HON HAI PRECISION IND T60H929 USB RF Module User Manual T60H929 00
HON HAI Precision Ind. Co., Ltd. USB RF Module T60H929 00
Users Manual
1
U S E R ’ S M A N U A L
T60H929.00
USB2.0 WLAN CARD
2
Contents
SECTION ONE: INTRODUCTION............................................................................................3
1.1 FEATURES ............................................................................................................................... 3
1.1.1 WIRELESS LAN FUNCTION ...................................................................................................... 3
1.2:FCC NOTICE ..................................................................................................................................4
1.2.1 FCC COMPLIANCE ...................................................................................錯誤! 尚未定義書籤。
1.2.2 FCC CLASS B STATEMENT.......................................................................錯誤! 尚未定義書籤。
SECTION TWO: WIRELESS UTILITY AND CONFIGURATION.......................................5
2-1 WINDOWS 98/ME/2000 WIRELESS UTILITY...................................................................................... 5
SECTION THREE: WINDOWS XP WIRELESS UTILITY AND CONFIGURATION.......... 10
3-1 WINDOWS XP WIRELESS UTILITY................................................................................................... 10
APPENDIX A GLOSSARY................................................................................................................16
The information contained in this manual has been verified at the time of this manual printing. The
manufacturer reserves the right to make any changes and improvements in the product described in this
manual at any time and without notice.
All registered trademarks are the property of their respective owners.

HON HAI PRECISION IND. CO., LTD.
3
Section One: Introduction
The Wireless 802.11b/g USB2.0 Module is available 54 Mbps solution in the 2.4-GHz band, compatible with
the IEEE 802.11b standard , the 802.11g standard USB2.0 Specification and USB Electro mechanical
Specification Revision 2.0. It allow user to switch to different vendors’ Access Points through the wireless
networks and to prevent from eavesdropping. The 802.11g data rate provides for 54, 48, 36, 24, 18, 12, 9,
6Mbps, and 802.11b data rate provides for 11,5.5,2,1 Mbps. The 802.11g mode supports encryption using
both 64-bit or 128-bit WEP.
1.1 Features
1.1.1 Wireless LAN Function
Form Factor & Bus Interface Form Factor : Not standard, Interface: USB 2.0.
Wireless LAN Compliance Compatible with IEEE 802.11b standard and IEEE802.11g
standard and USB2.0 Specification.
Operating Frequency 2.4 ~ 2.497GHz ISM band
Modulation Schemes 802.11g:
64QAM(54Mbps,48Mbps),16QAM(36Mbps, 24Mbps),
QPSK(18Mbps,12Mbps), BPSK(9Mbps, 6Mbps)
802.11b:
CCK (11 Mbps, 5.5Mbps), DQPSK (2 Mbps), DBPSK (1 Mbps)
Channel Numbers IEEE 802.11b compliant
1 ~ 11 channels for United States
1 ~ 13 channels for Europe
1 ~ 13 or 14 channels for Japan
WLAN Data Rate The IEEE802.11g data rate provides for 54 auto fallback 48,
36, 24, 18, 12, 9, 6 and IEEE802.11b data rate provides for 11
auto fallback to 5.5, 2 and 1Mbps.
Spreading 11-chip Barker Sequence
Media Access Protocol CSMA/CA with ACK
Transmitter Output Power Typ. 802.11b 17.5+/-1.5 dBm
Typ. 802.11g 13.5+/-1.5 dBm
Antenna Type Integrated diversity switch with Printed Antenna.
Operating Voltage 5.0VDC
Radio On / Off
Dynamic Rate Shifting Automatic fallback
Network Architecture Ad-hoc, Infrastructure
Operating Systems Windows 98/Me/2000/XP

HON HAI PRECISION IND. CO., LTD.
4
1.2 FCC Notice
Federal Communication Commission Interference Statement
This equipment has been tested and found to comply with the limits for a Class B digital device, pursuant to Part
15 of the FCC Rules. These limits are designed to provide reasonable protection against harmful interference in
a residential installation. This equipment generates, uses and can radiate radio frequency energy and, if not
installed and used in accordance with the instructions, may cause harmful interference to radio communications.
However, there is no guarantee that interference will not occur in a particular installation. If this equipment does
cause harmful interference to radio or television reception, which can be determined by turning the equipment
off and on, the user is encouraged to try to correct the interference by one of the following measures:
- Reorient or relocate the receiving antenna.
- Increase the separation between the equipment and receiver.
- Connect the equipment into an outlet on a circuit different from that
to which the receiver is connected.
- Consult the dealer or an experienced radio/TV technician for help.
This device complies with Part 15 of the FCC Rules. Operation is subject to the following two conditions: (1)
This device may not cause harmful interference, and (2) this device must accept any interference received,
including interference that may cause undesired operation.
FCC Caution: Any changes or modifications not expressly approved by the party responsible for compliance
could void the user's authority to operate this equipment.
IMPORTANT NOTE:
FCC Radiation Exposure Statement:
This equipment complies with FCC radiation exposure limits set forth for an uncontrolled environment.
This transmitter must not be co-located or operating in conjunction with any other antenna or transmitter.
FOXCONN declared that T60H929 is limited in CH1~11 from 2412 to 2462 MHz by specified firmware
controlled in USA.
1.3 Canada Notice
Industry Canada Statement
Operation is subject to the following two conditions:
1) this device may not cause interference and
2) this device must accept any interference, including interference that may cause undesired operation of the
device
To prevent radio interference to the licensed service, this device is intended to be operated indoors and away
from windows to provide maximum shielding.
