X86 Assembly Language Reference Manual
User Manual:
Open the PDF directly: View PDF ![]() .
.
Page Count: 204 [warning: Documents this large are best viewed by clicking the View PDF Link!]
2550 Garcia Avenue
Mountain View, CA 94043
U.S.A.
x86 Assembly Language
Reference Manual
A Sun Microsystems, Inc. Business

Please
Recycle
1995 Sun Microsystems, Inc. 2550 Garcia Avenue, Mountain View, California 94043-1100 U.S.A.
All rights reserved. This product or document is protected by copyright and distributed under licenses restricting its use,
copying, distribution and decompilation. No part of this product or document may be reproduced in any form by any means
without prior written authorization of Sun and its licensors, if any.
Portions of this product may be derived from the UNIX® system, licensed from UNIX Systems Laboratories, Inc., a wholly
owned subsidiary of Novell, Inc., and from the Berkeley 4.3 BSD system, licensed from the University of California. Third-party
software, including font technology in this product, is protected by copyright and licensed from Sun’s Suppliers.
RESTRICTED RIGHTS LEGEND: Use, duplication, or disclosure by the government is subject to restrictions as set forth in
subparagraph (c)(1)(ii) of the Rights in Technical Data and Computer Software clause at DFARS 252.227-7013 and FAR 52.227-19.
The product described in this manual may be protected by one or more U.S. patents, foreign patents, or pending applications.
TRADEMARKS
Sun, Sun Microsystems, the Sun logo, SunSoft, the SunSoft logo, Solaris, SunOS, OpenWindows, DeskSet, ONC, ONC+, and NFS
are trademarks or registered trademarks of Sun Microsystems, Inc. in the United States and other countries. UNIX is a registered
trademark in the United States and other countries, exclusively licensed through X/Open Company, Ltd. OPEN LOOK is a
registered trademark of Novell, Inc. PostScript and Display PostScript are trademarks of Adobe Systems, Inc.
All SPARC trademarks are trademarks or registered trademarks of SPARC International, Inc. in the United States and other
countries. SPARCcenter, SPARCcluster, SPARCompiler, SPARCdesign, SPARC811, SPARCengine, SPARCprinter, SPARCserver,
SPARCstation, SPARCstorage, SPARCworks, microSPARC, microSPARC-II, and UltraSPARCare licensed exclusively to Sun
Microsystems, Inc. Products bearing SPARC trademarks are based upon an architecture developed by Sun Microsystems, Inc.
The OPEN LOOK® and Sun™ Graphical User Interfaces were developed by Sun Microsystems, Inc. for its users and licensees.
Sun acknowledges the pioneering efforts of Xerox in researching and developing the concept of visual or graphical user
interfaces for the computer industry. Sun holds a non-exclusive license from Xerox to the Xerox Graphical User Interface, which
license also covers Sun’s licensees who implement OPEN LOOK GUI’s and otherwise comply with Sun’s written license
agreements.
X Window System is a trademark of X Consortium, Inc.
THIS PUBLICATION IS PROVIDED “AS IS” WITHOUT WARRANTY OF ANY KIND, EITHER EXPRESS OR IMPLIED,
INCLUDING, BUT NOT LIMITED TO, THE IMPLIED WARRANTIES OF MERCHANTABILITY, FITNESS FOR A
PARTICULAR PURPOSE, OR NON-INFRINGEMENT.
THIS PUBLICATION COULD INCLUDE TECHNICAL INACCURACIES OR TYPOGRAPHICAL ERRORS. CHANGES ARE
PERIODICALLY ADDED TO THE INFORMATION HEREIN, THESE CHANGES WILL BE INCORPORATED IN NEW
EDITIONS OF THE PUBLICATION. SUN MICROSYSTEMS, INC. MAY MAKE IMPROVEMENTS AND/OR CHANGES IN
THE PRODUCT(S) AND/OR THE PROGRAMS(S) DESCRIBED IN THIS PUBLICATION AT ANY TIME.

iii
Contents
Preface. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . xvii
1. Assembler Input . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1
Introduction . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1
Source Files in Assembly Language Format. . . . . . . . . . . . . . . . 2
File Organization. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 2
Statements. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3
Values and Symbol Types. . . . . . . . . . . . . . . . . . . . . . . . . . . . 4
Expressions. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 6
Expression Syntax . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 7
Expression Semantics (Absolute vs. Relocatable) . . . . . . . . 9
Machine Instruction Syntax . . . . . . . . . . . . . . . . . . . . . . . . . . 10
Instruction Description . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 12
Pseudo Operations . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 14
General Pseudo Operations . . . . . . . . . . . . . . . . . . . . . . . . . . 14
Symbol Definition Pseudo Operations . . . . . . . . . . . . . . . . . 19

iv x86 Assembly Language Reference Manual—November 1995
2. Instruction-Set Mapping . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 21
Introduction . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 22
Notational Conventions . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 23
References. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 26
Segment Register Instructions . . . . . . . . . . . . . . . . . . . . . . . . . . . 26
Load Full Pointer (lds,les, lfs, lgs, and lss) . . . . . . . . . . . . . 26
Pop Stack into Word (pop). . . . . . . . . . . . . . . . . . . . . . . . . . . 27
Push Word/Long onto Stack (push). . . . . . . . . . . . . . . . . . . 28
I/O Instructions. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 29
Input from Port (in, ins) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 29
Output from Port (out, outs) . . . . . . . . . . . . . . . . . . . . . . . . . 31
Flag Instructions. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 32
Load Flags into AH Register (lahf) . . . . . . . . . . . . . . . . . . . . 32
Store AH into Flags (sahf). . . . . . . . . . . . . . . . . . . . . . . . . . . . 33
Pop Stack into Flag (popf). . . . . . . . . . . . . . . . . . . . . . . . . . . 33
Push Flag Register Onto Stack (pushf) . . . . . . . . . . . . . . . . 34
Complement Carry Flag (cmc). . . . . . . . . . . . . . . . . . . . . . . . 35
Clear Carry Flag (clc). . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 35
Set Carry Flag (stc). . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 36
Clear Interrupt Flag (cli). . . . . . . . . . . . . . . . . . . . . . . . . . . . . 36
Set Interrupt Flag (sti). . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 37
Clear Direction Flag (cld) . . . . . . . . . . . . . . . . . . . . . . . . . . . . 37
Set Direction Flag (std) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 38
Arithmetic Logical Instructions . . . . . . . . . . . . . . . . . . . . . . . . . . 38

Contents v
Integer Addition (add) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 38
Integer Add With Carry (adc) . . . . . . . . . . . . . . . . . . . . . . . . 39
Integer Subtraction (sub) . . . . . . . . . . . . . . . . . . . . . . . . . . . . 40
Integer Subtraction With Borrow (sbb) . . . . . . . . . . . . . . . . 41
Compare Two Operands (cmp) . . . . . . . . . . . . . . . . . . . . . . . 42
Increment by 1 (inc). . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 43
Decrease by 1 (dec) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 44
Logical Comparison or Test (test) . . . . . . . . . . . . . . . . . . . . . 45
Shift (sal, shl, sar, shr) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 46
Double Precision Shift Left (shld) . . . . . . . . . . . . . . . . . . . . . 48
Double Precision Shift Right (shrd). . . . . . . . . . . . . . . . . . . . 49
One’s Complement Negation (not) . . . . . . . . . . . . . . . . . . . . 50
Two’s Complement Negation (neg). . . . . . . . . . . . . . . . . . . . 50
Check Array Index Against Bounds (bound). . . . . . . . . . . . 51
Logical And (and) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 52
Logical Inclusive OR (or) . . . . . . . . . . . . . . . . . . . . . . . . . . . . 54
Logical Exclusive OR (xor) . . . . . . . . . . . . . . . . . . . . . . . . . . . 55
Multiply and Divide Instructions . . . . . . . . . . . . . . . . . . . . . . . . 56
Signed Multiply (imul) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 57
Unsigned Multiplication of AL, AX or EAX(mul) . . . . . . . 58
Unsigned Divide (div). . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 60
Signed Divide (idiv) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 61
Conversion Instructions . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 62
Convert Byte to Word (cbtw) . . . . . . . . . . . . . . . . . . . . . . . . . 62

vi x86 Assembly Language Reference Manual—November 1995
Convert Word to Long (cwtl) . . . . . . . . . . . . . . . . . . . . . . . . . 63
Convert Signed Word to Signed Double Word (cwtd) . . . . 63
Convert Signed Long to Signed Double Long (cltd) . . . . . . 64
Decimal Arithmetic Instructions . . . . . . . . . . . . . . . . . . . . . . . . . 64
Decimal Adjust AL after Addition (daa) . . . . . . . . . . . . . . . 64
Decimal Adjust AL after Subtraction (das). . . . . . . . . . . . . . 65
ASCII Adjust after Addition (aaa). . . . . . . . . . . . . . . . . . . . . 65
ASCII Adjust after Subtraction (aas). . . . . . . . . . . . . . . . . . . 66
ASCII Adjust AX after Multiply (aam) . . . . . . . . . . . . . . . . . 67
ASCII Adjust AX before Division (aad) . . . . . . . . . . . . . . . . 68
Coprocessor Instructions. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 69
Wait (wait, fwait) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 69
String Instructions . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 69
Move Data from String to String (movs). . . . . . . . . . . . . . . . 70
Compare String Operands (cmps). . . . . . . . . . . . . . . . . . . . . 71
Store String Data (stos) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 72
The Load String Operand (lods) . . . . . . . . . . . . . . . . . . . . . . 73
Compare String Data (scas) . . . . . . . . . . . . . . . . . . . . . . . . . . 75
Look-Up Translation Table (xlat) . . . . . . . . . . . . . . . . . . . . . . 76
Repeat String Operation (rep, repnz, repz) . . . . . . . . . . . . . 77
Procedure Call and Return Instructions . . . . . . . . . . . . . . . . . . . 78
Far Call — Procedure Call (lcall) . . . . . . . . . . . . . . . . . . . . . . 78
Near Call — Procedure Call (call) . . . . . . . . . . . . . . . . . . . . . 79
Return from Procedure (ret). . . . . . . . . . . . . . . . . . . . . . . . . . 80

Contents vii
Long Return (lret) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 81
Enter/Make Stack Frame for Procedure Parameters (enter) 82
High Level Procedure Exit (leave). . . . . . . . . . . . . . . . . . . . . 83
Jump Instructions. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 83
Jump if ECX is Zero (jcxz). . . . . . . . . . . . . . . . . . . . . . . . . . . . 83
Loop Control with CX Counter (loop, loopnz, loopz). . . . . 84
Jump (jmp, ljmp) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 85
Interrupt Instructions . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 87
Call to Interrupt Procedure (int, into) . . . . . . . . . . . . . . . . . . 87
Interrupt Return (iret) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 89
Protection Model Instructions . . . . . . . . . . . . . . . . . . . . . . . . . . . 90
Store Local Descriptor Table Register (sldt) . . . . . . . . . . . . . 90
Store Task Register (str). . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 90
Load Local Descriptor Table Register (lldt) . . . . . . . . . . . . . 91
Load Task Register (ltr). . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 92
Verify a Segment for Reading or Writing (verr, verw) . . . . 92
Store Global/Interrupt Descriptor Table Register (sgdt, sidt) 93
Load Global/Interrupt Descriptor Table (lgdt, lidt) . . . . . . 94
Store Machine Status Word (smsw). . . . . . . . . . . . . . . . . . . . 95
Load Machine Status Word (lmsw) . . . . . . . . . . . . . . . . . . . . 96
Load Access Rights (lar) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 96
Load Segment Limit (lsl). . . . . . . . . . . . . . . . . . . . . . . . . . . . . 97
Clear Task-Switched (clts). . . . . . . . . . . . . . . . . . . . . . . . . . . . 98
Adjust RPL Field of Selector (arpl) . . . . . . . . . . . . . . . . . . . . 99

viii x86 Assembly Language Reference Manual—November 1995
Bit Instructions. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 100
Bit Scan Forward (bsf). . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 100
Bit Scan Reverse (bsr) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 100
Bit Test (bt) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 101
Bit Test And Complement (btc) . . . . . . . . . . . . . . . . . . . . . . . 102
Bit Test And Reset (btr). . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 102
Bit Test And Set (bts). . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 103
Exchange Instructions . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 103
Compare and Exchange (cmpxchg)[486] . . . . . . . . . . . . . . . 103
Floating-Point Transcendental Instructions . . . . . . . . . . . . . . . . 104
Floating-Point Sine (fsin) . . . . . . . . . . . . . . . . . . . . . . . . . . . . 104
Floating-Point Cosine (fcos) . . . . . . . . . . . . . . . . . . . . . . . . . . 104
Floating-Point Sine and Cosine (fsincos) . . . . . . . . . . . . . . . 104
Floating-Point Constant Instructions. . . . . . . . . . . . . . . . . . . . . . 105
Floating-Point Load One (fld) . . . . . . . . . . . . . . . . . . . . . . . . 105
Processor Control Floating-Point Instructions. . . . . . . . . . . . . . 105
Floating-Point Load Control Word (fldcw). . . . . . . . . . . . . . 105
Floating-Point Load Environment (fldenv) . . . . . . . . . . . . . 106
Miscellaneous Floating-Point Instructions . . . . . . . . . . . . . . . . . 106
Floating-Point Different Reminder (fprem) . . . . . . . . . . . . . 106
Floating-Point Comparison Instructions. . . . . . . . . . . . . . . . . . . 106
Floating-Point Unsigned Compare (fucom). . . . . . . . . . . . . 106
Floating-Point Unsigned Compare And Pop (fucomp) . . . 107
Floating-Point Unsigned Compare And Pop Two (fucompp)107

Contents ix
Load and Move Instructions. . . . . . . . . . . . . . . . . . . . . . . . . . . . . 108
Load Effective Address (lea). . . . . . . . . . . . . . . . . . . . . . . . . . 108
Move (mov) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 109
Move Segment Registers (movw) . . . . . . . . . . . . . . . . . . . . . 109
Move Control Registers (mov). . . . . . . . . . . . . . . . . . . . . . . . 110
Move Debug Registers (mov). . . . . . . . . . . . . . . . . . . . . . . . . 111
Move Test Registers (mov) . . . . . . . . . . . . . . . . . . . . . . . . . . . 111
Move With Sign Extend (movsx). . . . . . . . . . . . . . . . . . . . . . 112
Move With Zero Extend (movzb) . . . . . . . . . . . . . . . . . . . . . 112
Pop Instructions. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 113
Pop All General Registers (popa) . . . . . . . . . . . . . . . . . . . . . 113
Push Instructions . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 114
Push All General Registers (pusha). . . . . . . . . . . . . . . . . . . . 114
Rotate Instructions. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 114
Rotate With Carry Left (rcl) . . . . . . . . . . . . . . . . . . . . . . . . . . 114
Rotate With Carry Right (rcr). . . . . . . . . . . . . . . . . . . . . . . . . 115
Rotate Left (rol) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 116
Rotate Right (ror). . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 117
Byte Instructions . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 118
Byte Set On Condition (setcc). . . . . . . . . . . . . . . . . . . . . . . . . 118
Byte Swap (bswap) [486]. . . . . . . . . . . . . . . . . . . . . . . . . . . . . 120
Exchange Instructions . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 120
Exchange And Add (xadd) [486] . . . . . . . . . . . . . . . . . . . . . . 120
Exchange Register / Memory With Register (xchg) . . . . . . 120

xx86 Assembly Language Reference Manual—November 1995
Miscellaneous Instructions . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 121
Write Back and Invalidate Cache (wbinvd) [486 only] . . . . 121
Invalidate (invd) [486 only]. . . . . . . . . . . . . . . . . . . . . . . . . . 122
Invalidate Page (invlpg) [486 only] . . . . . . . . . . . . . . . . . . . . 122
LOCK Prefix (lock). . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 122
No Operation (nop). . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 123
Halt (hlt) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 124
Real Transfer Instructions. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 125
Load Real (fld) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 125
Store Real (fst) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 125
Store Real and Pop (fstp) . . . . . . . . . . . . . . . . . . . . . . . . . . . . 126
Exchange Registers (fxch). . . . . . . . . . . . . . . . . . . . . . . . . . . . 126
Integer Transfer Instructions . . . . . . . . . . . . . . . . . . . . . . . . . . . . 127
Integer Load (fild) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 127
Integer Store (fist) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 127
Integer Store and Pop (fistp). . . . . . . . . . . . . . . . . . . . . . . . . . 127
Packed Decimal Transfer Instructions. . . . . . . . . . . . . . . . . . . . . 128
Packed Decimal (BCD) Load (fbld) . . . . . . . . . . . . . . . . . . . . 128
Packed Decimal (BCD) Store and Pop (fbstp) . . . . . . . . . . . 128
Addition Instructions . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 129
Real Add (fadd) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 129
Real Add and Pop (faddp) . . . . . . . . . . . . . . . . . . . . . . . . . . . 129
Integer Add (fiadd) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 129
Subtraction Instructions . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 130

Contents xi
Subtract Real and Pop (fsub) . . . . . . . . . . . . . . . . . . . . . . . . . 130
Subtract Real (fsubp) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 130
Subtract Real Reversed (fsubr). . . . . . . . . . . . . . . . . . . . . . . . 130
Subtract Real Reversed and Pop (fsubrp). . . . . . . . . . . . . . . 131
Integer Subtract (fisubrp) . . . . . . . . . . . . . . . . . . . . . . . . . . . . 131
Integer Subtract Reverse (fisubr) . . . . . . . . . . . . . . . . . . . . . . 131
Multiplication Instructions. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 132
Multiply Real (fmul) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 132
Multiply Real and Pop (fmulp) . . . . . . . . . . . . . . . . . . . . . . . 132
Integer Multiply (fimul) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 132
Division Instructions. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 133
Divide Real (fdiv). . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 133
Divide Real and Pop (fdivp). . . . . . . . . . . . . . . . . . . . . . . . . . 133
Divide Real Reversed (fdivr) . . . . . . . . . . . . . . . . . . . . . . . . . 133
Divide Real Reversed and Pop (fdivrp) . . . . . . . . . . . . . . . . 134
Integer Divide (fidiv). . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 134
Integer Divide Reversed (fidivr) . . . . . . . . . . . . . . . . . . . . 134
Miscellaneous Arithmetic Operations. . . . . . . . . . . . . . . . . . . . . 136
Square Root (fsqrt). . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 136
Scale (fscale) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 136
Partial Remainder (fprem) . . . . . . . . . . . . . . . . . . . . . . . . . . . 136
Round to Integer (frndint) . . . . . . . . . . . . . . . . . . . . . . . . . . . 137
Extract Exponent and Significand (fxtract). . . . . . . . . . . . . . 137
Absolute Value (fabs) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 137

xii x86 Assembly Language Reference Manual—November 1995
Change Sign (fchs). . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 138
Comparison Instructions. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 138
Compare Real (fcom). . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 138
Compare Real and Pop (fcomp). . . . . . . . . . . . . . . . . . . . . . . 139
Compare Real and Pop Twice (fcompp) . . . . . . . . . . . . . . . . 139
Integer Compare (ficom). . . . . . . . . . . . . . . . . . . . . . . . . . . . . 139
Integer Compare and Pop (ficomp). . . . . . . . . . . . . . . . . . . . 140
Test (ftst) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 140
Examine (fxam) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 140
Transcendental Instructions . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 141
Partial Tangent (fptan) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 141
Partial Arctangent (fpatan). . . . . . . . . . . . . . . . . . . . . . . . . . . 142
2x - 1 (f2xm1) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 142
Y * log2 X (fyl2x) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 142
Y * log2 (X+1) (fyl2xp1) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 143
Constant Instructions . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 143
Load log2E (fldl2e) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 143
Load log210 (fldl2t). . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 143
Load log10 2 (fldlg2). . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 144
Load loge 2 (fldln2) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 144
Load pi (fldpi) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 144
Load + 0 (fldz) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 145
Processor Control Instructions. . . . . . . . . . . . . . . . . . . . . . . . . . . 145
Initialize Processor (finit, fnint) . . . . . . . . . . . . . . . . . . . . . . . 145

Contents xiii
No Operation (fnop) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 145
Save State (fsave, fnsave) . . . . . . . . . . . . . . . . . . . . . . . . . . . . 146
Store Control Word (fstcw, fnstcw) . . . . . . . . . . . . . . . . . . . . 146
Store Environment (fstenv, fnstenv) . . . . . . . . . . . . . . . . . . . 146
Store Status Word (fstsw, fnstsw). . . . . . . . . . . . . . . . . . . . . . 147
Restore State (frstor) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 147
CPU Wait (fwait, wait) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 147
Clear Exceptions (fclex, fnclex) . . . . . . . . . . . . . . . . . . . . . . . 148
Decrement Stack Pointer (fdecstp). . . . . . . . . . . . . . . . . . . . . 148
Free Registers (ffree) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 148
Increment Stack Pointer (fincstp). . . . . . . . . . . . . . . . . . . . . . 149
3. Assembler Output. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 151
Introduction . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 151
Object Files in Executable and Linking Format (ELF). . . . . . . . 152
ELF Header. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 153
Section Header. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 155
Sections . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 159
Symbol Tables. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 162
String Tables . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 164
A. Using the Assembler Command Line . . . . . . . . . . . . . . . . . . . . 167
Assembler Command Line. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 167
Assembler Command Line Options . . . . . . . . . . . . . . . . . . . . . . 168
Disassembling Object Code . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 169
Index . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 171

xiv x86 Assembly Language Reference Manual—November 1995

xv
Tables
Table 1-1 Object File Sections . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 6
Table 1-2 Operators Supported by the Assembler. . . . . . . . . . . . . . . . . . . 6
Table 1-3 Syntactical Rules of Expressions . . . . . . . . . . . . . . . . . . . . . . . . . 8
Table 1-4 8-bit (byte) General Registers. . . . . . . . . . . . . . . . . . . . . . . . . . . . 11
Table 1-5 16-bit (word) General Registers. . . . . . . . . . . . . . . . . . . . . . . . . . 11
Table 1-6 32-bit (long ) General Registers . . . . . . . . . . . . . . . . . . . . . . . . . . 12
Table 1-7 Description of Segment Registers . . . . . . . . . . . . . . . . . . . . . . . . 12
Table 2-1 Condition Codes . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 25
Table 2-2 Logical AND. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 53
Table 2-3 Inclusive OR. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 54
Table 2-4 Exclusive XOR . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 56
Table 2-5 Clearing OF and CF flags — imul. . . . . . . . . . . . . . . . . . . . . . . . 57
Table 2-6 Clearing OF and CF flags — mul . . . . . . . . . . . . . . . . . . . . . . . . 59
Table 2-7 idiv Register Assignment. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 62
Table 2-8 Handling a Carry. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 66
Table 2-9 How aas Handles a Carry. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 67

xvi x86 Assembly Language Reference Manual—November 1995
Table 2-10 setcc Condition List. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 119
Table 2-11 Floating-point Opcodes . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 135
Table 3-1 Object File Types . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 155
Table 3-2 Section Attribute Flags . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 157
Table 3-3 Section Types . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 157
Table 3-4 Predefined User Sections . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 161
Table 3-5 Predefined Non-User Sections. . . . . . . . . . . . . . . . . . . . . . . . . . . 161
Table 3-6 Symbol Types. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 164
Table 3-7 Symbol Bindings . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 164

xvii
Preface
This preface is a brief description of the SunOS™ assembler that runs on x86.
This preface also includes a list of documents that can be used for reference.
The SunOS assembler that runs on x86, referred to as the “SunOS x86” in this
manual, translates source files that are in assembly language format into object
files in linking format.
In the program development process, the assembler is a tool to use in
producing program modules intended to exploit features of the Intel®
architecture in ways that cannot be easily done using high level languages and
their compilers.
Whether assembly language is chosen for the development of program
modules depends on the extent to which and the ease with which the language
allows the programmer to control the architectural features of the processor.
The assembly language described in this manual offers full direct access to the
x86 instruction set. The assembler may also be used in connection with SunOS
5.1 macro preprocessors to achieve full macro-assembler capability.
Furthermore, the assembler responds to directives that allow the programmer
direct control over the contents of the relocatable object file.
This document describes the language in which the source files must be
written. The nature of the machine mnemonics governs the way in which the
program’s executable portion is written. This document includes descriptions
of the pseudo operations that allow control over the object file. This facilitates
the development of programs that are easy to understand and maintain.

xviii x86 Assembly Language Reference Manual—November 1995
Before You Read This Book
Use the following documents as references:
•Intel 80386 Programmer’s Reference Manual
•i486™ Microprocessor Programmer Reference Manual (1990)
•Intel 80387 Programmer’s Reference Manual (1987)
•System V Application Binary Interface Intel 386 Processor Supplement
•System V Application Binary Interface
•SVID System V Interface Definition
You should also become familiar with the following:
•Man pages: as(1), ld(1), cpp(1), mn(4),cof2elf(1) (elf - Executable and
Linking Format), elf(3E), dis(1), a.out(5).
•ELF-related sections of the Programming Utilities manual.
How This Book Is Organized
This document is organized into the following chapters:
Chapter 1, “Assembler Input,” describes the overall structure required by the
assembler for input source files.
Chapter 2, “Instruction-Set Mapping,” describes the instruction set mappings
for the SunOS x86 processor.
Chapter 3, “Assembler Output,” provides an overview of ELF (Executable and
Linking Format) for the relocatable object files produced by the assembler.
Appendix A, “Using the Assembler Command Line,” describes the assembler
command line options.

