Inside Secure DESKREAD TAG READER User Manual USERS MANUAL
Inside Secure TAG READER USERS MANUAL
USERS MANUAL
© INSIDE Secure - 2011 - All rights reserved
deskRead user manual
Document Type:
User manual
Reference:
<Document Reference> v1
Release Date:
2011 05 05
File Name:
unsyncMAN_NFC_1107_751-1.0_DRAFT_CONFIDENTIAL_DeskRead user manual.docx
Security Level:
INSIDE General Business Use
Author
Verifier
Name
(Role)
Name
(Role)
Date:
Date:

deskRead user manual
INSIDE General Business Use Document
Page:
2/11
Date:
2011 05 05
Reference:
<Document Reference> v1
© INSIDE Secure - 2011 - All rights reserved
HISTORY
Version
Date
Author
Comments
X.Y
mmm dd, yyyy
Name
Creation

deskRead user manual
INSIDE General Business Use Document
Page:
3/11
Date:
2011 05 05
Reference:
<Document Reference> v1
© INSIDE Secure - 2011 - All rights reserved
Published by:
Inside Secure
41, Parc Club du Golf
13856 Aix-en-Provence Cedex 3
France
Tel.: +33 (0)4 42 39 63 00 - Fax: +33 (0)4 42 39 63 19
E-mail: info@insidefr.com - Web site: http://www.insidesecure.com
All products are sold subject to Inside Secure Terms & Conditions of Sale and the provisions of any
agreements made between Inside Secure and the Customer. In ordering a product covered by
this document the Customer agrees to be bound by those Terms & Conditions and agreements
and nothing contained in this document constitutes or forms part of a contract (with the
exception of the contents of this Notice). A copy of Inside Secure' Terms & Conditions of Sale is
available on request. Export of any Inside Secure product outside of the EU may require an export
Licence.
The information in this document is provided in connection with Inside Secure products. No
license, express or implied, by estoppel or otherwise, to any intellectual property right is granted
by this document or in connection with the sale of Inside Secure products. EXCEPT AS SET FORTH
IN INSIDE SECURE' TERMS AND CONDITIONS OF SALE, INSIDE SECURE OR ITS SUPPLIERS OR
LICENSORS ASSUME NO LIABILITY WHATSOEVER AND DISCLAIMS ANY EXPRESS, IMPLIED OR
STATUTORY WARRANTY RELATING TO ITS PRODUCTS INCLUDING, BUT NOT LIMITED TO, THE IMPLIED
WARRANTY OF MERCHANTABILITY, SATISFACTORY QUALITY, FITNESS FOR A PARTICULAR PURPOSE,
OR NON-INFRINGEMENT. IN NO EVENT SHALL INSIDE SECURE BE LIABLE FOR ANY DIRECT, INDIRECT,
CONSEQUENTIAL, PUNITIVE, EXEMPLARY, SPECIAL OR INCIDENTAL DAMAGES (INCLUDING, WITHOUT
LIMITATION, DAMAGES FOR LOSS OF PROFITS, LOSS OF REVENUE, BUSINESS INTERRUPTION, LOSS OF
GOODWILL, OR LOSS OF INFORMATION OR DATA) NOTWITHSTANDING THE THEORY OF LIABILITY
UNDER WHICH SAID DAMAGES ARE SOUGHT, INCLUDING BUT NOT LIMITED TO CONTRACT, TORT
(INCLUDING NEGLIGENCE), PRODUCTS LIABILITY, STRICT LIABILITY, STATUTORY LIABILITY OR
OTHERWISE, EVEN IF INSIDE SECURE HAS BEEN ADVISED OF THE POSSIBILITY OF SUCH DAMAGES.
Inside Secure makes no representations or warranties with respect to the accuracy or
completeness of the contents of this document and reserves the right to make changes to
specifications and product descriptions at any time without notice. Inside Secure does not make
any commitment to update the information contained herein. Inside Secure advises its customers
to obtain the latest version of device data sheets to verify, before placing orders, that the
information being relied upon by the customer is current. Inside Secure products are not
intended, authorized, or warranted for use as critical components in life support devices, systems
or applications, unless a specific written agreement pertaining to such intended use is executed
between the manufacturer and Inside Secure. Life support devices, systems or applications are
devices, systems or applications that (a) are intended for surgical implant to the body or (b)
support or sustain life, and which defect or failure to perform can be reasonably expected to
result in an injury to the user. A critical component is any component of a life support device,
system or application which failure to perform can be reasonably expected to cause the failure
of the life support device, system or application, or to affect its safety or effectiveness.