Equipment (or its transmit antenna) that is installed outdoors is subject to licensing.
HON HAI PRECISION IND. CO., LTD.
5
Section Two: Wireless Utility and Configuration
The following sections describe the Wireless Network Configuration Utility. This utility provides quick access and
friendly interface to configure the card setup.
2-1 Windows 98/ME/2000 Wireless Utility
After installation is completed, a Wireless LAN Utility icon will appear in Desktop screen. Click it, then you will see the
screen below. If you cannot find the icon, you can select “Start” ->”Program”->”Wireless LAN Configuration Utility” Icon.
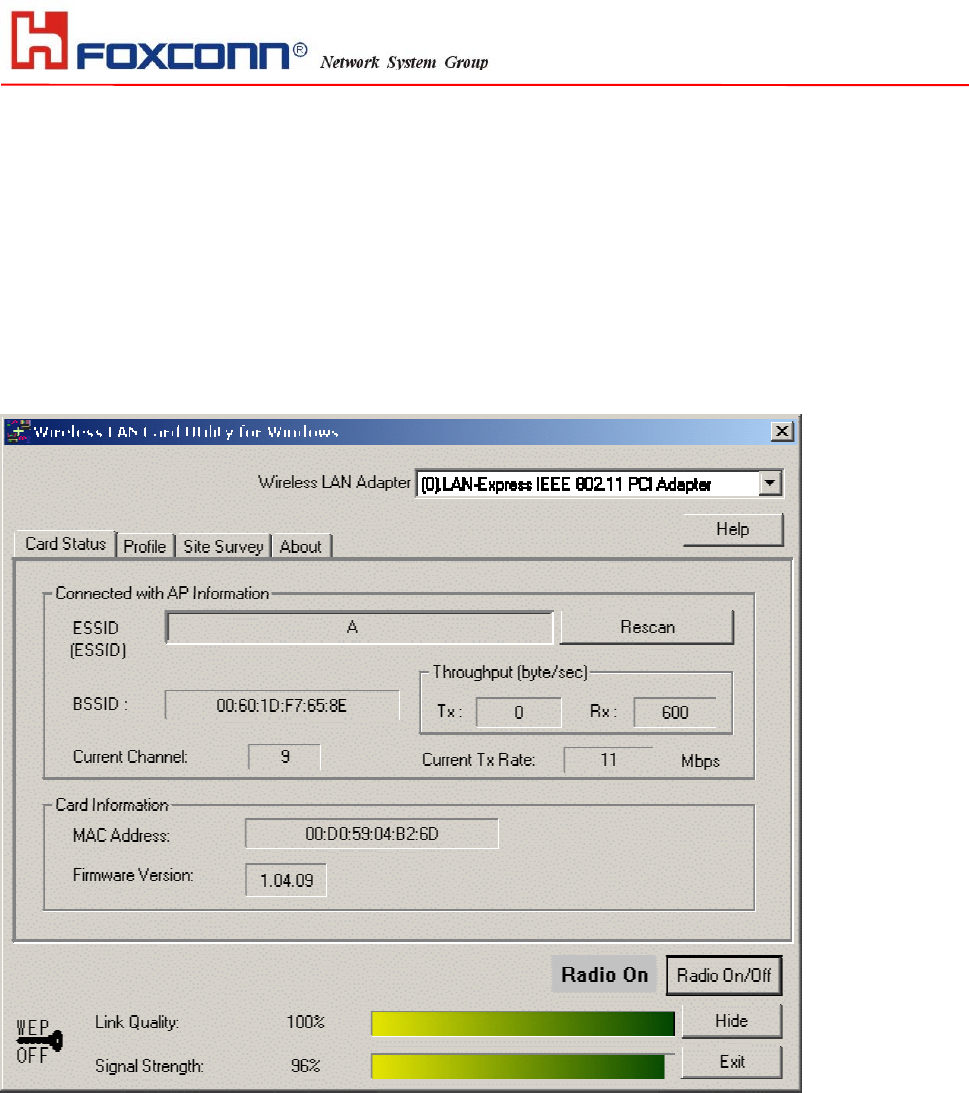
Card Status
You can see the AP information that your card connected. In this page you also can find Firmware Version , MAC Address
and Frequency Domain.
ESSID: An acronym for Extended Service Set Identifier, ESSID is the unique name shared among all clients and Access
Points in a wireless network. The ESSID must be identical for all clients or Access Points participating in the same network.
The ESSID is case sensitive and must not exceed 32 characters. Press ‘Rescan’ it will scan the specific ESSID that your
profile set. If your profile set the ESSID to be ANY, then while you press ‘Rescan’, it will scan AP in the nearby area and
choose the stronger one. From Link Quality and Signal Strength, you can tell the wireless transmission quality.
HON HAI PRECISION IND. CO., LTD.
