Global Sun Technology WLUD245418S 802.11g 54 Mbps Wireless USB Dongle User Manual Product Specification
Global Sun Technology Inc 802.11g 54 Mbps Wireless USB Dongle Product Specification
Contents
- 1. DoC
- 2. Users Manual Revised
Users Manual Revised
Product: IEEE 802.11g 54Mbps Wireless USB Dongle
Model: WL UD 2454 18S0
802.11g Wireless
USB Dongle
USER MANUAL
Marketing Dept.
Editorial:
Maggie Huang
Approved By:
George Chou
DOCUMENT
REV. 1.0
802.11g Wireless USB Dongle
USER MANUAL
REV. DATA 09/01/2004
22
1
GST Confidential
Product: IEEE 802.11g 54Mbps Wireless USB Dongle
Model: WL UD 2454 18S0
Version History
Version H/W Description Date Editor
V1.0 Jack Chen Create the file 1 Sept.2004 Maggie
22
2
GST Confidential
Product: IEEE 802.11g 54Mbps Wireless USB Dongle
Model: WL UD 2454 18S0
Contents
1. Introduction ...............................................................................................4
1.1 Product Feature................................................................................4
1.2 System Requirement ........................................................................4
2. Getting Start...............................................................................................5
2.1 LED Indicators ..................................................................................5
2.2 Install the 802.11g Wireless USB Dongle .........................................5
3. Configuration................................................................................................9
3.1 Net Status ...........................................................................................9
3.2 Site Scan ..........................................................................................10
3.3 Statistics............................................................................................12
3.4 Encryption.........................................................................................13
3.5 Info....................................................................................................14
3.6 Profile................................................................................................16
4. Glossary ......................................................................................................18
22
3
GST Confidential
Product: IEEE 802.11g 54Mbps Wireless USB Dongle
Model: WL UD 2454 18S0
1. Introduction
1.1 Product Feature
● Compliance with IEEE 802.11g and 802.11b standards
● Highly efficient design mechanism to provide unbeatable performance
● Achieving data rate up to 54Mbps for 802.11g and 11Mps for 802.11b with
wide range coverage
● Strong network security with WEP and WPA support
● Auto-switch between the two standards, IEEE 802.11b and 802.11g
● Driver/Utility support most commonly used operating systems including
Windows 2000/XP.
● Pen size which is easy to carry provides users the most mobility and
flexibility.
● Support USB 2.0 and USB 1.1 at the same time, especially for USB 2.0 the
data rate reaches 480MBytes.
1.2 System Requirement
● Windows 2000 and XP operating systems
● PC with Pentium III 600MHz system or above is recommended
● Equipped with at least one PC USB socket or PC USB adapter, USB 1.1 at
least.
● One CD-ROM drive
22
4
GST Confidential
Product: IEEE 802.11g 54Mbps Wireless USB Dongle
Model: WL UD 2454 18S0
2. Getting Start
2.1 LED Indicators
The Power LED will be ON when the unit is powered up.
The Link LED will be Blinking indicates a WLAN connection.
2.2 Install the 802.11g Wireless USB Dongle
1. Before insert USB Dongle into the PC USB of your computer, please install
the Utility Program first. Make sure that the 802.11g Wireless USB Dongle
is NOT inserted into the USB slot.
NOTE: all the snapped images of installation mentioned in this manual are
based on Windows XP. For other windows operating system, all the
procedures are the same but the screens are not the exactly same.
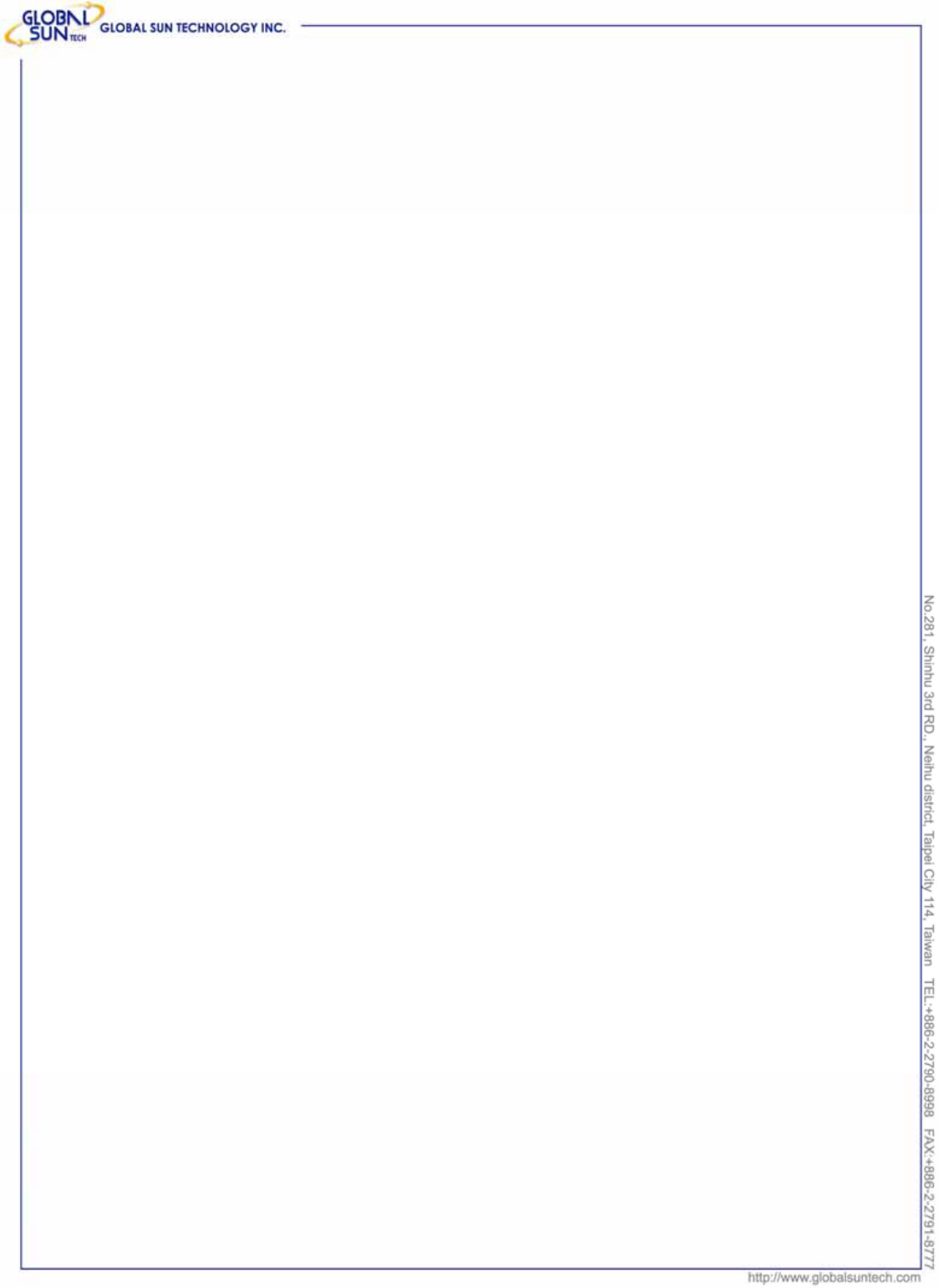
2. Turn on the computer. Insert the CD into the CD-ROM Drive. Please select
“USB Dongle” and then click the “Install”.
InstallShield Wizard will automatically start. Please click “Next” to continue.
22
5
GST Confidential
Product: IEEE 802.11g 54Mbps Wireless USB Dongle
Model: WL UD 2454 18S0
3. Setup WLAN Driver and Utility. Please click “Next “ to continue.
If user wants to change the installation folder, press “Brower” to change the
directory or press “Next” to continue.
