Intel 533ANH Intel WiFi Link 5300 User Manual Contents
Intel Mobile Communications Intel WiFi Link 5300 Contents
Intel >
Contents
- 1. XP User Guide 1 of 2
- 2. XP User Guide 2 of 2
- 3. User Manual 1
- 4. User Manual 2
- 5. User Manual
XP User Guide 1 of 2



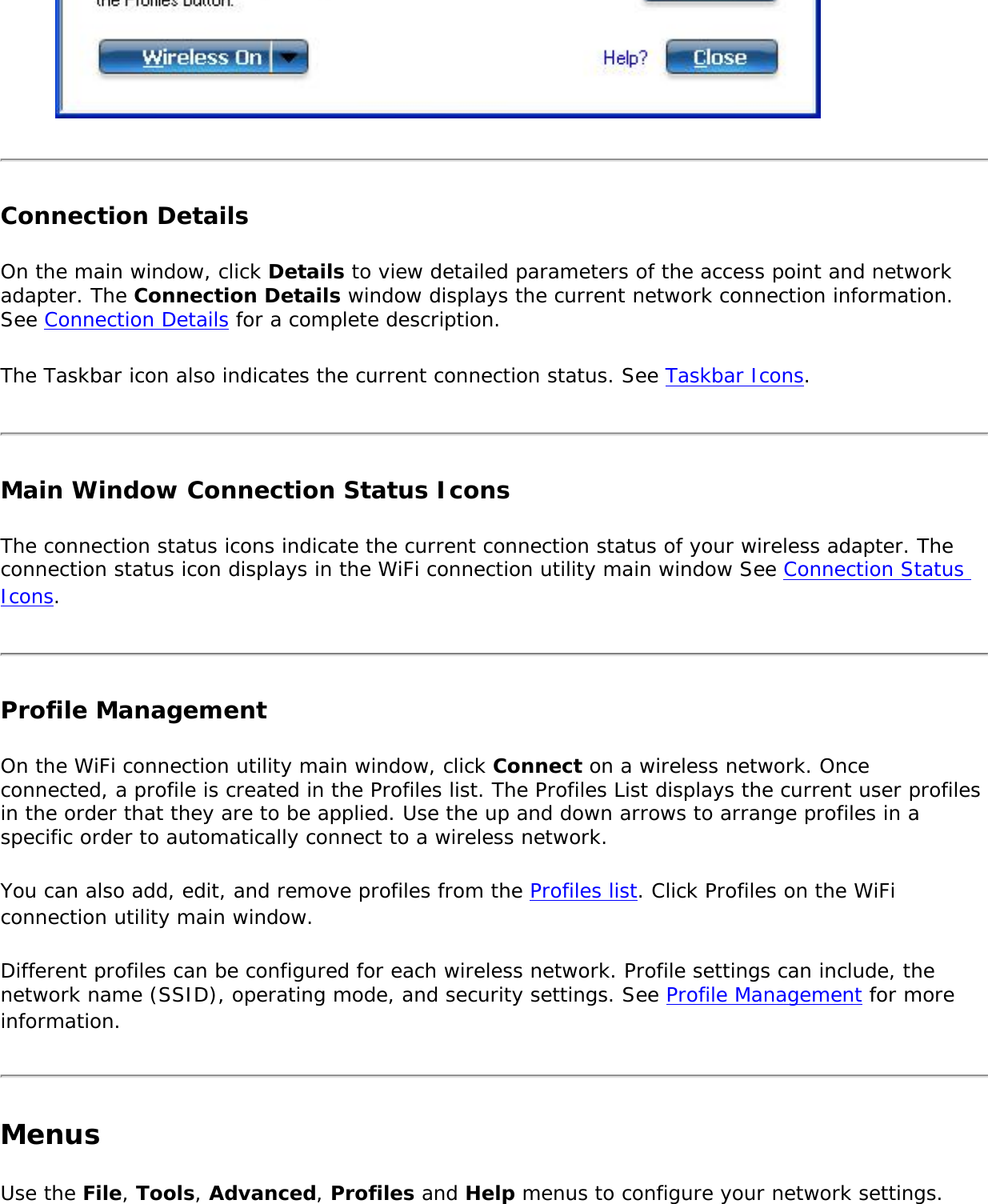
![Name DescriptionFile Exit: Closes the WiFi connection utility main window.Tools Application Settings: Use to set system wide connection preferences. See Application Settings for information.Intel Wireless Troubleshooter: Use to resolve wireless network connection problems. See Intel Wireless Troubleshooter for more information.Manual Diagnostics Tool: The Manual Diagnostics Tool lets you run a set of diagnostics tests that verify the functionality of your wireless adapter. See Manual Diagnostics Tool for more information.Administrator Tool: Used by administrators or the person who has administrator privileges on this computer to configure shared