Intel 9462NG Intel Dual Band Wireless-AC 9462 User Manual Intel WiFi Adapter Information Guide
Intel Mobile Communications Intel Dual Band Wireless-AC 9462 Intel WiFi Adapter Information Guide
Intel >
Contents
- 1. User Manual
- 2. User Manual 1
- 3. User Manual 2
User Manual
















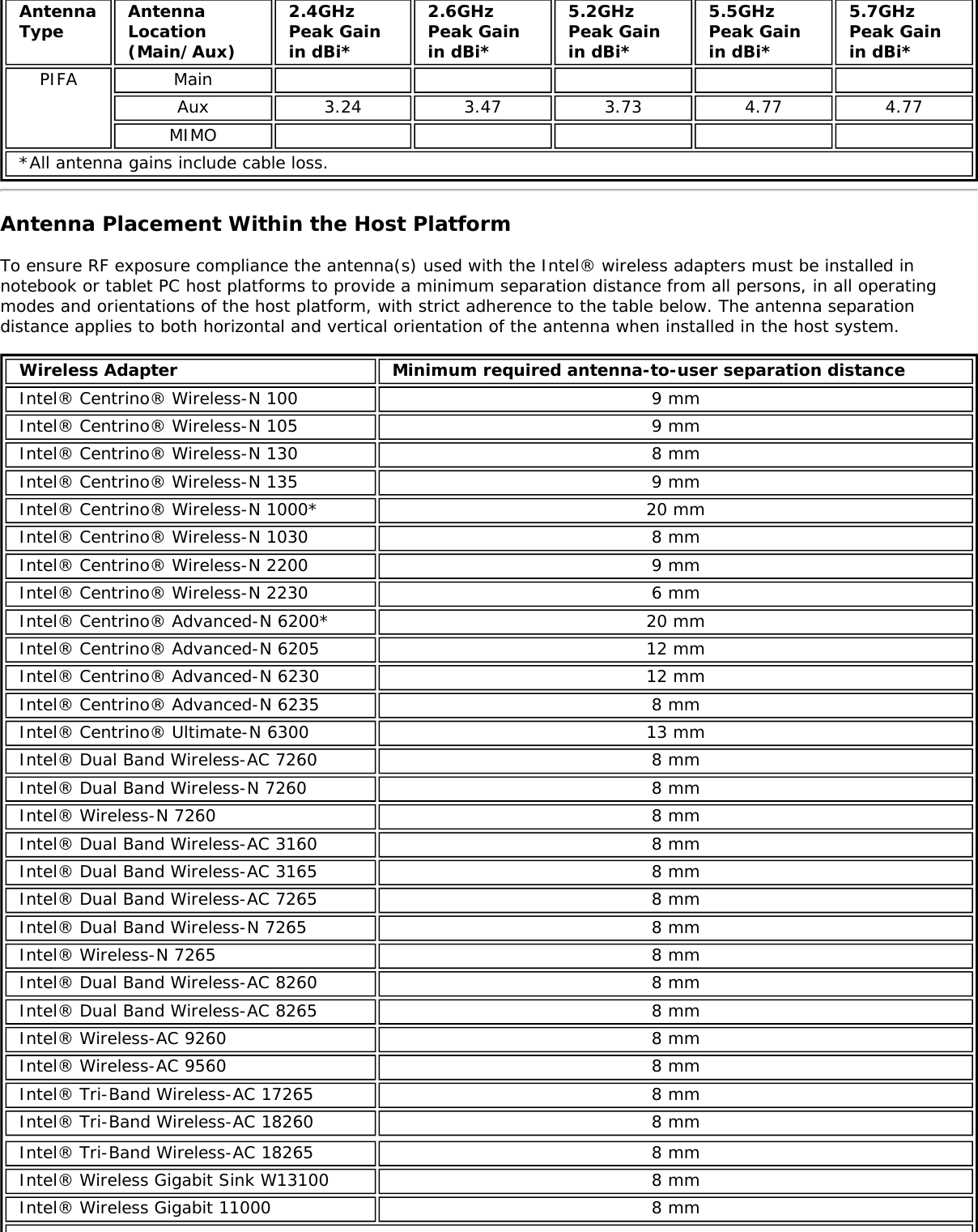

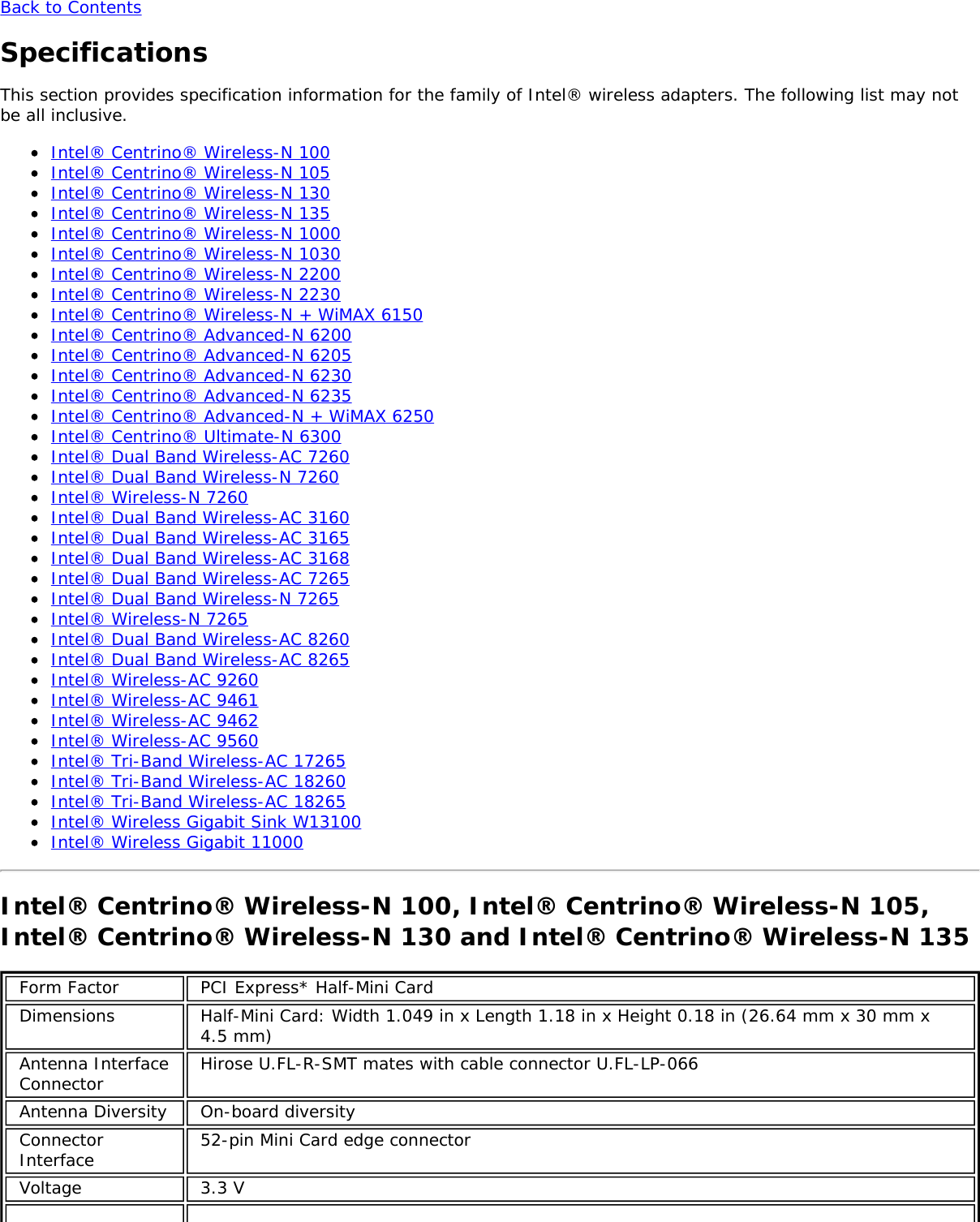
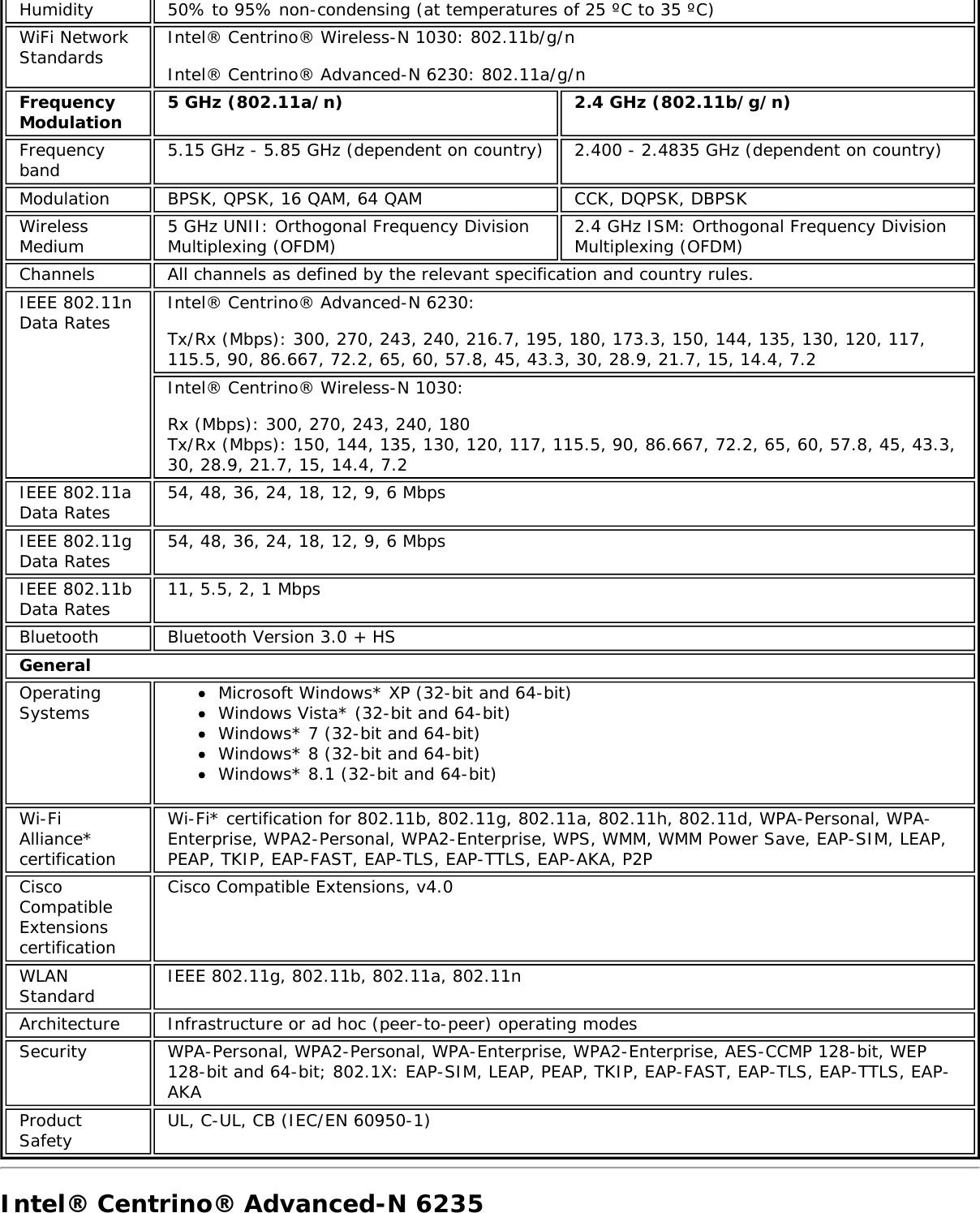
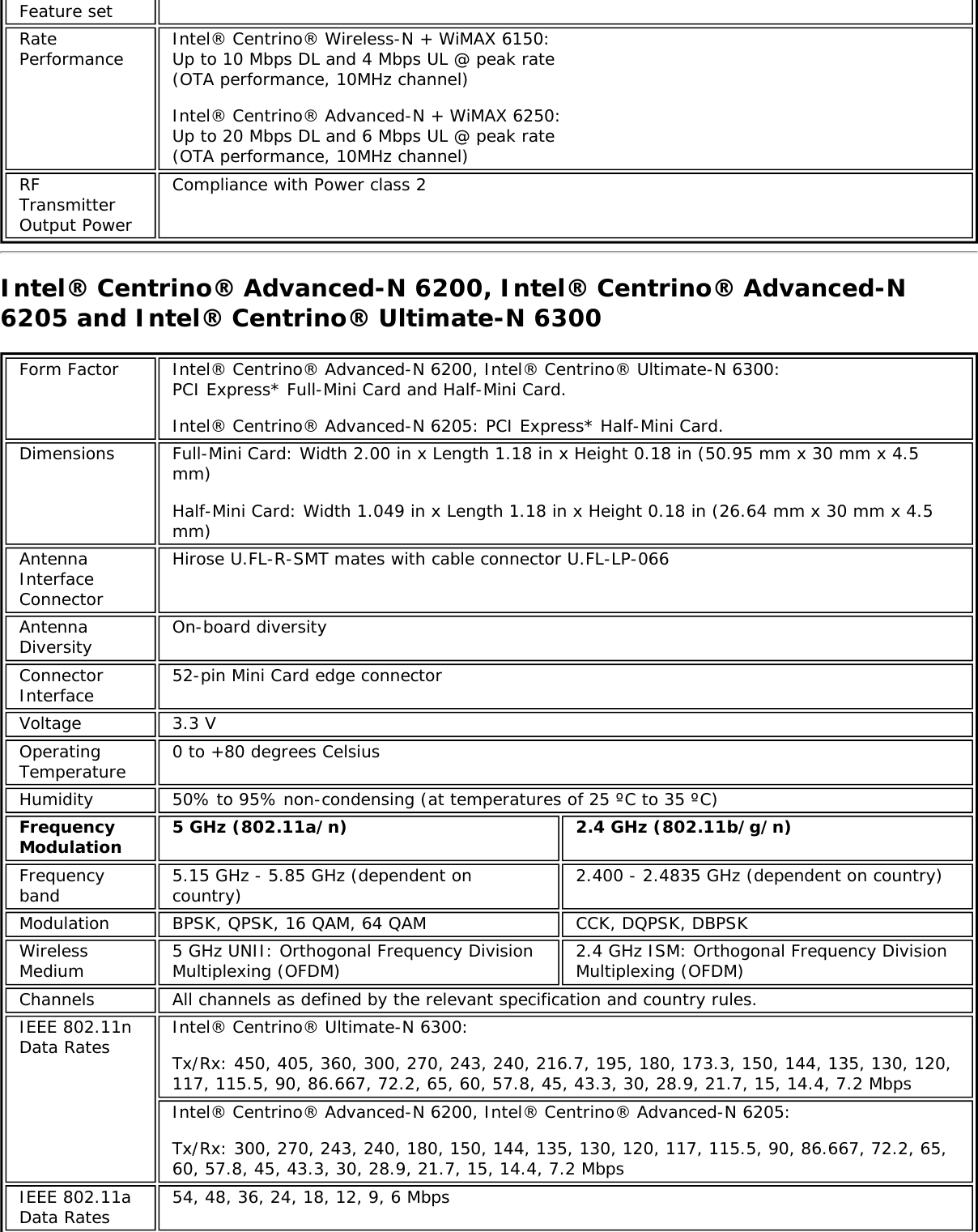
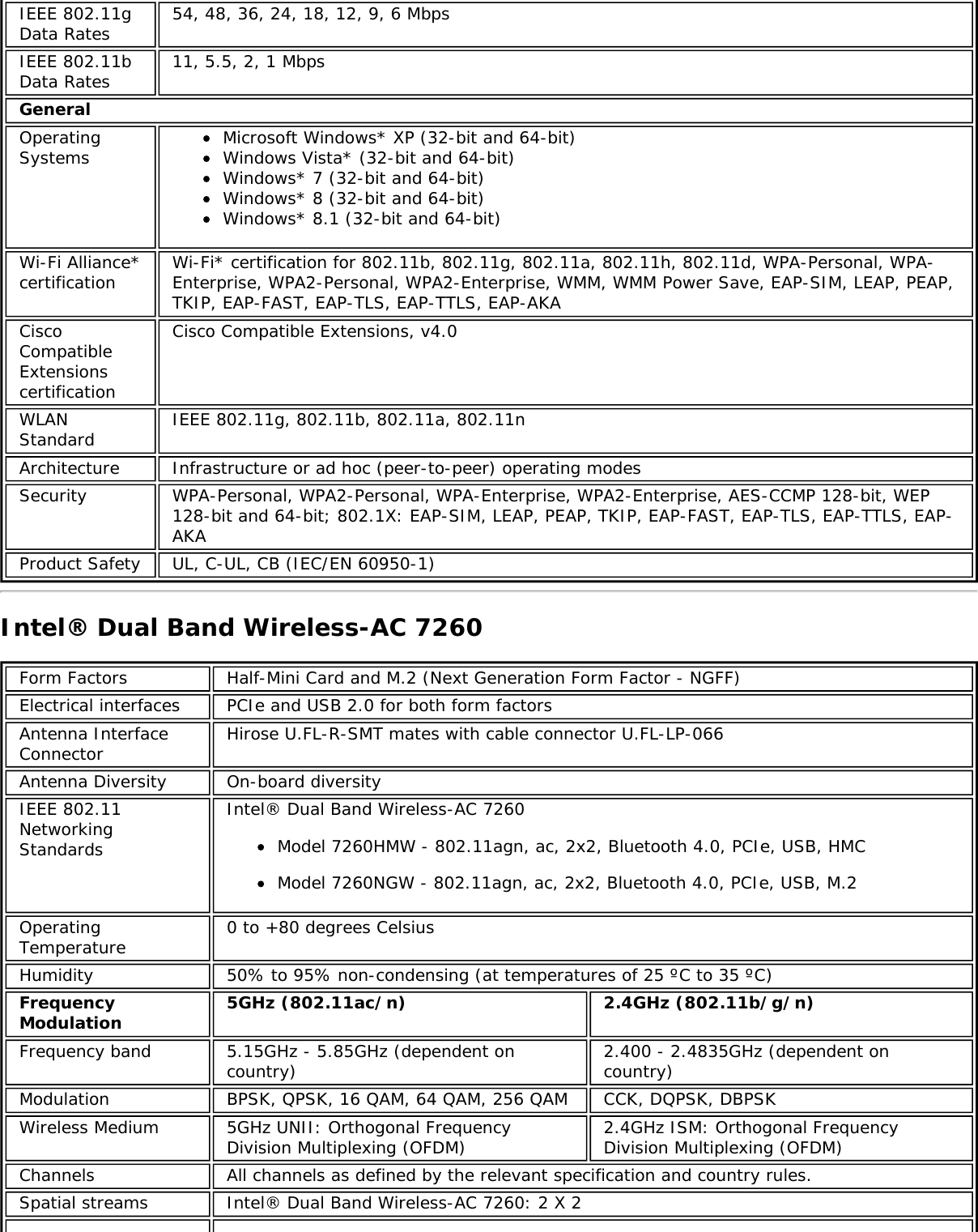
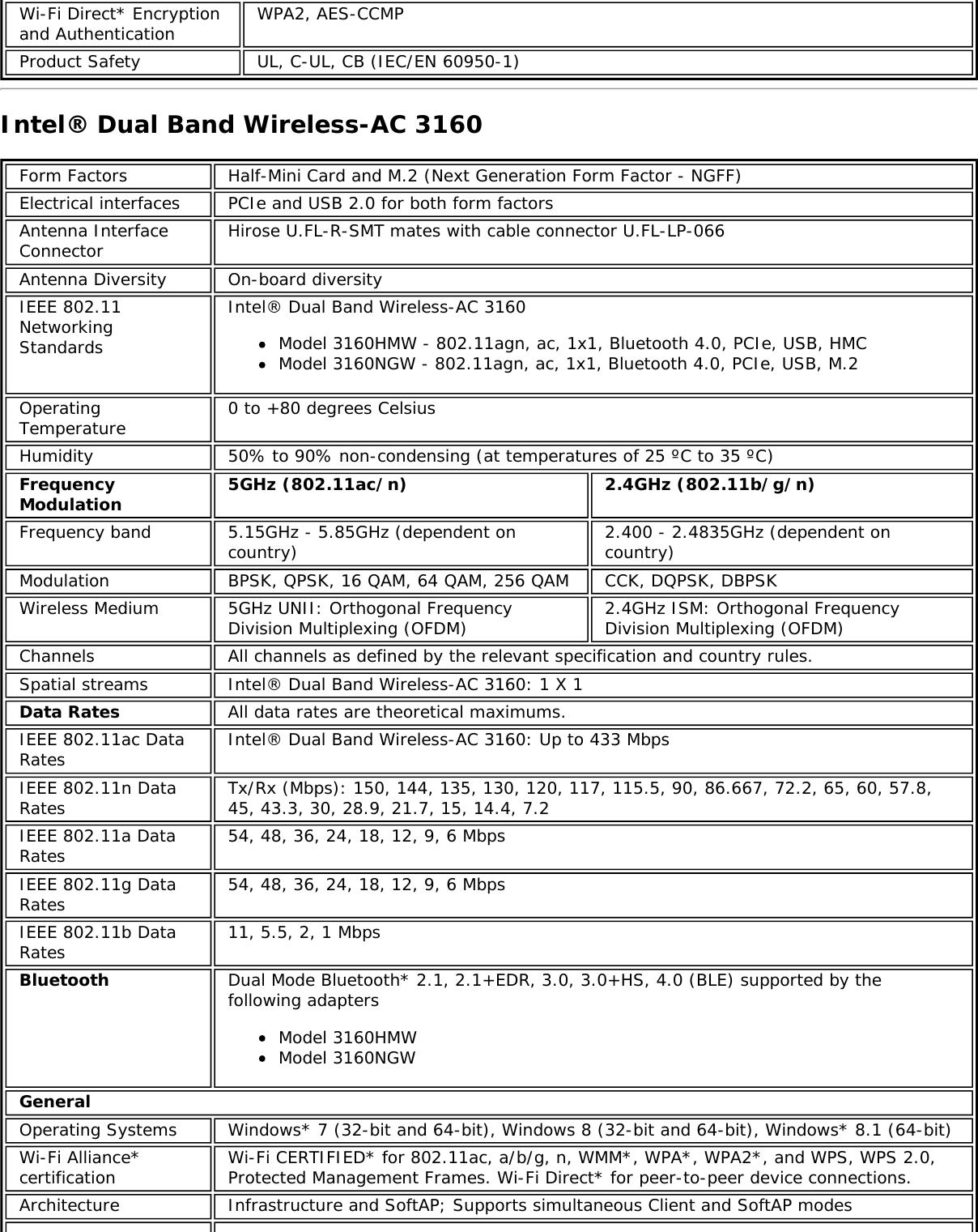
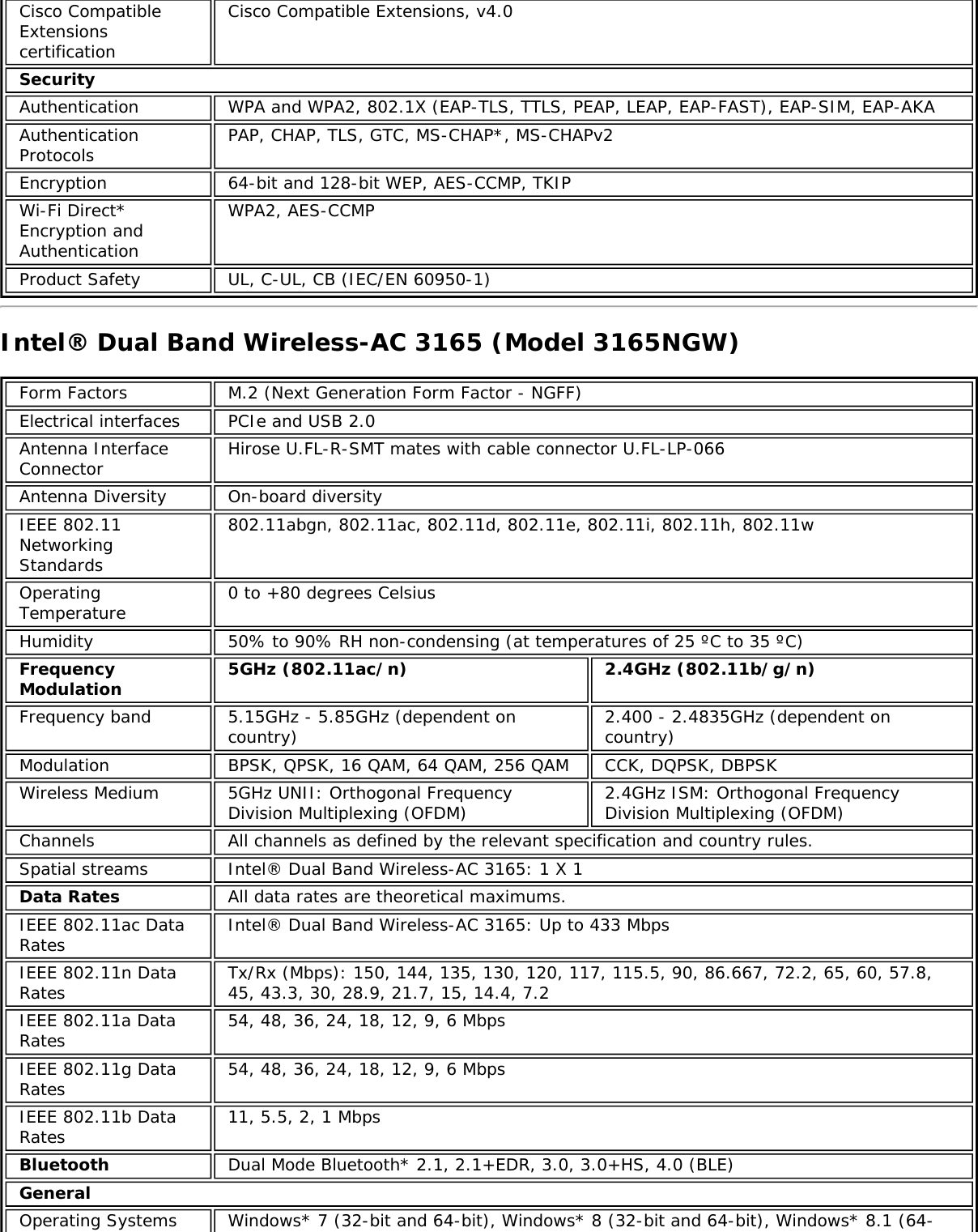
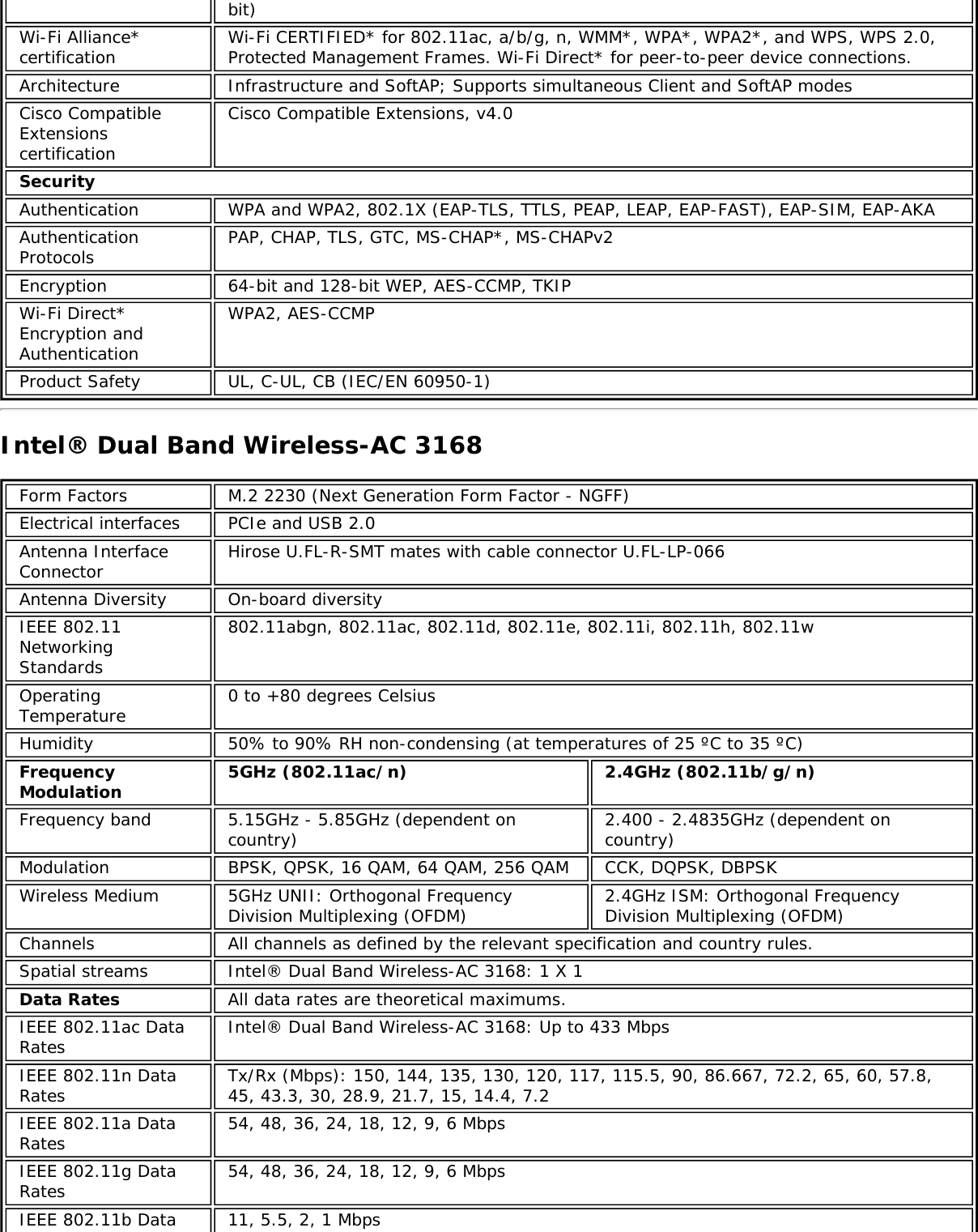
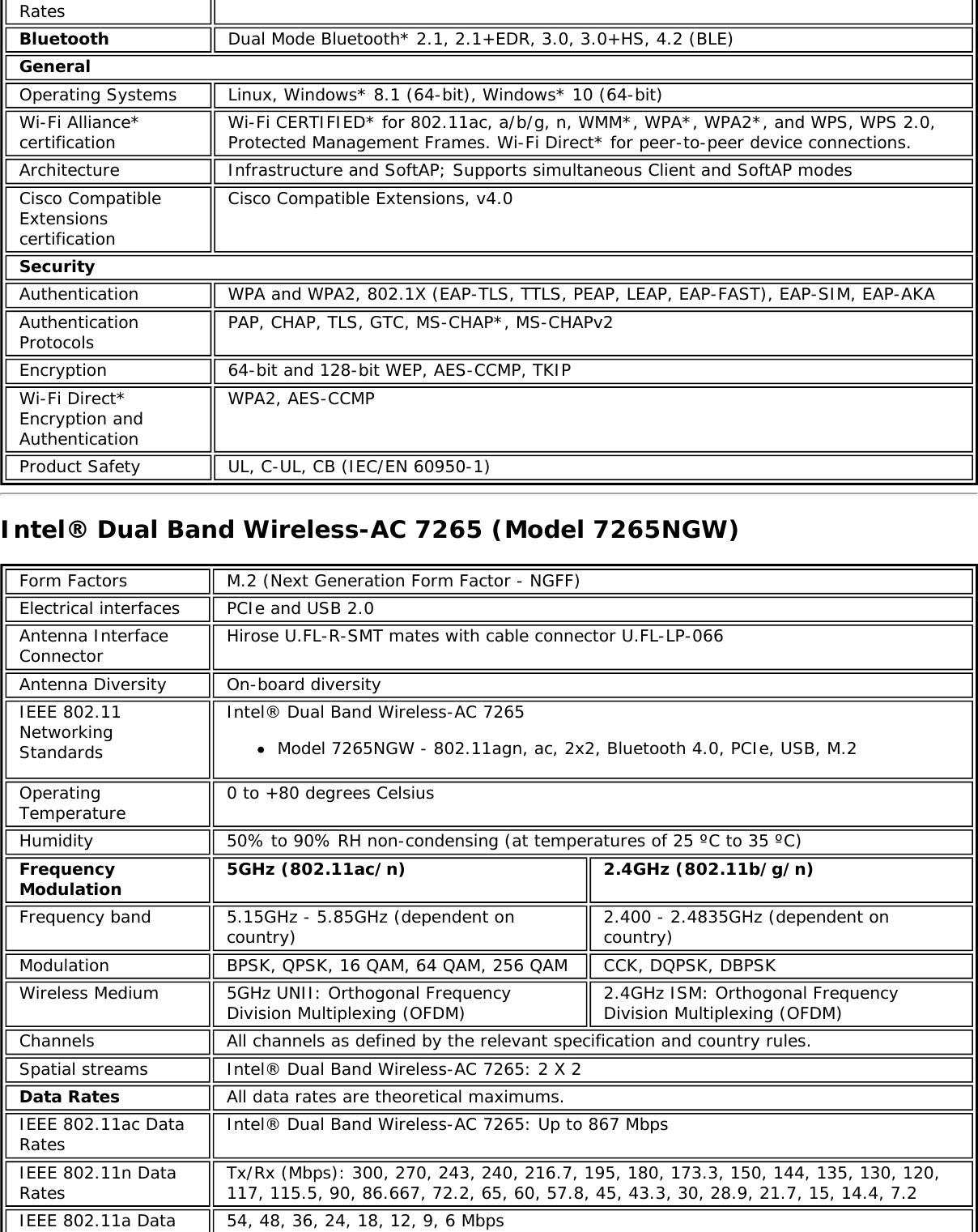
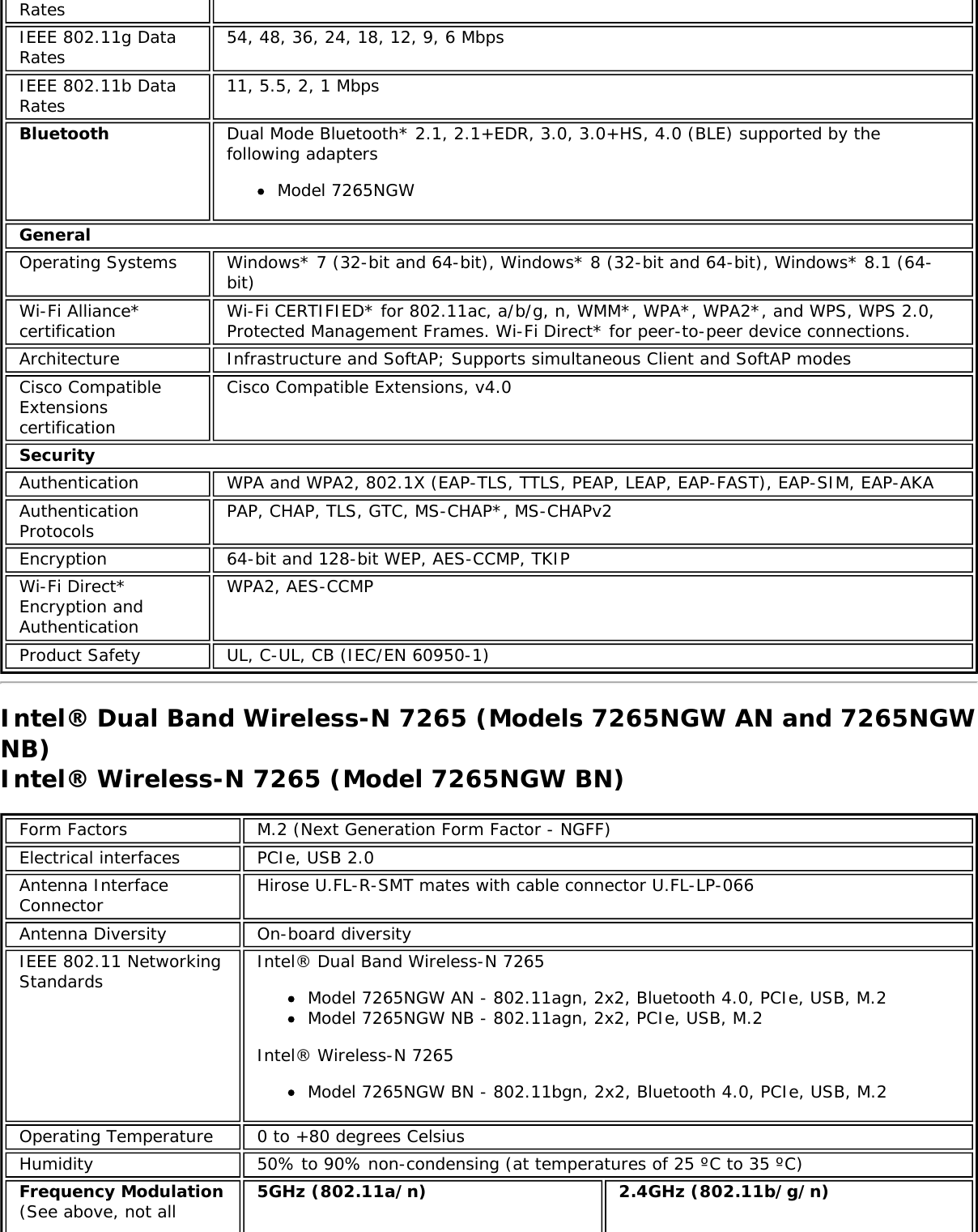
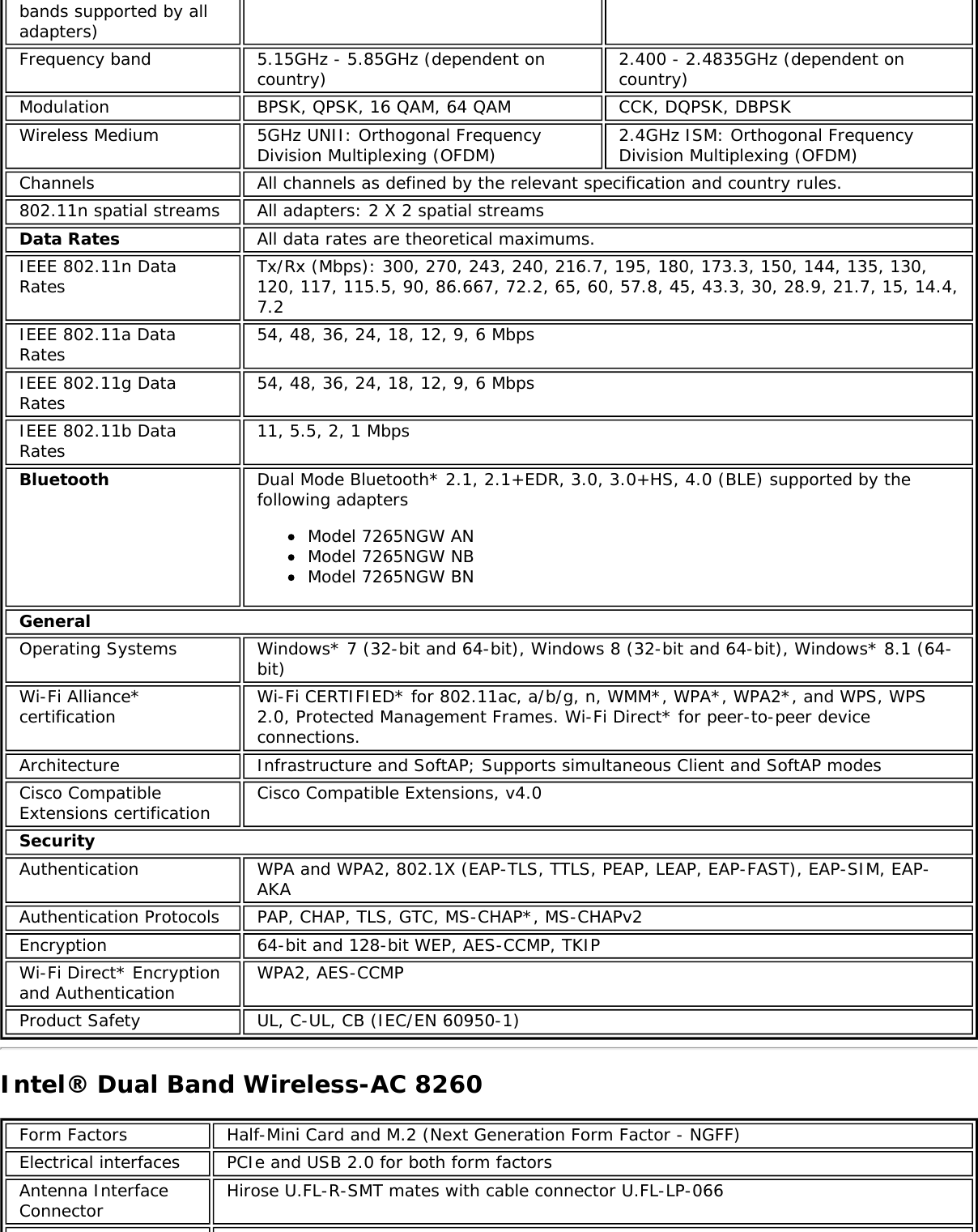
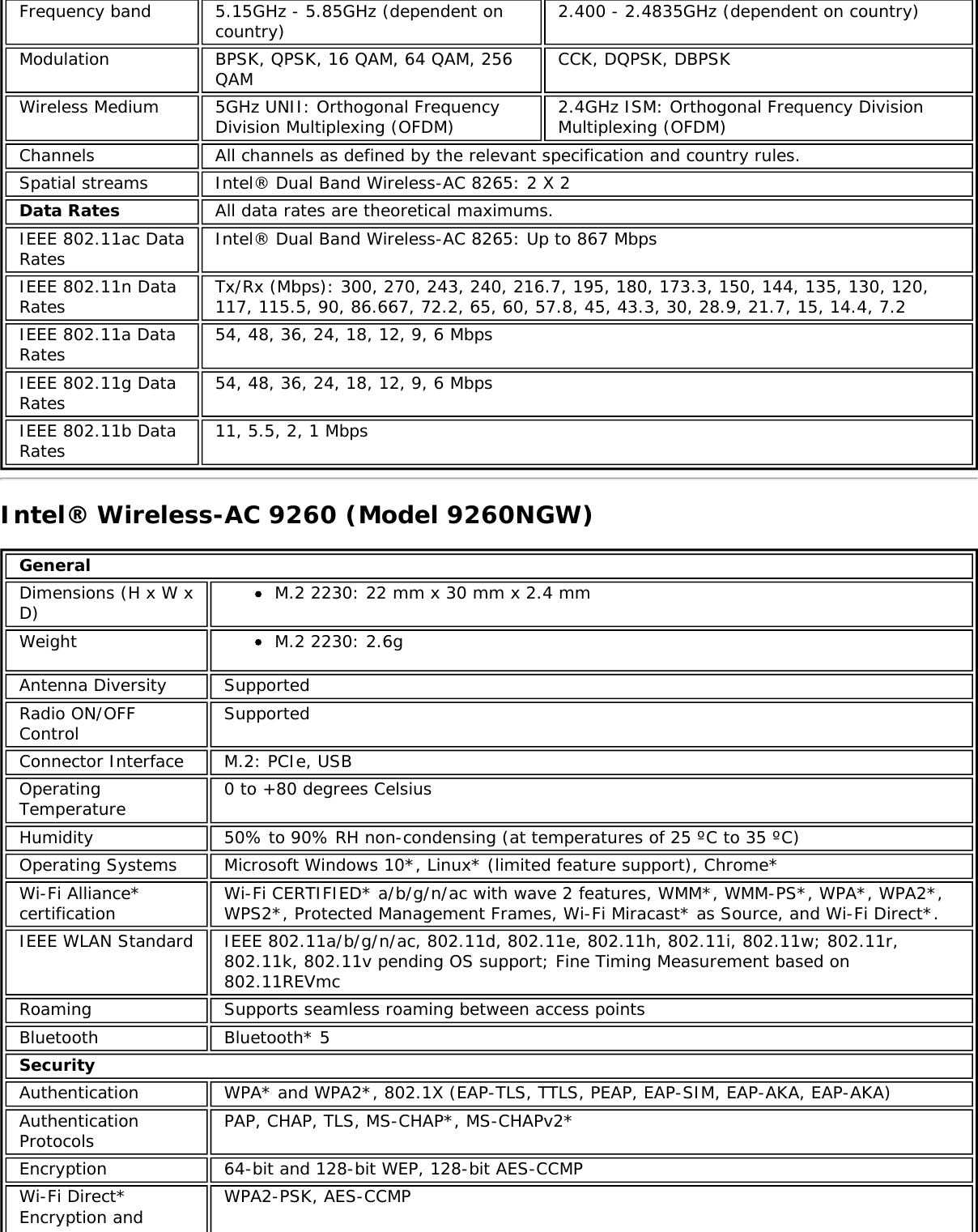
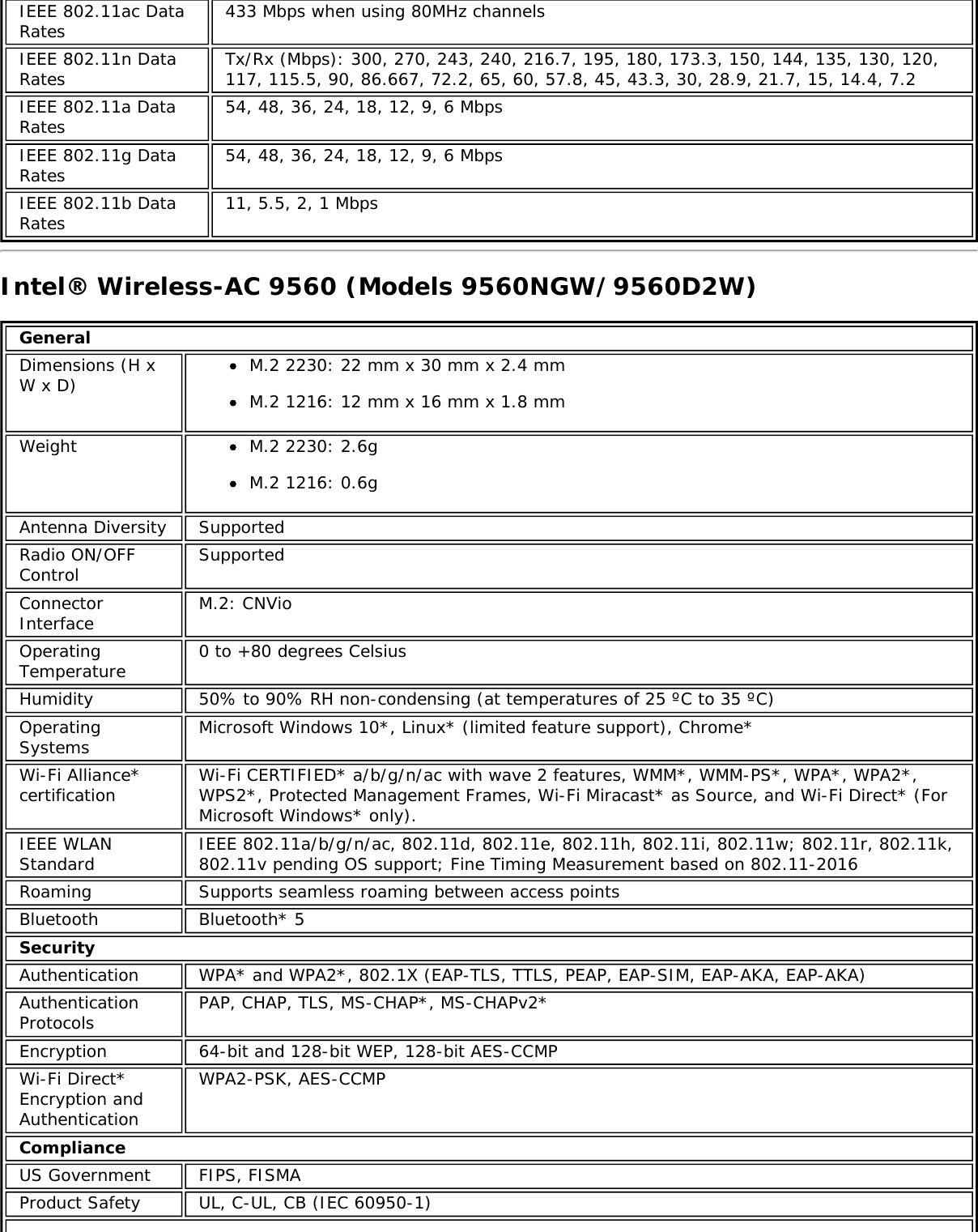
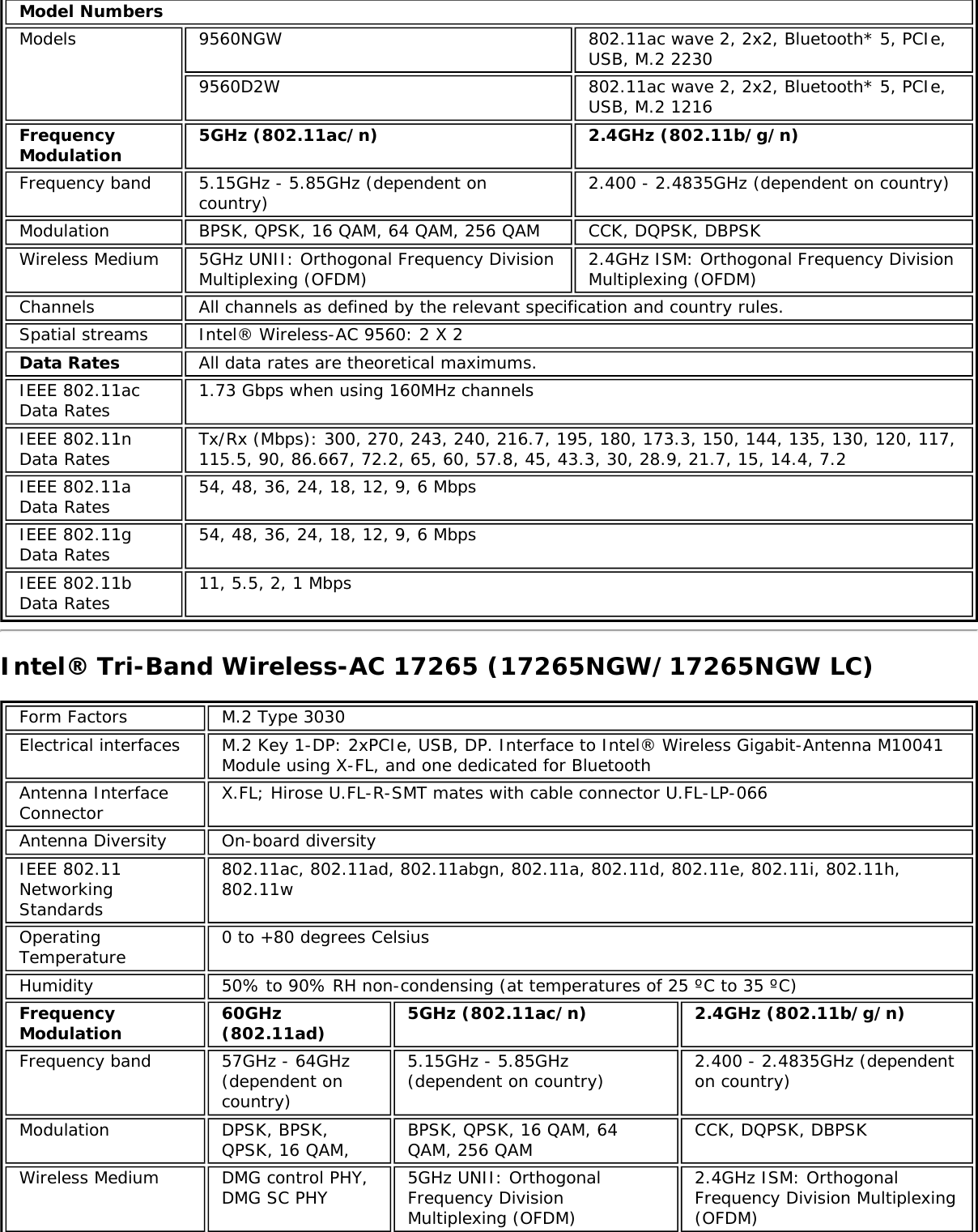
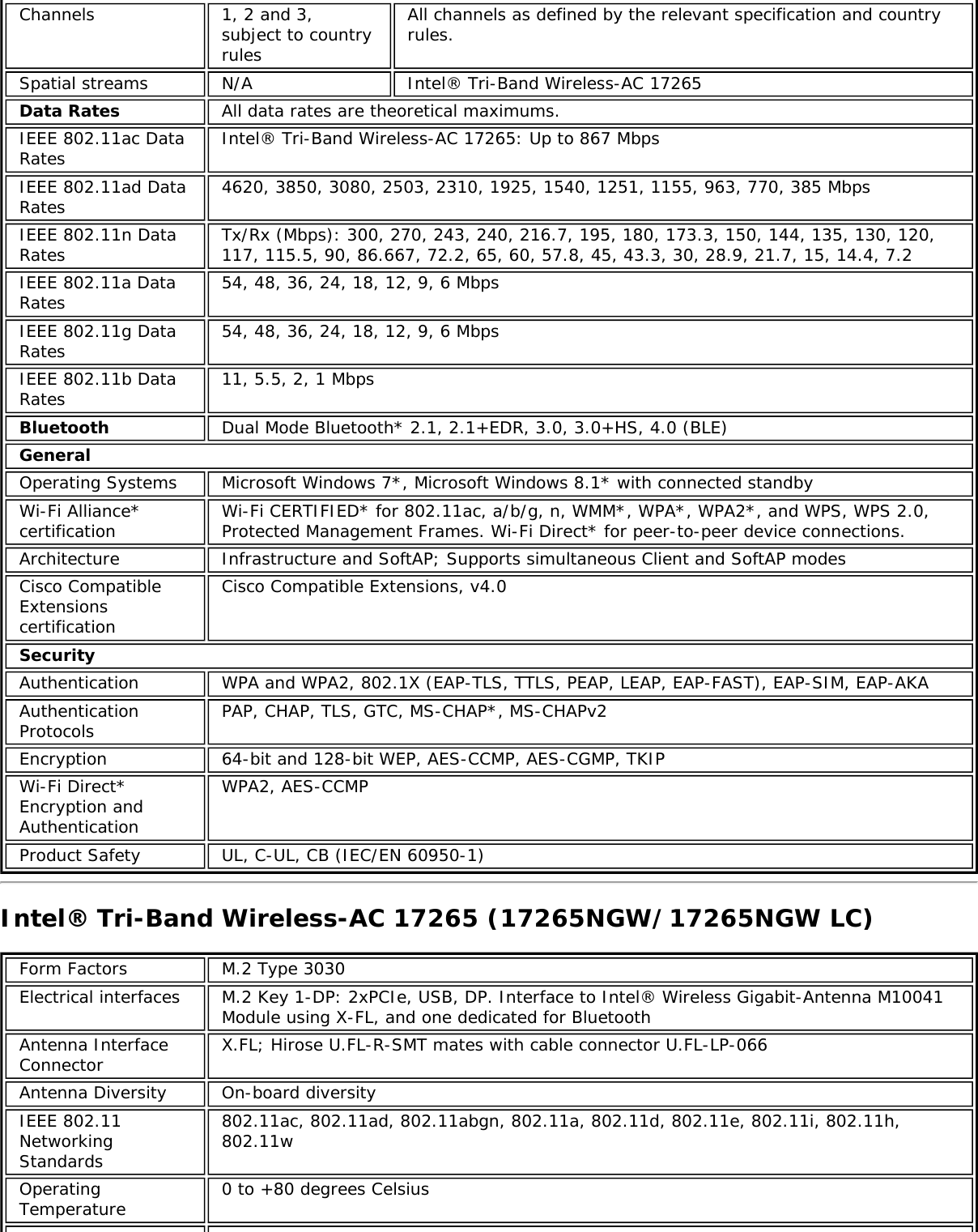
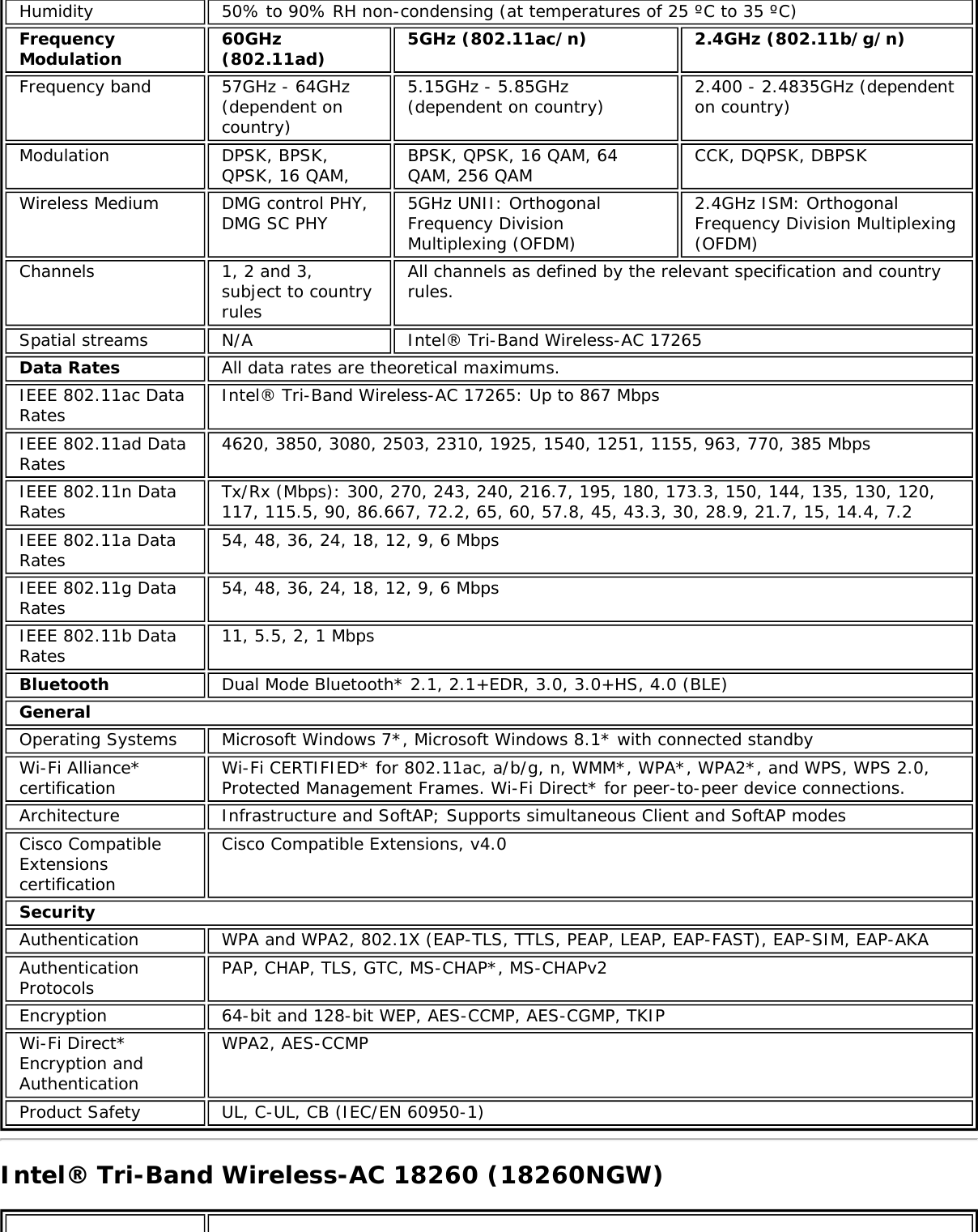
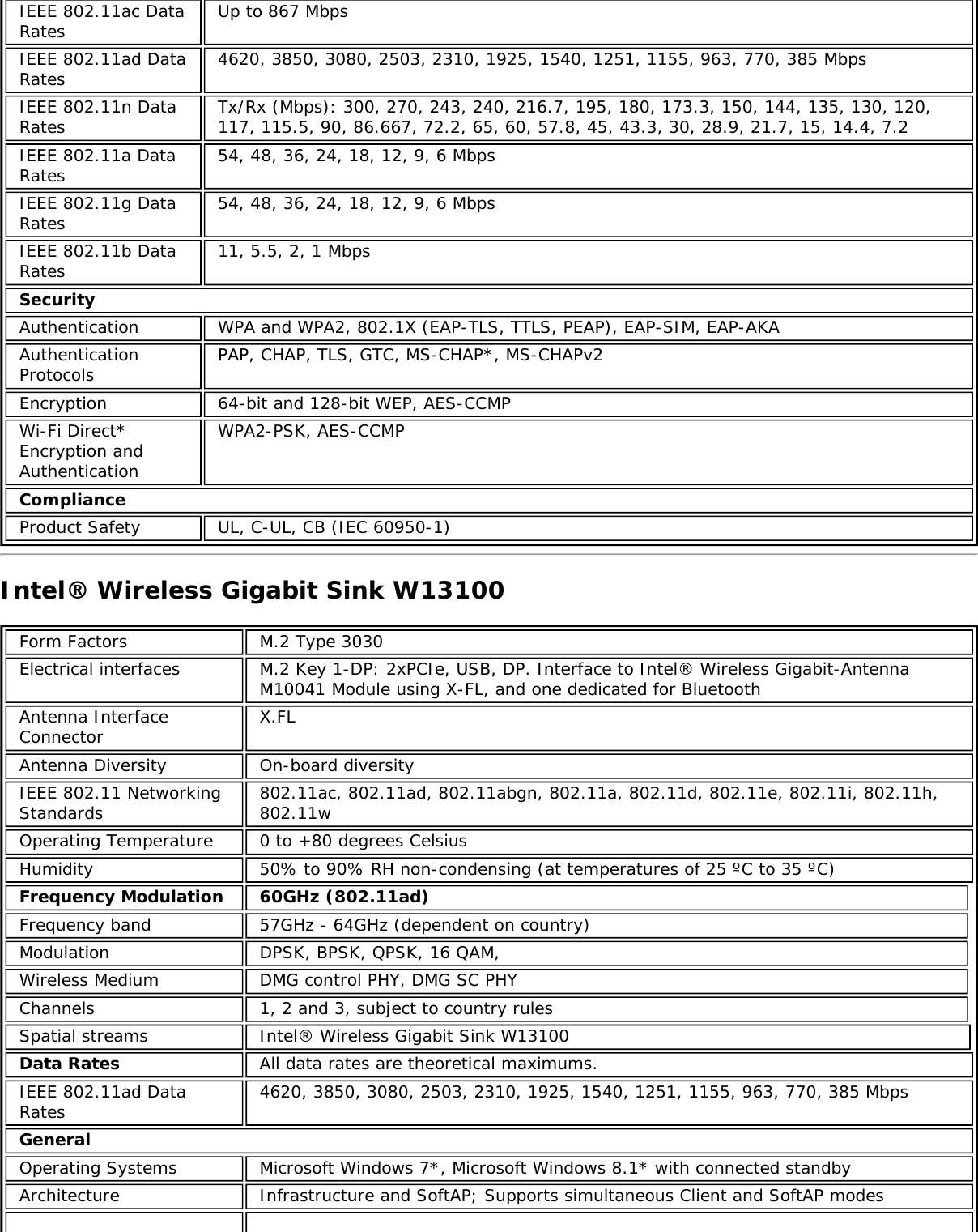
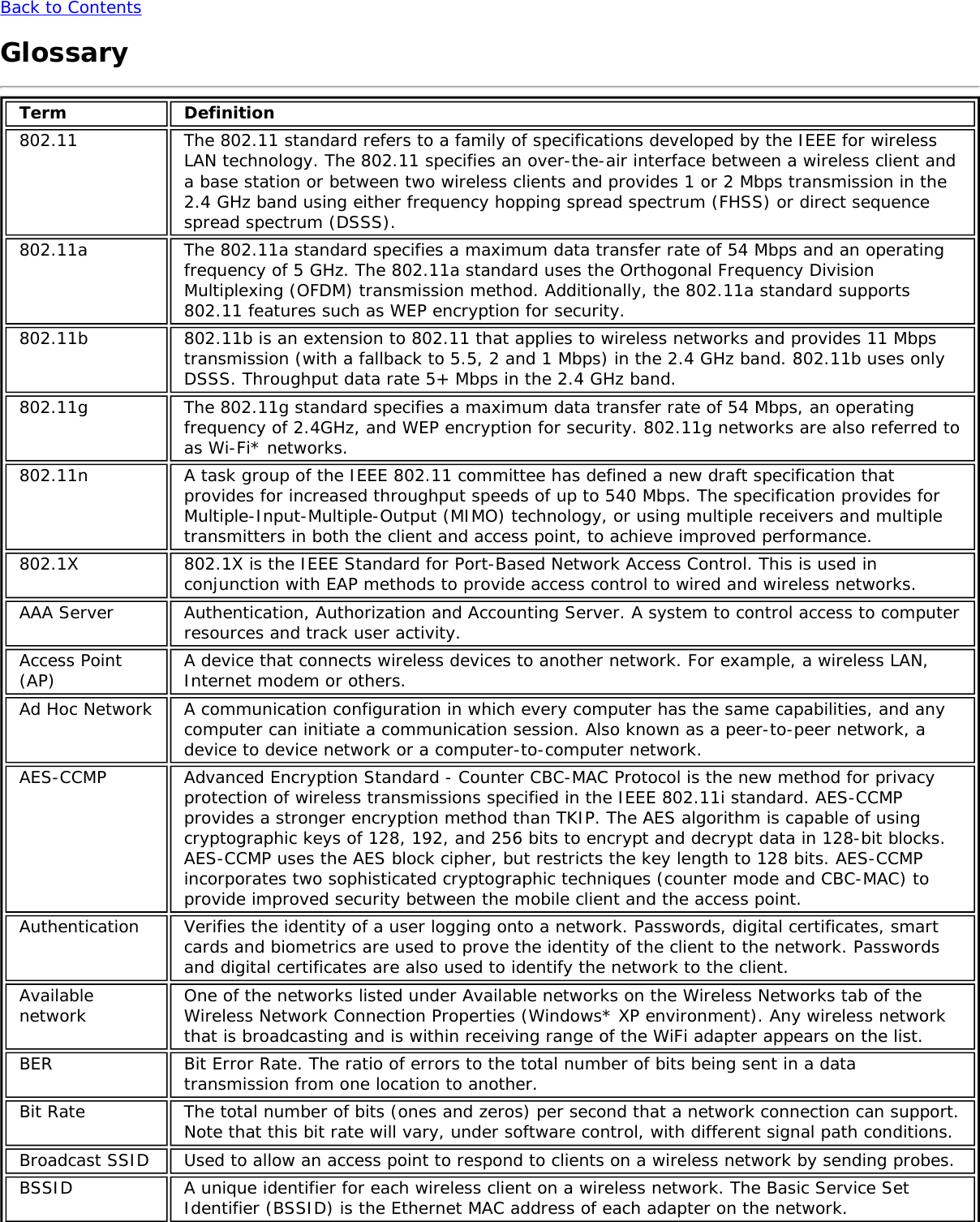
![Form Factors M.2 Type 2230Electrical interfaces M.2 Key 1-DP: 2xPCIe, USB, DP. Interface to Intel® Wireless Gigabit-Antenna M10041or M10042 Module using X-FL (single coax cable to carry power, IF and control)Dimensions 22 mm x 30 mm x S3 [1.5mm Max (Top Side)/ 0.1mm max (bottom side)]Antenna InterfaceConnector X.FL; Hirose U.FL-R-SMT mates with cable connector U.FL-LP-066Antenna Diversity On-board diversityIEEE 802.11NetworkingStandardsIEEE 802.11abgn, 802.11ac, 802.11ad, 802.11d, 802.11e, 802.11i, 802.11h, 802.11wOperatingTemperature 0 to +80 degrees CelsiusHumidity 50% to 90% RH non-condensing (at temperatures of 25 ºC to 35 ºC)FrequencyModulation 60GHz(802.11ad) 5GHz (802.11ac/n) 2.4GHz (802.11b/g/n)Frequency band 57GHz - 64GHz(dependent oncountry)5.15GHz - 5.85GHz(dependent on