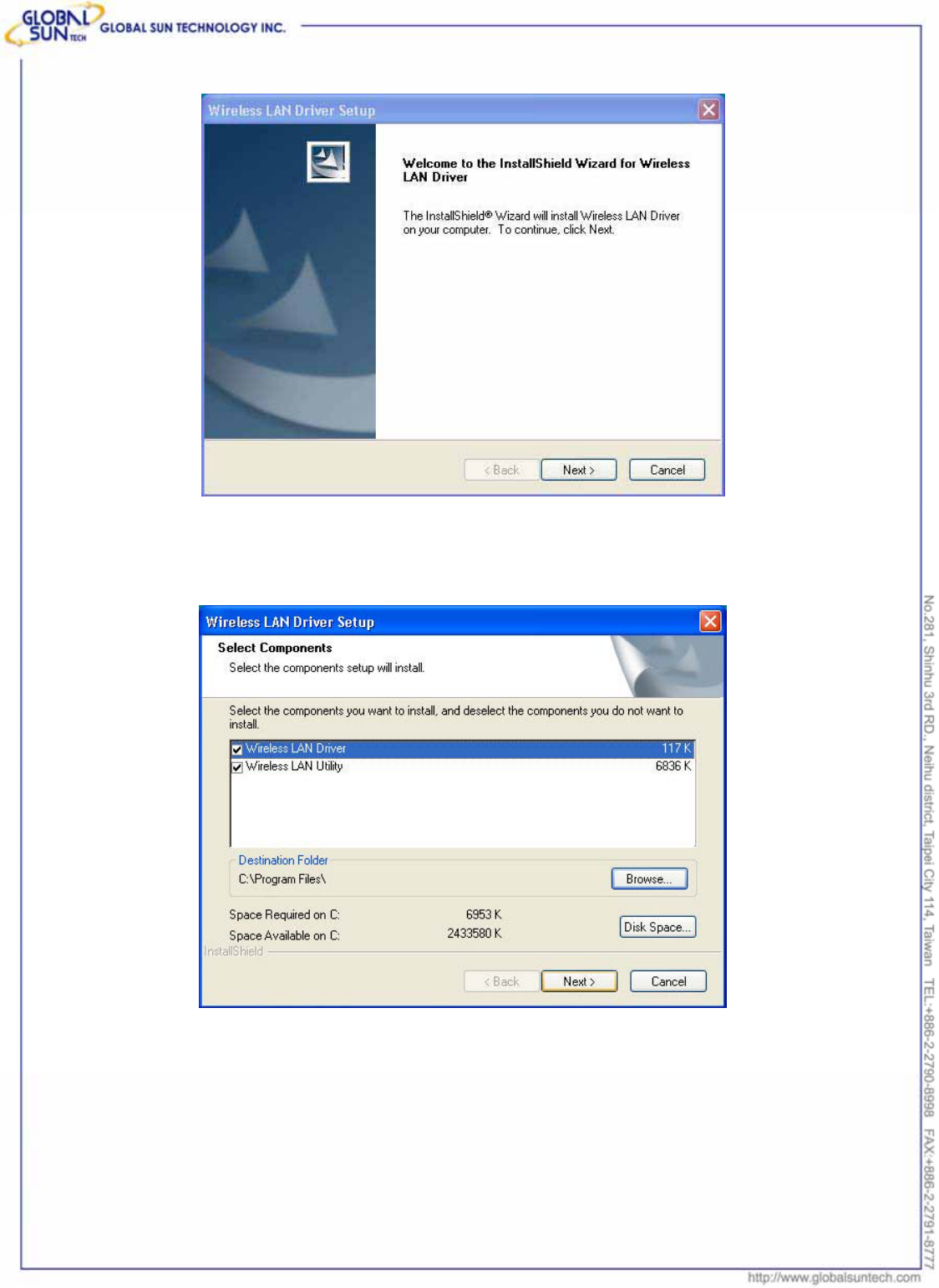
4. Click “Finish“ to complete installation.
22
6
GST Confidential
Product: IEEE 802.11g 54Mbps Wireless USB Dongle
Model: WL UD 2454 18S0
5. After installing Utility, insert the 802.11g Wireless USB Dongle into the USB
receptacle. Window 2000/XP will detect the device automatically.
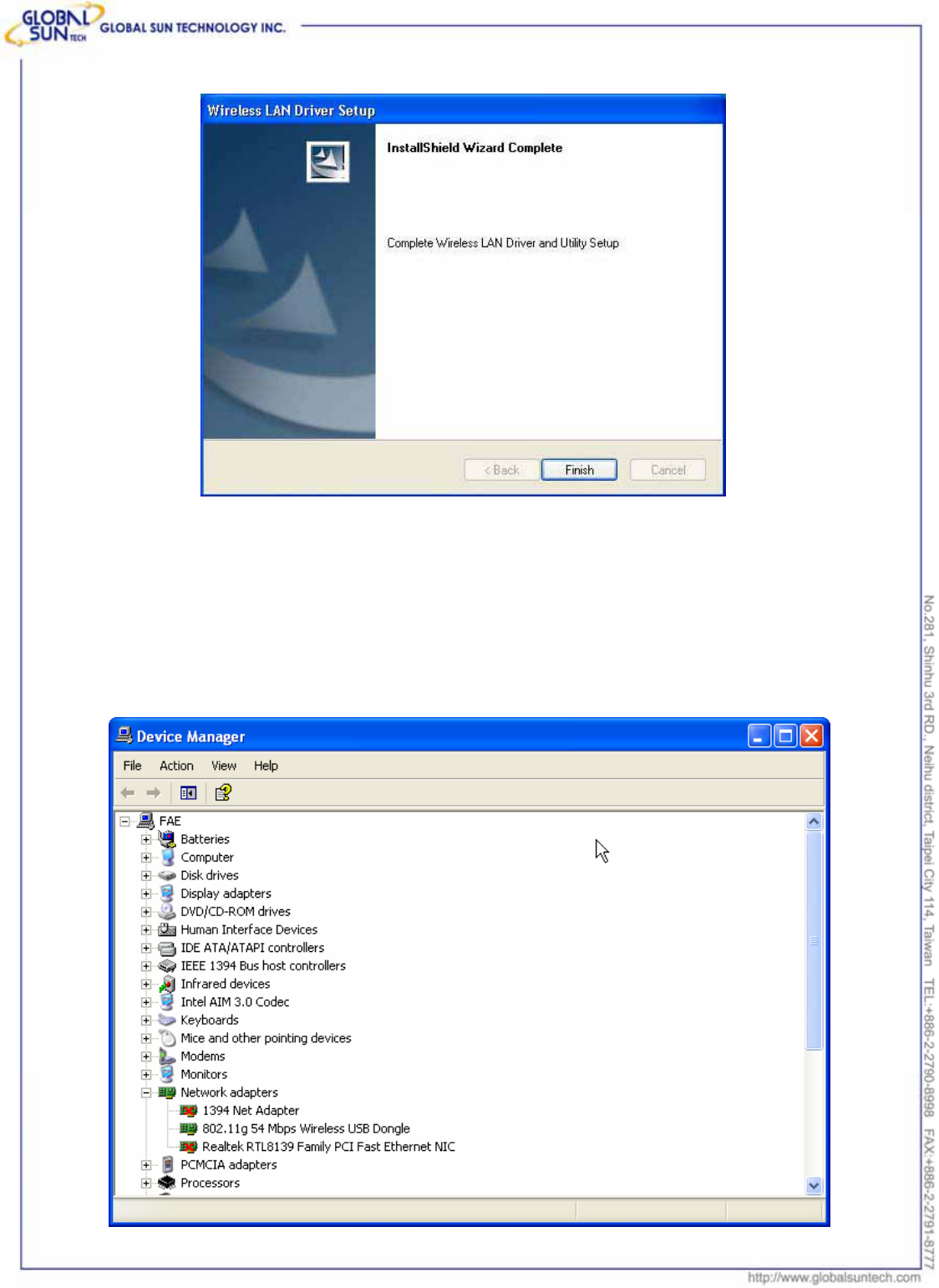
6. To make sure if the installation is successful, please check it through the
device management.
