LINKSYS WRE54G Wireless-G Range Expander User Manual
LINKSYS LLC Wireless-G Range Expander
LINKSYS >
User Manual

A Division of Cisco Systems, Inc.
®
Model No.
Range Expander
Wireless-G
WRE54G
User Guide
GHz
2.4
802.11g
WIRELESS
Chapter 1: Introduction
Welcome
WRE54G Wireless-G Range Expander is a standard WLAN repeater device. It can repeat and extend wireless signal
coverage on Linksys wireless AP/router.
Features
z Supports 64 / 128 bit WEP encryption in 802.11b/802.11g wireless LAN.
z Wireless operation provides data rate at 11, 5.5, 2, and 1Mbps with auto fallback for 802.11b WLAN card and also
provide rate at 6, 9, 12, 18, 24, 36, 48, and 54Mbps for 802.11g WLAN card.
z Configurable through your networked PC’s Web browser
z Configurable through Setup Wizard
z Backup and restore configuration
z Support auto-configuration and infrastructure operation modes. Under auto-configuration operation mode, WRE54G
will detect and connect to the Linksys wireless AP/Router with strongest signal in the environment. Infrastructure
operation mode allows user configure the WRE54G via setup wizard.
z Password protected configuration or management sessions for web access
z Built-in HTTP Server for setup and management via any browser easily
z Support 64/128 bit WEP encryption.

Chapter 2: Planning your Wireless Network
The Repeater’s Functions
Simply put, the Wireless-G Range Expander can increase the coverage
area of an ESS.
Network Topology
A wireless local area network (WLAN) is exactly like a regular local area
network (LAN), except that each computer in the WLAN uses a wireless
device to connect to the network. Computers in a WLAN share the same
frequency channel and SSID, which is an identification name for wireless
devices.
Ad-Hoc versus Infrastructure Mode
Unlike wired networks, wireless networks have two different modes in
which they may be set up: infrastructure and ad-hoc. An infrastructure
configuration is a WLAN and wired LAN communicating to each other
through an access point. An ad-hoc configuration is wireless-equipped computers communicating directly with each other. Choosing between these
two modes depends on whether or not the wireless network needs to share data or peripherals with a wired network or not. If the computers on the
wireless network need to be accessed by a wired
network or need to share a peripheral, such as a printer, with the wired network computers, the wireless network should be set up in infrastructure
mode.
The basis of infrastructure mode centers around an access point, which serves as the main point of communications in a wireless network. Access
points transmit data to PCs equipped with wireless network cards, which can roam within a certain radial range of the access point. Multiple access
points can be arranged to work in succession to extend the roaming range.
If the wireless network is relatively small and needs to share resources only with the other computers on the wireless network, then the ad-hoc
mode can be used. Ad-hoc mode allows computers equipped with wireless transmitters and receivers to communicate directly with each other,
eliminating the need for an access point. The drawback of this mode is that, in Ad-Hoc mode, wireless-equipped computers are not able to
communicate with computers on a wired network. And, of course, communication between the wireless-equipped computers is limited by the
distance and interference directly between them.

Chapter 3: Getting to Know the Wireless-G Range
Expander
The Side Panel
Auto configuration port is where you will connect the power adapter.
Reset Button You can use an object, such as a stretched paper clip, to press the Reset
button and then release the button to reset the device to its factory-default settings.
The Top Panel
The LEDs on the top panel of the Wireless-G Range Expander indicate the information about
power and network activity.
Power Blue. The Power LED lights up when the Wireless-G Range Expander is powered on.
Link Blue. The Link LED lights whenever there is a successful wireless connection.

Chapter 4: Connecting the Wireless-G Range
Expander
The Setup Wizard will take you through all the steps necessary to configure the Wireless-G
Range Expander. Before you start it, your notebook or desktop computer must already be part
of a wireless network.
1. Power on your Access Point and make sure cables are properly connected.
2. In order to configure the Wireless-G Range Expander you mush already be connected to a
wireless Access Point.
