5 13 May 2014
standing authorities are narrowly defined and generally require significant advance coordination within the
DOD and the Department of State. As such, they are of limited value to ongoing counterinsurgency
operations.
COMMANDER’S EMERGENCY RESPONSE PROGRAM
13-52. The Commanders’ Emergency Response Program is a statutory authorization to obligate funds
from the DOD operation and maintenance appropriation for the primary purpose of authorizing U.S.
military commanders to carry out small-scale projects designed to meet urgent humanitarian relief
requirements or urgent reconstruction requirements within their areas of responsibility that provide an
immediate and direct benefit to the people of Afghanistan. When authorized, Commanders’ Emergency
Response Program authority is found in annual NDAAs. Notably, the authority to use Commanders’
Emergency Response Program in Iraq was specifically repealed, eliminating the use of Commanders’
Emergency Response Program in Iraq. The Commanders’ Emergency Response Program is one of the most
important authorities commanders have in Afghanistan.
13-53. Some NDAAs include waiver authority for certain contracting requirements for the Commanders’
Emergency Response Program, enabling the use of streamlined contracting procedures. For example, one
NDAA provided that, “[f]or purposes of the exercise of the authority provided by this section or any other
provision of law making funding available for the [Commanders’ Emergency Response Program] ... the
Secretary may waive any provision of law not contained in this section that would (but for the waiver)
prohibit, restrict, limit, or otherwise constrain the exercise of that authority.” As a result, the Secretary of
Defense has periodically waived the Competition in Contracting Act requirements for Commanders’
Emergency Response Program-funded projects. Therefore, Commanders’ Emergency Response
Program-funded projects did not need to follow the competition requirements of the Federal Acquisition
Regulation.
13-54. In addition to being authorized for certain types of projects to assist the civilian population affected
by an insurgency, Commanders’ Emergency Response Program funds are often available for payment to
host-nation civilians in certain specified situations. For example, under the Commanders’ Emergency
Response Program for Afghanistan, appropriated funds may be used to repair property damage that results
from U.S., multinational, or supporting military operations that are not otherwise compensable under the
Foreign Claims Act. These funds can also be used for condolence payments to individual civilians for the
death or physical injury resulting from U.S., multinational, or supporting military operations that are not
compensable under the Foreign Claims Act. Such payments include payments to surviving spouse or kin of
defense or police personnel killed because of U.S., multinational, or supporting military operations. On the
other hand, Commanders’ Emergency Response Program for Afghanistan funds may not be used to pay
rewards or fund any type of weapon buy-back program. Instead, a provision in U.S. Code authorizes a
rewards problem.
GLOBAL TRAIN AND EQUIP OR BUILDING PARTNER CAPACITY
13-55. Other NDAA provisions have recently authorized DOD to build the capacity of foreign military
forces in support of overseas contingency operations. Current NDAA Train and Equip authority allows
DOD to build the capacity of a foreign country's national military forces in order for that country to—
- Conduct counterterrorist operations.
- Participate in or support military and stability operations in which the U.S forces are a
participant.
This authority includes building the capacity of maritime security forces conducting counterinsurgency
operations.
GLOBAL SECURITY CONTINGENCY FUND
13-56. Congress has used the NDAA to authorize the Global Security Contingency Fund, which provides
funds to the Secretary of State or Secretary of Defense to provide assistance to designated countries for the
purposes of enhancing the country’s national military forces, and other national security forces that conduct

Legal Considerations
13 May 2014 FM 3-24/MCWP 3-33.5 13-13
border and maritime security, internal defense, and counterterrorism operations. Funds provided may also
be used for the justice sector, including law enforcement and prisons, rule of law programs, and
stabilization efforts in a country in those cases in which the Secretary of State, in consultation with the
Secretary of Defense, determines that the conflict or instability in a country or region challenges the
existing capability of civilian providers to deliver such assistance. Funds come from both DOD operation
and maintenance appropriations and Department of State funds.
HUMAN RIGHTS VETTING
13-57. Congress typically limits when it funds training or equipment for foreign security forces under
provisions commonly known as the Leahy Amendment or Leahy vetting procedures. If the Department of
State has credible information that the foreign security force unit identified to receive the training or
equipment has engaged in a consistent pattern of gross violations of internationally recognized human
rights, Congress prohibits funding. Such prohibitions impose a requirement upon Department of State and
DOD. These departments must vet the proposed recipient units against a database of credible reports of
human rights violations.
CLAIMS AND SOLATIA
13-58. Under certain conditions, the U.S. government makes payments to host-nation civilians. The
Foreign Claims Act permits certain claims to be filed against the U.S. government. In some countries,
solatia payments are available.
FOREIGN CLAIMS ACT
13-59. Under the Foreign Claims Act, claims by host-nation civilians for property losses, injury, or death
caused by service members or the civilian component of the U.S. forces may be paid to promote and
maintain friendly relations with a host nation. Claims that result from noncombat activities or negligent or
wrongful acts or omissions are payable. Claims that are not payable under the Foreign Claims Act include
losses from combat, contractual matters, domestic obligations, and claims that are either not in the best
interest of the U.S. to pay or that are contrary to public policy. Because payment of claims requires
adjudication of the claim and because many claims prove, upon investigation, to be not payable, U.S. forces
must be careful not to raise expectations by promising payment.
SOLATIA
13-60. If U.S. forces are conducting counterinsurgency in a country where payments in sympathy or
recognition of loss are common, solatia payments to accident victims may be legally payable. Solatia
payments are not claims payments. They are payments in money or in kind to a victim or to a victim’s
family as an expression of sympathy or condolence. The payments are customarily made immediately and
generally are nominal. The individual or unit involved in the damage has no legal obligation to pay;
compensation is simply offered as an expression of remorse according to local custom. Solatia payments
should not be made without prior coordination with the combatant command.
ESTABLISHING THE RULE OF LAW
13-61. Establishing the rule of law is a key goal and end state in counterinsurgency. Defining that end
state requires extensive coordination between the instruments of U.S. power, a host nation, and
multinational partners. Attaining that end state is usually the mission of host-nation authorities,
international and intergovernmental organizations, the Department of State, and other U.S. government
agencies, with, in some cases, support from U.S. forces. Some key aspects of the rule of law include—

Chapter 13
13-14 FM 3-24/MCWP 3-33.5 13 May 2014
- A government that derives its powers from the governed and competently manages, coordinates,
and sustains collective security, as well as political, social, and economic development. This
includes national, regional, and local government.