22
7
GST Confidential

Product: IEEE 802.11g 54Mbps Wireless USB Dongle
Model: WL UD 2454 18S0
7. Once the installation is successful, a utility program icon will show in the
taskbar. To lunch the utility, just double click the icon.
22
8
GST Confidential
Product: IEEE 802.11g 54Mbps Wireless USB Dongle
Model: WL UD 2454 18S0
3. Configuration
3.1 Net Status
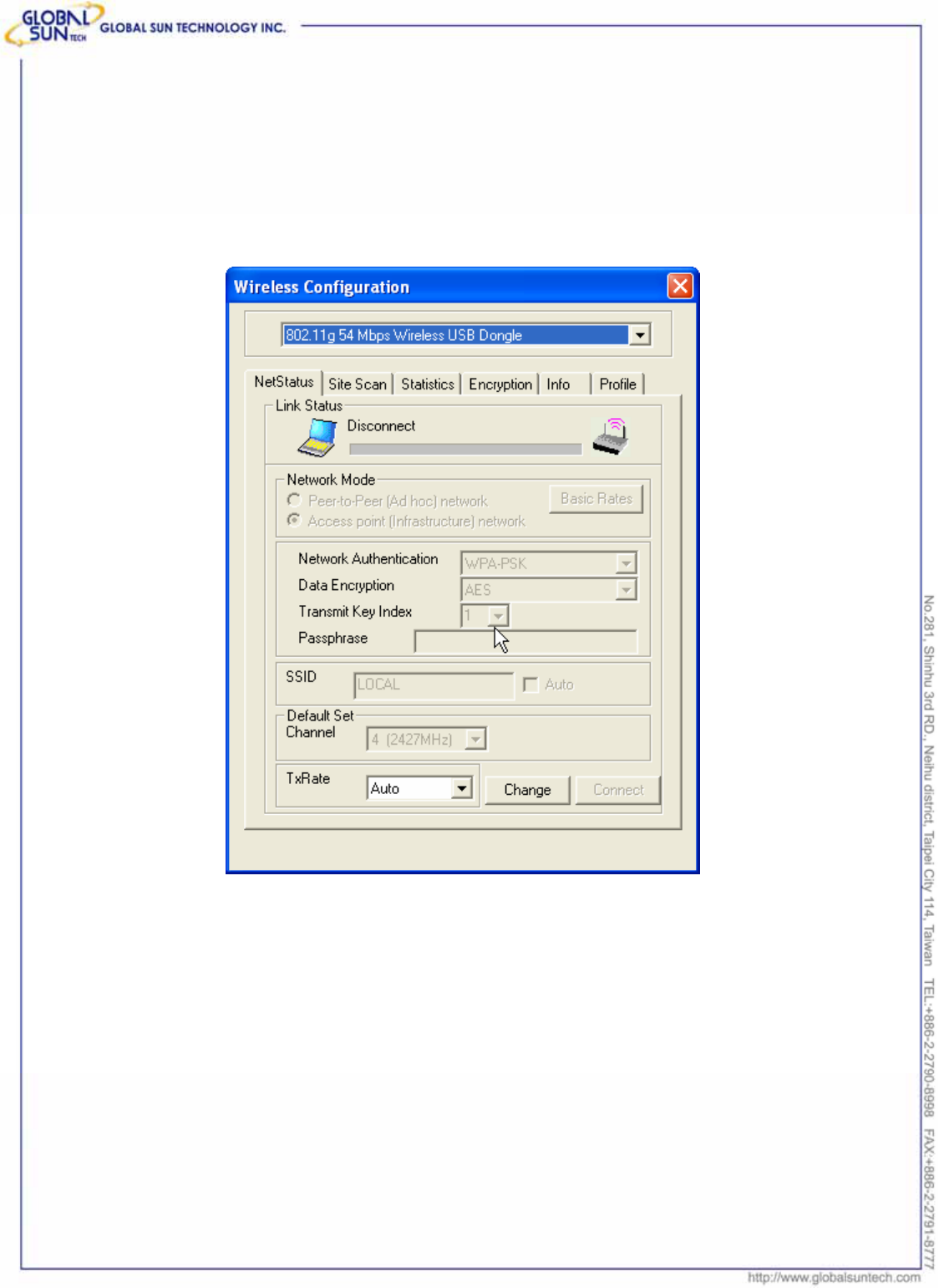
The default page is as below after launch the Utility program.
Link Status: Shows the network linking status.
Network Mode: Shows the current wireless mode used for wireless
communication, including Peer to Peer and Access point network. User can also
change Transmit/Receive Rate via press “Basic Rates” button, it’s not
recommended to change the settings.
Network Authentication: Shows the current encryption mode used for wireless
networking.
z Data encryption: Open System, Share-Key System, Auto Switch and WPA-PSK
z Transmit Key Index: The channel responding to the access point or router.
z Passphrase: Value of the encryption key.
22
9
GST Confidential
Product: IEEE 802.11g 54Mbps Wireless USB Dongle
Model: WL UD 2454 18S0
SSID: Shows the SSID associated, which must be same as the AP in order to
establish the communication.
Default Set Channel: Shows the current associated channel.
TxRate: Shows the current transmitting data rate. Default set in auto. It can be
changed by selecting available data rate. It’s not recommended to change the
settings.
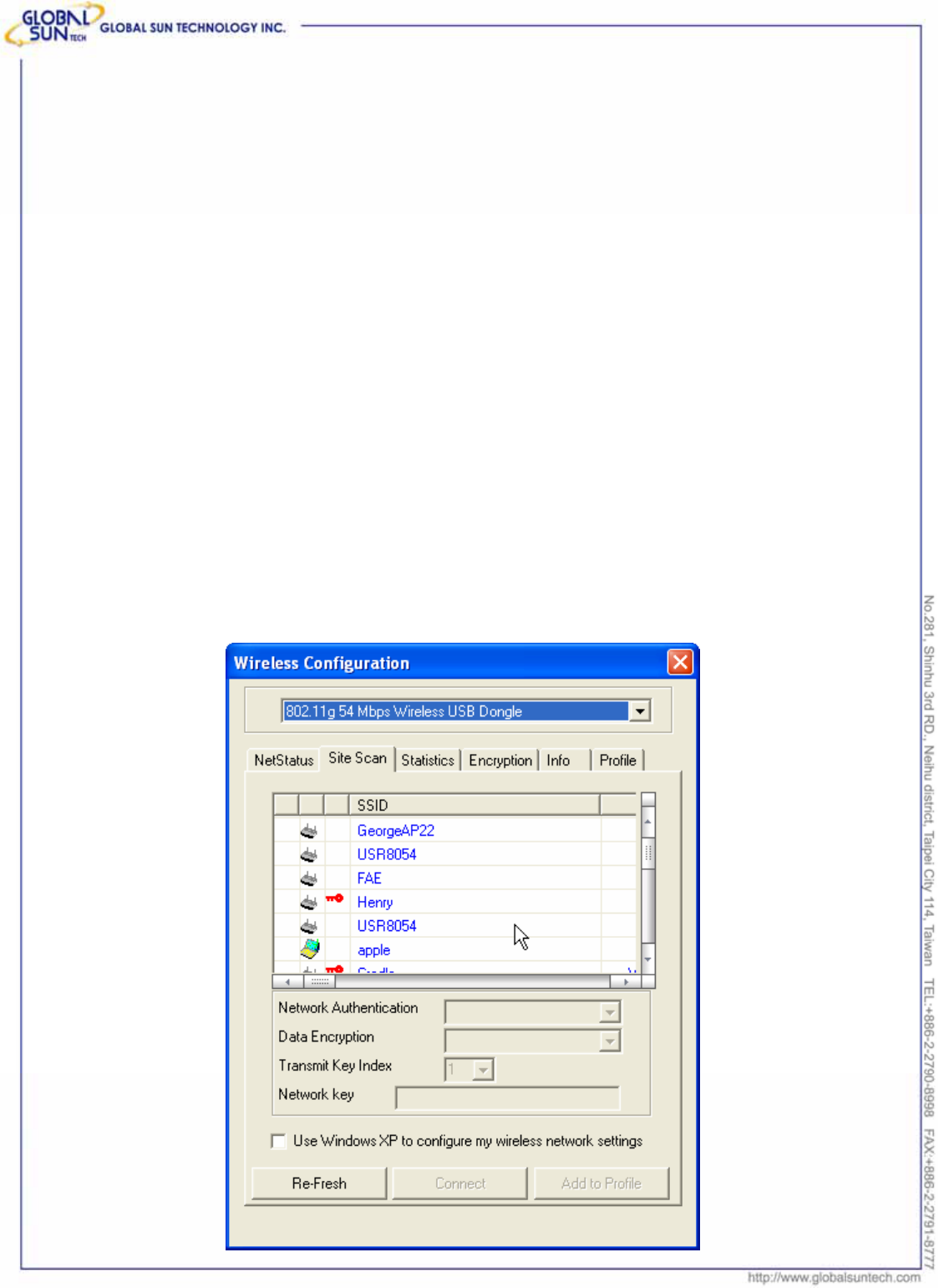
3.2 Site Scan
This page allows to enable the site scan function to scan for the available
wireless network (Wireless clients and Access Points ) and establish the
wireless communication with one.