Preface xix
What Typographic Changes Mean
The following table describes the typographic changes used in this book.
Shell Prompts in Command Examples
The following table shows the default system prompt and superuser prompt
for the C shell, Bourne shell, and Korn shell.
Table P-1 Typographic Conventions
Typeface or
Symbol Meaning Example
AaBbCc123 The names of commands,
files, and directories;
on-screen computer output
Edit your .login file.
Use ls -a to list all files.
machine_name% You have mail.
AaBbCc123 What you type, contrasted
with on-screen computer
output
machine_name% su
Password:
AaBbCc123 Command-line placeholder:
replace with a real name or
value
To delete a file, type rm filename.
AaBbCc123 Book titles, new words or
terms, or words to be
emphasized
Read Chapter 6 in User’s Guide.
These are called class options.
You must be root to do this.
Table P-2 Shell Prompts
Shell Prompt
C shell prompt machine_name%
C shell superuser prompt machine_name#
Bourne shell and Korn shell
prompt $
Bourne shell and Korn shell
superuser prompt #

xx x86 Assembly Language Reference Manual—November 1995
1
Assembler Input 1
The SunOS x86 assembler translates source files in the assembly language
format specified in this document into relocatable object files for processing by
the link editor. This translation process is called assembly. The main input
required to assemble a source file in assembly language format is that source
file itself.
This chapter has the following organization:
Introduction
In whatever manner it is produced, the source input file must have a certain
structure and content. The specification of this structure and content
constitutes the syntax of the assembly language. A source file may be produced
by one of the following:
•A programmer using a text editor
•A compiler as an intermediate step in the process of translating from a high-
level language to executable code
•An automatic program generator
•Some other mechanism.
Introduction page 1
Source Files in Assembly Language Format page 2
Pseudo Operations page 14

2x86 Assembly Language Reference Manual—November 1995
1
The assembler may also allow ancillary input incidental to the translation
process. For example, there are several invocation options available. Each such
option exercised constitutes information input to the assembler. However, this
ancillary input has little direct connection to the translation process, so it is not
properly a subject for this manual. Information about invoking the assembler
and the available options appears in the as(1) man pages.
This chapter describes the overall structure required by the assembler for input
source files. This structure is relatively simple: the input source file must be a
sequence of assembly language statements. This chapter also begins the
specification of the contents of the input source file by describing assembly
language statements as textual objects of a certain form.
This document completes the specification by presenting detailed assembly
language statements that correspond to the Intel instruction set and are
intended for use on machines that run SunOS x86 architecture. For more
information on assembly language instruction sets, please refer to the product
documentation from Intel Corporation.
Source Files in Assembly Language Format
This section details the following:
•file organization
•statements
•values and symbols
•expressions
•machine instruction syntax
File Organization
Input to the assembler is a text file consisting of a sequence of statements. Each
statement ends with the first occurrence of a newline character (ASCII LF), or
of a semicolon (;) that is not within a string operand or between a slash and a
newline character. Thus, it is possible to have several statements on one line.

Assembler Input 3
1
To make programs easy to read, understand and maintain, however, it is good
programming practice not to have more than one statement per line. As
indicated above, a line may contain one or more statements. If several
statements appear on a line, they must be separated by semicolons (;).
Statements
This section outlines the types of statements that apply to assembly language.
Each statement must be one of the following types:
•An empty statement is one that contains nothing other than spaces, tabs, or
formfeed characters.
Empty statements have no meaning to the assembler. They can be inserted
freely to improve the appearance of a source file or of a listing generated
from it.
•An assignment statement is one that gives a value to a symbol. It consists of
a symbol, followed by an equal sign (=), followed by an expression.
The expression is evaluated and the result is assigned to the symbol.
Assignment statements do not generate any code. They are used only to
assign assembly time values to symbols.
•Apseudo operation statement is a directive to the assembler that does not
necessarily generate any code. It consists of a pseudo operation code,
optionally followed by operands. Every pseudo operation code begins with
a period (.).
•Amachine operation statement is a mnemonic representation of an executable
machine language instruction to which it is translated by the assembler. It
consists of an operation code, optionally followed by operands.
Furthermore, any statement remains a statement even if it is modified in either
or both of the following ways:
•Prefixing a label at the beginning of the statement.
A label consists of a symbol followed by a colon (:). When the assembler
encounters a label, it assigns the value of the location counter to the label.
•Appending a comment at the end of the statement by preceding the
comment with a slash (/).

4x86 Assembly Language Reference Manual—November 1995
1
The assembler ignores all characters following a slash up to the next
occurrence of newline. This facility allows insertion of internal program
documentation into the source file for a program.
Values and Symbol Types
This section presents the values and symbol types that the assembler uses.
Values
Values are represented in the assembler by numerals which can be faithfully
represented in standard two’s complement binary positional notation using 32
bits. All integer arithmetic is performed using 32 bits of precision. Note,
however, that the values used in an x86 instruction may require 8, 16, or 32
bits.
Symbols
A symbol has a value and a symbol type, each of which is either specified
explicitly by an assignment statement or implicitly from context. Refer to the
next section for the regular definition of the expressions of a symbol.
The following symbols are reserved by the assembler:
.Commonly referred to as dot. This is the location counter while assembling a
program. It takes on the current location in the text,data, or bss section.
.text
This symbol is of type text. It is used to label the beginning of a .text section
in the program being assembled.
.data
This symbol is of type data. It is used to label the beginning of a data section
in the program being assembled.
.bss
This symbol is of type bss. It is used to label the beginning of a .bss section
in the program being assembled.

Assembler Input 5
1
.init
This is used with C++ programs which require constructors.
.fini
This is used with C++ programs which require destructors.
Symbol Types
Symbol type is one of the following:
undefined
A value is of undefined symbol type if it has not yet been defined. Example
instances of undefined symbol types are forward references and externals.
absolute
A value is of absolute symbol type it does not change with relocation.
Example instances of absolute symbol types are numeric constants and
expressions whose proper sub-expressions are themselves all absolute.
text
A value is of text symbol type if it is relative to the .text section.
data
A value is of data symbol type if it is relative to the .data section.
bss
A value is of bss symbol type if it is relative to the .bss section.
You can give any of these symbol types the attribute EXTERNAL.
Sections
Five of the symbol types are defined with respect to certain sections of the
object file into which the assembler translates the source file. This section
describes symbol types.
6x86 Assembly Language Reference Manual—November 1995
1
If the assembler translates a particular assembly language statement into a
machine language instruction or into a data allocation, the translation is
associated with one of the following five sections of the object file into which
the assembler is translating the source file:
An optional section, .comment, may also be produced (see Chapter 3,
“Assembler Output”).
The section associated with the translated statement is .text unless the
original statement occurs after a section control pseudo operation has directed
the assembler to associate the statement with another section.
Expressions
The expressions accepted by the x86 assembler are defined by their syntax and
semantics. The following are the operators supported by the assembler:
Table 1-1 Object File Sections
Section Purpose
text This is an initialized section. Normally, it is read-only and
contains code from a program. It may also contain read-only
tables
data This is an initialized section. Normally, it is readable and
writable. It contains initialized data. These can be scalars or
tables.
bss This is an initialized section. Space is not allocated for this
segment in the object file.
init This is used with C++ programs that require constructors.
fini This is used by C++ programs that require destructors.
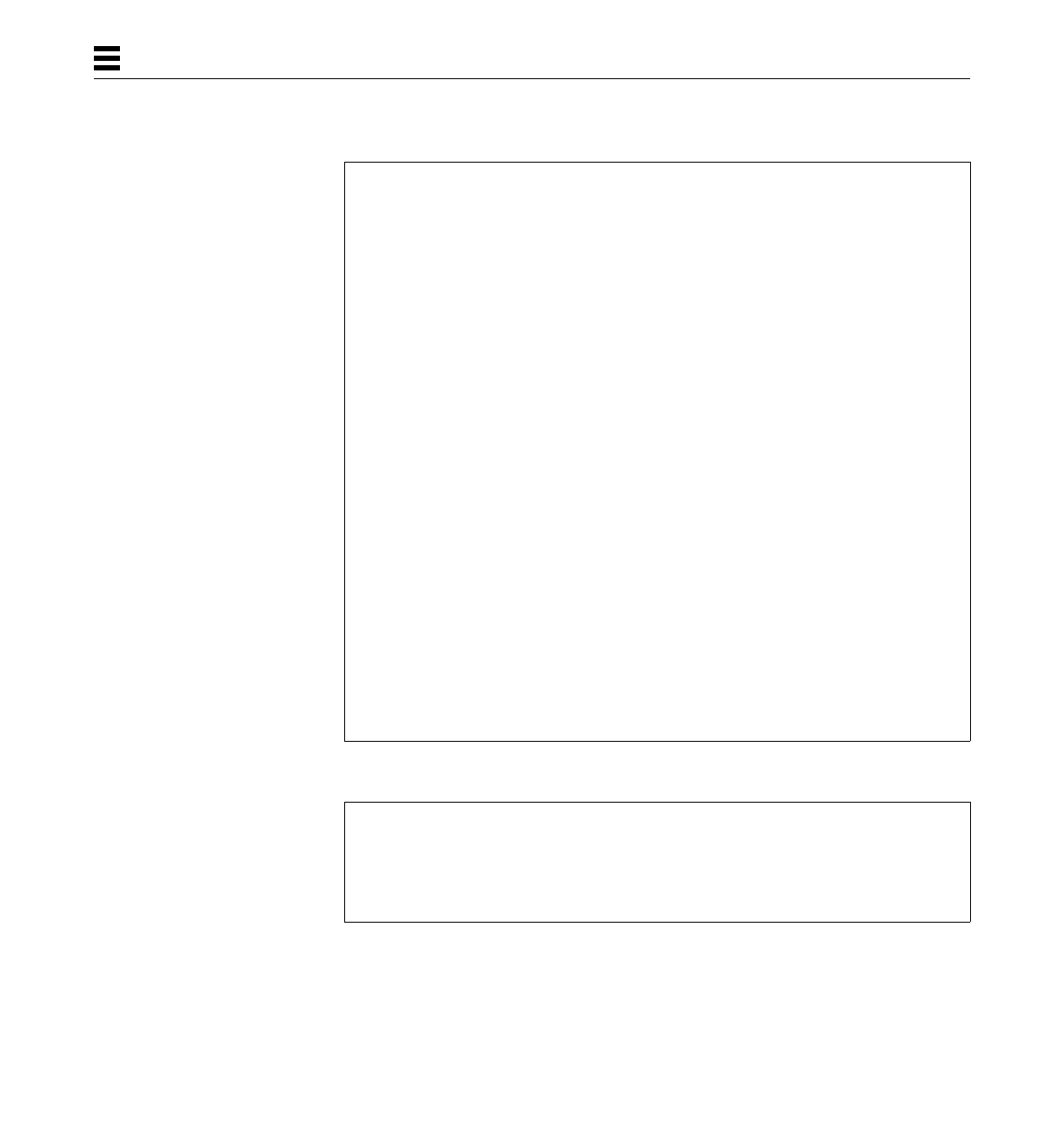
Table 1-2 Operators Supported by the Assembler
Operator Action
+Addition
-Subtraction
\* Multiplication
\/ Division
Assembler Input 7
1
Expression Syntax
Table 1-3 shows syntactic rules, the non terminals are represented by lowercase
letters, the terminal symbols are represented by uppercase letters, and the
symbols enclosed in double quotes are terminal symbols. There is no
precedence assigned to the operators. You must use square brackets to
establish precedence.
&Bitwise logical and
|Bitwise logical or
>> Right shift
<< Left shift
\% Remainder operator
!Bitwise logical and not
Table 1-2 Operators Supported by the Assembler
Operator Action
8x86 Assembly Language Reference Manual—November 1995
1
Table 1-3 Syntactical Rules of Expressions
The terminal nodes are given by the following regular expressions:
expr : term
| expr "+" term
| expr "-" term
| expr "\*" term
| expr "\/" term
| expr "&" term
| expr "|" term
| expr ">>" term
| expr "<<" term
| expr "\%" term
| expr "!" term
;
term : id
| number
| "-" term
| "[" expr "]"
| "<o>" term
| "<s>" term
;
id : LABEL
;
number : DEC_VAL
| HEX_VAL
| OCT_VAL
| BIN_VAL
;
LABEL = [a-zA-Z_][a-zA-Z0-9_]*:
DEC_VAL = [1-9][0-9]*
HEX_VAL = 0[Xx][0-9a-fA-F][0-9a-fA-F]*
OCT_VAL = 0[0-7]*
BIN_VAL = 0[Bb][0-1][0-1]*
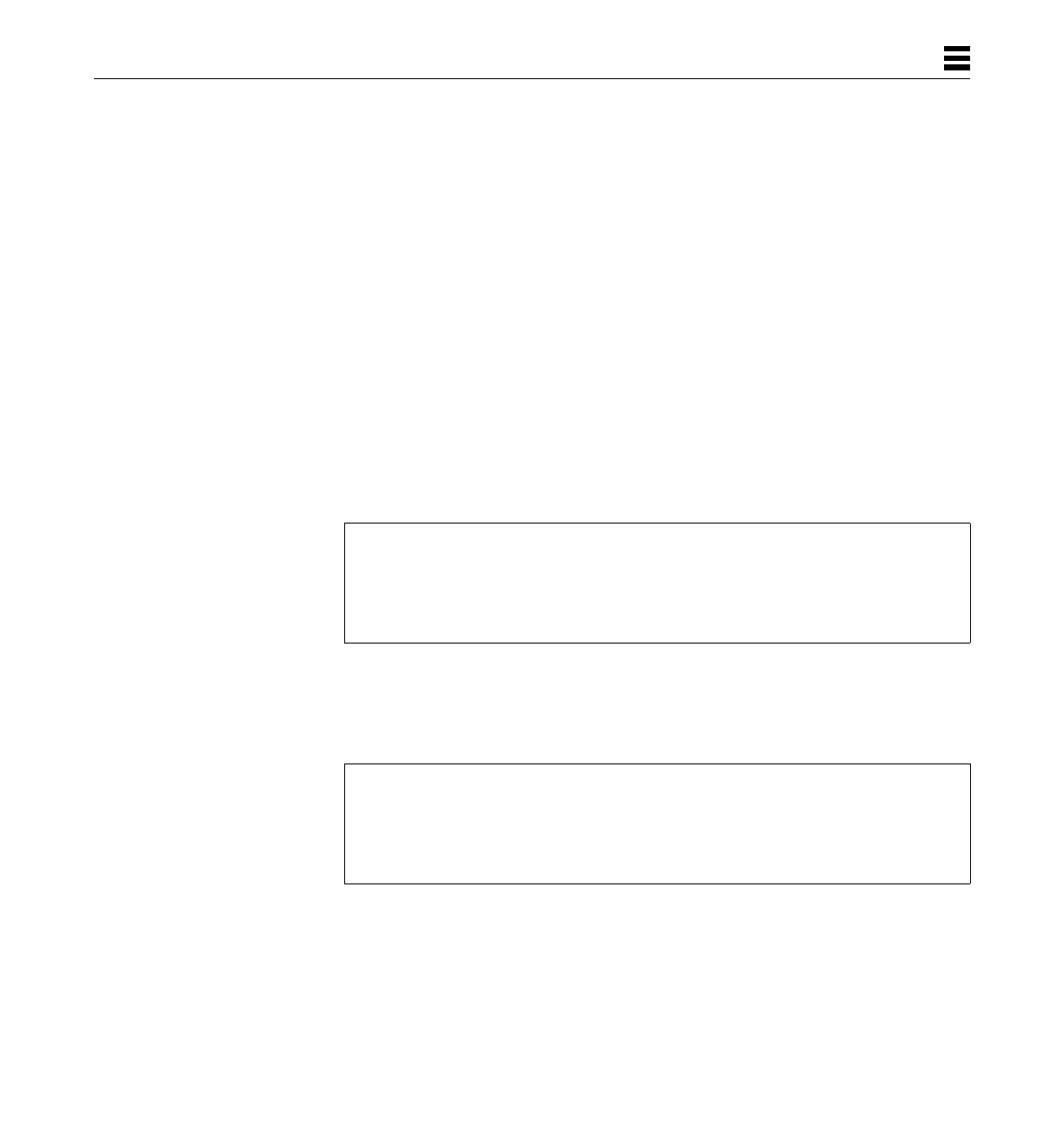
Assembler Input 9
1
In the above regular expressions, choices are enclosed in square brackets; a
range of choices is indicated by letters or numbers separated by a dash (-); and
the asterisk (*) indicates zero or more instances of the previous character.
Expression Semantics (Absolute vs. Relocatable)
Semantically, the expressions fall into two groups, absolute and relocatable.
The equations later in this section show the legal combinations of absolute and
relocatable operands for the addition and subtraction operators. All other
operations are only legal on absolute-valued expressions.
All numbers have the absolute attribute. Symbols used to reference storage,
text, or data are relocatable. In an assignment statement, symbols on the left
side inherit their relocation attributes from the right side.
In the equations below, a is an absolute-valued expression and r is a
relocatable-valued expression. The resulting type of the operation is shown to
the right of the equal sign.
In the last example, you must declare the relocatable expressions before taking
their difference.
Following are some examples of valid expressions:
a + a = a
r + a = r
a - a = a
r - a = r
r - r = a
label
$label
[label + 0x100]
[label1 - label2]
$[label1 - label2]
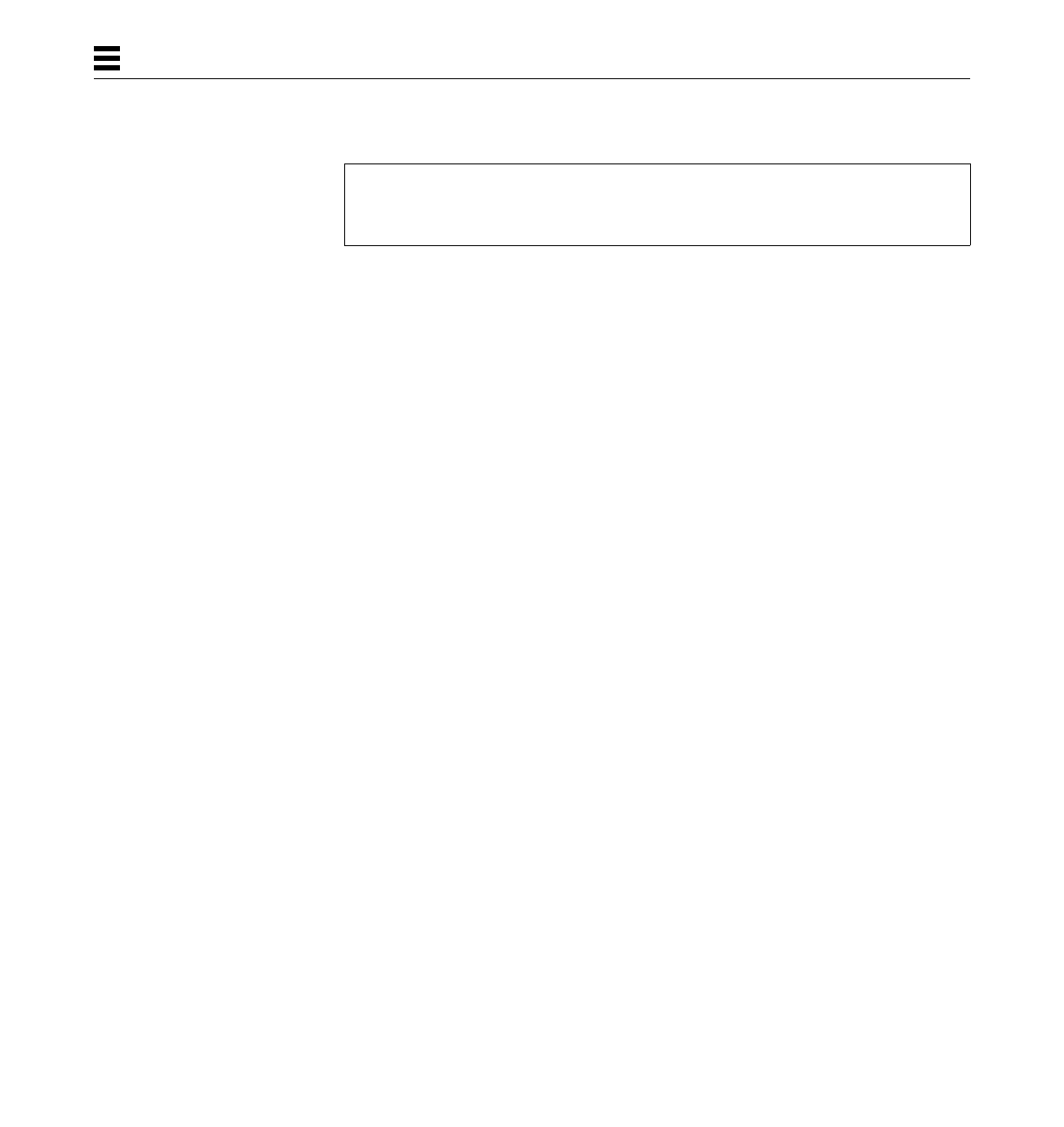
10 x86 Assembly Language Reference Manual—November 1995
1
Following are some examples of invalid expressions:
Machine Instruction Syntax
This section describes the instructions that the assembler accepts. The detailed
specification of how the particular instructions operate is not included; for this,
see Intel’s 80386 Programmer’s Reference Manual.
The following list describes the three main aspects of the SunOS x86 assembler:
•All register names use the percent sign (%) as a prefix to distinguish them
from symbol names.
•Instructions with two operands use the left one as the source and the right
one as the destination. This follows the SunOS operating environment
assembler convention, and is reversed from Intel’s notation.
•Most instructions that can operate on a byte, word, or long may have b,w, or
l appended to them. When an opcode is specified with no type suffix, it
usually defaults to long. In general, the SunOS assembler derives its type
information from the opcode, where the Intel assembler can derive its type
information from the operand types. Where the type information is derived
motivates the b,w, and l suffixes used in the SunOS assembler. For
example, in the instruction movw $1,%eax the w suffix indicates the operand
is a word.
Operands
Three kinds of operands are generally available to the instructions: register,
memory, and immediate. Full descriptions of each type appear in “Notational
Conventions” on page 23. Indirect operands are available only to jump and call
instructions.
The assembler always assumes it is generating code for a 32-bit segment. When
16-bit data is called for (e.g., movw %ax, %bx), the assembler automatically
generates the 16-bit data prefix byte.
[$label - $label]
[label1 * 5]
(label + 0x20)
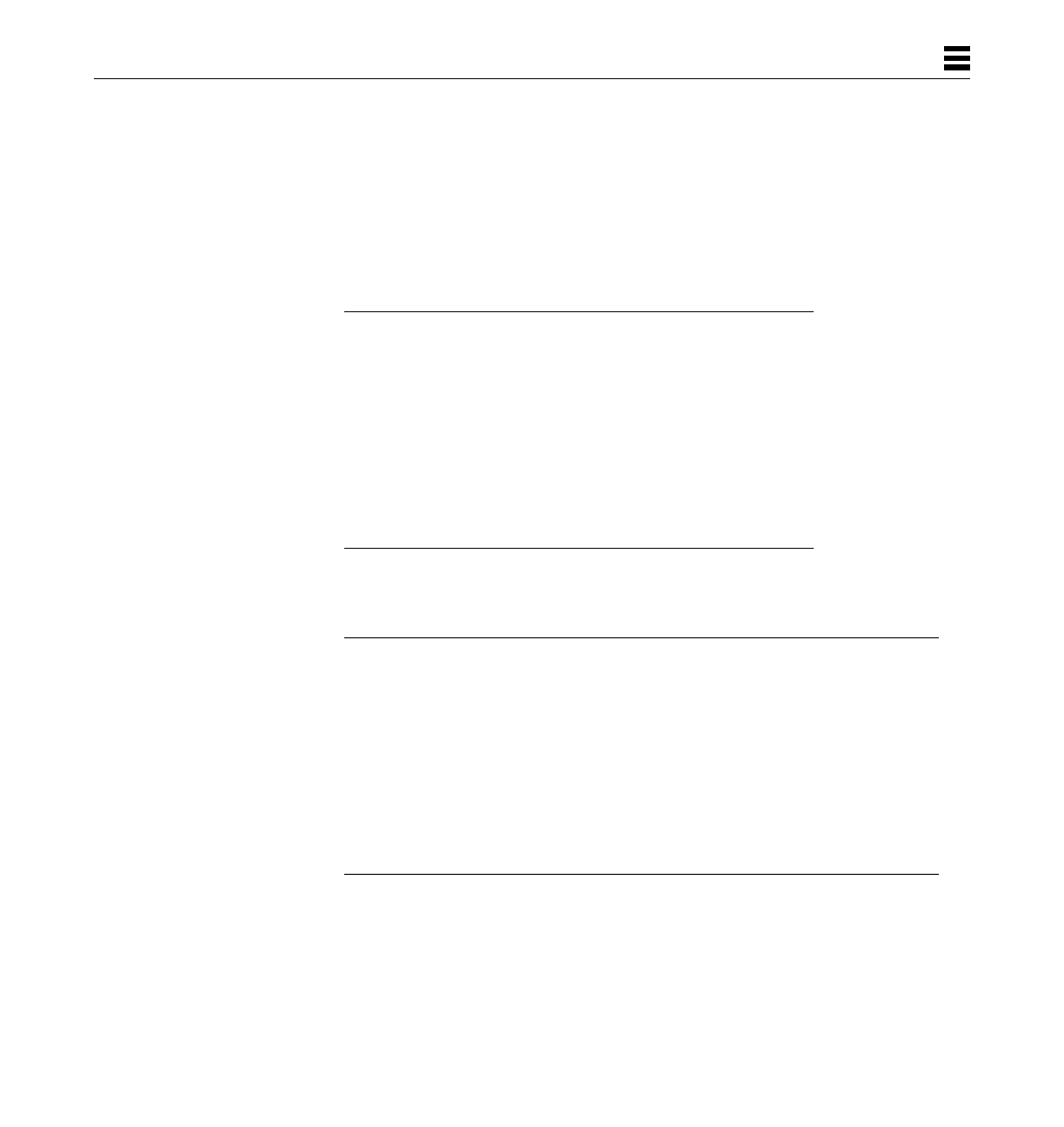
Assembler Input 11
1
Byte, word, and long registers are available on the x86 processor. The
instruction pointer (%eip) and flag register (%efl) are not available as explicit
operands to the instructions. The code segment (%cs) may be used as a source
operand but not as a destination operand.
The names of the byte, word, and long registers available as operands and a
brief description of each follow. The segment registers are also listed.
Table 1-4 8-bit (byte) General Registers
%al Low byte of %ax register
%ah High byte of %ax register
%cl Low byte of %cx register
%ch High byte of %cx register
%dl Low byte of %dx register
%dh High byte of %dx register
%bl Low byte of %bx register
%bh High byte of %bx register
Table 1-5 16-bit (word) General Registers
%ax Low 16-bits of %eax register
%cx Low 16-bits of %ecx register
%dx Low 16-bits of %edx register
%bx Low 16-bits of %ebx register
%sp Low 16-bits of the stack pointer
%bp Low 16-bits of the frame pointer
%si Low 16-bits of the source index register
%di Low 16-bits of the destination index register
12 x86 Assembly Language Reference Manual—November 1995
1
Instruction Description
This section describes the SunOS x86 instruction syntax.
The assembler assumes it is generating code for a 32-bit segment, therefore, it
also assumes a 32-bit address and automatically precedes word operations
with a 16-bit data prefix byte.
Table 1-6 32-bit (long ) General Registers
%eax 32-bit general register
%ecx 32-bit general register
%edx 32-bit general register
%ebx 32-bit general register
%esp 32-bit stack pointer
%ebp 32-bit frame pointer
%esi 32-bit source index register
%edi 32-bit destination index register
Table 1-7 Description of Segment Registers
%cs Code segment register; all references to the instruction space
use this register
%ds Data segment register, the default segment register for most
references to memory operands
%ss Stack segment register, the default segment register for
memory operands in the stack (i.e., default segment register for
%bp, %sp, %esp, and %ebp)
%es General-purpose segment register; some string instructions use
this extra segment as their default segment
%fs General-purpose segment register
%gs General-purpose segment register
Assembler Input 13
1
Addressing Modes
Addressing modes are represented by the following:
•All the items in the square brackets are optional, but at least one is
necessary. If you use any of the items inside the parentheses, the
parentheses are mandatory.
•sreg is a segment register override prefix. It may be any segment register. If
a segment override prefix is present, you must follow it by a colon before
the offset component of the address. sreg does not represent an address by
itself. An address must contain an offset component.
•offset is a displacement from a segment base. It may be absolute or
relocatable. A label is an example of a relocatable offset. A number is an
example of an absolute offset.
•base and index can be any 32-bit register. scale is a multiplication factor
for the index register field. Its value may be 1, 2, 4, 8 to indicate the
number to multiply by. The multiplication then occurs by 1, 2, 4, and 8.
Refer to Intel’s 80386 Programmer’s Reference Manual for more details on x86
addressing modes.
Following are some examples of addresses:
movl var, %eax
Move the contents of memory location var into %eax.
movl %cs:var, %eax
Move the contents of the memory location var in the code segment into
%eax.
movl $var, %eax
Move the address of var into %eax.
movl array_base(%esi), %eax
Add the address of memory location array_base to the contents of %esi
to get an address in memory. Move the contents of this address into %eax.
[sreg:][offset][([base][,index][,scale])]

14 x86 Assembly Language Reference Manual—November 1995
1
movl (%ebx, %esi, 4), %eax
Multiply the contents of %esi by 4 and add this to the contents of %ebx to
produce a memory reference. Move the contents of this memory location
into %eax.
movl struct_base(%ebx, %esi, 4), %eax
Multiply the contents of %esi by 4, add this to the contents of %ebx, and
add this to the address of struct_base to produce an address. Move the
contents of this address into %eax.
Expressions and Immediate Values
An immediate value is an expression preceded by a dollar sign:
immediate: "$" expr
Immediate values carry the absolute or relocatable attributes of their
expression component. Immediate values cannot be used in an expression,
and should be considered as another form of address, i.e., the immediate
form of address.
immediate: "$" expr "," "$" expr
The first expr is 16 bits of segment. The second expr is 32 bits of offset.
Pseudo Operations
The pseudo-operations listed in this section are supported by the x86
assembler.
General Pseudo Operations
Below is a list of the pseudo operations supported by the assembler. This is
followed by a separate listing of pseudo operations included for the benefit of
the debuggers (dbx(1)).
.align val
The align pseudo op causes the next data generated to be aligned modulo
val.val should be a positive integer value.