country) 2.400 - 2.4835GHz (dependenton country)Modulation DPSK, BPSK,QPSK, 16 QAM, BPSK, QPSK, 16 QAM, 64QAM, 256 QAM CCK, DQPSK, DBPSKWireless Medium DMG control PHY,DMG SC PHY 5GHz UNII: OrthogonalFrequency DivisionMultiplexing (OFDM)2.4GHz ISM: OrthogonalFrequency Division Multiplexing(OFDM)Channels 1, 2 and 3,subject to countryrulesAll channels as defined by the relevant specification and countryrules.Spatial streams N/A Intel® Tri-Band Wireless-AC 18260Data Rates All data rates are theoretical maximums.IEEE 802.11ac DataRates Intel® Tri-Band Wireless-AC 18260: Up to 867 MbpsIEEE 802.11ad DataRates 4620, 3850, 3080, 2503, 2310, 1925, 1540, 1251, 1155, 963, 770, 385 MbpsIEEE 802.11n DataRates Tx/Rx (Mbps): 300, 270, 243, 240, 216.7, 195, 180, 173.3, 150, 144, 135, 130, 120,117, 115.5, 90, 86.667, 72.2, 65, 60, 57.8, 45, 43.3, 30, 28.9, 21.7, 15, 14.4, 7.2IEEE 802.11a DataRates 54, 48, 36, 24, 18, 12, 9, 6 MbpsIEEE 802.11g DataRates 54, 48, 36, 24, 18, 12, 9, 6 MbpsIEEE 802.11b DataRates 11, 5.5, 2, 1 MbpsBluetooth Dual Mode Bluetooth* 2.1, 2.1+EDR, 3.0, 3.0+HS, 4.0 (BLE), 4.1GeneralOperating Systems Microsoft Windows 7*, Microsoft Windows 8.1* with connected standbyWi-Fi Alliance*certification Wi-Fi CERTIFIED* for 802.11ac, a/b/g, n, WMM*, WPA*, WPA2*, and WPS, WPS 2.0,Protected Management Frames. Wi-Fi Direct* for peer-to-peer device connections.Architecture Infrastructure and SoftAP; Supports simultaneous Client and SoftAP modesCisco CompatibleExtensionscertificationCisco Compatible Extensions, v4.0Security](https://usermanual.wiki/Intel/9462NG.User-Manual/User-Guide-3671027-Page-66.png)
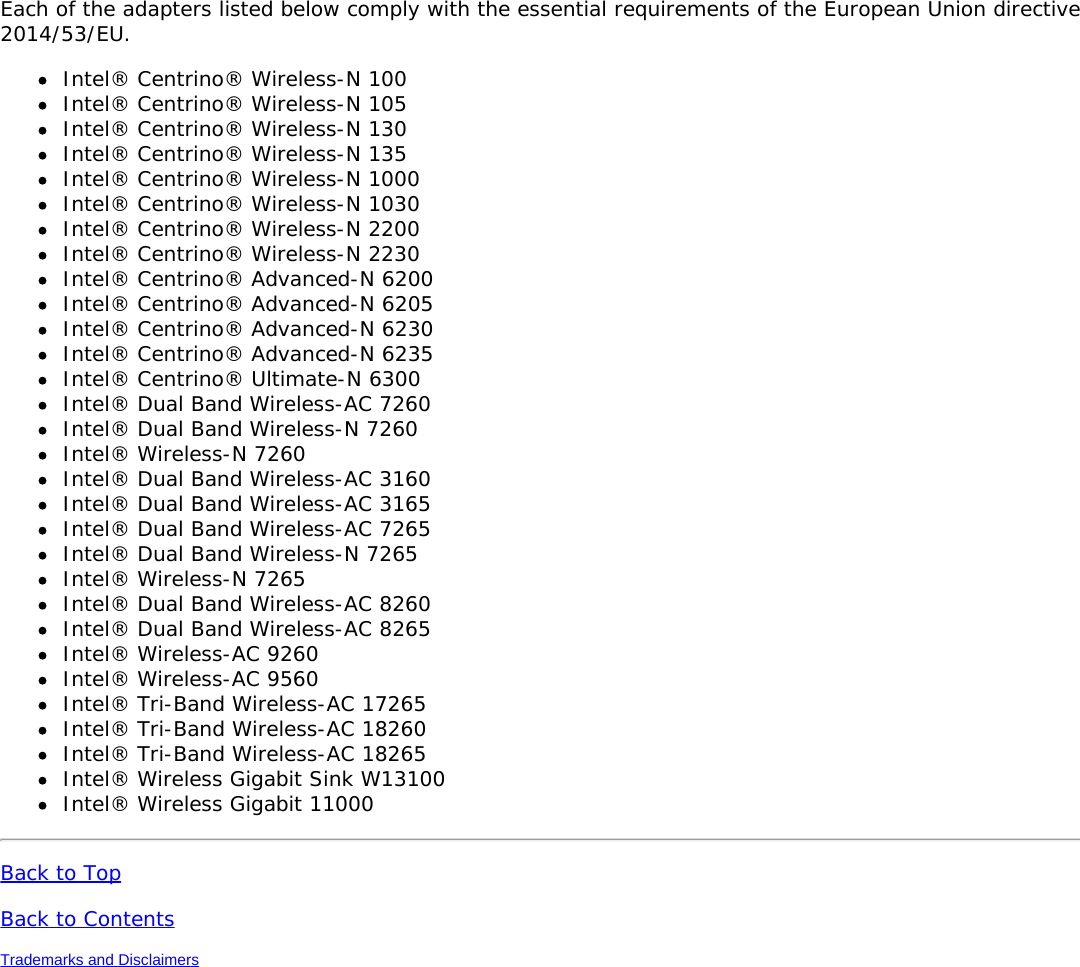
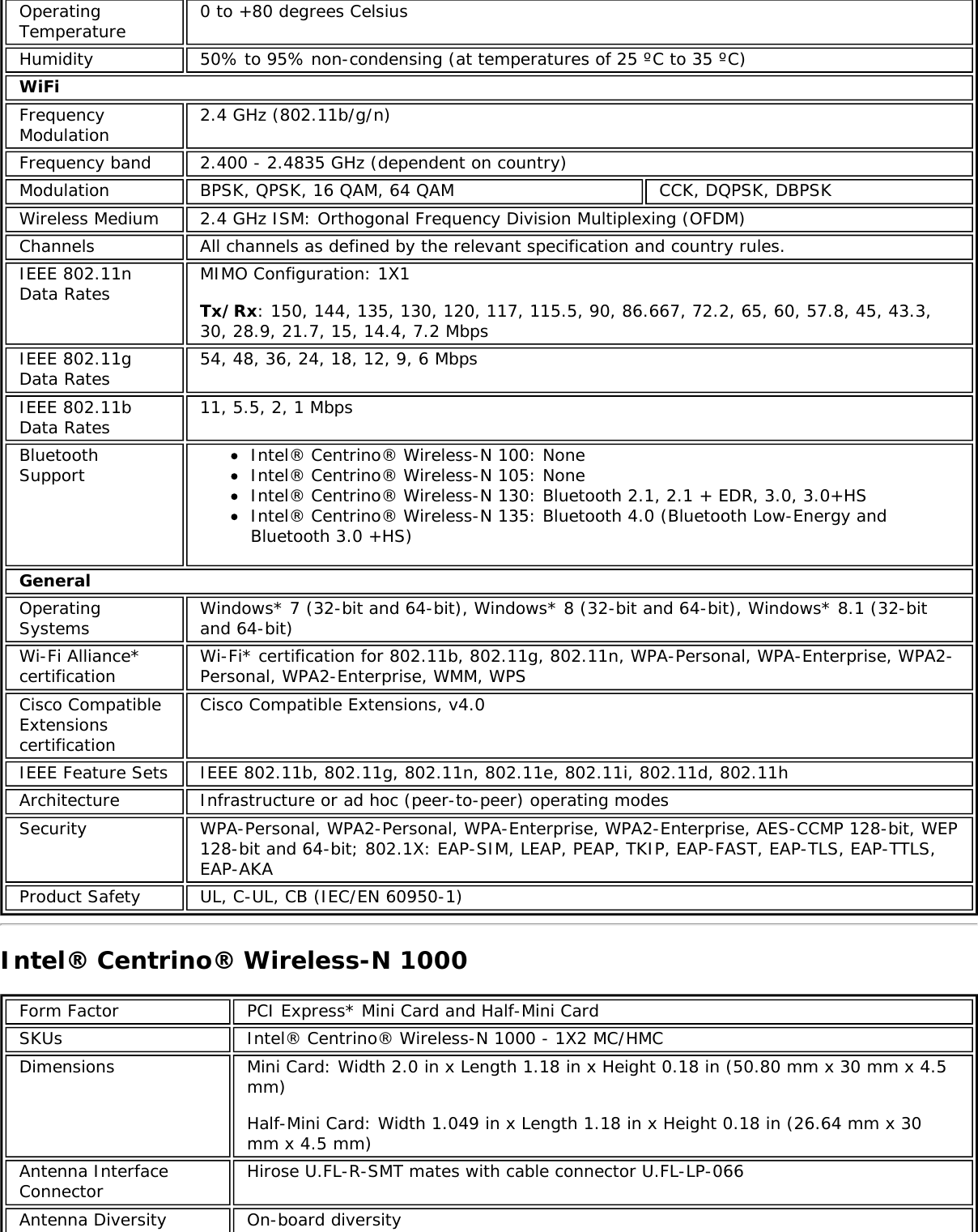
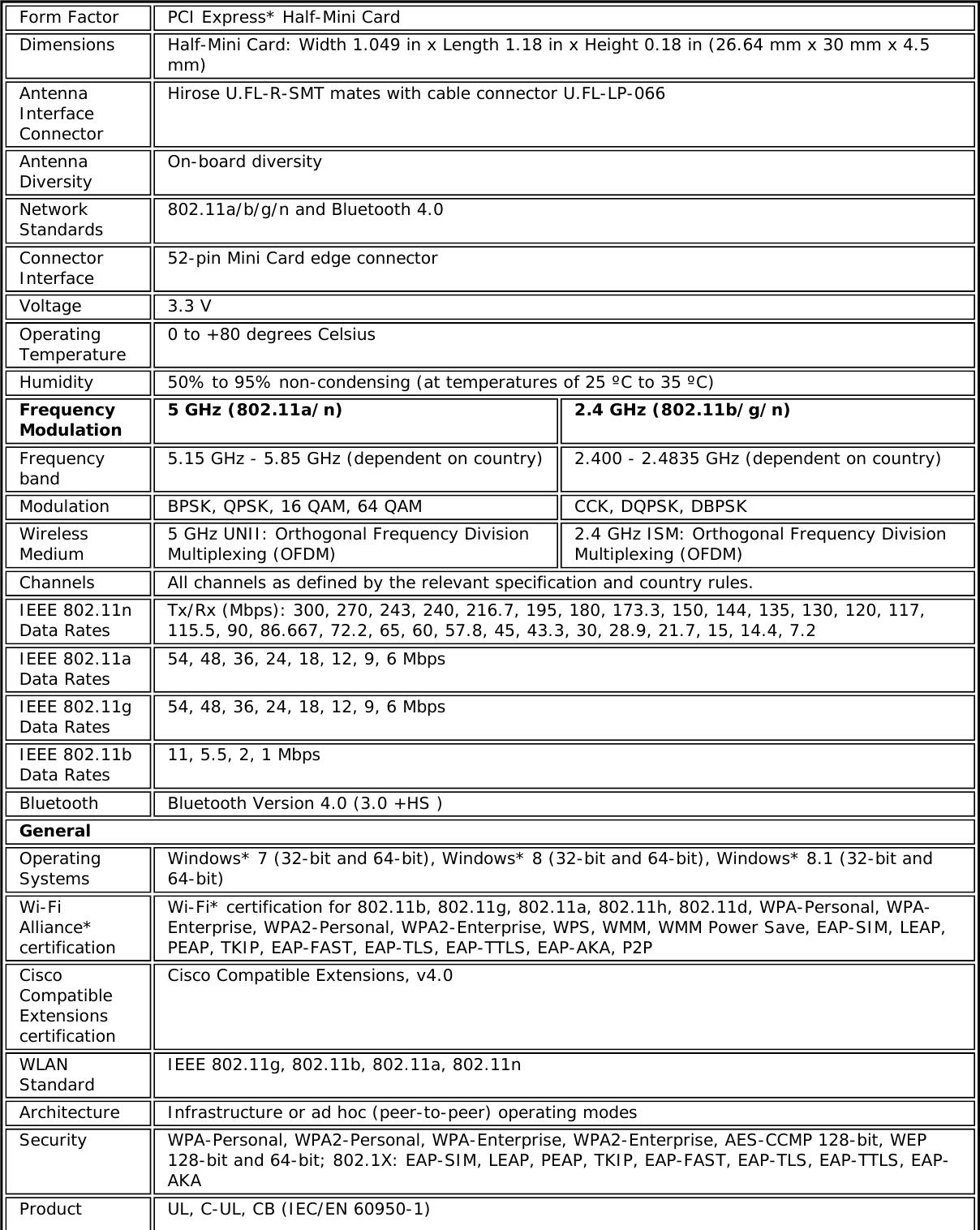
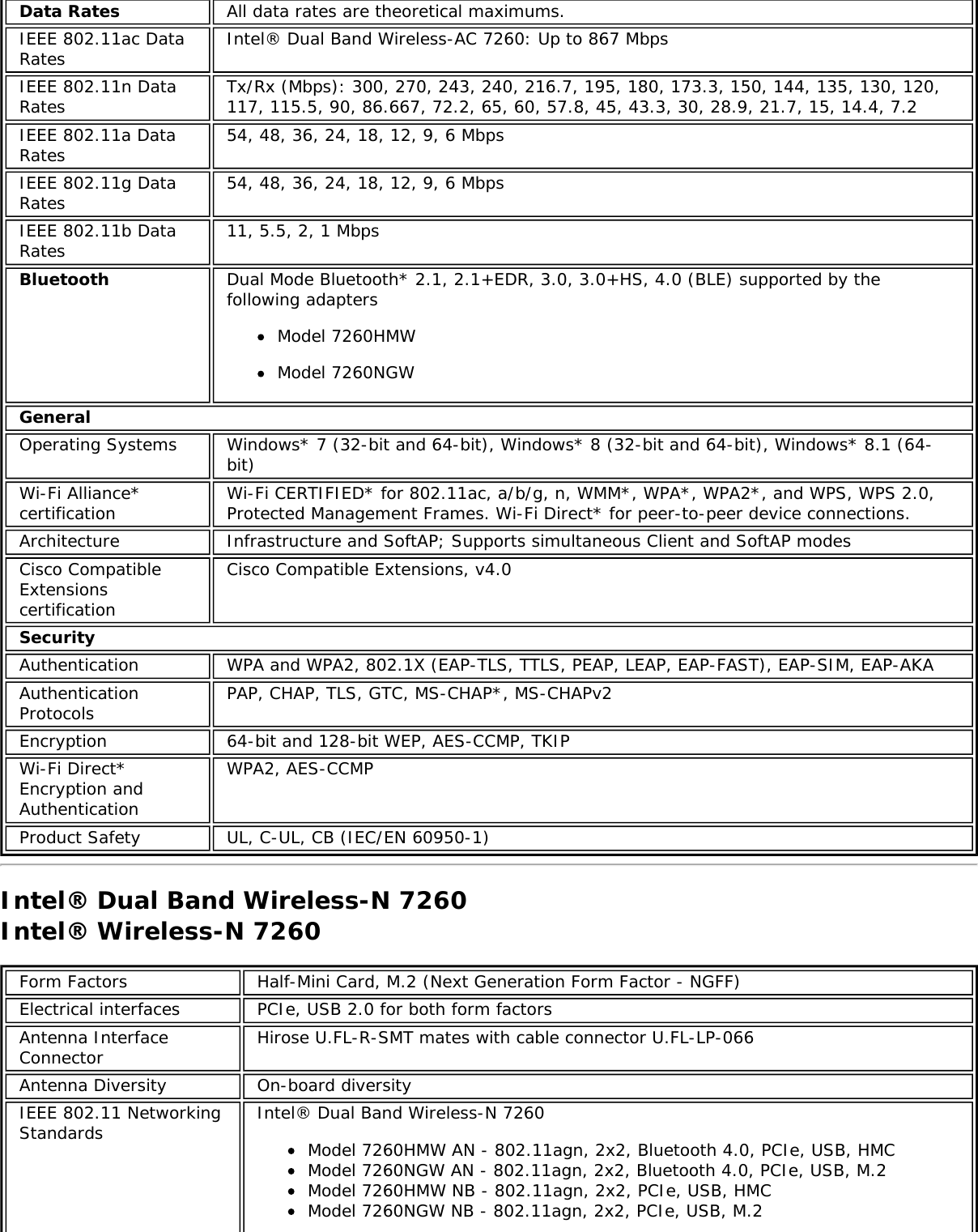
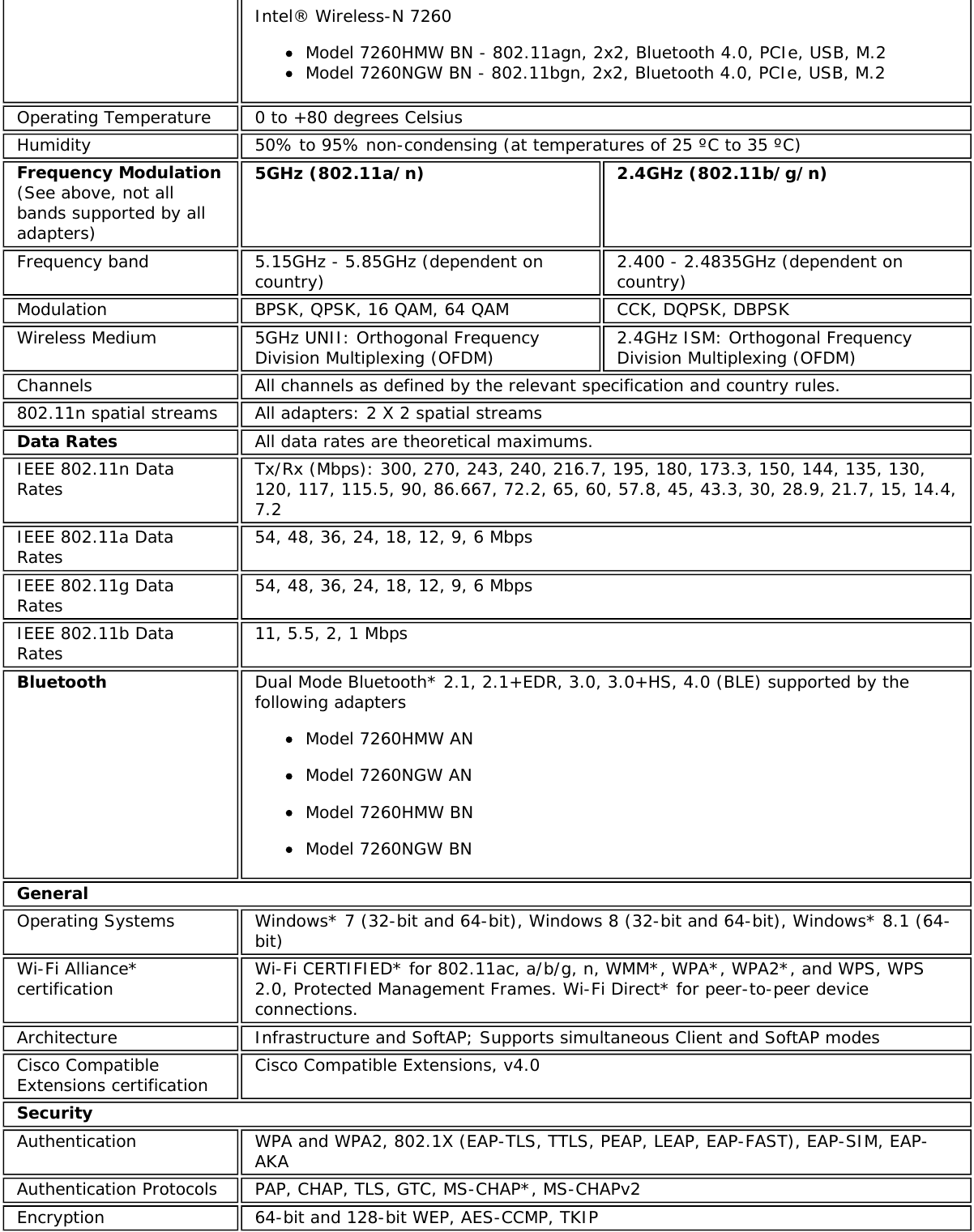