Users can choose one of the networking devices first, key in properly information
required by the device (it might be an access point, wireless router or another
wireless lan card), press “connect” to start connection.
22
10
GST Confidential
Product: IEEE 802.11g 54Mbps Wireless USB Dongle
Model: WL UD 2454 18S0
SSID: Service Set Identifier, which is a unique name shared among all clients
and nodes in a wireless network. The SSID must be identical for each clients
and nodes in the wireless network.
Network Authentication: 4 options are available.
z Open system: the sender and receiver do not share secret key for communication.
Instead, each party generates its own key-pairs and asks the other party to accept it.
The key is regenerated when the connection is established every time.
z Shared-Key system: the sender and receiver share the common key for data
communication and the key are used for extended the time length.
z Auto Switch: depends on the communication to establish, and automatically use the
proper authentication mode.
z WPA-PSK: It’s a new encryption technology, but not all the access point or router
supports this function.
Data Encryption: While using WPA-PSK, there are two encryption way to do
enable, TKIP and AES.
Transmit Key Index: select one of the 4 keys to use.
Network Key: enter values to these fields, either in HEX or ASCII formats.
Use Window XP to configure my wireless network settings: Check the box
to use the Window XP “Zero Configuration” program to configure the settings,
instead of this utility. Use the default utility with the box unchecked.
22
11
GST Confidential
Product: IEEE 802.11g 54Mbps Wireless USB Dongle
Model: WL UD 2454 18S0
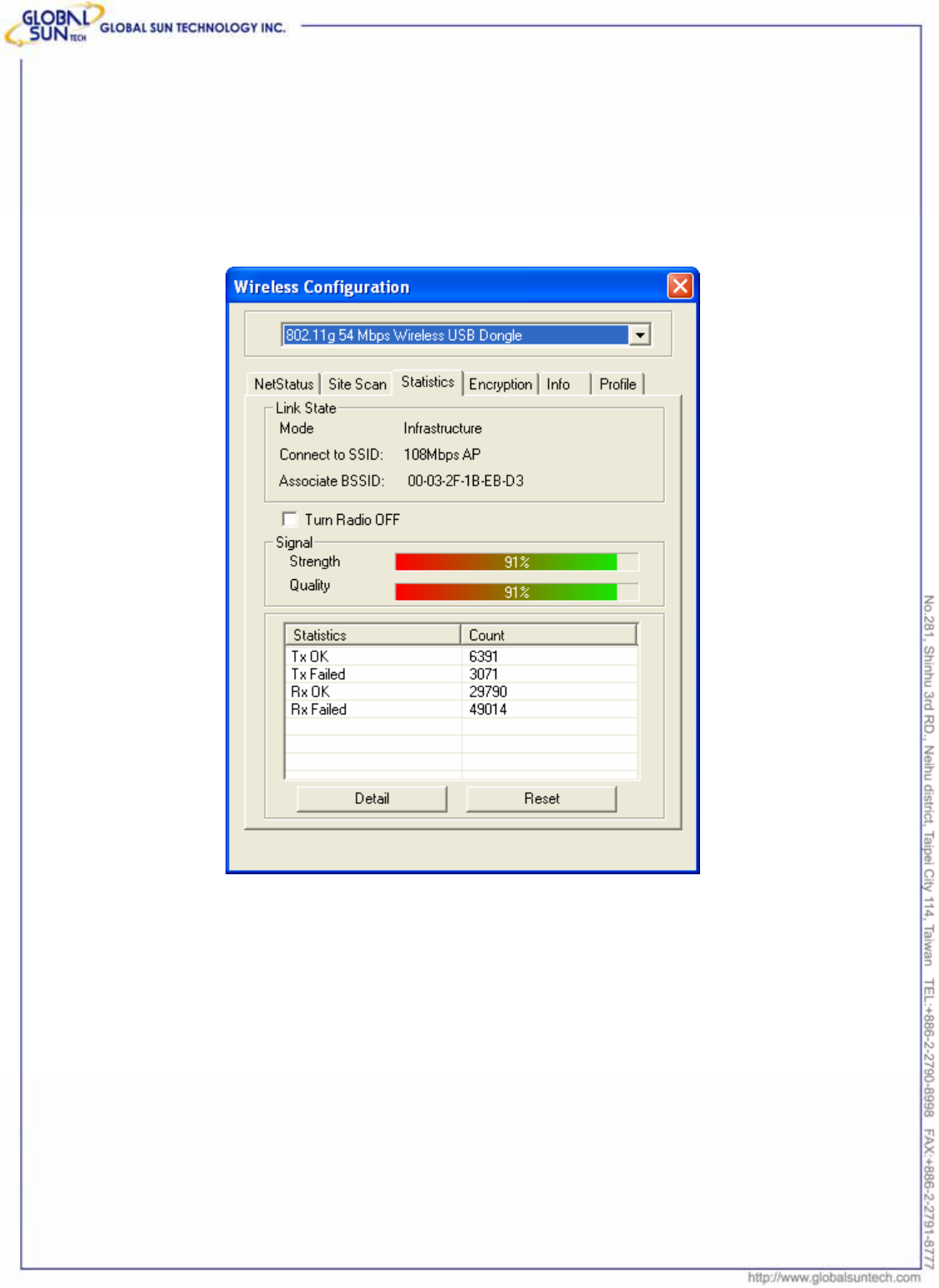
3.3 Statistics
This is the page shows the linking information, signal strength and quality.
Further more, user can see transmit and receive statistics. If check the Turn
Radio Off, the radio interface will be turned off.
Link Quality: Shows the link quality of the 802.11g wireless LAN USB Dongle
with the Access Point when operating under Infrastructure mode.
Signal Strength: Shows the wireless signal strength of the connection between
the 802.11g Wireless LAN USB Dongle with the Access Point.
Statistics & Count: Shows the statistics of data transfer.