6
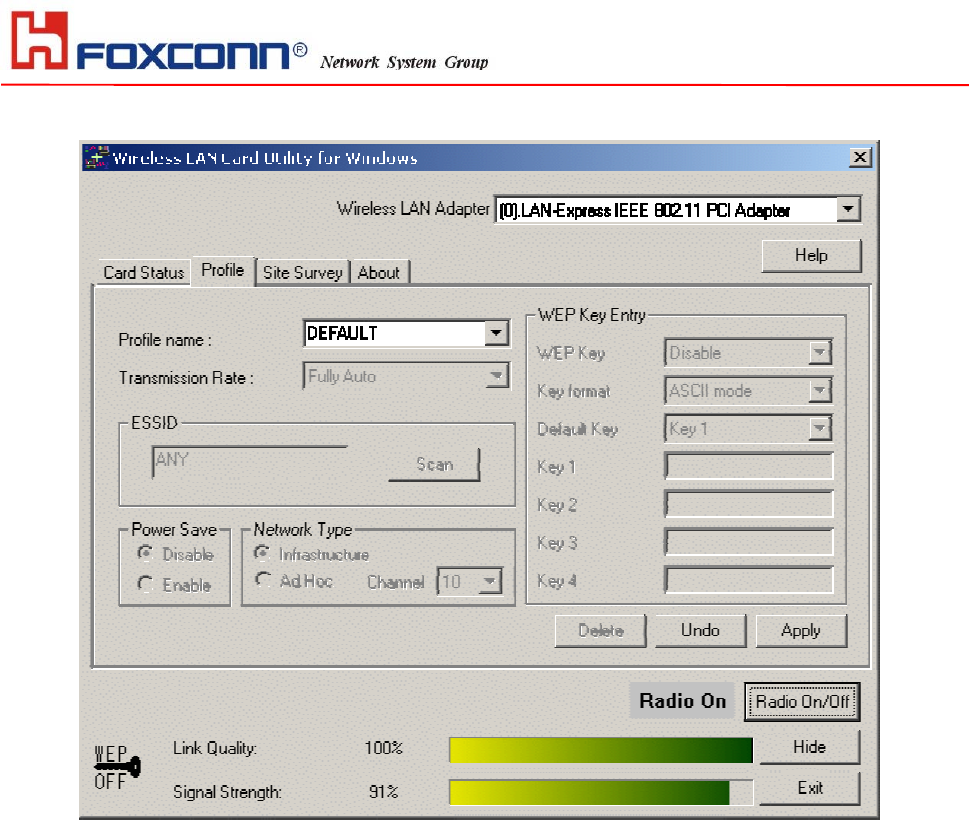
Profile
If you want to use default Profile setting, then choose the DEFAULT at profile name.
If you want to setup your own profile, then select PROFILE1 and you can change this PROFILE1 name to the one you like.
There are two network types:
Ad-Hoc: This mode is used for a simple peer-to-peer network. It offers file sharing between wireless clients without a
wireless Access Point (AP).
Infrastructure: This mode allows a wireless LAN to be integrated into an existing wired network through an AP.
Infrastructure type networks also permit roaming between Access Points while maintaining connection to all network
resources. Infrastructure mode provides additional features, such as WEP security, power saving and extended range.
ESSID: You can either choose specific AP or connect to any AP in the nearby area.
Power Save: enable it, so it will be triggered when your computer system is inactive.
HON HAI PRECISION IND. CO., LTD.
7
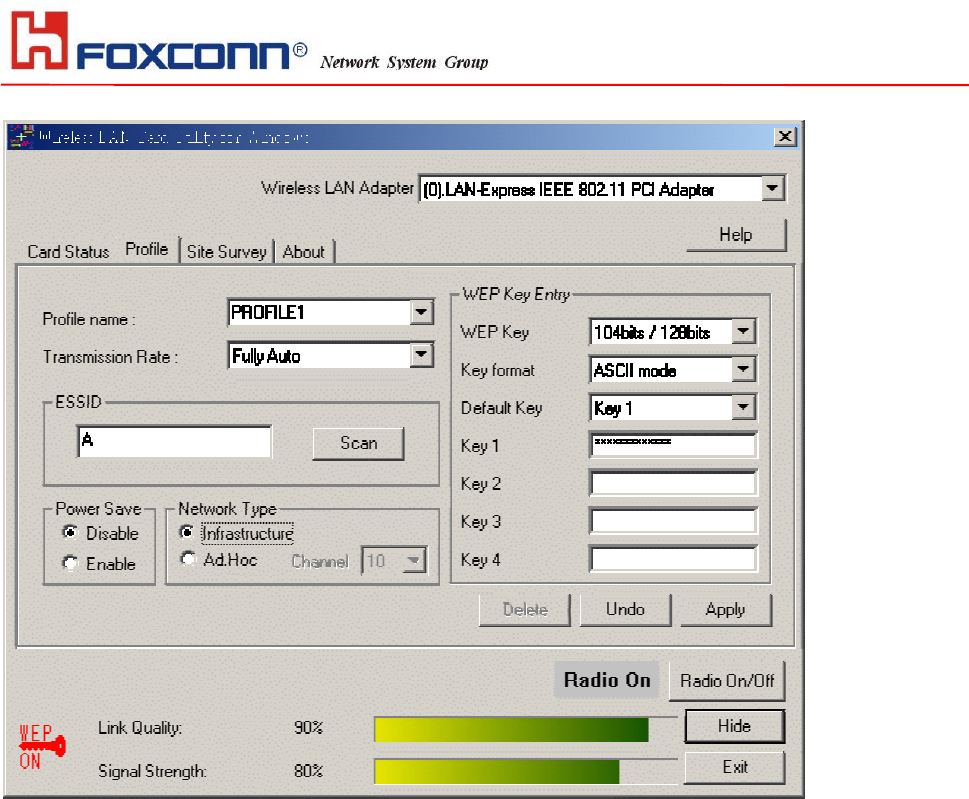
WEP Key: Wired Equivalent Privacy, WEP is an encryption scheme used to protect your wireless data communications.
WEP uses a combination of 40-bit keys,128-bit keys to provide data encryption for your wireless network. AP and wireless
card should use the same WEP key in order to communication.