profiles (Pre-logon/Common, Persistent, and Voice over IP [VoIP]). The Administrator Tool can also be used by an Information Technology department to configure user settings within the WiFi connection utility and to create custom install packages to export to other systems. See Administrator Tool for more information.NOTE: The Administrator Tool is available only if it installed during a custom installation of the Intel(R) PROSet/Wireless WiFi software. See Install Additional Software Featuresfor more information on custom installation.Advanced Adapter Settings: Displays Adapter Settings that are equivalent to the settings in the Microsoft Windows Advanced settings. See Adapter Settings for information.To access Adapter Settings from Microsoft Windows:● Double-click Network Connections from the Windows Control Panel.● Right-click the Wireless Network Connection.● Select Properties from the menu.● Click Configure to display the Advanced settings for the adapter.Advanced Statistics: Select to view detailed information about the wireless adapter and connection. See Advanced Statistics for more information.Use Windows to manage Wi-Fi: Select to enable Microsoft Windows XP as the wireless manager. See Microsoft Windows XP Wireless Zero Configuration for more information.](https://usermanual.wiki/Intel/533ANH.XP-User-Guide-1-of-2/User-Guide-964560-Page-8.png)
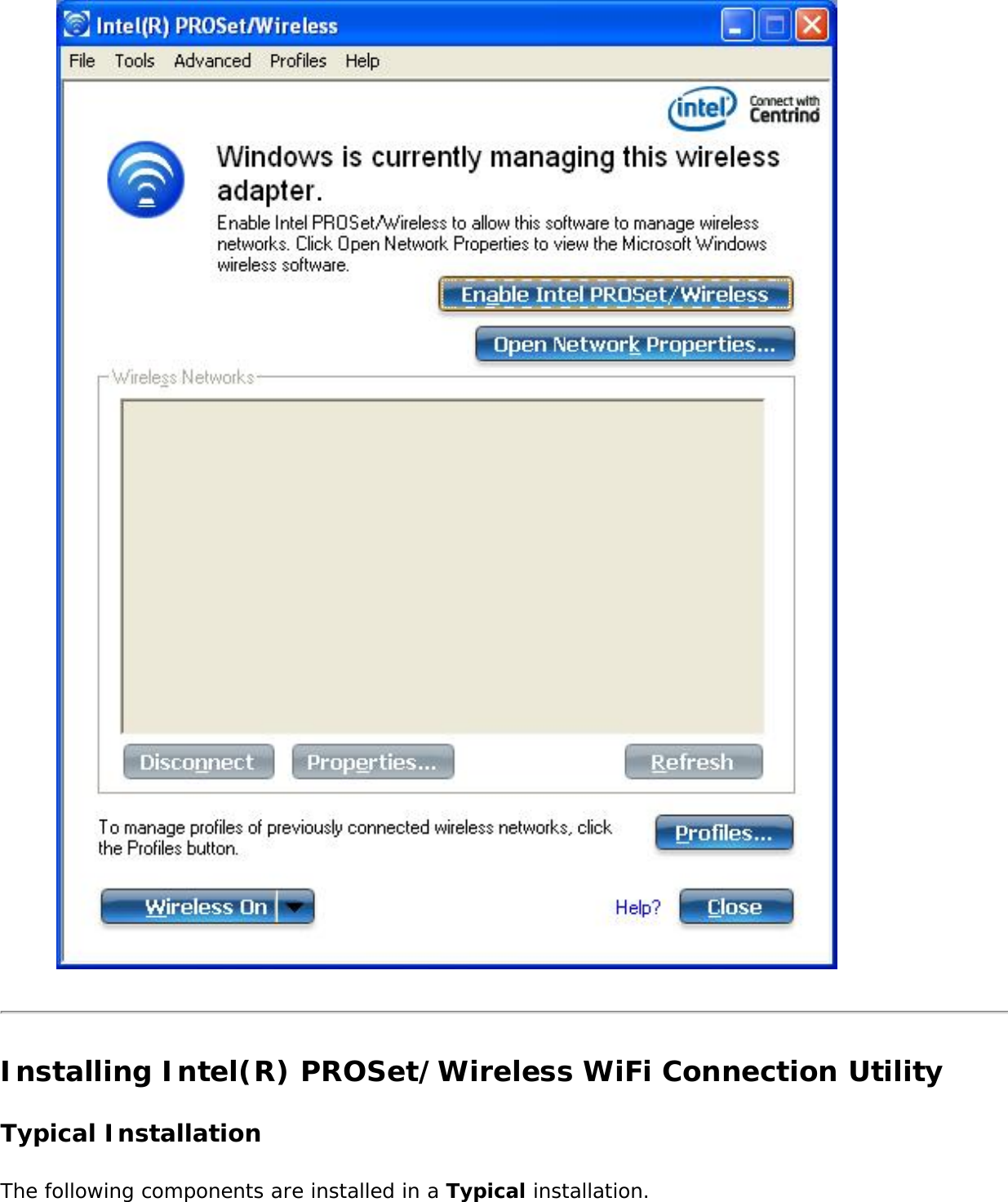


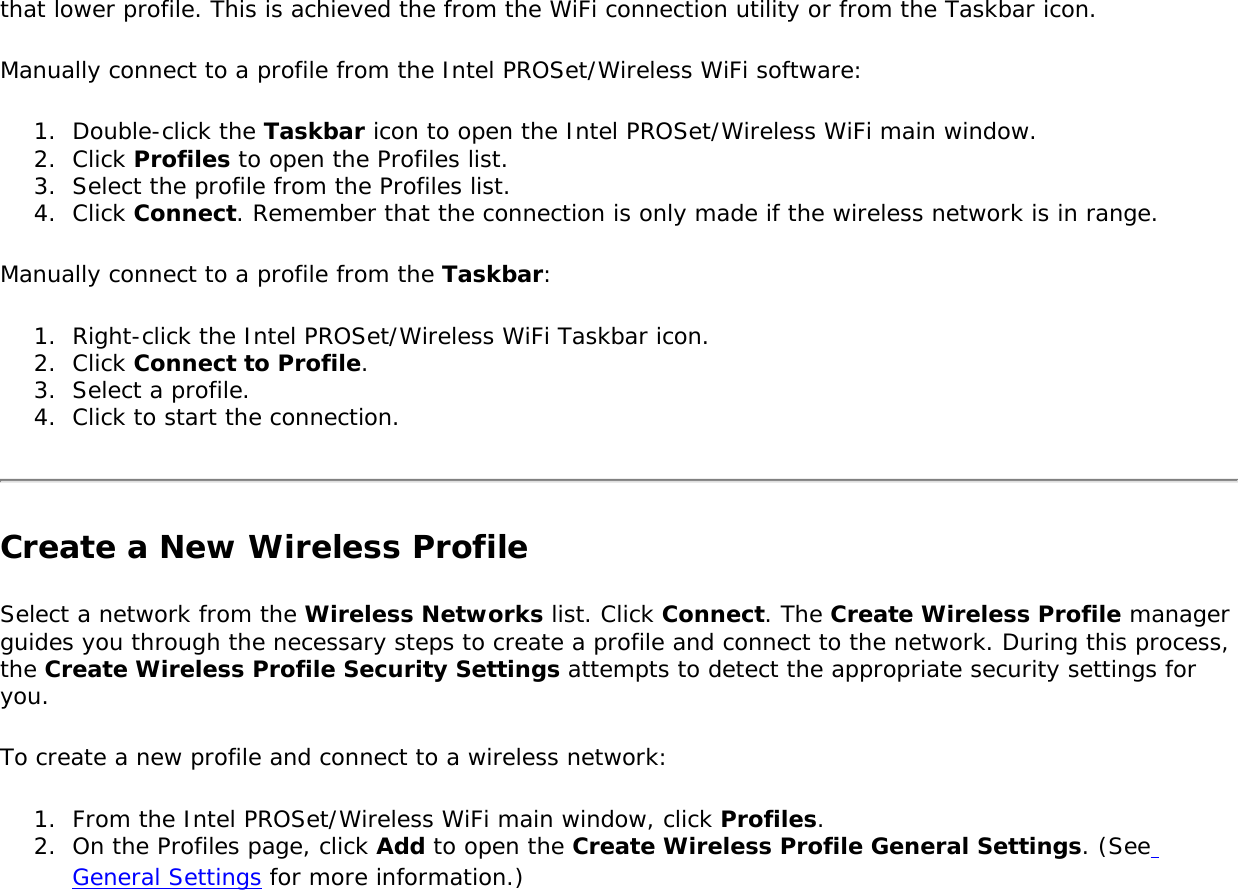
![operating mode being used, and whether security encryption is enabled. These icons display next to the profile name in the Profiles list.Name DescriptionProfile Name The Profile Name is your name for this network. It can be anything that helps you identify this network. For example, My Home Network, Coffee Shop on A Street.Network Name Name of the wireless network (SSID) or computer.Connection Icons: The network profile status icons indicate