- Sustainable security institutions. These include a civilian-controlled military as well as police,
court, and penal institutions, all of which should be perceived by the local population as fair,
just, and transparent.
- Fundamental human rights. The United Nations Declaration on Human Rights and the
International Convention for Civil and Political Rights provide a guide for applicable human
rights. However, the latter provides for derogation from certain rights during an officially
proclaimed state of public emergency that threatens the life of the nation. Respect for the full
panoply of human rights should be the goal of a host nation; derogation and violation of these
rights by host-nation security forces, in particular, often provides an excuse for insurgent
activities.
13-62. In times of extreme unrest and insurgency, host-nation legal structures—courts, prosecutors,
defense assistance, and prisons—may cease to exist or function. Under these conditions, counterinsurgents
may need to undertake a significant role in the reconstruction of the host-nation judicial system to establish
legal procedures and systems to deal with captured insurgents and common criminals. During judicial
reconstruction, counterinsurgents can expect to be involved in providing sustainment and security support.
They can expect to provide legal support and consultation to the host-nation judicial entities. Even when
judicial functions are restored, counterinsurgents may still have to provide logistic and security support to
judicial activities for a prolonged period. This support continues as long as insurgents continue to disrupt
activities that support the legitimate rule of law.
13-63. Rule of law is a principle under which all persons, institutions, and entities, public and private,
including the state itself, are accountable to laws that are publicly promulgated, equally enforced, and
independently adjudicated, and that are consistent with international human rights principles. In assessing
rule of law, counterinsurgency planners should consider the end state for which the host nation should
strive. While the form of the rule of law among different states may differ markedly, the effects should be
similar. Some effects from the application of rule of law include the following:
- The state monopolizes the use of force in the resolution of disputes.
- Individuals are secure in their persons and property.
- The state is itself bound by law and does not act arbitrarily.
- The law can be readily determined and is stable enough to allow individuals to plan their affairs.
- Individuals have meaningful access to an effective and impartial legal system.
- The state protects basic human rights and fundamental freedoms.
- Individuals rely on the existence of justice institutions and the content of law in the conduct of
their daily lives.
13-64. While no nation achieves these effects entirely, counterinsurgent efforts should support and
reinforce host-nation rule of law efforts to approach them. Rule of law operations can become a key line of
effort for counterinsurgents. Because many variables—whether cultural, economic, institutional, or
operational—affect rule of law and rule of law operations, no single approach to assessment or
implementation can be established.
13-65. In counterinsurgency environments, it is likely that justice mechanisms will have either collapsed
or be in serious need of rebuilding. Given the time and resources required to establish a fully functional
judicial system, counterinsurgents may need to support interim justice mechanisms—mechanisms to
provide justice in communities even while permanent judicial mechanisms are being developed. Such
interim justice mechanisms may use simplified formal mechanisms or informal justice mechanisms such as
traditional customs or other forms of community-based dispute resolution. Interim justice development and
institutional capacity building should be mutually reinforcing. Overall, progress in the rule of law is far
more rapid when building the capacity of police, prosecutors, judiciary, civil dispute resolution, and
corrections occurs simultaneously rather than sequentially.
13-66. Transitional justice mechanisms (truth commissions, trials and amnesties, purges from office, and
reparations) address past violations of human rights and humanitarian law. They can be effective in

Legal Considerations
13 May 2014 FM 3-24/MCWP 3-33.5 13-15
building the rule of law and reducing support for an insurgency. Trials and amnesties are important
components of reconciliation and reintegration. Truth commissions can serve the same function, and can
simultaneously expose the legal and humanitarian violations of an insurgency to a population and the
world. Counterinsurgency forces should coordinate with civilian leaders and consider including these
processes in their operations.
13-67. In some parts of the world, formal state-sanctioned and state-run courts are not the primary method
for resolving disputes. Instead, people resolve disputes through traditional customs and processes. For
example, many Afghans rely on shura and jirga, councils of community leaders who mediate conflicts. In
seeking to establish the rule of law, counterinsurgents need to understand what traditional forms of justice
already exist in a community. Counterinsurgents should consider whether these systems should be
integrated into the formal legal system, and they should also consider whether they can rely on those
traditional systems of justice as interim mechanisms while more formal court systems are being developed.
13-68. Counterinsurgents must be attentive to both civil and criminal justice. The criminal justice system
includes police, court systems, and corrections facilities. Its goal is to incapacitate, punish, deter, and
rehabilitate criminals. The civil justice system addresses disputes that are not of a criminal nature, such as
contract or property disputes. When the institutions of justice have collapsed or need to be rehabilitated, the
absence of both civil and criminal justice can cause instability and frustration in local communities. The
rule of law requires functioning systems for addressing both criminal and civil justice.
13-69. Helping a society develop a functioning civil and criminal legal system can be essential to counter
an insurgency. A knowledge of the host-nation legal system may help a commander determine the best
means to aid that development. Because a legal system develops over time within each society,
understanding its development and history helps explain its relevance to society. Laws and norms that
make little sense on the outside may have deep cultural and historic roots. The Army and the Marine Corps
legal communities can help a commander better understand the legal environment and how to help
reestablish and reinforce the rule of law.
13-70. Counterinsurgents should inform and educate the media, local community, host nation, and public
at large about applicable law of war provisions, U.S. and host-nation laws, and the obligations of those
participating in hostilities. Providing this information can help build trust and legitimacy by helping locals
and the media understand the rules U.S. forces follow and the safeguards they apply in operations. Legal
preparation of the battlefield can also help delegitimize the insurgents, as locals and the media will better
understand the insurgents’ violation of the laws.
This page intentionally left blank.

13 May 2014 FM 3-24/MCWP 3-33.5 Source Notes-1
Source Notes
These are the sources used, quoted, or paraphrased in this publication. They are listed
by page number. Where material appears in a paragraph, both page and paragraph
number are listed. Boldface indicates the titles of historical vignettes.
1-3 The Laos Insurgency: Christopher Paul. “Laos, 1959-1975” in Paths to Victory: Detailed
Insurgency Case Studies. Rand National Defense Research Institute. 2013, 147-156.
2-2 The Anbar Province Operational Environment: Dr. William Knarr. “Al-Sahawa: An
Awakening in Al Qaim.” in The Combating Terrorism Exchange Journal. May 2013, 5-30.
4-4. para 4-44. Mao Zedong. On Guerrilla War. London: Cassel, 1965.
4-12 External Support for the Tamil Tigers: Colin P. Clarke. “Sri Lanka, 1976-2009” in Paths
to Victory: Detailed Insurgency Case Studies. Rand National Defense Research Institute.