KEY Format: You can choose to enter ASCII Characters (0~9, a~z, A~Z) or Hexadecimal number (0~9, a~f, A~F)
Default Key: The current KEY you choose.
KEY1~4: If you choose 40-bit keys, then you must enter 5 ASCII Characters or 10 Hexadecimal numbers. If you choose
128-bit keys, then you must enter 13 ASCII Characters or 26 Hexadecimal numbers.
HON HAI PRECISION IND. CO., LTD.
8
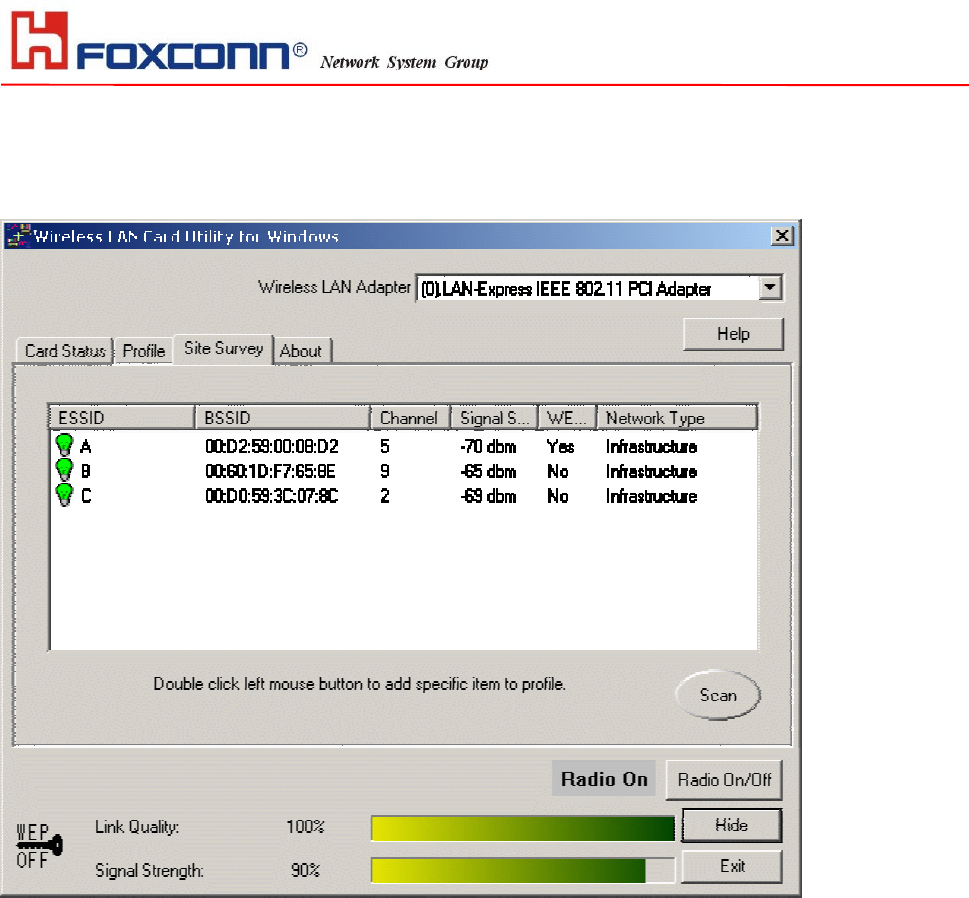
Site Survey
Use the Site Survey Tool. You can identify each channel transmission quality.
HON HAI PRECISION IND. CO., LTD.
9
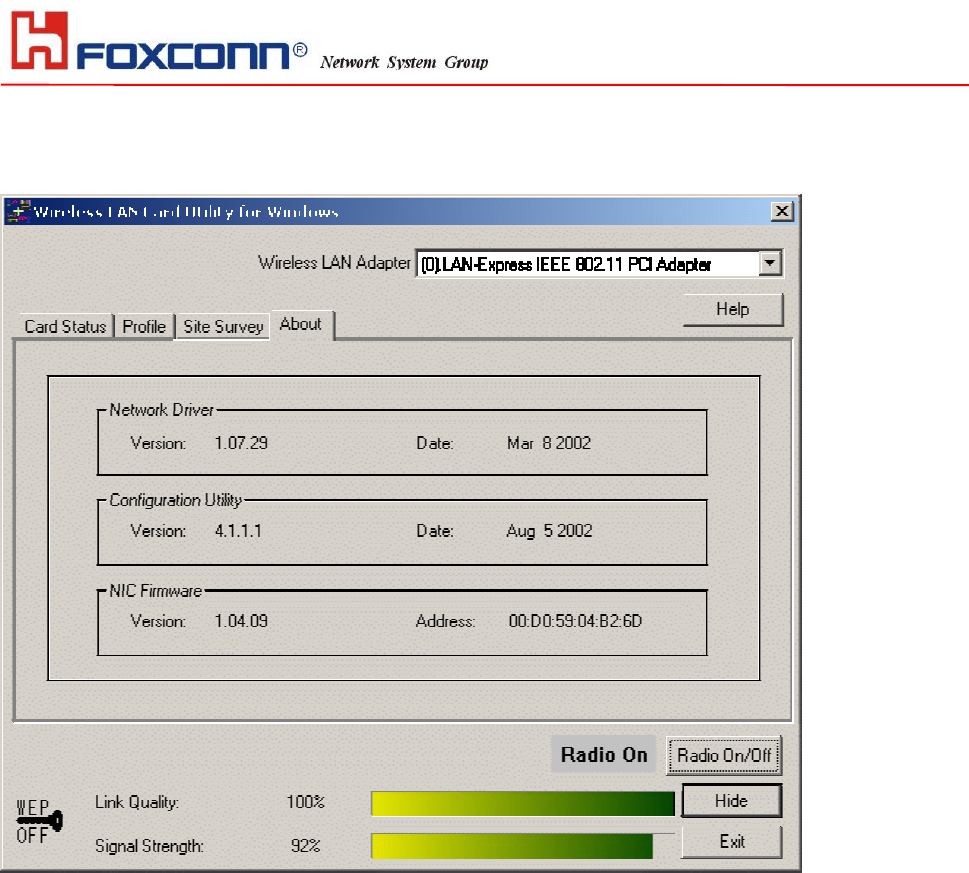
About
Use the About, you can see the information of Network Driver, Configuration Utility and Firmware Version.
