Manual
User Manual:
Open the PDF directly: View PDF ![]() .
.
Page Count: 76

Bern University of Applied Sciences
BTI7301 - PROJECT 1
Mail Server Set-Up &
Security-Hardening Script
User Manual
Authors:
Fridolin Zurlinden
Ismael Riedo
Jan Henzi
Tutor:
Dr. Simon Kramer
January 23, 2019
Abstract
This paper gives you an overview understanding, what is this hardening script about and what
happens on the server when you execute it. It escorts you through every step of the installation.
Starting with the run options, then firewall, DNS, internal user management, SSH, mail, and at the
end the web part. It demonstrates the contrast between a non-hardened and a hardened server by this
script. Gives you a full manual how to configure your email client and it concludes everything with
some future works ideas.

User Manual Internet Server Set-Up & Security-Hardening Script
Contents
Abstract
List of Figures 5
1 Introduction 6
1.1 Prerequisits........................................... 7
1.1.1 Ubuntu18.04Server.................................. 7
1.1.2 Domain ......................................... 7
1.1.3 Minimal Linux knowledge . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 7
1.2 Architectureoverview ..................................... 8
2 Walkthrough 9
2.1 Codedirectorytree....................................... 9
2.2 Overview ............................................ 10
2.2.1 Completerun...................................... 10
2.2.2 Rerunrun........................................ 11
2.2.3 Overview process diagram . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 12
2.3 Firewall ............................................. 13
2.3.1 Firewall process diagram . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 15
2.4 DNS............................................... 16
2.4.1 DNS architecture diagram . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 18
2.4.2 DNSprocessdiagram ................................. 19
2.4.3 Multipledomains.................................... 19
2.5 Usermanagement........................................ 20
2.5.1 Actions ......................................... 20
2.5.2 User management process diagram . . . . . . . . . . . . . . . . . . . . . . . . . . 22
2.6 SSH ............................................... 23
2.6.1 Configuration...................................... 23
2.6.2 SSHprocessdiagram.................................. 25
2.7 E-Mail.............................................. 26
2.7.1 Configurations ..................................... 26
2.7.2 E-Mailprocessdiagram ................................ 31
2.7.3 Multiple e-mail addresses . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 31
2.8 Web ............................................... 32
2.8.1 Web architecture diagram . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 33
3 Hardening Tests 34
3.1 Firewall ............................................. 34
3.2 DNS............................................... 37
3.2.1 Domainnameresolver................................. 37
3.2.2 AuthoritativeDNS................................... 39
3.3 SSH ............................................... 40
3.3.1 SSHdaemon ...................................... 40
3.4 E-Mail.............................................. 42
3.4.1 E-Mail server configuration . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 42
3.4.2 E-Mailheader...................................... 44
3.5 Web ............................................... 45
Contents Page 3 of 76

User Manual Internet Server Set-Up & Security-Hardening Script
4 E-Mail Client configuration 47
4.1 MailonmacOSMojave .................................... 47
4.1.1 Mailserverconfig.................................... 47
4.1.2 MailSMTPsettings .................................. 48
4.1.3 MailIMAPTLSsetting................................ 49
5 Future Work 50
5.1 Extendedfunctionalities.................................... 50
5.1.1 Multipledomains.................................... 50
5.1.2 Multiple e-mail addresses . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 50
5.1.3 Webapplicationserver................................. 50
5.2 MoreHardening ........................................ 50
5.3 Containerization ........................................ 51
5.4 CodeMigration......................................... 51
6 Conclusion 52
7 License 53
7.1 MITlicense........................................... 53
8 Glossary 54
Bibliography 57
Appendices 58
Contents Page 4 of 76

User Manual Internet Server Set-Up & Security-Hardening Script
List of Figures
1.1 Architectureoverview ..................................... 8
2.1 Setupprocessdiagram..................................... 12
2.2 Firewallprocessdiagram.................................... 15
2.3 ArchitectureDNS........................................ 18
2.4 DNSprocessdiagram ..................................... 19
2.5 User management process diagram . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 22
2.6 SSHprocessdiagram...................................... 25
2.7 Emailprocessdiagram..................................... 31
2.8 ArchitectureWeb........................................ 33
3.1 Firewall (without DNS) BEFORE .............................. 34
3.2 Firewall (with DNS) BEFORE ................................ 35
3.3 Firewall setup AFTER .................................... 36
3.4 Name resolver BEFORE ................................... 37
3.5 Name resolver details BEFORE ............................... 37
3.6 Name resolver AFTER .................................... 38
3.7 Name resolver details AFTER ................................ 38
3.8 Authoritative DNS test BEFORE .............................. 39
3.9 Authoritative DNS test AFTER ............................... 39
3.10 SSH daemon BEFORE ................................... 40
3.11 SSH daemon AFTER ..................................... 41
3.12 Mail BEFORE (emailsecuritygrader.com) . . . . . . . . . . . . . . . . . . . . . . . . . . 42
3.13 Mail BEFORE (hardenize.com) ............................... 42
3.14 Mail AFTER (emailsecuritygrader.com) . . . . . . . . . . . . . . . . . . . . . . . . . . 43
3.15 Mail AFTER (hardenize.com) ................................ 43
3.16 Mail header BEFORE .................................... 44
3.17 Mail header AFTER ..................................... 44
3.18 Web BEFORE ......................................... 45
3.19 Web AFTER ......................................... 46
4.1 Mailserverconfig........................................ 47
4.2 MailSMTPsettings ...................................... 48
4.3 MailIMAPTLSsetting .................................... 49
List of Figures Page 5 of 76

User Manual Internet Server Set-Up & Security-Hardening Script
1 Introduction
In this document, we descripted a full installation of follow components: Firewall, DNS, SSH, Email
and Web. As well, we show you all possibilities you can take within the provided script. We let you
understand that the components are hardened and give you some thoughts about the future. Everything
start with the walkthrough chapter, a complete walkthrough through the scripts explained based on
the output. You can quickly and clearly follow up what is happening where and how. There is an
overview code directory tree, which indicates all the scripts which are made. After it starts with all
the components, which will be installed.
•Overview: This Section is about the main script, which bundles all components. The user also
has the possibility to create his individual setup and if necessary to perform uninstallation and
modifications on a second run.
•Firewall:The firewall can be extended with additional rules with the help of a configuration file.
The file can be found in the “files” directory under the name “fw.conf”.
•DNS: In the DNS part, two DNS servers will be installed. Both are from nlnetlabs: unbound
and NSD. Unbound is used as resolver, to handle all requests from this server and NSD is used
as authoritative name server. Such a separation increases security.
•User management: Since some services also require Unix users, scripts have been written to
make it easier to create and assign users to services. Both the mail part and the SSH part need
such users.
•SSH: The SSH part is not only about making the server more secure by forbidding the root user
to log in, but also about equipping new or existing users with right and ssh keys so that a login
is still possible via specific users.
•Email: A secure mail server with postfix is set up in the email part. Unix users are also required
here.
•Web: In the web part nginx and apache are used. The nginx is used as reverse proxy and the
apache as frontend webserver.
Results are important, so the hardening Tests section is about giving you a feeling about what one
can expect from a successful complete run of the script. Based on common hardening pages and tools,
tests were made to show how secure the server is, before the script and after a complete run of the
scripts.
•Firewall: The firewall tests were performed with nmap. The results of the firewall test can seem
a bit irritating at first: more ports are open than before. However, this makes sense, because
certain ports are needed by the services. What is open or closed before also depends on the host
of the server.
•DNS: It was important not only to make a DNS secure, but also to make it independent. With
the own resolver this was very successful and so the user of the scripts has a DNS detached from
big companies like Google or Cloudflare.
•SSH: Apart from forbidding the root user from logging in, we also made sure that after the SSH
configuration only algorithms are used that are currently considered as secure.
•Mail: With secure protocols and antispam measures, the mail server was configured so that it
received very good marks during the tests. We tested it with https://emailsecuritygrader.com
and https://www.hardenize.com.
CHAPTER 1. INTRODUCTION Page 6 of 76

User Manual Internet Server Set-Up & Security-Hardening Script
•Web: Also the web part could be tested via https://www.hardenize.com . There we also achieved
very good values.
In addition, you will find a small step-by-step guide (currently only macOS guide) to set up the email
client to work with your server. Moreover, in the conclusion we discuss about extended functionali-
ties like multiple domains / e-mail addresses, more hardening possibilities, containerization and code
migration. At the very end, you find all configured config files of each component.
1.1 Prerequisits
In order to start a complete run of the scripts, it is worth making some things ready in advance so that
the run can go clean and fast.
1.1.1 Ubuntu 18.04 Server
You need your own Ubuntu Server (Version 18.04), which is an accessible from the internet. You need
root access.
1.1.2 Domain
You need your own domain. A free test domain can easily be found with a small search in any web
search engine.
1.1.3 Minimal Linux knowledge
The script is in command line only, so you need some minimal Linux knowledge. You should know how
to navigate and execute a command inside the terminal.
CHAPTER 1. INTRODUCTION Page 7 of 76

User Manual Internet Server Set-Up & Security-Hardening Script
2 Walkthrough
2.1 Code directory tree
.
dns
dns.sh
dns_nsd.sh
dns_unbound.sh
nsd
configBackwardsZoneDNS_nsd.sh
configDNS_nsd.sh
configForwardZoneDNS_nsd.sh
finalisationDNS_nsd.sh
installDNS_nsd.sh
testDNS_nsd.sh
unbound
configDNSAccess_unbound.sh
configDNSHardening_unbound.sh
configDNSListening_unbound.sh
finalisationDNS_unbound.sh
installDNS_unbound.sh
testDNS_unbound.sh
uninstall_dns.sh
files
fw.conf -> fw/fw.conf
fw
controllTraffic.sh
enableUfw.sh
fw.conf
fw.sh
specificConfigurations.sh
uninstall_fw.sh
mail
alias.sh
checkDomain.sh
clientCertificate.sh
dkim.sh
dmarc.sh
dnsRecords.sh
dovecot.sh
hardeningMail.txt
mail.sh
restart.sh
spf.sh
tls.sh
uninstall_mail.sh
setup.sh
ssh
config.sh
restart.sh
ssh.sh
sshkeys.sh
utils
checkPackage.sh
chooseIp.sh
getAllIpv4.sh
getAllIpv6.sh
getIpv4.sh
getIpv6.sh
logging.sh
removeFolder.sh
removePackage.sh
revIpv4.sh
summary.sh
user.sh
valid_ipv4.sh
web
apache
configureApache.sh
enableApache.sh
nginx
configureNginx.sh
enableNginx.sh
nginxCertConfig.sh
uninstall_web.sh
web.sh
DNS
The DNS setup is based on two complety independent servers:
•nsd as authoritative nameserver (queries from the inter-
net to this domain).
•unbound as local dns resolver (queries from this host).
Firewall
The firewall configuration is loaded from this file (files/fw.conf).
Standard ports are already defined, additional ports can be
specified in this file.
Anti-spam measures
Following DNS based anti-spam measures are configured for the
mailserver. They makes sure spam mail is recognized during
recieving and all sent mails, reach their destination without
being classified as spam from the recieving side:
•DKIM
•DMARC
•SPF
Entrypoint
This is the main entrypoint for the setup (./setup.sh). From
here on the user is guided through the whole setup process.
Webserver
As webserver two components interact together:
•Nginx is used as a reverse proxy to terminate SSL con-
nections and provide a secure HTTPS connection.
•Apache is used as a web server to provide webpages,
could later also be used as application server (see section
5.1.3).
CHAPTER 2. WALKTHROUGH Page 9 of 76
User Manual Internet Server Set-Up & Security-Hardening Script
2.2 Overview
2.2.1 Complete run
In this section we make a full configuration with the administartions script “setup.sh”. We describe
every step.
First, we will install the ufw (uncomplicated firewall), which will then be configured by the script.
1<INFO > - Tue Jan 8 11:14:31 UTC 2019 - No M o dification Flag found . Seems to be the
fi rst run . Wi ll sta rt h ar de ning now .
2*** Q U E S T I O N *** Do you wish to per f o rm a c o m plete run (Firewall , DNS , SSH , Mail , Web )
[ y/ n ]? y
3<INFO > - Tue Jan 8 11:14:39 UTC 2019 - Com p l e t e run set to true
4
5[...]
At the end of the whole configuration a modification flag is set, which is checked at a rerun. So you
have the option modify and delete at a later time (visible in the next section).
1
2[...]
3
4<INFO > - Tue Jan 8 11:25:19 UTC 2019 - Set modification Flag .
5<INFO > - Tue Jan 8 11:25:19 UTC 2019 - Done . Finished with config u r at i o ns
CHAPTER 2. WALKTHROUGH Page 10 of 76

User Manual Internet Server Set-Up & Security-Hardening Script
2.2.2 Rerun run
If you run the script again at a later time, there are some small changes in the possibilities. New you
will have the option “Modify”, which makes it possible to configure all or certain components again (in
the example only the firewall was configured again), or also the option “Delete”, with which you could
remove certain components.
1*** QUESTION *** Modification Flag found . Please choose option : modif y / uninstall [m /
2u ]? m
3<INFO > - Wed Jan 9 08:45:33 UTC 2019 - Modifica t i on choosen
4*** Q U E S T I O N *** Do you wish to per f o rm a c o m plete run (Firewall , DNS , SSH , Mail , Web )
[ y/ n ]? n
5<INFO > - Wed Jan 9 08:45:34 UTC 2019 - Complete run set to false .
6<INFO > - Wed Jan 9 08:45:34 UTC 2019 - Star t the specific selection for s ing le parts .
7*** QUESTION *** Do you wish to perform action on fw [ y/ n]? y
8<INFO > - Wed Jan 9 08:45:36 UTC 2019 - Action for fw set to true
9*** QUESTION *** Do you wish to pe r form acti on on dns [y / n]? n
10 <INFO > - Wed Jan 9 08:45:37 UTC 2019 - Action for dns set to false ( w il l sk ip it ) .
11 *** QUESTION *** Do you wish to pe r form acti on on ssh [y / n]? n
12 <INFO > - Wed Jan 9 08:45:37 UTC 2019 - Action for ssh set to false ( w il l sk ip it ) .
13 *** QUESTION *** Do you wish to pe rform action on mail [y /n ]? n
14 <INFO > - Wed Jan 9 08:45:40 UTC 2019 - Action for mail set to false ( w il l sk ip it ) .
15 *** QUESTION *** Do you wish to pe r form acti on on web [y / n]? n
16 <INFO > - Wed Jan 9 08:45:43 UTC 2019 - Action for web set to false ( w il l sk ip it ) .
17
18 [...]
19
20 <INFO > - Wed Jan 9 08:45:55 UTC 2019 - Set modif i c atio n Flag .
21 <INFO > - Wed Jan 9 08:45: 5 5 UTC 2019 - Done . Finished with config u rat i ons
Explanation of [...]
At this point specific components are configured, which are explained separately in this document. This
section is only about the administration script, which triggers the whole processes.
CHAPTER 2. WALKTHROUGH Page 11 of 76
User Manual Internet Server Set-Up & Security-Hardening Script
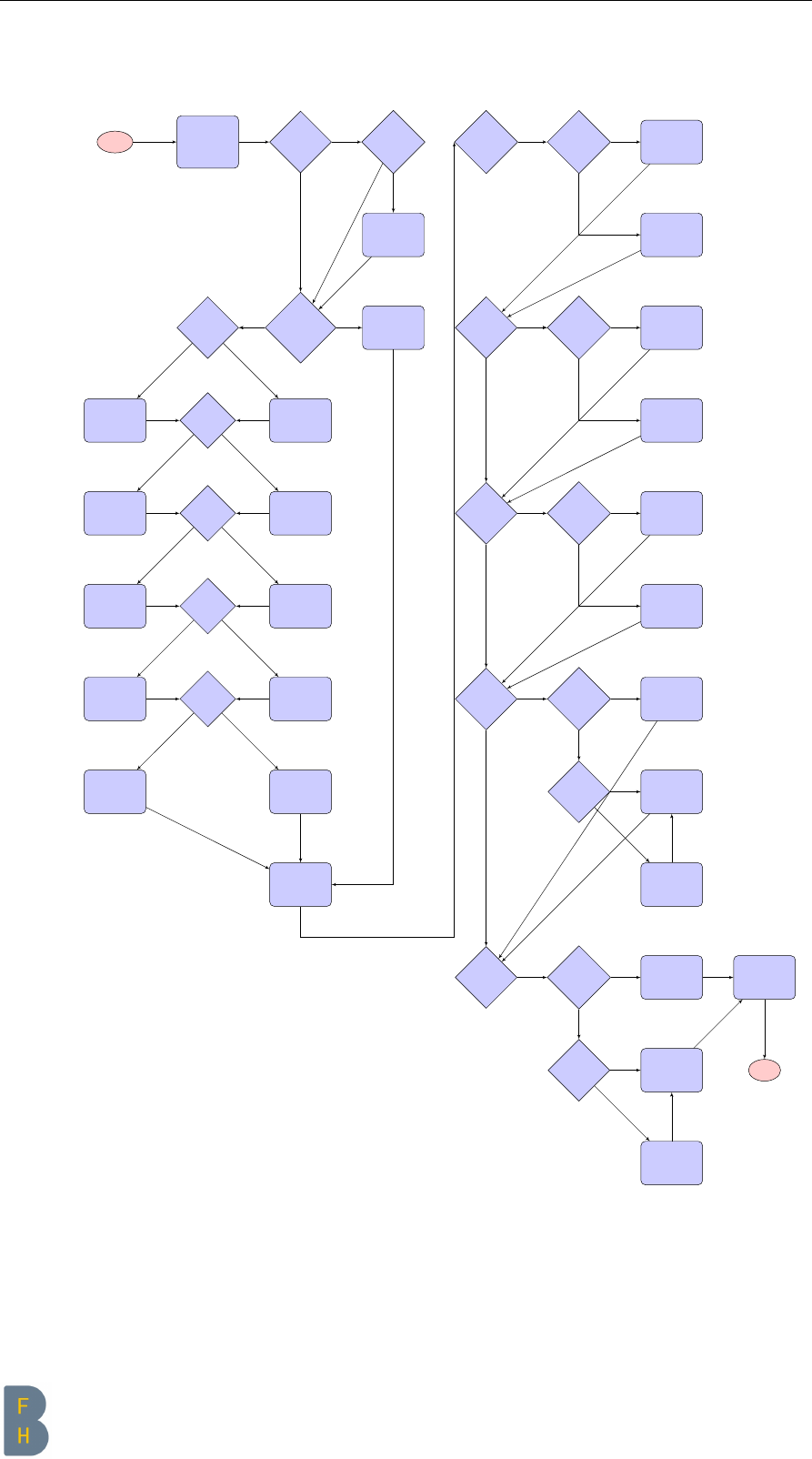
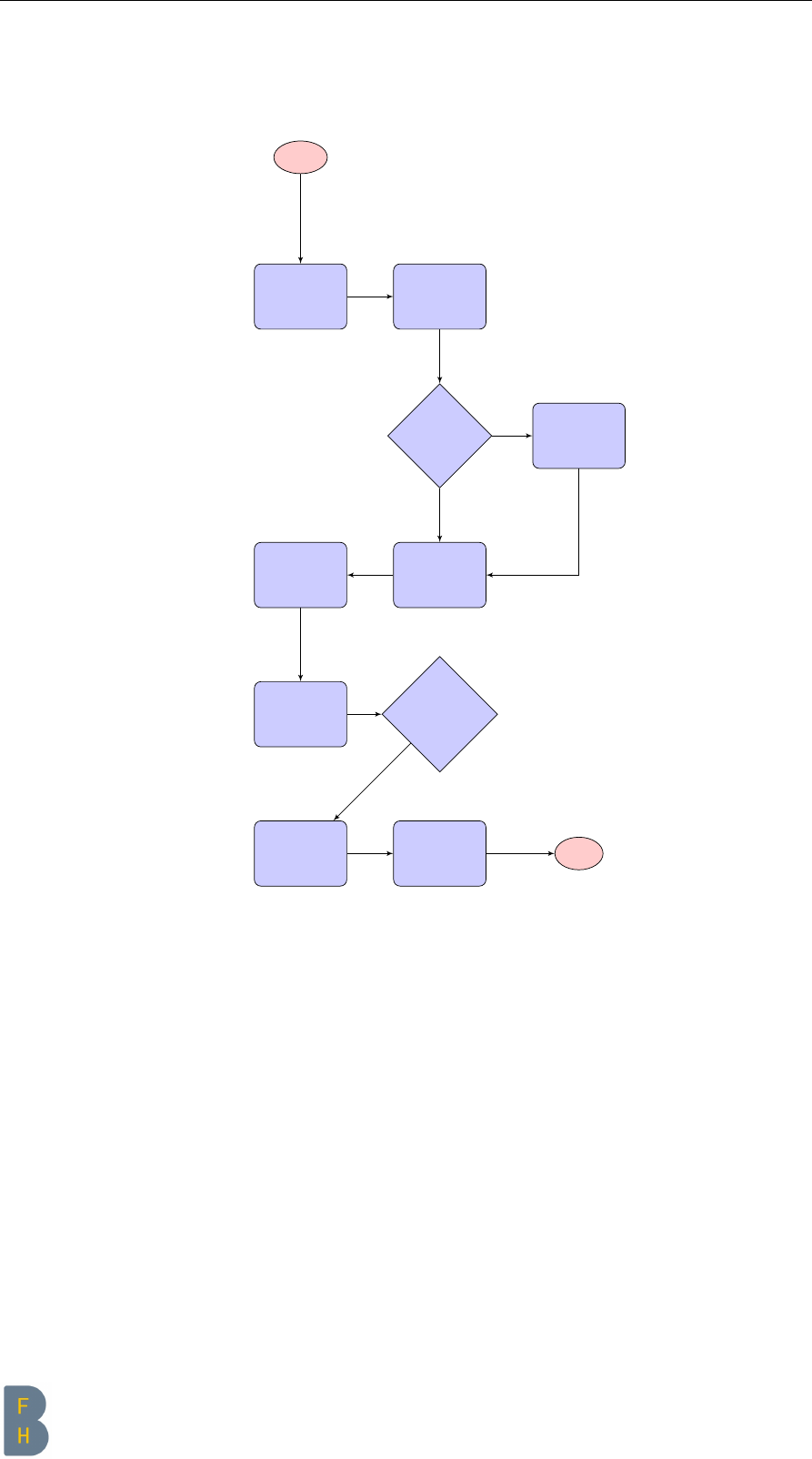
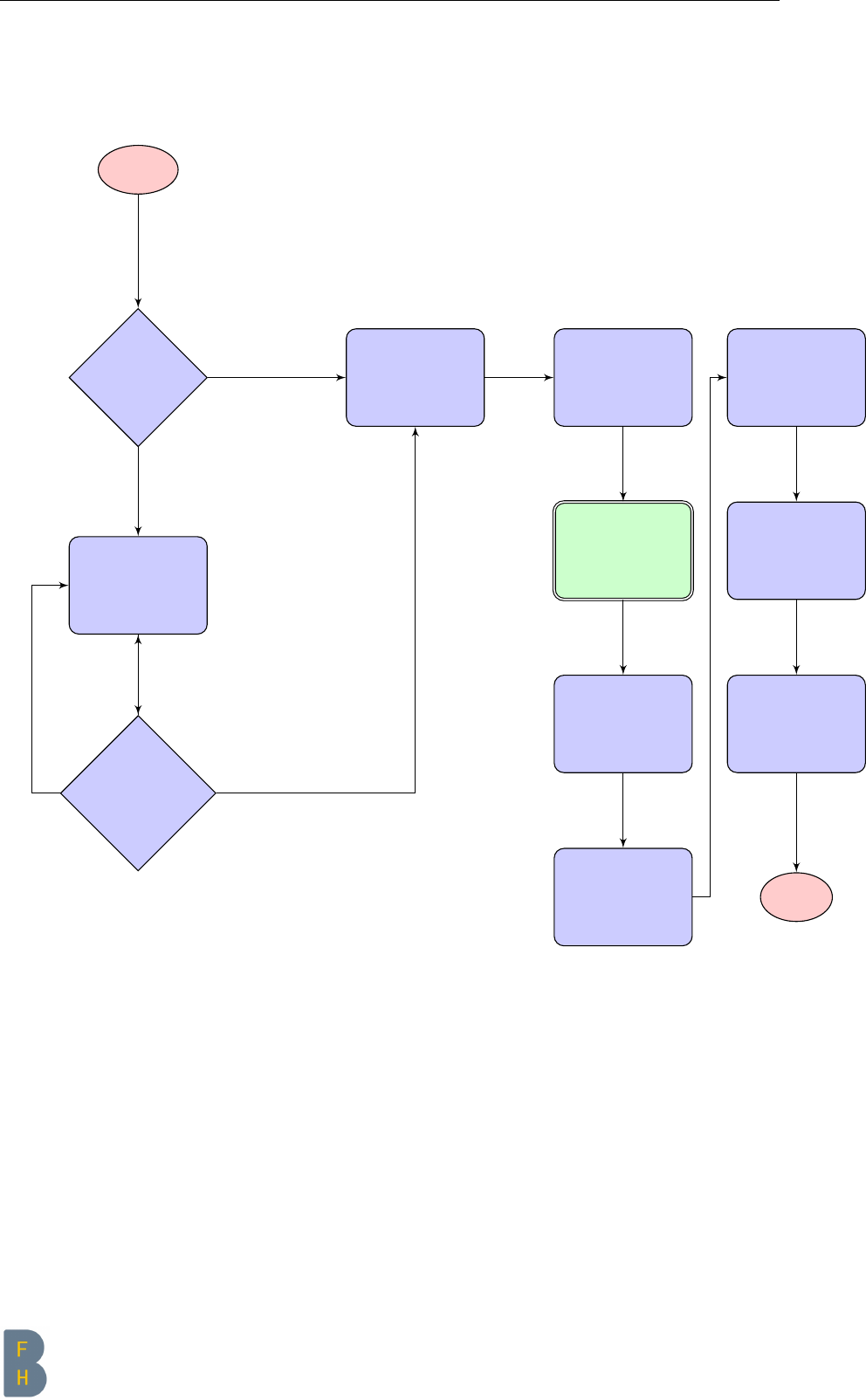
2.2.3 Overview process diagram
start
Initialize
all Flags
(Firewall,
DNS, Mail,
SSH, WEB,
Uninstall)
Check if
first run
Uninstall or
Modify?
Set Uninstall
Flag to 1
Choose if
you want a
full setup
Set all
Flags to 1
Setup
Firewall?
Setup DNS?
Set FW
Falg to 1
Set FW
Falg to 0
Setup SSH?
Set DNS
Falg to 1
Set DNS
Falg to 0
Setup Mail?
Set SSH
Falg to 1
Set SSH
Falg to 0
Setup Web?
Set Mail
Falg to 1
Set Mail
Falg to 0
Set Web
Falg to 1
Set Web
Falg to 0
Done Set
Flags
Firewall
Flag = 1?
Uninstall
Flag = 1? Start Unin-
stall Firewall
Start Firewall
Config-
urations
Start Unin-
stall DNS
Start DNS
Config-
urations
Uninstall
Flag = 1?
DNS Flag =
1?
Skip
Start SSH
Config-
urations
Uninstall
Flag = 1?
SSH Flag =
1?
Start Unin-
stall Mail
Uninstall
Flag = 1?
Mail Flag =
1?
DNS Flag =
1?
Start Mail
Config-
urations
Start DNS
Config-
urations
Web Flag =
1?
Uninstall
Flag = 1? Start Unin-
stall Web
Start Web
Config-
urations
Start DNS
Config-
urations
DNS Flag =
1?
Set first run
done Flag
End
no
yes no
yes
no
yes
no
yes
no
yes
no
yes
no
yes
no
yes yes
yes
yes
yes
yes
yesyes
yes
yes
yes
yes
yes
no
no
no
no
no
no
no
no
no
no
no
yes
Figure 2.1: Setup process diagram
CHAPTER 2. WALKTHROUGH Page 12 of 76