the different connection states of the adapter with a wireless network, the type of operating mode being used, and whether network security is being used. Blue circle: The wireless adapter is associated with an access point or computer (Device to Device [ad hoc] mode). If a profile has 802.1X security enabled, this indicates that the wireless adapter is associated and authenticated.Indicates Network (infrastructure) mode.Indicates Device to Device (ad hoc) mode.Indicates an Administrator profile. The wireless network uses Security encryption.Indicates that this network is on the Exclude list, e.g. is set for manual rather than automatic connection. When on the Exclude list, to connect the user must connect manually. Arrows Use the arrows to position profiles in a preferred order for auto-connection. ● Up-arrow: Move the position of a selected profile up in the Profiles list. ● Down-arrow: Move the position of a selected profile down in the Profiles list. Connect Connect the selected profile for the wireless network.Add Opens the Create Wireless Profile General Settings, which are used to create a new profile. See Create a New Profile for more information.Remove Removes a selected profile from the Profiles list. See Remove a Profile for more information.Properties Used to edit the contents of an existing profile. You can also double-click a profile in the Profiles list to edit the profile. See Edit an Existing Profile for more information.Export/Import: Imports and exports user-based profiles to and from the Profiles list. Wireless profiles can be automatically imported into the Profiles list. See Export or Import Profiles for more information.Close Closes the profile management window.Help? Provides help information for this page. Connect to a ProfileWhen you are in range of a wireless network that has a matching profile you are automatically connected to that network. If a network