HON HAI PRECISION IND. CO., LTD.
10
Section Three: Windows XP Wireless Utility and Configuration
3-1 Windows XP Wireless Utility
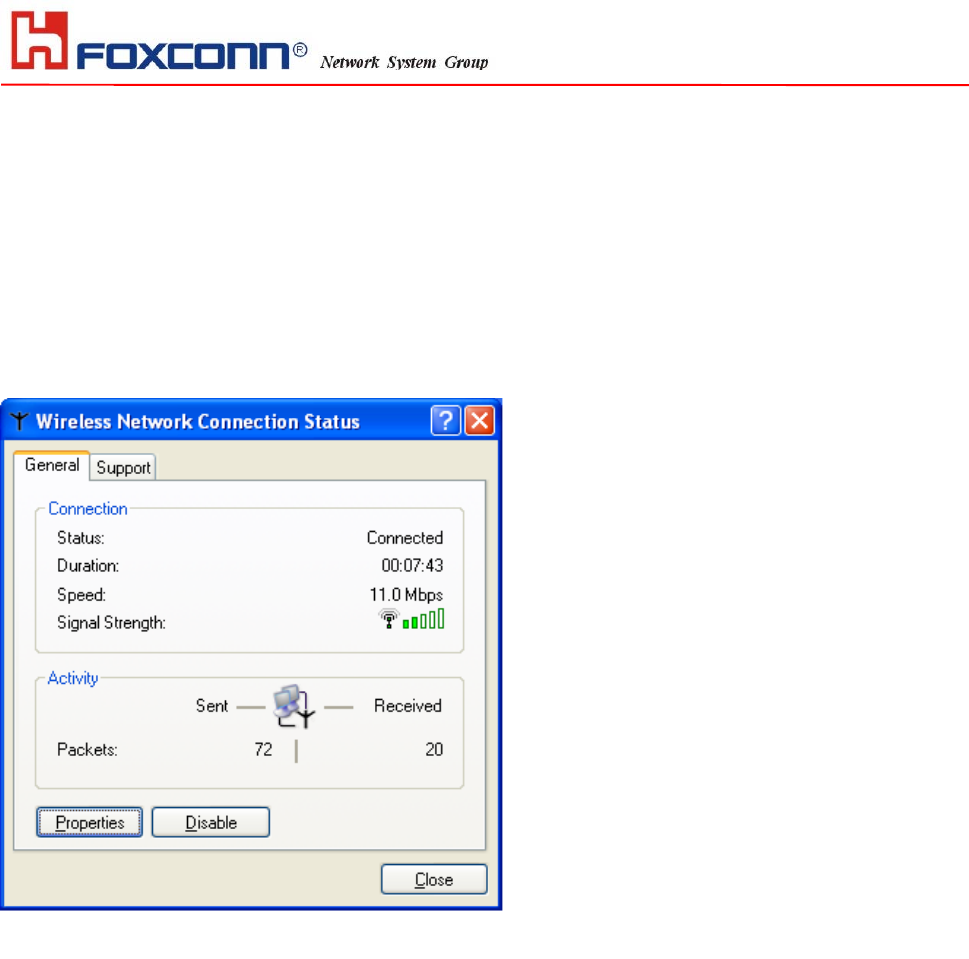
1. To configure the wireless card setting, you can select Start\Settings\Network Connection in the Windows
XP. Choose the wireless network connection, then you will see below screen. From this screen, you can see
wireless connection status and wireless signal level.