User Manual Internet Server Set-Up & Security-Hardening Script
2.3 Firewall
In this section we make a full Firewall configuration. We describe every step.
First, we will install the ufw (uncomplicated firewall), which will then be configured by the script.
1<INFO > - Tue Jan 8 11:14:39 UTC 2019 - St arting Firewall Co n figur a t ions .
2<INFO > - Tue Jan 8 11:14:39 UTC 2019 - Will install ’ ufw ’ now . Ple ase w ai t ...
3..............
4<INFO > - Tue Jan 8 1 1 : 1 4 : 5 2 UTC 2019 - Package ’ ufw ’ is installe d now .
After the successful installation it goes on with a basic security. This includes enabling all traffic
out and blocking all traffic in. So that nobody is locked out of his own server right at the beginning,
seperat ssh on port 22 is enabled and configured as the only access from outside at this time.
1<INFO > - Tue Jan 8 11:14:53 UTC 2019 - Ufw is enabled now .
2<FW > - Tue Jan 8 11:14:53 UTC 2019 - UFW enable done .
3<INFO > - Tue Jan 8 11:14:53 UTC 2019 - Star t Firewall Hardening . ( close all non
re levant ports )
4<INFO > - Tue Jan 8 11:14:54 UTC 2019 - All incoming and outgoing tr affic is ha n d e l e d
now .
5<FW > - Tue Jan 8 11:14:54 UTC 2 019 - T raffi c controll d one .
6<INFO > - Tue Jan 8 1 1 : 1 4 : 5 4 UTC 2019 - Activate SSH Connection for host ’ XYZ ’.
After setting up the base security, special configurations are loaded, which the user can add by
himself. He does this by adding the necessary rules to the config-file “fw.conf” in the folder “files”.
The user has the possibility to say whether he wants to allow (ALLOW) or deny (DENY) a certain
access. Listed in the output are the minimum accesses needed for a comlete run of the scripts. These
configurations are already present in the configuration file by default. At the very end a list of the now
activated rules will be displayed.
1<INFO > - Tue Jan 8 11:14:55 UTC 2019 - Looking for Firewall Confi g file for specific
configurations
2<INFO > - Tue Jan 8 11 : 1 4 : 5 5 UTC 2019 - File Found . /root/files/fw.conf
3# SSH
4<INFO > - Tue Jan 8 11:15:19 UTC 2019 - Working on ’ al lo w 2 2/ tcp ’ .
5<INFO > - Tue Jan 8 11:15:19 UTC 2019 - Working on ’ al lo w 2 2/ udp ’ .
6# DNS
7<INFO > - Tue Jan 8 11:15:20 UTC 2019 - Working on ’ al lo w 5 3/ tcp ’ .
8<INFO > - Tue Jan 8 11:15:20 UTC 2019 - Working on ’ al lo w 5 3/ udp ’ .
9# MAIL
10 <INFO > - Tue Jan 8 11:15:20 UTC 2019 - Working on ’ al lo w 2 5/ tcp ’ .
11 <INFO > - Tue Jan 8 11:15:20 UTC 2019 - Working on ’ al lo w 2 5/ udp ’ .
12 # SECURE SMTP
13 <INFO > - Tue Jan 8 11:15:21 UTC 2019 - Working on ’ al lo w 465 / t cp ’.
14 <INFO > - Tue Jan 8 11:15:21 UTC 2019 - Working on ’ al lo w 465 / u dp ’.
15 # IMAP
16 <INFO > - Tue Jan 8 11:15:21 UTC 2019 - Working on ’ al lo w 143 / t cp ’.
17 <INFO > - Tue Jan 8 11:15:21 UTC 2019 - Working on ’ al lo w 143 / u dp ’.
18 # IMAP TLS
19 <INFO > - Tue Jan 8 11:15:21 UTC 2019 - Working on ’ al lo w 993 / t cp ’.
20 <INFO > - Tue Jan 8 11:15:22 UTC 2019 - Working on ’ al lo w 993 / u dp ’.
21 # HTTP HTTPS
22 <INFO > - Tue Jan 8 11:15:22 UTC 2019 - Working on ’ al lo w 8 0/ tcp ’ .
23 <INFO > - Tue Jan 8 11:15:22 UTC 2019 - Working on ’ al lo w 443 / t cp ’.
24 <INFO > - Tue Jan 8 11:15:22 UTC 2019 - Done Specific co n f igura t i ons .
25 <FW > - Tue Jan 8 11:1 5 : 2 2 UTC 2019 - Specific Con f i gu r a ti o n s of UFW done .
26 <INFO > - Tue Jan 8 1 1:1 5:22 UTC 2019 - Fi rewall Con figu rat ions done .
27 Status: active
28
29 To Action From
CHAPTER 2. WALKTHROUGH Page 13 of 76

User Manual Internet Server Set-Up & Security-Hardening Script
30 -- -- - --- ----
31 22/ tcp ALLOW An y w h e r e
32 22/ udp ALLOW An y w h e r e
33 53/ tcp ALLOW An y w h e r e
34 53/ udp ALLOW An y w h e r e
35 25/ tcp ALLOW An y w h e r e
36 25/ udp ALLOW An y w h e r e
37 465/ tcp ALLOW An y w h e r e
38 465/ udp ALLOW An y w h e r e
39 143/ tcp ALLOW An y w h e r e
40 143/ udp ALLOW An y w h e r e
41 993/ tcp ALLOW An y w h e r e
42 993/ udp ALLOW An y w h e r e
43 80/ tcp ALLOW An y w h e r e
44 443/ tcp ALLOW An y w h e r e
45 22/ tcp ( v6 ) AL LO W An yw he re ( v6 )
46 22/ udp ( v6 ) AL LO W An yw he re ( v6 )
47 53/ tcp ( v6 ) AL LO W An yw he re ( v6 )
48 53/ udp ( v6 ) AL LO W An yw he re ( v6 )
49 25/ tcp ( v6 ) AL LO W An yw he re ( v6 )
50 25/ udp ( v6 ) AL LO W An yw he re ( v6 )
51 46 5/ t cp ( v6 ) AL LO W An yw he re ( v6 )
52 46 5/ u dp ( v6 ) AL LO W An yw he re ( v6 )
53 14 3/ t cp ( v6 ) AL LO W An yw he re ( v6 )
54 14 3/ u dp ( v6 ) AL LO W An yw he re ( v6 )
55 99 3/ t cp ( v6 ) AL LO W An yw he re ( v6 )
56 99 3/ u dp ( v6 ) AL LO W An yw he re ( v6 )
57 80/ tcp ( v6 ) AL LO W An yw he re ( v6 )
58 44 3/ t cp ( v6 ) AL LO W An yw he re ( v6 )
59
60 <FW > - Tue Jan 8 11:15:22 UTC 2019 - UFW Conf i g ur a t io n s done .
61 <FW > - Tue Jan 8 11:15:22 UTC 2019 - Actions on Firewall Done
CHAPTER 2. WALKTHROUGH Page 14 of 76
User Manual Internet Server Set-Up & Security-Hardening Script
2.3.1 Firewall process diagram
Here we have process diagram of how the script works with all possible outcomes.
start
Start Firewall
Configuration Enable
Firewall
check if
already
active
Activate
Done Ac-
tivation
Deny Incom-
ing Traffic
Allow
Outgoing
Traffic
Load
Specific
Configura-
tions
Activate All
Specific Rules
Done Firewall
Config-
urations
End
yes
no
Figure 2.2: Firewall process diagram
CHAPTER 2. WALKTHROUGH Page 15 of 76
User Manual Internet Server Set-Up & Security-Hardening Script
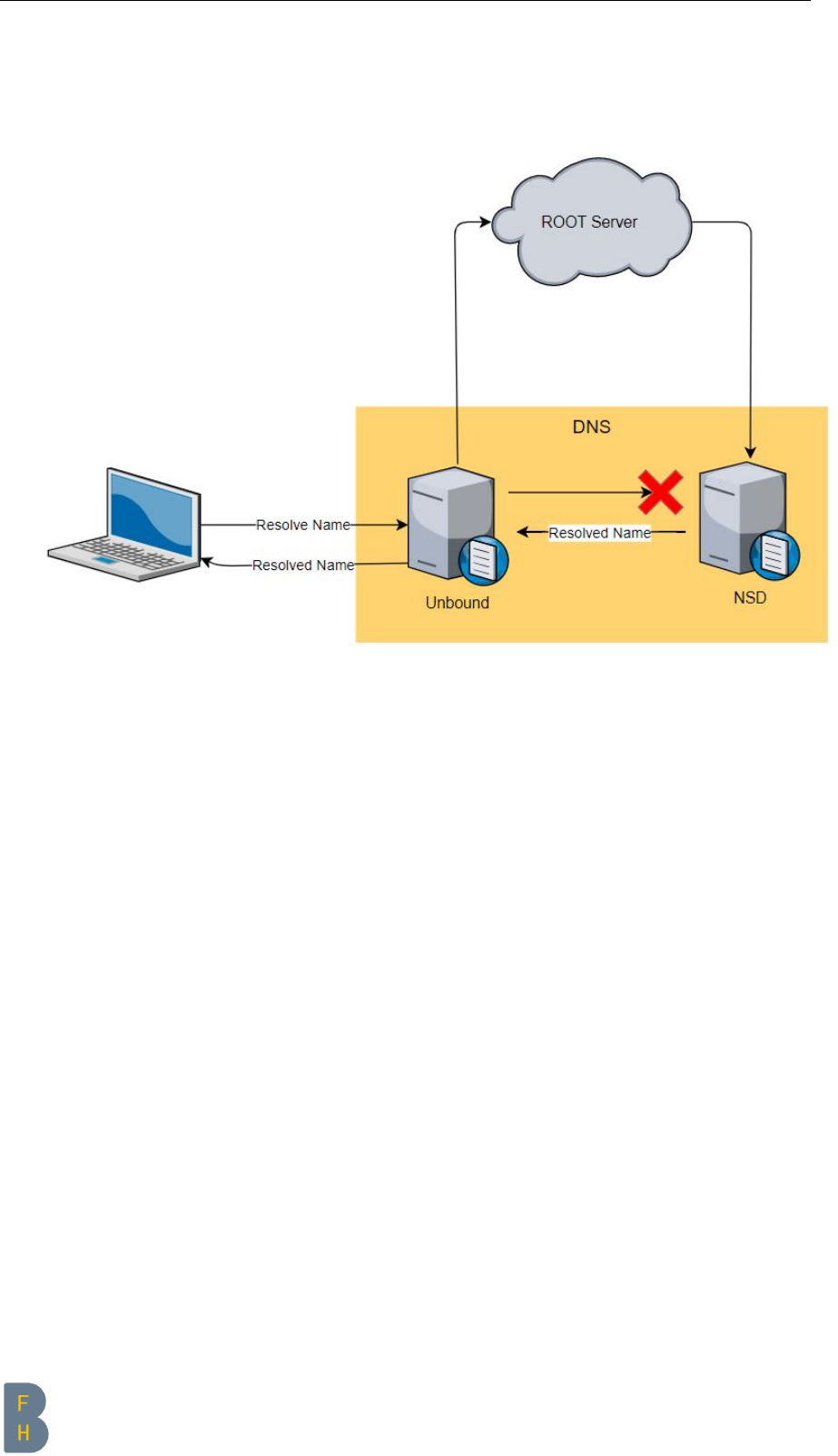
2.4 DNS
In this section we make a full DNS configuration. We describe every step.
First we install unbound , a DNS resolver which will be used from now for all DNS requests from this
server.
1<INFO > - Tue Jan 8 11 : 1 5 : 2 2 UTC 2019 - Starting DNS Conf i gur a tio n s .
2* NOTE * We install two DNS Server , one for i n t e r n al DNS requests ( for this s erv er and /
or home clients ) and one aut h o rit a tiv e DNS Server for your domai n
3* PART 0: We insta ll the basic confi gura tion for un bound - we come back to it later
4<INFO > - Tue Jan 8 11:15:22 UTC 2019 - Install DNS
5<INFO > - Tue Jan 8 11:15:24 UTC 2019 - Will install ’unbound’ now . Pl eas e wait ...
6............
7<INFO > - Tue Jan 8 11:15:36 UTC 2019 - Package ’unbound’ is in st al led now .
8<INFO > - Tue Jan 8 1 1:15: 37 UTC 2019 - Co nfigur e DNS Ha rd ening ( Hide version , use
root - hints file , use trust - anch ored zones for DNSSEC requests )
9<INFO > - Tue Jan 8 11:15:37 UTC 2019 - Configure DNS Ports , IPs
10 <INFO > - Tue Jan 8 11:15:37 UTC 2019 - Server will list en with l o c a lhost on port 53
11 <INFO > - Tue Jan 8 11:15:37 UTC 2019 - Co n f i g ure DNS Ac cess
12 <INFO > - Tue Jan 8 11:15:37 UTC 2019 - Co n f i g ure this Client
13 <INFO > - Tue Jan 8 11 : 1 5 : 3 7 UTC 2019 - Se rver will use localhost as DNS
After we continue with the authoritative Name Server: NSD, have ready your domain (high-
lighted).
1* PART 1: We st art with the a utho rit ativ e Name Serv er : NSD
2
3!! CAUT I ON !! you need your own domain - IF NOT the server wont be functional
4DO NOT use a domai n which does not bel ong to you , it may be i llegal
5* NOTE * If you want to test it only , you can get a free domain like . tk or .ga - just
search in your f a v o r i t e web search engine ( duckduckgo , google etc ..)
6
7Press enter to continue
8
9*** Q U E S T I O N *** do you have your own domain ? (y /n / abort ) y
10 <INFO > - Tue Jan 8 11:15:59 UTC 2019 -
11
12 *** Q U E S T I O N *** please enter your domain : examplerun.cf
13
14 *** QUESTION *** is e xampler un . cf cor rect ? (y/ n/ abort ) y
15
16 <INFO > - Tue Jan 8 11:16:15 UTC 2019 - We will configure the aut h o rit a tiv e DNS
Server with the domain : examplerun.cf
Once the domain is set, check if the follow output is your extern IP, if yes continue.
1*** Q U E S T I O N *** is this 104.248.137.212 your external IP address ? (y ( default)/n/
abort ) y
2<INFO > - Tue Jan 8 11:16:48 UTC 2019 - We will configure the aut h o rit a tiv e DNS Server
with this: 104.248.137.212
3<INFO > - Tue Jan 8 11:16:48 UTC 2019 - Install auth o r it a t ive DNS for : examplerun.cf
4<INFO > - Tue Jan 8 11:16:48 UTC 2019 - Will install ’ nsd ’ now . Ple ase w ai t ...
5..........
6<INFO > - Tue Jan 8 11:16:57 UTC 2019 - Package ’ nsd ’ is i nstalled now .
7<INFO > - Tue Jan 8 11:16:59 UTC 2019 - Will install ’ ldns utils ’ now . Pl eas e wait ...
8........
9<INFO > - Tue Jan 8 11:17:06 UTC 2019 - Package ’ l dns utils ’ is i nstall ed now .
10 <INFO > - Tue Jan 8 11:17:06 UTC 2019 - Co n f i g ure NSD
11 <INFO > - Tue Jan 8 11:17:06 UTC 2019 - Co n f i g ure Forward Zone
12 <INFO > - Tue Jan 8 11:17:06 UTC 2019 - Co n f i g ure Backward Zone
13 <INFO > - Tue Jan 8 11:17:06 UTC 2019 - Fina l steps
14 <INFO > - Tue Jan 8 11 : 1 7 : 1 1 UTC 2019 - Test NSD
CHAPTER 2. WALKTHROUGH Page 16 of 76
User Manual Internet Server Set-Up & Security-Hardening Script
Now you can change, as described, your domain (Glue Records).
1PART 2: You have a full func t i o nal a u t hor i tat i v e Name Serve r BUT your domain hoster
does not know it !
2!! VERY I M P ORTANT !! GO to your domai n hoster , change the name serv er for your domain
to :
3ns1.examplerun.cf with IP: 104.248.137.212
4ns2.examplerun.cf with IP: 104.248.137.212
5!! VERY IMPORTANT !! DO the same for the Glue Records , with the same name server and
IPs
6NOTE : It may take some time to change it - if you have d iffi c ulti e s with this part use
your favorite web searc h engin e
7
8If you are done , press enter to c o n t i nu e
In the last part, if you use the server in your home/work network you can make the domain resolver
we installed (unbound) accessible for your local clients. Mostly it is not the case so you can continue
with “enter”. At the end we test to resolve a ipv4 and a ipv6 address.
1PART 3: *** QUESTION *** Do you rent this server or is it in your internal ne t work
area ? If you dont know what it means just press enter . ( intern / < enter > ( default)
)<enter>
2<INFO > - Tue Jan 8 11 : 1 7 : 4 0 UTC 2019 - Test local DNS
3<INFO > - Tue Jan 8 11:17:40 UTC 2019 - Test ipv4 address
4www . goo gle . com . 3600 IN A 21 6. 58 .2 10 .4
5<INFO > - Tue Jan 8 11:17:40 UTC 2019 - Test ipv6 address
6ipv6 . goo gle . com . 60 4800 IN CN AME ipv 6 .l . goog le . com .
7ipv6 . l . googl e . com . 3600 IN AAA A 2 a00 : 14 50 :4 00 5: 800 :: 20 0 e
8
9Success f u lly in s t a l l e d NSD and Unbound
And we are done with the DNS part!
CHAPTER 2. WALKTHROUGH Page 17 of 76

User Manual Internet Server Set-Up & Security-Hardening Script
2.4.2 DNS process diagram
Here we have process diagram of how the script works with all possible outcomes.
start
Install default
unbound
configuration
Info for user
Has domain
Message
for user
Ask
domainname
end
Domainname
correct
Gets first IP
Check if IP
>1 availble
Asks if
IPAdress is
correct
Make
optionlist
with all IPs
Choose IP
Reverse IPv4
Install NSD
Info for user
Check if IP
>0 availble end
Usage
Unbound
Local Area
Check if IP
>1 availble
Make
optionlist
with all IPs
Choose IP
Reconfiger
Unbound
Local Area
no
yes
abort
Domain Name
no
abort
yes
>1
yes
no = 1
= 0
>0
localhost
local area
>1
= 1
Figure 2.4: DNS process diagram
2.4.3 Multiple domains
After installation you can use multiple sub domains of your domain. All domains will be resolved,
as it is configured with a wild-card: (in this example) *.examplerun.cf. As the script was designed
for someone with basic understanding of computer technology, to have multiple domains on the same
server is not possible.
CHAPTER 2. WALKTHROUGH Page 19 of 76