3. Power on your Wireless-G Range Expander by connecting your Wireless-G Range Expander
to a power outlet.
4. Once the Wireless-G Range Expander is powered on, you can access it in your wireless
network.
5. Insert the Setup Wizard CD into the CD-ROM driver of your PC or notebook that has already
be part of a wireless network.
6. The screen should appear on your monitor. If it does not, this means the auto-run is not
functioning. Start the auto-run manually by clicking the Start button, selecting Run, and typing
D:\setup.exe (if “D” is your CD-ROM drive). Click the Setup button to run the Setup Wizard.
7. Click the Next button to continue or Exit to exit the Setup Wizard.
8. The next screen to appear will display a list of the access points on your network, along with
the status information for each access point. If there is only one access point on your
network, it will be the only one displayed. If there are more than one displayed, select the
Access Point you want to connect to. Once you have connected to an Access Point, the
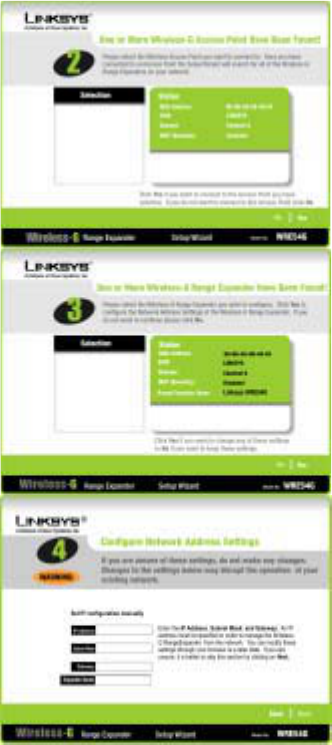
Setup Wizard will search for all of the Wireless-G Range Expanders on your network.
9. Click the Yes button to continue or No to exit the Setup Wizard.
10. The Security screen shows the WEP key. If you would like to use Wired Equivalent Privacy
(WEP) encryption for your wireless network., enter the required information on the screen.
z WEP. In order to utilize WEP encryption, select the WEP setting from the pull-down
menu, 64-bit (10 hex digits) or 128-bit (26 hex digits). If you do not wish to utilize
WEP encryption, make sure Disabled is selected. The Access Point’s WEP
encryption is unique to Linksys and may conflict with other vendors’ WEP encryption.
z Passphrase. Instead of manually entering WEP keys, you can enter a Passphrase.
This Passphrase is used to generate one or more WEP keys. It is case-sensitive and
should not be longer than 16 alphanumeric characters. (The Passphrase function is
compatible with Linksys wireless products only. If you want to communicate with
non-Linksys wireless products, you will need to enter your WEP keys manually on
the non-Linksys wireless products.)
11. If you entered a passphrase, then the Key 1 field will display the automatically generated
WEP key. If you did not enter a passphrase, then enter a WEP key in the Key 1 field. Each
device in your wireless network must use the same WEP key for the network to function
properly.
z Key 1. WEP keys enable you to create an encryption scheme for wireless LAN
transmissions. If the WEP key hasn’t been automatically generated, then manually
enter a set of values. (Do not leave the field blank, and do not enter all zeroes. These
are not valid key values.) If you are using 64-bit WEP encryption, then each key must
consist of exactly 10 hexadecimal characters. If you are using 128-bit WEP
encryption, then each key must consist of exactly 26 hexadecimal characters. Valid
hexadecimal characters are “0”-“9” and “A”-“F”.
12. Next button to continue or Back to return to the previous page.
13. Select the Wireless-G Range Expander you want to configure. Click Yes to configure the
Network Address Settings of the Wireless-G Range Expander. If you do not want to continue,
click No.
14. You can manually set IP configuration. Enter an IP Address, Subnet Mask, Gateway, and
Expander Name appropriate for your network. If you are unsure of these settings, you can
skip this selection by just clicking on Next.