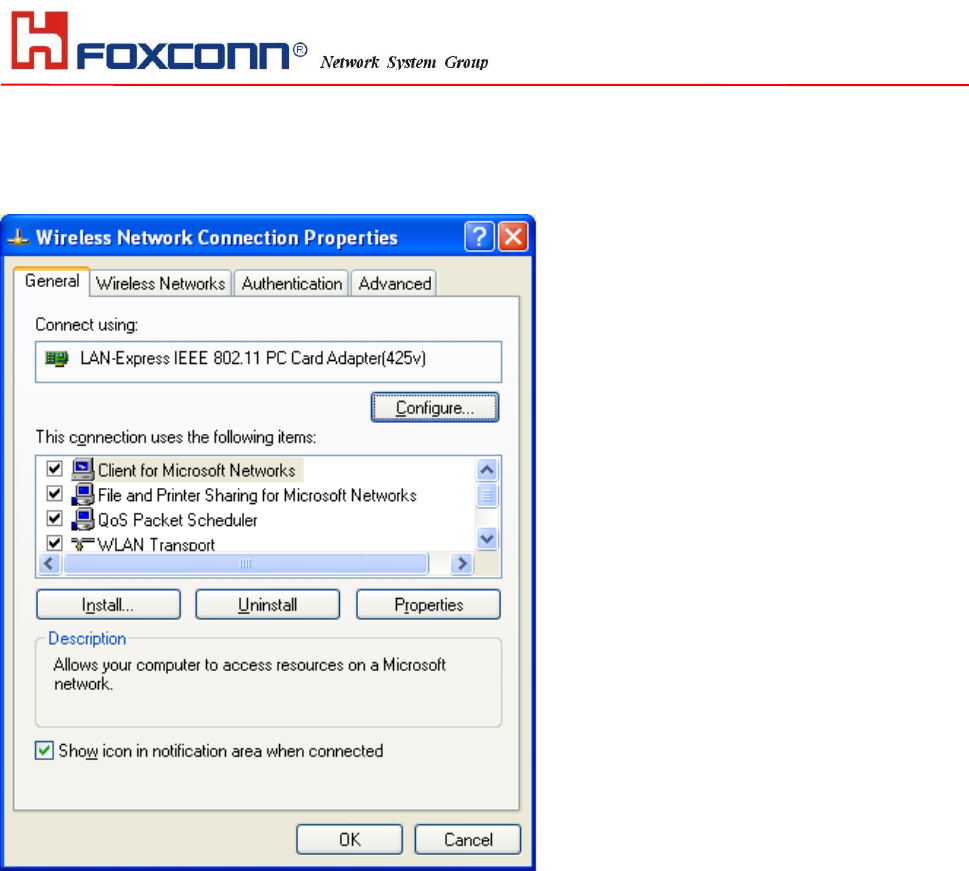
2. Select ‘Properties’ in the above screen. The following windows will show up.
HON HAI PRECISION IND. CO., LTD.
11
In ‘General’ page, Wireless LAN card information and networking protocol have been displayed. Extra
networking protocol can be installed in this page.
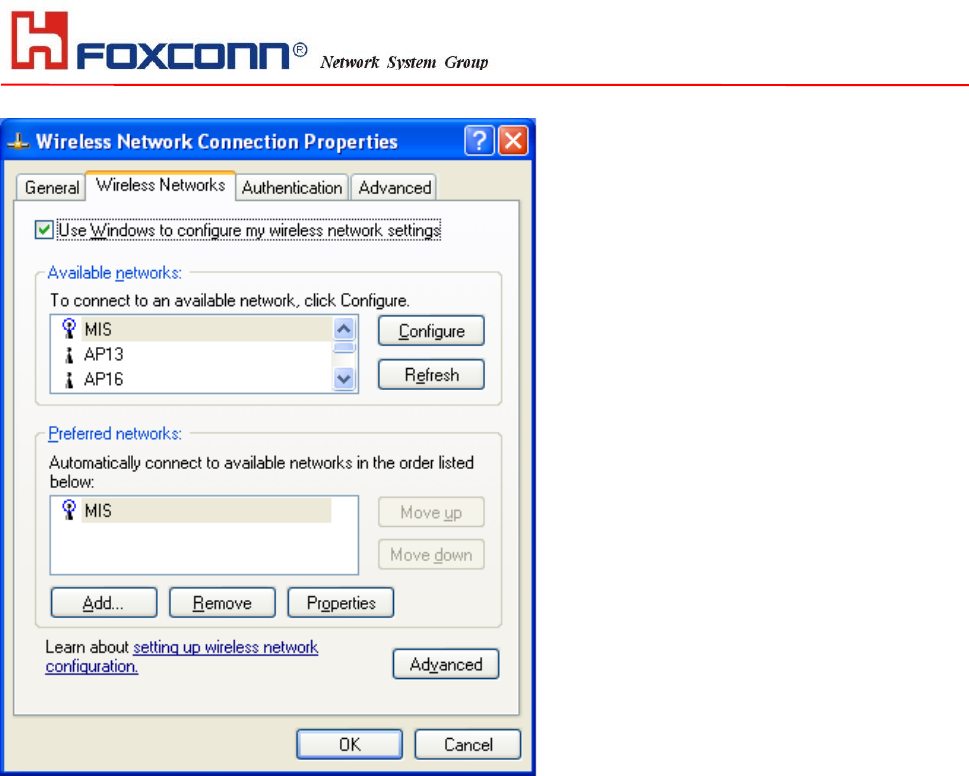
3. Select Wireless Networks page, you can see available wireless networks in your nearby area. You can add your preferred
wireless Access Point to your list, so your wireless card will search for specific wireless networks.
HON HAI PRECISION IND. CO., LTD.
12
Configure
To connect to an existing access point (infrastructure) network, under Available networks, click the network name, and
then click ‘Configure’ to setup wireless security and data encryption.
Reflesh
To update the list of available networks that are within range of your computer, click Refresh.
Add
To connect to an access point (infrastructure) network that you know is available but that does not appear under Available
networks, under Preferred networks, click Add. In Wireless Network Properties, specify the network name (Service Set
Identifier).
Remove
To remove a wireless network from the list of preferred networks.
HON HAI PRECISION IND. CO., LTD.