22
12
GST Confidential
Product: IEEE 802.11g 54Mbps Wireless USB Dongle
Model: WL UD 2454 18S0
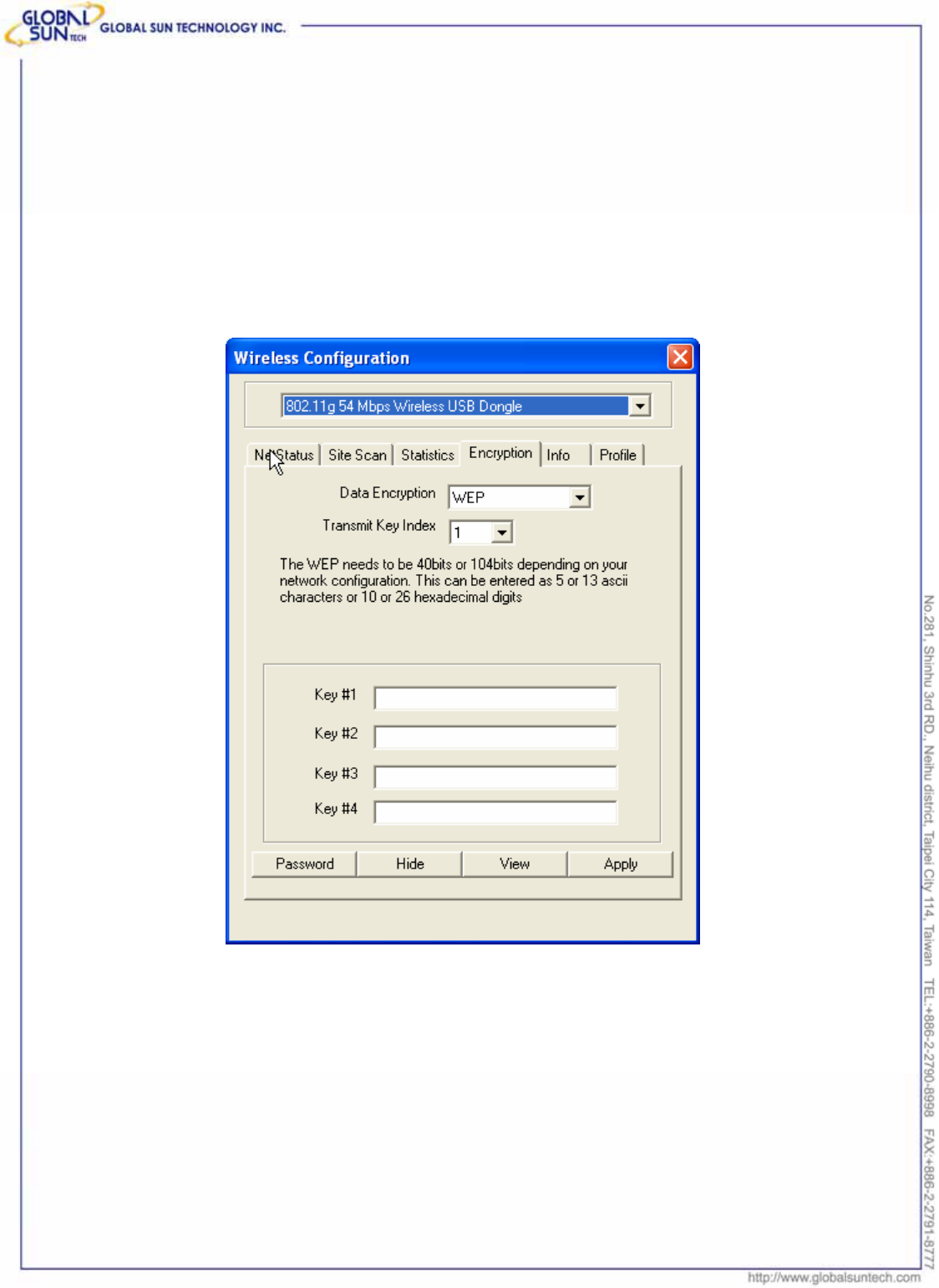
3.4 Encryption
This is the page where configures the encryption settings of 802.11g 54Mbps
Wireless USB Dongle. Users can see the original encryption value with clicking
on the “View” button, “Password” to change the value, “Hide” to make the
password invisible, and “Apply” to make the new settings change.
22
13
GST Confidential
Product: IEEE 802.11g 54Mbps Wireless USB Dongle
Model: WL UD 2454 18S0
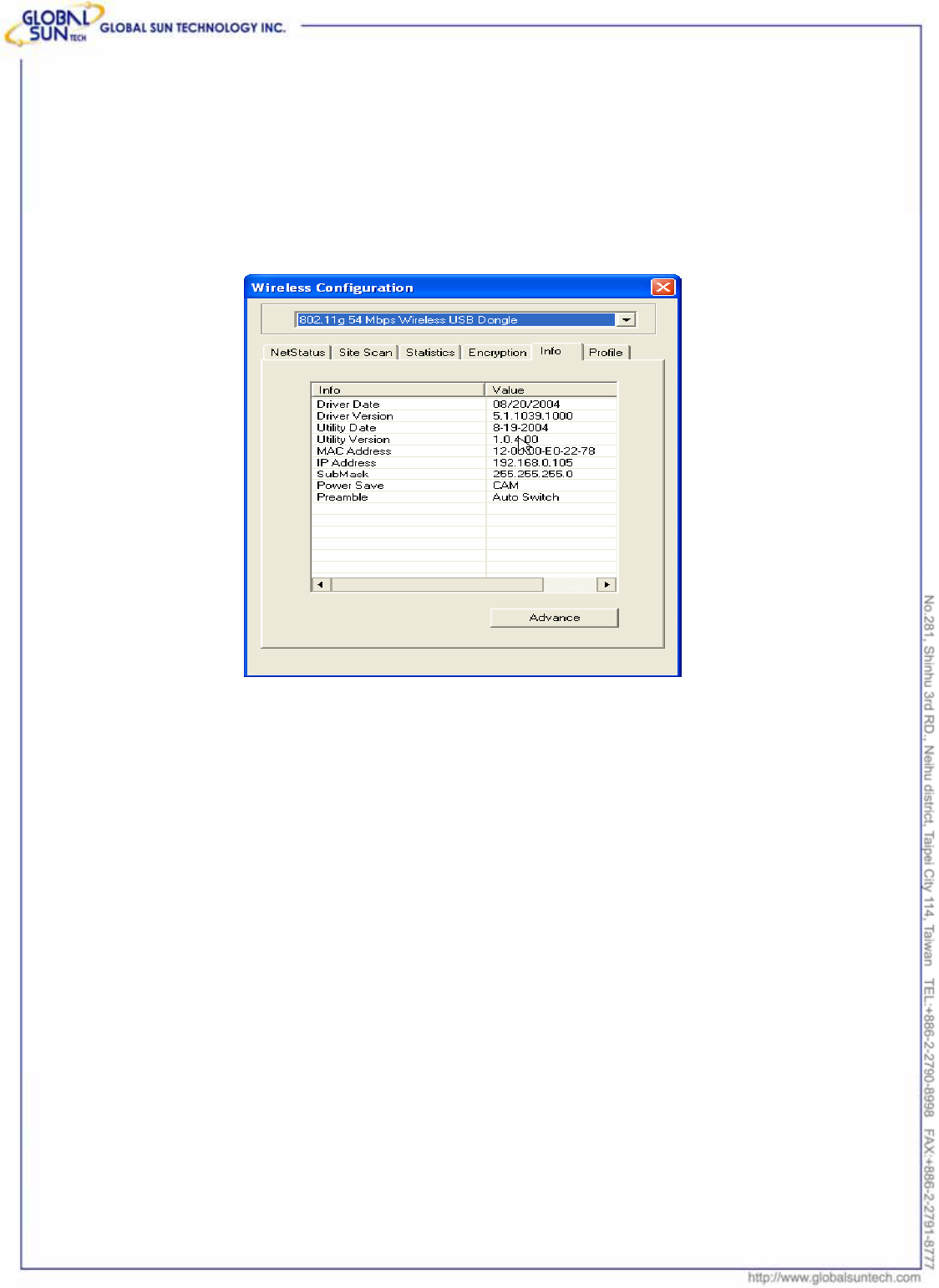
3.5 Info
This page displays some information about 802.11g 54Mbps Wireless USB
Dongle utility, which includes Driver Date, Driver Version, Utility Date, Utility
Version, MAC Address, IP Address, SubMask, Power Save and Preamble.