Assembler Input 15
1
.bcd val
The.bcd pseudo op generates a packed decimal (80-bit) value into the
current section. This is not valid for the.bss section. val is a nonfloating-
point constant.
.bss
The.bss pseudo op changes the current section to.bss.
.bss tag, bytes
Define symbol tag in the.bss section and add bytes to the value of dot
for.bss. This does not change the current section to.bss.bytes must be a
positive integer value.
.byte val [, val]
The.byte pseudo op generates initialized bytes into the current section.
This is not valid for.bss. Each val must be an 8-bit value.
.comm name, expr [, alignment]
The.comm pseudo op allocates storage in the .data section. The storage is
referenced by the symbol name, and has a size in bytes of expr. expr
must be a positive integer. name cannot be predefined. If the alignment is
given, the address of the name is aligned to a multiple of alignments.
.data
The data pseudo op changes the current section to .data.
.double val
The .double pseudo op generates an 80387 64 bit floating-point constant
(IEEE 754) into the current section. Not valid in the .bss section. val is a
floating-point constant. val is a string acceptable to atof(3); that is, an
optional sign followed by a non-empty string of digits with optional
decimal point and optional exponent.
.even
The .even pseudo op aligns the current program counter (.) to an even
boundary.

16 x86 Assembly Language Reference Manual—November 1995
1
.file "
string
"
The .file op creates a symbol table entry where string is the symbol name
and STT_FILE is the symbol table type. string specifies the name of the
source file associated with the object file.
.float val
The .float pseudo op generates an 80387 32 bit floating-point constant
(IEEE 754) into the current section. This is not valid in the .bss section. val
is a floating-point constant. val is a string acceptable to atof(3); that is, an
optional sign followed by a non-empty string of digits with optional
decimal point and optional exponent.
.globl
symbol
[,
symbol
]*
The globl op declares each symbol in the list to be global; that is, each
symbol is either defined externally or defined in the input file and accessible
in other files; default bindings for the symbol are overridden.
•A global symbol definition in one file satisfies an undefined reference to the
same global symbol in another file.
•Multiple definitions of a defined global symbol is not allowed. If a defined
global symbol has more than one definition, an error occurs.
Note – This pseudo-op by itself does not define the symbol.
.ident “string”
The .ident pseudo op creates an entry in the comment section containing
string. string is any sequence of characters, not including the double
quote (").
.lcomm name, expr
The .lcomm pseudo op allocates storage in the .bss section. The storage is
referenced by the symbol name, and has a size of expr. name cannot be
predefined, and expr must be a positive integer type. If the alignment is
given, the address of name is aligned to a multiple of alignment.

Assembler Input 17
1
.local
symbol
[,
symbol
]*
Declares each symbol in the list to be local; that is, each symbol is defined in
the input file and not accessible in other files; default bindings for the
symbol are overridden. These symbols take precedence over weak and global
symbols.
Because local symbols are not accessible to other files, local symbols of the
same name may exist in multiple files.
Note – This pseudo-op by itself does not define the symbol.
.long val
The .long pseudo op generates a long integer (32-bit, two’s complement
value) into the current section. This pseudo op is not valid for the .bss
section. val is a nonfloating-point constant.
.nonvolatile
Defines the end of a block of instruction. The instructions in the block may
not be permuted. This pseudo-op has no effect if:
•The block of instruction has been previously terminated by a Control
Transfer Instruction (CTI) or a label
•There is no preceding .volatile pseudo-op
.section section_name [, attributes]
Makes the specified section the current section.
The assembler maintains a section stack which is manipulated by the section
control directives. The current section is the section that is currently on top of
the stack. This pseudo-op changes the top of the section stack.
•If section_name does not exist, a new section with the specified name and
attributes is created.
•If section_name is a non-reserved section, attributes must be included the first
time it is specified by the .section directive.
.set name, expr
The .set pseudo op sets the value of symbol name to expr. This is
equivalent to an assignment.

18 x86 Assembly Language Reference Manual—November 1995
1
.string “str”
This pseudo op places the characters in str into the object module at the
current location and terminates the string with a null. The string must be
enclosed in double quotes (""). This pseudo op is not valid for the .bss
section.
.text
The .text pseudo op defines the current section as .text.
.value expr [,expr]
The .value pseudo op is used to generate an initialized word (16-bit, two’s
complement value) into the current section. This pseudo op is not valid in
the .bss section. Each expr must be a 16-bit value.
.version string
The .version pseudo op puts the C compiler version number into the
.comment section.
.volatile
Defines the beginning of a block of instruction. The instructions in the
section may not be changed. The block of instruction should end at a
.nonvolatile pseudo-op and should not contain any Control Transfer
Instructions (CTI) or labels. The volatile block of instructions is terminated
after the last instruction preceding a CTI or label.
.weak
symbol
[,
symbol
]
Declares each symbol in the list to be defined either externally, or in the input
file and accessible to other files; default bindings of the symbol are
overridden by this directive.
•Aweak symbol definition in one file satisfies an undefined reference to a
global symbol of the same name in another file.
•Unresolved weak symbols have a default value of zero; the link editor does
not resolve these symbols.
•If a weak symbol has the same name as a defined global symbol, the weak
symbol is ignored and no error results.
Note – This pseudo-op does not itself define the symbol.

Assembler Input 19
1
symbol =expr
Assigns the value of expr to symbol.
Symbol Definition Pseudo Operations
.def name
The .def pseudo op starts a symbolic description for symbol name. See
endef.name is a symbol name.
.dim expr [,expr]
The .dim pseudo op is used with the .def pseudo op. If the name of a
.def is an array, the expressions give the dimensions; up to four
dimensions are accepted. The type of each expression should be positive.
.endef
The .endef pseudo op is the ending bracket for a .def.
.file name
The .file pseudo op is the source file name. Only one is allowed per
source file. This must be the first line in an assembly file.
.line expr
The .line pseudo op is used with the .def pseudo op. It defines the
source line number of the definition of symbol name in the .def. expr
should yield a positive value.
.ln line [,addr]
This pseudo op provides the relative source line number to the beginning of
a function. It is used to pass information through to sdb.
.scl expr
The .scl pseudo op is used with the .def pseudo op. Within the .def it
gives name the storage class of expr. The type of expr should be positive.

20 x86 Assembly Language Reference Manual—November 1995
1
.size expr
The .size pseudo op is used with the .def pseudo op. If the name of a
.def is an object such as a structure or an array, this gives it a total size of
expr. expr must be a positive integer.
.stabs
name type
0
desc valu
e
.stabn
type
0
desc value
The .stabs and .stabn pseudo ops are debugger directives generated by
the C compiler when the -g option are used. name provides the symbol table
name and type structure. type identifies the type of symbolic information
(i.e., source file, global symbol, or source line). desc specifies the number of
bytes occupied by a variable or type, or the nesting level for a scope symbol.
value specifies an address or an offset.
.tag str
The .tag pseudo op is used in conjunction with a previously defined .def
pseudo op. If the name of a .def is a structure or a union, str should be
the name of that structure or union tag defined in a previous .def-.endef
pair.
.type expr
The .type pseudo op is used within a .def-.endef pair. It gives name
the C compiler type representation expr.
.val expr
The .val pseudo op is used with a .def-.endef pair. It gives name (in
the .def) the value of expr. The type of expr determines the section for
name.
21
Instruction-Set Mapping 2
This chapter describes the instruction set mappings for the SunOS x86
processor. For more details of the operation and a summary of the exceptions,
please refer to the i486 Microprocessor Programmer’s Reference Manual from Intel
Corporation.
This chapter is organized as follows:
Introduction page 22
Segment Register Instructions page 26
I/O Instructions page 29
Flag Instructions page 32
Arithmetic Logical Instructions page 38
Multiply and Divide Instructions page 56
Conversion Instructions page 62
Decimal Arithmetic Instructions page 64
Coprocessor Instructions page 69
String Instructions page 69
Procedure Call and Return Instructions page 78
Jump Instructions page 83
Interrupt Instructions page 87
Protection Model Instructions page 90
Bit Instructions page 100
Exchange Instructions page 103
22 x86 Assembly Language Reference Manual—November 1995
2
Introduction
Although the Intel processor supports address-size attributes of either 16 or 32
bits, the x86 assembler only supports address-size attributes of 32 bits. The
operand-size is either 16 or 32 bits. An instruction that accesses 16-bit words or
32-bit longs has an operand-size attribute of either 16 or 32 bits.
Floating-Point Transcendental Instructions page 104
Floating-Point Constant Instructions page 105
Processor Control Floating-Point Instructions page 105
Miscellaneous Floating-Point Instructions page 106
Floating-Point Comparison Instructions page 106
Load and Move Instructions page 108
Pop Instructions page 113
Push Instructions page 114
Rotate Instructions page 114
Byte Instructions page 118
Exchange Instructions page 120
Miscellaneous Instructions page 121
Real Transfer Instructions page 125
Integer Transfer Instructions page 127
Packed Decimal Transfer Instructions page 128
Addition Instructions page 129
Subtraction Instructions page 130
Multiplication Instructions page 132
Division Instructions page 133
Miscellaneous Arithmetic Operations page 136
Comparison Instructions page 138
Transcendental Instructions page 141
Constant Instructions page 143
Processor Control Instructions page 145
Instruction-Set Mapping 23
2
Notational Conventions
The notational conventions used in the instructions included in this chapter are
described below:
•The mnemonics are expressed in a regular expression-type syntax.
•When a group of letters is separated from other letters by a bar (|) within
square brackets or curly braces, then the group of letters between the bars or
between a bar and a closing bracket or brace is considered an atomic unit.
For example, fld[lst] means fldl,flds, or fldt;fst{ls} means fst,
fstl, or fsts; and fild{l|ll} means fild,fildl, or fildll.
•Square brackets ([]) denote choices, but at least one is required.
•Alternatives enclosed within curly braces ({}) denote that you can use one
or none of them
•The vertical bar separates different suffixes for operators or operands. For
example, the following indicates that an 8-, 16-, or 32-bit immediate value is
permitted in an instruction:
•The SunOS operators are built from the Intel operators by adding suffixes to
them. The 80387, 80486 deals with three data types: integer, packed decimal,
and real.
The SunOS assembler is not typed; the operator has to carry with it the type
of data item it is operating on. If the operation is on an integer, the following
suffixes apply: none for Intel’s short(16 bits), l for Intel’s long (32 bits),
and ll for Intel’s longlong(64 bits). If the operator applies to reals, then: s
is short (32 bits), l is long (64 bits), and t is temporary real(80 bits).
•reg[8|16|32] defines a general-purpose register, where each number
indicates one of the following:
imm[8|16|32]
32: %eax, %ecx, %edx, %ebx, %esi, %edi, %ebp, %esp
16: %ax, %cx, %dx, %bx, %si, %di, %bp, %sp
8: %al, %ah, %cl, %ch, %dl, %dh, %bl, %bh

24 x86 Assembly Language Reference Manual—November 1995
2
•imm[8|16|32|48] — an immediate value. You define immediate values
using the regular expression syntax previously described (see also
Expressions and Immediate Values on page 210). If there is a choice between
operand sizes, the assembler will choose the smallest representation.
•mem[8|16|32|48|64|80] — a memory operand; the 8, 16, 32, 48, 64, and
80 suffixes represent byte, word, long (or float), inter-segment, double, and
long double memory address quantities, respectively.
•creg — a control register; the control registers are: %cr0,%cr2,%cr3, or
%cr4.
•r/m[8|16|32] is a general-purpose register or memory operand; the
operand type is determined from the suffix. They are: 8 = byte, 16 = word,
and 32 = long. The registers for each operand size are the same as
reg[8|16|32] above.
•dreg is a debug register; the debug registers are: %db0,%db1,%db2,%db3,
%db6,%db7.
•sreg is a segment register. The 16-bit segment registers are: %cs,%ds,%ss,
%es,%fs, and %gs.
•treg is a test register. The test registers are: %tr6 and %tr7.
•freg is floating-point registers %st (%st(0)), %st(1) - %st(7).
•An instruction can act on zero or more operands. An operand can be any of
the following:
•an immediate operand (in the instruction itself)
•a register (32-bit genera, segment, or status/instruction register), (16-bit
word register), and (8-bit byte register).
•a pointer to a memory location.
•an I/O port
•Instruction syntax is:
operand1 → operand2
where operand1 and operand2 are operated on and the result stored in
operand2. The → arrow shows the direction. The direction is opposite of
that described in the Intel Corporation i486 Microprocessor Programmer’s
Reference Manual.
Instruction-Set Mapping 25
2
•disp[8|32] — the number of bits used to define the distance of a relative
jump; because the assembler only supports a 32-bit address space, only 8-bit
sign extended and 32-bit addresses are supported.
•immPtr — an immediate pointer; when the immediate form of a long call or
a long jump is used, the selector and offset are encoded as an immediate
pointer. An immediate pointer consists of $imm16,$imm32 where the first
immediate value represents the segment and the second represents the
offset.
•cc — condition codes; the 30 condition codes are:
Table 2-1 Condition Codes
aabove
ae above or equal
bbelow
be below or equal
ccarry
eequal
ggreater
ge greater than or equal to
lless than
le less than or equal to
na not above
nae not above or equal to
nb not below
nbe not below or equal to
nc not carry
ne not equal
ng not greater than
nge not greater than or equal to
nl not less than
nle not less than or equal to
26 x86 Assembly Language Reference Manual—November 1995
2
References
This document presumes that you are familiar with the manner in which the
Intel instruction sets function. For more information on specific instruction
descriptions, please refer to the Intel Corporation i486 Microprocessor
Programmer’s Reference Manual.
Segment Register Instructions
The following are the segment register instructions supported by the x86
processor.
Load Full Pointer
(
lds
,
les,lfs,lgs, and lss)
Operation
mem[32|48] → reg[16|32]
no not overflow
np not parity
ns not sign
nz not zero
ooverflow
pparity
pe parity even
po parity odd
ssign
zzero
lds{wl} mem[32|48], reg[16|32]
les{wl} mem[32|48], reg[16|32]
lfs{wl} mem[32|48], reg[16|32]
lgs{wl} mem[32|48], reg[16|32]
lss{wl} mem[32|48], reg[16|32]
Table 2-1 Condition Codes (Continued)

Instruction-Set Mapping 27
2
Description
Reads a full pointer from memory and stores it in the specified segment
register (DS, ES, FS, GS or SS) with a 16- or 32-bit offset value.
Example
Load a 16-bit pointer from memory location 0x44444444 into the DX register:
Load a 32-bit pointer from memory location 0x33333333 into the EDX
register:
Pop Stack into Word (pop)
Operation
stack → r/m[16|32]
stack → segment register
Description
Replaces the previous contents of the register or memory operand with a
word or long from the top of the stack.
Replaces the previous contents of the segment register operand with a long.
For a word, SP + 2; for a long, SP + 4.
ldsw 0x44444444, %dx
ldsl 0x33333333, %edx
pop{wl} r/m[16|32]
pop{l} [%ds|%ss|%es|%fs|%gs]

28 x86 Assembly Language Reference Manual—November 1995
2
Example
Replace the contents of the memory location pointed to by the EDI register,
plus an offset of 4, with the word from the top of the stack:
Replace the contents of the memory location pointed to by the EAX register
with the long from the top of the stack:
Push Word/Long onto Stack (push)
Operation
r/m[16|32] → stack
segment register → stack
Description
For a word, SP - 2; for a long, SP - 4. Replaces the new top of stack, pointed
to by SP, with the register, memory, immediate, or segment register operand.
popw 4(edi)
popl %eax
push{wl}r/m[16|32]
push{wl}imm[8|16|32]
push{l} [%cs|%ds|%ss|%es|%fs|%gs]
Instruction-Set Mapping 29
2
Example
Replaces the new top of stack with the 16-bit immediate value, -126:
Replaces the new top of stack with the 32-bit immediate value, 23456789:
Replaces the new top of stack with the content of the AX register:
Replaces the new top of stack with the content of the EBX register:
I/O Instructions
Input from Port (in,ins)
Operation
imm[8|16|32] → [AL|AX|EAX]
DX → [AL|AX|EAX]
DX → ES:(E)DI
pushw $-126
pushl $23456789
pushw %ax
pushl %ebx
in{bwl} imm8
in{bwl} (%dx)
ins{bwl}

30 x86 Assembly Language Reference Manual—November 1995
2
Description
in transfers a byte, word, or long from the immediate port into the byte,
word, or long memory address pointed to by the AL, AX, or EAX register,
respectively.
The second form of the in instruction transfers a byte, word, or long from a
port (0 to 65535), specified in the DX register, into the byte, word, or long
memory address pointed to by the AL, AX, or EAX register, respectively.
When an 8-bit port is specified, the upper-eight bits of the port address will
be 0.
The ins instruction transfers a string from a port specified in the DX register
to the memory byte or word pointed to by the ES:destination index. Load
the desired port number into the DX register and the desired destination
address into the DI or EDI index register before executing the ins
instruction. After a transfer occurs, the destination-index register is
automatically incremented or decremented as determined by the value of
the direction flag (DF). The index register is incremented if DF = 0 (DF
cleared by a cld instruction); it is decremented if DF = 1 (DF set by a std
instruction). The increment or decrement count is 1 for a byte transfer, 2 for
a word, and 4 for a long. Use the rep prefix with the ins instruction for a
block transfer of CX bytes or words.
Example
Transfer an immediate 8-bit port address into the AL register:
Transfer a 16-bit port address, specified in the DX register, into the AX
register:
Transfer a string from the port address, specified in the DX register, into the
ES:destination index register:
inb $0xff
inw (%dx)
insl

Instruction-Set Mapping 31
2
Output from Port (out,outs)
Operation
[AL|AX|EAX] → imm[8|16|32]
[AL|AX|EAX] → DX
ES:(E)DI → DX
Description
Transfers a byte, word, or long from the memory address pointed to by the
content of the AL, AX, or EAX register to the immediate 8-, 16-, or 32-bit
port address.
The second form of the out instruction transfers a byte, word, or long from
the AL, AX, or EAX registers respectively to a port (0 to 65535), specified by
the DX register.
The outs instruction transfers a string from the memory byte or word
pointed to by the ES:source index to the port addressed in the DX register.
Load the desired port number into the DX register and the desired source
address into the SI or ESI index register before executing the outs
instruction. After a transfer occurs, the destination-index register is
automatically incremented or decremented as determined by the value of
the direction flag (DF). The index register is incremented if DF = 0 (DF
cleared by a cld instruction); it is decremented if DF = 1 (DF set by a std
instruction). The increment or decrement count is 1 for a byte transfer, 2 for
a word, and 4 for a long. Use the rep prefix with the outs instruction for a
block transfer of CX bytes or words.
out{bwl} imm8
out{bwl} (%dx)
outs{bwl}
32 x86 Assembly Language Reference Manual—November 1995
2
Example
Transfer a word from the AX register into the 16-bit port address, 0xff:
Transfer a long from the EAX register into the 32-bit port address specified
by the DX register:
Transfer a string from the memory byte or word pointed to by the ES:source
index to the port addressed in the DX register:
Flag Instructions
Load Flags into AH Register (lahf)
Operation
SF:ZF:xx:AF:xx:PF:xx:CF → AH
Description
Transfers the low byte of the flags word to the AH register. The bits (lsb to
msb) are: sign, zero, indeterminate, auxiliary carry, indeterminate, parity,
indeterminate, and carry.
Example
Transfer the flags word into the AH register:
outw $0xff
outl (%dx)
outsl
lahf
lahf

Instruction-Set Mapping 33
2
Store AH into Flags (sahf)
Operation
AH → SF:ZF:xx:AF:xx:PF:xx:CF
Description
Loads flags (sign, zero, indeterminate, auxiliary carry, indeterminate, parity,
indeterminate, and carry) with values from the AH register.
Example
Load values from the AH register into the flags word:
Pop Stack into Flag (popf)
Operation
stack → flags register
Description
Pops the word or long from the top of the stack and stores the value in the
flags register. Stores a word in FLAGS; stores a long in EFLAGS.
sahf
sahf
popf{wl}

34 x86 Assembly Language Reference Manual—November 1995
2
Example
Pops the word from the top of the stack and stores it in the flags register:
Pops the long from the top of the stack and stores it in the eflags register:
Push Flag Register Onto Stack (pushf)
Operation
flags register → stack
Description
For a word, SP - 2 and copies FLAGS to the new top of stack pointed to by
SP. For a long, SP - 4 and copies EFLAGS to the new top of stack pointed to
by SS:eSP.
Example
Pushes the flags register onto the top of the stack:
Pushes the eflags register onto the top of the stack:
popfw
popfl
pushf{wl}
pushfw
pushfl
Instruction-Set Mapping 35
2
Complement Carry Flag (cmc)
Operation
not CF → CF
Description
Reverses the setting of the carry flag; affects no other flags.
Example
Reverse the setting of the carry flag:
Clear Carry Flag (clc)
Operation
0→ CF
Description
Sets the carry flag to zero; affects no other flags.
Example
Clear the carry flag:
cmc
cmc
clc
clc
36 x86 Assembly Language Reference Manual—November 1995
2
Set Carry Flag (stc)
Operation
1→ CF
Description
Sets the carry flag to 1.
Example
Set the carry flag:
Clear Interrupt Flag (cli)
Operation
0→ IF
Description
Clears the interrupt flag if the current privilege level is at least as privileged
as IOPL; affects no other flags. External interrupts disabled at the end of the
cli instruction or from that point on until the interrupt flag is set.
Example
Clear the interrupt flag:
stc
stc
cli
cli
Instruction-Set Mapping 37
2
Set Interrupt Flag (sti)
Operation
1→ IF
Description
Sets the interrupt flag to 1.
Example
Set the interrupt flag:
Clear Direction Flag (cld)
Operation
0→ DF
Description
Clears the direction flag; affects no other flags or registers. Causes all
subsequent string operations to increment the index registers, (E)SI and/or
(E)DI, used during the operation.
Example
Clear the direction flag:
sti
sti
cld
cld