15. Click the Next button to continue or Back to return to the previous page.
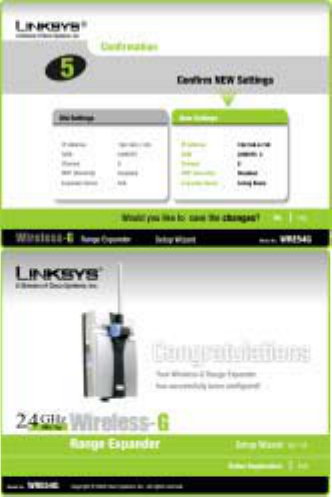
16. The next screen will allow you to review your settings. If these settings are correct, click the
Yes button to save these settings. If there are any problems with the settings, click the No
button to exit the Setup Wizard.
17. Congratulations! At this point, the configuration performed with the Setup Wizard is
complete. Click the Exit button to exit the Setup Wizard.
Appendix A: Glossary
802.11a - An IEEE wireless networking standard that specifies a maximum data transfer rate of 54Mbps and an
operating frequency of 5GHz.
802.11b - An IEEE wireless networking standard that specifies a maximum data transfer rate of 11Mbps and an
operating frequency of 2.4GHz.
802.11g - An IEEE wireless networking standard that specifies a maximum data transfer rate of 54Mbps, an
operating frequency of 2.4GHz, and backward compatibility with 802.11b devices.
Access Point - Device that allows wireless-equipped computers and other devices to communicate with a wired
network. Also used to expand the range of a wireless network.
Adapter - This is a device that adds network functionality to your PC.
Ad-hoc - A group of wireless devices communicating directly with each other (peer-to-peer) without the use of
an access point.
Bandwidth - The transmission capacity of a given device or network.
Bit - A binary digit.
Bridge - A device that connects two different kinds of local networks, such as a wireless network to a wired
Ethernet network.
Broadband - An always-on, fast Internet connection.
Browser - A browser is an application program that provides a way to look at and interact with all the
information on the World Wide Web.
DDNS (Dynamic Domain Name System) - The capability of having a website, FTP, or e-mail server-with a
dynamic IP address-use a fixed domain name.
Default Gateway - A device that forwards Internet traffic from your local area network.
DHCP (Dynamic Host Configuration Protocol) - A protocol that lets one device on a local network, known as a
DHCP server, assign temporary IP addresses to the other network devices, typically computers.
Domain - A specific name for a network of computers.
DSSS (Direct-Sequence Spread-Spectrum) - A type of radio transmission technology that includes a redundant
bit pattern to lessen the probability of data lost during transmission. Used in 802.11b networking.
Dynamic IP Address - A temporary IP address assigned by a DHCP server.
Encryption - Encoding data to prevent it from being read by unauthorized people.
Ethernet - An IEEE standard network protocol that specifies how data is placed on and retrieved from a common
transmission medium.
Firmware - 1. In network devices, the programming that runs the device. 2. Programming loaded into read-only
memory (ROM) or programmable read-only memory (PROM) that cannot be altered by end-users.
Gateway - A system that interconnects networks.
Hardware - The physical aspect of computers, telecommunications, and other information technology devices.
HTTP (HyperText Transport Protocol) - The communications protocol used to connect to servers on the World
Wide Web.
IEEE (The Institute of Electrical and Electronics Engineers) - An independent institute that develops networking
standards.
Infrastructure - Currently installed computing and networking equipment.
Infrastructure Mode - Configuration in which a wireless network is bridged to a wired network via an access
point.
IP (Internet Protocol) - A protocol used to send data over a network.
IP Address - The address used to identify a computer or device on a network.
IPCONFIG - A Windows 2000 and XP utility that displays the IP address for a particular networking device.
IPSec (Internet Protocol Security) - A VPN protocol used to implement secure exchange of packets at the IP layer.
LAN (Local Area Network) - The computers and networking products that make up the network in your home or
office.
MAC (Media Access Control) Address - The unique address that a manufacturer assigns to each networking
device.