The security of any system in which the product is used will depend on the system's security as a
whole. Where security or cryptography features are mentioned in this document this refers to
features which are intended to increase the security of the product under normal use and in
normal circumstances. (c) Inside Secure 2011. All Rights Reserved. Inside Secure(r), Inside Secure

deskRead user manual
INSIDE General Business Use Document
Page:
4/11
Date:
2011 05 05
Reference:
<Document Reference> v1
© INSIDE Secure - 2011 - All rights reserved
logo and combinations thereof, and others are registered trademarks or tradenames of Inside
Secure or its subsidiaries. Other terms and product names may be trademarks of others.

deskRead user manual
INSIDE General Business Use Document
Page:
5/11
Date:
2011 05 05
Reference:
<Document Reference> v1
© INSIDE Secure - 2011 - All rights reserved
TABLE OF CONTENTS
1 INTRODUCTION................................................................................................... 5
2 MAIN FEATURES ................................................................................................. 6
3 CONTENT .......................................................................................................... 6
4 CONTROL SOFTWARE ......................................................................................... 6
5 THE RF DETECTOR ............................................................................................ 8
6 DESKREAD DEVICE ............................................................................................ 8
6.1 Use cases ......................................................................................................... 9
7 TROUBLESHOOTING ......................................................................................... 10
APPENDIX A - LIST OF TABLES .................................................................................. 11
APPENDIX B - LIST OF FIGURES ................................................................................ 11
1 INTRODUCTION
Thank you for choosing Inside Secure’s deskRead NFC device.
deskRead is designed to support NFC application developpers with a full-featured NFC hardware
platform that allows practical testing of NFC contactless applications.
Once connected to a personnal computer, deskRead will bring the same NFC functionnality than
an integrated NFC enabled Handset or smart device. It is then possible to develop and test NFC
applications that use Open NFC API, before porting to an embedded target that implements
Open NFC.
Emulator based third party handset applications development environments may also provide
hardware NFC device connection to enable physical testing of the emulated applications.
Open NFC API is available as Open source software for multiple OS or virtual machine porting
including Androïd, WindowsCE and Java JSR 257 and can be downloaded from
http://www.open-nfc.org
deskRead is not a commercial contactless reader device: it is not designed to be
widely deployed as point of sale or NFC end user homes and desktops NFC reader. It is
only supported by Inside’s proprietary software and is not a standard PC/SC
contactless reader.
This device complies with part 15 of the FCC Rules. Operation is subject to the following two
conditions: (1) This device may not cause harmful interference, and (2) this device must accept
any interference received, including interference that may cause undesired operation
NOTE: THE MANUFACTURER IS NOT RESPONSIBLE FOR ANY RADIO OR TV INTERFERENCE CAUSED BY UNAUTHORIZED
MODIFICATIONS TO THIS EQUIPMENT. SUCH MODIFICATIONS COULD VOID THE USER’S AUTHORITY TO OPERATE THE EQUIPMENT

deskRead user manual
INSIDE General Business Use Document
Page:
6/11
Date:
2011 05 05
Reference:
<Document Reference> v1
© INSIDE Secure - 2011 - All rights reserved
2 MAIN FEATURES
Plug and play USB HID (human interface device) class device :
The HID class is the one that is used by keyboard, mouse or identification device and does
not require any driver installation with most of Operating Systems.
secuRead NFC routing device : provides NFC reader writer, card emulation and Peer-to-
Peer functionality to the secured host (SWP-UICC card) or primary control host (PC).
JavaCard secure element : the SecuRead version of the product provides embedded
JavaCard integrated circuit card : the deskRead with enabled feature can be presented
in front of any contactless reader and will be detected just like a standard JavaCard.
Optionnal UICC developper extension for third party UICC development tools.
3 CONTENT
deskRead device :
NFC tags
UICC extension
device :
RF detector device :
4 CONTROL SOFTWARE
deskRead is supported by Open NFC Connection Center software.
Connection center is a windows PC software that acts as a crosspoint for open NFC clients and
services. deskRead devices will be detected as NFC controller dervice provider.
When an Open NFC server is started, the connection center provides automatic connection to
the available NFC controller service.
Connection Center is not a control software as it is only used to set up a NFC controller
service, it does not perform any operation on the device as long as no Open NFC client (the
control application) has been started. Open NFC client example applications are provided
in the Open NFC download package.

deskRead user manual
INSIDE General Business Use Document
Page:
7/11
Date:
2011 05 05
Reference:
<Document Reference> v1
© INSIDE Secure - 2011 - All rights reserved
Open NFC API including Connection Center software and documentation can be freely
downloaded at http://www.open-nfc.org.