38 x86 Assembly Language Reference Manual—November 1995
2
Set Direction Flag (std)
Operation
1→ DF
Description
Sets the direction flag to 1, causing all subsequent string operations to
decrement the index registers, (E)SI and/or (E)DI, used during the
operation.
Example
Set the direction flag:
Arithmetic Logical Instructions
Integer Addition (add)
Operation
reg[8|16|32] + r/m[8|16|32] → r/m[8|16|32]
r/m[8|16|32] + reg[8|16|32] → reg[8|16|32]
imm[8|16|32] + r/m[8|16|32] → r/m[8|16|32]
std
std
add{bwl} reg[8|16|32], r/m[8|16|32]
add{bwl} r/m[8|16|32], reg[8|16|32]
add{bwl} imm[8|16|32], r/m[8|16|32]
Instruction-Set Mapping 39
2
Description
Integer adds operand1 to operand2 and stores the result in operand2.
When an immediate byte is added to a word or long, the immediate value is
sign-extended to the size of the word or long operand.
If you wish to decimal adjust (daa) or ASCII adjust (aaa) the add result, use
the form of add that stores the result in AL.
Example
Integer adds the 8-bit constant, -126, to the content of the AL register:
Integer adds the word contained in the effective address (addressed by the
EDI register plus an offset of 4) to the content of the DX register:
Integer adds the content of the EDX register to the effective address
(addressed by the EDI register plus an offset of 4):
Integer Add With Carry (adc)
Operation
(reg[8|16|32] + CF) + r/m[8|16|32] → r/m[8|16|32]
(r/m[8|16|32] + CF) + reg[8|16|32] → reg[8|16|32]
(imm[8|16|32] + CF) + r/m[8|16|32] → r/m[8|16|32]
addb $-126,%al
addw 4(%edi),%dx
addl %edx, 4(%edi)
adc{bwl} reg[8|16|32], r/m[8|16|32]
adc{bwl} r/m[8|16|32], reg[8|16|32]
adc{bwl} imm[8|16|32], r/m[8|16|32]
40 x86 Assembly Language Reference Manual—November 1995
2
Description
Integer adds operand1 and the carry flag to operand2 and stores the result
in operand2. adc is typically executed as part of a multi-byte or multi-word
add operation. When an immediate byte is added to a word or long, the
immediate value is sign-extended to the size of the word or long operand.
Example
Integer add the 8-bit content of the effective memory address (ESI register
plus an offset of 1) and the carry flag to the content of the address in the CL
register:
Integer add the 16-bit content of the effective memory address (EDI register
plus an offset of 4) and the carry flag to the content of the address in the DX
register:
Integer add the 32-bit content of the address in the EDX register and the
carry flag to the effective memory address (EDI register plus an offset of 4):
Integer Subtraction (sub)
Operation
r/m[8|16|32] − reg[8|16|32] → r/m[8|16|32]
reg[8|16|32] − r/m[8|16|32] → reg[8|16|32]
r/m[8|16|32] − imm[8|16|32] → r/m[8|16|32]
adcb 1(%esi), %cl
adcw 4(%edi), %dx
adcl %edx, 4(%edi)
sub{bwl} reg[8|16|32], r/m[8|16|32]
sub{bwl} r/m[8|16|32], reg[8|16|32]
sub{bwl} imm[8|16|32], r/m[8|16|32]
Instruction-Set Mapping 41
2
Description
Subtracts operand1 from operand2 and stores the result in operand2. When
an immediate byte value is subtracted from a word, the immediate value is
sign-extended to the size of the word operand before the subtract operation
is executed.
If you wish to decimal adjust (das) or ASCII adjust (aas) the sub result, use
the form of sub that stores the result in AL.
Example
Integer subtract the 8-bit constant, -126, from the content of the effective
address (addressed by the ESI register plus an offset of 1):
Integer subtract the 16-bit constant, 1234, from the content of the effective
address (addressed by the EDI register plus an offset of 4):
Integer subtract the 32-bit content of the EDX register from the effective
address (addressed by the EDI register plus an offset of 4):
Integer Subtraction With Borrow (sbb)
Operation
r/m[8|16|32] − (reg[8|16|32] + CF) → r/m[8|16|32]
reg[8|16|32] − (r/m[8|16|32] + CF) → reg[8|16|32]
r/m[8|16|32] − (imm[8|16|32] + CF) → r/m[8|16|32]
subb $-126, 1(%esi)
subw $1234, 4(%edi)
subl %edx, 4(%edi)
sbb{bwl} reg[8|16|32], r/m[8|16|32]
sbb{bwl} r/m[8|16|32], reg[8|16|32]
sbb{bwl} imm[8|16|32], r/m[8|16|32]

42 x86 Assembly Language Reference Manual—November 1995
2
Description
Subtracts (operand1 and the carry flag) from operand2 and stores the result
in operand2. When an immediate byte value is subtracted from a word, the
immediate value is sign-extended to the size of the word operand before the
subtract operation is executed.
Example
Integer subtract the 8-bit content of the CL register plus the carry flag from
the effective address (addressed by the ESI register plus an offset of 1):
Integer subtract the 16-bit constant, -126, plus the carry flag from the AL
register:
Integer subtract the 32-bit constant, 12345678, plus the carry flag from the
effective address (addressed by the EDI register plus an offset of 4):
Compare Two Operands (cmp)
Operation
r/m[8|16|32] − reg[8|16|32]
reg[8|16|32] − r/m[8|16|32]
r/m[8|16|32] − imm[8|16|32]
sbbb %cl, 1(%esi)
sbbw $-126, %al
sbbl $12345678, 4(%edi)
cmp{bwl} reg[8|16|32], r/m[8|16|32]
cmp{bwl} r/m[8|16|32], reg[8|16|32]
cmp{bwl} imm[8|16|32], r/m[8|16|32]
Instruction-Set Mapping 43
2
Description
Subtracts operand1 from operand2, but does not store the result; only
changes the flags. cmp is typically executed in conjunction with conditional
jumps and the setcc instruction. If an operand greater than one byte is
compared to an immediate byte, the immediate byte value is first sign-
extended.
Example
Compare the 8-bit constant, 0xff, with the content of the AL register:
Compare the 16-bit content of the DX register with the effective address
(addressed by the EDI register plus an offset of 4):
Compare the 32-bit content of the effective address (addressed by the EDI
register plus an offset of 4) to the EDX register:
Increment by 1 (inc)
Operation
r/m[8|16|32] + 1 → r/m[8|16|32]
Description
Adds 1 to the operand and does not change the carry flag. Use the add
instruction with an immediate value of 1 to change the carry flag,.
cmpb $0xff, %al
cmpw %dx, 4(%edi)
cmpl 4(%edi), %edx
inc{bwl} r/m[8|16|32]

44 x86 Assembly Language Reference Manual—November 1995
2
Example
Add 1 to the contents of the byte at the effective address (addressed by the
ESI register plus an offset of 1):
Add 1 to the 16-bit contents of the AX register:
Add 1 to the 32-bit contents at the effective address (addressed by the EDI
register):
Decrease by 1 (dec)
Operation
r/m[8|16|32] − 1 → r/m[8|16|32]
Description
Subtracts 1 from the operand. Does not change the carry flag. To change the
carry flag, use the sub instruction with an immediate value of 1.
incb 1(%esi)
incw %ax
incl 4(%edi)
dec{bwl}r/m[8|16|32]
Instruction-Set Mapping 45
2
Example
Subtract 1 from the 8-bit contents of the effective address (addressed by the
ESI register plus an offset of 1):
Subtract 1 from the 16-bit contents of the BX register:
Subtract 1 from the 32-bit contents of the effective address (addressed by the
EDI register plus an offset of 4):
Logical Comparison or Test (test)
Operation
reg[8|16|32] and r/m[8|16|32] → r/m[8|16|32]
r/m[8|16|32] and reg[8|16|32] → reg[8|16|32]
imm[8|16|32] and r/m[8|16|32] → r/m[8|16|32]
Description
Performs a bit-wise logical AND of the two operands. The result of a bit-
wise logical AND is 1 if the value of that bit in both operands is 1;
otherwise, the result is 0. test discards the results and modifies the flags.
The OF and CF flags are cleared; SF, ZF and PF flags are set according to the
result.
decb 1(%esi)
decw %bx
decl 4(%edi)
test{bwl}reg[8|16|32], r/m[8|16|32]
test{bwl}r/m[8|16|32], reg[8|16|32]
test{bwl}imm[8|16|32], r/m[8|16|32]
46 x86 Assembly Language Reference Manual—November 1995
2
Example
Perform a logical AND of the constant, 0xff, and the 8-bit contents of the
effective address (addressed by the ESI register plus an offset of 1):
Perform a logical AND of the 16-bit contents of the DX register and the
contents of the effective address (addressed by the EDI register plus an
offset of 4):
Perform a logical AND of the constant, 0xffeeddcc, and the 32-bit contents
of the effective address (addressed by the EDI register plus an offset of 4):
Shift (sal,shl,sar,shr)
Operation
shift-left r/m[8|16|32] by imm8 → r/m[8|16|32]
shift-left r/m[8|16|32] by %cl → r/m[8|16|32]
shift-right r/m[8|16|32] by imm8 → r/m[8|16|32]
shift-right r/m[8|16|32] by %cl → r/m[8|16|32]
testb $0xff, 1(%esi)
testw %dx, 4(%edi)
testl $0xffeeddcc, 4(%edi)
sal{bwl} imm8, r/m[8|16|32]
sal{bwl} %cl, r/m[8|16|32]
shl{bwl} imm8, r/m[8|16|32]
shl{bwl} %cl, r/m[8|16|32]
sar{bwl} imm8, r/m[8|16|32]
sar{bwl} %cl, r/m[8|16|32]
shr{bwl} imm8, r/m[8|16|32]
shr{bwl} %cl, r/m[8|16|32]

Instruction-Set Mapping 47
2
Description
sal (or its synonym shl) left shifts (multiplies) a byte, word, or long value
for a count specified by an immediate value and stores the product in that
byte, word, or long respectively. The second variation left shifts by a count
value specified in the CL register. The high-order bit is shifted into the carry
flag; the low-order bit is set to 0.
sar right shifts (signed divides) a byte, word, or long value for a count
specified by an immediate value and stores the quotient in that byte, word,
or long respectively. The second variation right shifts by a count value
specified in the CL register. sar rounds toward negative infinity; the high-
order bit remains unchanged.
shr right shifts (unsigned divides) a byte, word, or long value for a count
specified by an immediate value and stores the quotient in that byte, word,
or long respectively. The second variation divides by a count value specified
in the CL register. shr sets the high-order bit to 0.
Example
Right shift, count specified by the constant (253), the 8-bit contents of the
effective address (addressed by the ESI register plus an offset of 1):
Right shift, count specified by the contents of the CL register, the 16-bit
contents of the effective address (addressed by the EDI register plus an
offset of 4):
Left shift, count specified by the constant (253), the 32-bit contents of the
effective address (addressed by the EDI register plus an offset of 4):
sarb $253, 1(%esi)
shrw %cl, 4(%edi)
shll $253, 4(%edi)
48 x86 Assembly Language Reference Manual—November 1995
2
Double Precision Shift Left (shld)
Operation
by imm8 shift-left r/m[16|32] bits reg[16|32] → r/m[16|32]
by reg[16|32] shift-left r/m[16|32] bits r/m[16|32] → r/m[16|32]
Description
shld double-precision left shifts a 16- or 32-bit register value into a word or
long for the count specified by an immediate value, MODULO 32 (0 to 31).
The result is stored in that particular word or long.
The second variation of shld double-precision left shifts a 16- or 32-bit
register or memory value into a word or long for the count specified by
register CL MODULO 32 (0 to 31).The result is stored in that particular
word or long.
shld sets the SF, ZF, and PF flags according to the value of the result; CS is
set to the value of the last bit shifted out; OF and AF are undefined.
Example
Use the count specified by the constant, 253, to double-precision left shift a
16-bit register value from the DX register to the effective address (addressed
by the EDI register plus an offset of 4):
Use the count specified (%CL MOD 32) by the 32-bit EDX register to double-
precision left shift a 32-bit memory value at the effective address (addressed
by the EDI register plus an offset of 4):
shld{wl}imm8, reg[16|32], r/m[16|32]
shld{wl}%cl, reg[16|32], r/m[16|32]
shldw $253, %dx, 4(%edi)
shldl %cl,%edx, 4(%edi)
Instruction-Set Mapping 49
2
Double Precision Shift Right (shrd)
Operation
by imm8 shift-right r/m[16|32] bits reg[16|32] → r/m[16|32]
by reg[16|32] shift-right r/m[16|32] bits r/m[16|32] → r/m[16|32]
Description
shrd double-precision right shifts a 16- or 32-bit register value into a word
or long for the count specified by an immediate value MODULO 32 (0 to
31). The result is stored in that particular word or long.
The second variation of shrd double-precision right shifts a 16- or 32-bit
register or memory value into a word or long for the count specified by
register CL MODULO 32 (0 to 31).The result is stored in that particular
word or long.
shrd sets the SF, ZF, and PF flags according to the value of the result; CS is
set to the value of the last bit shifted out; OF and AF are undefined.
Example
Use the count specified by the constant, 253, to double-precision right shift a
16-bit register value from the DX register to the effective address (addressed
by the EDI register plus an offset of 4):
Use the count specified (%CL MOD 32) by the 32-bit EDX register to
double-precision right shift a 32-bit memory value at the effective address
(addressed by the EDI register plus an offset of 4)
shrd{wl}imm8, reg[16|32], r/m[16|32]
shrd{wl}%cl, reg[16|32], r/m[16|32]
shrdw $253, %dx, 4(%edi)
shrdl %cl,%edx, 4(%edi)

50 x86 Assembly Language Reference Manual—November 1995
2
One’s Complement Negation (not)
Operation
not r/m[8|16|32] → r/m[8|16|32]
Description
Inverts each bit value of the byte, word, or long; that is, every 1 becomes a 0
and every 0 becomes a 1.
Example
Invert each of the 8-bit values at the effective address (addressed by the ESI
register plus an offset of 1):
Invert each of the 16-bit values at the effective address (addressed by the
EDI register plus an offset of 4):
Invert each of the 32-bit values at the effective address (addressed by the
EDI register plus an offset of 4):
Two’s Complement Negation (neg)
Operation
two’s-complement r/m[8|16|32] → r/m[8|16|32]
not{bwl} r/m[8|16|32]
notb 1(%esi)
notw 4(%edi)
notl 4(%edi)
neg{bwl} r/m[8|16|32]

Instruction-Set Mapping 51
2
Description
Replace the value of the byte, word, or long with its two’s complement; that
is, neg subtracts the byte, word, or long value from 0, and puts the result in
the byte, word, or long respectively.
neg sets the carry flag to 1, unless initial value of the byte, word, or long is
0. In this case neg clears the carry flag to 0.
Example
Replace the 8-bit contents of the effective address (addressed by the ESI
register plus an offset of 1) with its two’s complement:
Replace the 16-bit contents of the effective address (addressed by the EDI
register plus an offset of 4) with its two’s complement:
Replace the 32-bit contents of the effective address (addressed by the EDI
register plus an offset of 4) with its two’s complement:
Check Array Index Against Bounds (bound)
Operation
r/m[16|32] bound reg[16|32] → CC is unchanged
negb 1(%esi)
negw 4(%edi)
negl 4(%edi)
bound{wl}reg[16|32], r/m[16|32]

52 x86 Assembly Language Reference Manual—November 1995
2
Description
Ensures that a signed array index (16- or 32-bit register) value falls within
the upper and lower bounds of a block of memory. The upper and lower
bounds are specified by a 16- or 32-bit register or memory value. If the
signed array index value is not within the bounds, an Interrupt 5 occurs; the
return EIP points to the bound instruction.
Example
Check the 16-bit signed array index value in the AX register against the
doubleword with the upper and lower bounds specified by DX:
Check the 32-bit signed array index value in the EAX register against the
doubleword with the upper and lower bounds specified by EDX:
Logical And (and)
Operation
reg[8|16|32] land r/m[8|16|32] → r/m[8|16|32]
r/m[8|16|32] land reg[8|16|32] → reg[8|16|32]
imm[8|16|32] land r/m[8|16|32] → r/m[8|16|32]
boundw %ax, %dx
boundl %eax, %edx
and{bwl} reg[8|16|32], r/m[8|16|32]
and{bwl} r/m[8|16|32], reg[8|16|32]
and{bwl} imm[8|16|32], r/m[8|16|32]
Instruction-Set Mapping 53
2
Description
Performs a logical AND of each bit in the values specified by the two
operands and stores the result in the second operand.
Example
Perform an 8-bit logical AND of the CL register and the contents of the
effective address (addressed by the ESI register plus an offset of 1):
Perform a 16-bit logical AND of the constant, 0xffee, and the contents of the
effective address (addressed by the AX register):
Perform a 32-bit logical AND of the contents of the effective address
(addressed by the EDI register plus an offset of 4) and the EDX register:
Table 2-2 Logical AND
Values Result
0 LAND 0 0
0 LAND 1 0
1 LAND 0 0
1 LAND 1 1
andb %cl, 1(%esi)
andw $0xffee, %ax
andl 4(%edi), %edx
54 x86 Assembly Language Reference Manual—November 1995
2
Logical Inclusive OR (or)
Operation
reg[8|16|32] LOR r/m[8|16|32] → r/m[8|16|32]
r/m[8|16|32] LOR reg[8|16|32] → reg[8|16|32]
imm[8|16|32] LOR r/m[8|16|32] → r/m[8|16|32]
Description
Performs a logical OR of each bit in the values specified by the two
operands and stores the result in the second operand.
or{bwl} reg[8|16|32], r/m[8|16|32]
or{bwl} r/m[8|16|32], reg[8|16|32]
or{bwl} imm[8|16|32], r/m[8|16|32]
Table 2-3 Inclusive OR
Values Result
0 LOR 0 0
0 LOR 1 1
1 LOR 0 1
1 LOR 1 1

Instruction-Set Mapping 55
2
Example
Perform an 8-bit logical OR of the constant, 0xff, and the AL register:
Perform a 16-bit logical OR of the constant, 0xff83, and the contents of the
effective address (addressed by the EDI register plus an offset of 4):
Perform a 32-bit logical OR of the EDX register and the contents of the
effective address (addressed by the EDI register plus an offset of 4):
Logical Exclusive OR (xor)
Operation
reg[8|16|32] XOR r/m[8|16|32] → r/m[8|16|32]
r/m[8|16|32] XOR reg[8|16|32] → reg[8|16|32]
imm[8|16|32] XOR r/m[8|16|32] → r/m[8|16|32]
orb $0xff, %al
orw $0xff83, 4(%edi)
orl %edx, 4(%edi)
xor{bwl} reg[8|16|32], r/m[8|16|32]
xor{bwl} r/m[8|16|32], reg[8|16|32]
xor{bwl} imm[8|16|32], r/m[8|16|32]
56 x86 Assembly Language Reference Manual—November 1995
2
Description
Performs an exclusive OR of each bit in the values specified by the two
operands and stores the result in the second operand.
Example
Perform a 8-bit exclusive OR of the constant, 0xff, and the AL register:
Perform a 16-bit exclusive OR of the constant, 0xff83, and the contents of the
effective address (addressed by the EDI register plus an offset of 4):
Perform a 32-bit exclusive OR of the EDX register and the contents of the
effective address (addressed by the EDI register plus an offset of 4):
Multiply and Divide Instructions
When the type suffix is not included in a multiply or divide instruction, it
defaults to a long.
Table 2-4 Exclusive XOR
Values Result
0 XOR 0 0
0 XOR 1 1
1 XOR 0 1
1 XOR 1 0
xorb $0xff, %al
xorw $0xff83, 4(%edi)
xorl %edx, 4(%edi)
Instruction-Set Mapping 57
2
Signed Multiply (imul)
Operation
r/m8 × AL → AX
r/m16 × AX → DX:AX
r/m32 × EAX → EDX:EAX
r/m[16|32] × reg[16|32] → reg|16|32]
imm[16|32] × r/m[16|32] → reg|16|32]
Description
The single-operand form of imul executes a signed multiply of a byte,
word, or long by the contents of the AL, AX, or EAX register and stores the
product in the AX, DX:AX or EDX:EAX register respectively.
The two-operand form of imul executes a signed multiply of a register or
memory word or long by a register word or long and stores the product in
that register word or long.
The three-operand form of imul executes a signed multiply of a 16- or 32-
bit immediate by a register or memory word or long and stores the product
in a specified register word or long.
imul clears the overflow and carry flags under the following conditions:
imulb r/m8
imulw r/m16
imul{l} r/m32
imul{wl}r/m[16|32], reg[16|32]
imul{bwl}imm[16|32], r/m[16|32], reg[16|32]
Table 2-5 Clearing OF and CF flags — imul
Instruction Form Condition for Clearing OF and CF
r/m8 × AL → AX AL = sign-extend of AL to 16 bits
r/m16 × AX → DX:AX AX= sign-extend of AX to 32 bits
r/m32 × EAX → EDX:EAX EDX:EAX= sign-extend of EAX to 32 bits
r/m[16|32] × reg[16|32] → reg|16|32] Product fits exactly within reg[16|32]
imm[16|32] × r/m[16|32] → reg|16|32] Product fits exactly within reg[16|32]
58 x86 Assembly Language Reference Manual—November 1995
2
Example
Perform an 8-bit signed multiply of the AL register and the contents of the
effective address (addressed by the ESI register plus an offset of 1):
Perform a 16-bit signed multiply of the constant, -126, and the contents of
the effective address (addressed by the EDI register plus an offset of 4).
Store the result in the DX register:
Perform a 32-bit signed multiply of the constant, 12345678, and the contents
of the effective address (addressed by the EDI register plus an offset of 4).
Store the result in the EDX register:
Unsigned Multiplication of AL,AX or EAX(mul)
Operation
r/m8 × AL → AX
r/m16 × AX → DX:AX
r/m32 × EAX → EDX:EAX
imulb 1(%esi)
imulw $-126, 4(%edi), %dx
imull $12345678, 4(%edi), %edx
mul{bwl} r/m[8|16|32]
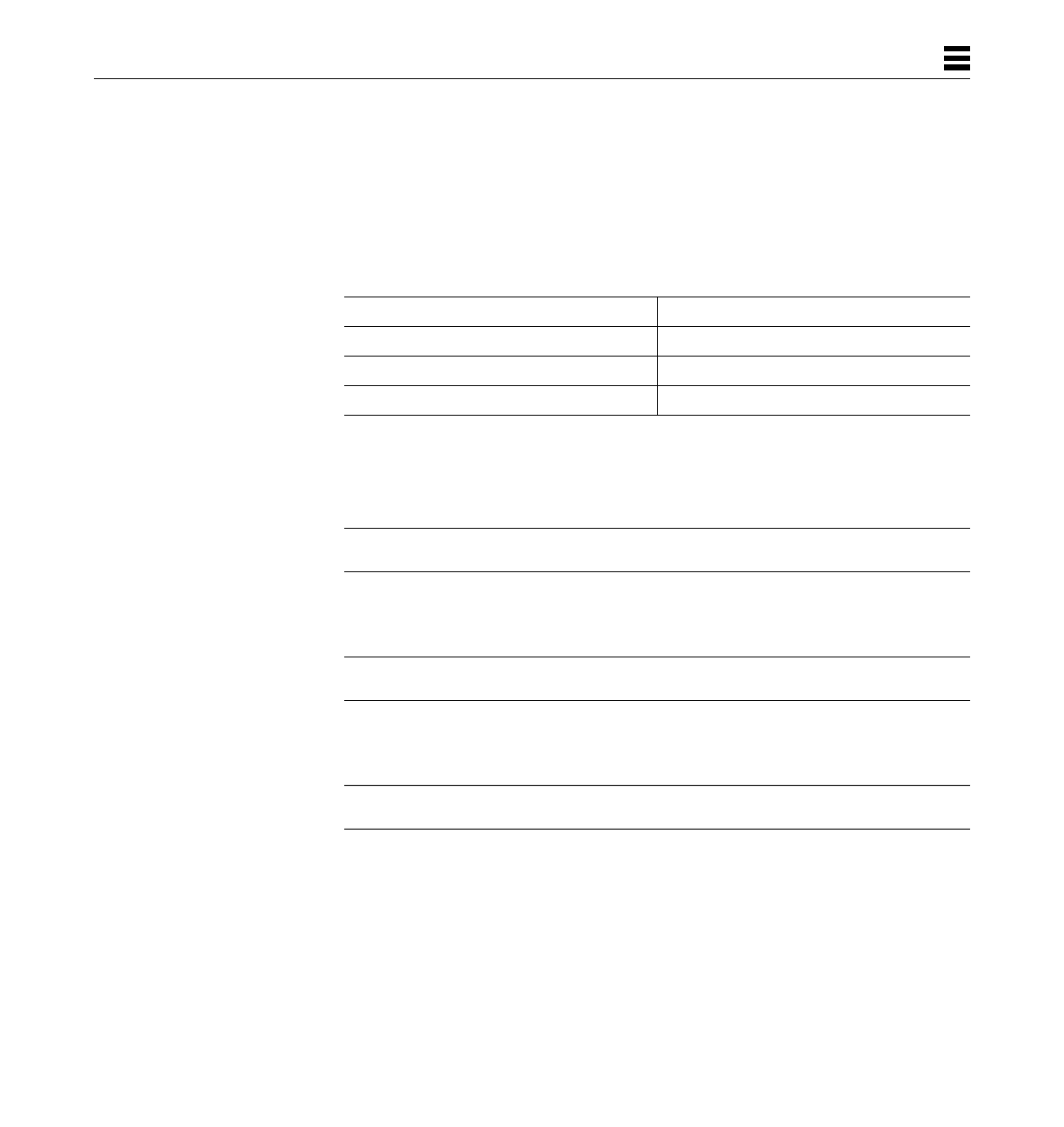
Instruction-Set Mapping 59
2
Description
mul executes a unsigned multiply of a byte, word, or long by the contents of
the AL, AX, or EAX register and stores the product in the AX, DX:AX or
EDX:EAX register respectively.
mul clears the overflow and carry flags under the following conditions:
Example
Perform an 8-bit unsigned multiply of the AL register and the contents of
the effective address (addressed by the ESI register plus an offset of 1):
Perform a 16-bit unsigned multiply of the AL register and the contents of
the effective address (addressed by the EDI register plus an offset of 4):
Perform a 32-bit unsigned multiply of the AL register and the contents of
the effective address (addressed by the EDI register plus an offset of 1):
Table 2-6 Clearing OF and CF flags — mul
Instruction Form Condition for Clearing OF and CF
r/m8 × AL → AX clear to 0 if AH is 0; otherwise, set to 1
r/m16 × AX → DX:AX clear to 0 if DX is 0; otherwise, set to 1
r/m32 × EAX → EDX:EAX clear to 0 if EDX is 0; otherwise, set to 1
mulb 1(%esi)
mulw 4(%edi)
mull 1(%edi)

