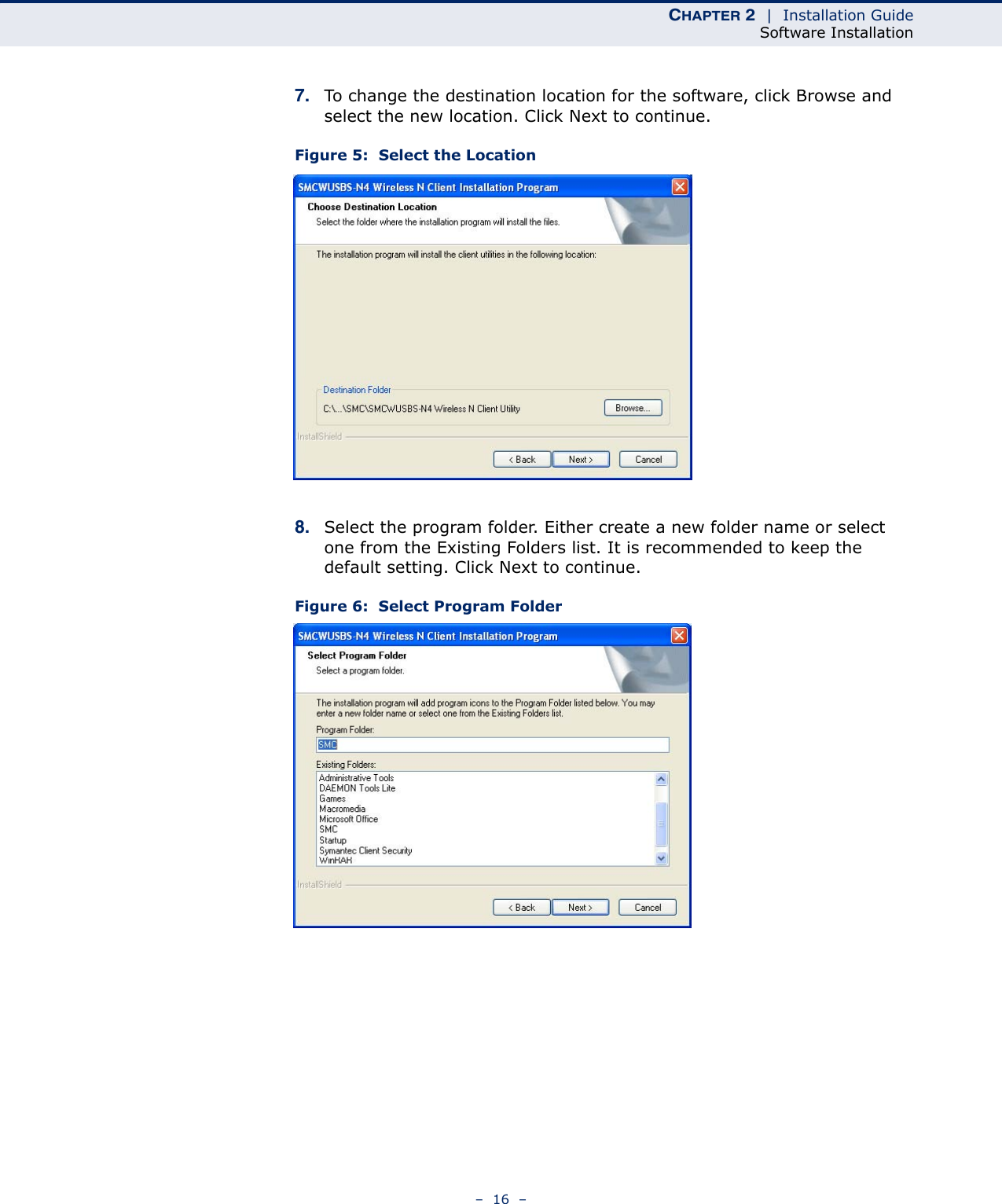
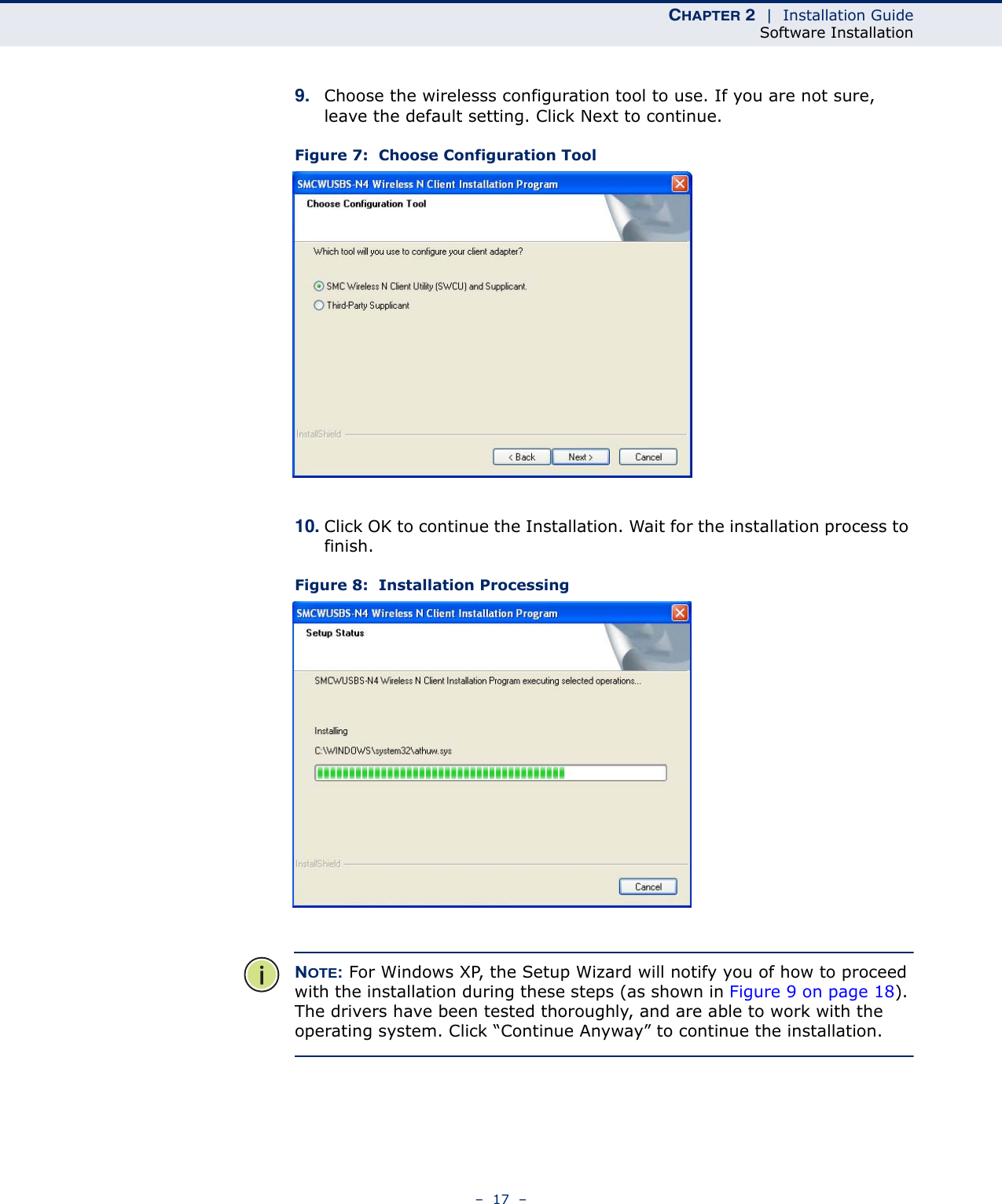
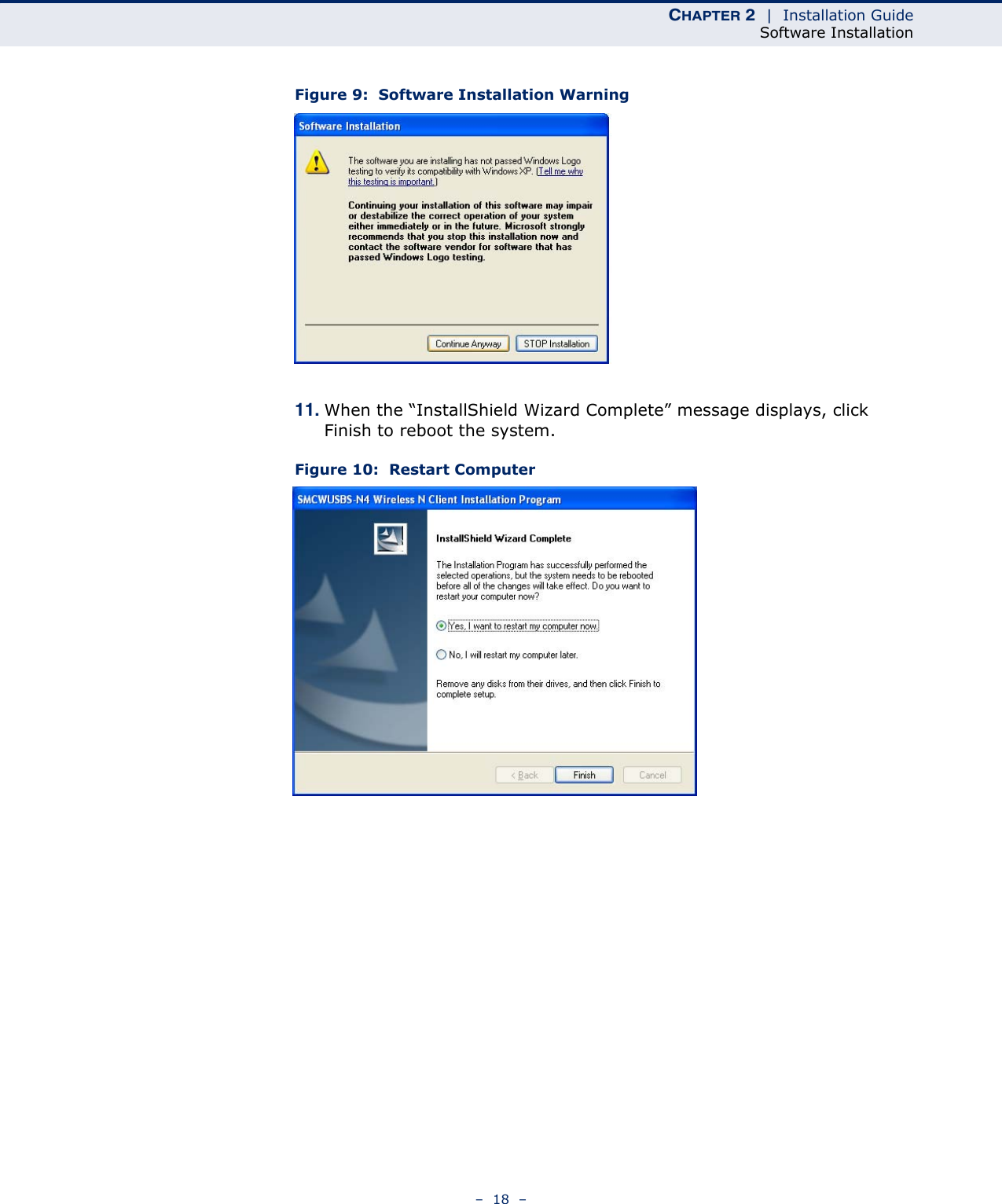