with a lower priority profile is also in range you can force the connection to](https://usermanual.wiki/Intel/533ANH.XP-User-Guide-1-of-2/User-Guide-964560-Page-35.png)






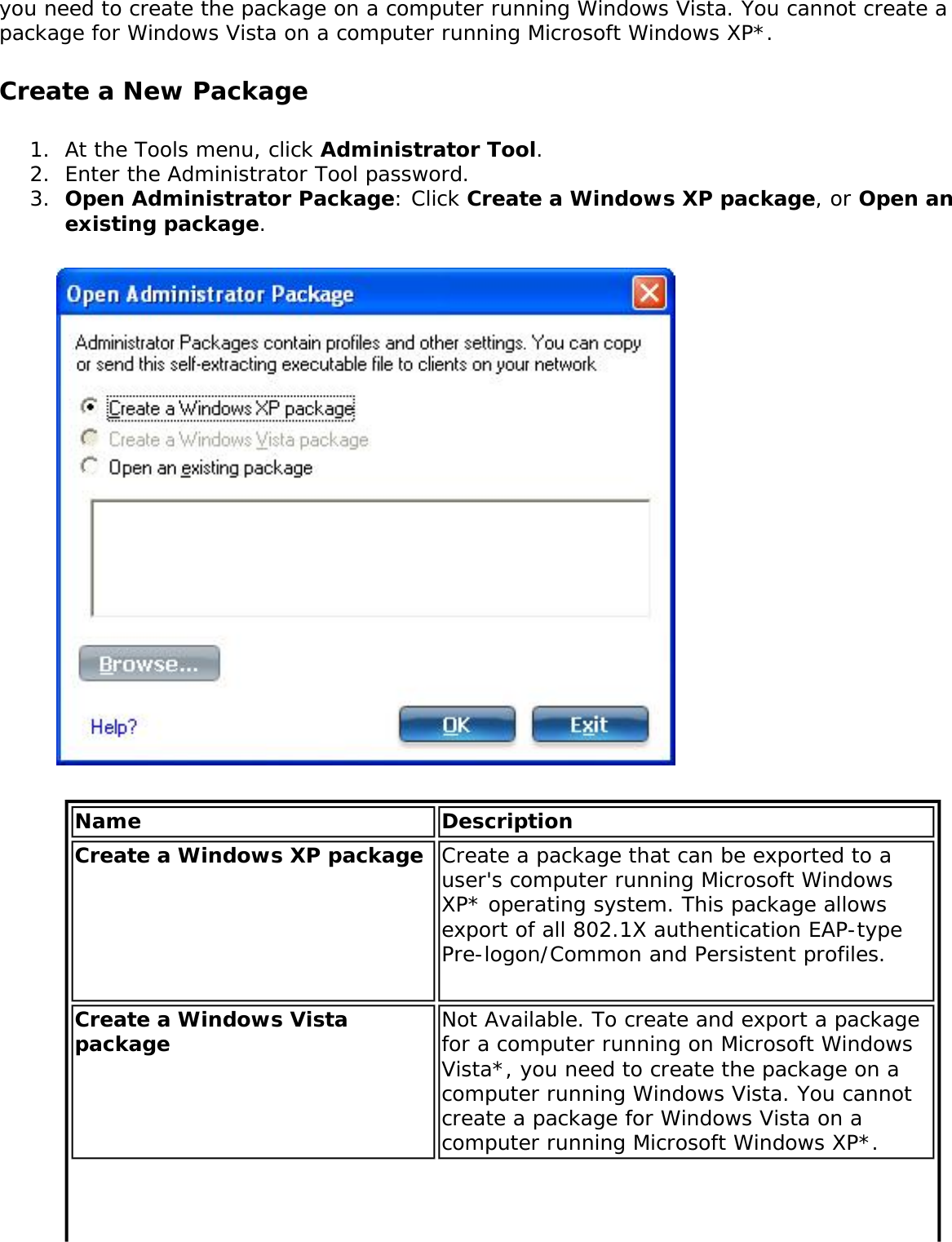



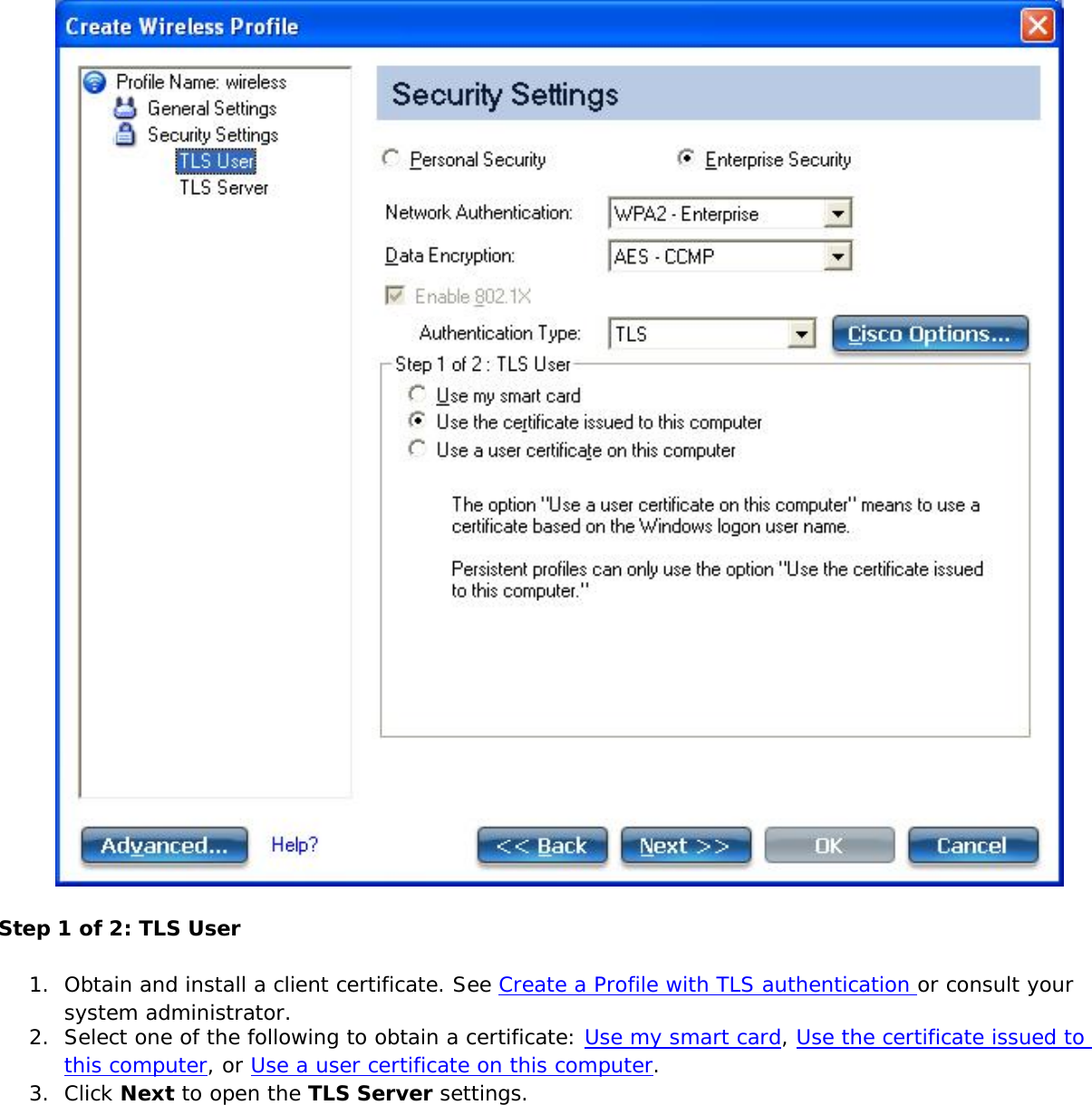

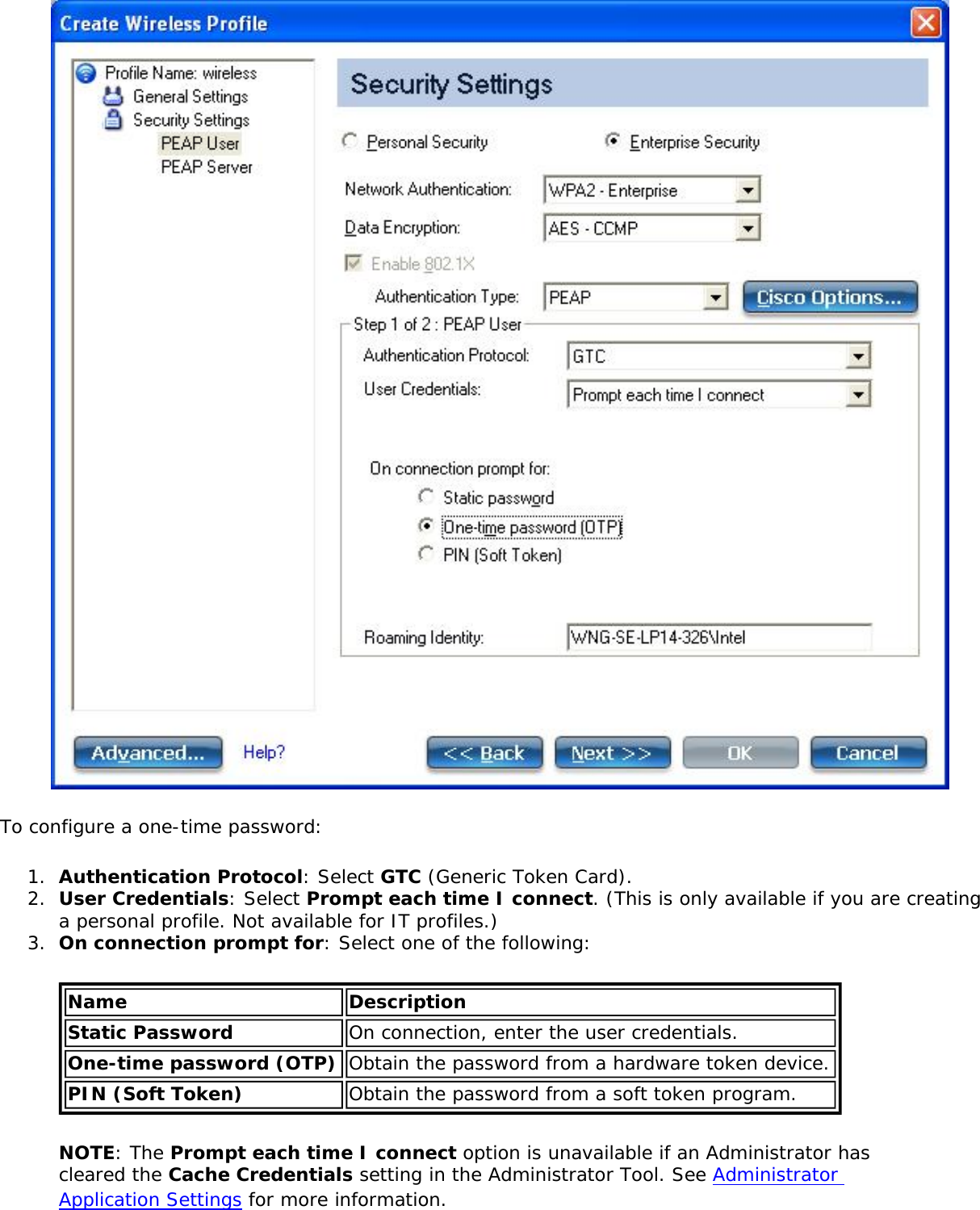
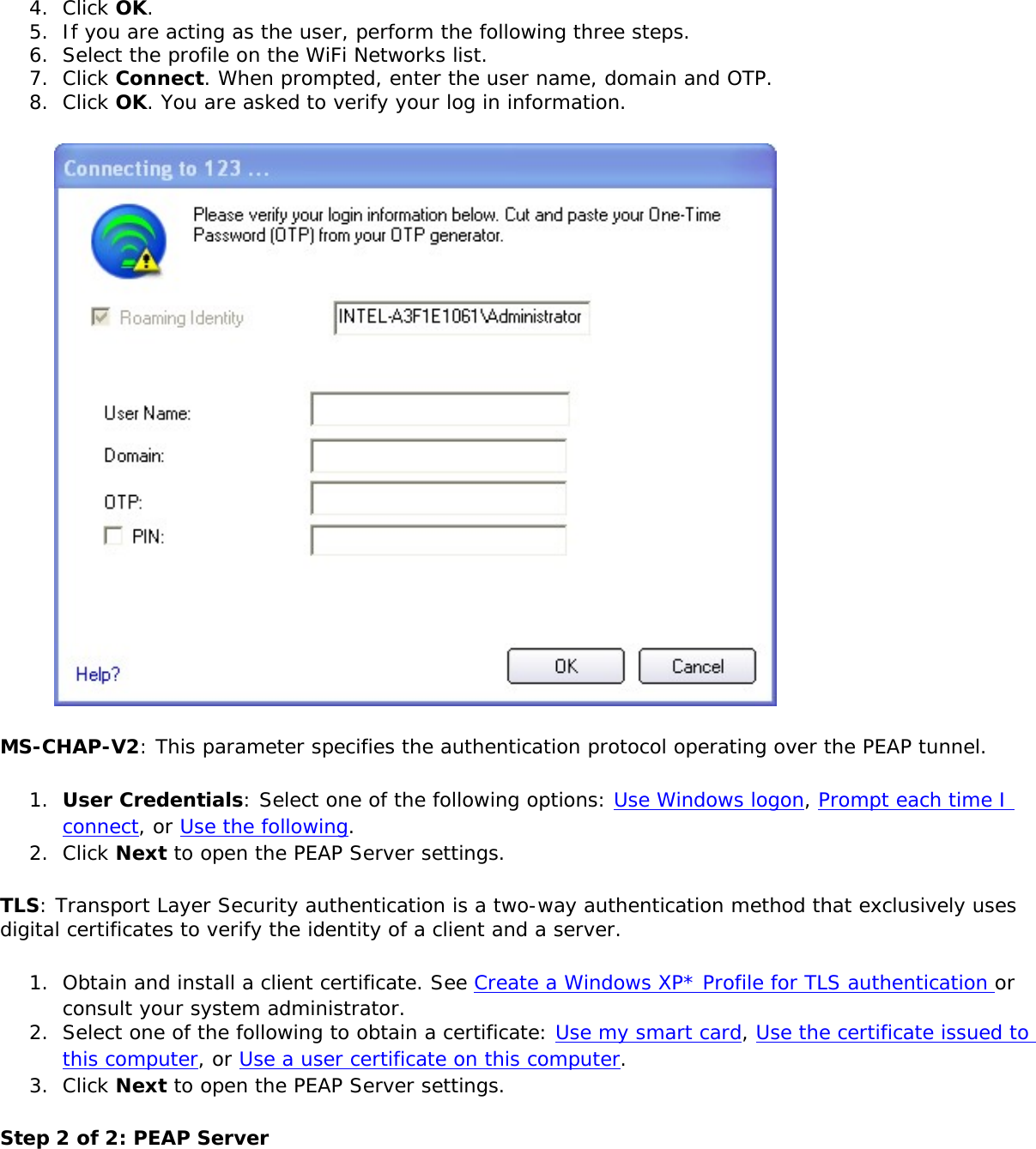
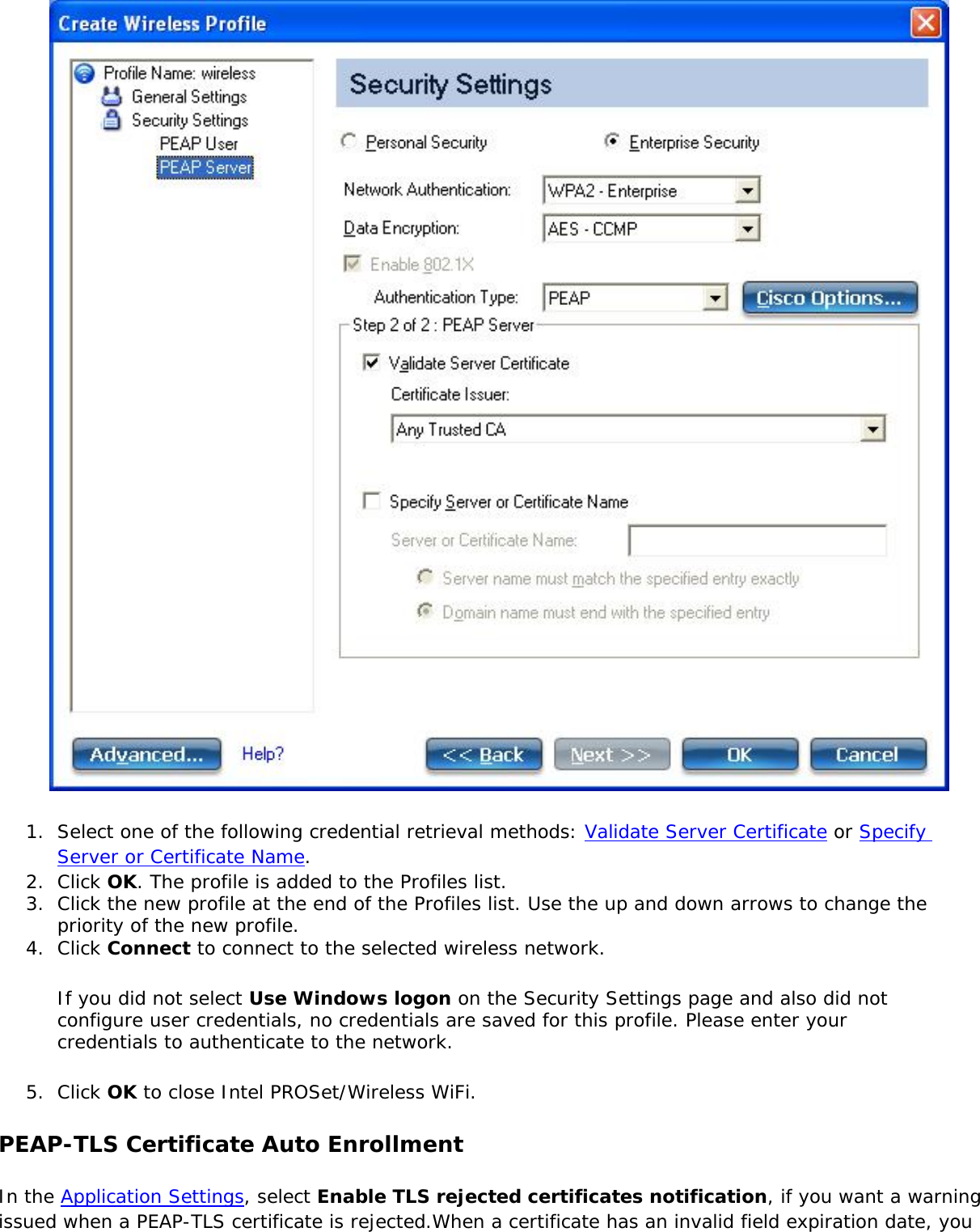

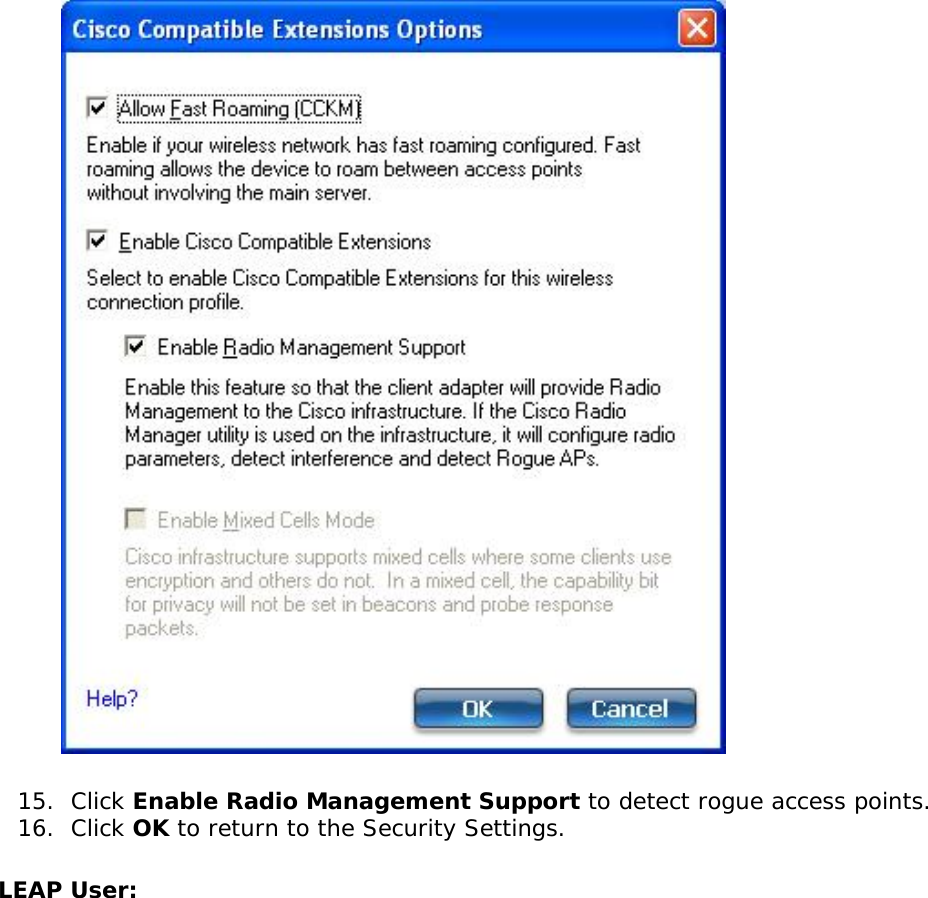
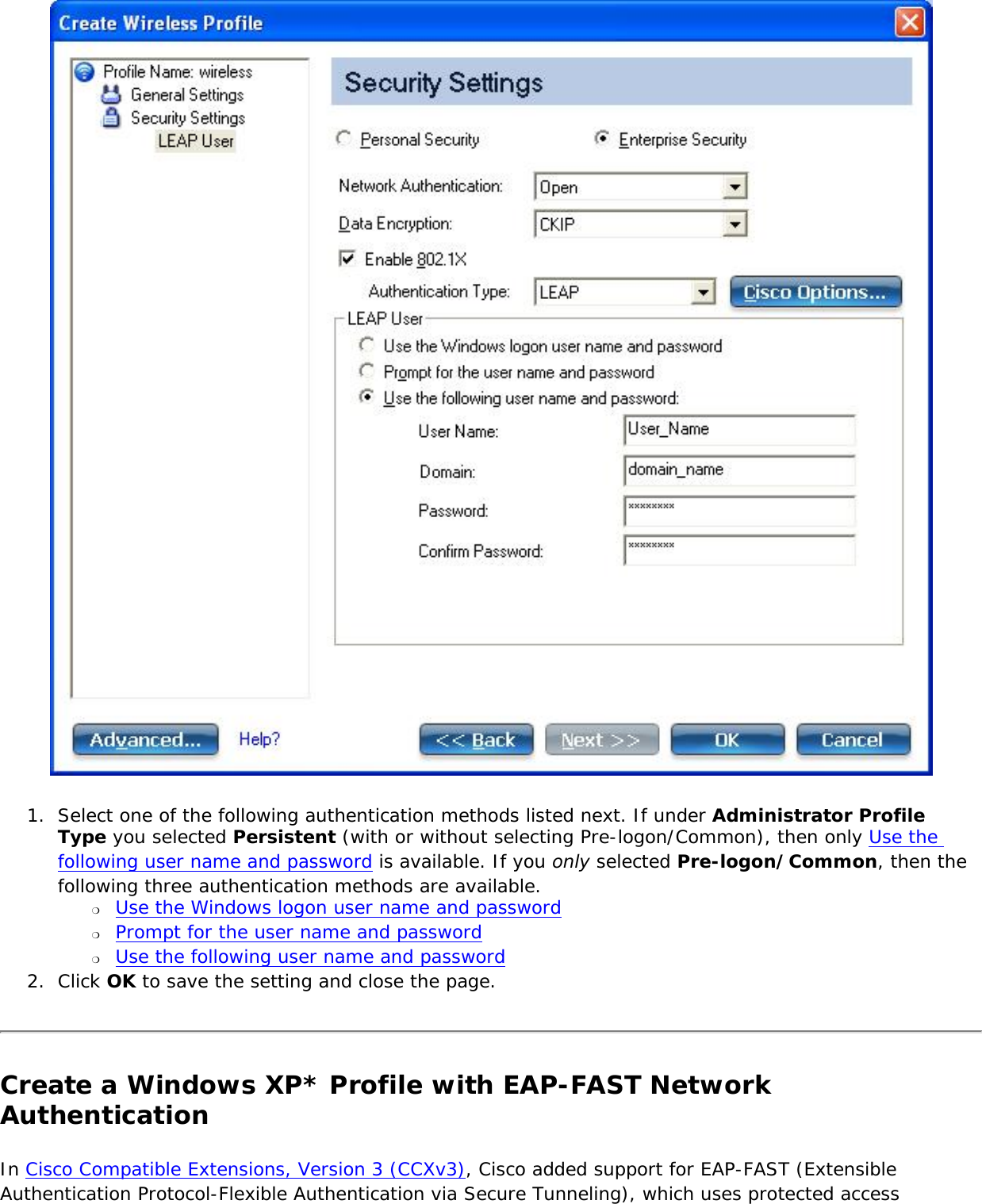

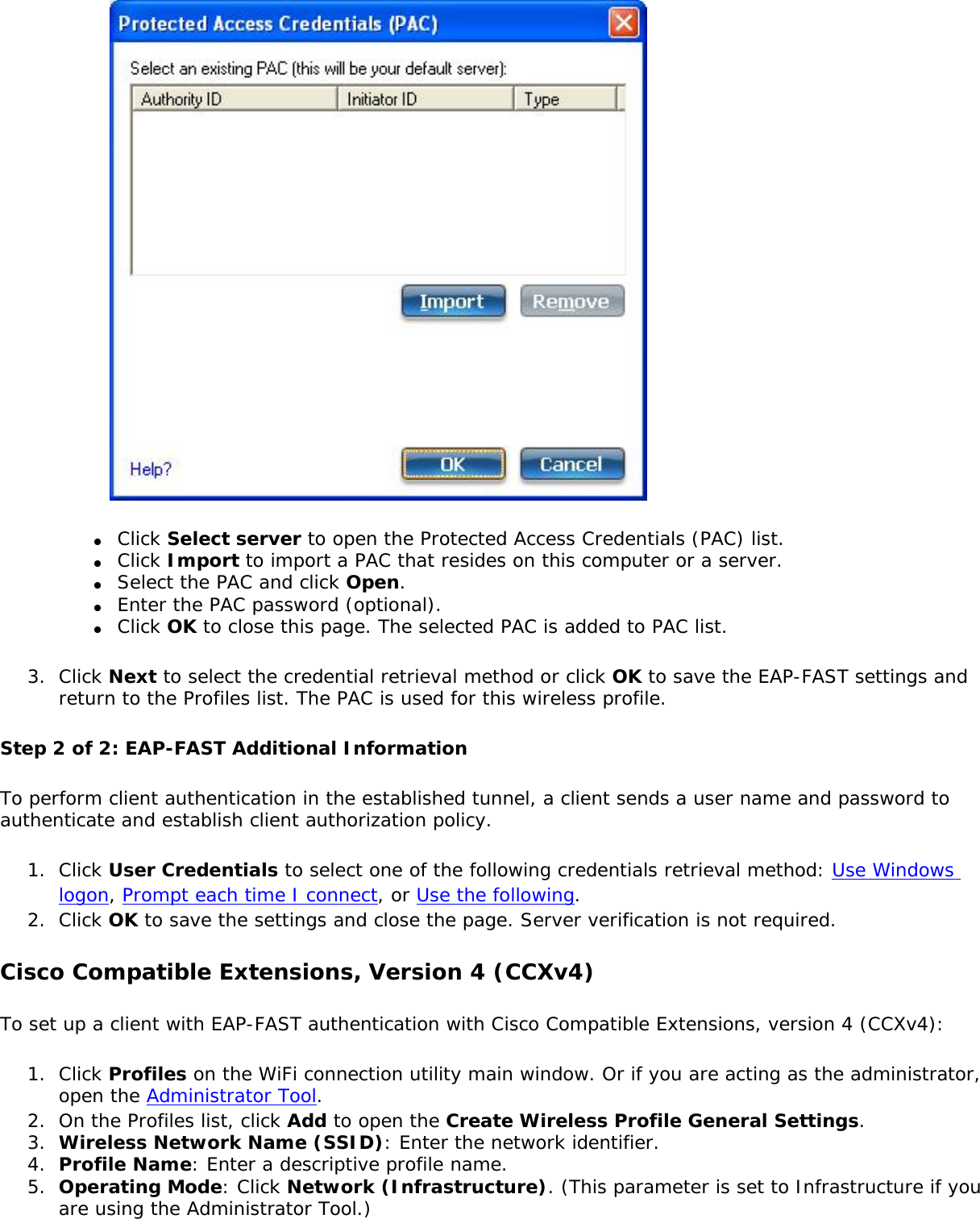
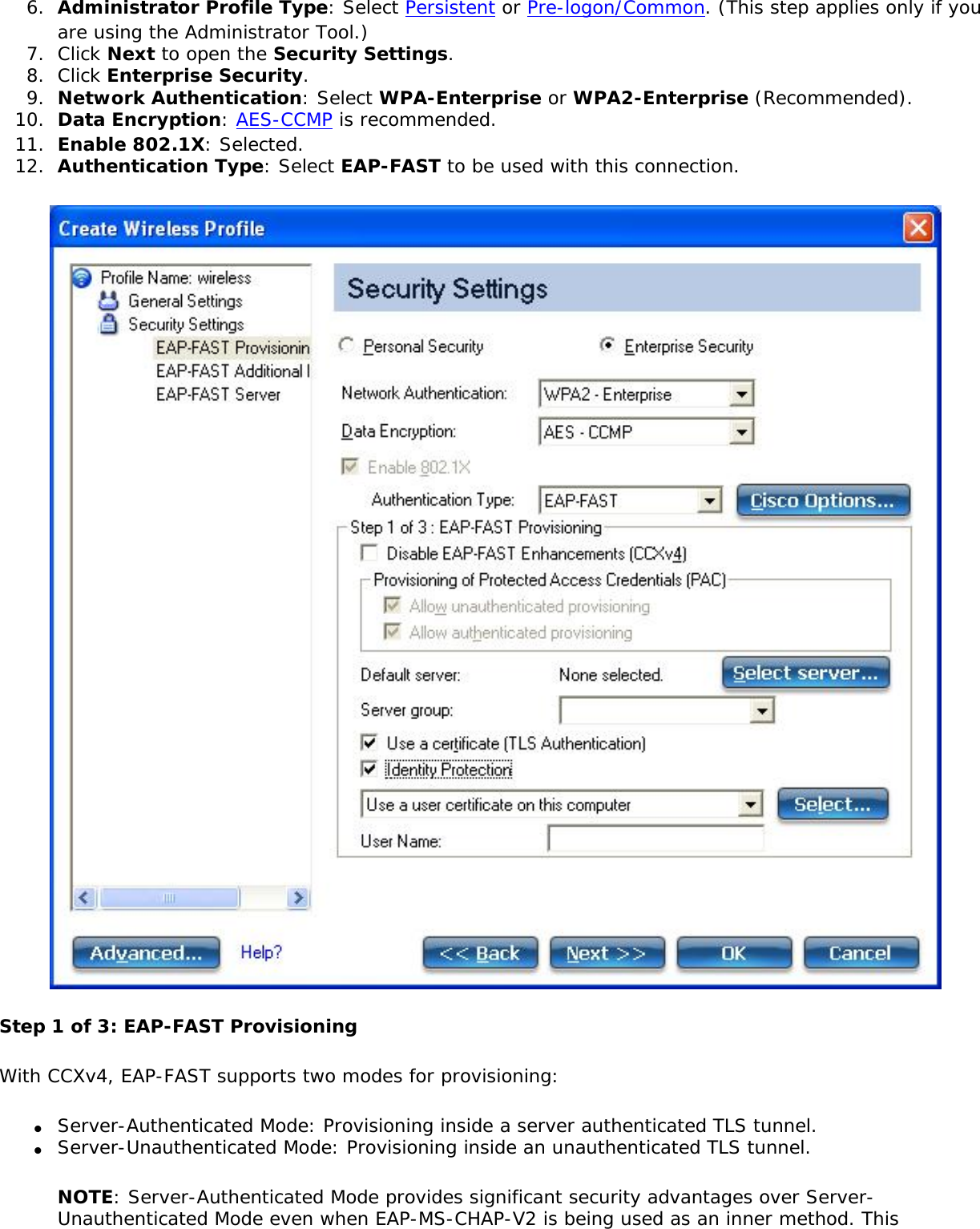

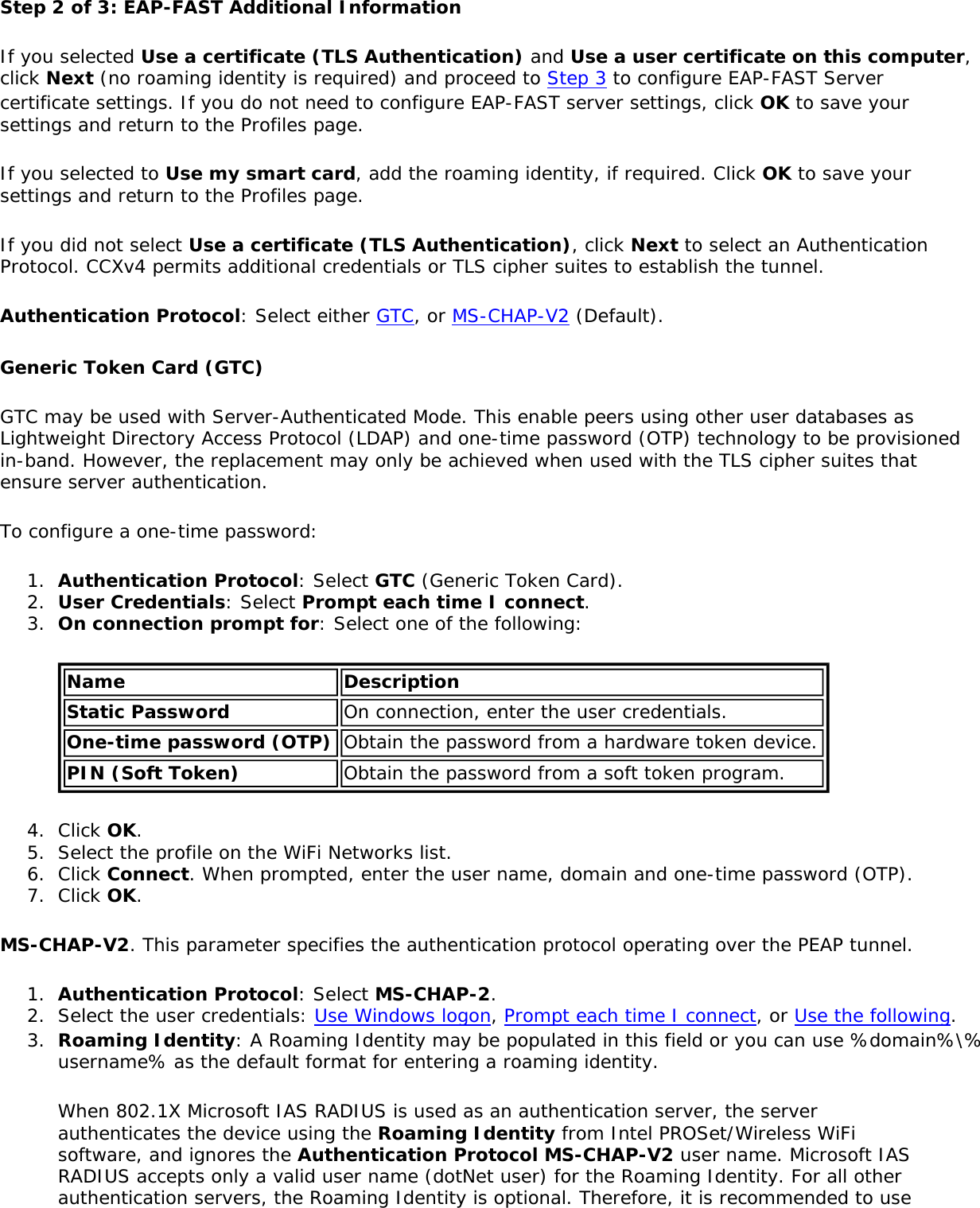








![network through data encryption. The TLS Handshake Protocol allows the server and client to provide mutual authentication and to negotiate an encryption algorithm and cryptographic keys before data is transmitted. Only available for PEAP authentication type.Cisco FeaturesCisco LEAP Cisco LEAP (Cisco Light EAP) is a server and client 802.1X authentication