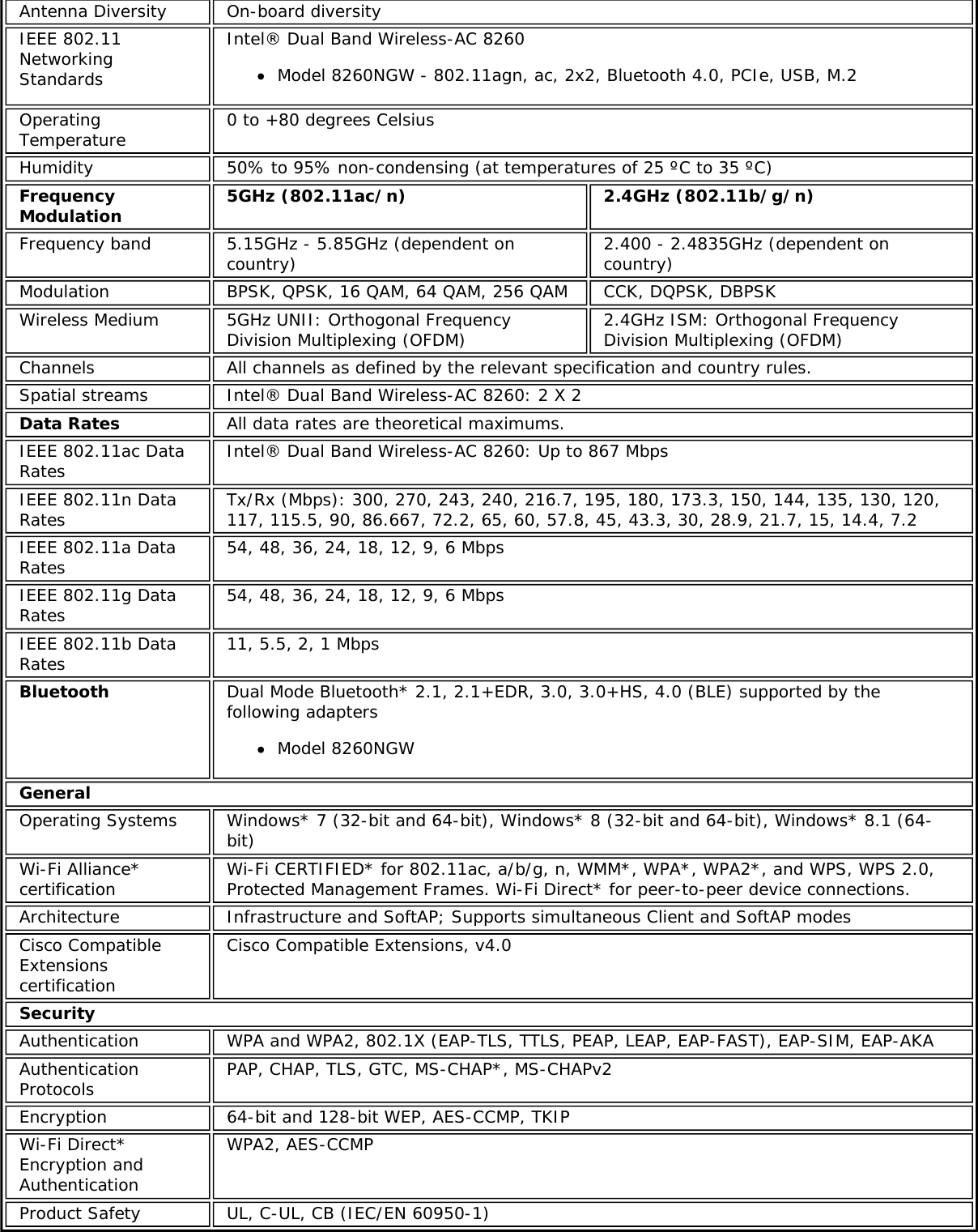
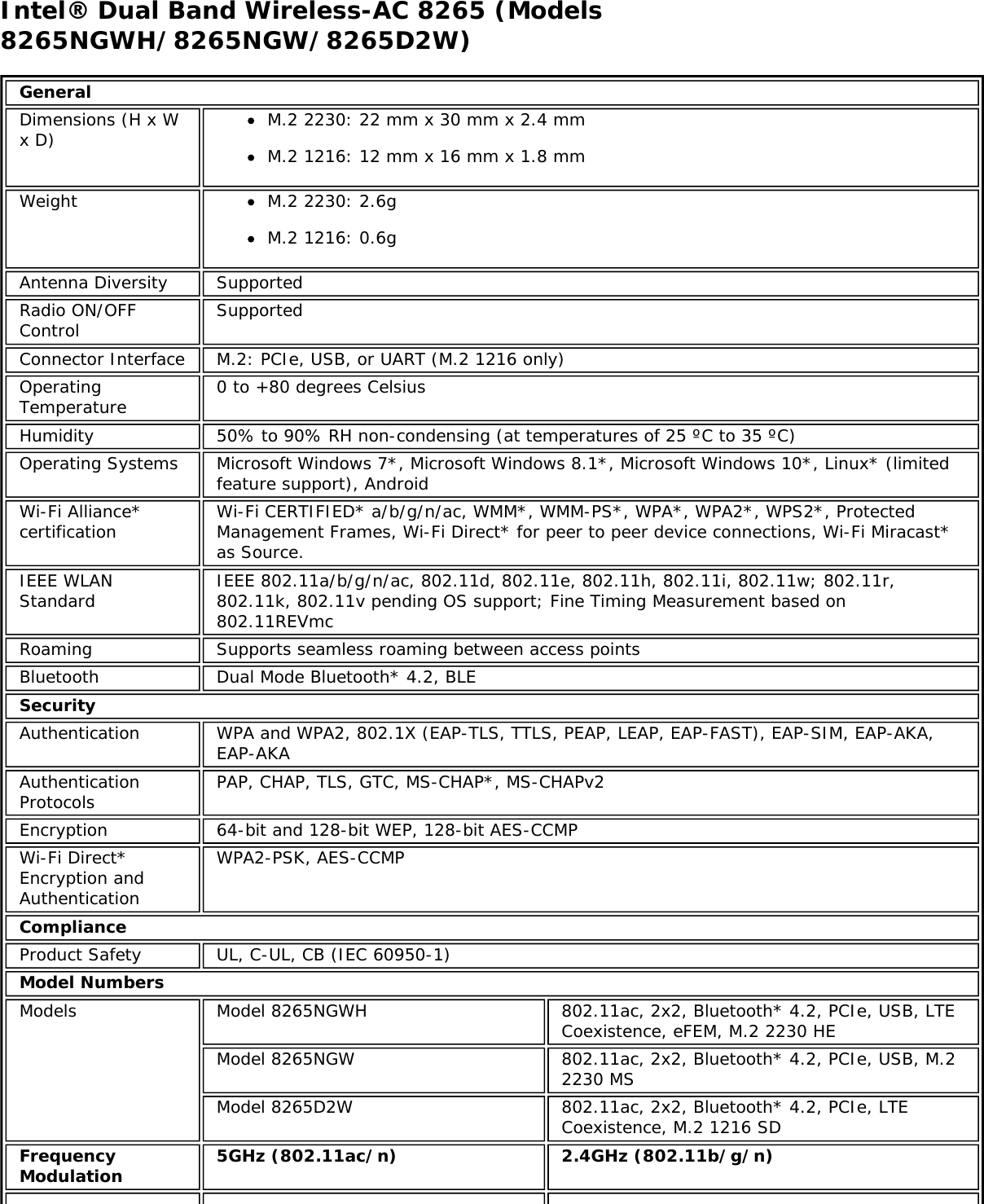
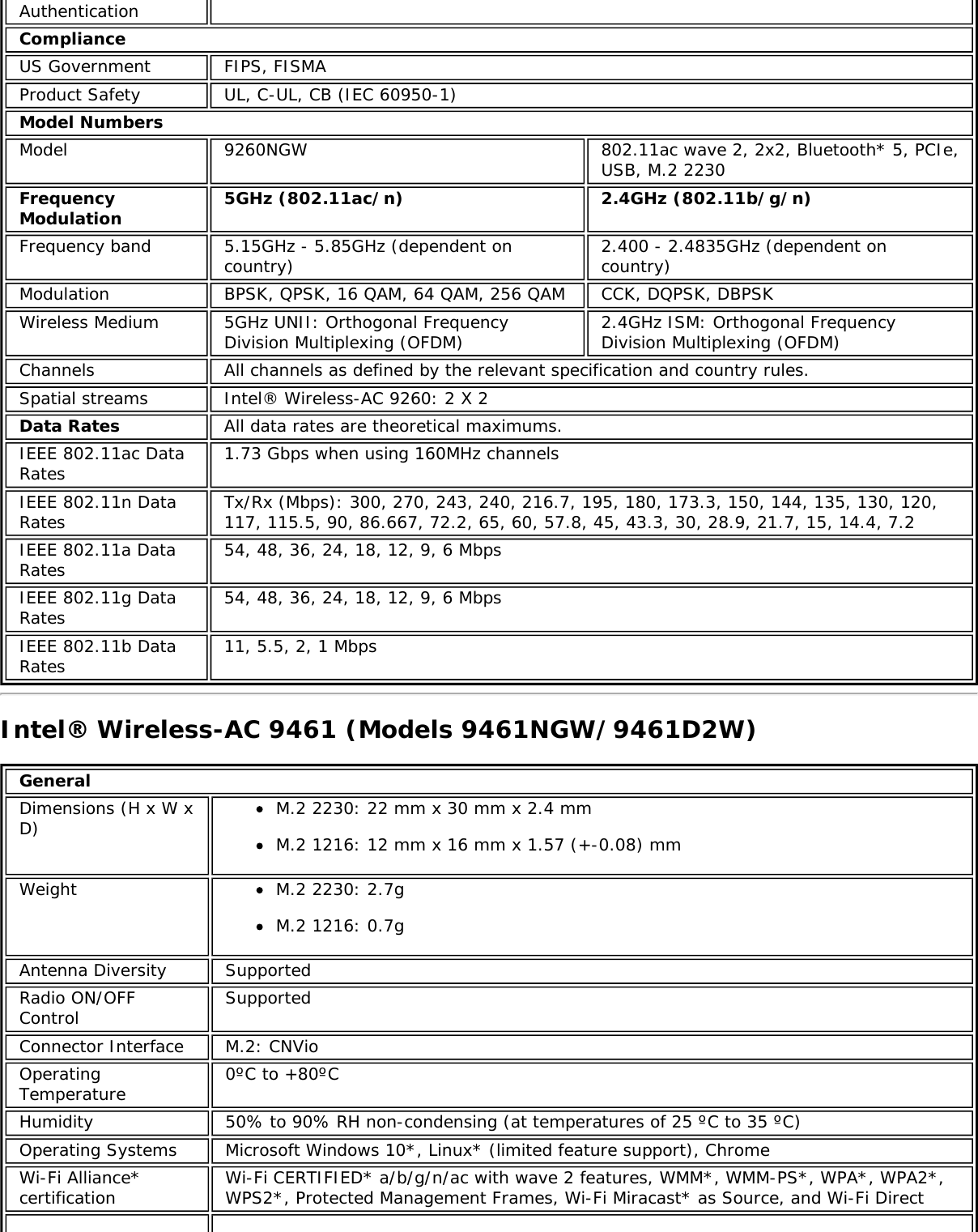
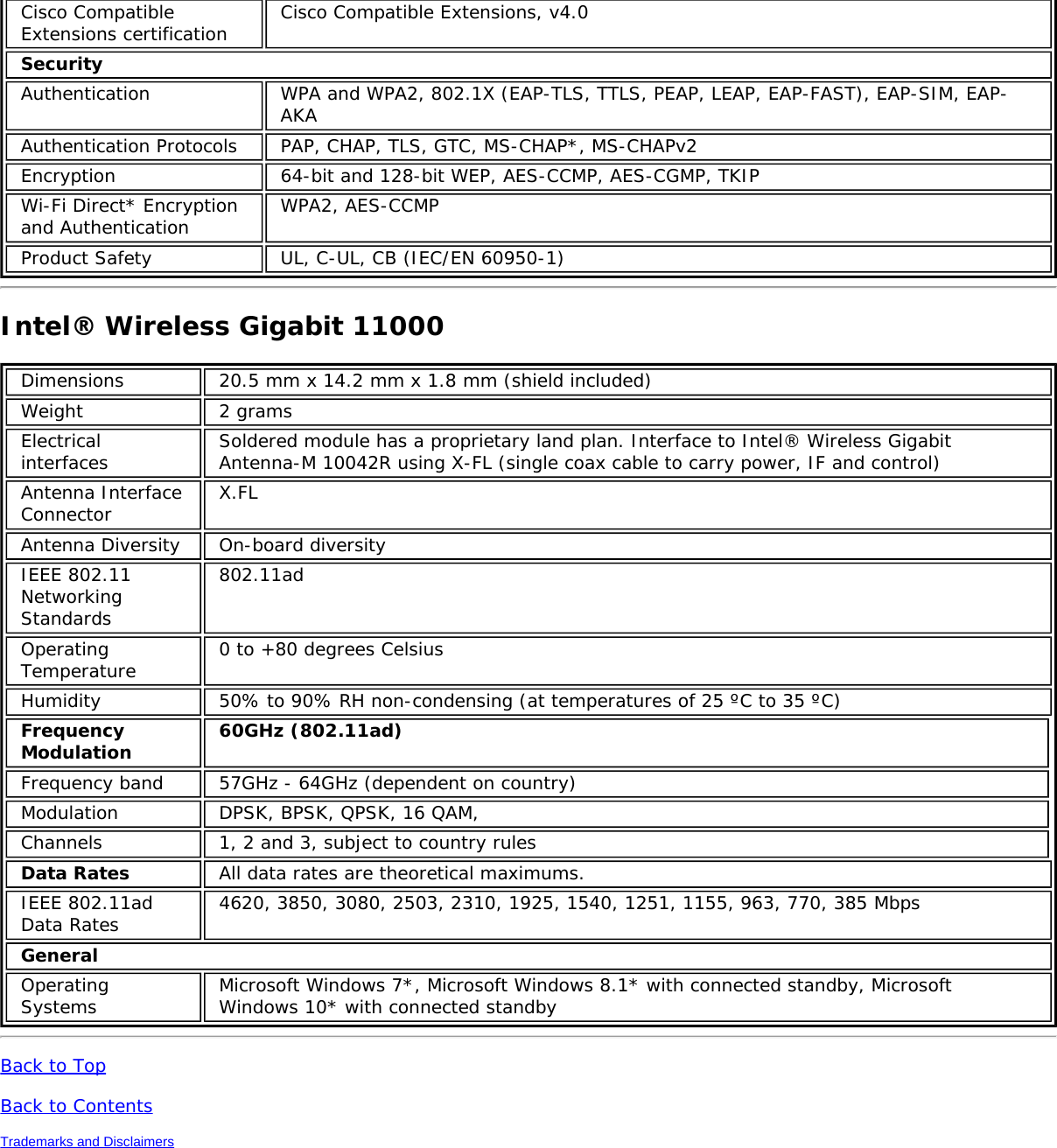
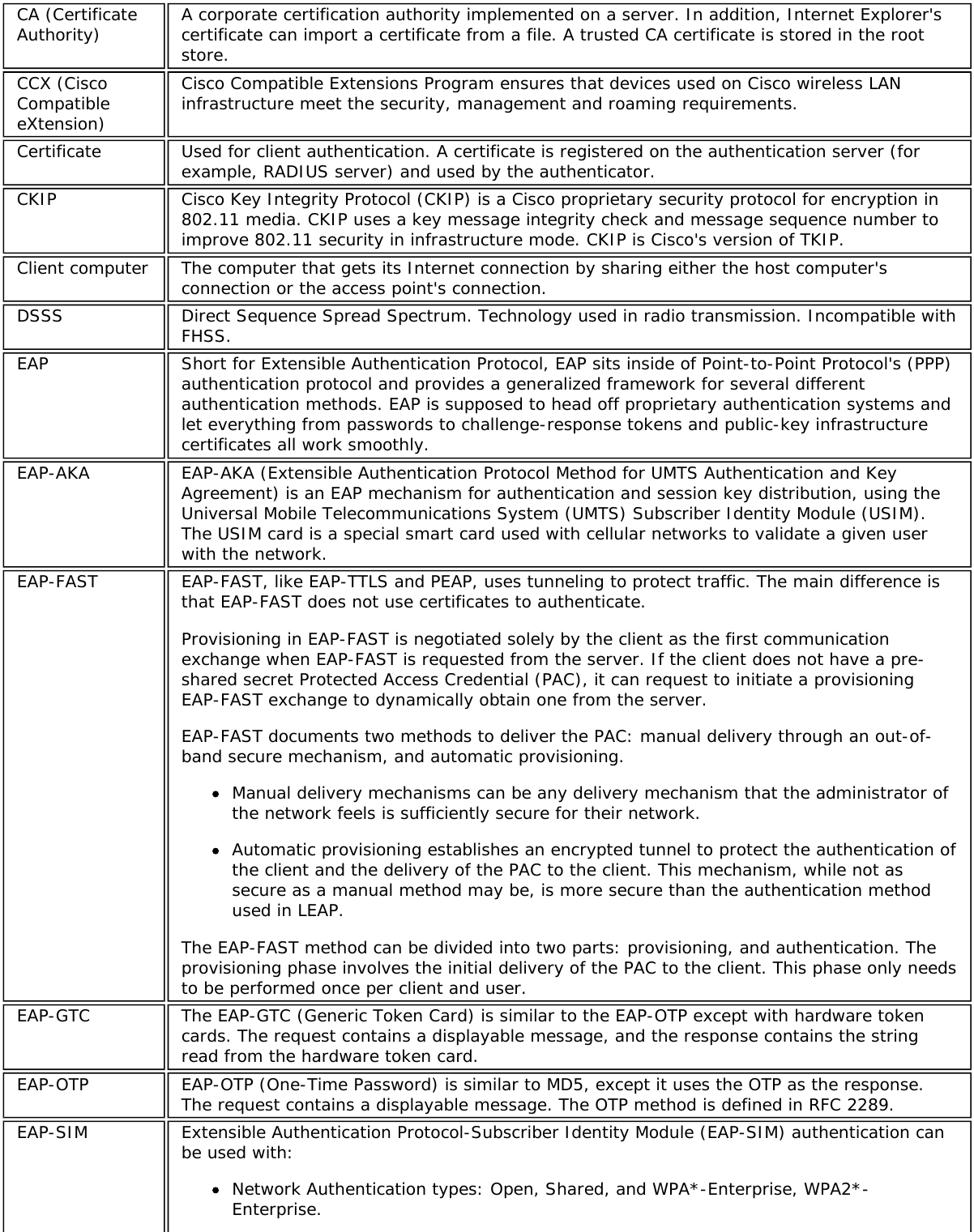
![Authentication WPA and WPA2, 802.1X (EAP-TLS, TTLS, PEAP, LEAP, EAP-FAST), EAP-SIM, EAP-AKAAuthenticationProtocols PAP, CHAP, TLS, GTC, MS-CHAP*, MS-CHAPv2Encryption 64-bit and 128-bit WEP, AES-CCMP, AES-CGMP, TKIPWi-Fi Direct*Encryption andAuthenticationWPA2, AES-CCMPProduct Safety UL, C-UL, CB (IEC/EN 60950-1)Intel® Tri-Band Wireless-AC 18265 (18265NGW)GeneralDimensions (H x Wx D) M.2 2230: 22 mm x 30 mm x 2.4 mm [1.5mm Max (Top Side)/ 0.1mm Max (BottomSide)]Weight M.2 2230: 2.4gAntenna Diversity SupportedRadio ON/OFFControl SupportedConnector interface M.2: PCIe, USB Interface to Intel® Wireless Gigabit-Antenna M10101 Module using X-FL(single coax cable to carry power, IF and control)OperatingTemperature(Adapter Shield)0 to +80 ºCHumidity Non-Operating 50% to 90% RH non-condensing (at temperatures of 25 ºC to 35 ºC)Operating Systems Microsoft Windows 7*, Microsoft Windows 8.1*, Microsoft Windows 10, Linux* (limitedfeature support), AndroidWi-Fi Alliance Wi-Fi CERTIFIED* a/b/g/n/ac, WMM*, WMM-PS*, WPA*, WPA2*, WPS2, ProtectedManagement Frames, Wi-Fi Direct* for peer to peer device connections, Wi-Fi Miracastas SourceIEEE WLANStandard IEEE 802.11a/b/g/n/ac, 802.11d, 802.11e, 802.11h, 802.11i, 802.11w; 802.11r,802.11k, 802.11v pending OS support; Fine Timing Measurement based on802.11REVmcRoaming Supports seamless roaming between respective access pointsBluetooth Dual Mode Bluetooth* 4.2, BLEFrequencyModulation 60GHz(802.11ad) 5GHz (802.11ac/n) 2.4GHz (802.11b/g/n)Frequency band 57GHz - 64GHz(dependent oncountry)5.15GHz - 5.85GHz(dependent on country) 2.400 - 2.4835GHz (dependenton