2013, 423-439.
6-2 Command in Counterinsurgency: Excerpt from Chapter 5, “Regimental Command in
Counterinsurgency” in Counterinsurgency Leadership in Afghanistan, Iraq, and Beyond.
Marine Corps University Press, Quantico, Virginia. 2011, 51-54.
7-3 If a Tactic Works in This Province, it Might Not Work in The Next: The Case of the
Dan Aw Patan District, Afghanistan, 2010: Donald P. Wright, unpublished article, Combat
Studies Institute, Fort Leavenworth, Kansas. 2013.
8-1 Intelligence and the Shining Path: Christopher Paul. Rand National Defense Research
Institute. 2013.
9-2 Shape-Clear-Hold-Build-Transition: The Huks: Molly Dunigan. “Philippines (Huk
Rebellion) 1946-1956” in Paths to Victory: Detailed Insurgency Case Studies. Rand National
Defense Research Institute. 2013, 31-39.
10-4 para 10-47. Afghanistan Youth National and Social Organization. www.aynso.org
11-2 Security Cooperation in El Salvador: Christopher Paul. Rand National Defense Research
Institute. 2013.
12-5 Measuring Effectiveness and Performance in Vietnam: Christopher Paul. “South
Vietnam, 1960-1975” in Paths to Victory: Detailed Insurgency Case Studies. Rand National
Defense Research Institute. 2013, 177-197.
This page intentionally left blank.

13 May 2014 FM 3-24/MCWP 3-33.5 Glossary-1
Glossary
The glossary lists acronyms and terms with Army, multi-Service, or joint definitions.
Where Army and joint definitions are different, (Army) precedes the definition. The
proponent manual for terms is listed in parentheses after the definition. Terms for
which the Army and Marine Corps have agreed on a common definition are followed
by (Army-Marine Corps).
SECTION I—ACRONYMS AND ABBREVIATIONS
ABCA American, British, Canadian, Australian, and New Zealand
ADP Army doctrine publication
ADRP Army doctrine reference publication
ASCOPE areas, structures, capabilities, organizations, people, events
ATTP Army tactics, techniques, and procedures
COIN counterinsurgency
DA Department of the Army
DOD Department of Defense
DODD Department of Defense directive
DODI Department of Defense instruction
FM field manual
JP joint publication
G-2 assistant chief of staff, intelligence
G-3 assistant chief of staff, operations
MACV Military Assistance Command, Vietnam
MCDP Marine Corps doctrine publication
MCO Marine Corps order
MCRP Marine Corps reference publication
MCWP Marine Corps warfighting publication
MOE measure of effectiveness
MOP measure of performance
NDAA National Defense Authorization Act
NGO nongovernmental organization
S-2 intelligence staff officer
S-3 operations staff officer
SOF special operations forces
STANAG standardization agreement
TC training circular
U.S. United States
USC United States Code

Glossary
Glossary-2 FM 3-24/MCWP 3-33.5 13 May 2014
SECTION II—TERMS
all-source intelligence
Intelligence products and/or organizations and activities that incorporate all sources of information in
the production of finished intelligence. (JP 2-0)
area of interest
That area of concern to the commander, including the area of influence, areas adjacent thereto, and
extending into enemy territory. This area also includes areas occupied by enemy forces who could
jeopardize the accomplishment of the mission. (JP 3-0)
area of operations
An operational area defined by the joint force commander for land and maritime forces that should be
large enough to accomplish their missions and protect their forces. (JP 3-0)
assessment
1. A continuous process that measures the overall effectiveness of employing joint force capabilities
during military operations. 2.Determination of the progress toward accomplishing a task, creating a
condition, or achieving an objective. (JP 3-0)
base
A locality from which operations are projected or supported. (JP 4-0)
biometrics
The process of recognizing an individual based on measurable anatomical, physiological, and
behavioral characteristics. (JP 2-0)
center of gravity
The source of power that provides moral or physical strength, freedom of action, or will to act. (JP 5-0)
clear
A tactical mission task that requires the commander to remove all enemy forces and eliminate
organized resistance within an assigned area. (FM 3-90-1)
combat outpost
A reinforced observation post capable of conducting limited combat operations. (FM 3-90-2)
command
The authority that a commander in the armed forces lawfully exercises over subordinates by virtue of
rank or assignment. (JP 1)
control
(Army) The regulation of forces and warfighting functions to accomplish the mission in accordance
with the commander’s intent. (ADP 6-0)
counterinsurgency
Comprehensive civilian and military efforts designed to simultaneously defeat and contain insurgency
and address its root causes. (JP 3-24)
country team
The senior, in-country, United States coordinating and supervising body, headed by the chief of the
United States diplomatic mission, and composed of the senior member of each represented United
States department or agency, as desired by the chief of the United States diplomatic mission.
(JP 3-07.4)
cyberspace
A global domain within the information environment consisting of the interdependent network of
information technology infrastructures and resident data, including the Internet, telecommunications
networks, computer systems, and embedded processors and controllers. (JP 1-02)

Glossary
13 May 2014 FM 3-24/MCWP 3-33.5 Glossary-3
end state
The set of required conditions that defines achievement of the commander’s objectives. (JP 3-0)
foreign internal defense
Participation by civilian and military agencies of a government in any of the action programs taken by
another government or other designated organization to free and protect its society from subversion,
lawlessness, insurgency, terrorism, and other threats to its security. (JP 3-22)
human intelligence
(joint) A category of intelligence derived from information collected and provided by human sources.
(JP 2-0) (Army) The collection by a trained human intelligence collector of foreign information from
people and multimedia to identify elements, intentions, composition, strength, dispositions, tactics,
equipment, and capabilities. (FM 2-22.3)
information environment
The aggregate of individuals, organizations, and systems that collect, process, disseminate, or act on
information. (JP 3-13)
information fratricide
The result of employing information-related capabilities in a way that causes effects in the information
environment that impede the conduct of friendly operations or adversely affect friendly forces.