User Manual Internet Server Set-Up & Security-Hardening Script
2.5 User management
The usermanagment is used whenever a list of users on the unix system must be selected for a service.
In the following subsections you find a brief overview of all the available actions.
2.5.1 Actions
Here you find a short example for each action, inputs are highlighted.
Help
The help text displays at the start of the function end everytime the command help ist entered.
1<INFO > - Mon Jan 14 09:44:29 UTC 2019 - Doing user h a n d l i n g for SSH config u r at i o n
2Usage :
3This function helps you manage the users on this system and select the ones
you wish to provision for the ssh service .
4Following act ion s are ava i l a b l e :
5help : Di splay this help
6di s play : Show all unix users on this system
7add : Add a unix user to this system (this implies the
select action)
8delete : Remove a unix user from this system (this implies the
un select action )
9select : Add an ex i s t i n g unix user to the list of users which
will be pro v i sion e d for the servi c e ssh
10 un s e l e c t : Remove a user from the list of users w hich will be
provisioned for the s e rvice ssh
11 show : Show the list of users which will be provisione d for
the s e rvice ssh
12 quit: Exit this fun c t i o n
Display
Show all unix users on the system:
1<INFO > - Mon Jan 14 09:44:29 UTC 2019 - Number of users s e l e c t e d : 0
2*** Q U E S T I O N *** what actio n do you like to choose ? ( help / displa y /add / delete / sele ct /
un select / show / quit ) display
3
4<INFO > - Mon Jan 14 09 : 4 4 : 4 2 UTC 2019 - Display i n g users for this system
5root
6sync
Add
Add a unix user to the system (this implies the select action)
1<INFO > - Mon Jan 14 09:44:42 UTC 2019 - Number of users s e l e c t e d : 0
2*** Q U E S T I O N *** what actio n do you like to choose ? ( help / displa y /add / delete / sele ct /
un select / show / quit ) add
3
4<INFO > - Mon Jan 14 09 : 4 5 : 0 7 UTC 2019 - Adding user for this system
5*** Q U E S T I O N *** please enter the desired username to be added ? alice
6
7id : ’alice’: no such user
8Adding user ’ a li ce ’ ...
9Adding new group ’ al ic e ’ (1000) ...
CHAPTER 2. WALKTHROUGH Page 20 of 76

User Manual Internet Server Set-Up & Security-Hardening Script
10 Adding new user ’ a li ce ’ ( 1000) with group ’ a li ce ’ ...
11 Cr e a t i n g home d i r e c tory ’/ home / a lic e ’ ...
12 Co p ying files from ’ / etc / ske l ’ ...
13 Enter new UNIX p a s sword :
14 Retype new UNIX password :
15 passwd : pa ssword up dat ed success fully
16 Ch a n g i n g the user i n f orma t i on for alice
17 Enter the new value , or press ENTER for the default
18 Full Name []:
19 Room Number []:
20 Work Phone []:
21 Home Phone []:
22 Other []:
23 Is the inform a t i on correct ? [Y /n ] y
24 <INFO > - Mon Jan 14 09 : 4 5 : 2 2 UTC 2019 - Succ e ssfu l l y added user alice , adding it to
the list for ssh
25
26 *** QUESTION *** Do you want to add sudo priv i l e g es for the user alice ? (y /N ) y
27 <INFO > - Mon Jan 14 09 : 4 5 : 2 8 UTC 2019 - Adding sudo privi l e g es for user alice
28 <INFO > - Mon Jan 14 09 : 4 5 : 2 8 UTC 2019 - Succe s s fuly added sudo privi l e g es for user
alice
Show
Show the list of users which will be provisioned for the service
1<INFO > - Mon Jan 14 09:45:28 UTC 2019 - Number of users s e l e c t e d : 1
2*** Q U E S T I O N *** what actio n do you like to choose ? ( help / displa y /add / delete / sele ct /
un select / show / quit ) alice
3<INFO > - Mon Jan 14 09 : 4 5 : 4 6 UTC 2019 - Display i n g s e l e c t e d users for service ssh
4<INFO > - Mon Jan 14 09:45:46 UTC 2019 - alice
Unselect
Remove a user from the list of users which will be provisioned for the service
1<INFO > - Mon Jan 14 09:45:46 UTC 2019 - Number of users s e l e c t e d : 1
2*** Q U E S T I O N *** what actio n do you like to choose ? ( help / displa y /add / delete / sele ct /
un select / show / quit ) unselect
3<INFO > - Mon Jan 14 09 : 4 5 : 5 6 UTC 2019 - Unsel e c ting user for servi c e ssh
4*** Q U E S T I O N *** please enter the desired username to be re m oved from s e lection ?
alice
5<INFO > - Mon Jan 14 09 : 4 5 : 5 9 UTC 2019 - Remov e d alice from selection for ssh
Select
Add an existing unix user to the list of users which will be provisioned for the service
1<INFO > - Mon Jan 14 09:45:59 UTC 2019 - Number of users s e l e c t e d : 0
2*** Q U E S T I O N *** what actio n do you like to choose ? ( help / displa y /add / delete / sele ct /
un select / show / quit ) select
3<INFO > - Mon Jan 14 09 : 4 6 : 0 7 UTC 2019 - Selecting user for se r v ice ssh
4*** Q U E S T I O N *** please enter the desired username to be selec ted ? alice
5<INFO > - Mon Jan 14 09 : 4 6 : 0 9 UTC 2019 - Selected alice for ssh
CHAPTER 2. WALKTHROUGH Page 21 of 76

User Manual Internet Server Set-Up & Security-Hardening Script
Delete
Remove a unix user from the system (this implies the unselect action)
1<INFO > - Mon Jan 14 09:46:13 UTC 2019 - Number of users s e l e c t e d : 1
2*** Q U E S T I O N *** what actio n do you like to choose ? ( help / displa y /add / delete / sele ct /
un select / show / quit ) delete
3<INFO > - Mon Jan 14 09 : 4 6 : 2 0 UTC 2019 - Removing user for this system
4*** Q U E S T I O N *** please enter the desired username to be de l eted ? sync
5Re m o v i n g files ...
6Re m o v i n g user ’ s yn c ’ ...
7Wa rni ng : group ’nogroup’ has no more members .
8Done.
9<INFO > - Mon Jan 14 09 : 4 6 : 2 3 UTC 2019 - Succ e ssfu l l y deleted user sync
Quit
Exit the function
1<INFO > - Mon Jan 14 09:46:46 UTC 2019 - Number of users s e l e c t e d : 1
2*** Q U E S T I O N *** what actio n do you like to choose ? ( help / displa y /add / delete / sele ct /
un select / show / quit ) quit
2.5.2 User management process diagram
Here we have process diagram of how the script works with all possible outcomes.
start
Enter
username User exists Create user
Enter
additional
user
Add sudo
privileges
Add to
sudo group
end
Yes
No
Yes
No
No
Yes
Figure 2.5: User management process diagram
CHAPTER 2. WALKTHROUGH Page 22 of 76

User Manual Internet Server Set-Up & Security-Hardening Script
2.6 SSH
2.6.1 Configuration
This is an example of the SSH configuration part, all inputs are highlighted in yellow.
User management ssh
Here is a minimal example for the ssh user handling, for further information see section 2.5
1<SSH > - Mon Jan 14 09: 4 4 : 2 9 UTC 2019 - Per f orm actions on SSH
2<SSH > - Mon Jan 14 09: 4 4 : 2 9 UTC 2019 - Per f orm install on SSH
3<INFO > - Mon Jan 14 09:44:29 UTC 2019 - Doing user h a n d l i n g for SSH config u r at i o n
4Usage :
5This function helps you manage the users on this system and select the ones
you wish to provision for the ssh service .
6Following act ion s are ava i l a b l e :
7help : Di splay this help
8di s play : Show all unix users on this system
9add : Add a unix user to this system (this implies the
select action)
10 delete : Remove a unix user from this system (this implies the
un select action )
11 select : Add a existing unix user to the list of users which
will be pro v i sion e d for the servi c e ssh
12 un s e l e c t : Remove a user from the list of users w hich will be
provisioned for the s e rvice ssh
13 show : Show the list of users which will be provisione d for
the s e rvice ssh
14 quit: Exit this fun c t i o n
15
16 <INFO > - Mon Jan 14 09:44:42 UTC 2019 - Number of users s e l e c t e d : 0
17 *** Q U E S T I O N *** what actio n do you like to choose ? ( help / displa y /add / delete / sele ct /
un select / show / quit ) add
18
19 <INFO > - Mon Jan 14 09 : 4 5 : 0 7 UTC 2019 - Adding user for this system
20 *** Q U E S T I O N *** please enter the desired username to be added ? alice
21
22 id : ’alice’: no such user
23 Adding user ’ a li ce ’ ...
24 Adding new group ’ al ic e ’ (1000) ...
25 Adding new user ’ a li ce ’ ( 1000) with group ’ a li ce ’ ...
26 Cr e a t i n g home d i r e c tory ’/ home / a lic e ’ ...
27 Co p ying files from ’ / etc / ske l ’ ...
28 Enter new UNIX p a s sword :
29 Retype new UNIX password :
30 passwd : pa ssword up dat ed success fully
31 Ch a n g i n g the user i n f orma t i on for alice
32 Enter the new value , or press ENTER for the default
33 Full Name []:
34 Room Number []:
35 Work Phone []:
36 Home Phone []:
37 Other []:
38 Is the inform a tion correc t ? [Y / n] y
39 <INFO > - Mon Jan 14 09 : 4 5 : 2 2 UTC 2019 - Succ e ssfu l l y added user alice , adding it to
the list for ssh
40
41 *** QUESTION *** Do you want to add sudo priv i l e g es for the user alice ? (y /N ) y
42 <INFO > - Mon Jan 14 09 : 4 5 : 2 8 UTC 2019 - Adding sudo privi l e g es for user alice
43 <INFO > - Mon Jan 14 09 : 4 5 : 2 8 UTC 2019 - Succe s s fuly added sudo privi l e g es for user
alice
44
45 <INFO > - Mon Jan 14 09:46:46 UTC 2019 - Number of users s e l e c t e d : 1
CHAPTER 2. WALKTHROUGH Page 23 of 76

User Manual Internet Server Set-Up & Security-Hardening Script
46 *** Q U E S T I O N *** what actio n do you like to choose ? ( help / displa y /add / delete / sele ct /
un select / show / quit ) quit
SSH key generation
For every user a personal ssh key-pair is generated, the user has to enter the passphrase. When the
setup is complete the user can download all his keys, certificates and passphrases from the server.
1<INFO > - Mon Jan 14 09 : 4 6 : 5 5 UTC 2019 - Leavi n g user m a nageme n t
2<INFO > - Mon Jan 14 09 : 4 6 : 5 5 UTC 2019 - Generat i n g SSH keys for users
3<INFO > - Mon Jan 14 09:46:55 UTC 2019 - Ge n e rating SSH key for user alice
4<INFO > - Mon Jan 14 09 : 4 6 : 5 5 UTC 2019 - IMPORTANT - make sure you remember ALL the
passphras e s and save your keys to some secure lo c a t i o n - IMPORTANT
5
6<INFO > - Mon Jan 14 09:46:55 UTC 2019 - IM P O R T A N T - !!! passphr a s e MUST be minimum 5
characters long!!! - IMPO R T A N T
7Generating public/private rsa key pair .
8Enter pa ssphr ase ( empty for no pass p h r ase ): ********
9Enter same passphr ase again : ********
10 Your i de nt if ic at io n has b een sa ve d in / hom e / alic e /. s sh / i d_rsa .
11 Your public key h as b ee n saved in / home / a lic e /. ssh / i d_rsa . pub .
12 The k ey f in ge rp ri nt is :
13 SHA256 :82 nk 2iy0lS6n + KJdIIfGeR / T Bbk glLo xihM ZVMd Yif0 al ice@e xampl erun . cf
14 The ke ys r an do ma rt i mag e i s :
15 + -- -[ RSA 4096] - - - -+
16 ....*+o. ..
17 . o.+o . ..
18 o ... . ..
19 o .+o E ...
20 o .*++ S o.
21 o ...+ o.Bo.
22 . .o+=
23 ..o+=o
24 ..oo+=o
25 +- -- -[ SH A256 ] -- -- -+
26 <INFO > - Mon Jan 14 09 : 5 7 : 4 5 UTC 2019 - IMPORTANT - This is your private key , this is
the only thing you need right to save . All of your certi f i cate and keys are saved
to your home . You need this key to do wnload t hem . - IM PORTANT
27 ----- BEG IN RSA P RIV ATE KEY -- -- -
28 Proc - Type : 4, E NCRYPTED
29 DEK - Info : AES -128 - CBC ,8 B5 BF D4 85 A8 05 BA 253 16 C2 1C 26 6C CD CF
30
31 BC h9 X2 Lo 6j xZ Bt VR pr li AhC p / TVX +60 E Px Bu 59 sU VW uk On B8C Ky / bq Eh kO b6D Vsh
32 ...
33 VrxQPgOeipL3zr54Zq9SY6NC2BCu5OygDHWXsKwrBTnx0Hi262jo6bX7Kqmog4qX
34 --- -- END RSA P RIV AT E KEY - -- - -
SSH hardening & cleanup
At the end the user keys are moved to the corresponding user home and the SSH configuration is
hardenend [5]:
•Root login is not permited
•Passwort login is not permited
•X11 is not permited
•Only secure alogrithms are permited
CHAPTER 2. WALKTHROUGH Page 24 of 76

User Manual Internet Server Set-Up & Security-Hardening Script
1<INFO > - Mon Jan 14 09 : 5 7 : 4 5 UTC 2019 - Cleaning up ..
2<INFO > - Mon Jan 14 09 : 5 7 : 4 5 UTC 2019 - Hardening SSH da emon co nfig
3
4<INFO > - Mon Jan 14 09 : 5 7 : 4 5 UTC 2019 - Hardening sshd confi g ( disabl e X11Forwar ding ,
enable d o m a i nname lookup , disable root login , enabling only strong al g o r i thms )
5
6<INFO > - Mon Jan 14 09 : 5 7 : 4 5 UTC 2019 - Hardening complete
7
8<INFO > - Mon Jan 14 09 : 5 7 : 4 5 UTC 2019 - Finishing up , rest a r t ing services
9
10 <INFO > - Mon Jan 14 09 : 5 7 : 4 5 UTC 2019 - Restart i n g all c o m p o nents for SSH
11
12 <INFO > - Mon Jan 14 09:57:45 UTC 2019 - SSH daemon confi g ura t i on complete .
13 <SSH > - Mon Jan 14 09:57:45 UTC 2019 - Actions on SSH Done
2.6.2 SSH process diagram
Here we have a process diagram of how the script works with all possible outcomes.
start
User man-
agement
Generate
SSH Keys
Set Per-
missions
Hardening
SSH Config
Install SSH
Guard
Restart
Services
End
Figure 2.6: SSH process diagram
CHAPTER 2. WALKTHROUGH Page 25 of 76

User Manual Internet Server Set-Up & Security-Hardening Script
2.7 E-Mail
2.7.1 Configurations
This is an example of the Email configuration part, all inputs are highlighted in yellow.
Package installation
First all the neccessary packages are installed, this includes:
•postfix
•mailutils
•letsencrypt
•dovecot
•opendkim
•opendmarc
•zip
1<Mail > - Mon Jan 14 11 : 2 9 : 5 2 UTC 2019 - Perform i n s tall on Mail
2<INFO > - Mon Jan 14 11 : 2 9 : 5 2 UTC 2019 - Se t t ing up MX and SPF re c ords in dns
3
4<INFO > - Mon Jan 14 11 : 2 9 : 5 2 UTC 2019 - Appending DNS recor d s for the mailse r v e r to
zonefile
5
6<INFO > - Mon Jan 14 11 : 2 9 : 5 2 UTC 2019 - Reloading zone files ..
7
8<INFO > - Mon Jan 14 11 : 2 9 : 5 2 UTC 2019 - Install i n g mails e r v e r packages ( postfix ,
mailutils , dove cot )
9<INFO > - Mon Jan 14 11 : 3 0 : 1 5 UTC 2019 - Will install ’ po stf ix - p cr e ’ now . Please wait
...
10 ......
11 <INFO > - Mon Jan 14 11 : 3 0 : 2 1 UTC 2019 - Packa g e ’ p ost fix - p cr e ’ is i nstalled n ow .
12 <INFO > - Mon Jan 14 11 : 3 0 : 2 1 UTC 2019 - Will install ’ postfix - policyd - spf - p ython ’ no w .
Please wait ...
13 .......
14 <INFO > - Mon Jan 14 11 : 3 0 : 2 7 UTC 2019 - Packa g e ’ postfix - policyd - spf - python ’ is
installed now .
15 <INFO > - Mon Jan 14 11 : 3 0 : 2 8 UTC 2019 - Will install ’ mailutils ’ now . Pl eas e wait ...
16 ........
17 <INFO > - Mon Jan 14 11 : 3 0 : 3 6 UTC 2019 - Packa g e ’ m ai lu tils ’ is i nstalle d now .
18 <INFO > - Mon Jan 14 11 : 3 0 : 3 6 UTC 2019 - Will install ’letsencrypt’ now . Pl eas e wait ...
19 ...............
20 <INFO > - Mon Jan 14 11 : 3 0 : 5 1 UTC 2019 - Packa g e ’letsencrypt’ is i nstal led now .
21 <INFO > - Mon Jan 14 11 : 3 0 : 5 1 UTC 2019 - Will install ’ do vec ot - c or e ’ now . Please wait
...
22 .....................
23 <INFO > - Mon Jan 14 11 : 3 1 : 1 1 UTC 2019 - Packa g e ’ d ove cot - c or e ’ is i nstalled n ow .
24 <INFO > - Mon Jan 14 11 : 3 1 : 1 1 UTC 2019 - Will install ’ do vec ot - i ma pd ’ no w . Pl ease wai t
...
25 ..............
26 <INFO > - Mon Jan 14 11 : 3 1 : 2 4 UTC 2019 - Packa g e ’ d ove cot - i ma pd ’ is in st al led now .
27 <INFO > - Mon Jan 14 11 : 3 1 : 2 5 UTC 2019 - Will install ’ op en dk im ’ n ow . Pl ease wai t ...
28 ........
29 <INFO > - Mon Jan 14 11 : 3 1 : 3 3 UTC 2019 - Packa g e ’ o pe nd kim ’ is i ns ta lled now .
30 <INFO > - Mon Jan 14 11 : 3 1 : 3 3 UTC 2019 - Will install ’ op end kim - t oo ls ’ n ow . Pl ease wai t
...
31 ......
32 <INFO > - Mon Jan 14 11 : 3 1 : 3 8 UTC 2019 - Packa g e ’ o pen dki m - t oo ls ’ is i ns talled n ow .
CHAPTER 2. WALKTHROUGH Page 26 of 76

User Manual Internet Server Set-Up & Security-Hardening Script
33 <INFO > - Mon Jan 14 11 : 3 1 : 3 9 UTC 2019 - Will install ’ opendmarc ’ now . Pl eas e wait ...
34 ..........
35 <INFO > - Mon Jan 14 11 : 3 1 : 4 8 UTC 2019 - Packa g e ’ o pe nd marc ’ is i nstalle d now .
36 <INFO > - Mon Jan 14 11 : 3 1 : 4 8 UTC 2019 - Will install ’zip ’ now . Pl ease wait ...
37 ......
38 <INFO > - Mon Jan 14 11 : 3 1 : 5 4 UTC 2019 - Packa g e ’ zip ’ is i nstalled n ow .
Client certificates
The setup allows only logins with personal certificates, the following are generated here. This is a
minimal configuration for the user managment, for further information see section 2.5
1<INFO > - Mon Jan 14 1 1 :31:54 UTC 2019 - Configu r e Mail Hardening (TLS , SPF , DKIM ,
DMARC , dovecot , client certific ate login )
2Usage :
3This function helps you manage the users on this system and select the ones
you wish to provision for the mail s erv ice .
4Following act ion s are ava i l a b l e :
5help : Display this help
6di s play : Show all unix users on this system
7add : Add a unix user to this system (this impl i es the select
action)
8delete : Remove a unix user from this system (this implies the
un select action )
9select : Add a existing unix user to the list of users which will
be provisioned for the servic e mail
10 un s e l e c t : Remove a user from the list of users which will be
provisioned for the s e rvice mail
11 show : Show the list of users which will be p r ovis i o n ed for the
se r vice mail
12 quit: Exit this fun c t i o n
13
14 <INFO > - Mon Jan 14 11:34:31 UTC 2019 - Number of users s e l e c t e d : 0
15 *** Q U E S T I O N *** what actio n do you like to choose ? ( display / add / delete / se lect /
un select / show / quit ) select
16
17 <INFO > - Mon Jan 14 11 : 3 4 : 3 3 UTC 2019 - Selecting user for se r v ice mail
18
19 *** Q U E S T I O N *** please enter the desired username to be selec t e d ? alice
20
21 <INFO > - Mon Jan 14 11 : 3 4 : 3 5 UTC 2019 - Selected alice for mail
22
23 <INFO > - Mon Jan 14 11:34:35 UTC 2019 - Number of users s e l e c t e d : 1
24 *** Q U E S T I O N *** what actio n do you like to choose ? ( display / add / delete / se lect /
un select / show / quit ) quit
25 <INFO > - Mon Jan 14 11 : 3 4 : 3 9 UTC 2019 - Leavi n g user m a nageme n t
Postfix configuration
In this setup postfix acts as the SMTP Server to send an recieve mail. The script now configures all
the neccessary postfix components [4]:
•User mappings (alias, canonical)
•Service users
•TLS (letsencrypt)
•Anti spam measures (SPF, DKIM, DMARC)
CHAPTER 2. WALKTHROUGH Page 27 of 76
User Manual Internet Server Set-Up & Security-Hardening Script
1
2<INFO > - Mon Jan 14 11 : 3 4 : 3 9 UTC 2019 - Mapping users to mail ad d r esses
3
4<INFO > - Mon Jan 14 11:34:39 UTC 2019 - Adding users to alias and canonical file
5
6<INFO > - Mon Jan 14 11 : 3 4 : 3 9 UTC 2019 - Adding sup p l em e n tar y p ostmas t e r user for dmarc
reporting
7
8<INFO > - Mon Jan 14 11 : 3 4 : 3 9 UTC 2019 - Setti n g up TLS with l etse n c r ypt
9
10 <INFO > - Mon Jan 14 11 : 3 4 : 3 9 UTC 2019 - Runni n g l e t senc r y pt to obtain a ce r tifi c a t e
11
12 <INFO > - Mon Jan 14 11 : 3 4 : 4 0 UTC 2019 - Will install ’certbot’ now . P lease wai t ...
13 ...
14 <INFO > - Mon Jan 14 11 : 3 4 : 4 2 UTC 2019 - Packa g e ’certbot’ is i nstalled now .
15 Sa ving d ebu g l og to / var / log / le tsen cry pt / le tsen cry pt . log
16 Pl u gins selected : Au t h ent i cat o r standalone , Installe r None
17 Obtaining a new certificate
18 Performing the following cha l l e nges :
19 http -01 c h allenge for mail . examp l e r un . cf
20 Waiting for verification...
21 Cl e a n i n g up challenges
22
23 IMPORTANT NOTES :
24 - C on g ra tu la t io ns ! Yo ur c er ti fi ca te a nd ch ai n hav e be en s ave d at :
25 / etc / le ts enc rypt / l ive / m ail . exam pleru n . cf / f ul lc hain . pem
26 Your key file has been saved at :
27 / etc / le ts enc rypt / l ive / m ail . exam pleru n . cf / p rivkey . pem
28 Your cert will expire on 2019 -04 -14. To obtain a new or tweaked
29 version of this cert i f icat e in the future , simply run certbot
30 ag ain . To non - i nt er ac ti ve ly ren ew * a ll * of y ou r ce rti fica tes , r un
31 " cert bot r en ew "
32
33 - Your acc o unt cr e d entia l s have been saved in your Ce r tbot
34 con fi gur at ion d irectory at / e tc / let sen cryp t . You s hou ld m ake a
35 secure backup of this fo lde r now . This c on fi gu ra ti on d irectory will
36 also c o n tain ce r t ific a t es and private keys o b tained by C e rtbot so
37 making reg u lar backups of this folder is id ea l .
38
39 - If you like Certbot , please c onsider su p p o rting our work by :
40
41 Do na ti ng to IS RG / L ets E nc ryp t : ht tp s : // lets encr ypt . org / d onate
42 Do na ti ng to EFF : ht tp s : // eff . org / do nate - le
43
44 <INFO > - Mon Jan 14 11:34:50 UTC 2019 - Co nfigu r i ng TLS for postfix
45
46 <INFO > - Mon Jan 14 11:34:51 UTC 2019 - TLS confi g u ra t i on for po s t fix complete
47
48 <INFO > - Mon Jan 14 11 : 3 4 : 5 1 UTC 2019 - Restart i n g p ostfix servic e
49
50 <INFO > - Mon Jan 14 11 : 3 4 : 5 3 UTC 2019 - Se t t ing up SPF ( anti spam measur e )
51
52 <INFO > - Mon Jan 14 11 : 3 4 : 5 3 UTC 2019 - Adding SPF confi g ura t i on to u nbound
53
54 <INFO > - Mon Jan 14 11 : 3 4 : 5 3 UTC 2019 - Adding SPF confi g ura t i on to p ostfix con fig
55
56 <INFO > - Mon Jan 14 11 : 3 4 : 5 3 UTC 2019 - Setting up DKIM ( anti spam measure )
57
58 <INFO > - Mon Jan 14 11 : 3 4 : 5 3 UTC 2019 - Creating users for DKIM
59
60 <INFO > - Mon Jan 14 11 : 3 4 : 5 3 UTC 2019 - Confi g u ring opendkim
61
62 opendkim - genk ey : gen erating private key
63 opendkim - genk ey : private key writ t en to 20190 1 1 411. private
64 opendkim - genk ey : ext racting public key
CHAPTER 2. WALKTHROUGH Page 28 of 76