country)Modulation DPSK, BPSK,QPSK, 16 QAM, BPSK, QPSK, 16 QAM, 64QAM, 256 QAM CCK, DQPSK, DBPSKWireless Medium DMG control PHY,DMG SC PHY 5GHz UNII: OrthogonalFrequency DivisionMultiplexing (OFDM)2.4GHz ISM: OrthogonalFrequency Division Multiplexing(OFDM)Channels 1, 2 and 3,subject to countryrulesAll channels as defined by the relevant specification and countryrules.Spatial streams N/A Intel® Tri-Band Wireless-AC 18265Data Rates All data rates are theoretical maximums.](https://usermanual.wiki/Intel/9462NG.User-Manual/User-Guide-3671027-Page-67.png)
![This package is an SSL implementation written by Eric Young (eay@cryptsoft.com). The implementation was writtenso as to conform with Netscape's SSL.This library is free for commercial and non-commercial use as long as the following conditions are adhered to. Thefollowing conditions apply to all code found in this distribution, be it the RC4, RSA, lhash, DES, etc., code; not justthe SSL code. The SSL documentation included with this distribution is covered by the same copyright terms exceptthat the holder is Tim Hudson (tjh@cryptsoft.com).Copyright remains Eric Young's, and as such any Copyright notices in the code are not to be removed. If this packageis used in a product, Eric Young should be given attribution as the author of the parts of the library used. This can bein the form of a textual message at program startup or in documentation (online or textual) provided with thepackage.Redistribution and use in source and binary forms, with or without modification, are permitted provided that thefollowing conditions are met:1. Redistributions of source code must retain the copyright notice, this list of conditions and the followingdisclaimer.2. Redistributions in binary form must reproduce the above copyright notice, this list of conditions and thefollowing