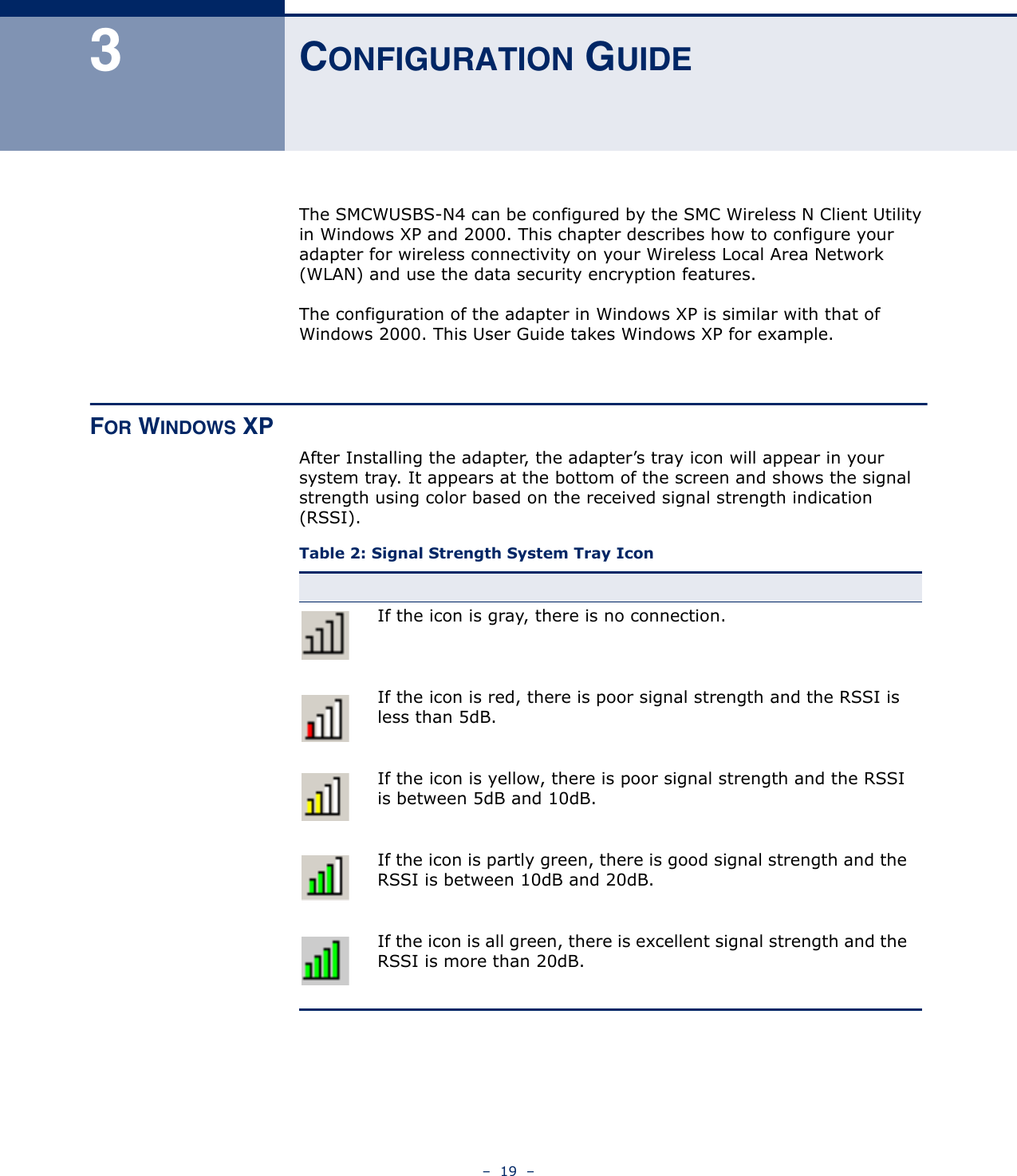
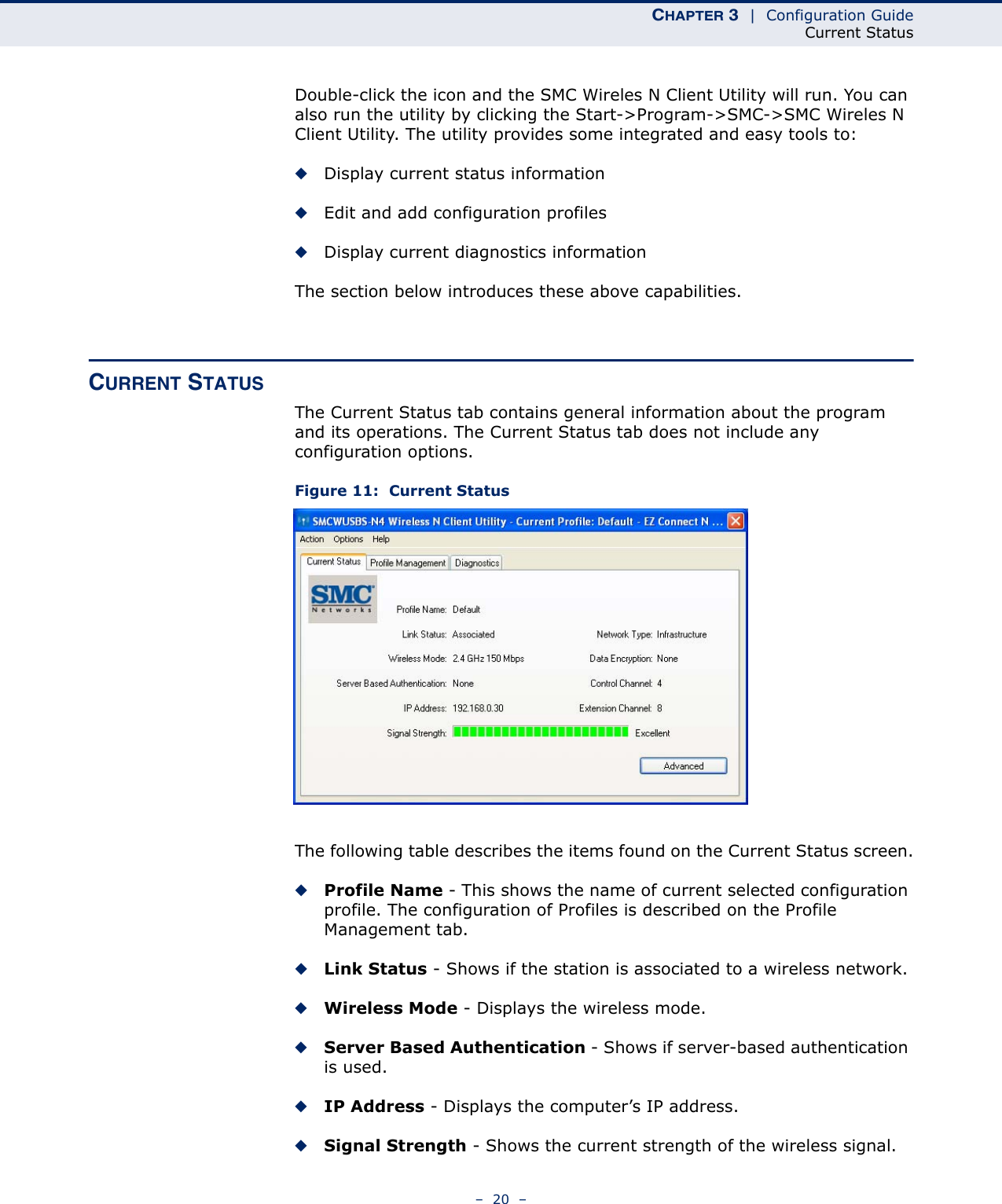
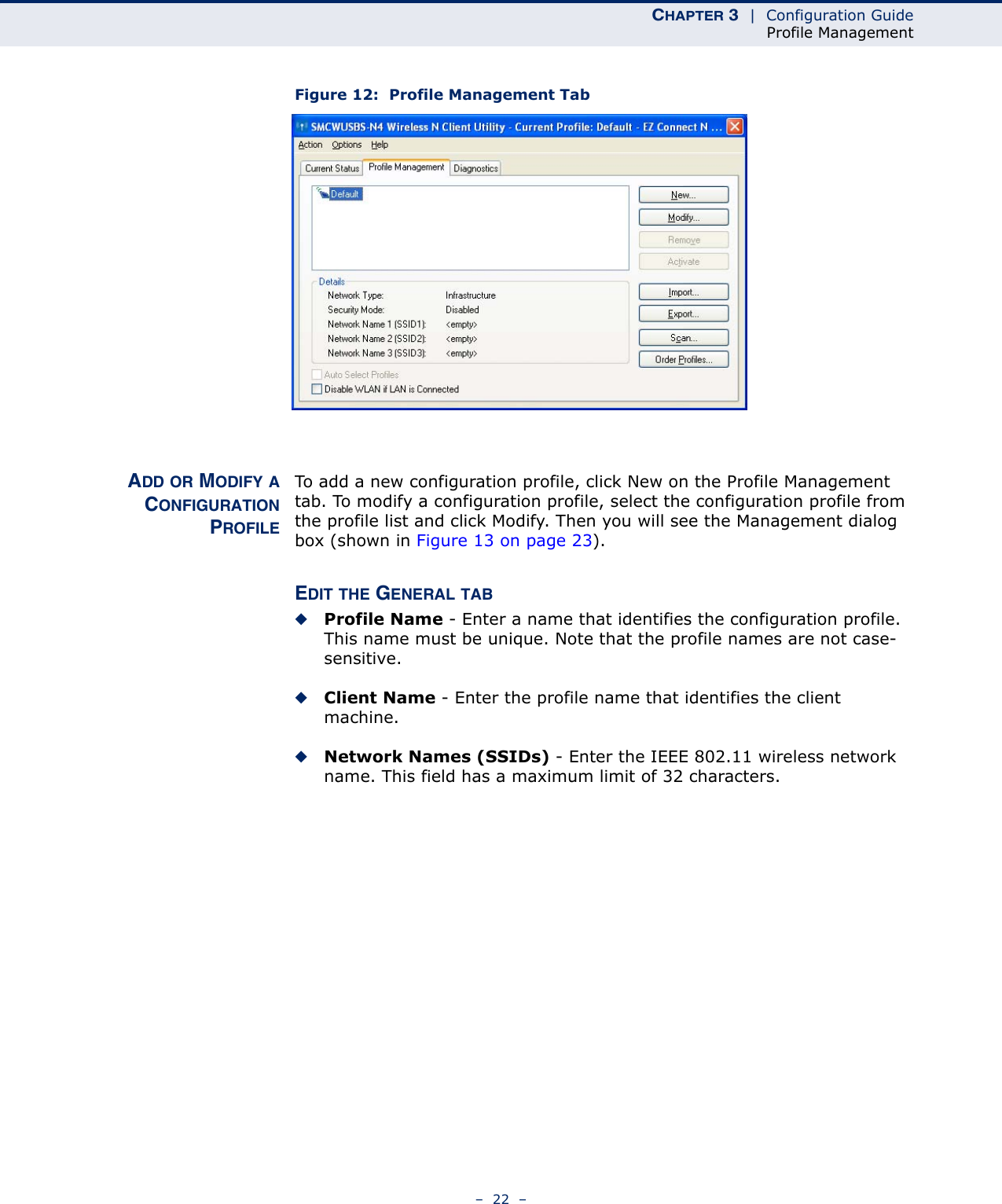