deskRead user manual
INSIDE General Business Use Document
Page:
8/11
Date:
2011 05 05
Reference:
<Document Reference> v1
© INSIDE Secure - 2011 - All rights reserved
5 THE RF DETECTOR
The RF detector device is useful to check NFC reader operation
mode: when it is placed on the active area, the RF field energy
powers the LED. The LED is blinking when the device is waiting for
a card. The LED brights continuously when it waits for a removed
tag answer. The wait timeout before the reader resumes card
detection (LED blink) may be long, up to several tens of seconds,
depending on the card communication protocol settings.
The RF detector should not be used when a card is
being read as it might prevent communication with the
card
6 DESKREAD DEVICE
Three power modes are available : Handset ON, Battery OFF (power by the field), and Handset
OFF (Battery LOW).
When using the device, the power mode is signalled thanks to the dual color LED.
Before the device connection to the USB port, it is in battery off
mode. It can be used to perform card emulation from a secure
element if previously setup.
After the device is connected to the USB port or after PC startup,
the LED remains OFF as long as no control software is started.
In this mode, the device may be used for battery low card
emulation from secure elements hosts as previously defined from
control software. It is not possible to read a card and any card shall
be removed in order to perform a transaction with a remote reader.
After the device has been started by control software such as NFC
Desk, the LED turns red for battery on mode.
It is then possible to read a card and perform card emulation under the
PC software control.
After the control software is stopped, the LED turns orange. The device is
now back to battery low mode. This mode is similar to battery off mode with higher performance.
deskRead user manual
INSIDE General Business Use Document
Page:
9/11
Date:
2011 05 05
Reference:
<Document Reference> v1
© INSIDE Secure - 2011 - All rights reserved
No card can be read or written. The device may perform card emulation from secure elements
hosts depending on control software setup.
To go back to battery off mode, remove the USB cable.
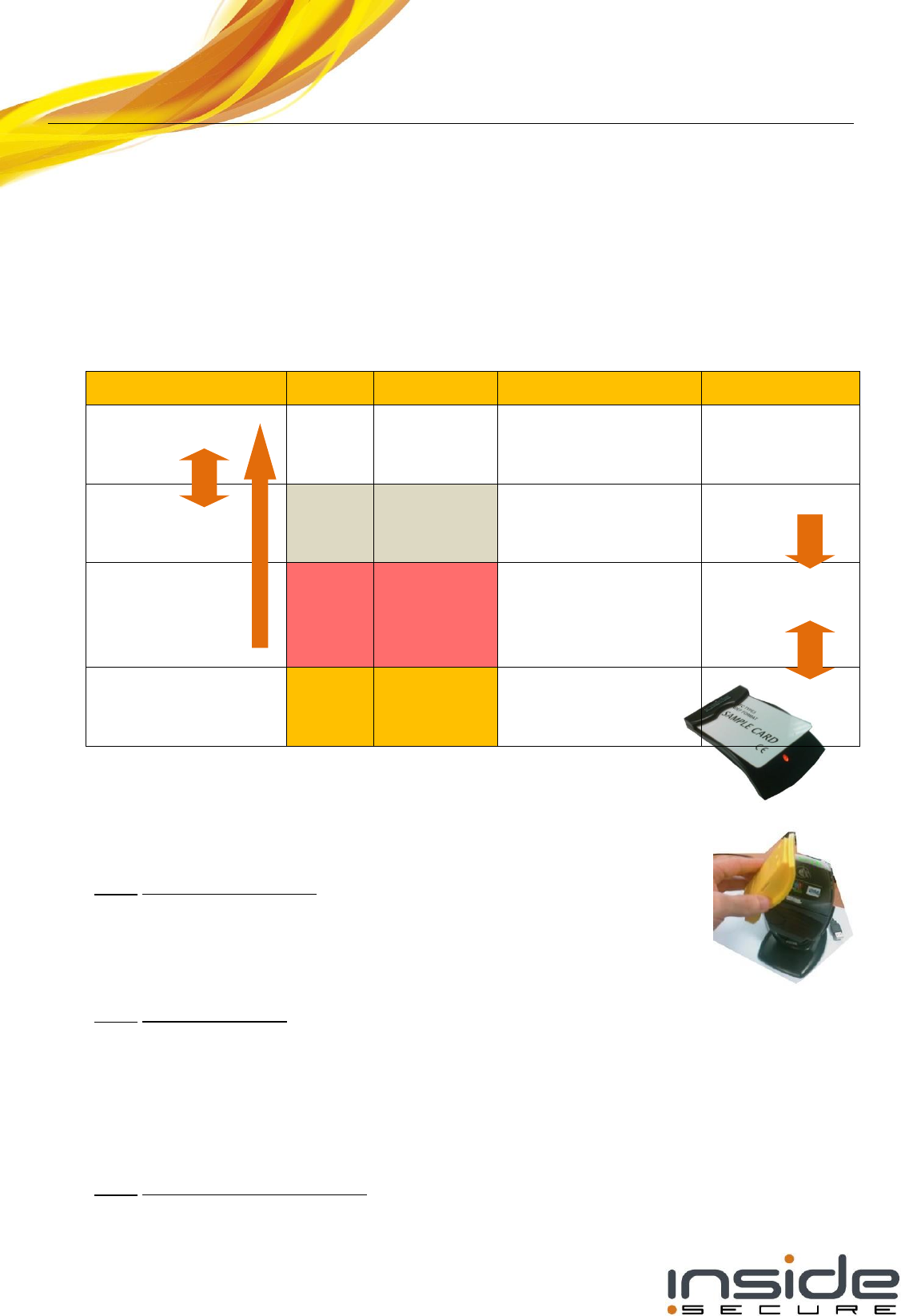
Note : the battery low mode will be signalled differently, depending on the control software status