User Manual Internet Server Set-Up & Security-Hardening Script
65 opendkim - genk ey : DNS TXT record w ritte n to 2019011 411. txt
66
67 <INFO > - Mon Jan 14 11 : 3 4 : 5 4 UTC 2019 - Reloading systemd unit s
68
69 <INFO > - Mon Jan 14 11 : 3 4 : 5 5 UTC 2019 - Generat i n g DNS records for opendkim
70
71 <INFO > - Mon Jan 14 11:34:55 UTC 2019 - Setting up DMARC ( anti spoofing measur e )
72
73 <INFO > - Mon Jan 14 11 : 3 4 : 5 5 UTC 2019 - Conf i gurt i n g opendmarc
74
75 <INFO > - Mon Jan 14 11 : 3 4 : 5 5 UTC 2019 - Reloading systemd unit s
76
77 <INFO > - Mon Jan 14 11 : 3 4 : 5 5 UTC 2019 - Adding DNS r e cords for op e n d m a r c
78
79 <INFO > - Mon Jan 14 11 : 3 4 : 5 5 UTC 2019 - Integ r a ting op e n d m a r c into pos t fix
Dovecot configuration
Dovecot acts as the IMAP server to enable clients to fetch mail from the server. The authentication is
done via client certificates [11]. At the end the generated certificates for the user can be downloaded
over a secure SSH connection. This includes:
•Dovecot SSL (letsencrypt)
•Authentication via certificates
•Preparation of artifacts (ZIP file with certificates) and download command
1<INFO > - Mon Jan 14 11 : 3 4 : 5 5 UTC 2019 - Con f i guri n g dovecot as imap server
2
3<INFO > - Mon Jan 14 11 : 3 4 : 5 5 UTC 2019 - Confi g u ring dovecot
4
5<INFO > - Mon Jan 14 11 : 3 4 : 5 5 UTC 2019 - Confi g u ring dovecot ser v ice
6
7<INFO > - Mon Jan 14 11 : 3 4 : 5 5 UTC 2019 - Confi g u ring dovecot SSL
8
9<INFO > - Mon Jan 14 11 : 3 4 : 5 5 UTC 2019 - Confi g u ring dovecot SSL
10
11 <INFO > - Mon Jan 14 11 : 3 4 : 5 5 UTC 2019 - Confi g u ring external auth ext e n s i o n
12
13 <INFO > - Mon Jan 14 11 : 3 4 : 5 5 UTC 2019 - Confi g u ring postfix for client certificates
14
15 <INFO > - Mon Jan 14 11 : 3 4 : 5 5 UTC 2019 - Confi g u ring client c e rtifi c a te a u t he n t ic a tio n
16
17 <INFO > - Mon Jan 14 11 : 3 4 : 5 7 UTC 2019 - Generat i n g cer t i f icat e authority , please enter
a pa s sphrase when promted :
18
19 Enter New CA Key Passphra s e : ******
20 Re - Ent er New CA Key Passphrase : ******
21 Generating RSA private key , 4096 bit long modulus
22 ........................................................................
23 ........................................................................
24 ........................................................................
25 ....................................++
26 ..................++
27 e is 65537 (0 x010001 )
28 Enter pass phras e for / r oot / src / E as yRSA -3. 0. 5/ pk i / private/ ca . key : ******
29 / ro ot / s rc
30
31 <INFO > - Mon Jan 14 11:35:07 UTC 2019 - Ge n e rating key and ce r t ific a t e for user alice
32 <INFO > - Mon Jan 14 11 : 3 5 : 0 7 UTC 2019 -
IMPORTANT - make sure you remember ALL the passphrases! You can download your certificate and key
33 after the setup. - IMPORTANT
CHAPTER 2. WALKTHROUGH Page 29 of 76

User Manual Internet Server Set-Up & Security-Hardening Script
34
35 Signature ok
36 su bj ec t = CN = alic e , e ma i lA dd re ss = a li c e@ ex am p le ru n . cf
37 Getting CA Private Key
38 Enter pass phras e for / etc / ssl / private/ e xa mp l er un . cf . ca . k ey :
39
40 <INFO > - Mon Jan 14 11 : 3 5 : 1 3 UTC 2019 -
IMPORTANT - certificate and key for the user "alice" are saved to his home. He can download it
41 later over a secure SSH connection - IMPORTANT
42
43 <INFO > - Mon Jan 14 11 : 3 5 : 1 3 UTC 2019 - Cleaning up ..
44 <INFO > - Mon Jan 14 11 : 3 5 : 1 3 UTC 2019 - Creating zip file for alice user arti f a c t s
45 adding : id_rs a ( deflated 24%)
46 ad ding : id _rsa . pub ( deflated 2 0% )
47 adding : alice . example r u n . cf . clientcer t . pem ( deflated 27%)
48 <INFO > - Mon Jan 14 11 : 3 5 : 1 3 UTC 2019 - This is your command to do w n l o a d your files
to your local direct o r y ( rsync needs to be inst a l l e d on your client ):
49 rsync -e \ssh -i PATH TO YOUR SSH PRIVATE KEY" --remove-source-files -av alice@examplerun.cf:/home/ali
50 ce/alice artifacts.zip ./
51 <INFO > - Mon Jan 14 11 : 3 5 : 1 3 UTC 2019 - Finishing up , rest a r t ing services
52
53 <INFO > - Mon Jan 14 11 : 3 5 : 1 3 UTC 2019 - Restarting all c o m p o nents of the m ailser v e r
54
55 <INFO > - Mon Jan 14 11 : 3 5 : 1 7 UTC 2019 - Mailser v e r co n f ig u r ati o n complete .
56 <Mail > - Mon Jan 14 11 : 3 5 : 1 7 UTC 2019 - Actions on Mail Done
CHAPTER 2. WALKTHROUGH Page 30 of 76
User Manual Internet Server Set-Up & Security-Hardening Script
2.7.2 E-Mail process diagram
Here we have process diagram of how the script works with all possible outcomes.
start
Domain or
subdomain
Choose
subdomain
Subdomain
part of
domain
Write
MX entry Install mail
packages
User man-
agement
Create
alias files
Configure
Mailserver
Genereate
certificate
authority
Genereate
client
certificates
Resatrt
service
End
Domain
Subdomain
Yes
No
no
Figure 2.7: Email process diagram
2.7.3 Multiple e-mail addresses
With the user management you can create multiple users. All of them will get their own mail address.
In this version of the script it is not possible to have multiple mail addresses per user. See subsection
5.1.2.
CHAPTER 2. WALKTHROUGH Page 31 of 76

User Manual Internet Server Set-Up & Security-Hardening Script
2.8 Web
The web part was developed in addition to the mandatory requirements. It runs through without the
user having to do anything. For these reasons (especially the second one), the descriptions are also
rather small. The code snippets here above show how a clean run without errors looks like. In the web
part, as in all other parts, everything necessary will be installed first.
1<INFO > - Tue Jan 8 11 : 2 4 : 2 1 UTC 2019 - Starting WEB Conf i gur a tio n s .
2<INFO > - Tue Jan 8 11:24:21 UTC 2019 - Will install ’ ng in x ’ now . Pl eas e wait ...
3...........
4<INFO > - Tue Jan 8 11:24:32 UTC 2019 - Package ’ n gin x ’ is i ns talle d now .
5<INFO > - Tue Jan 8 11:24:33 UTC 2019 - Will install ’certbot’ now . Pl eas e wait ...
6....
7<INFO > - Tue Jan 8 11:24:36 UTC 2019 - Package ’certbot’ is in st al led now .
8<INFO > - Tue Jan 8 11:24:36 UTC 2019 - Will install ’ python - certbo t - ng inx ’ now .
Please wait ...
9.......
10 <INFO > - Tue Jan 8 11:24:43 UTC 2019 - Package ’ python - cer tbot - ngin x ’ is in s t alled
now .
11 <INFO > - Tue Jan 8 11:24:43 UTC 2019 - Will install ’apache2’ now . Pl eas e wait ...
12 ..............
13 <INFO > - Tue Jan 8 11:24:57 UTC 2019 - Package ’apache2’ is in st al led now .
As the next step after installation, the nginix is configured.
1<INFO > - Tue Jan 8 11:24:57 UTC 2019 - St arting nginx Con f igu r ati o ns .
2<INFO > - Tue Jan 8 11:24:57 UTC 2019 - Ngin x is al ready activated .
3<INFO > - Tue Jan 8 11:24:57 UTC 2019 - Star t Nginx Hardening . (TLS , r e d i r e c t http - >
https , se c u i r t y headers , no server token , timeouts )
With openssl a certificate will be created in a next step. The certificate is then used for ssl termination.
1<INFO > - Tue Jan 8 11:24:57 UTC 2019 - Star t openssl to generate a ssl pem file .
2Generating DSA parameters , 4096 bit long prime
3.............+.......+.....+.........+..............
4+++++++++++++++++++++++++++++++++++++++++++++++++++*
5.............+..+.+.................+.....+...+.....
6.........+......+.......+...........................
7< INFO > - T ue Jan 8 1 1:2 5: 08 UTC 2 019 - Don e . Yo ur fi le is lo ca ted her e : / etc / ssl /
dh 4096 . pe m . Will st art c ertb ot .
8Sa ving d ebu g l og to / var / log / le tsen cry pt / le tsen cry pt . log
9Pl ugi ns selected : Auth e nticat o r nginx , Installer nginx
10 Obtaining a new certificate
11 Performing the following cha l l e nges :
12 http -01 c h allenge for e xa mp le ru n . cf
13 http -01 c h allenge for www . exampleru n . cf
14 Waiting for verification...
15 Cl e a n i n g up challenges
16
17 IMPORTANT NOTES :
18 - C on g ra tu la t io ns ! Yo ur c er ti fi ca te a nd ch ai n hav e be en s ave d at :
19 / etc / le ts enc rypt / l ive / exam pleru n . cf / f ul lc hain . pem
20 Your key file has been saved at :
21 / etc / le ts enc rypt / l ive / exam pleru n . cf / p rivkey . pem
22 Your cert will expire on 2019 -04 -08. To obtain a new or tweaked
23 version of this cert i f icat e in the future , simply run certbot
24 ag ain . To non - i nt er ac ti ve ly ren ew * a ll * of y ou r ce rti fica tes , r un
25 " cert bot r en ew "
26 - If you like Certbot , please c onsider su p p o rting our work by :
27
28 Do na ti ng to IS RG / L ets E nc ryp t : ht tp s : // lets encr ypt . org / d onate
29 Do na ti ng to EFF : ht tp s : // eff . org / do nate - le
CHAPTER 2. WALKTHROUGH Page 32 of 76

User Manual Internet Server Set-Up & Security-Hardening Script
Nginx will then be hardened [12]:
•Enable secure SSL protocols only (>=TLSv1.2)
•Secure cipher sets (no known vulnerabilities)
•Redirect all connections from HTTP to HTTPS
•Turn off server tokens
1<INFO > - Tue Jan 8 11:25:19 UTC 2019 - Will remo ve default sites of nginx
2<INFO > - Tue Jan 8 11:25:19 UTC 2019 - Will start to setup nginx . conf file
3<INFO > - Tue Jan 8 11:25:19 UTC 2019 - Done . Your file is located under ’/ e tc / n gin x /
ng in x . conf ’ .
4<INFO > - Tue Jan 8 11 : 2 5 : 1 9 UTC 2019 - Will start specific C onf i gur a tio n s
5<INFO > - Tue Jan 8 11:25:19 UTC 2019 - Done . Your file is located under ’/ e tc / n gin x /
conf . d/ exampl e r u n .cf . conf ’.
6<INFO > - Tue Jan 8 11 : 2 5 : 1 9 UTC 2019 - Will check Syn tax and activate .
7nginx : the conf igura tion file / etc / ng inx / nginx . conf sy nta x is ok
8nginx : co nf igura tion file / etc / nginx / ngi nx . conf test is succes sful
In the next and last step the apache will be configured. This setup places apache behind nginx
as pure webserver. All connections are passed through nginx where SSL is terminated. Later on it
would be possible to extend this setup with a WAF like ModSecurity which would provide an aditional
security layer. See section 5.2.
1<INFO > - Tue Jan 8 11:25:19 UTC 2019 - St arting apach e C o nfigu r a tions .
2<INFO > - Tue Jan 8 11:25:19 UTC 2019 - Apache is already ac tivated .
3<INFO > - Tue Jan 8 11:25:19 UTC 2019 - Foun d enabled default site , re m o v i n g symlink
4<INFO > - Tue Jan 8 11 : 2 5 : 1 9 UTC 2019 - Will Setup a default mini webpage .
5<INFO > - Tue Jan 8 11 : 2 5 : 1 9 UTC 2019 - Will Setup a se p e r a t e ports . conf file .
6<INFO > - Tue Jan 8 11 : 2 5 : 1 9 UTC 2019 - Will Setup avaibl e sites .
7<INFO > - Tue Jan 8 11 : 2 5 : 1 9 UTC 2019 - Will check Syn tax and activate .
8Syntax OK
2.8.1 Web architecture diagram
For a better understanding of how the proxy server interacts with the web server, see this small diagram.
Figure 2.8: Architecture Web
CHAPTER 2. WALKTHROUGH Page 33 of 76
User Manual Internet Server Set-Up & Security-Hardening Script
3 Hardening Tests
3.1 Firewall
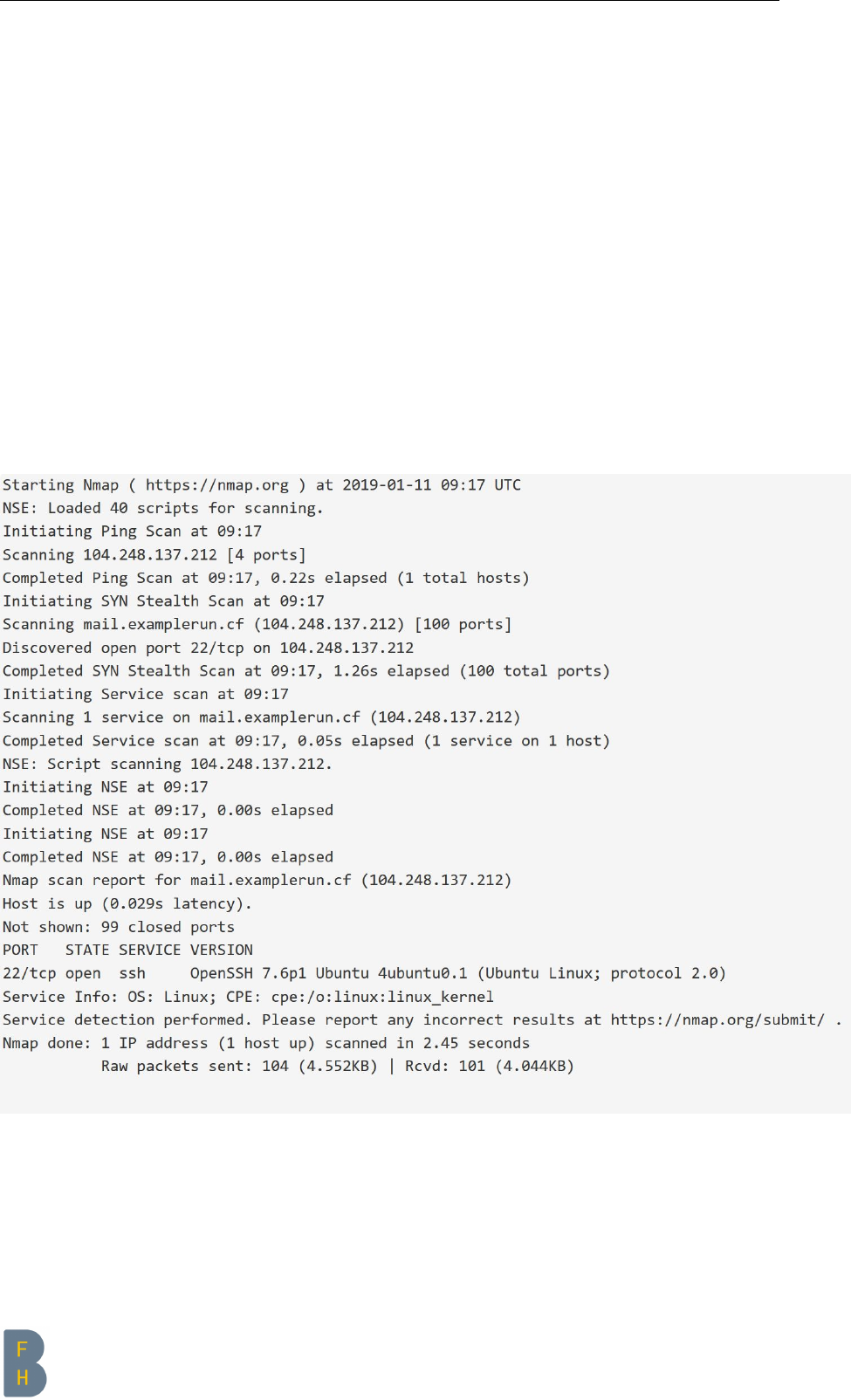
The firewall is an important factor in security. Open or incorrectly configured ports can quickly make a
server vulnerable, especially if you have other components running on it. The firewall was tested with
nmap [3]
BEFORE script
It should also be mentioned that the “before” run looks worse than the “after” run at first sight (more
open ports). This is because ports needed for the components must be opened. The rest of the traffic
is safely closed for this, so the server owner has control over it.
Figure 3.1: Firewall (without DNS) BEFORE
CHAPTER 3. HARDENING TESTS Page 34 of 76

User Manual Internet Server Set-Up & Security-Hardening Script
3.2 DNS
3.2.1 Domain name resolver
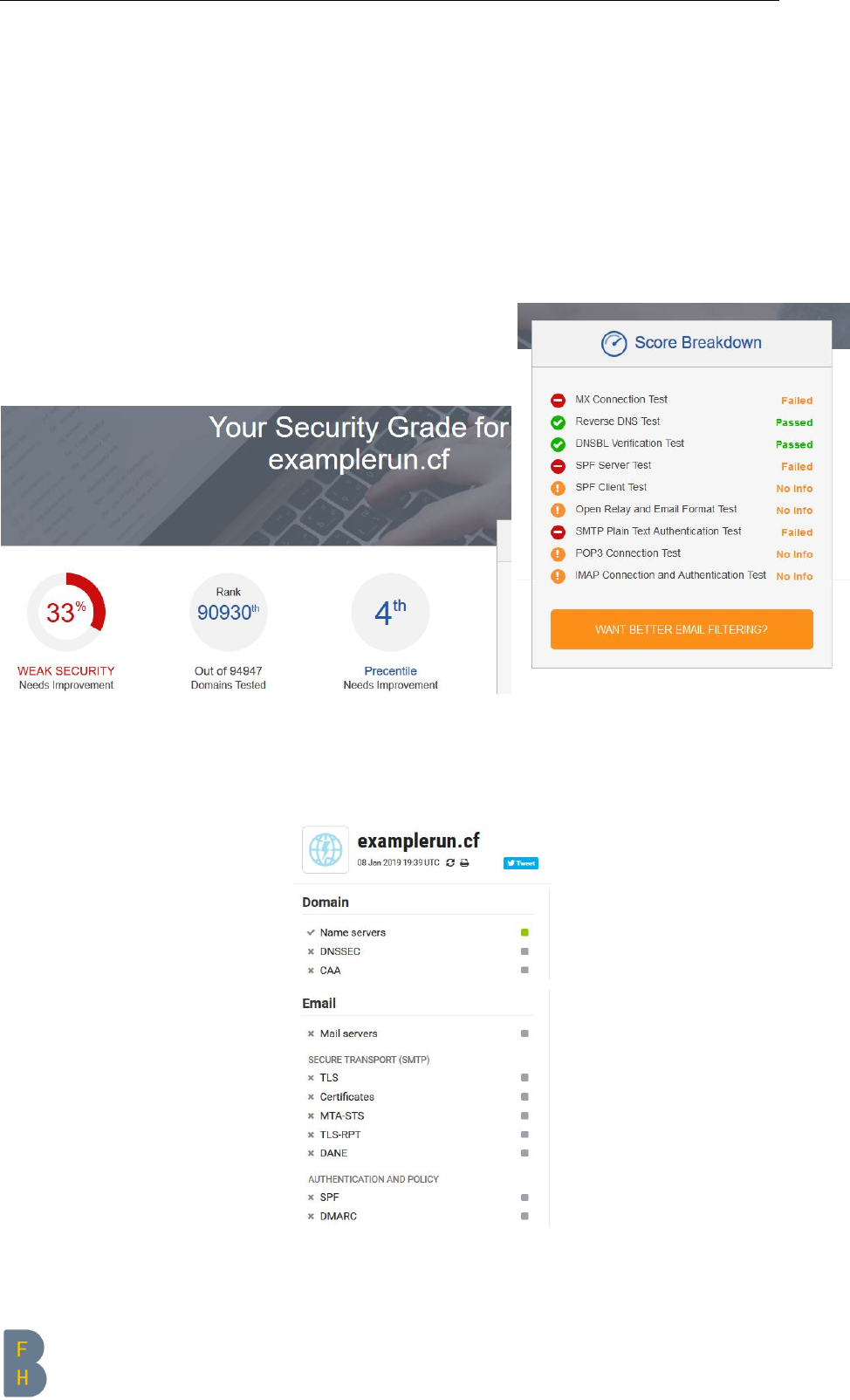
As you have a brand new server you are most probably have use a domain name resolver from a big
company like Google, Cloudfare etc. But after the script you have your own resolver which is even
better than the one which is by default configured.
BEFORE script
Before running the script you get a C from https://cmdns.dev.dns-oarc.net/ [8]
Figure 3.4: Name resolver BEFORE
Figure 3.5: Name resolver details BEFORE
CHAPTER 3. HARDENING TESTS Page 37 of 76