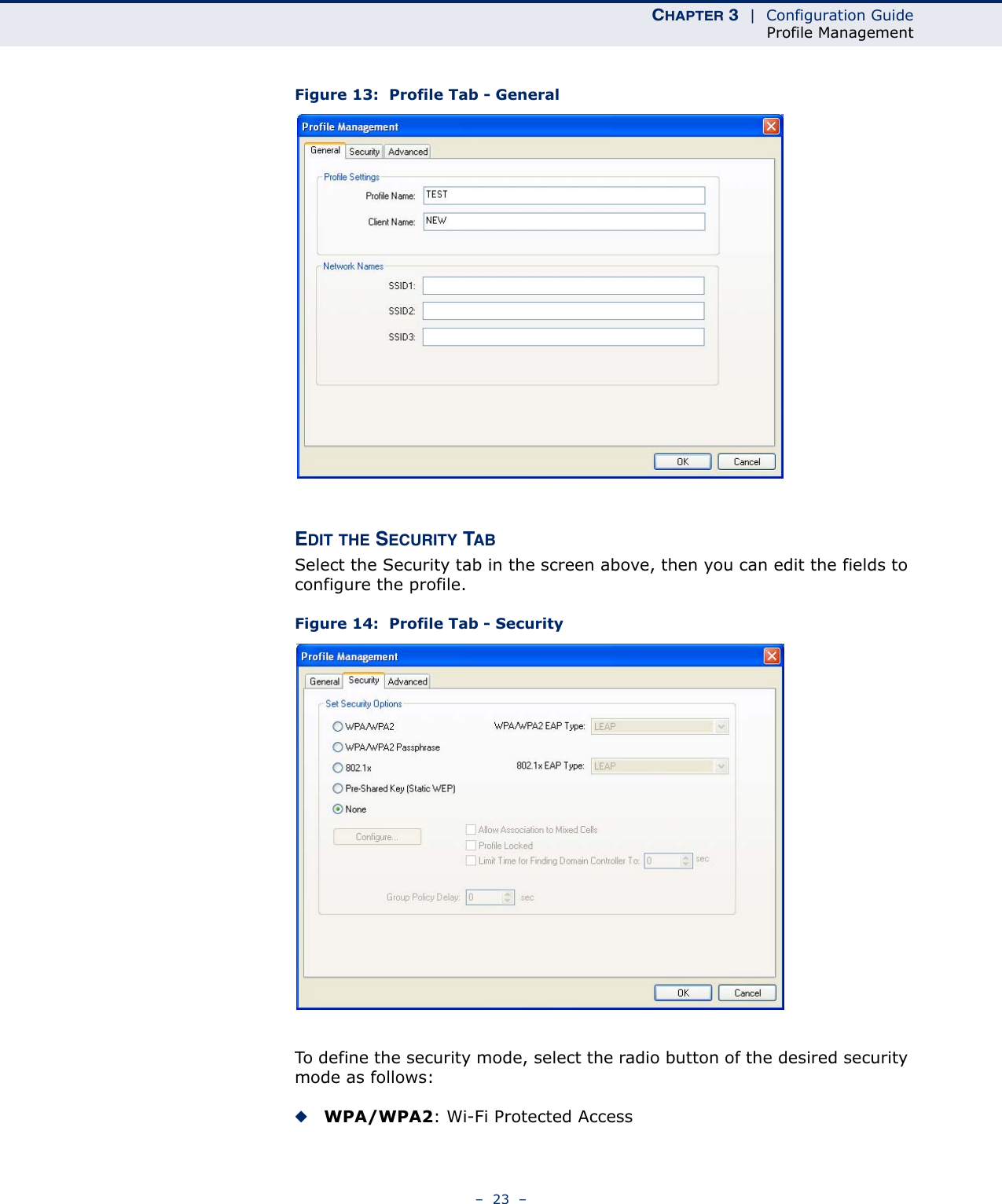
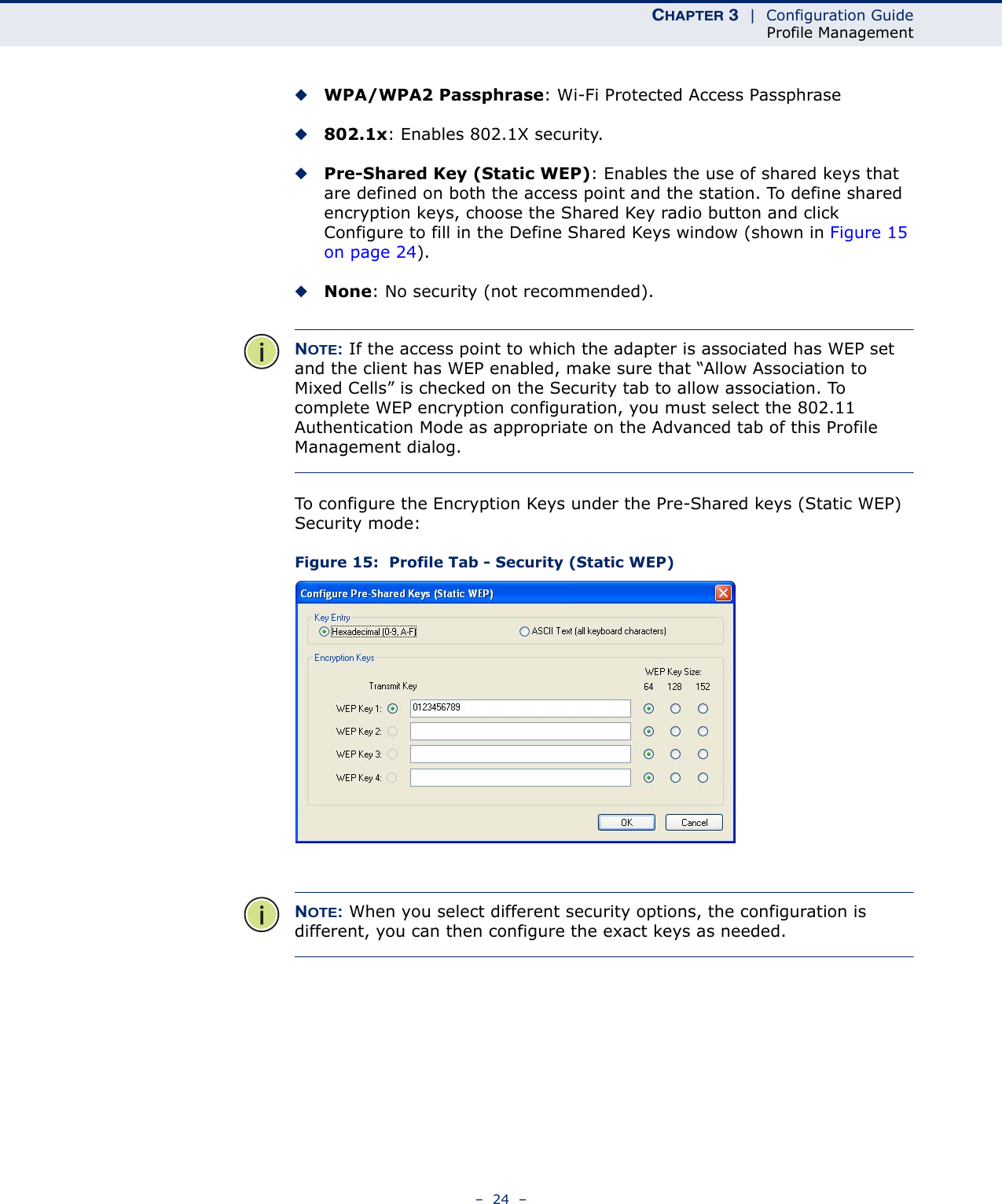