as summarized in the table below which also illustrates the different operational transitions when
connecting/disconnecting the device or when starting and stopping the control software.
USB cable
LED
Power Mode
Operation
Control Software
Non connected
OFF
Battery off
(power by
the field)
Card emulation from
secure element
Not applicable
Connected
NOT
VISIBLE
Battery low
(handset
OFF)
Card emulation from
secure element
Not started
Connected
RED
Battery on
(Handset ON)
Card emulation from
any host
Reader/writer
Started
Connected
ORANGE
Battery low
(Handset
OFF)
Card emulation from
secure element
Stopped
6.1 Use cases
6.1.1 Read/Write a card
deskRead casing offers an ID1 card landing area in order to provide a stable
card position during software avaluation. Depending on the card internal
antenna design, it may be needed to swap or rotate the card to ensure card
detection.
6.1.2 Emulate a card
When card emulation services are enabled, deskRead can be used just as a card, under the
control of a selected host.
The control software (primary host) may provide the emulated card application. When the
control software is not running, a secure element (UICC host or SE) usually provide securead
emulated card application. The routing of the contactless transaction to a secure element is
configured from the control software.
6.1.3 Peer-to-peer exchange.
deskRead user manual
INSIDE General Business Use Document
Page:
10/11
Date:
2011 05 05
Reference:
<Document Reference> v1
© INSIDE Secure - 2011 - All rights reserved
Two deskRead devices may be used as peer devices when held in front of each other
6.1.4 Secure elements hosted applications
Two types of secure elements car be used to manage NFC secure applications.
The SWP UICC is a NFC host as it is able to configure the NFC controller. The UICC is removable
and usually delivered by a network or service operator which controls the hosted contactless
and applications.
The NFC controller internal secure element is controlled by the device
manufacturer. Depending on the device manufacturer service
offering, this secure element may offer higher flexibility to applications
developpers as the device manufacturer may include secure
aplications APIs to the application developper’s environment.
Depending on the processor and OS security level, the control software
that runs into the device operating system may also provide secure
applications hosting from the primary host.