60 x86 Assembly Language Reference Manual—November 1995
2
Unsigned Divide (div)
Operation
AX ÷ r/m8 → AL
DX:AX ÷ r/m16 → AX
EDX:EAX ÷ r/m32 → EAX
Description
div executes unsigned division. div divides a 16-, 32-, or 64-bit register
value (dividend) by a register or memory byte, word, or long (divisor). The
quotient is stored in the AL, AX, or EAX register respectively.
The remainder is stored in AH, Dx, or EDX. The size of the divisor (8-, 16- or
32-bit operand) determines the particular register used as the dividend.
The OF, SF, ZF, AR, PF and CF flags are undefined.
div{bwl} r/m[8|16|32]
Instruction-Set Mapping 61
2
Example
Perform an 8-bit unsigned divide of the AX register by the contents of the
effective address (addressed by the ESI register plus an offset of 1) and store
the quotient in the AL register, and the remainder in AH:
Perform a 16-bit unsigned divide of the DX:AX register by the contents of
the effective address (addressed by the EDI register plus an offset of 4) and
store the quotient in the AX register, and the remainder in DX:
Perform a 32-bit unsigned divide of the EDX:EAX register by the contents of
the effective address (addressed by the EDI register plus an offset of 4) and
store the quotient in the EAX register, and the remainder in EDX:
Signed Divide (idiv)
Operation
AX ÷ r/m8 → AL
DX:AX ÷ r/m16 → AX
EDX:EAX ÷ r/m32 → EAX
divb 1(%esi)
divw 4(%edi)
divl 4(%edi)
idiv{bwl}r/m[8|16|32]

62 x86 Assembly Language Reference Manual—November 1995
2
Description
idiv executes signed division. idiv divides a 16-, 32-, or 64-bit register
value (dividend) by a register or memory byte, word, or long (divisor). The
size of the divisor (8-, 16- or 32-bit operand) determines the particular
register used as the dividend, quotient, and remainder.
If the resulting quotient is too large to fit in the destination, or if the divisor
is 0, an Interrupt 0 is generated. Non-integral quotients are truncated
toward 0. The remainder has the same sign as the dividend; the absolute
value of the remainder is always less than the absolute value of the divisor.
Example
Perform a 16-bit signed divide of the DX:AX register by the contents of the
effective address (addressed by the EDI register plus an offset of 4) and store
the quotient in the AX register
Conversion Instructions
Convert Byte to Word (cbtw)
Operation
sign-extend AL → AX
Table 2-7 idiv Register Assignment
Divisor Operand Size Dividend Quotient Remainder
byte AX AL AH
word DX:AX AX DX
long EDX:EAX EAX EDX
divw 4(%edi)
cbtw
Instruction-Set Mapping 63
2
Description
cbtw converts the signed byte in AL to a signed word in AX by extending
the most-significant bit (sign bit) of AL into all bits of AH.
Example
Convert Word to Long (cwtl)
Operation
sign-extend AX → EAX
Description
cwtl converts the signed word in AX to a signed long in EAX by extending
the most-significant bit (sign bit) of AX into two most-significant bytes of
EAX.
Example
Convert Signed Word to Signed Double Word (cwtd)
Operation
sign-extend AX → DX:AX
Description
cwtd converts the signed word in AX to a signed double word in DX:AX by
extending the most-significant bit (sign bit) of AX into all bits of DX.
cbtw
cwtl
cwtl
cwtd

64 x86 Assembly Language Reference Manual—November 1995
2
Example
Convert Signed Long to Signed Double Long (cltd)
Operation
sign-extend EAX → EDX:EAX
Description
cltd converts the signed long in EAX to a signed double long in EDX:EAX
by extending the most-significant bit (sign bit) of EAX into all bits of EDX.
Example
Decimal Arithmetic Instructions
Decimal Adjust AL after Addition (daa)
Operation
decimal-adjust AL → AL
Description
Use daa only after executing the form of an add instruction that stores a
two-BCD-digit byte result in the AL register. daa then adjusts AL to a two-
digit packed decimal result.
cwtd
cltd
cltd
daa

Instruction-Set Mapping 65
2
Example
Decimal adjust the two-BCD-digit in the AL register:
Decimal Adjust AL after Subtraction (das)
Operation
decimal-adjust AL → AL
Description
Use das only after executing the form of a sub instruction that stores a two-
BCD-digit byte result in the AL register. das then adjusts AL to a two-digit
packed decimal result.
Example
Decimal adjust the two-BCD-digit in the AL register:
ASCII Adjust after Addition (aaa)
Operation
ASCII-adjust AL → AL
daa
das
das
aaa
66 x86 Assembly Language Reference Manual—November 1995
2
Description
You use aaa only after executing the form of an add instruction that stores
a two-BCD-digit byte result in the AL register. aaa then adjusts AL to
contain the correct decimal result. The top nibble of AL is set to 0. To
convert AL to an ASCII result, follow the aaa instruction with:
Table 2-8 shows how aaa handles a carry.
Example
Adjust the AL register to contain the correct decimal result after an add
instruction that stores a two-BCD-digit byte.
ASCII Adjust after Subtraction (aas)
Operation
ASCII-adjust AL → AL
or %al, 0x30
Table 2-8 Handling a Carry
Carry Action
decimal carry AH + 1; CF and AF set to 1
no decimal carry AH unchanged; CF and AF cleared to 0
aaa
aas
Instruction-Set Mapping 67
2
Description
Use aas only after executing the form of an add instruction that stores a
two-BCD-digit byte result in the AL register. aas then adjusts AL to contain
the correct decimal result. The top nibble of AL is set to 0. To convert AL to
an ASCII result, follow the aas instruction with:
Table 2-9 shows how aas handles a carry.
Table 2-9 How aas Handles a Carry
Example
Adjust the AL register to contain the correct decimal result after a sub
instruction that stores a two-BCD-digit byte
ASCII Adjust AX after Multiply (aam)
Operation
AL ÷ 10 → AH
mod 10 AL → AL
Description
You use aam only after executing a mul instruction between two BCD digits
(unpacked). mul stores the result in the AX register. The result is less than
100 so it can be contained in the AL register (the low byte of the AX
or %al, 0x30
Carry Action
decimal carry AH - 1; CF and AF set to 1
no decimal carry AH unchanged; CF and AF cleared to 0
aas
aam
68 x86 Assembly Language Reference Manual—November 1995
2
register). aam unpacks the AL result by dividing AL by 10, stores the
quotient (most-significant digit) in AH, and stores the remainder (least-
significant digit) in AL.
Example
Adjust the AL register to contain the correct decimal result after a mul
instruction between two BCD digits:
ASCII Adjust AX before Division (aad)
Operation
AL + (AH × 10) → AL
0→ AH
Description
aad prepares two unpacked BCD digits for a division operation that yields
an unpacked result. The least-significant digit is in AL; the most-significant
in AH.
aad prepares the AL and AH registers:
AX is then equal to the binary equivalent of the original unpacked two-digit
BCD number.
aam
aad
AL + (AH × 10) → AL
0→ AH

Instruction-Set Mapping 69
2
Example
Adjust the AL and AH registers for a division operation by setting the AX
register equal to the original unpacked two-digit number:
Coprocessor Instructions
Wait (wait,fwait)
Description
wait — processor suspends instruction execution until the BUSY # pin is
inactive (high).
fwait — processor checks for pending unmasked numeric exceptions
before proceeding.
Example
Suspend instruction execution until not BUSY and check for exceptions:
String Instructions
All Intel string op mnemonics default to long.
aad
wait
fwait
wait
70 x86 Assembly Language Reference Manual—November 1995
2
Move Data from String to String (movs)
Operation
move {bwl} [(E)SI] → ES: (E)DI]
move {bwl} DS: [(E)SI] → ES: [(E)DI]
Description
Copies the byte, word, or long in [(E)SI] to the byte, word, or long in
ES:[(E)DI}. Before executing the move instruction, load the index values into
the SI source- and DI destination-index registers.
The destination operand must be addressable from the ES register; it cannot
span segments. A source operand, however, can span segments; the default
is DS.
After the data is moved, both the source- and destination-index registers are
automatically incremented or decremented as determined by the value of
the direction flag (DF). The index registers are incremented if DF = 0 (DF
cleared by a cld instruction); they are decremented if DF = 1 (DF set by a
std instruction). The increment/decrement count is 1 for a byte move, 2 for
a word, and 4 for a long.
For a block move of CX bytes or words, precede a movs instruction with a
rep prefix.
Example
Copy the 8-bit byte from the DS:[(E)SI] to the ES:[(E)DI] register.
movs{bwl}
movs{bwl} m[8|16|32], reg[16|32]
movsb

Instruction-Set Mapping 71
2
Compare String Operands (cmps)
Operation
compare DS:[(E)SI] with ES:[(E)DI]
Description
Compares the byte, word, or long in DS:[(E)SI] with the byte, word, or long
in ES:[(E)DI}. Before executing the cmps instruction, load the index values
into the SI source- and DI destination-index registers.
cmps subtracts the operand indexed by the destination-index from the
operand indexed by the source-index register.
After the data is compared, both the source- and destination-index registers
are automatically incremented or decremented as determined by the value
of the direction flag (DF). The index registers are incremented if DF = 0 (DF
cleared by a cld instruction); they are decremented if DF = 1 (DF set by a
std instruction). The increment/decrement count is 1 for a byte move, 2 for
a word, and 4 for a long.
For a block compare of CX or ECX bytes, words or longs, precede a cmps
instruction with a repz or repnz prefix.
cmps{bwl}

72 x86 Assembly Language Reference Manual—November 1995
2
Example
Compare the 8-bit byte in the DS:[(E)SI] register to the ES:[(E)DI] register.
Compare the 16-bit word in the DS:[(E)SI] register to the ES:[(E)DI] register.
Compare the 32-bit word in the DS:[(E)SI] register to the ES:[(E)DI] register.
Store String Data (stos)
Operation
store [AL|AX|EAX] → ES:[(E)DI]
Description
Transfers the contents of the AL, AX, or EAX register to the memory byte or
word addressed in the destination register relative to the ES segment. Before
executing the move instruction, load the index values into the DI
destination-index register.
The destination operand must be addressable from the ES register; it cannot
span segments.
After the data is transferred, the destination-index register is automatically
incremented or decremented as determined by the value of the direction flag
(DF). The index registers are incremented if DF = 0 (DF cleared by a cld
cmpsb
cmpsw
cmpsl
stos{bwl}

Instruction-Set Mapping 73
2
instruction); they are decremented if DF = 1 (DF set by a std instruction).
The increment/decrement count is 1 for a byte move, 2 for a word, and 4 for
a long.
For a block transfer of CX bytes, words or longs, precede a stos instruction
with a rep prefix.
Example
Transfer the contents of the AL register to the memory byte addressed in the
destination register, relative to the ES segment.
Transfer the contents of the AX register to the memory word addressed in
the destination register, relative to the ES segment
Transfer the contents of the EAX register to the memory double-word
addressed in the destination register, relative to the ES segment
The Load String Operand (lods)
Operation
load ES:[(E)DI] → [AL|AX|EAX]
stosb
stosw
stosl
lods{bwl}

74 x86 Assembly Language Reference Manual—November 1995
2
Description
Loads the memory byte or word addressed in the destination register into
the AL, AX, or EAX register. Before executing the lods instruction, load the
index values into the SI source-index register.
After the data is loaded, the source-index register is automatically
incremented or decremented as determined by the value of the direction flag
(DF). The index register is incremented if DF = 0 (DF cleared by a cld
instruction); it is decremented if DF = 1 (DF set by a std instruction). The
increment/decrement count is 1 for a byte move, 2 for a word, and 4 for a
long.
For a block transfer of CX bytes, words or longs, precede a lods instruction
with a rep prefix; however, lods is used more typically within a loop
construct where further processing of the data moved into AL, AX, or EAX
is usually required.
Example
Load the memory byte addressed in the destination register, relative to the
ES segment register, into the AL register.
Load the memory word addressed in the destination register, relative to the
ES segment register, into the AX register.
Load the memory double-word addressed in the destination register,
relative to the ES segment register, into the EAX register.
lodsb
lodsw
lodsl

Instruction-Set Mapping 75
2
Compare String Data (scas)
Operation
compare ES:[(E)DI] with [AL|AX|EAX]
Description
Compares the memory byte or word addressed in the destination register
relative to the ES segment with the contents of the AL, AX, or EAX register.
The result is discarded; only the flags are set.
Before executing the scas instruction, load the index values into the DI
destination-index register. The destination operand must be addressable
from the ES register; it cannot span segments.
After the data is transferred, the destination-index register is automatically
incremented or decremented as determined by the value of the direction flag
(DF). The index registers are incremented if DF = 0 (DF cleared by a cld
instruction); they are decremented if DF = 1 (DF set by a std instruction).
The increment/decrement count is 1 for a byte move, 2 for a word, and 4 for
a long.
For a block search of CX or ECX bytes, words or longs, precede a scas
instruction with a repz or repnz prefix.
scas{bwl}
76 x86 Assembly Language Reference Manual—November 1995
2
Example
Compare the memory byte addressed in the destination register, relative to
the ES segment, with the contents of the AL register.
Compare the memory word addressed in the destination register, relative to
the ES segment, with the contents of the AX register
Compare the memory byte double-word addressed in the destination
register, relative to the ES segment, with the contents of the EAX register
Look-Up Translation Table (xlat)
Operation
set AL to DS:[(E)BX + unsigned AL]
Description
Changes the AL register from the table index to the table entry. AL should
be the unsigned index into a table addressed by DS:BX (16-bit address) or
DS:EBX (32-bit address).
Example
Change the AL register from the table index to the table entry.
scasb
scasw
scasl
xlat
xlat
Instruction-Set Mapping 77
2
Repeat String Operation (rep,repnz,repz)
Operation
repeat string-operation until tested-condition
Description
Use the rep (repeat while equal), repnz (repeat while nonzero) or repz
(repeat while zero) prefixes in conjunction with string operations. Each
prefix causes the associated string instruction to repeat until the count
register (CX) or the zero flag (ZF) matches a tested condition.
Example
Repeat while equal: Copy the 8-bit byte from the DS:[(E)SI] to the ES:[(E)DI]
register.
Repeat while not zero: Compare the memory byte double-word addressed
in the destination register EDL, relative to the ES segment, with the contents
of the EAX register.
Repeat while zero:Transfer the contents of the EAX register to the memory
double-word addressed in the destination register EDL, relative to the ES
segment.
rep
repnz
repz
rep movsb
repnz scasl
repz stosl
78 x86 Assembly Language Reference Manual—November 1995
2
Procedure Call and Return Instructions
Far Call — Procedure Call (lcall)
Operation
far call ptr16:{16|32}
far call m16:{16|32}
Description
The lcall instruction calls intersegment (far) procedures using a full
pointer. lcall causes the procedure named in the operand to be executed.
When the called procedure completes, execution flow resumes at the
instruction following the lcall instruction (see the return instruction).
lcall ptr16:{16|32} uses a four-byte or six-byte operand as a long pointer
to the called procedure.
lcall m16:{16|32} fetches the long pointer from the specified memory
location.
In Real Address Mode or Virtual 8086 Mode, the long pointer provides 16
bits for the CS register and 16 or 32 bits for the EIP register. Both forms of
the lcall instruction push the CS and IP or EIP registers as a return address.
Example
Use a four-byte operand as a long pointer to the called procedure.
Fetch a long pointer from the memory location addressed by the edx
register, offset by 3.
lcall immptr
lcall *mem48
lcall $0xfebc, $0x12345678
lcall *3(%edx)
Instruction-Set Mapping 79
2
Near Call — Procedure Call (call)
Operation
near call rel{16|32}
near call r/m{16|32}
Description
The call instruction calls near procedures using a full pointer. call causes
the procedure named in the operand to be executed. When the called
procedure completes, execution flow resumes at the instruction following
the call instruction (see the return instruction).
call rel{16|32} adds a signed offset to address of the instruction following
the call instruction to determine the destination; that is, the displacement
is relative to the next instruction. The displacement value is stored in the
EIP register. For rel16, the upper 16 bits of EIP are cleared to zero resulting
in an offset value that does not exceed 16 bits.
call r/m{16|32} specifies a register or memory location from which the
absolute segment offset is fetched. The offset of the instruction following the
call instruction is pushed onto the stack. After the procedure completes,
the offset is popped by a near ret instruction within the procedure.
Both forms of the call instruction have no affect on the CS register.
Example
Program counter minus 0x11111111.
Add a signed offset value to the address of the next instruction.
call disp32
call *r/m32
call .-0x11111111
call *4(%edi)
80 x86 Assembly Language Reference Manual—November 1995
2
Return from Procedure (ret)
Operation
return to caller
Description
The ret instruction transfers control to the return address located on the
stack. This address is usually placed on the stack by a call instruction.
Issue the ret instruction within the called procedure to resume execution
flow at the instruction following the call.
The optional numeric (16- or 32-bit) parameter to ret specifies the number
of stack bytes or words to be released after the return address is popped
from the stack. Typically, these bytes or words are used as input parameters
to the called procedure.
For an intersegment (near) return, the address on the stack is a segment
offset that is popped onto the instruction pointer. The CS register remains
unchanged.
Example
Transfer control to the return address located on the stack.
Transfer control to the return address located on the stack. Release the next
16-bytes of parameters.
ret
ret imm16
ret
ret $-32767

Instruction-Set Mapping 81
2
Long Return (lret)
Operation
return to caller
Description
The lret instruction transfers control to a return address located on the
stack. This address is usually placed on the stack by an lcall instruction.
Issue the lret instruction within the called procedure to resume execution
flow at the instruction following the call.
The optional numeric (16- or 32-bit) parameter to lret specifies the number
of stack bytes or words to be released after the return address is popped
from the stack. Typically, these bytes or words are used as input parameters
to the called procedure.
For an intersegment (far) return, the address on the stack is a long pointer.
The offset is popped first, followed by the selector.
In Real Mode, CS and IP are loaded directly. In Protected mode, an
intersegment return causes the processor to check the descriptor addressed
by the return selector. The AR byte of the descriptor must indicate a code
segment of equal or lesser privilege (or greater or equal numeric value) than
the current privilege level. Returns to a lesser privilege level cause the stack
to be reloaded from the value saved beyond the parameter block.
lret
lret imm16

82 x86 Assembly Language Reference Manual—November 1995
2
Example
Transfer control to the return address located on the stack.
Transfer control to the return address located on the stack. Release the next
16-bytes of parameters.
Enter/Make Stack Frame for Procedure Parameters (enter)
Operation
make stack frame for procedure parameters
Description
Create the stack frame required by most block-structured high-level
languages. The imm16 operand specifies the number of bytes of dynamic
storage allocated on the stack for the routine being entered. The imm8
operand specifies the lexical nesting level (0 to 31) of the routine within the
high-level language source code. The nesting level determines the number
of stack frame pointers copied into the new stack frame from the preceding
frame.
Example
Create a stack frame with 0xfecd bytes of dynamic storage on the stack and
a nesting level of 0xff.
lret
lret $-32767
enter imm16, imm8
enter $0xfecd, $0xff

Instruction-Set Mapping 83
2
High Level Procedure Exit (leave)
Operation
set (E)SP to (E)BP, then pop (E)BP
Description
The leave instruction reverses the actions of an enter instruction. leave
copies the frame pointer to the stack point and releases the stack space
formerly used by a procedure for its local variables. leave pops the old
frame pointer into (E)BP, thus restoring the caller’s frame. A subsequent
ret nn instruction removes any arguments pushed onto the stack of the
exiting procedure.
Example
Copy the frame pointer to the stack pointer and release the stack space.
Jump Instructions
Jump if ECX is Zero (jcxz)
Operation
jump to disp8 if (E)CX is 0
leave
leave
jcxz disp8

84 x86 Assembly Language Reference Manual—November 1995
2
Description
The jcxz instruction tests the contents of the CX or ECX register for 0. jcxz
differs from other conditional jumps that it tests the flags, rather than (E)CX.
jcxz is useful at the beginning of a loop that terminates with a conditional
loop instruction; such as:
In this case, jcxz tests CX or ECX for 0 prior to entering the loop, thus
executing 0 times:
Example
Loop Control with CX Counter (loop,loopnz,loopz)
Operation
decrement count; jump to disp8 if count not equal 0
decrement count; jump to disp8 if count not equal 0 and ZF = 0
decrement count; jump to disp8 if count not equal 0 and ZF = 1
loopne .-126
jcxz .-126
...
loopne .-126
loop disp8
loopnz disp8
loopne disp8
loopz disp8
loope disp8

Instruction-Set Mapping 85
2
Description
loop decrements the count register; the flags register remains unchanged.
Conditions are checked for by the particular form of loop you used. If the
conditions match, a short jump is made to the address specified by the disp8
operand. The range of the disp8 operand, relative to the current instruction,
is +127 decimal bytes to -128 decimal bytes.
loop instructions provide iteration control and combine loop index
management with conditional branching. Prior to using the loop
instruction, load the count register with an unsigned iteration count. Then,
add the loop instruction at the end of a series of instructions to be iterated.
The disp8 operand points to the beginning of the iterative loop.
Example
Decrement the count register and when the count is not equal to zero, jump
short to the disp8 location.
Jump (jmp
,
ljmp)
Operation
jump short or near; displacement relative to next instruction
jump far (intersegment; 4- or 6-byte immediate address
jump if condition is met; displacement relative to next instruction
loopne .-126
jmp disp{8|16|32}
jmp *r/m{16|32}
ljmpimmPtr
ljmp*mem48
j
cc
disp{8|32}
86 x86 Assembly Language Reference Manual—November 1995
2
Description
The jmp instruction transfers execution control to a different point in the
instruction stream; records no return information.
Jumps with destinations of disp[8|16|32] or r/m[16|32] are near jumps and
do not require changes to the segment register value.
jmp rel{16|32} adds a signed offset to the address of the instruction
following the jmp instruction to determine the destination; that is, the
displacement is relative to the next instruction. The displacement value is
stored in the EIP register. For rel16, the upper 16 bits of EIP are cleared to
zero resulting in an offset value not to exceed 16 bits.
ljmp ImmPtr or *mem48 use a four- or six-byte operand as a long pointer to
the destination. In Real Address Mode or Virtual 8086 mode, the long
pointer provides 16 bits for the CS register and 16 or 32 bits for the EIP
register. In Protected mode, both long pointer forms consult the AR (Access
Rights) byte of the descriptor indexed by the selector part of the long
pointer. The jmp performs one of the following control transfers depending
on the value of the AR byte:
•A jump to a code segment at the same privilege level
•A task switch
Example
Jump to the relative effective address (addressed by the EDI register plus an
offset of 4):
Long jump, use 0xfebc for the CS register and 0x12345678 for the EIP
register:
Jump if not equal:
jmp *4(%edi)
ljmp $0xfebc, $0x12345678
jne .+10

Instruction-Set Mapping 87
2
Interrupt Instructions
Call to Interrupt Procedure (int,into)
Operation
interrupt 3 — trap to debugger
interrupt numbered by immediate byte
interrupt 4 — if overflow flag is 1
Description
The int instruction generates a software call to an interrupt handler. The
imm8 (0 to 255) operand specifies an index number into the IDT (Interrupt
Descriptor Table) of the interrupt routine to be called. In Protect Mode, the
IDT consists of an array of 8-byte descriptors; the descriptor for the
interrupt invoked must indicate an interrupt, trap, or task gate. In Real
int 3
int imm8
into
88 x86 Assembly Language Reference Manual—November 1995
2
Address Mode, the IDT is an array of four byte-long pointers. In Protected
and Real Address Modes, the base linear address of the IDT is defined by
the contents of the IDTR.
The into form of the int instruction implies interrupt 4. The interrupt
occurs only if the overflow flag is set.
The first 32 interrupts are reserved for system use. Some of these interrupts
are used for internally generated exceptions.
The int imm8 form of the interrupt instruction behaves like a far call except
that the flags register is pushed onto the stack before the return address.
Interrupt procedures return via the iret instruction, which pops the flags
and return address from the stack.
In Real Address Mode, the int imm8 pushes the flags, CS, and the return IP
onto the stack, in that order, then jumps to the long pointer indexed by the
interrupt number.
Example
Trap to debugger:
Trap to interrupt 0xff:
Trap to interrupt 4:
int $3
int $0xff
into

Instruction-Set Mapping 89
2
Interrupt Return (iret)
Operation
return →routine
Description
In Real Address Mode, iret pops CS, the flags register, and the instruction
pointer from the stack and resumes the routine that was interrupted. In
Protected Mode, the setting of the nested task flag (NT) determines the
action of iret. The IOPL flag register bits are changed when CPL equals 0
and the new flag image is popped from the stack.
iret returns from an interrupt procedure without a task switch if NT
equals 0. Returned code must be equally or less privileged than the
interrupt routine as indicated CS selector RPL bits popped from the stack. If
the returned code is less privileged, iret pops SS and the stack pointer from
the stack.
iret reverses the operation of an INT or CALL that caused the task switch
if NT equals 1.The task executing iret is updated and saved in its task
segment. The code that follows iret is executed if the task is re-entered.
Example
Resume the interrupted routine:
iret
iret
90 x86 Assembly Language Reference Manual—November 1995
2
Protection Model Instructions
Store Local Descriptor Table Register (sldt)
Operation
LDTR → r/m[16]
Description
The Local Descriptor Table Register (LDTR) is stored by sldt as indicated
by the effective address operand. LDTR is stored into the two-byte register
or the memory location.
sldt is not used in application programs. It is used only in operating
systems.
Example
Store the LDTR in the effective address (addressed by the EBX register plus
and offset of 5):
Store Task Register (str)
Operation
STR → r/m(16
Description
The contents of the task register is stored by sldt as indicated by the
effective address operand. STR is stored into the two-byte register or the
memory location.
sldtr/m16
sldt 5(%ebx)
str r/m16

Instruction-Set Mapping 91
2
Example
Store str in the effective address (addressed by the EBX register plus an
offset of 5):
Load Local Descriptor Table Register (lldt)
Operation
SELECTOR → LDTR
Description
LDTR is loaded by LLDT. The operand (word) contains a selector to a local
GDT (Global Descriptor Table). The descriptor registers are not affected.The
task state segment LDT field does not change.
The LDTR is marked invalid if the selector operand is 0. A #GP fault is
caused by all descriptor references (except LSL VERR, VERW, or LAR
instructions).
LLDT is not used in application programs. It is used in operating systems.
Example
Load the LLDT register from the effective address (addressed by the EBX
register plus and offset of 5):
str 5(%ebx)
lldt r/m16
lldt 5(%ebx)