disclaimer in the documentation and/or other materials provided with the distribution.3. All advertising materials mentioning features or use of this software must display the followingacknowledgement: "This product includes cryptographic software written by Eric Young (eay@cryptsoft.com)"The word 'cryptographic' can be left out if the routines from the library being used are not cryptographicrelated.4. If you include any Windows specific code (or a derivative thereof) from the apps directory (application code)you must include an acknowledgement: "This product includes software written by Tim Hudson(tjh@cryptsoft.com)"THIS SOFTWARE IS PROVIDED BY ERIC YOUNG "AS IS:' AND ANY EXPRESS OR IMPLIED WARRANTIES, INCLUDING,BUT NOT LIMITED TO, THE IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULARPURPOSE ARE DISCLAIMED. IN NO EVENT SHALL THE AUTHOR OR CONTRIBUTORS BE LIABLE FOR ANY DIRECT,INDIRECT, INCIDENTAL, SPECIAL, EXEMPLARY, OR CONSEQUENTIAL DAMAGES (INCLUDING, BUT NOT LIMITED TO,PROCUREMENT OF SUBSTITUTE GOODS OR SERVICES; LOSS OF USE, DATA, OR PROFITS; OR BUSINESSINTERRUPTION) HOWEVER CAUSED AND ON ANY THEORY OF LIABILITY, WHETHER IN CONTRACT, STRICTLIABILITY, OR TORT (INCLUDING NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY OUT OF THE USE OF THISSOFTWARE, EVEN IF ADVISED OF THE POSSIBILITY OF SUCH DAMAGE.The license and distribution terms for any publicly available version or derivative of this code cannot be changed. i.e.this code cannot simply be copied and put under another distribution license [including the GNU Public License.]zlib.h -- interface of the 'zlib' general purpose compression library, version 1.2.3, July18th, 2005Copyright (C) 1995-2005 Jean-loup Gailly and Mark AdlerThis software is provided 'as-is', without any express or implied warranty. In no event will