6.1.5 Secure element connectivity
Open NFC API implements the connectivity API that allows
exchange between the secure elments and the control software,
in order to display user feedback after a secure element has
performed a contactless transaction ;
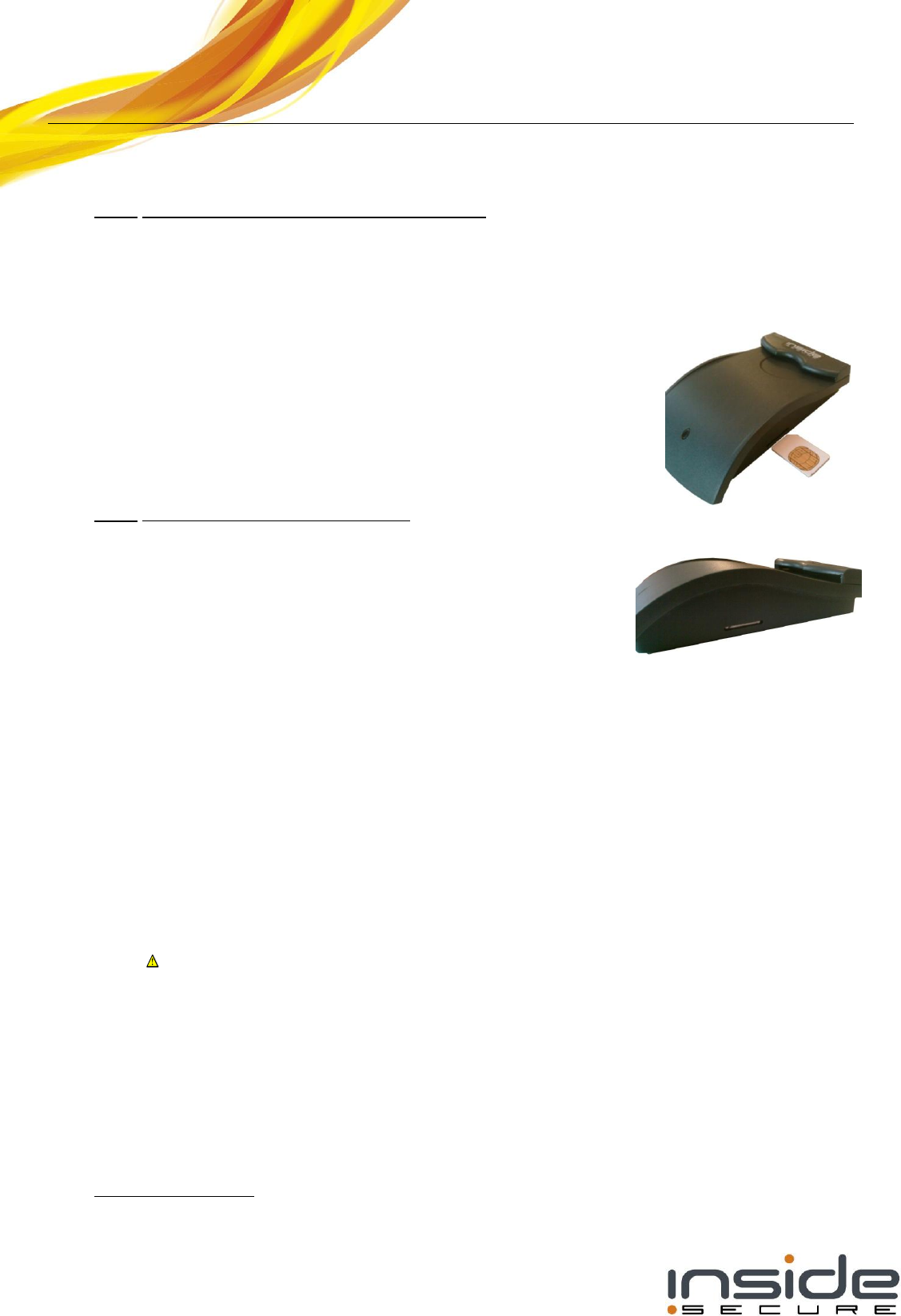
7 UICC
The UICC (not supplied) may be inserted as shown aside :
The UICC is correctly inserted after the click.
If the UICC cannot be fully inserted, make sure the notched corner is inserted first and the circuit
side up.
Use a sharp tool to insert the UICC.
To remove the UICC, use a sharp tool in order to push the UICC card and release the spring.
Do not remove or insert the UICC while the control software is running (LED RED).
It is advised to stop control software and disconnect USB connector before inserting or
removing the UICC, just the same as for standard handset. Otherwise, the control
software may stop responding or the UICC may be damaged or operating improperly.
After a new UICC inserted, it is necessary to run a control software and configure the UICC
access rights before it can be used in contactless applications.
8 TROUBLESHOOTING
Operationnal bitrate :

deskRead user manual
INSIDE General Business Use Document
Page:
11/11
Date:
2011 05 05
Reference:
<Document Reference> v1
© INSIDE Secure - 2011 - All rights reserved
USB HID device class is convenient as it is plug and play, however bitrate is limited to 64 bytes per
ms. Hence, the remaining bandwidth for NFC data is highly reduced, which provides low
performance for bandwidth consuming NFC applications and use cases such as P2P operation.
Open NFC application does not start :
Make sure the deskRead is properly detected in the Connection Center and the associated NFC
controller service is properly started. It is advised to stop the NFC controller service before
disconnecting the device. After the device is connected, the associated service has to be
started manually if the Connection Center was previously started.
APPENDIX A - LIST OF TABLES
Aucune entrée de table d'illustration n'a été trouvée.
APPENDIX B - LIST OF FIGURES
Aucune entrée de table d'illustration n'a été trouvée.