92 x86 Assembly Language Reference Manual—November 1995
2
Load Task Register (ltr)
Operation
r/m16 → Task Register
Description
The task register is loaded by LTR from the source register or memory
location specified by the operand. The loaded task state segment is tagged
busy. A task switch does not occur.
Example
Load the TASK register from the effective address (addressed by the EBX
register plus and offset of 5):
Verify a Segment for Reading or Writing (verr,verw)
Operation
1→ ZF (if segment can be read or written)
Description
VERR and VERW contains the value of a selector in the two-byte register or
memory operand. VERR and VERW determine if the indicated segment can
be reached in the current privilege level and whether it is readable (VERR)
or writable (VERW). If the segment can be accessed, the zero flag (ZF) is set
to 1, otherwise the zero flag is set to 0. For the zero flag to be set these
conditions must be met:
•The selector denotes a descriptor; the selector is “defined”.
ltr r/m16
ltr 5(%ebx)
verr r/m16
verw r/m16

Instruction-Set Mapping 93
2
•The selector is a code or data segment; not a task statement, LDT or a gate.
•For VERR, the segment must be readable, for VERW, writable.
•The descriptor privilege level (DPL) can be any value for VERR. otherwise
the DPL must have the same or less privilege as the current level and the
DPL of the selector.
Validation is performed as if the segment were loaded into DS, ES, FS, or GS
and the indicated write or read performed. The validation results are
indicated by the zero flag. The value of the selector cannot result in an
exception.
Example
Determine if the segment indicated by the effective address (addressed by
the EBX register plus an offset of 5) can be reached in the current privilege
level and whether it is readable (VERR):
Store Global/Interrupt Descriptor Table Register (sgdt,sidt)
Operation
DTR → mem48
Description
The contents of the descriptor table register is copied by sgdt/sidt to the
six bytes of memory specified by the operand. The first word at the effective
address is assigned the LIMIT field of the register. If the operand-size
attribute is 32-bits:
•The base field of the register is assigned to the next three bytes.
•The fourth byte is written as zero.
verr 5(%ebx)
sgdt mem48
sidt mem48

94 x86 Assembly Language Reference Manual—November 1995
2
•The last byte is undefined.
If the operand-size attribute is 16-bits, the 32-bit BASEfield of the register is
assigned to the next four bytes.
sgdt/sldt are not used in application programs, they are used in
operating systems.
Example
Copy the contents of the Global Descriptor Table Register to the specified
memory location:
Copy the contents of the Interrupt Descriptor Table Register to the effective
address (addressed by the EBX register plus an offset of 5):
Load Global/Interrupt Descriptor Table (lgdt,lidt)
Operation
MEM48 → GDTR
MEM48 → IDTR
Description
The GDTR and IDTR are loaded with a linear base address and limit value
from a six-byte operand in memory by the lgdt/lidt instructions. For a
16-bit operand:
•Load the register with a 16-bit limit and a 24-bit base.
sgdt 0x55555555
sidt 5 (%ebx)
lgdt mem48
lidt mem48

Instruction-Set Mapping 95
2
•The six-byte data operand high-order eight bits are not used.
For a 32-bit operand:
•Load the register with a 16-bit limit and a 32-bit base.
•The six-byte data operand high-order eight bits are used as the high-order
base address bits.
All 48-bits of the six-byte data operand are always stored into by the
sgdt/sidt instructions. For a 16-bit and a 32-bit operand, the upper eight-
bits are written with the high-order eight address bits. lgdt or lidt,
when used with a 16-bit operand to load the register stored by sgdt or
sidt, stores the upper eight-bits as zeros.
lgdt and lidt are not used in application programs; they are used in
operation system. lgdt and lidt are the only instructions that load a linear
address directly in 80386 Protected Mode.
Example
Load the Global/Interrupt Descriptor Table Register from memory address
0x55555555:
Store Machine Status Word (smsw)
Operation
MSW → r/m16
Description
The machine status word is stored by smsw in the two-byte register of
memory location pointed to by the effective address operand.
80386 machines should use MOV ..., CR0.
lgdt 0x55555555
lidt 0x55555555
smsw r/m16

96 x86 Assembly Language Reference Manual—November 1995
2
Example
Store the machine status word in the effective address (addressed by the
EBX register plus an offset of 5):
Load Machine Status Word (lmsw)
Operation
r/m16 → MSW
Description
The machine status word (part of CR0) is loaded by lmsw from the source
operand. lmsw can be used to switch to Protected Mode if followed by an
intersegment jump to clear the instruction queue. lmsw cannot switch back
to Real Address Mode.
lmsw is not used in application programs. It is used in operating systems.
Example
Load the machine status word from the contents of the effective address
(addressed by the EBX register plus an offset of 5):
Load Access Rights (lar)
Operation
r/m16 (masked by FF00) →r16
r/m32 (masked by 00FxFF00) → r32
smsw 5(%ebx)
lmsw r/m16
lmsw 5(%ebx)
lar r/m32, reg32

Instruction-Set Mapping 97
2
Description
If the selector is visible at the CPL (modified by the RPL) and is a valid
descriptor type, lar stores a form of the second doubleword of the
descriptor for the source selector. The designated register is loaded with the
double-word (high-order) of the descriptor masked by 00FxFF00, and the
zero flag is set to 1. The x in 00Fx ... indicates that these four bits loaded by
lar are undefined. The zero flag is cleared if the selector is invisible or of
the wrong type.
The 32-bit value is stored in the 32-bit destination register if the 32-bit
operand size is specified. If the 16-bit operand size is specified, the lower 16-
bits of this value are stored in the 16-bit destination register.
For lar, all data segment descriptors and code are valid.
Example
Load access rights from the contents of the effective address (addressed by
the EBX register plus an offset of 5) into the EDX register:
Load Segment Limit (lsl)
Operation
Selector rm16 (byte) → r16
Selector rm32 (byte) → r32
Selector rm16 (page) → r16
Selector rm32 (page) → r32
lar 5(%ebx) %edx
lsl r/m32, reg32
98 x86 Assembly Language Reference Manual—November 1995
2
Description
lsl loads a register with a segment limit (unscrambled). The descriptor
type must be accepted by lsl, and the source selector must be visible at the
CPL weakened by RPL. ZF is then set to 1. Otherwise, ZF is set to 0 and the
destination register is unchanged.
The segment limit is loaded as a byte value. A page value limit in the
descriptor is translated by lsl to a byte limit before lsl loads it in the
destination register (the 20-bit limit from the descriptor is shifted left 12 and
OR’d with 00000FFFH).
lsl stores the 32-bit granular limit in the 16-bit destination register.
For lsl, code and data segment descriptors are valid.
Example
Load a segment limit from the contents of the effective address (addressed
by the EBX register plus an offset of 5) into the EDX register.
Clear Task-Switched (clts)
Operation
0→ TS Flag in CR0
Description
The task-switched flag in register CR0 is cleared by clta. The TS Flag is set
by the 80386 for each task switch. The TS Flag is used as follows:
•If the TS Flag is set, each execution of the ESC instruction is trapped.
lsl 5(%ebx), %edx
clts

Instruction-Set Mapping 99
2
•If the TS Flag and the MP Flag are both set, execution of a Wait instruction
is trapped.
If a task switch is made after an ESC instruction is started, save the
processor extension context before a new ESC instruction can be run. The
fault handler resets the TS Flag and saves the context.
clts is not used in application program, it is used in operating systems.
clts can only be executed at privilege level 0.
Example
Clear the TS flag:
Adjust RPL Field of Selector (arpl)
Operation
If RPL 1 < RPL 2, 1 → ZF
Description
arpl has two operands. The first operand is a 16-bit word register or
memory variable that contains the value of a selector. The second operand is
a word register. If the RPL field of the second operand is greater than the
RPL field of the first operand, ZF is set to 1 and the RPL field of the first
operand is increased to match the RPL field of the second operand.
Otherwise, no change is made to the first operand and the ZF is set to 0.
arpl is not used in application programs, it is used in operating systems.
arpl guarantees that a selector to a subroutine does not request a privilege
greater than allowed. Normally, the second operand of arpl is a register
that contains the CS selector value of the caller.
clts
arplr16, r/m16

100 x86 Assembly Language Reference Manual—November 1995
2
Example
Bit Instructions
Bit Scan Forward (bsf)
Operation
(r/m = 0) 0 → ZF
(r/m ≠0) 0 → ZF
Description
bsf scans the bits, starting at bit 0, in the doubleword operand or the second
word. If the bits are all zero, ZF is cleared. Otherwise, ZF is set and the bit
index of the first set bit, found while scanning in the forward direction, is
loaded into the destination register.
Example
Bit Scan Reverse (bsr)
Operation
(r/m = 0) 0 → ZF
(r/m ≠0) 0 → ZF
arpl %sp, 5(%ebx)
bsf{wl} r/m[16|32], reg[16|32]
bsf 4(%edi), %edx
bsr{wl} r/m[16|32], reg[16|32]

Instruction-Set Mapping 101
2
Description
bsr scans the bits, starting at the most significant bit, in the doubleword
operand or the second word. If the bits are all zero, ZF is cleared. Otherwise,
ZF is set and the bit index of the first set bit found, while scanning in the
reverse direction, is loaded into the destination register
Example
Bit Test (bt)
Operation
BIT [LeftSRC, RightSRC] →CF
Description
The bit indicated by the first operand (base) and the second operand (offset)
are saved by bt into CF (carry flag).
Example
bsr 4(%edi), %edx
bt{wl} imm8, r/m[16|32]
bt{wl} reg[16|32], r/m[16|32]
btl $253, 4(%edi)
btl %edx, 4(%edi)
102 x86 Assembly Language Reference Manual—November 1995
2
Bit Test And Complement (btc)
Operation
BIT [LeftSRC, RightSRC] →CF
NOT BIT [LeftSRC, RightSRC] → BIT[LeftSRC, RightSRC]
Description
The bit indicated by the first operand (base) and the second operand (offset)
are saved by btc into CF (carry flag) and complements the bit.
Example
Bit Test And Reset (btr)
Operation
BIT[LeftSRC, RightSRC] → CF
0→ BIT[LeftSRC, RightSRC]
Description
The value of the first operand (base) and the second operand (bit offset) are
saved by btr into the carry flag and then it stores 0 in the bit.
Example
btc{wl} imm8, r/m[16|32]
btc{wl} reg[16|32], r/m[16|32]
btl $253, 4(%edi)
btl %edx, 4(%edi)
btr{wl} imm8, r/m[16|32]
btr{wl} reg[16|32], r/m[16|32]
btrl $253, 4(%edi)
btrl $edx, 4(%edi)
Instruction-Set Mapping 103
2
Bit Test And Set (bts)
Operation
BIT[LeftSRC, RightSRC] → CF
0→ BIT[LeftSRC, RightSRC]
Description
The value of the first operand (base) and the second operand (bit offset) are
saved by bts into the carry flag and then it stores 1 in the bit.
Example
Exchange Instructions
Compare and Exchange (cmpxchg)[486]
Example
bts{wl} imm8, r/m[16|32]
bts{wl} reg[16|32], r/m[16|32]
btsl $253, 4(%edi)
btsl $edx, 4(%edi)
cmpxchg{bwl}reg[8|16|32], r/m[8|16|32]
cmpxchgb %cl, 1(%esi)
cmpxchgl %edx, 4(%edi)
104 x86 Assembly Language Reference Manual—November 1995
2
Floating-Point Transcendental Instructions
Floating-Point Sine (fsin)
Example
Replace the contents of the top of the stack with its sine.
Floating-Point Cosine (fcos)
Example
Replace the contents of the top of the stack with its cos.
Floating-Point Sine and Cosine (fsincos)
Example
Replace the contents of the top of the stack with its sine and then push the
cosine onto the FPU stack.
fsin
fsin
fcos
fcos
fsincos
fsincos
Instruction-Set Mapping 105
2
Floating-Point Constant Instructions
Floating-Point Load One (fld)
Example
Use these constant instructions to push often-used values onto the FPU
stack.
Processor Control Floating-Point Instructions
Floating-Point Load Control Word (fldcw)
Example
Load the FPU control word with the value in the specified memory address.
fld1
fld12+
fld12e
fldpi
fldlg2
fldln2
fldz
fldl 2(%ecx)
fldcwr/m16
fldcw 2(%ecx)
106 x86 Assembly Language Reference Manual—November 1995
2
Floating-Point Load Environment (fldenv)
Example
Reload the FPU environment from the source-operand specified memory
space.
Miscellaneous Floating-Point Instructions
Floating-Point Different Reminder (fprem)
Example
Divide stack element 0 by stack element 1 and leave the remainder in stack
element 0.
Floating-Point Comparison Instructions
Floating-Point Unsigned Compare (fucom)
Description:
Compare stack element 0 with stack element (i). Use condition codes:
fldenvmem
fldenv 2(%ecx)
fprem1
fprem
fucomfreg
Instruction-Set Mapping 107
2
No compare: 111
(i) < stack 0: 000
(i) > stack 0: 001
(i) = stack 0: 100
Example
Compare stack element 0 with stack element 7.
Floating-Point Unsigned Compare And Pop (fucomp)
Description
Compare stack element 0 with stack element (i). Use condition codes shown for
fucom. Then pop the stack.
Example
Floating-Point Unsigned Compare And Pop Two (fucompp)
Description
Compare stack element 0 with stack element (i). Use condition codes shown for
fucom. Then pop the stack twice.
fucom %st(7)
fucompfreg
fucomp %st(7)
fucompp

108 x86 Assembly Language Reference Manual—November 1995
2
Example
Load and Move Instructions
Load Effective Address (lea)
Operation
Addr(m) → r16
Addr(m) → r32
Truncate to 16 bits(Addr(m)) → r16
Truncate to 16 bits(Addr(m)) → r32
Description
The offset part of the effective address is calculated by lea and stored in the
specified register. The specified register determines the operand-size
attribute if the instruction. The USE attribute of the segment containing the
second operand determines the address-size attribute.
Example
fucompp %st(7)
lea{wl} r/m[16|32], reg[16|32]
leal 0x33333333, %edx
Instruction-Set Mapping 109
2
Move (mov)
Operation
SRC → DEST
Description
mov stores or loads the following special registers in or from a general
purpose register.
•Control registers CR0, CR2, and CR3
•Debug registers DR0, DR1, DR2, DR3, DR6, and DR7
•Test registers TR6 and TR7
These instructions always use 32-bit operands.
Example
Move Segment Registers (movw)
Operation
r/m16 → Sreg
Sreg → r/m16
mov{bwl}imm[8|16|32], r/m[8|16|32]
mov{bwl}reg[8|16|32], r/m[8|16|32]
mov{bwl}r/m[8|16|32], reg[8|16|32]
movl %cr3, %ebp
movl %db7, %ebp
movl %ebp, %cr3
movl %ebp, %db7
movl %tr7, %ebp
movl %ebp, %tr7
movwsreg,r/m16
movwr/m16, sreg
110 x86 Assembly Language Reference Manual—November 1995
2
Description
movw copies the first operand to the second operand, including data from a
descriptor. The descriptor table entry for the selector contains the data for
the register. The DS and ES registers can be loaded with a null selector
without causing an exception. Use of DS or ES however, causes a #GP(0),
and no memory reference occurs.
All interrupts are inhibited until after the execution of the next instruction,
after a movw into SS. Special actions and checks result from loading a
segment register under Protected Mode.
Example
Move Control Registers (mov)
Operation
SRC → DEST
Description
This form of mov stores or loads the Control Register CR0, CR2, or CR4 to
or from a general purpose register.
These instructions are always used with 32-bit operands.
Example
movw %CS, 5(%ebx)
movw %(%ebx), %CS
mov{l}creg, reg32
mov{l}reg32, creg
movl %cr3, %ebp
movl %ebp, %cr3

Instruction-Set Mapping 111
2
Move Debug Registers (mov)
Operation
SRC → DEST
Description
This form of mov stores or loads the Debug Register DR1, DR2, or DR3, DR6,
and DR7 to or from a general purpose register.
These instructions are always used with 32-bit operands.
Example
Move Test Registers (mov)
Operation
SRC → DEST
Description
This form of mov stores or loads the Test Register TR6 or TR7 to or from a
general purpose register.
These instructions are always used with 32-bit operands.
mov{l}dreg, reg32
mov{l}reg32, dreg
movl %db7, %ebp
movl %ebp, %db7
mov{l}treg, reg32
mov{l}reg32, treg
112 x86 Assembly Language Reference Manual—November 1995
2
Example
Move With Sign Extend (movsx)
Operation
SignExtend(SRC) → DEST
Description
movsx reads the contents of the register or effective address as a word or
byte. movsx then sign-extends the 16- or 32-bit value to the operand-size
attribute of the instruction. The result is stored in the destination register by
movsx.
Example
Move With Zero Extend (movzb)
Operation
SignExtend(SRC) → DEST
movl %tr7, %ebp
movl %ebp, %tr7
movsx{wl}r/m8, reg[16|32]
movsxwl r/m16, reg32
movsxbl 1(%esi), %edx
movsxwl 5(%ebx), %edx
movzb[wl]r/m8, reg[16|32]
movzwl r/m16, reg32

Instruction-Set Mapping 113
2
Description
movzx reads the contents of the register or effective address as a word or
byte. movzx then sign-extends the 16- or 32-bit value to the operand-size
attribute of the instruction. The result is stored in the destination register by
movzx.
Example
Pop Instructions
Pop All General Registers (popa)
Operation
POP → r16
POP → r32
Description
The eight 16-bit general registers are popped by popa. However, the SP
value is not loaded into SP, It is discarded. popa restores the general
registers to their values before a previous pusha was executed. DI is the
first register popped.
The eight 32-bit registers are popped by popad. However, the ESP value is
not loaded into ESP, it is discarded. popad restores the general registers to
their values before a previous pushad was executed. EDI is the first register
popped.
Example
popa{wl}
popal

114 x86 Assembly Language Reference Manual—November 1995
2
Push Instructions
Push All General Registers (pusha)
Operation
SP → r16
SP → r32
Description
The 16-bit or 32-bit general registers are saved by pusha and pushad,
respectively. The stack pointer is decremented by 16 by pusha to hold the
eight word values. The stack pointer is decremented by 32 by pushad to
hold the eight doubleword values. The registers are pushed onto the stack in
the order received; the stack bytes appear in reverse order. DI or EDI is the
last stack pushed.
Example
Rotate Instructions
Rotate With Carry Left (rcl)
Operation
r/m high-order bit → CF
CF → r/m low-order bit
r/m → ShiftLeft
pusha{wl}
pushal
rcl{bwl}imm8, r/m[8|16|32]
rcl{bwl}%cl, r/m[8|16|32]

Instruction-Set Mapping 115
2
Description
The left rotate instruction shifts all bits in the register or memory operand
specified. The carry flag (CF) is included in the rotation. The most
significant bit is rotated to the carry flag, the carry flag is rotated to the least
significant bit position, all other bits are shifted to the left. The result
includes the original value of the carry flag.
The first operand value indicates how many times the rotate takes place.
The value is either the contents of the CL register or an immediate number.
For a single rotate, where the first operand is one, the overflow flag (OF) is
defined. For all other cases, OF is undefined. After the shift, the carry flag
bit is XORed with the most significant result bit.
Example
Rotate With Carry Right (rcr)
Operation
r/m high-order bit → CF
CF → r/m low-order bit
r/m → ShiftRight
Description
The right rotate instruction shifts all bits in the register or memory operand
specified. The carry flag (CF) is included in the rotation. The least significant
bit is rotated to the carry flag, the carry flag is rotated to the most significant
bit position, all other bits are shifted to the right. The result includes the
rclb $1, 1(%esi)
rclb $253, 1(%esi)
rclb %cl, 1(%esi)
rcll $1, 4(%edi)
rcll $253, 4(%edi)
rcll %cl, 4(%edi)
rcr{bwl}imm8, r/m[8|16|32]
rcr{bwl}%cl, r/m[8|16|32]

116 x86 Assembly Language Reference Manual—November 1995
2
original value of the carry flag.
The first operand value indicates how many times the rotate takes place.
The value is either the contents of the CL register or an immediate number.
For a single rotate, where the first operand is one, the overflow flag (OF) is
defined. For all other cases, OF is undefined. After the shift, the carry flag
bit is XORed with the two most significant result bits.
Example
Rotate Left (rol)
Operation
r/m high-order bit → CF
CF → r/m low-order bit
r/m → ShiftLeft
Description
The left rotate instruction shifts all bits in the register or memory operand
specified. The most significant bit is rotated to the carry flag, the carry flag is
rotated to the least significant bit position, all other bits are shifted to the
left. The result does not include the original value of the carry flag.
The first operand value indicates how many times the rotate takes place.
The value is either the contents of the CL register or an immediate number.
For a single rotate, where the first operand is one, the overflow flag (OF) is
defined. For all other cases, OF is undefined. After the shift, the carry flag
bit is XORed with the most significant result bit.
rcrb $1, 1(%esi)
rcrb $253, 1(%esi)
rcrb %cl, 1(%esi)
rcrl $1, 4(%edi)
rcrl $253, 4(%edi)
rcrl %cl, 4(%edi)
rol{bwl}imm8, r/m[8|16|32]
rol{bwl}%cl, r/m[8|16|32]

Instruction-Set Mapping 117
2
Example
Rotate Right (ror)
Operation
r/m high-order bit → CF
CF → r/m low-order bit
r/m → ShiftRight
Description
The right rotate instruction shifts all bits in the register or memory operand
specified. The least significant bit is rotated to the carry flag, the carry flag is
rotated to the most significant bit position, all other bits are shifted to the
right. The result does not include the original value of the carry flag.
The first operand value indicates how many times the rotate takes place.
The value is either the contents of the CL register or an immediate number.
For a single rotate, where the first operand is one, the overflow flag (OF) is
defined. For all other cases, OF is undefined. After the shift, the carry flag
bit is XORed with the two most significant result bits.
rclb $1, 1(%esi)
rclb $253, 1(%esi)
rclb %cl, 1(%esi)
rcll $1, 4(%edi)
rcll $253, 4(%edi)
rcll %cl, 4(%edi)
ror{bwl}imm8, r/m[8|16|32]
ror{bwl}%cl, r/m[8|16|32]

118 x86 Assembly Language Reference Manual—November 1995
2
Example
Byte Instructions
Byte Set On Condition (setcc)
Operation
ConditionTrue: 1 → r/m8
ConditionFalse: 0 → rm/8
Description
If the condition is met, set
cc
stores a one byte at the destination specified
by the effective address. If the condition is not met, set
cc
stores a zero
byte. Table 2-10 on page 119 lists the set
cc
condition options. Similar
condition options are separated by commas, followed by the flag condition.
rcrb $1, 1(%esi)
rcrb $253, 1(%esi)
rcrb %cl, 1(%esi)
rcrl $1, 4(%edi)
rcrl $253, 4(%edi)
rcrl %cl, 4(%edi)
set
cc
r/m8
Instruction-Set Mapping 119
2
Example
Table 2-10 set
cc
Condition List
Instruction (set+cc) Set Byte If:
seta, setnbe greater, not equal or less than, CF=0 & ZF=0
setae, setnc, setnb equal or greater, not carry, not less than, CF=0
setb, setc, setnae less than carry, carry = 1, not equal or greater than, CF=1
setbe, setna equal or less than, not greater than carry, CF=1 or ZF=1
sete, setz equal, zero, ZF=1
setg, setnle greater, ZF=0 or SF=OF. not equal or less, ZF=1 or SF ≠ OF
setge, setnl equal or greater, not less, SF = OF
setl, setnge less, not equal or greater, SF ≠OF
setle, setng equal or less, not greater, ZF = 1 and SF ≠OF
setne, setnz not equal, not zero, ZF = 0
setno not overflow, OF = 0
setns not sign, SF=0
seto overflow, OF = 1
setpe, setp parity even, parity, PF = 1
setpo, setnp parity odd, not parity, PF = 0
sets sign, SF = 1
set(cc) 1(%esi)
120 x86 Assembly Language Reference Manual—November 1995
2
Byte Swap (bswap) [486]
Example
Convert little/big endian to big/little endian by swapping bytes.
Exchange Instructions
Exchange And Add (xadd) [486]
Example
Exchange the byte contents of the ESI register with the byte register and
load the sum into the ESI register.
Exchange Register / Memory With Register (xchg)
Operation
DEST → temp
SRC → DEST
temp → SRC
bswapreg[16|32]
bswap %ebx
xadd{bwl}reg[8|16|32], r/m[8|16|32]
xaddb %cl, 1(%esi)
xchg{bwl}reg[8|16|32], r/m[8|16|32]
Instruction-Set Mapping 121
2
Description
Two operands, in either order, are exchanged by xchg. During the exchange,
BUS LOCK is asserted (regardless of the value of IOPL or the LOCK prefix)
if a memory operand is part of the exchange.
Example
Miscellaneous Instructions
Write Back and Invalidate Cache (wbinvd) [486 only]
Example
Write back and invalidate the cache.
xchgb %cl, 1(%esi) /*exchange byte register with EA byte */
xchgl %ebp, %eax
xchgl %ebx, %eax
xchgl %ecx, %eax
xchgl %edi, %eax
xchgl %edx, %eax
xchgl %edx, 4(%edi) /*exchange word register with EA word */
xchgl %esi, %eax
xchgl %esp, %eax
wbinvd
wbinvd
122 x86 Assembly Language Reference Manual—November 1995
2
Invalidate (invd) [486 only]
Example
Invalidate the entire cache.
Invalidate Page (invlpg) [486 only]
Example
Invalidate a single entry in the translation lookaside buffer.
LOCK Prefix (lock)
Operation
LOCK# → NEXT Instruction
Description
The LOCK # signal is asserted during execution of the instruction following
the lock prefix. This signal can be used in a multiprocessor system to
ensure exclusive use of shared memory while LOCK # is asserted. The bts
instruction is the read-modify-write sequence used to implement test-and-
run.
invd
invd
invlpgmem32
invlpg 5(%ebx)
lock
Instruction-Set Mapping 123
2
The lock prefix works only with the instructions listed here. If a lock
prefix is used with any other instructions, an undefined opcode trap is
generated.
Memory field alignment does not affect the integrity of lock.
If a different 80386 processor is concurrently executing an instruction that
has a characteristic listed here, locked access is not guaranteed. The
previous instruction:
•Does not follow a lock prefix
•Is not on the previous list of acceptable instructions
•A memory operand specified has a partial overlap with the destination
operand.
Example
No Operation (nop)
Operation
NO OPERATION
Description
No operations are performed by nop. The xchgl %eax, %eax instruction is
an alias for the nop instruction.
bt, bts, btr, btc m, r/imm
xchg r, m
xchg m, r
add, or, adc, sbb, and, sub, xor m, r/imm
not, neg, inc, dec m
lock
nop