(FM 3-13)
information operations
The integrated employment, during military operations, of information-related capabilities in concert
with other lines of operations to influence, disrupt, corrupt, or usurp the decisionmaking of adversaries
and potential adversaries while protecting our own. (JP 3-13)
information-related capability
A tool, technique, or activity employed within a dimension of the information environment that can be
used to create effects and operationally desirable conditions. (JP 3-13)
insurgency
The organized use of subversion and violence to seize, nullify, or challenge political control of a
region. Insurgency can also refer to the group itself. (JP 3-24)
intelligence
The product resulting from the collection, processing, integration, evaluation, analysis, and
interpretation of available information concerning foreign nations, hostile or potentially hostile forces
or elements, or areas of actual or potential operations. (JP 2-0)
intelligence preparation of the battlefield/battlespace
(Army-Marine Corps) A systematic process of analyzing and visualizing the portions of the mission
variables of threat/adversary, terrain, weather, and civil considerations in a specific area of interest and
for a specific mission. By applying intelligence preparation of the battlefield/battlespace, commanders
gain the information necessary to selectively apply and maximize operational effectiveness at critical
points in time and space. (FM 2-01.3/ MCRP 2-3A)
intergovernmental organization
An organization created by a formal agreement between two or more governments on a global,
regional, or functional basis to protect and promote national interests shared by member states.
(JP 3-08)
internal defense and development
The full range of measures taken by a nation to promote its growth and to protect itself from
subversion, lawlessness, insurgency, terrorism, and other threats to its security. (JP 3-22)
irregular warfare
A violent struggle among state and non-state actors for legitimacy and influence over the relevant
population(s). (JP 1)

Glossary
Glossary-4 FM 3-24/MCWP 3-33.5 13 May 2014
line of effort
In the context of joint operation planning, using the purpose (cause and effect) to focus efforts toward
establishing operational and strategic conditions by linking multiple tasks and missions. (JP 5-0)
line of operation
A line that defines the interior or exterior orientation of the force in relation to the enemy or that
connects actions on nodes and/or decisive points related in time and space to an objective(s). (JP 5-0)
measure of effectiveness
A criterion used to assess changes in system behavior, capability, or operational environment that is
tied to measuring the attainment of an end state, achievement of an objective, or creation of an effect.
(JP 3-0)
measure of performance
A criterion used to assess friendly actions that is tied to measuring task accomplishment. (JP 3-0)
mission command
The exercise of authority and direction by the commander using mission orders to enable disciplined
initiative within the commander’s intent to empower agile and adaptive leaders in the conduct of
unified land operations. (ADP 6-0)
mission orders
Directives that emphasize to subordinates the results to be attained, not how they are to achieve them.
(ADP 6-0)
nation assistance
Assistance rendered to a nation by foreign forces within that nation’s territory based on agreements
mutually concluded between nations. (JP 3-0)
nongovernmental organization
A private, self-governing, not-for-profit organization dedicated to alleviating human suffering; and/or
promoting education, health care, economic development, environmental protection, human rights, and
conflict resolution; and/or encouraging the establishment of democratic institutions and civil society.
(JP 3-08)
operational approach
A description of the broad actions the force must take to transform current conditions into those
desired at end state. (JP 3-0)
operational environment
A composite of the conditions, circumstances, and influences that affect the employment of
capabilities and bear on the decisions of the commander. (JP 3-0)
public affairs
Those public information, command information, and community engagement activities directed
toward both the external and internal publics with interest in the Department of Defense. (JP 3-61)
rules of engagement
Directives issued by competent military authority that delineate the circumstances and limitations
under which United States forces will initiate and/or continue combat engagement with other forces
encountered. (JP 1-04)
running estimate
The continuous assessment of the current situation used to determine if the current operation is
proceeding according to the commander’s intent and if planned future operations are supportable.
(ADP 5-0)

Glossary
13 May 2014 FM 3-24/MCWP 3-33.5 Glossary-5
security cooperation
All Department of Defense interactions with foreign defense establishments to build defense
relationships that promote specific US security interests, develop allied and friendly military
capabilities for self-defense and multinational operations, and provide US forces with peacetime and
contingency access to a host nation. (JP 3-22)
security force assistance
The Department of Defense activities that contribute to unified action by the US Government to
support the development of the capacity and capability of foreign security forces and their supporting
institutions. (JP 3-22)
site exploitation
A series of activities to recognize, collect, process, preserve, and analyze information, personnel,
and/or materiel found during the conduct of operations. (JP 3-31)
strike
An attack to damage or destroy an objective or a capability. (JP 3-0)
target audience
An individual or group selected for influence. (JP 3-13)
unified action
The synchronization, coordination, and/or integration of the activities of governmental and
nongovernmental entities with military operations to achieve unity of effort. (JP 1)
unity of command
The operation of all forces under a single responsible commander who has the requisite authority to
direct and employ those forces in pursuit of a common purpose. (JP 3-0)
unity of effort
Coordination and cooperation toward common objectives, even if the participants are not necessarily
part of the same command or organization, which is the product of successful unified action. (JP 1)
This page intentionally left blank.

13 May 2014 FM 3-24/MCWP 3-33.5 References-1
References
All URLs accessed on 1 May 2014.
REQUIRED PUBLICATIONS
These documents must be available to intended users of this publication.
ADRP 1-02. Terms and Military Symbols. 24 September 2013.
JP 1-02. Department of Defense Dictionary of Military and Associated Terms. 8 November 2010.
RELATED PUBLICATIONS
These documents contain relevant supplemental information.
MULTINATIONAL PUBLICATIONS
Most ABCA publications are available at http://www.abca-armies.org. The ABCA web site requires a
user ID and password.
ABCA Coalition Operations Handbook. 10 August 2010.
JOINT AND DEPARTMENT OF DEFENSE PUBLICATIONS
Most joint publications are available at http://www.dtic.mil/doctrine/new_pubs/jointpub.htm.
DODD 2310.01E. The Department of Defense Detainee Program. 5 September 2006.
DODD 3115.09. DoD Intelligence Interrogations, Detainee Debriefings, and Tactical Questioning.
11 October 2012.
DODD 5205.14. DoD Counter Threat Finance (CTF) Policy. 19 August 2010.
DODI 5525.11. Criminal Jurisdiction Over Civilians Employed By or Accompanying the Armed
Forces Outside the United States, Certain Service Members, and Former Service Members.
3 March 2005.
JP 1. Doctrine for the Armed Forces of the United States. 25 March 2013.
JP 1-04. Legal Support to Military Operations. 17 August 2011.
JP 2-0. Joint Intelligence. 22 October 2013.
JP 2-01.3. Joint Intelligence Preparation of the Operational Environment. 16 June 2009.
JP 3-0. Joint Operations. 11 August 2011.
JP 3-05. Special Operations. 18 April 2011.
JP 3-07.4. Joint Counterdrug Operations. 14 August 2013.
JP 3-08. Interorganizational Coordination During Joint Operations. 24 June 2011.
JP 3-13. Information Operations. 27 November 2012.
JP 3-16. Multinational Operations. 16 July 2013.