User Manual Internet Server Set-Up & Security-Hardening Script
3.2.2 Authoritative DNS
To setup a authoritative DNS is not easy, and mistakes are easily made.
BEFORE script
Before running the script if you do by hand, misconfiguration can happen. As you can see from
https://mxtoolbox.com/ [6].
Figure 3.8: Authoritative DNS test BEFORE
After script
If you do it with the script, everything will be fine.
Figure 3.9: Authoritative DNS test AFTER
CHAPTER 3. HARDENING TESTS Page 39 of 76

User Manual Internet Server Set-Up & Security-Hardening Script
3.3 SSH
3.3.1 SSH daemon
You recieve a server with a default SSH daemon setup from your provider or have one at home with a
default configuration from your Unix/Linux distro.
BEFORE script
Here we are testing a server with a default setup from https://digitalocean.com (the results might
differ, depending where your server is hosted).
Before the SSH daemon is hardened we recieve the following result, some of the “Key Exchange
Algorithms” and “MAC Algorithms” are weak [10].
Figure 3.10: SSH daemon BEFORE
CHAPTER 3. HARDENING TESTS Page 40 of 76
User Manual Internet Server Set-Up & Security-Hardening Script
3.4 E-Mail
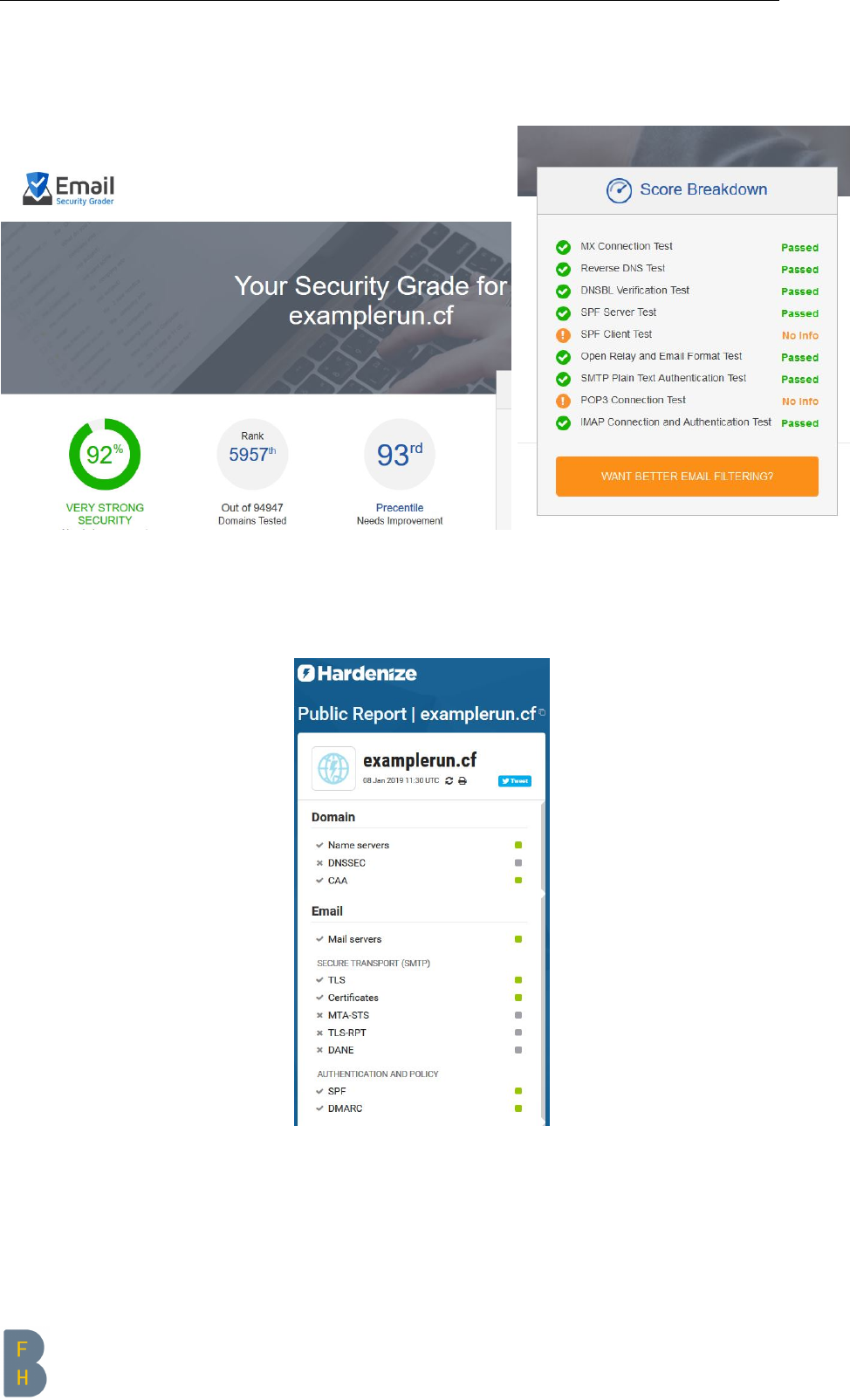
To run a E-Mail server is not easy at all. Even professional providers which should setup your email
server for you do mostly mistakes. A insecure email server is also very attractive for hackers.
3.4.1 E-Mail server configuration
BEFORE script
If you use a basic email configuration, your email server will mostly look like this (graded from:
https://www.hardenize.com [2], https://emailsecuritygrader.com [13])
(a) Rank (b) Details
Figure 3.12: Mail BEFORE (emailsecuritygrader.com)
Figure 3.13: Mail BEFORE (hardenize.com)
CHAPTER 3. HARDENING TESTS Page 42 of 76
User Manual Internet Server Set-Up & Security-Hardening Script
AFTER script
But if you configure your email server with the script, it will look like this:
(a) Rank (b) Details
Figure 3.14: Mail AFTER (emailsecuritygrader.com)
Figure 3.15: Mail AFTER (hardenize.com)
CHAPTER 3. HARDENING TESTS Page 43 of 76
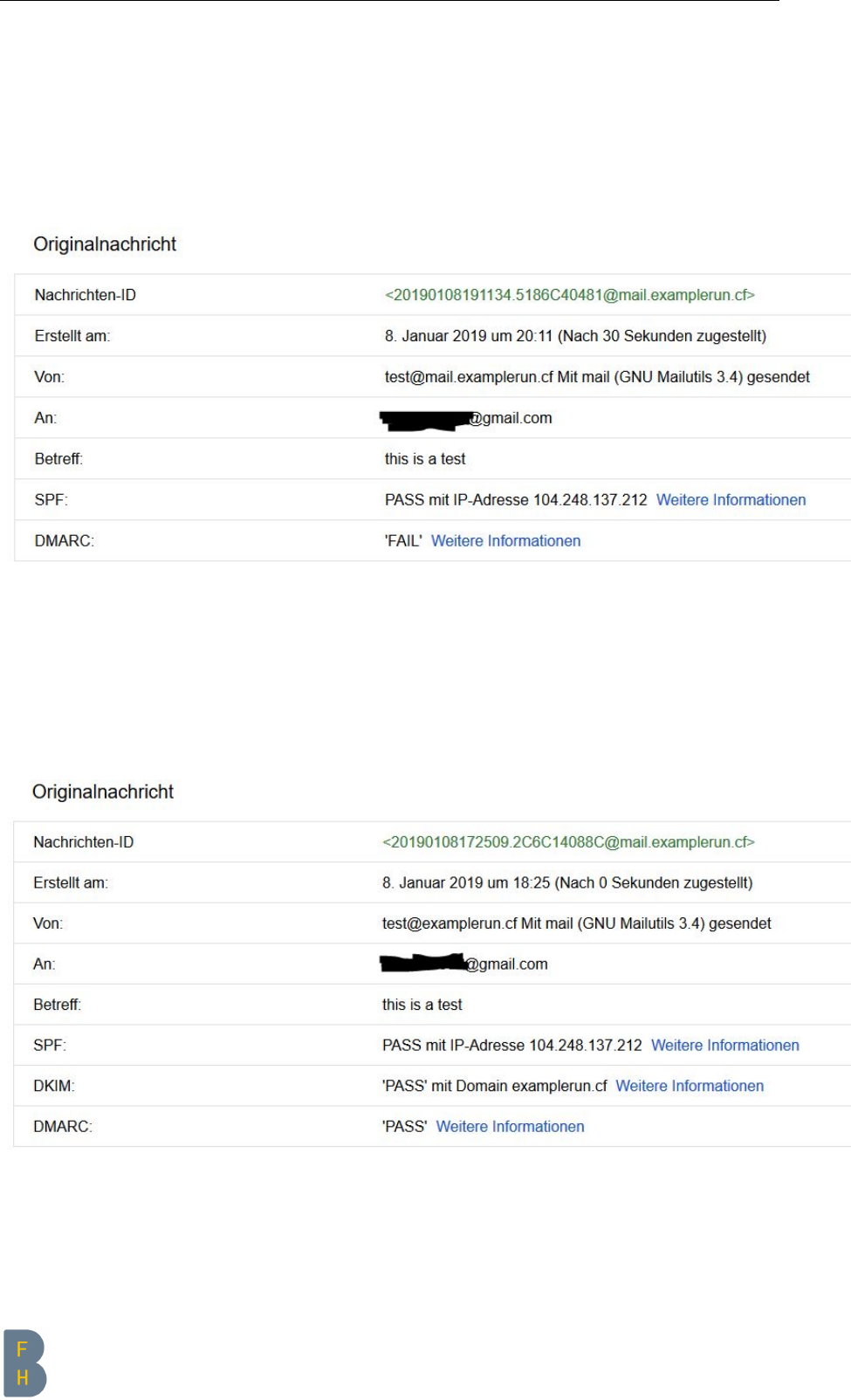
User Manual Internet Server Set-Up & Security-Hardening Script
3.4.2 E-Mail header
As well if you don’t want to end as SPAM your email header should be perfect, if you use the basic
configuration, it won’t be.
BEFORE script
Here how your header looks like before the script:
Figure 3.16: Mail header BEFORE
AFTER script
And here after:
Figure 3.17: Mail header AFTER
CHAPTER 3. HARDENING TESTS Page 44 of 76
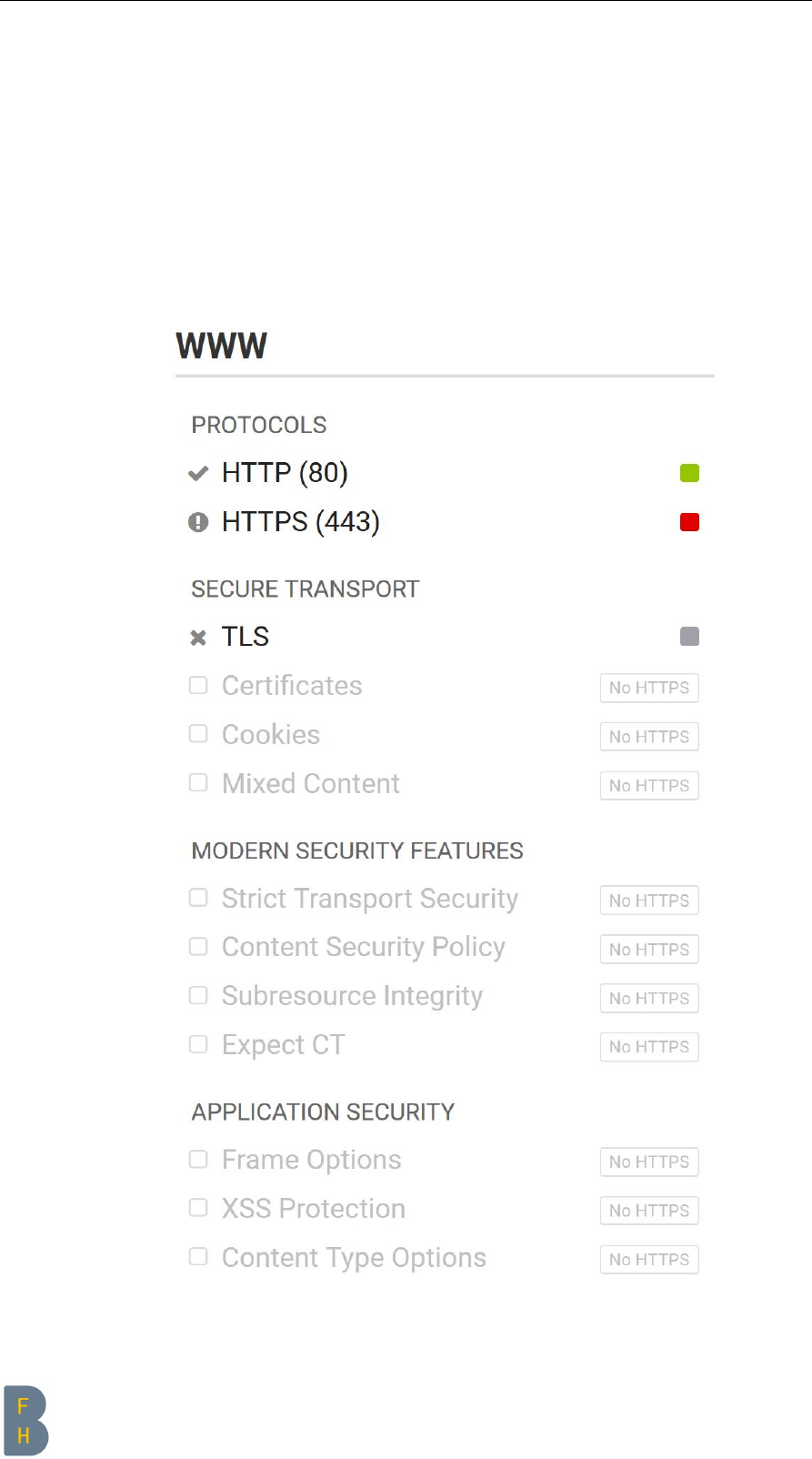
User Manual Internet Server Set-Up & Security-Hardening Script
3.5 Web
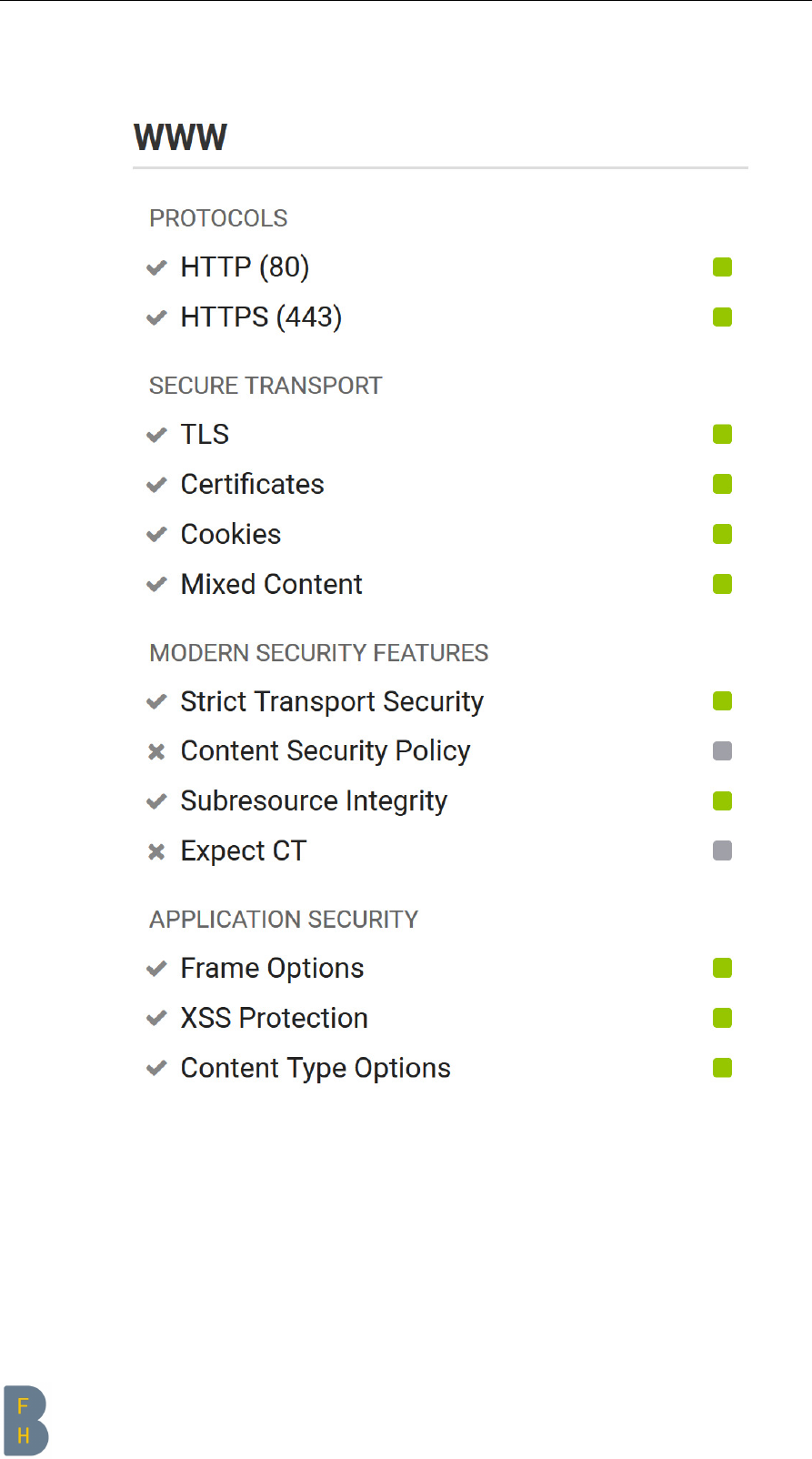
The web part could be tested very well with https://www.hardenize.com [2]. This is by the way
the same tool/website with which the email part was checked.
To test the “before” part properly, an nginx had to be installed on the server in advance. It was not
included by default on the servers used for testing. This is primarily about showing what it looks like
when an unconfigured web service is on the internet versus made more secure with the script from this
project.
BEFORE script
Figure 3.18: Web BEFORE
CHAPTER 3. HARDENING TESTS Page 45 of 76
User Manual Internet Server Set-Up & Security-Hardening Script
4 E-Mail Client configuration
After you set up your secure email server you might want to configure your e-mail client.
The mailserver is only accessible through imaps and requires a TLS certificate for authentication.
Therefor you need to set up your mail client with the appropriate configuration.
At the moment there is only one example for “Mail on macOS Mojave”.
4.1 Mail on macOS Mojave
4.1.1 Mail server config
Figure 4.1: Mail server config
CHAPTER 4. E-MAIL CLIENT CONFIGURATION Page 47 of 76

User Manual Internet Server Set-Up & Security-Hardening Script
5 Future Work
5.1 Extended functionalities
For somebody with basic needs the functionalities of this script is enough. But if we expand the
spectrum, there are still some exciting features missing. Why not have more than one domains on the
same server? Why not have multiple e-mail addresses? Why not choose your own address? This could
be important for somebody who has a small company for example.
5.1.1 Multiple domains
The base to have multiple domains is already set. With NSD you have a perfect authoritative name
server for multiple domains. NSD is not a hobby product, it is a very professional one. It is even used
for some root domains (see: https://en.wikipedia.org/wiki/NSD). The function to make one domain
zone is already here, so we “only” need to make more of it and guide the user through a new process.
5.1.2 Multiple e-mail addresses
Of course it would be interesting to have more than one email address per user. As well, if you want to
create an email address it would be nice if you can choose your own local-part (everything before the
@) of your address. Postfix is capable of all this things, but it won’t do it by it self. This part sounds
quite easy, but it is a complex process which is not defined and scripted yet.
5.1.3 Web application server
Instead of using Apache only as a plain web server it could be extended to act a PHP or CGI application
server with a database. This could be helpful if the user would like to run small applications next to
static website content.
5.2 More Hardening
After installing all components with the script, you have a decent hardened server. Still, it could be
more secure! There are things we could not configure for you in this project like:
•TLS 1.3 : An update of TLS 1.2, faster and more secure.
For more information about TLS 1.3, please check a the comparative study paper (TLS1.2vs1.3.pdf)
from our colleges Kandiah Rajina and Doukmak Anna. You can find the PDF in the same direc-
tory.
•DNSSEC : To secure your domain, but it needs some interaction with your top-level domain
registrar.
•E-Mail
MTA-STS: For more security in sending and receiving emails.
DANE: (needs DNSSEC) is a bridge between DNSSEC and TLS.
As well we would have liked to provide you some more components like:
•XMPP-IM WebRTC: For real-time communication.
•Tor Node: For growing the Tor network.
CHAPTER 5. FUTURE WORK Page 50 of 76

User Manual Internet Server Set-Up & Security-Hardening Script
•Snort-IDS: For network intrusion detection and prevention.
•WAF: To add an existing layer of security to the webserver. Especially when the webserver acts
as an application server.
All of those are candidates for future work. It may be done in a second project from our university...
or you?
5.3 Containerization
The idea of containerization is to put every component into a Docker container. The main benefit
would be that every component runs separated in a isolated environment.
•More modular: With a Docker container setup every component (DNS, SSH, Mail, Web) would
run in a separate container, which would make the setup more modular.
Note: The firewall is not useful in a container. It needs to be configured on the Docker host
to redirect the necessary ports to the right container.
•Platform independent: With the use of Docker containers the project could be set up on any
platform which supports a Docker Engine. This includes most of the modern Unix/Linux dis-
tributions and even Windows Systems. Inside of the containers there would still run a Ubuntu
image.
5.4 Code Migration
Our script collection is exclusively implemented with bash. So we are close to the operating system
and can directly fall back on commands of the operating system. Using other scripting languages or
perhaps even a high-level language (object-oriented) would probably be a pay off. With code migration
it is always a kind of ’trade off’ between what one likes, becoming more modern and/or simplifying.
•Python:
Also close to the linux operating system. Certain subrutienes would be simpler or smaller in
python and in general python is better readable and therefore easier to maintain.
•Ansible:
A very good example of modernization and machine independence. Ansible is very con-
temporary and migration to one or more ansible playbooks from our code would certainly be
possible.
When it comes to code migration, it must be mentioned that the primary focus is not on creating new
code parts, but on refactoring and migrating existing code. Of course, you can create new code in
parallel, but you won’t be able to avoid rewriting or moving existing code.
CHAPTER 5. FUTURE WORK Page 51 of 76

User Manual Internet Server Set-Up & Security-Hardening Script
6 Conclusion
Every user who exchanges information over the internet should have the privilge to do this in a secure
an anonymous matter. We built this script to provide every user, a maximal secure server, with a
minimal need of information. Altough we tried to cover as much aspects and components as possible
we saw, during our work, that there is much more to do. The further work which could build on top of
our project are written down in chapter 5. After all, we learnt a lot for the future and are hoping to
make the internet a little more secure for everyone of its users.
CHAPTER 6. CONCLUSION Page 52 of 76