124 x86 Assembly Language Reference Manual—November 1995
2
Example
Halt (hlt)
Operation
HLT →ENTER HALT STATE
Description
halt puts the 80386 in a HALT state by stopping instruction execution.
Execution is resumed by an nmi or an enabled interrupt. After a halt, if an
interrupt is used to continue execution, the saved CS:EIP or CS:IP value
points to the next instruction (after the halt).
The halt instruction is privileged.
Example
nop
hlt
Address Prefix
addr16
Data Prefix
data16
hlt

Instruction-Set Mapping 125
2
Real Transfer Instructions
Load Real (fld)
Operation
SRC → STACK ELEMENT 0
Description
The source operand is pushed onto the stack by fld. The register used
before the stack top-pointer is decremented, is the register number used if
the source is a register.
Example
Load stack element 7 onto stack element 0.
Store Real (fst)
Operation
STACK ELEMENT 0 → DESTINATION
Description
The current value of stack element 0 is copied to the destination. The
destination can be a single- or double-real memory operand or another
register.
fld{lst}
fld %st (7)
fst{ls}
126 x86 Assembly Language Reference Manual—November 1995
2
Example
Store the contents of stack element 7 onto stack element 0.
Store Real and Pop (fstp)
Operation
STACK ELEMENT 0 → DESTINATION THEN POP
Description
The current value of stack element 0 is copied to the destination. The
destination can be a single-, double-, or extended-real memory operand, or
another register. Then pop the stack register.
Example
Copy the contents of stack element 0 onto stack element 7 and pop stack
element 0.
Exchange Registers (fxch)
Example
Exchange the contents of stack element 0 and stack element 7.
%fst (7)
fstp{lst}
%fstp (7)
fxch
fxch %st(7)
Instruction-Set Mapping 127
2
Integer Transfer Instructions
Integer Load (fild)
Example
Convert the integer operand (signed) into extended-real and load it onto the
floating-point stack.
Integer Store (fist)
Example
Convert the value in stack element 0 into a signed integer and transfer the
result to register ECX with an offset of 2.
Integer Store and Pop (fistp)
Example
Convert the value in stack element 0 into a signed integer and transfer the
result to register ECX with an offset of 2, then pop the stack.
fild{l|ll}
fild 2(%eax)
fist{l}
fist 2(%ecx)
fistp{l|ll}
fistp 2(%ecx)
128 x86 Assembly Language Reference Manual—November 1995
2
Packed Decimal Transfer Instructions
Packed Decimal (BCD) Load (fbld)
Example
Convert the source operand (BCD) into extended-real and push it onto the
floating-point stack.
Packed Decimal (BCD) Store and Pop (fbstp)
Example
Convert the value in stack element 0 to a packed decimal integer and store
the result in register ECX with an offset of 2, and pop the stack.
fbld
fbld 2(%ecx)
fbstp
fbstp 2(%ecx)
Instruction-Set Mapping 129
2
Addition Instructions
Real Add (fadd)
Example
Add stack element 7 to stack element 0 and return the sum to stack element
0.
Real Add and Pop (faddp)
Example
Add stack element 0 to stack element 7 and return the sum to stack element
7, then pop the stack.
Integer Add (fiadd)
Example
Add the integer contents of register ECX to stack element 0.
fadd{ls}
fadd %st(7), %st
faddp
faddp %st, %st(7)
fiadd{l}
fiadd 2(%ecx)
130 x86 Assembly Language Reference Manual—November 1995
2
Subtraction Instructions
Subtract Real and Pop (fsub)
Example
Subtract stack element 7 from stack element 0 and return the difference to
stack element 0.
Subtract Real (fsubp)
Example
Subtract stack element 7 from stack element 0 and return the difference to
stack element 7, then pop the stack.
Subtract Real Reversed (fsubr)
Example
Subtract stack element 0 from stack element 7 and return the difference to
stack element 0.
fsub{ls}
fsub %st(7), %st
fsubp
fsubp %st, %st(7)
fsubr{ls}
fsubr %st(7), %st

Instruction-Set Mapping 131
2
Subtract Real Reversed and Pop (fsubrp)
Example
Subtract stack element 0 from stack element 7 and return the difference to
stack element 7, then pop the stack.
Integer Subtract (fisubrp)
Example
Subtract stack element 0 from the integer contents of register ECX (with an
offset of 2) and return the difference to register ECX, then pop the stack.
Integer Subtract Reverse (fisubr)
Example
Subtract stack element 0 from the integer contents of register ECX (with an
offset of 2) and return the difference to stack element 0.
fsubrp
fsubrp %st, %st(7)
fisubrp
fisubrp 2(%ecx)
fisubr{l}
fisubr 2(%ecx)
132 x86 Assembly Language Reference Manual—November 1995
2
Multiplication Instructions
Multiply Real (fmul)
Example
Multiply stack element 7 by stack element 0 and return the product to stack
element 0.
Multiply Real and Pop (fmulp)
Example
Multiply stack element 0 by stack element 7 and return the product to stack
element 7, then pop the stack.
Integer Multiply (fimul)
Example
Multiply the integer contents of register ECX by stack element 0, return the
product to register ECX.
fmul{ls}
fmul %st(7), %st
fmulp
fmulp %st, %st(7)
fimul{l}
fimul 2(%ecx)
Instruction-Set Mapping 133
2
Division Instructions
Divide Real (fdiv)
Example
Divide stack element 0 by stack element 7 and return the result to stack
element 0.
Divide Real and Pop (fdivp)
Example
Divide stack element 7 by stack element 0 and return the result to stack
element 7, then pop the stack.
Divide Real Reversed (fdivr)
Example
Divide stack element 0 by stack element 7 and return the result to stack
element 7.
fdiv{ls}
fdiv %st(7), %st
fdivp
fdivp %st, %st(7)
fdivr{ls}
fdivr %st, %st(7)

134 x86 Assembly Language Reference Manual—November 1995
2
Divide Real Reversed and Pop (fdivrp)
Example
Divide stack element 0 by stack element 7 and return the result to stack
element 7, then pop the stack.
Integer Divide (fidiv)
Example
Divide stack element 0 by the integer contents of register ECX, with an
offset of 2, and return the result to register ECX.
Integer Divide Reversed (fidivr)
Example
Divide the integer contents of register ECX, with an offset of 2, by stack
element 0 and return the result to stack element 0.
fdivrp
fdivrp %st, %st(7)
fidiv{l}
fidiv 2(%ecx)
fidivr{l}
fidivr 2(%ecx)
Instruction-Set Mapping 135
2
Floating-Point Opcode Errors
Warning – The SunOS x86 assembler generates the wrong object code for some
of the floating-point opcodes fsub,fsubr,fdiv, and fdivr when there are
two floating register operands, and the second op destination is not the zeroth
floating-point register. This error has been made to many versions of the USL
UNIX® system and would probably cause problems if it were fixed.
Replace the following instructions, in column 1, with their substitutions, in
column 2, for x86 platforms:
Table 2-11 Floating-point Opcodes
fsub %st,%st(n) fsubr %st, %st(n)
fsubp %st,%st(n) fsubrp %st, %st(n)
fsub fsubr
fsubr %st,%st(n) fsub %st, %st(n)
fsubrp %st,%st(n) fsubp %st, %st(n)
fsubr fsub
fdiv %st,%st(n) fdivr %st,%st(n)
fdivp %st,%st(n) fdivrp %st,%st(n)
fdiv fdivr
fdivr %st, %st(n) fdvir %st, %st(n)
fdivrp %st, %st(n) fdivp %st, %st(n)
fdivr fdiv

136 x86 Assembly Language Reference Manual—November 1995
2
Miscellaneous Arithmetic Operations
Square Root (fsqrt)
Example
Replace stack element 0 with the square root of its value.
Scale (fscale)
Example
Add the integer value in stack element 1 to the exponent of stack element 0
(multiplication and division by powers of 2).
Partial Remainder (fprem)
Example
Divide stack element 0 by stack element 1 and return the (partial) remainder
to stack element 0.
fsqrt
fsqrt
fscale
fscale
fprem
fprem

Instruction-Set Mapping 137
2
Round to Integer (frndint)
Example
Round the value in stack element 0 to an integer according to the FPU
control word RC field.
Extract Exponent and Significand (fxtract)
Example
Separate stack element 0 into its exponent and significand and return the
exponent to stack element 0, then push the significand onto the FPU stack.
Absolute Value (fabs)
Example
Replace stack element 0 with its absolute value.
frndint
frndint
fxtract
fxtract
fabs
fabs
138 x86 Assembly Language Reference Manual—November 1995
2
Change Sign (fchs)
Example
Replace the sign of stack element 0 with the opposite sign.
Comparison Instructions
Compare Real (fcom)
Example
Compare stack element 0 with stack element 7. Condition codes contain the
result: No compare=111, st 0 greater than st 7=000, st 0 less than st 7=001,
equal compare=100.
fchs
fchs
fcom{ls}
fcom %st(7)
Instruction-Set Mapping 139
2
Compare Real and Pop (fcomp)
Example
Compare stack element 0 with stack element 7. Condition codes contain the
result: No compare=111, st 0 greater than st 7=000, st 0 less than st 7=001,
equal compare=100, then pop the stack.
Compare Real and Pop Twice (fcompp)
Example
Compare stack element 0 with stack element 1. Condition codes contain the
result: No compare=111, st 0 greater than st 7=000, st 0 less than st 7=001,
equal compare=100, then pop the stack twice.
Integer Compare (ficom)
Example
Integer compare stack element 0 with the contents of register ECX (with an
offset of 2). Condition codes contain the result: No compare=111, st 0 greater
than st 7=000, st 0 less than st 7=001, equal compare=100,
fcomp{ls}
fcomp %st(7)
fcompp
fcompp
ficom{l}
ficom 2(%ecx)
140 x86 Assembly Language Reference Manual—November 1995
2
Integer Compare and Pop (ficomp)
Example
Integer compare stack element 0 with the contents of register ECX (with an
offset of 2). Condition codes contain the result: No compare=111, st 0 greater
than st 7=000, st 0 less than st 7=001, equal compare=100, then pop the
stack.
Test (ftst)
Example
Compare stack element 0 with the value 0.0. Condition codes contain the
result: No compare=111, st 0 greater than st 7=000, st 0 less than st 7=001,
equal compare=100,
Examine (fxam)
Example
Report the type of object in stack element 0. FPU flags C3, C2, and C0 return
the type:
ficomp{l}
ficomp 2(%ecx)
ftst
ftst
fxam
Instruction-Set Mapping 141
2
Transcendental Instructions
Partial Tangent (fptan)
Example
Replace stack element 0 with its tangent and push a value of 1 onto the FPU
stack.
Unsupported 000
NaN 001
Normal 010
Infinity 011
Zero 100
Empty 101
Denormal 110
fxam
fptan
fptan
142 x86 Assembly Language Reference Manual—November 1995
2
Partial Arctangent (fpatan)
Example
Divide stack element 1 by stack element 0, compute the arctangent and
return the result in radians to stack element 1, then pop the stack.
2x - 1 (f2xm1)
Example
Replace the contents of stack element 0 (st) with the value of (2st-1).
Y * log2 X (fyl2x)
Example
Compute the logarithm (base-2) of stack element 0 and multiply the result
by stack element 1 and return the result to stack element 1, then pop the
stack.
fpatan
fpatan
f2xm1
f2xm1
fyl2x
fy12x
Instruction-Set Mapping 143
2
Y * log2 (X+1) (fyl2xp1)
Example
Compute the logarithm (base-2) of stack element 0 plus 1.0 and multiply the
result by stack element 1 and return the result to stack element 1, then pop
the stack.
Constant Instructions
Load log2E (fldl2e)
Example
Push log2e onto the FPU stack
Load log210 (fldl2t)
Example
Push log210 onto the FPU stack.
fyl2xp1
fy12xpl
fldl2e
fldl2e
fldl2t
fldl2t
144 x86 Assembly Language Reference Manual—November 1995
2
Load log102 (fldlg2)
Example
Push log102 onto the FPU stack.
Load loge 2 (fldln2)
Example
Push log2e onto the FPU stack.
Load pi (fldpi)
Example
Push πonto the FPU stack.
fldlg2
fldlg2
fldln2
fldln2
fldpi
fldpi
Instruction-Set Mapping 145
2
Load + 0 (fldz)
Example
Push +0.0 onto the FPU stack.
Processor Control Instructions
Initialize Processor (finit,fnint)
Example
No Operation (fnop)
Example
fldz
fldz
finit
fninit
finit
fnop
fnop
146 x86 Assembly Language Reference Manual—November 1995
2
Save State (fsave,fnsave)
Example
Store Control Word (fstcw,fnstcw)
Example
Store Environment (fstenv,fnstenv)
Example
fsave
fnsave
fsave 2(%ecx)
fstcw
fnstcw
fstcw 2(%ecx)
fstenv
fnstenv
fstenv 2(%ecx)
Instruction-Set Mapping 147
2
Store Status Word (fstsw,fnstsw)
Example
Restore State (frstor)
Example
CPU Wait (fwait,wait)
Example
fstsw
fnstsw
fstsw %ax
frstor
frstor 2(%ecx)
fwait
wait
fwait
148 x86 Assembly Language Reference Manual—November 1995
2
Clear Exceptions (fclex,fnclex)
Example
Decrement Stack Pointer (fdecstp)
Example
Free Registers (ffree)
Example
fclex
fnclex
fclex
fdecstp
fdecstp
ffree
ffree %st(7)
Instruction-Set Mapping 149
2
Increment Stack Pointer (fincstp)
Example
Example:
fincstp
fincstp

150 x86 Assembly Language Reference Manual—November 1995
2

151
Assembler Output 3
This chapter is an overview of ELF (Executable and Linking Format) for the
relocatable object files produced by the assembler. The fully detailed definition
of ELF appears in the System V Application Binary Interface and the Intel 386
Processor Supplement.
This chapter is organized as follows:
Introduction
The main output produced by assembling an input assembly language source
file is the translation of that file into an object file in (ELF). ELF files produced
by the assembler are relocatable files that hold code and/or data. They are
input files for the linker. The linker combines these relocatable files with other
ELF object files to create an executable file or a shared object file in the next
stage of program building, after translation from source files into object files.
The three main kinds of ELF files are relocatable, executable and shared object
files.
The assembler can also produce ancillary output incidental to the translation
process. For example, if the assembler is invoked with the -V option, it can
write information to standard output and to standard error.
Introduction page 151
Object Files in Executable and Linking Format (ELF) page 152

152 x86 Assembly Language Reference Manual—November 1995
3
The assembler also creates a default output file when standard input or
multiple input files are used. Ancillary output has little direct connection to the
translation process, so it is not properly a subject for this manual. Information
about such output appears in as(1) manual page.
Certain assembly language statements are directives to the assembler
regarding the organization or content of the object file to be generated.
Therefore, they have a direct effect on the translation performed by the
assembler. To understand these directives, described in Chapter 2, “Instruction-
Set Mapping“, it is helpful to have some working knowledge of ELF, at least
for relocatable files.
Object Files in Executable and Linking Format (ELF)
Relocatable ELF files produced by the assembler consist of:
•An ELF header
•A section header table
•Sections
The ELF header is always the first part of an ELF file. It is a structure of fixed
size and format. The fields, or members, of the structure describe the nature,
organization and contents of the rest of the file. The ELF header has a field that
specifies the location within the file where the section header table begins.
The section header table is an array of section headers that are structures of
fixed size and format. The section headers are the elements of the array, or the
entries in the table. The section header table has one entry for each section in
the ELF file. However, the table can also have entries (section headers) that do
not correspond to any section in the file. Such entries and their array indices
are reserved. The members of each section header constitute information useful
to the linker about the contents of the corresponding section, if any.
All of a relocatable file’s information that does not lie within its ELF header or
its section header table lies within its sections. Sections contain most of the
information needed to combine relocatable files with other ELF files to produce
shared object files or executable files. Sections also contain the material to be
combined. For example, sections can hold:
•Relocation tables
•Symbol tables
•String tables

Assembler Output 153
3
Each section in an ELF file fills a contiguous (possibly empty) sequence of that
file’s bytes. Sections never overlap. However, the (set theoretic) union of a
relocatable ELF header, the section header table, and all the sections can omit
some of the bytes. Bytes of a relocatable file that are not in the ELF header, or
in the section header table, or in any of the sections constitute the inactive
space. The contents of a file’s inactive space, if any, are unspecified.
ELF Header
The ELF header is always located at the beginning of the ELF file. It describes
the ELF file organization and contains the actual sizes of the object file control
structures.
The ELF header consists of the following fields, or members, some have the
value 0 for relocatable files:
e_ident
This is a byte array consisting of the EI_NIDENT initial bytes of the ELF
header, where EI_NIDENT is a name for 16. The elements of this array mark
the file as an ELF object file and provide machine-independent data that can
be used to decode and interpret the file’s contents.
e_type
Identifies the object file type. A value of 1, that has the name ET_REL,
specifies a relocatable file. Table 3-1 describes all the object file types.
e_machine
Specifies the required architecture for an individual file. A value of 3, that
has the name EM_386, specifies Intel 80386. EM_486, specifies Intel 80486.
e_version
Identifies the version of this object file’s format. This field should have the
current version number, named EV_CURRENT.
e_entry
Virtual address where the process is to start. A value of 0 indicates no
associated entry point.

154 x86 Assembly Language Reference Manual—November 1995
3
e_phoff
Program header table’s file offset, in bytes. The value of 0 indicates no
program header. (Relocatable files do not need a program header table.)
e_shoff
Section header table’s file offset, in bytes. The value of 0 indicates no section
header table. (Relocatable files must have a section header table.)
e_flag
Processor-specific flags associated with the file. For the Intel 80386, this field
has value 0.
e_ehsize
ELF header’s size, in bytes.
e_phentsize
Size, in bytes, of entries in the program header table. All entries are the
same size. (Relocatable files do not need a program header table.)
e_phnum
Number of entries in program header table. A value of 0 indicates the file
has no program header table. (Relocatable files do not need a program
header table.)
e_shentsize
Size, in bytes, of the section header structure. A section header is one entry
in the section header table; all entries are the same size.
e_shnum
Number of entries in section header table. A value of 0 indicates the file has
no section header table. (Relocatable files must have a section header table.)
Assembler Output 155
3
e_shstrndx
Section header table index of the entry associated with the section name
string table. A value of SHN_UNDEF indicates the file does not have a section
name string table.
Section Header
The section header table has all of the information necessary to locate and
isolate each of the file’s sections. A section header entry in a section header
table contains information characterizing the contents of the corresponding
section, if the file has such a section.
Each entry in the section header table is a section header. A section header is a
structure of fixed size and format, consisting of the following fields, or
members:
sh_name
Specifies the section name. The value of this field is an index into the section
header string table section, wherein it indicates the beginning of a null-
terminated string that names the section.
sh_type
Categorizes the section’s contents and semantics. Table 3-3 describes the
section types.
Table 3-1 Object File Types
Type Value Description
none 0 No file type
rel 1 Relocatable file
exec 2 Executable file
dyn 3 Shared object file
core 4 Core file
loproc 0xff00 Processor-specific
hiproc 0xffff Processor-specific
156 x86 Assembly Language Reference Manual—November 1995
3
sh_flags
One-bit descriptions of section attributes. Table 3-2 describes the section
attribute flags.
sh_addr
Address where the first byte resides if the section appears in the memory
image of a process; a value of 0 indicates the section does not appear in the
memory image of a process.
sh_offset
Specifies the byte offset from the beginning of the file to the first byte in the
section.
Note – If the section type is SHT_NOBITS, the corresponding section occupies
no space in the file. In this case, sh_offset specifies the location at which the
section would have begun if it did occupy space within the file.
sh_size
Specifies the size, in byte units, of the section.
Note – Even if the section type is SHT_NOBITS,sh_size can be nonzero;
however, the corresponding section still occupies no space in the file.
sh_link
Section header table index link. The interpretation of this information
depends on the section type, as described in Table 3-3.
sh_info
Extra information. The interpretation of this information depends on the
section type, as described in Table 3-3.
sh_addralign
If a section has an address alignment constraint, the value in this field is the
modulus, in byte units, by which the value of sh_addr must be congruent
to 0; i.e., sh_addr = 0 (mod sh_addralign).
Assembler Output 157
3
For example, if a section contains a long (32 bits), the entire section must be
ensured long alignment, so sh_addralign has the value 4. Only 0 and
positive integral powers of 2 are currently allowed as values for this field. A
value of 0 or 1 indicates no address alignment constraints.
sh_entsize
Size, in byte units, for entries in a section that is a table of fixed-size entries,
such as a symbol table. Has the value 0 if the section is not a table of fixed-
size entries
Table 3-2 Section Attribute Flags
Flag Default Value Description
SHF_WRITE 0x1 Contains data that is writable during process execution.
SHF_ALLOC 0x2 Occupies memory during process execution. This attribute is off if a control
section does not reside in the memory image of the object file.
SHF_EXECINSTR 0x4 Contains executable machine instructions.
SHF_MASKPROC 0xf0000000 Reserved for processor-specific semantics.
Table 3-3 Section Types
Name Value Description
Interpretation by
sh_info sh_link
SHT_NULL 0 Marks section header as inactive; file has no
corresponding section. 0SHN_UNDEF
SHT_PROGBITS 1 Contains information defined by the
program, and in a format and with a
meaning determined solely by the program.
0SHN_UNDEF
SHT_SYMTAB 2 Is a complete symbol table, usually for link
editing. This table can also be used for
dynamic linking; however, it can contain
many unnecessary symbols.
Note: Only one section of this type is allowed
in a file
One greater than the
symbol table index of
the last local symbol.
The section
header index of
the associated
string table.