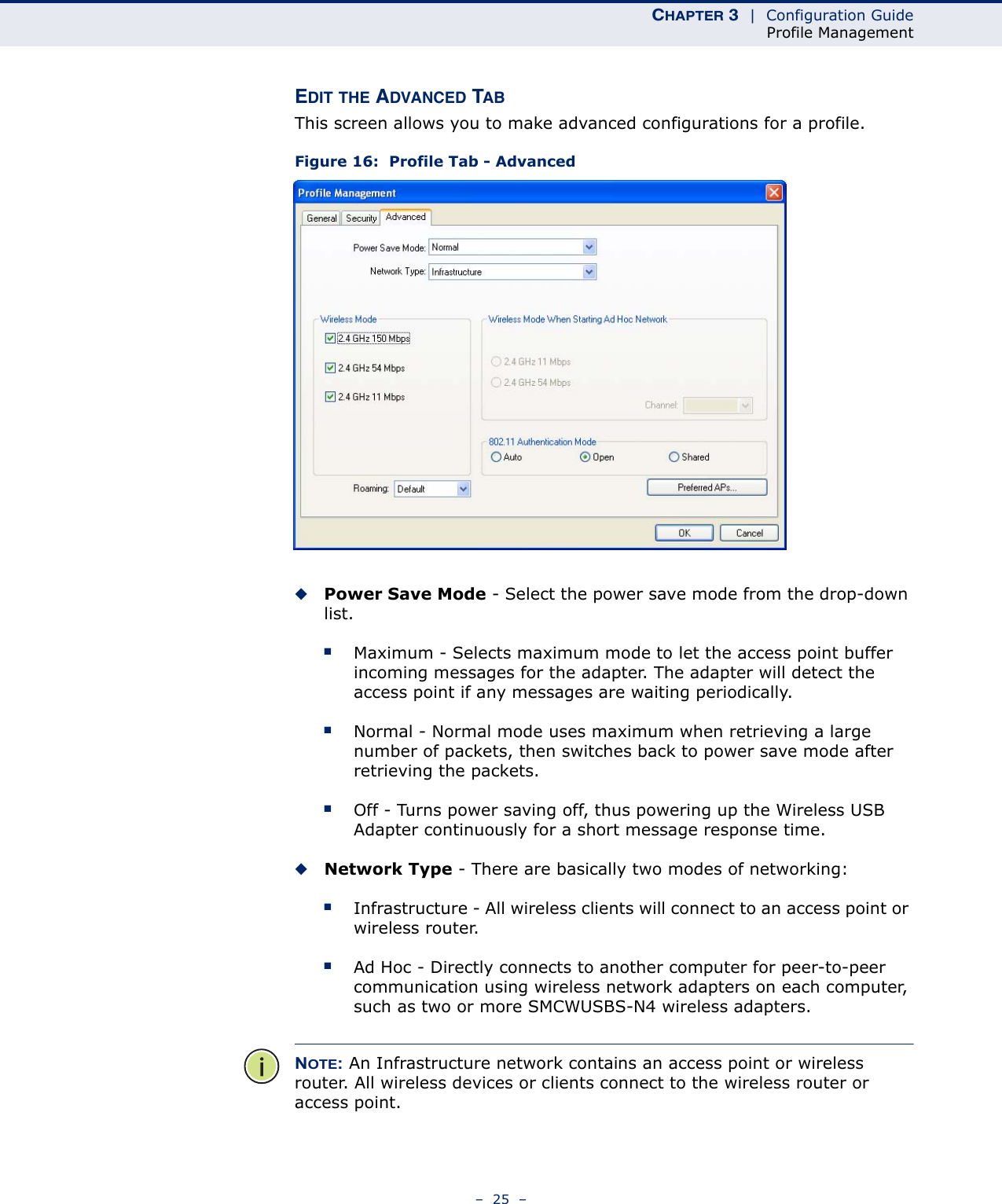
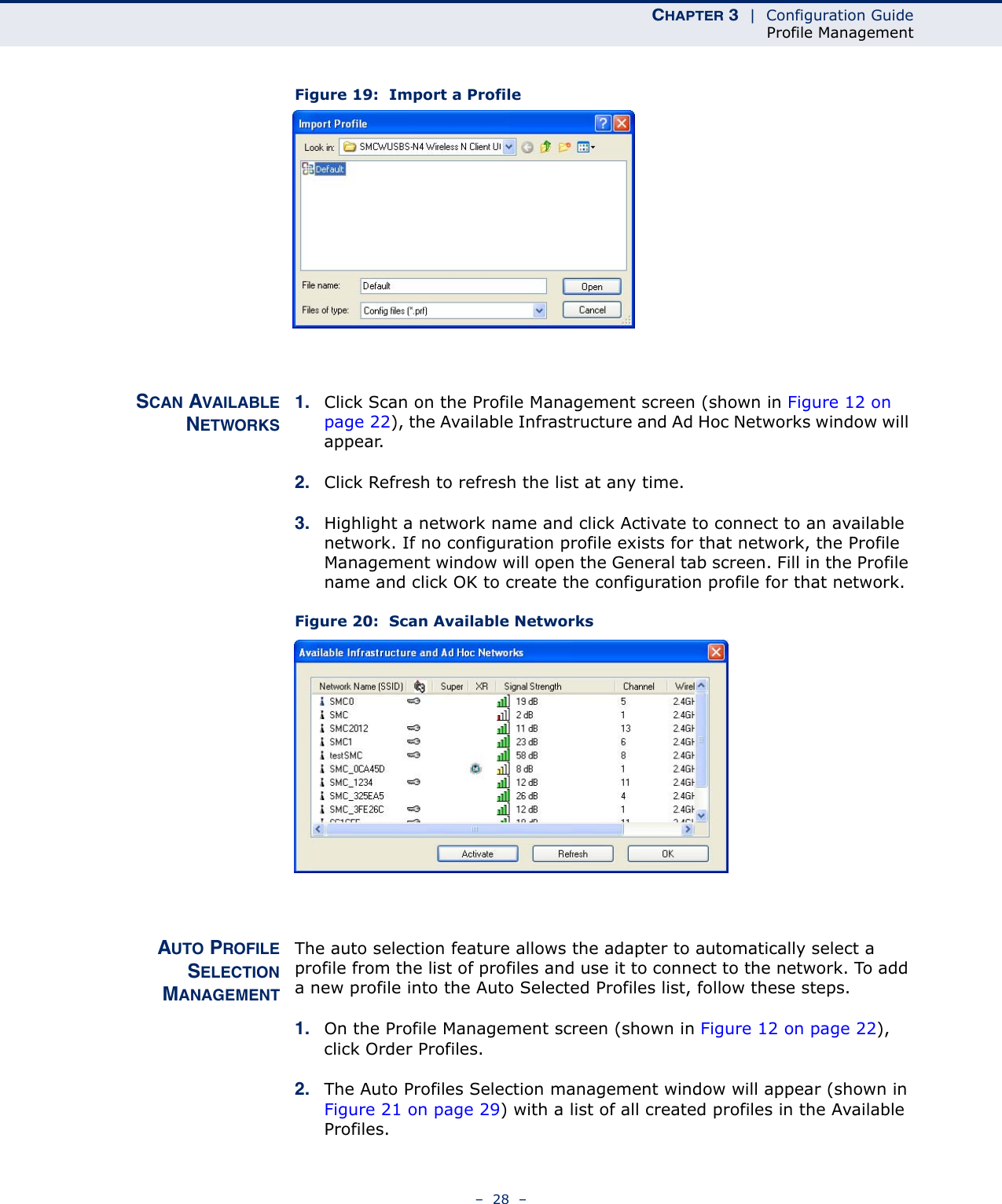
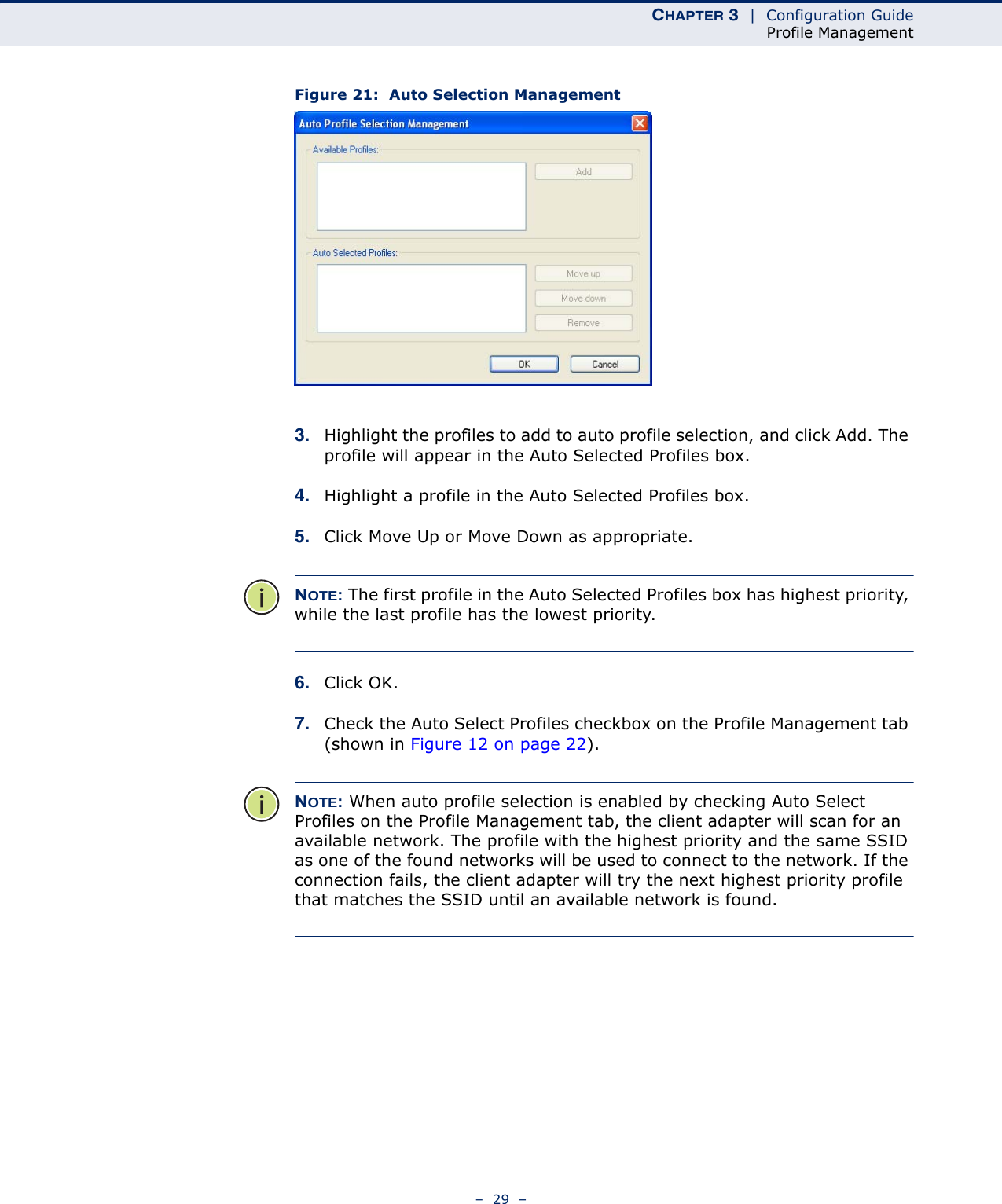
