2007 01 26 Nmap Quick Options Guide Professor Messer
Professor_Messer_Nmap_Quick_Reference_Guide
Professor_Messer_Nmap_Quick_Reference_Guide
Professor_Messer_Nmap_Quick_Reference_Guide
User Manual:
Open the PDF directly: View PDF ![]() .
.
Page Count: 2

SCAN OPTION SUMMARY
Scan Name Command
Syntax
Requires
Privileged
Access
Identifies
TCP
Ports
Identifies
UDP
Ports
TCP SYN Scan -sS YES YES NO
TCP connect() Scan -sT NO YES NO
FIN Stealth Scan -sF YES YES NO
Xmas Tree Stealth Scan -sX YES YES NO
Null Stealth Scan -sN YES YES NO
Ping Scan -sP NO NO NO
Version Detection -sV NO NO NO
UDP Scan -sU YES NO YES
IP Protocol Scan -sO YES NO NO
ACK Scan -sA YES YES NO
Window Scan -sW YES YES NO
RPC Scan -sR NO NO NO
List Scan -sL NO NO NO
Idlescan -sI YES YES NO
FTP Bounce Attack -b NO YES NO
PING OPTIONS
ICMP Echo Request Ping -PE, -PI
TCP ACK Ping -PA[portlist], -PT[portlist]
TCP SYN Ping -PS[portlist]
UDP Ping -PU[portlist]
ICMP Timestamp Ping -PP
ICMP Address Mask Ping -PM
Don’t Ping -P0, -PN, -PD
Require Reverse -R
Disable Reverse DNS -n
Specify DNS Servers --dns-servers
HOST AND PORT OPTIONS
Exclude Targets --exclude <host1 [,host2],...>
Exclude Targets in File --excludefile <exclude_file>
Read Targets from File -iL <inputfilename>
Pick Random Numbers for Targets -iR <num_hosts>
Randomize Hosts --randomize_hosts, -rH
No Random Ports -r
Source Port --source-port <portnumber>
Specify Protocol or Port Numbers -p <port_range>
Fast Scan Mode -F
Create Decoys -D <decoy1 [,decoy2][,ME],...>
Source Address -S <IP_address>
Interface -e <interface>
List Interfaces --iflist
LOGGING OPTIONS
Normal Format -oN <logfilename>
XML Format -oX <logfilename>
Grepable Format -oG <logfilename>
All Formats -oA <basefilename>
Script Kiddie Format -oS <logfilename>
Resume Scan --resume <logfilename>
Append Output --append-output
REAL-TIME INFORMATION OPTIONS
Verbose Mode --verbose, -v
Version Trace --version-trace
Packet Trace --packet-trace
Debug Mode --debug, -d
Interactive Mode --interactive
Noninteractive Mode --noninteractive
TUNING AND TIMING OPTIONS
Time to Live --ttl
Use Fragmented IP Packets -f, -ff
Maximum Transmission Unit --mtu <databytes>
Data Length --data-length <databytes>
Host Timeout --host-timeout <milliseconds>
Initial Round Trip Timeout --initial-rtt-timeout <milliseconds>
Minimum Round Trip Timeout --min-rtt-timeout <milliseconds>
Maximum Round Trip Timeout --max-rtt-timeout <milliseconds>
Maximum Parallel Hosts per Scan --max-hostgroup <number>
Minimum Parallel Hosts per Scan --min-hostgroup <number>
Maximum Parallel Port Scans --max-parallelism <number>
Minimum Parallel Port Scans --min-parallelism <number>
Minimum Delay Between Probes --scan-delay <milliseconds>
Maximum Delay Between Probes --max-scan-delay
Timing Policies --timing, -T<0|1|2|3|4|5>
MISCELLANEOUS OPTIONS
Quick Reference Screen --help, -h
Nmap Version --version, -V
Data Directory --datadir <directory_name>
Quash Argument Vector -q
Define Custom Scan Flags --scanflags <flagval>
(Uriel) Maimon Scan -sM
IPv6 Support -6
Send Bad TCP or UDP Checksum --badsum
Copyright © 2007 Professor Messer, LLC, All Rights Reservedhttp://www.ProfessorMesser.com SNC-201
NMAP
Professor Messer’s Quick Reference Guide to
OPERATING SYSTEM FINGERPRINTING
OS Fingerprinting -O
Limit System Scanning --osscan-limit
More Guessing Flexibility --osscan-guess, --fuzzy
Additional, Advanced, and Aggressive -A
VERSION DETECTION
Version Scan -sV
Don’t Exclude Any Ports --allports
Set Version Intensity --version-intensity
Enable Version Scanning Light --version-light
Enable Version Scan All --version-all
RUN-TIME INTERACTIONS
Display Run-Time Help ?