158 x86 Assembly Language Reference Manual—November 1995
3
SHT_STRTAB 3 Is a string table. A file can have multiple
string table sections. 0SHN_UNDEF
SHT_RELA 4 Contains relocation entries with explicit
addends. A file can have multiple relocation
sections.
The section header
index of the section to
where the relocation
applies.
The section
header index of
the associated
symbol table.
SHT_HASH 5 Is a symbol rehash table.
Note: Only one section of this type is allowed
in a file
0 The section
header index of
the symbol
table to which
the hash table
applies.
SHT_DYNAMIC 6 Contains dynamic linking information.
Note: Only one section of this type is allowed
in a file
0 The section
header index of
the string table
used by entries
in the section.
SHT_NOTE 7 Contains information that marks the file. 0 SHN_UNDEF
SHT_NOBITS 8 Contains information defined by the
program, and in a format and with a
meaning determined by the program.
However, a section of this type occupies no
space in the file, but the section header’s
offset field specifies the location at which the
section would have begun if it did occupy
space within the file.
0SHN_UNDEF
SHT_REL 9 Contains relocation entries without explicit
addends. A file can have multiple relocation
sections.
The section header
index of the section to
where the relocation
applies.
The section
header index of
the associated
symbol table.
SHT_SHLIB 10 Reserved. 0 SHN_UNDEF
Table 3-3 Section Types (Continued)
Name Value Description
Interpretation by
sh_info sh_link
Assembler Output 159
3
Note – Some section header table indices are reserved, and the object file does
not contain sections for these special indices.
Sections
A section is the smallest unit of an object file that can be relocated. Sections
containing the following material usually appear in relocatable ELF files:
•Executable text
•Read-only data
•Read-write data
•Read-write uninitialized data (only section header appears)
Sections do not need to occur in any particular order within the object file. The
sections of a relocatable ELF file contain all of the file information that is not
contained in the ELF header or in the section header table. The sections in any
ELF file must satisfy several conditions:
SHT_DYNSYM 11 Is a symbol table with a minimal set of
symbols for dynamic linking.
Note: Only one section of this type is allowed
in a file
One greater than the
symbol table index of
the last local symbol.
The section
header index of
the associated
string table.
SHT_LOPROC
SHT_HIPROC 0x700
00000
0x7ffff
fff
Lower and upper bounds of range of section
types reserved for processor-specific
semantics.
0 SHN_UNDEF
SHT_LOUSER
SHT_HIUSER 0x800
00000
0xfffff
fff
Lower and upper bounds of range of section
types reserved for application programs.
Note: Section types in this range can be used
by an application without conflicting with
system-defined section types.
0SHN_UNDEF
Table 3-3 Section Types (Continued)
Name Value Description
Interpretation by
sh_info sh_link

160 x86 Assembly Language Reference Manual—November 1995
3
1. Every section in the file must have one section header entry in the section
header table to describe the section. However, the section header table can
have section header entries that correspond to no section in the file.
2. Each section occupies one contiguous sequence of bytes within a file. The
section can be empty (even so, its section header entry in the section header
table can have a nonzero value for the field sh_size).
3. A byte in a file can reside in at most one section. Sections in a file cannot
overlap.
4. An object file can have inactive space. Inactive space is the set of all bytes in
the file that are not part of the ELF header, the section header table, the
program header table (for executable files), or of any section in the file. The
contents of the inactive space are unspecified.
Sections can be added for multiple text or data segments, shared data, user-
defined sections, or information in the object file for debugging.
Note – Not all of the sections where there are entries in the file section header
table need to be present.
Predefined Sections
Sections having certain names beginning with "." (dot) are predefined, with
their types and attributes already assigned. These special sections are of two
kinds: predefined user sections and predefined nonuser sections.
Predefined User Sections
Sections that an assembly language programmer can manipulate by issuing
section control directives in the source file are user sections. The predefined user
sections are those predefined sections that are also user sections.
Assembler Output 161
3
Table 3-4 lists the names of the predefined user sections and briefly describes
each.
Predefined Non-User Sections
Table 3-5 shows the predefined sections that are not user sections, because
assembly language programmers cannot manipulate them by issuing section
control directives in the source file.
Table 3-4 Predefined User Sections
Section Name Description
".bss" Uninitialized read-write data.
".comment" Version control information.
".data" & ".data1" Initialized read-write data.
".debug" Debugging information.
".fini" Runtime finalization instructions.
".init" Runtime initialization instructions.
".rodata" &
".rodata1"Read-only data.
".text" Executable instructions.
".line" Line # info for symbolic debugging.
".note" Special information from vendors or system builders.
Table 3-5 Predefined Non-User Sections
Section Name Description
".dynamic" Dynamic linking information.
".dynstr" Strings needed for dynamic linking.
".dynsym" Dynamic linking symbol table.
".got" Global offset table.
162 x86 Assembly Language Reference Manual—November 1995
3
Relocation Tables
Locations represent addresses in memory if a section is allocatable; that is, its
contents are to be placed in memory at program runtime. Symbolic references
to these locations must be changed to addresses by the link editor.
The assembler produces a companion relocation table for each relocatable
section. The table contains a list of relocations (that is, adjustments to locations
in the section) to be performed by the link editor.
Symbol Tables
The symbol table contains information to locate and relocate symbolic
definitions and references. The assembler creates the symbol table section for
the object file. It makes an entry in the symbol table for each symbol that is
defined or referenced in the input file and is needed during linking.
The symbol table is then used by the link editor during relocation. The symbol
table’s section header contains the symbol table index for the first non-local
symbol.
The symbol table contains the following information:
".hash" A symbol hash table.
".interp" The path name of a program interpreter.
".plt" The procedure linking table.
"rel
name
"&
".rela
name
"Relocation information. name is the section to which the
relocations apply. e.g., ".rel.text", ".rela.text".
".shstrtab" String table for the section header table names.
".strtab" The string table.
".symtab" The symbol table.
Table 3-5 Predefined Non-User Sections (Continued)
Section Name Description

Assembler Output 163
3
st_name
Index into the object file symbol string table. A value of zero indicates the
corresponding entry in the symbol table has no name; otherwise, the value
represents the string table index that gives the symbol name.
st_value
Value of the associated symbol. This value is dependent on the context; for
example, it can be an address, or it can be an absolute value.
st_size
Size of symbol. A value of 0 indicates that the symbol has either no size or
an unknown size.
st_info
Specifies the symbol type and binding attributes. Table 3-6 andTable 3-7
describe the symbol types and binding attributes.
st_other
Undefined meaning. Current value is 0.
st_shndx
Contains the section header table index to another relevant section, if
specified. As a section moves during relocation, references to the symbol
continue to point to the same location because the value of the symbol
changes as well.
164 x86 Assembly Language Reference Manual—November 1995
3
String Tables
Astring table is a section which contains null-terminated variable-length
character sequences, or strings. The object file uses these strings to represent
symbol names and file names. The strings are referenced by indices into the
string table section. The first and last bytes of a string table must be the null
character.
•A string table index can refer to any byte in the section.
Table 3-6 Symbol Types
Value Type Description
0 notype Type not specified.
1 object Symbol is associated with a data object; for example, a variable or an array.
2 func Symbol is associated with a function or other executable code. When another object file
references a function from a shared object, the link editor automatically creates a procedure
linkage table entry for the referenced symbol.
3 section Symbol is associated with a section. These types of symbols are primarily used for relocation.
4 file Gives the name of the source file associated with the object file.
13
15 loproc
hiproc Values reserved for processor-specific semantics.
Table 3-7 Symbol Bindings
Value Binding Description
0 local Symbol is defined in the object file and not accessible in other files. Local symbols of the same
name can exist in multiple files.
1 global Symbol is either defined externally or defined in the object file and accessible in other files.
2 weak Symbol is either defined externally or defined in the object file and accessible in other files;
however, these definitions have a lower precedence than globally defined symbols.
13
15 loproc
hiproc Values reserved for processor-specific semantics.

Assembler Output 165
3
•Empty string table sections are permitted if zero is the value of sh_size in
the section header entry for the string table in the section header table.
A string can appear multiple times and can also be referenced multiple times.
References to substrings can exist, and unreferenced strings are allowed.

166 x86 Assembly Language Reference Manual—November 1995
3
167
Using the Assembler Command Line A
This chapter describes how to invoke the assembler and use the command-line
options.
This chapter is organized as follows:
Assembler Command Line
Invoke the assembler command line as follows:
Note – The language drivers (such as cc and f77) invoke the assembler
command line with the fbe command. You can use either the as or fbe
command to invoke the assembler command line.
Assembler Command Line page 167
Assembler Command Line Options page 168
Disassembling Object Code page 169
as [options] [inputfile] ...

168 x86 Assembly Language Reference Manual—November 1995
A
The as command translates the assembly language source files, inputfile, into
an executable object file, objfile. The Intel assembler recognizes the file name
argument hyphen (-) as the standard input. It accepts more than one file name
on the command line. The input file is the concatenation of all the specified
files. If an invalid option is given or the command line contains a syntax error,
the Intel assembler prints the error (including a synopsis of the command line
syntax and options) to standard error output, and then terminates.
The Intel assembler supports #define macros, #include files, and symbolic
substitution through use of the C preprocessor
cpp
. The assembler invokes the
preprocessor before assembly begins if it has been specified from the command
line as an option. (See the -P option.)
Assembler Command Line Options
-Dname
-Dname=def
When the -P option is in effect, these options are passed to the
cpp
preprocessor without interpretation by the as command; otherwise, they are
ignored.
-Ipath
When the -P option is in effect, this option is passed to the
cpp
preprocessor without interpretation by the as command; otherwise, it is
ignored.
-m
This new option runs m4 macro preprocessing on input. The
m4
preprocessor is more powerful than the C preprocessor (invoked by the -P
option), so it is more useful for complex preprocessing. See the SunOS 5.x
Reference Manual for x86 for a detailed description of the m4 macro-processor.
-o outfile
Takes the next argument as the name of the output file to be produced. By
default, the .s suffix, if present, is removed from the input file and the .o
suffix is appended to form the output file name.

Using the Assembler Command Line 169
A
-P
Run
cpp
, the C preprocessor, on the files being assembled. The preprocessor
is run separately on each input file, not on their concatenation. The
preprocessor output is passed to the assembler.
-Q[y|n]
This new option produces the “assembler version” information in the
comment section of the output object file if the y option is specified; if the n
option is specified, the information is suppressed.
-s
This new option places all stabs in the .stabs section. By default, stabs are
placed in stabs.excl sections, that are stripped out by the static linker ld
during final execution. When the -s option is used, stabs remain in the final
executable because .stab sections are not stripped out by the static linker
ld.
-Uname
When the -P option is in effect, this option is passed to the
cpp
preprocessor without interpretation by the as command; otherwise, it is
ignored.
-V
This option writes the version information on the standard error output.
Disassembling Object Code
The dis program is the object code disassembler for ELF. It produces an
assembly language listing of the object file. For detailed information about this
function, see the dis(1) manual page.

170 x86 Assembly Language Reference Manual—November 1995
A

171
Index
A
addresses, 162
addressing mode
base and index, 13
offset, 13
scale, 13
segment register, 13
as command, 167
assembler (as)
addition instructions, 129
arithmetic logical instructions, 38 to
55
bit instructions, 100 to 103
byte instructions, 118 to 120
comparison instructions, 138 to 140
constant instructions, 143 to 145
conversion instructions, 62 to 64
coprocessor instructions, 69
decimal arithmetic instructions, 64 to
68
division instructions, 133 to 134
exchange instructions, 103, 120
expressions, 6, 14
flag instructions, 32 to 38
floating point comparison
instructions, 106 to 107
floating point constant
instructions, 105
floating point opcode errors, 135
floating point transcendental
instructions, 104
I/O instructions, 29
immediate values, 14
input format, 2 to 4
instruction descriptions, 12 to 25
addressing modes, 13 to 14
instructions
addition
fadd(), 129
faddp(), 129
fiadd(), 129
arithmetic logical
adc(), 39
add(), 38
and(), 52
bound(), 51
cmp(), 42
dec(), 44
inc(), 43
neg(), 50
not(), 50
or(), 54

172 x86 Assembly Language Reference Manual—November 1995
sal(), 46
sar(), 46
sbb(), 41
shl(), 46
shld(), 48
shr(), 46
shrd(), 49
sub(), 40
test(), 45
xor(), 55
arithmetic/logical, 38
bit bsf(), 100
bsr(), 100
bt(), 101
btc(), 102
btr(), 102
bts(), 103
bytebswap(), 120
setcc(), 118
comparison
fcom(), 138
fcomp(), 139
fcompp(), 139
ficom(), 139
ficomp(), 140
ftst(), 140
fxam(), 140
constant
fldl2e(), 143
fldl2t(), 143
fldlg2(), 144
fldln2(), 144
fldpi(), 144
fldz(), 145
conversion, 62
cbtw(), 62
cltd(), 64
cwtd(), 63
cwtl(), 63
coprocessor, 69
fwait(), 69
wait(), 69
decimal arithmetic, 64
aaa(), 65
aad(), 68
aam(), 67
aas(), 66
daa(), 64
das(), 65
division
fdiv(), 133
fdivr(), 133
fdivrp(), 134
fidiv(), 134
fidivr(), 134, 135
exchange
cmpxchg(), 103
xadd(), 120
xchg(), 120
flag clc(), 35
cld(), 37
cli(), 36
cmc(), 35
lahf(), 32
popf(), 33
pushf(), 34
sahf(), 33
stc(), 36
std(), 38
sti(), 37
floating point comparison

173
fucom(), 106
fucomp(), 107
fucompp(), 107
floating point constant
fld1(), 105
fld12+(), 105
fld12e(), 105
fldlg2(), 105
fldln2(), 105
fldpi(), 105
fldz(), 105
floating point transcendental
fcos(), 104
fsin(), 104
fsincos(), 104
I/O, 29
in(), 29
ins(), 29
out(), 31
outs(), 31
integer transfer
fild(), 127
fist(), 127
fistp(), 127
interrupt
int(), 87
into(), 87
iret(), 89
jump
jcc(), 85
jcxz(), 83
jmp(), 85
ljmp(), 85
loop(), 84
loope(), 84
loopne(), 84
loopnz(), 84
loopz(), 84
load and move
lea(), 108
mov(), 109, 110, 111
movsb(), 112
movsbwl(), 112
movw(), 109
movzwl(), 112
load full pointer
lds(), 26
les(), 26
lfs(), 26
lgs(), 26
lss(), 26
miscellaneous, 122
hlt(), 124
invd(), 122
invlp(), 122
lock(), 122
nop(), 123
wbinvd(), 121
miscellaneous arithmetic
operations
fabs(), 137
fchs(), 138
fprem(), 136
frndint(), 137
fscale(), 136
fsqrt(), 136
fxtract(), 137
miscellaneous floating point
fprem1(), 106
multiply
fimul(), 132
fmul(), 132
fmulp(), 132
multiply and divide

174 x86 Assembly Language Reference Manual—November 1995
div(), 60
idiv(), 61
imul(), 57
imulb(), 57
mul(), 58
packed decimal transfer
fbld(), 128
fbst(), 128
pop popa(), 113
pop stack into word
pop(), 27
procedure call, 78
procedure call and return
call(), 79
enter(), 82
lcall(), 78
leave(), 83
lret(), 81
ret(), 80
processor control
fclex(), 148
fdecstp(), 148
ffree(), 148
fincstp(), 149
finit(), 145
fnclex(), 148
fninit(), 145
fnop(), 145
fnsave(), 146
fnstcw(), 146
fnstenv(), 146
fnstsw(), 147
frstor(), 147
fsave(), 146
fstcw(), 146
fstenv(), 146
fstsw(), 147
wait(), 147
processor control floating point
fldcw(), 105
fldenv(), 106
protection model, 90 to 98
arpl(), 99
lar(), 96
lgdt(), 94
lidt(), 94
lldt(), 91
lmsw(), 96
lsl(), 97
ltr(), 92
sgdt(), 93
sidt(), 93
sldt(), 90
smsw(), 95
str(), 90
verr(), 92
verw(), 92
push
pusha(), 114
push stack into word
push(), 28
real transfer
fld(), 125
fst(), 125
fstp(), 126
fxch(), 126
return, 78
rotate
rcl(), 114
rcr(), 115
rol(), 116
ror(), 117
string, 69 to 77

175
cmps(), 71
lods(), 73
movs(), 70
rep(), 77
repnz(), 77
repz(), 77
scas(), 75
stos(), 72
xlat(), 76
subtraction
fisubr(), 131
fisubrp(), 131
fsub(), 130
fsubr(), 130
fsubrp(), 131
subp(), 130
transcendental
f2xm1(), 142
fptan(), 141, 142
fyl2x(), 142
fyl2xp1(), 143
integer transfer instructions, 127
interrupt instructions, 87 to 89
jump instructions, 83 to 85
load and move instructions, 108 to
112
miscellaneous arithmetic
operations, 136 to 138
miscellaneous instructions, 121 to124
mnemonics
addition, 129
arithmetic, 136
multiplication instructions, 132
multiply and divide instructions, 56
to 61
object file
.comment section, 6
operands
immediate, 10
memory, 10
overview, 10
register, 10
operations, dbx pseudo, 20
operations, general pseudo, 14 to 18
operators, 6
other floating point instructions, 106
packed decimal transfer
instructions, 128
pop instructions, 113
procedure call and return
instructions, 78 to 83
process control floating point
instructions, 105 to 106
processor control instructions, 145 to
149
protection model instructions, 90 to
99
push instructions, 114
real transfer instructions, 125 to 126
rotate instructions, 114 to 117
segment register instructions, 26 to 28
statements
assignment, 3
empty, 3
machine operation, 3
modifying, 3
pseudo operation, 3
string instructions, 69 to 77
subtraction instructions, 130 to 131
SunOS vs. Intel, mnemonics, 21 to
149
notational coventions, 23
symbols, 4
syntax rules, 7 to 10
transcendental instructions, 141 to
143
types, 4 to 5
values, 4 to 5
assembler command line, 167
assembler command line options, 168
assembly language, 1
C
cc language driver, 167

176 x86 Assembly Language Reference Manual—November 1995
command line options
-D, 168
-lpath, 168
-m, 168
-o outfile, 168
-P, 169
-Q, 169
-s, 169
-Uname, 169
-V, 169
D
default output file, 152
dis program, 169
disassembling object code, 169
E
ELF header
e_ehsize, 154
e_entry, 153
e_flag, 154
e_ident, 153
e_machine, 153
e_phentsize, 154
e_phnum, 154
e_phoff, 154
e_shentsize, 154
e_shnum, 154
e_shoff, 154
e_shstrndx, 155
e_type, 153
e_version, 153
ELF section, 159
predefined non-user section, 161
predefined user section, 160
ELF section header
sh_addr, 156
sh_addralign, 156
sh_entsize, 157
sh_flags, 156
sh_info, 156
sh_link, 156
sh_name, 155
sh_offset, 156
sh_size, 156
sh_type, 155
ELF string table, 164
ELF symbol table, 162
st_info, 163
st_name, 163
st_other, 163
st_shndx, 163
st_size, 163
st_value, 163
expression
absolute, 9
relocatable, 9
F
f77 language driver, 167
fbe command, 167
.file,16
G
.globl,16
H
hyphen (-), 168
I
-I option, 168
instructions
addition
fadd(), 129
faddp(), 129

177
fiadd(), 129
arithmetic logical
adc(), 39
add(), 38
and(), 52
bound(), 51
cmp(), 42
dec(), 44
inc(), 43
neg(), 50
not(), 50
or(), 54
sal(), 46
sar(), 46
sbb(), 41
shl(), 46
shld(), 48
shr(), 46
shrd(), 49
sub(), 40
test(), 45
xor(), 55
bit bsf(), 100
bsr(), 100
bt(), 101
btc(), 102
btr(), 102
bts(), 103
bytebswap(), 120
setcc(), 118
comparison
fcom(), 138
fcomp(), 139
fcompp(), 139
ficom(), 139
ficomp(), 140
ftst(), 140
fxam(), 140
constant
fldl2e(), 143
fldl2t(), 143
fldlg2(), 144
fldln2(), 144
fldpi(), 144
fldz(), 145
conversion
cbtw(), 62
cltd(), 64
cwtd(), 63
cwtl(), 63
coprocessor
fwait(), 69
wait(), 69
decimal arithmetic
aaa(), 65
aad(), 68
aam(), 67
aas(), 66
daa(), 64
das(), 65
division
fdiv(), 133
fdivr(), 133
fdivrp(), 134
fidiv(), 134
fidivr(), 134, 135
exchange
cmpxchg(), 103
xadd(), 120
xchg(), 120
flag clc(), 35
cld(), 37
cli(), 36
cmc(), 35
lahf(), 32
popf(), 33
pushf(), 34
sahf(), 33
stc(), 36
std(), 38
sti(), 37
floating point comparison
fucom(), 106
fucomp(), 107
fucompp(), 107
floating point constant
fld1(), 105
fld12+(), 105
fld12e(), 105

178 x86 Assembly Language Reference Manual—November 1995
fldlg2(), 105
fldln2(), 105
fldpi(), 105
fldz(), 105
floating point transcendental
fcos(), 104
fsin(), 104
fsincos(), 104
I/O in(), 29
ins(), 29
out(), 31
outs(), 31
integer transfer
fild(), 127
fist(), 127
fistp(), 127
interrupt
int(), 87
into(), 87
iret(), 89
jump
jcc(), 85
jcxz(), 83
jmp(), 85
ljmp(), 85
loop(), 84
loope(), 84
loopne(), 84
loopnz(), 84
loopz(), 84
load and move
lea(), 108
mov(), 109, 110, 111
movsb(), 112
movsbwl(), 112
movw(), 109
movzwl(), 112
load full pointer
lds(), 26
les(), 26
lfs(), 26
lgs(), 26
lss(), 26
miscellaneous
hlt(), 124
invd(), 122
invlp(), 122
lock(), 122
nop(), 123
wbinvd(), 121
miscellaneous arithmetic operations
fabs(), 137
fchs(), 138
fprem(), 136
frndint(), 137
fscale(), 136
fsqrt(), 136
fxtract(), 137
miscellaneous floating point
fprem1(), 106
multiply
fimul(), 132
fmul(), 132
fmulp(), 132
multiply and divide
div(), 60
idiv(), 61
imul(), 57
imulb(), 57
mul(), 58
packed decimal transfer
fbld(), 128
fbst(), 128
pop popa(), 113
pop stack into word
pop(), 27
procedure call and return
call(), 79
enter(), 82
lcall(), 78
leave(), 83
lret(), 81
ret(), 80
processor control
fclex(), 148
fdecstp(), 148
ffree(), 148
fincstp(), 149
finit(), 145
fnclex(), 148

179
fninit(), 145
fnop(), 145
fnsave(), 146
fnstcw(), 146
fnstenv(), 146
fnstsw(), 147
frstor(), 147
fsave(), 146
fstcw(), 146
fstenv(), 146
fstsw(), 147
wait(), 147
processor control floating point
fldcw(), 105
fldenv(), 106
protection model
arpl(), 99
lar(), 96
lgdt(), 94
lidt(), 94
lldt(), 91
lmsw(), 96
lsl(), 97
ltr(), 92
sgdt(), 93
sidt(), 93
sldt(), 90
smsw(), 95
str(), 90
verr(), 92
verw(), 92
push
pusha(), 114
push stack into word
push(), 28
real transfer
fld(), 125
fst(), 125
fstp(), 126
fxch(), 126
rotate
rcl(), 114
rcr(), 115
rol(), 116
ror(), 117
string
cmps(), 71
lods(), 73
movs(), 70
rep(), 77
repnz(), 77
repz(), 77
scas(), 75
stos(), 72
xlat(), 76
subtraction
fisubr(), 131
fisubrp(), 131
fsub(), 130
fsubr(), 130
fsubrp(), 131
subp(), 130
transcendental
f2xm1(), 142
fptan(), 141, 142
fyl2x(), 142
fyl2xp1(), 143
invoking, as command, 167
L
language drivers, 167
.local,17
M
-m option, 168
machine instruction syntax, 10
derived type information, 10
destination operand, 10
register name, 10
source operand, 10
multiple files, on as command line, 168
multiple sections, 160
multiple strings, in string table, 165
N
.nonvolatile,17

180 x86 Assembly Language Reference Manual—November 1995
notational conventions
condition codes, 25
control register, 24
distance of relative jump, 25
immediate pointer, 25
immediate value, 24
memory operand, 24
O
operands
byte register, 11
long register, 12
segment register, 12
word register, 11
operations, general pseudo, 14
.align val,14
.bcd val,15
.bss,15
.bss tag, bytes,15
.byte val,15
.comm name, expr,15
.data,15
.double val,15
.even,15
options
command line, 168
P
-P option, 169
predefined non-user sections, 161
predefined user sections, 160
Programming Utilities - SunOS 5.0, xviii
pseudo-operations, 14
Q
-Q option, 169
R
relocatable files, 151
relocation tables, 162
S
-s option, 169
.section,17
section header, 155
sections, 159
statements
append comment, 3, ?? to 4
assignment, 3
empty, 3
label prefix, 3
machine operation, 3
pseudo operation, 3
string tables, 164
strings
multiple references in string
table, 165
unreferenced in string table, 165
strings, multiple in string table, 165
sub-strings in string table
references to, 165
symbol, 19
symbol tables, 162
symbol types
absolute, 5
attribute, 5
bss, 5
data, 5
object file sections, 6
text, 5
undefined, 5
symbol, reserved
.bss, 4
.data, 4
.fini, 5
.init, 5
.text, 4
U
-U option, 169
V
-V option, 169

181
.volatile,18
W
.weak,18

182 x86 Assembly Language Reference Manual—November 1995

November 1995Copyright 1995 Sun Microsystems, Inc., 2550 Garcia Avenue, Mountain View, Californie 94043-1100 USA.
Tous droits réservés.Ce produit ou document est protégé par un copyright et distribué avec des licences qui en restreignent
l’utilisation, la copie et la décompliation. Aucune partie de ce produit ou de sa documentation associée ne peuvent Être
reproduits sous aucune forme, par quelque moyen que ce soit sans l’autorisation préalable et écrite de Sun et de ses bailleurs de
licence, s’il en a.
Des parties de ce produit pourront etre derivees du système UNIX®, licencié par UNIX Systems Laboratories Inc., filiale
entierement detenue par Novell, Inc. ainsi que par le système 4.3. de Berkeley, licencié par l’Université de Californie. Le logiciel
détenu par des tiers, et qui comprend la technologie relative aux polices de caractères, est protégé par un copyright et licencié par
des fourmisseurs de Sun.
LEGENDE RELATIVE AUX DROITS RESTREINTS : l’utilisation, la duplication ou la divulgation par l’administation
americaine sont soumises aux restrictions visées a l’alinéa (c)(1)(ii) de la clause relative aux droits des données techniques et aux
logiciels informatiques du DFAR 252.227- 7013 et FAR 52.227-19.
Le produit décrit dans ce manuel peut Être protege par un ou plusieurs brevet(s) americain(s), etranger(s) ou par des demandes
en cours d’enregistrement.
MARQUES
Sun, Sun Microsystems, le logo Sun, Solaris sont des marques deposées ou enregistrées par Sun Microsystems, Inc. aux Etats-
Unis et dans certains autres pays. UNIX est une marque enregistrée aux Etats-Unis et dans d’autres pays, et exclusivement
licenciée par X/Open Company Ltd. OPEN LOOK est une marque enregistrée de Novell, Inc., PostScript et Display PostScript
sont des marques d’Adobe Systems, Inc.
Toutes les marques SPARC sont des marques deposées ou enregitrées de SPARC International, Inc. aux Etats-Unis et dans
d’autres pays. SPARCcenter, SPARCcluster, SPARCompiler, SPARCdesign, SPARC811, SPARCengine, SPARCprinter,
SPARCserver, SPARstation, SPARCstorage, SPARCworks, microSPARC, microSPARC II et UltraSPARC sont exclusivement
licenciées a Sun Microsystems, Inc. Les produits portant les marques sont basés sur une architecture développée par Sun
Microsytems, Inc.
Les utilisateurs d’interfaces graphiques OPEN LOOK® et Sun™ ont été développés par Sun Microsystems, Inc. pour ses
utilisateurs et licenciés. Sun reconnait les efforts de pionniers de Xerox pour la recherche et le développement du concept des
interfaces d’utilisation visuelle ou graphique pour l’industrie de l’informatique. Sun détient une licence non exclusive de Xerox
sur l’interface d’utilisation graphique, cette licence couvrant aussi les licencies de Sun qui mettent en place OPEN LOOK GUIs et
qui en outre se conforment aux licences écrites de Sun.
Le système X Window est un produit du X Consortium, Inc.
CETTE PUBLICATION EST FOURNIE "EN L’ETAT" SANS GARANTIE D’AUCUNE SORTE, NI EXPRESSE NI IMPLICITE, Y
COMPRIS, ET SANS QUE CETTE LISTE NE SOIT LIMITATIVE, DES GARANTIES CONCERNANT LA VALEUR
MARCHANDE, L’APTITUDE DES PRODUITS A REPONDRE A UNE UTILISATION PARTICULIERE OU LE FAIT QU’ILS NE
SOIENT PAS CONTREFAISANTS DE PRODUITS DE TIERS.
CETTE PUBLICATION PEUT CONTENIR DES MENTIONS TECHNIQUES ERRONEES OU DES ERREURS
TYPOGRAPHIQUES. DES CHANGEMENTS SONT PERIODIQUEMENT APPORTES AUX INFORMATIONS CONTENUES
AUX PRESENTES, CES CHANGEMENTS SERONT INCORPORES AUX NOUVELLES EDITIONS DE LA PUBLICATION.
SUN MICROSYSTEMS INC. PEUT REALISER DES AMELIORATIONS ET/OU DES CHANGEMENTS DANS LE(S)
PRODUIT(S) ET/OU LE(S) PROGRAMME(S) DECRITS DANS DETTE PUBLICATION A TOUS MOMENTS.