JP 3-22. Foreign Internal Defense. 12 July 2010.
JP 3-24. Counterinsurgency. 22 November 2013.
JP 3-31. Command and Control for Joint Land Operations. 24 February 2014.
JP 3-57. Civil-Military Operations. 11 September 2013.
JP 3-61. Public Affairs. 25 August 2010.
JP 4-0. Joint Logistics. 16 October 2013.
JP 5-0. Joint Operation Planning. 11 August 2011.
ARMY PUBLICATIONS
Most Army doctrinal publications are available at http://www.apd.army.mil/.

References
References-2 FM 3-24/MCWP 3-33.5 13 May 2014
ADP 5-0. The Operations Process. 17 May 2012.
ADP 6-0. Mission Command. 17 May 2012.
ADRP 1. The Army Profession. 14 June 2013.
ADRP 2-0. Intelligence. 31 August 2012.
ADRP 3-07. Stability. 31 August 2012.
ADRP 5-0. The Operations Process. 17 May 2012.
ADRP 6-0. Mission Command. 17 May 2012.
AR 190-8/MCO 3461.1 Military Police: Enemy Prisoners of War, Retained Personnel, Civilian
Internees and Other Detainees. 1 October 1997.
ATP 3-07.20/MCRP 3-33.1G. IMSO Multi-Service Tactics, Techniques, and Procedures for Integrated
Monetary Shaping Operations. 26 April 2013.
ATP 5-19. Risk Management. 14 April 2014.
ATTP 2-91.6. Tactics, Techniques, and Procedures for Intelligence Support to Site Exploitation. 27
December 2010.
ATTP 3-39.20. Police Intelligence Operations. 29 July 2010.
FM 2-01.3/MCRP 2-3A. Intelligence Preparation of the Battlefield/Battlespace. 15 October 2009.
FM 2-22.3. Human Intelligence Collector Operations. 6 September 2006.
FM 3-05. Army Special Operations. 9 January 2014.
FM 3-07. Stability Operations. 6 October 2008.
FM 3-11/MCWP 3-37.1. Multi-Service Doctrine for Chemical, Biological, Radiological, and Nuclear
Operations. 1 July 2011.
FM 3-13. Inform and Influence Activities. 25 January 2013.
FM 3-22. Army Support to Security Cooperation. 22 January 2013.
FM 3-55. Information Collection. 3 May 2013.
FM 3-57. Civil Affairs Operations. 31 October 2011.
FM 3-90-1. Offense and Defense Volume 1. 22 March 2013.
FM 3-90-2. Reconnaissance, Security, and Tactical Enabling Tasks Volume 2. 22 March 2013.
FM 4-92. Contracting Support Brigade. 12 February 2010.
FM 6-05/MCWP 3-36.1. CF-SOF Multi-Service Tactics, Techniques, and Procedures for
Conventional Forces and Special Operations Forces Integration, Interoperability, and
Interdependence. 13 March 2014.
FM 27-10. The Law of Land Warfare. 18 July 1956.
TC 2-19.63. Company Intelligence Support Team. 9 November 2010.
TC 2-22.82. Biometrics-Enabled Intelligence. 21 March 2011.
TC 2-33.4. Intelligence Analysis. 1 July 2009.
MARINE CORPS PUBLICATIONS
Most Marine Corps publications are available at
http://www.marines.mil/News/Publications/ELECTRONICLIBRARY.aspx.
MCDP 1-0. Marine Corps Operations. 9 August 2011.
MCDP 1-1. Strategy. 12 November 1997.
MCDP 5. Planning. 21 July 1997.
MCDP 6. Command and Control. 4 October 1996.
MCO 5530.17. Marine Corps Identity Operations (IdOps). 13 November 2012.
MCWP 3-33.1. Marine Air-Ground Task Force Civil-Military Operations. 28 September 2011.
MCWP 5-1. Marine Corps Planning Process. 24 August 2010.
References
13 May 2014 FM 3-24/MCWP 3-33.5 References-3
UNITED STATES LAW
Most acts and public laws are available at http://thomas.loc.gov/home/thomas.php.
Detainee Treatment Act of 2005.
Executive Order 13491. Ensuring Lawful Interrogation. Available at http://www.archives.gov/federal-
register/executive-orders/2009-obama.html.
National Defense Authorization Act.
Title 10, United States Code. Armed Forces.
Title 22. United States Code. Foreign Relations and Intercourse.
The Uniform Code of Military Justice. Available at
http://www.law.cornell.edu/uscode/text/10/subtitle-A/part-II/chapter-47.
OTHER PUBLICATIONS
Geneva Conventions. Available at http://avalon.law.yale.edu/subject_menus/lawwar.asp .
The Hague Conventions. Available at http://avalon.law.yale.edu/subject_menus/lawwar.asp.
Interagency Conflict Assessment Framework. Office of the Coordinator for Reconstruction and
Stabilization, United States Department of State. July 2008. Available online:
http://toolkit.ineesite.org/toolkit/INEEcms/uploads/1151/Conflict_Assessment_Framework.pdf.
Mao Zedong. On Guerrilla War. London: Cassel, 1965.
NORTH ATLANTIC TREATY ORGANIZATION PUBLICATIONS
North Atlantic Treaty Organization publications are available at http://www.nato.int.
Allied Joint Publication 3.4.4. Allied Joint Doctrine for Counterinsurgency (COIN). 4 February 2011.
STANAG 2611. Allied Joint Doctrine for Counterinsurgency (COIN). 4 February 2011.
PRESCRIBED FORMS
None
REFERENCED FORMS
Unless otherwise indicated, DA forms are available on the Army Publishing Directorate (APD) Web
site (http://www.apd.army.mil/).
DA Form 2028. Recommended Changes to Publications and Blank Forms.
This page intentionally left blank.