User Manual Internet Server Set-Up & Security-Hardening Script
7 License
For all the work accomplished in this project we were inspired by a lot of resources. Especially by the
book “Linux Hardening in Hostile Networks: Server Security from TLS to Tor” [9], which provided a
lot of examples for our work. Furthermore a lot of very well written websites and online guides were
used:
•Dovecot and Postfix client certificate authentication [11]
•DMARC Setup [1]
•Configuring HTTPS servers [12]
Nevertheless we paid close attention not to copy any code nor modify any of the components we use.
Therefore all the outcome we produced in this project is our own work.
We decided to use the MIT license which has a wide acceptance in the open source community and
fits our needs for license without warranty.
7.1 MIT license
Copyright 2018 Ismael Riedo, Jan Henzi, Fridolin Zurlinden, Bern University of Applied Sciences
Permission is hereby granted, free of charge, to any person obtaining a copy of this software and
associated documentation files (the ”Software”), to deal in the Software without restriction, including
without limitation the rights to use, copy, modify, merge, publish, distribute, sublicense, and/or sell
copies of the Software, and to permit persons to whom the Software is furnished to do so, subject to
the following conditions:
The above copyright notice and this permission notice shall be included in all copies or substantial
portions of the Software.
THE SOFTWARE IS PROVIDED ”AS IS”, WITHOUT WARRANTY OF ANY KIND, EXPRESS
OR IMPLIED, INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF MERCHANTABIL-
ITY, FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT. IN NO EVENT
SHALL THE AUTHORS OR COPYRIGHT HOLDERS BE LIABLE FOR ANY CLAIM, DAMAGES
OR OTHER LIABILITY, WHETHER IN AN ACTION OF CONTRACT, TORT OR OTHERWISE,
ARISING FROM, OUT OF OR IN CONNECTION WITH THE SOFTWARE OR THE USE OR
OTHER DEALINGS IN THE SOFTWARE.
CHAPTER 7. LICENSE Page 53 of 76

User Manual Internet Server Set-Up & Security-Hardening Script
8 Glossary
Ansible Ansible is open source software that automates software provisioning, configuration manage-
ment, and application deployment. Ansible connects via SSH, remote PowerShell or via other
remote APIs. .
SOURCE: https://en.wikipedia.org/wiki/Ansible (software). 51
Apache The Apache HTTP Server, colloquially called Apache, is free and open-source cross-platform
web server software, released under the terms of Apache License 2.0. Apache is developed and
maintained by an open community of developers under the auspices of the Apache Software
Foundation.
SOURCE: https://en.wikipedia.org/wiki/Apache HTTP Server. 9
DANE DNS-based Authentication of Named Entities (DANE) is an Internet security protocol to allow
X.509 digital certificates, commonly used for Transport Layer Security (TLS), to be bound to
domain names using Domain Name System Security Extensions (DNSSEC)
SOURCE: https://en.wikipedia.org/wiki/DNS-based Authentication of Named Entities.
50
DKIM DomainKeys Identified Mail (DKIM) is an email authentication method designed to detect
forged sender addresses in emails, (email spoofing), a technique often used in phishing and email
spam.
SOURCE: https://en.wikipedia.org/wiki/DomainKeys Identified Mail. 9, 27
DMARC DMARC (Domain-based Message Authentication, Reporting and Conformance) is an email-
validation system designed to detect and prevent email spoofing, the use of forged sender addresses
often used in phishing and email spam. .
SOURCE: https://en.wikipedia.org/wiki/DMARC. 9, 27
DNS The Domain Name System (DNS) is a hierarchical decentralized naming system for computers,
services, or other resources connected to the Internet or a private network. It associates various
information with domain names assigned to each of the participating entities. Most prominently,
it translates more readily memorized domain names to the numerical IP addresses needed for
locating and identifying computer services and devices with the underlying network protocols.
SOURCE: https://en.wikipedia.org/wiki/Domain Name System. 9, 16
DNSSEC The Domain Name System Security Extensions (DNSSEC) is a suite of Internet Engineering
Task Force (IETF) specifications for securing certain kinds of information provided by the Domain
Name System (DNS) as used on Internet Protocol (IP) networks. It is a set of extensions to DNS
which provide to DNS clients (resolvers) origin authentication of DNS data, authenticated denial
of existence, and data integrity, but not availability or confidentiality.
SOURCE: https://en.wikipedia.org/wiki/Domain Name System Security Extensions. 50
Docker Docker is a computer program that performs operating-system-level virtualization, also known
as “containerization”. It was first released in 2013 and is developed by Docker, Inc.
SOURCE: https://en.wikipedia.org/wiki/Docker (software). 51
Glue Records Glue Records, or Nameserver Glue, relate a nameserver on the internet to an IP address.
This relationship is set up at the domain registrar for the main domain on which the nameservers
were created.
SOURCE: https://www.liquidweb.com/kb/what-are-glue-records/. 17
Glossary Page 54 of 76

User Manual Internet Server Set-Up & Security-Hardening Script
IMAP In computing, the Internet Message Access Protocol (IMAP) is an Internet standard protocol
used by email clients to retrieve email messages from a mail server over a TCP/IP connection.[1]
IMAP is defined by RFC 3501.
SOURCE: https://en.wikipedia.org/wiki/Internet Message Access Protocol. 29
ModSecurity ModSecurity, sometimes called Modsec, is an open-source web application firewall (WAF).
Originally designed as a module for the Apache HTTP Server, it has evolved to provide an array
of Hypertext Transfer Protocol request and response filtering capabilities along with other secu-
rity features across a number of different platforms including Apache HTTP Server, Microsoft
IIS and NGINX. It is a free software released under the Apache license 2.0.
SOURCE: https://en.wikipedia.org/wiki/ModSecurity. 33
MTA-STS MTA-STS (full name SMTP Mail Transfer Agent Strict Transport Security) is a new stan-
dard that aims to improve the security of SMTP by enabling domain names to opt into strict
transport layer security mode that requires authentication (valid public certificates) and encryp-
tion (TLS).
SOURCE: https://www.hardenize.com/blog/mta-sts. 50
Nginx Nginx is a web server which can also be used as a reverse proxy, load balancer, mail proxy and
HTTP cache. The software was created by Igor Sysoev and first publicly released in 2004.[9] A
company of the same name was founded in 2011 to provide support and Nginx plus paid software.
Nginx is free and open-source software, released under the terms of a BSD-like license.
SOURCE: https://en.wikipedia.org/wiki/Nginx. 9
nsd In Internet computing, NSD (for ”name server daemon”) is an open-source Domain Name System
(DNS) server. It was developed by NLnet Labs of Amsterdam in cooperation with the RIPE
NCC, from scratch as an authoritative name server (i.e., not implementing the recursive caching
function by design).
SOURCE: https://en.wikipedia.org/wiki/NSD. 9
Python Python is an interpreted, high-level, general-purpose programming language. Created by
Guido van Rossum and first released in 1991, Python has a design philosophy that emphasizes
code readability, notably using significant whitespace. It provides constructs that enable clear
programming on both small and large scales.
SOURCE: https://en.wikipedia.org/wiki/Python (programming language). 51
SMTP Simple Mail Transfer Protocol (SMTP) is an Internet standard for email transmission. First
defined by RFC 821 in 1982, it was updated in 2008 with Extended SMTP additions by RFC
5321; which is the protocol in widespread use today.
SOURCE: https://en.wikipedia.org/wiki/Simple Mail Transfer Protocolm. 27
SPF Sender Policy Framework (SPF) is an email authentication method designed to detect forged
sender addresses in emails (email spoofing), a technique often used in phishing and email spam.
SOURCE: https://en.wikipedia.org/wiki/Sender Policy Framework. 9, 27
SSH Secure Shell (SSH) is a cryptographic network protocol for operating network services securely
over an unsecured network.[1] Typical applications include remote command-line login and remote
command execution, but any network service can be secured with SSH.
SOURCE: https://en.wikipedia.org/wiki/Secure Shell. 23
SSL Transport Layer Security (TLS), and its now-deprecated predecessor, Secure Sockets Layer (SSL),[1]
are cryptographic protocols designed to provide communications security over a computer net-
work.[2] Several versions of the protocols find widespread use in applications such as web browsing,
email, instant messaging, and voice over IP (VoIP). Websites can use TLS to secure all commu-
nications between their servers and web browsers.
SOURCE: https://en.wikipedia.org/wiki/Transport Layer Security. 29
Glossary Page 55 of 76

User Manual Internet Server Set-Up & Security-Hardening Script
TLS Transport Layer Security (TLS), and its now-deprecated predecessor, Secure Sockets Layer (SSL),[1]
are cryptographic protocols designed to provide communications security over a computer net-
work.[2] Several versions of the protocols find widespread use in applications such as web browsing,
email, instant messaging, and voice over IP (VoIP). Websites can use TLS to secure all commu-
nications between their servers and web browsers.
SOURCE: https://en.wikipedia.org/wiki/Transport Layer Security. 27
Tor Tor is free software for enabling anonymous communication. The name is derived from an acronym
for the original software project name ”The Onion Router”. Tor directs Internet traffic through
a free, worldwide, volunteer overlay network consisting of more than seven thousand relays to
conceal a user’s location and usage from anyone conducting network surveillance or traffic analysis.
SOURCE: https://en.wikipedia.org/wiki/Tor (anonymity network). 50
ufw The default firewall configuration tool for Ubuntu is ufw. Developed to ease iptables firewall
configuration, ufw provides a user friendly way to create an IPv4 or IPv6 host-based firewall. By
default UFW is disabled.
SOURCE: https://help.ubuntu.com/community/UFW. 13
unbound Unbound is a validating, recursive, and caching DNS resolver product from NLnet Labs. It
is distributed free of charge in open-source form under the BSD license.
SOURCE: https://en.wikipedia.org/wiki/Unbound (DNS server). 9
WAF A web application firewall (or WAF) filters, monitors, and blocks HTTP traffic to and from a
web application. A WAF is differentiated from a regular firewall in that a WAF is able to filter the
content of specific web applications while regular firewalls serve as a safety gate between servers.
By inspecting HTTP traffic, it can prevent attacks stemming from web application security flaws,
such as SQL injection, cross-site scripting (XSS), file inclusion, and security misconfigurations.
SOURCE: https://en.wikipedia.org/wiki/Web application firewall. 33, 51
WebRTC WebRTC (Web Real-Time Communication) is a free, open-source project that provides web
browsers and mobile applications with real-time communication (RTC) via simple application
programming interfaces (APIs). It allows audio and video communication to work inside web
pages by allowing direct peer-to-peer communication, eliminating the need to install plugins or
download native apps.Supported by Google, Microsoft, Mozilla, and Opera, WebRTC is being
standardized through the World Wide Web Consortium (W3C) and the Internet Engineering
Task Force (IETF).
SOURCE: https://en.wikipedia.org/wiki/WebRTC. 50
wild-card In software, a wildcard character is a kind of placeholder represented by a single character,
such as an asterisk (*), which can be interpreted as a number of literal characters or an empty
string. It is often used in file searches so the full name need not be typed.
SOURCE: https://en.wikipedia.org/wiki/Wildcard character. 19
Glossary Page 56 of 76

User Manual Internet Server Set-Up & Security-Hardening Script
Bibliography
[1] Global Cyber Alliance. DMARC Setup. 2016. url:https://dmarcguide.globalcyberalliance.
org (visited on 10/24/2018).
[2] Hardenize. Hardenize. 2018. url:https://www.hardenize.com (visited on 10/25/2018).
[3] Gordon ”Fyodor” Lyon Insecure.Com LLC. The Official Nmap Project Guide to Network Discov-
ery and Security Scanning. 2011. url:https://nmap.org/book/port-scanning- tutorial.
html (visited on 10/25/2018).
[4] Todd Knarr Linode. Configure SPF and DKIM With Postfix on Debian 8. 2018. url:https:
/ / www . linode . com / docs / email / postfix / configure - spf - and - dkim - in - postfix - on -
debian-8/ (visited on 10/25/2018).
[5] Michael Boelen Linux Audit. OpenSSH security and hardening. 2018. url:https : / / linux -
audit.com/audit-and-harden-your-ssh-configuration/ (visited on 10/25/2018).
[6] MXToolbox. MX Lookup. 2018. url:https://mxtoolbox.com/ (visited on 10/25/2018).
[7] NLnet Labs. unbound & nsd. 2018. url:https://github.com/NLnetLabs (visited on 10/25/2018).
[8] OARC, Inc. Check My DNS. 2017. url:https://www.dns- oarc.net/oarc/services/cmdns
(visited on 10/25/2018).
[9] Kyle Rankin. Linux Hardening in Hostile Networks: Server Security from TLS to Tor. Addison
Wesley, 2017.
[10] Rebex. Rebex. 2018. url:https://sshcheck.com (visited on 10/25/2018).
[11] Giel van Schijndel. Dovecot and Postfix client certificate authentication. 2017. url:https:/ /
blog. mortis . eu / blog / 2017 / 06 / dovecot - and - postfix - with - client - cert - auth . html
(visited on 10/24/2018).
[12] Igor Sysoev and Brian Mercer. Configuring HTTPS servers. 2018. url:http://nginx.org/en/
docs/http/configuring_https_servers.html (visited on 10/25/2018).
[13] Vircom. Email Security Grader. 2018. url:https://emailsecuritygrader.com/ (visited on
10/25/2018).
Bibliography Page 57 of 76
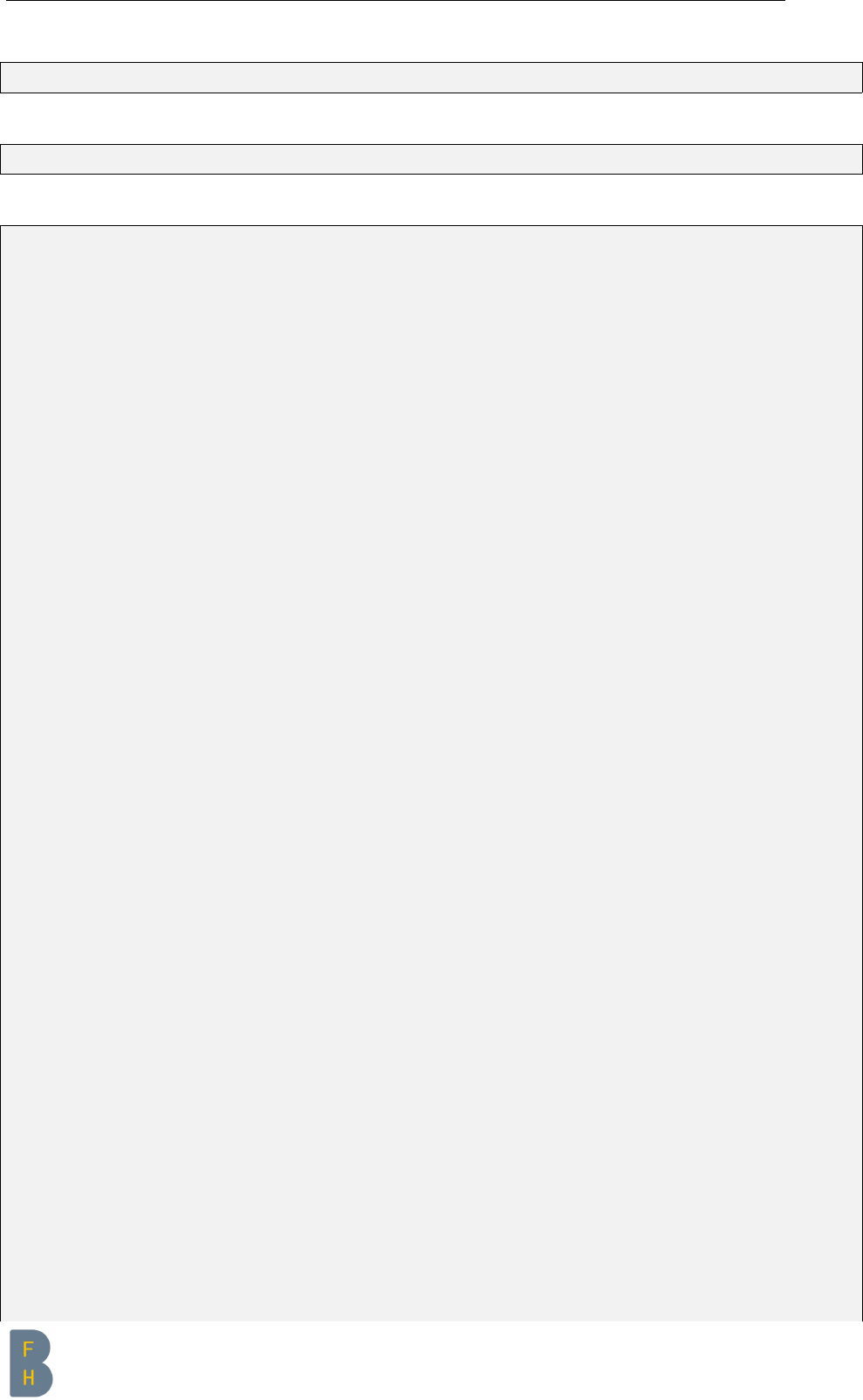
User Manual Internet Server Set-Up & Security-Hardening Script
configFiles/dns/unbound/unbound.conf
1include: " / etc / u nbound / u nbound . c on f .d /*. con f "
configFiles/dns/unbound/access.conf
1server:
configFiles/dns/unbound/hardening.conf
1# ## SO URCE : ht tps :// cal om el . or g / un bo un d_ dns . h tml ###
2server:
3# enab le to not answer id . server and hostname . bind queries .
4hide - identity : yes
5
6# e nable to not answer version . serve r and versio n .bind quer ies .
7hide - version : yes
8
9# Read the root hints from this file . Default is nothing , usi ng built in
10 # hints for the IN class . The file has the format of zone files , with root
11 # nameserver names and addresses only . The default may become outdated ,
12 # when serve rs change , therefore it is good p ractice to use a root - hin ts
13 # f il e . get one f ro m http s :// ww w . in ternic . net / d omai n / nam ed . roo t
14 root - hints : " / va r / lib / u nboun d / ro ot . h int s "
15
16 # Will trust glue only if it is within the servers authority .
17 # H arden against out of zone rrsets , to avoid spoofing attempts .
18 # Ha r d e n i n g q ueries multiple name servers for the same data to make
19 # spoofing si gnifi cantl y ha rder and does not manda te dnssec .
20 harden - g lu e : yes
21
22 # Require DNSSEC data for trust - a n c h o red zones , if such data is absent , the
23 # zone becom es bo gu s . Ha rde n again st receiving dnssec - stripped data . If you
24 # turn it off , failin g to v a l i d a t e dnskey data for a trust a n chor will trigger
25 # insecur e mode for that zone ( like wit h o ut a t rusta n c hor ) . Default on ,
26 # which i n sists on dnssec data for trust - anchored zones .
27 harden - dnssec - stripped : yes
28
29 # Use 0 x20 - encoded random bits in the query to foil spoof attempt s .
30 # h tt p :// too ls . iet f . org / htm l / draft - vixie - dnsext - dns0 x20 -00
31 # While upper and lower case letters are allowed in domain names , no si g n ifi c a nce
32 # is attached to the case . That is , two names with the same spelling but
33 # di f ferent case are to be treated as if id e n t ical . This means calomel . org is the
34 # s am e as C aLoMeL . Org w hic h is the s am e as C AL OME L . ORG .
35 use - caps - for - id : yes
36
37 # the t im e to liv e ( TTL ) val ue l ow er bound , in seconds . Defaul t 0.
38 # If more than an hour could easily give trouble due to stale data .
39 cache - min - ttl : 360 0
40
41 # the t im e to liv e ( TTL ) val ue cap for R Rse ts and me ss ages in the
42 # cache . Items are not c ached for longer . In se c onds .
43 cache - max - ttl : 86 40 0
44
45 # perform prefetch ing of close to expi red message cache e ntr ies . If a client
46 # requests the dns lo okup and the TTL of the cached hostname is g oing to
47 # expire in less than 10% of its TTL , unbound will (1 st ) return the ip of the
48 # host to the client and (2 nd ) pre - fetch the dns r equest from the remo te dns
49 # serv er . This metho d has been shown to increase the amo unt of cached hits by
50 # local c l ients by 10% on a v e rage .
51 pr efetch : yes
52
53 # numb er of t h reads to create . 1 disables threading . This shou ld equal the number
54 # of CPU cores in the machine . Our example machine has 4 CPU cores .
55 num - threads : 1
56
57 ## Unbound Optimiz a t ion and Speed Tweaks ###
Page 59 of 76