Mbps (Megabits Per Second) - One million bits per second; a unit of measurement for data transmission.
Network - A series of computers or devices connected for the purpose of data sharing, storage, and/or
transmission between users.
Node - A network junction or connection point, typically a computer or work station.
OFDM (Orthogonal Frequency Division Multiplexing) - A type of modulation technology that separates the data
stream into a number of lower-speed data streams, which are then transmitted in parallel. Used in 802.11a,
802.11g, and powerline networking.
Packet - A unit of data sent over a network.
Passphrase - Used much like a password, a passphrase simplifies the WEP encryption process by automatically
generating the WEP encryption keys for Linksys products.
Roaming - The ability to take a wireless device from one access point's range to another without losing the
connection.
Router - A networking device that connects multiple networks together, such as a local network and the Internet.
Software - Instructions for the computer. A series of instructions that performs a particular task is called a
"program".
SSID (Service Set IDentifier) - Your wireless network's name.
Static IP Address - A fixed address assigned to a computer or device that is connected to a network.
Static Routing - Forwarding data in a network via a fixed path.
Subnet Mask - An address code that determines the size of the network.
Topology - The physical layout of a network.
Upgrade - To replace existing software or firmware with a newer version.
Upload - To transmit a file over a network.
URL (Uniform Resource Locator) - The address of a file located on the Internet.
WAN (Wide Area Network) - The Internet.
WEP (Wired Equivalent Privacy) - A method of encrypting data transmitted on a wireless network for greater
security.
WLAN (Wireless Local Area Network) - A group of computers and associated devices that communicate with
each other wirelessly.
Appendix B: Regulatory Information
FCC STATEMENT
This product has been tested and complies with the specifications for a Class B digital device, pursuant to Part 15
of the FCC Rules. These limits are designed to provide reasonable protection against harmful interference in a
residential installation. This equipment generates, uses, and can radiate radio frequency energy and, if not
installed and used according to the instructions, may cause harmful interference to radio communications.
However, there is no guarantee that interference will not occur in a particular installation. If this equipment does
cause harmful interference to radio or television reception, which is found by turning the equipment off and on,
the user is encouraged to try to correct the interference by one or more of the following measures:
• Reorient or relocate the receiving antenna
• Increase the separation between the equipment or devices
• Connect the equipment to an outlet other than the receiver's
• Consult a dealer or an experienced radio/TV technician for assistance
FCC Radiation Exposure Statement
This equipment complies with FCC radiation exposure limits set forth for an uncontrolled environment. This
equipment should be installed and operated with minimum distance 20cm between the radiator and your body.
FCC Caution: To assure continued compliance, any changes or modifications not expressly approved by the party
responsible for compliance could void the user's authority to operate this equipment.
This device complies with Part 15 of the FCC Rules. Operation is subject to the following two conditions: (1) This
device may not cause harmful interference, and (2) this device must accept any interference received, including
interference that may cause undesired operation.
This transmitter must not be co-located or operating in conjunction with any other antenna or transmitter.
Cisco-Linksys, LLC declares that WRE54G ( FCC ID: Q87-WRE54G ) is limited in
CH1~CH11 by specified firmware controlled in U.S.A.

Appendix C: Contact Information
Wireless-G Range Expander
Appendix C: Contact Information
Need to contact Linksys?
Visit us online for information on the latest products and updates
to your existing products at: http://www.linksys.com or
ftp.linksys.com
Can't find information about a product you want to buy
on the web? Do you want to know more about networking
with Linksys products? Give our advice line a call at: 800-546-5797 (LINKSYS)
Or fax your request in to: 949-261-8868
If you experience problems with any Linksys product,
you can call us at: 800-326-7114
Don't wish to call? You can e-mail us at: support@linksys.com
If any Linksys product proves defective during its warranty period,
you can call the Linksys Return Merchandise Authorization
department for obtaining a Return Authorization Number at: 949-261-1288
(Details on Warranty and RMA issues can be found in the Warranty
Information section in this Guide.)