the authors be held liablefor any damages arising from the use of this software. Permission is granted to anyone to use this software for anypurpose, including commercial applications, and to alter it and redistribute it freely, subject to the followingrestrictions:1. The origin of this software must not be misrepresented; you must not claim that you wrote the originalsoftware. If you use this software in a product, an acknowledgment in the product documentation would beappreciated but is not required.2. Altered source versions must be plainly marked as such, and must not be misrepresented as being the originalsoftware.3. This notice may not be removed or altered from any source distribution.Jean-loup Gailly jloup@gzip.orgMark Adler madler@alumni.caltech.edu](https://usermanual.wiki/Intel/9462NG.User-Manual/User-Guide-3671027-Page-71.png)




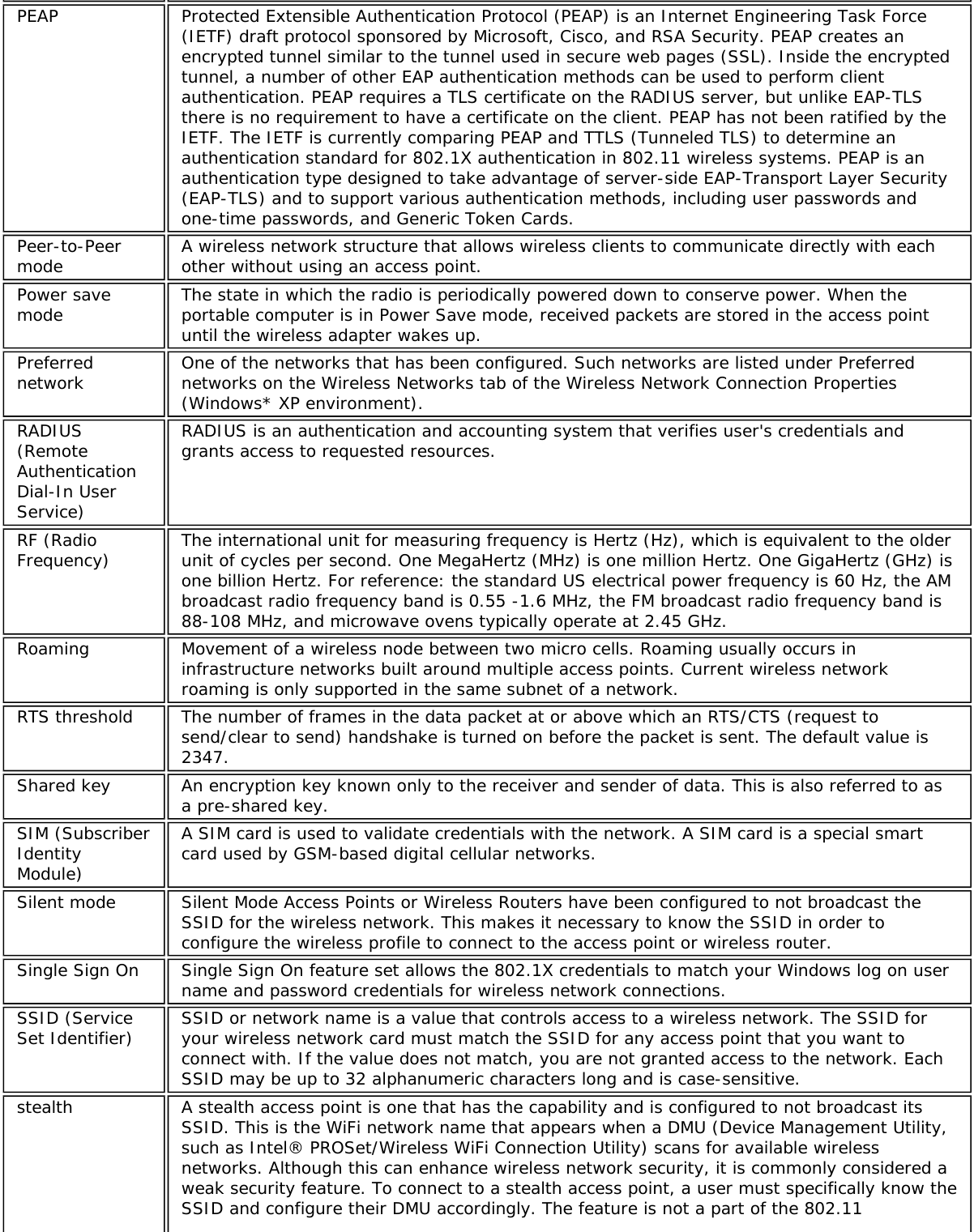
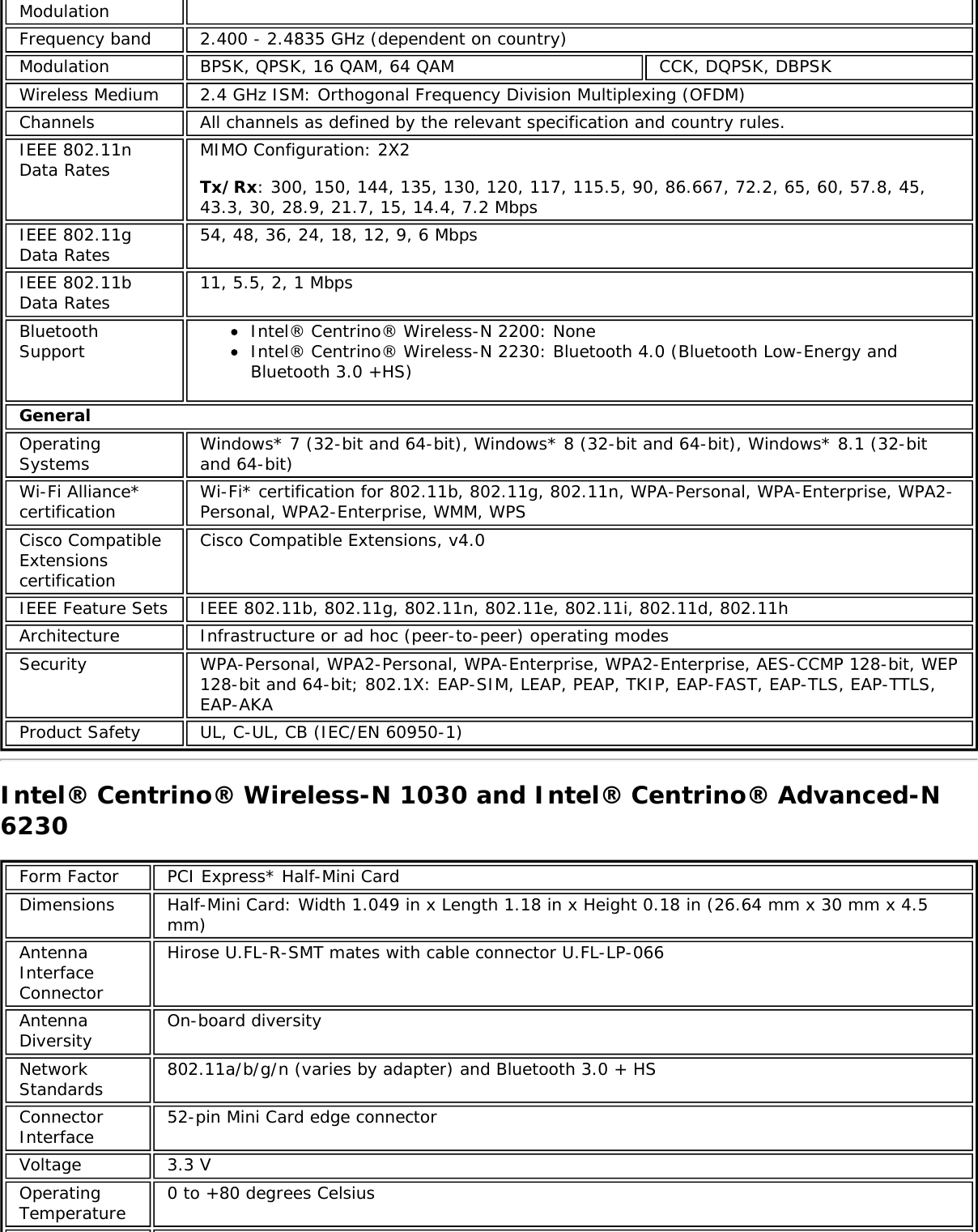
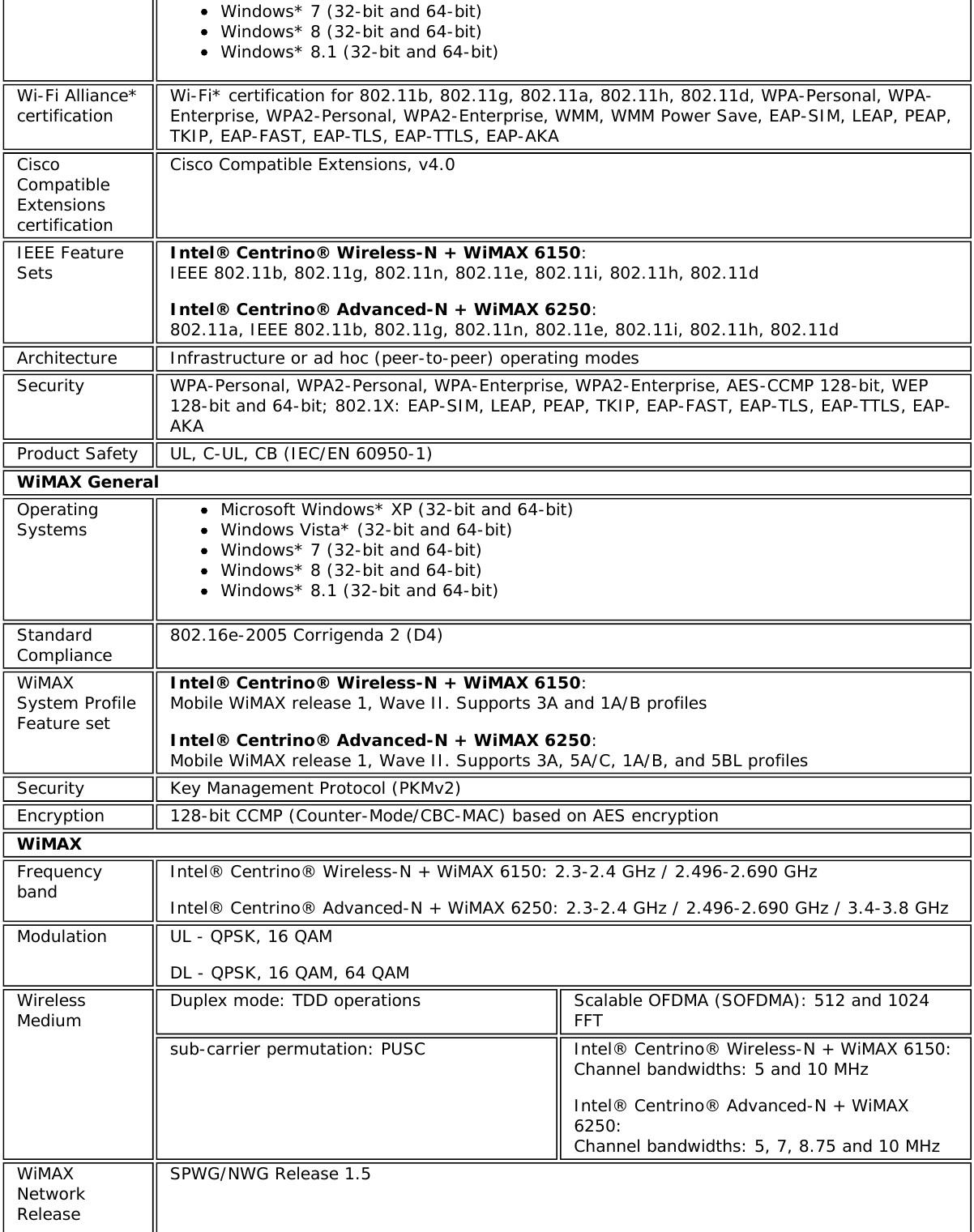
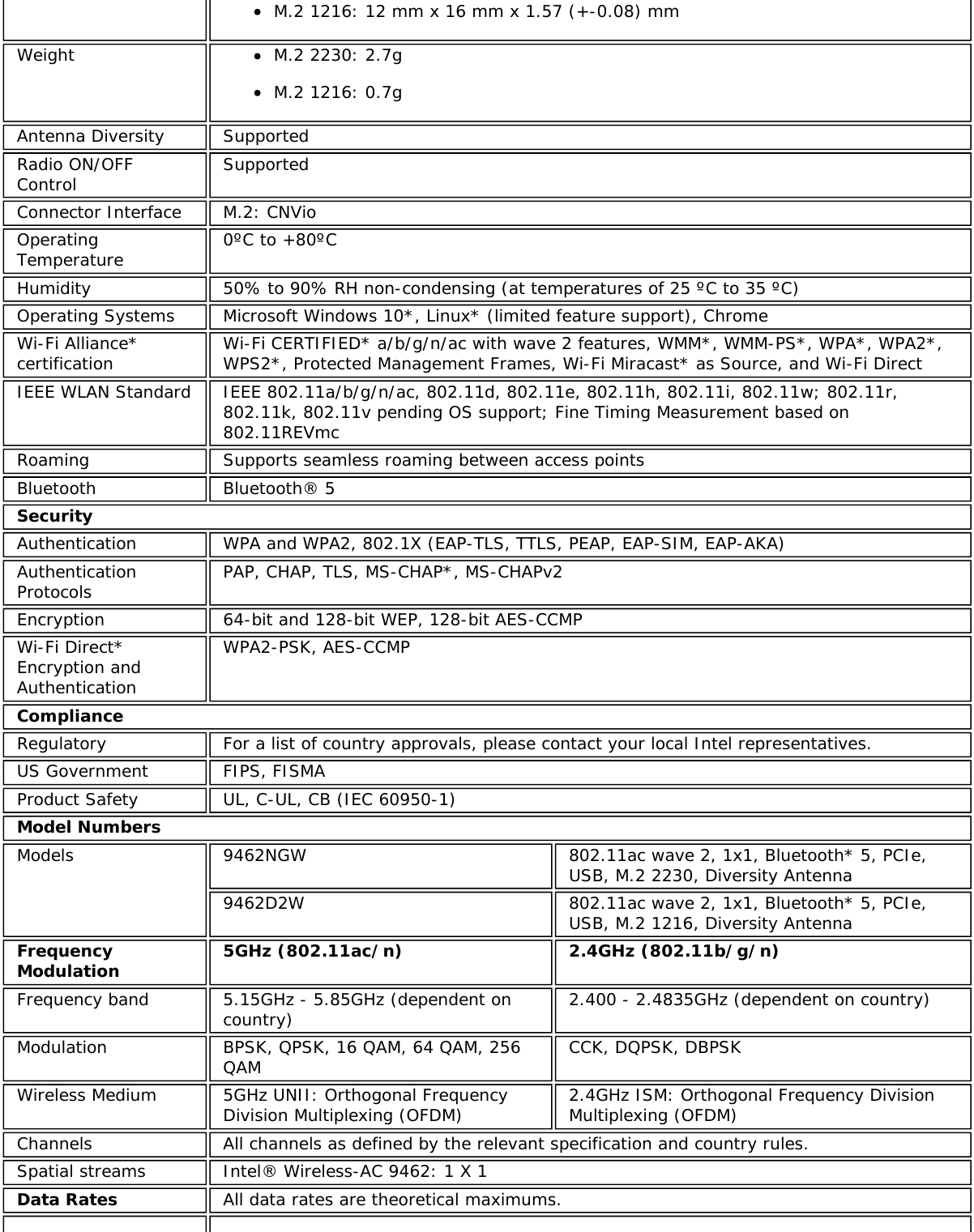
![specification, and is known by differing names by various vendors: closed mode, privatenetwork, SSID broadcasting.TKIP (TemporalKey IntegrityProtocol)Temporal Key Integrity protocol improves data encryption. Wi-Fi Protected Access* uses itsTKIP. TKIP provides important data encryption enhancements including a re-keying method.TKIP is part of the IEEE 802.11i encryption standard for wireless networks. TKIP is the nextgeneration of WEP, the Wired Equivalency Protocol, which is used to secure 802.11 wirelessnetworks. TKIP provides per packet key mixing, a message integrity check and a re-keyingmechanism, thus fixing the flaws of WEP.TLS (TransportLayer Security) A type of authentication method using the Extensible Authentication Protocol (EAP) and asecurity protocol called the Transport Layer