13
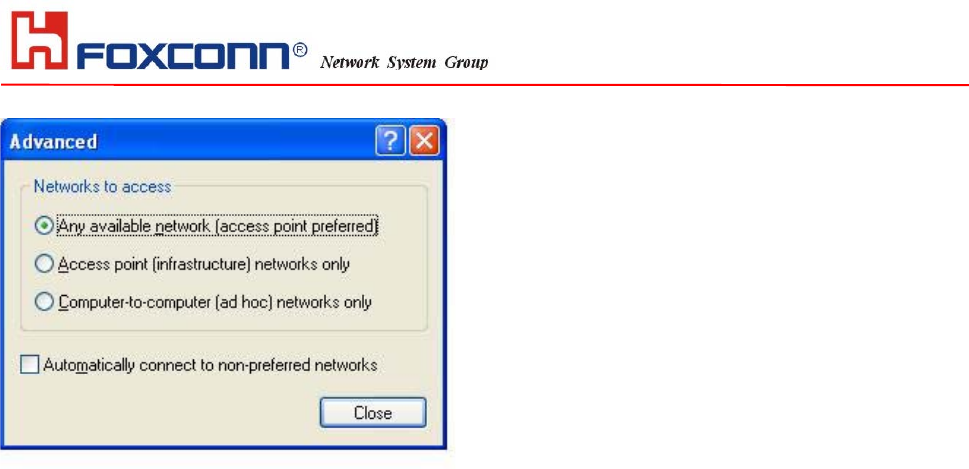
Advanced
*If your network are configuring to a computer-to-computer (ad hoc) network, select ‘Computer-to-computer (ad hoc)
network only’.
*If you want to connect to a computer-to-computer and access point (infrastructure) networks are within range of your
computer, click ‘Access point (infrastructure)network only’.
*If you want to connect to a computer-to-computer (ad hoc) network and both computer-to-computer and access point
(infrastructure) networks are within range of your computer, click ‘Any available network (access point preferred)’.
To automatically connect to available networks that do not appear in the Preferred networks list, click Advanced, and then
select the Automatically connect to non-preferred networks check box.
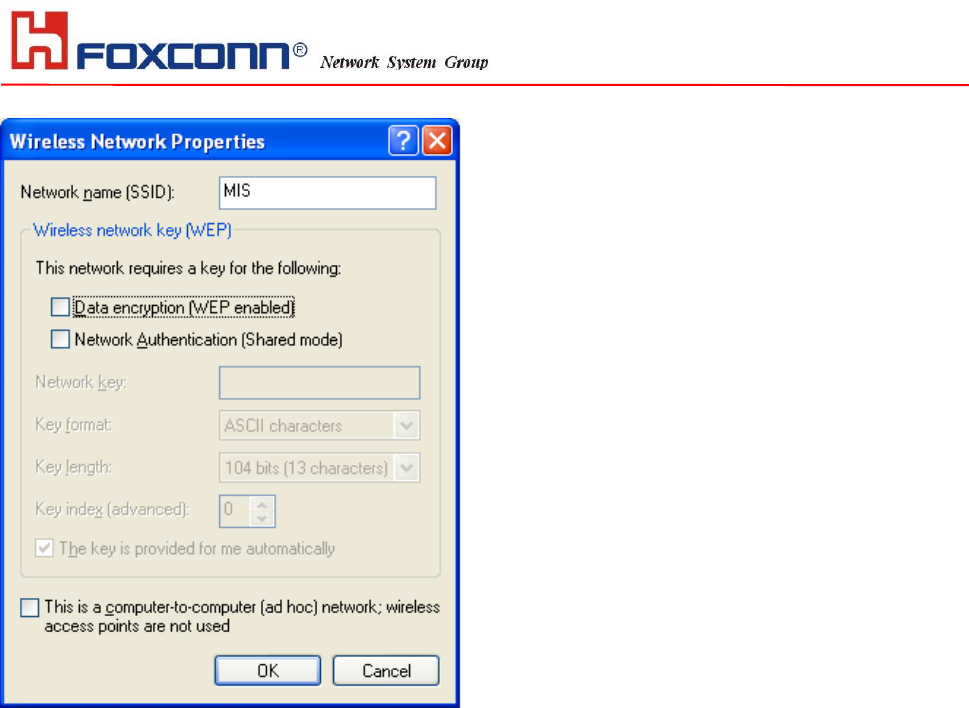
Define your network name (SSID) in the following windows, so your can join a specific wireless network. Check AP has
WEP on or not. You wireless network will need to have same WEP setting with AP in order to communicate. If your
wireless network don’t have any AP, check the ‘This is computer-to computer (ad-hoc) network; wireless access points
are not used’
HON HAI PRECISION IND. CO., LTD.