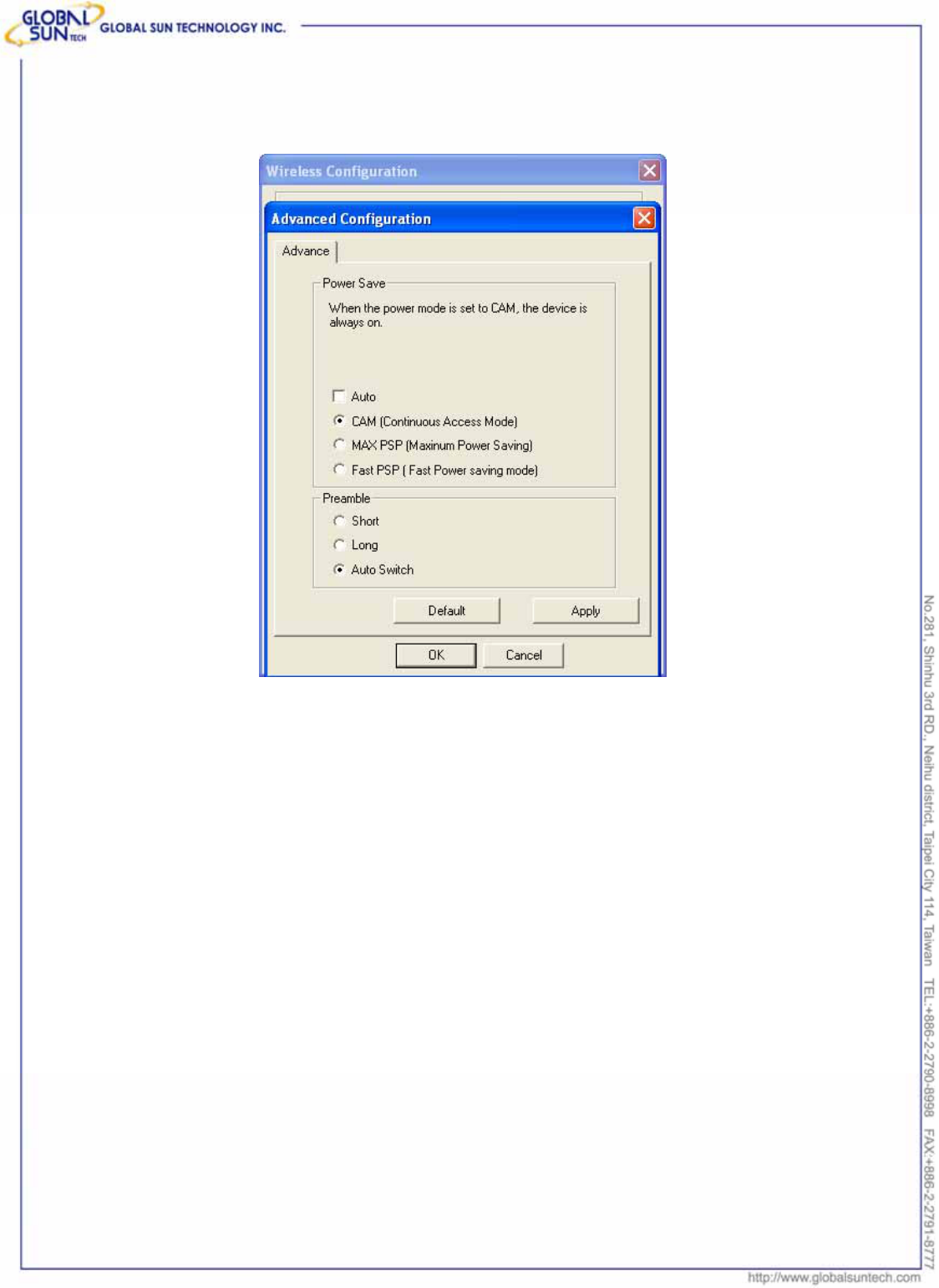
Advance: Users can enter the Advance property page to configure the settings
of Power Save and Preamble.
Power Save: There are 3 modes for power save, including CAM (Continuous
Access Mode), MAX PSP (Maximum Power Saving) and Fast PSP (Fast Power
Saving). The default setting is CAM (Continuous Access Mode).
Preamble: There are 3 options for Preamble, including Long, Short and Auto
Switch, and default setting is Auto Switch.
z Short Preamble: Transmit data with Short Preamble, with enable this function, the
transmit speed will lower than Long preamble format, but not so easily impacted by
interference as Long Preamble.
z Long Preamble: Transmit data with Long Preamble, with enable this function, the
transmit speed will higher than Short Preamble format, but easily impacted by
interference.
z Auto Switch: Driver will choose the properly preamble format depends on the outside
interference automatically. The default setting for Preamble is Auto Switch, and
22
14
GST Confidential
Product: IEEE 802.11g 54Mbps Wireless USB Dongle
Model: WL UD 2454 18S0
recommended not been changed.
22
15
GST Confidential
Product: IEEE 802.11g 54Mbps Wireless USB Dongle
Model: WL UD 2454 18S0
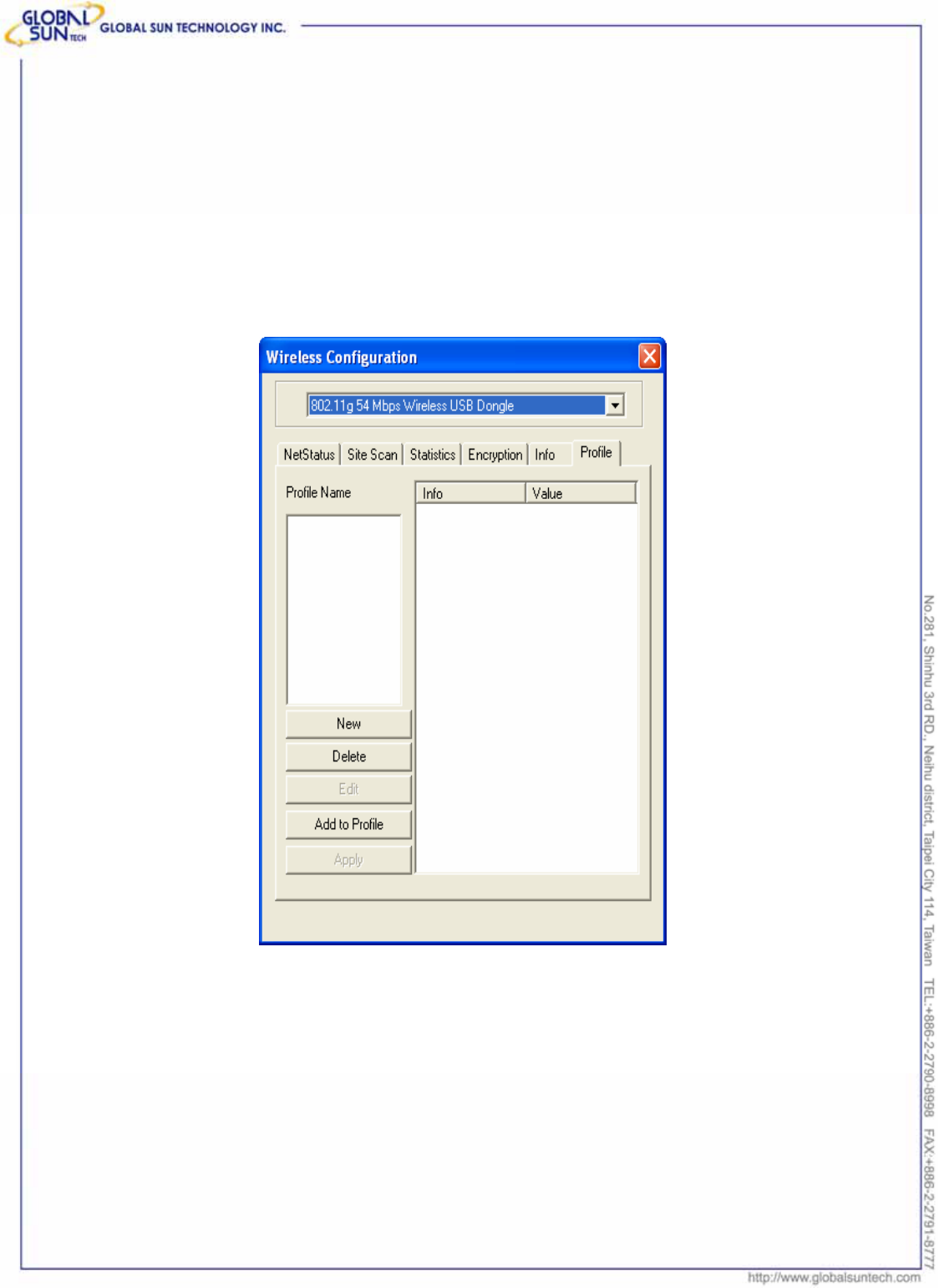
3.6 Profile
This page is for creating, editing, and deleting any available networks to the
profile. Once add new profile to the table, users can access the networking
devices without redundant effort, Wireless USB Dongle will link to the device
based on the profile automatically.