through a user-supplied logon password. When a wireless access point communicates with a Cisco LEAP-enabled RADIUS (Cisco Secure Access Control Server [ACS]), Cisco LEAP provides access control through mutual authentication between client wireless adapters and the wireless networks and provides dynamic, individual user encryption keys to help protect the privacy of transmitted data.Cisco Rogue Access Point Security FeatureThe Cisco Rogue access point feature provides security protection from an introduction of a rogue access point that could mimic a legitimate access point on a network in order to extract information about user credentials and authentication protocols that could compromise security. This feature only works with Cisco's LEAP authentication. Standard 802.11 technology does not protect a network from the introduction of a rogue access point. See LEAP Authentication for more information.802.11b and 802.11g Mixed Environment Protection ProtocolSome access points, for example Cisco 350 or Cisco 1200, support environments in which not all client stations support WEP encryption; this is called Mixed-Cell Mode. When these wireless networks operate in "optional encryption" mode, client stations that join in WEP mode, send all messages encrypted, and stations that use standard mode send all messages unencrypted. These access points broadcast that the network does not use encryption but allow clients that use WEP mode. When "Mixed-Cell" is enabled in a profile, it lets you connect to access points that are configured for "optional encryption."CKIPCisco Key Integrity Protocol (CKIP) is Cisco proprietary security protocol for encryption in 802.11 media. CKIP uses the following features to improve 802.11 security in infrastructure mode:● Key Permutation (KP)● Message Sequence Number](https://usermanual.wiki/Intel/533ANH.XP-User-Guide-1-of-2/User-Guide-964560-Page-104.png)