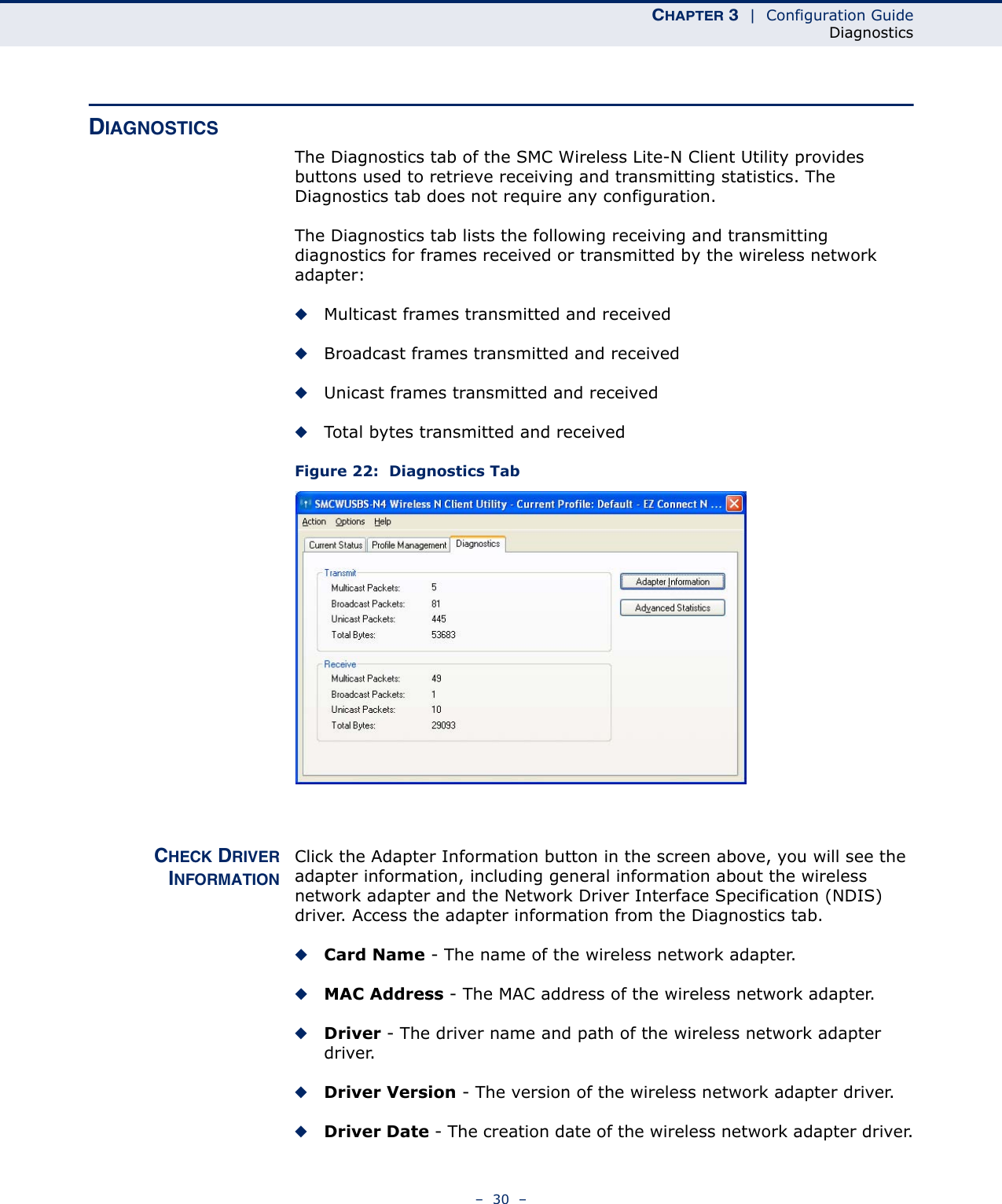
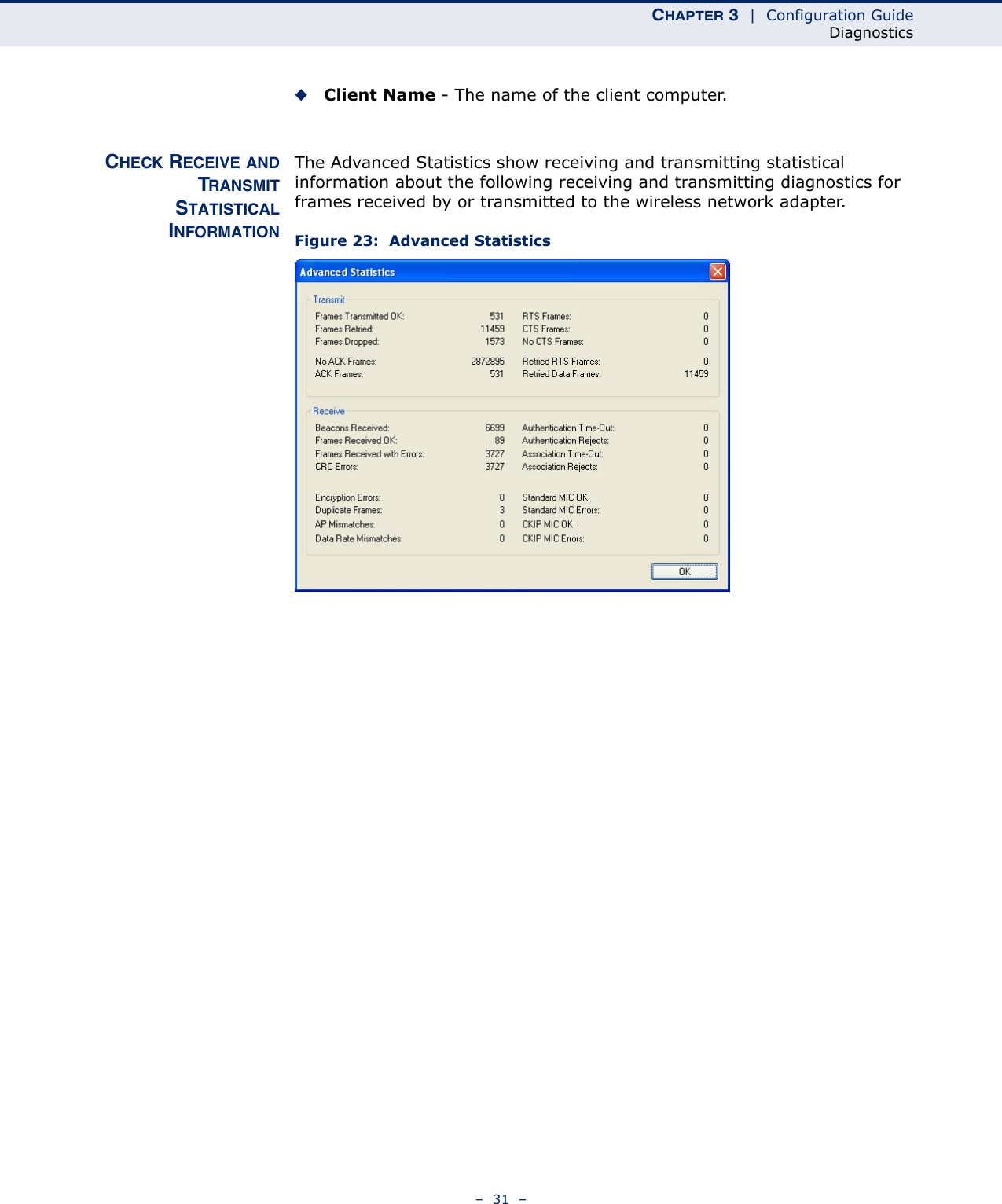
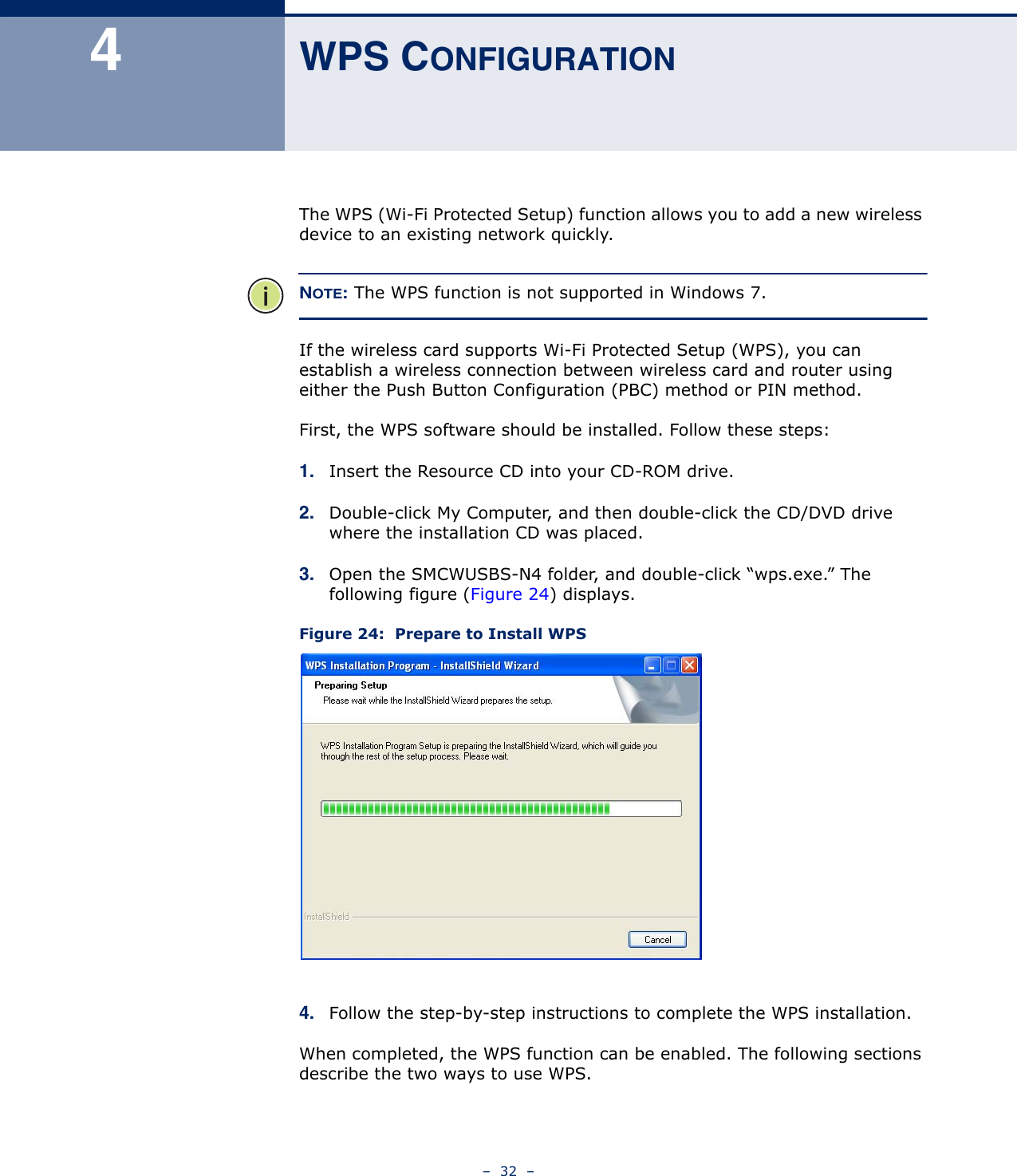