13 May 2014 FM 3-24/MCWP 3-33.5 Index-1
Index
Entries are by paragraph number
A
accountability, 10-71
activities, and disposition, 5-2–
5-17
political, 5-4–5-9
support, 5-18–5-29
acts, terrorist, 5-12–5-13
adaptability, 4-36–4-37
advising, 11-26
all-source intelligence, 8-7–8-11
defined, 8-7
analytical frameworks, other,
4-104–4-105
application of criminal laws, of a
host nation, 13-37–13-38
approaches, insurgent, 4-40–4-45
area of interest, defined, 2-14
area of operations, defined, 2-12
armed conflict, non-international,
13-33–13-38
assessing, a cultural situation,
3-9–3-15
and developing a host-nation
force, 11-6–11-19
assessment, cell, 12-30–12-32
considerations, 12-9–12-18
defined, 12-1
frameworks, 12-5
methods, 12-6–12-8
assessments, 12-1–12-37
assist a foreign government,
authority to, 13-3–13-5
assistance to police, general
prohibition on, 13-5
associated threats, 5-30–5-48
attack, the network, 7-47–7-55
authority, for foreign internal
defense, 13-4
to assist a foreign government,
13-3–13-5
auxiliary forces, 4-81–4-84
B
base, defined, 7-80
basic rules, Soldier’s and
Marine’s, 13-30–13-32
basing, 7-80–7-83
biometric-enabled intelligence,
8-22–8-24
biometrics, defined, 8-22
border considerations, 7-71–7-79
broad indicators of progress,
12-28–12-29
build, 9-31–9-33
building, capacity, 10-65
building partner capacity, or global
train and equip, 13-55
C
capabilities, intelligence-related,
8-21–8-31
capacity, building, 10-65
cell, assessment, 12-30–12-32
center of gravity, 7-20–7-22
defined, 7-20
civil considerations, and mission
variables, 2-45–2-46
civilian personnel, and
contractors, 13-48
claims, and solatia, 13-58–13-60
clear, 9-17–9-22
clear, defined, 9-17
cognitive, dimension, 2-34
combat outpost, defined, 7-83
command, defined, 6-2
in counterinsurgency, 6-2–6-6
responsibility, 13-46
command and control, and
mission command, 6-1–6-21
commander’s emergency
response program, 13-52–
13-57
Common Article 3, Geneva
Convention, 13-34–13-36
communications, 5-24
comprehensive, effort, 1-47–1-48
conceptual, planning, 7-13–7-34
considerations, assessment,
12-9–12-18
border, 7-71–7-79
legal, 13-1–13-70
operational, 7-46–7-83
other operational, 7-62–7-83
remote area, 7-63–7-70
context, understanding the
strategic, 1-1–1-92
contractors, and civilian
personnel, 13-48
control, and legitimacy, 1-27–1-33
defined, 6-2
conventional tactics, 5-14–5-17
conventional forces and special
operations forces,
synchronization, 6-15–6-21
coordination, 1-52–1-58
countering an insurgency, U.S.
strategy and policy for, 1-10–
1-13
countering insurgencies, direct
methods for, 9-1–9-57
indirect methods for, 10-1–
10-71
counterinsurgency, command,
6-2–6-6
defined, 1-3
headquarters use in, 6-7–6-14
money usage principles in,
10-63–10-71
paradoxes, 7-2–7-12
counterinsurgent forces must
understand the environment,
1-79
counterinsurgent forces should
prepare for a long-term
commitment, 1-85
counterintelligence, 8-18
counter threat finance, 4-25, 5-21,
7-30, 9-49, 10-39, 10-40, 10-54,
country team, 1-65–1-66
defined, 1-65
criminal organizations, 5-42–5-45
cultural advisor, and green cell,
3-17–3-22
cultural situation, assessing a,
3-9–3-15
culture, 3-1–3-25
organizing to understand,
3-16–3-24
understanding, 3-4–3-8
cyberspace, defined, 8-6
demographic and urbanization
trends, 2-3–2-7
Index
Entries are by paragraph number.
Index-2 FM 3-24/MCWP 3-33.5 13 May 2014
D
Department of State, 1-63–1-68
designing measures of
effectiveness and performance,
12-22–12-27
Detainee Treatment Act of 2005,
13-40
detention, and internment
standards, 13-42
and interrogation, 13-39–13-43
develop simple, flexible plans,
through mission orders, 7-31–
7-34
developing, and assessing a
host-nation security force,
11-6–11-19
host-nation security forces,
11-32–11-40
measurement criteria, 12-19–
12-37
dimension, cognitive, 2-34
informational, 2-34
physical, 2-34
diplomacy, and negotiation,
10-20–10-24
direct action, 1-5, 1-12, 6-5, 6-16,
direct enablers, other, 9-41–9-57
direct methods for countering
insurgencies, 9-1–9-57
directed telescope technique,
12-33–12-37
discrimination, 13-19–13-25
disposition and activities, 5-2–
5-17
DOD funds generally not
expendable by commanders for
this purpose, 13-51
doing nothing is sometimes the
best action, 7-7
dynamics of insurgency, 4-46–
4-105
E
economic, variable, 2-25–2-31
effort, and unity of command,
1-49–1-51
comprehensive, 1-47–1-48
lines of and operation, 7-23–
7-30
whole-of-government, 1-41–
1-46
eighth dynamic, organizational
and operational patterns, 4-76–
4-77
elements, organizational, 4-78
emergency response program,
commander’s, 13-52–13-57
empower the lowest levels, 1-91
end state, defined, 7-23
enforcing discipline of U.S. forces,
13-44–13-48
environment and geography,
fourth dynamic, 4-59–4-61
establishing the rule of law,
13-61–13-70
ethical application of landpower in
unified action, 1-36–1-40
external support, fifth dynamic,
4-62–4-64
F
failing or failed states, 2-7
fifth dynamic, external support,
4-62–4-64
first dynamic, leadership, 4-49–
4-53
flexibility, 10-70
forces, auxiliary, 4-81–4-84
multinational, 1-67–1-68
Foreign Claims Act, 13-59
foreign forces, training and
equipping, 13-49–13-51
foreign internal defense, authority
for, 13-4
defined, 11-27
forensic-enabled intelligence,
8-25–8-27
fourth dynamic, environment and
geography, 4-59–4-61
framework,
shape-clear-hold-build-transitio
n, 9-5–9-40
frameworks, assessment, 12-5
fundamentals, and prerequisites,
insurgency, 4-1–4-105
insurgency, 4-29–4-105
intelligence, 8-2–8-6
fusion centers, 8-12–8-13
G
general orders, 13-47
general prohibition on assistance
to police, 13-5
generational engagement, 10-7–
10-19
Geneva Convention, Common
Article 3, 13-34–13-36
global security contingency fund,
13-56
global train and equip or building
partner capacity, 13-55
globalization, 2-5
government and forces, host
nation, 1-60
green cell and cultural advisor,
3-17–3-22
guerilla units, 4-80
H
headquarters use, in
counterinsurgency, 6-7–6-14
hold, 9-23–9-30
honor, 13-29
host nation, application of criminal
laws, 13-37–13-38
government and forces, 1-60
ownership, 10-64
transfer of detainees to, 13-43
working with forces, 11-1–
11-45
host-nation security forces,
developing, 11-32–11-40
human intelligence, 8-14–8-17
defined, 8-14
human rights vetting, 13-57
human terrain system, 3-23–3-25
humanity, unnecessary suffering
or superfluous injury, 13-16–
13-18
I
identify, 10-28–10-30
identify, separate, isolate,
influence, and reintegrate,
10-25–10-53
ideology, second dynamic, 4-54–
4-55
if a tactic works this week, it might
not work next week; if it works
in this province, it might not
work in the next, 7-10–7-11
indirect enablers, other, 10-54–
10-71
indirect methods for countering
insurgencies, 10-1–10-71
indoctrination, and training, 5-22–
5-23
influence, 10-41–10-45
influence neutral, networks, 7-58
information, operations, 7-84–7-96
variable, 2-33–2-36
information collection and
intelligence, surveillance, and
reconnaissance, 8-19–8-20
Index
Entries are by paragraph number.