Increase / Decrease Verbosity v / V
Increase / Decrease Debugging d / D
Increase / Decrease Packet Tracing p / P
Any Other Key Print Status
Copyright © 2007 Professor Messer, LLC, All Rights Reservedhttp://www.ProfessorMesser.com SNC-201
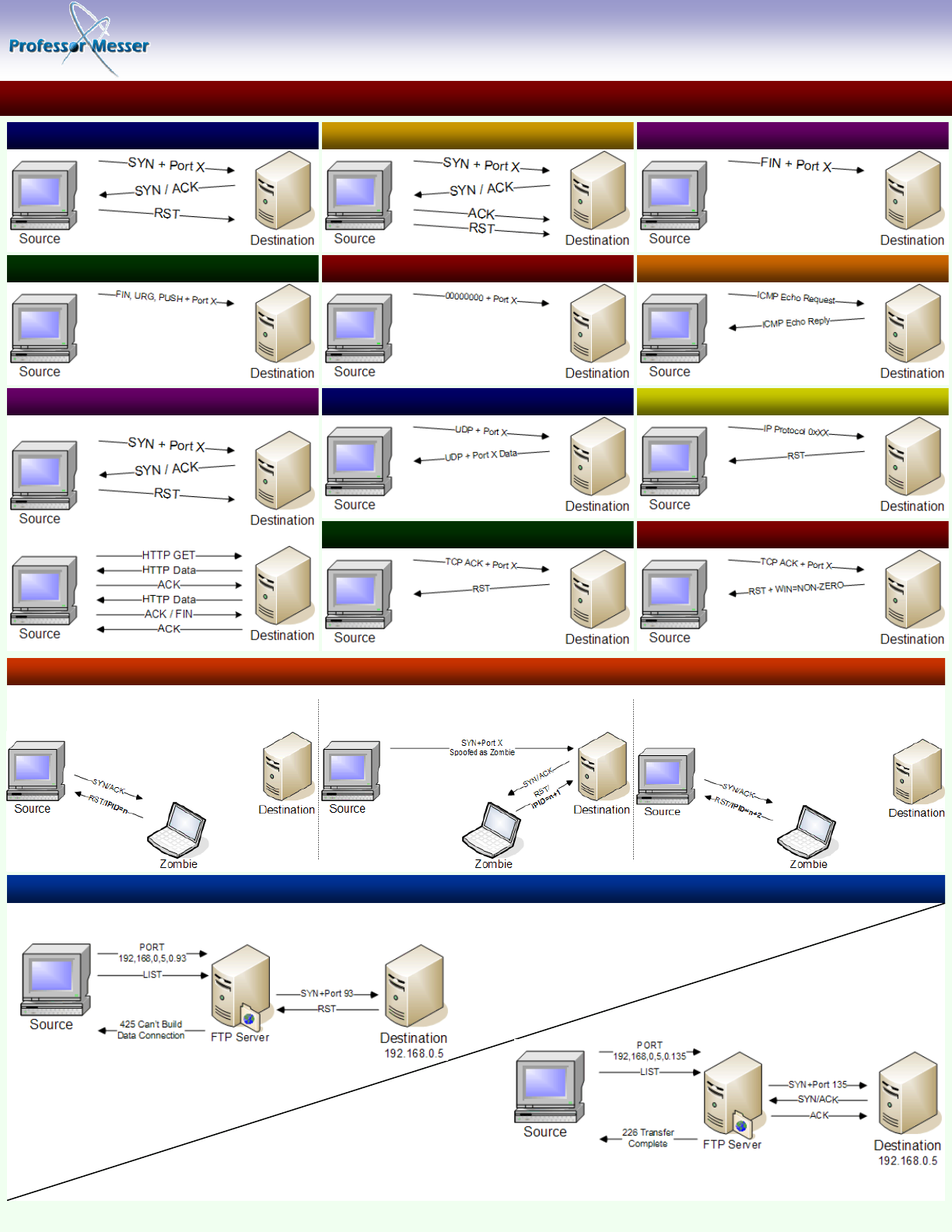
TCP SYN SCAN (-sS)
Identifying Open Ports with Nmap
TCP connect() SCAN (-sT)
TCP FIN SCAN (-sF)
TCP XMAS TREE SCAN (-sX)
TCP NULL SCAN (-sN)
TCP PING SCAN (-sP)
VERSION DETECTION SCAN (-sV)
UDP SCAN (-sU)
TCP ACK SCAN (-sA)
IP PROTOCOL SCAN (-sO)
TCP WINDOW SCAN (-sW)
IDLESCAN (-sI <zombie host:[probeport]>)
FTP BOUNCE ATTACK (-b <ftp_relay_host>)
Version scan identifies open ports with a TCP SYN scan...
...and then queries the port with a customized signature.
Step 1: Nmap sends a SYN/ACK to the zombie workstation to
induce a RST in return. This RST frame contains the initial IPID
that nmap will remember for later.
Step 2: Nmap sends a SYN frame to the destination address,
but nmap spoofs the IP address to make it seem as if the SYN
frame was sent from the zombie workstation.
Step 3: Nmap repeats the original SYN/ACK probe of the zom-
bie station. If the IPID has incremented, then the port that was
spoofed in the original SYN frame is open on the destination
device.
A closed port will result with the FTP server informing the source station that the FTP server can’t build the connection.
An open port completes the transfer over the specified connection.
NMAP
Professor Messer’s Quick Reference Guide to