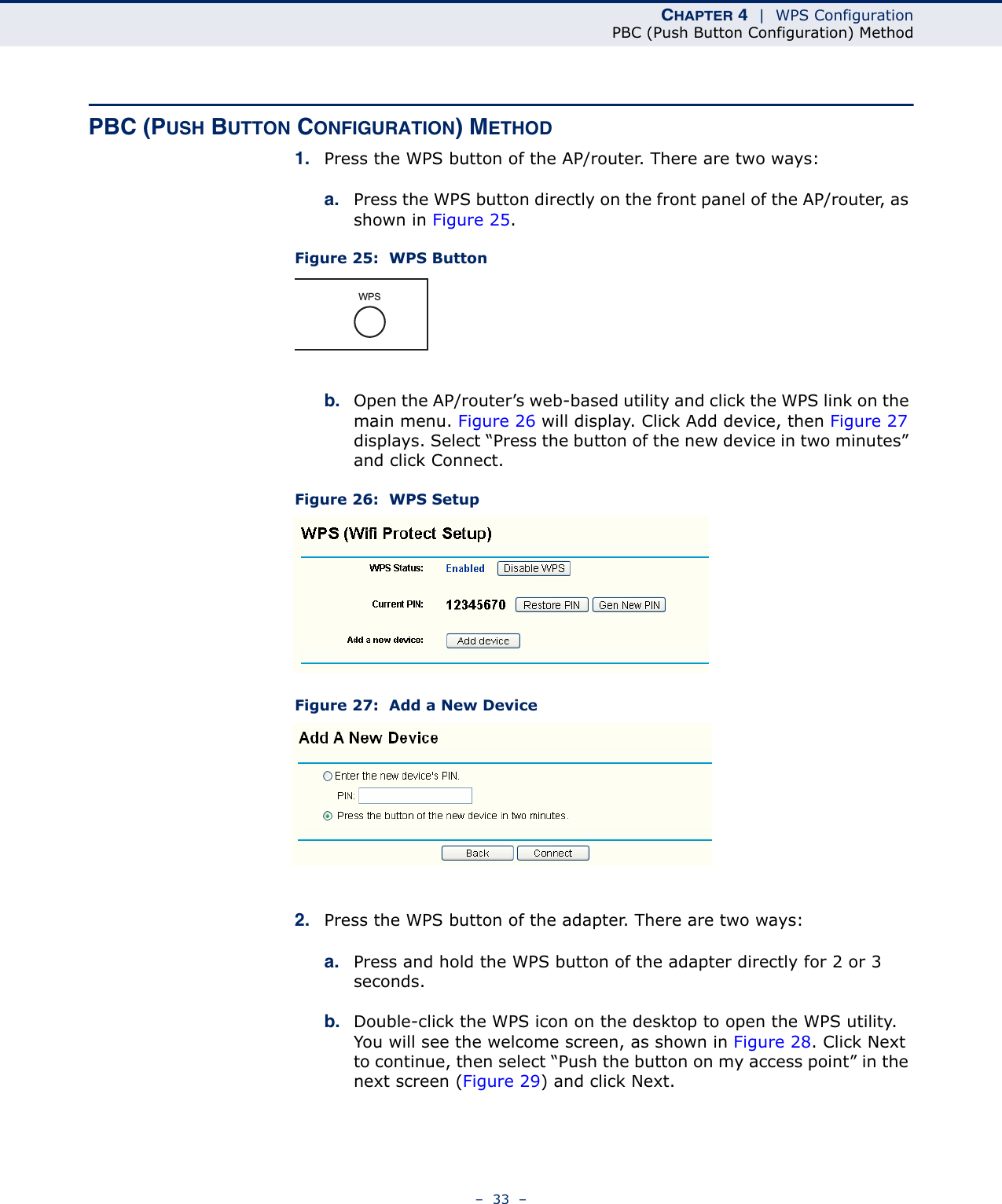
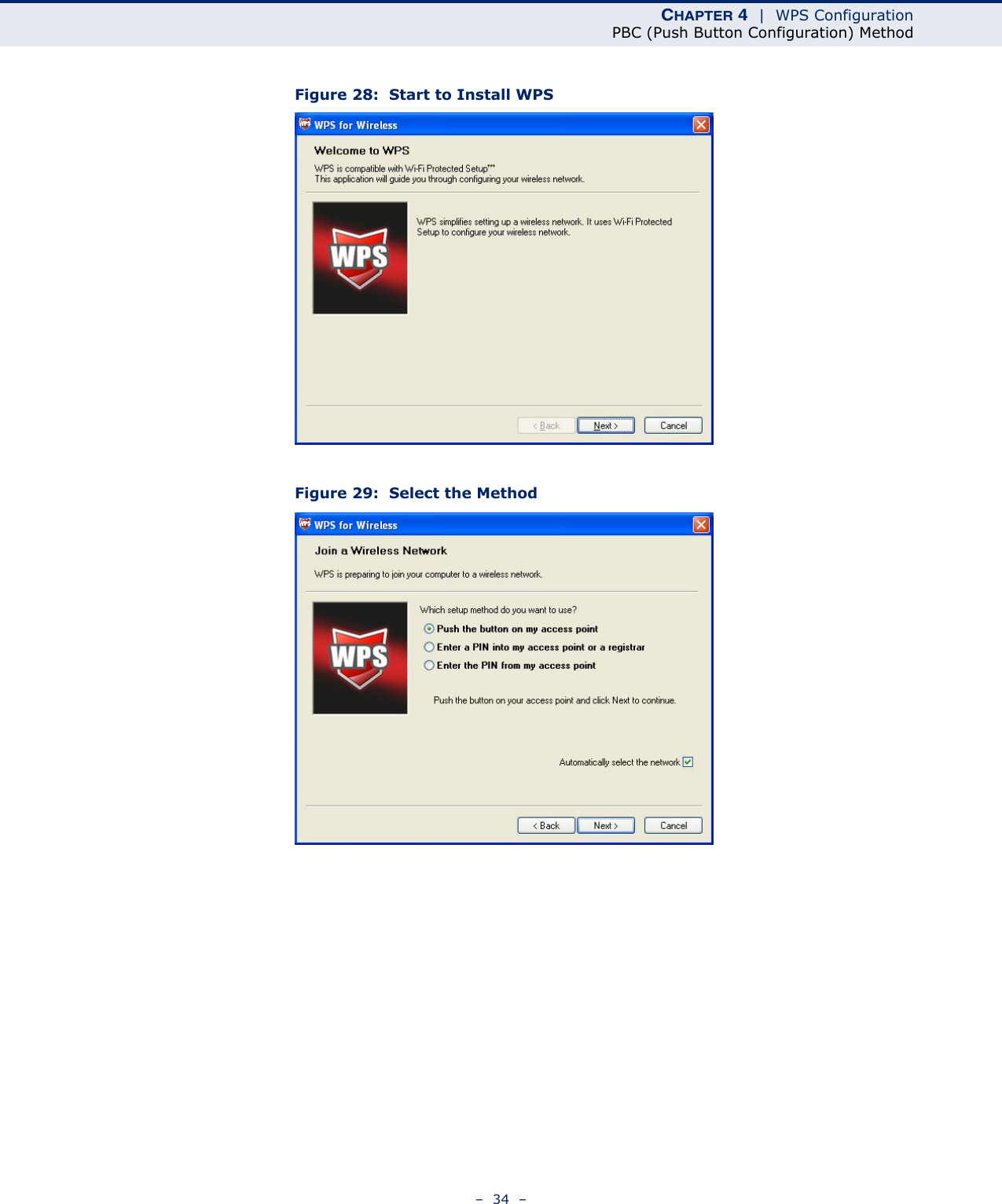
Edgecore Networks SMCWUSBSN4 EZ Connect TM N 150 Mbps Wireless N USB Adapter User Manual SMCWUSBS N4 User maual rev1
Edgecore Networks Corporation EZ Connect TM N 150 Mbps Wireless N USB Adapter SMCWUSBS N4 User maual rev1
SMCWUSBS-N4_User maual_rev1