User Manual Internet Server Set-Up & Security-Hardening Script
58
59 # the number of slabs to use for cache and must be a power of 2 times the
60 # n umber of num - threa d s set above . more slabs reduce lock contention , but
61 # fragment memo ry usage .
62 msg - cache - slabs : 8
63 rrset - cache - s labs : 8
64 infra - cache - s labs : 8
65 key - cache - slabs : 8
66
67 # Increase the mem ory size of the cache . Use r o ughly twice as much rrset cache
68 # memor y as you use msg cache memory . Due to malloc overhead , the total memor y
69 # usage is likel y to rise to double (or 2.5 x) the total cache memory . The test
70 # box has 4 gig of ram so 256 meg for rrset allows a lot of room for cac h eed objects .
71 rrset - cache - size : 256 m
72 msg - cache - si ze : 1 28 m
73
74 # buffer size for UDP port 53 incoming ( SO_RCVBUF socket option ) . This sets
75 # the kernel b uffer larger so that no m e s s a g e s are lost in spikes in the t r affic .
76 so - rcvbu f : 1m
77
78 # Should a d d i tional section of s ecure me s sage also be kept clean of unsecure
79 # data . Useful to sh ield the users of this validator from p o t e n tial bogus
80 # data in the a dditio n a l section . All unsigned data in the additiona l section
81 # is removed from secure messages .
82 val - clean - additi o n a l : yes
83
84 # If nonzero , unwanted replies are not only reported in statistics , but also
85 # a running total is kept per thread . If it reac h e s the threshold , a w a rning
86 # is printed and a defensive acti on is taken , the cache is c l eared to flush
87 # potential po ison out of it . A suggest e d value is 10000000 , the de f ault is
88 # 0 ( turned off ) . We think 10 K is a good value .
89 unwanted - reply - th reshold : 10000
90
91 # R educe EDNS reasse m b l y buffer size .
92 # Suggested by the u nbound man page to reduce fragm e n ta t i on r e a s s embly problems
93 edns - bu ffer - si ze : 14 72
configFiles/dns/unbound/listening.conf
1server:
2# set dns listening for ipv4
3interface : 12 7.0.0.1
4
5# set dns listening for ipv6
6interface : ::1
7
8# port to answer queries from
9port : 53
10
11 # E nable IPv4 , " yes " or " no ".
12 do - ip4 : yes
13
14 # E nable IPv6 , " yes " or " no ".
15 do - ip6 : yes
16
17 # E nable UDP , " yes " or " no ".
18 do - udp : yes
19
20 # E nable TCP , " yes " or " no ".
21 do - tcp : yes
configFiles/dns/unbound/qname–minimisation.conf
1server:
2# Send minimum am ount of inf o r mati o n to upstream se r v ers to enhance
3# privacy . Only sends mi nim um re qui red labels of the QNAME and sets
Page 60 of 76
User Manual Internet Server Set-Up & Security-Hardening Script
4# QTYPE to NS when possible .
5
6# See RF C 7 81 6 " DNS Qu ery Na me M in im is at ion to I mp rov e P riv ac y " for
7# details.
8
9qname - m i n imisat i o n : yes
configFiles/dns/unbound/root–auto–trust–anchor–file.conf
1server:
2# The f o l l owing line will c o n f i gure unbound to per f o rm c r ypt o g rap h ic
3# D NSSEC valid ation using the root trust anchor .
4auto - trust - anc ho r - fi le : " / var / lib / u nb oun d / ro ot . key "
configFiles/dns/nsd/nsd.conf
1
2server:
3# un co mment to s pecify sp ec ific int erface s to b in d ( d efa ul t all ) .
4ip - address : 104.24 8.137 .212
5#ip - address :
6
7# port to answer qu e r ies on . default is 53.
8port : 53
9
10 # N umbe r of NSD se rvers to fo rk .
11 server - c ount : 1
12
13 # listen only on IPv4 connect i o n s
14 ip4 - only : yes
15
16 # don ’ t answer VER SIO N .BIND and VE RSIO N . SERVER CHAOS class queries
17 hide - version : yes
18
19 # id en ti fy t he s erv er ( CH TXT ID . S ER VE R en tr y ) .
20 identity: " "
21
22 logfile: " / var / log / nsd . log "
23
24 # The directory for zonefile : files .
25 zonesdir: " / etc / nsd / z one s "
26 pidfile: " / etc / nsd / nsd . pid "
27 us ername : nsd
28
29 pattern:
30 na me : e xa mp le ru n . cf
31 zo ne fi le : e xa mp le ru n . cf . fo rw ard
32 pattern:
33 name: 212.137.248.104.in -addr.arpa
34 zo nefile : ex a mplerun . cf . backwar d
configFiles/dns/nsd/examplerun.cf.backward
1
2$ORIGIN 212.137.248.104.in -addr.arpa.
3$TTL 1800
4
5@ IN SOA ns1 . example r u n . cf . ns2 . examplerun . cf . (
62019010917 ; serial number
728800 ; Refresh
87200 ; Retry
912 0 9600 ; Exp ire
10 86400 ; Min TTL
11 )
12
13 NS ns1 . exampleru n . cf .
Page 61 of 76
User Manual Internet Server Set-Up & Security-Hardening Script
14 NS ns2 . exampleru n . cf .
15 ; PTR
16 IN P TR e xa mp le ru n . cf .
17 IN PTR mail . examplerun . cf .
configFiles/dns/nsd/examplerun.cf.forward
1
2$O RI GI N e xa mp le r un . cf . ; de fa ul t zo ne d om ai n
3$TTL 86400 ; defaul t time to live
4
5
6@ IN SOA ns1 . example r u n . cf . ns2 . examplerun . cf . (
72019010917 ; serial number
828800 ; Refresh
97200 ; Retry
10 12 0 9600 ; Exp ire
11 86400 ; Min TTL
12 )
13
14 NS ns1 . exampleru n . cf .
15 NS ns2 . exampleru n . cf .
16 MX 10 mail . exampleru n . cf .
17
18 examplerun . cf . IN CAA 0 issue " l et se ncr ypt . o rg "
19 examplerun . cf . IN CAA 0 iodef " m ai lt o : p o st ma st er @ ex a mp le r un . c f "
20
21 IN A 104.2 4 8 .1 3 7. 2 1 2
22 IN TXT " v= s pf1 mx a ˜ all "
23 ns1 IN A 1 0 4.2 4 8. 1 3 7. 2 12
24 ns2 IN A 1 0 4.2 4 8. 1 3 7. 2 12
25 www IN A 1 0 4.2 4 8. 1 3 7. 2 12
26 * IN A 104.2 4 8.1 3 7. 2 12
27
28 mail IN A 1 04 . 24 8 . 13 7 .21 2
29 IN TXT " v= s pf1 mx a ˜ all "
30 201901091 7 . _ domaink e y IN TXT (
31 "v = DKIM1 \059 h= sha256 \059 k = rsa \059 s = email \059 p= "
32 "MIIBIjANBgkqhkiG9w0BAQEFAAOCAQ8AMIIBCgKCAQEA6N+
Xk5S5yT9WNMgbIS7CvNKdWFKpSR7Tfo6trV0Ml6O6BHsFiSp5U5"
33 " kbQ / v rK / xg x9c 4k5 BI Ok / yL / jd /O / Bq jT GDnC / pL8 9SL1 Ne5Z +
vW1 h 4F E w9 gmw k 3e t scU P 0C Y ZZ s5P g vD l BPg fW yi tr jy + p Yl xs F BOR X ZP l rpQ R FnNY pS R /
eA XW F3 RE li O7 Nq uS Sec 98 5d pb ZW Q /3 MHm "
34 "W8ZVwv5oDfh/kMQ9727qMxpOED0ZQyml2kPpdHK87Rg9zGOJDJs880RC3lsd+6
tukf7fYyj51TvpRtndLPrbutKdFgi3eMMDkQXam+d8f3YHQoiMF7lR0pD2oOcH5glELX7gc6MwIDAQAB"
)
35 _adsp . _dom ainkey IN TXT " dkim = a ll "
36 _dmarc IN TXT " v= D MAR C1 \059 p= q uarantin e \059 sp = q uarantin e \05 9 adki m =r \059 aspf = r \059
fo = 1\ 05 9 rf = a frf \0 59 rua = m ai lto : p os t ma st e r@ ex a mp le r un . cf "
configFiles/ssh/sshd.config
1# $OpenBSD : sshd_config ,v 1.101 2017/03/14 07:19:07 djm Exp $
2
3# This is the ssh d server system - wide c onf igur ati on file . See
4# ss h d _config (5) for more inf o r mation .
5
6# T hi s ssh d was compiled w it h PAT H =/ usr / bin :/ bin :/ u sr / s bi n :/ s bi n
7
8# The s t r a t e gy used for options in the def a u lt ss h d _con f i g s h ipped with
9# Open S S H is to specify o p t ions with their default value where
10 # possible , but leave them comment e d . Uncommen t e d o p tions override the
11 # default v al ue .
12
13 # Port 22
14 # Addres s F amily any
Page 62 of 76
User Manual Internet Server Set-Up & Security-Hardening Script
15 # Listen A d dress 0.0.0.0
16 # Listen A d dress ::
17
18 # H ost Ke y / etc / ssh / s sh _h os t_ rs a_ ke y
19 # H ost Ke y / etc / ssh / s sh _h ost _e cd sa _k ey
20 #HostKey /etc/ssh/ssh_host_ed25519_key
21
22 # Ci p hers and keying
23 # RekeyLimit default none
24
25 # Logging
26 #SyslogFacility AUTH
27 # Lo gLevel INFO
28
29 # Authentication:
30
31 #LoginGraceTime 2m
32 Permi t Roo t Lo g in no
33 #StrictModes yes
34 #MaxAuthTries 6
35 #MaxSessions 10
36
37 #PubkeyAuthentication yes
38
39 # E xpect . ss h / au tho ri ze d_ ke ys 2 to be d is re ga rded by de fault in f utu re .
40 # A ut ho ri zed Ke ys Fi le . ss h / au th or iz ed _k ey s . ssh / a uth or iz ed _k ey s2
41
42 #AuthorizedPrincipalsFile none
43
44 #AuthorizedKeysCommand none
45 #AuthorizedKeysCommandUser nobody
46
47 # For t hi s to wor k you w ill a lso need ho st ke ys in / etc / ssh / s sh _k no wn _h os ts
48 #HostbasedAuthentication no
49 # Change to yes if you don ’t trust ˜/. ssh / kn o w n_hos t s for
50 # HostbasedAuthentication
51 #IgnoreUserKnownHosts no
52 # Don ’ t read the user ’ s ˜/. rhosts and ˜/. shosts files
53 #IgnoreRhosts yes
54
55 # To disable tunn eled cl ear text pas swords , ch ange to no here !
56 Pass w or dA u th en t ic at i on no
57 #PermitEmptyPasswords no
58
59 # C hange to yes to enab le challenge - response passwords ( be ware issues with
60 # some PAM modules and t h r eads )
61 ChallengeResponseAuthentication no
62
63 # Ke r b e r o s options
64 # Kerb e ros A ut h enti ca t io n no
65 #KerberosOrLocalPasswd yes
66 #KerberosTicketCleanup yes
67 #KerberosGetAFSToken no
68
69 # GSSAPI opt i o ns
70 #GSSAPIAuthentication no
71 #GSSAPICleanupCredentials yes
72 #GSSAPIStrictAcceptorCheck yes
73 #GSSAPIKeyExchange no
74
75 # Set this to ’yes ’ to enable PAM authentica t i on , account processing ,
76 # and sessio n p r o c essing . If this is enabled , PAM authe n t ic a t io n will
77 # be allowed through the C ha l le ng eR es po ns eA ut h en ti ca ti on and
78 # Pass w or d Aut h en t ic a tio n . Dependin g on your PAM con f iguration ,
79 # PAM aut h ent i cat i on via Ch a ll en ge Re sp on se Au t he nt ic at io n may bypass
80 # the s e t ting of " Pe rmi t RootL o gin yes
Page 63 of 76
User Manual Internet Server Set-Up & Security-Hardening Script
81 # If you just want the PAM account and s e ssion c hecks to run without
82 # PAM authent i c ation , then enable this but set P as s wo r dA ut h en ti c at io n
83 # and ChallengeResponseAuthentication to ’no’.
84 UsePAM yes
85
86 #AllowAgentForwarding yes
87 # Allo w Tc p Fo r wa r di n g yes
88 #GatewayPorts no
89 X11For w a rdi n g no
90 #X11DisplayOffset 10
91 # X11Us e Loc a lhost yes
92 # PermitTTY yes
93 PrintMotd no
94 #PrintLastLog yes
95 #TCPKeepAlive yes
96 # Us eLogin no
97 #PermitUserEnvironment no
98 # Compressi o n d elayed
99 #ClientAliveInterval 0
100 #ClientAliveCountMax 3
101 #UseDNS no
102 # P idF il e / var / run / ss hd . p id
103 # MaxStartu p s 1 0:30:100
104 #PermitTunnel no
105 # Chroo t Dir e ctory none
106 # Versi o nAd d endum none
107
108 # no default banner path
109 # Ba nner none
110
111 # Allow client to pass locale environ m e nt variabl e s
112 AcceptEnv LANG L C_ *
113
114 # override de f ault of no s ubsyst e m s
115 Subsystem sf tp / usr / lib / o penssh / sftp - s erve r
116
117 # Example of o verri ding settings on a per - user basi s
118 # Match User ano ncvs
119 # X 11 F o rwa r din g no
120 # Allow T cp F or w ar d in g no
121 # P e r m itTTY no
122 # F orc e C omm a n d cvs server
123 Host K e yA l go r it h ms ssh - ed25519 - cert - v01 @ o pens s h .com , ssh - rsa - cert - v0 1 @ope n s sh .com ,ssh -
ed25519 ,ssh - rsa , ecdsa - sha2 - nistp521 - cert - v0 1 @ope n s sh .com , ecdsa - sha2 - nistp384 - cert -
v 01 @o pe ns sh .com , ec dsa - sha2 - n ist p25 6 - cert - v0 1@ op en ss h . com , ecds a - sh a2 - n ist p52 1 , ec dsa
- sha2 - n ist p38 4 , ec dsa - sha2 - n is tp 25 6
124
125 K ex Al go ri t hm s c ur ve 255 19 - s ha 25 6@ li bs sh . org , ecdh - sha2 - n ist p5 21 , ecdh - sha2 - n ist p38 4 , ecdh -
sha2 - nistp256 , diffie - hellman - group - exchange - sh a25 6
126 MA Cs hmac - sha2 -51 2 - et m@ op e ns sh . com , hmac - sha2 -25 6 - et m@ op e ns sh . com , umac -128 - e tm @o pe n ss h .
com , hmac - s ha2 -51 2 , hm ac - sha2 -2 56 , umac - 128 @ op ens sh . com
127 Ci p hers chacha20 - po l y130 5 @ open s sh . com , aes256 - gc m @openssh . com , aes128 - gcm@open s s h .com ,
aes 256 - ctr , aes1 92 - ctr , aes128 - c tr
configFiles/mail/main.cf
1# See / usr / share / postfix / main . cf . dist for a commented , more complete versio n
2
3
4# Debian specific : Specifying a file name will cause the first
5# line of that file to be used as the name . The Debian defa u l t
6# is / etc / m ai lname .
7# m yorigin = / etc / m ai lname
8
9smtpd_b a n ner = $ m y host n a m e ESMTP $ma i l _ n ame ( Ubuntu )
10 biff = no
11
Page 64 of 76

User Manual Internet Server Set-Up & Security-Hardening Script
12 # appending . doma in is the MUA ’s job .
13 append_dot_mydomain = no
14
15 # Uncomment the next line to g e nerate " d elayed mail " wa r n i n g s
16 # dela y _w a rn i ng _ ti m e = 4 h
17
18 readme_directory = no
19
20 # See h tt p :// www . p os tfix . org / C OM PAT IB IL IT Y_ RE AD ME . h tm l -- d ef aul t to 2 on
21 # fresh installs .
22 compatibility_level = 2
23
24 # TLS parame t e r s
25 sm tp d_ tl s_ ce rt _f ile = / e tc / let sen cryp t / live / m ail . ex ample run . cf / f ul lc hain . pem
26 sm tp d_ tl s_ ke y_ fi le = / etc / l et se nc ry pt / l ive / m ail . exa mpler un . cf / p rivkey . pe m
27 smtpd_ u s e_t l s = yes
28 smt pd _t ls_ se ss io n_c ac he _d ata ba se = btree : ${ da ta_d irect ory }/ smtpd_ scache
29 sm tp _t ls_ se ss ion _c ac he_ da ta bas e = bt ree :/ va r / lib / p ostfi x / s mt p_ tl s_ se ss io n_c ac he
30
31 # See / usr / s har e / doc / p ostfix / T LS _R EAD ME . gz in the p ostf ix - doc p ackage fo r
32 # informati o n on enabling SSL in the smtp client .
33
34 smtp d_ r el ay _ re st ri c ti on s = permit_mynetworks , perm i t _sa s l _au t hen t i cat e d ,
permit _ t ls_ a ll_ c l ie n t cer t s , r ej ec t _u na ut h _d es ti n at io n
35 myhostname = mail . examplerun . cf
36 alias_maps = hash:/ e tc / a liases
37 alias_database = hash:/ etc / a liases
38 my or igin = / etc / m ai lname
39 mydest i nation = $myhostname , $mydomain , mail . exampl e r u n .cf , lo calhost . examplerun . cf ,
localhost
40 relayhost =
41 mynetworks = 127.0.0.0/ 8 [:: ffff : 12 7 .0. 0 .0 ] / 10 4 [ ::1]/128
42 mail b ox _ si z e_ l im i t = 0
43 recipient_delimiter = +
44 inet_ i nte r fa c es = all
45 inet_protocols = all
46 sender_canonical_maps = hash:/ etc / p ostfix / c an oni cal
47 my do ma in = e xa mp le ru n . cf
48 smtp_tls_security_level = may
49 smtp_tls_note_starttls_offer = yes
50 smtp_tls_loglevel = 1
51 # ## https :// ac cess . r edhat . com / a rt icle s /1 468593
52 smt p d_ tl s_ m an da to ry _p ro t oc ol s = ! SSLv2 , ! SSLv3 , ! TLSv1 , ! TLSv1 .1
53 smtp d _t l s_ p ro to c ol s = ! SSLv2 , ! SSLv3 , ! TLSv1 , ! TLSv1 .1
54 smt p _t ls _ ma nd at or y_ p ro to co ls = ! SSLv2 , ! SSLv3 , ! TLSv1 , ! TLSv1 .1
55 smtp _ tl s _p r ot o co l s = ! SSLv2 , ! SSLv3 , ! TLSv1 , ! TLSv1 .1
56 smtp _t l s_ ex c lu de _c i ph er s = EXP , MEDIUM , LOW , DES , 3DES , SSLv2
57 smt p d_ t ls _e xc l ud e_ ci p he rs = EXP , MEDIUM , LOW , DES , 3 DES , SSLv2
58 tl s_ hi gh _c ip he rl ist = kEECD H :+ kEECDH + SHA : kED H :+ k ED H + SHA :+ kED H + CA ME LLIA : k ECD H :+ k ECD H +
SHA : kRSA :+ kRSA + SHA :+ kRSA + CA M E L L I A :! aNULL :! eNULL :! SSLv2 :! RC4 :! MD5 :! DES :! EXP :! SEED :!
IDEA :!3 DES :! SHA
59 tls_ p re em p t_ ci p he rl i st = yes
60 smtp_tls_ciphers = high
61 smtpd_tls_ciphers = high
62 policyd - spf_ti m e_lim i t = 3600
63 smt p d_ re c ip ie nt _r es t ri ct io ns = r e jec t _ una u t h_pi p e lin i n g , reject _ n on_ f q dn_ r e ci p i ent ,
rej ect _un kno wn_ rec ipi ent _do ma in , p ermit_mynetworks , c he ck_ po li cy _se rv ic e unix :
pr iva te / policyd - spf , r ejec t_rb l_cl i ent zen . spamhaus . org , re ject _rbl _ clie nt bl .
sp am cop . net
64 # START O pendKIM & O penDMARC
65 milte r _pr o to c ol = 6
66 milter_default_action = accept
67 smtpd_ m i lte r s = local :/ opendkim / opendkim . sock , local :/ op endmarc / opendmarc . sock
68 non_smtpd_milters = local :/ opendkim / opendkim . sock , local :/ op endmarc / opendmarc . sock
69 # END OpendKIM & O pe nD MARC
70 sm tp d_ tl s_ CA fi le = / etc / ssl / c ert s / exam pleru n . cf . ca . crl . pem
Page 65 of 76
User Manual Internet Server Set-Up & Security-Hardening Script
71 tls_append_default_CA = no
configFiles/mail/master.cf
1#
2# Postfix mas ter process con f i gur a tio n file . For details on the format
3# of the file , see the master (5) manual page ( comma n d : " man 5 mas ter " or
4# on - lin e : http :// www . p os tfix . org / m aste r .5. htm l ).
5#
6# Do not forge t to exec ute " pos tfix re loa d " aft er e diti ng this file .
7#
8# ==========================================================================
9# se r vice type private unp riv chr oot wakeup maxproc command + args
10 # ( yes ) ( y es ) ( no ) ( nev er ) (1 00 )
11 # ==========================================================================
12 smtp inet n - y - - smtpd
13 # smtp inet n - y - 1 postscreen
14 # smtpd pass - - y - - smtpd
15 # dnsbl o g unix - - y - 0 dnsblog
16 # tlsproxy unix - - y - 0 tl s p r o x y
17 # submissi o n inet n - y - - smtpd
18 # -o sysl o g_name = postfix / submi s sion
19 -o smtpd_tls_security_level=encrypt
20 -o s mt pd _sa sl _a ut h_ ena bl e = yes
21 -o smtpd_tls_ask_ccert=yes
22 # -o smtpd_tls_security_level=encrypt
23 # -o s mt pd _sa sl _a ut h_ en ab le = yes
24 # -o smtpd_tls_auth_only=yes
25 # -o smtpd_reject_unlisted_recipient=no
26 # -o smtpd_client_restrictions=$mua_client_restrictions
27 # -o s m tp d _he l o_ r est r ic t ion s = $ mu a _he l o_ r estr ic t io n s
28 # -o smtpd_sender_restrictions=$mua_sender_restrictions
29 # -o smtpd_recipient_restrictions=
30 # -o s mtp d_r ela y_r est ric tio ns = p ermi t_sasl _authe nticat ed , reject
31 # -o m i lte r _ma c ro_ d aem on_n ame = O R I GINATING
32 # smtps inet n - y - - smtpd
33 # -o sysl o g_name = postfix / smtps
34 # -o smtpd_tls_wrappermode=yes
35 # -o s mt pd _sa sl _a ut h_ en ab le = yes
36 # -o smtpd_reject_unlisted_recipient=no
37 # -o smtpd_client_restrictions=$mua_client_restrictions
38 # -o s m tp d _he l o_ r est r ic t ion s = $ mu a _he l o_ r estr ic t io n s
39 # -o smtpd_sender_restrictions=$mua_sender_restrictions
40 # -o smtpd_recipient_restrictions=
41 # -o s mtp d_r ela y_r est ric tio ns = p ermi t_sasl _authe nticat ed , reject
42 # -o m i lte r _ma c ro_ d aem on_n ame = O R I GINATING
43 # 628 inet n - y - - qmqpd
44 pickup unix n - y 60 1 pickup
45 cl e anup unix n - y - 0 cleanup
46 qmgr unix n - n 300 1 qmgr
47 # qmgr unix n - n 300 1 oqmgr
48 tlsmgr unix - - y 1000? 1 t lsmgr
49 re w rite unix - - y - - trivial - rewrite
50 bounce unix - - y - 0 bo unce
51 defer unix - - y - 0 bounce
52 trace unix - - y - 0 bounce
53 verify unix - - y - 1 ve rify
54 flush unix n - y 1000? 0 flush
55 pr o x y m a p unix - - n - - proxymap
56 proxywrite unix - - n - 1 proxymap
57 smtp unix - - y - - smtp
58 relay unix - - y - - smtp
59 -o sysl og_name = postfix / $s ervic e _name
60 # -o s m t p_ h el o _t i me o ut =5 -o s mt p _c o nn ec t _t i me o ut =5
61 showq unix n - y - - showq
62 error unix - - y - - error
63 retry unix - - y - - error
Page 66 of 76

User Manual Internet Server Set-Up & Security-Hardening Script
64 di s card unix - - y - - discard
65 local unix - n n - - local
66 vi r tual unix - n n - - virtual
67 lmtp unix - - y - - lmtp
68 anvil unix - - y - 1 anvil
69 scache unix - - y - 1 sc ache
70 #
71 # ====================================================================
72 # In t e rfaces to non - Po stfix software . Be sure to examine the man ual
73 # pages of the non - Postfix softw are to find out what options it wants .
74 #
75 # Many of the following services use the P ostfix pipe (8) delivery
76 # agent . See the pipe (8) man page for infor m a tion about ${ recipient }
77 # and other message envelope option s .
78 # ====================================================================
79 #
80 # maildrop . See the P ostf ix MAILD ROP_ R EADM E file for detai ls .
81 # A lso s peci fy i n m ai n . cf : m ai l dr o p_ d es ti na t io n _r ec i pi e nt _ li m it =1
82 #
83 ma i l d r o p unix - n n - - pipe
84 fl ags = D Rh u use r = vmail ar gv =/ us r / bin / m aildrop -d ${ r ec ip ient }
85 #
86 # ====================================================================
87 #
88 # Recen t Cyrus versions can use the ex i s t i n g " lmtp " master . cf entry .
89 #
90 # Specify in cyru s . conf :
91 # lmtp cmd =" l mt pd -a " listen =" l ocal host : lmtp " proto = t cp4
92 #
93 # Specify in main . cf one or more of the following :
94 # m ai lb ox _t ra nsp ort = lmt p : inet : l ocalhost
95 # v ir tu al _t ra nsp ort = lmt p : inet : l ocalhost
96 #
97 # ====================================================================
98 #
99 # Cyrus 2.1.5 ( Amos Gou aux )
100 # Also specify in main.cf: cyrus_destination_recipient_limit=1
101 #
102 # cyrus unix - n n - - pipe
103 # user = cyrus argv =/ cyrus / bin / delive r -e -r $ { sender } -m $ { ext e n s i o n } ${ user }
104 #
105 # ====================================================================
106 # Old e xampl e of delivery via C yrus .
107 #
108 #old - cyrus unix - n n - - pipe
109 # flag s =R user = cyrus argv =/ cyrus / bin / deliv er -e -m ${ extension } $ { user }
110 #
111 # ====================================================================
112 #
113 # See the P ost fix U UCP_REA DME file for conf igura t ion details .
114 #
115 uucp unix - n n - - pipe
116 flags = Fqhu user = uucp argv = uux -r -n -z - a$sender - $n e x t hop !rmail ( $re c i p i ent )
117 #
118 # Other external delivery method s .
119 #
120 ifmail unix - n n - - pipe
121 fl ags = F use r = ftn arg v =/ usr / lib / i fmail / ifmail - r $ nexthop ( $ recipi ent )
122 bsmtp unix - n n - - pipe
123 flags = Fq . user = bsmtp argv =/ usr / lib / bsm tp / b sm tp - t$nexth op - f$ sender $recipien t
124 scalemail - backend unix - n n - 2 pipe
125 fl ags = R use r = scalemail argv =/ usr / lib / s ca lema il / bin / s cal em ail - s tor e $ { ne xthop } $ { use r
} $ { extension }
126 ma i lman unix - n n - - pipe
127 fl ags = FR use r = lis t arg v =/ usr / lib / m ai lma n / bin / p ostf ix - to - m ai lma n . py
128 ${ nexthop } $ { user }
Page 67 of 76