13 May 2014 FM 3-24/MCWP 3-33.5 Index-3
information environment, defined,
2-33
information fratricide, defined,
7-95
information operations, defined,
7-84
informational dimension, 2-34
information-related capability,
defined, 7-84
infrastructure, targeted threat,
9-44–9-49
variable, 2-37–2-40
insurgencies, networked, 4-88–
4-103
insurgency, defined, 1-3
dynamics of, 4-46–4-105
fundamentals, 4-29–4-105
prerequisites, 4-10–4-28
prerequisites and
fundamentals, 4-1–4-105
threat characteristics, 5-1–5-48
insurgent, approaches, 4-38–4-45
legitimacy and control, 4-31
organizational structure, 4-34
strategies, 4-30–4-39
strengths and weaknesses,
5-25–5-29
integrated, 11-25
integrated monetary shaping
operations, 10-56–10-71
intelligence, 8-1–8-31
all-source, 8-7–8-11
biometric-enabled, 8-22–8-24
defined, 8-2
forensic-enabled, 8-25–8-27
fundamentals, 8-2–8-6
human, 8-14–8-17
intelligence drives operations,
1-80–1-82
intelligence preparation of the
battlefield/battlespace, defined,
8-3
intelligence, surveillance, and
reconnaissance, and
information collection, 8-19–
8-20
intelligence-related capabilities,
8-21–8-31
intergovernmental organization,
defined, 1-74
internal defense and
development, defined, 1-35
internal support, sixth dynamic,
4-65–4-69
internment, and detention
standards, 13-42
interrogation, and detention,
13-39–13-43
interrogation field manual, 13-41
intrastate, war, 4-2–4-9
irregular warfare, defined, 1-2
isolate, 10-35–10-40
J-K
joint force, 1-61–1-62
joint phasing mode, 11-29–11-31
L
land forces and the range of
military operations, 1-14–1-26
large scale combat, 1-2, 1-18,
1-19, 1-20
law of war, 13-10–13-13
lead nation, 11-23
leadership, 4-79
first dynamic, 4-49–4-53
learn and adapt, 1-90
legal considerations, 13-1–13-70
legitimacy, 1-2, 1-24, 1-36, 1-38,
1-53, 1-78, 1-82–1-84, 1-88,
2-33, 2-40, 3-1, 3-13, 4-21,
4-24, 4-30, 4-31, 4-34, 4-43,
4-49, 4-51, 4-53, 4-73, 4-80,
5-4, 5-6, 5-8, 5-10, 5-12, 5-17,
5-47, 6-19, 7-4, 7-8, 7-9, 7-36,
7-37, 7-38, 7-42, 7-58, 8-14,
8-24, 9-18, 9-33, 9-43–9-46,
9-48, 9-57, 10-5, 10-9, 10-16,
10-31, 10-71, 11-2, 11-16,
12-13, 12-24, 13-47, 13-70
legitimacy and control, 1-27–1-33
insurgent, 4-31
legitimacy is the main objective,
1-78
line of effort, defined, 7-25
line of operation, defined, 7-24
lines of operation and effort, 7-23–
7-30
M
manage information and
expectations, 1-86–1-87
many important decisions are not
made by generals, 7-12
Marine’s basic rules, 13-30–13-32
means, 4-23–4-28
measure of effectiveness, defined,
12-20
measure of performance, defined,
12-20
measurement criteria, developing,
12-19–12-37
measures of effectiveness ,
designing, 12-22–12-27
measures of performance,
designing, 12-22–12-27
methods, assessment, 12-6–12-8
military tactics, 5-11–5-17
variable, 2-20–2-24
Military Justice, Uniform Code of,
13-45
military necessity, 13-14–13-15
militias, nongovernment, 5-46–
5-48
mission command and command
and control, 6-1–6-21
defined, 6-2
mission orders, defined, 7-34
develop simple, flexible plans
through, 7-31–7-34
mission variables and civil
considerations, 2-45–2-46
mission-specific rules of
engagement, 13-7–13-8
money usage principles in
counterinsurgency, 10-63–
10-71
motive, 4-14–4-22
multinational, forces, 1-67–1-68
rules of engagement, 13-9
N
nation assistance, and security
cooperation, 10-3–10-6
defined, 10-3
negotiation and diplomacy, 10-20–
10-24
network, attack the, 7-47–7-55
networked insurgencies, 4-88–
4-103
networks, influence neutral, 7-58
neutralize threat, 7-59–7-61
support friendly, 7-56–7-57
neutralize threat networks, 7-59–
7-61
nongovernment militias, 5-46–
5-48
nongovernmental organization,
defined, 1-69
nongovernmental organizations,
1-69–1-73
Index
Entries are by paragraph number.