Security (TLS). EAP-TLS uses certificates whichuse passwords. EAP-TLS authentication supports dynamic WEP key management. The TLSprotocol is intended to secure and authenticate communications across a public networkthrough data encryption. The TLS Handshake Protocol allows the server and client to providemutual authentication and to negotiate an encryption algorithm and cryptographic keysbefore data is transmitted.TTLS (TunneledTransport LayerSecurity)These settings define the protocol and the credentials used to authenticate a user. In TTLS,the client uses EAP-TLS to validate the server and create a TLS-encrypted channel betweenthe client and server. The client can use another authentication protocol. Typically password-based protocols challenge over this encrypted channel to enable server validation. Thechallenge and response packets are sent over a non-exposed TLS encrypted channel. TTLSimplementations today support all methods defined by EAP, as well as several older methods(CHAP, PAP, MS-CHAP and MS-CHAP-V2). TTLS can easily be extended to work with newprotocols by defining new attributes to support new protocols.WEP (WiredEquivalentPrivacy)Wired Equivalent Privacy, 64- and 128-bit (64-bit is sometimes referred to as 40-bit). This isa low-level encryption technique designed to give the user about the same amount ofprivacy that he would expect from a LAN. WEP is a security protocol for wireless local areanetworks (WLANs) defined in the 802.11b standard. WEP is designed to provide the samelevel of security as that of a wired LAN. WEP aims to provide security by data over radiowaves so that it is protected as it is transmitted from one end point to another.WEP Key Either a pass phrase or hexadecimal key.The pass phrase must be 5 ASCII characters for 64-bit WEP or 13 ASCII characters for 128-bit WEP. For pass phrases, 0-9, a-z, A-Z, and ~!