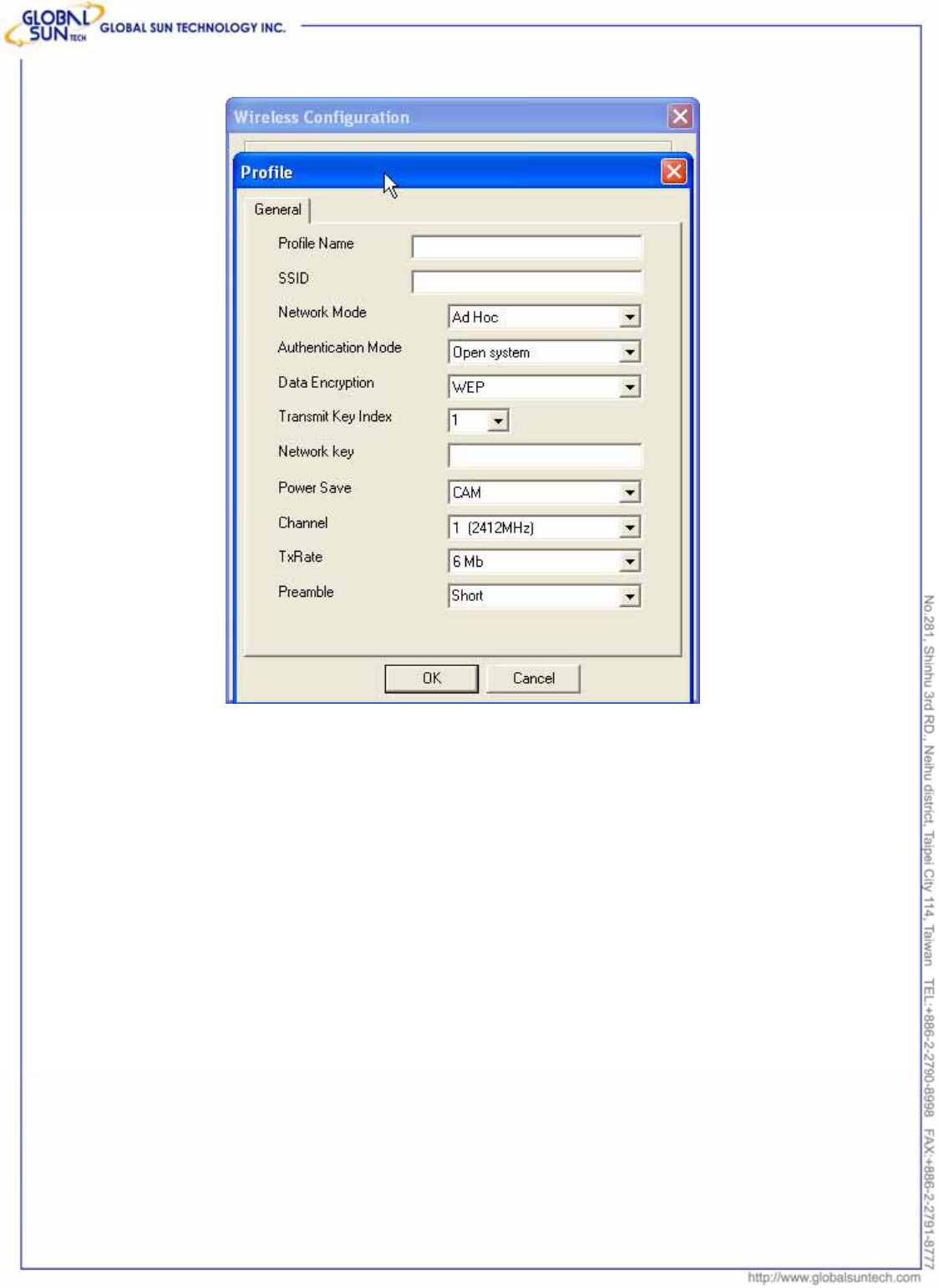
The profile information is the same as the previous settings. Users can configure
the Profile Name, SSID, Network Mode, and other items as the following picture.
22
16
GST Confidential
Product: IEEE 802.11g 54Mbps Wireless USB Dongle
Model: WL UD 2454 18S0
22
17
GST Confidential
Product: IEEE 802.11g 54Mbps Wireless USB Dongle
Model: WL UD 2454 18S0
4. Glossary
Access Point: An internetworking device that seamlessly connects wired and
wireless networks.
Ad-Hoc: An independent wireless LAN network formed by a group of computers,
each with a network adapter.
AP Client: One of the additional AP operating modes offered by 54Mbps Access
Point, which allows the Access Point to act as an Ethernet-to-Wireless Bridge,
thus a LAN or a single computer station can join a wireless ESS network through
it.
ASCII: American Standard Code for Information Interchange, ASCII, is one of
the two formats that you can use for entering the values for WEP key. It
represents English letters as numbers from 0 to 127.
Authentication Type: Indication of an authentication algorithm which can be
supported by the Access Point:
1. Open System: Open System authentication is the simplest of the available
authentication algorithms. Essentially it is a null authentication algorithm. Any
station that requests authentication with this algorithm may become
authenticated if 802.11 Authentication Type at the recipient station is set to
Open System authentication.
2. Shared Key: Shared Key authentication supports authentication of stations as
either a member of those who knows a shared secret key or a member of those
who does not.
Backbone: The core infrastructure of a network, which transports information
from one central location to another where the information is unloaded into a
local system.
Bandwidth: The transmission capacity of a device, which is calculated by how
much data the device can transmit in a fixed amount of time expressed in bits
per second (bps).
Beacon: A beacon is a packet broadcast by the Access Point to keep the
network synchronized. Included in a beacon are information such as wireless
LAN service area, the AP address, the Broadcast destination addresses, time
stamp, Delivery Traffic Indicator Maps, and the Traffic Indicator Message (TIM).
Bit: A binary digit, which is either -0 or -1 for value, is the smallest unit for data.
Bridge: An internetworking function that incorporates the lowest 2 layers of the
OSI network protocol model.
Browser: An application program that enables one to read the content and
interact in the World Wide Web or Intranet.
22
18
GST Confidential
Product: IEEE 802.11g 54Mbps Wireless USB Dongle
Model: WL UD 2454 18S0
BSS: BSS stands for “Basic Service Set”. It is an Access Point and all the LAN
PCs that associated with it.
Channel: The bandwidth which wireless Radio operates is divided into several
segments, which we call them “Channels”. AP and the client stations that it
associated work in one of the channels.
CSMA/CA: In local area networking, this is the CSMA technique that combines
slotted time -division multiplexing with carrier sense multiple access/collision
detection (CSMA/CD) to avoid having collisions occur a second time. This works
best if the time allocated is short compared to packet length and if the number of
situations is small.
CSMA/CD: Carrier Sense Multiple Access/Collision Detection, which is a LAN
access method used in Ethernet. When a device wants to gain access to the
network, it checks to see if the network is quiet (senses the carrier). If it is not, it
waits a random amount of time before retrying. If the network is quiet and two
devices access the line at exactly the same time, their signals collide. When the
collision is detected, they both back off and wait a random amount of time before
retrying.