14
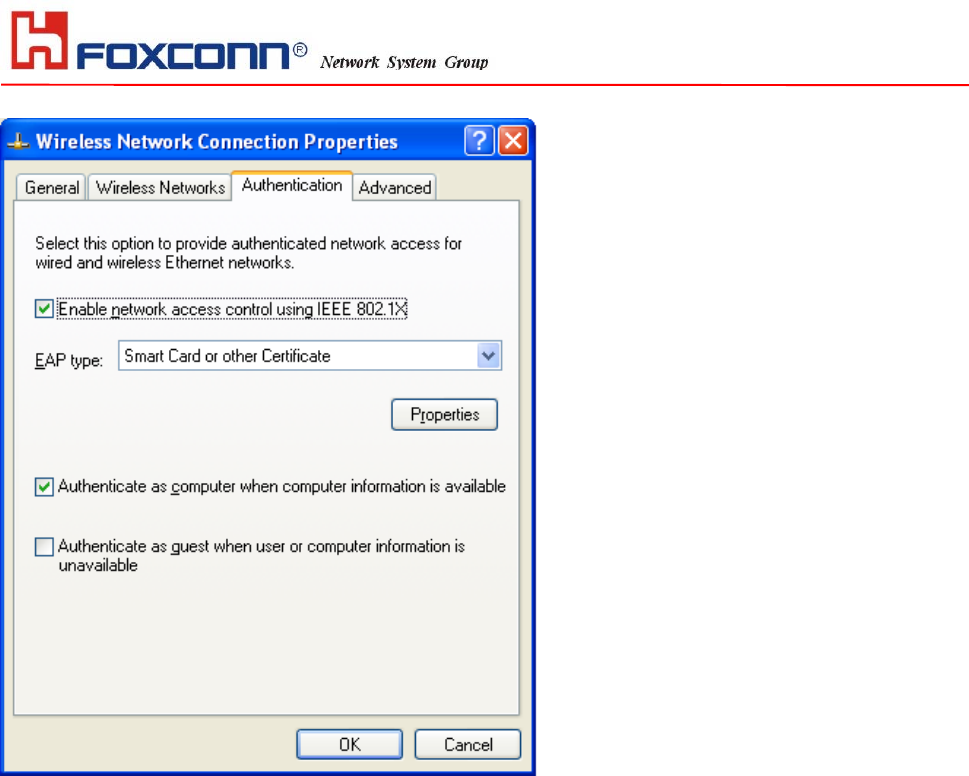
This window provides authentication via 802.1X. 802.1X, an IEEE standard that
provides an authentication framework for 802-based LANs. 802.1X takes advantage
of an existing authentication protocol known as the Extensible Authentication
Protocol. 802.1x, giving someone secure, encrypted, wireless access on a Microsoft
network will be as easy as setting a flag on the users domain account.
What does this mean for the Home Network user?
802.1x will ensure that if and when you make the change over to Wireless Ethernet, your neighbor will not be
able to access your wireless LAN!
HON HAI PRECISION IND. CO., LTD.
15
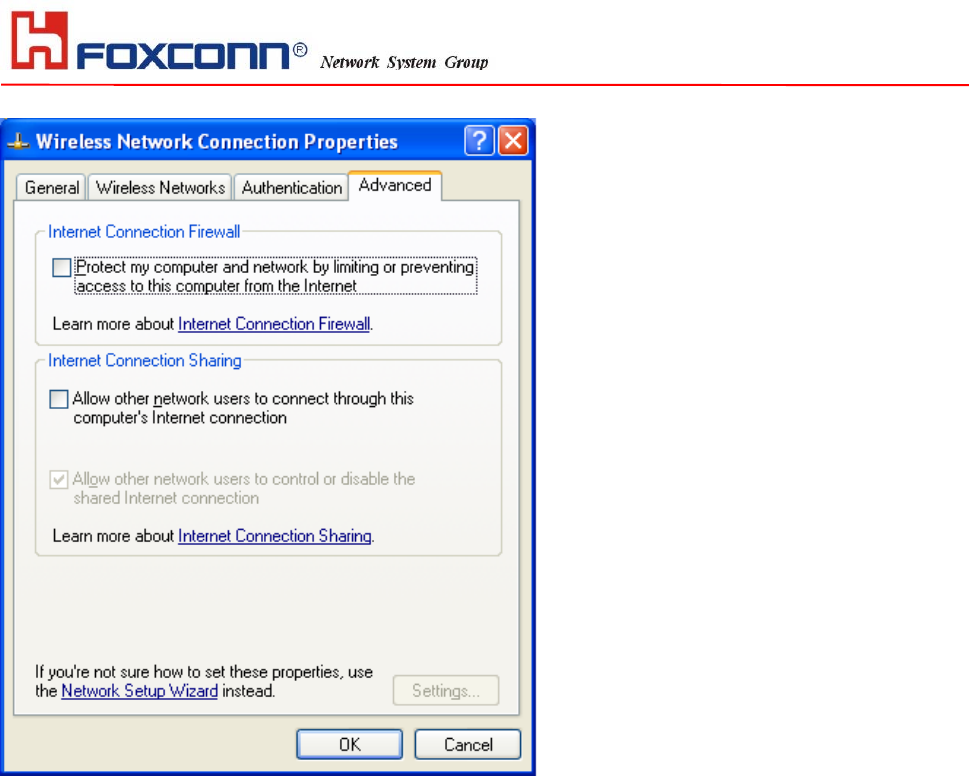
The ‘Advanced’ window offers Firewall and Internet Connection Sharing functions.
Depends on your networking environment, you can select below functions.
HON HAI PRECISION IND. CO., LTD.
16
Appendix A Glossary
Access Point - An internetworking device that seamlessly connects wired and wireless networks together.
Ad-Hoc - Ad-Hoc is a peer- to-peer wireless network without Access Point. A group of wireless clients consistent an
independent wireless LAN.
Backbone - The core infrastructure of a network, the portion of the network that transports information from one central
location to another central location. The information is then off-loaded onto a local system.
BSS - Stands for “Basic Service Set.” An Access Point associated with several wireless stations.
ESS - Stands for “Extended Service Set.” More than one BSS can be configured as an Extended Service Set. An ESS is
basically a roaming domain.
Ethernet - A popular local area data communications network, originally developed by Xerox Corp., which accepts
transmission from computers and terminals. Ethernet operates on 10/100 Mbps transmission rate over shielded coaxial
cable or over shielded twisted pair telephone wire.
Infrastructure - An integrated wireless and wired LAN is called an Infrastructure configuration.
Roaming - A function that allows one to travel with a mobile end system (wireless LAN mobile station, for example)
through the territory of a domain (an ESS, for example) while continuously connecting to the infrastructure.