@#$%^&*()_+|`-={}|[]\:";'<>?,./ are allvalid characters.The hex key must be 10 hexadecimal characters (0-9, A-F) for 64-bit WEP or 26hexadecimal characters (0-9, A-F) for 128-bit WEP.Wi-Fi*(WirelessFidelity)Is meant to be used generically when referring of any type to 802.11 network, whether802.11b, 802.11a, or dual-band.WiMAX WiMAX, the Worldwide Interoperability for Microwave Access, is a telecommunicationstechnology aimed at providing wireless data over long distances in a variety of ways, frompoint-to-point links to full mobile cellular type access. It is based on the IEEE 802.16standard. The name WiMAX was created by the WiMAX Forum, which was formed in June2001 to promote conformance and interoperability of the standard. The forum describesWiMAX as "a standards-based technology enabling the delivery of last mile wirelessbroadband access as an alternative to cable and DSL."Wireless router A stand-alone wireless hub that allows any computer that has a wireless network adapter tocommunicate with another computer within the same network and to connect to theInternet.WLAN (WirelessLocal-AreaNetwork)A type of local-area network that uses high-frequency radio waves rather than wires tocommunicate between nodes.WPA* (Wi-FiProtectedAccess)This is a security enhancement that strongly increases the level of data protection andaccess control to a wireless network. WPA is an interim standard that will be replaced withthe IEEE's 802.11i standard upon its completion. WPA consists of RC4 and TKIP and providessupport for BSS (Infrastructure) mode only. WPA and WPA2 are compatible.WPA2* (Wi-Fi This is the second generation of WPA that complies with the IEEE TGi specification. WPA2](https://usermanual.wiki/Intel/9462NG.User-Manual/User-Guide-3671027-Page-82.png)