User Manual Internet Server Set-Up & Security-Hardening Script
129
130 policy d - spf unix - n n - 0 spa wn
131 user = pol ic yd - spf arg v =/ usr / bin / pol icyd - spf
configFiles/mail/canonical.conf
1
2te st @m ai l . e xa mp le ru n . cf t es t @e xa mp l er un . c f
3ro ot @m ai l . e xa mp le ru n . cf p os tm as t er @e x am pl e ru n . cf
configFiles/mail/aliases.conf
1
2test:test
3postmaster : root
configFiles/mail/opendmarc.conf
1# This is a basic con f igu r a tio n that can easily be adap t e d to suit a standard
2# in s tall a t ion . For more ad v a n c e d options , see o p e ndkim . conf (5) and / or
3# / u sr / s har e / doc / o pe nd marc / examples / o pe nd marc . c on f . sa mple .
4
5## AuthservID ( strin g )
6## defaults to MTA name
7##
8## Sets the " authserv - id " to use when g e n e r ating the Authent i cation - R e sults :
9## header field after verifying a message . If the string " HOSTNAM E " is
10 ## provided , the name of the host runni n g the filt er ( as returned by the
11 ## gethost n a m e (3) function ) will be used .
12 #
13 # AuthservID name
14
15 ## Fail u reR e por t s { true | false }
16 ## default " false "
17 ##
18 ## En a bles gene r a t i on of failure reports when the DMARC test fails and the
19 ## purported sender of the message has requested such reports . Re ports are
20 ## formatted per RFC6 591 .
21 #
22 # FailureReports false
23
24 ## Pi d File path
25 ## default ( none )
26 ##
27 ## Specifies the path to a file that shoul d be c reated at process start
28 # # c on ta in in g th e pr oc es s I D .
29 #
30 Pi d File / var / run / op e n d m arc / opendmarc . pid
31
32 ## PublicSuffixList path
33 ## default ( none )
34 ##
35 ## Specifies the path to a file that contains top - level do m ains ( TLDs ) that
36 ## will be used to compute the O rg a n iz a t io n a l Domain for a given domain name ,
37 ## as d e s c r i b e d in the DMARC s p eci f ica t i on . If not provided , the filter will
38 ## not be able to d e t ermine the Org a ni z a ti o n al Domain and only the presented
39 ## domain will be evaluated .
40 #
41 Pu bl ic Su ff ix Li st / usr / shar e / p ubl ics uff ix
42
43 ## Reje c tFa i lur e s { true | false }
44 ## default " false "
45 ##
46 ## If set , me s s a g e s will be r e j e c ted if they fail the DMARC evaluation , or
47 ## temp - failed if ev aluation could not be c ompleted . By default , no message
48 ## will be re j e c t e d or temp - fail ed rega r d l ess of the outcom e of the DMARC
Page 68 of 76

User Manual Internet Server Set-Up & Security-Hardening Script
49 ## evaluation of the me ssa ge . Instead , an Authentication - Result s header
50 ## f ie ld will be add ed .
51 #
52 # RejectFailures false
53
54 ## Socket socketsp e c
55 ## default ( none )
56 ##
57 ## Specifies the socket that should be e stab l i shed by the f ilter to receive
58 ## connect ions from sendmail (8) in order to p rov ide service . socketspec is
59 ## in one of two f or ms : loc al : path , which cr eate s a UNIX do main sock et at
60 ## the specified path , or inet : port [ @ho st ] or i net6 : port [ @h os t ] which c rea tes
61 ## a TCP socket on the specified port for the appro priate protocol fam ily .
62 ## If the host is not given as either a hostname or an IP address , the
63 ## socket will be listening on all inte r f a ces . This option is ma n d a t o ry
64 ## either in the conf i gur a t ion file or on the c o mmand line . If an IP
65 ## ad d ress is used , it must be enclosed in square brackets .
66 #
67 Socket local :/ var / run / opend m a r c / o p endmarc . sock
68
69 ## Syslog { true | false }
70 ## default " false "
71 ##
72 ## Log via calls to sy slog (3) any interesti n g a c t i v i t y .
73 #
74 Syslog true
75
76 ## Sy slog Faci lit y faci lity - name
77 ## default " mail "
78 ##
79 ## Log via calls to syslog (3) using the named facility . The f a c i l i ty names
80 ## are the same as the ones a l lowed in syslog .conf (5) .
81 #
82 # SyslogFacility mail
83
84 ## Tru s te d Au t hs e rv I Ds string
85 ## default HOSTNAME
86 ##
87 # # S pe ci fi es o ne or m ore " a ut hse rv - id " v al ue s t o t rus t as re la yi ng t ru e
88 ## upstrea m DKIM and SPF re sults . The defau l t is to use the name of
89 ## the MTA p r ocessi n g the message . To spec i f y a list , separate each entry
90 ## with a comma . The key word " HOSTNAME " will be replaced by the name of
91 ## the host r u n ning the fi lter as reported by the geth o s t name (3) function .
92 #
93 # Trus t ed A ut h se r vI D s H O S T N A M E
94
95 ## UMask mask
96 ## default ( none )
97 ##
98 ## Request s a s p e c i f i c p e rmis s i ons mask to be used for file creation . This
99 ## only really applies to creation of the soc ket when Socke t speci f i e s a
100 ## UNIX domain socket , and to the H i s t oryF i l e and PidFile (if any ); tempor a r y
101 ## files are n o rmally created by the mkst e m p (3) f u n c t i o n that enforces a
102 ## specifi c file mode on creation reg ardless of the p rocess umas k . See
103 ## umask (2) for more info r m a tion .
104 #
105 UMask 0002
106
107 ## Us erID user [: group ]
108 ## default ( none )
109 ##
110 ## Attempt s to become the sp ecified us erid be fore starting operations .
111 ## The process will be a s s i g n e d all of the gr oups and pri m ary group ID of
112 ## the named user id unle ss an al t e r n a t e group is s p e c i f i e d .
113 #
114 UserID opendmarc
Page 69 of 76

User Manual Internet Server Set-Up & Security-Hardening Script
115 AutoResta r t Yes
116 Auto Re star tRa te 10/1 h
117 Pi d File / var / spool / postfix / opendmarc / opendmarc . pid
118 Socket local :/ var / spool / postf i x / op e n d m arc / opendmarc . sock
119 AuthservID mail . ex a m plerun . cf
120 Trus t edAu t hse r vIDs mail . examplerun . cf
121 Syslog true
122 SyslogFacility mail
123 UMask 0002
124 UserID opendmarc : opendmarc
configFiles/mail/opendkim.conf
1# This is a basic con f igu r a tio n that can easily be adap t e d to suit a standard
2# in s tall a t ion . For more ad v a n c e d options , see o p e ndkim . conf (5) and / or
3# / usr / share / doc / opendkim / examples / opendkim . conf . sam ple .
4
5# Log to s yslog
6Syslog yes
7# Required to use local socket with MTAs that access the socket as a non -
8# pr i vileged user ( e. g. Postfix )
9UMask 007
10
11 # S ig n for exa mp le . com w it h key in / etc / dkimkeys / d ki m . ke y u sin g
12 # se lector ’2007 ’ (e .g . 2007 . _ do ma ink ey . e xa mpl e . com )
13 # Domai n e xam pl e . com
14 # K eyF il e / etc / dkimkeys / d kim . key
15 # Se lector 2007
16
17 # Commonly - used options ; the commented - out versions show the defaults .
18 #Canonicalization simple
19 # Mode sv
20 # SubDomains no
21
22 # S ocket smtp :// localhost
23 #
24 # ## Sock et sock e t s p ec
25 # ##
26 # ## Names the socket where this filter should liste n for milter co n n ectio n s
27 # ## from the MTA . R e q u i r e d . Should be in one of these forms :
28 # ##
29 # ## inet : port @ a ddr e s s to listen on a sp e c i f i c i n t e r f a c e
30 # ## inet : port to listen on all in t e r f aces
31 # ## local :/ path / to / socket to listen on a UNIX domain socket
32 #
33 # So cket inet :8892 @localhost
34 Socket local :/ var / run / o pe ndkim / o pe ndkim . soc k
35
36 ## Pi d File filename
37 # ## de fa ul t ( n on e )
38 # ##
39 # ## Name of the file where the filter should write its pid bef ore beginning
40 # ## n orm al o pe ra ti on s .
41 #
42 Pi dFi le / var / run / opendkim / opendkim . pid
43
44
45 # Always oversign From ( sign using actual From and a null From to prev e n t
46 # ma li ci ou s s ig na tu re s h ead er fi el ds ( Fr om an d / or o th er s ) b et we en t he si gn er
47 # and the verifier . From is oversigned by d efault in the Debi an pacakge
48 # because it is often the i d e ntity key used by reputation systems and thus
49 # somewhat security sensitive .
50 Overs i gnH e ad e rs From
51
52 ## ResolverConfiguration filename
53 ## default ( none )
54 ##
Page 70 of 76

User Manual Internet Server Set-Up & Security-Hardening Script
55 ## Specifies a co n f igu r ati o n file to be passed to the Unbound l ibrary that
56 ## perform s DNS q ueries a p p l y i n g the DNSSEC protocol . See the Unb o u nd
57 ## docum e nta t i on at http :// unb o u nd . net for the expecte d content of this file .
58 ## The r esults of using this and the Trus t An c h or F ile setting at the same
59 ## time are undefined .
60 ## In Debian , / etc / unbound / unbound . conf is s hip ped as part of the Suggested
61 ## unbound package
62
63 # Reso l ver Con figu rat ion / etc / unbound / unb oun d .conf
64
65 ## Trus t An c h or F il e fi lename
66 ## default ( none )
67 ##
68 ## Specifies a file from which trust anchor data sh ould be read when doing
69 ## DNS que r i es and applying the DNSSEC protocol . See the Unbound d o cum e nta t i on
70 ## at http :// unbound . net for the expected fo rmat of this file .
71
72 Tr us tA nc ho rF il e / usr / sha re / dn s / root . ke y
73
74 ## Userid userid
75 # ## de fa ul t ( n on e )
76 # ##
77 # ## Change to user " userid " before starting no rmal operation ? May include
78 # ## a group ID as well , s e p a r a t ed from the userid by a colon .
79 #
80 UserID opendkim
81 # This is a basic con f igu r a tio n that can easily be adap t e d to suit a standard
82 # in s tall a t ion . For more ad v a n c e d options , see o p e ndkim . conf (5) and / or
83 # / usr / share / doc / opendkim / examples / opendkim . conf . sam ple .
84
85 # Log to s yslog
86 Syslog yes
87 # Required to use local socket with MTAs that access the socket as a non -
88 # pr i vileged user ( e. g. Postfix )
89 UMask 002
90 # Op e n D K I M user
91 # Re m e m b e r to add user postf i x to gro up opendkim
92 UserID opendkim
93
94 # Map d omains in From addresses to keys used to sign messages
95 Ke yT able / etc / opendkim / key . t abl e
96 Signing T able refile :/ etc / op e n d k i m / signing . table
97
98 # Hosts to ignore when verifying sig n a t ures
99 Ex te rn al Ig no re Li st / etc / o pe ndkim / t ru ste d . hos ts
100 Int er nal Ho sts / etc / o pendkim / t ru ste d . hos ts
101
102 # Commonly - used options ; the commented - out versions show the defaults .
103 Canon ica liza tion r elax ed / sim ple
104 Mode sv
105 SubDomains no
106 # ADSPAction continue
107 AutoRestart no
108 Auto Re star tRa te 10/ 1 M
109 Background yes
110 DNSTimeout 5
111 Sign atur eAlg ori thm rsa - sh a256
112
113 # Always oversign From ( sign using actual From and a null From to prev e n t
114 # ma li ci ou s s ig na tu re s h ead er fi el ds ( Fr om an d / or o th er s ) b et we en t he si gn er
115 # and the verifier . From is oversigned by d efault in the Debi an package
116 # because it is often the i d e ntity key used by reputation systems and thus
117 # somewhat security sensitive .
118 Overs i gnH e ad e rs From
119 # ## U BU NT U 18 .1 0
120 Pi dFi le / var / spool / postfi x / o p e ndkim / opendkim . pid
Page 71 of 76

User Manual Internet Server Set-Up & Security-Hardening Script
121 Socket local :/ var / spool / postfix / op endkim / op endkim . sock
configFiles/mail/signing.table
1* @exampler u n . cf exampl e r u n
configFiles/mail/trusted.hosts
1127.0.0.1
2::1
3localhost
4ex am pl er un . cf
5ma il . e xa mp le ru n . cf
configFiles/mail/users–external.conf
1test:::::::
configFiles/mail/dovecot.conf
1## Dovecot config u rat i o n file
2! i nc lu de_ try / usr / s har e / dove co t / protoco ls . d /*. pr ot ocol
3
4! i ncl ud e conf . d /*. conf
5
6auth default {
7mechanisms = plain login external
8user = root
9socket listen {
10 client {
11 path = / var / sp oo l / postf ix / private / auth
12 mode = 0660
13 user = postfix
14 group = postfi x
15 }
16 }
17 }
configFiles/mail/10–auth.conf
1
2##
3## Aut h ent i cat i on pro c e s s e s
4##
5
6# disa b le_ p la i ntex t_ a ut h = yes
7
8auth_ssl_username_from_cert = yes
9
10 auth_ m ech a ni s ms = plain login external
11
12 ! i ncl ud e auth - s yst em . c onf . ext
13 ! include auth - passwdfile . conf . ext
configFiles/mail/10–ssl.conf
1
2##
3## SSL s e t t i n g s
4##
5
6ssl = yes
7
8ss l_ cert = </ et c / le ts en cr ypt / l ive / m ail . exa mpler un . cf / f ul lchai n . pem
9ss l _key = </ etc / le t s e ncrypt / live / mail . ex amplerun . cf / privkey . pem
Page 72 of 76

User Manual Internet Server Set-Up & Security-Hardening Script
10
11 ss l_ca = </ et c / ssl / cert s / ex ample run . cf . ca . crl . pem
12
13 ss l_ cl ie nt _c a_ di r = / etc / ssl / c er ts
14
15 ssl_ v er if y _c li e nt _c e rt = yes
16
17 ssl_cert_username_field = CN
18
19 # DH p ar ame ters len gth to use .
20 ssl_dh_parameters_length = 1024
21
22 # SSL protocols to use
23 ssl_p rotoc ols = ! S SLv2 ! SSLv3
24
25 # SSL cipher s to use
26 ss l_ ci ph er _l is t = kE ECD H :+ kEECD H + SHA : k ED H :+ k ED H + SH A :+ k ED H + CA ME LLIA : k ECD H :+ kEC DH + SHA :
kRSA :+ kRSA + SHA :+ kRSA + CAMELLIA :! aNULL :! eNULL :! SSLv2 :! RC4 :! MD5 :! DES :! EXP :! SEED :! IDEA
:!3DES
27
28 # P refer the server ’ s order of ci phers over client ’ s .
29 ssl_prefer_server_ciphers = yes
30
31 # SSL e xtr a op ti ons . Currentl y support ed op ti ons are :
32 # no _comp r essio n - Disable compress i o n .
33 # no_ t i c k e t - Disa b l e SSL session t ickets .
34 #ssl_options =
configFiles/mail/auth–passwdfile.conf.ext
1
2# Au th en tic ati on for passwd - file us ers . Included from 10 - auth . conf .
3#
4# passwd - like file with specified location .
5# < doc / wiki / Au thData b a se . PasswdFil e . txt >
6
7passdb {
8dr ive r = passwd - file
9# the PLAIN scheme prevents us from havi ng to hash the empty stri ng
10 ar gs = sch em e = P LAI N u se rn am e_ f or ma t =% u / e tc / d ov ec ot / us ers - e xt er na l
11
12 # t his op ti on r eq uir es D ov ec ot 2. 2. 28 ( or t he p at ch ) , wi th out it th is s etu p
13 # is insecure becau s e it p e rmits logi ns with the empty string as password
14 mechanisms = external
15
16 # explicitly permi t empty passwords
17 overr i de_ f ie l ds = no p a s s word
18 }
19
20 userdb {
21 dr ive r = passwd - file
22 ar gs = u se rn am e_ fo r ma t =% u / etc / d ov ec ot / u ser s - e xt er na l
23 }
configFiles/fw/fw.conf
1# SSH
2allow - tcp - 22
3allow - udp - 22
4# DNS
5allow - tcp - 53
6allow - udp - 53
7# MAIL
8allow - tcp - 25
9allow - udp - 25
10 # SECURE SMTP
Page 73 of 76
User Manual Internet Server Set-Up & Security-Hardening Script
11 allow - tcp - 465
12 allow - udp - 465
13 # IMAP
14 allow - tcp - 143
15 allow - udp - 143
16 # IMAP TLS
17 allow - tcp - 993
18 allow - udp - 993
19 # HTTP HTTPS
20 allow - tcp - 80
21 allow - tcp - 443
configFiles/web/nginx/nginx.conf
1user www - data ;
2worker_processes auto;
3pid / run / ngi nx . pid ;
4in clude / etc / nginx / modules - en abl ed /*. conf ;
5
6events {
7work e r_ c on n ec t io n s 768;
8# multi_accept on;
9}
10
11 http {
12 ##
13 # Basic S e t t i n g s
14 ##
15
16 se nd fi le on ;
17 t cp _n op us h on ;
18 tcp_nodelay on;
19 keepalive_timeout 65;
20 types_hash_max_size 2048;
21 ser ver _t ok ens o ff ;
22
23 # ser v er _n am e s_ ha sh _b uc ke t _s iz e 64;
24 # se rv er _n am e_ in_ re di re ct off ;
25
26 in clude / etc / nginx / mime . type s ;
27 de fa ul t_ ty pe a pp li ca ti on / octet - s trea m ;
28
29 ##
30 # Lo g ging Settings
31 ##
32
33 access _log / var / log / n gin x / ac cess . lo g ;
34 error_log / var / log / n gin x / er ror . log ;
35
36 ##
37 # Gzip Settings
38 ##
39
40 gz ip on ;
41
42 # gz ip _v ar y on ;
43 # gzip_proxied any;
44 # gzip_ c omp _ le v el 6;
45 # gzip_buffers 16 8k;
46 # gzip_http_version 1.1;
47 # gz ip_t ypes text / p lai n tex t /css a pp lica tion / json a pplica tion / javas cript text / xml
applicati o n / xml a pplicati o n / xml + rss text / ja vascript ;
48
49 ##
50 # Virtual Host Configs
51 ##
52
Page 74 of 76
User Manual Internet Server Set-Up & Security-Hardening Script
53 in cl ude / et c / ngi nx / c on f .d /*. con f ;
54 }
configFiles/web/nginx/conf.d/examplerun.cf.conf
1server {
2li sten 443 ssl ;
3li sten [ ::]:443 ssl ;
4server_na m e e xamplerun . cf www . ex amplerun . cf defau l t_ser v er ;
5
6ssl_prefer_server_ciphers on;
7ssl_pr o t oco l s TLSv1 .1 TLSv1 .2;
8s sl _c i ph e rs E CD HE - E CD SA - A ES 256 - GC M - S HA 38 4 : E CD HE - RS A - AE S2 56 - GCM - S H A3 84 : EC DH E -
ECDS A - CHAC HA2 0 - P OL Y1 305 : ECDHE - RSA - CHAC HA 20 - P OLY1305 : ECDHE - EC DSA - AES 12 8 - GCM
- S HA2 56 : E CDHE - RSA - AES1 28 - GCM - S HA2 56 : E CDHE - EC DSA - AES 256 - S HA 384 : E CDHE - RSA -
AES256 - S HA384 : ECDHE - ECDSA - AES128 - SH A256 : ECDHE - RSA - AES128 - S HA2 56 ;
9
10 ss l_ se ss io n_ ca ch e s har ed : SSL :5 0 m;
11 ssl_session_timeout 5m;
12
13 ss l_ ce rt if ic at e / etc / l et se nc ry pt / l ive / exa mpler un . cf / f ul lcha in . pem ; # managed
by Certbot
14 ss l_ ce rt if ic at e_ key / etc / l et se ncr ypt / l iv e / exampl erun . cf / p ri vke y . pem ; # managed
by Certbot
15
16 ssl_ dhpa ram / etc / s sl / d h409 6 . pem ;
17
18 add_header Strict - Transport - Security " max - ag e = 3 15 36 0 00 ; i n cl u de S ub D om a in s "
always;
19 a dd _h ea de r X - C on tent - T ype - O pt io ns "nosniff" always;
20 a dd _h e ad er X - Xss - P r ot ec t io n " 1; mode = block " always;
21 a dd _h ea de r X - Fra me - O pt io ns " SA M E O RIGIN " always;
22 add_header Referrer - Polic y " same - o ri gin " always;
23
24 access _log / var / log / n gin x / ex ampler un . cf _s sl _ac ce ss . l og ;
25 error_log / var / log / n gin x / exa mpler un . cf _ss l_e rr or . log ;
26
27 lo c a t i o n / {
28 p ro xy _ se t_ he a de r X - Real - IP $ re mo t e_ ad dr ;
29 p ro xy _s e t_ he a de r X - F orw ard ed - Fo r $r e mo te _a dd r ;
30 prox y_se t_h eade r Host $host ;
31 proxy_pass http :// 1 27 . 0. 0 .1 : 80 8 0;
32 }
33 }
34
35 server {
36 listen 80;
37 listen [::]:80;
38 server_na m e e xamplerun . cf www . ex amplerun . cf defau l t_ser v er ;
39
40 access _log / var / log / n gin x / ex ampler un . cf_acce ss . log ;
41 error_log / var / log / n gin x / exa mpler un . c f_ error . log ;
42
43 return 301 https :// $hos t $req u es t _ uri ;
44 }
configFiles/web/apache2/ports.conf
1Listen 8080
2# vim : syntax = apa che ts =4 sw =4 sts =4 sr noet
configFiles/web/apache2/sites–available/examplerun.cf.conf
1
2< Virt ualH ost 127.0.0. 1: 8080 >
3Se rv er Na me e xa mp le ru n . cf
Page 75 of 76

User Manual Internet Server Set-Up & Security-Hardening Script
4ServerName www . example r u n . cf
5ServerAdmin webmaster@examplerun.cf
6Doc ume ntR oot / var / w ww / exam pleru n
7
8# L ogLevel i nf o s sl : w ar n
9
10 Er ro rLog $ { A PA CH E_ LO G_ DI R }/ is mu . ga_error . log
11 CustomLog ${ APA C HE_LO G _DIR }/ ismu . ga _ a c c e ss . log c ombi ned
12 </VirtualHost >
13
14 # vim : syntax = apa che ts =4 sw =4 sts =4 sr noet
Page 76 of 76