Index-4 FM 3-24/MCWP 3-33.5 13 May 2014
non-international armed conflict,
13-33–13-38
O
objectives, third dynamic, 4-56–
4-58
operation, lines of and effort,
7-23–7-30
operational, and planning
considerations, 7-1–7-96
considerations, 7-46–7-83
variables, 2-8–2-44
operational approach, 1-9, 1-12,
1-13, 1-20, 1-77, 6-5, 6-7, 6-9,
6-12, 7-13, 7-14, 7-15, 7-16,
7-18, 7-19, 7-23, 7-27, 7-46,
7-84, 9-3, 9-5, 9-7, 11-11,
defined, 1-13
operational environment, defined,
2-8
understanding an , 2-1–2-46
operations, information, 7-84–7-96
integrated monetary shaping,
10-56–10-71
opportunists, 5-31–5-41
opportunity, 4-11–4-13
orders, general, 13-47
organizational elements, 4-78
organizational and operational
patterns, eighth dynamic, 4-76–
4-77
organizations, criminal, 5-42–5-45
nongovernmental, 1-69–1-73
other, 1-74–1-76
organizing to understand culture,
3-16–3-25
other, analytical frameworks,
4-104–4-105
direct enablers, 9-41–9-57
indirect enablers, 10-54–10-71
operational considerations,
7-62–7-83
organizations, 1-74–1-76
ownership, host nation, 10-64
P
paradoxes, counterinsurgency,
7-2–7-12
parallel, 11-22
planning, 11-41–11-45
partnered, 11-24
partners, unified action, 1-59–1-76
partnership, 10-69
phasing and timing, seventh
dynamic, 4-70–4-75
physical dimension, 2-34
physical environment, variable,
2-41–2-42
planning, and operational
considerations, 7-1–7-96
conceptual, 7-13–7-34
parallel, 11-41–11-45
security cooperation, 11-27–
11-45
political activities, 5-4–5-9
variable, 2-16–2-19
political, economic, and
violence-centered insurgencies,
4-32
population control, 5-10
prerequisites, and fundamentals,
insurgency, 4-1–4-105
insurgency, 4-10–4-28
progress, broad indicators of,
12-28–12-29
proliferation of weapons, 2-6
proportionality, 13-26–13-28
public affairs, defined, 7-94
R
reintegrate, 10-46–10-53
relationship of an insurgency to
the economy, 4-33
relationships, 11-20–11-26
remote area, considerations,
7-63–7-70
responsibility, command, 13-46
root cause, 1-1–1-3, 1-26, 1-42,
1-47, 1-79, 2-2, 4-9, 4-14–
4-22, 4-27, 4-38, 4-49, 4-54,
5-7, 5-39, 5-43, 9-12, 9-15,
9-17, 9-21, 9-31, 9-33, 9-57,
10-4, 10-9, 10-20–10-24, 10-26,
11-5, 12-10, 12-14
rule of law, establishing, 13-61–
13-70
rules of engagement, 13-6–13-9
defined, 13-6
mission-specific, 13-7–13-8
multinational, 13-9
running estimate, defined, 8-20
S
second dynamic, ideology, 4-54–
4-55
security cooperation, defined,
10-5
nation assistance, 10-3–10-6
planning, 11-27–11-45
security force assistance, defined,
11-27
security under the rule of law is
essential, 1-83–1-84
selectivity, 10-67–10-68
sense of time, 4-35
separate, 10-31–10-34
seventh dynamic, phasing and
timing, 4-70–4-75
shape, 9-15–9-16
shape-clear-hold-build-transition,
framework, 9-5–9-40
site exploitation, 8-28–8-31
defined, 8-28
sixth dynamic, internal support,
4-65–4-69
social, variable, 2-32
solatia, 13-60
and claims, 13-58–13-60
Soldier’s basic rules, 13-30–13-32
some of the best weapons for
counterinsurgents do not shoot,
7-8
sometimes, the more force is
used, the less effective it is, 7-5
sometimes, the more you protect
your force, the less secure you
may be, 7-4
special operations forces, 1-57,
8-8, 9-16, 6-13, 6-15–6-17,
6-19–6-21
standards for detention and
internment, 13-42
states, failing or failed, 2-7
strategic principles, 1-77–1-92
strategies, insurgent, 4-30–4-39
strengths, insurgent, 5-25–5-29
strike, 9-50–9-57
defined, 9-50
support activities, 5-18–5-29
support friendly networks, 7-56–
7-57
support the host nation, 1-92
sustainability, 10-66
synchronization, conventional
forces and special operations
forces, 6-15–6-21
T
tactics, conventional, 5-14–5-17
military, 5-11–5-17
target audience, defined, 7-85
Index
Entries are by paragraph number.
13 May 2014 FM 3-24/MCWP 3-33.5 Index-5
targeted threat infrastructure,
9-44–9-49
technique, directed telescope,
12-33–12-37
terrorist acts, 5-12–5-13
the host nation doing something
tolerably is normally better than
us doing it well, 7-9
the more successful the
counterinsurgency is, the less
force can be used and the more
risk must be accepted, 7-6
the range of military operations,
land forces and, 1-14–1-26
third dynamic, objectives, 4-56–
4-58
threat characteristics, insurgency,
5-1–5-48
threats, associated, 5-30–5-48
time, variable, 2-43–2-44
training and indoctrination, 5-22–
5-23
training and equipping foreign
forces, 13-49–13-51
transfer of detainees to the host
nation, 13-43
transition, 9-34–9-40
transitions, 7-35–7-45
trends, demographic and
urbanization, 2-3–2-7
U
U.S. strategy and policy to counter
an insurgency, 1-10–1-13
unconventional warfare, 5-23
underground, 4-85–4-87
understanding, an operational
environment, 2-1–2-46
culture, 3-4–3-8
the strategic context, 1-1–1-92
unified action, 1-34–1-76
unified action, defined, 1-34
ethical application of
landpower in, 1-36–1-40
partners, 1-59–1-76
understanding, 1-34–1-76
Uniform Code of Military Justice,
13-45
unity of command and effort,
1-49–1-51
unity of command, defined, 1-49
unity of effort, defined, 1-51
urbanization, trends, 2-3–2-7
use the appropriate level of force,
1-88–1-89
V
variable, economic, 2-25–2-31
information, 2-33–2-36
infrastructure, 2-37–2-40
military, 2-20–2-24
physical environment, 2-41–
2-42
political, 2-16–2-19
social, 2-32
time, 2-43–2-44
variables, operational, 2-8–2-44
vetting, human rights, 13-57
W-X-Y-Z
war, intrastate, 4-2–4-9
weaknesses, insurgent, 5-25–5-29
weapons proliferation, 2-6
whole-of-government effort, 1-41–
1-46
working with host-nation forces,
11-1–11-45
This page intentionally left blank.

FM 3-24
MCWP 3-33.5
13 May 2014
By Order of the Secretary of the Army:
RAYMOND T. ODIERNO
General, United States Army
Chief of Staff
Official:
GERALD B. O’KEEFE
Administrative Assistant to the
Secretary of the Army
1412701
BY DIRECTION OF THE COMMANDANT OF THE MARINE CORPS:
DISTRIBUTION:
Active Army, Army National Guard, and U.S. Army Reserve: To be distributed in accordance with the
initial distribution number 121724, requirements for FM 3-24.
Marine Corps: PCN 143 000124 00
This page intentionally left blank.

PIN: 083748-000