DHCP: Dynamic Host Configuration Protocol, which is a protocol that lets
network administrators manage and allocate Internet Protocol (IP) addresses in
a network. Every computer has to have an IP address in order to communicate
with each other in a TCP/IP based infrastructure network. Without DHCP, each
computer must be entered in manually the IP address. DHCP enables the
network administrators to assign the IP from a central location and each
computer receives an IP address upon plugged with the Ethernet cable
everywhere on the network.
DSSS: Direct Sequence Spread Spectrum. DSSS generates a redundant bit
pattern for each bit to be transmitted. This bit pattern is called a chip (or chipping
code). The longer the chip, the greater the probability that the original data can
be recovered. Even if one or more bits in the chip are damaged during
transmission, statistical techniques embedded in the radio can recover the
original data without the need for retransmission. To an unintended receiver,
DSSS appears as low power wideband noise and is rejected (ignored) by most
narrowband receivers.
Dynamic IP Address: An IP address that is assigned automatically to a client
station in a TCP/IP network by a DHCP server.
Encryption: A security method that uses a specific algorithm to alter the data
transmitted, thus prevent others from knowing the information transmitted.
ESS: ESS stands for “Extended Service Set”. More than one BSS is configured
22
19
GST Confidential
Product: IEEE 802.11g 54Mbps Wireless USB Dongle
Model: WL UD 2454 18S0
to become Extended Service Set. LAN mobile users can roam between different
BSSs in an ESS.
ESSID: The unique identifier that identifies the ESS. In infrastructure association,
the stations use the same ESSID as AP’s to get connected.
Ethernet: A popular local area data communications network, originally
developed by Xerox Corp., that accepts transmission from computers and
terminals. Ethernet operates on a 10/100 Mbps base transmission rate, using
a shielded coaxial cable or over shielded twisted pair telephone wire.
Fragmentation: When transmitting a packet over a network medium,
sometimes the packet is broken into several segments, if the size of packet
exceeds that allowed by the network medium.
Fragmentation Threshold: The Fragmentation Threshold defines the number
of bytes used for the fragmentation boundary for directed messages. The
purpose of "Fragmentation Threshold" is to increase the transfer reliability thru
cutting a MAC Service Data Unit (MSDU) into several MAC Protocol Data Units
(MPDU) in smaller size. The RF transmission can not allow to transmit too big
frame size due to the heavy interference caused by the big size of transmission
frame. But if the frame size is too small, it will create the overhead during the
transmission.
Gateway: a device that interconnects networks with different, incompatible
communication protocols.
HEX: Hexadecimal, HEX, consists of numbers from 0 – 9 and letters from A – F.
IEEE: The Institute of Electrical and Electronics Engineers, which is the largest
technical professional society that promotes the development and application of
electrotechnology and allied sciences for the benefit of humanity, the
advancement of the profession. The IEEE fosters the development of standards
that often become national and international standards.
Infrastructure: An infrastructure network is a wireless network or other small
network in which the wireless network devices are made a part of the network
through the Access Point which connects them to the rest of the network.
ISM Band: The FCC and their counterparts outside of the U.S. have set aside
bandwidth for unlicensed use in the ISM (Industrial, Scientific and Medical) band.
Spectrum in the vicinity of 2.4GHz, in particular, is being made available
worldwide.
MAC Address: Media Access Control Address is a unique hex number
assigned by the manufacturer to any Ethernet networking device, such as a
network adapter, that allows the network to identify it at the hardware level.
Multicasting: Sending data to a group of nodes instead of a single destination.
22
20
GST Confidential
Product: IEEE 802.11g 54Mbps Wireless USB Dongle
Model: WL UD 2454 18S0
Multiple Bridge – One of the additional AP operating modes offered by 54Mbps
Access Point, which allows a group of APs that consists of two or more APs to
connect two or more Ethernet networks or Ethernet enabled clients together.
The way that multiple bridge setups is based on the topology of Ad-Hoc mode.
Node: A network junction or connection point, typically a computer or
workstation.
Packet: A unit of data routed between an origin and a destination in a network.
PLCP: Physical layer convergence protocol
PPDU: PLCP protocol data unit
Preamble Type: During transmission, the PSDU shall be appended to a PLCP
preamble and header to create the PPDU. Two different preambles and headers
are defined as the mandatory supported long preamble and header which
interoperates with the current 1 and 2 Mbit/s DSSS specification as described in
IEEE Std 802.11-1999, and an optional short preamble and header. At the
receiver, the PLCP preamble and header are processed to aid in demodulation
and delivery of the PSDU. The optional short preamble and header is intended
for application where maximum throughput is desired and interoperability with
legacy and non-short-preamble capable equipment is not consideration. That is,
it is expected to be used only in networks of like equipment that can all handle
the optional mode. (IEEE 802.11b standard)
PSDU: PLCP service data unit
Roaming: A LAN mobile user moves around an ESS and enjoys a continuous
connection to an Infrastructure network.
RTS: Request To Send. An RS-232 signal sent from the transmitting station to
the receiving station requesting permission to transmit.
RTS Threshold: Transmitters contending for the medium may not be aware of
each other. RTS/CTS mechanism can solve this “Hidden Node Problem”. If the
packet size is smaller than the preset RTS Threshold size, the RTS/CTS
mechanism will NOT be enabled.
SSID: Service Set Identifier, which is a unique name shared among all clients
and nodes in a wireless network. The SSID must be identical for each clients
and nodes in the wireless network.
Subnet Mask: The method used for splitting IP networks into a series of
sub-groups, or subnets. The mask is a binary pattern that is matched up with the
IP address to turn part of the host ID address field into a field for subnets.
TCP/IP: Transmission Control Protocol/ Internet Protocol. The basic
communication language or protocol of the Internet. It can also be used as a
communications protocol in a private network, i.e. intranet or internet. When you
22
21
GST Confidential
Product: IEEE 802.11g 54Mbps Wireless USB Dongle
Model: WL UD 2454 18S0
are set up with direct access to the Internet, your computer is provided with a
copy of the TCP/IP program just as every other computer that you may send
messages to or get information from also has a copy of TCP/IP.
Throughput: The amount of data transferred successfully from one point to
another in a given period of time.
WEP: Wired Equivalent Privacy (WEP) is an encryption scheme used to protect
wireless data communication. To enable the icon will prevent other stations
without the same WEP key from linking with the AP.
Wireless Bridge – One of the additional AP operating modes offered by
54mpbs Access Point, which allows a pair of APs to act as the bridge that
connects two Ethernet networks or Ethernet enabled clients together.
22
22
GST Confidential
Federal Communication Commission Interference Statement
This equipment has been tested and found to comply with the limits for
a Class B digital device, pursuant to Part 15 of the FCC Rules. These
limits are designed to provide reasonable protection against harmful
interference in a residential installation. This equipment generates,
uses and can radiate radio frequency energy and, if not installed and
used in accordance with the instructions, may cause harmful
interference to radio communications. However, there is no guarantee
that interference will not occur in a particular installation. If this
equipment does cause harmful interference to radio or television
reception, which can be determined by turning the equipment off and
on, the user is encouraged to try to correct the interference by one of
the following measures:
- Reorient or relocate the receiving antenna.
- Increase the separation between the equipment and receiver.
- Connect the equipment into an outlet on a circuit different from that
to which the receiver is connected.
- Consult the dealer or an experienced radio/TV technician for help.
This device complies with Part 15 of the FCC Rules. Operation is
subject to the following two conditions: (1) This device may not cause
harmful interference, and (2) this device must accept any interference
received, including interference that may cause undesired operation.
FCC Caution: Any changes or modifications not expressly approved by
the party responsible for compliance could void the user's authority to
operate this equipment.
IMPORTANT NOTE:
FCC Radiation Exposure Statement:
This equipment complies with FCC radiation exposure limits set forth for an
uncontrolled environment.
This transmitter must not be co-located or operating in conjunction with any
other antenna or transmitter.
Highest SAR Value: 0.273W/kg